Patents
Literature
2301 results about "Random number generation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A random number generator (RNG) is a device that generates a sequence of numbers or symbols that cannot be reasonably predicted better than by a random chance. Random number generators can be true hardware random-number generators (HRNG), which generate genuinely random numbers, or pseudo-random number generators (PRNG), which generate numbers that look random, but are actually deterministic, and can be reproduced if the state of the PRNG is known.
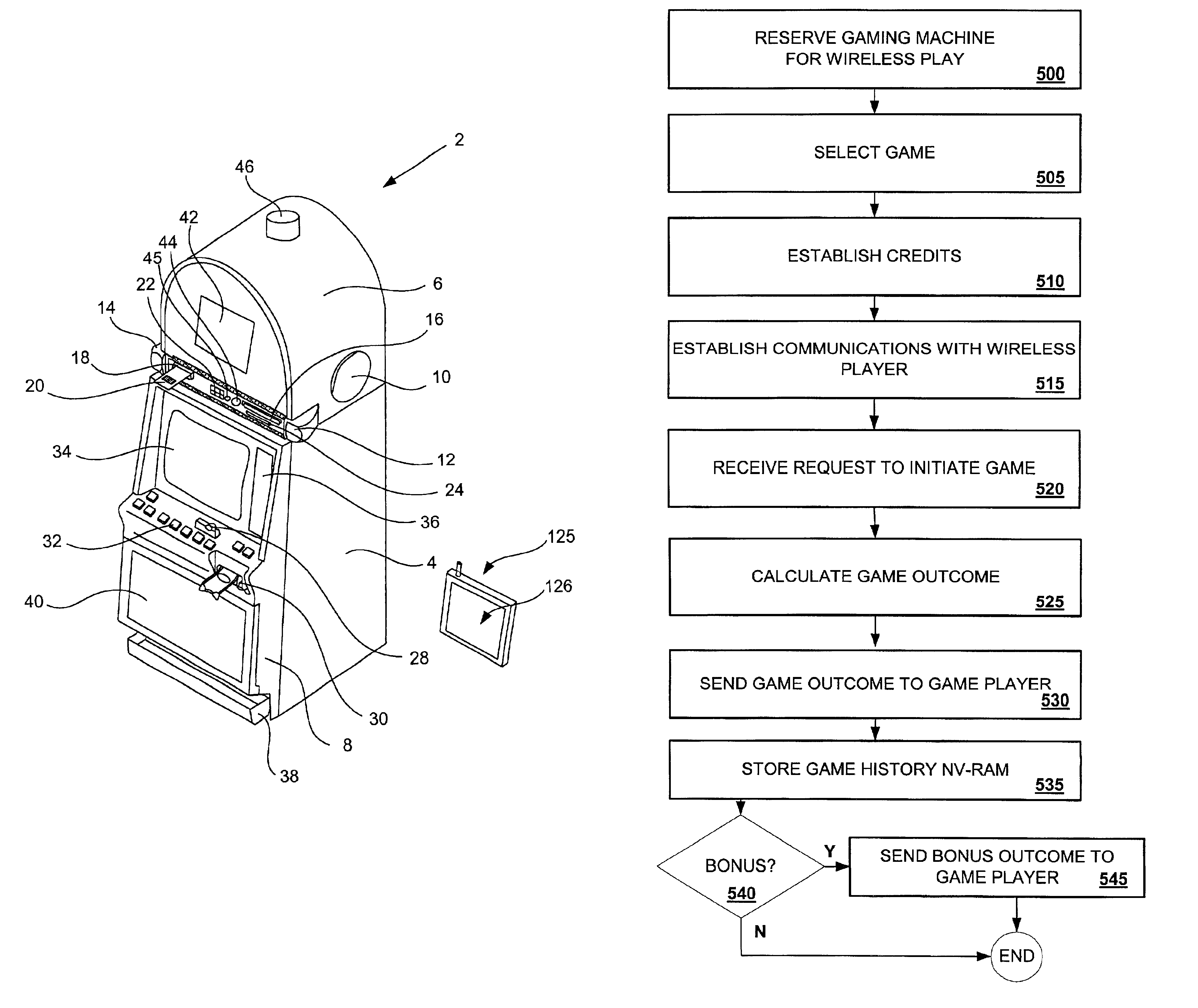
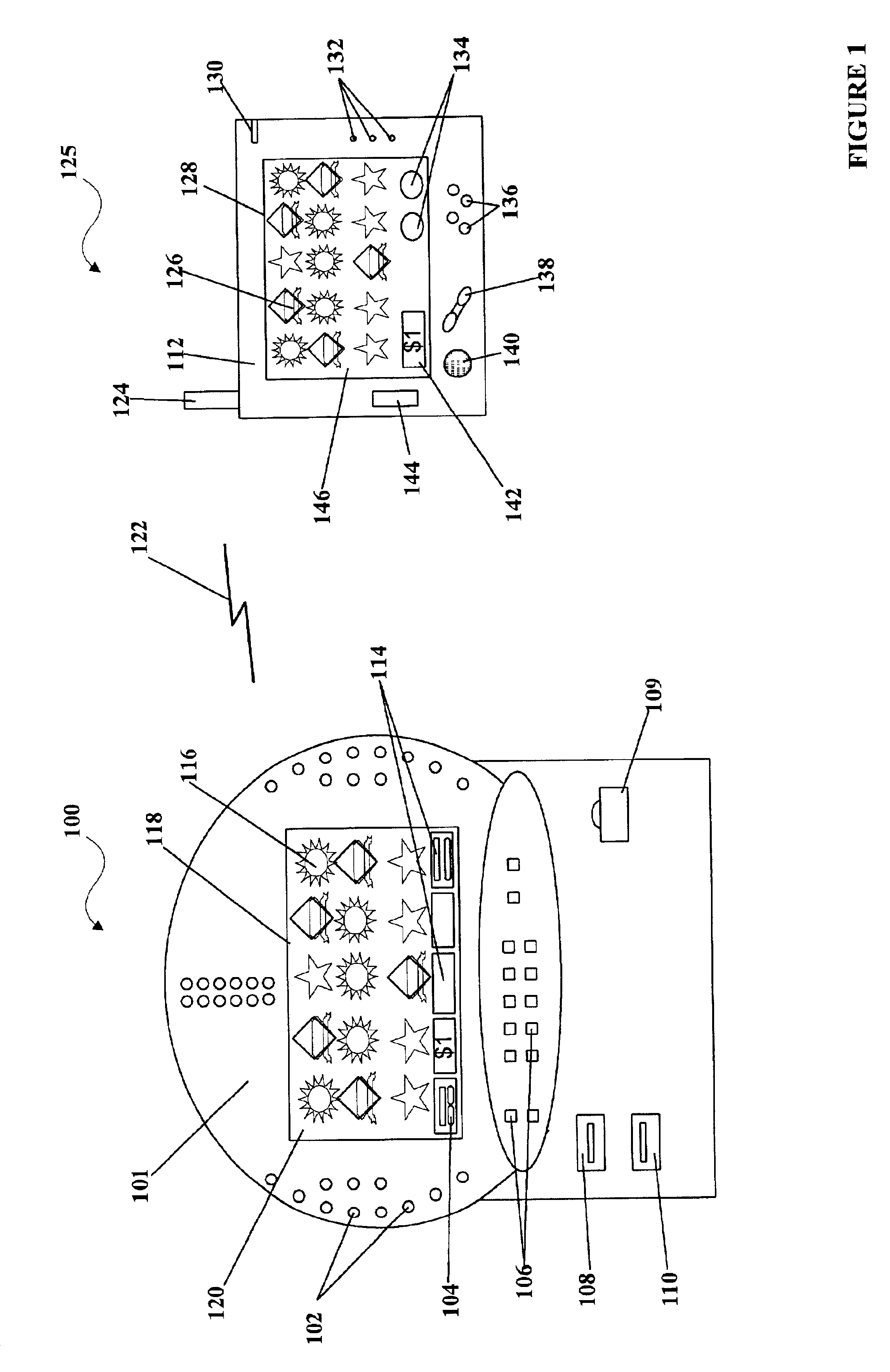
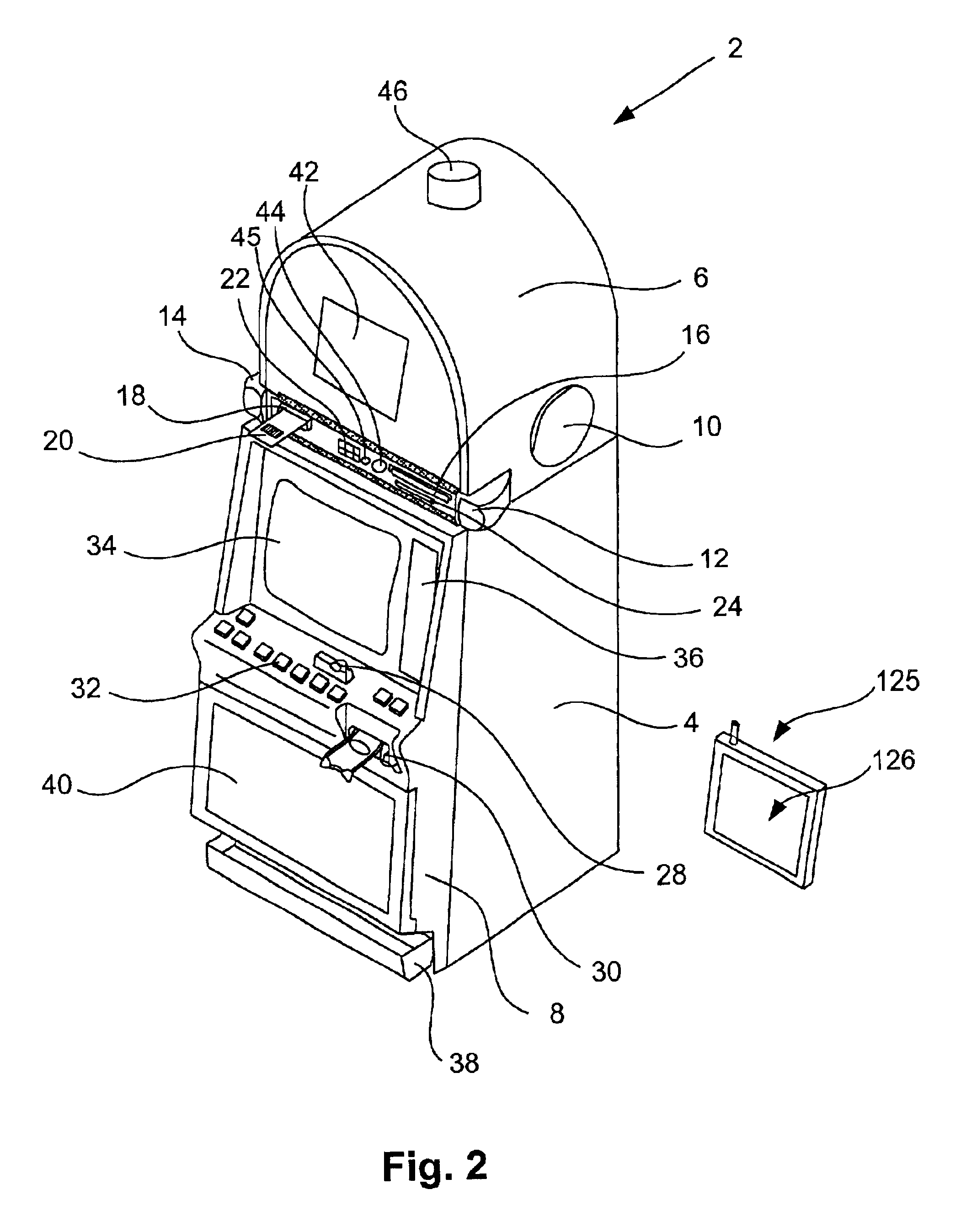
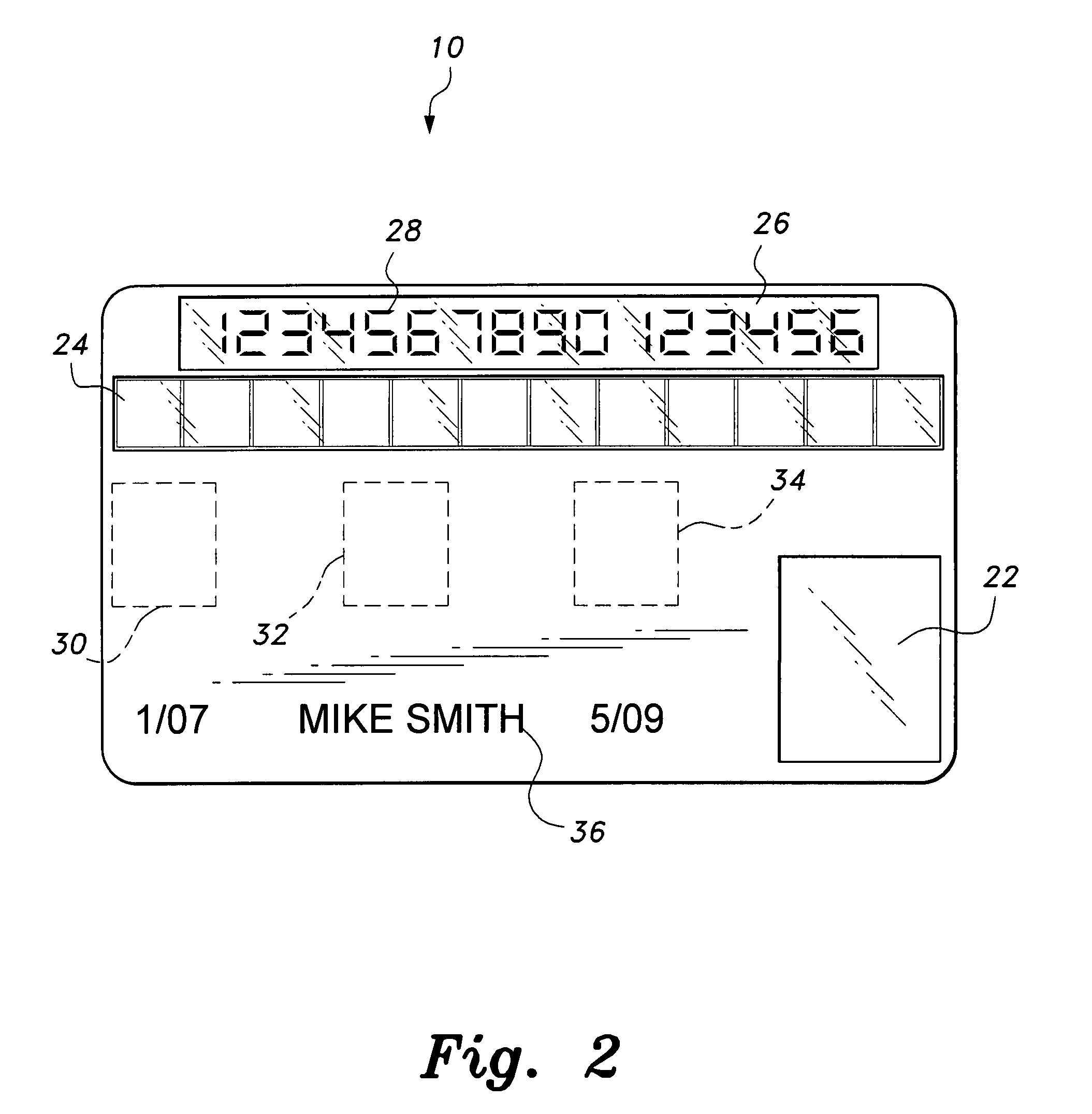
Wireless game player
InactiveUS6846238B2Apparatus for meter-controlled dispensingVideo gamesRelevant informationGame player
A disclosed gaming machine provides methods and apparatus for operating a wireless game player that presents a game of chance executed on a gaming machine in communication with the wireless game player. In one embodiment, the wireless game player is a hand-held mobile device, electronically linked to a licensed gaming machine via a wireless connection. All random number generation (RNG) events, game outcomes, meter information, game related information, and all cash transactions are maintained in the licensed (controlled) gaming machine and not the wireless game player. The wireless game player may be used anywhere within the legal areas of the casino and it has the capability of identifying who is using it. For example, a biometric input device, such as a finger print reader may be used on the wireless game player to identify the player. Thus, the issue of under-age or excluded players is addressed.
Owner:IGT
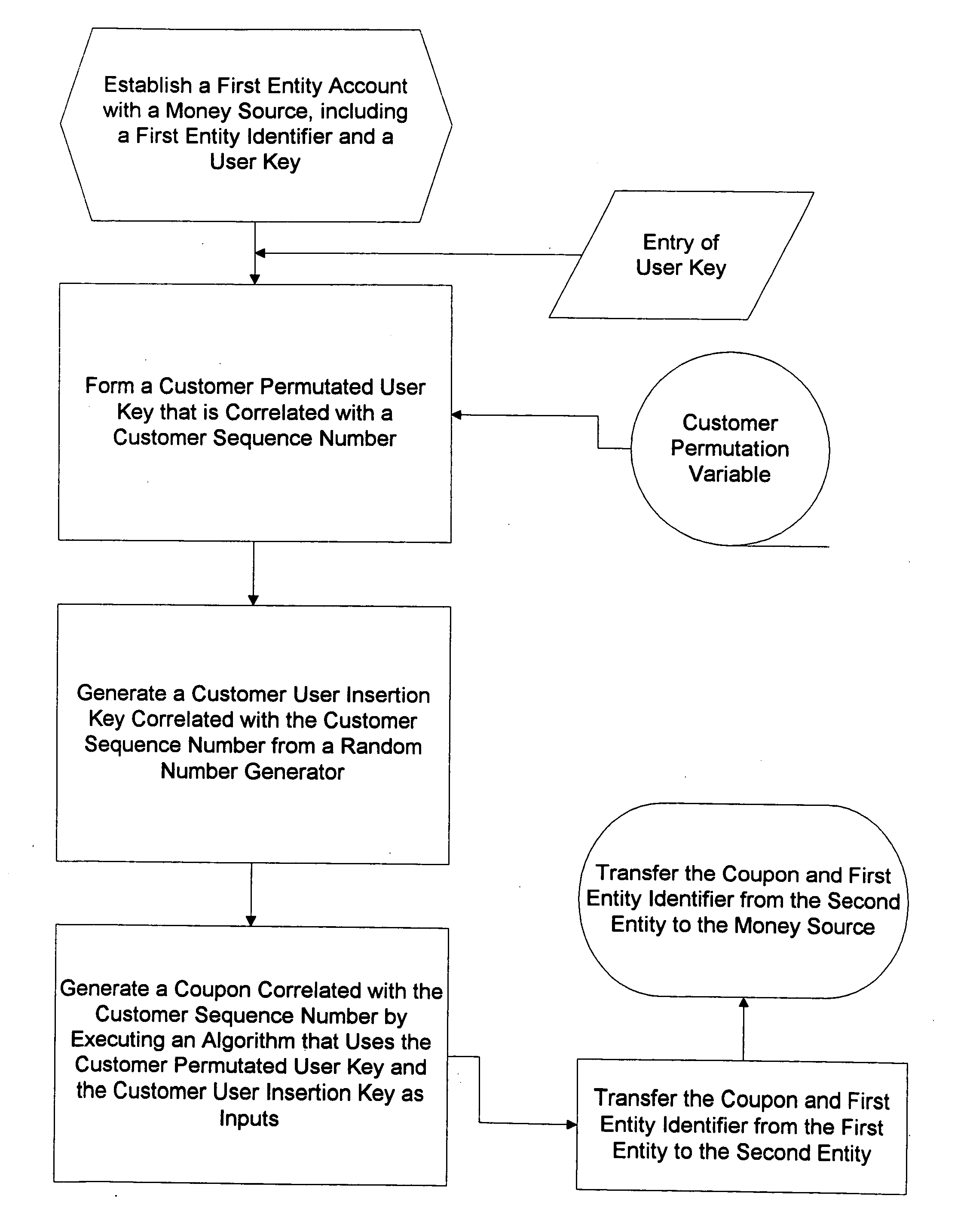
Method for generating customer one-time unique purchase order numbers
InactiveUS20050080747A1Anonymous user systemsRecord carriers used with machinesCredit cardPersonal identification number
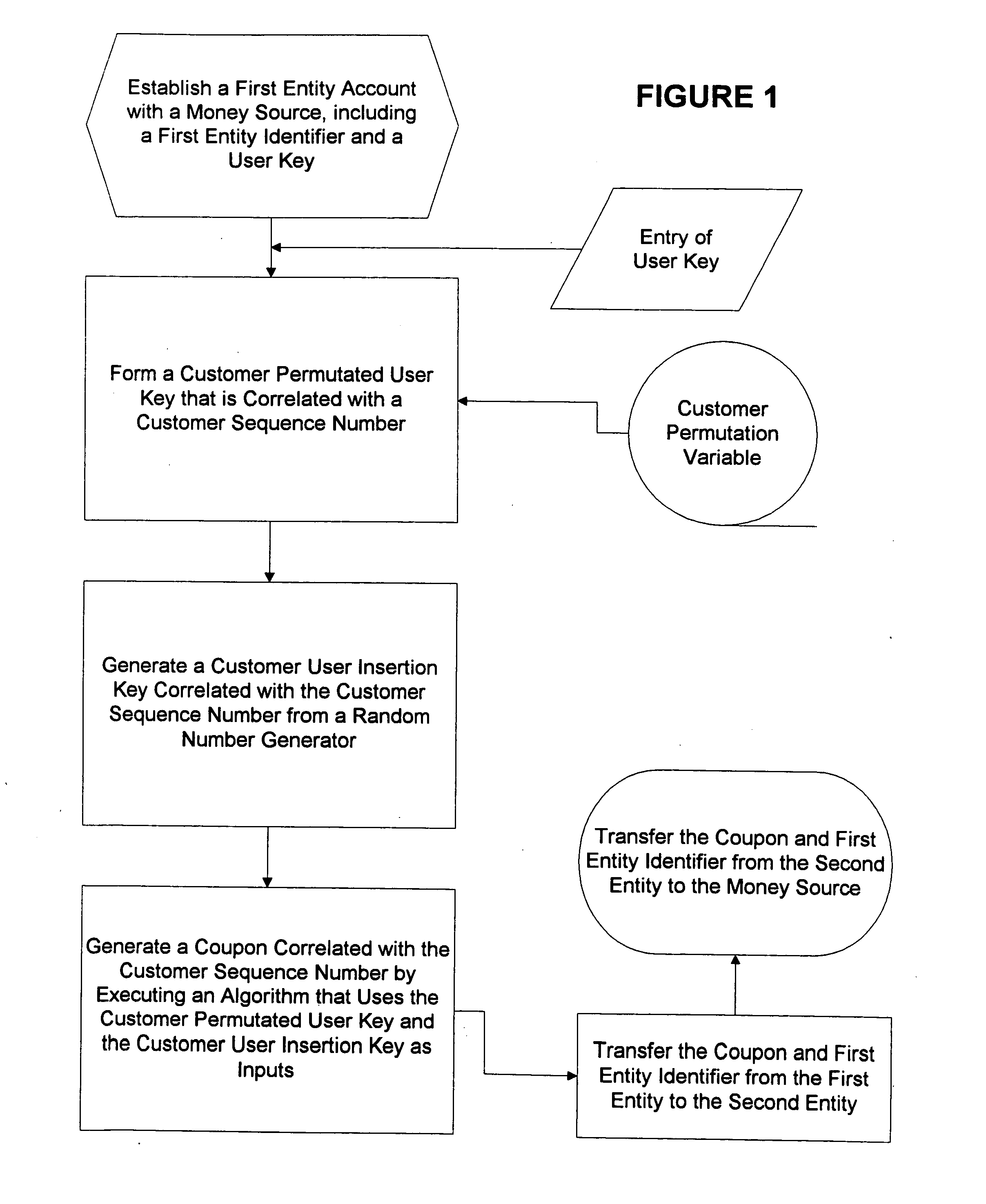
Multiple secure transactions are provided through use of a method that uses customer one-time unique purchase order numbers (“Coupons”) generated by an algorithm that uses a permutated user key and a user insertion key as input variables. A user key (such as a Personal Identification Number, or “PIN”) is combined with a permutation variable that is correlated with a customer sequence number to create the permutated user key. A random number generator is used to generate the user insertion key correlated with the customer sequence number. The algorithm can insert the permutated user key into a user account number through use of the user insertion key. A Coupon is validated by confirming that it is contained in a set of money source Coupons generated by a money source using the user key and a random number generator that is synchronized with the random number used to generate Coupons. Once a Coupon is validated, the matching money source Coupon and all earlier generated money source Coupons are deleted from the set, and a new set is generated. If a preselected number of Coupons are not validated for a chosen entity, an invalid user account number will be set. Coupons can be used for credit card or bank card transactions, and they can be generated without changing fixed digits of traditional twenty digit account numbers.
Owner:PRIVASYS
Wireless game player
A disclosed gaming machine provides methods and apparatus for operating a wireless game player that presents a game of chance executed on a gaming machine in communication with the wireless game player. In one embodiment, the wireless game player is a hand-held mobile device, electronically linked to a licensed gaming machine via a wireless connection. All random number generation (RNG) events, game outcomes, meter information, game related information, and all cash transactions are maintained in the licensed (controlled) gaming machine and not the wireless game player. The wireless game player may be used anywhere within the legal areas of the casino and it has the capability of identifying who is using it. For example, a biometric input device, such as a finger print reader may be used on the wireless game player to identify the player. Thus, the issue of under-age or excluded players is addressed.
Owner:IGT
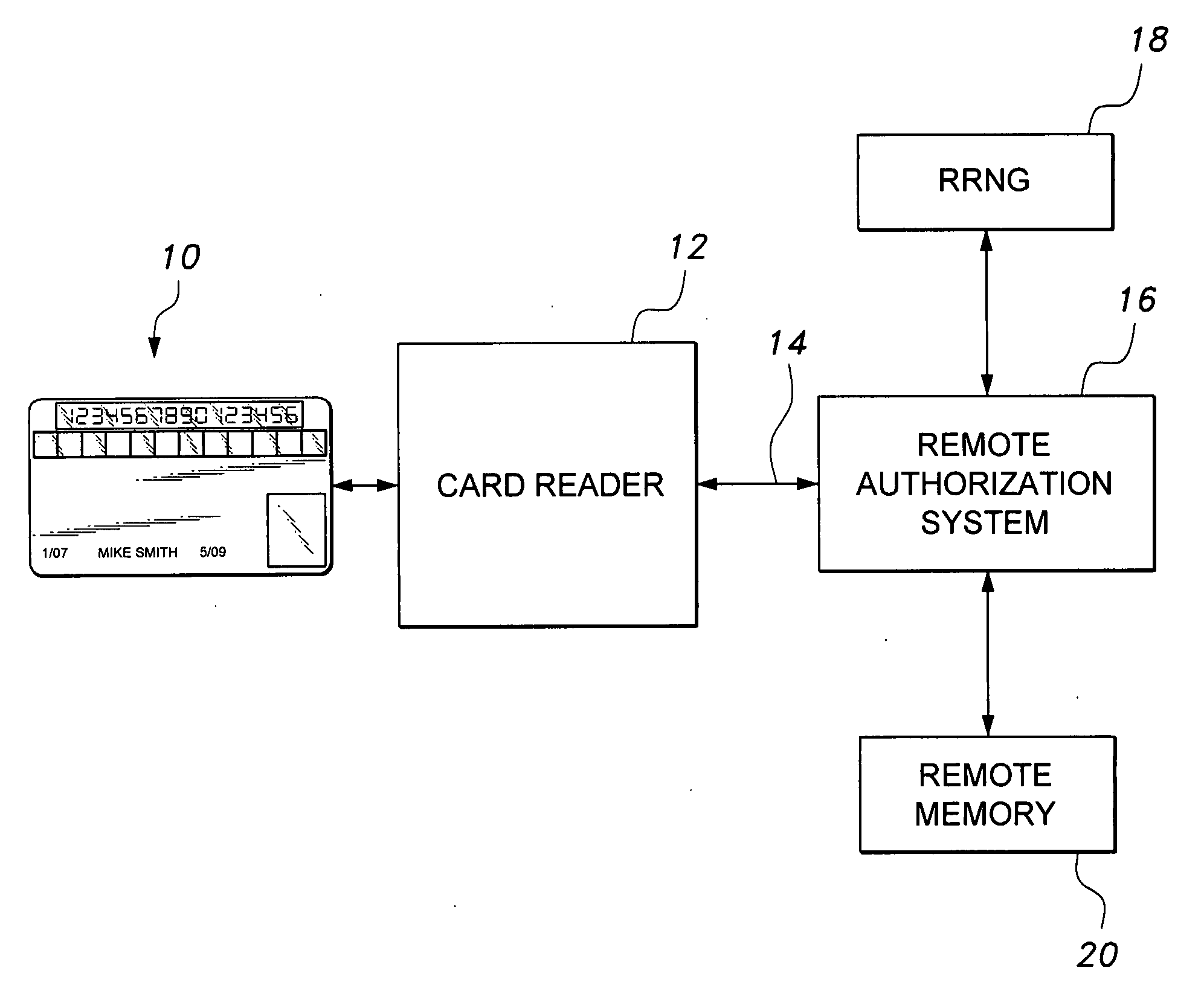
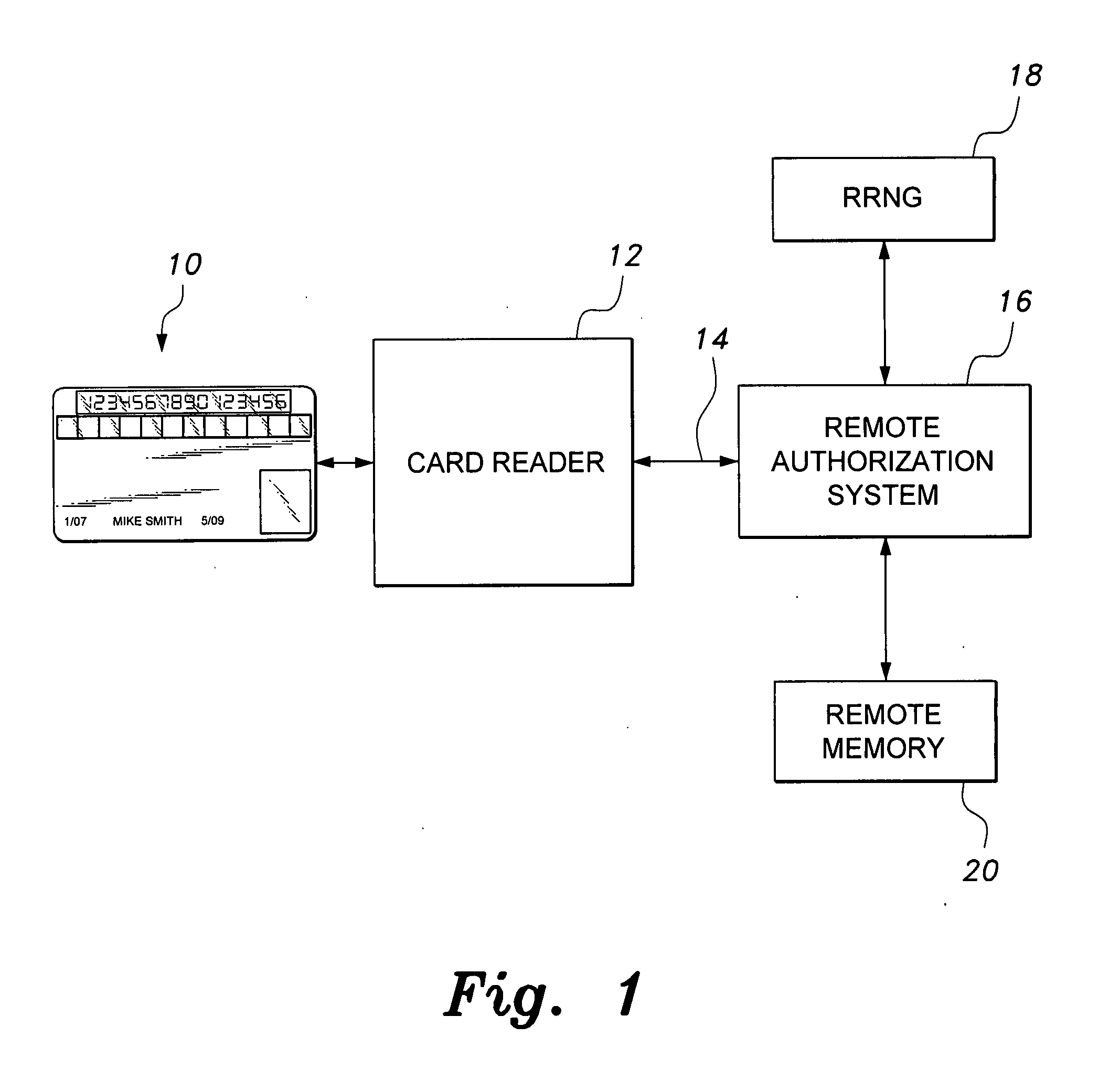
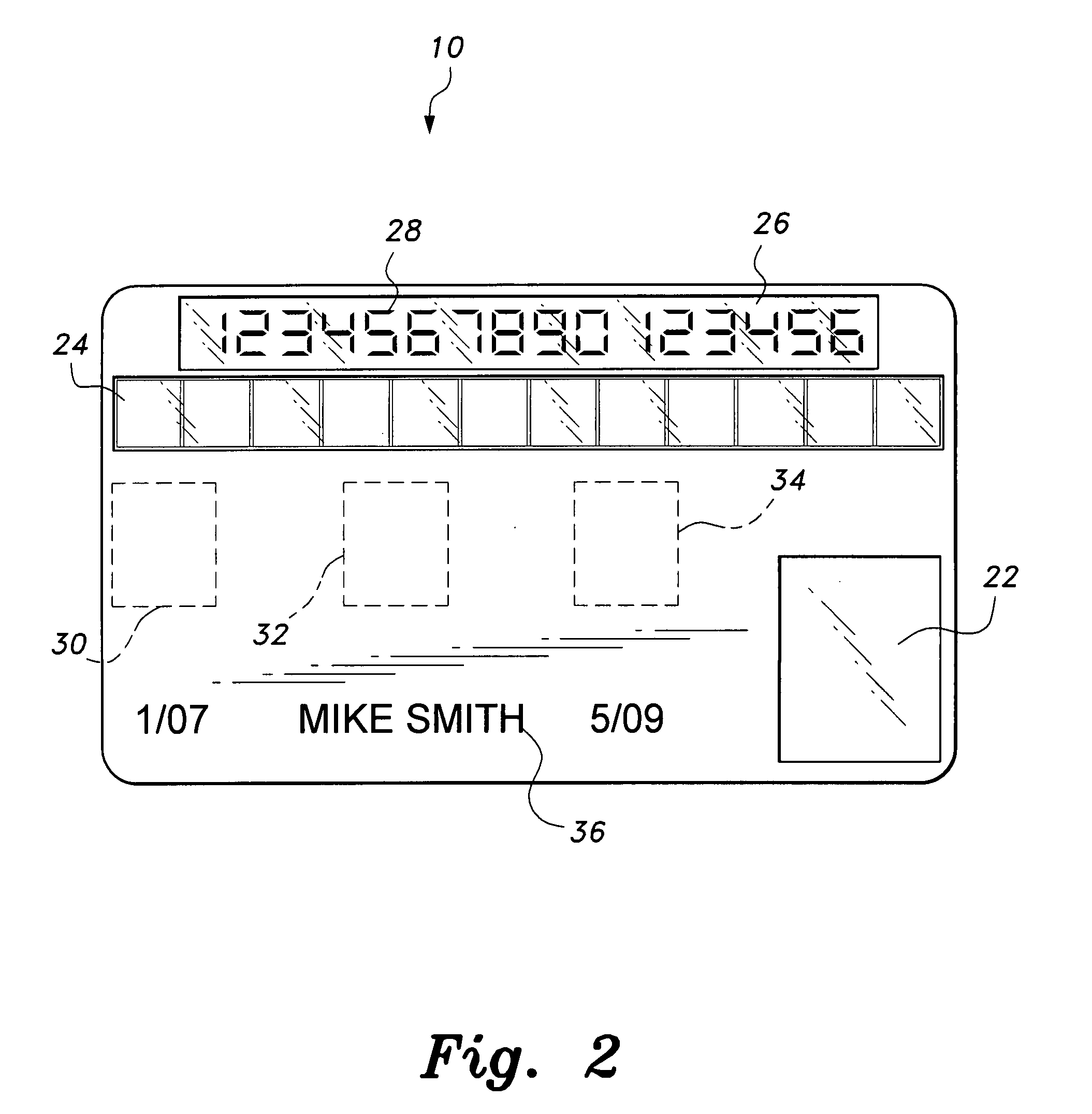
Smart card with random temporary account number generation
The smart card with random temporary account number generation provides an authenticating system coupled with an access or transaction card, such as a credit card. The card includes first and second memory storage media, with the first memory medium containing a plurality of temporary account or authentication numbers. The card also has a biometric sensor, such as a fingerprint scanner, and the second memory stores the biometric parameters of the authorized user. A processor compares the biometric parameters with the measured biometric readings to enable the card. The processor has a random number generator, allowing for the randomized selection of one of the account numbers stored in the first memory, thus providing a temporary account number for the transaction. A remote site includes an identical random number generator and set of account numbers, allowing the temporary account number to be verified and then discarded, following the transaction.
