Patents
Literature
60883 results about "Computer network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
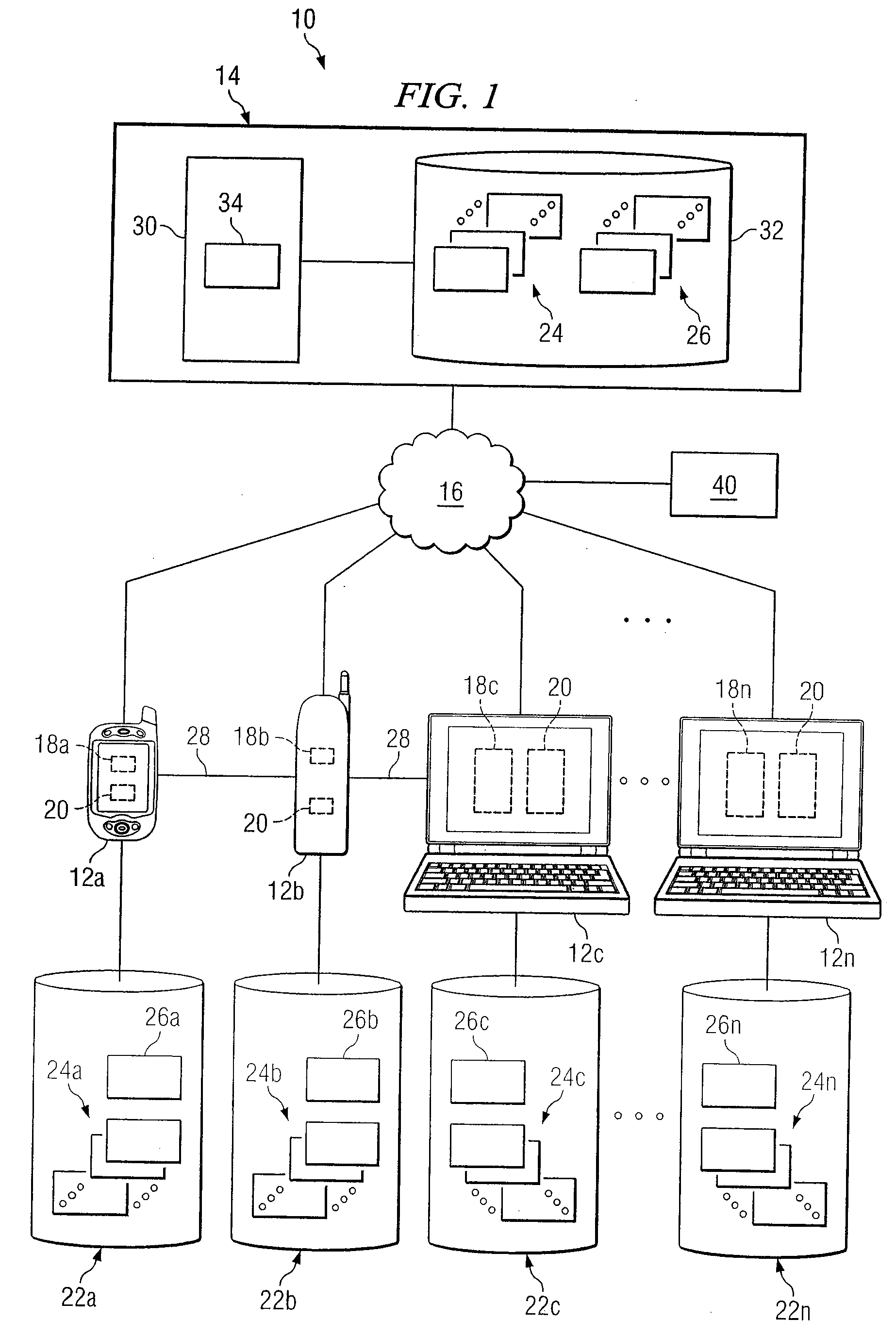
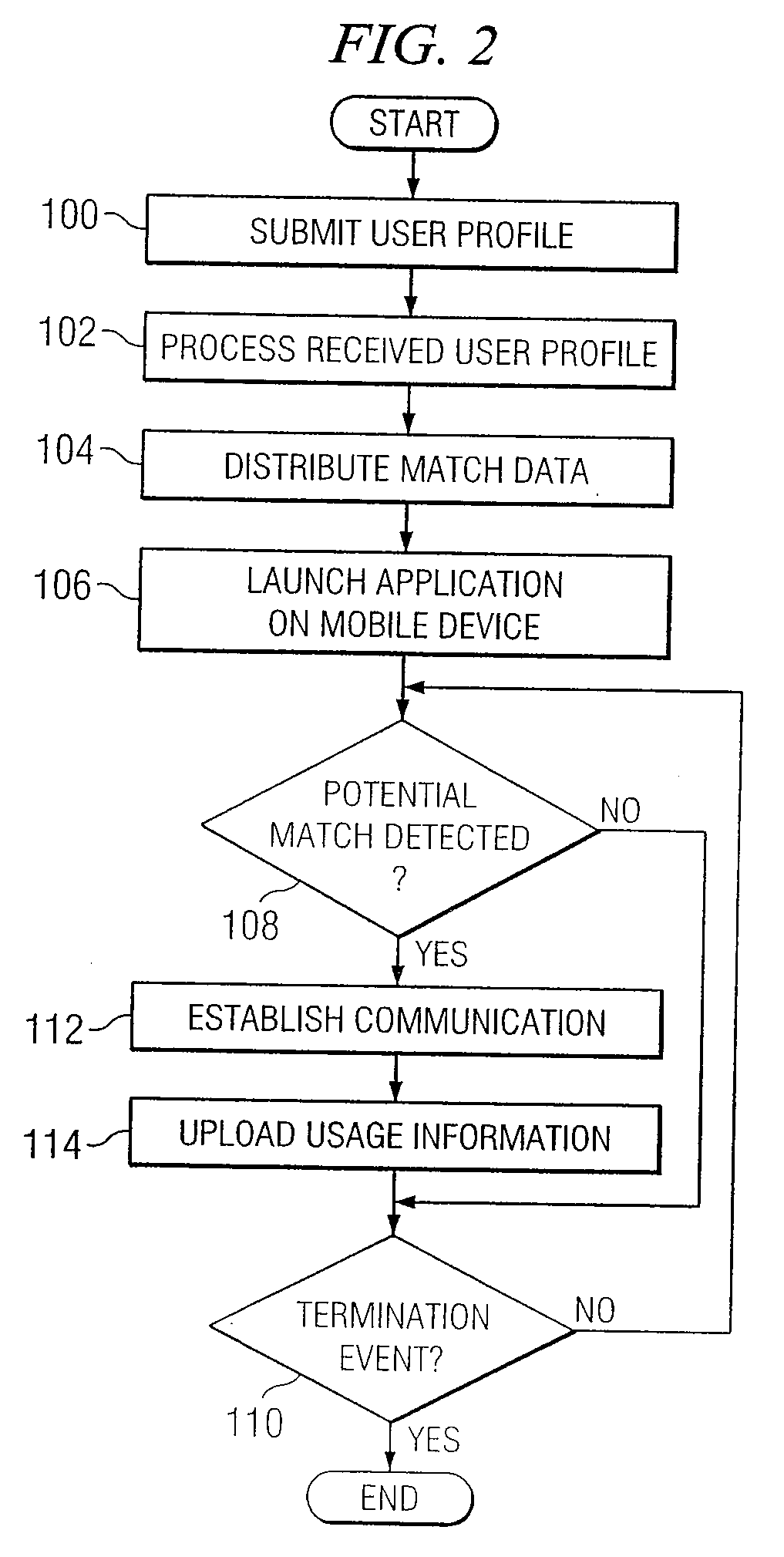
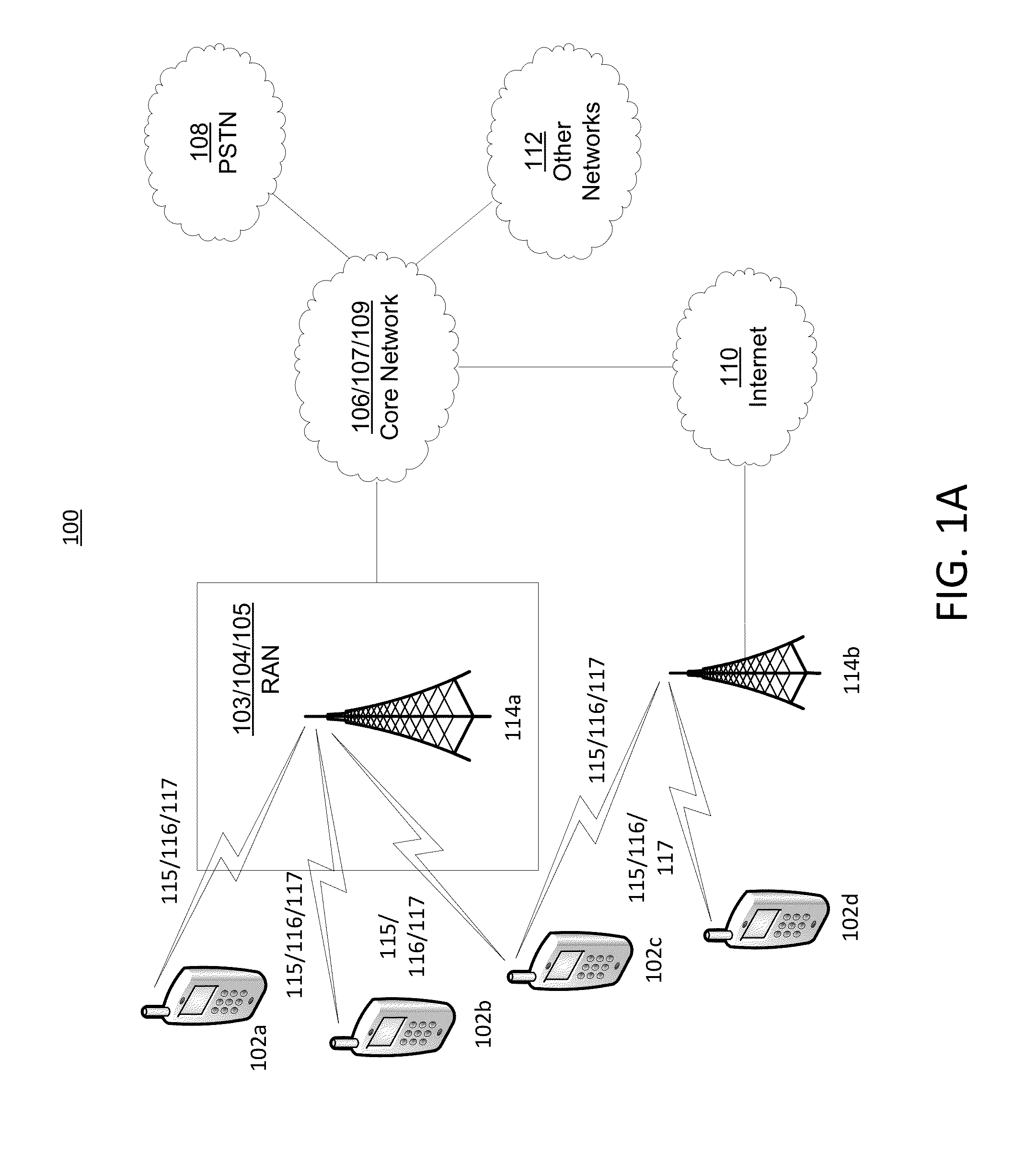
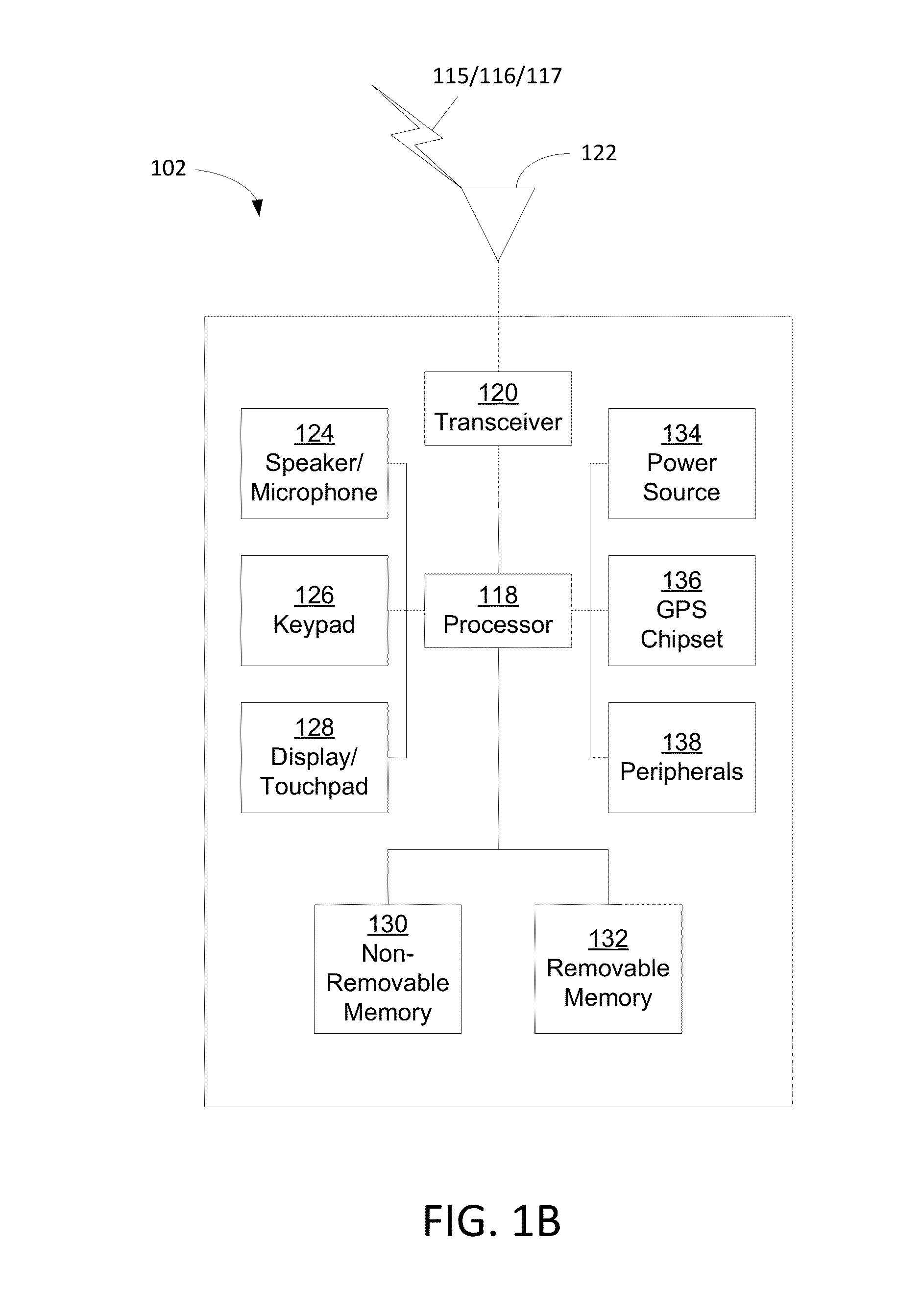
A computer network is a digital telecommunications network which allows nodes to share resources. In computer networks, computing devices exchange data with each other using connections (data links) between nodes. These data links are established over cable media such as wires or optic cables, or wireless media such as Wi-Fi.
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
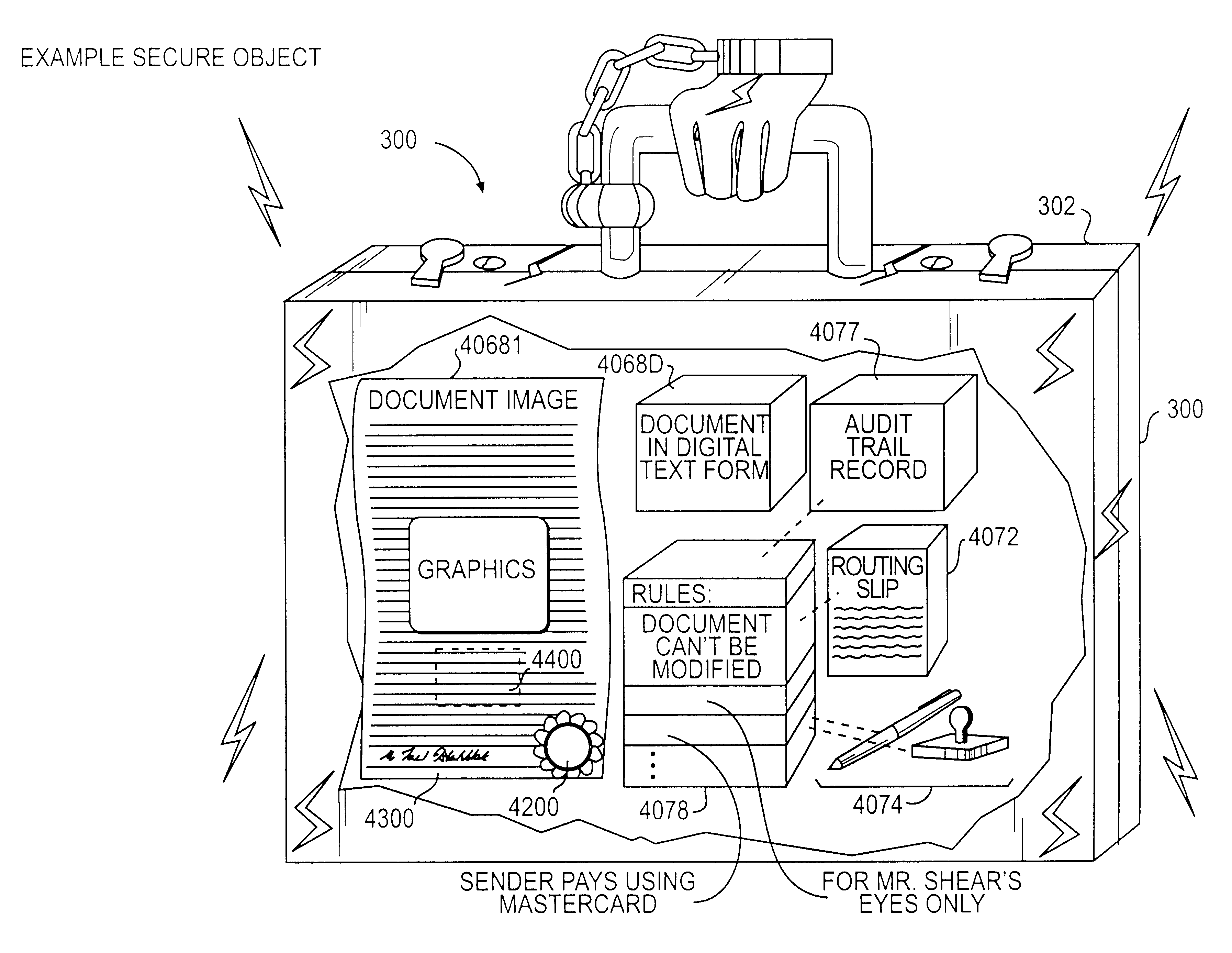
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
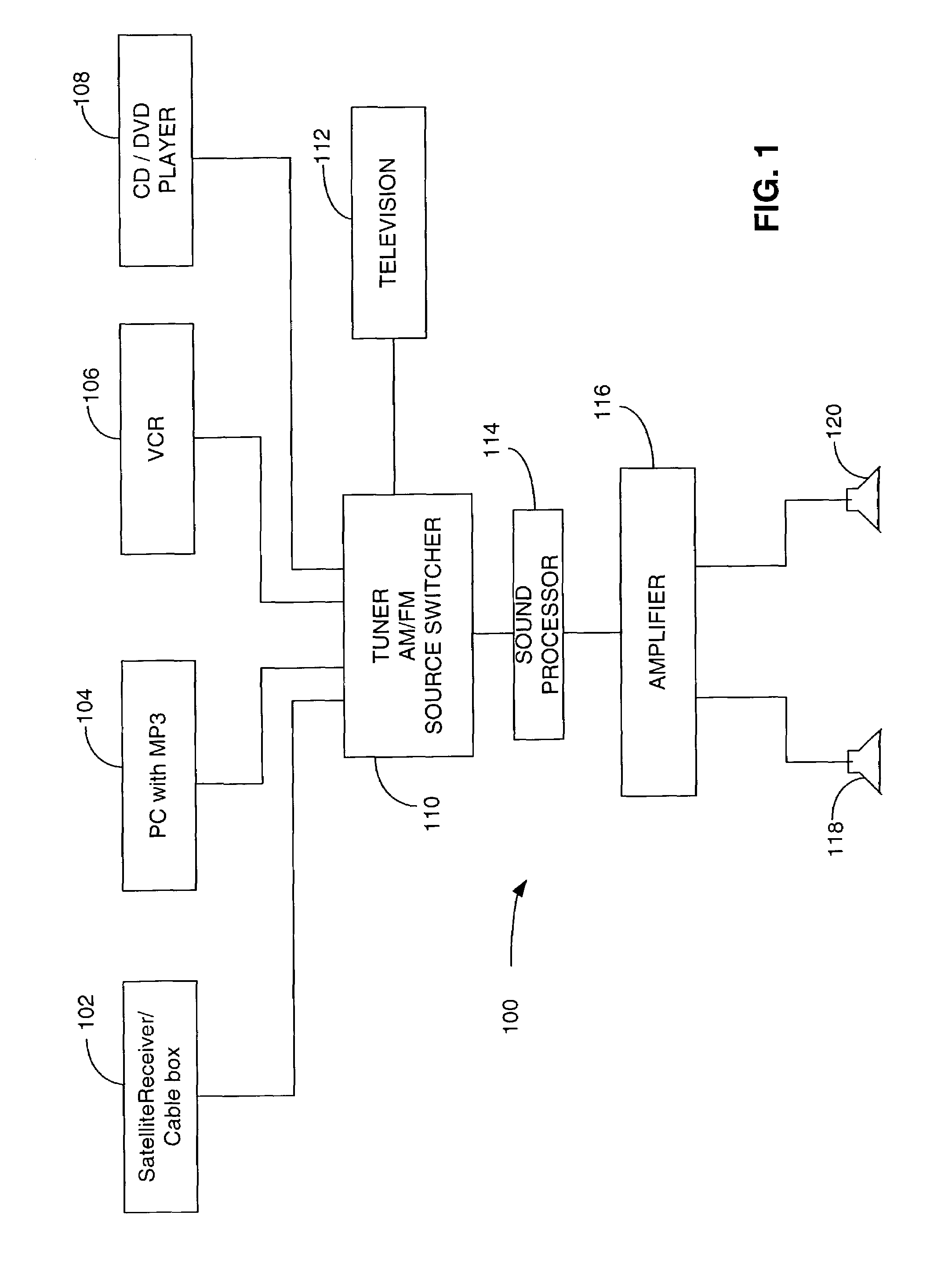
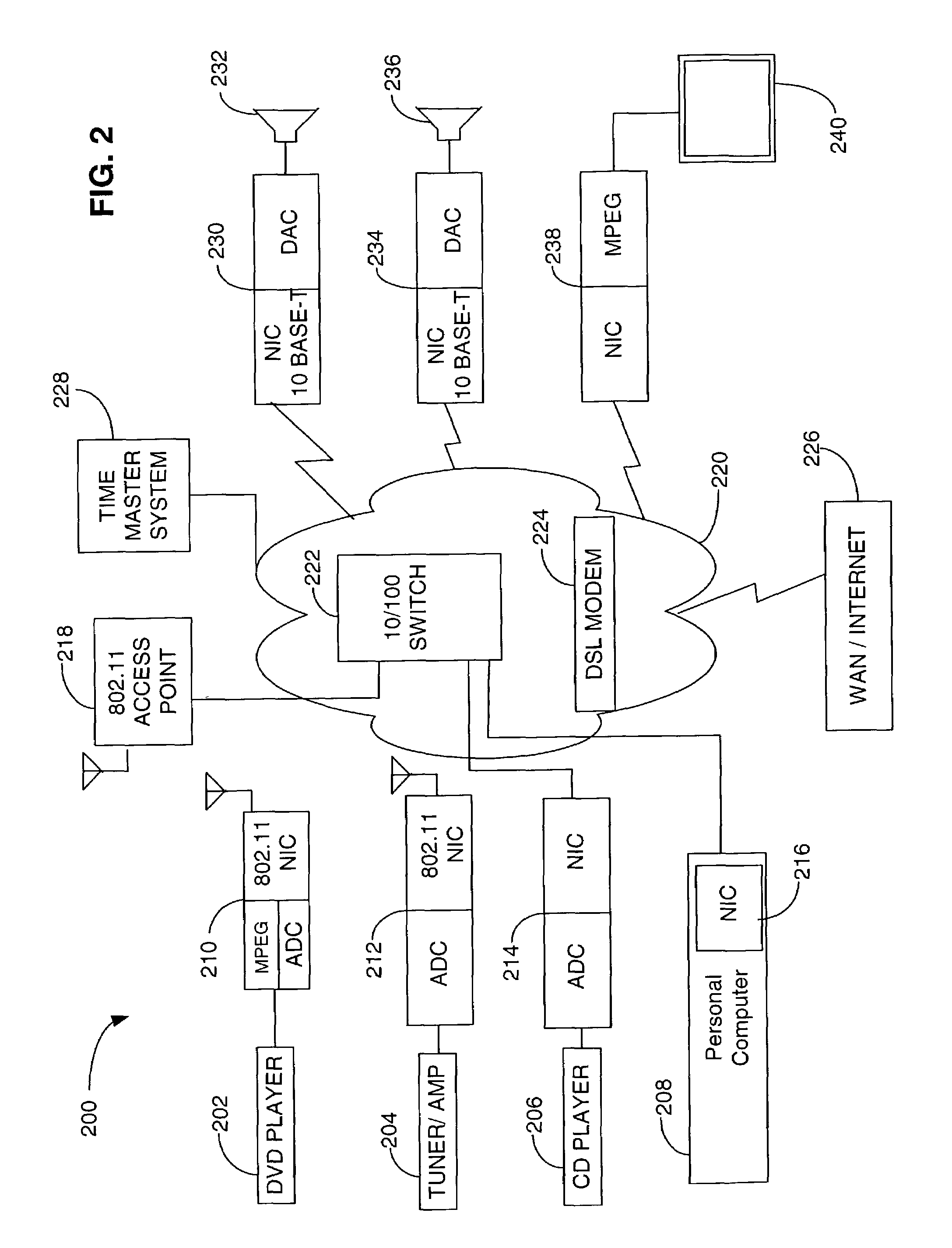
Method and system for disaggregating audio/visual components
ActiveUS7295548B2Improve user experiencePlural information simultaneous broadcastTwo-way working systemsComputer networkBrick
The present invention is directed to a method and system for disaggregating and connecting A / V components, and communicating A / V content stream information. An A / V stream from a source device is packaged for transmission over an IP network to one or more output devices. A brick device enables the integration of legacy A / V systems into the network supported A / V system. The brick device operates to provide analog signal and IP protocol conversion, along with the synchronization of received A / V stream data packets. The rendering and play of the A / V stream content on multiple output devices is synchronized to overcome distortions and other network idiosyncrasy and to facilitate a pleasant user experience.
