Patents
Literature
912 results about "IPsec" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
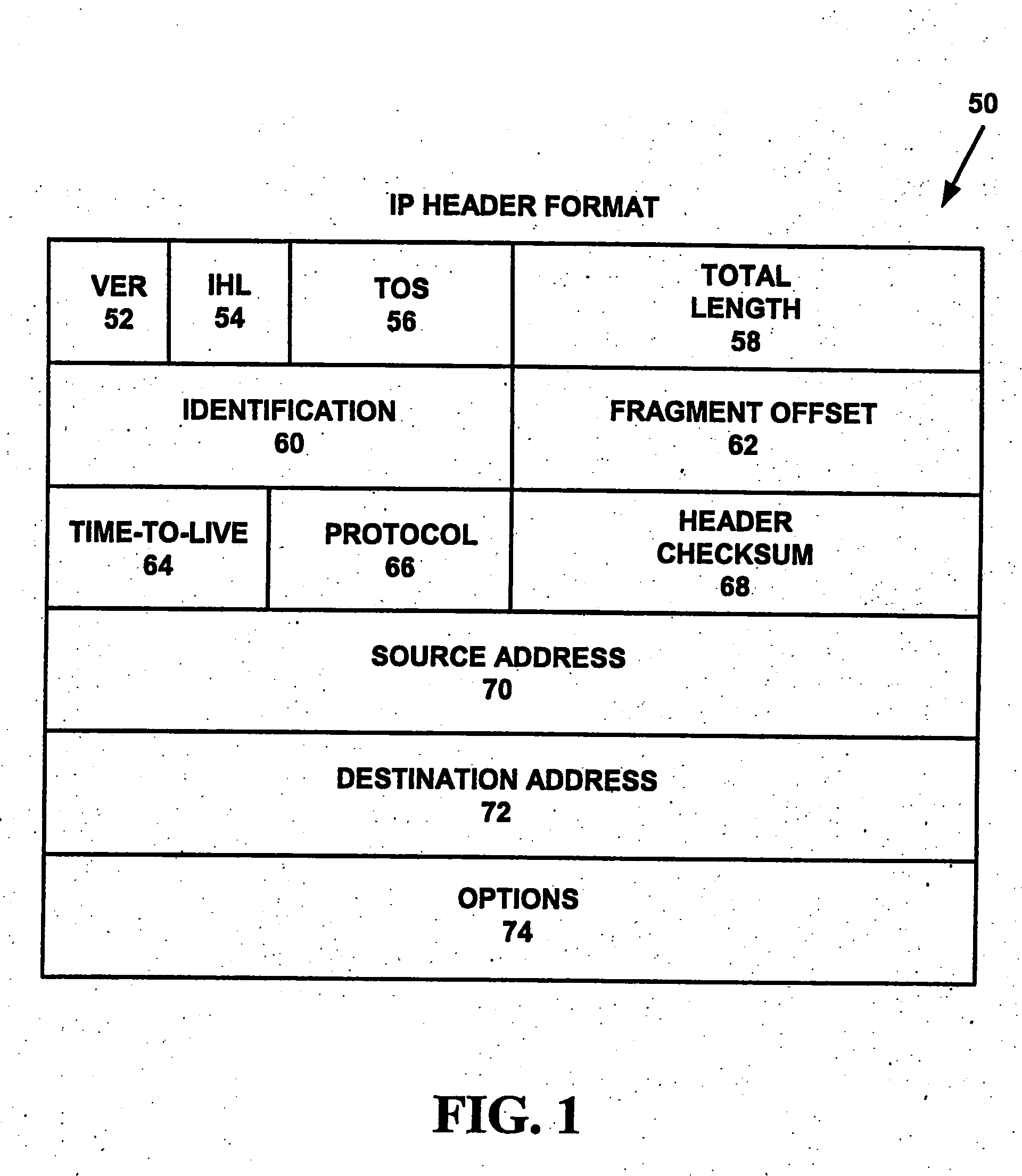
In computing, Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data sent over an Internet Protocol network. It is used in virtual private networks (VPNs).
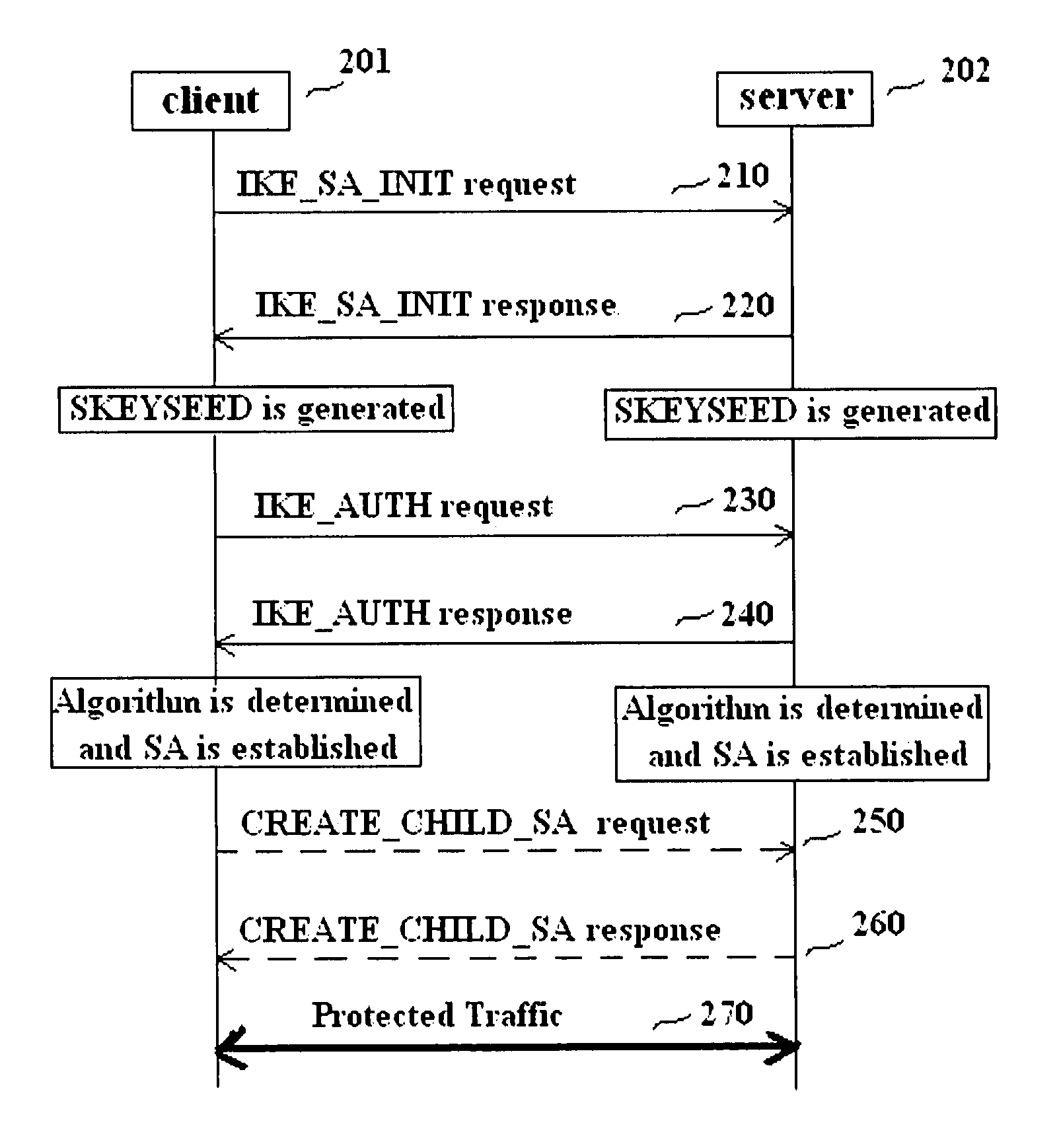
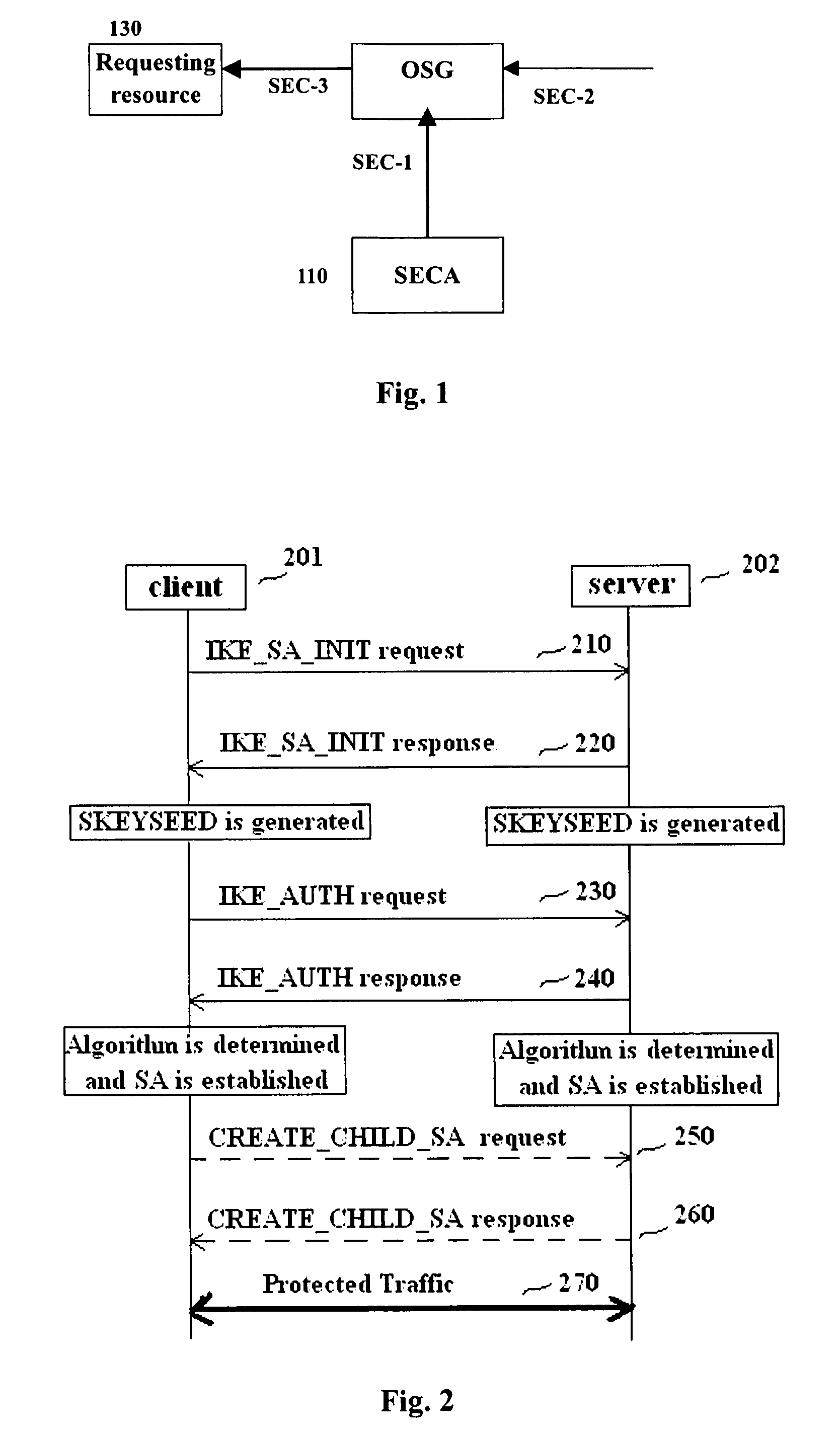
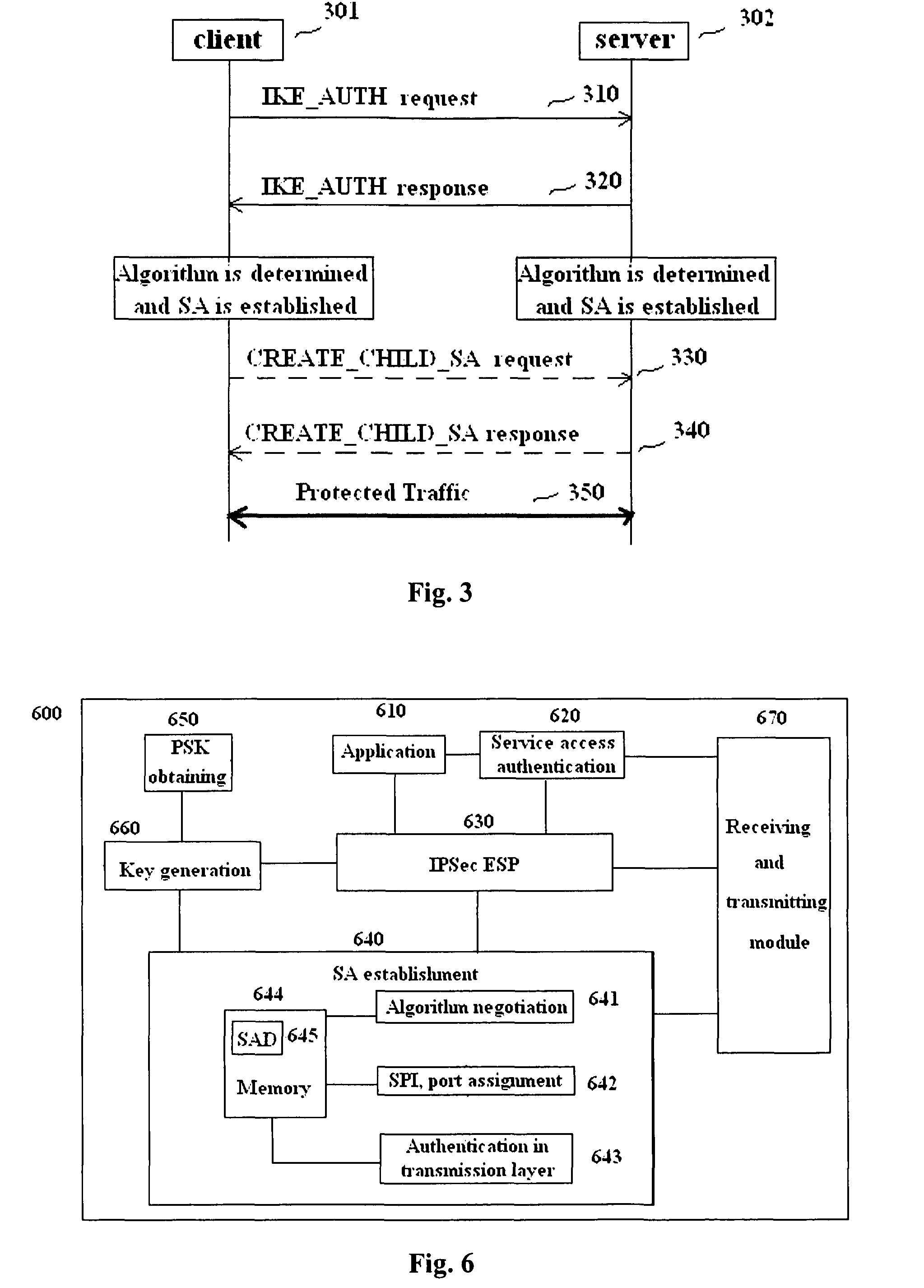
Methods and entities using IPSec ESP to support security functionality for UDP-based traffic
ActiveUS8639936B2Improve efficiencyOptimize procedureUser identity/authority verificationComputer security arrangementsTraffic capacityIPsec
Owner:ALCATEL LUCENT SAS
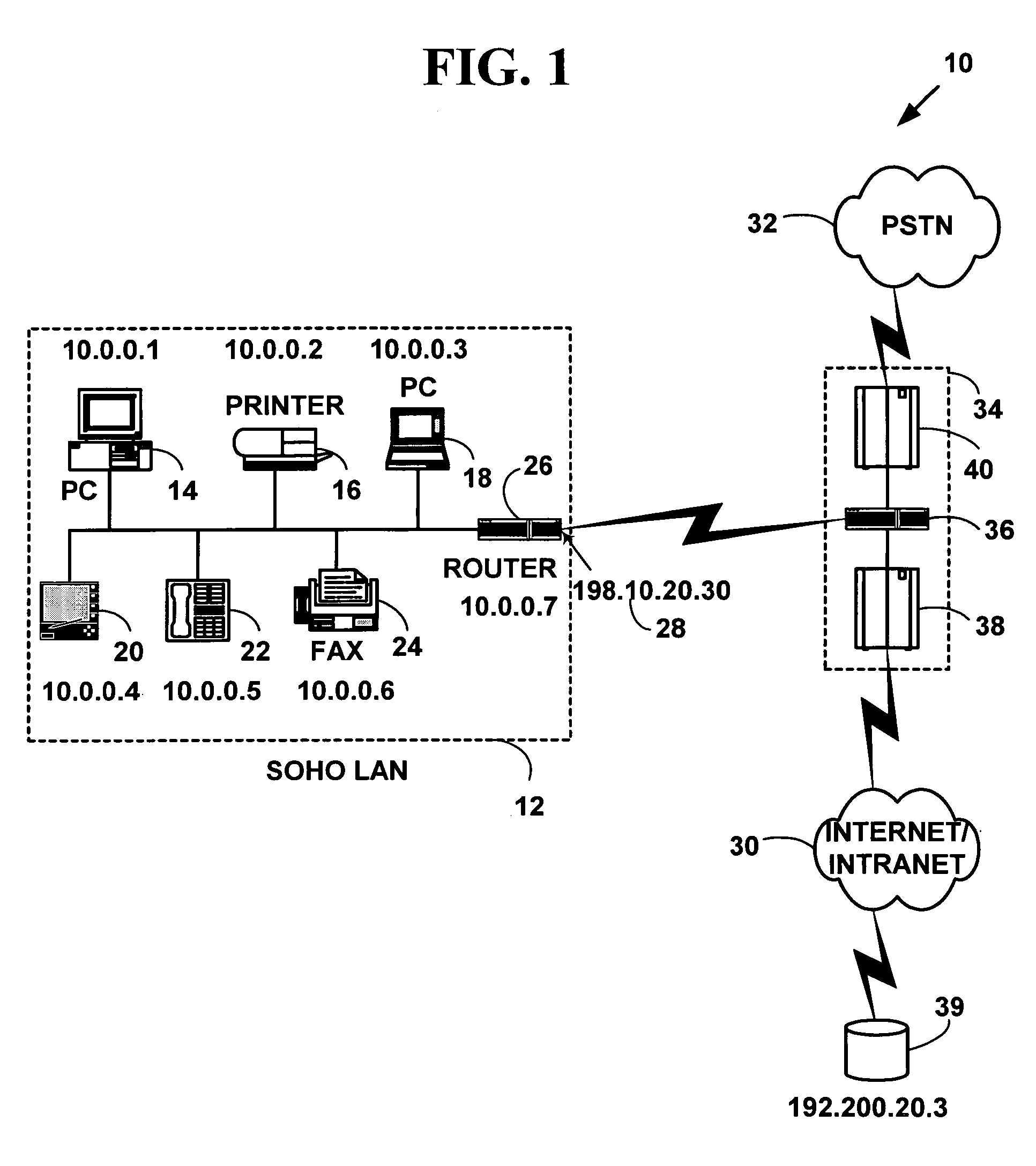
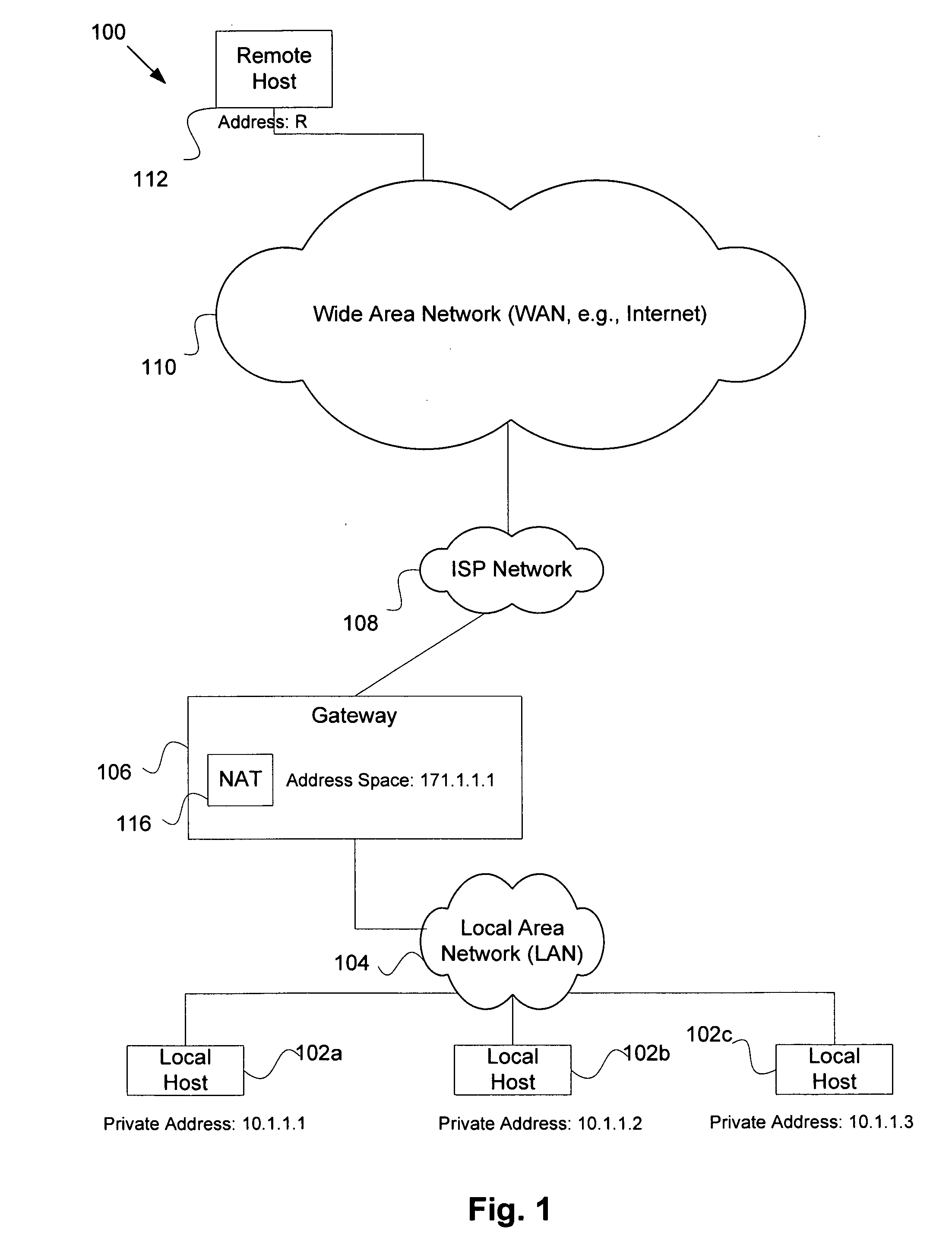
Method and system for distributed network address translation with network security features
InactiveUS7032242B1Digital data processing detailsUser identity/authority verificationSecurity associationIp address
A method and system for distributed network address translation with security features. The method and system allow Internet Protocol security protocol (“IPsec”) to be used with distributed network address translation. The distributed network address translation is accomplished with IPsec by mapping a local Internet Protocol (“IP”) address of a given local network device and a IPsec Security Parameter Index (“SPI”) associated with an inbound IPsec Security Association (“SA”) that terminates at the local network device. A router allocates locally unique security values that are used as the IPsec SPIs. A router used for distributed network address translation is used as a local certificate authority that may vouch for identities of local network devices, allowing local network devices to bind a public key to a security name space that combines a global IP address for the router with a set of locally unique port numbers used for distributed network address translation. The router issues security certificates and may itself be authenticated by a higher certificate authority. Using a security certificate, a local network device may initiate and be a termination point of an IPsec security association to virtually any other network device on an IP network like the Internet or an intranet. The method and system may also allow distributed network address translation with security features to be used with Mobile IP or other protocols in the Internet Protocol suite.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
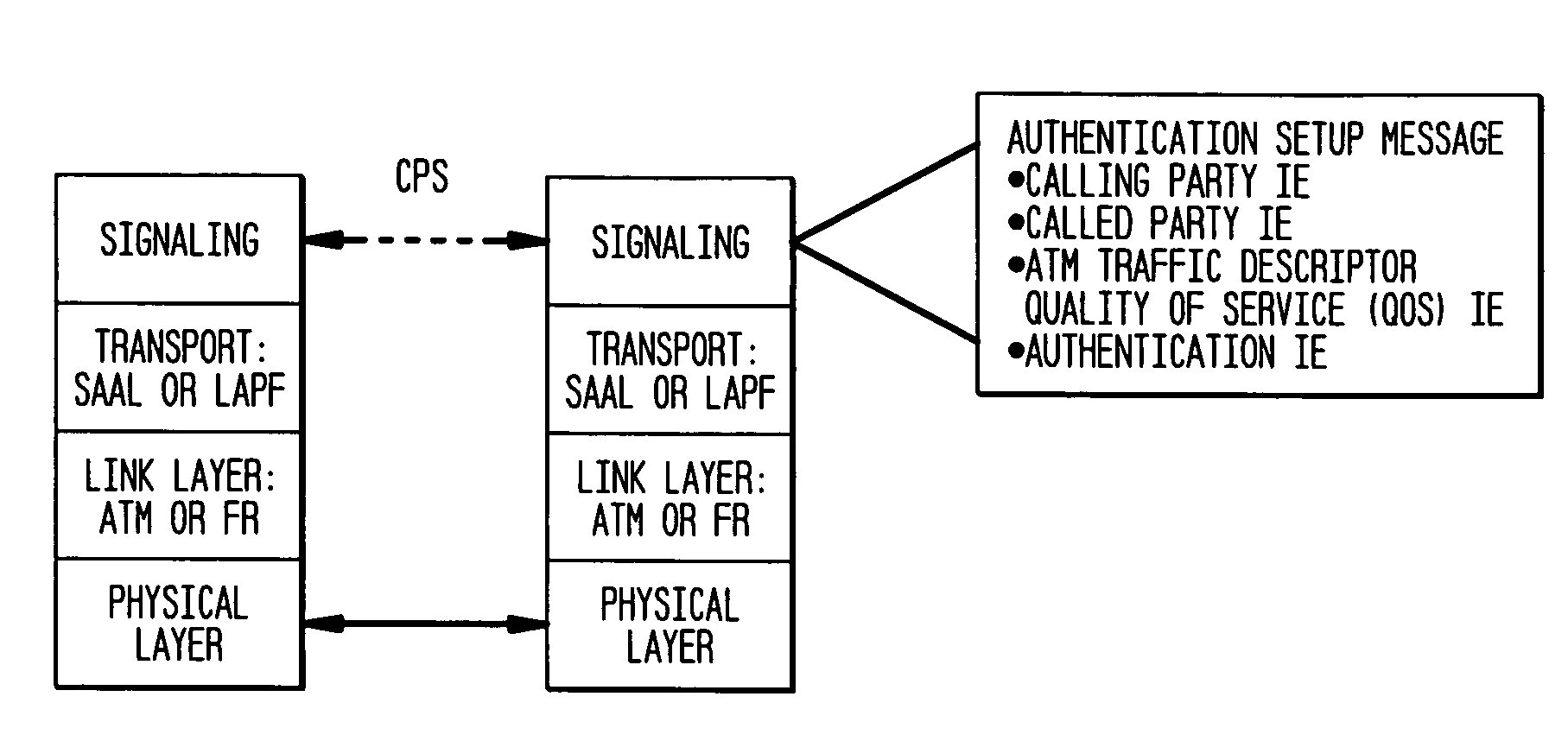
Authentication mechanisms for call control message integrity and origin verification
The present invention incorporates methodologies developed in the Internet Engineering Task Force (IETF) Internet Protocol Security (IPSEC) Working Group into asynchronous transfer mode (ATM) and frame relay (FR) signaling to provide message integrity and origin authentication. In one implementation the invention provides a virtual private network (VPN) infrastructure with call control message integrity, origin verification, and transit network filtering. The invention utilizes a set of control plane messages based on the IPSEC authentication header (AH) methodology to provide these security mechanisms for ATM and FR network switching equipment and signaling protocols. This abstract itself is not intended to limit the scope of this patent. The scope of the present invention is pointed out in the appending claims.