Owner:HEWTON ALFRED
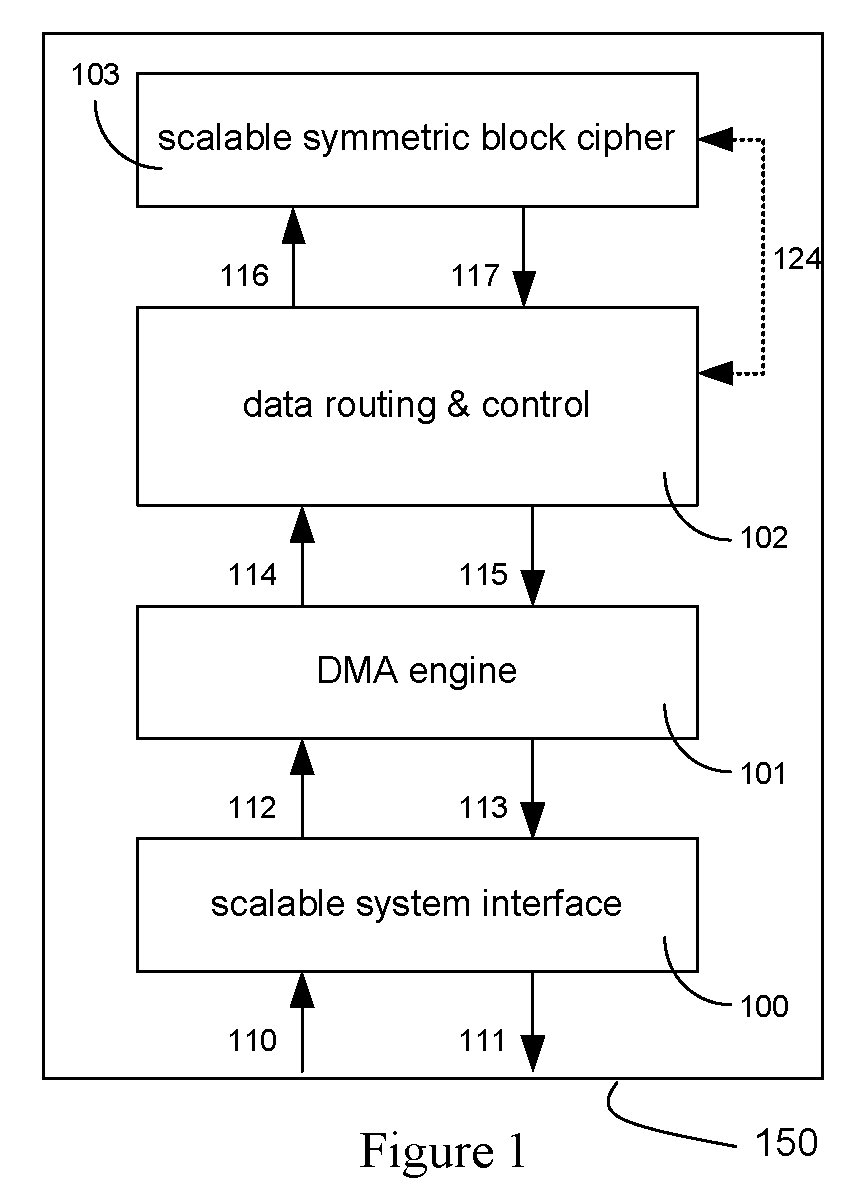
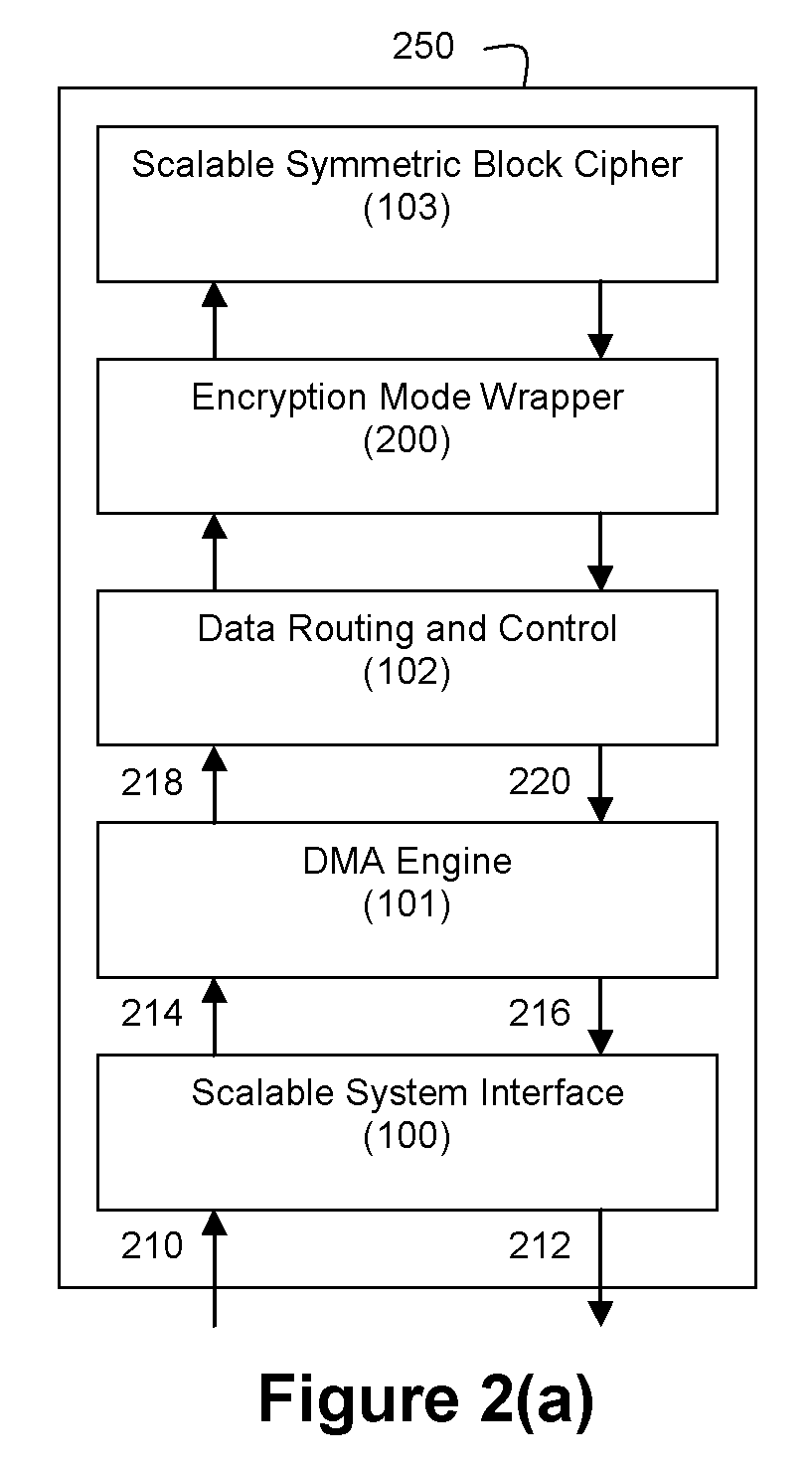
Method and Apparatus for Hardware-Accelerated Encryption/Decryption
ActiveUS20090060197A1Avoid contactMaximize availabilityEncryption apparatus with shift registers/memoriesSecret communicationMultiple encryptionComputer hardware
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
Smart card with random temporary account number generation
Owner:HEWTON ALFRED
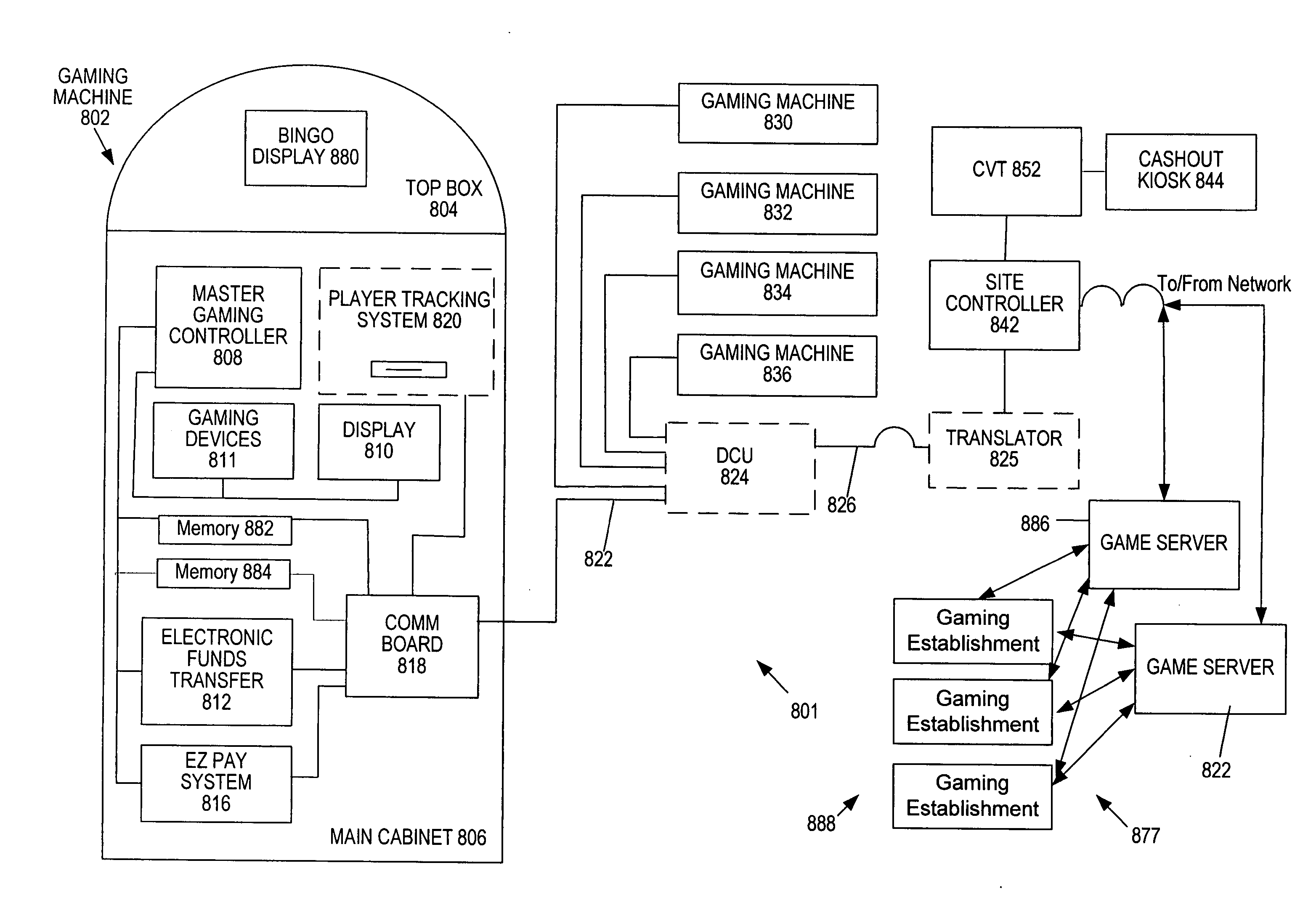
Class II/Class III hybrid gaming machine, system and methods
ActiveUS20060111168A1Raise priorityApparatus for meter-controlled dispensingVideo gamesClass iiiNumber generator
The present invention provides a gaming machine that can play both Class II and Class III games. Some implementations provide a gaming machine that has certain features (e.g., a true random number generator or “RNG”) enabled for Class III play and disabled for Class II play. Some aspects of the invention provide methods for determining when a Class III game is available. Other aspects of the invention allow a player to “line up” for a desired Class III game while playing another game, such as a Class II game or another Class III game, on the same gaming machine until the desired Class III game is available. Some such implementations grant higher priority to certain players according to their gaming history, e.g., as indicated by player tracking / player loyalty data. Alternative aspects of the invention allocate available Class III games in other ways, e.g., by playing a Class II game for a chance to play a Class III game, by lottery, or otherwise. Player tracking information may be shared and / or combined for Class II and Class III game play and may be used to determine gaming history.
Owner:IGT
Anonymous authenticated communications
InactiveUS7234059B1Maintaining anonymityKey distribution for secure communicationPublic key for secure communicationComputer networkElectronic communication
Owner:SANDIA NAT LAB
Financial trading game
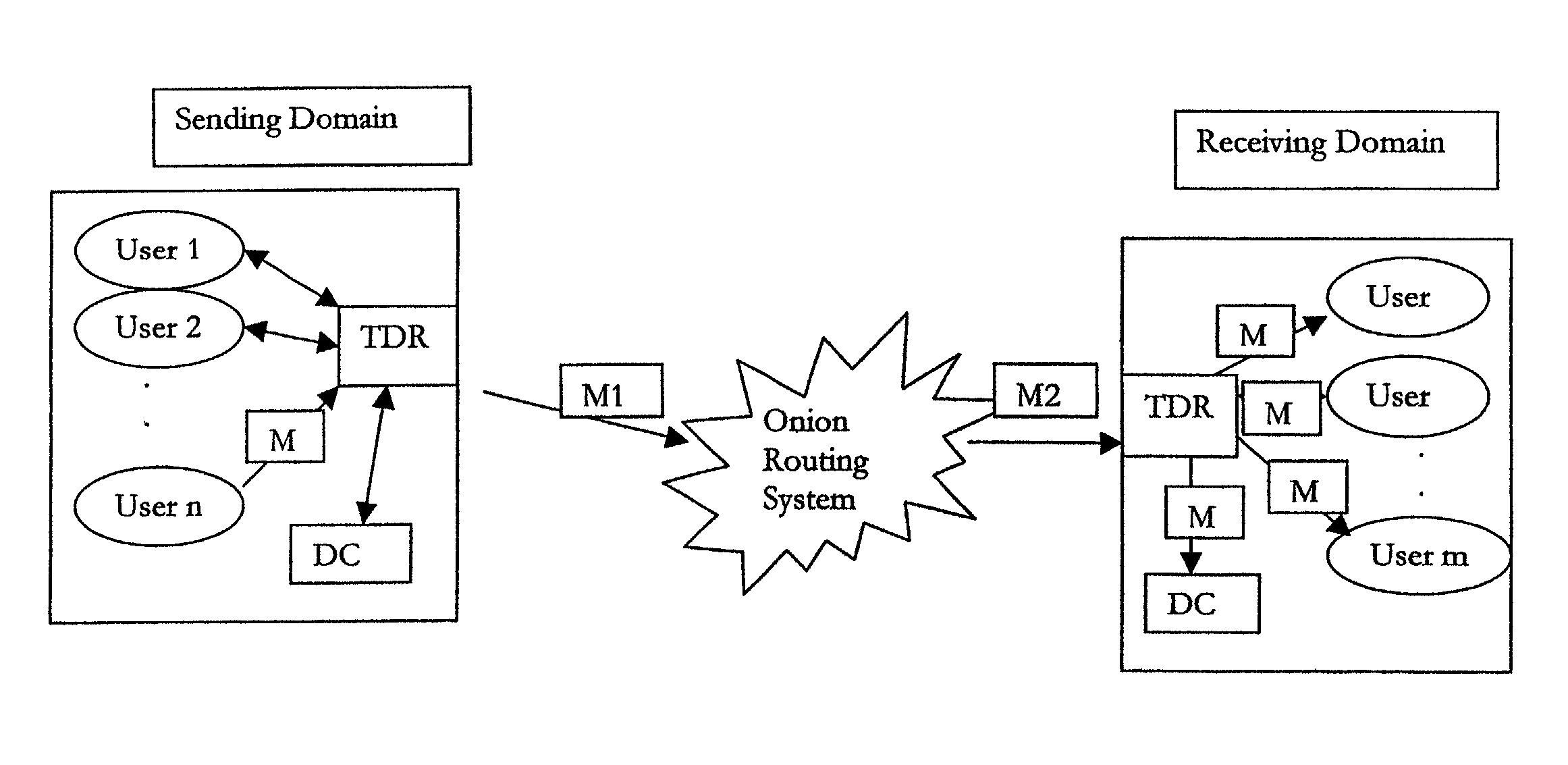
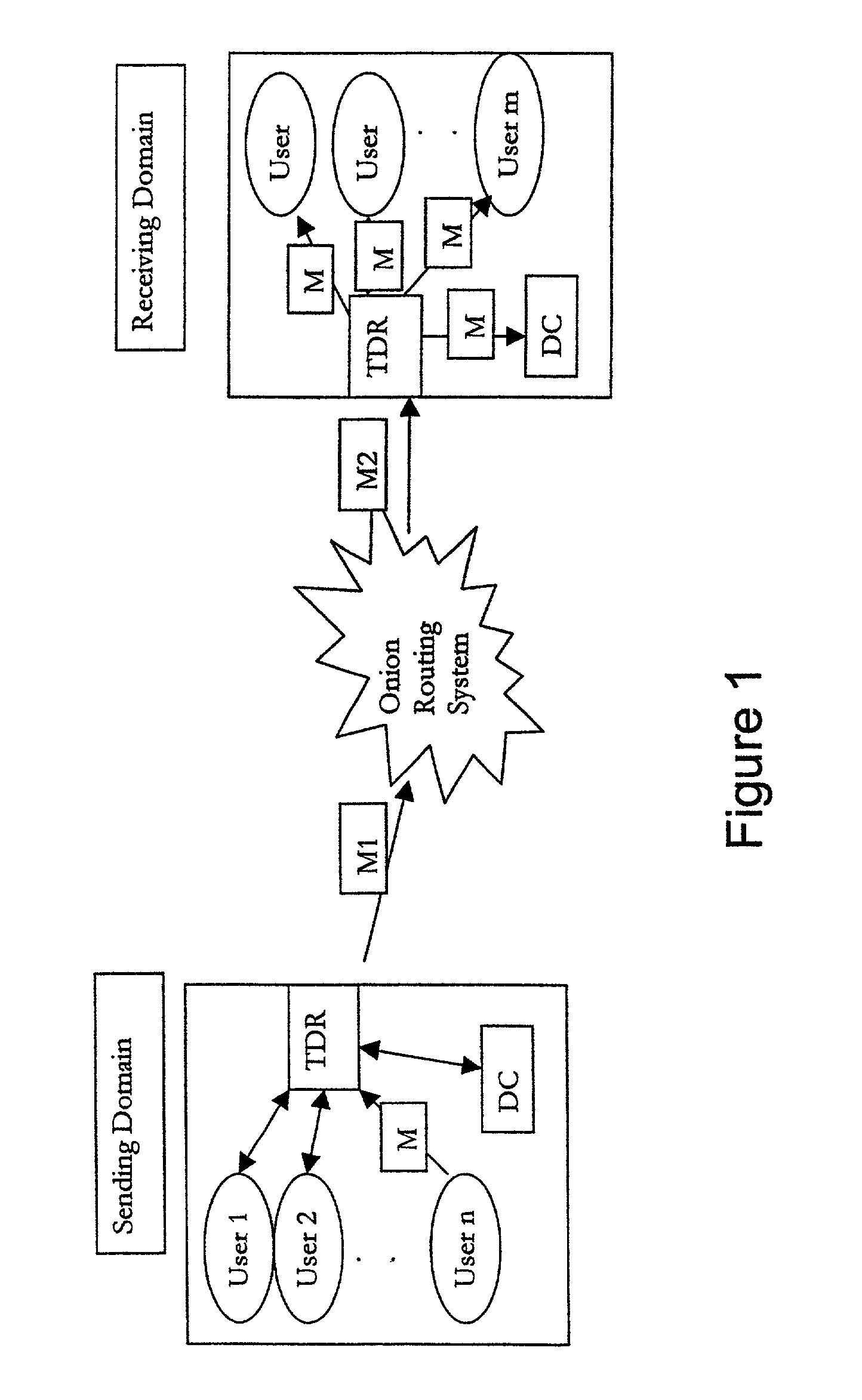
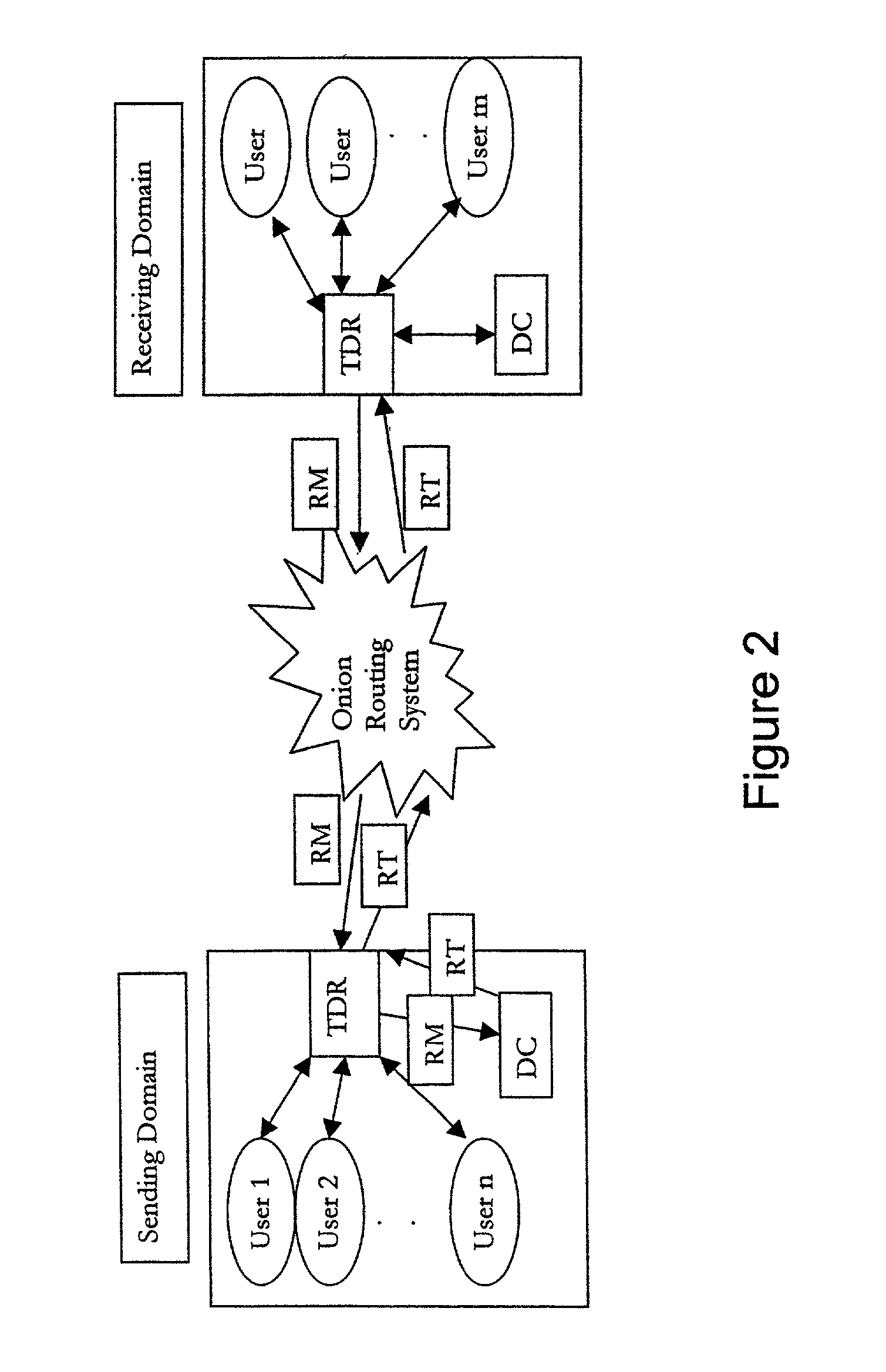
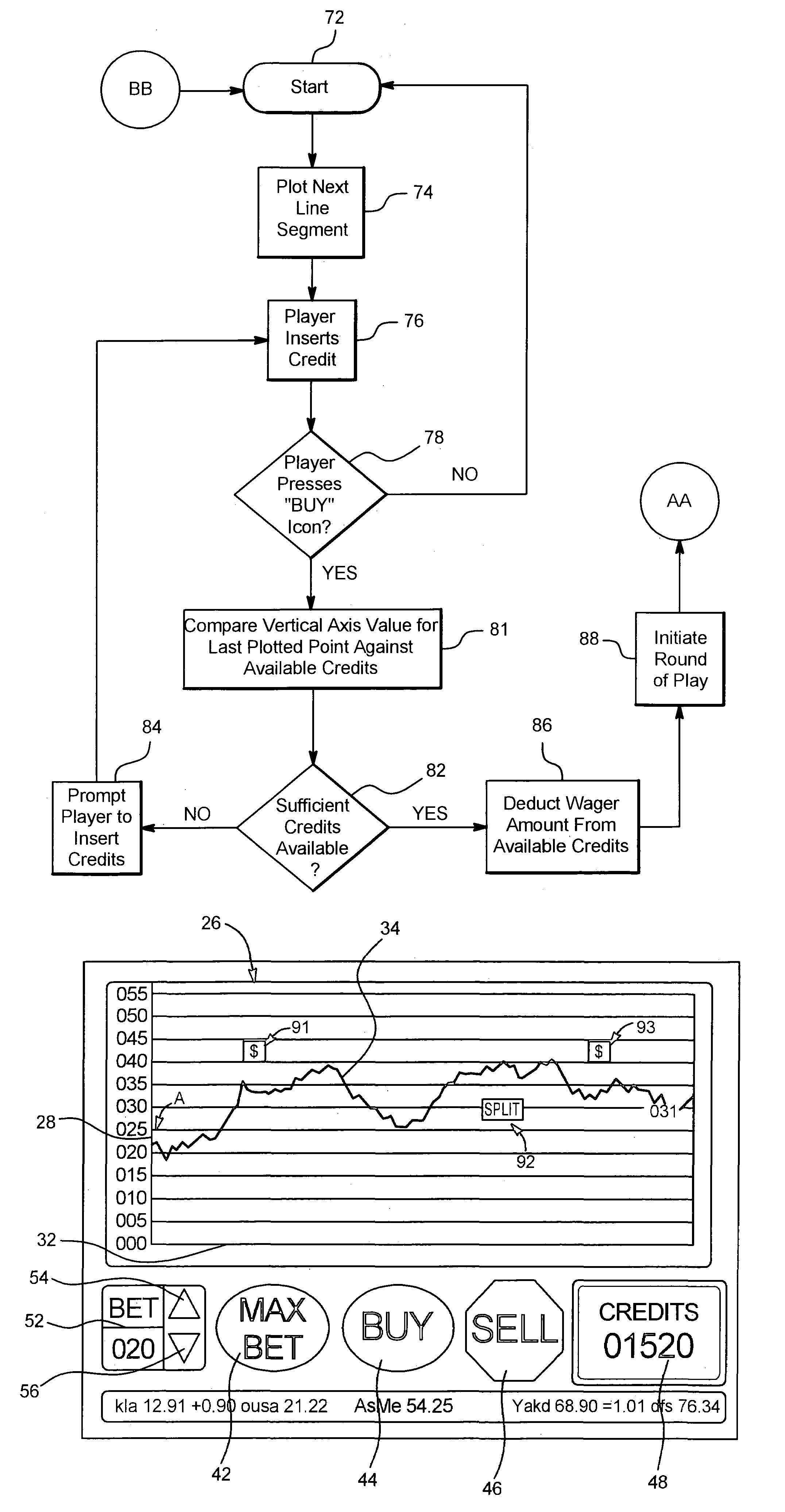
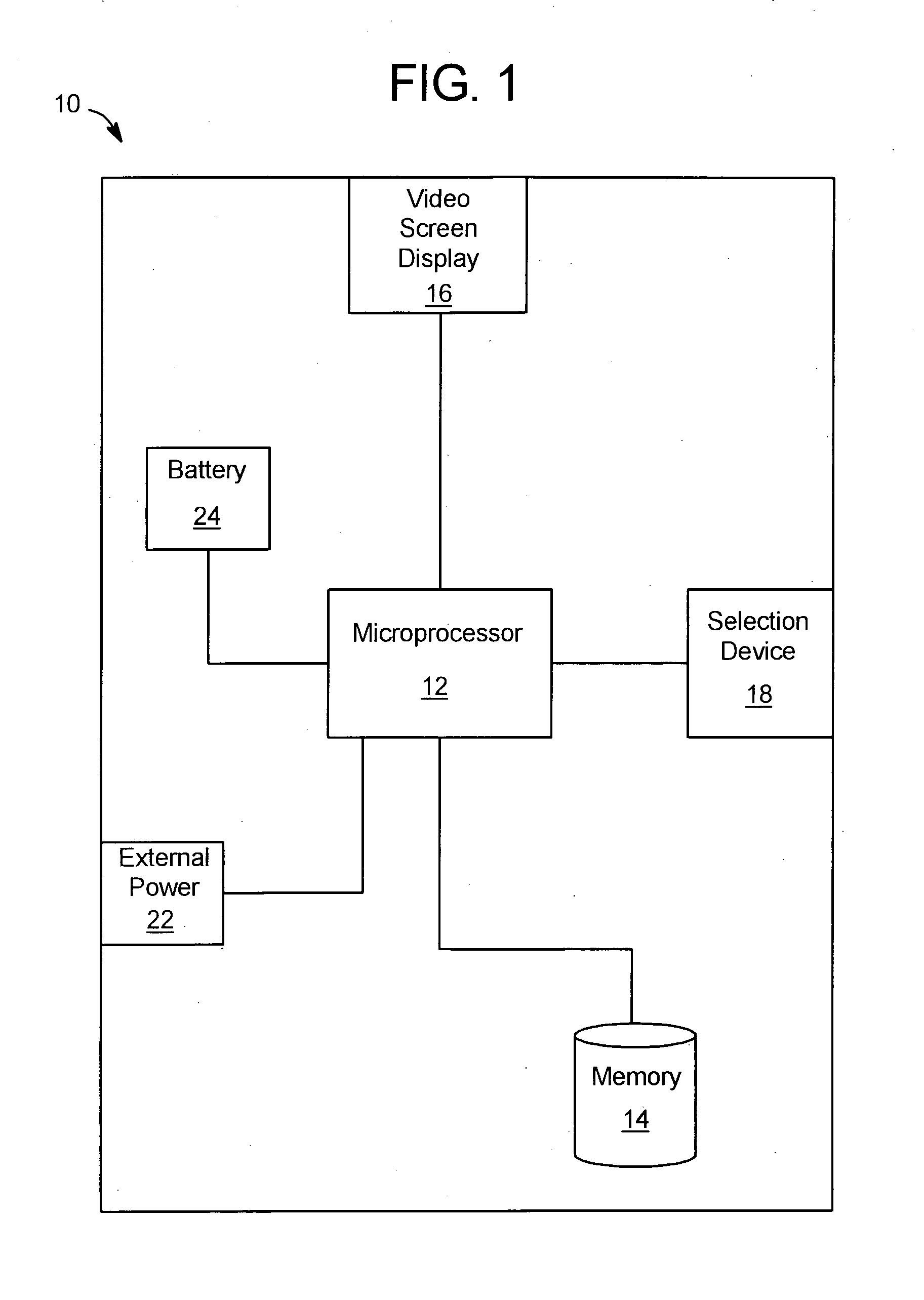
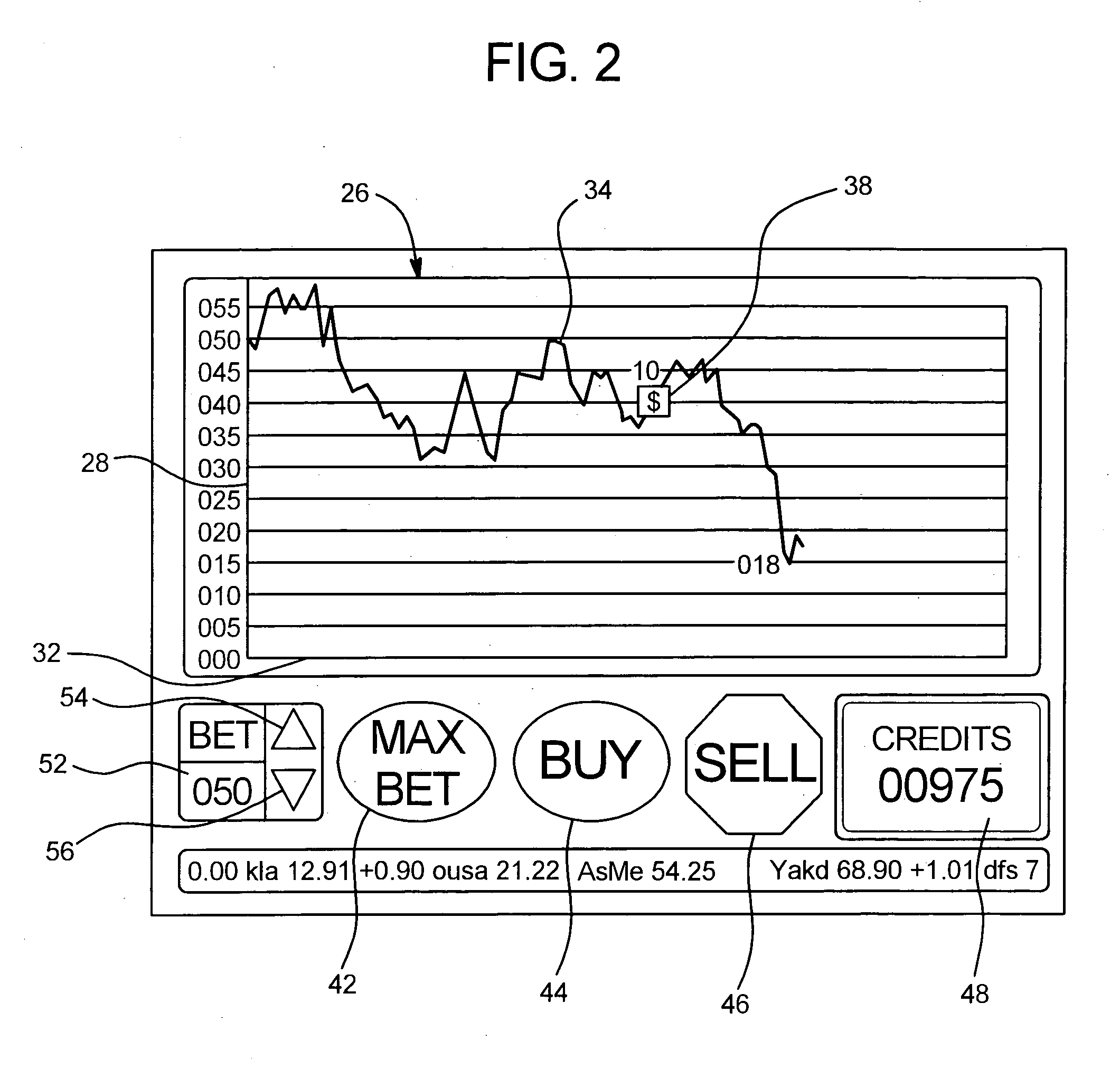
InactiveUS7040982B1Increase valueApparatus for meter-controlled dispensingVideo gamesPoint plottingDisplay device
This invention relates generally to a game, and more particularly to an electronic game that simulates trading securities on an exchange. The game of the present invention is preferably played as a video gaming machine for gambling purposes. A computing device is provided having, among other things, a video screen display on which a line chart is displayed. The computing device also includes a selection device, which provides a means by which the player interacts with the computing device to “buy” or “sell”. The line chart includes a vertical axis that corresponds to the value or price of one or more securities, and a horizontal axis that corresponds to time. A segmented line is plotted on the line chart during a round of play. A random number generator randomly determines the vertical axis value for each point plotted along the segmented line.
