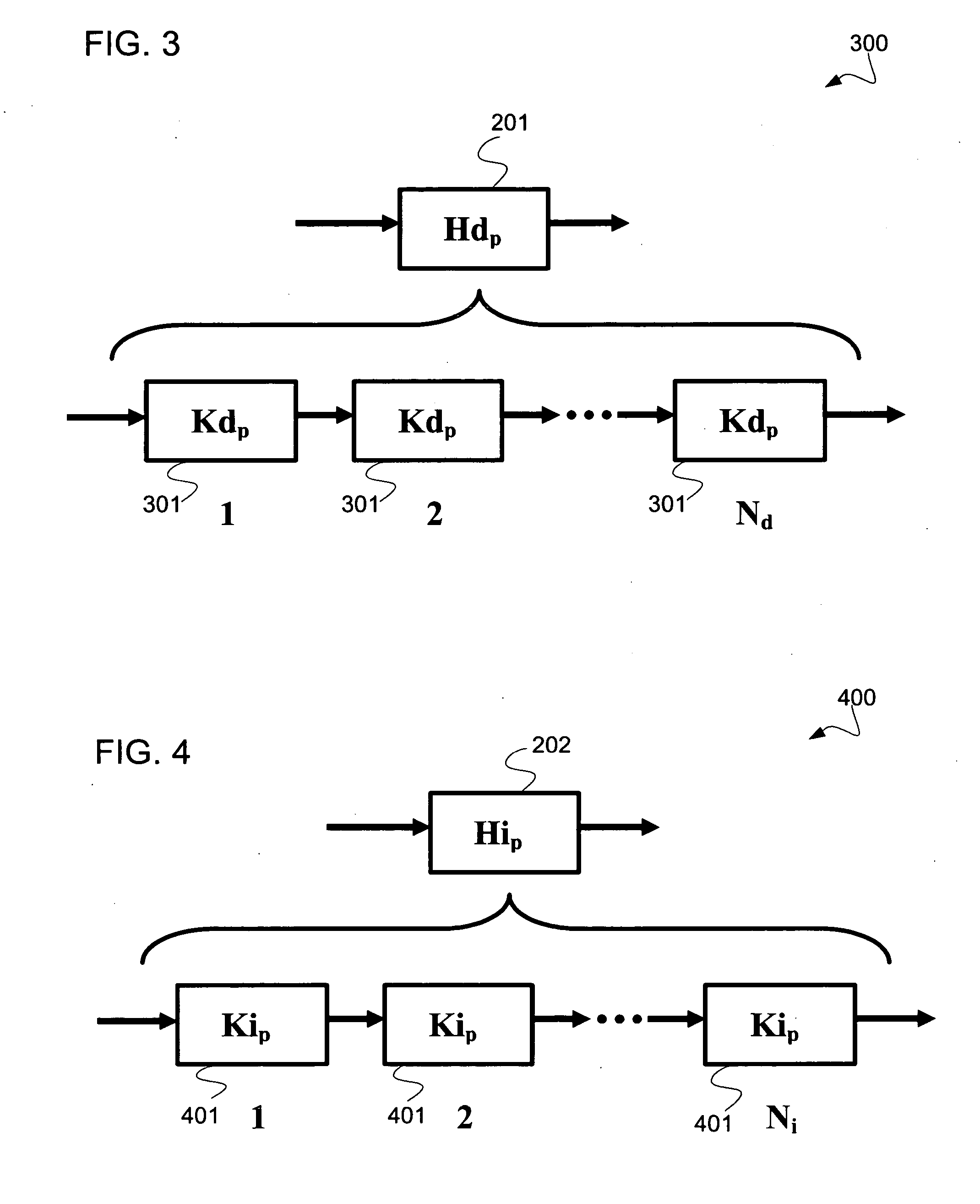
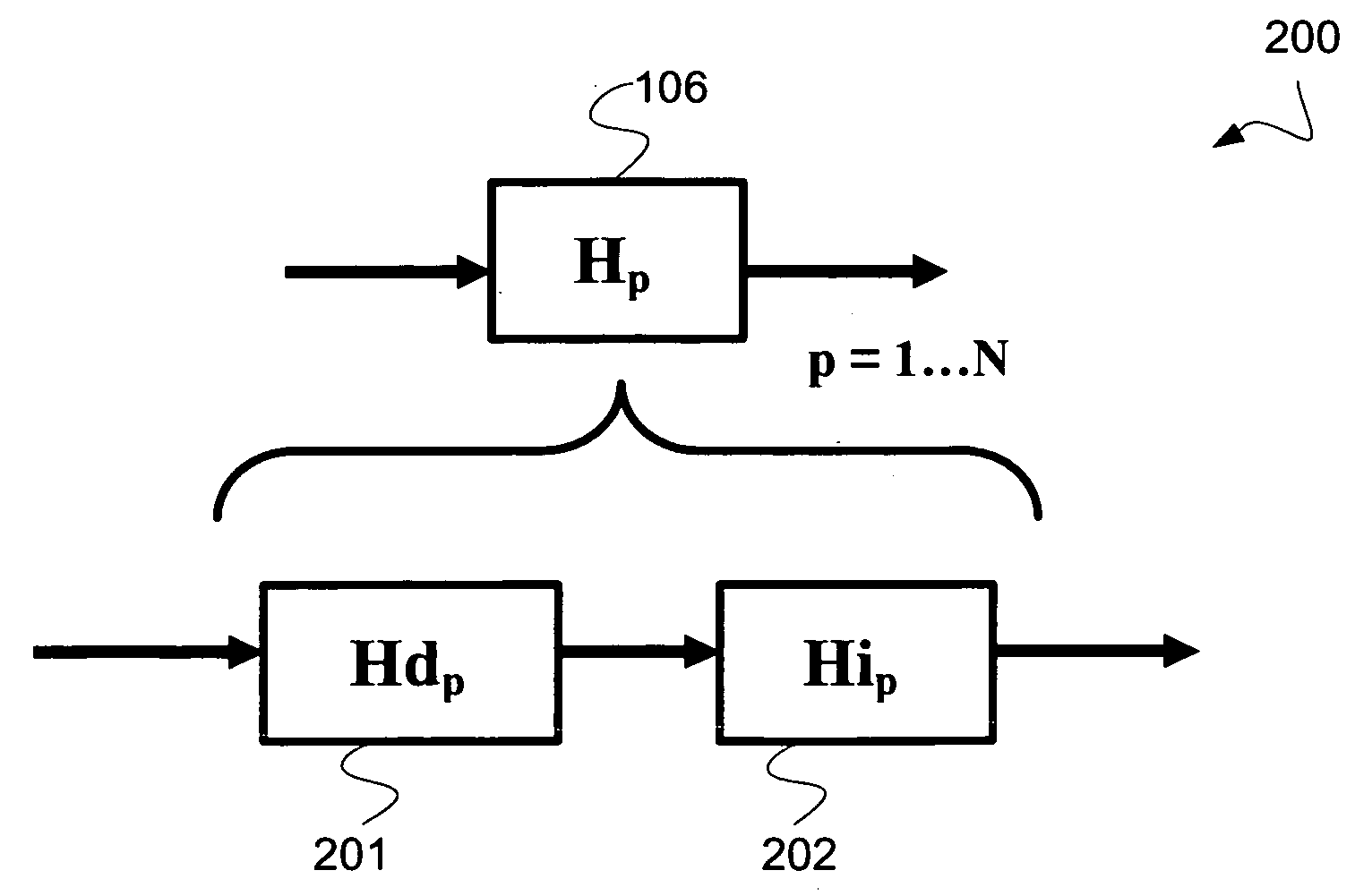
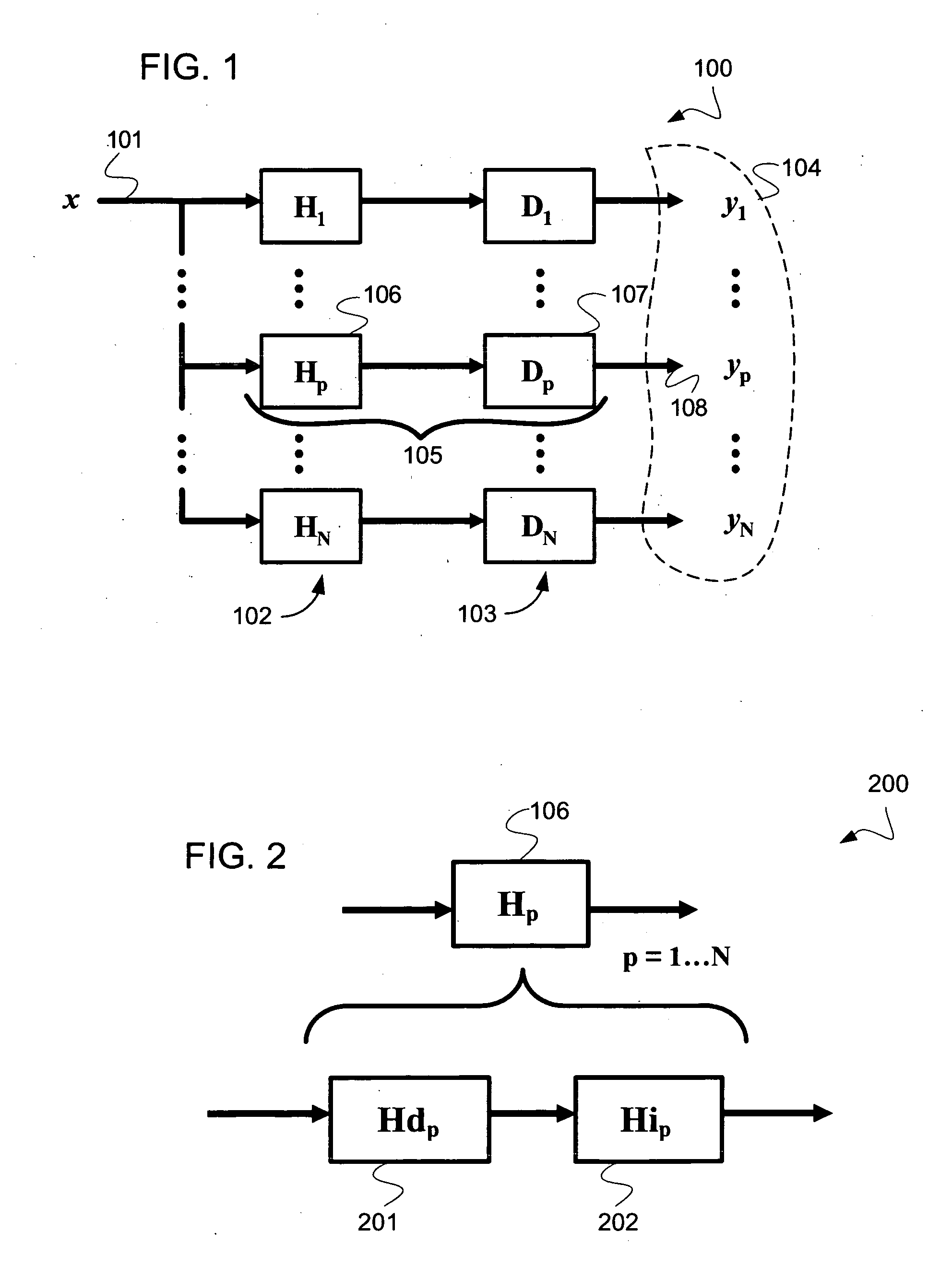
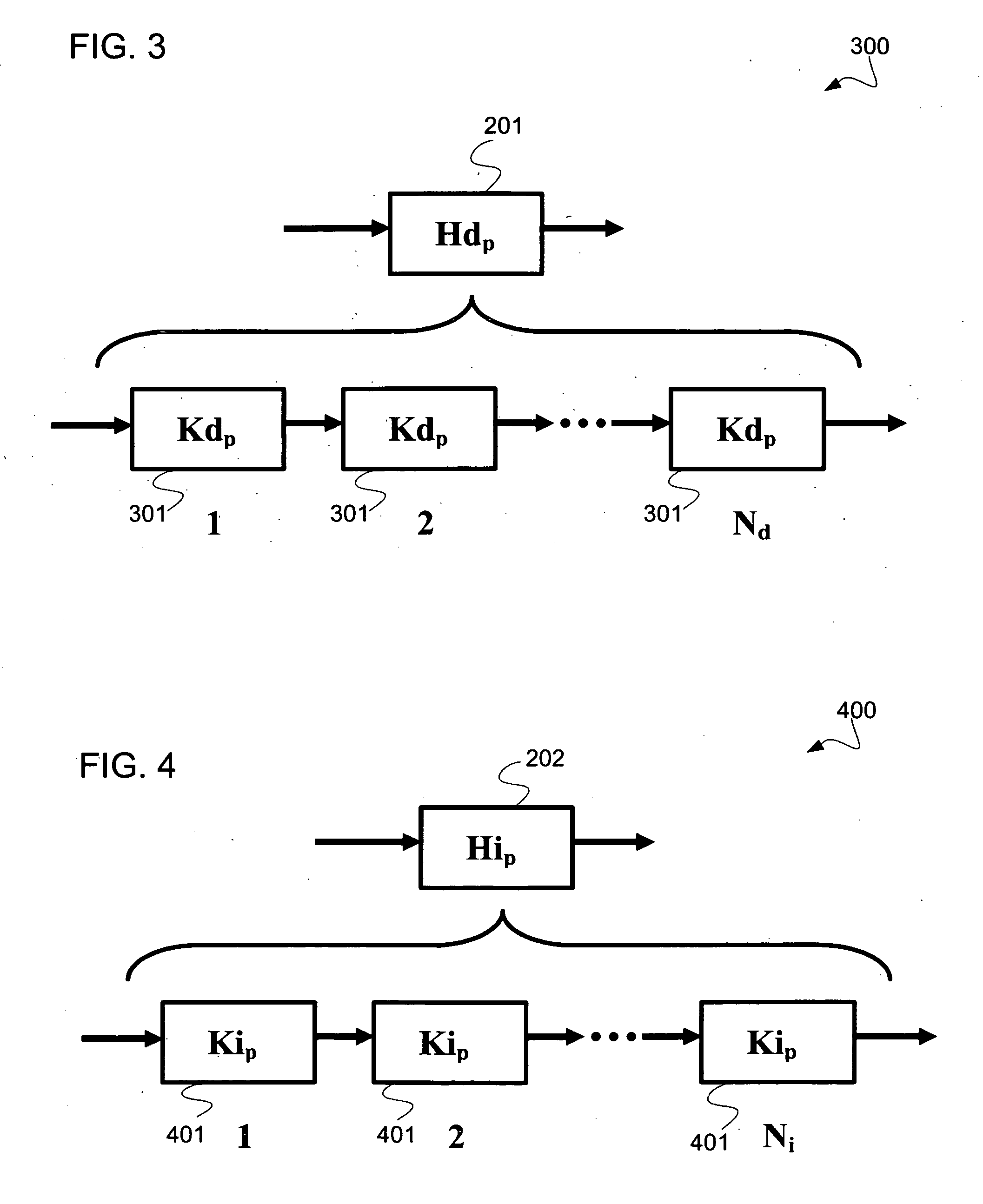
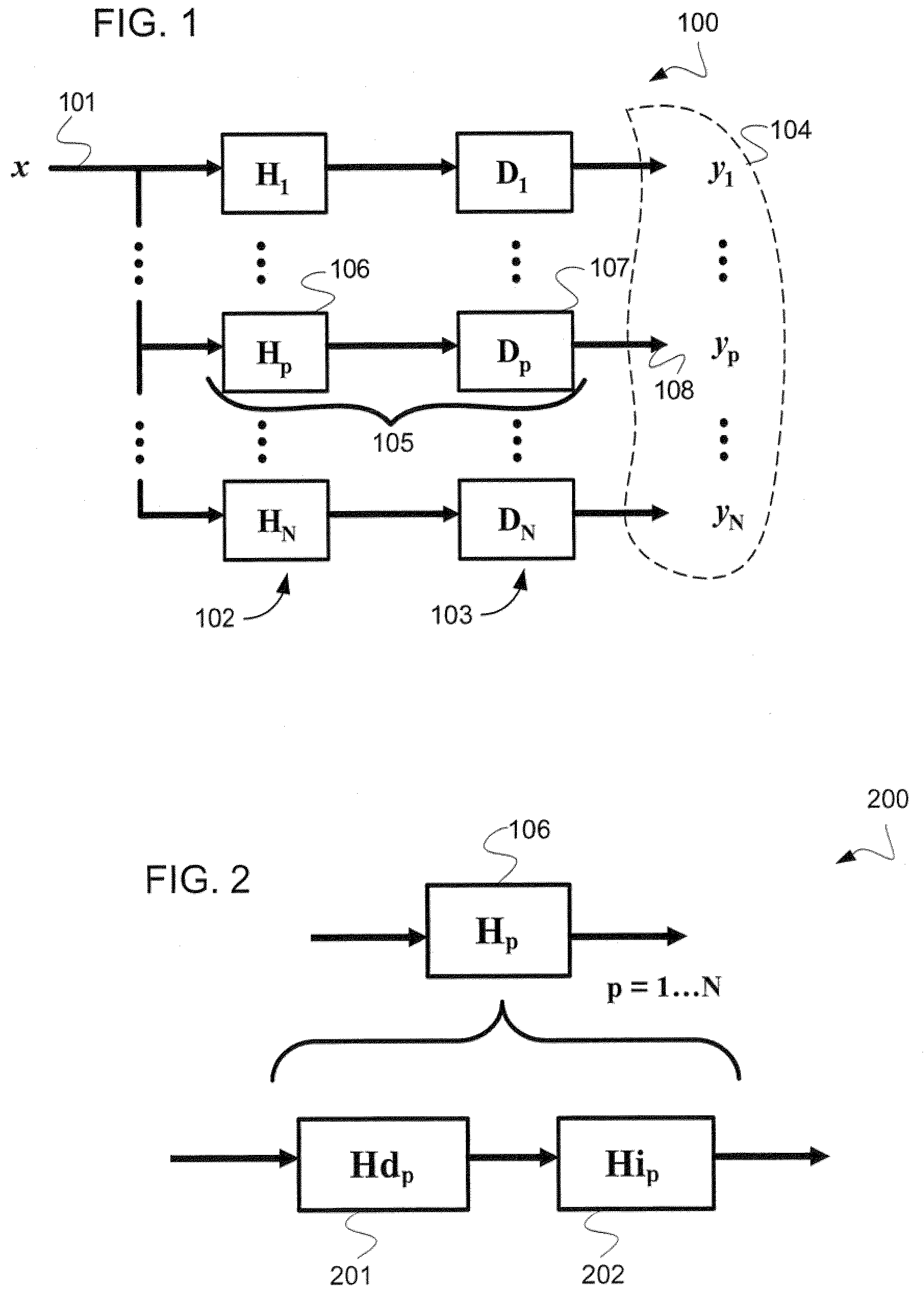
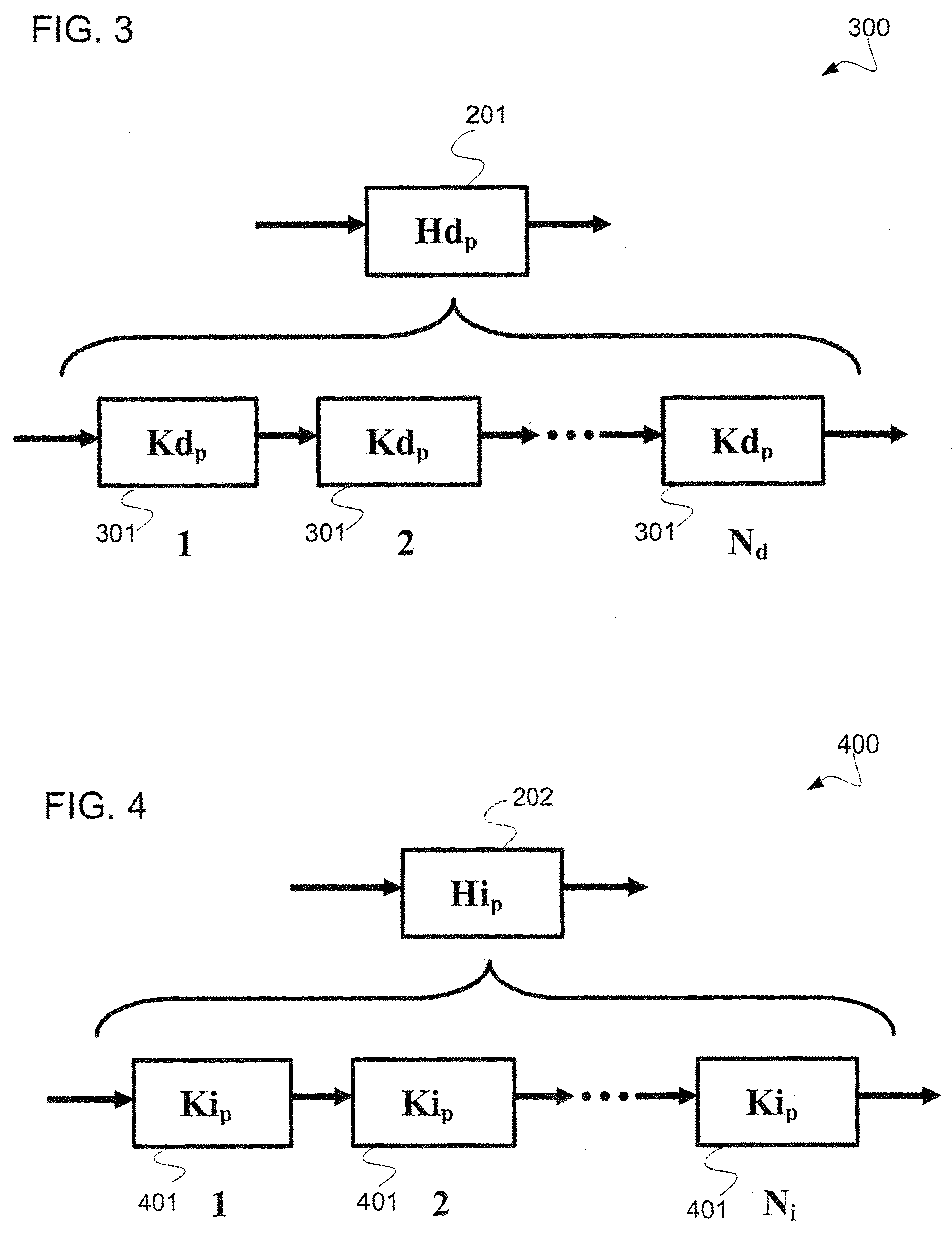
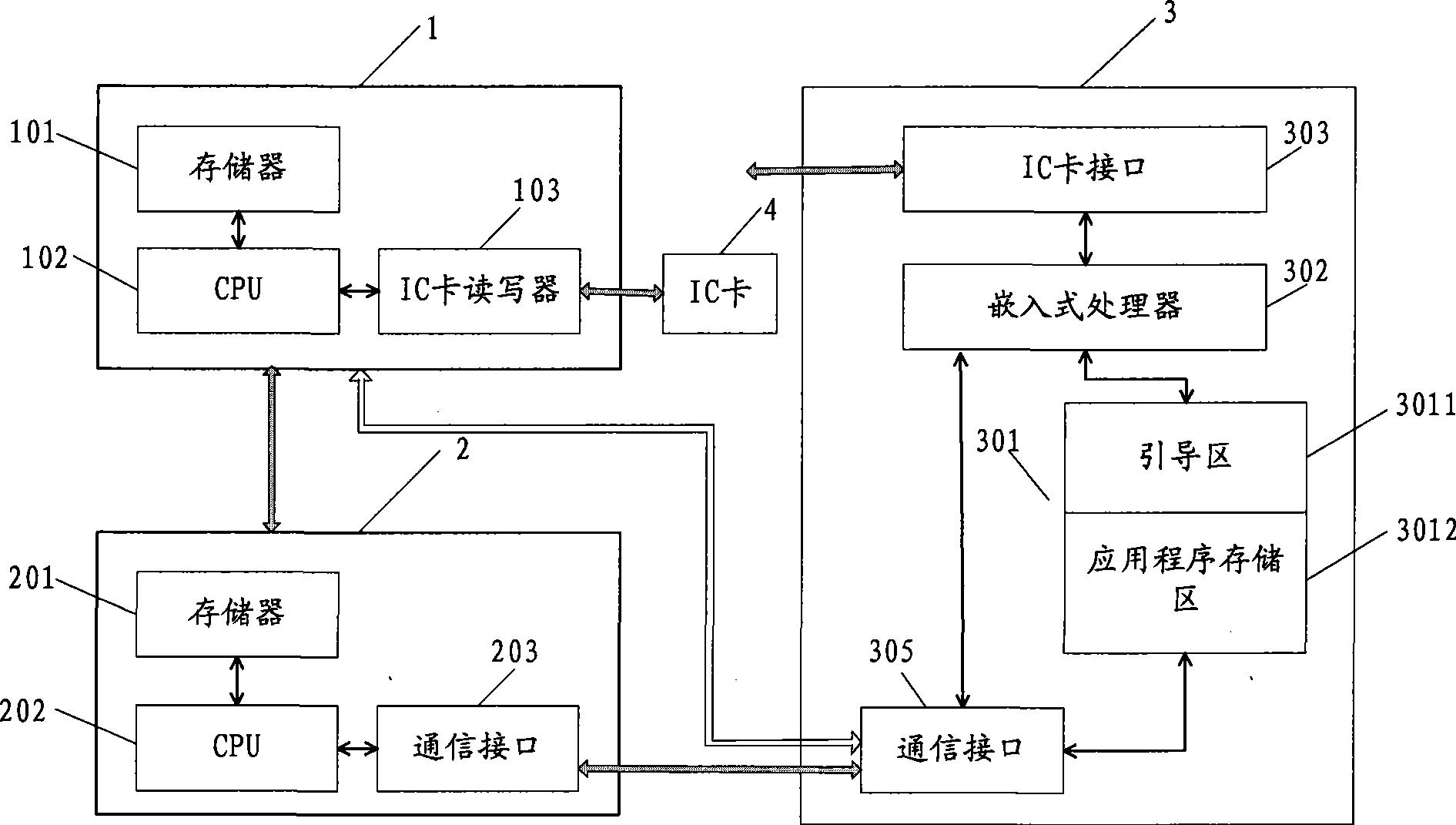
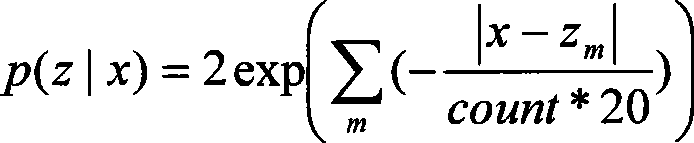Patents
Literature
238 results about "Embedded hardware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
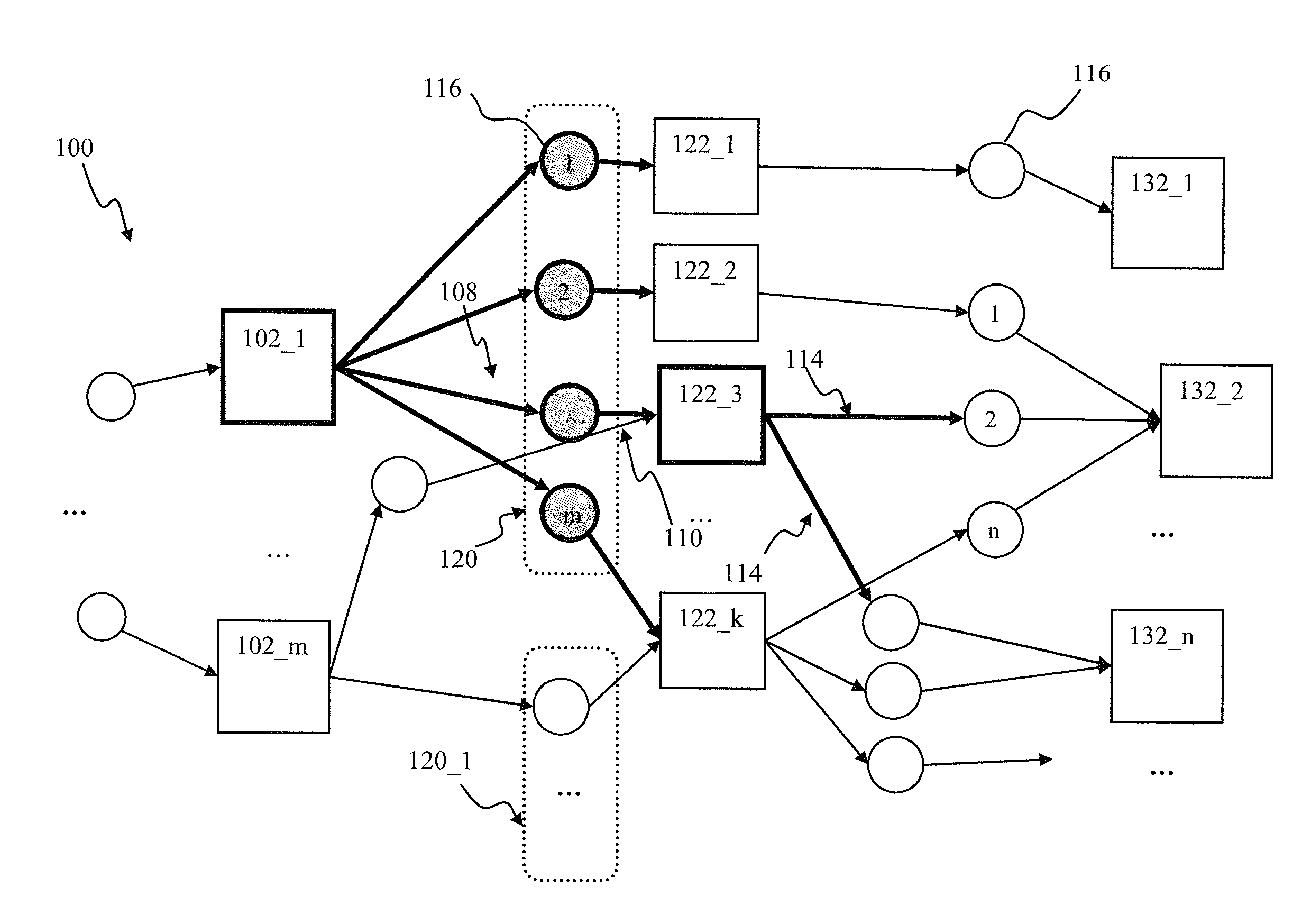
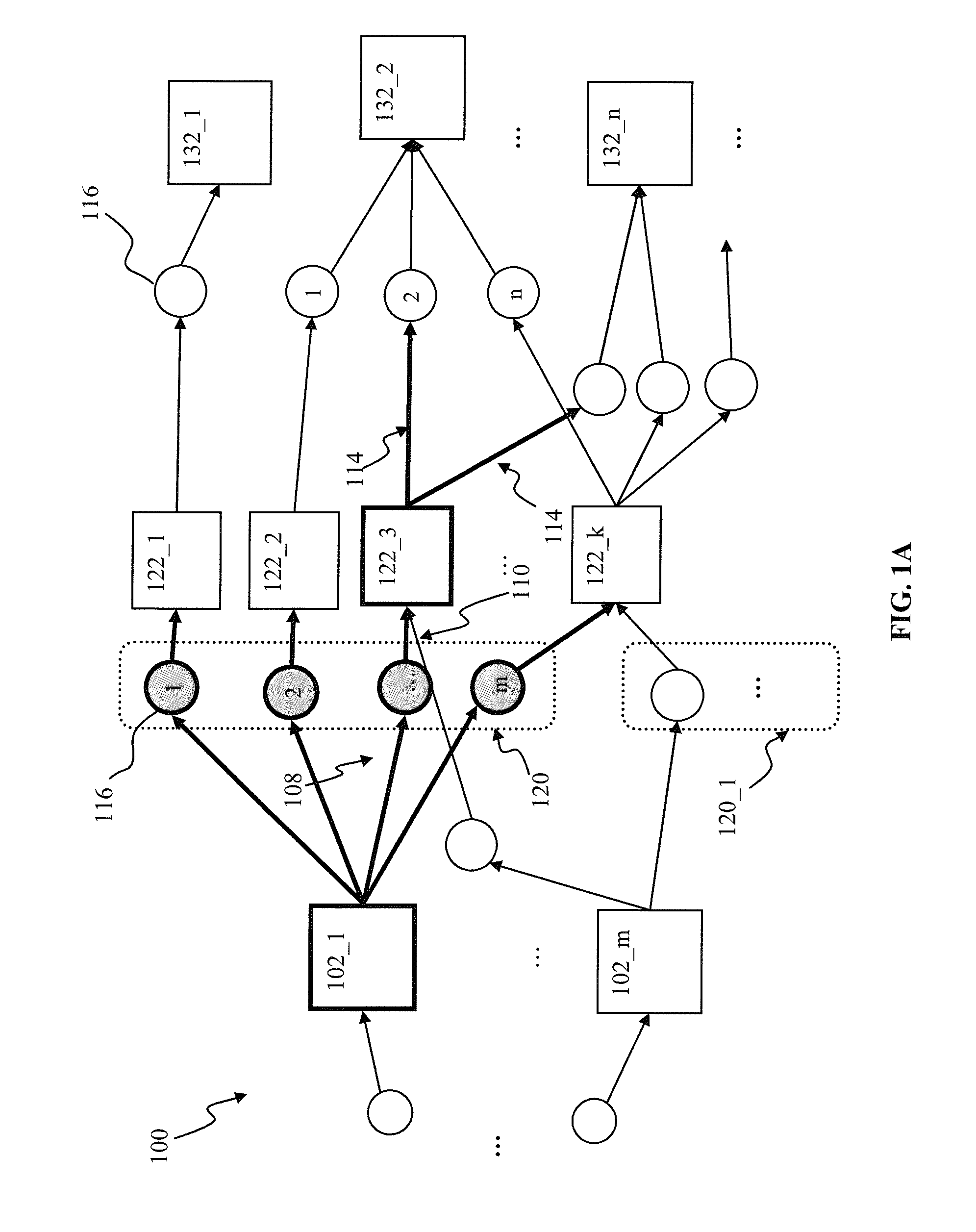
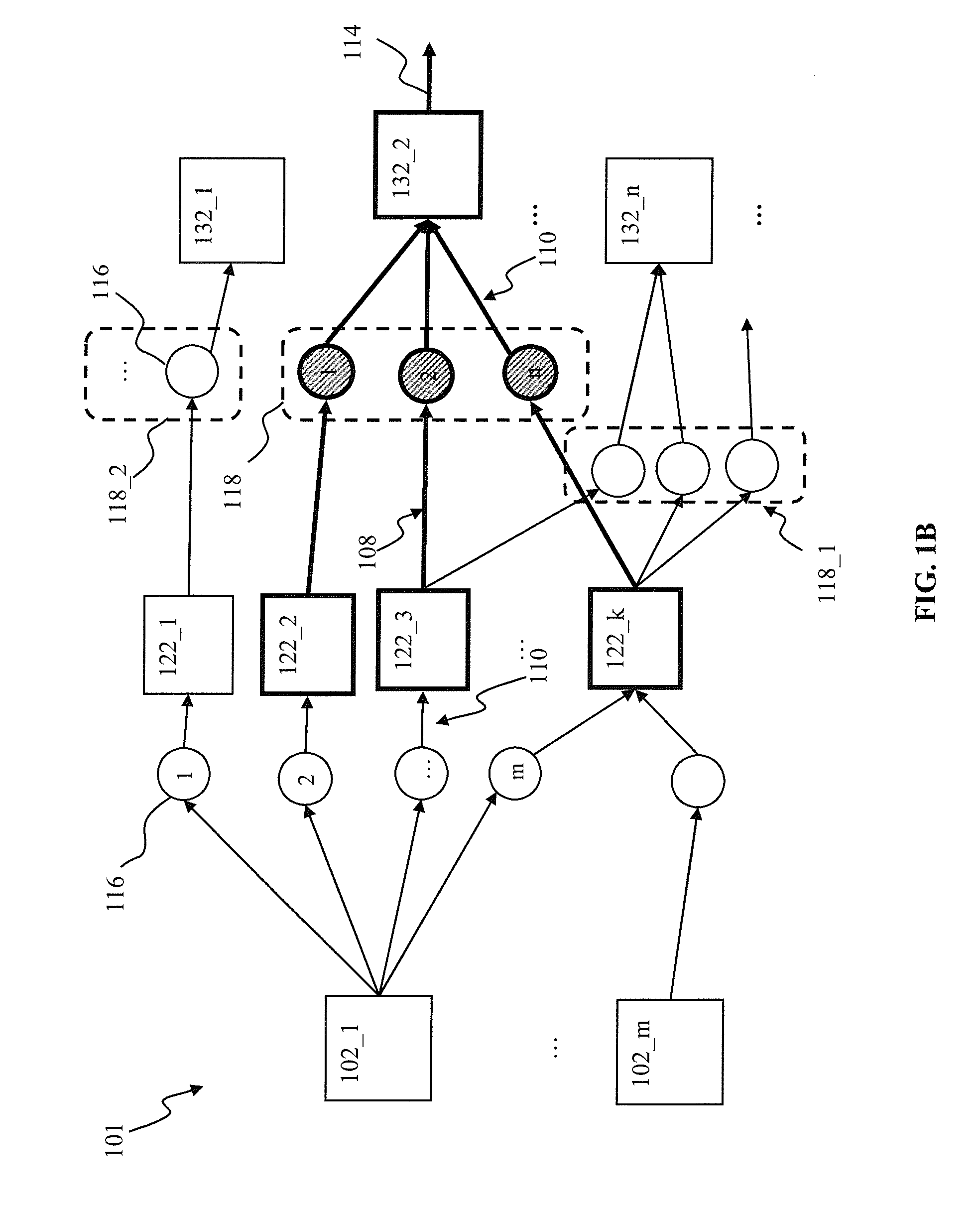
Apparatus and methods for synaptic update in a pulse-coded network
InactiveUS20130073491A1Reducing memory bus overheadReduce overheadDigital computer detailsDigital dataSynapseSpiking neural network
Apparatus and methods for efficient synaptic update in a network such as a spiking neural network. In one embodiment, the post-synaptic updates, in response to generation of a post-synaptic pulse by a post-synaptic unit, are delayed until a subsequent pre-synaptic pulse is received by the unit. Pre-synaptic updates are performed first following by the post-synaptic update, thus ensuring synaptic connection status is up-to-date. The delay update mechanism is used in conjunction with system “flush” events in order to ensure accurate network operation, and prevent loss of information under a variety of pre-synaptic and post-synaptic unit firing rates. A large network partition mechanism is used in one variant with network processing apparatus in order to enable processing of network signals in a limited functionality embedded hardware environment.
Owner:QUALCOMM INC
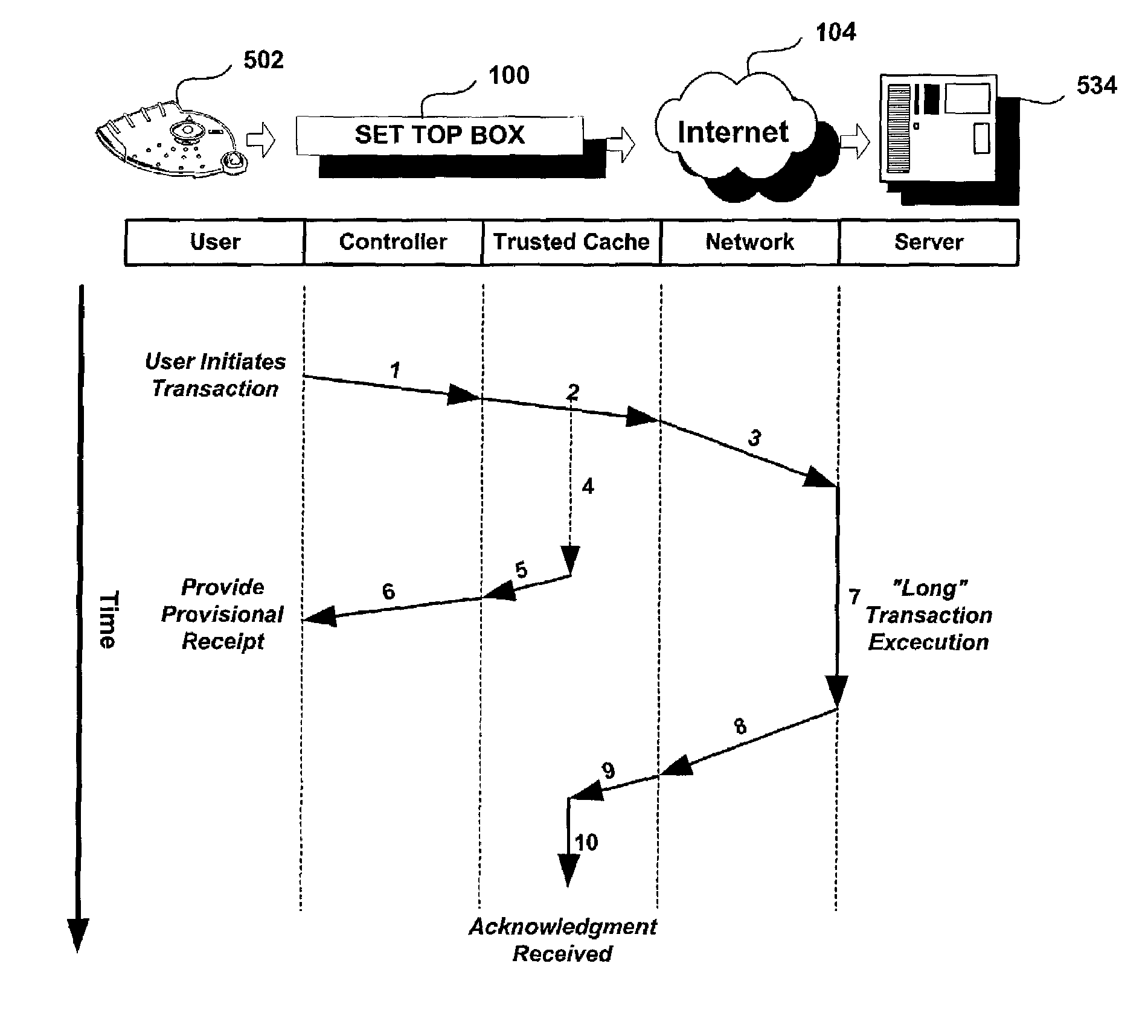
Trusted transactional set-top box
InactiveUS7346917B2Poor resolutionMaximum safetyTelevision system detailsAnalogue secracy/subscription systemsPrivate networkThe Internet
A set top box (STB) includes a trusted transactional cache and associated transactional protocol and enables e-commerce transactions to be securely committed to a remote server extremely quickly and with little network overhead. The invention does away with the user concern of whether the transaction was successful. The STB operates equally well on robust private networks as on unpredictable Internet or wireless networks, and avoids upsetting users who would otherwise have to wait in front of a display screen for confirmation of completion of the transaction after a temporary communication failure with the central site. The method may advantageously be used to provide cost-effective micro-payments solutions. The STB may include a dual headed display capability in which data and video maybe be directed to separate displays. The STB may feature an embedded ticket printer, as well as an embedded barcode scanner. This enables non computer literate users to more conveniently track transactions committed via the STB, or to take advantage of promotional coupons. The STB features an embedded hardware true Random Number Generator to produce maximum entropy encryption keys, therefore providing maximum secure and fool-proof means to protect private data using government authorized encryption schemes.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
System and method for signal decomposition, analysis and reconstruction
ActiveUS20060200035A1Digital technique networkCharacter and pattern recognitionDecompositionComputer science
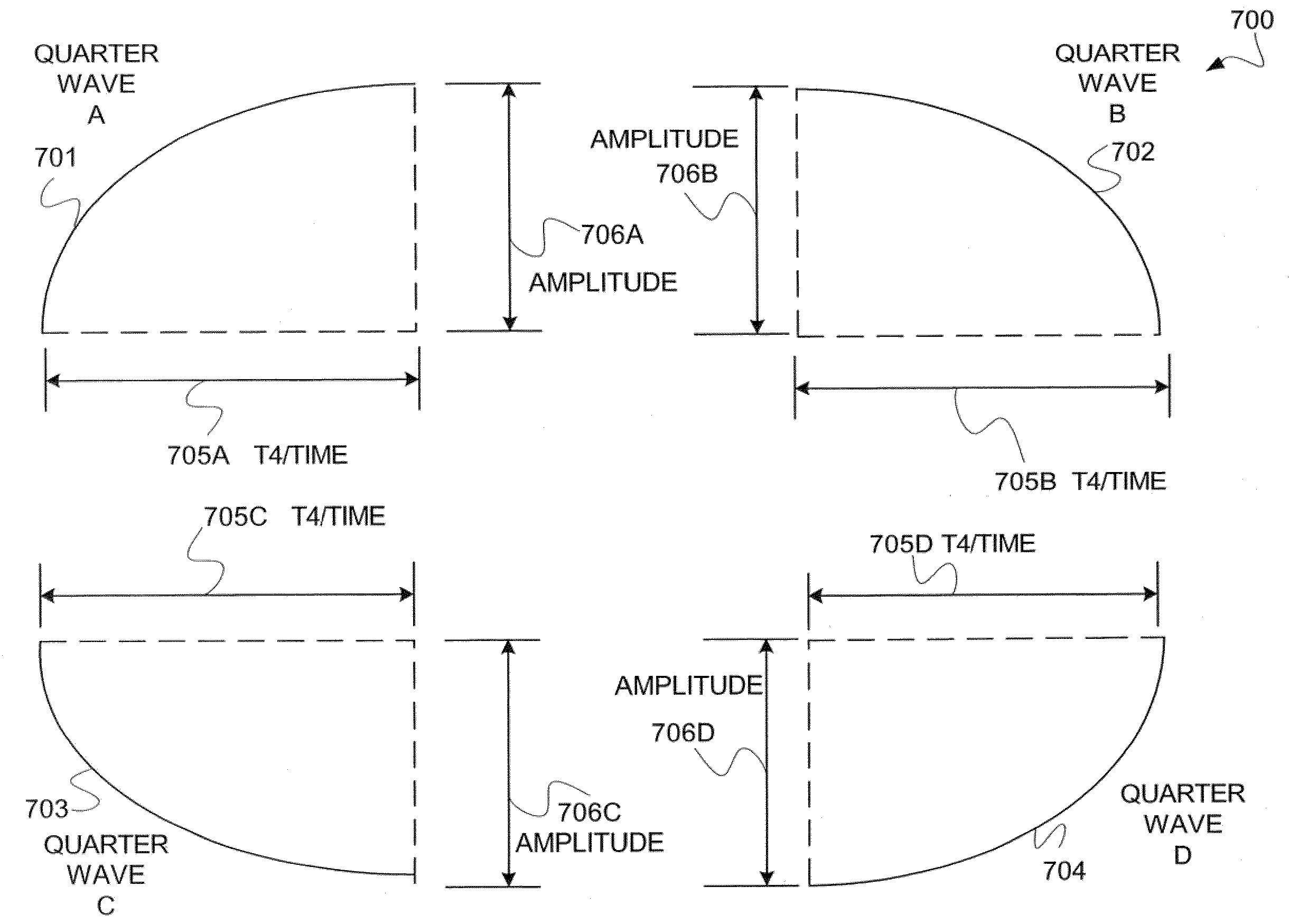
The present invention provides a system and method for representing quasi-periodic (“qp”) waveforms comprising, representing a plurality of limited decompositions of the qp waveform, wherein each decomposition includes a first and second amplitude value and at least one time value. In some embodiments, each of the decompositions is phase adjusted such that the arithmetic sum of the plurality of limited decompositions reconstructs the qp waveform. These decompositions are stored into a data structure having a plurality of attributes. Optionally, these attributes are used to reconstruct the qp waveform, or patterns or features of the qp wave can be determined by using various pattern-recognition techniques. Some embodiments provide a system that uses software, embedded hardware or firmware to carry out the above-described method. Some embodiments use a computer-readable medium to store the data structure and / or instructions to execute the method.
Owner:MURATA VIOS INC
Apparatus for signal decomposition, analysis and reconstruction
ActiveUS20060200034A1Digital technique networkCharacter and pattern recognitionDecompositionComputer science
The present invention provides a system and method for representing quasi-periodic (“qp”) waveforms comprising, representing a plurality of limited decompositions of the qp waveform, wherein each decomposition includes a first and second amplitude value and at least one time value. In some embodiments, each of the decompositions is phase adjusted such that the arithmetic sum of the plurality of limited decompositions reconstructs the qp waveform. These decompositions are stored into a data structure having a plurality of attributes. Optionally, these attributes are used to reconstruct the qp waveform, or patterns or features of the qp wave can be determined by using various pattern-recognition techniques. Some embodiments provide a system that uses software, embedded hardware or firmware to carry out the above-described method. Some embodiments use a computer-readable medium to store the data structure and / or instructions to execute the method.
Owner:MURATA VIOS INC
