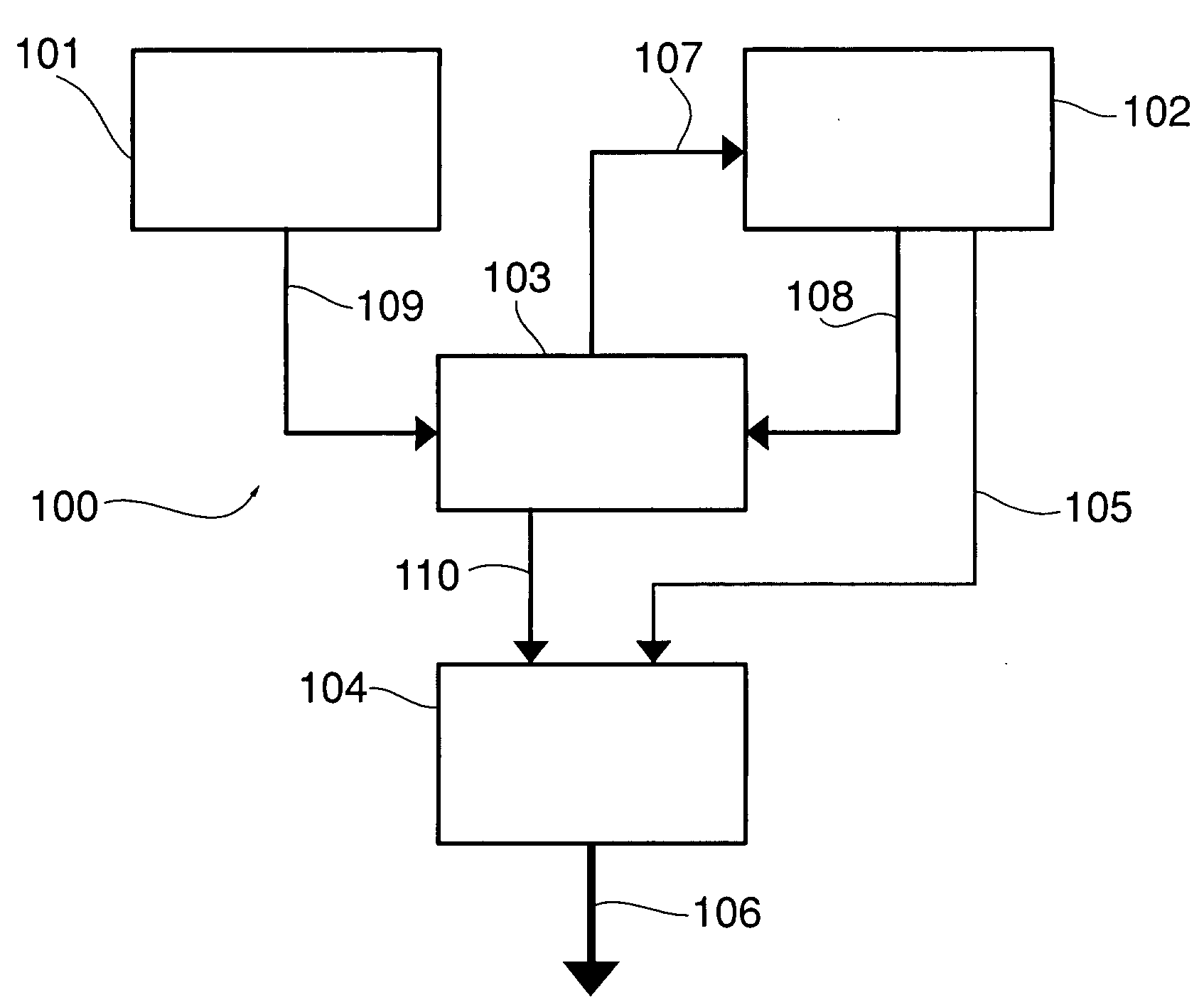
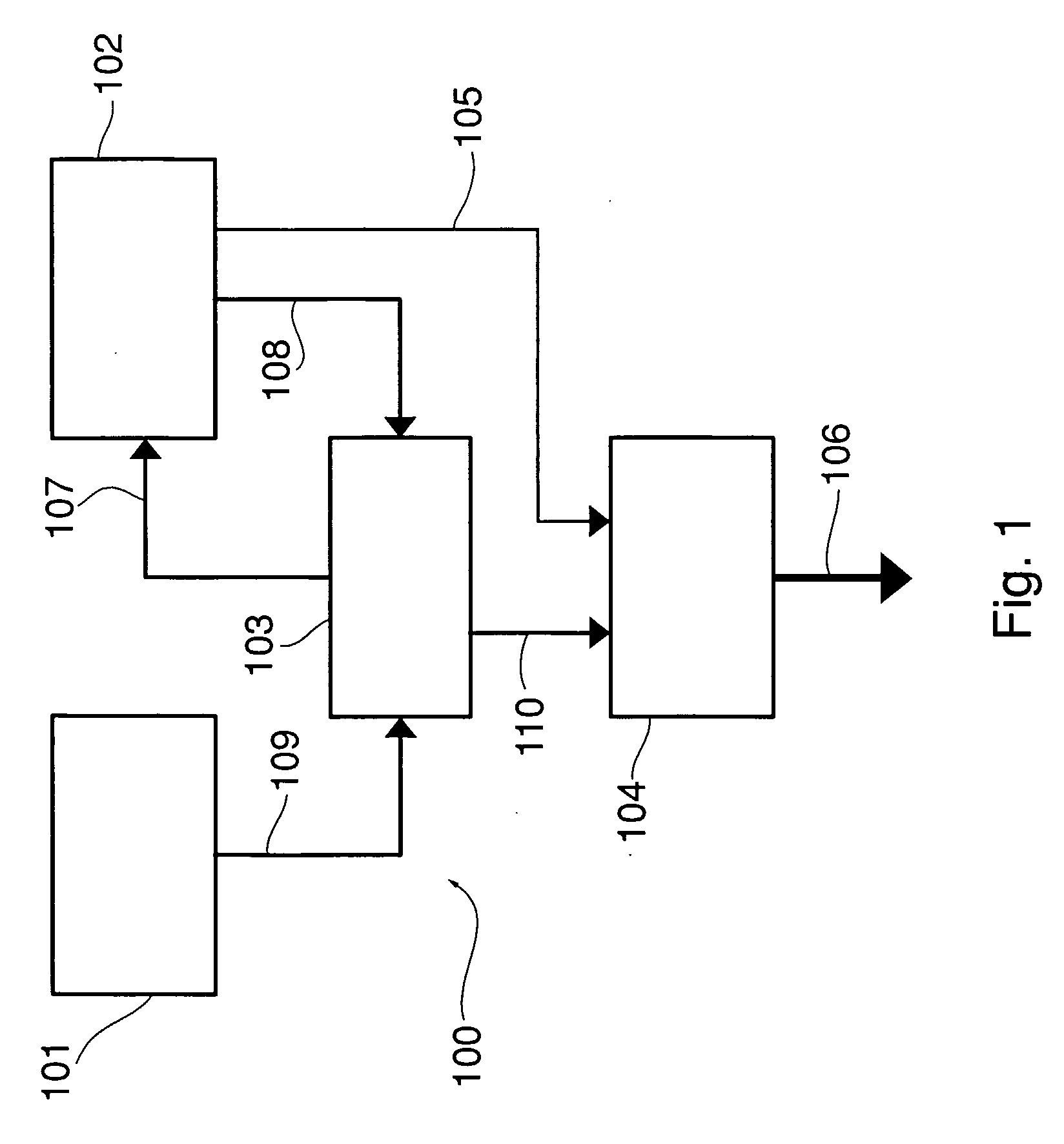
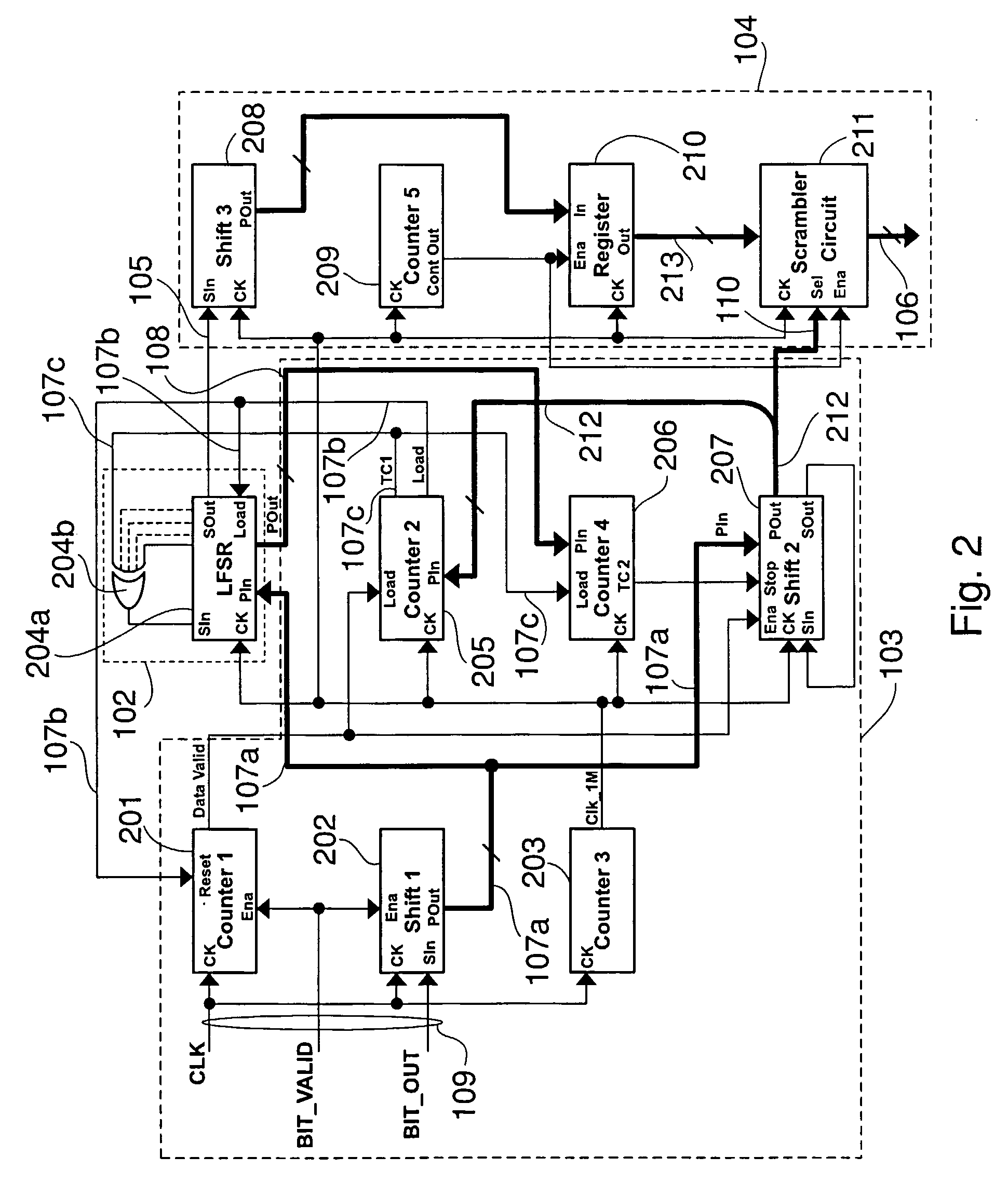
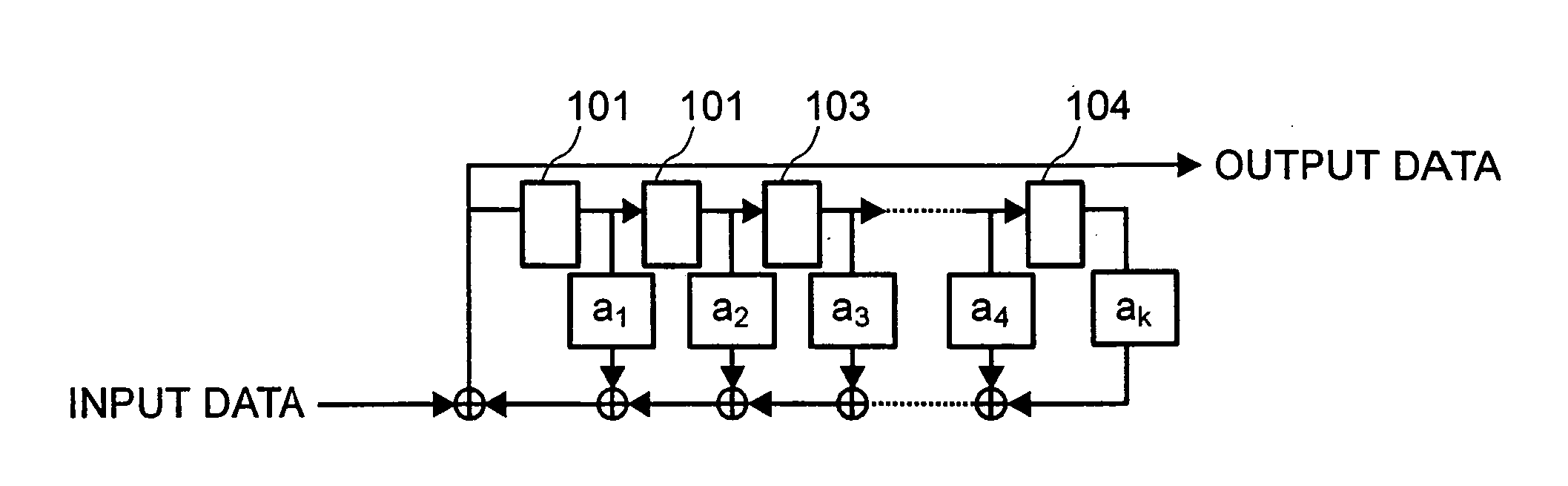
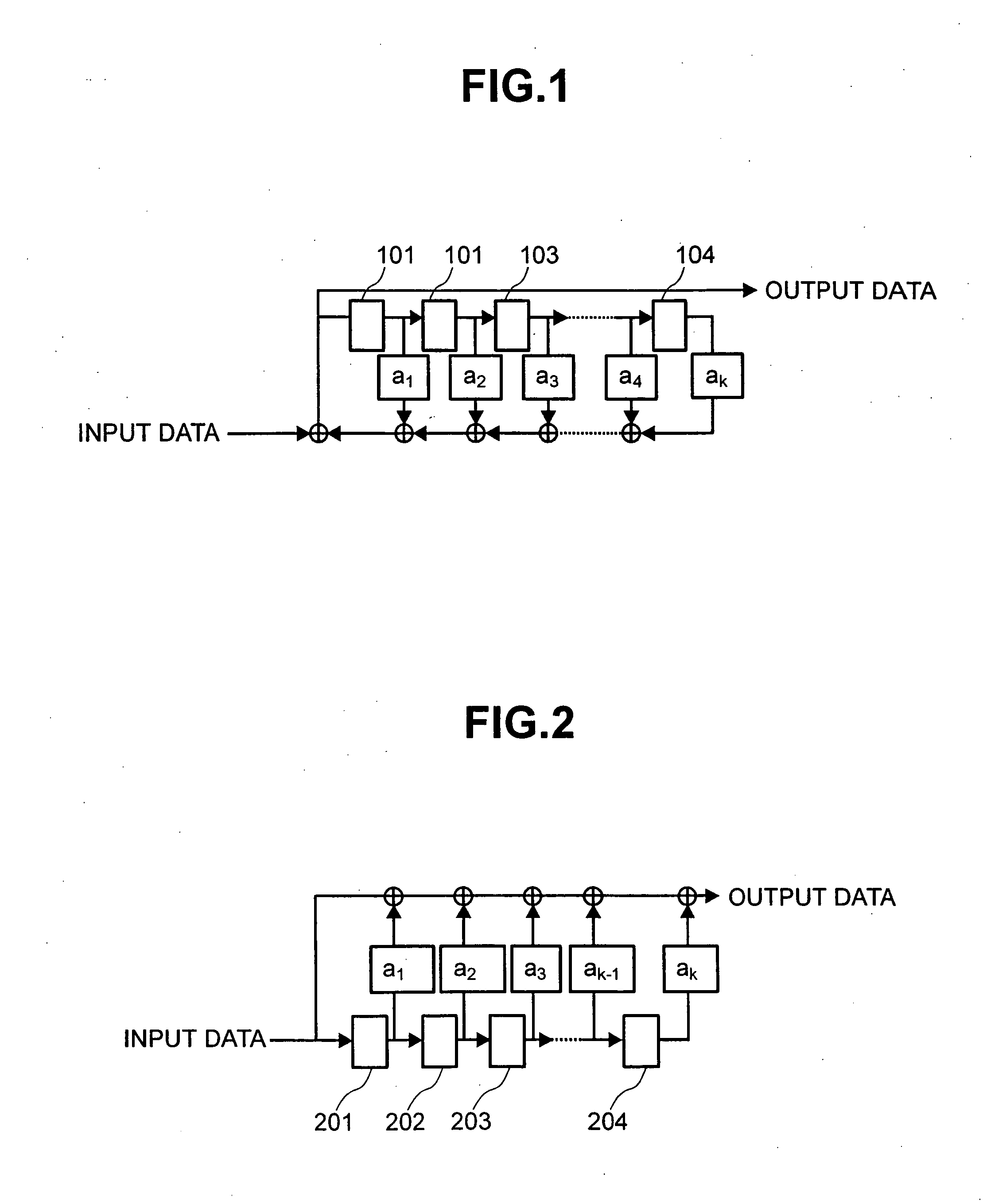
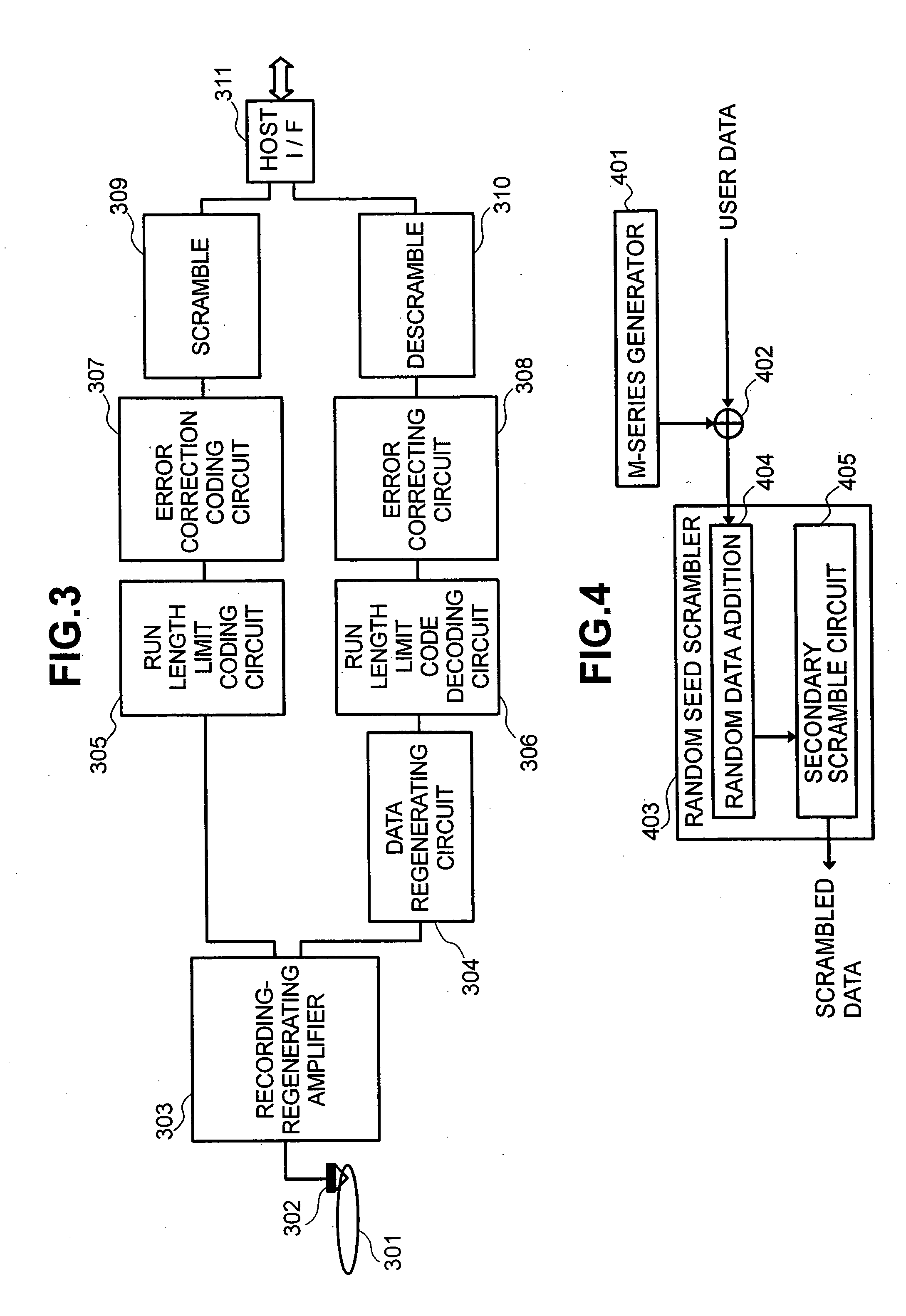
Patents
Literature
327 results about "Random seed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A random seed (or seed state, or just seed) is a number (or vector) used to initialize a pseudorandom number generator. For a seed to be used in a pseudorandom number generator, it does not need to be random. Because of the nature of number generating algorithms, so long as the original seed is ignored, the rest of the values that the algorithm generates will follow probability distribution in a pseudorandom manner.
