Patents
Literature
336 results about "Wireless security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
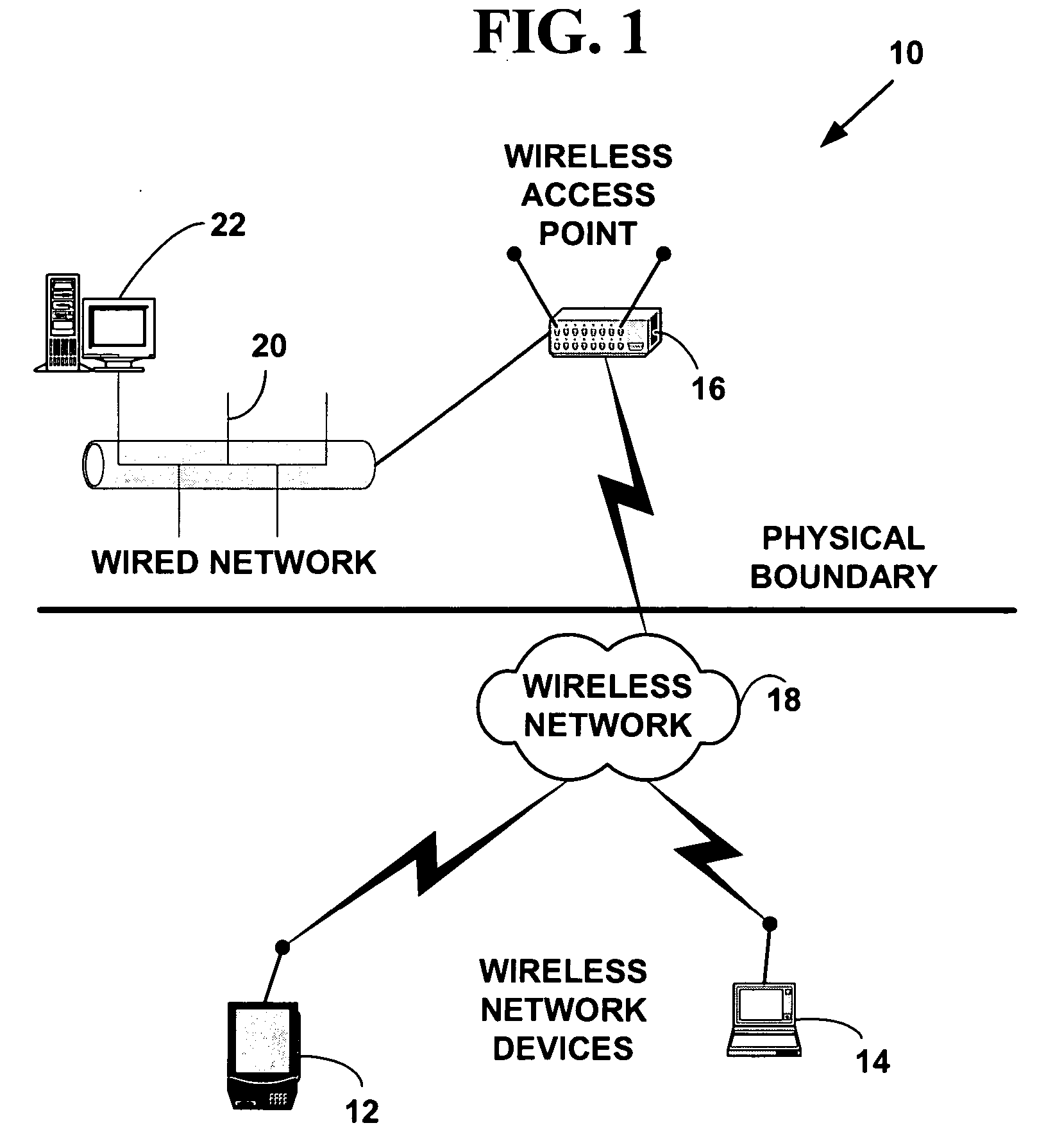
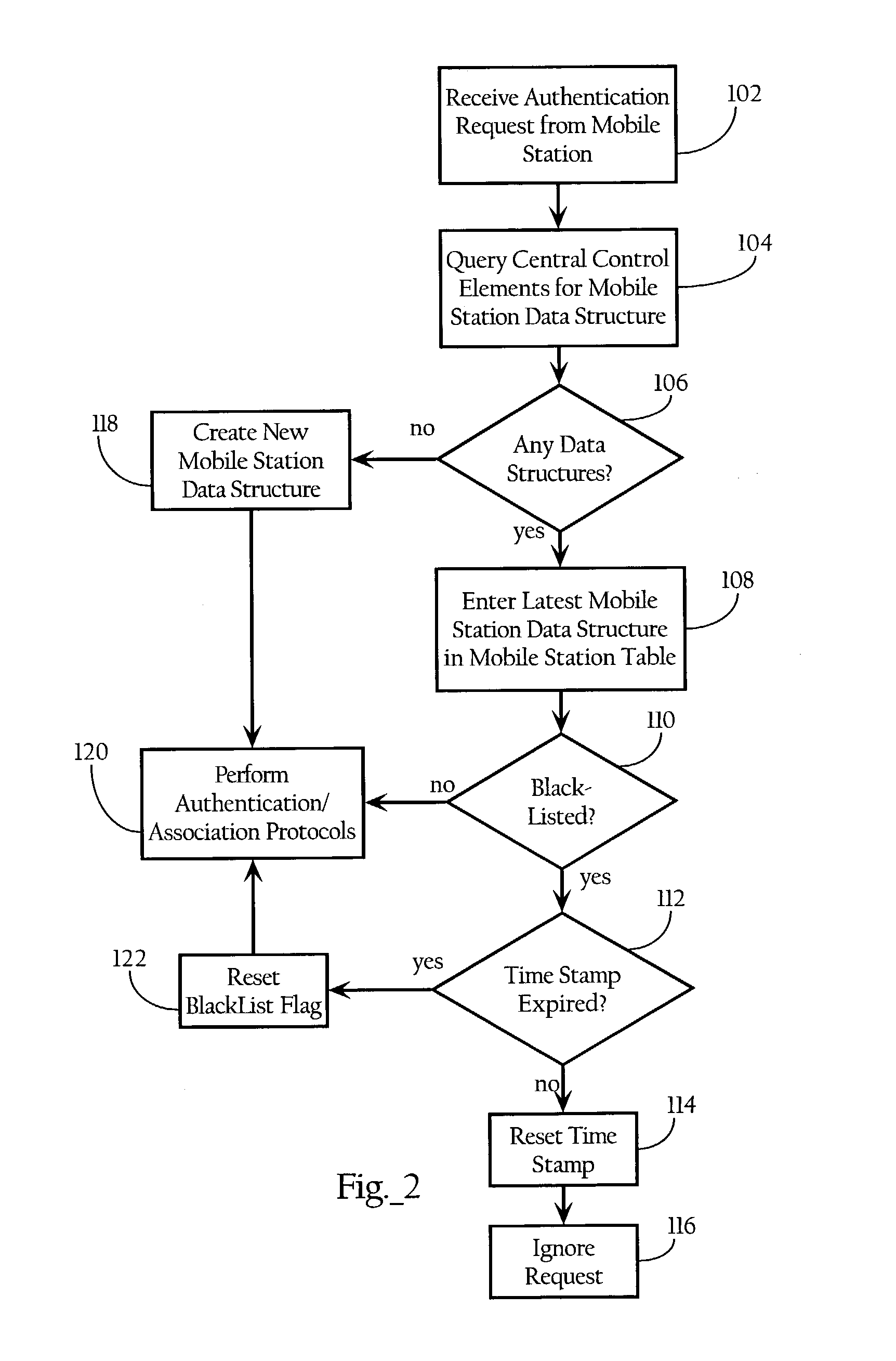
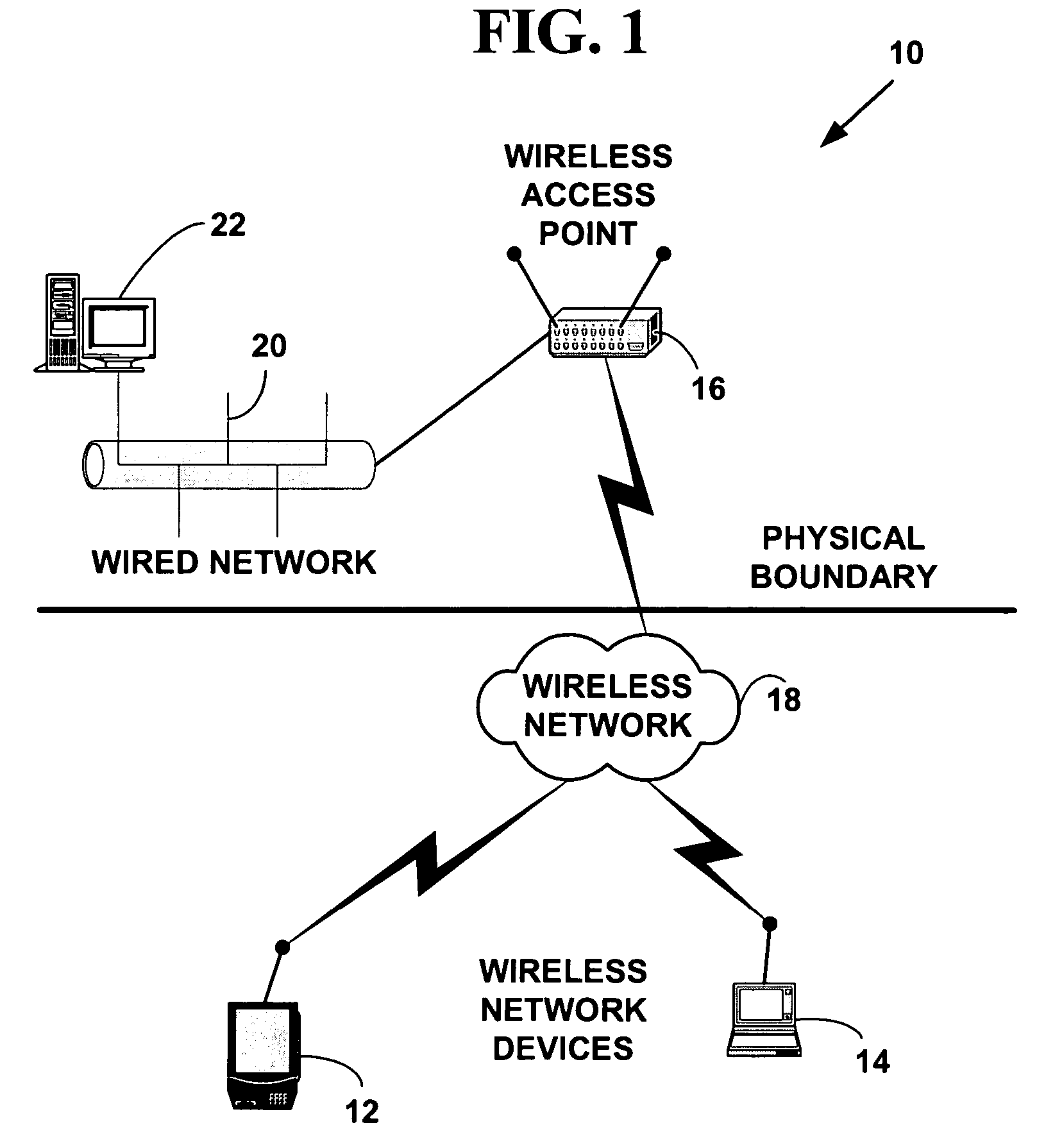
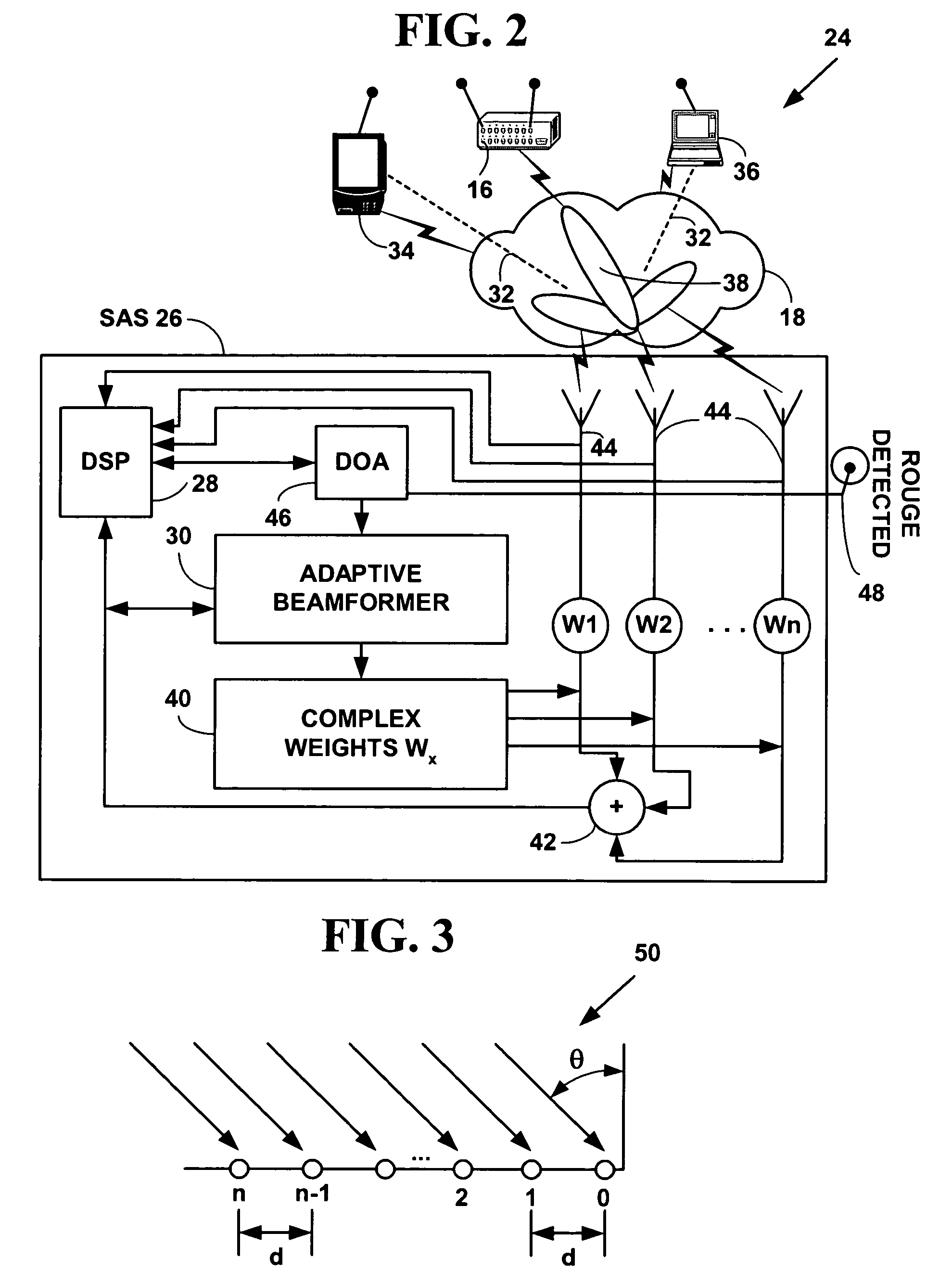
Wireless security is the prevention of unauthorized access or damage to computers or data using wireless networks, which include Wi-Fi networks. The most common type is Wi-Fi security, which includes Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard: the password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1997, which was superseded in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP. Enterprises often enforce security using a certificate-based system to authenticate the connecting device, following the standard 802.1X.
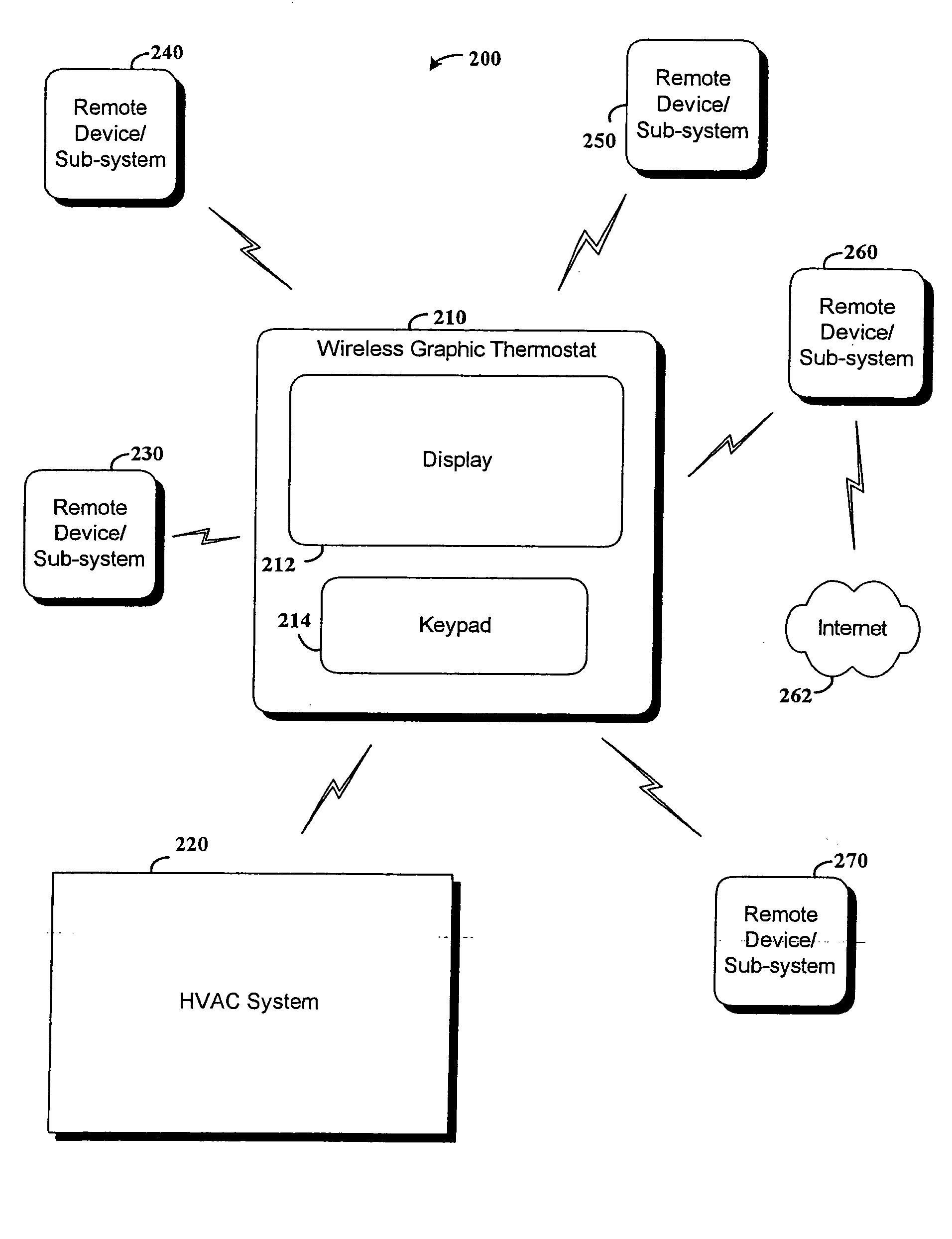
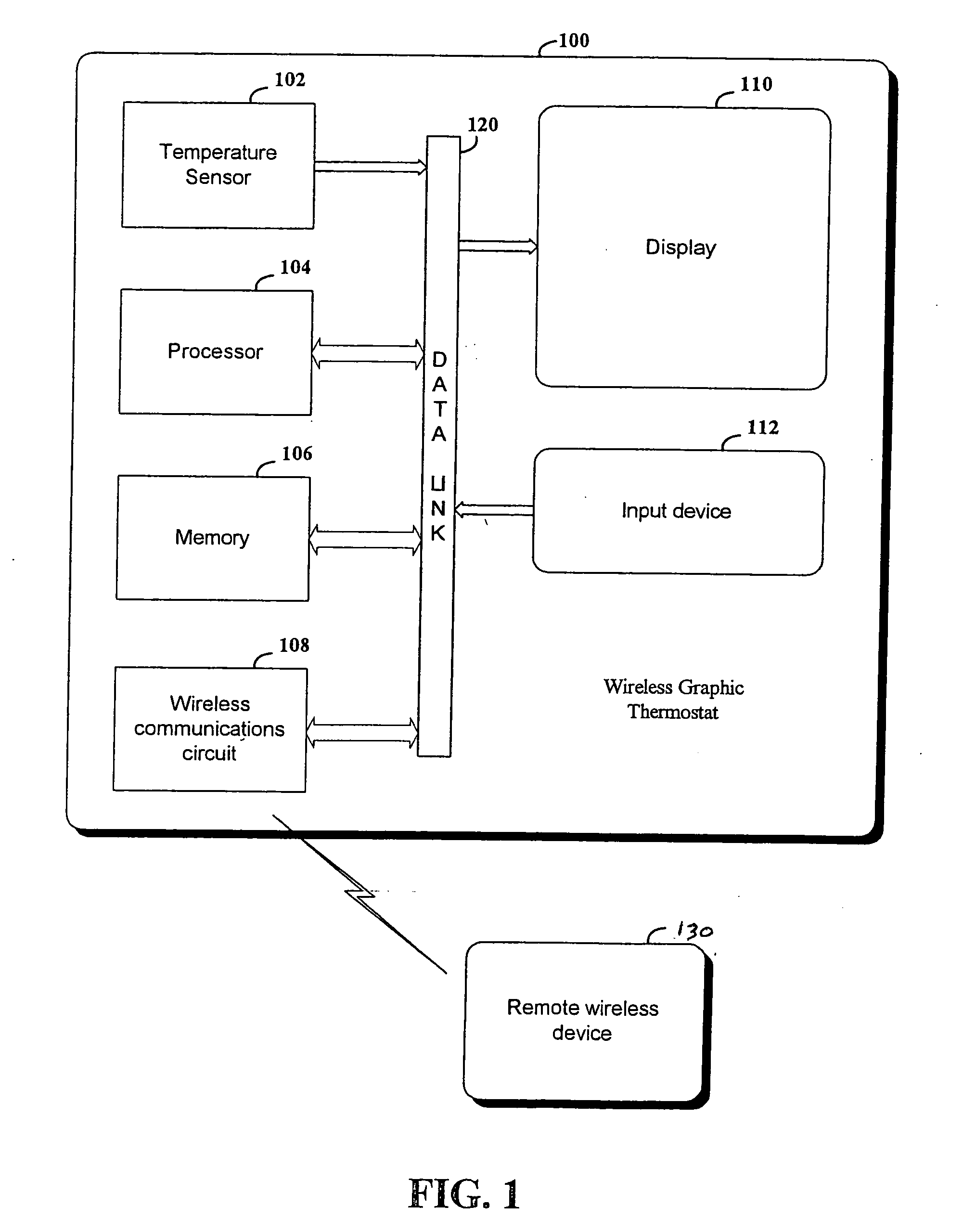
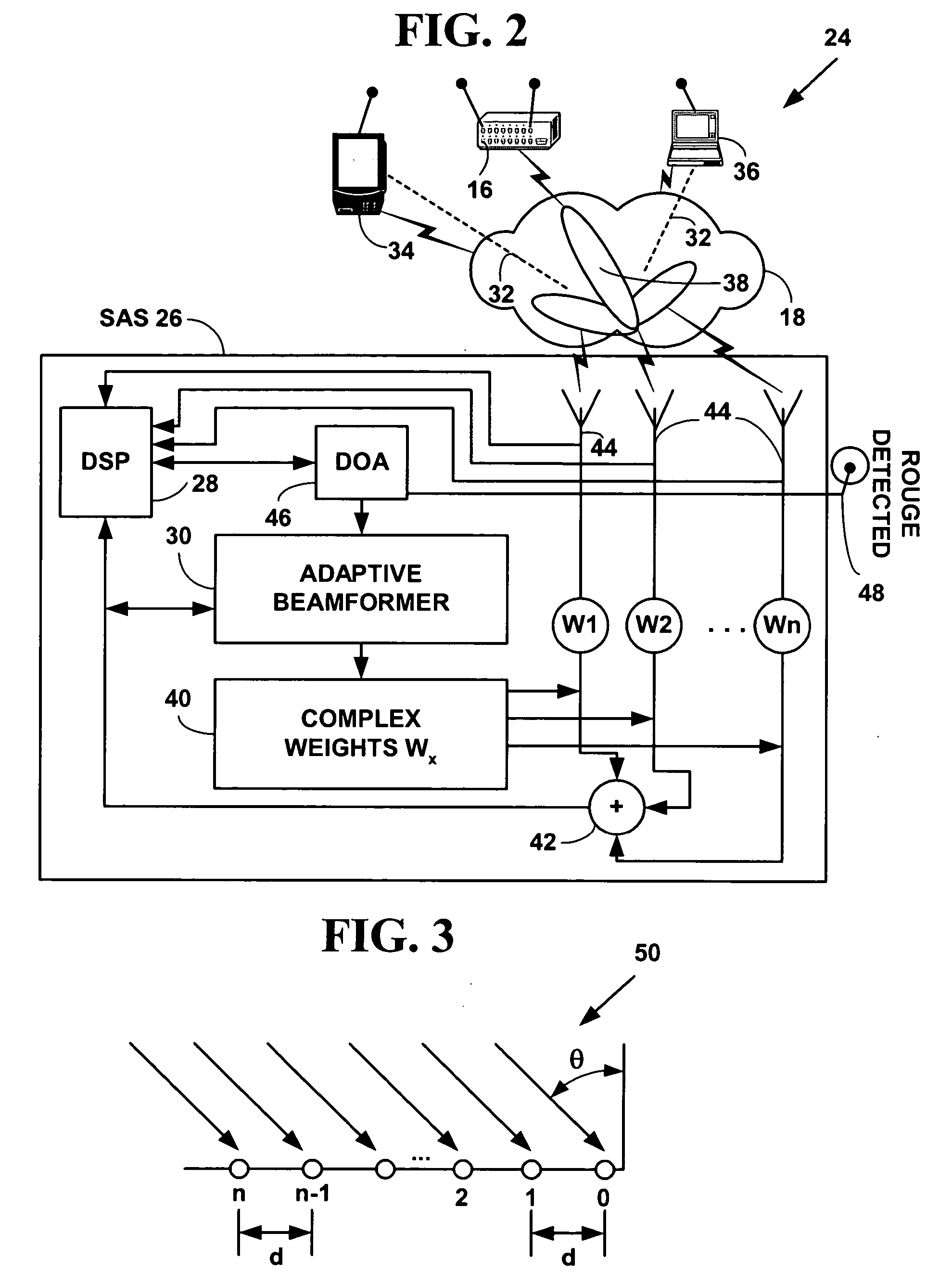
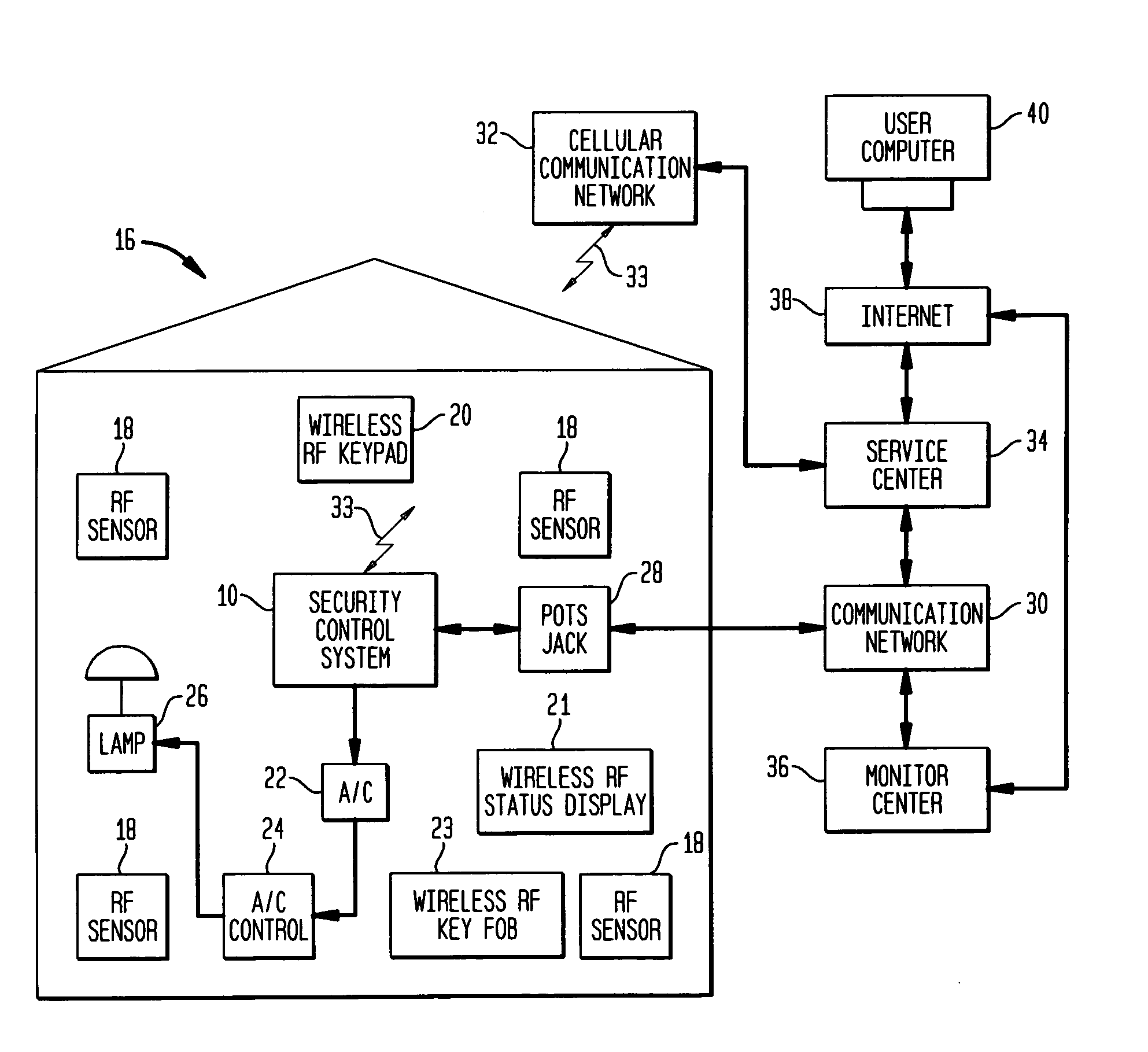
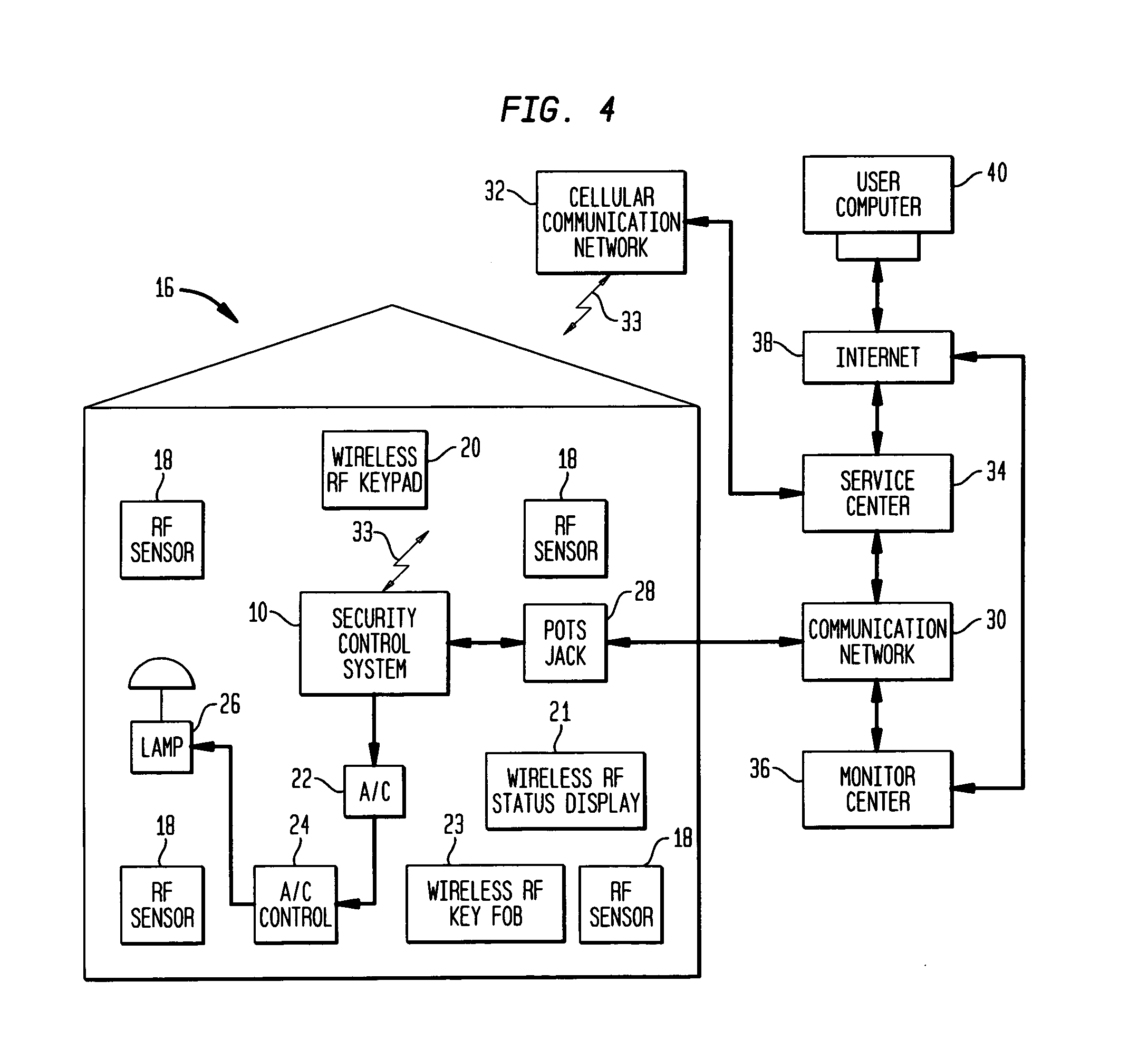
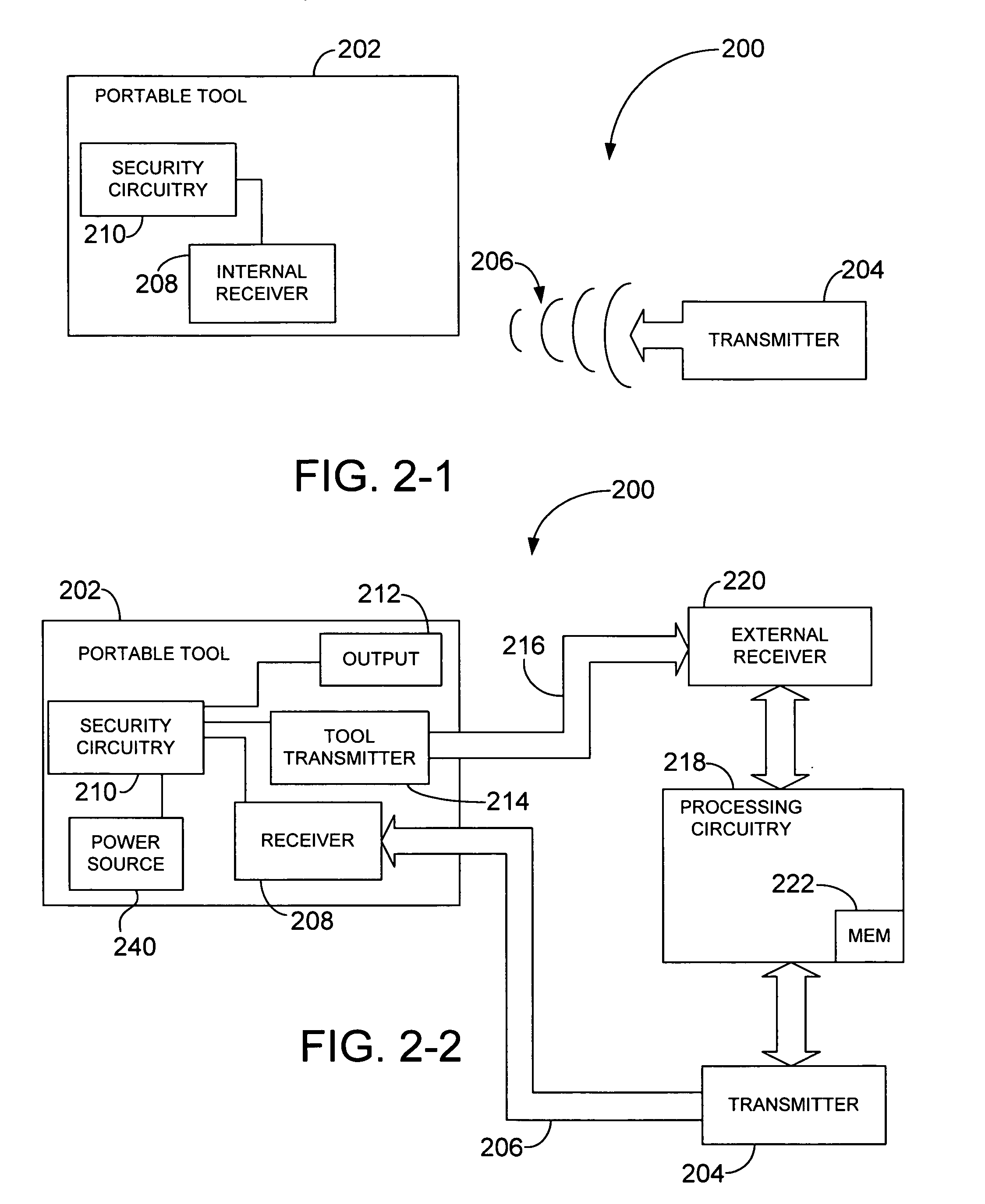
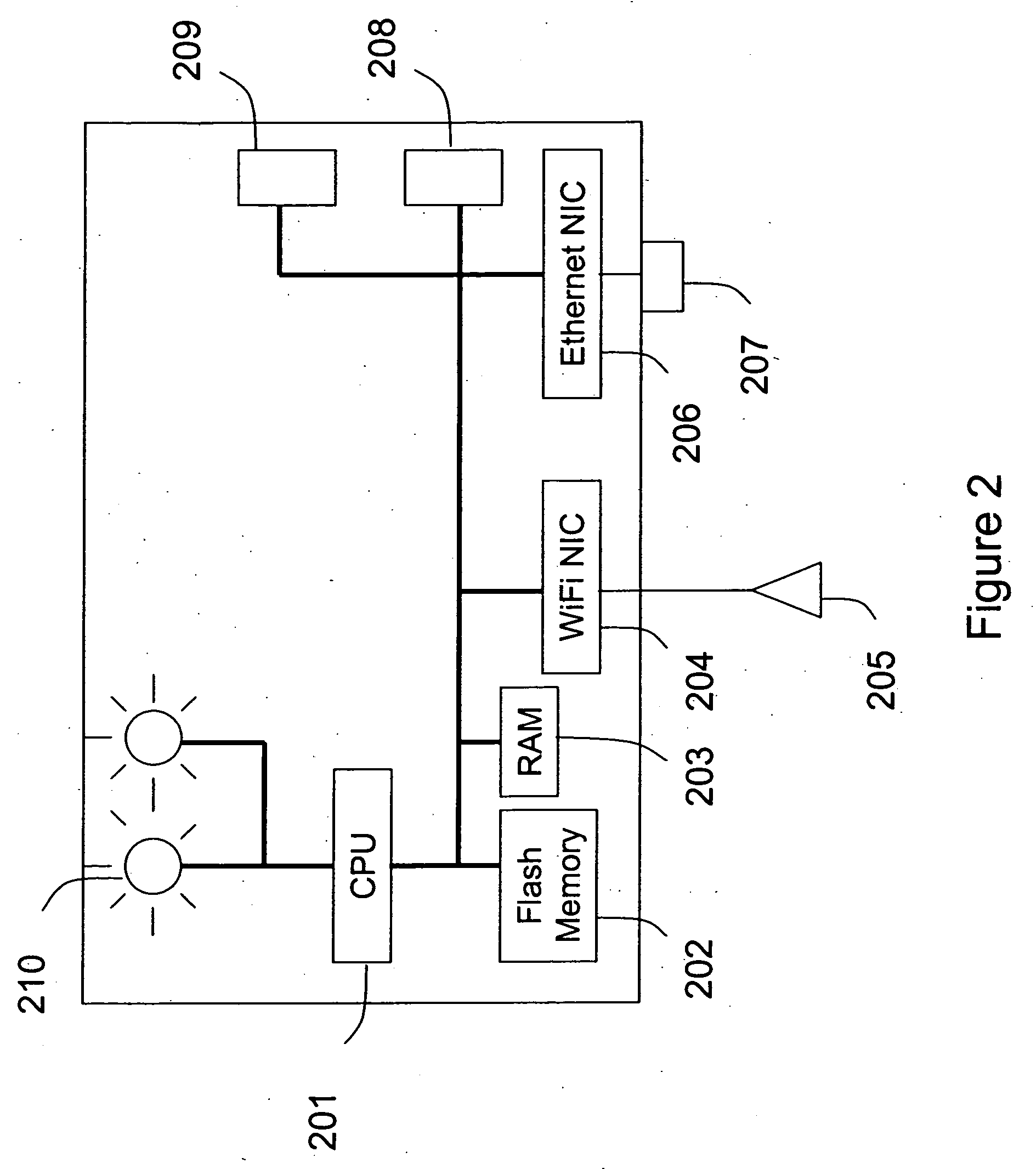
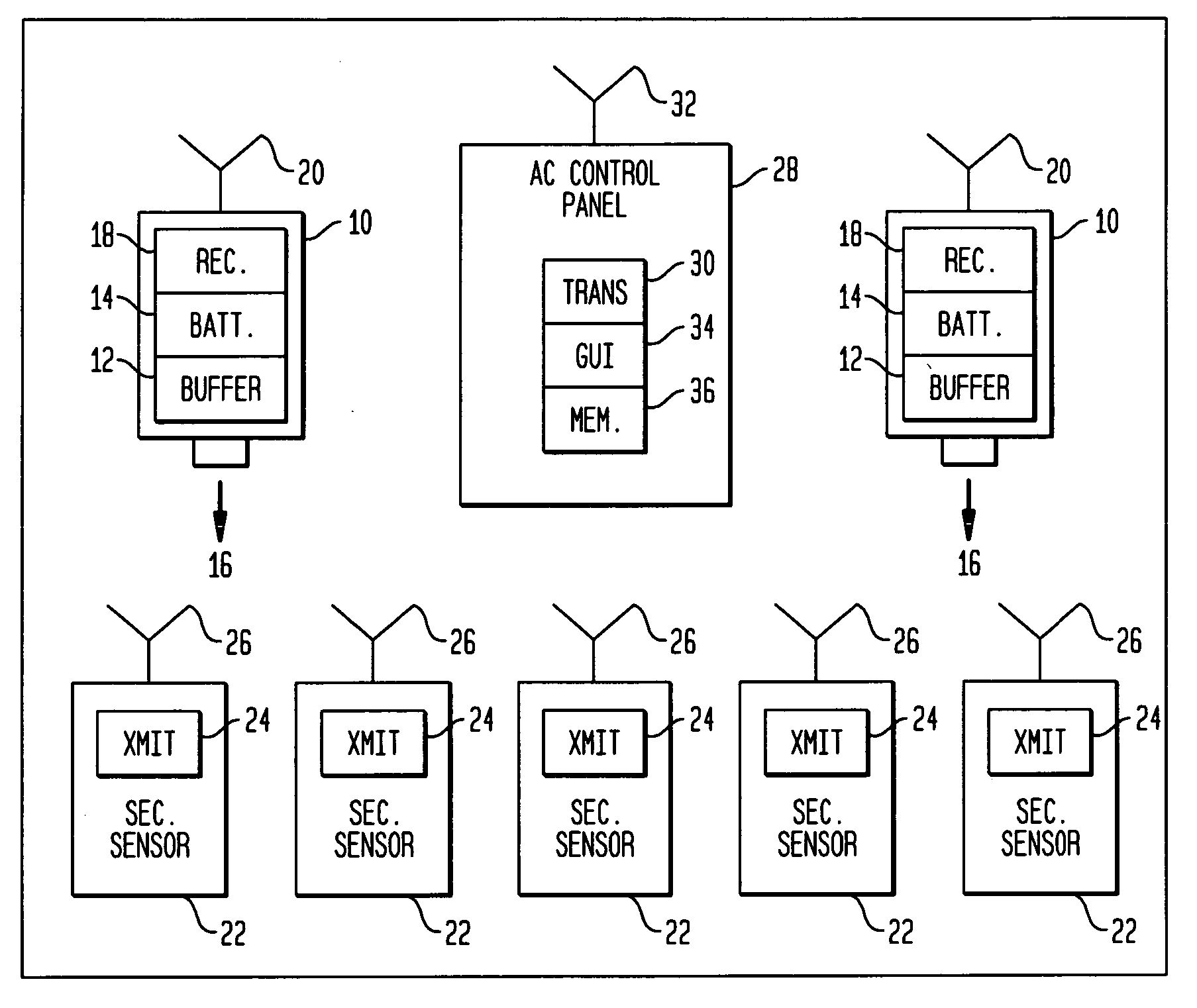
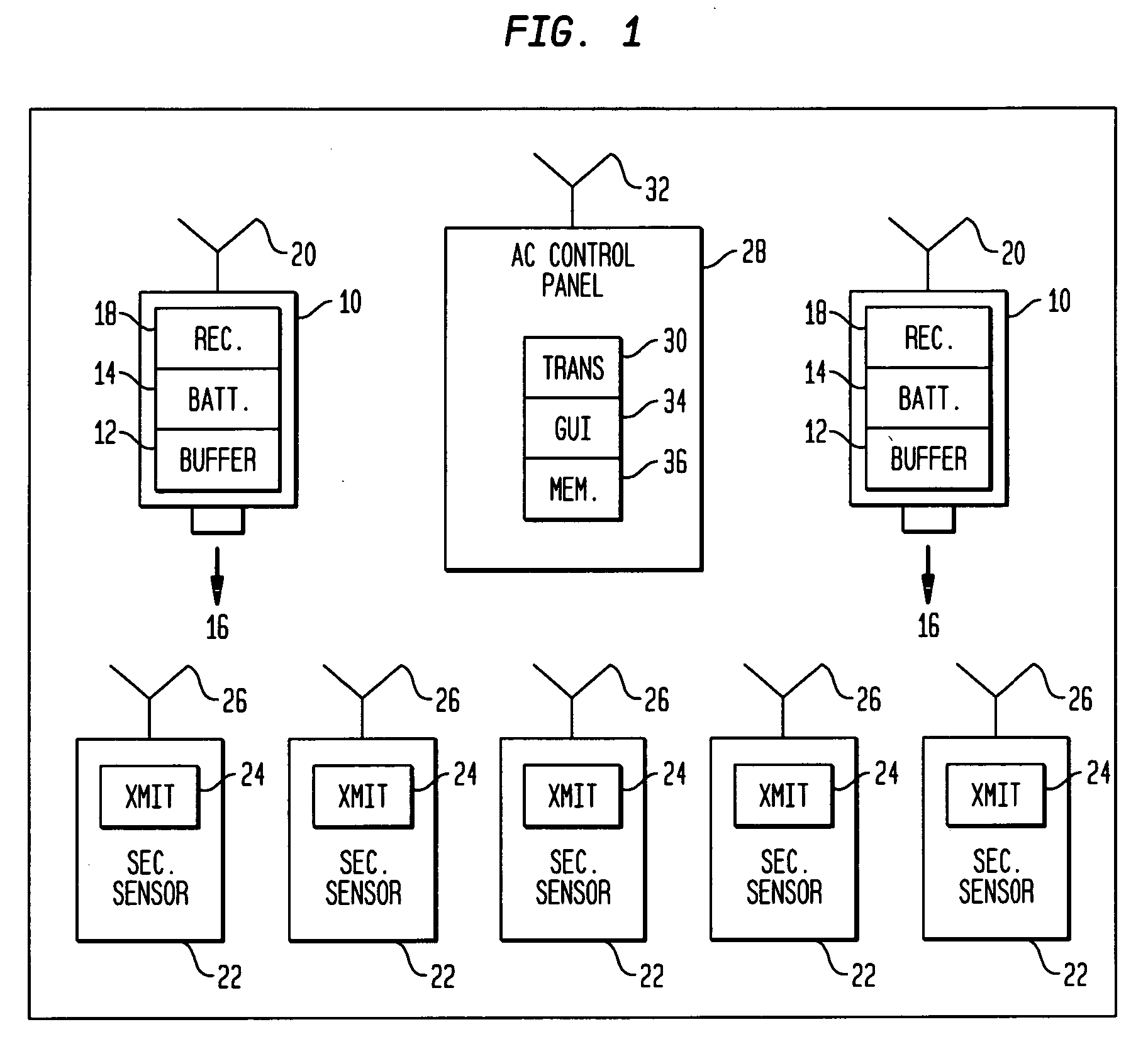
RF interconnected HVAC system and security system
InactiveUS20050270151A1Easy programmingMechanical apparatusSpace heating and ventilation safety systemsWireless controlThermostat