Machine-to-Machine Visual Code Generation and Recognition Method and System for Device Communications
Various embodiments of a machine-to-machine visual code generation and recognition method and a corresponding system are disclosed. In one embodiment, a first machine gathers real-time hardware setting information of the first machine, and subsequently generates a first QR code that embeds hardware setting information of the first machine. The first QR code is displayed to a display panel connected to the first machine, and a second machine with a camera captures the first QR code, and deciphers the first QR code to determine communication compatibility between the first machine and the second machine. Then, the second machine formulates a response that incorporates its own real-time hardware setting information, and generates a second QR code that embeds the second machine's response to the first machine. Subsequently, the first machine scans the second QR code from the second machine's display panel, and registers the second machine's hardware setting information.
Owner:HUANG JEFFREY
Blocked convolution optimization method and device for convolution neural network
ActiveCN107437110AResource Constraint Issues EliminatedAlleviate resource constraintsNeural architecturesPhysical realisationNerve networkAlgorithm
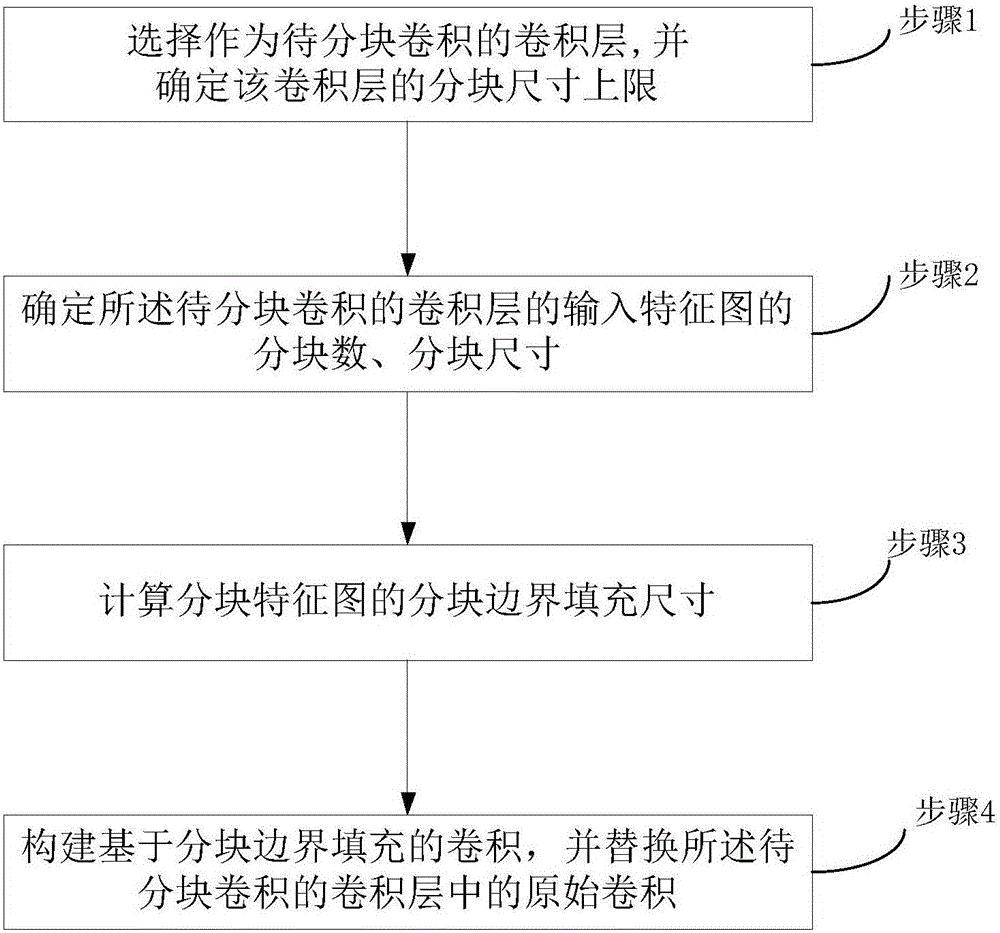
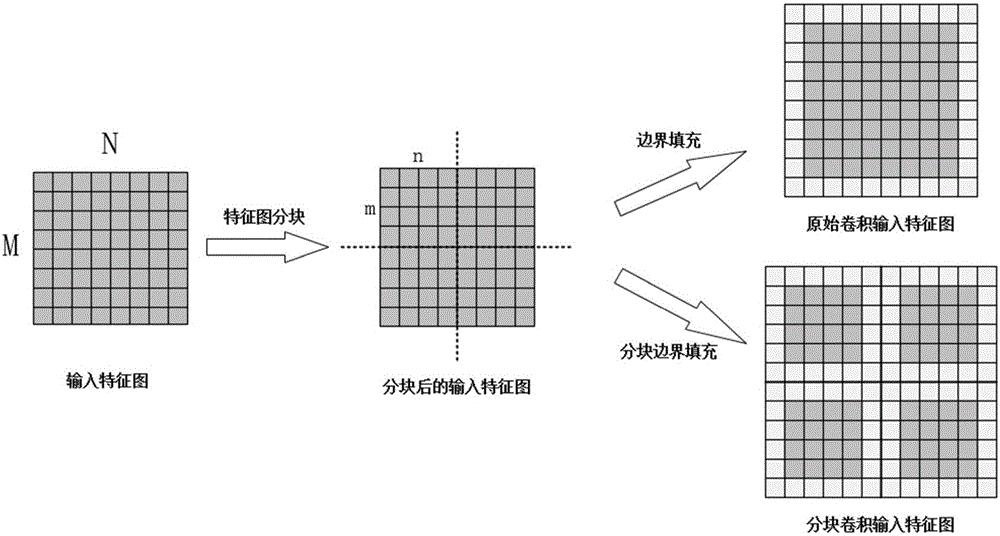
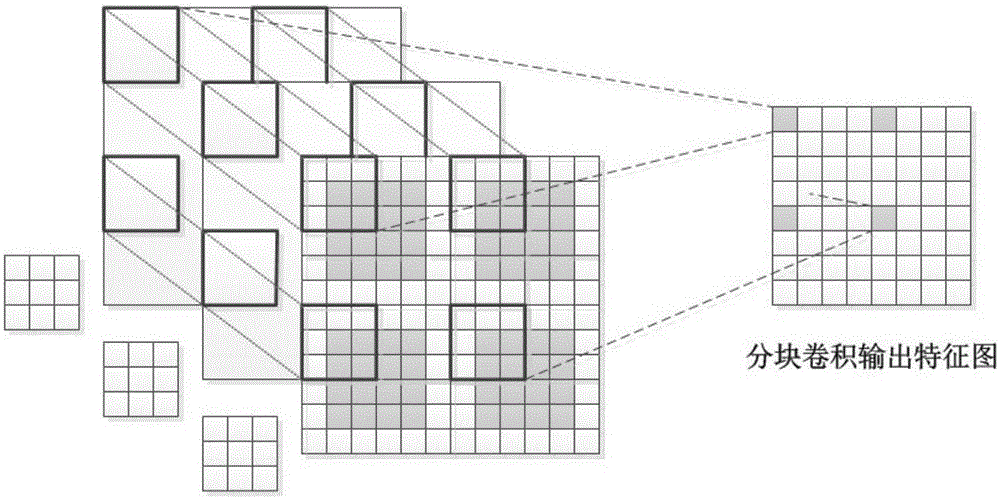
The invention relates to the field of deep neural networks and provides a blocked convolution optimization method and a device for a convolution neural network, so as to solve the bottleneck problem of convolution operation in a hardware processing system in the neural network. The optimization method comprises steps: a to-be-blocked convolution layer is selected, and the upper limit of the block size is determined; according to the upper limit of the block size, a block number and the block size of an input feature map are determined; based on the block number, the block size, the size of a convolution kernel, the size of the input feature map and the filling size of an input feature map boundary, the block boundary filling size of a block feature map is calculated; and based on the block number, the block size and the block boundary filling size, a convolution based on the block boundary filling is built to replace the original convolution. The resource constraint problem of the convolution neural network during operation of an embedded hardware platform is greatly alleviated, the burst length is improved maximally when a memory is read and written, the throughput is improved, the time delay is reduced, and the efficiency is improved.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Internet of Things intelligent gateway for multi-data protocol conversion
ActiveCN106878163AExchange minimizationEfficient use ofNetwork connectionsThe InternetTechnical standard
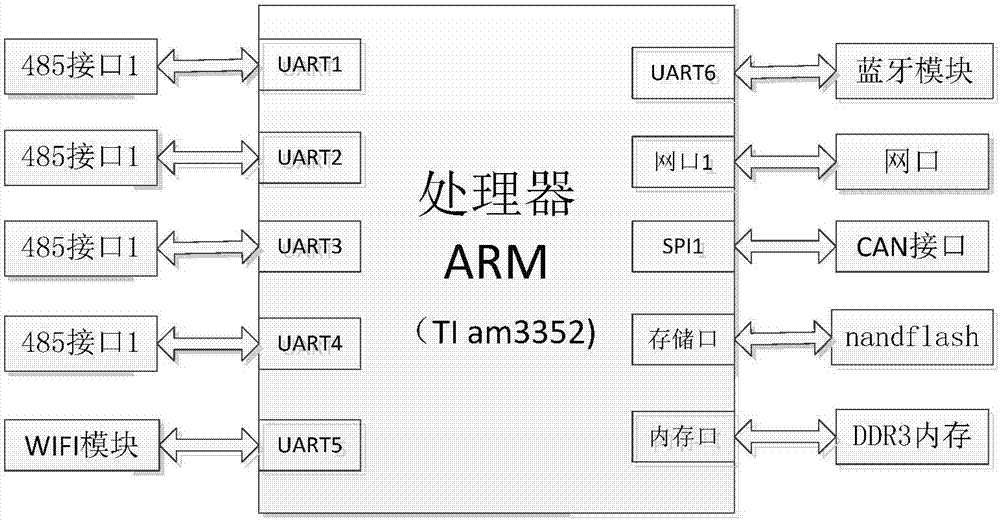
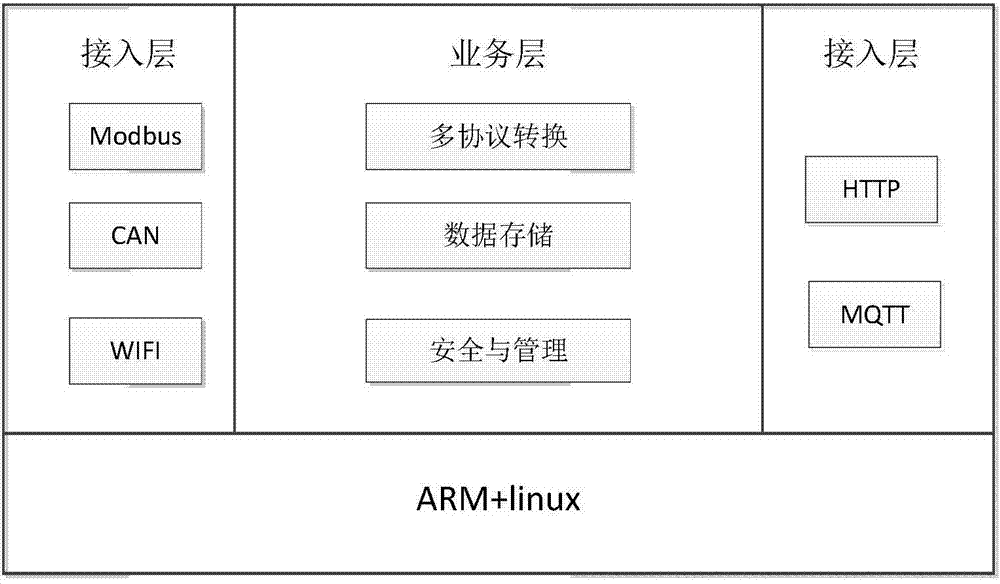
The invention discloses an Internet of Things intelligent gateway for multi-data protocol conversion, and belongs to the technical field of the Internet of Things intelligent gateway. The intelligent gateway comprises the following functions: equipment management, multi-protocol accessing, protocol conversion and standard data format data transmission; the Internet of Things intelligent gateway comprises three parts: an embedded hardware platform, an operation system and application software. The intelligent gateway has the advantage that the predicament that multiple node and multiple protocol equipment is accessed into the Internet of Things cloud platform in low efficiency and high complexity is solved. The equipment access of multi-protocol is supported, and Internet of Things protocol data can be uploaded the cloud platform, thereby facilitating the popularization and transplanting of the intelligent gateway in the industrial and urban Internet of Things project. By adding an equipment management and configuration module, the use of the user is greatly facilitated.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
Method and system for dynamically distributing embedded virtual memory
InactiveCN102193814AEstablish a scheduling mechanismIncrease the monitoring mechanism of real-time memory pre-occupancyMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationVirtual memoryVirtualization
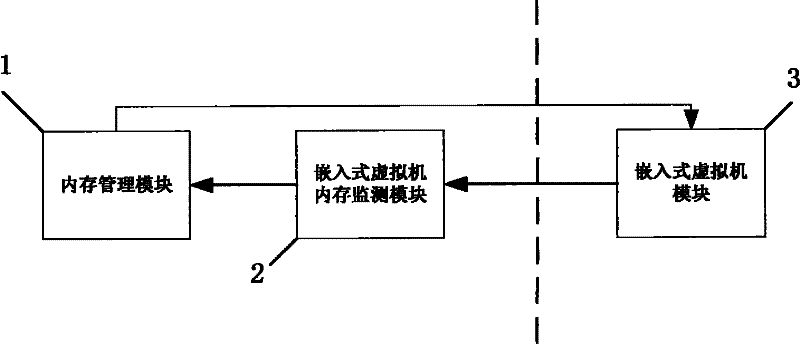
The invention discloses a method and a system for dynamically distributing an embedded virtual memory. By the method for dynamically distributing the memory, memory resource waste due to the conventional embedded virtual fixed memory distribution can be avoided effectively. The system comprises a memory management module, an embedded virtual machine memory monitoring module and an embedded virtual machine module, wherein the virtual machine memory monitoring module is used for monitoring a real-time memory requirement condition of an embedded system in real time; the memory management module is used for initializing memory distribution, establishing an initialized memory mapping table and updating the memory distribution and the memory mapping table in real time according to a monitoring situation of the virtual machine memory monitoring module; and the embedded virtual machine module is used for generating an embedded hardware virtual environment and running an embedded operating system, and performing various embedded applications on the embedded operating system.