Owner:IGT
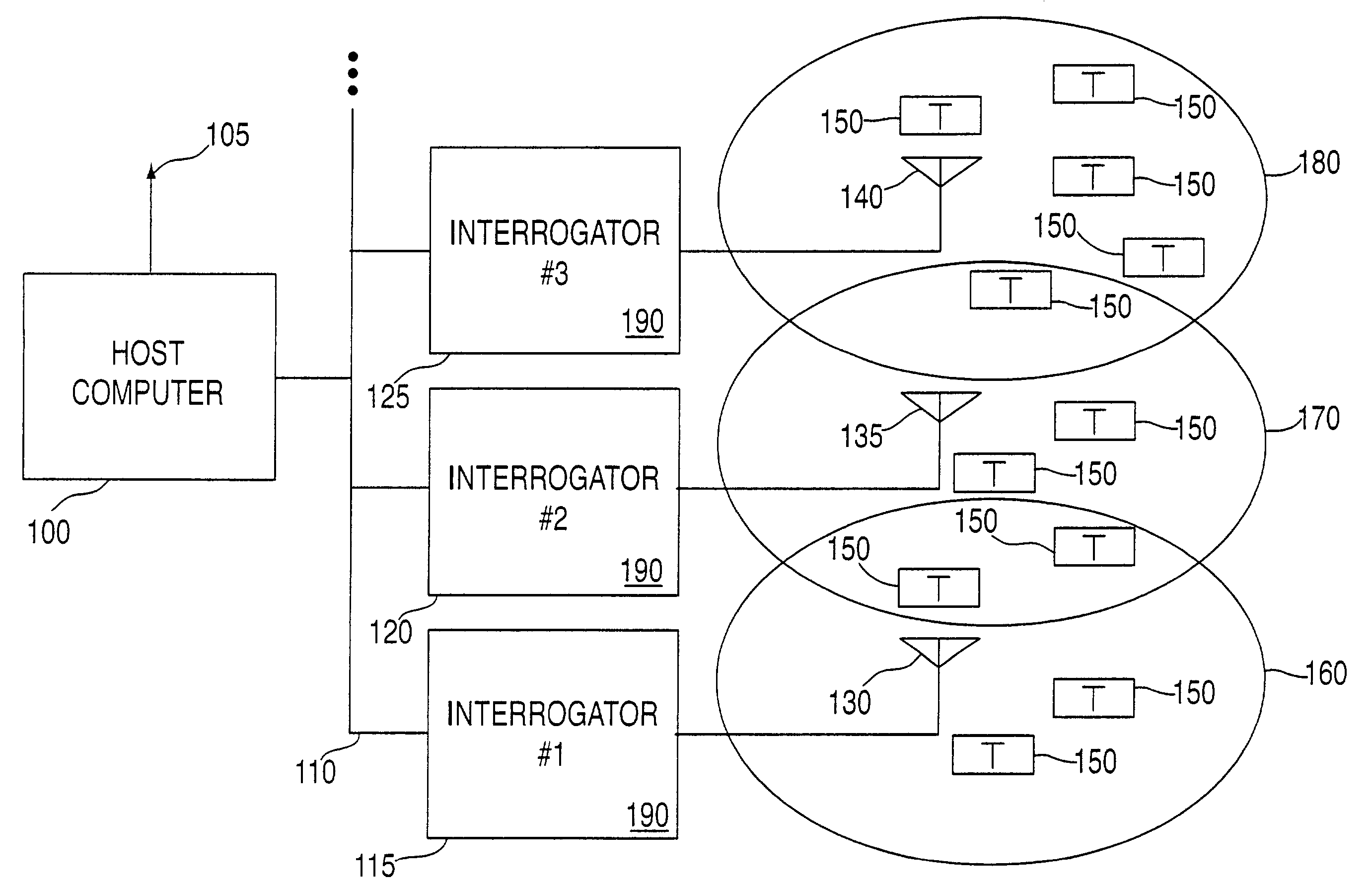
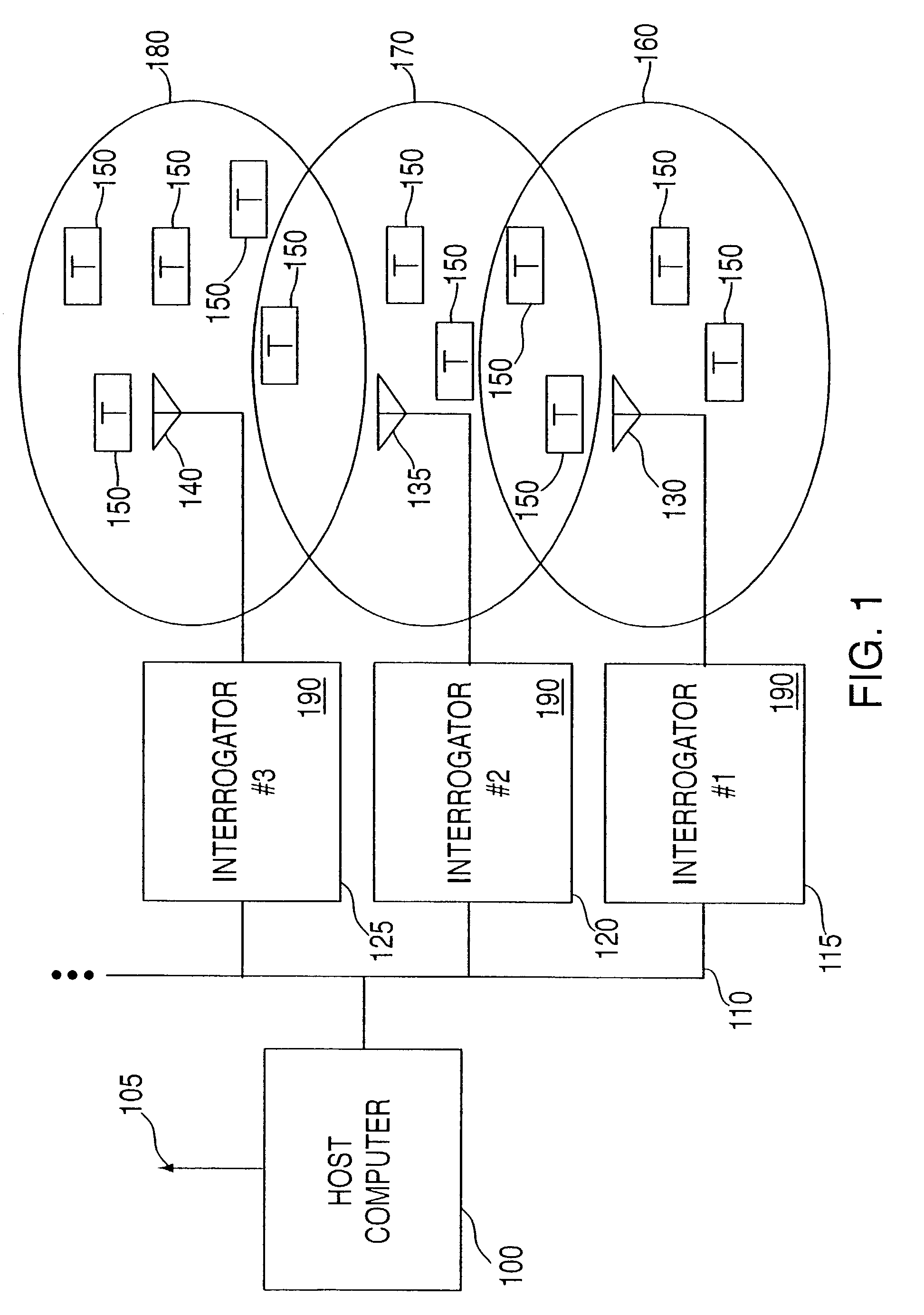
Method and system for communicating with and tracking RFID transponders
ActiveUS7253717B2Reduce the valueMemory record carrier reading problemsCo-operative working arrangementsNear neighborNumber generator
An RFID system and method for communicating between a host computer, one or more interrogators connected to the host computer, and a large body of transponders distributed within an area covered by the interrogators. Each transponder originally has a common identification code, and upon initialization by the host computer internally generates a unique identification code based upon an internally generated random number. The host, through the interrogators, reads each of the identification codes associated with each transponder by iteratively transmitting a read identification code command along with a controlled variable. Each transponder compares the received controlled variable to an internally generated random number, and selectively transmits its identification code based upon the outcome of this comparison. After the completion of each read identification code iteration, the host adjusts the controlled variable based upon the responses received in the previous iteration. Preferably, communications between the interrogators and the transponders are DSSS signals in TDMA format, and the transponders use the random number generator to assign a time slot for transmission of their response. Each interrogator includes an antenna system utilizing a switch matrix to connect multiple antennas having different polarizations, which ensures that all transponders within the range of the interrogator receive the signals from the interrogator. In a further aspect, the interrogators are arranged in groups, each group in nearest neighbor format, to reduce the time for reading the transponders and the emissions generated when more than one interrogator is active at the same time.
Owner:TERRESTRIAL COMMS LLC
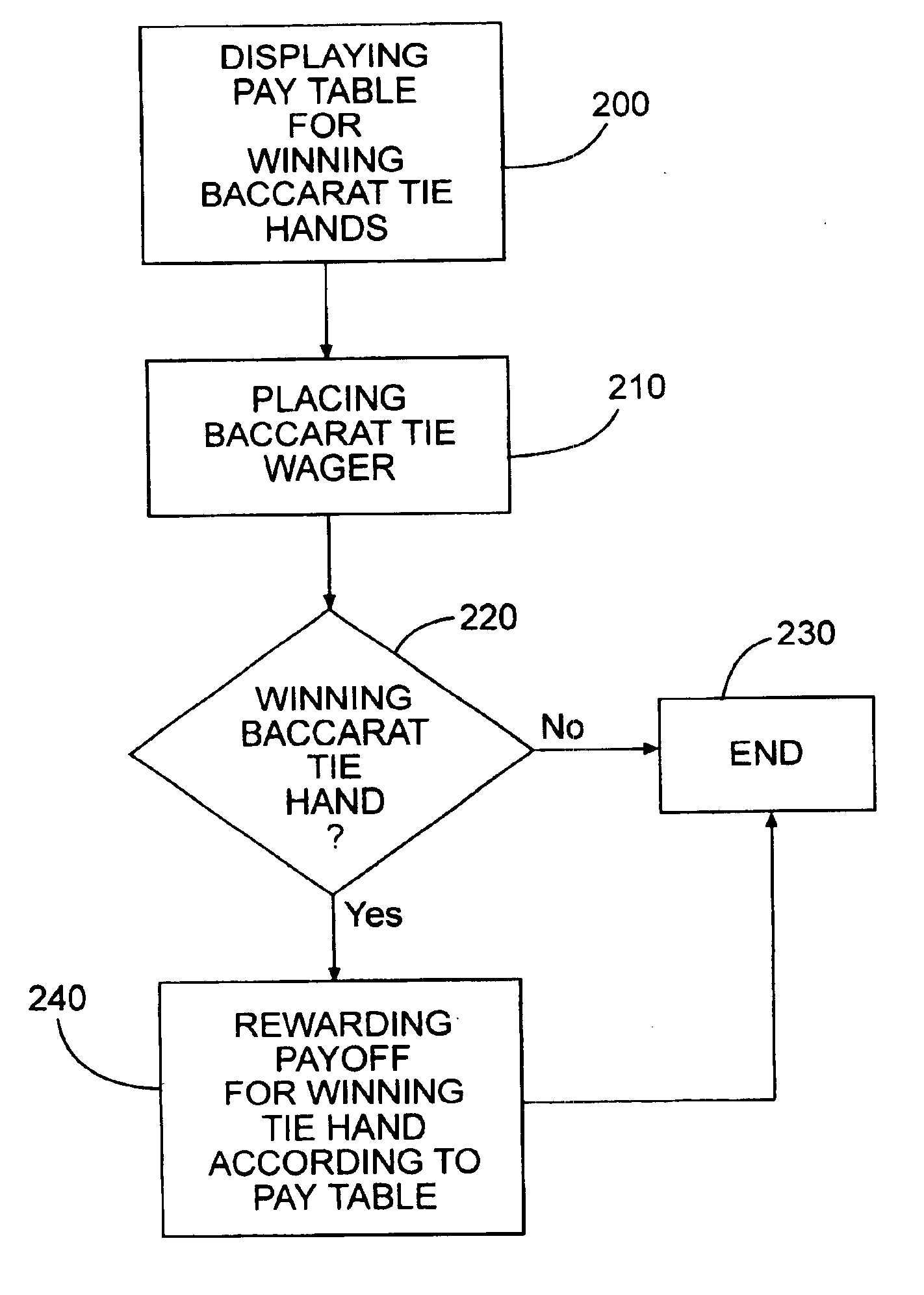
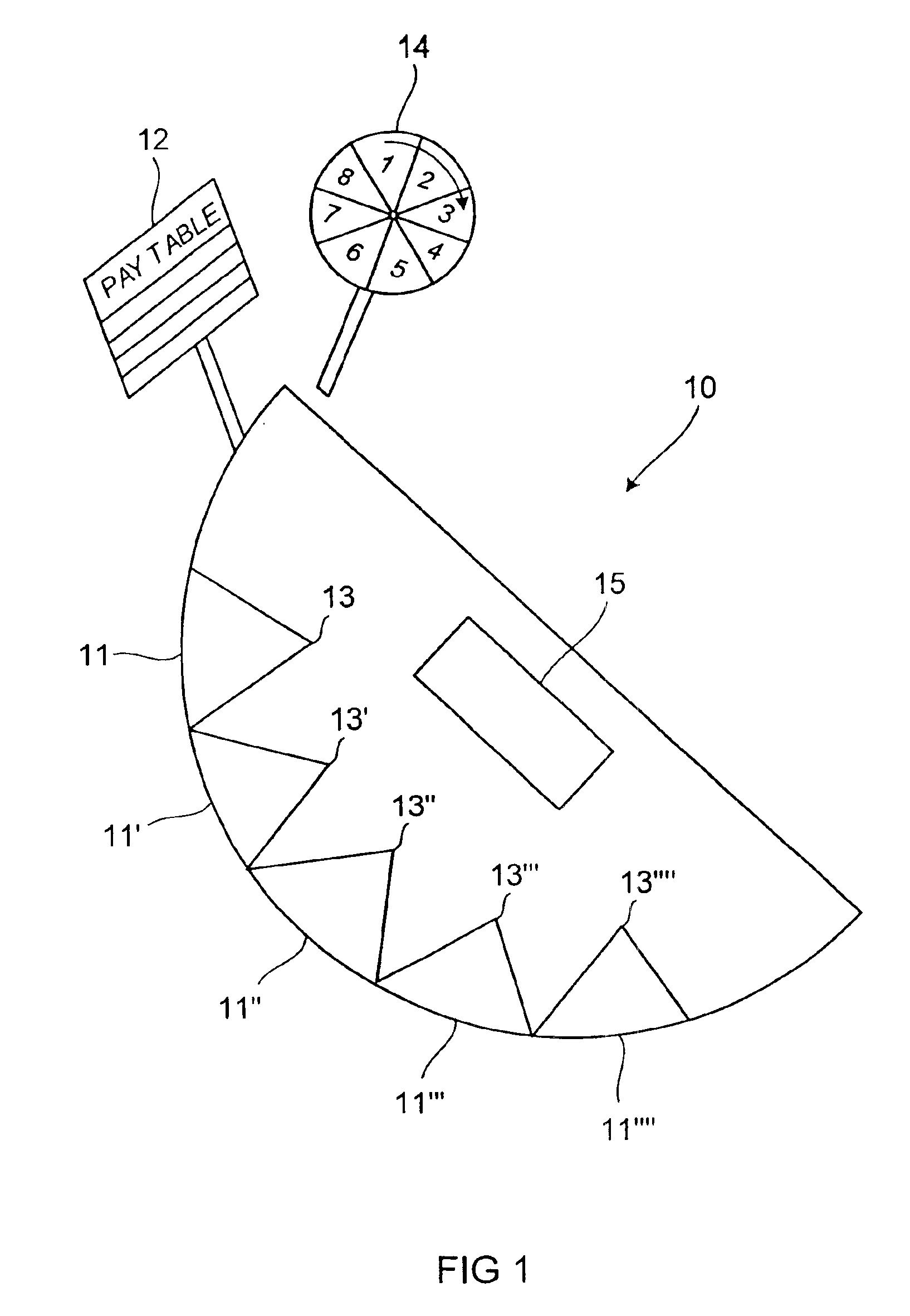
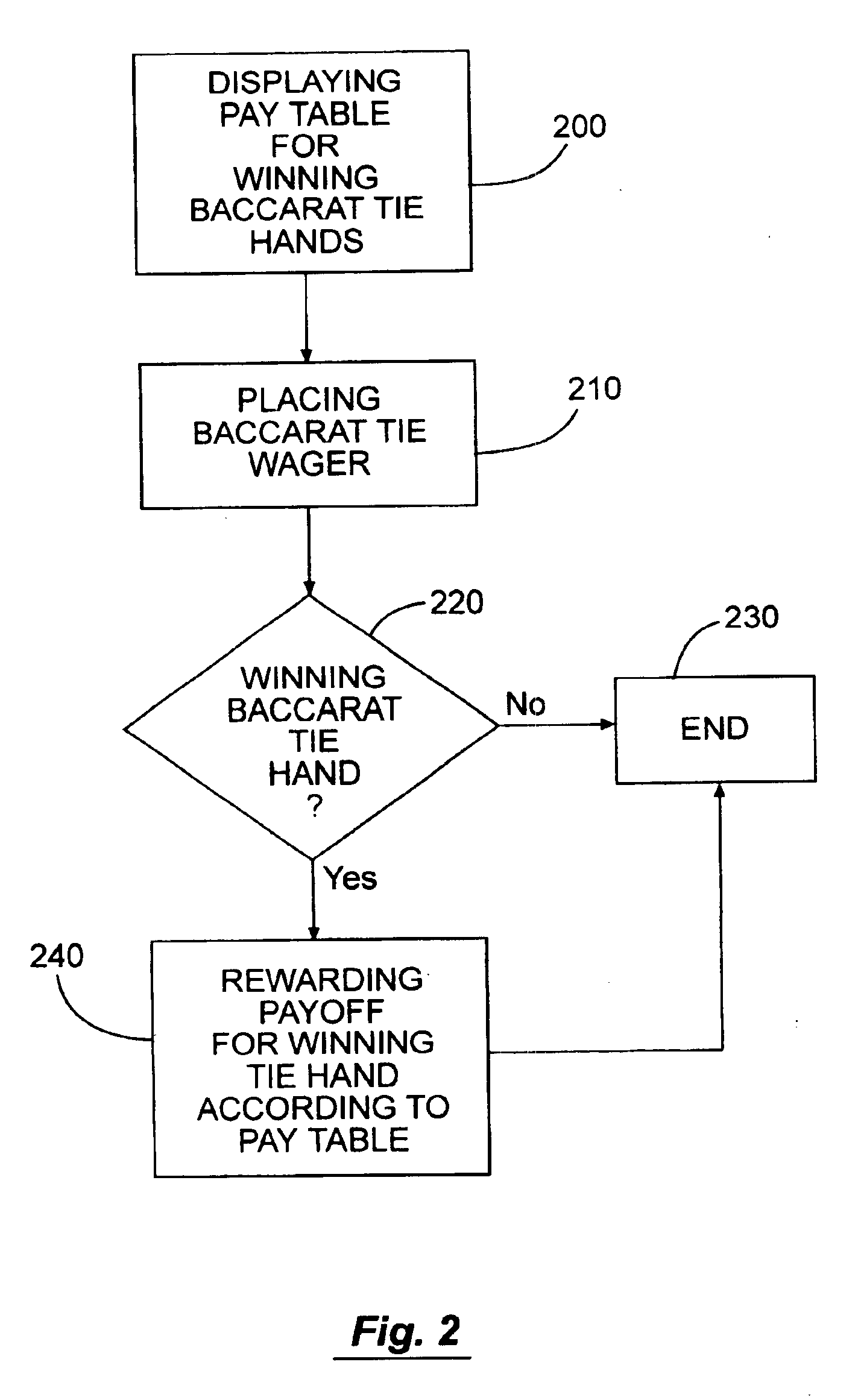
Method for wagering on baccarat tie
InactiveUS6916245B1Large revenue sharingBoard gamesVideo gamesNumber generatorArtificial intelligence
A method of playing and wagering on a game of chance with community events has the steps of identifying the community event; accepting wagers from players on the event; generating a chance event during play, and rewarding the players from the pool if the event occurs during the chance event. The step of rewarding each player includes determining the amount of each player's reward per that player's wager and splitting the pool among all those that wager. Dealing cards, spinning a wheel or drawing numbered balls generates a chance event after accepting wagers. Adding to the pool at least a portion of the wagers and increasing the pool when the event does not occur are steps. The step of bases the reward of each player on the proportion of the fraction of total wagers made by all wagering players during that game of chance that the amount of the player's wager represented. An apparatus has a pay table ranking events and a wagering place to accept individual wagers from players on the occurrence of the event. A random number generator establishes chance events and the pool connects to the wagering place. The pool receives a portion of the accepted wagers and rewards winners relative to the amount of that player's wager whenever the event occurs.