An interconnected wireless HVAC (heating, ventilation, air conditioning) system and wireless security system, which are interconnected and communicate with each other through the use of a common wireless technology, including the same selected frequency, modulation and a set of common protocols. The Wireless HVAC system includes wireless thermostats, which can communicate with and control both the HVAC system and the security system, and the wireless security system includes wireless controls or keypads, which can communicate with and control both the security system and the HVAC system. The universal wireless infrastructure can be expanded to provide communication or control of additional user or manufacturer installed wireless devices or systems through the universal wireless home infrastructure.
Owner:HONEYWELL INT INC
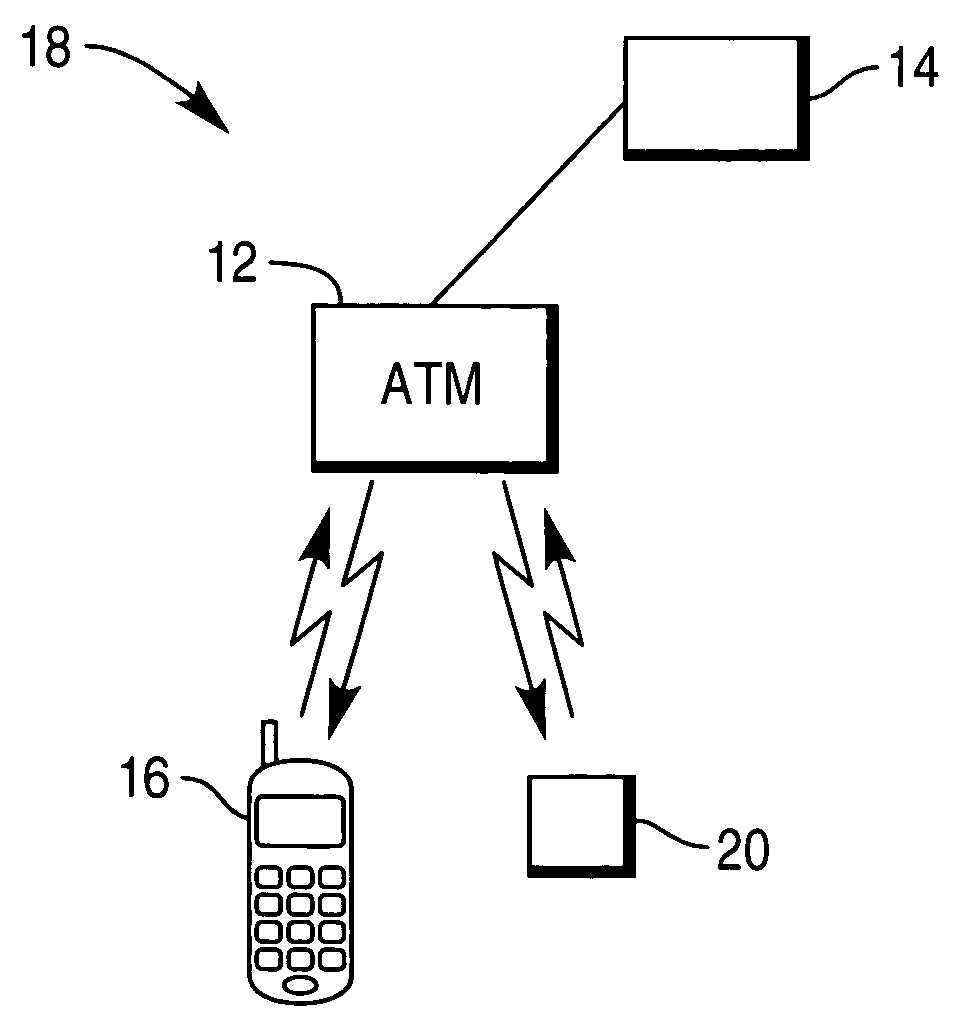
Wireless security module
ActiveUS7350230B2Digital data processing detailsComputer security arrangementsTelecommunications networkComputer module
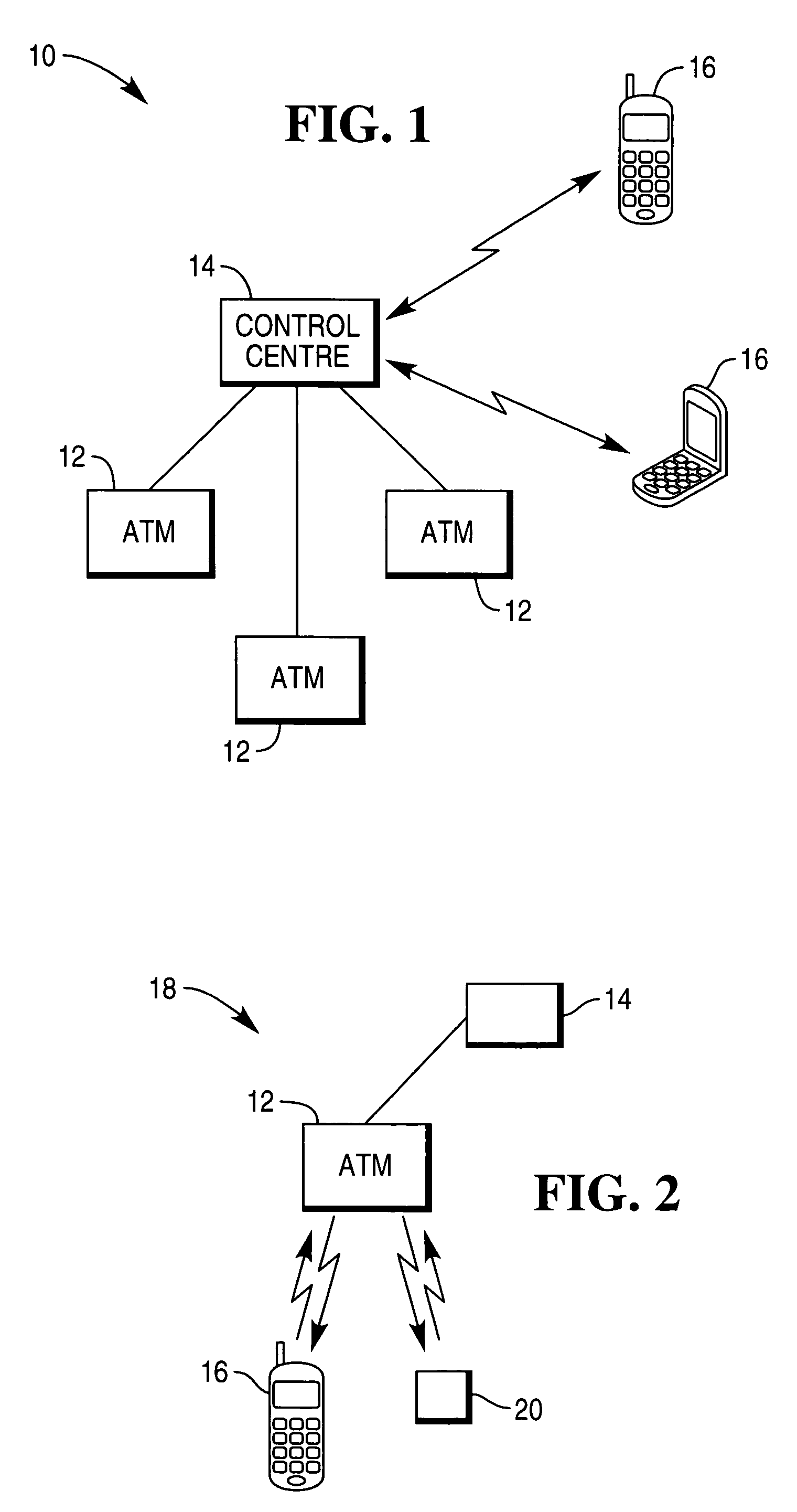
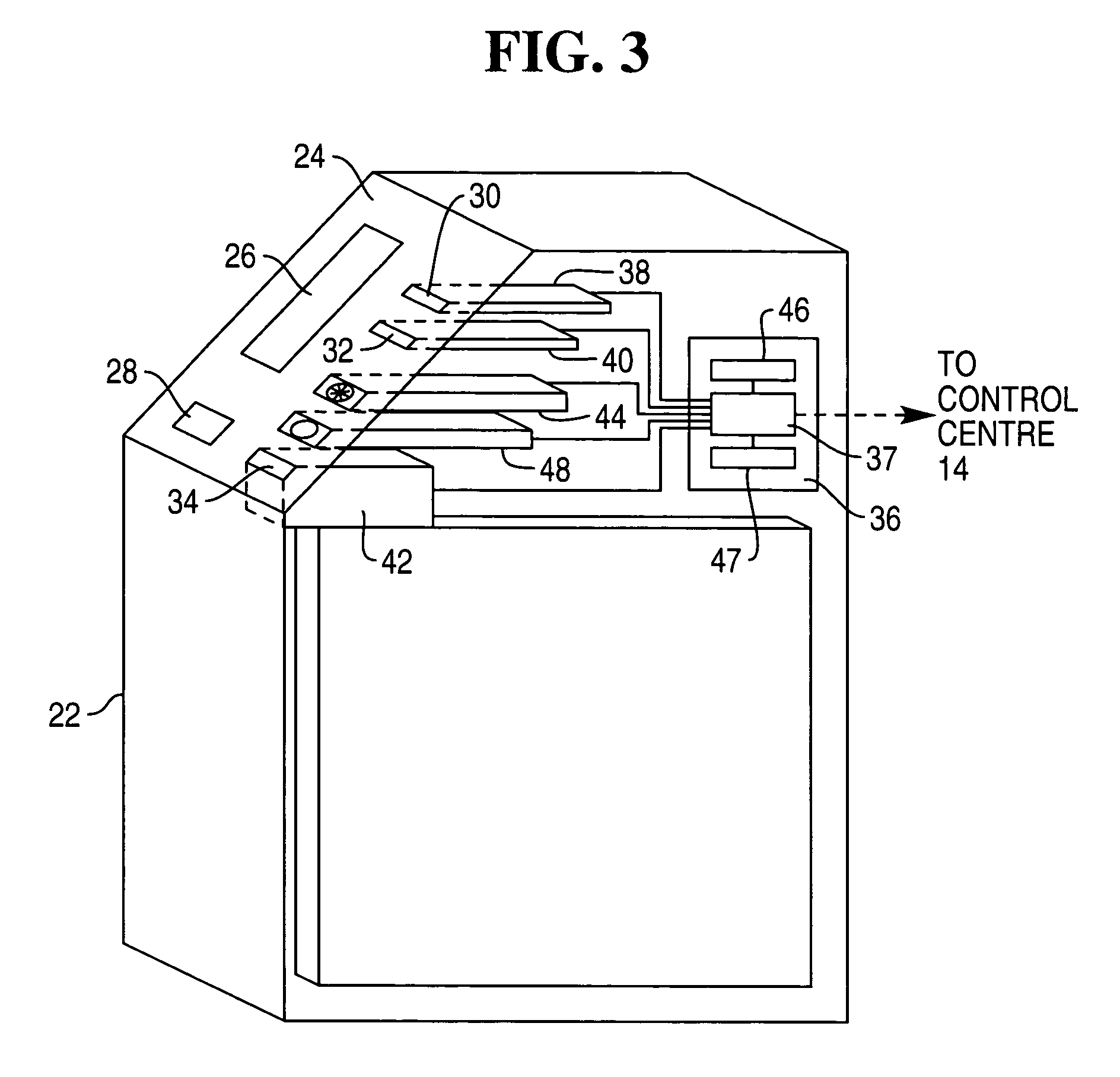
A wireless security module (20) adapted to authenticate a mobile device (16), such as a mobile telephone, thereby to allow communication between the mobile device and a terminal (12), such as a self-service terminal. The wireless security module (20) is paired with the mobile device (16) and is adapted to send an authentication signal to the mobile device (16) or the terminal (12) using a wireless communication path, such as a telecommunications network or an IR link or a Bluetooth connection.