Owner:SHANGHAI BAIHAN NETWORK TECH
Variable threshold transistor for the Schottky FPGA and multilevel storage cell flash arrays
InactiveUS20060044018A1Low powerImprove performanceMultistate logicSolid-state devicesSchottky barrierMulti-level cell
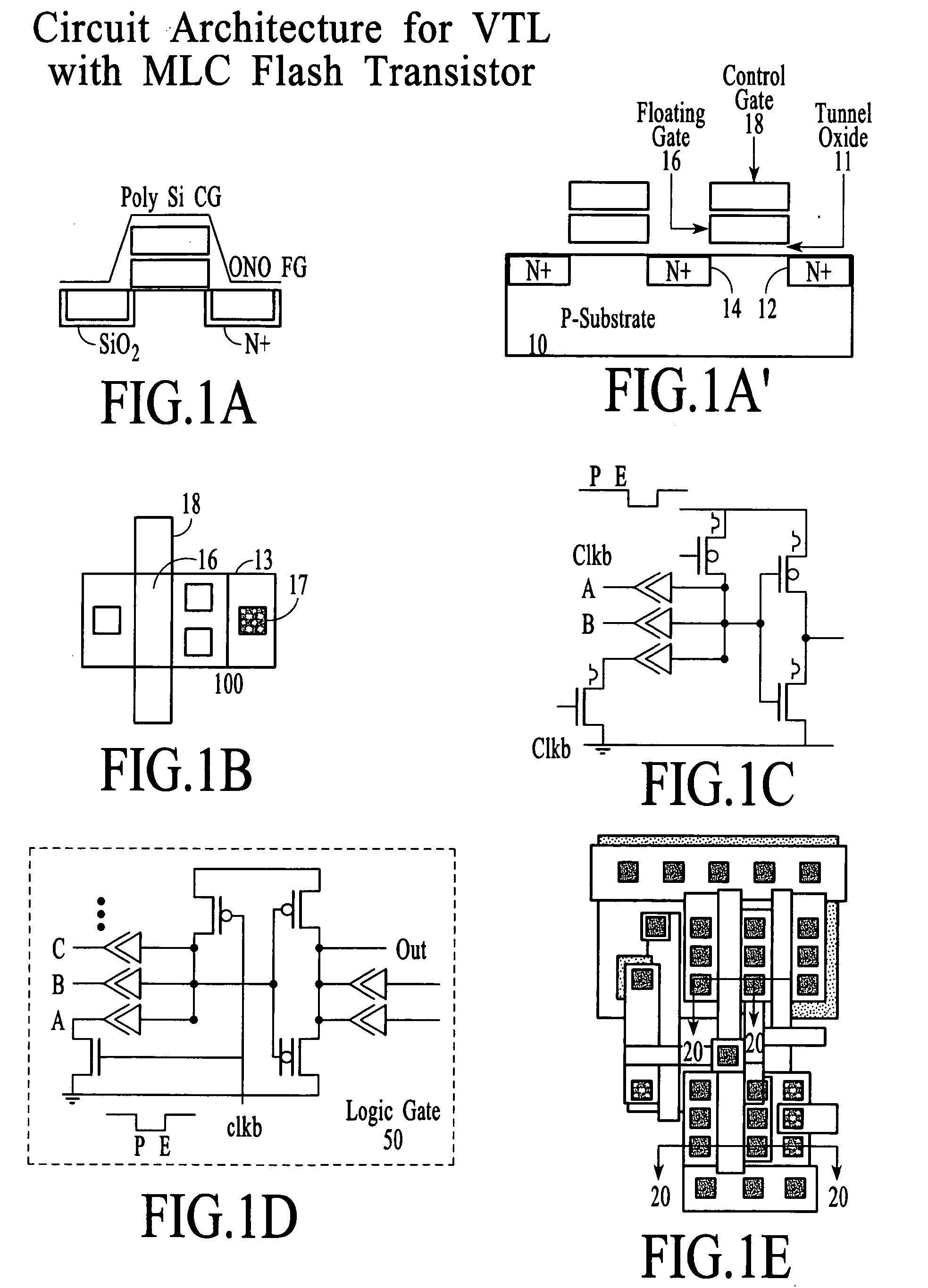
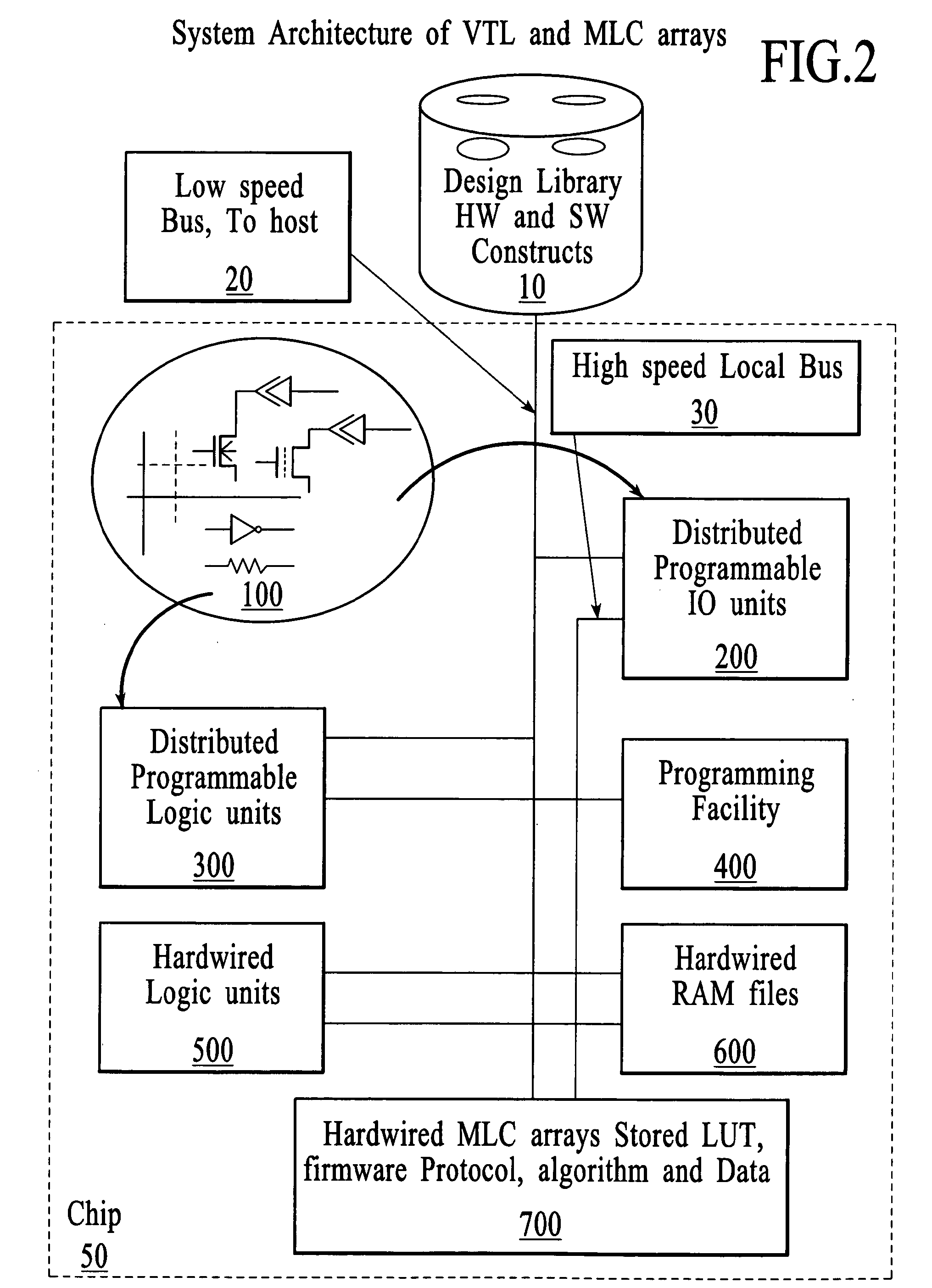
An IC solution utilizing mixed FPGA and MLC arrays is proposed. The process technology is based on the Schottky CMOS devices comprising of CMOS transistors, low barrier Schottky barrier diode (SBD), and multi-level cell (MLC) flash transistors. Circuit architectures are based on the pulsed Schottky CMOS Logic (SCL) gate arrays, wherein a variable threshold NMOS transistor may replace the regular switching transistor. During initialization windows, existing FPGA programming techniques can selectively adjust the VT of the switching transistor, re-configure the intra-connections of the simple SCL gates, complete all global interconnections of various units. Embedded hardware arrays, hardwired blocks, soft macro constructs in one chip, and protocols implementations are parsed. A wide range of circuit applications involving generic IO and logic function generation, ESD and latch up protections, and hot well biasing schemes are presented. The variable threshold transistors thus serve 3 distinctive functions. It acts as an analog device to store directly nonvolatile information in SCL gates. It couples the diode tree logic functions. Finally, it stores and operates large amount of information efficiently. The mixed SCL type FPGA and MLC storages shall emerge as the most compact logic and memory arrays in Si technology. Low power, high performance, and high capacity ICs are designed to mix and replace conventional CMOS-TTL circuits. The idea of multi-value logic composed of binary, ternary, and quaternary hardware and firmware is also introduced.
Owner:SUPER TALENT ELECTRONICS
Method and apparatus for protecting software against unauthorized use
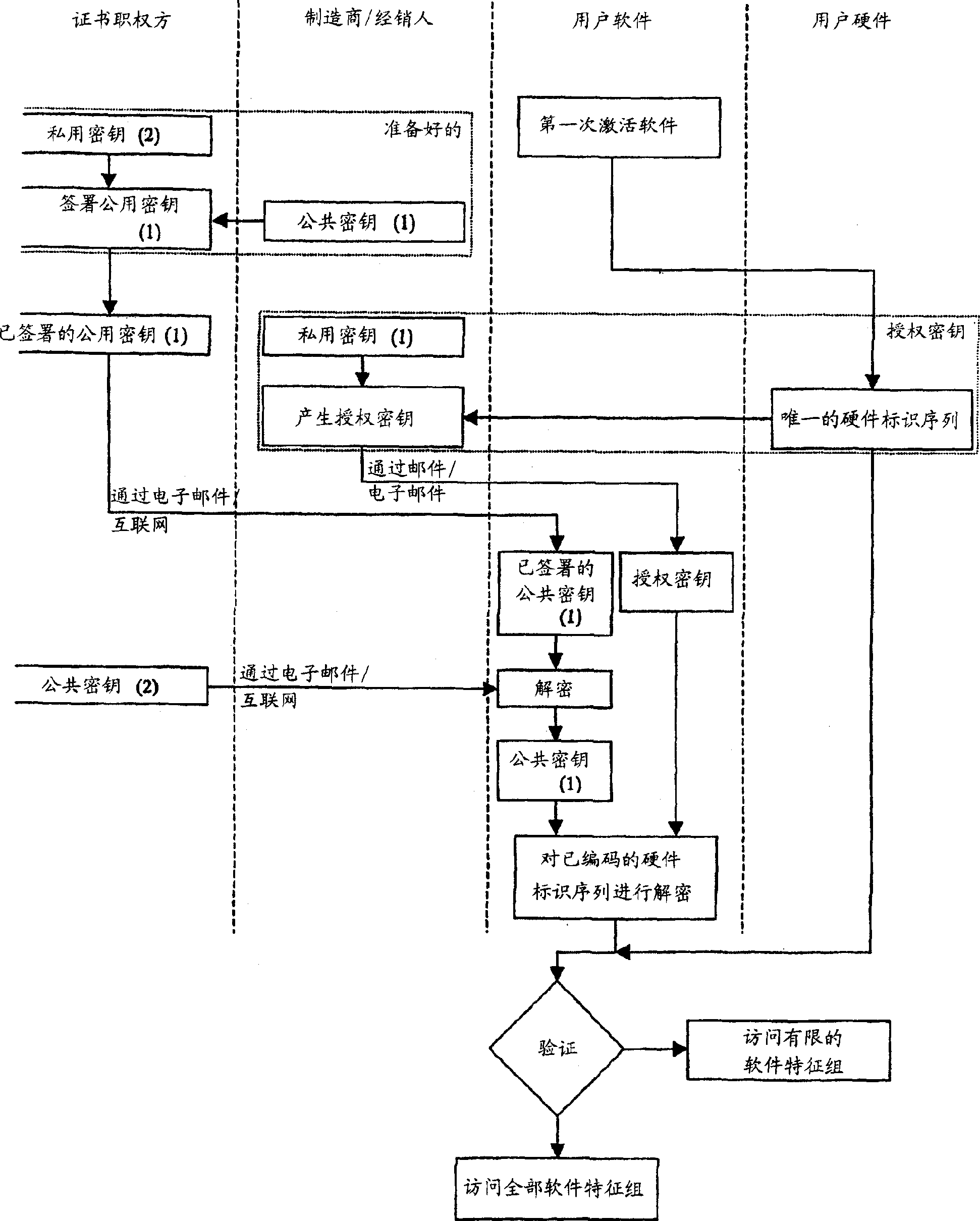
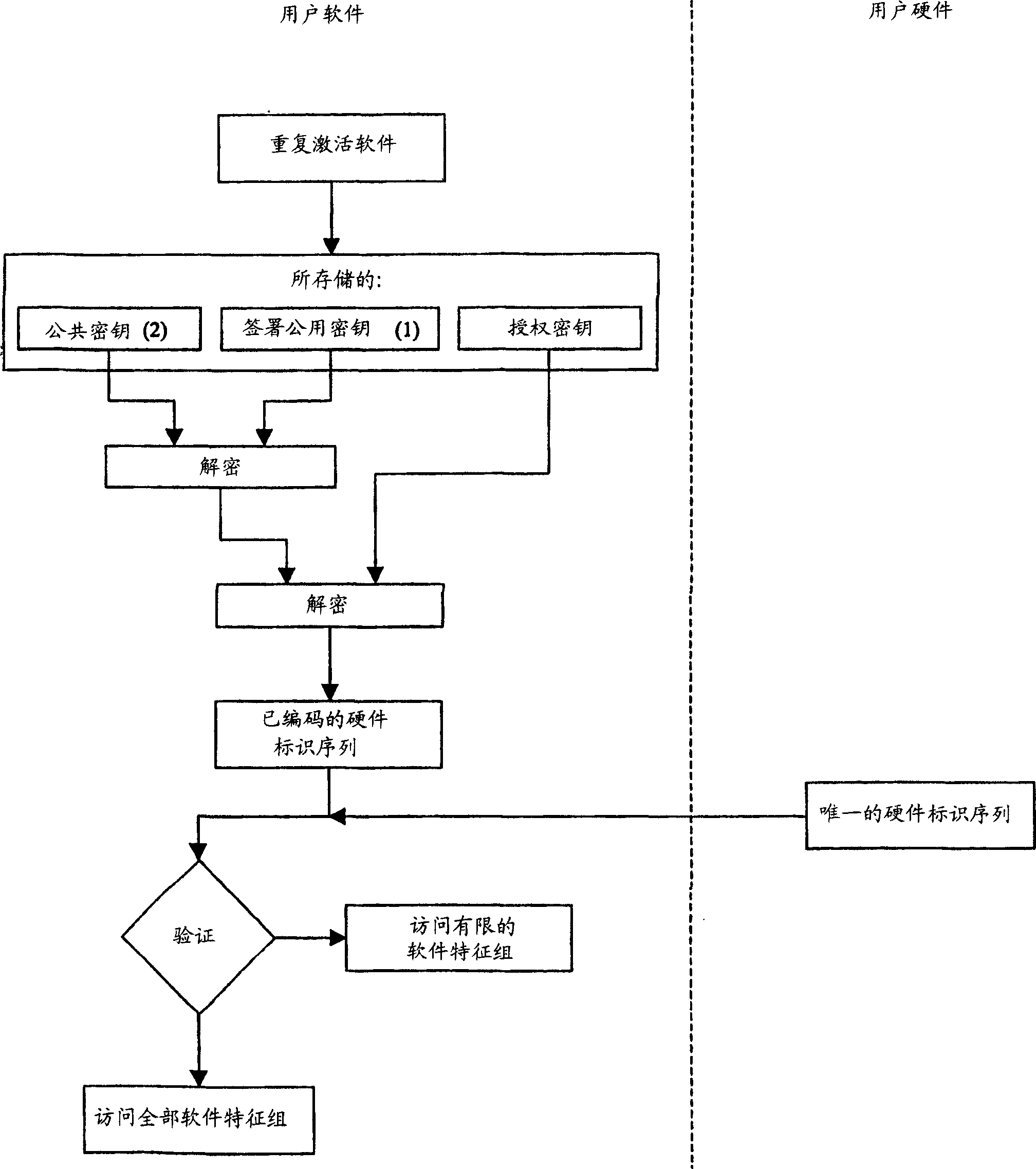
InactiveUS7313828B2Low costOptimal codeKey distribution for secure communicationDigital data processing detailsBiological activationSerial code
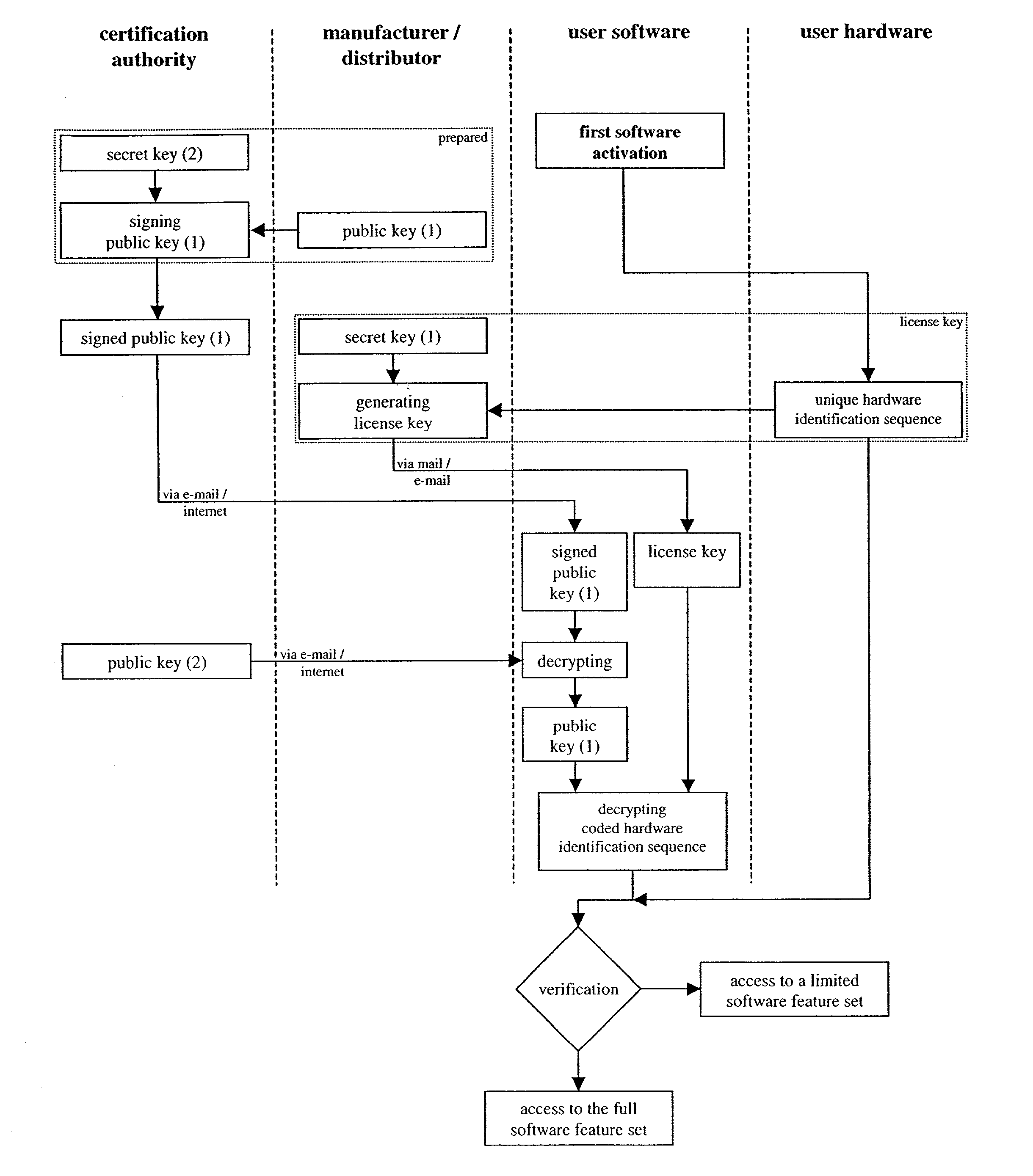
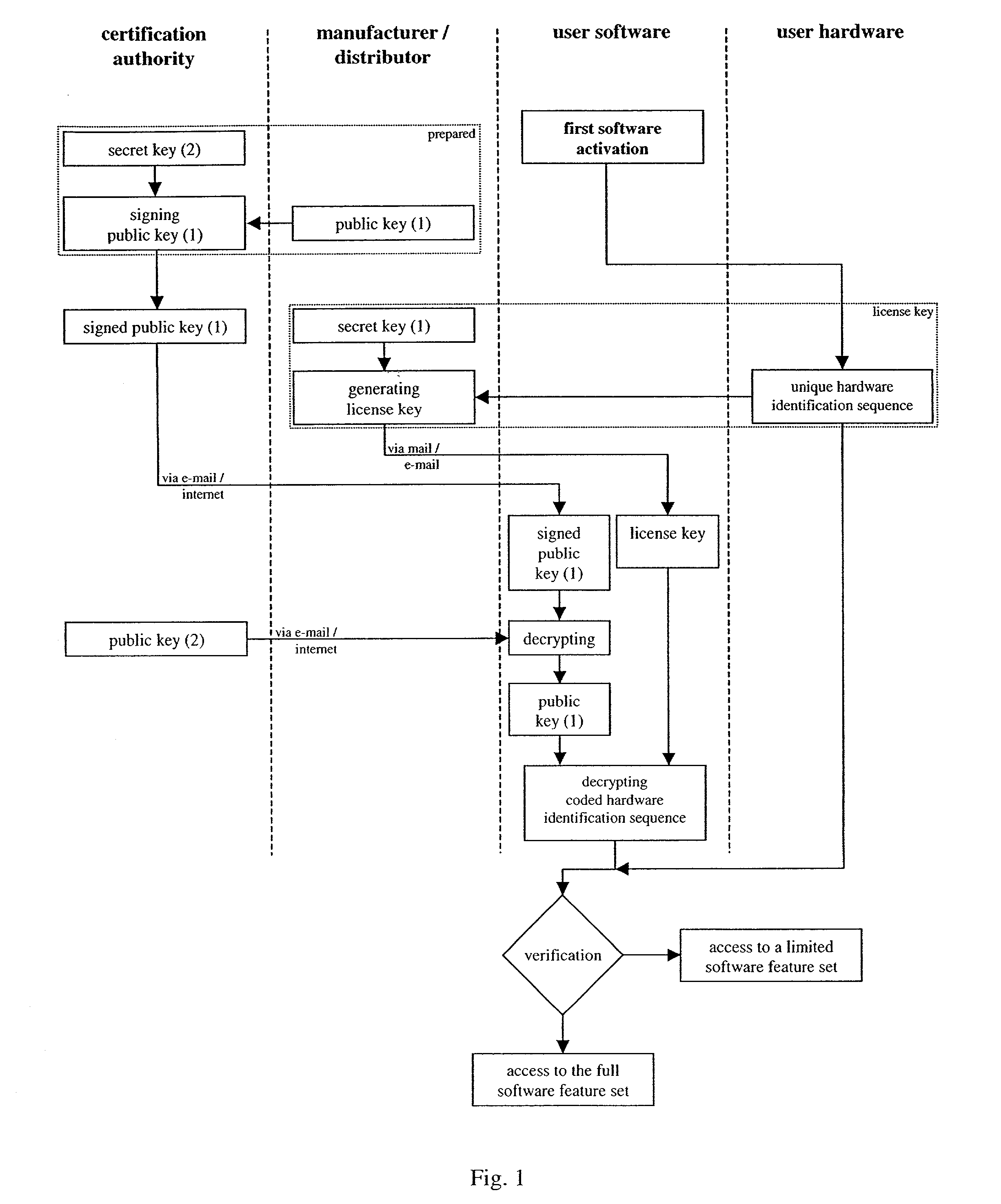
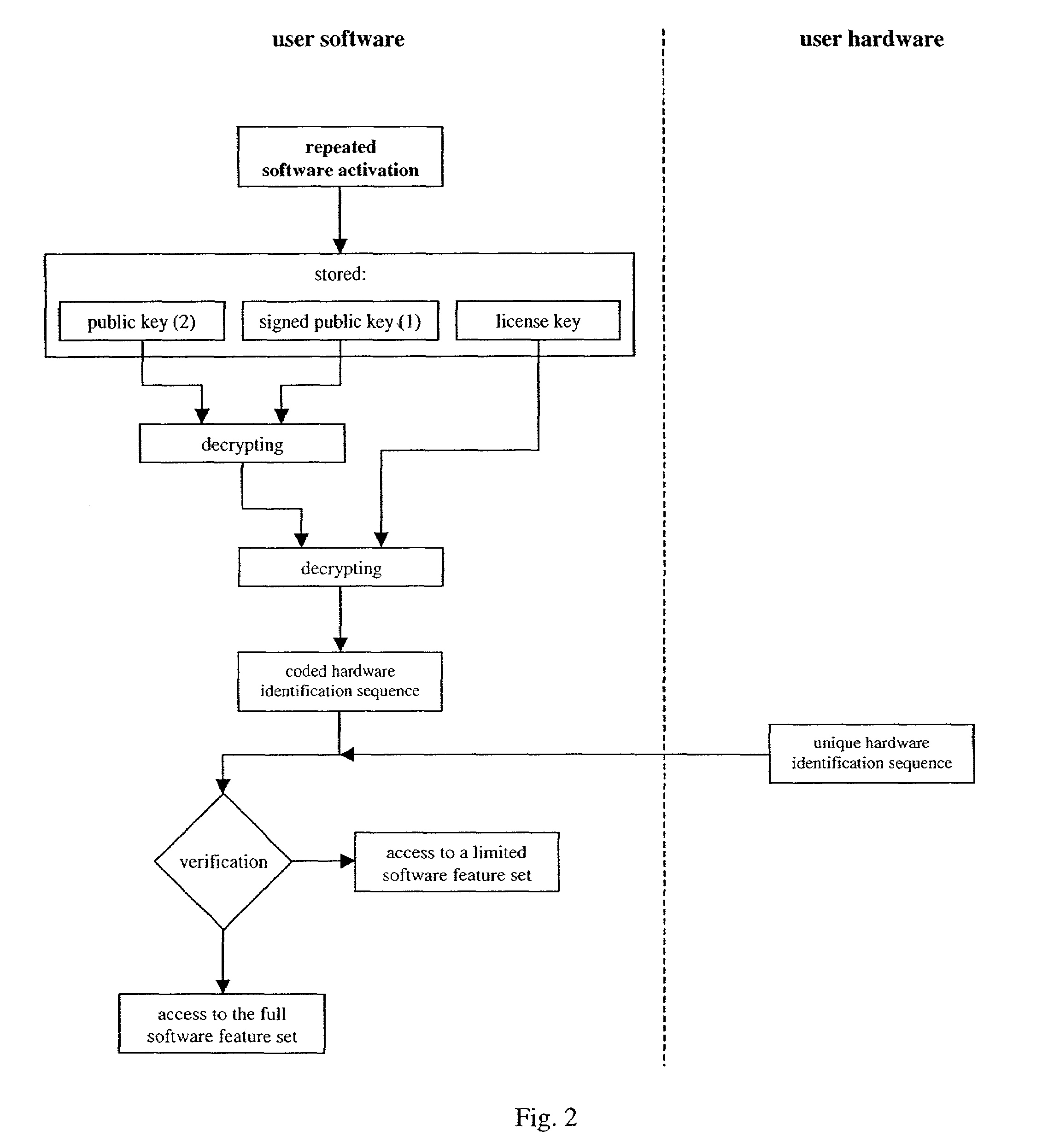
A method and apparatus which protects software against unauthorized use which is bound to at least one certain hardware device. The hardware device includes unique hardware identification sequences like unique hardware numbers / addresses, serial numbers or other embedded hardware characterization sequences. A special license key has to be passed to the software at the first activation. The license key contains among other things encrypted hardware identification sequences which are compared with the read out sequences of the accessible hardware devices. The use of the software features is permitted if the sequences match.