Owner:MICROSOFT TECH LICENSING LLC
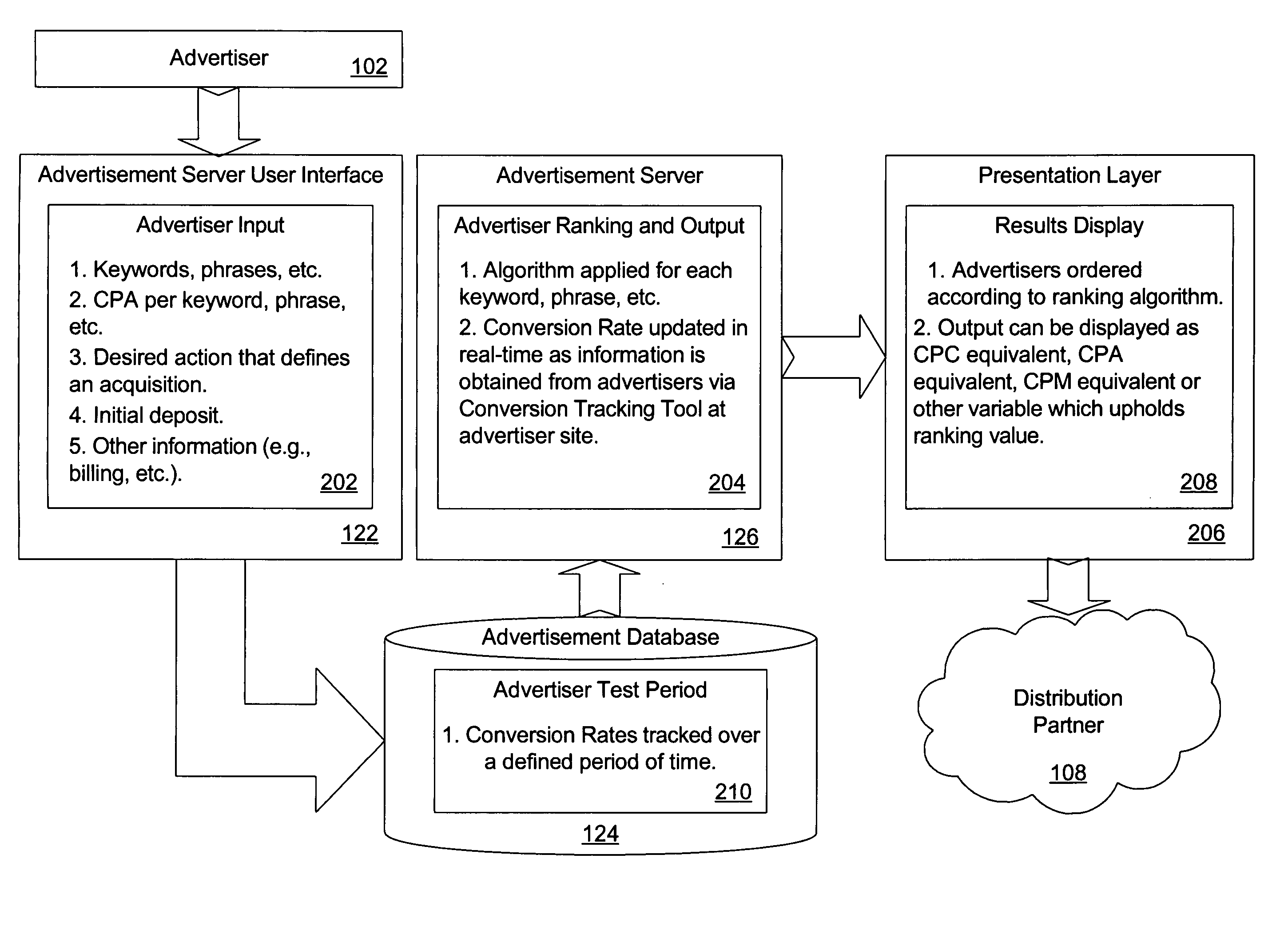
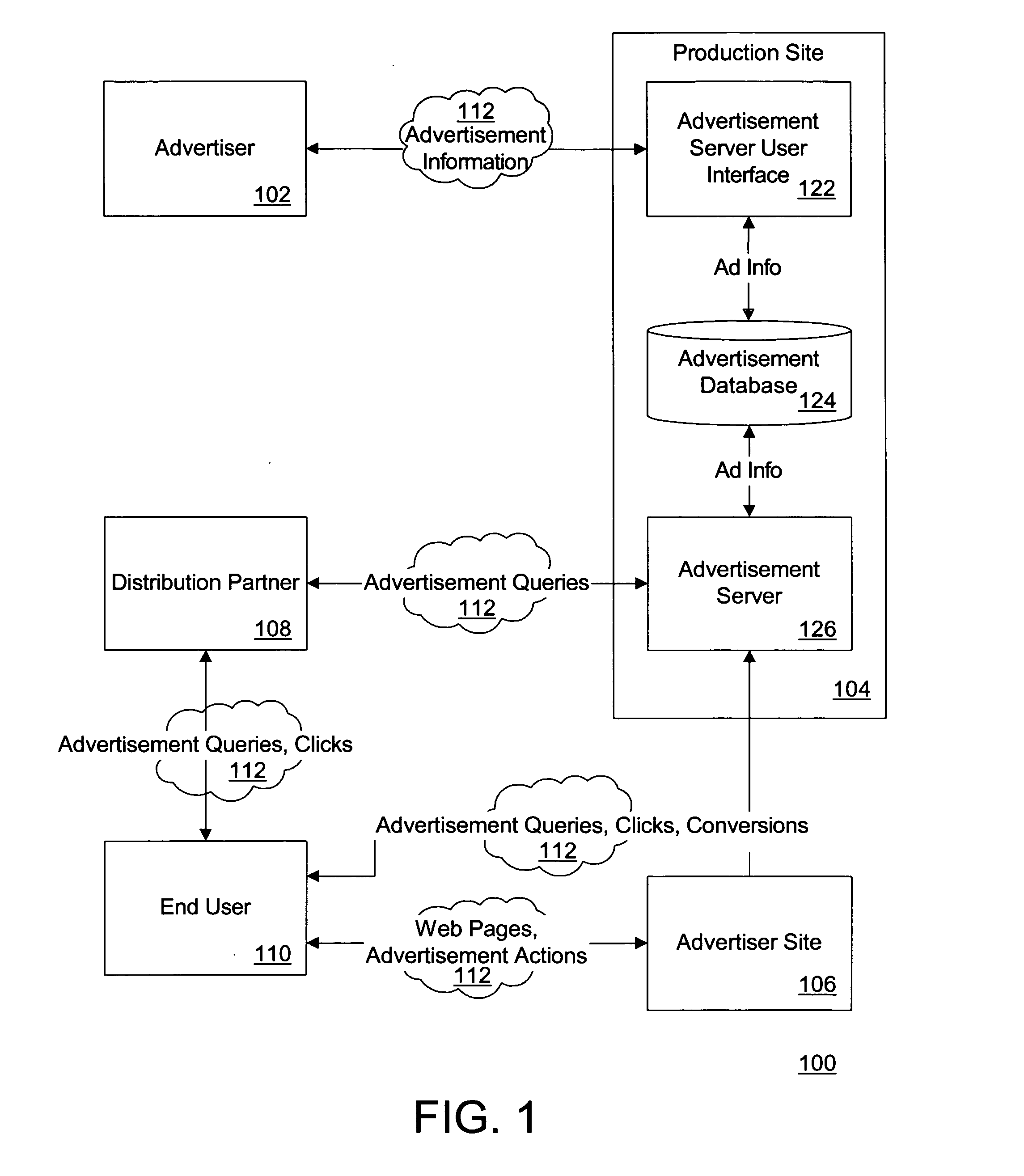
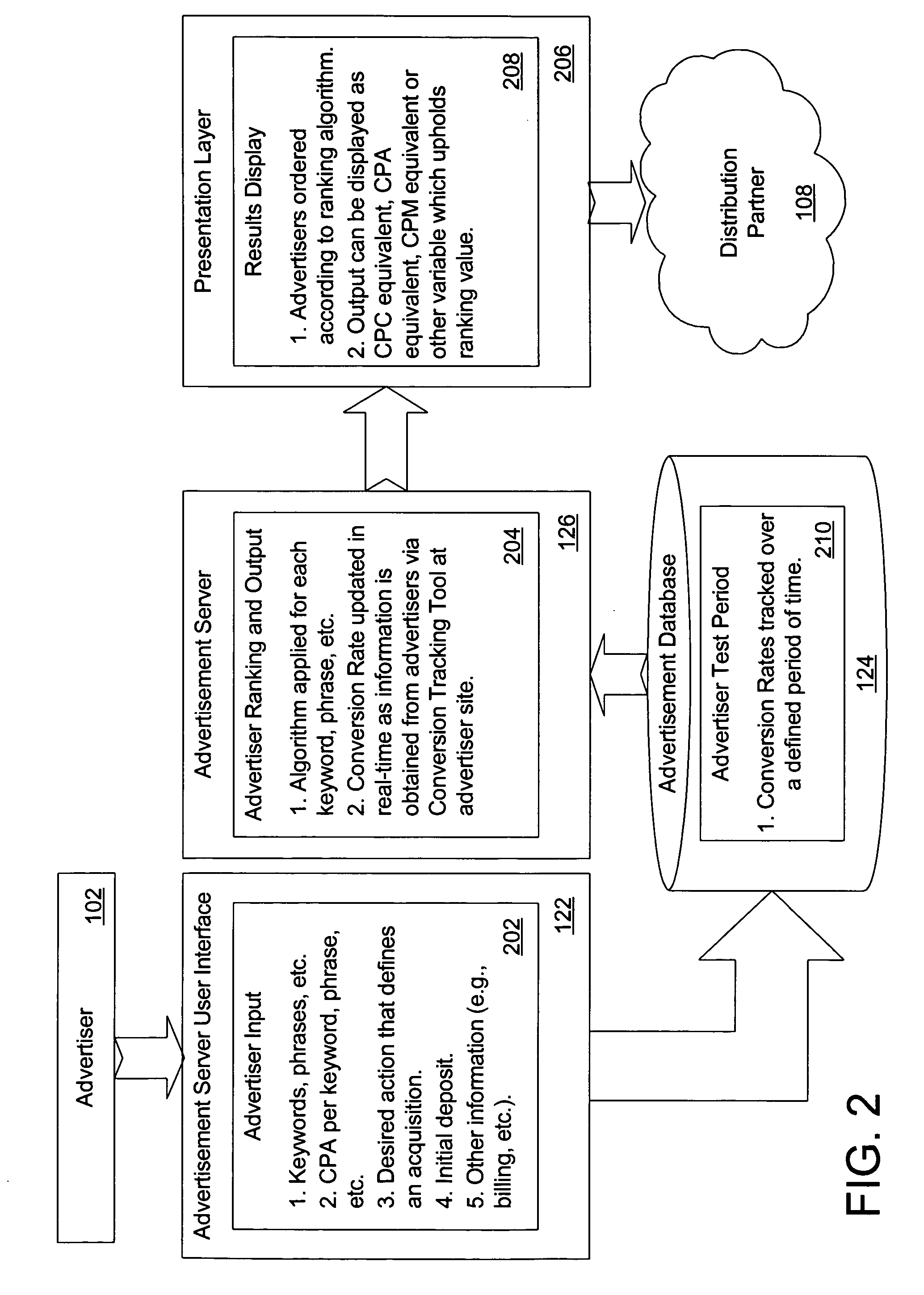
Performance-based online advertising system and method
ActiveUS20050097204A1AdvertisementsDigital data processing detailsOnline advertisingCost per acquisition
A system, method, and computer program product for online advertising, including computing and dynamically updating a cost-per-click (CPC) value of an advertisement for an advertisement traffic source based on a variable; and automatically uploading and distributing the advertisement to the traffic source. The variable includes price, advertisement traffic source, and / or advertiser variableS. Further embodiments include dynamically updating an advertisement listing that has a cost-per-acquisition (CPA)-based value with associated CPC or cost-per-1000 (CPM) values; and distributing the advertisement listing to an advertisement distribution network that serves the listing based on the CPC or CPM values. The distribution network includes CPC-based, CPA-based, and / or CPM-based distribution networks. Further embodiments include determining a CPC value for a CPA-based advertisement; and placing the advertisement on an advertising network at the determined CPC based on a ratio of an expected number of conversions at a CPA value divided by a number of clicks at the CPC.
Owner:MARCHEX
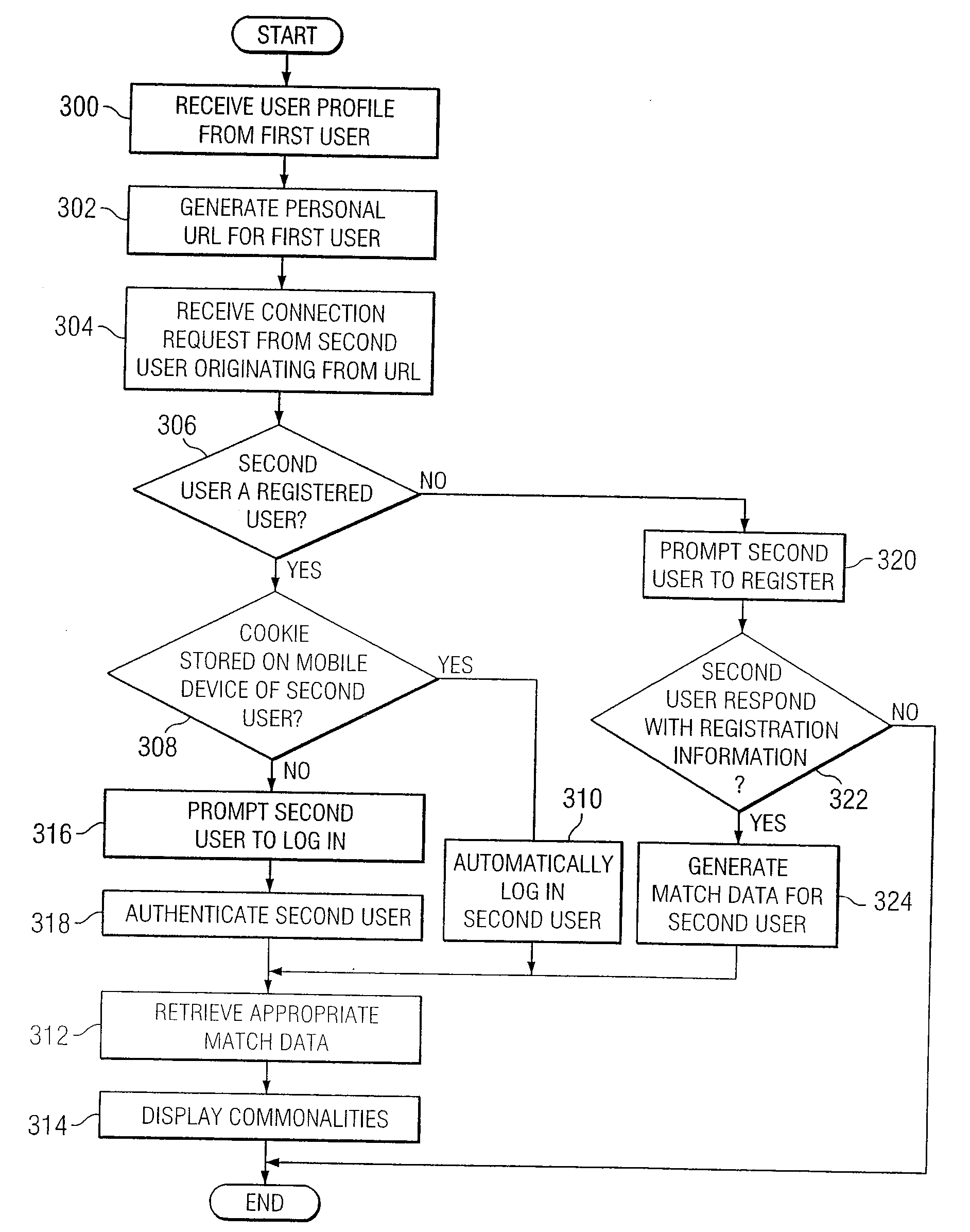
System and method for providing communication services to mobile device users incorporating proximity determination
InactiveUS20070030824A1Disadvantages can be reduced eliminatedWeb data retrievalTelephonic communicationComputer networkMobile device
In certain embodiments, a method for proximity determination includes receiving one or more network identifiers, each associated with a corresponding network, from a first mobile device. The method further includes receiving one or more network identifiers, each associated with a corresponding network, from a second mobile device. The method further includes processing the network identifiers received from the first and second mobile devices to determine whether the first mobile device and the second mobile device are in proximity to one another.
Owner:JAMBO NETWORKS
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS20070121596A1Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
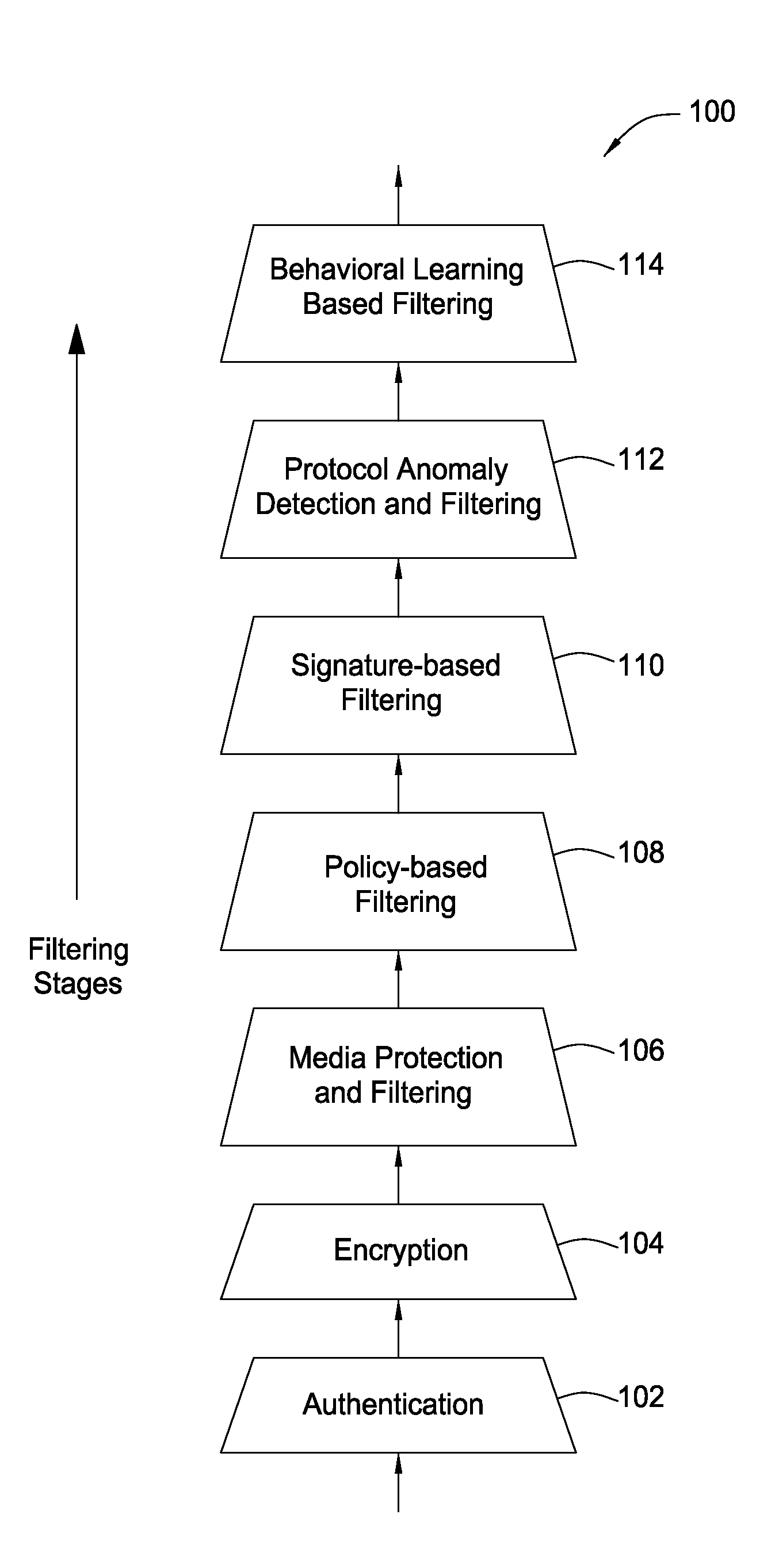
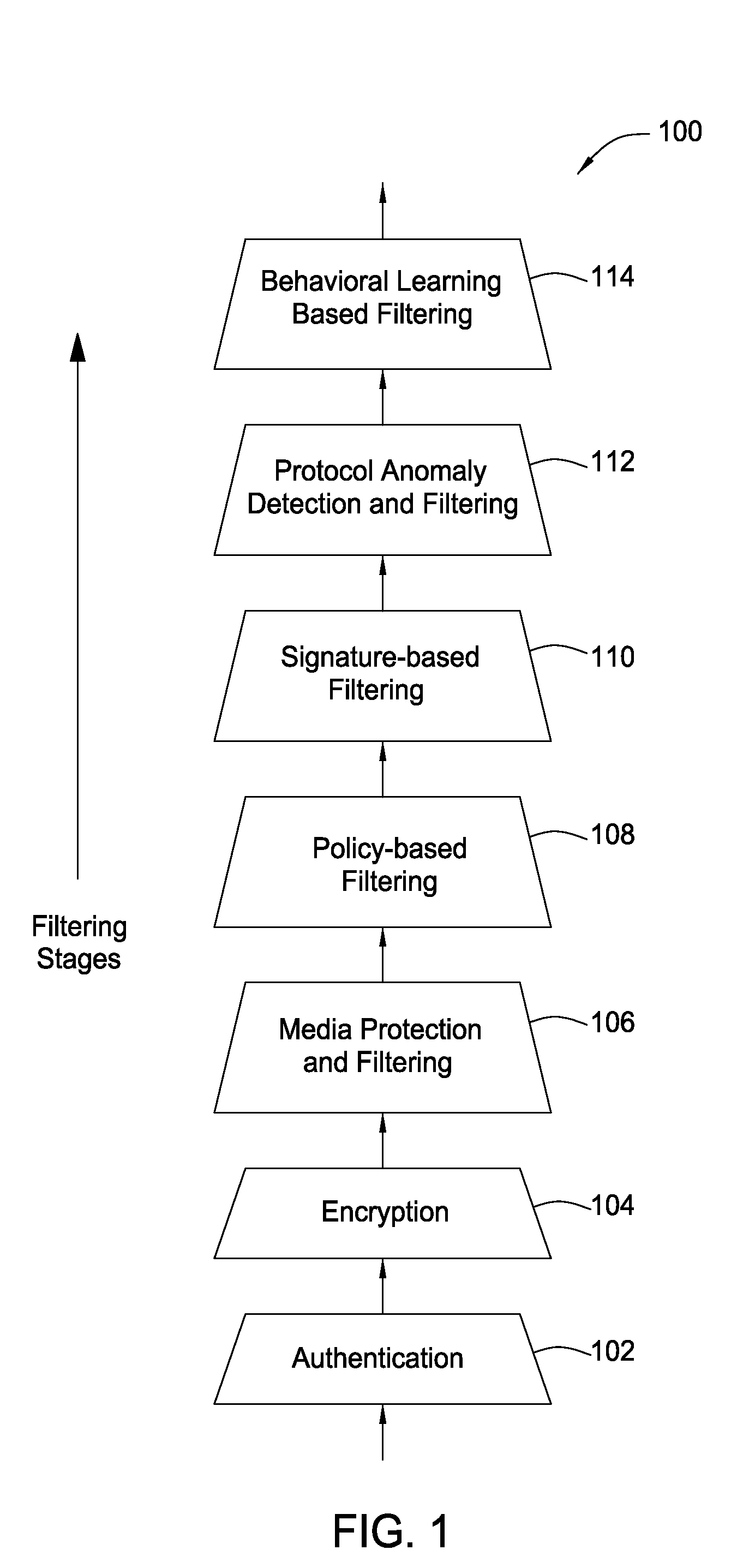
The present invention provides a system, method and apparatus for providing network level and nodal level vulnerability protection in VoIP networks by receiving a communication, filtering the received communication using three or more stages selected from the group comprising a media protection and filtering plane, a policy based filtering plane, a signature based filtering plane, a protocol anomaly detection and filtering plane and a behavioral learning based filtering plane, and either allowing or denying the received communication based the filtering step. The stages are applicable to one or more protocols including SIP, IMS, UMA, H.248, H.323, RTP, CSTA / XML or a combination thereof. In addition, the stages can be implemented within a single device or are distributed across a network (e.g., SIP network, a UMA network, an IMS network or a combination thereof).
