Patents
Literature
200 results about "Authentication header" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
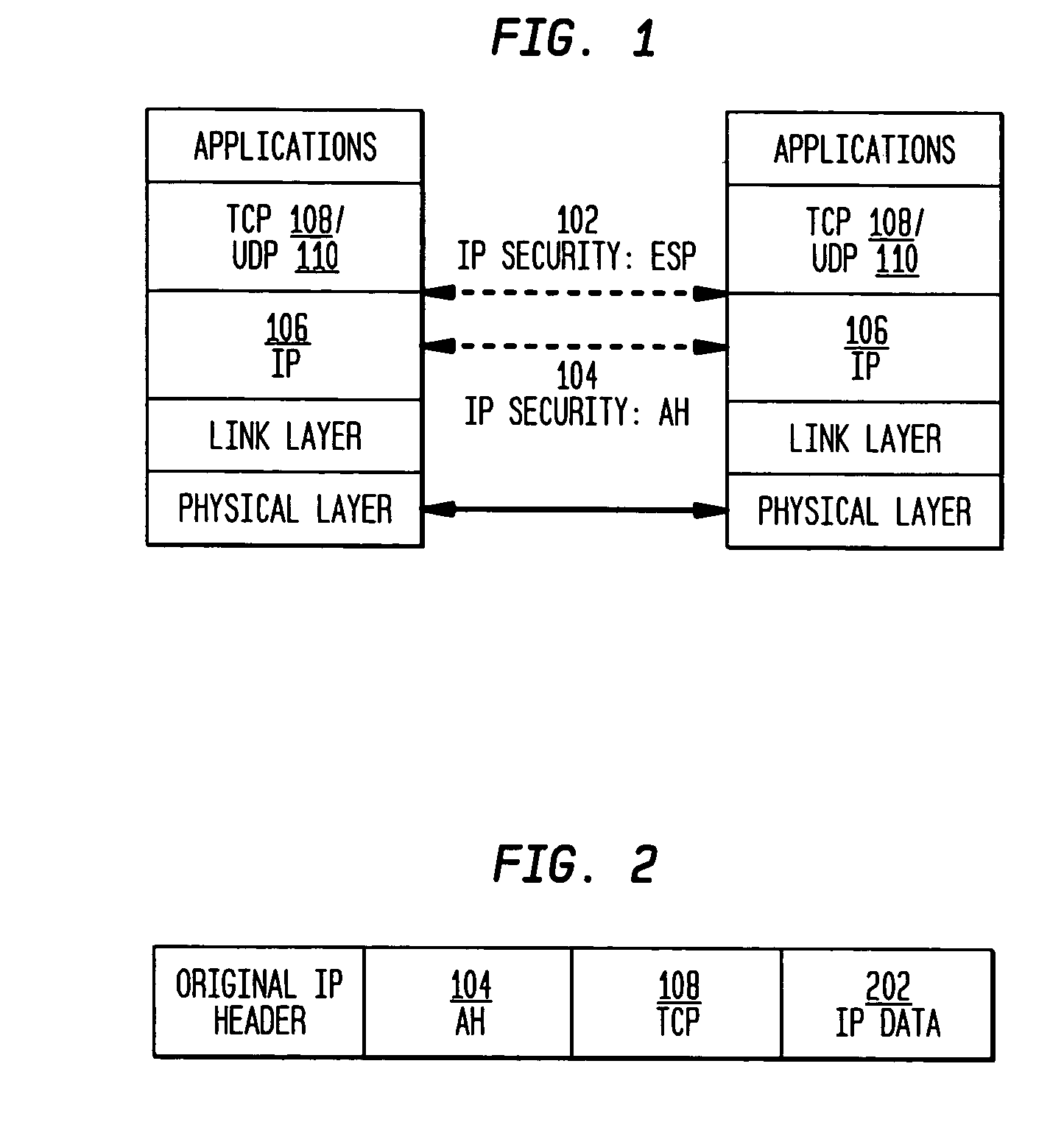
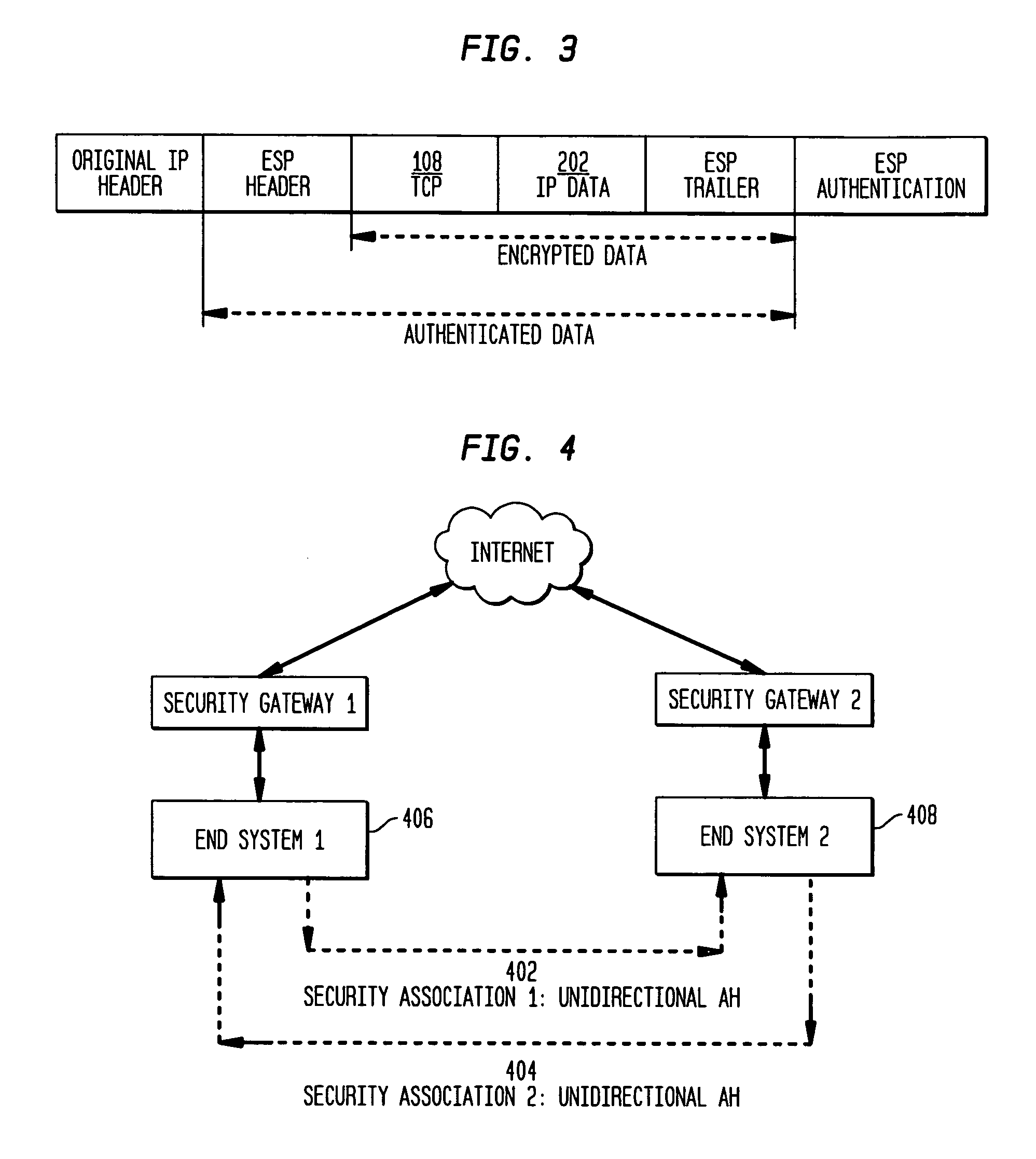
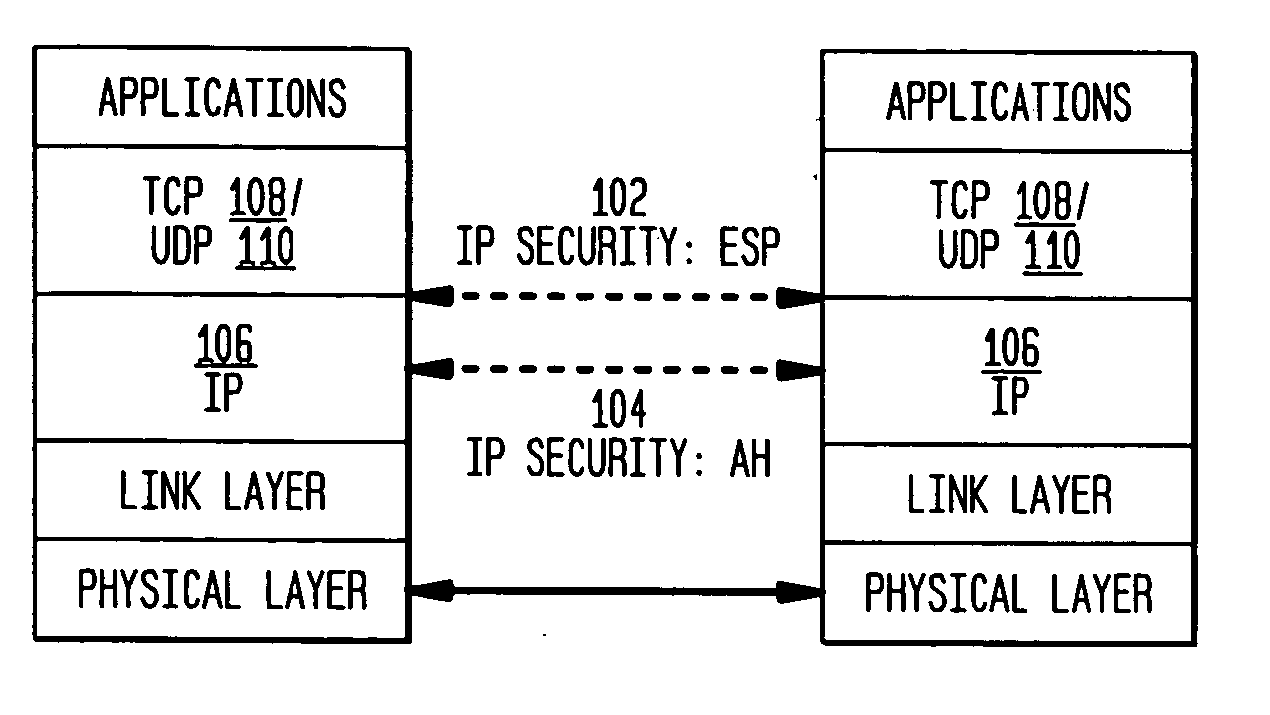
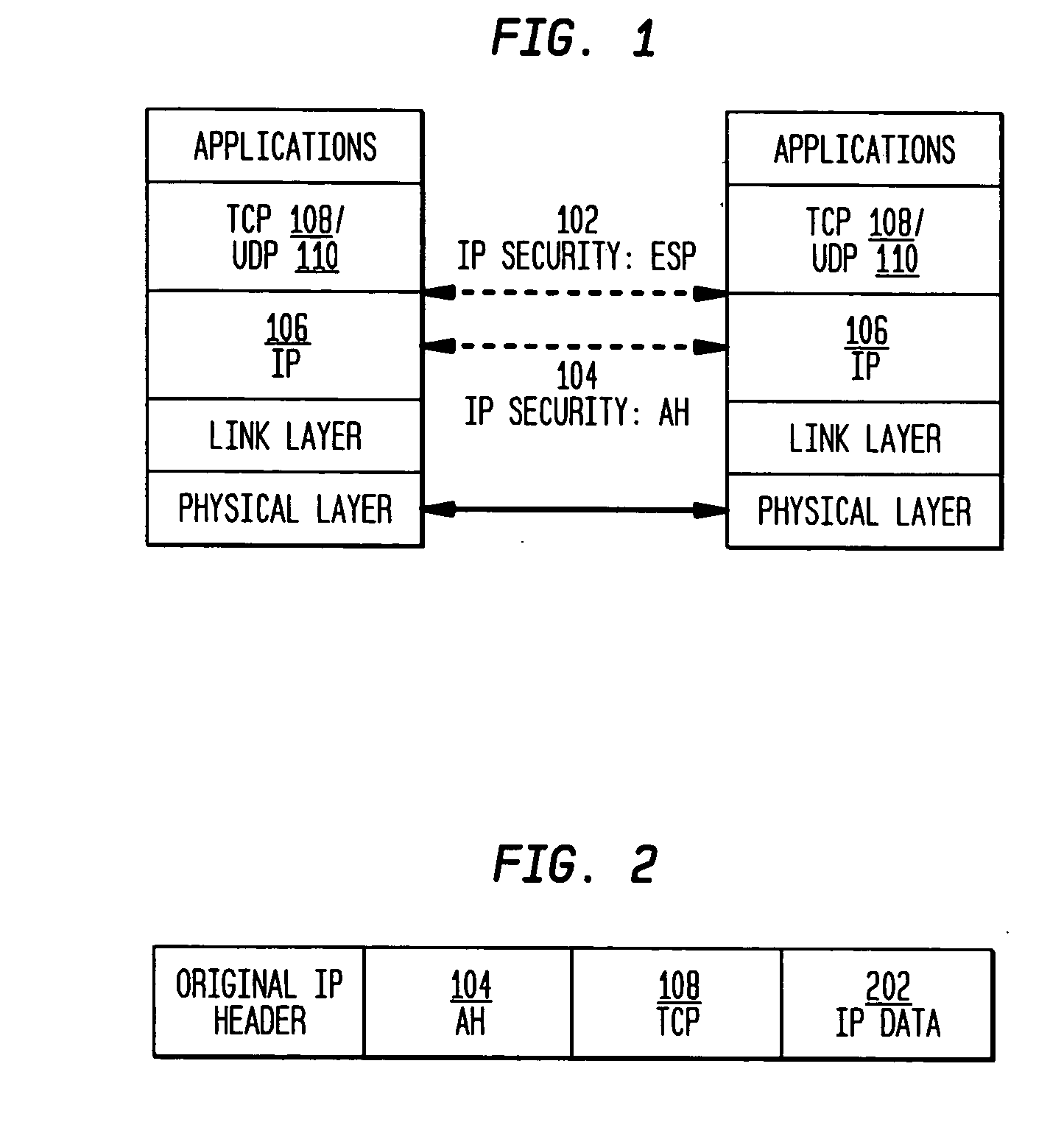
Authentication Header. The Authentication Header (AH) protocol provides data origin authentication, data integrity, and replay protection. However, AH does not provide data confidentiality, which means that all of your data is sent in the clear.
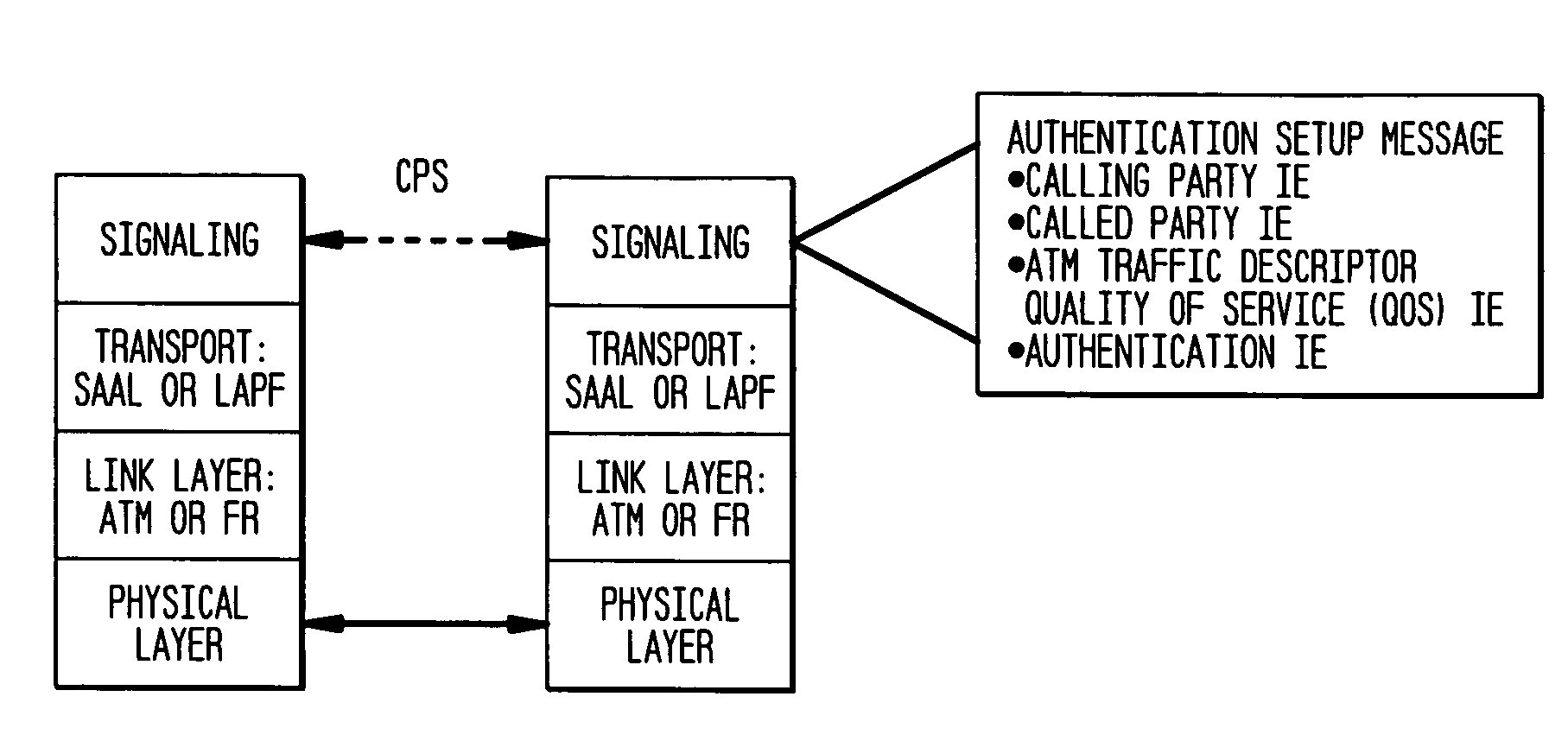
Authentication mechanisms for call control message integrity and origin verification
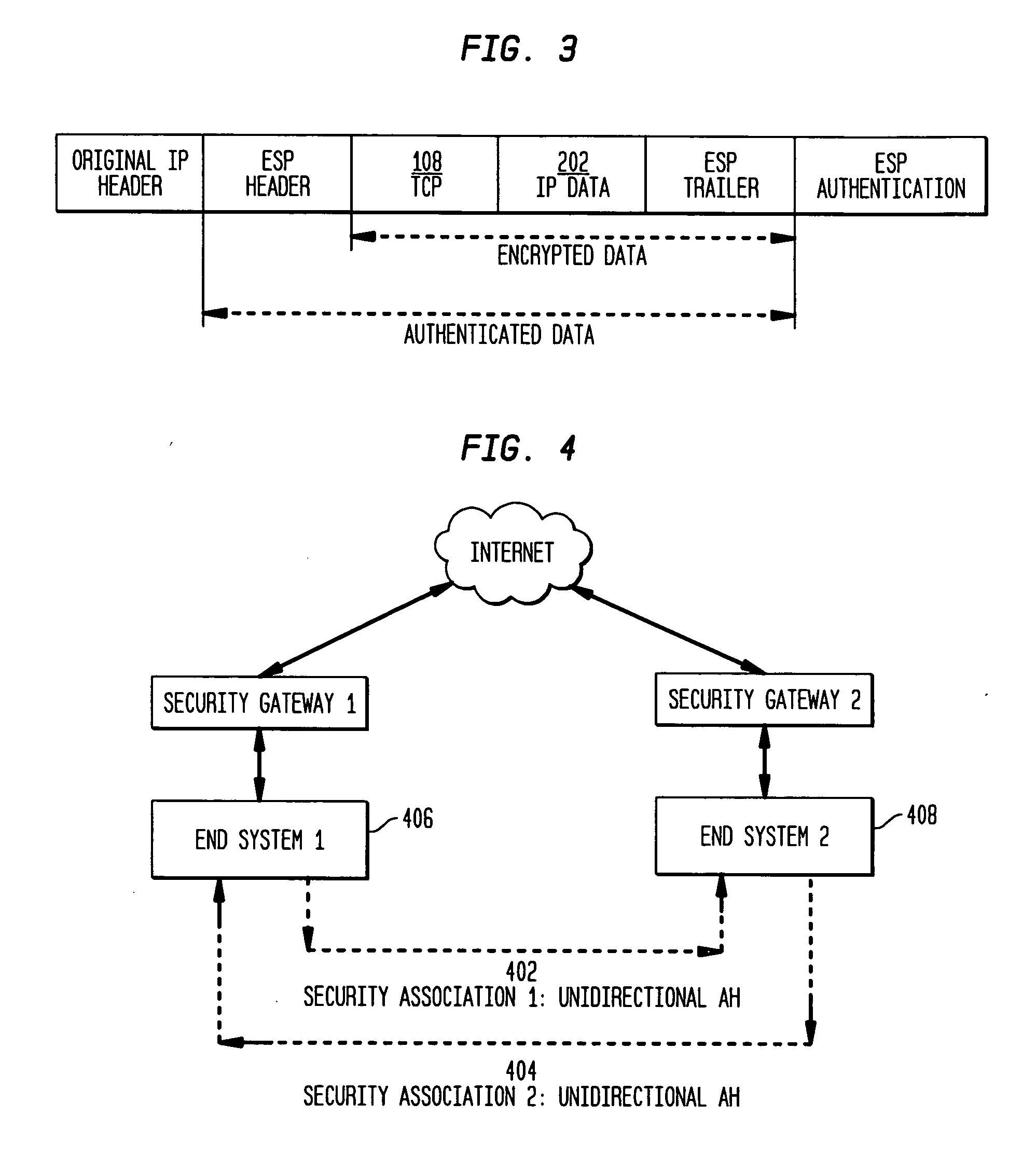
The present invention incorporates methodologies developed in the Internet Engineering Task Force (IETF) Internet Protocol Security (IPSEC) Working Group into asynchronous transfer mode (ATM) and frame relay (FR) signaling to provide message integrity and origin authentication. In one implementation the invention provides a virtual private network (VPN) infrastructure with call control message integrity, origin verification, and transit network filtering. The invention utilizes a set of control plane messages based on the IPSEC authentication header (AH) methodology to provide these security mechanisms for ATM and FR network switching equipment and signaling protocols. This abstract itself is not intended to limit the scope of this patent. The scope of the present invention is pointed out in the appending claims.
Owner:ALCATEL-LUCENT USA INC
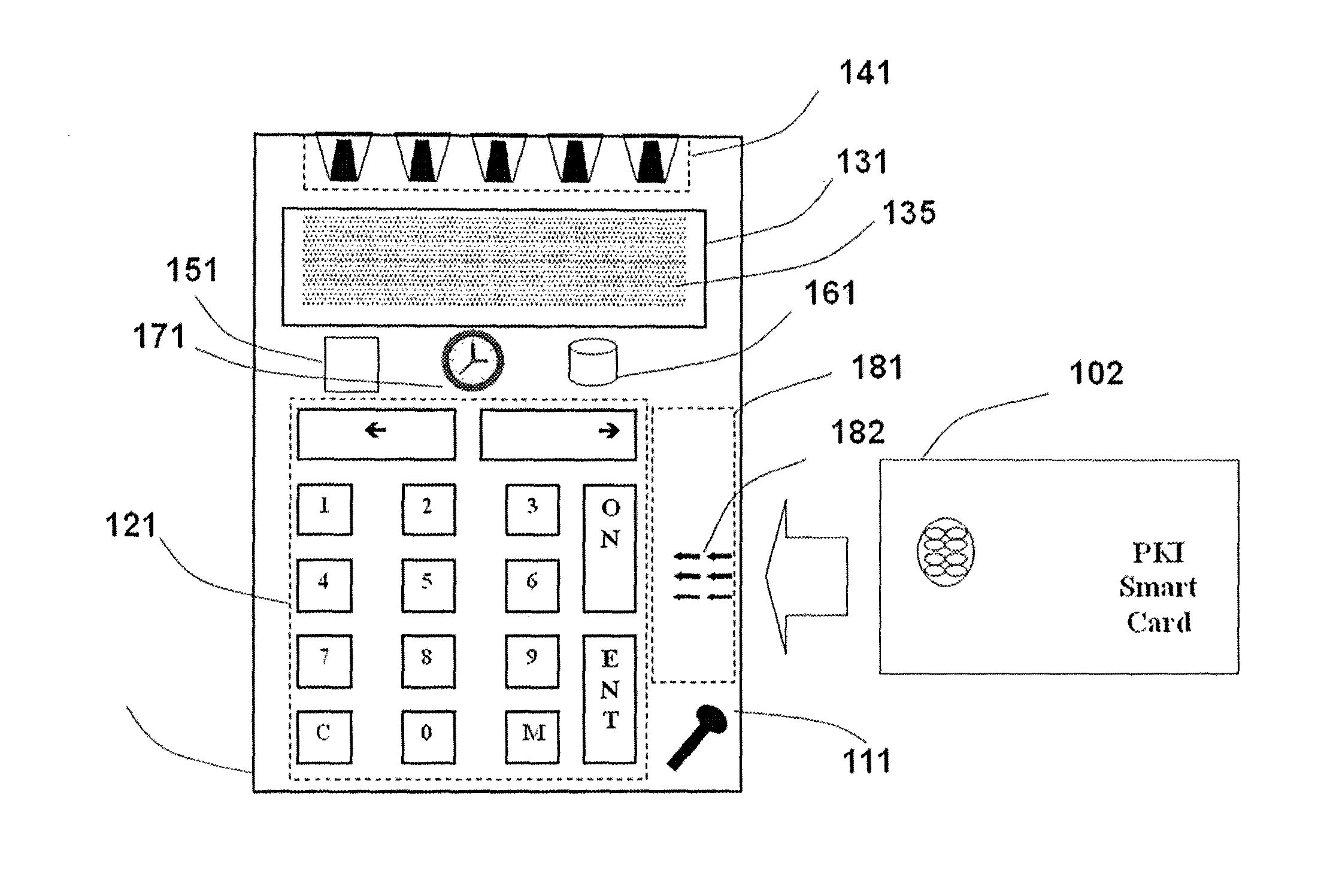
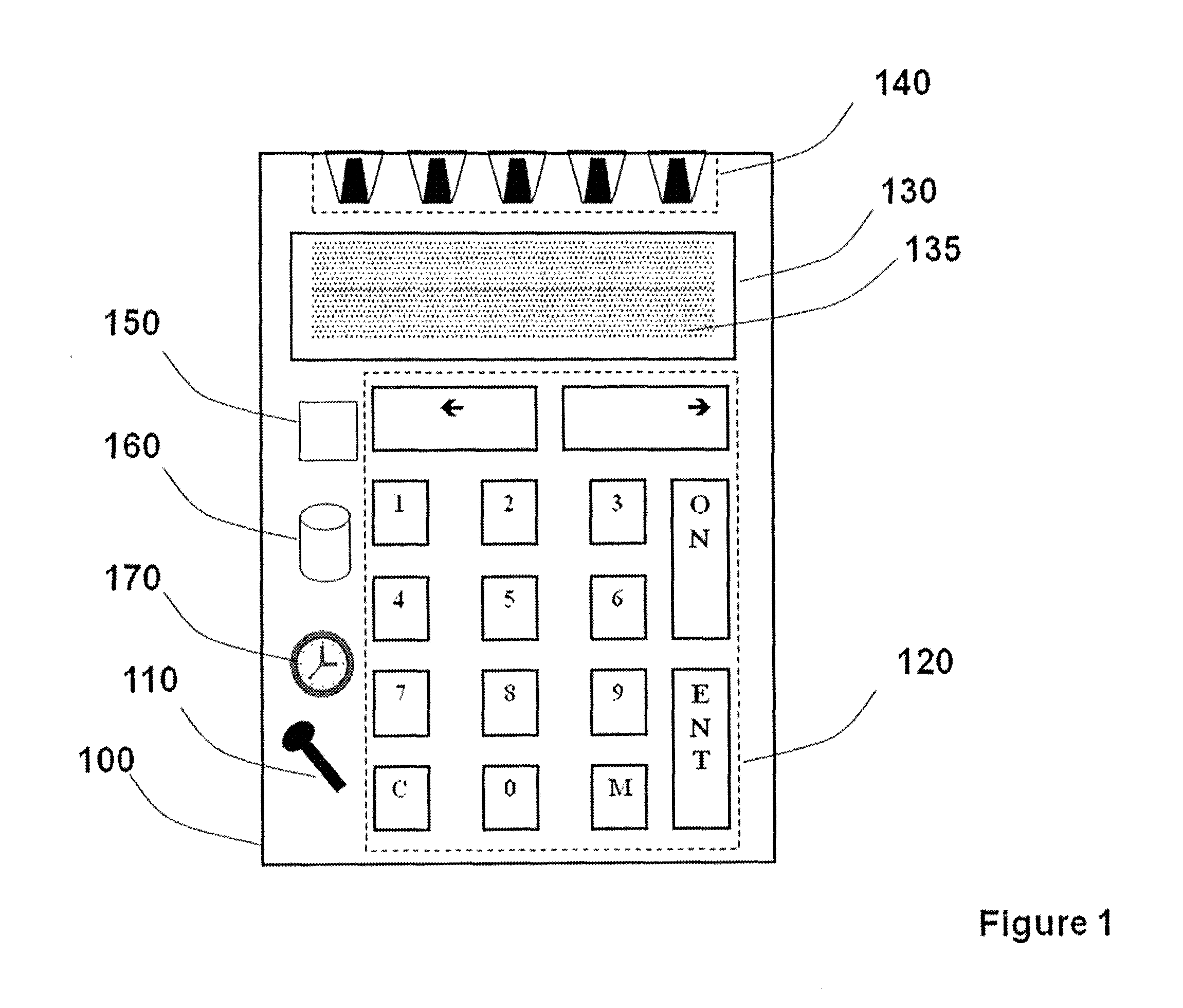
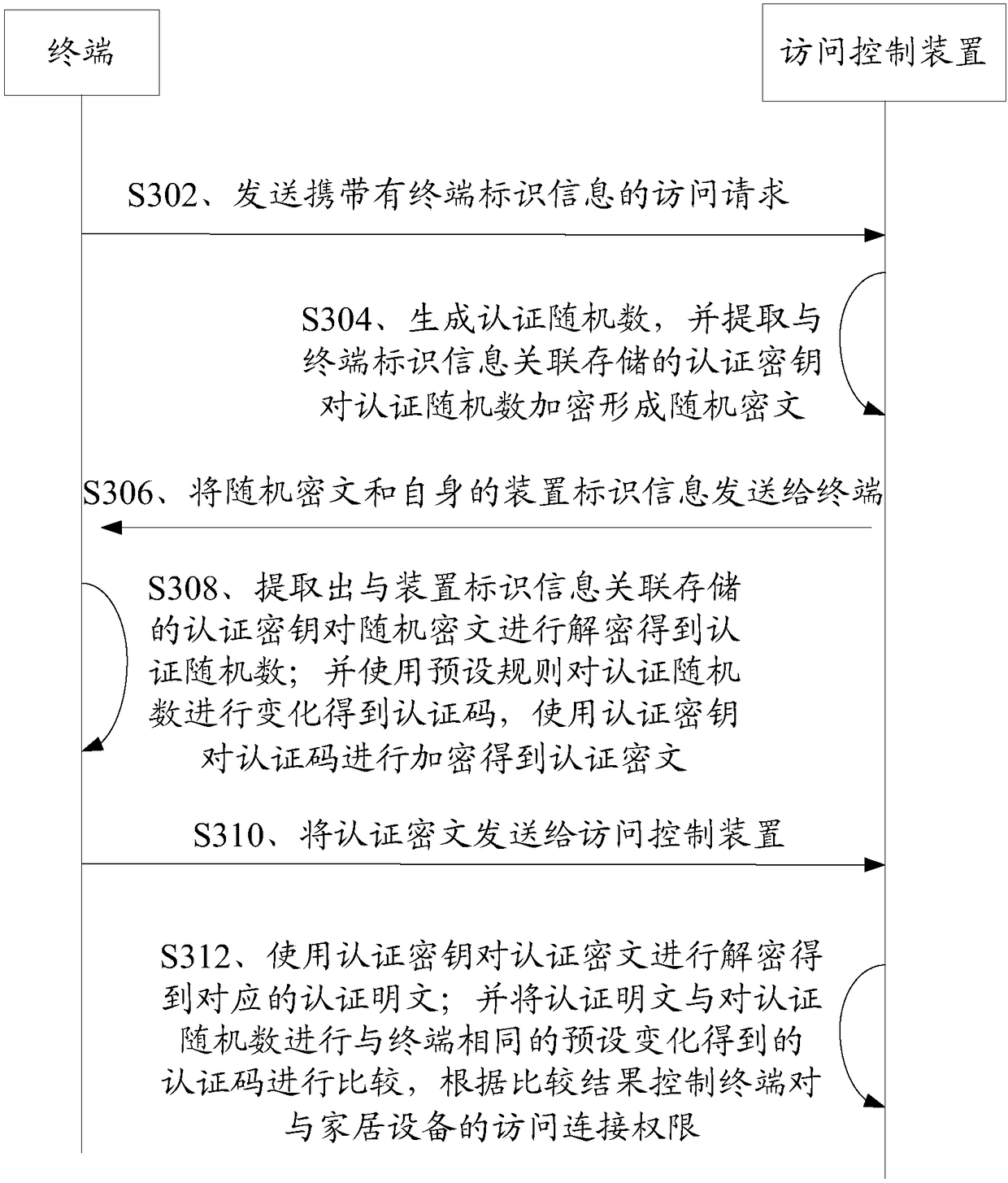
Strong authentication token with visual output of pki signatures
InactiveUS20130198519A1Improve securityUser identity/authority verificationDigital data authenticationDisplay deviceSecret code
A handheld authentication device comprising a data processor and a display is adapted to: generate an input value; submit the input value to an asymmetric cryptographic operation; obtain the result of said asymmetric cryptographic operation; generate an authentication message substantially comprising the result of the asymmetric cryptographic operation; encode the authentication message into one or more images; and display these images on the display. A method for securing computer-based applications remotely accessed by a user comprises capturing images displayed on the display of an authentication device of the user whereby these images have been encoded with an authentication message generated by the authentication device and whereby the authentication message comprises the result of an asymmetric cryptographic operation on an input value; decoding the images to retrieve the authentication message; retrieving the result of the asymmetric cryptographic operation from the authentication message; verifying the authentication message.
