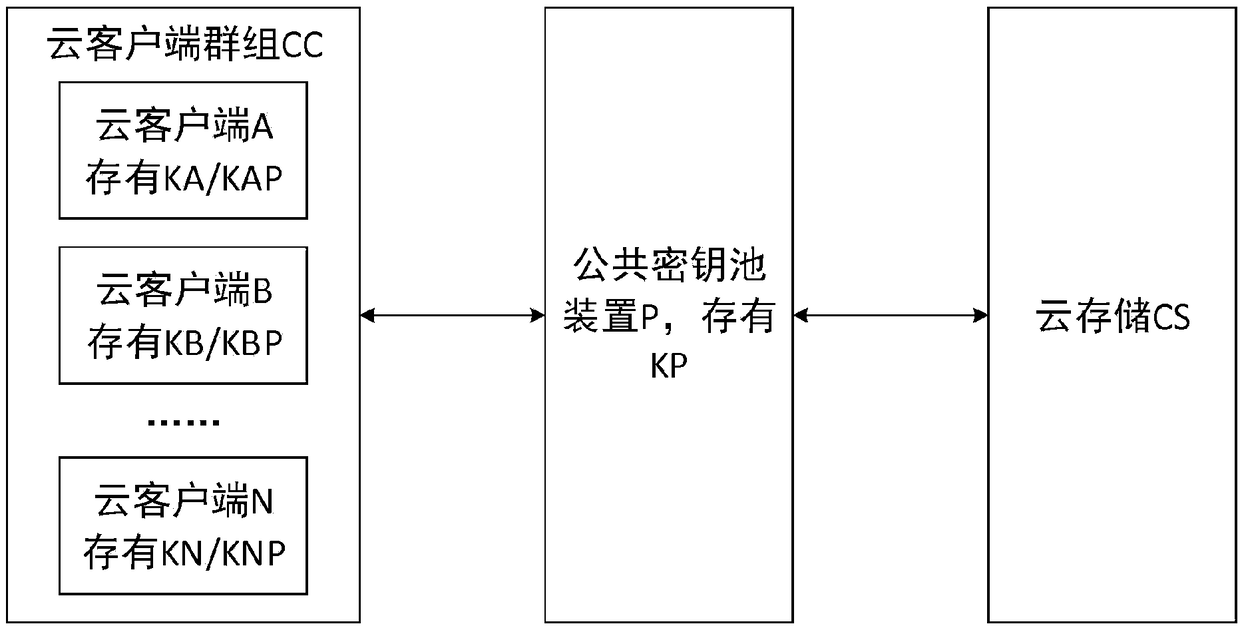
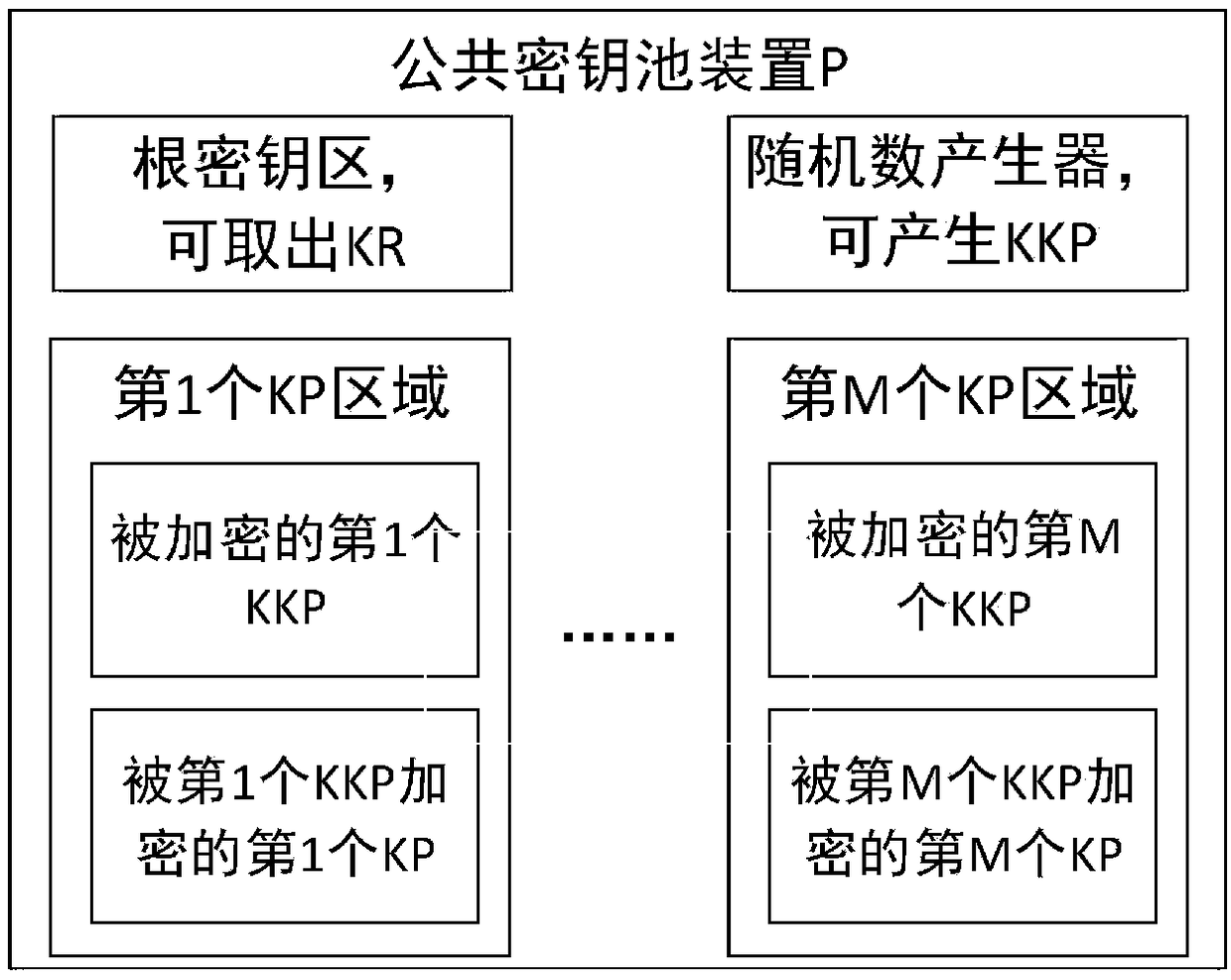
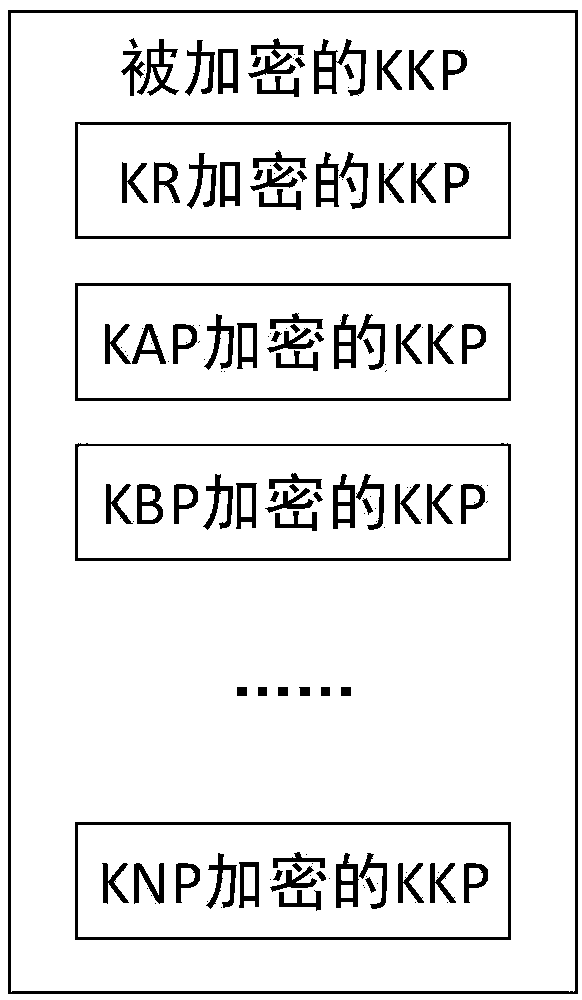
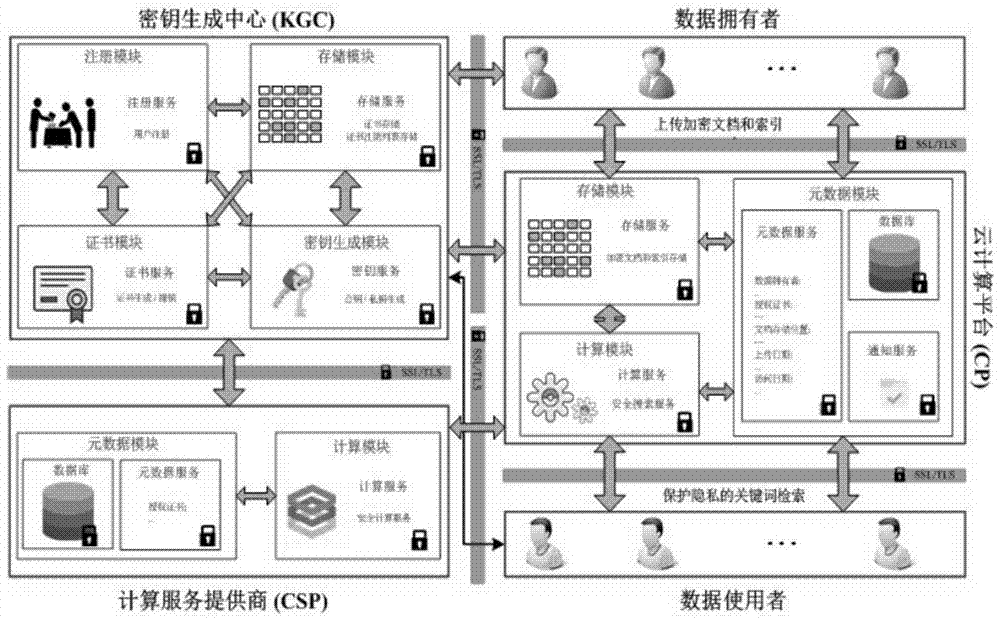
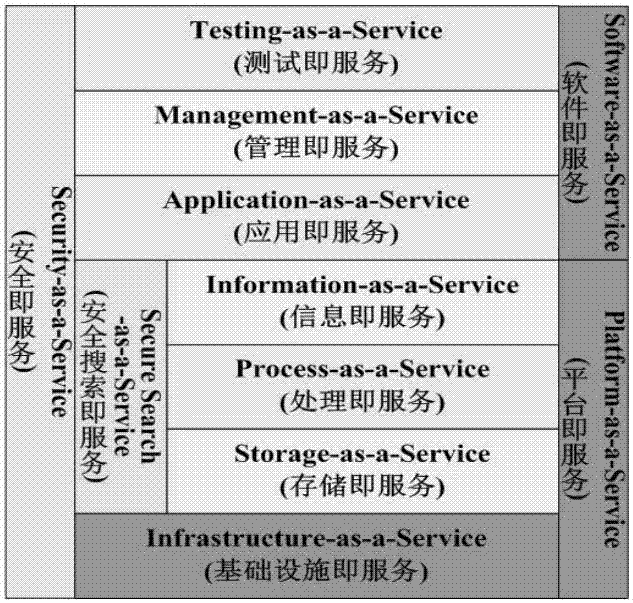
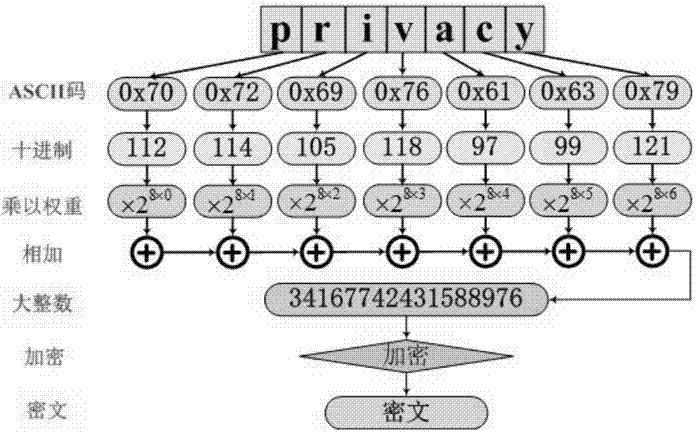
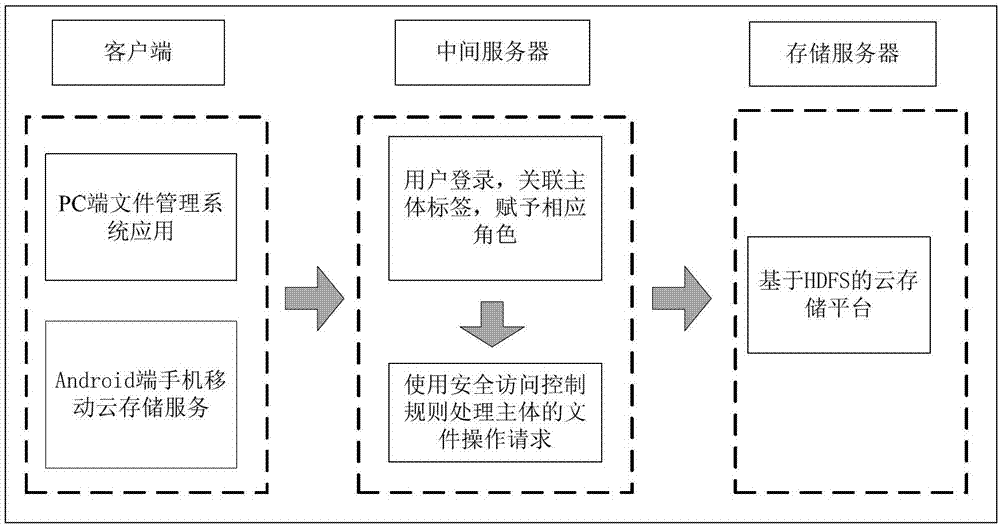
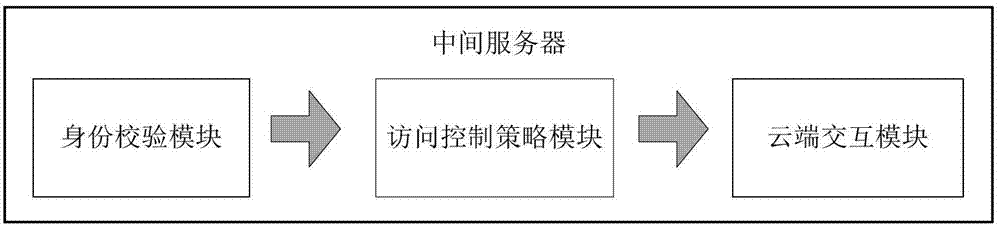
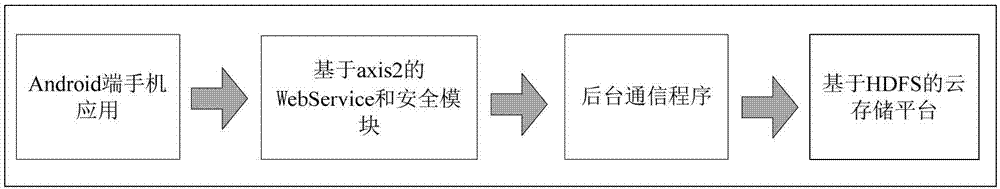
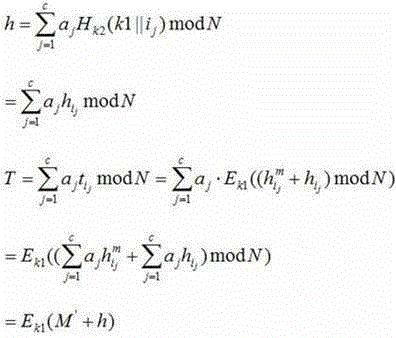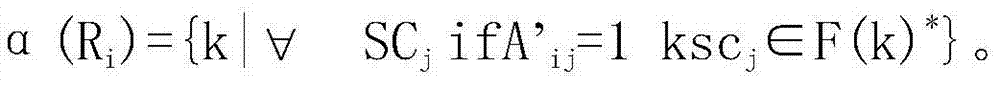Patents
Literature
72 results about "Cloud storage security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Cloud Storage Data Encryption Method, Apparatus and System
InactiveUS20120134491A1Reduced strengthReduce the amount of dataComputer security arrangementsSecret communicationComputer hardwarePlaintext
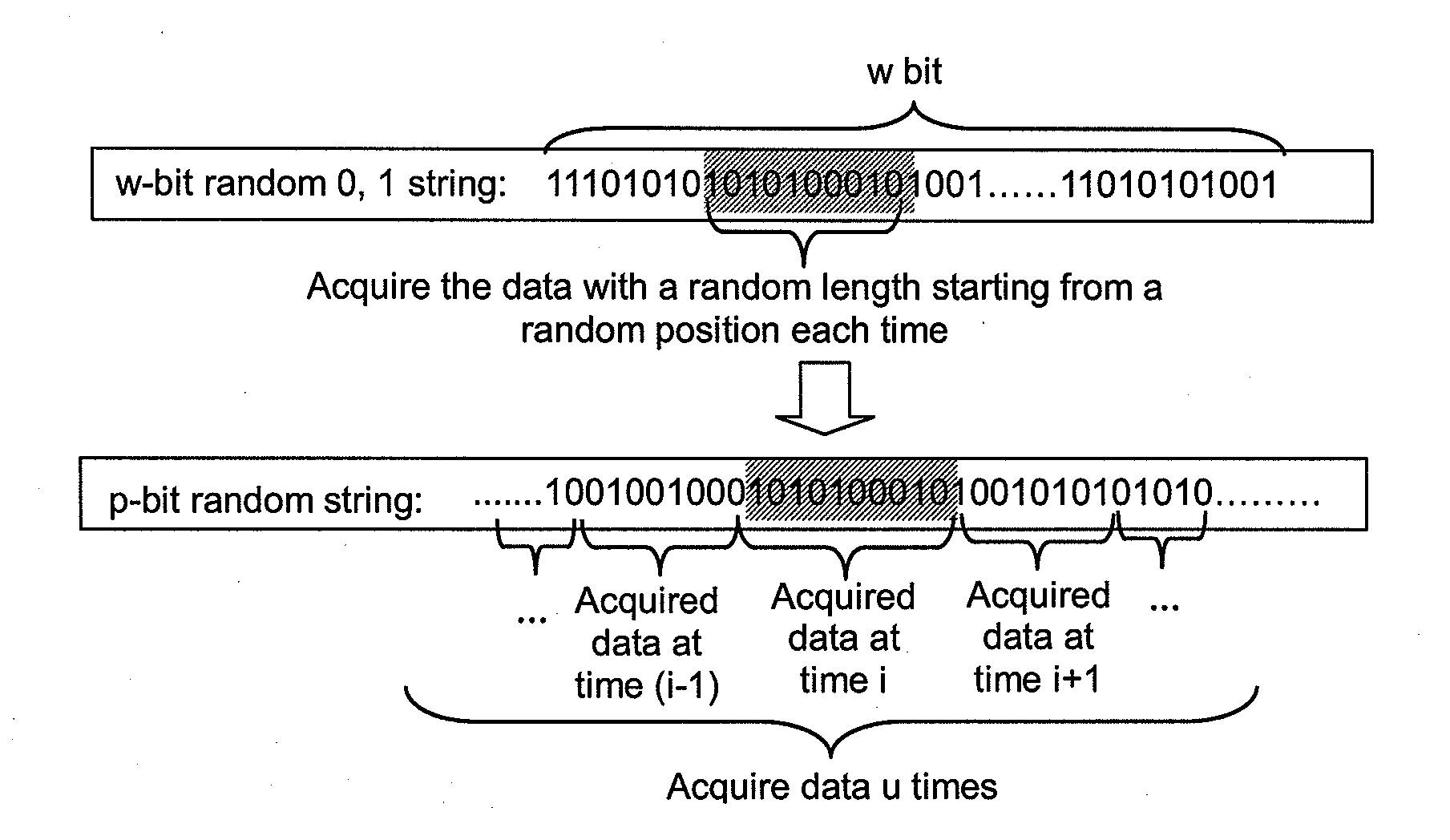
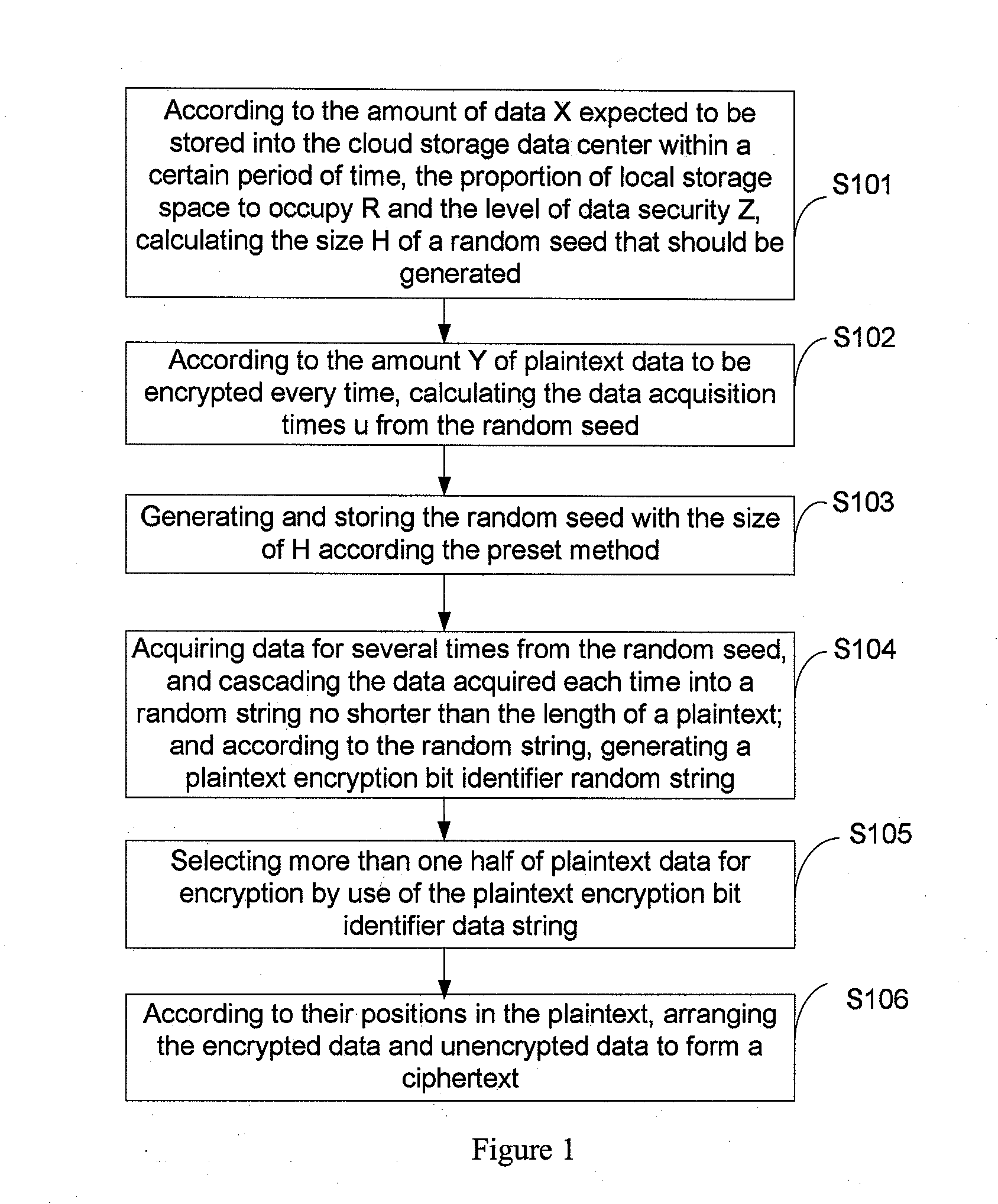
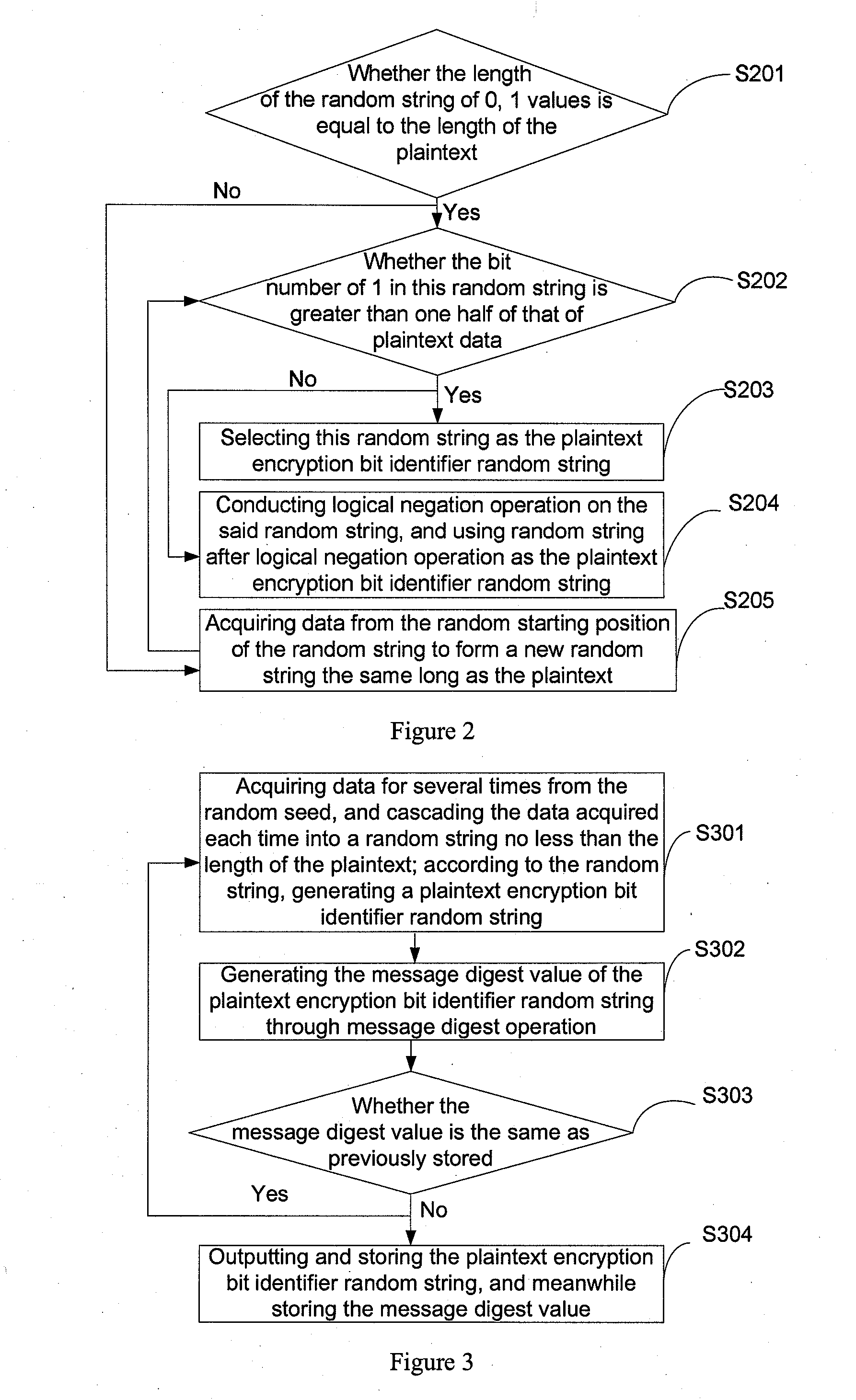
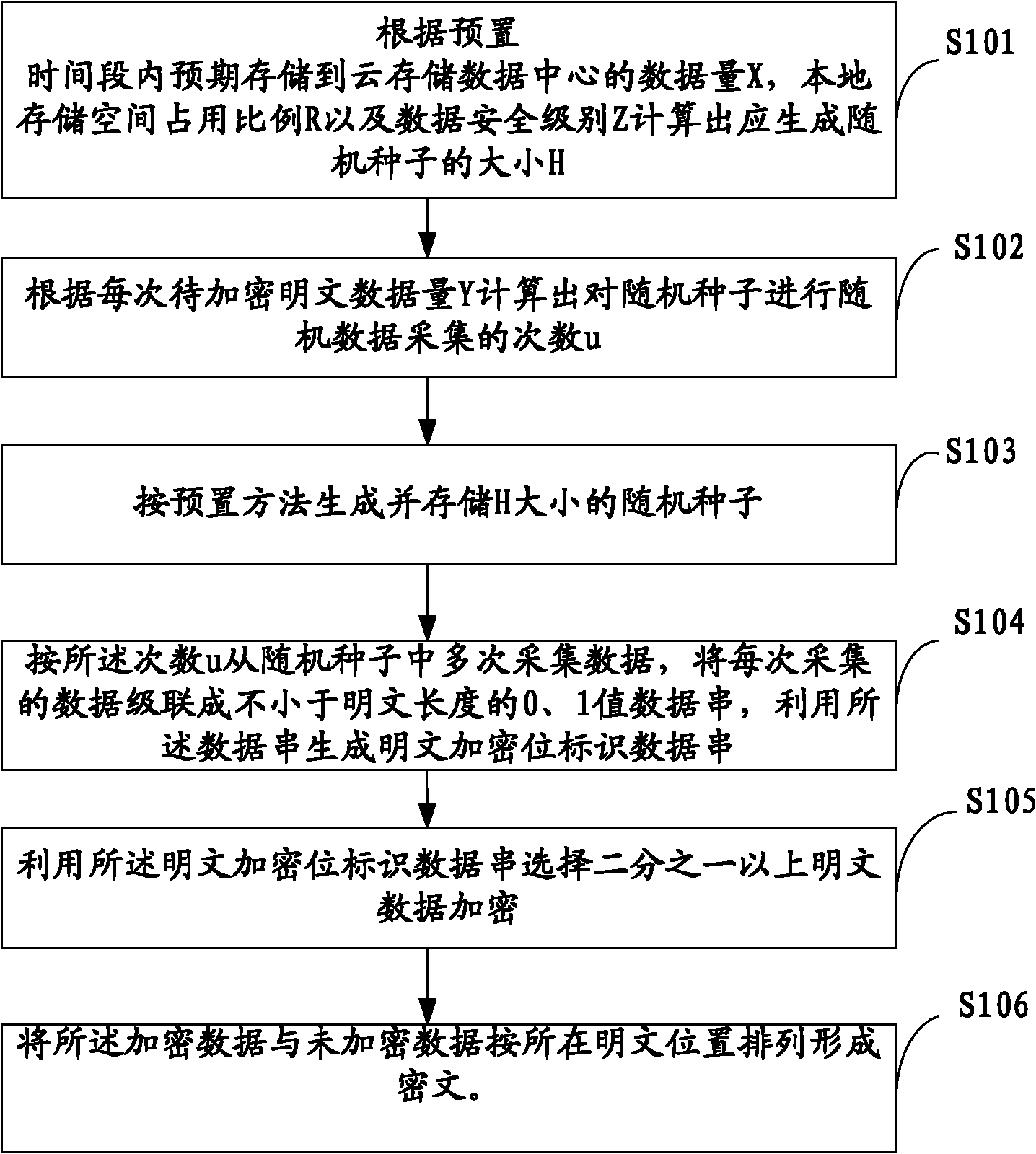
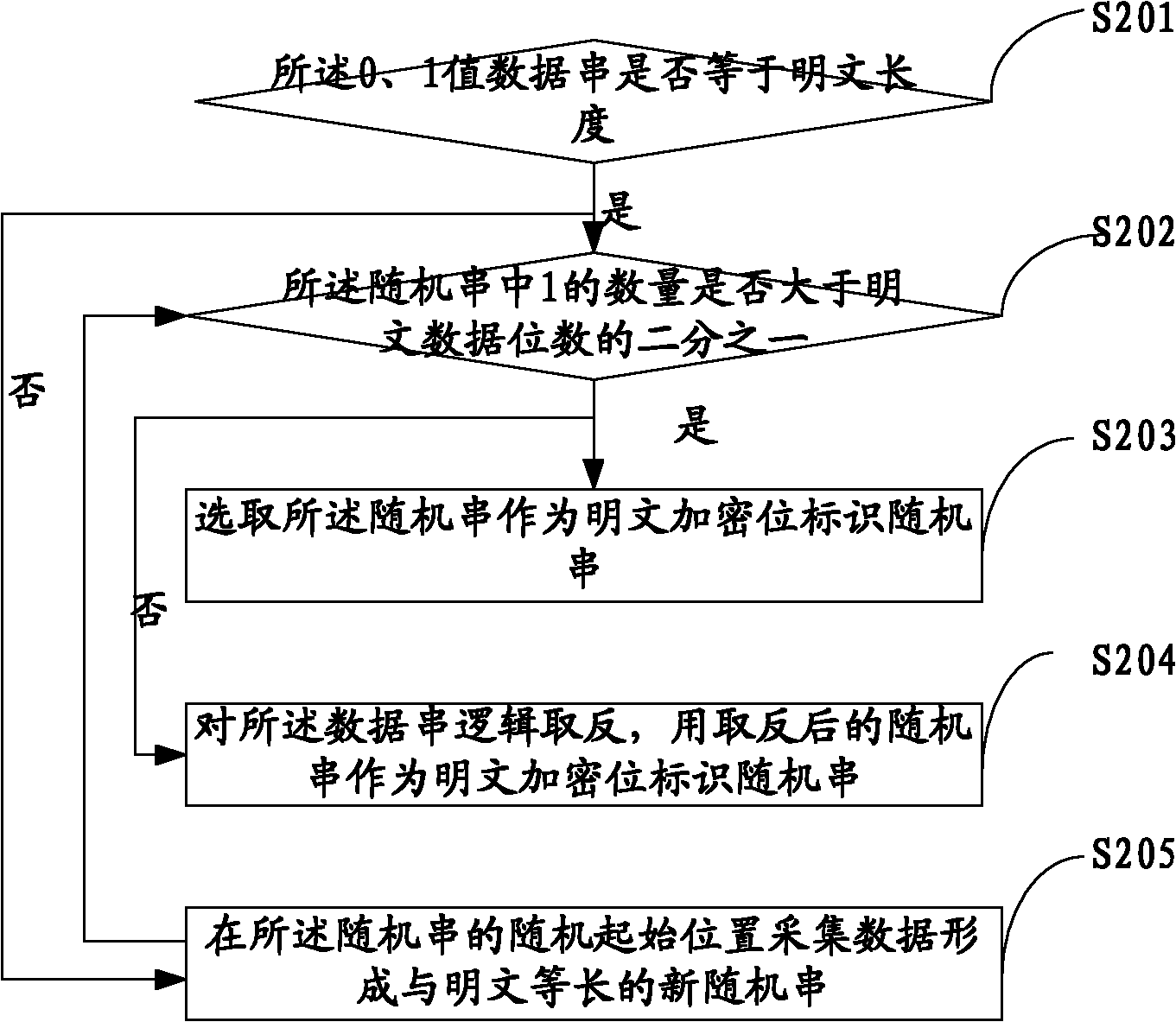
This present application relates to the field of cloud storage security technology, and in particular, relates to a cloud storage data encryption method, apparatus and system. The method comprises: according to the amount of data X expected to be stored within the preset time, the proportion of local storage space R and the security level of data Z, calculating the size H of a random seed that should be generated; according to the amount Y of plaintext data every time, calculating the times u of random seed acquired; according to the times u, acquiring data from the generated random seed with the size of H for several times to generate a plaintext encryption bit identifier data string; by use of the data string, selecting more than one half of the plaintext data for encryption to form a ciphertext. This application also provides a cloud storage data encryption apparatus and system. This invention has reduced the amount of encrypted data to be stored without sacrifice in the degree of data security protection, thus greatly improves the cloud storage data encryption and decryption performance.
Owner:BEIJING Z & W TECH CONSULTING
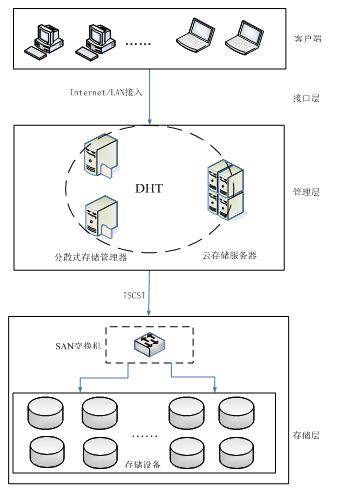
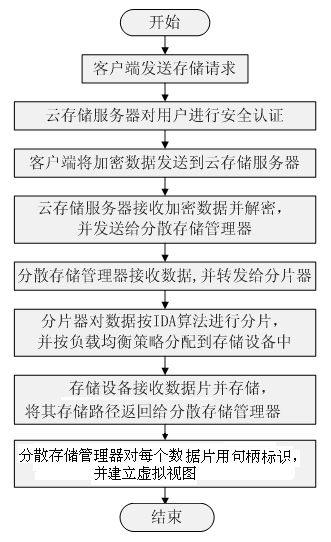
Distributed storage oriented cloud storage security architecture and data access method thereof
InactiveCN102088491AImprove usabilityImprove reliabilityTransmissionStorage area networkConfidentiality
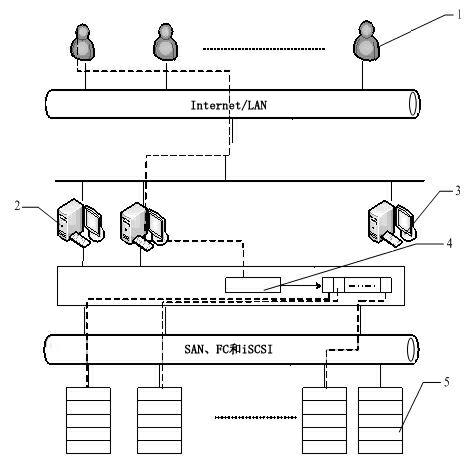