Owner:NCR CORP
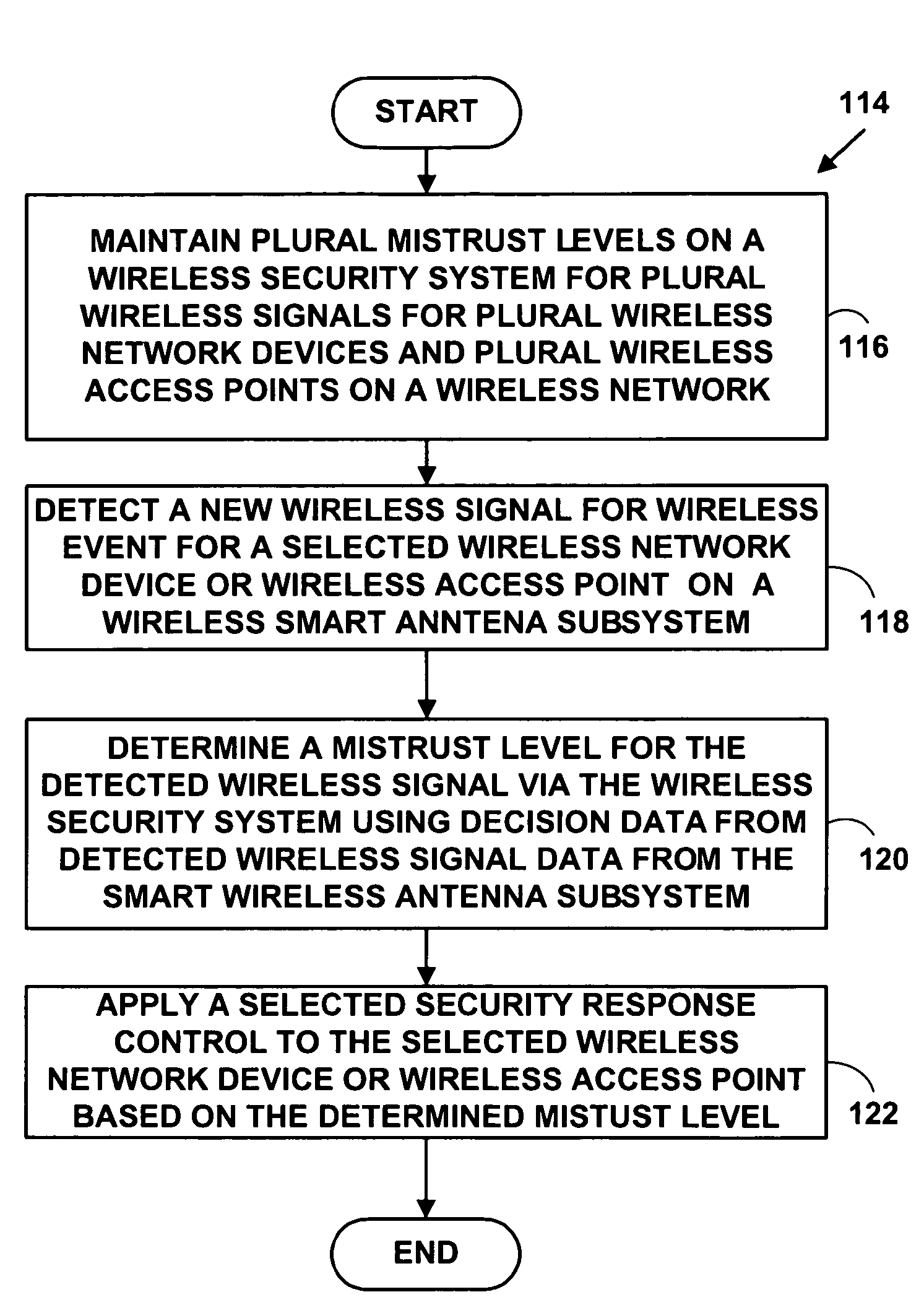
Method and system for wireless intrusion detection prevention and security management
ActiveUS20050037733A1Spatial transmit diversityUnauthorised/fraudulent call preventionSystems managementIntrusion detection and prevention
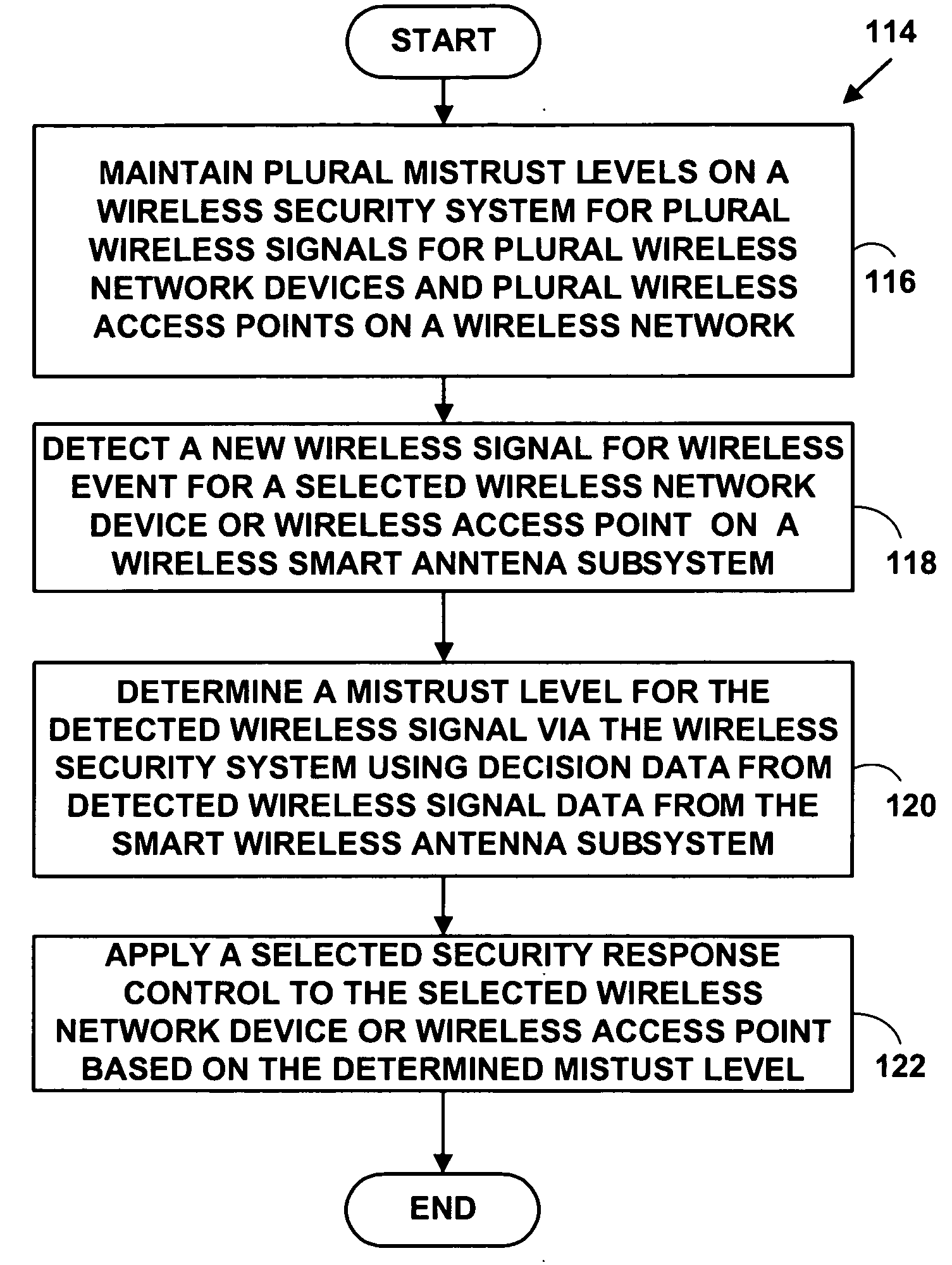
A method and system for wireless intrusion detection, prevention and security management. The method and system provides autonomous wireless intrusion detection and prevention, with minimal or no operator intervention. The method and system integrates a physical layer (e.g., OSI layer 1) a smart wireless radio frequency (RF) antenna subsystem with a data-link layer (e.g., OSI layer 2) wireless security system management platform.
Owner:3E TECH INT
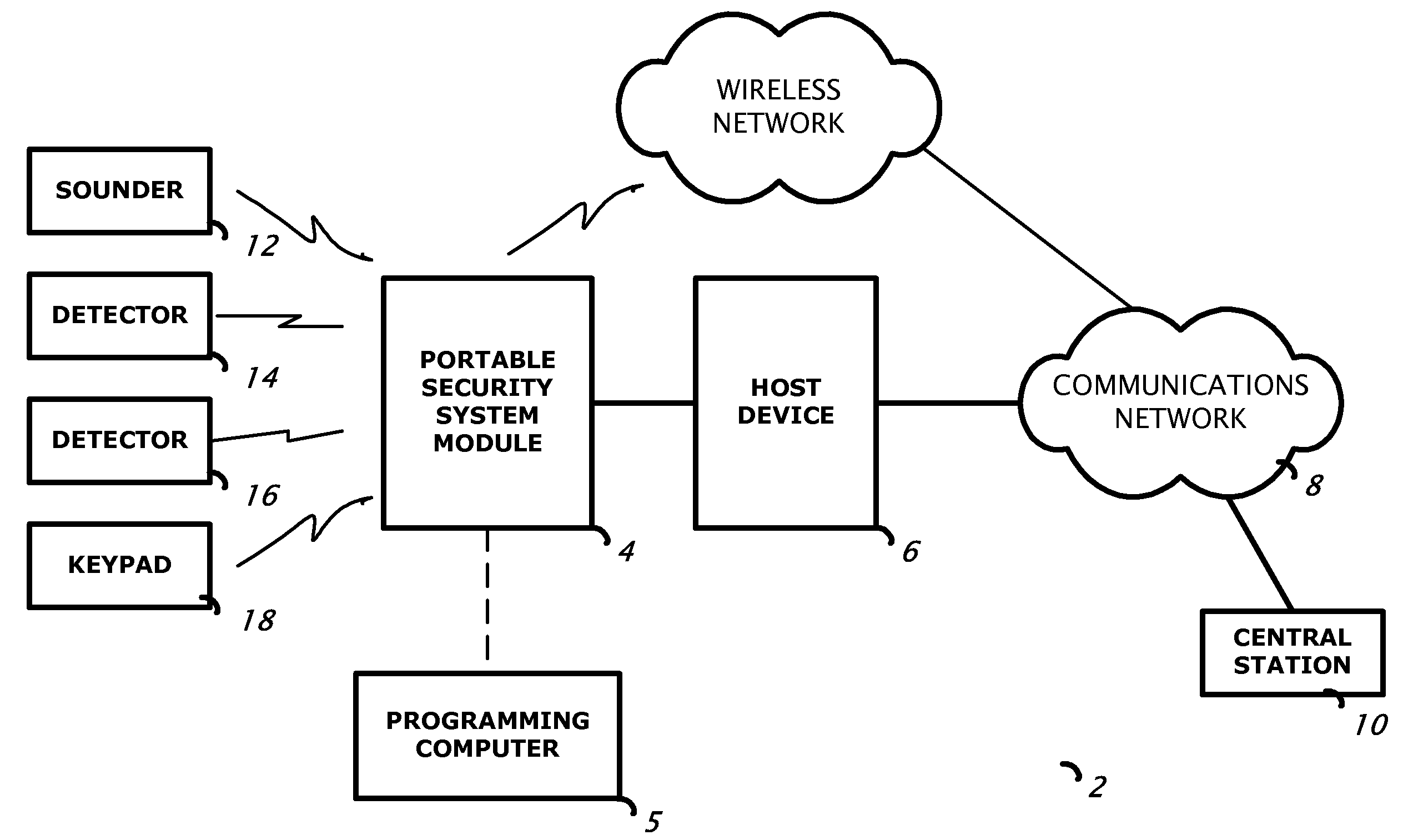
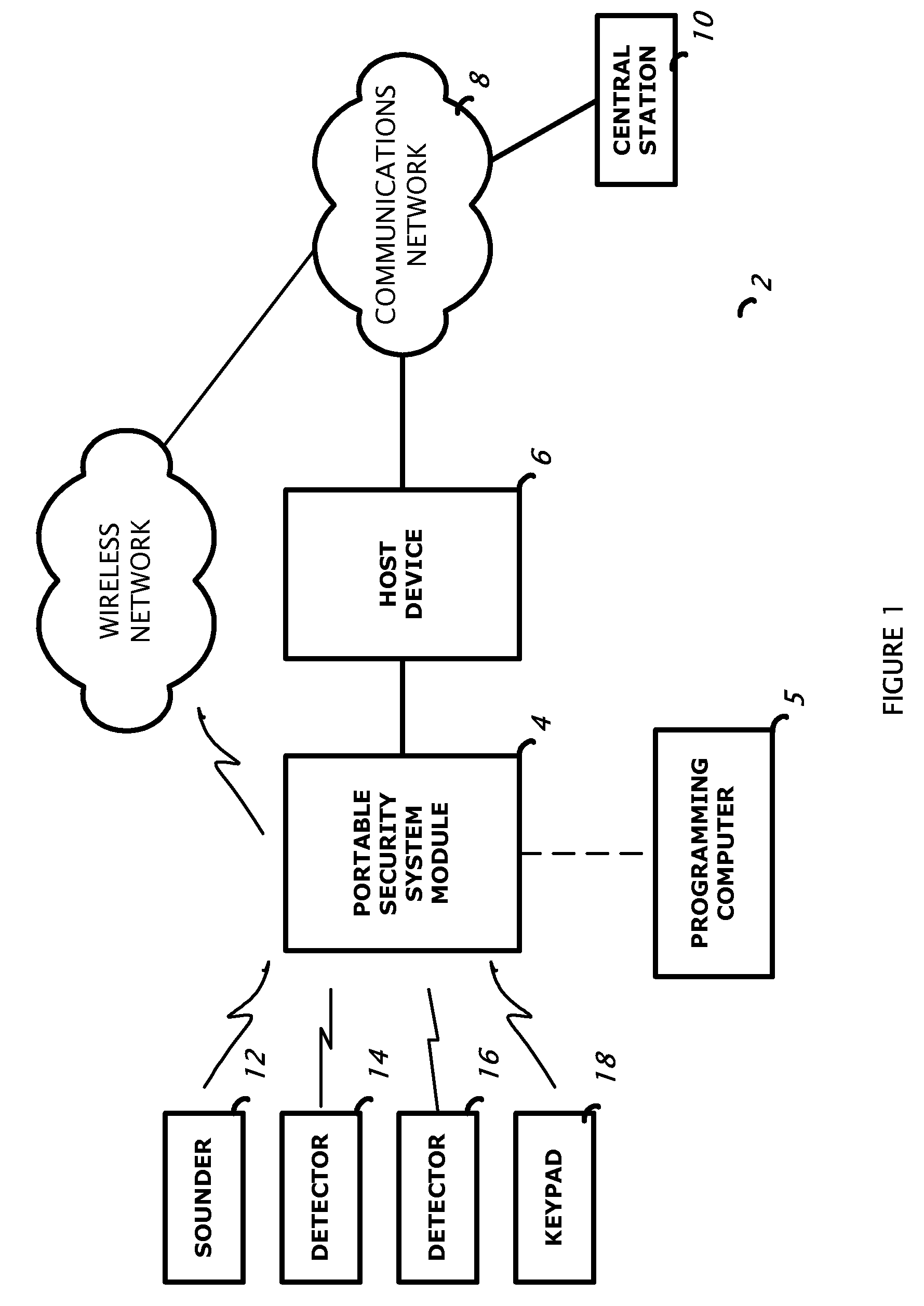
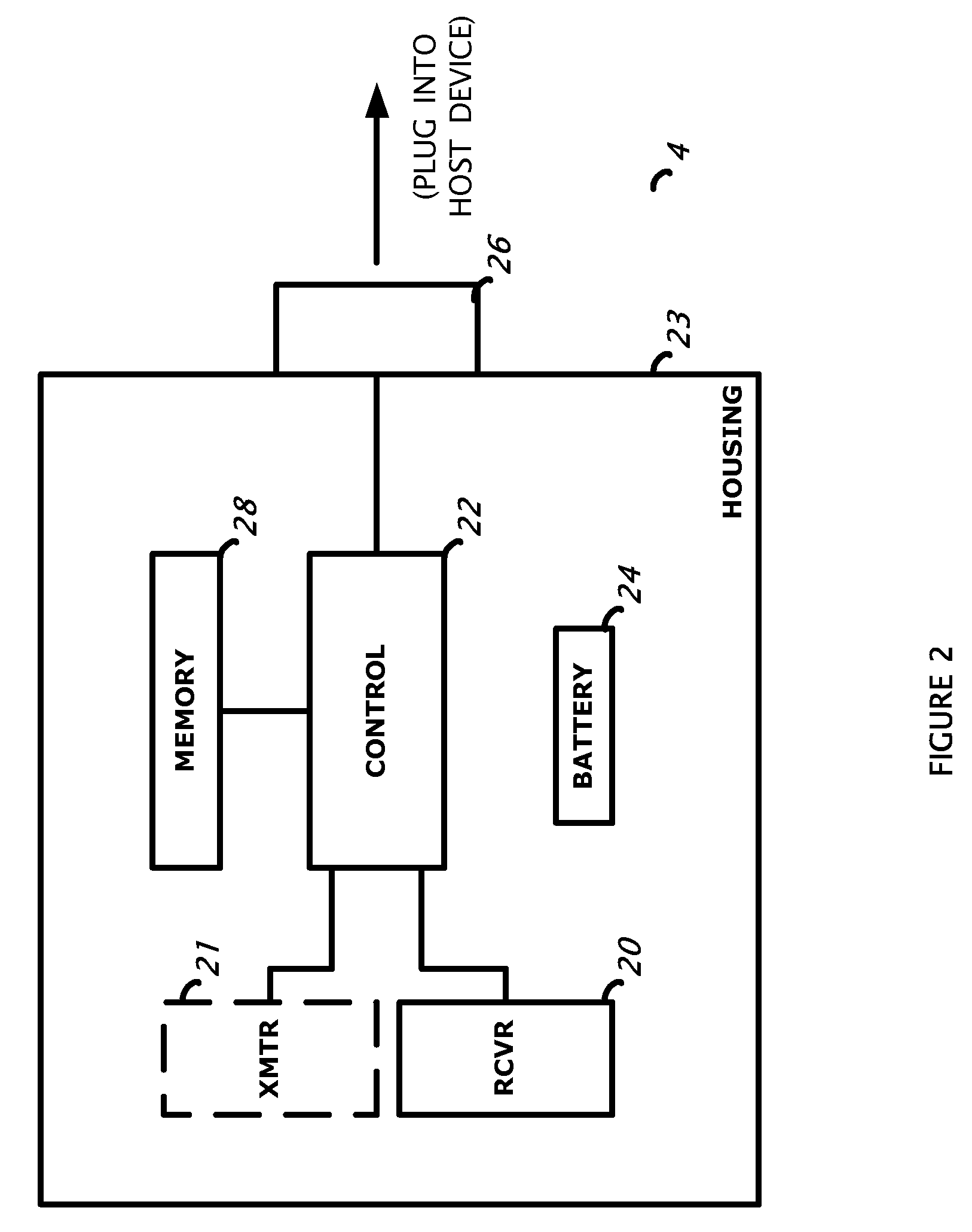
Security system control module
ActiveUS20080316024A1Eliminate requirementsEasy to installFrequency-division multiplex detailsTime-division multiplexNetwork Communication ProtocolsControl circuit
A security system control module with a portable housing including a wireless receiver, control circuitry, nonvolatile memory, and a data connector. The receiver receives data transmissions from at least one wireless security device that monitors a condition of a premises in which the wireless security device is installed. The data connector exchanges data between the control circuitry and an external host device, and it also accepts from the external host device primary operating power for operating the wireless receiver, the control circuitry, and the nonvolatile memory. The control circuitry is adapted to process signals in accordance with a preprogrammed configuration file stored in the nonvolatile memory, the signals received via the wireless receiver from a wireless security device, and to communicate with an external computer located remotely from the external host device via the data connector using a first communications protocol.
Owner:HONEYWELL INT INC
Security control and communication system and method
ActiveUS6999562B2Convenient programmingEasy to installFrequency-division multiplex detailsTelephonic communicationTransceiverDisplay device
An integrated security control system and method which integrate the functions of a wireless security system control panel and a radio transceiver in an integrated security control system unit. The integrated control unit includes a first telephone communication system for communicating security system data by wired telephone communications, and a second radio frequency (RF) cellular communication system for communicating security system data by communications through an RF communication network. The cellular communication system is the primary communication network for reporting a security event, thereby leaving the first telephone communication system open for telephone communications during the reporting of a security event. A separate unit of the security system, such as a wireless RF status display or a wireless RF keypad, is provided with a beeper transducer for sounding entry and exit beeps. The separate unit is positioned at a separate location from the integrated security control system unit, such that the entry beeps do not alert an entering person to the location of the integrated security control system unit. When a security event is triggered, the control unit delays activating a security alarm sounder in the control unit until after the second RF communication system has finished transmitting the alarm message.
