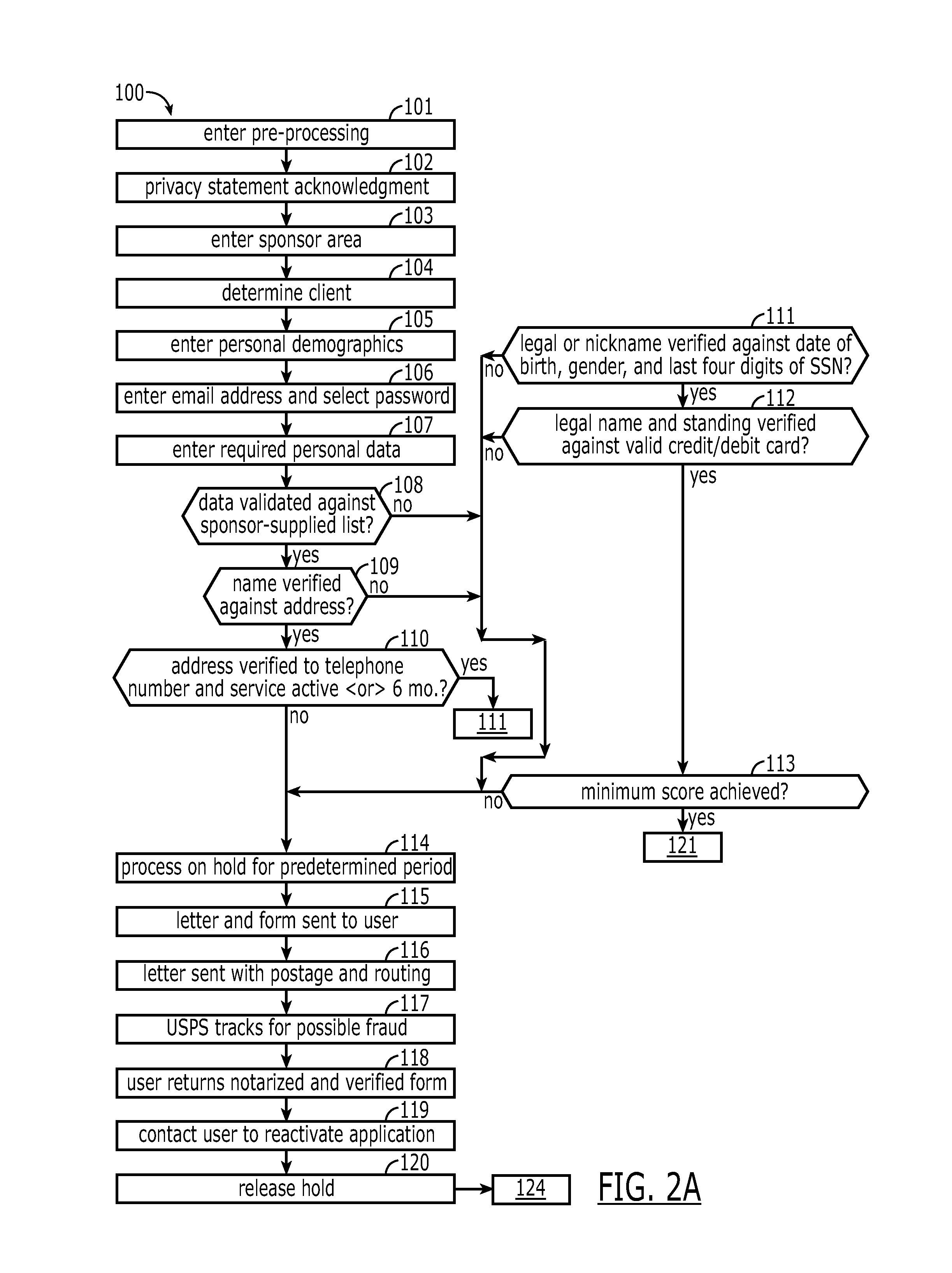
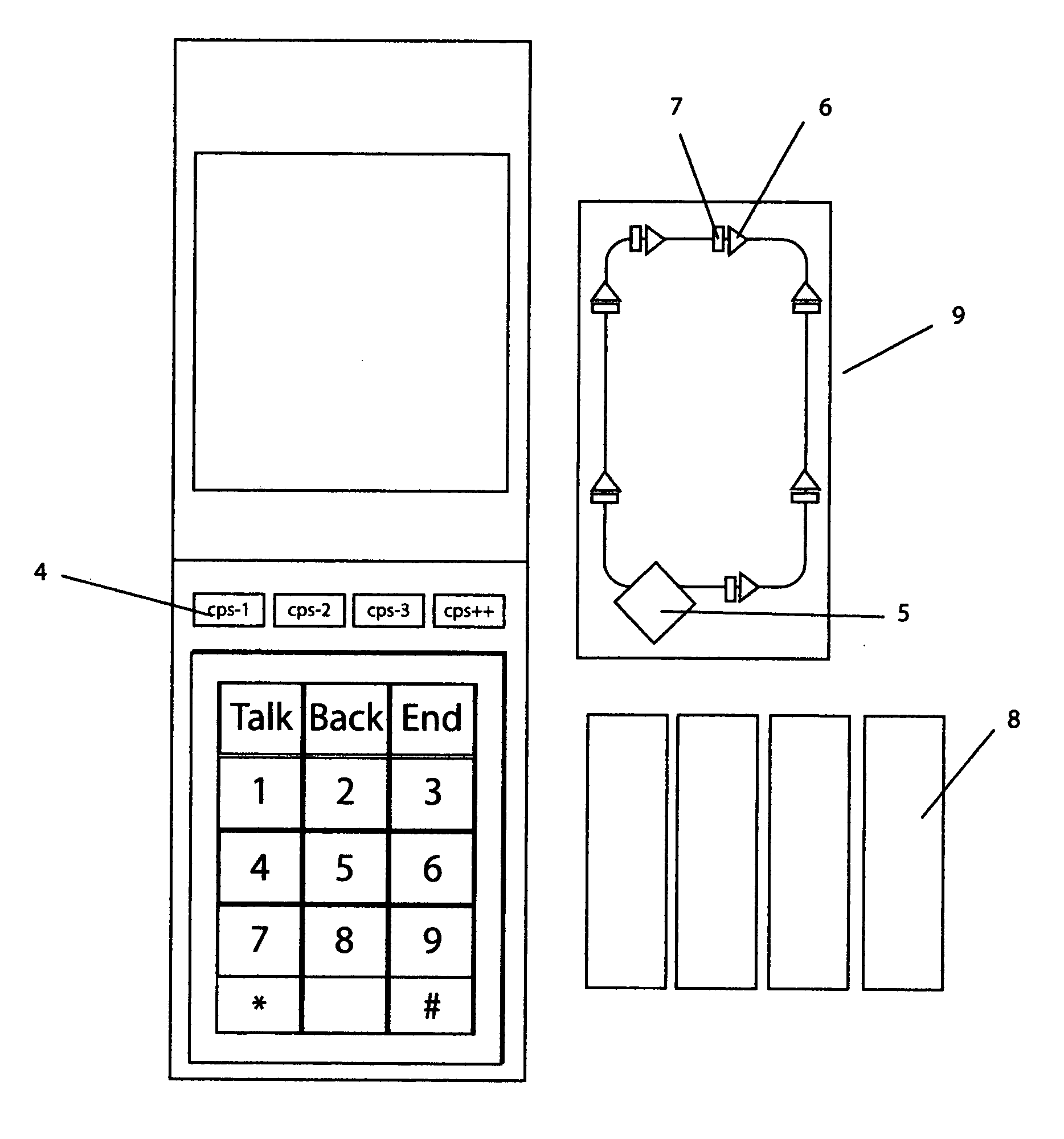
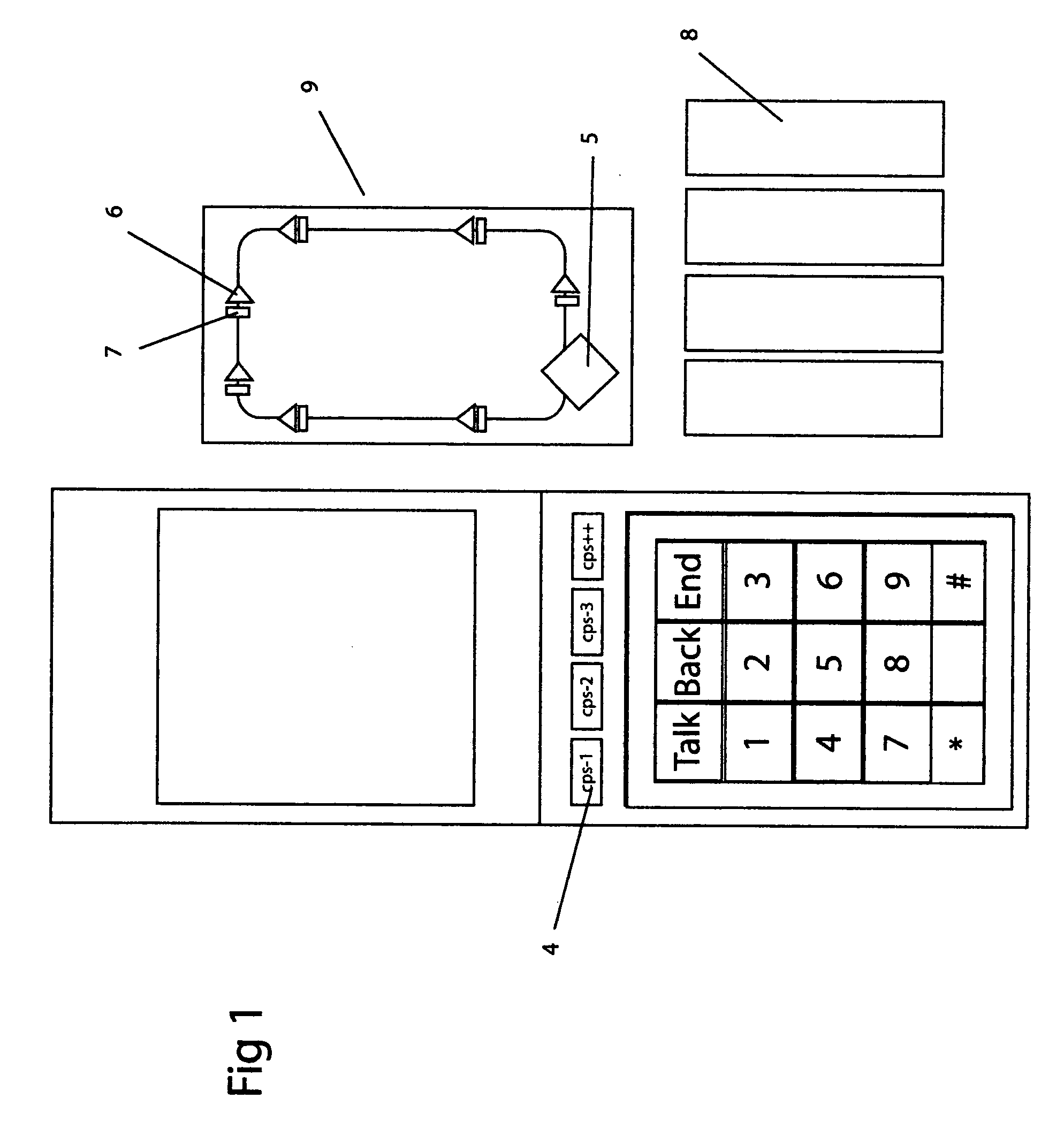
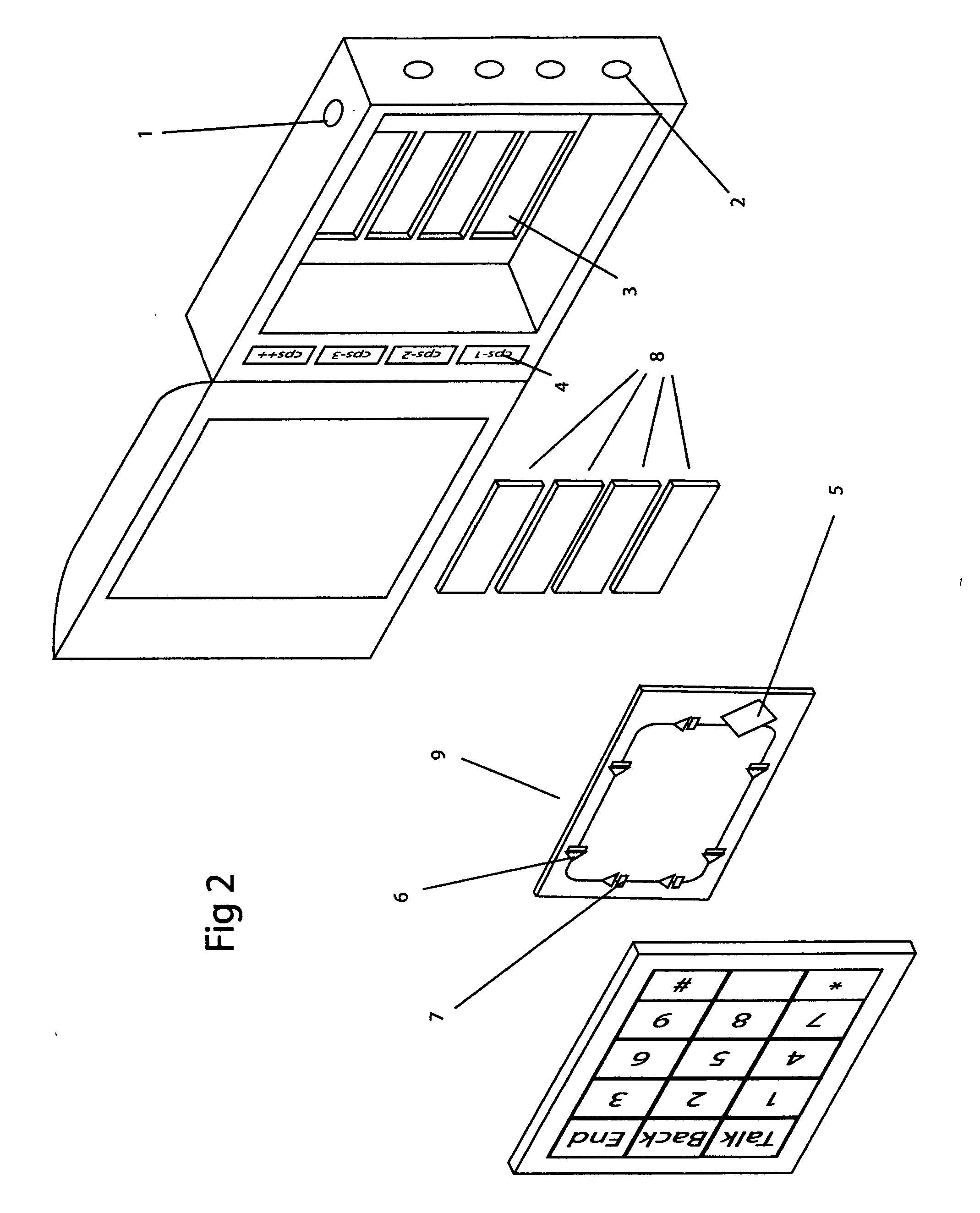
Patents
Literature
127 results about "Digital security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
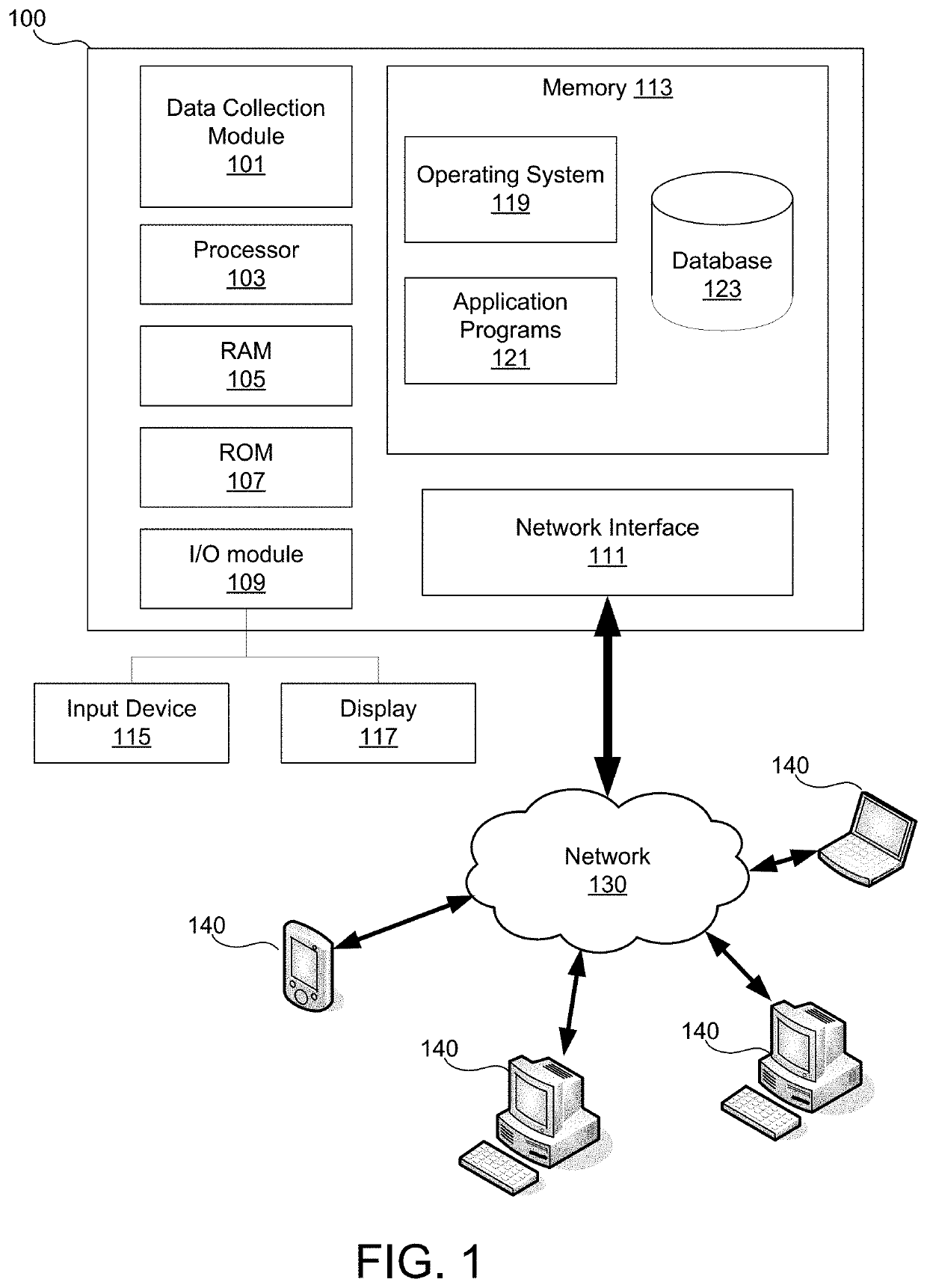
Digital Security refers to various ways of protecting computer's internet account and files from intrusion by an outside user.
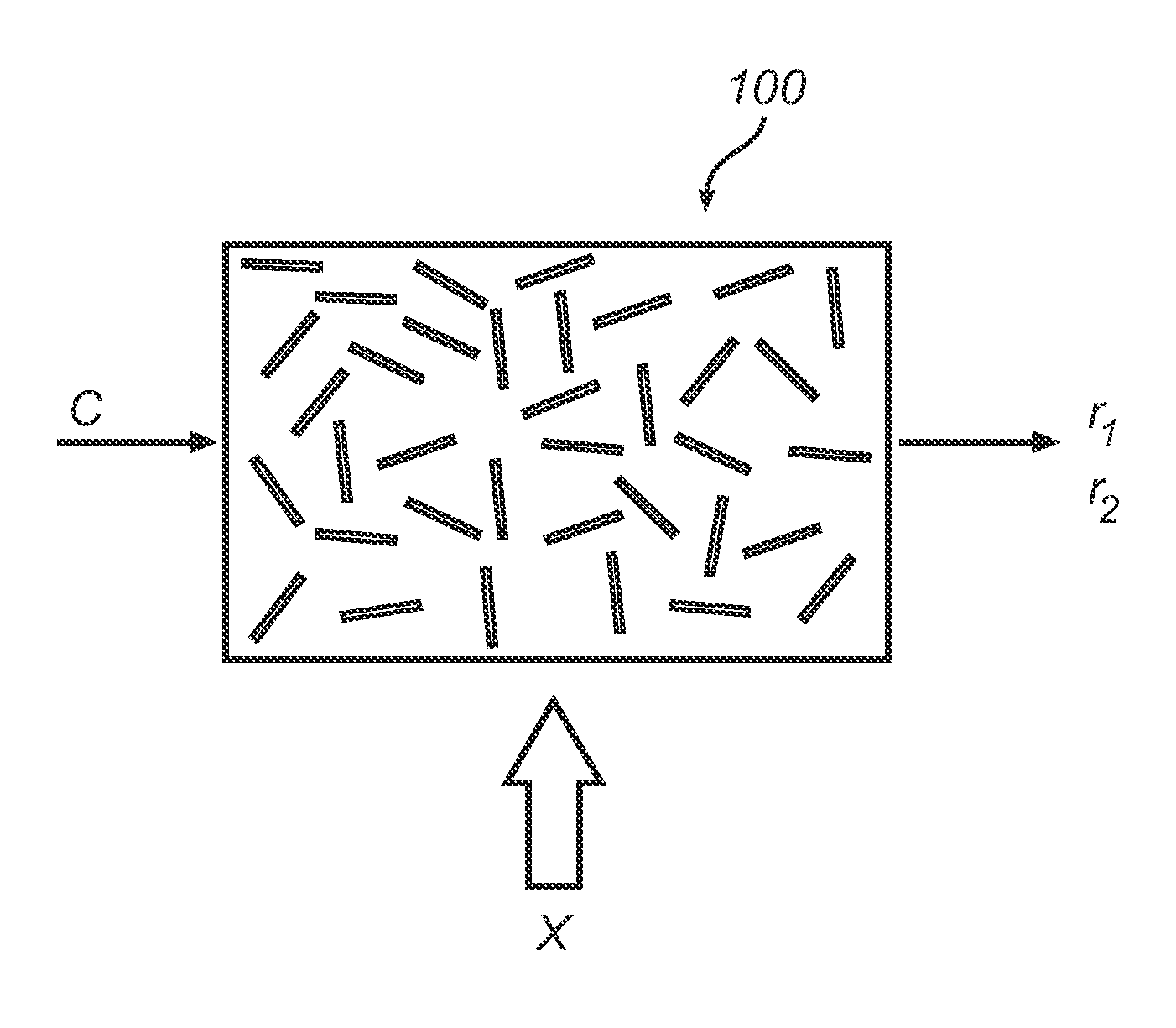
Digital security multimedia sensor
InactiveUS7023913B1Quality improvementImprove accuracyColor television with pulse code modulationColor television with bandwidth reductionImage transferBiological activation
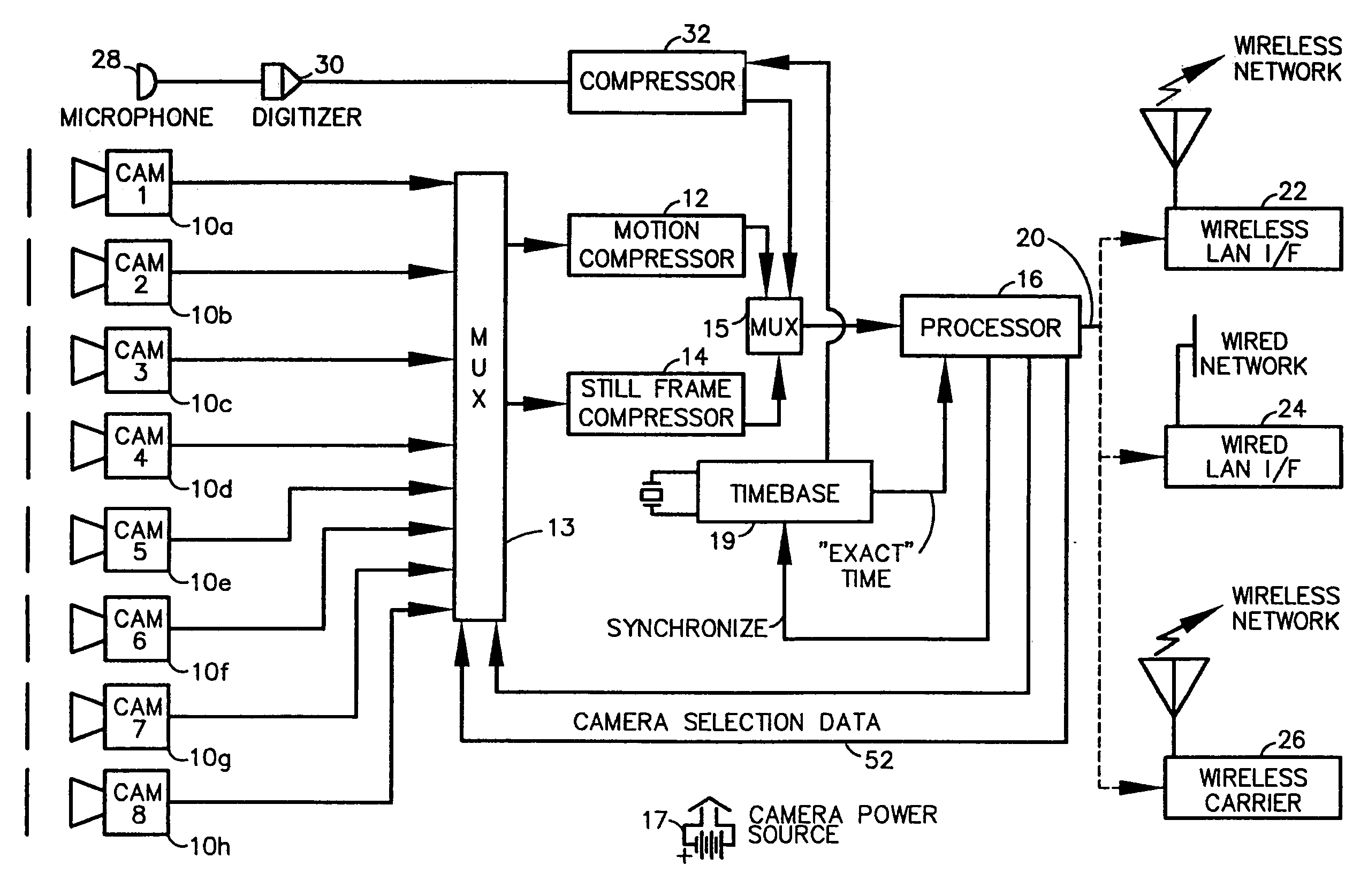
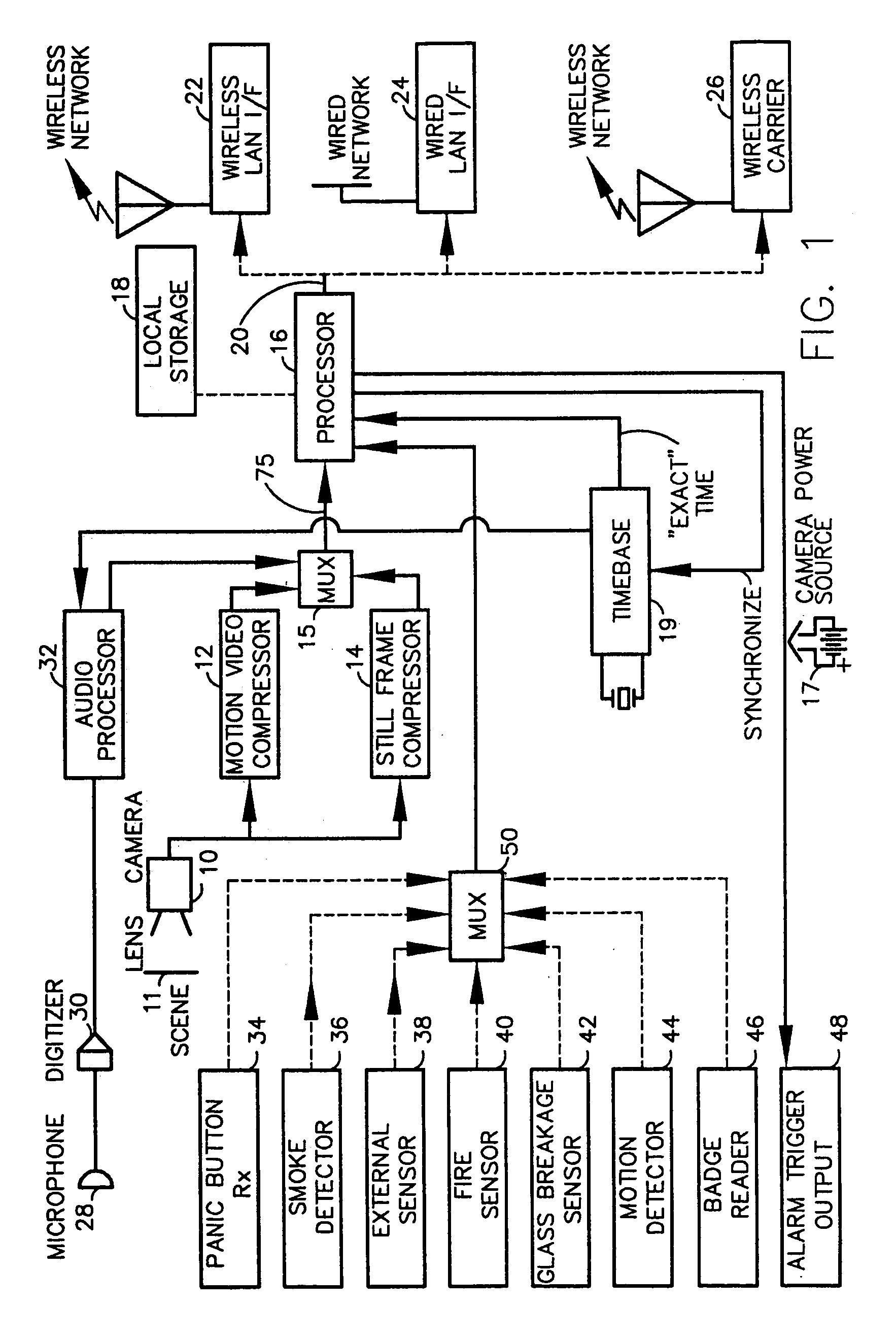
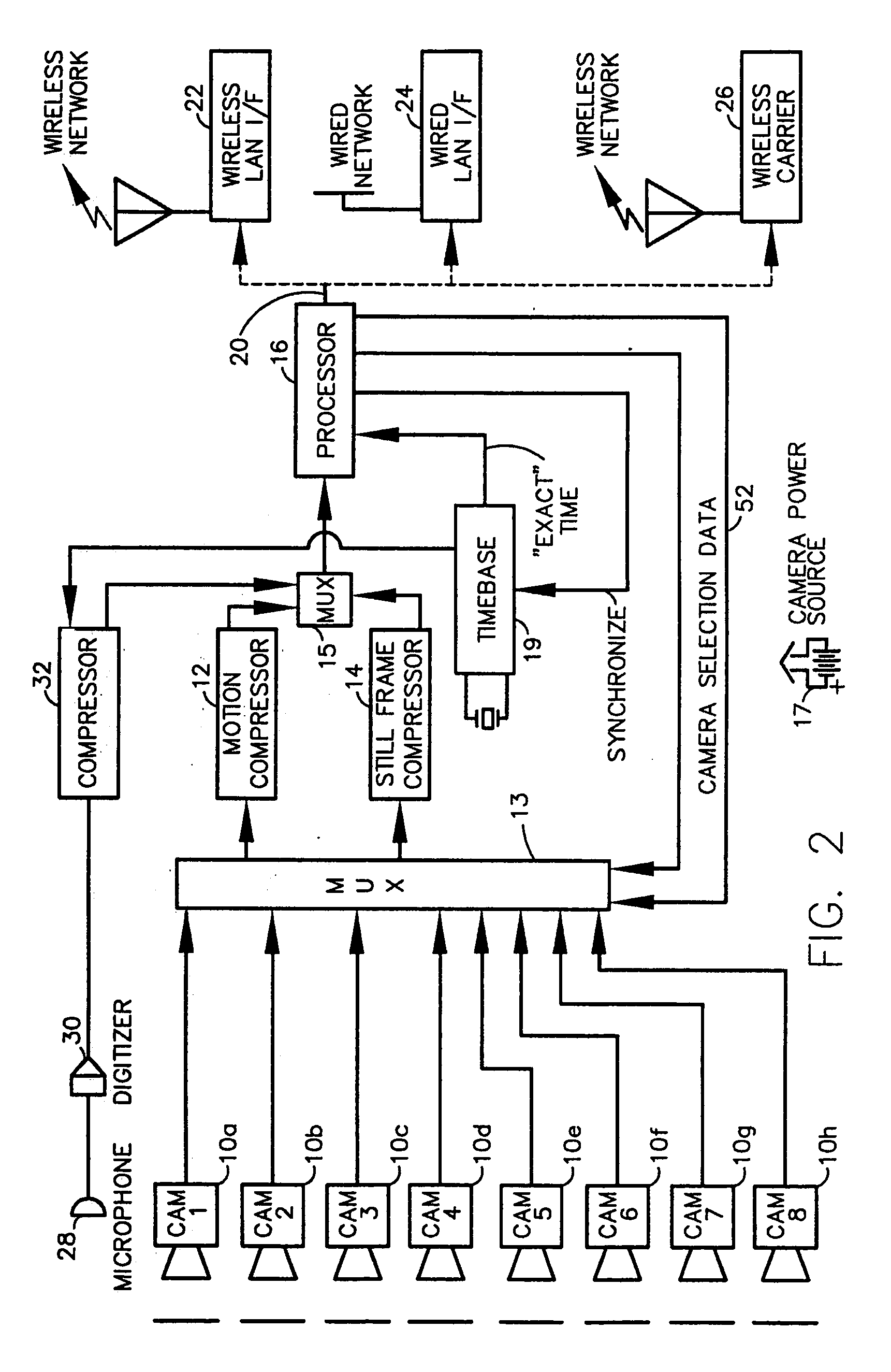
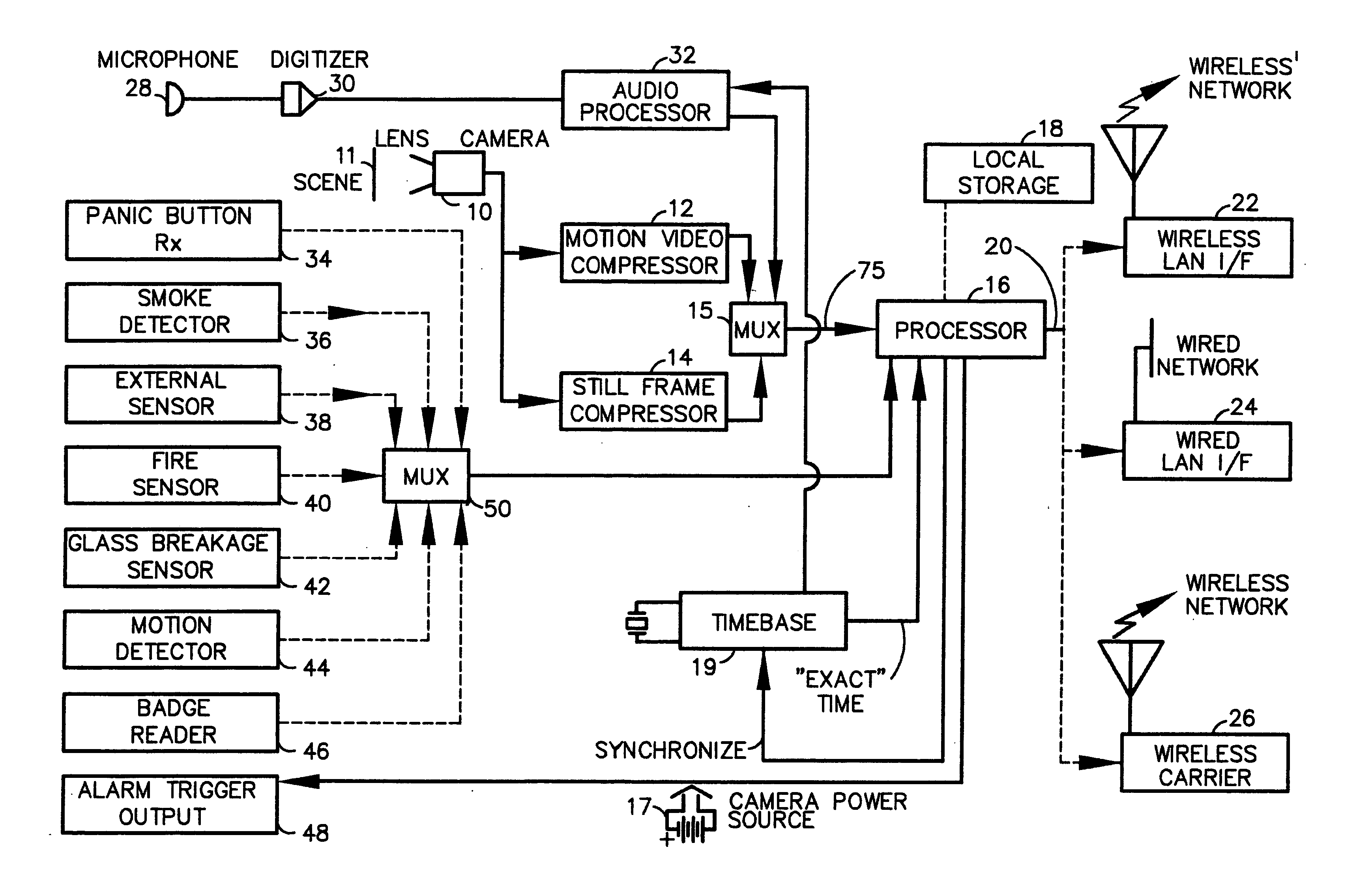
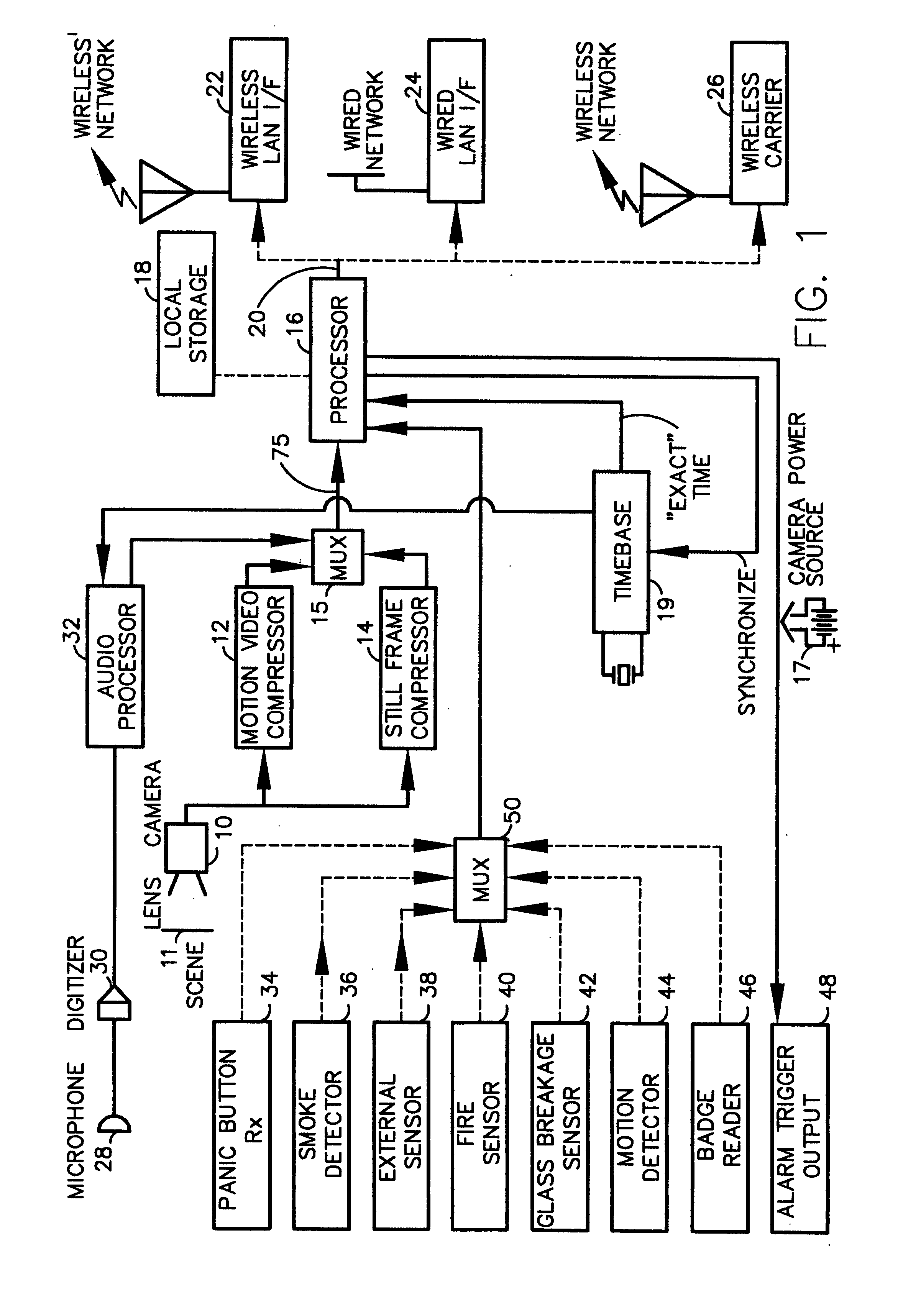
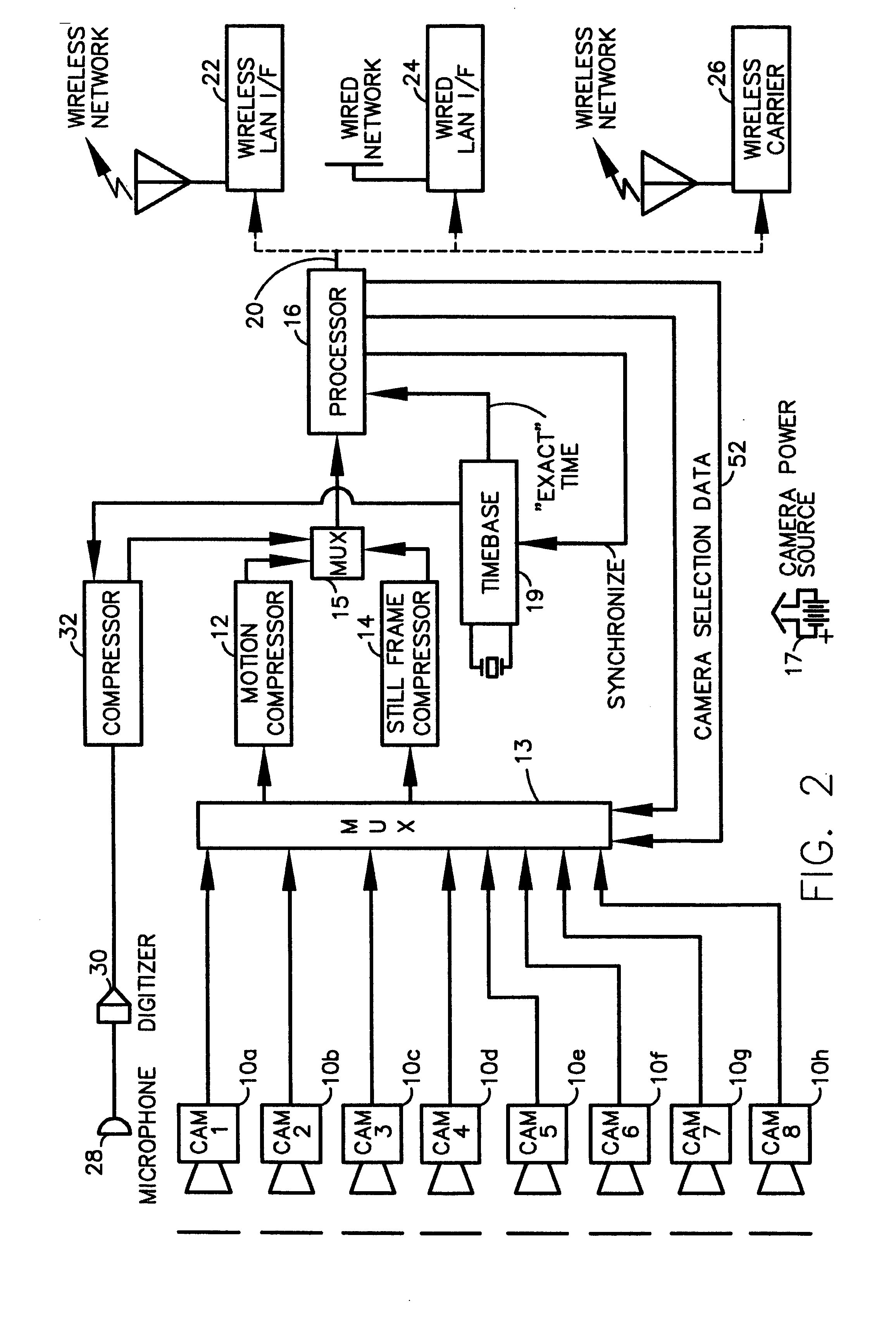
A fully digital camera system provides high-resolution still image and streaming video signals via a network to a centralized, server supported security and surveillance system. The digital camera for collects an image from one or more image transducers, compressing the image and sending the compressed digital image signal to a receiving station over a digital network. A plurality of image transducers or sensors may be included in a single camera unit, providing array imaging such as full 360 degree panoramic imaging, universal or spherical imaging and field imaging by stacking or arranging the sensors in an array. The multiple images are then compressed and merged at the camera in the desired format to permit transmission of the least amount of data to accomplish the desired image transmission. The camera also employs, or connects to, a variety of sensors other than the traditional image sensor. Sensors for fire, smoke, sound, glass breakage, motion, panic buttons, and the like, may be embedded in or connected to the camera. Data captured by these sensors may be digitized, compressed, and networked to detect notable conditions. An internal microphone and associated signal processing system may be equipped with suitable signal processing algorithms for the purpose of detecting suitable acoustic events and their location. In addition, the camera is equipped with a pair of externally accessible terminals where an external sensor may be connected. In addition, the camera may be equipped with a short-range receiver that may detect the activation of a wireless ‘panic button’ carried by facility personnel. This ‘panic button’ may employ infrared, radio frequency (RF), ultrasonic, or other suitable methods to activate the camera's receiver.
Owner:PR NEWSWIRE
Digital security multimedia sensor
InactiveUS20050207487A1Ensure effective disseminationEfficient routingColor television with pulse code modulationColor television with bandwidth reductionImage compressionBiological activation
A fully digital camera system provides high-resolution still image and streaming video signals via a network to a centralized, server supported security and surveillance system. The digital camera for collects an image from one or more image transducers, compressing the image and sending the compressed digital image signal to a receiving station over a digital network. A plurality of image transducers or sensors may be included in a single camera unit, providing array imaging such as full 360 degree panoramic imaging, universal or spherical imaging and field imaging by stacking or arranging the sensors in an