The invention discloses a distributed storage oriented cloud storage security architecture and a data access method thereof. The distributed cloud storage oriented security architecture comprises a cloud storage server, a distributed storage manager, a wafer breaker and storage devices, wherein the distributed storage manager and the cloud storage server are respectively connected with a client-side; the distributed storage manager and the cloud storage server are connected by a fiber channel (FC) or a routing switch; the wafer breaker is imbedded in the distributed storage manager; the distributed storage manager is connected with the storage devices by the FC or Iscsi; and the storage devices are connected by a network attached storage (NAS) or a storage area network (SAN). The storage devices are located at different places and are redundant mutually, thus improving the fault-tolerant ability of the devices and the optimal storage use ratio; the wafer breaker is used for carrying out fragment on stored data, so that the data are fragmented into data fragments which can not be identified by other authentication systems, and the fragmented data have relative confidentiality and security in the process of network transmission and data storage; and the storage devices and the server are the devices with higher cost performance, thus reducing the cost.
Owner:XI'AN UNIVERSITY OF ARCHITECTURE AND TECHNOLOGY
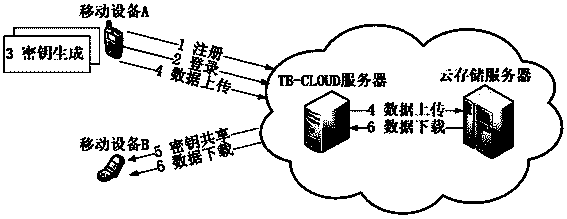
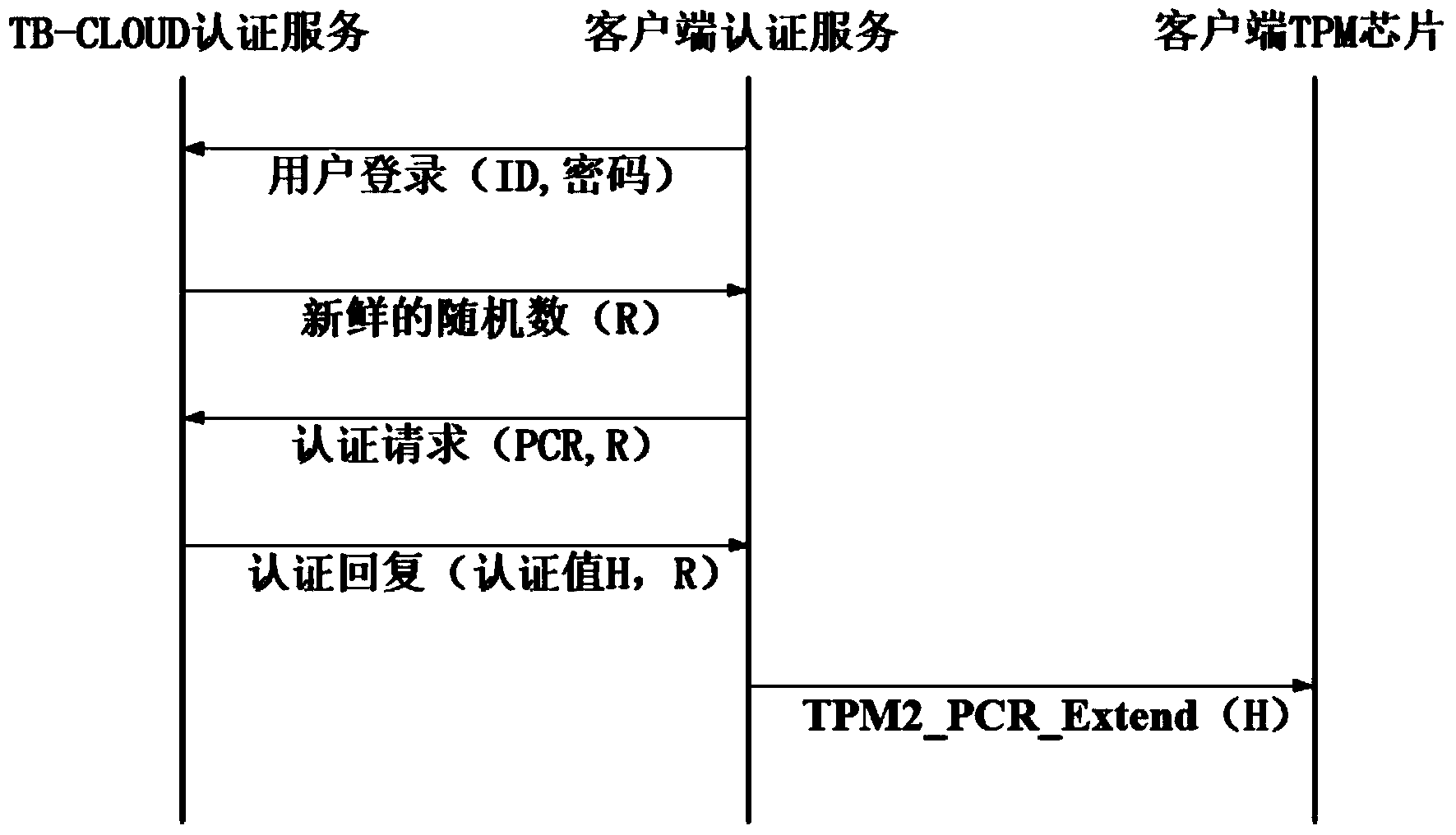
Credible data access control method applied to cloud storage of mobile devices
ActiveCN103763315AReduce the amount of data interactionConfidenceTransmissionCryptographic key generationKey size
The invention relates to a credible data access control method applied to cloud storage of mobile devices. The credible data access control method includes six steps including user registering, user login, secret key generation, data encryption uploading, data downloading and decryption in three stages. The first step is user registering, the second step is user login with an authentication process, the third step is encryption secret key generation, the fourth step is user data encryption uploading, the fifth step is secret key sharing among the multiple mobile devices, and the sixth step is data downloading and decryption. According to the credible data access control method, transmitting of a credible chain in the secret key exchanging process is guaranteed by a user through a mobile TPM chip, the length of a secret key is reduced through encryption based on a elliptic curve, it is guaranteed that the multiple mobile devices can safely share the secret key, compared with a traditional server terminal or client terminal data encryption method provided by a cloud storage service provider, the credible data access control method is safe, reliable, high in confidence degree and small in interaction data amount, and the good practical value and the wide application prospect are achieved in the technical field of cloud storage safety.