Owner:ONESPAN NORTH AMERICA INC
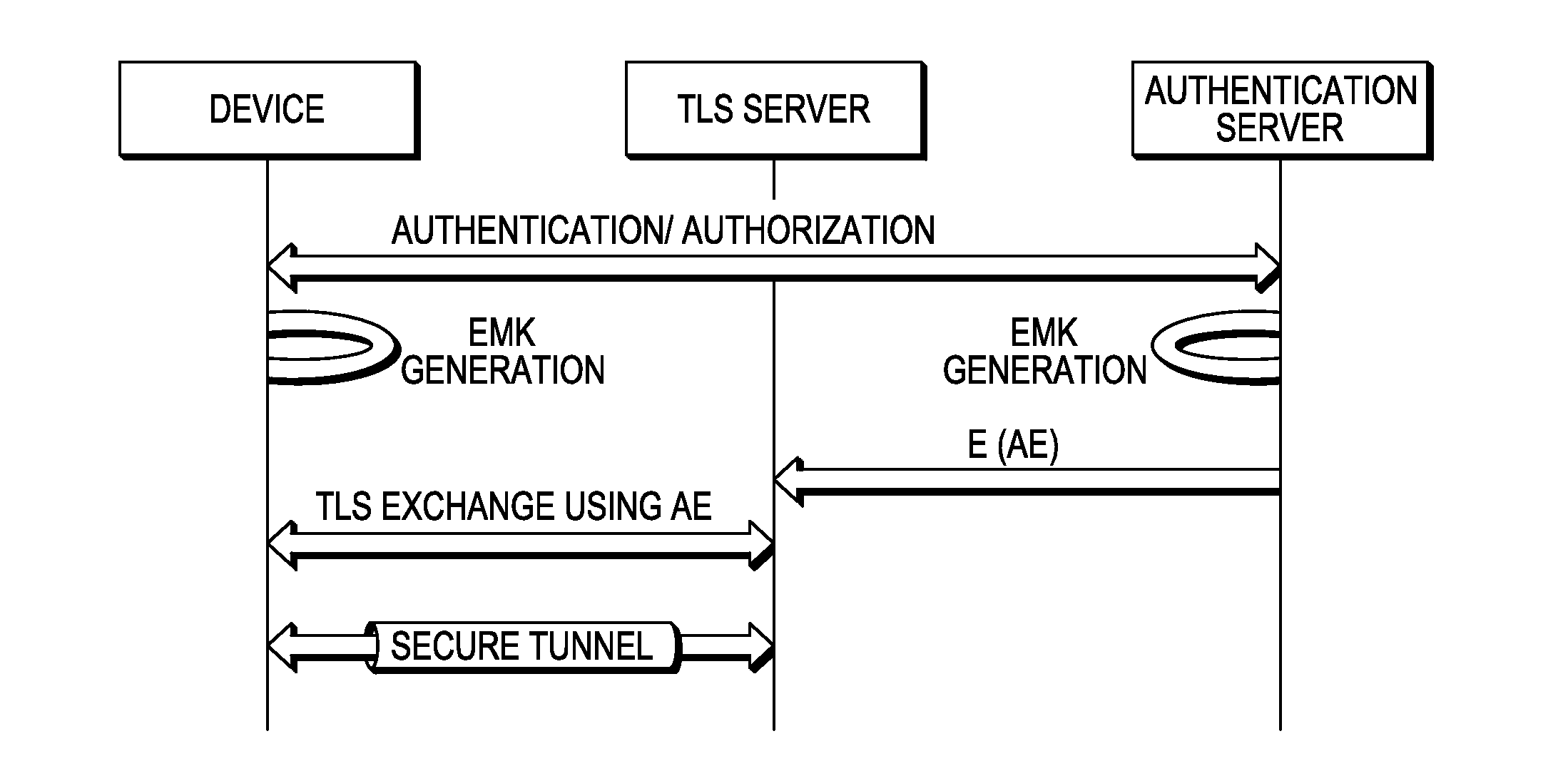
System and method for cognizant transport layer security (CTLS)
ActiveUS20120042160A1Not availableDigital data processing detailsUser identity/authority verificationCommunications systemAuthentication server
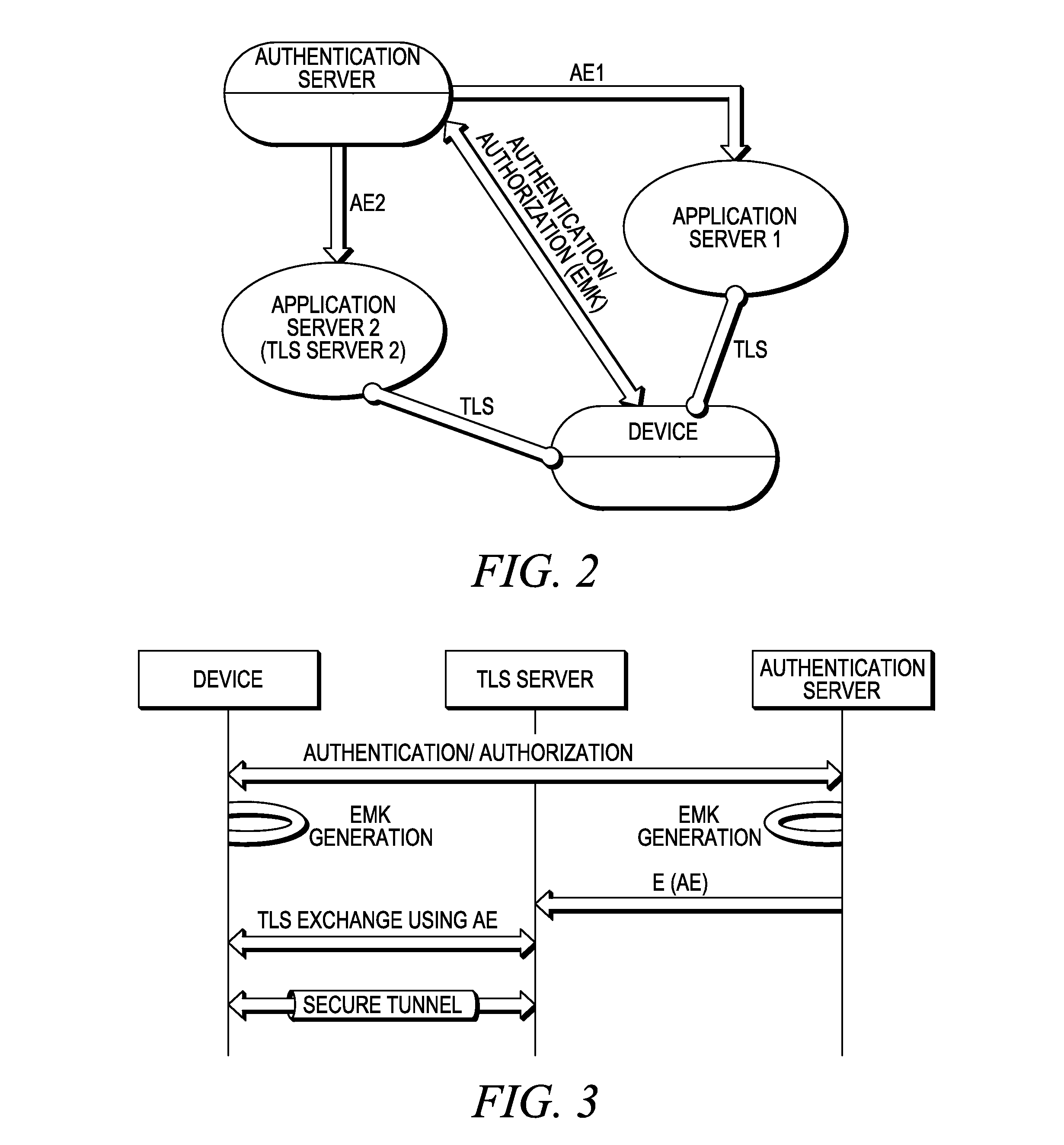
A method of authentication and authorization over a communications system is provided. Disclosed herein are systems and methods for creating a cryptographic evidence, called authentication / authorization evidence, AE, when a successful authentication / authorization between a client and an authentication server is complete. There are a variety of methods for generating AE. For instance, the AE can be data that is exchanged during the authentication signaling or data that results from it. A distinctive point being that AE results from the authentication process and is used as prior state for the following TLS exchange. An example for creation of AE, is as follows: EAP authentications typically result in an Extended Master Session Key (EMSK). The EMSK can be used to create an Evidence Master Key (EMK) that can then be used to create AE for a variety of servers.
Owner:GOOGLE TECH HLDG LLC
Login token generation and authentication method, device thereof, and storage medium
InactiveCN109150910AImprove interaction securityAvoid harmUser identity/authority verificationAccess timeValidation methods
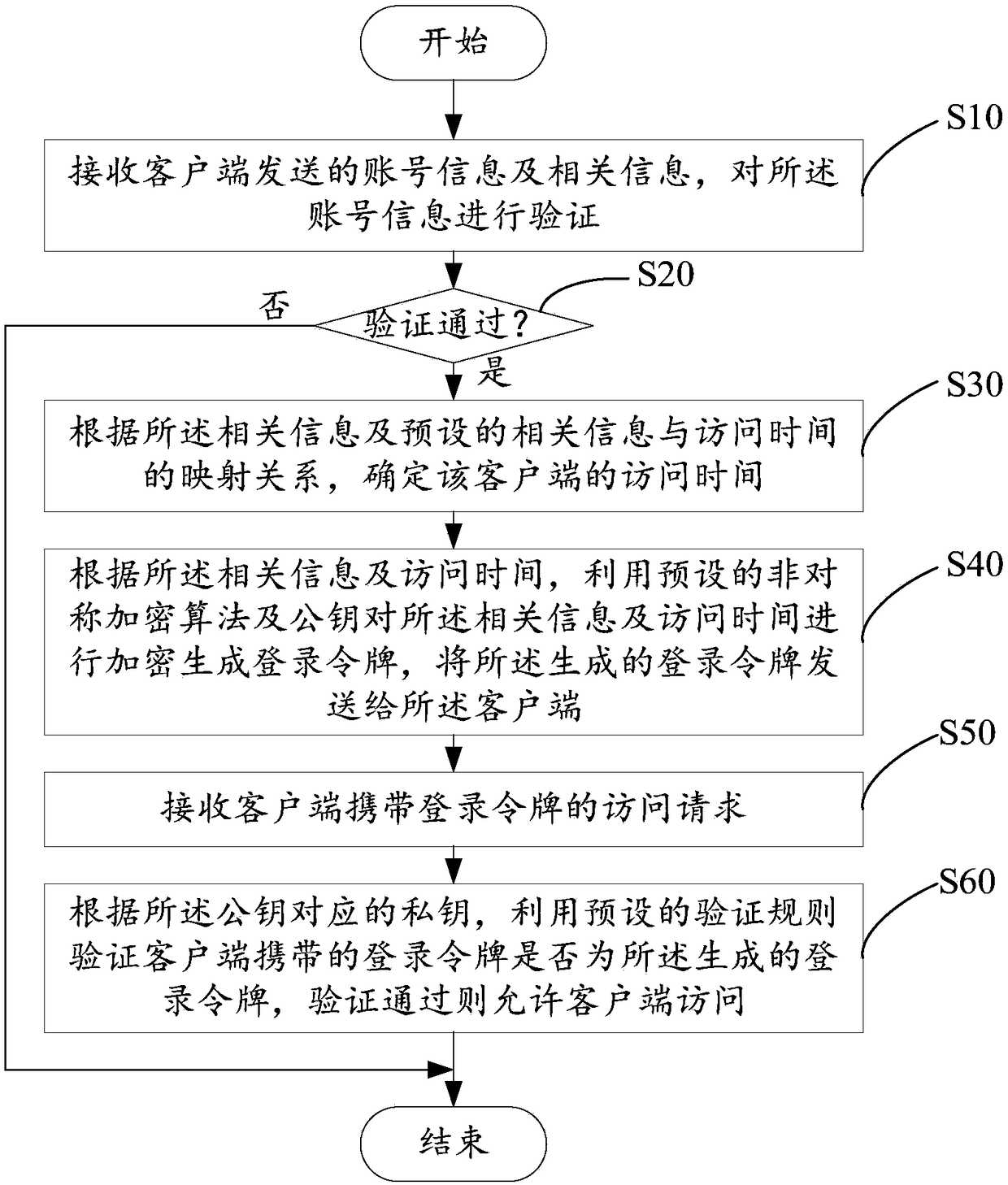
The present invention relates to security techniques, and discloses a login token generation and authentication method, an electronic device thereof and a storage medium. That method comprises the steps of receiving account information and related information sent by a client, verifying the account information, and when the verification is passed, determining the access time of the client according to the mapping relationship between the related information and the preset related information and the access time. Then, according to the related information and the access time, the related information and the access time are encrypted by using a public key and a preset asymmetric encryption algorithm to generate a login token, and the login token is transmitted to the client. Finally, an access request of a client carrying a login token is received, whether the login token carried by the client is the generated login token is verified by using a preset authentication rule according to a private key corresponding to the public key, and permits the client to access if the authentication is passed. By using the method, the device thereof and the storage medium, the safety of informationexchange in the interaction process between the client and the server can be improved, and the hidden danger of safety can be reduced.
Owner:PING AN TECH (SHENZHEN) CO LTD
Authentication method of mobile terminal uniqueness based on software digital certificate
ActiveCN103167491AImprove authentication strengthNot afraid to stealUser identity/authority verificationSecurity arrangementApplication serverComputer terminal
The invention discloses an authentication method of mobile terminal uniqueness based on a software digital certificate, and belongs to the technical field of computers and information safety. The method specifically comprises the following steps: (1), a safe client side is installed on a mobile terminal, a certificate request relevant to equipment information is generated so as to be registered by a server side; a digital certificate is issued to the mobile terminal by the server side, and relevance between the digital certificate and the equipment is achieved. (2), when the method is used, random information is sent to the mobile terminal by the server side, the information is received by the safe client side, the random information is signed by using a private key of the digital certificate of the equipment, and the signing data are sent to the server side. The signature is verified by a public key of the digital certificate by an application server, and a communication opposite terminal identity is confirmed. The method is capable of verifying the mobile terminal commendably and enhancing intensity of authentication on the basis that hardware authentication equipment is not added.
Owner:KOAL SOFTWARE CO LTD
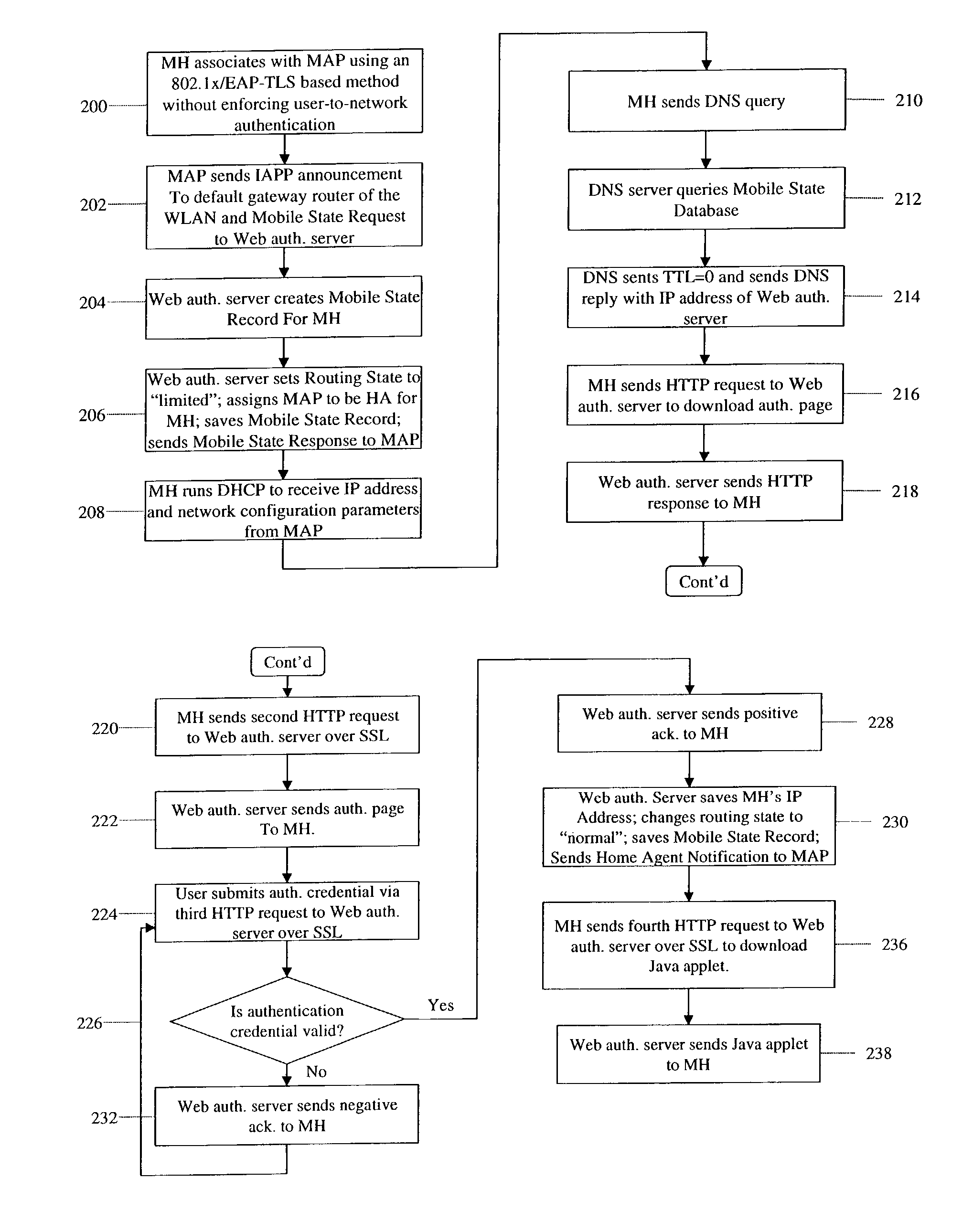
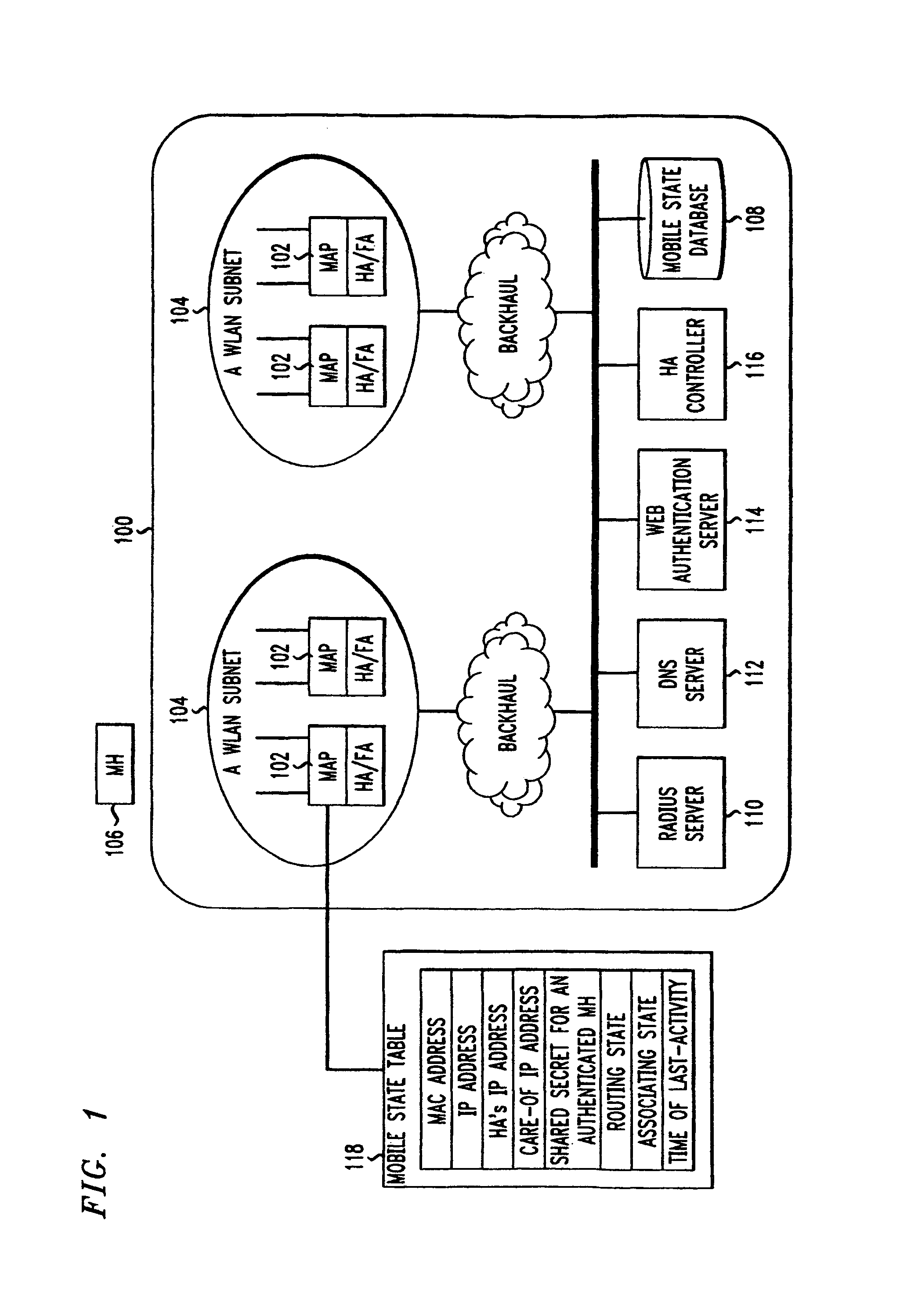
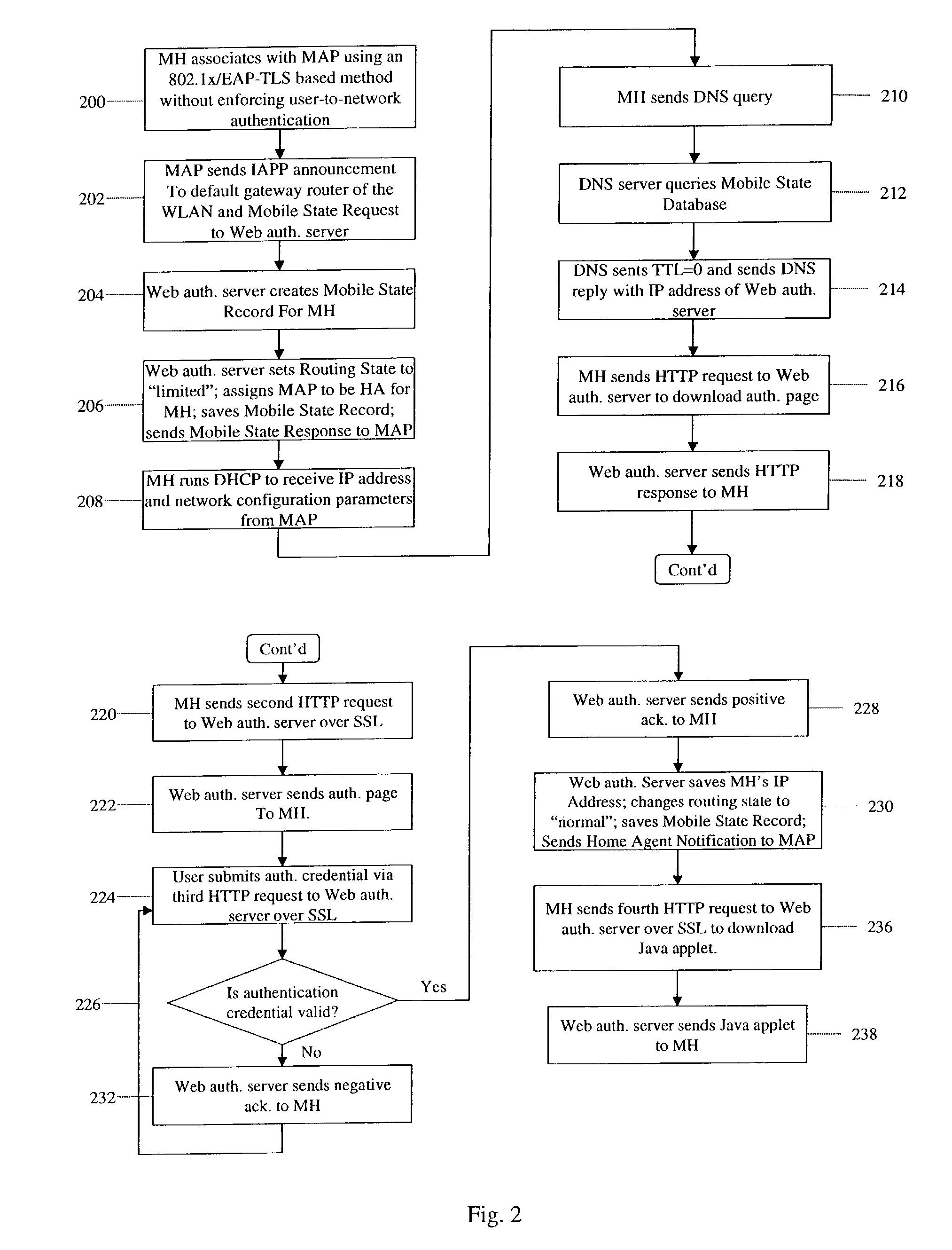
Zero-configuration secure mobility networking technique with web-based authentication interface for large WLAN networks
InactiveUS8817757B2Authentication is convenientAvoid attackNetwork traffic/resource managementNetwork topologiesIp addressUser authentication
A zero-configuration secure mobility networking technique for WLANs is provided, utilizing split link-layer and a Web-based authentication. The link-layer authentication process facilitates network-to-user authentication and generation of session-specific encryption keys for air traffic using digital certificates to prevent man-in-the-middle attacks without requiring users to have pre-configured accounts. Although any WLAN host can pass the link-layer authentication and obtain link connectivity, the WLAN only allows the host to obtain IP networking configuration parameters and to communicate with a Web-based authentication server prior to initiating the Web-based authentication process that is responsible for user-to-network authentication. The Web-based authentication server employs a Web page for initial authentication and a Java applet for consequent authentications. In the Web page, registered users can manually, or configure their Web browsers to automatically, submit their authentication credentials; new users can open accounts, make one-time payments, or refer the Web-based authentication server to other authentication servers where they have accounts. Once a user is authenticated to the WLAN, the user's mobile host obtains full IP connectivity and receives secure mobility support from the WLAN. The mobile host always owns a fixed IP address as it moves from one access point to another in the WLAN. All wireless traffic between the mobile host and the WLAN is encrypted. Whenever the mobile host moves to a new access point, a Java applet (or an equivalent client-side program delivered over Web) enables automatic authentication of the mobile host to the WLAN. In addition, the ZCMN method supports dynamic load balancing between home agents. Thus, a mobile host can change home agents during active sessions.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
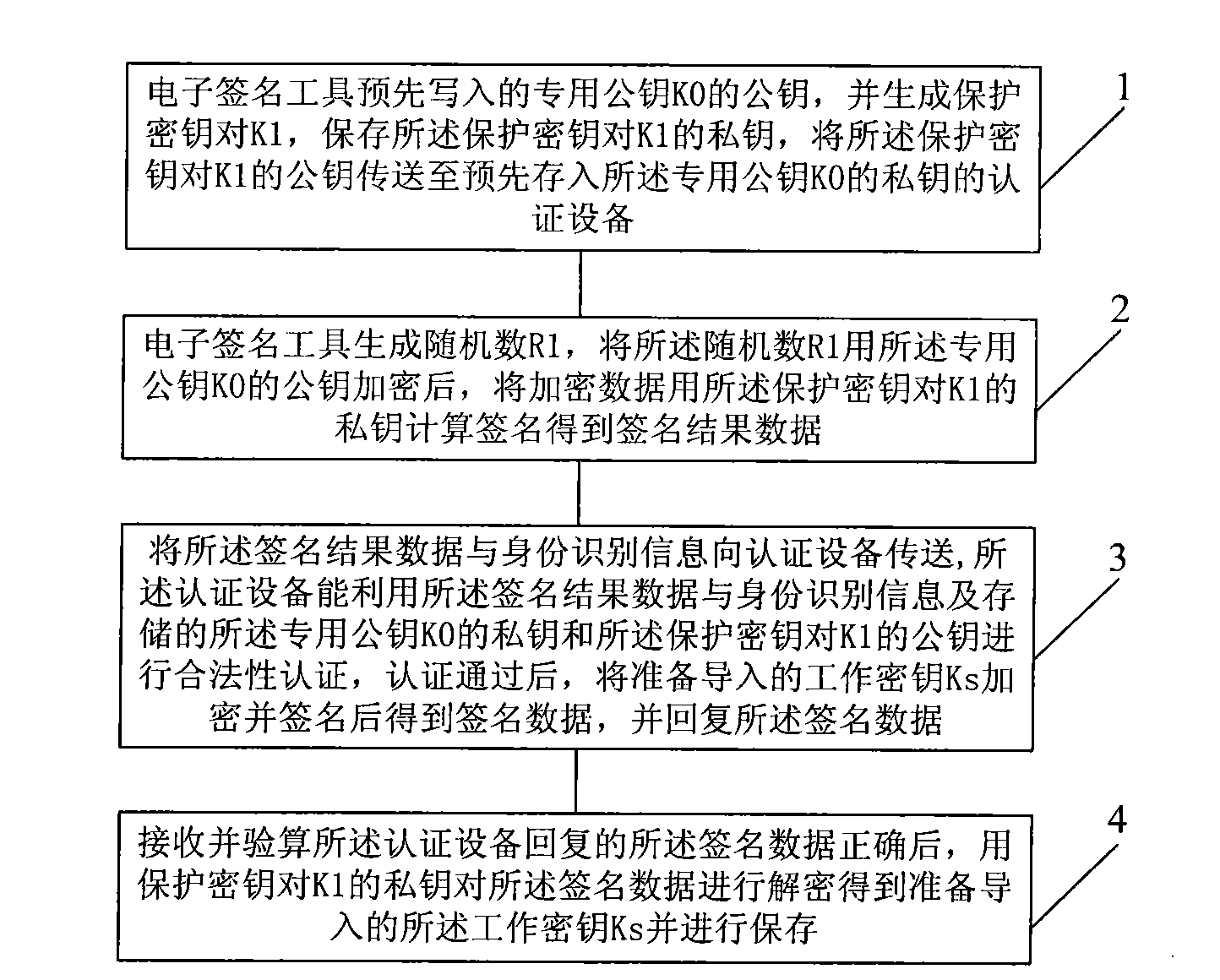
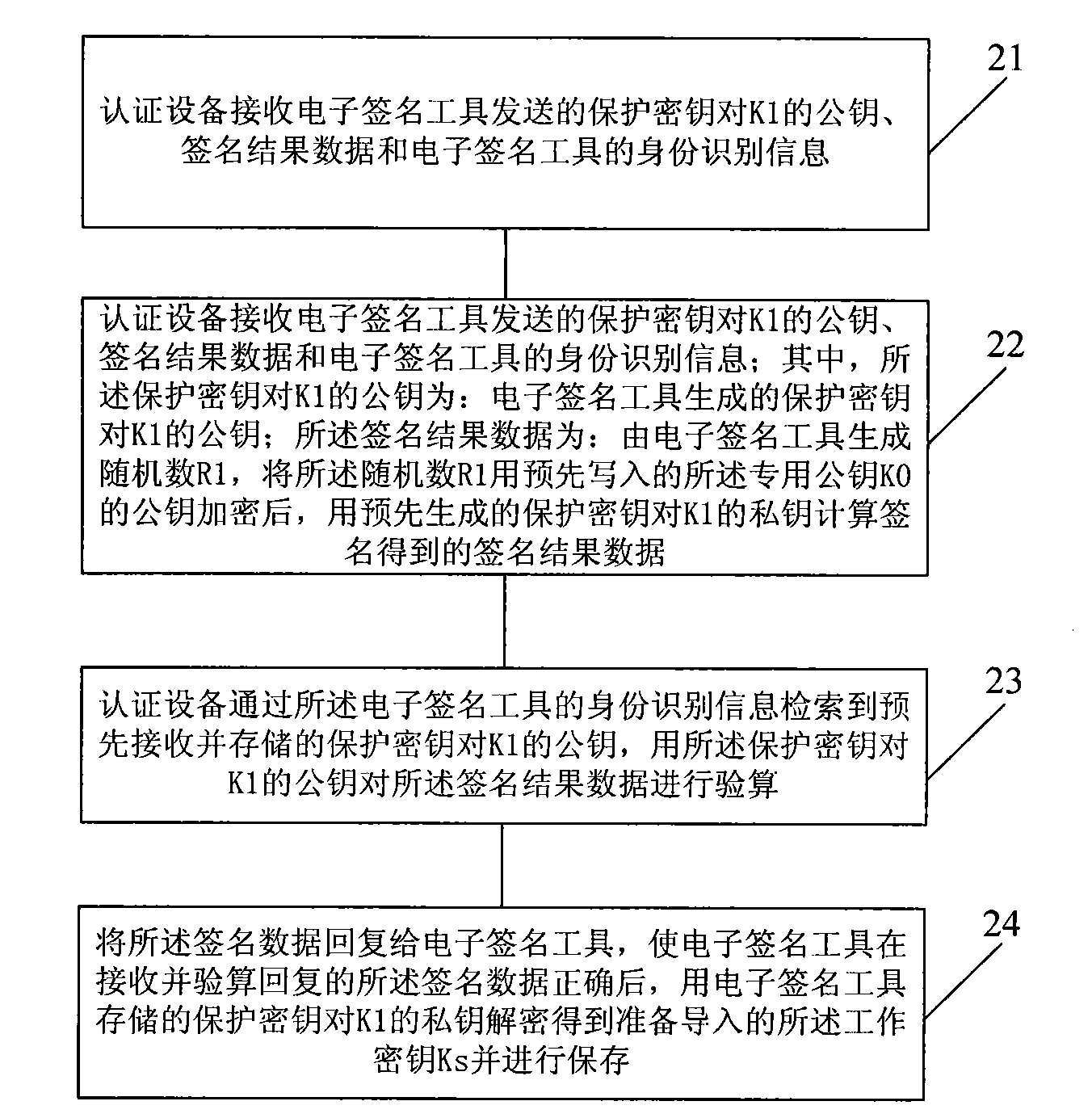
Method for importing secret keys safely, electronic signature tool, authentication device and system
ActiveCN101989991AImprove securityImprove conveniencePublic key for secure communicationUser identity/authority verificationThe InternetAuthentication system
The invention discloses a method for importing secret keys safely, an electronic signature tool, an authentication device and an authentication system. The method comprises the following steps: generating a random number R1, encrypting the random number R1 by a public key of pre-written special public keys K0 so as to obtain encrypted data, and carrying out calculated signature on the encrypted data by a private key of pre-generated and stored protection secret key pair K1 so as to obtain signature result data; transmitting the signature result data and identification information to an authentication device, wherein the private key of the special public key K0 and the public key of the protection secret key pair K1 are stored in the authentication device; after carrying out validity authentication by the authentication device according to the signature result data, the identification information, the stored private key of the special public key K0 and the stored public key of the protection secret key pair K1, encrypting and signing a working secret key Ks to be imported so as to form signature data for response; and receiving and decrypting the signature data replied by the authentication device so as to obtain imported working secret key Ks. The method for importing the secret keys safely is not dependent on specific security environments; and by using the method for importing the secret keys safely, the working secret keys can be imported into electronic signature tools via Internet.