array. The multiple images are then compressed and merged at the camera in the desired format to permit transmission of the least amount of data to accomplish the desired image transmission. The camera also employs, or connects to, a variety of sensors other than the traditional image sensor. Sensors for fire, smoke, sound, glass breakage, motion, panic buttons, and the like, may be embedded in or connected to the camera. Data captured by these sensors may be digitized, compressed, and networked to detect notable conditions. An internal microphone and associated signal processing system may be equipped with suitable signal processing algorithms for the purpose of detecting suitable acoustic events and their location. In addition, the camera is equipped with a pair of externally accessible terminals where an external sensor may be connected. In addition, the camera may be equipped with a short-range receiver that may detect the activation of a wireless ‘panic button’ carried by facility personnel. This ‘panic button’ may employ infrared, radio frequency (RF), ultrasonic, or other suitable methods to activate the camera's receiver.
Owner:PR NEWSWIRE
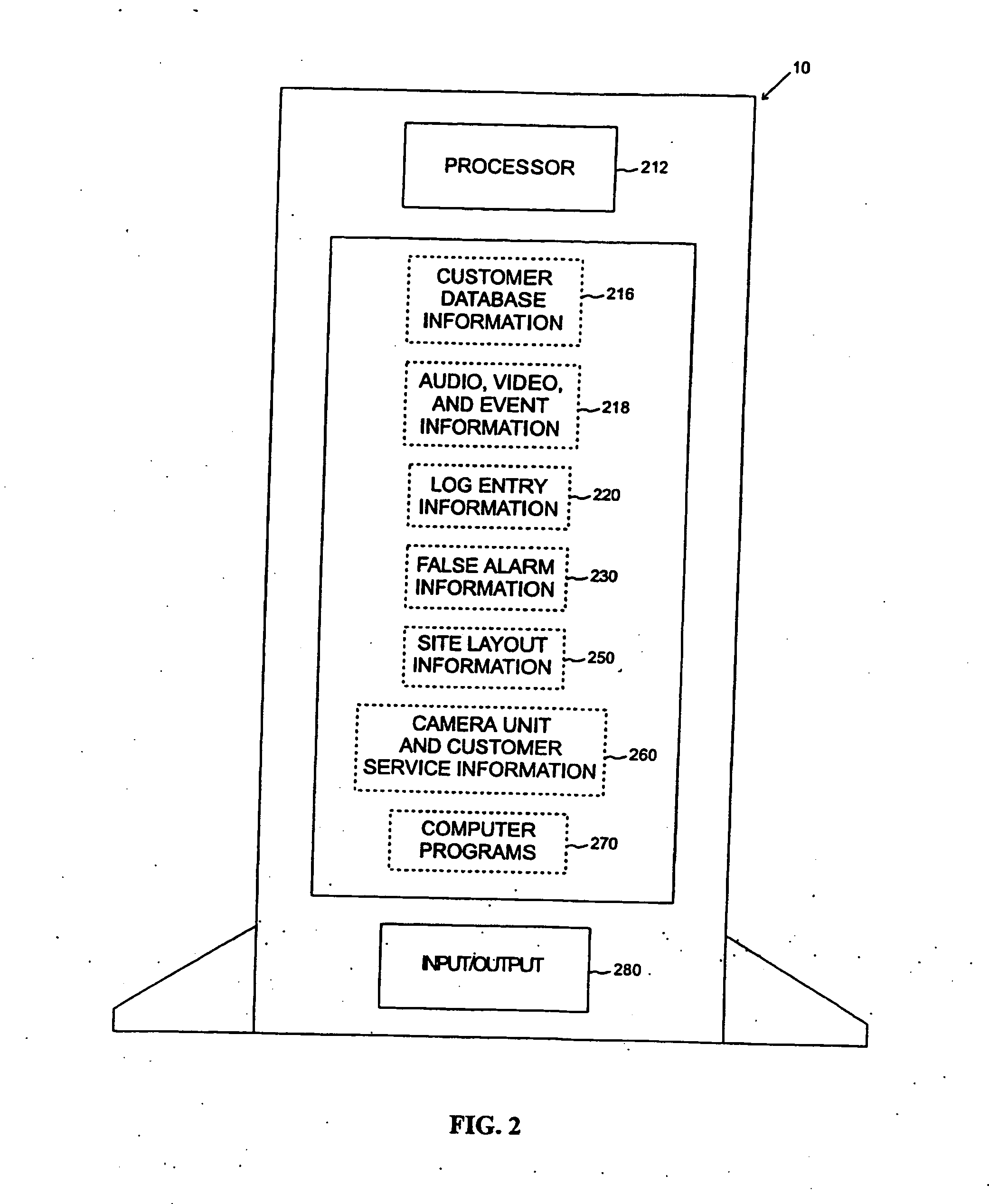
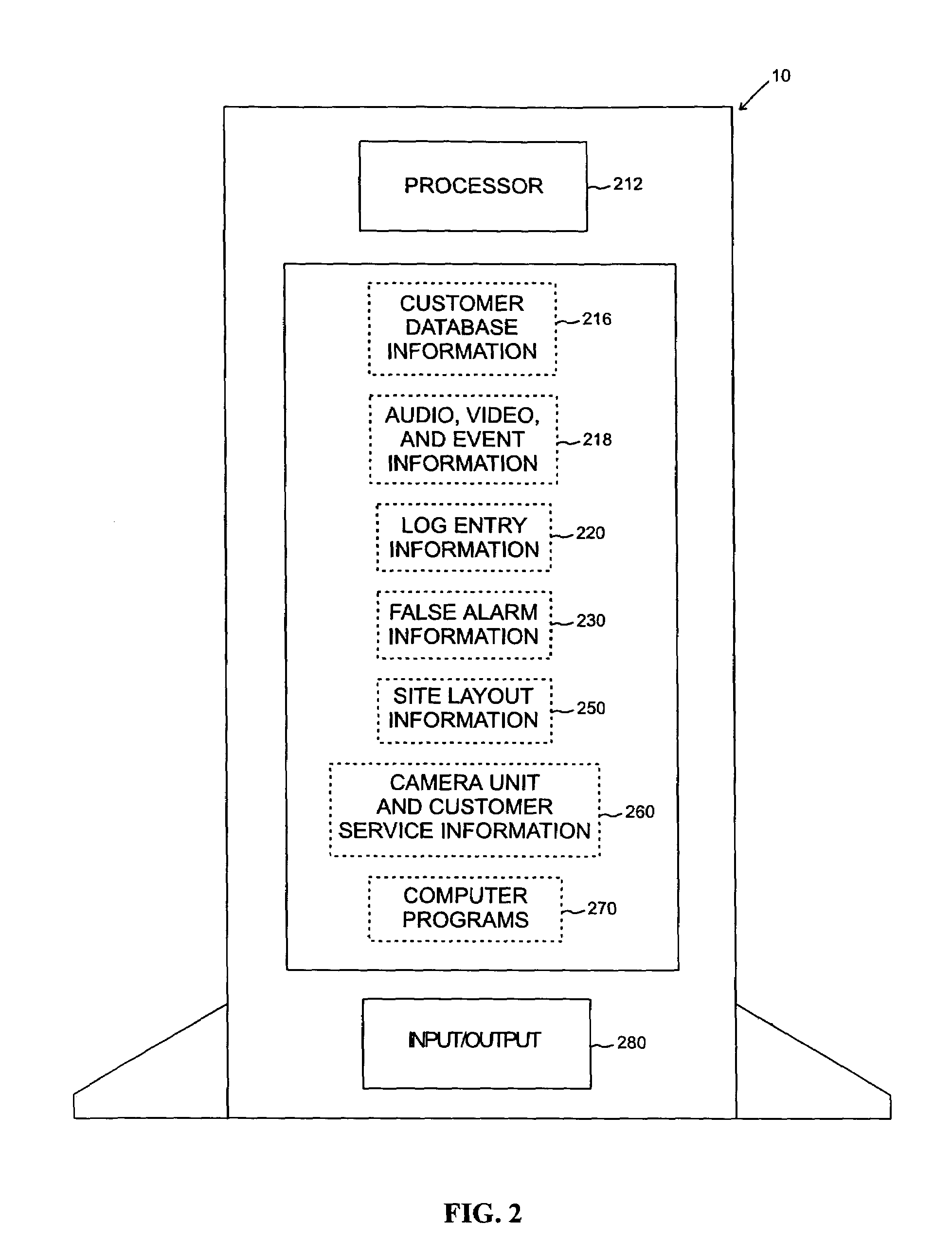
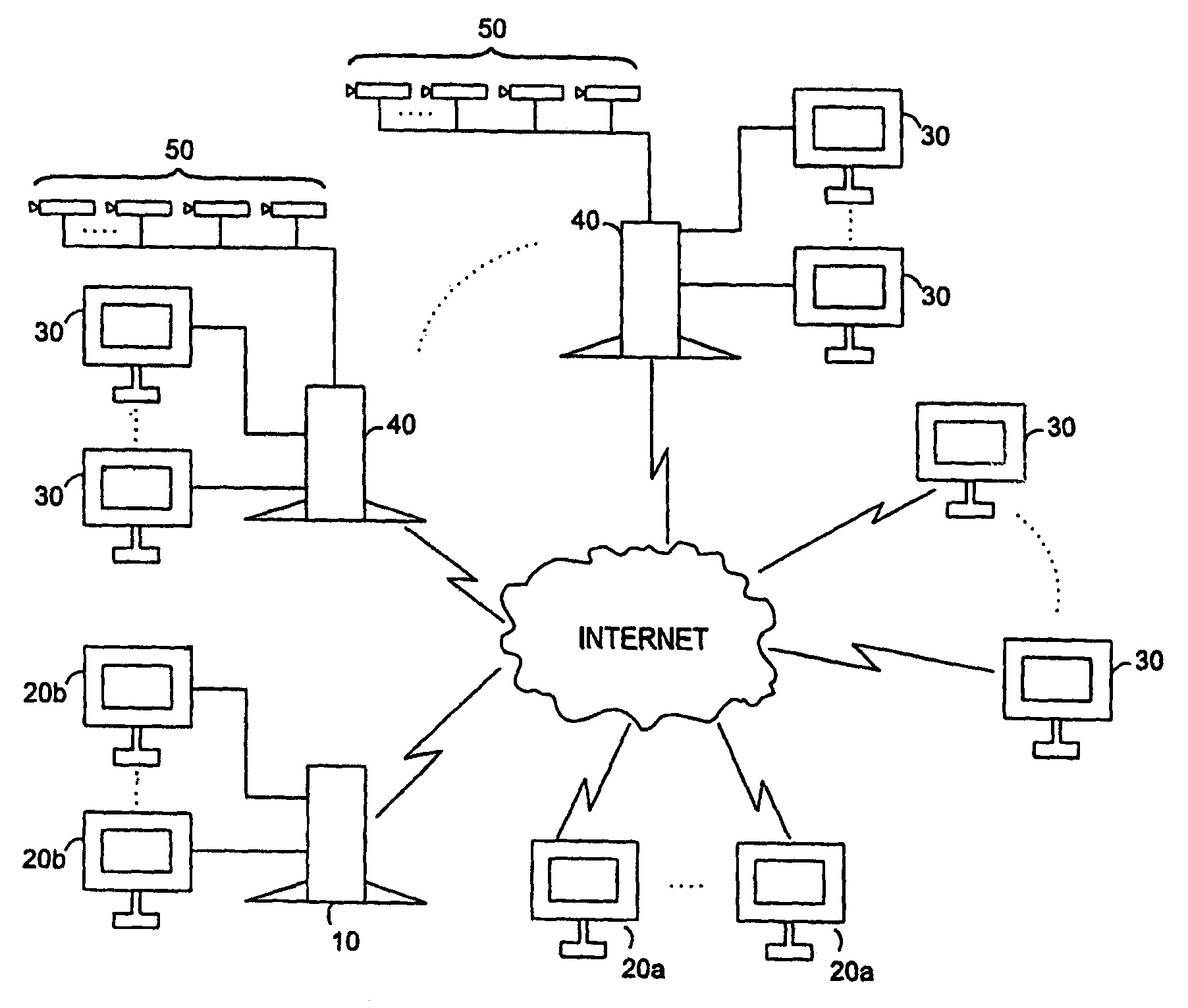
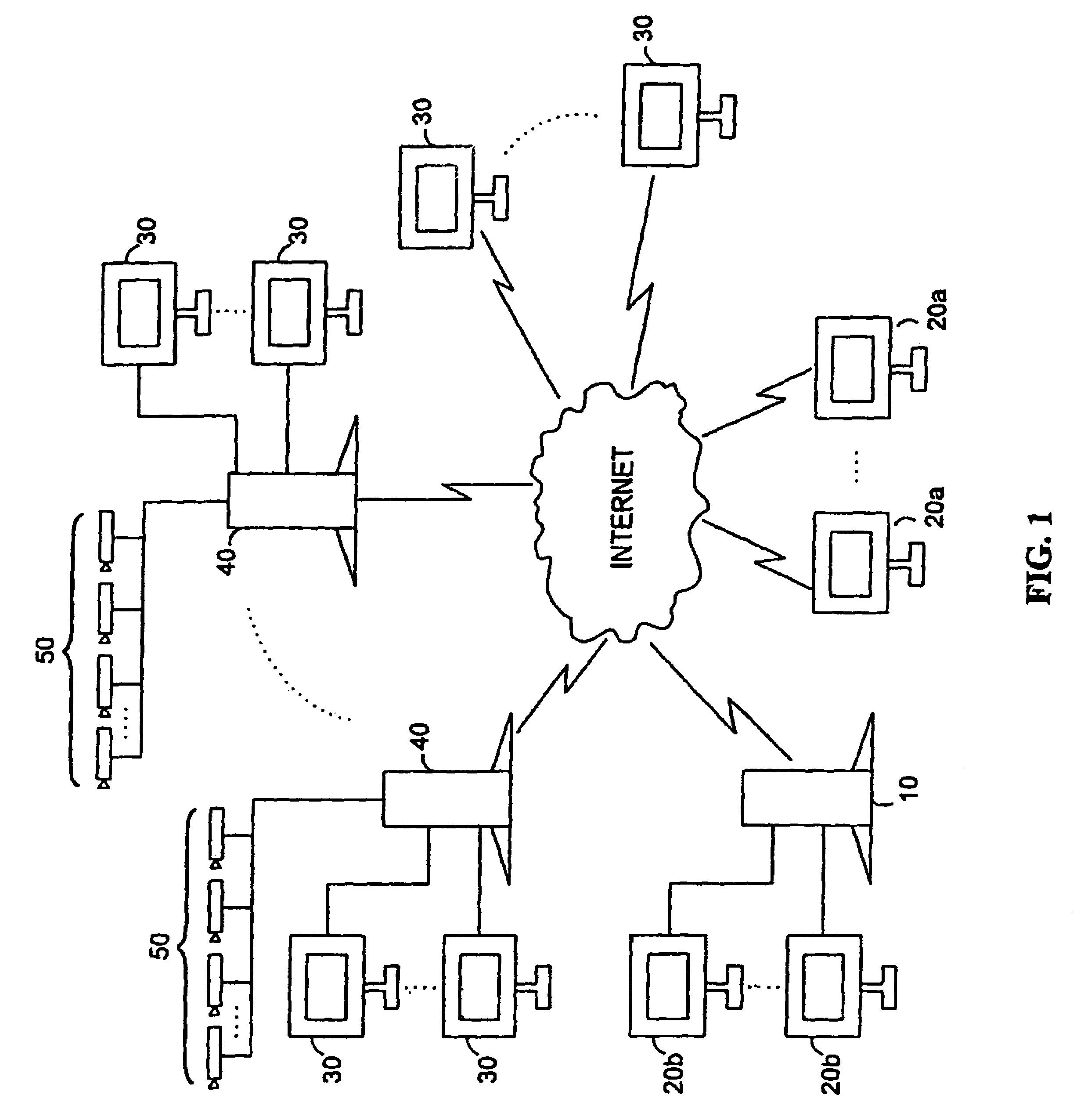
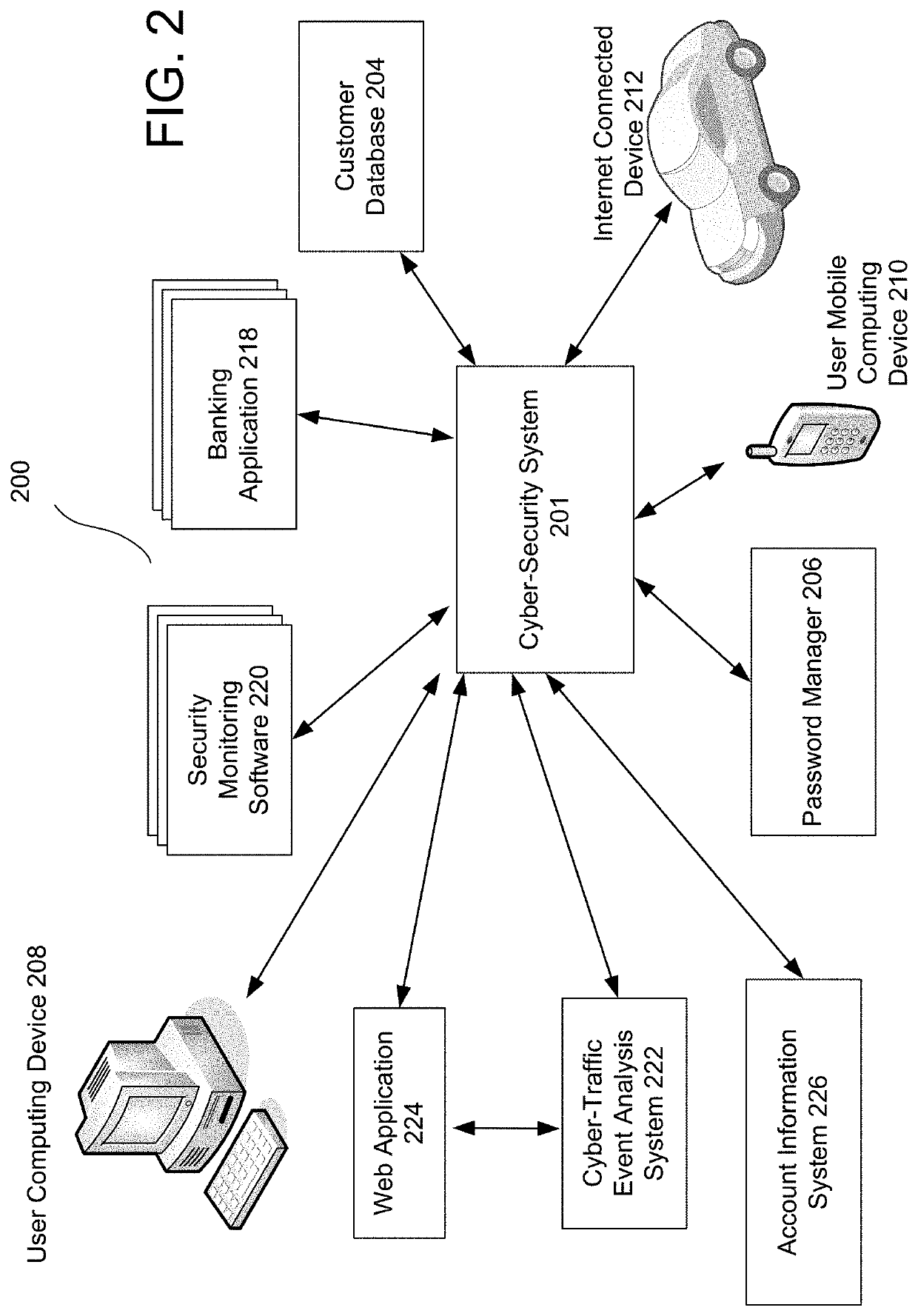
Networked digital security system and methods
InactiveUS20060053459A1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningWeb serviceWorkstation
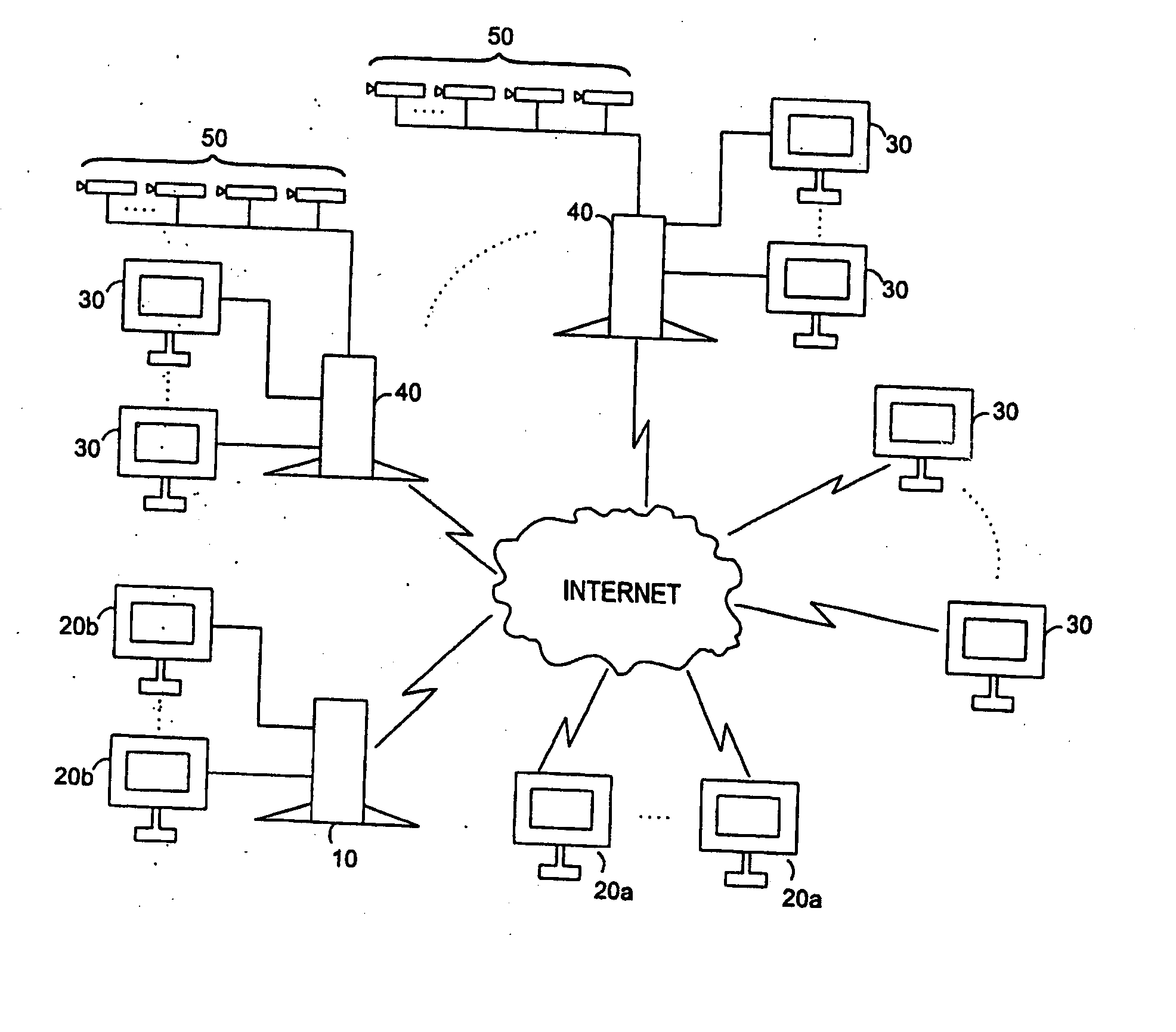
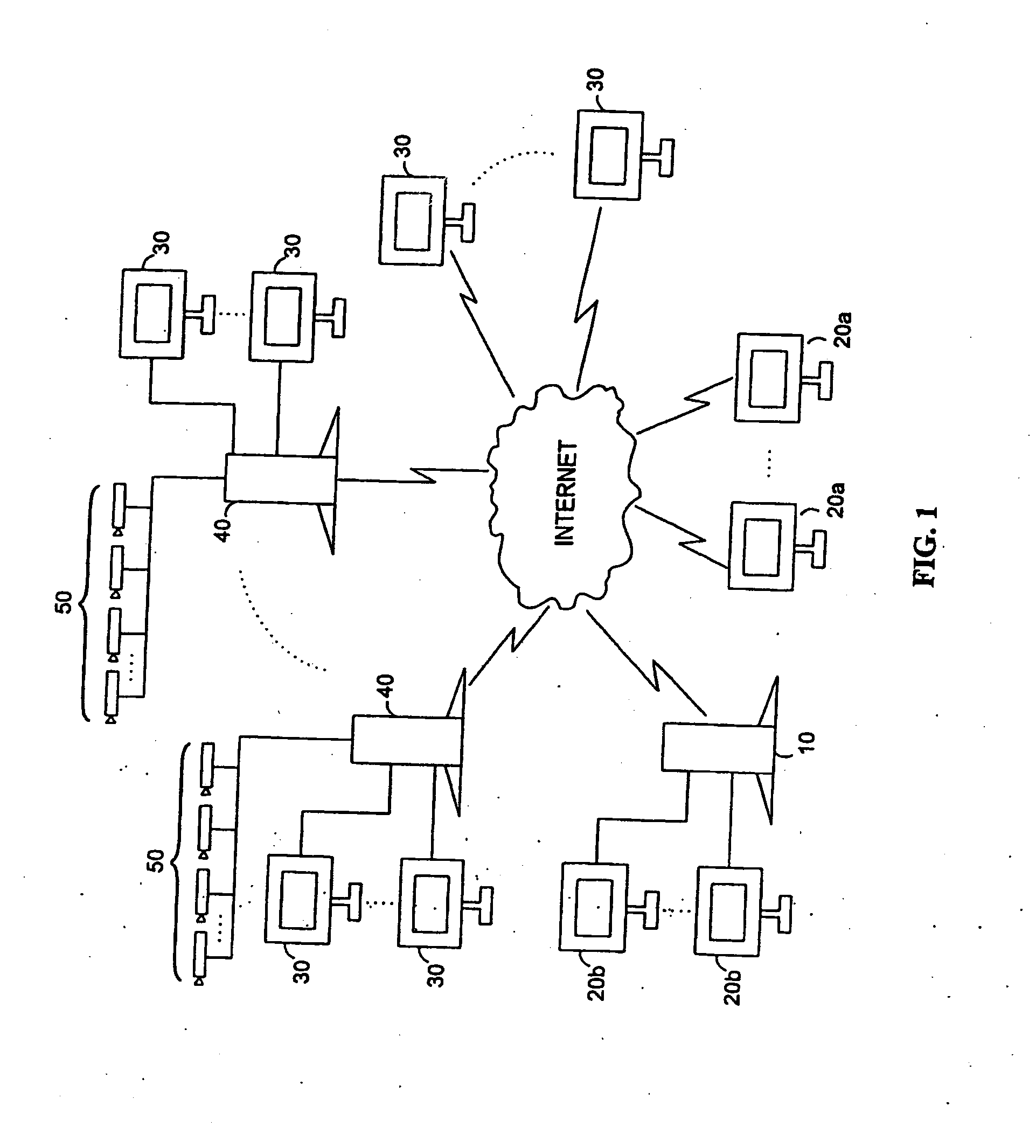
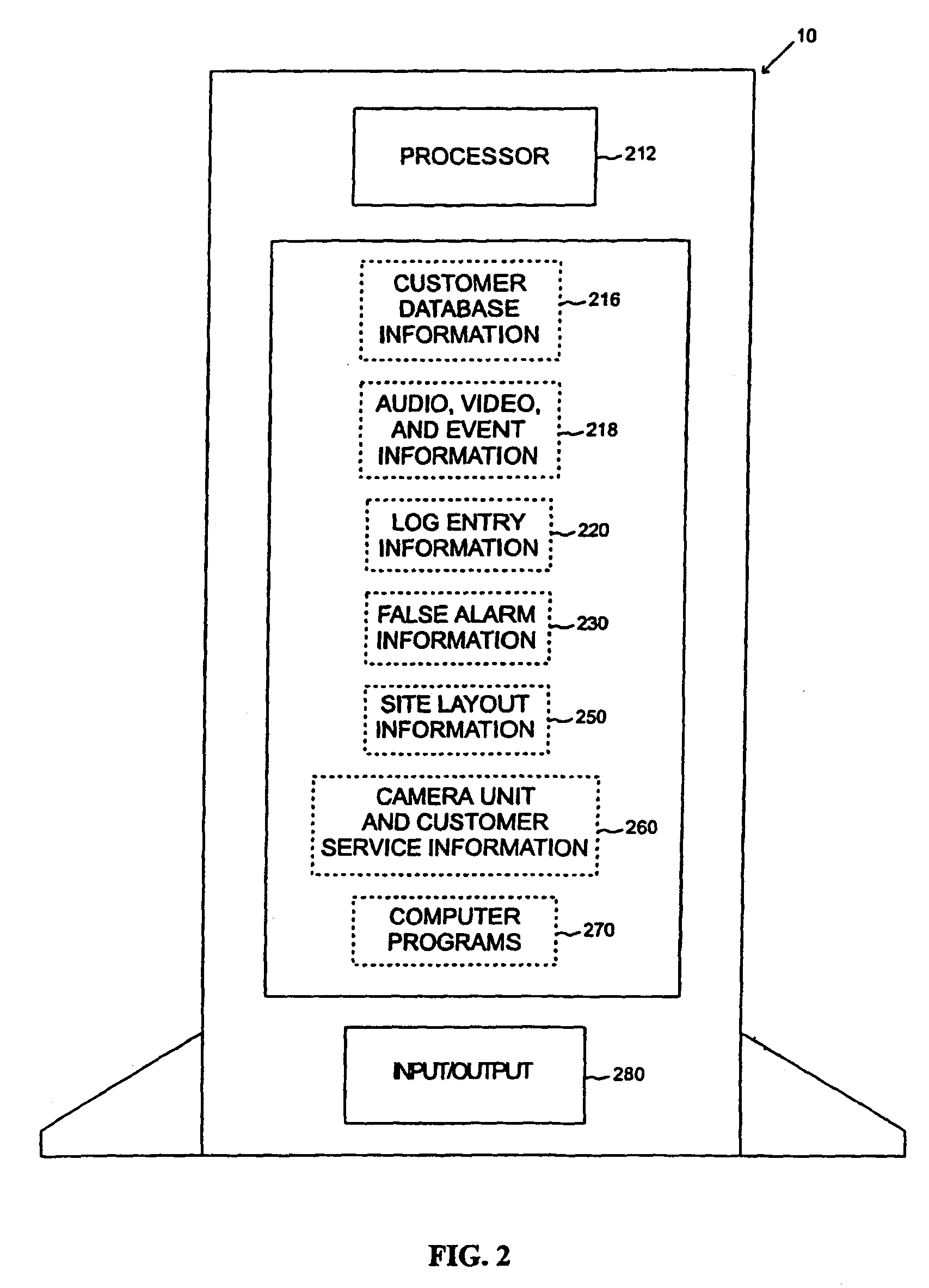
A networked digital security system is disclosed that preferably includes a centralized administrator web server coupled via a communication network such as the Internet to a plurality of customer servers and-a plurality of customer work stations. The centralized web server advantageously provides a point of control and management of the networked digital security system. The customer servers and customer work stations are preferably located at the customer's monitored sites. The customer servers are coupled to one or more intelligent camera units, which are preferably fully integrated intelligent units that gather, analyze, and transmit video, audio, and associated detected alarm event information to their associated customer server and the administrator web server. The camera units also include an intelligent automatic gain controller, an encoder buffer controller, and a network bandwidth priority controller. The system supports several compression algorithm standards.
Owner:AXCESS INT INC
Networked digital security system and methods
InactiveUS6954859B1Digital data processing detailsMultiple digital computer combinationsWeb serviceWorkstation
A networked digital security system is disclosed that preferably includes a centralized administrator web server coupled via a communication network such as the Internet to a plurality of customer servers and a plurality of customer work stations. The centralized web server advantageously provides a point of control and management of the networked digital security system. The customer servers and customer work stations are preferably located at the customer's monitored sites. The customer servers are coupled to one or more intelligent camera units, which are preferably fully integrated intelligent units that gather, analyze, and transmit video, audio, and associated detected alarm event information to their associated customer server and the administrator web server. The camera units also include an intelligent automatic gain controller, an encoder buffer controller, and a network bandwidth priority controller. The system supports several compression algorithm standards.