Owner:BEIHANG UNIV
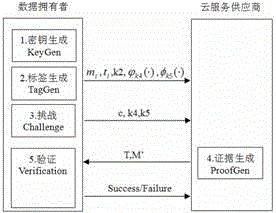
Cloud storage data security auditing method allowing group-user identity revocation
InactiveCN103501352AAudit validAvoid complex calculationsUser identity/authority verificationThird partyCloud storage security
The invention discloses a cloud storage data security auditing method allowing group-user identity revocation. The cloud storage data security auditing method comprises the following six steps: (1) generating keys (KeyGen); (2) calculating resign keys (ReKey); (3) generating signs (Sigh); (4) generating resigns (ReSign); (5) generating proofs (GenProof); (6) checking the proofs (CheckProof). Not only can shared data be effectively audited by a third party auditor after group-user identities are revoked, but also the security of the method is further enhanced compared with the existing method for solving a public auditing protocol allowing group-user identity revocation. As a result, the method disclosed by the invention can enhance the confidence of people in cloud storage security and further promote the health development of cloud storage environments.
Owner:BEIHANG UNIV
Method for cloud storage security control
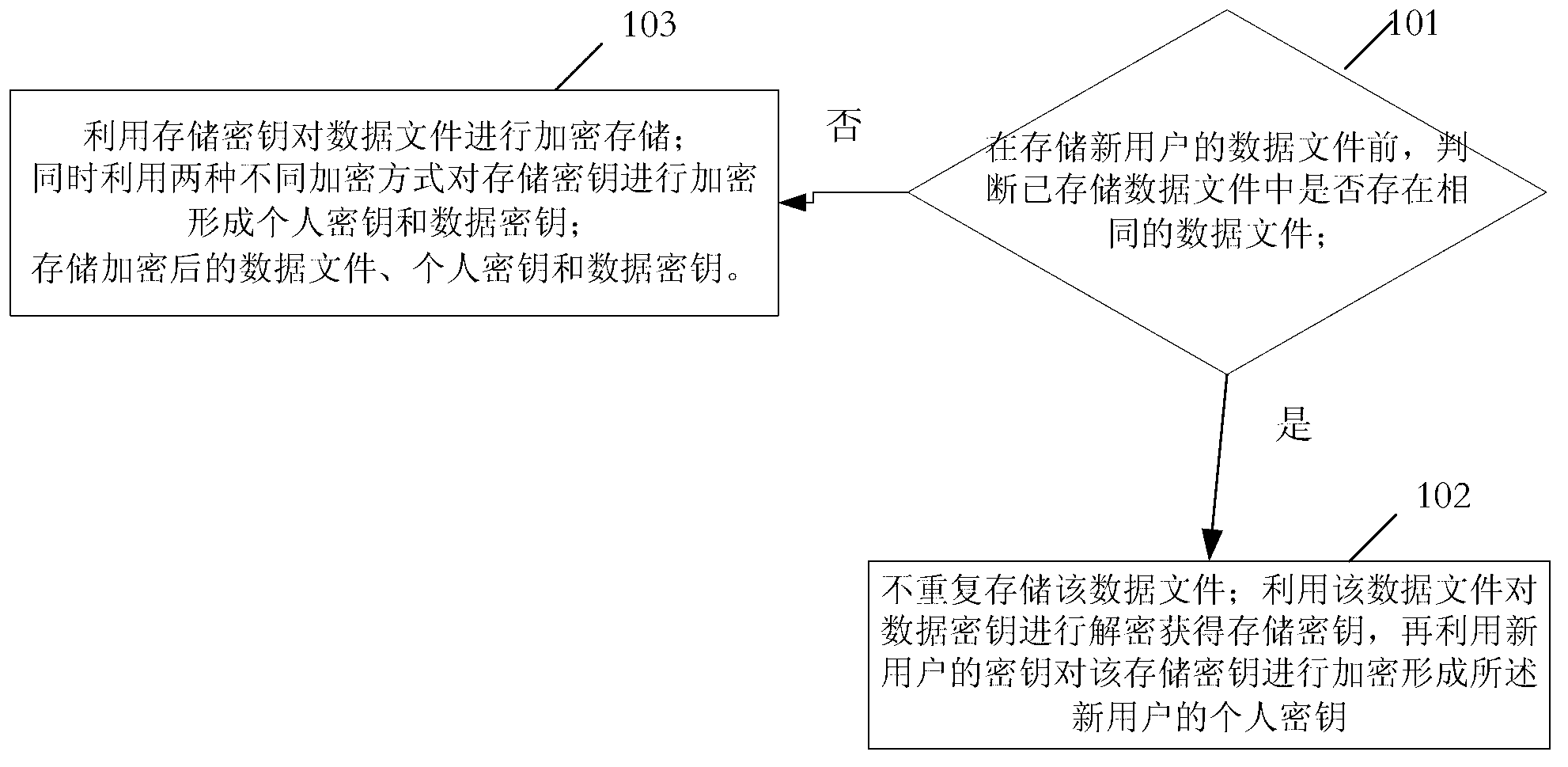
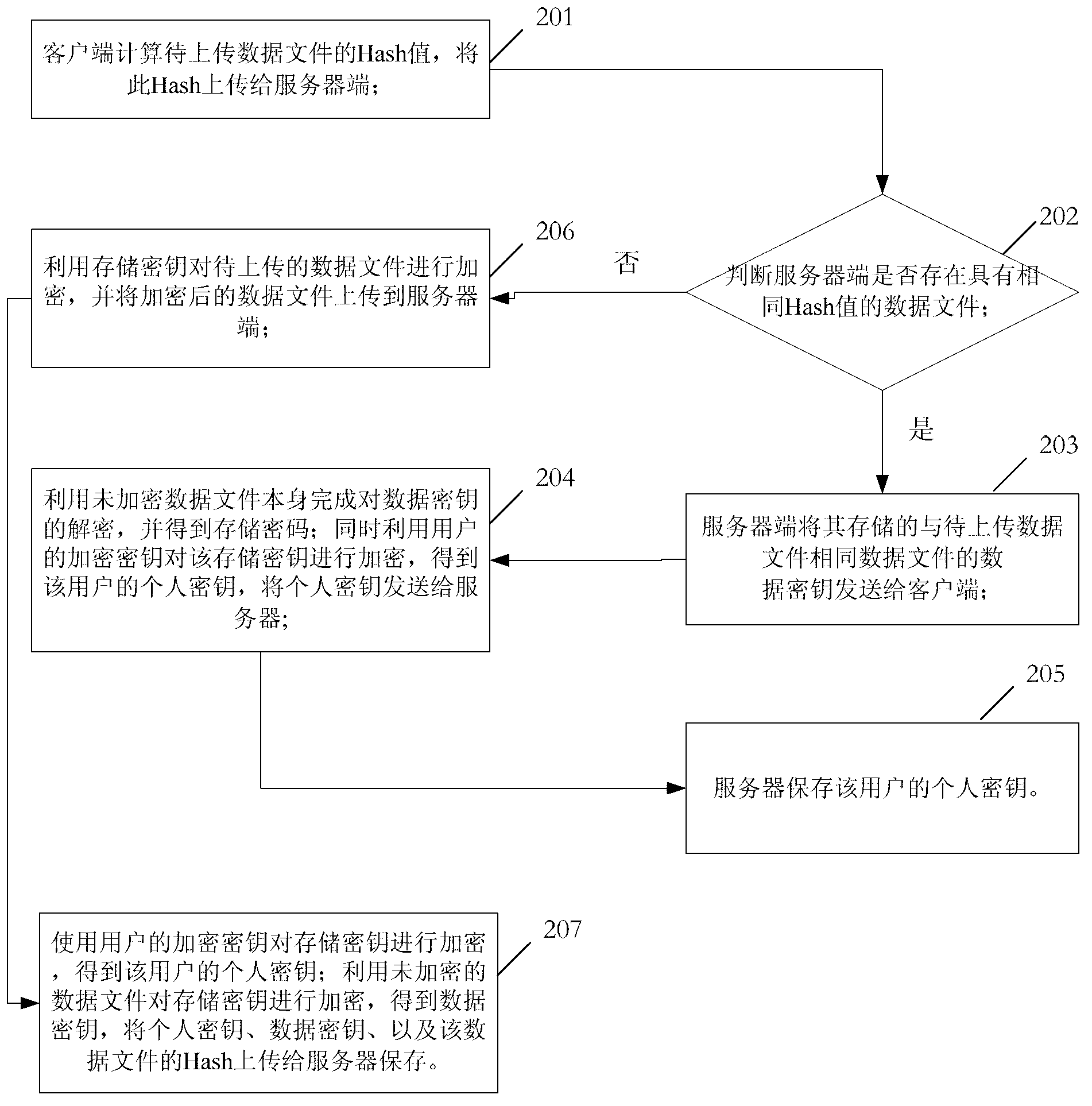
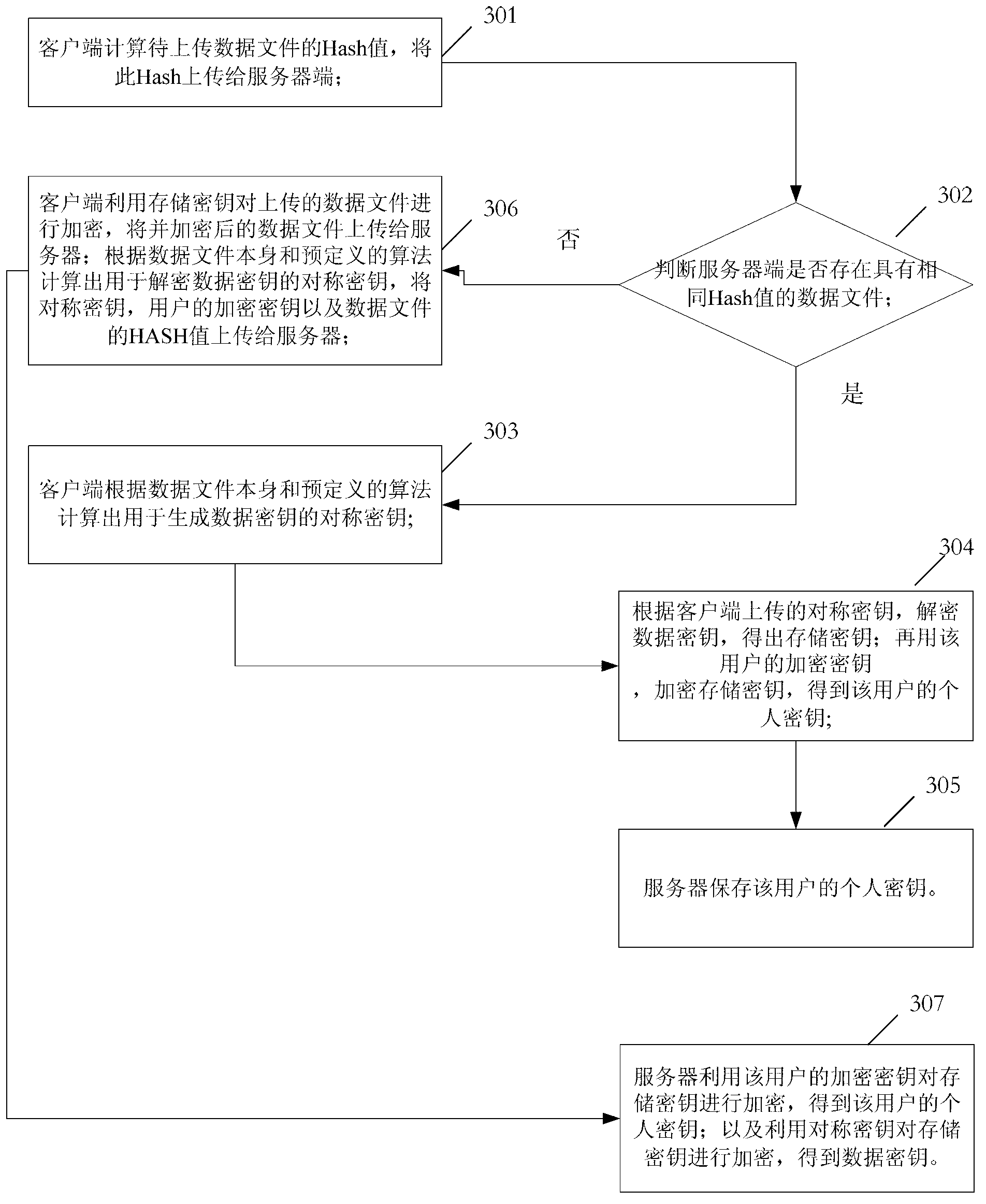
ActiveCN103236934AUser identity/authority verificationComputer security arrangementsPlaintextPassword
The embodiment of the invention discloses a method for cloud storage security control, which is used for solving the problems that since shared storage is commonly adopted during the storage in the prior art, and service providers need to control private keys, the security of private keys is low. The method comprises the steps of encrypting a private key issued to each user through two different encryption modes, so as to form a first cryptographic key and a second cryptographic key, storing the first cryptographic key and the second cryptographic key, receiving answers to security problems input by the user after decryption failure of the first cryptographic key through user passwords, deciphering the second cryptographic key through the answers to the security problems, so as to obtain a clear cryptographic key, resetting the user passwords, and encrypting the clear cryptographic key obtained by deciphering the answers to the security problems, so as to form a new first cryptographic key to be stored.
Owner:北京书生信息技术有限公司
Cloud storage system and data management method thereof
ActiveCN102638568AEnsure safetyUser identity/authority verificationCloud storage securityData management
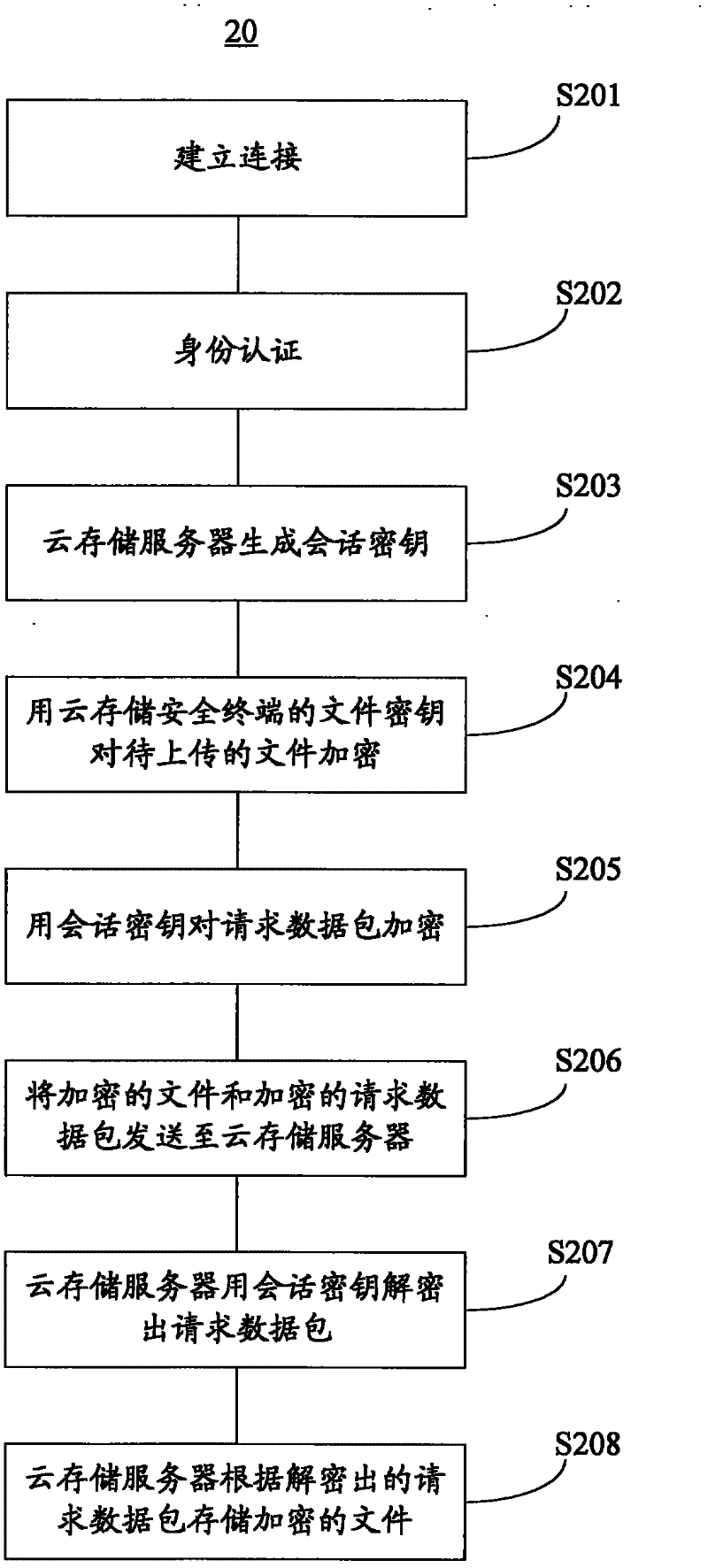
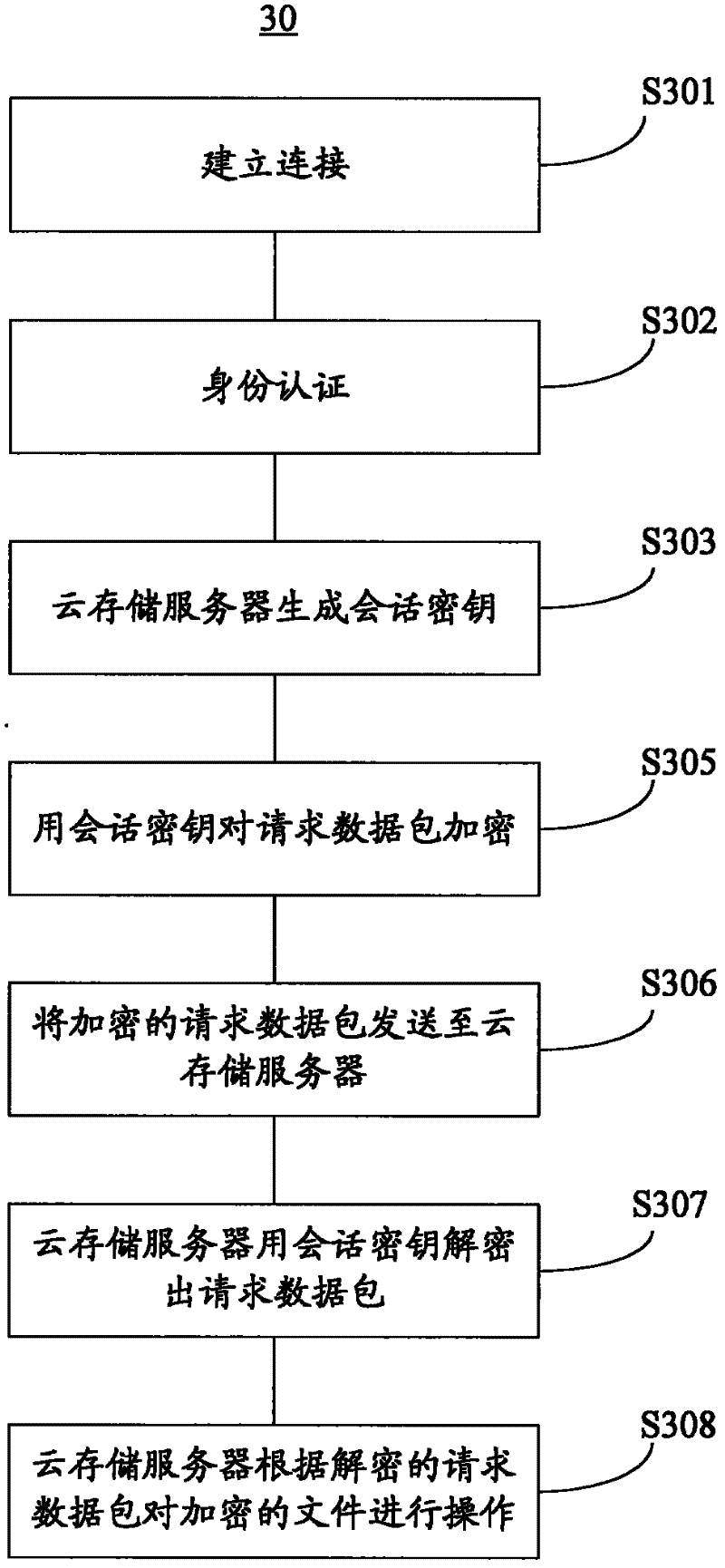
The invention discloses a cloud storage system and a data management method thereof. The cloud storage system comprises a cloud storage server, a client side and a cloud storage safety terminal, wherein the cloud storage server is configured to store file data of multiple users; the client side is configured to be capable of operating client side software so as to establish connection with the cloud storage server; and the cloud storage safety terminal with a file encryption key is configured to be capable of establishing connection with the client side. The file data stored in the cloud storage server are the data encrypted with the file encryption key of the cloud storage safety terminal. According to the scheme, safety of the data is guaranteed by hardware certification of the cloud storage safety terminal.