Interactive Electronic Book Operating Systems And Methods
ActiveUS20080222552A1High interactive representationRich book effectDigital data processing detailsDigital computer detailsOperational systemRandom seed
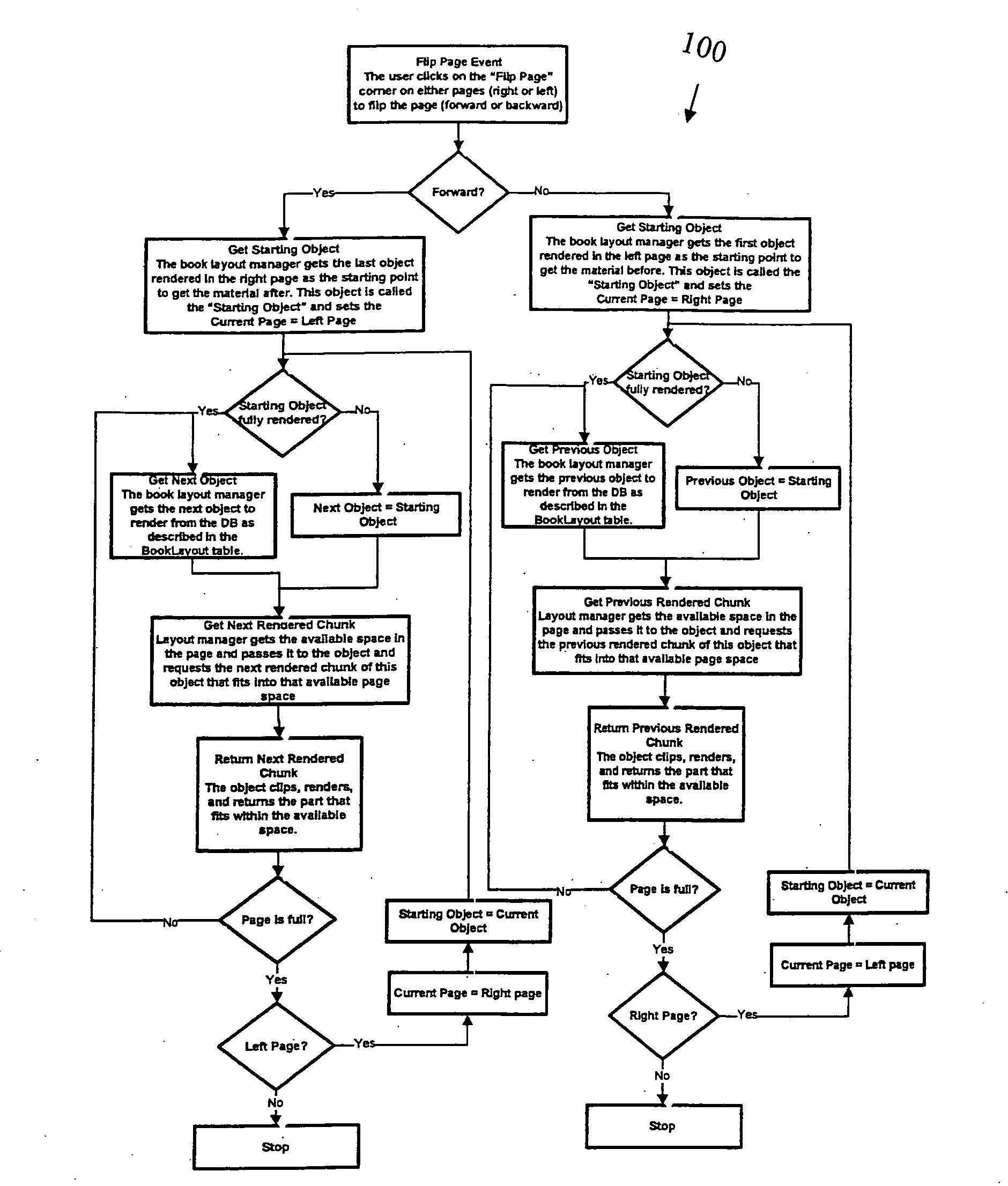
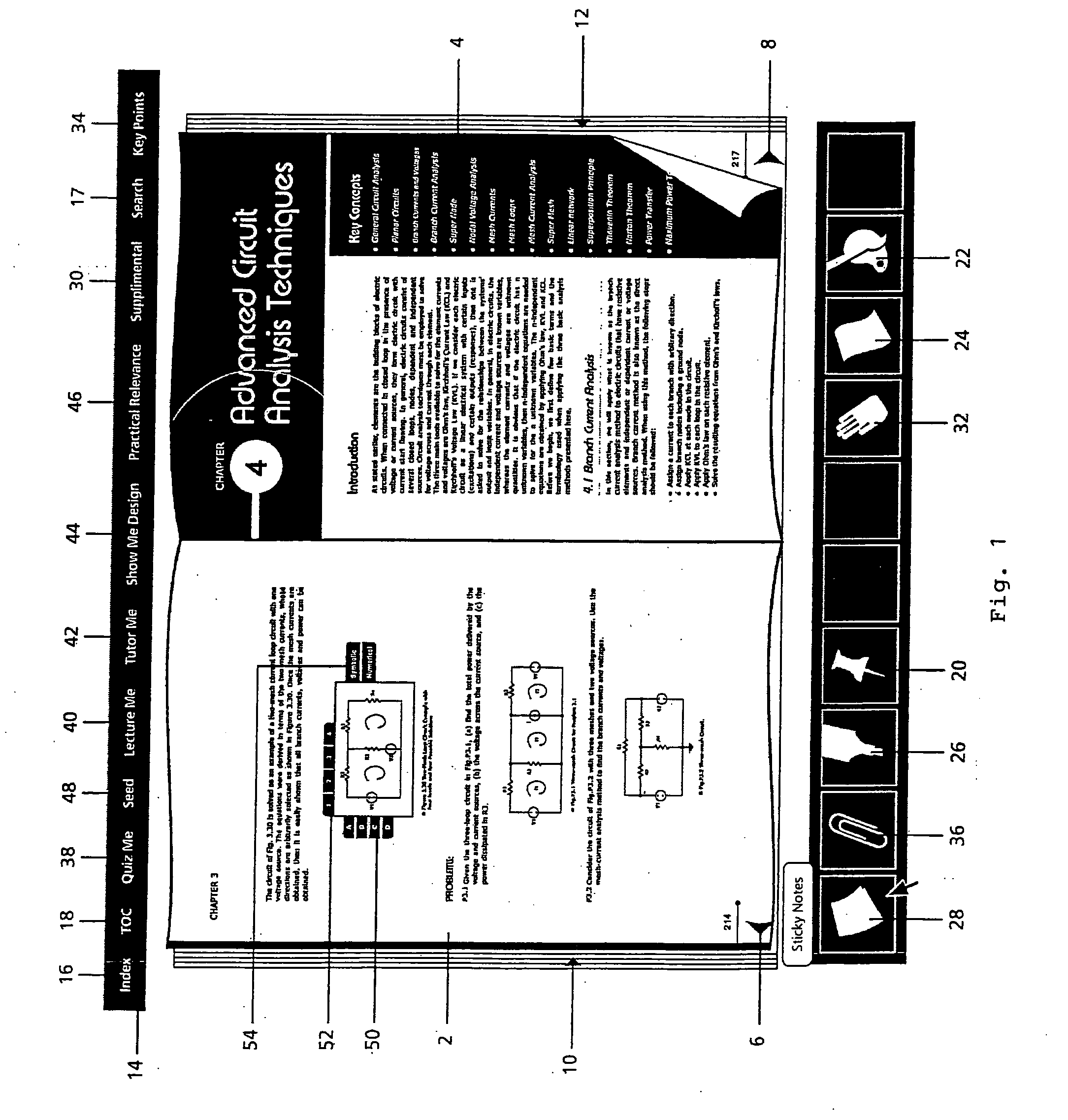
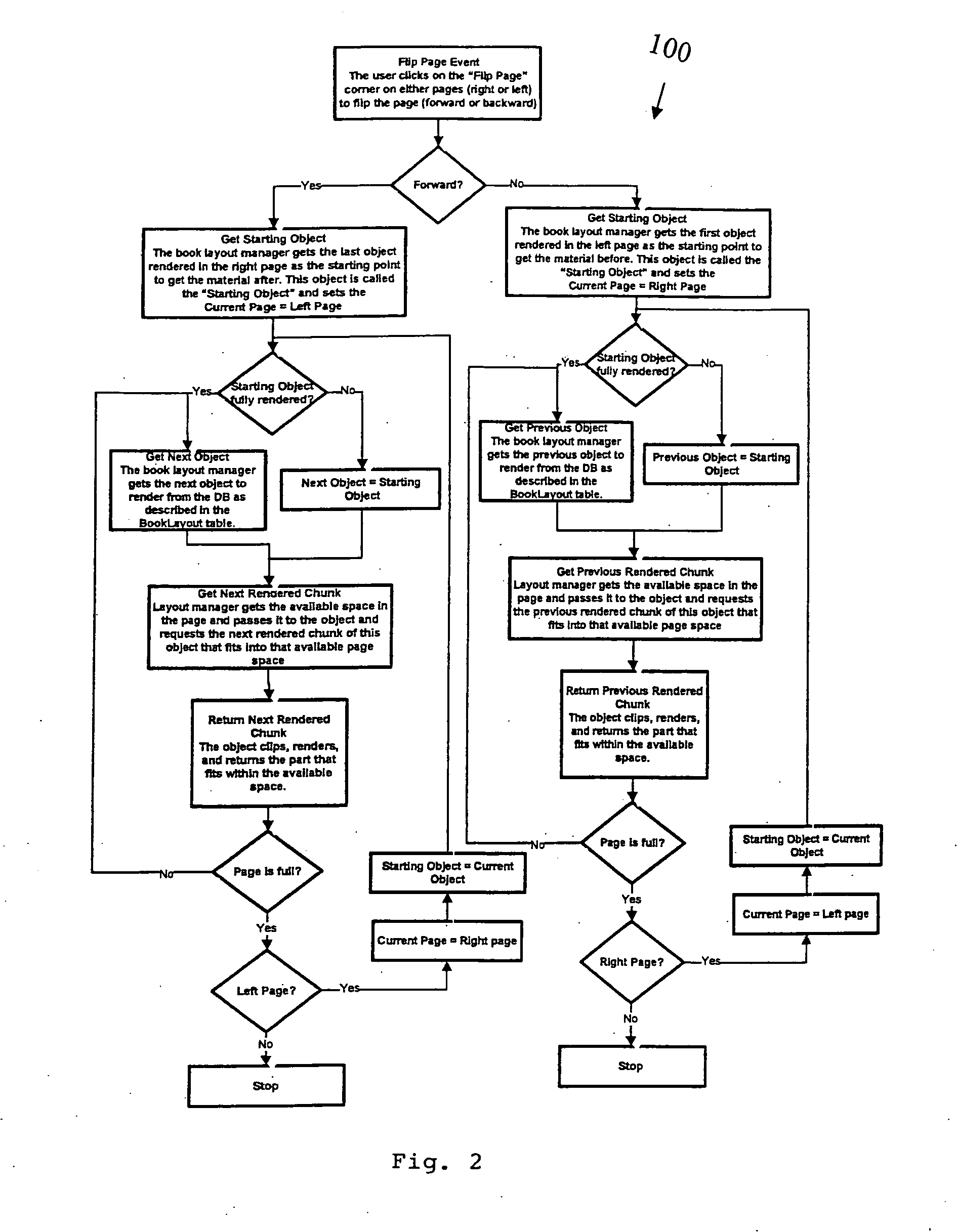
Interactive electronic book operating systems and methods for displaying and allowing customization of content of scientific, engineering and other technical and professional digital books. The systems and methods allow for a single screen for displaying digital books covering scientific and technical topics having a classical look and feel on operating platforms(such as portable laptops, desktops, and small handheld displays) that are capable of running the Java Virtual Machine. The display screen can include icon toolbars about the screen and / or directly on the screen to manipulate the pages and content of the digital book. The icons can allow for forward and backward page turning, generating of dynamic indexing and tables of contents, bookmarking, color themes, floating pages, highlighting, adding sticky notes, hiding selected content on the pages, quizzing the reader, lecturing the reader, tutoring the reader, showing the reader additional designs and practical relevance, and allowing the instructor to generate uniform seed numbers for problems and designs and / or allowing the instructor to generate random seed values for problems and designs.