Owner:AXCESS INT INC
Networked digital security system and methods
InactiveUS7952609B2Analogue secracy/subscription systemsColor television detailsWeb serviceWorkstation
A networked digital security system is disclosed that preferably includes a centralized administrator web server coupled via a communication network such as the Internet to a plurality of customer servers and-a plurality of customer work stations. The centralized web server advantageously provides a point of control and management of the networked digital security system. The customer servers and customer work stations are preferably located at the customer's monitored sites. The customer servers are coupled to one or more intelligent camera units, which are preferably fully integrated intelligent units that gather, analyze, and transmit video, audio, and associated detected alarm event information to their associated customer server and the administrator web server. The camera units also include an intelligent automatic gain controller, an encoder buffer controller, and a network bandwidth priority controller. The system supports several compression algorithm standards.
Owner:AXCESS INT INC
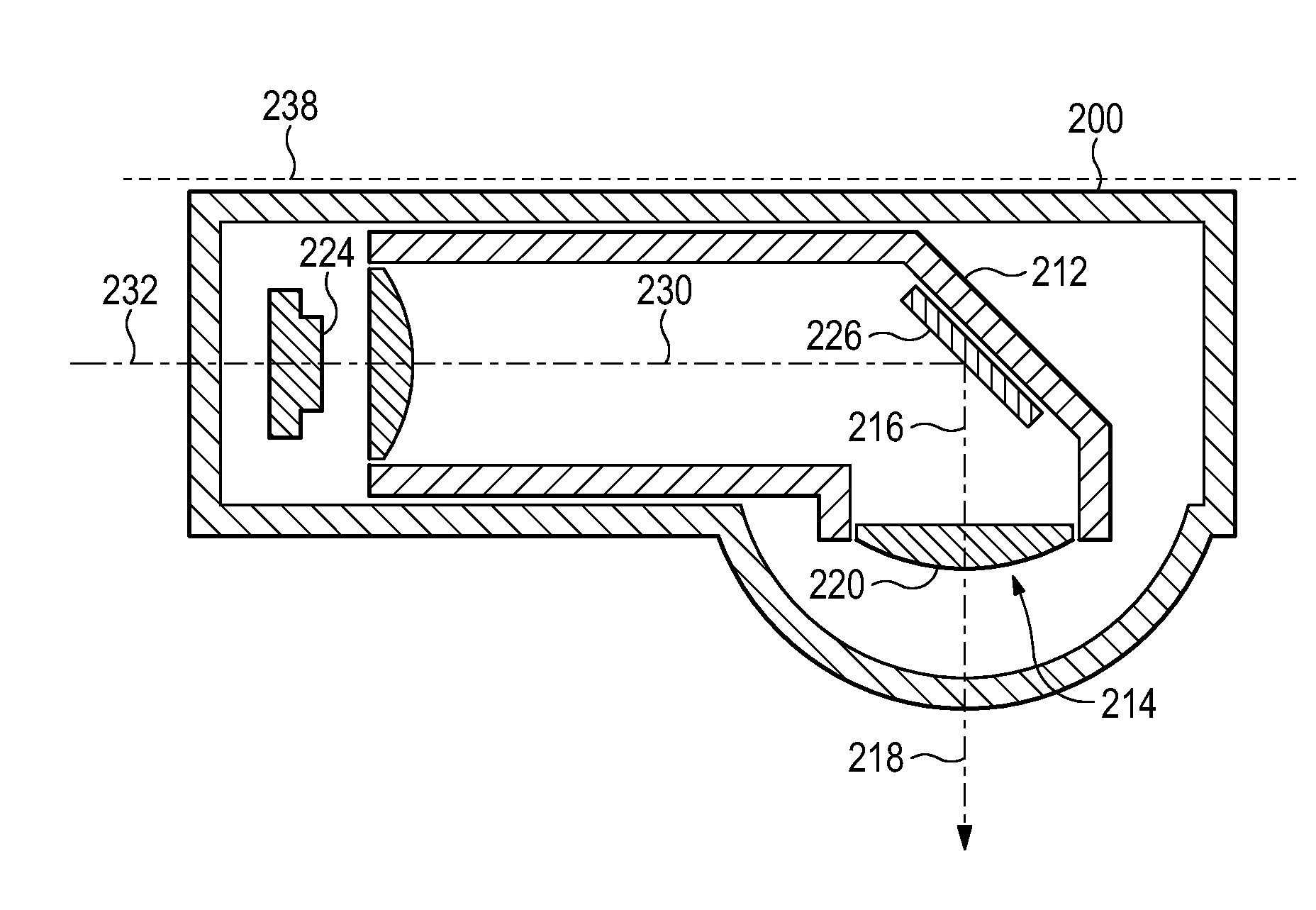
Compact dome camera
A compact video capture system is provided with a folded optical assembly to reduce a relative system size while providing improved lens performance. The folded lens and optical assembly allow for an improved lens resolution and zoom capability while not overly restricting an F number in a compact dome camera. These compact video systems may be implemented in CCTV dome cameras or digital security cameras to improve image recording while being small enough to be discretely mounted. In one instance, the optical assembly includes a first lens system with a light gathering entrance oriented in a first optical axis direction, an image sensor configured to detect light gathered by the lens system oriented in a second optical axis direction, and an optical folding element disposed along the optical path to redirect light along the optical path by changing a traveling direction of the light.
Owner:THEIA TECH
Zoned based security administration for data items
InactiveUS20050039001A1Digital computer detailsUnauthorized memory use protectionComputerized systemSecurity rule
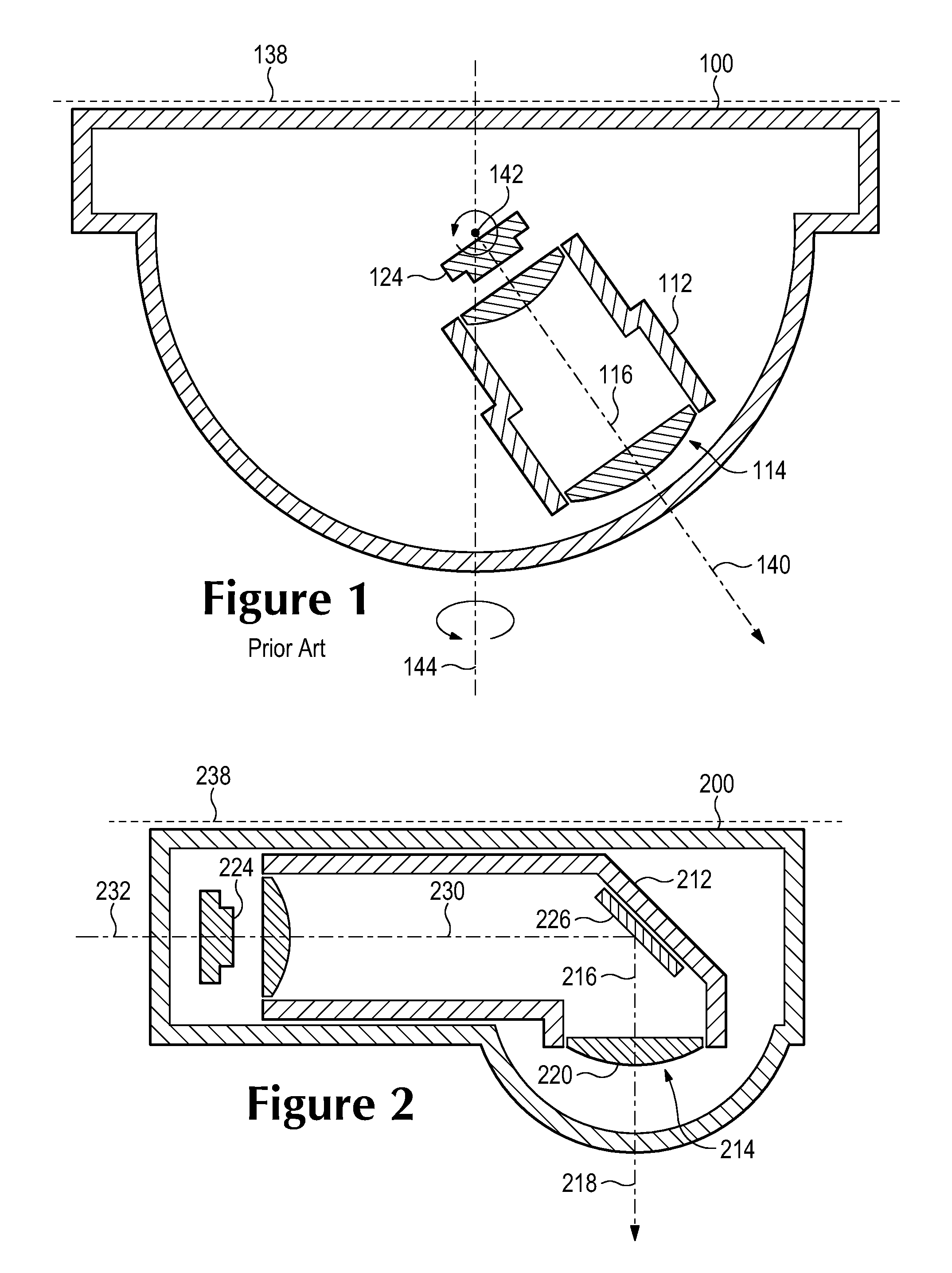
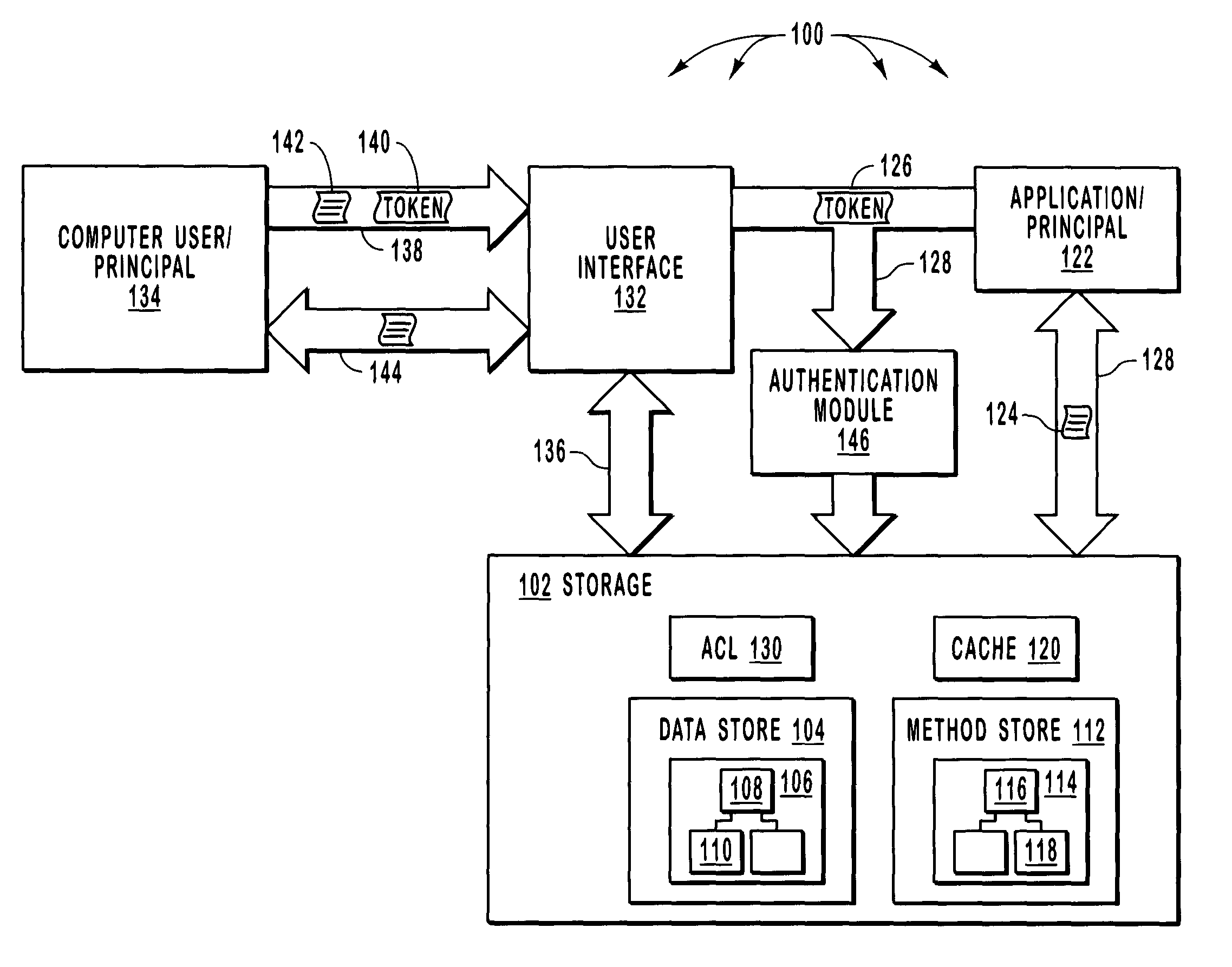
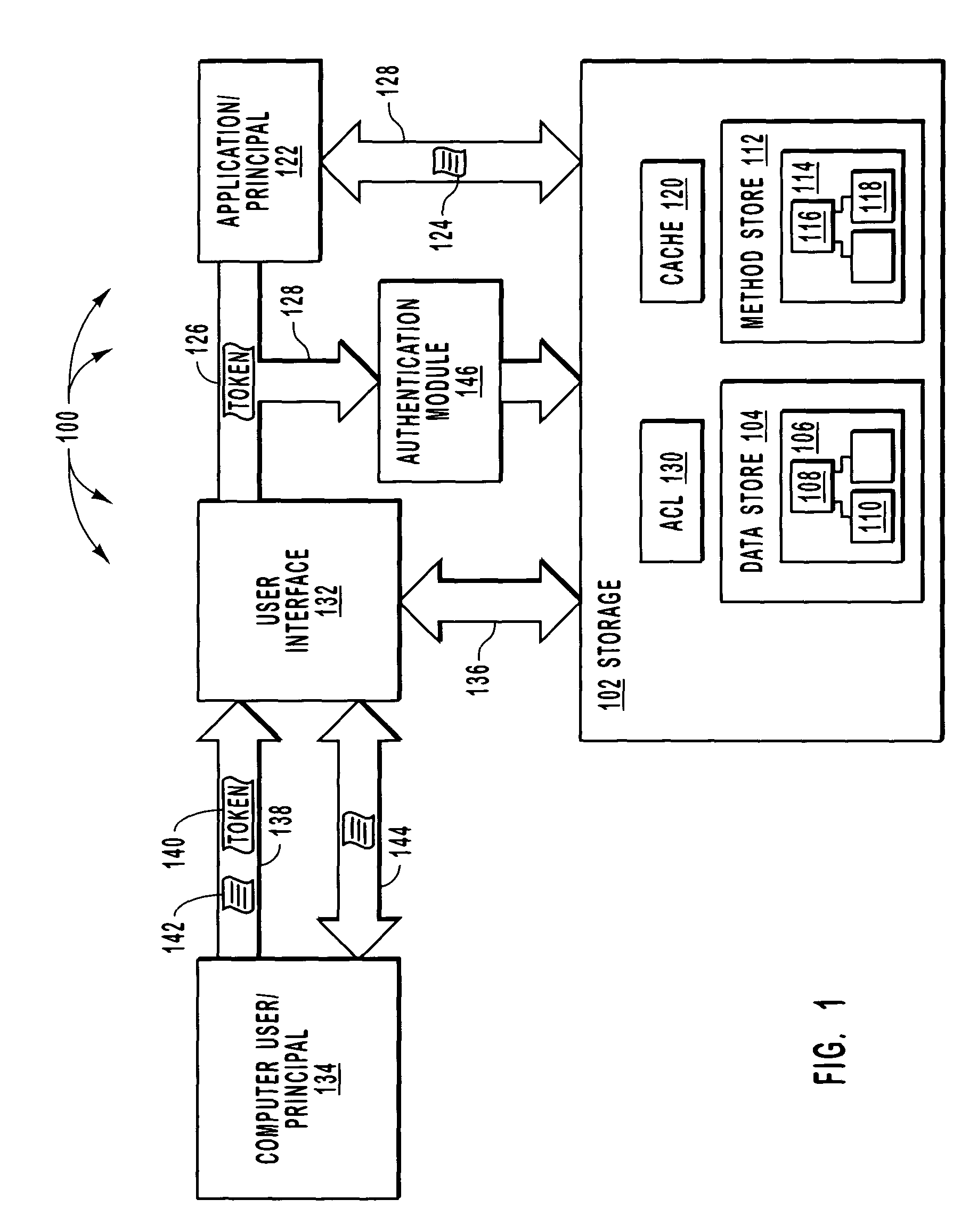
Administering digital security is disclosed. Data and method items are stored on a computer system in a volume. The volume is divided up into non-overlapping security zones. Each item exists in a security zone. Security rules are granted to principals where the security rules apply to items in a particular zone. The security rules specify what principals have what rights; such as read, write delete and execute; to what items. Administrative rights can be delegated by principals by splitting a security zone to form two security zones. Principals who have administrative rights to the security zone assign additional principals to one of the security zones while maintaining all administrative rights to the other zone. Thus principals can retain certain administrative rights to certain items exclusively to themselves while delegating administrative rights to other items to other principals.