Owner:NETAK TECH KO LTD
OTP-based cloud storage data storing method, device and system
InactiveCN101986663AProtection securityPrivacy protectionUser identity/authority verificationConfidentialityData center
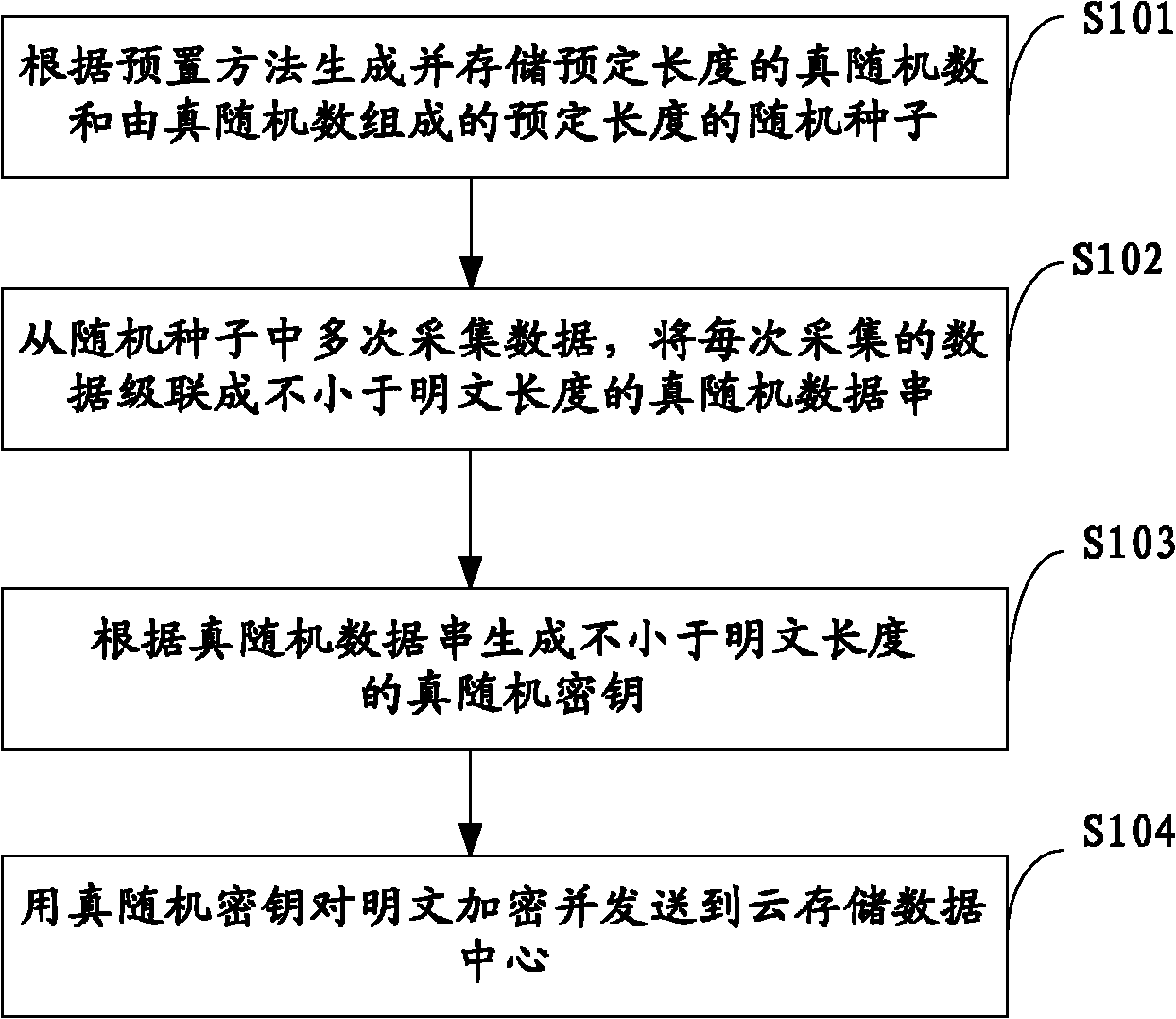
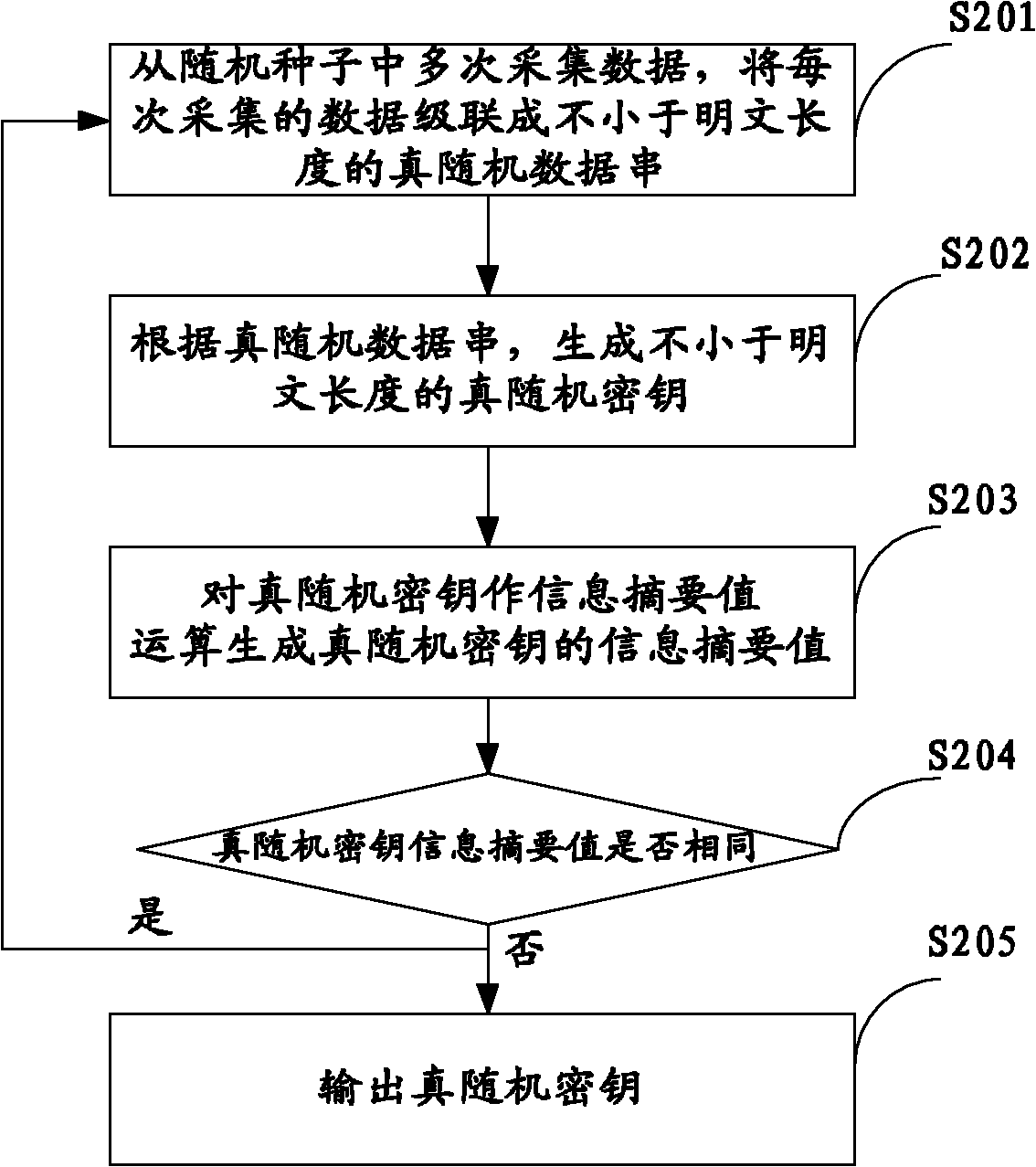
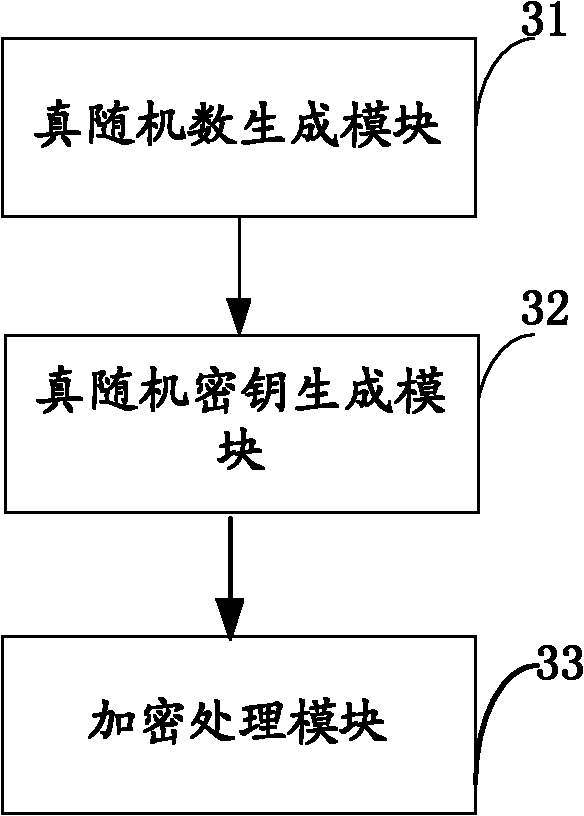
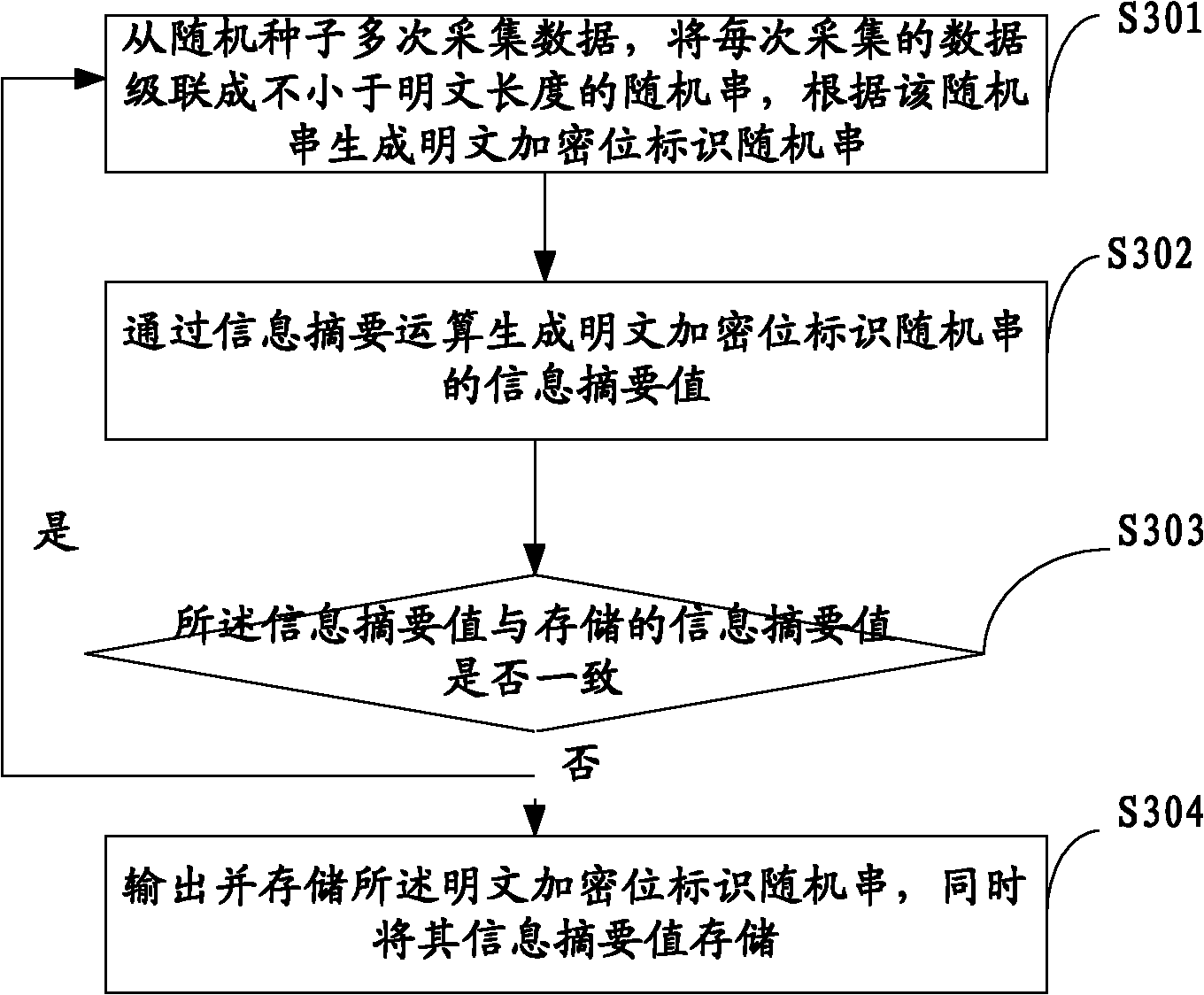
The invention belongs to the technical field of cloud storage security, and particularly relates to an OTP-based (one-time pad-based) cloud storage data storing method, an OTP-based cloud storage data storing device and an OTP-based cloud storage data storing system. The method comprises the following steps of: generating and storing a true random number of predetermined length and a random seed consisting of the true random number and with predetermined length according to a preset method; repeatedly acquiring data from the random seed, and cascading the data acquired each time into a true random data string not shorter than a plain text length; and generating a true random key not shorter than the plain text length according to the true random data string, encrypting the plain text and sending the encrypted plain text to a cloud storage data center. The invention also provides the OTP-based cloud storage data storing device and the OTP-based cloud storage data storing system. The method, the device and the system generate and store the true random key with enough number and without repeated use by using relatively small plain text storage space, effectively protect the security and the privacy of the cloud storage data and improve the confidentiality of the cloud storage data.