Owner:UNIV OF CENT FLORIDA RES FOUND INC
Cloud Storage Data Encryption Method, Apparatus and System
InactiveUS20120134491A1Reduced strengthReduce the amount of dataComputer security arrangementsSecret communicationComputer hardwarePlaintext
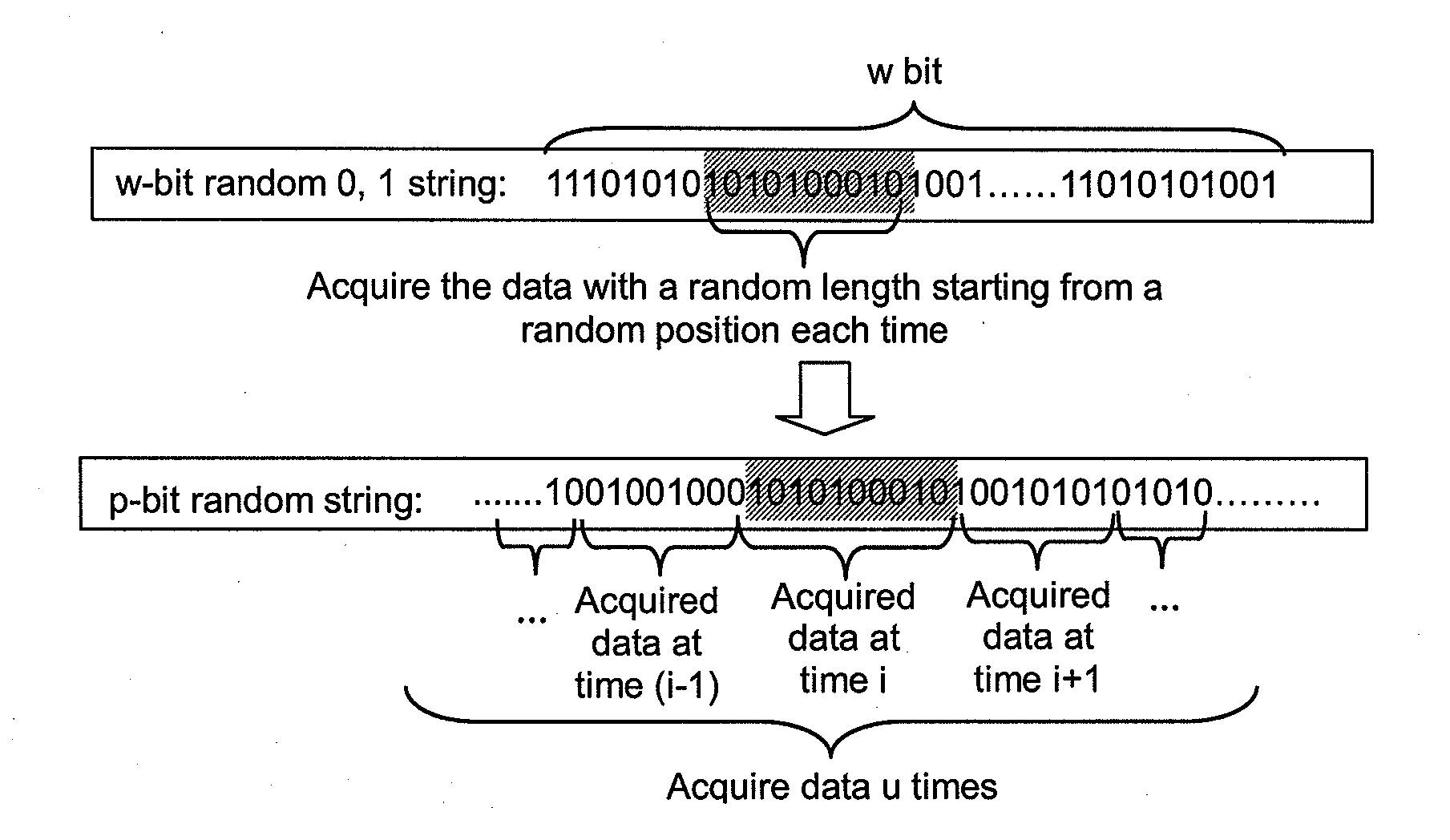
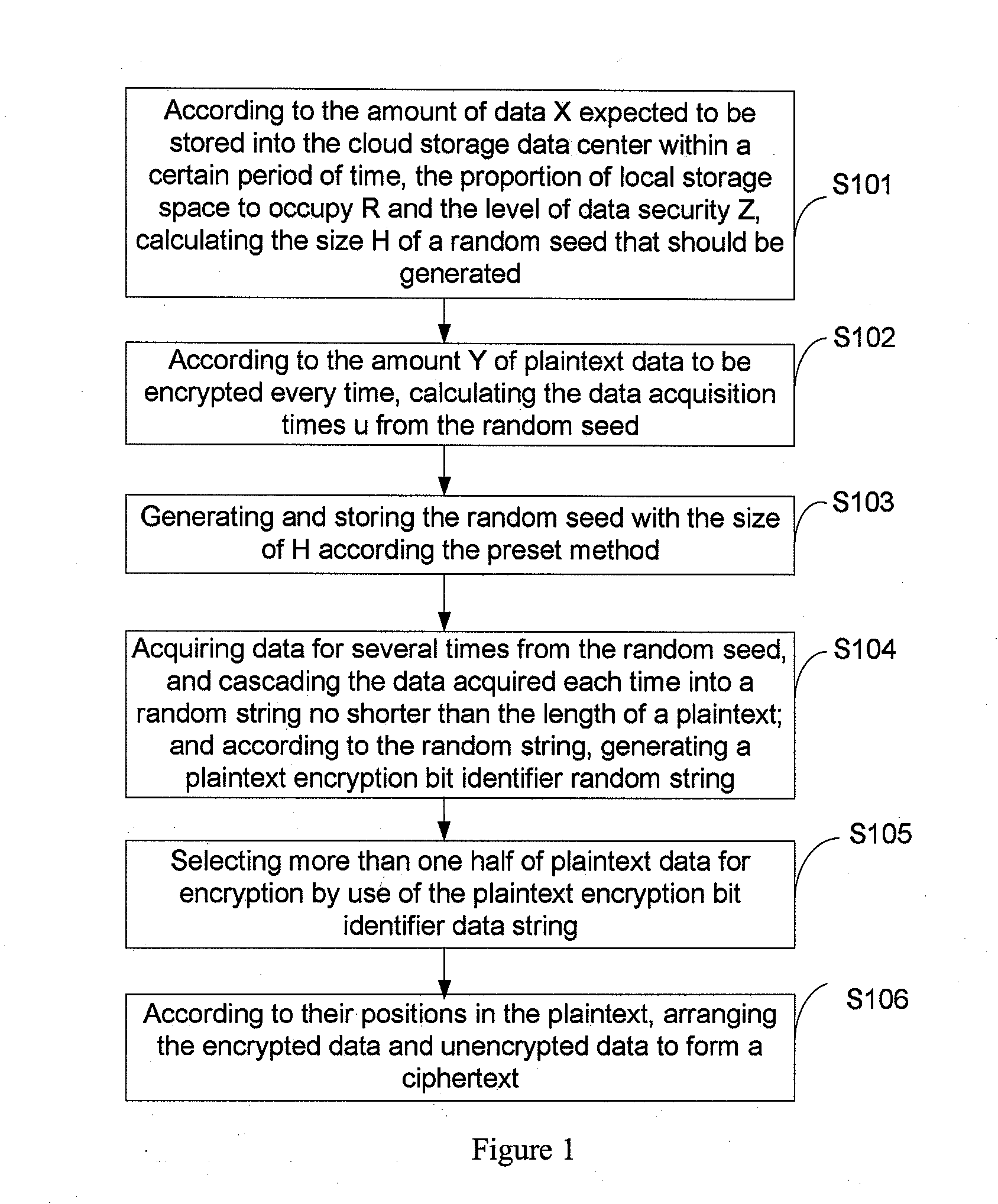
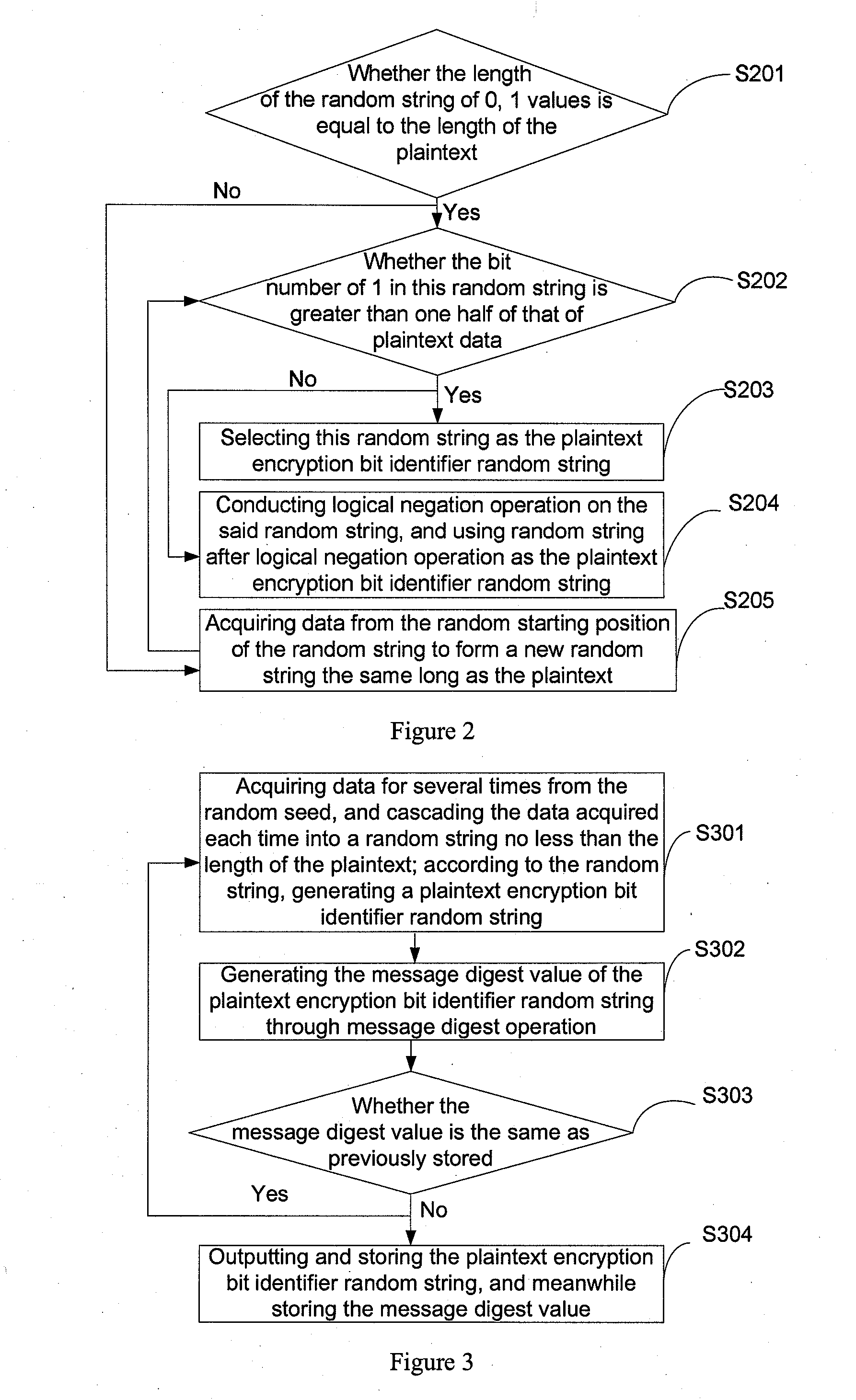
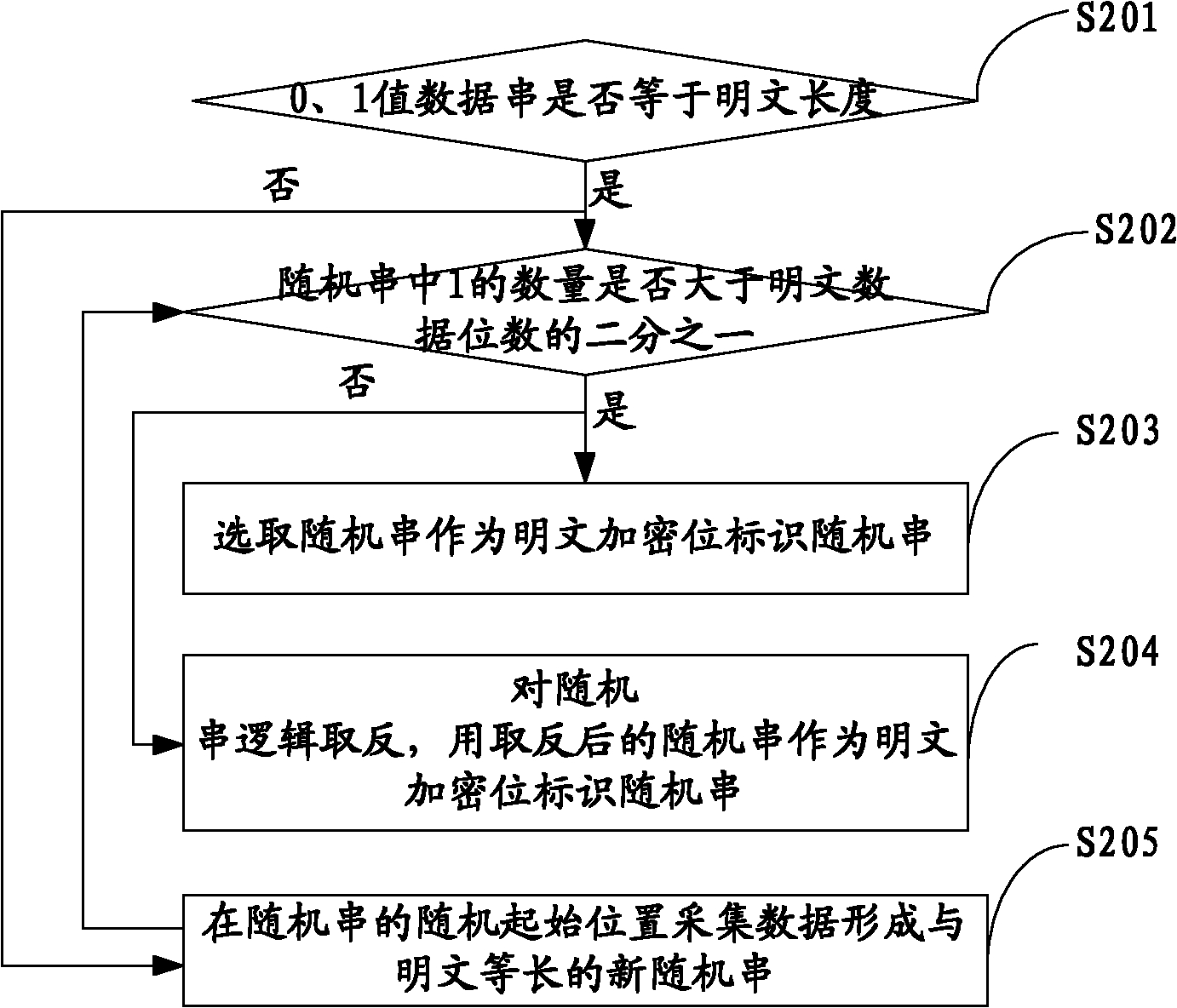
This present application relates to the field of cloud storage security technology, and in particular, relates to a cloud storage data encryption method, apparatus and system. The method comprises: according to the amount of data X expected to be stored within the preset time, the proportion of local storage space R and the security level of data Z, calculating the size H of a random seed that should be generated; according to the amount Y of plaintext data every time, calculating the times u of random seed acquired; according to the times u, acquiring data from the generated random seed with the size of H for several times to generate a plaintext encryption bit identifier data string; by use of the data string, selecting more than one half of the plaintext data for encryption to form a ciphertext. This application also provides a cloud storage data encryption apparatus and system. This invention has reduced the amount of encrypted data to be stored without sacrifice in the degree of data security protection, thus greatly improves the cloud storage data encryption and decryption performance.
Owner:BEIJING Z & W TECH CONSULTING
Method and system for updating certification key
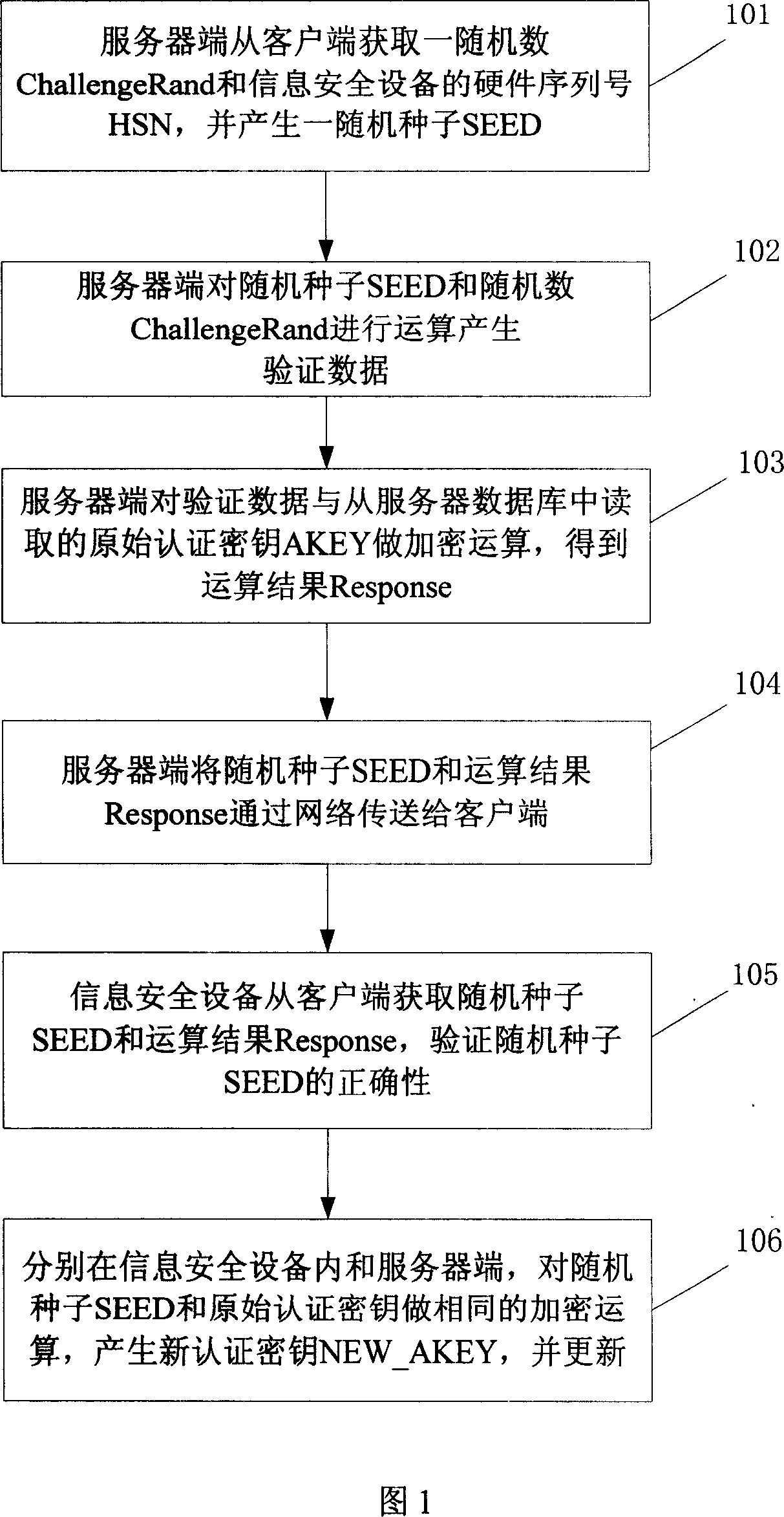
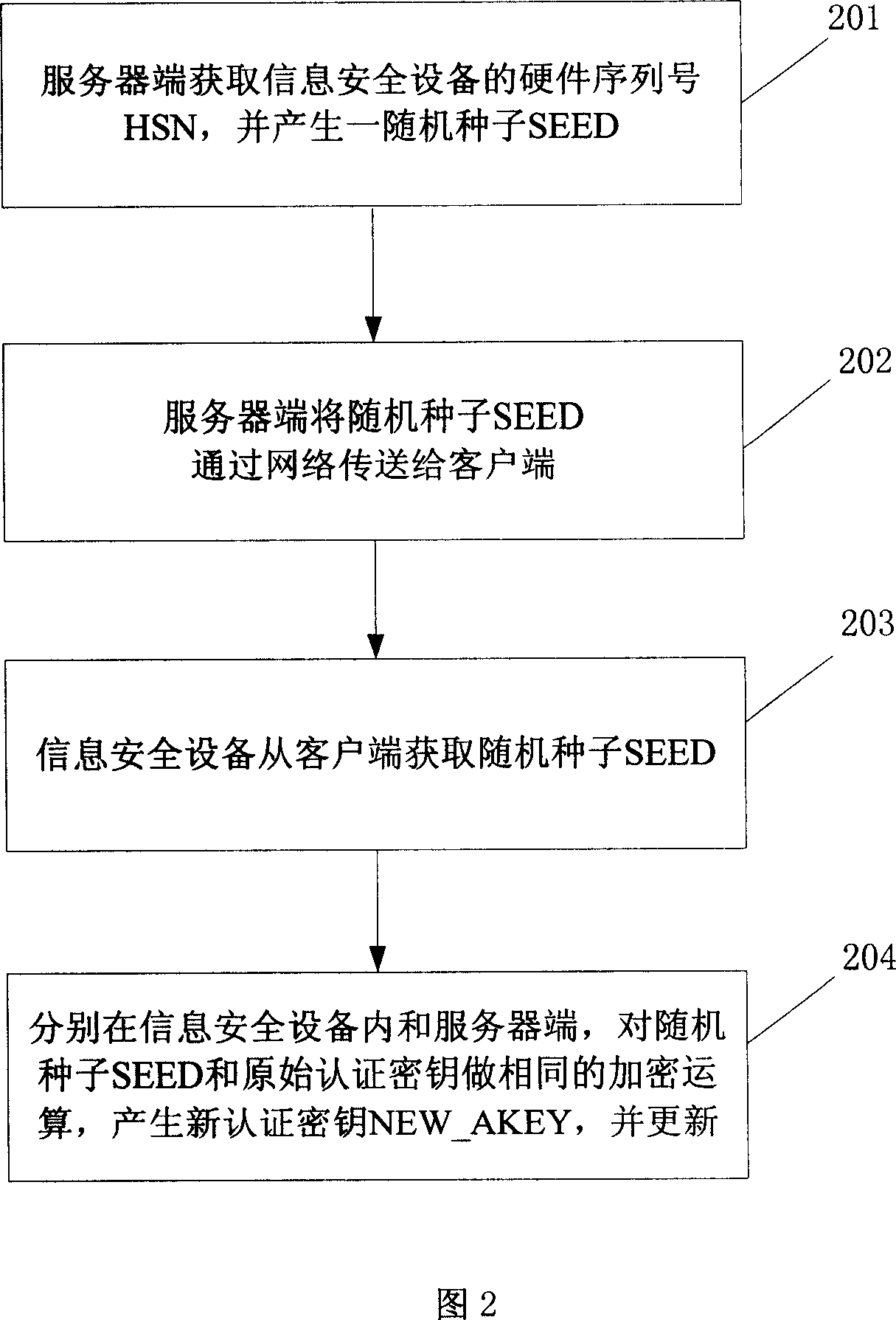
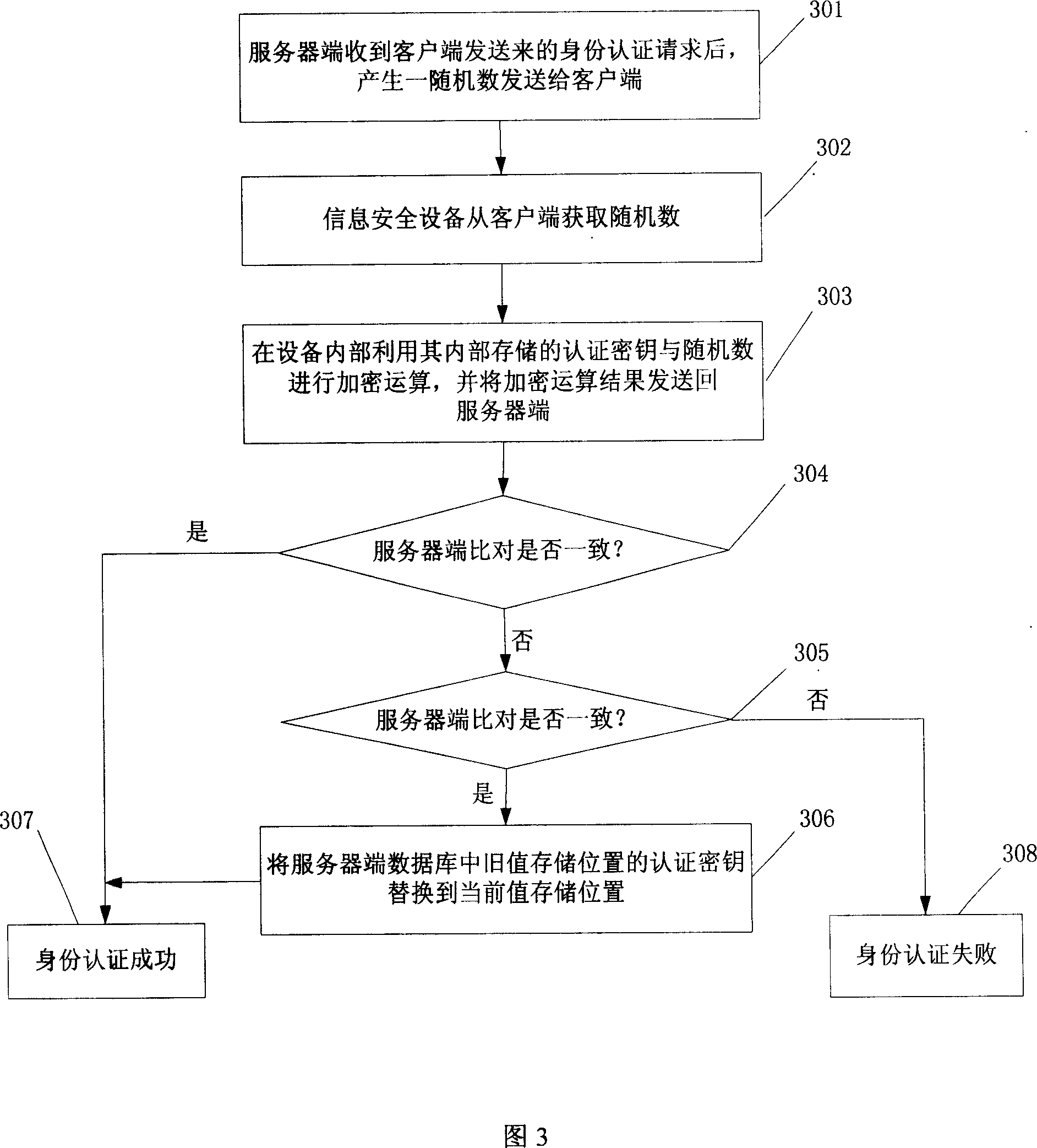
The invention is to solve issues: not security of transferring authentication cipher key through network by using plaintext; and managing bother, and high cost by using cryptograph format to transfer authentication cipher (AC). The disclosed method for updating AC remotely includes steps: server end calculates random seed and random number to generate verification data; server end carries out encryption operation for original AC and verification data, and transfers random seed and result of encryption operation to client end; information security equipment validates correctness of random seed; carrying out same encryption operation for random seed and original AC inside the information security equipment, and at server end so as to generate new AC, which is in use for updating AC inside the information security equipment, and database in server. The invention also discloses system for updating AC.
