Method for importing secret keys safely, electronic signature tool, authentication device and system
An electronic signature tool and a technology for authentication equipment, applied in the field of electronic technology applications, can solve problems such as high security requirements and inconvenience, and achieve the effects of simple processing and improved security and convenience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
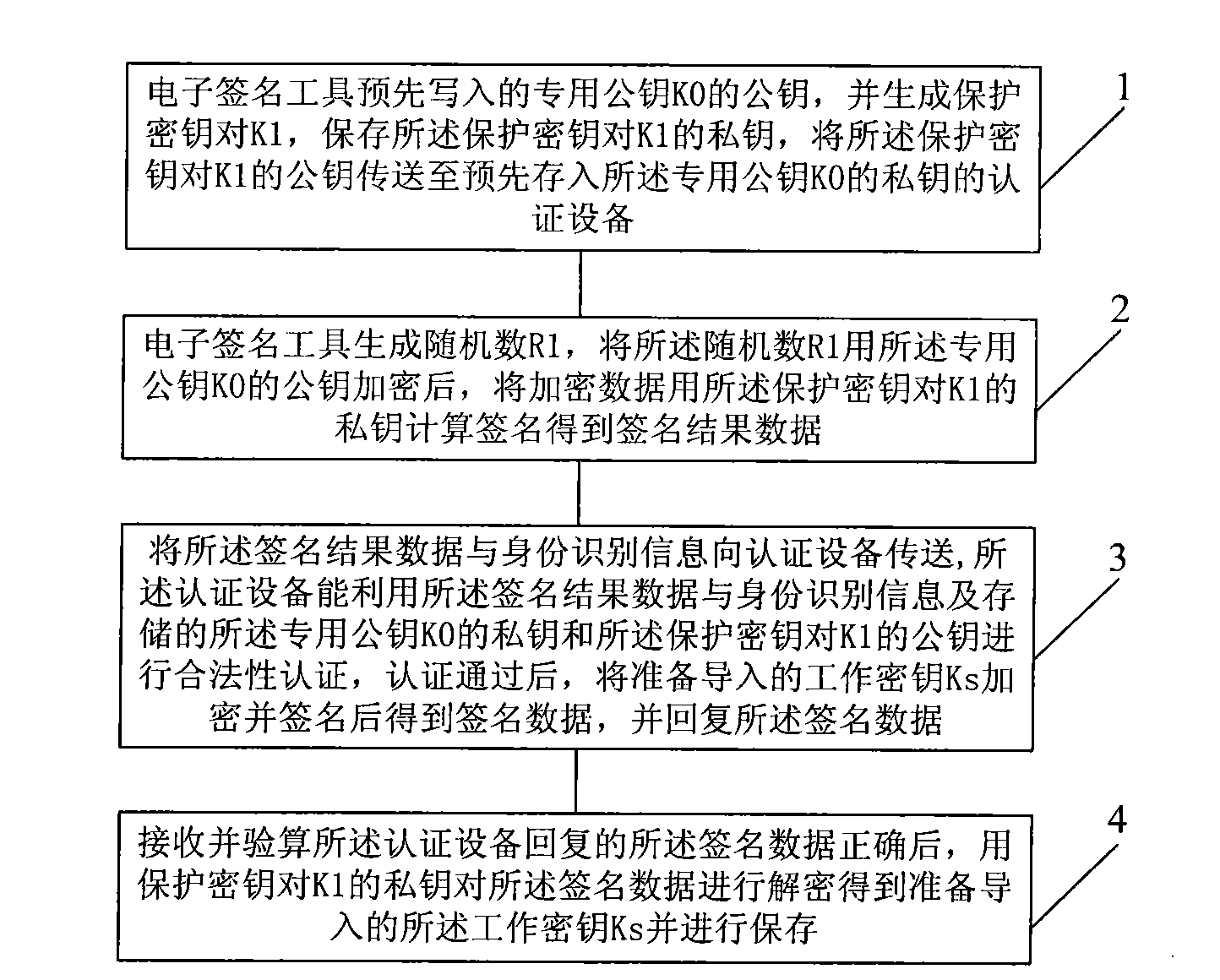
[0048] This embodiment provides a method for securely importing a key, which is used to securely import a working key to an electronic signature tool (such as a USBKey device), such as figure 1 As shown, the method includes:
[0049] Step 1, the electronic signature tool pre-writes the public key of the dedicated public key K0, and generates a protection key pair K1, saves the private key of the protection key pair K1, and transmits the public key of the protection key pair K1 To the authentication device pre-stored with the private key of the dedicated public key K0;
[0050] Step 2: Generate a random number R1, encrypt the random number R1 with the pre-written public key of the dedicated public key K0 to obtain encrypted data, and use the pre-generated and saved protection key to calculate the signature with the private key of K1 Get the signature result data;
[0051] Step 3, send the signature result data and identification information (which can be the serial number of ...