Owner:TENDYRON CORP
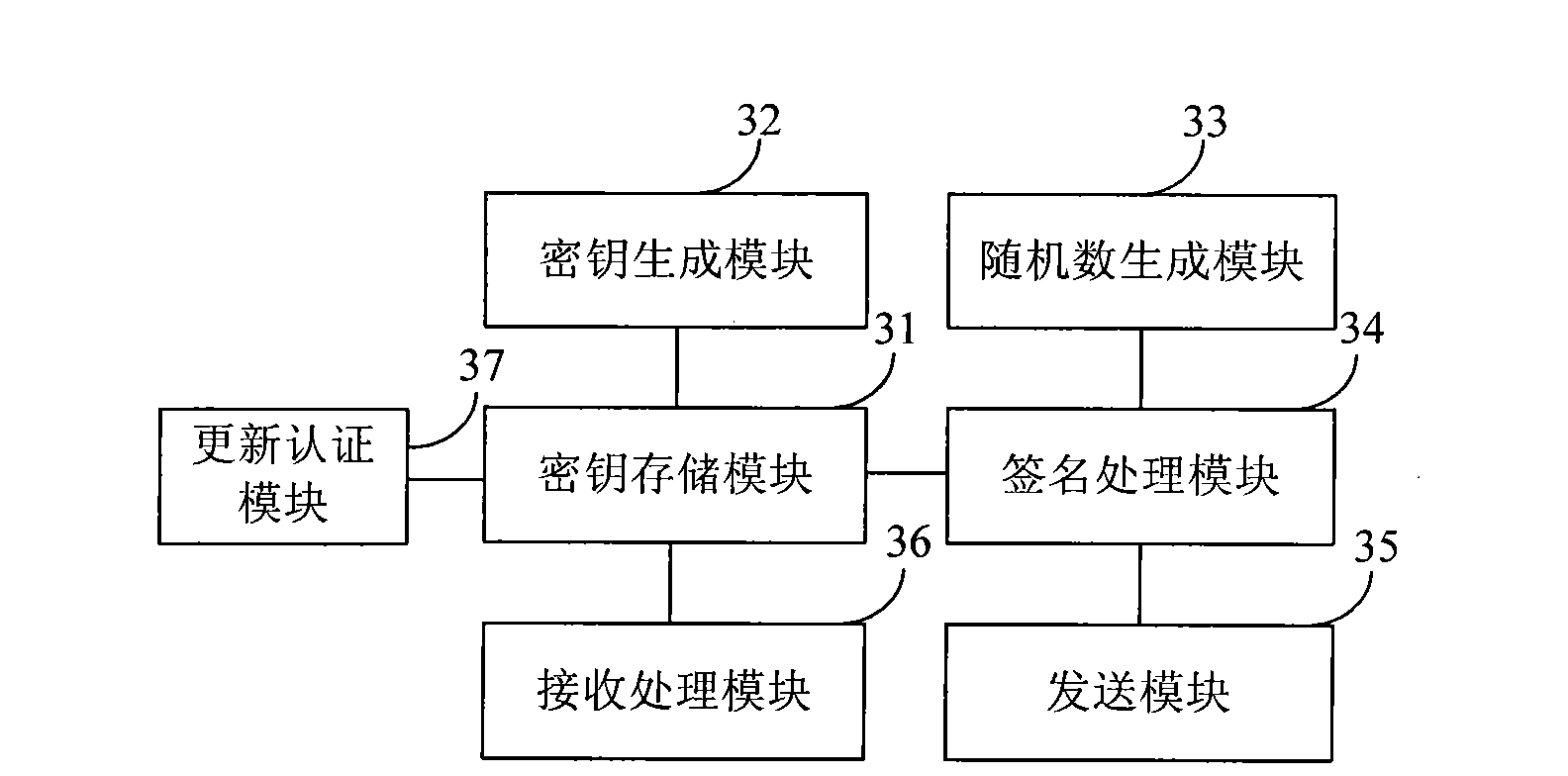
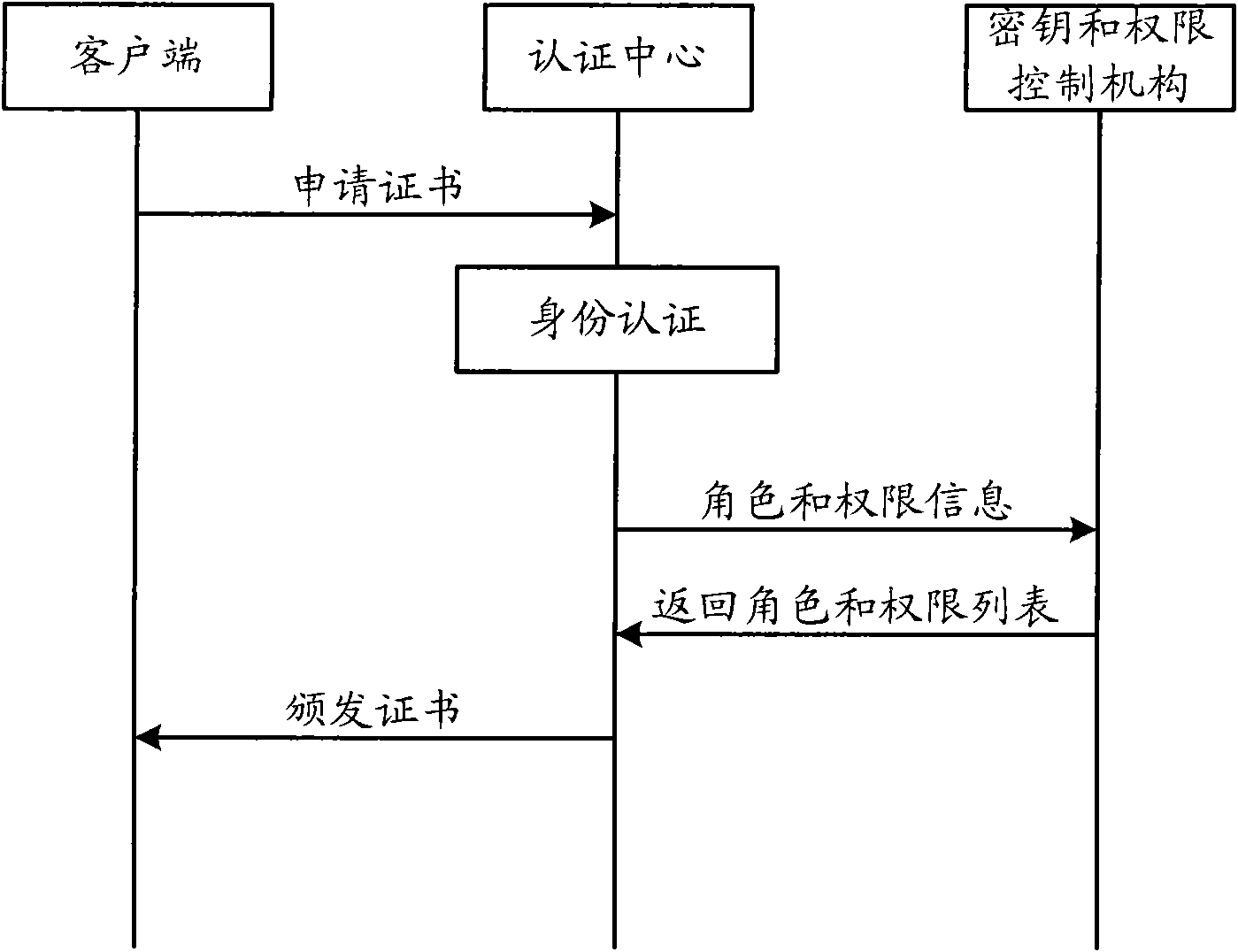
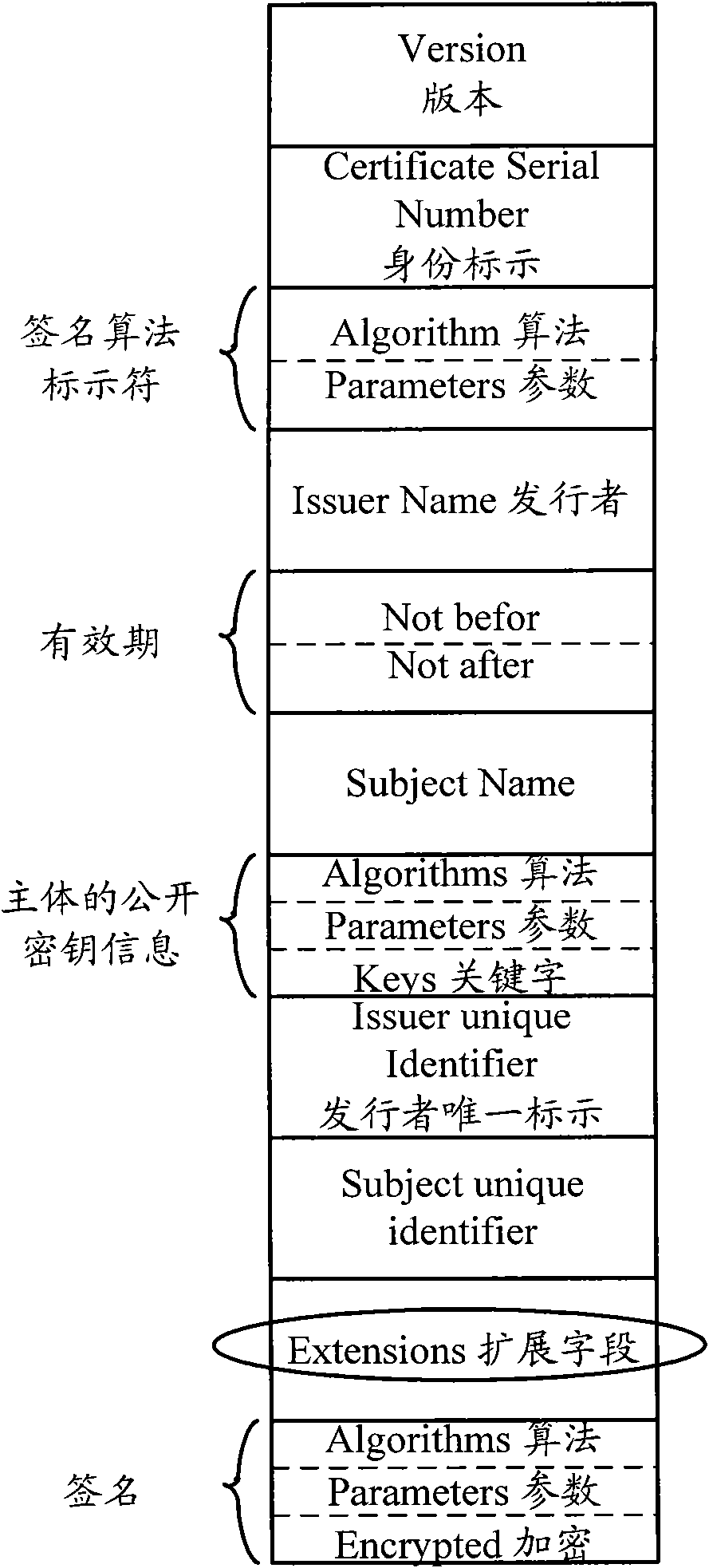
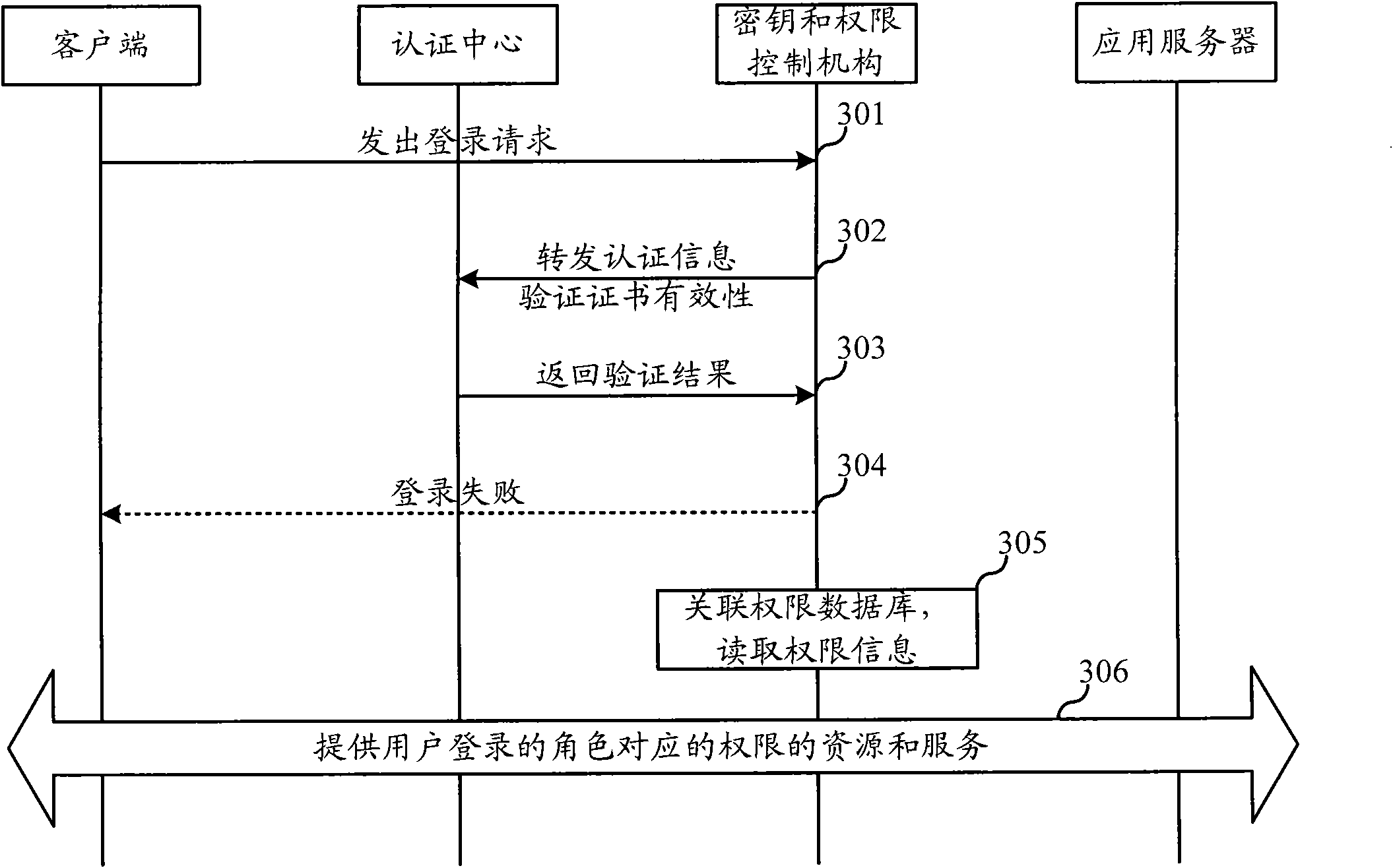
Fusion and authentication method and system of identity and authority in industrial control system
ActiveCN102420690AKeep intactIncrease storage spaceUser identity/authority verificationSupporting systemThird party
The invention discloses a fusion and authentication method and system of identity and authority in an industrial control system. The method comprises the following steps of: storing role information of a user into an identity certificate through fusing an attribute certificate and the identity certificate; setting an authority database; saving authority information corresponding to different roles of the user; first, authenticating the identity of the user while the user logs into the system; extracting the authority information of the user according to the user name information and a role information association authority database in the identity certificate after passing the authentication; and providing resources corresponding to the authority to the user by the system. Therefore, the industrial control system can finish the user identity authentication and complicated authority authentication in the industrial field only by supporting one reliable third party and using one certificate under the situation of support system security grade. The two certificates are combined into one so that the management is more convenient. The specific authorities of the user in different roles are saved in the authority database; and larger information storage space and more complete preservation of the information are obtained.
Owner:ASAT CHINA TECH
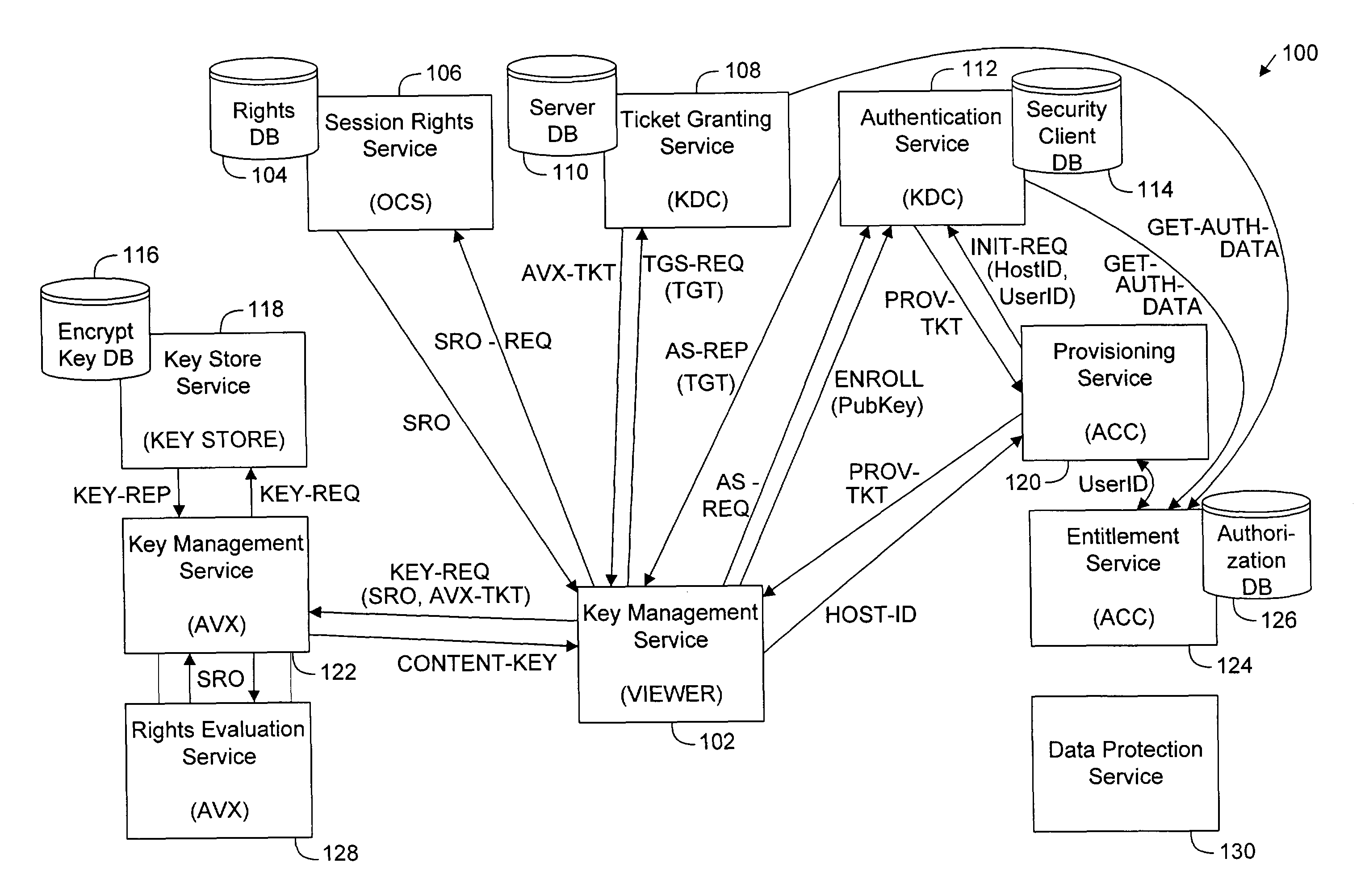
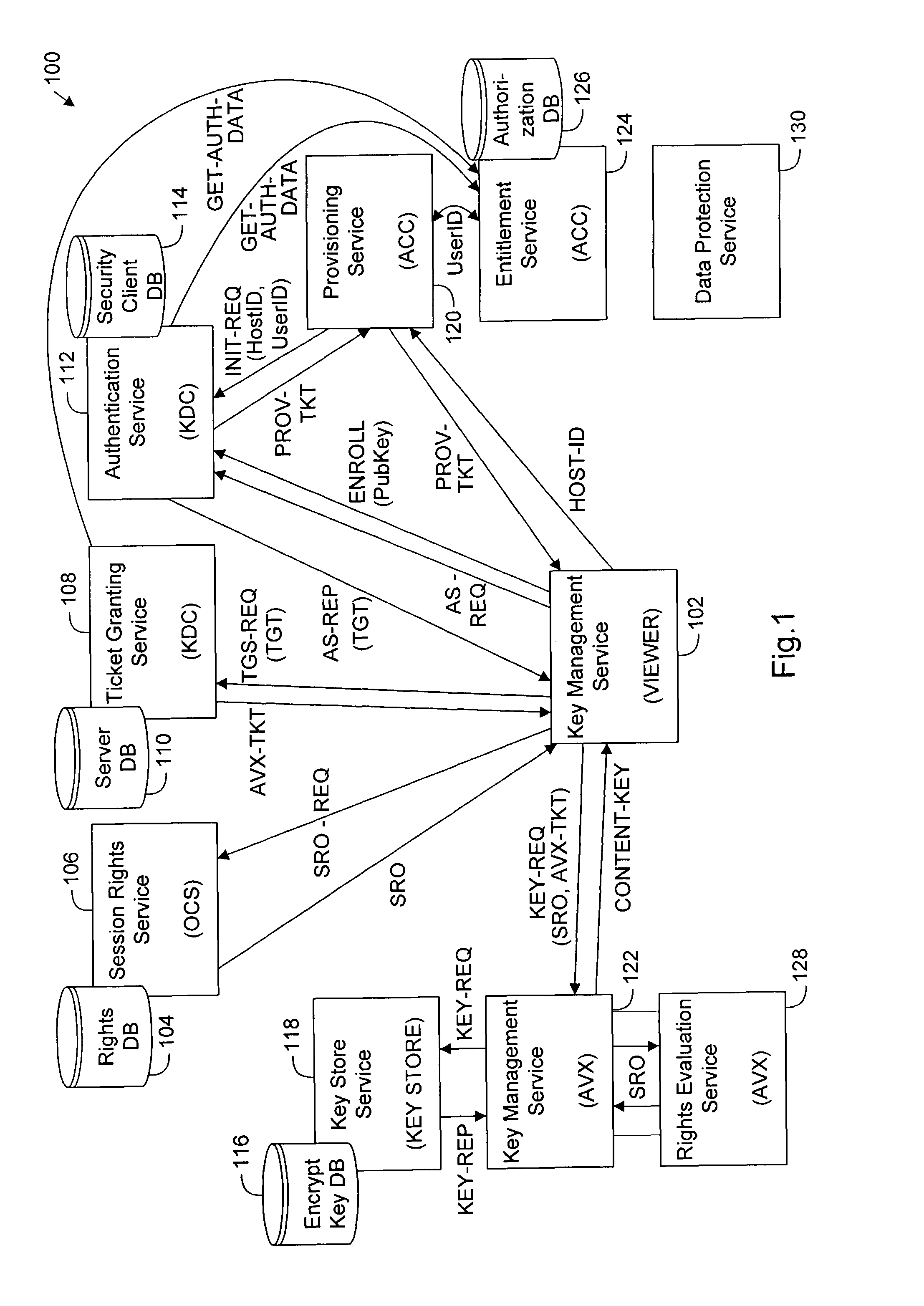
System for digital rights management using distributed provisioning and authentication
ActiveUS8364951B2Key distribution for secure communicationDigital data processing detailsContent distributionUser identifier
Owner:GOOGLE TECH HLDG LLC
Authentication mechanisms for call control message integrity and origin verification
ActiveUS20050243798A1Provide securityMultiple digital computer combinationsProgram controlTransit networkFrame Relay
The present invention incorporates methodologies developed in the Internet Engineering Task Force (IETF) Internet Protocol Security (IPSEC) Working Group into asynchronous transfer mode (ATM) and frame relay (FR) signaling to provide message integrity and origin authentication. In one implementation the invention provides a virtual private network (VPN) infrastructure with call control message integrity, origin verification, and transit network filtering. The invention utilizes a set of control plane messages based on the IPSEC authentication header (AH) methodology to provide these security mechanisms for ATM and FR network switching equipment and signaling protocols. This abstract itself is not intended to limit the scope of this patent. The scope of the present invention is pointed out in the appending claims.