Owner:NOKIA TECHNOLOGLES OY
Portable blindman independent navigation system
ActiveCN101797197AImprove detection accuracyLow costInstruments for road network navigationWalking aidsOperational systemNavigation system
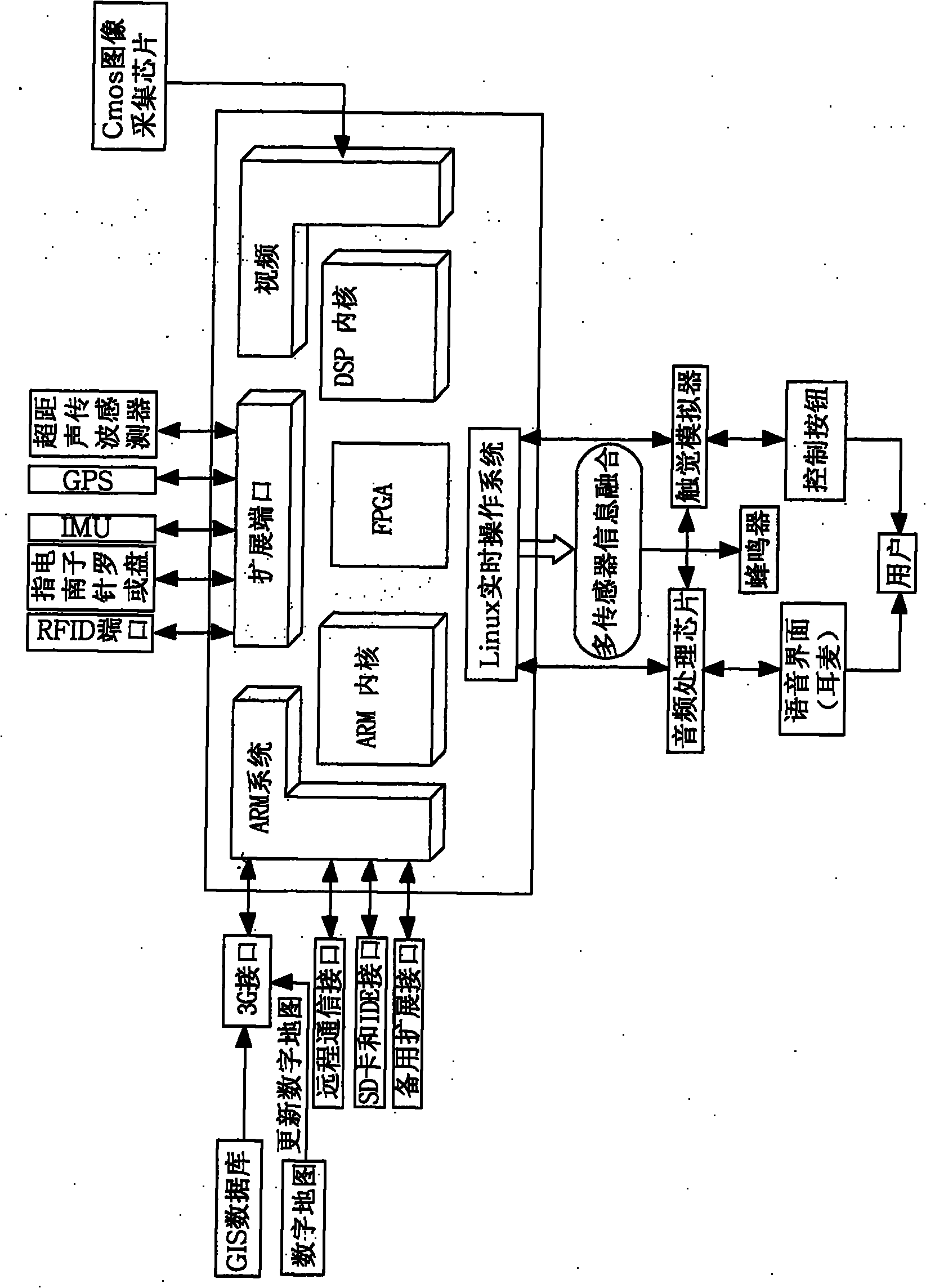
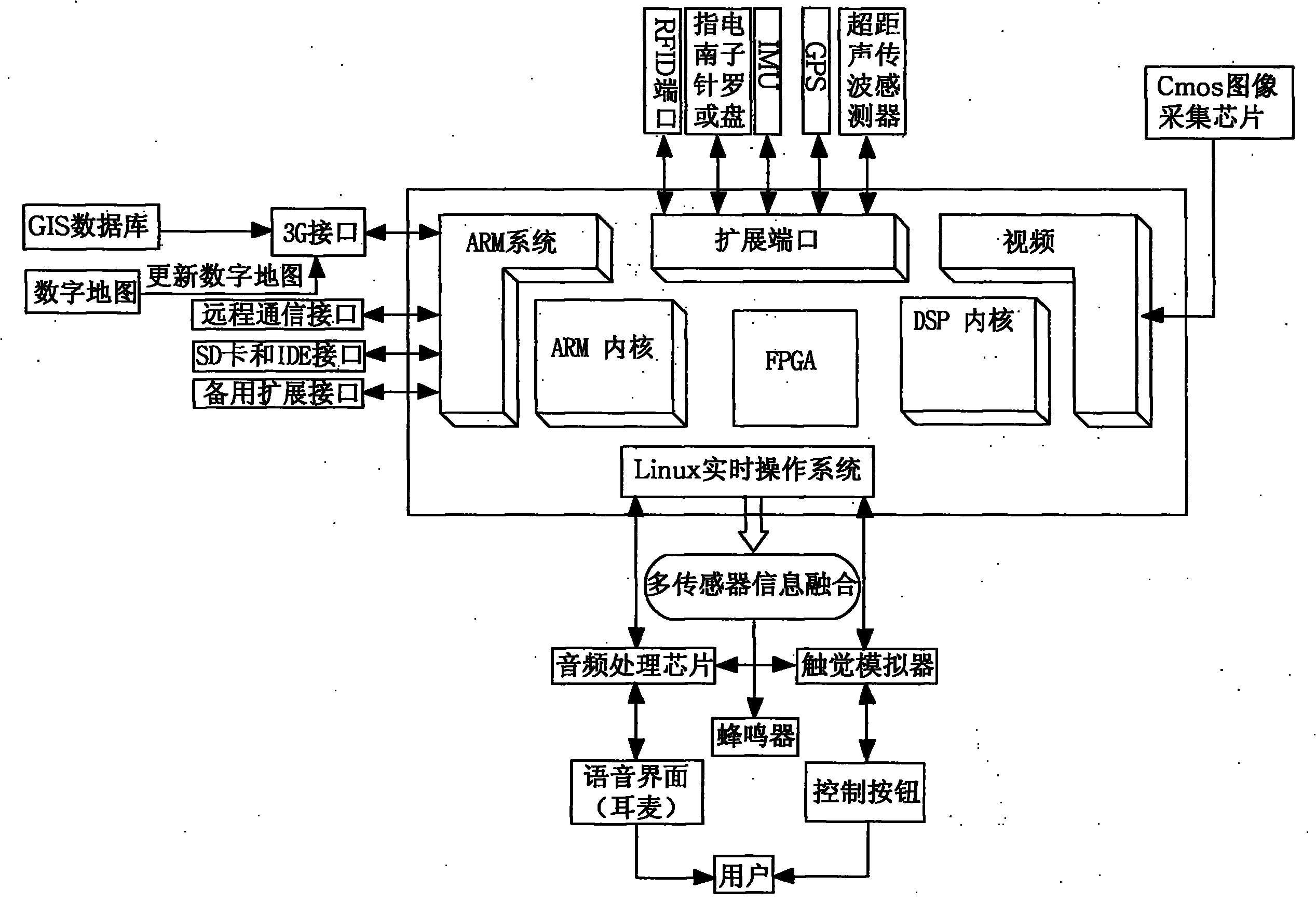
The invention relates to the technical field of navigation systems, in particular to a portable blindman independent navigation system. The portable blindman independent navigation system is a main glasses body, which comprises a glasses framework, pinhole cameras arranged on both sides of the main glasses framework, a GPS (Global Position System) arranged in the middle of the main glasses body, earphones arranged at the tail ends of the glasses framework and embedded hardware systems arranged in lenses of the main glasses body; wherein the embedded hardware systems arranged in the lenses of the main glasses body comprise extension ports, ARM (Advanced RISC Machines, RISC is short for Reduced Instruction-Set Computer) systems, videos, ARM inner cores, DSP (Digital Signal Processor) inner cores, FPGs and Linux real-time operation systems. In the portable blindman independent navigation system, the embedded systems are used for carrying out three-dimensional information extraction on binocular images acquired by the pinhole cameras, a built-in navigation map and GPS information are used for comparison to acquire relevant information of positions, directions, front barriers and the like and converting results into voice signals to inform blindmen.
Owner:VISIONNAV ROBOTICS SHENZHEN LTD
Apparatus for signal decomposition, analysis and reconstruction
The present invention provides a system and method for representing quasi-periodic (“qp”) waveforms comprising, representing a plurality of limited decompositions of the qp waveform, wherein each decomposition includes a first and second amplitude value and at least one time value. In some embodiments, each of the decompositions is phase adjusted such that the arithmetic sum of the plurality of limited decompositions reconstructs the qp waveform. These decompositions are stored into a data structure having a plurality of attributes. Optionally, these attributes are used to reconstruct the qp waveform, or patterns or features of the qp wave can be determined by using various pattern-recognition techniques. Some embodiments provide a system that uses software, embedded hardware or firmware to carry out the above-described method. Some embodiments use a computer-readable medium to store the data structure and / or instructions to execute the method.
Owner:MURATA VIOS INC
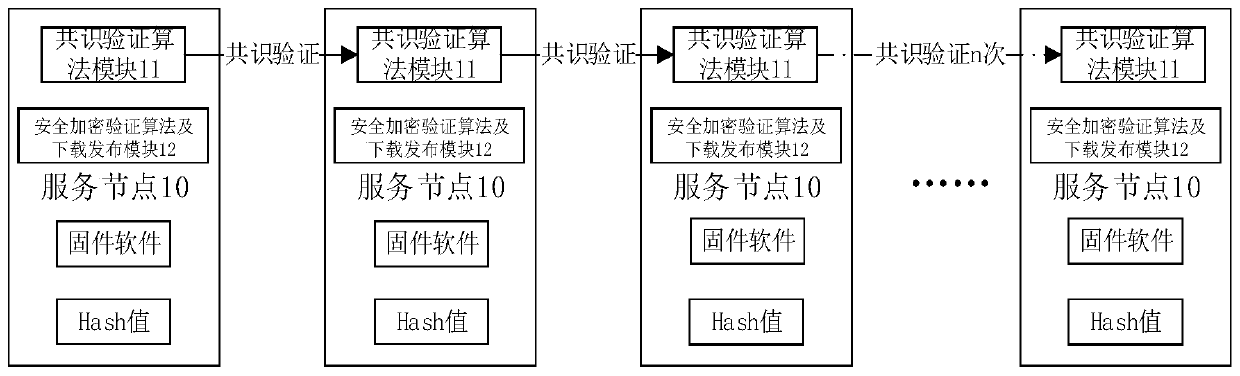
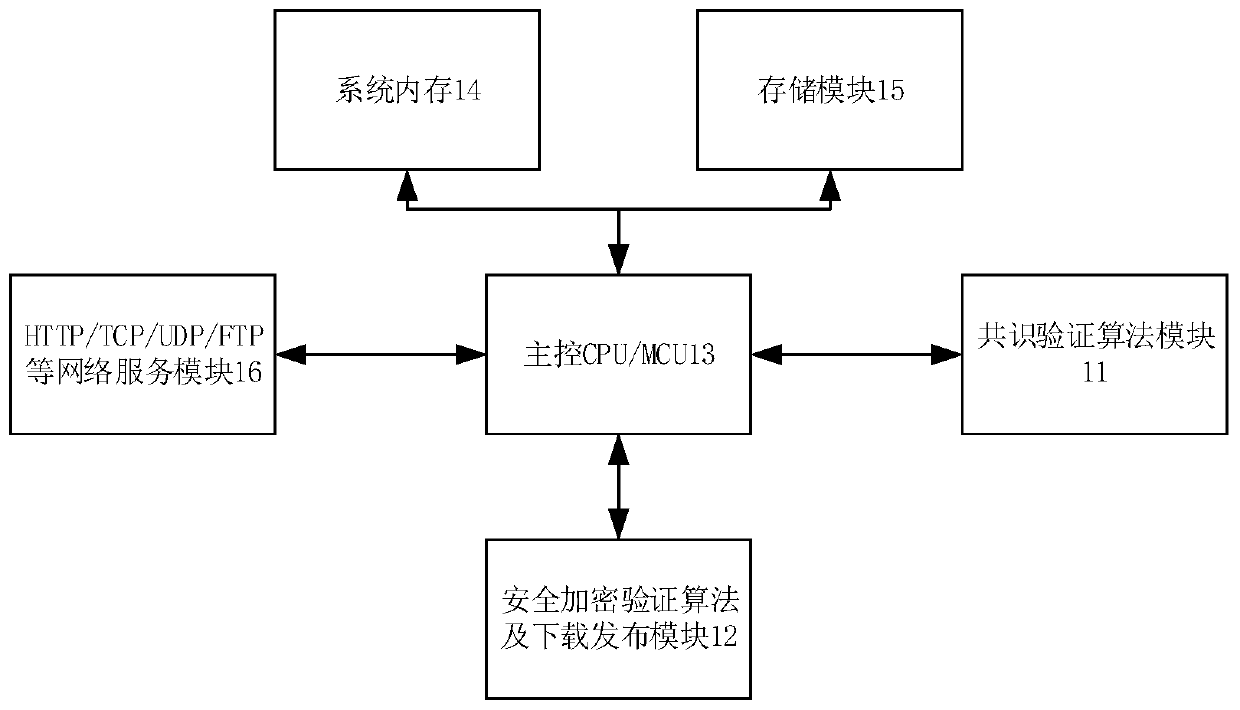
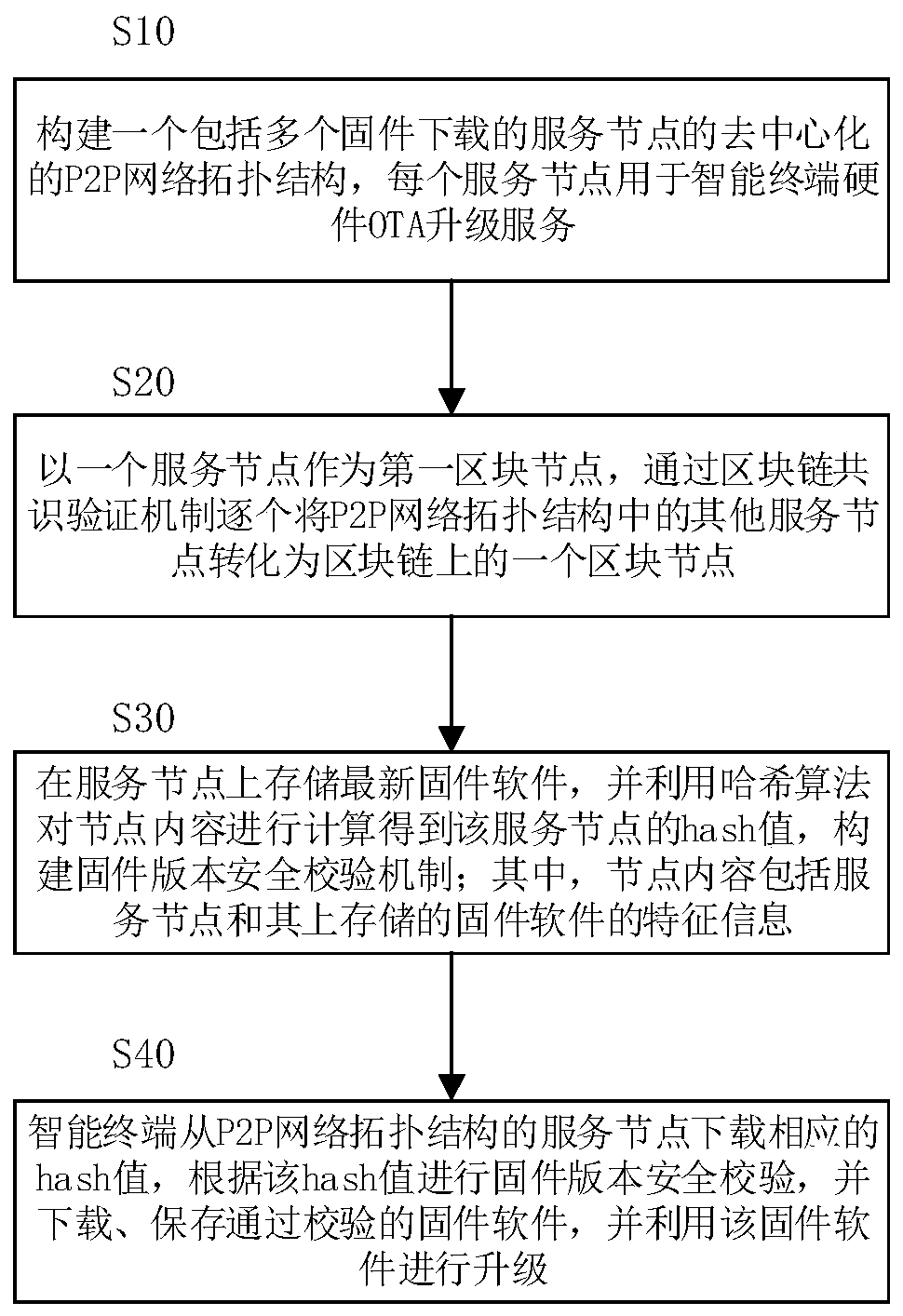
System and method for realizing OTA upgrade of embedded hardware based on block chain
ActiveCN109889589AUpgrade does not affectImprove upgrade reliabilityUser identity/authority verificationData switching networksComputer networkFirmware version
The invention discloses a system and a method for realizing OTA upgrade of embedded hardware based on a block chain. The method comprises the following steps: constructing a P2P network topological structure comprising a plurality of service nodes downloaded by firmware; taking one service node as a first block node, and converting other service nodes in the P2P network into one block node on theblock chain one by one through a block chain consensus verification mechanism; storing the latest firmware software on the service node, and calculating the node content by using a Hash algorithm to obtain a Hash value of the service node; wherein the node content comprises feature information of the service node and firmware software stored on the service node; and the intelligent terminal downloads the corresponding hash value from the service node of the P2P network, carries out firmware version security verification according to the hash value, downloads and stores the verified firmware software, and upgrades the firmware software. The safe and credible P2P network topological structure is established by using the block chain technology, and the OTA upgrading reliability and safety ofthe intelligent terminal are improved.