Owner:FEITIAN TECHNOLOGIES
System and method for building and exchanging encrypted passwords between a client and server
InactiveUS6182220B1User identity/authority verificationDigital data authenticationPasswordRandom seed
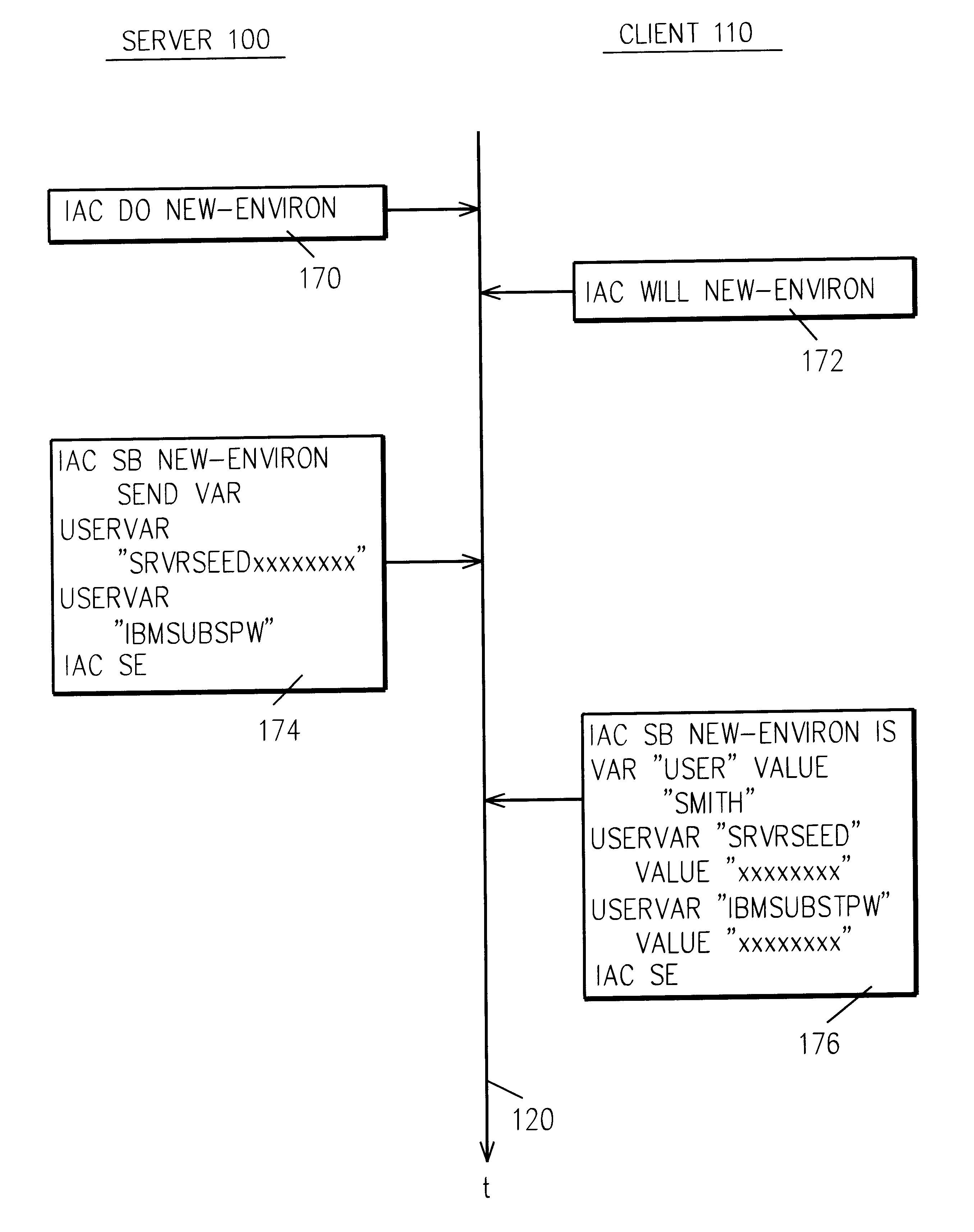
A method and system is provided for communicating encrypted user passwords from a client to a server. During new environment negotiations, the server communicates to the client a server random seed value. The client then generates a client random seed value and, using the client random seed value, the server random seed value, and the user variable name, an encrypted user password. The client then communicates to the server the client random seed, the user variable name and the encrypted user password. Then the server validates the encrypted user password using the server random seed, the client random seed and the user variable name.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH +1
Method and apparatus for providing authentication in a communication system
InactiveUS7123719B2User identity/authority verificationSecret communicationCommunications systemRandom seed
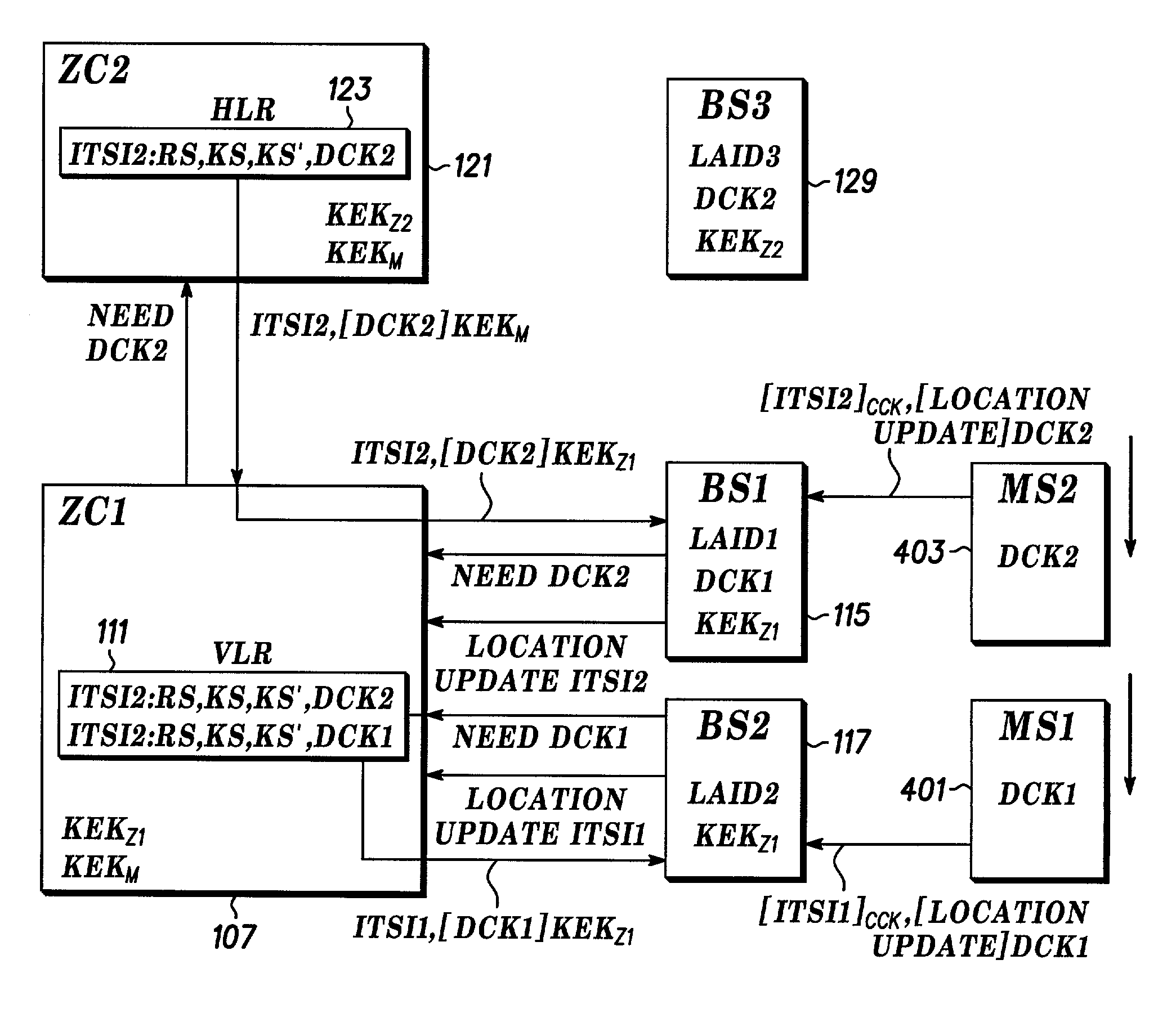
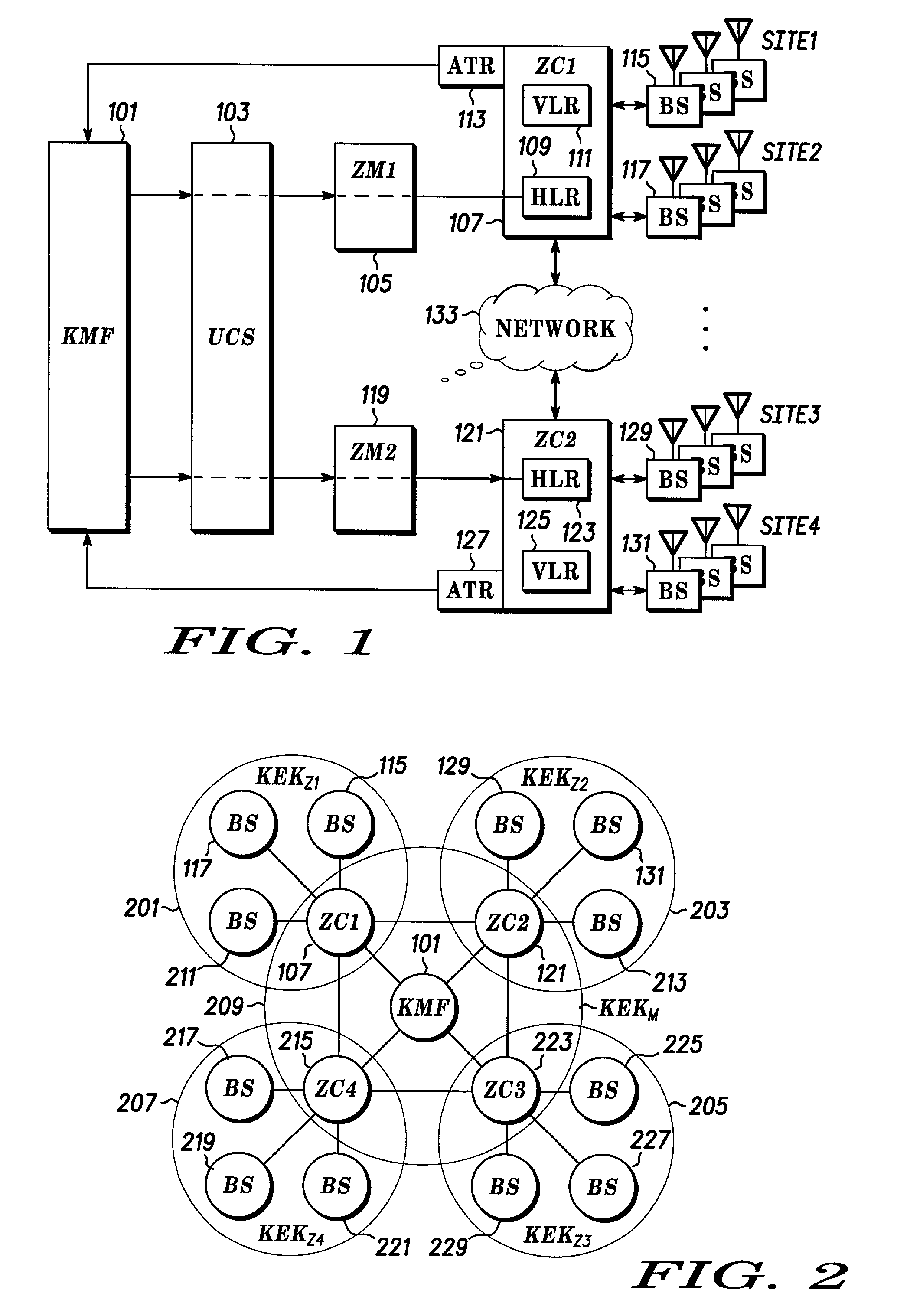
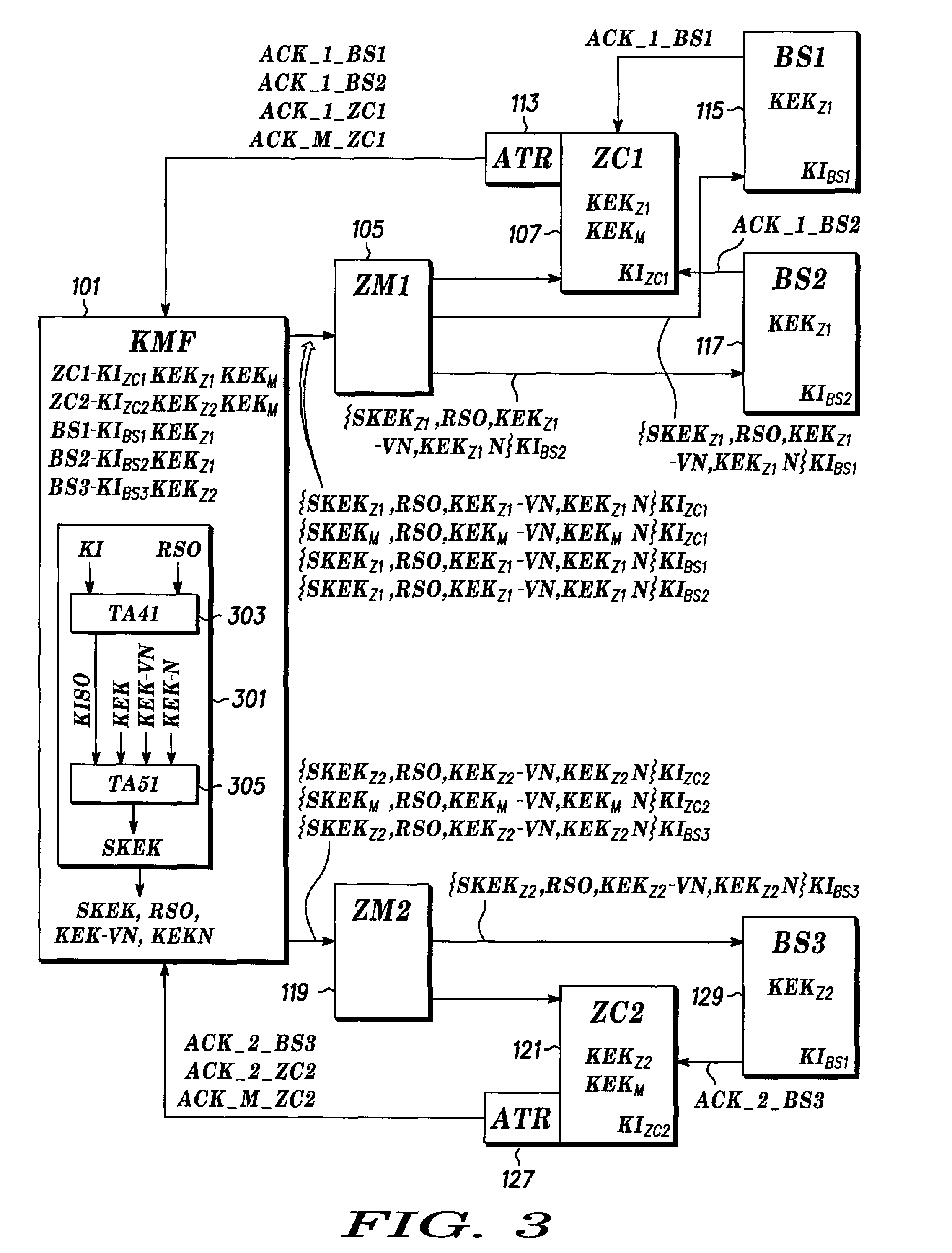
A method includes receiving an authentication request from a mobile station (401) and determining whether to forward the request to an authentication agent. When it is determined to forward the request, the request is forwarded to the authentication agent (107). A random number and a random seed are received from the authentication agent (107). The random number and the random seed are forwarded to the mobile station (401). A response to the random number and the random seed from the mobile station (401) is received and forwarded to the authentication agent (107). The authentication agent (107) compares the response with an expected response. When the authentication agent (107) authenticates the mobile station (401), a derived cipher key is received from the authentication agent (107).