Owner:ADEMCO INC
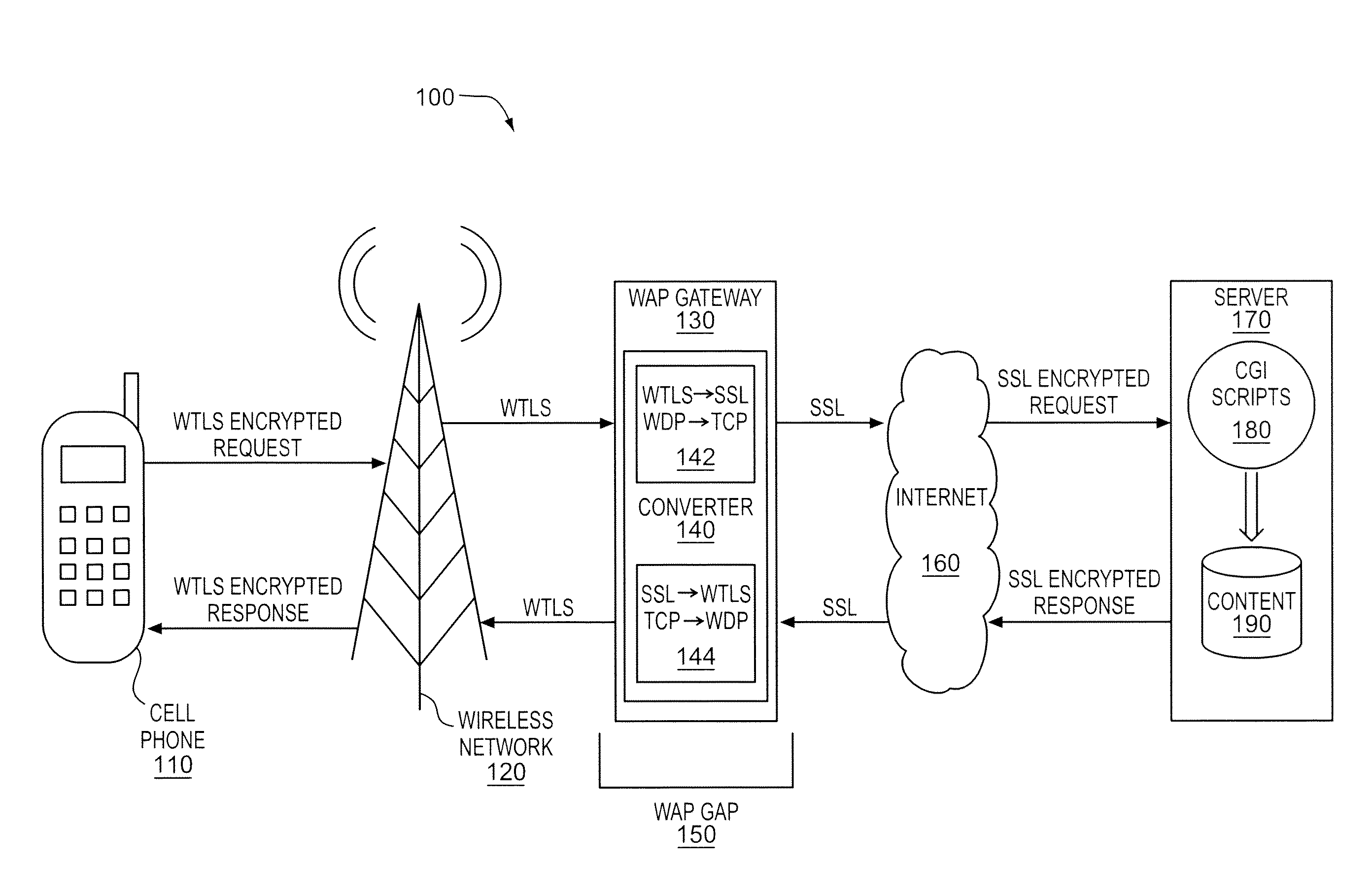
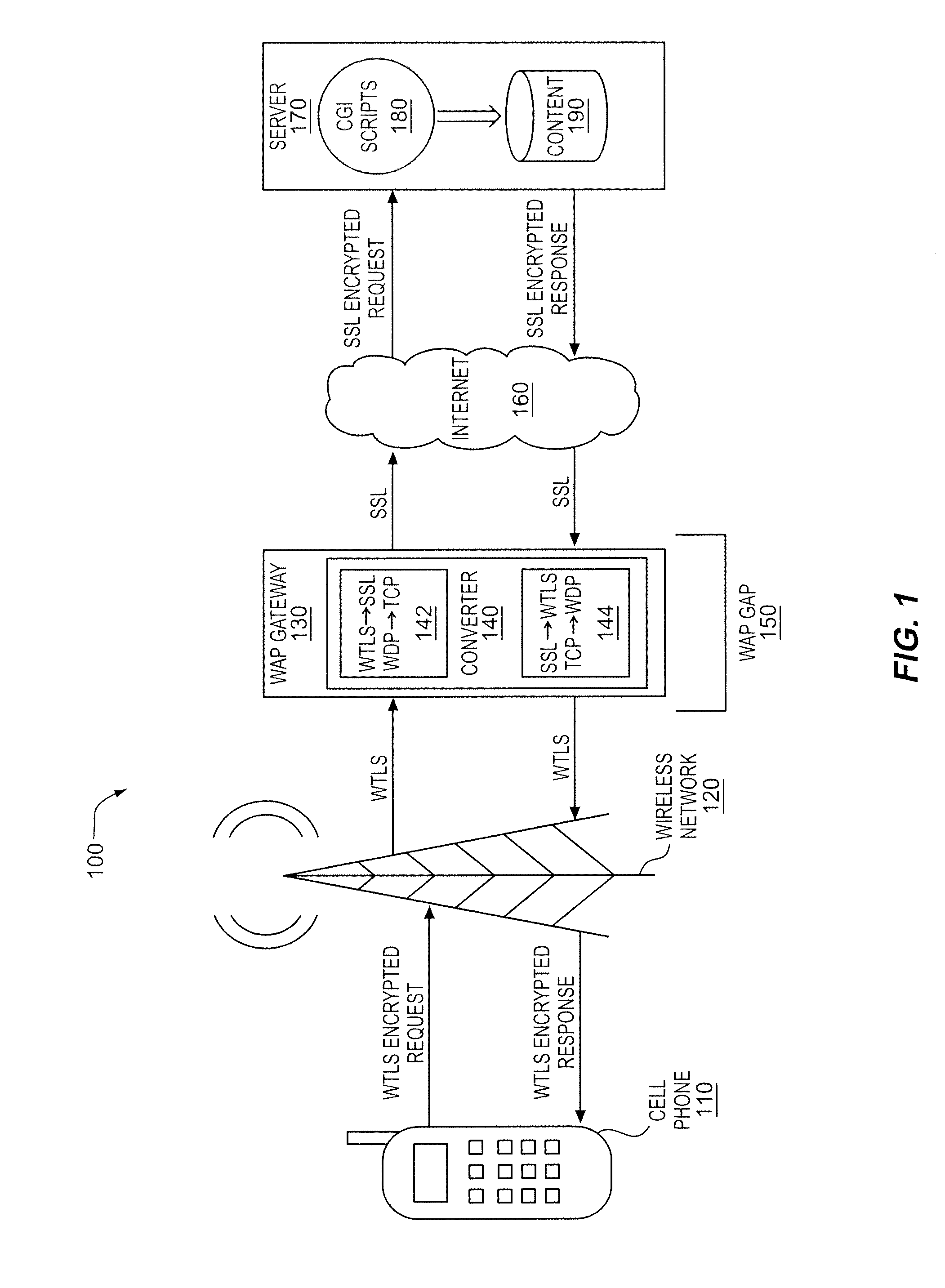
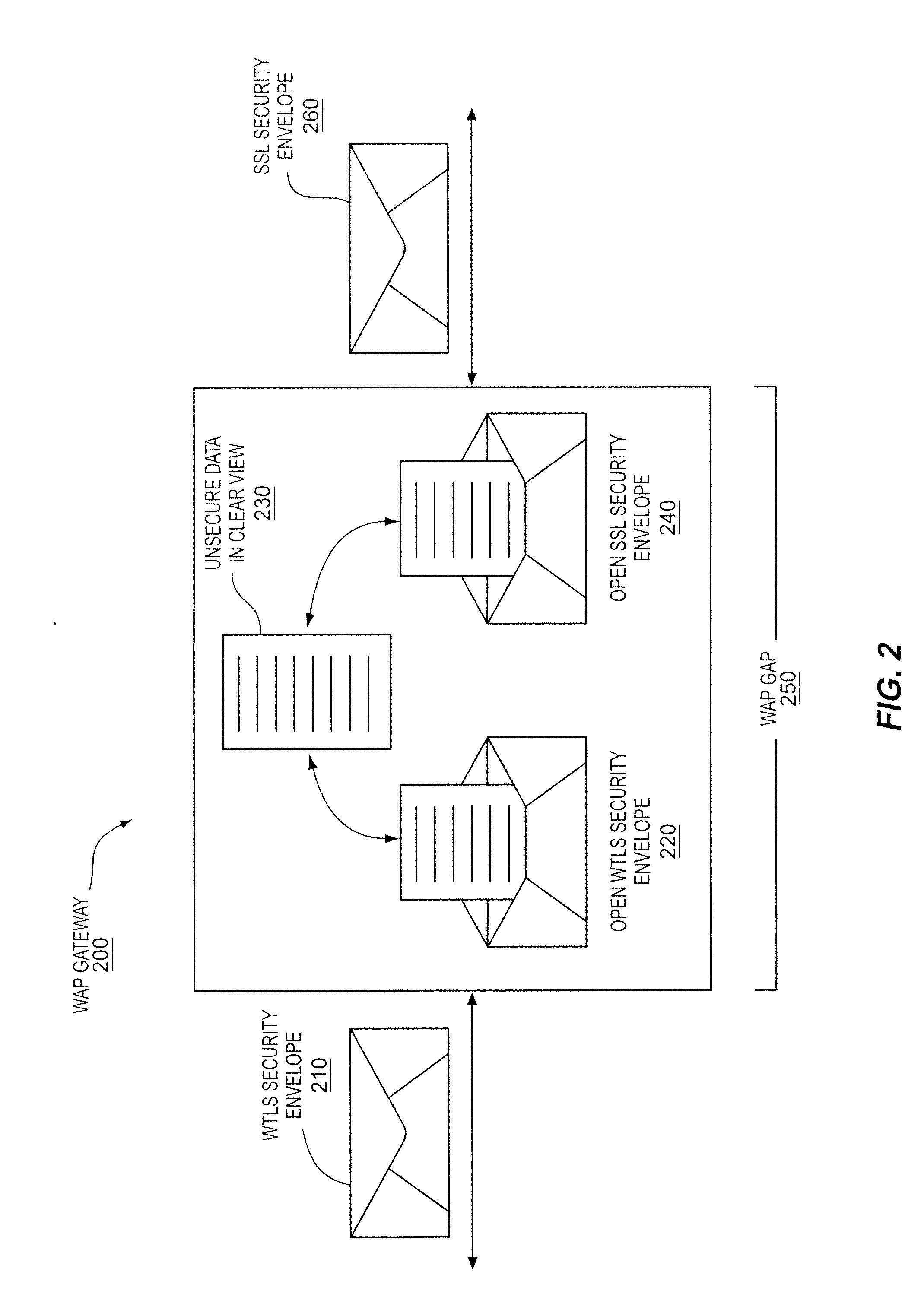
Selecting a security format conversion for wired and wireless devices
InactiveUS8522337B2Multiple digital computer combinationsSecret communicationComputer networkSelection system
A selection system and method to receive an indication of a security format from a network and to select one of a plurality of security format conversions based on the received indication is described. The indication may be an indication of a wireless security format such as WTLS used by a wireless access device or a wired security format such as SSL used by a wired access device and the security format conversion selected based on the indication may be to another secured format or a plain data format. The indication may include an indication of a port and an indication of a security feature that is supported by the access device.
Owner:INTEL CORP
Theft prevention device for automotive vehicle service centers
ActiveUS7119686B2Electric signal transmission systemsMultiple keys/algorithms usageMobile vehicleEngineering
Owner:MIDTRONICS
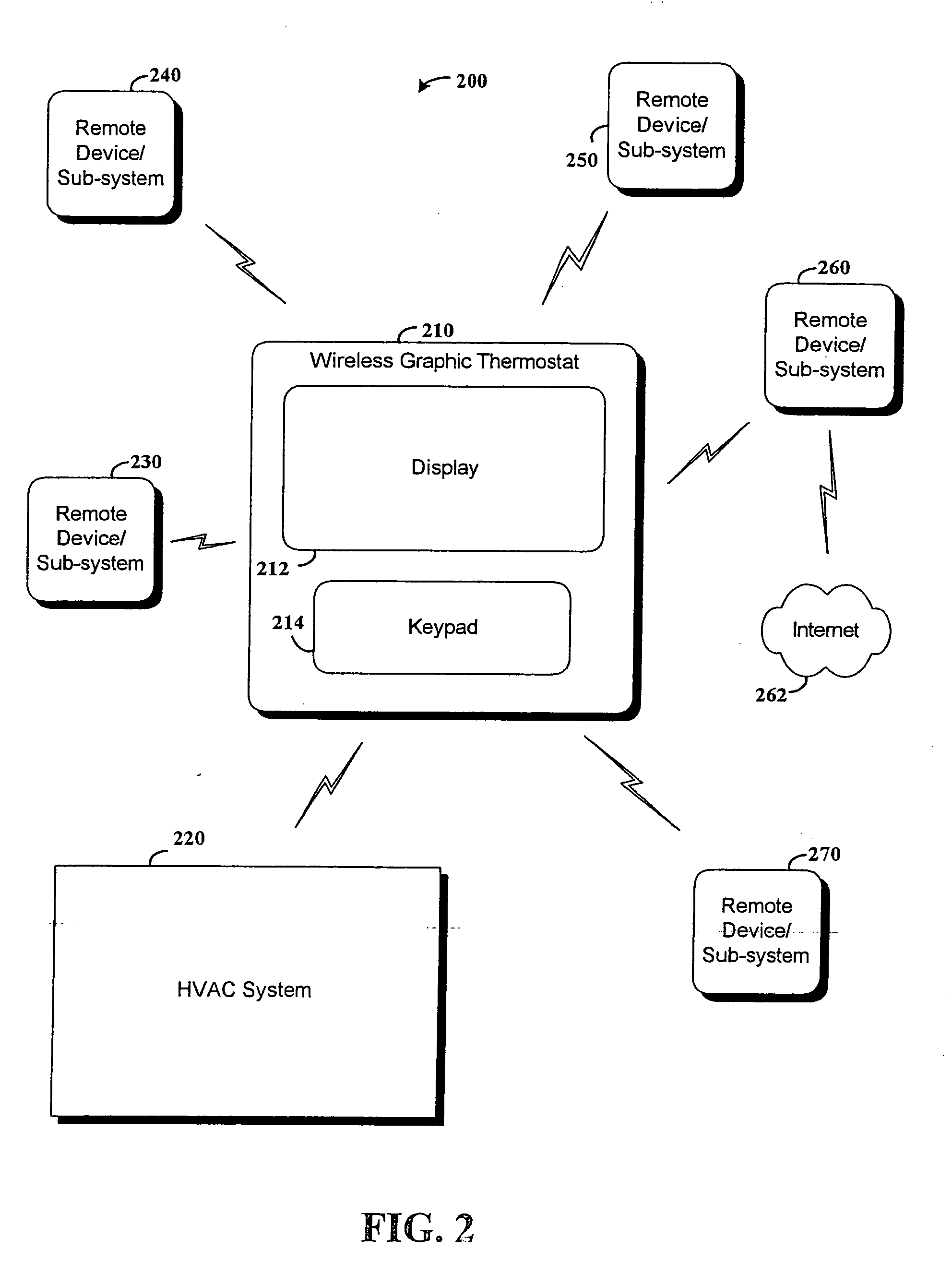
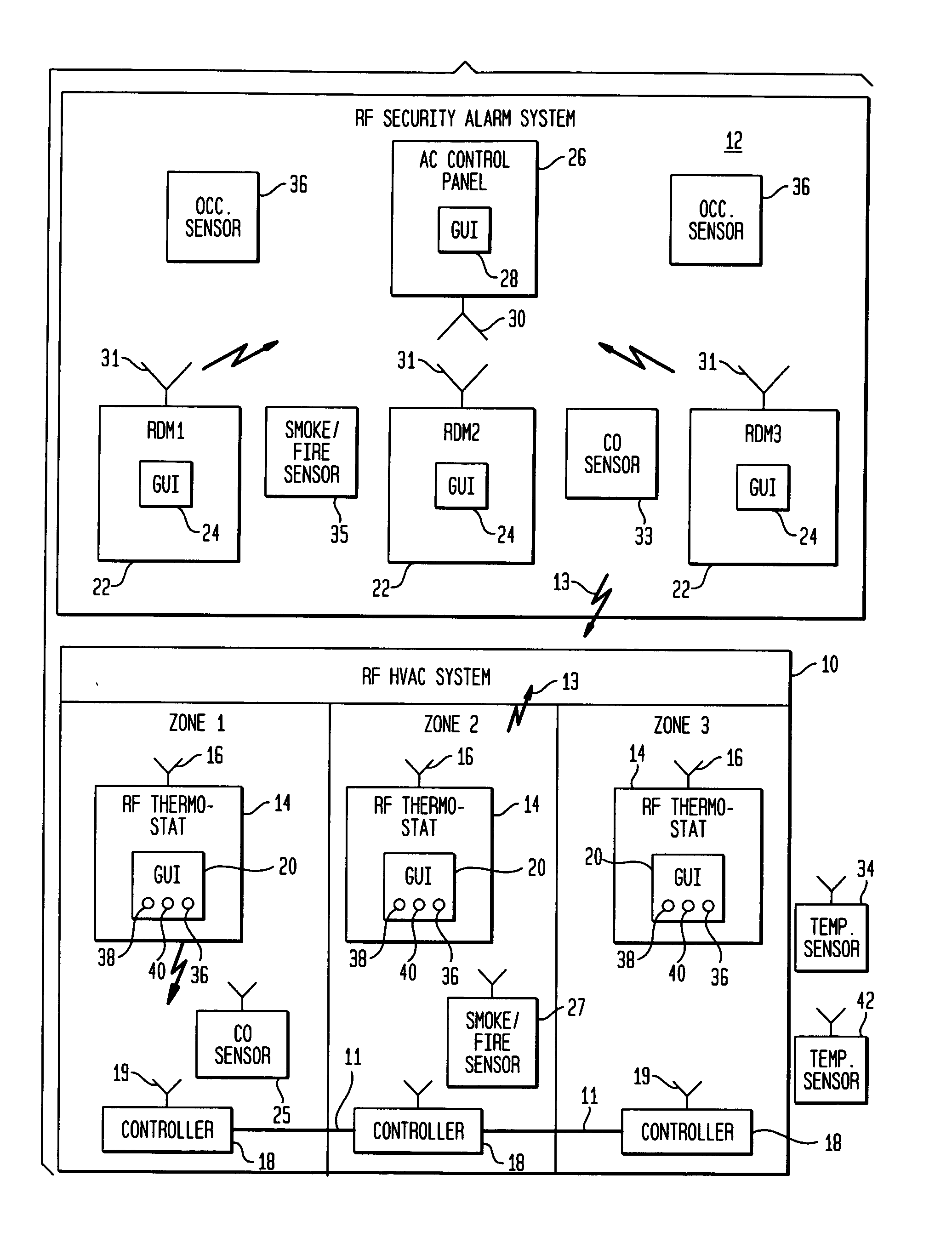
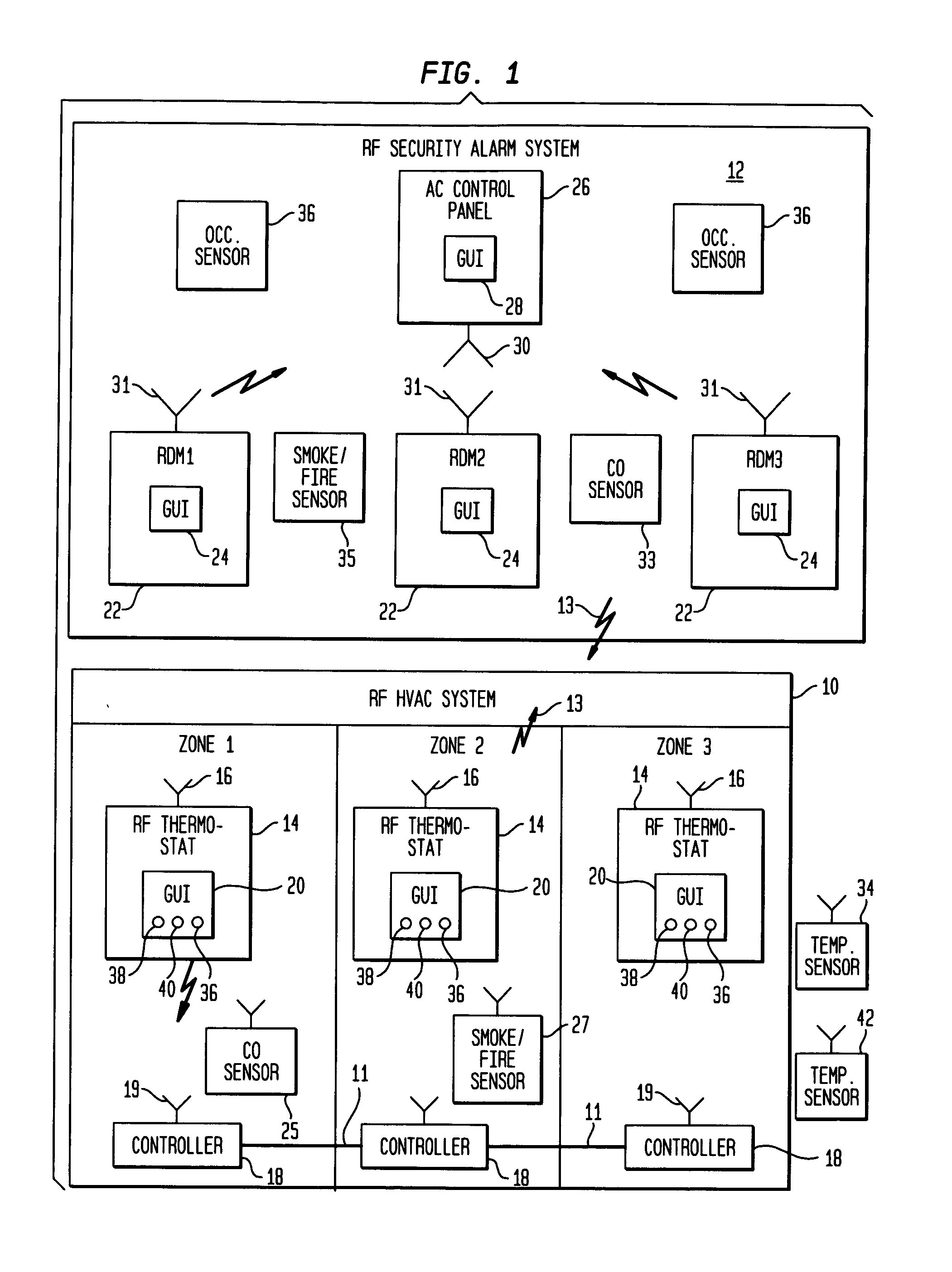
RF interconnected HVAC system and security system
InactiveUS20050040943A1EasilyMechanical apparatusSpace heating and ventilation safety systemsWireless controlEngineering
An interconnected wireless RF HVAC (heating, ventilation, air conditioning) system and wireless RF security system, which are interconnected and communicate with each other through the use of a common wireless RF technology, including the same selected frequency, modulation and a set of common protocols. The RF wireless HVAC system includes wireless RF thermostats which can communicate with and control both the HVAC system and the security system, and the wireless RF security system includes wireless RF controls or keypads which can communicate with and control both the security system and the HVAC system. The universal RF infrastructure can be expanded to provide communication or control of additional user or manufacturer installed wireless RF devices or systems through the universal RF home infrastructure.
Owner:HONEYWELL INT INC
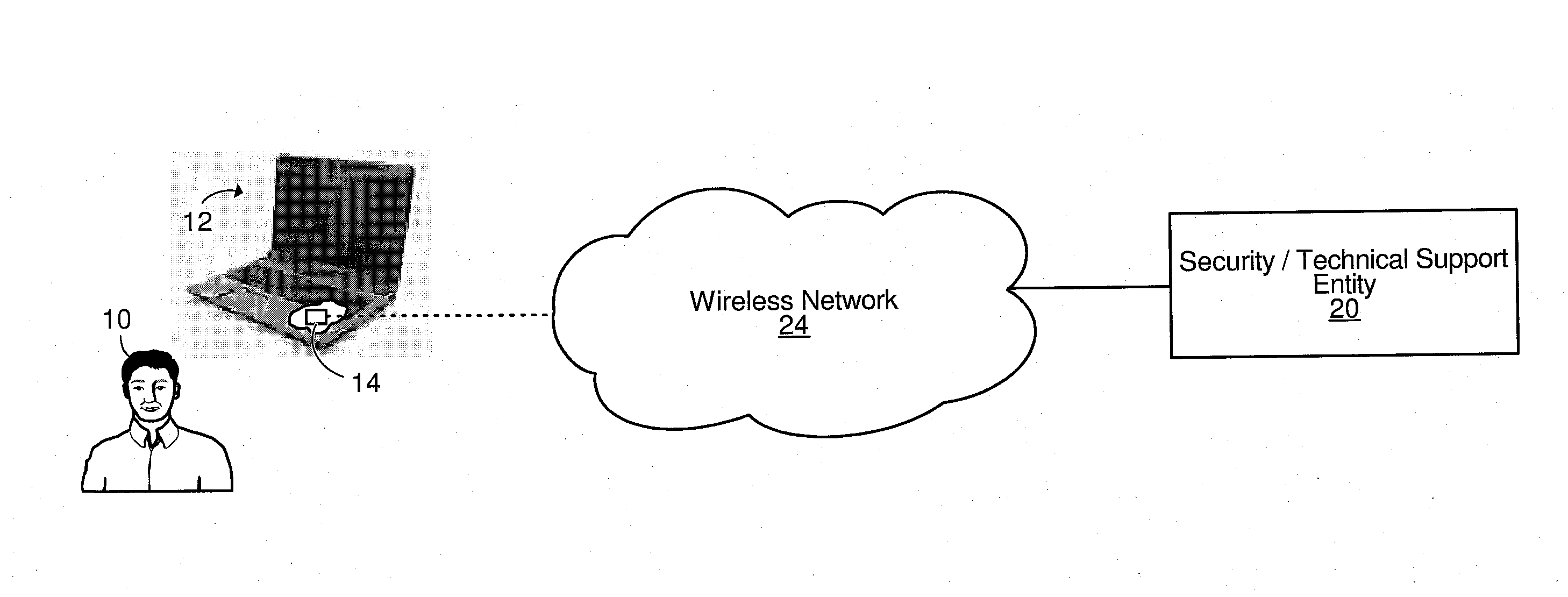
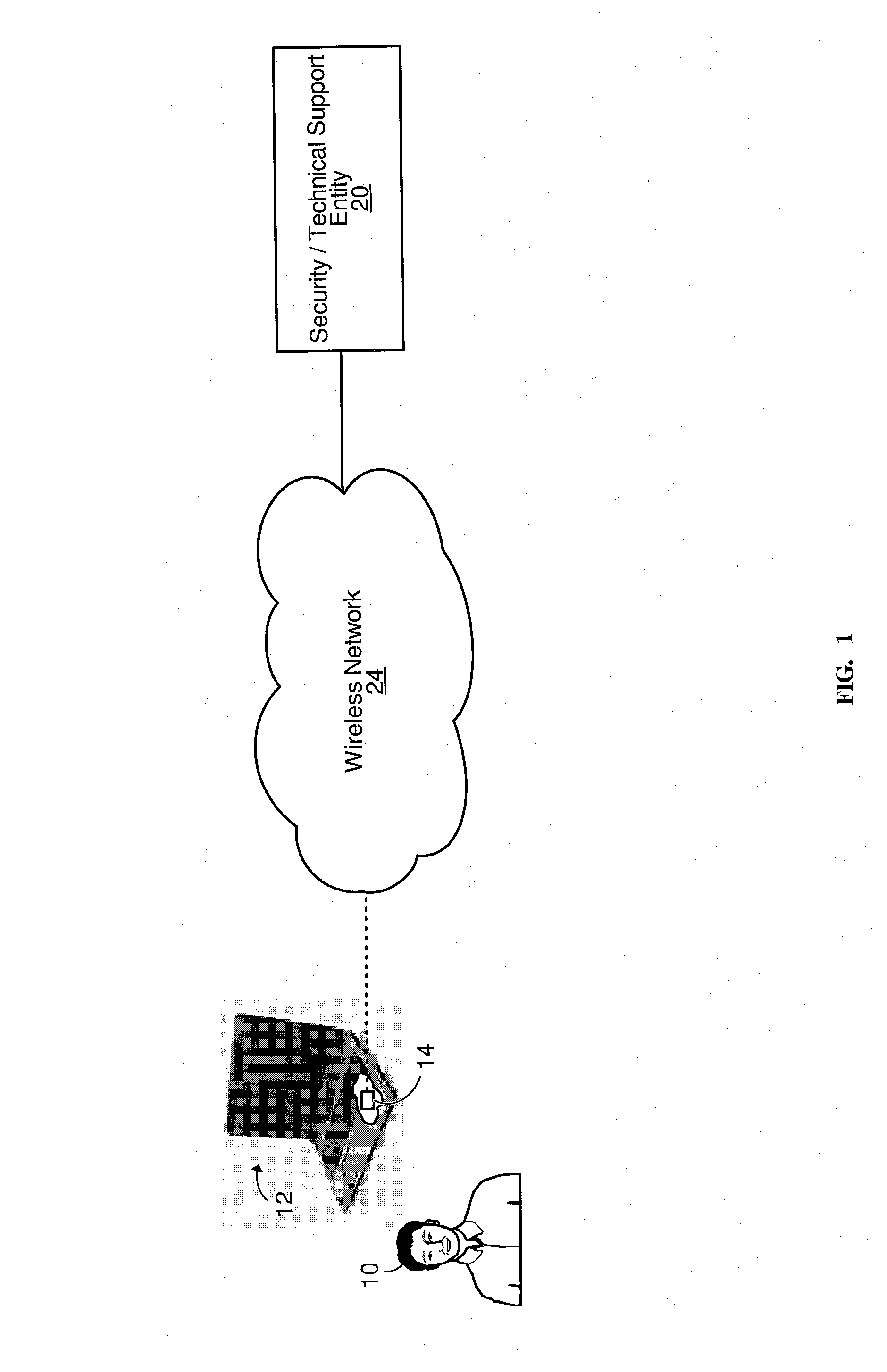
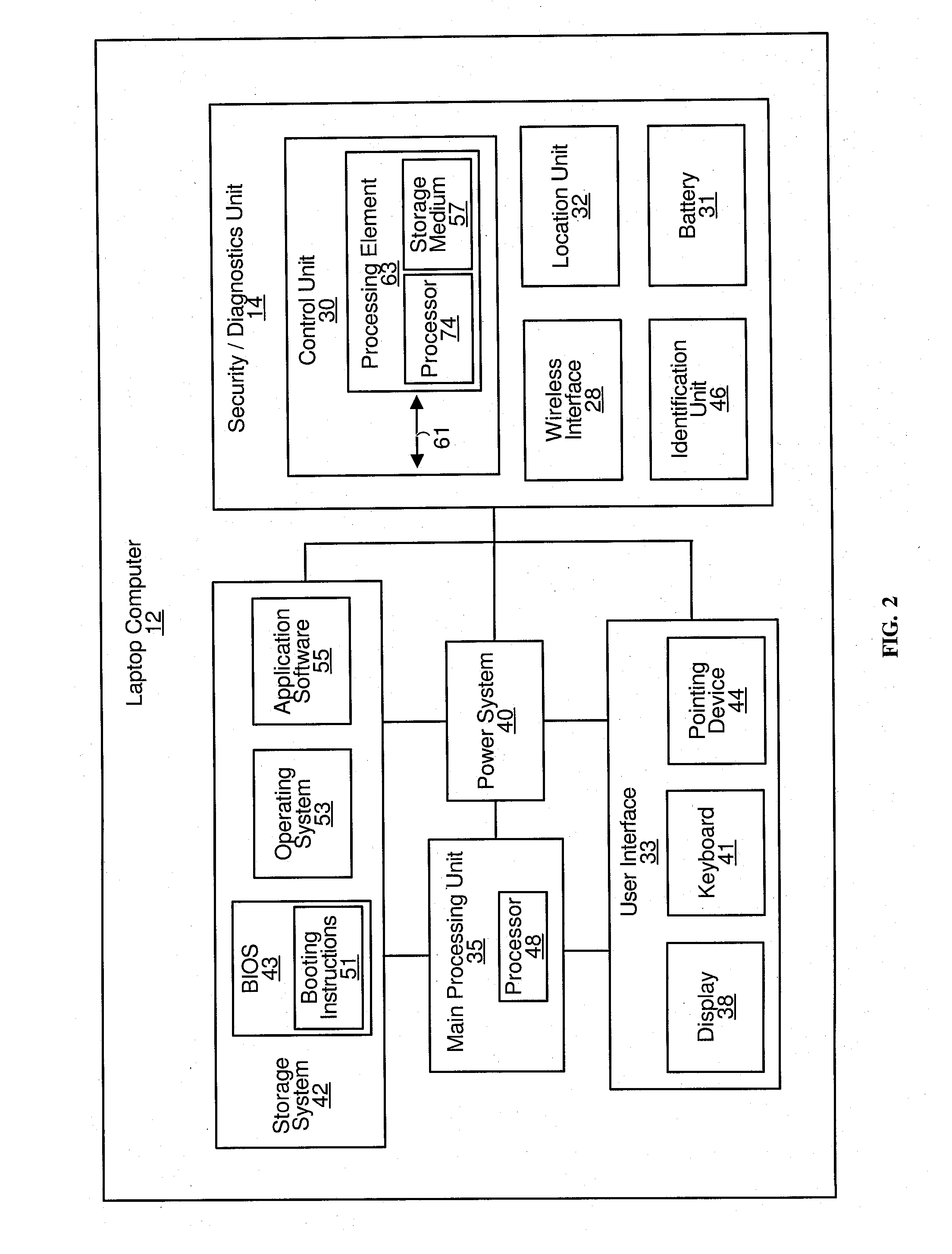
Methods and systems for providing a wireless security service and/or a wireless technical support service for personal computers
InactiveUS20100218012A1Promote recoveryError detection/correctionVolume/mass flow measurementComputer hardwarePersonal computer
Methods and systems for providing a wireless security service and / or a wireless technical support service for a personal computer. The personal computer comprises a control unit for processing information conveyed by signals transmitted over a wireless network and received by a wireless interface of the personal computer. By processing this information, the control unit may: send at least one command for execution by a power management controller of the personal computer such that, upon executing the at least one command, the power management controller changes a power state of the personal computer (e.g., powers off the personal computer and prevents the personal computer from being powered on, or powers on the personal computer); cause booting software to become corrupted; cause various technical support operations (diagnostics and / or maintenance operations) to be performed on the personal computer; and / or cause the wireless interface to transmit over the wireless network information regarding a boot sequence of the personal computer.
