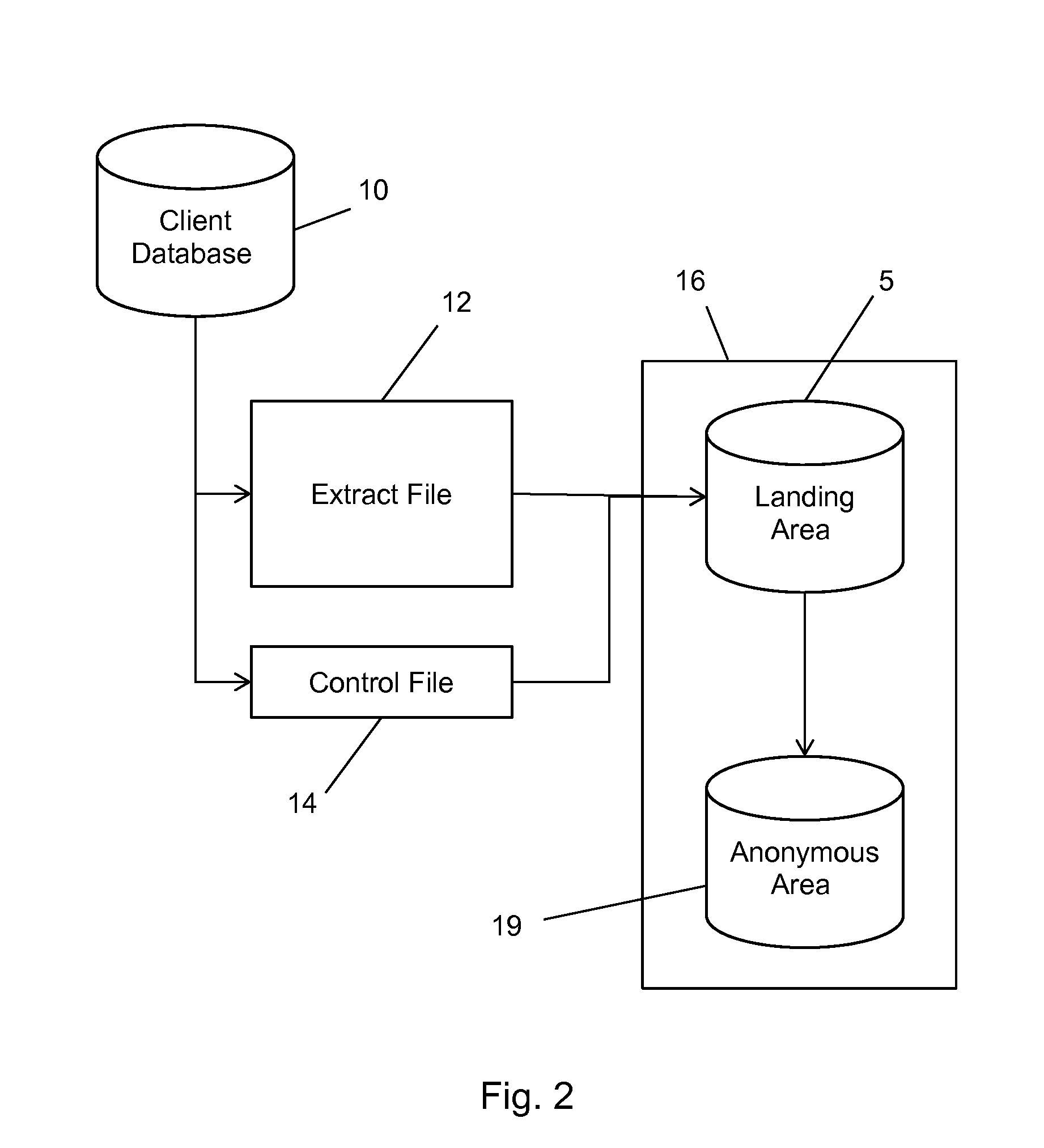
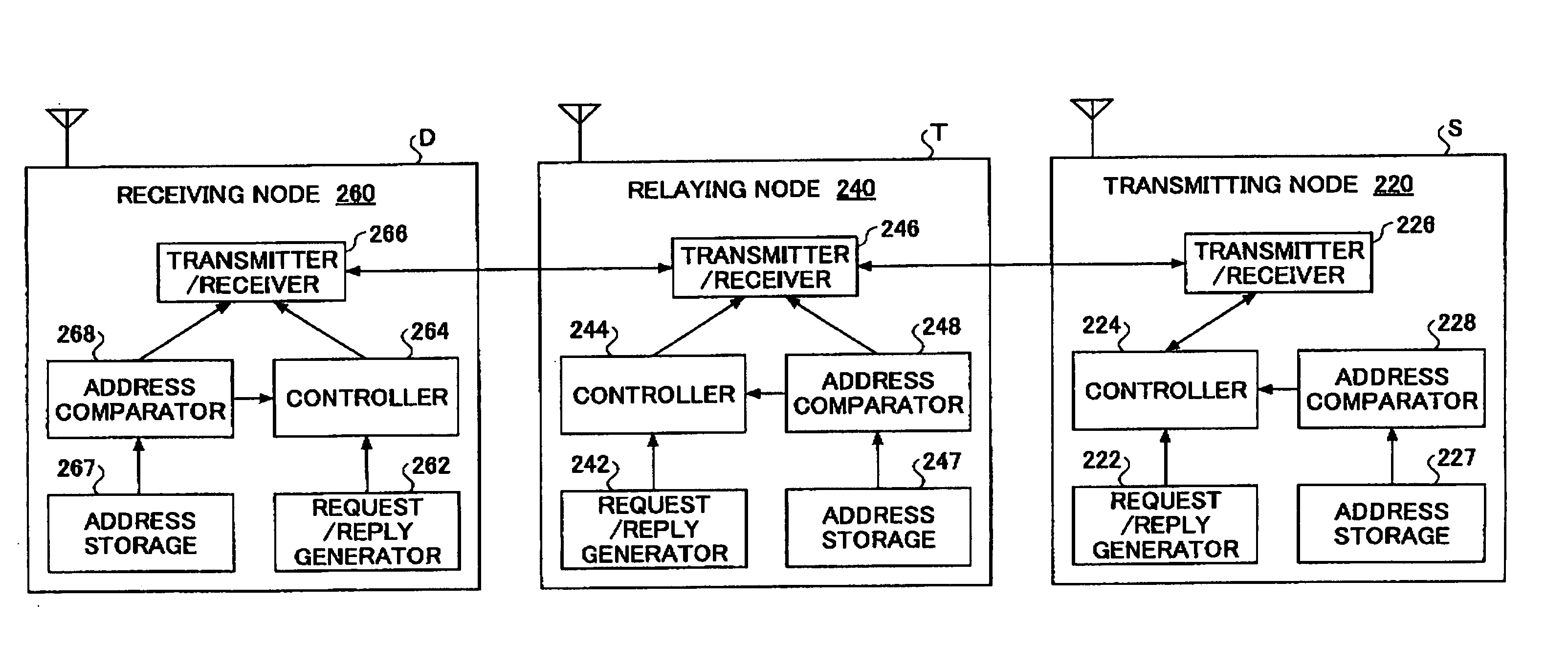
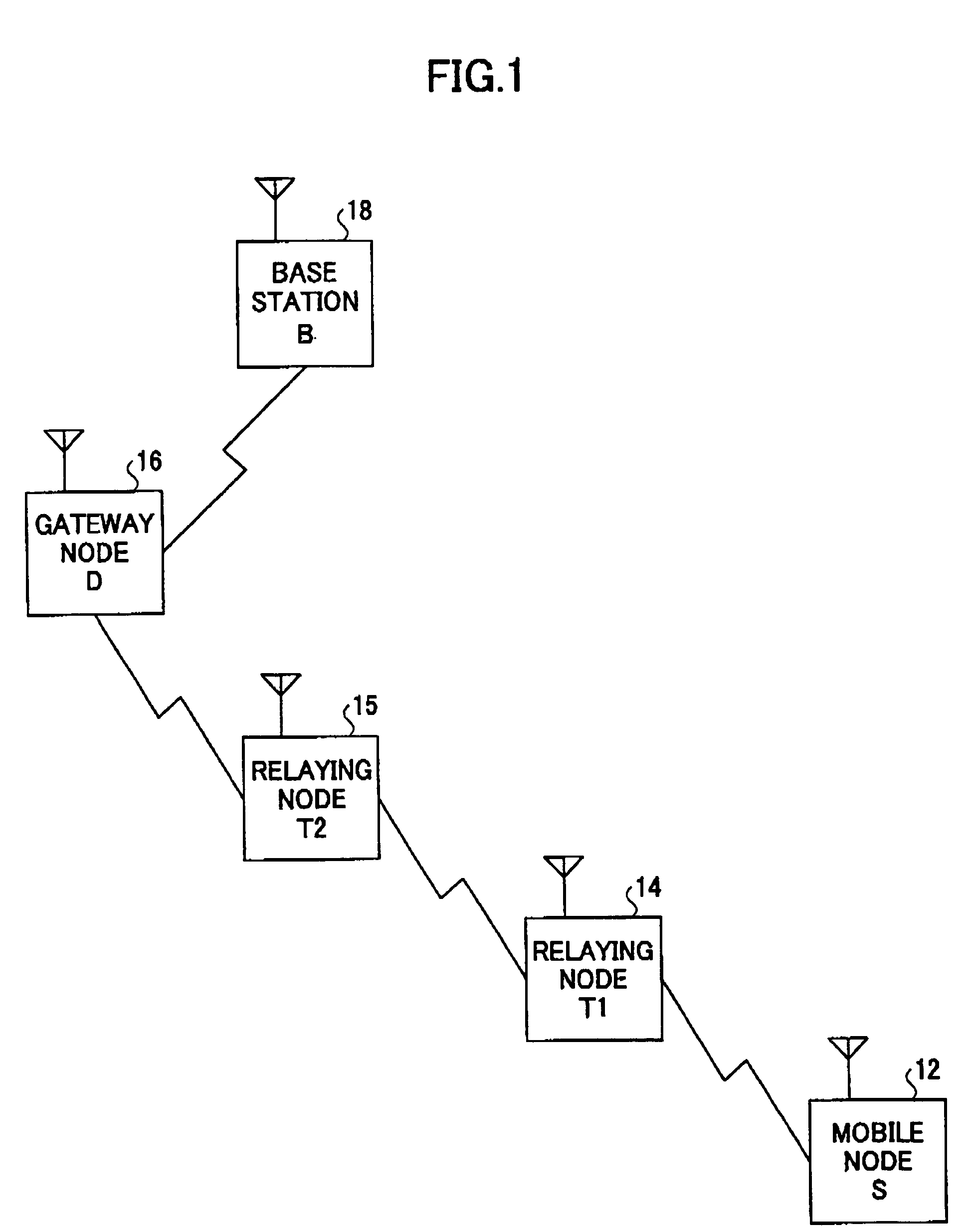
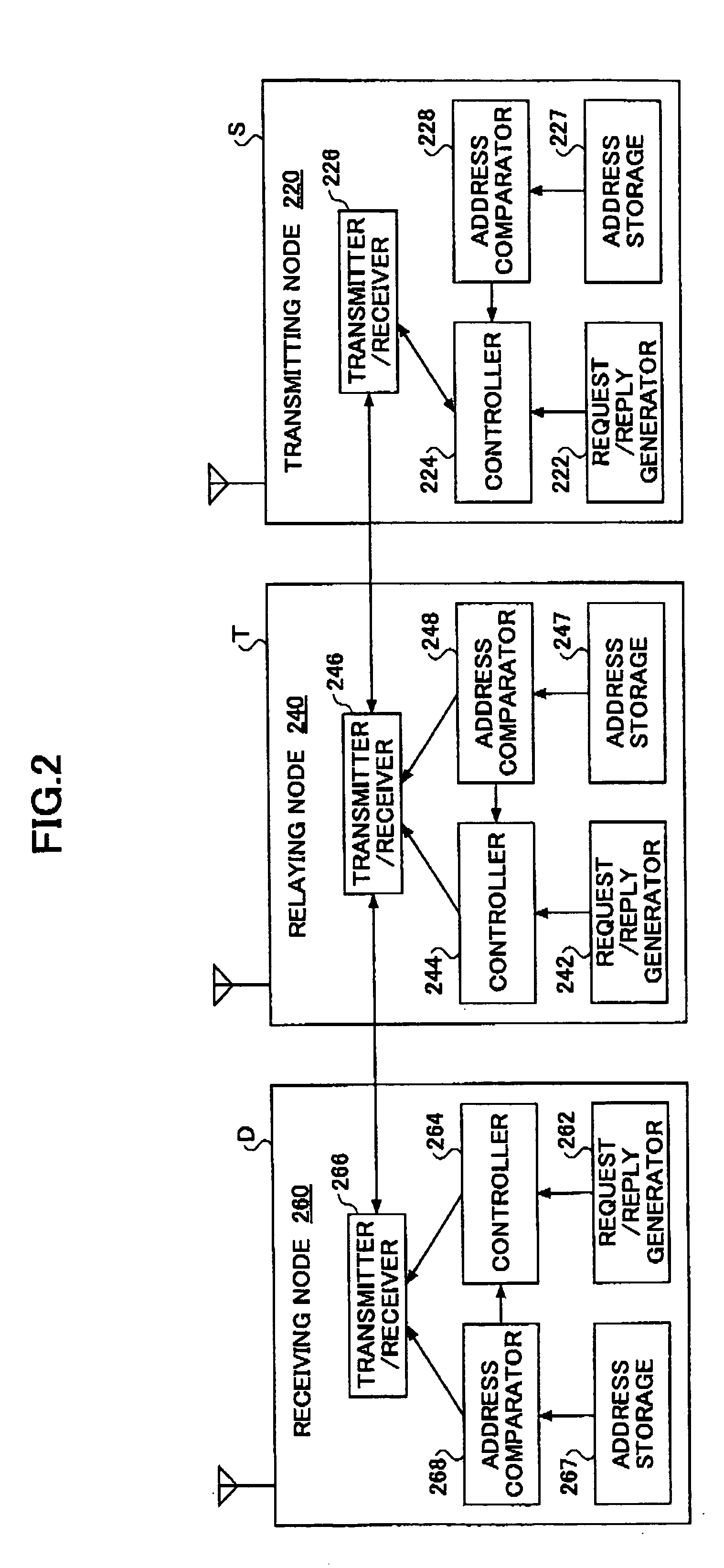
Patents
Literature
460results about How to "Improve privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
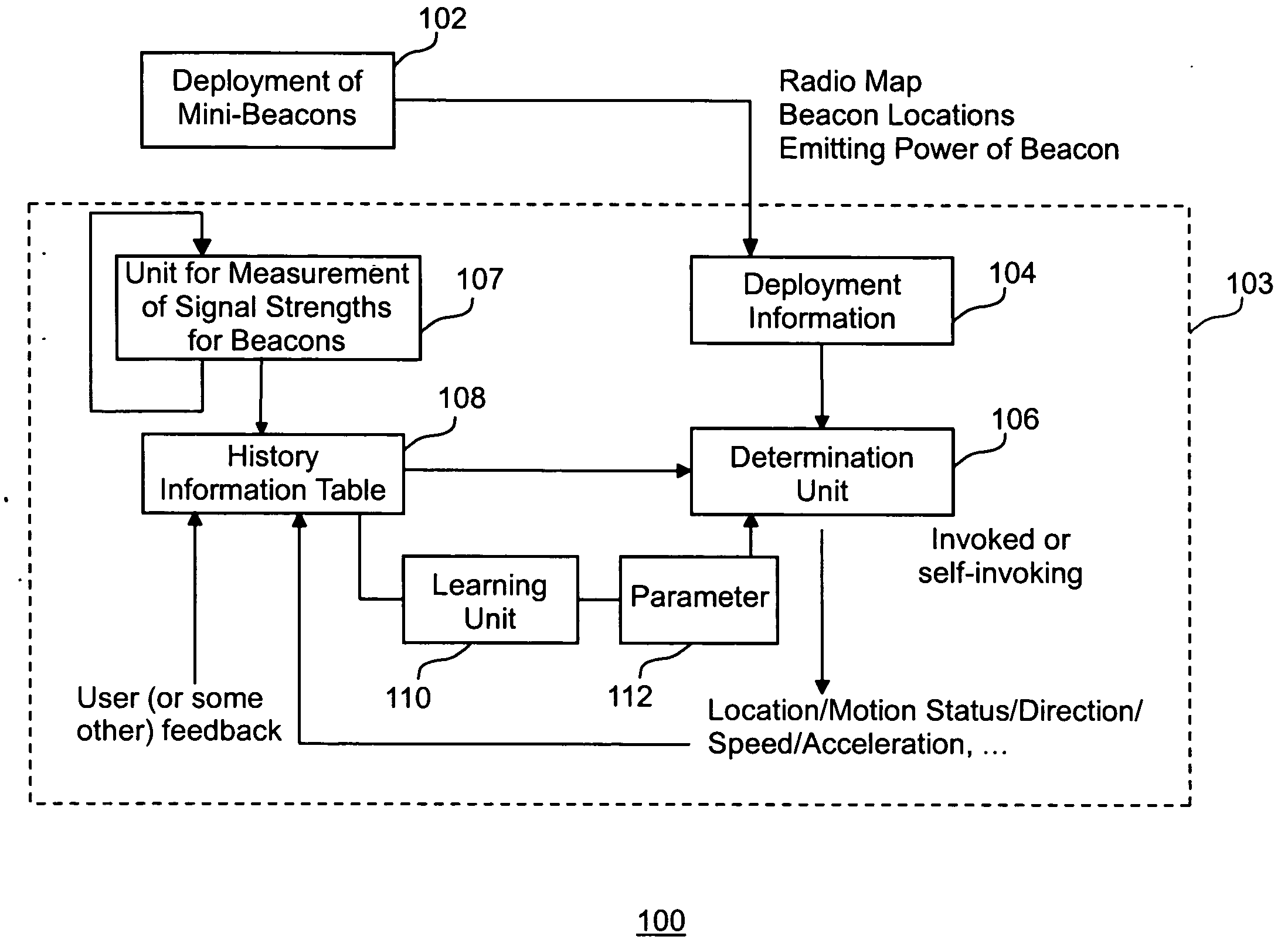
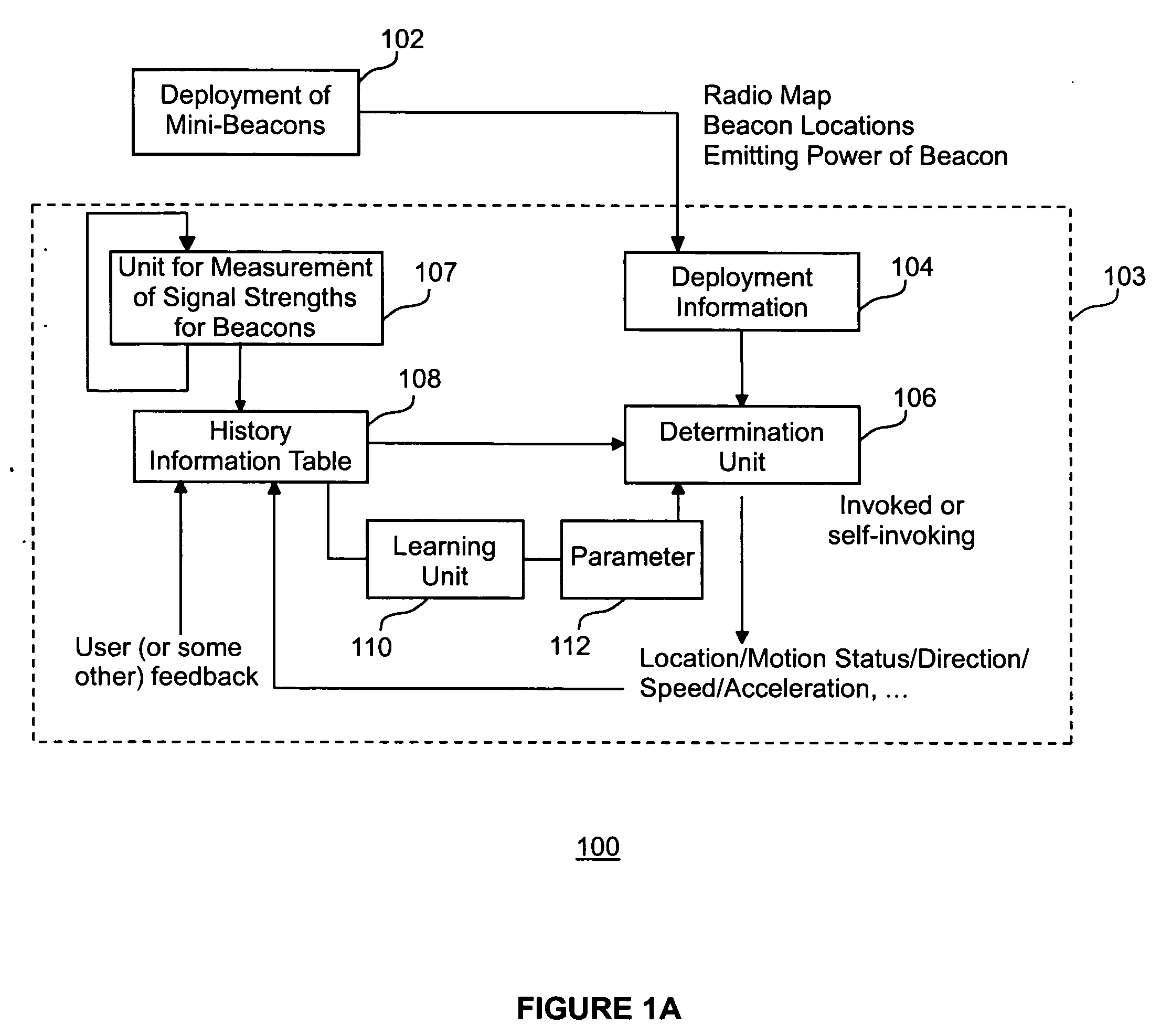
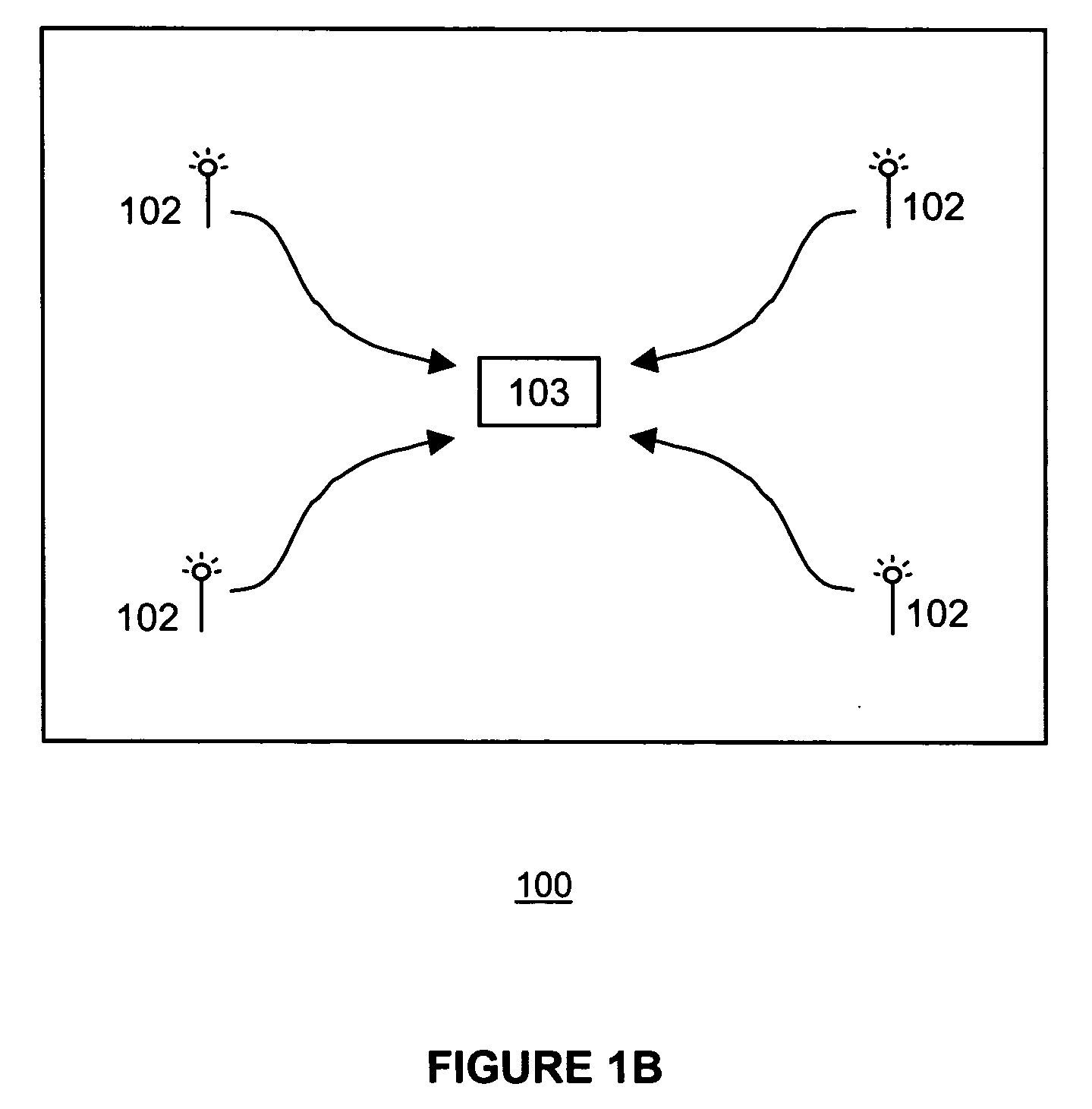
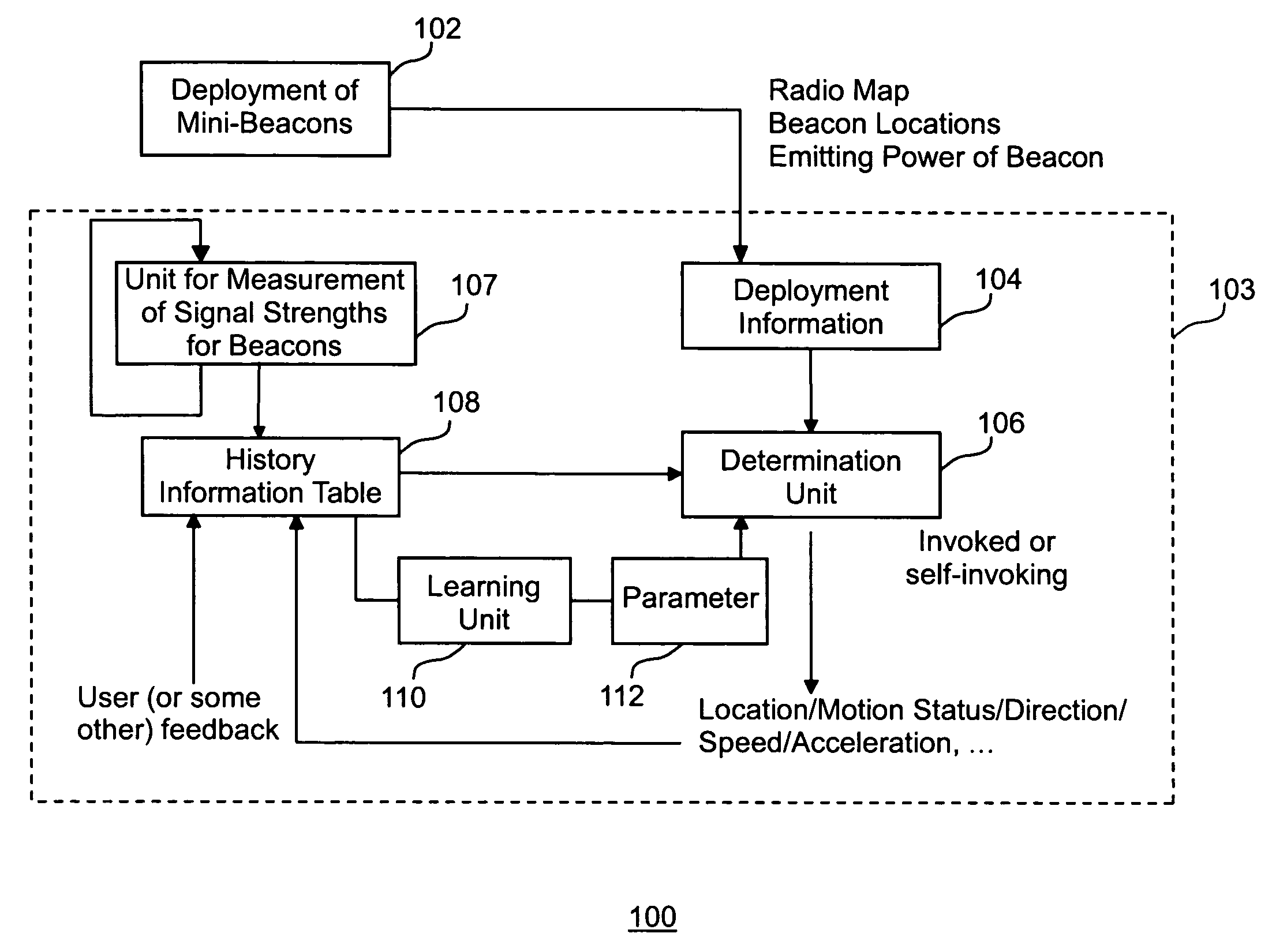
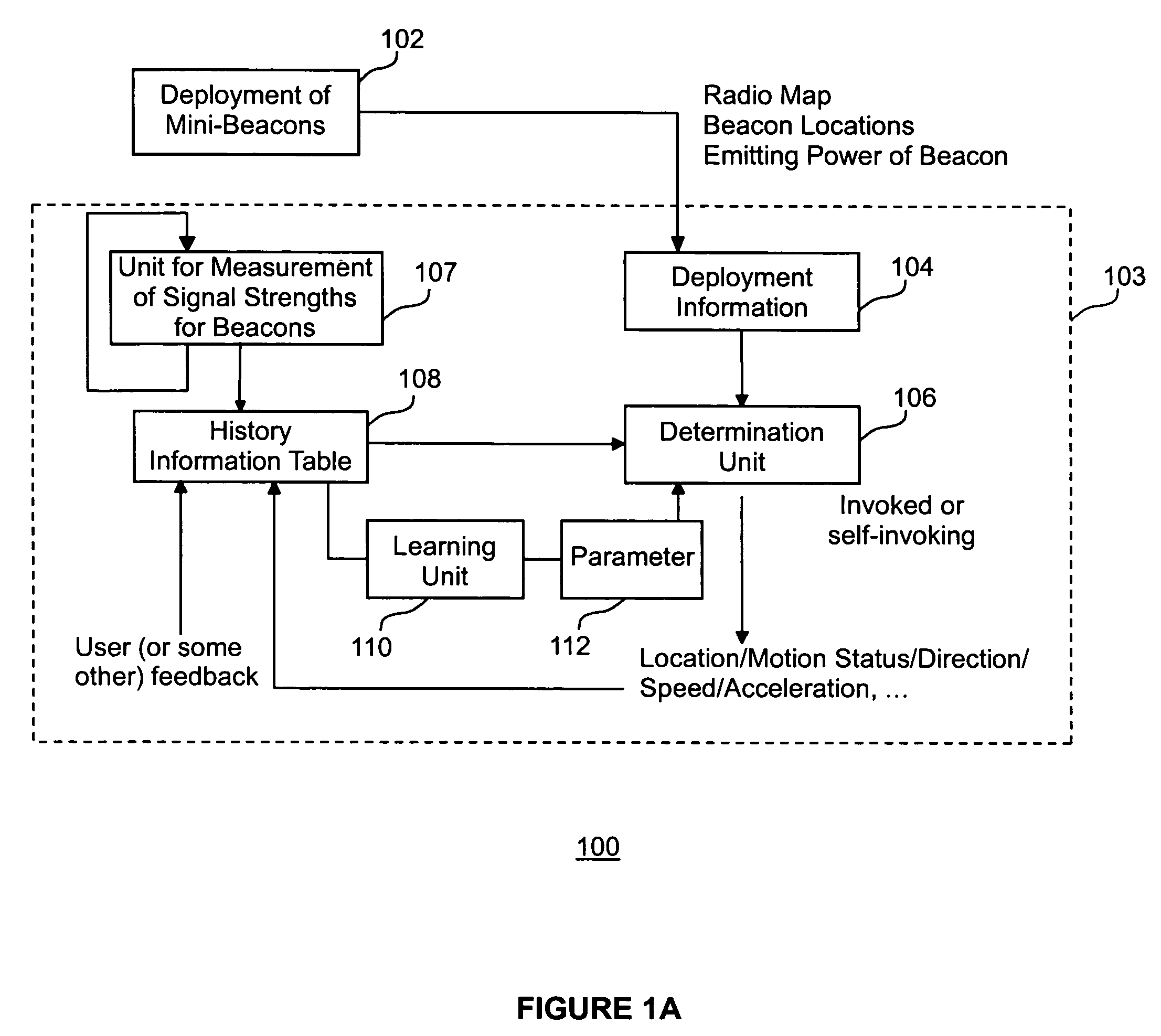
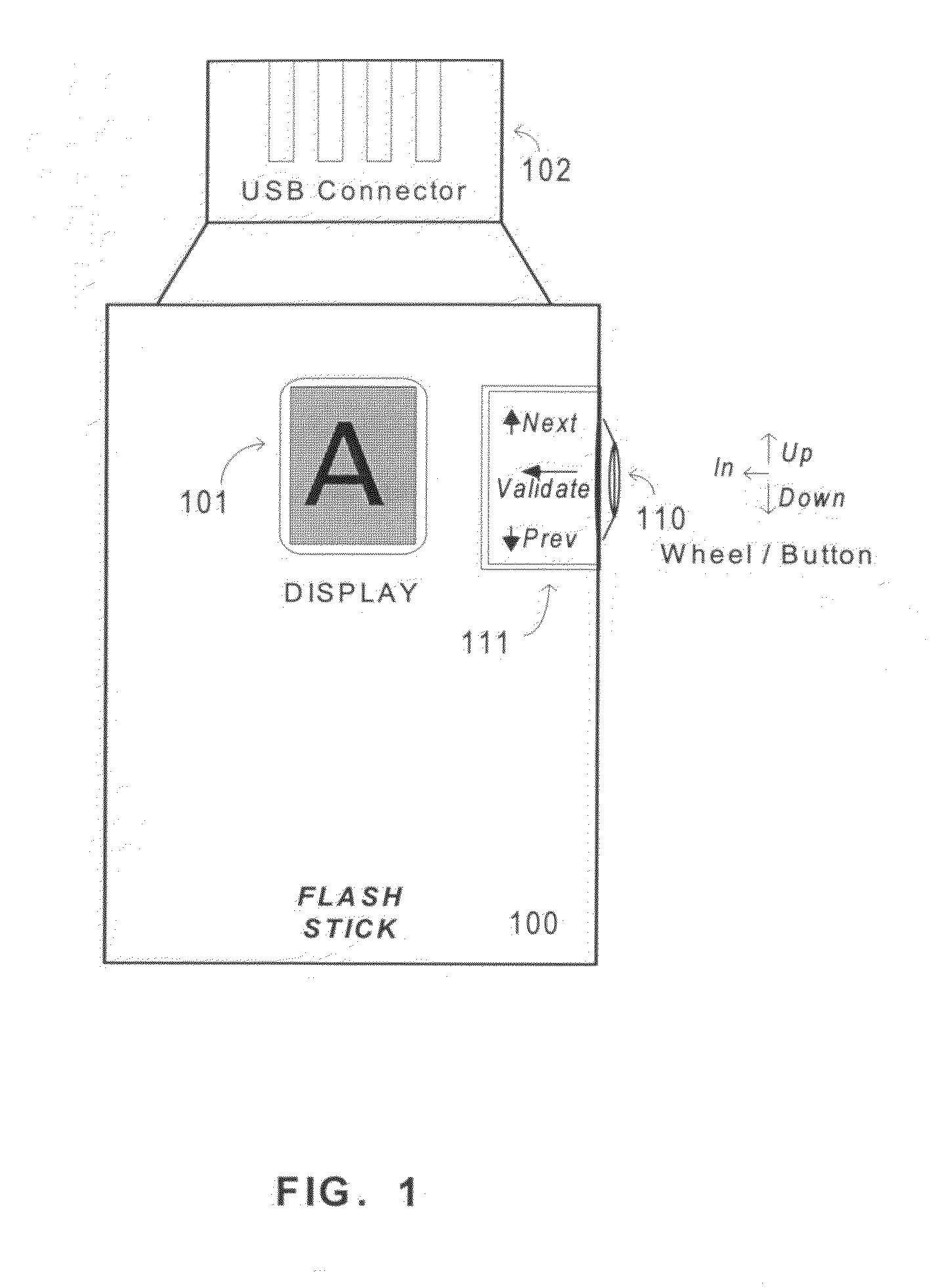
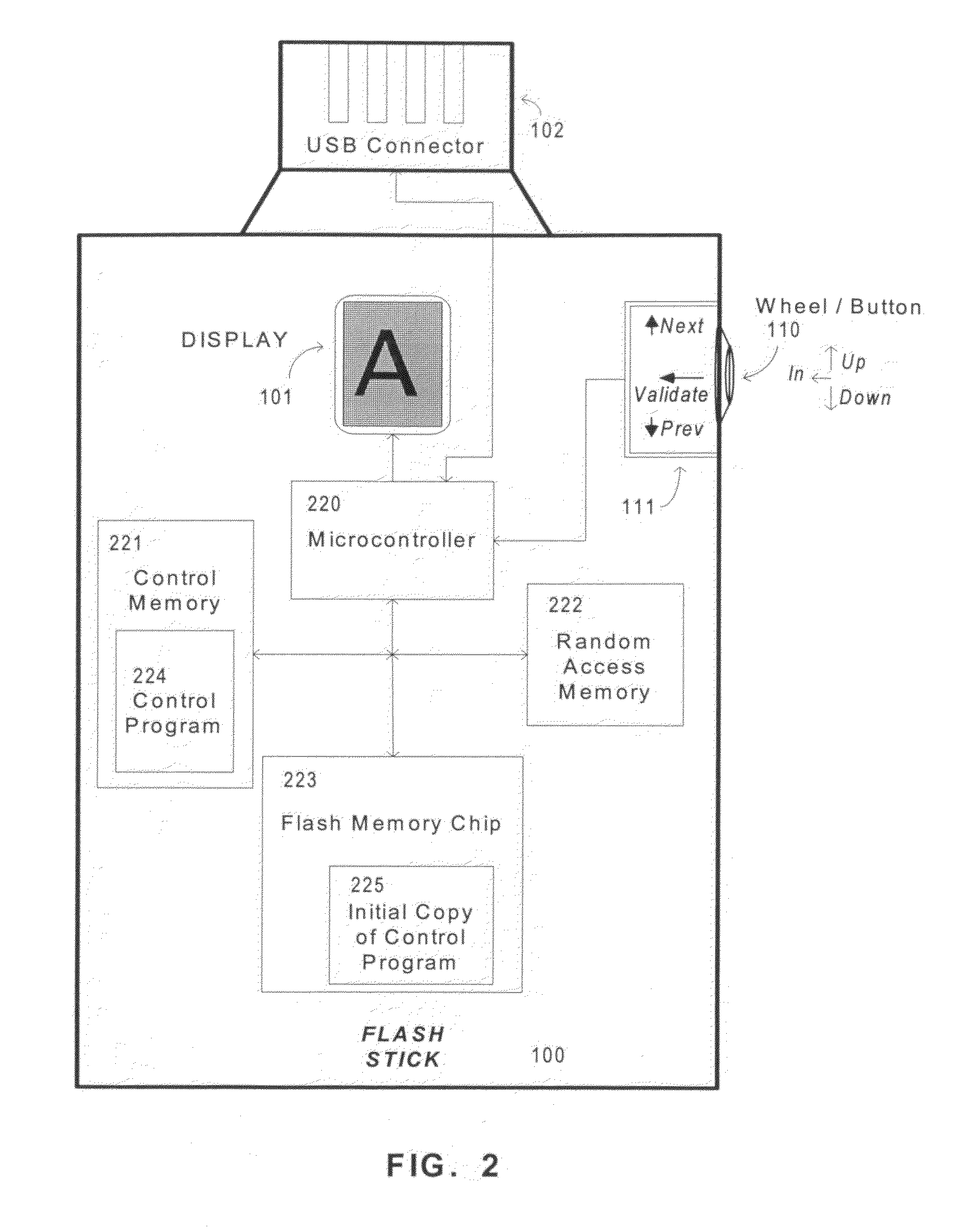
Method and apparatus for location determination using mini-beacons
InactiveUS20050136845A1Few burdenLow costReceivers monitoringBeacon systems using radio wavesLocation determinationSignal strength
A system and method uses wireless communication devices as beacons to determine the relative location of another target wireless communication device. The beacons transmit identifying information that the target device can use to determine the identity of the beacon. The target device can measure the received intensity of the beacon transmissions and determine an associated beacon that best satisfies a specified criteria (e.g., largest signal strength) using a procedure of the present invention that discriminates between multiple beacons.
Owner:FUJITSU LTD
Method and apparatus for location determination using mini-beacons
InactiveUS7751829B2Low costImprove privacy protectionReceivers monitoringBeacon systems using radio wavesLocation determinationCommunication device
A system and method uses wireless communication devices as beacons to determine the relative location of another target wireless communication device. The beacons transmit identifying information that the target device can use to determine the identity of the beacon. The target device can measure the received intensity of the beacon transmissions and determine an associated beacon that best satisfies a specified criteria (e.g., largest signal strength) using a procedure of the present invention that discriminates between multiple beacons.
Owner:FUJITSU LTD
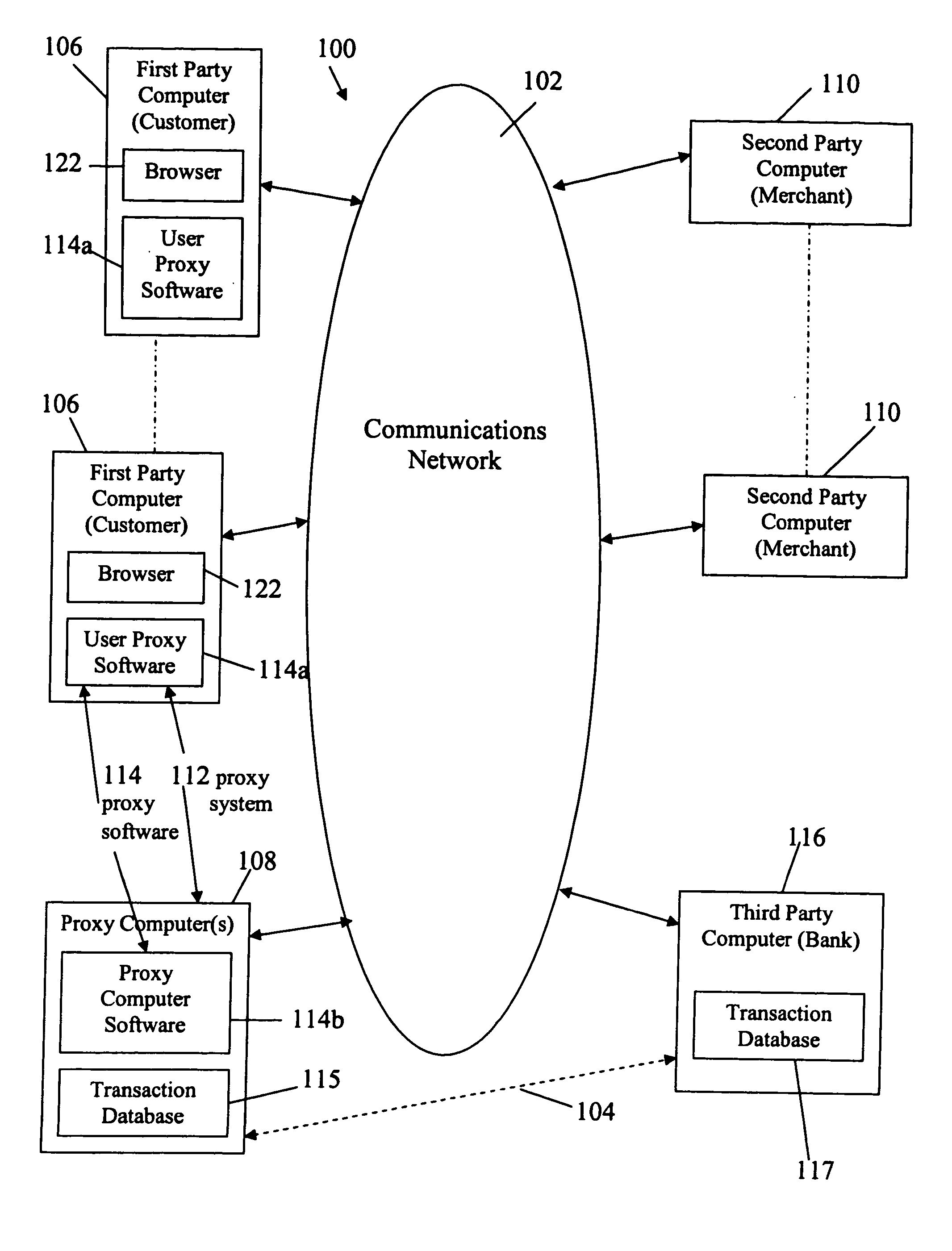
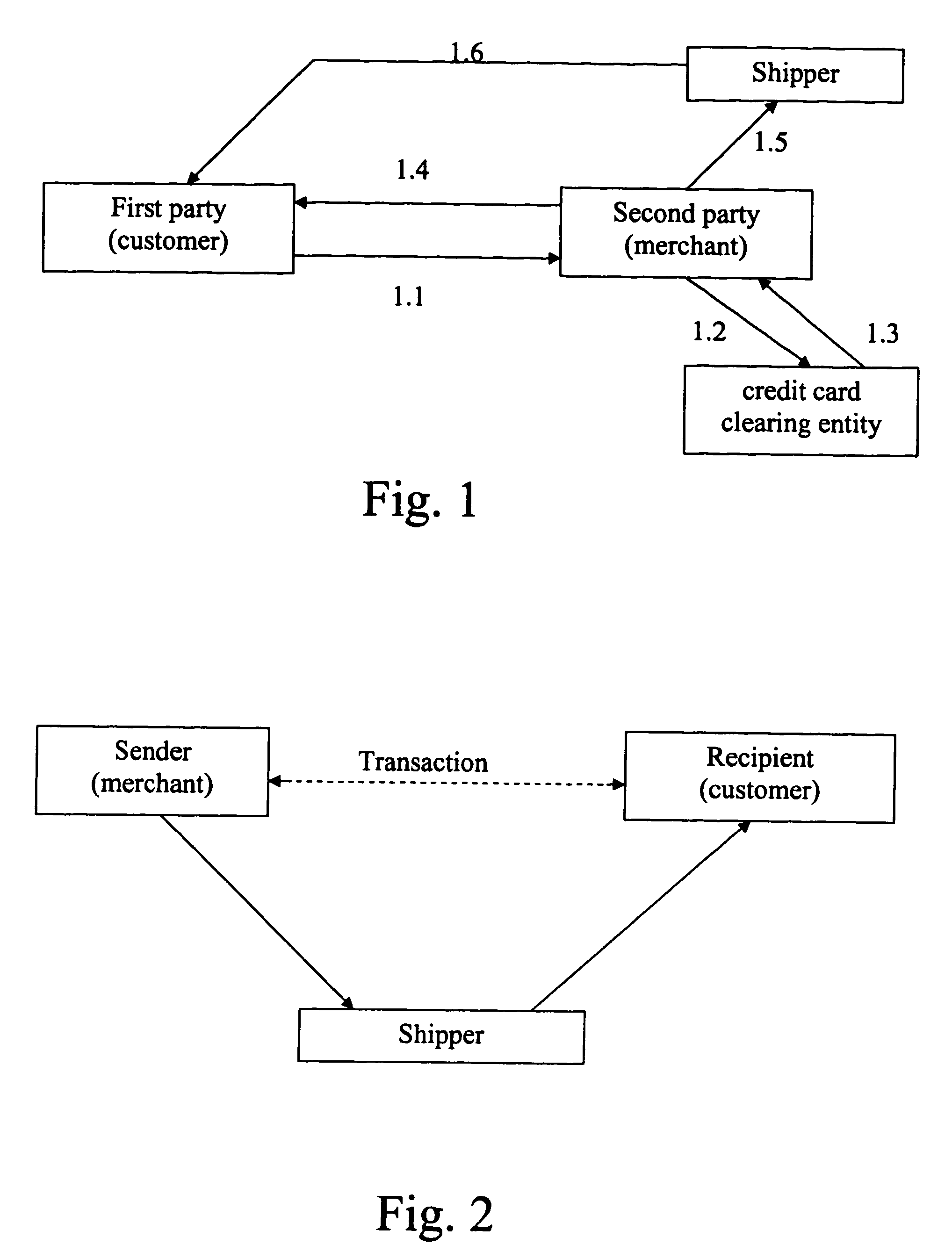
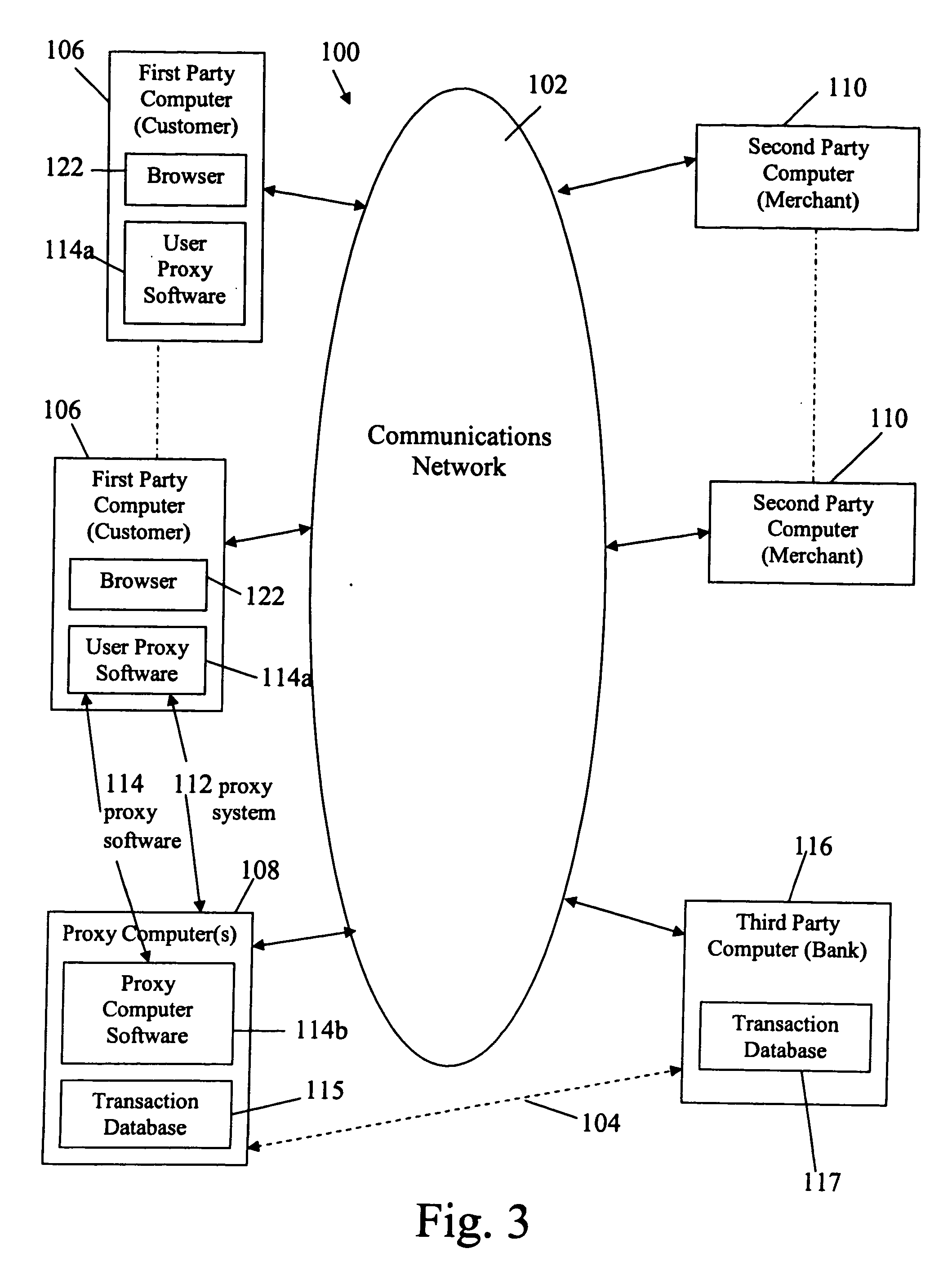
Electronic purchase of goods over a communications network including physical delivery while securing private and personal information of the purchasing party
InactiveUS20060247982A1Improve privacy protectionReduce collectionBuying/selling/leasing transactionsLogisticsCredit cardThird party
E-commerce which secures private and personal information of purchaser / users. E-commerce which may include delivery of a good ordered or purchased over a network (e.g., the Internet) to a purchaser / user, and / or arranging for electronic payment of the good is accomplished while securing private and personal information of purchaser / users, which may include the user's identity and address (and those of the user's computer), and financial information. E-commerce transactions include the purchasing or otherwise