Owner:AVAYA INC
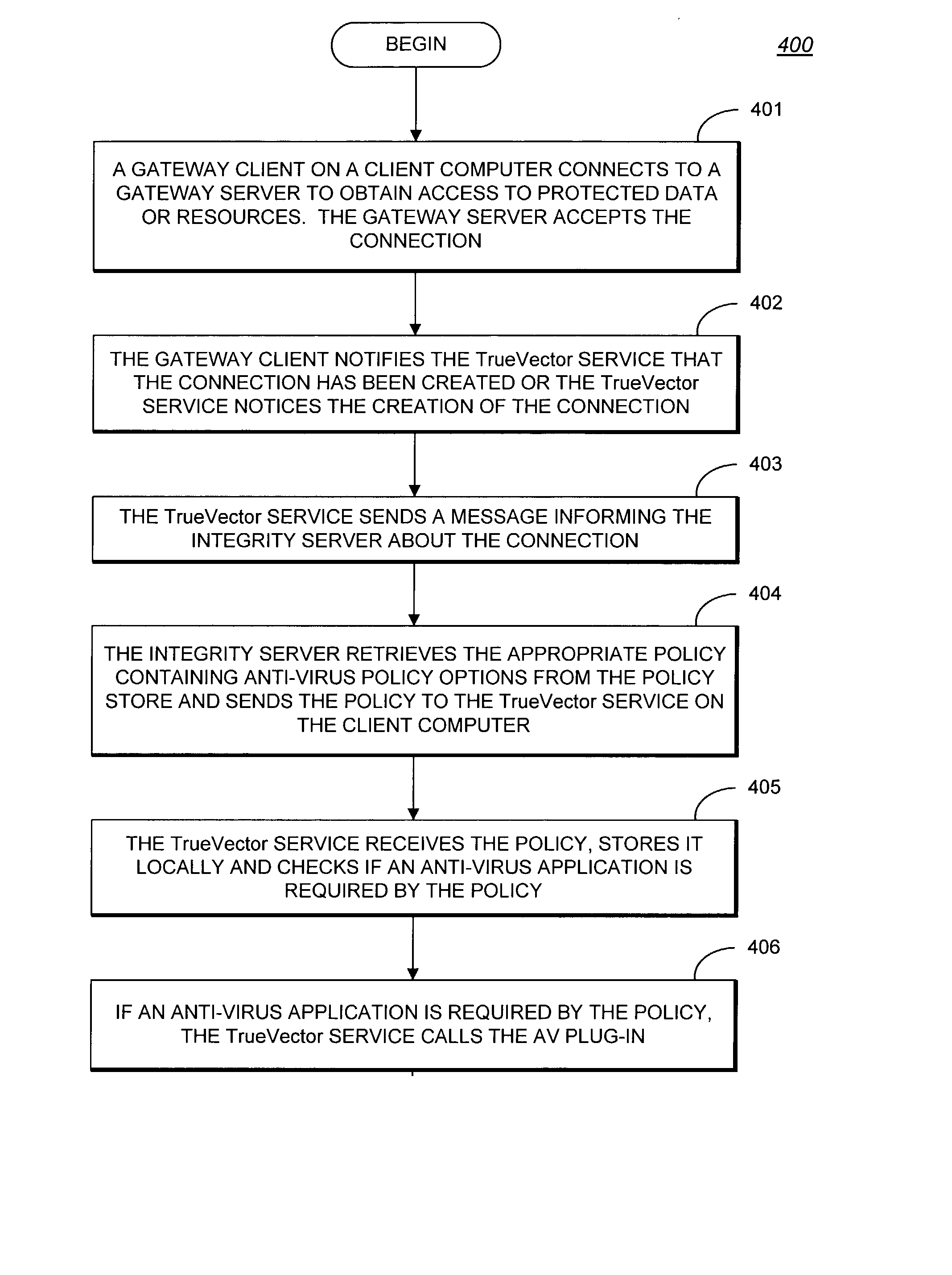
System and methods providing anti-virus cooperative enforcement
InactiveUS6873988B2Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
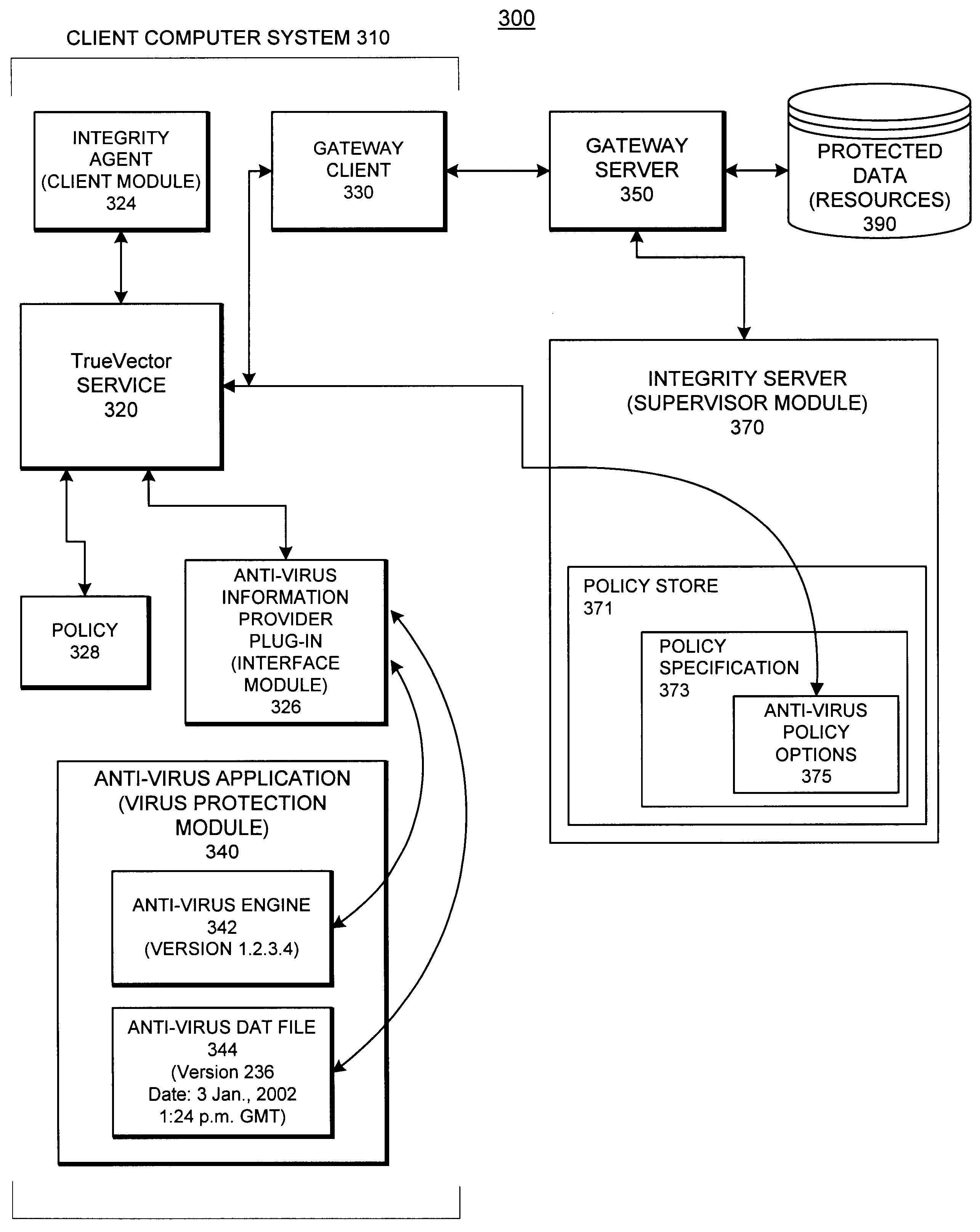
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
System and methodology for security policy arbitration
ActiveUS20030177389A1Multiple digital computer combinationsProgram controlComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
System and method for providing context sensitive recommendations to digital services
ActiveUS20040043758A1Reducing or minimizing the processing load and memoryReduces privacy concernInterconnection arrangementsDigital data information retrievalComputer networkRelevant information
A system and method is disclosed to provide recommendations to a wireless device, based on stored bookmark / short-cut data. When a wireless device accesses services, data pertaining to the service access, along with any context related information is transmitted within the wireless device, or to a remote server. The data is processed in conjunction with bookmarks / short-cuts specified within the device, and are organized and presented to the wireless device in accordance with preference instructions specified within the wireless device.
Owner:NOKIA TECHNOLOGLES OY
Dynamic parameter adjustment for LTE coexistence
Coexistence gaps may permit one radio access technology (RAT) to coexists with another RAT by providing period in which one RAT may be silent and another may transmit. Methods may account for the RAT traffic and for the presence of other secondary users in a channel. Methods may be provided to dynamically change the parameters of a coexistence gap pattern, such as the duty cycle, to adapt to both the RAT traffic and the presence of other secondary users. Methods may include PHY methods, such as synchronization signal (PSS / SSS) based, MIB based, and PDCCH based, MAC CE based methods, and RRC Methods. Measurements may be provided to detect the presence of secondary users, and may include reporting of interference measured during ON and OFF durations, and detection of secondary users based on interference and RSRP / RSRQ measurements.
Owner:INTERDIGITAL PATENT HLDG INC
System and methods providing anti-virus cooperative enforcement
InactiveUS20030055994A1Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
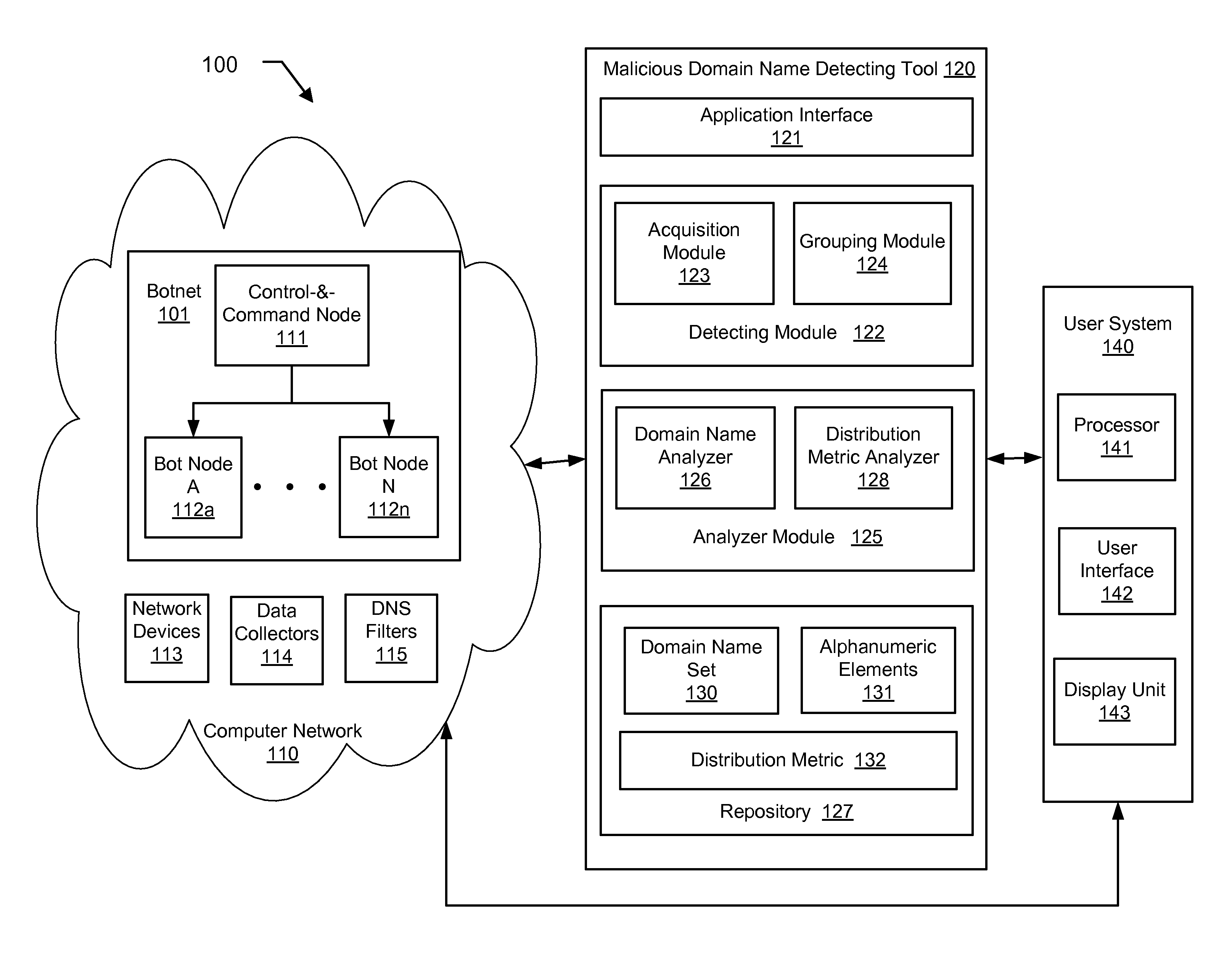
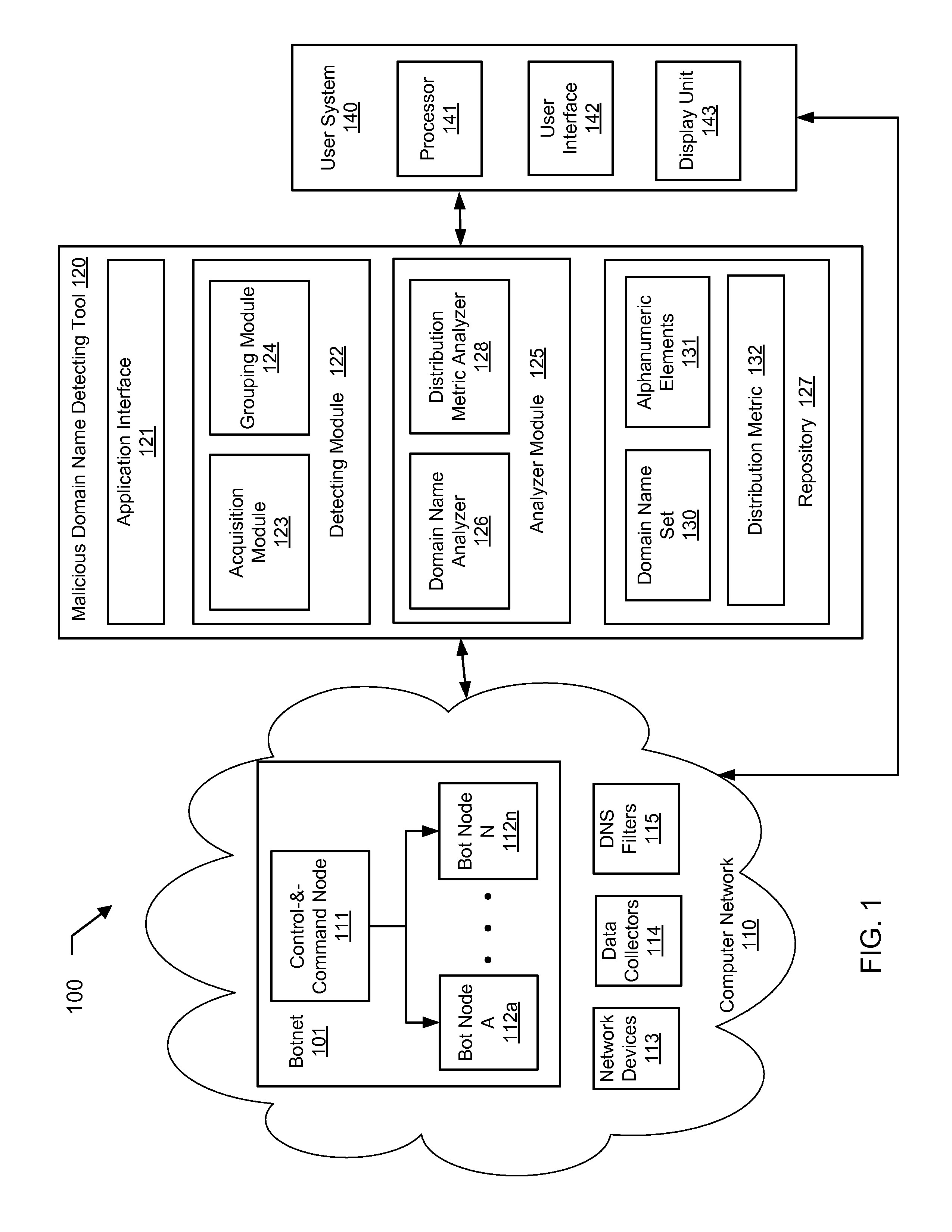
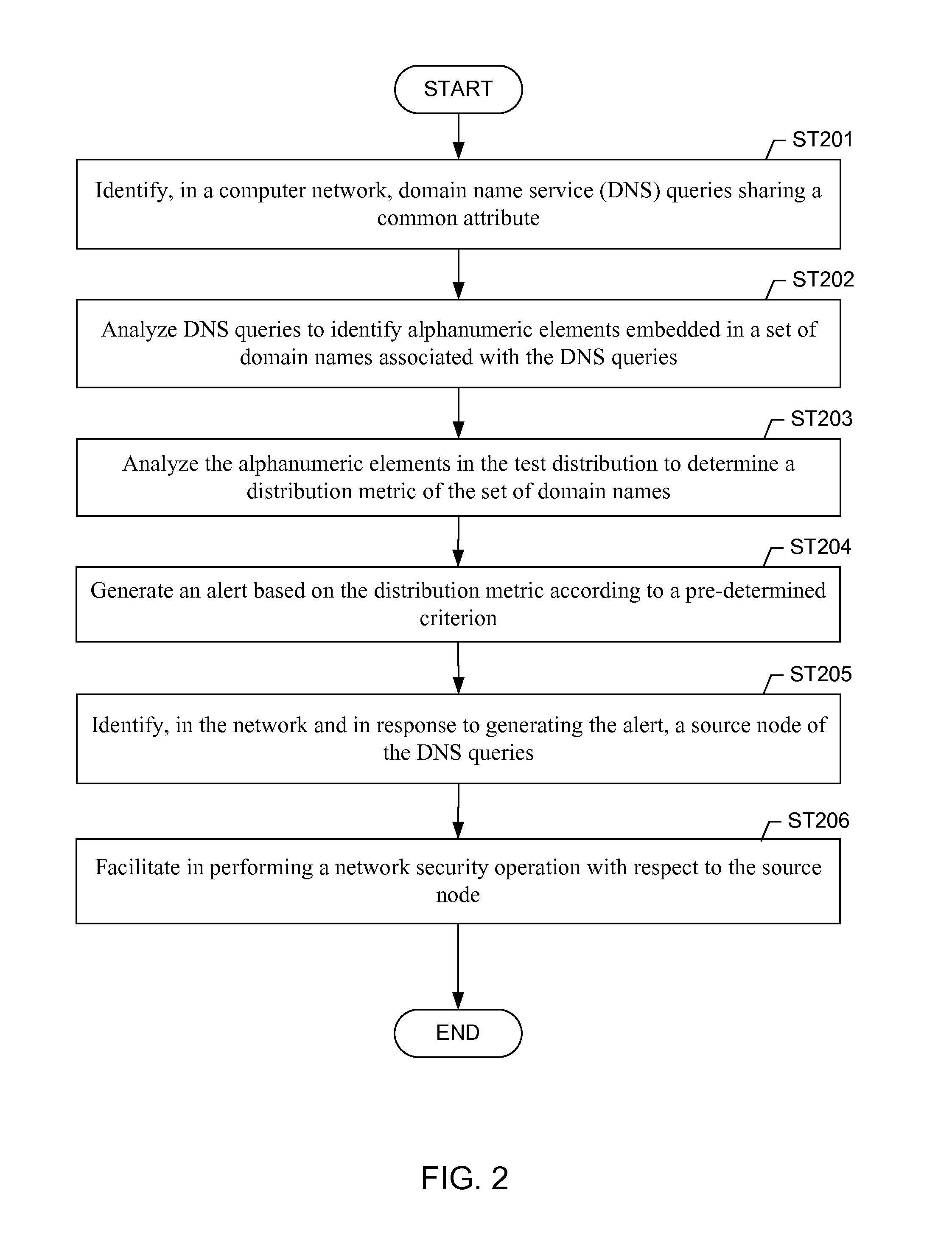
Detecting DNS fast-flux anomalies
A method for detecting automatically generated malicious domain names in a network. The method includes identifying a plurality of domain name service (DNS) queries in the network, wherein the plurality of DNS queries share a common attribute, analyzing, using a central processing unit (CPU) of a computer, the plurality of DNS queries to identify a plurality of alphanumeric elements embedded in a set of domain names associated with the plurality of DNS queries, analyzing, using the CPU, the plurality of alphanumeric elements to determine a distribution metric of the set of domain names, and generating an alert based on the distribution metric according to a pre-determined criterion.
Owner:THE BOEING CO
System architecture for and method of processing packets and/or cells in a common switch
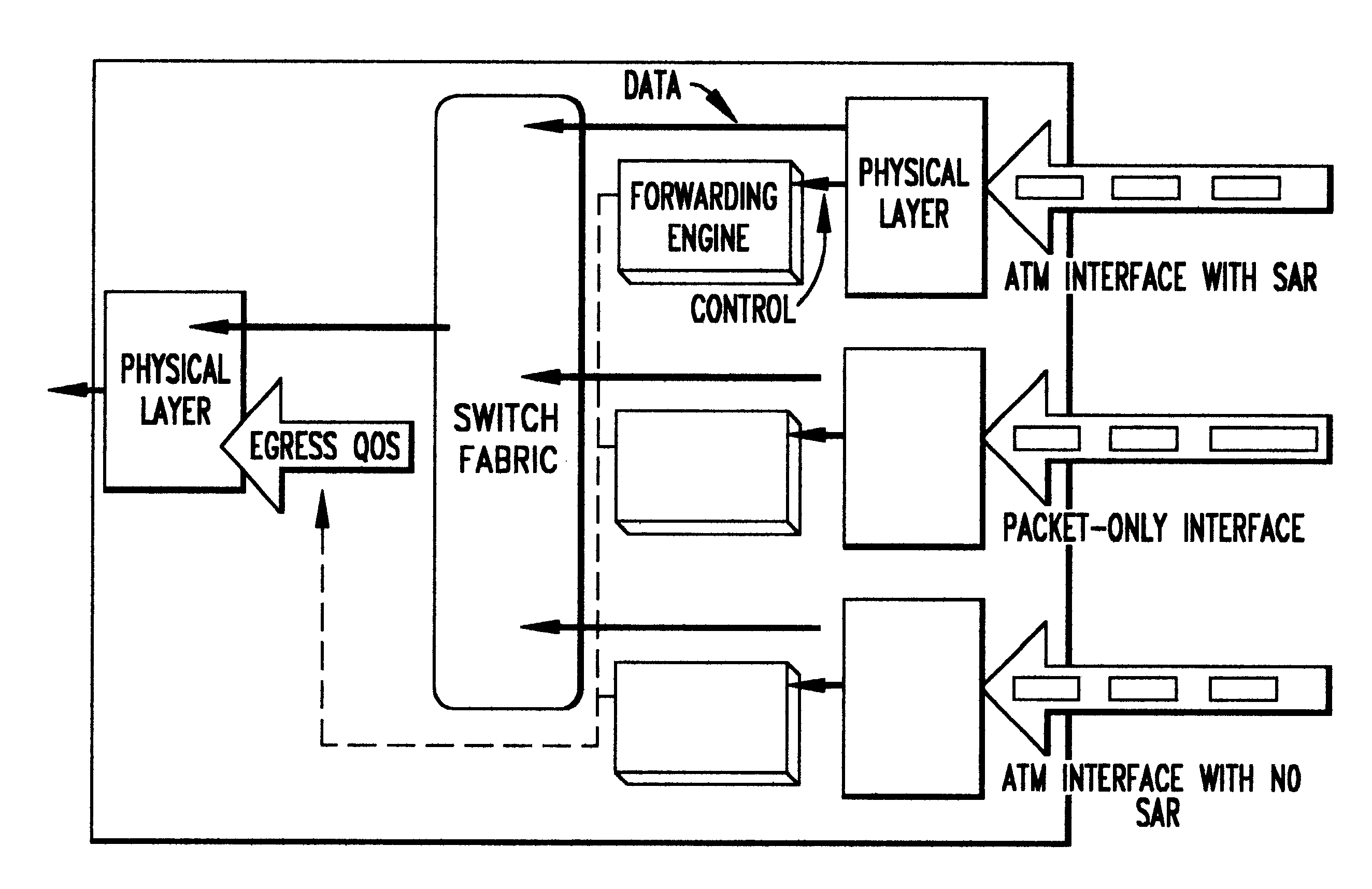
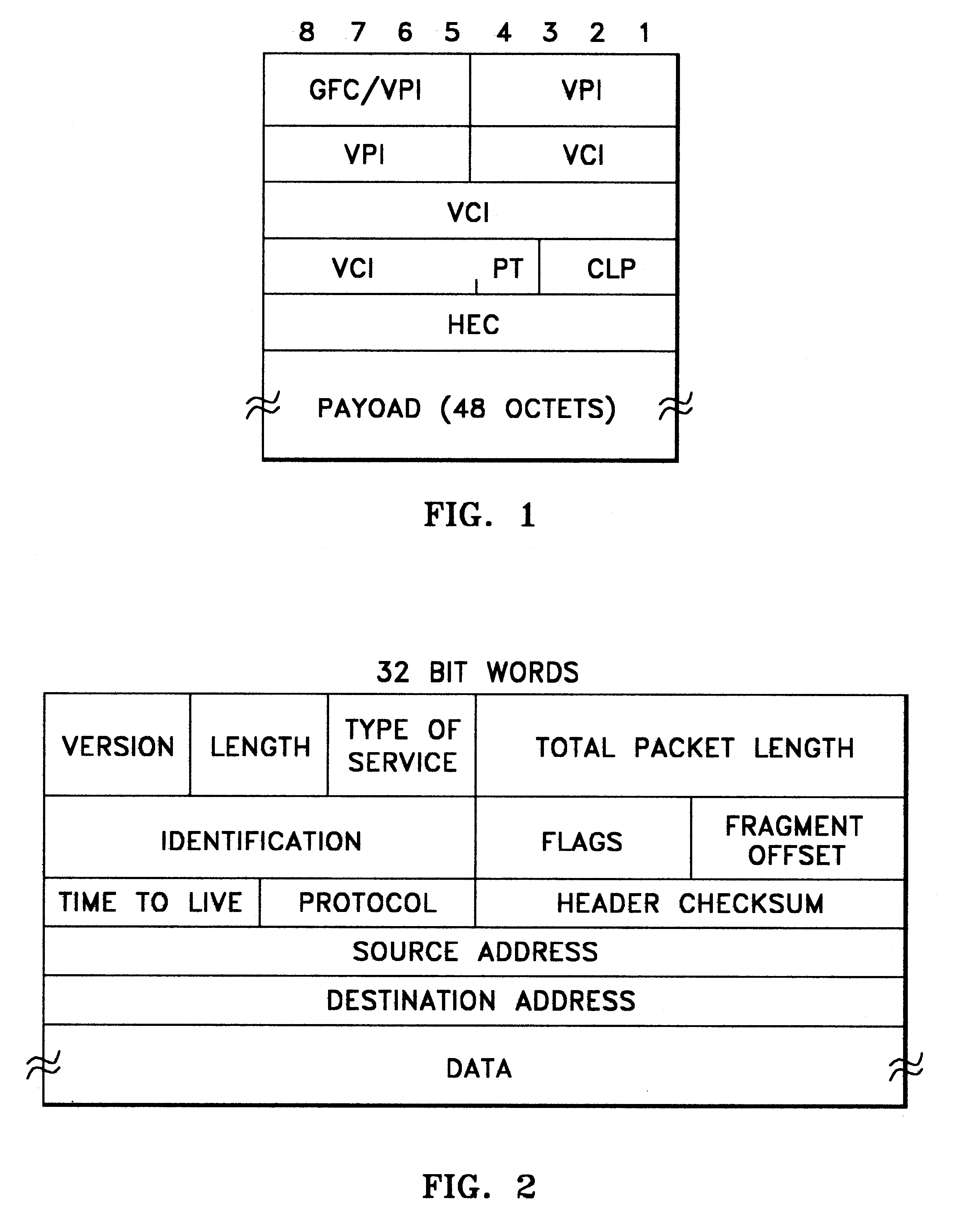
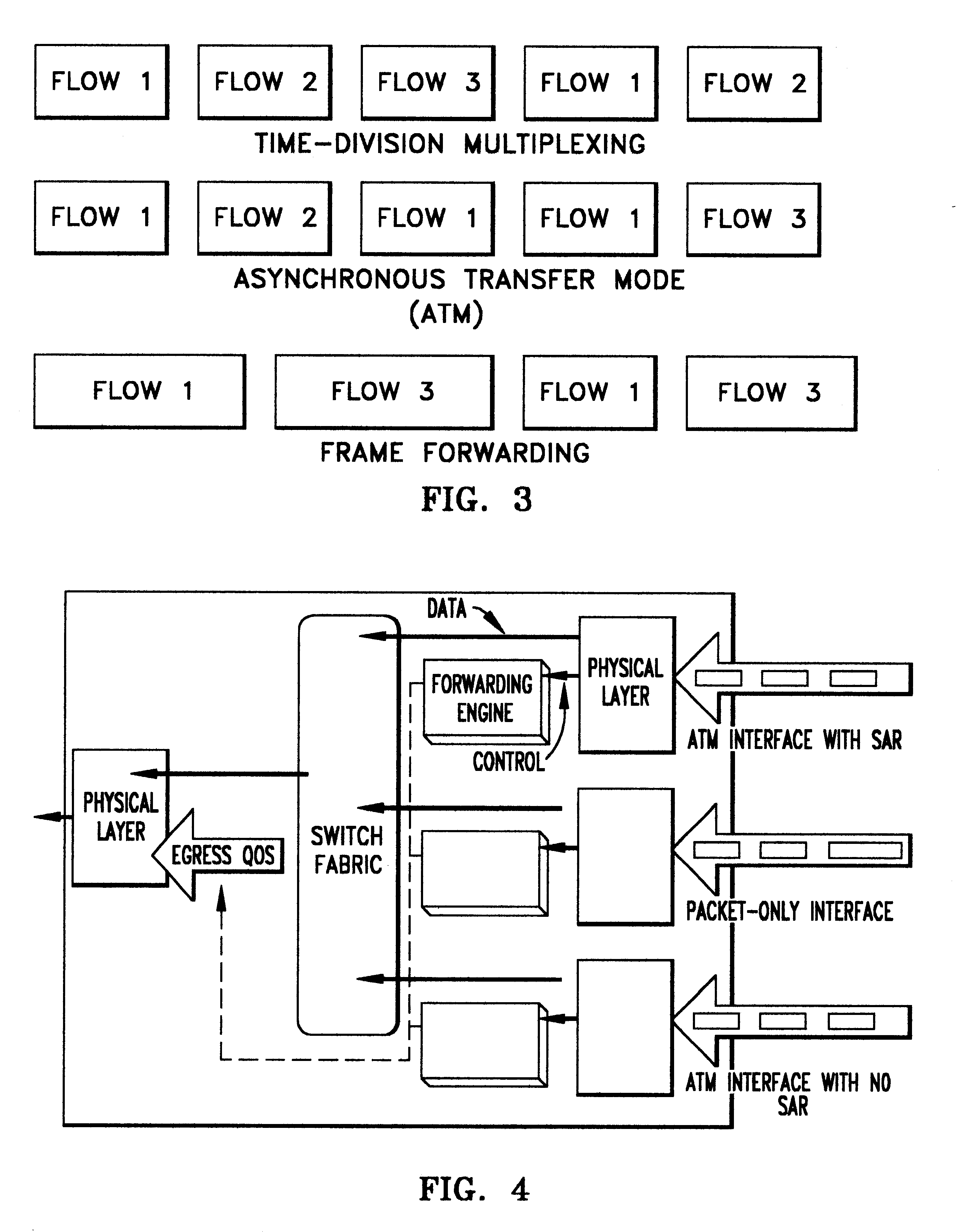
InactiveUS6259699B1Without impacting performance aspectPromote resultsData switching by path configurationStore-and-forward switching systemsAtm switchingQos management
A novel networking architecture and technique for transmitting both cells and packets or frames across a common switch fabric, effected, at least in part, by utilizing a common set of algorithms for the forwarding engine (the ingress side) and a common set of algorithms for the QoS management (the egress part) that are provided for each I / O module to process packet / cell information without impacting the correct operation of ATM switching and without transforming packets into cells for transfer across the switch fabric.