Owner:PEAK POSITIONING CORP
Distributed wireless network security system
ActiveUS7342906B1Frequency-division multiplex detailsUnauthorised/fraudulent call preventionWireless securityLink layer security
Methods, apparatuses and systems enabling a distributed wireless network security system. In one embodiment, the present invention provides a wireless network system where security policies are automatically distributed and uniformly implemented across wireless network access points. Embodiments of the present invention address the situation where a malicious user moves to a different access point within a wireless network environment after failing to properly authenticate and / or associate at a first access point. Embodiments of the present invention enable an integrated, multi-layer network security system, wherein a security mechanism at one layer (e.g., link layer security mechanisms) can set policies based on information gleaned from operation of a security mechanism at another layer (e.g., application layer authentication servers).
Owner:CISCO TECH INC
Wireless security system and method
ActiveUS7373508B1Key distribution for secure communicationDigital data processing detailsClient-sideComputer science
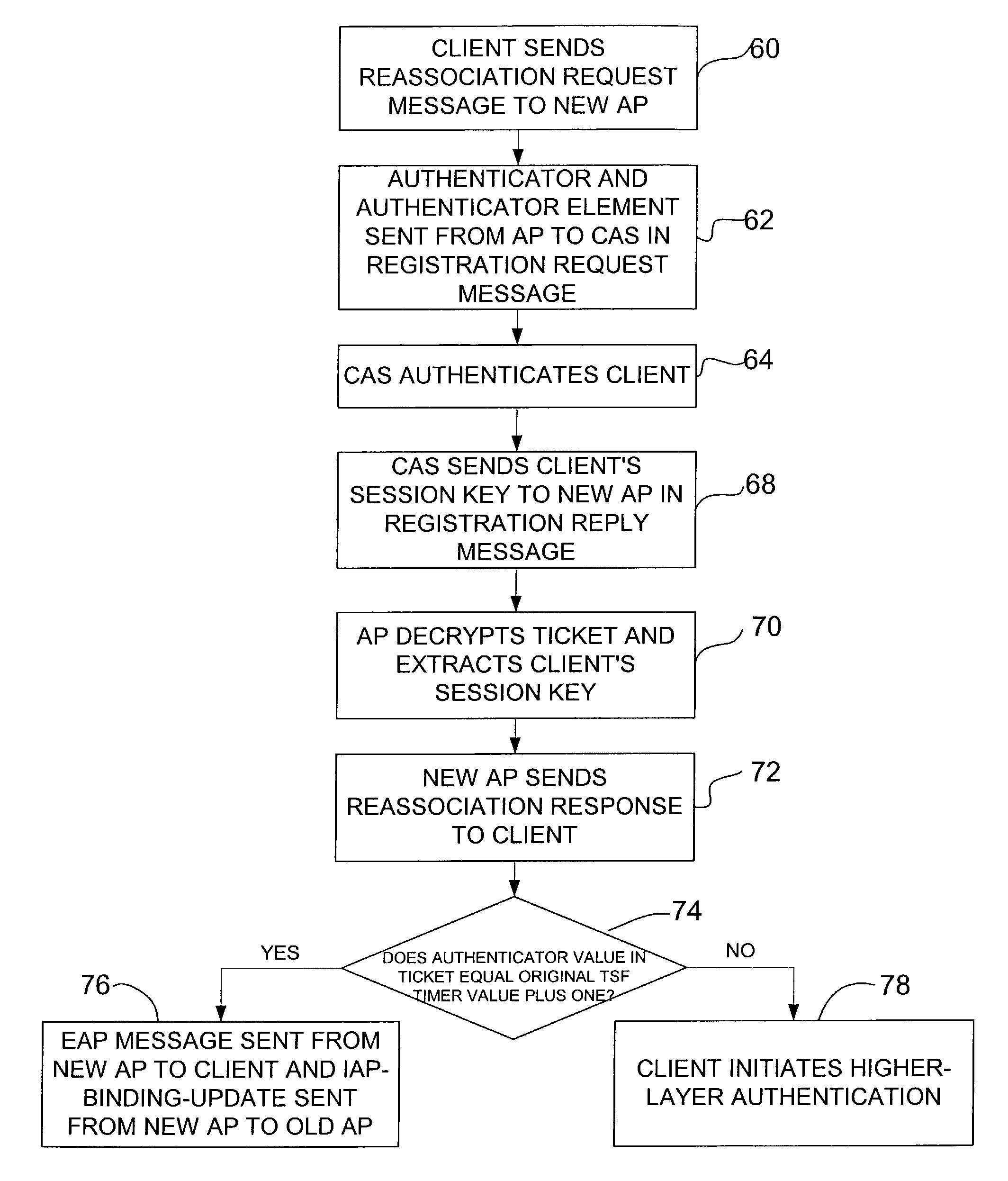
A method for reauthentication during client roaming in a wireless network system. The network has at least one access server and a plurality of access points registered with the access server. The method includes receiving a registration request at the access server from a new access point for a roaming client registered with the access server and sending a client's session key to the new access point in a registration reply upon authentication of the registration request. The client's session key is configured for use by the new access point to authenticate the client and establish keys for the client. A method for secure context transfer during client roaming is also disclosed.
Owner:CISCO TECH INC
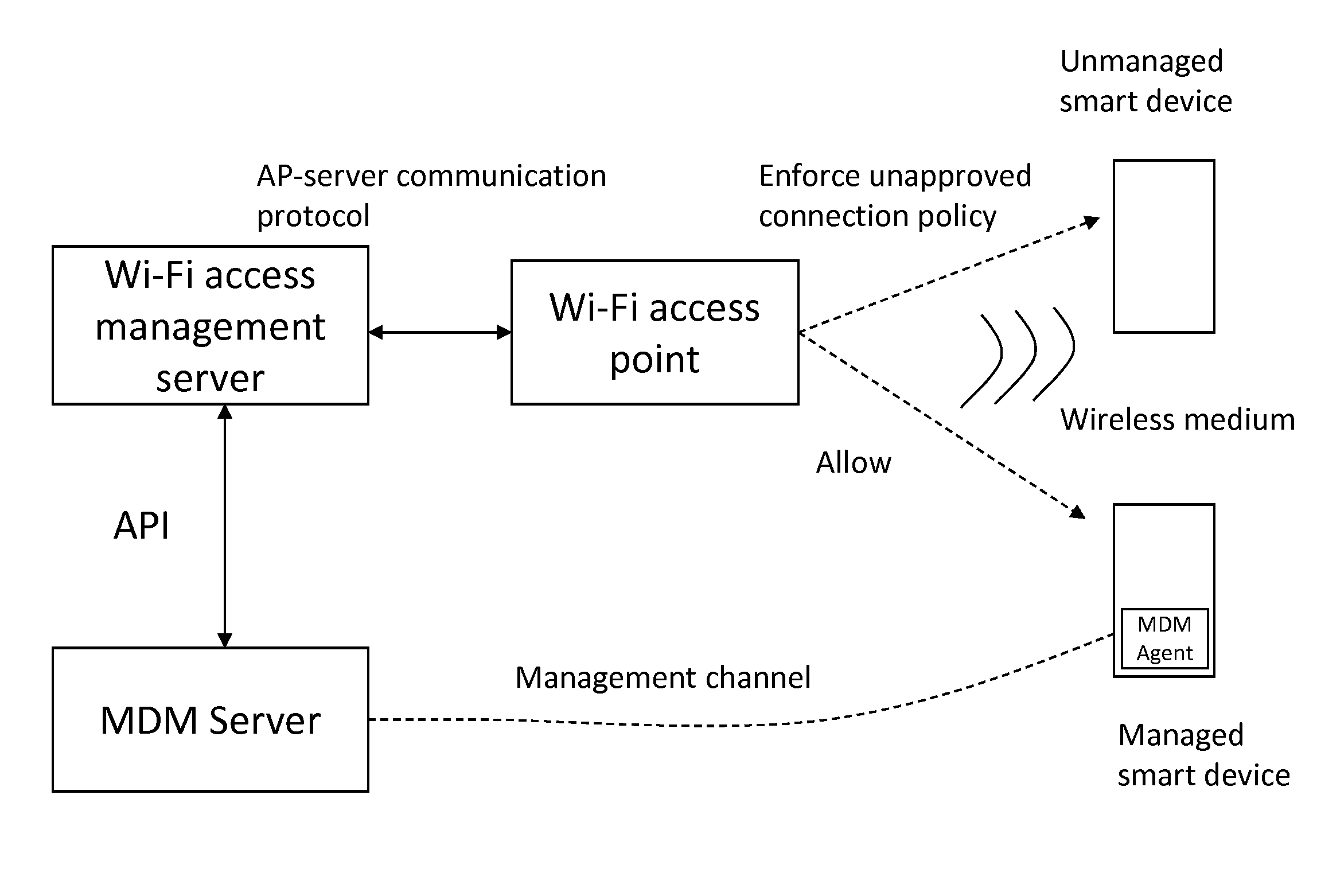
Monitoring of smart mobile devices in the wireless access networks
InactiveUS20130007848A1Improve securityDigital data processing detailsComputer security arrangementsAccess networkWireless mesh network
A method for smart mobile devices monitoring in wireless local area networks. The method includes installing a wireless security monitoring system or a wireless access system in a local area network. The method includes configuring the wireless security monitoring system or the wireless access system to communicate with a mobile device management (MDM) system. The method includes detecting a wireless client connecting to the wireless local area network and identifying the wireless client to be a smart mobile device. Moreover, the method includes receiving an indication at the wireless security monitoring system or the wireless access system from the MDM system regarding whether the wireless client is a managed device or not. The method also includes classifying the wireless client as approved or unapproved smart mobile device based at least upon the indication received from the MDM system.
Owner:AIRTIGHT NETWORKS
Radio Transmission Method
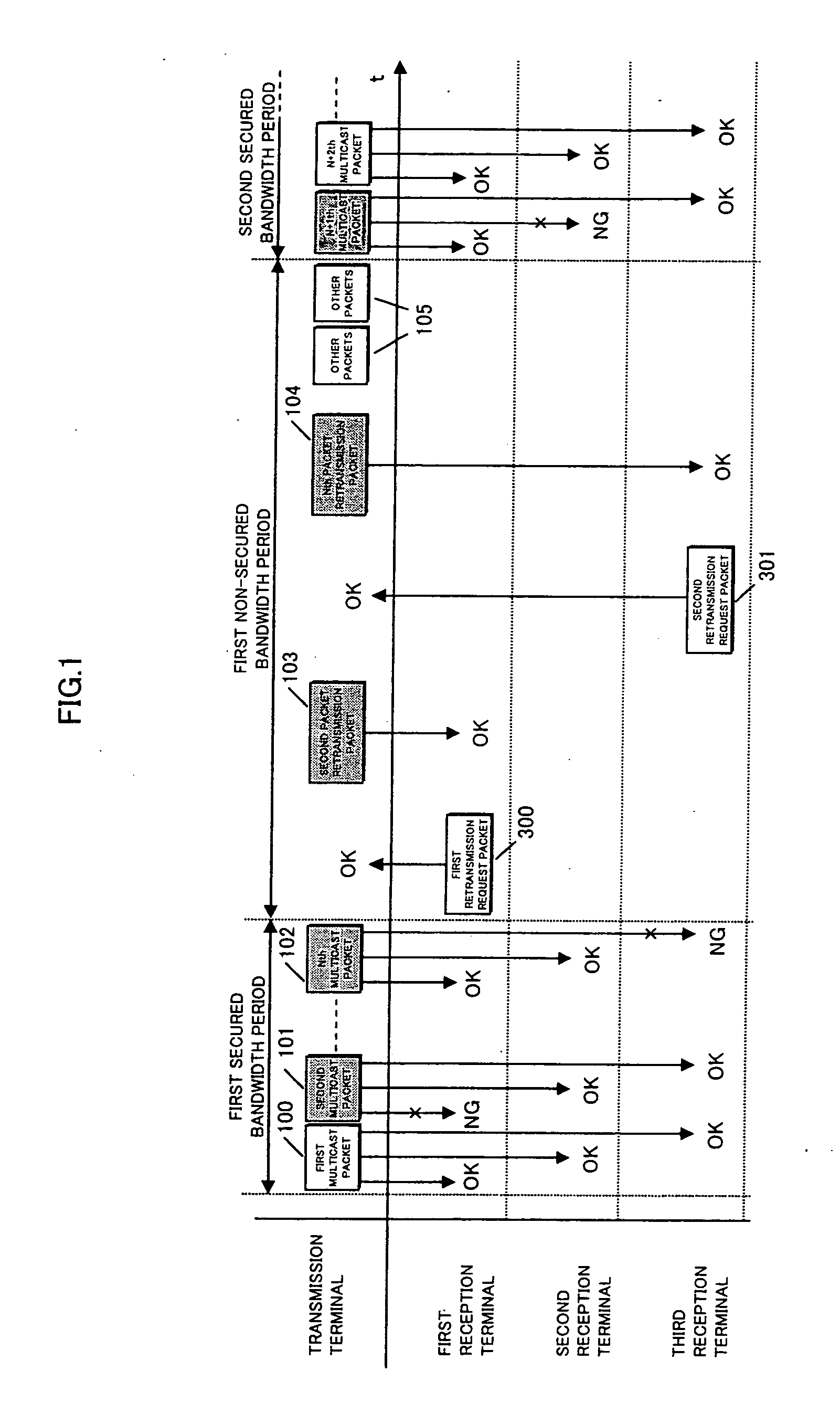
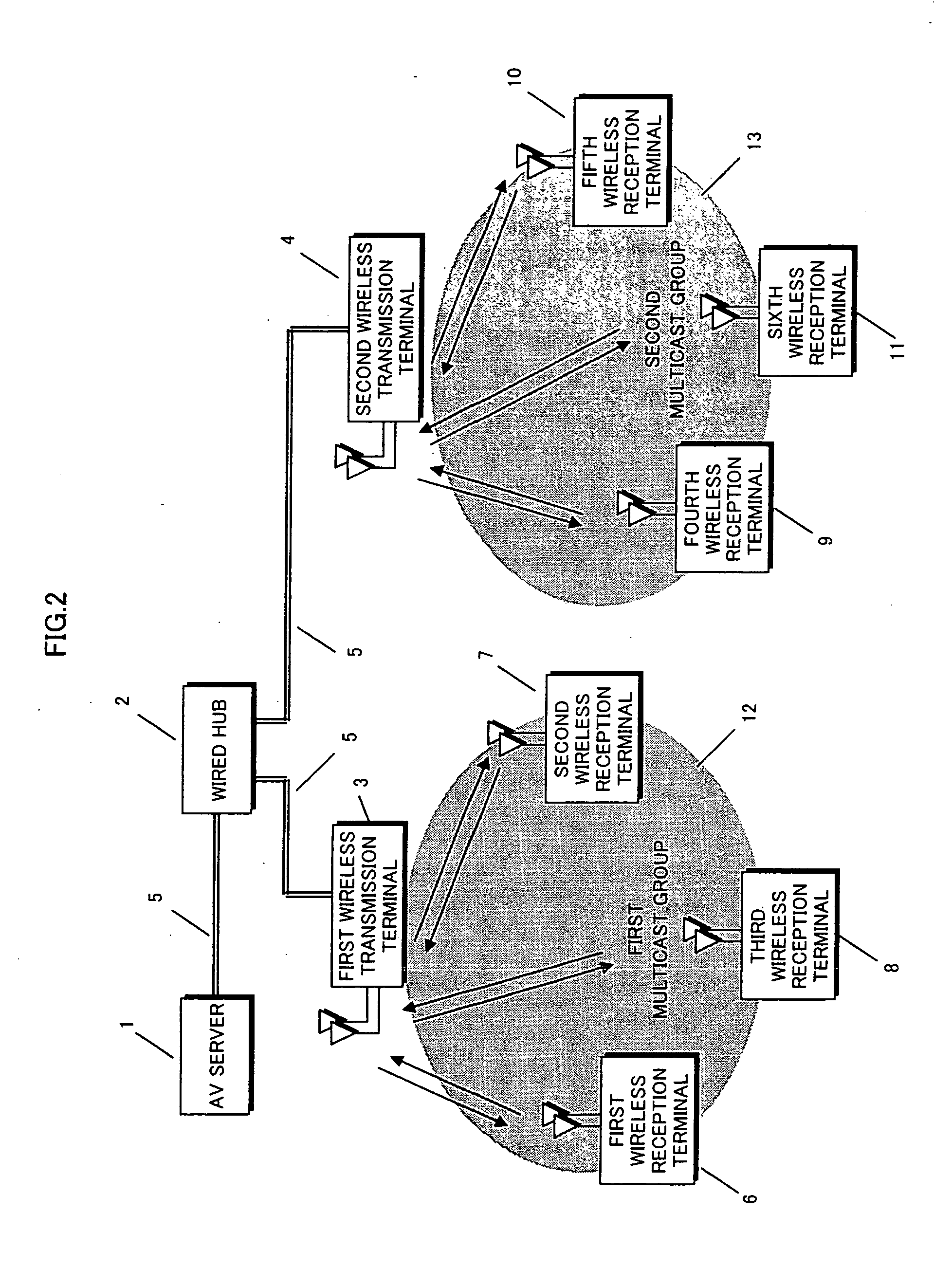
InactiveUS20080192661A1Improve reliabilityImprove utilization efficiencyError prevention/detection by using return channelData switching by path configurationMulticast packetsWireless security
Retransmission control and retransmission are performed at a lower priority than the transmission of multicast packets from a transmission apparatus to two or more reception apparatuses. A communication apparatus performs wireless multicast transmission to reliable transmit packets. In a transmission side terminal, sequence numbers are attached at a layer higher than the Mac layer to each of secured-bandwidth or priority control-type Mac layer multicast packets, and in a plurality of reception side terminals, missing packets are detected using the sequence numbers, and bandwidth other than the secured bandwidth or lower priority packets are used to perform retransmission requests. The transmission terminal retransmits data using bandwidth other than the secured bandwidth or lower priority packets, thereby enabling favorable reception of audio, video and data when transmitting the audio, video and data in real-time to the reception terminals using wireless secured bandwidth-type or priority control-type Mac layer multicast transmission.
Owner:PANASONIC CORP
Method and apparatus for monitoring multiple network segments in local area networks for compliance with wireless security policy
InactiveUS20060193300A1Prevent unauthorized wireless accessMinimizes human effortNetwork topologiesRadio/inductive link selection arrangementsGeographic regionsComputer science
Method and system for monitoring a plurality of network segments in a local area network within a selected geographic region is provided. The monitoring is performed to check compliance with one or more wireless security policies. The method comprises providing a network monitoring device and coupling the network monitoring device to a connection port of the local are network. Moreover, the method includes providing one or more sniffers that are adapted to interact with a wireless medium. The sniffers are spatially disposed within and / or in a vicinity of the selected geographic region. The method includes determining a connectivity status of at least one wireless access device to the local area network.
Owner:AIRTIGHT NETWORKS
Method and system for wireless intrusion detection prevention and security management
ActiveUS7295831B2Spatial transmit diversityUnauthorised/fraudulent call preventionSystems managementIntrusion detection and prevention
Owner:3E TECH INT
Tool tracking apparatus
InactiveUS7928845B1Electric signalling detailsBurglar alarm by hand-portable articles removalLED displayElectrical battery
A tool tracking apparatus constructed by a base monitoring station that has electronic circuitry, an LED display panel and an audible alarm; a power supply including a battery power backup for the base monitoring station; a perimeter loop wire electrically connected to the base monitoring system defining an extended area in which at least one tool is protected or can be located; at least one wireless security tag fixedly attached to the at least one tool for rounding a second audible alarm when the locate button on the base monitoring station is pushed or for triggering the first audible alarm when the at least one wireless security tag approaches the perimeter loop wire at a distance less than a preset distance.
Owner:LAROSA WILLIAM A
Method and apparatus for authenticating a wireless access point
InactiveUS7885639B1Unauthorised/fraudulent call preventionMultiple keys/algorithms usageMedia access controlWireless security
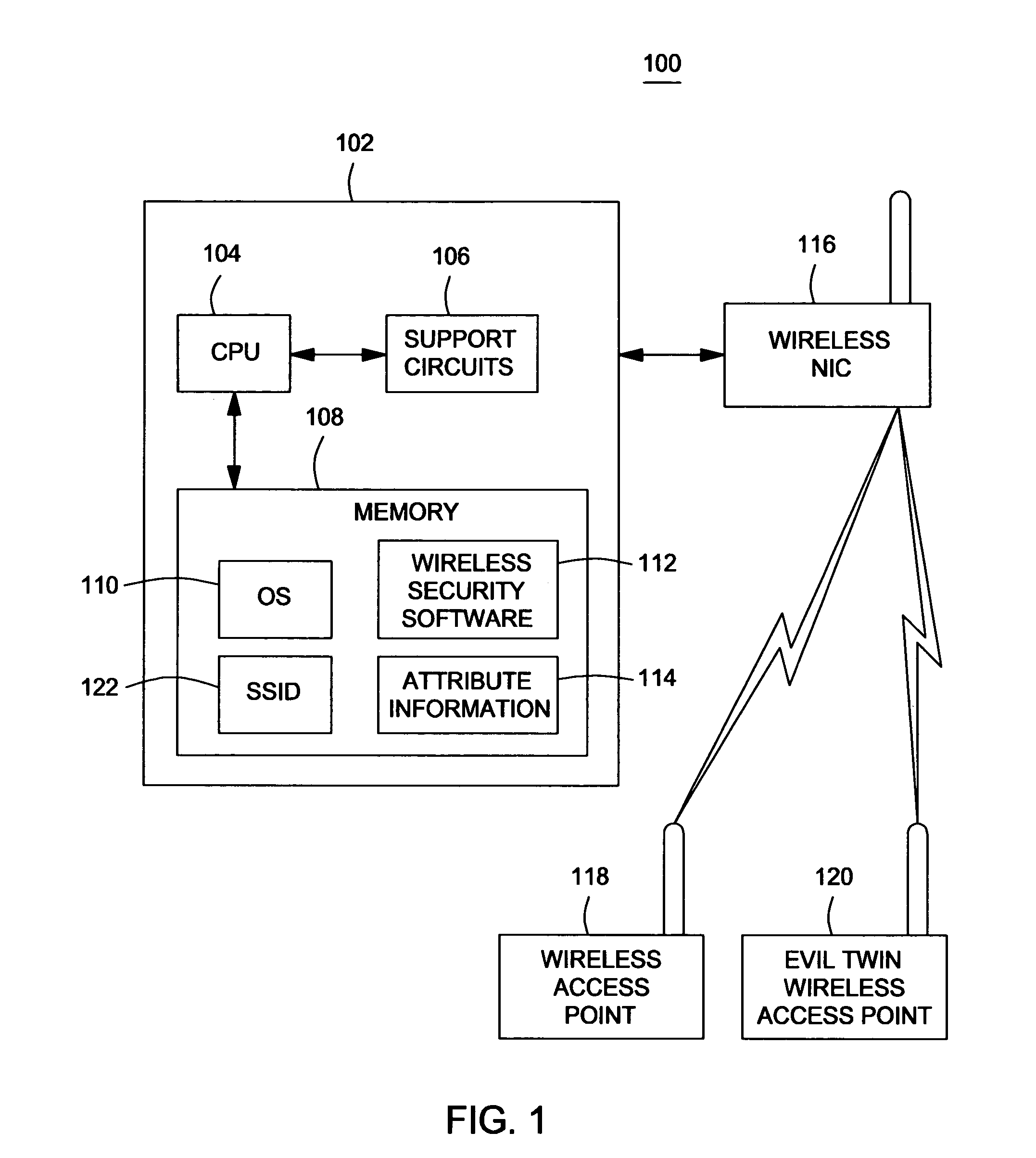
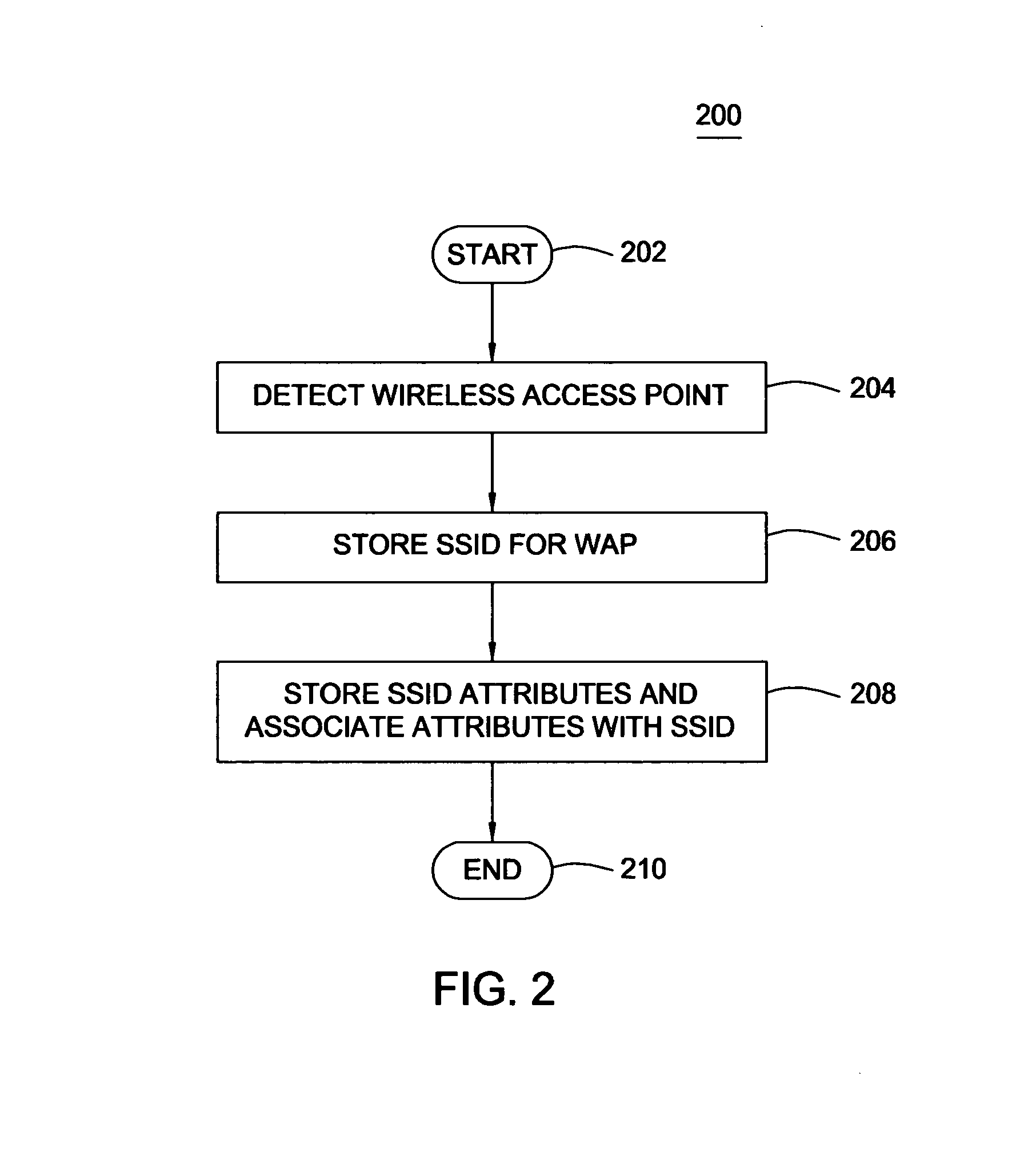
A method, system and computer-readable medium for authenticating a wireless access point is described. The method comprises upon initially connecting to the wireless access point, storing a first service set identifier associated with the wireless access point, storing a first media access control address for the wireless access point and associating the first media access control address for the wireless access point with the first service set identifier for the wireless access point. The system comprises a computing device for executing wireless security software wherein the wireless security software upon initial connection of the computing device to the wireless access point, stores a first service set identifier associated with the wireless access point, stores a first media access control address for the wireless access point and associates the first media access control address for the wireless access point with the first service set identifier for the wireless access point.
