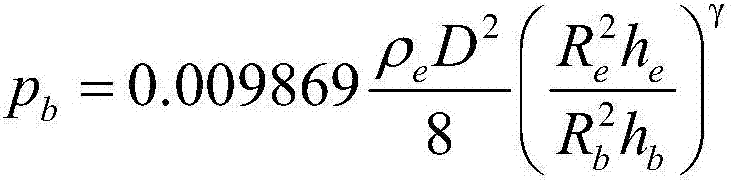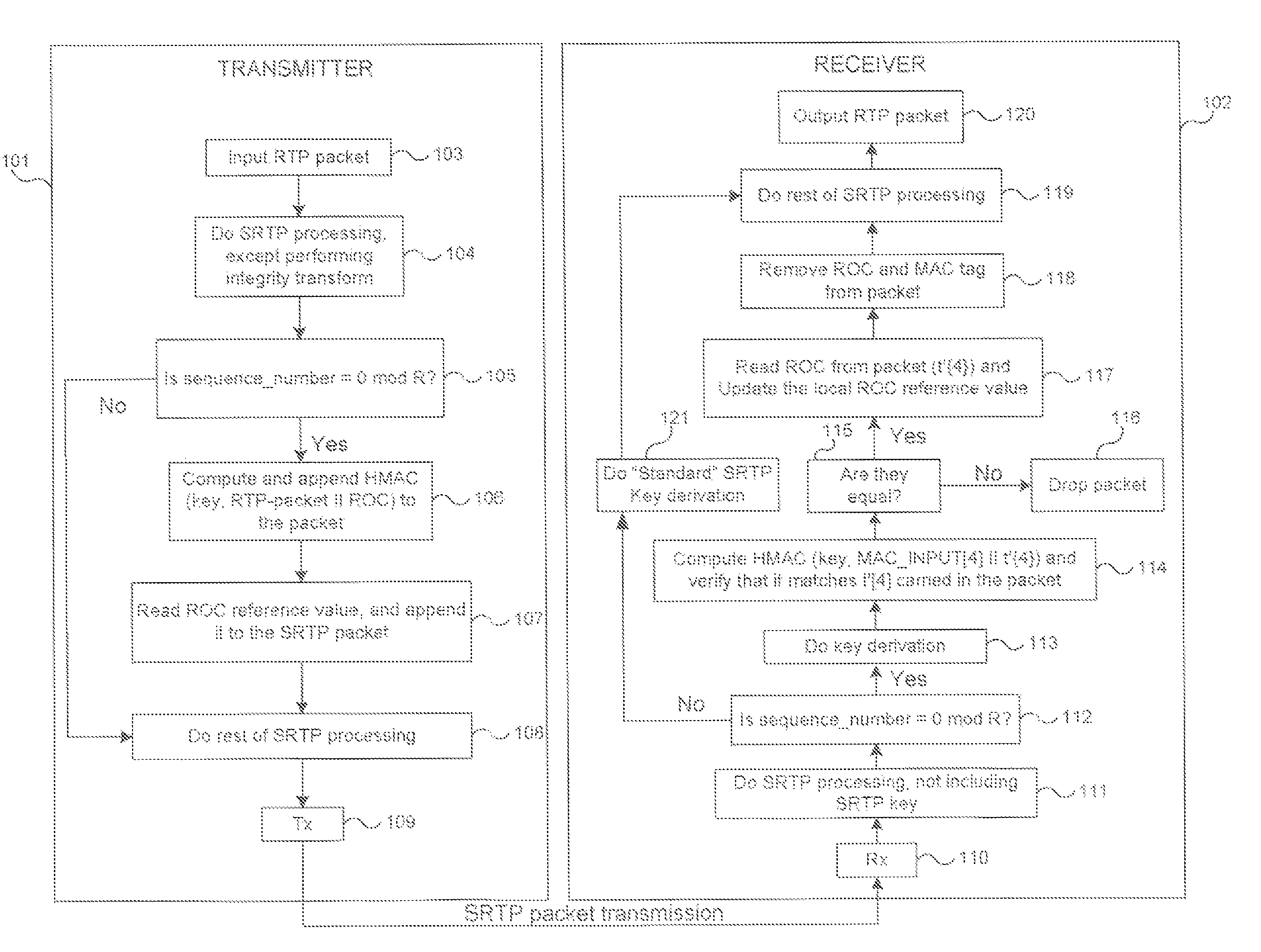Patents
Literature
48 results about "Task force" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
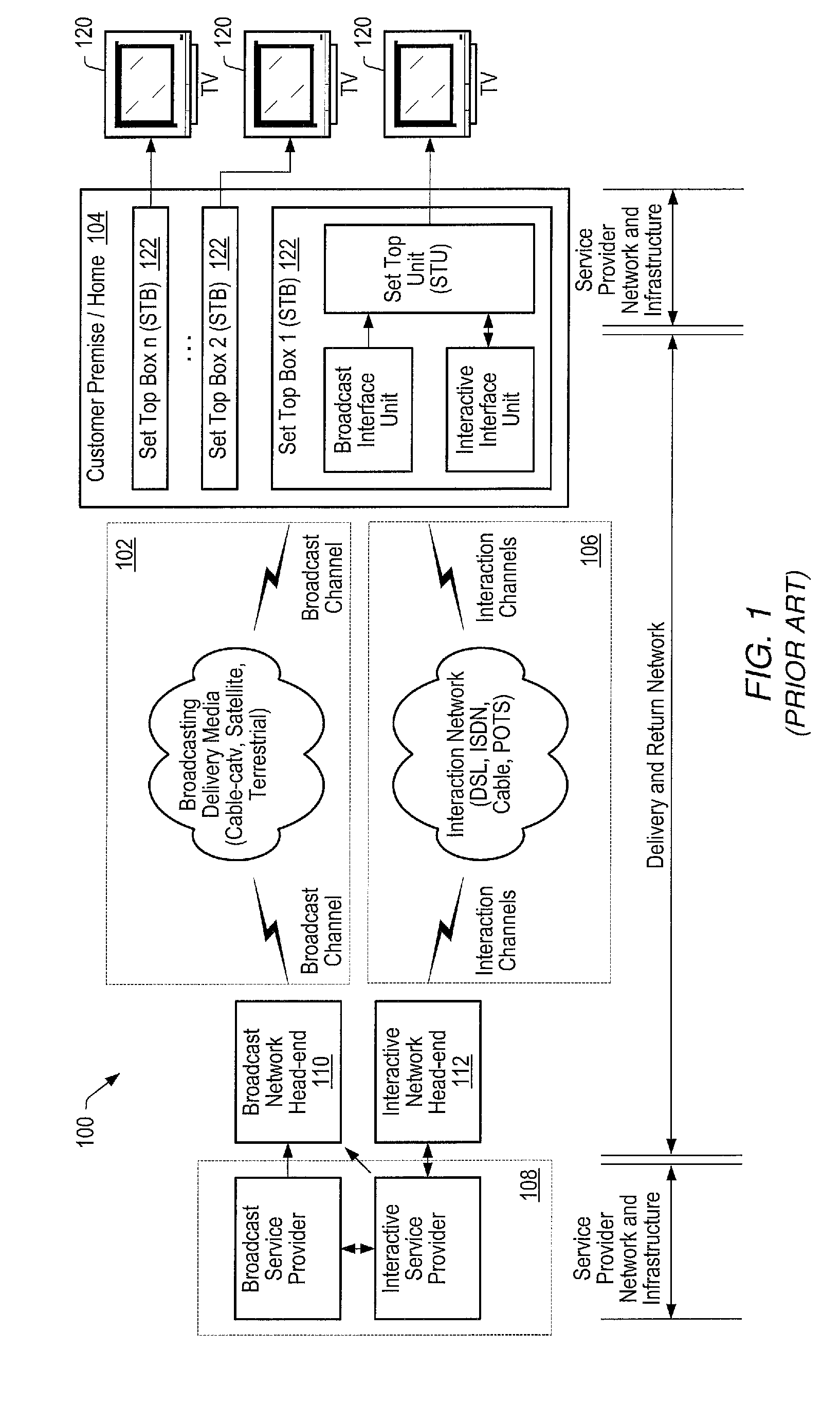
A task force (TF) is a unit or formation established to work on a single defined task or activity. Originally introduced by the United States Navy, [citation needed] the term has now caught on for general usage and is a standard part of NATO terminology.
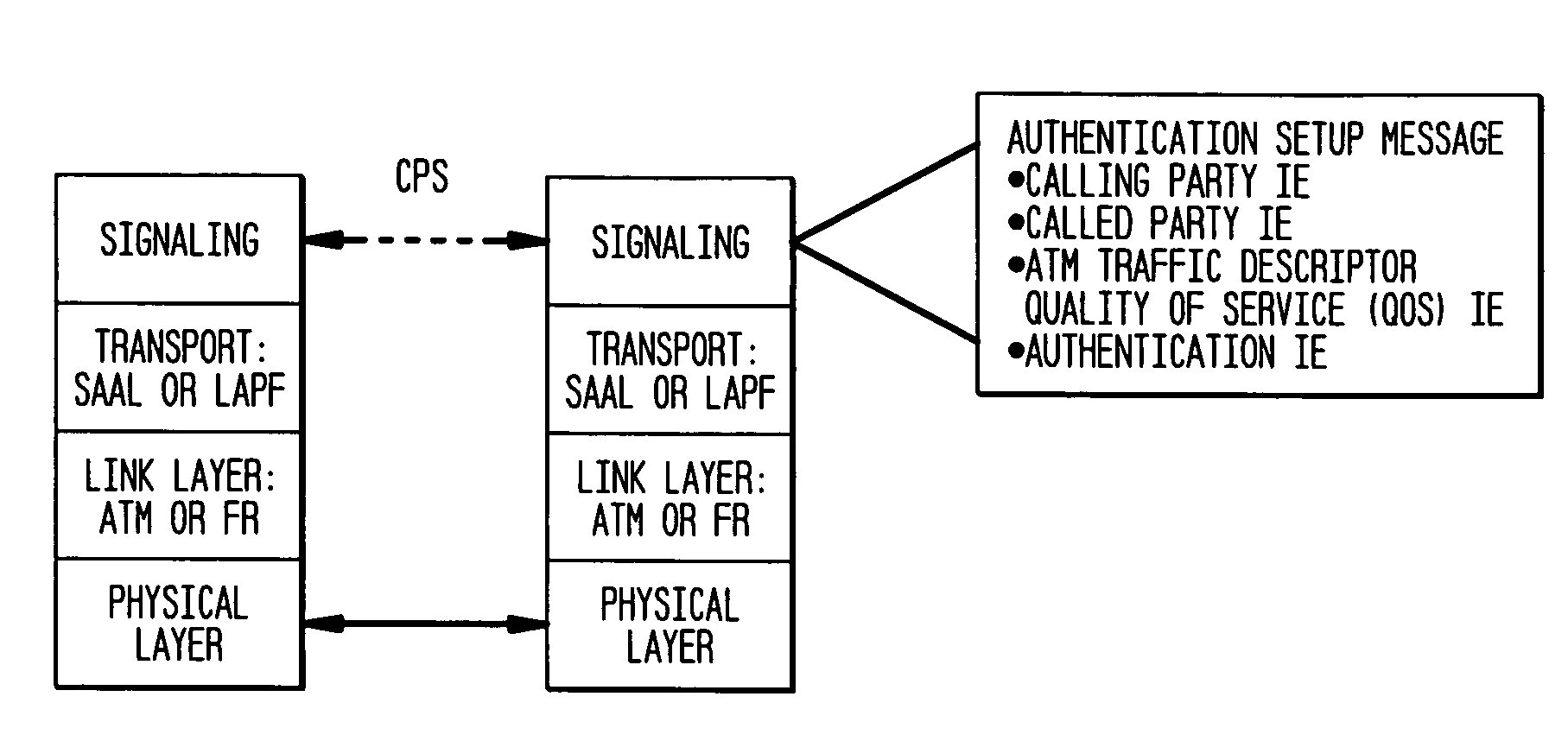
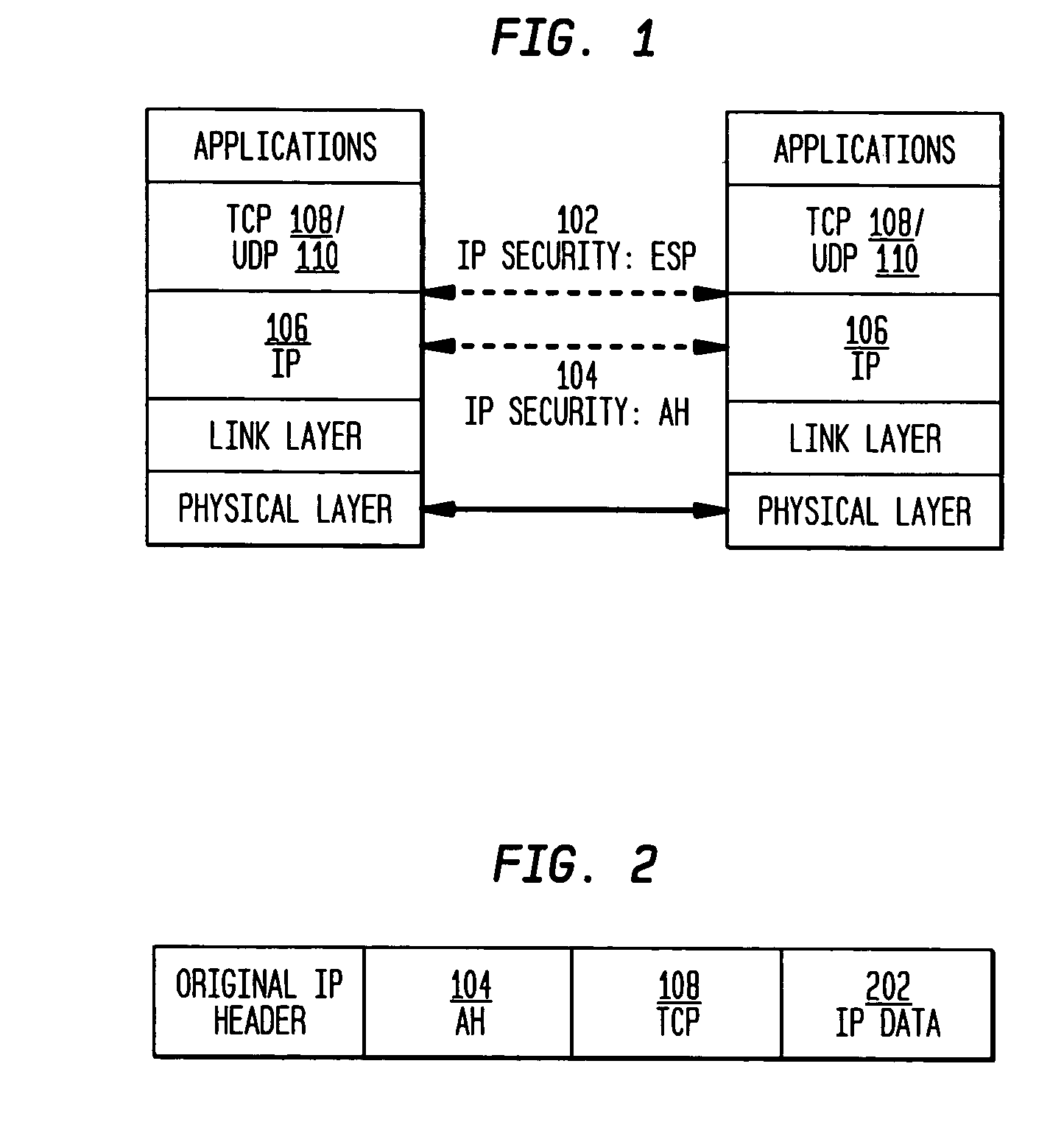
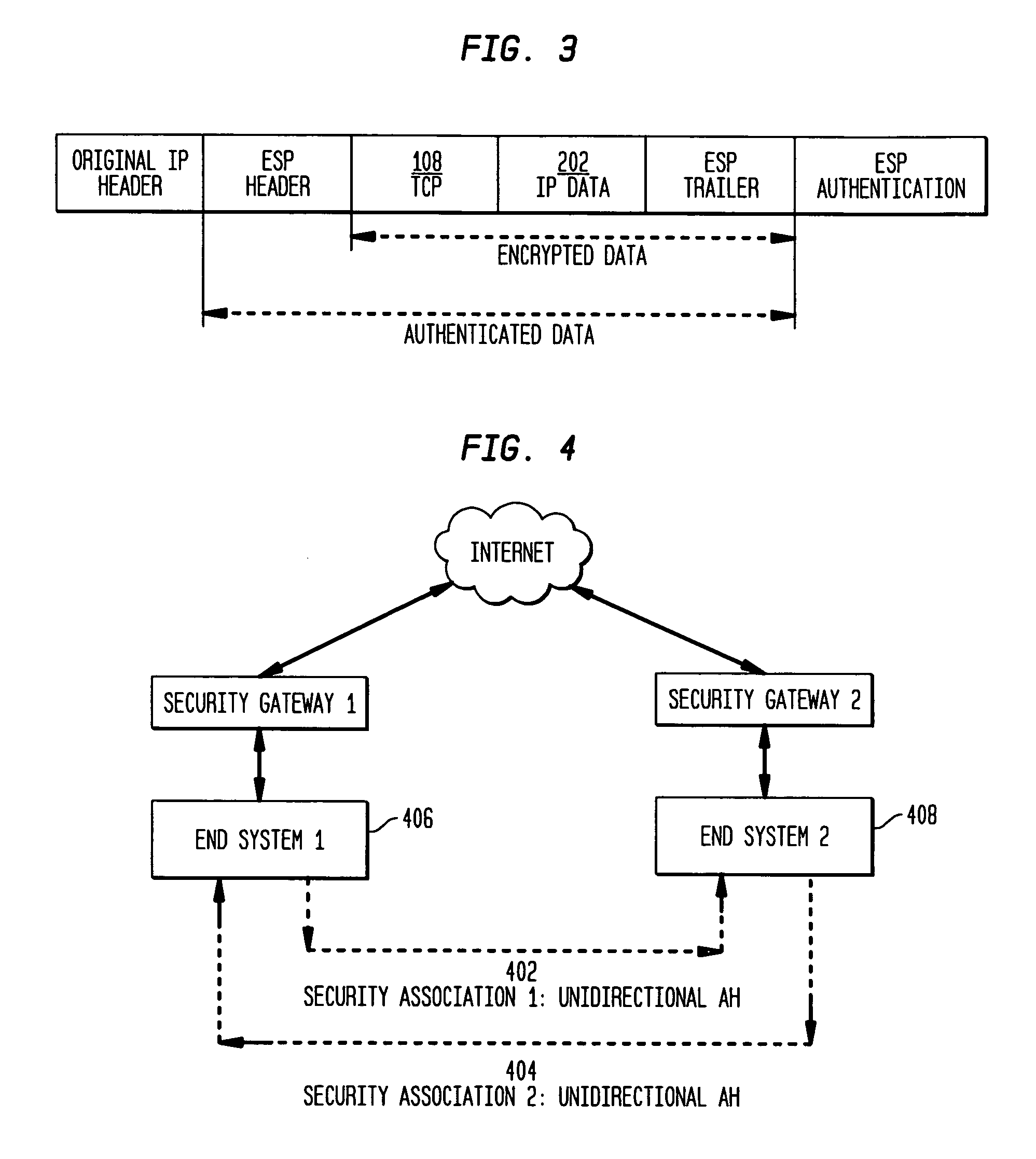
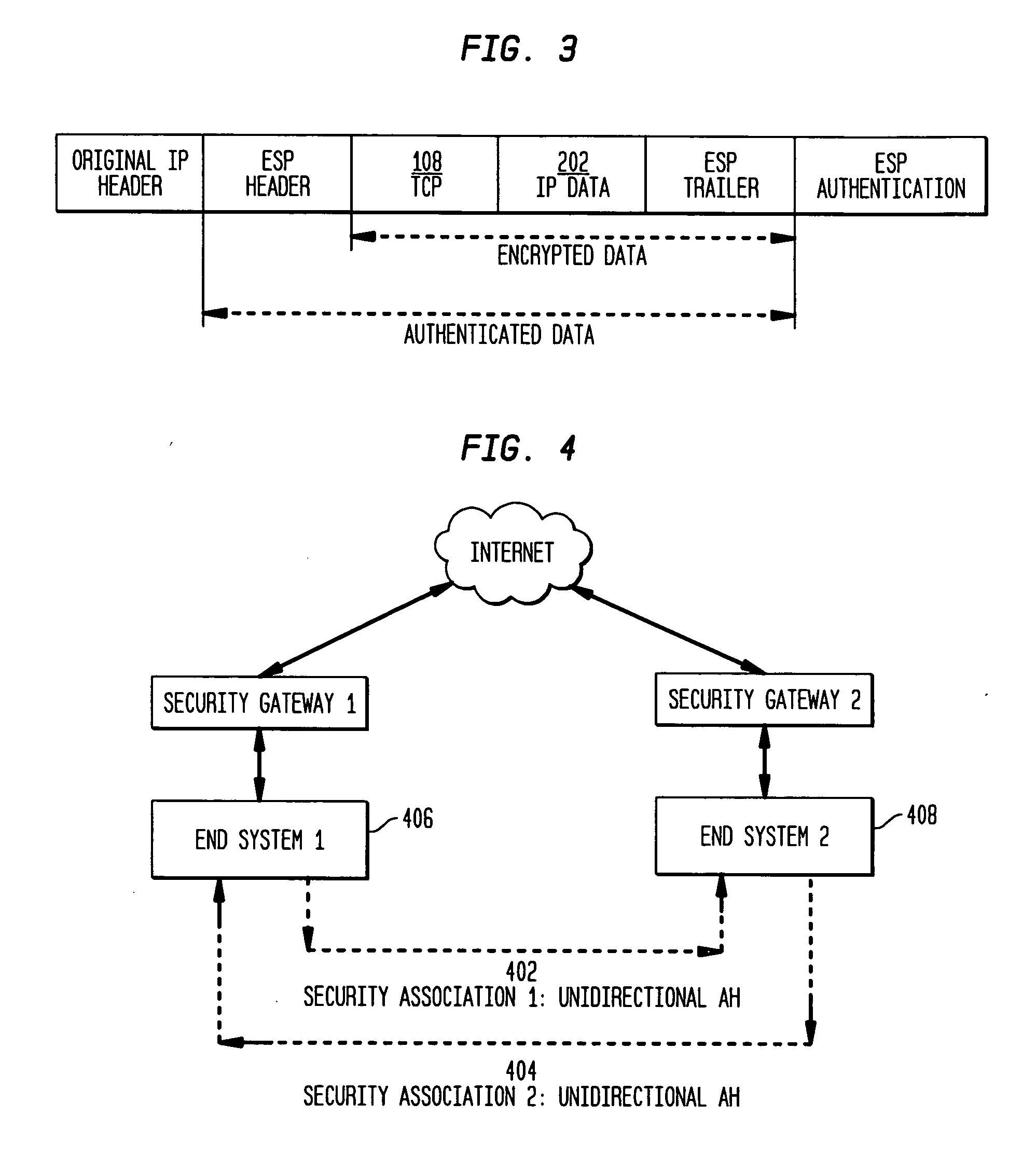
Authentication mechanisms for call control message integrity and origin verification
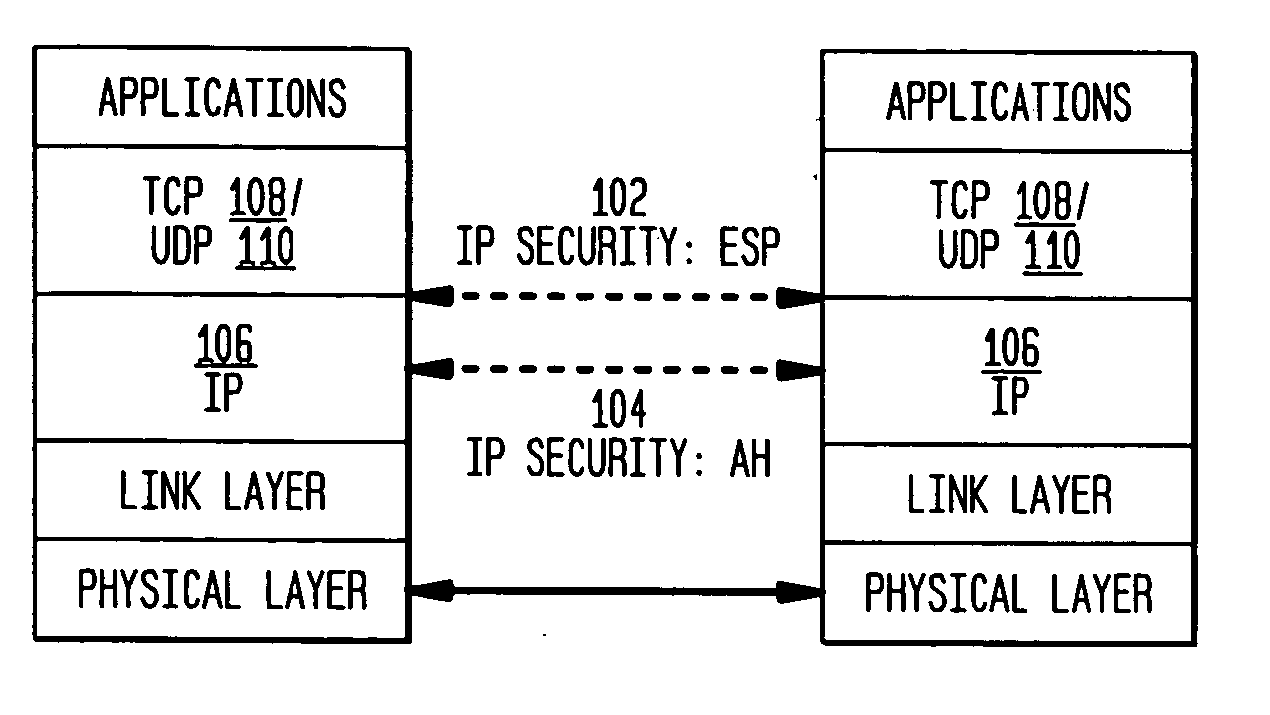
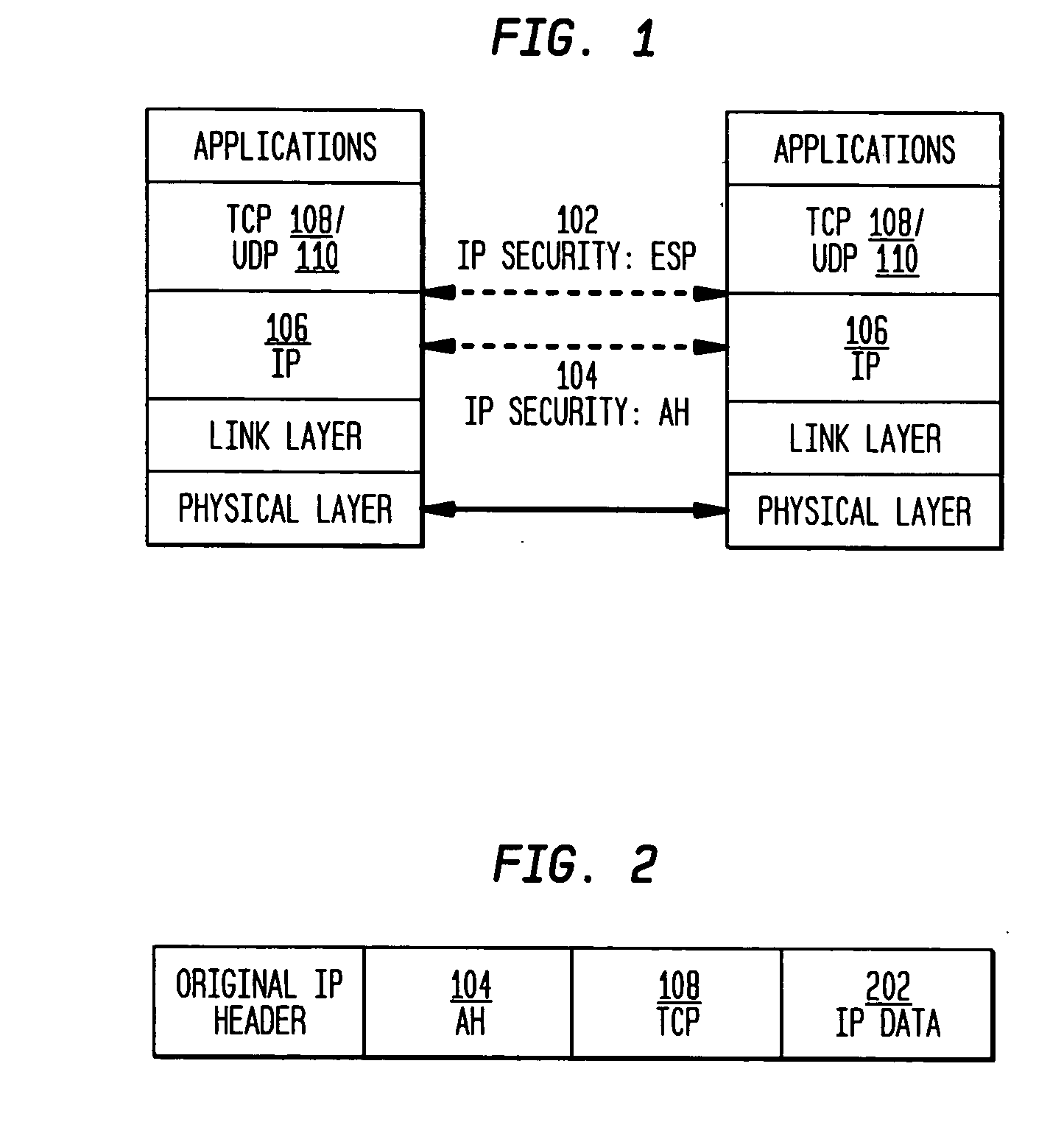
The present invention incorporates methodologies developed in the Internet Engineering Task Force (IETF) Internet Protocol Security (IPSEC) Working Group into asynchronous transfer mode (ATM) and frame relay (FR) signaling to provide message integrity and origin authentication. In one implementation the invention provides a virtual private network (VPN) infrastructure with call control message integrity, origin verification, and transit network filtering. The invention utilizes a set of control plane messages based on the IPSEC authentication header (AH) methodology to provide these security mechanisms for ATM and FR network switching equipment and signaling protocols. This abstract itself is not intended to limit the scope of this patent. The scope of the present invention is pointed out in the appending claims.