Owner:ALCATEL-LUCENT USA INC
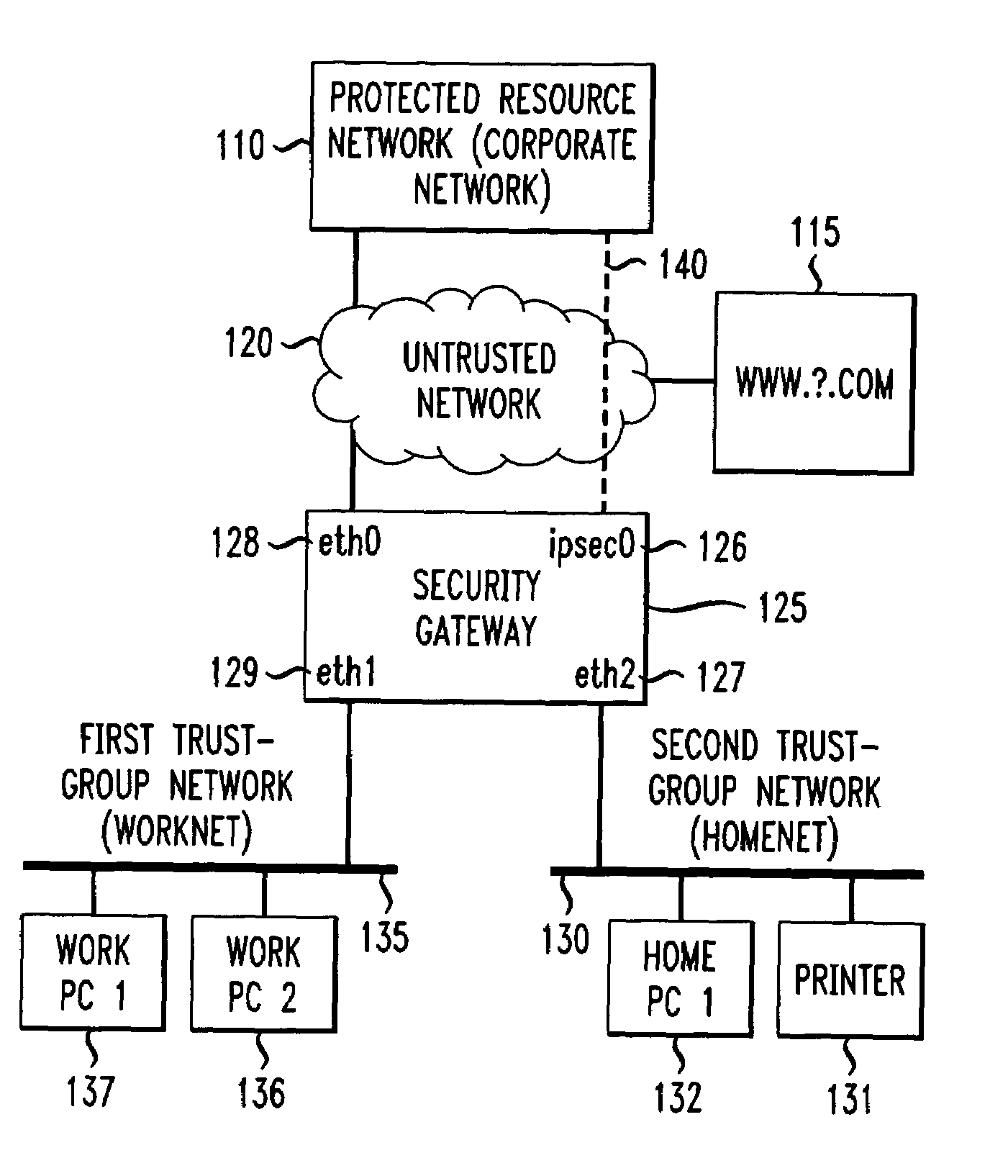
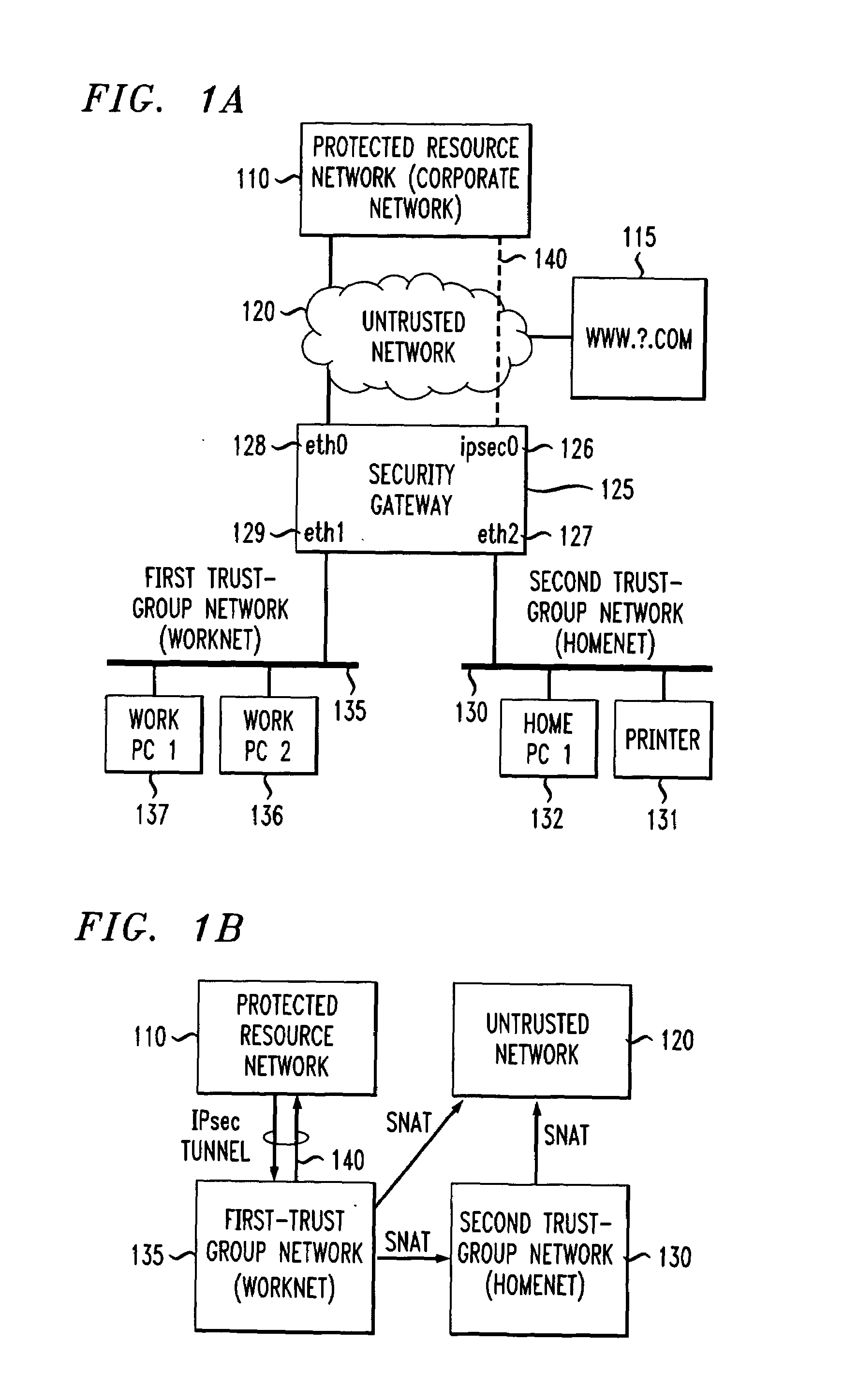
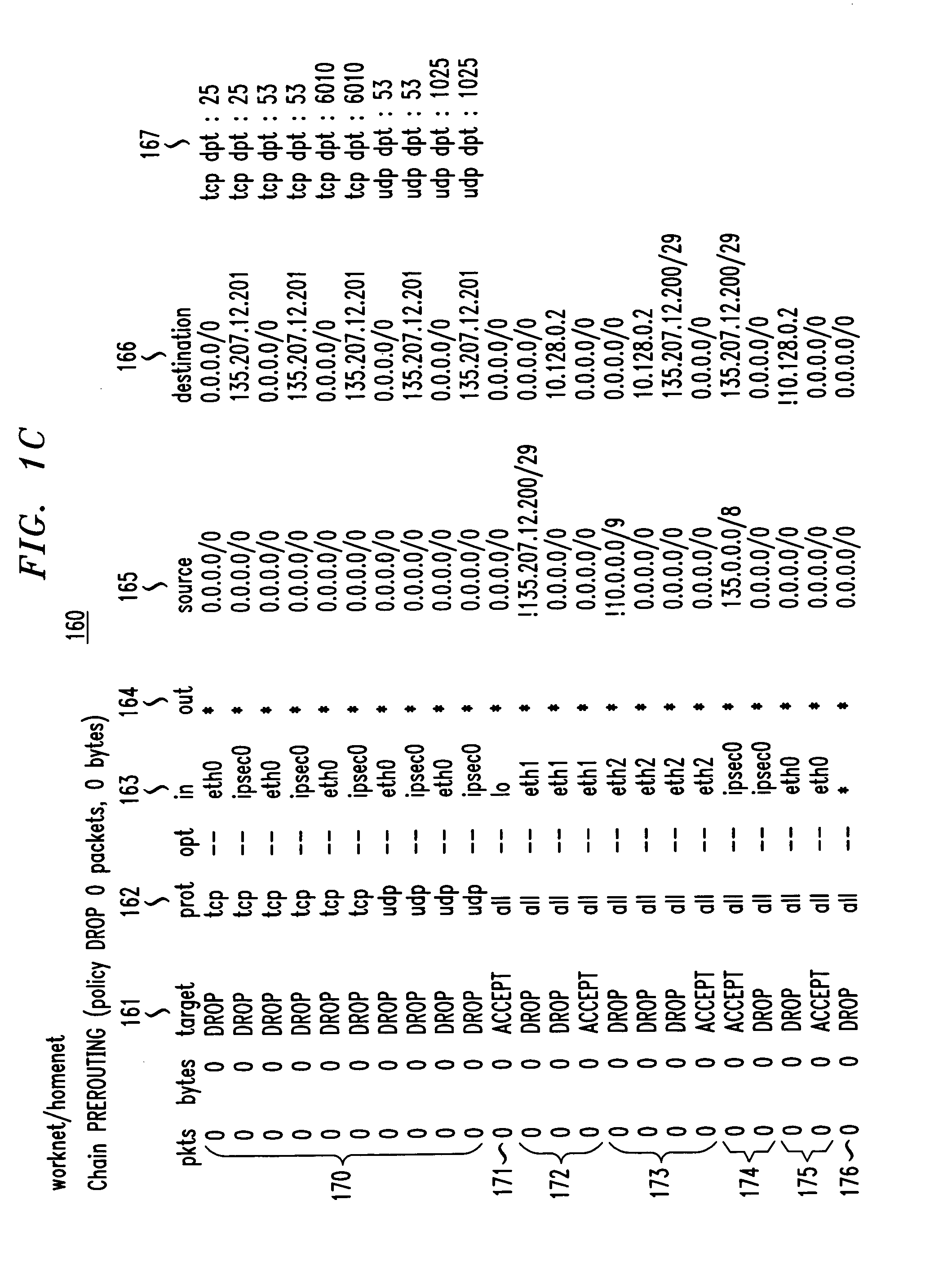
Method and apparatus for securely connecting a plurality of trust-group networks, a protected resource network and an untrusted network
InactiveUS7131141B1Improve securityMultiple digital computer combinationsProgram controlPrivate networkIp address
A security gateway provides a secure connection among one or more networks and a protected resource network. One of the local networks may be connected to the remote private network via a VPN IPsec tunnel. The networks may be local networks that share resources without compromising the security of the protected resource network. The local networks may have access to an untrusted network such as the Internet, sharing a single connection through the security gateway. Dynamic source network address translation is used to permit access from the network connected to the protected resource network to other, less trusted networks while concealing the actual IP addresses of hosts within that network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
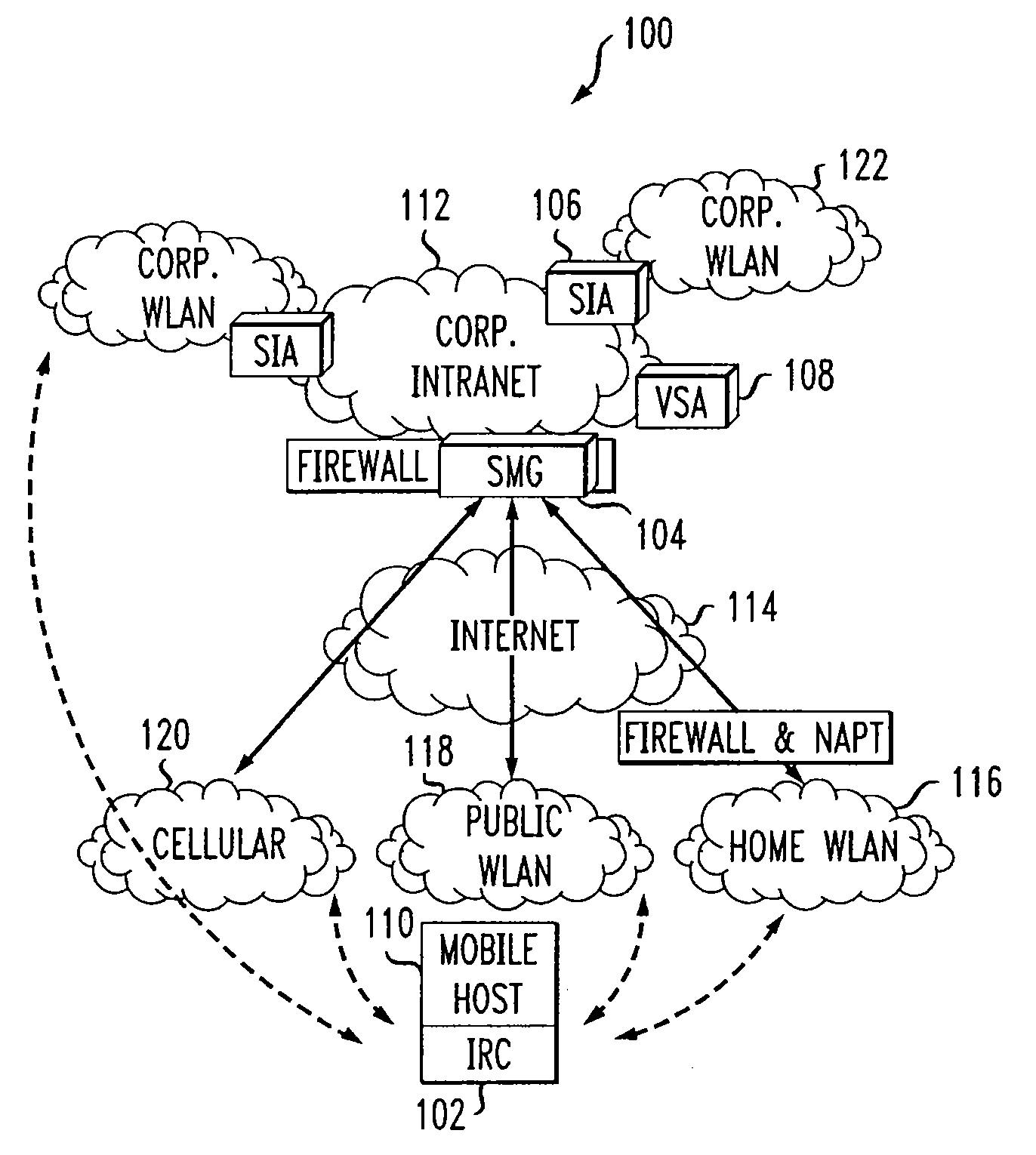
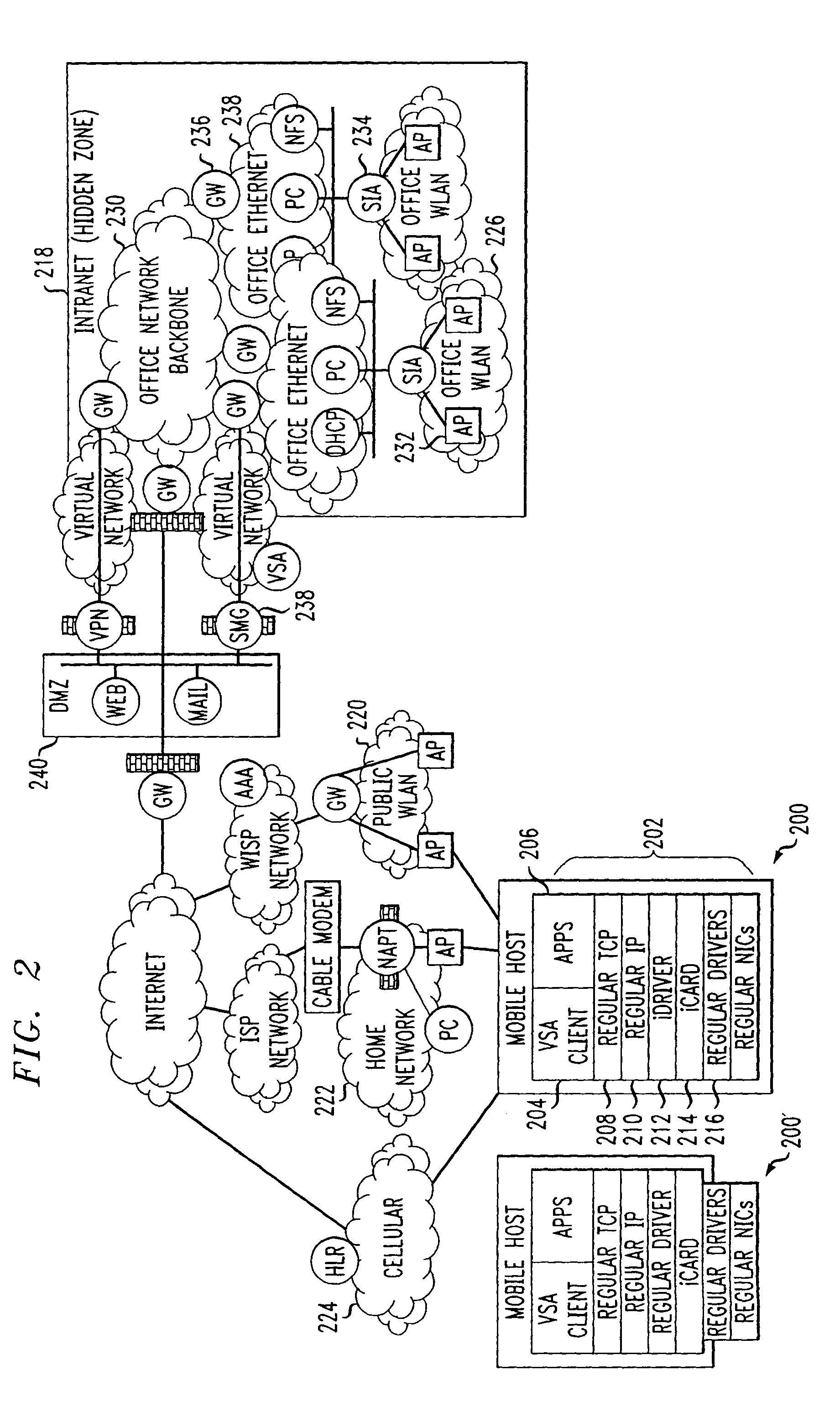
System and method to support networking functions for mobile hosts that access multiple networks
InactiveUS7441043B1Multiple digital computer combinationsWireless network protocolsModem deviceIp address
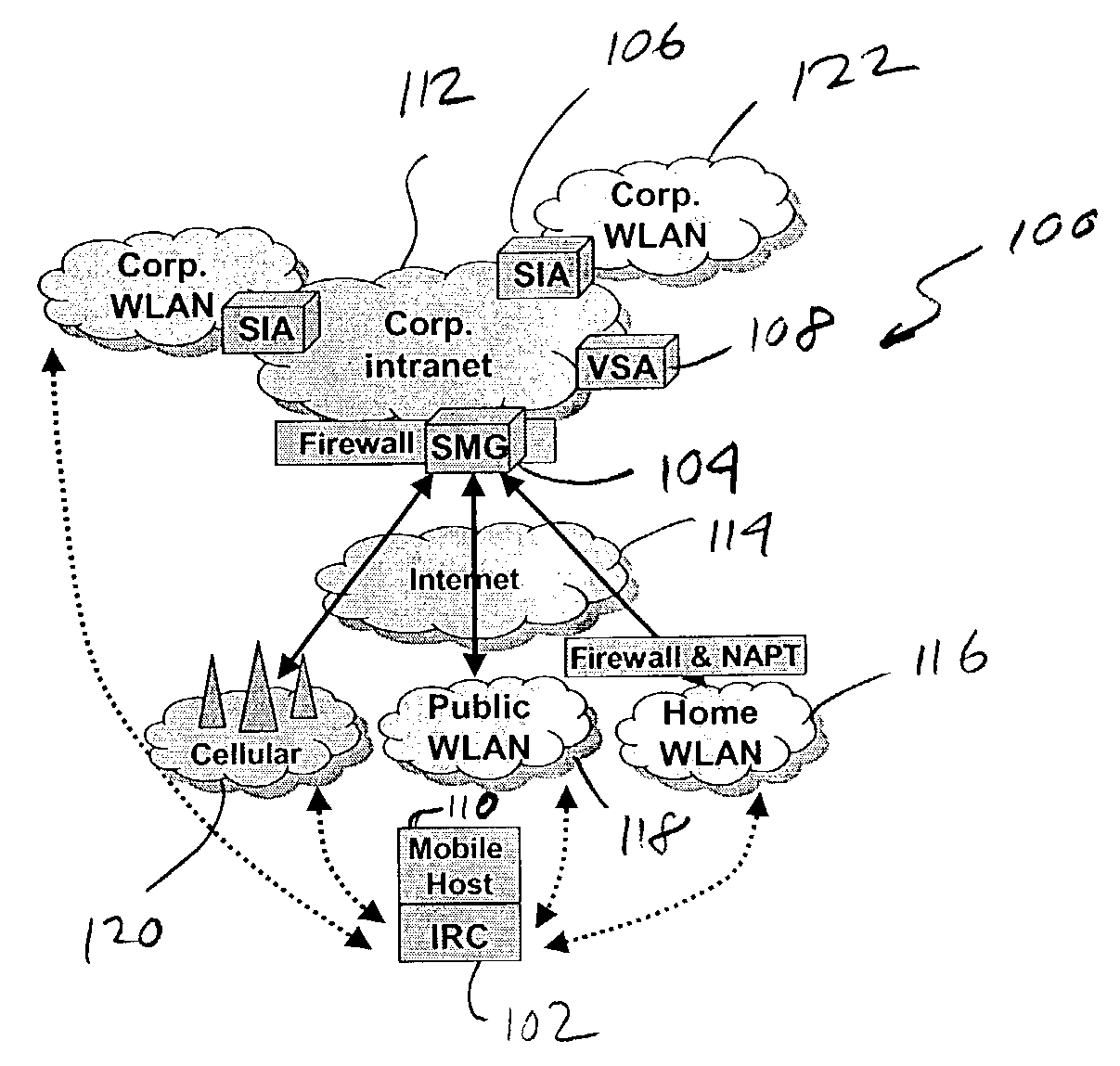
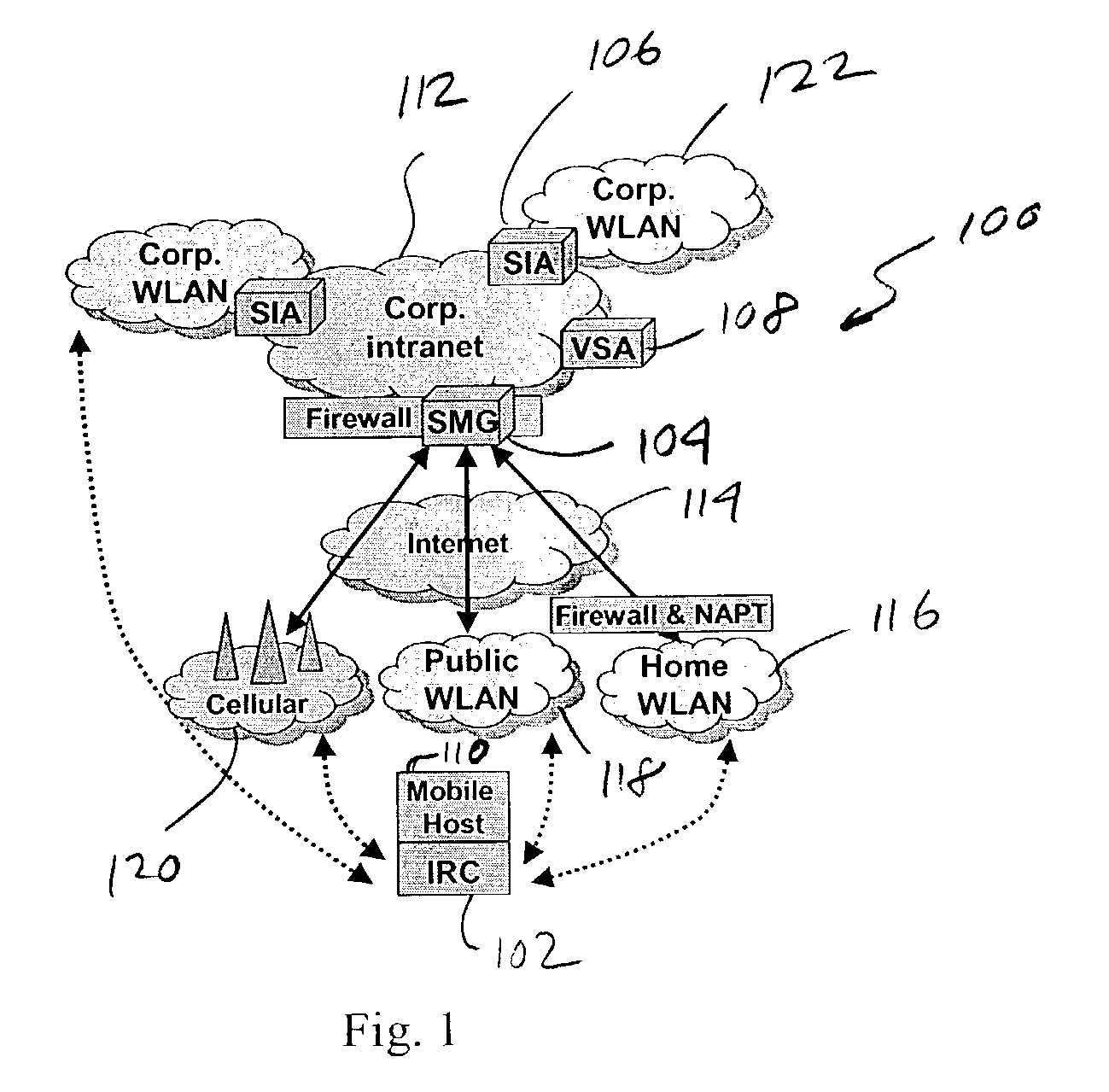
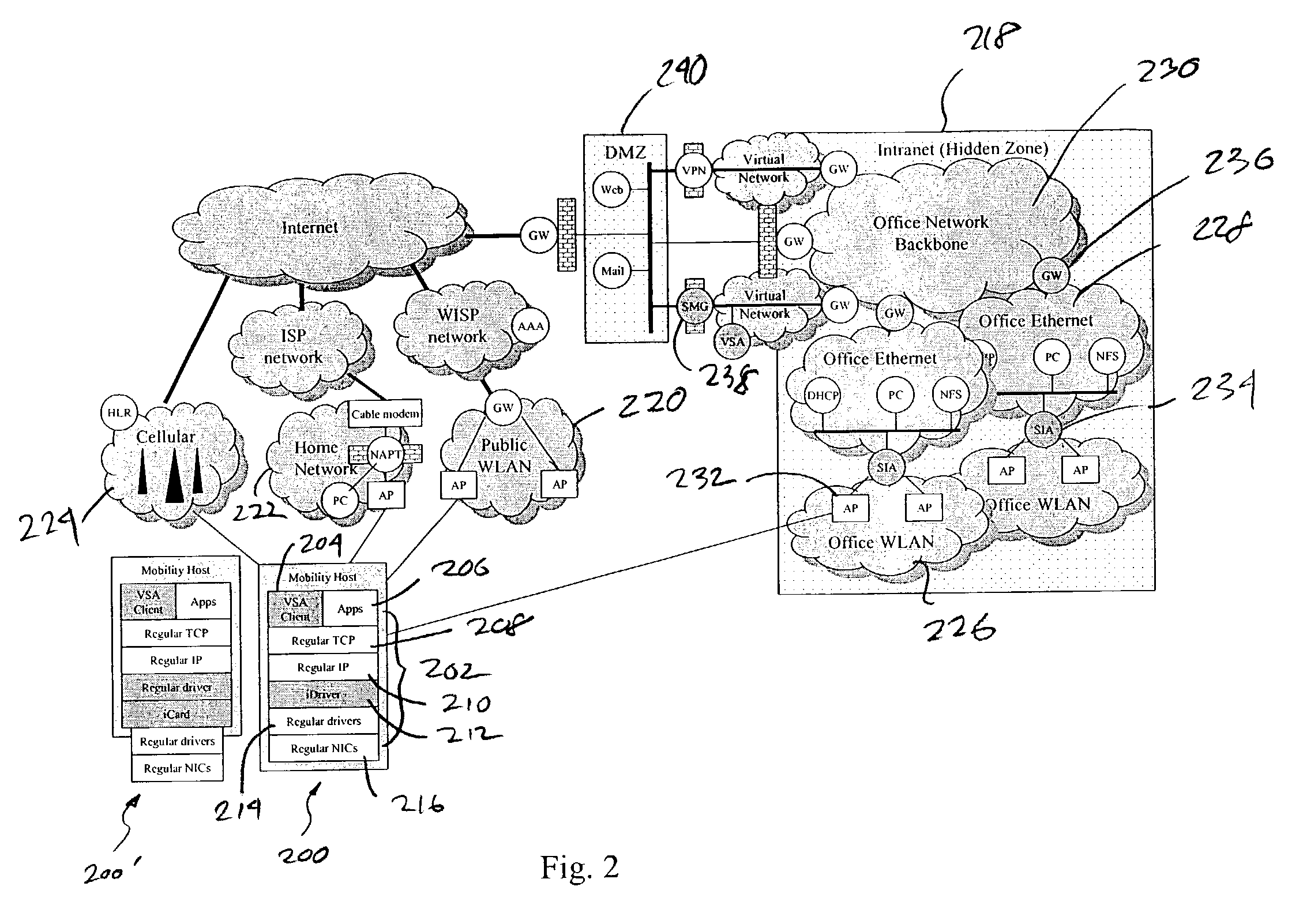
An IP-based corporate network architecture and method for providing seamless secure mobile networking across office WLAN, home WLAN, public WLAN, and 2.5G / 3G cellular networks for corporate wireless data users. The system includes Internet roaming clients (IRCs), a secure mobility gateway (SMG), optional secure IP access (SIA) gateways, and a virtual single account (VSA) server. The IRC is a special client tool installed on a mobile computer (laptop or PDA) equipped with a WLAN adaptor and a cellular modem. It is responsible for establishing and maintaining a mobile IPsec tunnel between the mobile computer and a corporate intranet. The SMG is a mobile IPsec gateway installed between the corporate intranet and the Internet. It works in conjunction with the IRC to maintain the mobile IPsec tunnel when the mobile computer is connected on the Internet via a home WLAN, a public WLAN, or a cellular network. The SIA gateway is a special IPsec gateway installed in the middle of the wired corporate intranet and an office WLAN. It works with the IRC to ensure data security and efficient use of corporate IP addresses when the mobile computer is connected to the office WLAN. The VSA server manages authentication credentials for every corporate user based on a virtual single account concept. The Internet Roaming system can provide secure, always-on office network connectivity for corporate users no matter where they are located using best available wireless networks.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
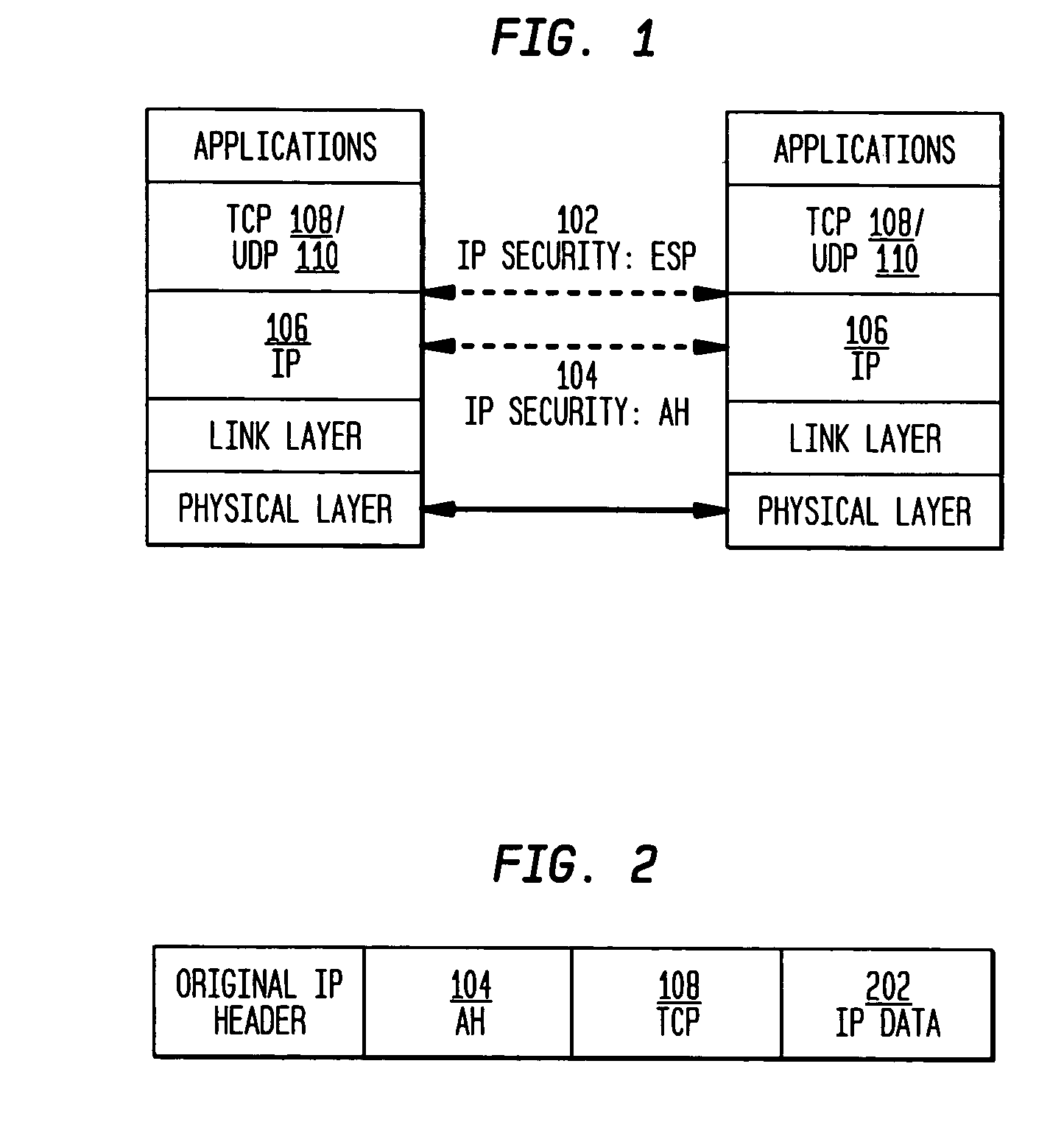
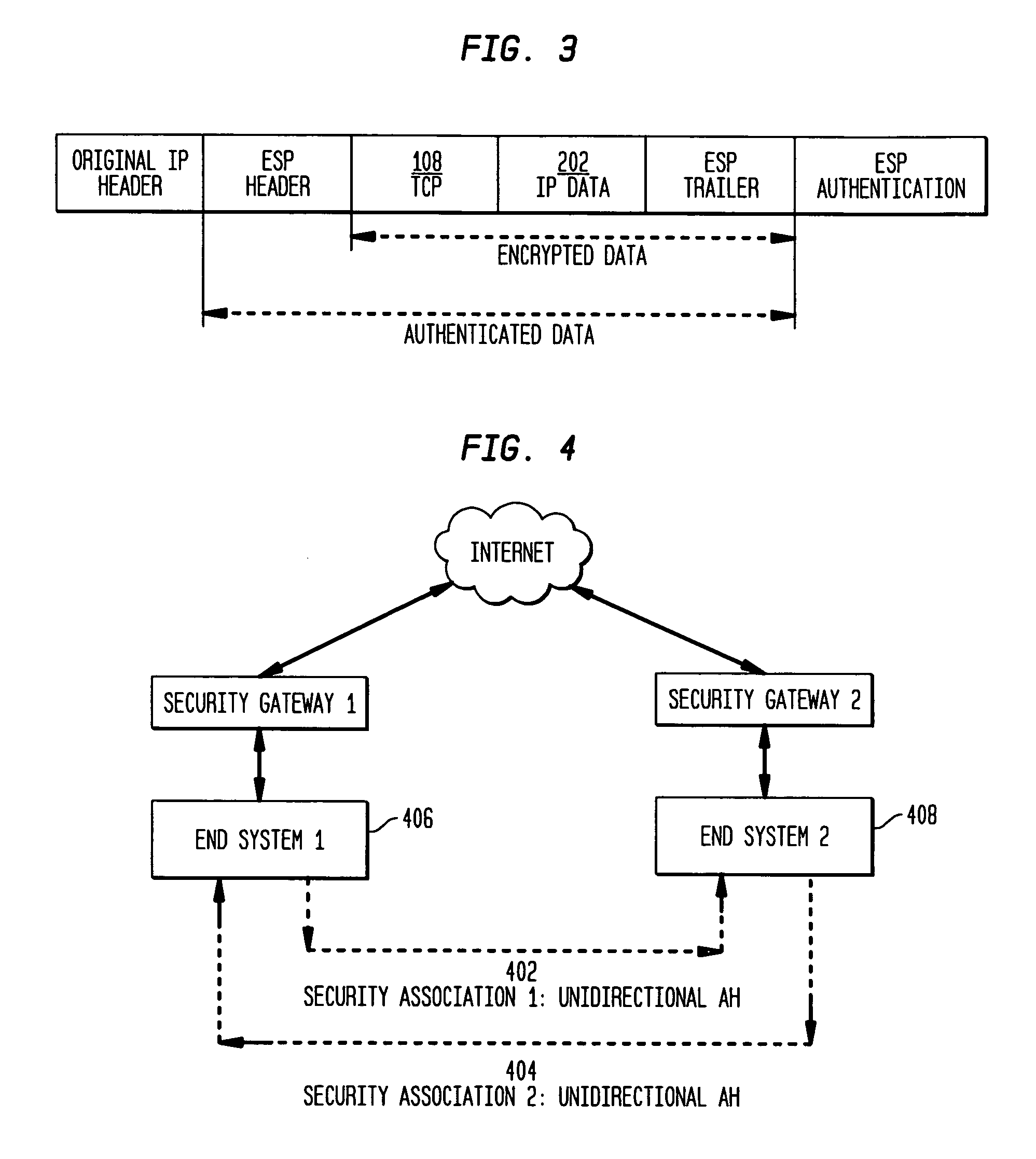
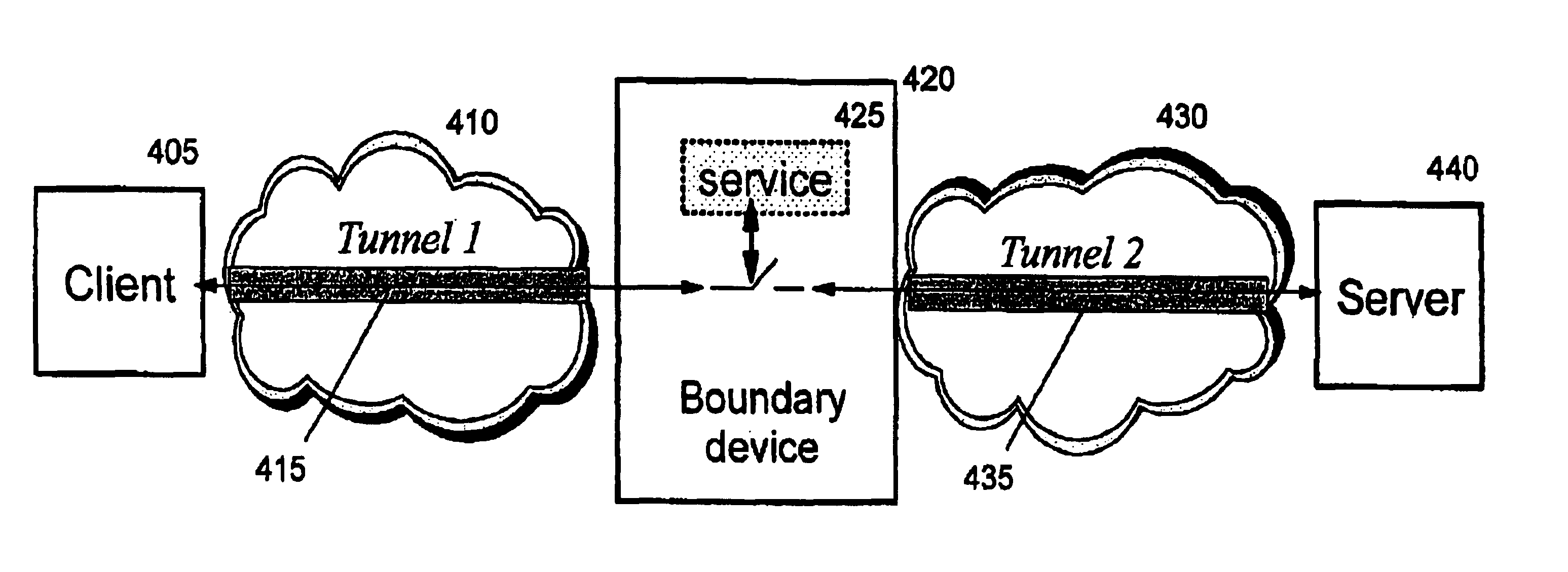