Owner:WSOU INVESTMENTS LLC +1
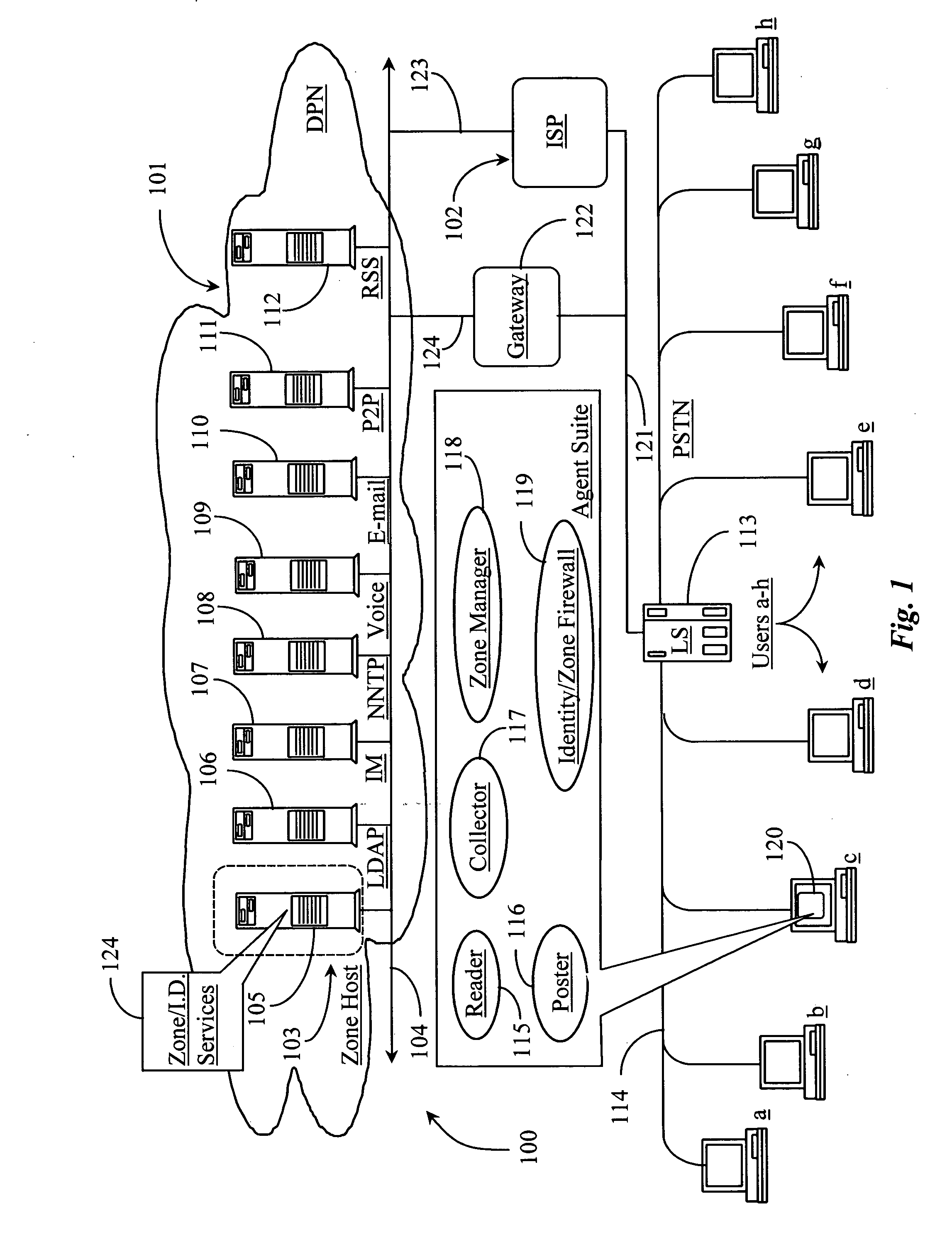
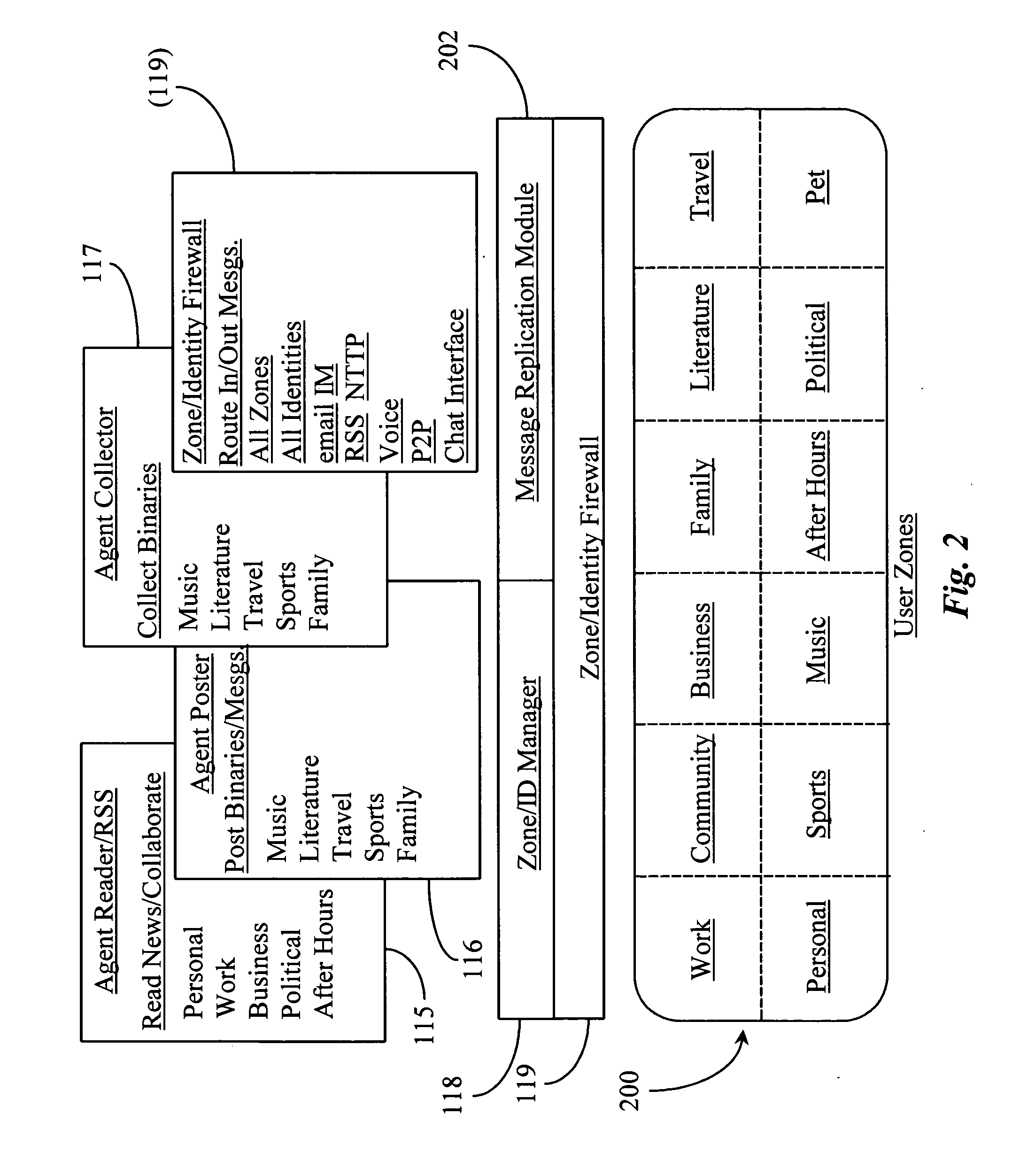
Methods and apparatus for identifying and facilitating a social interaction structure over a data packet network
ActiveUS20050198299A1Operation be completeServices signallingMultiple digital computer combinationsComputer networkSoftware suite
A software suite for managing the publishing and consumption of information and payload data across one or more transport protocols supported by a data-packet-network includes a posting application for publishing the information and payload data, and a consuming application for accessing and consuming the information and payload data. In a preferred embodiment the posting application enables posting of information that is consumable separately from the payload data wherein the information richly describes the payload data including provision of instructions for sampling the payload data before consuming the payload data.
Owner:FORTE INTERNET SOFTWARE
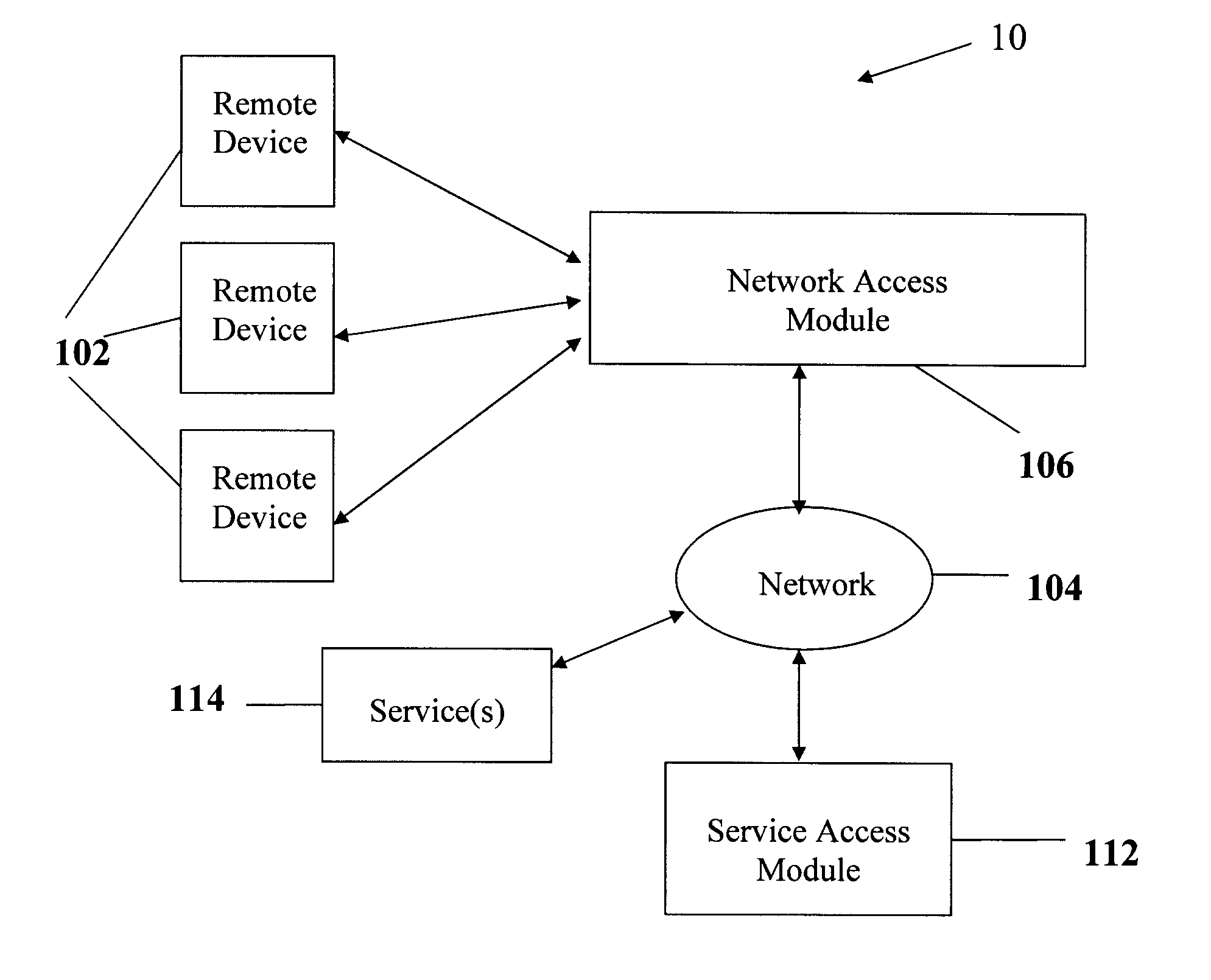
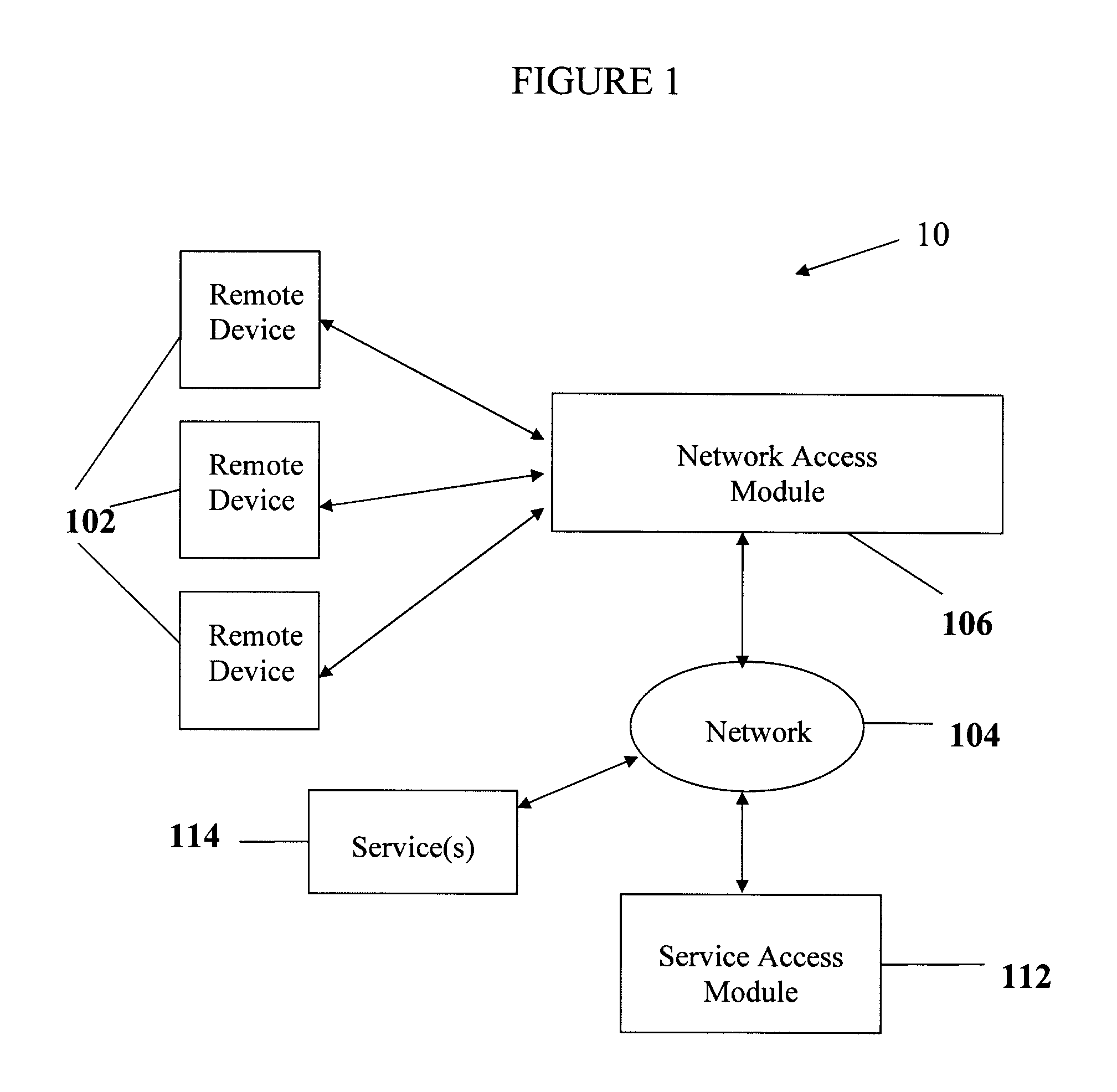
Remote service access system and method
InactiveUS20100107225A1Limited accessDigital data processing detailsMultiple digital computer combinationsData validationComputer network
A wireless service access system and method are disclosed. One aspect of the disclosed system provides a remote device wireless access to one or more services over a communication network, the system comprising a network access module adapted for communicating wirelessly with the remote device and for receiving therefrom identifying data; and a service access module, communicatively linked to the network access module, for authenticating the remote device based on the identifying data and authorizing access to the one or more services thereto via the network access module.
Owner:DATAVALET TECH
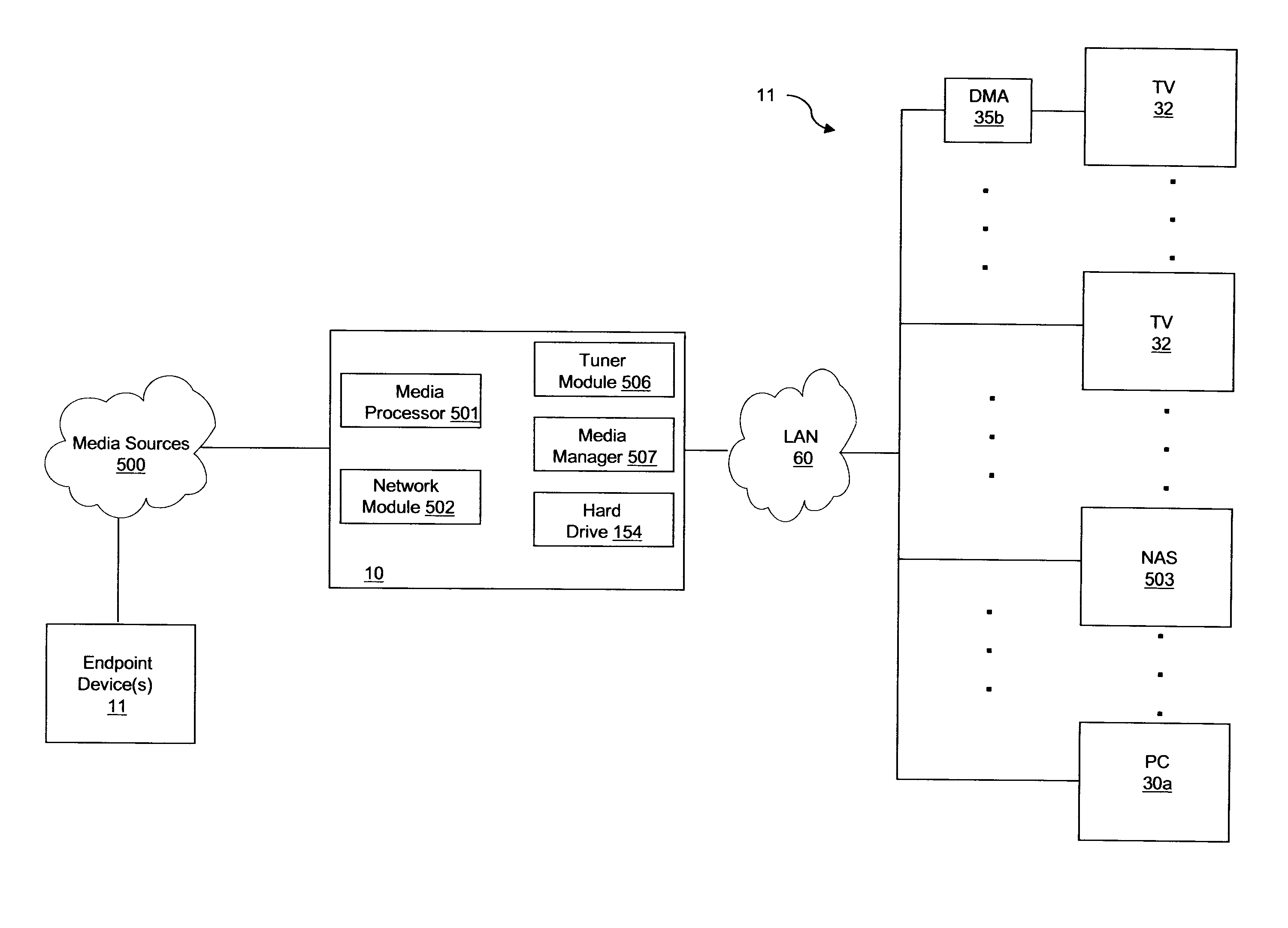
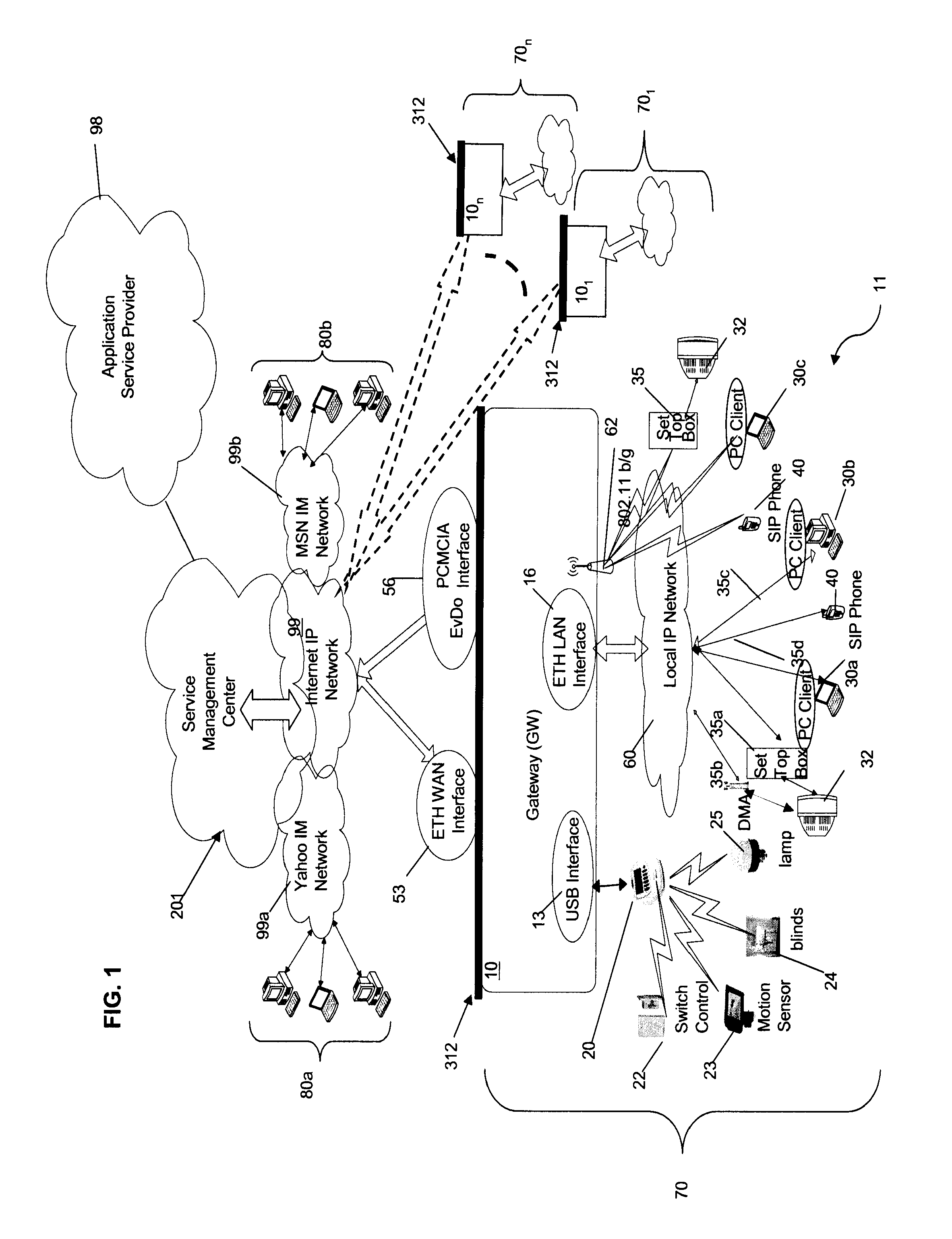
System And Method To Acquire, Aggregate, Manage, And Distribute Media
ActiveUS20080168523A1Simplify overall management of serviceReduce complexityMultiplex communicationBilling/invoicingComputer networkData format
A media content manager residing at a user premises having a tuner coupled to at least one media source operable to selectively receive at least one media stream of at least one type of media content. The media content manager also including a media processor coupled to the tuner and operable to receive the at least one media stream and convert the media stream to a predetermined data format, the at least one media stream comprising metadata. Additionally, the media content manages has a media manager coupled to the media processor and operable to receive the at least one media stream in the predetermined data format and direct the media stream to a selected media player device coupled to the media processor. Furthermore, the media content manager includes a storage device coupled to the media manager and operable to receive and store the at least one media stream in the predetermined data format.
Owner:KIP PROD P1 LP
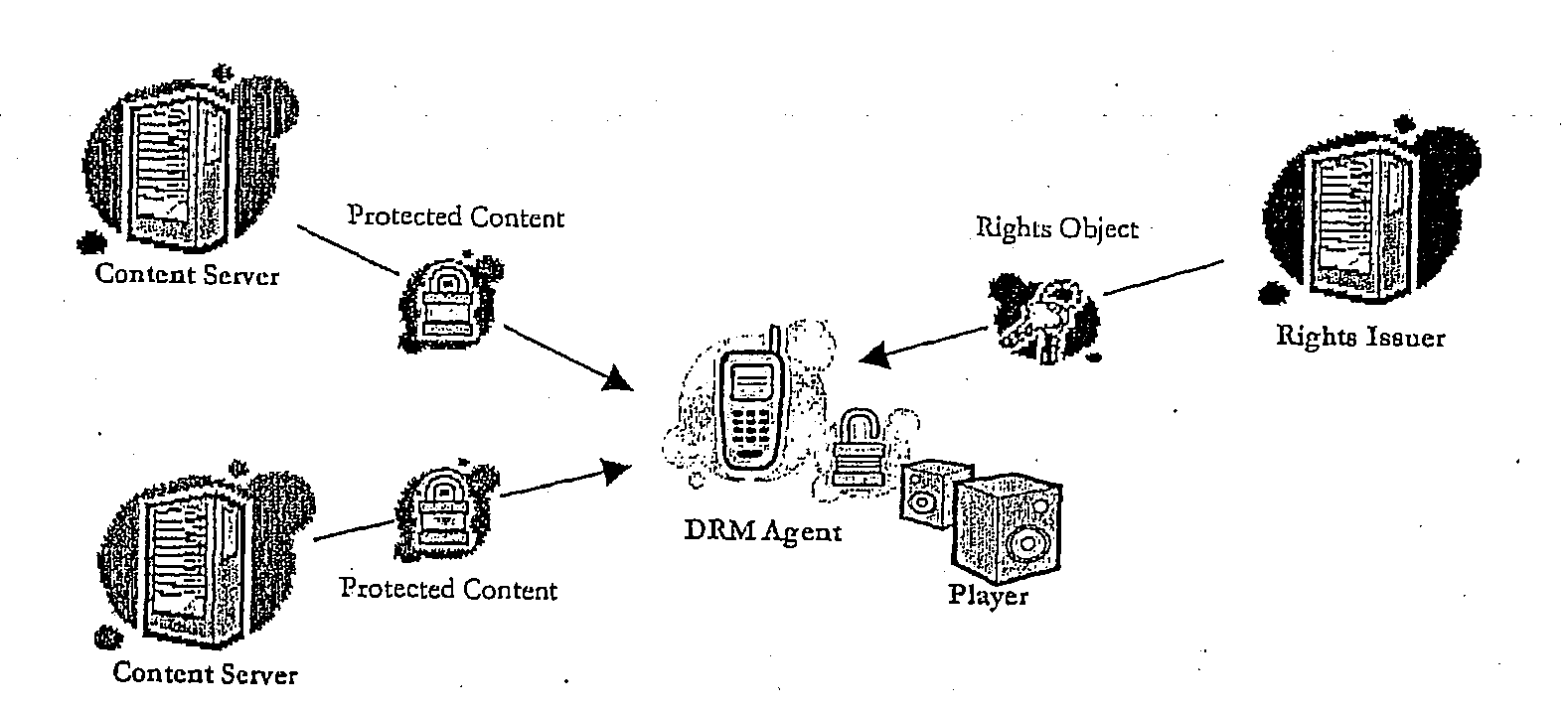
Method of Providing Digital Rights Management for Music Content by Means of a Flat-Rate Subscription
ActiveUS20100031366A1Reliable and goodEasy to manageMetering/charging/biilling arrangementsDigital data processing detailsOperational systemComputer network
The invention enables digital music content to be downloaded to and used on a portable wireless computing device. An application running on the wireless device has been automatically adapted to parameters associated with the wireless device without end-user input (e.g. the application has been configured in dependence on the device OS and firmware, related bugs, screen size, pixel number, security models, connection handling, memory etc. This application enables an end-user to browse and search music content on a remote server using a wireless network; to download music content from that remote server using the wireless network and to playback and manage that downloaded music content. The application also includes a digital rights management system that enables unlimited legal downloads of different music tracks to the device and also enables any of those tracks stored on the device to be played so long as a subscription service has not terminated.