Owner:ALCATEL-LUCENT USA INC
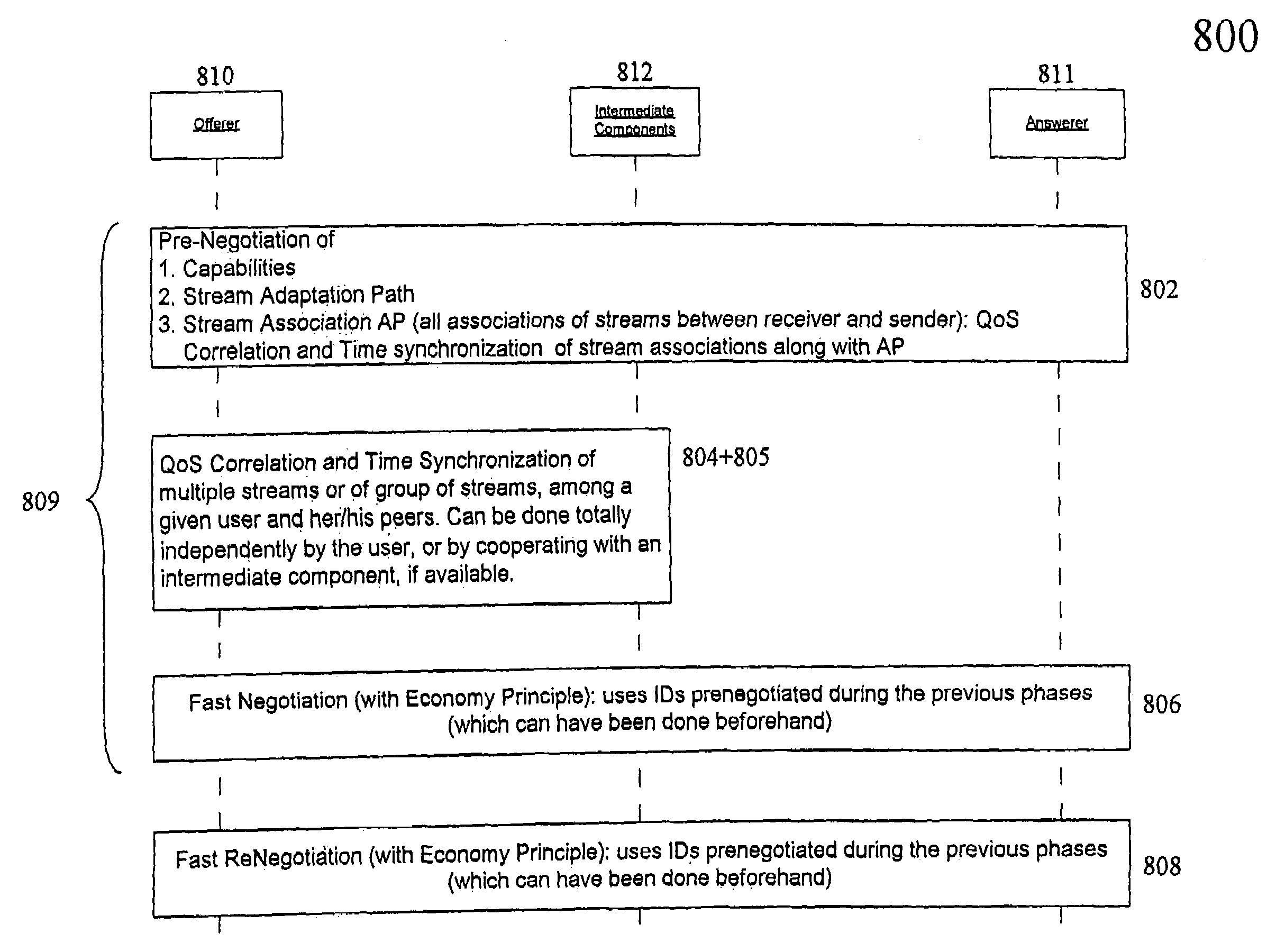
Model for enforcing different phases of the end-to-end negotiation protocol (E2ENP) aiming QoS support for multi-stream and multimedia applications
ActiveUS7602723B2Dynamic characteristicCoupling device connectionsError preventionMulti streamExtensible markup
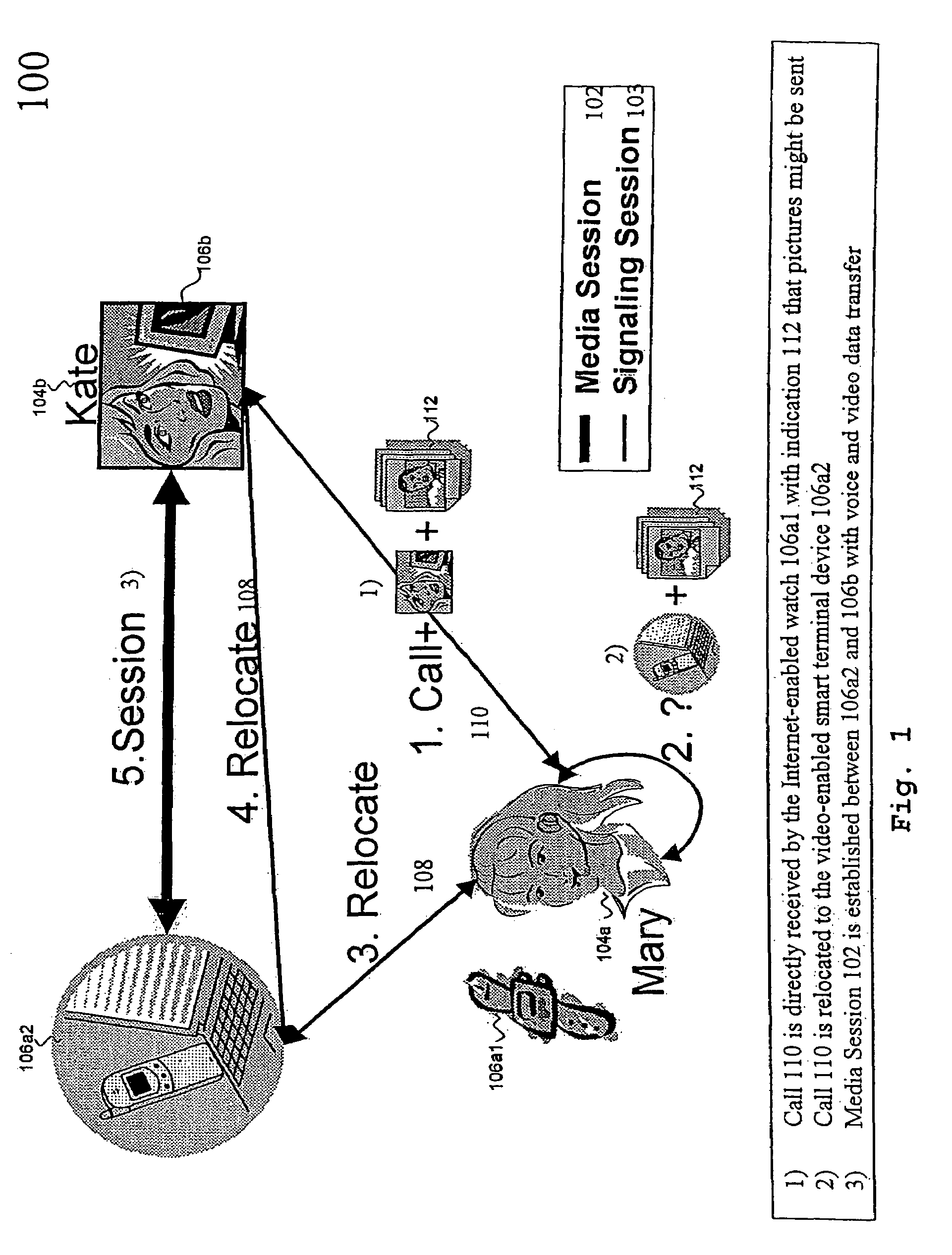
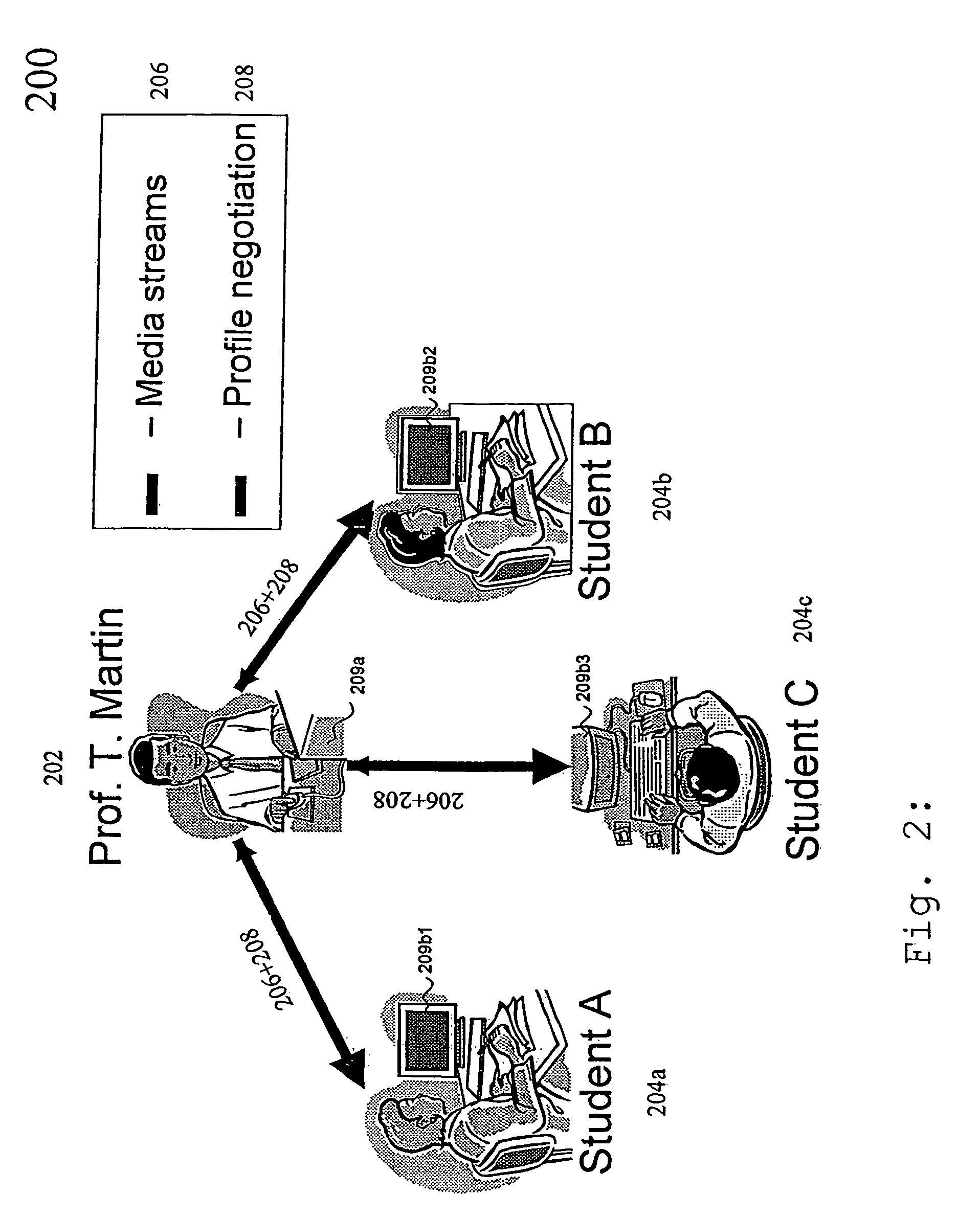
The underlying invention generally relates to the field of mobile computing in a networking environment with distributed multimedia applications and technologies. More specifically, it is directed to the concept of the End-to-End Negotiation Protocol (E2ENP) phases, which enable a pre-negotiation (802, 804, 805), fast negotiation (806) and a fast, dynamic renegotiation (808) of the end-to-end quality and capabilities for telecommunication sessions (102), for multiple configurations of two or a multiplicity of end peers and / or intermediate components in a consistent, reliable, and incremental way by enabling the mobile users' applications to efficiently and timely react to QoS violations. In this context, the invention proposes a model for defining user profiles and terminal capability information in such a way that hierarchical QoS contract specifications (1108), e.g. compelling correlations (804) across different sets of QoS contracts (1108) for related media streams (206), can be enforced and used for deriving negotiable information. As a reference implementation of this concept, this invention proposes a novel usage of the Session Initiation Protocol (SIP, 910) standardized by the Internet Engineering Task Force (IETF) in conjunction with extensions of the Session Description Protocol Next Generation (SDPng, 912) specification based on the Extensible Markup Language (XML) in order to implement concepts of the End-to-End QoS Negotiation Protocol (E2ENP, 908).
Owner:SONY DEUT GMBH +1
Method and system for key management in voice over internet protocol
InactiveUS7730309B2Eliminate needEasy to implementKey distribution for secure communicationUnauthorised/fraudulent call preventionSession Initiation ProtocolDiffie–Hellman key exchange
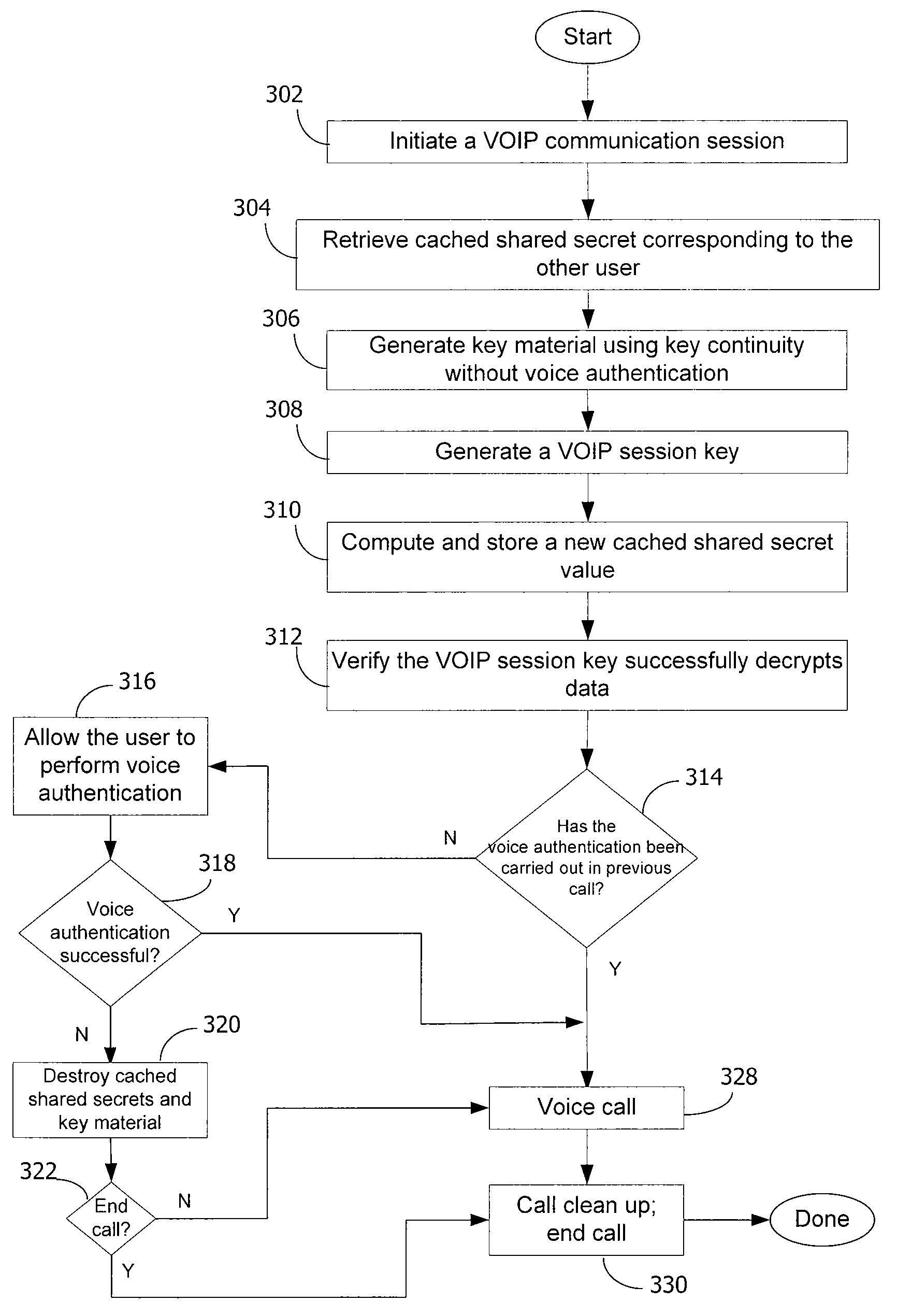
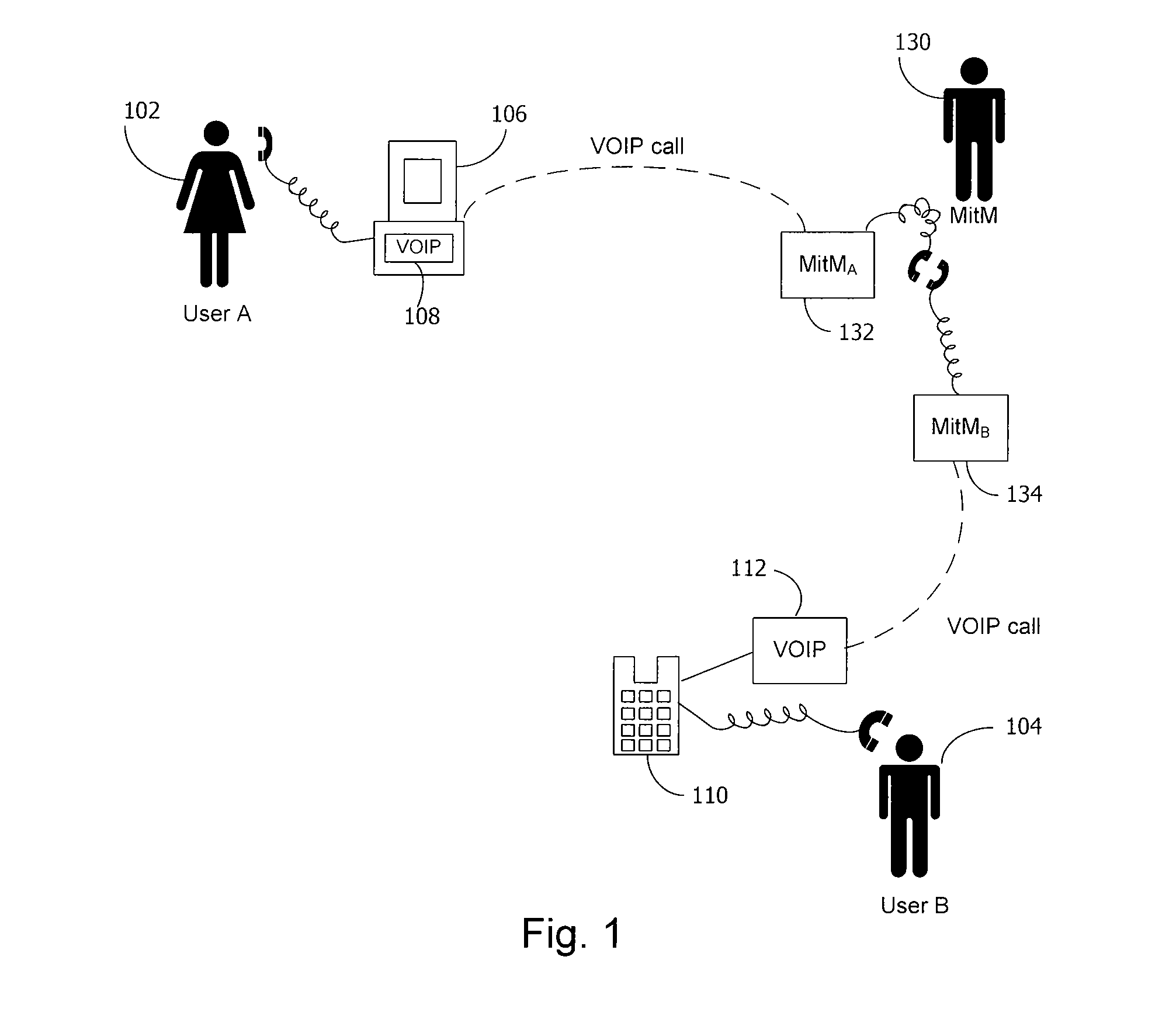
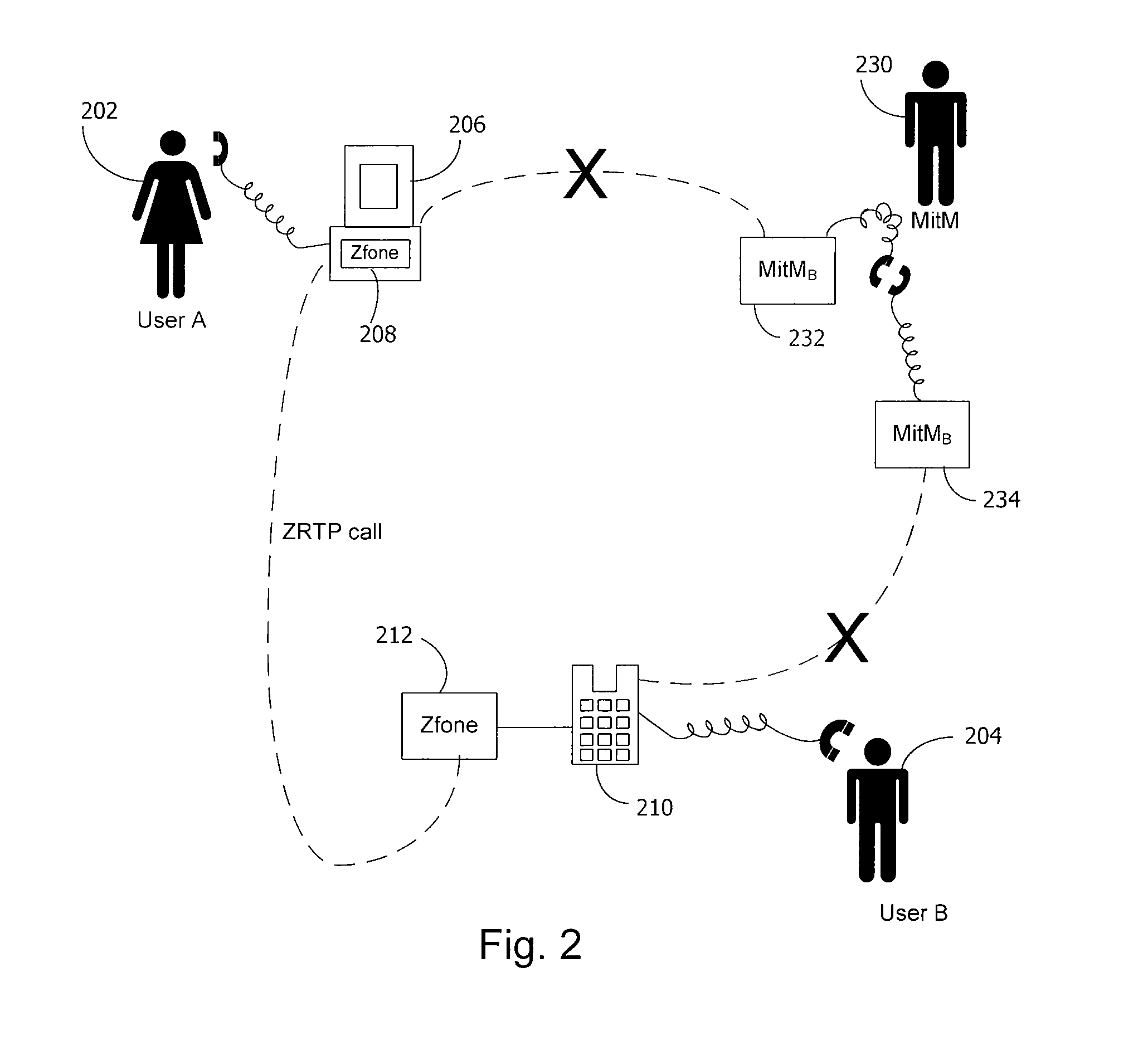
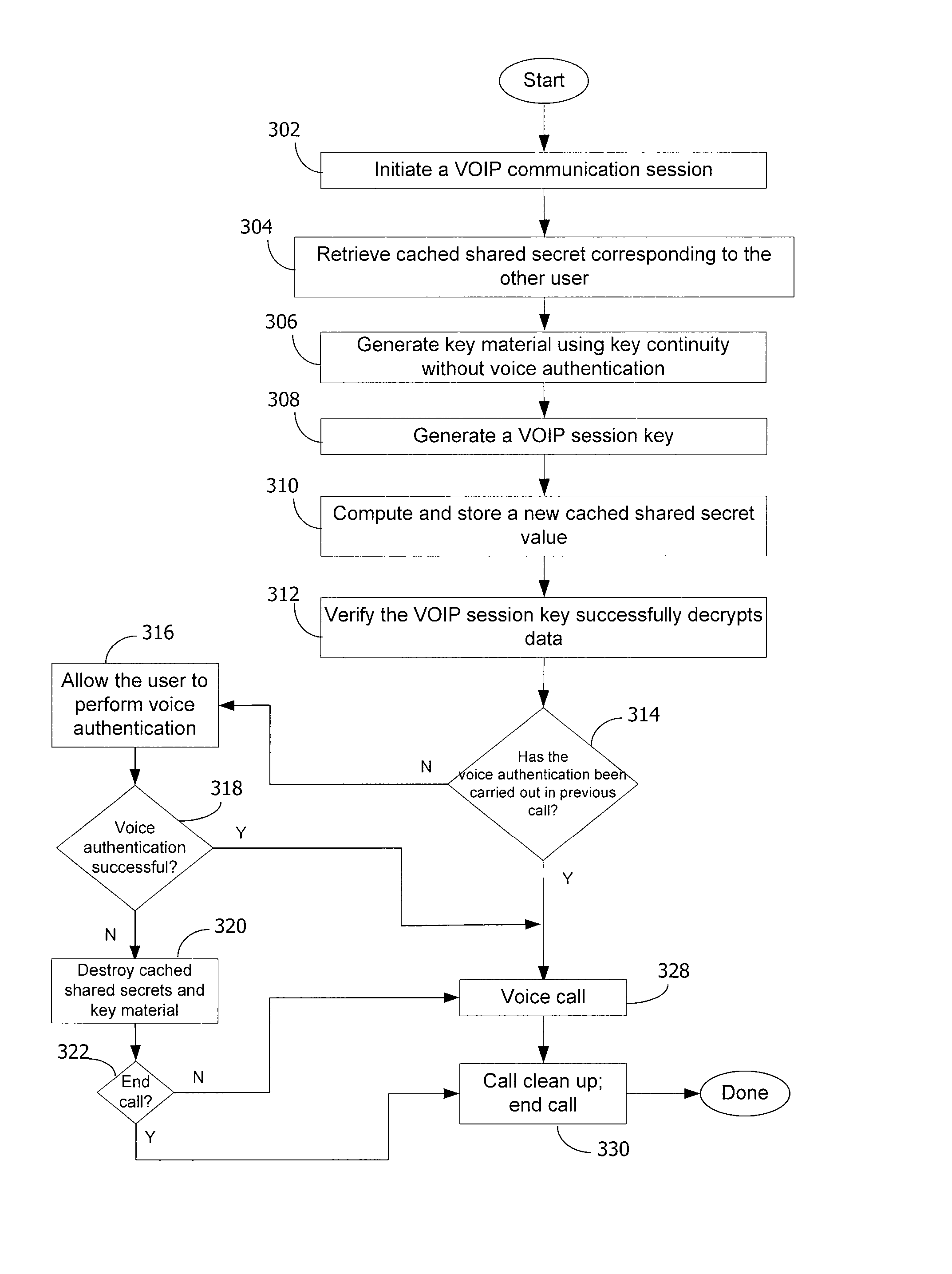
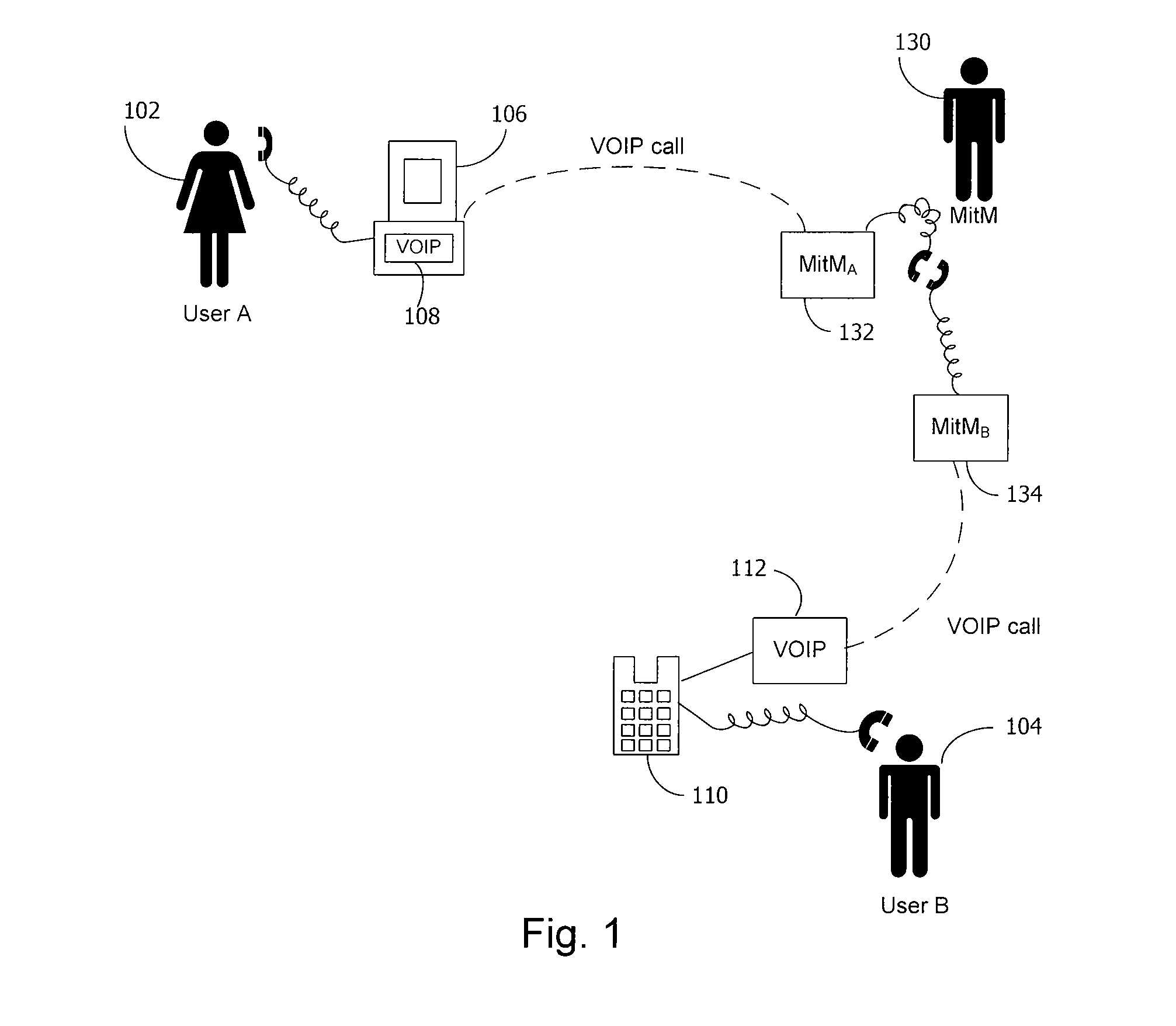
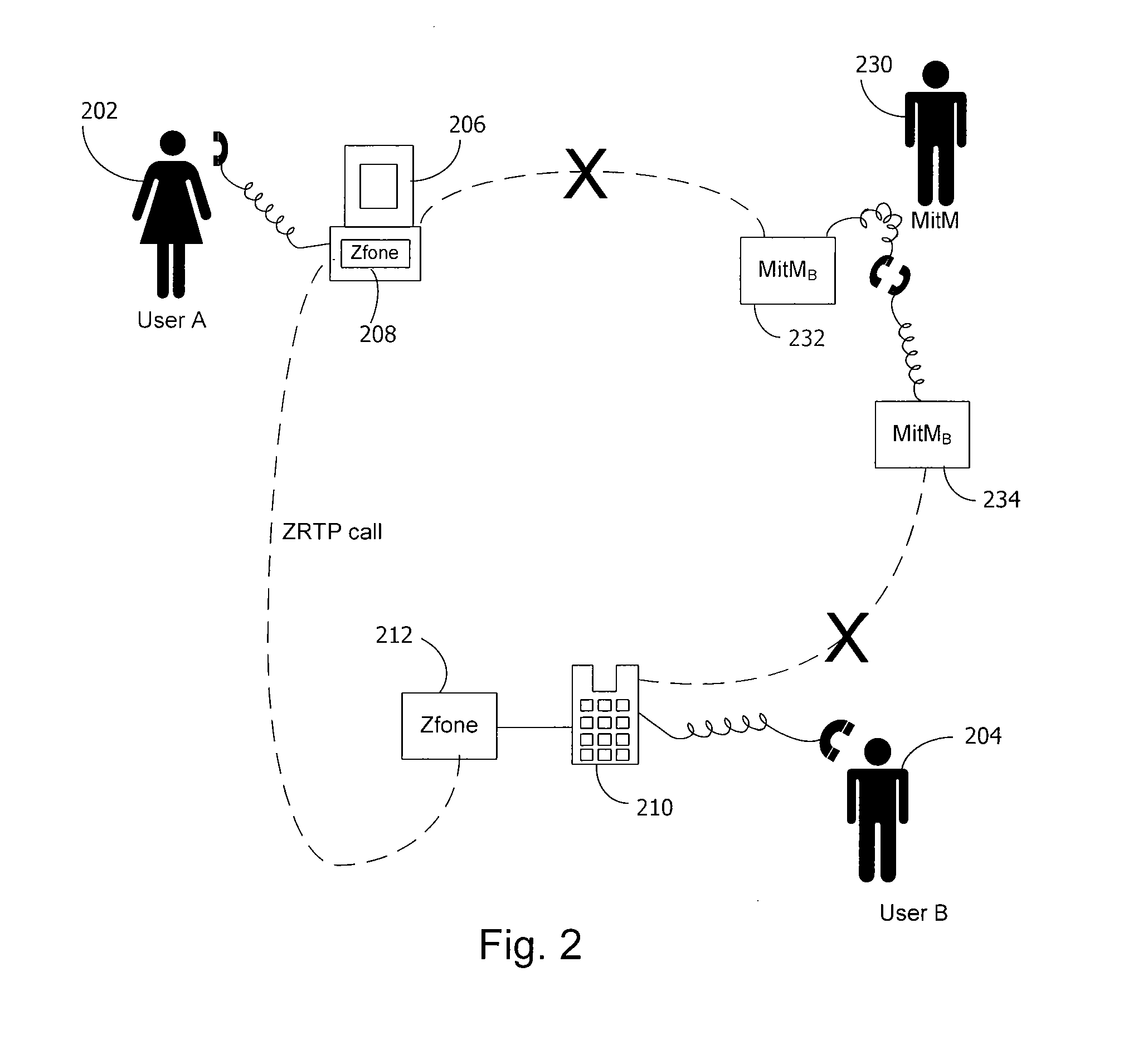
A method and system for a secure telephone protocol are disclosed, which can be implemented using current Voice over IP (VoIP) protocols, Session Initiation Protocol (SIP, as specified in the Request for Comment (RFC) 3261 from the Internet Engineering Task Force (IETF)), Real Time Transport Protocol (RTP, as specified in RFC 3550), and Secure RTP (SRTP, as specified in RFC 3711). The secure telephone protocol can include a shared secret value that is cached and then re-used later to authenticate a long series of session keys to be used for numerous separate secure phone calls over a long period of time, thereby providing cryptographic key continuity without the need for voice authentication. In an embodiment, the secure telephone protocol can utilize the Diffie-Hellman key exchange during call setup, and AES for encrypting the voice stream.