Owner:CA TECH INC
Method and apparatus for setting up wireless LAN of device
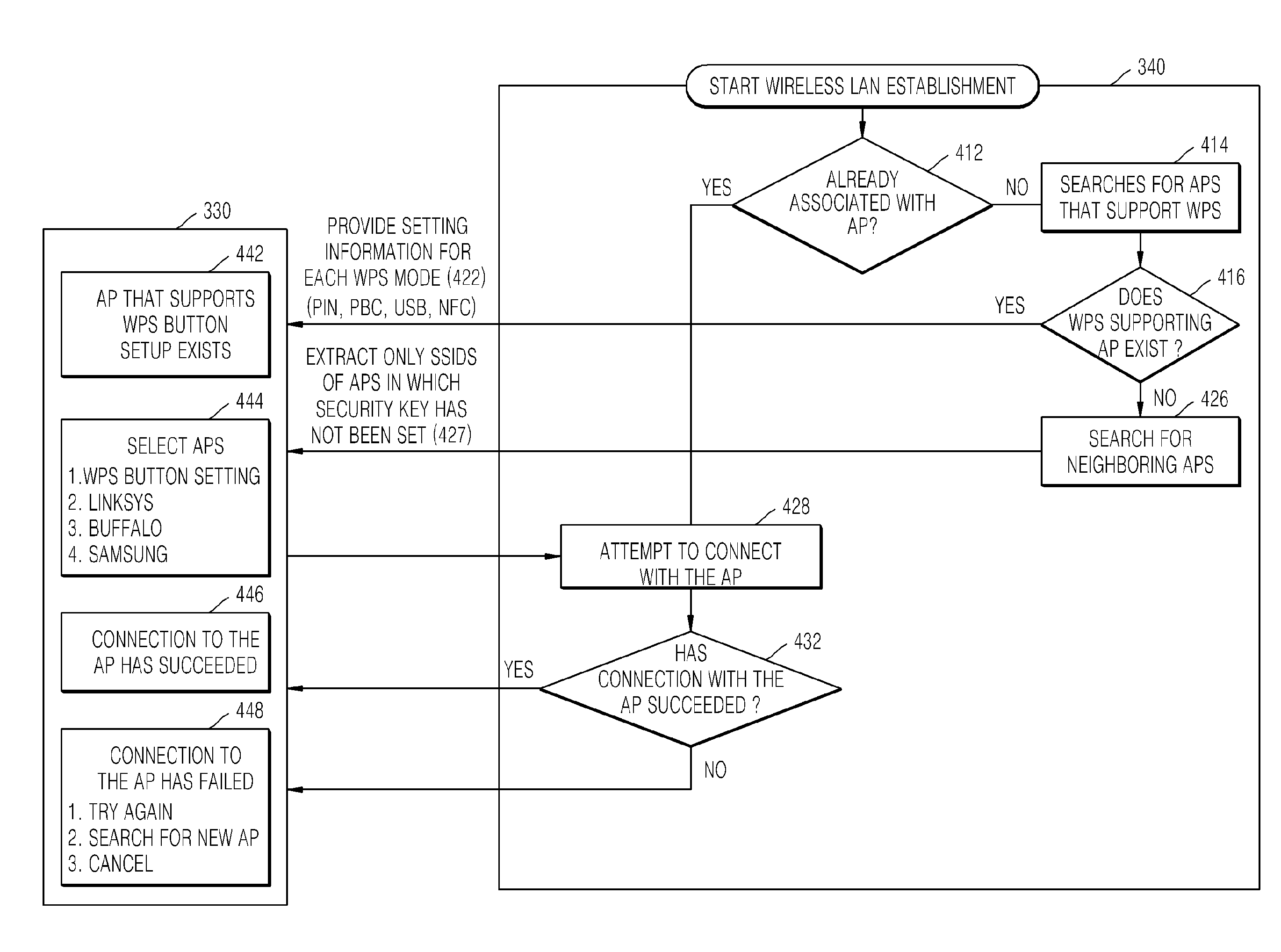
InactiveUS20090271709A1Simple interfaceInput/output for user-computer interactionAssess restrictionWireless lanComputer science
Owner:SAMSUNG ELECTRONICS CO LTD
Wireless security communication method and system
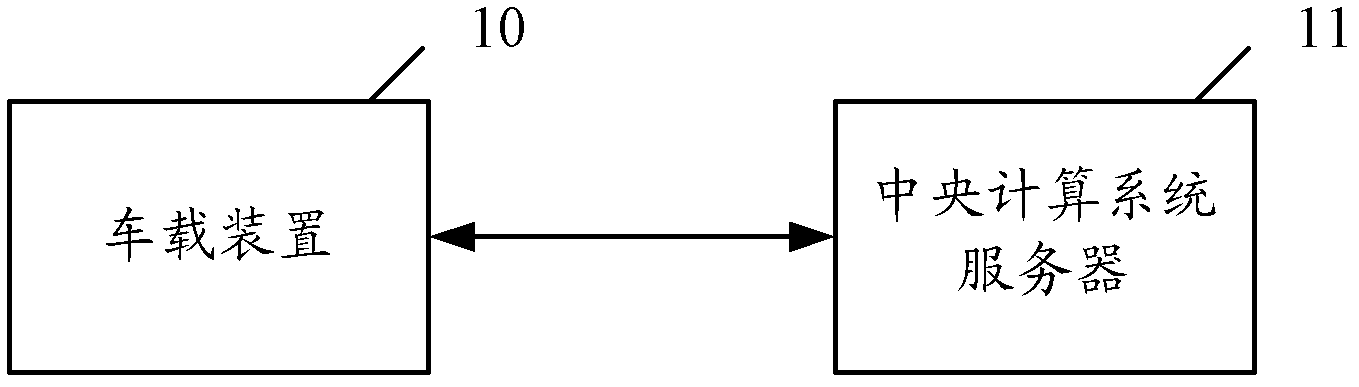
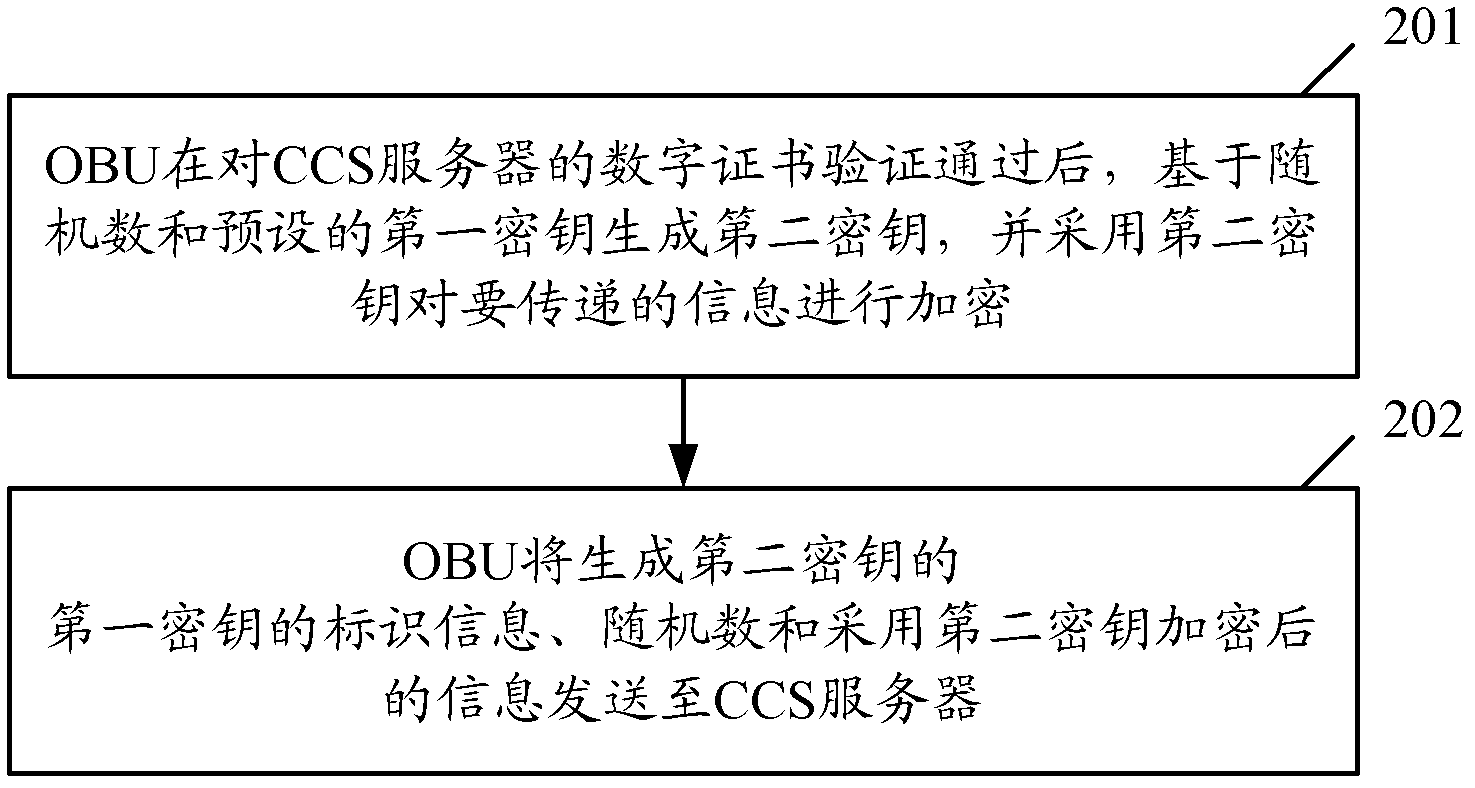
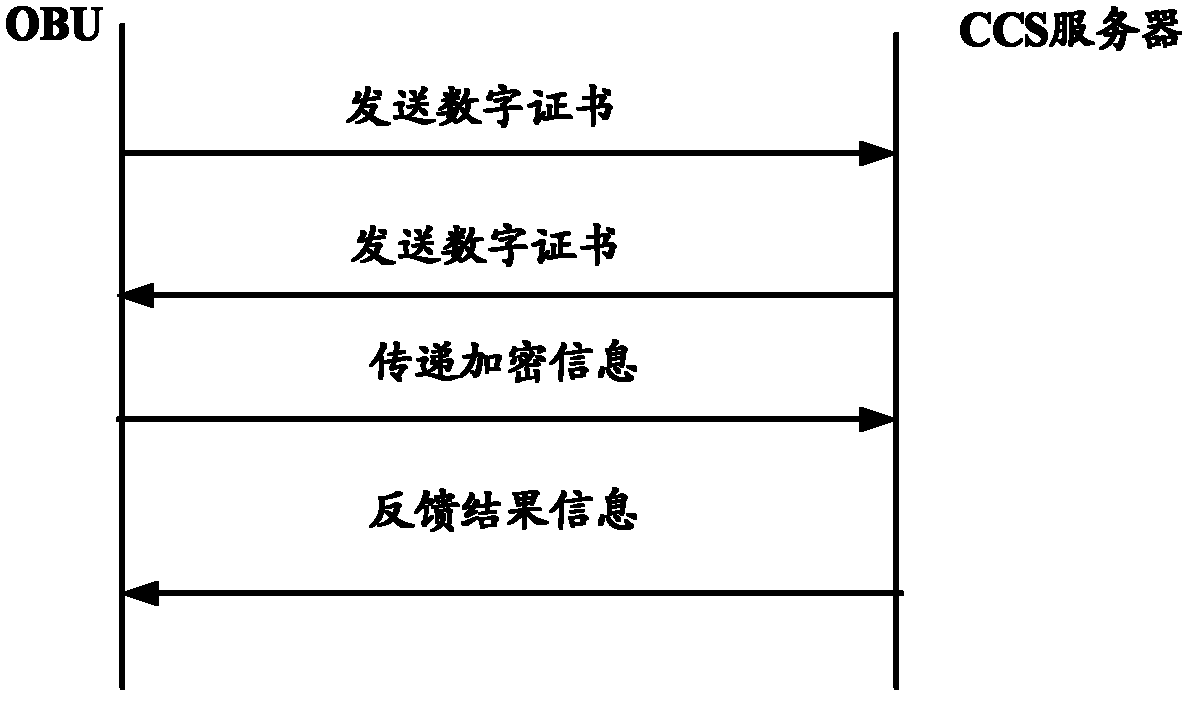
The invention discloses a wireless security communication method and system for ensuring the security of wireless communication in an intelligent transportation system, improving the data processing efficiency and reducing the complexity of security communication. The method comprises the following steps: at least one first secret key and identification information thereof are respectively stored in an OBU (On-Board Unit) and a CCS (Central Computer System) server; and the OBU is used for generating a second secret key on the basis of a random number and the first secret key after a digital certificate of the CCS server is passed through verification, encrypting information to be transmitted by adopting the second secret key, and then sending the identification information of the first secret key and the random number which generate the second secret key, and the information encrypted by the second secret key to the CCS server. The invention simultaneously discloses a wireless security communication system.
Owner:BEIJING WATCH DATA SYST
Wireless security, telemetry and control system
InactiveUS6980124B2Easy to installReduce manufacturing costVehicle testingFrequency-division multiplex detailsControl systemEngineering
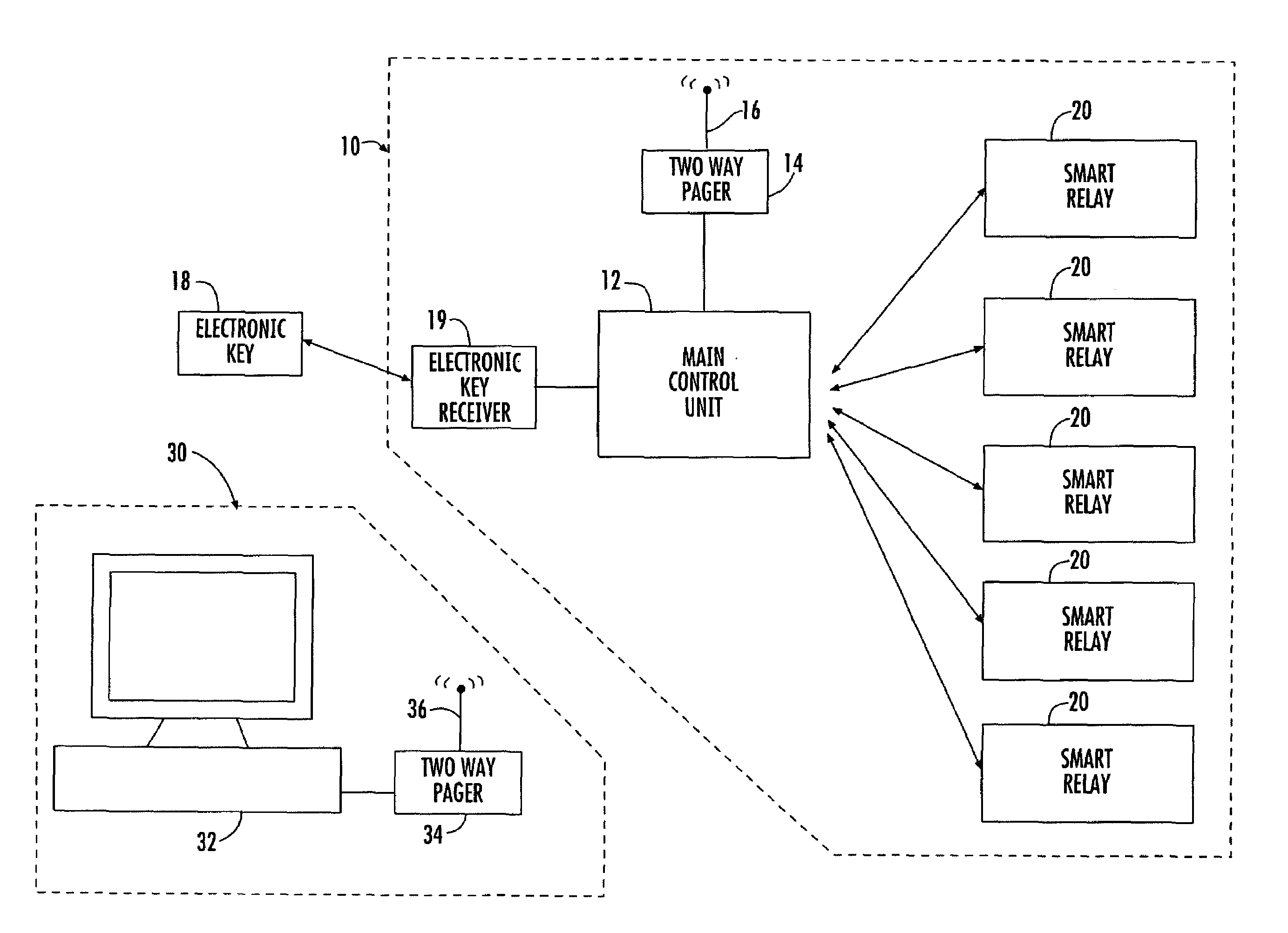
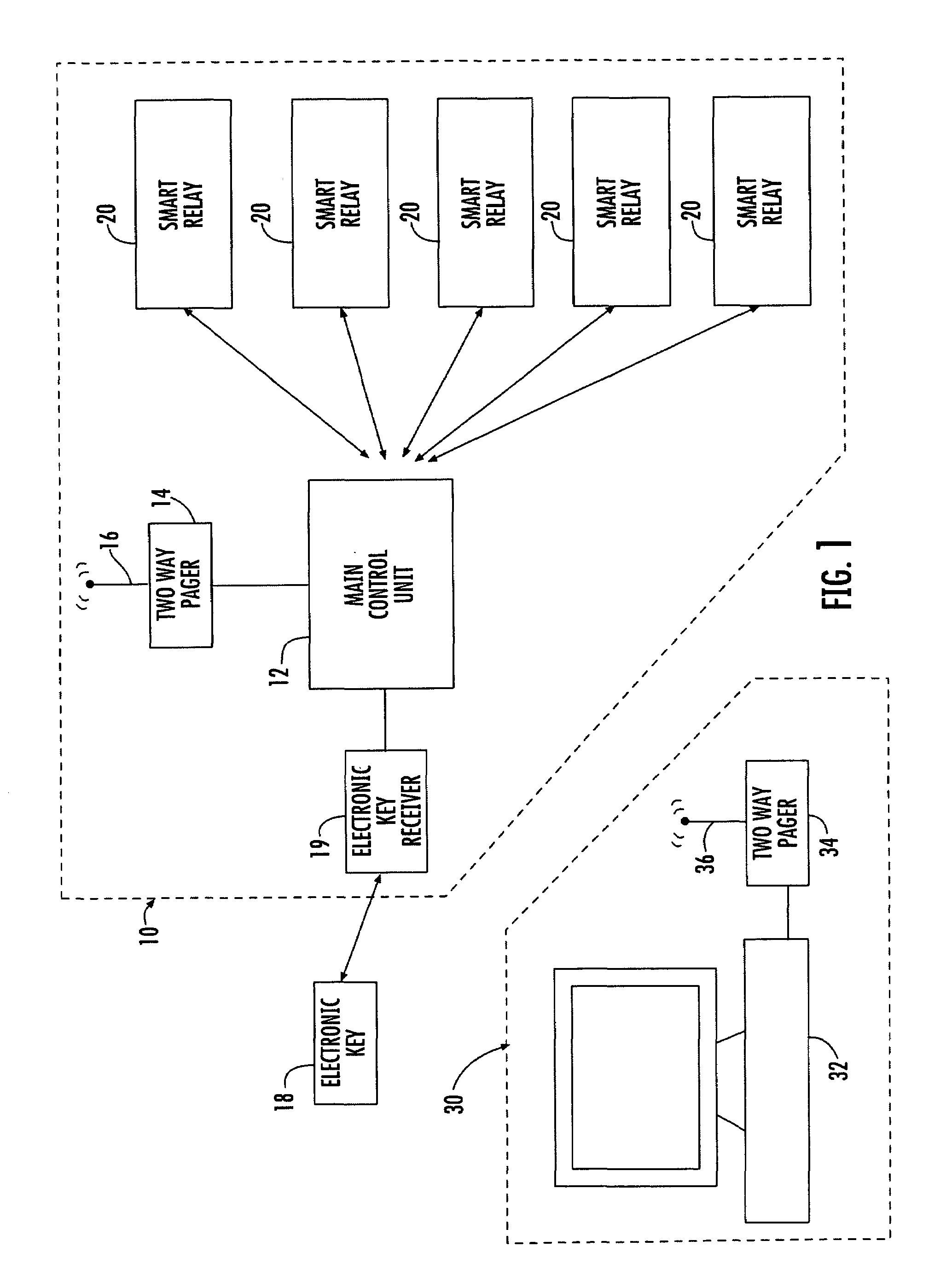
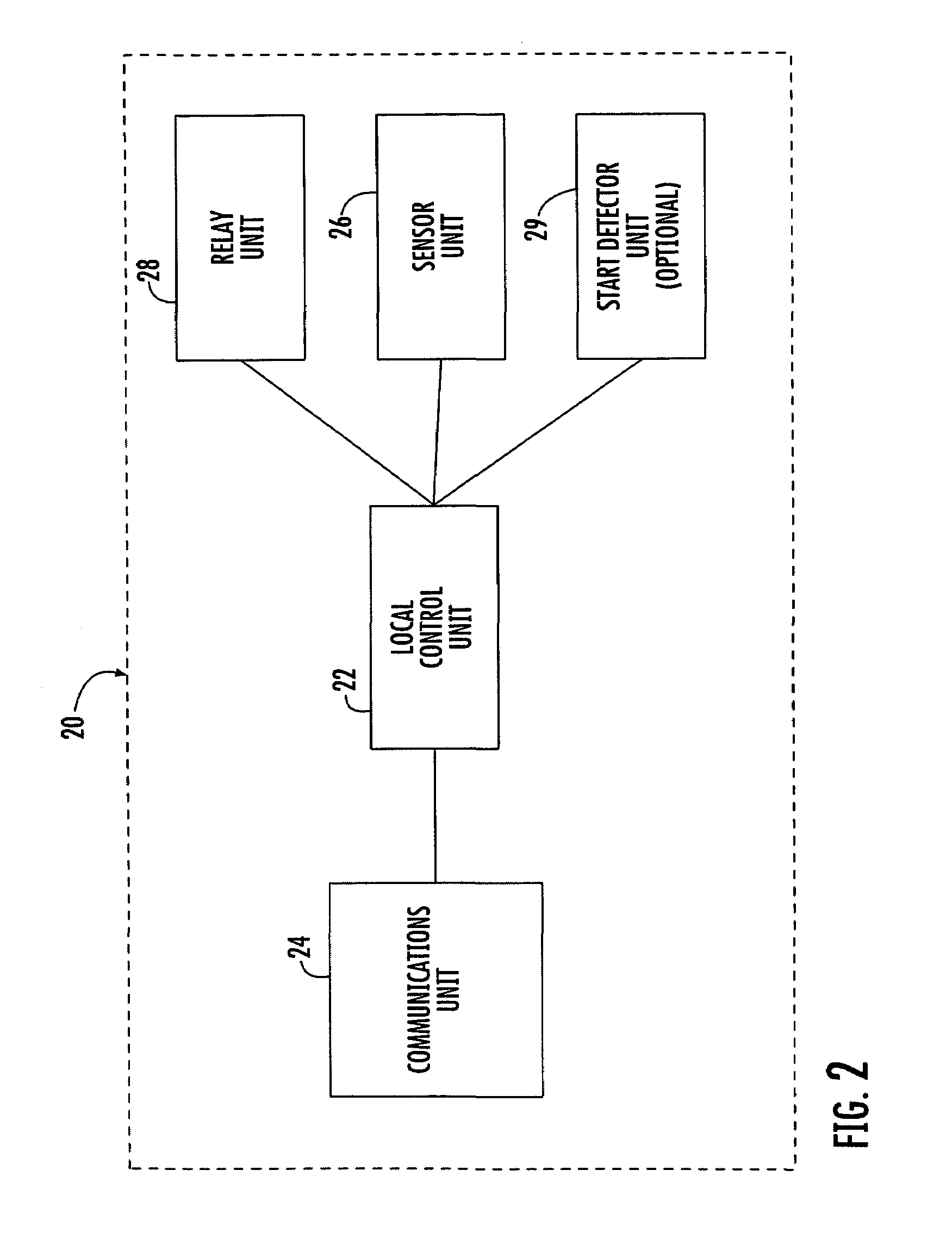
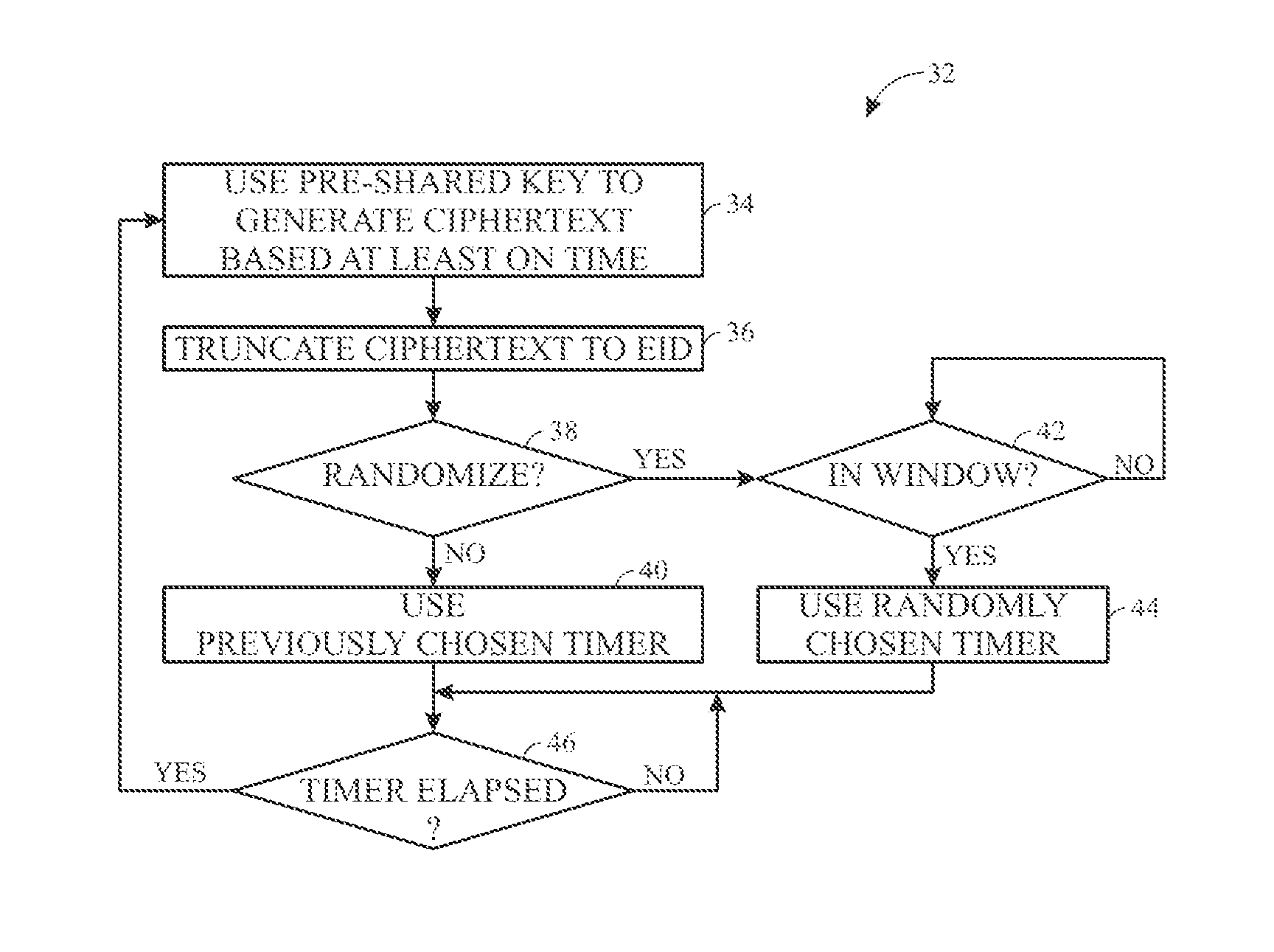
The present invention relates to a security, telemetry and control system which utilizes wireless communication between a control unit and smart relay(s) within the vehicle and also utilizes wireless communication between the vehicle and a remote base station to monitor and protect a vehicle or piece of equipment against unauthorized users and thieves.