Owner:MOTOROLA SOLUTIONS INC
Cloud Storage Data Access Method, Apparatus and System Based on OTP
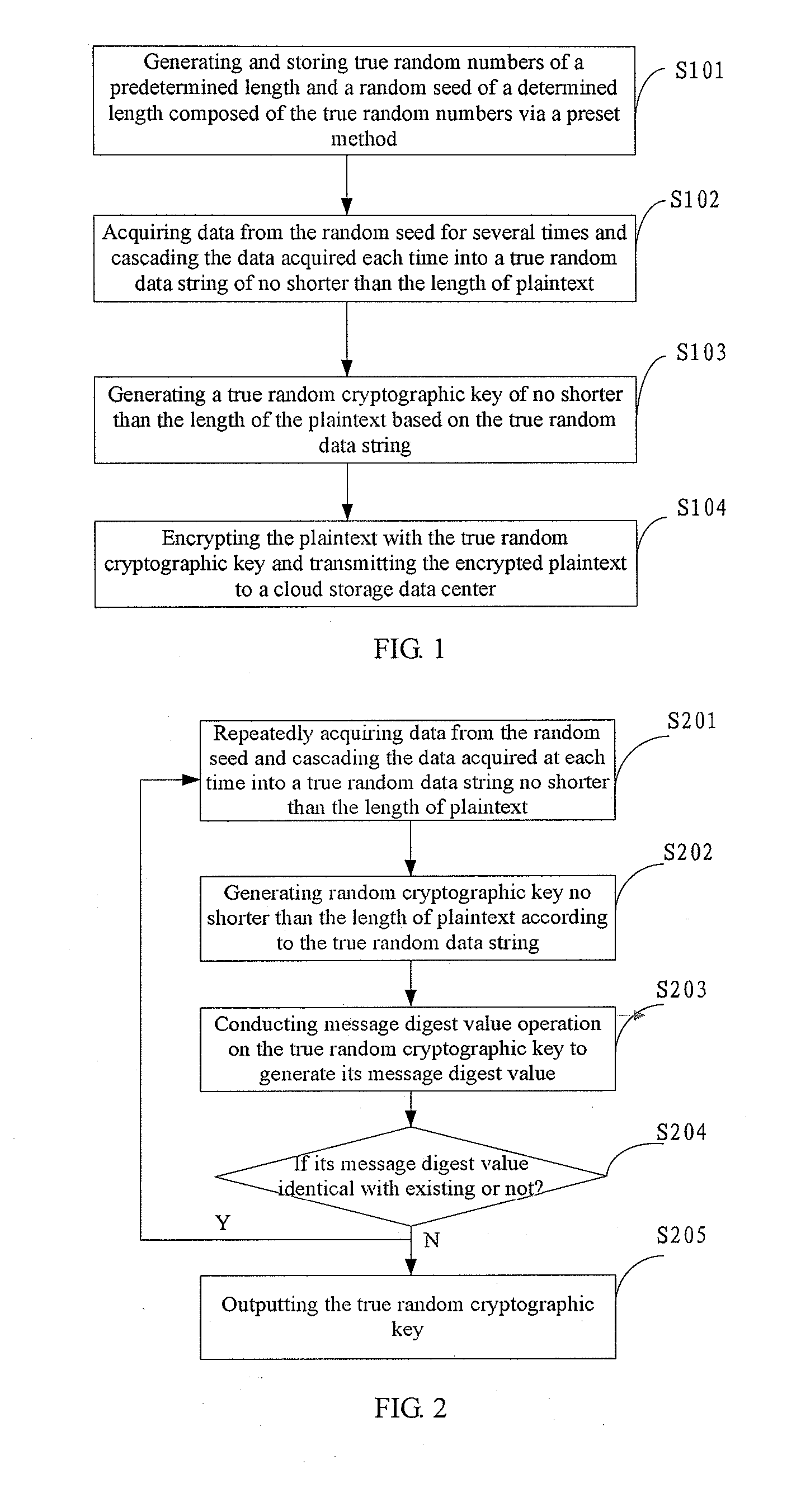
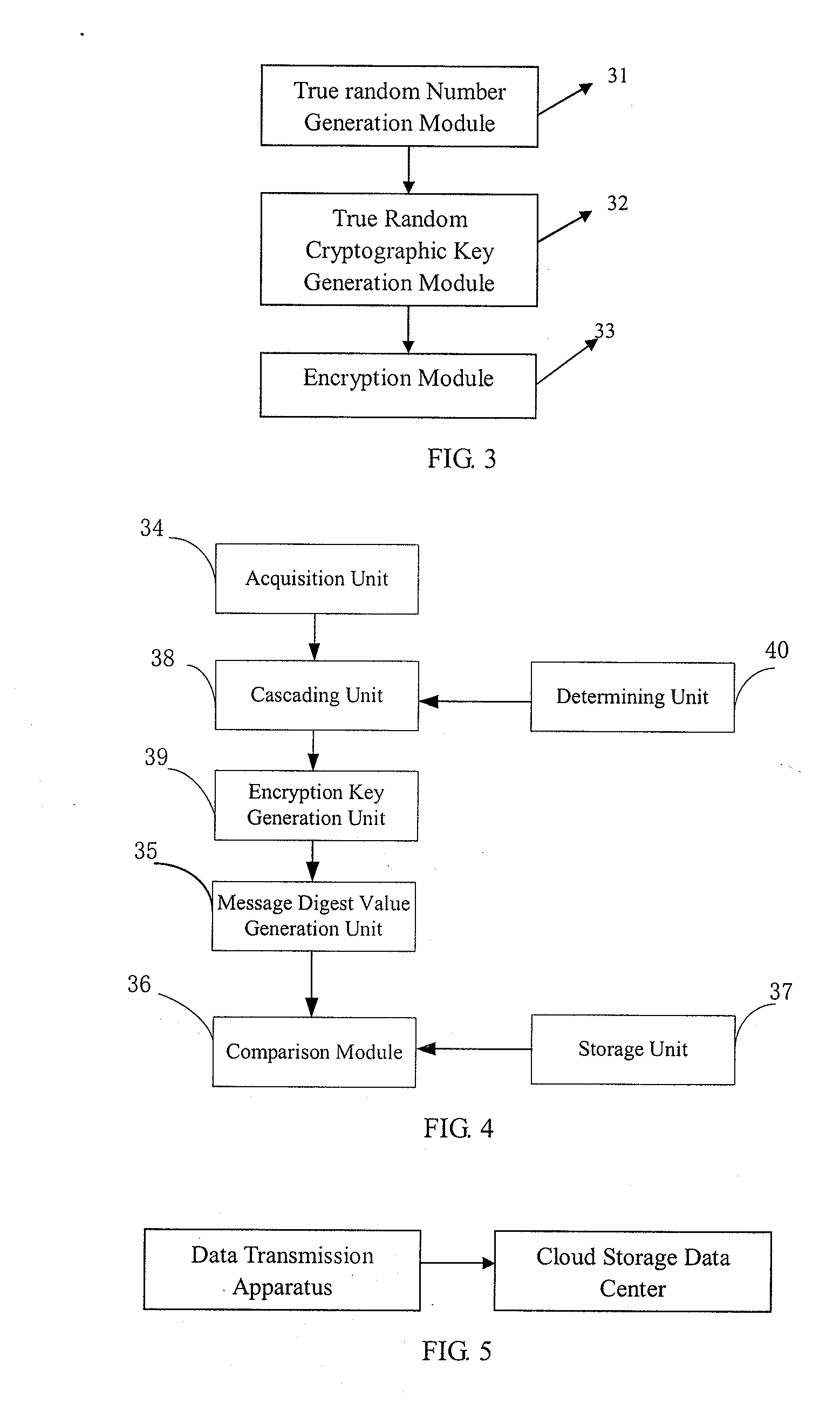
InactiveUS20120134495A1Small storage space occupancyStrengthens cloud storage data securityMemory loss protectionDigital data processing detailsPlaintextComputer hardware
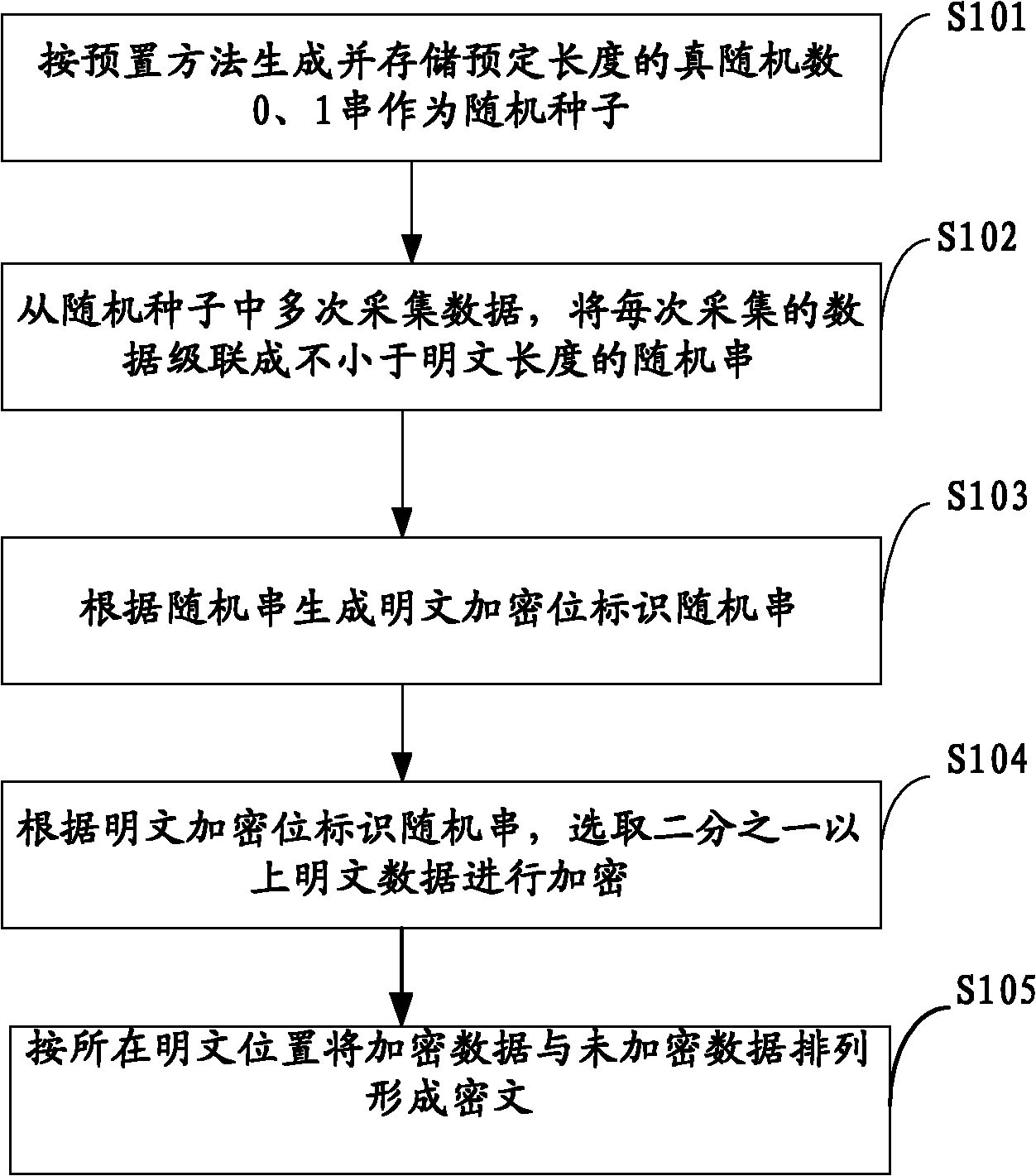
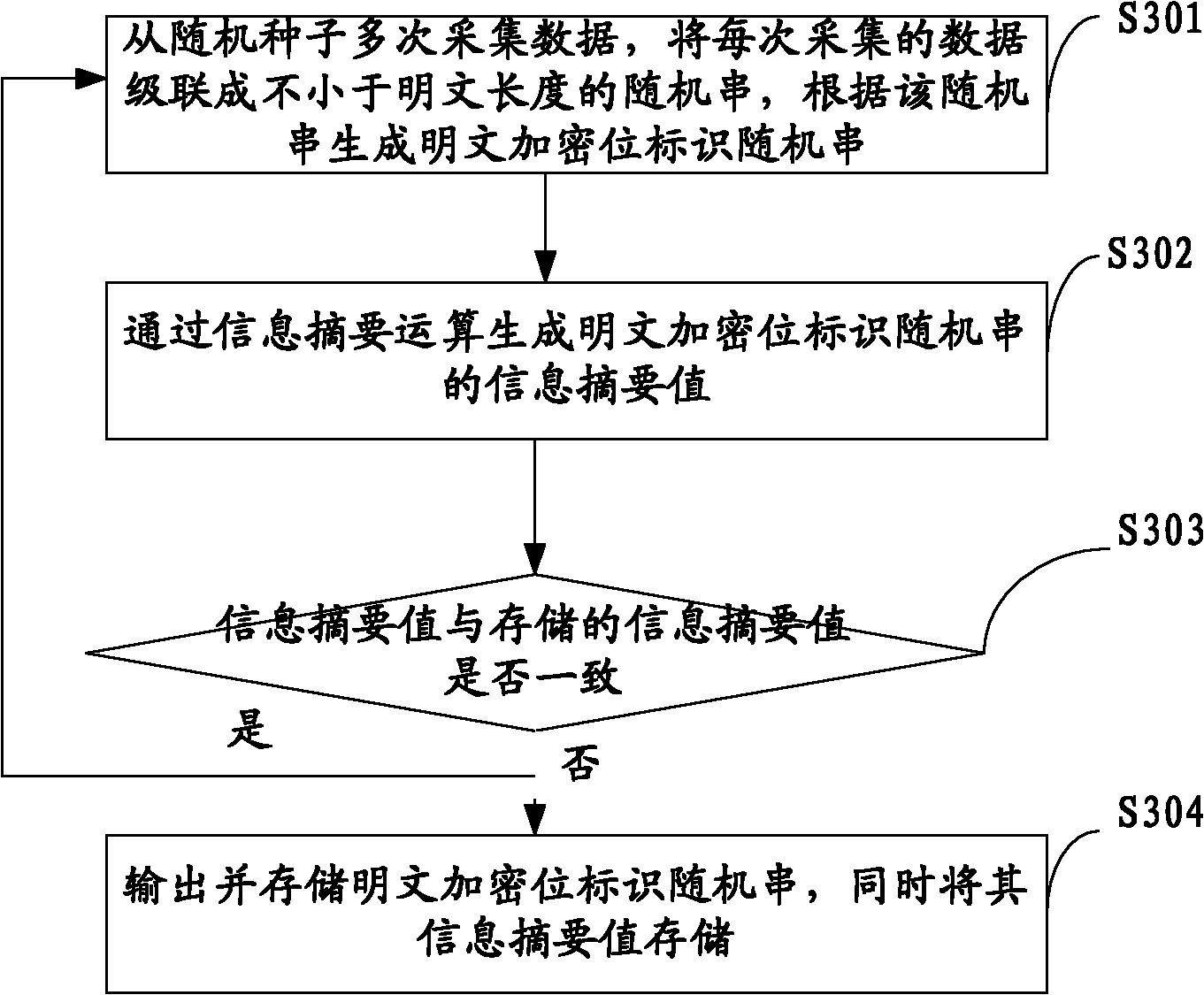
The present application relates to cloud storage technology and especially relates to a cloud storage data access method, apparatus and system based on OTP. This method includes: generating and storing true random numbers of a predetermined length and a random seed of a predetermined length composed of the true random numbers via a preset method; acquiring data from the random seed for several times and cascading the data acquired each time into a true random data string of no shorter than the length of plaintext; based on the true random data string, generating a true random cryptographic key of no shorter than the length of the plaintext, encrypting the plaintext using this cryptographic key and transmitting ciphertext to a cloud storage data center. This application also provides a cloud storage data access apparatus and system based on OTP. The method, apparatus and system introduced by this invention can generate and store sufficient true random cryptographic key with relatively small physical space occupancy in comparison with that of plaintext, thereby enabling OTP to be applied into cloud storage data security protection.