Owner:ZIMMERMANN PHILIP R
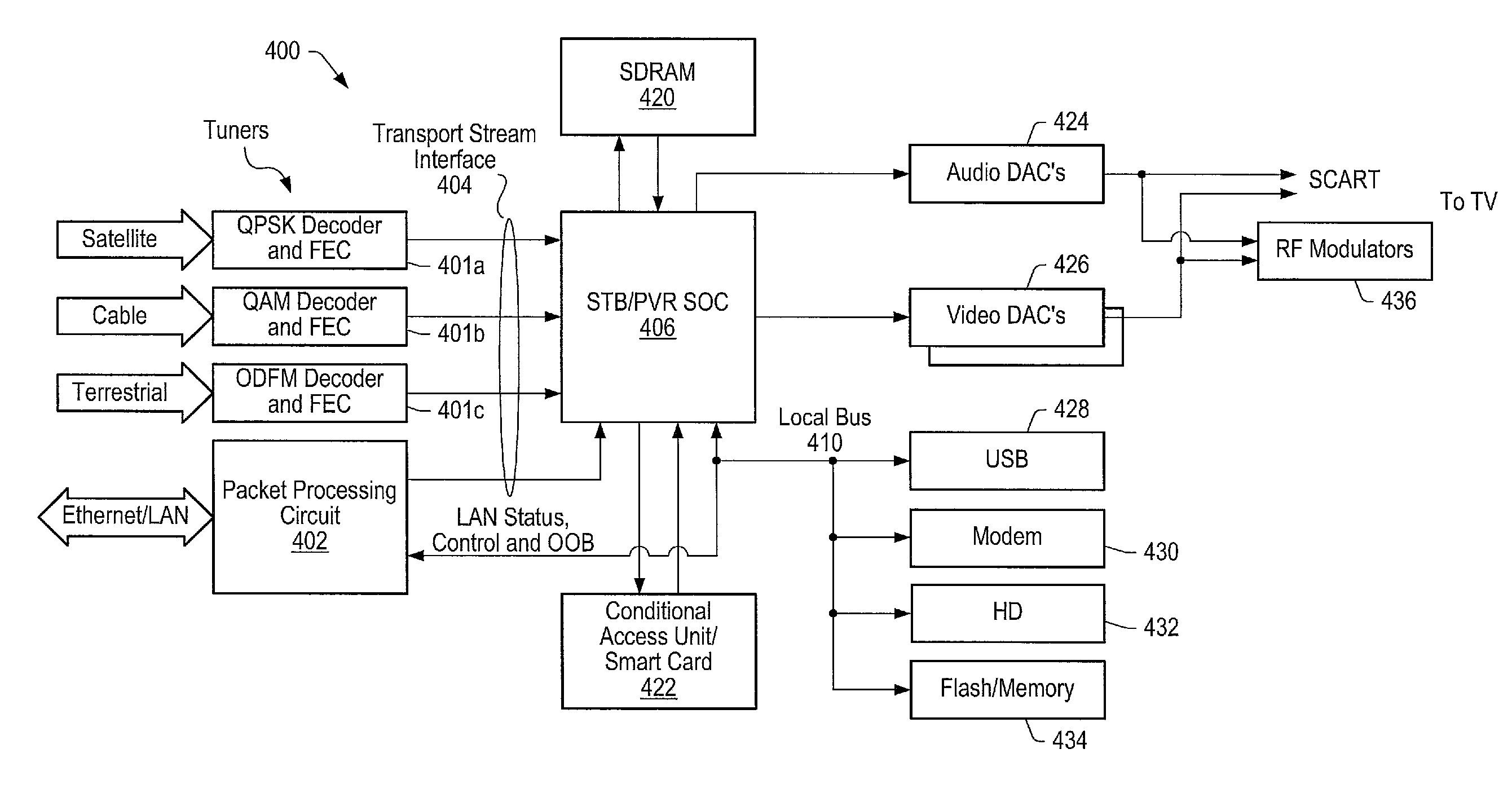
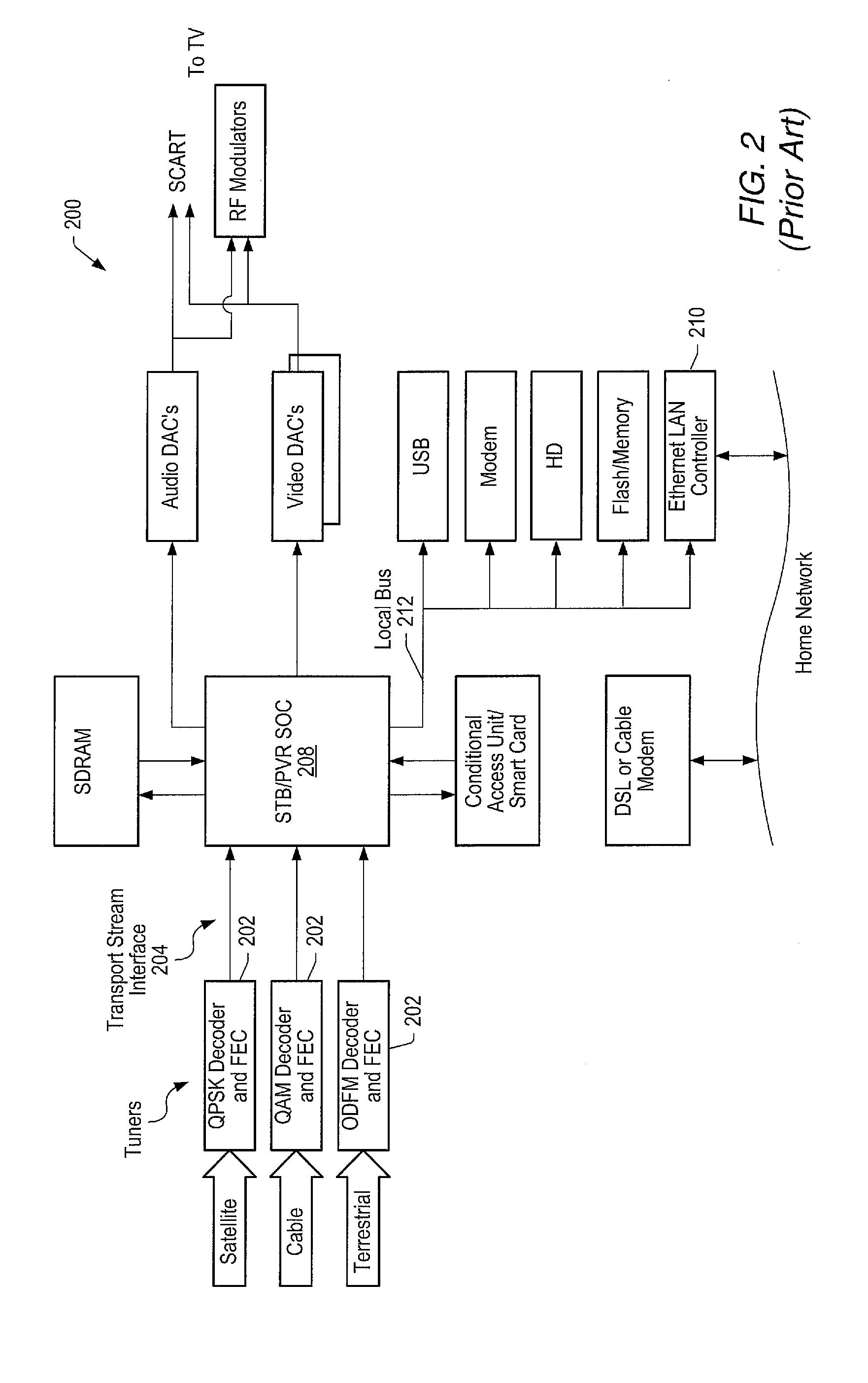
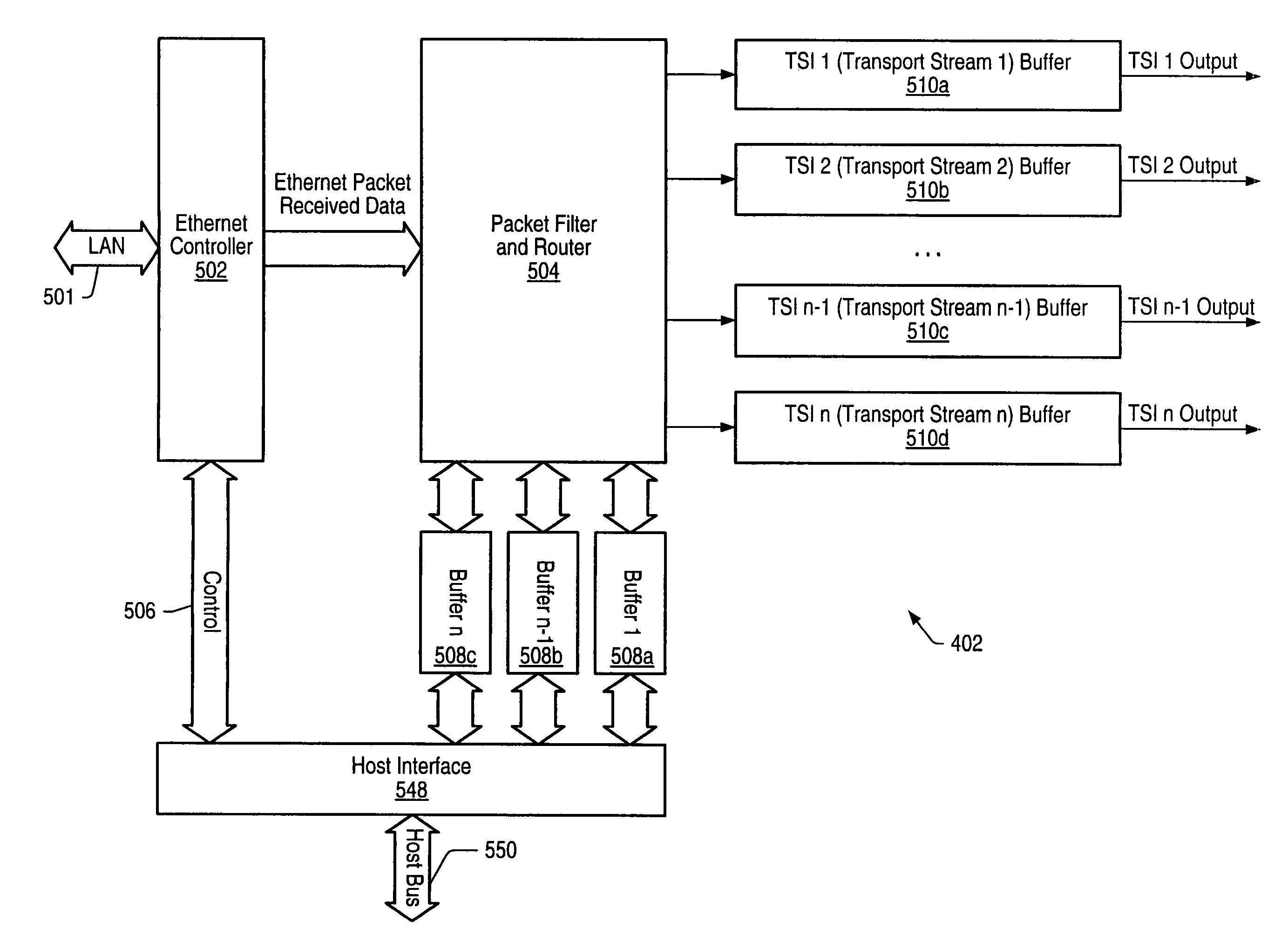
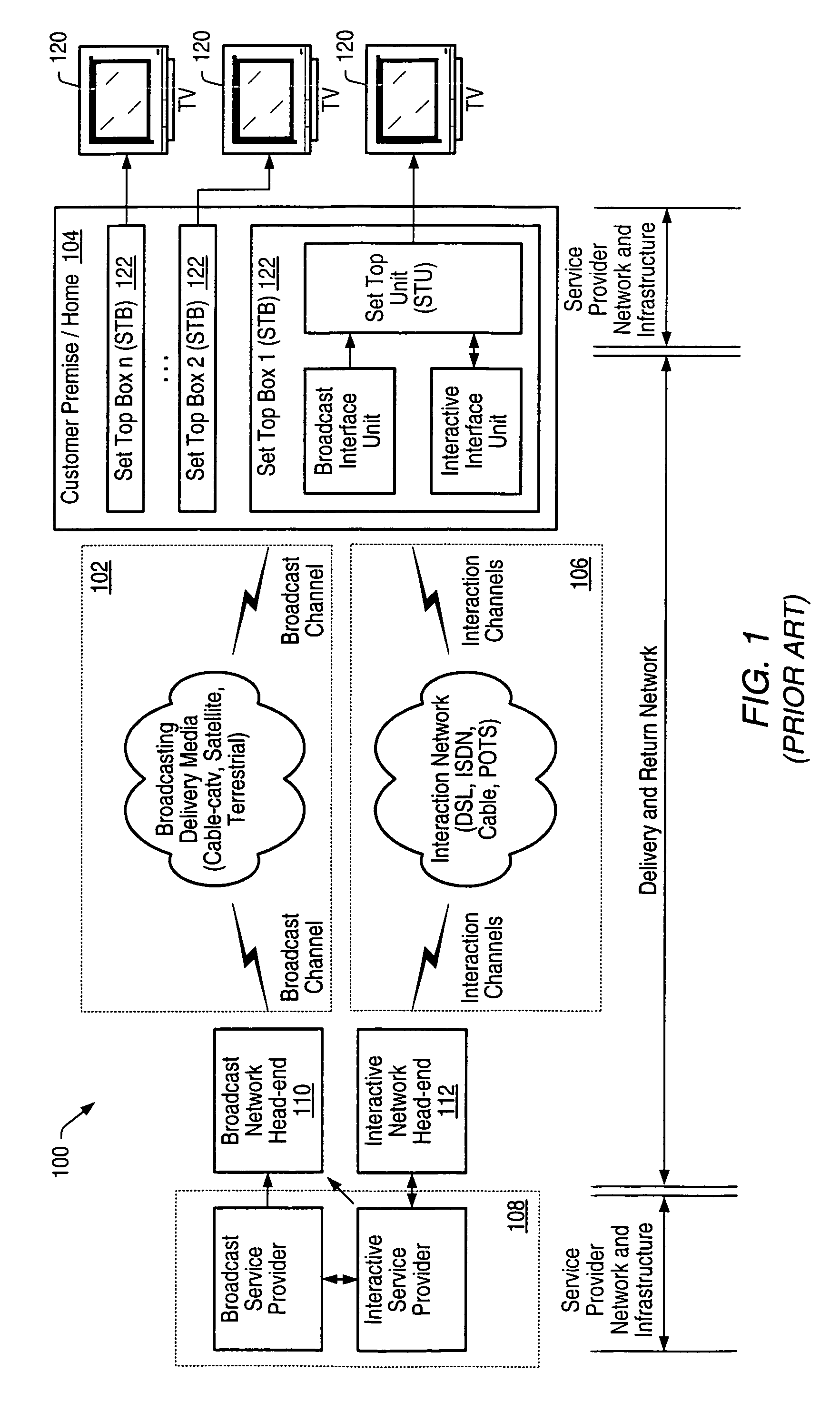
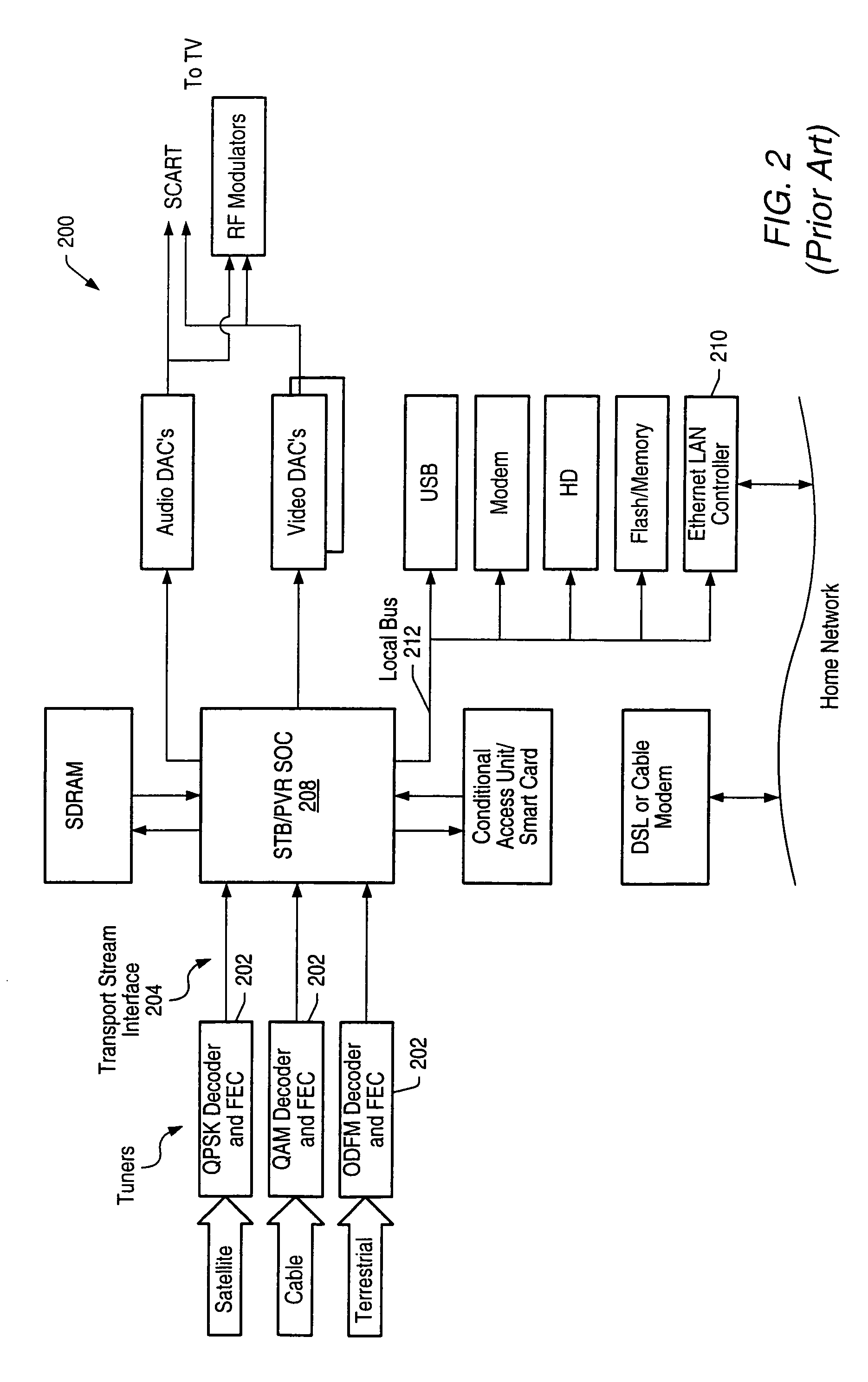
High speed ethernet MAC and PHY apparatus with a filter based ethernet packet router with priority queuing and single or multiple transport stream interfaces
ActiveUS20060174032A1Performance levelImprove efficiencySpecial service provision for substationDigital computer detailsData streamThe Internet
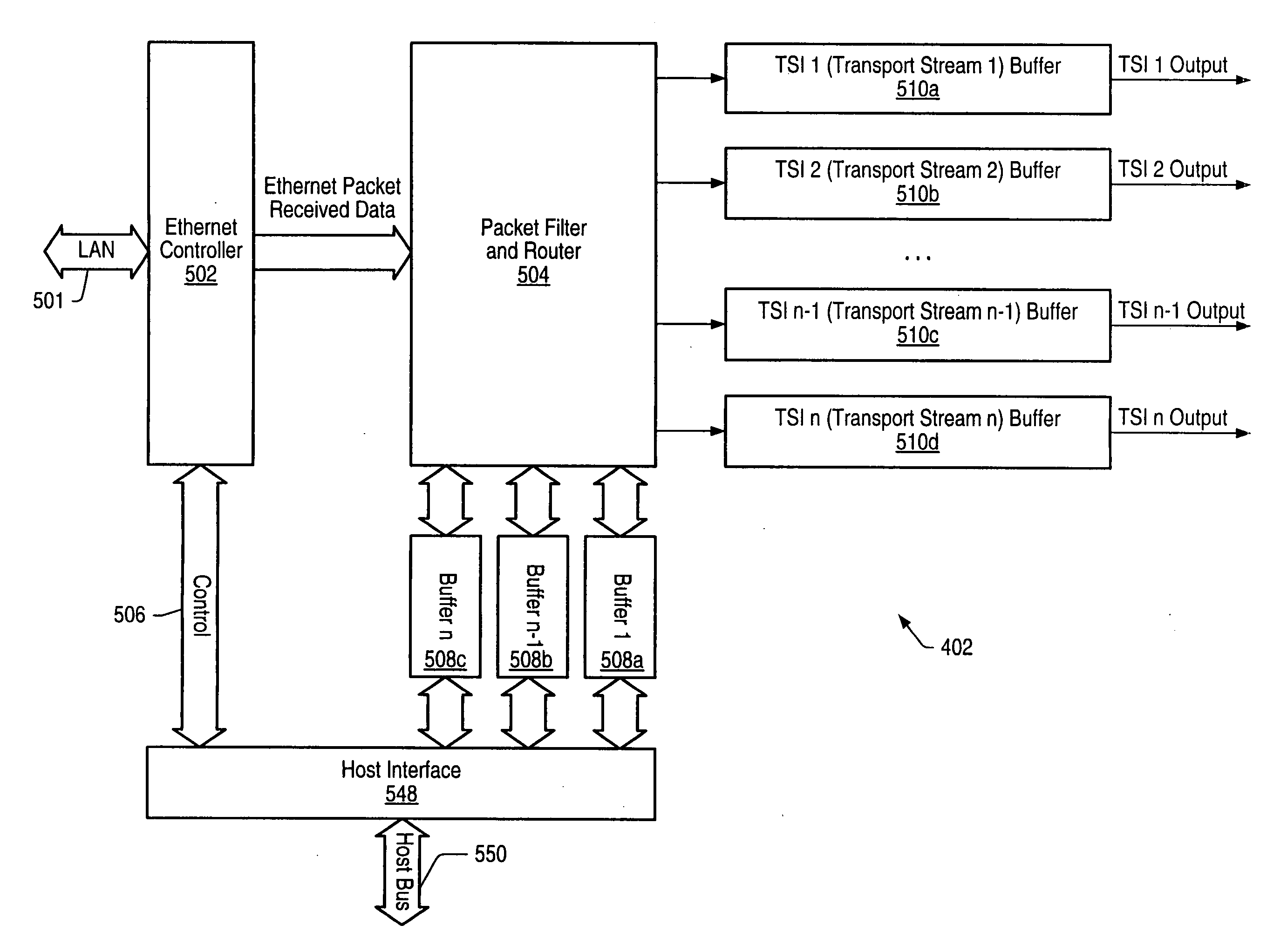
In one embodiment, an audio-visual content delivery system, such as a set-top box / personal video recorder system, is configured to interface with a local area network (LAN). A packet processing circuit comprised in the system may be configured to filter and route Ethernet packet data received from the LAN to specific ports and / or queues without host processor intervention. The packet processing circuit may utilize a set of filter and routing mechanisms configurable in hardware to interpret various Internet Engineering Task Force (IETF) networking transport protocols, and may transfer the packet data in a format recognized by a variety of consumer subsystems, each of which may be coupled to the decoder. The packet processing circuit may be implemented as a semiconductor device, and may allow encapsulated application data, (encapsulated using standardized encapsulation techniques), to be routed to a plurality of different types of application sinks or processors, forming a point-to-point or multi-point serial or parallel data stream over a standard transport covering numerous levels of the ISO data communications stack.