Owner:TIKTOK PTE LTD
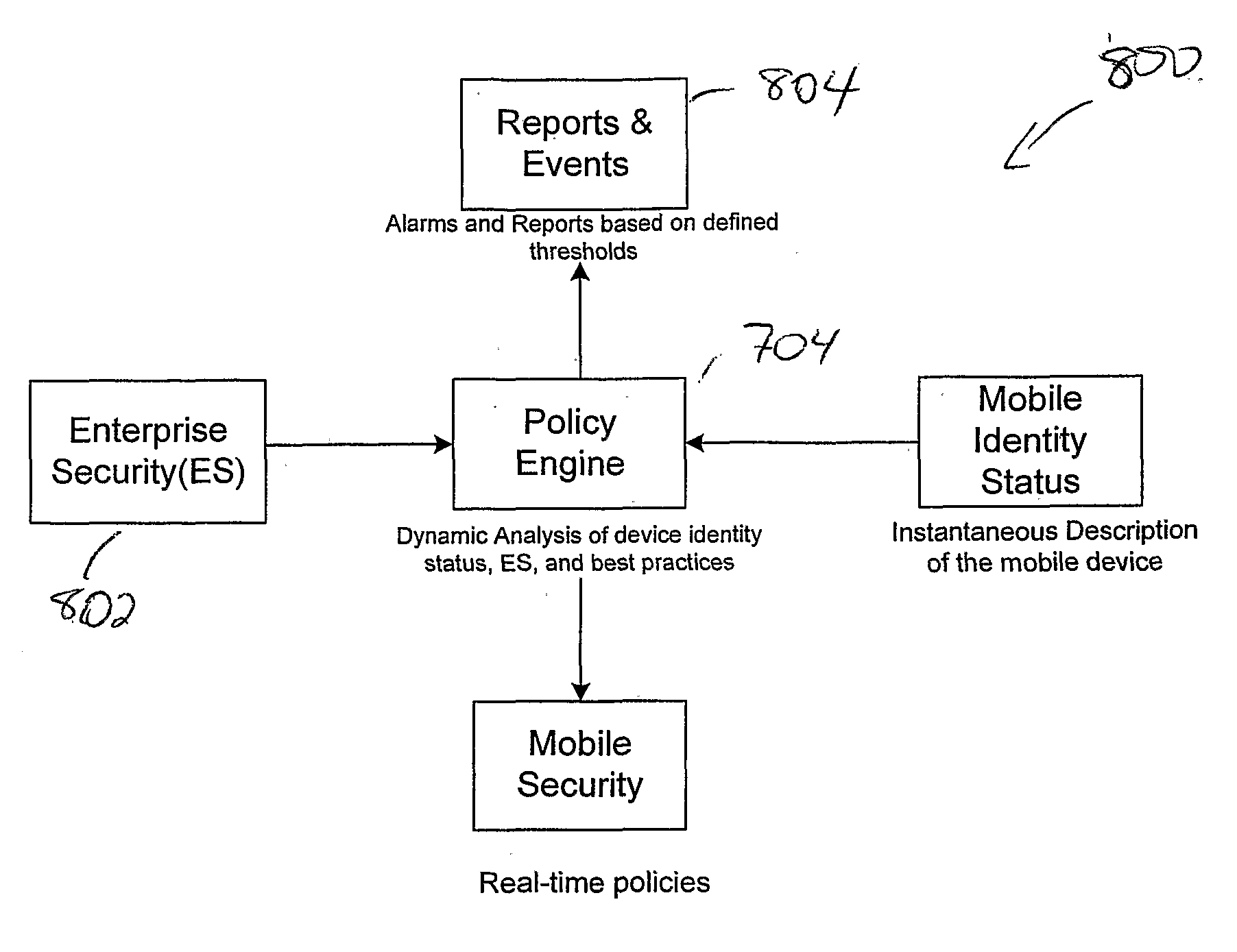
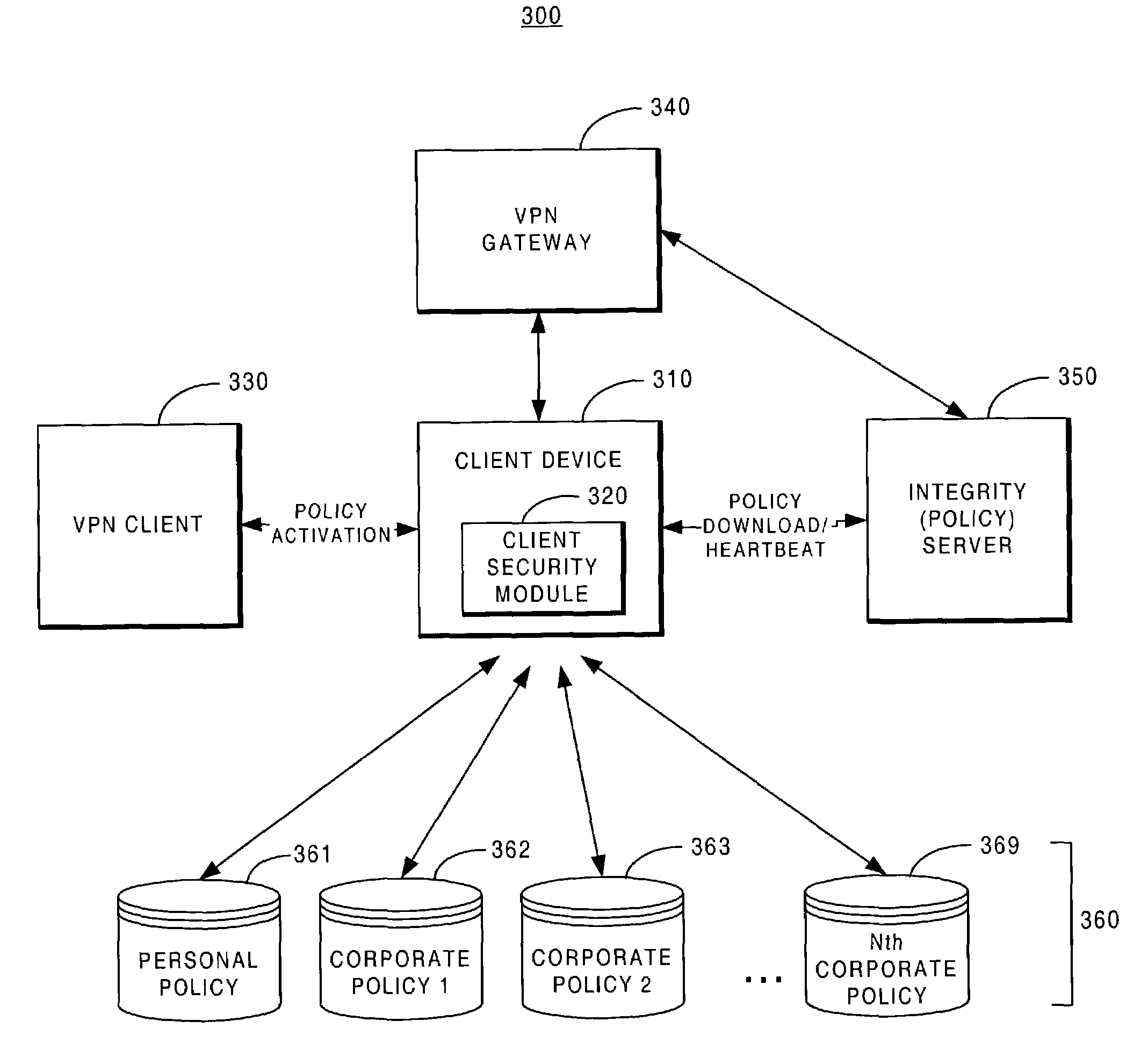
System and method for enforcing a security policy on mobile devices using dynamically generated security profiles
ActiveUS20070143824A1Eliminate needComplete banking machinesPayment architectureComputer networkSecurity parameter
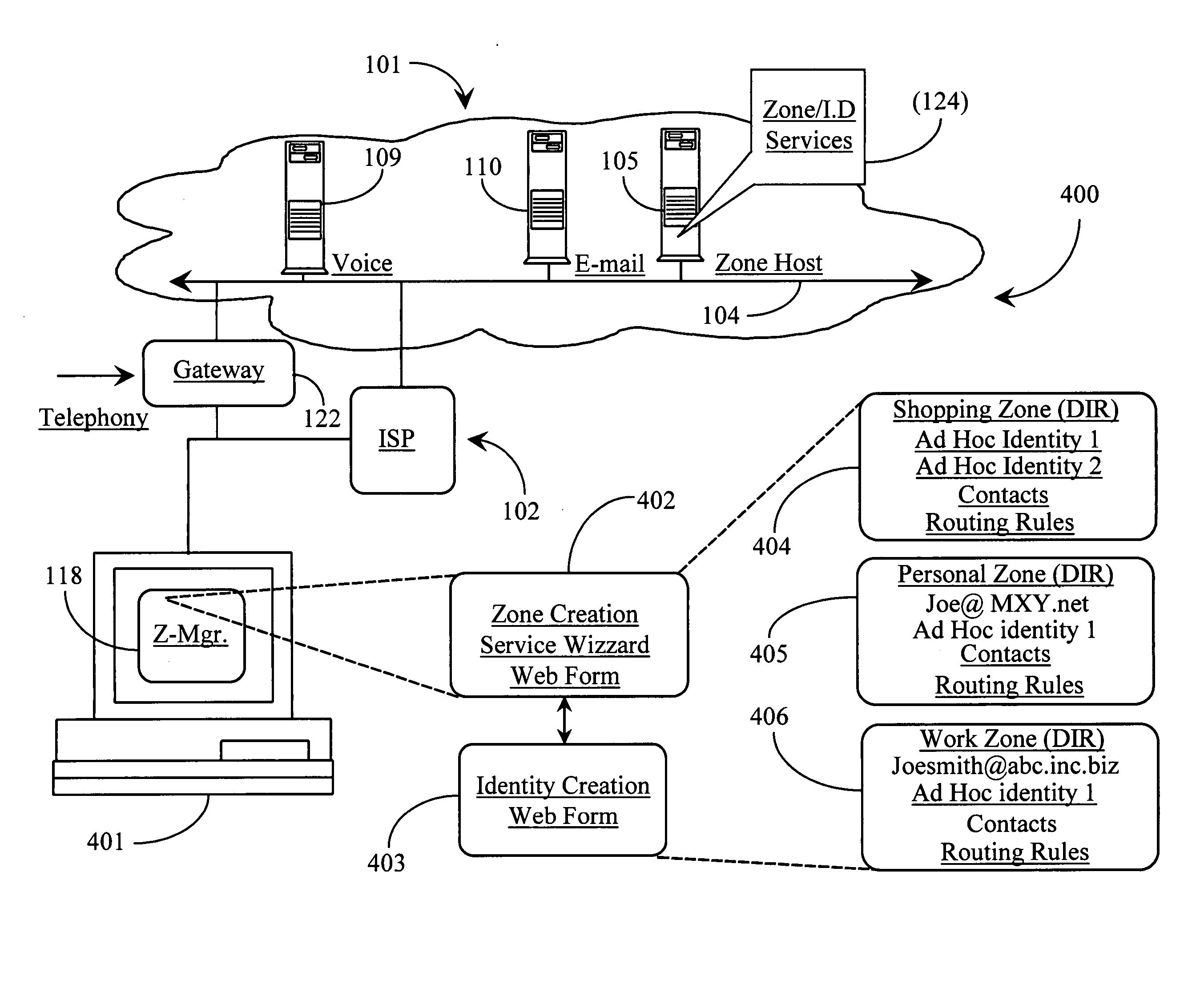
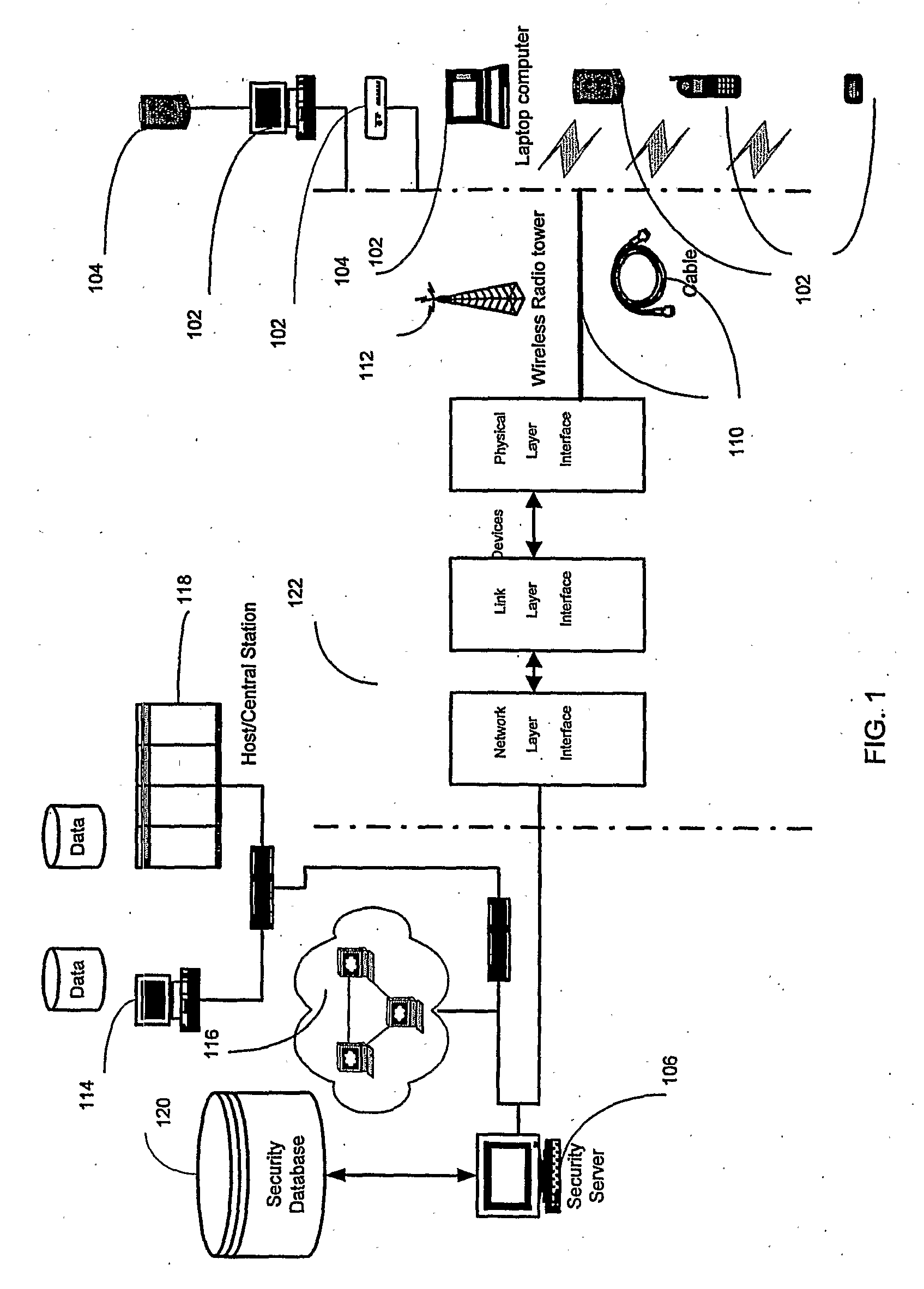
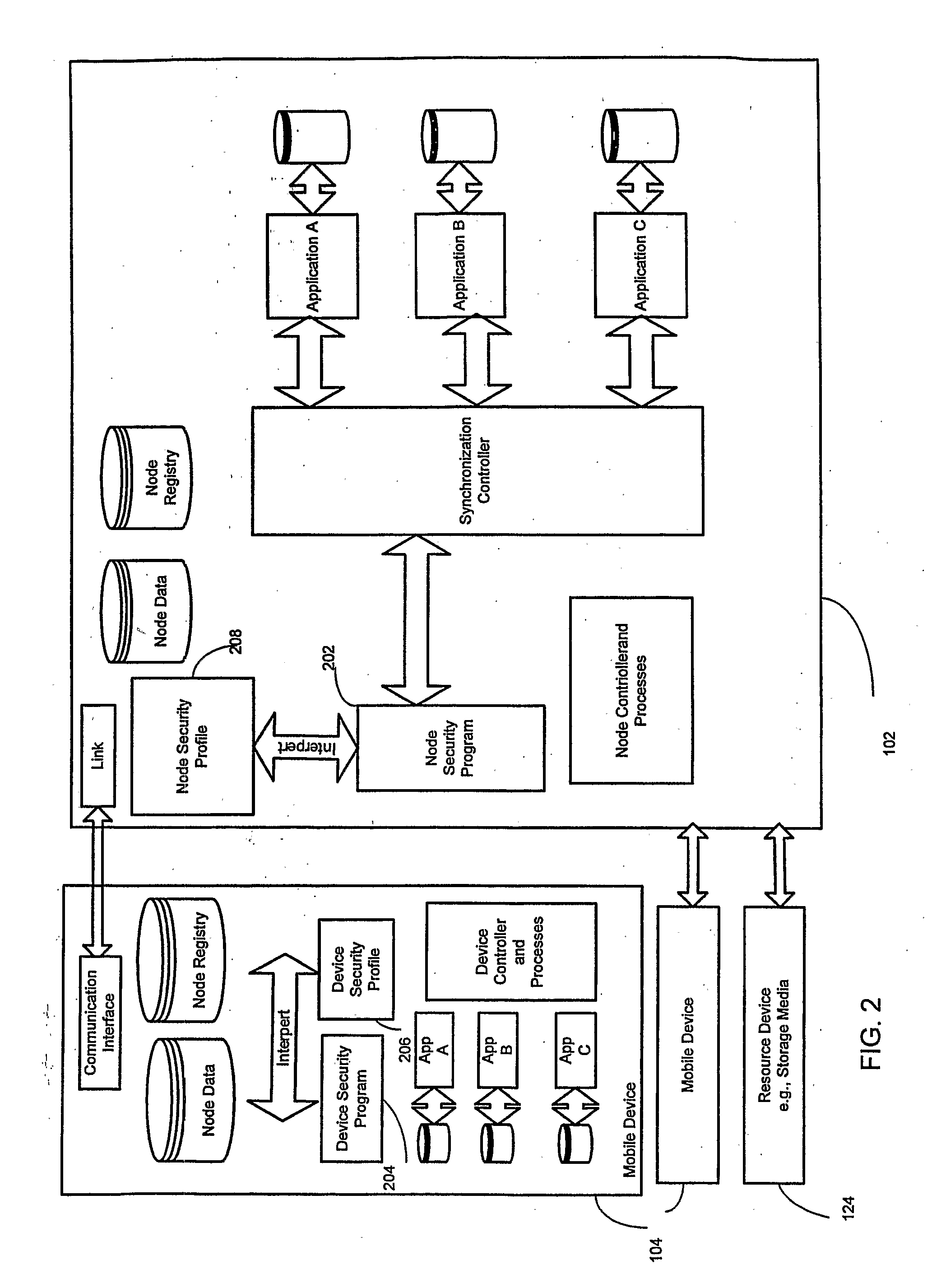
A system and method for enforcing security parameters that collects information from a source relating to a mobile device (104). Based on the collected information, an identity status for the mobile device (104) is determined that uniquely identifies the mobile device (104) and distinguishes it from other mobile devices. The identity status of the mobile device (104) can be determined when the mobile device (104) connects to a computing node source (102) or when the mobile device (104) accesses a resource (124) within the network. A security profile based on the identity status of the mobile device (104) is generated and the security profile is applied to the mobile device (104).
Owner:TRUST DIGITAL
Domain name routing
InactiveUS6119171AImprove service qualityEasy to useTime-division multiplexData switching by path configurationDomain nameComputer network
The present invention provides for a Domain Name Router (DNR) that uses domain names to route data sent to a destination on a network (e.g., a stub network). Each corporate entity or stub network can be assigned one or a small number of global addresses. Each of the hosts on the stub network can be assigned a global address. When a source entity sends data to a destination entity with a local address, the data is sent to the DNR using a global address. The source entity embeds the destination's domain name and its own domain name inside the data. The DNR extracts the destination's domain name from the data, translates that domain name to a local address and sends the data to the destination.