Owner:IGRS ENG LAB
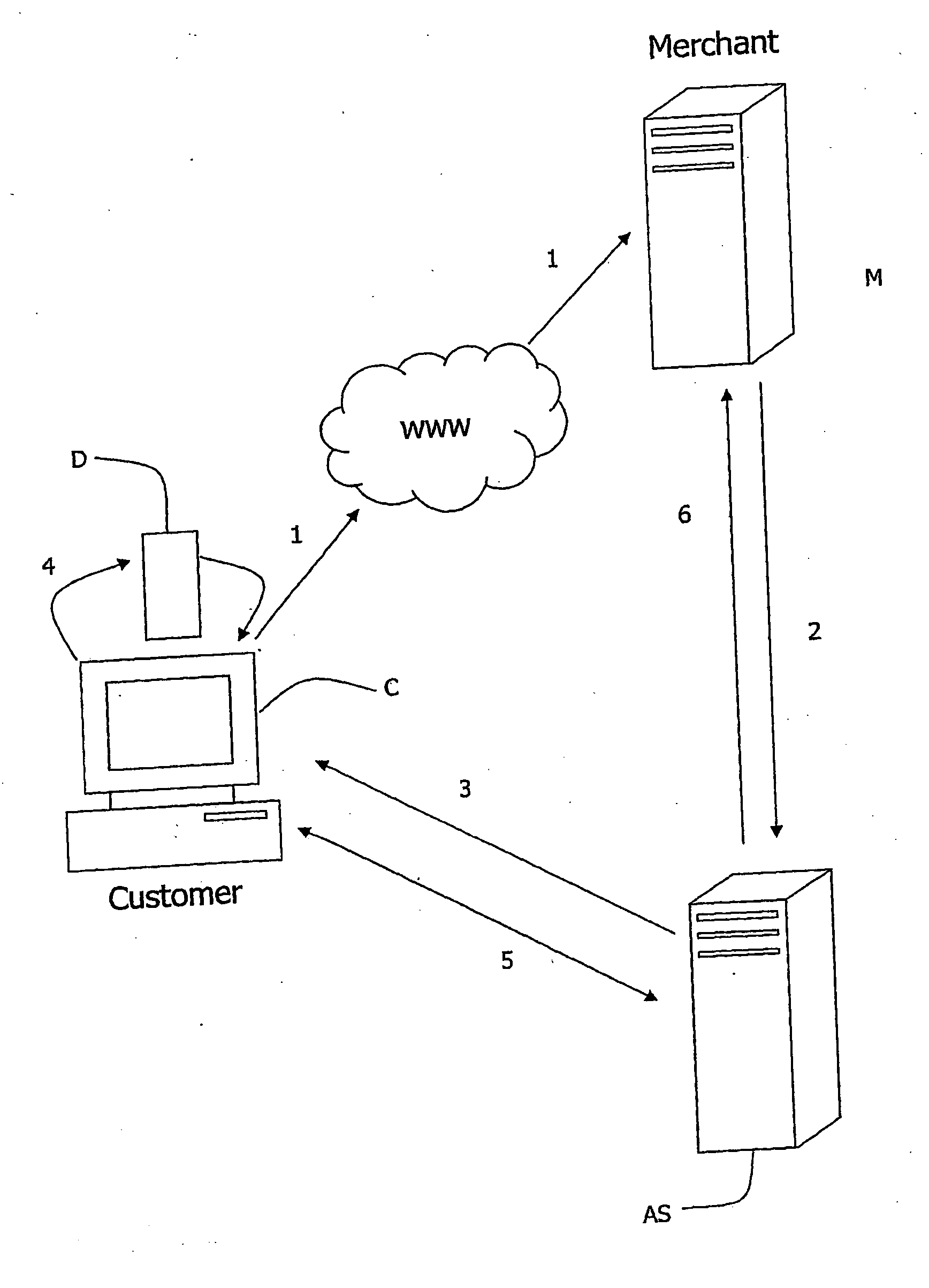
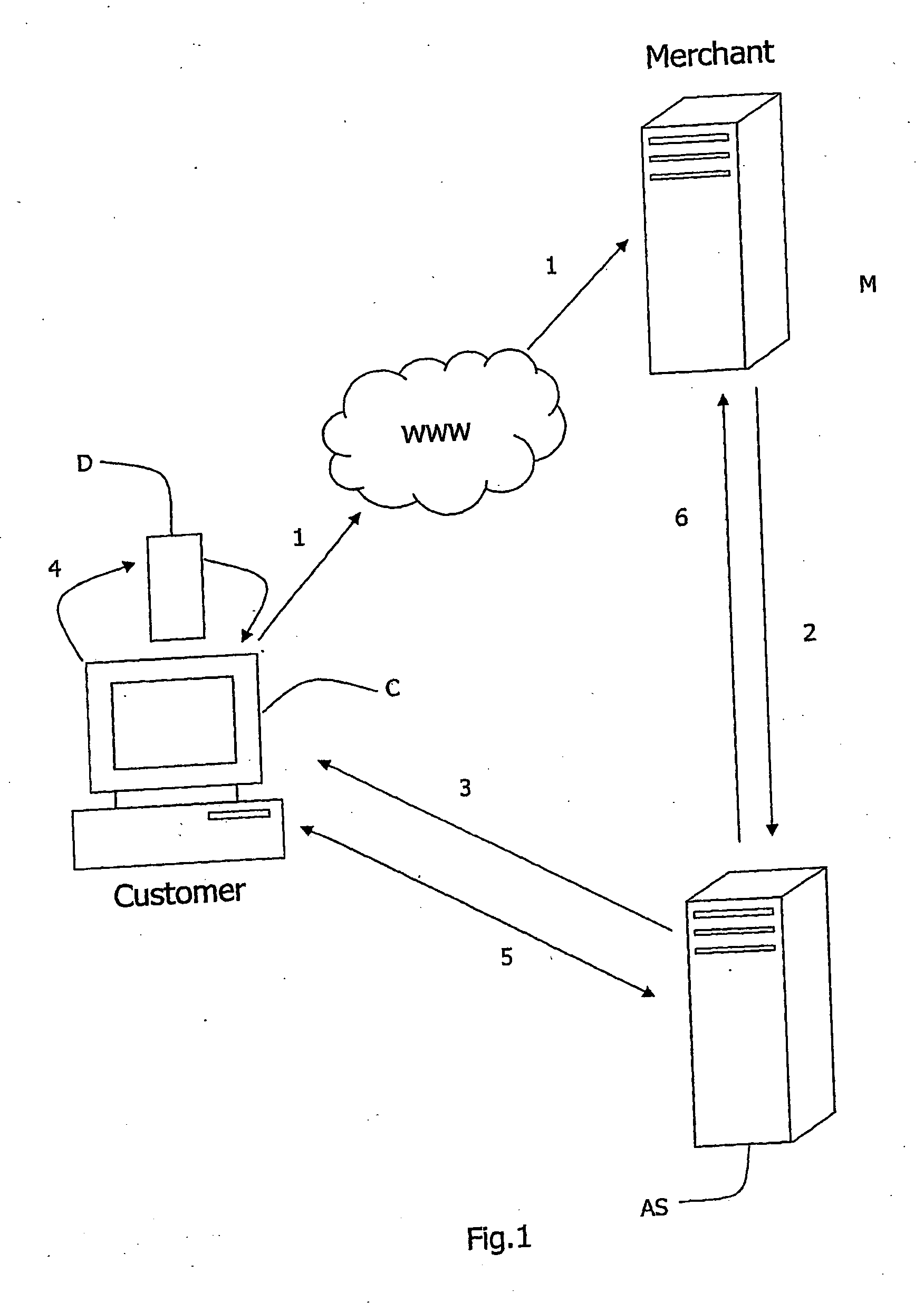
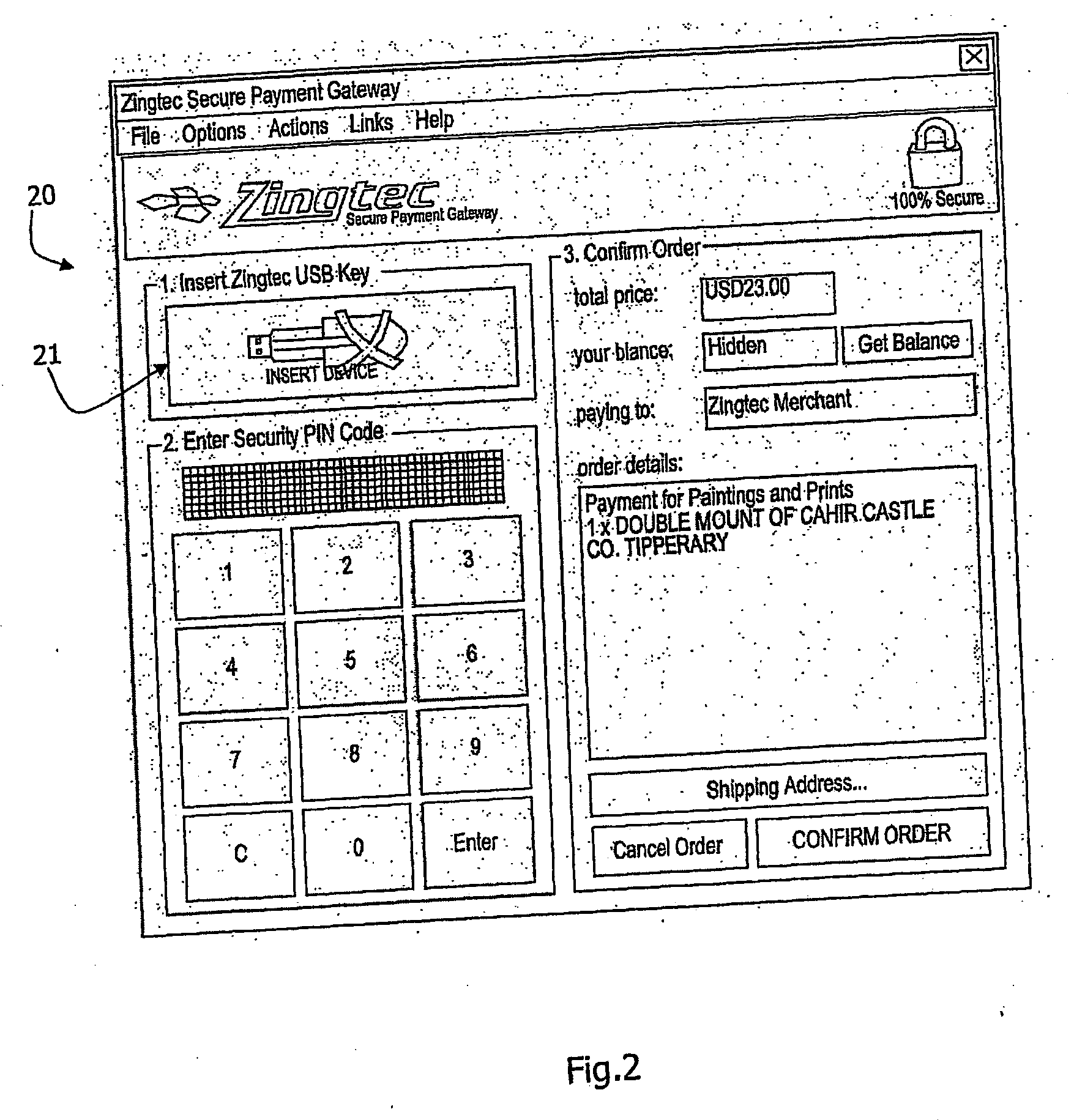
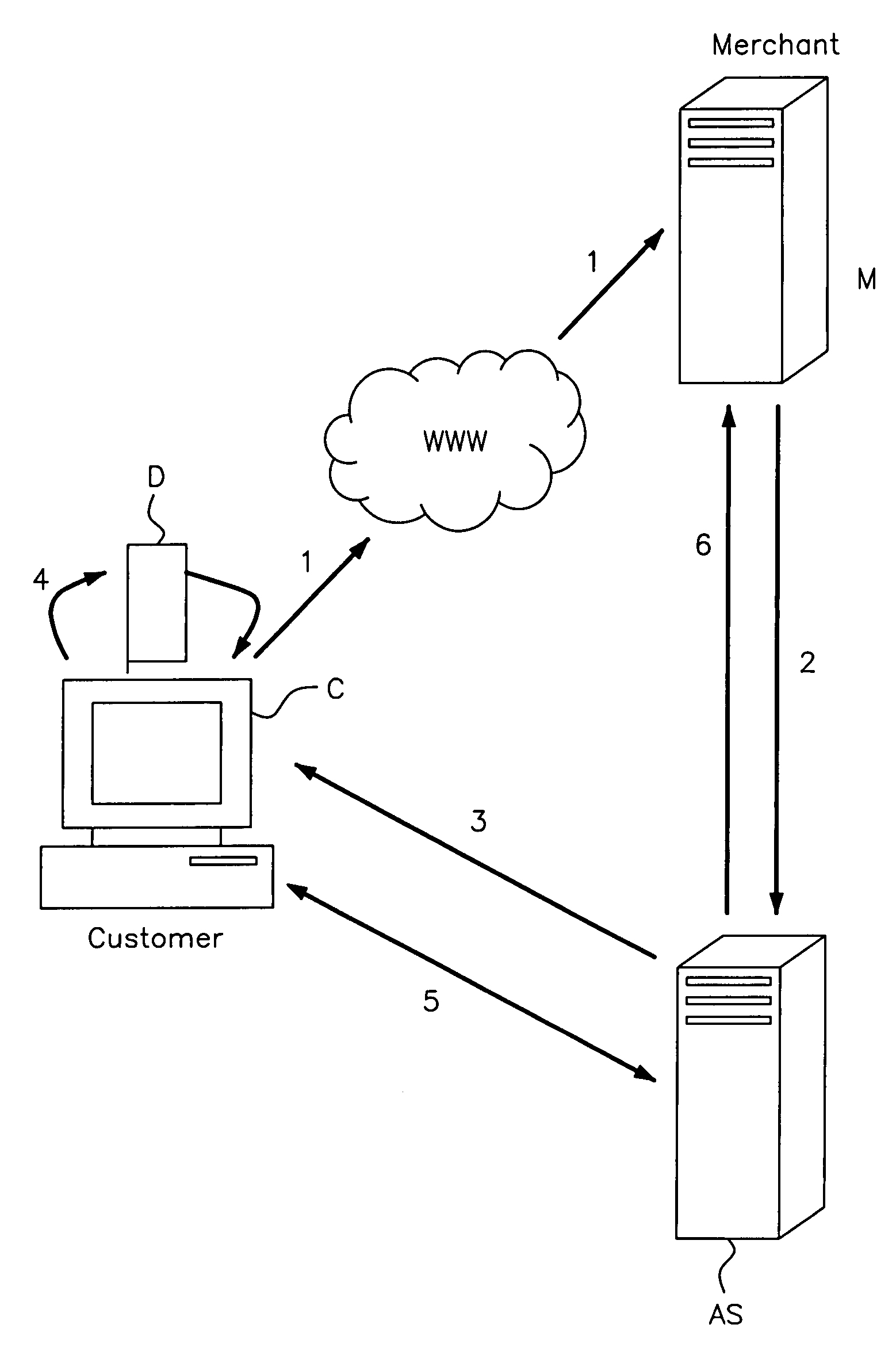
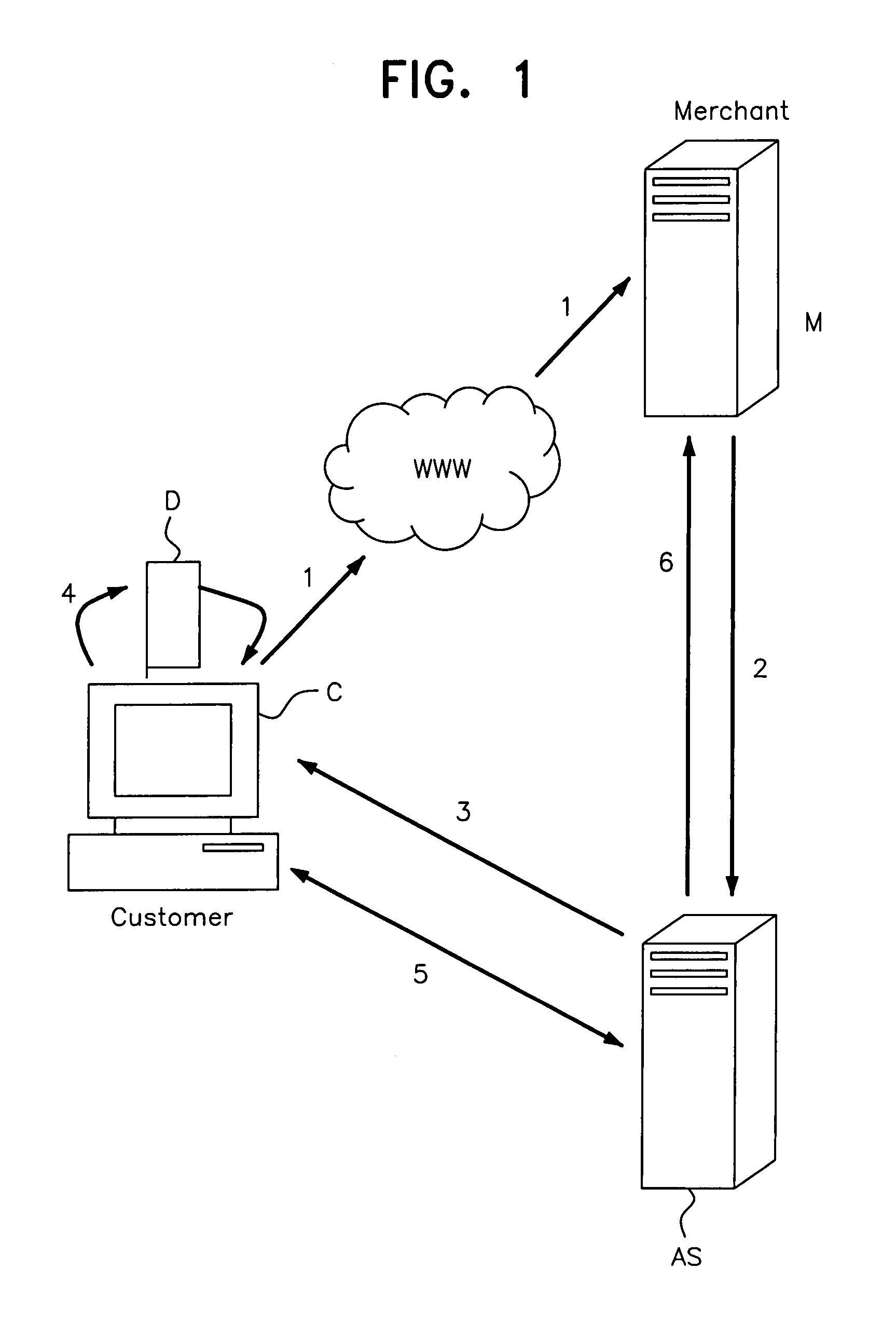
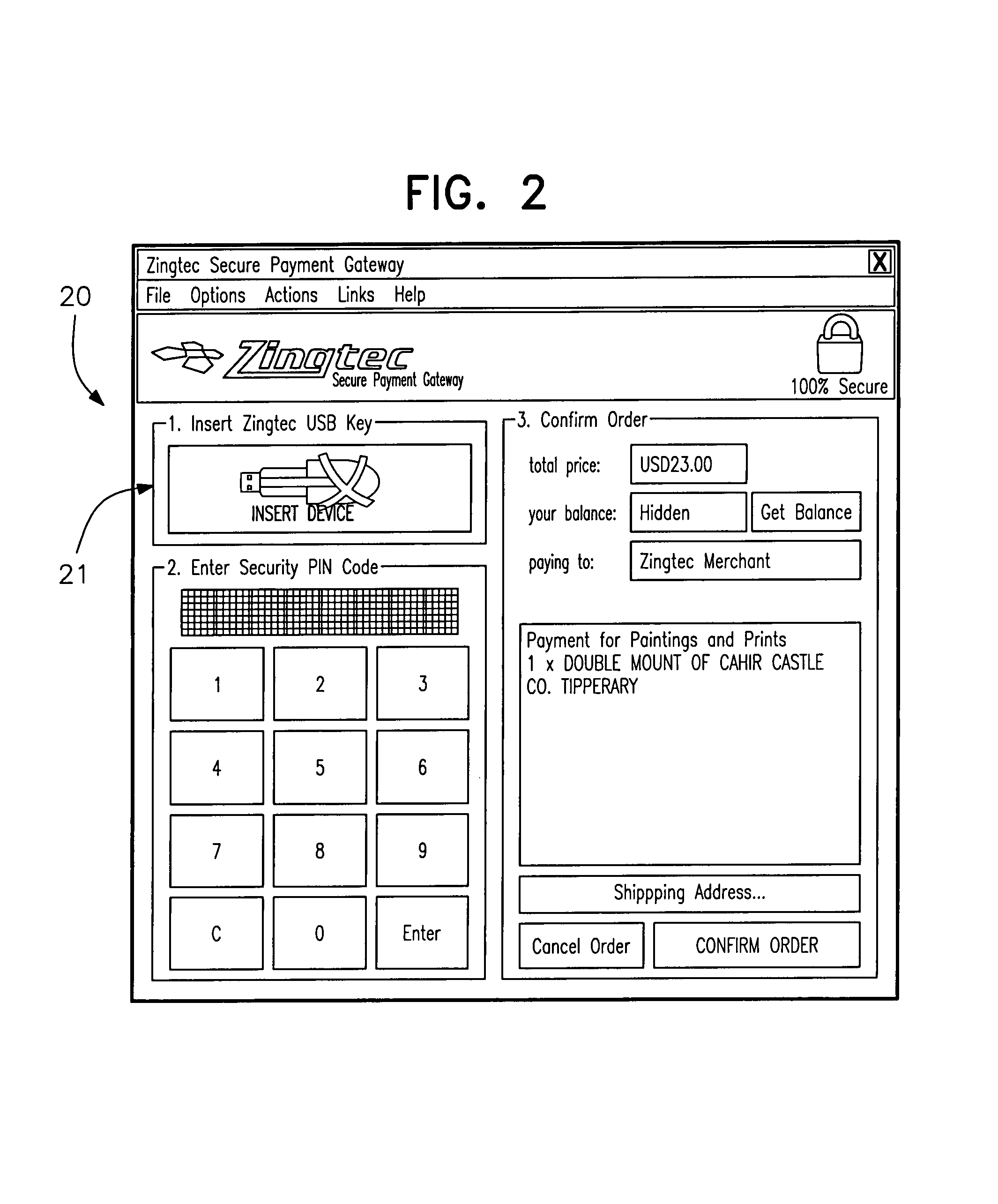
Transaction processing
InactiveUS20060089919A1Complete banking machinesDigital data processing detailsMerchant servicesPayment
A customer inserts a security device (D) into the USB port of his computer (C). When a transaction request confirmation (1) is transmitted to a merchant server (M), the merchant server (M) instructs an account server (AS). The account server (AS) performs customer verification, and payment (either with a local account or remote financial institute server). The account server (AS) communicates directly (3, 5) with the customer computer (C) with an encryption mechanism utilising security data read from the security device (D) and a time stamp. A security key for the security device is updated after each transaction and an embedded hardware key is also used.
Owner:ZINGTECH
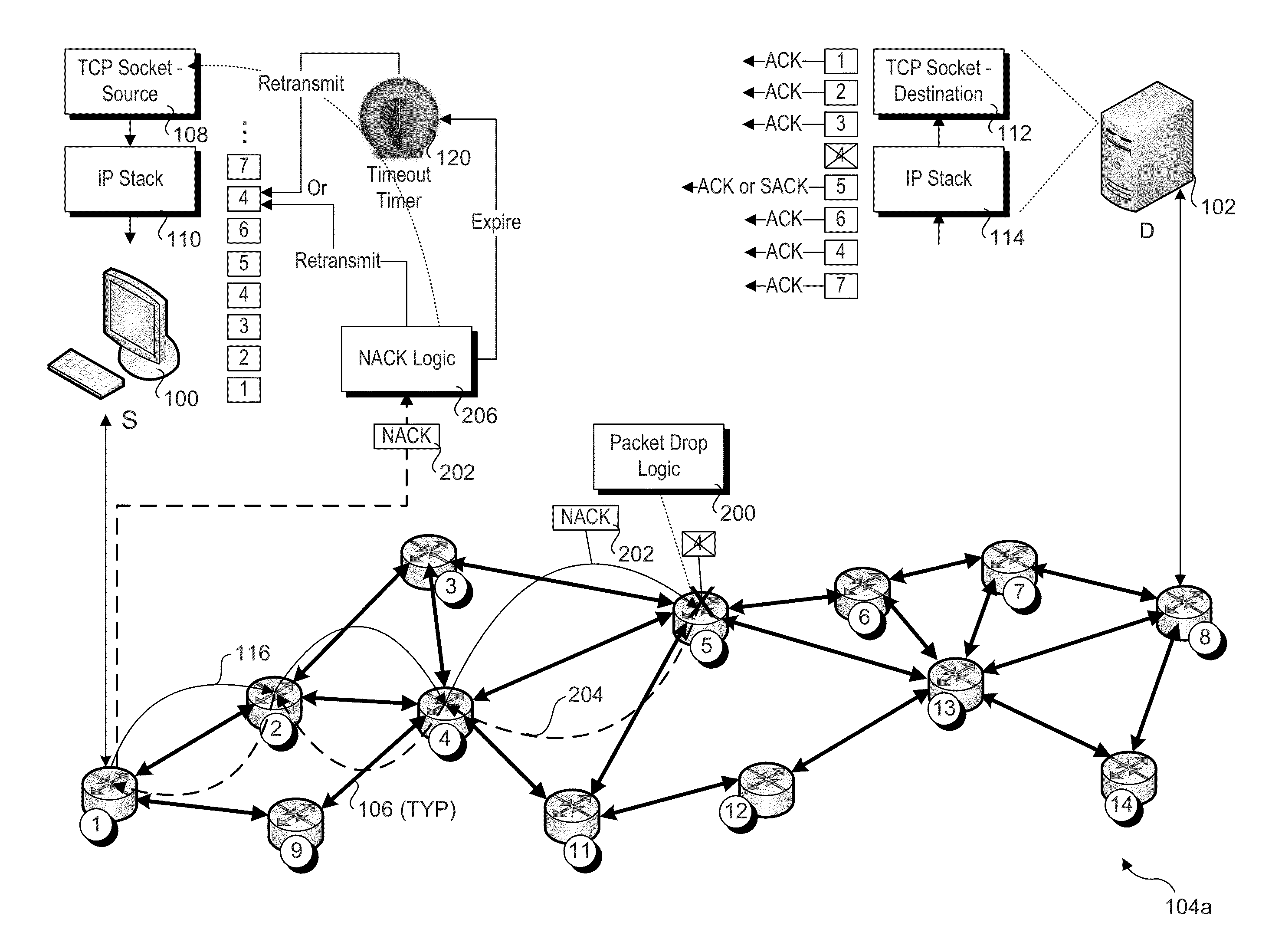
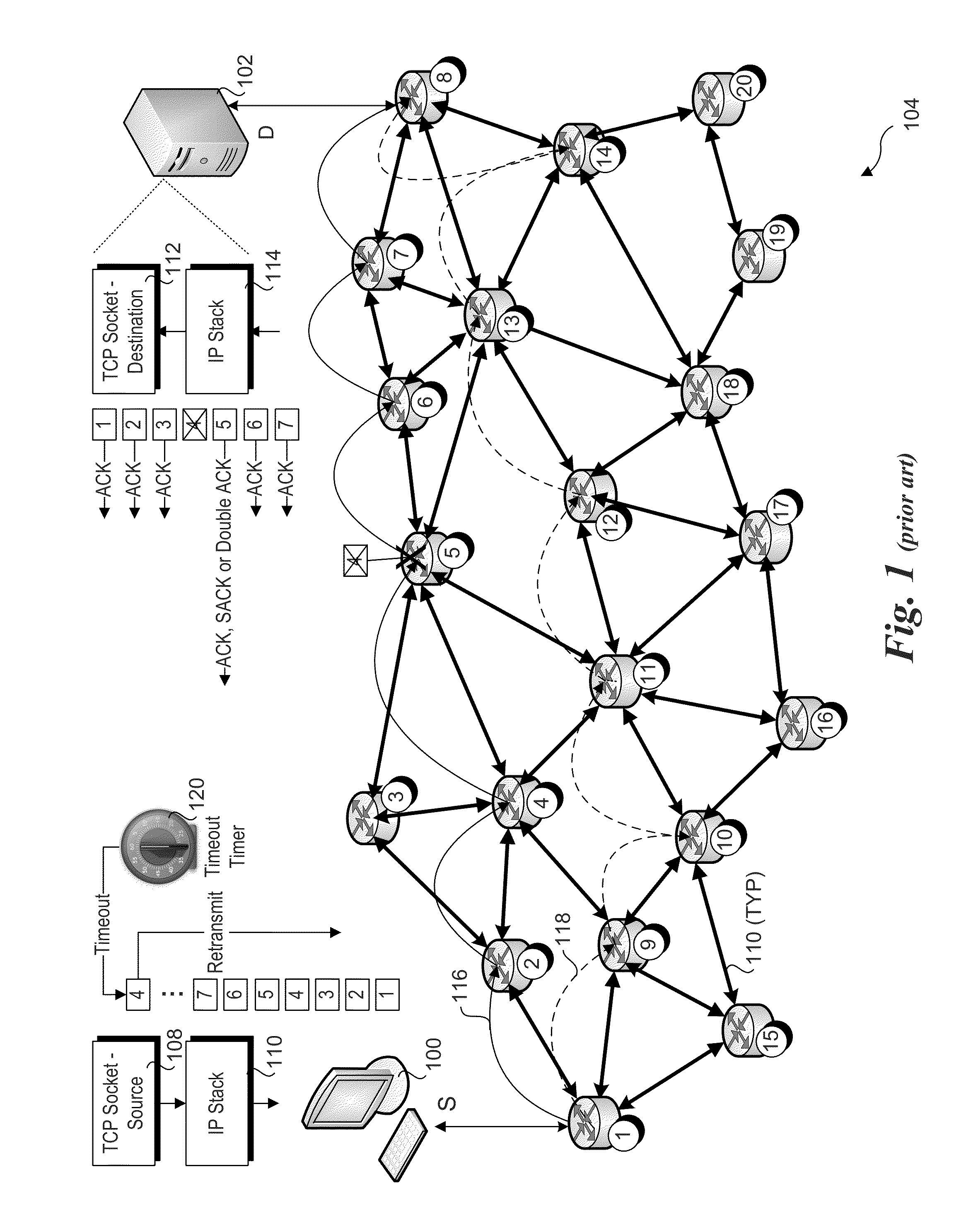
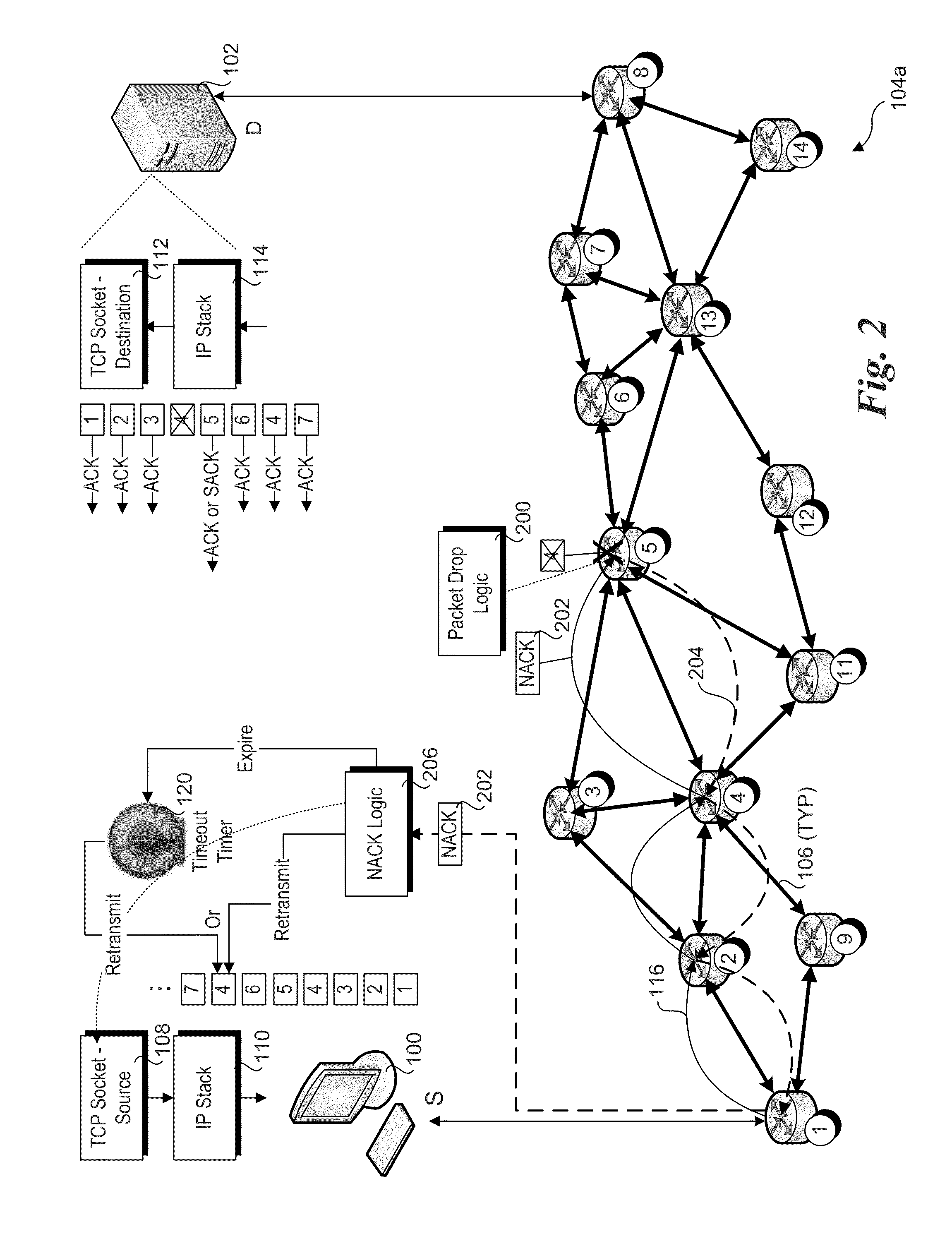
Notification by network element of packet drops
ActiveUS20140153574A1Error prevention/detection by using return channelData switching by path configurationNetwork packetEmbedded hardware
Methods and apparatus for implementing notification by network elements of packet drops. In response to determining a packet is to be dropped, a network element such as a switch or router determines the source of the packet and returns a dropped packet notification message to the source. Upon receipt of notification, networking software or embedded hardware on the source causes the dropped packet to be retransmitted. The notification may also be sent from the network element to the destination computer to inform networking software or embedded logic implemented by the destination computer that the packet was dropped and notification to the source has been sent, thus alleviating the destination from needing to send a Selective ACKnowledge (SACK) message to inform the source the packet was not delivered. (Too narrow)
Owner:INTEL CORP
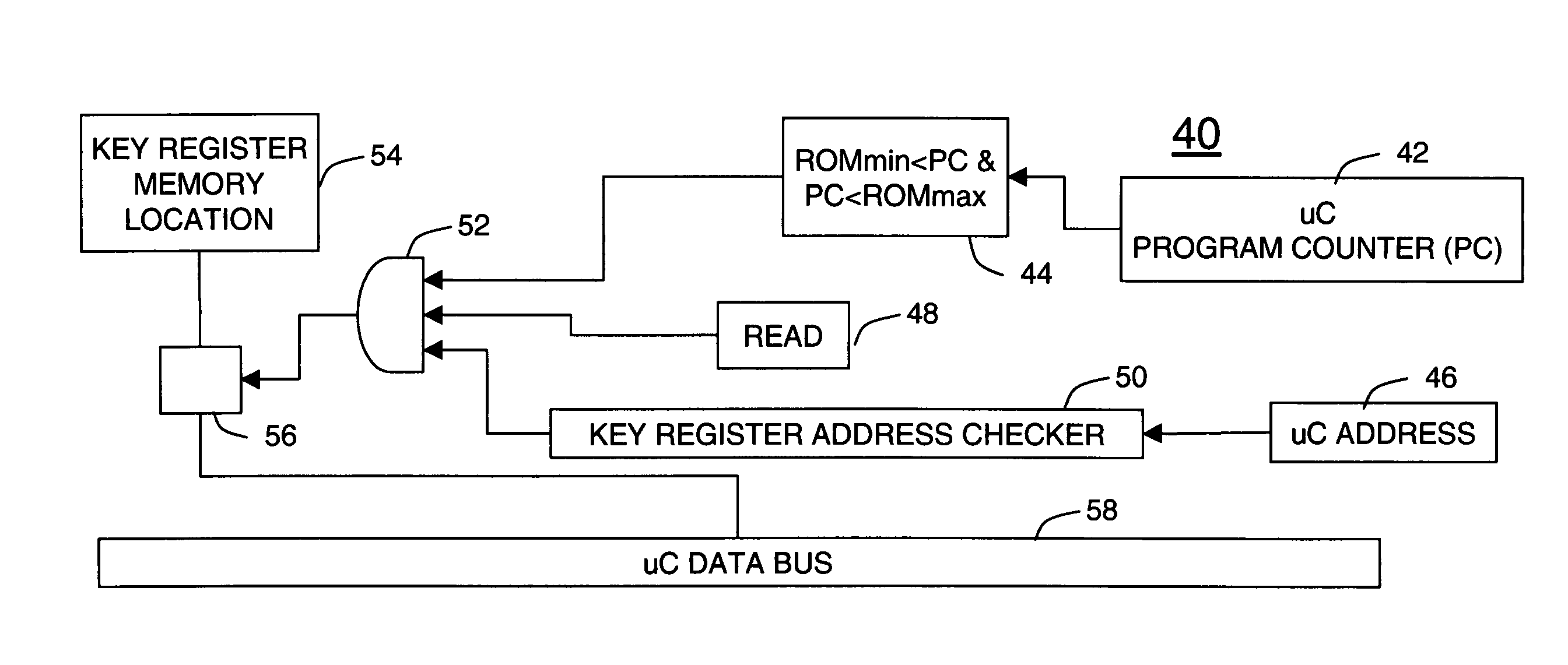
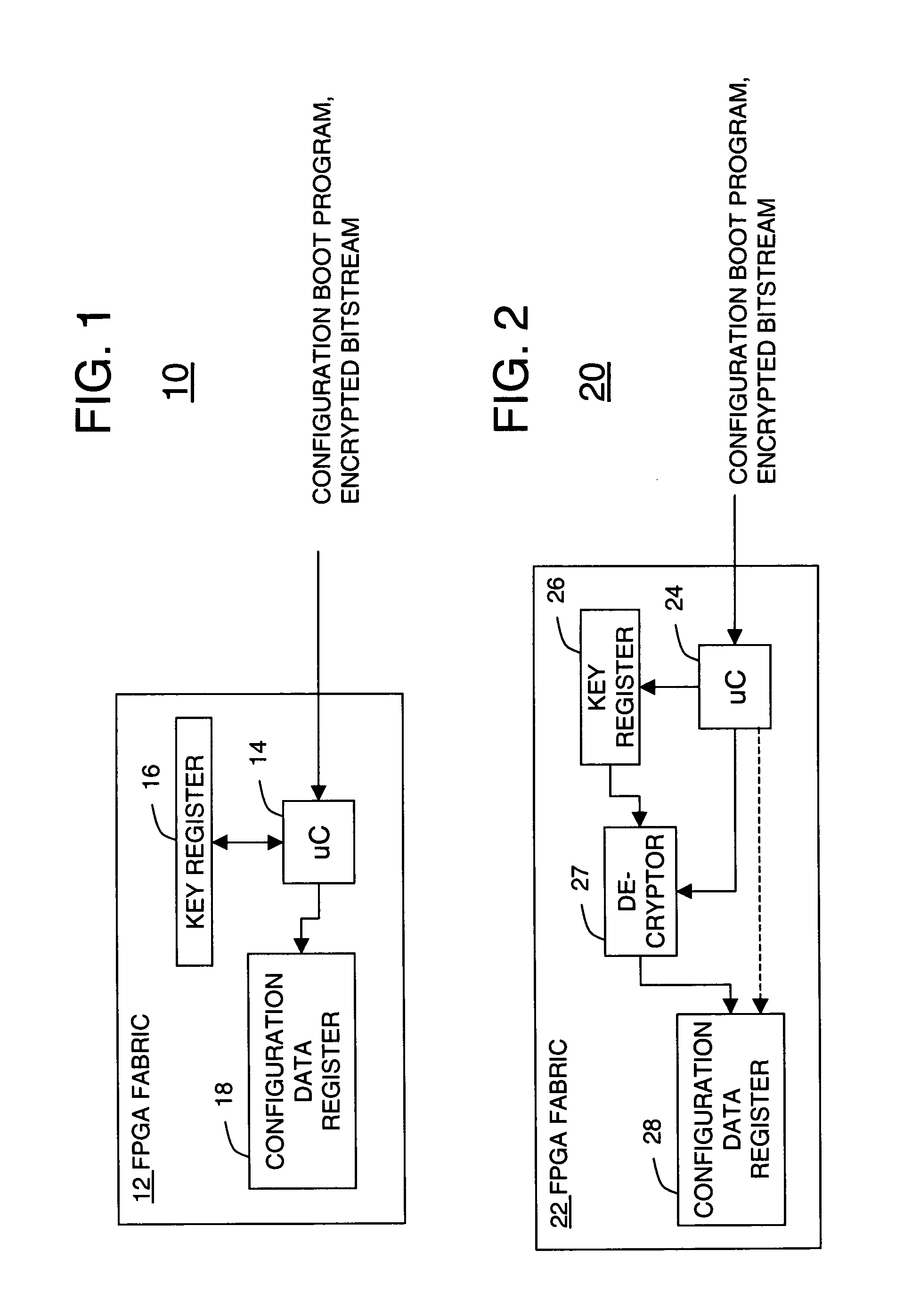
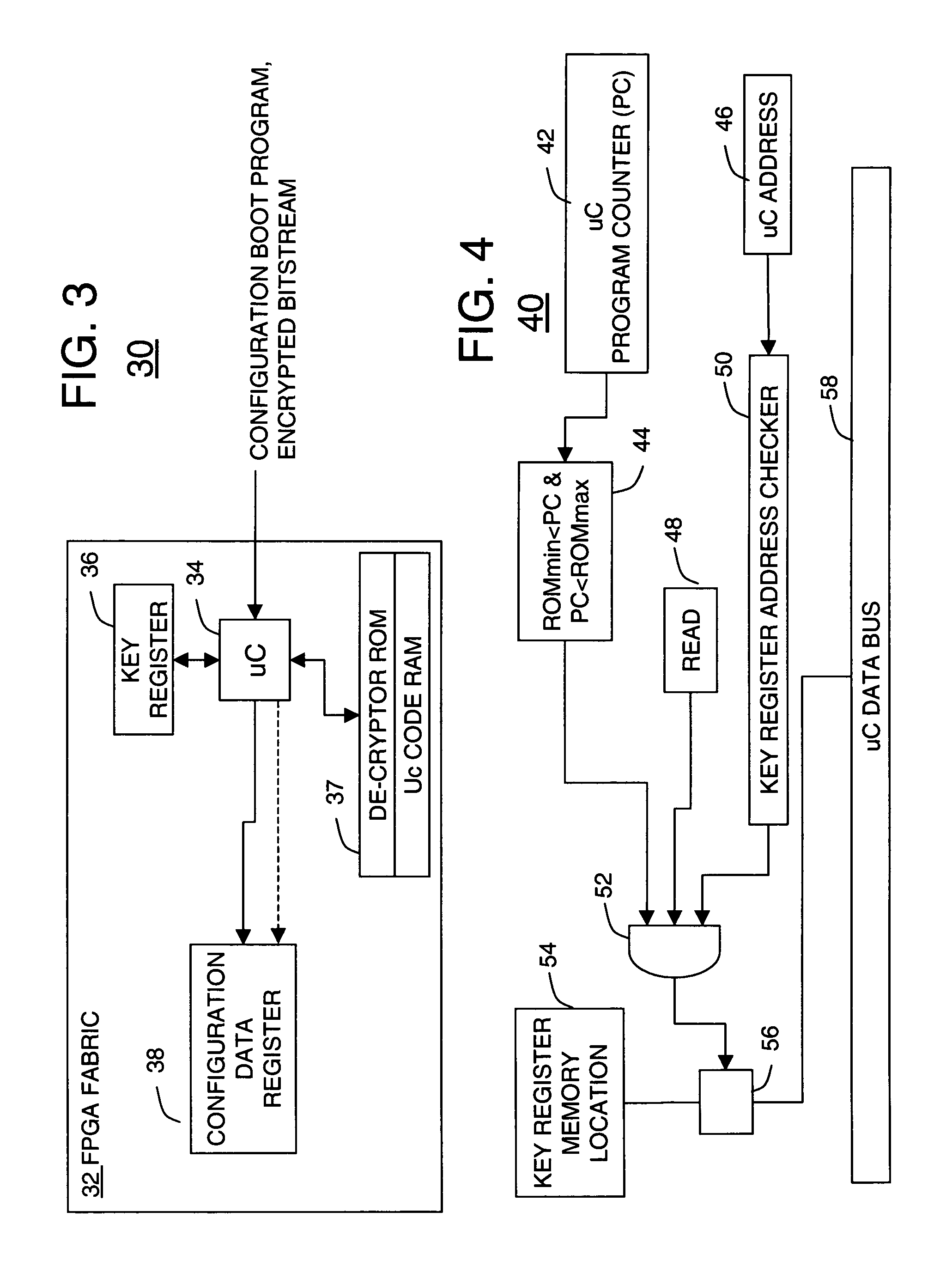
System and method for securing using decryption keys during FPGA configuration using a microcontroller