Owner:MICROCHIP TECH INC
Method and system for key management in voice over internet protocol
InactiveUS20070157026A1Eliminate needEasy to implementKey distribution for secure communicationUnauthorised/fraudulent call preventionSession Initiation ProtocolDiffie–Hellman key exchange
A method and system for a secure telephone protocol are disclosed, which can be implemented using current Voice over IP (VoIP) protocols, Session Initiation Protocol (SIP, as specified in the Request for Comment (RFC) 3261 from the Internet Engineering Task Force (IETF)), Real Time Transport Protocol (RTP, as specified in RFC 3550), and Secure RTP (SRTP, as specified in RFC 3711). The secure telephone protocol can include a shared secret value that is cached and then re-used later to authenticate a long series of session keys to be used for numerous separate secure phone calls over a long period of time, thereby providing cryptographic key continuity without the need for voice authentication. In an embodiment, the secure telephone protocol can utilize the Diffie-Hellman key exchange during call setup, and AES for encrypting the voice stream.
Owner:ZIMMERMANN PHILIP R
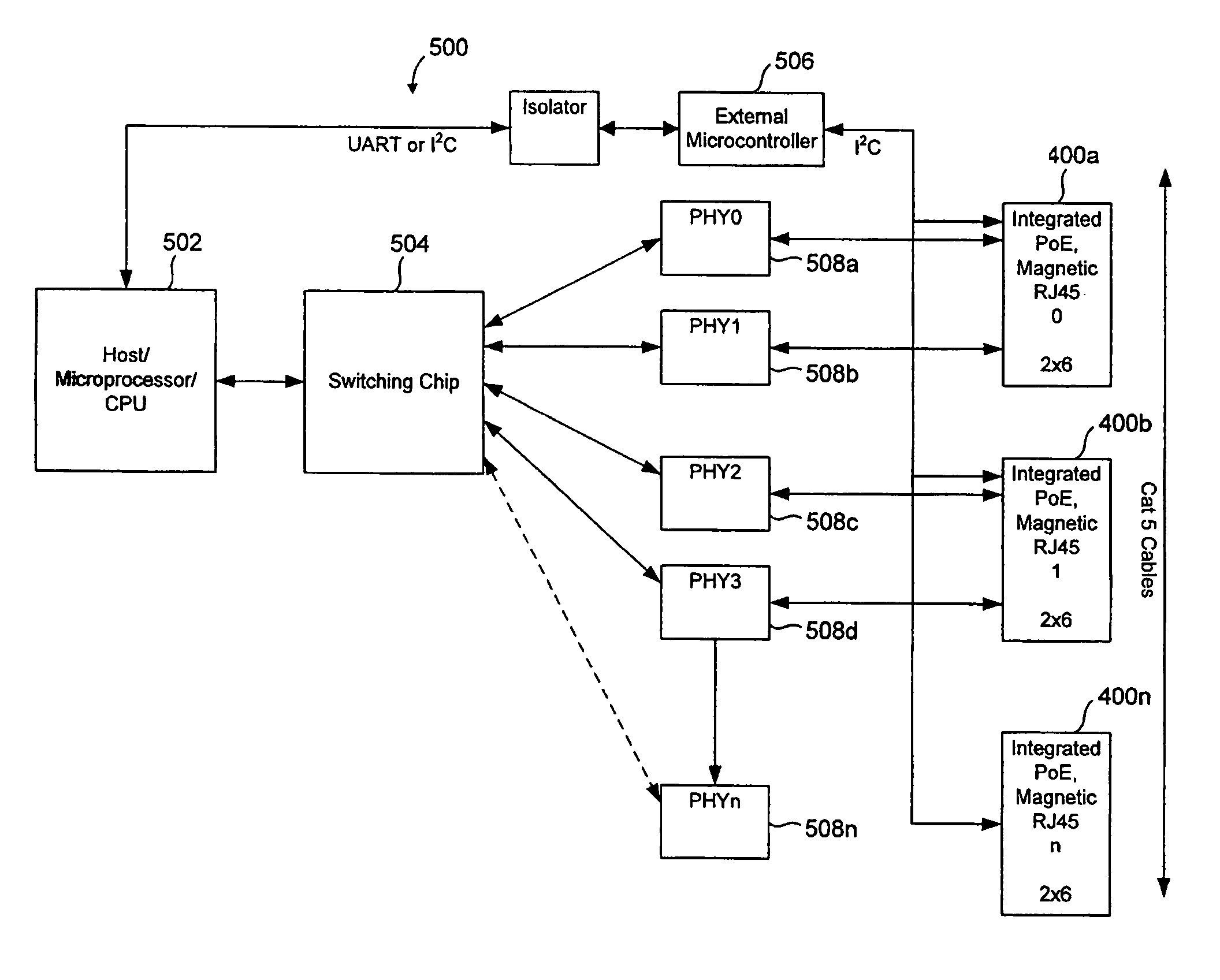
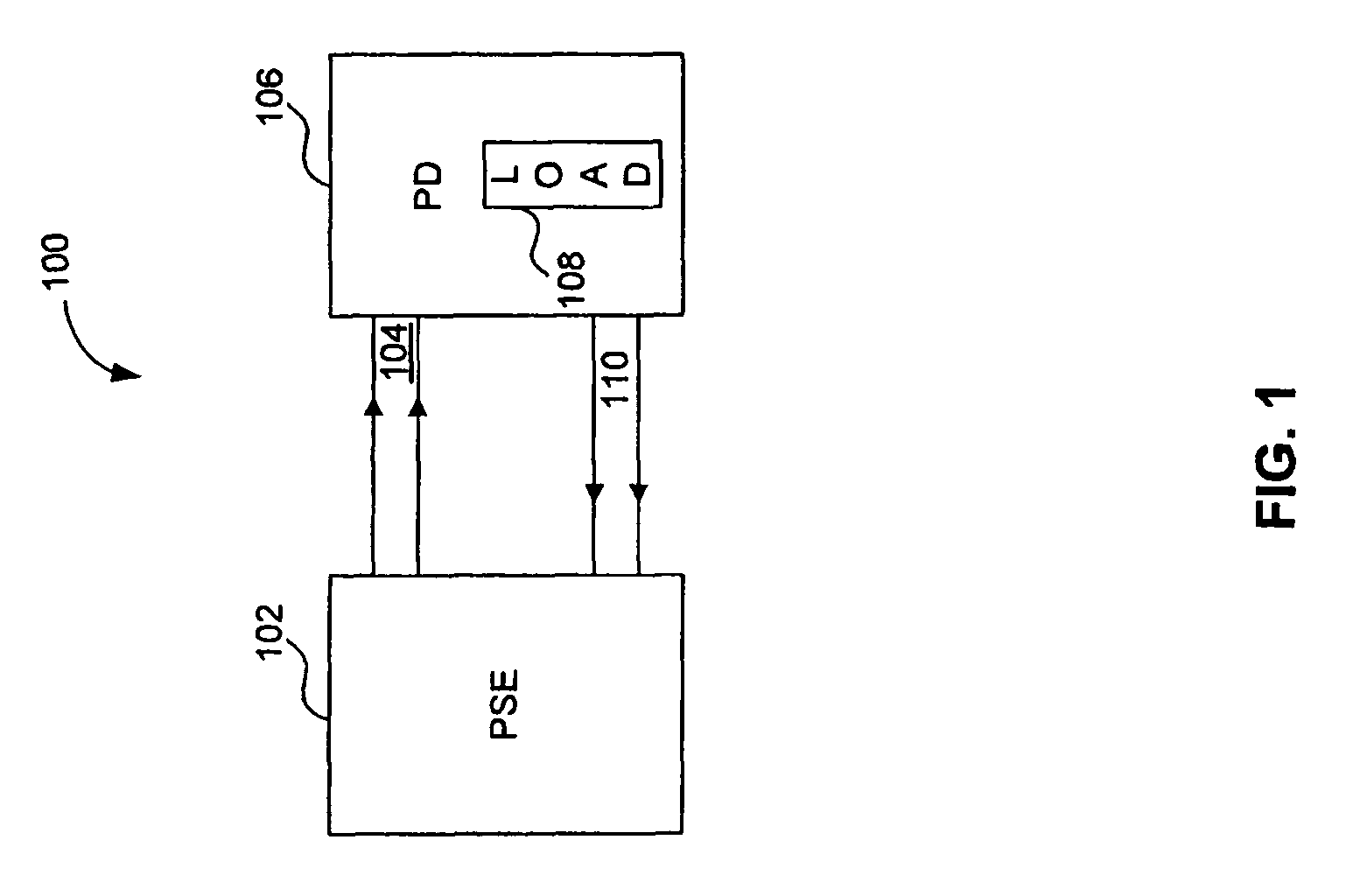
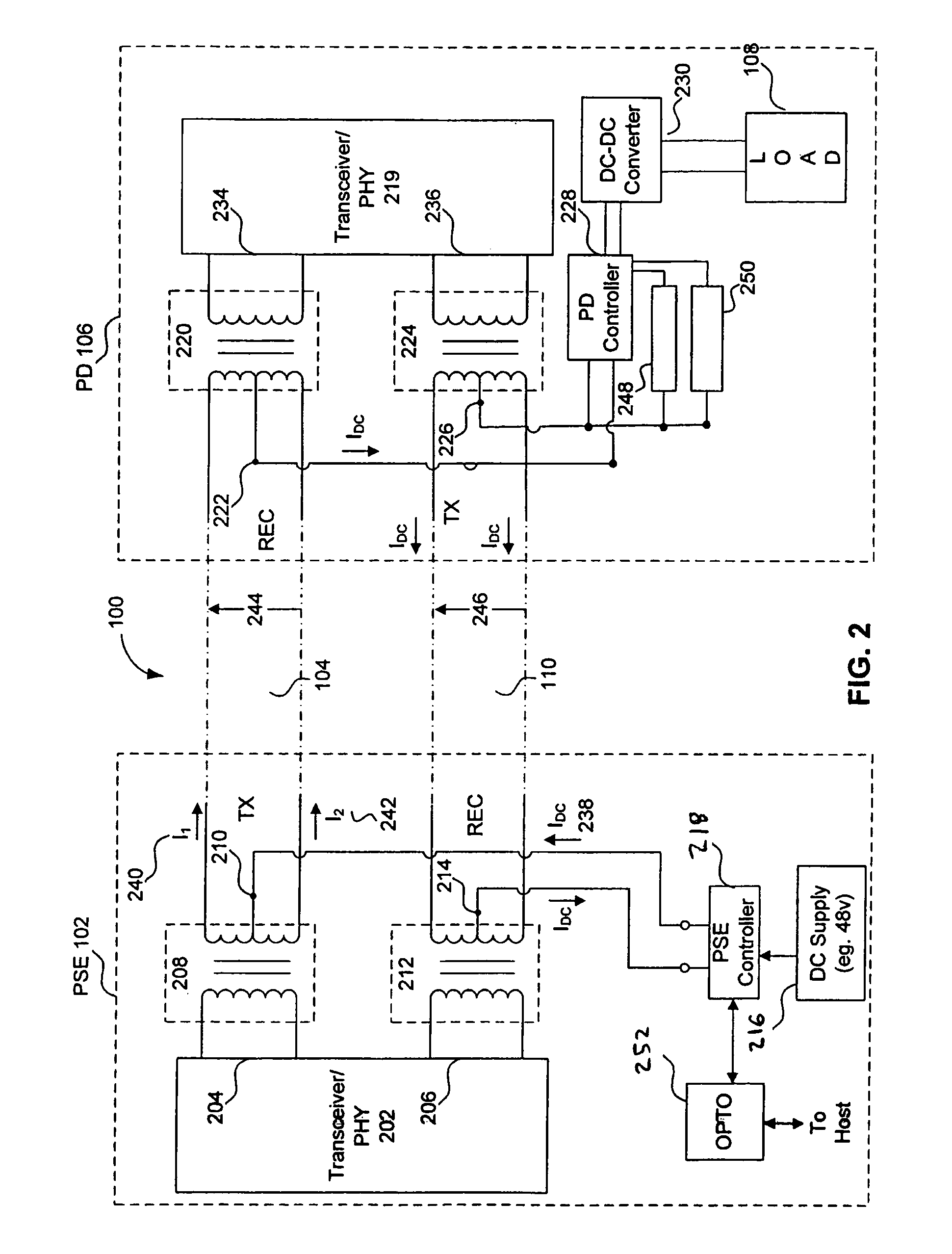
Power over ethernet connector with integrated power source equipment (PSE) controller supporting high power applications
ActiveUS8037324B2Volume/mass flow measurementPower supply for data processingElectricityComputer module
Owner:AVAGO TECH INT SALES PTE LTD
Authentication mechanisms for call control message integrity and origin verification
ActiveUS20050243798A1Provide securityMultiple digital computer combinationsProgram controlTransit networkFrame Relay
The present invention incorporates methodologies developed in the Internet Engineering Task Force (IETF) Internet Protocol Security (IPSEC) Working Group into asynchronous transfer mode (ATM) and frame relay (FR) signaling to provide message integrity and origin authentication. In one implementation the invention provides a virtual private network (VPN) infrastructure with call control message integrity, origin verification, and transit network filtering. The invention utilizes a set of control plane messages based on the IPSEC authentication header (AH) methodology to provide these security mechanisms for ATM and FR network switching equipment and signaling protocols. This abstract itself is not intended to limit the scope of this patent. The scope of the present invention is pointed out in the appending claims.
Owner:ALCATEL-LUCENT USA INC
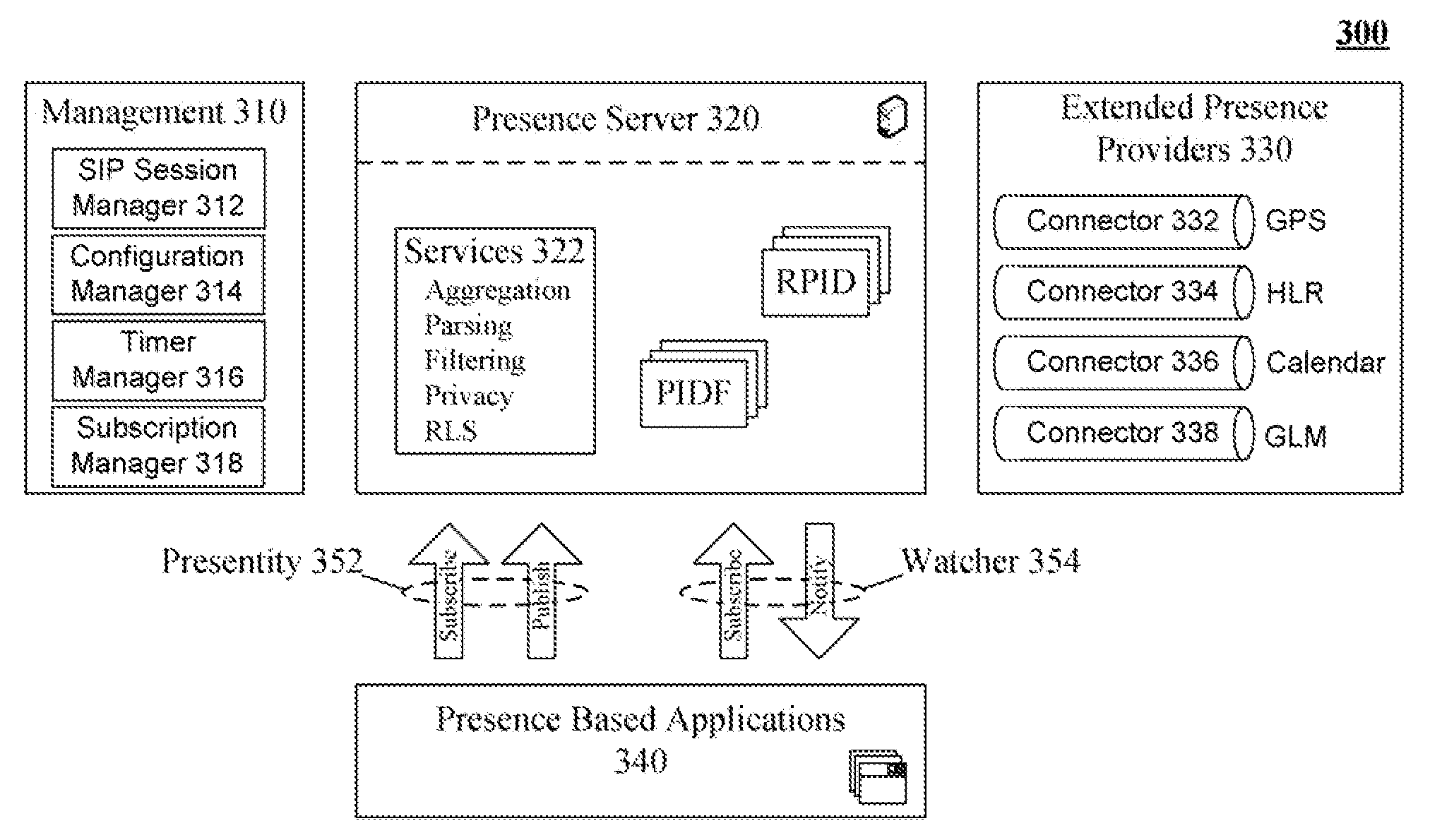
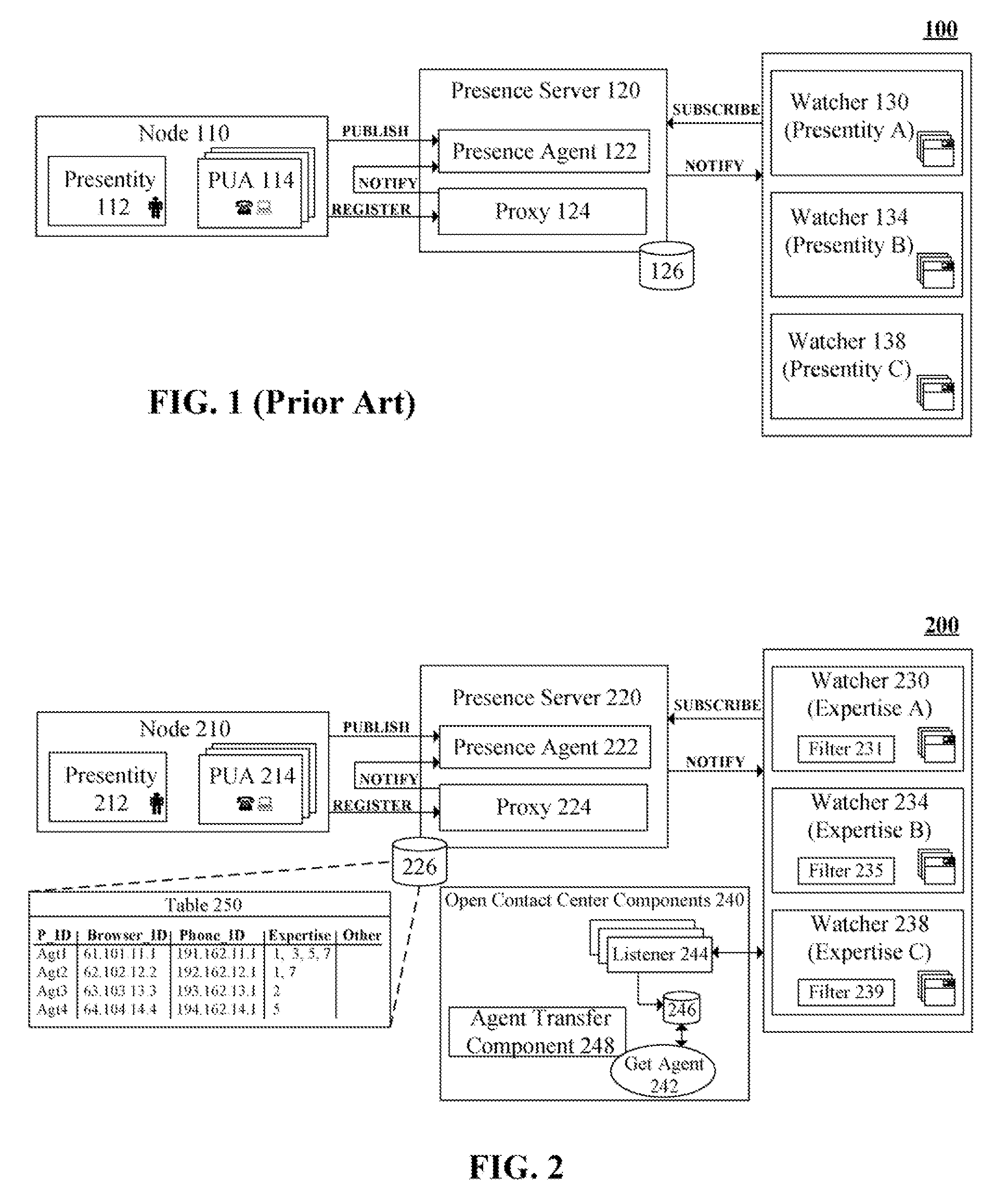
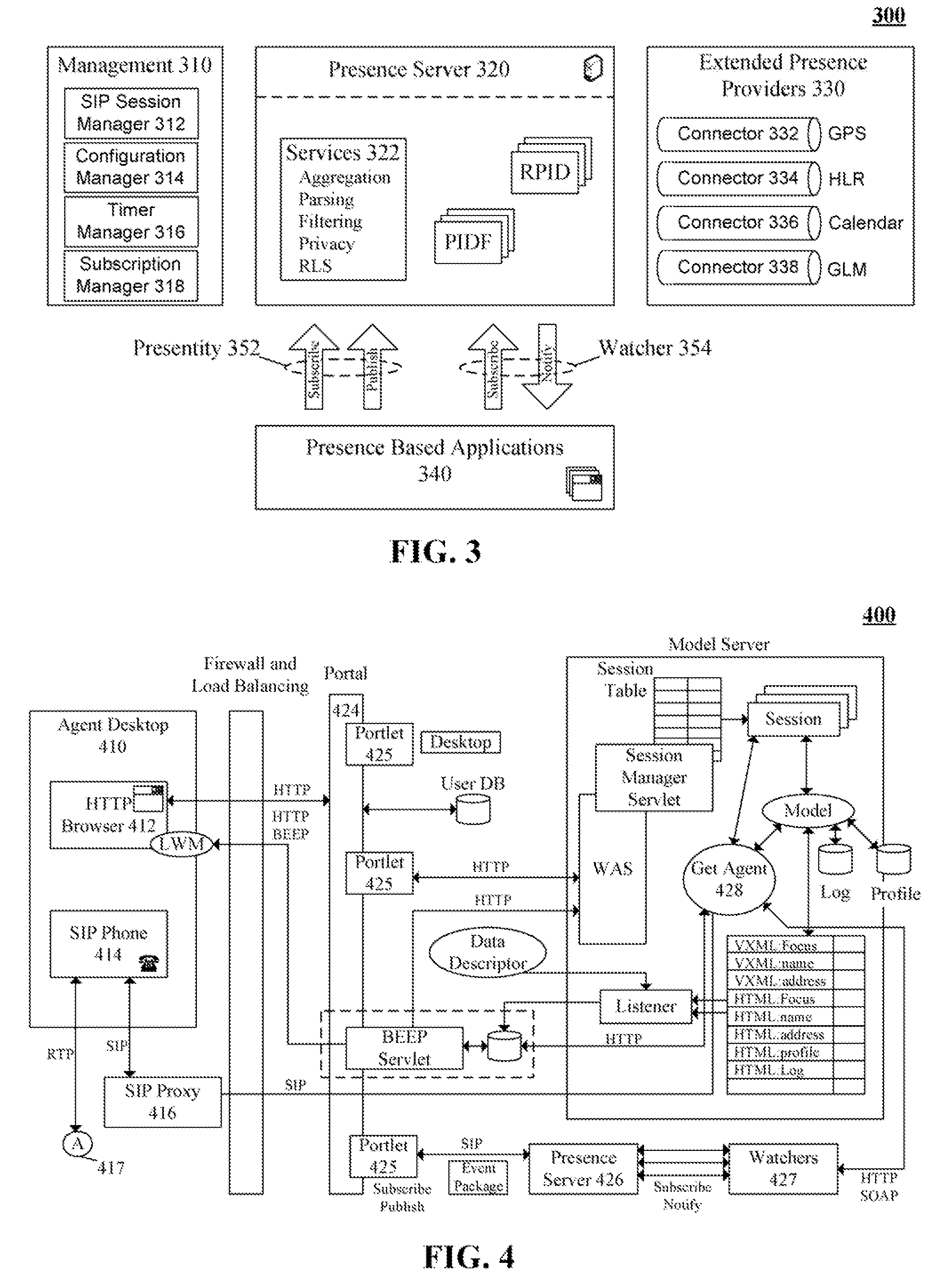
Skills based routing in a standards based contact center using a presence server and expertise specific watchers
ActiveUS20080205628A1Special service for subscribersManual exchangesSession Initiation ProtocolThe Internet
The present invention discloses a presence management system for a contact center including a presence server, a data store, and one or more watchers. The presence server can accept, manage, and distribute presence information using Session Initiation Protocol (SIP) based messages in conformance with an open standard, such as an Internet Engineering Task Force (IETF) based standard. The data store can be communicatively linked to the presence server and can be configured to store the presence information. The stored presence information can include presence information for multiple contact center agents, wherein for each agent the stored presence information includes an element for expertise of the associated agent. The watchers can subscribe to the presence information managed by the presence server. Each of the watchers can correspond to a unique expertise. The watcher associated with an expertise can watch presence information for all of the contact center agents having that expertise.