Establishing consistent, end-to-end protection for a user datagram
A method, system, and computer program product for providing consistent, end-to-end protection within a computer network for user datagrams (i.e. packets) traveling through the network. The network may comprise network segments that are conventionally assumed to be secure (such as those found in a corporate intranet) as well as network segments in non-secure networks (such as the public Internet or corporate extranets). Because security breaches may in fact happen in any network segment when datagrams are unprotected, the present invention discloses a technique for protecting datagrams throughout the entire network path by establishing cascaded tunnels. The datagrams may be exposed in cleartext at the endpoints of each tunnel, thereby enabling security gateways to perform services that require content inspection (such as network address translation, access control and authorization, and so forth). The preferred embodiment is used with the “IPSec” (Internet Protocol Security Protocol) and “IKE” (Internet Key Exchange) protocols, thus providing a standards-based solution.
Owner:IBM CORP
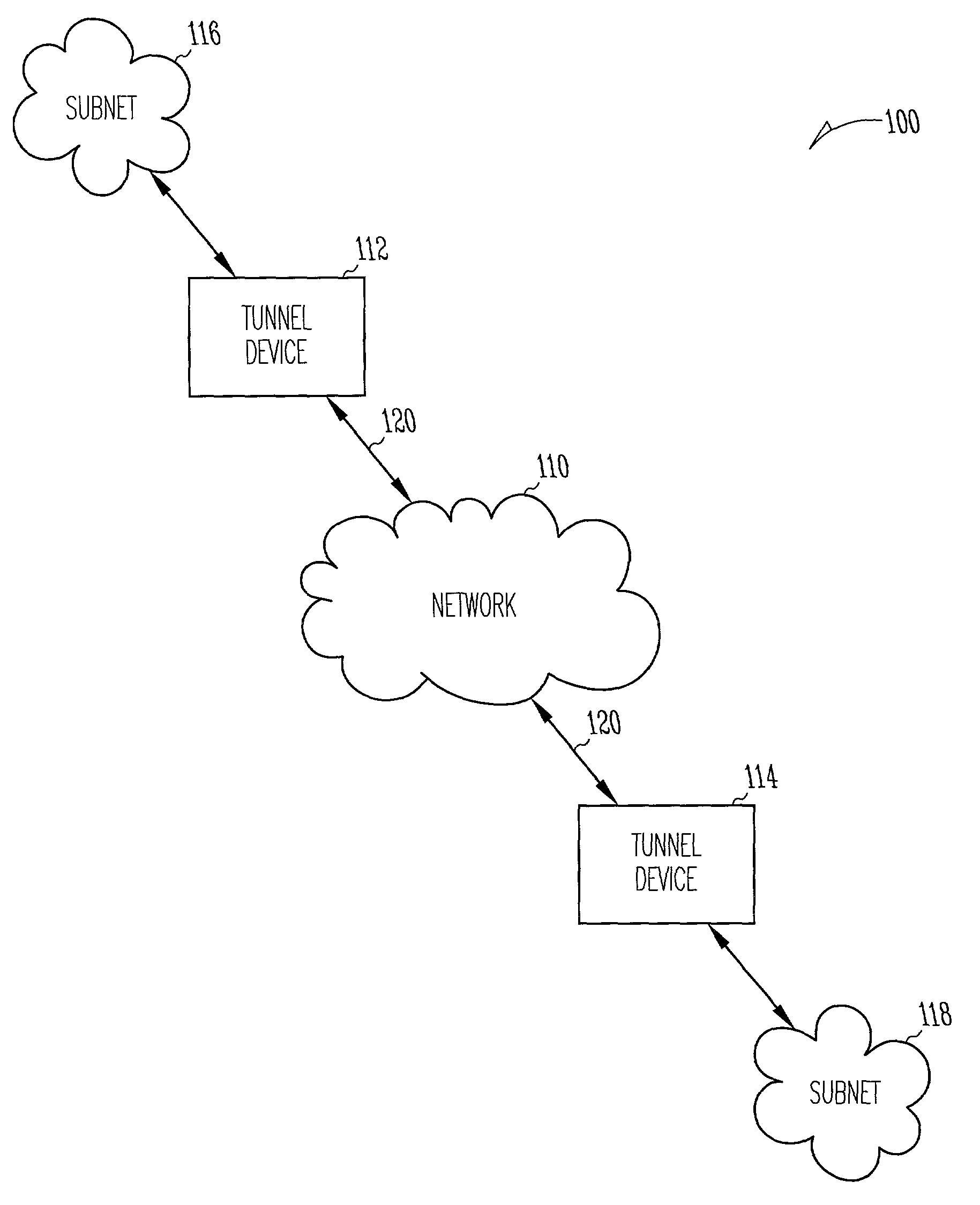
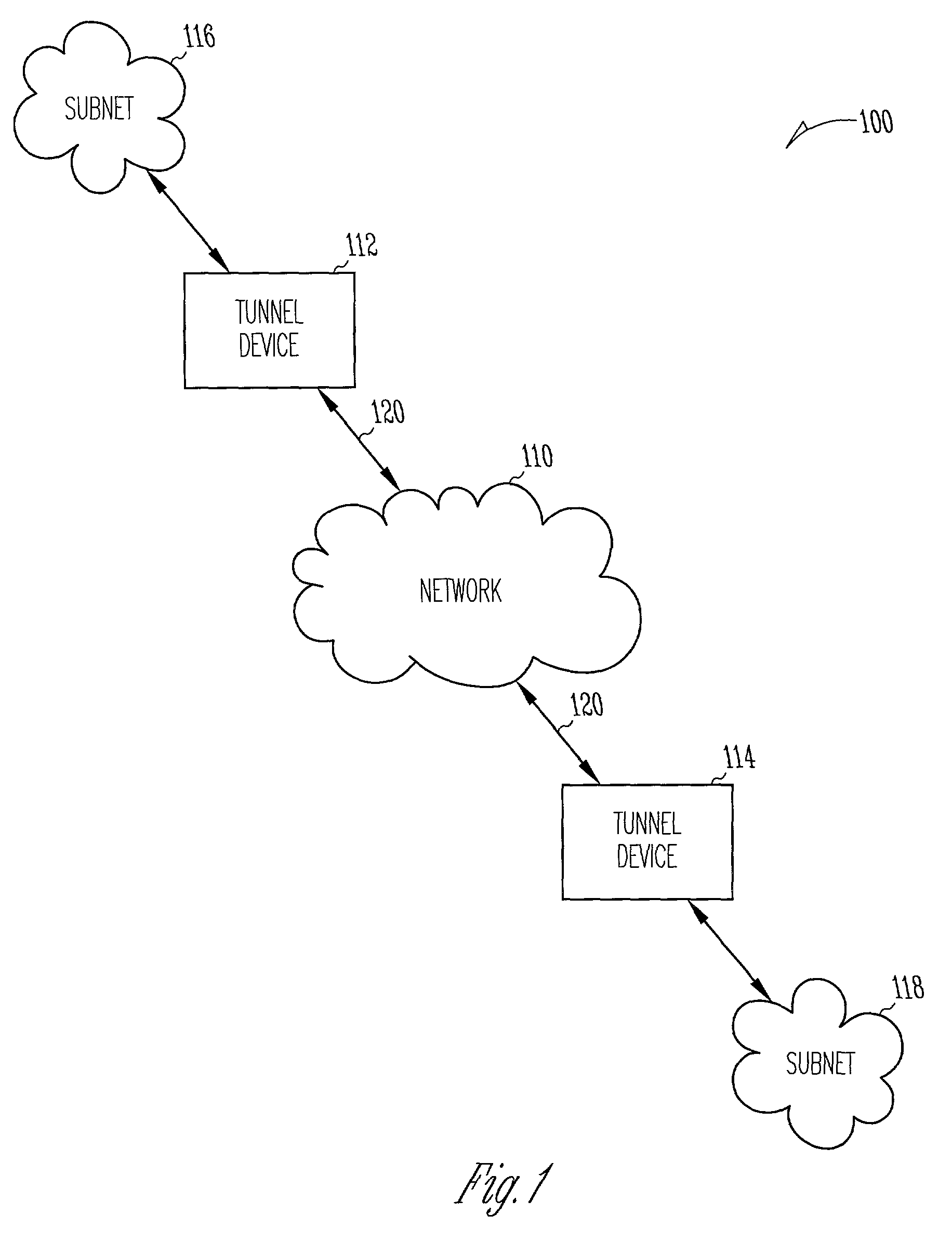
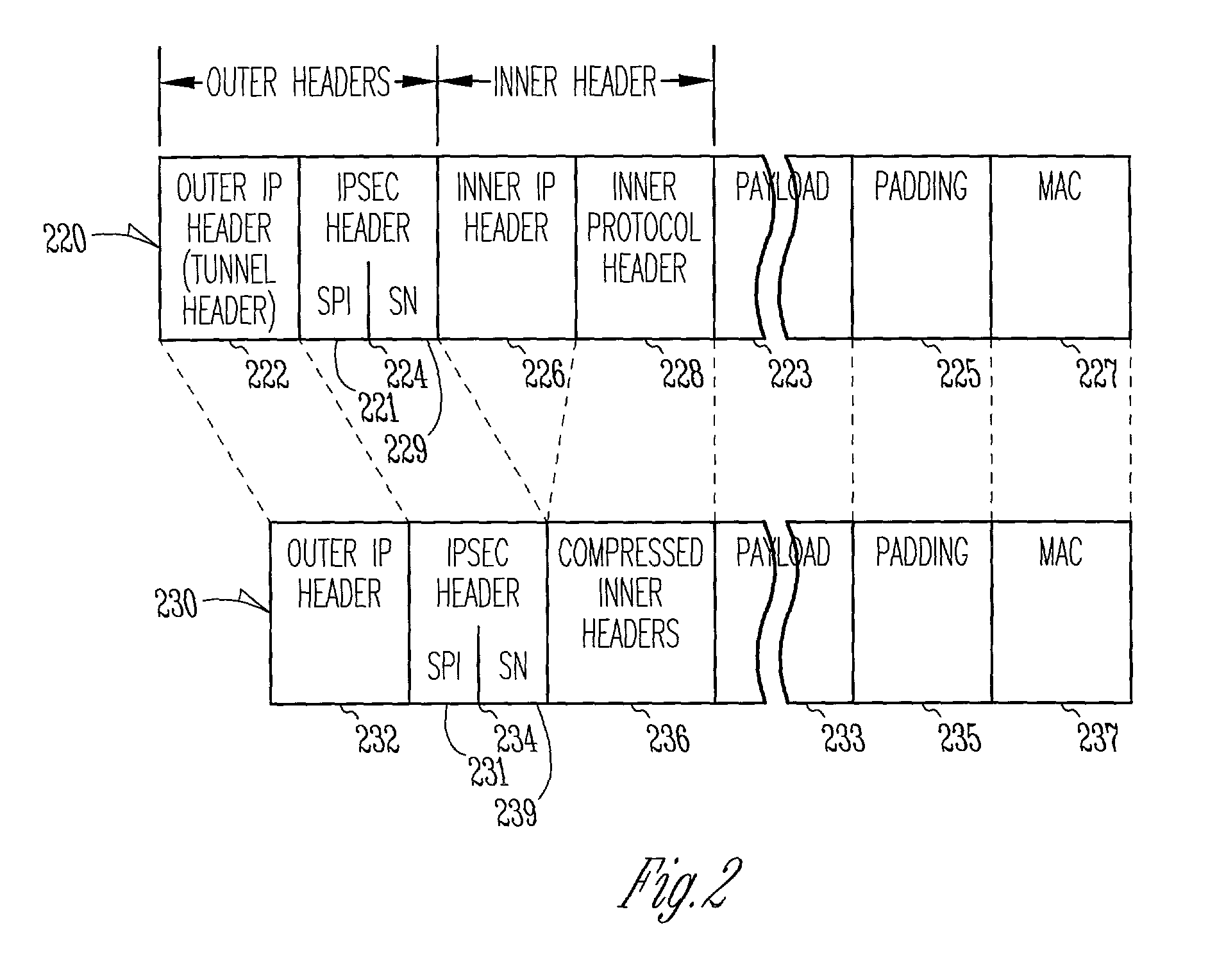
System and method for communicating IPSec tunnel packets with compressed inner headers
Compression of inner headers of IPSec tunnel packets is achieved by storing an inner IP header and an inner protocol header in a context sub-table associated with the security association database entry at a destination tunnel device. IPSec tunnel packets having compressed inner headers may be identified by the LSBs of the SPI number in the IPSec header. The SPI number may also identify whether the IPSec tunnel packet is a TCP packet. A portion of padding in the encapsulated portion may identify a particular context sub-table used for decompressing the inner headers. The context sub-table may be updated as portions of the inner headers change.
Owner:HARRIS CORP
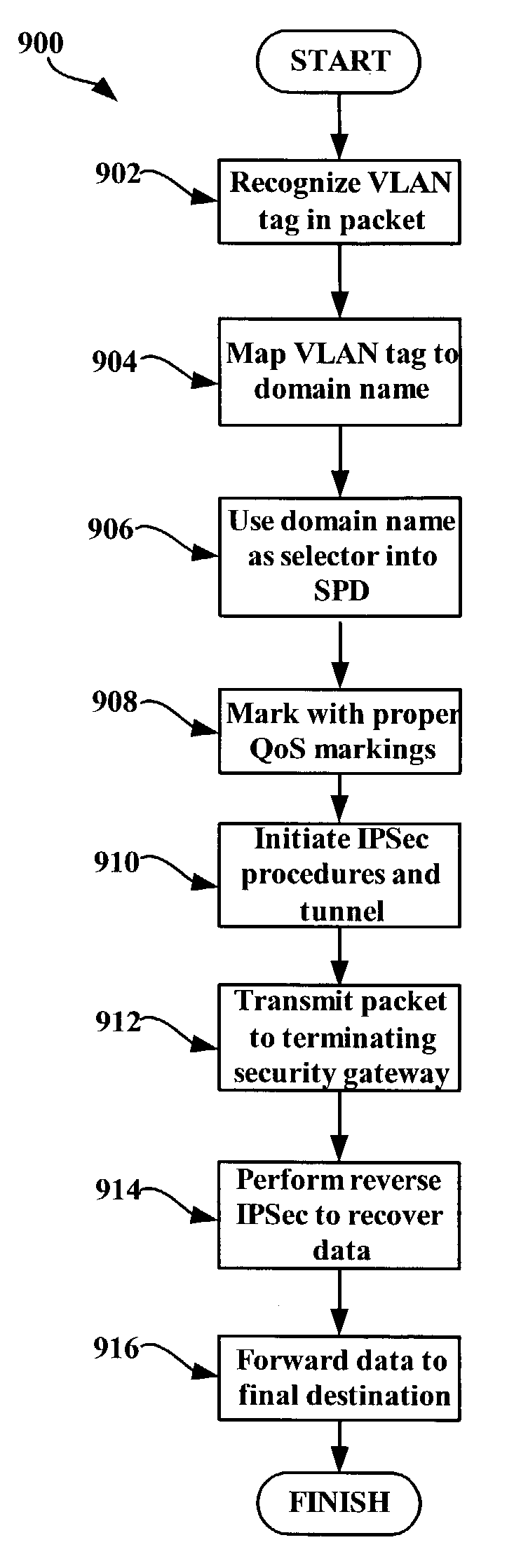
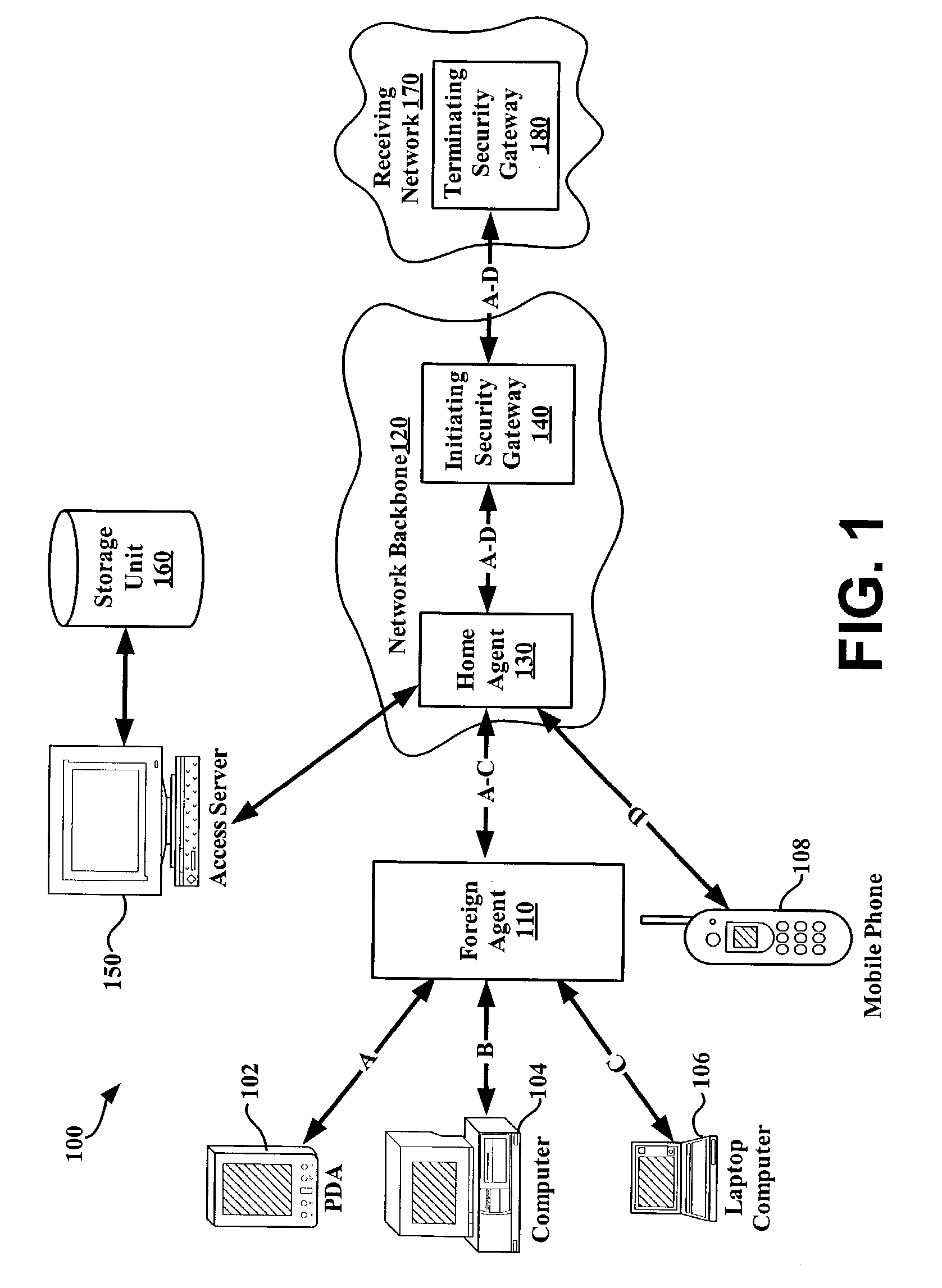
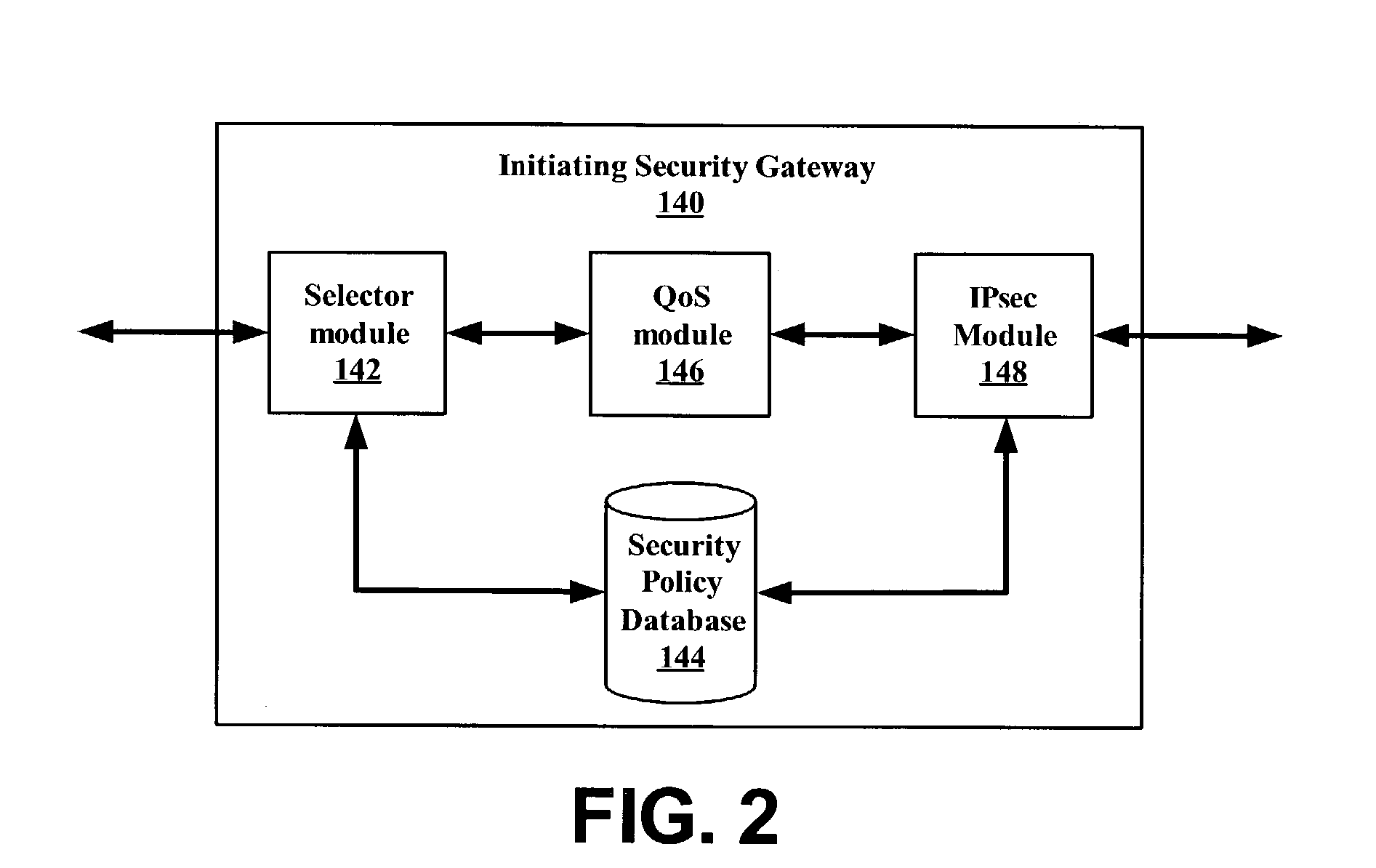
System and method for using virtual local area network tags with a virtual private network
An exemplary system and method for using a network access system, such as a virtual private network (VPN), are provided. A user device may have a user session with a home agent. Additionally, an initiating security gateway may be in communication with the home agent, and a terminating security gateway may be in communication with the initiating security gateway via a tunnel (e.g., Internet Protocol in Internet Protocol (IP-in-IP) or Internet Protocol security (IPsec) tunnel). Further, a virtual local area network (VLAN) tag associated with the user session may map to a selector operable in a security policy database. The selector may be used to find a security policy defining an IPsec procedure, and the security policy may be applied to the tunnel. Also, the initiating security gateway may also include a Quality of Service (QoS) module that determines QoS markings for a packet traveling along the tunnel.