A system for securely using decryption keys during FPGA configuration includes a FPGA having a microcontroller for receiving a bitstream having an encrypted bitstream portion as well as a configuration boot program. The configuration boot program can be code that runs on an embedded hardware microcontroller or a software microcontroller. The system further includes a key storage register coupled to the microcontroller for storing key data from the microcontroller, a decryptor coupled to the key storage register, and a configuration data register in the FPGA. Preferably, only the decryptor can read from the key storage register and the configuration data register cannot be read by the microcontroller after the decryptor is used.
Owner:XILINX INC
Method to protect software against unauthorized use
InactiveCN1582422ADigital data processing detailsInternal/peripheral component protectionSoftware engineeringSerial code
The present invention describes a method to protect software against unauthorized use which is bound to at least one certain hardware device. This hardware device comprise unique hardware identification sequences like unique hardware numbers / addresses, serial numbers or other embedded hardware characterization sequences. A special license key has to be passed to the software for enabling activation. The license key contains among other things encrypted hardware identification sequences which are compared with the read out sequences of the accessible hardware devices. The use of the software features is permitted if the sequences match.
Owner:NOKIA TECH OY
Intelligent domestic system and safety implementing method
InactiveCN101141348ALow costImprove computing powerCharacter and pattern recognitionData switching by path configurationOperational systemComputer module
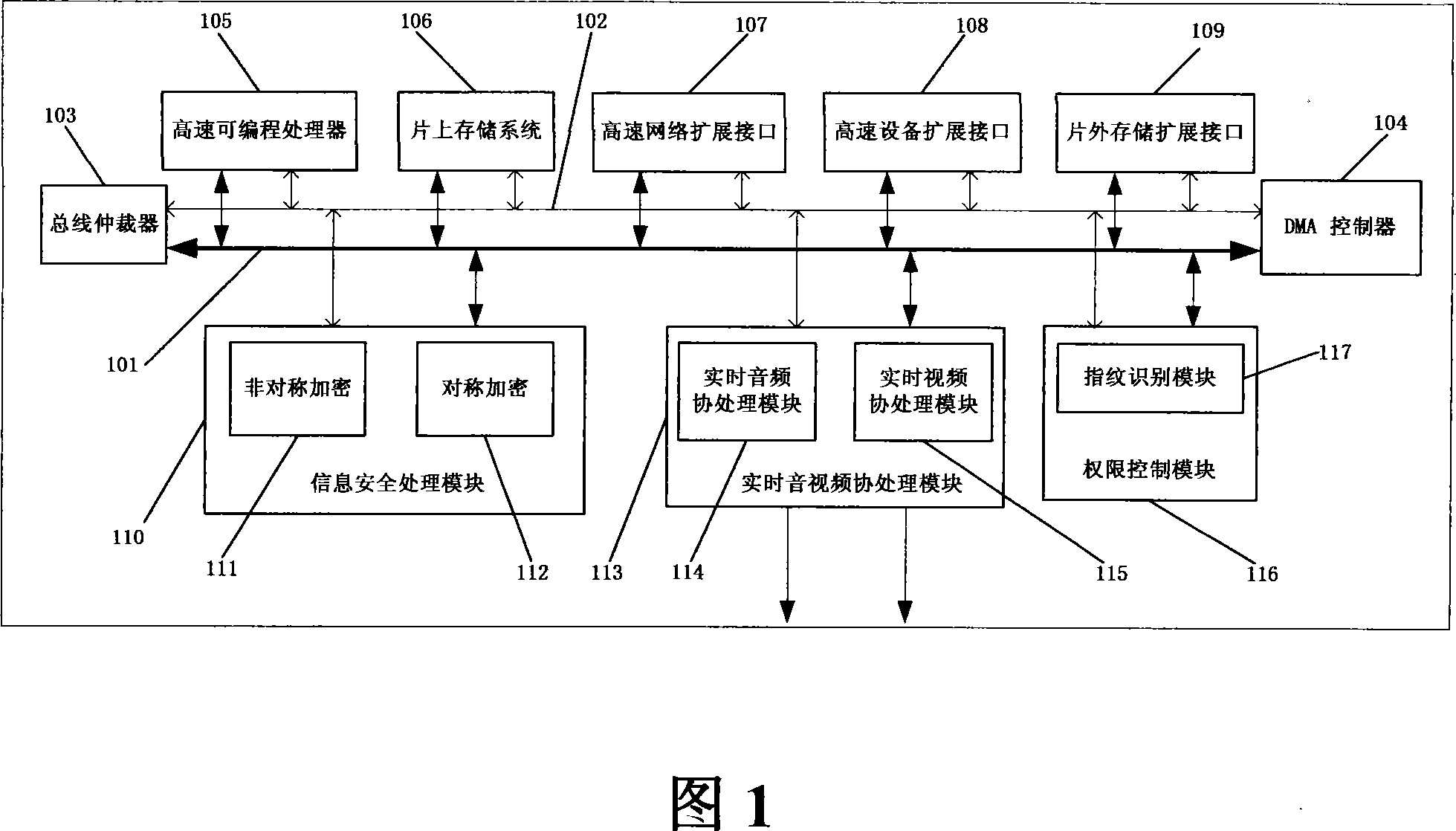
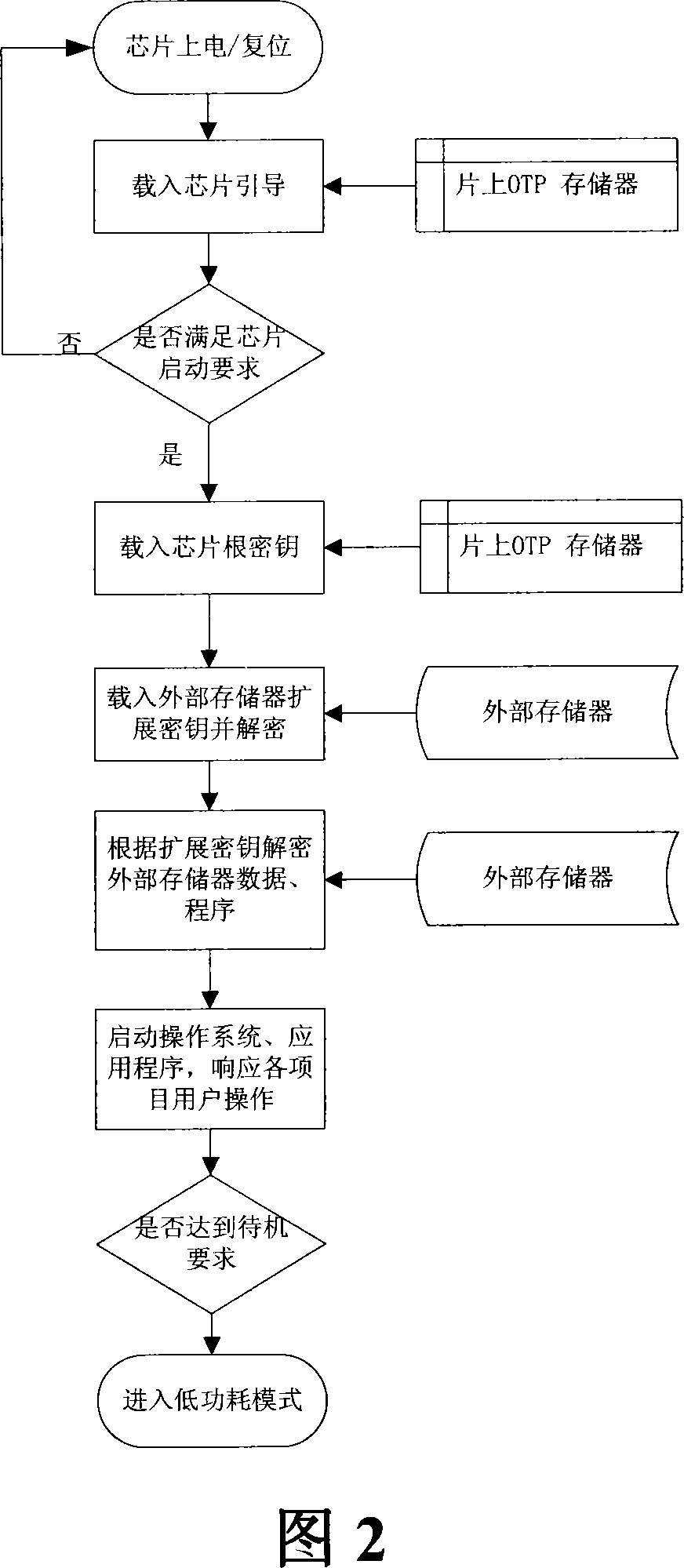
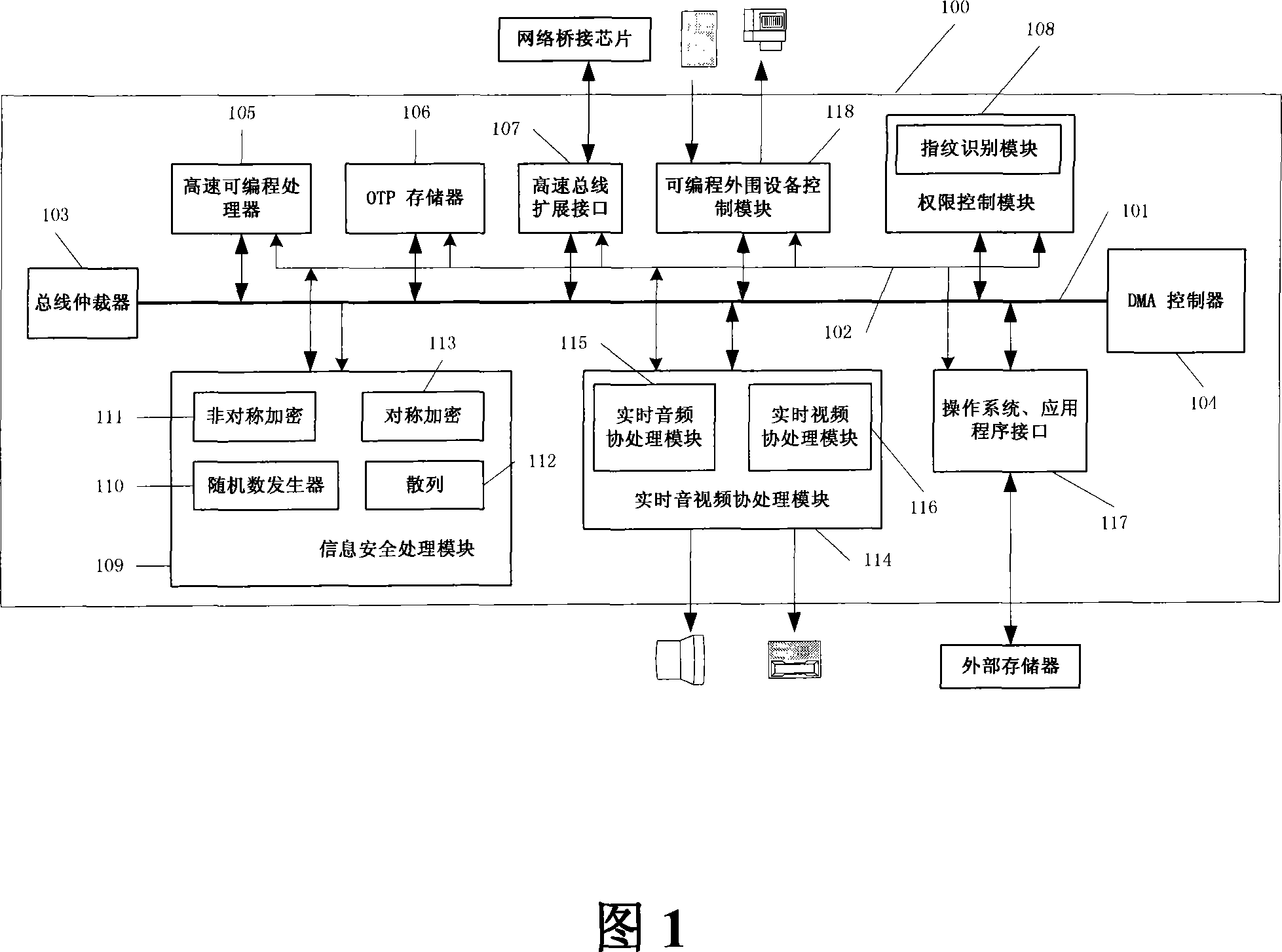
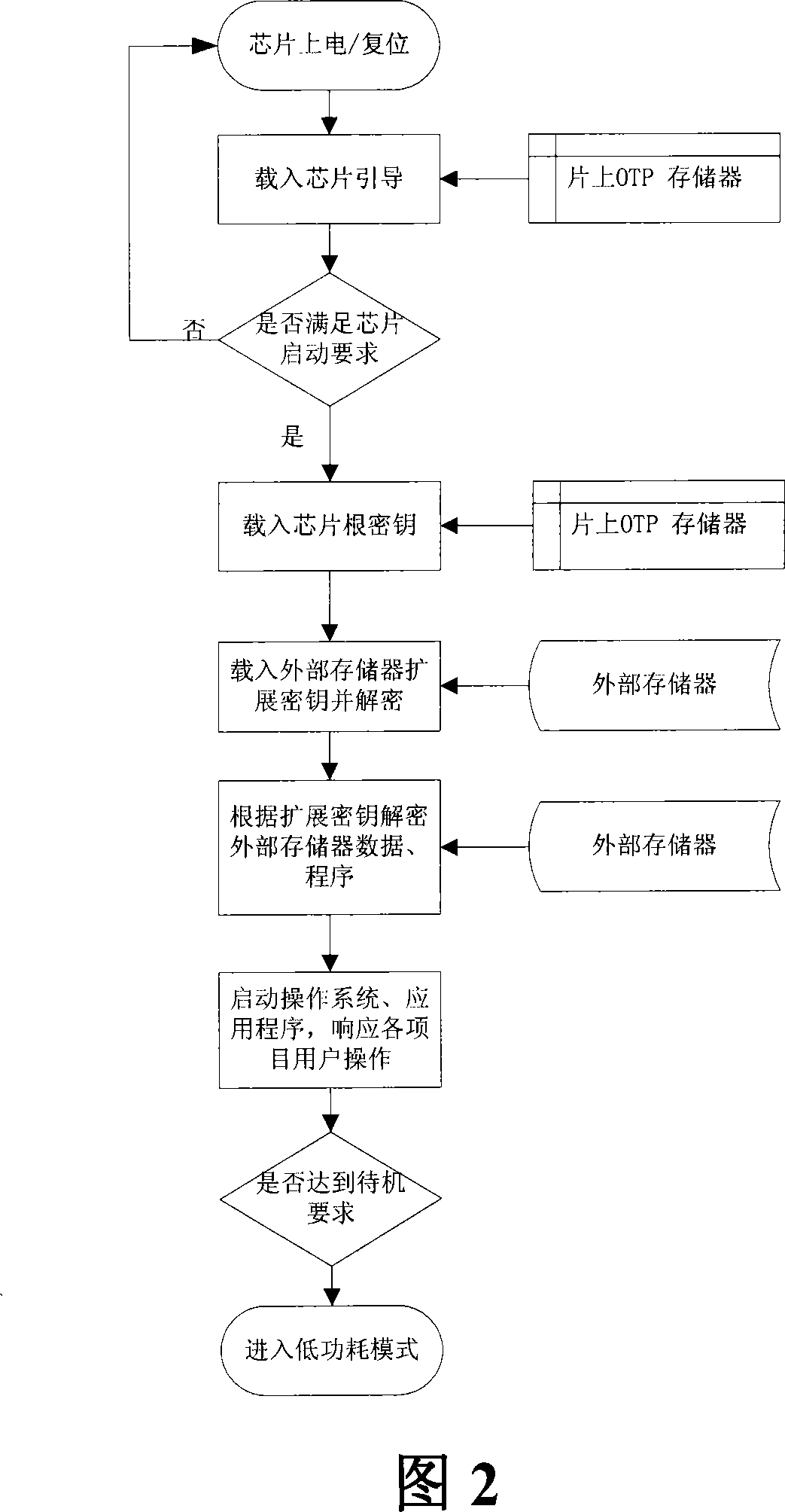
The utility model relates to an intelligent household system, which comprises a local device with the flush-type hardware support platform and a PC client. Both the local device and the local PC client are connected to LAN. The flush-type hardware support platform comprises a flush-type chip and a peripheral device. The flush-type chip consists of a bus system, a memory expansion port on chip, a high speed programmable processor, an operating system and an application program. The local PC client is used to control the local device; also, the flush-type chip includes a storage system on chip and a information safety processing module; the storage system on chip and the information safety processing module are connected to the bus system; the storage system on chip is used to store the bootstrap program and the root key; the information safety processing module is used to encrypt and / or decrypt data and and / or application program. The utility model has such technical results as the system is automatically realized, so that the computer platform's support is not necessary. Thus, the system's complexity is simplified and the terminal system's cost is obviously lowered.