Owner:IBM CORP
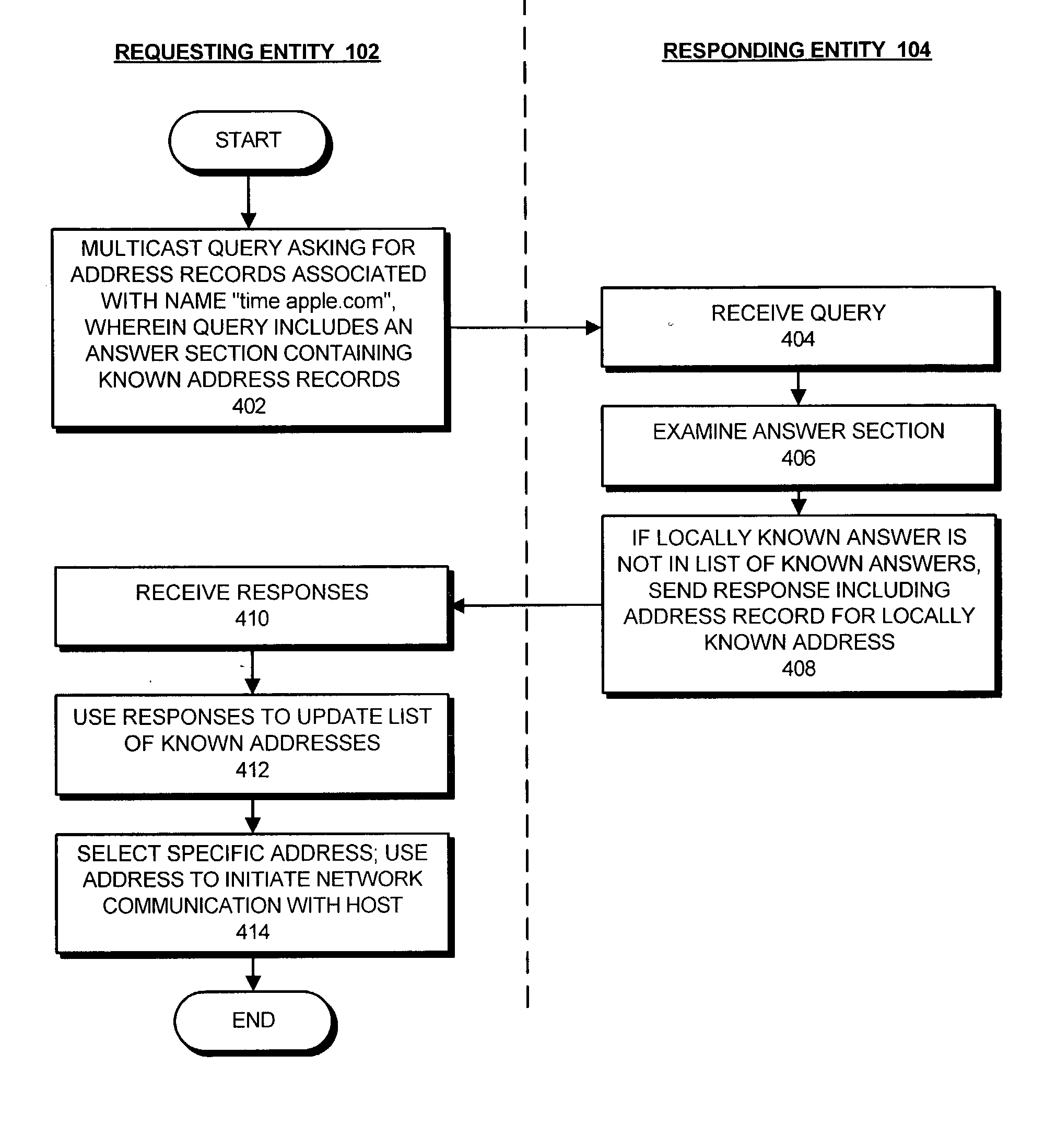
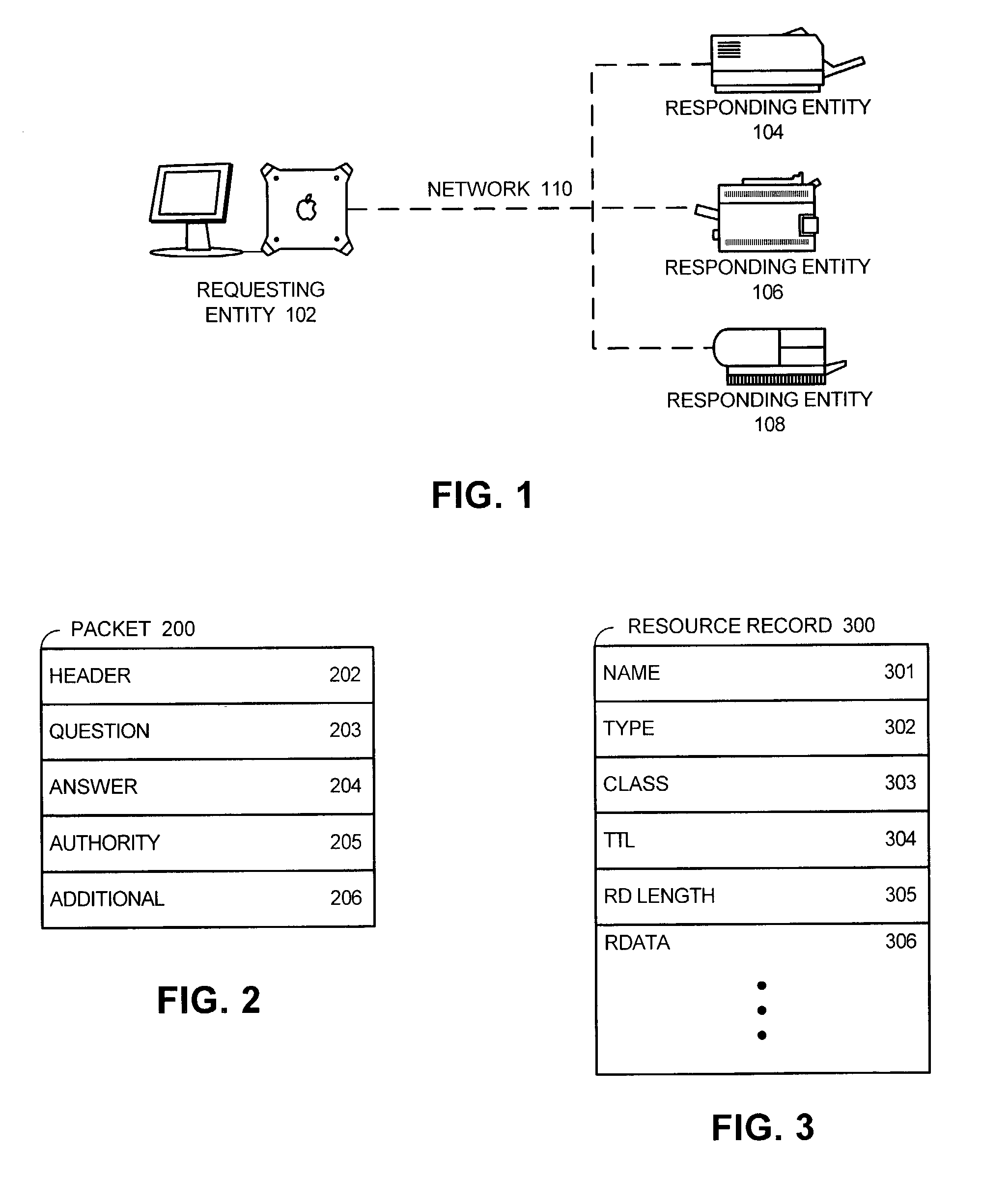
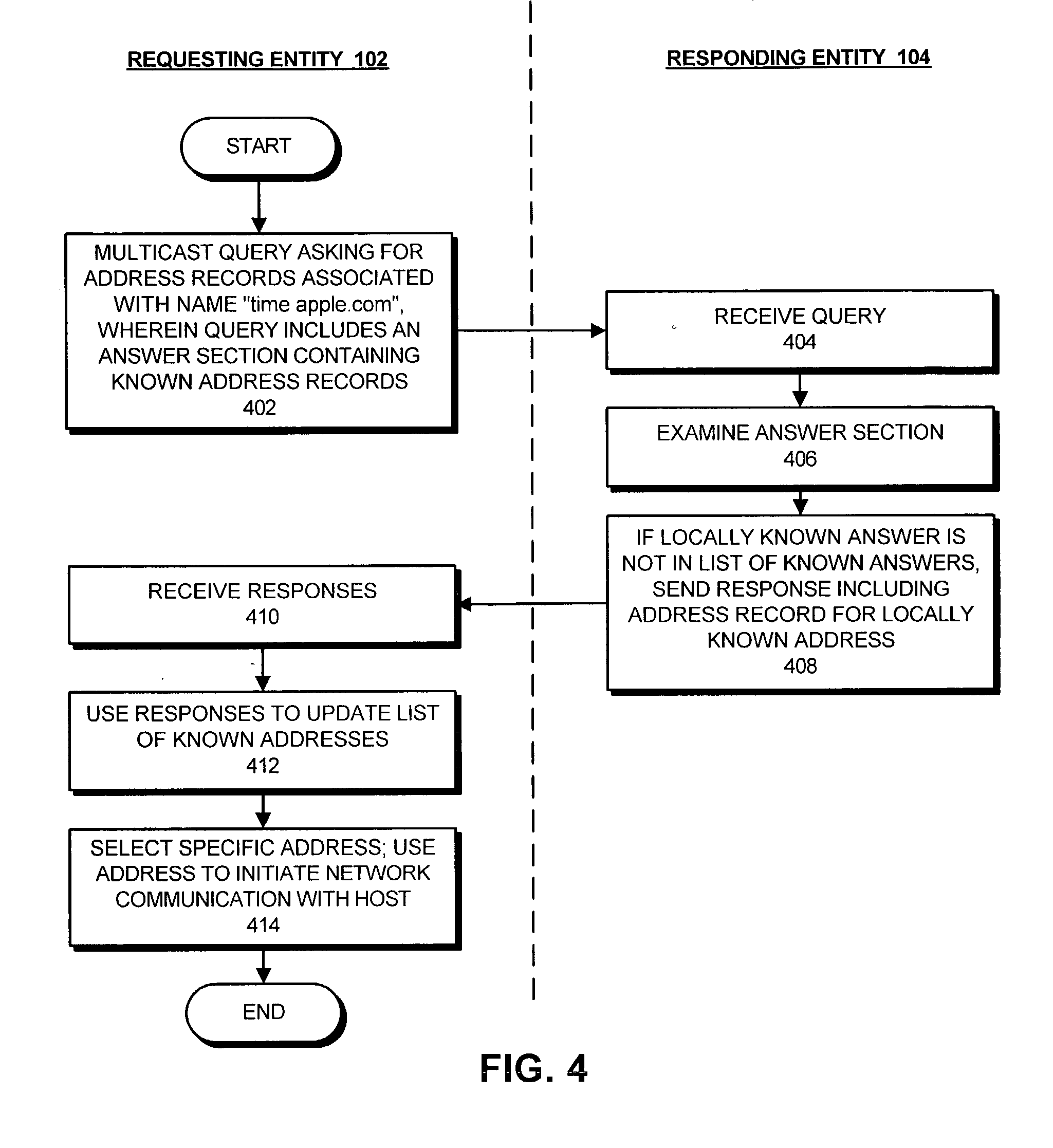
Method and apparatus for supporting duplicate suppression when issuing multicast queries using DNS-format message packets
Domain Name System (DNS) Queries and DNS Responses both use the same packet format. The DNS packet format, defined by Internet Engineering Task Force (IETF) Protocol Standard 13 (RFC 1035) includes a header section, a question section, an answer section, an authority record section and an additional record section. In conventional DNS Queries, the header section and the question section are used; the answer section, authority record section and additional record section are empty. In the present invention, when issuing a query, the client places the question in the question section as usual, but then places all the answers it already knows into the (previously empty) answer section of the query. When receiving a query, a responder first checks to make sure that the answer it is about to give is not already included in the answer section of the query. If the answer is listed in the answer section of the query, it means that the client already has that information, and doesn't need to be told again. In this way, when a client issues its first multicast query, it may receive many responses. When the client issues a subsequent query, it indicates the list of responses it successfully received by listing them in the answer section, and then only receives responses that were missed the first time. In the normal course of operation, this means that by the second or third transmission of the query, no further responses are generated on the network, and the client can then issue occasional periodic queries without eliciting a flood of responses every time.
Owner:APPLE INC
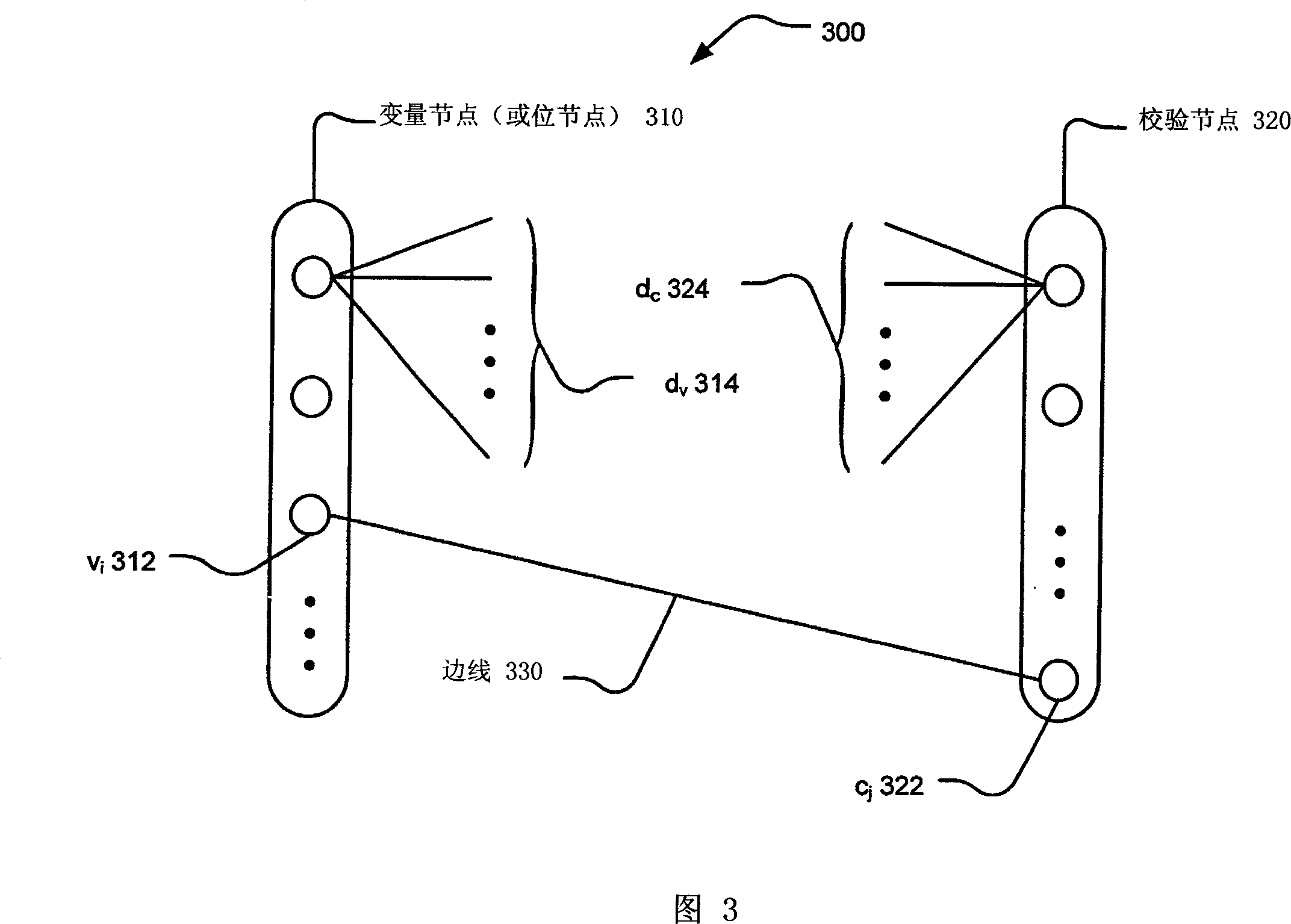
Construction of LDPC (Low Density Parity Check) codes using GRS (Generalized Reed-Solomon) code
Construction of LDPC (Low Density Parity Check) codes using GRS (Generalized Reed-Solomon) code. A novel approach is presented by which a GRS code may be employed to generate a wide variety of types of LDPC codes. Such GRS based LDPC codes may be employed within various types of transceiver devices implemented within communication systems. This approach may be employed to generate GRS based LDPC codes particular designed for various application arenas. As one example, such a GRS based LDPC code may be specifically designed for use in communication systems that operate in accordance with any standards and / or recommended practices of the IEEE P802.3an (10GBASE-T) Task Force.
Owner:AVAGO TECH INT SALES PTE LTD
Method for Identifying Real-Time Traffic Hop by Hop in an Internet Network
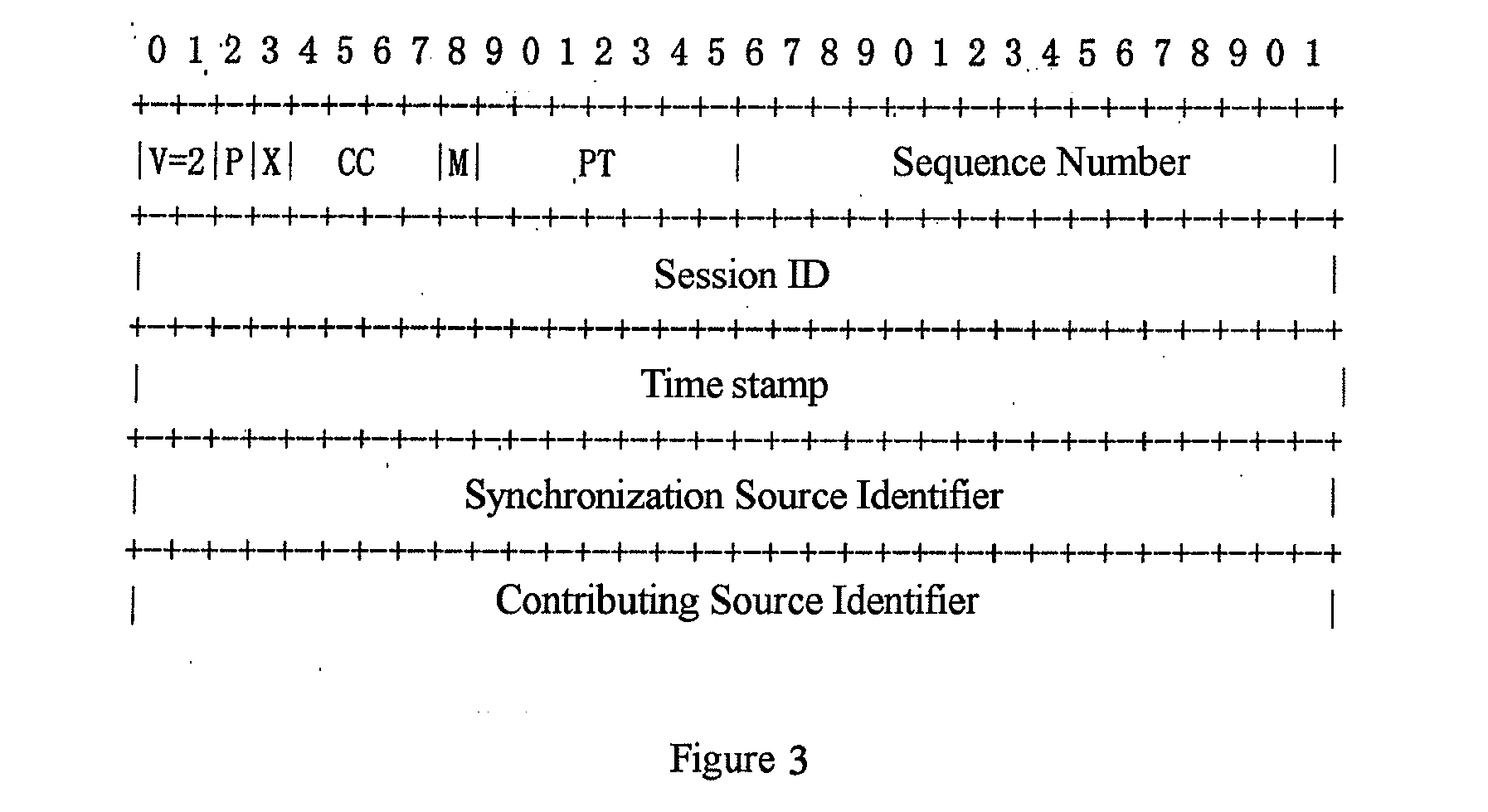
A method for identifying real-time traffic hop by hop in an Internet network including a sender, a receiver, and routers in the network is provided. The method comprises steps of registering source port number and / or destination port number of the UDP respectively for RTP, RTCP and RTSP with the Internet Assigned Numbers Authority (IANA) under the Internet Engineering Task Force (IETF) arrangement, then in one aspect, adding in the UDP header a Session ID field for identifying the session. The method can be used to identify the frames of the Real-time Transport Protocol (RTP) hop by hop during the packet's transmission, and to provide priority for real-time traffic transport so as to provide a QoS guarantee for real-time traffic even in the case of dramatically increasing network traffic.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG
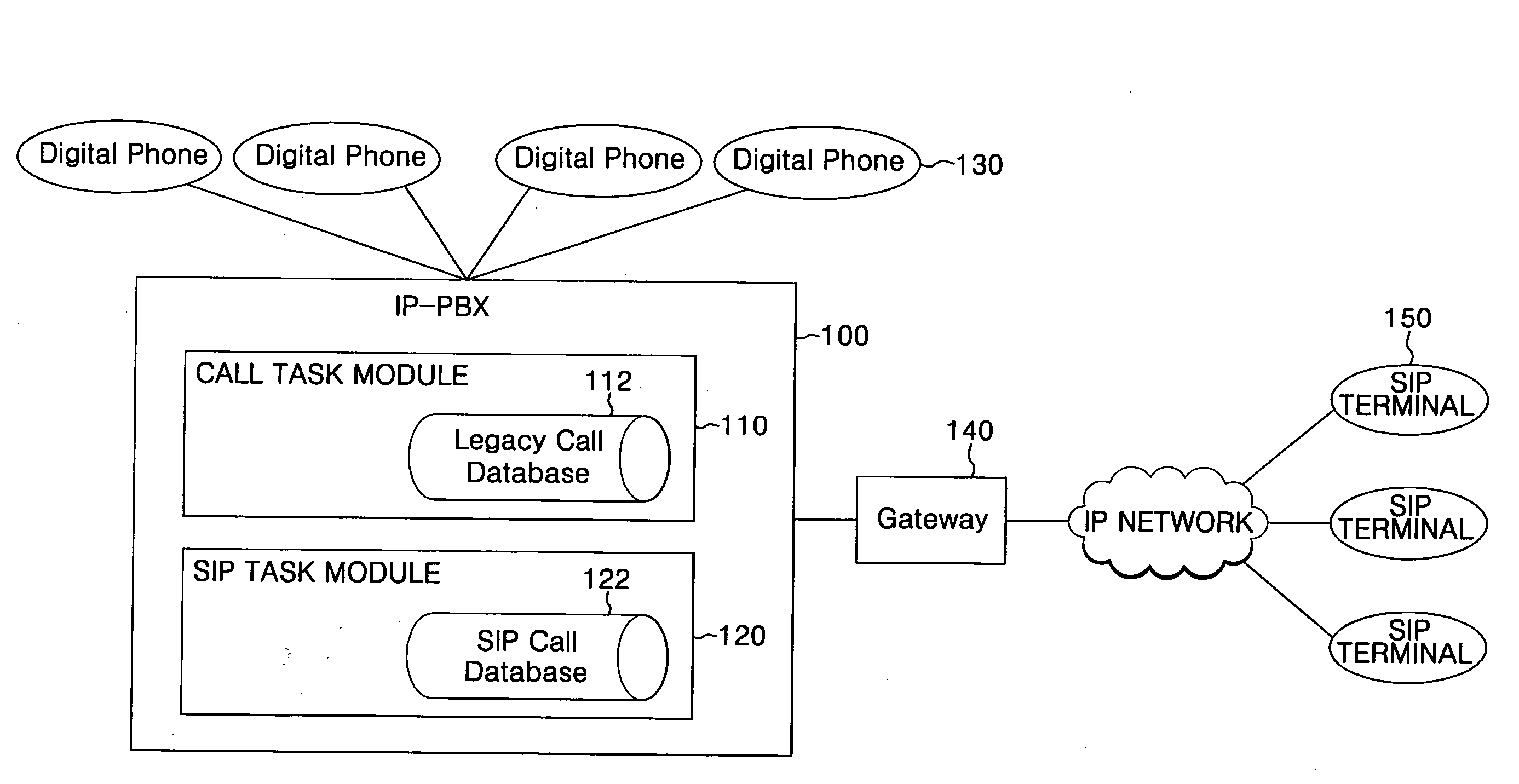
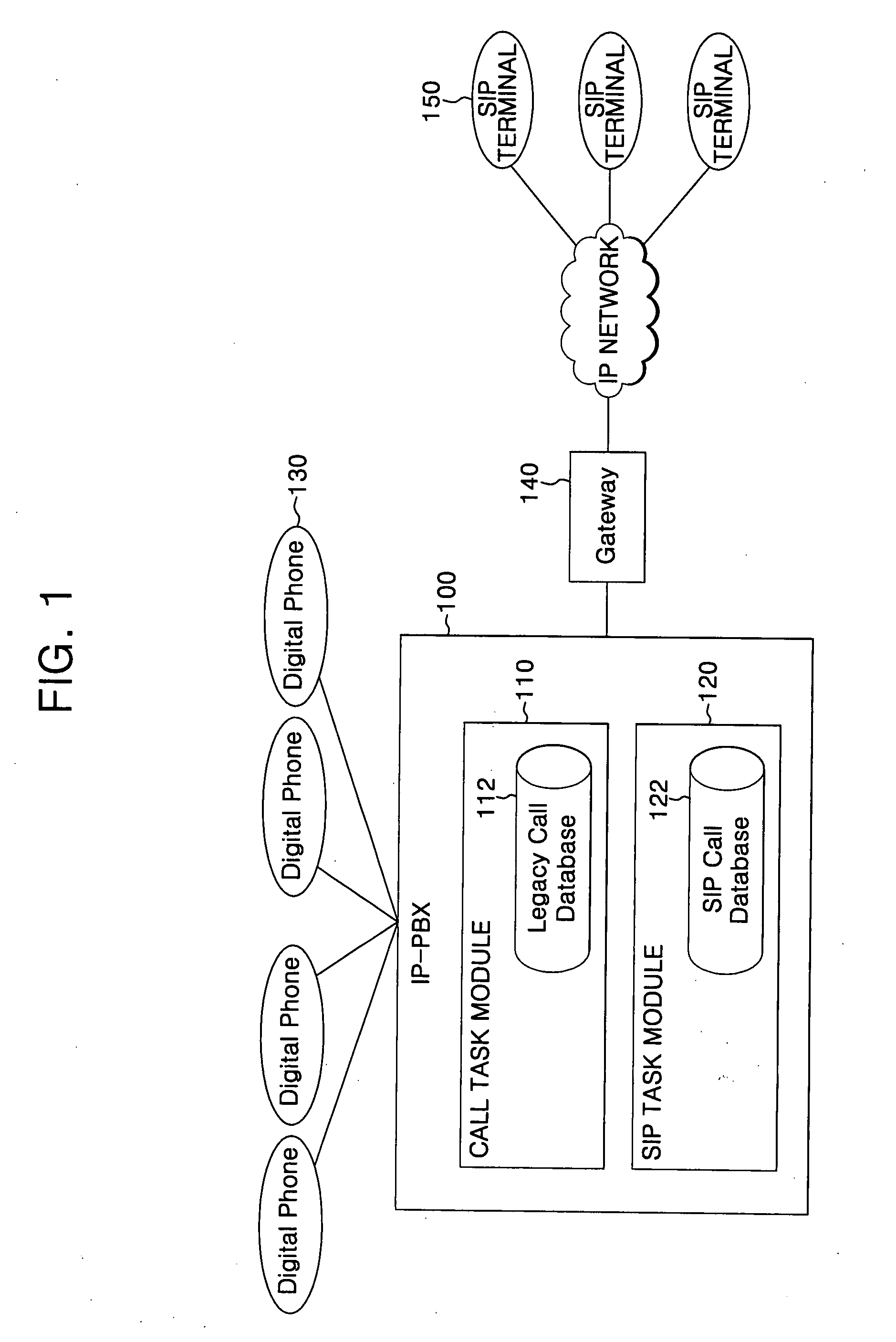
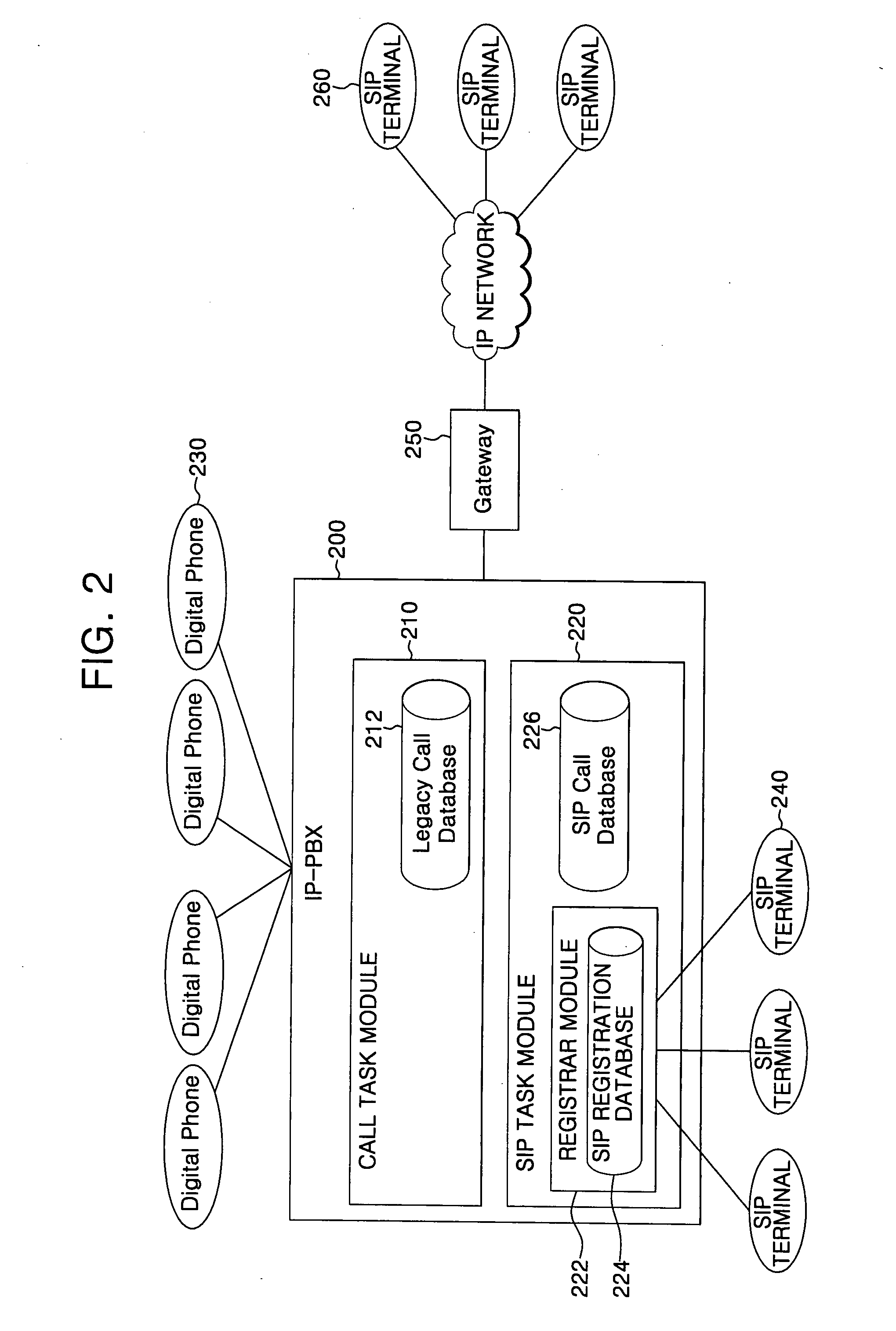
IP-PBX system and method for linking VoIP terminal therewith
InactiveUS20070206585A1Automatic exchangesNetworks interconnectionSession Initiation ProtocolTTEthernet
An Internet protocol (IP)-private branch exchange (PBX) system and a method for linking the system with a Voice over Internet Protocol (VoIP) terminal. The IP-PBX system and method allow the VoIP terminal to be registered at an extension of the IP-PBX system, the VoIP terminal supporting a protocol, e.g., H.323 or session initiation protocol (SIP), standardized by a standardization organization, e.g., the International Telecommunication Union (ITU), the Internet Engineering Task Force (IETF), or the European Telecommunications Standards Institute (ETSI).