Owner:MICROSOFT TECH LICENSING LLC
System and method for digital authentication
InactiveUS20160078430A1Database updatingFinanceCommunication interfaceApplication programming interface
Owner:CAPITAL ONE SERVICES
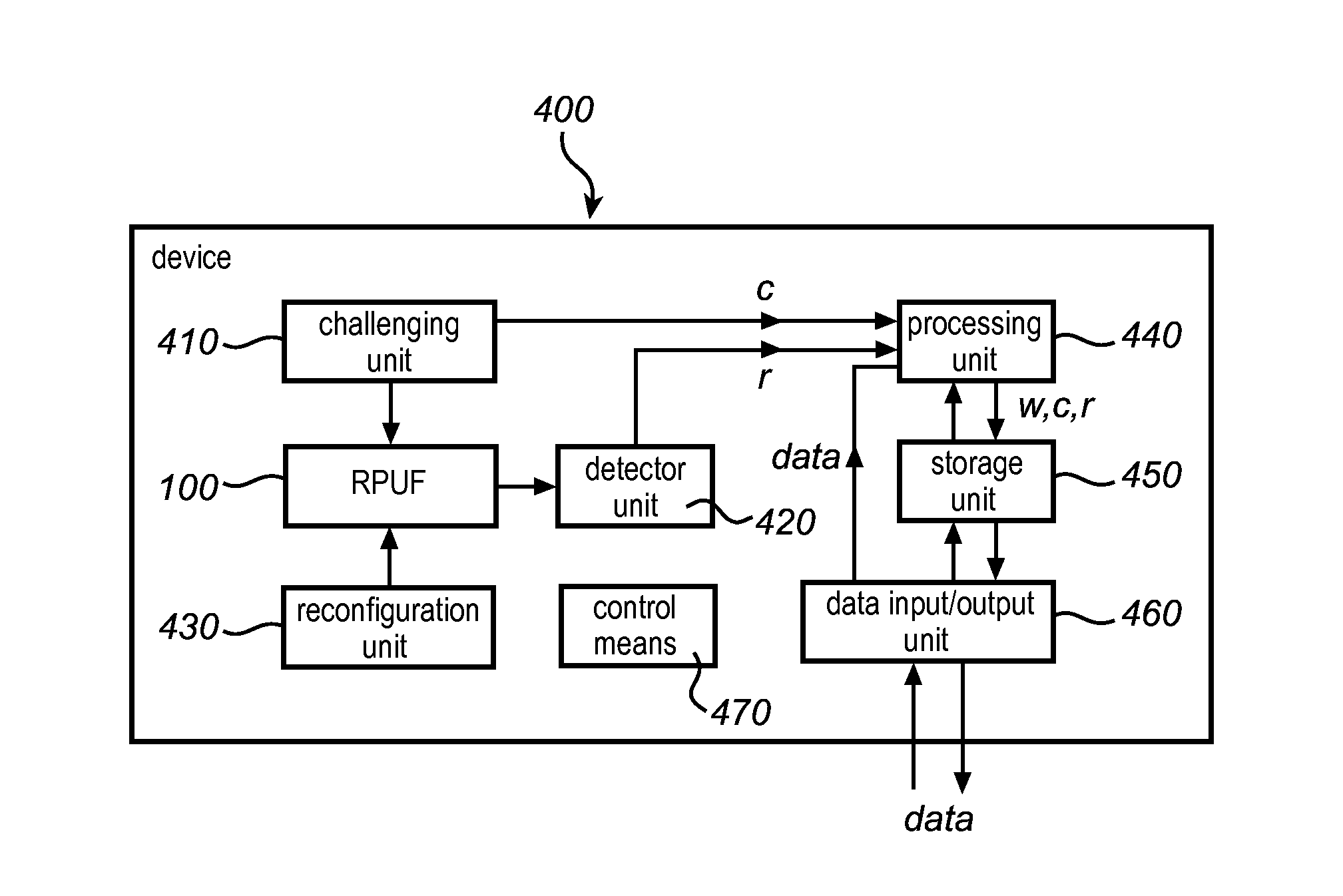
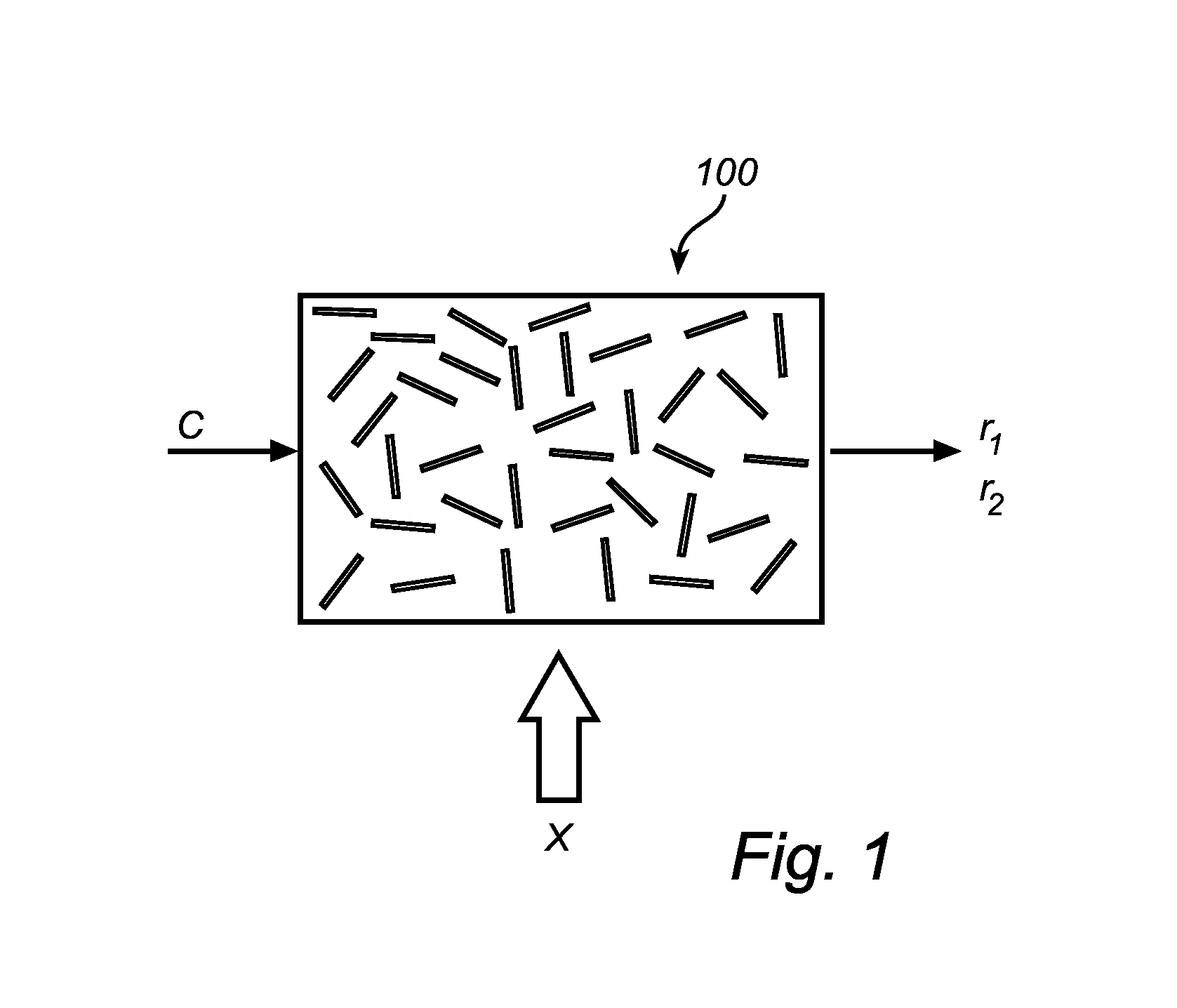
Method and device for providing digital security
ActiveUS20100176920A1Mitigate such drawbackEfficient use ofElectric signal transmission systemsMultiple keys/algorithms usagePhysical systemDigital security
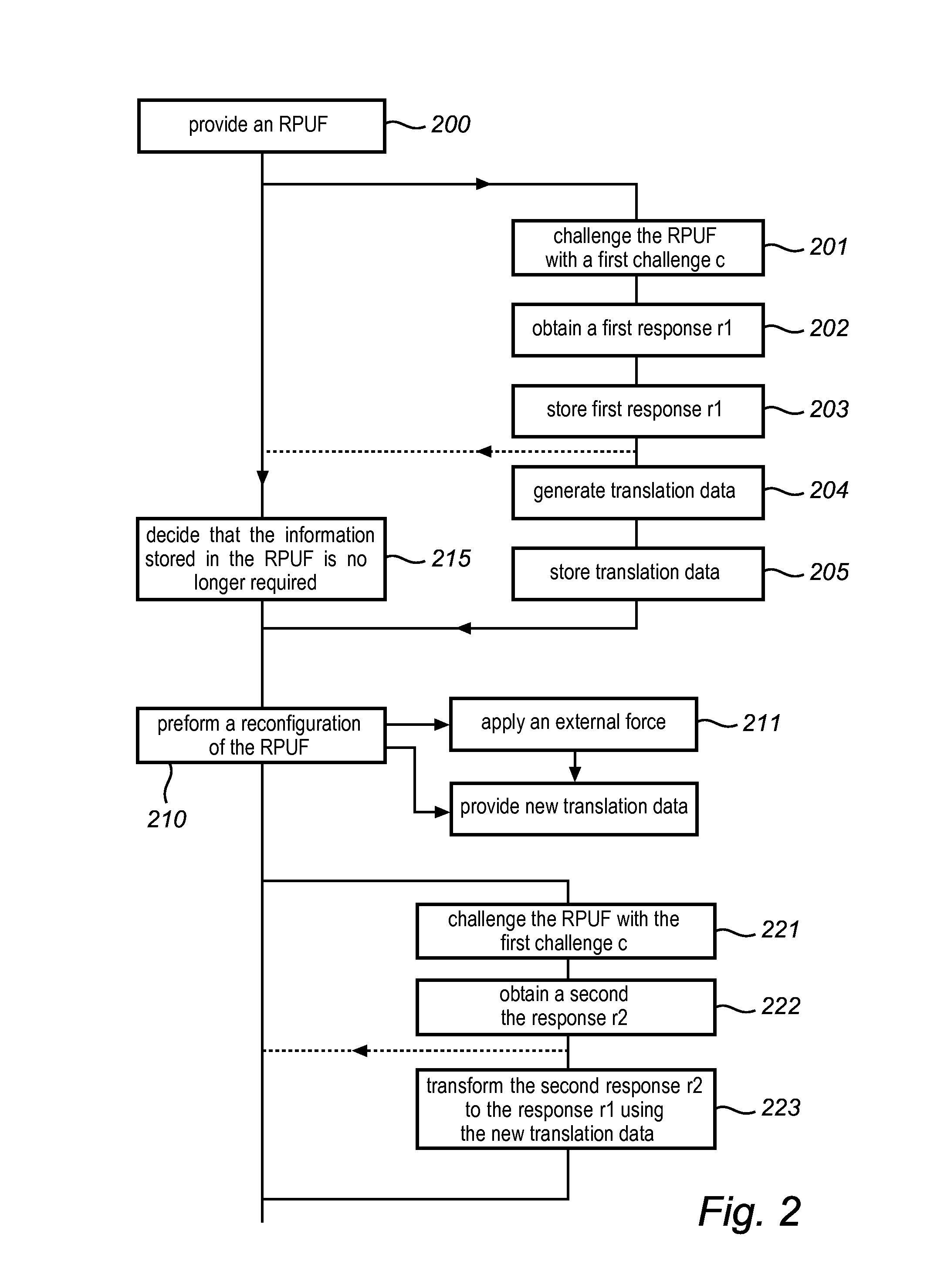
This invention relates to a method and system for providing digital security by means of a reconfigurable physical uncloneable function, RPUF. The RPUF comprises a physical system constituted by distributed components arranged to generate a first response when receiving a first challenge at a point of the physical system. The physical reconfiguring of the RPUF comprises redistributing the components such that they generate a second response, which differs from said first response, when again applying the first challenge at the point. The reconfiguration step is further utilized in providing secure storage for digital items. The digital item is data of any kind, including data that needs to be accessed and updated, i.e. which is dynamic in nature. The method is exemplified by implementations such as secure storage of a key, a secure counter and a seed generator.
Owner:INTRINSIC ID
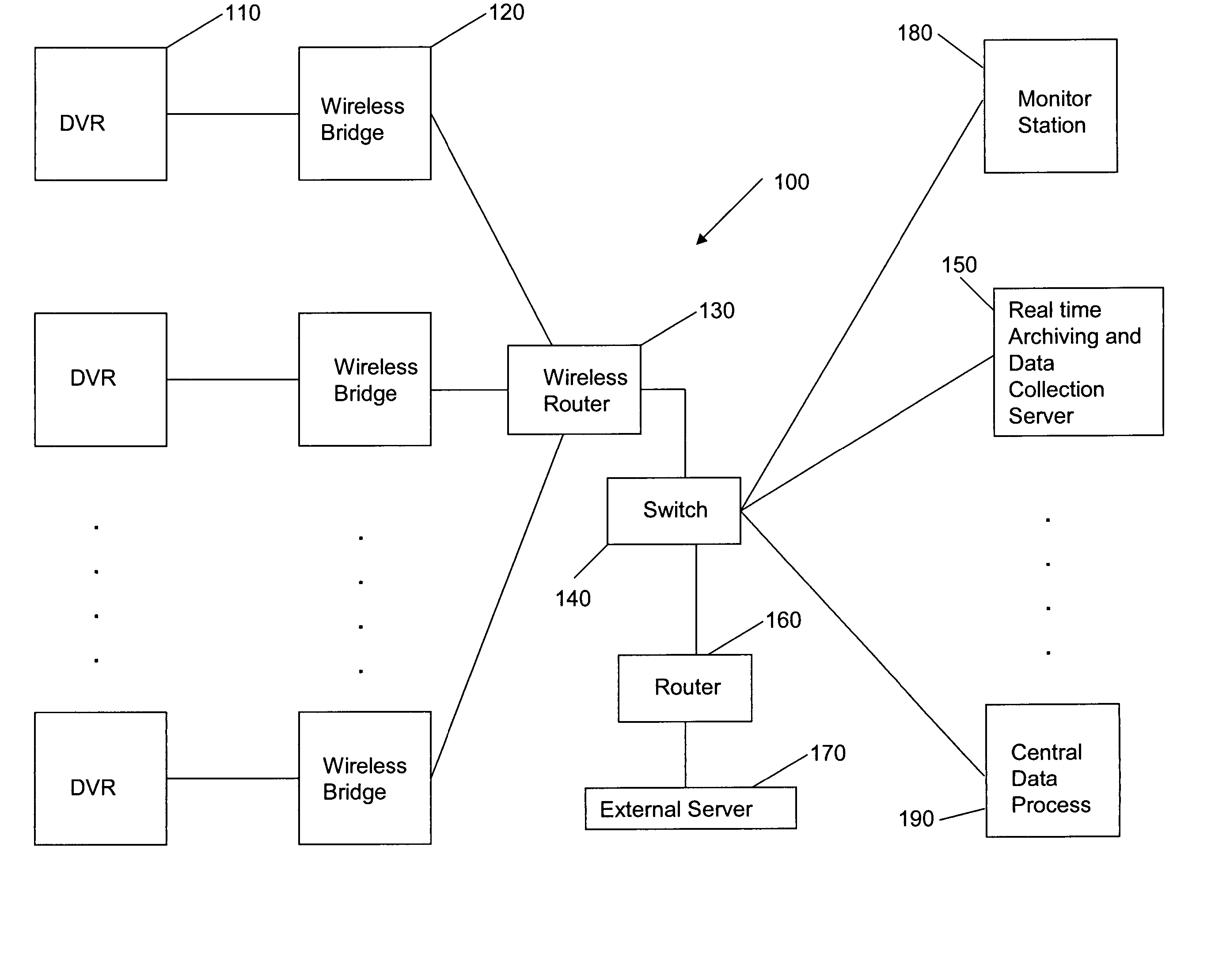
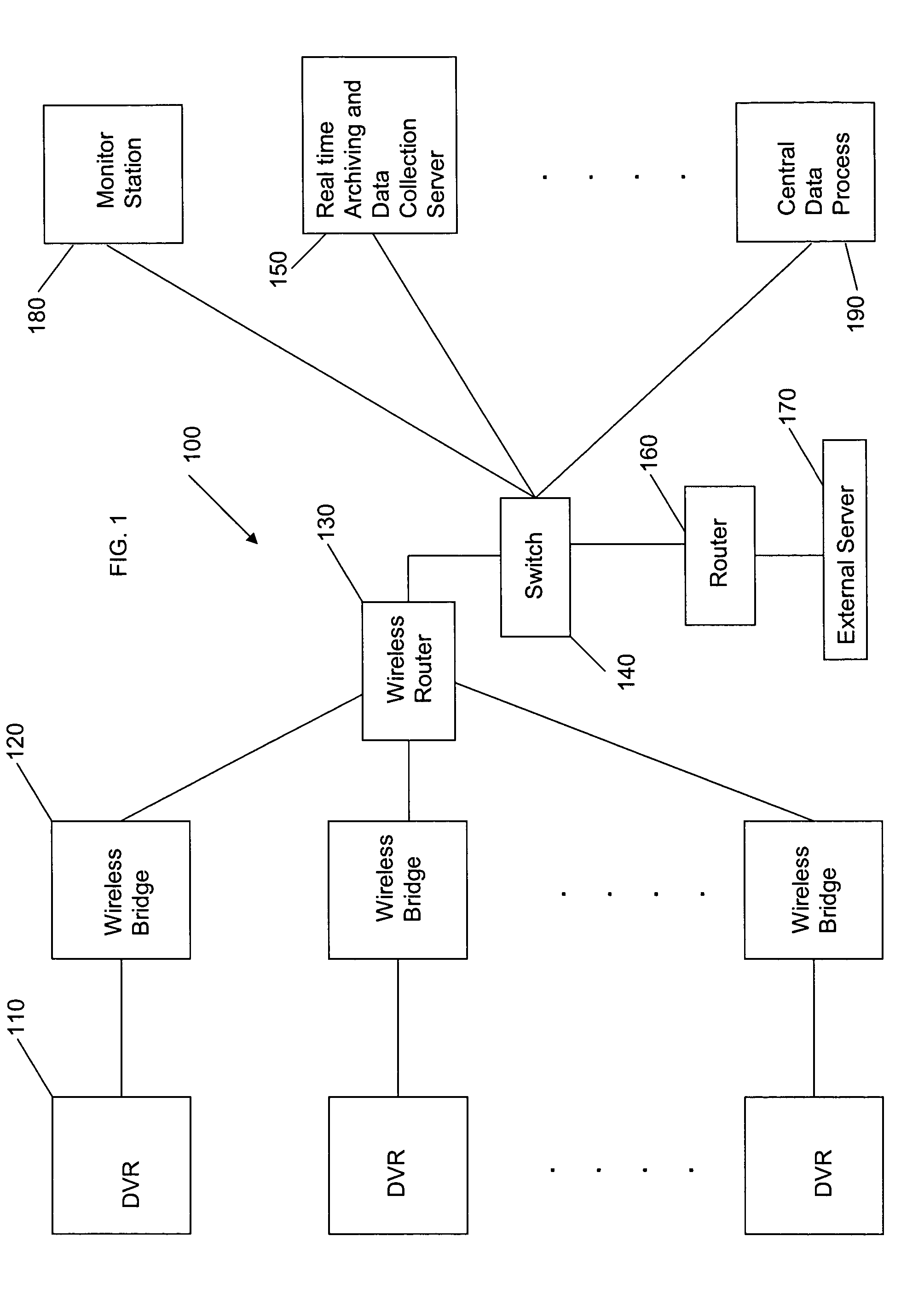
Mobile digital security system and method
InactiveUS20050066371A1Closed circuit television systemsTwo-way working systemsDigital videoComputer network
A mobile digital security system includes a digital video recorder disposed in each of at least one mobile unit and operable to generate a digital video / data signal, a wireless interface coupled to the digital video recorder for encapsulating and transmitting the digital video / data signal, a wireless device coupled to the wireless interface through a wireless network for receiving the encapsulated and transmitted digital video / data signal, and a server for processing the received digital video / data signal.
Owner:LU BIN
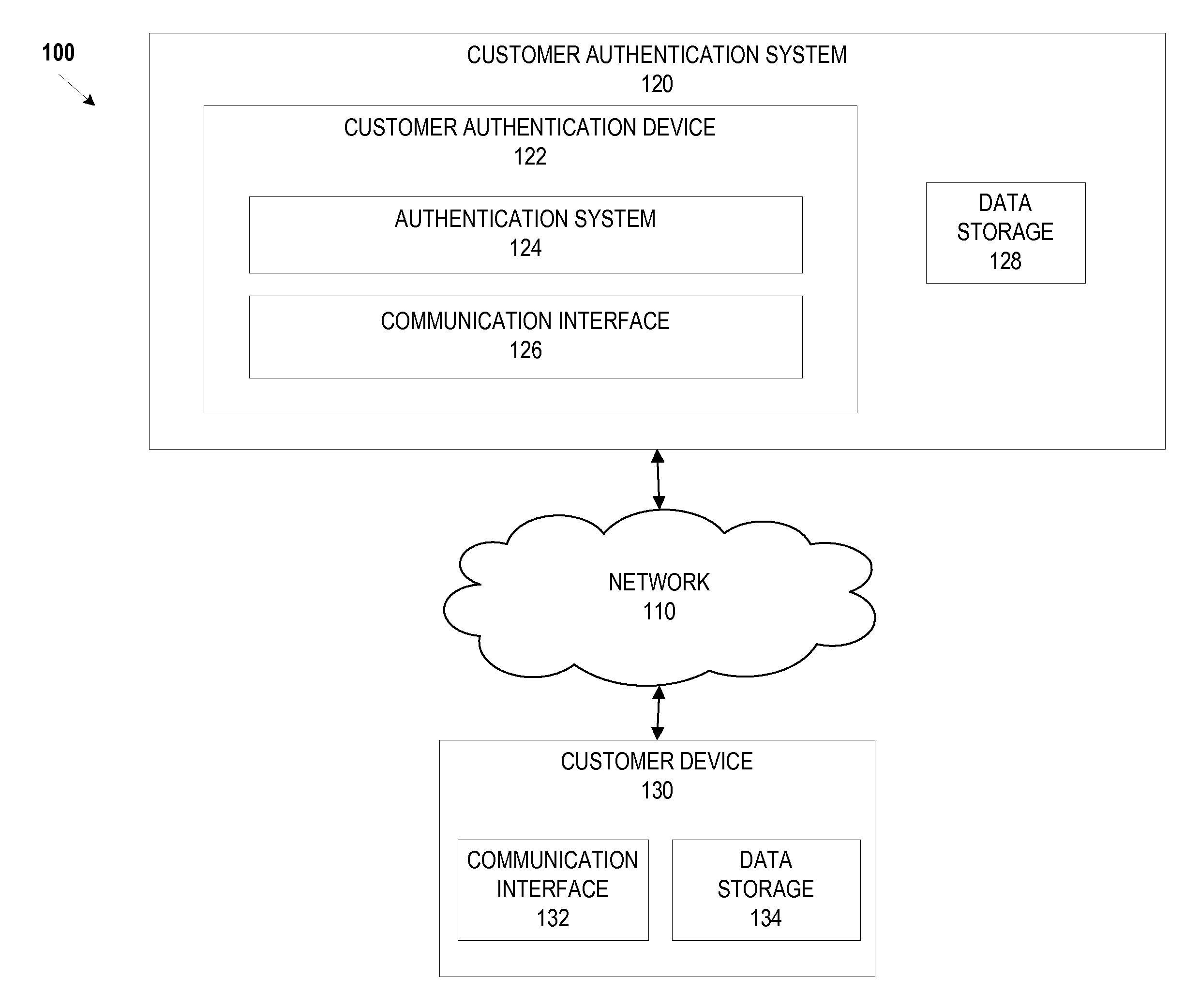
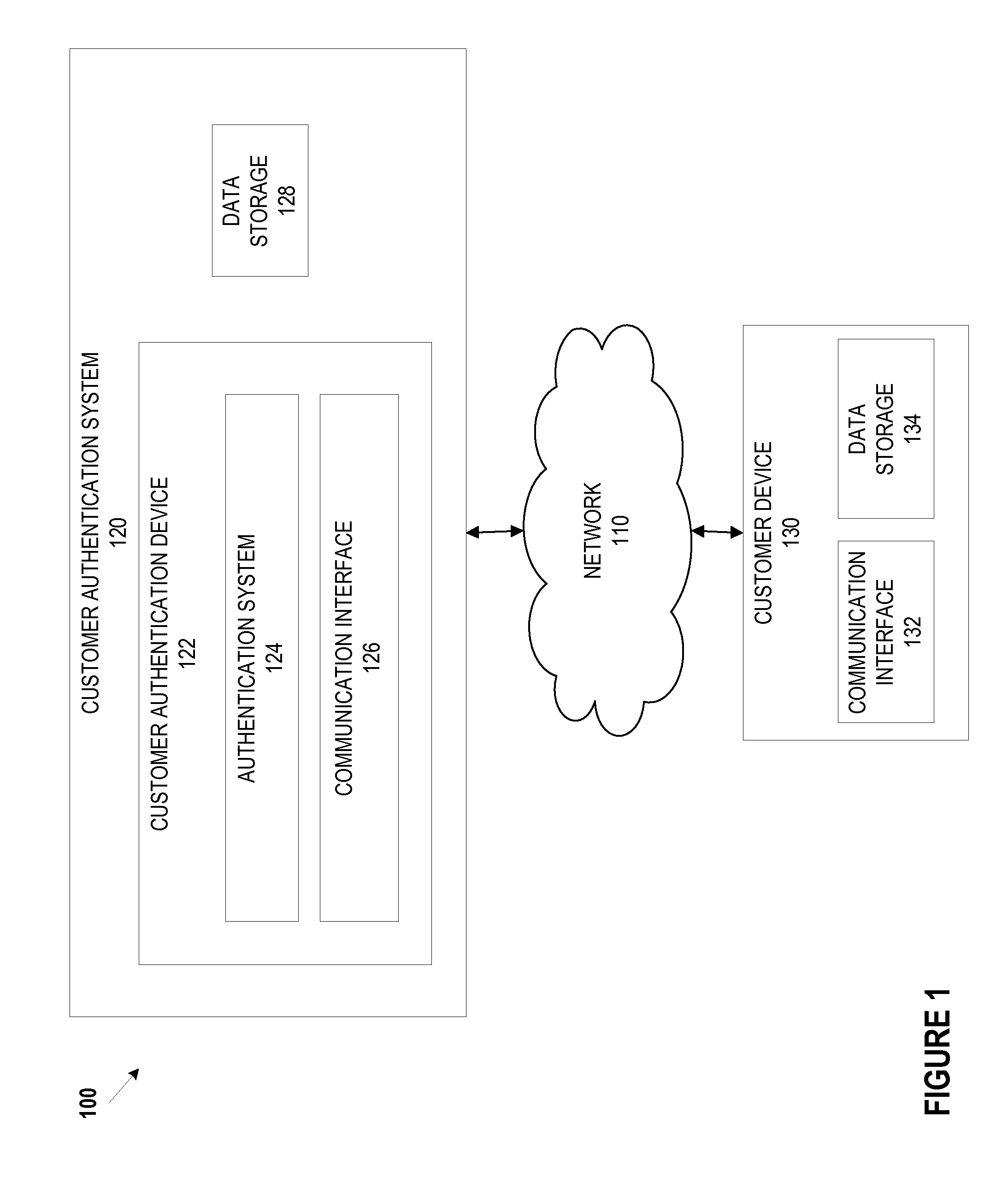
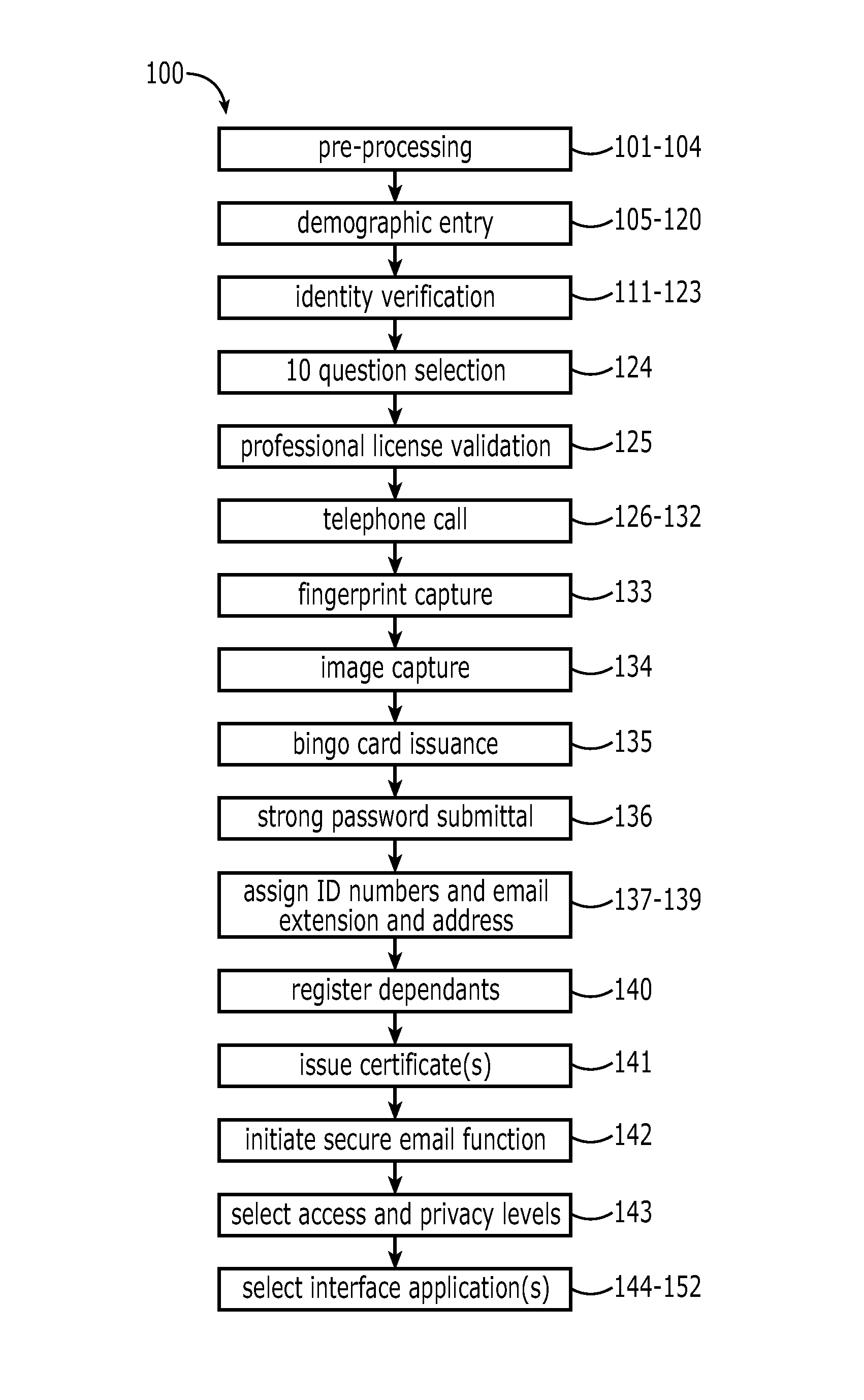
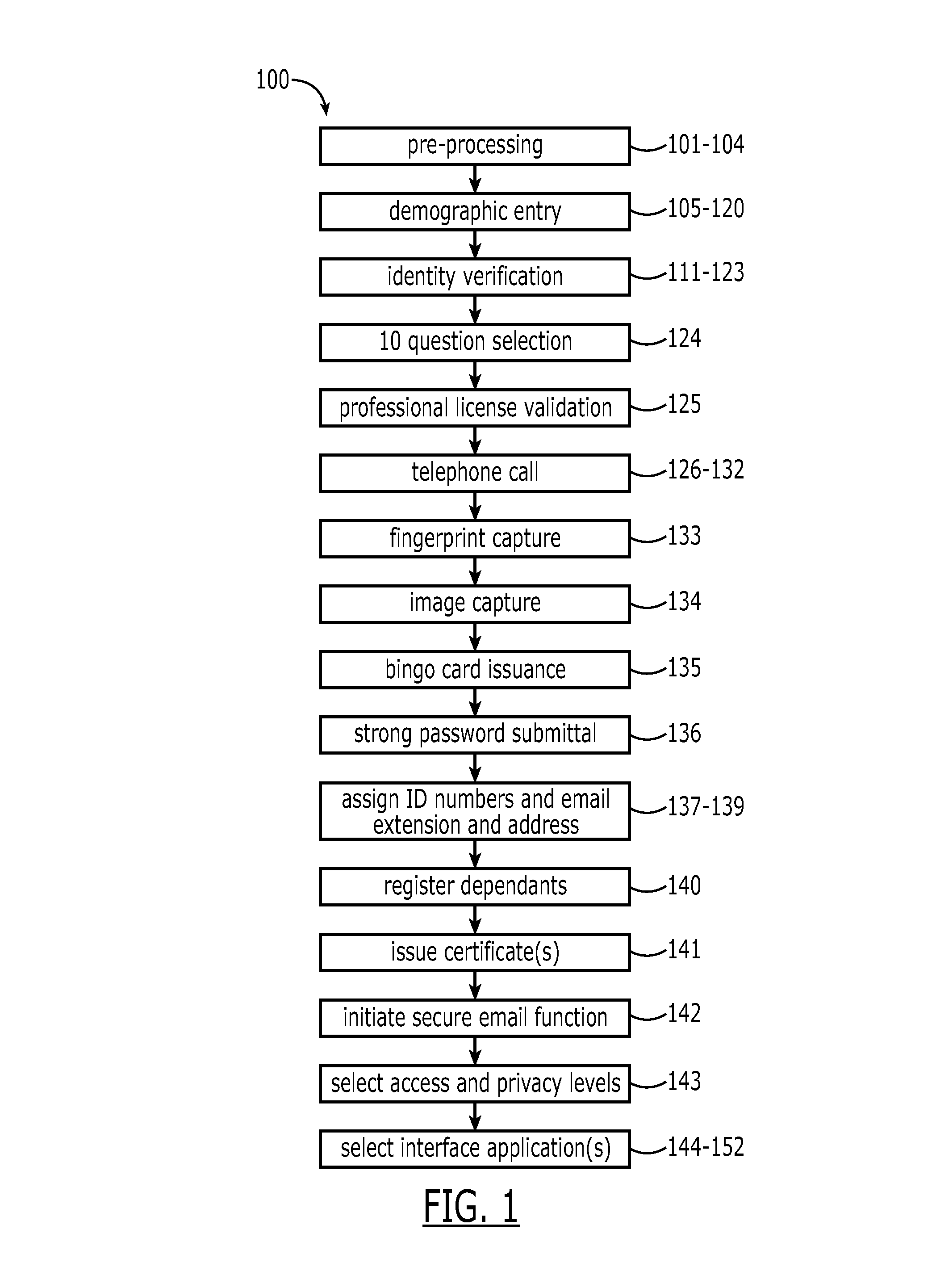
Identity validation and verification system and associated methods
A computer implemented system and method verify and validate a user identity for enrollment in a secure personal dataset accessing system. A personal dataset includes identifiable attributes of the user. Using a computer, authenticity of an asserted user identity includes electronically verified identifiable attributes to form the personal dataset. A biometric identifier of the user is automatically captured for validating the identifiable attributes by confirming that the asserted identity matches the identifiable attributes. A traceable e-audit trail is provided in an enterprise infrastructure and bench mark performance indicator. A digital security element is generated and results in the user electronically receiving a password and a unique electronic address is assigned to the user. The digital security element is then transmitted to the user from the computer and enables electronic access to the personal dataset relating to the user, the personal dataset having been authenticated through the verification and validation.