Owner:VALTRUS INNOVATIONS LTD
Process and system providing internet protocol security without secure domain resolution
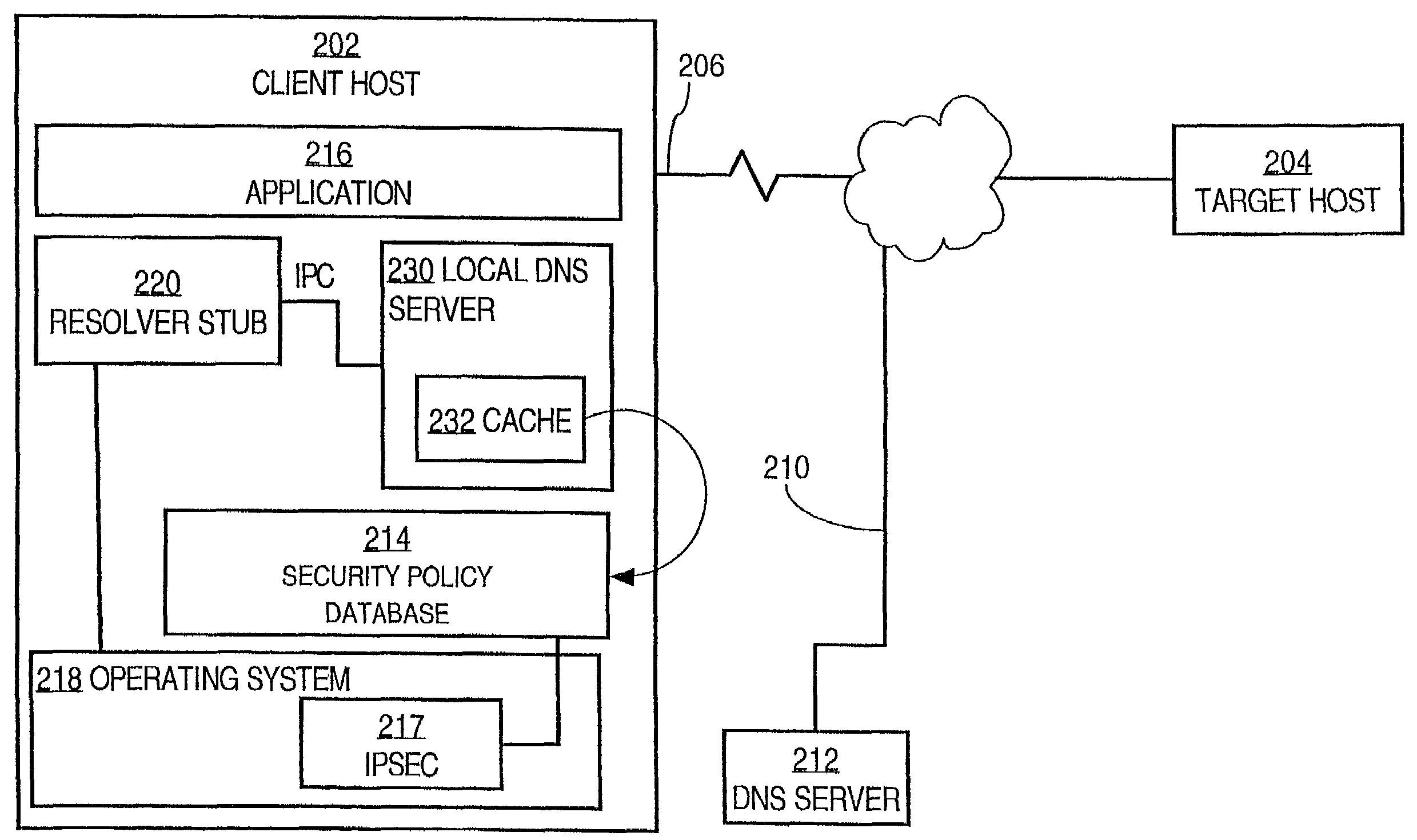
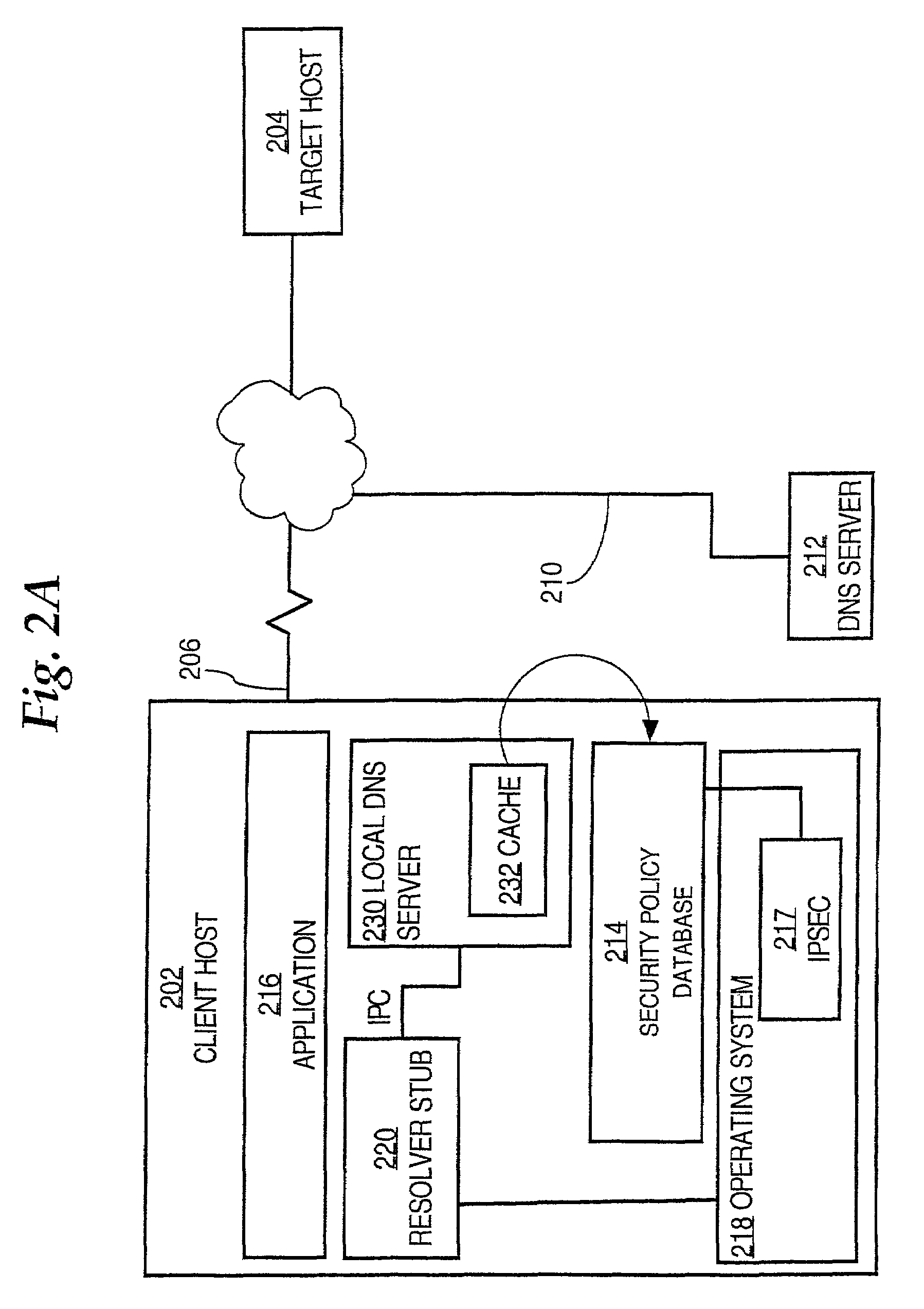
A system and method providing Internet protocol security without secure domain name resolution are disclosed. A processor that periodically needs to resolve domain names into network addresses has a local DNS server that includes a secure IPSEC cache, a resolver function, a security policy database, and an IPSEC layer. The cache is readable only by the IPSEC layer. Resolved domain names are cached with process and transaction identifiers that uniquely associate the resolved names with an application process and time. When resolution is needed, the cache is used to ensure that IP addresses are resolved from names that came from the application. As a result, IPSEC connections may be established without use of DNSSEC to provide secure domain name resolution.
Owner:CISCO TECH INC
Virtual private network (VPN)-as-a-service with load-balanced tunnel endpoints
ActiveUS20150188823A1Facilitate (VPN)-as-a-serviceEfficient use ofError preventionFrequency-division multiplex detailsPlaintextData stream
A mechanism to facilitate a private network (VPN)-as-a-service, preferably within the context of an overlay IP routing mechanism implemented within an overlay network. The overlay provides delivery of packets end-to-end between overlay network appliances positioned at the endpoints. During such delivery, the appliances are configured such that the data portion of each packet has a distinct encryption context from the encryption context of the TCP / IP portion of the packet. By establishing and maintaining these distinct encryption contexts, the overlay network can decrypt and access the TCP / IP flow. This enables the overlay network provider to apply one or more TCP optimizations. At the same time, the separate encryption contexts ensure the data portion of each packet is never available in the clear at any point during transport. According to another feature, data flows within the overlay directed to a particular edge region may be load-balanced while still preserving IPsec replay protection.
Owner:AKAMAI TECH INC
Secure communication methods and systems
InactiveUS20060020787A1Reduce signal delayMultiple digital computer combinationsWireless network protocolsSecure communicationSecurity association
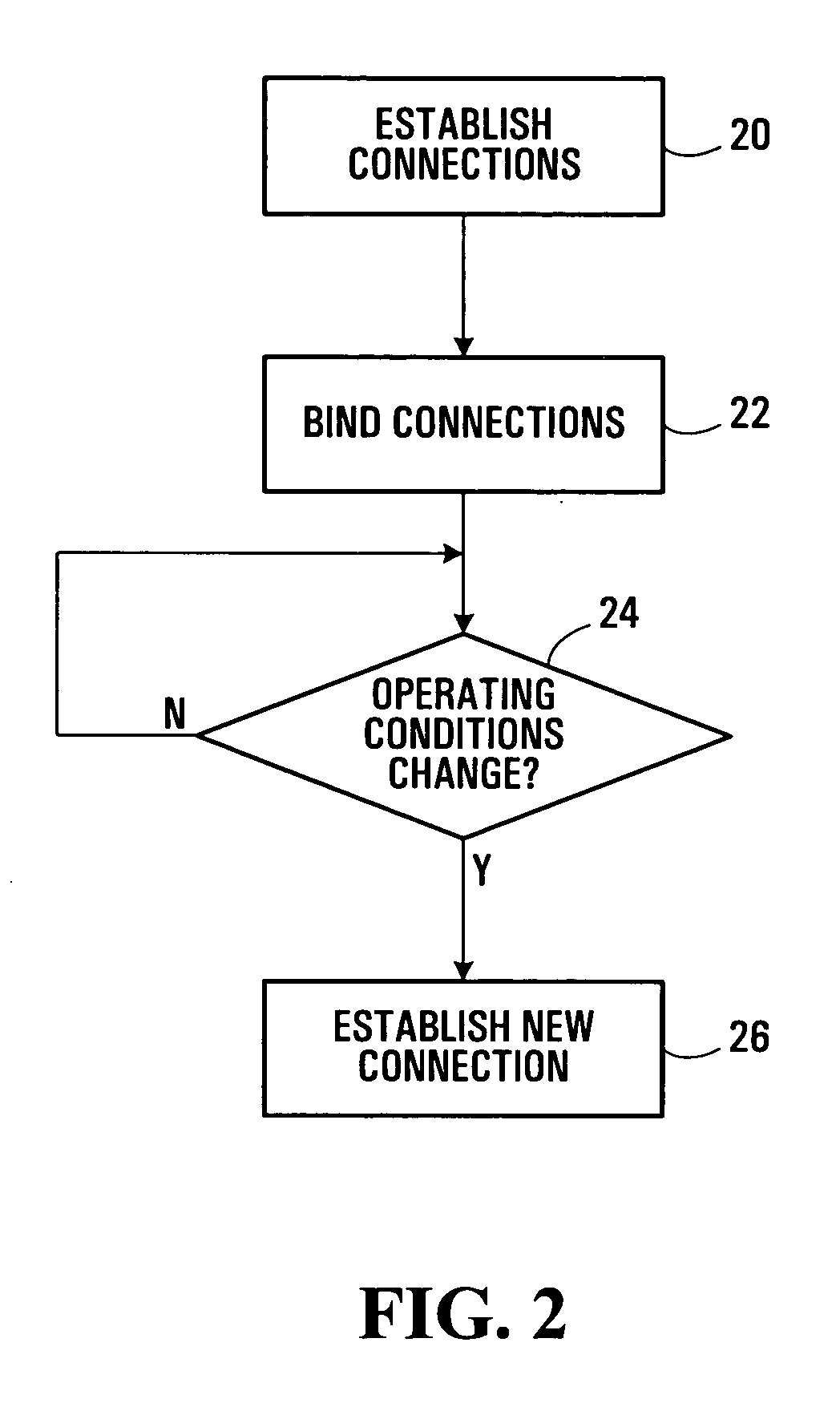
Methods and systems for secure communications are provided. Secure end-to-end connections are established as separate multiple secure connections, illustratively between a first system and an intermediate system and between a second system and an intermediate system. The multiple secure connections may be bound, by binding Internet Protocol Security Protocol (IPSec) Security Associations (SAs) for the multiple connections, for example, to establish the end-to-end connection. In the event of a change in operating conditions which would normally require the entire secure connection to be re-established, only one of the multiple secure connections which form the end-to-end connection is re-established. Separation of end-to-end connections in this manner may reduce processing resource requirements and latency normally associated with re-establishing secure connections.
Owner:RPX CORP
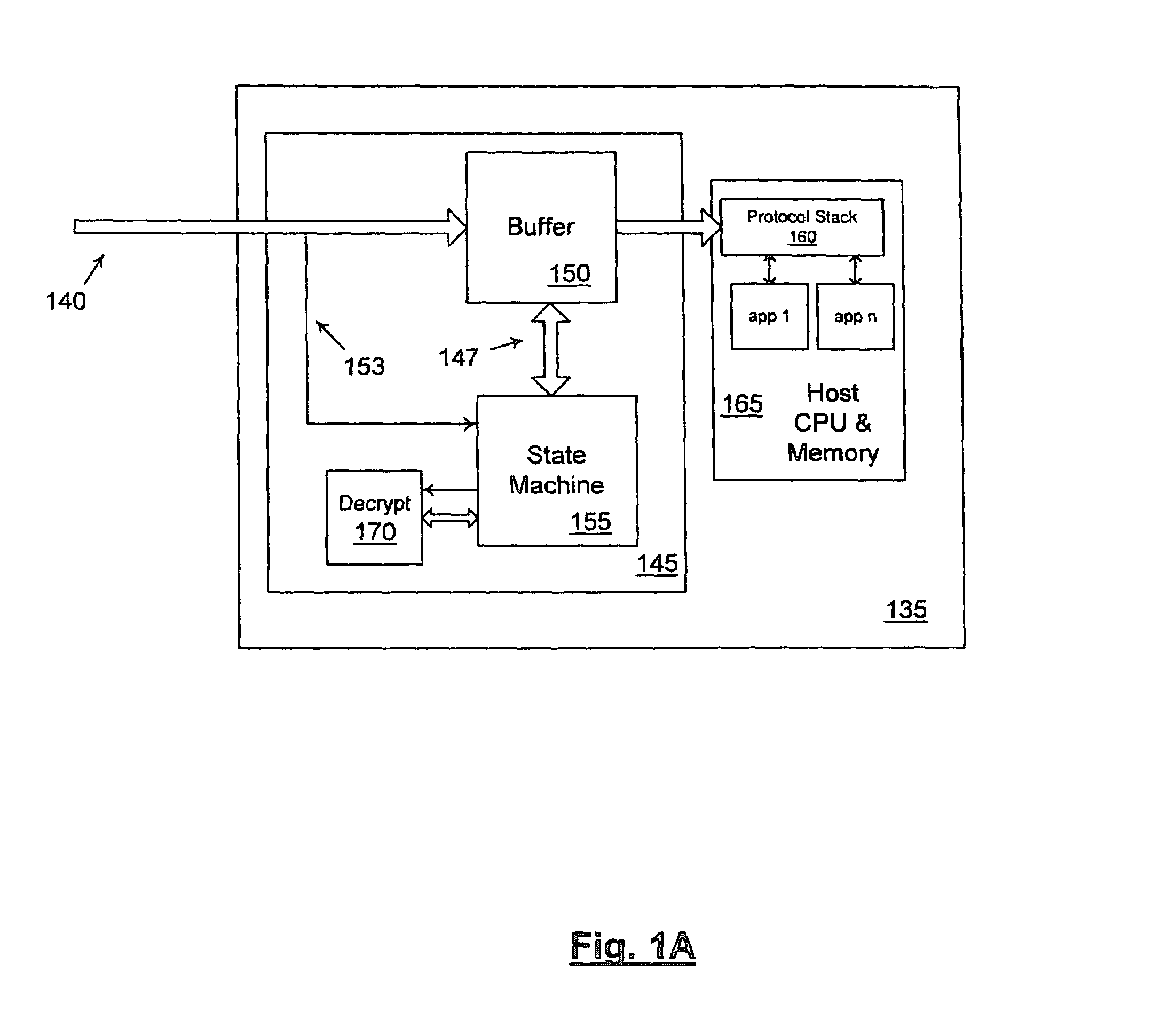
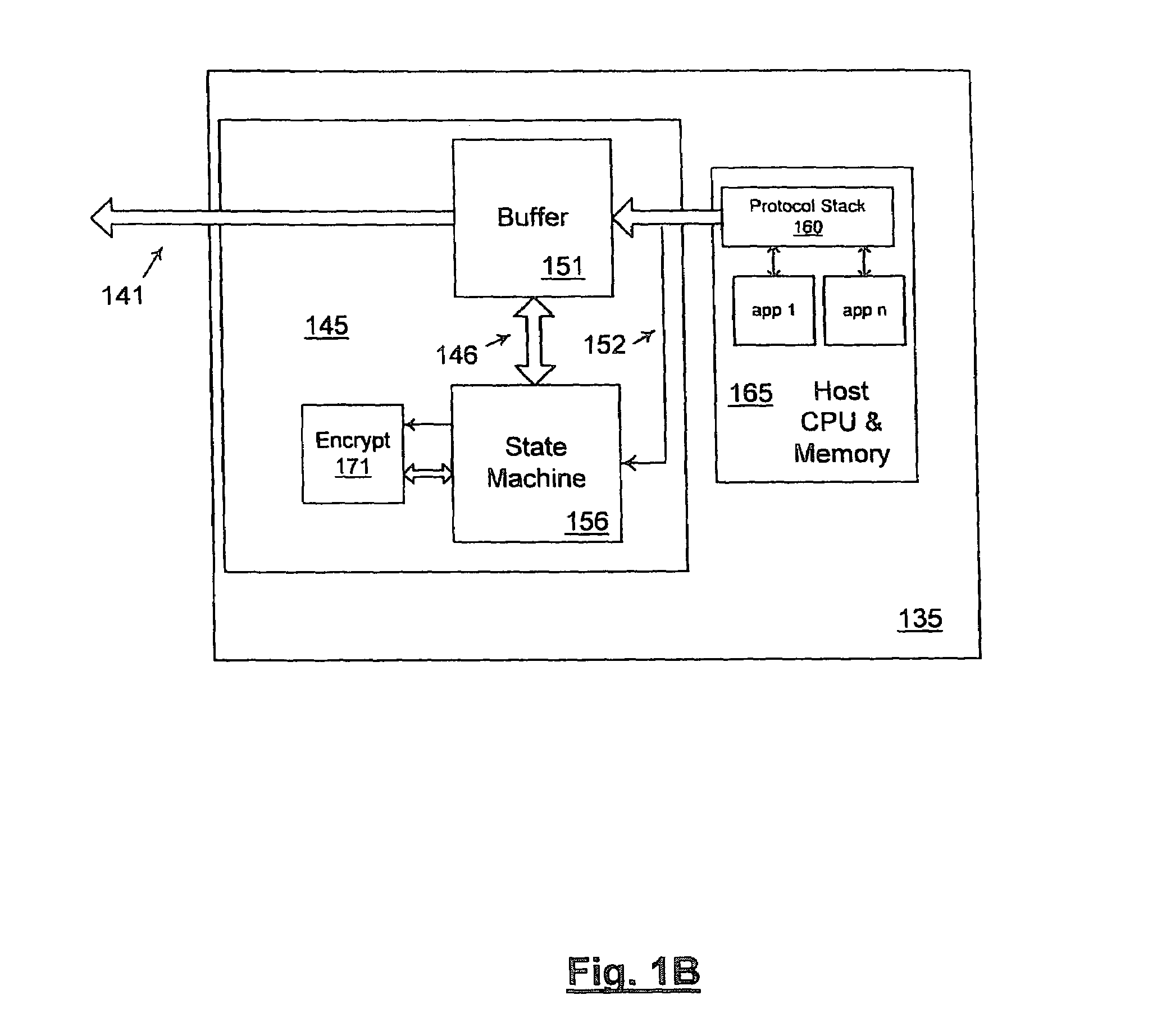
Method and apparatus for secure internet protocol (IPSEC) offloading with integrated host protocol stack management
ActiveUS20060104308A1Requires minimizationDigital data processing detailsTime-division multiplexComputer hardwareSecurity association
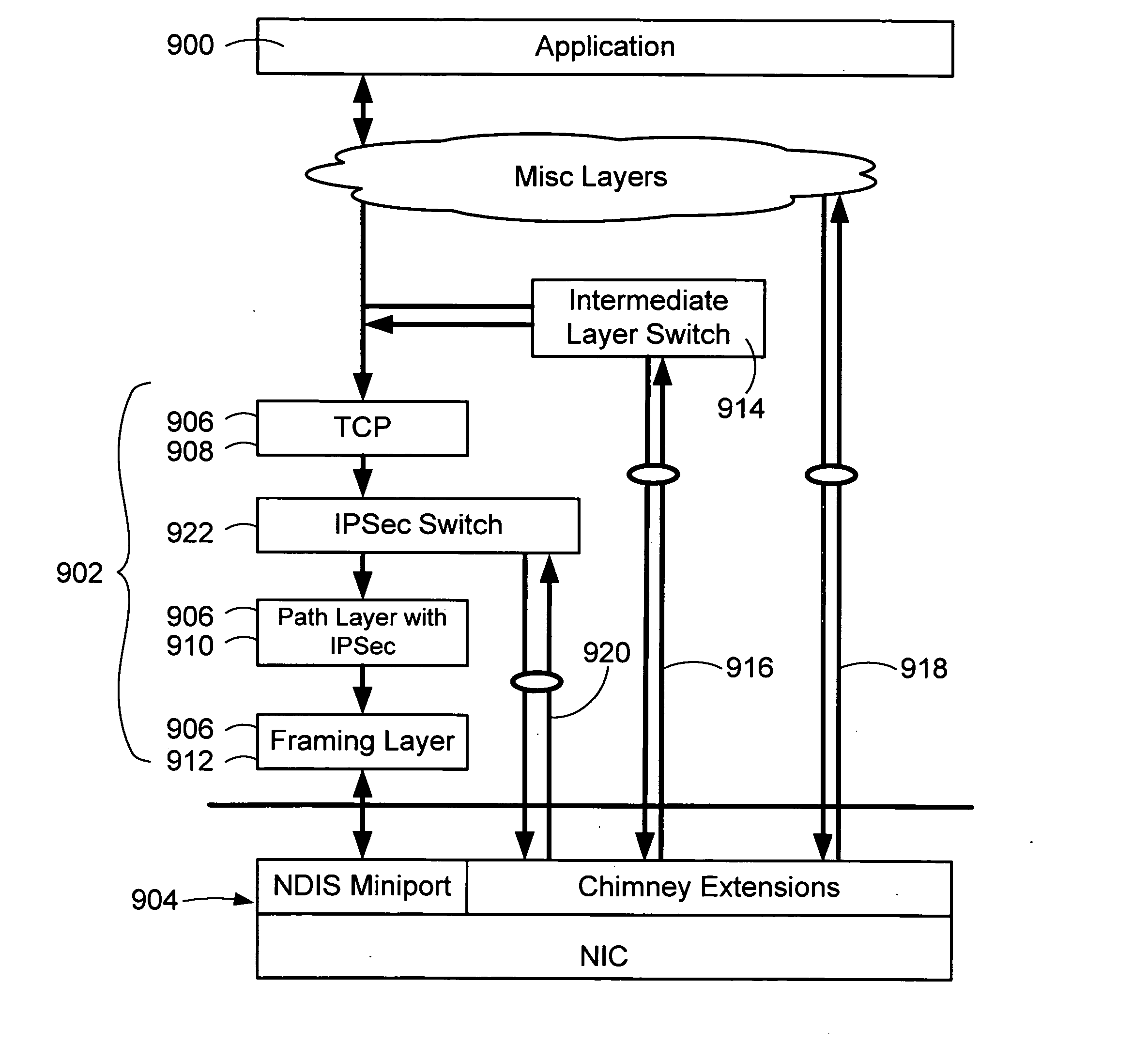
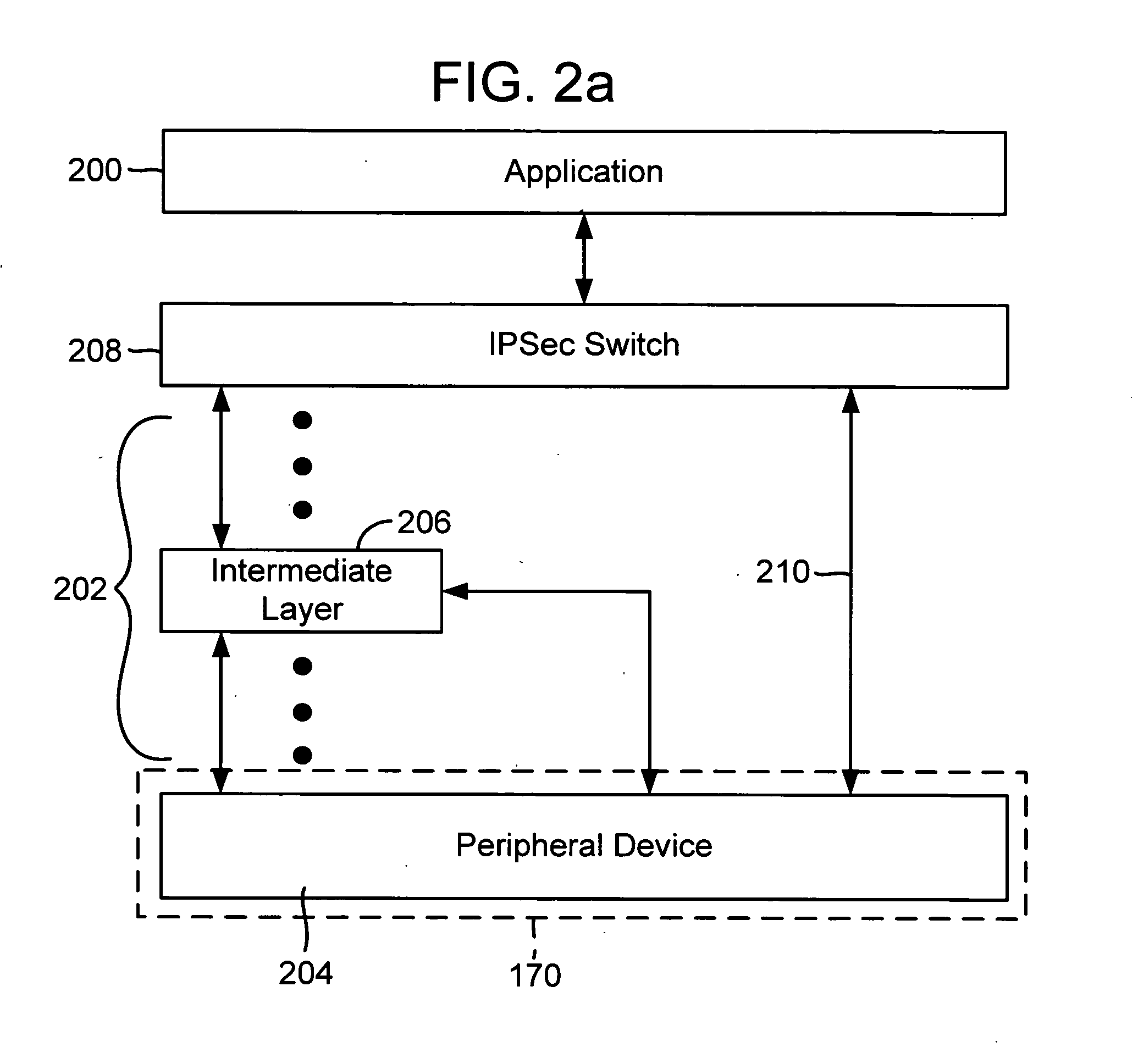
The invention provides mechanisms for transferring processor control of secure Internet Protocol (IPSec) security association (SA) functions between a host and a target processing devices of a computerized system, such as processors in a host CPU and a NIC. In one aspect of the invention, the computation associated with authentication and / or encryption is offloaded while the host maintains control of when SA functions are offloaded, uploaded, invalidated, and re-keyed. The devices coordinate to maintain metrics for the SA, including support for both soft and hard limits on SA expiration. Timer requirements are minimized for the target. The offloaded SA function may be embedded in other offloaded state objects of intermediate software layers of a network stack.