Owner:ALCATEL-LUCENT USA INC
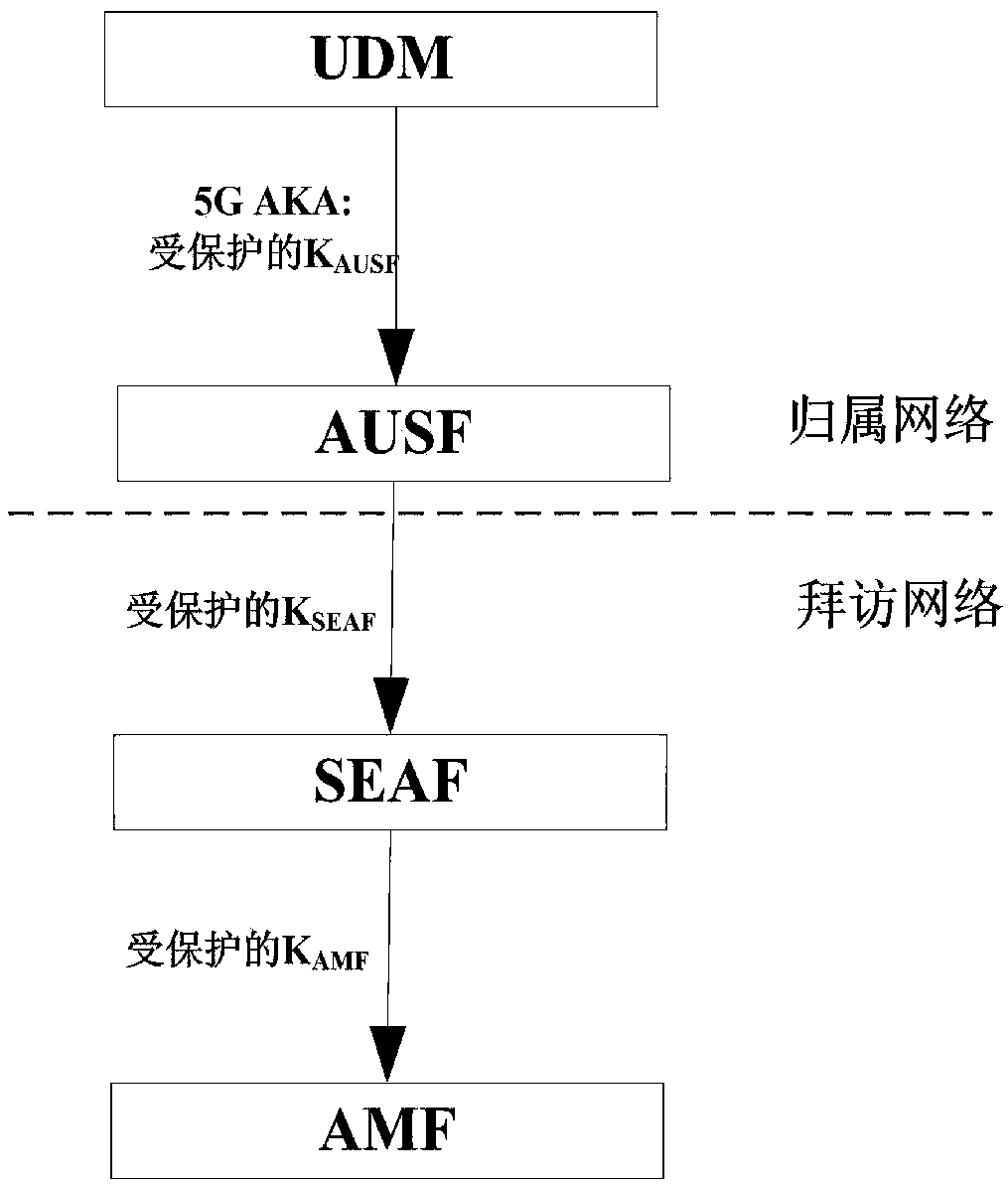
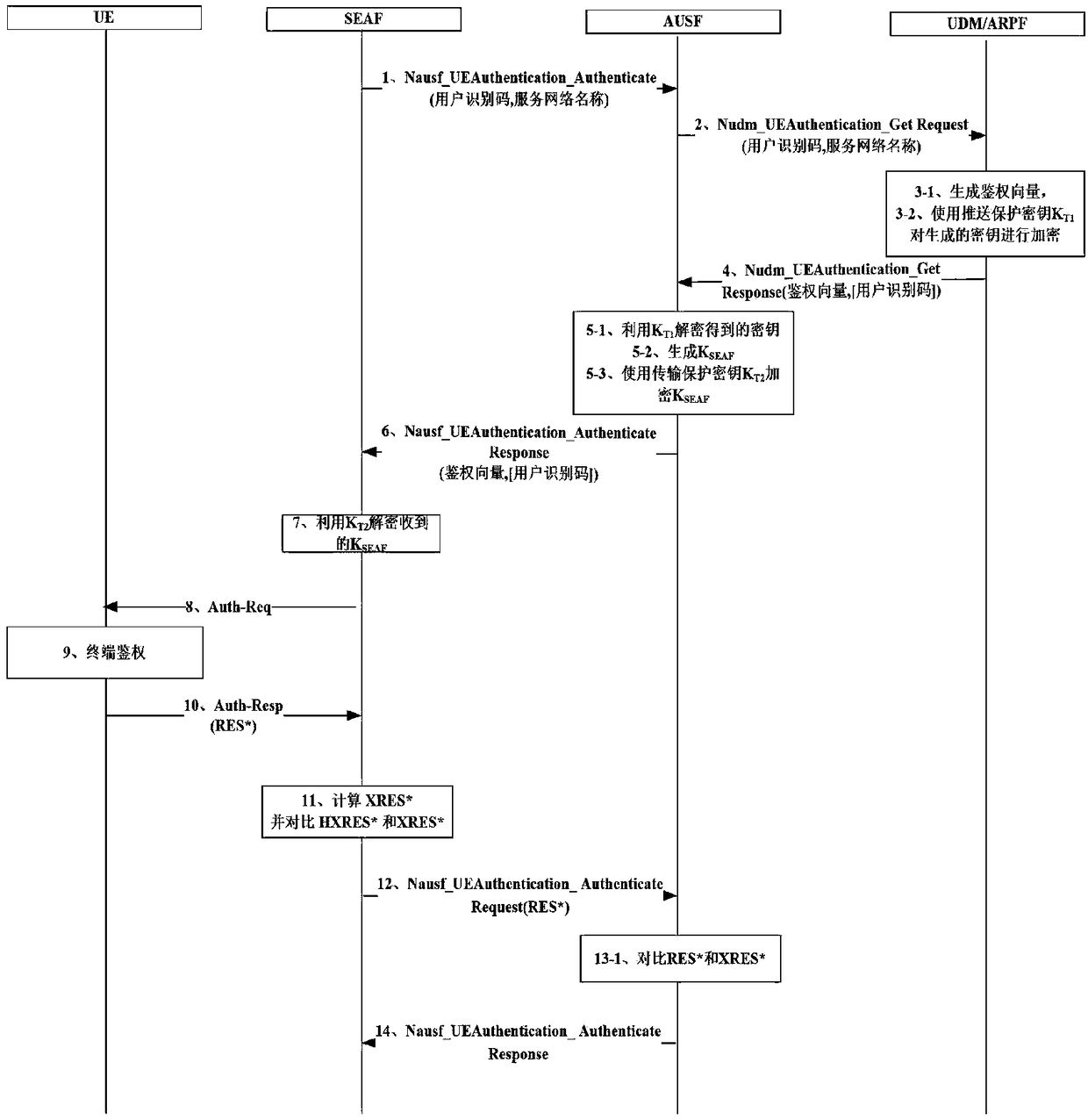
A method for enhancing security of authentication process between network elements of core network based on 5G AKA
ActiveCN109041057AImplement negotiated updatesPrevent leakageSecurity arrangementComputer terminalSecurity enhancement
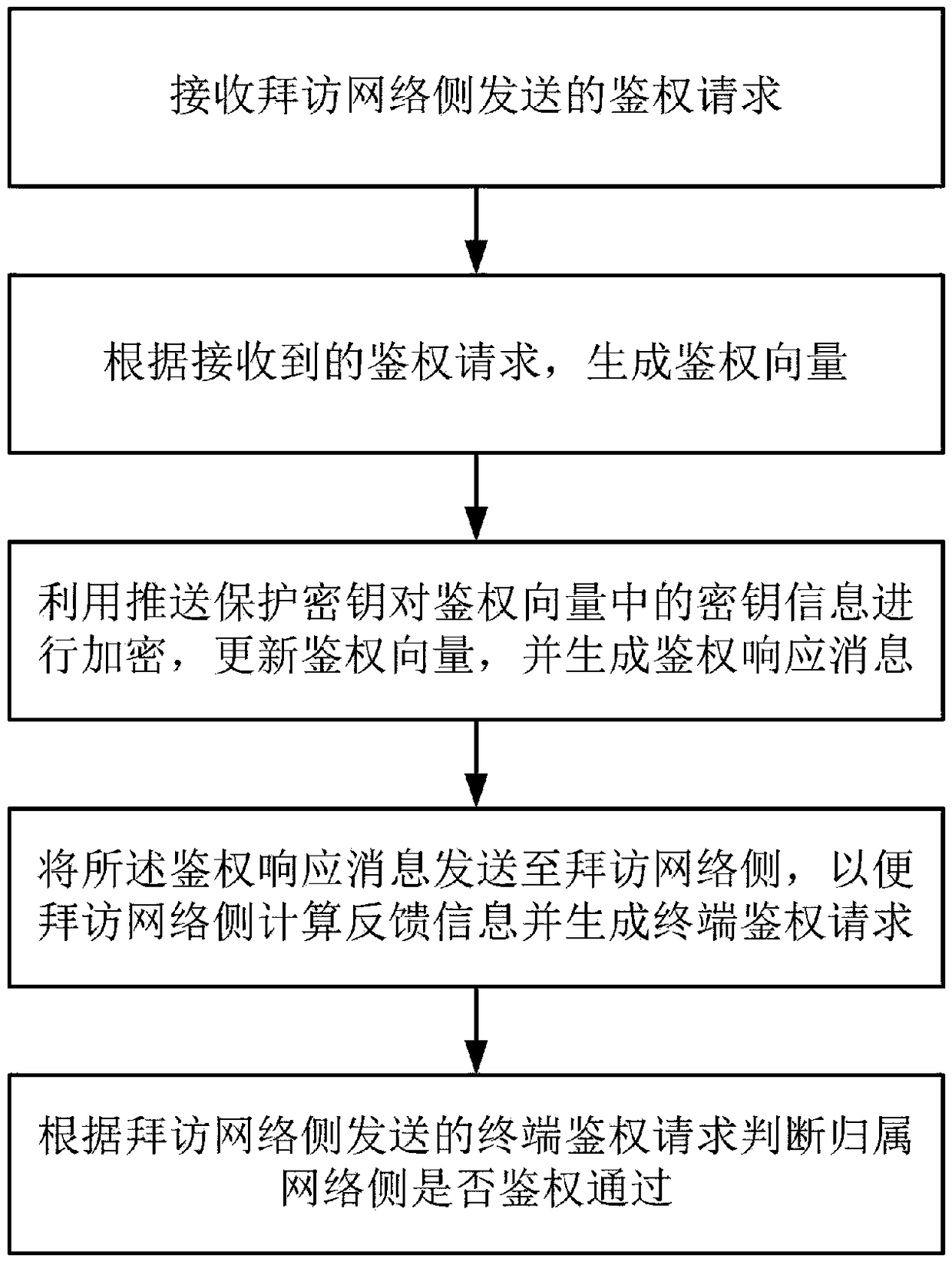
The invention relates to a method for enhancing the security of authentication process between core network elements based on 5G AKA, belonging to the technical field of mobile communication, which solves the problem that key information such as key, user identity and the like caused by the prior plaintext transmission mode are stolen. The invention relates to a security enhancement method for enhancing security of authentication process between network elements of core network based on 5G AKA, which is applied to a home network side. The method comprises the following steps: receiving authentication request sent by a visiting network side; generating an authentication vector according to the received authentication request; encrypting the key information in the authentication vector by using the push protection key, updating the authentication vector, and generating an authentication response message; sending the authentication response message to the visiting network side so that thevisiting network side calculates feedback information and generates a terminal authentication request; according to the terminal authentication request sent by the visiting network side, judging whether or not the home network side has passed the authentication. By encrypting the key information transmitted between the network elements of the core network, the security of the authentication process between the network elements of the core network is effectively enhanced.
Owner:XINGTANG TELECOMM TECH CO LTD +1
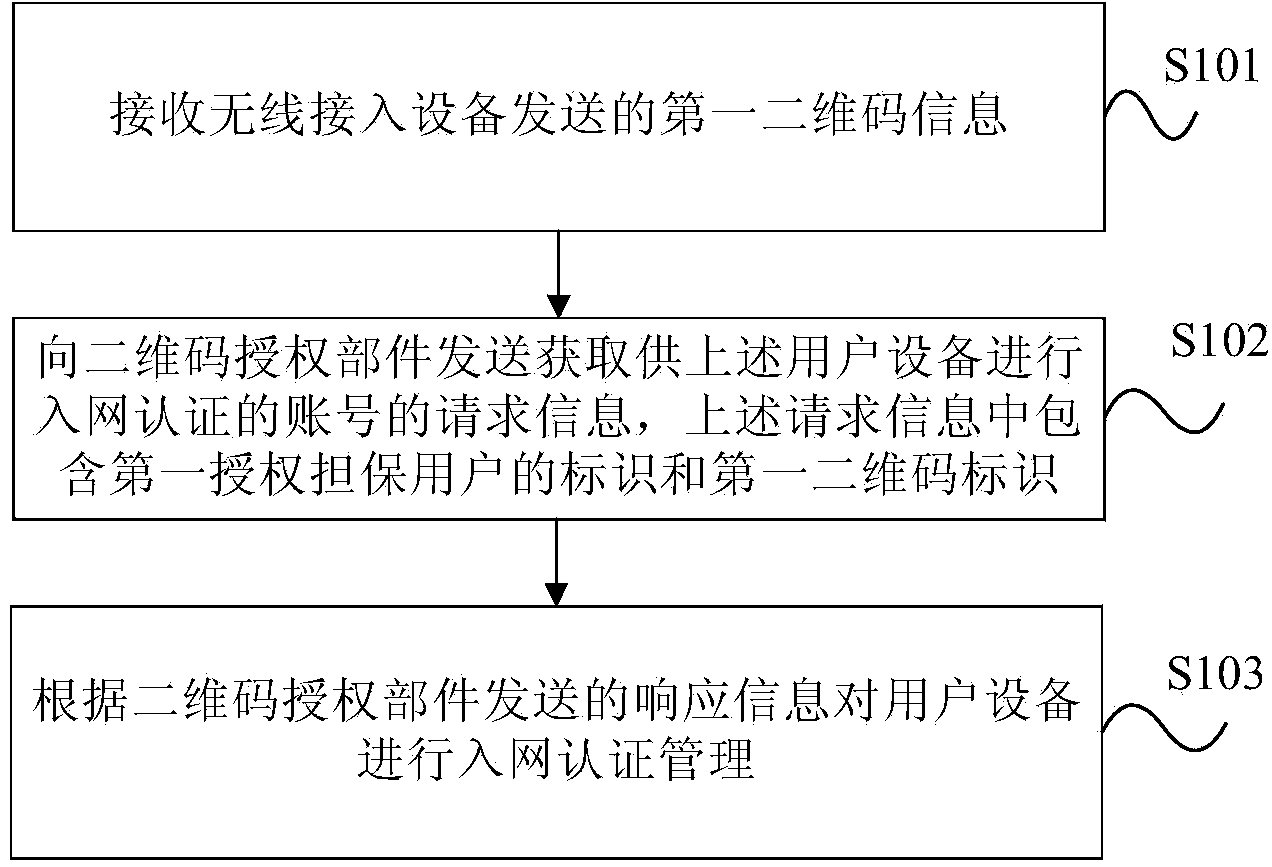
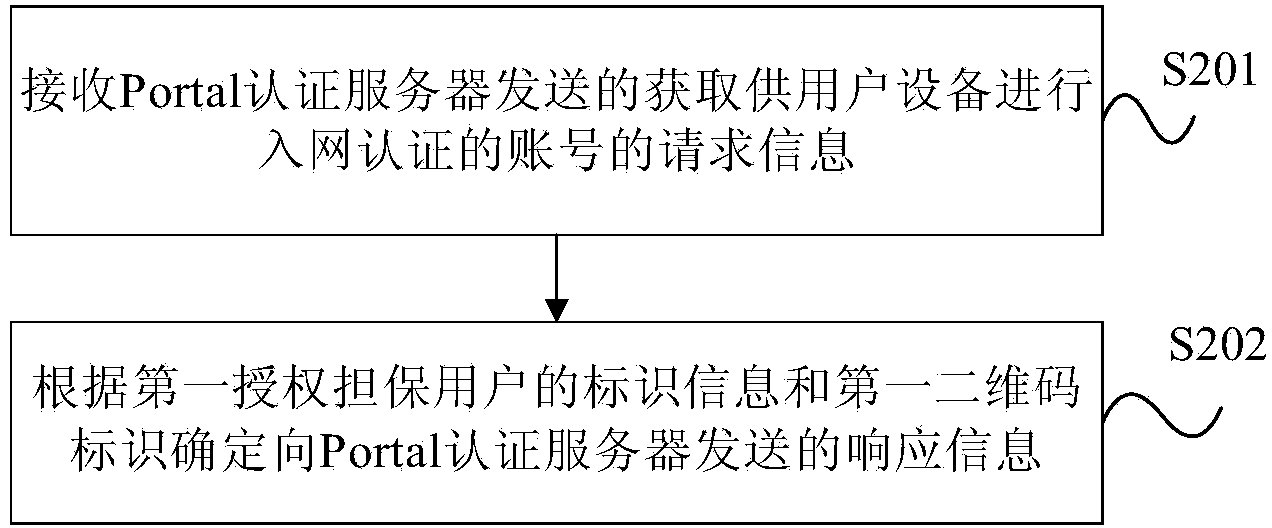
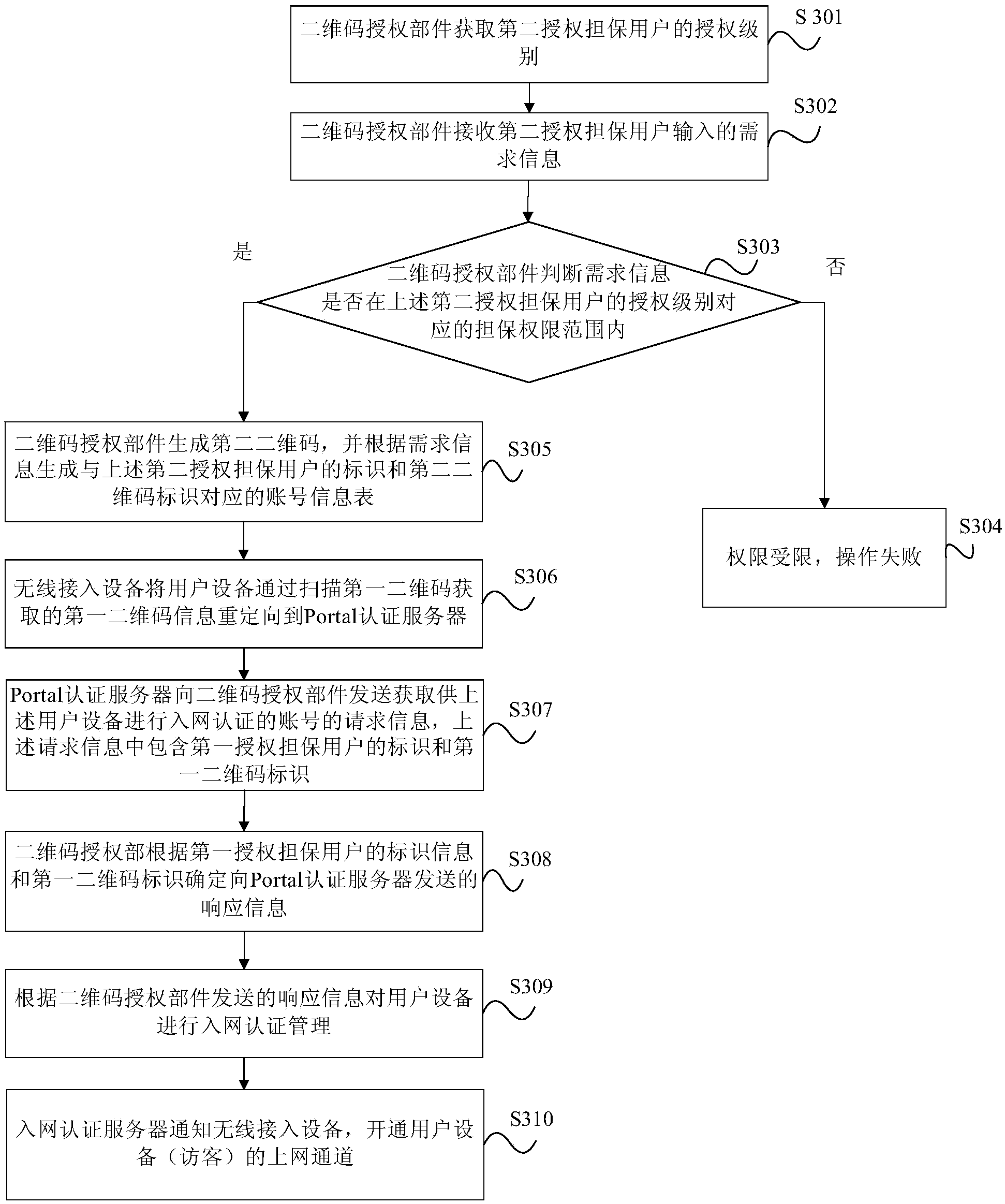
Authentication method, device and system based on two-dimensional code
ActiveCN103532971AImprove the efficiency of authorization authenticationTransmissionSensing by electromagnetic radiationDimensional modelingAuthentication server
The embodiment of the invention provides an authentication method, a device and a system based on a two-dimensional code. The method comprises the steps that first two-dimensional code information sent by wireless access equipment is received by a Portal authentication server, wherein the first two-dimensional code information is information acquired by user equipment by scanning the two-dimensional code, and comprises a first authorization guarantee user marker and a first two-dimensional code marker; request information for acquiring an account number allowing the user equipment to perform network access authentication is sent to a two-dimensional code authorization component, wherein the request information comprises the first authorization guarantee user marker and the first two-dimensional code marker; the two-dimensional code authorization component obtains a relation between the user equipment and a first authorization guarantee user; response information is sent to the Portal authentication server according to the first authorization guarantee user marker and the first two-dimensional code marker; and the Portal authentication server performs network access authentication management on the user equipment according to the response information sent by the two-dimensional code authorization component. The method, the device and the system improve the efficiency of use authority authentication of a wireless network.
Owner:上海锐山网络有限公司
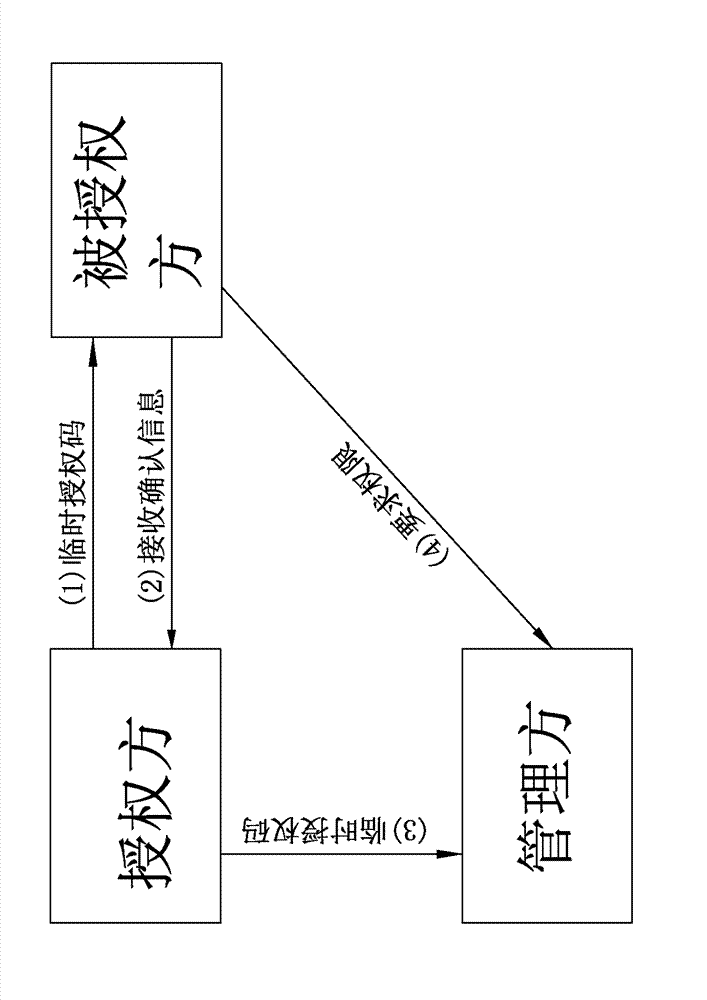
Temporary authorization method for mobile communication equipment of authorizing party and authorized party and temporary authorization management method and device for manager
InactiveCN103401868AReduce loadReduce workloadUser identity/authority verificationInternet privacyComputerized system
The invention relates to the technical field of permission use of mobile communication equipment, in particular to a temporary authentication method of mobile communication equipment. The method comprises the following steps that the authenticating party generates temporary authentication information and performs information confirmation between the authenticating party and the authenticated party by adopting an encryption communication way; the authenticating party automatically transmits authentication information to the manager after the authenticating party and the authenticated party confirm the information; and the manager records and confers the temporary permission of the authenticated party. Due to the adoption of the authentication method, the authentication safety can be ensured, the manager is not required to perform each operation, convenience is brought to the operation, the temporary authentication time is shortened effectively, and the authentication contents can be adjusted flexibly. According to the method, a functional module framework is established, and a computer system is controlled to complete operation via computer program instructions. Moreover, the invention further provides specific methods based on the authenticating party, the authenticated party and the manager respectively for the method.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
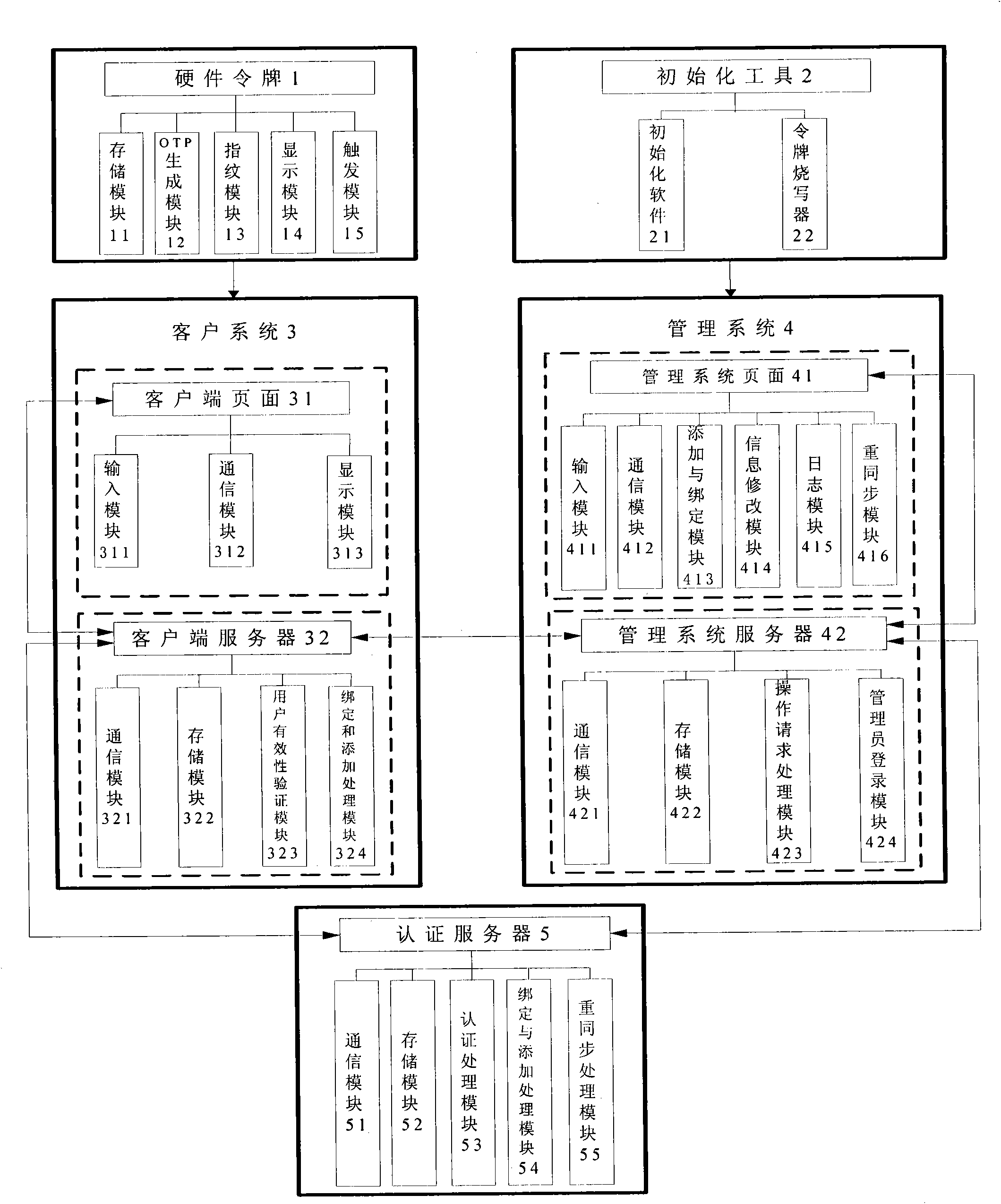
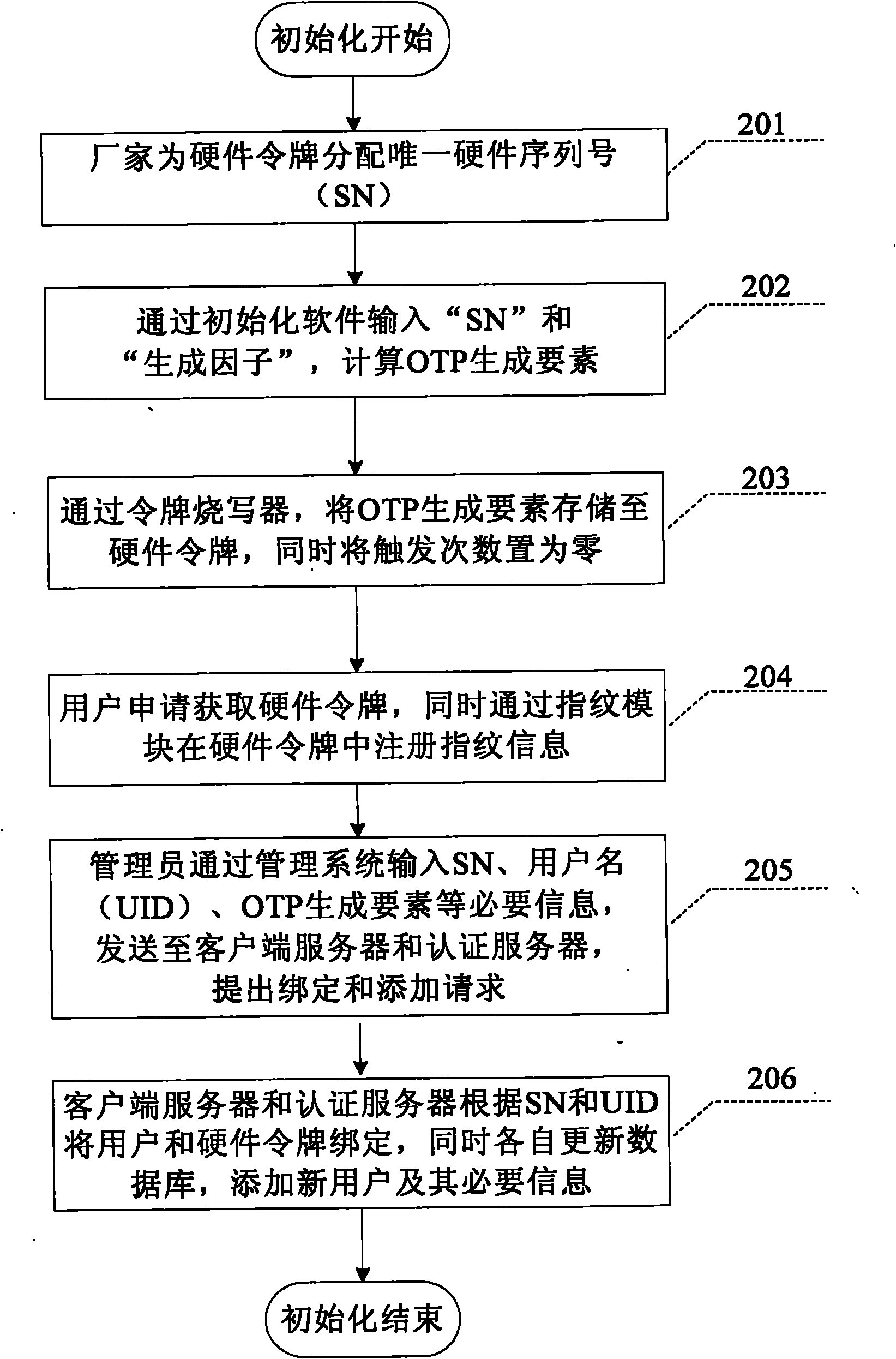
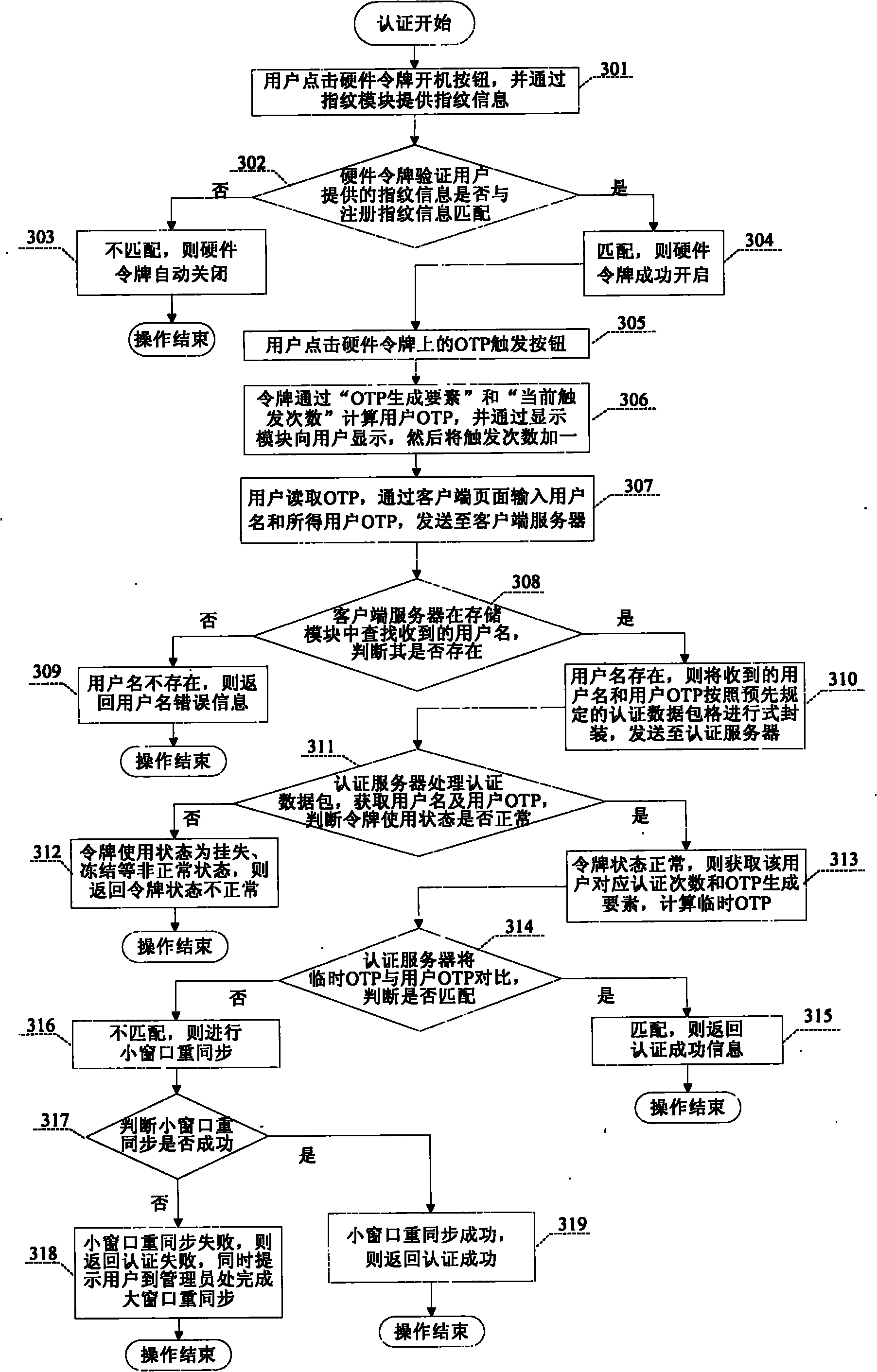
One-time password authentication system and authentication method used for B/S (Browser/Server) network structure
The invention relates to a one-time password (OTP) authentication system and authentication method used for a B / S (Browser / Server) network structure. The authentication system comprises a hardware token, an initializing tool, a client system, a management system and au authentication server. The initializing tool completes the initialization flow of the hardware token; the hardware token provides an OTP required by authentication for a user; the user inputs the OTP into the client system, and the client system sends the OTP to the authentication server; the authentication server completes the authentication process and returns the result back to the client system, and the client system finally feeds back the result to the user; the management system completes system management and maintenance and sends a management operation request to the authentication server and a client server as specified; and the authentication server and the client server receive the request, complete the operation and return the operation result. The authentication method comprises system initialization, login authentication and system management and comprises eight specific steps. User authentication and system management can be completed by the browser page mode, so that the invention has the advantages of convenient use, easy maintenance, practical value and broad application prospects.