Owner:BEIJING Z & W TECH CONSULTING
Method of using machine learning to predict hard disk fault
InactiveCN107392320AImprove failure accuracyAvoid lossDetecting faulty computer hardwareReliability/availability analysisPrediction rateCloud storage security
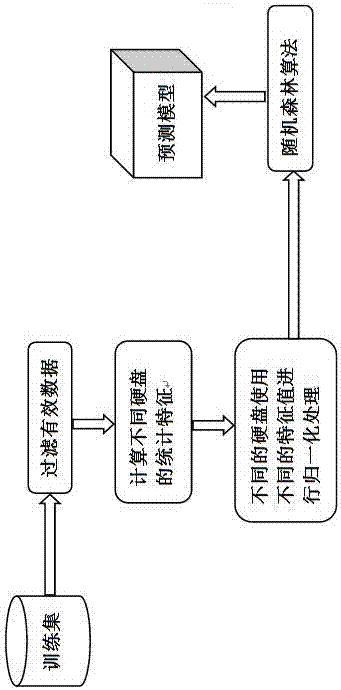
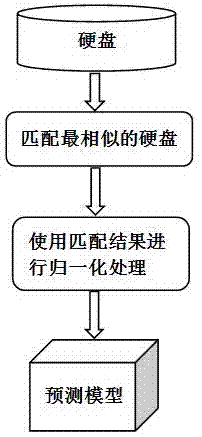
The present invention provides a method of using the machine learning to predict a hard disk fault, and belongs to the cloud storage safety technology field. The method of the present invention uses the mass smart data sets provided by the blackblaze, according to the condition that the smart data of the hard disks of different brands is distributed unevenly, uses a random forest algorithm to train and model the historical data, generates a fault prediction model, and enables the fault prediction rate to be improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
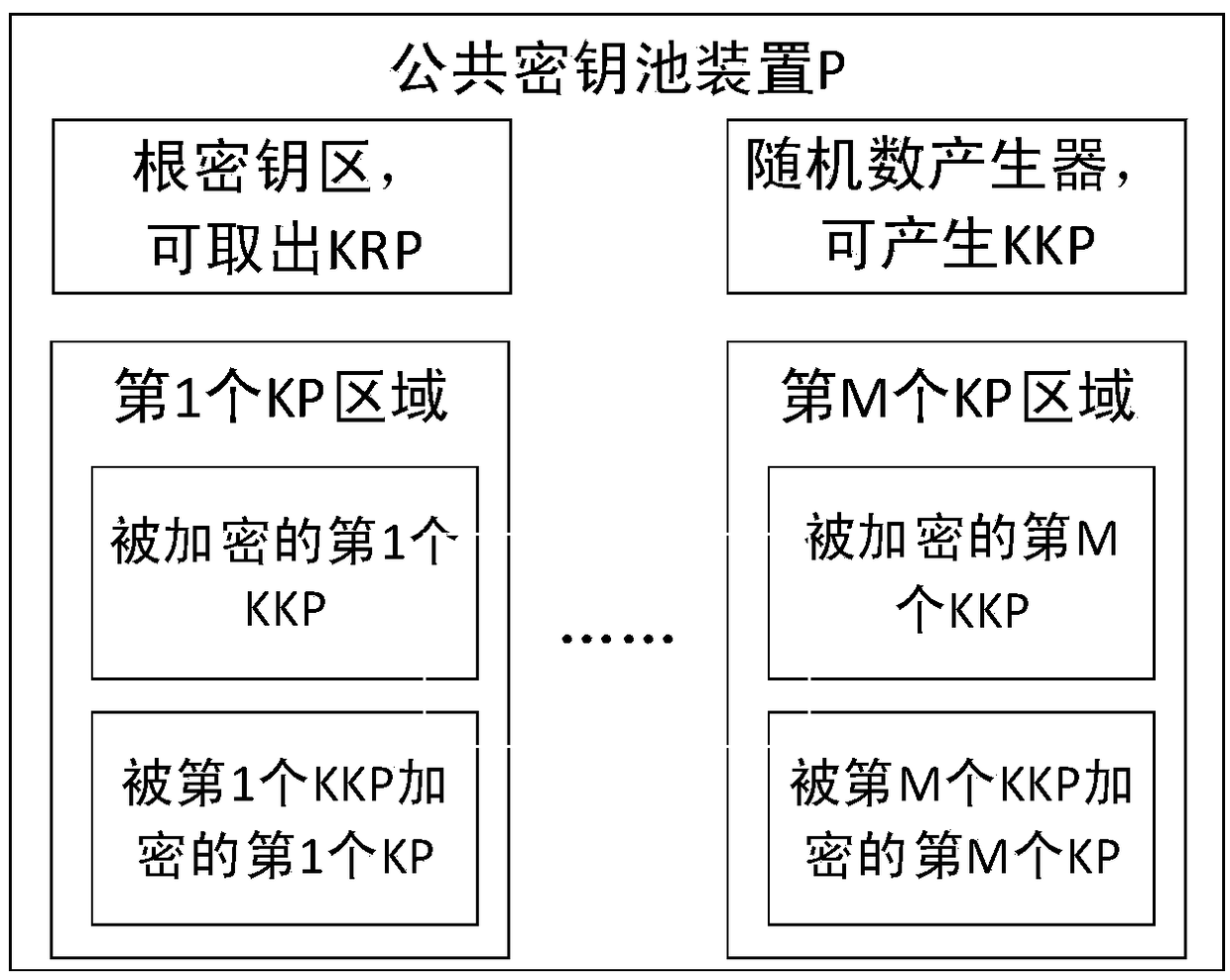
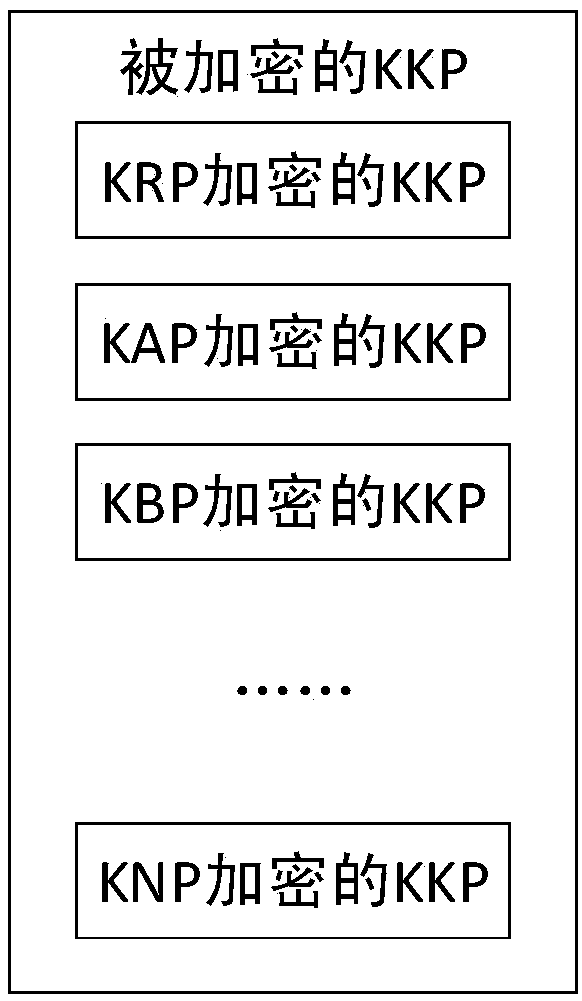
Anti-quantum computing cloud storage security control method and system based on public key pool
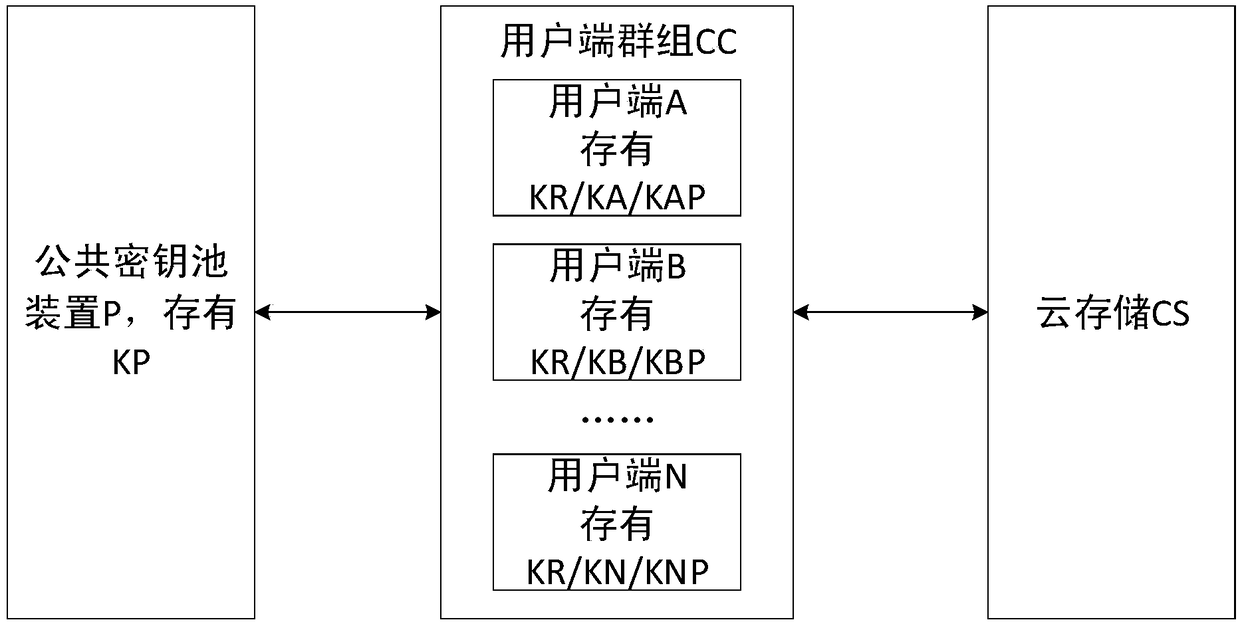
ActiveCN109150519AAvoid crackingKey distribution for secure communicationCloud storage securityData file
The invention relates to an anti-quantum cloud storage security control method and system based on a public key pool. The user side uploads the data file encrypted by a file key to a server, wherein the file key is generated by combination of the file key true random number generated by the quantum key card and the key pool device; the server receives the stores the user side relevant data; and the user side downloads the personal key, the public key true random number and the encrypted data file and generates the file key by using combination of the file key true random number and the key pool device so as to decrypt and obtain the data film. The server side cannot contact all the keys and the plaintext data files of the user side and the user side only discloses the encrypted public keyand stores the public key by the key card, and the key card is the independent hardware isolation equipment and the possibility of key stealing by the malicious software or the malicious operation canbe greatly reduced. The quantum computer cannot obtain the user public key and then cannot obtain the corresponding private key so that the scheme is not liable to be decoded by the quantum computer.
Owner:RUBAN QUANTUM TECH CO LTD
A method and system for cloud storage security control based on key pool
ActiveCN109104276AGuaranteed true randomnessImprove securityKey distribution for secure communicationComputer hardwareCloud storage security
The invention discloses a cloud storage security control method and system based on key pool, the user end uploads the data file encrypted by the file key to the server, the user end is provided witha quantum key card, the file key is generated by using the true random number generated by the quantum key card, and the user end also uploads the true random number to the server. A server receives and stores data files and true random numbers from a client. The user terminal downloads the true random number and the data file encrypted by the file key, and the user terminal uses the true random number to generate the file key in the quantum key card configured by the user terminal to decrypt the data file. In the cloud storage process, the server can not access the file key and the decrypteddata file, which solves the security concerns of the client for the cloud storage data, and uses the true random number generated by the quantum key card to generate the true random file key, so as toimprove the security of the key and ensure the security of the execution environment of the encrypted program at the client.
Owner:RUBAN QUANTUM TECH CO LTD
A cloud storage security control method and system based on a public key pool
ActiveCN108989033AAddress the danger of theftAddress security concernsKey distribution for secure communicationControl systemCloud storage security
The invention discloses a cloud storage security control method and a cloud storage security control system based on a public key pool. A user end uploads the data file encrypted by the file key to the server, and the user end is provided with a quantum key card. The file key is generated by combining the true random number generated by the quantum key card with the key pool device, and the user end uploads the true random number to the server. The server receives and stores data files and true random numbers from the client. The user terminal downloads a true random number and a data file encrypted by using a file key, and combines the true random number with the key pool device to generate a file key, and decrypts the file to obtain a data file. In the cloud storage process, the server can not access the file key and the decrypted data file, which solves the security concerns of the client for the cloud storage data, the true random number generated by the quantum key card is used togenerate the true random file key, so as to improve the security of the key and ensure the security of the execution environment of the encrypted program at the client.
Owner:RUBAN QUANTUM TECH CO LTD
A proxy cloud storage security control method and system based on public key pool
ActiveCN108985099AImprove securityEnsure safetyDigital data protectionCloud storage securityData file
The invention discloses a proxy cloud storage security control method and system based on a public key pool. A user end uploads the data file to the key pool device, and the key pool device uploads the data file encrypted by the file key to the server. The file key is generated by the true random number generated by the quantum key card of the user end, and the user end uploads the true random number to the server through the key pool device. The server receives and stores data files and true random numbers from the client. The user end sends a read request to the key pool device, the key pooldevice downloads the true random number and the cipher text of the data file, the true random number generates a file key, decrypts the obtained data file and transmits the file to the user end. In the cloud storage process, the server can not access the file key and the decrypted data file, which can solve the security concerns of the cloud storage data. The quantum key card is utilized to generate the true random number to generate the true random file key, so the security of the key is improved and the security of the user-side encryption program execution environment is ensured.
Owner:RUBAN QUANTUM TECH CO LTD
Searchable encryption method based on wildcard character in cloud storage safety
ActiveCN107256248AFlexible AuthorizationFlexible revocationDigital data protectionSpecial data processing applicationsCiphertextCloud storage security
The invention relates to a searchable encryption method based on wildcard character in cloud storage safety. The method comprises the following steps that: setting a document to be uploaded; extracting a keyword set; encrypting the keyword set; selecting a random number as a document encryption key, and encrypting the document encryption key; encrypting the document to be uploaded to obtain a ciphertext, and sending the ciphertext to a cloud computing platform; input a query keyword set, generating a query trapdoor, carrying out signature, and sending the signature to the cloud computing platform; verifying a query signature by the cloud computing platform, and executing a search algorithm by the cloud computing platform; transmitting a keyword index and the query trapdoor into a keyword matching protocol to obtain an encryption matching result; carrying out decryption to obtain a search result; according to the search result, returning a corresponding ciphertext by the cloud computing platform; and recovering the document encryption key, and recovering the document. By use of the method, the keyword search of at most two wildcard characters can be supported, the wildcard character can appear on any position of the keyword, and a plurality of random characters can be represented.
Owner:FUZHOU UNIV
Distributed file system-based mobile cloud storage safety access control method
The invention provides a distributed file system-based mobile cloud storage safety access control method. The method comprises the following steps that 1, users send a file access request of cloud storage to a cloud storage platform; 2, an intermediate server loads user security policy configuration information; 3, the intermediate server is relevant with a user access request according to the configuration information to generate a permission expression; 4, the intermediate server solves the permission expression by a permission judgment method; and 5, a storage server processes an operating request of the users on files according to a solving result of the expression. According to the method, loss caused by traversal and recursion is avoided, and the performance of a system is improved substantially by optimizing a permission verification mechanism and analyzing and solving the permission expression, so that usability and high efficiency of a safety access control technology are improved.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
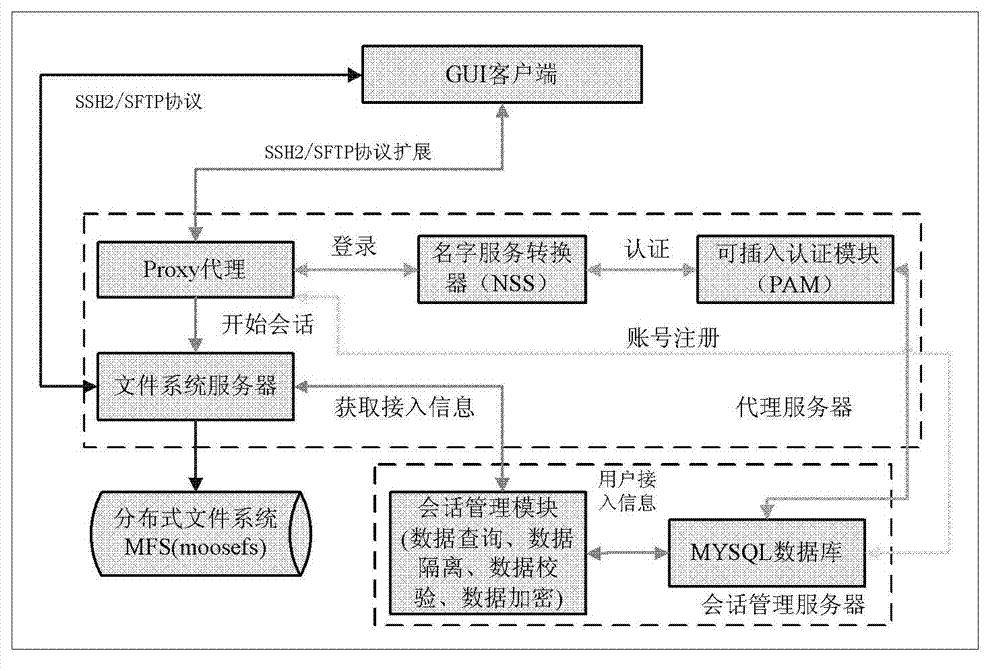
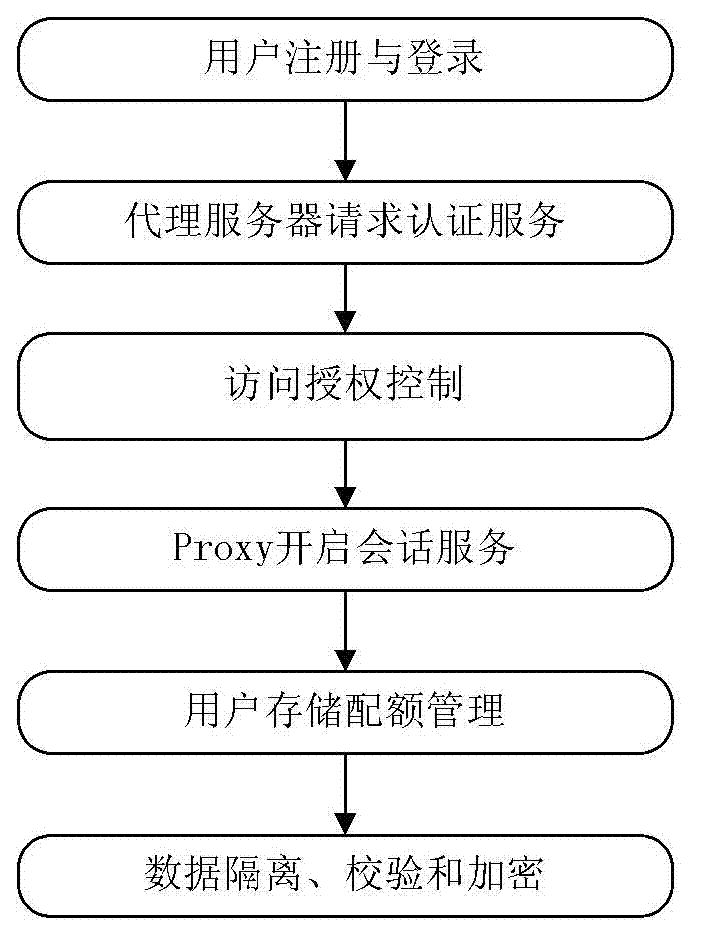
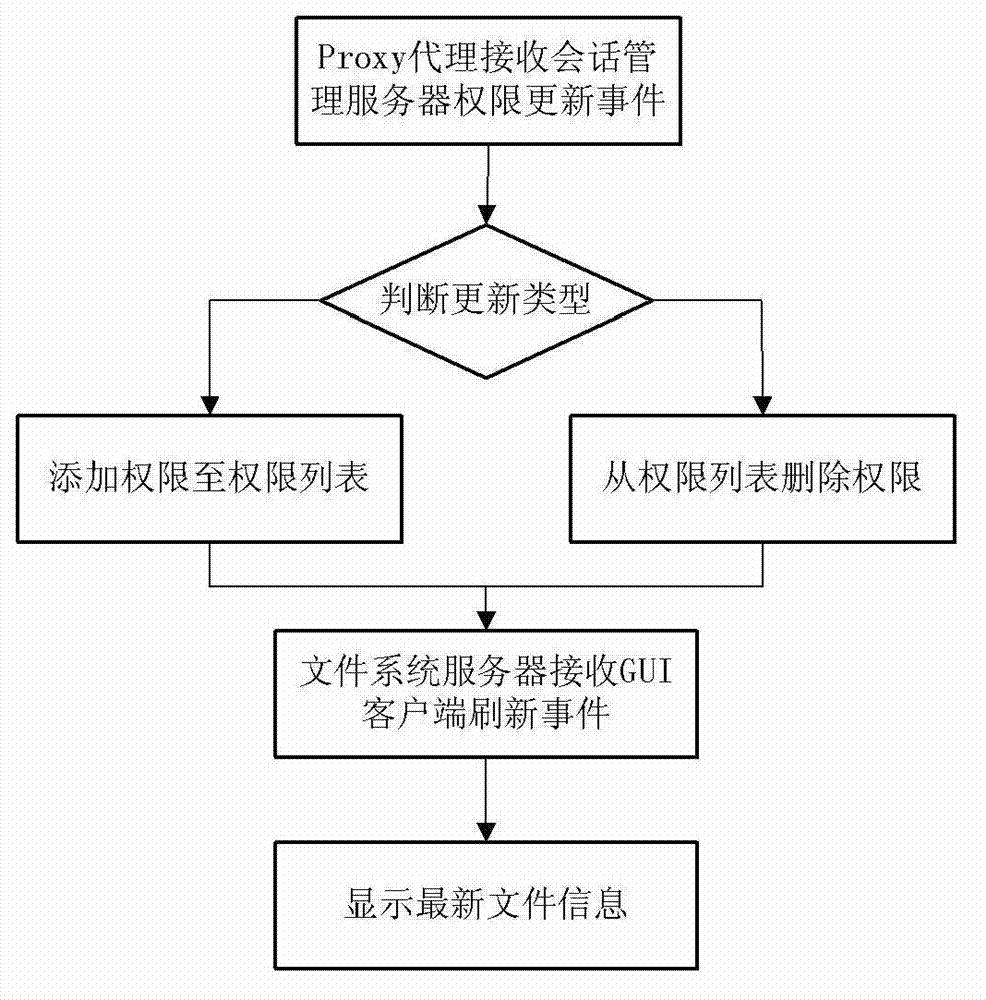
Safety management method of cloud memory system based on session management server
The invention discloses a safety management method of a cloud memory system based on a session management server. The safety management method comprises that registering and login are carried out by a user, a proxy server requests certification service, authorization control is accessed, session service is opened by a Proxy, the user stores quota management, and isolation, checking and encryption of data are conducted. Through the adoption of the safety management method, the user can safely manage and protect the data from a cloud memory system overall state, through the session management server, synchronous update and searching for user information and file system information are established between data bases, multi-user access and authorization management are supported, and the quota management of the user information is optimized, In addition, the function of data protection and recovery of users of the cloud memory system is finished based on a damaged data checking and isolation strategy of the session management server, and further, user data can be prevented from being falsified through data integrity checking and a reliable encryption mechanism.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI +1
Cloud storage data storage and retrieval method, device and system
InactiveCN102063587AImprove securityReduce lossesComputer security arrangementsTransmissionData retrievalData center
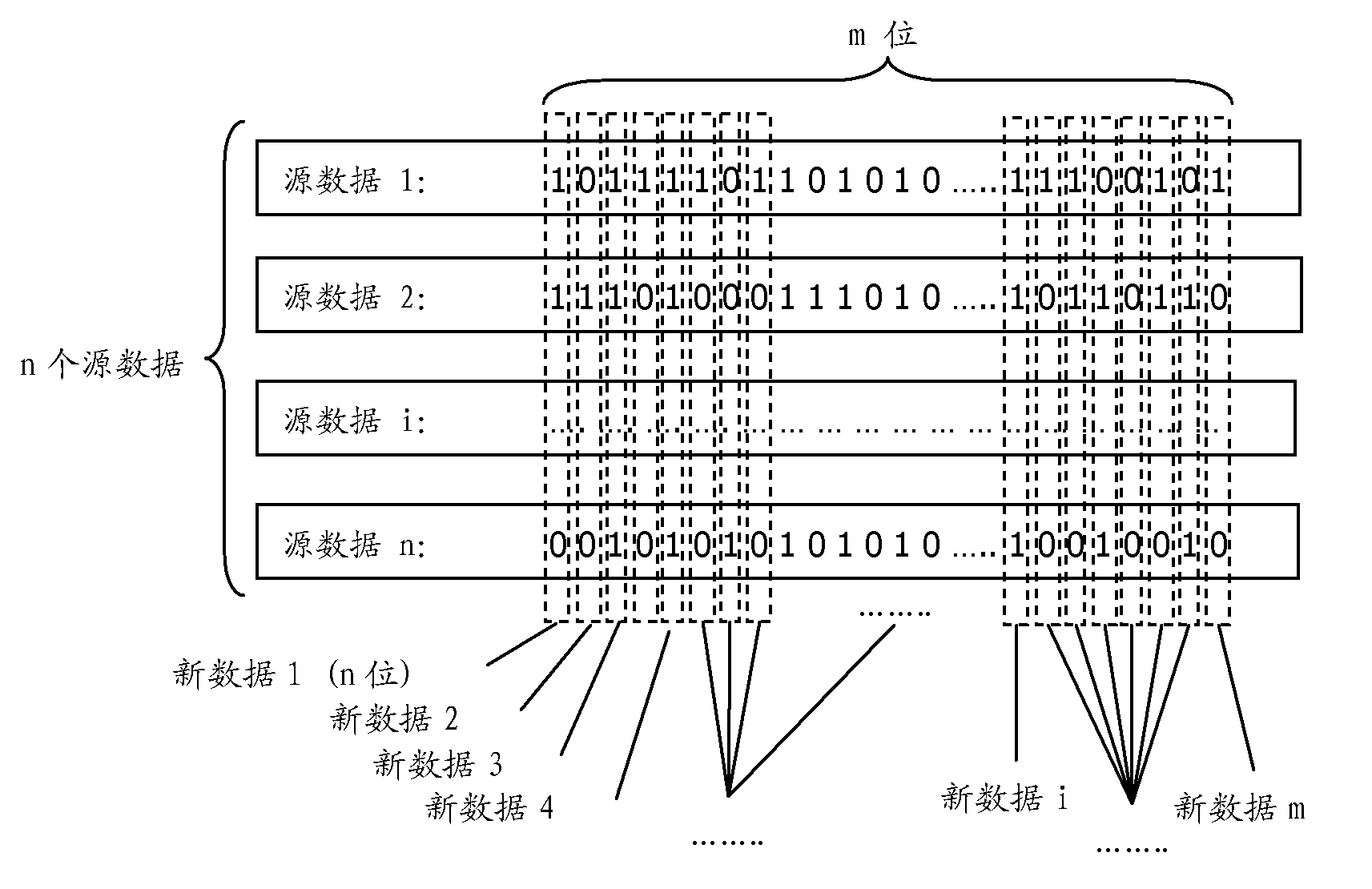
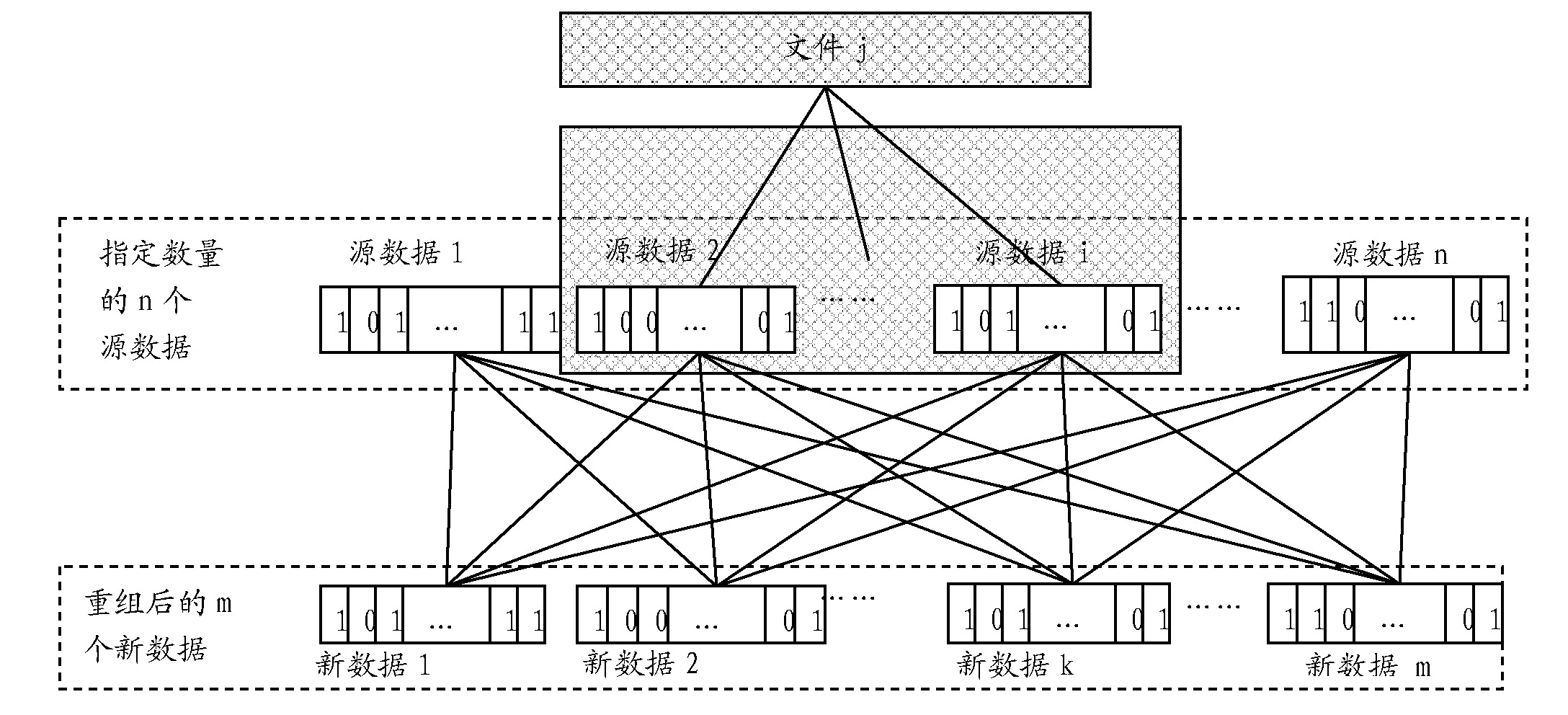
The invention relates to a cloud storage data storage and retrieval method, device and system, belonging to the technical field of cloud storage safety. The data storage method comprises the following steps: grouping source data to be stored according to a preset grouping policy; restructuring the content of the source data by taking the groups as units to form new data; and transmitting the new data to a cloud storage data center for storage. The data retrieval method comprises the following steps: retrieving the accessed data from the cloud storage data center according to an access request; acquiring data restoring information corresponding to the accessed data; and restoring the accessed data into the source data according to the data restoring information. The invention also provides the cloud storage data storage and retrieval device and system. The invention greatly improves the safety of data stored in the cloud storage data center and greatly reduces the possible loss for users caused by data leakage.