Owner:MICROSOFT TECH LICENSING LLC
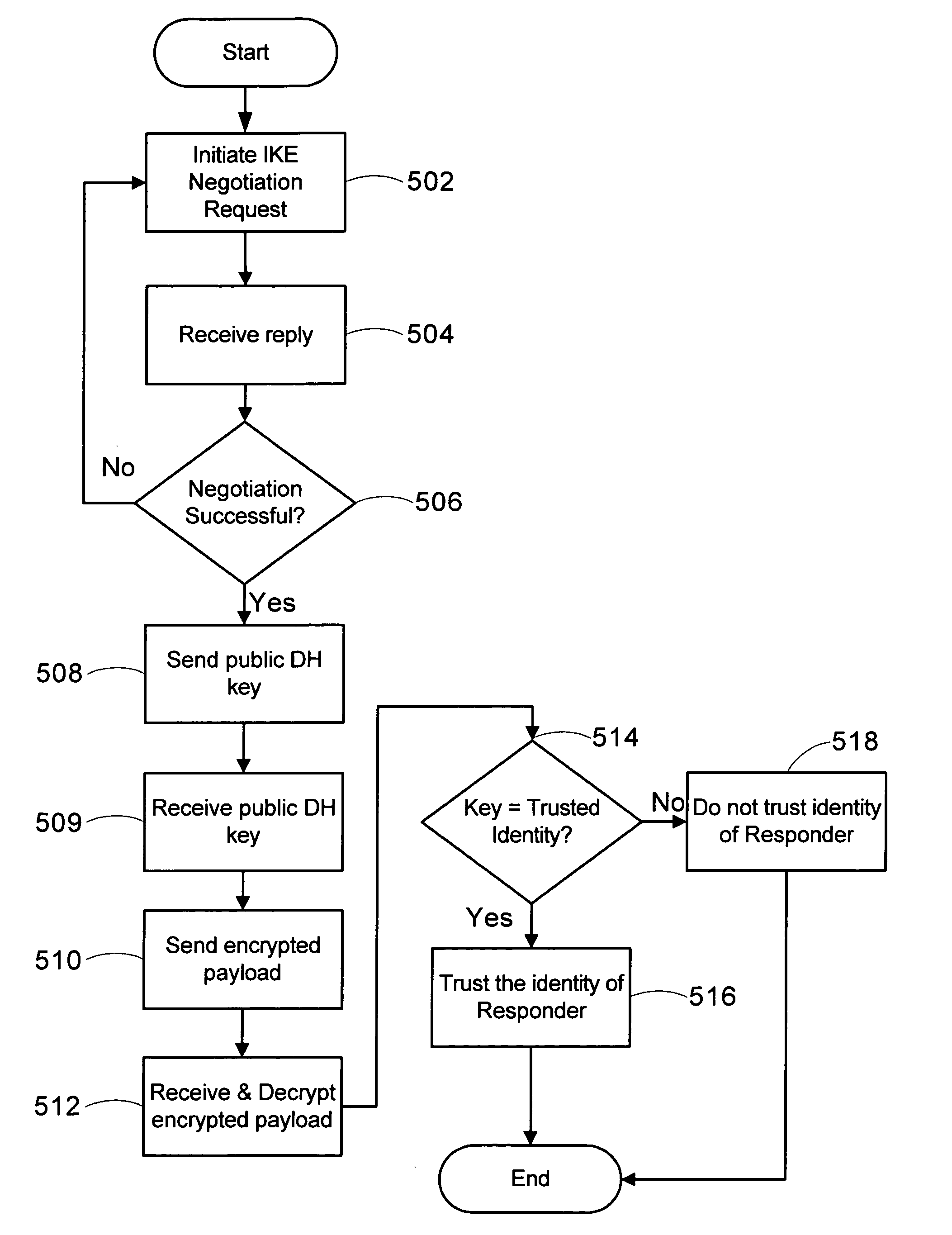
Use of static Diffie-Hellman key with IPSec for authentication
InactiveUS20050149732A1Ensure confidentialityNetwork traffic/resource managementComputer controlIPsecShared secret
Embodiments of the invention authenticate devices and establish secure connections between devices using static Diffie-Hellman key pairs. A first device obtains in a trusted manner a static DH public key of a second device prior to negotiation. The second device negotiates a secure connection to the first device using a shared secret created from the static DH public key, which serves as both a claim on the second device's identity and an encryption key. The static DH public key can be used to establish subsequent secure, authenticated communications sessions.
Owner:ROVI TECH CORP
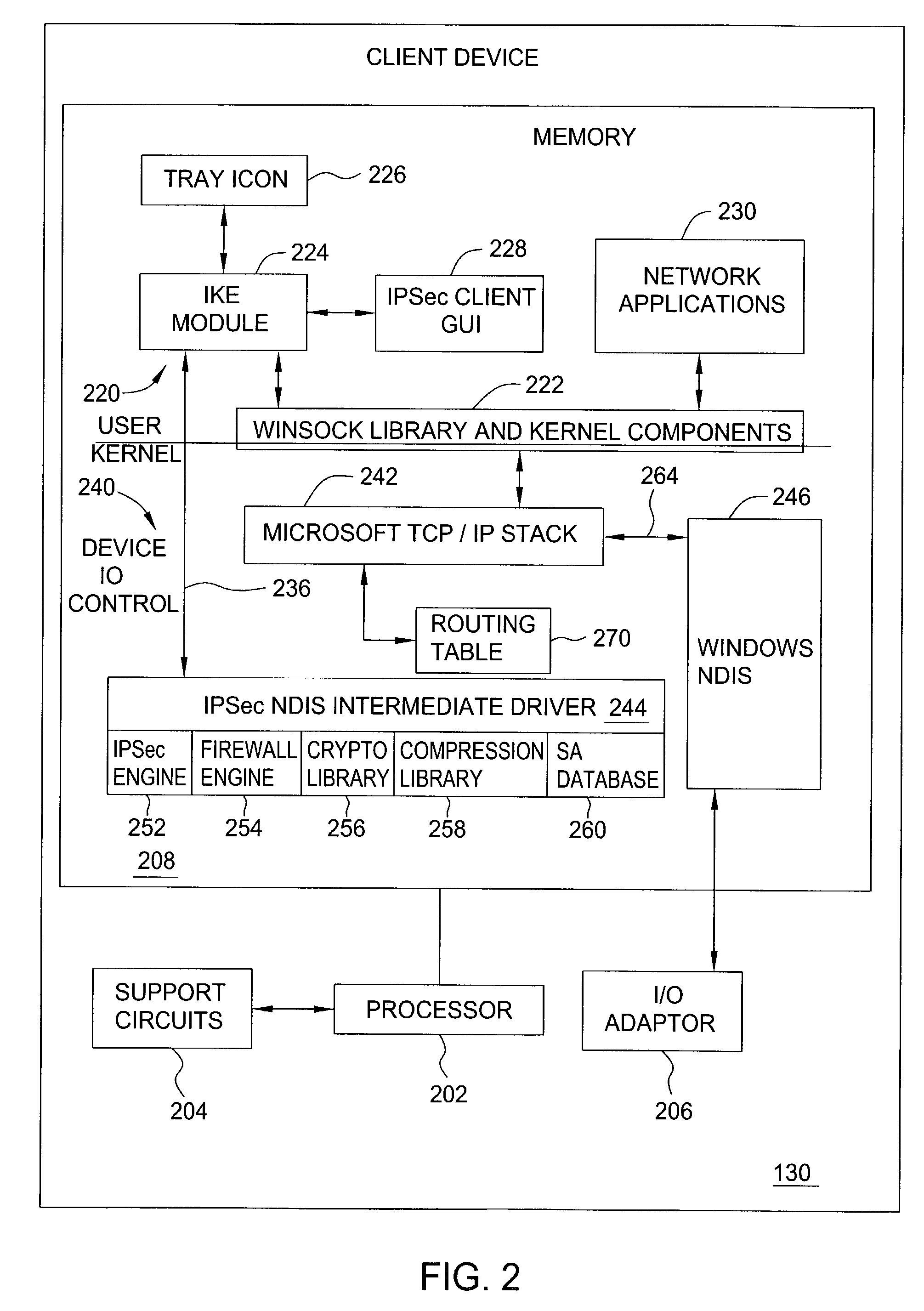
System and method for improved network security
InactiveUS6915437B2Improve performanceImprove securityDigital data processing detailsUser identity/authority verificationTraffic capacityInternet Key Exchange
Owner:MICROSOFT TECH LICENSING LLC
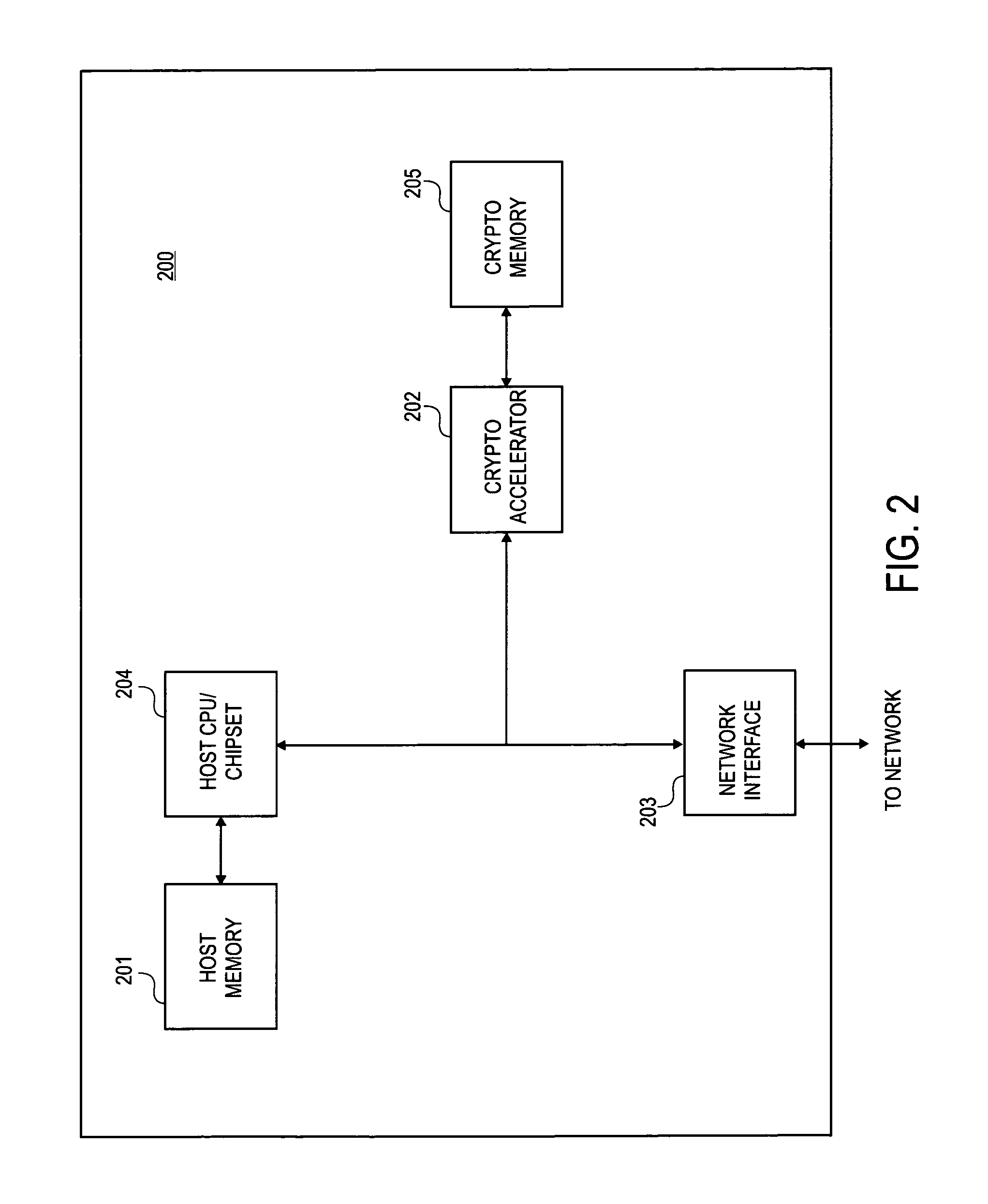
Method and circuit to accelerate IPSec processing
ActiveUS7017042B1Unauthorized memory use protectionHardware monitoringNetwork packetSecurity association
Methods and apparatus' for performing IPSec processing on an IP packet being transmitted onto a network and being received from a network are described. The methods and apparatus' further described perform IPSec processing inline which results in a reduced number of transfers over the system bus, reduced utilization of system memory, and a reduced utilization of the system CPU. An IP packet which requires IPSec processing enters an acceleration device. In one embodiment, the acceleration device is coupled to a security policy database (SPD) and security association database (SAD). IPSec processing is performed at the acceleration device without sending the IP Packet to system memory for processing.
Owner:DIGITAL ARCHWAY +1
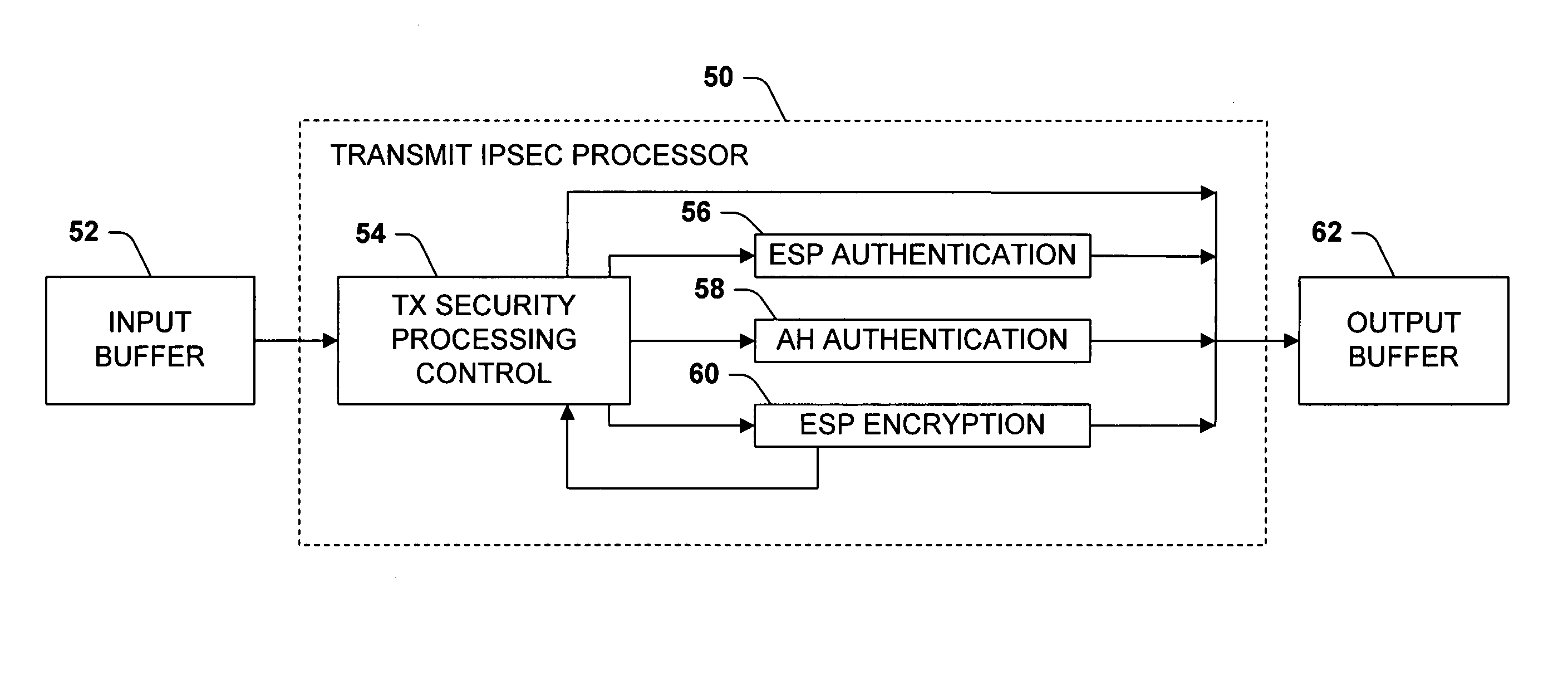
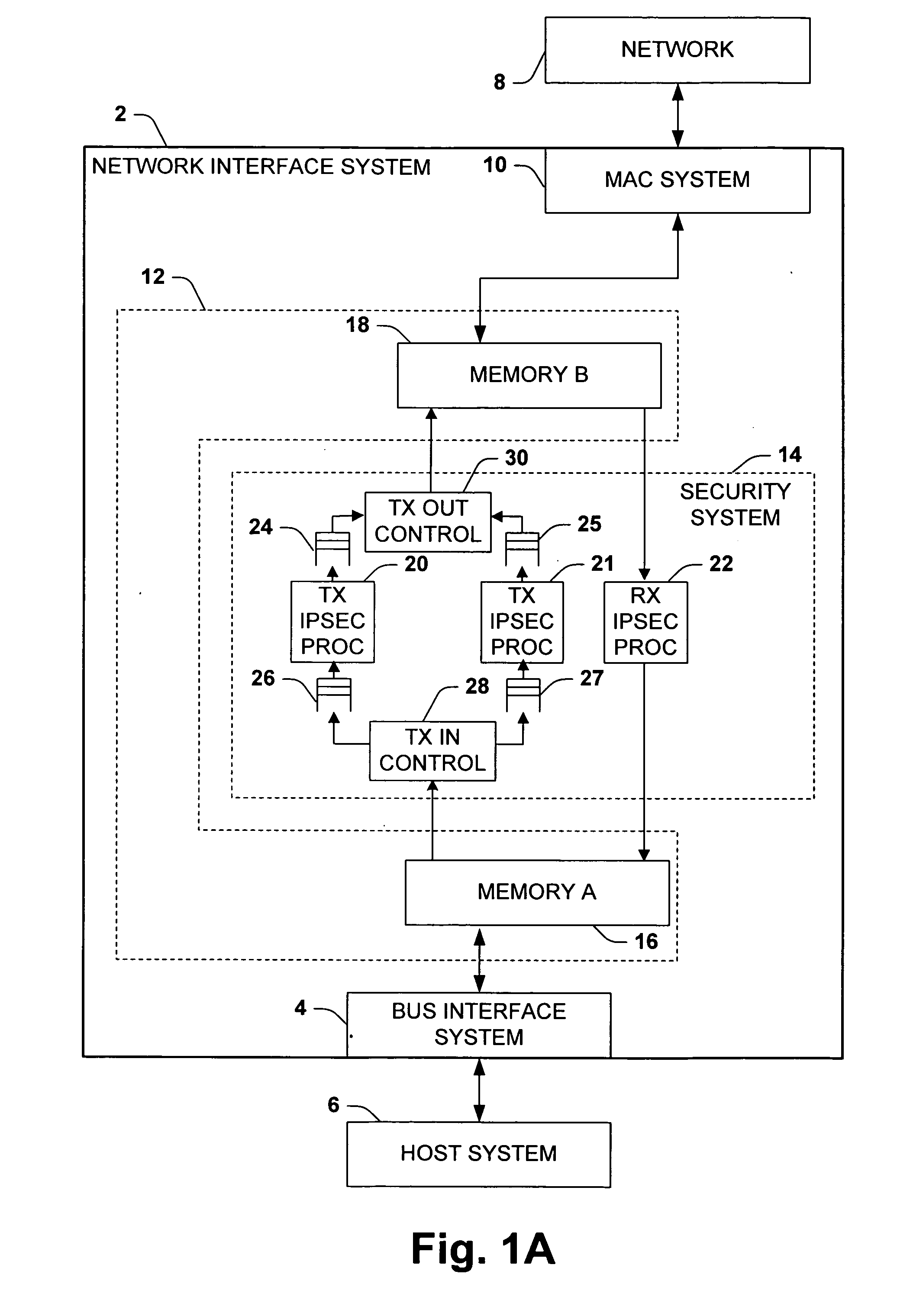
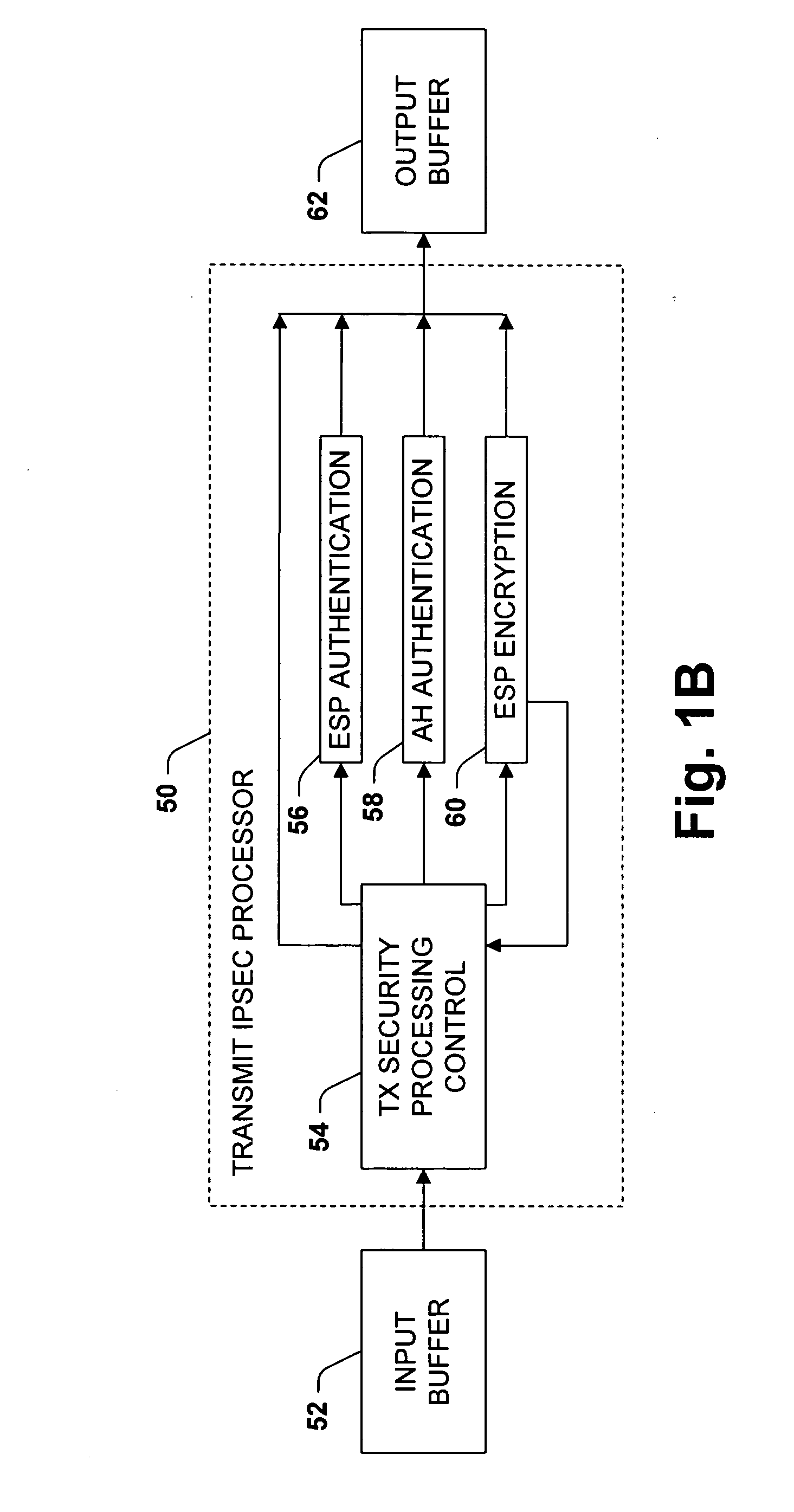
Two parallel engines for high speed transmit IPSEC processing
ActiveUS20050198531A1Avoid spreadingEliminates a potential bottleneckDigital data processing detailsUnauthorized memory use protectionControl systemIPsec
The invention relates to a network interface system for interfacing a host system with a network. The network interface system includes a bus interface system, a media access control system, and a security system. The network interface offloads IPsec processing from the host processor. According to the invention, the security system includes two processors for encrypting and authenticating the outgoing data. Outgoing data packets are sent alternately to one or the other processor, whereby transmission processing can be accelerated relative to receive processing.