Owner:KRAGH JAMES F
Methods of operation for plug-in wireless safety device
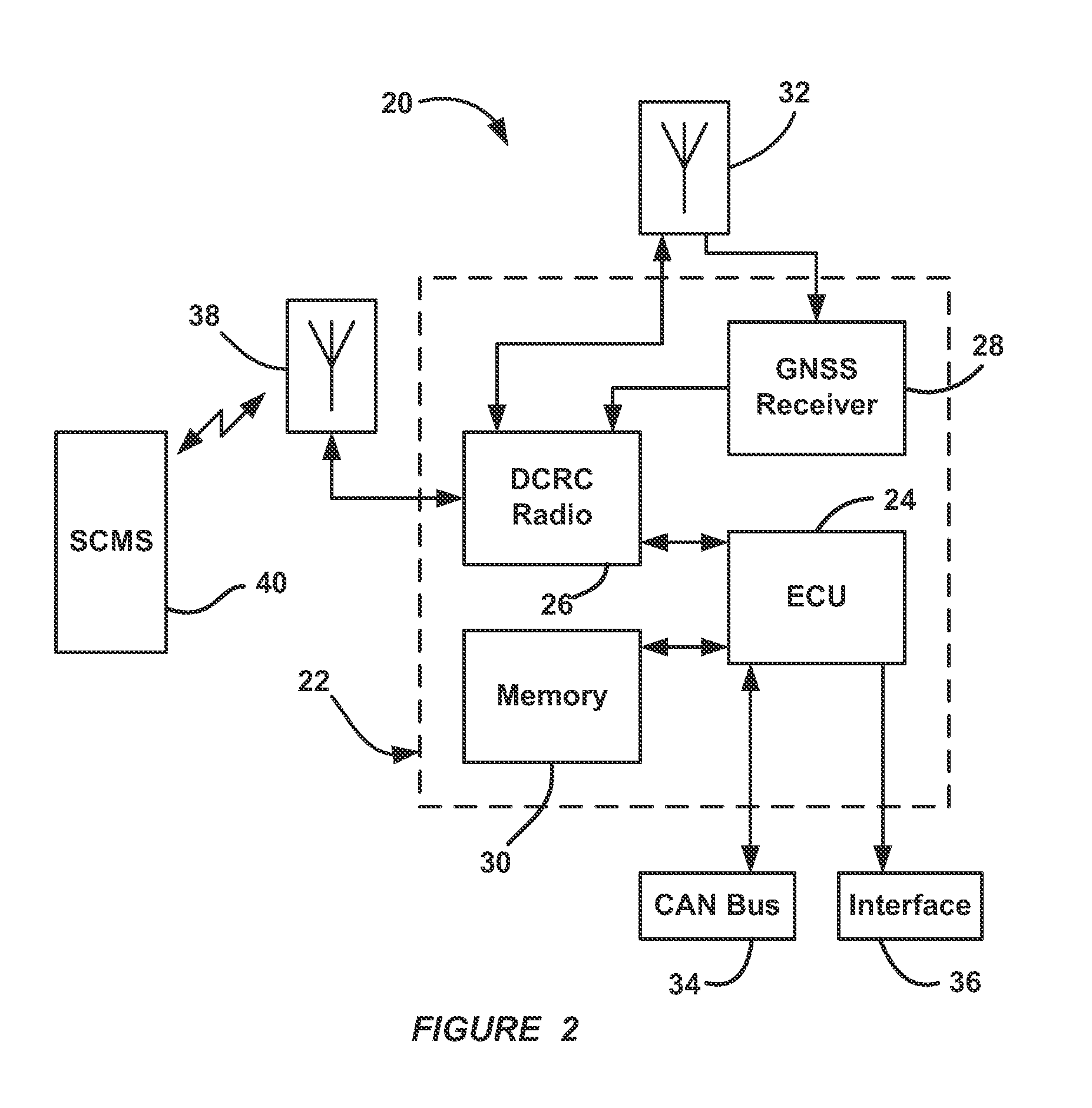
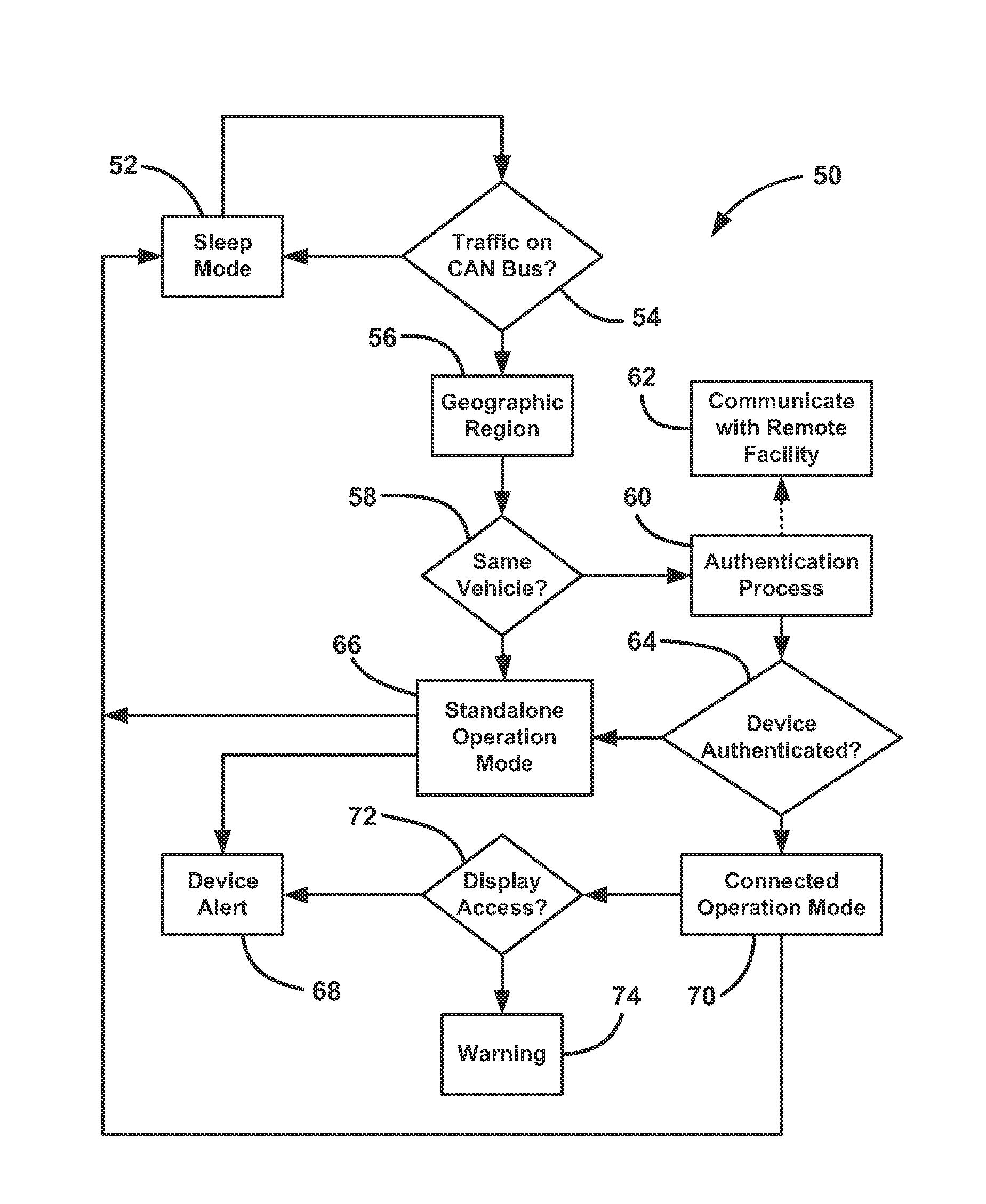
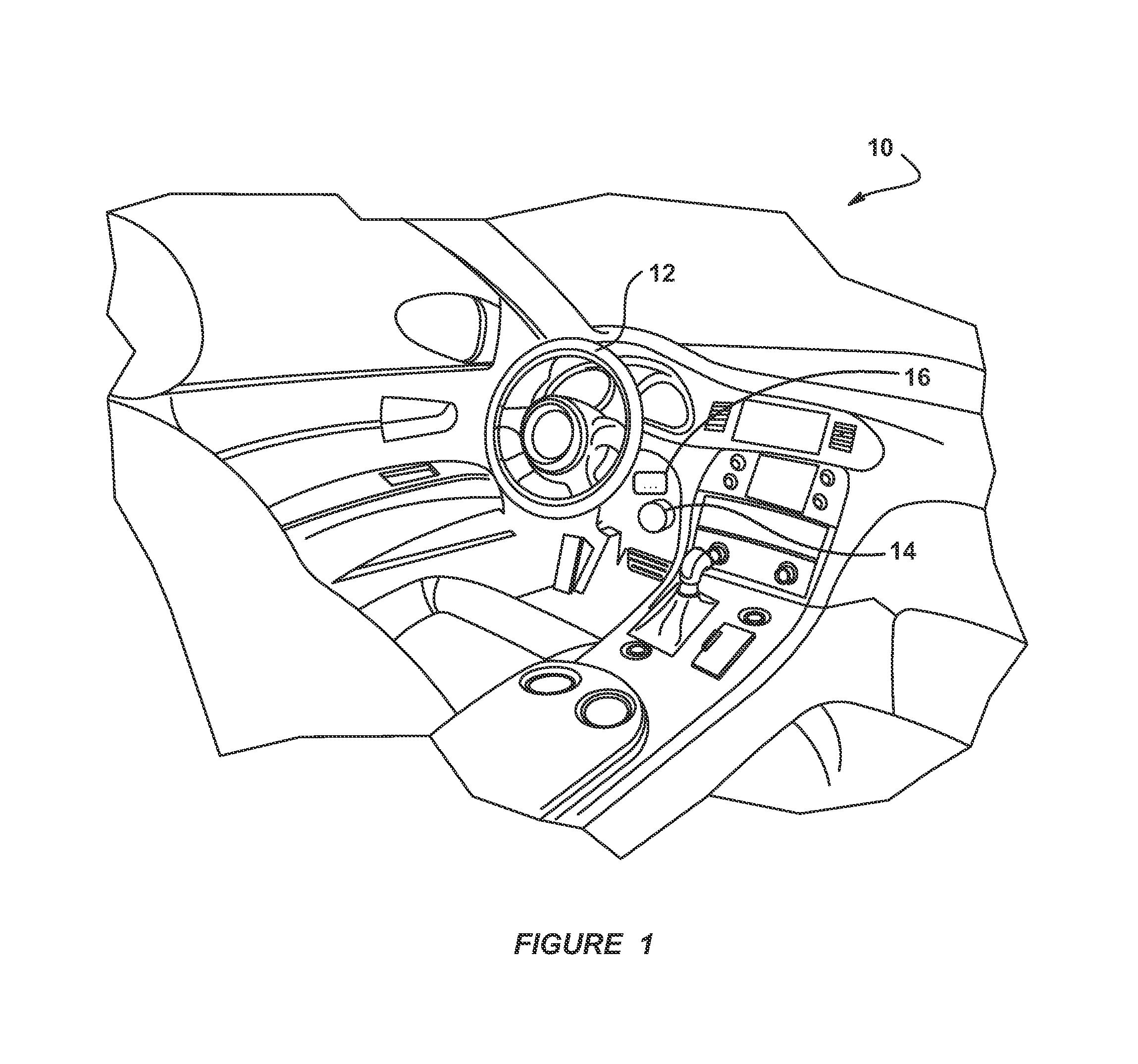
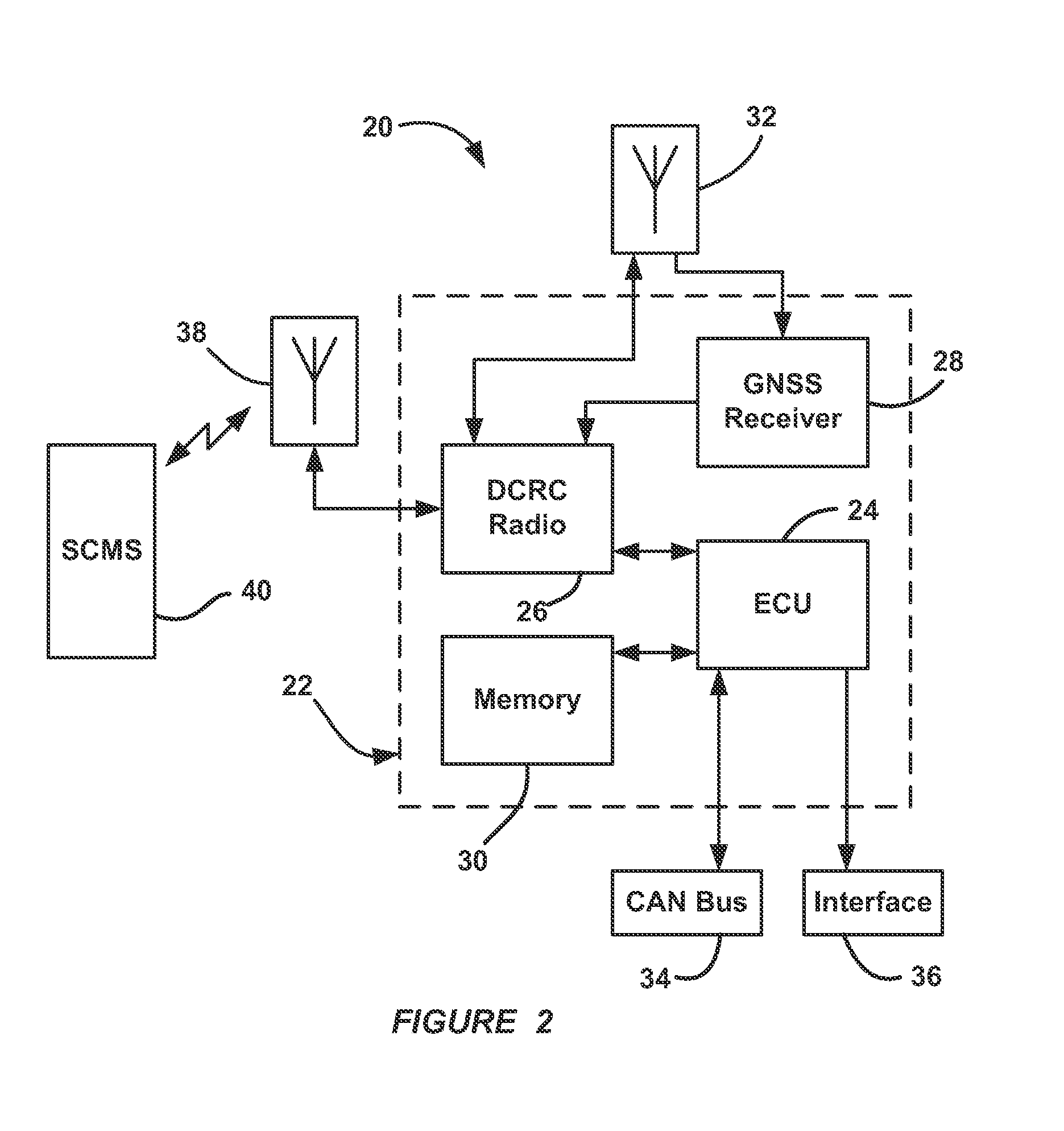
InactiveUS20150005981A1Transmission systemsRegistering/indicating working of vehiclesElectricityCommunications system
An aftermarket plug-in safety device that allows a vehicle to communicate with other vehicles or infrastructures in a V2X communications system. The device includes a radio for transmitting and receiving signals and a GPS receiver for receiving GPS signals and providing vehicle position data. The device also includes a memory for storing digital security certificates and vehicle application data and a processor configured to be put in electrical communication with a vehicle CAN bus. The processor receives vehicle location signals from the GPS receiver, files from the memory and signals from the radio and providing signals for transmission to the radio. The processor identifies the vehicle that the plug-in device is coupled to and provides data on the CAN bus identifying the device. The processor also performs self-configuring operations based on type of vehicle, access to vehicle systems and location of the vehicle.
Owner:GM GLOBAL TECH OPERATIONS LLC
Digital Visualization and Perspective Manager
Methods, computer-readable media, software, and apparatuses may assist a consumer in keeping track of a consumer's accounts in order to prevent unauthorized access or use of the consumer's identified accounts. Upon discovery of a consumer's accounts, the methods, computer-readable media, software, and apparatuses may determine information that may be shared, used, or transferred by the companies, institutions, or organizations for each of the discovered accounts. The determined information may be visually displayed to the consumer along with recommendations regarding digital safety.
Owner:ALLSTATE INSURANCE
Digital security surveillance system
InactiveUS20070166001A1Easy to operateLow costTelevision system detailsAnalogue secracy/subscription systemsExternal storageDVD recorder
A digital security surveillance system allows a user to store selected security surveillance feeds while the user is simultaneously watching or reviewing another feed. User control commands are accepted and sent through the system. The system parses the resulting digital stream and generates identifying information associated with at least one video segment of the digital stream. The video segments are stored on a storage device. When a security surveillance feed is requested for display, a corresponding stored digital stream is found and its video segments are extracted from the storage device and sent to a decoder that converts the digital stream into display output signals. The security surveillance feeds can be simultaneously sent to an external storage device such as a DVD recorder or VCR.
Owner:TIVO SOLUTIONS INC
Cryptographic methods and devices for pseudo-random generation, encrypting data, and cryptographically hashing a message
InactiveUS20100142705A1Improve protectionHardware implementationEncryption apparatus with shift registers/memoriesSecret communicationComputer hardwareData sequences
The invention relates to the general field of digital security and more particularly cryptography. In particular it proposes a device and a method of encrypting a sequence of data. The invention also relates to a cryptographic device (1) and a cryptographic method of generating a pseudo-random data sequence (13) and their favored use in the field of digital security, in particular for encrypting and decrypting data and for cryptographically hashing messages.
Owner:ORIDAO
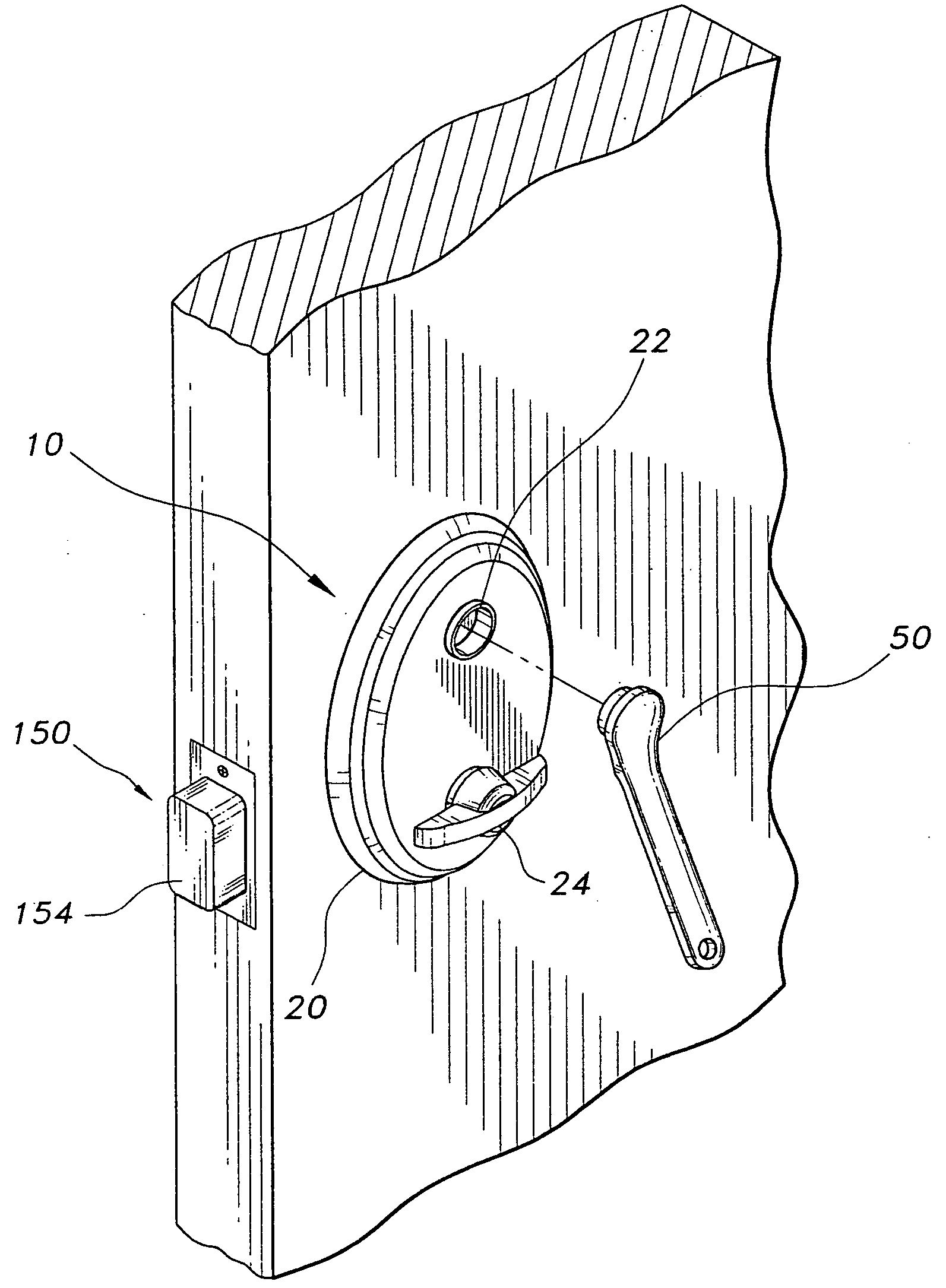
Deadbolt lock with electronic touch-key
InactiveUS7069755B2Save livesEasy to replaceAnti-theft cycle devicesAnti-theft devicesMicrocomputerMotor drive
Owner:LIES WILLIAM B +3
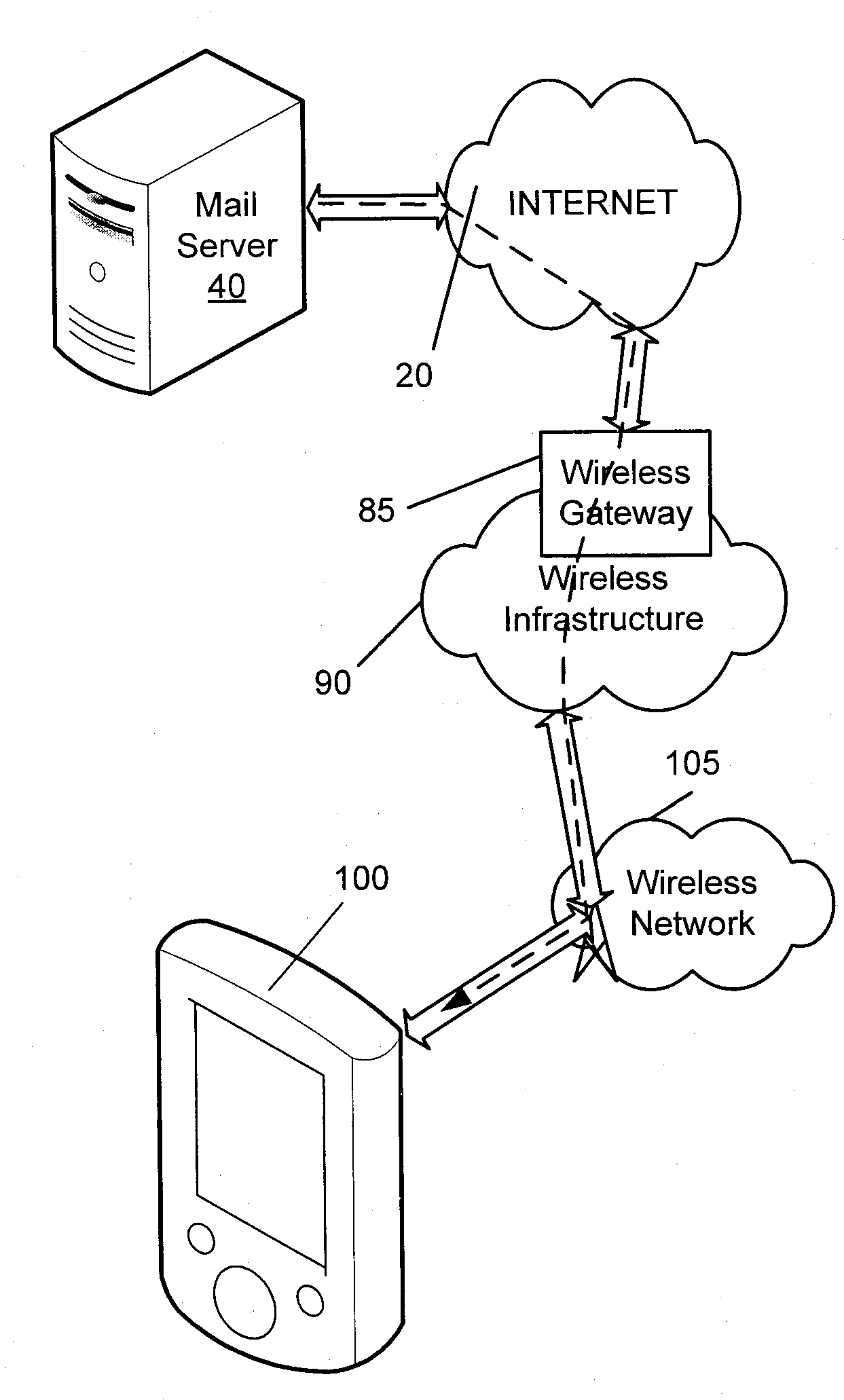
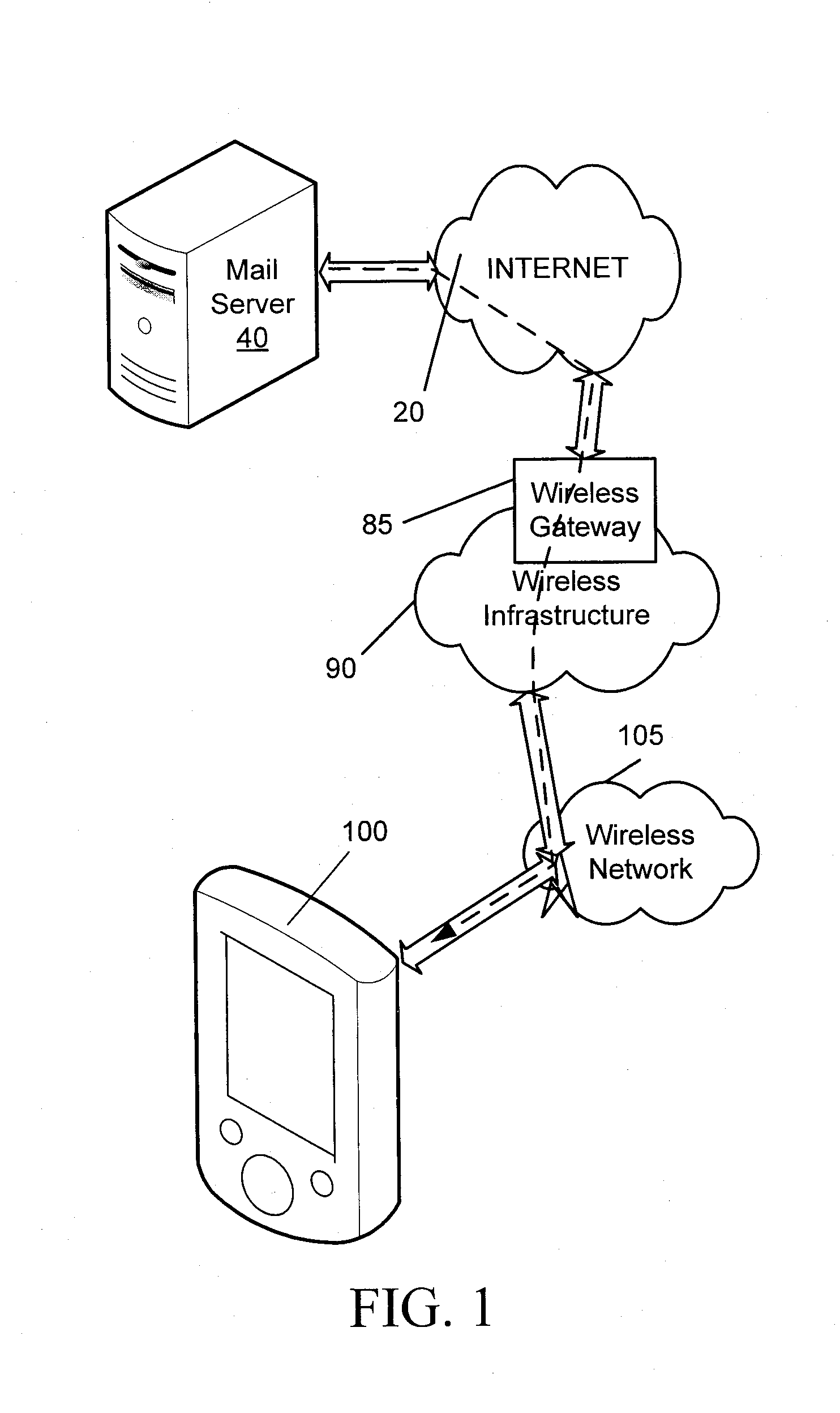
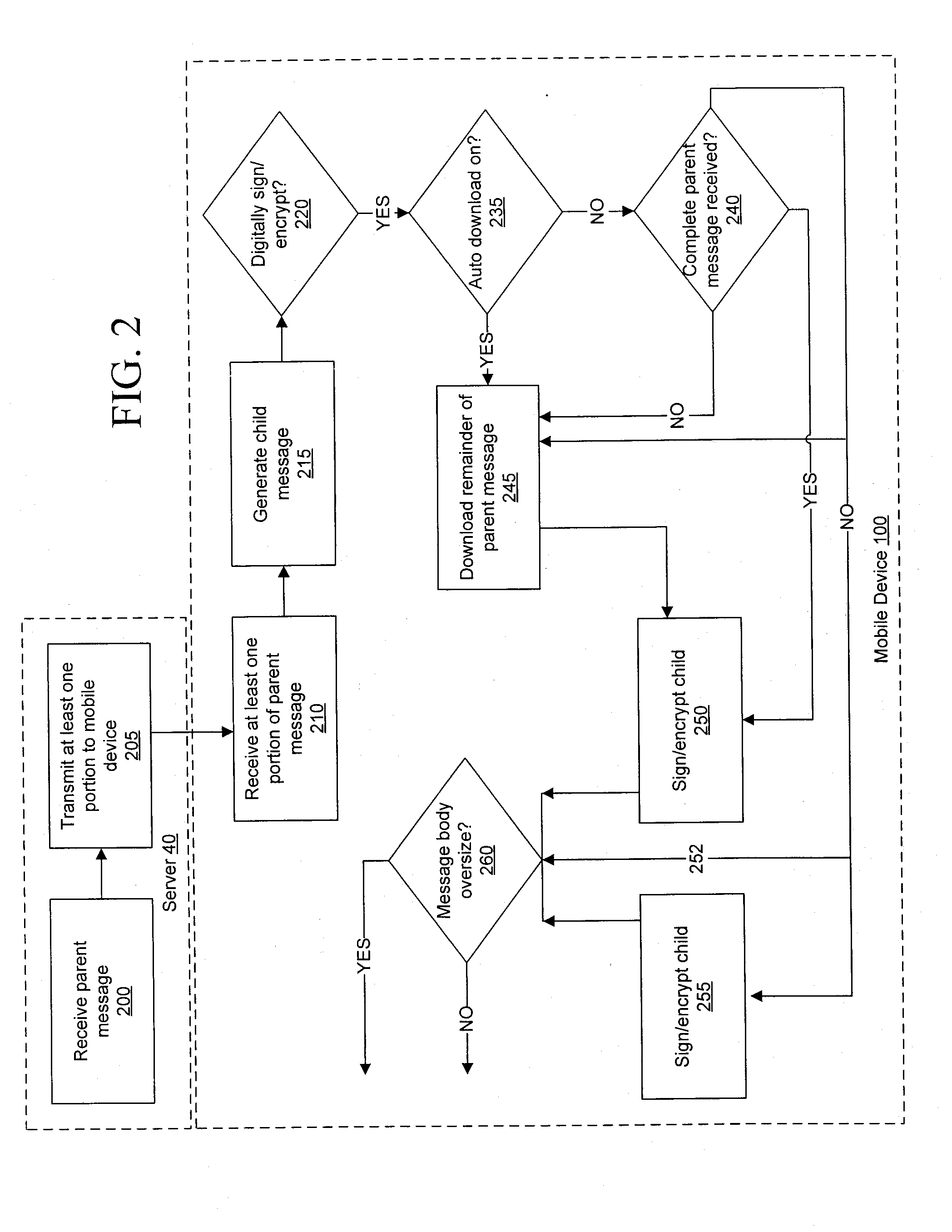
Secure message handling on a mobile device
ActiveUS20090034729A1Public key for secure communicationUser identity/authority verificationComputer hardwareMessage handling
Systems, methods, and software for providing digital security to a child message transmitted from a mobile device to a messaging server, where the mobile device typically does not transmit the parent message with the child message to the messaging server. Whether to apply digital security, such as encryption or a digital signature, or both, is determined, and if the mobile device does not include a complete copy of a parent message for insertion into the child message, the mobile device selectively downloads the parent message from the messaging server prior to the computation of a digital signature or prior to encryption. The systems and methods may also provide a check of the child message size, when the child message includes inserted parent content, to ensure that the child message does not exceed any prescribed limits on message size.