Owner:PROGRESSIVE GAMING INT +1
Method and Apparatus for Ad Hoc Mesh Routing
ActiveUS20080002599A1Reduce probabilityBlocking in networkError prevention/detection by using return channelTransmission systemsSignal qualityMesh routing
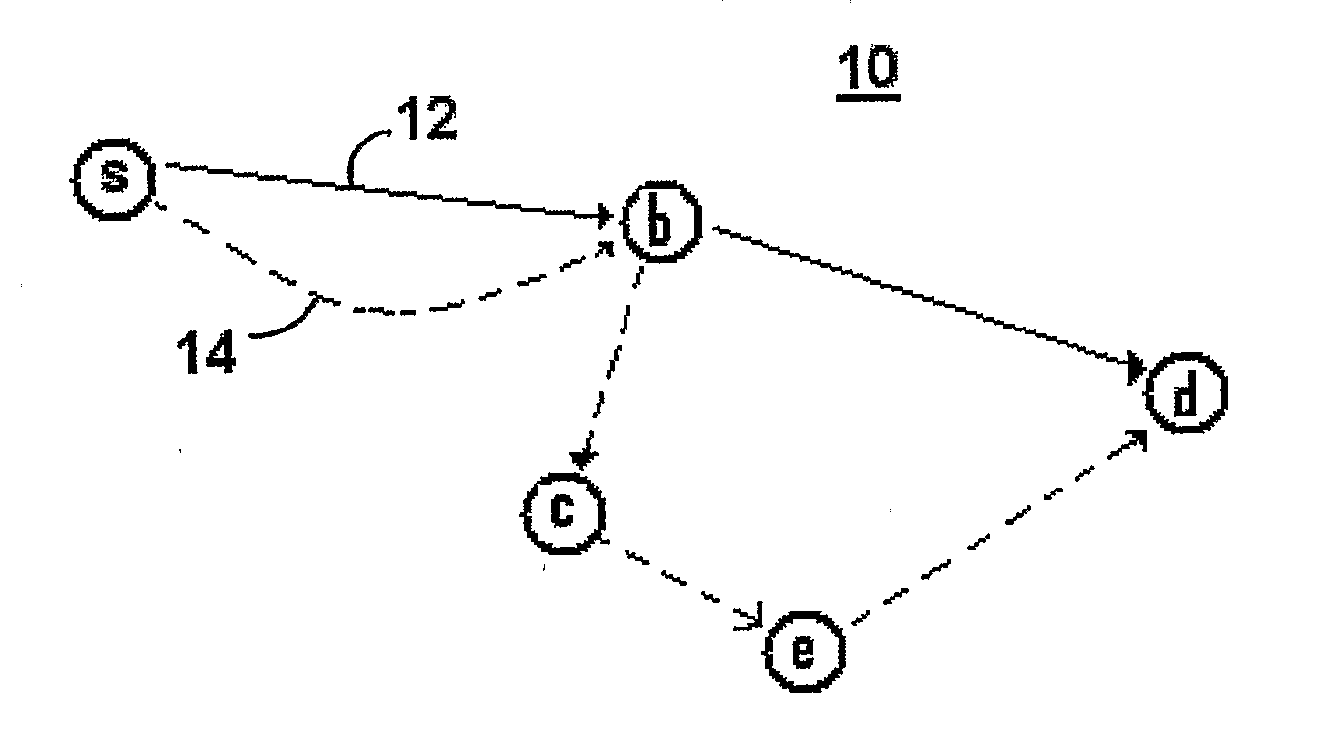
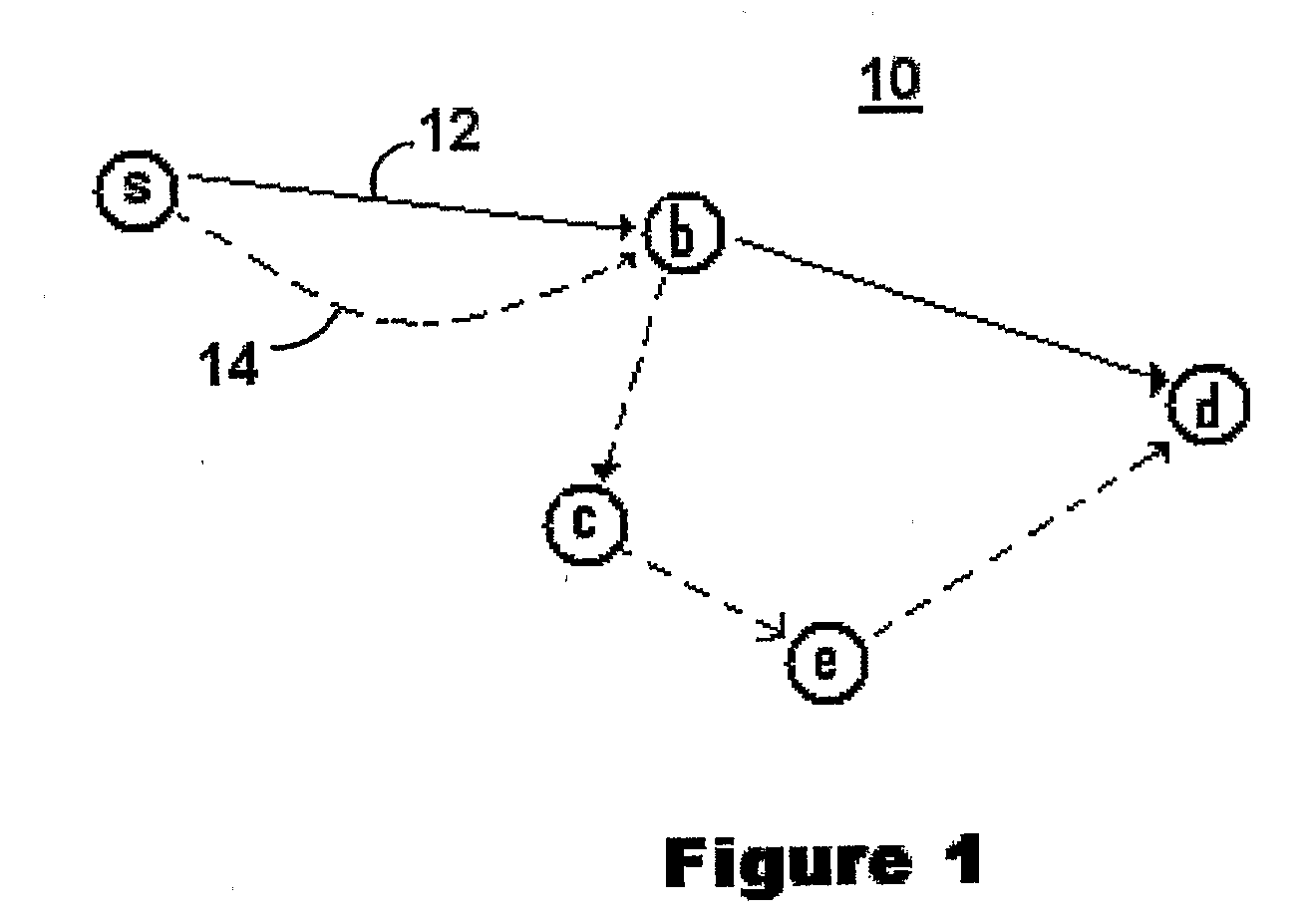
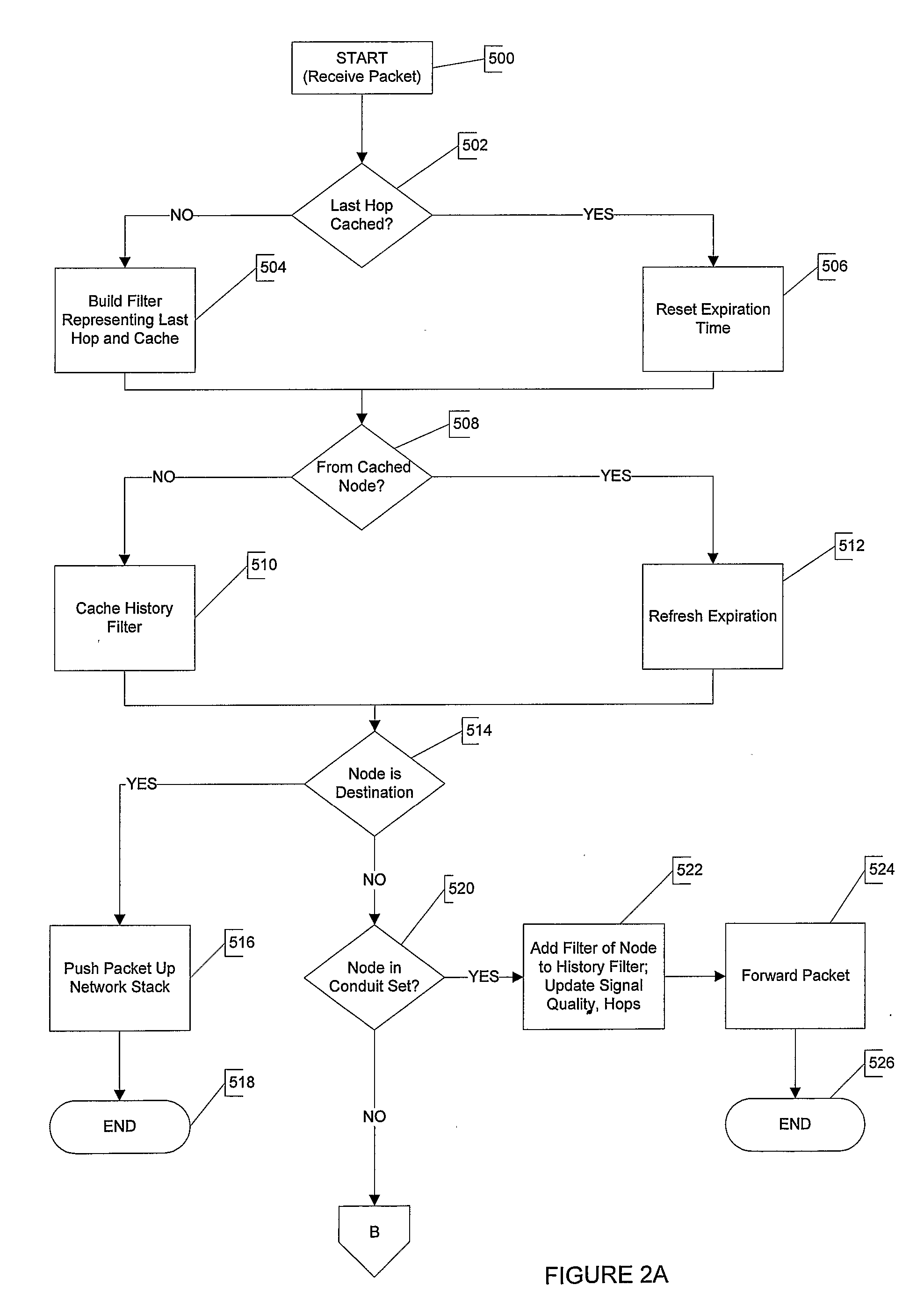
Packets are routed in a wireless mesh network by assigning a probability of packet retransmission based on certain factors which may include the number of hops the packet has made, whether the destination is within a certain number of known hops of the receiving node, the number of nearby nodes, whether the receiving node is a member of a past known route to the destination and / or whether a nearby neighbor of the receiving node is a member of a past known route to the destination. Once a probability is assigned, a random number generator may be used to make a decision between retransmitting the packet and dropping the packet. Signal quality may also be used as a factor in the probability of retransmission. In a preferred embodiment, Bloom filters are used to store information in the header of a data packet containing the identifiers of forwarding nodes and the identifiers of nodes on a previously-successful route from the source to the destination.
Owner:YAU JOHNNY +1
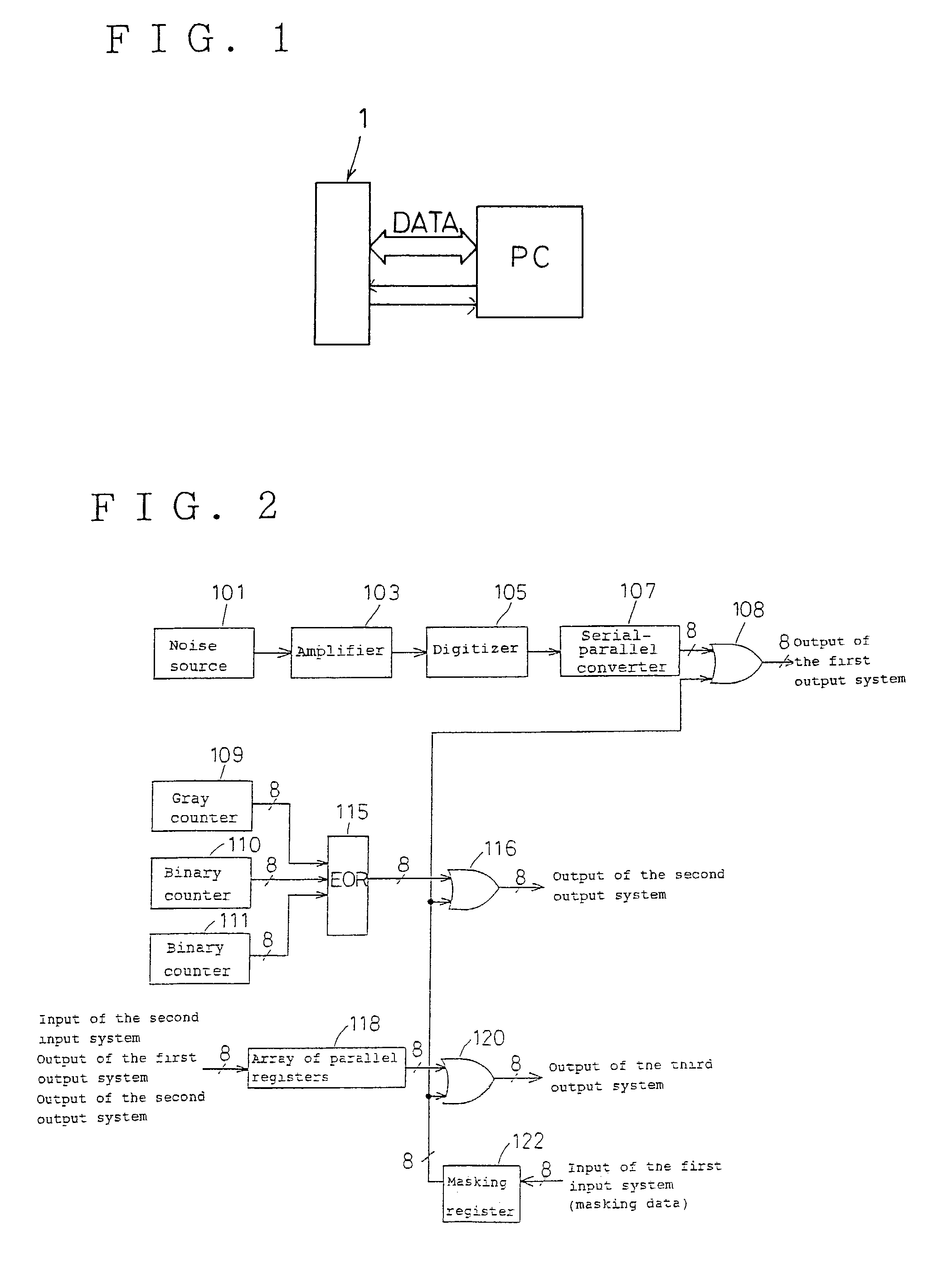
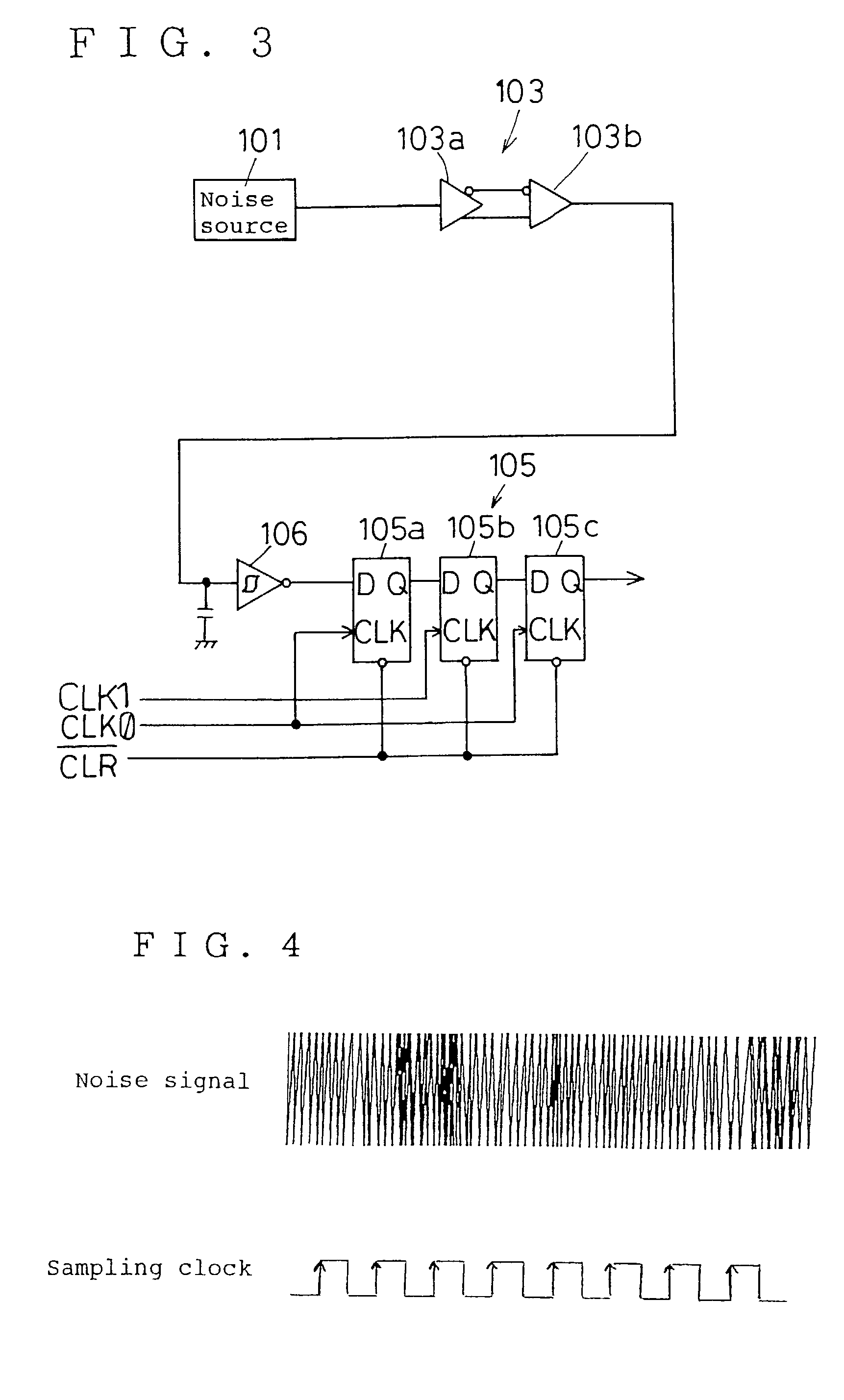
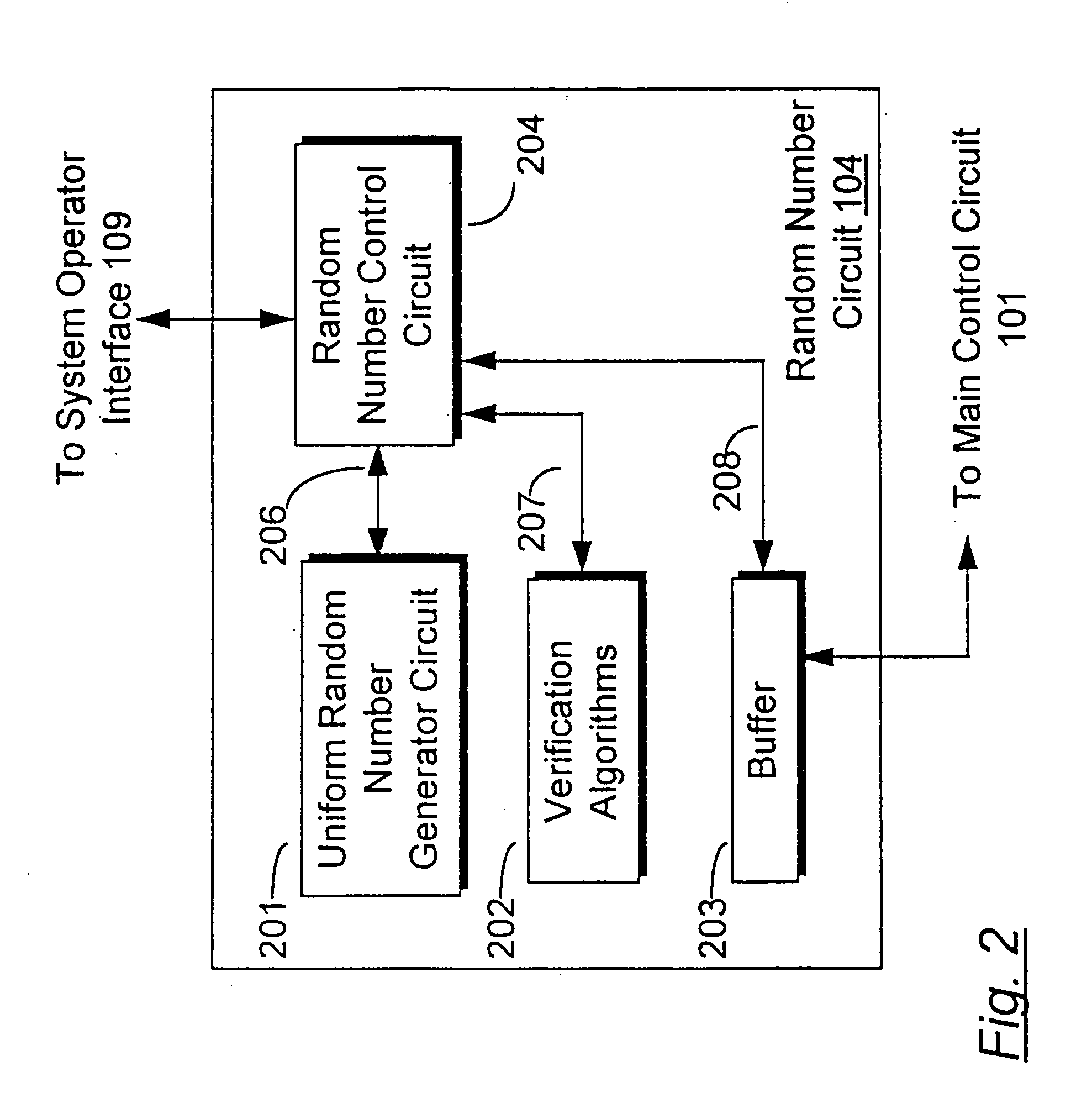
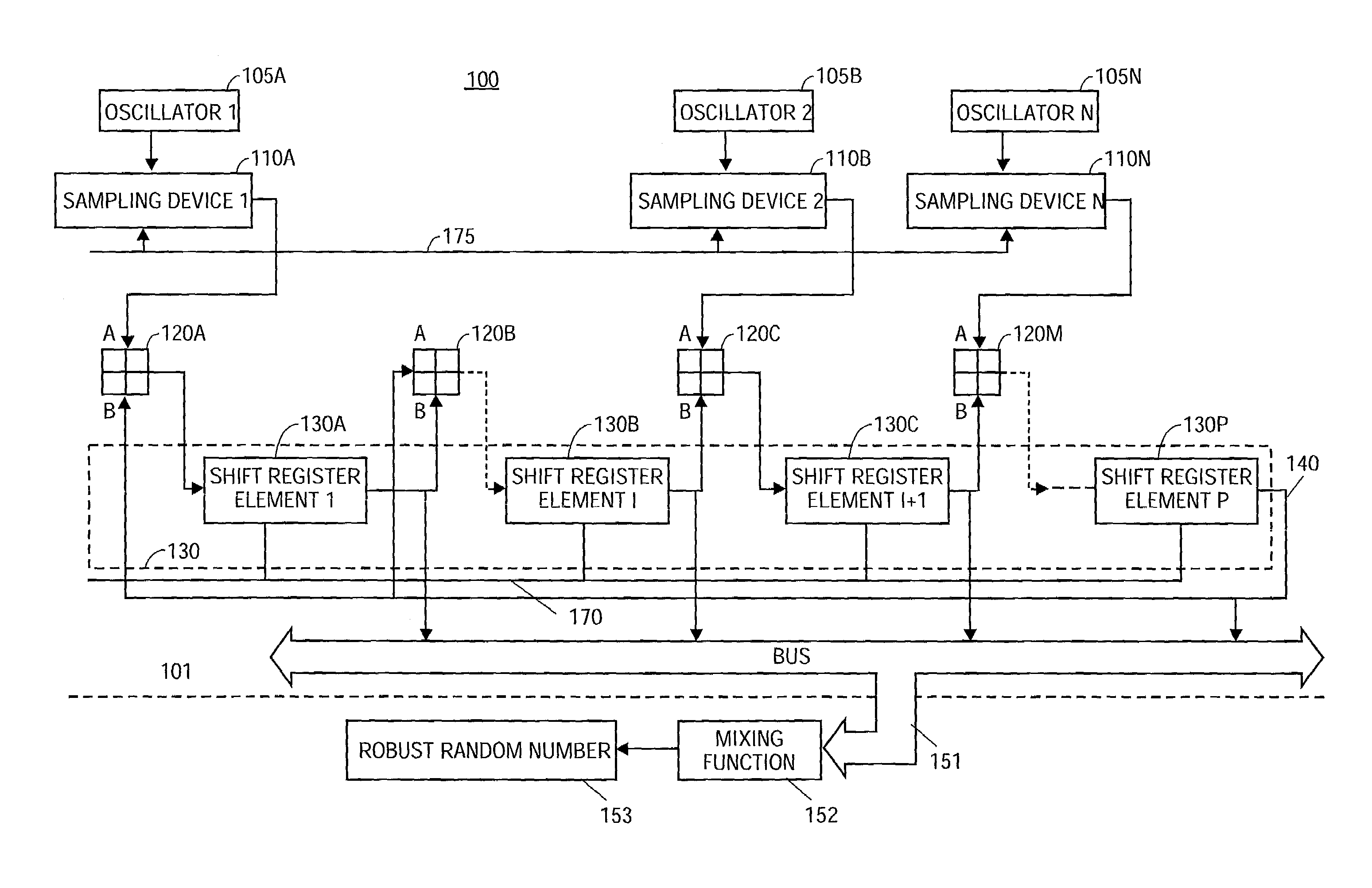
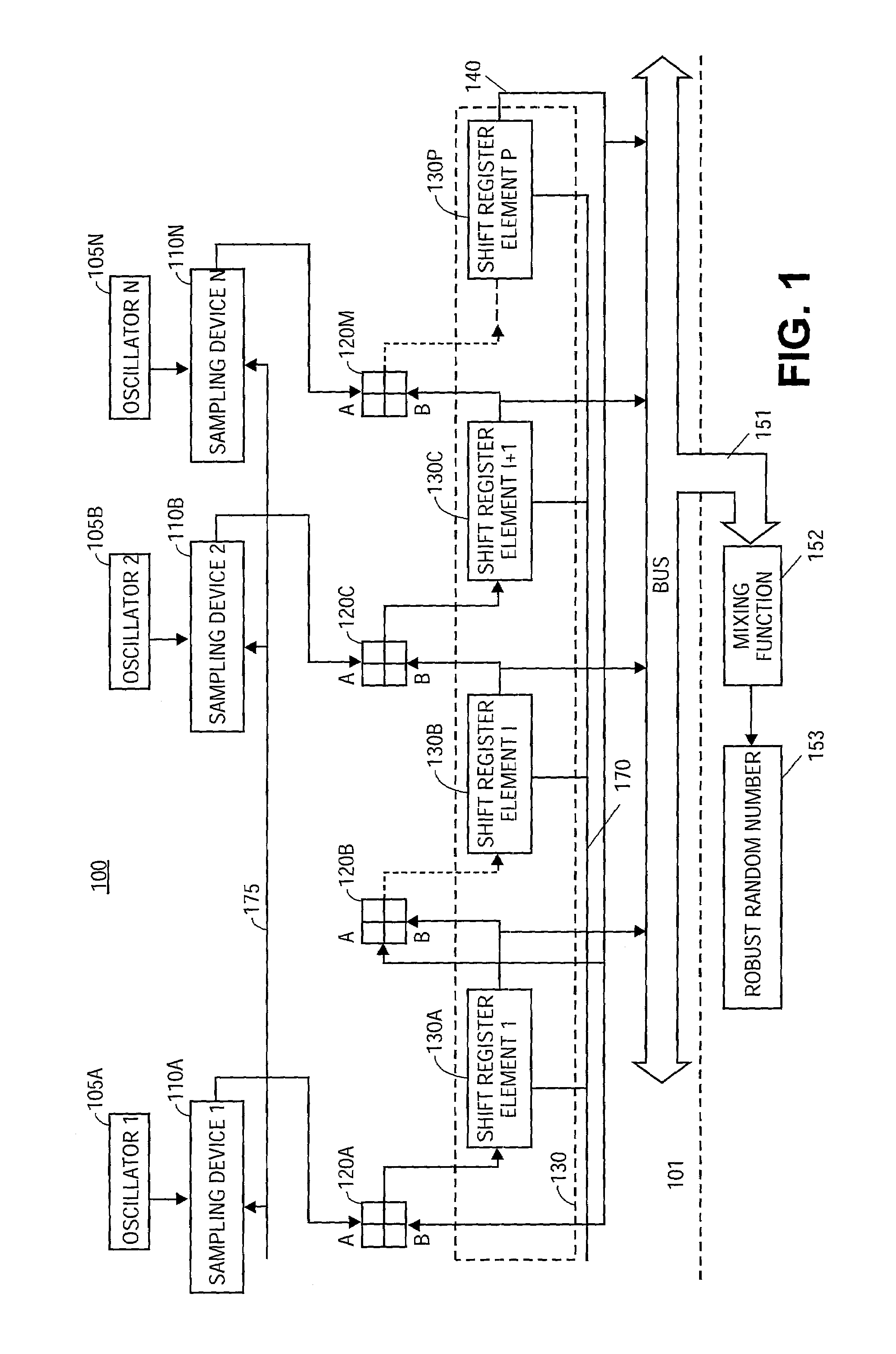
Random number generator
InactiveUS7124157B2Promote generationStable structureRandom number generatorsDigital function generatorsAudio power amplifierNumber generator
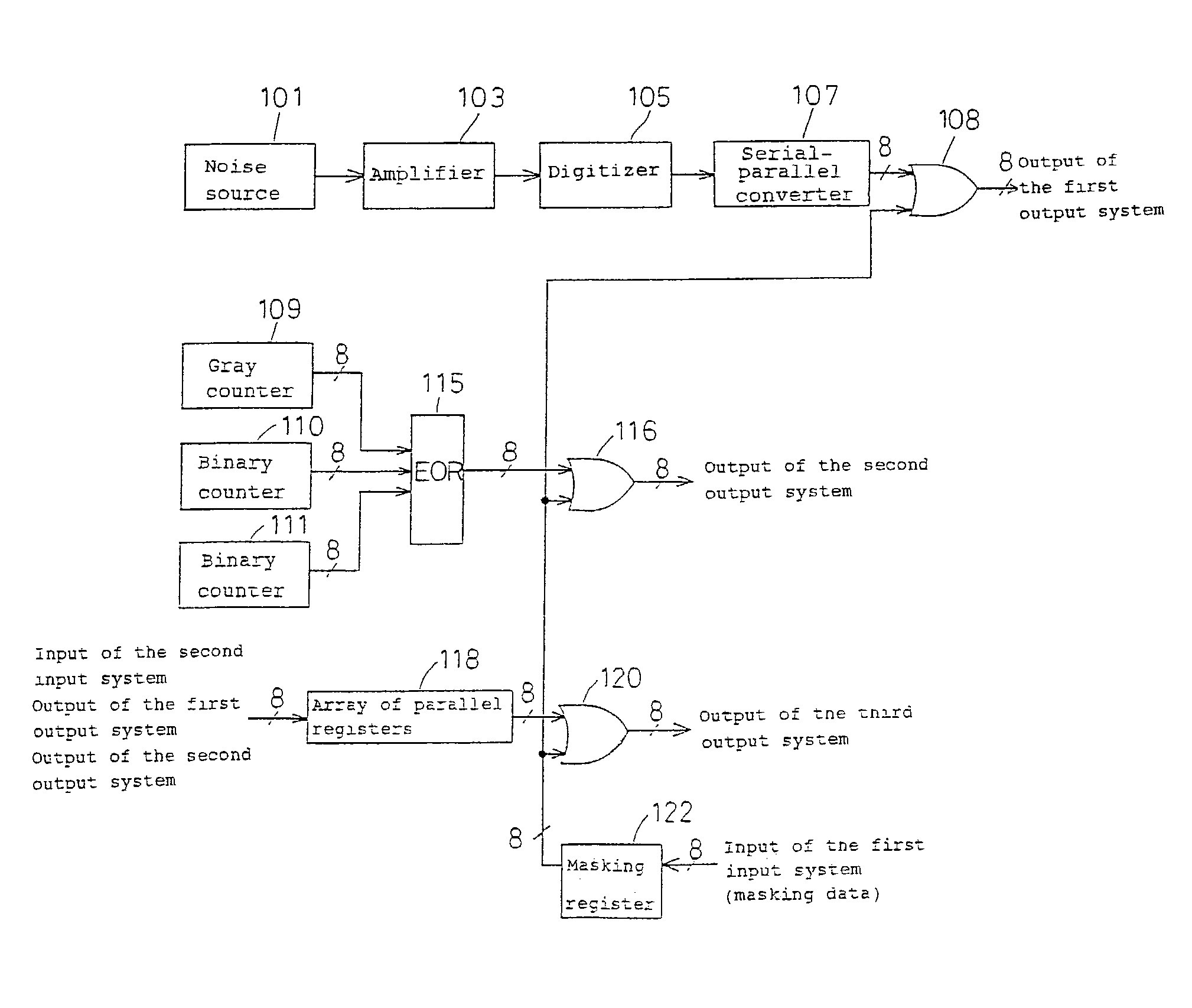
A random number generator having a simple construction which generates physical random numbers necessary for encryption. The random number generator has an amplifier to amplify noise signals generated from a noise source and digitizer to digitize the amplified noise signals. The digitizer includes a serial register.