ordering of goods electronically by user, who may be a consumer or retail customer, and for delivery of goods to a shipping or electronic address designated by the user or to a physical or virtual depot for pick-up by the user, while providing complete anonymity of the user with respect to an electronic vendor, who may be a merchant or retailer. Proxy software is provided for user computers, one or more proxy computers, or both, for users to communicate with vendors anonymously over the network, provide for delivery of an ordered good and provide for electronic payment, while securing the user's private information. Delivery of a good includes shipping from a vendor to a depot using the depot name and address, and then either re-shipping from the depot to an address designated by the user which is withheld from the vendor, or held at the depot for anonymous pick-up. The proxy software provides for a proxy party to deal with a vendor and arrange payment from a bank or credit card company to the vendor based on an account that the proxy party has with the bank. The proxy party is not required where the purchaser / user is provided with a transaction identity by a third party bank, for example, which masks the true identity of the purchaser who, however, is known to the bank, as is his, her or its shipping address.
Owner:IPRIVACY
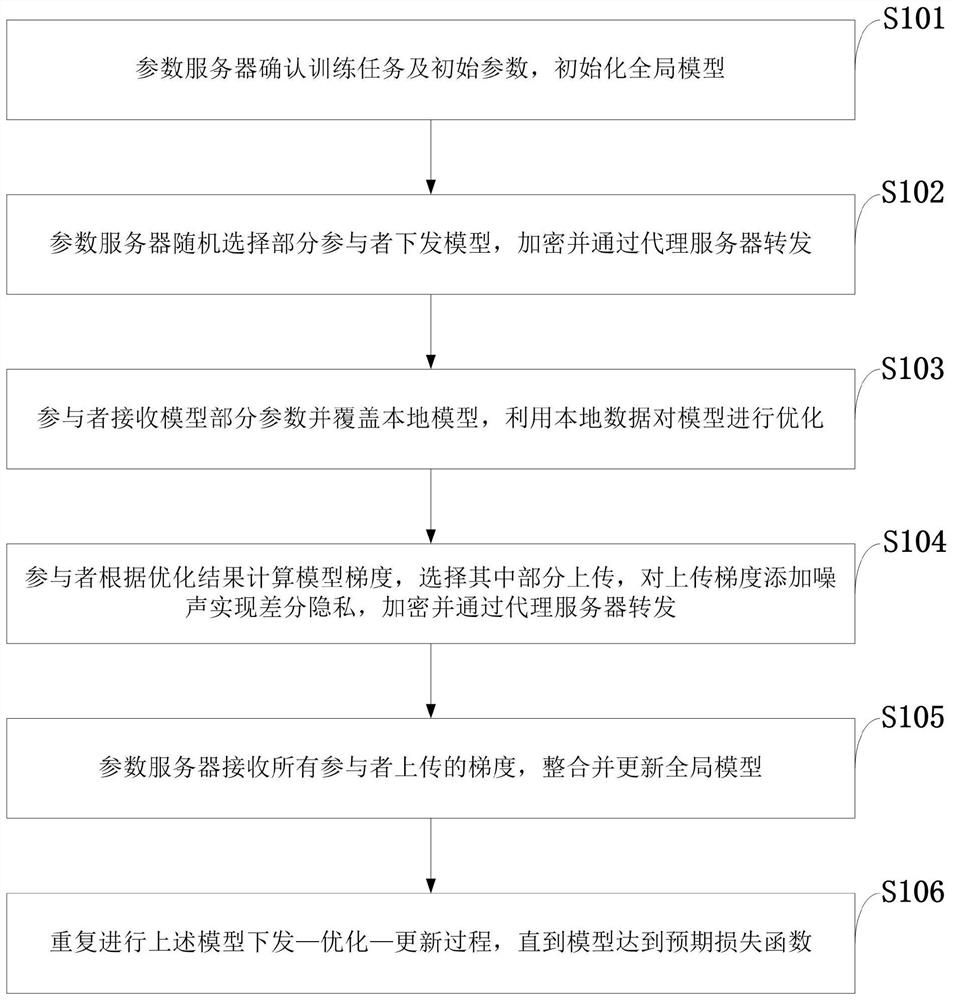
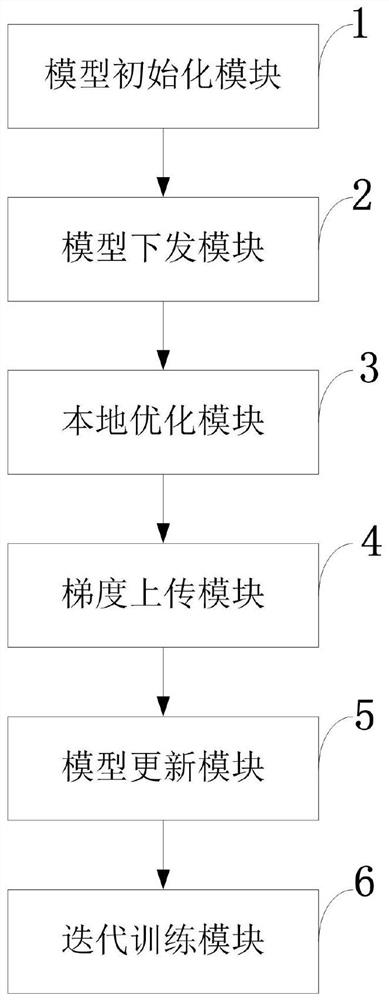
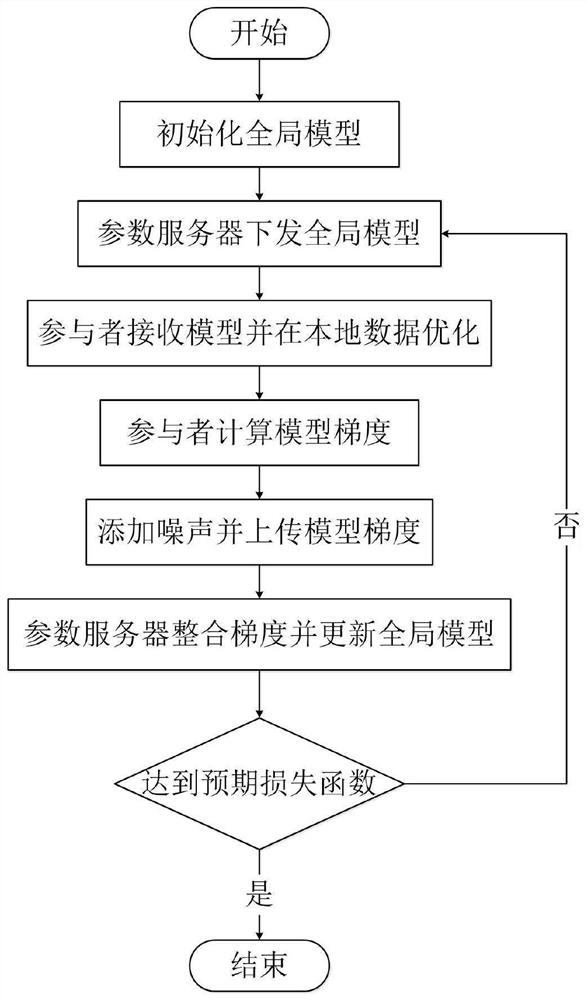
Federated learning information processing method and system, storage medium, program and terminal
ActiveCN111611610ARealize identity anonymityGuaranteed separation effectDigital data protectionNeural architecturesInformation processingData privacy protection
The invention belongs to the technical field of wireless communication networks, and discloses a federated learning information processing method and system, a storage medium, a program, and a terminal. A parameter serve confirms a training task and an initial parameter and initialize a global model. The parameter server randomly selects part of participants to issue model parameters, encrypts themodel parameters and forwards the model parameters through the proxy server; the participants receive part of parameters of the model and cover the local model, and the model is optimized by using local data; the participant calculates a model gradient according to an optimization result, selects a part of the model gradient for uploading, adds noise to the uploading gradient to realize differential privacy, encrypts the uploading gradient and forwards the uploading gradient through the proxy server; the parameter server receives the gradients of all participants, and integrates and updates the global model; and the issuing-training-updating process of the model is repeated until an expected loss function is achieved. According to the invention, data privacy protection is realized; the communication overhead of a parameter server is reduced, and anonymity of participants is realized.
