Centralized safety control method and device
A security control, centralized technology, applied in the field of communication, can solve the problems of waste of resources, complex operation, low security, etc., to achieve the effect of reducing performance requirements, reducing complexity, and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0063] An embodiment of the present invention provides a centralized security control method, such as figure 1 As shown, the method includes:
[0064] Step S101, after the central node detects that the smart device enters the local network, it mutually checks the identity with the smart device, and when the verification is passed, stores the digital security certificate and public key of the smart device, and adds the smart device to the security device list;
[0065] In this step, the central node and the smart device verify each other's identity by verifying the digital security certificate of the other party; wherein, when the smart device does not have a digital security certificate, the central node generates a digital security certificate for the smart device.
[0066] Step S102, the central node generates a session key for the smart device and sends it to the smart device;
[0067] Preferably, in this step, after receiving the request sent by the smart device to join ...
Embodiment 2
[0073] An embodiment of the present invention provides a centralized security control method, such as figure 2 shown, including the following steps:
[0074] Step S201, after the smart device joins the network to which the central node belongs, it mutually checks the identity with the central node, and stores the digital security certificate and public key of the central node after the verification is passed;
[0075] Step S202, the smart device receives the session key sent by the central node, and uses the session key to initiate a query request for the security device list to the central node, and selects the target of the session in the security device list fed back by the central node equipment;
[0076] Step S203, the smart device conducts a session with the target device through the central node.
[0077] It can be known from the description of Embodiments 1 and 2 that the centralized security control method provided by the embodiment of the present invention has a c...
Embodiment 3
[0080] The embodiment of the present invention elaborates the centralized security control method provided by the present invention in more detail by combining specific application scenarios. In this embodiment, the central node is defaulted as an intelligent gateway. Of course, in the present invention, the central node is not limited to being an intelligent Gateway, as long as a certain device satisfies that it is the control center of the entire system, it establishes a session, and other smart devices will join this session. Security Manager runs on this device and maintains a list of security devices, then this device can be used as The central node described in the present invention.
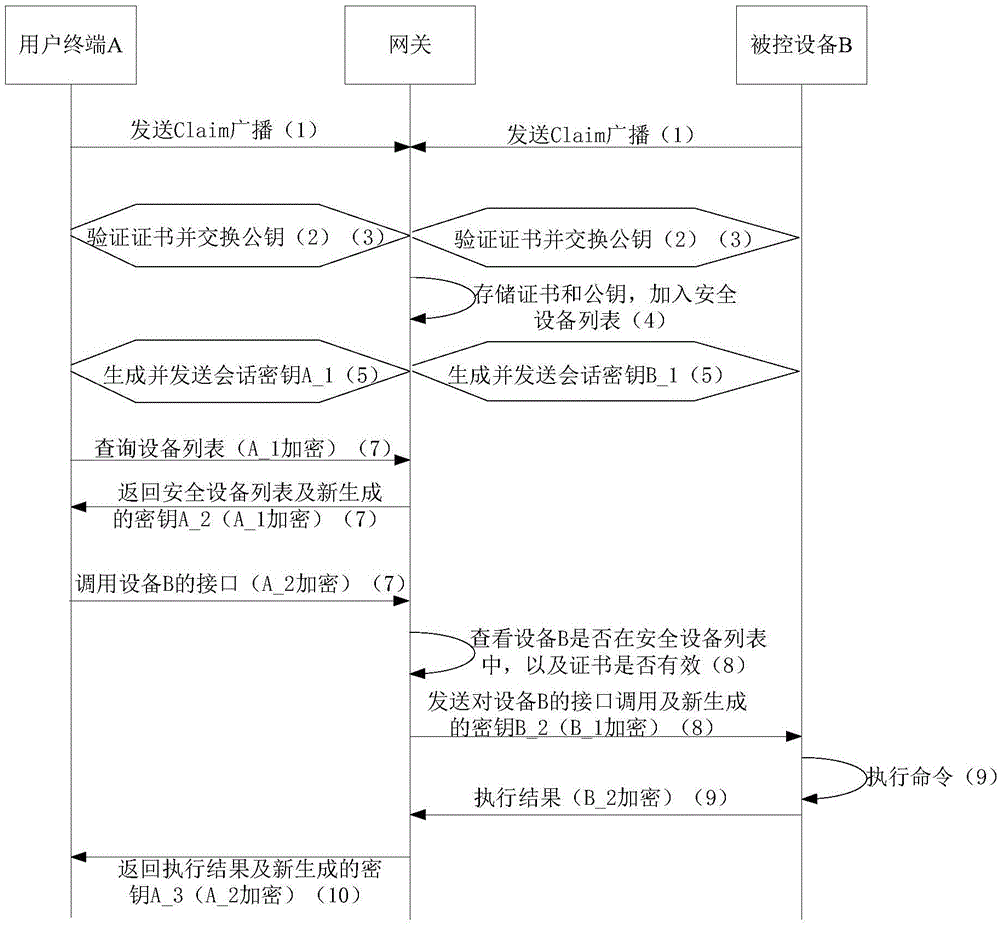
[0081] like image 3 As shown, the centralized security control method described in this embodiment includes the following steps:
[0082] (1) After the smart home appliance enters the Internet of the local device, it sends a Claim broadcast.
[0083] (2) After the Security Manager on th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com