Owner:HMI
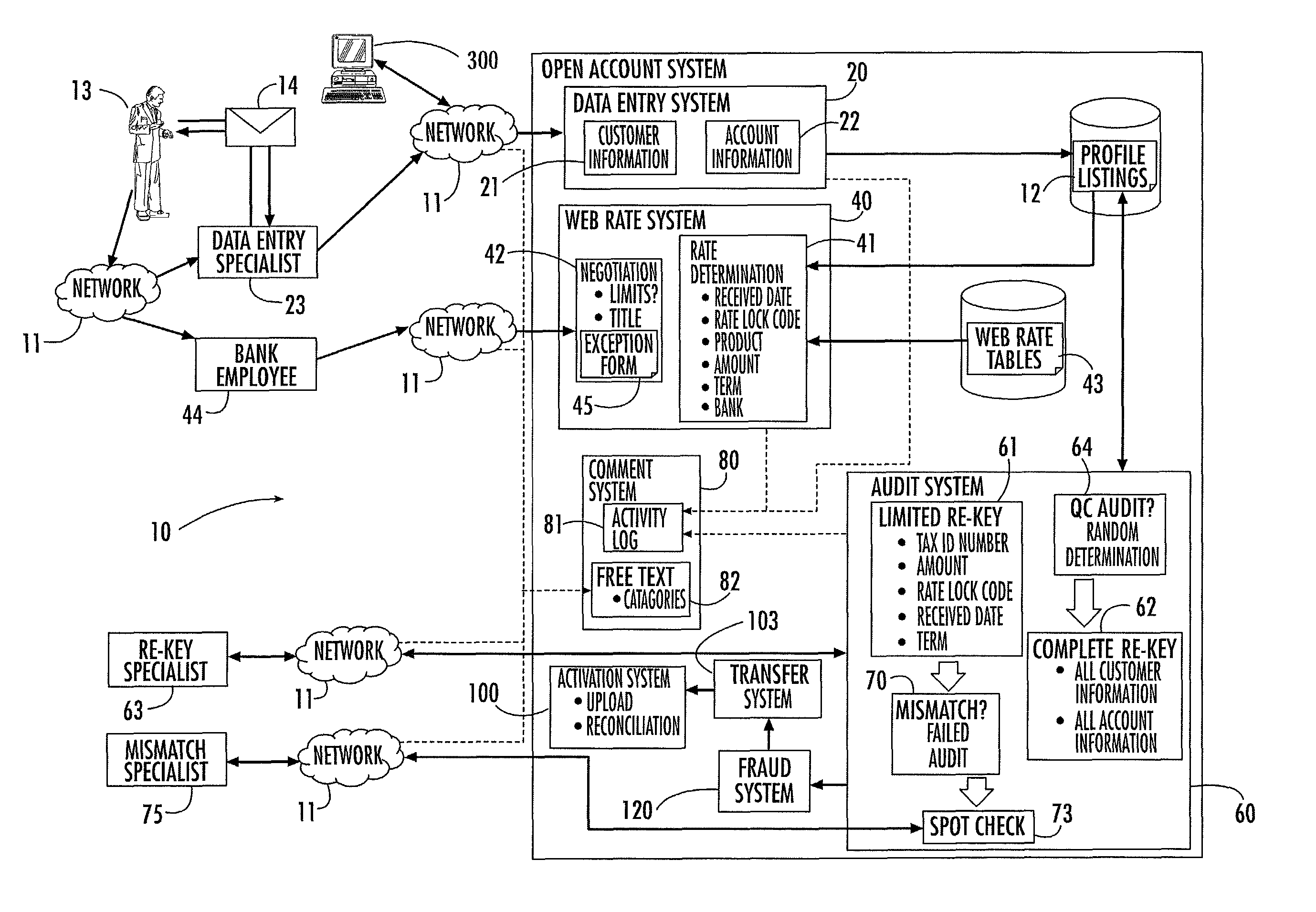
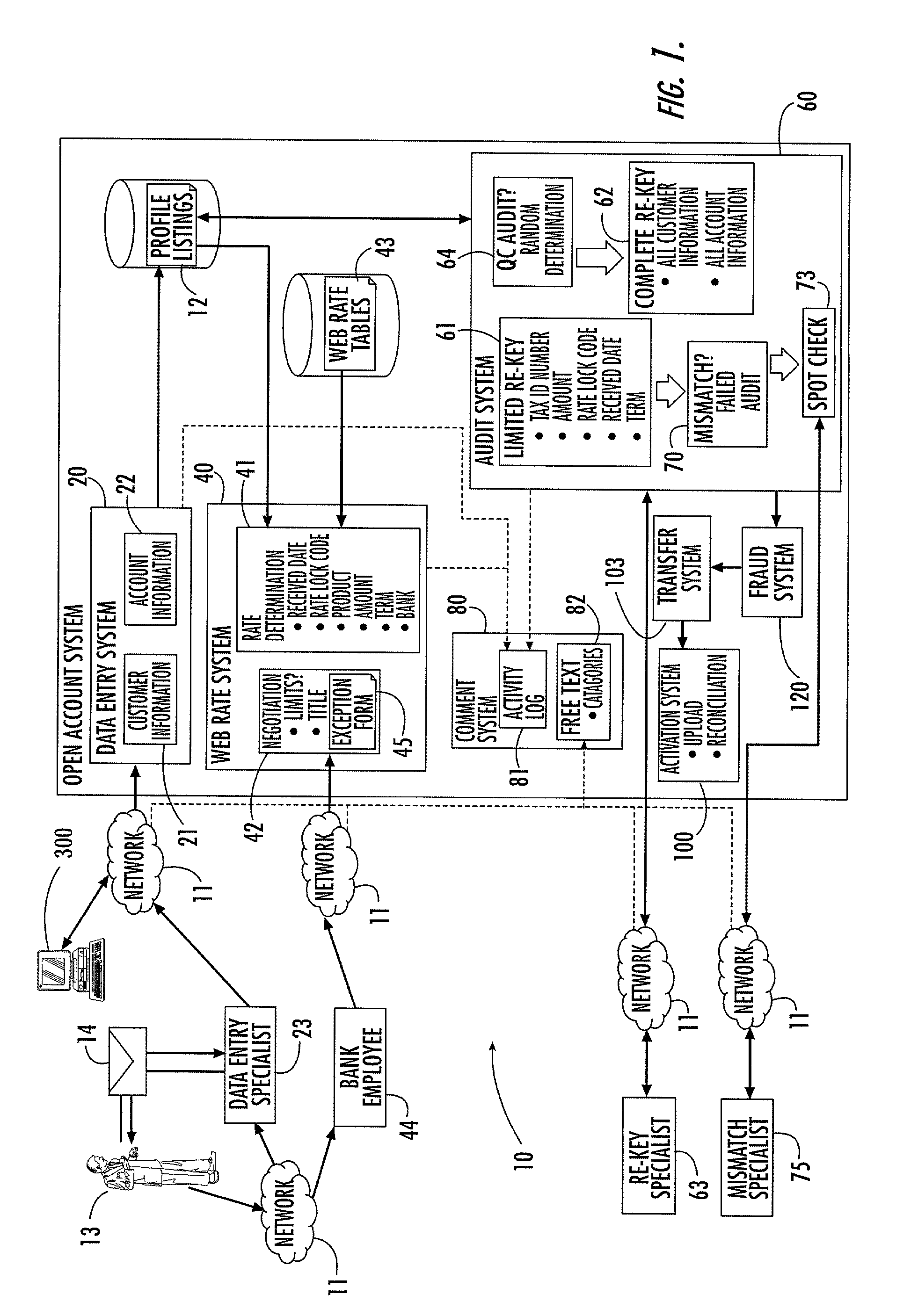
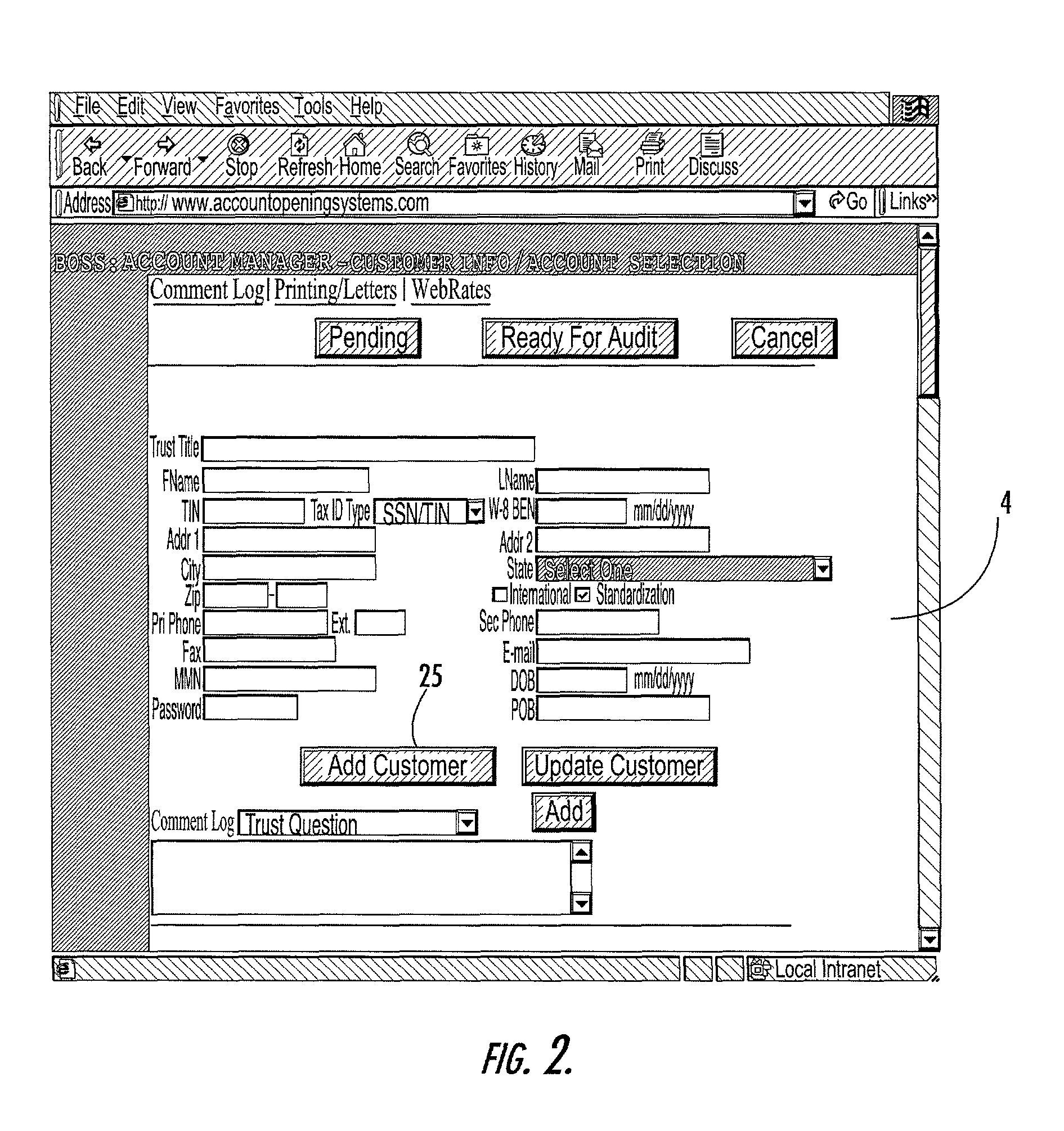
Account opening system, method and computer program product
ActiveUS8224723B2Improve accuracyImprove efficiencyFinancePayment architectureFile allocationBank account
A system that facilitates opening of a bank account by banking personnel for a customer. The account opening system includes an automatic rate determination feature that uses customer information, account information and other criteria to determine an account interest rate. The rate determination system may also mediate rate negotiation between a personal banker and the customer by limiting the increase in rate awarded by the personal banker. An auditing system assigns numbers to a series of profiles, each describing a request to open an account. Profiles to be audited are determined by generating random numbers that fall within the range of assigned profile numbers. Random number generation is repeated until a threshold percentage of profiles have been selected for auditing. The account opening system includes a system for tracking the progress of the account application and for organizing information recorded by the personal banker during interactions with the customer.
Owner:JPMORGAN CHASE BANK NA +1
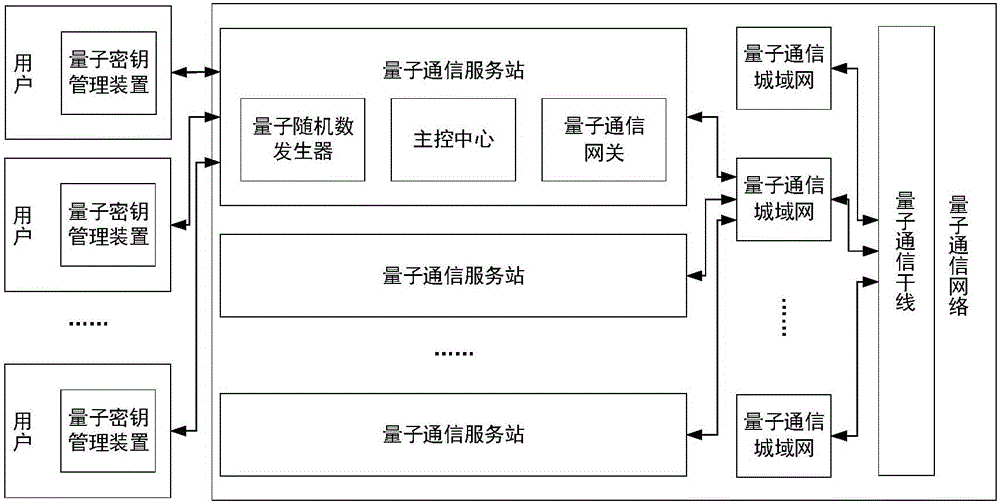
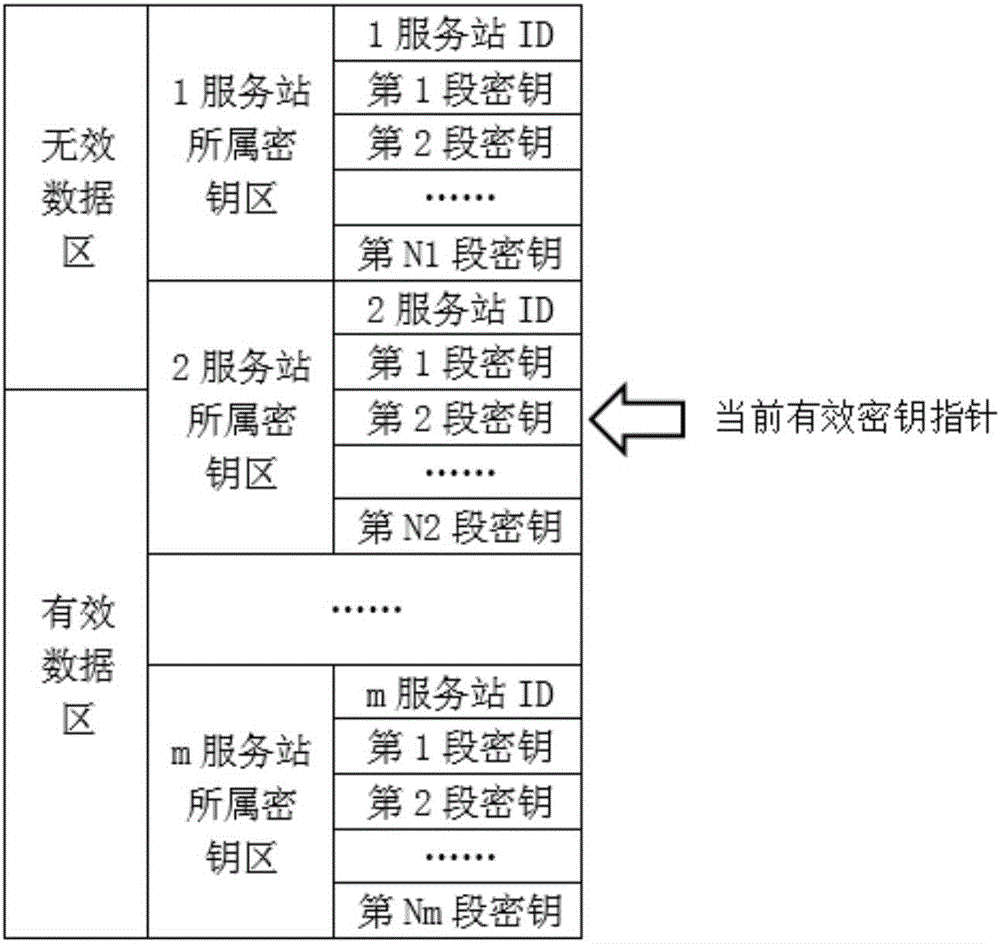
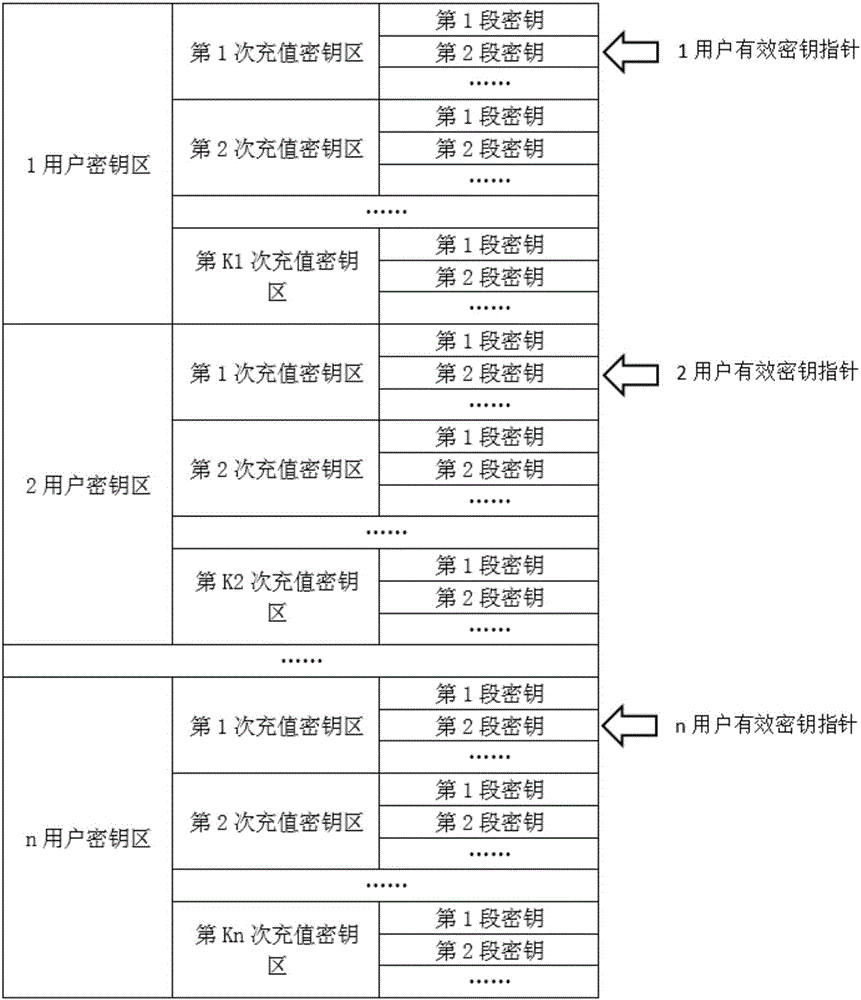
Quantum communication service station, quantum key management device, key configuration network, and key configuration method
ActiveCN106452740AAddress access security issuesAchieve coverageKey distribution for secure communicationSecurity questionKey distribution
The invention discloses a quantum communication service station, a quantum key management device, a key configuration network, and a key configuration method. The key configuration method comprises the following steps: responding to a key distribution request; authenticating a user of the key distribution request; writing a key generated with a true random number into a quantum key management device of the authenticated user. The key configuration method is different from the existing quantum key distribution QKD method in that key distribution of ultra high security is realized by pairing quantum key management devices and service stations at the end of a quantum communication network, the problem about access security at the end of a quantum communication network is solved, and terminal access is not a weak link of a quantum communication scheme. The quantum communication network can completely cover and replace the classic communication network in service.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
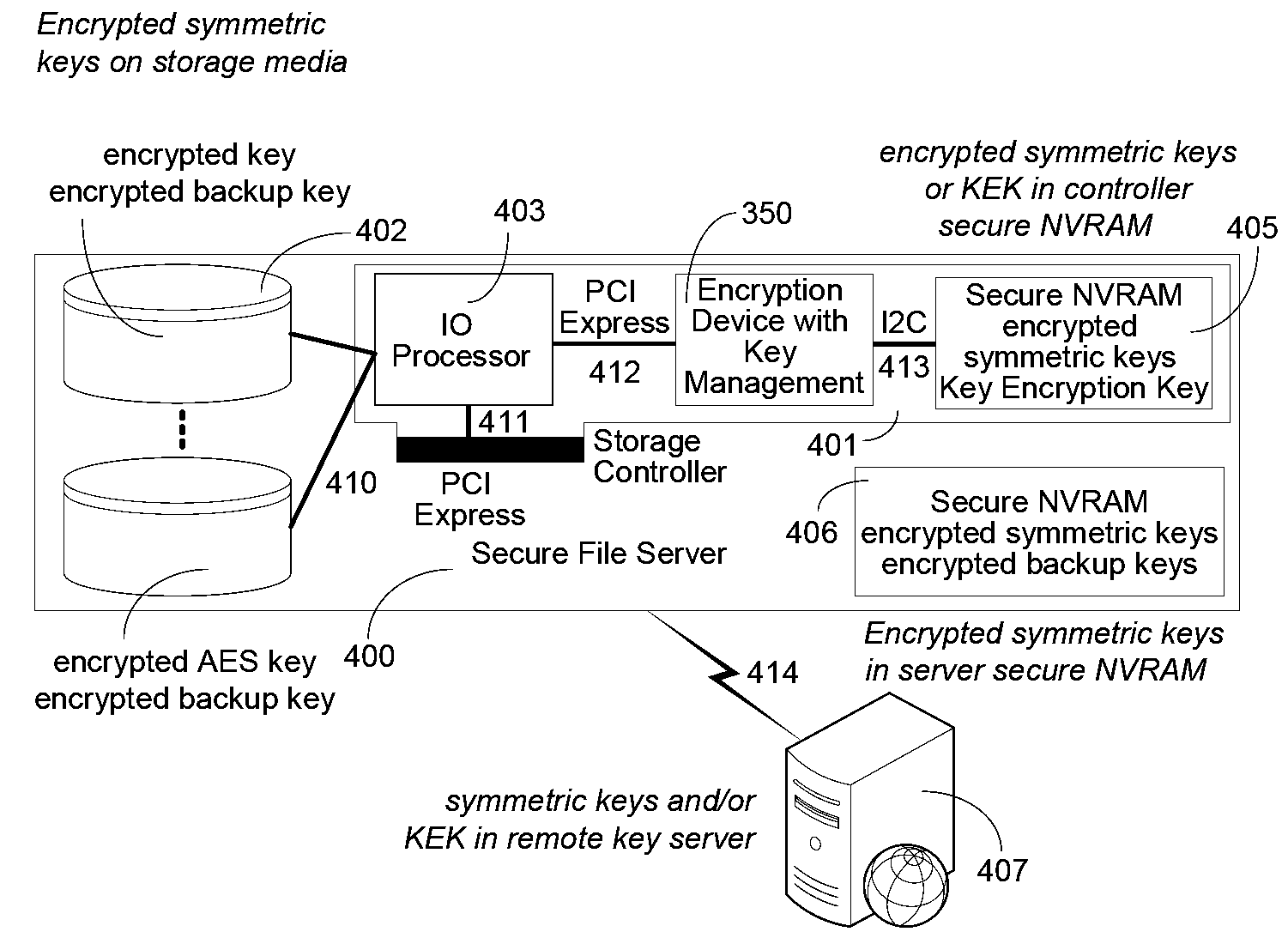
System and method for enhanced security of storage devices
ActiveUS9921978B1Unauthorized memory use protectionInternal/peripheral component protectionComputer hardwareEngineering
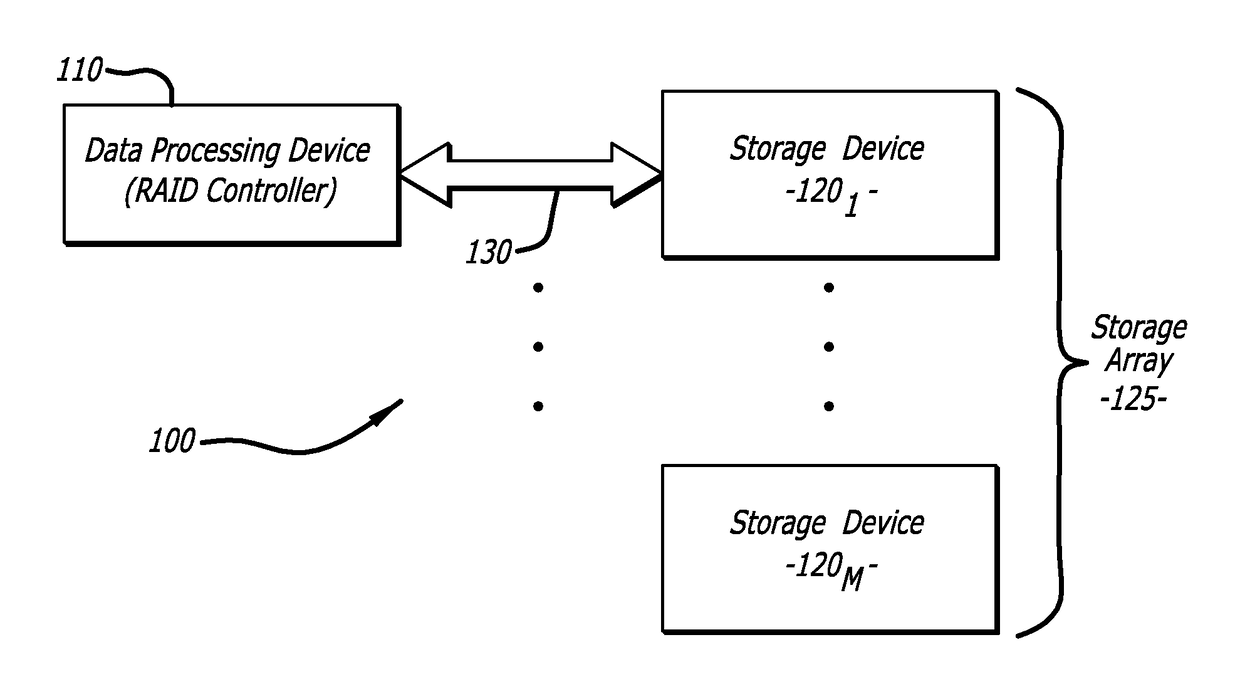
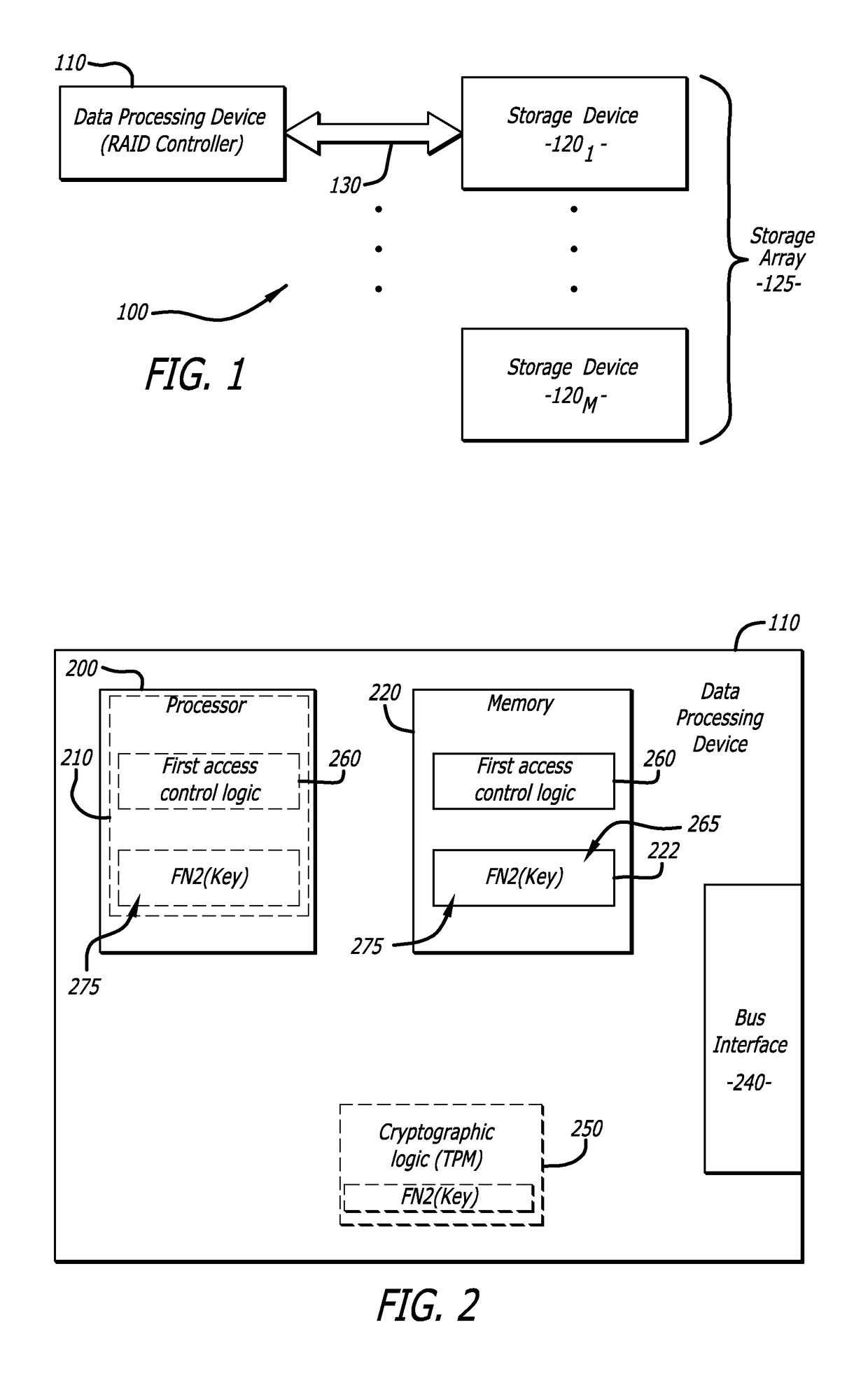
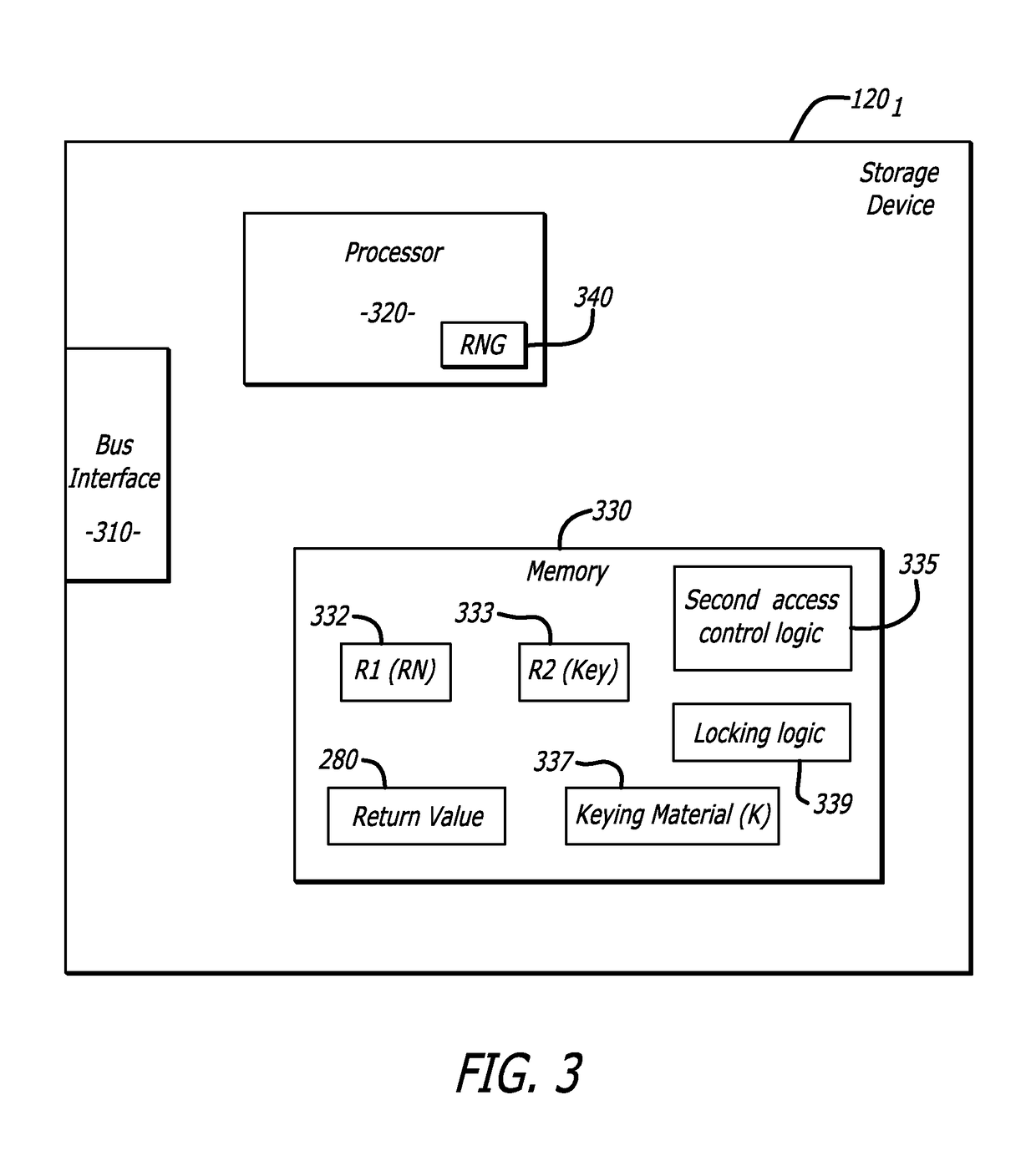
A storage device features a processor and a random number generation which are communicatively coupled to a memory. The memory comprises an access control logic that is configured to (i) transmit a first message that comprises information associated with a random number generated by the random number generator and a first keying material, (ii) receive a second message in response to the first message, the second message comprises information generated using at least the random number, (iii) recover information from the second message, the recovered information comprises information generated using at least pre-stored keying material and a return value being based on the random number, (iv) compare the return value from the recovered information with the random number, and (v) alter an operating state of the storage device from a locked state to an unlocked state upon the return value matching the random number, the unlocked state allows one or more devices to control storage device including accessing stored content within the storage device.