Owner:CHENGDU FINCHOS ELECTRONICS
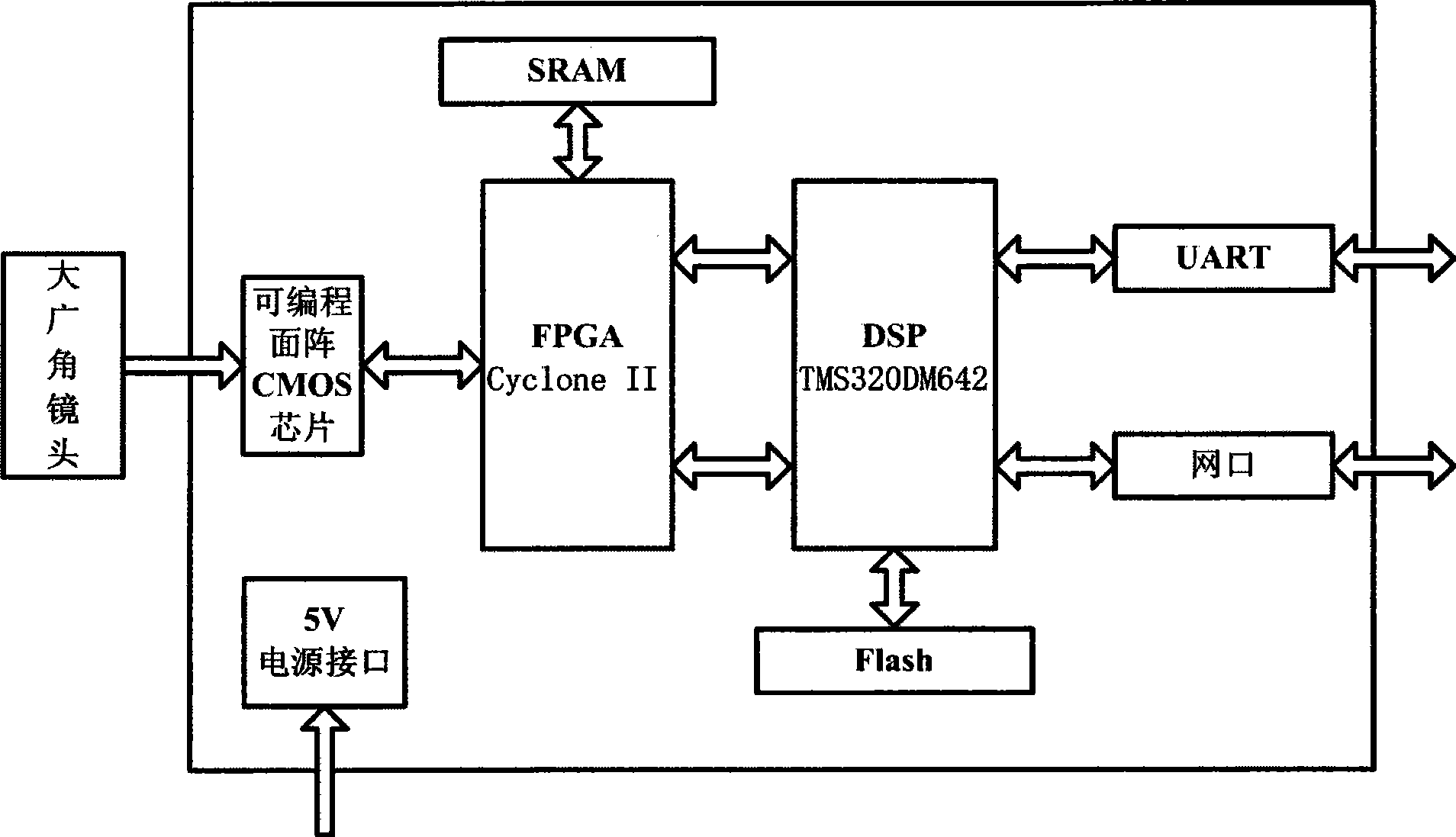
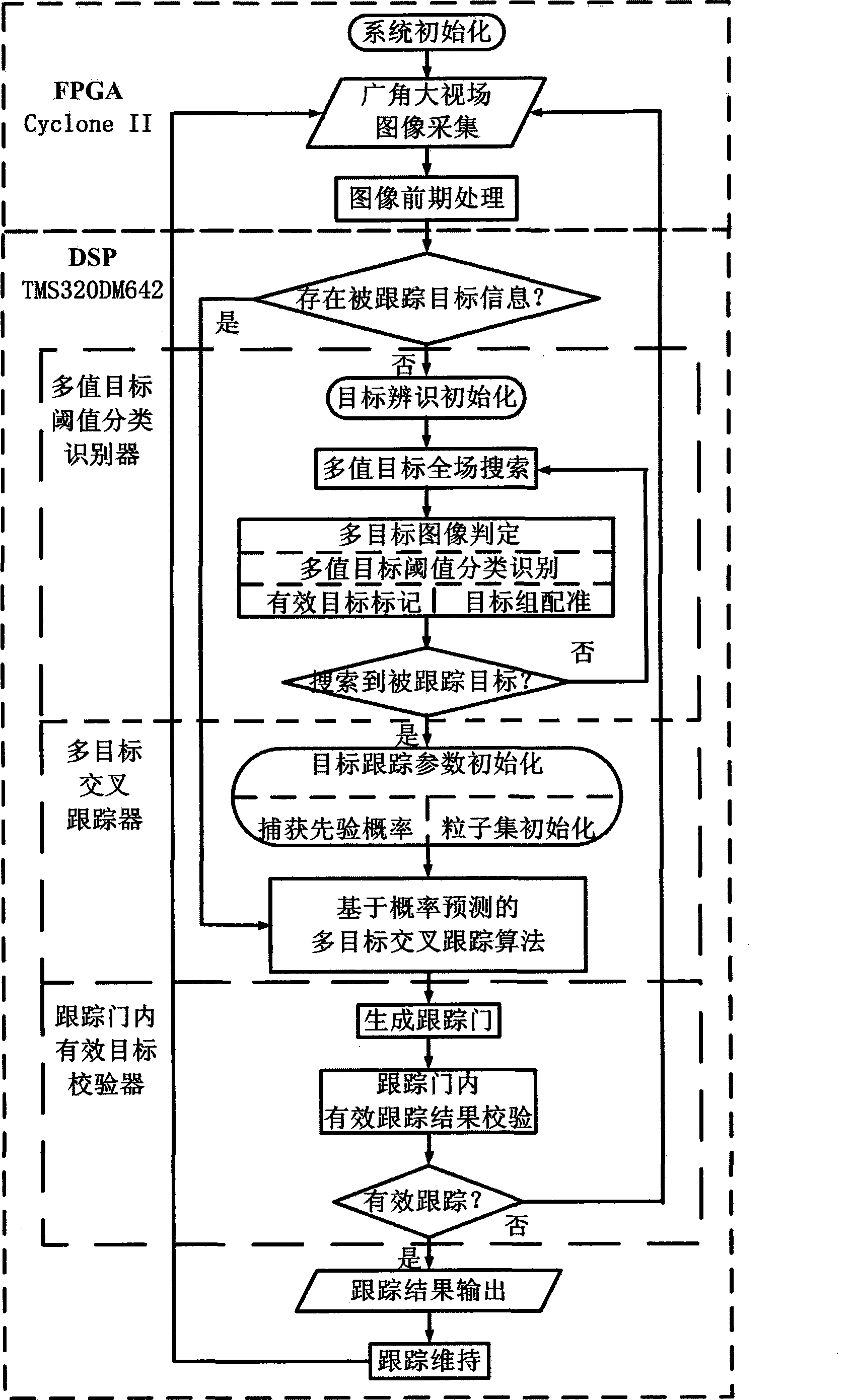
Wide-angle lens-based FPGA & DSP embedded multi-valued targets threshold categorization tracking device
InactiveCN101447075AQuality improvementAvoid target lossTelevision system detailsImage analysisMulti target trackingEmbedded system
The invention provides a wide-angle lens-based FPGA & DSP embedded multi-valued targets threshold categorization tracking device and relates to an embedded system for identifying and tracking multi-targets in a video stream and a related algorithm. Image collection is completed by a wide-angle lens and a color area array CMOS chip; digital image pretreatment, such as digital filtering, image enhancement and the like, is carried out by the FPGA; the algorithms such as multi-valued targets threshold categorization identification, marking registration and the like are realized in a main processor with the DSP as a core; an improved image-tracking program which is based on multi-targets cross operation of a probabilistic forecasting model generates a tracking gate in real time; a target tester in the tracking gate controls and tracks a process and outputs a target value. The wide-angle lens-based multi-valued targets threshold categorization tracking device supported by an embedded hardware platform has wide application prospect in the aspects of dynamic photography, security monitoring, maneuvering target detecting, multi-targets tracking, automatic navigation of vehicles, etc. The device especially has the advantage in constructing an airborne target tracking system with small structure volume and low power consumption.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
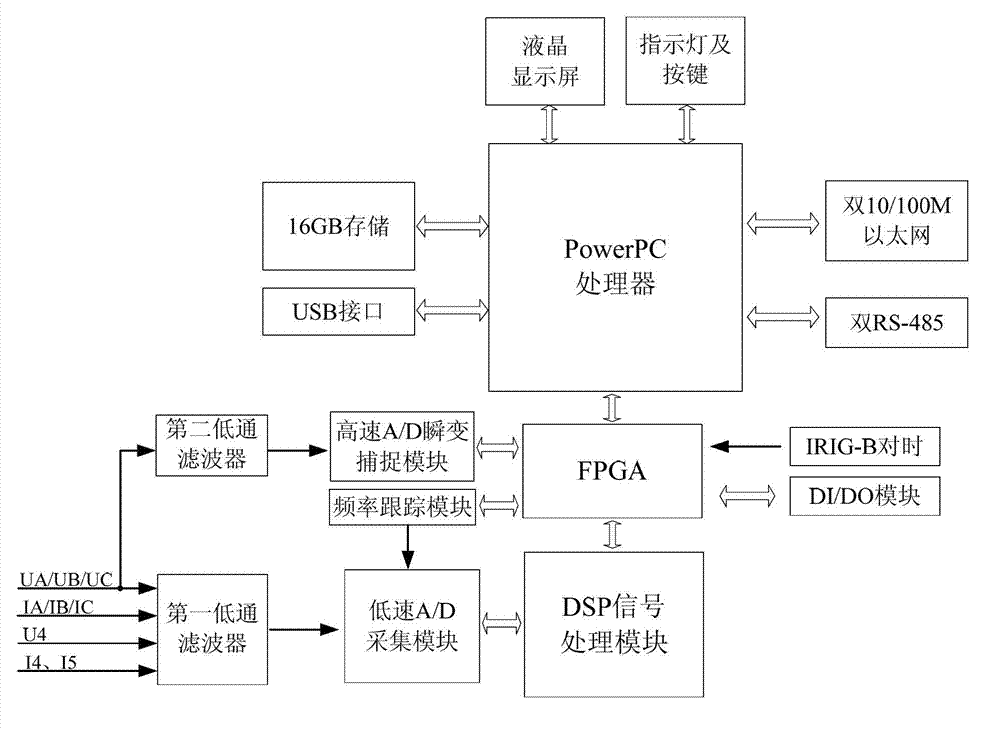
On-line electric energy quality monitoring device
ActiveCN102759675ACapable of capturing high-speed transient signalsElectrical testingPower qualityDigital signal processing
The invention discloses an on-line electric energy quality monitoring device. A hardware platform is an embedded hardware platform and is in a complex structure consisting of a Power PC (Personal Computer) functional unit, an FPGA (Field Programmable Gate Array) functional unit and a DSP (Digital Signal Processing) functional unit, wherein the Power PC functional unit is independent of the DSP functional unit; and data interaction is performed between the Power PC functional unit and the DSP functional unit through a double-port RAM (Random Access Memory) configured in the FPGA functional unit. The conventional normal electric energy quality device has a high-speed transient signal acquisition function by only increasing limited cost. The on-line electric energy quality monitoring device is widely applied to nonlinear load and impact load, including on-line monitoring of conventional electric energy quality index parameters at places with more serious transient interference such as equipment connection and lightning strike on a power grid; and when a high-speed voltage transient abnormal event occurs, the current transient signal can be automatically acquired and truly and completely recorded, and basis support is provided for failure analysis of devices and equipment on a power supply line.
Owner:深圳市中电软件有限公司
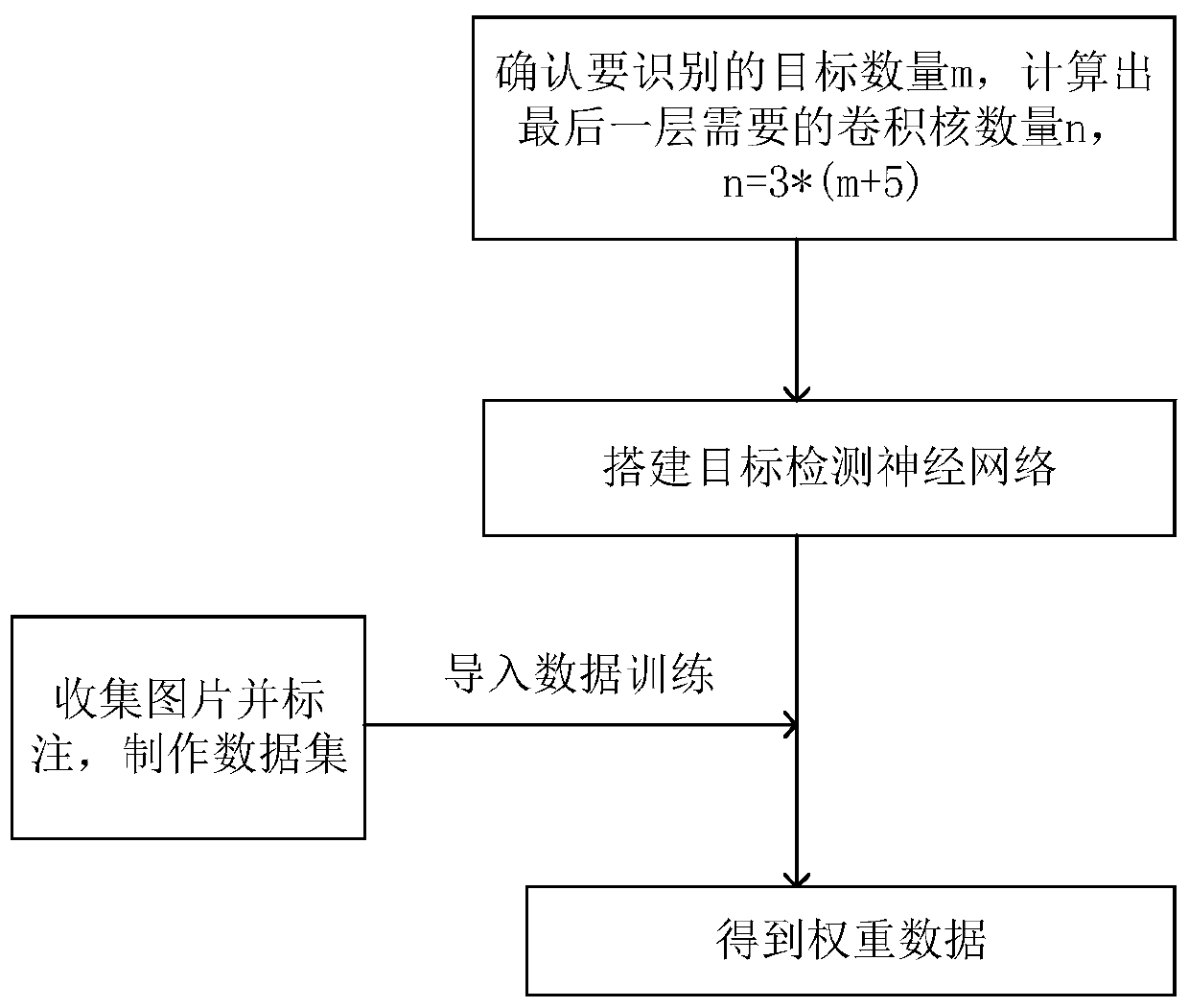
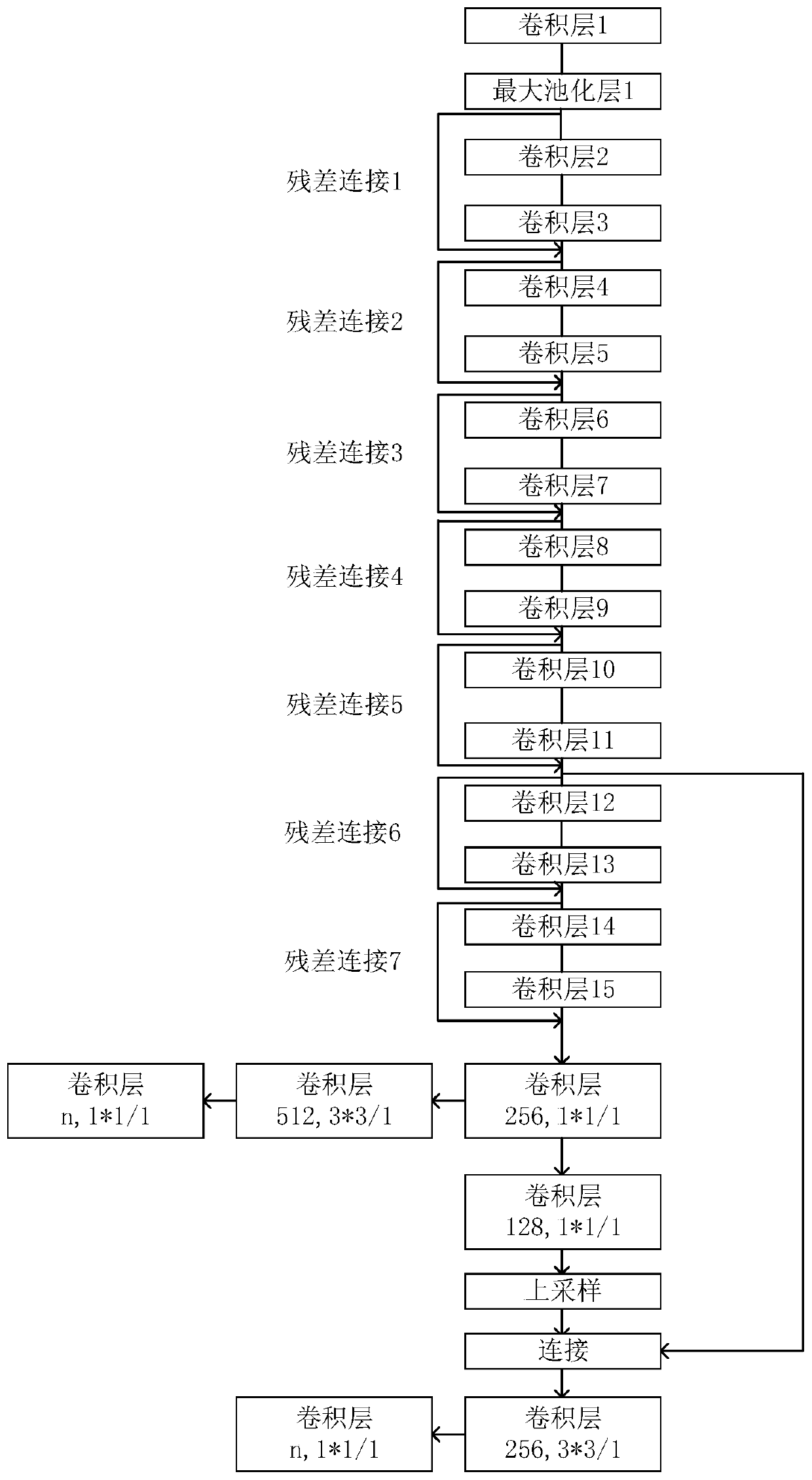
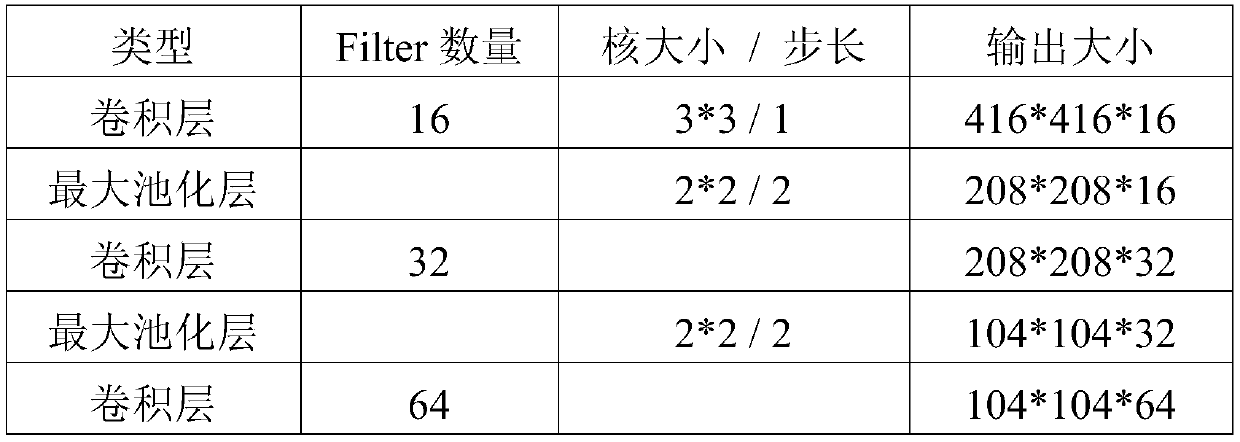
Improved target detection method based on residual network
ActiveCN110210621ASmall amount of calculationGuaranteed real-timeNeural architecturesNeural learning methodsData setFeature extraction
The invention discloses an improved target detection method based on a residual network, based on YOLO V3-tiny network, features are extracted through continuous convolution operation, finally, pictures are divided into 13*13 grids, for each grid unit, a detection frame of a target with a center point falling into the grid unit is predicted through three anchor frames. The method specifically comprises the following steps of determining the number of types of the target to be identified to form a data set; establishing a target detection neural network; obtaining training weight files. Throughthe lightweight target detection network YOLOV3-tiny, the calculation amount is small, the target detection task can be carried out in the embedded hardware, and the real-time performance is ensured.According to the method, the original feature extraction network is replaced by the residual network resnet18, and for the feature extraction network with the same layer number, the feature extraction capability of the network can be improved by adding the residual structure by the residual network, so that the target detection precision can be improved on the premise that the detection speed isnot reduced.
Owner:DALIAN UNIV OF TECH
Transaction processing
A customer inserts a security device (D) into the USB port of his computer (C). When a transaction request confirmation (1) is transmitted to a merchant server (M), the merchant server (M) instructs an account server (AS). The account server (AS) performs customer verification, and payment (either with a local account or remote financial institute server). The account server (AS) communicates directly (3, 5) with the customer computer (C) with an encryption mechanism utilising security data read from the security device (D) and a time stamp. A security key for the security device is updated after each transaction and an embedded hardware key is also used.
Owner:ZINGTECH
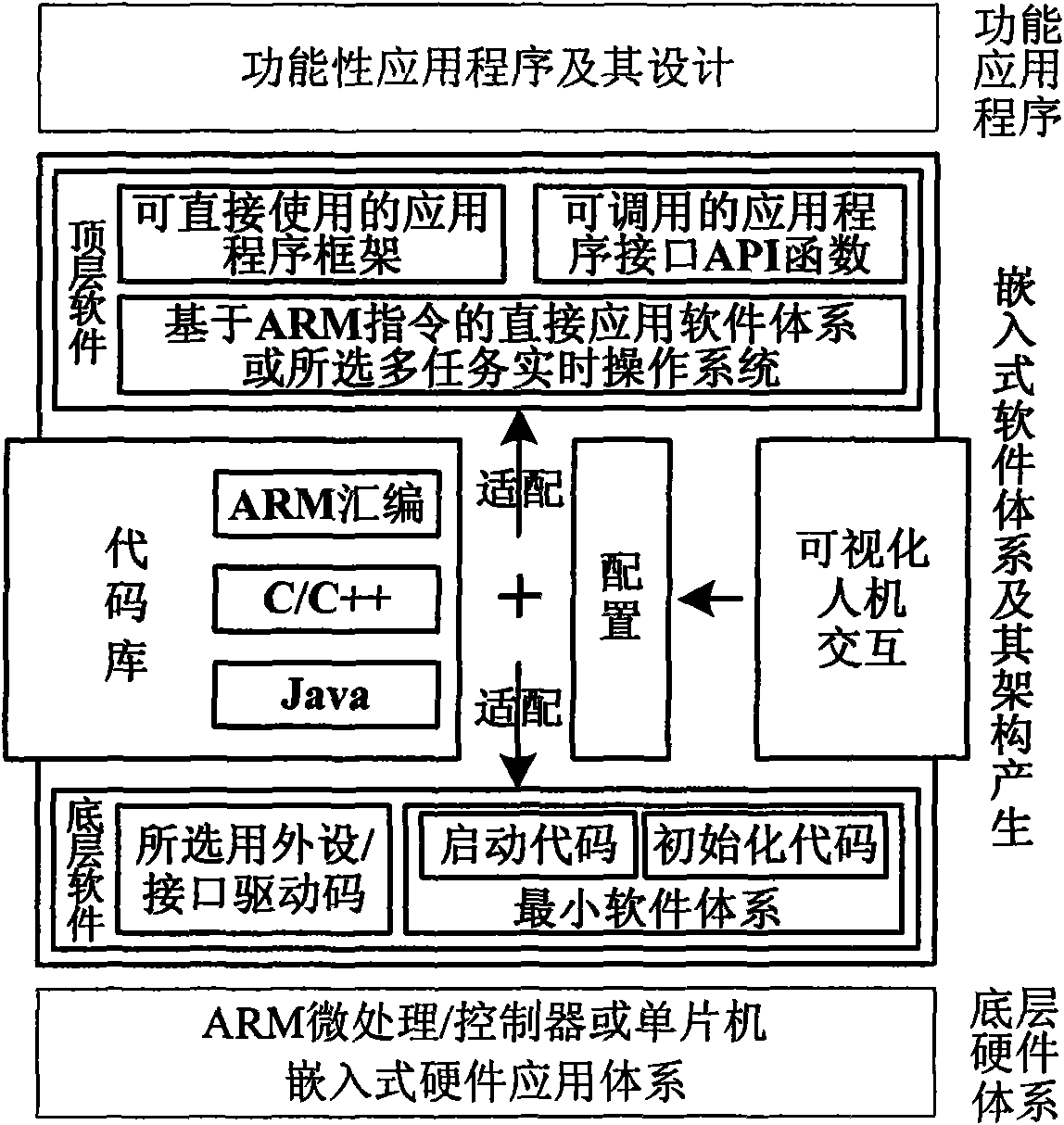
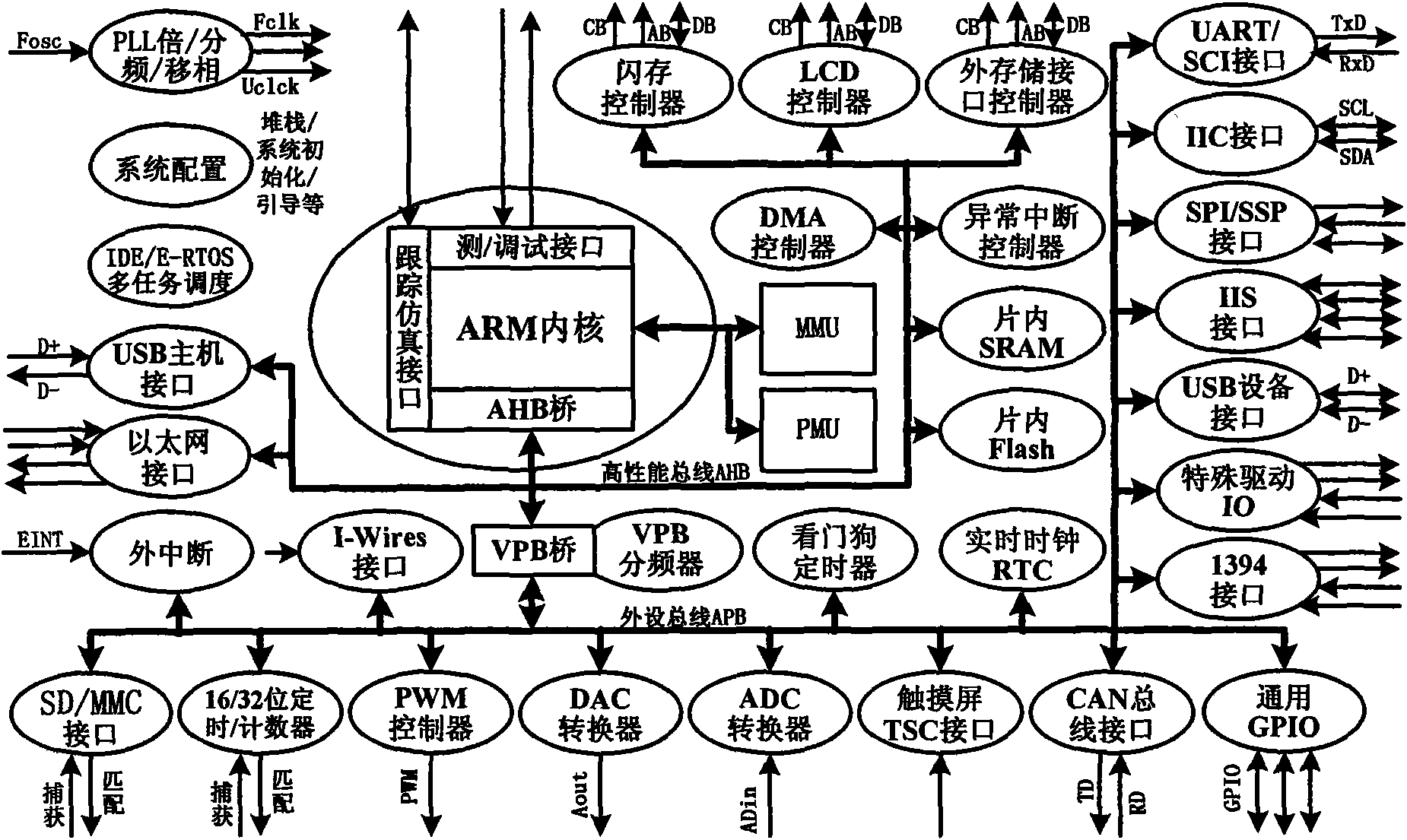
Software system configuring tool of ARM series microprocessor
InactiveCN101551747ASimplify the design processShorten the development cycleSpecific program execution arrangementsHuman–machine interfaceOperational system
The invention, software system configuring tool of ARM series microprocessor, realizes quick configuration of imbedded application software system of various ARM microprocessors / controllers, obtains practical configuration based on ARM microprocessors / controllers, with rich program code base based on bottom hardware and strong adaptability of embedded hardware system, established on embedded ARM hardware system, and by means of simple and easily used visual human-machine interface, downwards forms bottom software composed of a minimal software system containing starting codes, system initializing codes and the like, and external and interface drivers, and upwards forms top software composed of a board support package based on direct software system of ARM instruction set or selected multi-tasking real-time operating system, callable application program interface function library and directly useable application program framework, by combining embedded extensive and rich code database and by means of adaptation and optimization stage by stage. The software system configuring tool is applied to design of embedded system, reduces development cycle to the utmost, research and development costs and threshold, strengthens reliability and high efficiency of system, and smoothly realizes design of functional application program so as to promote embedded products into market fast.