Owner:AUTOSAFE INT
Security for wireless broadcasts
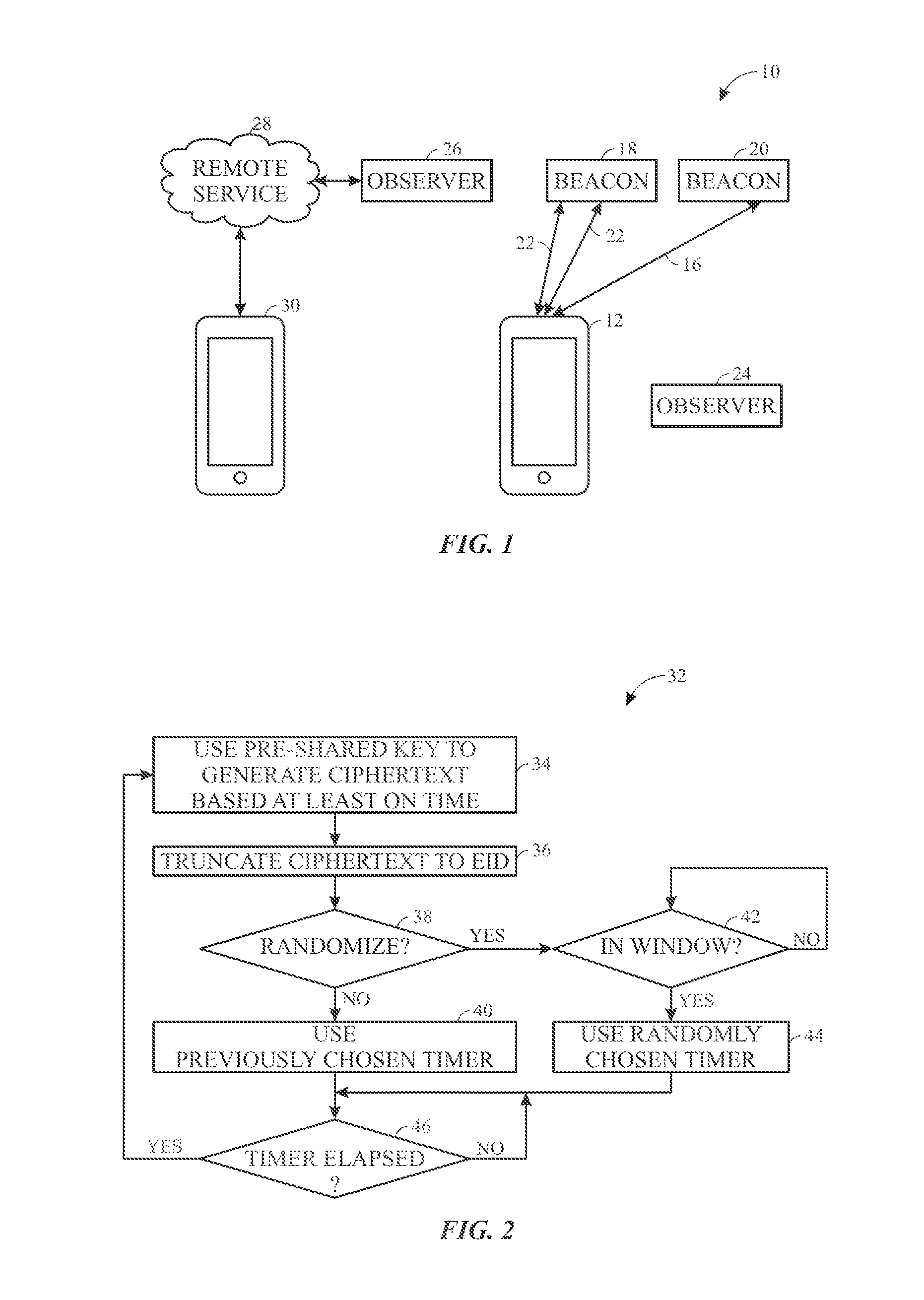
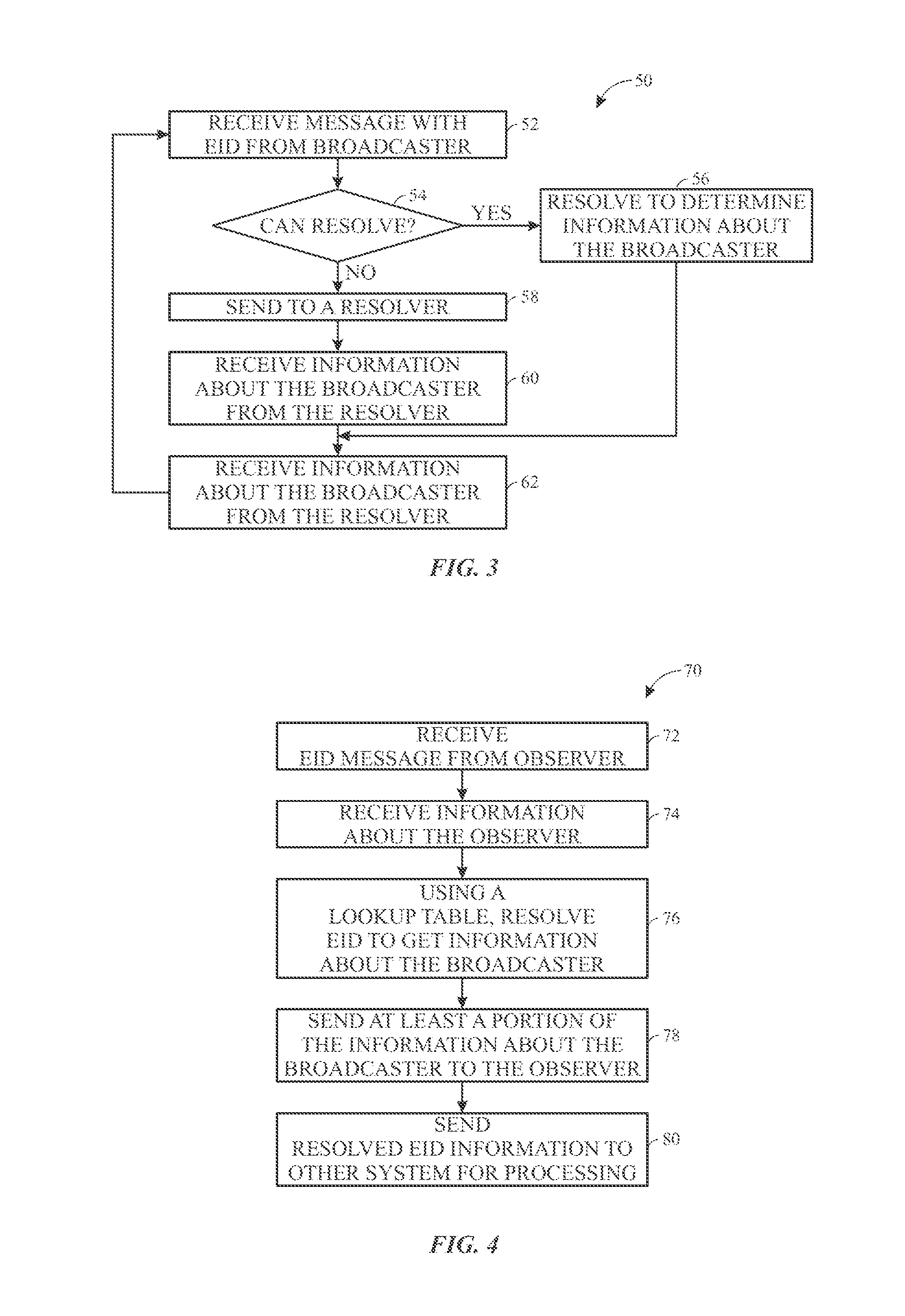
ActiveUS20170013450A1Short range communication serviceSecurity arrangementWireless broadcastWireless broadcasting
Methods and systems are provided for concealing identifying data that may be used to identify a beacon or device in broadcasts unless an observer device is able to directly or indirectly, via an authorized resolver device, translate an encrypted broadcast into the identifiable information. The wireless security scheme disclosed herein also pertains to resolving the concealed data messages to obtain the identifiable information.
Owner:GOOGLE LLC
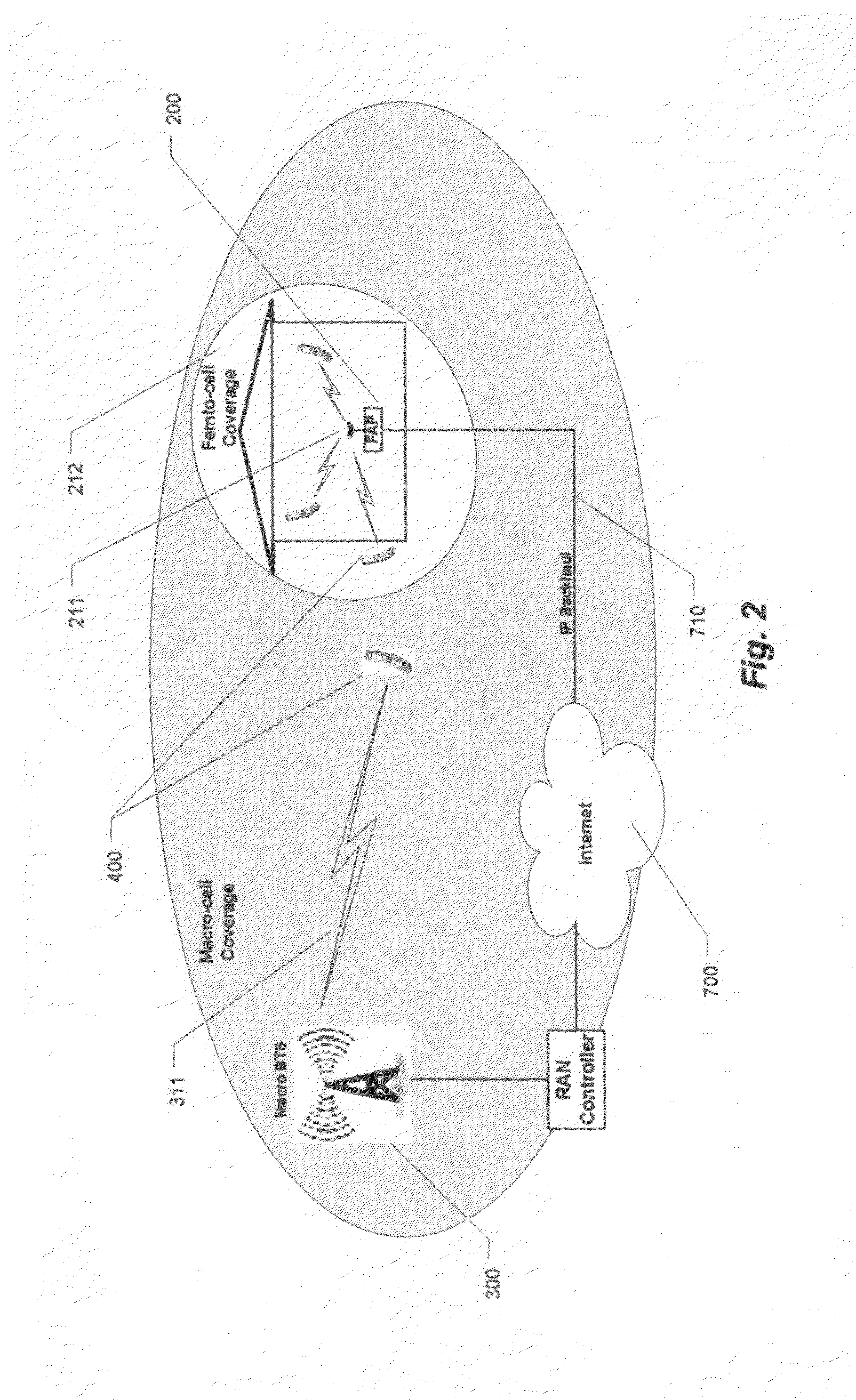
Mobile Femto-cell in a Wireless Safety Network
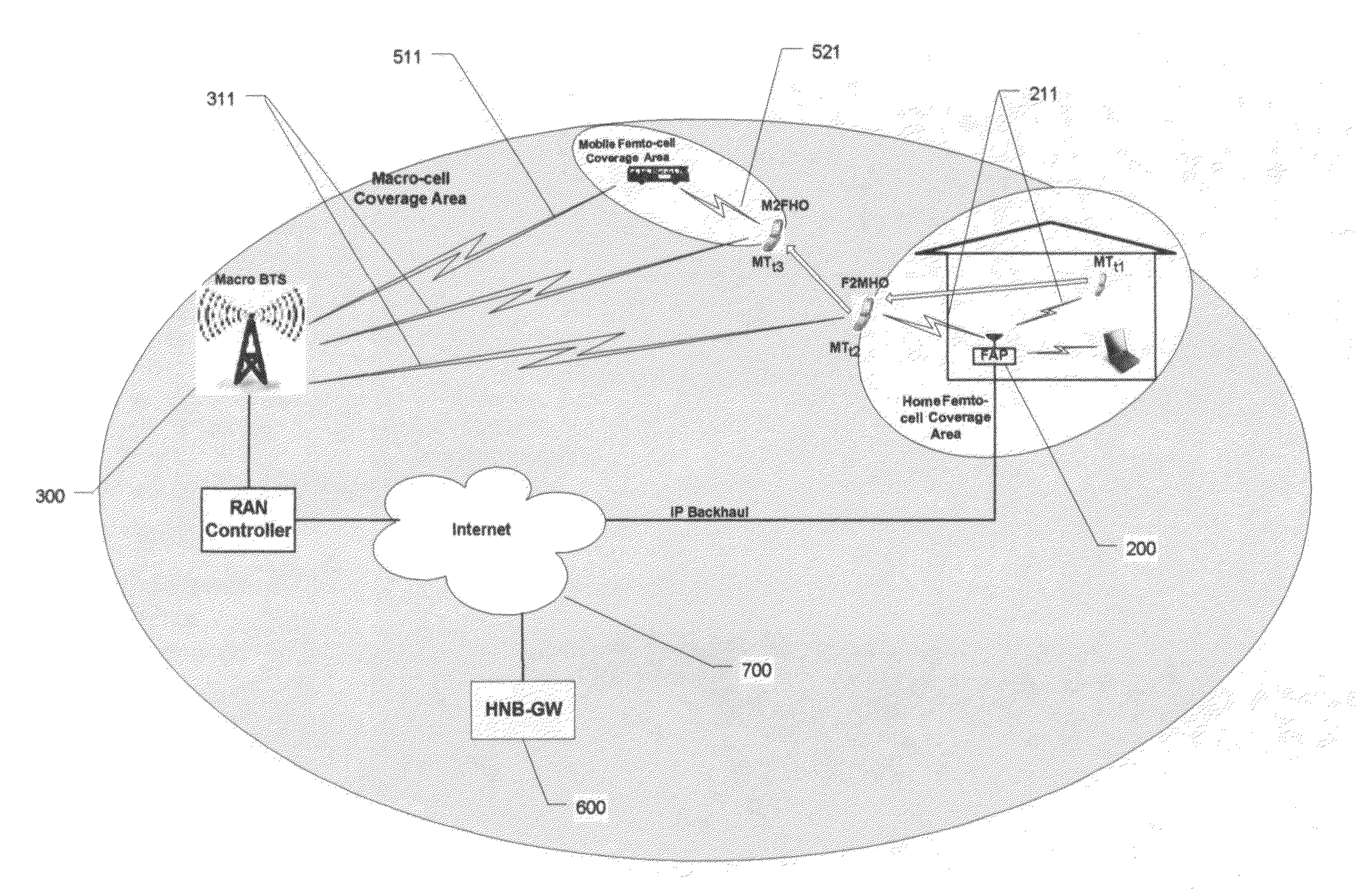
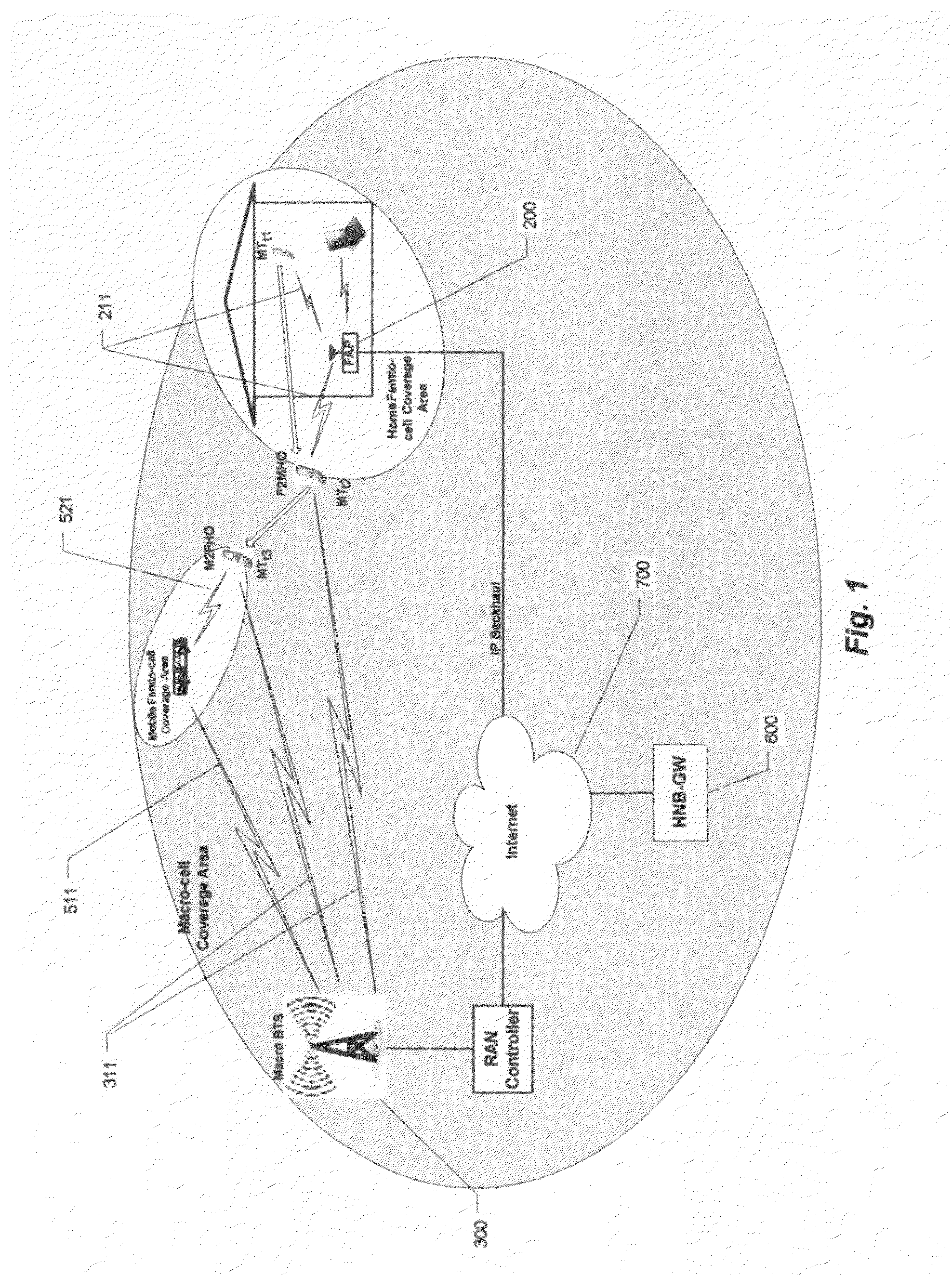
ActiveUS20110217947A1Provide experienceIncrease macro-cell capacity qualityNetwork topologiesConnection managementEngineeringPicocell
This invention provides wireless safety network through the integration of mobile femto-cells (mFAP), into macro-cellular system. Such network provides safety management for students during their travel to and from school through the supervision of handovers between home and mobile femto-cell and the macro-cellular environment as well as supervision of class attendance, emergency function, and other services.