Owner:ADVANCED MICRO DEVICES INC
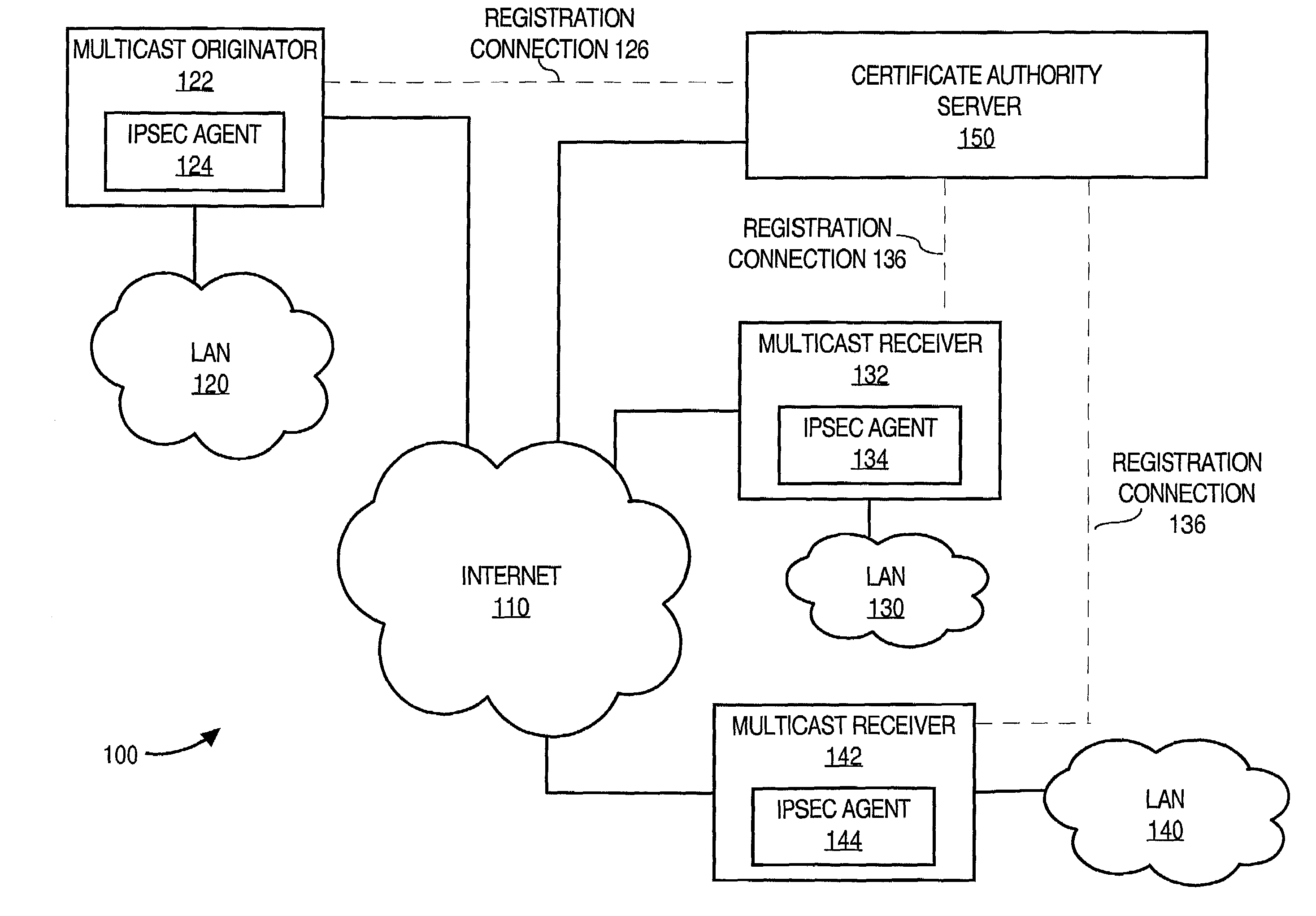
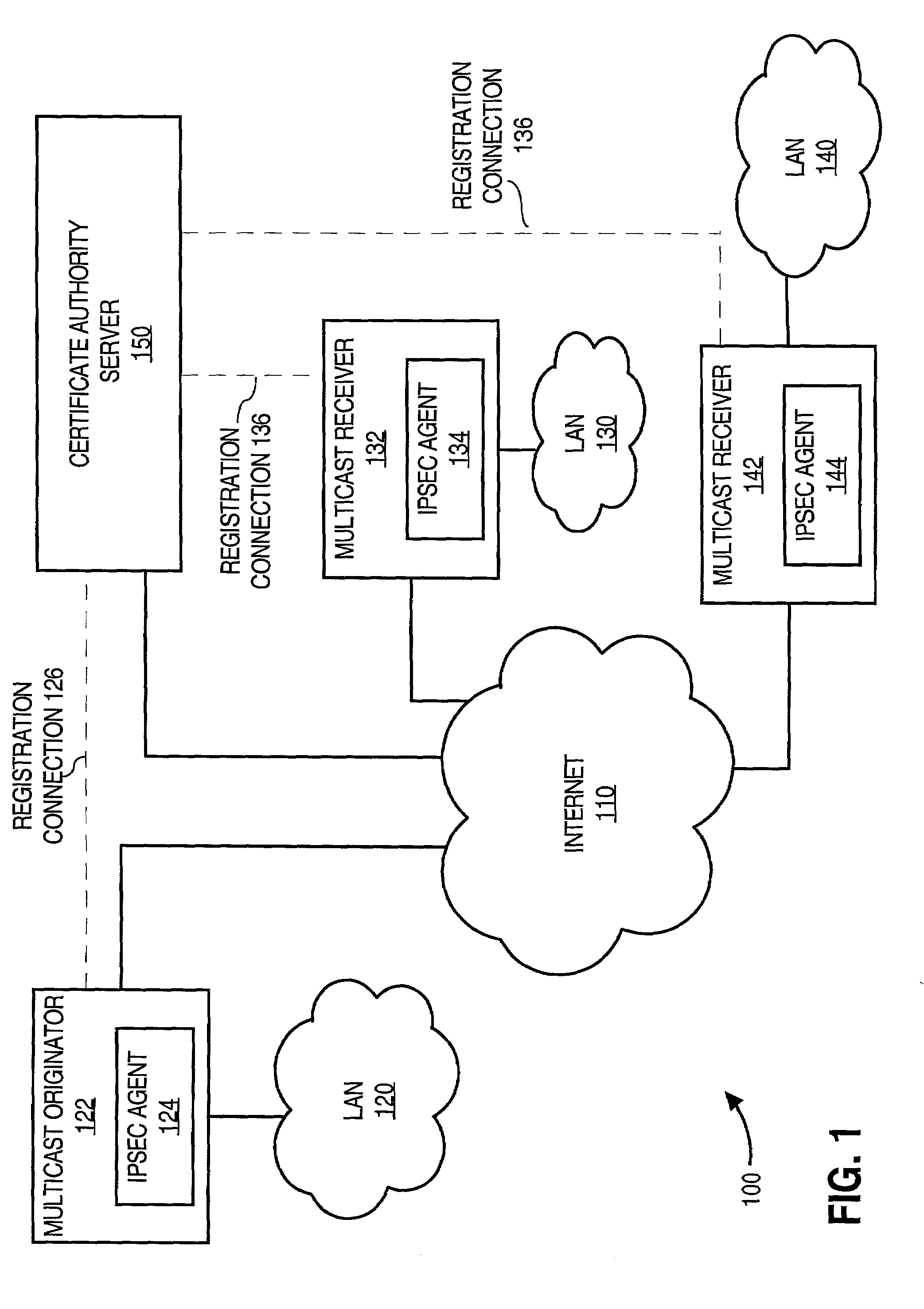
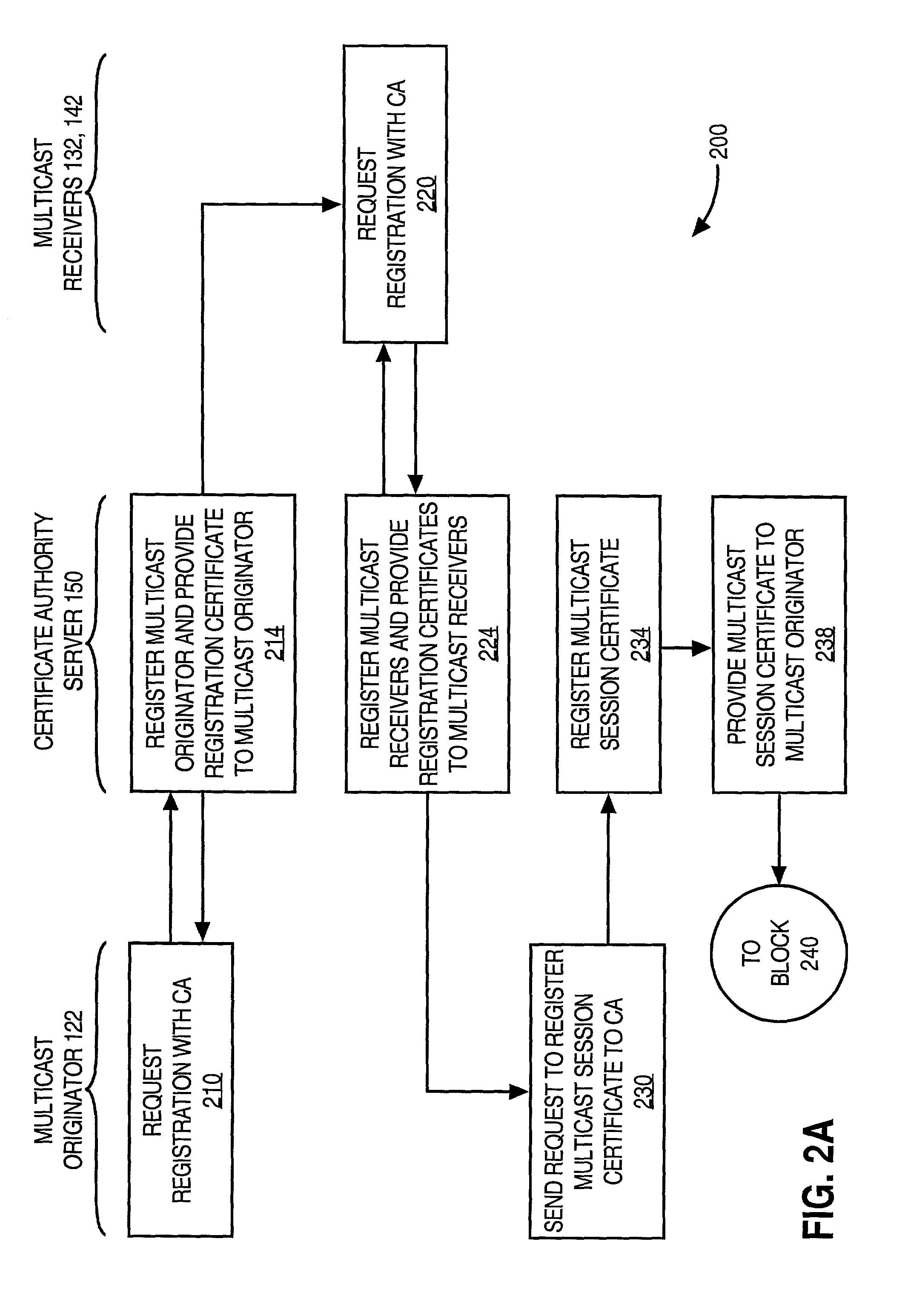
Facilitating secure communications among multicast nodes in a telecommunications network
An approach for facilitating secure communications among multicast nodes in a telecommunications network is disclosed. A source node sends an encryption key and an identifier to an authoritative node that stores the encryption key and associates the identifier with the encryption key. The source node encrypts data using the encryption key and sends the encrypted data with the identifier in a multicast. The multicast destination nodes retrieve the encryption key from the authoritative node based on the identifier and then decrypt the multicast. A list of administrative nodes, a list of authorized nodes, and an expiration time may be used to manage the encryption key. The authoritative node may be a certificate authority or key distribution center, and the source node may encrypt the multicast using the Internet security protocol (IPsec) or secure socket layer (SSL). Thus, communications among multicast nodes may be efficiently secured in a scalable manner.
Owner:CISCO TECH INC
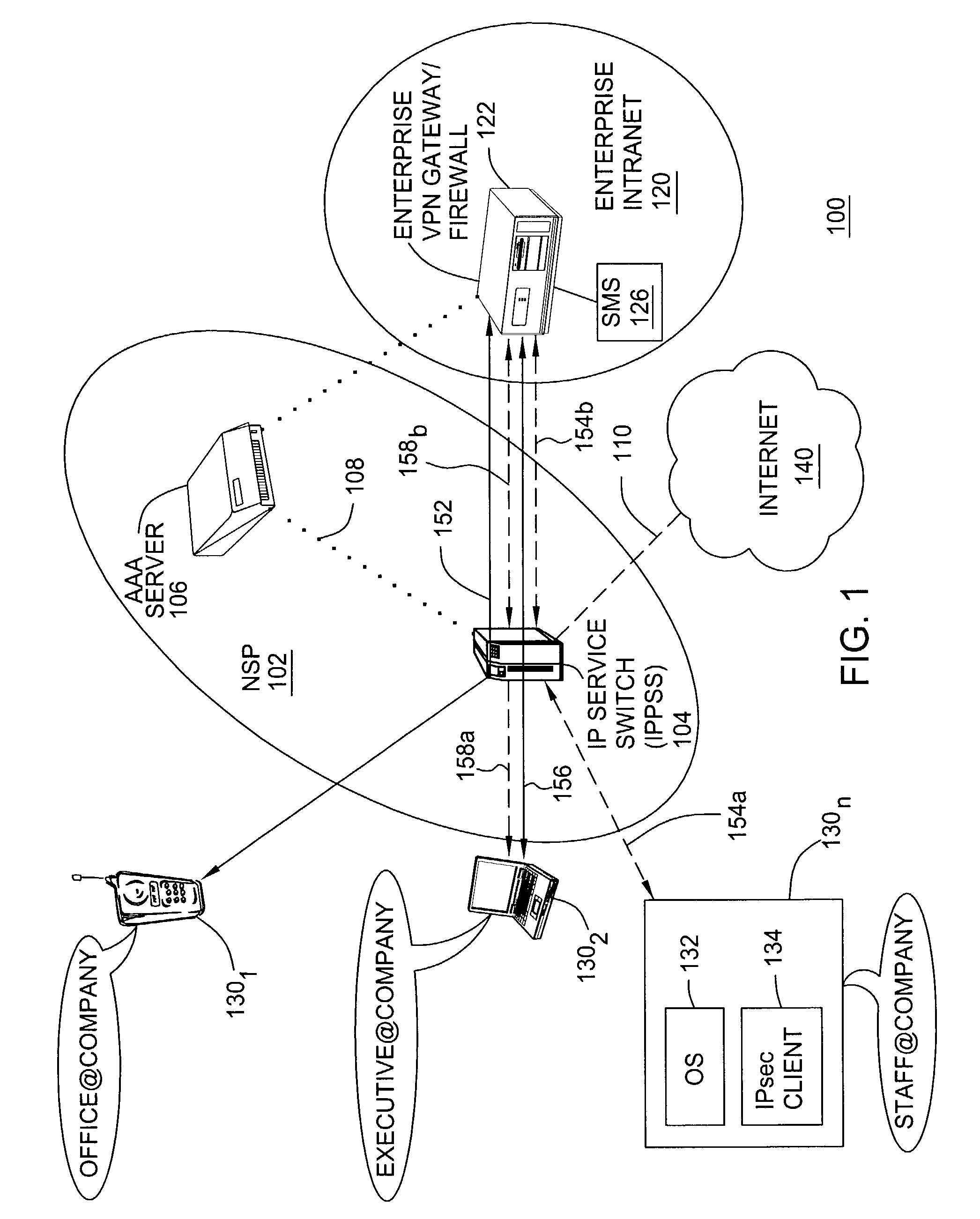
Method and apparatus for providing adaptive VPN to enable different security levels in virtual private networks (VPNs)
ActiveUS7478427B2Computer security arrangementsMultiple digital computer combinationsRouting tableIp address
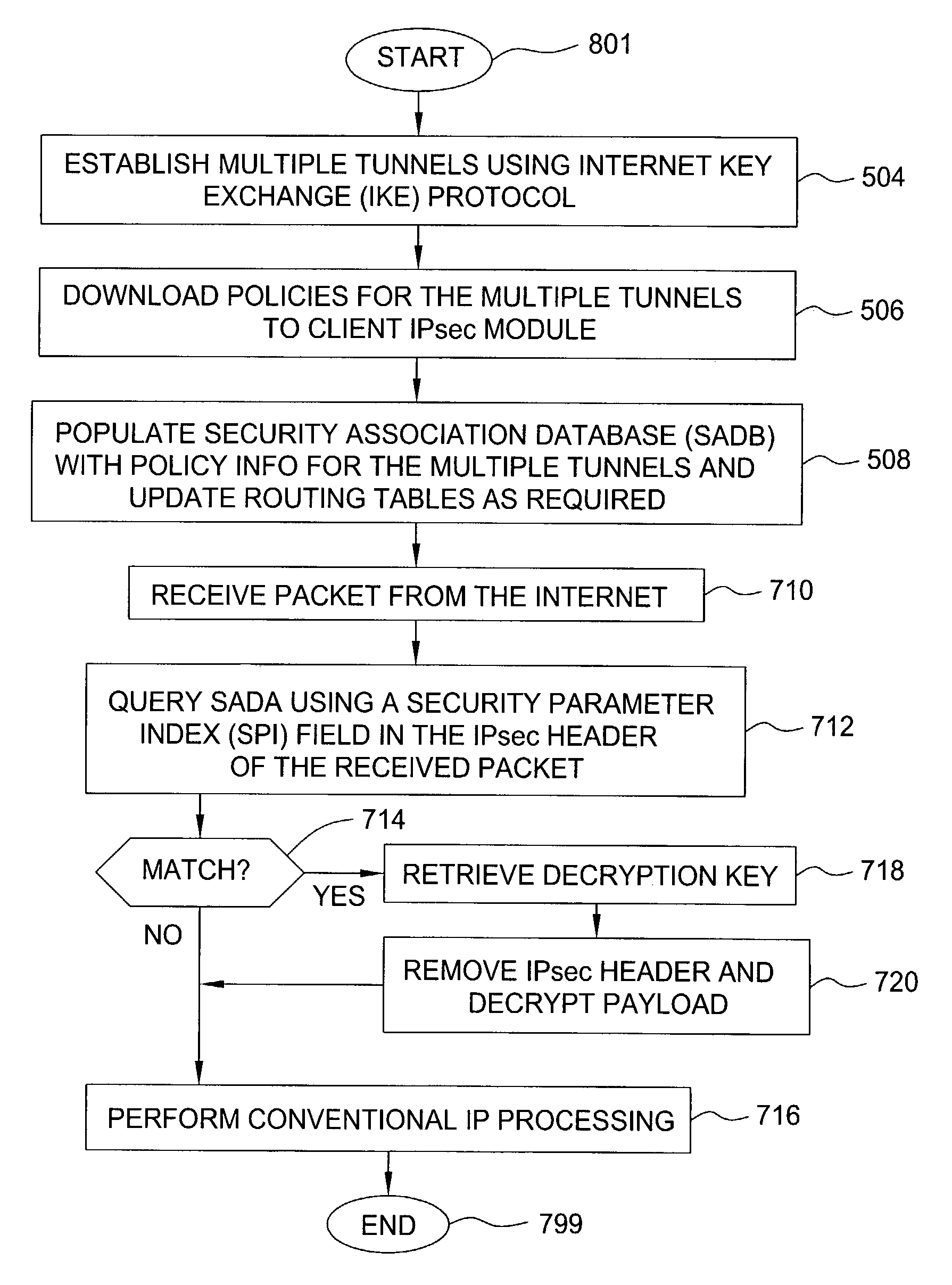
A method and apparatus for providing at least two virtual private network VPN tunnels from a client device in a VPN network having an enterprise gateway and a network VPN gateway. The method and apparatus includes a client device having an Internet Key Exchange (IKE) module for establishing the at least two tunnels using an IKE protocol wherein a first tunnel is an end-to-end VPN tunnel to the enterprise gateway, and a second tunnel is a network-based tunnel to the network VPN gateway. An IPsec Network Driver Interface interfaces with the IKE module, which includes a security authentication database (SADB) that stores downloaded enterprise security policies respectively for each of the at least two tunnels. A routing table stores IP addresses of local presences and hosts respectively associated with the at least two tunnels, whereby packets are routed over the at least two tunnels based on the downloaded policies.
Owner:ALCATEL-LUCENT USA INC
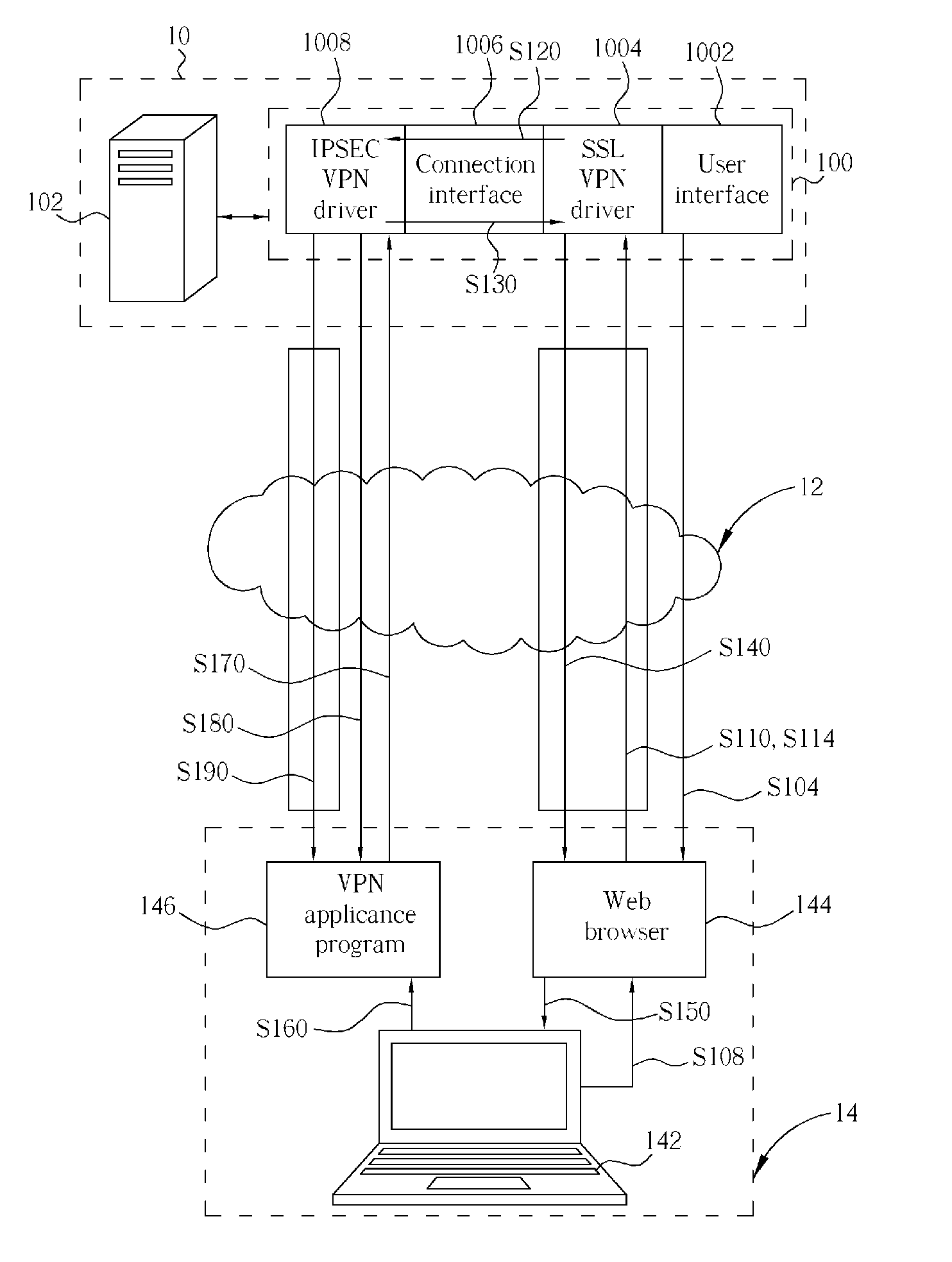
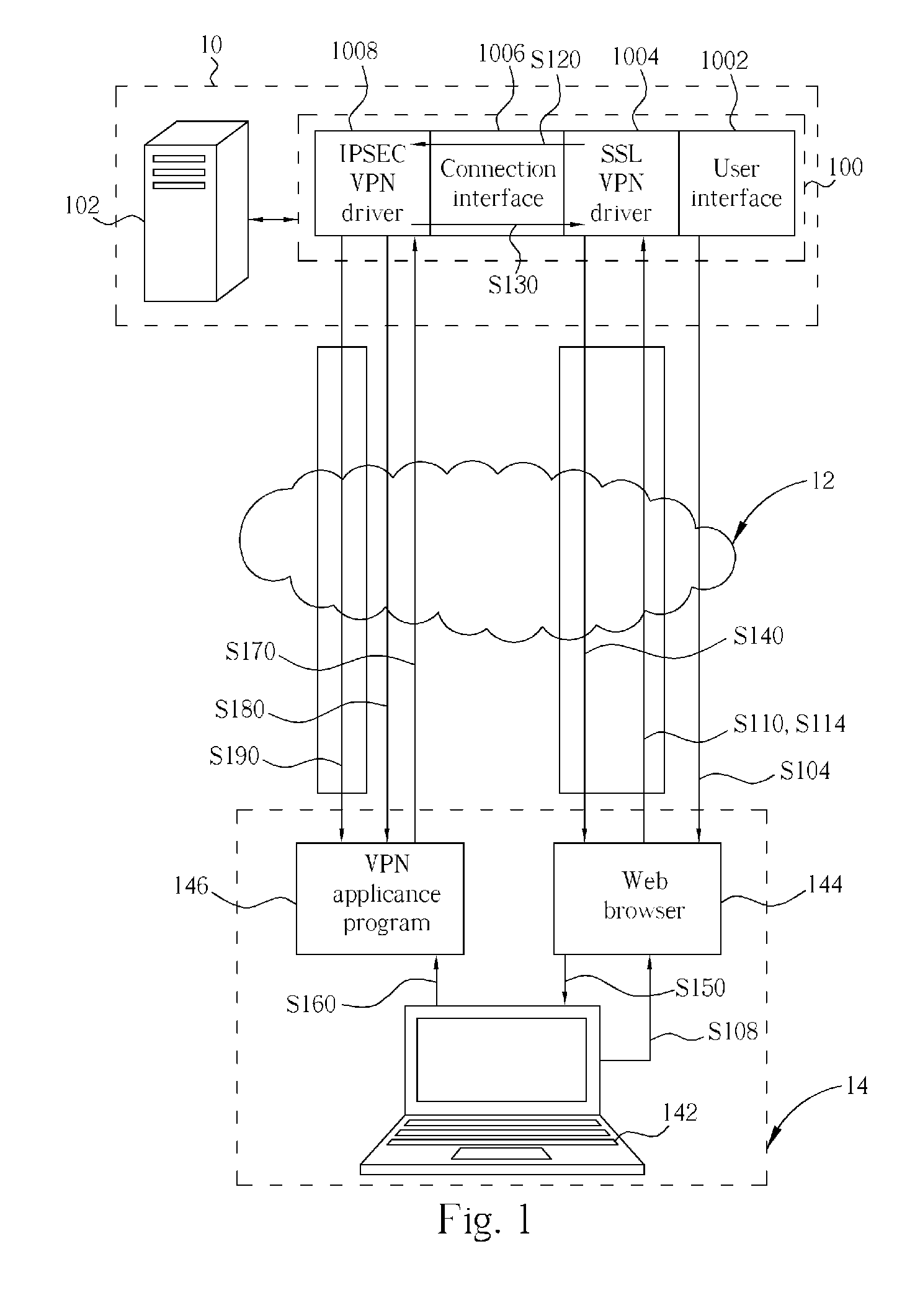
Security gateway utilizing SSL protocol protection and related method
InactiveUS20060005008A1Improve securitySecure transmissionSecuring communicationNetworked systemIPsec
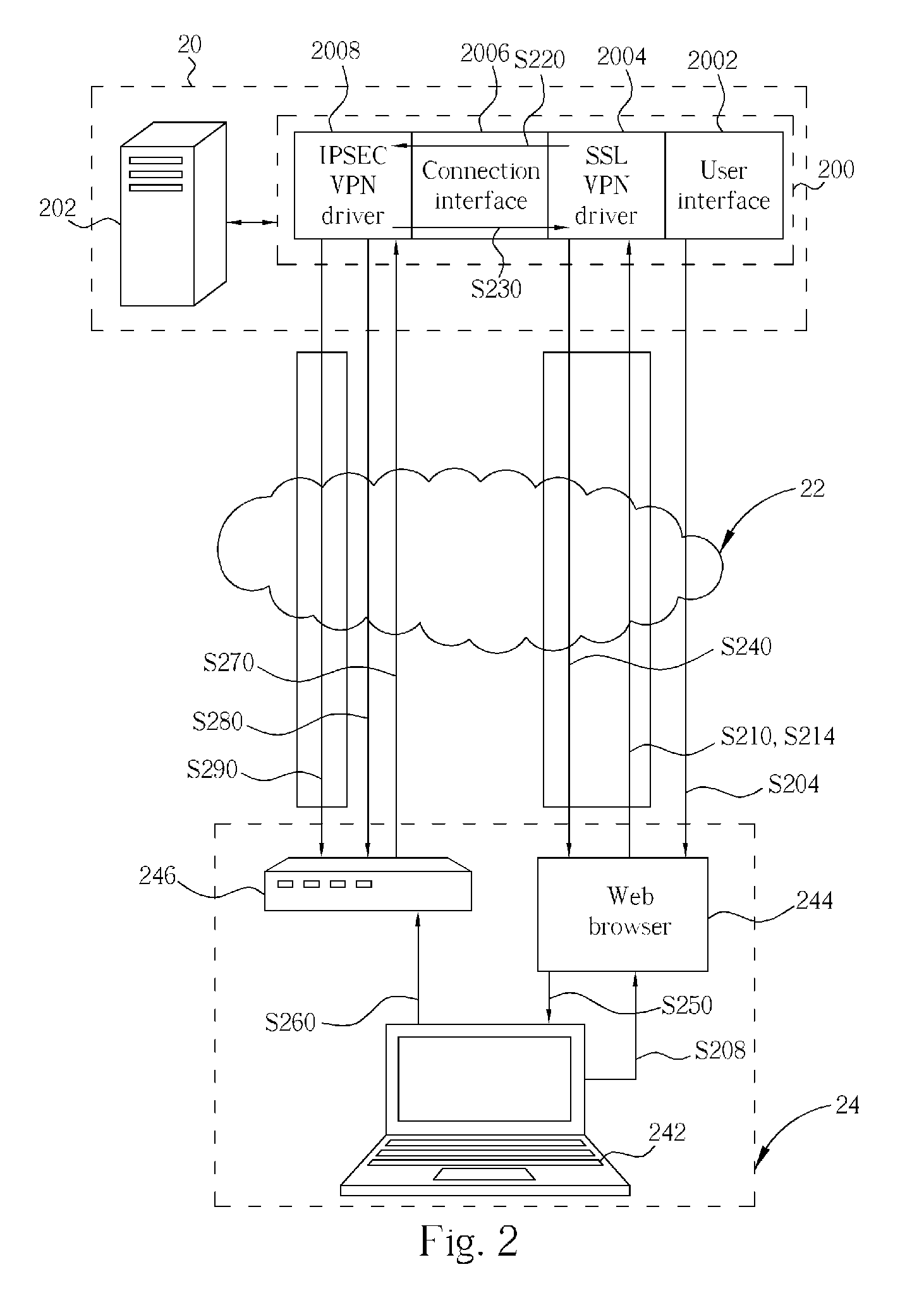
A security gateway, for use in a network system for linking at least a client end and a server end, includes a user interface, a SSL VPN driver, a connection interface and an IPSEC VPN driver. The security gateway supports IPSEC and SSL protocols. Before establishing an IPSEC VPN between a client end and a server end, the security gateway will perform ID authentication for the user of the client end with a widely-used SSL protocol, so as to establish a SSL VPN between a server end and a client end. When the ID of the client end is authorized, a configuration file comprising the SA is generated and then safely sent to the client end through the SSL VPN tunnel. After the client end receives and executes the configuration file having the SA, an IPSEC VPN tunnel between the server end and the client end is established.
Owner:ICP ELECTRONICS
System and methods for providing network quarantine using IPsec
A system and method for ensuring that machines having invalid or corrupt states are restricted from accessing host resources are provided. A quarantine agent (QA) located on a client machine acquires statements of health from a plurality of quarantine policy clients. The QA packages the statements and provides the package to a quarantine enforcement client (QEC). The QEC sends the package to a quarantine Health Certificate Server (HCS) with a request for a health certificate. If the client provided valid statements of health, the HCS grants the client health certificate that may be used in IPsec session negotiation.