Owner:BEIHANG UNIV
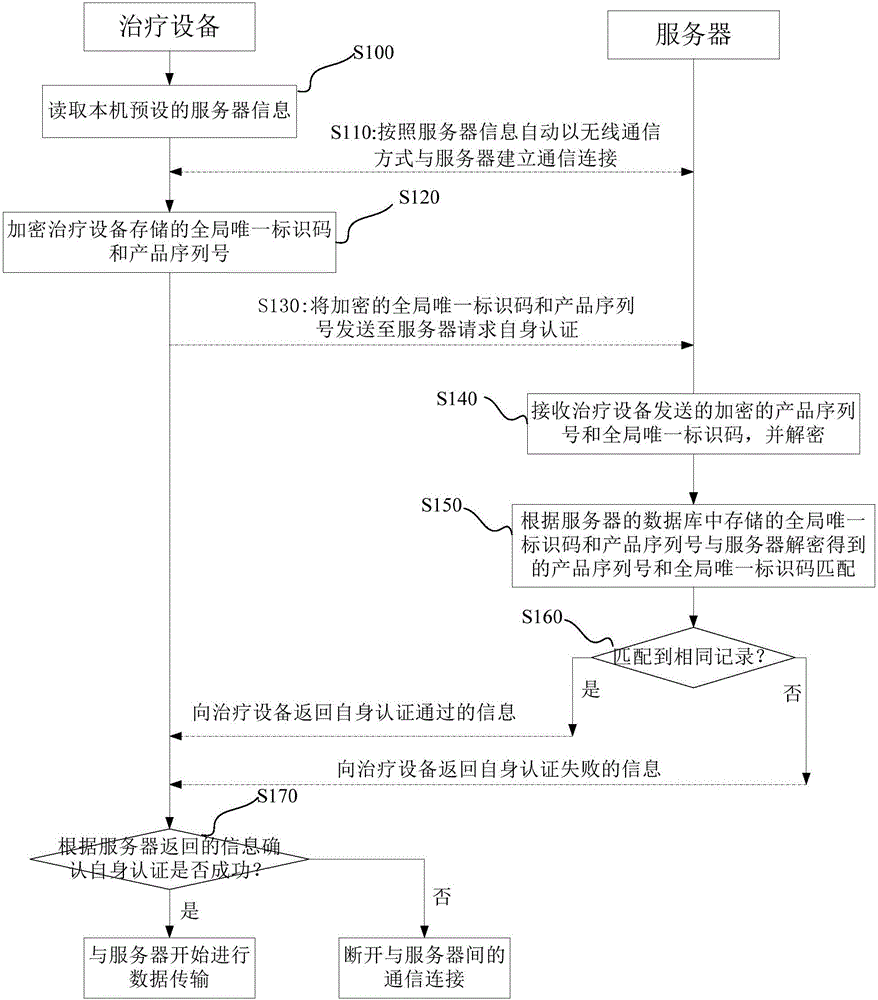
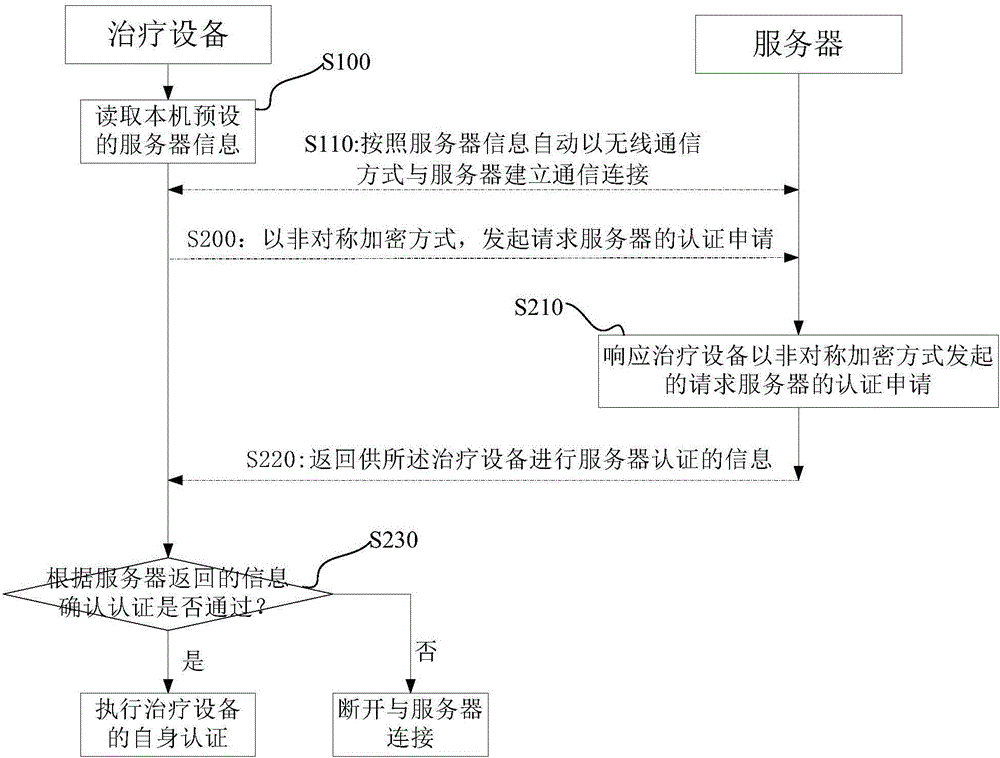
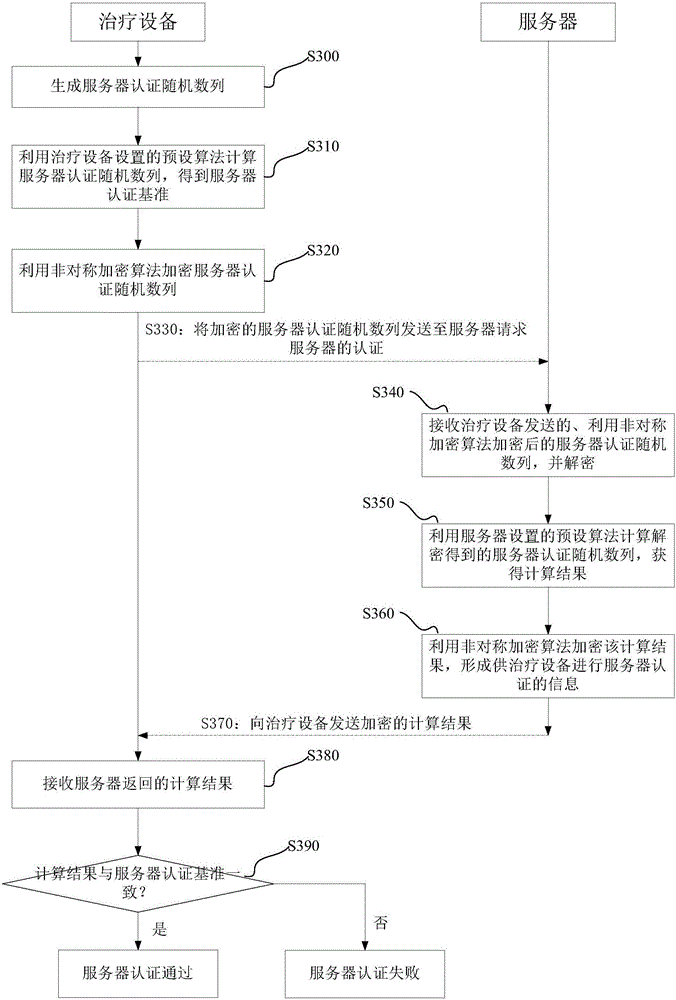
Authentication method, authentication device, authentication system and treatment equipment
ActiveCN105871857AAvoid same-identity situationsPrevent peepingTransmissionData transmissionAuthentication system
The invention discloses an authentication method, an authentication device, an authentication system and treatment equipment. The authentication method comprises the steps of reading server information which is preset by a local machine, automatically establishing communication connection according to the server information in a wireless communication manner; and initiating self authentication by the treatment equipment, wherein self authentication comprises reading a global unique identification code and a product serial number which are pre-stored by the local machine; encrypting the global unique identification code and the product serial number which are stored in the treatment equipment, and transmitting the encrypted global unique identification code and the product serial number to a server for requesting self authentication; confirming a self authentication result according to information which returns from the server; if self authentication passes, starting data transmission with the server; and if self authentication fails, disconnecting communication connection with the server. The authentication method, the authentication device, the authentication system and the treatment equipment reduce operation difficulty and complexity in identity authentication.
Owner:BMC MEDICAL
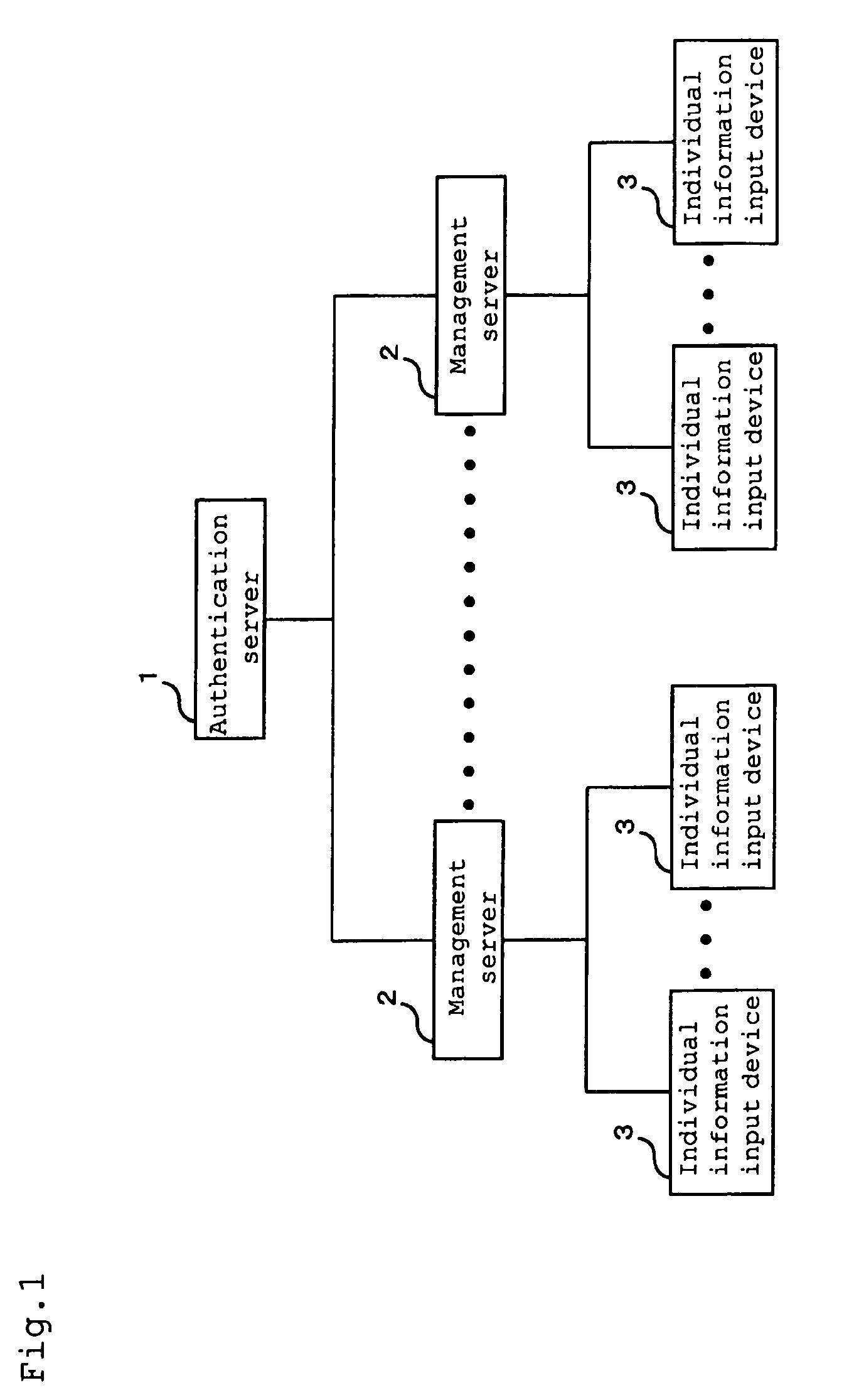
Authentication system
ActiveUS8866586B2Easy to findImprove securityElectric signal transmission systemsTicket-issuing apparatusAuthentication serverElectronic information
[PROBLEMS] To provide an authentication system improving authentication accuracy of existence of a registered person and easily find an unauthorized act to improve the security in a system by performing authentication using coincidence / non-coincidence of biometrics information and temporal / spatial authentication when performing individual authentication via a network by using electronic information which is easily tampered, easily leaks out, and is easily stolen. [MEANS FOR SOLVING PROBLEMS] An authentication server (1) includes a database for managing individual information on a registered person to be authenticated. Moreover, the authentication server (1) is connected to a plurality of management servers (2) via a communication network and correlates the individual information transmitted from an individual information input device (3) via the management server (2) with the individual information in the database, thereby authenticating the existence of the registered person.
Owner:IHC CORP
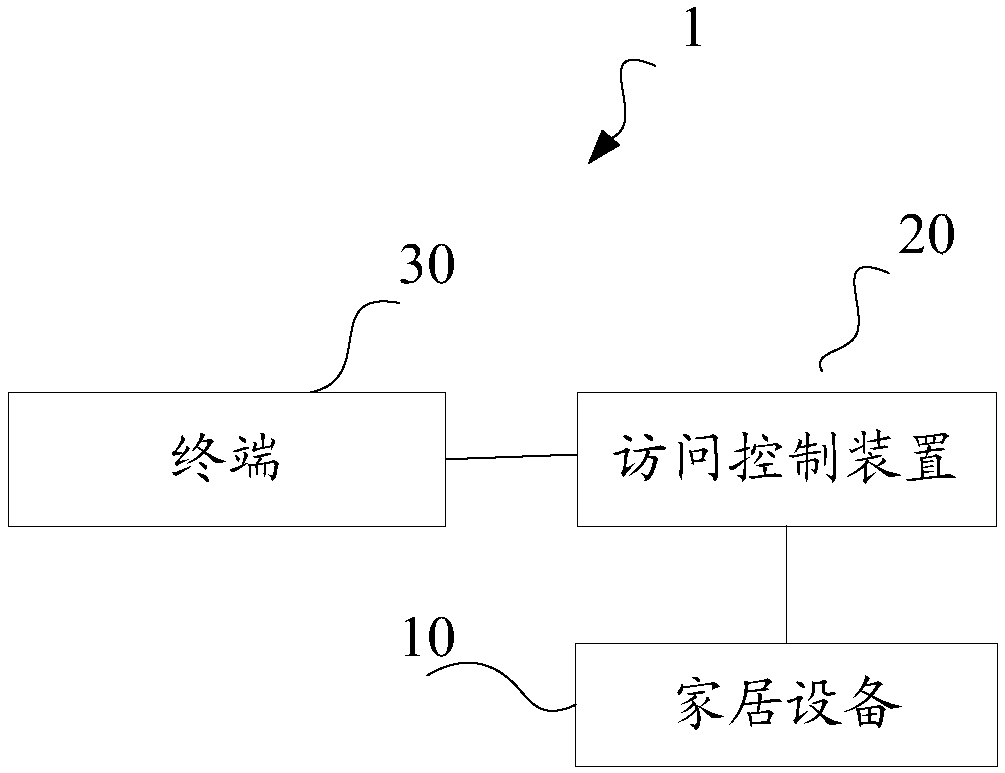
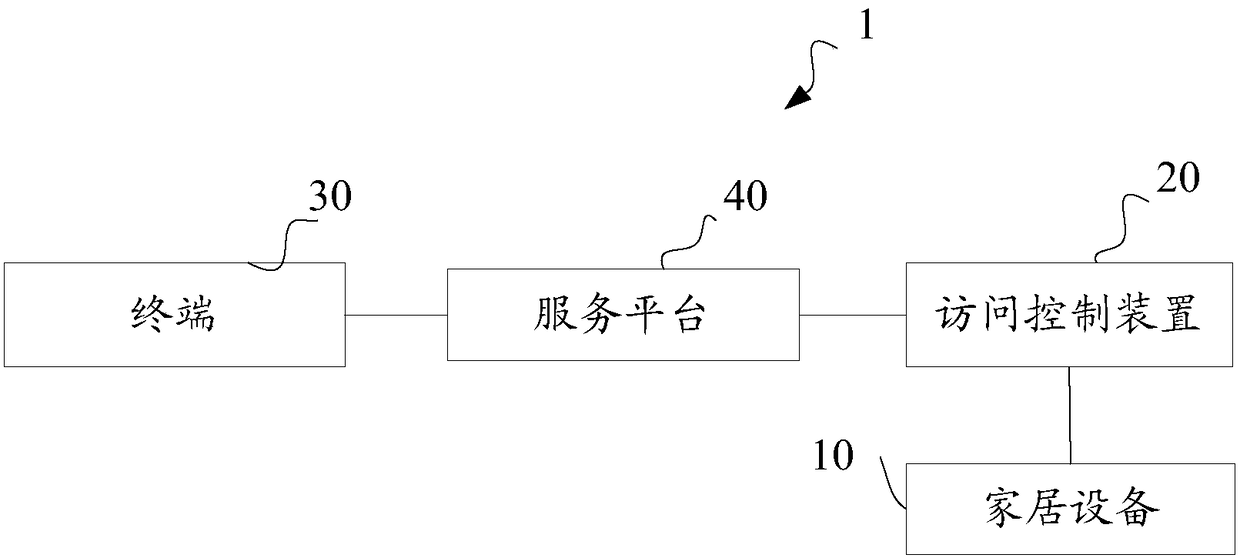
Access control method and apparatus, terminal and Internet of Things home system
InactiveCN108809914AEnsure safetyPrevent replay attacksKey distribution for secure communicationPlaintextThe Internet
The invention discloses an access control method and apparatus, a terminal and an Internet of Things home system. The access control apparatus is in communication connection with a home device, and the access of the terminal to the home device needs to be authenticated by the access control apparatus based on an authentication key and an authentication code; the authentication key is associated with apparatus identification information and terminal identification information on the terminal side and the access control apparatus side respectively, therefore, the uniqueness of the keys of the both authentication parties is ensured, and then it can be ensured that the authenticated terminal is a legitimate terminal. In addition, since the final authentication result is performed according toa comparison result between the authentication code and the authentication plaintext, the terminal is required to have the correct authentication key and a preset rule at the same time, and the doubleverification mode ensures the security of the authentication. An authentication random number is randomly generated in each authentication process, so that the replay attack on the Internet of Thingshome system can be prevented, the authentication effectiveness is further improved, and the security of the Internet of Things home system is ensured.
Owner:NATIONZ TECH INC
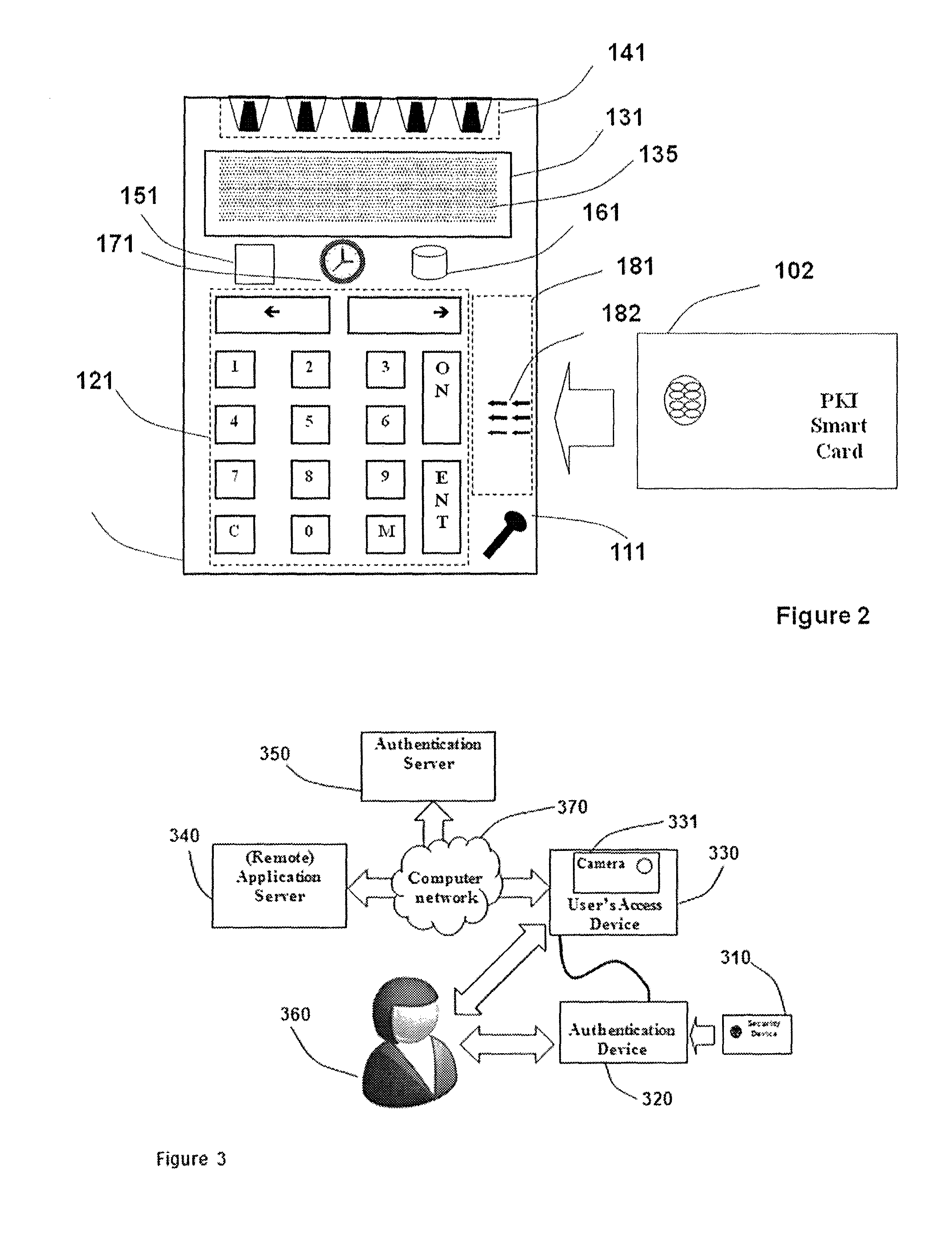
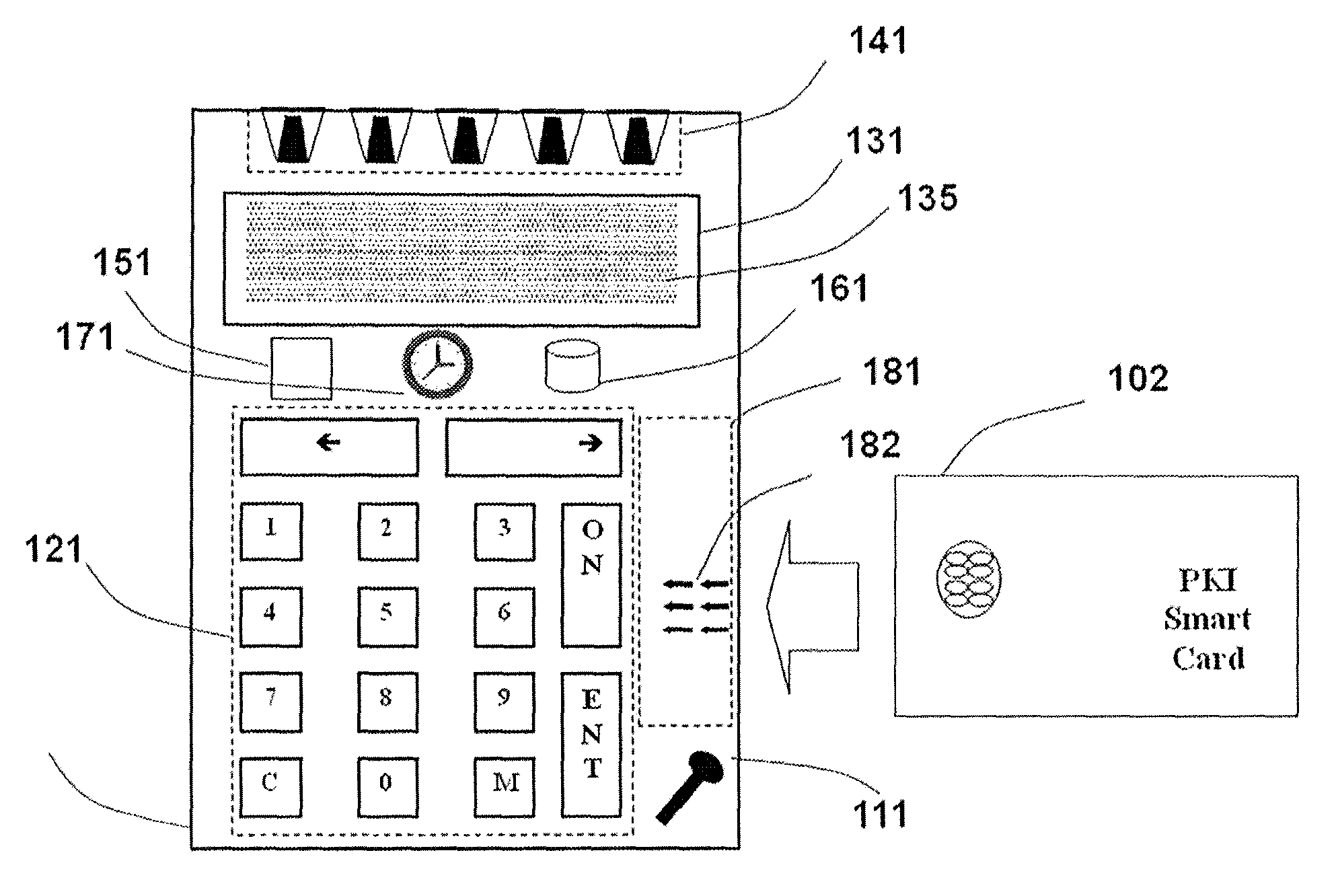
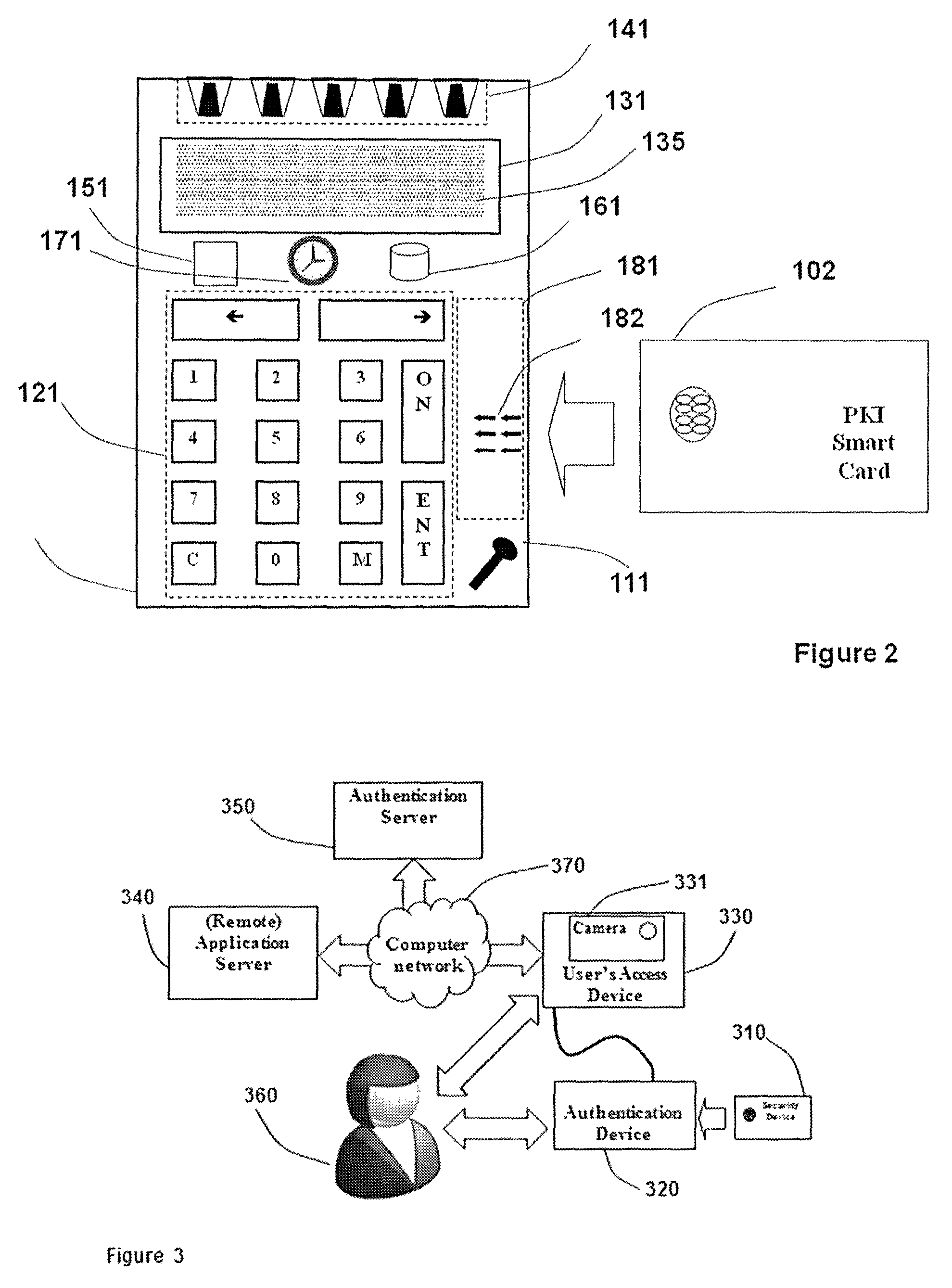
Strong authentication token with visual output of PKI signatures
InactiveUS8966268B2User identity/authority verificationDigital data authenticationDisplay deviceSecret code
A handheld authentication device comprising a data processor and a display is adapted to: generate an input value; submit the input value to an asymmetric cryptographic operation; obtain the result of said asymmetric cryptographic operation; generate an authentication message substantially comprising the result of the asymmetric cryptographic operation; encode the authentication message into one or more images; and display these images on the display. A method for securing computer-based applications remotely accessed by a user comprises capturing images displayed on the display of an authentication device of the user whereby these images have been encoded with an authentication message generated by the authentication device and whereby the authentication message comprises the result of an asymmetric cryptographic operation on an input value; decoding the images to retrieve the authentication message; retrieving the result of the asymmetric cryptographic operation from the authentication message; verifying the authentication message.