Embodiment 2
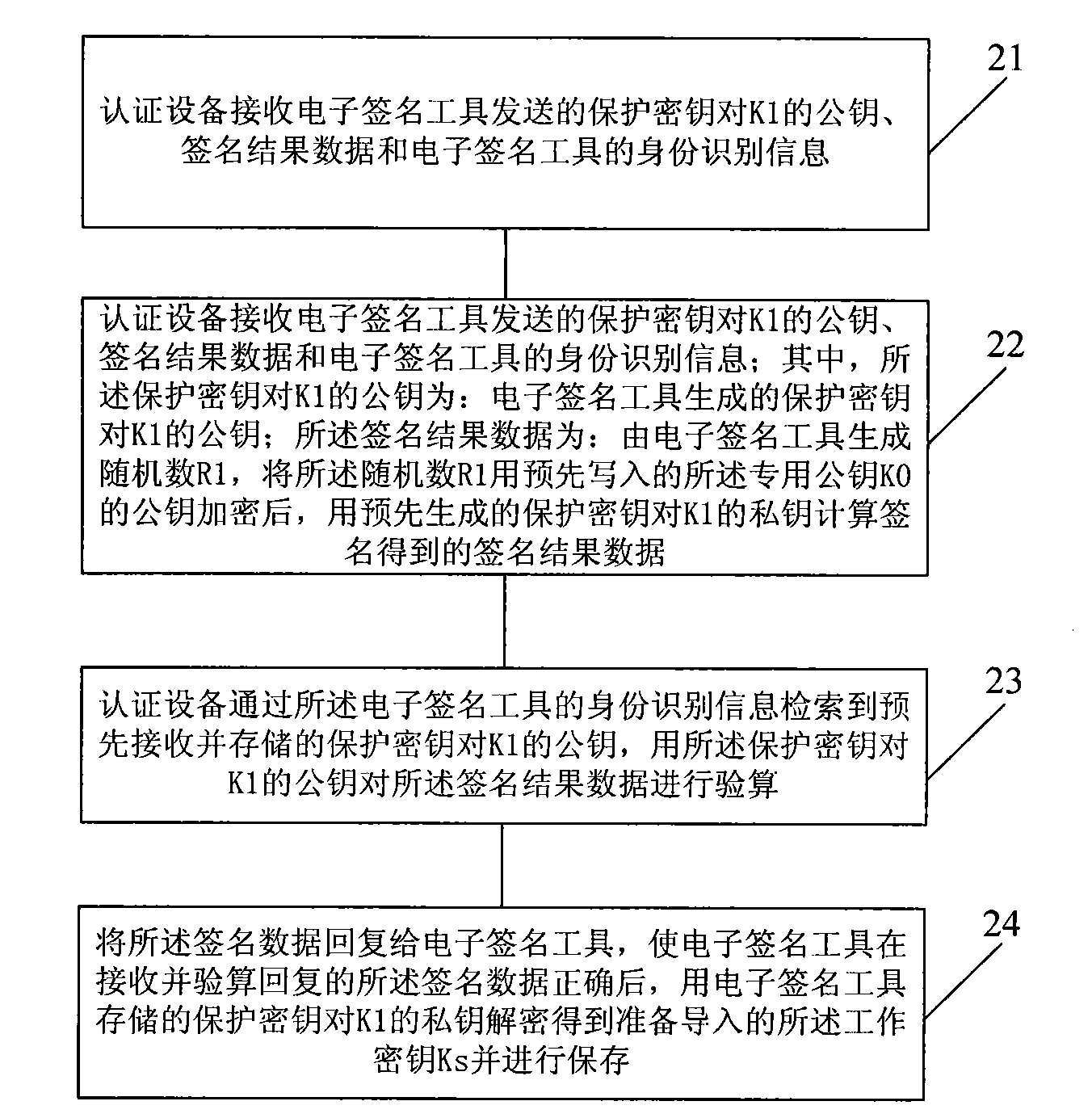
[0058] This embodiment provides a method for securely importing a key, which is used to securely import a working key into an electronic signature tool, such as figure 2 As shown, the method includes:
[0059] Step 21, the authentication device receives the public key of the protection key pair K1 sent by the electronic signature tool, the signature result data and the identification information of the electronic signature tool; wherein, the public key of the protection key pair K1 is: generated by the electronic signature tool The public key of the protected key pair K1; the signature result data is: the random number R1 is generated by the electronic signature tool, and after the random number R1 is encrypted with the public key of the pre-written special public key K0, it is encrypted with The signature result data obtained by calculating and signing the private key of K1 with the pre-generated protection key;
[0060] Step 22: The authentication device retrieves the pre-...