Owner:FIREEYE SECURITY HLDG US LLC
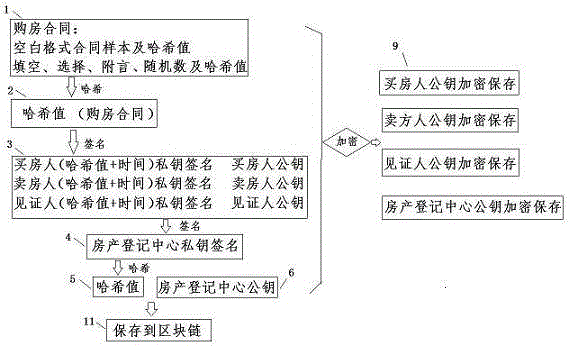
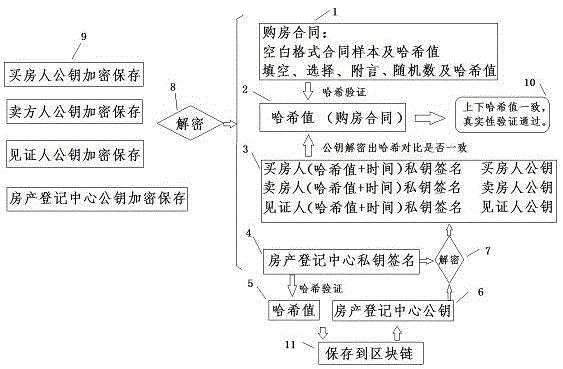
Block chain information archiving and privacy protection method
ActiveCN105610578APrevent tamperingEasy retrievalKey distribution for secure communicationThird partyPrivacy protection
The invention discloses a block chain information archiving and privacy protection method. The block chain information archiving and privacy protection method comprises the steps of adding random number generation Hash values to information needing archiving; then signing by an interest-related person or a eyewitness and generating Hash values; and finally recording at a block chain. Some information needing archiving is formatting and separable formatting information and self-filling information respectively stored and subjected to Hash verification, such as gap-filling information, selection information, postscript information, random number information (for preventing brute force attack). Data which are encrypted by using a public key only can be decrypted by a relevant person who knows the original information by using a private key; a third party verifies true and false of the information; and the encrypted information can be disclosed for a judicial institution if judiciary involvement is needed.
Owner:苏州交链科技有限公司 +1
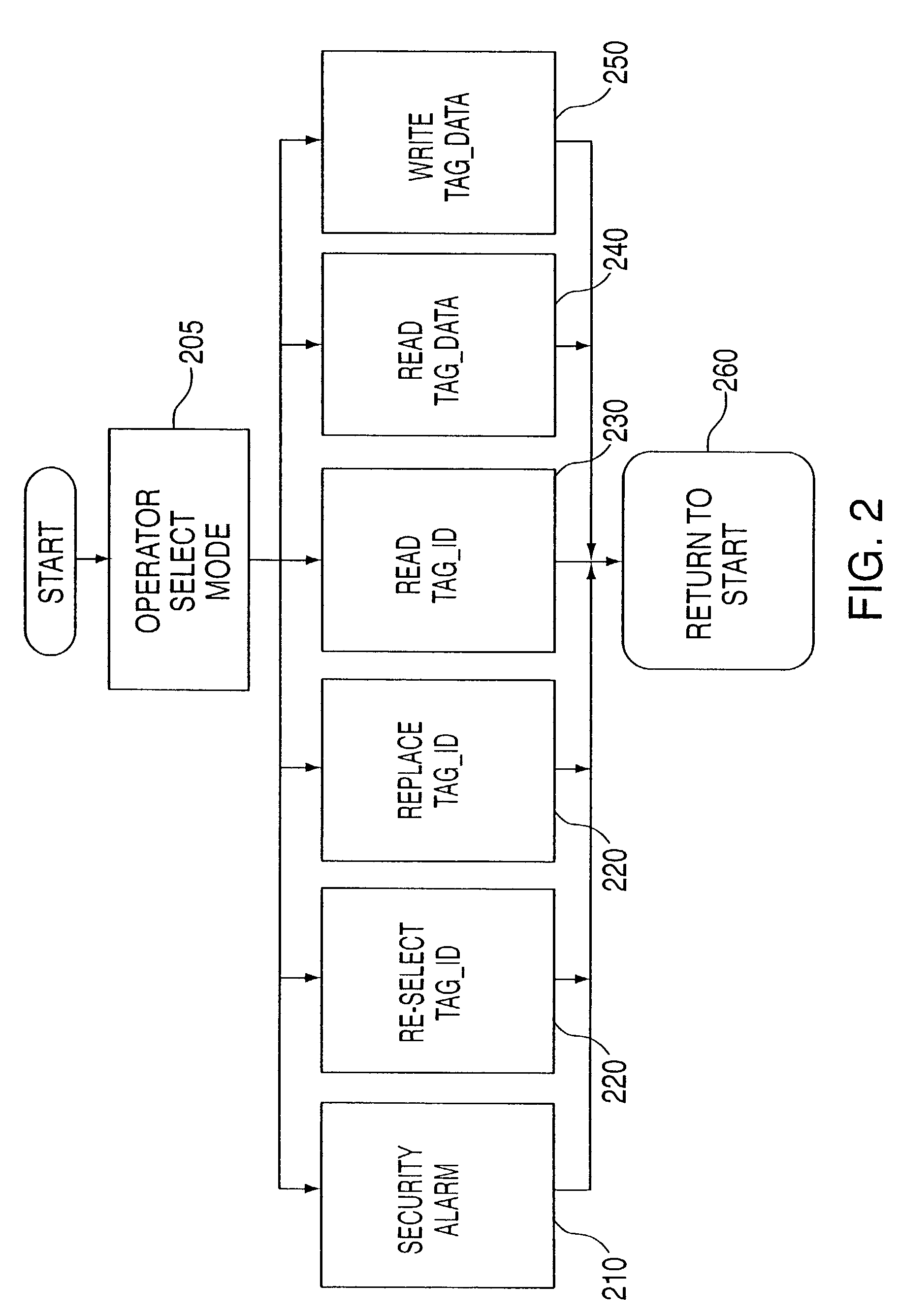
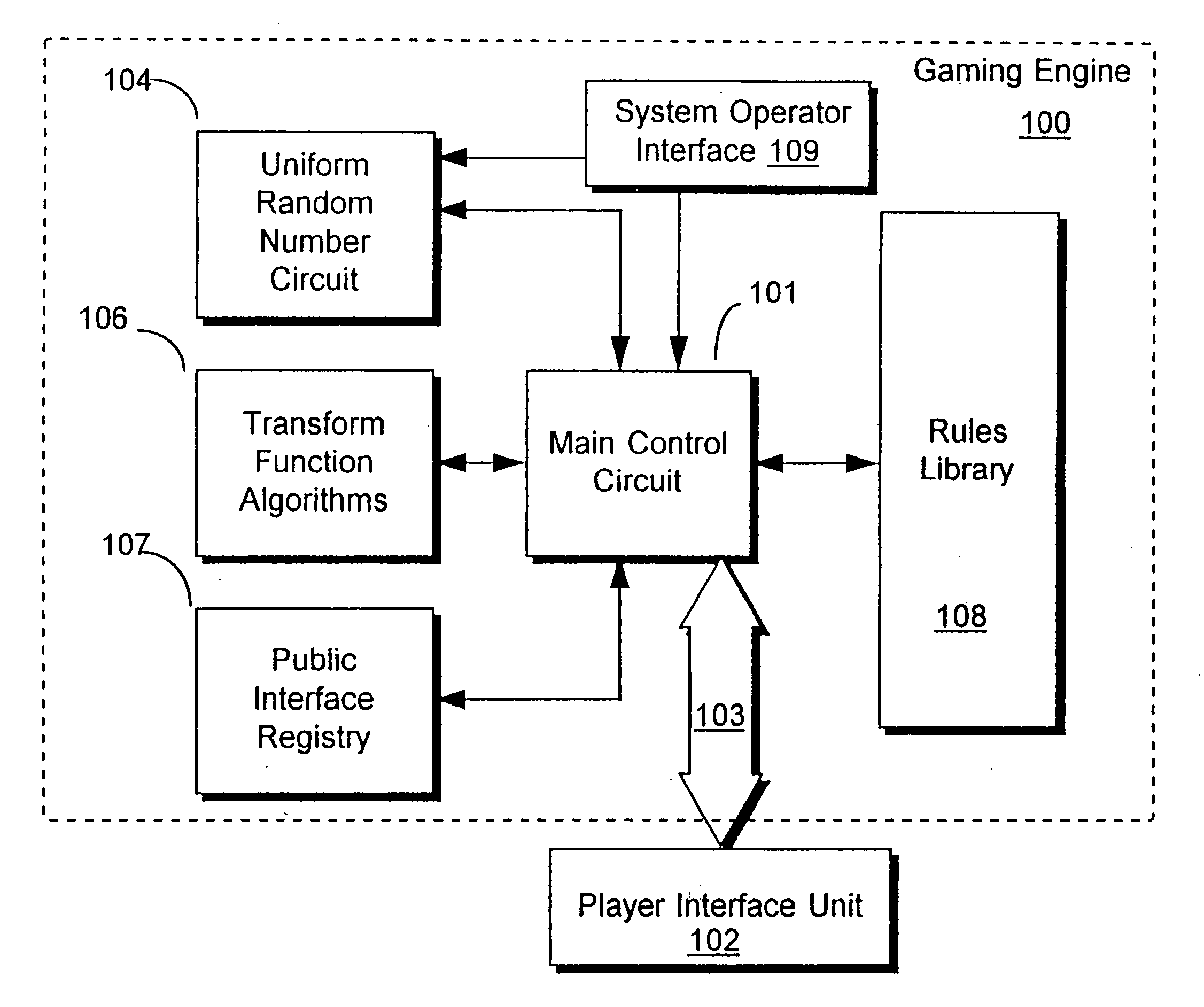
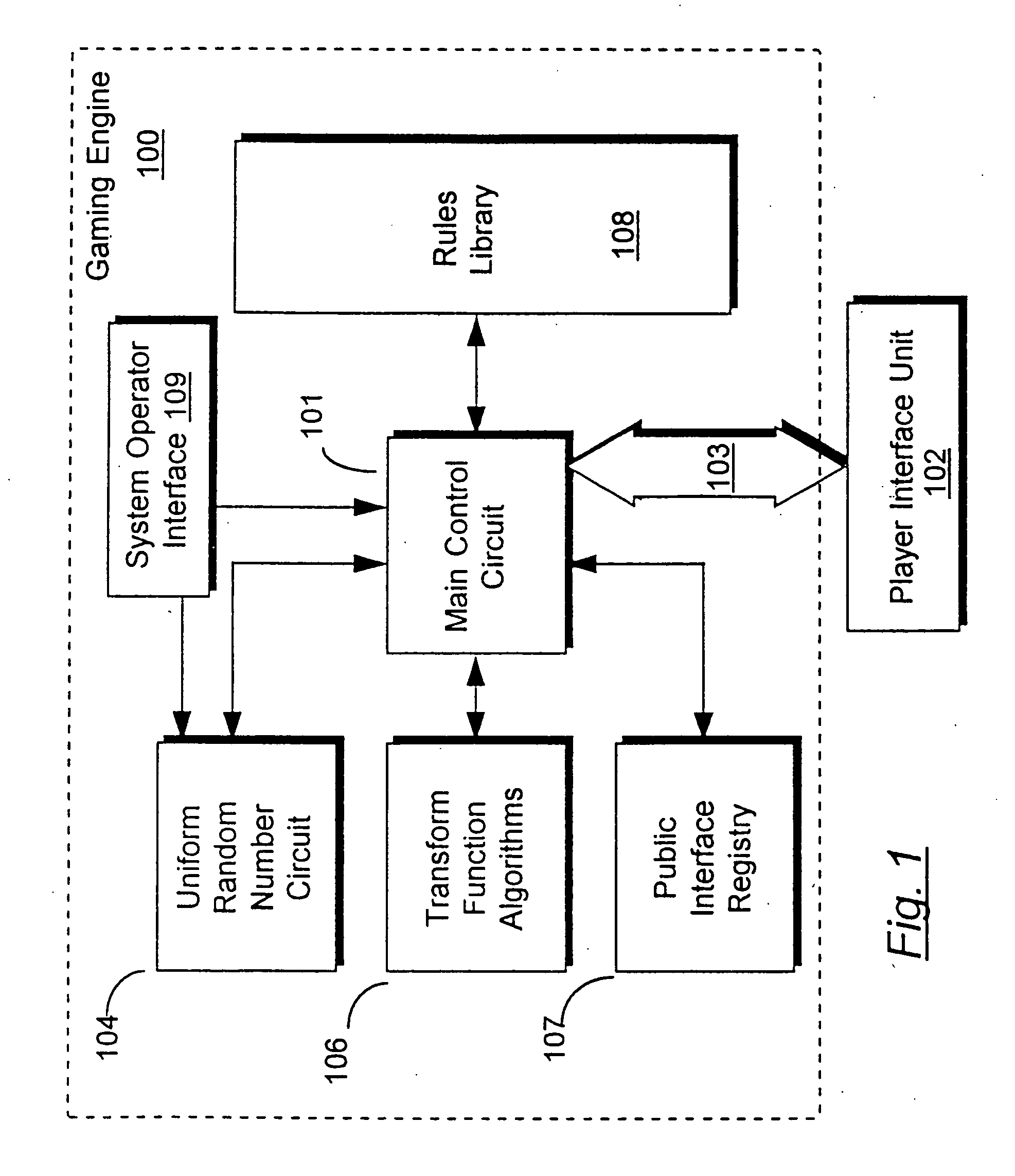
Method for control of gaming systems and for generating random numbers
InactiveUS20060165235A1Convenient timeImprove efficiencyRandom number generatorsMultiple digital computer combinationsArray data structureNumber generator
An apparatus for implementing a game having a deterministic component and a non-deterministic component wherein a player uses the game through at least one player interface unit. Each player interface unit generates a player record indicating player-initiated events. A random number generator provides a series of pseudo-random numbers and a rules library stores indexed rules for one or more games. An interface registry stores mapping records where the mapping records are used to associate the player-initiated events to pre-selected rules in the rules library. A control means is coupled to the player interface to receive the output of the player interface unit, coupled to the interface registry, the rules library, and the random number generator. The control means processes the player record and returns an output record to the player interface unit where the output record is determined by executing the game's rules with reference to the pseudo-random numbers and predefined combinatorial algorithms for selecting sets of the pseudo-random numbers.
Owner:ZYNGA
Agile network protocol for secure communications with assured system availability
InactiveUS7010604B1Reduce network loadSmall sizeKey distribution for secure communicationData stream serial/continuous modificationDiscriminatorComputer hardware
A plurality of computer nodes communicates using seemingly random IP source and destination addresses and (optionally) a seemingly random discriminator field. Data packets matching criteria defined by a moving window of valid addresses are accepted for further processing, while those that do not meet the criteria are rejected. In addition to “hopping” of IP addresses and discriminator fields, hardware addresses such as Media Access Control addresses can be hopped. The hopped addresses are generated by random number generators having non-repeating sequence lengths that are easily determined a-priori, which can quickly jump ahead in sequence by an arbitrary number of random steps and which have the property that future random numbers are difficult to guess without knowing the random number generator's parameters. Synchronization techniques can be used to re-establish synchronization between sending and receiving-nodes. These techniques include a self-synchronization technique in which a sync field is transmitted as part of each packet, and a “checkpoint” scheme by which transmitting and receiving nodes can advance to a known point in their hopping schemes. A fast-packet reject technique based on the use of presence vectors is also described. A distributed transmission path embodiment incorporates randomly selected physical transmission paths.
Owner:VIRNETX
Additional hash functions in content-based addressing
ActiveUS7373345B2Eliminate malicious hash attackEliminate attackData processing applicationsDigital data information retrievalComputer hardwareHash function
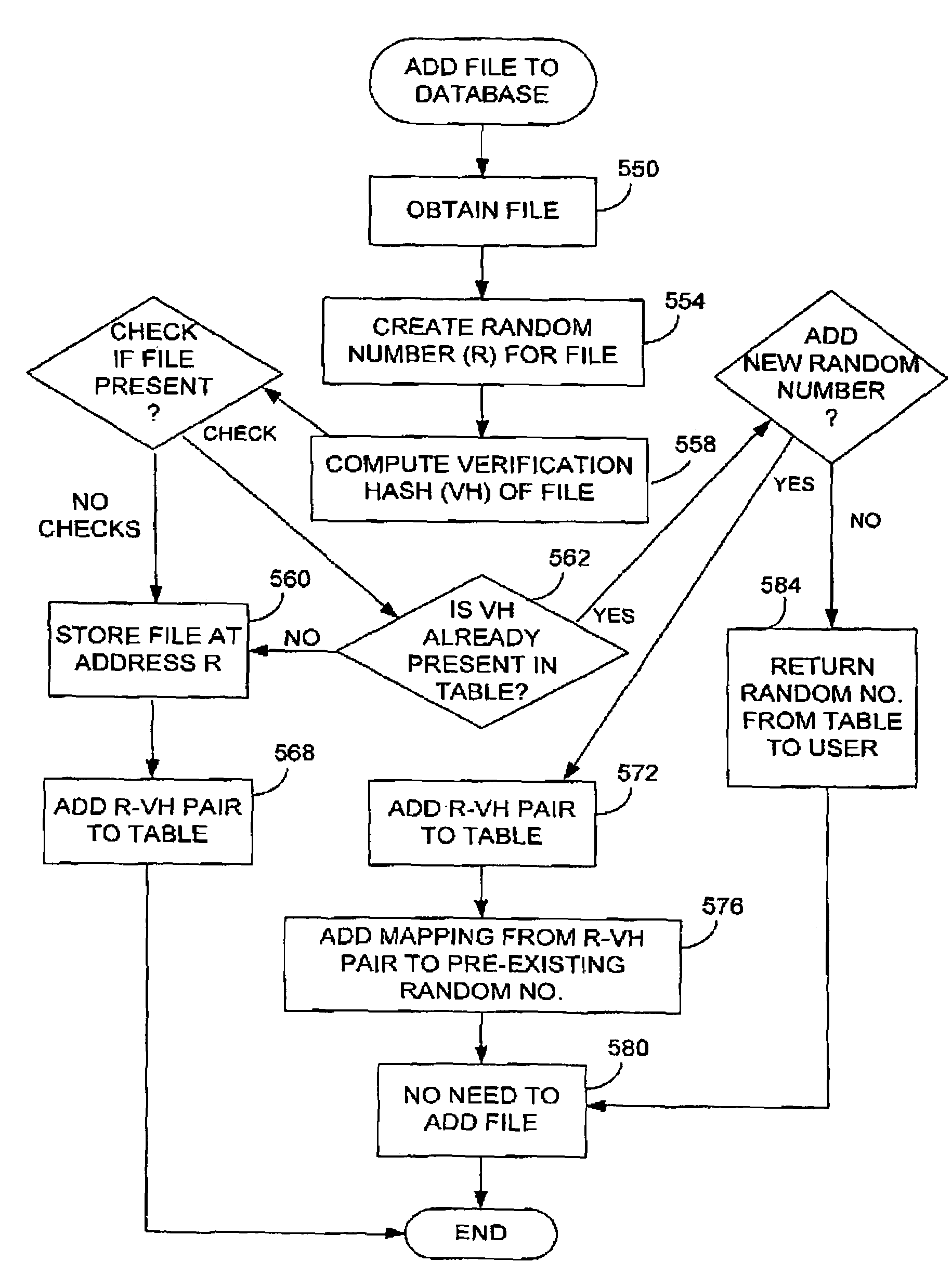
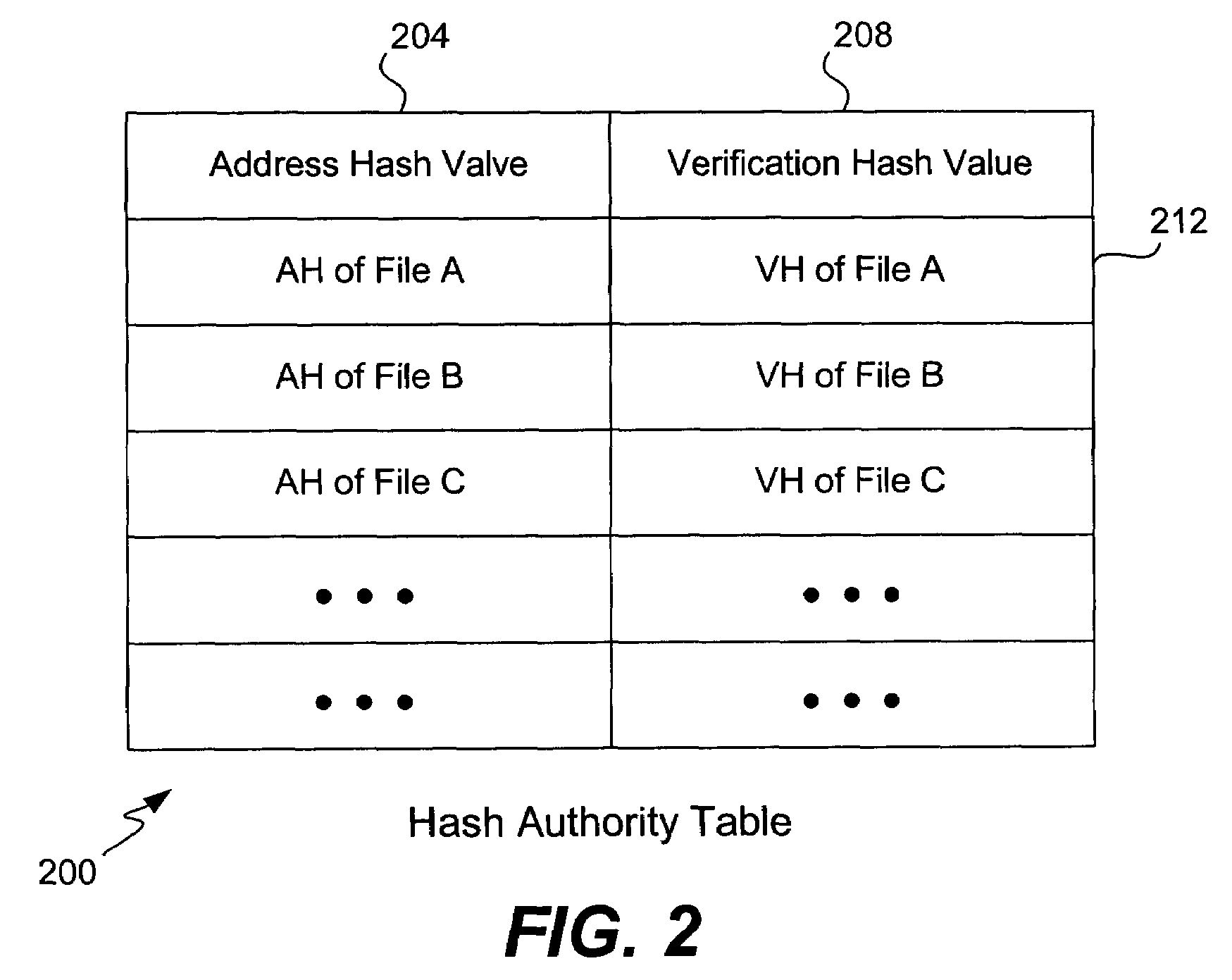
A hash function used for content addressing is different from the hash function used for content verification. Adding a file to a database involves storing both hash function values in a table as pair. Verifying the integrity of a file believed to be a duplicate in a database, or when retrieving a file, makes use of the verification hash function. Files can be continuously checked. A multi-level database can be used. A second hash function can be added to an existing system. A verification hash function can be upgraded and more than one content verification hash function can be used. In a variation, a random number generator is used instead of a hash function for content addressing; the verification hash function is also used. Files addressed using a random number are added or retrieved from a database and their verification hash values are checked. Time stamps and digital signatures are used for security.
Owner:DATACORE SOFTWARE
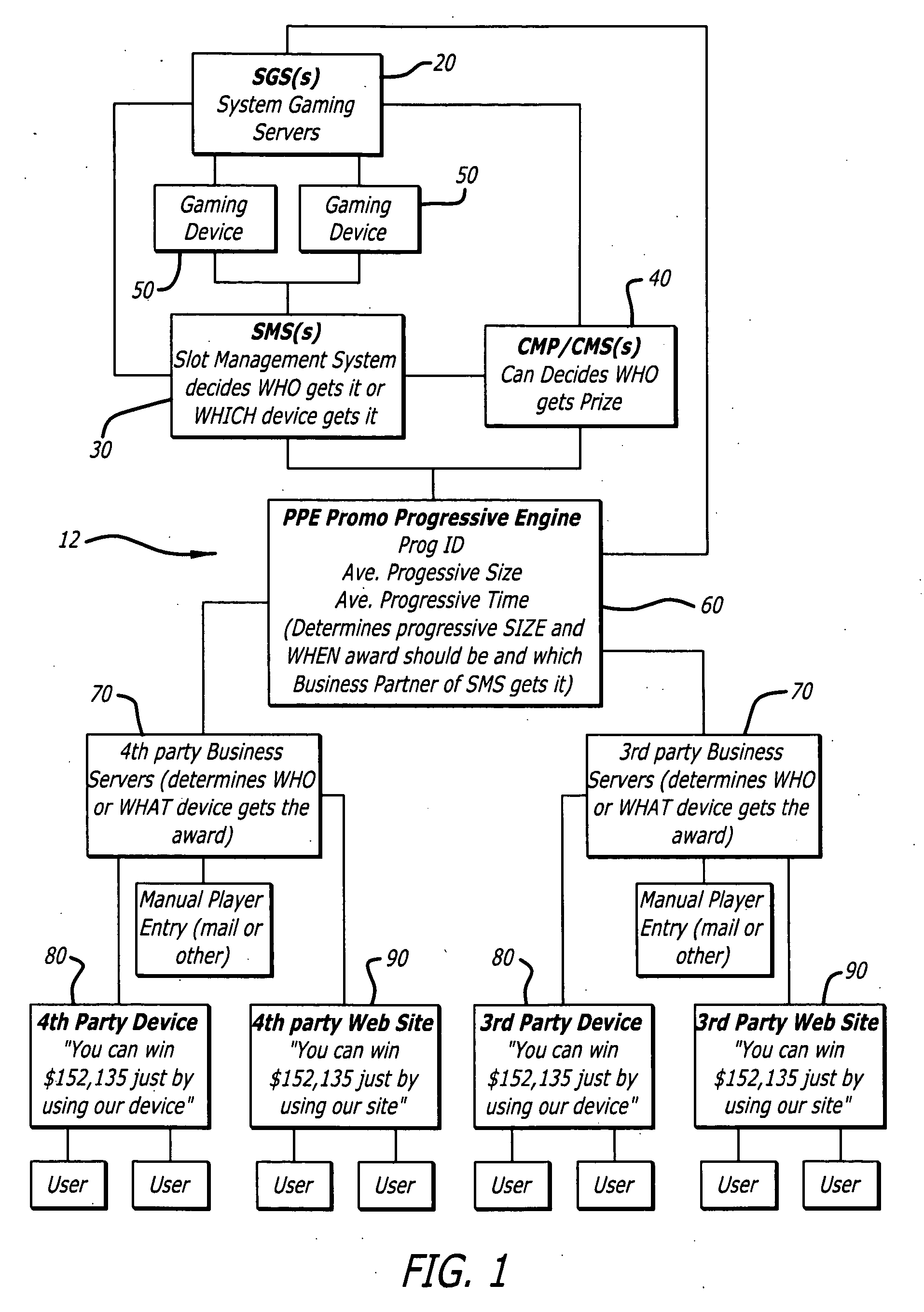
Progressive game and processing system thereof
InactiveUS20070060320A1Create perceptionAchieve levelingApparatus for meter-controlled dispensingVideo gamesArtificial intelligenceComputer science
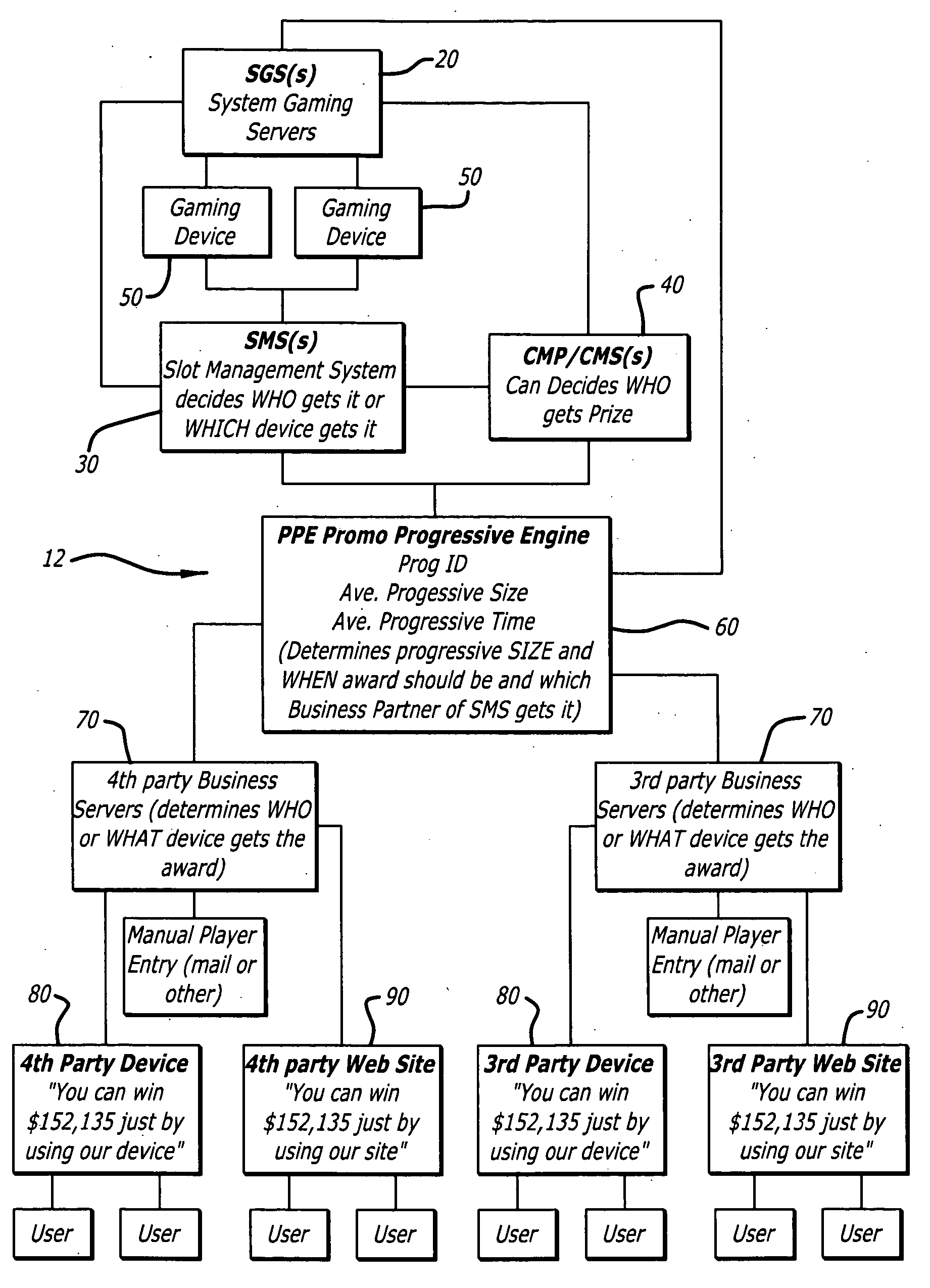
A progressive game is implemented on a gaming system, wherein the gaming system includes one or more gaming machines connected to a game server, and wherein the progressive game has a progressive prize value that increases according to a progressive prize growth rate. The progressive game includes a selectable targeted progressive prize value, a selectable targeted progressive prize time, and one or more enticement factors. The progressive prize growth rate is calculated using the selectable targeted progressive prize value, the selectable targeted progressive prize time, and the one or more enticement factors. Additionally, a random number generation algorithm tests to determine if there is a progressive prize win at each predetermined time period. The selectable targeted progressive prize time is used to calculate the predetermined time period for testing for a progressive prize win. If a progressive prize win has not been identified, the progressive prize value is incremented by the progressive prize growth rate. If a progressive prize win has been identified, a random number generation algorithm determines one or more winners of the progressive prize.