Owner:ONESPAN NORTH AMERICA INC
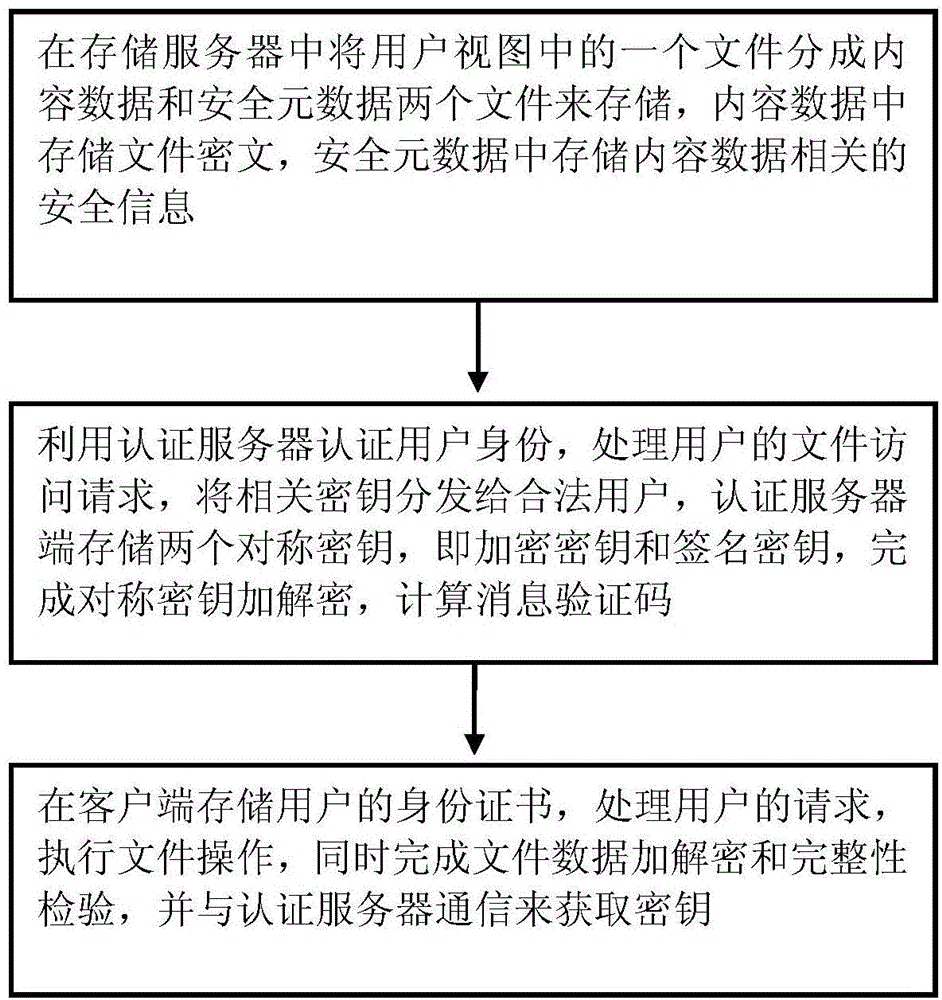
Mass data storage system and processing method
The invention provides a mass data storage system and a processing method. The system comprises a storage server, an authentication server and a client, wherein the storage server is used for storing content data and safety data files; the authentication server serves as the root trusted by the whole system and is used for authenticating the identities of users, processing a file access request of the users and distributing relevant keys to legal users, and only an authentication server encryption key and an authentication server signing key are stored in the authentication server; the client is used for processing the request of the users, executing file operation and meanwhile completing file data encryption and decryption and integrity check, and the client is in communication with the authentication server so as to acquire the keys. The mass data storage system guarantees data privacy, integrity and access control safety in a common network and a cloud storage environment, reduces safety dependency on the storage server, and is simple in logic structure and high in expandability.
Owner:CHENGDU SCENE TECH
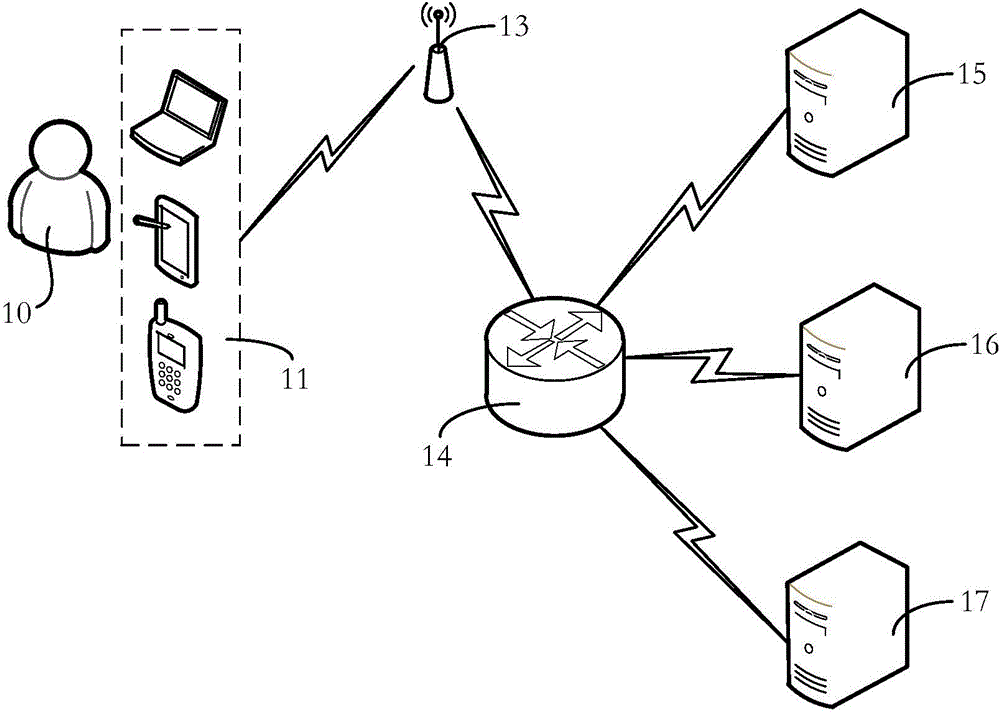
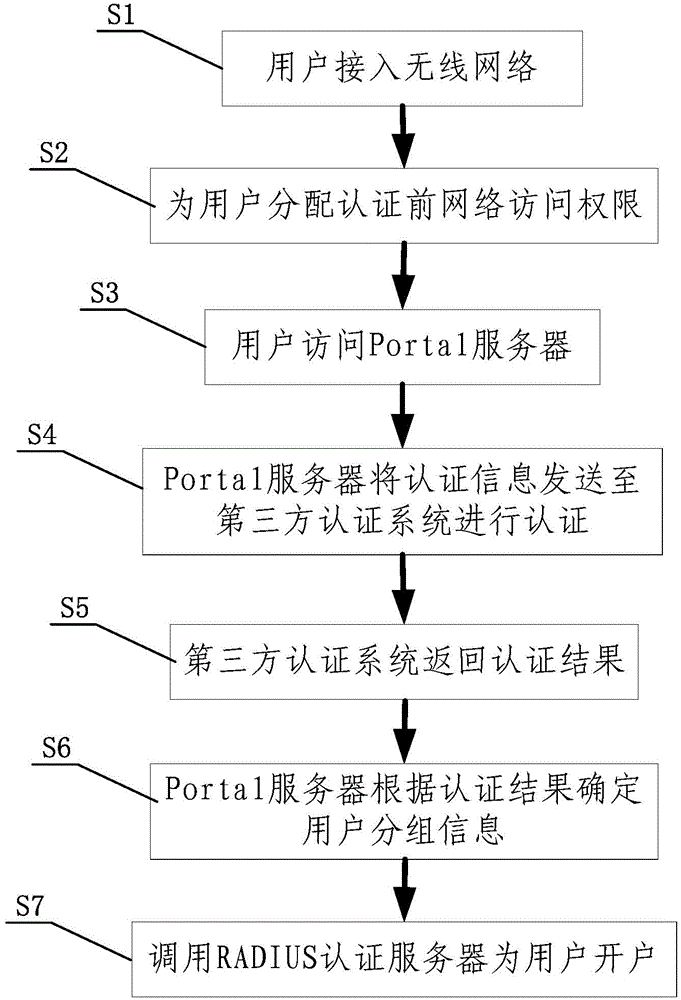
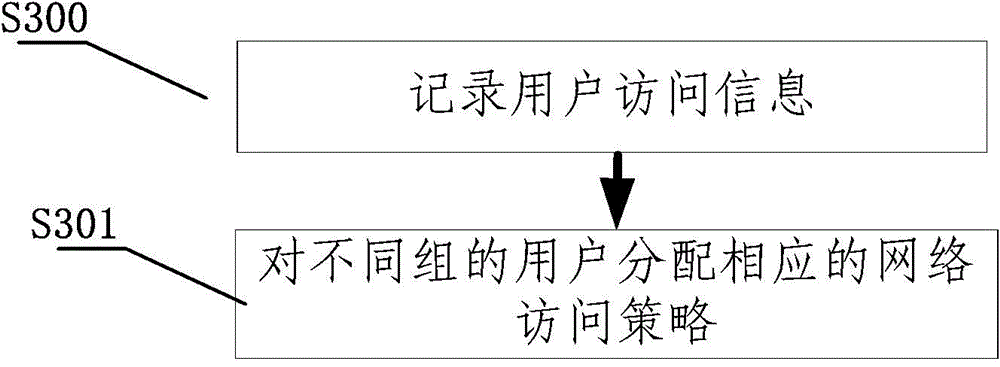
Method and system of network real name authentication
InactiveCN104158824AImplementation of real-name authenticationTake advantage ofUser identity/authority verificationThird partyAuthentication server
The invention relates to a method and a system of network real name authentication. The method comprises the following steps that: a user is connected to a wireless network; a network access permission before authentication is distributed for the user; the user visits a Portal server; the Portal server transmits the authentication information to a third-party authentication system to authenticate; the third-party authentication system returns an authentication result; the Portal server determines user grouping information according to the authentication result; and an RADIUS (Remote Authentication Dial In User Service) authentication server is transferred to open an account to the user. Through the method and the system which are provided by the invention, the unified real name authentication can be implemented to be greatly beneficial for improving accuracy and safety of real name authentication; meanwhile, the existing resources are fully utilized to avoid wasting of resources.
Owner:解芳
Wireless communications device and authentication processing method
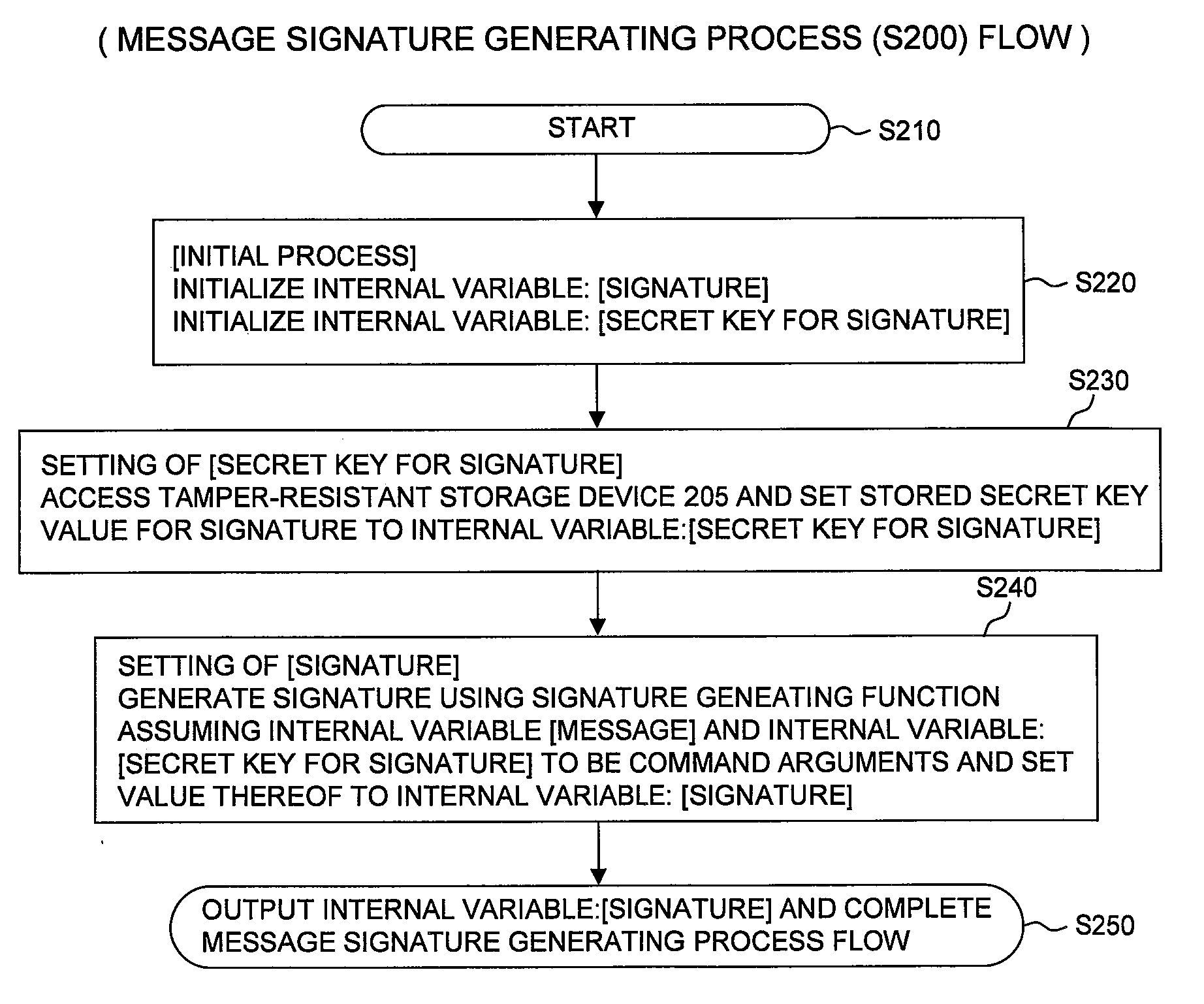
ActiveUS20120311340A1Multiple keys/algorithms usageUser identity/authority verificationHash-based message authentication codeDigital signature
An authentication method is provided which is capable of performing message authentication within an allowable time regardless of the magnitude of the number of messages and performing message authentication high in accuracy within a range for which the allowable time allows. Upon transmission by wireless communications with another mobile or a fixed station, a message authentication code of communication data and a digital signature are generated (S200 and S300). The generated message authentication cod and digital signature are transmitted with being added to the communication data. Upon reception, whether authentication should be done using either one of the message authentication code and the digital signature included in received information is determined according to its own state for the authentication (S400 and S500). This state includes, for example, a load state of a central processing unit or the like that performs an authentication process.
Owner:RENESAS ELECTRONICS CORP
Wireless adhoc communication system, terminal, authentication method for use in terminal, encryption method, terminal management method, and program for enabling terminal to perform those methods
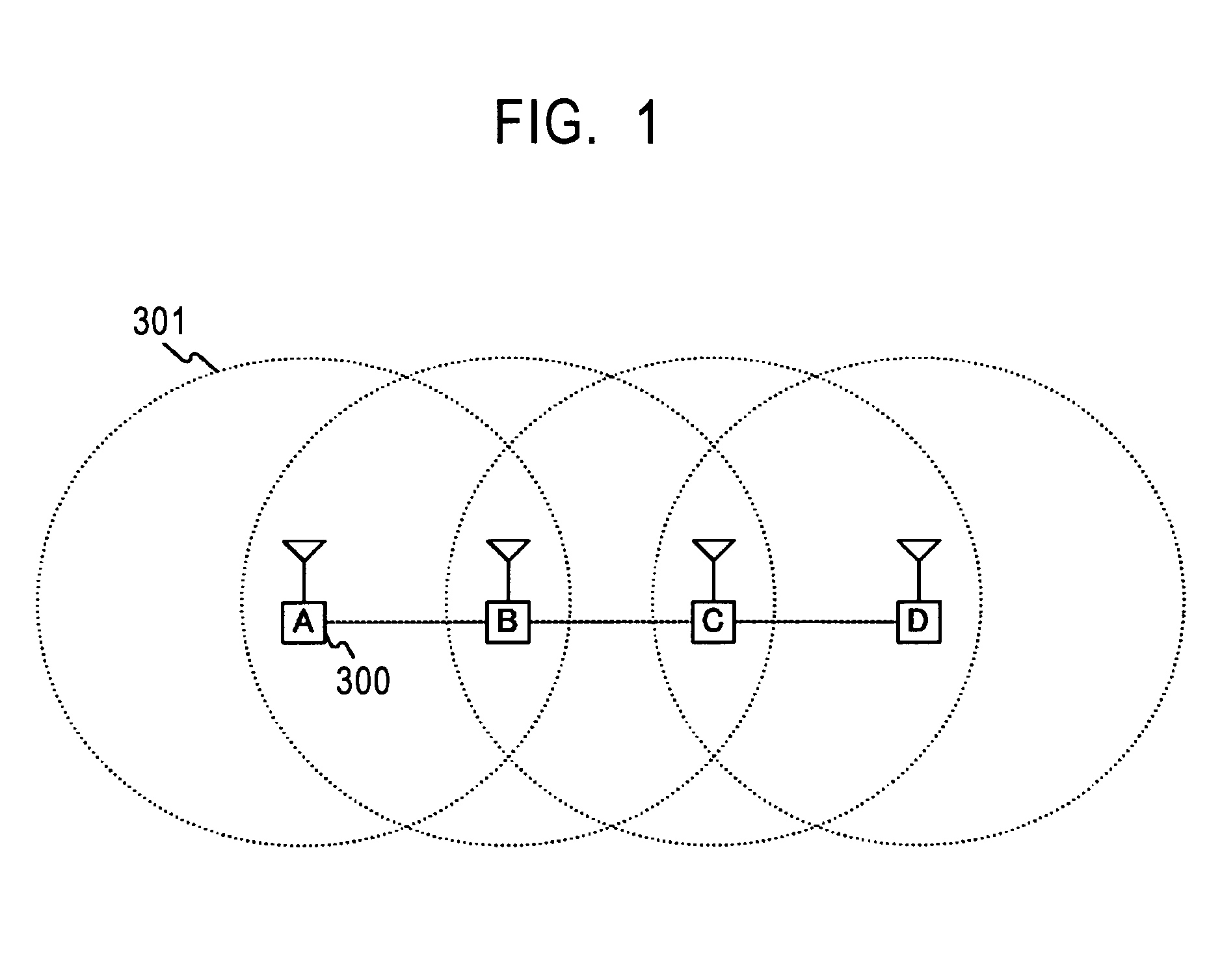
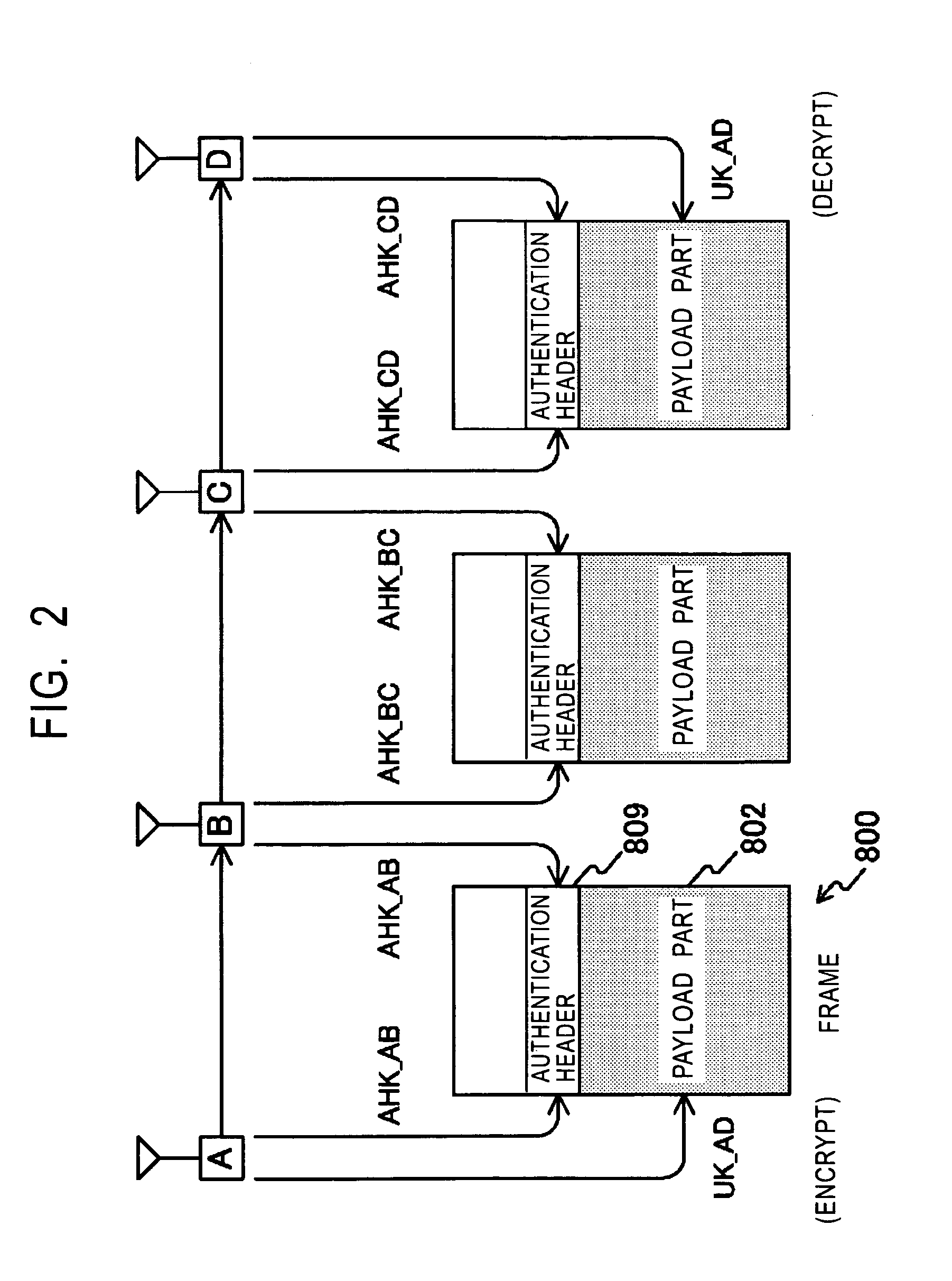
InactiveUS7292842B2Secrecy of the payloadSecrecy of the payload can be ensuredKey distribution for secure communicationUnauthorised/fraudulent call preventionComputer hardwareCommunications system
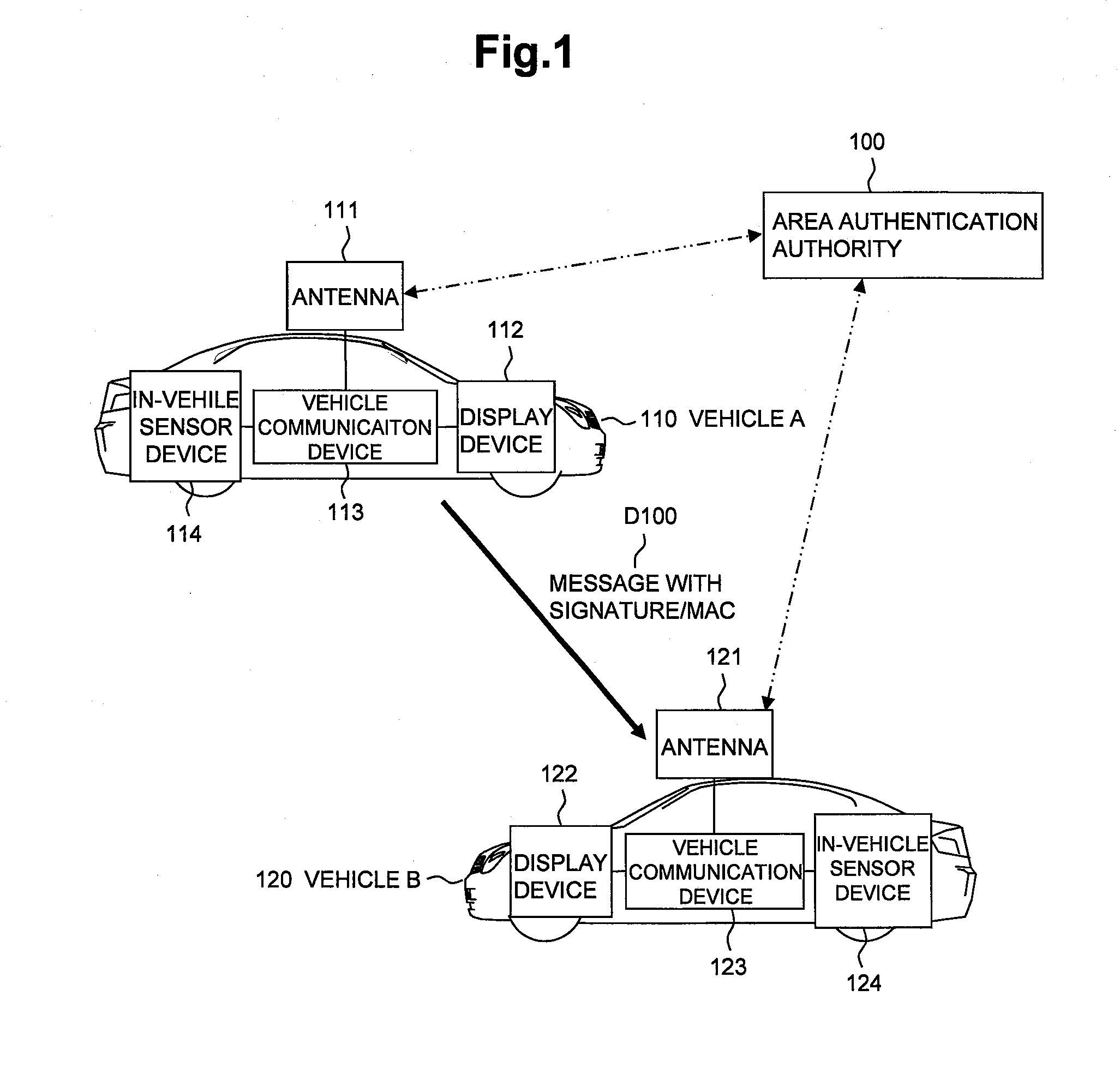
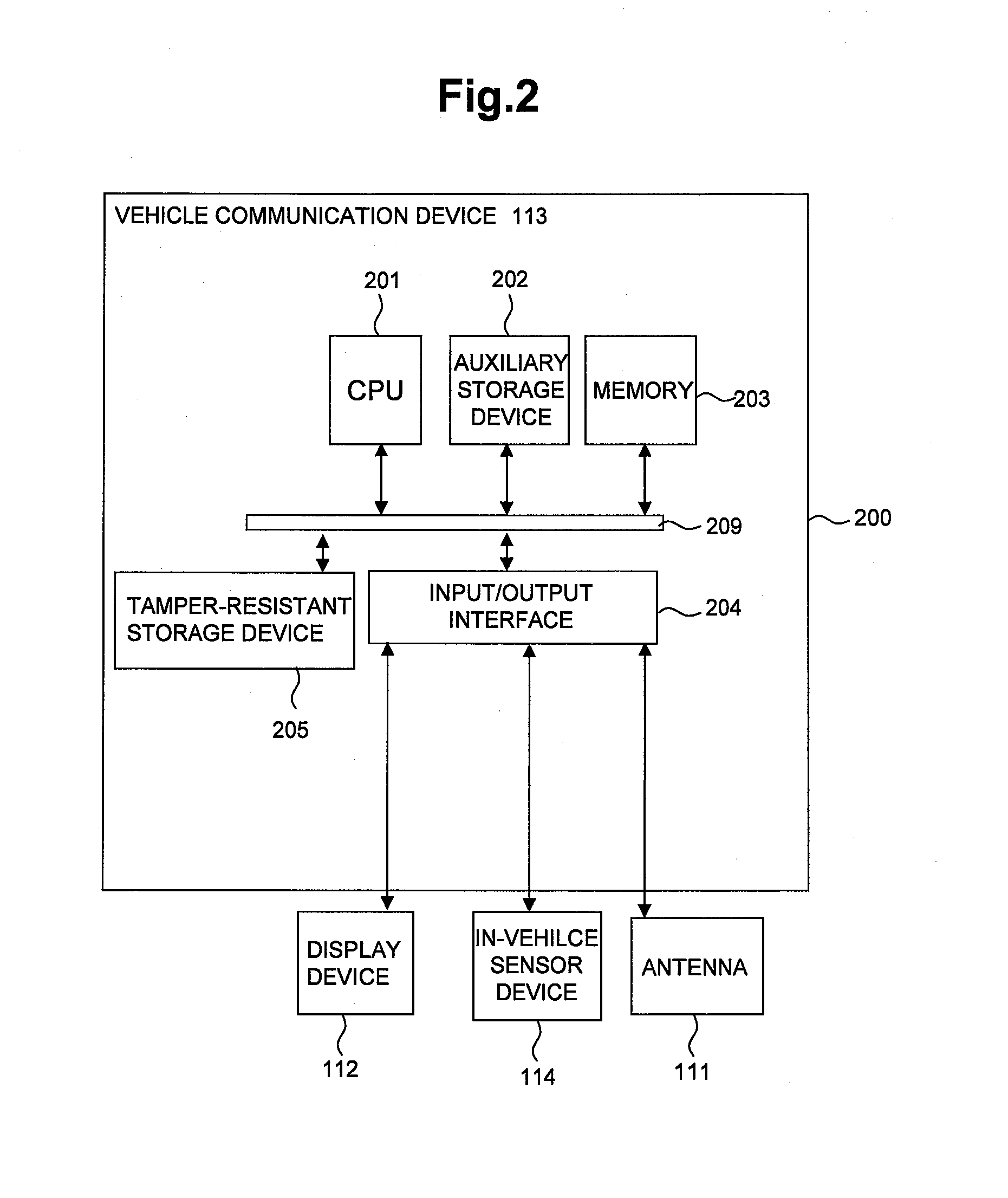
Frame transmission source authentication is performed among terminals involved in delivery in a wireless adhoc communication system. A first terminal generates a keyed hashed value by using an authentication header key determined with respect to a second terminal, and gives it to an authentication header of a frame. The second terminal generates a keyed hashed value by using the authentication header key determined with respect to the first terminal, and compares it with the authentication header given to the frame. If the keyed hashed value generated at the second terminal matches the authentication header, it is confirmed that the frame has been transmitted from the first authenticated valid terminal. The first terminal encrypts a payload part by using a unicast encryption key determined with respect to a third terminal. This encrypted payload part can be decrypted only by the third terminal having the unicast encryption key.