Embodiment 3
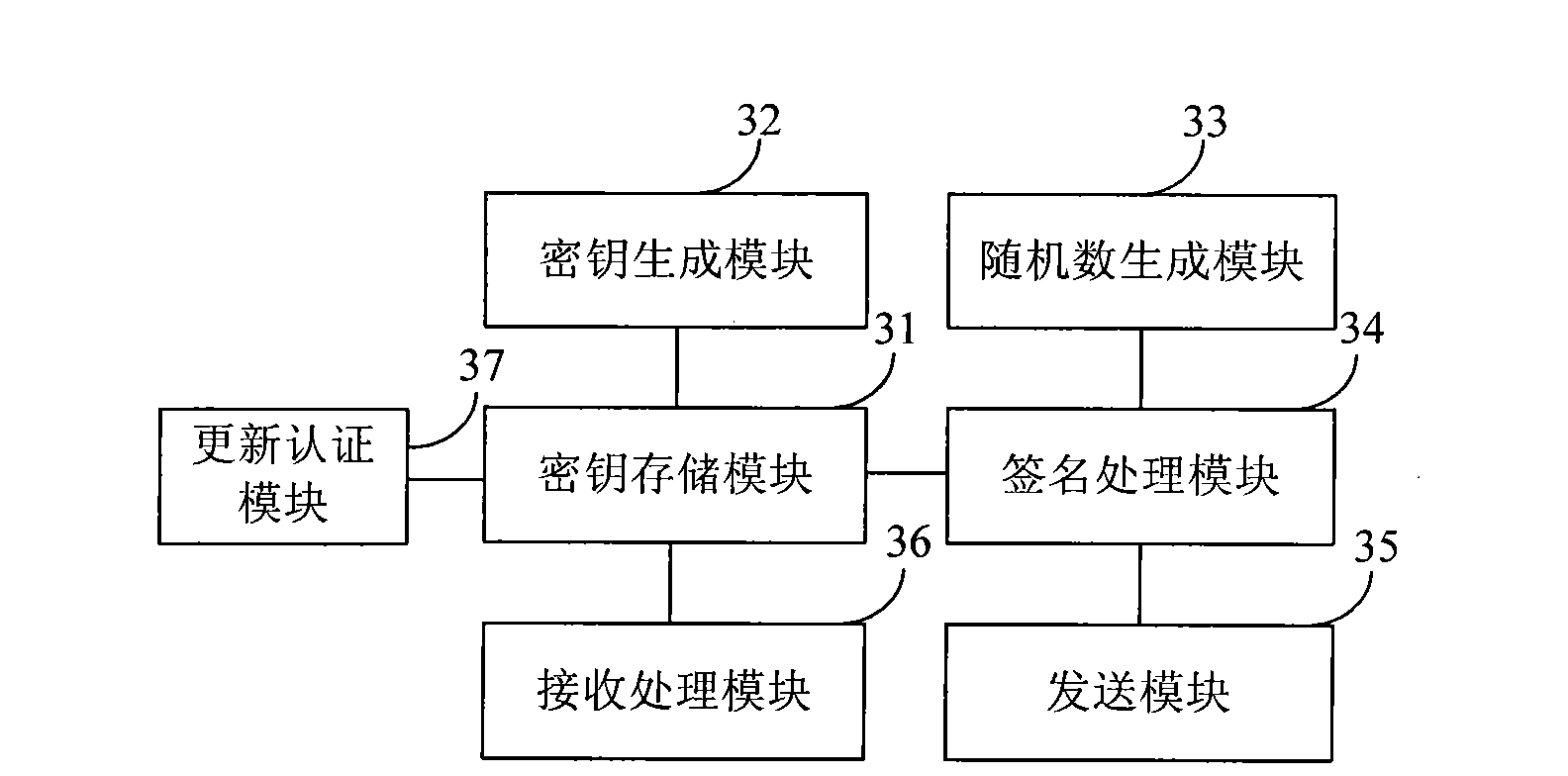
[0074] This embodiment provides an electronic signature tool, which can communicate with the authentication device of the background system, and use the network to safely import the work key, such as image 3 As shown, the electronic signature tool includes: a key storage module 31, a key generation module 32, a random number generation module 33, a signature processing module 34, a sending module 35 and a receiving processing module 36;
[0075] Wherein, the key storage module 31 is used to save the public key of the dedicated public key K0 written in advance, and save the private key of the protection key pair K1 generated by the key generation module 32, and save the receiving processing module 36 to receive The working key Ks obtained after processing the signature data replied by the authentication device;
[0076] The key generation module 32 is configured to generate a protection key pair K1, and store the private key of the protection key pair K1 in the key storage mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com