Owner:F POSZAT HU +1
Applications processor including a database system, for use in a wireless location system
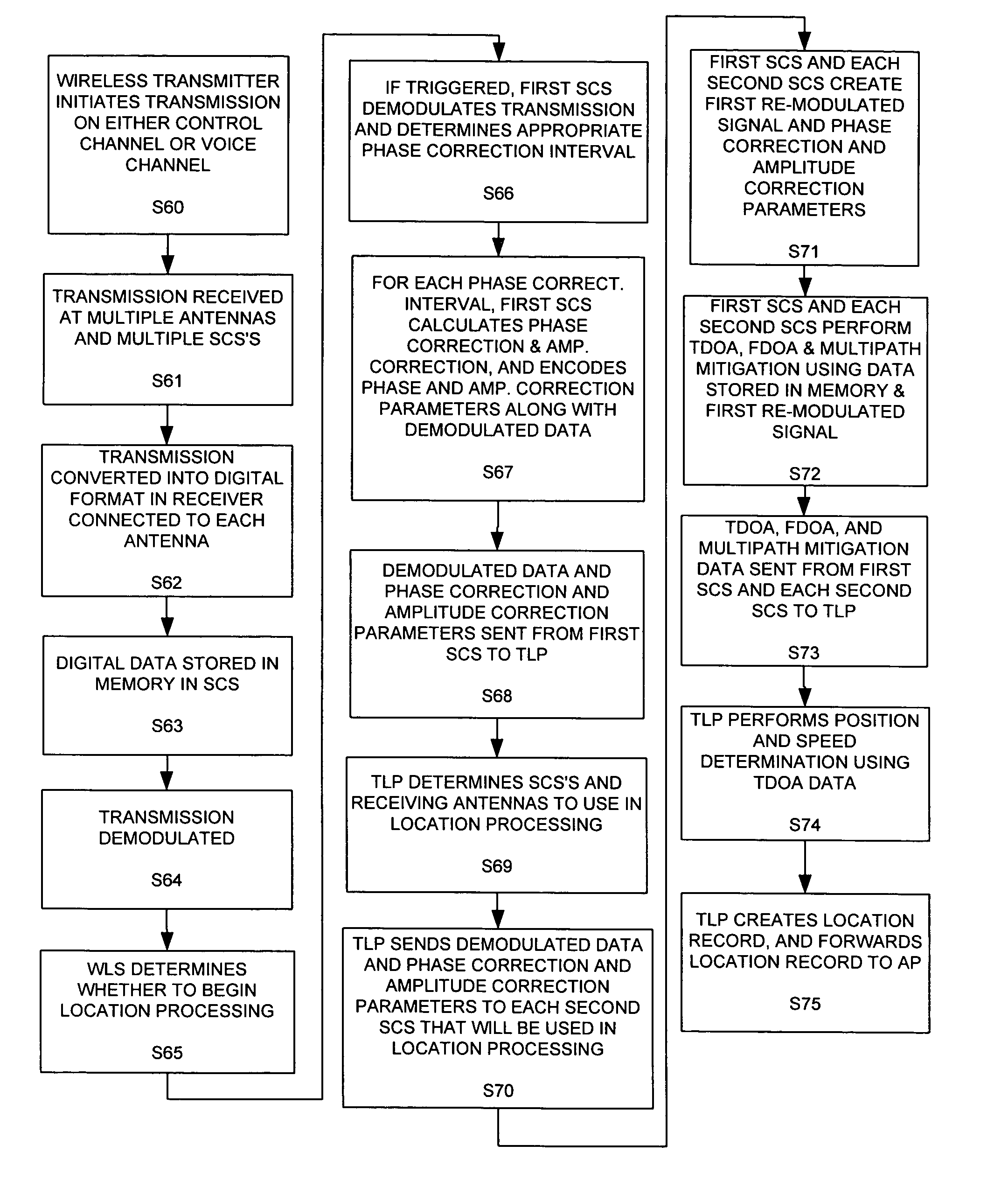
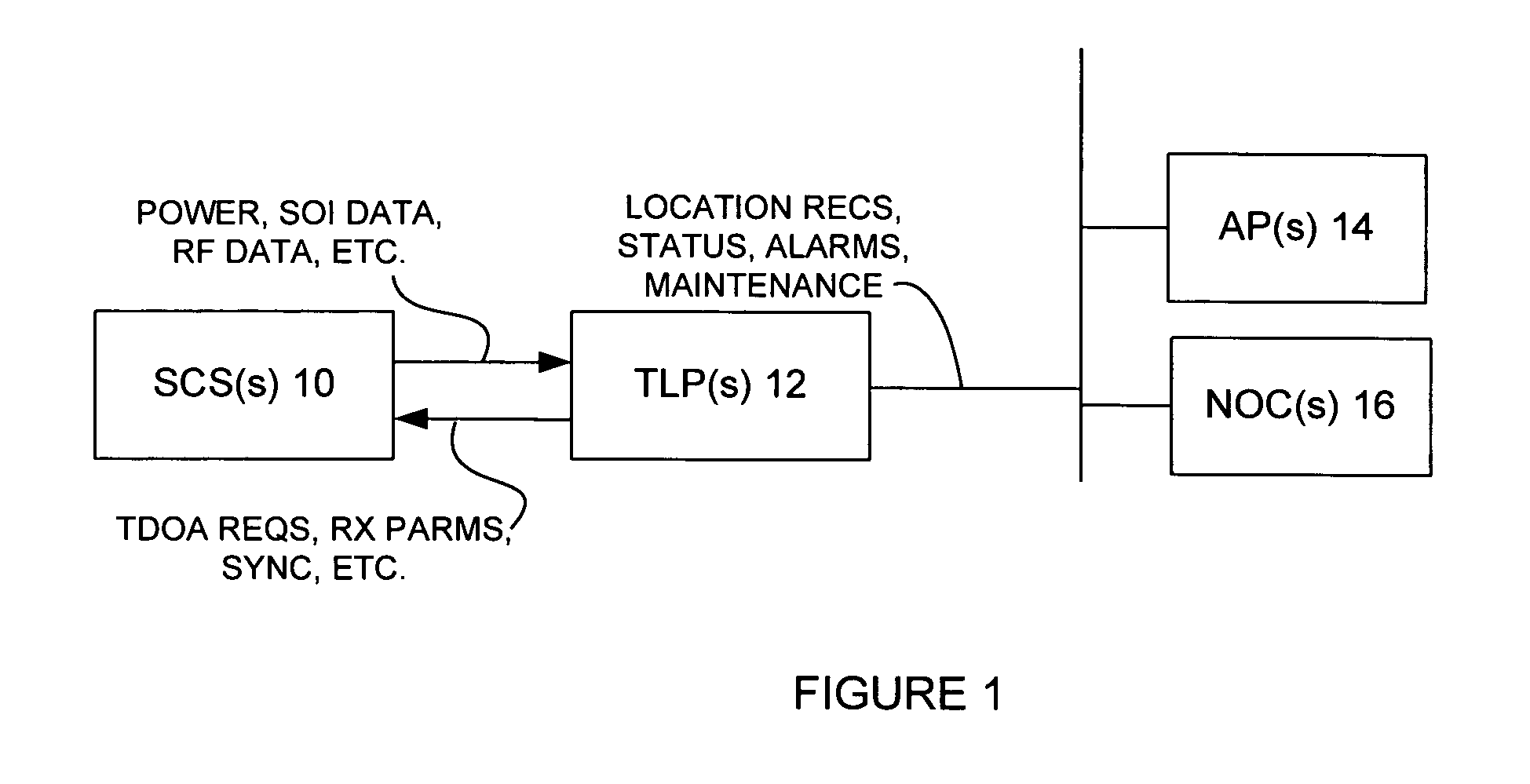
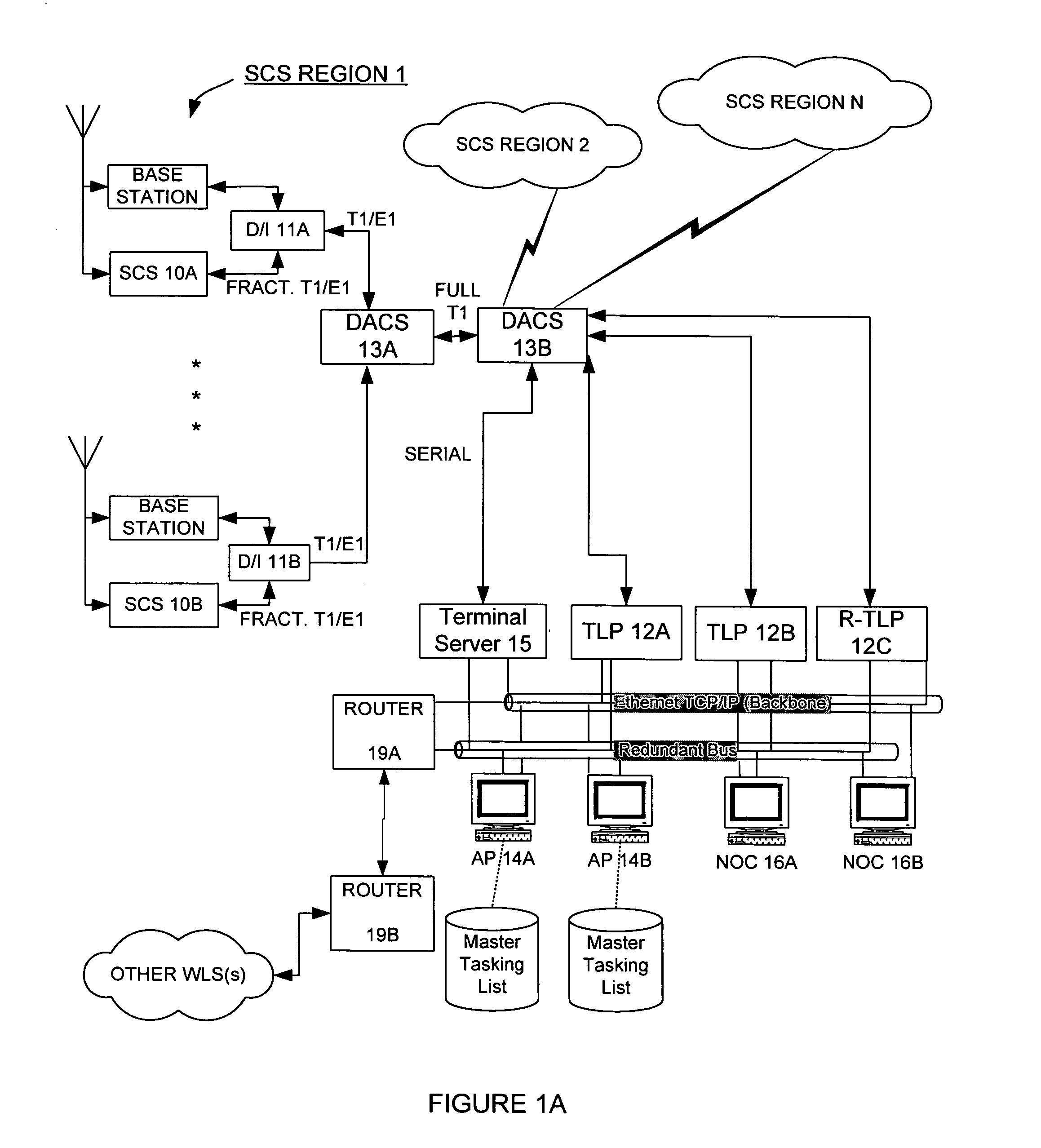
InactiveUS7271765B2Emergency connection handlingDirection finders using radio wavesComputer networkCollection system
An Applications Processor (14) including a centralized database system is used in a wireless location system (WLS). The APs 14 may be used to manage resources in the WLS, including signal collection systems (SCSs 10) and TDOA location processors (TLPs 12). Each AP 14 contains a database containing triggers for the WLS. The WLS can be programmed to locate only certain pre-determined types of transmissions. When a transmission of a pre-determined type occurs, then the WLS is triggered to begin location processing. Each AP 14 also contains applications interfaces that permit a variety of applications to securely access the WLS. These applications may access location records in real time or non-real time, create or delete certain types of triggers, or cause the WLS to take other actions. Each AP 14 is also capable of certain post-processing functions.
Owner:TRUE POSITION INC
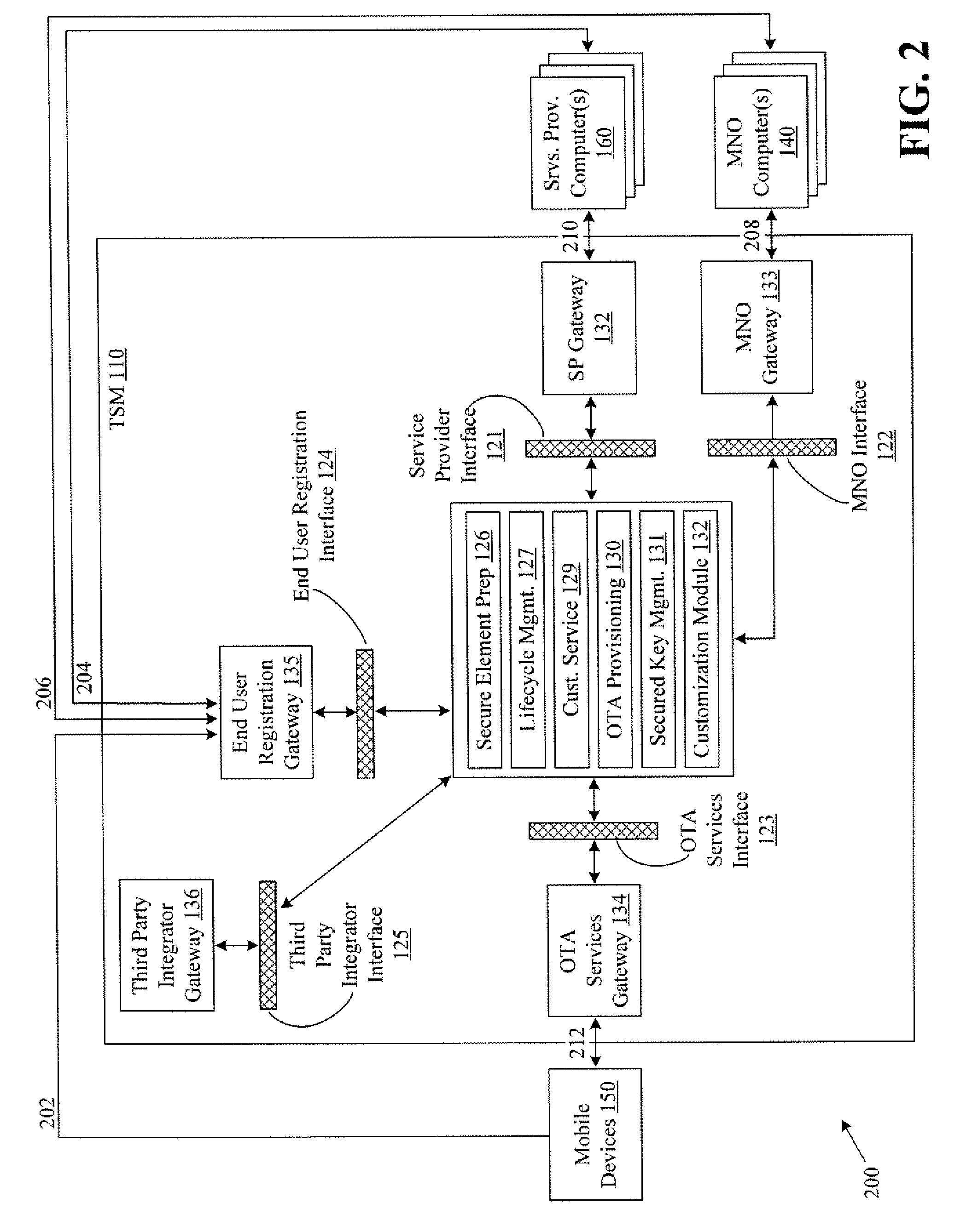
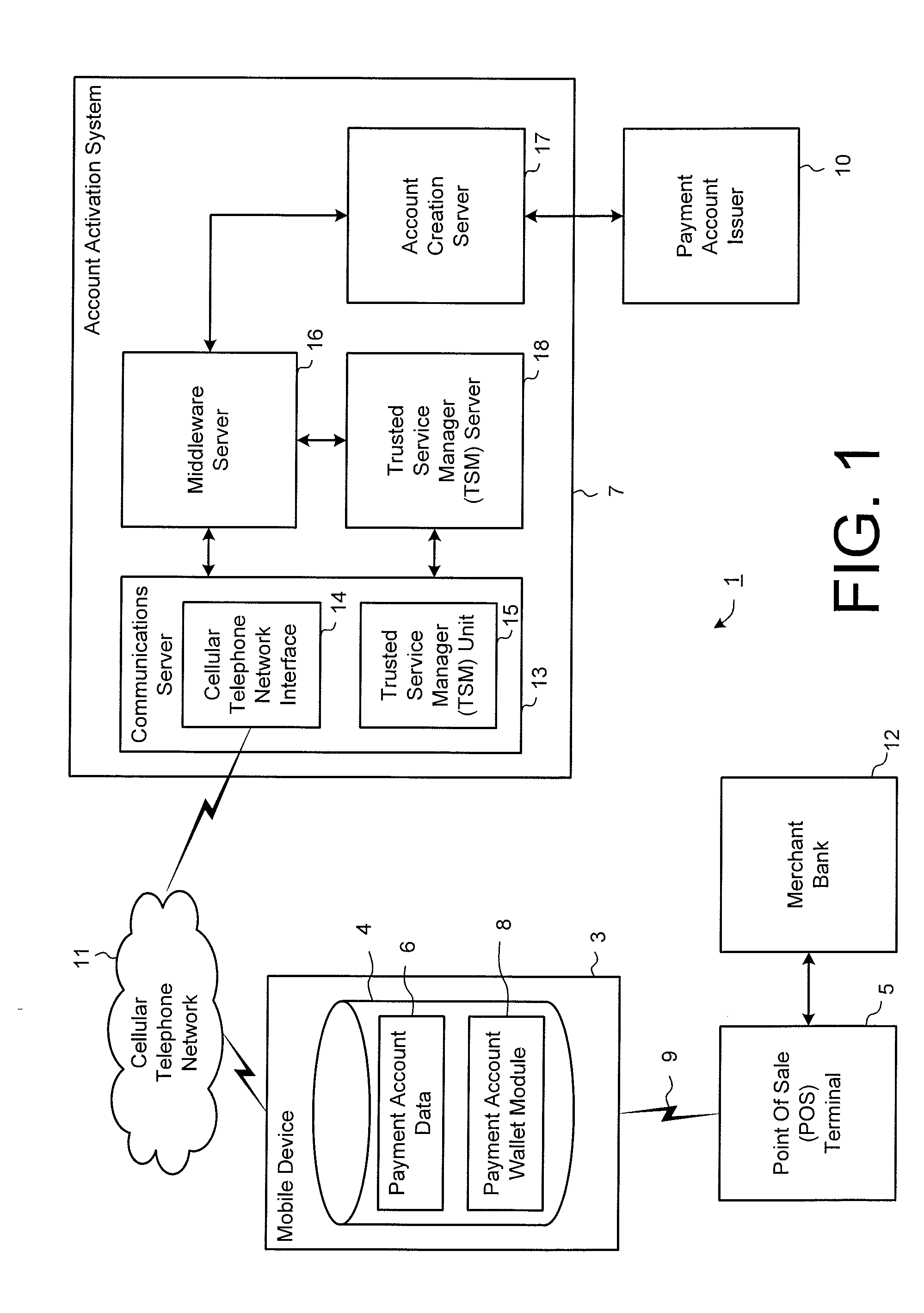
Systems and methods for providing trusted service management services
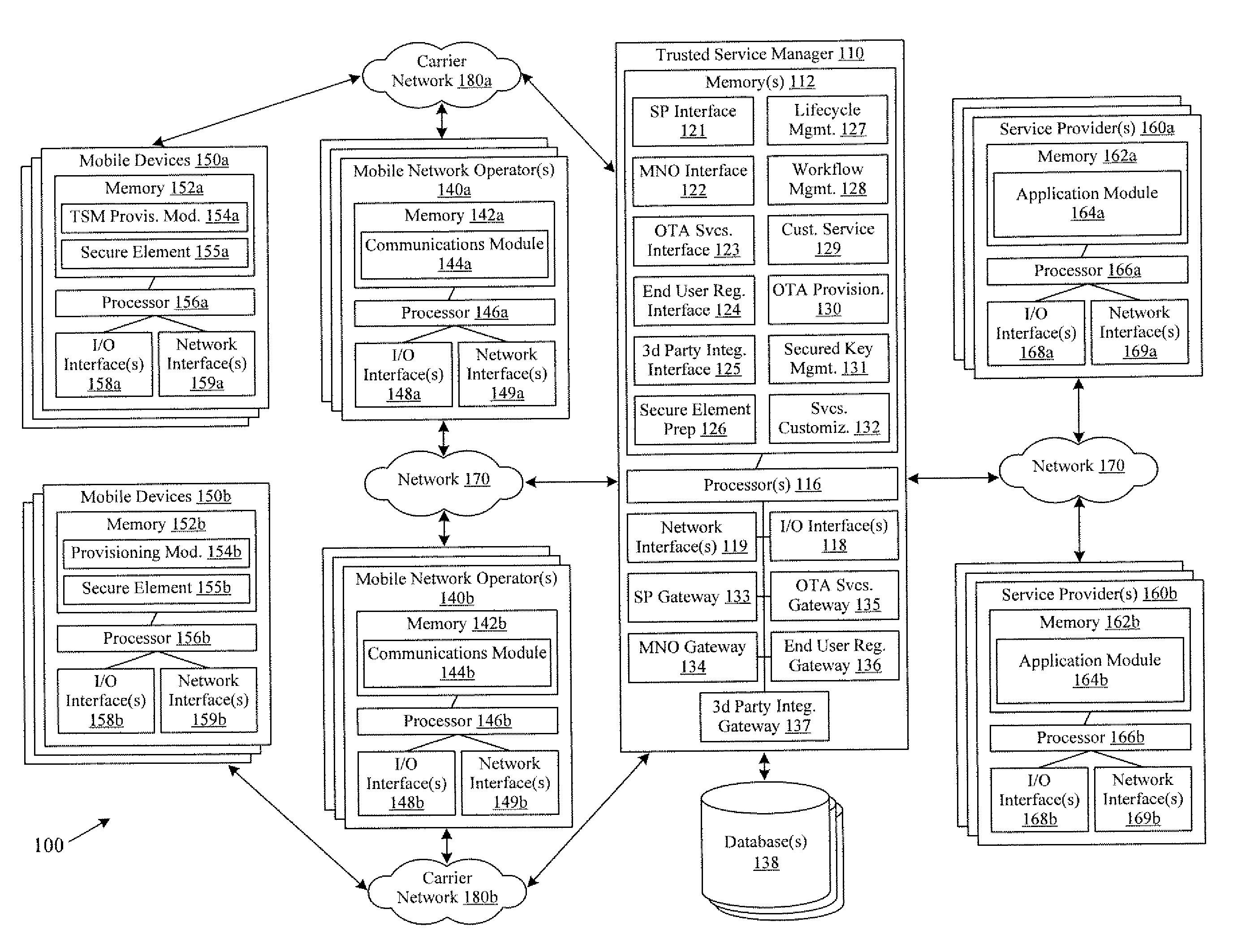
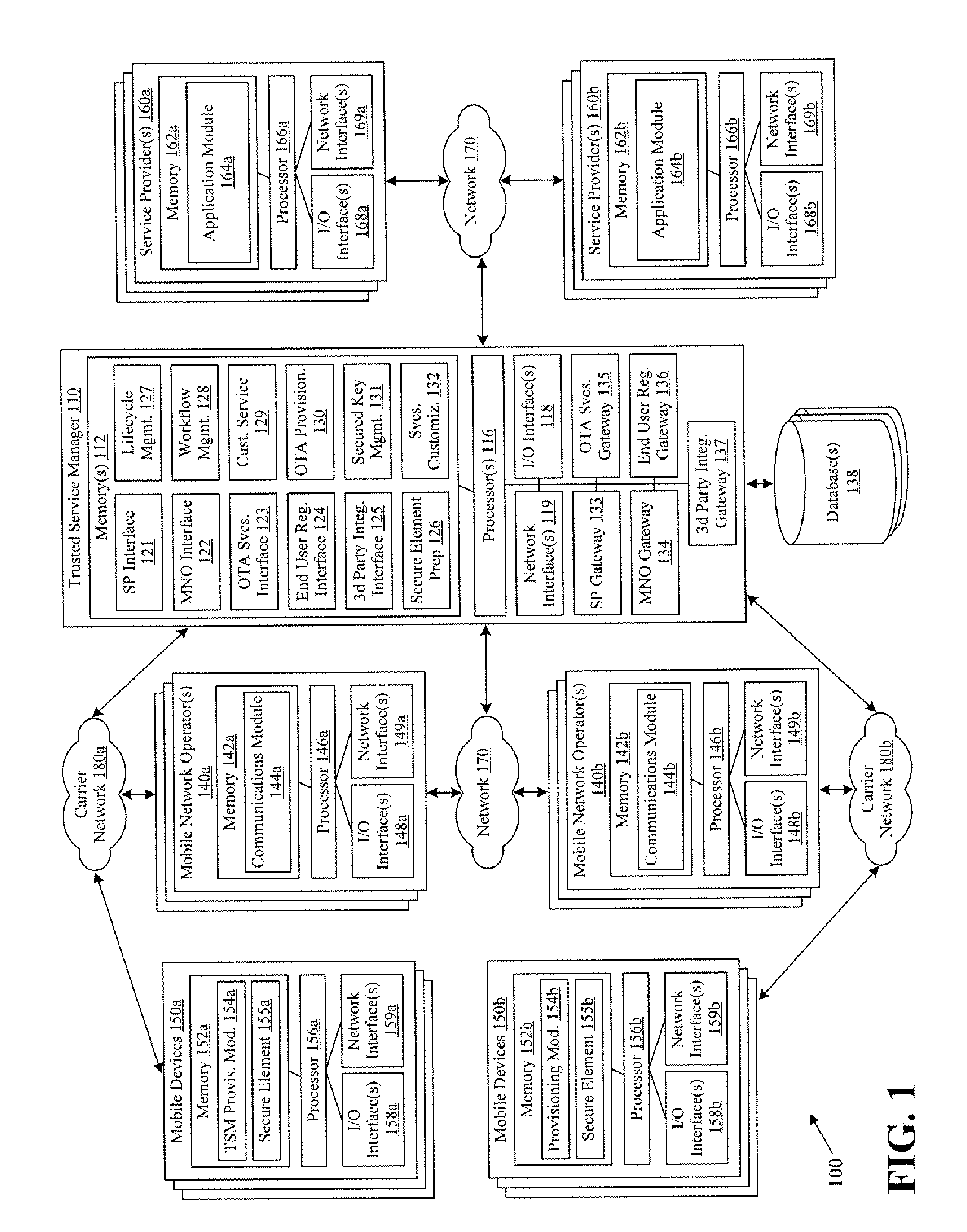
InactiveUS20100291904A1Easy maintenanceOptimize networkService provisioningSpecial service for subscribersService provisionMobile device
Embodiments of the invention provide systems and methods for providing trusted service management services. According to one embodiment, a system can include at least one service provider gateway operable to receive and transmit messages with multiple service providers; at least one mobile network operator gateway operable to receive and transmit messages with multiple mobile network operators; at least one provisioning gateway operable to transmit mobile device application data with multiple mobile devices and to receive messages from the plurality of mobile devices. The system can further include a processor operable to execute computer-executable instructions to: facilitate service provider communications by providing a common service provider interface for the service providers; facilitate mobile network operator communications by providing a common mobile network operator interface for the mobile network operators; facilitate provisioning multiple mobile device applications with the mobile devices; and facilitate communications with the mobile devices.