Owner:XIDIAN UNIV
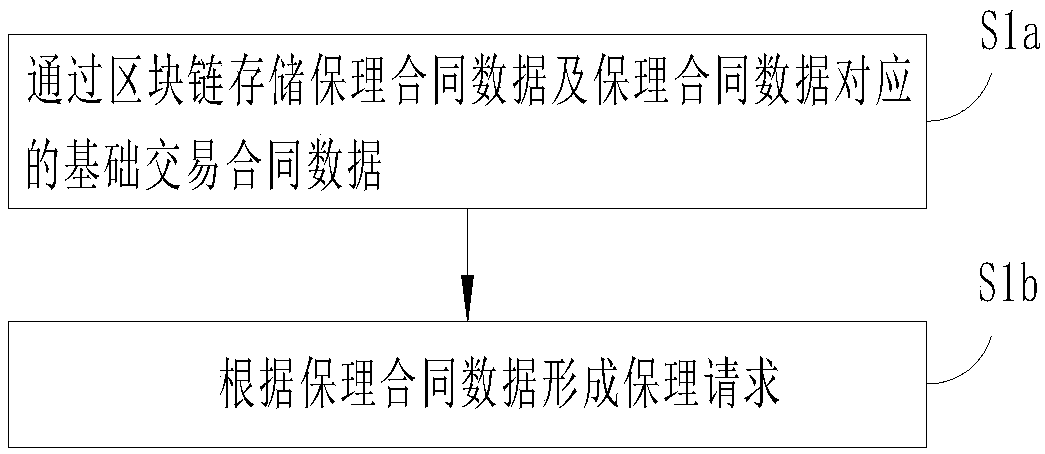
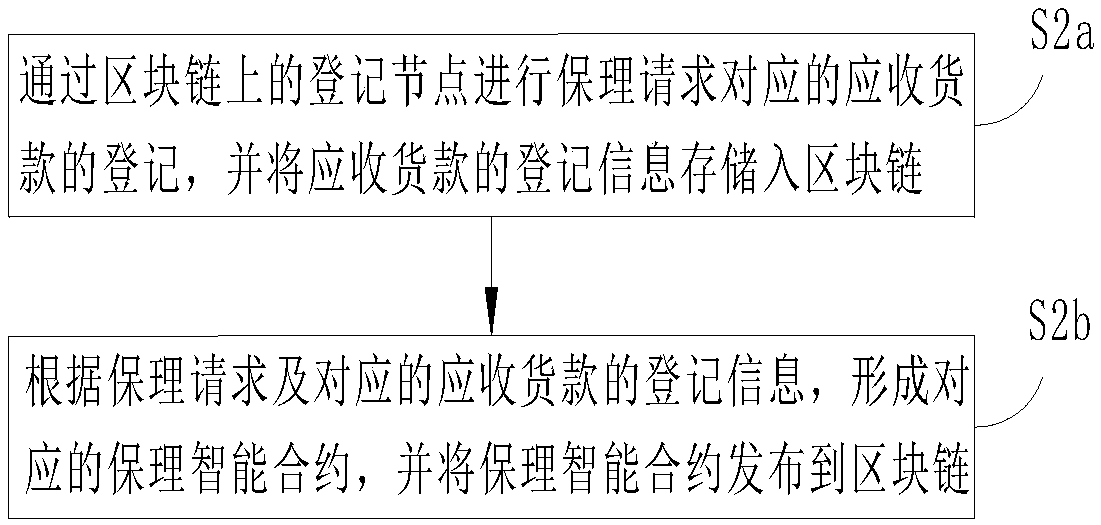
Method and system for processing factoring information based on blockchain
InactiveCN108122159AImprove settlement efficiencyConfidence and reliabilityFinanceBuying/selling/leasing transactionsSmart contractComputer science
The invention provides a method and a system for processing factoring information based on a blockchain. The method for processing the factoring information comprises the following steps: receiving afactoring request transmitted by a user; forming a corresponding factoring smart contract according to the factoring request; identifying user information related to the factoring smart contract on the blockchain; carrying out endorsement verification on the factoring smart contract by an endorsement verification node corresponding to the user information, on the blockchain; when the factoring smart contract passes the endorsement verification, changing ownership information corresponding to the factoring request by the factoring smart contract. The method and the system for processing the factoring information based on the blockchain, provided by the invention, provide fidelity and traceability of service data for all parties participating in factoring service by applying the characteristics of non-deletability, temper resistance, multi-maintenance, account book sharing and the like of blockchain data. Besides, the fulfillment of factoring service is finished by the factoring smart contract, service data cannot be tempered, and the difficulty of information mutual recognition of all the parties participating in the factoring service in the prior art is overcome.
Owner:CHINA CHAIN TECH CO LTD
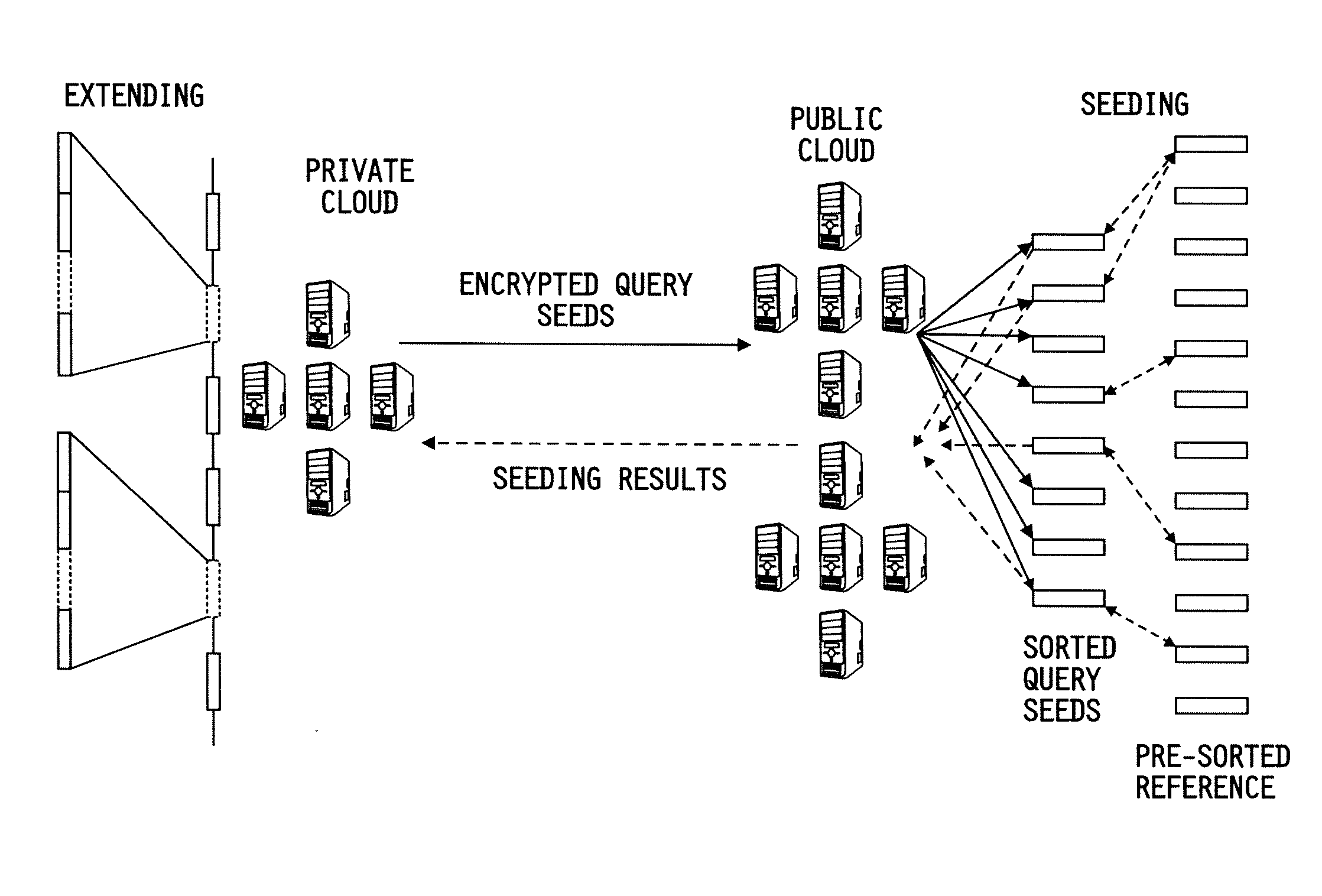
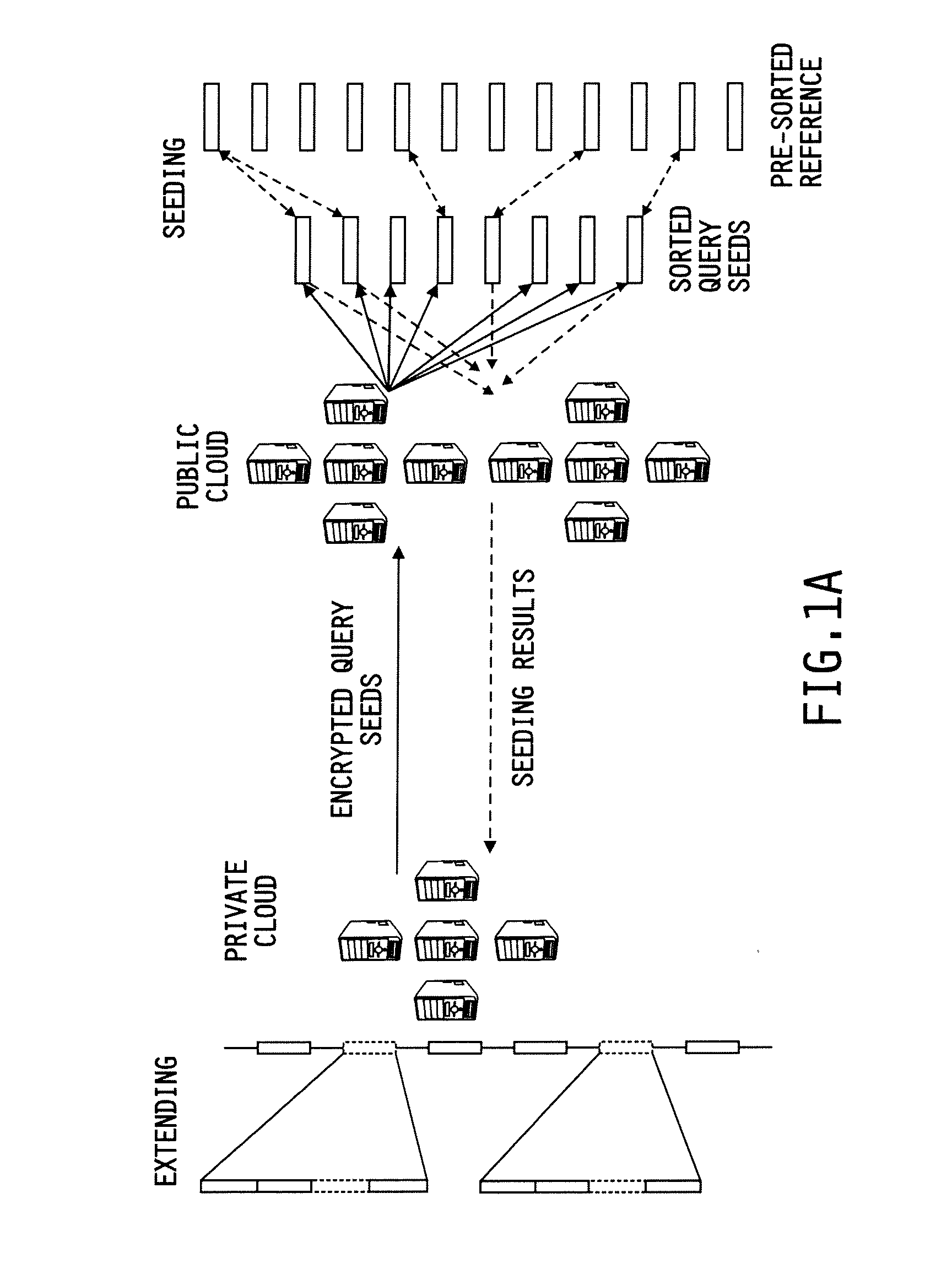
Secure and scalable mapping of human sequencing reads on hybrid clouds
ActiveUS20140075183A1Improve privacy protectionLow costSequence analysisSecuring communicationPhacusPrivacy protection
System and methods are provided for performing privacy-preserving, high-performance, and scalable DNA read mapping on hybrid clouds including a public cloud and a private cloud. The systems and methods offer strong privacy protection and have the capacity to process millions of reads and allocate most of the workload to the public cloud at a small overall cost. The systems and methods perform seeding on the public cloud using keyed hash values of individual sequencing reads' seeds and then extend matched seeds on the private cloud. The systems and methods are designed to move the workload of read mapping from the extension stage to the seeding stage, thereby ensuring that the dominant portion of the overhead is shouldered by the public cloud.
Owner:INDIANA UNIV RES & TECH CORP
Depository receipt application transaction system and method based on blockchain
ActiveCN107844976AThere is no problem of rapid data expansionGood privacy protectionPayment protocolsSpecial data processing applicationsPrivacy protectionReceipt
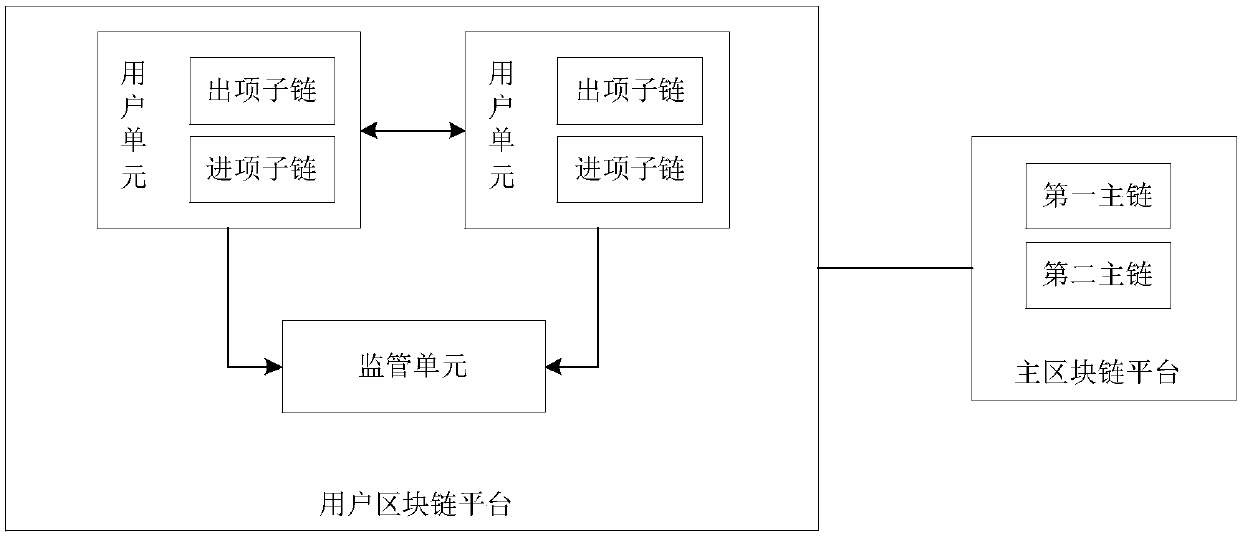
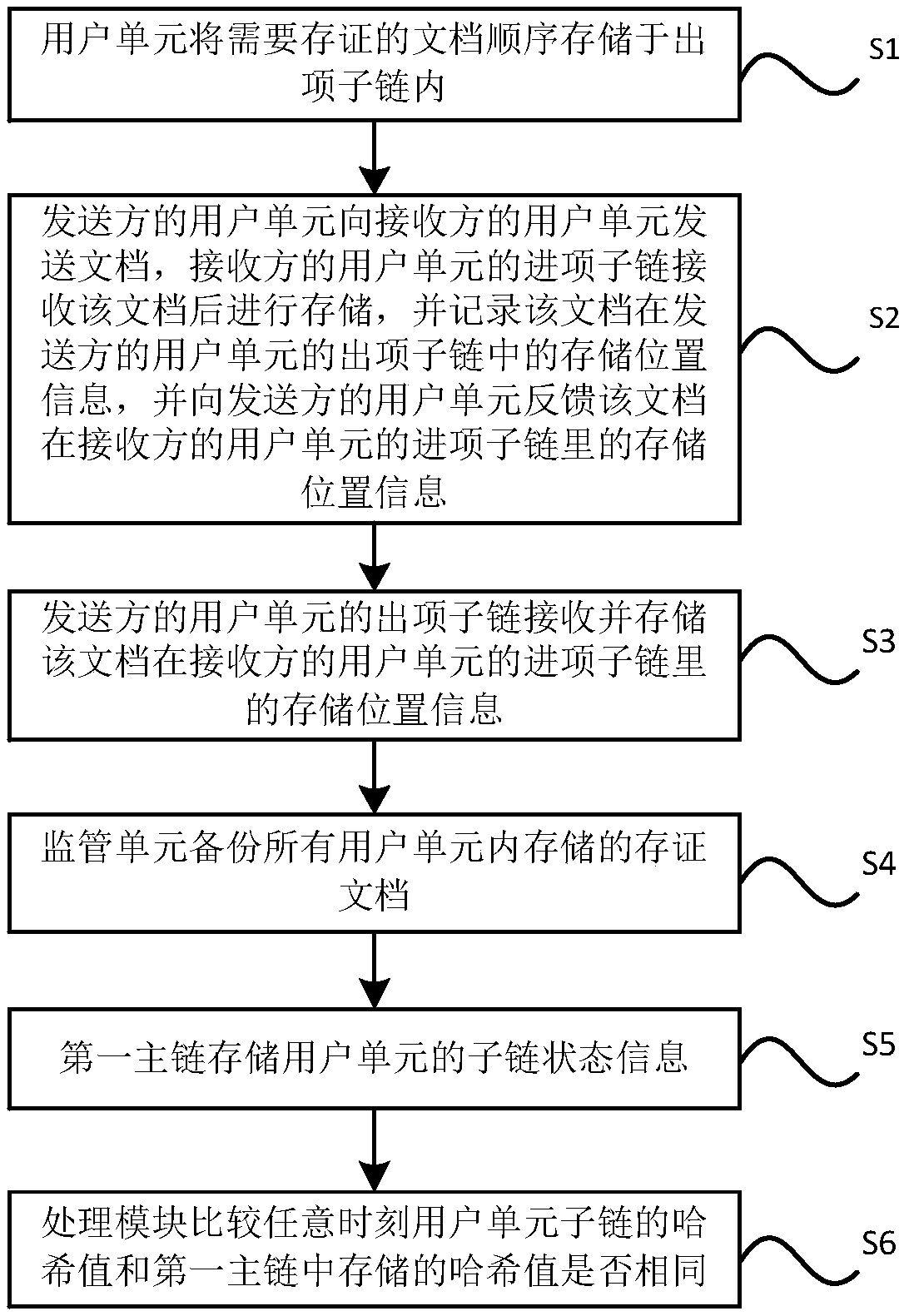
The invention discloses a depository receipt application transaction system based on blockchain, and relates to the technical field of blockchain. The system comprises a user blockchain platform, a main blockchain platform, and a processing module. The user blockchain platform comprises at least two user units and a supervision unit, and each user unit comprises an expenditure item subchain and anincome item subchain, wherein the expenditure item subchain is used for storing a depository receipt document generated by a user, and the income item subchain is used for storing the depository receipt document received by the user. The supervision unit is used for the backup of the depository receipt documents stored in all user units. The main blockchain platform comprises a first main chain and a second main chain, wherein the first main chain is used for storing the subchain state information of each user unit, and the second main chain is used for storing the address of each user unit.The processing module is used for comparing whether the Hash values of the subchains of the user units are the same as a Hash value stored in the first block chain at any time or not. According to theinvention, the processing performance of the system is not limited by the number of users, and a problem that data is rapidly expanded is solved. The system has a good privacy protection function, and can effectively prevent the document data from being tampered.
Owner:WUHAN TIANYU INFORMATION IND
Partitioned block chain network and method for realizing partition query by same
ActiveCN107766542AReduce the spreadImprove privacy protectionFinanceDigital data protectionData privacy protectionTransaction data
The invention discloses a partitioned block chain network. The block chain network consists of multiple nodes; according to visible permissions of the nodes to different transaction data, part or allof the nodes are divided in one or more partitions; the interior of the same partition is completely visible for the transaction data, and different partitions are invisible for the transaction data;according to the permissions of the nodes participating in a consensus process, all the nodes are classified: the nodes capable of participating in the consensus process of all the partitions are global consensus nodes, the nodes only capable of participating in the consensus process of the partitions where the nodes are located are partition consensus nodes, and the nodes incapable of participating in any consensus process are synchronous nodes; each node has a partition identifier; and each node stores transaction fingerprints of all historical transaction data. By partitioning and classifying the nodes in the block chain network, the query of the historical transaction data is limited in the same partition, so that the propagation range of the historical transaction data is greatly reduced and the data privacy protection effect is improved.
Owner:上海分布信息科技有限公司
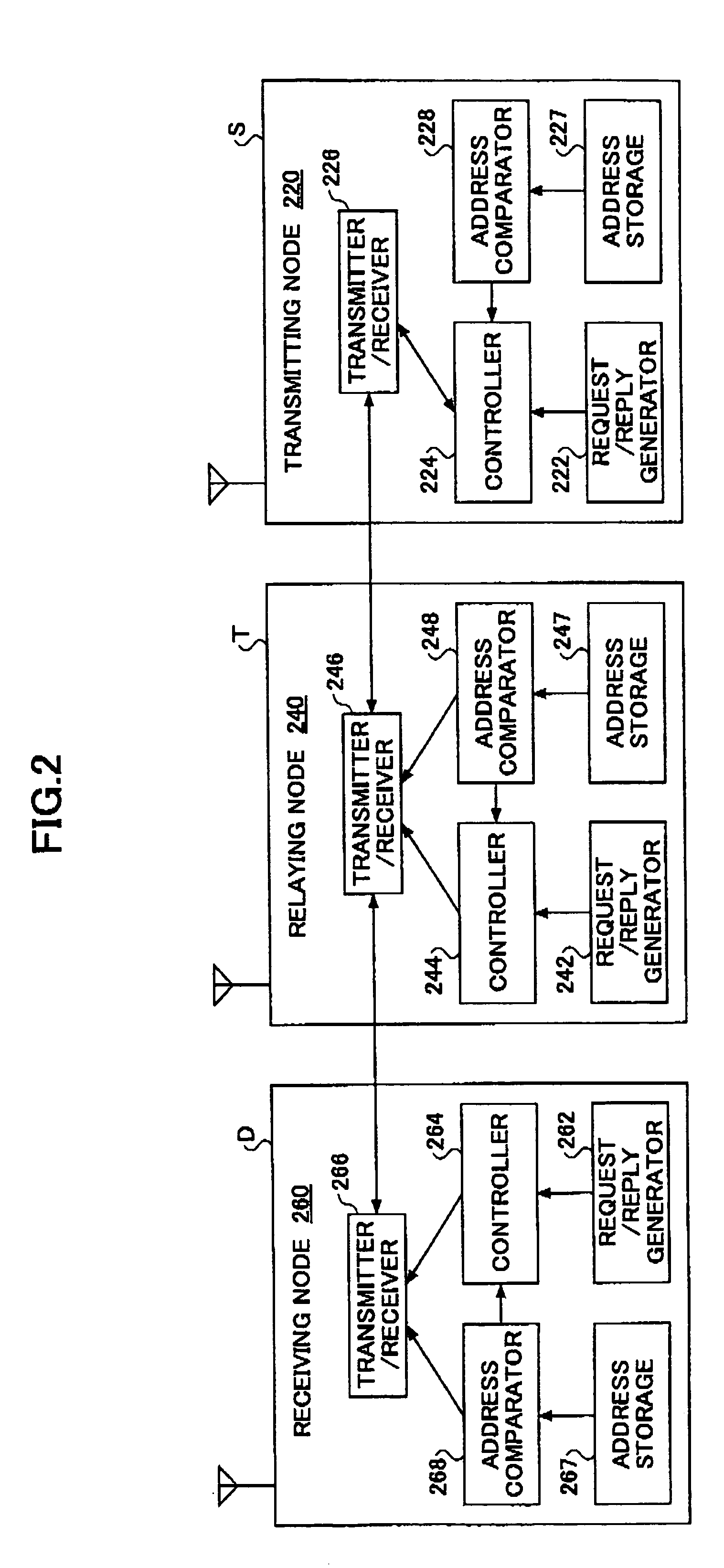
Mobile node, an ad hoc network routing controlling method and an ad hoc network system
ActiveUS7486651B2Reduce riskImprove privacy protectionKey distribution for secure communicationUnauthorised/fraudulent call preventionCommunication unitDigital signature
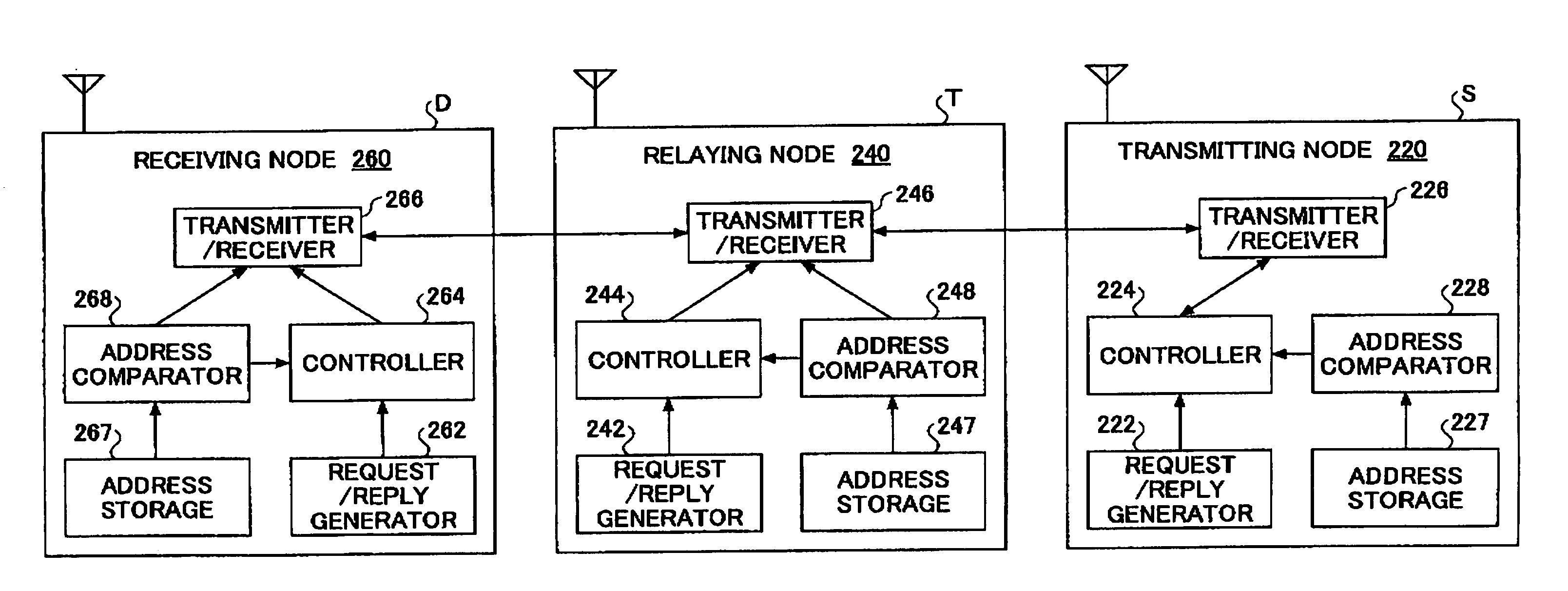
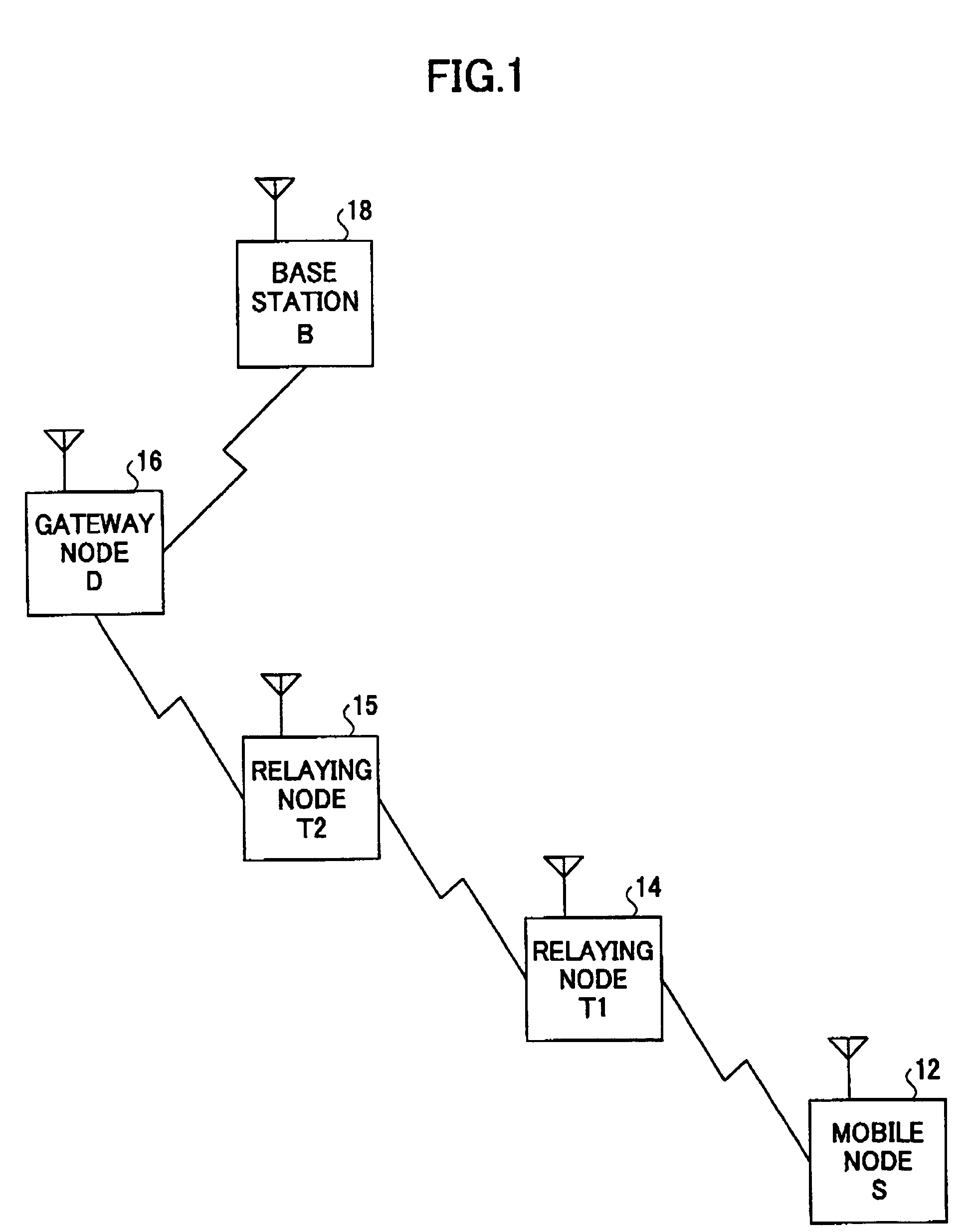
A mobile node (400) capable of establishing an ad hoc network routing is disclosed. The mobile node comprises a transmitting / receiving unit (426) for communicating with other communication unit and a routing request generator (422) for generating a routing request message for requiring an ad hoc network routing. The mobile node further comprises: an address storage (427) for storing an address of the mobile node (400) and an address of a receiving node; a random number generator (430) for generating a random number; a certificate issuing unit (440) for issuing a certificate of the mobile node (400); a digital signature creator (450) for creating a digital signature of the mobile node (400); and a controller (424) for transmitting / receiving the routing request message accompanied by the address of the mobile node, the address of the receiving node, the random number, the certificate and the digital signature via the transmitting / receiving unit, according to an ad hoc network protocol.