Owner:BEIJING Z & W TECH CONSULTING
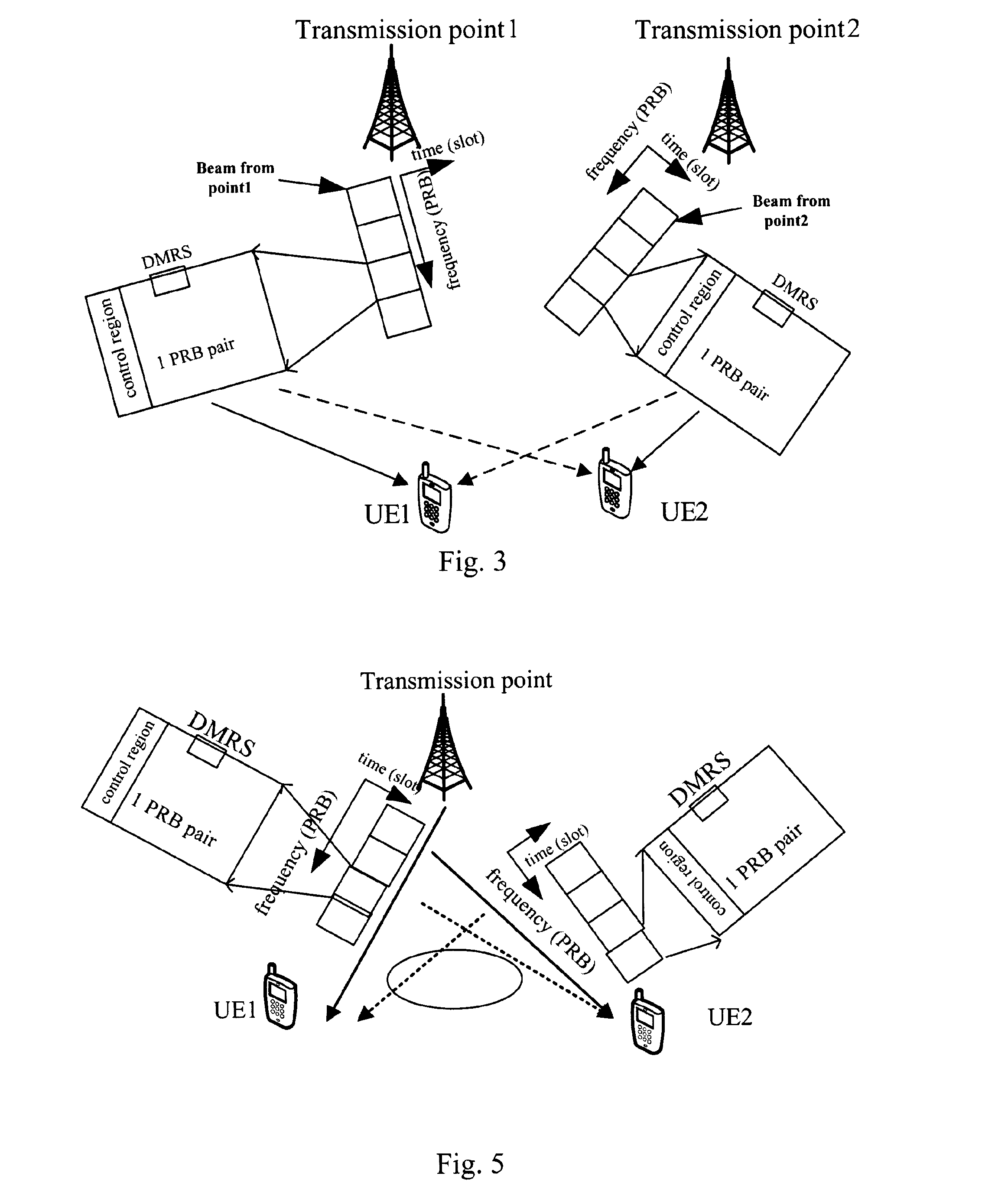
Method of scrambling signals, transmission point device and user equipment using the method
ActiveUS20140071936A1Reduce signaling overheadConflicting requirementMulti-frequency code systemsPilot signal allocationResource blockRandom seed
Method of scrambling signals, transmission point device and user equipment using the method are provided. The method is for scrambling signals assigned on predetermined radio resources of at least one layer of resource blocks with the same time and frequency resources, and comprises the steps of: sending an ID table to a user equipment through higher layer signaling, the ID table being a subset of the whole ID space and containing available IDs for the user equipment; notifying the user equipment an ID in the ID table to be used through physical layer signaling or UE specific higher layer signaling; generating a random seed based on the notified ID; initializing a scrambling sequence by the random seed; and scrambling the signals with the initialized scrambling sequence. The method of the disclosure, by combining physical layer signaling and higher layer signaling, may notify the used group ID and the blind detection space to a UE, the blind detection for the UE is enabled and the signaling overhead is reduced.
Owner:SUN PATENT TRUST
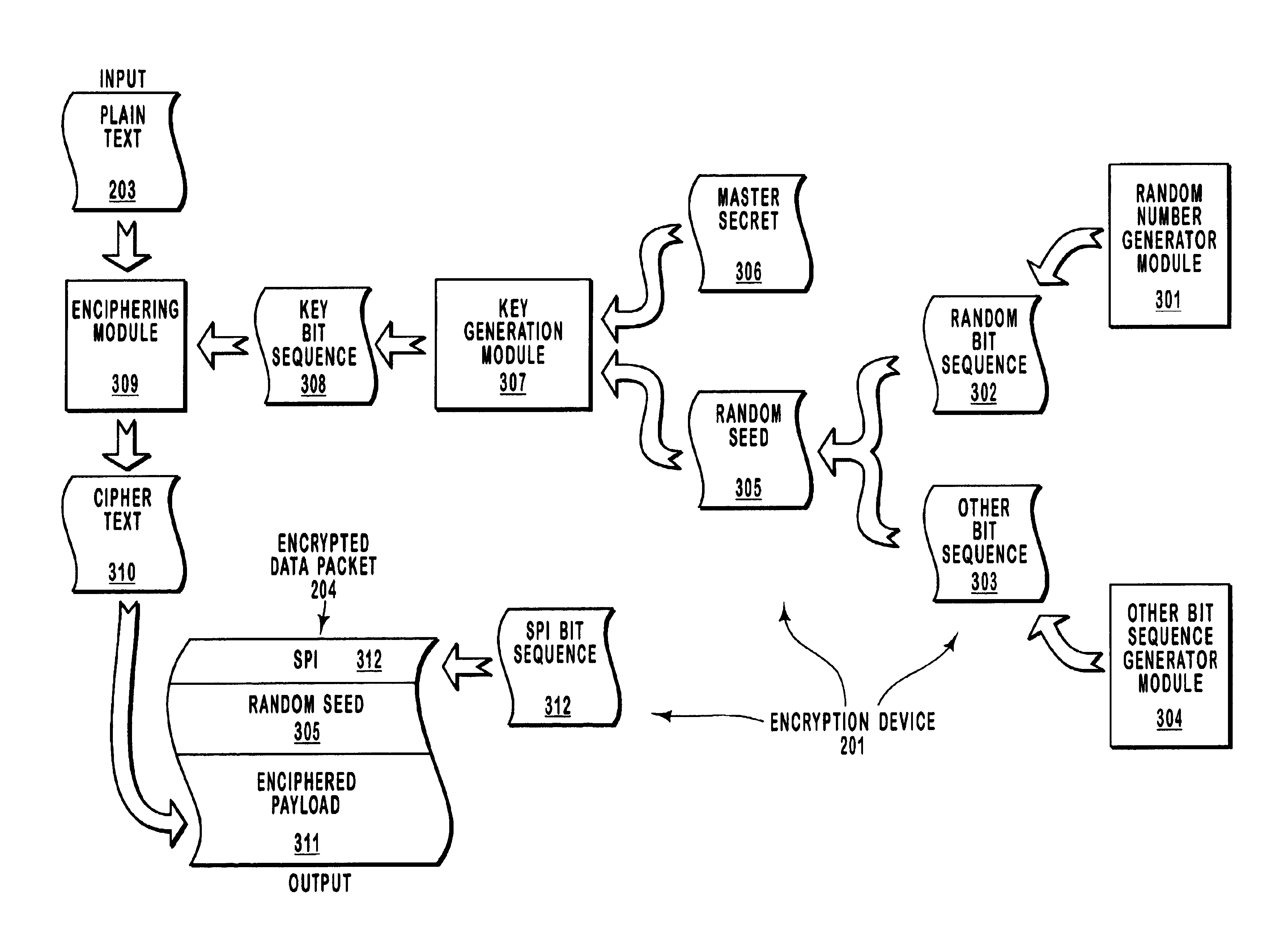
Methods and systems for generating encryption keys using random bit generators
InactiveUS6931128B2Reduce rewardAvoid breakingKey distribution for secure communicationSecret communicationNetwork packetRandom seed
A security key, such as an encryption key, is generated so as to make it more difficult for eavesdroppers to identify the key. Specifically, a cryptographically secure random number generator generates a random bit sequence that is included in a seed. This random seed is provided along with a negotiated master secret to a key generation module. The key generation module may implement a pseudo random function that is in accordance with the Transport Layer Security (TLS) protocol or the Wireless Transport Layer Security (WTLS) protocol. This key may then be used to encrypt a plain text message to form an encrypted data packet. The encrypted data packet also includes the random seed in unencrypted form. The encrypted data packet may be transmitted over a public network to a recipient with reduced risk of eavesdropping.
Owner:MICROSOFT TECH LICENSING LLC
Random set-based cluster tracking
InactiveUS7193557B1Precise processQuickly and accurately resolves tracking of objectPosition fixationDirection findersTimestampState parameter
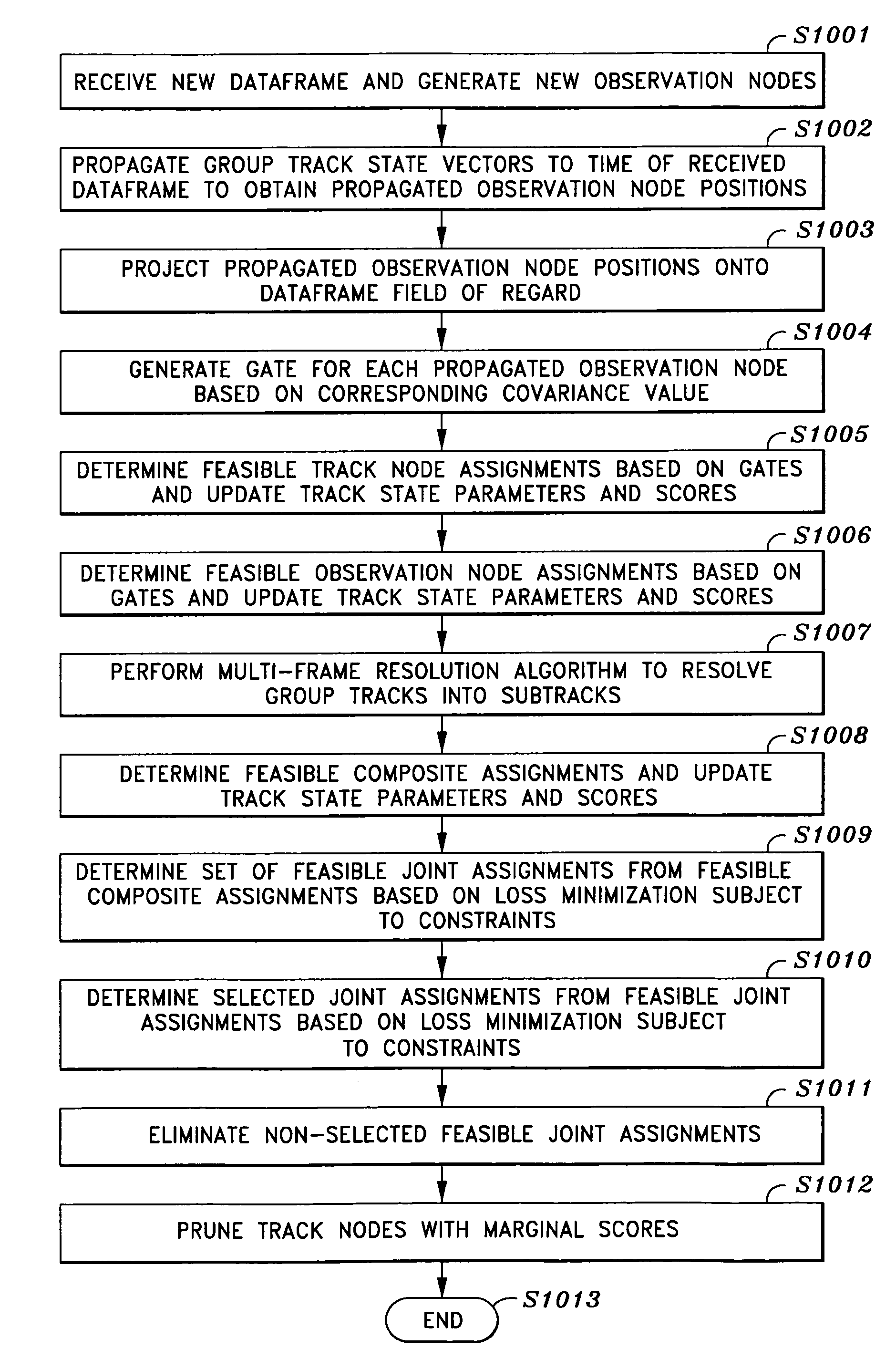
Tracking objects by receiving a dataframe from a detection sensor device, the dataframe containing a timestamp and data corresponding to each detected object, generating new observation nodes for each detected object, propagating group track state parameters to obtain posterior observable positions and projecting them onto the received dataframe, generating gates for the posterior observable positions and projecting them onto the received dataframe, determining feasible track node and feasible observation node assignments based on the proximity of the new observation nodes to the gates, updating track node state parameters and corresponding scores, performing a multi-frame resolution algorithm to resolve group track nodes into subtrack nodes, determining a set of feasible composite assignments for composite sets of track nodes and observation nodes, updating track node state parameters and corresponding scores, and determining a selected set of joint assignments based on the feasible composite assignments and their respective scores.
Owner:LOCKHEED MARTIN CORP
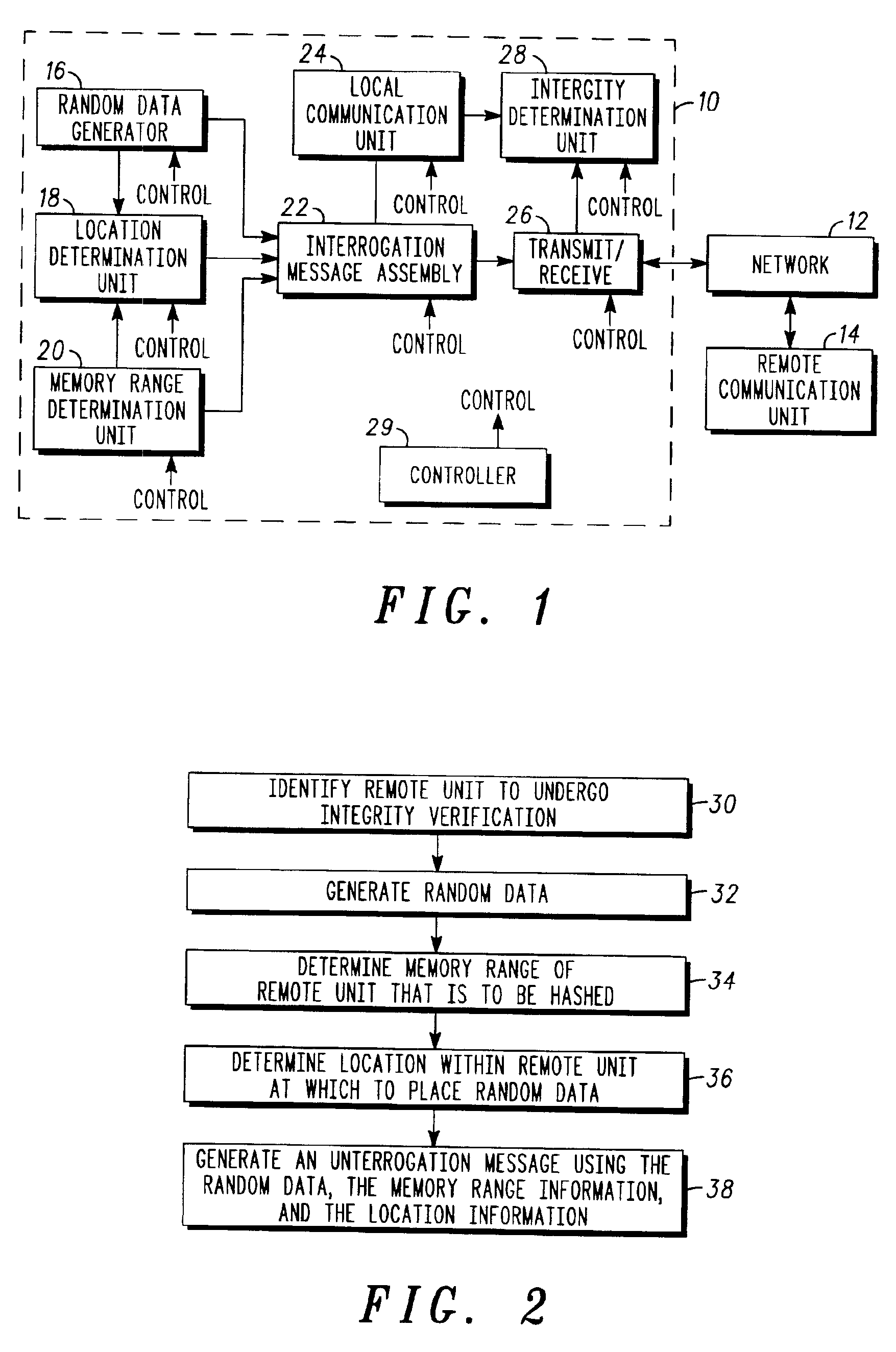
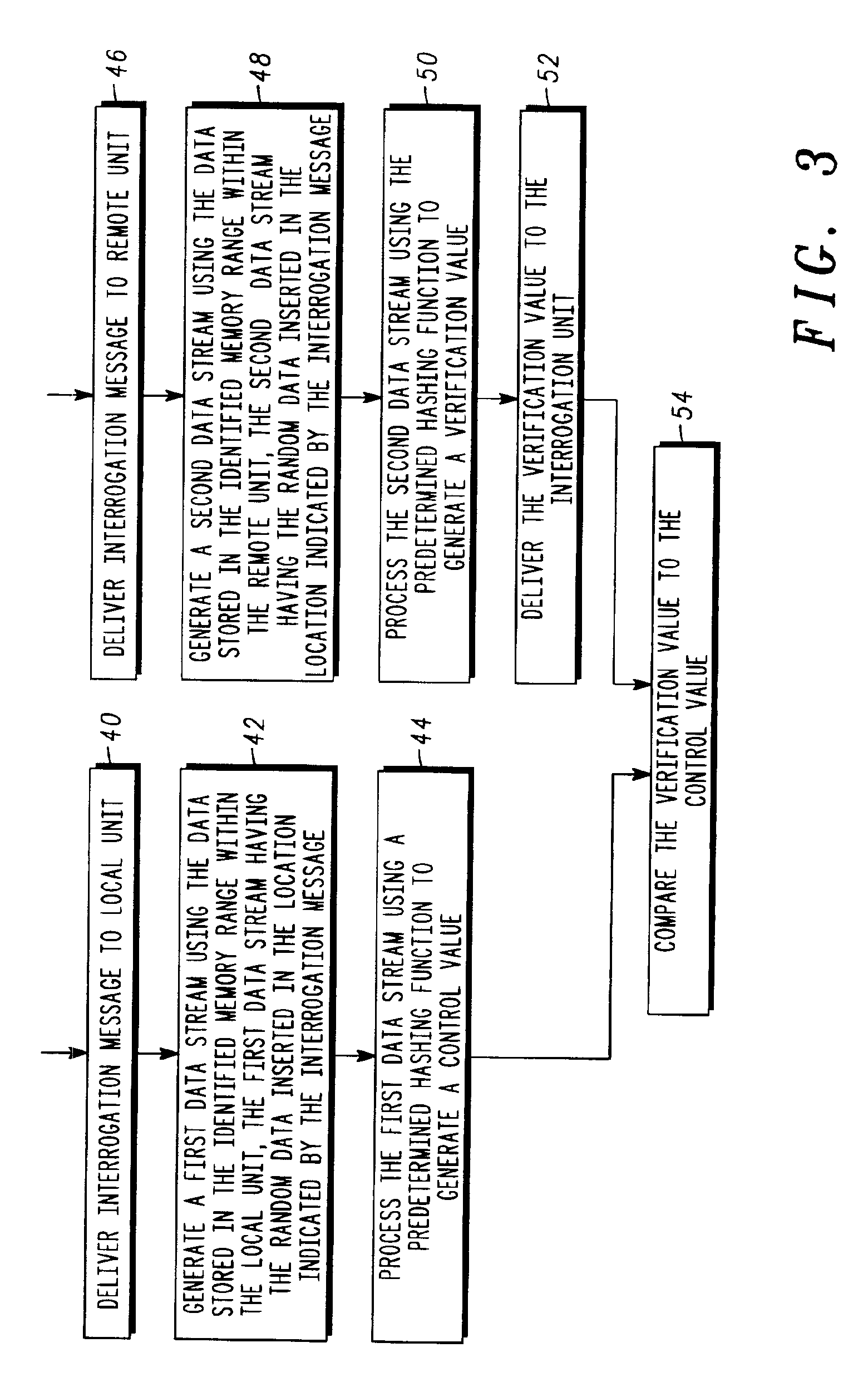
Remote system integrity verification
InactiveUS6925566B1Unauthorized memory use protectionHardware monitoringCommunications systemData stream
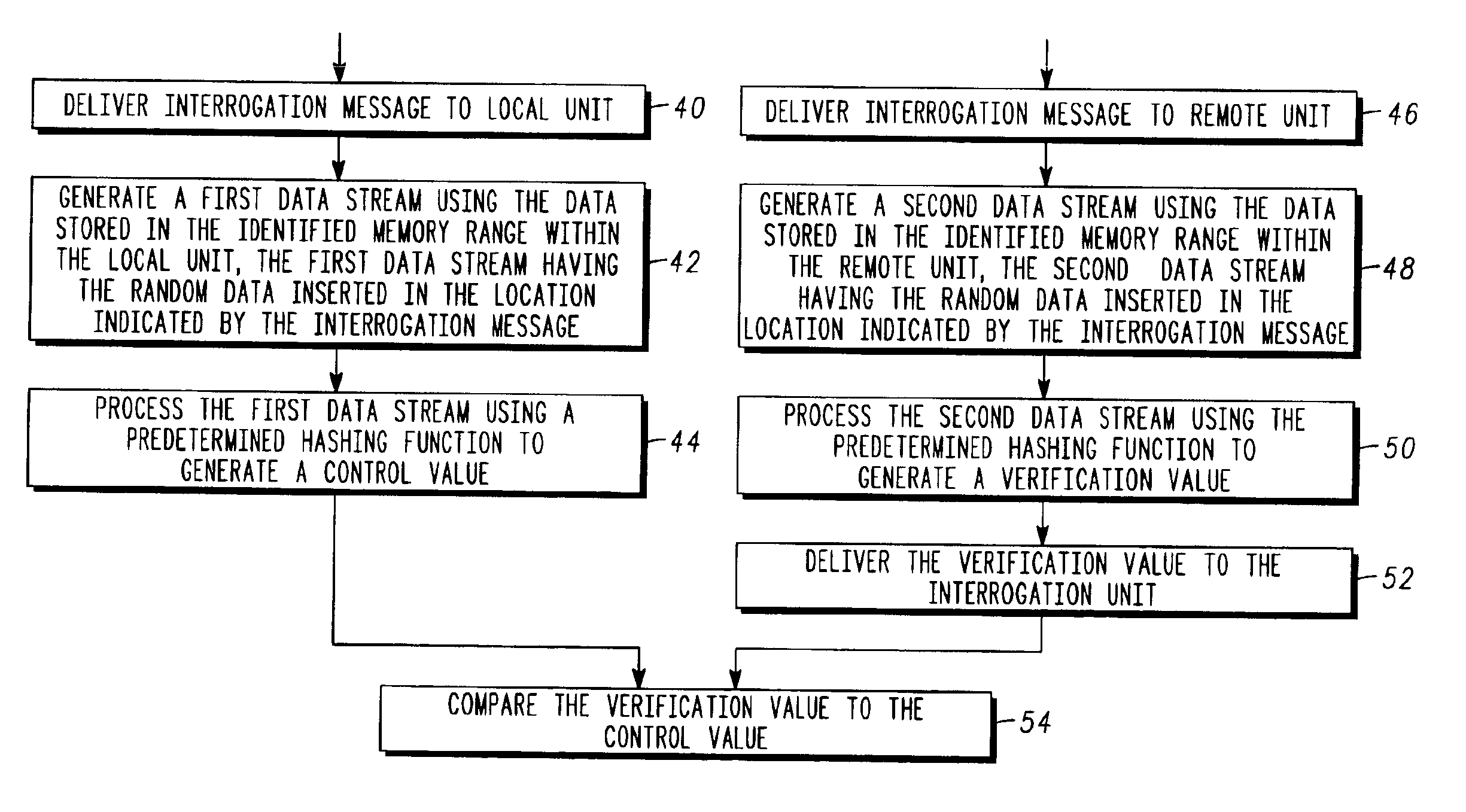
The integrity of a remote communication unit (14) in a communication system is verified by comparing a hash value generated within the remote unit (14) to a hash value generated within a local unit (24). An interrogation message is generated within an interrogating entity (10) that includes a random seed value, memory range information identifying a memory range within the remote unit that is to be hashed, and position information identifying a position at which the random seed value is to be located within a data stream generated within the remote unit (14). The interrogation message is then delivered to the remote unit (14) which then performs a hashing operation based upon the parameters within the interrogation message to generate a hash value. The hash value is then returned to the interrogating entity (10) for comparison with a control value.