Owner:SAMSUNG ELECTRONICS CO LTD
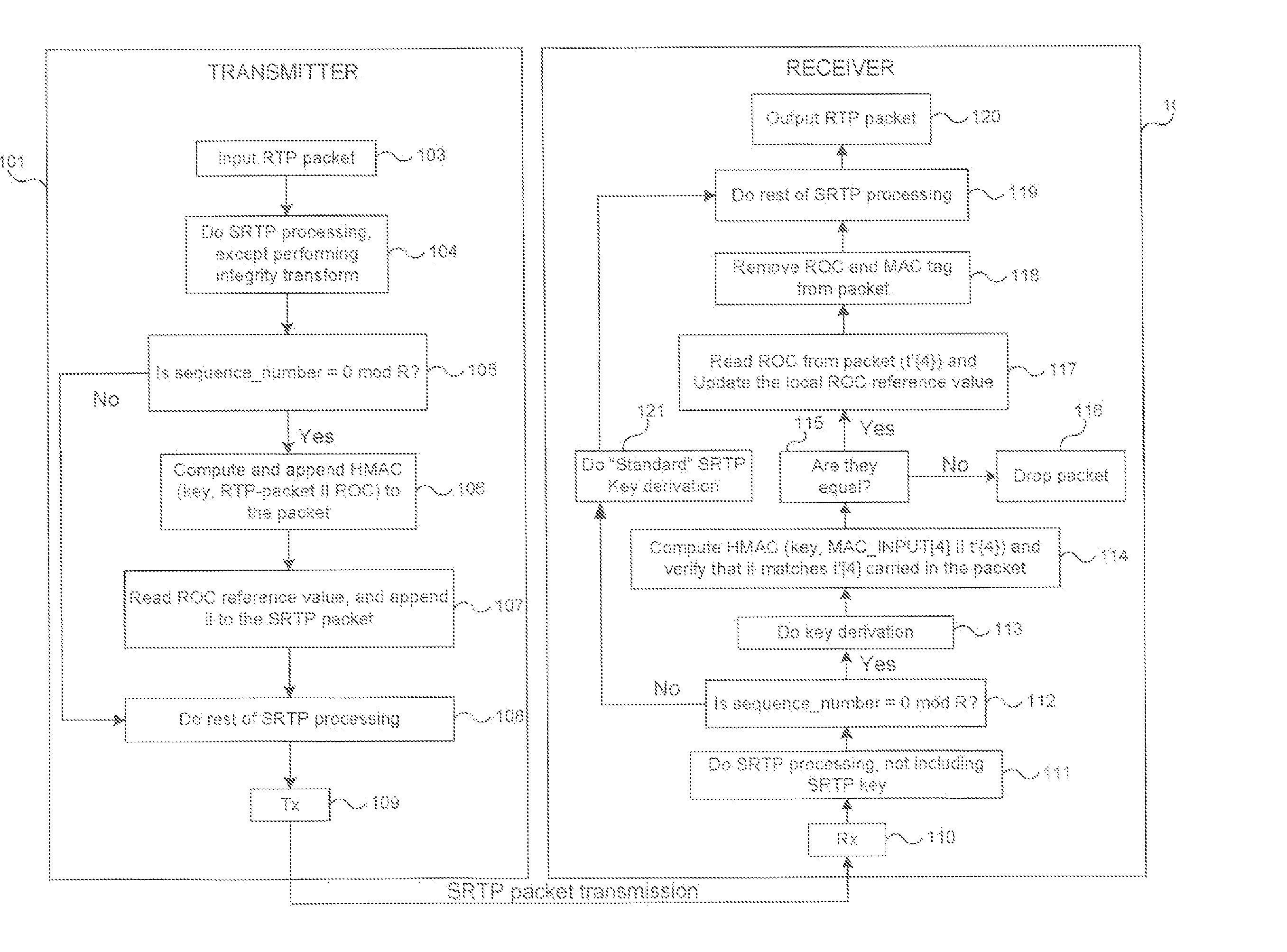
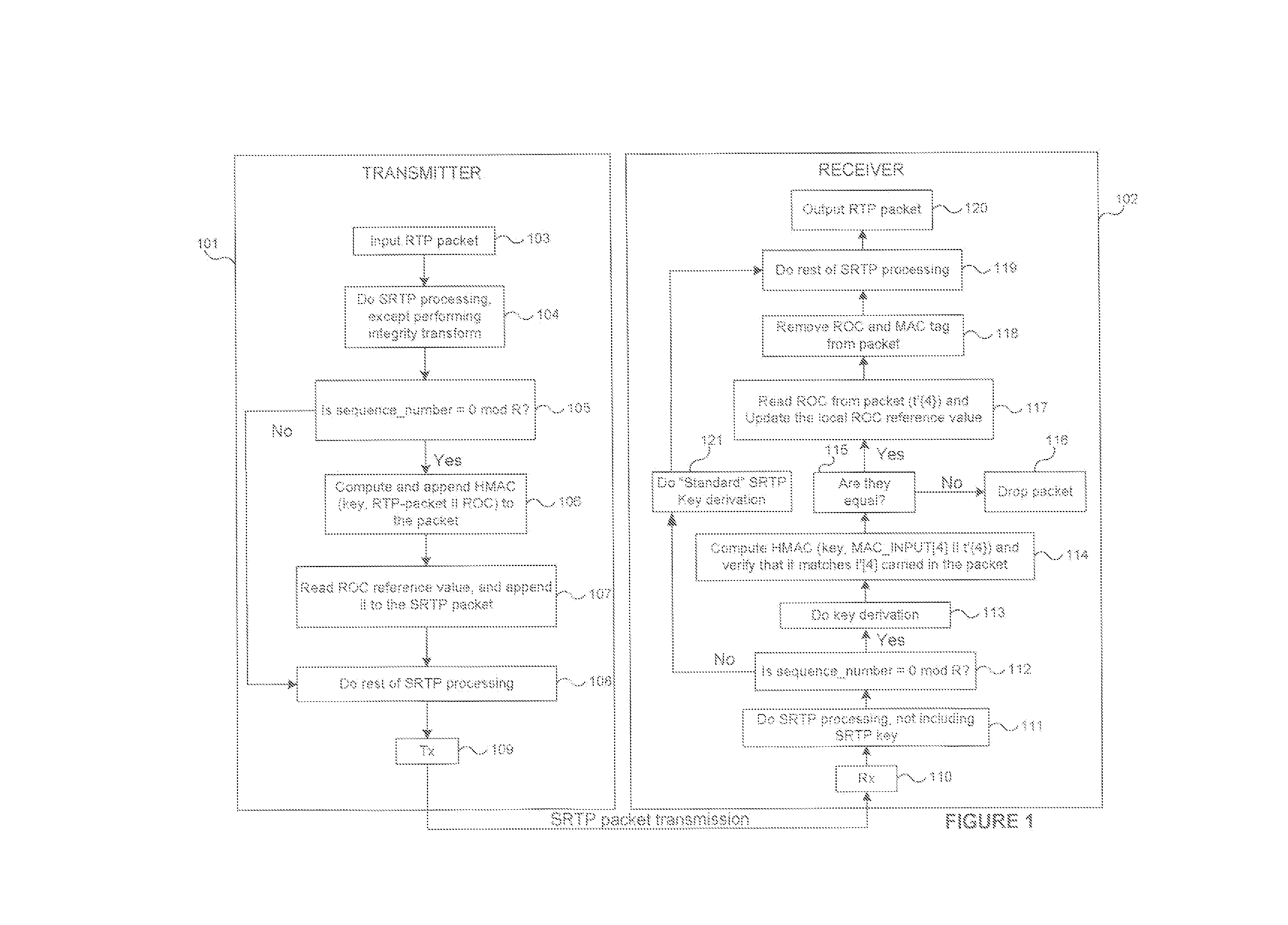
Methods for secure and bandwidth efficient cryptographic synchronization
ActiveUS20070113085A1Efficient use of bandwidthEasy to useSynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageTransmission protocolSecure Real-time Transport Protocol
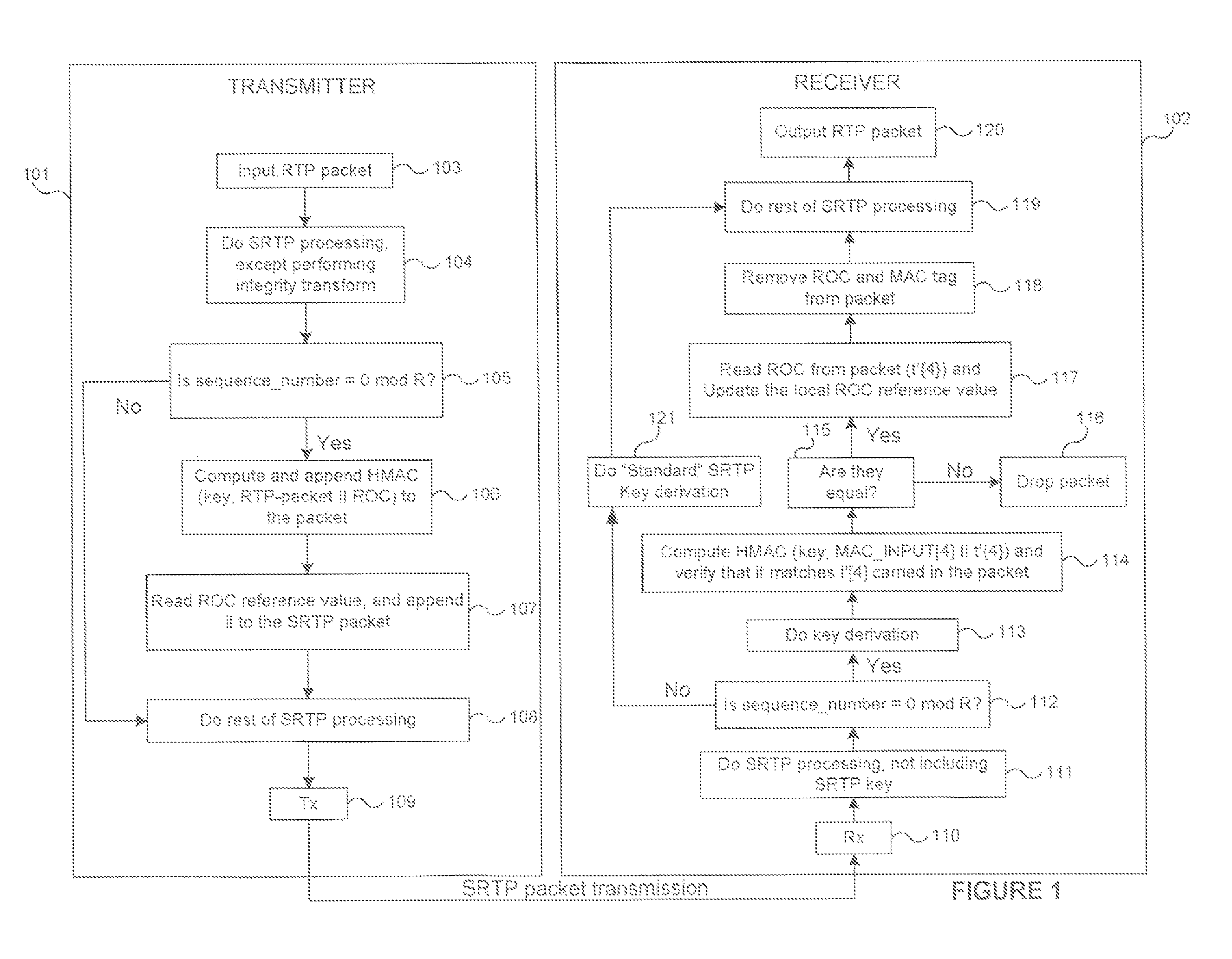
Methods for cryptographic synchronization of data packets. A roll-over counter (ROC) value is periodically appended to and transmitted with a data packet when a function of the packet sequence number equals a predetermined value. The ROC effectively synchronizes the cryptographic transformation of the data packets. Although the disclosed methods are generally applicable to many transmission protocols, they are particularly adaptable for use in systems wherein the data packets are transmitted to a receiver using the Secure Real-Time Transport Protocol (SRTP) as defined in Internet Engineering Task Force (IETF) Request for Comments (RFC) 3711.
Owner:TELEFON AB LM ERICSSON (PUBL)
Apparatus and method for implementing instruction support for the camellia cipher algorithm
A processor including instruction support for implementing the Camellia block cipher algorithm may issue, for execution, programmer-selectable instructions from a defined instruction set architecture (ISA). The processor may include a cryptographic unit that may receive instructions for execution. The instructions include one or more Camellia instructions defined within the ISA. In addition, the Camellia instructions may be executable by the cryptographic unit to implement portions of a Camellia cipher that is compliant with Internet Engineering Task Force (IETF) Request For Comments (RFC) 3713. In response to receiving a Camellia F( )-operation instruction defined within the ISA, the cryptographic unit may perform an F( ) operation, as defined by the Camellia cipher, upon a data input operand and a subkey operand, in which the data input operand and subkey operand may be specified by the Camellia F( )-operation instruction.
Owner:SUN MICROSYSTEMS INC
System and Method for Managing Cognitive Bandwidth to Prevent Failure of Valuable Tasks Requiring Cognition
InactiveUS20150248532A1Increase valueImprove efficiencyHealth-index calculationMedical automated diagnosisCountermeasureTask force
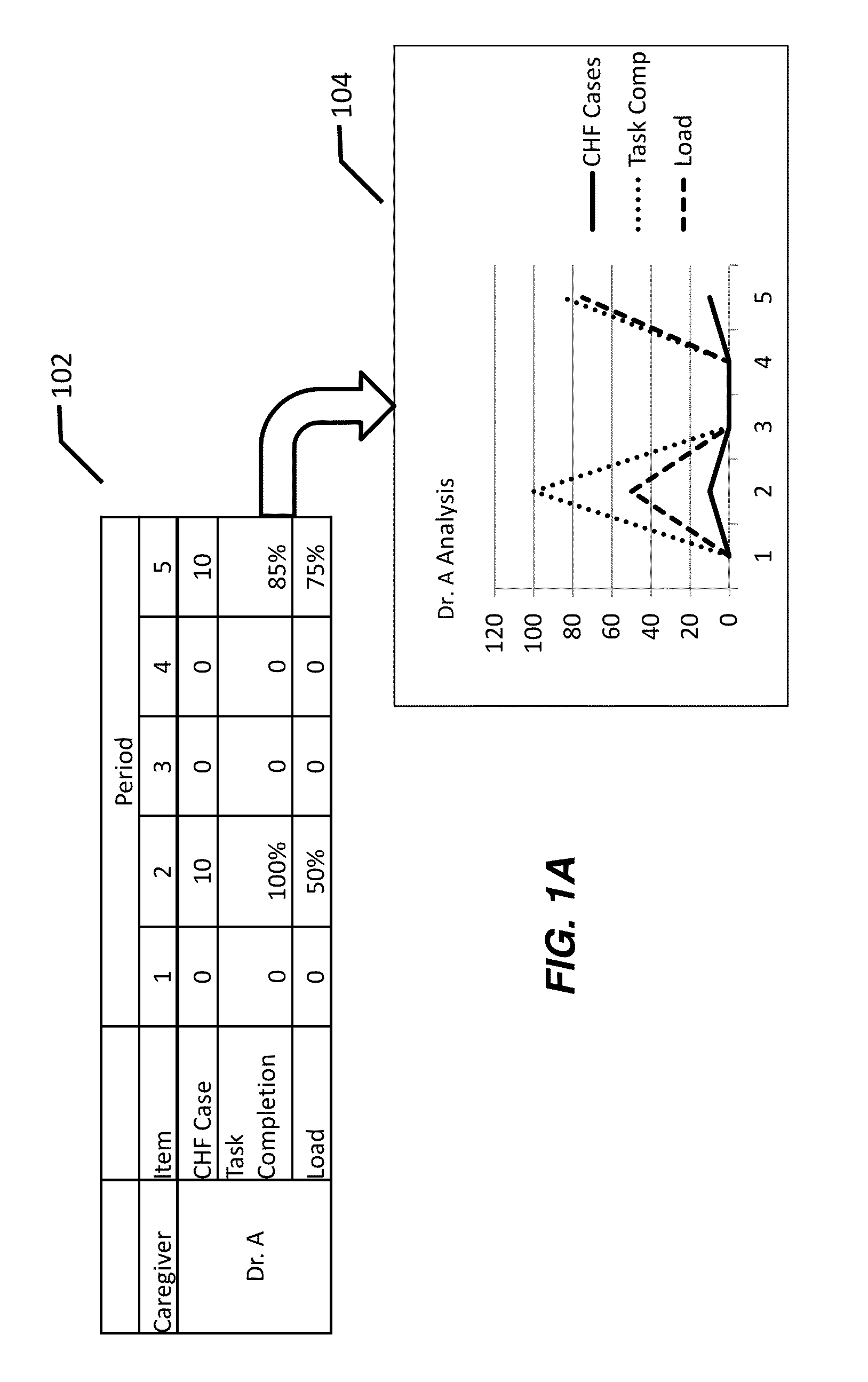
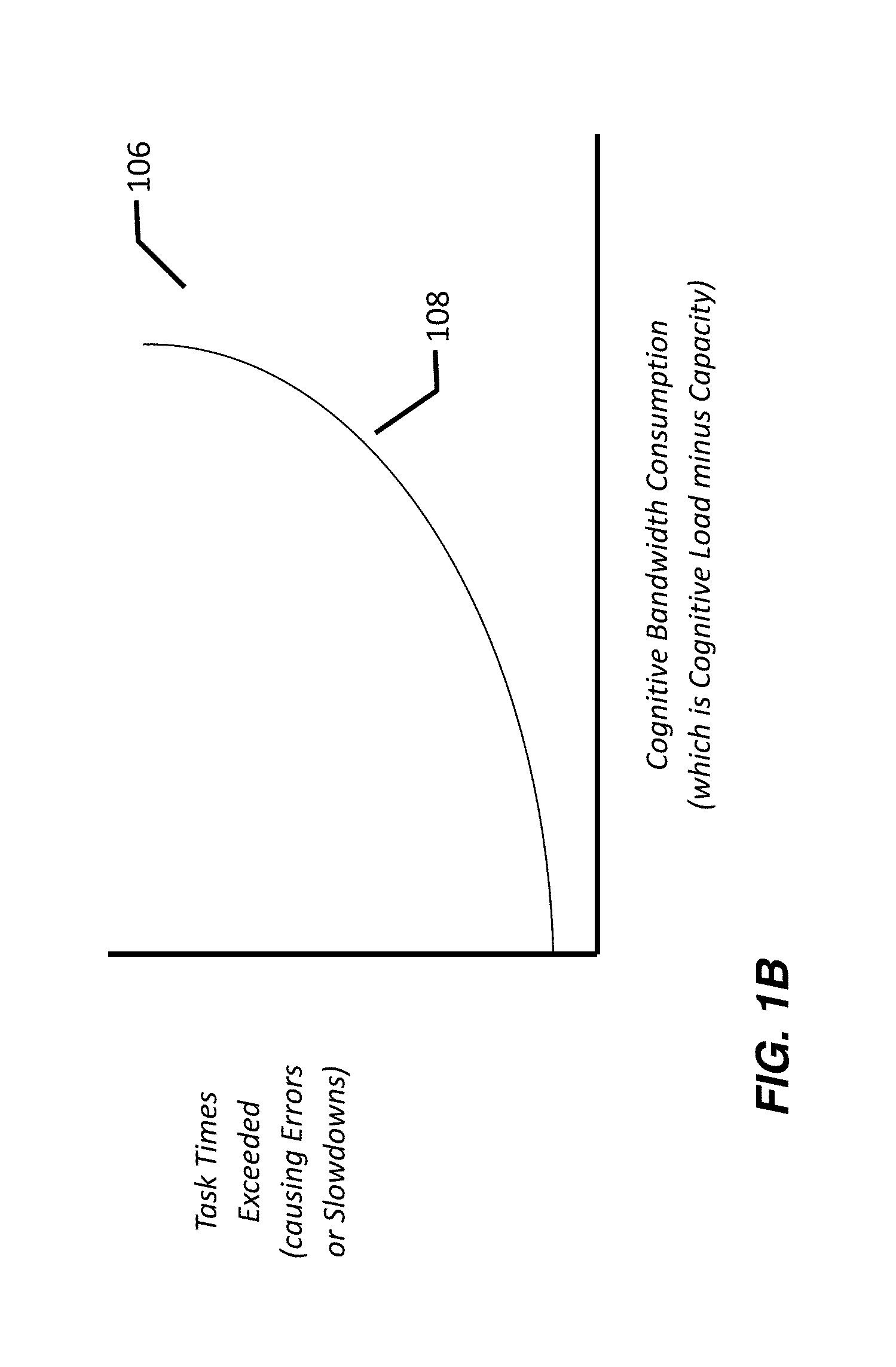
Process mining and tipping point analysis is used to determine tasks at risk. Tasks At Risk Intervention lead time analysis determines whether those tasks at risk can be performed in an opportunity window cost-effectively and at a high rate of success by the current task force. Load balancing can be used to offload fungible tasks at risk to flexible resources that can perform those tasks at risk for the highest value opportunities to micro-target tasks at risk with specific countermeasures, perhaps partitioned among several task force members to ensure can be done within the window of opportunity, to ensure their success. The flexible cognitive resources performing fungible tasks can be housed in a hub resource facility to centralize load balancing and obtain scale economies benefits from the shared capacity.
Owner:RAJASENAN TERRY
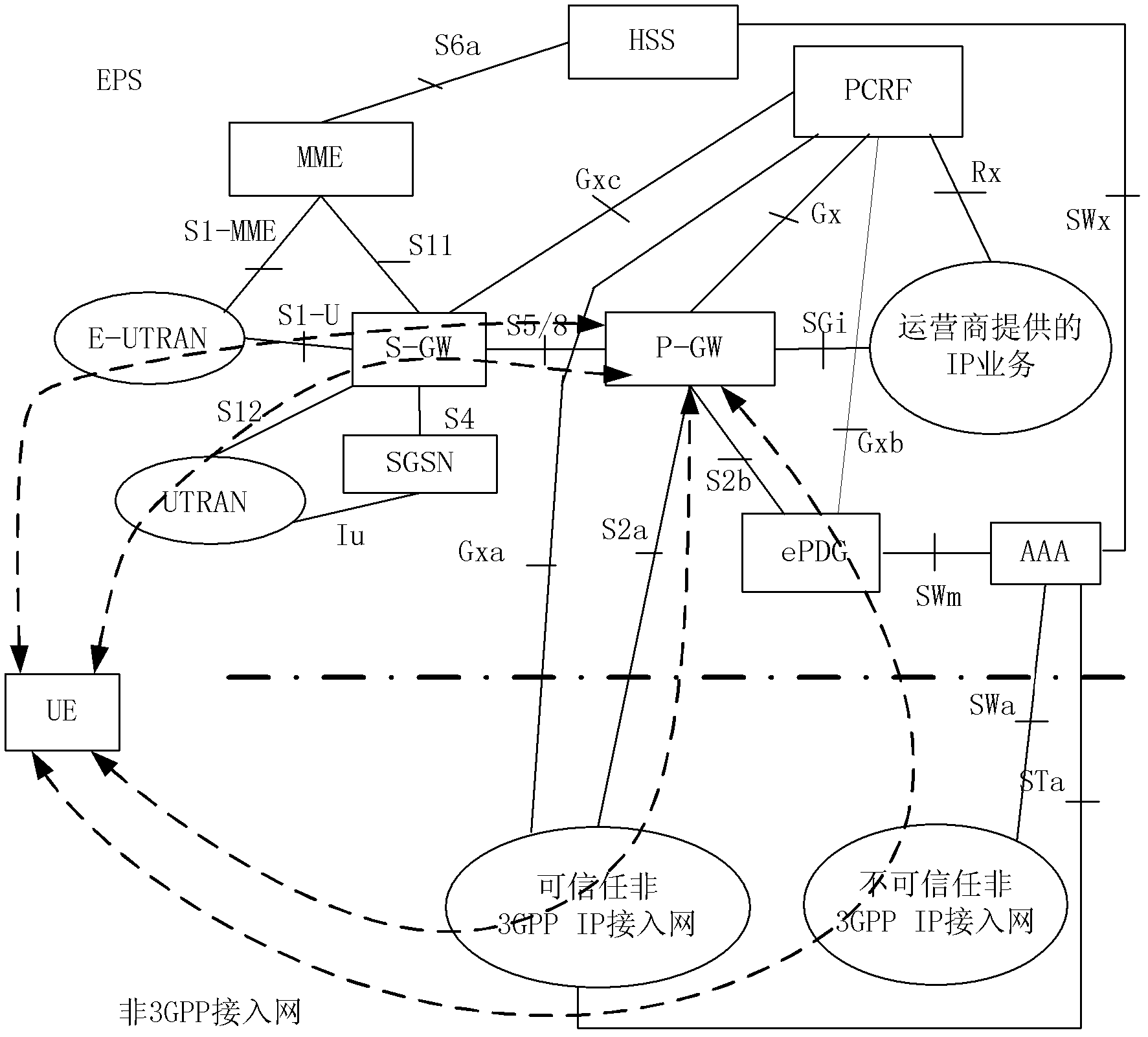
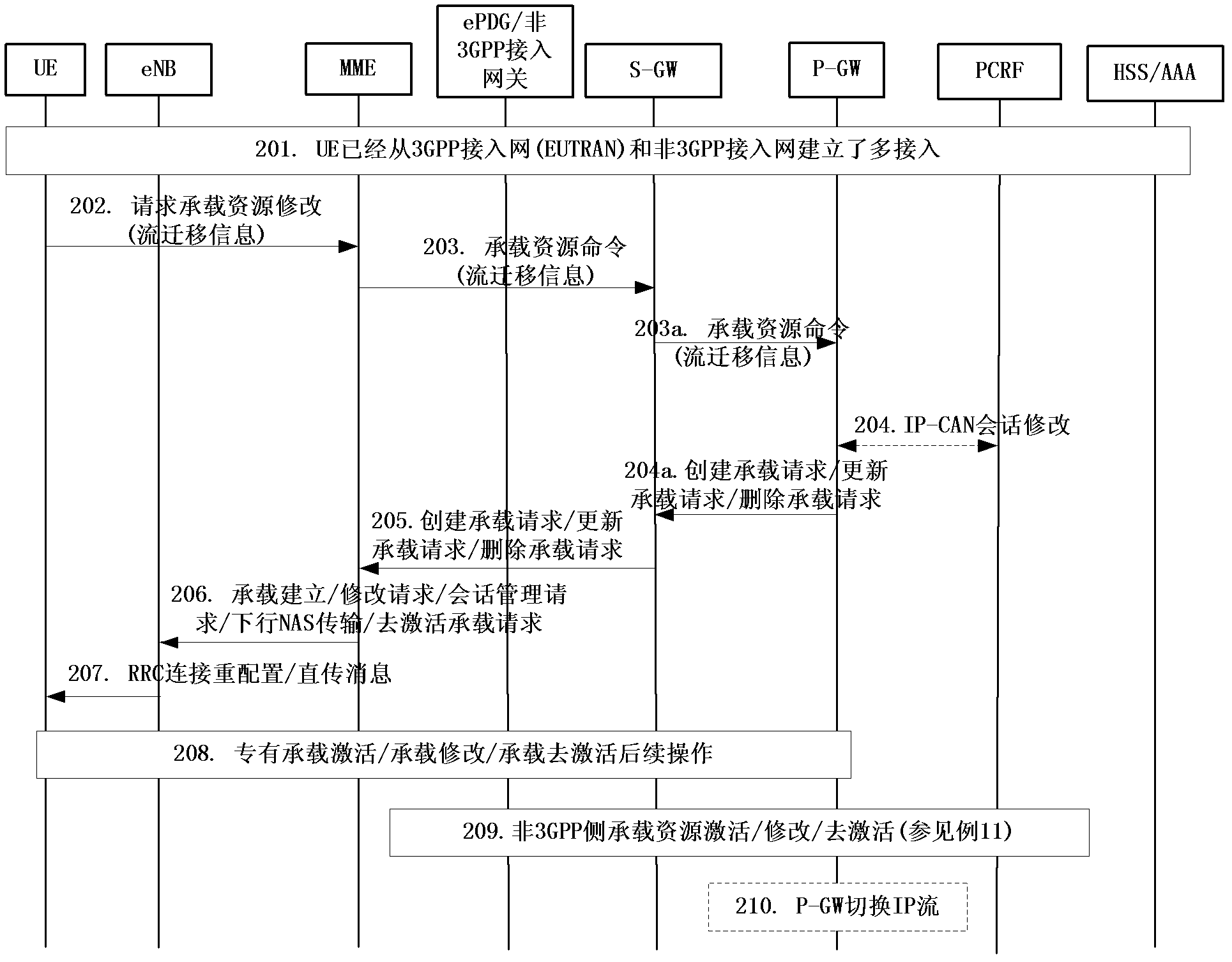
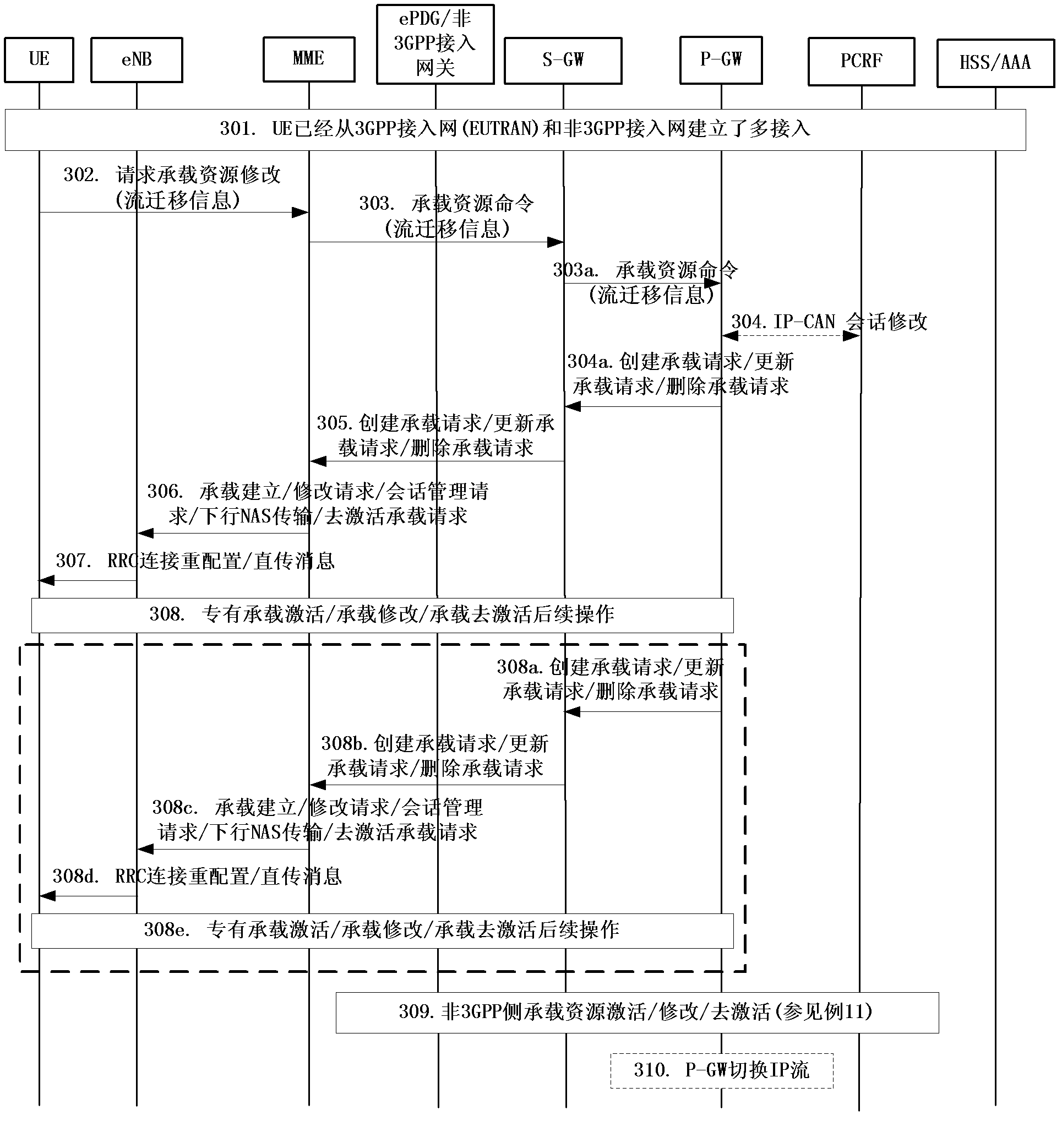
Implementing method of flow migration, terminal and grouped data network gateway
InactiveCN103024823AAvoid modificationImplement stream migrationNetwork traffic/resource managementConnection managementAccess networkThe Internet
The invention discloses an implementing method of flow migration, a terminal and a grouped data network gateway, and is capable of avoiding modification on a non-3rd generation partnership project (3GPP) access network and an internet engineering task force (IETF) protocol and simplifying an operation procedure, wherein the method comprises a step of: establishing a plurality of accesses of same public data network (PDN) connection on a terminal, and migrating a dataflow by the P-GW by a 3GPP network signaling and packet work gateway (P-GW) negotiation flow migration information; the P-GW comprises a receiving module and a flow migrating module, wherein the receiving module is used for receiving the flow migration information transmitted by the terminal, and the flow migrating module is used for migrating dataflow according to the flow migration information received by the receiving module; the terminal comprises a connection establishing module and a negotiation module, wherein the connection establishing module is used for establishing the plurality of accesses in the same PDN connection; and the negotiation module is used for negotiating the flow migration information with the P-GW through the 3GPP network signaling after the plurality of accesses of the same PDN connection are established by the connection establishing module.