Owner:GOOGLE LLC
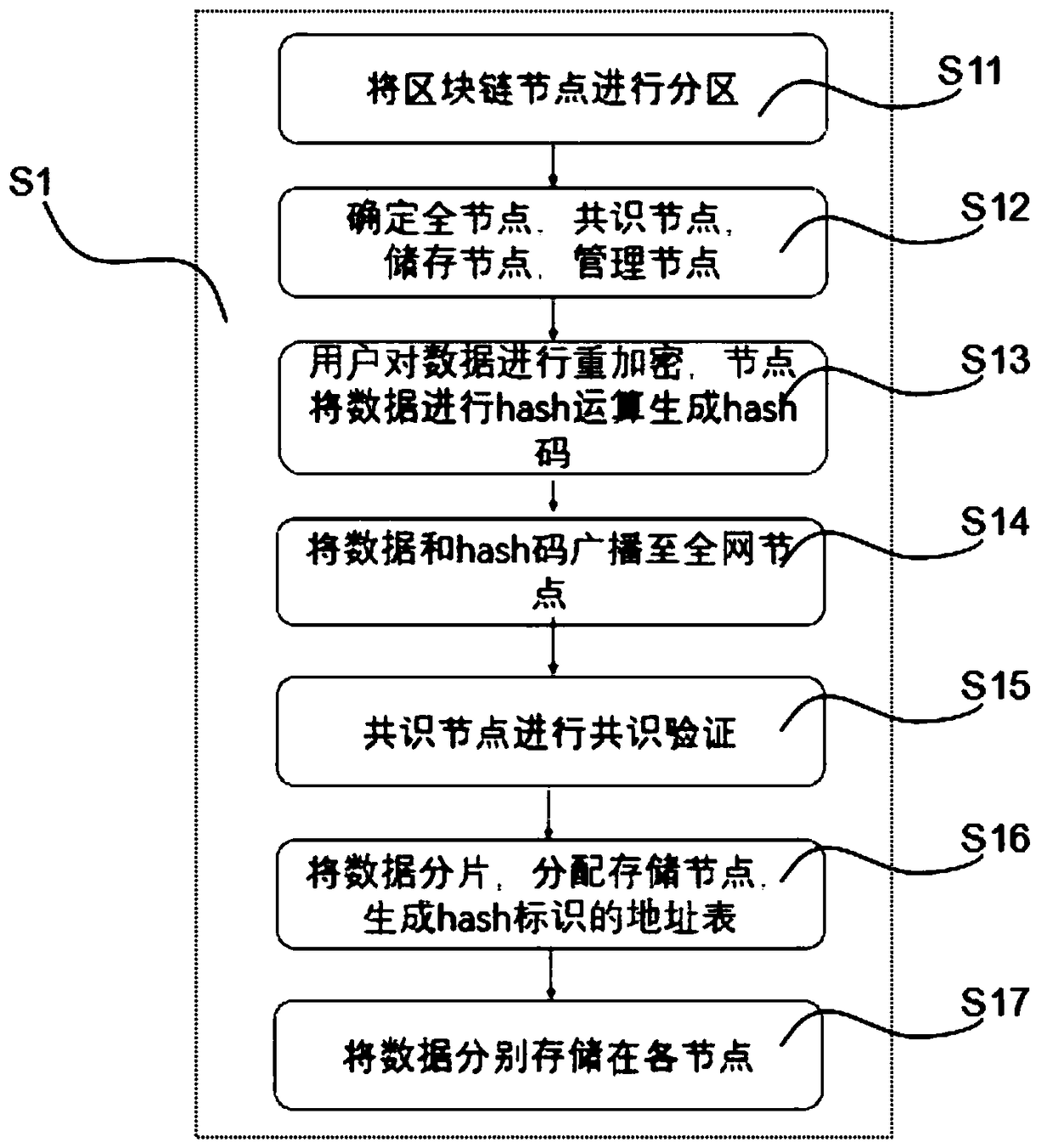
Game data partition storage method based on block chain hash addressing and re-encryption
ActiveCN109327512AImprove securityImprove privacyUser identity/authority verificationVideo gamesStructure of Management InformationEncryption
The invention relates to a game data partition storage method based on block chain hash addressing and re-encryption. The method comprises a data partition storage step and a data check step, whereinthe data partition storage step specifically comprises: partitioning block chain nodes into a full node, a consensus node, a storage node and a management node; performing hash operation on the node data to generate hash code; broadcasting the hash codes to nodes throughout the network; performing consensus verification by using hash values; generating a storage address table corresponding to thehash values; and respectively storing the data on the nodes according to the generated storage address table corresponding to the hash values. According to the game data partition storage method basedon block chain hash addressing and re-encryption, by performing fragmentation and partition storage on the data, the data have m pieces of redundancy, the stored data are fragmented, so that the dataprivacy is improved, and the nodes are classified, and different nodes are responsible for different functions, thereby reducing the resource waste, and the hierarchical node structure improves the scalability and the pluggability of the architecture.
Owner:广东微链科技有限公司
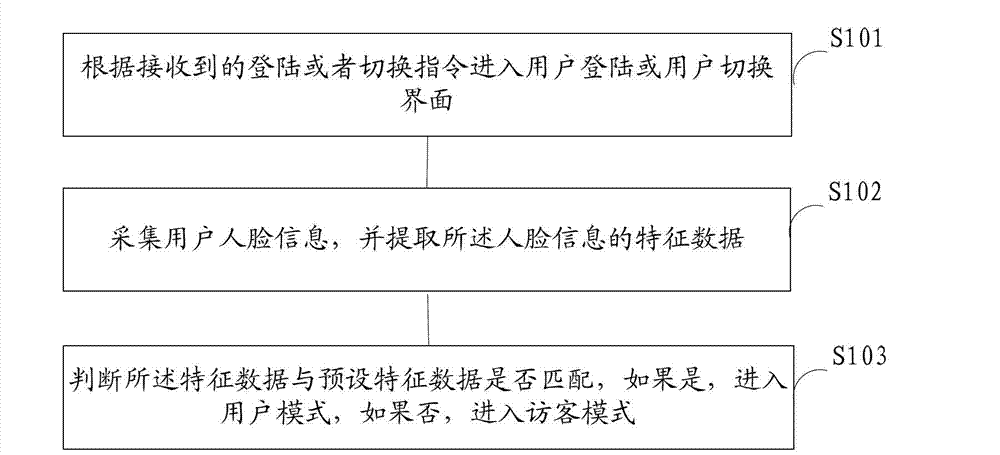
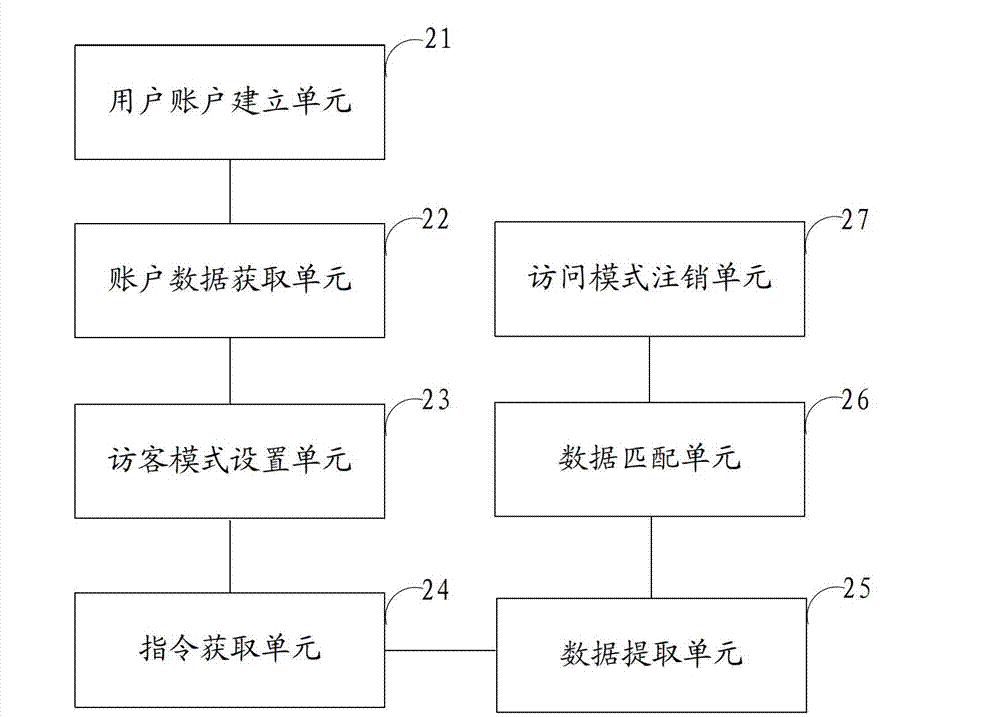
User login/switching method and system, and mobile terminal
InactiveCN102932518AImprove privacy protectionEasy loginSubstation equipmentComputer scienceUser interface
The invention is suitable for the field of mobile terminals, and provides a user login / switching method and a user login / switching system, and a mobile terminal. The method comprises the following steps of: entering into a user login interface or a user switching interface according to a received login or switching instruction; acquiring user face information, and extracting characteristic data of the face information; and judging whether the characteristic data are matched with preset characteristic data, if so, entering into a user mode, otherwise, entering into a visitor mode. By the method, a user can enter into a use mode corresponding to the preset characteristic data by acquiring the face characteristic data, so that user login or user switching is convenient and easy.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
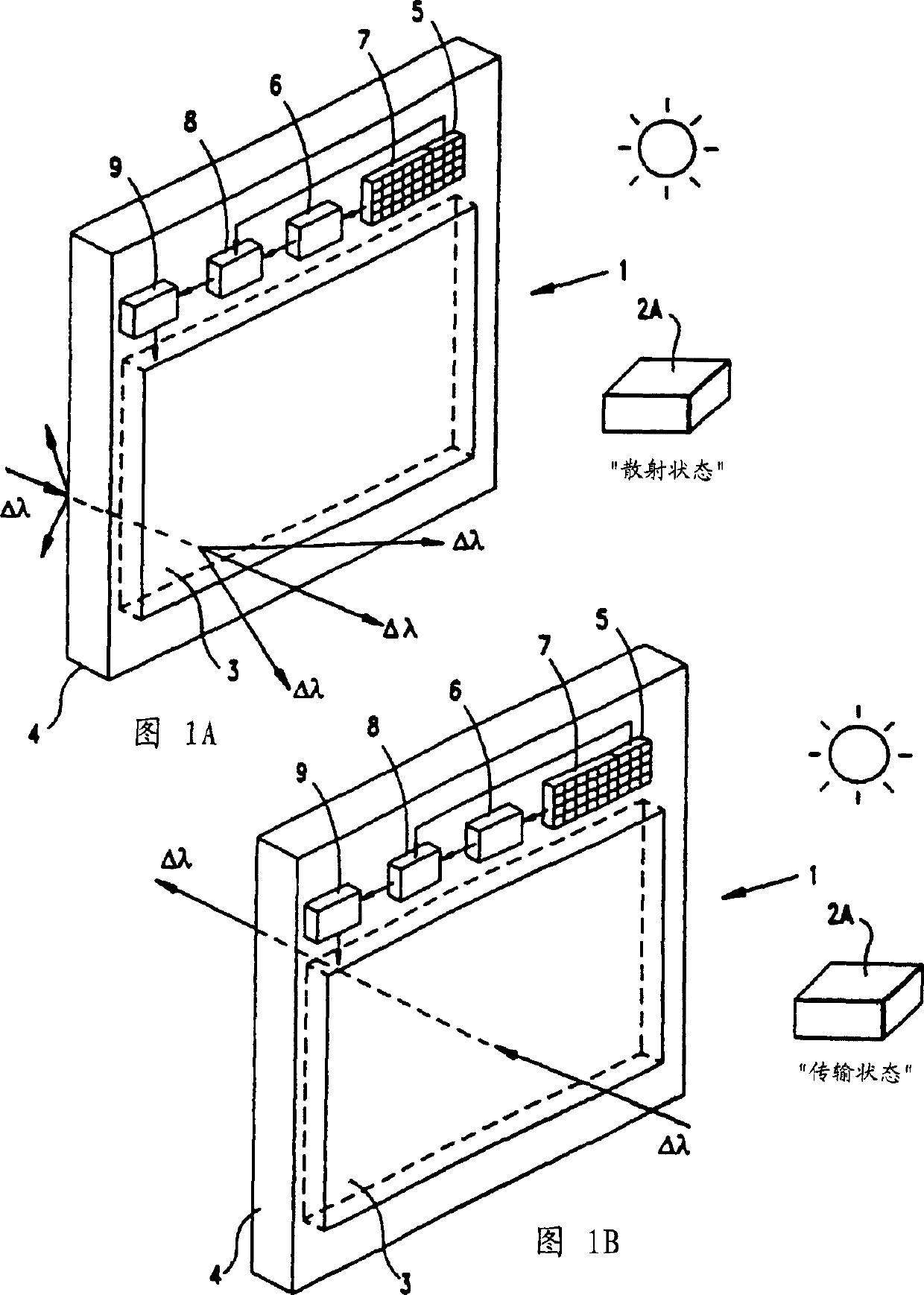
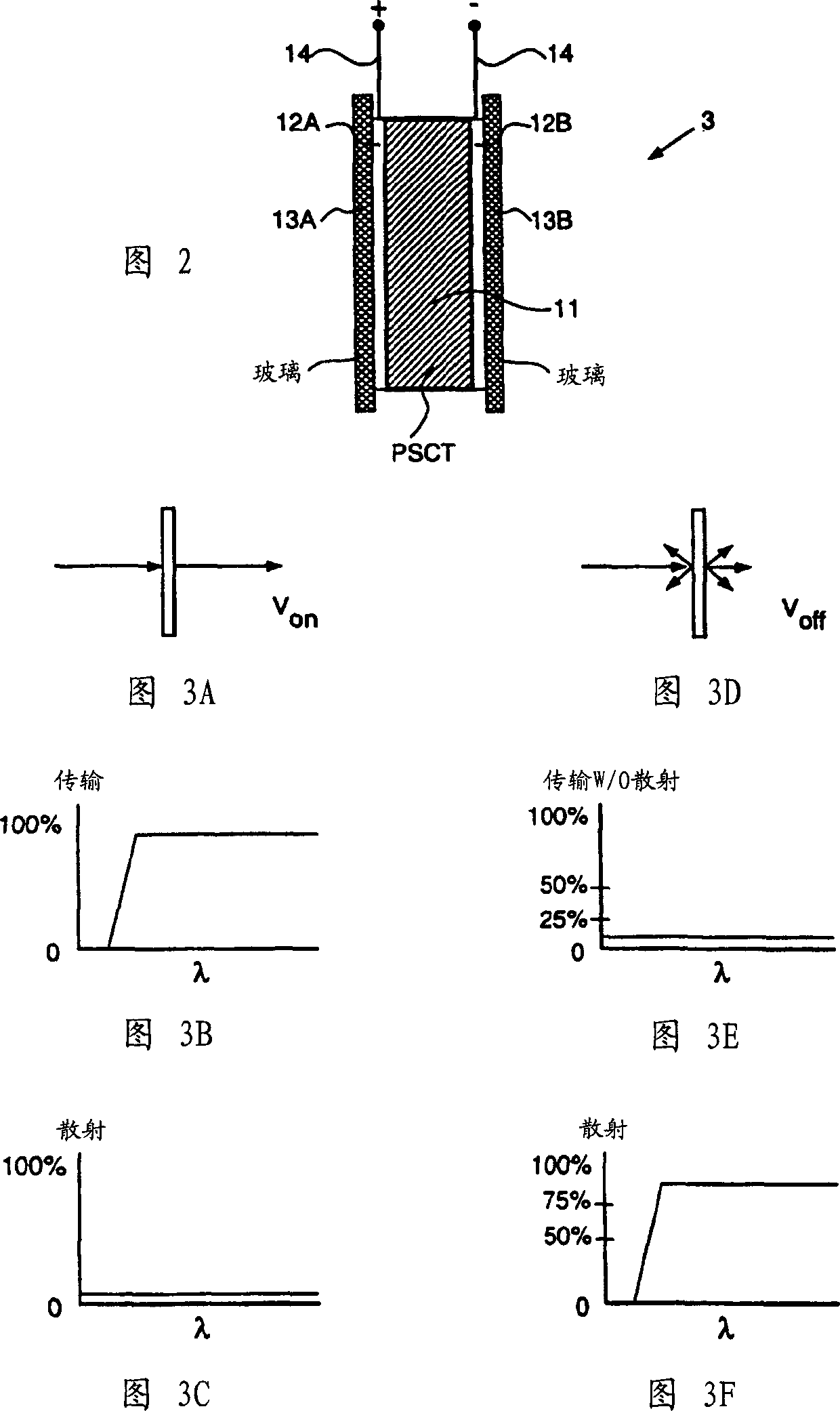
Electro-optical glazing structures having scatthering and transparent modes of operation
InactiveCN1359479AAvoid deficienciesAvoid disadvantagesLiquid crystal compositionsDoor/window protective devicesEngineeringOperation mode
Electro-optical glazing structures having total-scattering and total-transparent modes of operation which are electrically-switchable for use in dynamically controlling electromagnetic radiation flow in diverse applications.
Owner:REVEO
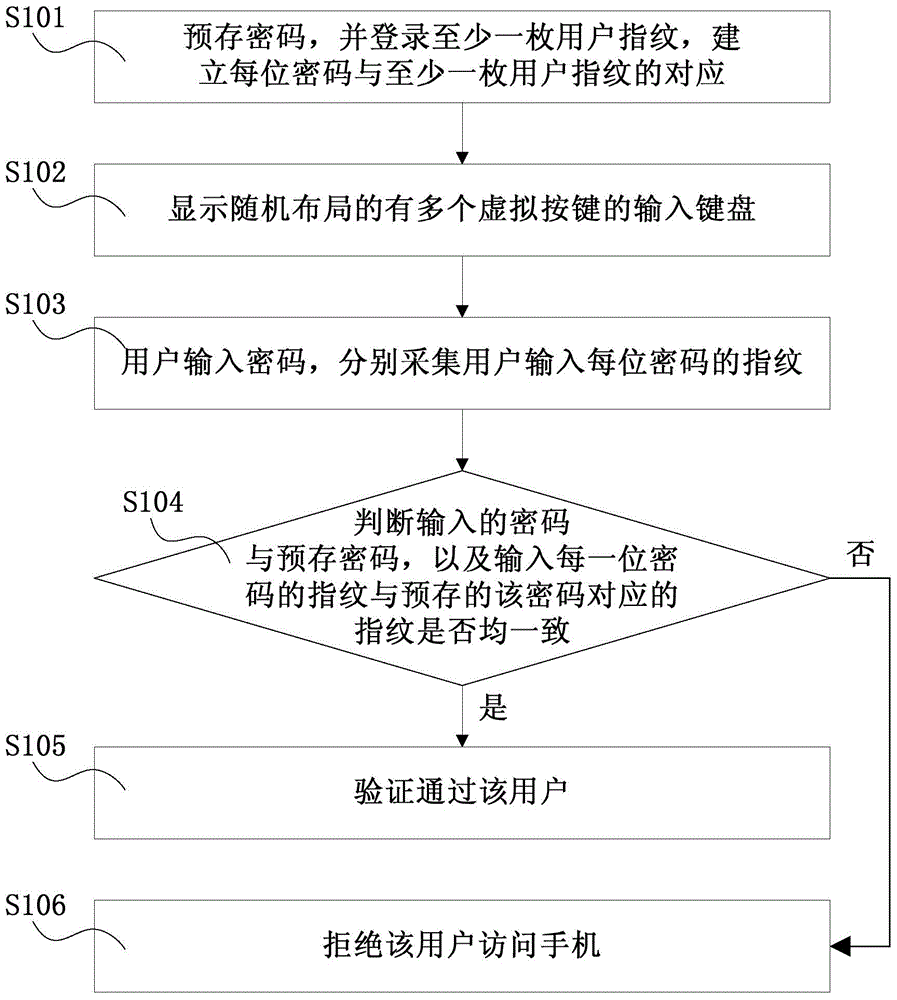
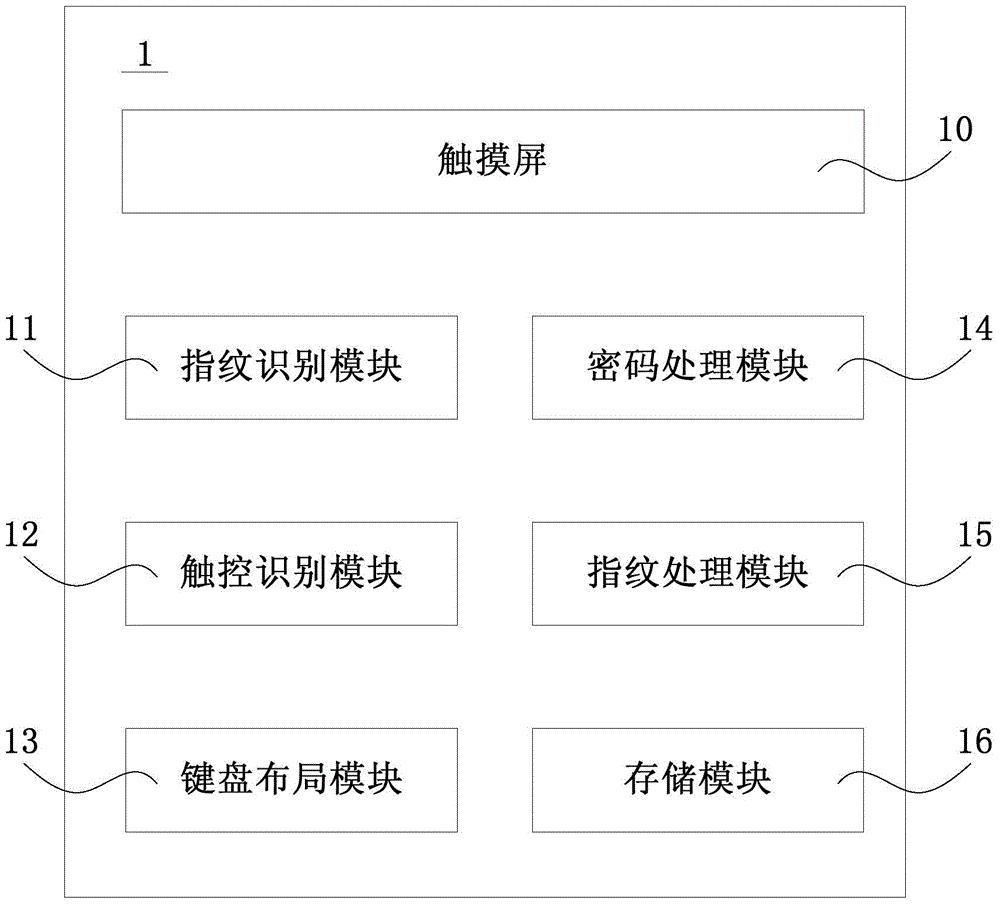
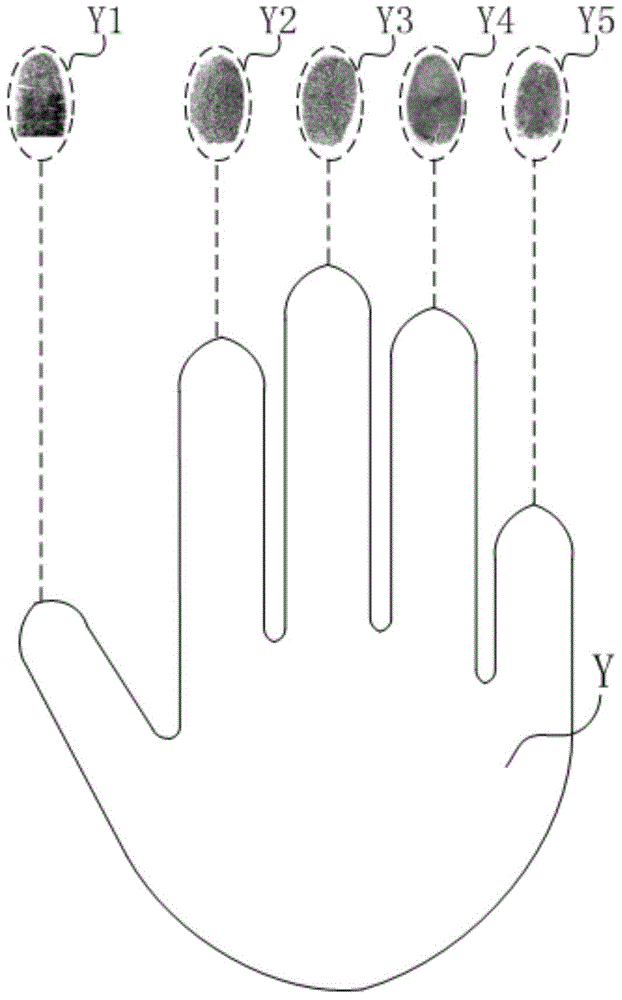
Fingerprint and password combined type verification method and device thereof
InactiveCN104091103AIncrease the difficulty of cracking verificationImprove privacy protectionDigital data authenticationPrivacy protectionConfidentiality
The invention discloses a fingerprint and password combined type verification method and a device thereof. The fingerprint and password combined type verification method and the device thereof are used in an electronic device with a touch screen, and the touch screen has the fingerprint recognition function and the touch recognition function at the same time. The method includes the following steps that an input keyboard which is provided with a plurality of virtual keys is displayed, and if an input password is the same as a pre-stored password and each fingerprint for operating the virtual keys is matched with a corresponding pre-stored user fingerprint, verification is successful. By means of the fingerprint and password combined type verification method and the device thereof, cracking verification difficulty is greatly increased, and privacy protection to the electronic device is improved; the practicability of the method is almost the same as the practicability in an existing mode, under the condition that user difficulty is not increased, the password cannot be cracked by others easily, and hence the confidentiality which is far higher than that of an existing verification mode is achieved.