Owner:FIRST DATA
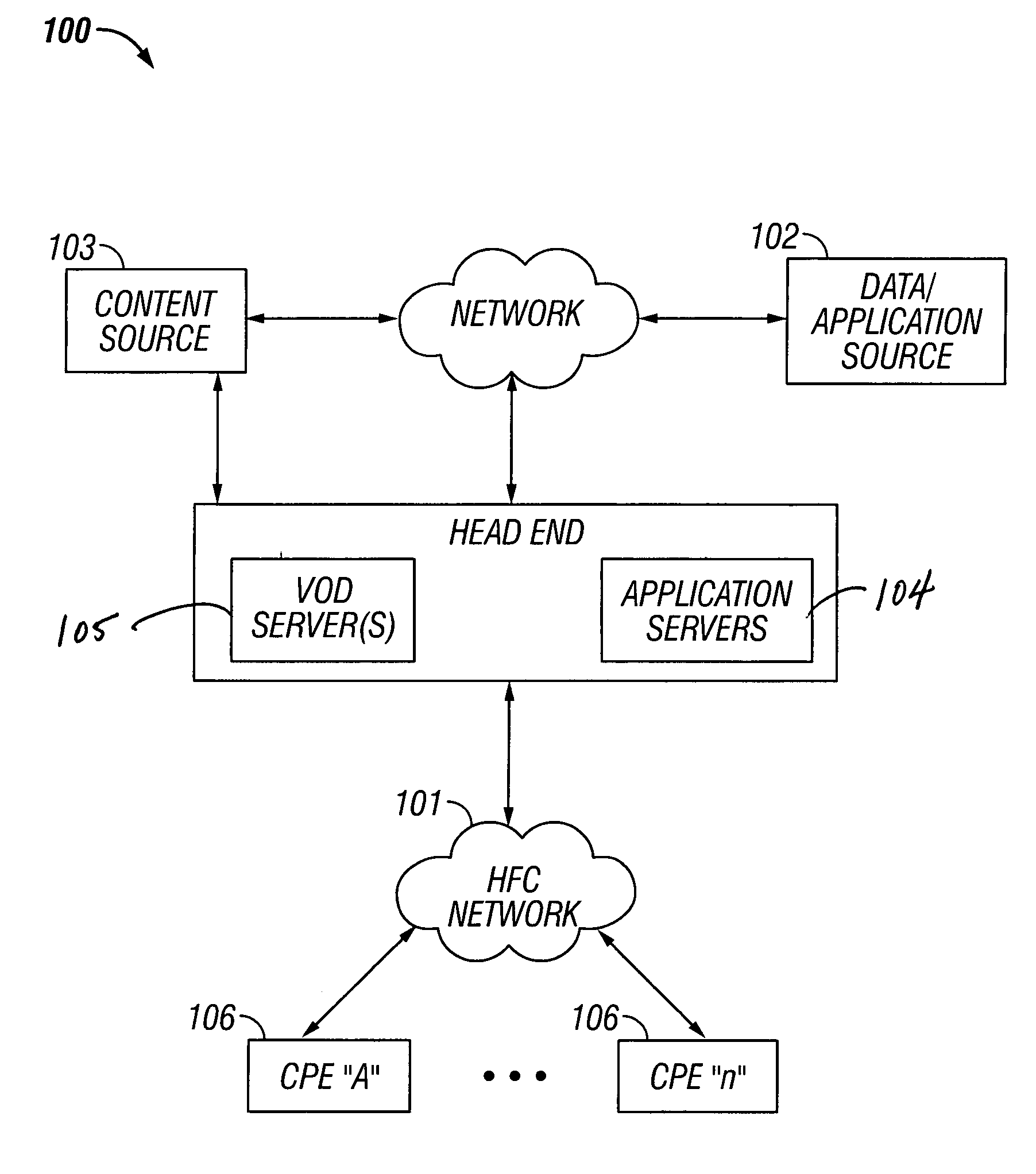
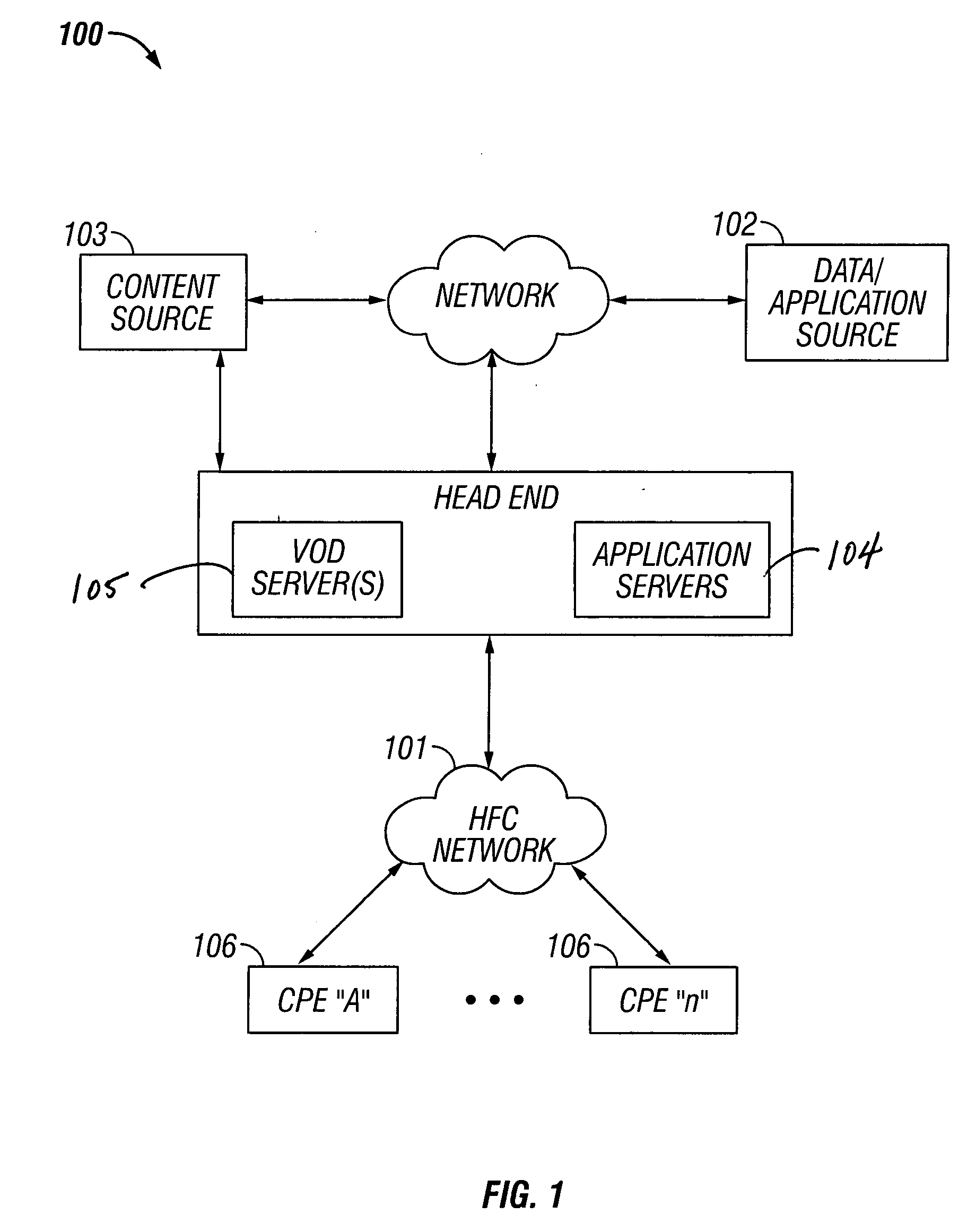
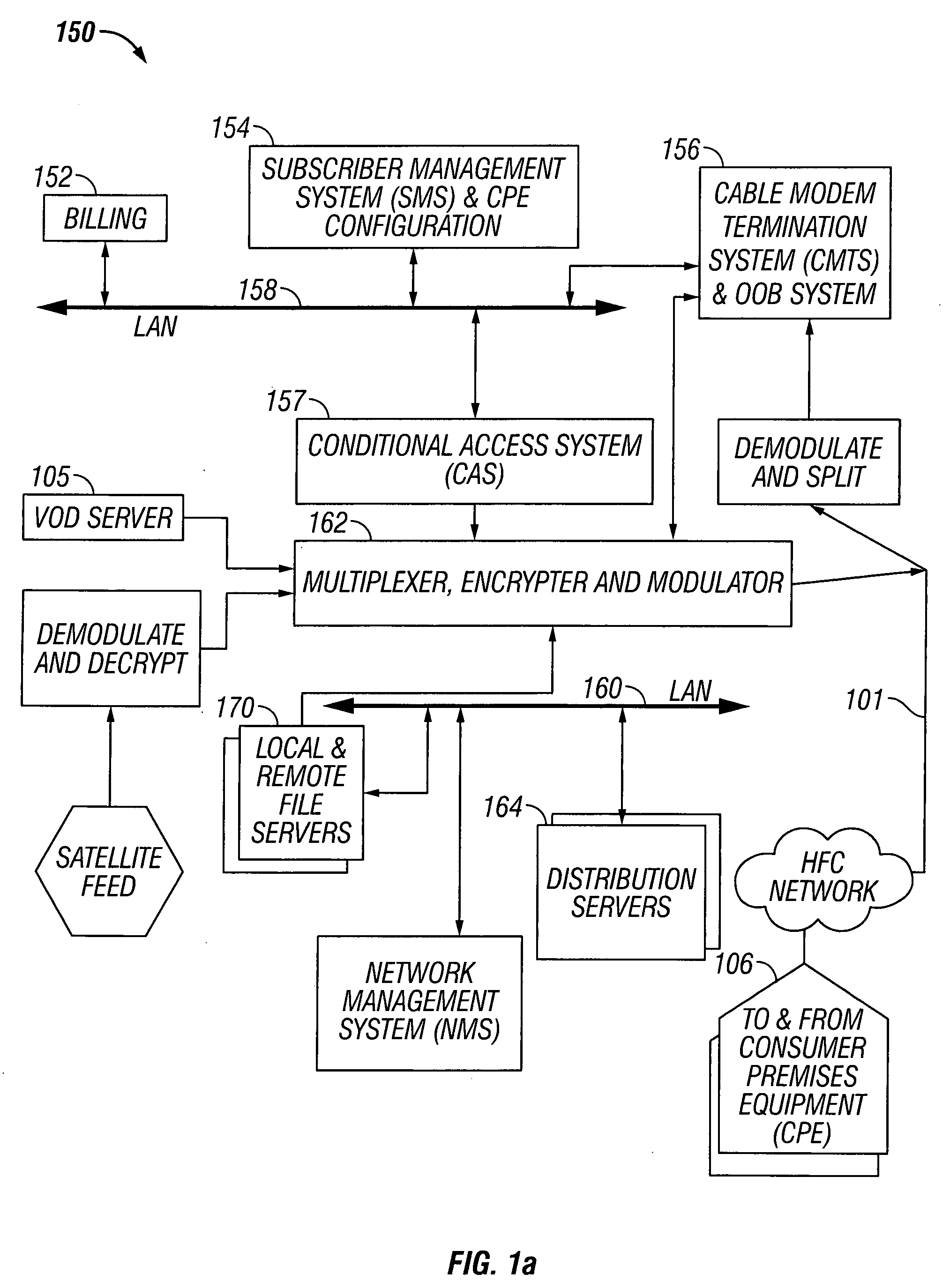
Premises gateway apparatus and methods for use in a content-based network
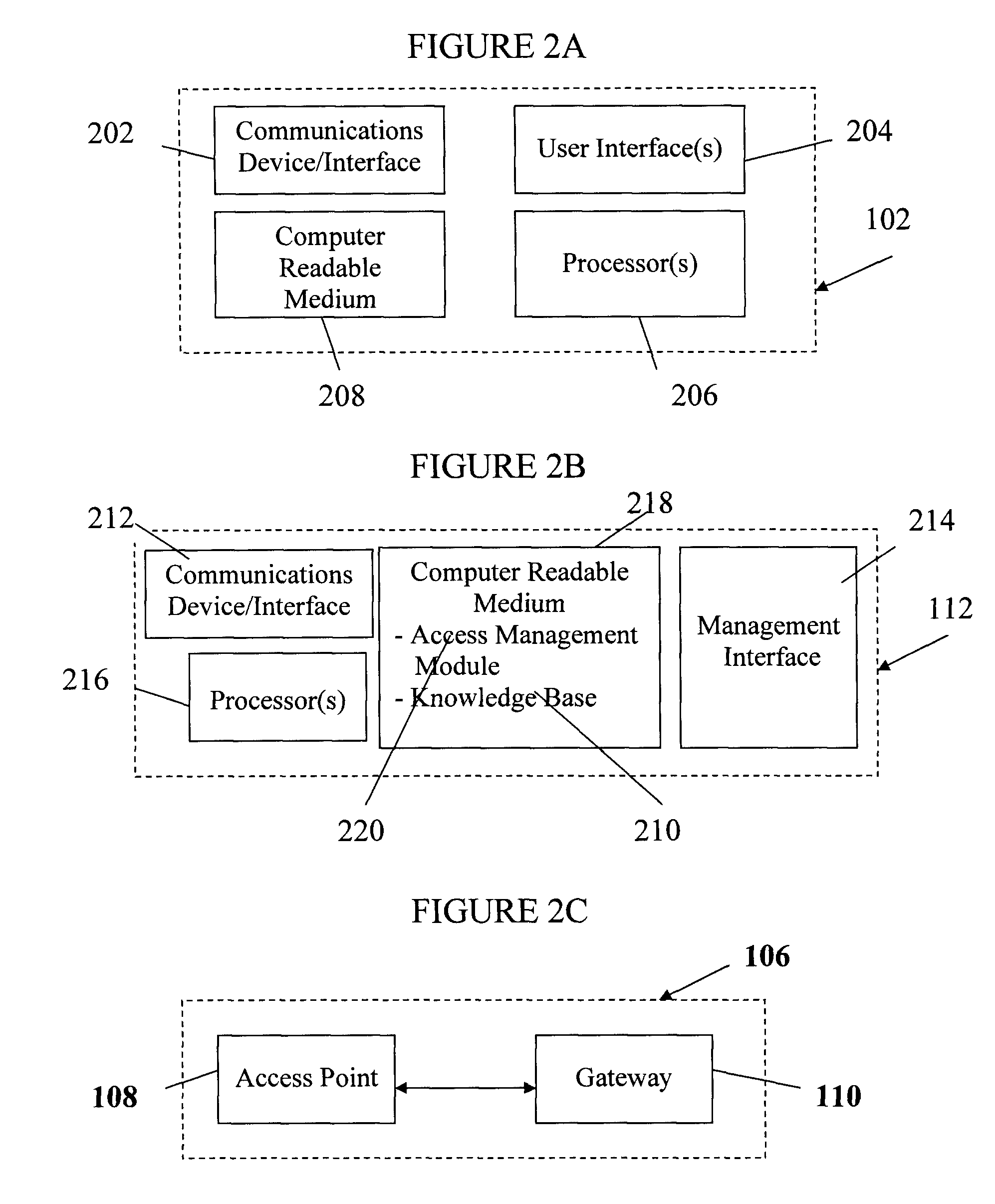
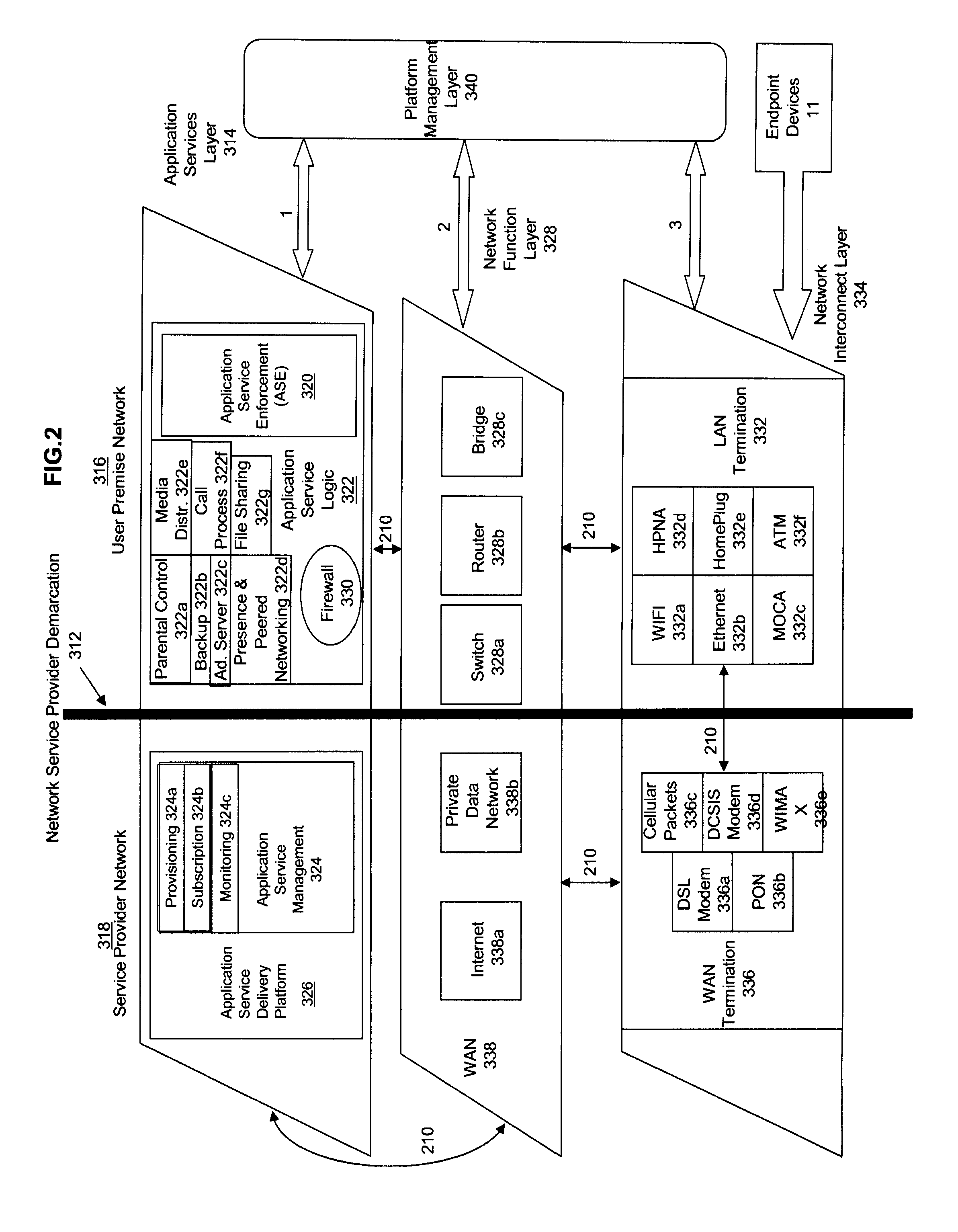
ActiveUS20080313691A1Satisfies needColor television signals processingNetwork topologiesDigital videoComputer network
Apparatus and methods for premises gateway functions that integrate or unify functions typically distributed across multiple devices within a content-based network. In one embodiment, the out-of-band (OOB) signaling functionality normally provided in each of a set-top-box (STB) and digital video recorder (DVR) are unified into a common OOB (e.g., DOCSIS) capable premises gateway device, thereby obviating OOB tuners and related components from each device. In another variant, the premises gateway is adapted for all-IP operation, such as for use with IP-based computers and IP set-top boxes, etc. Fully unified variants are also disclosed, wherein the DVR and / or STB functions are physically integrated within the premises gateway.
Owner:TIME WARNER CABLE ENTERPRISES LLC
System and method for simulating an application for subsequent deployment to a device in communication with a transaction server
InactiveUS20060047665A1Minimal modificationDigital data processing detailsTextiles and paperCommunication interfaceComputer network
A system and method for simulating a wireless application for subsequent deployment on a mobile device, the mobile device configured for using the deployed application to communicate over a network with a data source through a transaction server. The method and system comprising executing the simulated application to generate at least one message configured for receipt by the simulated communication interface of the transaction server; simulating the server communication interface for receiving the message and for transmitting the asynchronous message intended for transmission to the data source via the interface; establishing a connection to the network by a development tool and transmitting the asynchronous message over the network to the data source; wherein the simulated server communication interface is used to monitor the status (i.e. a return value if any) of the transmitted asynchronous message.
Owner:MALIKIE INNOVATIONS LTD
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protocol) gateways simultaneously
ActiveUS7039037B2Time-division multiplexData switching by path configurationCyber operationsComputer network
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYST INC
Generalized entity network translation (GENT)
ActiveUS20150244690A1Many choicesGood conditionUser identity/authority verificationPublic key infrastructure trust modelsSystem integrationRoot certificate
Generalized Entity Network Translation provides new state of the art methodology for extending RKI techniques into a truly generalized framework capable of operating at exceptional levels of authenticity without the need for roots, certificate authorities, or other static points in an infrastructure. More astounding is its ability to create trusted authentic entity relationships that require no externally stored state outside of the shared context between discrete peers. The present invention provides, among other things, novel improvements to blockchain-derived systems and provides strong proof of ownership, renewal, roll-backs, and localized state and many blockchain systems more palatable choices for system integration.
Owner:ENT TECH
Multimedia publishing system for wireless devices
InactiveUS20060256130A1Cathode-ray tube indicatorsWebsite content managementComputer networkApplication software
A dynamic publishing system for delivery and presentation of multimedia on a wireless device, such as a PDA or mobile telephone. A presentation server dynamically compiles application data based on scene description data for one or more media objects, and sends the application data to the wireless device for presentation of the media objects. The wireless device has a media player that is able to process the application data at an object level for the objects in response to events, and control the presentation. The application data includes content, layout and control logic data for the media objects.
Owner:ACTIVESKY
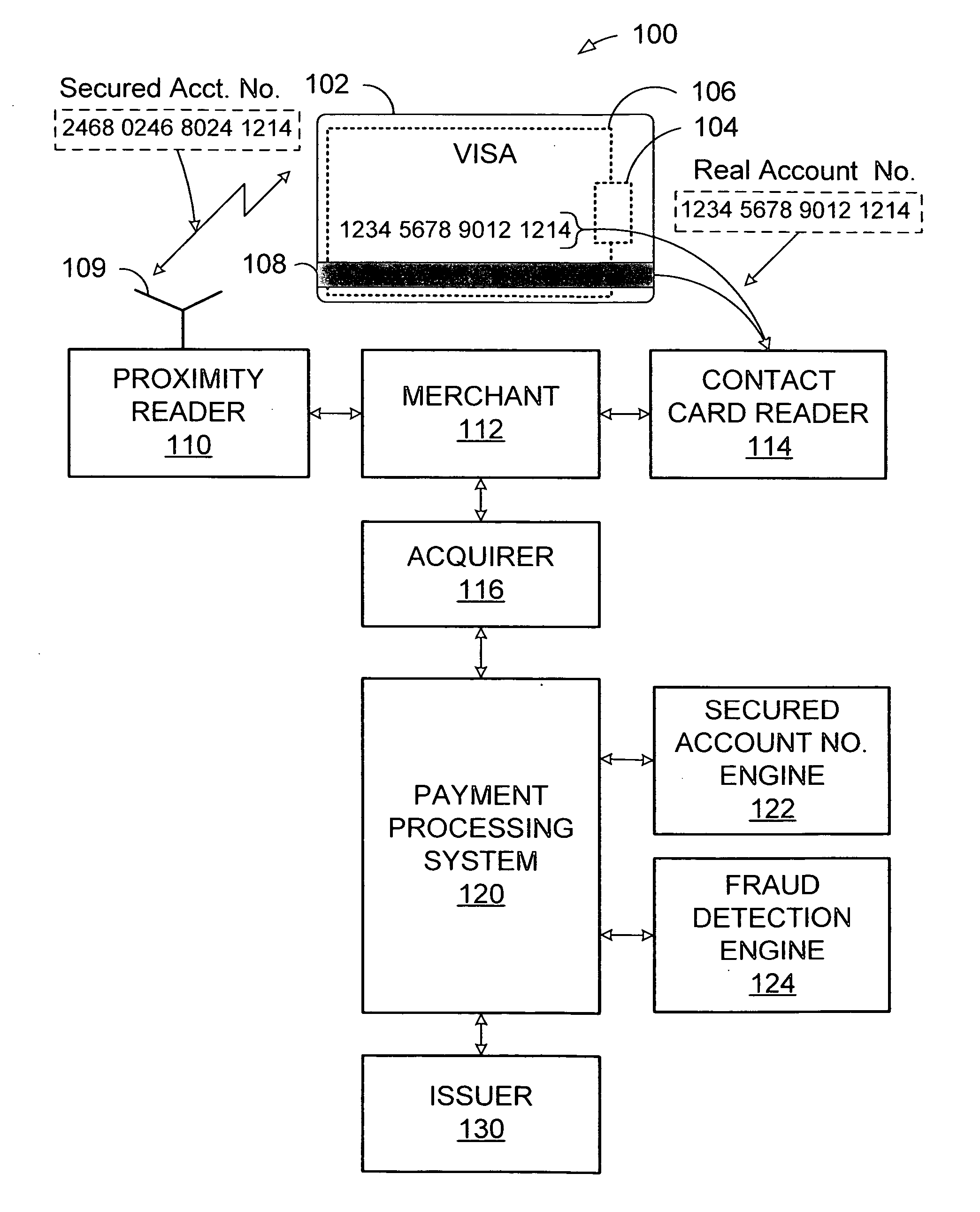
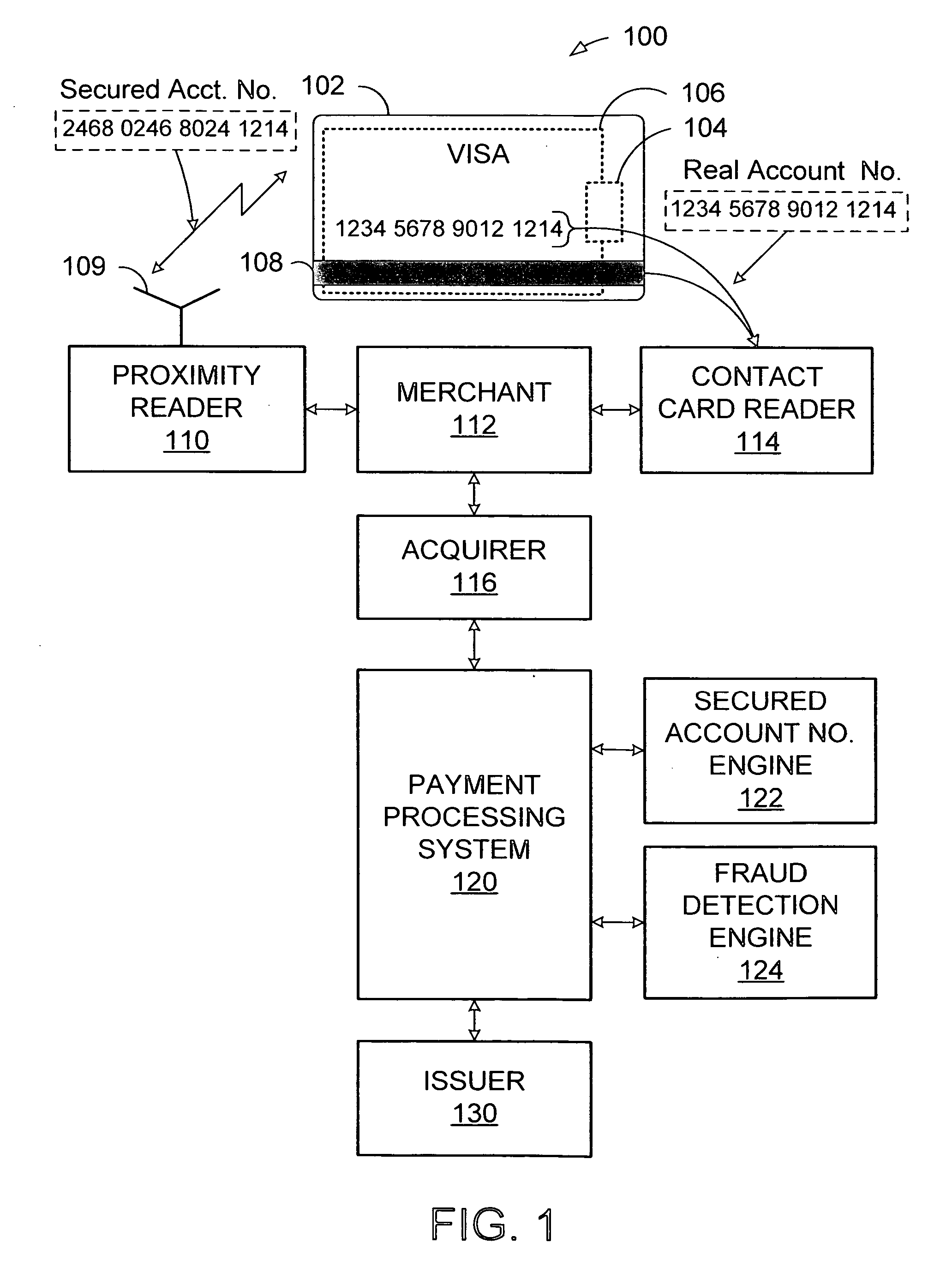
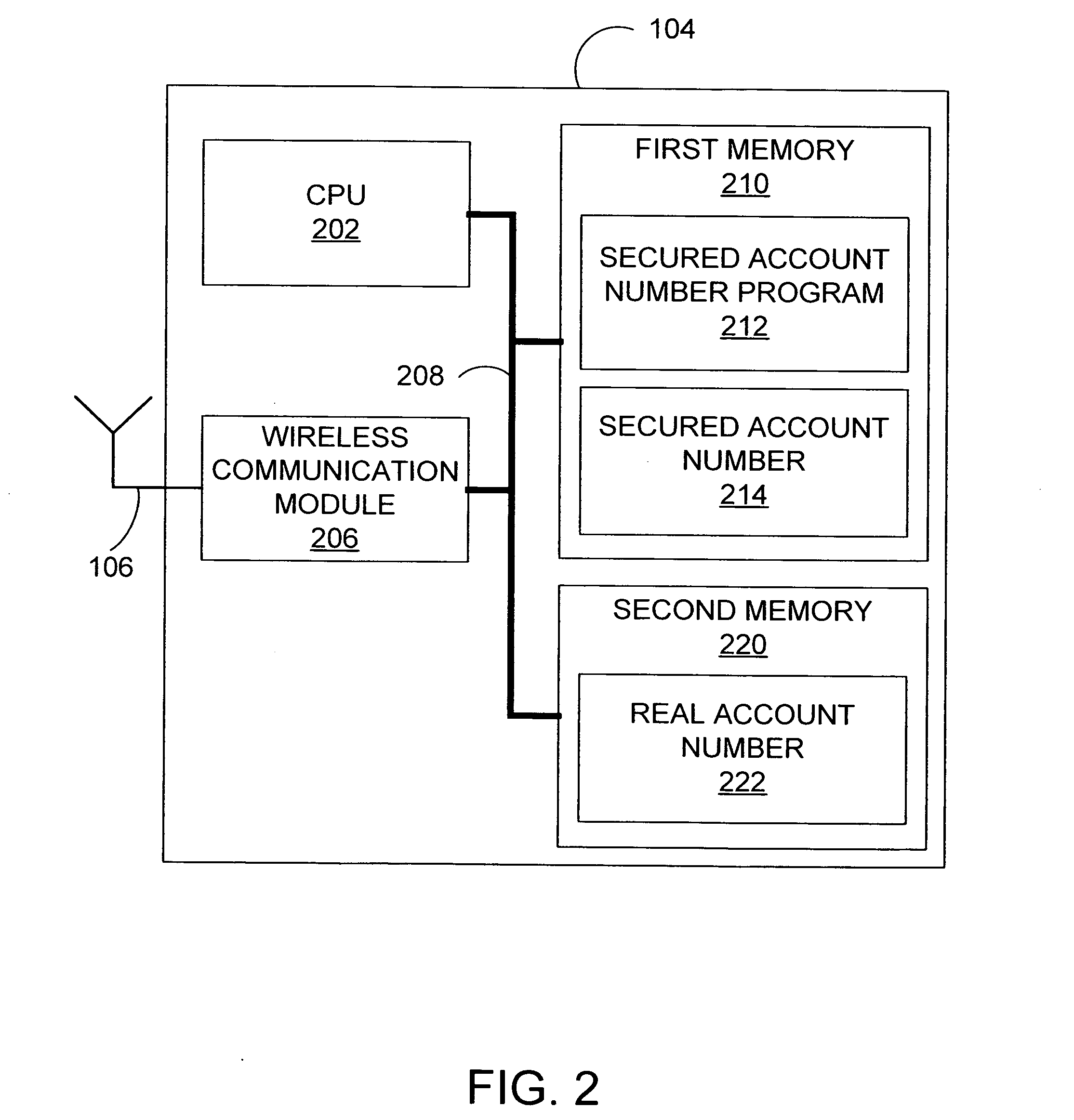
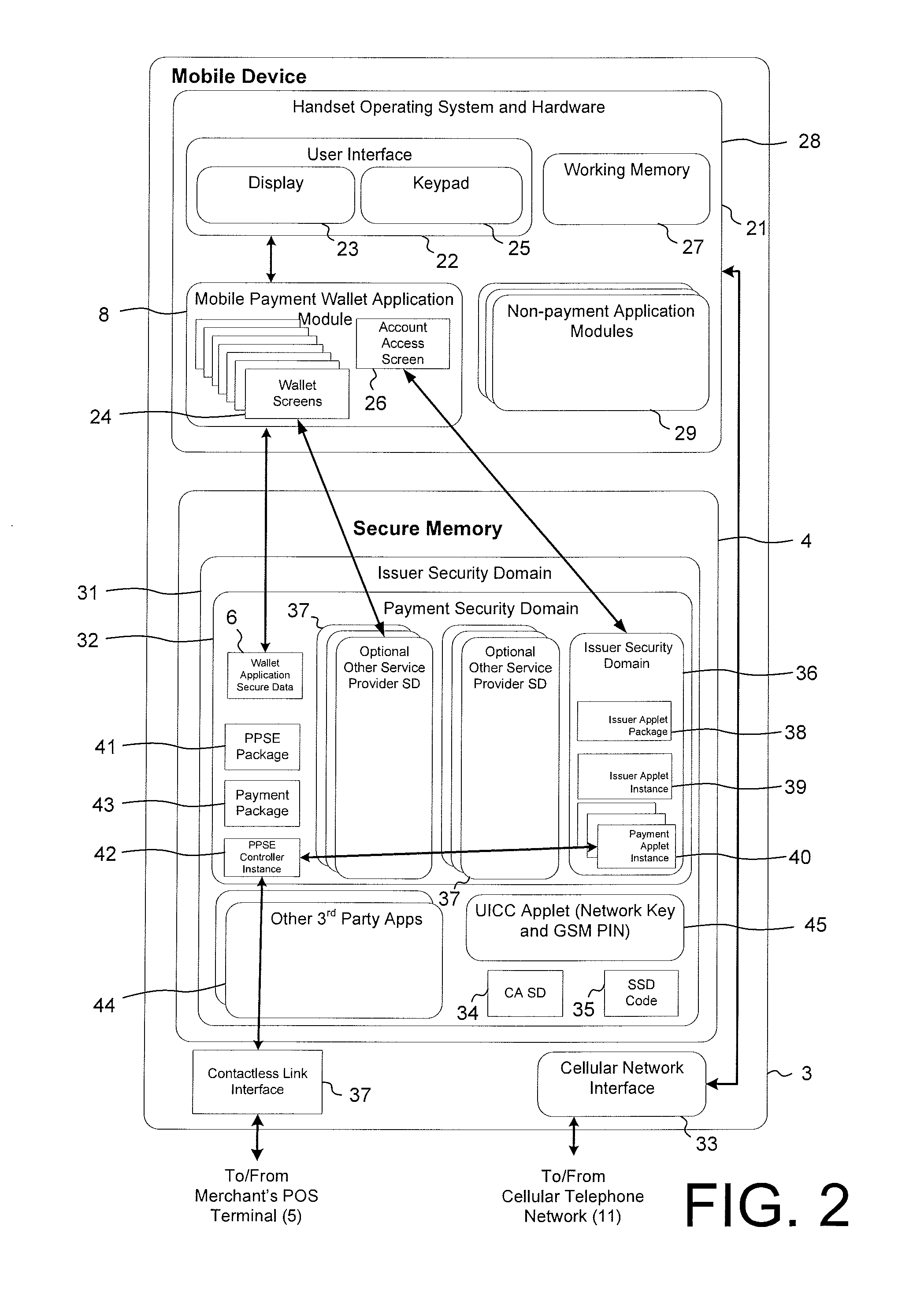
System and method for secured account numbers in proximity devices
A method and system for using a secured account number for processing proximity types of wireless financial transactions associated with portable consumer proximity devices is disclosed. In one embodiment, the method includes receiving a proximity type of wireless financial transaction request along with a secured account number from a portable proximity consumer device such as a contactless smart card, converting the secured account number to the user's real account number, and transmitting the financial transaction request along with the user's real account number to the issuer of the user's real account number for authorization and processing.