Owner:ZTE CORP
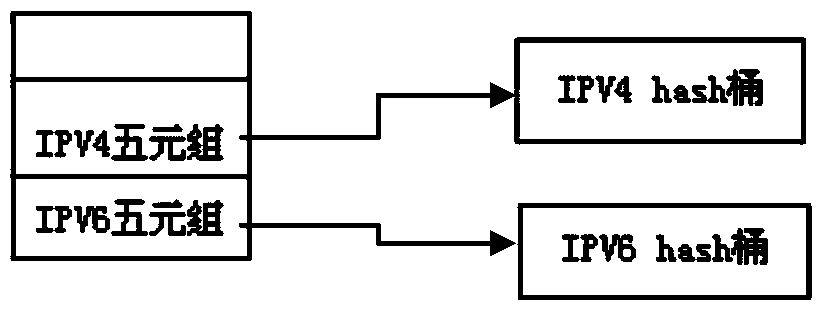
Method and equipment for forwarding datagram based on NAT 64 (Network Address Translation 64)
InactiveCN103634216ASolve performance deficienciesImprove performanceData switching networksConnection tableNetwork addressing
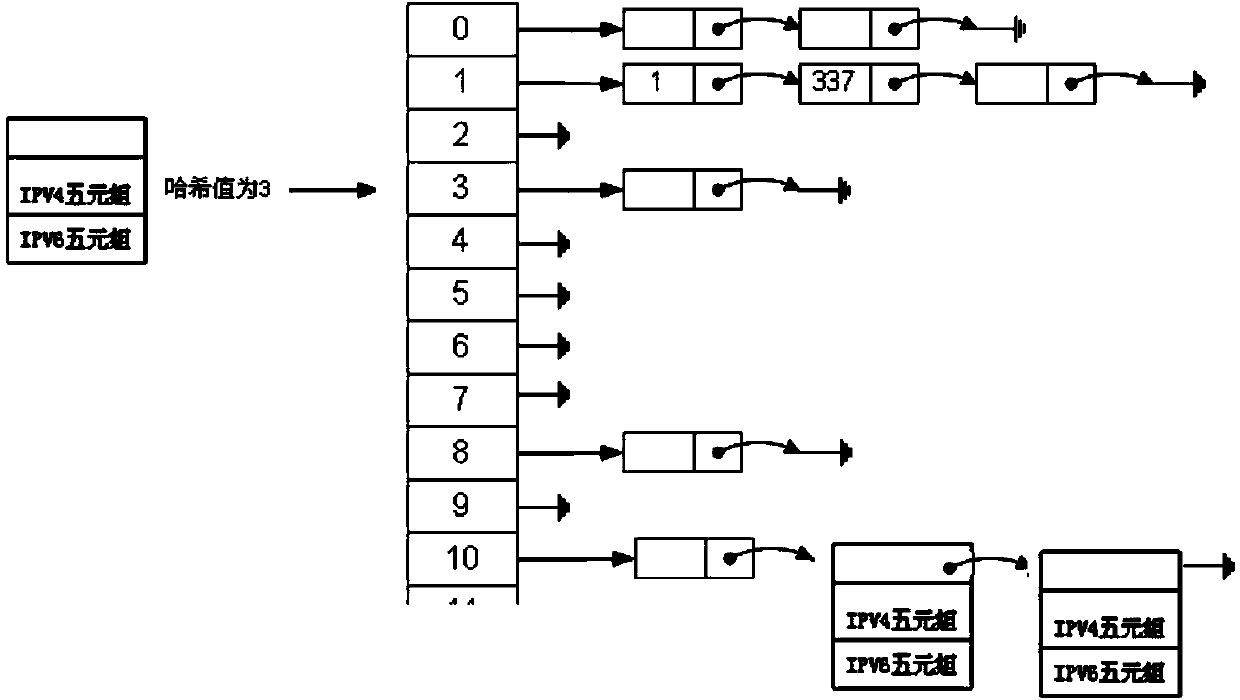
The invention provides a method and equipment for forwarding a datagram based on NAT 64 (Network Address Translation 64). The method and the equipment are used for solving the problems in the prior art that most of the content of the Internet is available to IPv4 (Internet Protocol version 4) only, the condition that IPv6 (Internet Protocol version 6) terminal users often need to access IPv4 content is unavoidable, the conversion of the network addresses and protocols of the IPv6 and IPv4 under the protocols of TCP (transmission control protocol), UDP (User Datagram Protocol) and ICMP (Internet Control Message Protocol) is realized by a NAT 64 technology designed by an IETF (Internet Engineering Task Force), however, forwarding equipment realizes the conversion of the network addresses and protocols mainly through traversing an address mapping table in a current NAT 64 implementation mode, and in the case of a large number of users, the searching efficiency is low, the system resource occupation is too large, and then the performance can be lowered seriously. According to the method and the equipment, the efficiency of converted address searching during the intercommunication between the IPv4 and the IPv6 is greatly increased through establishing an IPv4 and IPv6 mixed connection table and searching in a Hash manner, and then, the overall performance is improved.
Owner:OPZOON TECH
System for the operational activation of banking ATM networks and method for the management of banking ATM equipment network
InactiveUS20100070413A1Improve responsePromoting improvements in the consumer marketFinancePayment architectureBiological activationTask force
The “SYSTEM FOR THE OPERATIONAL ACTIVATION OF BANKING ATM NETWORKS AND METHOD FOR THE MANAGEMENT OF BANKING ATM EQUIPMENT NETWORK” is more particularly related to a system (1) of operational activation of banking ATM networks and a method for the management of banking ATM equipment networks, prominently developed to provide the market with the best levels of quality, knowledge, and availability, moreover, allowing for the aforementioned ATM networks to be managed in a total or partial form, through its pieces of equipment and financing institutions and, besides that, in the segment of modes of payment, the system also becomes responsible for the administration of the capture terminals of the services of Electronic Funds Transfer (EFT) and, in that way, it ensures a tool which allows for greater efficacy in the monitoring and the reduction of the length of time of catering to the operational demands, promoting greater expeditiousness and flexibility in the operational processes, ensuring greater efficacy in the monitoring of the parks of terminals, also reducing the length of activation time of the field task forces.
Owner:TECH BANCARIA SA
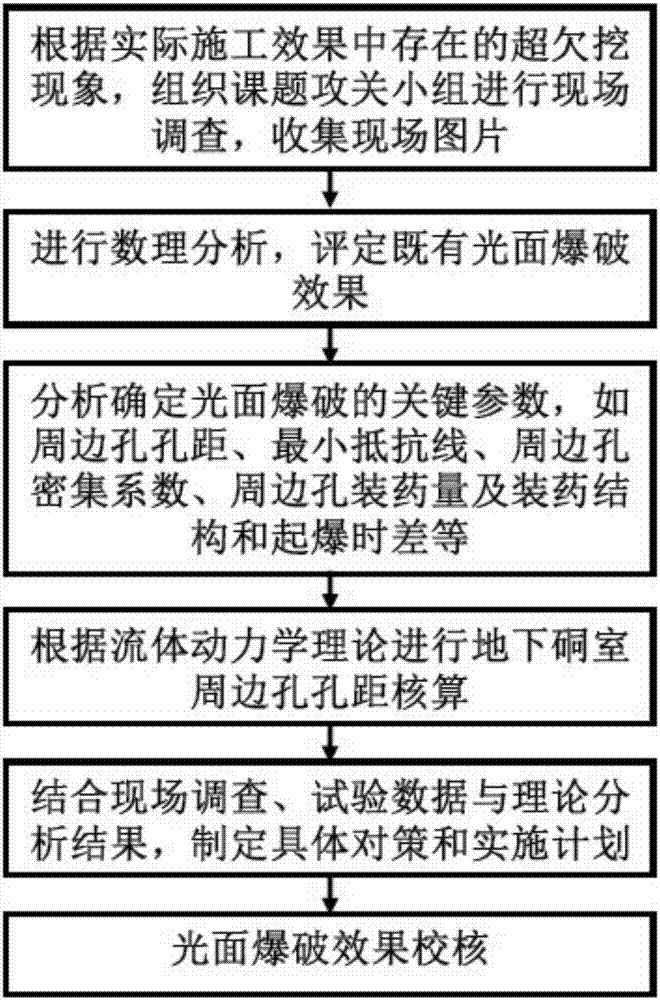
Smooth blasting method for controlling flatness of profile surface for underground chamber
The invention discloses a smooth blasting method for controlling flatness of profile surface for an underground chamber. The method comprises the following steps: 1) organizing topic task force to investigate on site according to the over-under-excavation phenomenon in a practical construction effect, and collecting site pictures; 2) carrying out mathematical analysis and evaluation to ensure that a smooth blasting effect is achieved; 3) analyzing key parameters determining smooth blasting, wherein the key parameters comprise hole spacing of peripheral holes, minimum resistant line, close coefficients of the peripheral holes, charge quantity and charging structure of the peripheral holes, blasting interval and the like; 4) calculating the hole spacing of the peripheral holes of the underground chamber according to fluid-dynamic theory; 5) making specific countermeasures and implementation plans under the combination of field investigation, test data and theoretical analysis results; and 6) checking the smooth blasting effect. The method has the characteristics of saving construction cost, improving construction quality and improving economic benefit, and is applicable to smooth blasting of the underground chamber in the fields of water conservancy and hydropower engineering , tunnel engineering, underground space structure and the like.
Owner:HOHAI UNIV
Active defensive type graphic-model integrated operation monitoring system based on DMTF-CIM (Distributed Management Task Force-CompuServe Information Manager) model
InactiveCN105260811AGuaranteed stabilityGuaranteed feasibilityResourcesData informationData acquisition
The invention relates to an active defensive type graphic-model integrated operation monitoring system based on a DMTF-CIM (Distributed Management Task Force-CompuServe Information Manager) model, and is applied to monitoring objects, such as master station equipment, key applications and important data in a first region, a second region, a third region and a fourth region in a safety area having automatic power dispatching. The operation monitoring system mainly comprises a DMTF-CIM model definition module, a monitoring object modelling module, a monitoring object graphic-model conversion module, a monitoring object data acquisition module, a task management module and an alarm management module; an acquisition server in the monitoring object data acquisition module is connected to a monitoring object in the second region of the safety area through a core switch in the second region of the safety area and acquires operation data information; and the acquisition server formats operating data information through the DMTF-CIM model and then stores the operating data information in a database server in the second region of the safety area. Related functions of the DMTF-CIM model definition module, the monitoring object modelling module and the monitoring object graphic-model conversion module are realized.
Owner:STATE GRID CORP OF CHINA +1
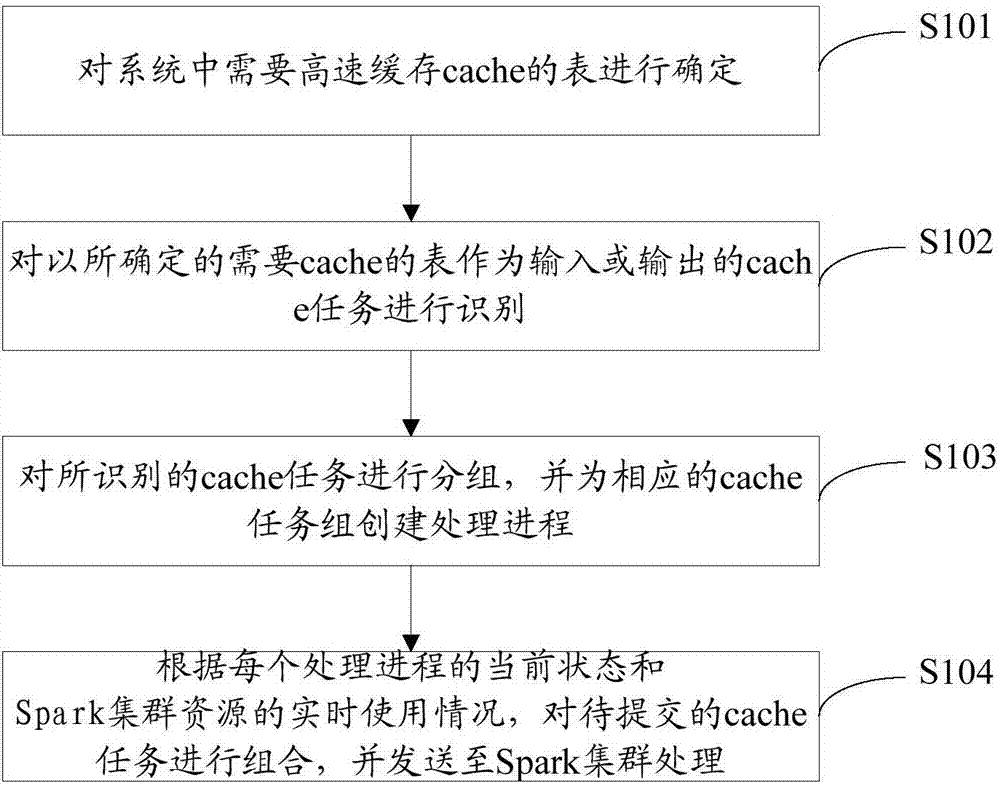
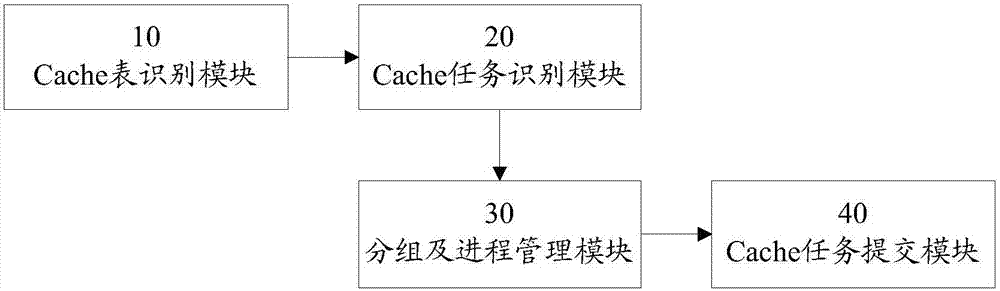
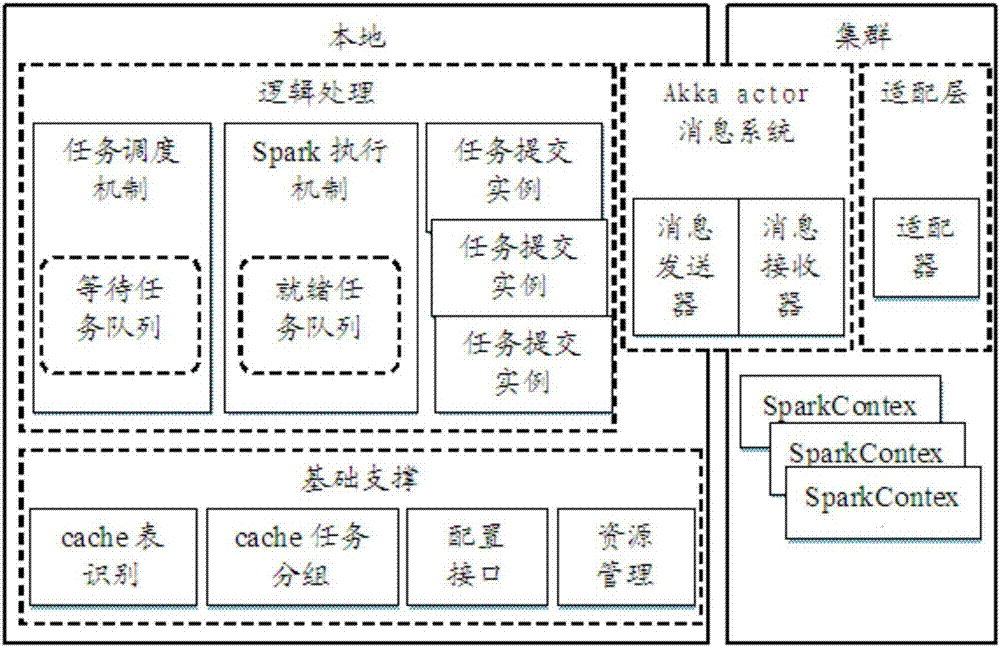
Method and device for improving Spark operation efficiency
InactiveCN107544844AImprove parallelismGuaranteed uptimeResource allocationParallel computingTask force
The invention discloses a method and a device for improving Spark operation efficiency, and relates to the field of big data analysis and processing. The method comprises the following steps that: determining a table which needs to be cached in a system; identifying a cache task which takes the determined table which needs to be cached as input or output; grouping the identified cache task, and creating a processing process for the corresponding cache task group; and according to the current state of each processing process and the real-time use situation of Spark cluster resources, combiningcache tasks to be submitted, and sending the combined cache tasks to be submitted to a Spark cluster to be processed. By use of the embodiment of the invention, the system resources of the cluster canbe fully utilized, tables and contents to be cached are reasonably determined, the process is dynamically decided and scheduled, a degree of parallelism is increased to a maximum degree under a situation that resources permit, and a purpose of improving the Spark operation efficiency is achieved.
Owner:ZTE CORP
Construction of LDPC (low density parity check) codes using GRS (generalized reed-solomon) code
InactiveCN1933336AError preventionError correction/detection using multiple parity bitsCommunications systemTransceiver
Construction of LDPC (Low Density Parity Check) codes using GRS (Generalized Reed-Solomon) code. A novel approach is presented by which a GRS code may be employed to generate a wide variety of types of LDPC codes. Such GRS based LDPC codes may be employed within various types of transceiver devices implemented within communication systems. This approach may be employed to generate GRS based LDPC codes particular designed for various application arenas. As one example, such a GRS based LDPC code may be specifically designed for use in communication systems that operate in accordance with any standards and / or recommended practices of the IEEE P802.3an (10GBASE-T) Task Force.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
High Speed Ethernet MAC and PHY Apparatus with a Filter Based Ethernet Packet Router with Priority Queuing and Single or Multiple Transport Stream Interfaces