Owner:NANCHANG OUFEI BIOLOGICAL IDENTIFICATION TECH +3
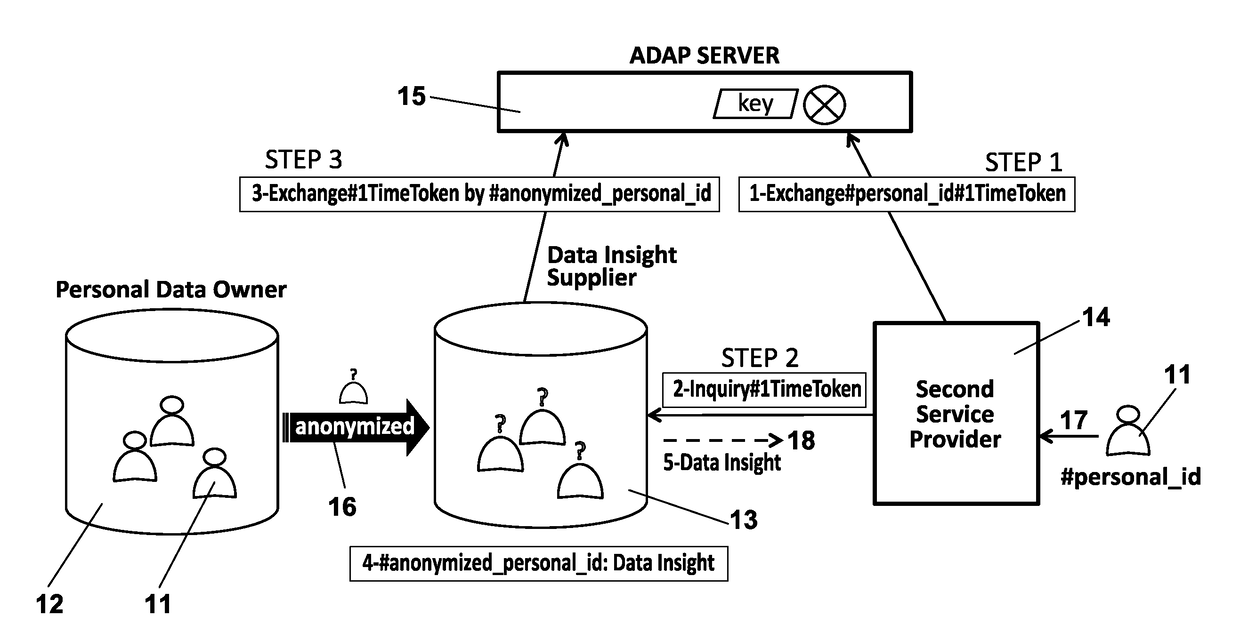
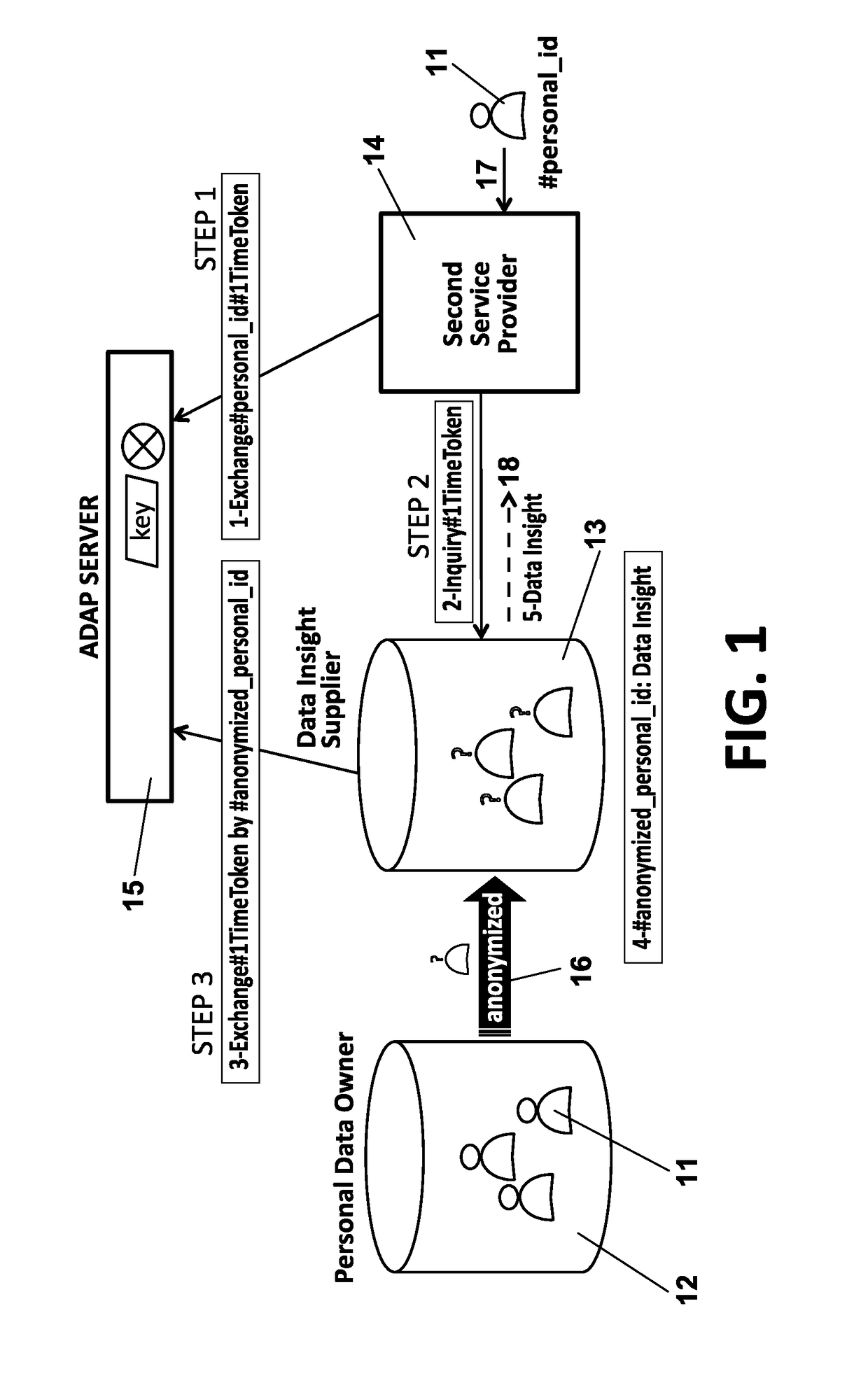
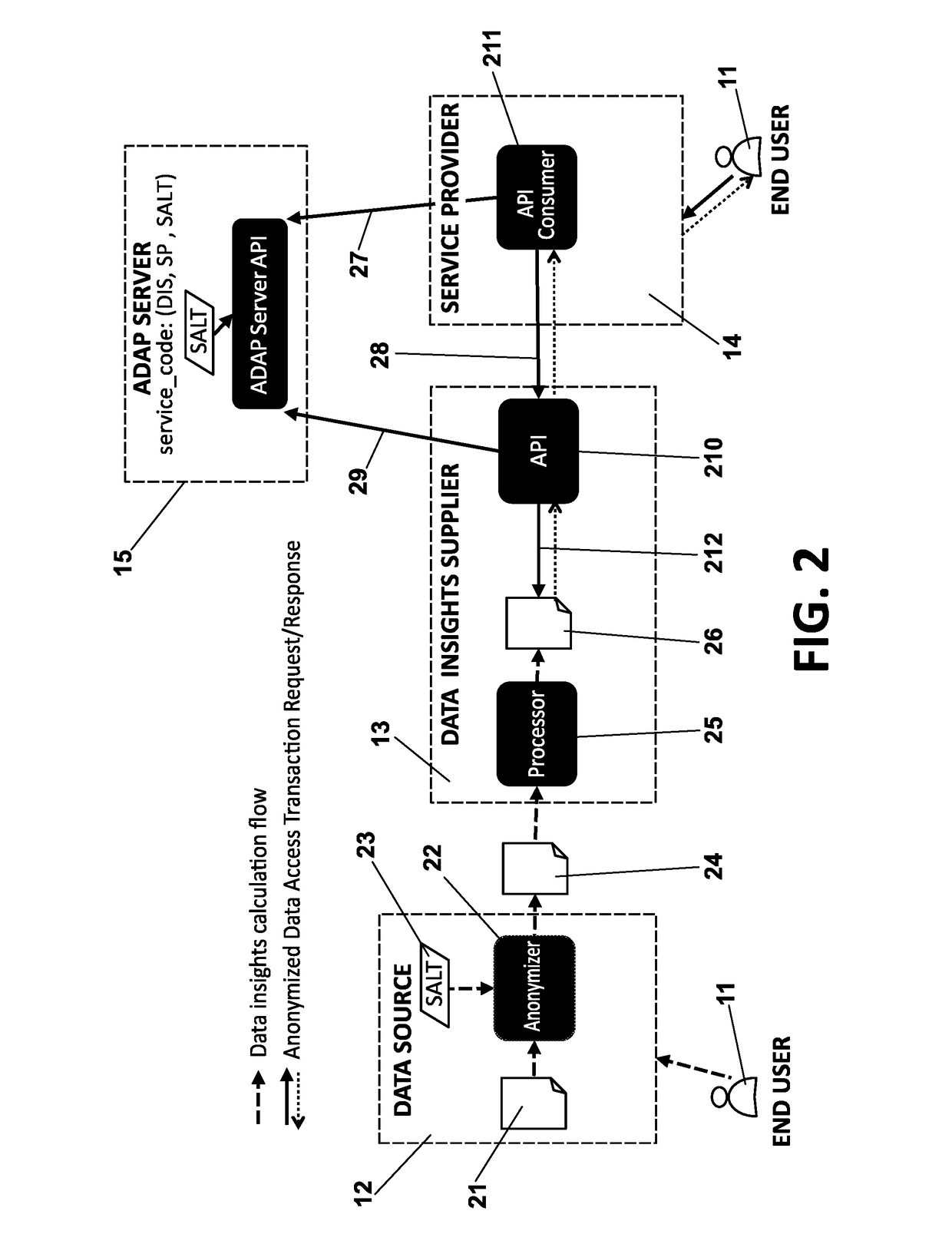
Methods, apparatus and system for improved access of consumer's personal data
InactiveUS20170132431A1Improve scalabilityIncrease flexibilityUser identity/authority verificationDigital data protectionInternet privacyEngineering
Methods, apparatus and system to access personal data of a consumer (generated when said user is operating with a first service provider) by a second service provider, maintaining the privacy of the consumer. The proposed invention allows accessing data belonging to a certain consumer (for example, data generated when using a certain telecommunications service) by another entity providing services to the user (for example a bank) without sending the personal identification of the consumer. The proposed invention adds more flexibility, saves resources and increases scalability, efficiency and privacy.
Owner:TELEFONICA DIGITAL ESPANA
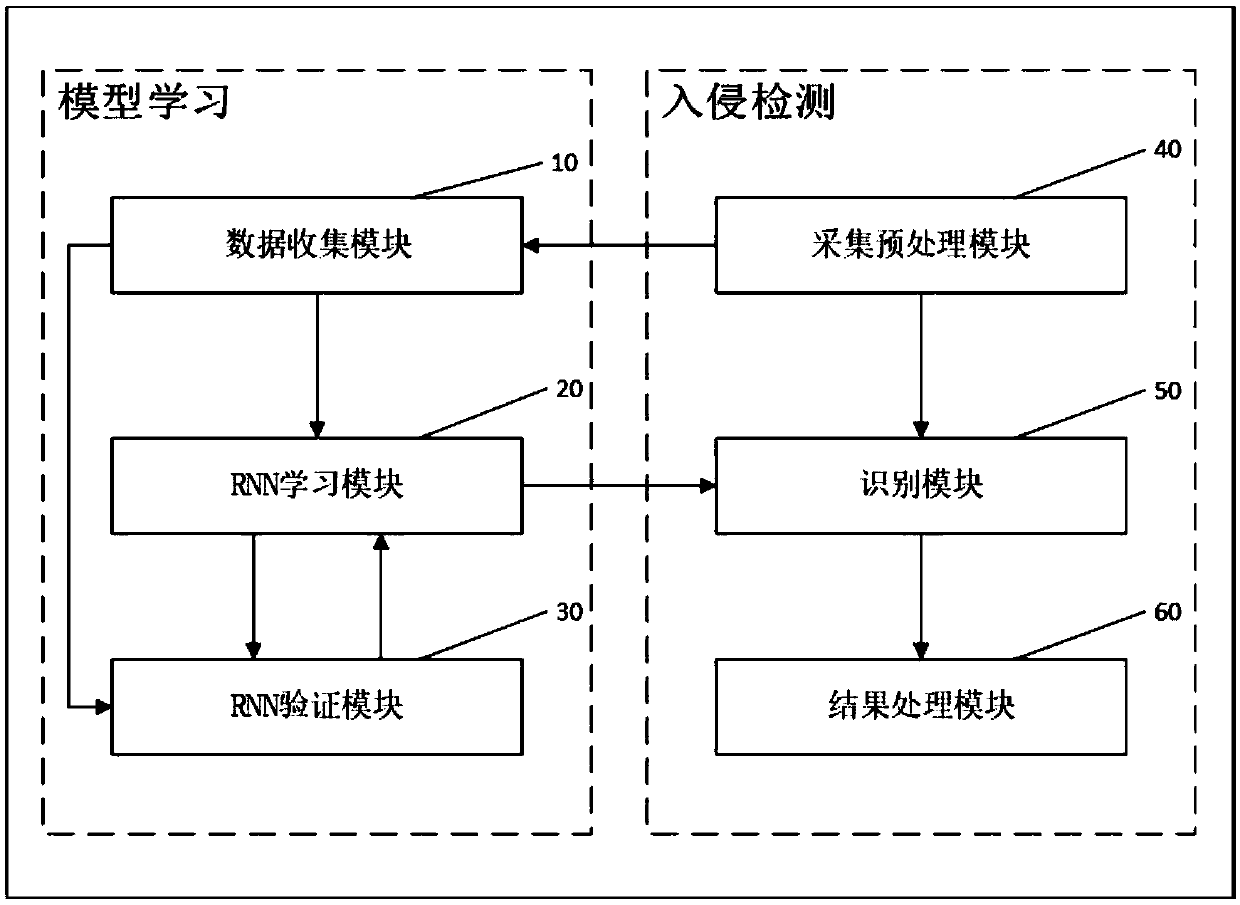
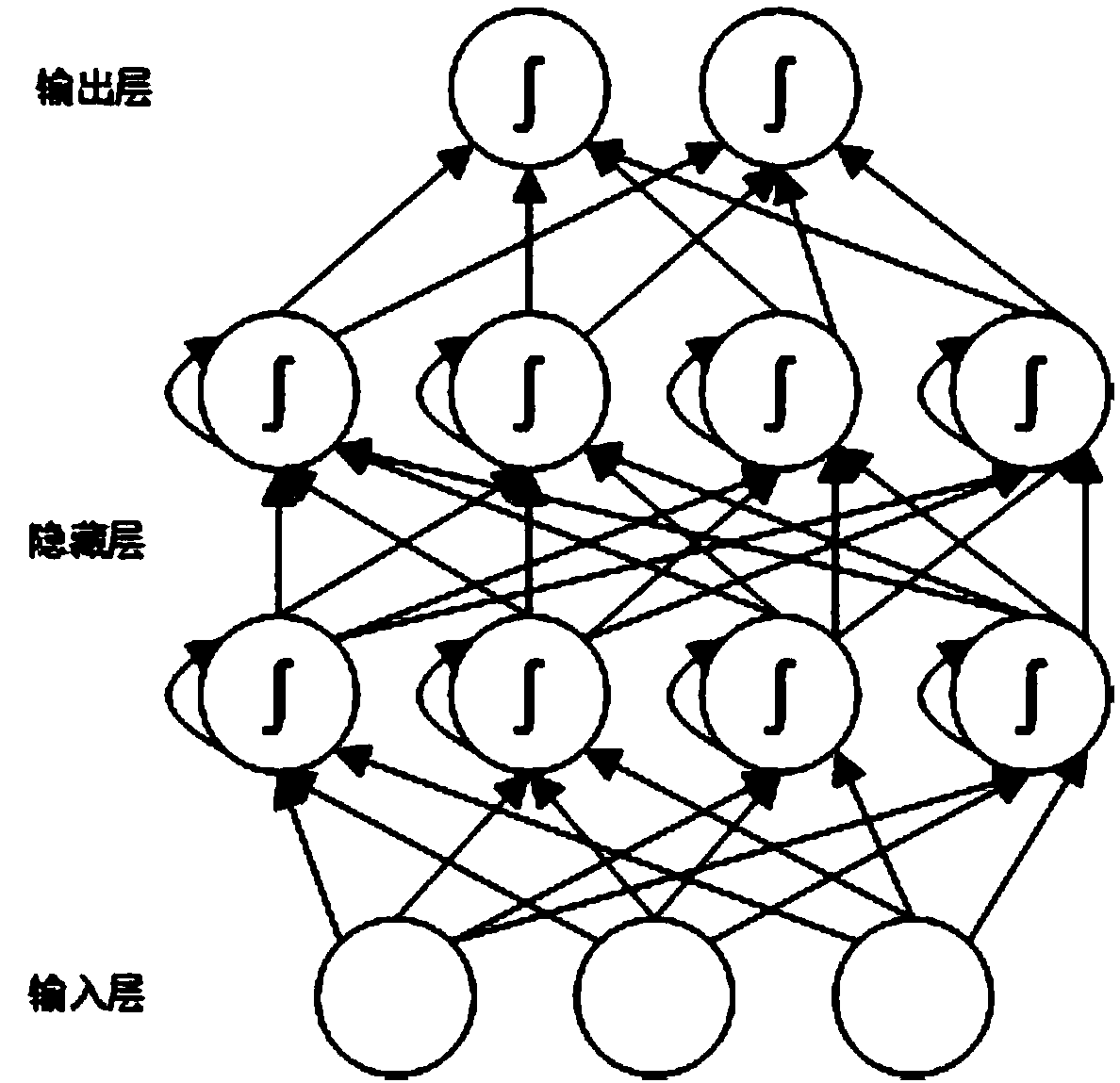
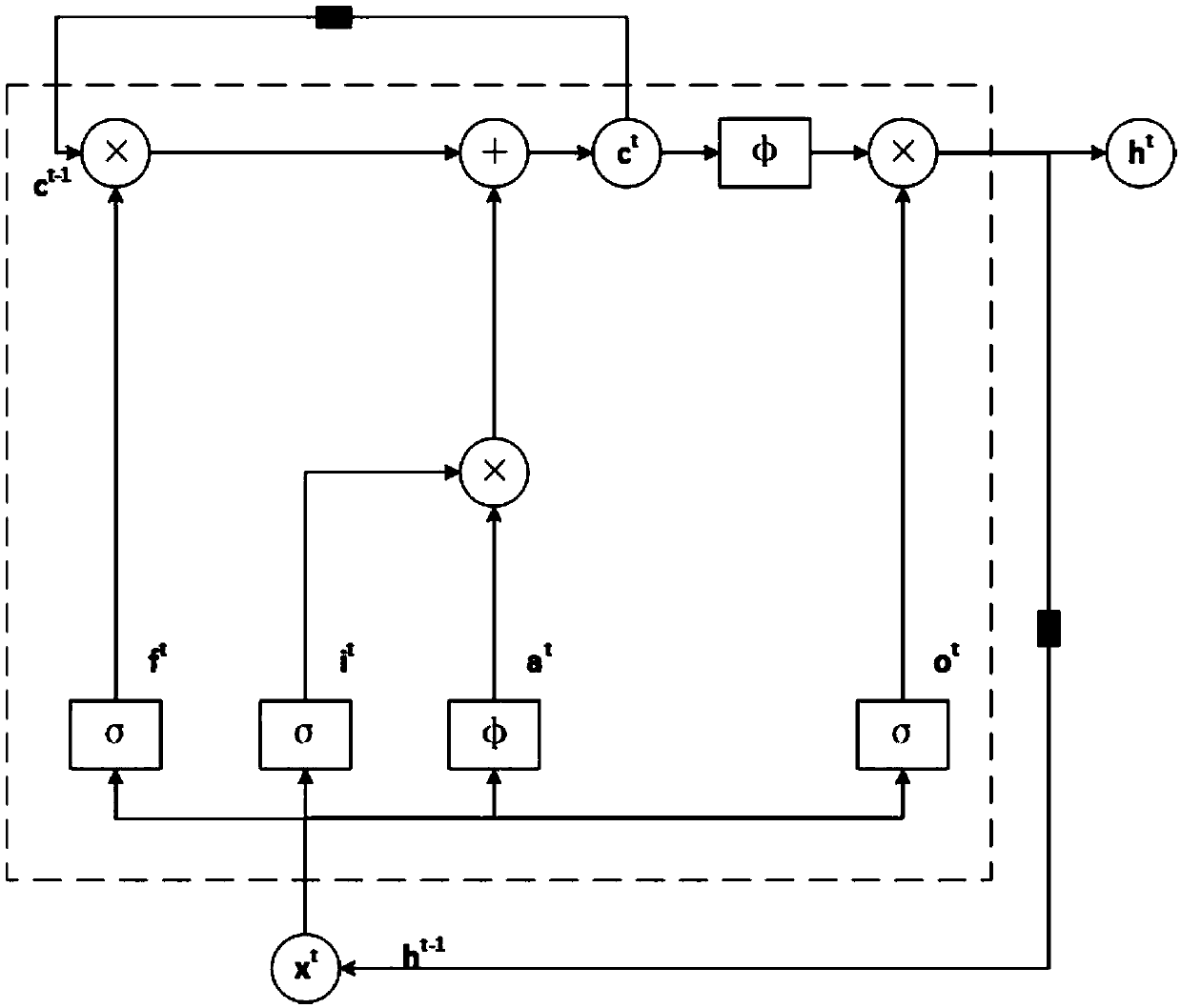
A wireless local area network intrusion detection method and system based on deep learning
ActiveCN109698836AIncrease processing granularityPrivacy protectionData switching networksConfidentialityUsability
The invention discloses a wireless local area network intrusion detection system based on deep learning, and relates to the field of network space security. The system comprises model learning and intrusion detection, the model learning is responsible for pre-constructing an RNN neural network, and intrusion detection uses the constructed RNN neural network to complete an intrusion detection taskin real time. An LSTM recurrent neural network is adopted to carry out classification prediction on data traffic of a wireless local area network with a time sequence characteristic; the type of the target network traffic sequence is judged according to the output predicted by the identification module; The intrusion behavior in the target network is identified, different granularity processing isperformed according to the set priorities and processing methods, early warning and prevention are performed on possible information security problems, the confidentiality, the usability and the integrity of the wireless local area network are guaranteed, and the security level of the wireless local area network is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
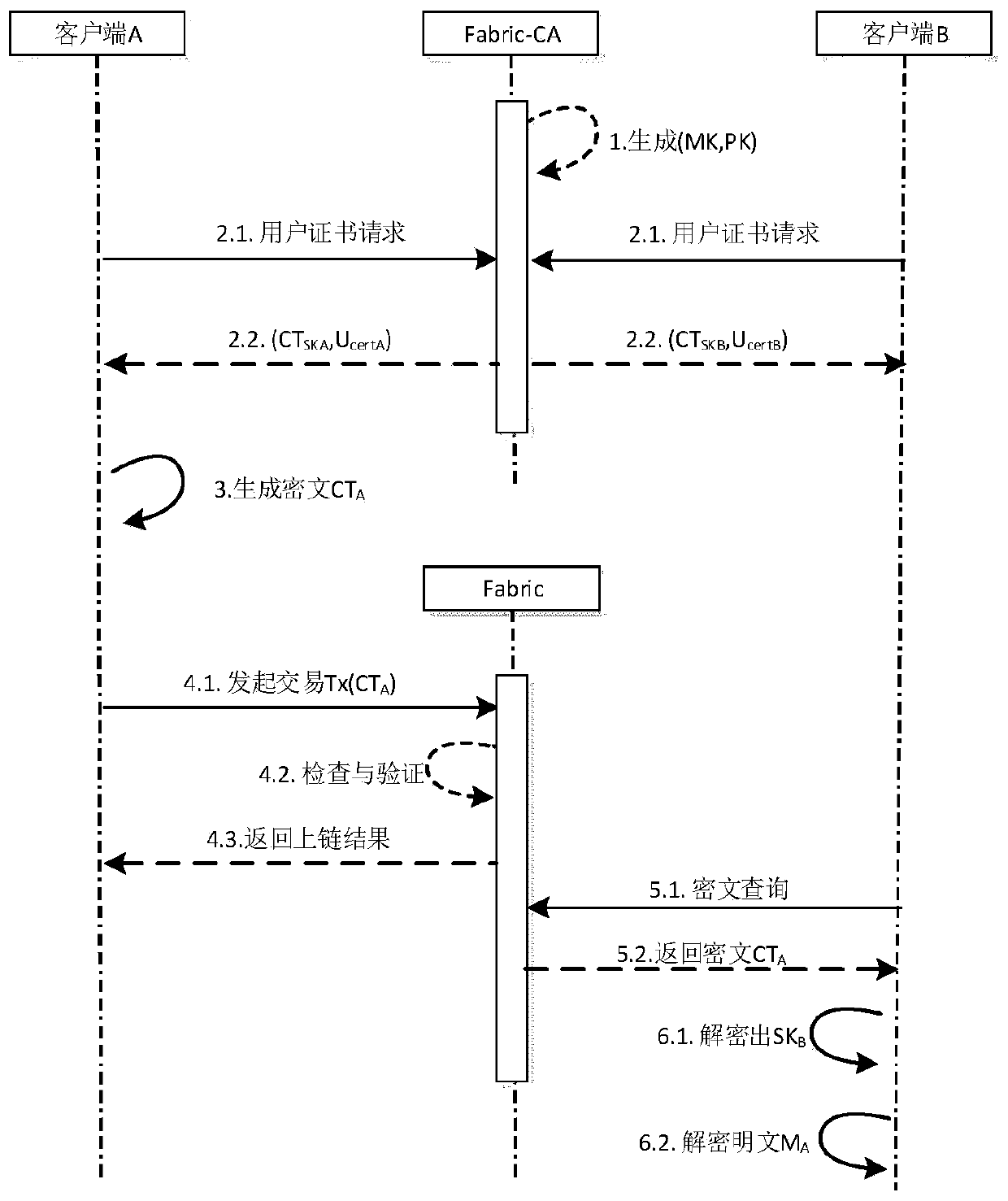
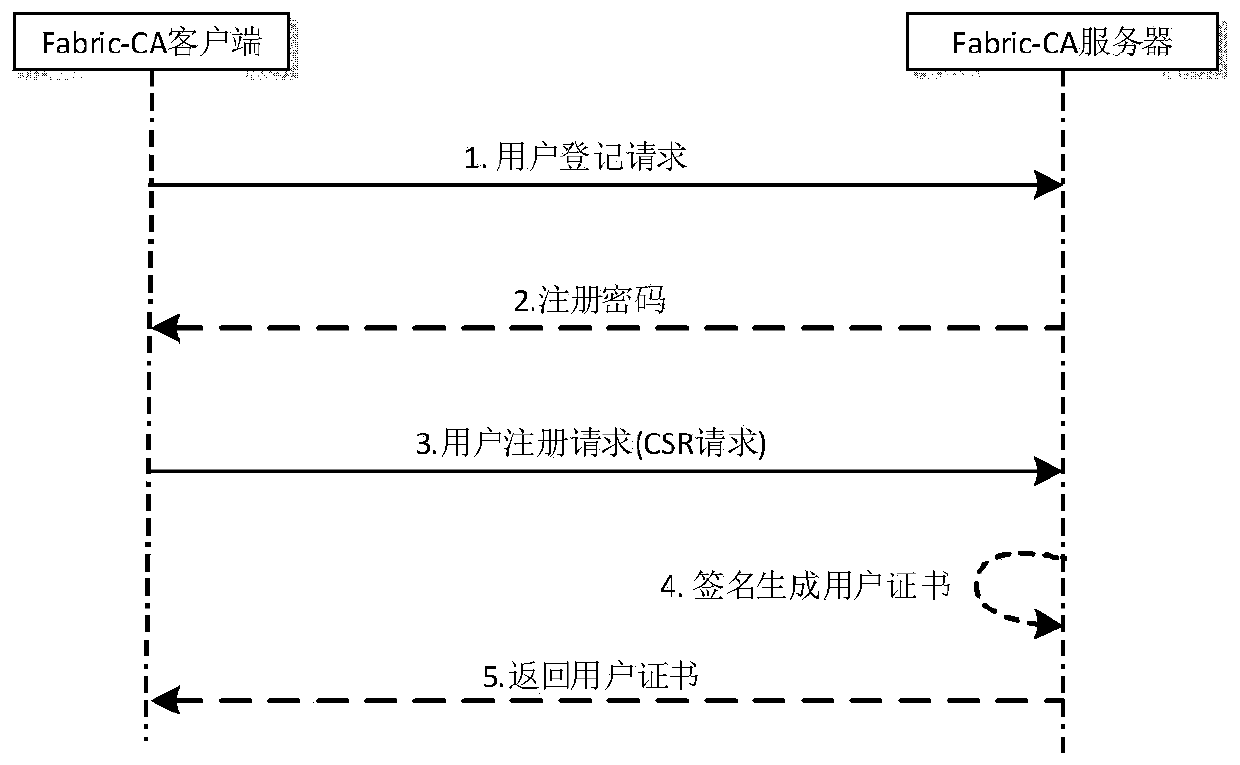
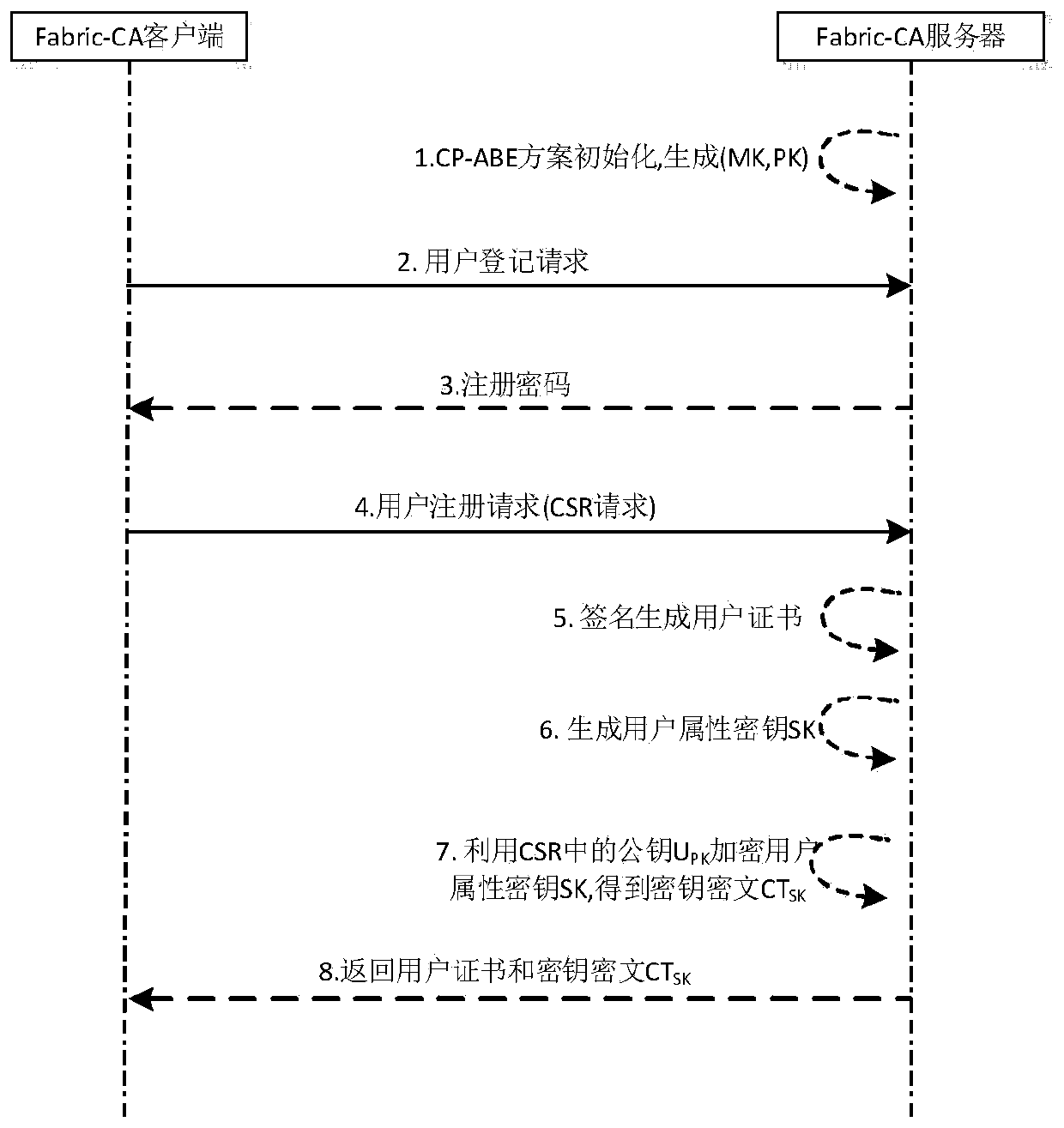
Alliance block chain data access control method based on CP-ABE algorithm
ActiveCN111371561AAddress privacy breachesRealize fine-grained encryption access control functionKey distribution for secure communicationPublic key for secure communicationAlgorithmCiphertext
The invention discloses an alliance blockchain data access control method based on a CP-ABE algorithm, which comprises the following steps: (1) a key generation stage: generating a master key MK and apublic parameter PK in a CP-ABE scheme in the stage, generating a user certificate and an attribute key ciphertext according to a user certificate request, and returning the user certificate and theattribute key ciphertext to a client; (2) a data encryption and chaining stage: in the stage, encrypting private data into a ciphertext by using a CP-ABE scheme, and performing chaining operation on the ciphertext; and (3) an access control stage: after the ciphertext transaction information is requested, the client firstly decrypts the attribute key ciphertext to obtain the attribute key, and further decrypts the ciphertext according to the attribute key to obtain plaintext private data. On the premise of ensuring safe distribution of the user attribute key, the method can be used for effectively realizing privacy protection and encryption access control functions of the uplink data of the super account book block chain.