Owner:MICROSOFT TECH LICENSING LLC
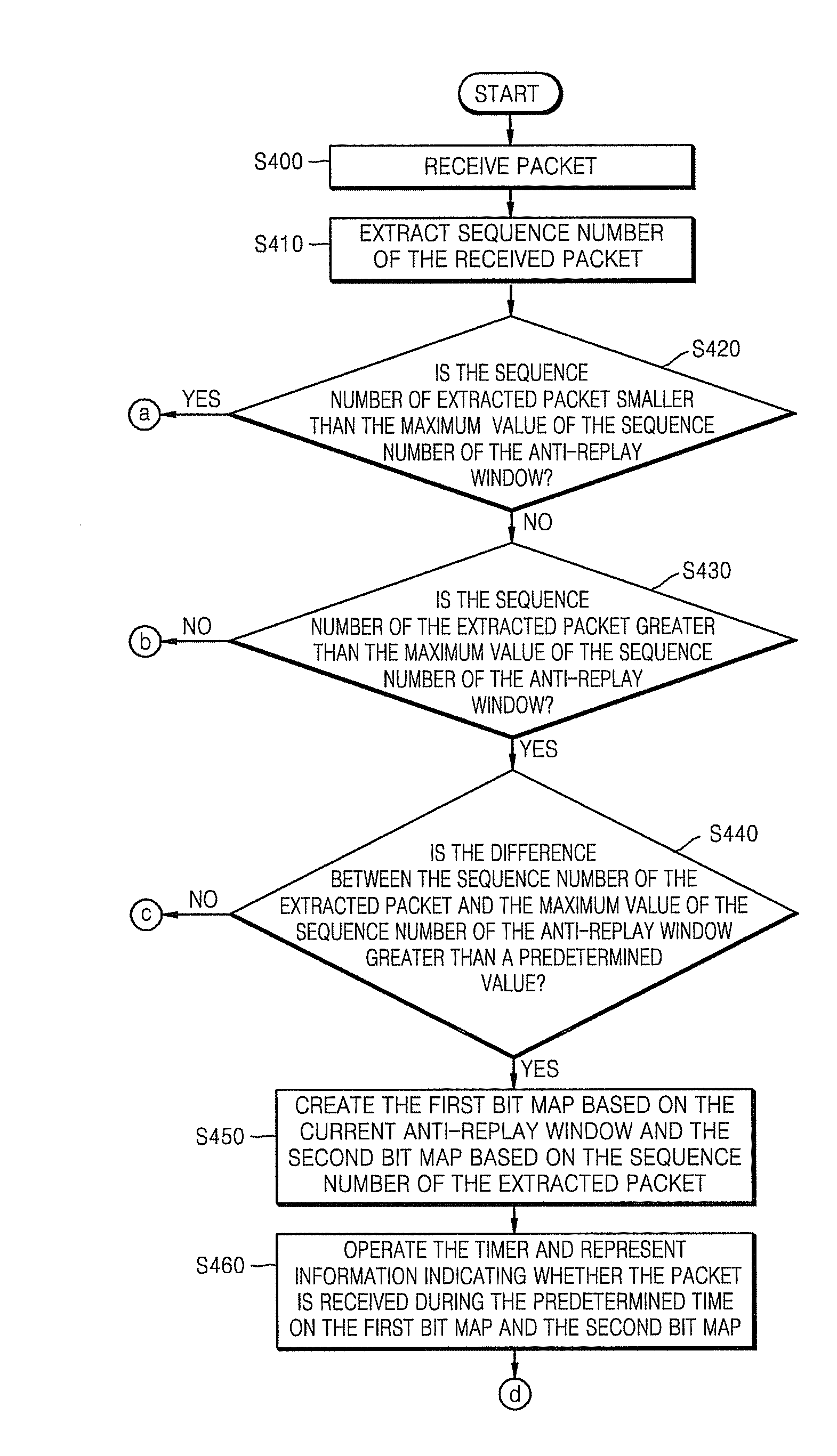
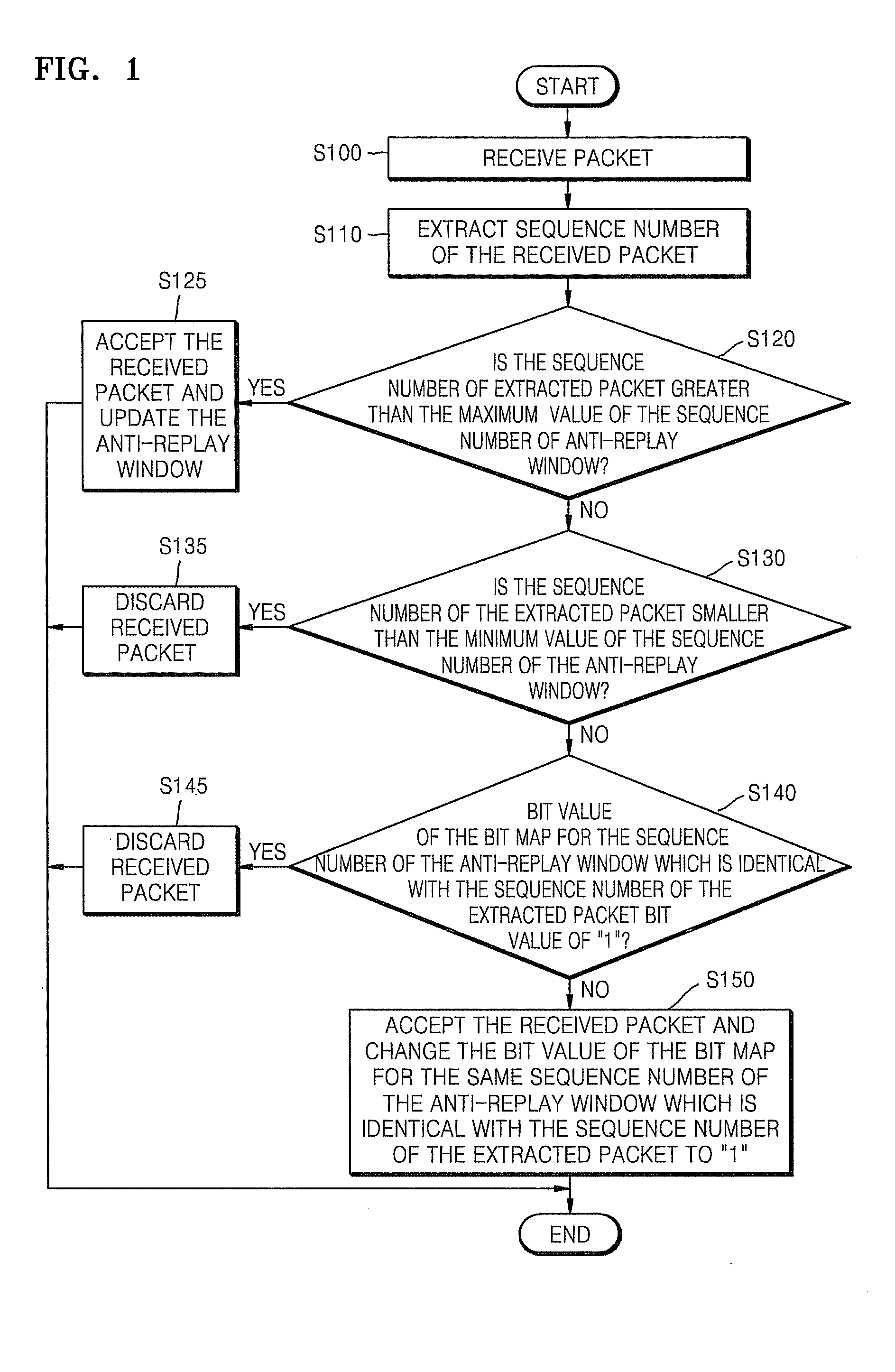
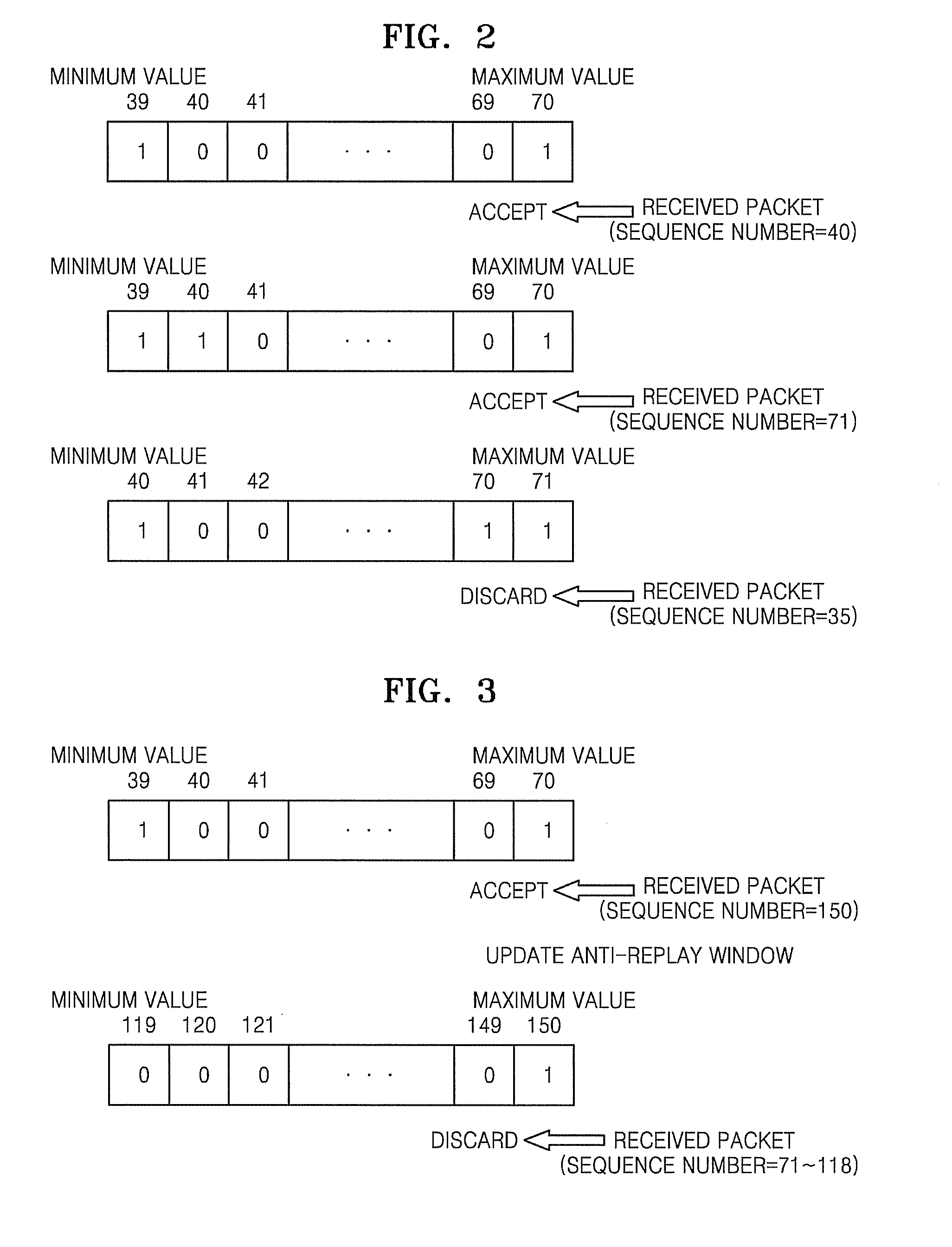
Method and Apparatus for Updating Anti-Replay Window in Ipsec
InactiveUS20080295163A1Error prevention/detection by using return channelData taking preventionIPsecComputer science
A method and apparatus for updating an anti-replay window in Internet Protocol Security (IPSec). The method includes determining whether a difference between a sequence number extracted from a received packet and a maximum value of a sequence number of an anti-replay window is greater than a predetermined value; if it is determined that the difference is greater than the predetermined value, creating a first bit map based on a size of the anti-replay window and a second bit map based on the sequence number extracted from the received packet, respectively; comparing the number of bit values in the first bit map of packets received during a predetermined time with the number of bit values in the second bit map of packets received during the predetermined time, and updating the anti-replay window.
Owner:SAMSUNG ELECTRONICS CO LTD
High performance IPSEC hardware accelerator for packet classification
InactiveUS7003118B1Increase the burdenDeterioration in throughputData switching by path configurationMultiple digital computer combinationsIPsecHardware implementations
An architecture for a high performance IPSEC accelerator. The architecture includes components for scanning fields of packets, programming an IPSEC services device according to the scanned fields, and modifying the scanned packet with an output from the IPSEC security services device. Preferably, the architecture is implemented in hardware, and attached to a host machine. Hardware devices, fast in comparison to software processing and network speeds, allows the computationally intensive IPSEC processes to be completed in real-time and reduce or eliminate bottlenecks in the path of a packet being sent or received to / from a network.
Owner:HEWLETT PACKARD DEV CO LP
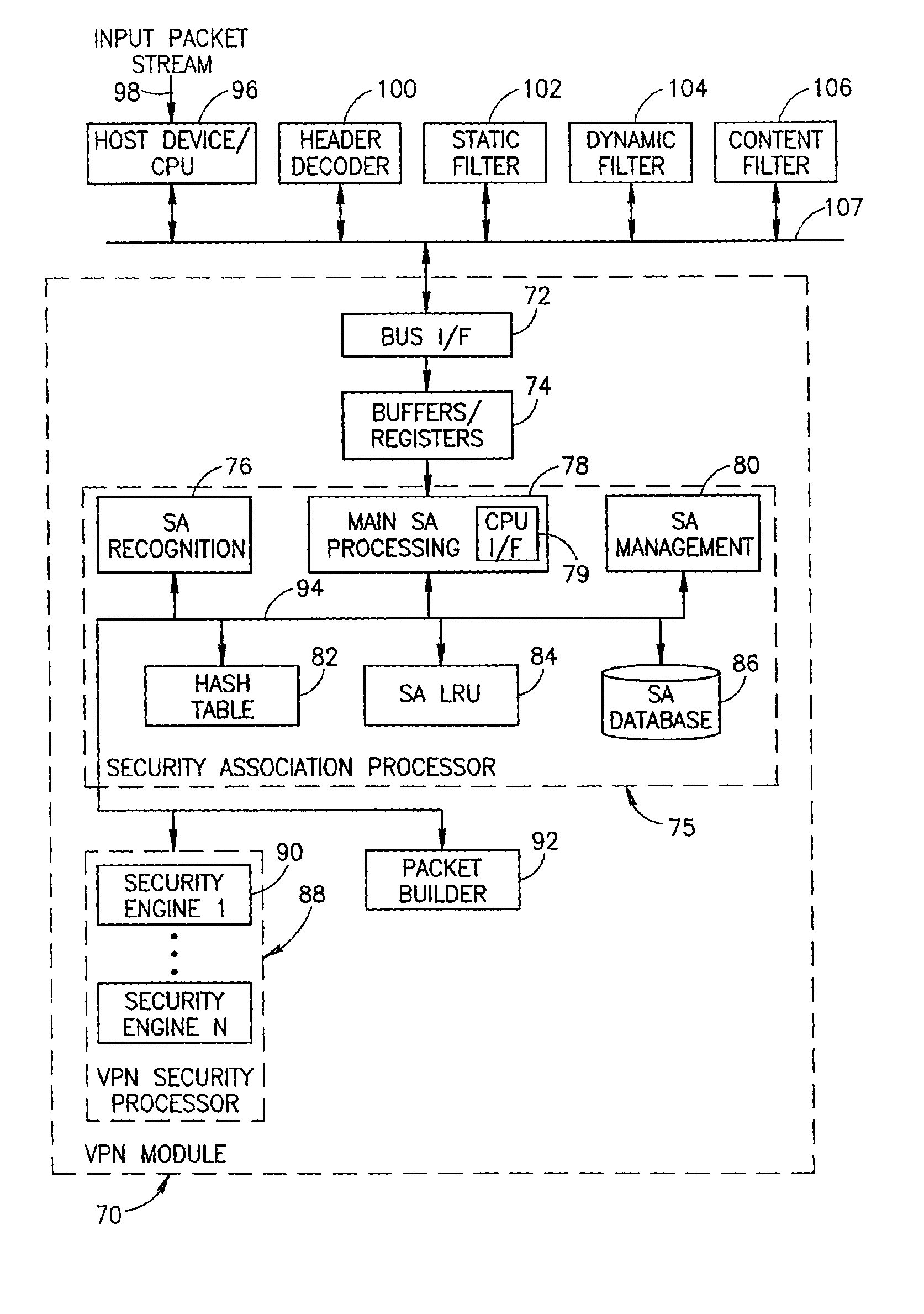
Virtual private network mechanism incorporating security association processor
ActiveUS7107464B2Low costLow-cost implementationMultiple digital computer combinationsProgram controlSecurity associationPrivate network
A novel and useful virtual private network (VPN) mechanism and related security association processor for maintaining the necessary security related parameters to perform security functions such as encryption, decryption and authentication. A security association database (SAD) and related circuitry is adapted to provide the necessary parameters to implement the IPSec group of security specifications for encryption / decryption and authentication. Each security association (SA) entry in the database comprises all the parameters that are necessary to receive and transmit VPN packets according to the IPSec specification.
Owner:TELECOM ITALIA SPA
Method to provide dynamic Internet Protocol security policy service
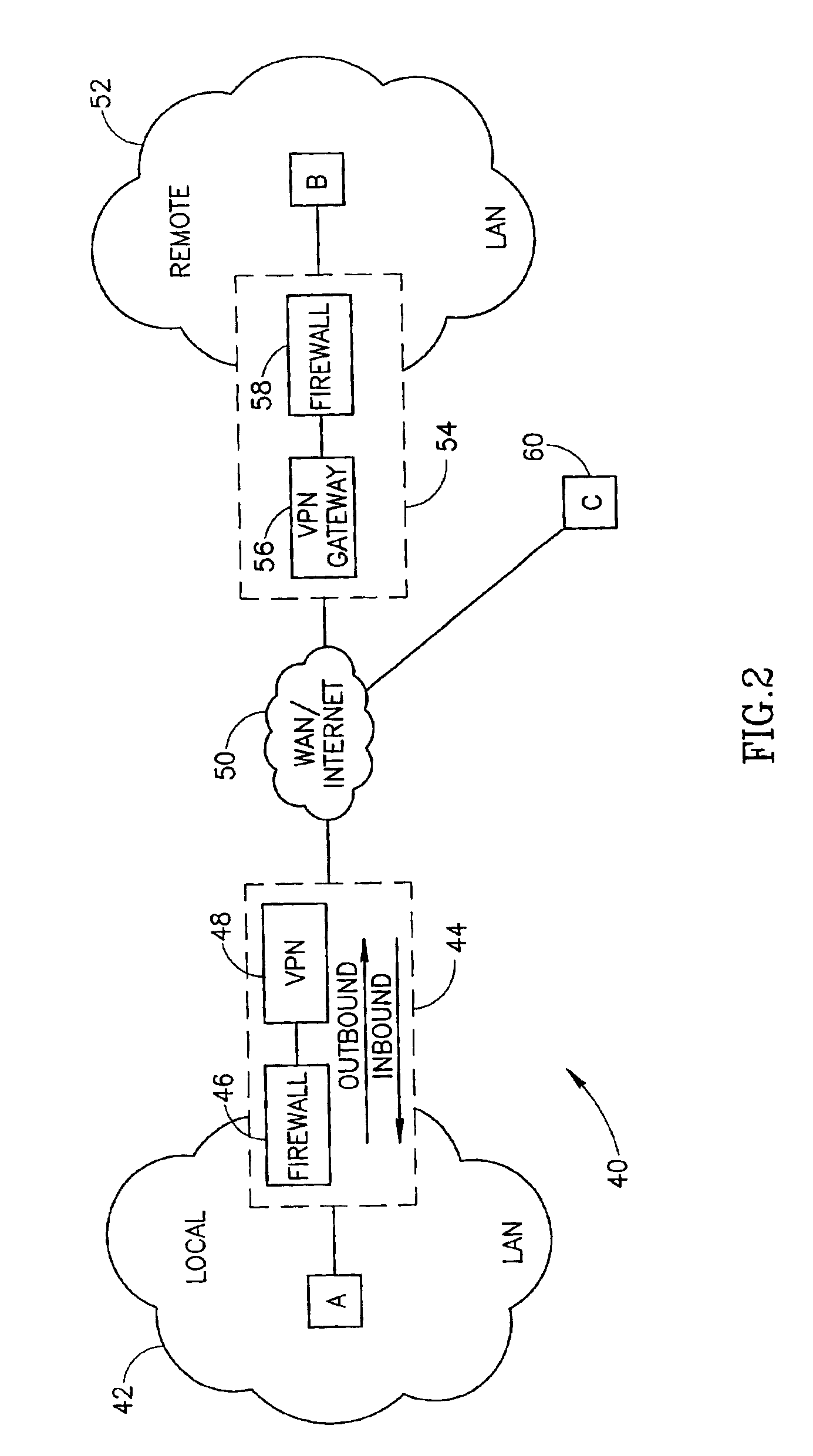
InactiveUS20050063352A1Wireless network protocolsRadio/inductive link selection arrangementsComputer networkForeign agent
A mobile node may roam away from its home network to a foreign network. The mobile node may communicate using the Mobile Internet Protocol, and it may use Internet Protocol security to communicate with its home network. A foreign agent on the foreign network and a home agent on the home network may dynamically link a policy to be used for a Internet Protocol security session between the foreign agent and the home agent. The foreign agent and the home agent may dynamically create a filter to be used for the Internet Protocol Security session.
Owner:UTSTARCOM INC
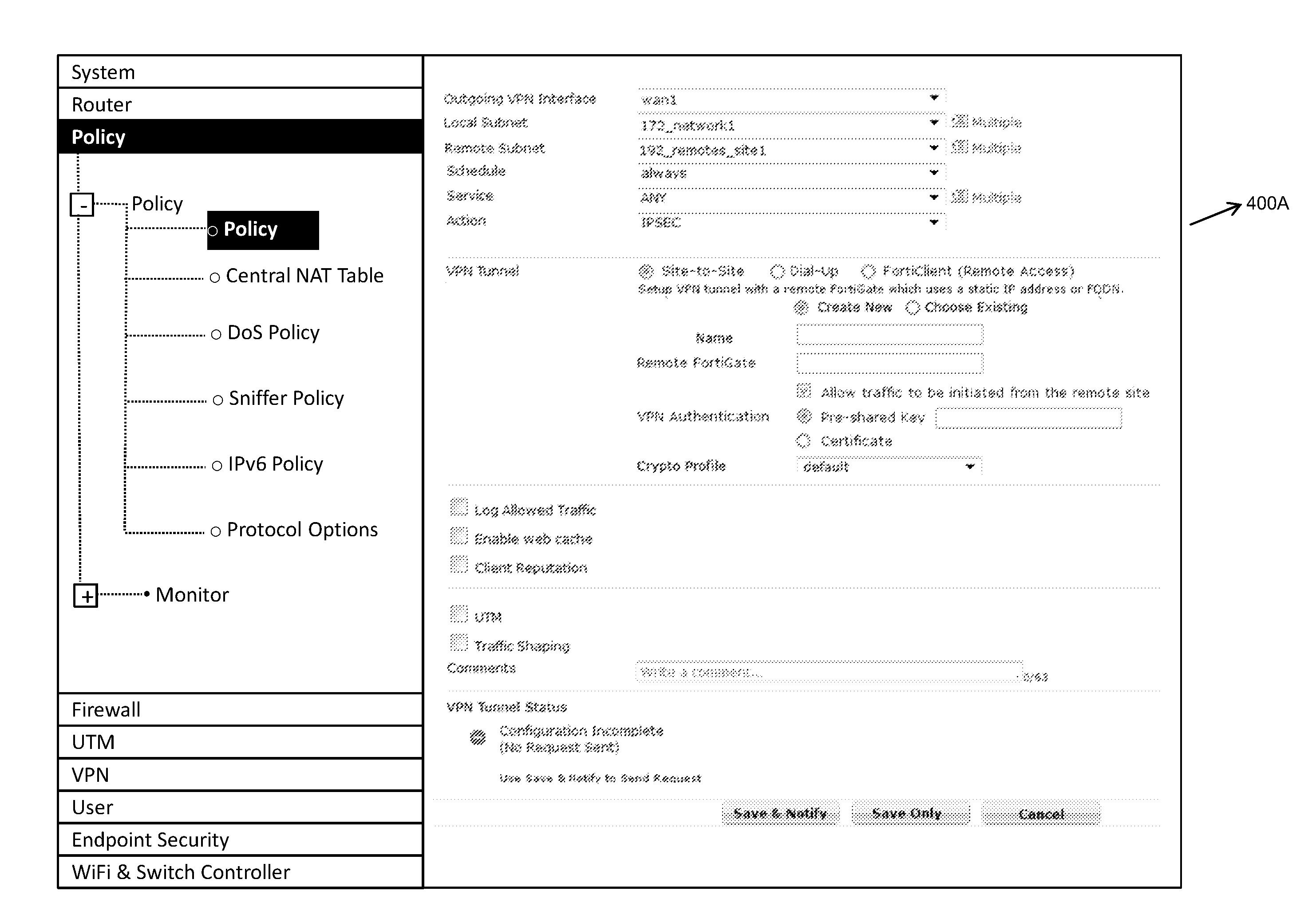
Policy-based configuration of internet protocol security for a virtual private network
ActiveUS20130298182A1Computer security arrangementsData switching networksInternet protocol suiteIPsec
A method for performing policy-based configuration of Internet Protocol Security (IPSec) for a Virtual Private Network (VPN) is provided. According to one embodiment, a browser-based interface of a network device displays a policy page through which multiple settings may be configured for a VPN connection. The settings include a type of IPSec tunnel to be established between the network device and a peer. One or more parameter values corresponding to one or more of the settings are received and responsive thereto a policy file is created or modified corresponding to the VPN connection. The policy file has contained therein multiple parameter values corresponding to the settings. Establishment of the VPN connection between the network device and the peer is requested based on the parameter values contained within the policy file by sending a notification request, including the policy file, from the network device to the peer.
Owner:FORTINET
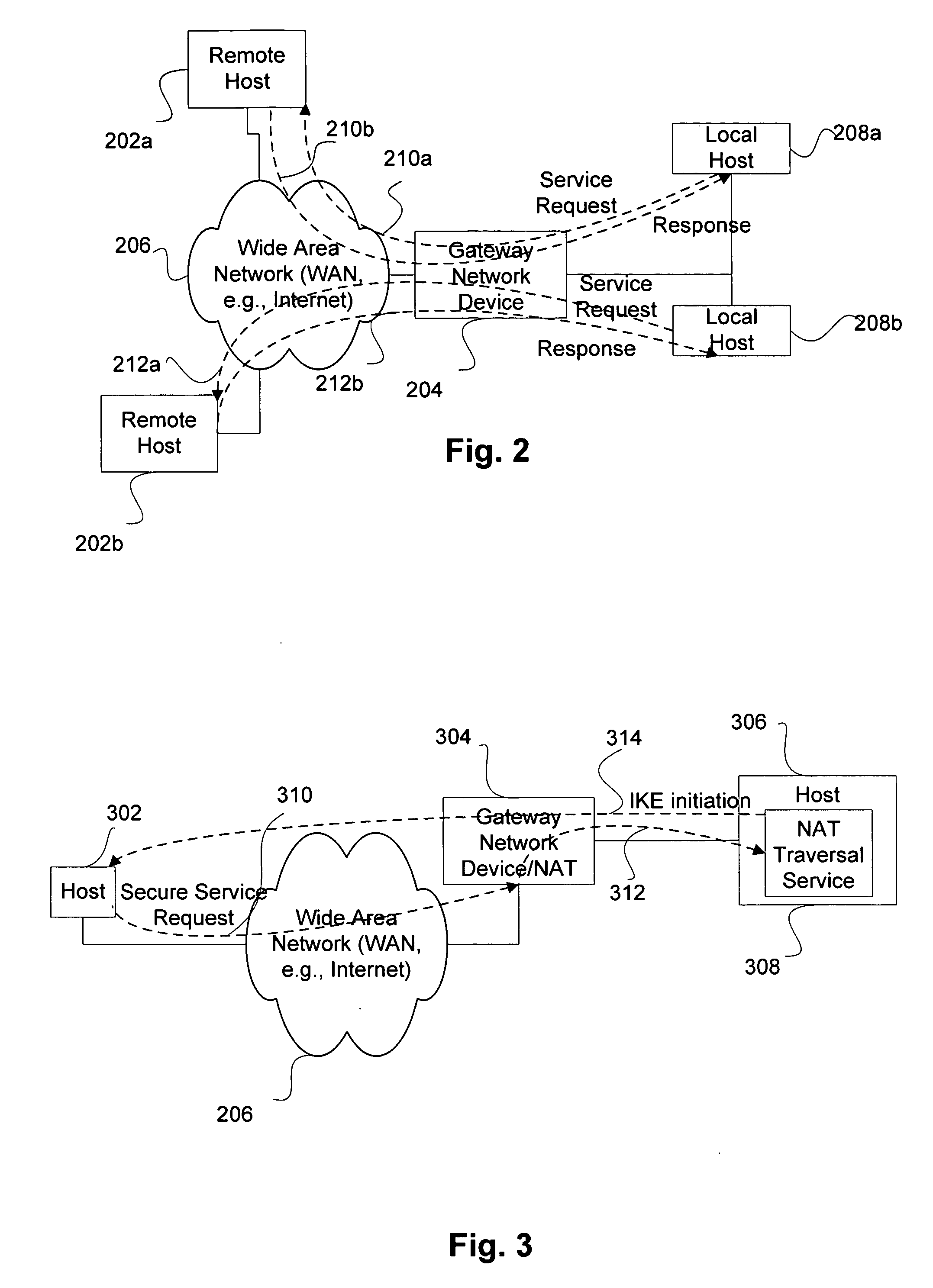
Service for NAT traversal using IPSEC
Disclosed are methods and apparatus for methods and apparatus for facilitating a secure connection between a first and a second node in a computer network where one or both of the nodes may or may not reside behind a network address translation (NAT) enabled gateway. Embodiments of the present invention provide a seamless integration by providing a uniform solution for establishing secure connections, such as IPSEC, between two nodes irrespective of whether they are behind a NAT-enabled gateway or not. In general, a gateway is operable to receive a request from a remote host for a secure connection to a local host that within the home network of the gateway. The gateway then forwards this received request to a NAT traversal service. The NAT traversal service receives the request and then automatically sends an initiation message to set up a secure session, e.g., performing authentication and exchanging keys. In a specific aspect, the setup data utilizes an IKE (Internet Key Exchange) initiation message that is sent to the originator of the request via the gateway. Upon receipt of this initiation message, the gateway is then able to set up a two way connection to allow other setup data to flow between the remote and local hosts to complete the setup session and then secure data to flow between the remote and local hosts in a secure communication session, such as in IPSec or VPN session.