Owner:IPCOMM
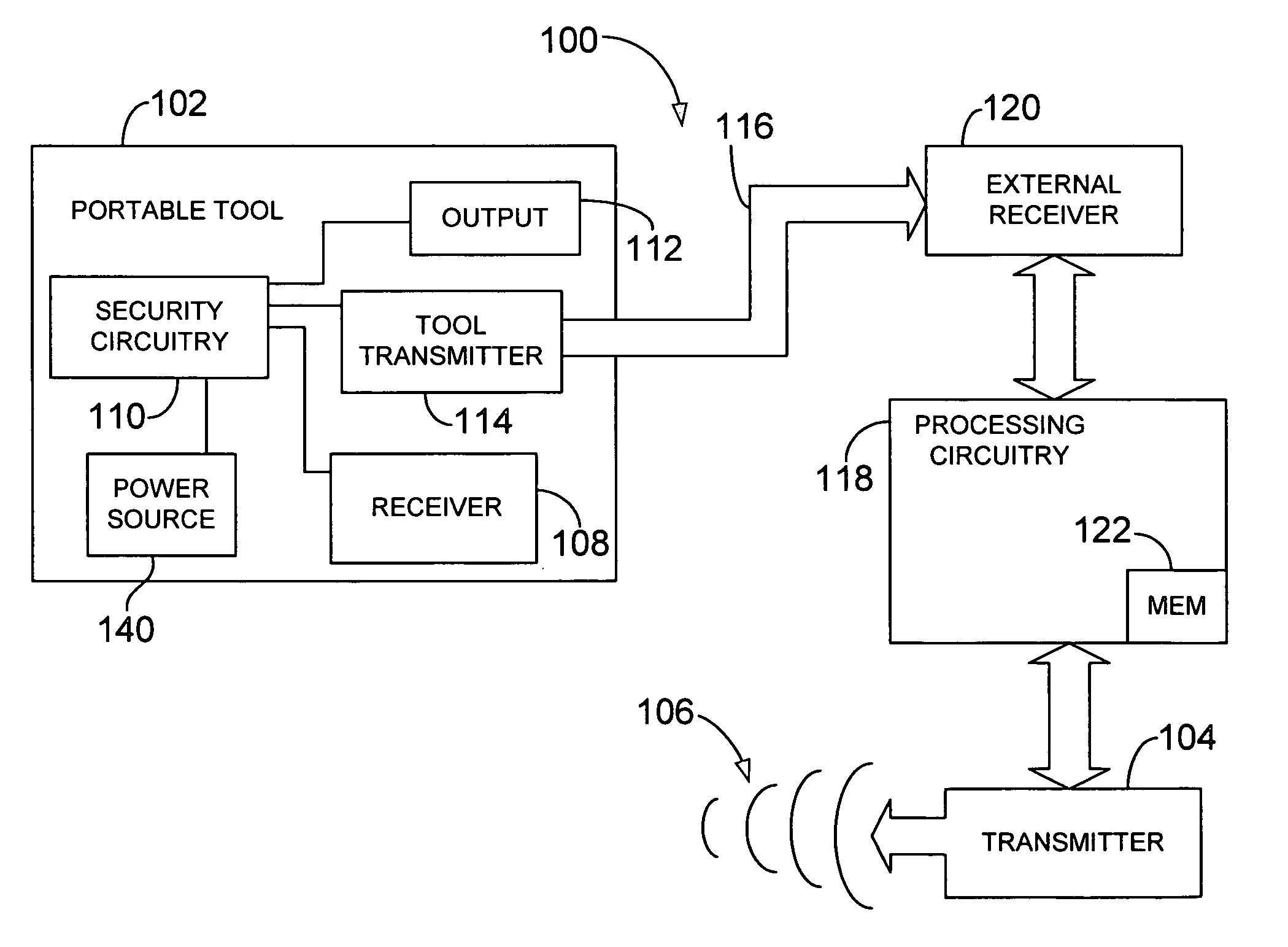
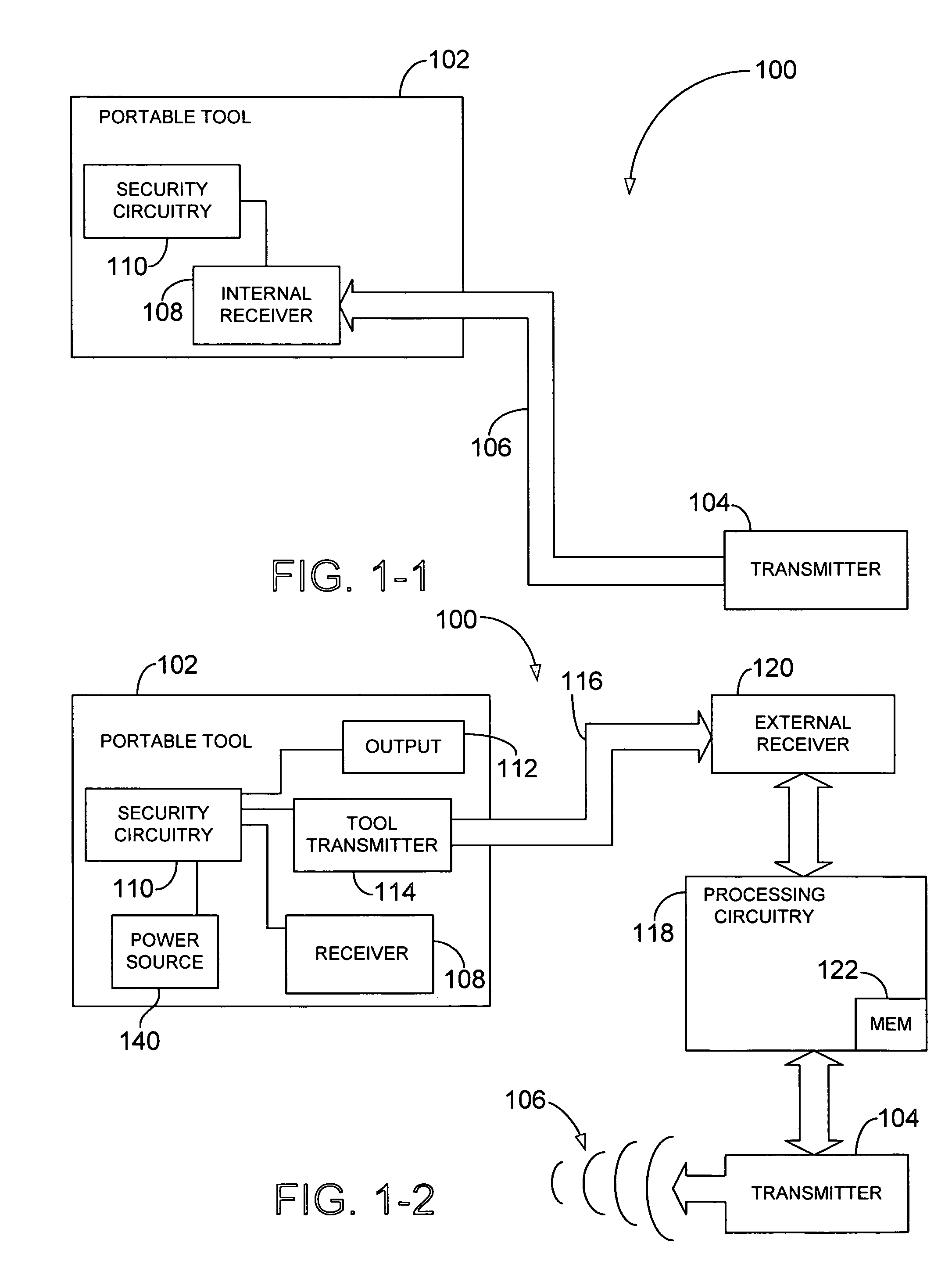
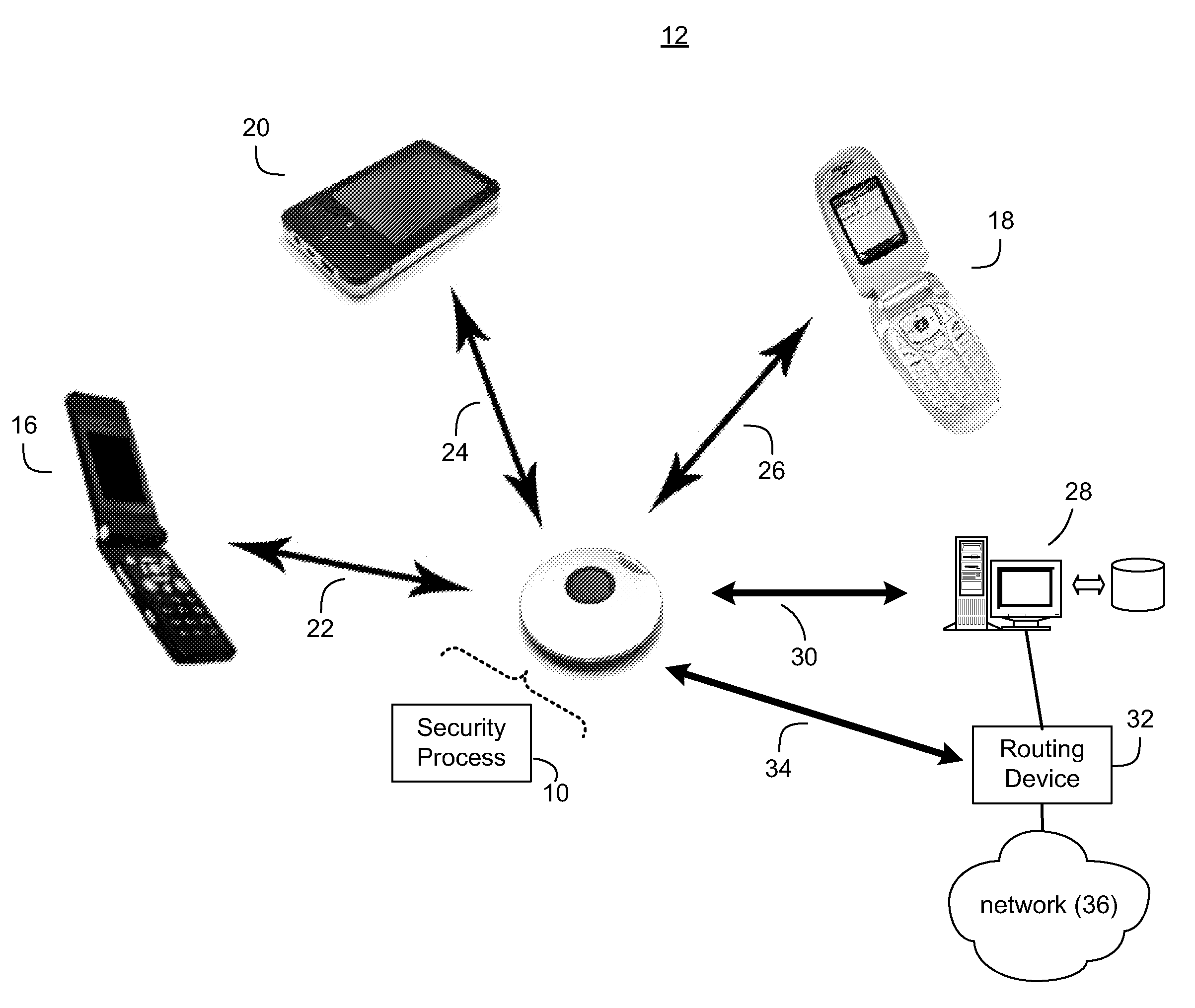
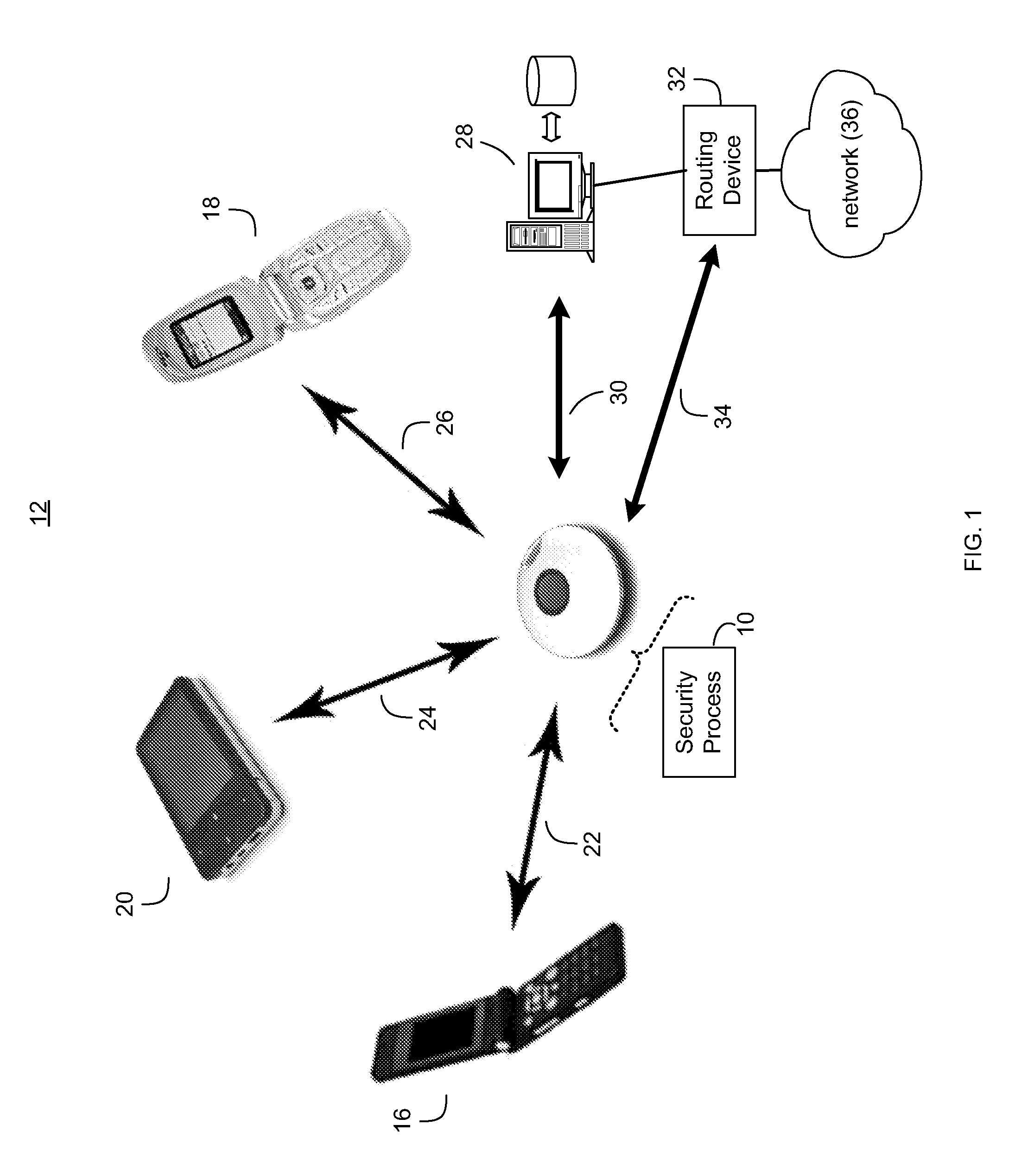
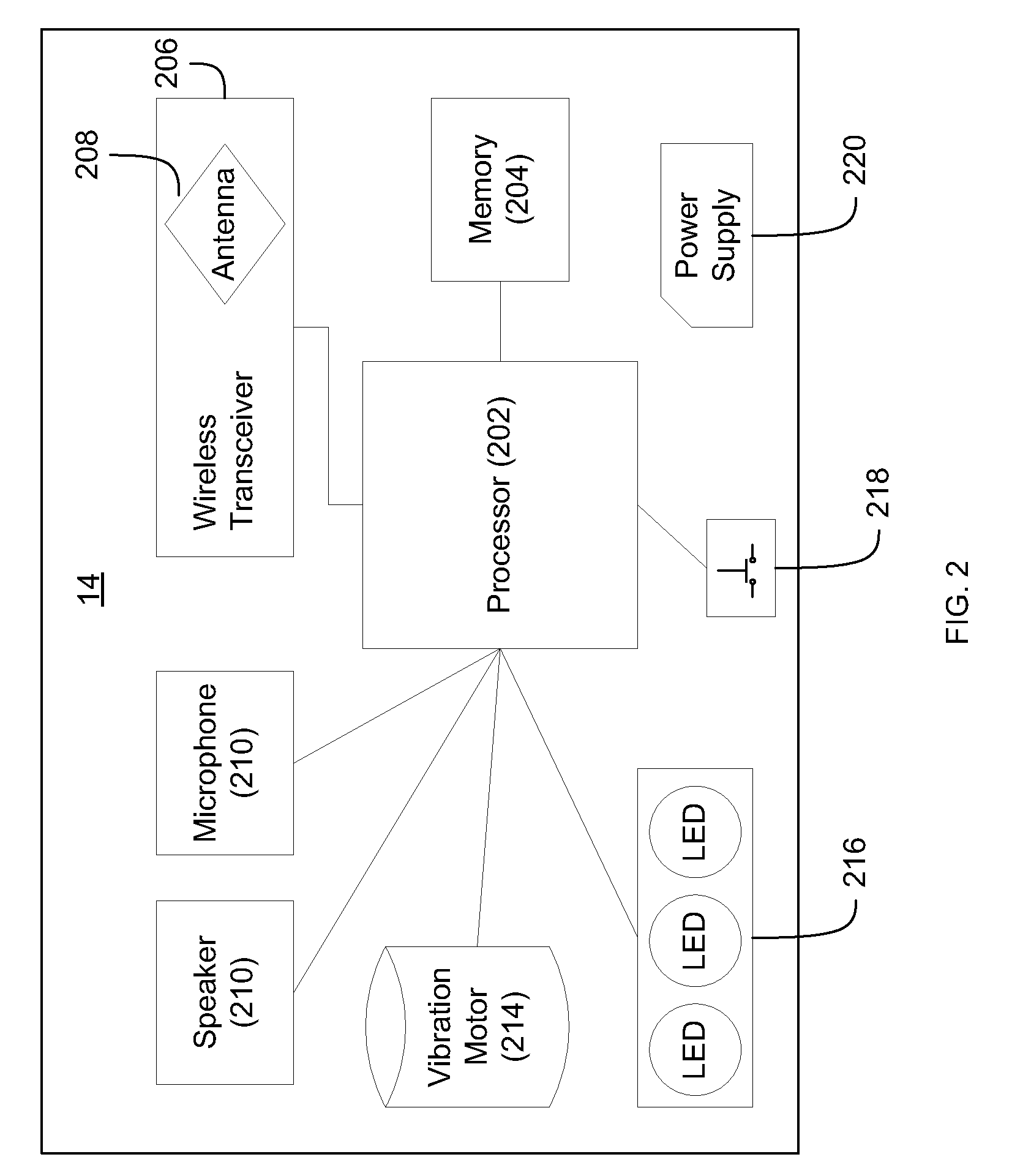
Wireless security device and method
ActiveUS20110059720A1Alarms using portable personal devicesEmergency connection handlingProtocol ProfileBluetooth
A wireless security device and method includes implementing, by a wireless security device, one or more Bluetooth wireless protocol profiles for connecting to one or more Bluetooth enabled devices. A Bluetooth enabled telephony device may be paired with the wireless security device using one or more Bluetooth wireless protocol profiles. The wireless security device may send a command to the telephony device over the wirelessly paired Bluetooth connection, to the telephony device. The command may cause the telephony device to place a telephone call to an emergency telephone number. Once the telephone call is placed, a prerecorded emergency message may be sent from the wireless security device to the telephony device, causing the telephony device to play the prerecorded emergency message.
Owner:ZOMM LLC
Wireless security video system with a pre-alarm buffer
InactiveUS20050128295A1Reduce power consumptionColor television detailsClosed circuit television systemsVideo recordingWireless security
Security systems are disclosed in which intrusion security sensors provided on the perimeter of a protected space immediately activate a plurality of wireless RF, battery operated, low current drain security video cameras elsewhere in the protected space to enable pre-alarm video recording by the security video cameras. Each security video cameras is capable of operating in a standby inactive video mode, providing a low electrical power consumption, or in an active video recording mode. Each security sensor includes an RF transmitter for transmitting an RF security / alarm event message indicating detection of a security / alarm event. Upon detection of an alarm event by a security sensor, the security sensor transmits an RF security / alarm event message which causes the security system video cameras to awaken from the standby inactive video mode into the active video recording mode.
Owner:HONEYWELL INT INC
Methods of operation for plug-in wireless safety device
InactiveUS20150005981A1Transmission systemsRegistering/indicating working of vehiclesElectricityCommunications system
An aftermarket plug-in safety device that allows a vehicle to communicate with other vehicles or infrastructures in a V2X communications system. The device includes a radio for transmitting and receiving signals and a GPS receiver for receiving GPS signals and providing vehicle position data. The device also includes a memory for storing digital security certificates and vehicle application data and a processor configured to be put in electrical communication with a vehicle CAN bus. The processor receives vehicle location signals from the GPS receiver, files from the memory and signals from the radio and providing signals for transmission to the radio. The processor identifies the vehicle that the plug-in device is coupled to and provides data on the CAN bus identifying the device. The processor also performs self-configuring operations based on type of vehicle, access to vehicle systems and location of the vehicle.
Owner:GM GLOBAL TECH OPERATIONS LLC
Concealed wireless sensor with external antenna
ActiveUS6952165B2Easy to installEasy to receiveBurglar alarm by openingElectric signalling detailsLine sensorElectrical battery
A wireless security device, such as a door or window motion sensor, that can be mounted almost entirely within a recess of a door, window or frame, with only the antenna mounted on the surface of the door or window jamb. The wireless security device has a housing suitable for being embedded within a structure such as a door, window or frame. In the housing are a security sensor circuit adapted to generate an alarm signal when activated, a radio frequency (RF) transmitter connected to the security sensor circuit for transmitting an RF signal when the alarm signal is generated, and a power source (such as a battery, piezoelectric element, solar cell or fuel cell) for supplying operating power to the security sensor circuit and the RF transmitter. A substantially flat surface mountable strip is located in proximity to the housing and is suitable for being mounted outside (i.e. along the surface of the structure). The surface mountable strip has an antenna that is coupled to the RF transmitter for emitting electromagnetic energy corresponding to the RF signal from the transmitter. In addition, the embedded antenna provides a predictable transmission pattern resulting in increased range and reliability.
Owner:ADEMCO INC
Wireless secure device
InactiveUS7224801B2Internal/peripheral component protectionSecret communicationComputer hardwareJoystick
A method and apparatus for securely connecting one or more wireless peripheral devices such as keyboards, mice, gamepads, remote controllers, joysticks and one or more host systems such as personal computers or workstations, the secure connection reducing the vulnerability of wireless communications between a wireless peripheral device and a host system to accidental or malicious interference or eavesdropping.
Owner:LOGITECH EURO SA
Systems and Methods for Wireless Security Using Distributed Collaboration of Wireless Clients
ActiveUS20070217371A1Easy to deployIncrease exposureUnauthorised/fraudulent call preventionMemory loss protectionWireless securityClient system
Owner:EXTREME NETWORKS INC
Transmit power control for wireless security
ActiveUS20060056636A1Increase transmit powerEnergy efficient ICTPower managementTransmitted powerWireless security
The present invention provides a method for establishing a secure channel between wireless devices. The method involves reducing the transmit power of the devices in conjunction with placing the devices in close proximity to one another. By reducing the transmit power, wireless communications between the devices cannot be detected by other devices beyond the short transmission range. The devices then generate and exchange encryption keys using the reduced-power transmissions in order to establish a secure, encrypted communications channel. Once the secure channel is established, the devices increase their transmit power back to normal operating levels, allowing them to be moved further apart while maintaining secure wireless communications.
Owner:QUALCOMM INC +1
Security system of wireless industrial control network, and method for implementing security policy
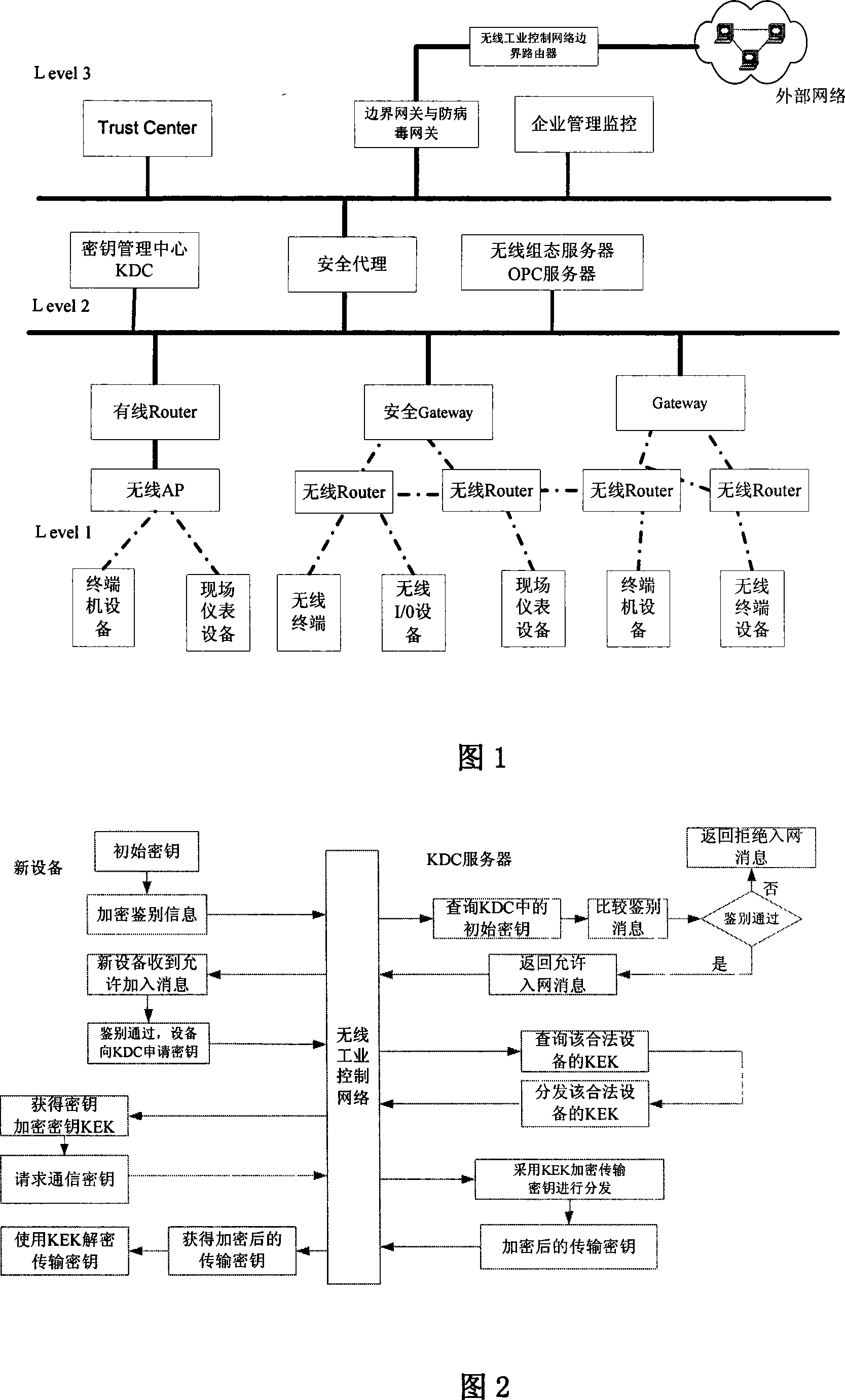
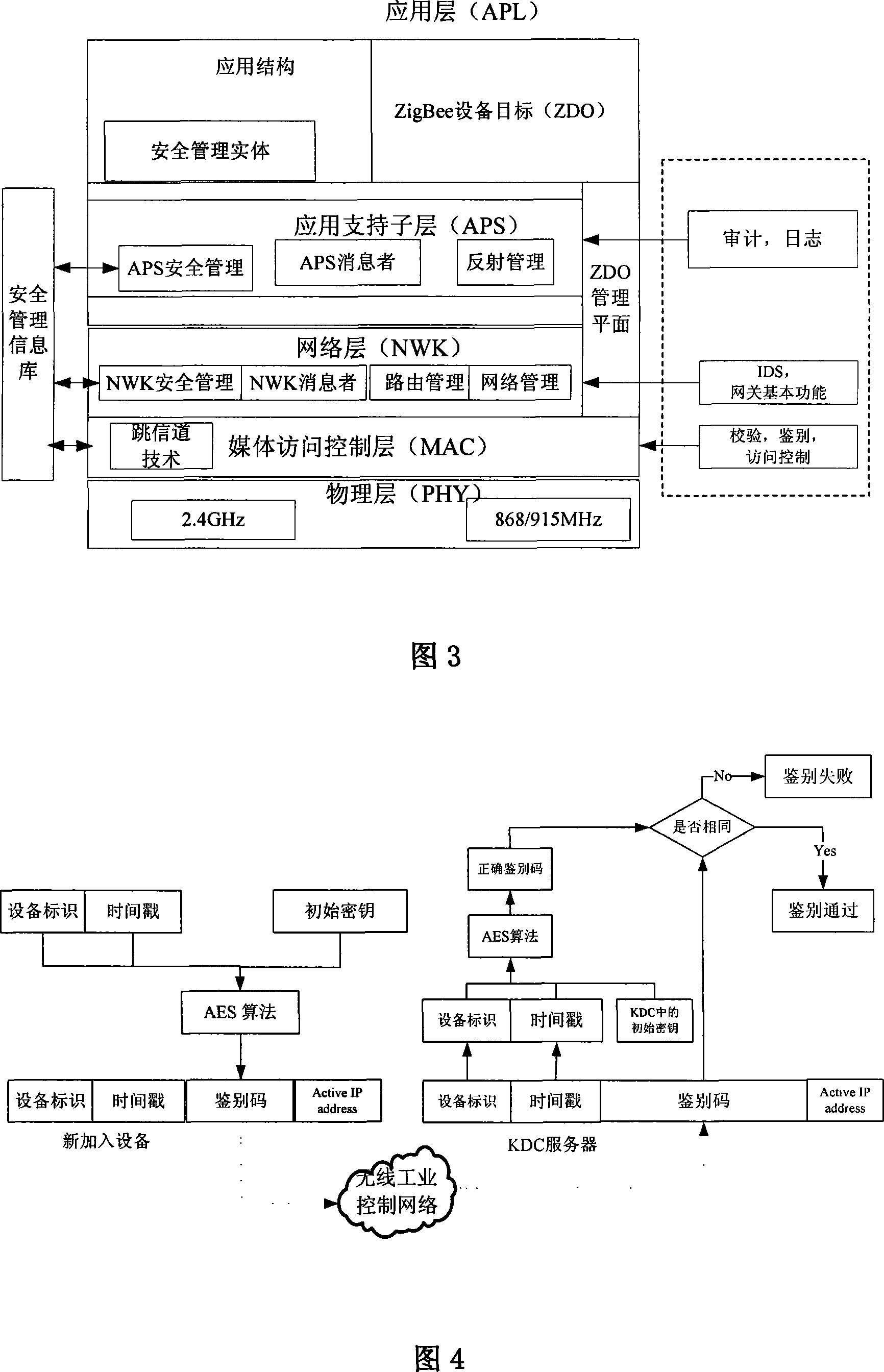
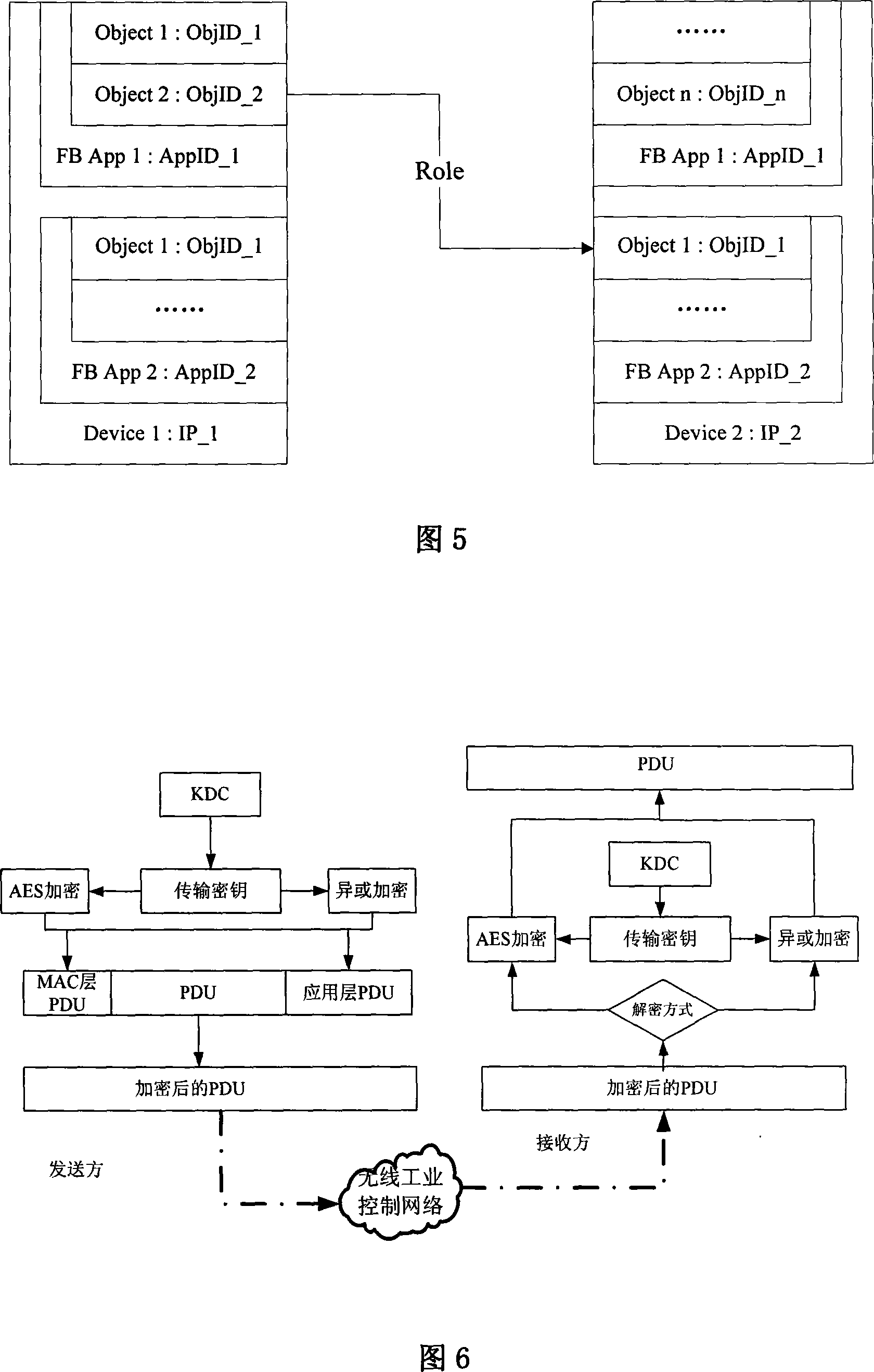
InactiveCN101094056AGuaranteed uptimeNormal production orderKey distribution for secure communicationData switching by path configurationInformation repositoryStructure of Management Information
The technical scheme of this invention is that dividing the wireless industry control net (WICN) into three net sections: a enterprise managing layer, a process controlling layer and field equipment layer. According to the hiberarchy of WICN, a WICN safety managing system is built. This system defines the built WICN into 4 safety levels. According to the access control list in the sever pool of the key administration center KDC, via the mechanism of key managing and the equipment verifying basis on KDC, the wireless safety gateway, the wireless net safety application managing entity and the wireless safety managing info database, different safety precautions are applied on the various layers and various safety levels of nets. This invention suits the industry field control to solve effectively the safety problems of resource and data comm. within the WICN and ensures the normal system running.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com