Owner:HUAXIN CONSULTATING CO LTD
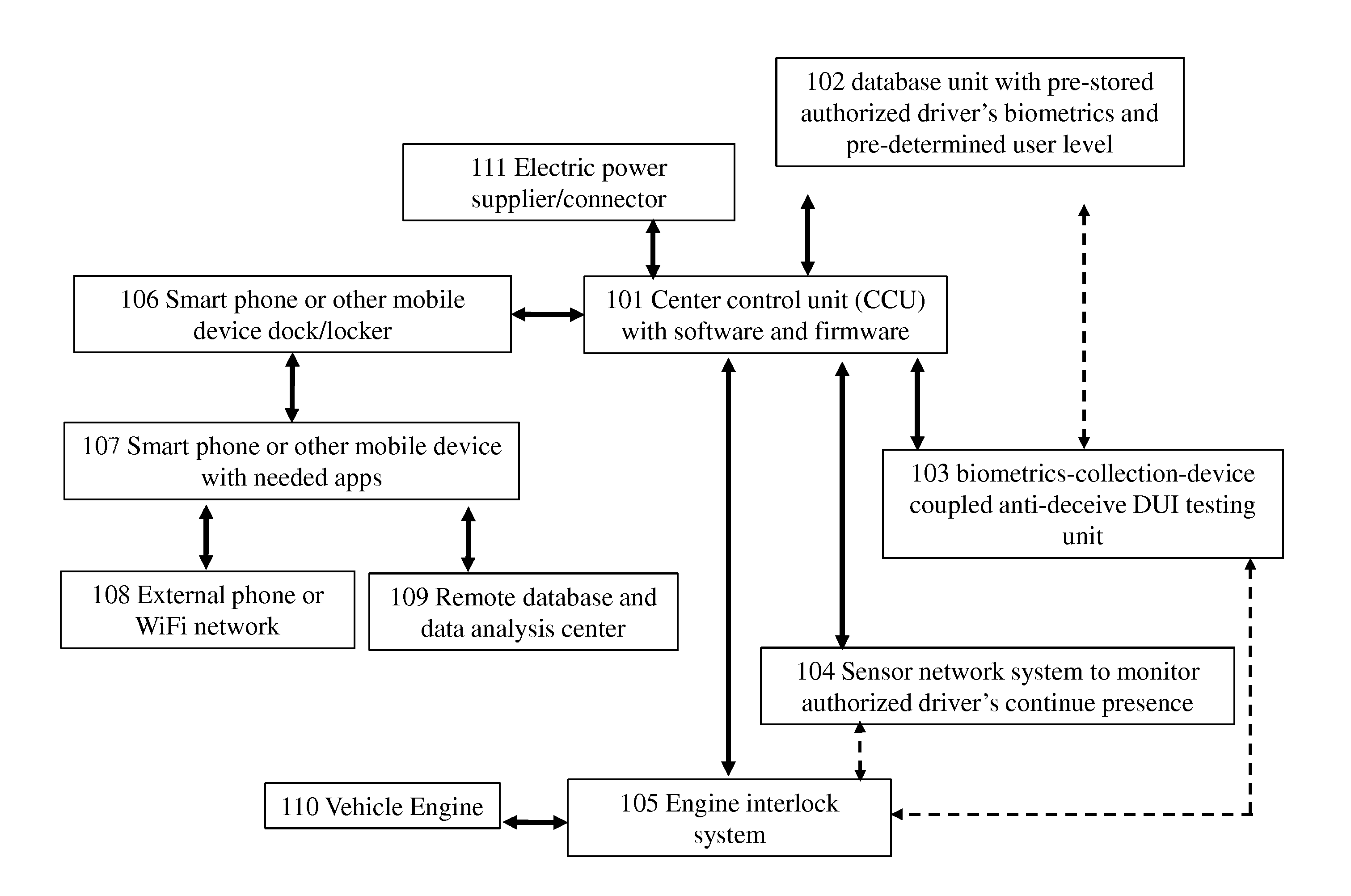
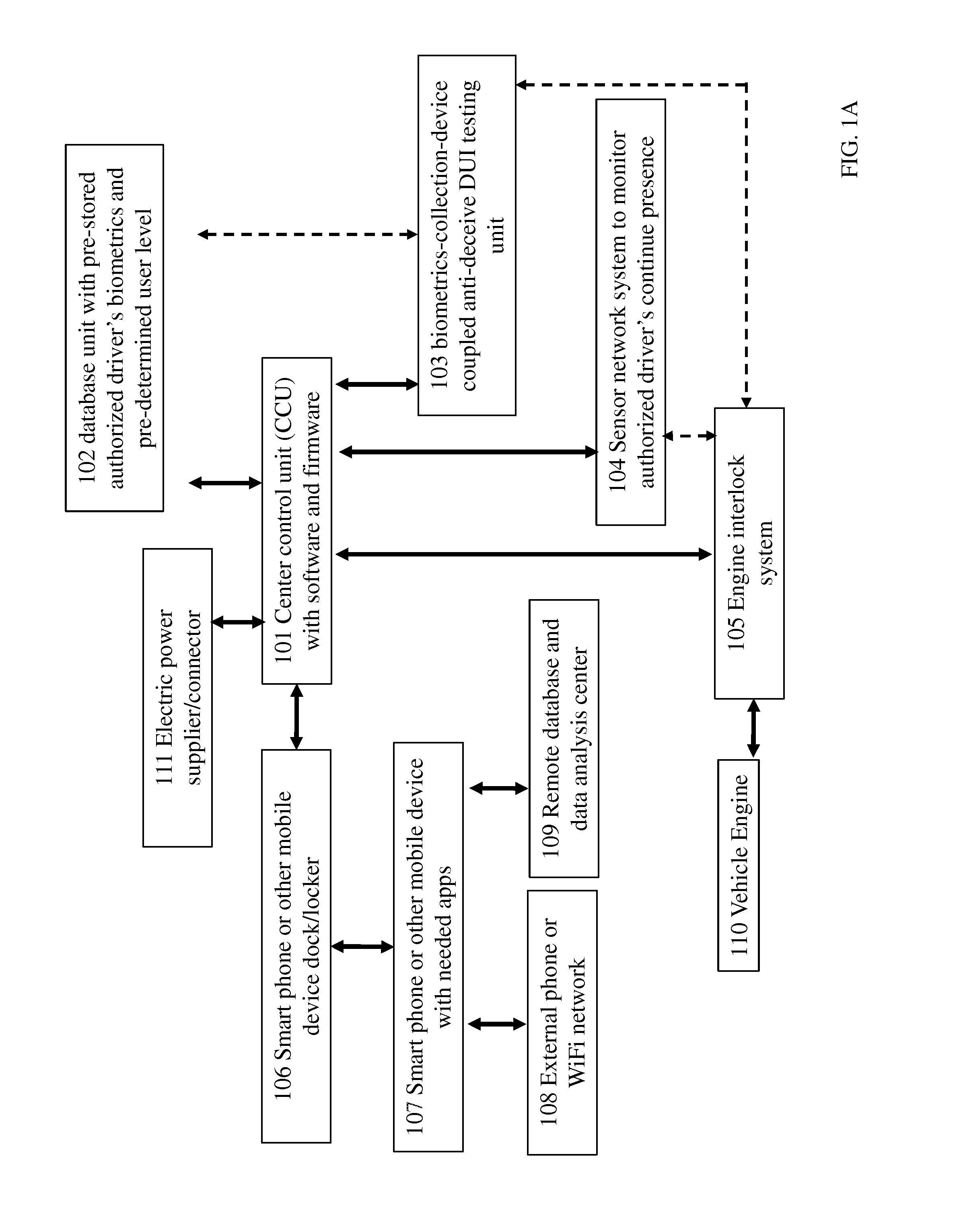
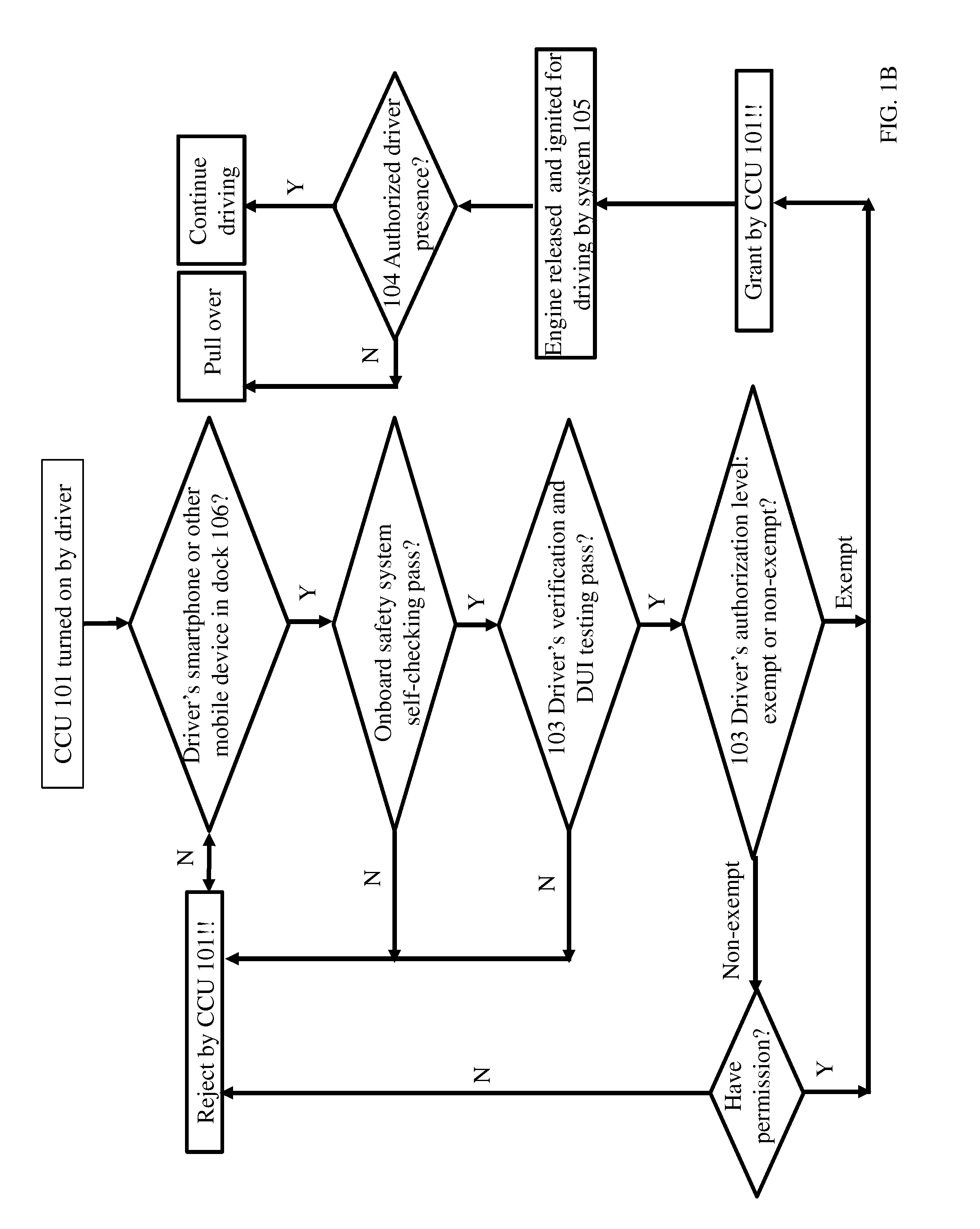
Vehicle Onboard Safety System
ActiveUS20150360696A1Improve privacy protectionPerson identificationSensorsDistractionDriver/operator
Vehicle onboard safety systems against deception during driving-under-influence (DUI) test, using cheiloscopy sensor or bite mark sensor as biometrics have been invented. The systems have an engine interlock system, which controls the engine ignition based on the onboard DUI testing result. The systems also have a smart phone locker designed to take the smart phone away from the driver in order to avoid any driving distraction, while allowing connection to external network and resource through tethering.
Owner:GE YI +1
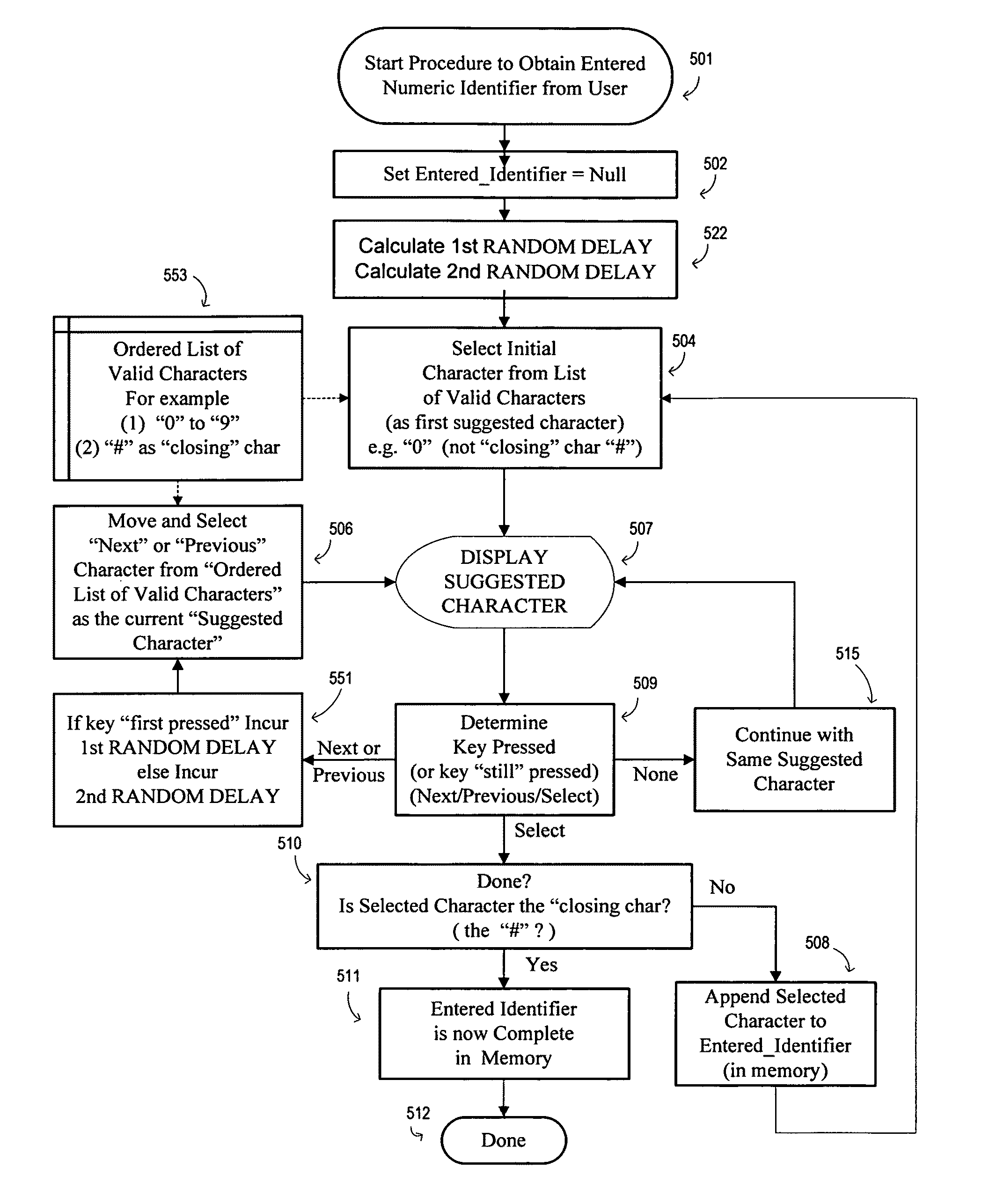
Entering an identifier with security improved by time based randomization of input steps based upon time
ActiveUS20100153735A1Improve securityImprove privacy protectionMemory loss protectionError detection/correctionInternet privacyUser input
A secure method, apparatus or computer program incorporates a method for entering private information such as a user identifier, password or other secret code comprising at least one symbol or character. According to method in one illustrated embodiment, the user selects characters for input starting from presentation of an initial suggested character, moving under user control to presentation of a user's desired input character, and then followed by the selection by the user of that presented character as a character for data input. The method includes randomizing the timing of the display and / or reaction time to user input so that the number and timing of the key presses required to select any specific desired character for input is made unpredictable. This makes it difficult during entry of information to determine by covert means what specific information is being entered.
Owner:BULL HN INFORMATION SYST INC
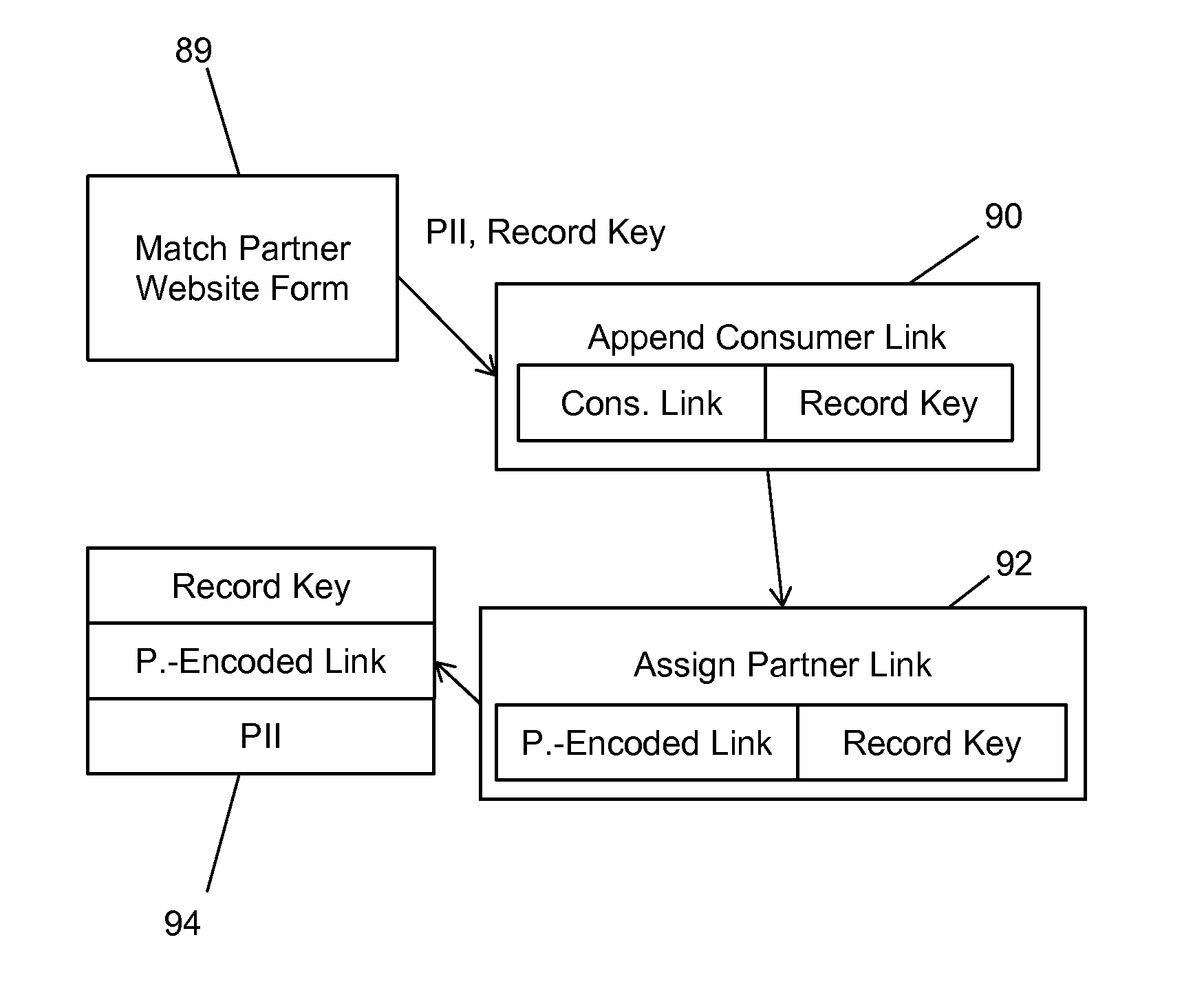
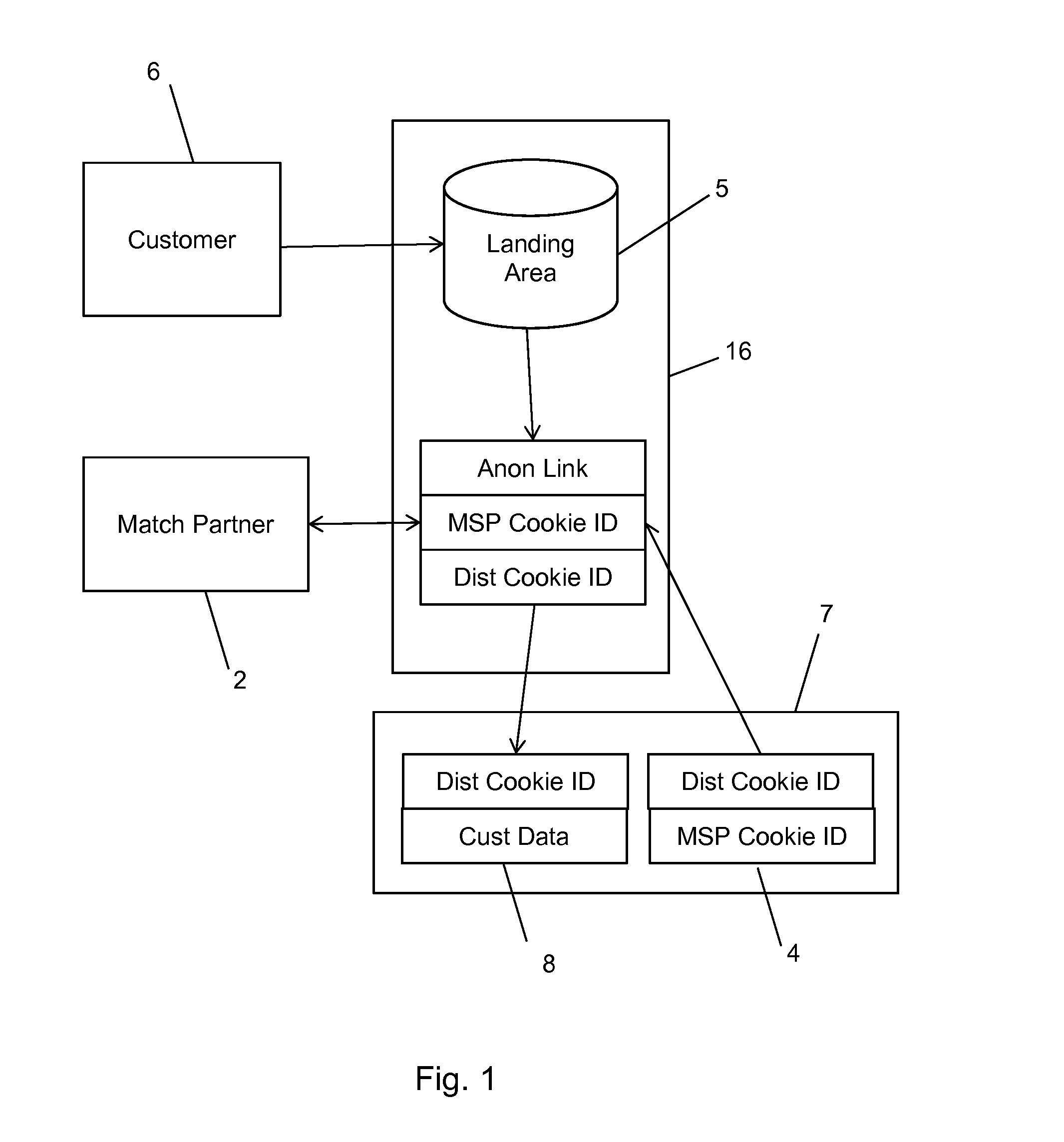
Apparatus and Method for Bringing Offline Data Online While Protecting Consumer Privacy
ActiveUS20150081565A1Precise positioningIncreased marketingAdvertisementsComputer security arrangementsInternet privacyOnline and offline
A method and system for bringing together online and offline advertising uses anonymous links that are associated with consumer data. The anonymous links allow processing without personally identifiable information (PII) in a secure environment. Data is matched using the anonymous links, and further using identifiers that are encrypted for use in connection with individual match distribution partners. The method and system allows a marketer to utilize offline data to precisely target advertisements without the use of PII, and to perform analytics concerning the use of the online advertisements to more precisely determine the effectiveness of multichannel marketing efforts.
Owner:LIVERAMP
Mobile node, an ad hoc network routing controlling method and an ad hoc network system
ActiveUS20050195814A1Avoid riskReduce riskKey distribution for secure communicationNetwork topologiesSelf-organizing networkAd hoc network routing
A mobile node (400) capable of establishing an ad hoc network routing is disclosed. The mobile node comprises a transmitting / receiving unit (426) for communicating with other communication unit and a routing request generator (422) for generating a routing request message for requiring an ad hoc network routing. The mobile node further comprises: an address storage (427) for storing an address of the mobile node (400) and an address of a receiving node; a random number generator (430) for generating a random number; a certificate issuing unit (440) for issuing a certificate of the mobile node (400); a digital signature creator (450) for creating a digital signature of the mobile node (400); and a controller (424) for transmitting / receiving the routing request message accompanied by the address of the mobile node, the address of the receiving node, the random number, the certificate and the digital signature via the transmitting / receiving unit, according to an ad hoc network protocol.