Owner:MALIKIE INNOVATIONS LTD
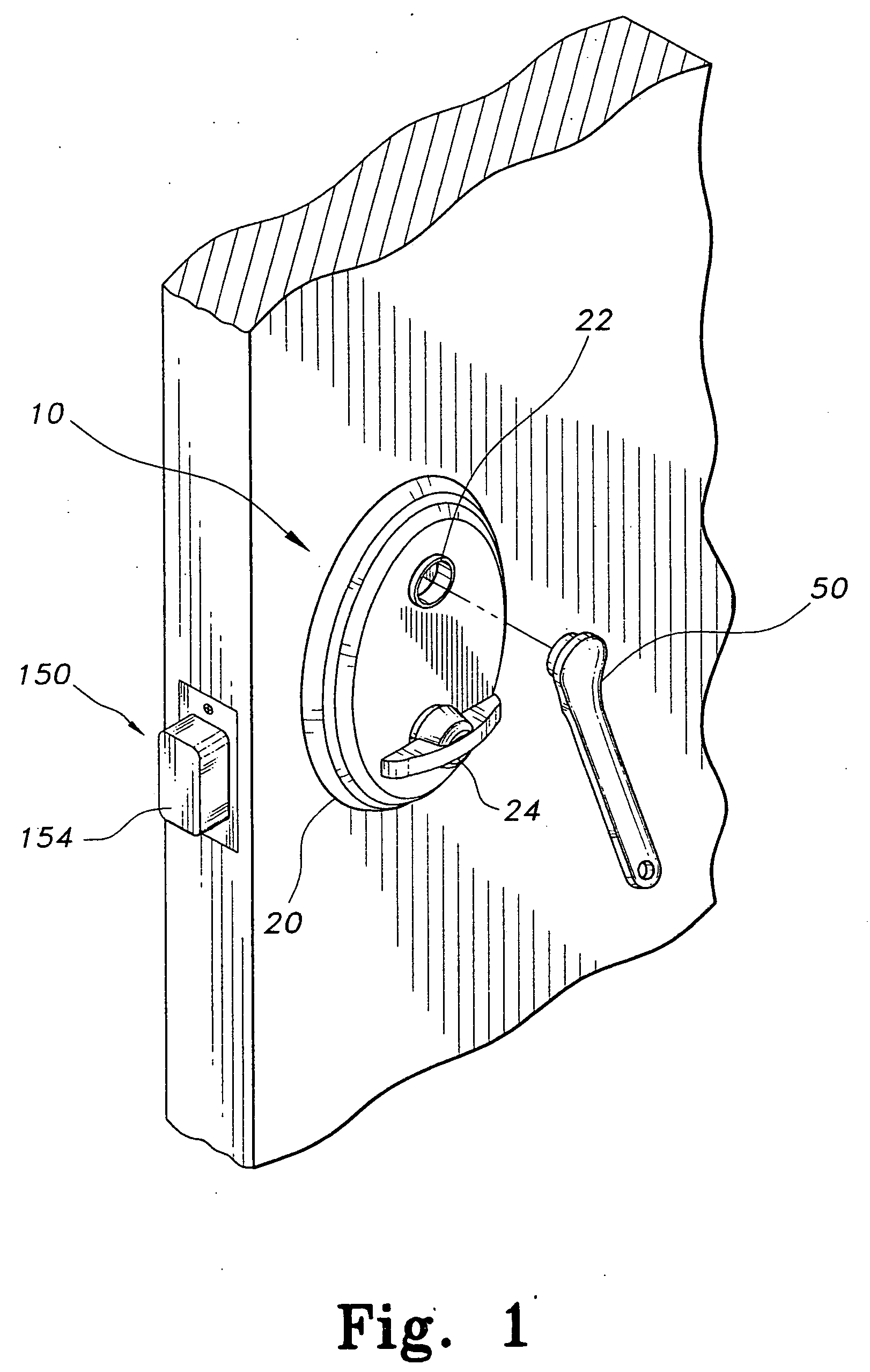
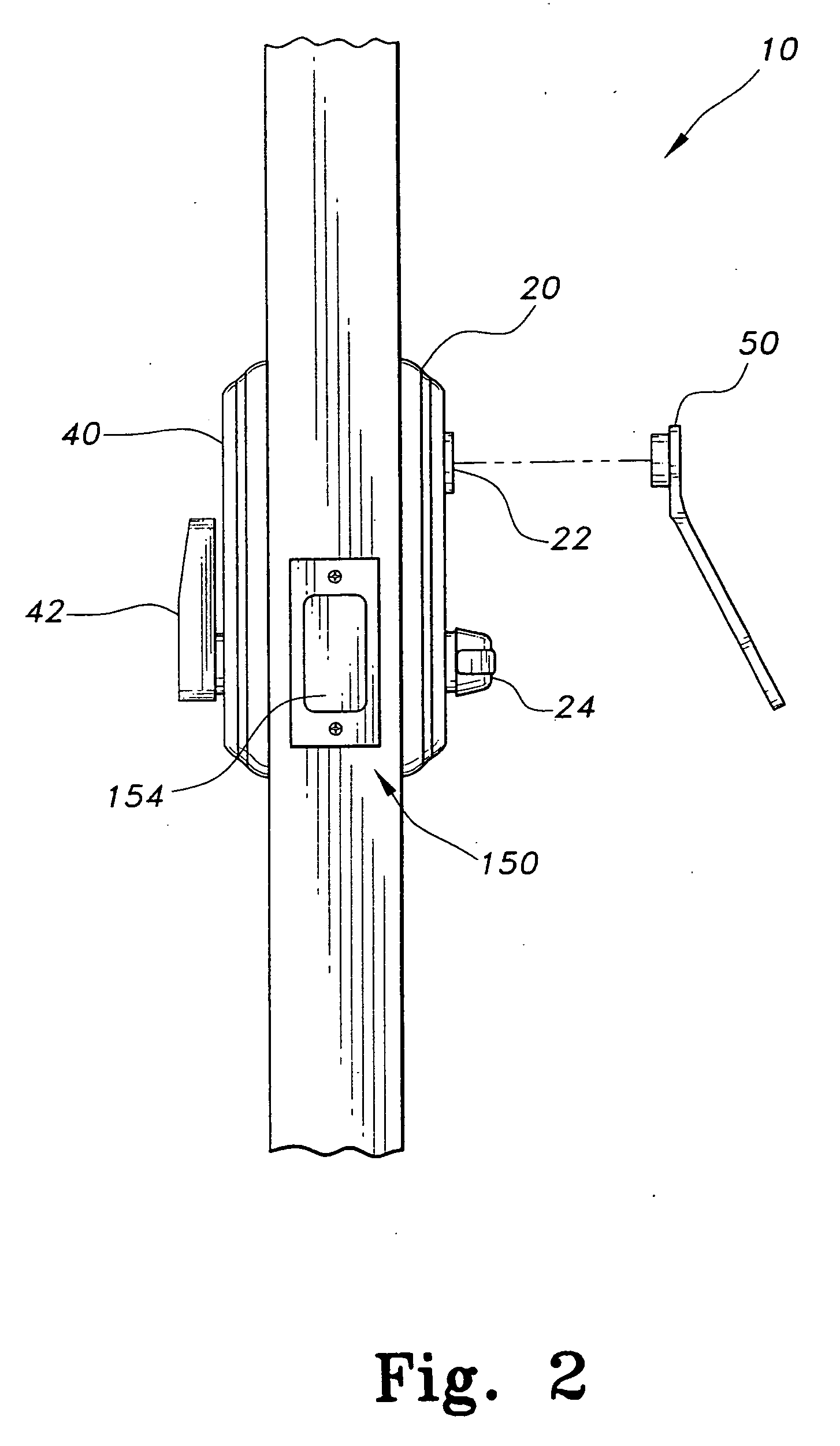
Deadbolt lock with electronic touch-key
InactiveUS20050144994A1Easy to replaceReduce stepsAnti-theft cycle devicesAnti-theft devicesMicrocomputerMotor drive
A deadbolt lock has a housing and a deadbolt latch mounted to the housing. The deadbolt latch has a bolt that is moveable between an extended, locked position, and a retracted, unlocked position. An outside thumb-turn rotatably mounted to the housing. A motor-driven axial clutch is connected between the deadbolt latch and the outside thumb-turn. The bolt is movable by the thumb-turn only when the clutch is engaged. A microcomputer disposed within the housing. An electric motor is connected between the microcomputer and the clutch for engaging and disengaging the clutch. An electronic touch-key reader is disposed in the housing. The electronic touch-key reader is electronically connected to the microcomputer and is capable of reading a digital security code from an electronic touch-key applied thereto. The microprocessor actuates the electric motor to engage the clutch only when an authorized digital security code is read by the electronic touch-key reader.
Owner:LIES WILLIAM B +3
Method and device for providing digital security
ActiveUS8446250B2Mitigate such drawbackEfficient use ofElectric signal transmission systemsMultiple keys/algorithms usagePhysical systemDigital security
This invention relates to a method and system for providing digital security by means of a reconfigurable physical uncloneable function, RPUF. The RPUF comprises a physical system constituted by distributed components arranged to generate a first response when receiving a first challenge at a point of the physical system. The physical reconfiguring of the RPUF comprises redistributing the components such that they generate a second response, which differs from said first response, when again applying the first challenge at the point. The reconfiguration step is further utilized in providing secure storage for digital items. The digital item is data of any kind, including data that needs to be accessed and updated, i.e. which is dynamic in nature. The method is exemplified by implementations such as secure storage of a key, a secure counter and a seed generator.
Owner:INTRINSIC ID
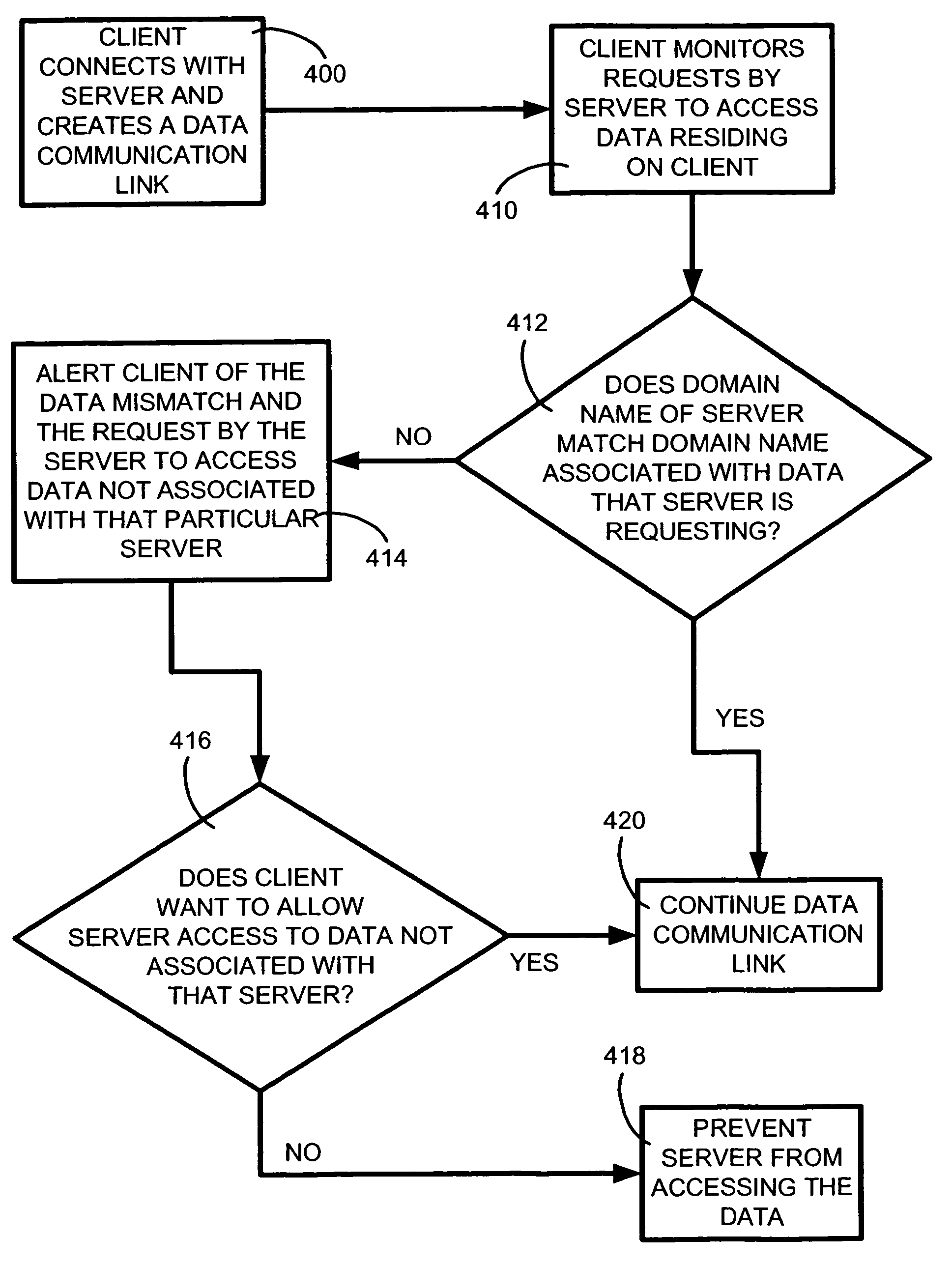
System and method for alerting computer users of digital security intrusions
InactiveUS6973580B1Digital data processing detailsUser identity/authority verificationGraphicsComputer users
The present invention is embodied in a system and method for monitoring and alerting remote client users of digital intrusions of their computers by host servers. In general, the present invention monitors actions taken by host servers relating to information about the remote client and displays graphical alerts when a digital intrusion or a breach of security occurs during a network connection, such as a connection to the Internet, with the host server. Specifically, the present invention monitors certain aspects of the remote client user s interaction with host servers. Based on certain interaction, such as an attempt by the host server to retrieve non-related information about the remote client, the remote client user can be provided with a graphical alert. This allows the remote client user to make an informed decision whether or not to allow certain host server sites to retrieve the client user s personal information.