Owner:CISCO TECH INC
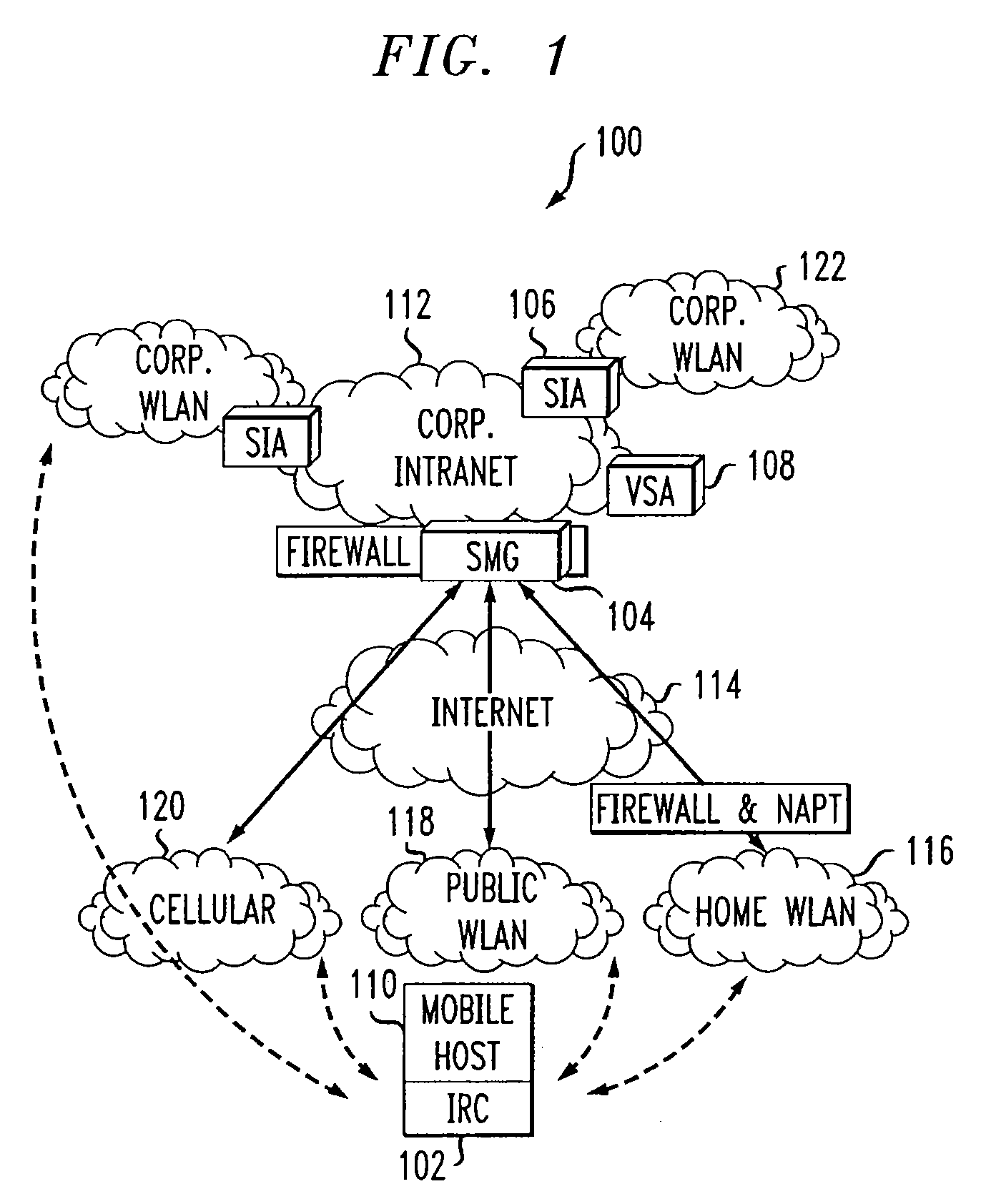
System and method to support networking functions for mobile hosts that access multiple networks
InactiveUS20090022152A1Data switching by path configurationWireless network protocolsModem deviceIp address
An IP-based corporate network architecture and method for providing seamless secure mobile networking across office WLAN, home WLAN, public WLAN, and 2.5 G / 3 G cellular networks for corporate wireless data users. The system includes Internet roaming clients (IRCs), a secure mobility gateway (SMG), optional secure IP access (SIA) gateways, and a virtual single account (VSA) server. The IRC is a special client tool installed on a mobile computer (laptop or PDA) equipped with a WLAN adaptor and a cellular modem. It is responsible for establishing and maintaining a mobile IPsec tunnel between the mobile computer and a corporate intranet. The SMG is a mobile IPsec gateway installed between the corporate intranet and the Internet. It works in conjunction with the IRC to maintain the mobile IPsec tunnel when the mobile computer is connected on the Internet via a home WLAN, a public WLAN, or a cellular network. The SIA gateway is a special IPsec gateway installed in the middle of the wired corporate intranet and an office WLAN. It works with the IRC to ensure data security and efficient use of corporate IP addresses when the mobile computer is connected to the office WLAN. The VSA server manages authentication credentials for every corporate user based on a virtual single account concept. The Internet Roaming system can provide secure, always-on office network connectivity for corporate users no matter where they are located using best available wireless networks.
Owner:AT&T INTPROP II L P
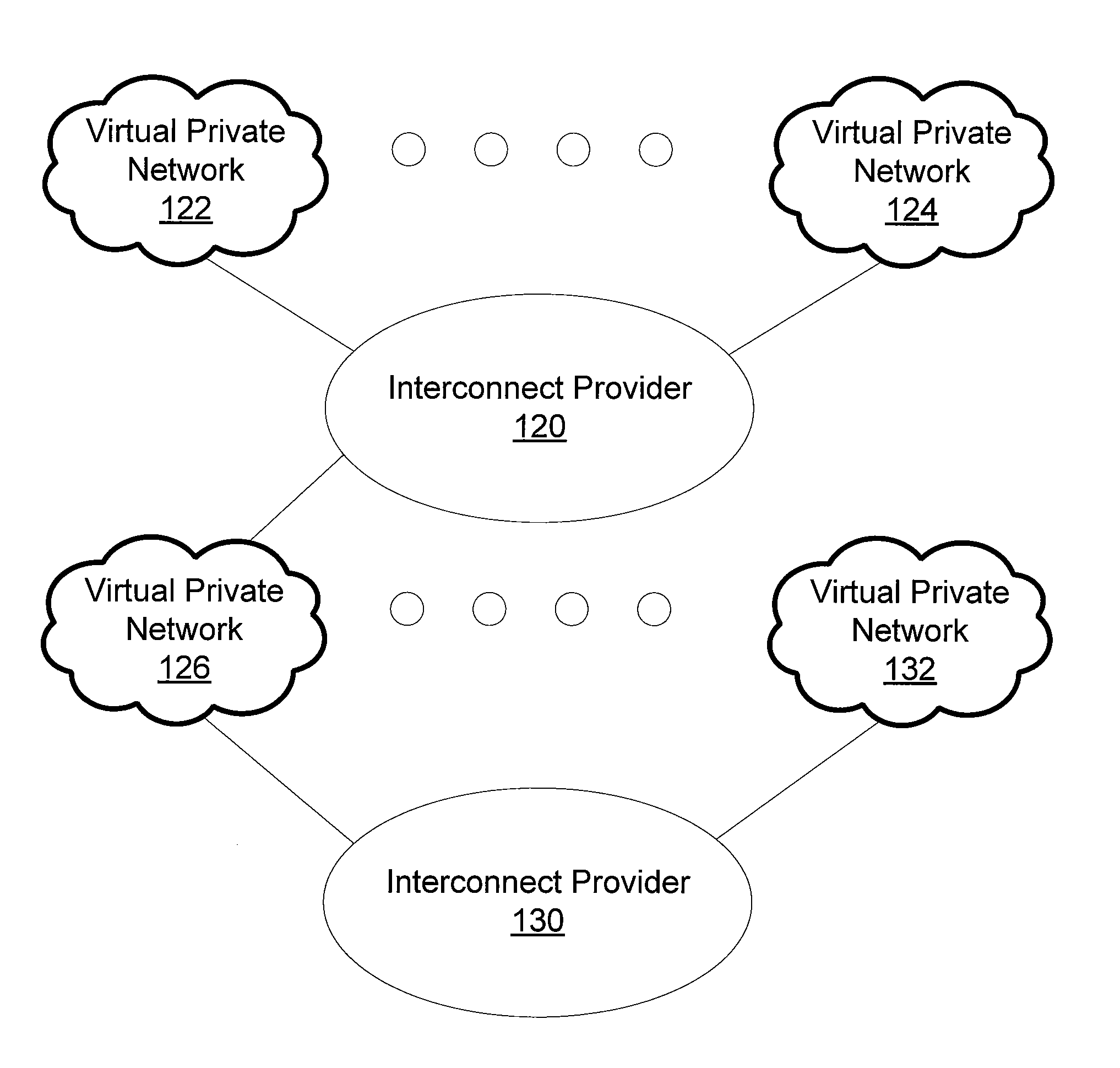
System and method for interconnecting multiple virtual private networks
A system and method for interconnecting multiple VPNs, each using multiple service providers, while offering a minimum standard of end-to-end connection quality and reliability is described. The system and method utilizes an overseer that resolves end-to-end issues across multiple interconnected virtual private networks. When connecting multiple virtual private networks, multiple interconnect providers are interconnected so that the end-to-end service quality standard is met. The certification of service providers, exchange points, transit service providers and IPSec devices permits interoperability for encryption, integrity and authentication across the product of all IPSec vendors. When two subscribers both use certified IPSec equipment then they can provide each other with controlled access to each other's networks.
Owner:ANXEBUSINESS
Securing network traffic by distributing policies in a hierarchy over secure tunnels
A technique for securing message traffic in a data network using a protocol such as IPsec, and more particularly various methods for distributing security policies among peer entities in a network while minimizing the passing and storage of detailed policy or key information except at the lowest levels of a hierarchy.
Owner:CIPHEROPTICS
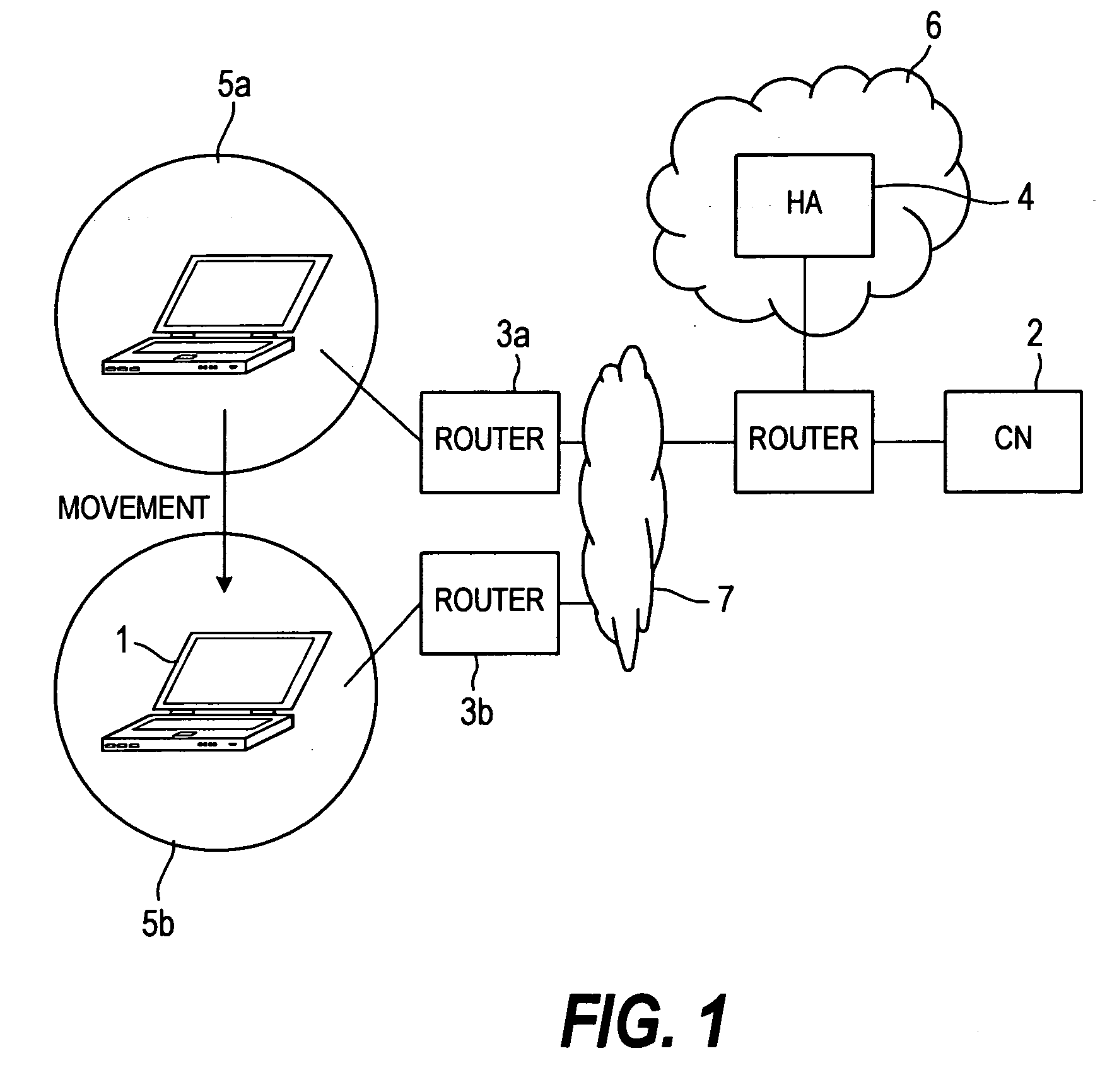
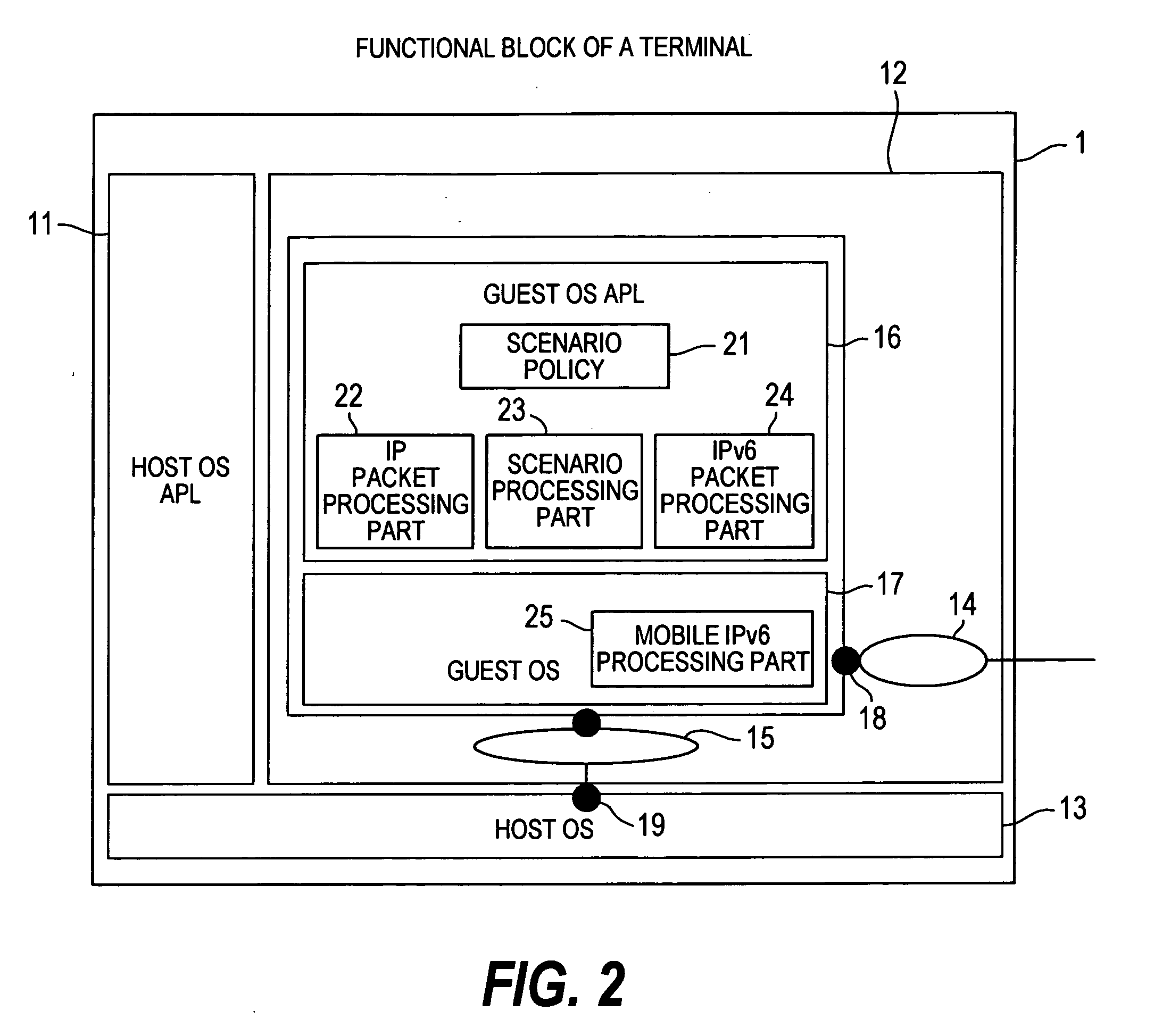
Terminal and communication system
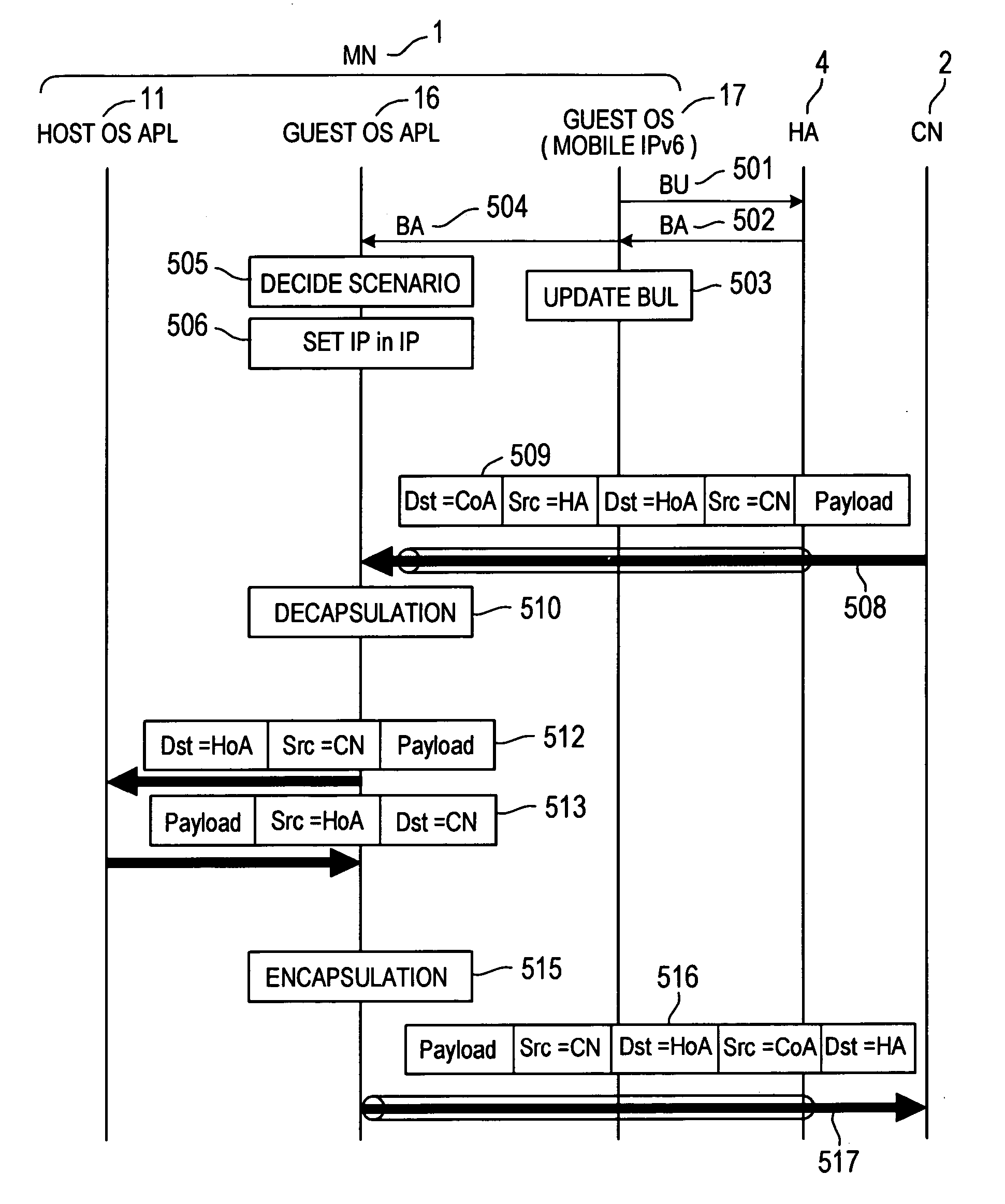
InactiveUS20070081512A1More complicated processComplicated processTime-division multiplexMultiprogramming arrangementsCommunications systemMethod selection
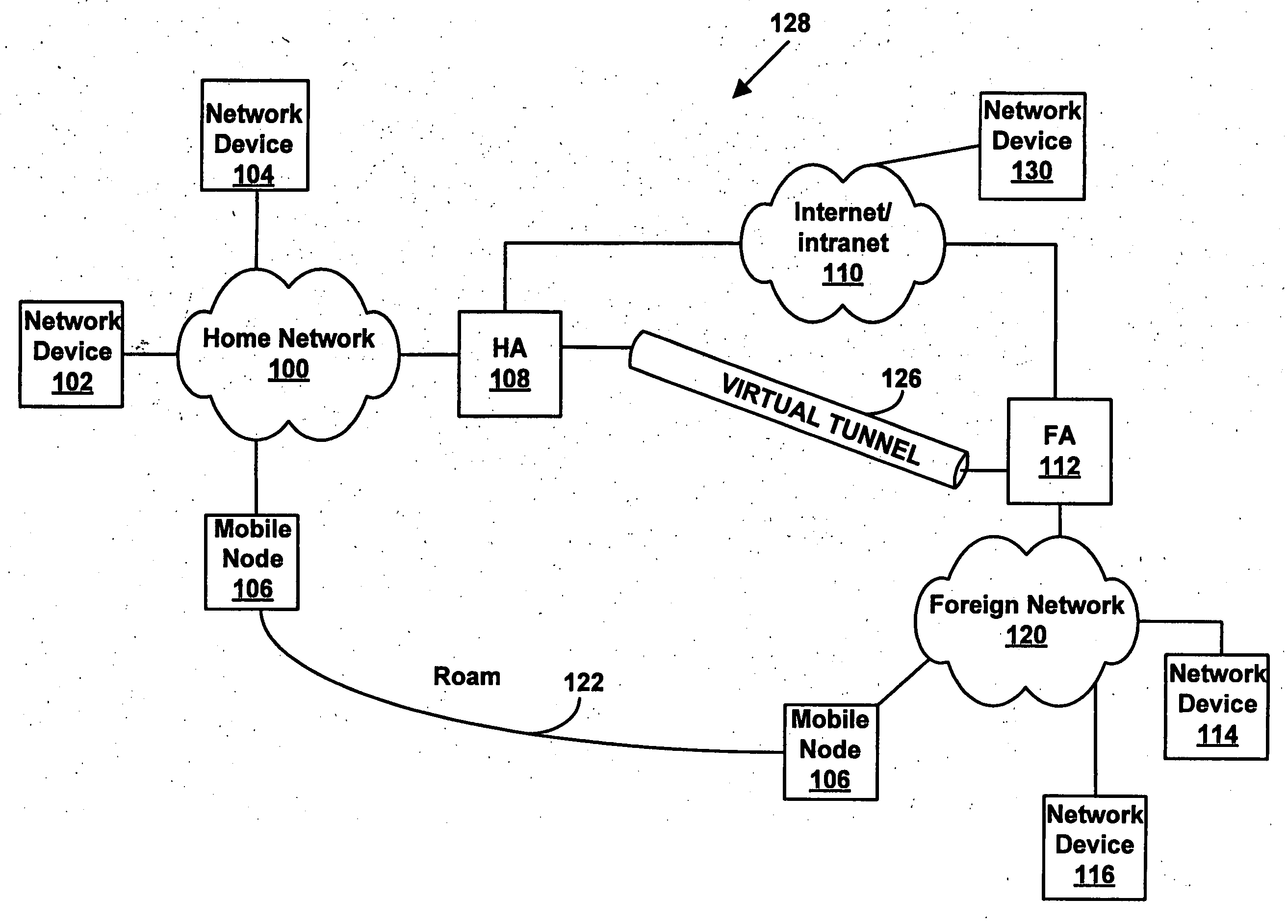
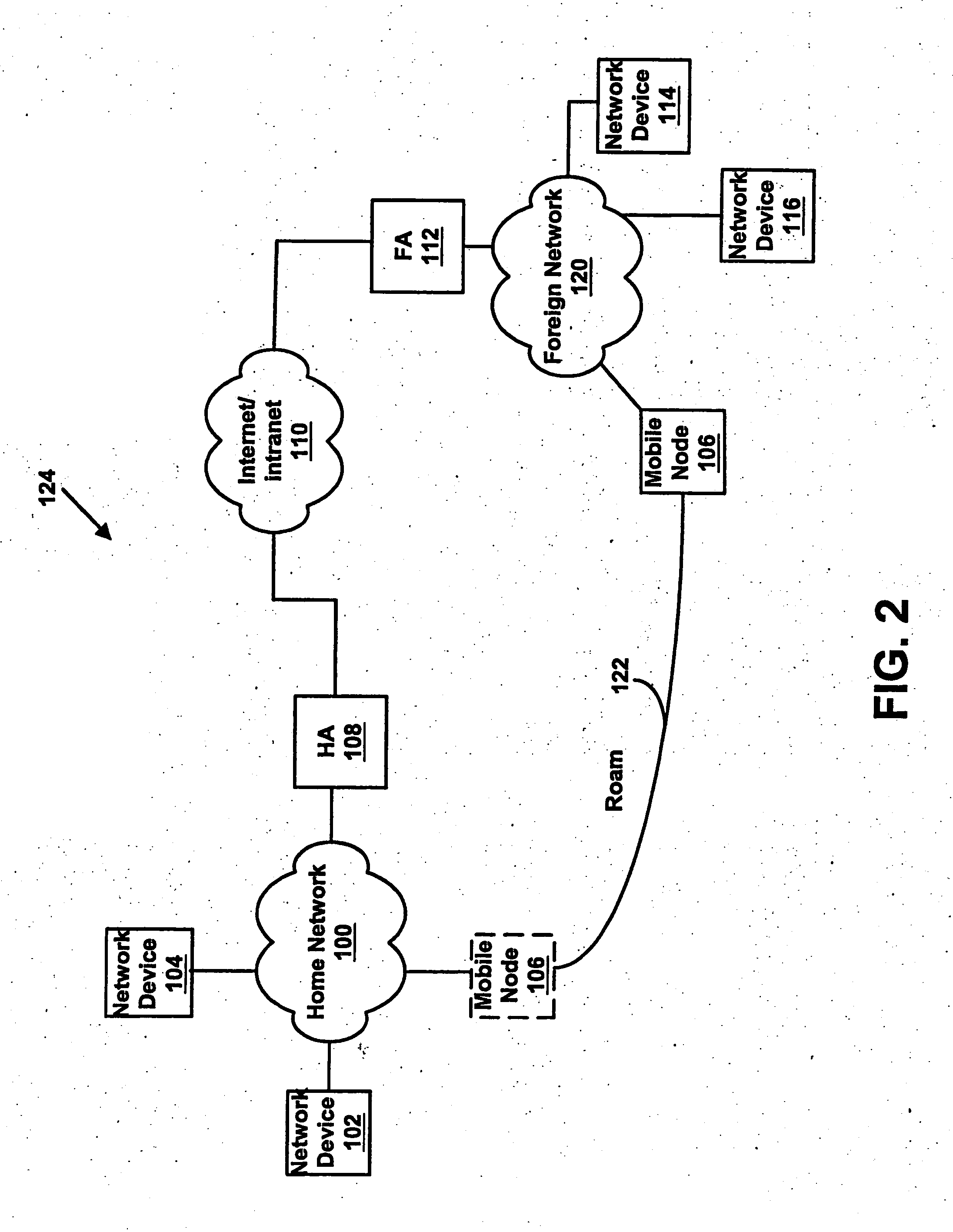
By assigning a fixed home address to an MN, Mobile IPv6 assures the arrival of each content at the MN 1. In order to allow the user to receive a Mobile IPv6 service, it is necessary to provide the MN 1 with a Mobile IPv6 function for making applications conform to IPv6. However, there are only few such MNs 1. In addition, the MN 1 does not have a function for implementing an IPsec process repeatedly on a packet transmitted to and received from another apparatus. A scenario processing port 23 employed in the MN 1 includes a means, which is used for selecting a process according to a communication method and carrying out the selected process when a response to a Mobile IPv6 location registration message is received. By providing the scenario processing port 23 with a means for selecting a communication method, a function can be added to the MN 1 with ease. In addition, by providing the MN 1 with a means for implementing an IPsec process a plurality of times, it is possible to provide a communication apparatus according to a security management configuration.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com