Owner:BEIJING Z & W TECH CONSULTING
Cloud storage method and system for file
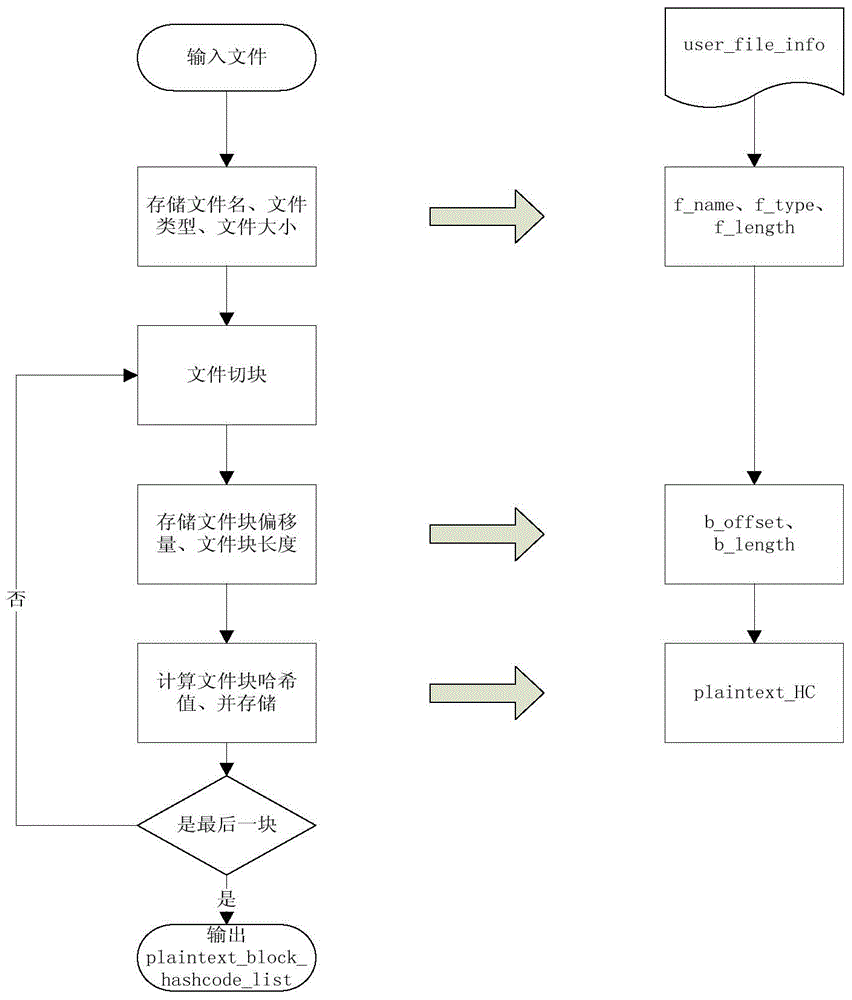
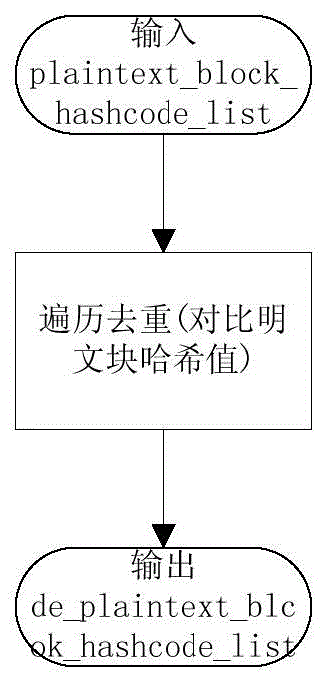
InactiveCN104902010AImprove securityImprove storage efficiencyTransmissionComputer hardwarePlaintext
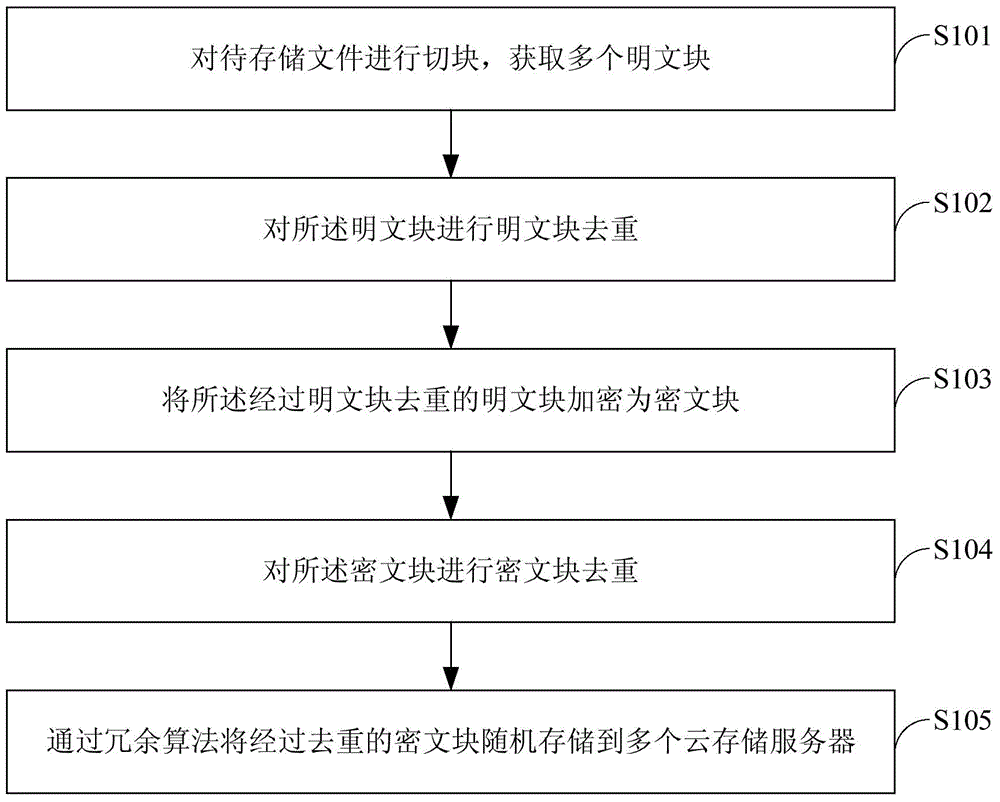
The invention is applied to the field of cloud storage, and provides a cloud storage method and system for a file. The method comprises the following steps: segmenting a file to be stored to obtain multiple plaintext blocks; performing plaintext block de-weighting on the plaintext blocks; encrypting the plaintext blocks subjected to the plaintext block de-weighting into cryptograph blocks; performing cryptograph block de-weighting on the cryptograph blocks; and storing the cryptograph blocks subjected to the de-weighting on multiple cloud storage servers through a redundancy algorithm. According to the embodiments of the invention, the multiple plaintext blocks are obtained through segmenting the file to be stored, the plaintext block de-weighting is performed on the plaintext blocks, the plaintext blocks subjected to the plaintext block de-weighting are encrypted into cryptograph blocks, the cryptograph block de-weighting is performed on the cryptograph blocks, and the cryptograph blocks are stored on the multiple cloud storage servers through the redundancy algorithm, such that the storage efficiency of cloud storage is improved through segmentation and de-weighing, and the cloud storage security is enhanced through encryption.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Dynamic adaptive secure cloud storage method considering node reliability
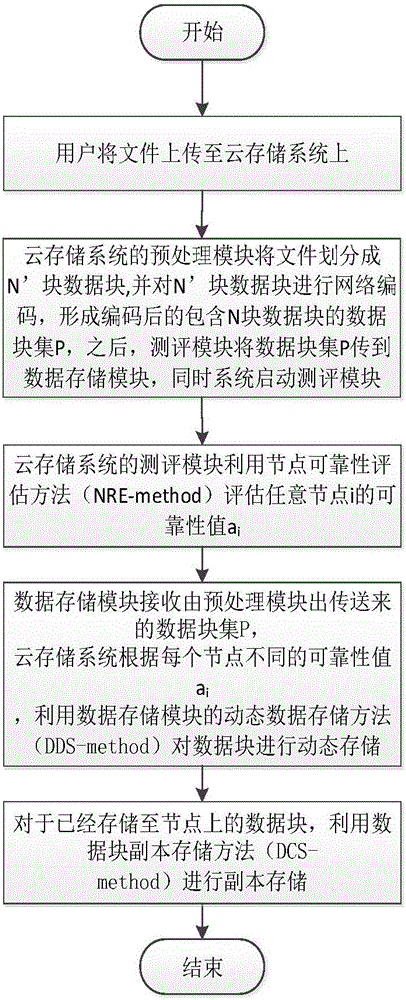
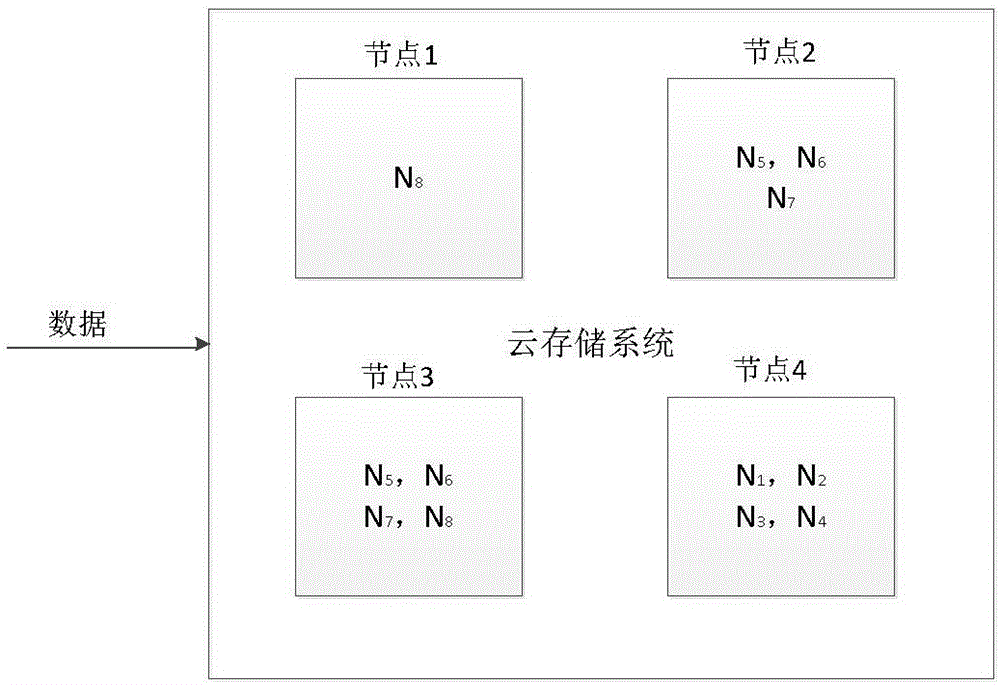
ActiveCN106230982AReduce the number of failuresNo need for copy storageData switching networksStorage securityCloud storage security
The invention belongs to the field of cloud storage security, and specifically relates to a dynamic adaptive secure cloud storage method considering node reliability. The method provided by the invention comprises the steps that a cloud storage system preprocesses a file uploaded to the cloud by using a preprocessing module; the cloud storage system detects any node by using an evaluation module through a node reliability evaluation method; and a data storage module receives a data block set sent by the preprocessing module. By adopting the method provided by the invention, the historical fault times of a cloud storage node can be detected, a reliability value is set for each node according to a detection result, and resources are dynamically distributed according to the reliability value, so that the data storage security is ensured while meeting the load balancing demand. Transcript storage is carried out on nodes with lower reliability values to ensure lower redundancy than pure copy, so that the storage cost is reduced.
Owner:HARBIN ENG UNIV
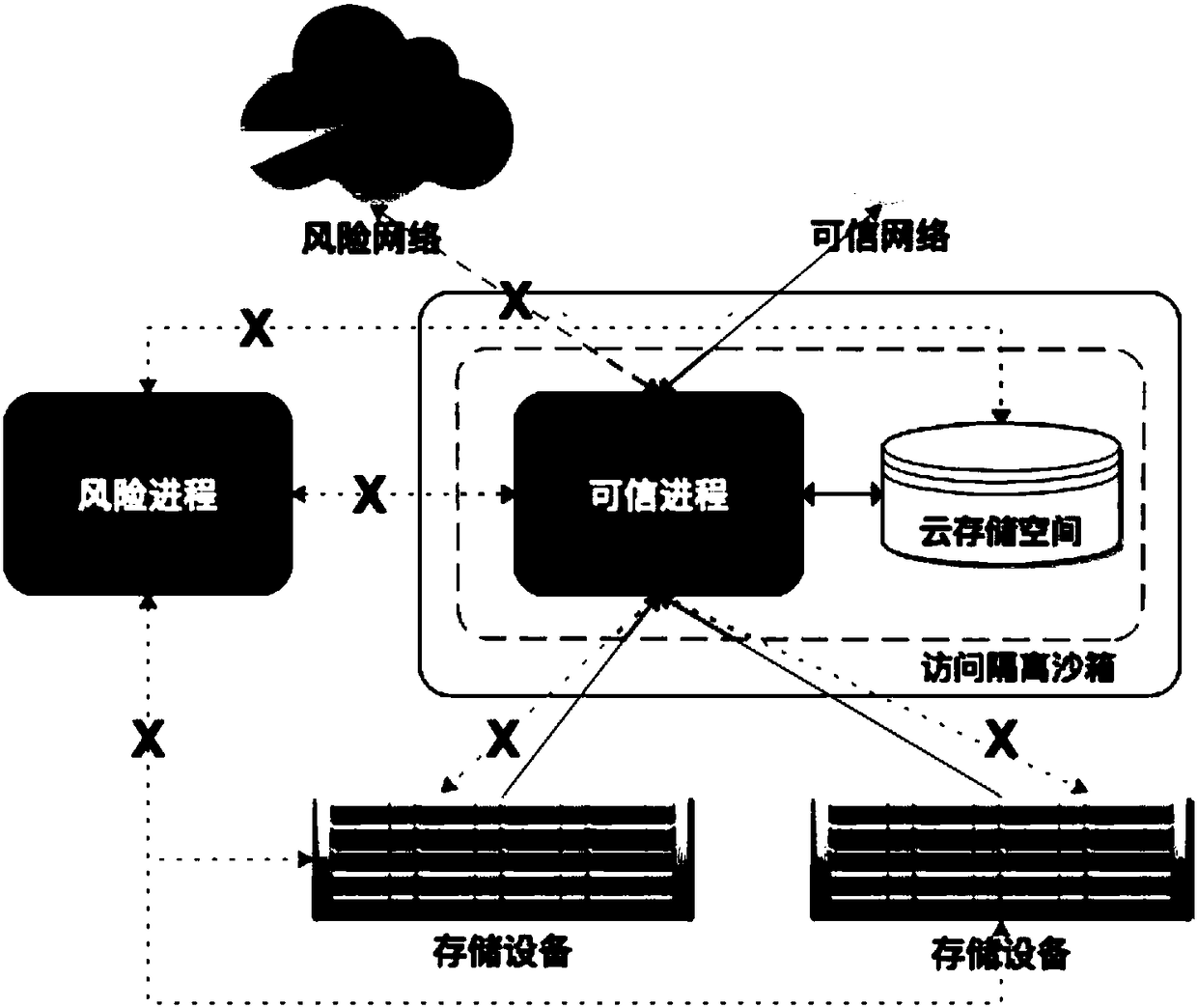
Cloud storage security access method based on sandbox technology
InactiveCN108133153ASecure AccessTroubleshoot access to storage resourcesInternal/peripheral component protectionStorage securityAccess method
The invention belongs to the technical field of cloud storage security, and particularly relates to a cloud storage security access method based on a sandbox technology. The method is applied to a cloud storage environment and implemented based on an access isolation sandbox under the cloud storage environment, and a cloud storage space and a trusted process module are arranged in the access isolation sandbox; compared with the prior art, the cloud storage security access method solves the problem of the cloud storage environment how to access storage resources safely and reliably. The accessisolation sandbox is introduced to restrict the use of trusted processes and cloud storage data and isolate a risk environment and risk processes, and thereby safeguarding the data security access under the cloud storage environment.