Owner:VISA USA INC (US)
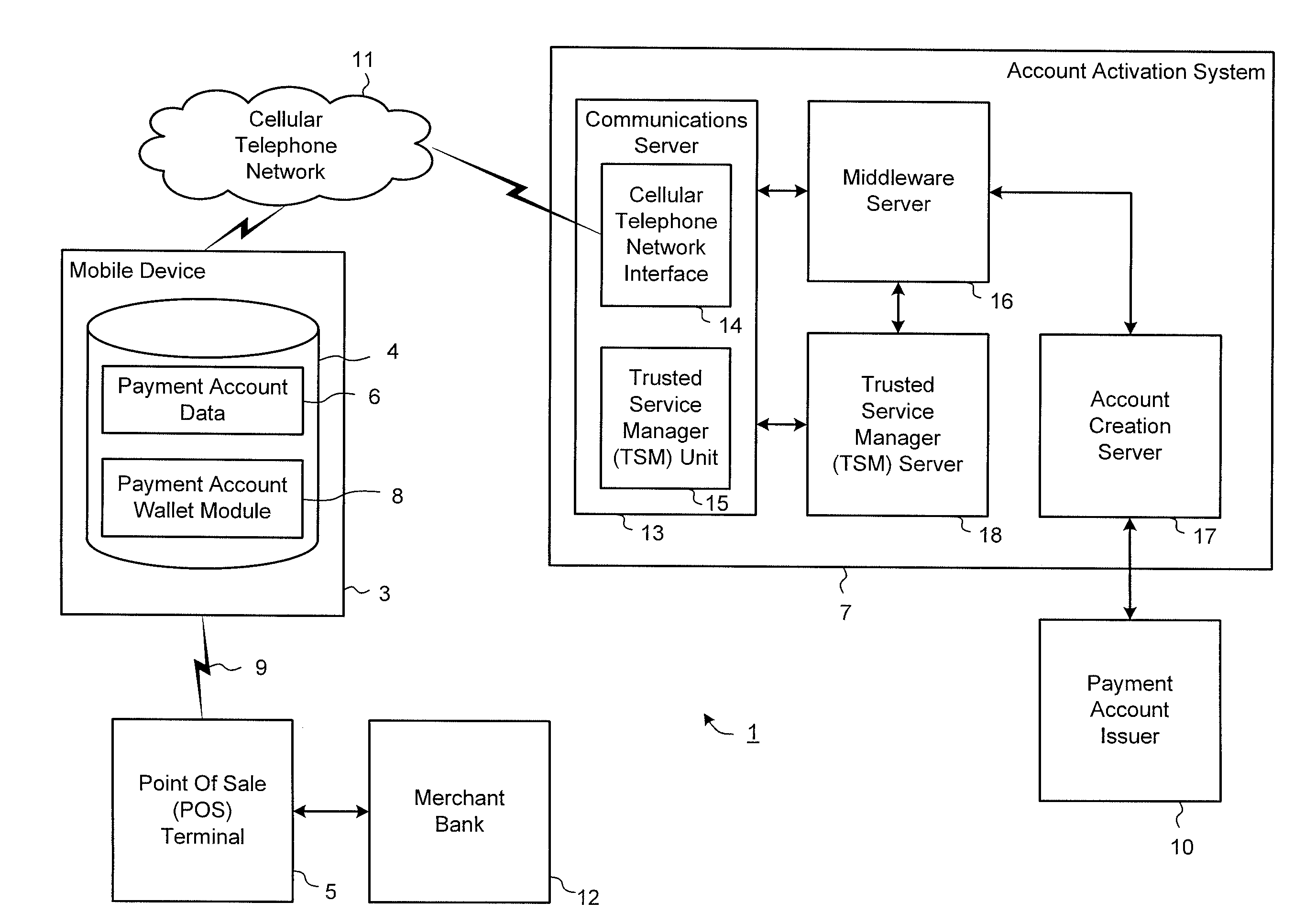
Secure account provisioning
ActiveUS20120078735A1Promote activationFinancePoint-of-sale network systemsComputer networkUser authentication
A mobile payment system and method are described that facilitates the secure and real time user authentication and activation of a mobile payment account for a user portable electronic device over a communications network.
Owner:BARCLAYS EXECUTION SERVICES LTD
System and methodology for security policy arbitration
ActiveUS7546629B2Multiple digital computer combinationsSecret communicationComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
Electronic purchase of goods over a communications network including physical delivery while securing private and personal information of the purchasing party
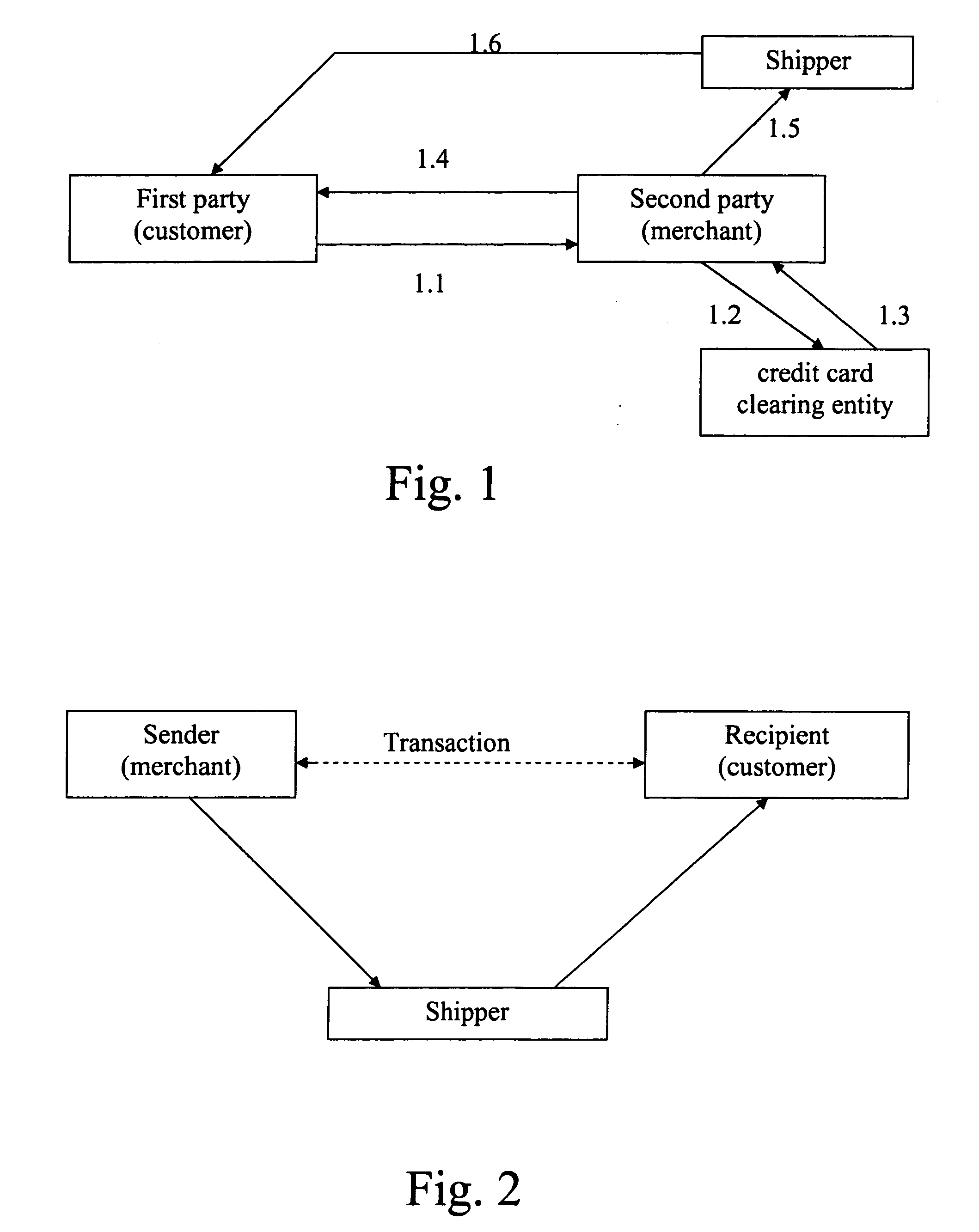
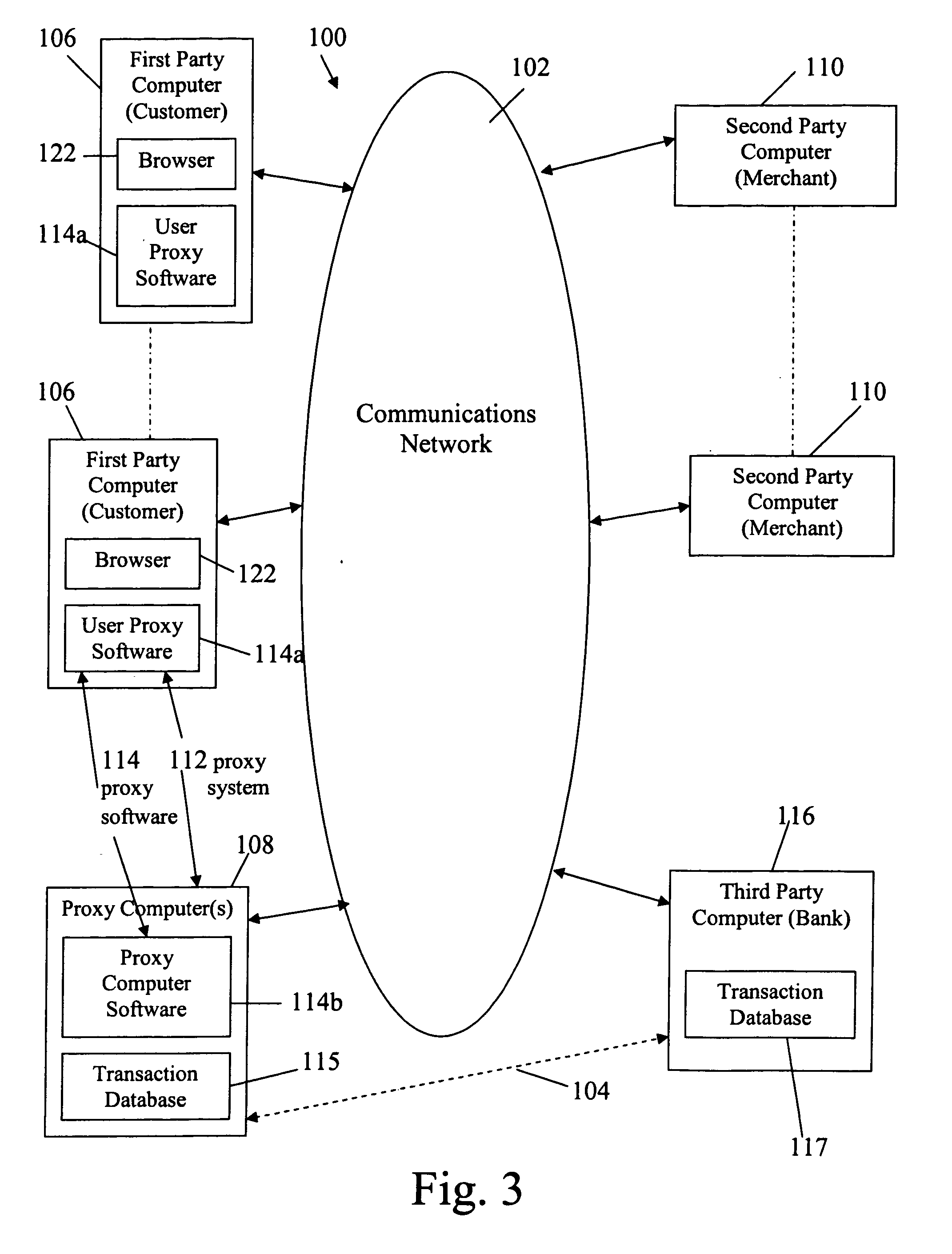
InactiveUS7069249B2Improve privacy protectionReduce collectionSecret communicationBuying/selling/leasing transactionsPaymentComputer network
E-commerce which may include delivery of a good ordered or purchased over a network (e.g., the Internet) to a purchaser / user, and / or arranging for electronic payment of the good is accomplished while securing private and personal information of purchasers / users. Proxy software is provided for user computers, one or more proxy computers, or both, for users to communicate with vendors anonymously over the network, provide for delivery of an ordered good and provide for electronic payment, while securing the user's private information.
Owner:IPRIVACY
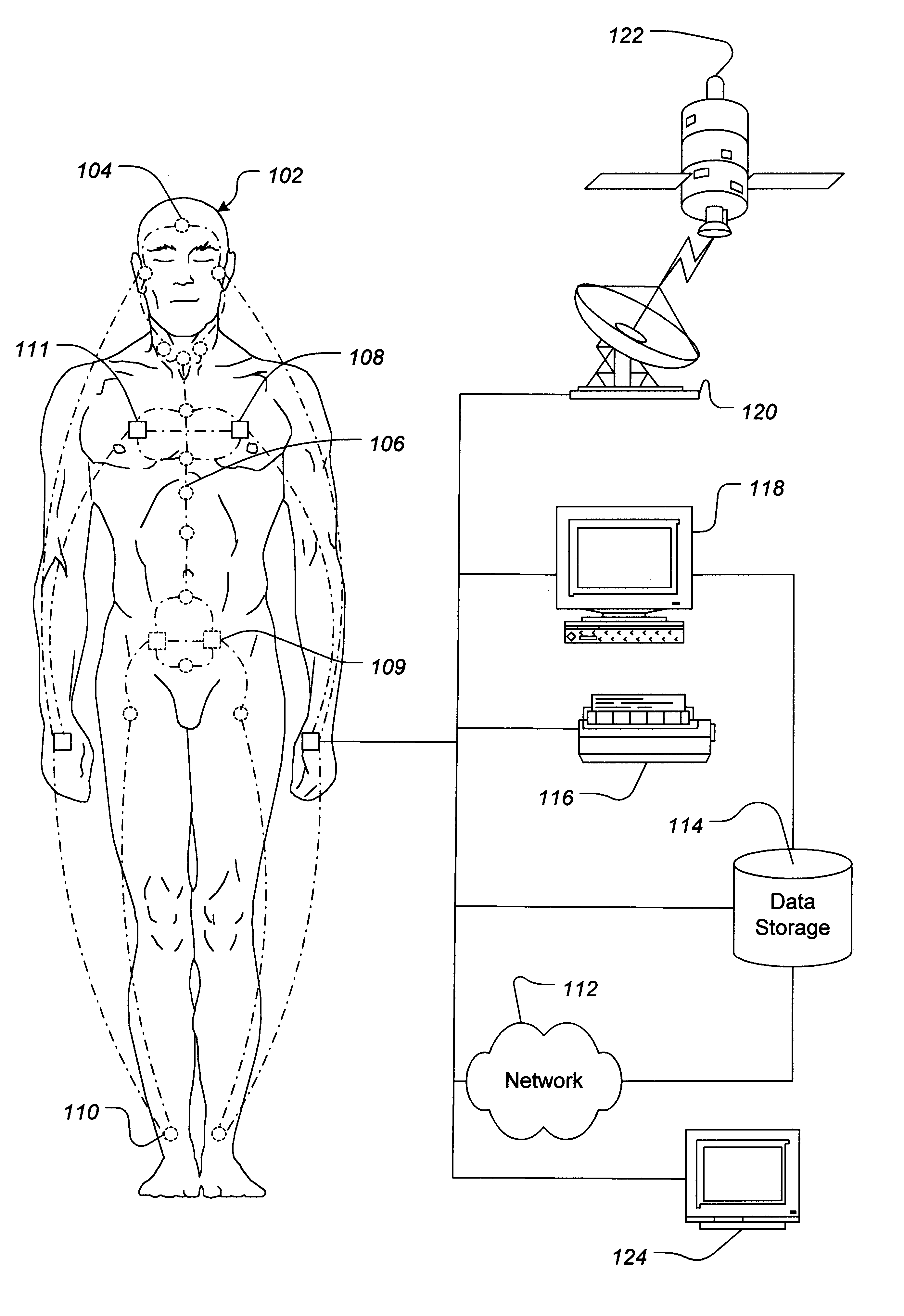
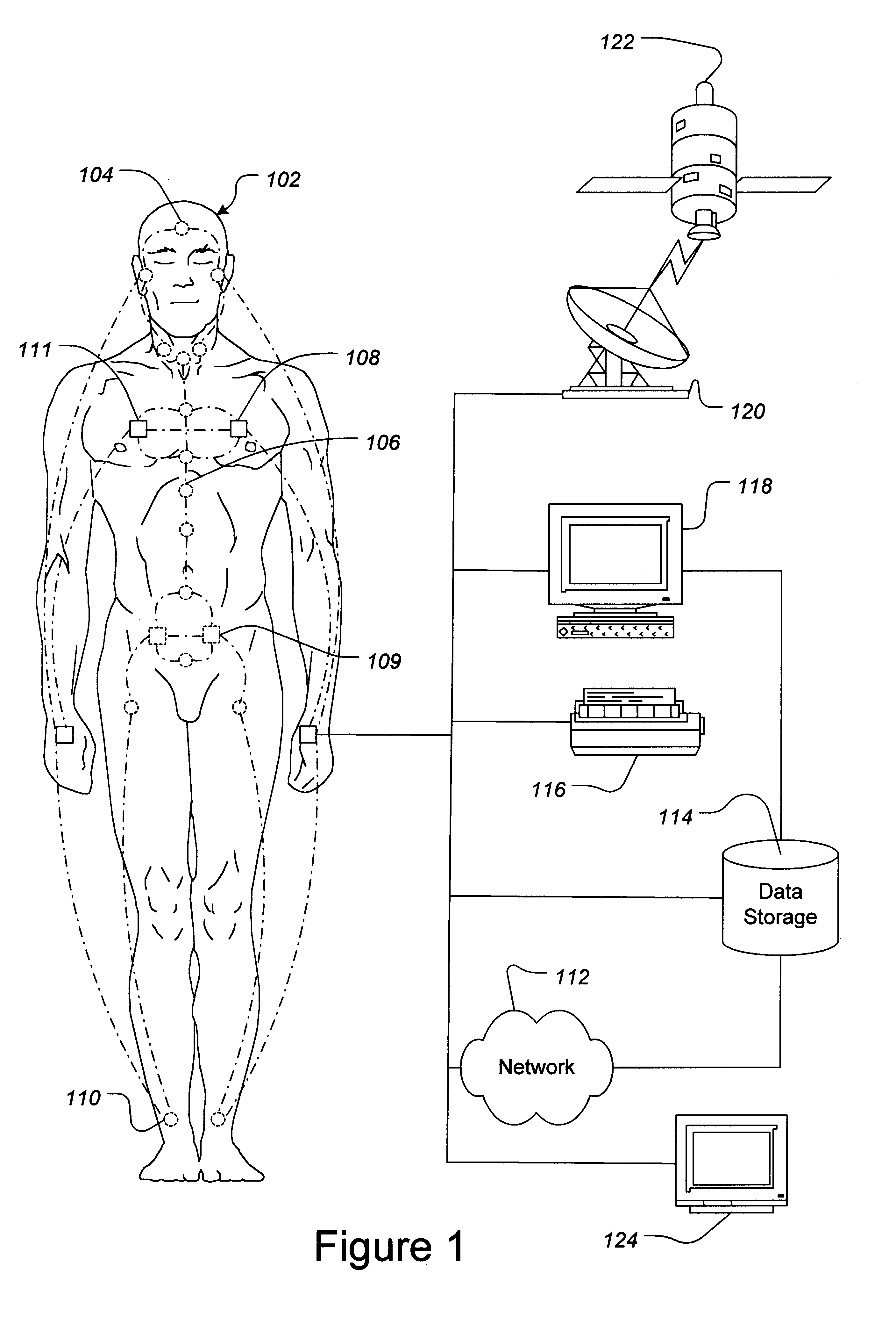
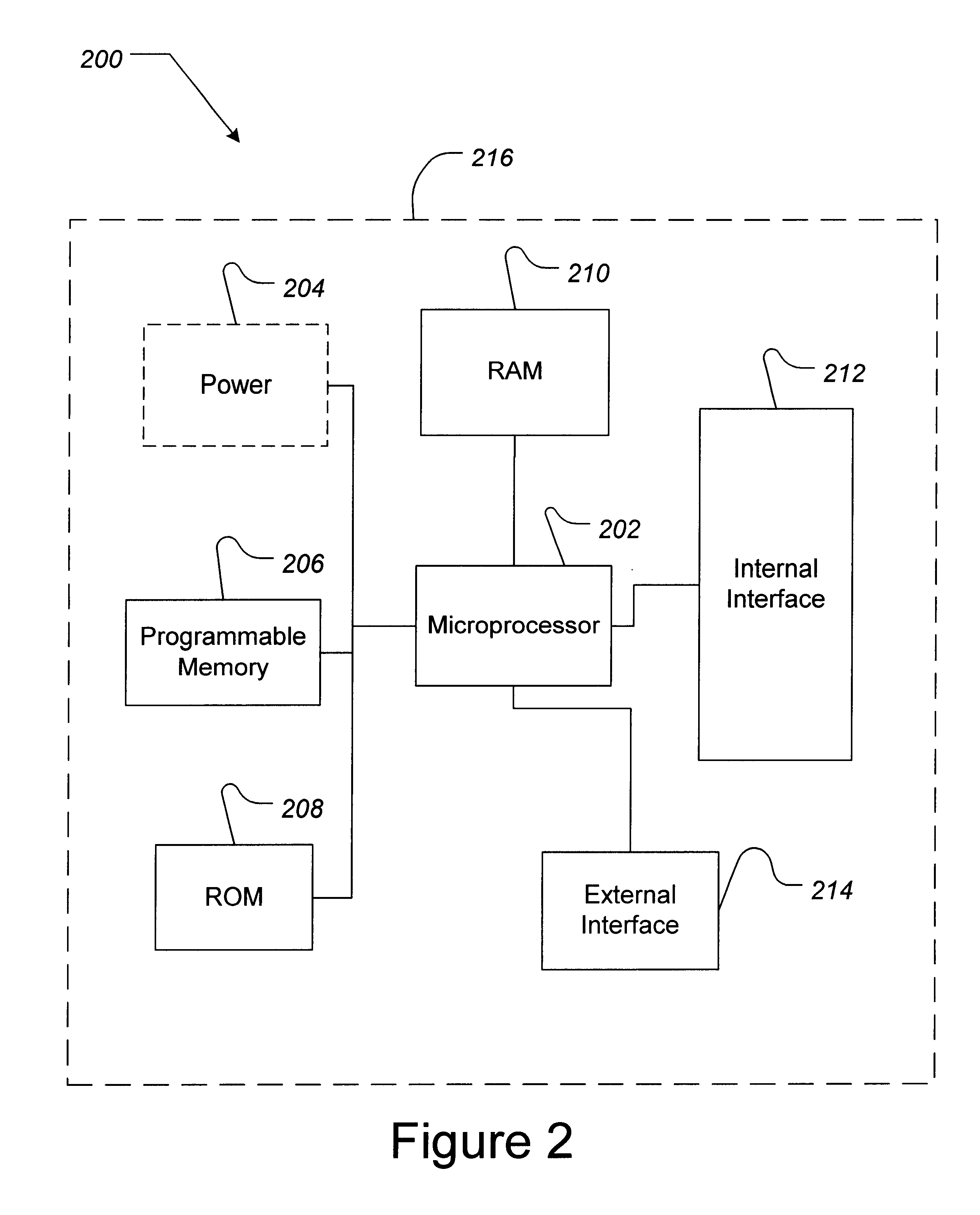
Network for implanted computer devices
A network device that can be implanted in a subject is described. The device is configured to communicate over a computer network. In one embodiment, the device of the invention includes an internal interface in physiological communication with the subject. The internal interface is coupled with, and configured to send signals to, a processor. The processor is configured to receive and process the signals, and is further configured to communicate over a computer network with another such device. Such devices can be used to monitor and communicate information regarding a host's physiological status, monitor and / or control artificial organs and prosthetic devices, and / or dispense medication.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com