ActiveUS20130010795A1Performance levelImprove efficiencySpecial service provision for substationData switching by path configurationData streamThe Internet
An audio-visual content delivery system includes an interface to communicate with a local area network (LAN). A packet processing circuit in the system may filter and route Ethernet packet data received from the LAN, to specific ports and / or queues without host processor intervention. The packet processing circuit may utilize a set of filter and routing mechanisms configurable in hardware to interpret various Internet Engineering Task Force networking transport protocols, and may transfer the packet data in a format recognized by a variety of consumer subsystems, each of which may be coupled to the packet processing circuit. The packet processing circuit may be implemented as a semiconductor device, and may allow encapsulated application data to be routed to a plurality of different types of application sinks or processors, forming a point-to-point or multi-point serial or parallel data stream over a standard transport covering numerous levels of the ISO data communications stack.
Owner:STANDRD MICROSYSTEMS CORPORATION
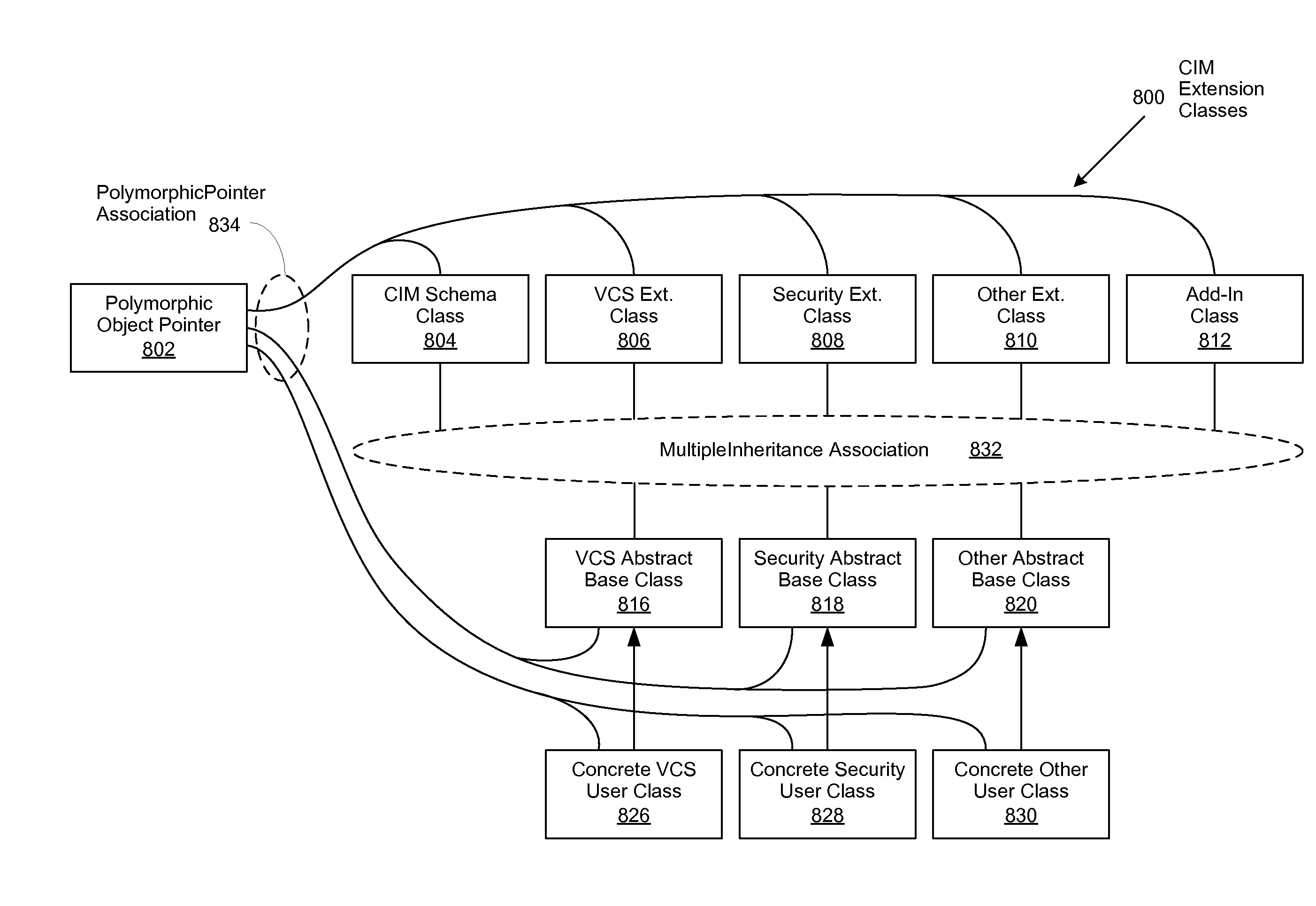
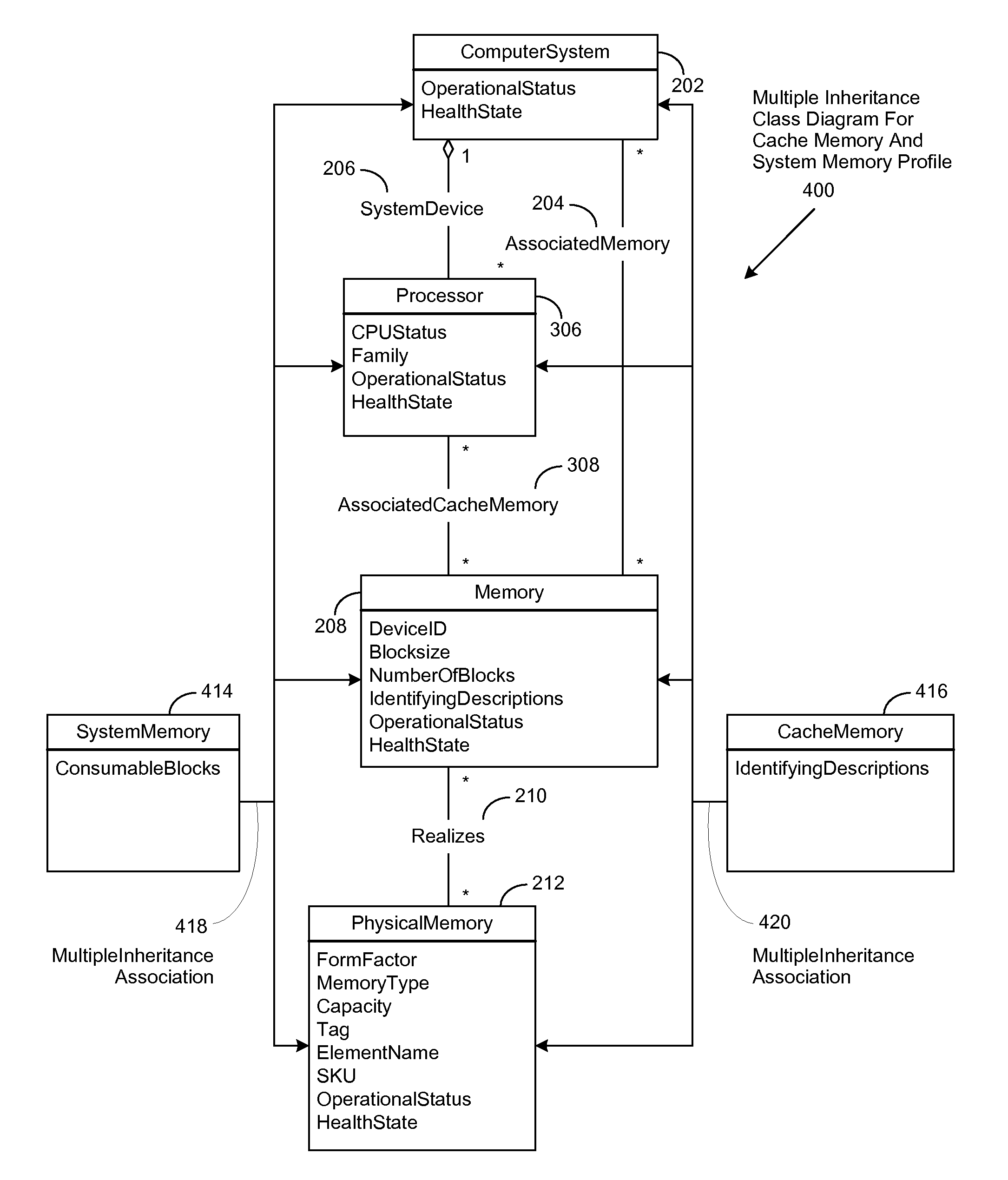
Method to support dynamic object extensions for common information model (CIM) operation and maintenance
ActiveUS8387069B2Reduce ambiguityImprove integrityObject oriented databasesSpecific program execution arrangementsData integrityStructure of Management Information
Owner:DELL PROD LP
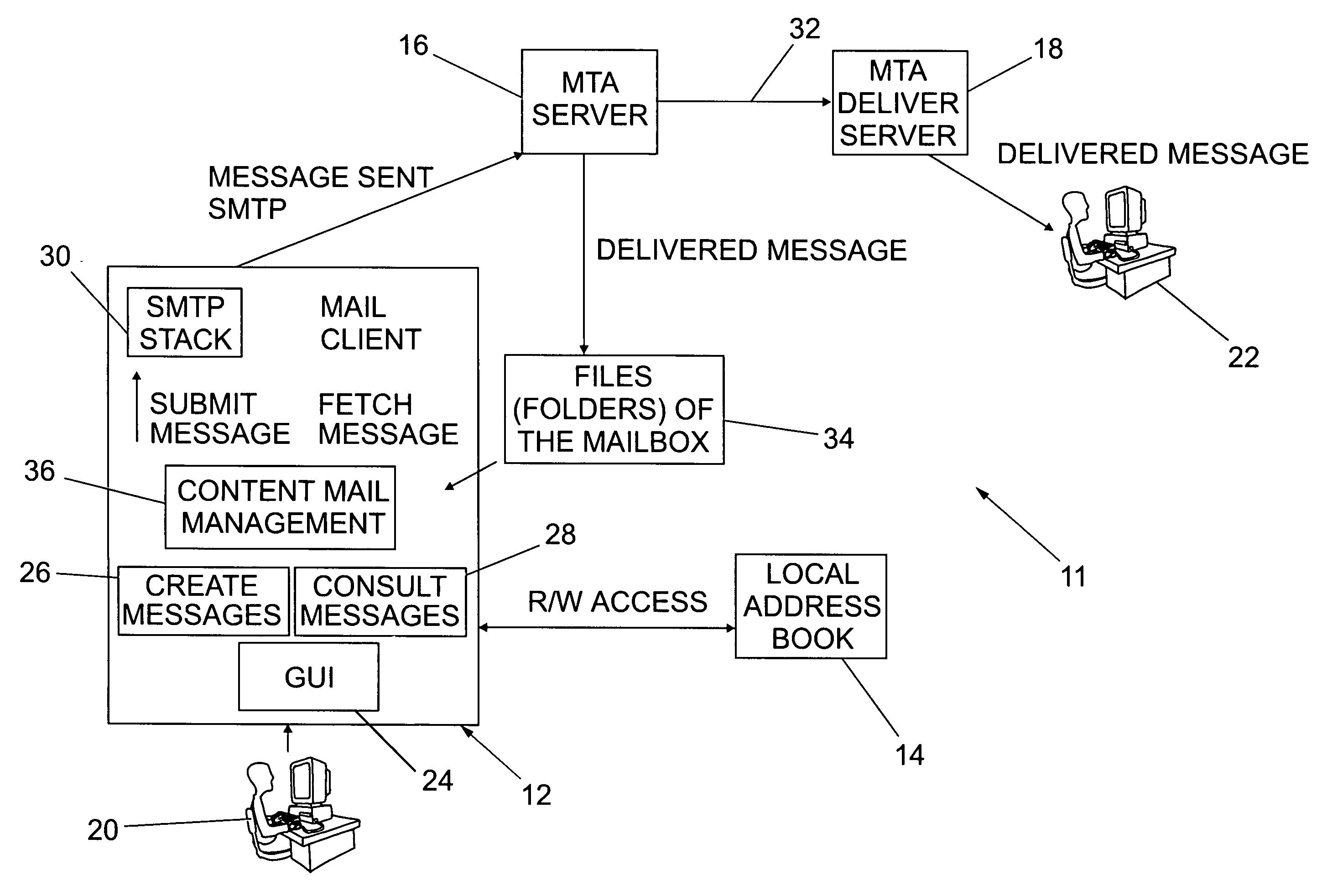
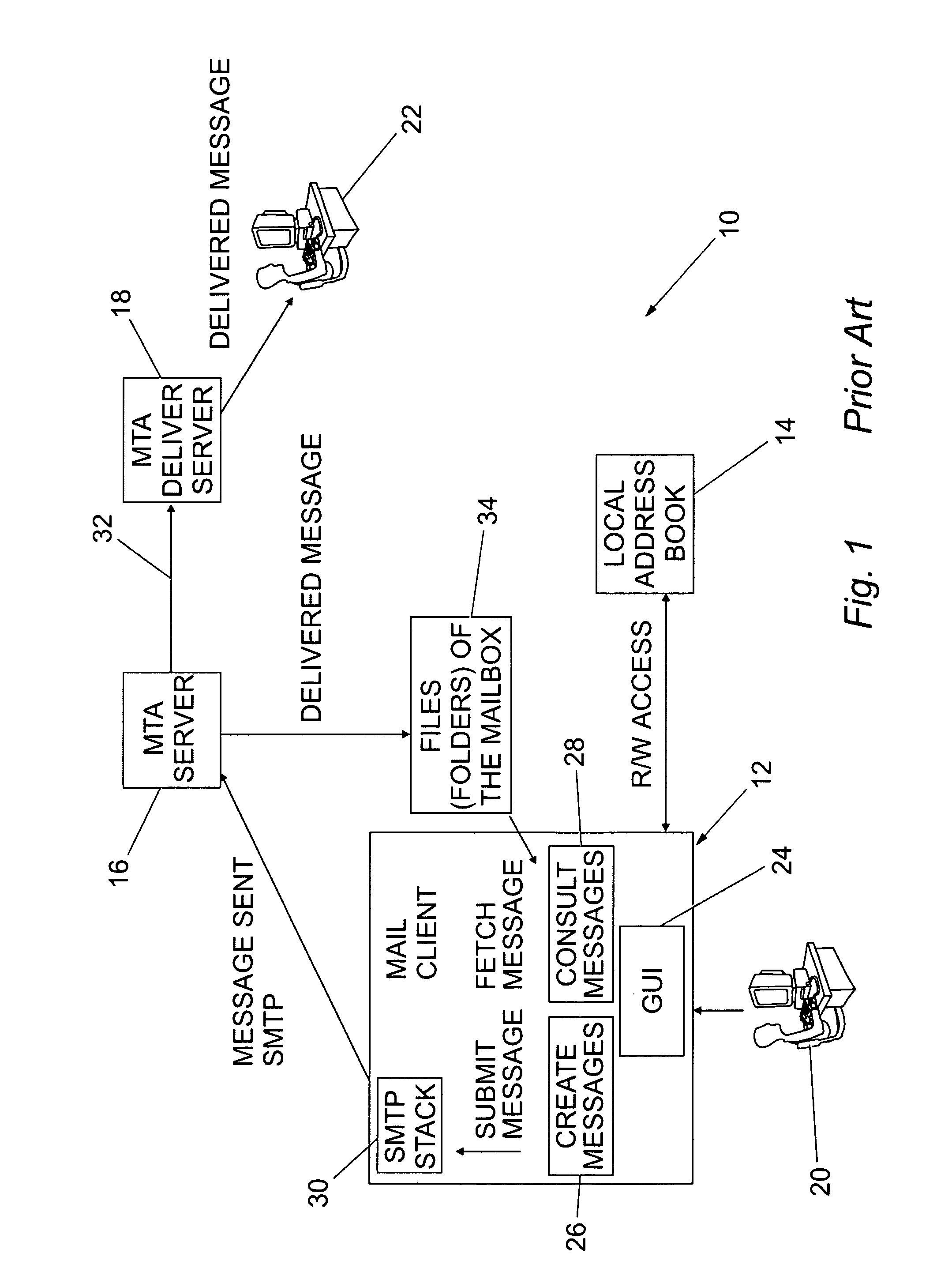
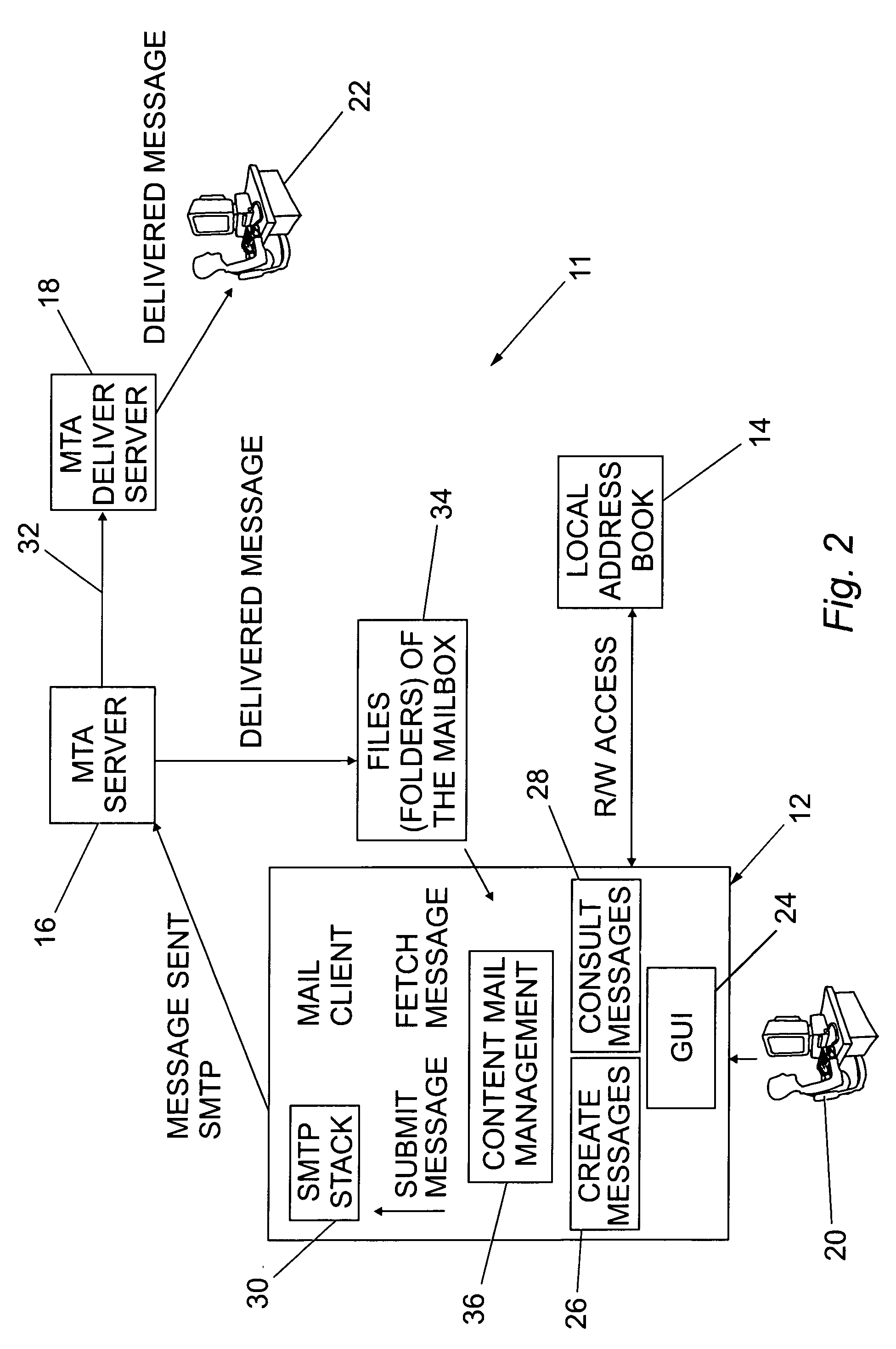
Electronic mail management system
InactiveUS8849918B2Less-difficult to track relatedDigital data processing detailsMultiple digital computer combinationsThe InternetEmail management
An electronic mail management system and method is disclosed comprising a control table for storing information related to sent and received messages of an email client, wherein the stored information relates to header fields of the received and sent messages and, in particular, to fields as defined in Internet Engineering Task Force standard RFC 2822. The system monitors the control table to identify received messages which relate to sent messages and also to identify sent messages which have not been responded to by the recipients of the sent message. The email client displays received messages stored in the control table hierarchically according to the related sent message and also displays the status of the messages in the control table.
Owner:INT BUSINESS MASCH CORP
Methods for secure and bandwidth efficient cryptographic synchronization
ActiveUS7725709B2Efficient synchronizationSynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageTransmission protocolNetwork packet
Methods for cryptographic synchronization of data packets. A roll-over counter (ROC) value is periodically appended to and transmitted with a data packet when a function of the packet sequence number equals a predetermined value. The ROC effectively synchronizes the cryptographic transformation of the data packets. Although the disclosed methods are generally applicable to many transmission protocols, they are particularly adaptable for use in systems wherein the data packets are transmitted to a receiver using the Secure Real-Time Transport Protocol (SRTP) as defined in Internet Engineering Task Force (IETF) Request for Comments (RFC) 3711.
Owner:TELEFON AB LM ERICSSON (PUBL)
Optimum managing method and system for elevator group
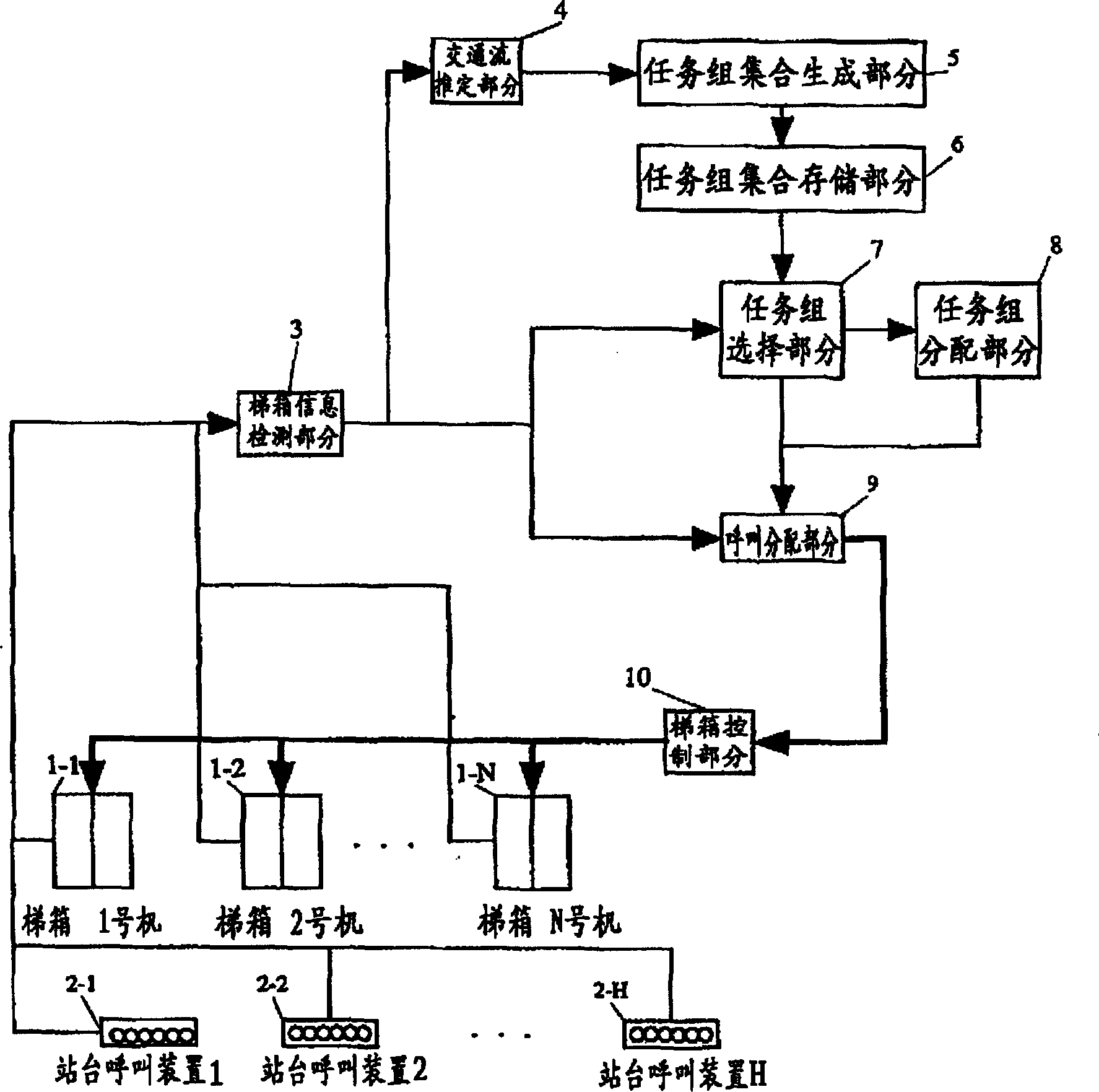
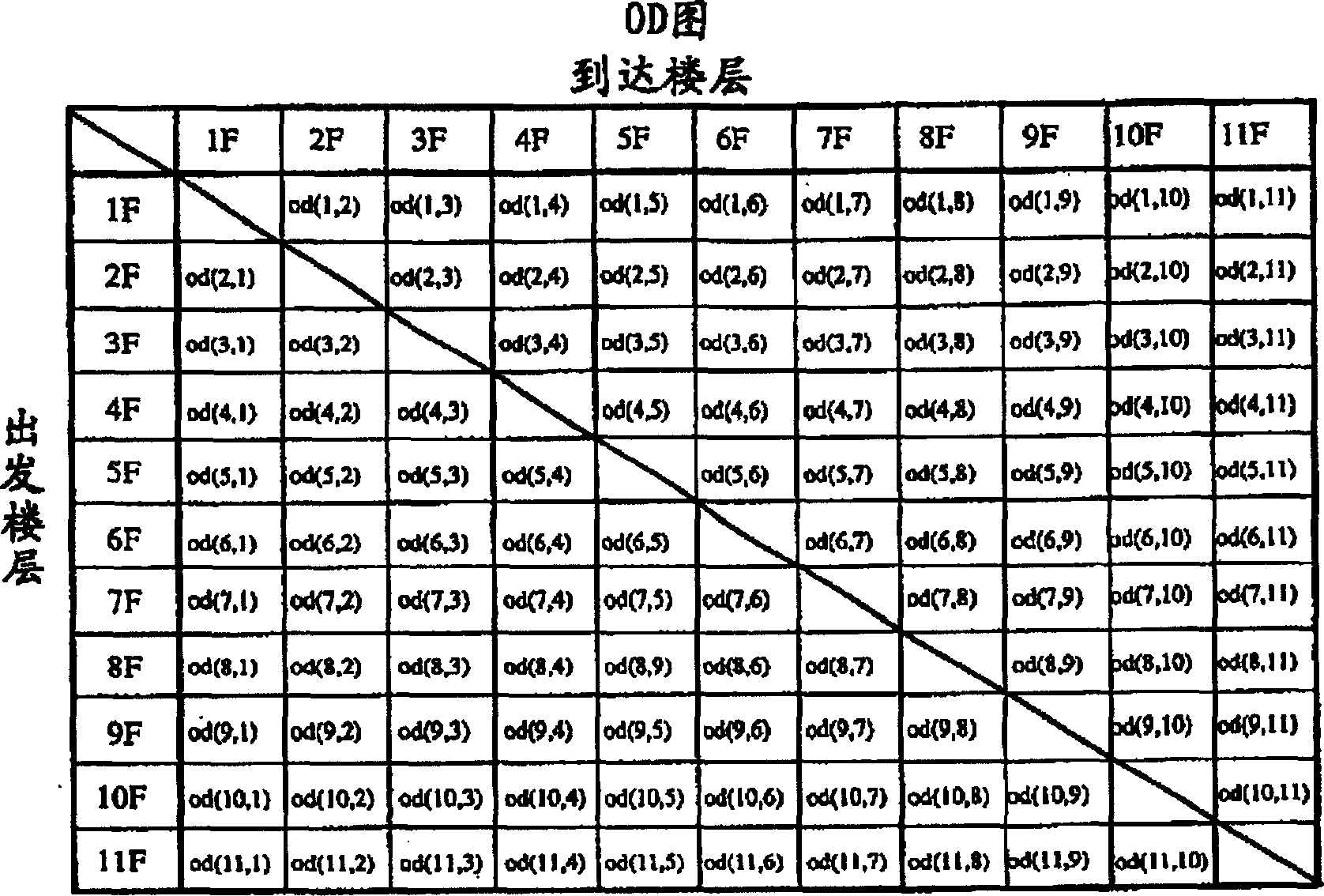
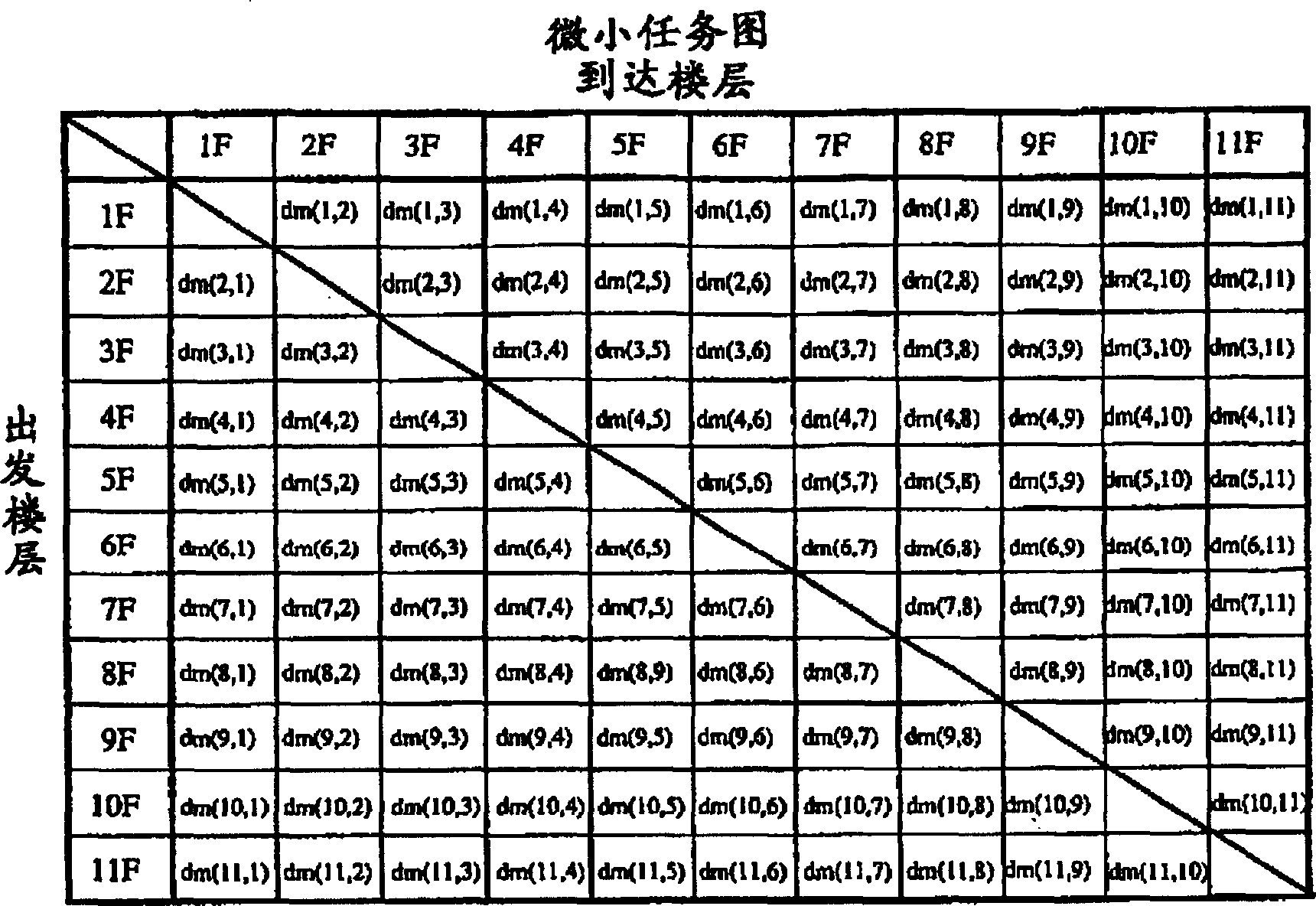
InactiveCN1231409CImprove delivery capacityImprove operational efficiencyElevatorsSimulationHigh effectiveness
The present invention provides an optimal management method and system of an elevator group capable of realizing optimized operation, simple call allocation calculation, and high-speed calculation. In the optimal management method and system of elevator groups, an element on the line list representing the relationship between the departure floor and the arrival floor that the elevator car can provide services is called a task unit, and an elevator can provide services at a time The combination of task units is called a task group, and the set of task groups prepared for the entire elevator group is called a task group set. By dynamically assigning this task group set to the elevator group, the elevators can be operated efficiently.
Owner:MITSUBISHI ELECTRIC CORP
High speed ethernet MAC and PHY apparatus with a filter based ethernet packet router with priority queuing and single or multiple transport stream interfaces
ActiveUS8281031B2Performance levelImprove efficiencySpecial service provision for substationData switching by path configurationData streamThe Internet
In one embodiment, an audio-visual content delivery system, such as a set-top box / personal video recorder system, is configured to interface with a local area network (LAN). A packet processing circuit comprised in the system may be configured to filter and route Ethernet packet data received from the LAN to specific ports and / or queues without host processor intervention. The packet processing circuit may utilize a set of filter and routing mechanisms configurable in hardware to interpret various Internet Engineering Task Force (IETF) networking transport protocols, and may transfer the packet data in a format recognized by a variety of consumer subsystems, each of which may be coupled to the decoder. The packet processing circuit may be implemented as a semiconductor device, and may allow encapsulated application data, (encapsulated using standardized encapsulation techniques), to be routed to a plurality of different types of application sinks or processors, forming a point-to-point or multi-point serial or parallel data stream over a standard transport covering numerous levels of the ISO data communications stack.
Owner:MICROCHIP TECH INC
Short length LDPC (Low Density Parity Check) code and modulation adapted for high speed Ethernet applications
InactiveUS20060041821A1Error correction/detection using LDPC codesCode conversionNetwork Communication ProtocolsParity-check matrix
A short length LDPC (Low Density Parity Check) code and modulation adapted for high speed Ethernet applications. In some instances, the short length-LDPC code and modulation may be employed within the recommended practices currently being developed by the IEEE 802.3an (10GBASE-T) Task Force. The IEEE 802.3an (10GBASE-T) Task Force has been commissioned to develop and standardize communications protocol adapted particularly for Ethernet operation over 4 wire twisted pair cables. A new LDPC code, some possible embodiments of constellations and the corresponding mappings, as well as possible embodiments of various parity check matrices, H, of the LDPC code are presented herein to provide for better overall performance than other proposed LDPC codes existent in the art of high speed Ethernet applications. Moreover, this proposed LDPC code may be decoded using a communication device having much less complexity than required to decode other proposed LDPC codes existent in this technology space.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
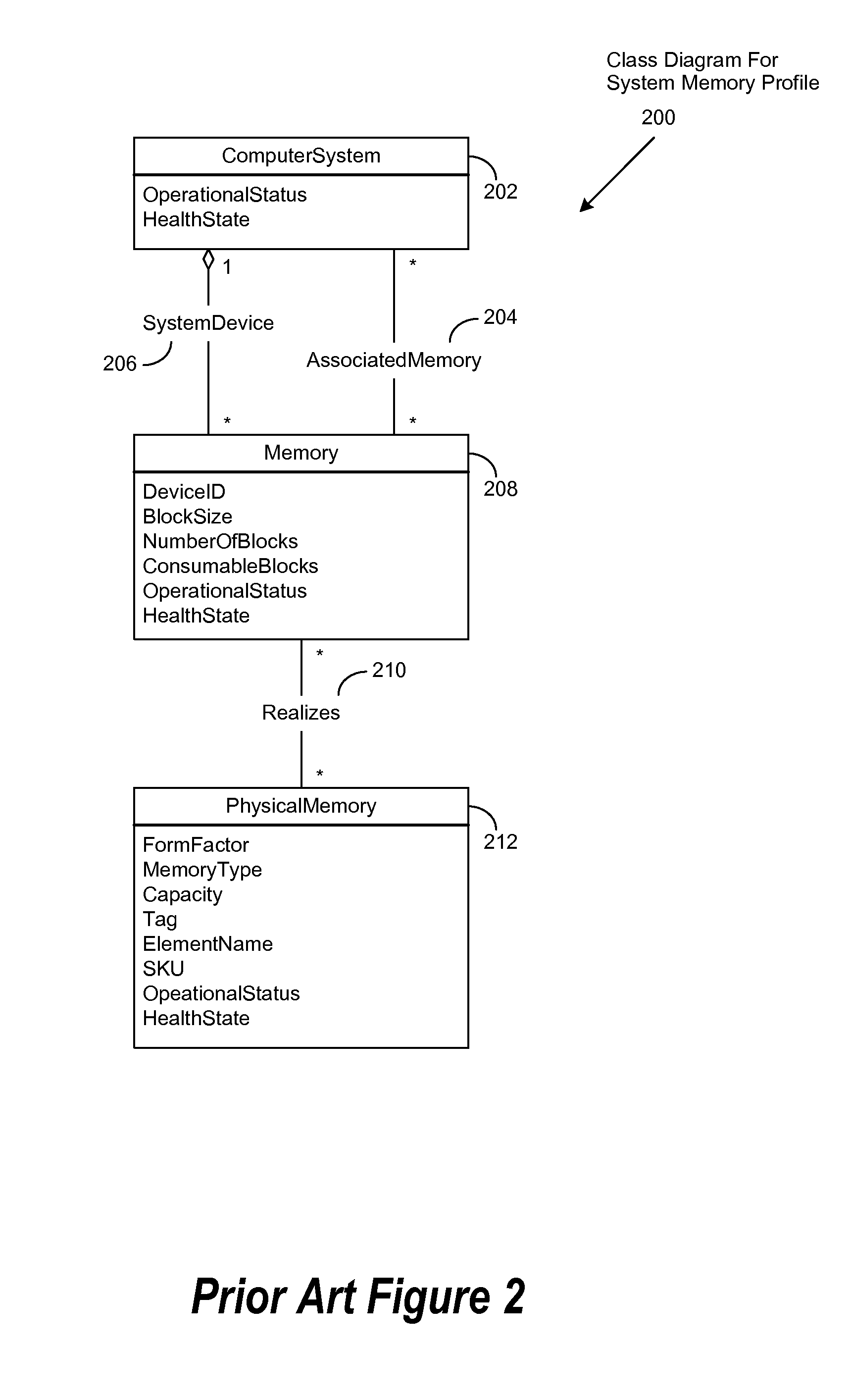
Method to support dynamic object extensions for common information model (CIM) operation and maintenance
ActiveUS20080127073A1Reduce ambiguityImprove integrityObject oriented databasesSpecific program execution arrangementsData integrityAmbiguity
An improved system and method is disclosed for making the Common Information Model (CIM), produced by the Distributed Management Task Force (DMTF), more flexible and extensible without requiring changes to it or its existing implementations. MultipleInheritance associations are implemented to define extension abstract classes for managed element information and to create static and dynamic add-in classes, all operable to reference the CIM schema class. Ambiguity is mitigated by not allowing properties of different data types to have the same name in super classes that are used for MultipleInheritance associations. Data integrity is facilitated by merging class properties of the same name and data type through the use of a Min algorithm. Concrete user classes are derived from new abstract classes such that management functionality is enabled for managed element properties. A polymorphic object pointer is implemented using a PolymorphicPointer association to facilitate traversal or the resulting class hierarchies and inheritance trees.
Owner:DELL PROD LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com