Owner:GOOGLE LLC
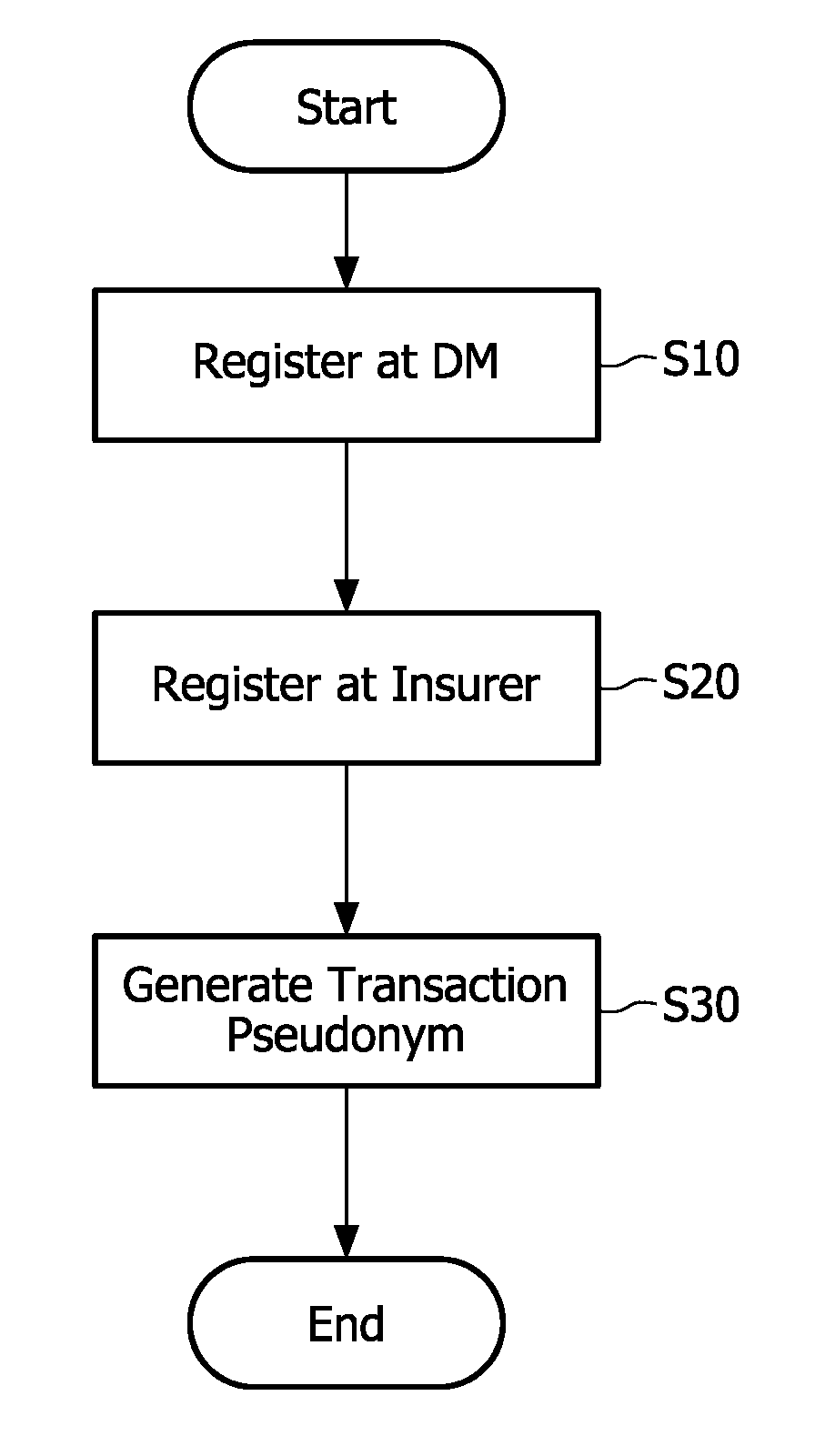
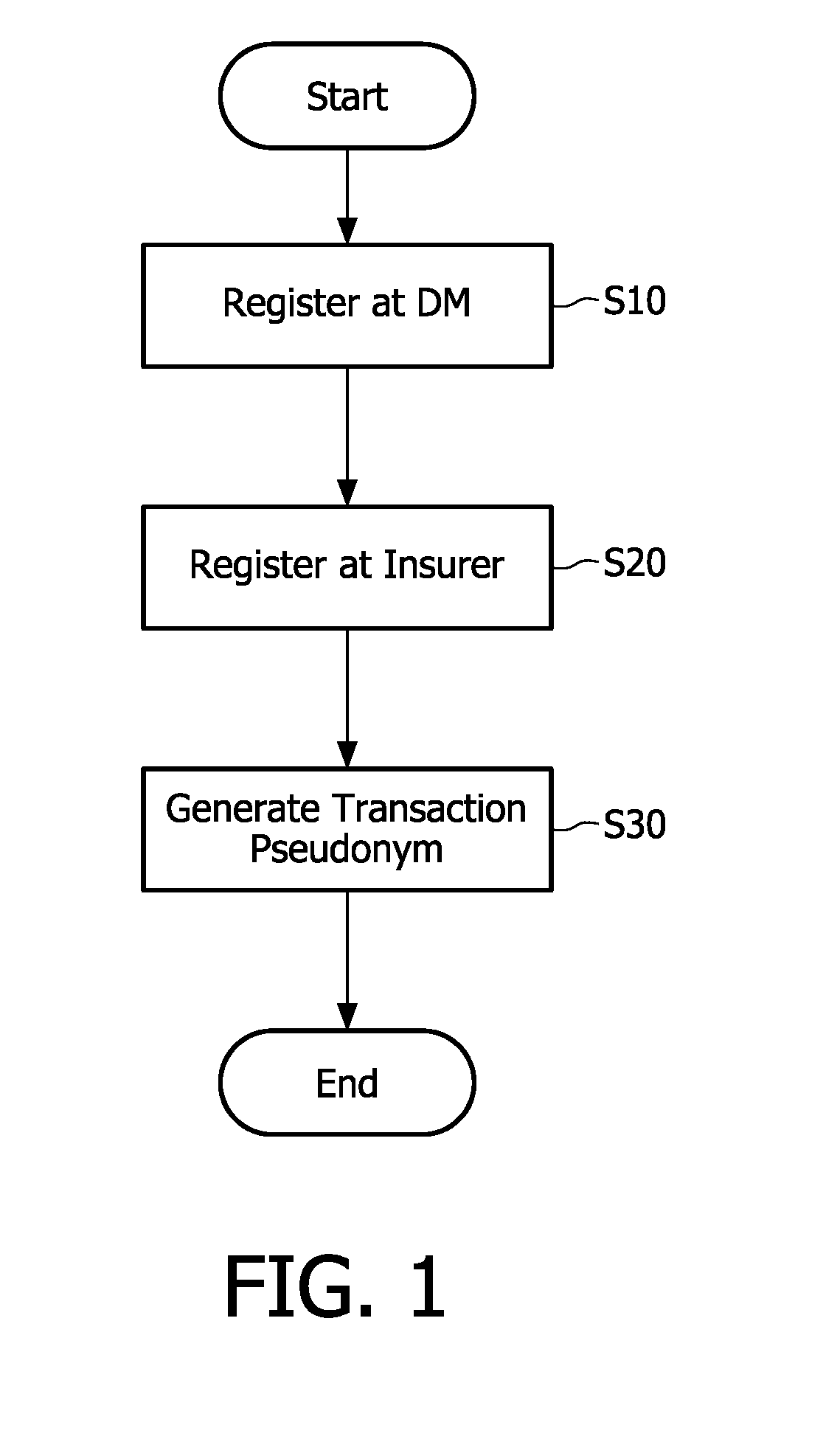
Secure authentication of lectronic prescriptions
InactiveUS20100169218A1Improve privacy protectionPrivacy protectionData processing applicationsDrug and medicationsSecure authenticationPseudonymity
The invention relates to a system for authenticating electronic prescriptions, the system comprising an acquisition unit for acquiring an electronic prescription for authentication, the electronic prescription comprising a transaction number, a first pseudonym, and a signature of a first participant using a transaction pseudonym, the first pseudonym indicating the first participant's registration at a first privacy officer; a generation unit for generating the transaction pseudonym based on the first pseudonym, the transaction number and a registration key corresponding to the first pseudonym and being shared between the first participant and a second privacy officer; and a validation unit for verifying the first participant's registration at the second privacy officer and the authenticity of the signature based on the registration key and the transaction pseudonym. As the transaction pseudonym depends on registrations at two privacy officers and a transaction number for a real-time prescription, the participant's privacy can be well protected from each privacy officer.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
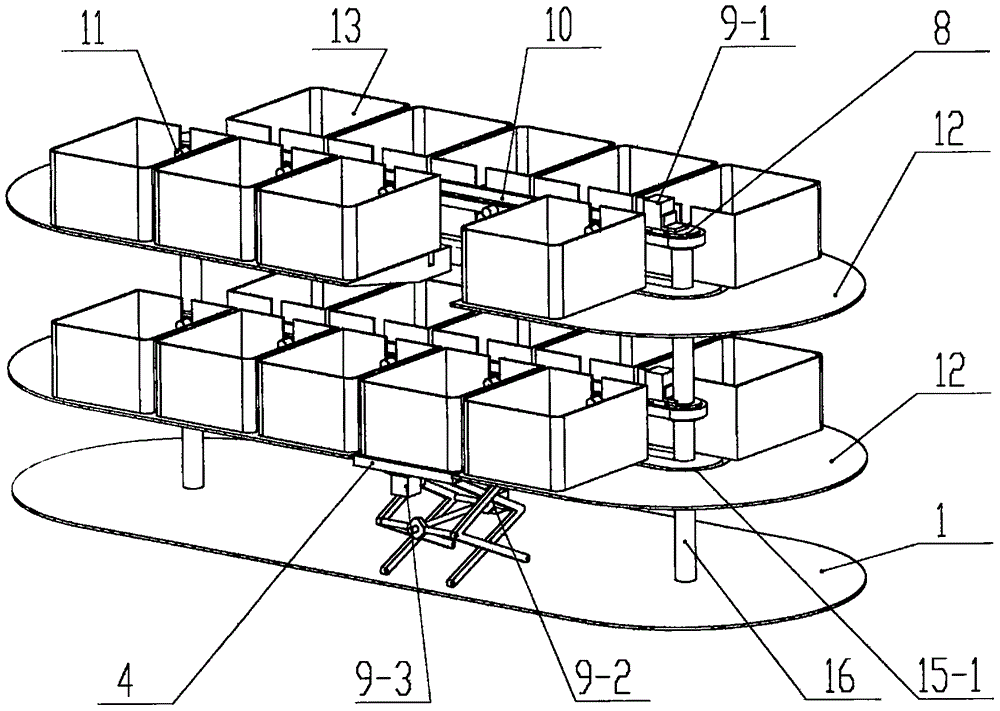
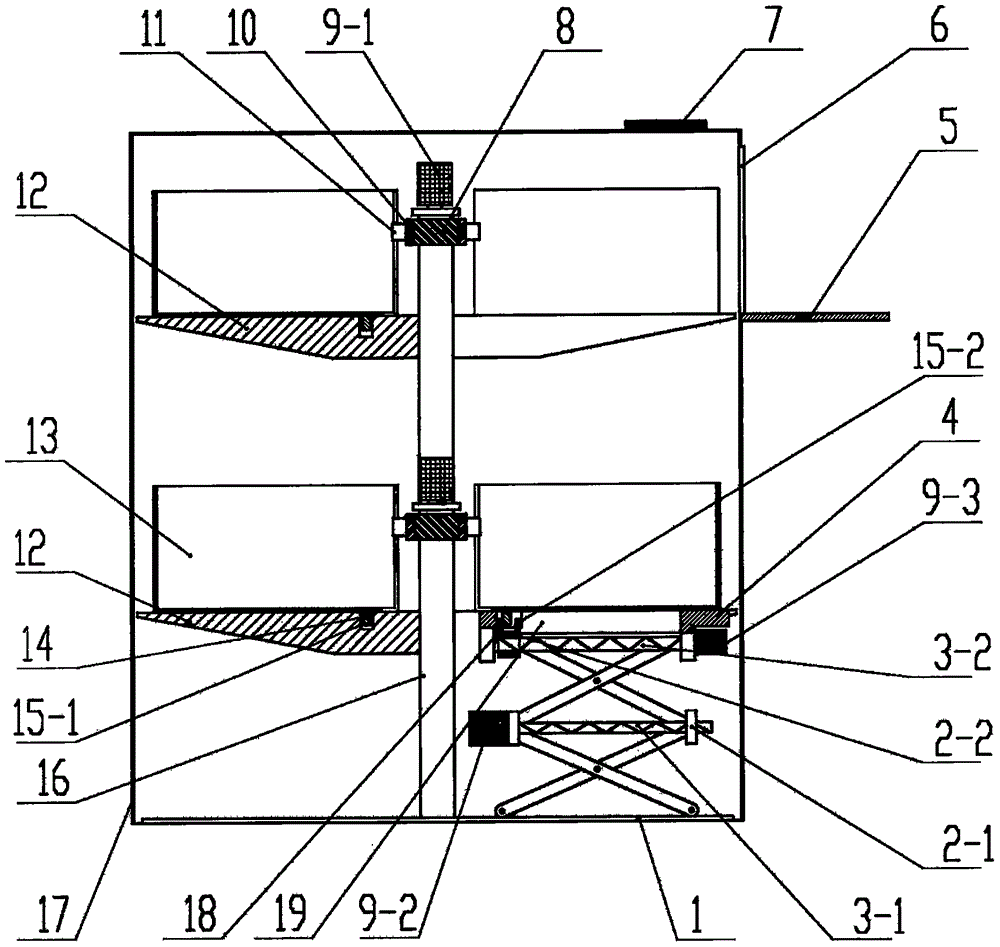
Intelligent storage cabinet
The invention discloses an intelligent storage cabinet, which comprises a cabinet body, wherein a man-machine interaction control unit and an access opening are formed in the cabinet body; a carrying and collecting plate is arranged on the access opening; a base, a support post, a plurality of horizontal support platforms, a plurality of storage boxes, a driving device, a support plate, an ascending and descending device, a push-pull device and a power distribution box are arranged in the cabinet body; an annular guide groove and a plurality of storage boxes are arranged on each horizontal support platform; the support plate is arranged on the ascending and descending device; an auxiliary guide groove is formed in the support plate; the push-pull device is arranged at the bottom of the support plate; the driving device is arranged on each horizontal support platform, and is used for driving the plurality of storage boxes to slide along the annular guide groove and the auxiliary guide groove; the man-machine interaction control unit, the driving device, the ascending and descending device and the push-pull device are electrically connected with the power distribution box; the driving device, the ascending and descending device and the push-pull device are connected with the man-machine interaction control unit. The intelligent storage cabinet has the advantages that the automatic finding can be realized; the storage boxes to be accessed can be automatically conveyed to the access opening position; the accessing is convenient and safe.
Owner:时长永
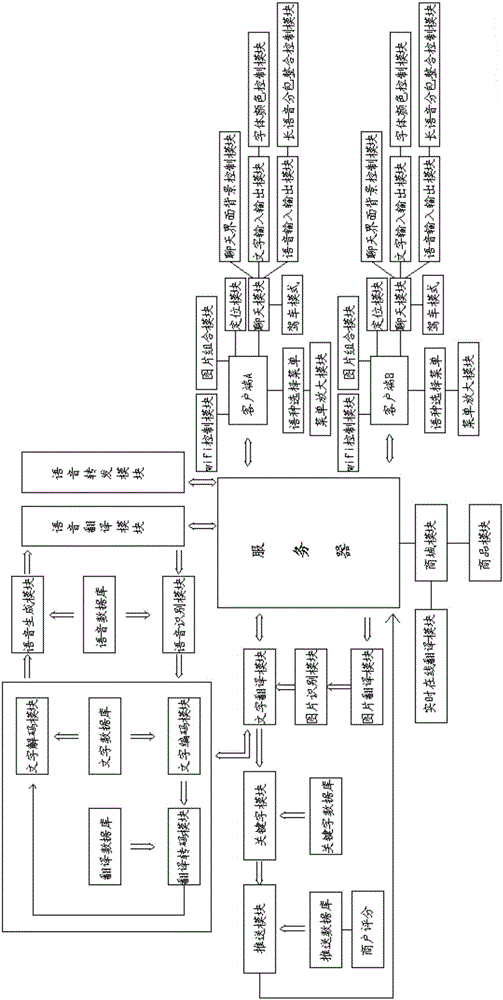
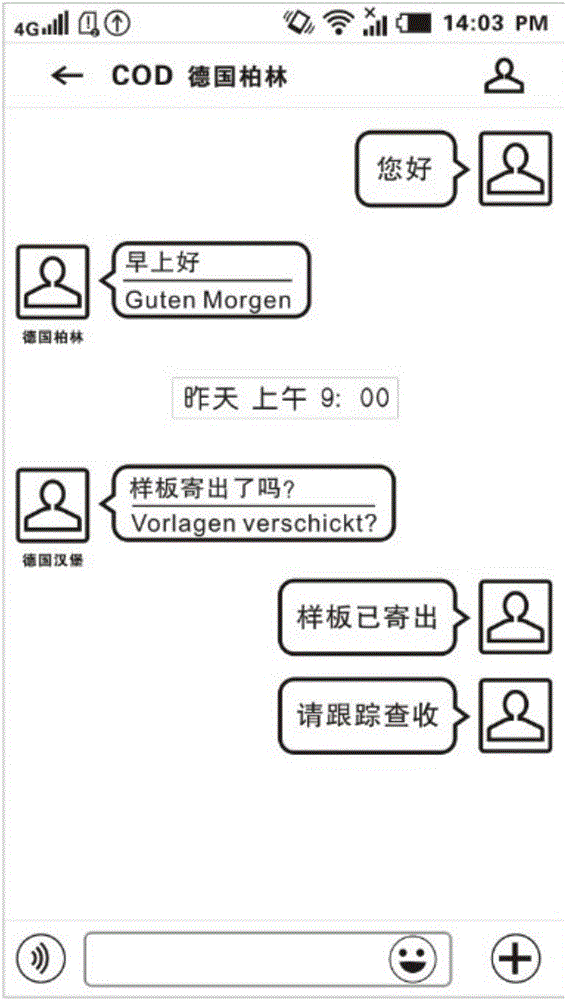
Online translation and chat system
InactiveCN106682967AIt is convenient to chat with each otherEasy accessNatural language translationBuying/selling/leasing transactionsUser needsClient-side
The invention discloses an online translation and chat system. The system comprises a client and a server, which are in communication connection. The system also comprises a translation module, a chat module, a shopping mall module, a voice conversion module and a keyword searching module. The system greatly facilitates the chat between users speaking in different languages through quickly and autonomously translating the chat contents of two sides, wherein the translation comprises the recognition and translation of text, voice and images. Moreover, the system is provided with the shopping mall module, thereby facilitating the real-time translation of goods information, and bringing convenience to the people speaking various languages for shopping. The system achieves a function of voice forwarding, and greatly facilitates the voice chat. For the text and voice information in the daily chat process, the keyword module is used for searching matched goods or merchant information for keywords, generates push information, displays the push information at a chat interface, greatly brings convenience to a user for obtaining the needed goods or merchant information, and provides push information which is practical and effective and is close to the demands of the user.
Owner:胡开标
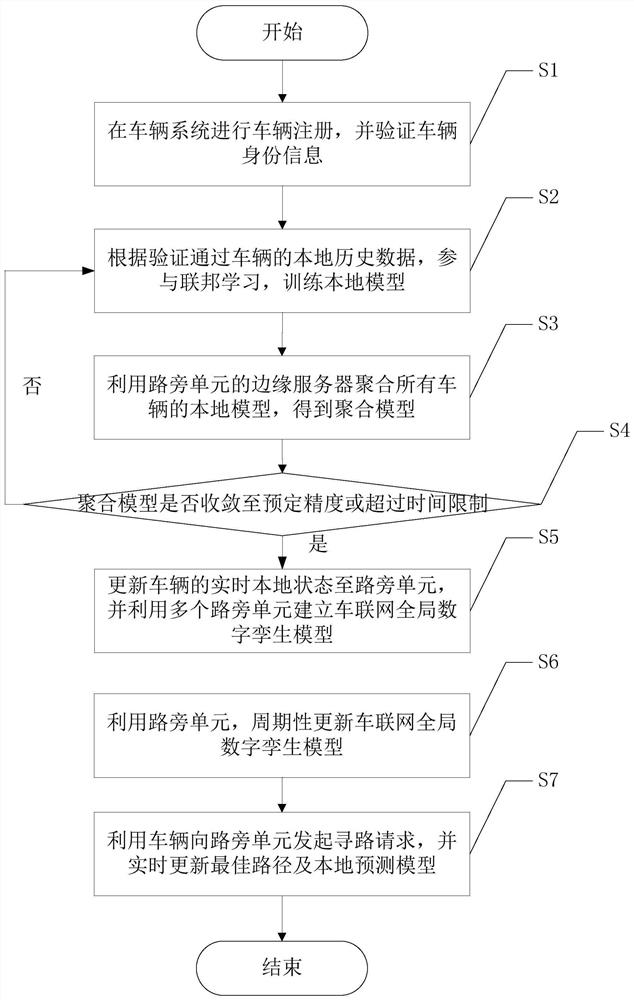
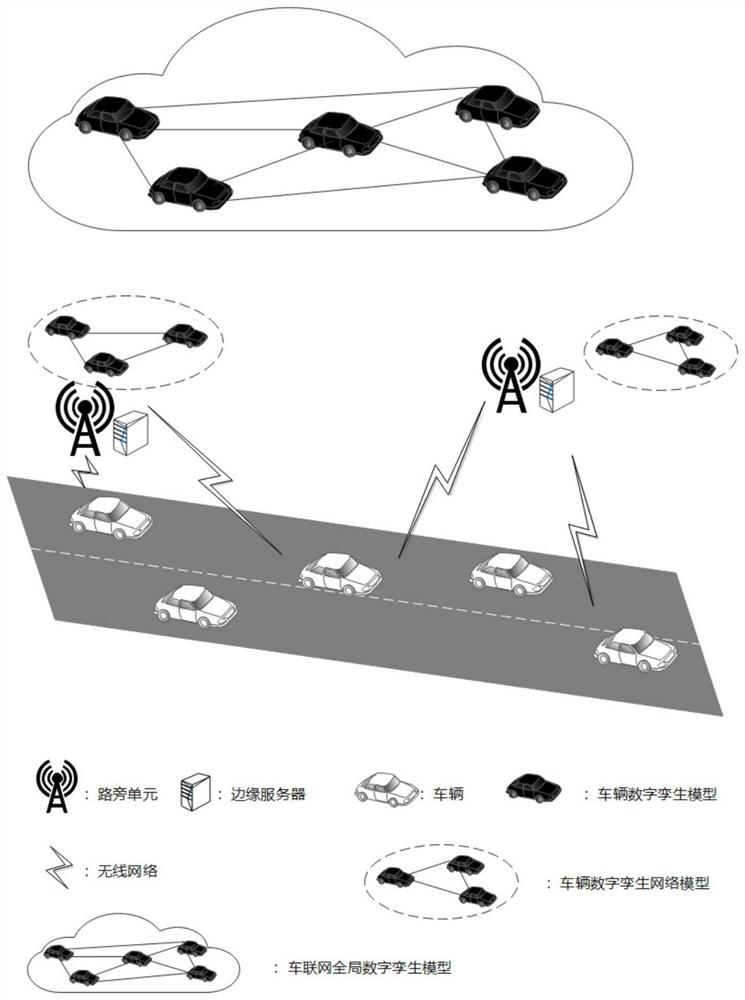
Intelligent traffic path planning method based on federated learning and digital twinning
ActiveCN112700639AReduce riskReduce latencyDetection of traffic movementParticular environment based servicesTraffic predictionSimulation
The invention discloses an intelligent traffic path planning method based on federated learning and digital twinning. The method comprises the following steps of: S1, carrying out vehicle registration in a vehicle system, and verifying the identity information of vehicles; S2, according to the local historical data of the vehicles, participating in federated learning, and training a local model; S3, aggregating the local models of all the vehicles to obtain an aggregation model; S4, judging whether the aggregation model converges to preset precision or exceeds a time limit or not, if yes, entering the step S5, and otherwise, returning to the step S2; S5, establishing an Internet-of-vehicles global digital twinning model; S6, periodically updating the Internet-of-vehicles global digital twinning model; and S7, initiating a path finding request to a roadside unit, and updating the optimal path and the local prediction model in real time. The planning method provided by the invention is applied to the field of Internet of vehicles, so as to solve the problems of low flow prediction and path planning accuracy, high time delay and privacy leakage risk in the current road traffic system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
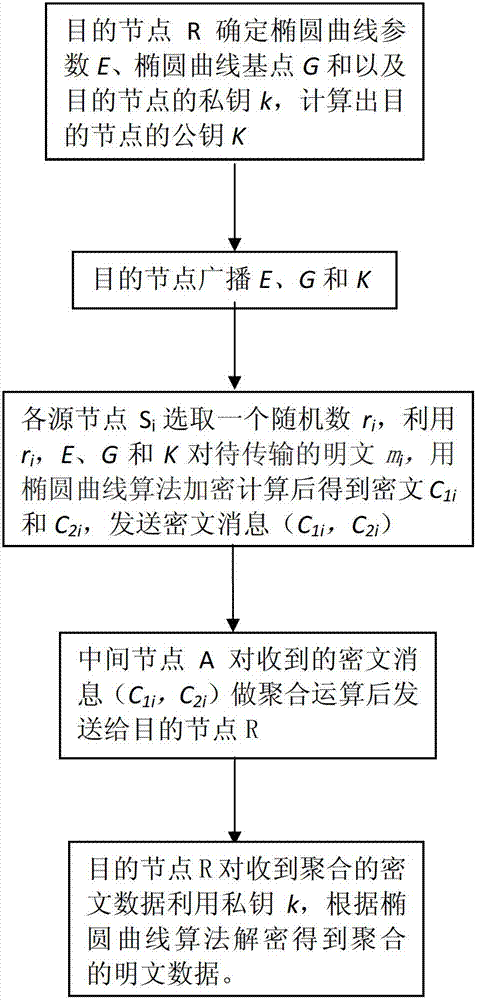
Privacy protection method during data aggregation of wireless sensor network
InactiveCN102833740ASmall number of public key digitsCalculation speedSecurity arrangementPlaintextWireless mesh network
The invention discloses a privacy protection method during data aggregation of a wireless sensor network. Privacy protection in a data addition aggregation process and a multiplication aggregation process is realized on the basis of an elliptical curve algorithm. The privacy protection method comprises the following steps of: determining, by a target node, an elliptical curve parameter and a private key k, calculating a public key K and broadcasting the elliptical curve parameter and the public key K; encrypting, by each source node, a plain text by an elliptical curve algorithm by using a random number, the elliptical curve parameter and the public key K and transmitting a cipher text message; performing, by a middle node, aggregation operation on the received cipher text message and transmitting an aggregation result to the target node; and decrypting, by the target node, the received aggregated cipher text data by using the private key k according to the elliptical curve algorithm to obtain aggregated plain text data. Compared with the prior art, an elliptical curve encryption technology adopted in the invention has the advantages of small public key digit, high calculation speed and the like, and two aggregation operation modes of addition aggregation and multiplication aggregation can be realized.