Owner:SONY CORP
Electronic medical record safety system
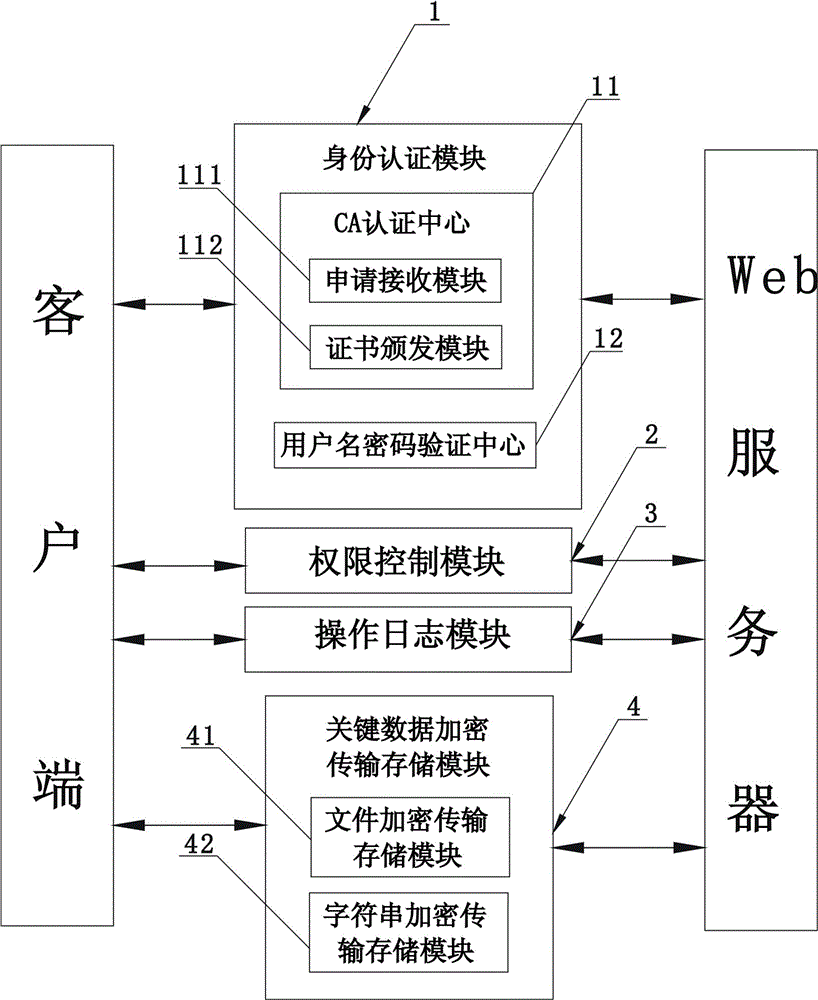
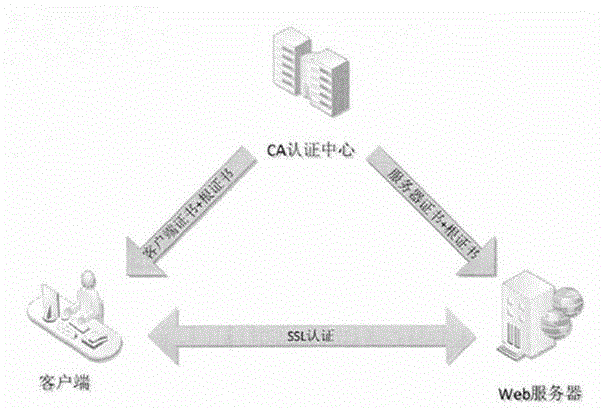
InactiveCN104392405AGuaranteed credibilityGuaranteed legalityData processing applicationsUser identity/authority verificationMedical recordPassword
The invention provides an electronic medical record safety system, comprising an identity authentication module, an authority control module, an operational log module and a key data encryption, transmission and storage module. The identity authentication module comprises a CA authentication centre and a user name and password authentication centre; the CA authentication centre and the user name and password authentication centre are combined to identify identities of users logged in the electronic medical record safety system. The authority control module is used for controlling authorities of users subjected to the authentication of the identity authentication module and based on the relation among users, roles and authorities. The operational log module is used for tracing and recording login and amendment records of users subjected to the authentication of the identity authentication module. The key data encryption, transmission and storage module is used for encrypting, transmitting and storing key data in the electronic medical record system.
Owner:杭州银江智慧健康集团有限公司
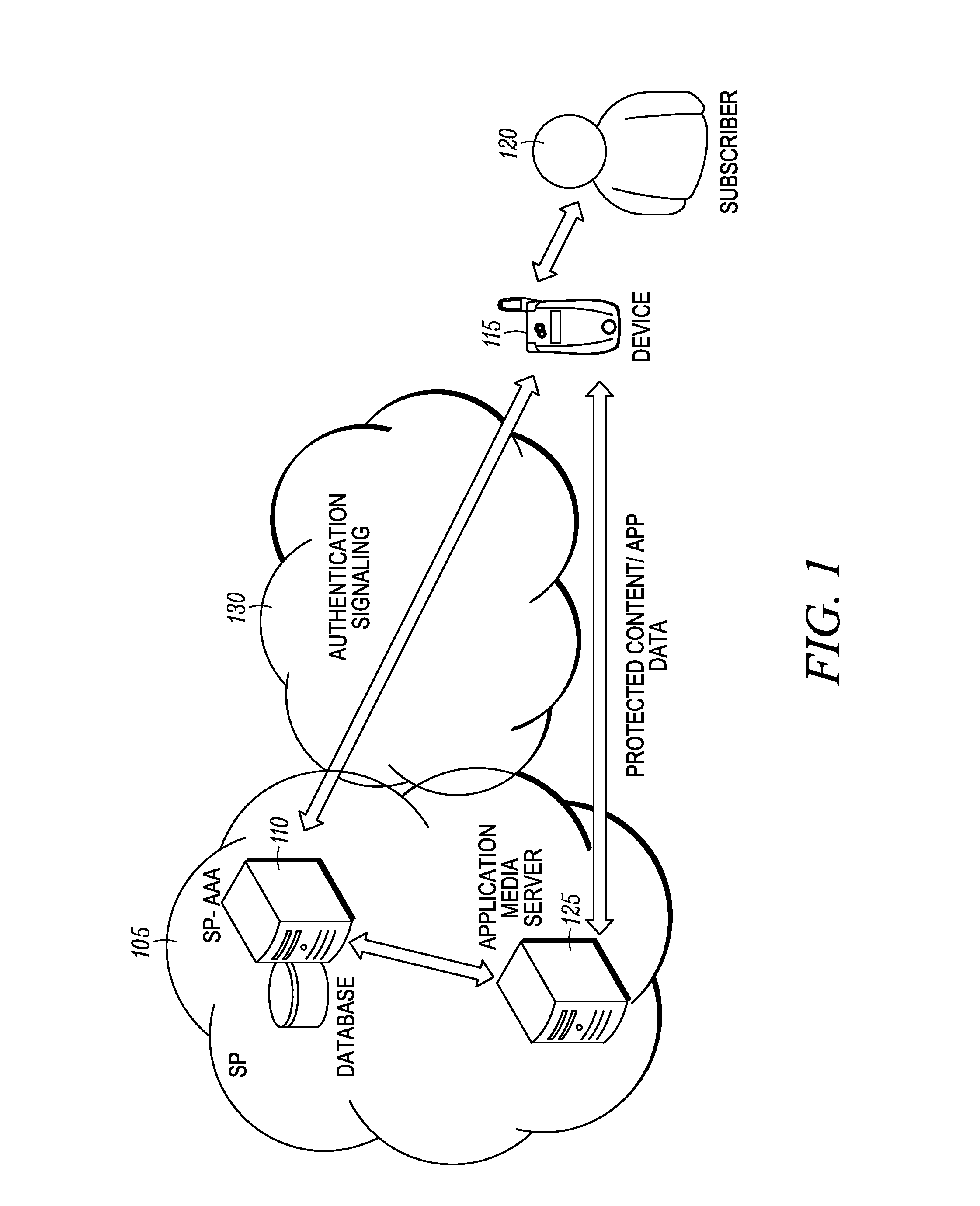
Providing remote services to legacy applications
ActiveUS7945949B2Digital data processing detailsComputer security arrangementsServer agentVoice communication
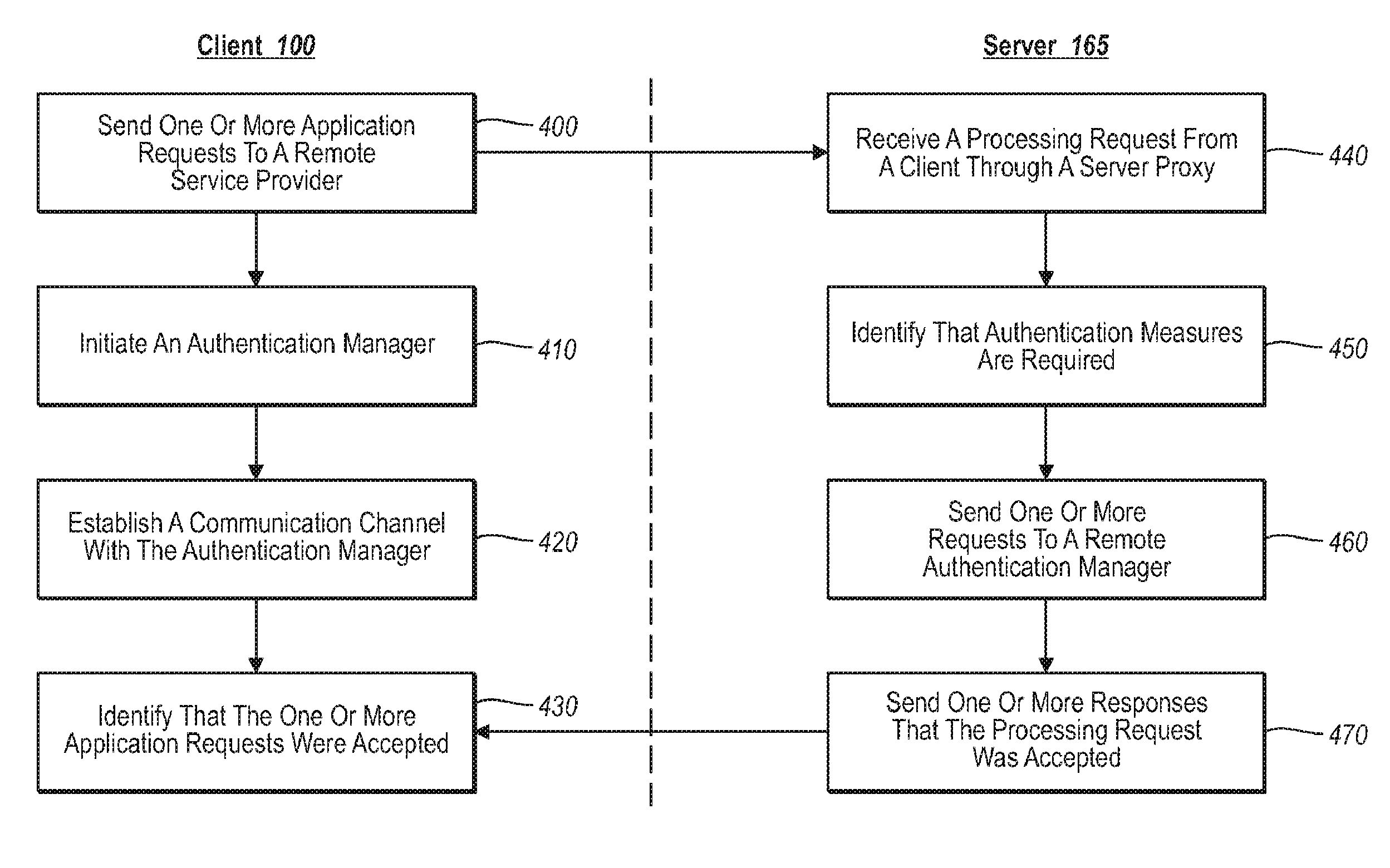
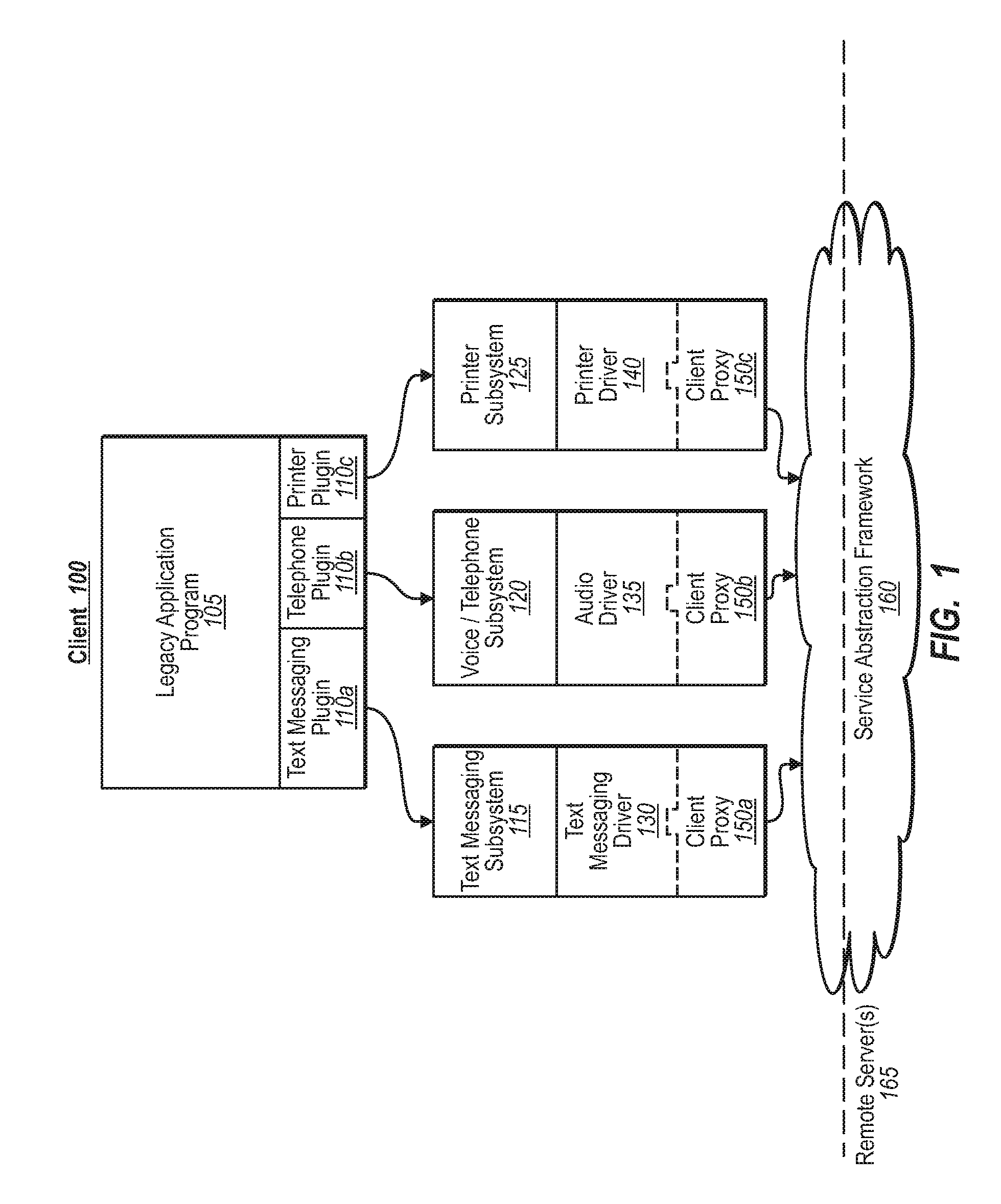
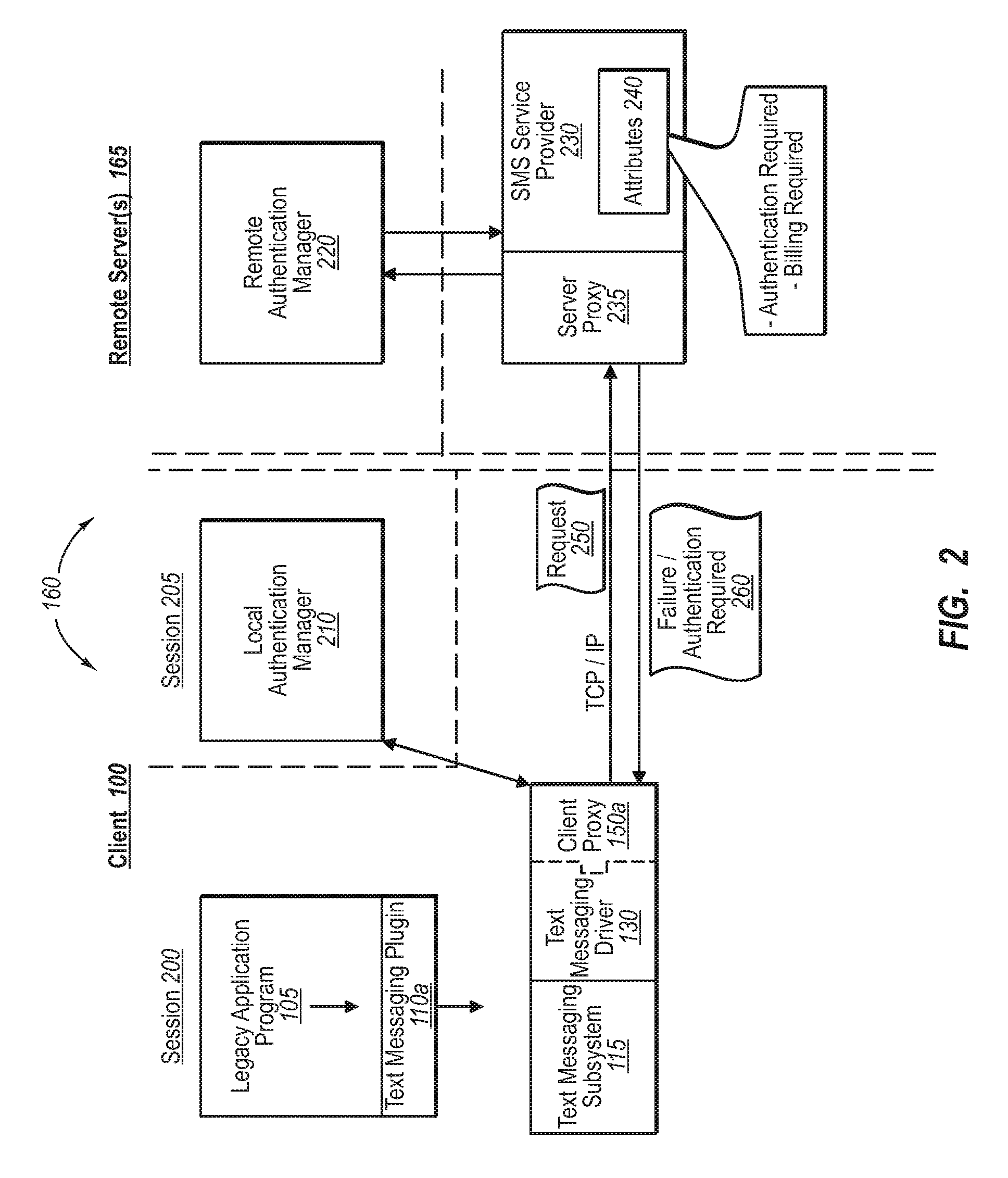
A developer can provide complex services to existing legacy applications using one or more components configured to tap into a service abstraction framework. In one implementation, for example, a developer of a remote service provider adds one or more authentication attributes to the remote service provider, and further creates a local client driver that incorporates a client proxy. When a legacy application generates a function request (e.g., to print, send a text message, initiate a voice communication), the client proxy intercepts the request through an appropriate communication subsystem, and relays the request to the server proxy. The server proxy determines the extent to which authentication measures may be required. If required, the client proxy can initiate out-of-band processing with various authentication managers to validate / process the request at the remote service provider.
Owner:MICROSOFT TECH LICENSING LLC
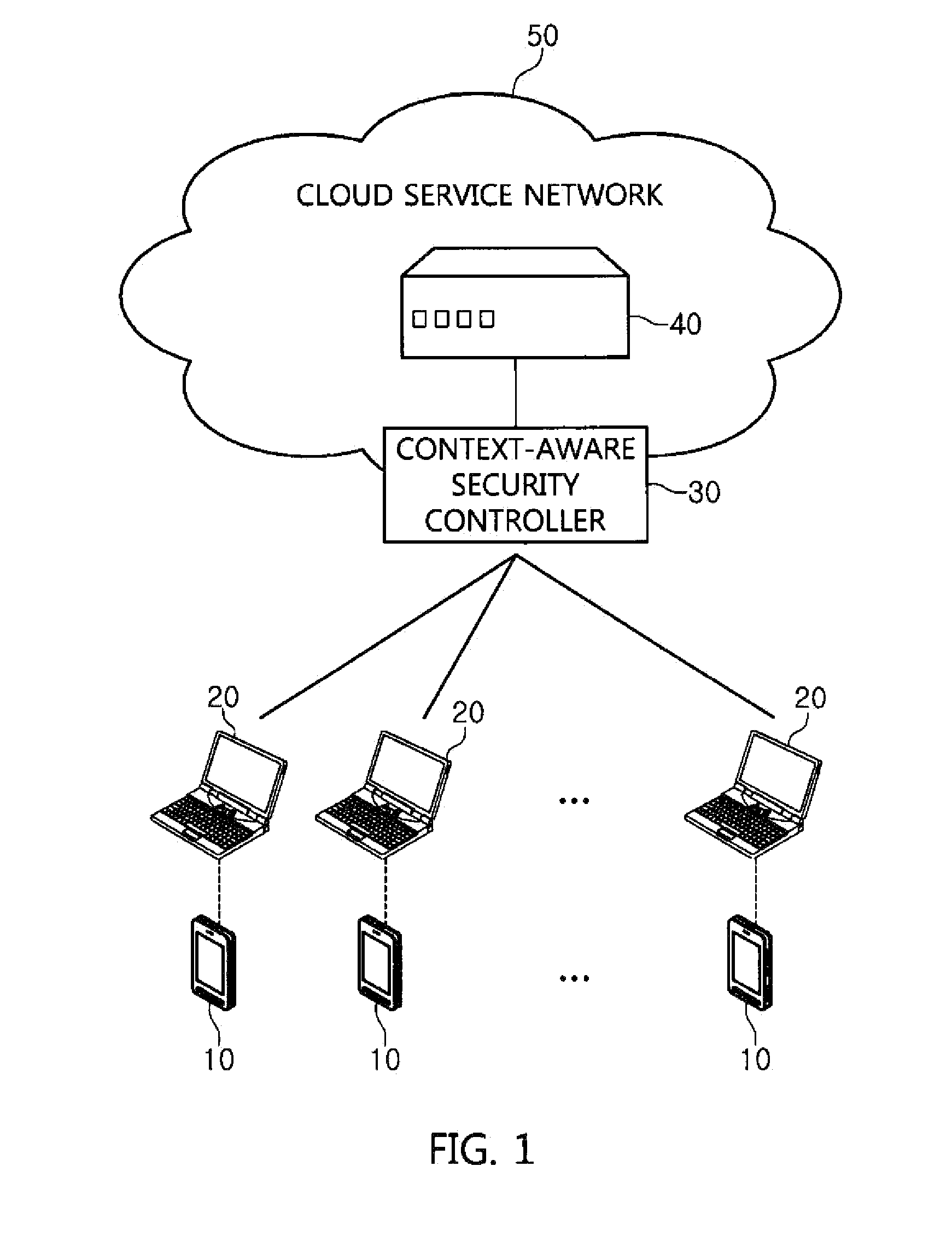
Apparatus, method and system for context-aware security control in cloud environment
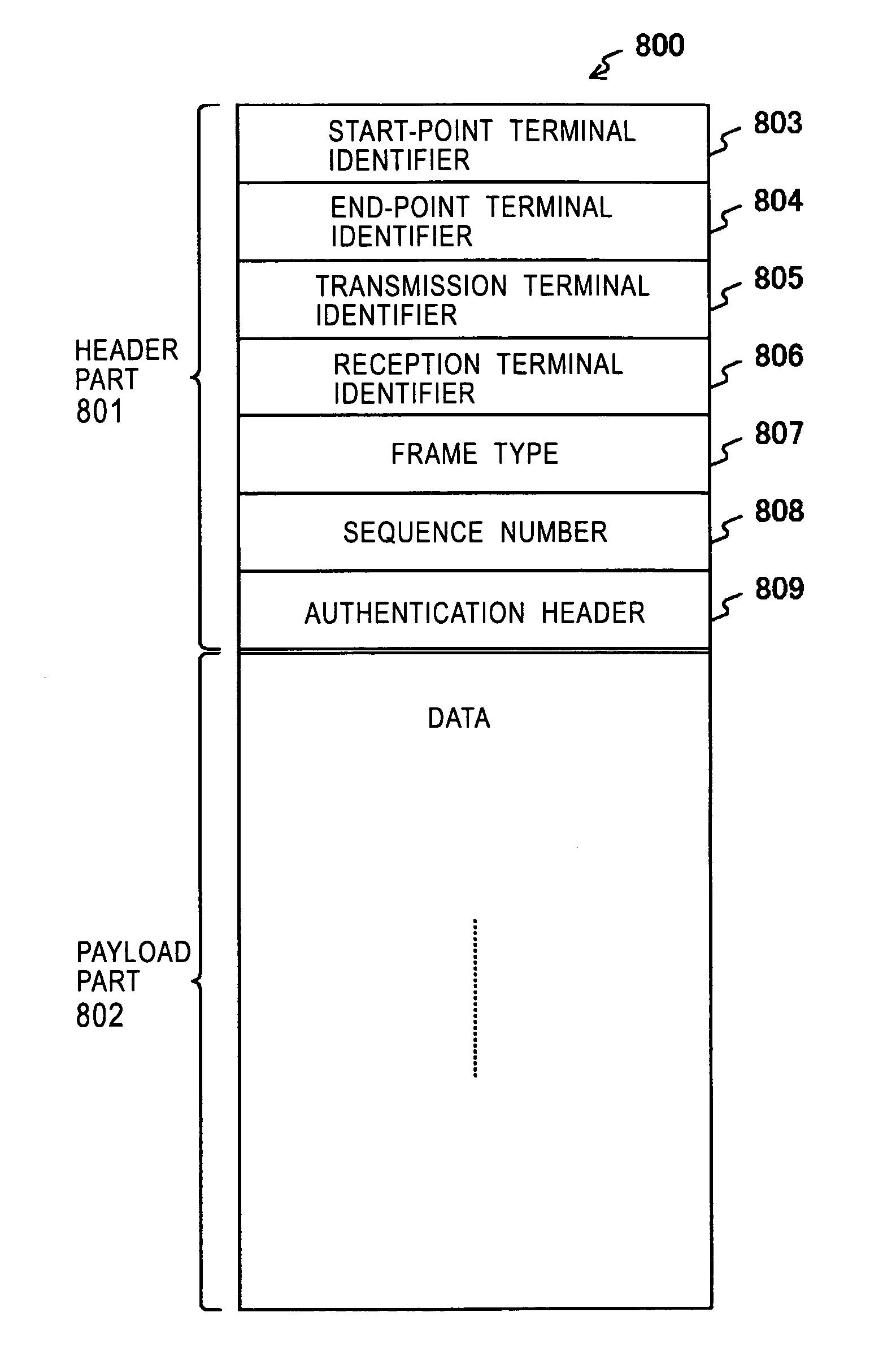
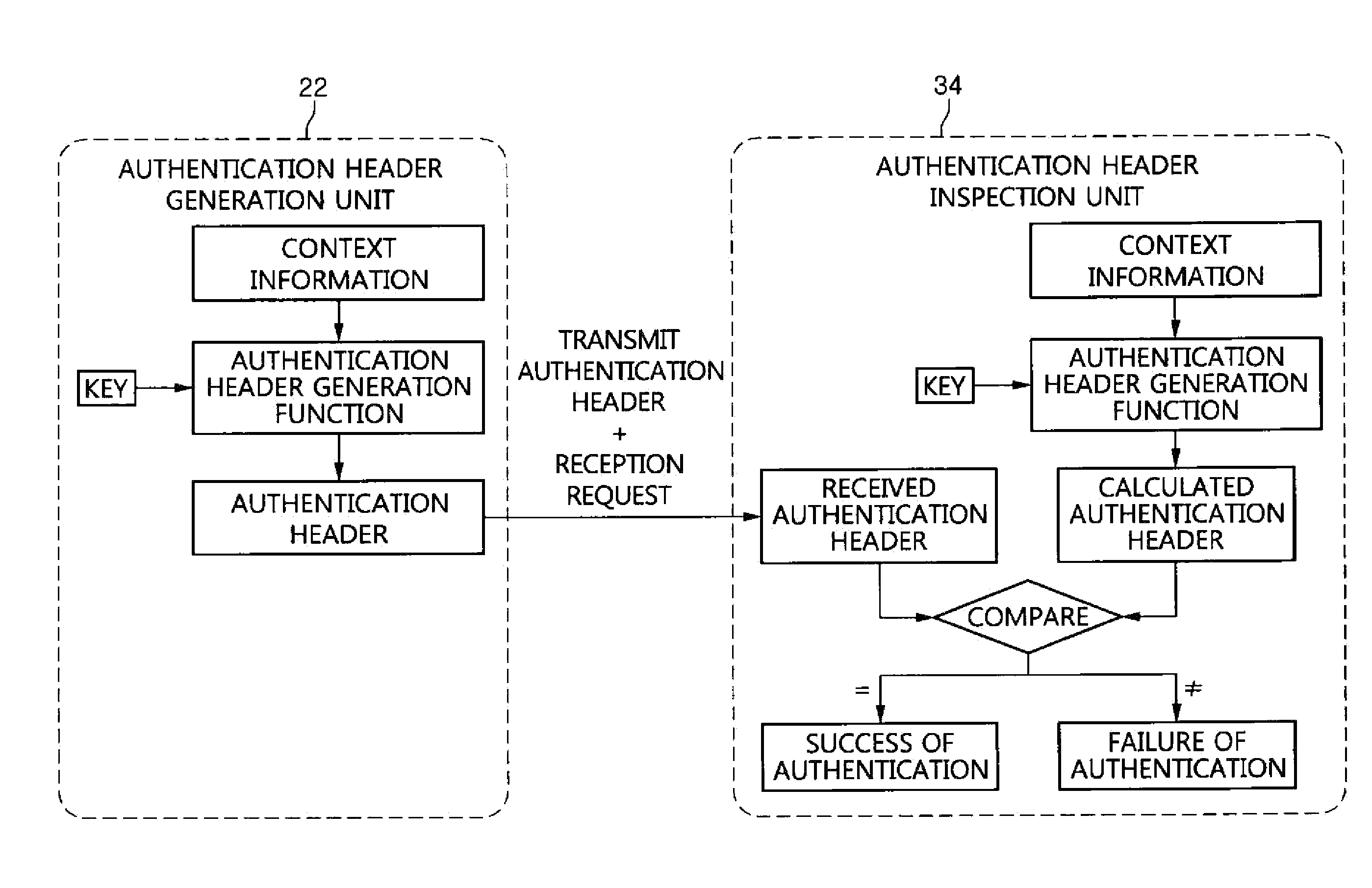
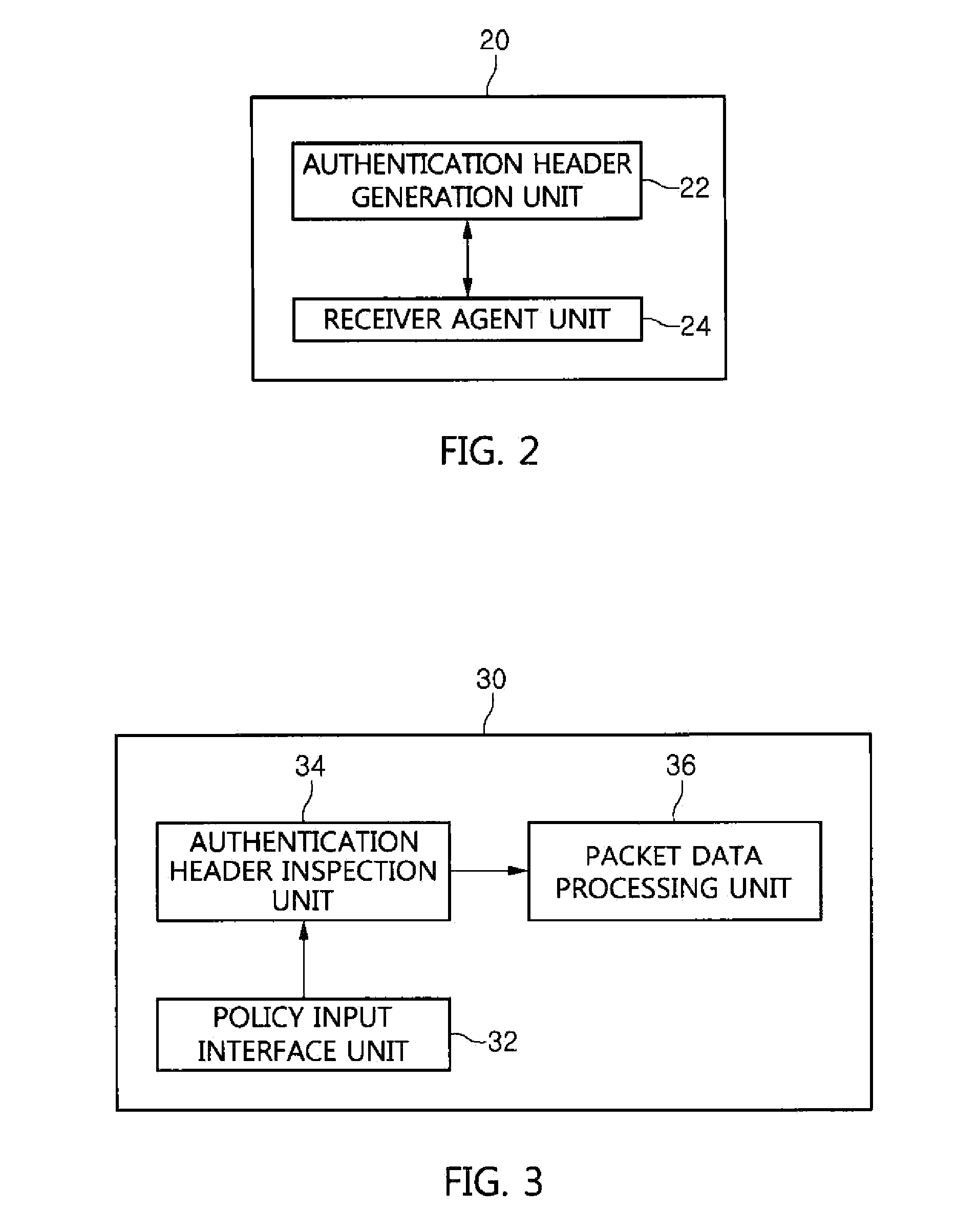
An apparatus, method and system for context-aware security control in a cloud environment are provided. The apparatus includes an authentication header inspection unit and a packet data processing unit. The authentication header inspection unit generates an authentication header based on the received context information and key of a user, compares the generated authentication header with the authentication header of packet data received from a remote user terminal, and outputs the results of the comparison. The packet data processing unit performs one of the transmission, modulation and discarding of packet data from the cloud server of a cloud service network based on the results of the comparison by the authentication header inspection unit.