Owner:BALLY GAMING INC
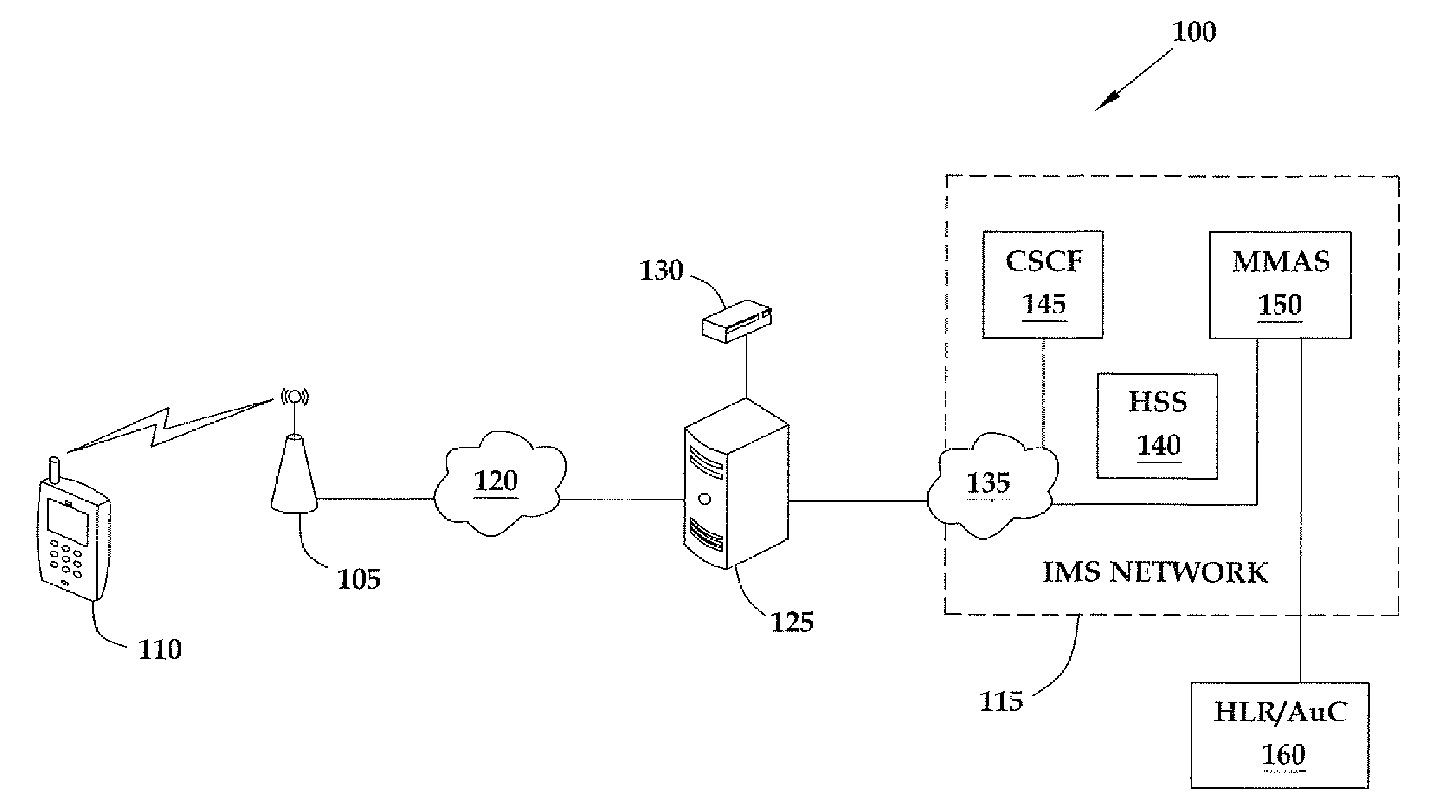
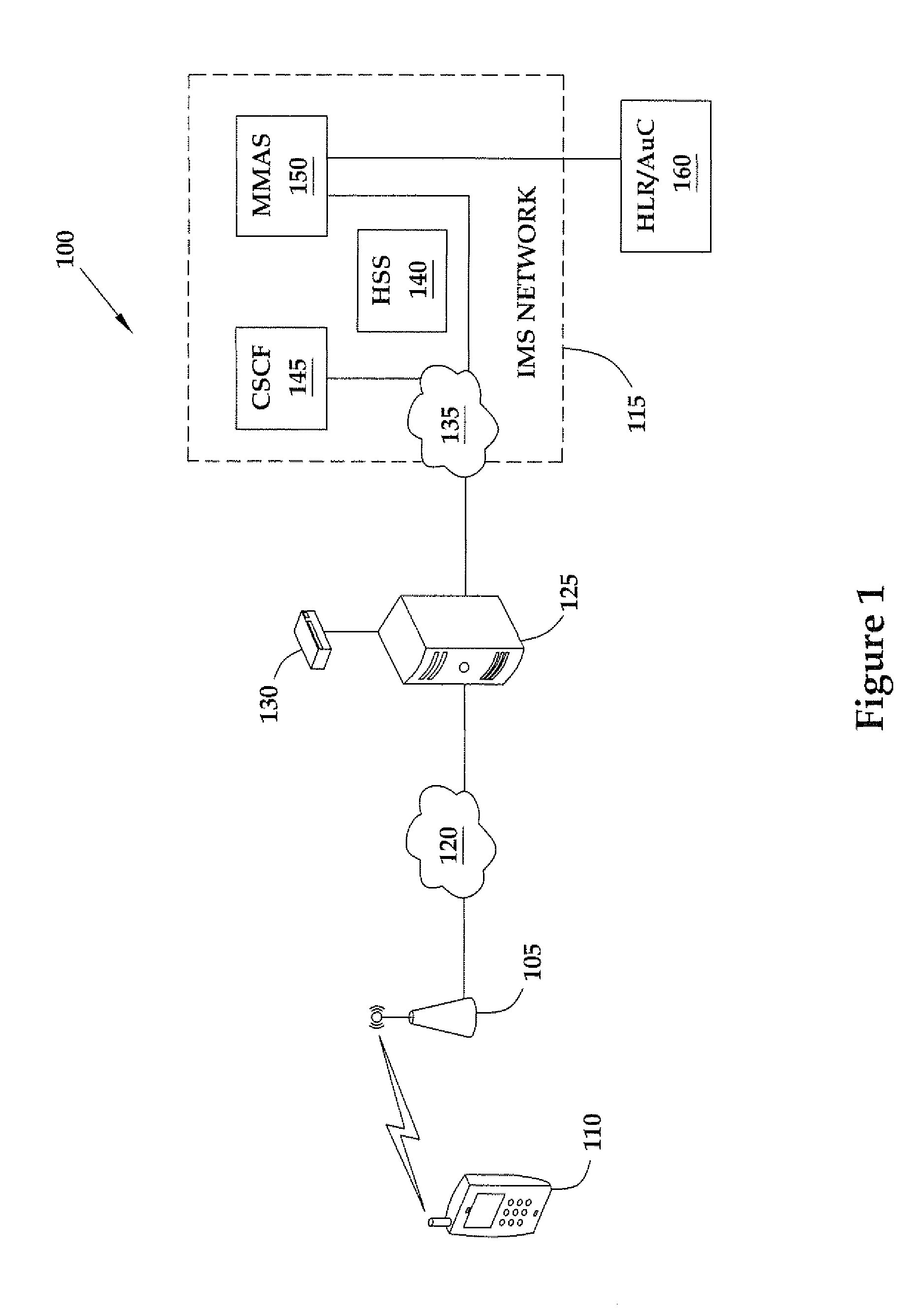
Method for authenticating a mobile unit attached to a femtocell that operates according to code division multiple access
ActiveUS20090191844A1Unauthorised/fraudulent call preventionDigital data processing detailsCode division multiple accessAuthentication server
The present invention provides a method involving a femtocell in communication with an Internet Protocol Multimedia Subsystem (IMS) network. In one embodiment, the femtocell operates according to code division multiple access (CDMA) standards. The method includes receiving, from the femtocell and at a first secure entity in the IMS network, first authentication information generated by the mobile unit using a first random number broadcast by the femtocell in a global challenge. The method also includes receiving, from a second secure entity in the secure network, at least one security key formed based on the global challenge and second authentication information for uniquely challenging the mobile unit. In one embodiment, the second secure entity is a CDMA-based authentication server. The method further includes providing the security key(s) to the femtocell in response to authenticating the mobile unit based upon the second authentication information.
Owner:ALCATEL LUCENT SAS
Tamper detection countermeasures to deter physical attack on a security asic
ActiveUS20130104252A1Error detection/correctionVolume/mass flow measurementCountermeasureNumber generator
Various embodiments of the present invention relates generally to an integrated circuit, and more particularly, to systems, devices and methods of incorporating a tamper detection countermeasure into a security ASIC to deter physical attacks. The tamper detection countermeasure architects an active mesh to cover a sensitive area in the security ASIC. A plurality of time-varying random numbers is generated by a random number generator (RNG), and the active mesh is driven and configured according to these random numbers. During tamper detection cycles, the active mesh is monitored with respect to the plurality of random numbers that is directly provided by the RNG. Upon a tampering attempt, a flag signal is generated and used to initialize subsequent anti-tampering actions. The active mesh may be controlled and monitored based on time-varying codes, and therefore, an adversary may not easily bypass the active mesh and attack the sensitive area.
Owner:MAXIM INTEGRATED PROD INC
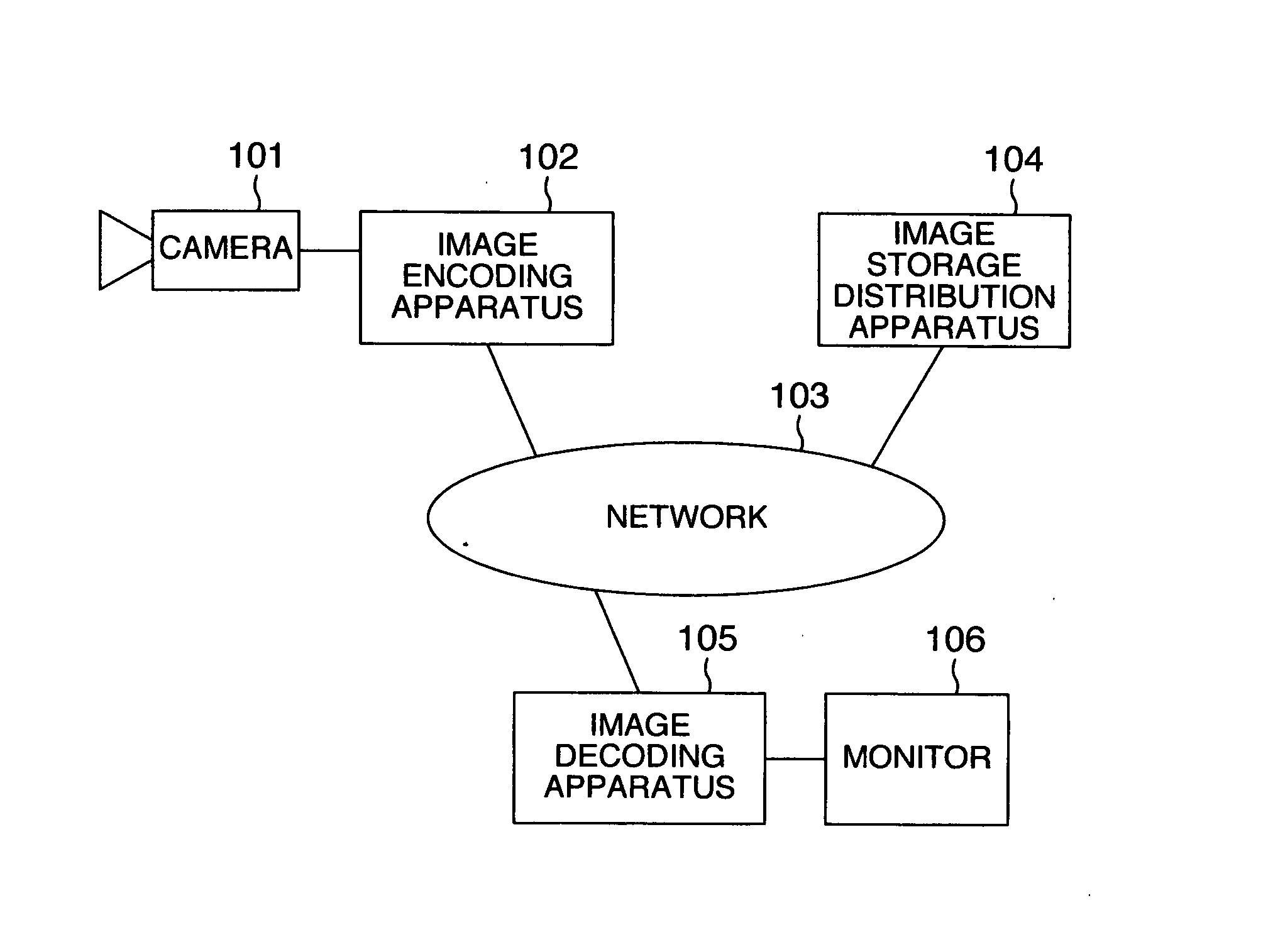
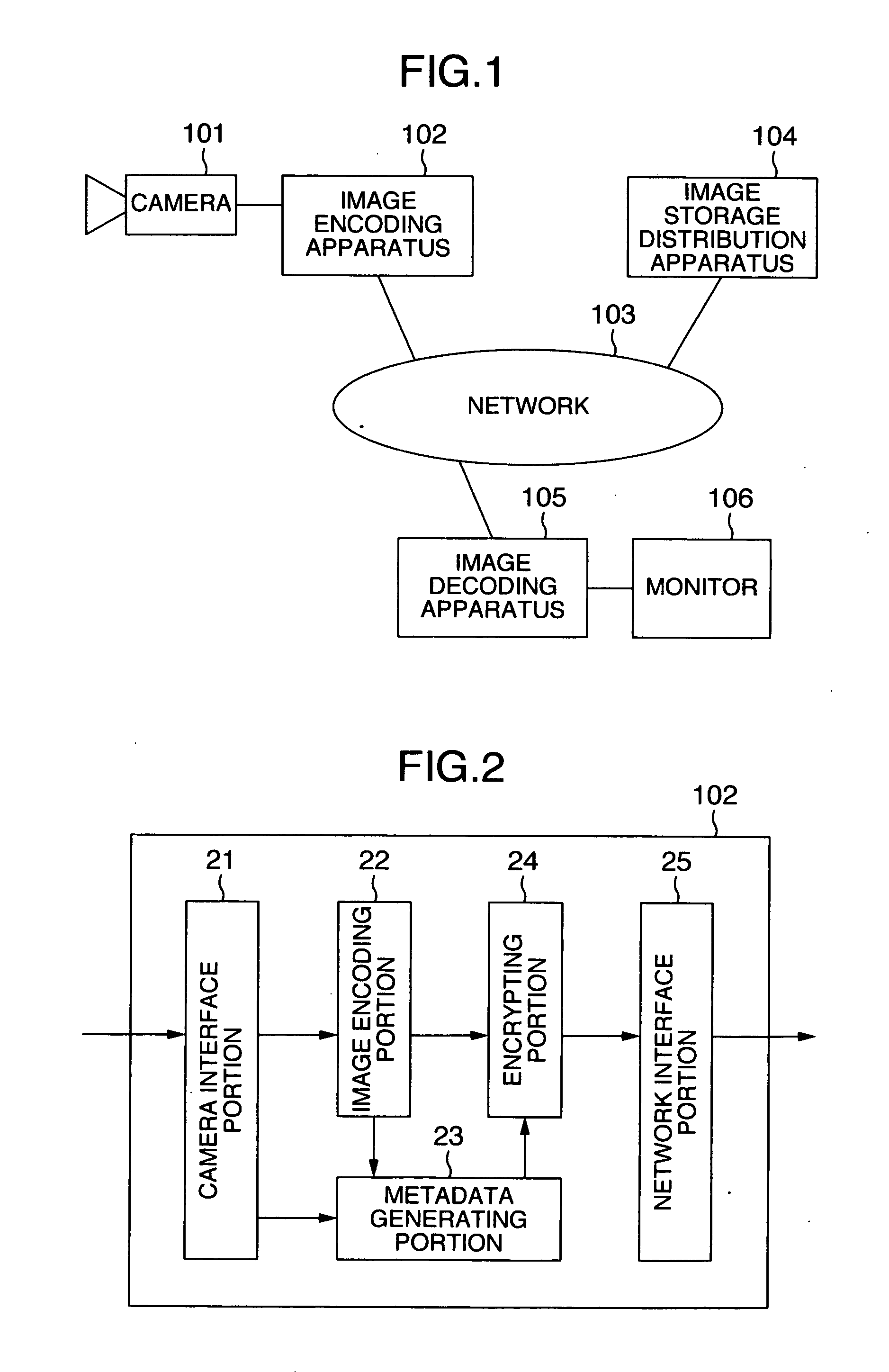
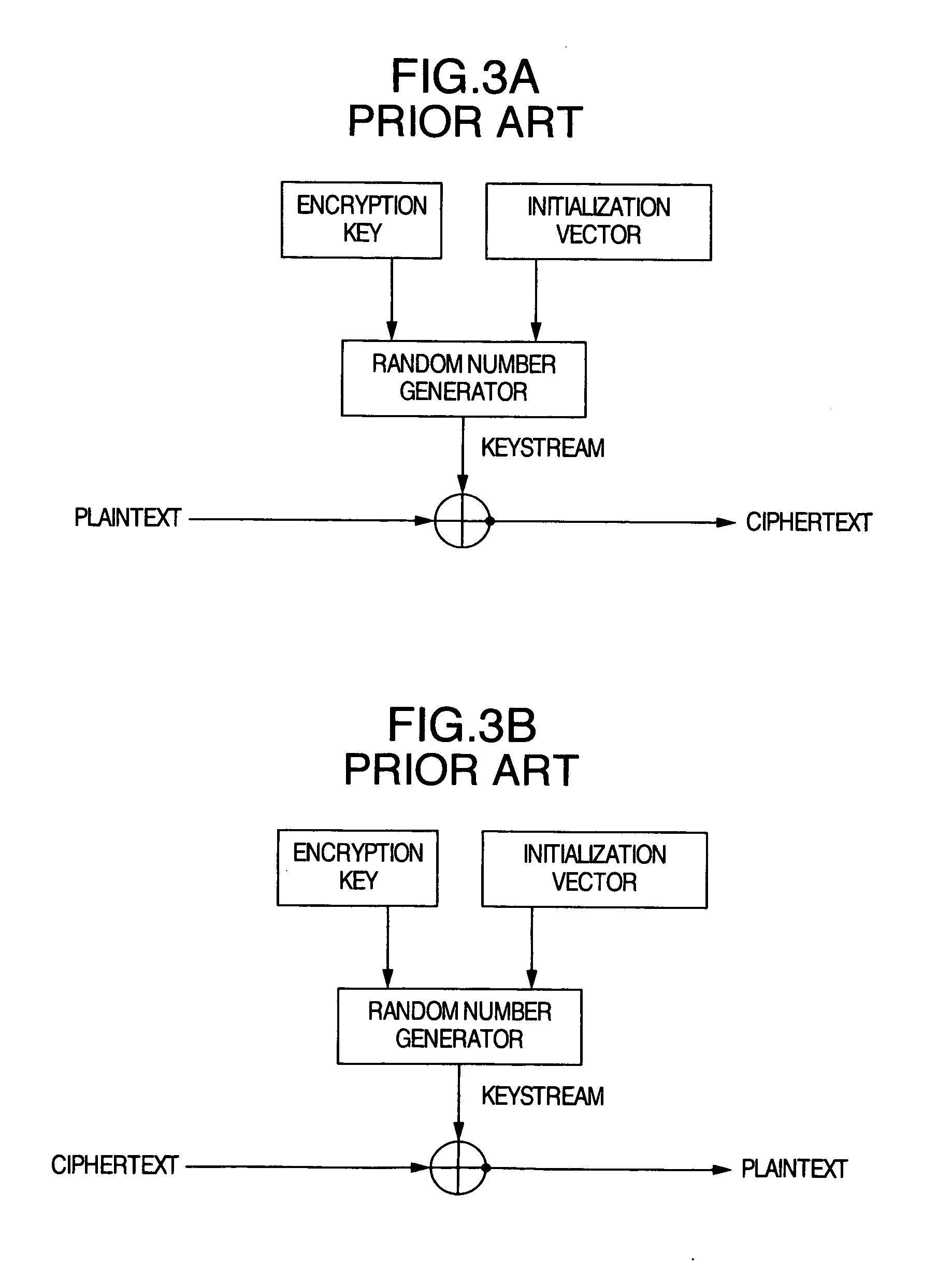
Encryption method, encryption apparatus, data storage distribution apparatus and data delivery system
InactiveUS20060056625A1Effective encryptionKey distribution for secure communicationData taking preventionComputer hardwareData shipping
Data to be encrypted is effectively encrypted by a data delivery system for encrypting the data to be encrypted with a transmitting apparatus and decrypting a cipher thereof with a receiving apparatus. In a configuration for encrypting and decrypting the data to be encrypted by using a random number sequence generated by a random number generating portion for generating the random number sequence uniquely decided from an input parameter, the transmitting apparatus generates the input parameter to perform encryption based on metadata of the data to be encrypted while the receiving apparatus generates the input parameter to perform cipher decryption based on the metadata embedded in the data to be encrypted.
Owner:KOKUSA ELECTRIC CO LTD
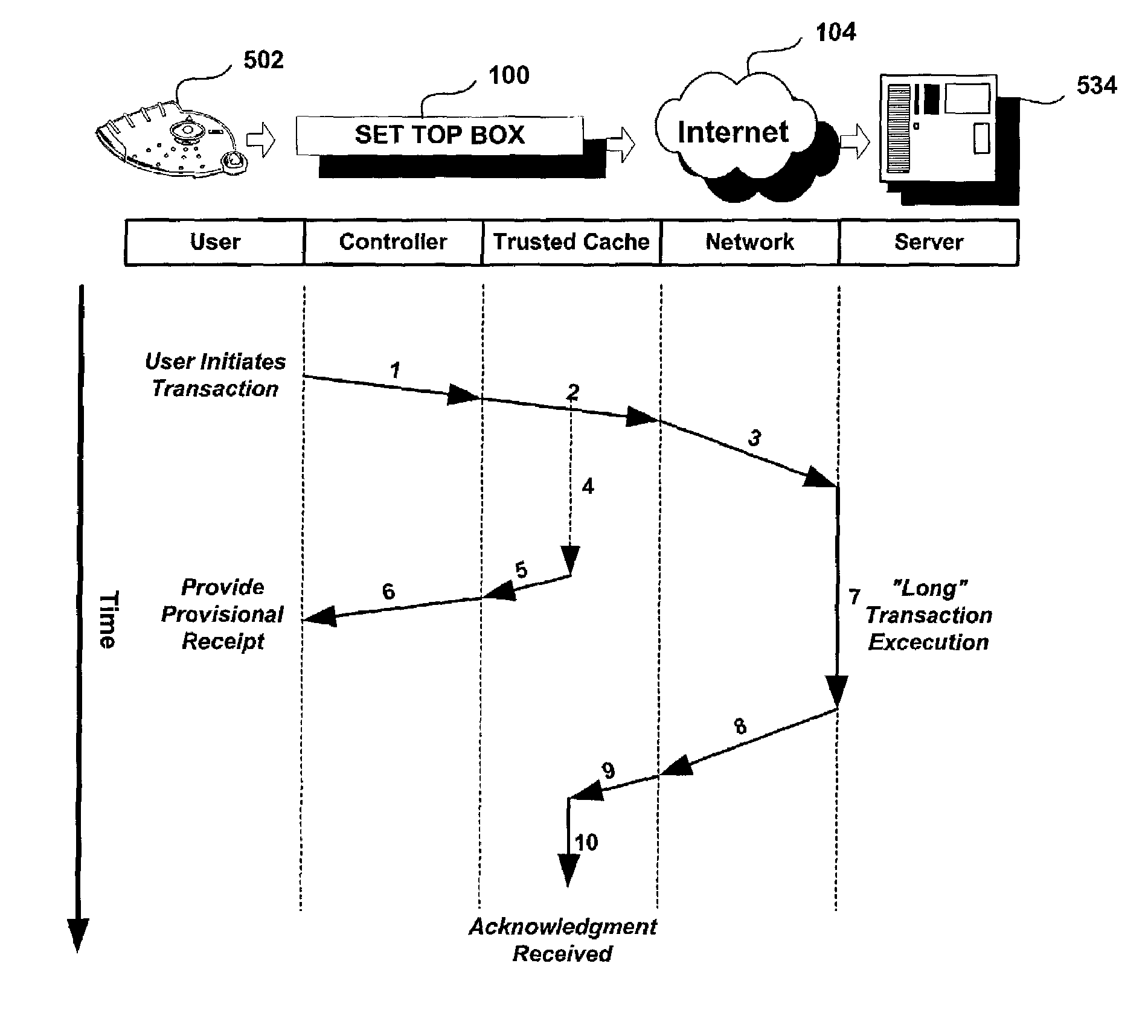
Trusted transactional set-top box
InactiveUS7346917B2Poor resolutionMaximum safetyTelevision system detailsAnalogue secracy/subscription systemsPrivate networkThe Internet
A set top box (STB) includes a trusted transactional cache and associated transactional protocol and enables e-commerce transactions to be securely committed to a remote server extremely quickly and with little network overhead. The invention does away with the user concern of whether the transaction was successful. The STB operates equally well on robust private networks as on unpredictable Internet or wireless networks, and avoids upsetting users who would otherwise have to wait in front of a display screen for confirmation of completion of the transaction after a temporary communication failure with the central site. The method may advantageously be used to provide cost-effective micro-payments solutions. The STB may include a dual headed display capability in which data and video maybe be directed to separate displays. The STB may feature an embedded ticket printer, as well as an embedded barcode scanner. This enables non computer literate users to more conveniently track transactions committed via the STB, or to take advantage of promotional coupons. The STB features an embedded hardware true Random Number Generator to produce maximum entropy encryption keys, therefore providing maximum secure and fool-proof means to protect private data using government authorized encryption schemes.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
Random number generator
A random number generator comprising an oscillator with an output signal dependant upon a random source, a sampling device to sample the output signal from the oscillator to obtain a sampled oscillator output, and a fixed frequency clock driven linear feedback shift register (LFSR) communicatively coupled to the sampling device via a digital gate to receive the sampled oscillator output, and to provide a random number at an output of the LFSR. Additionally, the random number generator may comprise an optional mixing function communicatively coupled to the LFSR to read the random number, and to insert the random number into an algorithm to obtain a robust random number.
Owner:MARVELL ASIA PTE LTD
Video pachinko on a video platform as a gaming device
InactiveUS7125333B2Apparatus for meter-controlled dispensingVideo gamesNumber generatorRandom number generation
A disclosed gaming machine presents pachinko games to a player playing the gaming machine. In some embodiments, a player may initiate a new pachinko game on the gaming machine while the outcome of a previous pachinko game is being presented to the player. The wagers on each game may be different. Also, a player may input parameters into the gaming machine that affect the game outcome presentation. For a number of different games, two or more game outcomes may be presented simultaneously to the player on the gaming machine. However, the game outcomes determined by the gaming machine are independent of one another and do not depend on the game outcome presentation. Normally, the game outcomes are determined using a random number generator and a pay table stored in a memory on the gaming machine.