Owner:IBM CORP
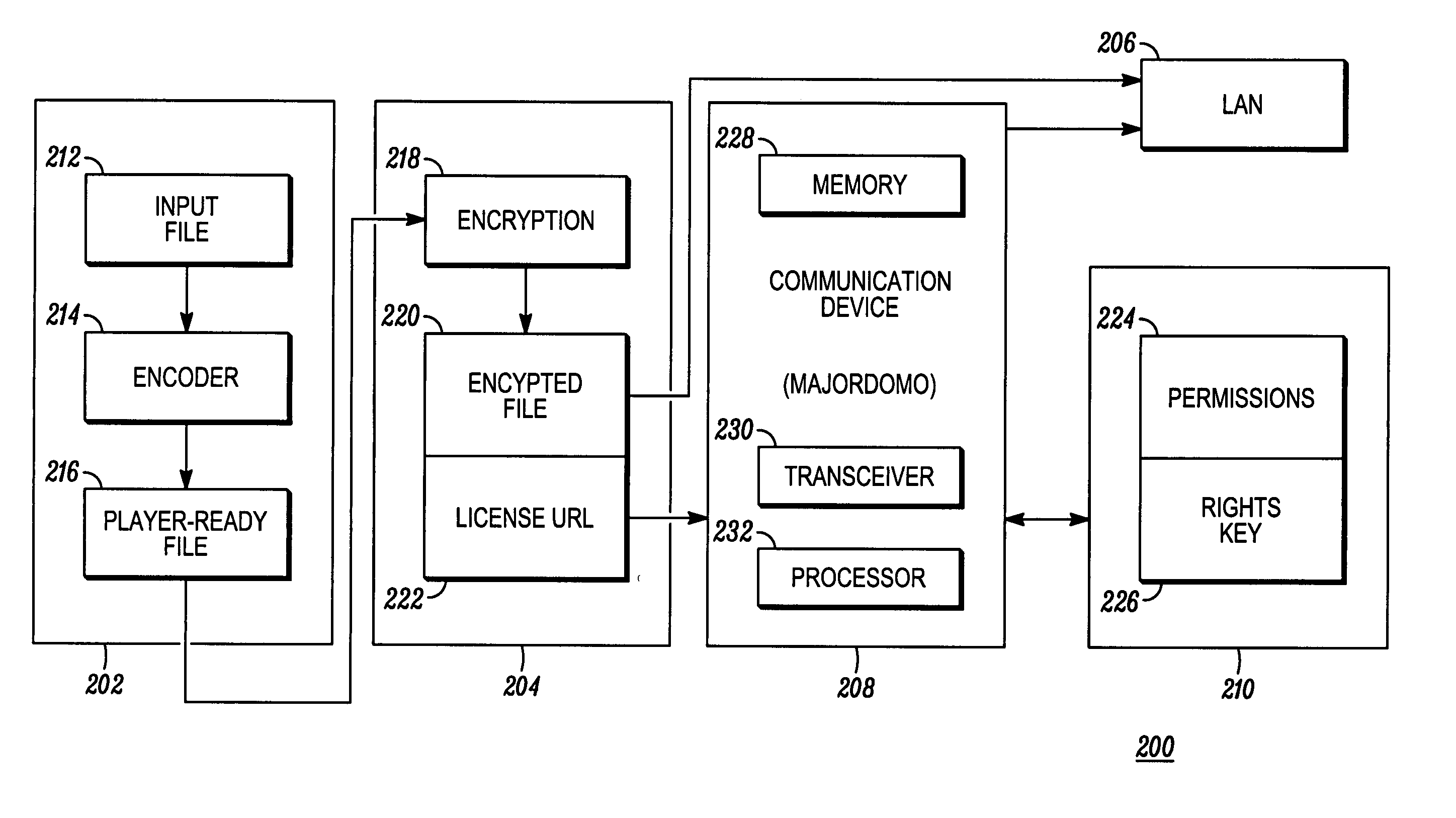
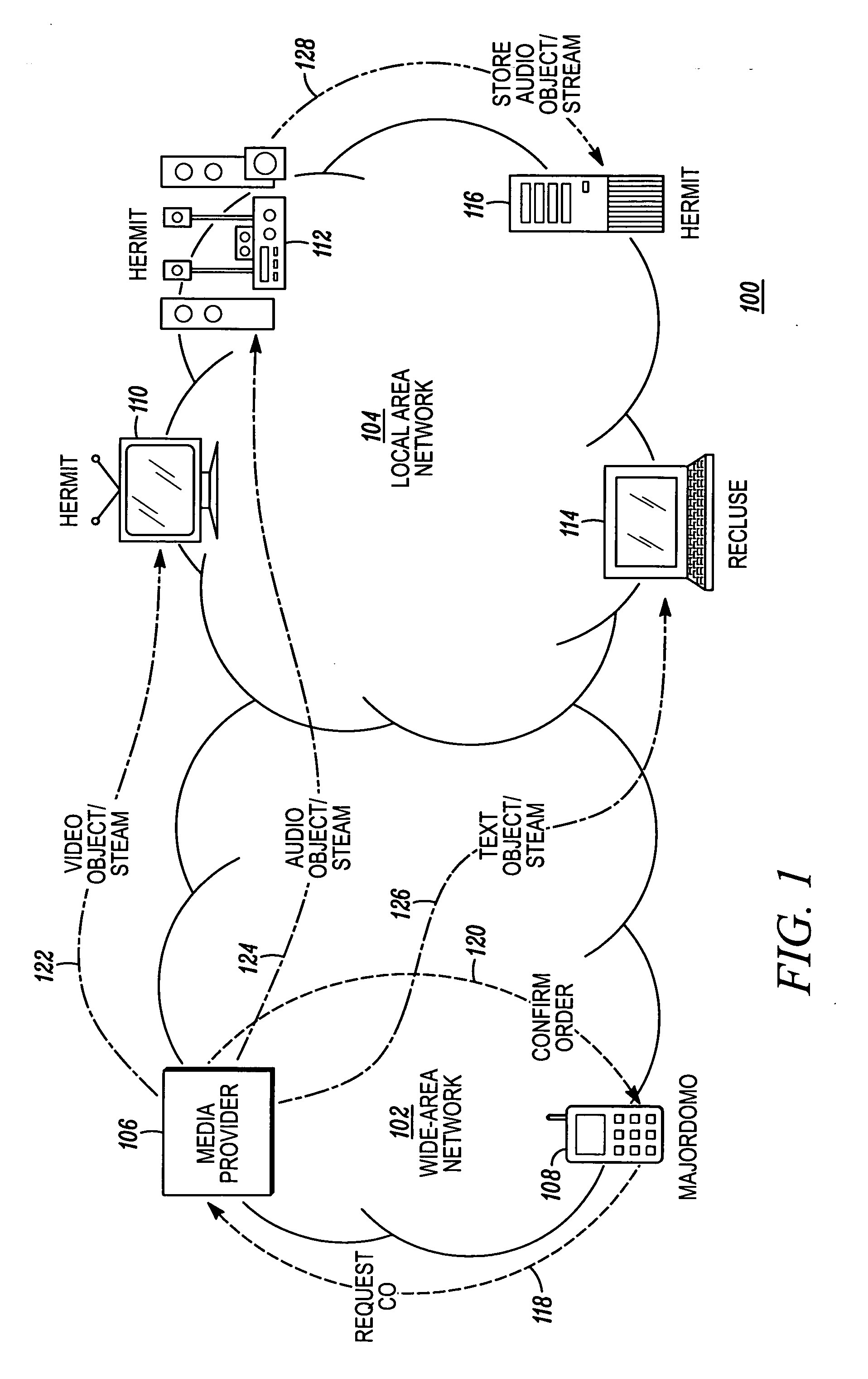
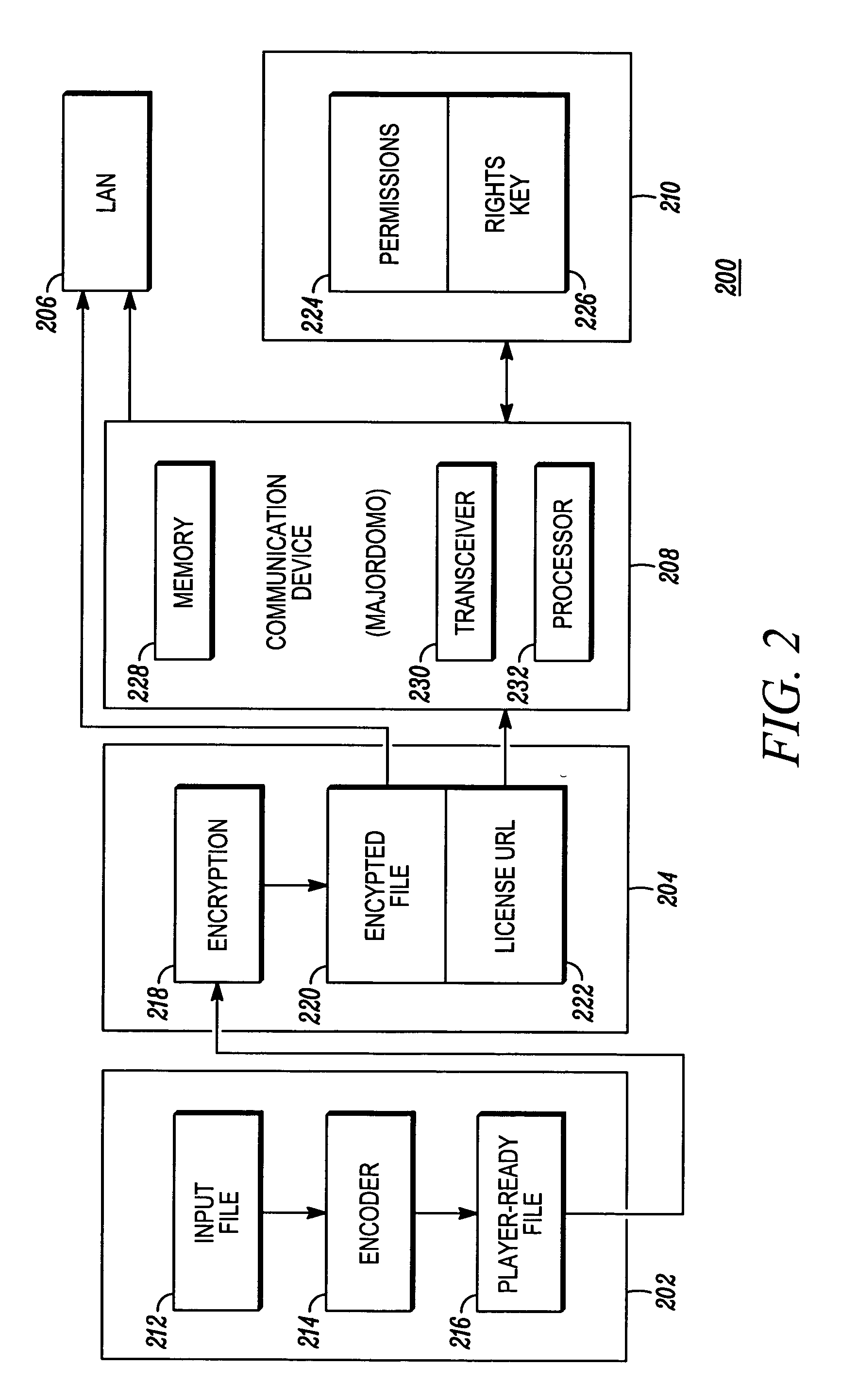
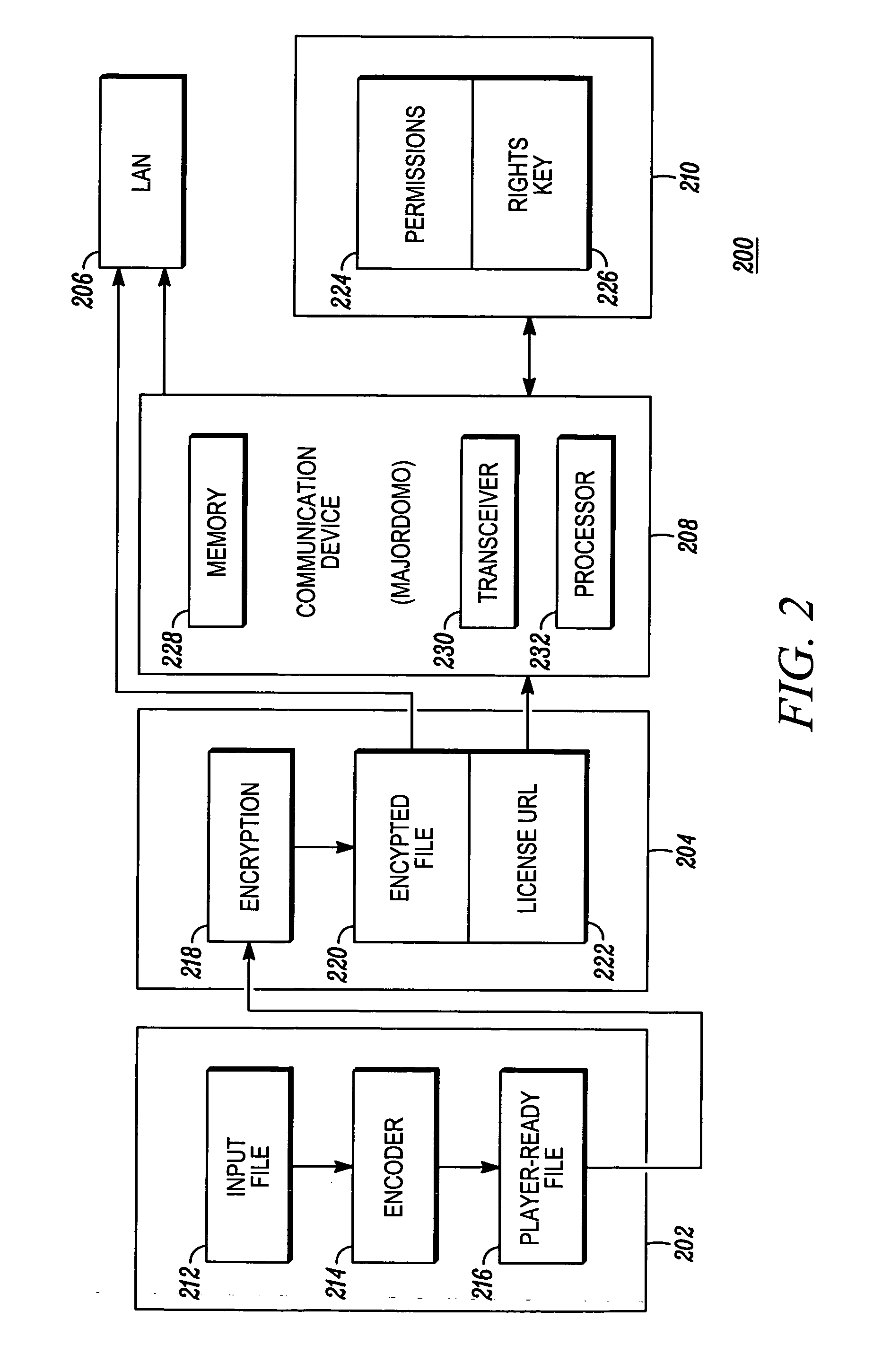
Digital security for distributing media content to a local area network
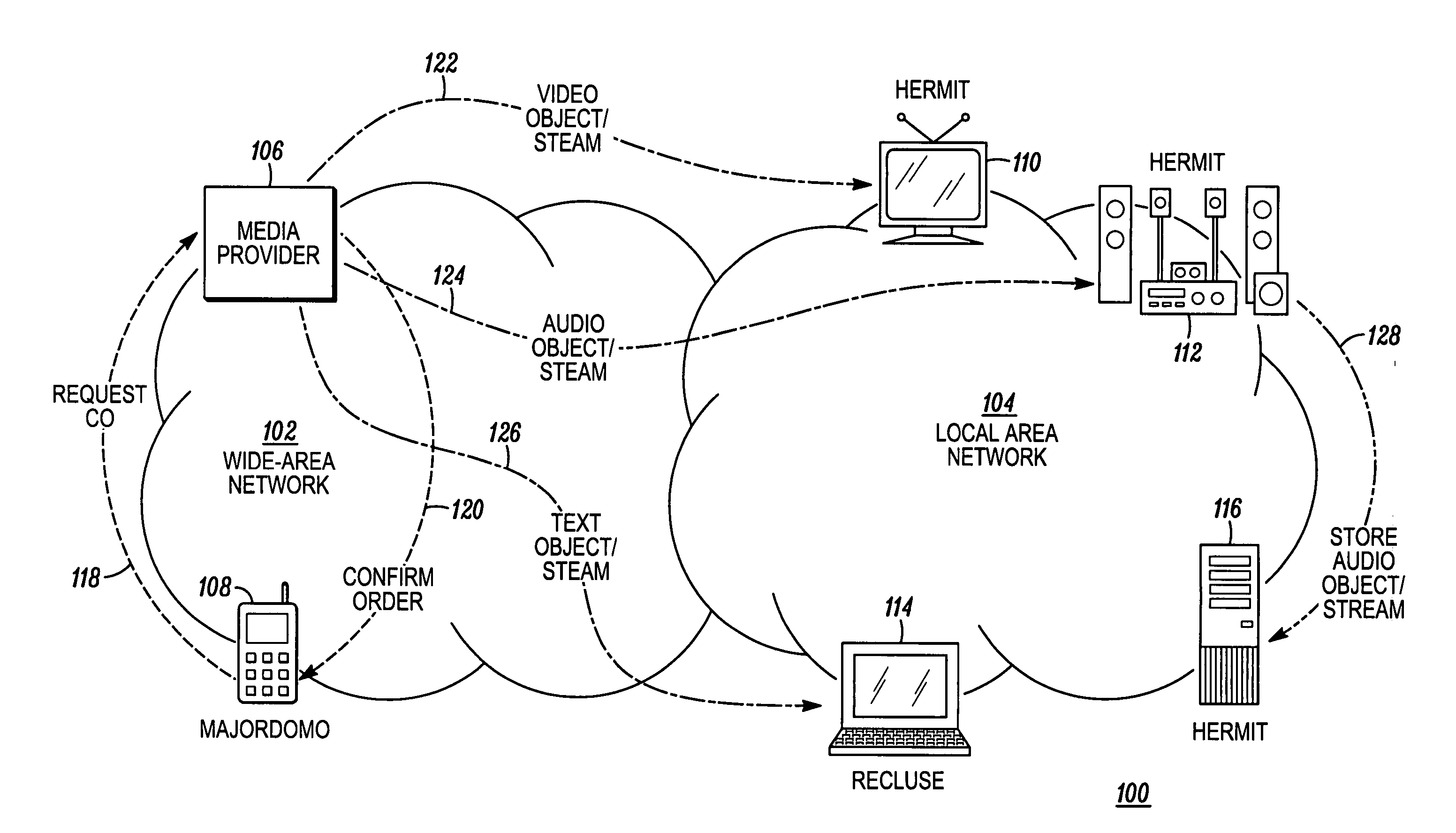
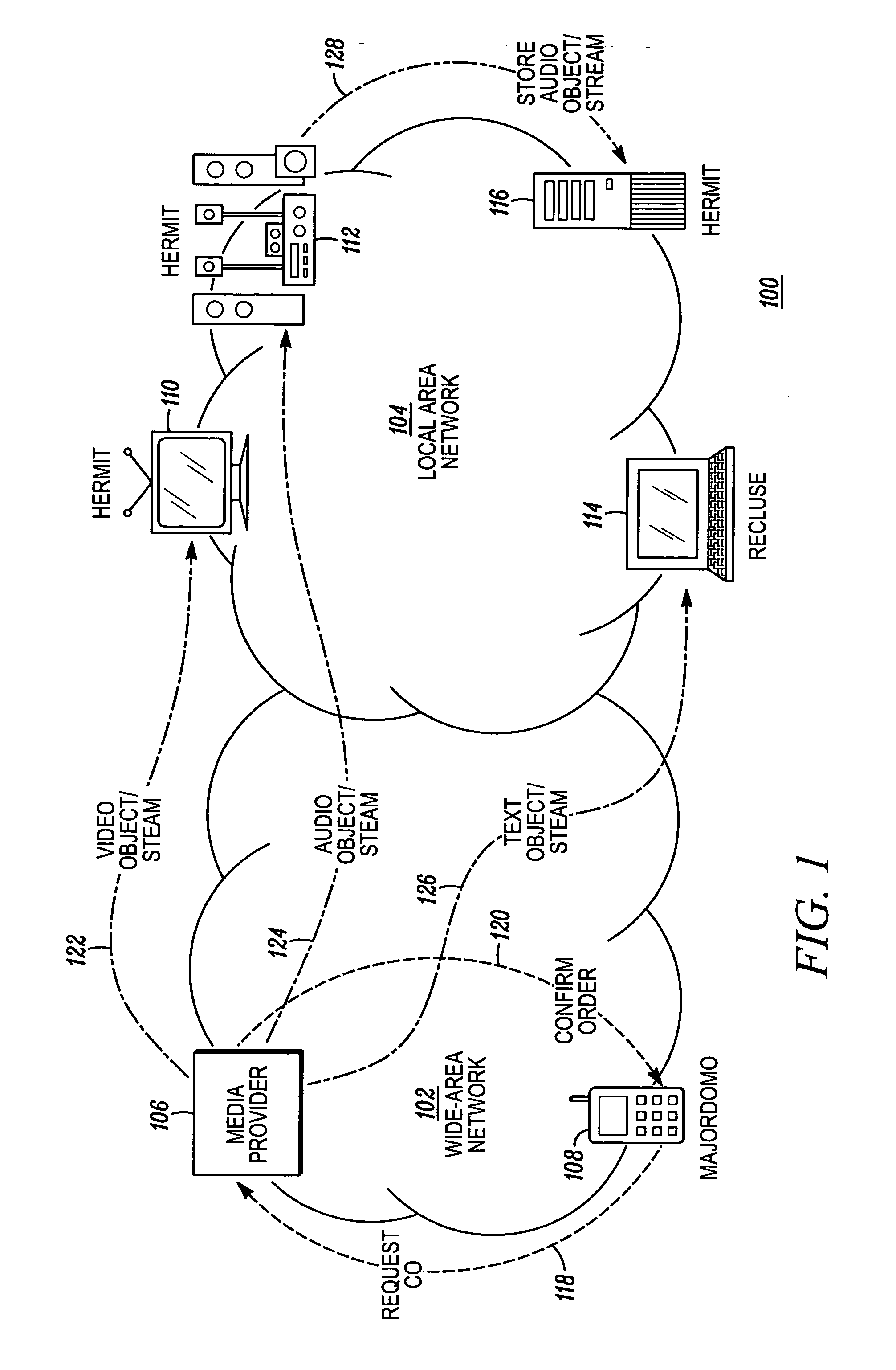
InactiveUS20070088660A1Digital computer detailsProgram/content distribution protectionThird partyKey storage
A digital security system (100) for distributing media content to a local area network (104). The system (100) comprises a media provider (106), media devices (110-116) for receiving media content from the media provider (106) and a remote agent (108) for communicating with the media provider (106) and the media devices (110-116). The media provider (106), or associated third party, has encrypted media content and a content key corresponding to the encrypted media content. Each media device (110-116) has content storage for receiving the encrypted media content, and key storage for receiving the content key. The remote agent (108) obtains the content key from the media provider, (106) encrypts the content key with a network privacy key, and send the encrypted content key to the media devices (110-116). When the media devices (110-116) receive the encrypted media content from the media provider (106), they will be able to decrypt the encrypted content key using the network privacy key and decrypt the encrypted media content using the decrypted content key.
Owner:MOTOROLA INC
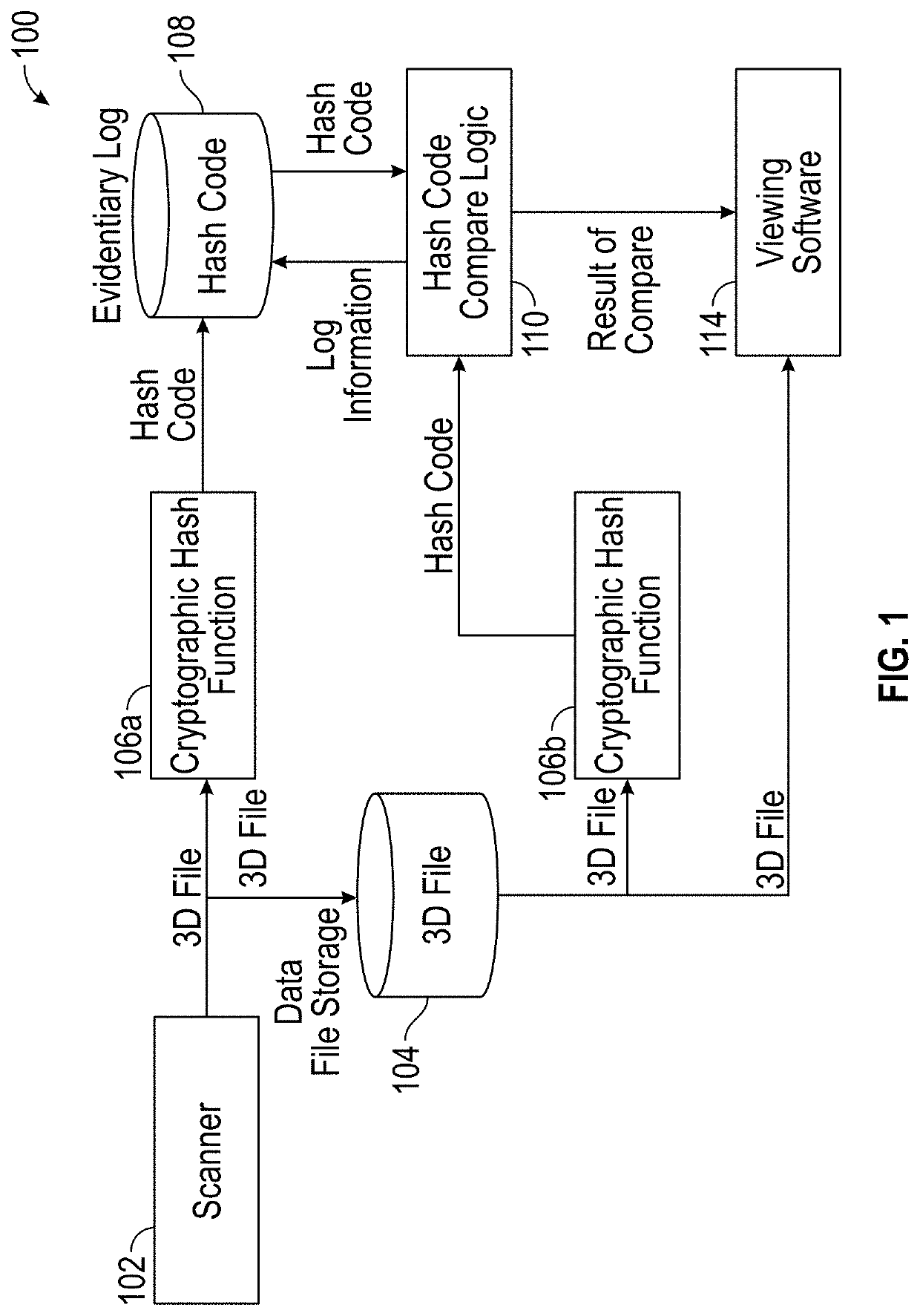
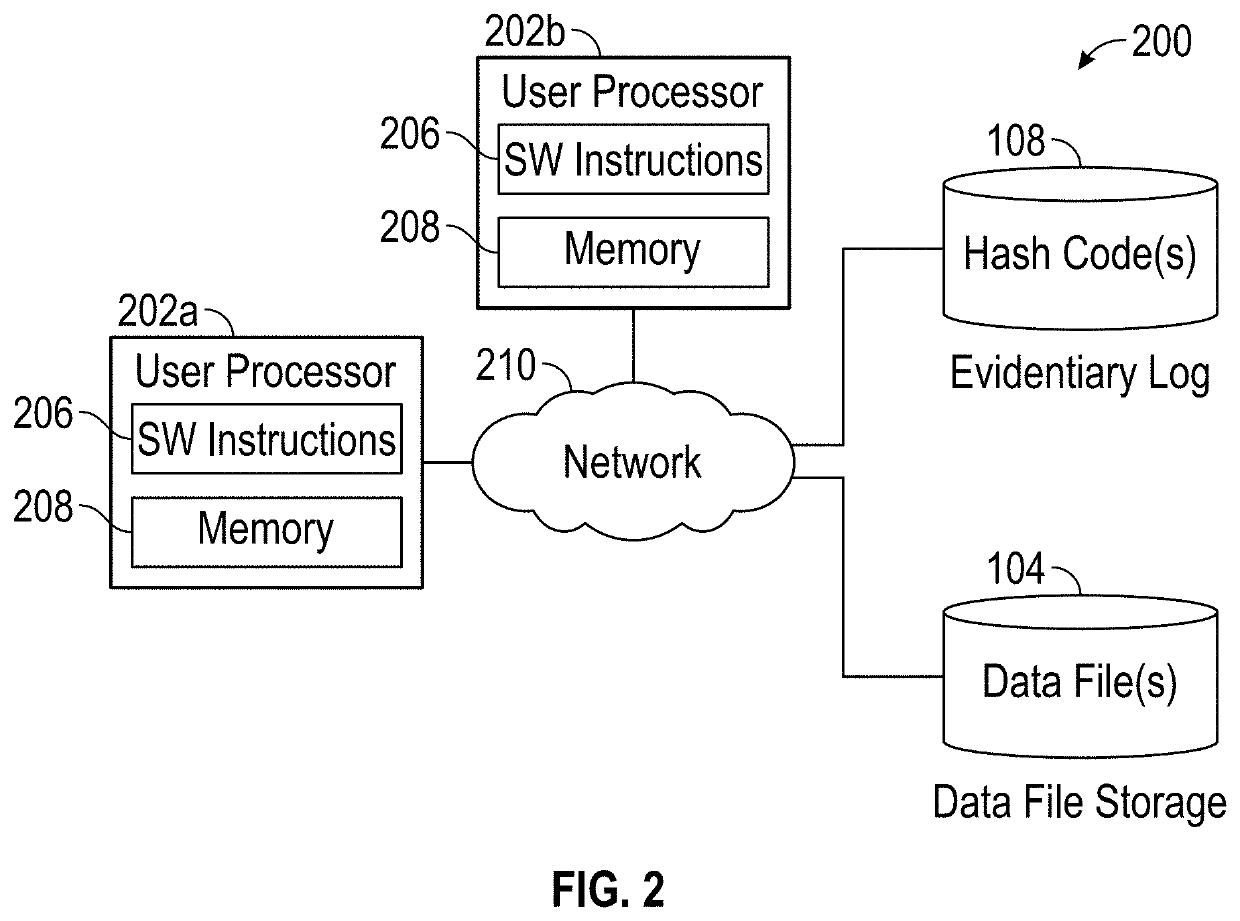
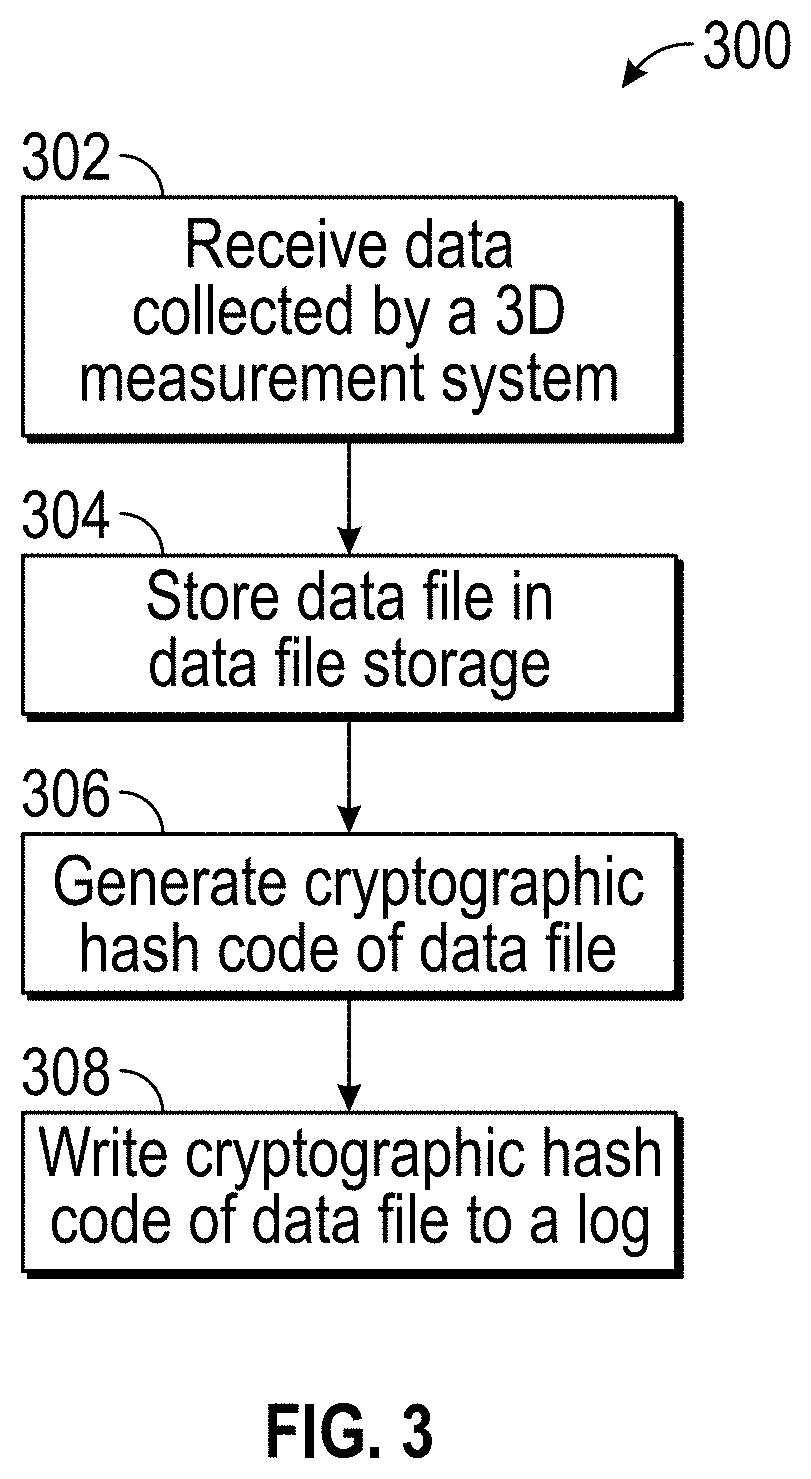
Securing data acquired by coordinate measurement devices
Securing data acquired by coordinate measurement devices including receiving a request from a requestor to access a data file including data that was acquired by a coordinate measurement device. The data file is retrieved and the content of the data file is authenticated. The authenticating includes retrieving an expected digital security attribute previously calculated by a digital security function based on content of the data file prior to the data file being retrieved. The authenticating also includes applying the digital security function to the data file to calculate an actual digital security attribute, and comparing the expected digital security attribute to the actual digital security attribute. Based on the comparing, a value of valid or not valid is assigned to an output of the authenticating.
Owner:FARO TECH INC
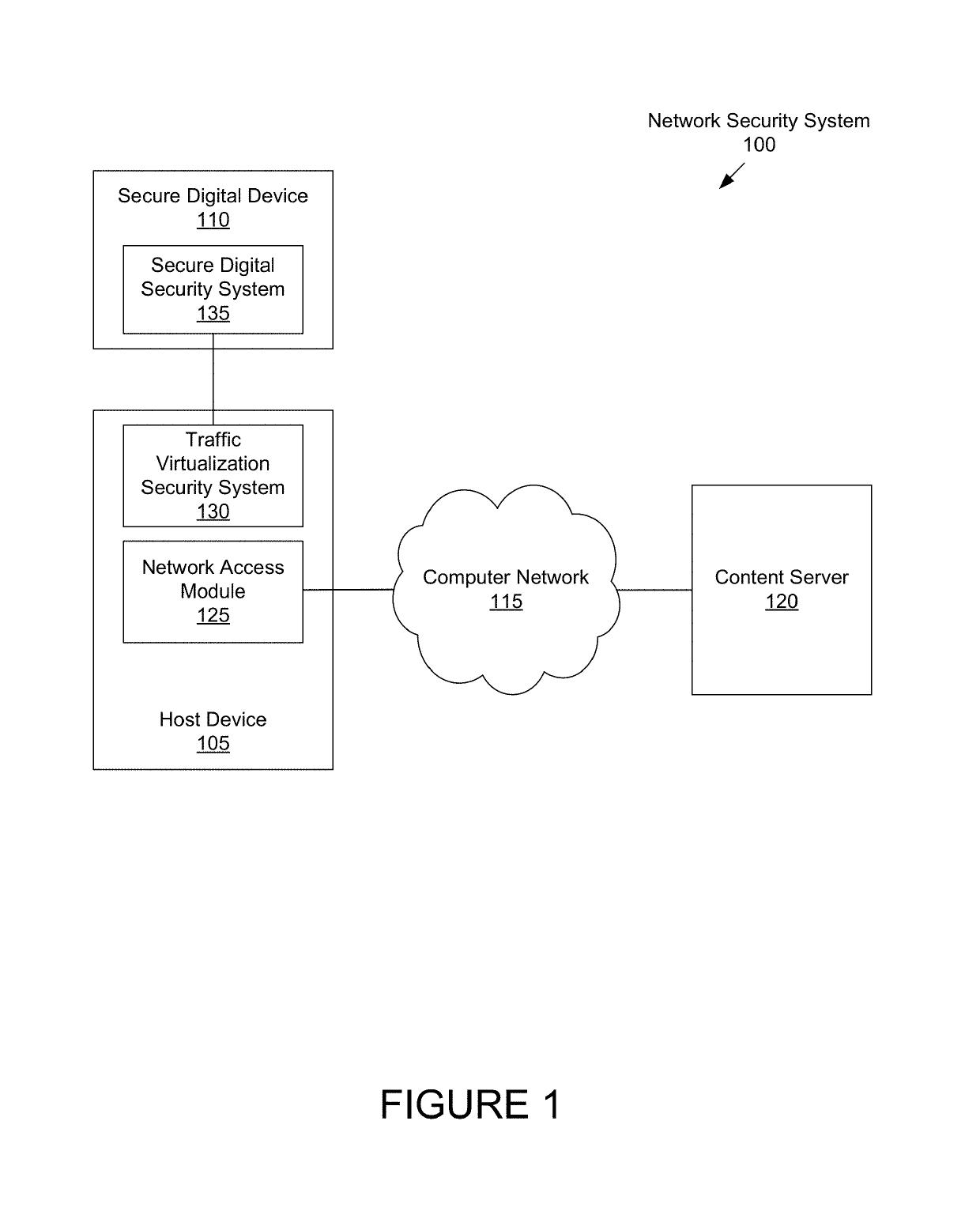
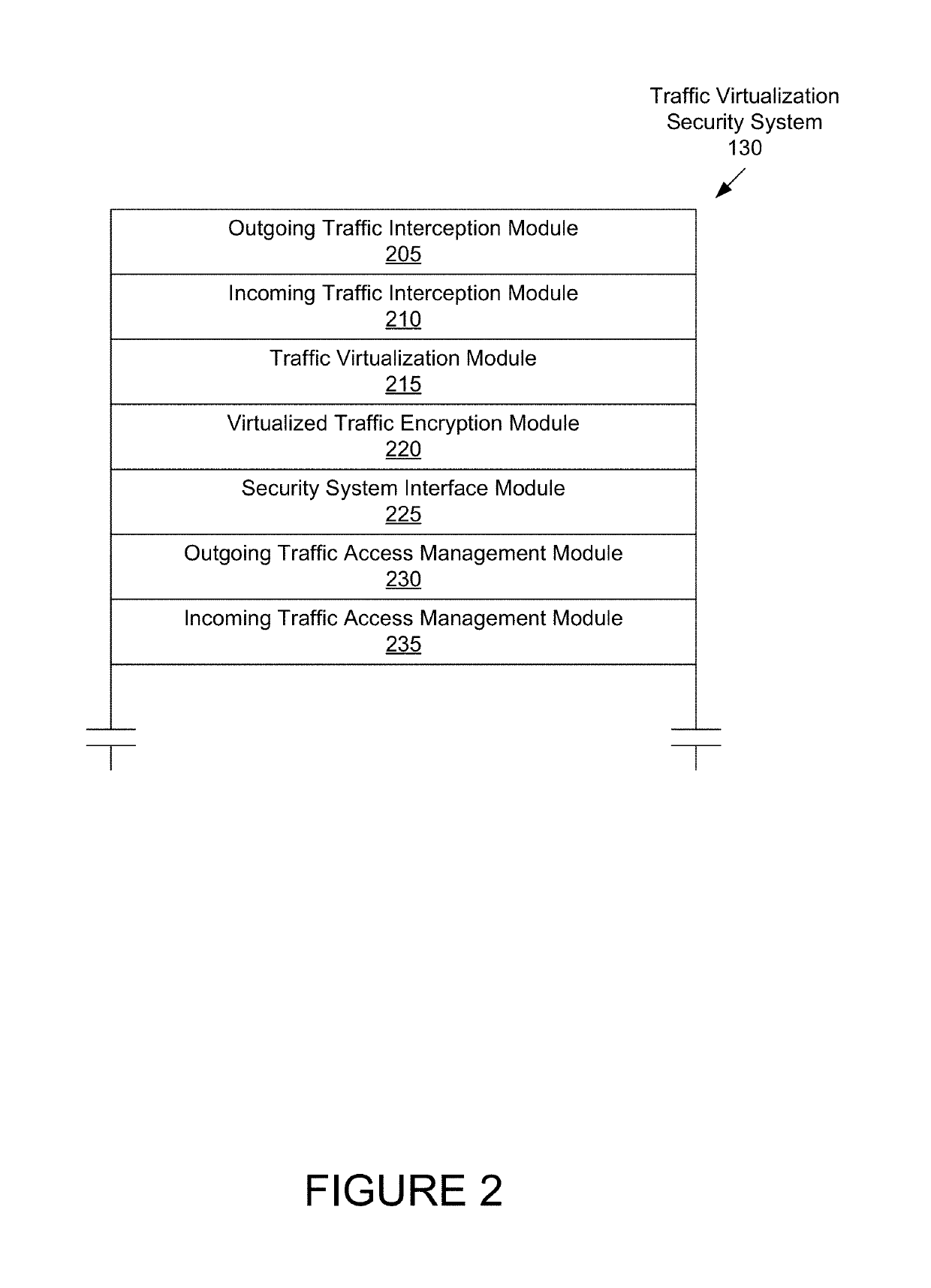
Systems and methods for providing network security using a secure digital device
A system may include a traffic interception module configured to intercept network traffic of a host device. A traffic virtualization module may be configured to generate a virtual file on the host device containing the intercepted network traffic. A security system interface module may be configured to provide the virtual file to a secure digital security system over a virtualized file interface coupling the host device to the secure digital security system, and to receive instructions to allow or to deny the network traffic from the secure digital security system over the virtualized file interface. A traffic access management module may be configured to allow or to deny the network traffic based on the instructions.