Owner:河南博元电力科技股份有限公司 +4
Production management system and safety implementation method
InactiveCN101145228ASolve the problem of own security (platform security)Real-time acquisitionUser identity/authority verificationTotal factory controlOperational systemApplication software
The invention provides a production management system, which comprises a client embedded hardware support platform and a data server used for receiving and publishing production management information. Both the client embedded hardware support platform and the data server are assessed to a local area network (LAN). The client embedded hardware support platform comprises an embedded chip and peripherals, wherein the embedded chip comprises a bus system, an application program interface and a high-speed programmable processor. The embedded hardware support platform contains an operation system and application programs. The peripherals include an external memory and / or a network bridging chip. The embedded chip also comprises a disposable programmable memory and an information safety processing module, and the disposable programmable memory and the information safety processing module are both accessed to the bus system. The disposable programmable memory is used for storing programs and root keys; the information safety processing module is used for encrypting and / or decrypting data and / or programs. The invention solves the safety problem of the embedded chip itself and also the network.
Owner:CHENGDU FINCHOS ELECTRONICS
Embedded high-performance heterogeneous computing platform based on FPGA and ARM
InactiveCN103226541AStrong complementarityImprove efficiencyGeneral purpose stored program computerExtensibilityComputer science
The invention relates to the field of computer hardware, belongs to the field of embedded hardware platforms, and in particular discloses an embedded high-performance heterogeneous computing platform based on an FPGA (field programmable gate array) and an ARM (advanced reduced instruction-set computer machine). The embedded high-performance heterogeneous computing platform integrates the advantages of the FPGA and the ARM, is high in transmission and processing speed, good in expandability, and high in reliability; defects in the prior art are overcome; complementation of software and hardware systems is achieved; and the system performance is improved. The embedded high-performance heterogeneous computing platform comprises an information input system, wherein the information input system is connected with an information output system after connected with an ARM module and an FPGA module.
Owner:江苏复芯物联网科技有限公司
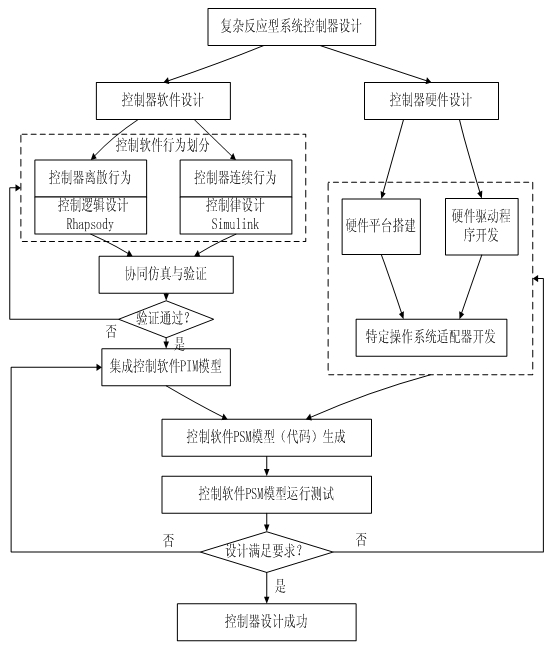
Design method of complex reaction type system controller
InactiveCN102012673APromote rapid developmentReduce development costsAdaptive controlModel driven developmentOperational system
The invention discloses a design method of a complex reaction type system controller, belonging to the field of controller design. In the method, a mode that control software and an embedded hardware platform are in parallel is adopted. The method comprises the following steps: dividing the controller into a logic part and a control law part according to the complex reaction type system attributes; respectively establishing a model for the two parts by using the idea of model driving development, and combining the logic part and the control law part of the controller by using the model integration mode of model importing, thereby forming complete complex reaction type system control software irrelevant to the platform; and finally, converting a personal information management (PIM) model into a platform specific model (PSM) by using a specific operating system adapter, and downloading the PSM model to the designed hardware platform, thereby completing the design of the complex reaction type system controller. By using the design method, the design personnel can concentrate on the construction of the complex reaction type system logic model without considering the editing of the controller software, thereby greatly enhancing the development efficiency of the complex reaction type system controller.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Portable wireless network detection evidence-obtaining system
InactiveCN104159244AConvenient for dynamic expansionReduce power consumptionHigh level techniquesWireless communicationOperational systemEmbedded operating system
The invention discloses a portable wireless network detection evidence-obtaining system which comprises an embedded hardware platform, as well as an embedded operating system module and an application platform module based on the embedded hardware platform, wherein the embedded hardware platform comprises an embedded mainboard and a wireless network card module; the wireless network card module specifically comprises a network interface controller, a baseband processor, a medium frequency processing unit, a radio frequency processing unit, a transmitting-receiving module and an antenna sequentially connected. According to the invention, a system framework taking a modularization architecture as a main body, the hardware platform based on a low-power and high-performance arm embedded platform, and a software platform taking a customized safe embedded Linux operating system as a backbone are realized, and the technologies such as wireless network drive optimization, concurrence multithreading real-time monitoring and multimode wireless security detection are combined and adopted, so that the problems about miniaturization, mobility and low energy consumption of equipment are effectively solved, and the perfect wireless detection function is realized through multiple innovative technologies.
Owner:王强
Media live broadcast method based on 4G wireless private network
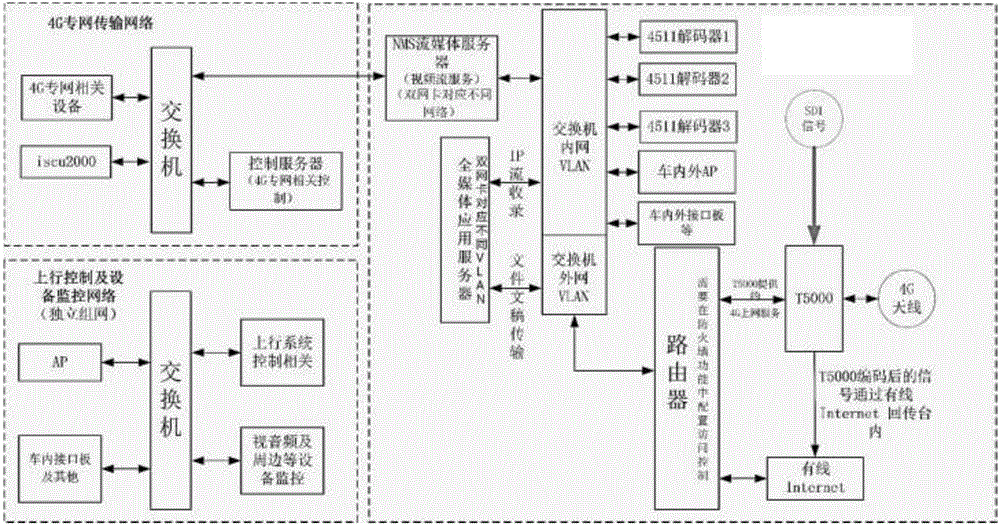
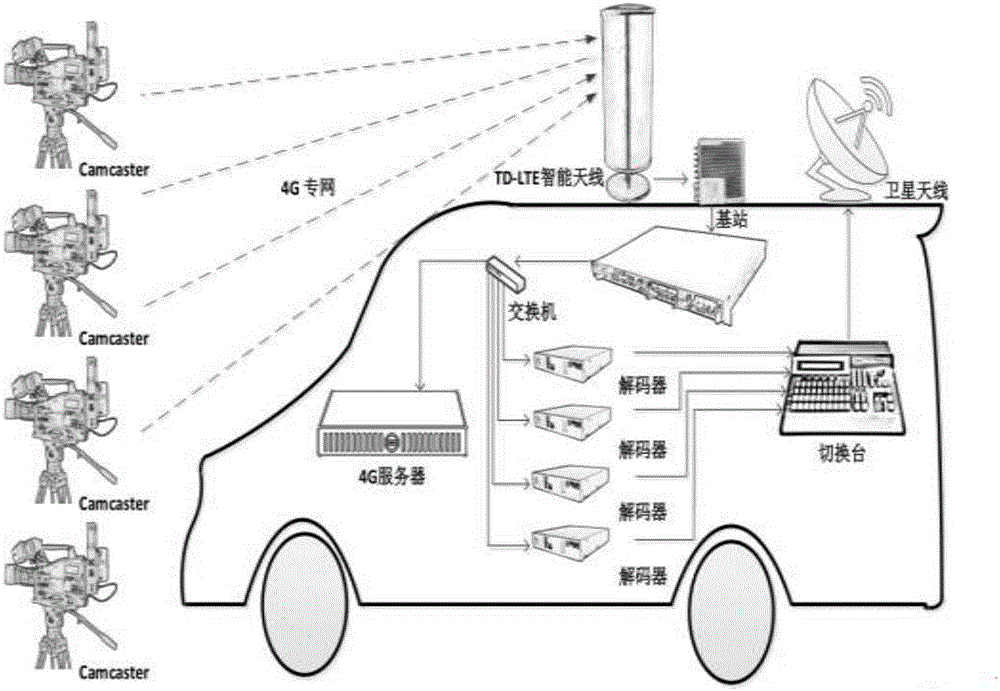
InactiveCN106804014AVarious forms of expressionRealize ITTelevision system detailsGHz frequency transmissionCommunications systemPrivate network
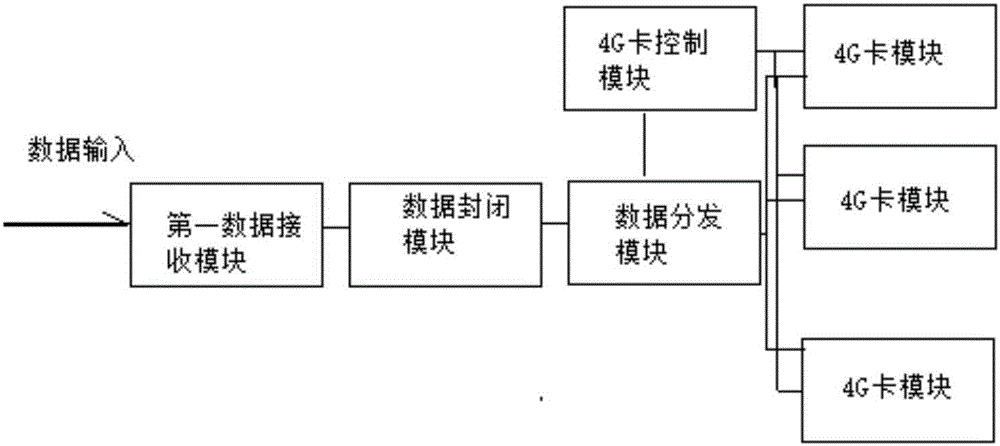
The invention provides a media live broadcast method based on a 4G wireless private network. Mobile audio and video live broadcasting and graphical and textual data transmission are performed based on 4G multi-card binding cooperation. A 4G wireless private network transmission system is a set of TD-LTE standard communication system based on the special band and is composed of front-end video and audio acquisition equipment, a 4G wireless private network base station, an NMS-receiving media server and a high definition decoder. The audio and video signal transmission process is that IP encoding is performed on the baseband SDI signals outputted by multi-position cameras through respective acquisition and transmission equipment and then the signals are transmitted to the 4G wireless private network base station. The 4G wireless private network base station transmits the received IP stream signals to the NMS media server through the private network. The NMS media server distributes the received IP stream signals to the high definition decoder so as to complete reduction of the IP stream to the baseband SDI signals. The audio and video front-end acquisition equipment is equipped with an embedded hardware encoding module and multiple 4G wireless private network transmission modules, and the SDI signals are encoded and then the IP stream signals are outputted so that high-code-rate IP signal stable transmission can be realized.
Owner:JIANGSU BROADCASTING CORPORATION
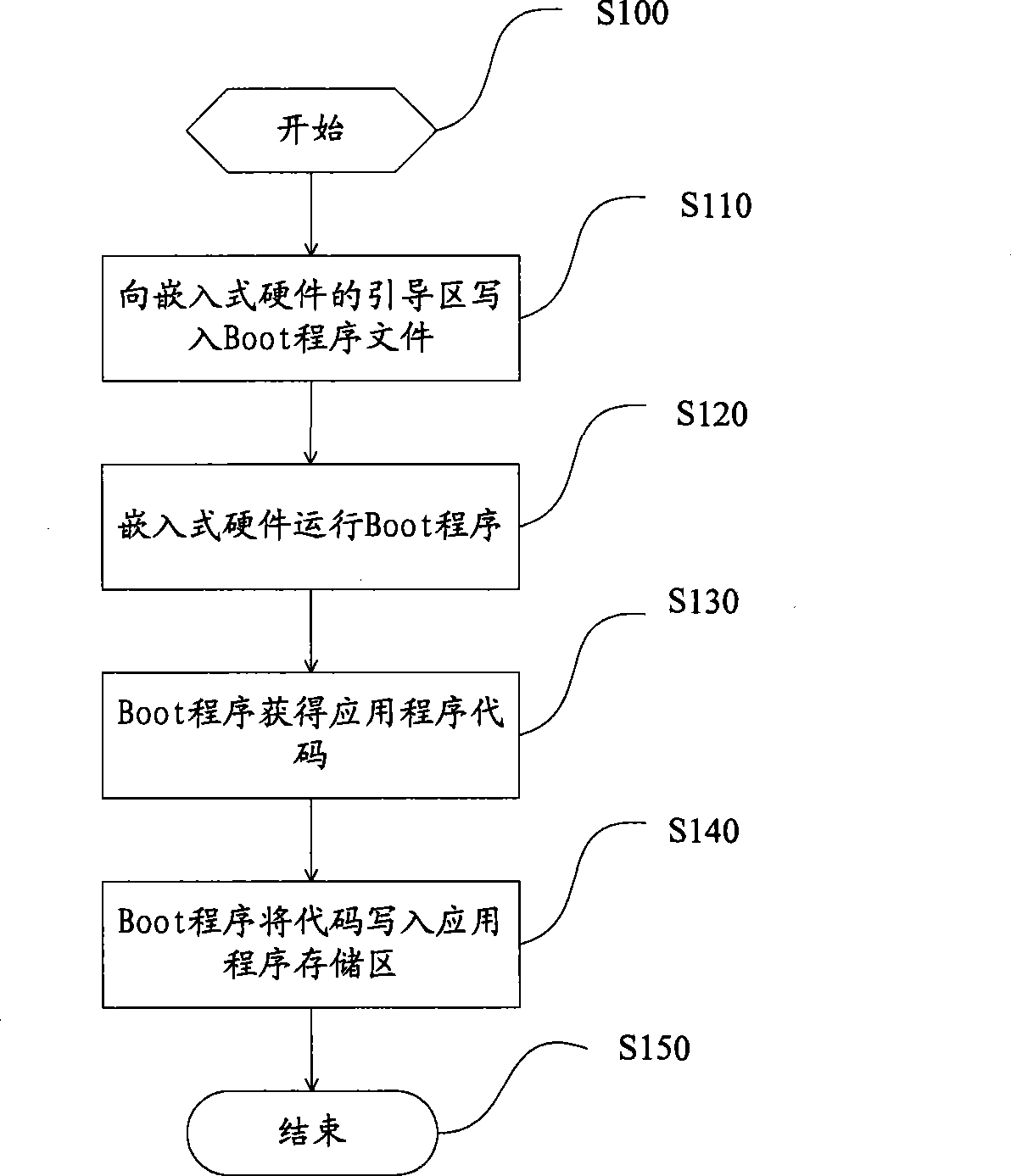
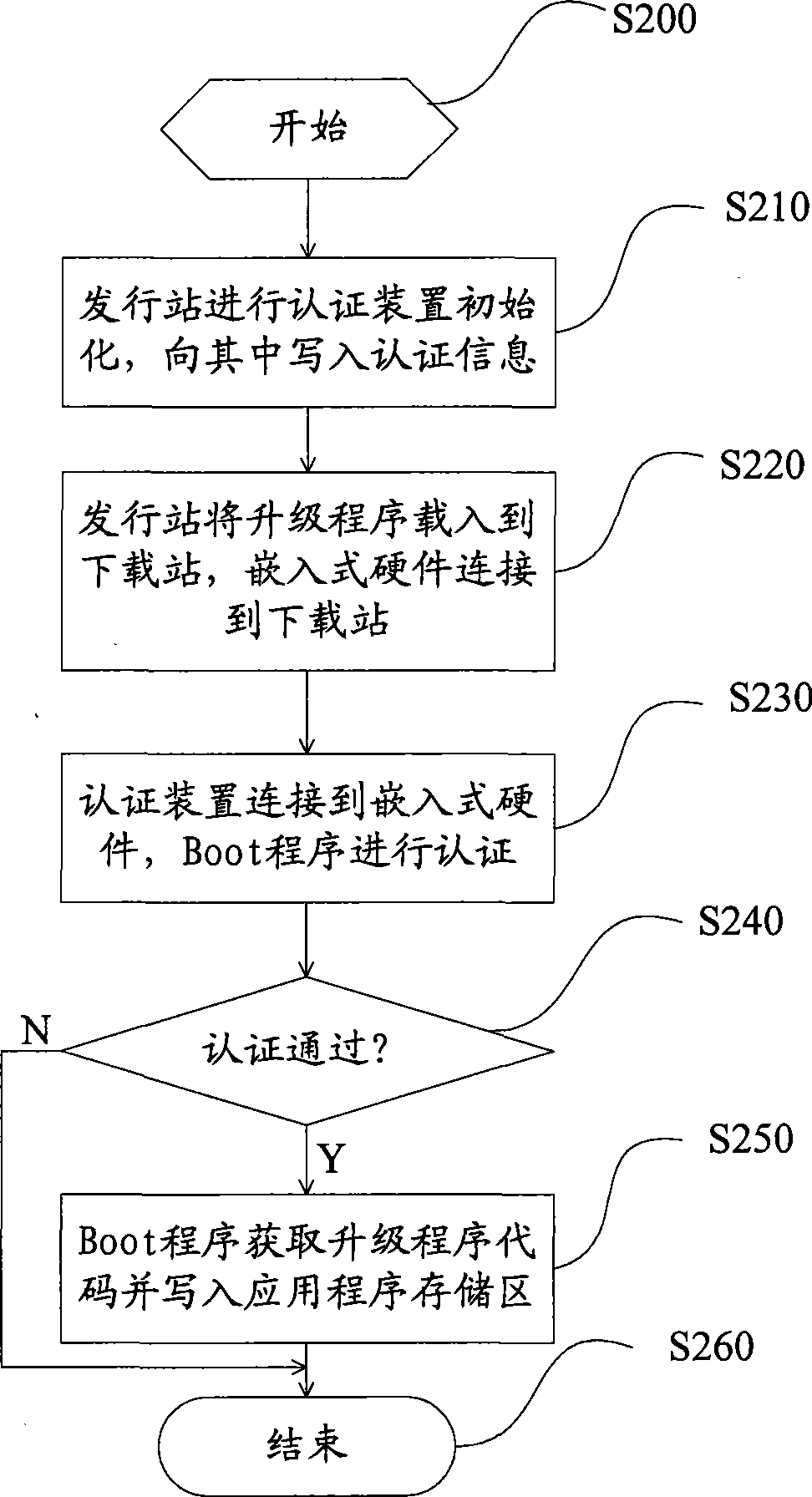
Program downloading control method
InactiveCN101419557AUpdate flexibleUpdate changeableProgram loading/initiatingApplication softwareBoot sector
A program download control method comprises a program initial writing and program upgrade download. The program initial writing comprises the following steps: a Boot program file is written in a boot sector of embedded hardware; the embedded hardware is started and the Boot program runs and writes an application program code in an application program memory area after acquiring the application program code. The program upgrade download comprises the following steps: an issue station initializes an certification device and writes certification information in the certification device; an upgrade program is loaded to a download station, and the embedded hardware is connected to the download station; the certification device is connected to the embedded hardware, and the Boot program performs certification; certification is judged; if the certification is successful, the Boot program downloads the upgrade program and writes an upgrade program code to the application program memory area for ending; and if the certification fails, the step is directly finished, therefore, flexible right control on the program download is realized in two aspects which are the software and the hardware.
Owner:AEROSPACE INFORMATION
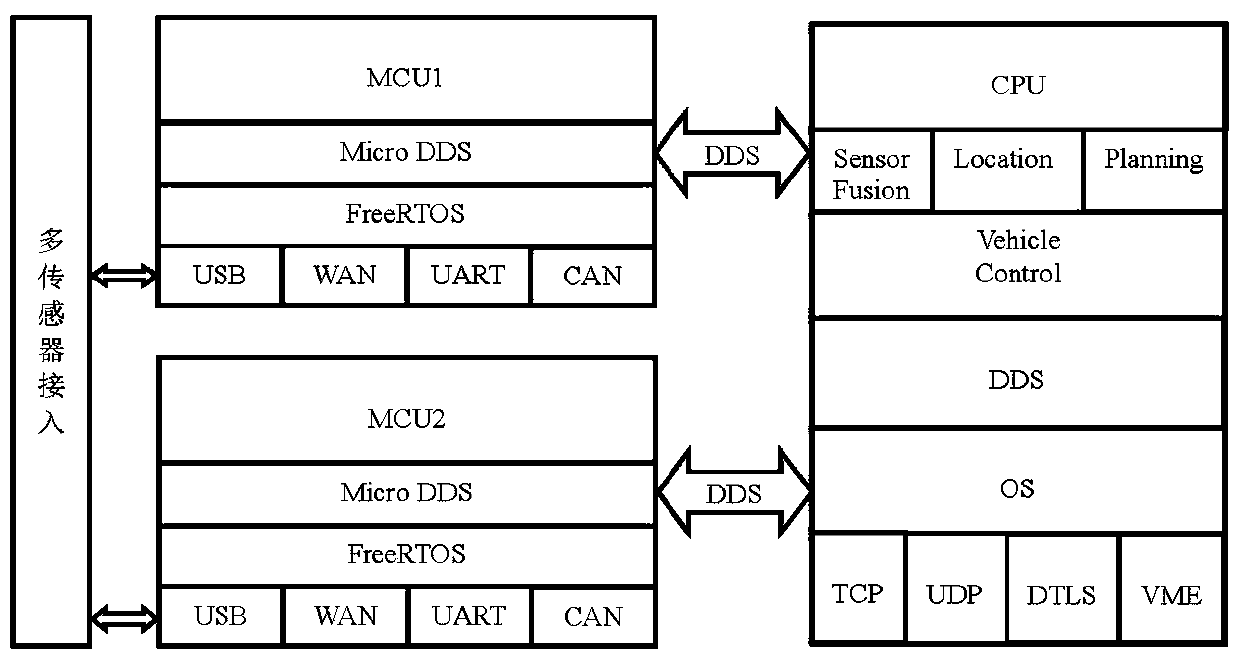
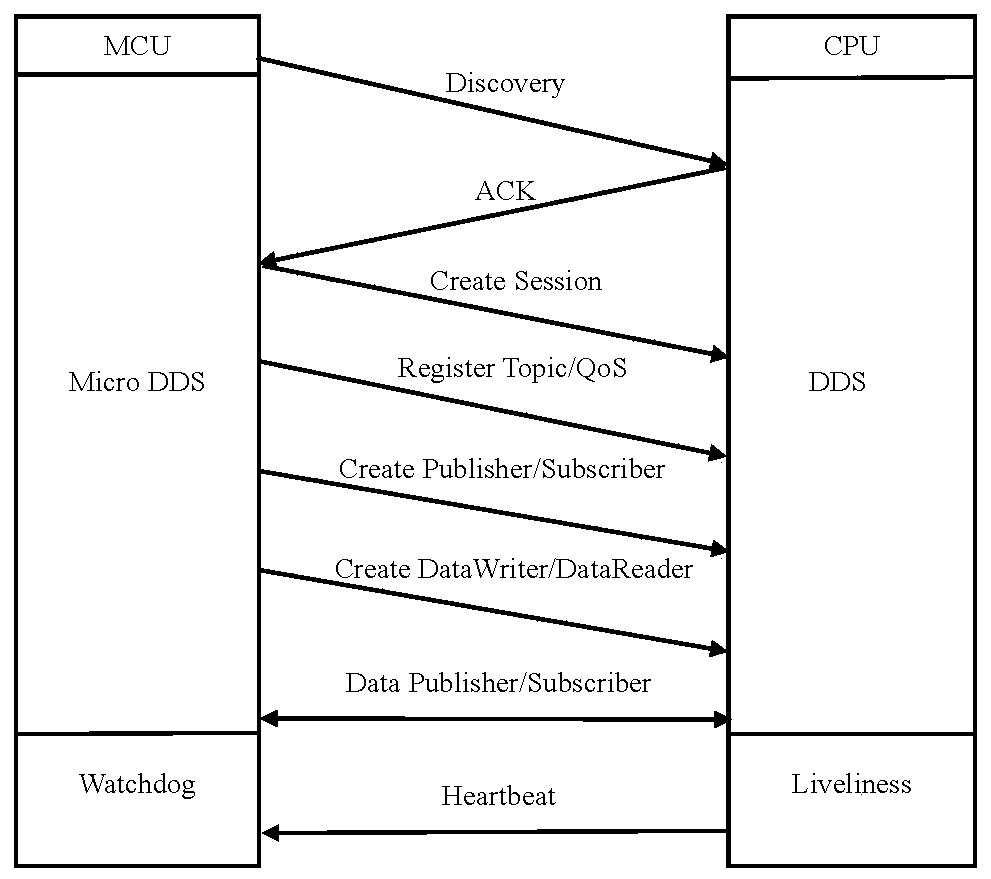
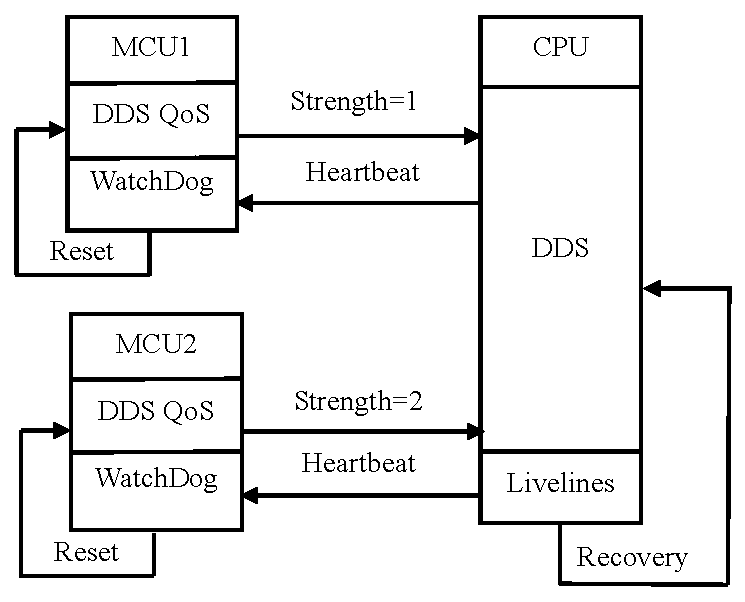
Method for realizing DDS service on embedded sensor access platform
ActiveCN110209514AImprove stabilityRapid deploymentInterprogram communicationTransmissionReal-time operating systemHardware redundancy
The invention relates to a method for realizing a DDS service on an embedded sensor access platform, and the method comprises the steps: taking embedded hardware as the sensor access platform, carrying an embedded real-time operation system, and carrying out the message communication with a data processing unit through employing the DDS service. According to the invention, the sensor access platform is constructed based on an embedded manner, so that low-cost hardware redundancy backup can be realized; meanwhile, DDS service is realized based on an embedded mode, complete DDS service is formedwith the data processing unit, and a perfect abnormal recovery mechanism is provided.
Owner:AUTOCORE INTELLIGENT TECH NANJING CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com