Owner:北京京航计算通讯研究所
Method, device and system for encrypting cloud storage data
ActiveCN102006300AReduce the amount of encryptionImprove performanceComputer security arrangementsSecuring communicationComputer hardwareCloud storage security
Owner:BIGKNOW (BEIJING) DATA TECH CO LTD
Safe data storage method
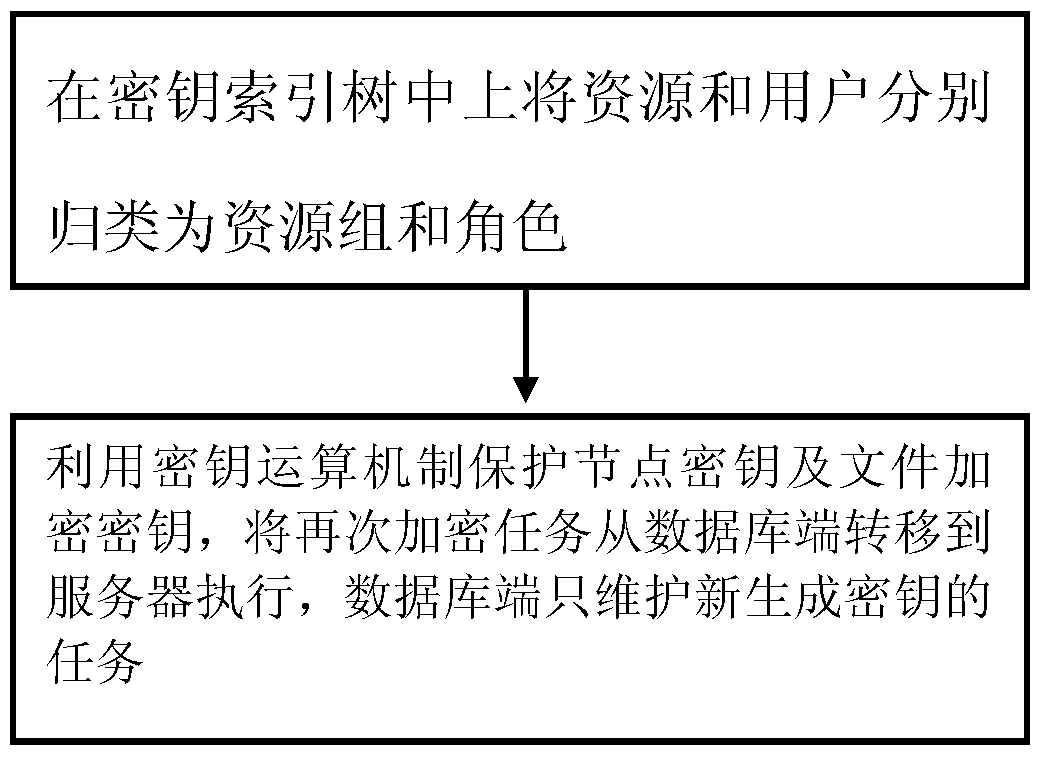
InactiveCN104811448AReduce complexityReduce overheadKey distribution for secure communicationEncryptionCloud storage security
The invention provides a safe data storage method. The safe data storage method comprises the following steps of respectively classifying resources and users into a resource group and characters in a secret key index tree, protecting a node key and a file encryption key through a key calculation mechanism, transferring an once more encryption task from a data base terminal to a server to be executed and enabling the data base terminal to maintain a new generated key task. The safe data storage method further reduces cloud storage safety performance costs effectively, reduces the maintenance quantity of the data base terminal and establishes an effectively key and a data updating strategy.
Owner:GUANGXI POWER GRID CORP
File cloud storage security solution method and system
InactiveCN105871892ASolve confidentiality issuesImprove securityTransmissionSoftware engineeringCloud storage security
The invention provides a file cloud storage security solution method and system. The method is divided into two parts, namely encryption and decryption. The encryption method includes the steps that a computer is loaded with a softdog, a file encryption secret key in the softdog is obtained in an authentication mode, the secret key is utilized to conduct encryption on a file required to be encrypted, and the encrypted file is unloaded to a cloud server. The decryption method includes the steps that the cloud server is started, the encrypted file is downloaded, a local computer is loaded with the softdog, the file encryption secret key in the softdog is obtained in an authentication mode, the encrypted file is decrypted through the secret key, and the original file is obtained. By means of the file cloud storage security solution method and system, the file can be encrypted to the maximum degree and protected against losses.
Owner:BEIJING UNION UNIVERSITY
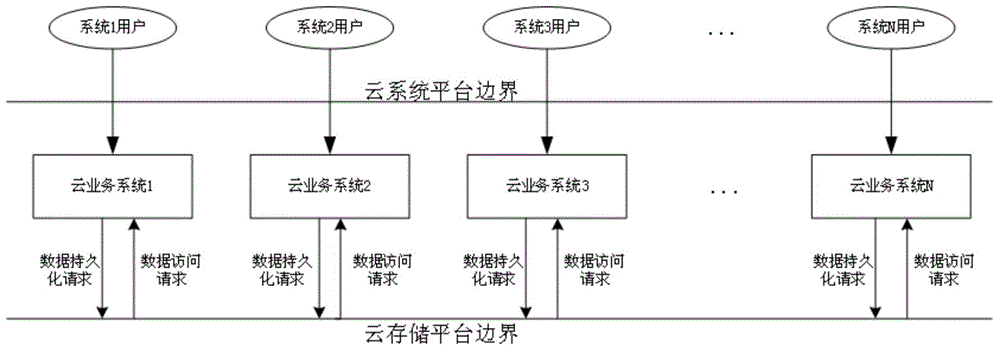
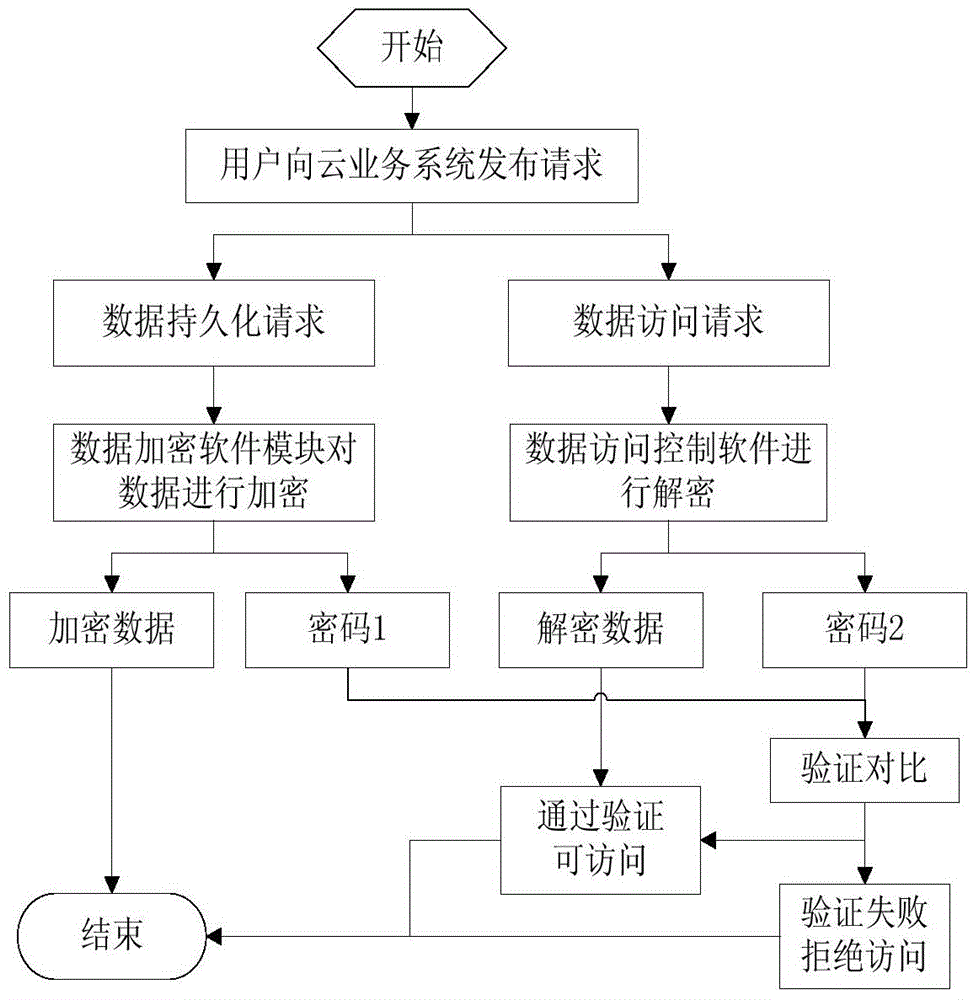
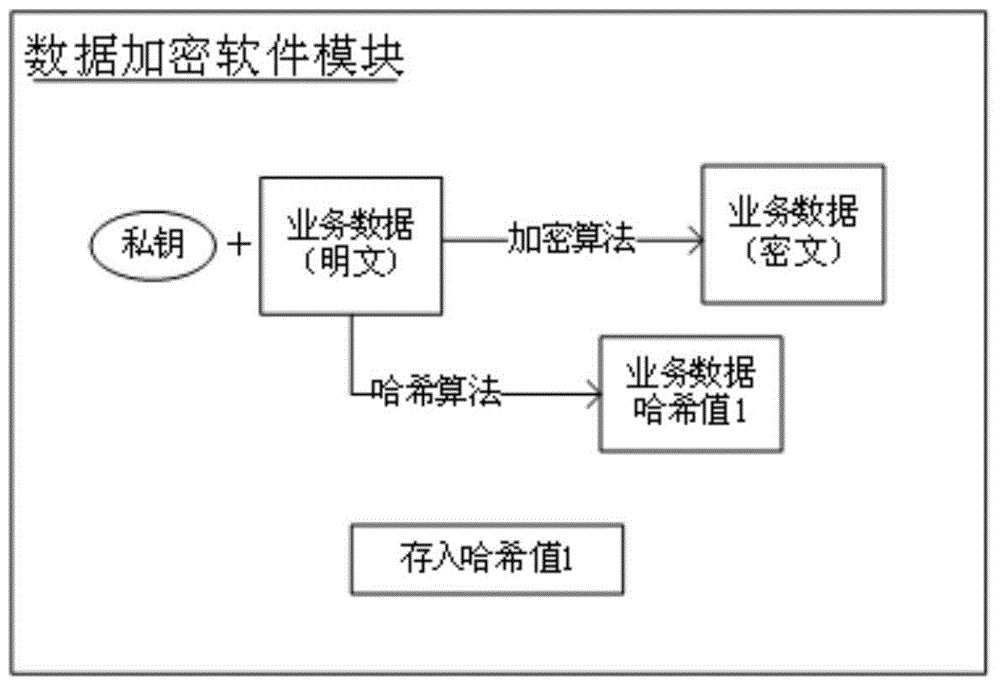
Cloud storage security realization method based on data encryption and access control
The invention provides a cloud storage security realization method based on data encryption and access control. The method comprises the following steps: when a user issuing a data persistence request to a cloud service system, the service system transmitting the data persistence request to a cloud storage platform, a data encryption software model performing encryption processing on data, and finishing data storage; when the user issues a data access request to the cloud service system, the service system transmitting the data access request to the cloud storage platform, a data access control software module performing access control on access data to determine whether to the data access request is allowed, and if the data access request is allowed, allowing access to the data after encryption; and if the access is allowed, ending the access so as to ensure the security of the data stored by the user in the cloud storage platform in a distributed mode. According to the invention, the encryption processing and the access control are performed on the data so that the data between systems of a cloud platform rejects mutual access, and thus the data security is guaranteed.
Owner:STATE GRID CORP OF CHINA +1
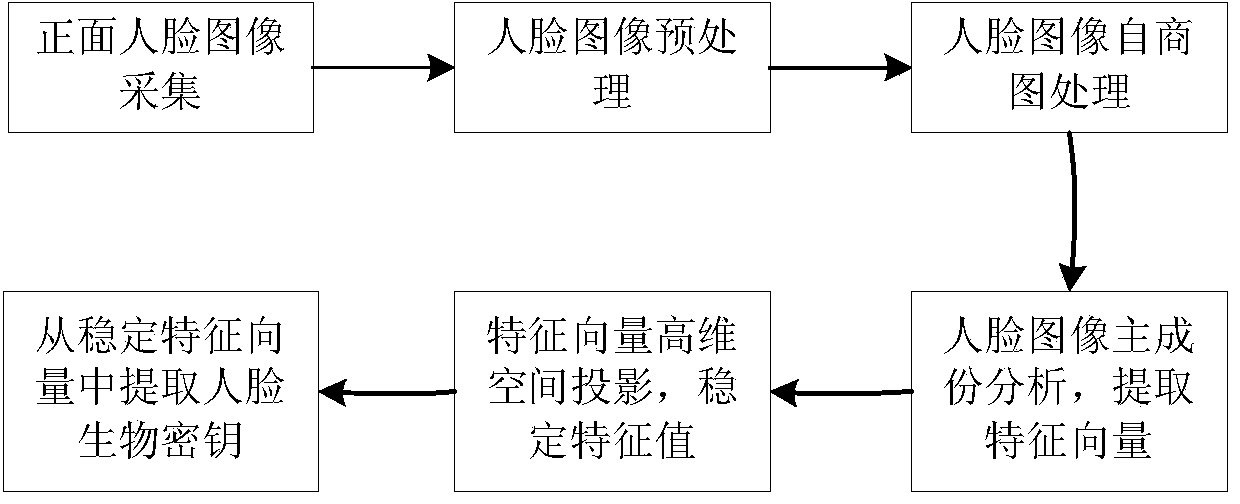
Face image biological key generating method
ActiveCN103886235AChanging the network biometric authentication modeCharacter and pattern recognitionDigital data authenticationFeature vectorCloud storage security
The invention provides a face image biological key generating method. The face image biological key generating method includes steps of subjecting face images of users to characteristic space conversion, projecting the face images into a higher space, stabilizing facial feature information into an acceptable fluctuation range in the higher space, extracting digital sequences from stabilized feature vectors, and encoding in the digital sequences to generate a biological key. By adopting the face image biological key generating method, no face information of the users is required to be stored in mobile terminals and identification servers, and the face images of the users are also dispensed with transmission in the network. The users generate (user names and secret keys) pairs by acquiring the face images of their own and perform network identity authentication by various authentication methods derived from the (user names and secret keys) pairs. The private data of the users are subjected to direct encipherment protection by the method supporting the face biological secret key, and the method can be extended to application in the field of cloud storage safety. As long as key space of the face biological secret keys is larger enough, high safety can be guaranteed.
Owner:HANGZHOU DIANZI UNIV
Efficient searchable symmetric encryption method and system with forward and backward security
ActiveCN110457915AAchieving Retrieval ComplexityEfficient retrievalDigital data protectionOther databases indexingCiphertextCloud storage security
Owner:HUAZHONG UNIV OF SCI & TECH +1
Data possession proof scheme
ActiveCN105227549AImprove execution speedImprove securityTransmissionThird partyCloud storage security
The invention discloses a data possessionproof scheme, belonging to the field of information security and being suitable for a cloud storage security management technology. In the scheme, a key generation module, a label generation module, a challenge module, a proof generation module and a verification module are included. The scheme only needs addition, subtraction, multiplication and modular arithmetic and supports modification and additional operations of data blocks, data possession proof of multiple duplicates and third-party verifiable data possessionproof. The scheme disclosed by the invention has the advantages of high security, low computational expense and low requirements for storage space and traffic, and provides a new research orientation for developing the data possession proof scheme.
Owner:SHANGHAI GUAN AN INFORMATION TECH
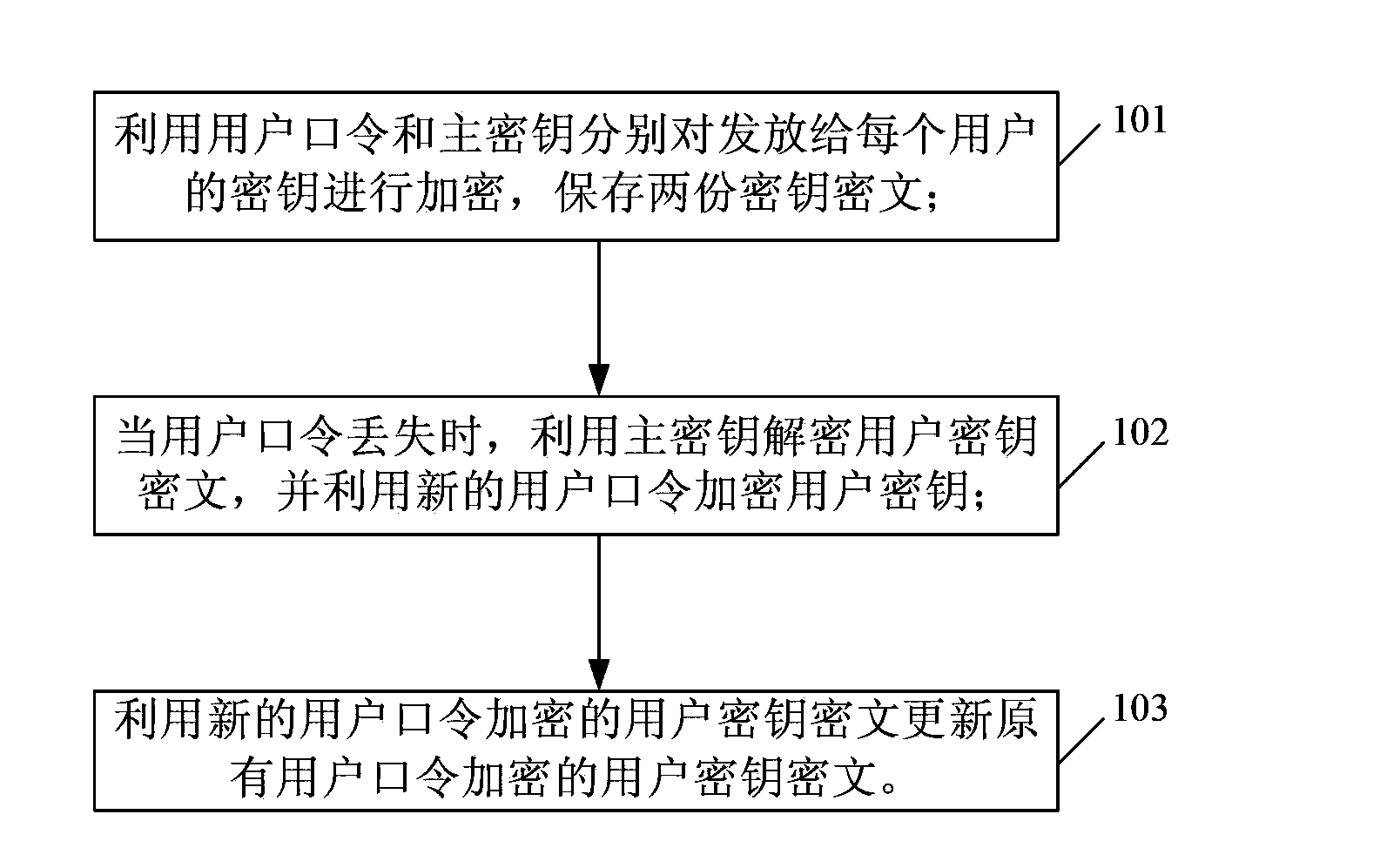
Cloud storage safety control method
Disclosed is a method for security control of cloud storage, which ensures the security of a cloud storage key. The method includes: encrypting a key issued to each user using a user password and a master key respectively, and storing two pieces of key ciphertext; when the user password is lost, decrypting the user key using the master key, and encrypting the user key using a new user password; and updating the user key ciphertext which is encrypted by the original user password using a piece of user key ciphertext which is encrypted by the new user password.