Owner:IGT
Quantum noise random number generator
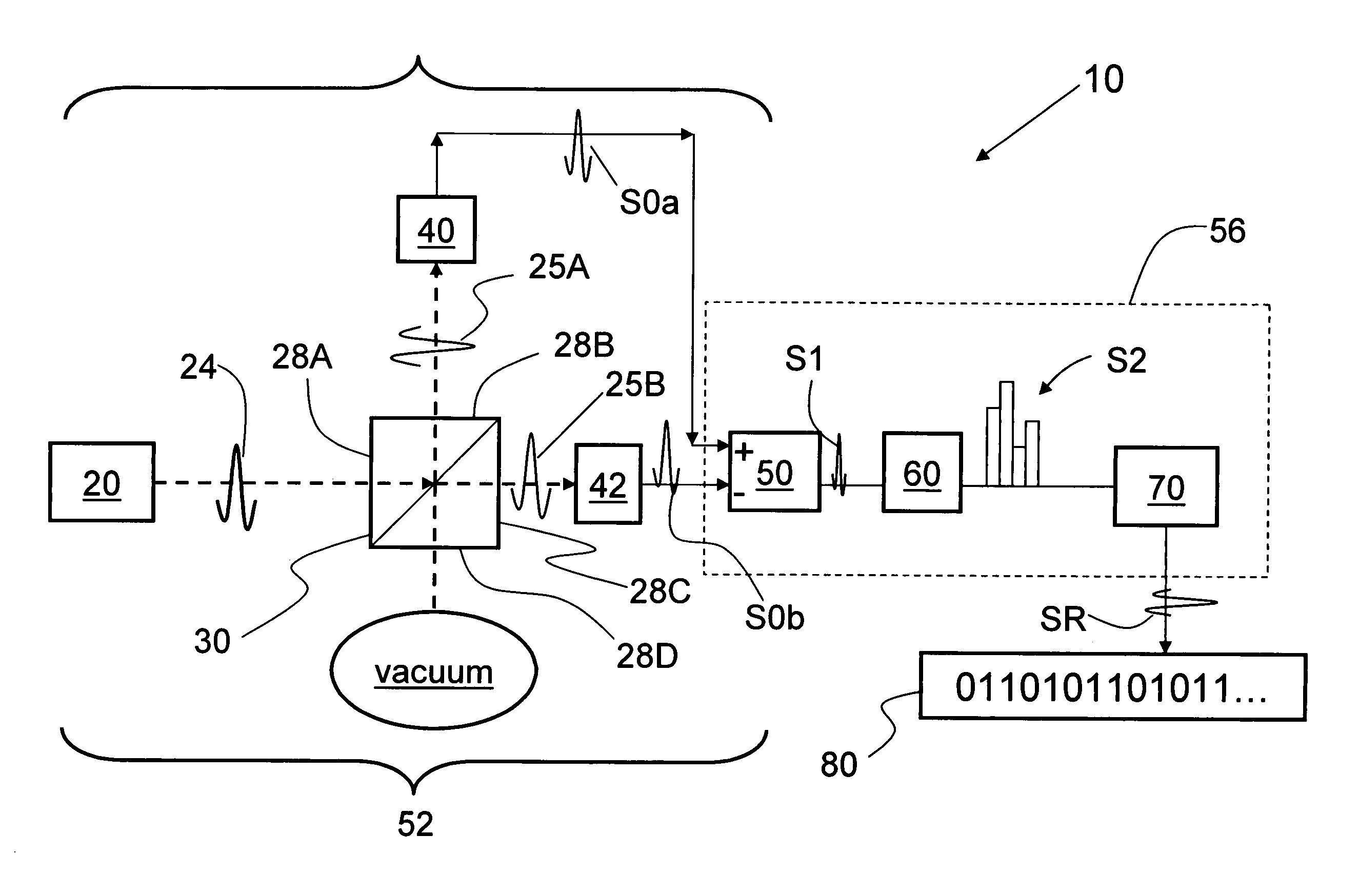
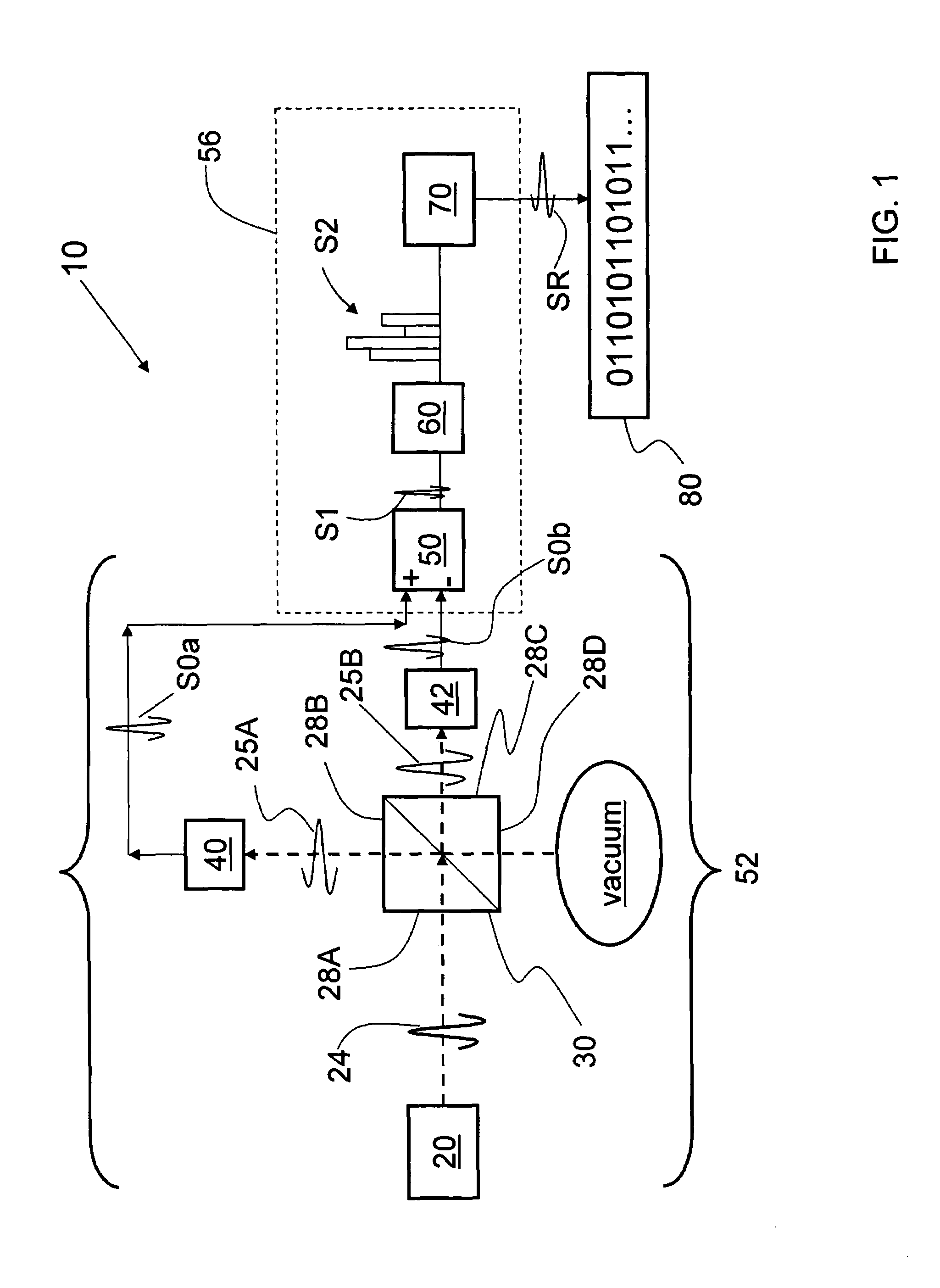
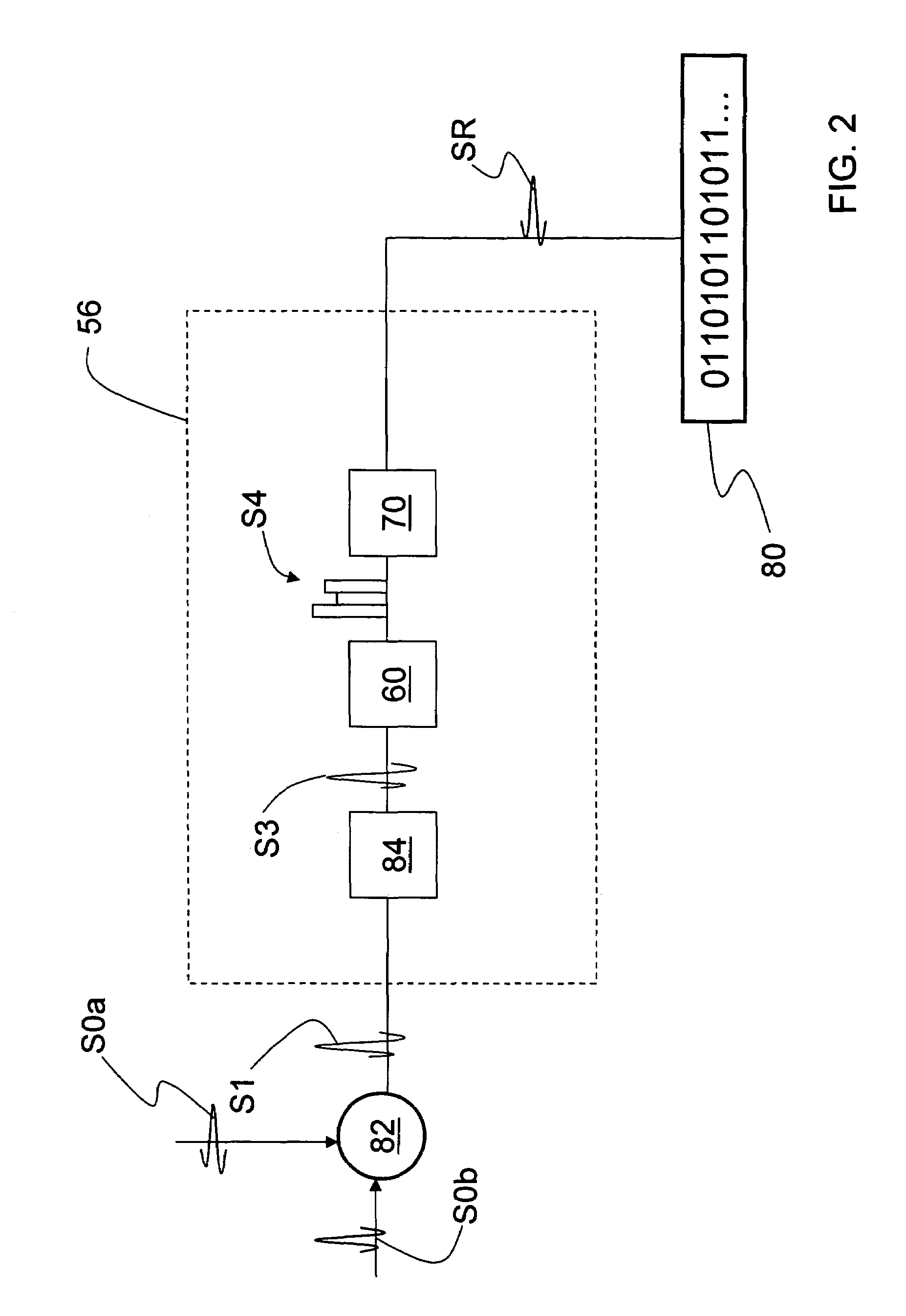
A quantum noise random number generator system that employs quantum noise from an optical homodyne detection apparatus is disclosed. The system utilizes the quantum noise generated by splitting a laser light signal using a beamsplitter having four ports, one of which receives one of which is receives the laser light signal, one of which is connected to vacuum, and two of which are optically coupled to photodetectors. Processing electronics process the difference signal derived from subtracting the two photodetector signals to create a random number sequence. Because the difference signal associated with the two photodetectors is truly random, the system is a true random number generator.
Owner:MAGIQ TECH INC
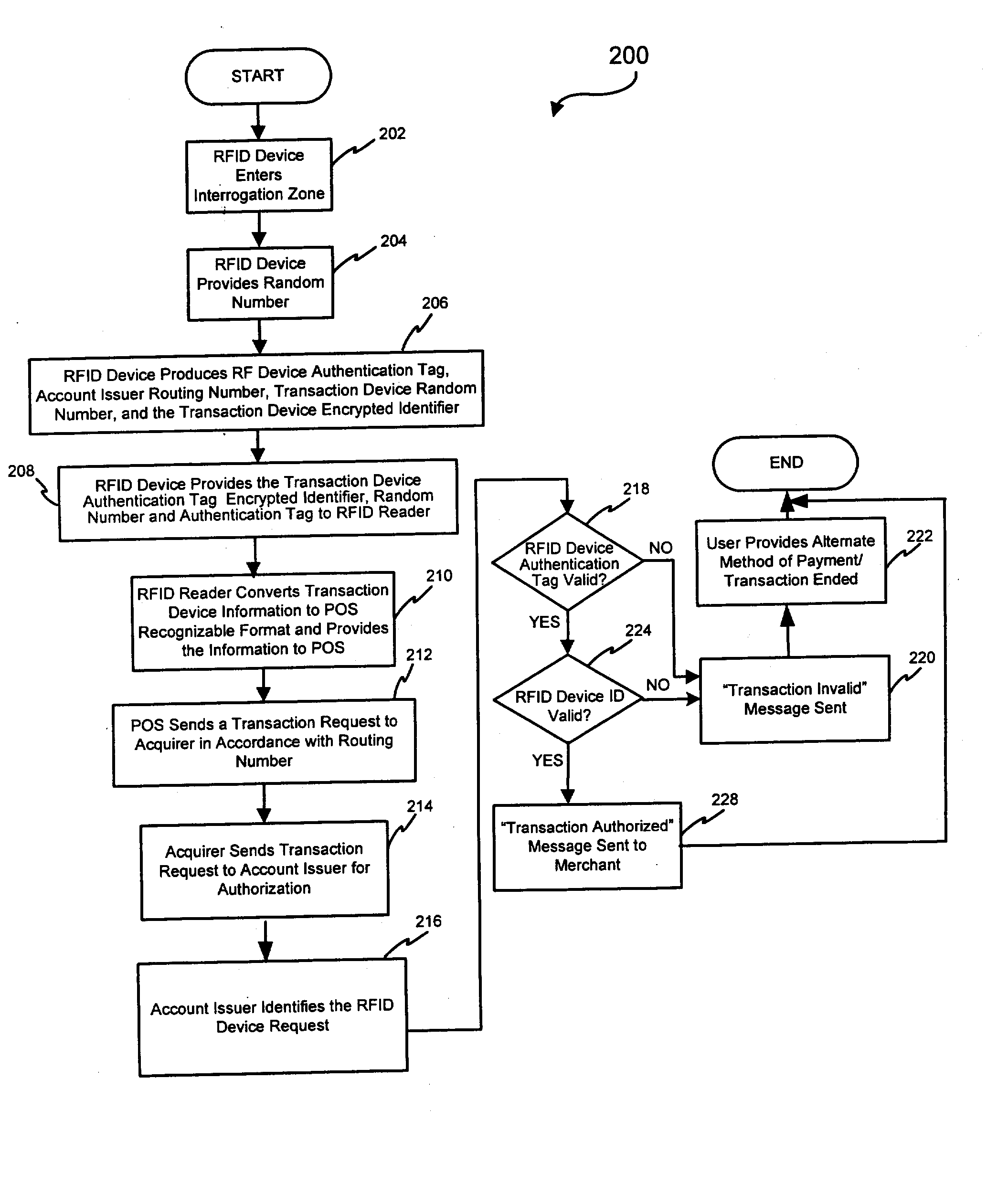
System and method for securing RF transactions using a radio frequency identification device including a random number generator
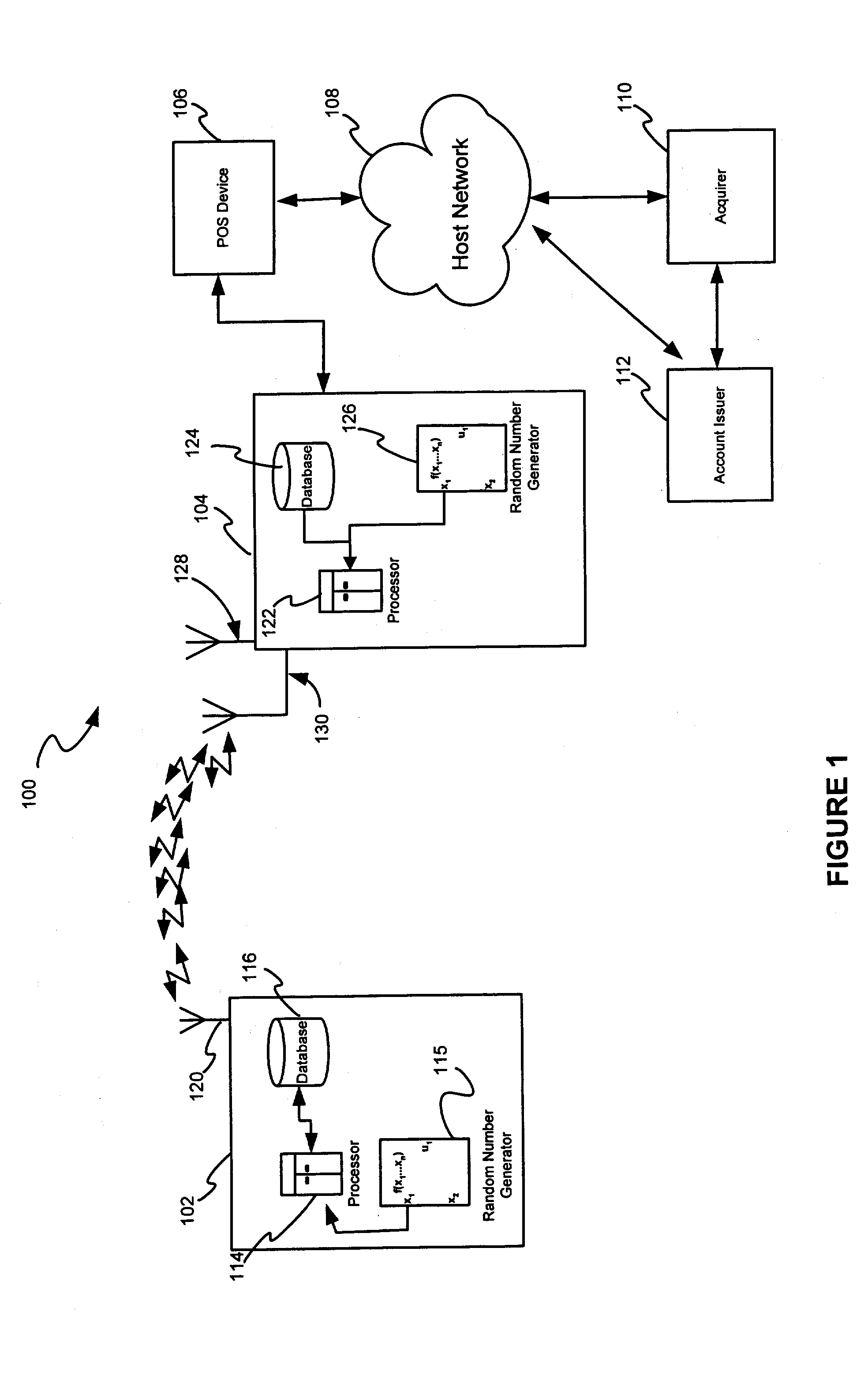
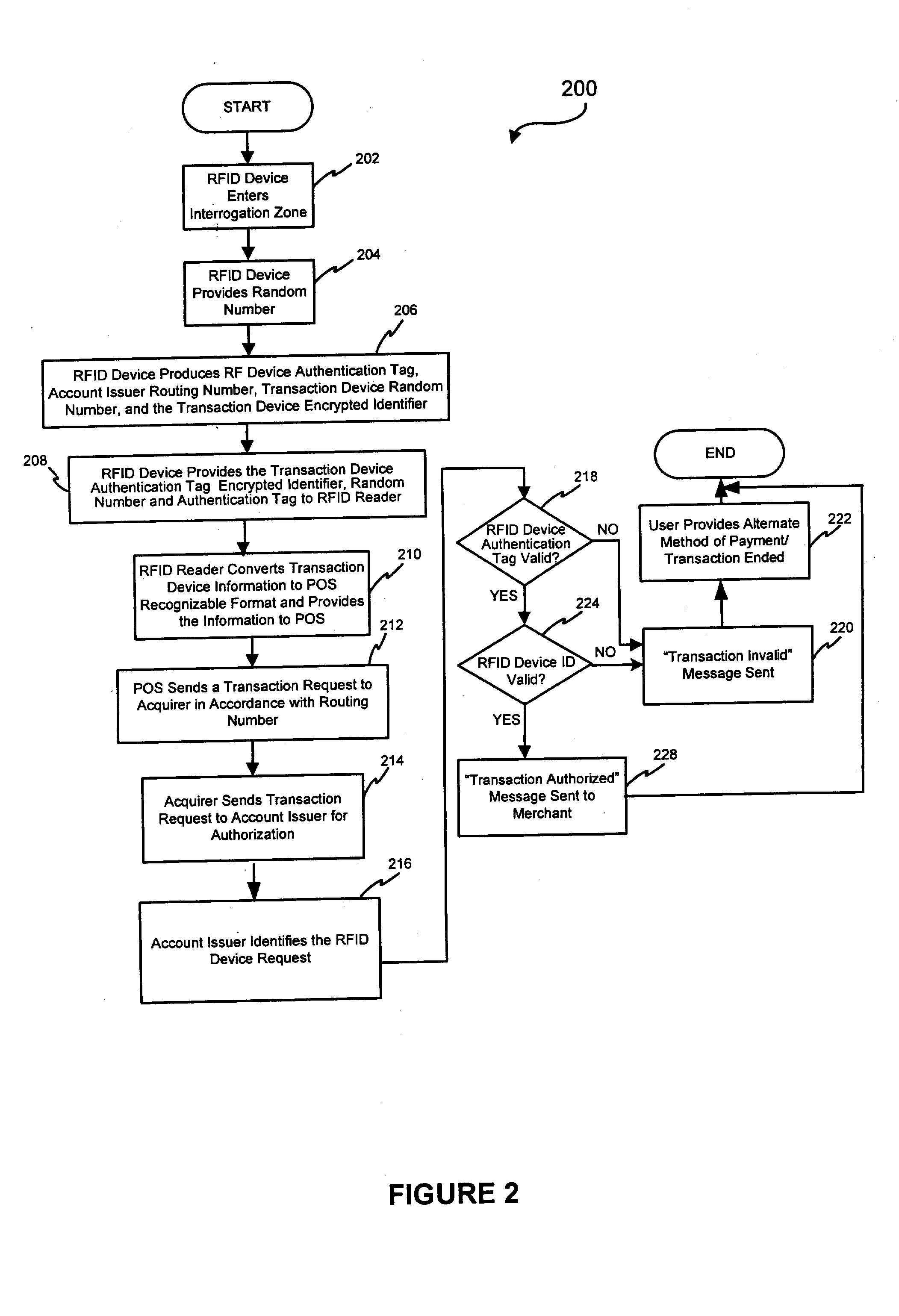
InactiveUS20050071231A1Individual entry/exit registersPayment circuitsIdentification deviceNumber generator
A system and method for securing a Radio Frequency (RF) transaction using a RF identification device (RFID) transaction device is provided. The method includes a RFID transaction device including a random number generator for generating a random number. The random number may be used by an account issuer to verify the validity of a RFID transaction device or RFID reader communicating on the RF transactions network. The authorizing agent may receive the random number and compare the random number to a device validating code.
Owner:LIBERTY PEAK VENTURES LLC
Countermeasure against denial-of-service attack on authentication protocols using public key encryption
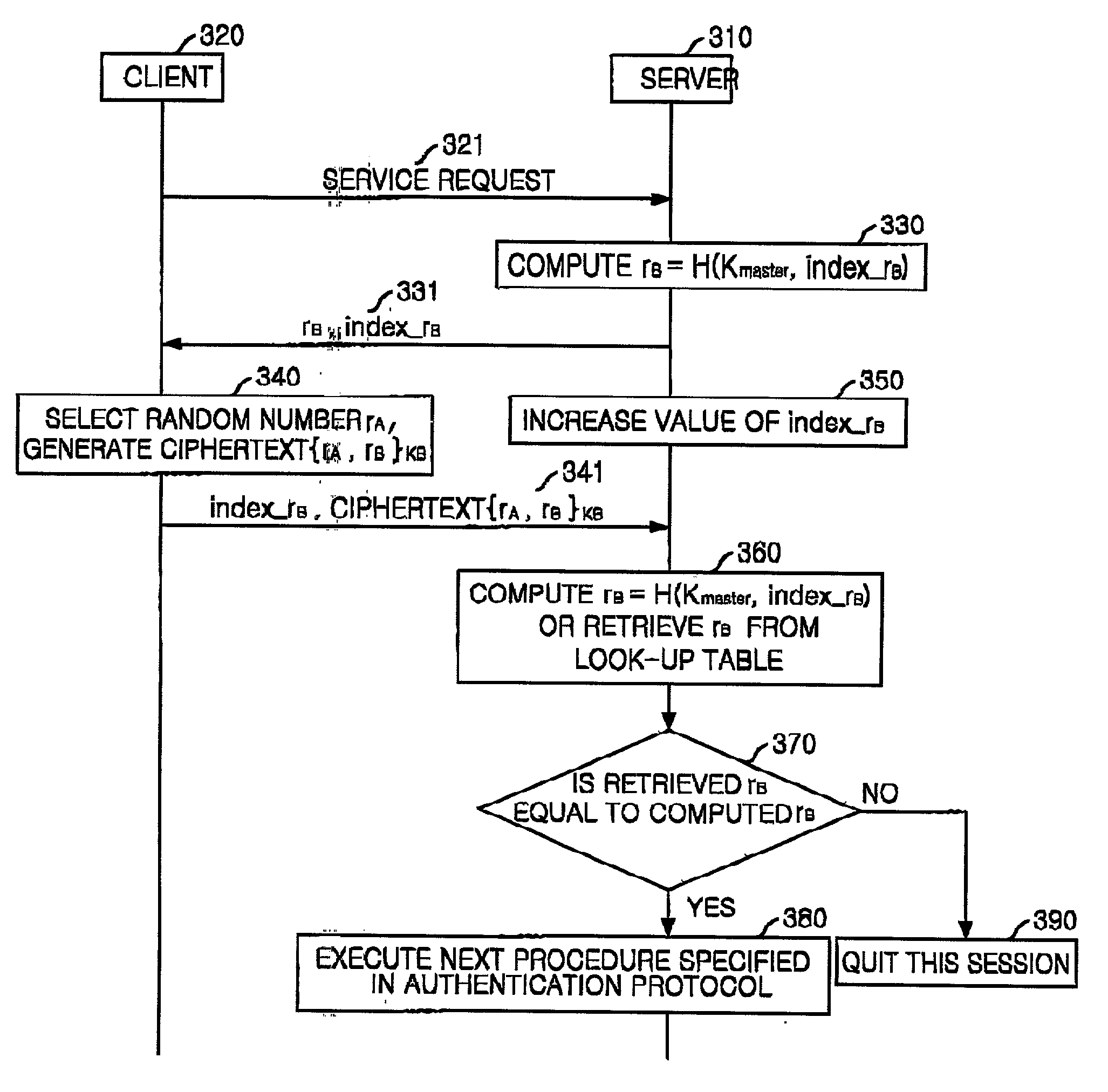
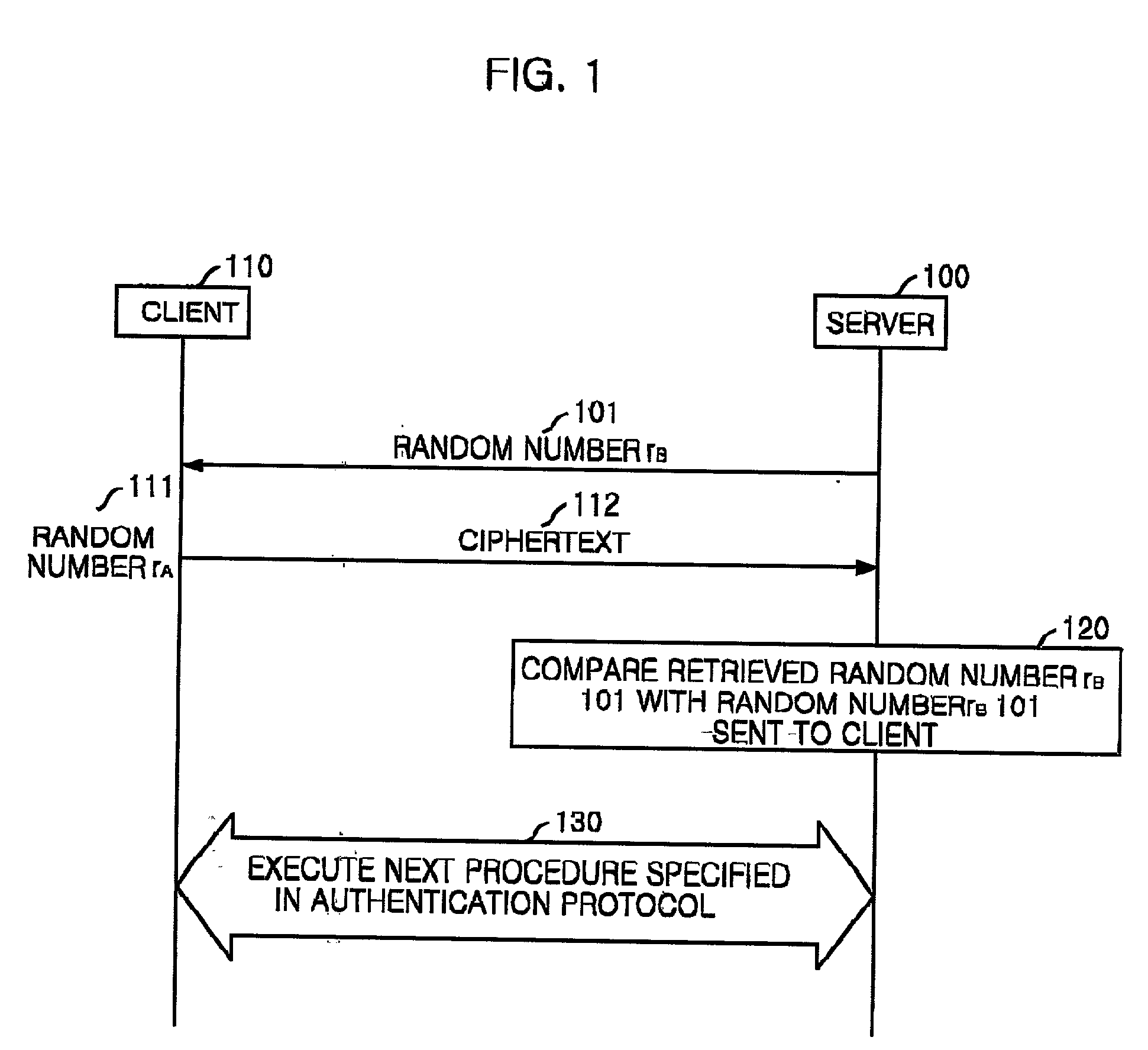
InactiveUS20020073322A1Public key for secure communicationUser identity/authority verificationClient-sideProtocol for Carrying Authentication for Network Access
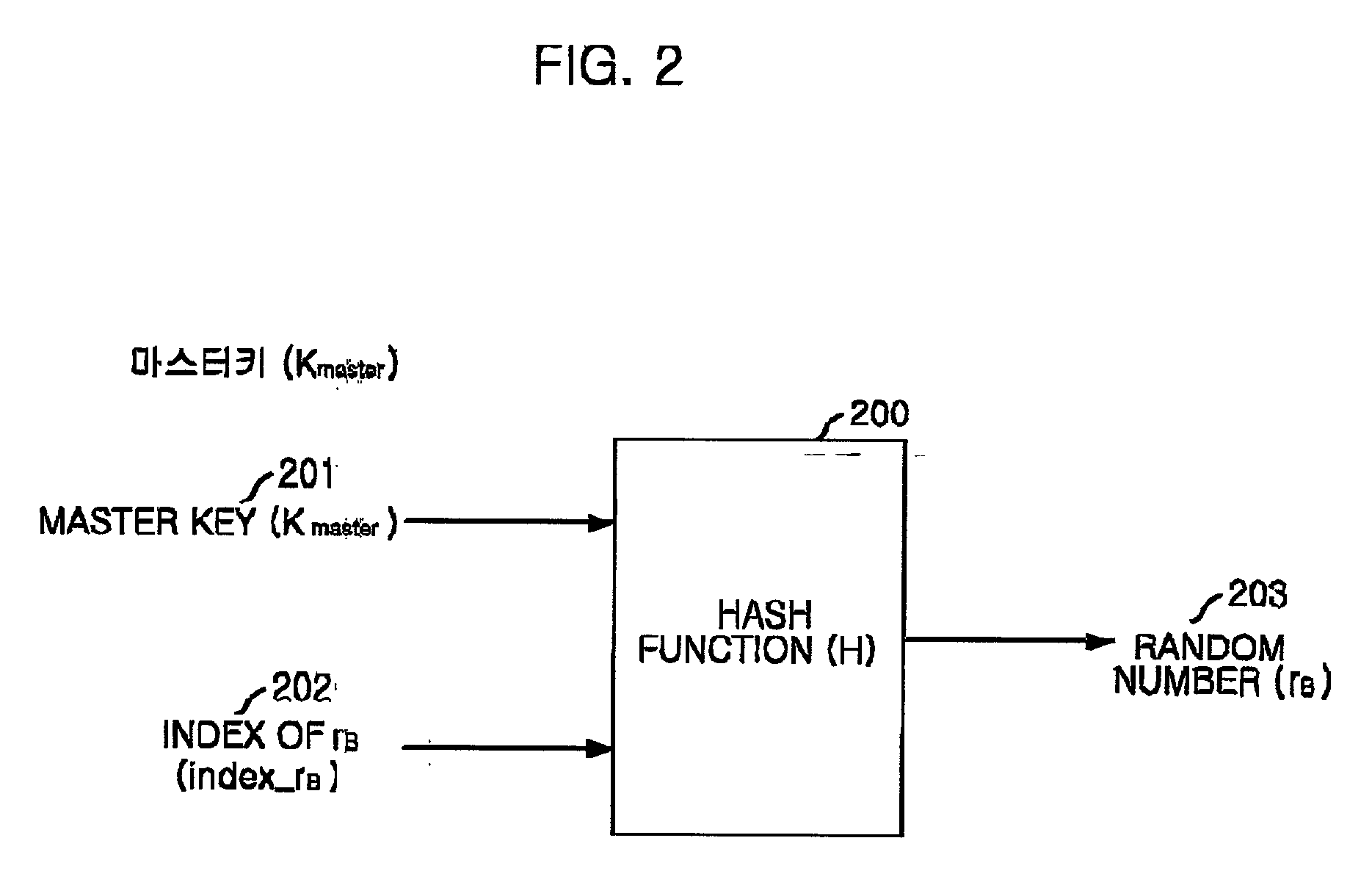
The present invention gives robustness for the denial-of-service to the authentication protocol itself, loads no additional public key computation, and is applicable to any authentication protocol in which the client authenticates the server by sending the client's random number encrypted under the public key of the server. The method for defeating a denial-of-service attack for use in a communication system in which the client sends a ciphertext of a random number chosen by the client encrypted under a public key of the server to authenticate the server includes the steps of: (a) the server's generating a random number rB in response to a service request from the client and sending the random number to the client; (b) the server's receiving the ciphertext which the client produced by using the random number rB from the client and a random number rA of the client; (c) the server's recovering a random number rB from the ciphertext received from the client and comparing the recovered random number with the random number sent to the client; and (d) if the random numbers match at the step (c), providing the service, and, otherwise, denying the service.
Owner:KT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com