Owner:ELECTRONICS & TELECOMM RES INST
NFC (near field communication)-based point-to-point trusted authentication method
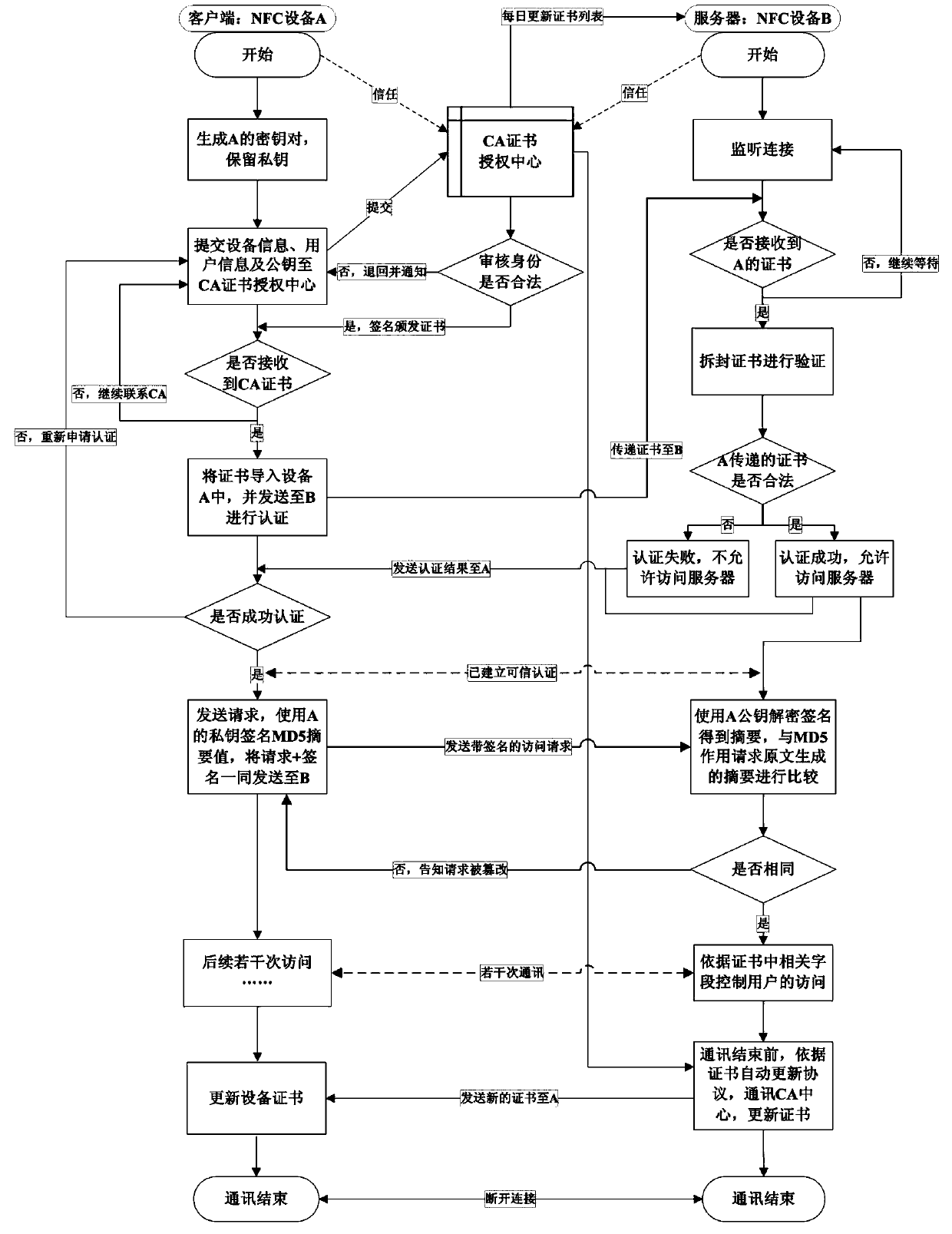
InactiveCN104219055AAchieve accessAchieve immediacyKey distribution for secure communicationUser identity/authority verificationDigital signatureTransfer procedure
The invention provides an NFC (near field communication)-based point-to-point trusted authentication method. The method includes that a client NFC device generates an own key pair and sends an own public key, device information and personal identity information to a CA (certificate authority); after verifies the identity, the CA issues a certificate to the device, to be specific, the certificate is used for achieving identity authentication with an NFC server and accompanied with digital signing message of a publisher in a CA center; an access is provided for the digital certificate into the client NFC device, thus the device can perform the relative access through the certificate of its own; in case that the access to the NFC server for the identity authentication is required, the client NFC device transmits the own certificate to the NFC server through an established secret passage. According to the arrangement, the safe, reliable, flexible, convenient, resource-saving and multi-functional authentication is achieved during the NPC point-to-point transmission.
Owner:TIANJIN UNIV
Network authentication system on basis of switchboards and authentication method for network authentication system
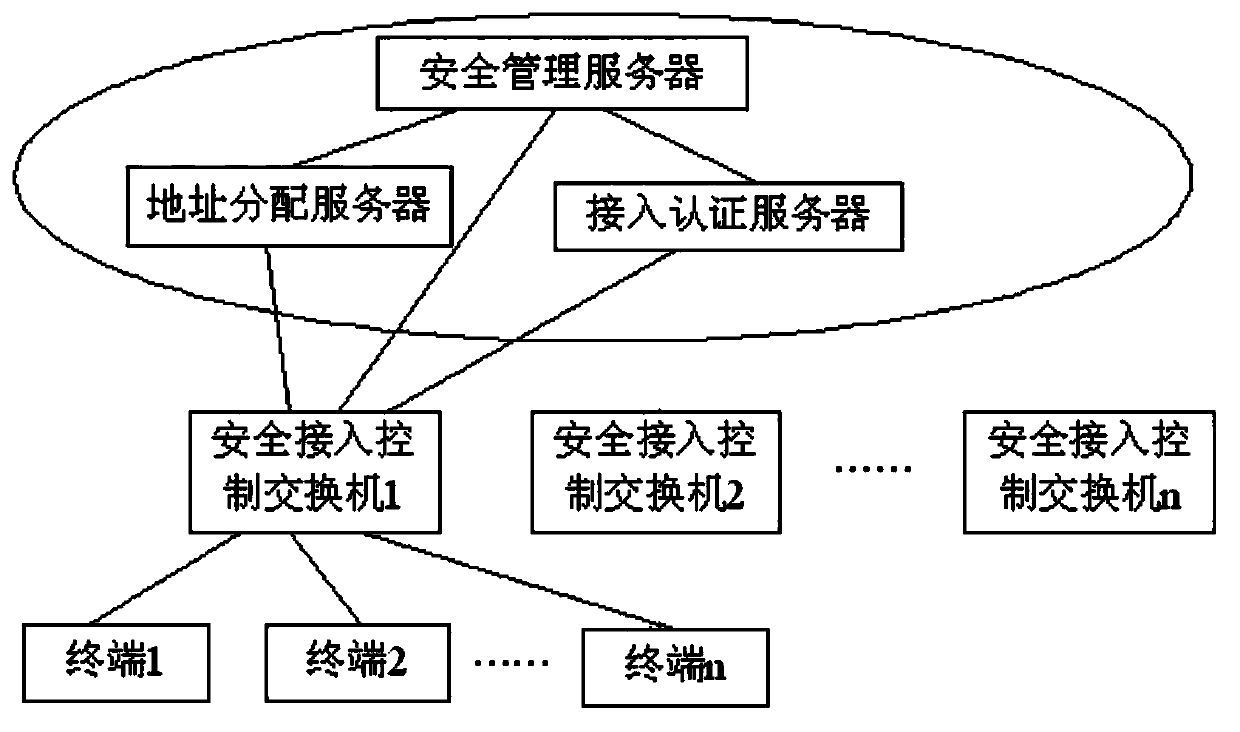
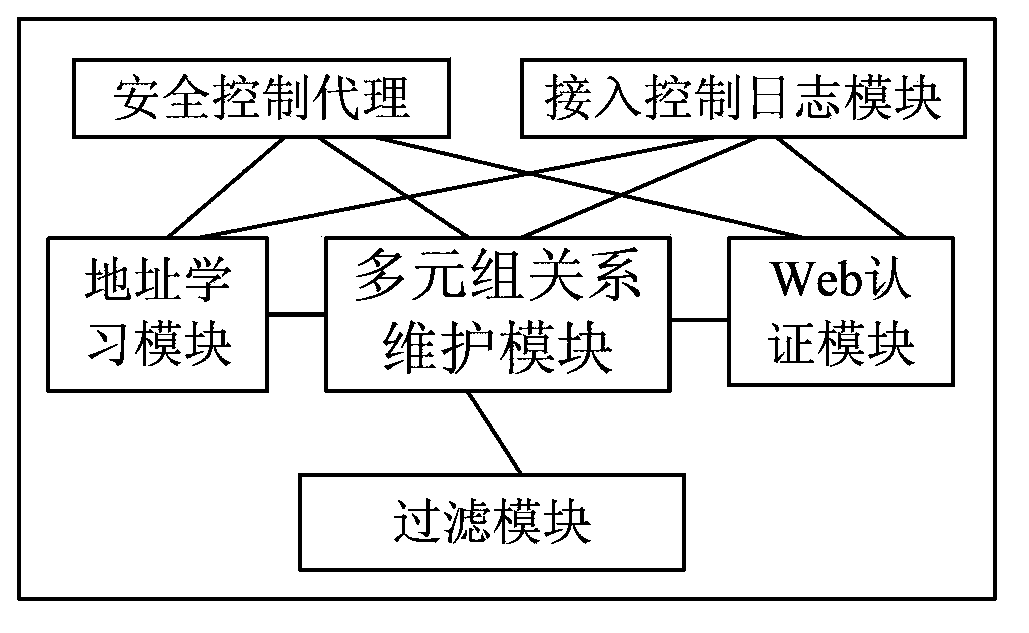
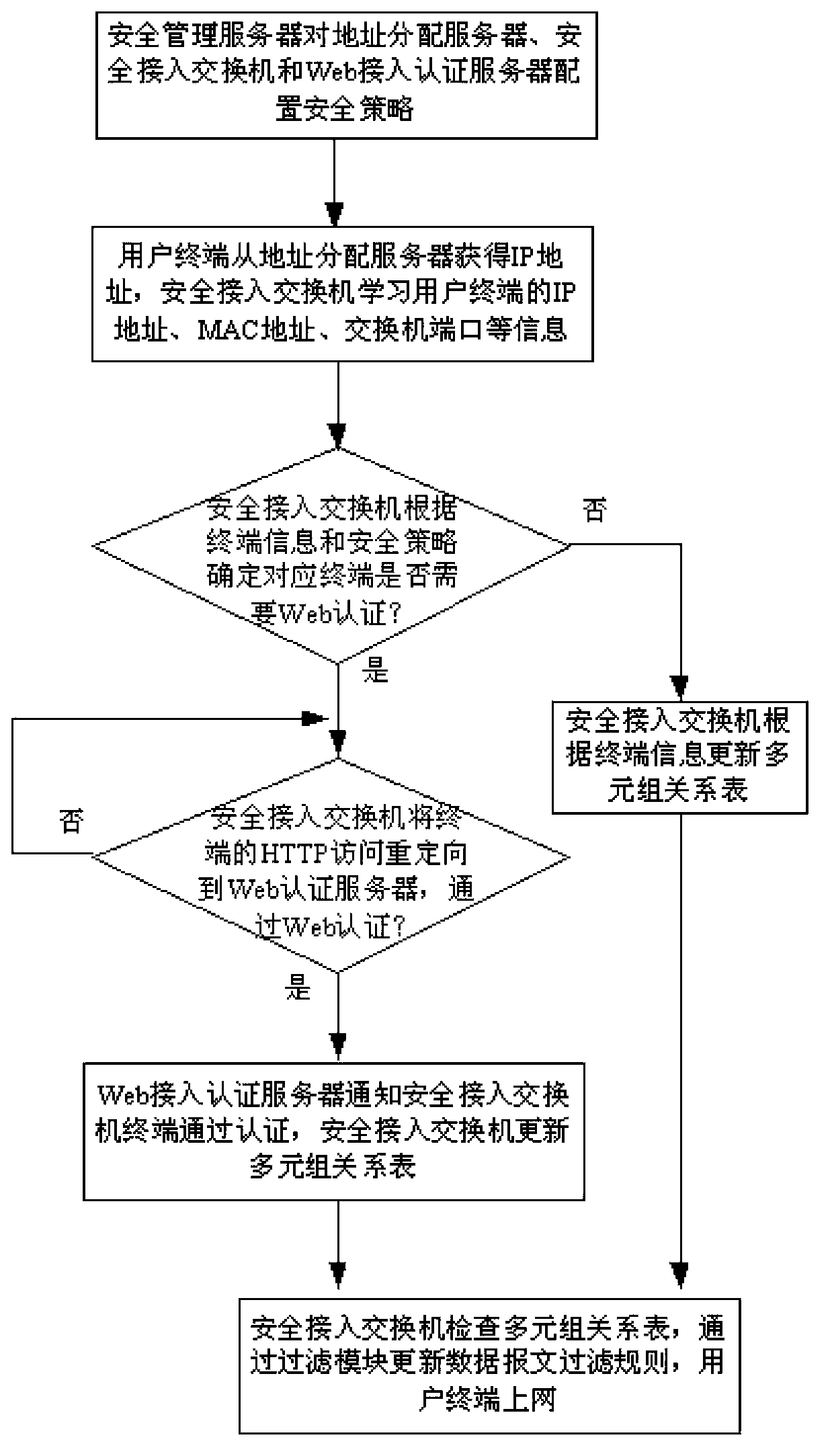
ActiveCN103428211AImprove securityIncrease credibilityTransmissionWeb authenticationRelevant information
The invention discloses a network authentication system on the basis of switchboards. The network authentication system comprises the security access control switchboards, a security management server, an address allocation server, a Web access authentication server and user terminals. The invention further discloses an authentication method applied to the network authentication system on the basis of the switchboards. The authentication method includes steps that 1, the security management server configures security strategies; 2, the user terminals access a network, and the security access control switchboards learn relevant information of the user terminals; 3, the security access control switchboards determine whether the user terminals need Web authentication to surf the network or not according to the relevant information of the user terminals and the security strategies; 4, the Web authentication server authenticates users if the user terminals need the Web authentication; 5, the security access control switchboards allow the user terminals to surf the network if the users are successfully authenticated. The network authentication system and the authentication method have the advantages that the Web authentication bound with multiple elements can be performed on the network access users, so that the network authentication security is improved, the network reliability is enhanced, and the like.
Owner:SOUTH CHINA UNIV OF TECH
User anonymous identity authentication protocol based on k-pseudonym set in wireless network
ActiveCN104283899AReduce resource consumptionTransmissionSecurity arrangementWireless mesh networkUser authentication
The invention discloses a user anonymous identity authentication protocol based on a k-pseudonym set in a wireless network. In the protocol, a user sends the information includes the k-pseudonym set of the true identity label of the user and the information encrypted through the true user shared key to an authentication server, the authentication server completes user authentication within the range of the traversal and the calculation of k pieces of user information; the average number of users needing traversal is half the sum of k and 1, and two types of methods for constructing the k-pseudonym set are provided at the same time. According to the protocol, anonymous authentication is achieved on the basis of a shared key by introducing the k-pseudonym set, and the resource loss, generated during anonymous authentication, of the user and the authentication server is lowered.
Owner:XIDIAN UNIV
Digital certificate-based unified authentication login method for integrating multiple application systems
ActiveCN103560888AProtection securityEasy to operateUser identity/authority verificationPasswordAuthorization
The invention discloses a digital certificate-based unified authentication login method for integrating multiple application systems. A legal digital certificate signed and issued for a user, an authentication method of the digital certificate replaces an original authentication method of a user name and a password; a unified authentication platform is established, and unified certification service is provided for all the information application systems; the information application systems have access to the platform, login authentication and authorization are performed, and unified authentication login is completed. When the method is used, safety of the information application systems is improved, losses caused by early leak of the user name and the password are reduced, and signature of the digital certificate guarantees traceability of operation in the information application systems; due to the fact that the unified authentication platform is established, user information resources can be shared in a concentrated mode and are convenient to manage and maintain; on the basis of the OAuth2.0 protocol, an open interface is provided, and therefore new application information systems can have access to the platform more easily; the unified authentication login and single-point login function is provided, operation of the user is facilitated, and working efficiency is improved.
Owner:江苏先安科技有限公司
Fast authentication for inter-domain handovers
ActiveUS20150271668A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsAdministrative domainElliptic curve Diffie–Hellman
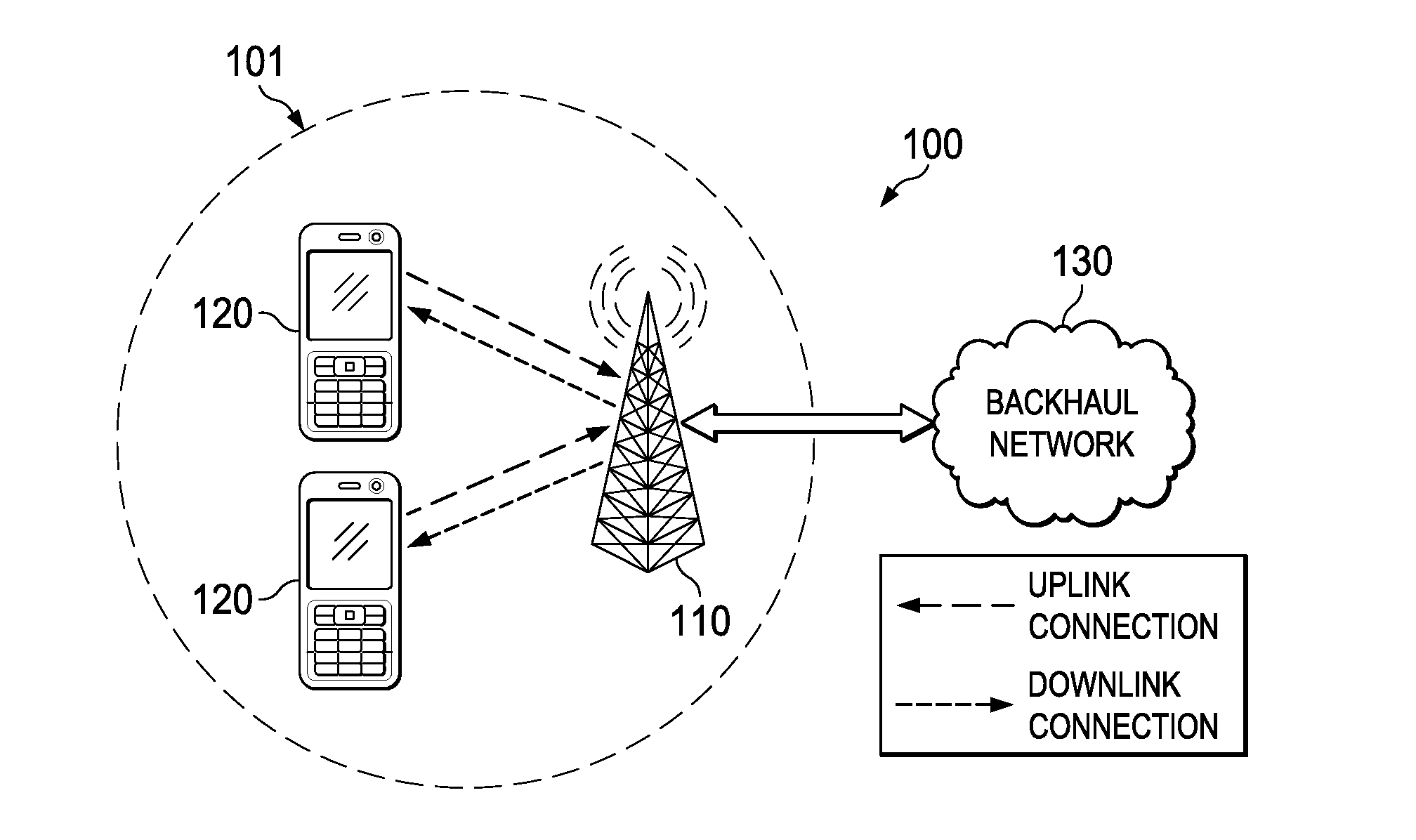
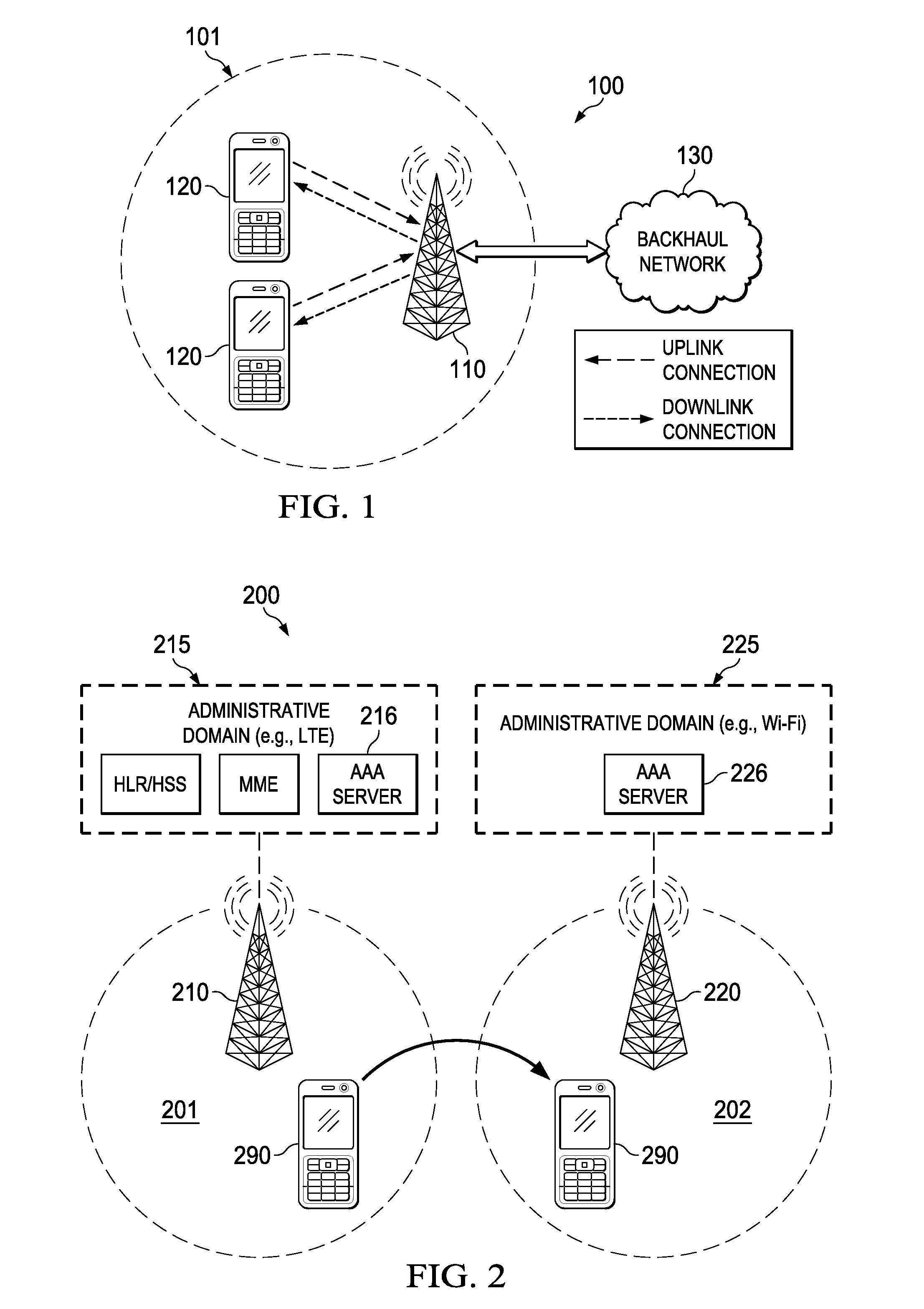
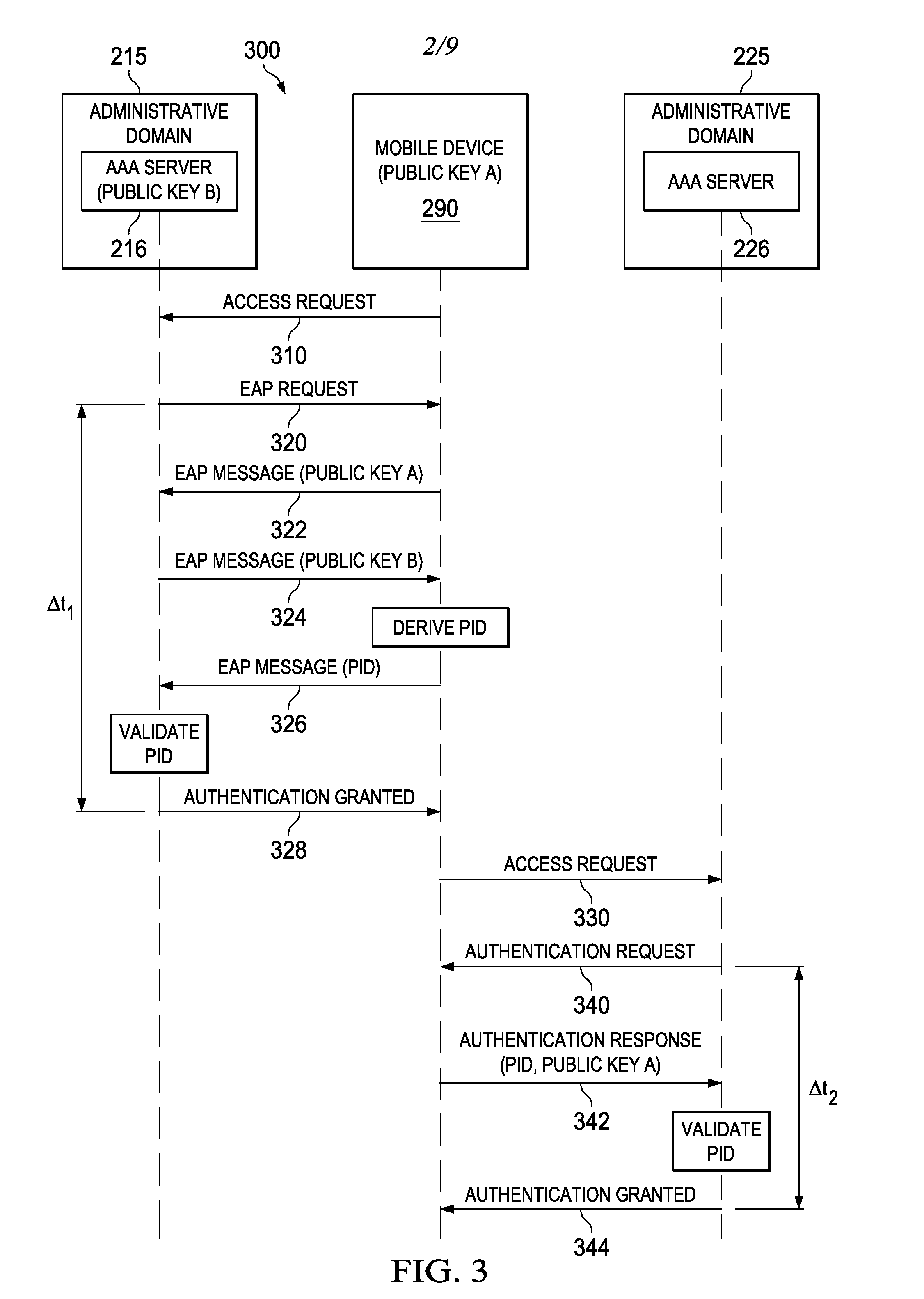
Fast mobile device authentication can be achieved during inter-domain handovers between administrative domains operating under a federated service agreement using pseudonym identifications (PID). Specifically, the mobile device may derive a PID when obtaining authentication in a first wireless network, and then use the PID to obtain fast authentication in a second wireless network. The PID may be generated during an Elliptic curve Diffie-Hellman (ECDH) authentication procedure using public keys associated with the mobile device and the first wireless network. The PID (or a derivative thereof) may then be provided to an authentication server in a second wireless network for validation. The PID may be validated by the second authentication server via online or offline validation procedures. The PID can also be used as an electronic coupon for accessing the second network.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com