Owner:JIANGSU UNIV OF SCI & TECH +1
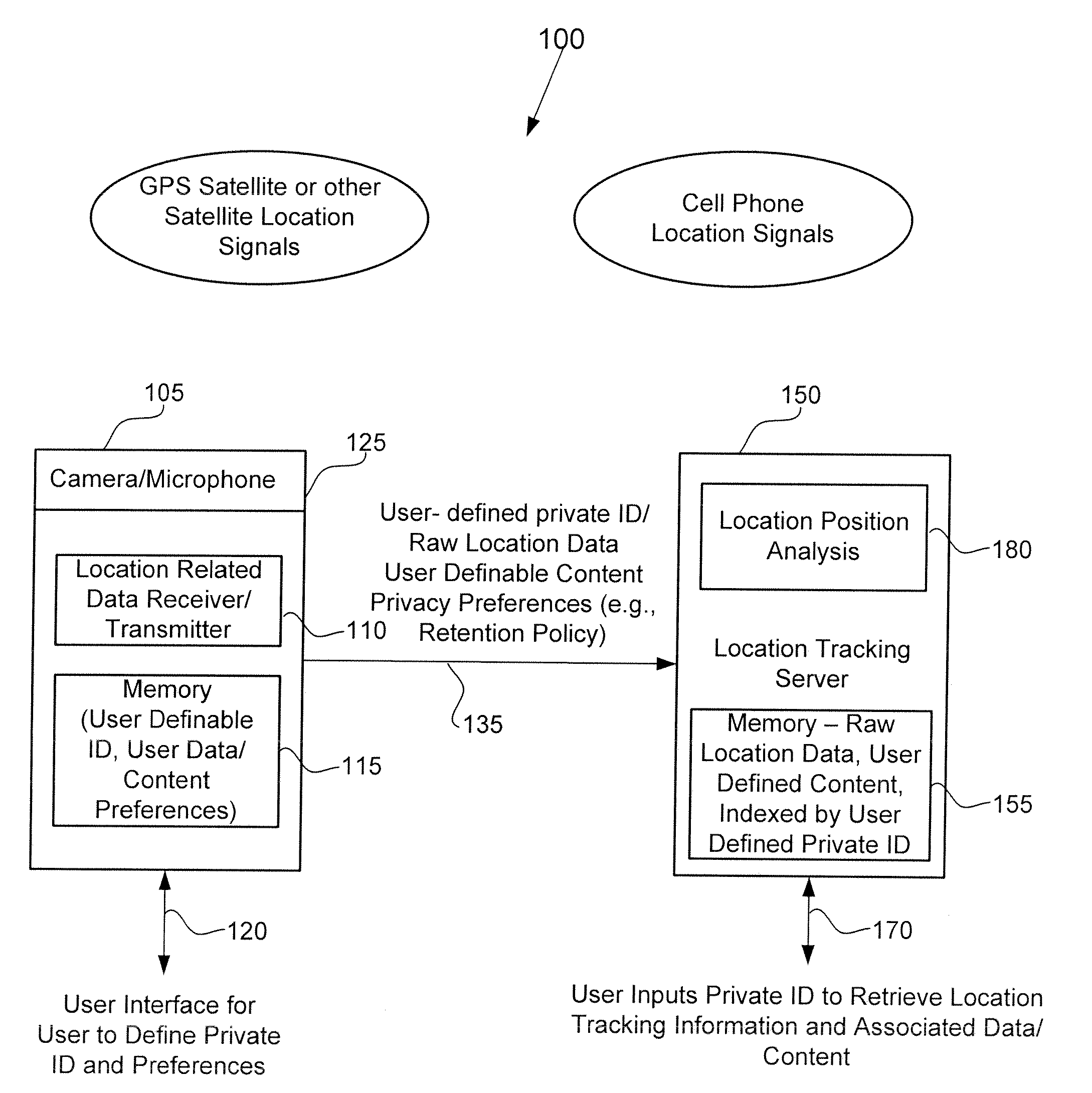
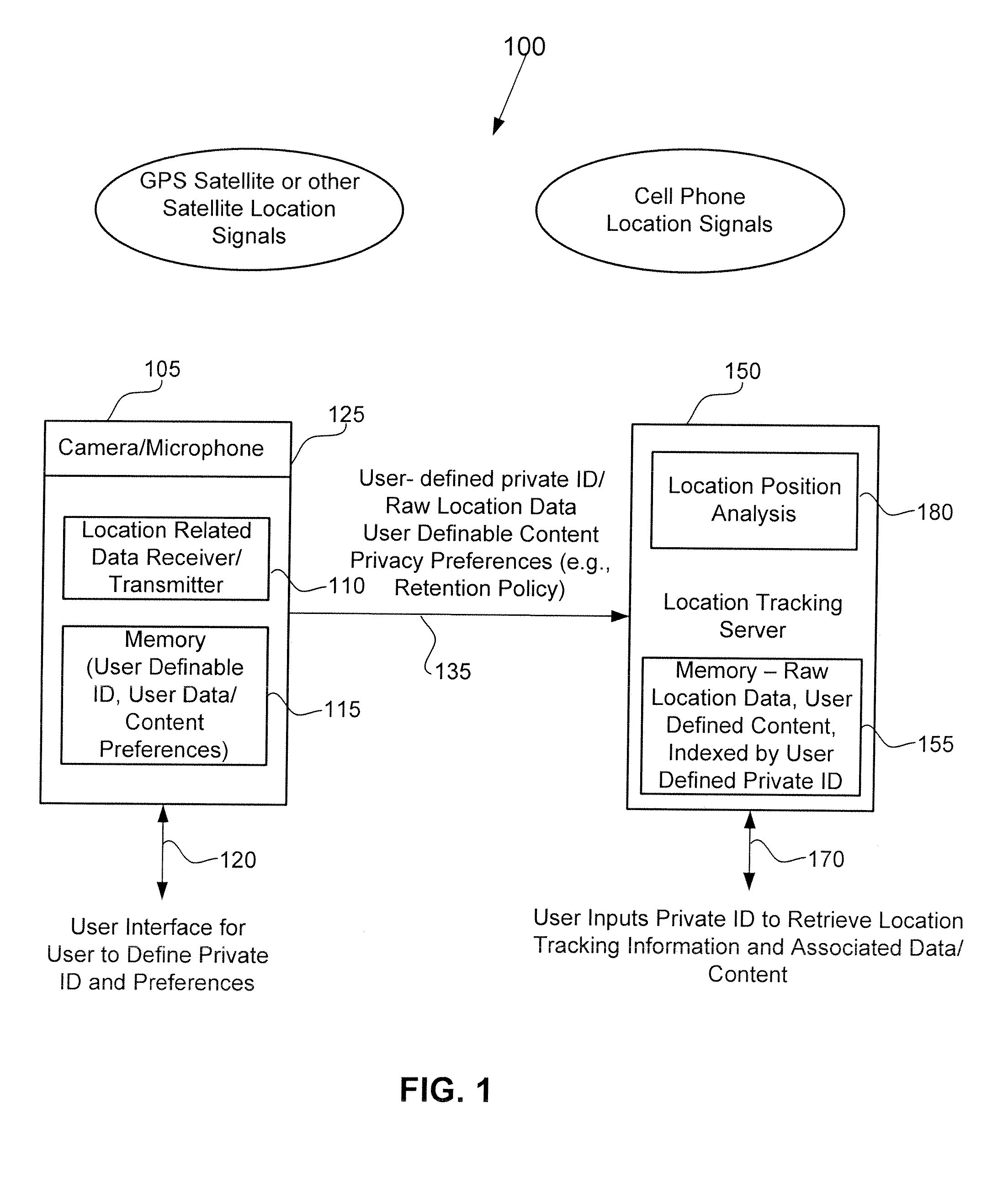
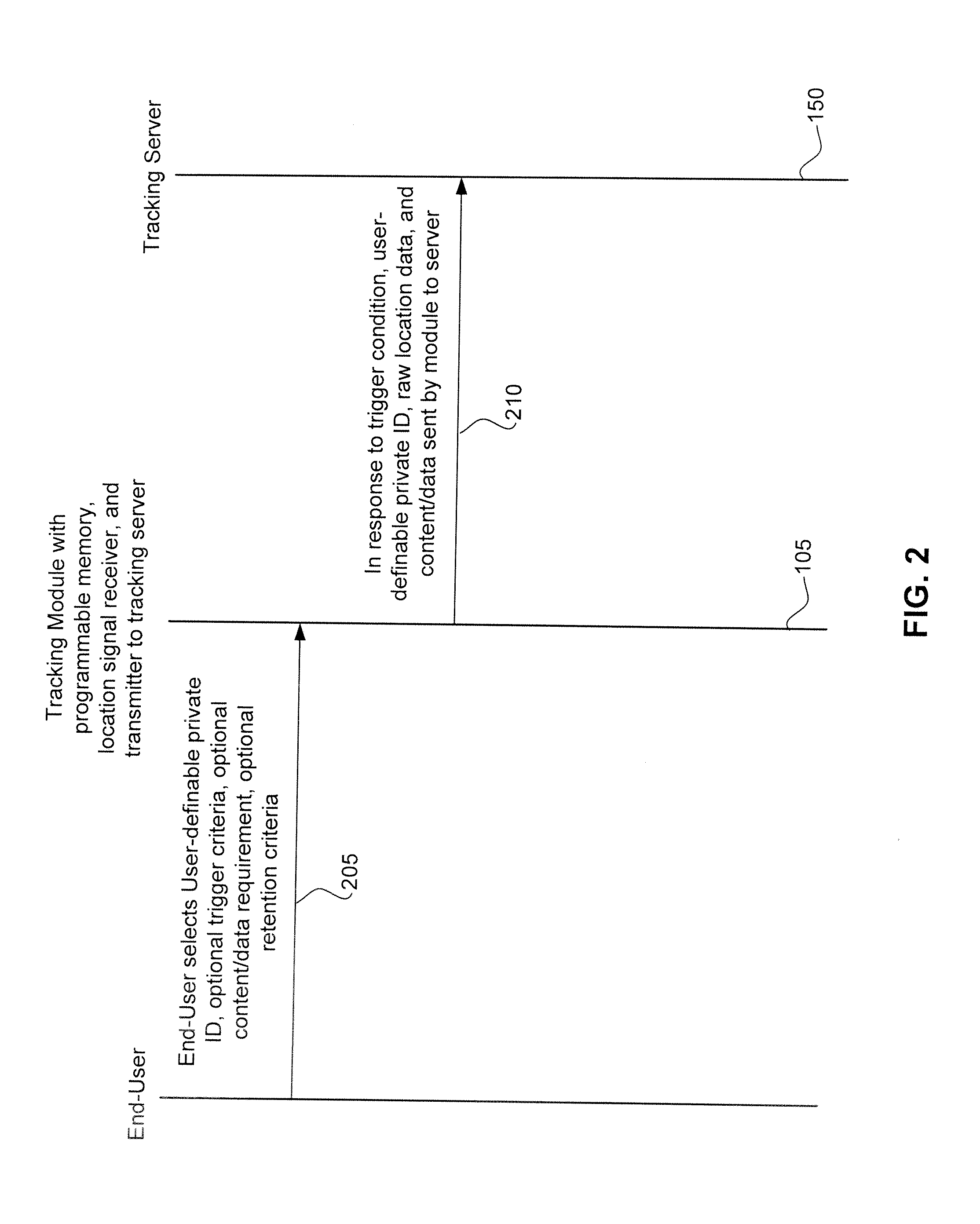
Tracking System With User-Definable Private ID For Improved Privacy Protection
ActiveUS20090224970A1Improve privacy protectionDirection finders using radio wavesPosition fixationLocation trackingPrivacy protection
A location tracking service includes a location tracking server and individual tracking modules. An individual tracking module can be attached or embedded in a consumer product. Each tracking module is programmable by an end-user to include a private ID that is sent along with tracking data to the location tracking server. The end-user can define and edit the private ID in the tracking module independent of the location tracking service to improve privacy protection. The tracking data may include raw (unprocessed) location data to reduce processing requirements at the tracking module.
Owner:OMNIVISION TECH INC
Identity information management method and system based on block chain technology
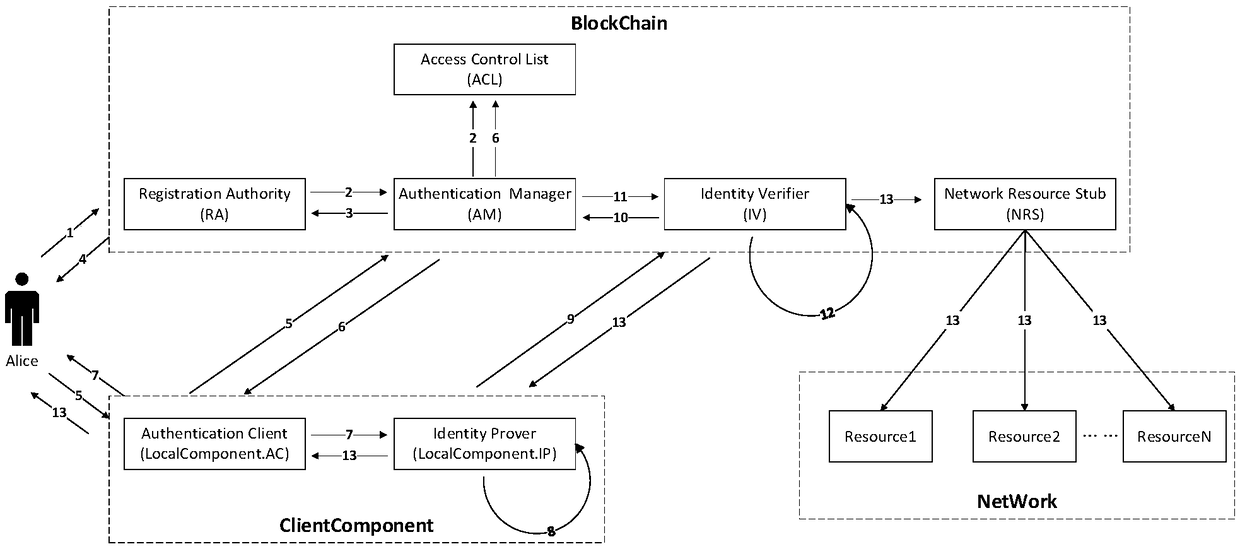
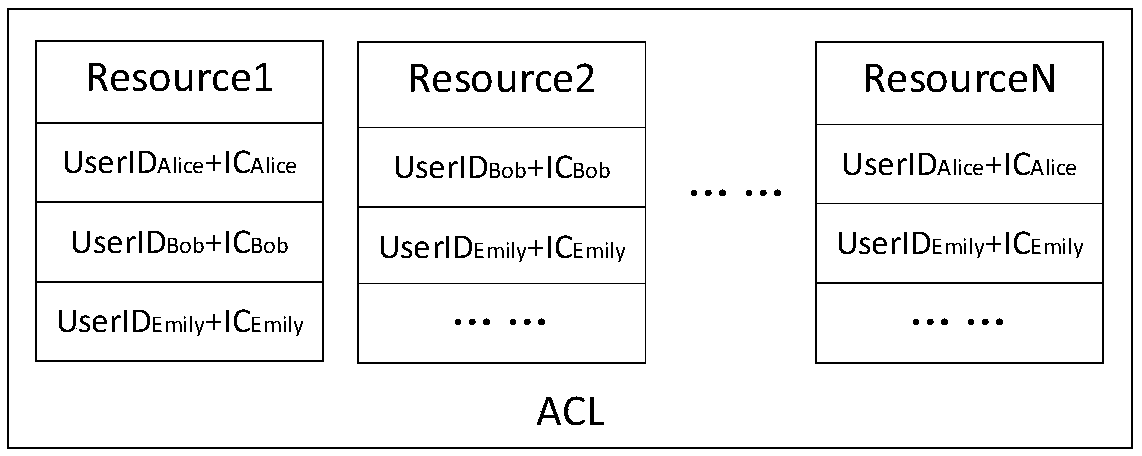
ActiveCN109347799AImprove privacy protectionStrong security protectionUser identity/authority verificationPrivacy protectionChain network
The invention discloses an identity information management method and system based on block chain technology. The method comprises the following steps: identifying user identity through a block chainnetwork so as to protect personal privacy information; and performing identity verification on a user according to the identified user identity through the block chain network and the user module. Theidentity information management method disclosed by the invention has the advantages that unified identity management infrastructure with strong privacy protection, strong security protection and strong audit accountability is constructed based on the block chain network, and the unified identity management infrastructure can provide identity identification, identity verification, authorization,audit accountability and like services.
Owner:宁波图灵奇点智能科技有限公司
Searchable encryption method based on wildcard character in cloud storage safety
ActiveCN107256248AFlexible AuthorizationFlexible revocationDigital data protectionSpecial data processing applicationsCiphertextCloud storage security
The invention relates to a searchable encryption method based on wildcard character in cloud storage safety. The method comprises the following steps that: setting a document to be uploaded; extracting a keyword set; encrypting the keyword set; selecting a random number as a document encryption key, and encrypting the document encryption key; encrypting the document to be uploaded to obtain a ciphertext, and sending the ciphertext to a cloud computing platform; input a query keyword set, generating a query trapdoor, carrying out signature, and sending the signature to the cloud computing platform; verifying a query signature by the cloud computing platform, and executing a search algorithm by the cloud computing platform; transmitting a keyword index and the query trapdoor into a keyword matching protocol to obtain an encryption matching result; carrying out decryption to obtain a search result; according to the search result, returning a corresponding ciphertext by the cloud computing platform; and recovering the document encryption key, and recovering the document. By use of the method, the keyword search of at most two wildcard characters can be supported, the wildcard character can appear on any position of the keyword, and a plurality of random characters can be represented.
Owner:FUZHOU UNIV
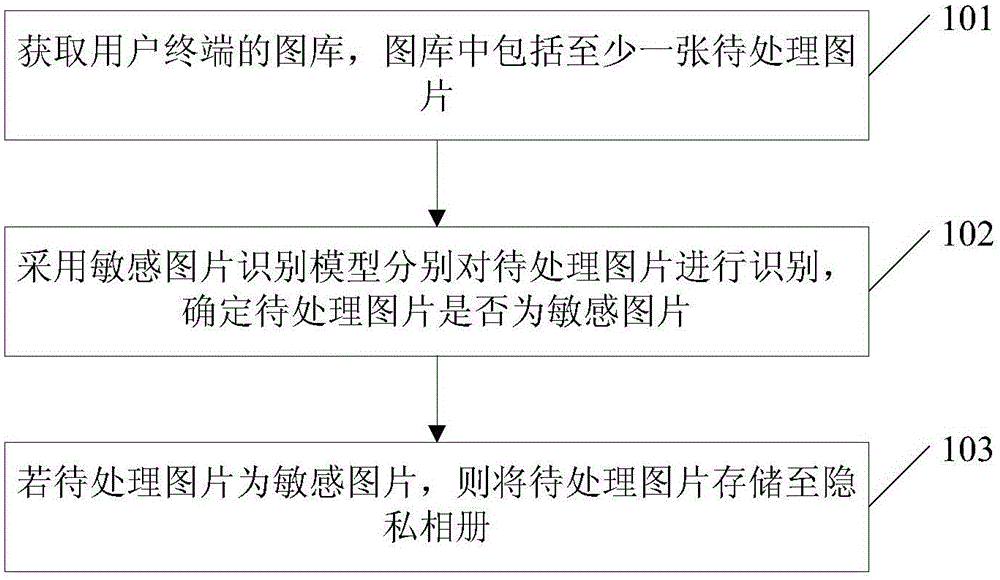
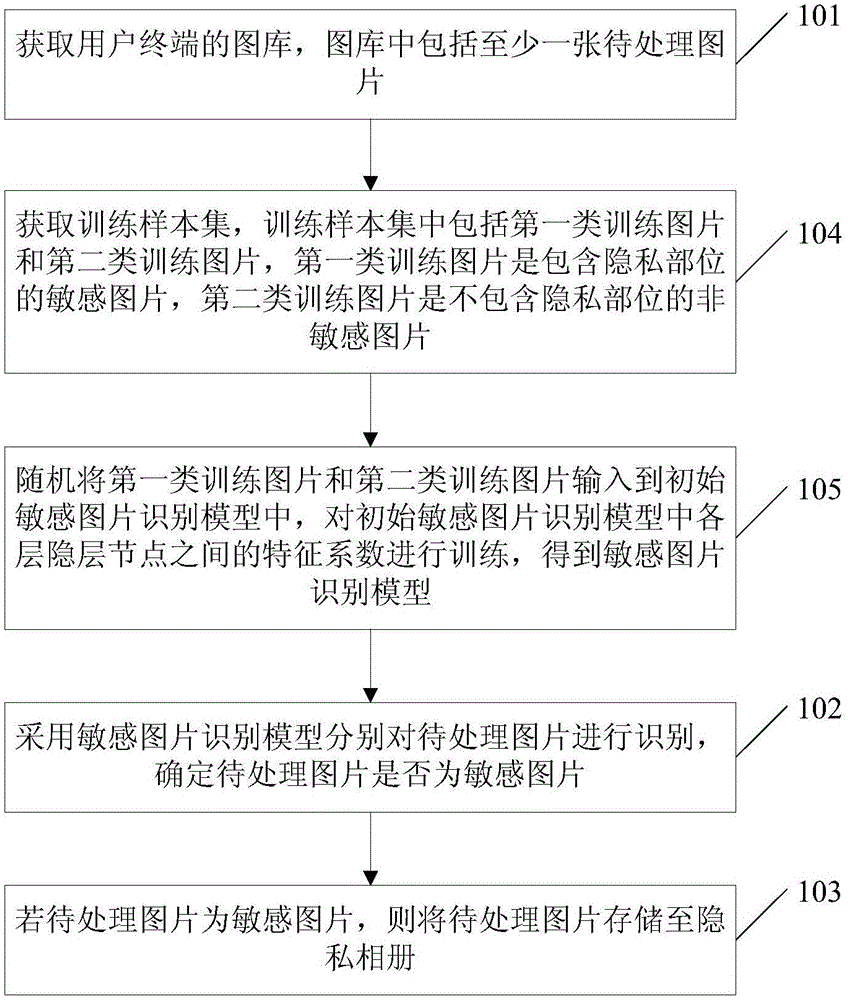
Sensitive picture identification method and apparatus, and server
ActiveCN105095911AImprove recognition efficiencyPrevent leakageImage enhancementImage analysisPrivacy protectionComputer terminal
The invention relates to a sensitive picture identification method and apparatus, and a server. The method comprises the following steps: identifying pictures to be processed in a picture database of a user terminal by use of a sensitive picture identification model, determining whether the pictures to be processed are sensitive pictures, and when the pictures to be processed are sensitive pictures, storing the pictures to be processed in a private photo album. According to the invention, the method can automatically identify and process the pictures to be processed in the picture database, prevents a user from manually selecting the sensitive pictures and removing the sensitive pictures to the private photo album, is time-saving and labor-saving, improves the identification efficiency of the sensitive pictures, improves the privacy protection intensity and prevents leakage of the sensitive pictures.
Owner:XIAOMI INC
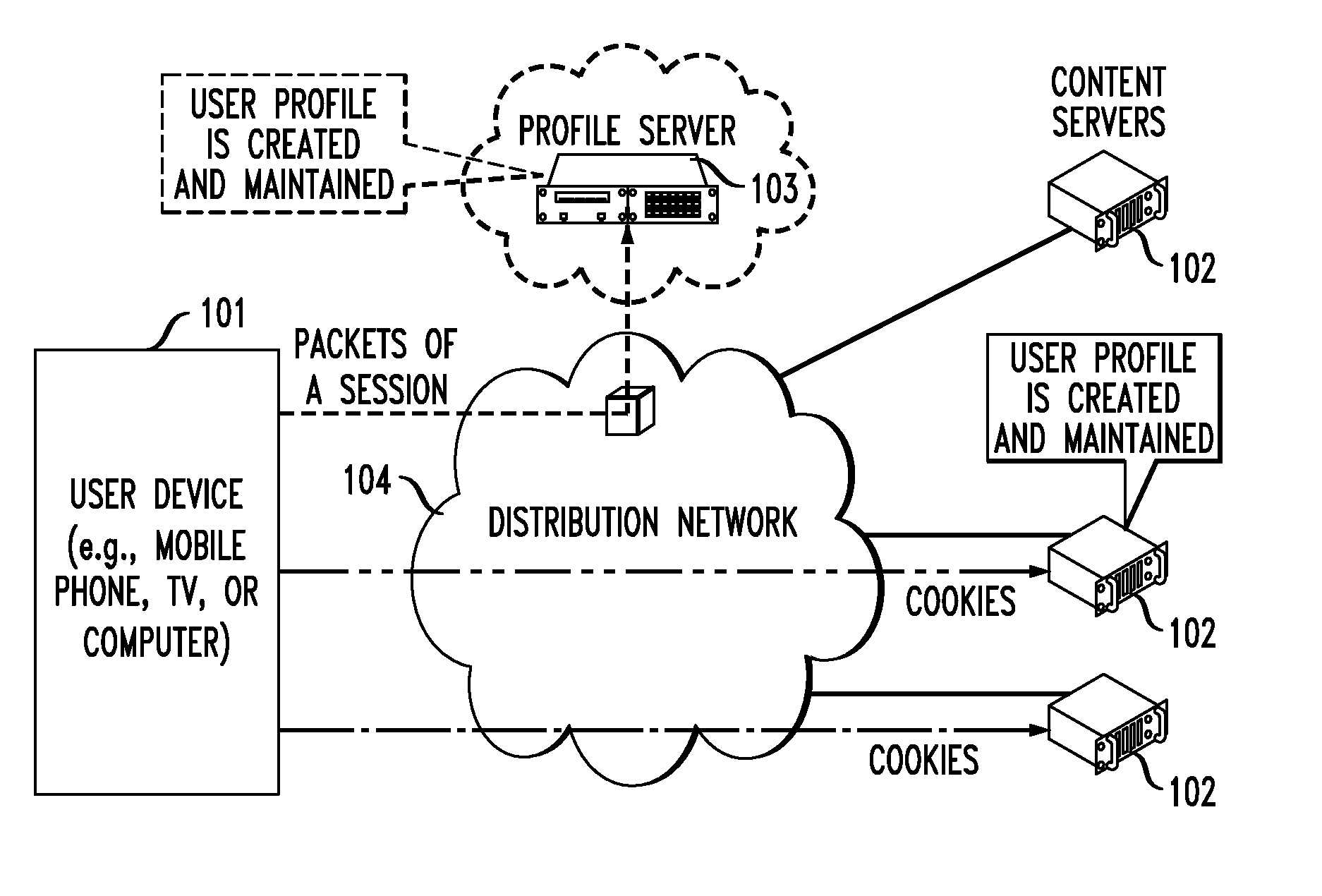
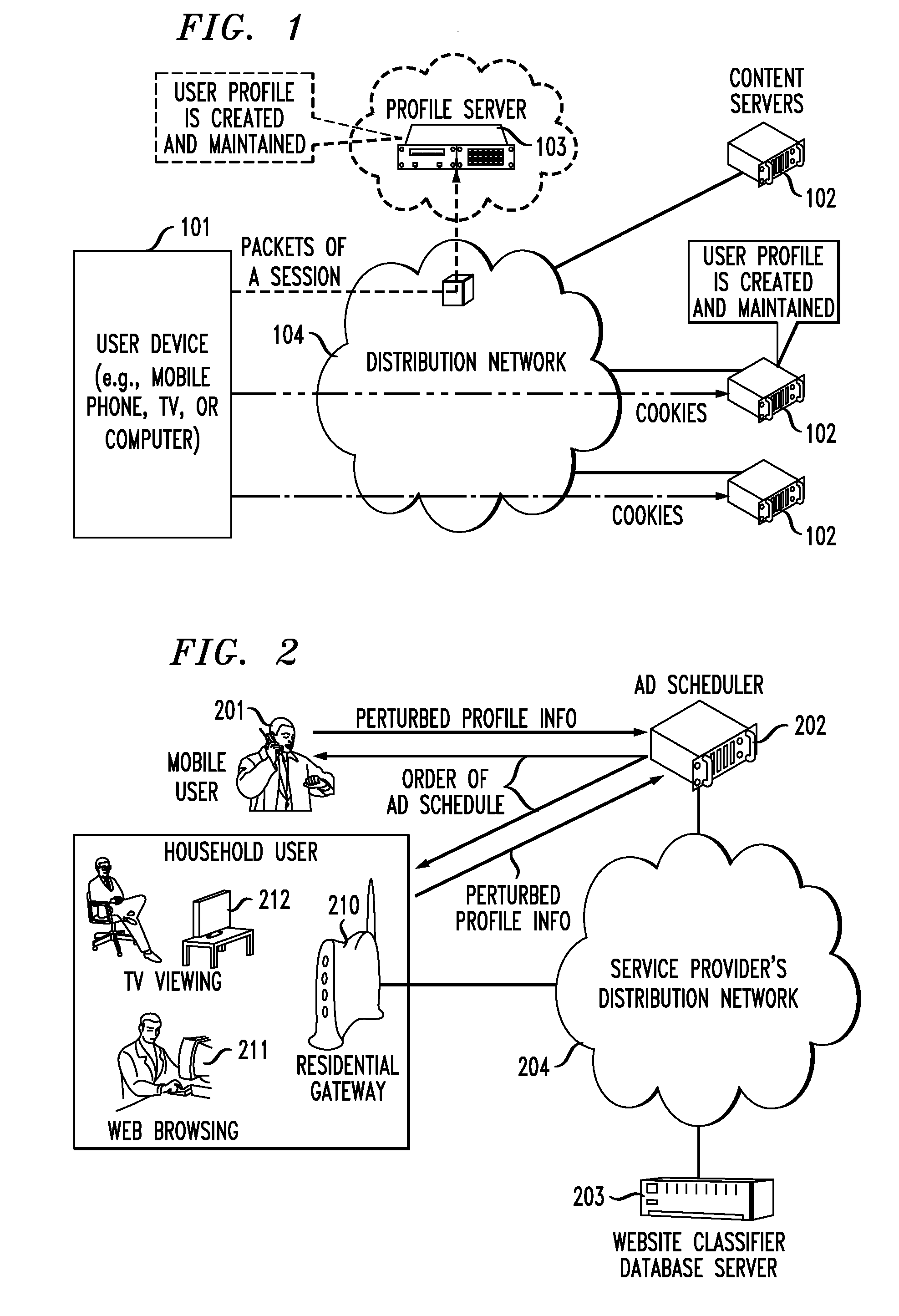
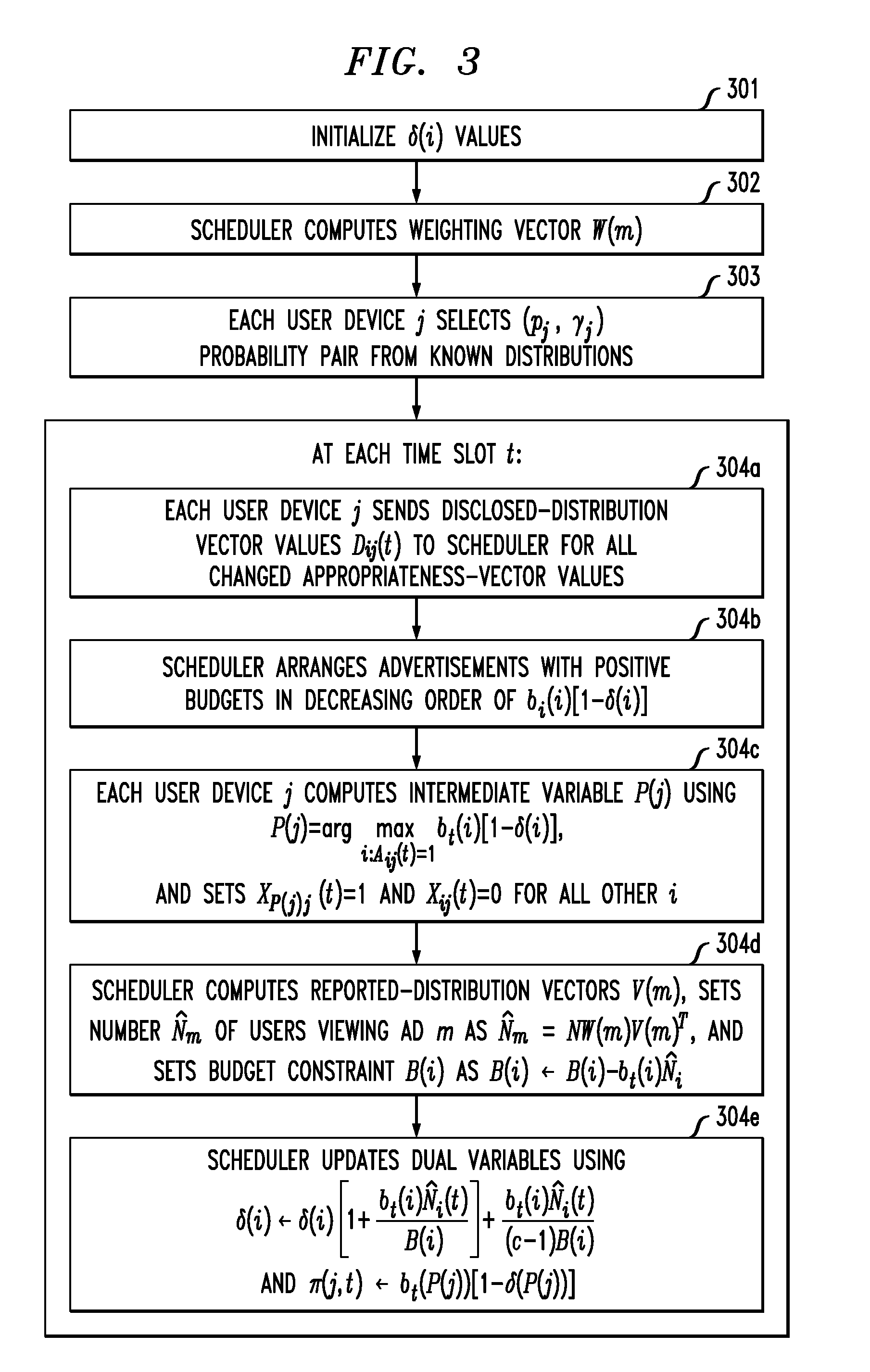
Privacy-preserving advertisement targeting using randomized profile perturbation
InactiveUS20130060601A1Privacy protectionTotal revenue maximizationMarketingOnline algorithmInternet privacy
A distribution and scheduling system for advertisements that targets ads to users and maximizes service-provider revenue without having full knowledge of user-profile information. Each user device stores a user profile and is pre-loaded with a set of ads that could possibly be shown during a timeslot. Each user device selects and displays an ad based on the user profile but does not identify the selected ad to the service provider. Instead, the user devices provide perturbed user-profile information in the form of Boolean vectors, which the service provider uses in conjunction with a guaranteed-approximation online algorithm to estimate the number of users that saw a particular ad. Thus, the service provider can charge advertisers for the number of times their ads are viewed, without knowing the users' profiles or which ads were viewed by individual users, and users can view the targeted ads while maintaining privacy from the service provider.
Owner:ALCATEL LUCENT SAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com