Owner:北京书生信息技术有限公司
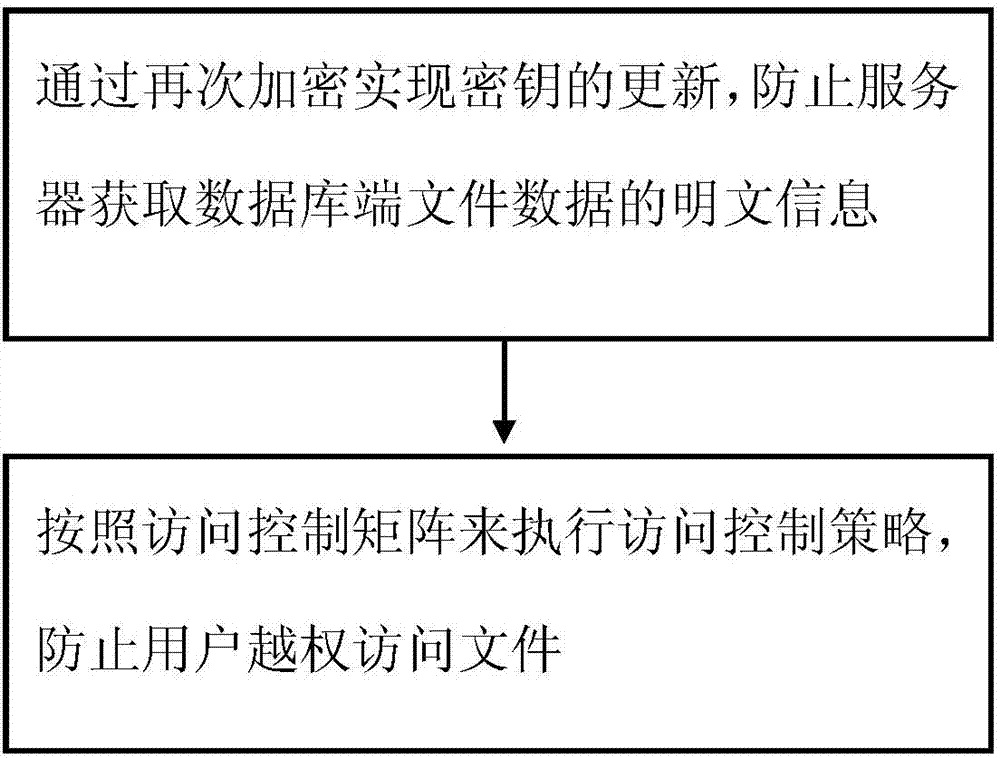
Safe content access method
The invention provides a safe content access method used for encrypting a file in a cloud computing environment. The safe content access method comprises the following steps: updating a secrete key through re-encryption to prevent a server from acquiring the plaintext information of file data of a database side; executing an access control policy according to an access control matrix to prevent a user from performing unauthorized file access. According to the safe content access method, the safety performance cost of cloud storage is further safely and effectively reduced, the maintenance quantity of the database side is decreased, and an efficient secrete key and data updating policy is constructed.
Owner:成都创屹远景科技有限公司
Cloud storage encryption method, device and equipment and storage medium
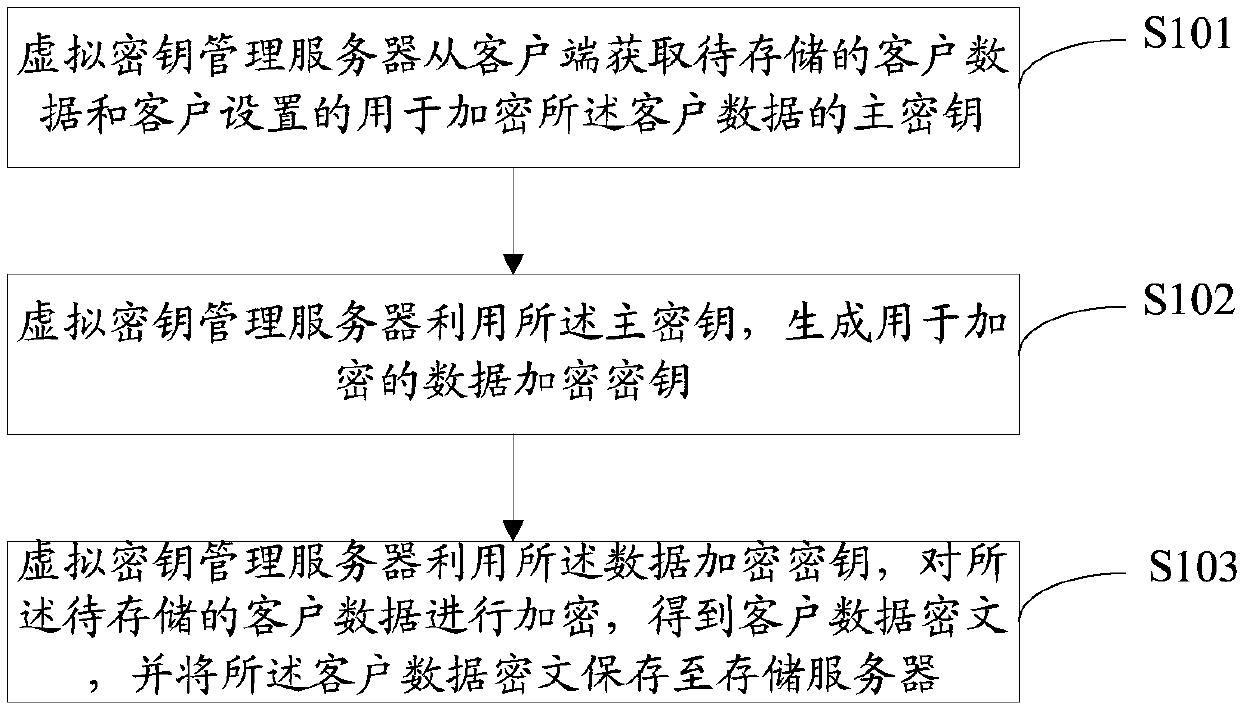
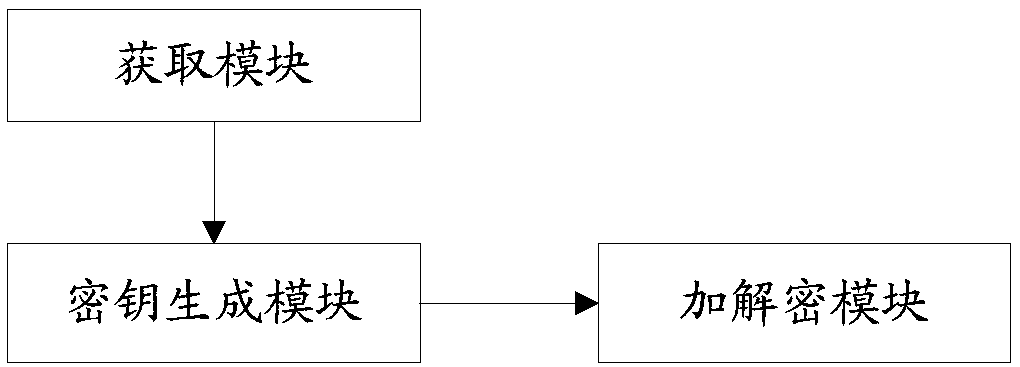
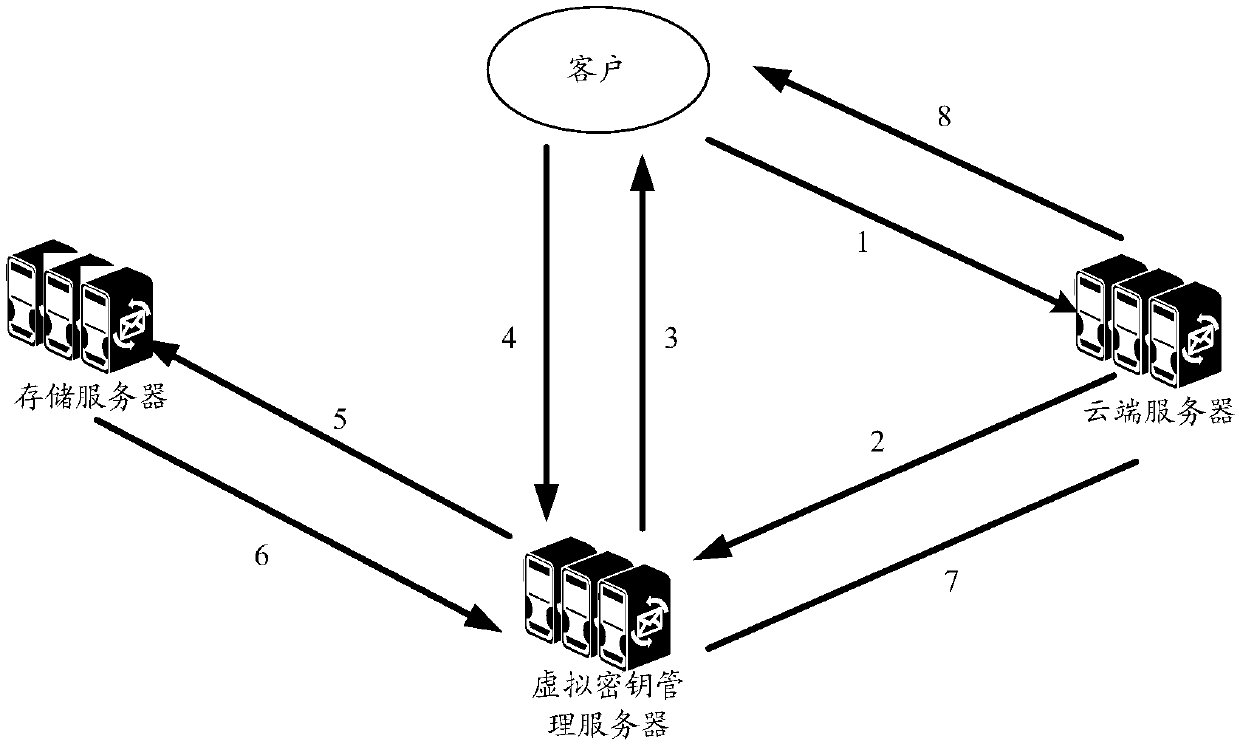
The invention discloses a cloud storage encryption method, device and equipment and a storage medium, and relates to the field of data encryption of a cloud computing data center, the method comprisesthe following steps: a virtual key management server acquires client data to be stored and a master key set by a client and used for encrypting the client data from a client; The virtual key management server generates a data encryption key for encryption by using the main key; And the virtual key management server encrypts the client data to be stored by using the data encryption key to obtain aclient data ciphertext, and stores the client data ciphertext to a storage server. Based on the cloud computing virtualization technology and the data encryption technology, the embodiment of the invention can effectively manage the secret key for encryption, improve the authentication security and the secret key security of the cloud computing data center, and improve the cloud storage securityof the cloud computing data center.
Owner:ZTE CORP
Cloud storage security deduplication method and device based on Merkel hash tree
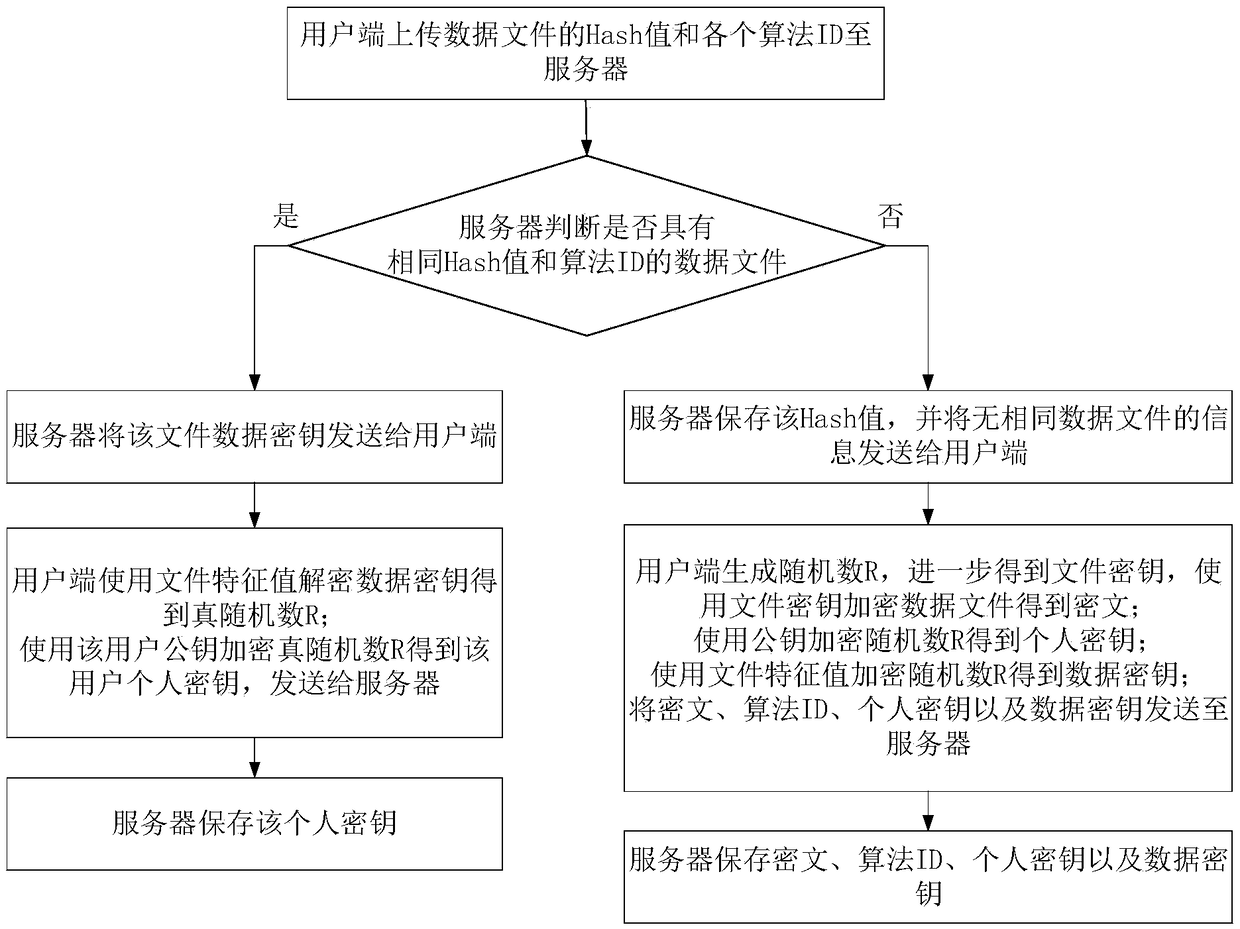
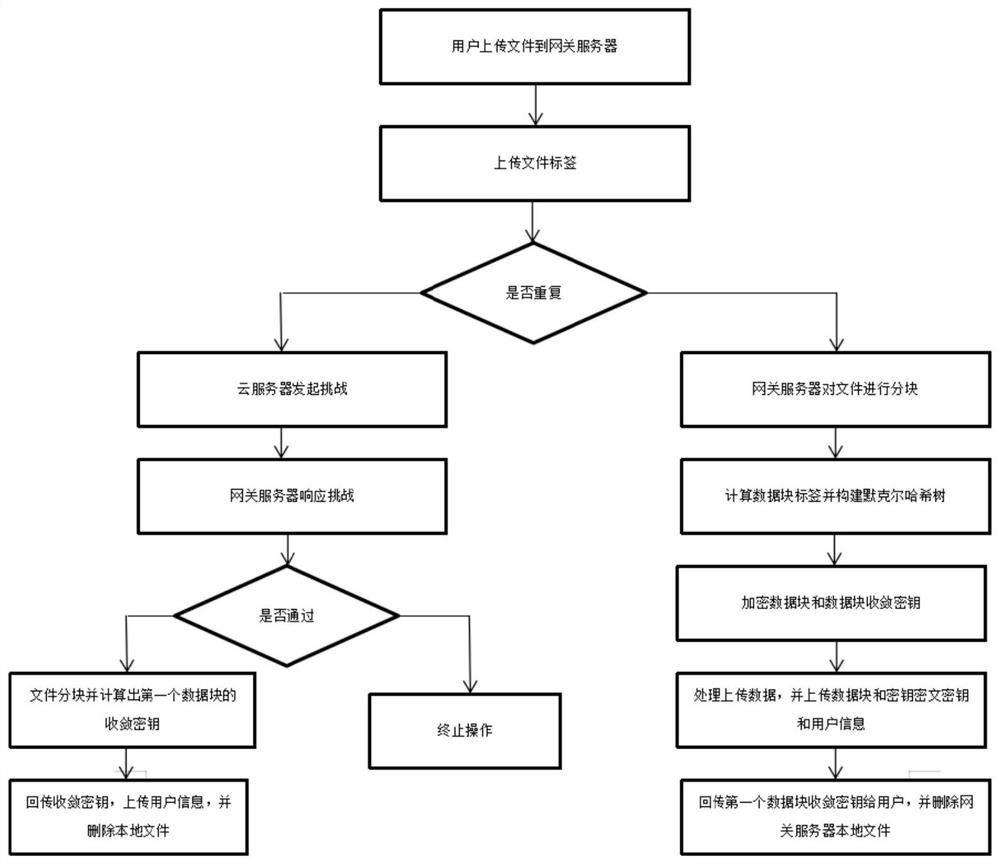
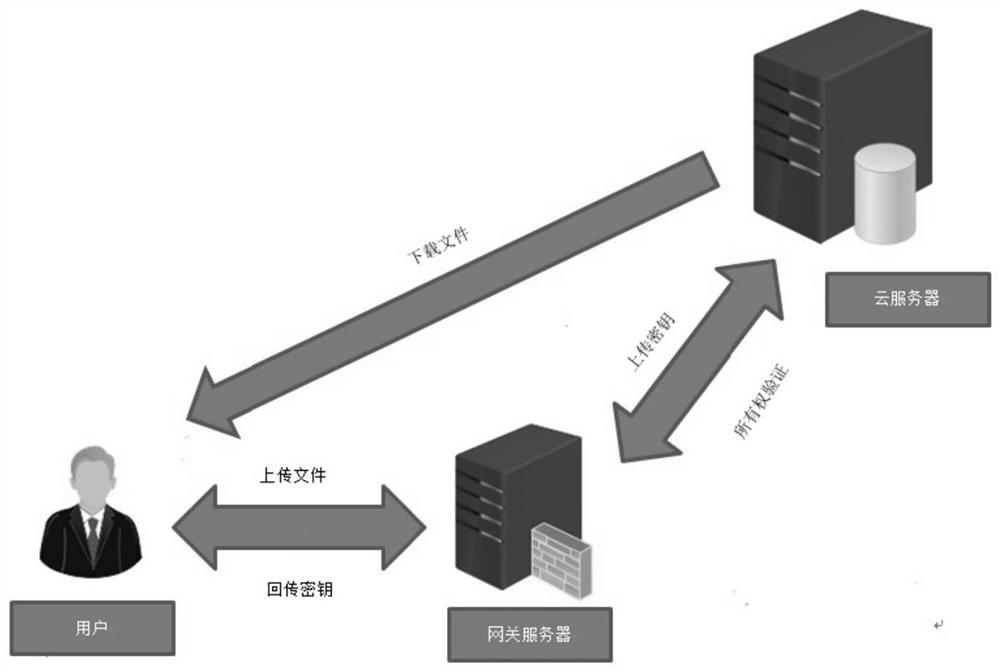
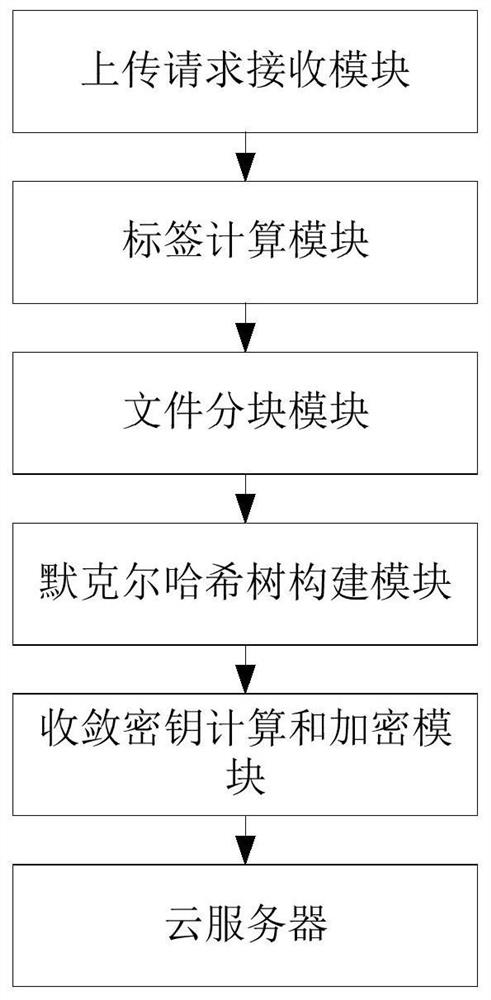
PendingCN112565434AReduce in quantityReduce sizeInput/output to record carriersTransmissionUser verificationCloud storage security
The invention provides a cloud storage security deduplication method based on a Merkel hash tree, and the method comprises the steps that a gateway server calculates a label of a to-be-uploaded file,and uploads the label to a cloud server; the cloud server judges whether the uploaded label exists or not; if so, the cloud server operates an ownership certification protocol to carry out ownership verification, and the cloud server data is allowed to be accessed only after the user passes the verification; and if not, the gateway server blocks the file to be uploaded into n data blocks, constructs a Merkel hash tree, converges key calculation and encrypts. The invention provides a cloud storage security deduplication method based on a Merkel hash tree and a gateway server, the gateway serveris erected between a user and the cloud server to carry out the flow confusion of an uploaded file, so as to resist an attacker; and valuable information is obtained from private data uploaded by a user through a honest and curious server by adopting a key chain mechanism, and meanwhile, the quantity and the size of files locally stored by the user are reduced.
Owner:GUANGDONG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com