Owner:CDC PROPRIETE INTELLECTUELLE
Control method and system for wireless channel access competition
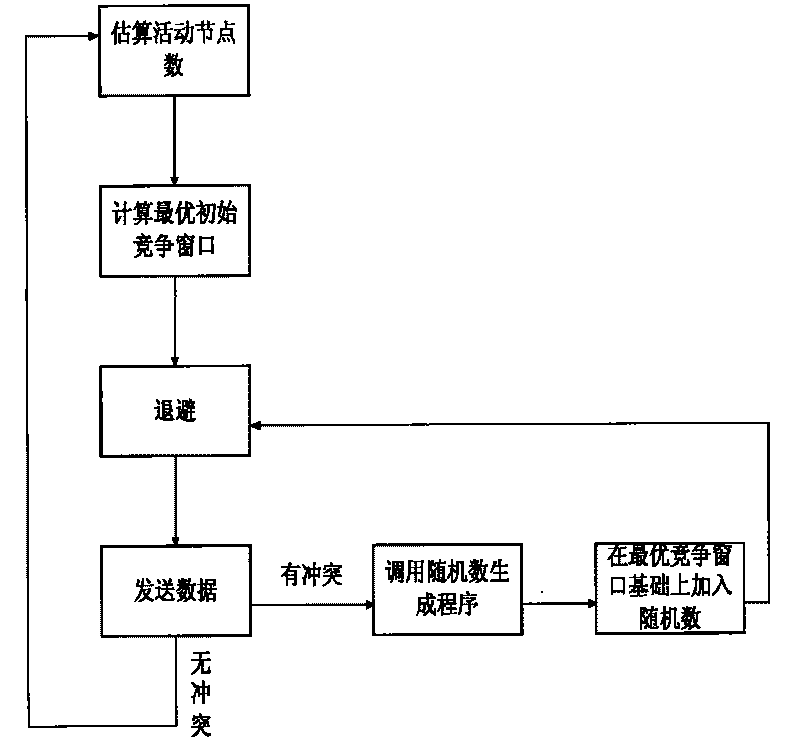
InactiveCN101695195AIncrease backoff timeImprove throughputWireless communicationRandom seedCalculation methods
The invention discloses control method and system for wireless channel access competition. The computing method of the optimal contention window is provided on the basis of an IEEE802.11 standard, and the original back off algorithm of an MAC protocol is improved. The invention is firstly characterized by deeply analyzing the thruput and the delay performance of a wireless network, and provides the method for dynamically computing the optimal contention window in a real-time mode according to the number of active nodes in the wireless network. Moreover, the invention provides a new back off mode which comprises the following steps of firstly, computing the optimal contention window according to the number of the calculated active nodes in the network; secondly, adding a random seed algorithm; and when conflict occurs in the wireless channel, the back off algorithm is increased by a random value on the basis of the optimal contention window instead of doubling the original window. Therefore, the conflict of channel competition by each active node is avoided, the access delay of media is also shortened, and the thruput and the utilization rate of the wireless network are both improved.
Owner:COMMUNICATION UNIVERSITY OF CHINA
Method of managing user key for broadcast encryption
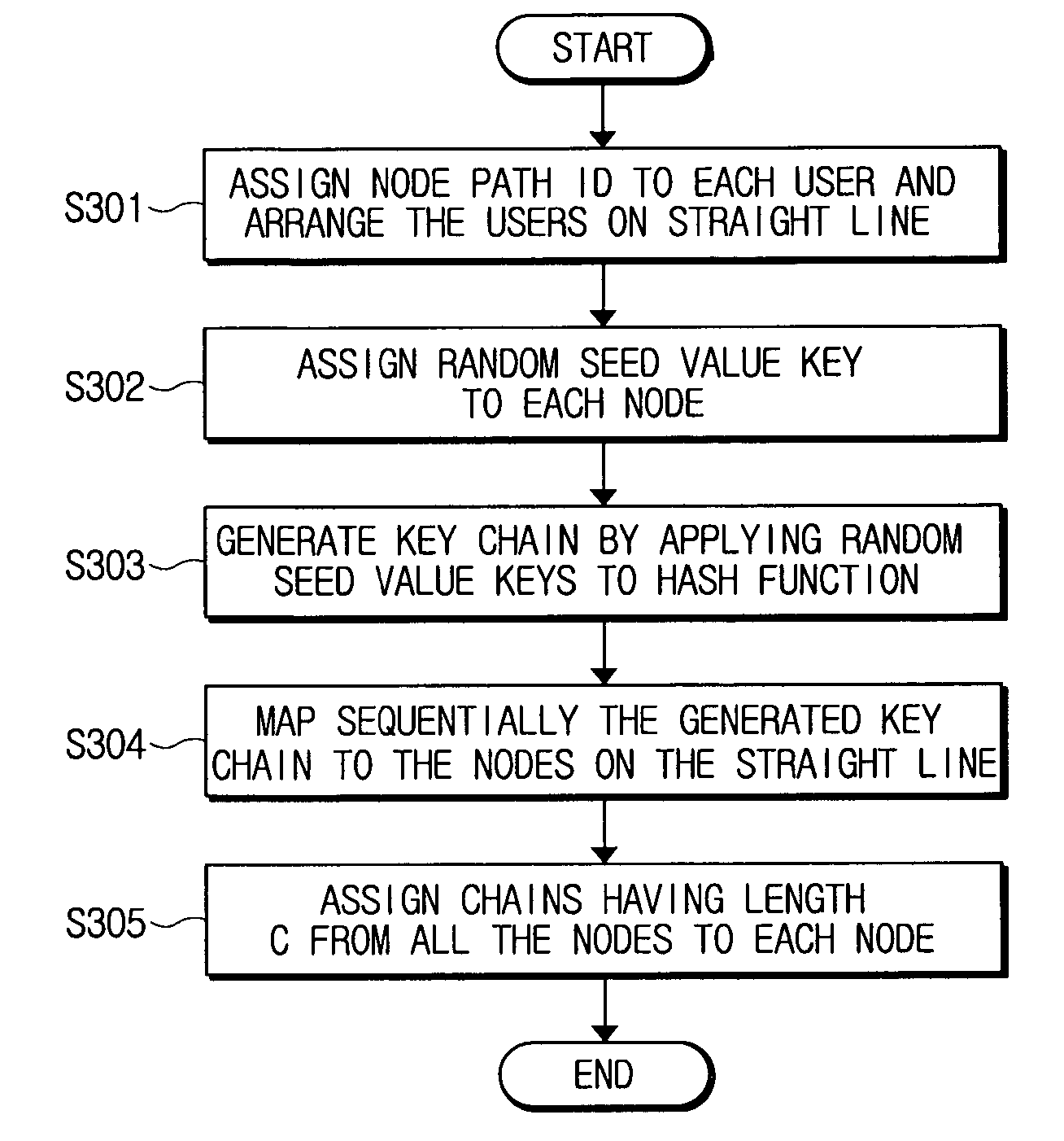
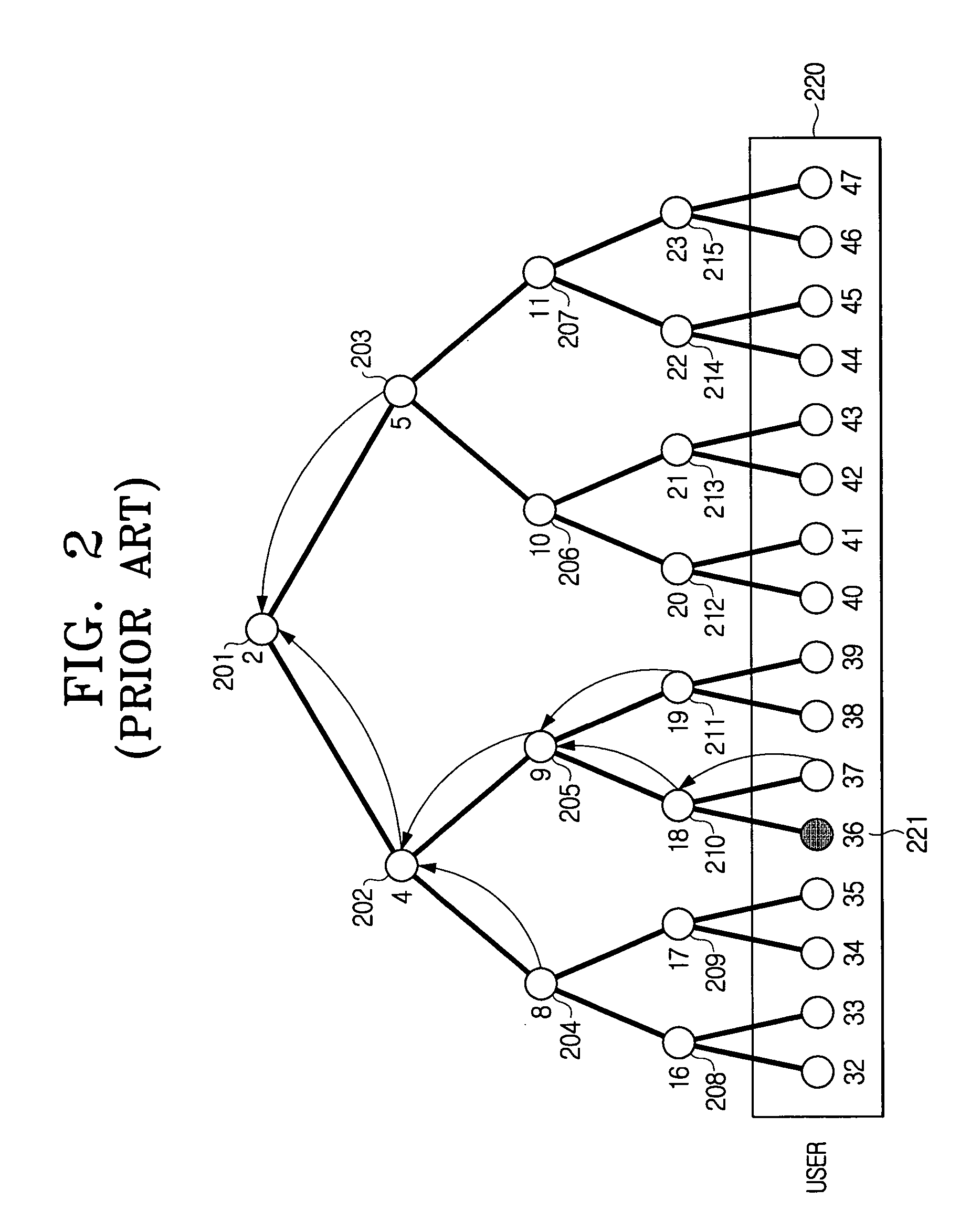
ActiveUS20060129805A1Reduce transmission overheadKey distribution for secure communicationUser identity/authority verificationHash functionSubset difference
A user key management method for a broadcast encryption includes assigning node path identifiers (IDs) to nodes arranged in sequence; assigning random seed value keys to the nodes according to the node path IDs; generating key values by repeatedly applying a hash function to the assigned random seed value keys; and assigning the generated key values to the nodes in sequence. Accordingly, it is possible to reduce the transmission overhead that is most important matter in the broadcast encryption to less than the number of the revoked users. Further, there is an advantage that the transmission overhead of the exemplary embodiments of the present invention is remarkably reduced compared with the Subset Difference method.
Owner:SAMSUNG ELECTRONICS CO LTD
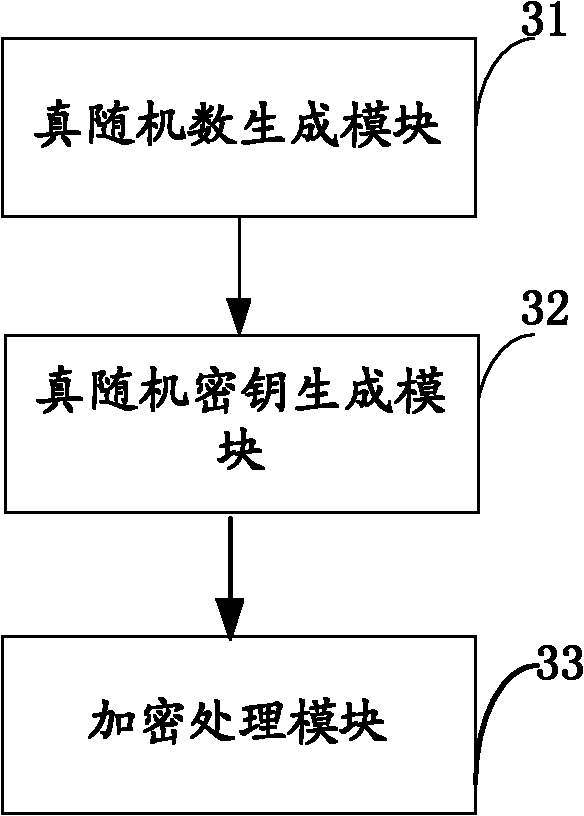
Secret key and true random number generator and method for generating secret key and true random number
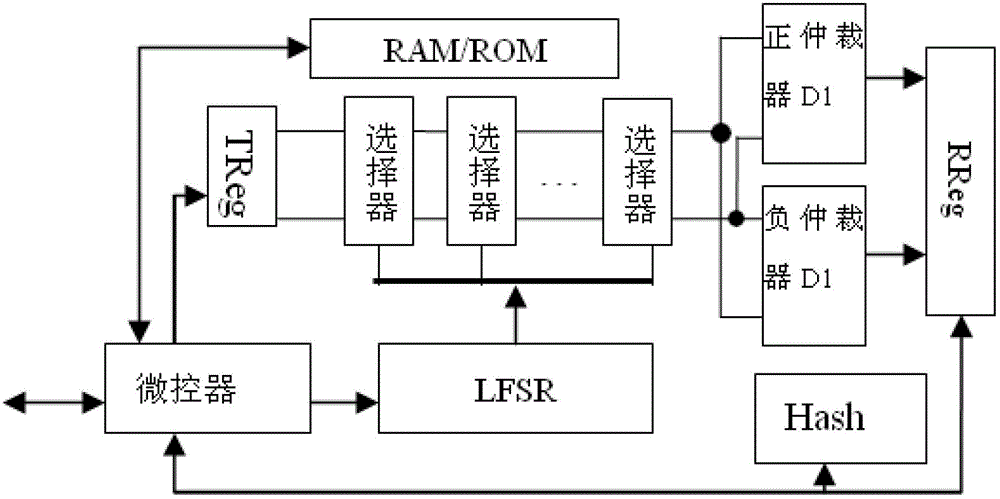
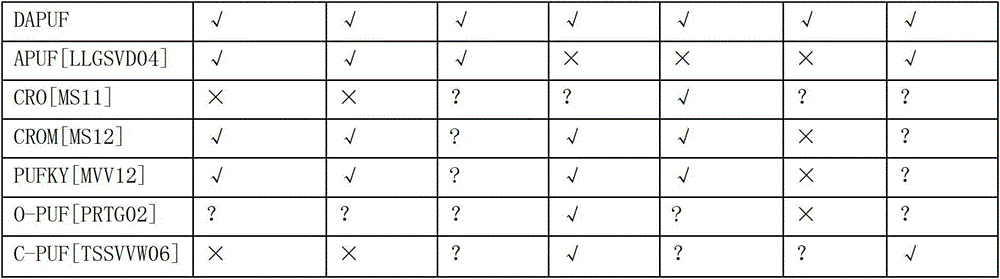
InactiveCN103188075AReduce areaHigh speedKey distribution for secure communicationGeneration processMicrocontroller
The invention discloses a secret key and true random number generator and a method for generating a secret key and a true random number. The generator comprises a double-arbiter physically unclonable function (DAPUF), a trigger signal generation register (TReg), a response acquisition register (RReg), a microcontroller, a linear feedback shift register (LFSR), a Hash engine, a volatile memory and a nonvolatile memory. The invention also aims at providing a method for generating the secret key and the true random number. The method comprises the steps of: (1) initialization process of the secret key; (2) reconstruction process of the secret key; (3) initialization process of the true random number; and (4) the generation process of the true random number. The secret key and the true random number which are obtained by combining the response of the DAPUF with the steps in the method have the effects that (1) the error rate of the generated secret key is decided by the noise of the DAPUF and the election times of a majority of election methods, and the error rate of the generated secret key can be reduced unlimitedly; and (2) the LFSR is updated for a number of times, so that a random seed becomes an uncertain entropy source, and after the response which is generated by taking the uncertain entropy source as challenge is treated by the Hash, so that the output true random number meets the pseudo-randomness.