Owner:CUPP COMPUTING
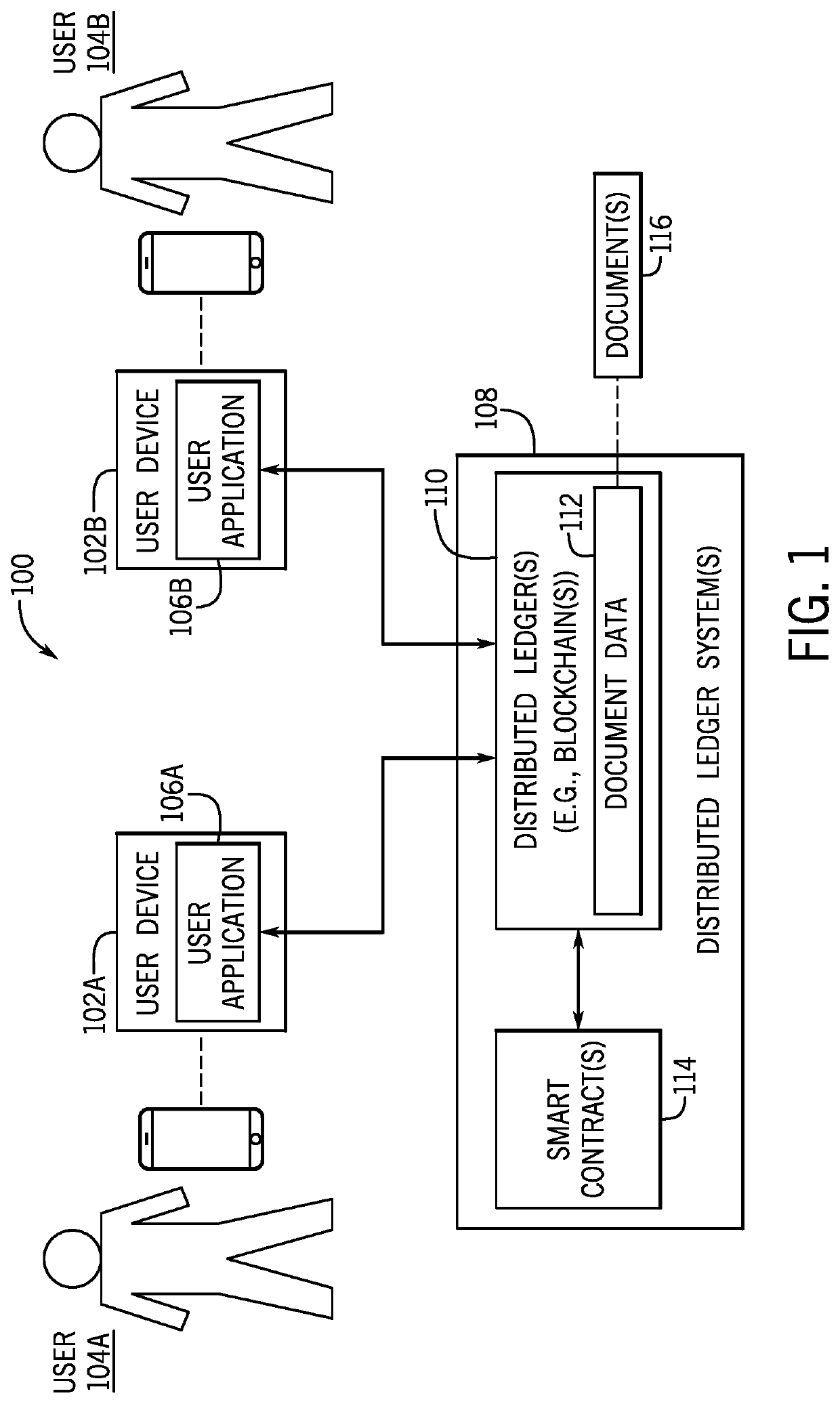
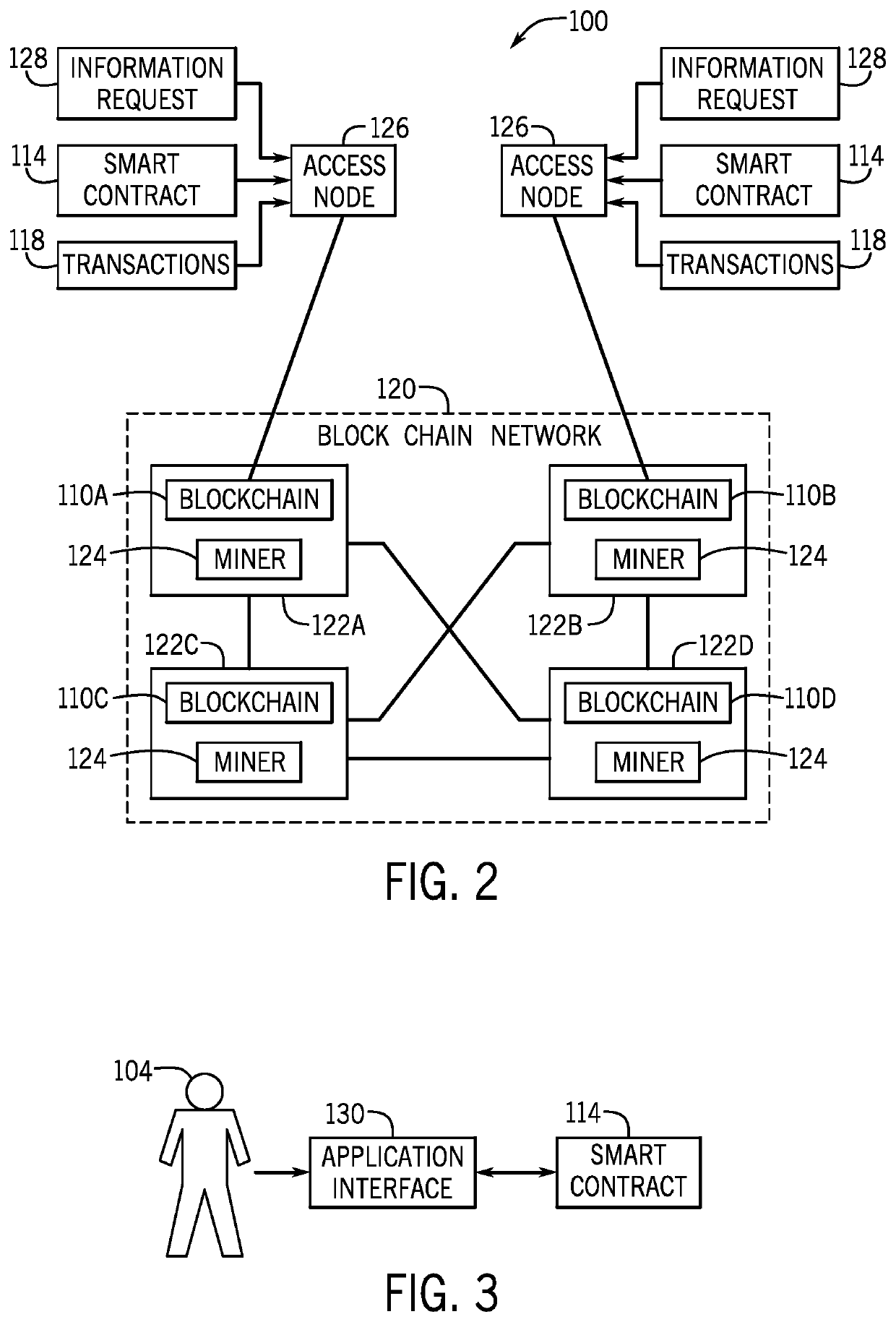
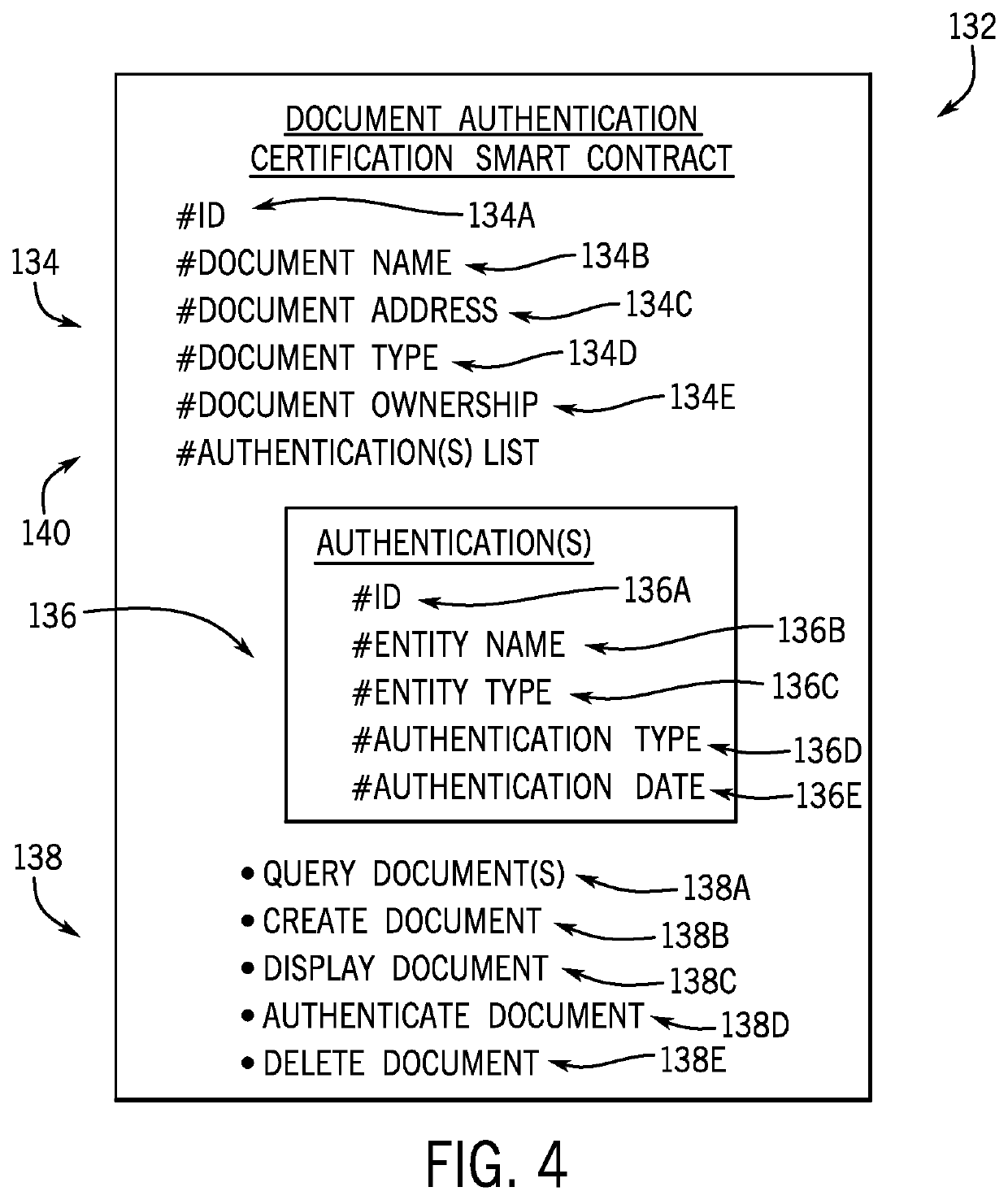
Document authentication certification with blockchain and distributed ledger techniques
ActiveUS11170092B1Guaranteed automatic operationEncryption apparatus with shift registers/memoriesUser identity/authority verificationNetwork onUnique identifier
Embodiments are described herein for document authentication certification using information stored on a distributed ledger such as a blockchain. A distributed ledger may securely store document data describing the document. Use of a distributed ledger may provide an immutable, readily auditable record of the history of the document. Each user participating in the system may be assigned a unique identifier to be used for conducting transactions on the distributed ledger network. A user may also be provided with a digital security token such as a cryptographic key that is useable to authenticate the user and enable access to the document data stored on the distributed ledger(s).
Owner:USAA
Methods of operation for plug-in wireless safety device
InactiveUS8930041B1Registering/indicating working of vehiclesDigital data processing detailsElectricityCommunications system
An aftermarket plug-in safety device that allows a vehicle to communicate with other vehicles or infrastructures in a V2X communications system. The device includes a radio for transmitting and receiving signals and a GPS receiver for receiving GPS signals and providing vehicle position data. The device also includes a memory for storing digital security certificates and vehicle application data and a processor configured to be put in electrical communication with a vehicle CAN bus. The processor receives vehicle location signals from the GPS receiver, files from the memory and signals from the radio and providing signals for transmission to the radio. The processor identifies the vehicle that the plug-in device is coupled to and provides data on the CAN bus identifying the device. The processor also performs self-configuring operations based on type of vehicle, access to vehicle systems and location of the vehicle.
Owner:GM GLOBAL TECH OPERATIONS LLC
Privacy proxy of a digital security system for distributing media content to a local area network
A local area network (504) for providing Media Provider control and user privacy when distributing media content to the local area network (504). The local area network (504) comprises media devices (510-514) and a proxy (528). The media devices (510-514) provide a description of the capabilities of the media devices (510-514) to a Media Provider (506) in response to receiving a query for the capabilities of the media devices (510-514) from the Media Provider (506). The media devices (510-514) also receive media content directed to the media devices (510-514) from the Media Provider (506). The media content includes content objects based on the capabilities of the media devices (510-514). The proxy (528) translates between generic device names known to the Media Provider (506) and physical device addresses corresponding to the media devices (510-514).
Owner:MOTOROLA INC
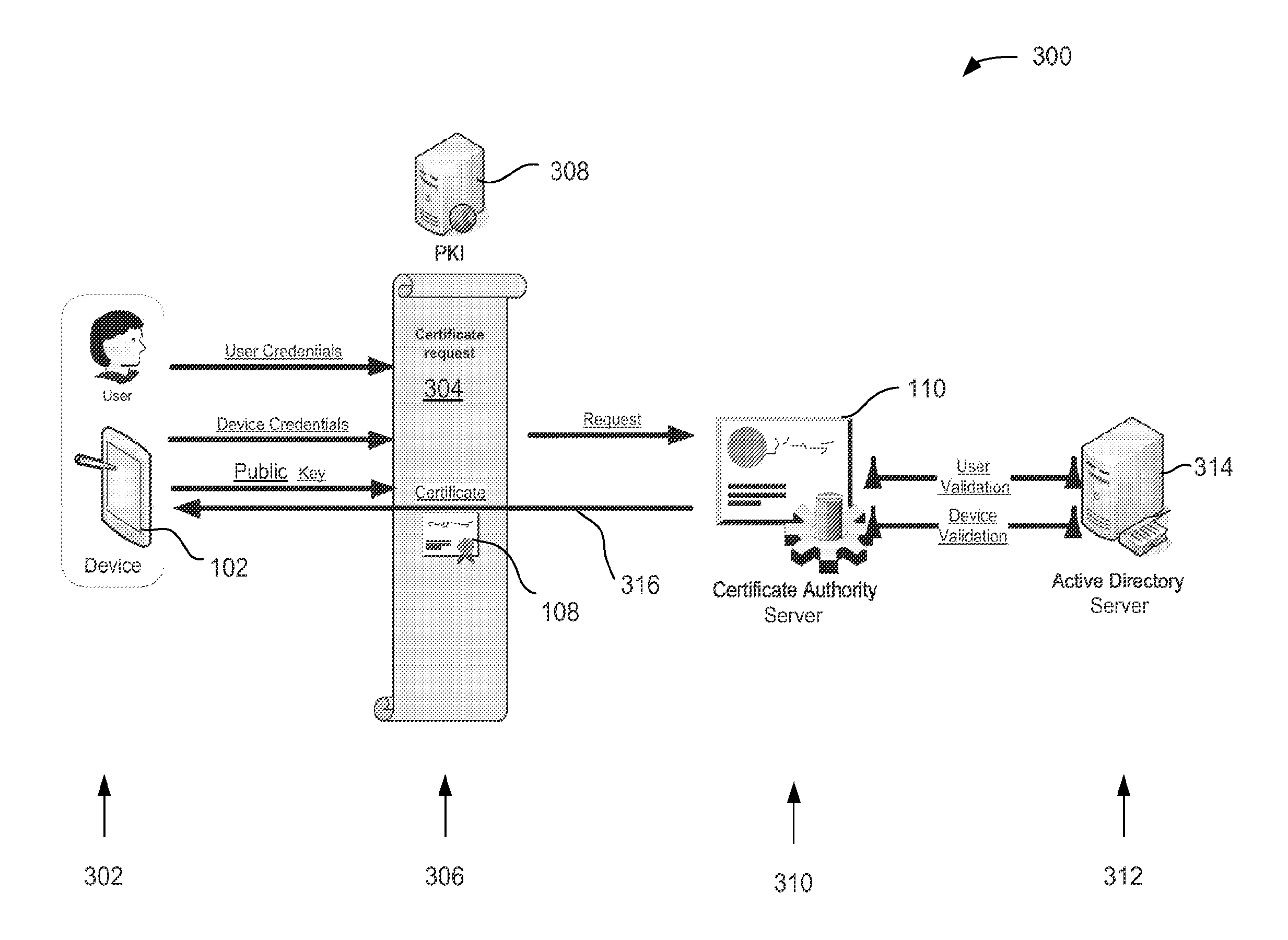
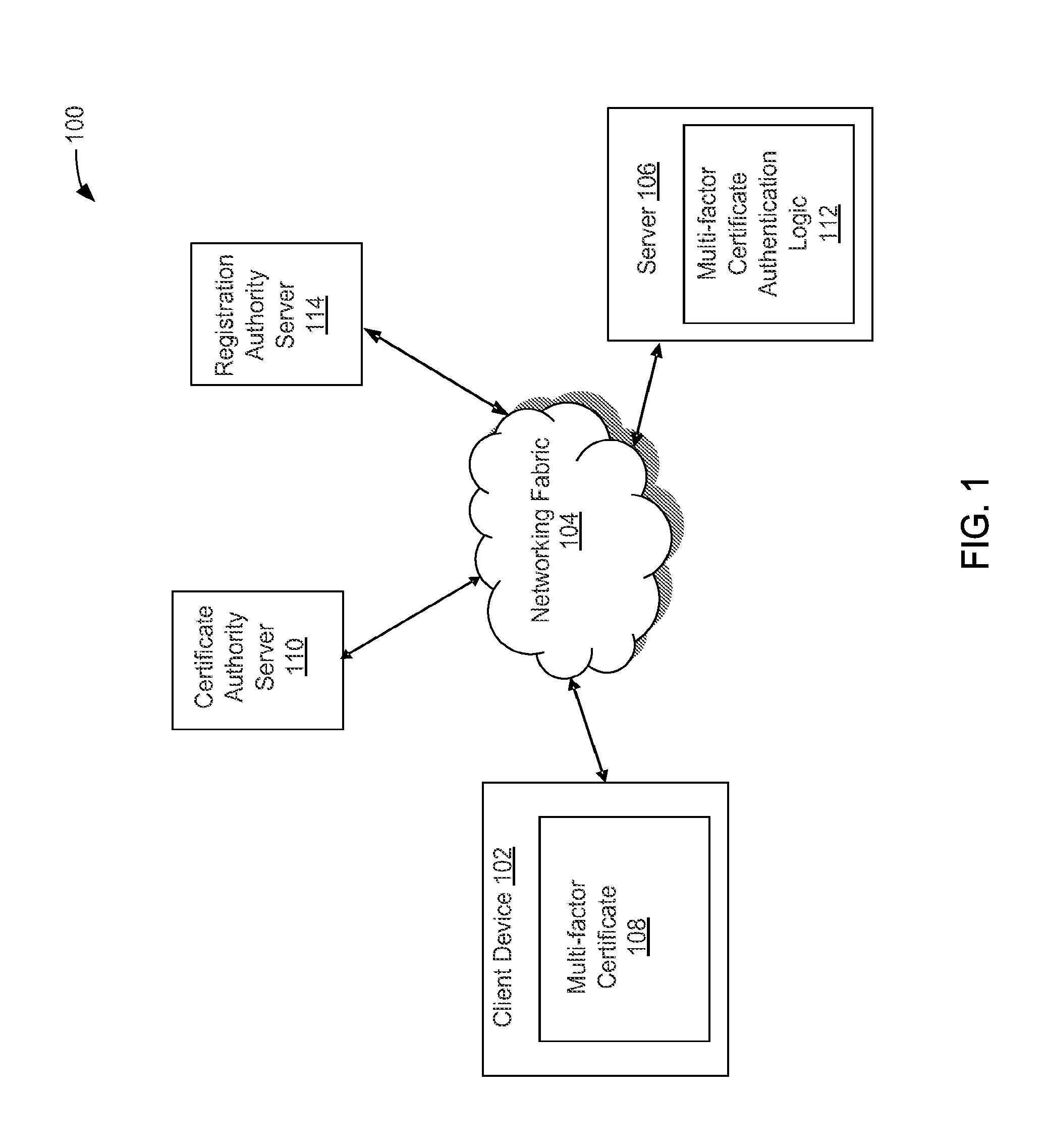
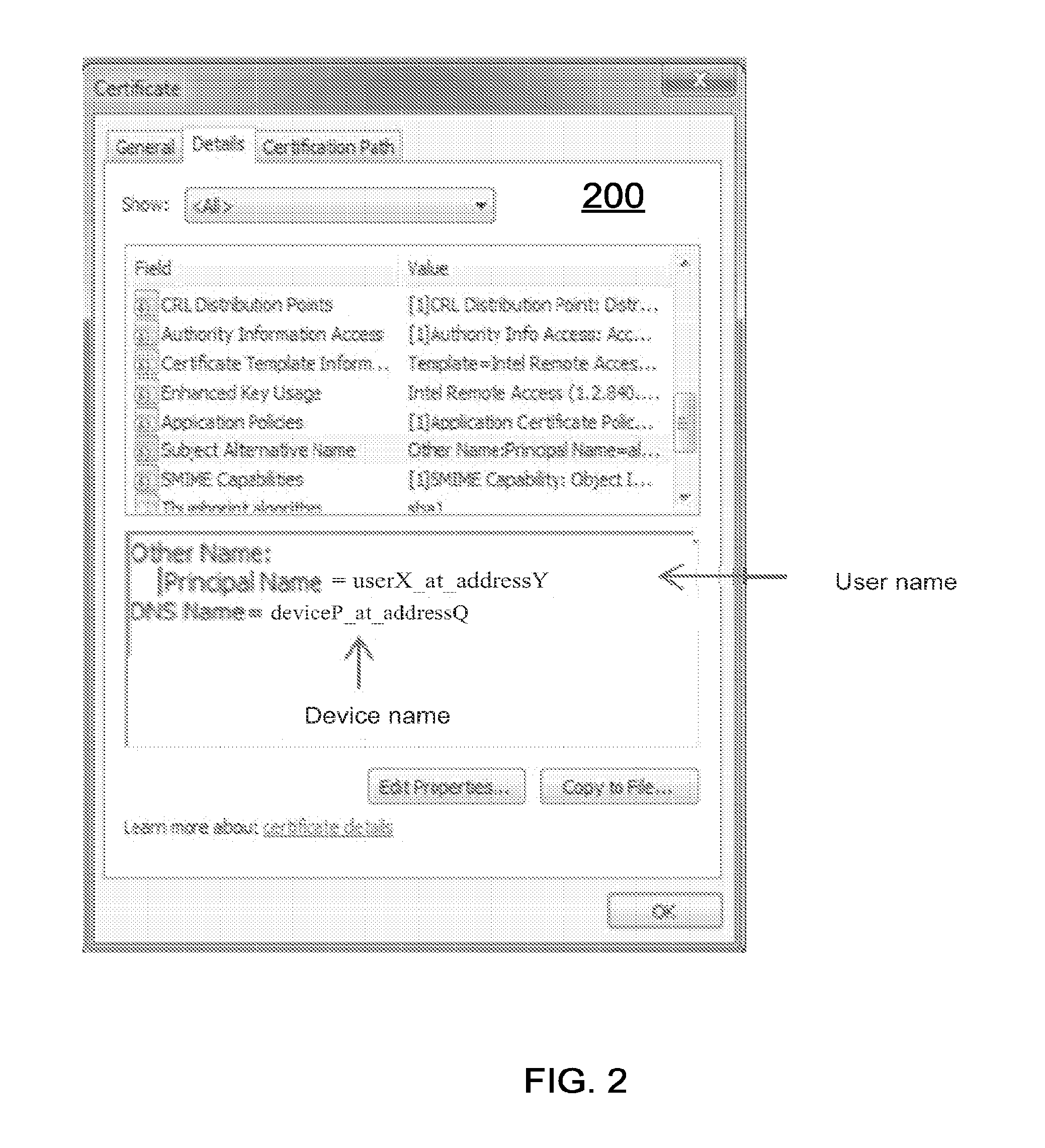
Multi-factor certificate authority
Disclosed herein is a certificate authority server configured to provide multi-factor digital certificates. A processor readable medium may include a plurality of instructions configured to enable a certificate authority server of a certificate authority, in response to execution of the instructions by a processor, to receive a request to provide a multi-factor digital security certificate by digitally signing a certificate request having a plurality of factors and a cryptographic key, wherein a first of the plurality of factors is an identifier of a device and a second of the plurality of factors is an identifier of a user of the device. The instructions are also configured to enable the certificate authority server to associate the cryptographic key with the plurality of factors and issue the digital security certificate based on the certificate request. Also disclosed is a method of using a multi-factor digital certificate as part of the authorization process to implicitly bind the plurality of factors. Other embodiments may be described and claimed.
Owner:INTEL CORP
Universal cellular circuit board
InactiveUS20060199614A1Improve the security systemNeed for manySpectrum investigationSubstation equipmentService provisionDigital security
A system and apparatus that allows cell phone users to control the roaming features of their service from one telecommunication network (i.e., cellular service provider) to another at the device level, independently of a particular primary network. More specifically, it intends to perform primary functions using the principles of (SoC) design, allowing an array of third party smart cards to share the motherboard of the universal cellular circuit, thus, allowing for ease of switching service providers by simply pushing a button on the apparatus. In addition, this device is equipped with a digital security diagnostic port (DSDP), allowing the scanning of the physical layer of the cellular circuit for unwanted / unexpected chips and other digital security breaches. For the cause of unprecedented efforts to accelerate the design, production, implementation, and distribution of new technologies (SoC design, ESL design, Robotics . . . ), this invention addresses a future threat to human-computer interactions (HCI) and public safety.
Owner:INFOSENSE TECH & RES
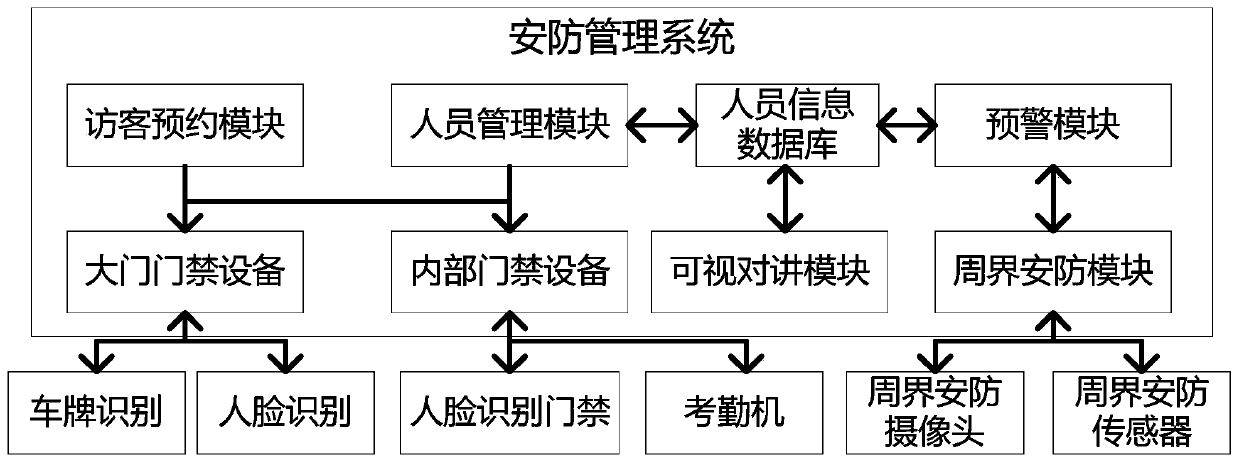
Warning method for campus based on face recognition
InactiveCN109727352AImprove securityReduce work stressRegistering/indicating time of eventsData processing applicationsSecurity systemDigitization
The invention relates to the field of Internet of Things and intelligent security, and specifically discloses a warning method for a campus based on face recognition. The method comprises a personnelmanagement module, a warning module, a visitor reservation module, a perimeter security module, and a visual intercom module. The personnel management module is used for managing access authority andmonitoring personnel access. The warning module is used for pushing warning information to parents and teaching staffs. The visitor reservation module is used for temporary visitors to apply for access authorization. The perimeter security module is used for monitoring and recording a perimeter alarm device and sending out a warning signal. The visual intercom module for communication between security personnel and the teaching staffs and information query. According to the warning method for the campus based on face recognition, a smart camera with face recognition and license plate recognition is combined with a perimeter security device and attendance system to form a complete set of digital security system for the campus, so that the security system for the campus can further realize comprehensive intelligent and automated supervision, the pressure on the security personnel is reduced, and the security level of the campus is improved.
Owner:广东粤众互联信息技术有限公司
Centralized safety control method and device
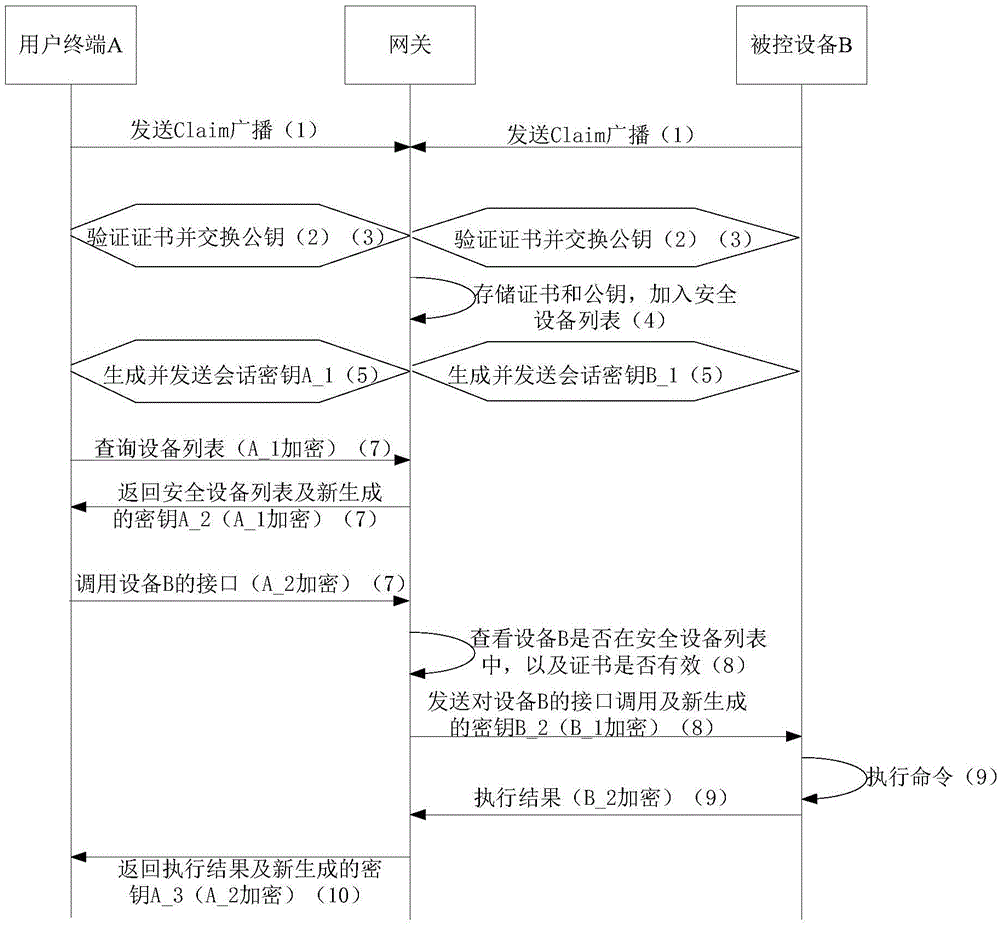
ActiveCN105007164ASimple security policyReduce performance requirementsUser identity/authority verificationSafety controlSecurity policy
The invention discloses a centralized safety control method and a centralized safety control device. The method comprises the steps as follows: a central node checks identity with the intelligent device after monitoring that some intelligent device accesses a local network, and stores a digital security certificate and a public key of the intelligent device after the check is passed, and adds the intelligent device in a safety equipment list; the central node generates a conversation key for the intelligent device and transmits the conversation key to the intelligent device; the central node transmits the safety equipment list, which has been encrypted by using the conversation key to the intelligent device based on an inquiring request of the intelligent device so that the intelligent device could select target equipment for conversation; the central node transfers the conversation information interacted by the intelligent device and the target equipment while the intelligent device initiates a conversation with the selected target equipment. The method and the device of the invention change a point-to-point security policy into centralized safety control, thereby reducing the performance requirement, operation complexity and cost of the intelligent device.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com