Owner:GUANGZHOU UNIVERSITY +5
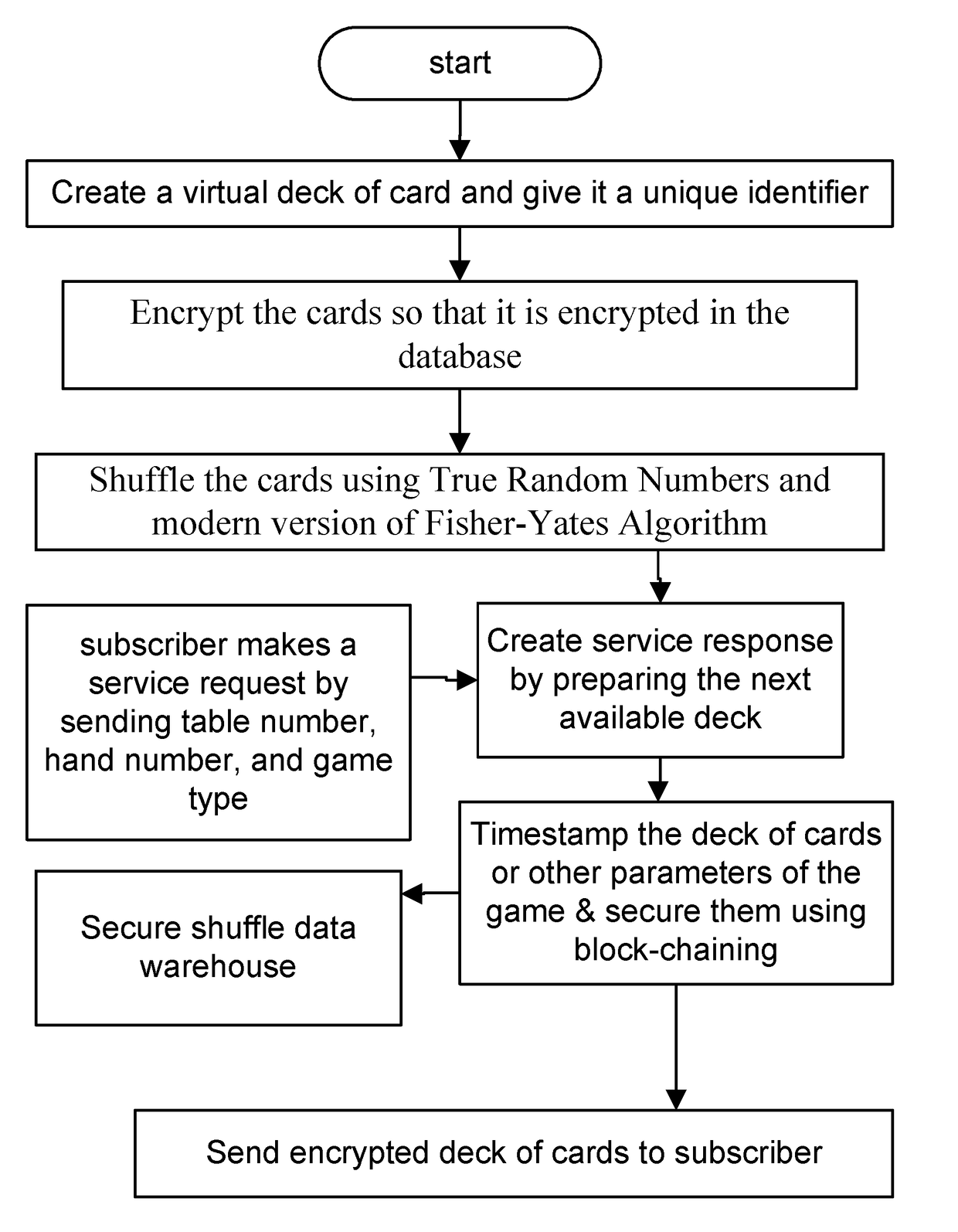
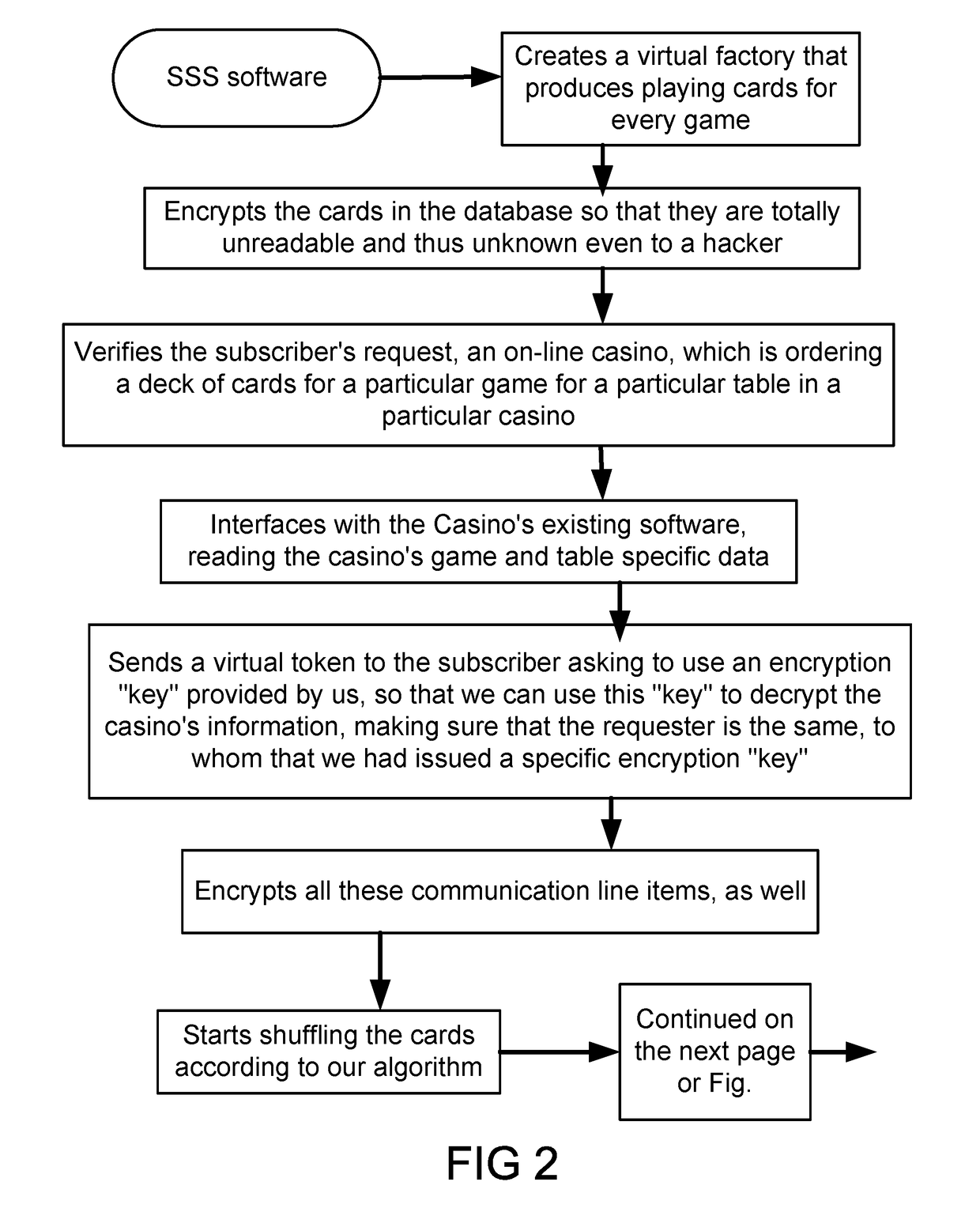
System and method for public verification of a gambling website or gaming event
InactiveUS20170161991A1Increase in sizeApparatus for meter-controlled dispensingComputer hardwareRandom seed
In one example, we describe a method and system to solve the following problem for on-line gambling industry or gaming or on-line software or entertainment, which has to deal with two significant issues, as examples: (1) The integrity of the cards, the dice, or any random event generator; and (2) The possibility of cheating. On the first problem, the question is how would one know that the cards are not stacked to either favor the house / dealer in the case of Blackjack, or in the case of poker, the cards are not stacked as to favor betting and increasing the size of the pot and the rake. We have developed a software platform that delivers secure, encrypted cards, or other random seed generated event game, through a process that makes it virtually impossible for the integrity of the game to be compromised without detection. More variations and examples are discussed here.
Owner:AYATI ARYO +1
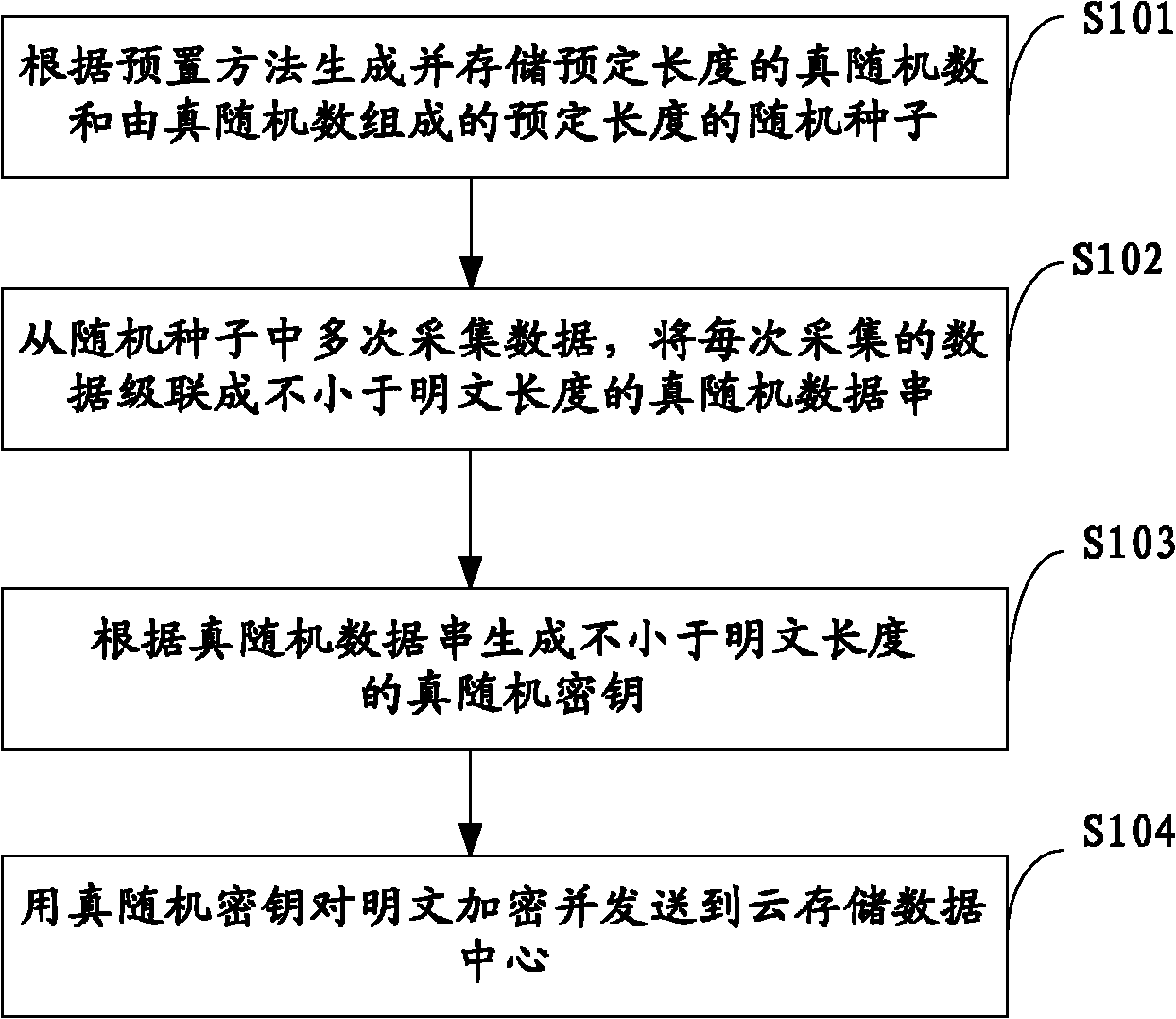
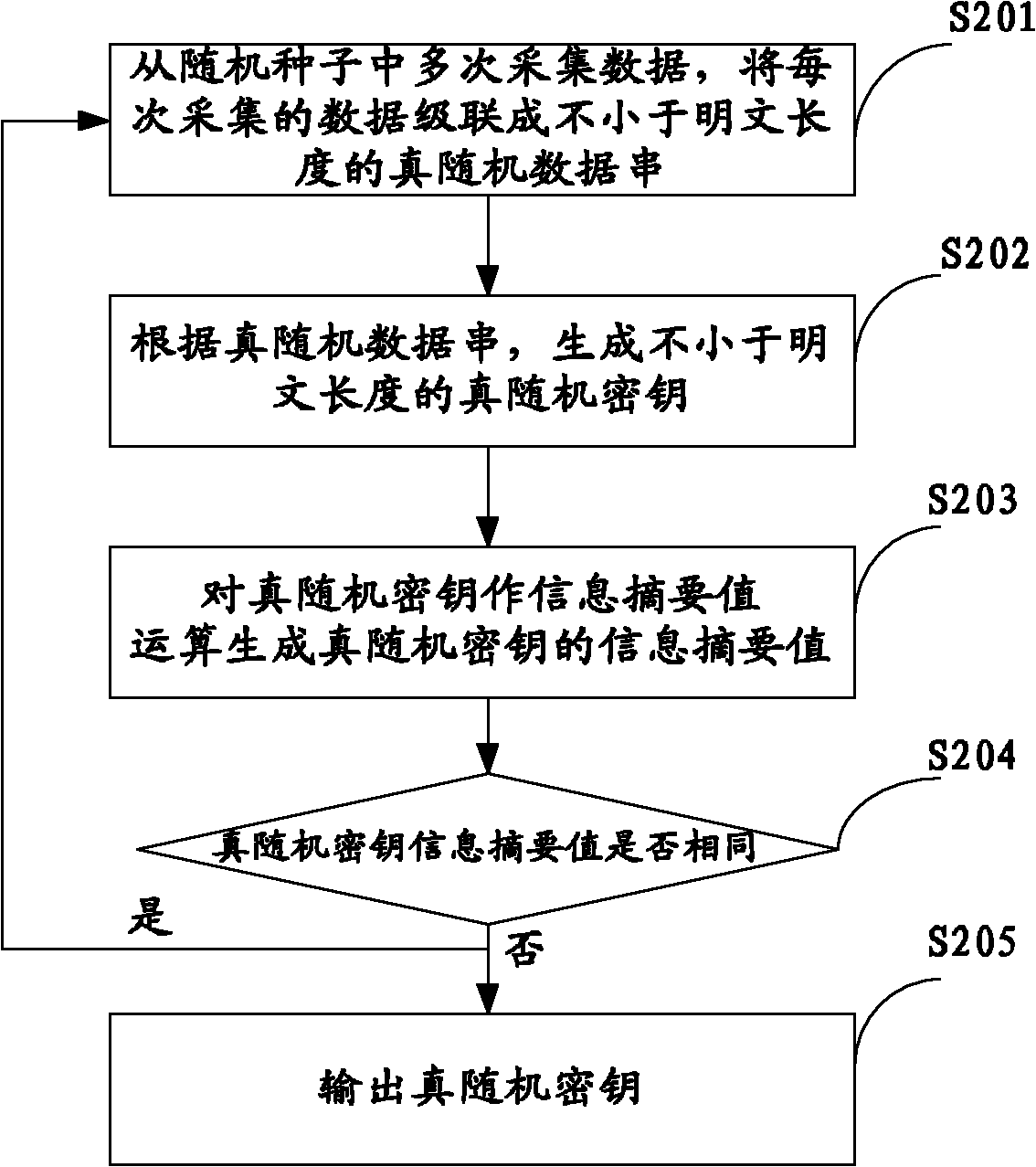
OTP-based cloud storage data storing method, device and system
InactiveCN101986663AProtection securityPrivacy protectionUser identity/authority verificationConfidentialityData center
The invention belongs to the technical field of cloud storage security, and particularly relates to an OTP-based (one-time pad-based) cloud storage data storing method, an OTP-based cloud storage data storing device and an OTP-based cloud storage data storing system. The method comprises the following steps of: generating and storing a true random number of predetermined length and a random seed consisting of the true random number and with predetermined length according to a preset method; repeatedly acquiring data from the random seed, and cascading the data acquired each time into a true random data string not shorter than a plain text length; and generating a true random key not shorter than the plain text length according to the true random data string, encrypting the plain text and sending the encrypted plain text to a cloud storage data center. The invention also provides the OTP-based cloud storage data storing device and the OTP-based cloud storage data storing system. The method, the device and the system generate and store the true random key with enough number and without repeated use by using relatively small plain text storage space, effectively protect the security and the privacy of the cloud storage data and improve the confidentiality of the cloud storage data.
Owner:BEIJING Z & W TECH CONSULTING
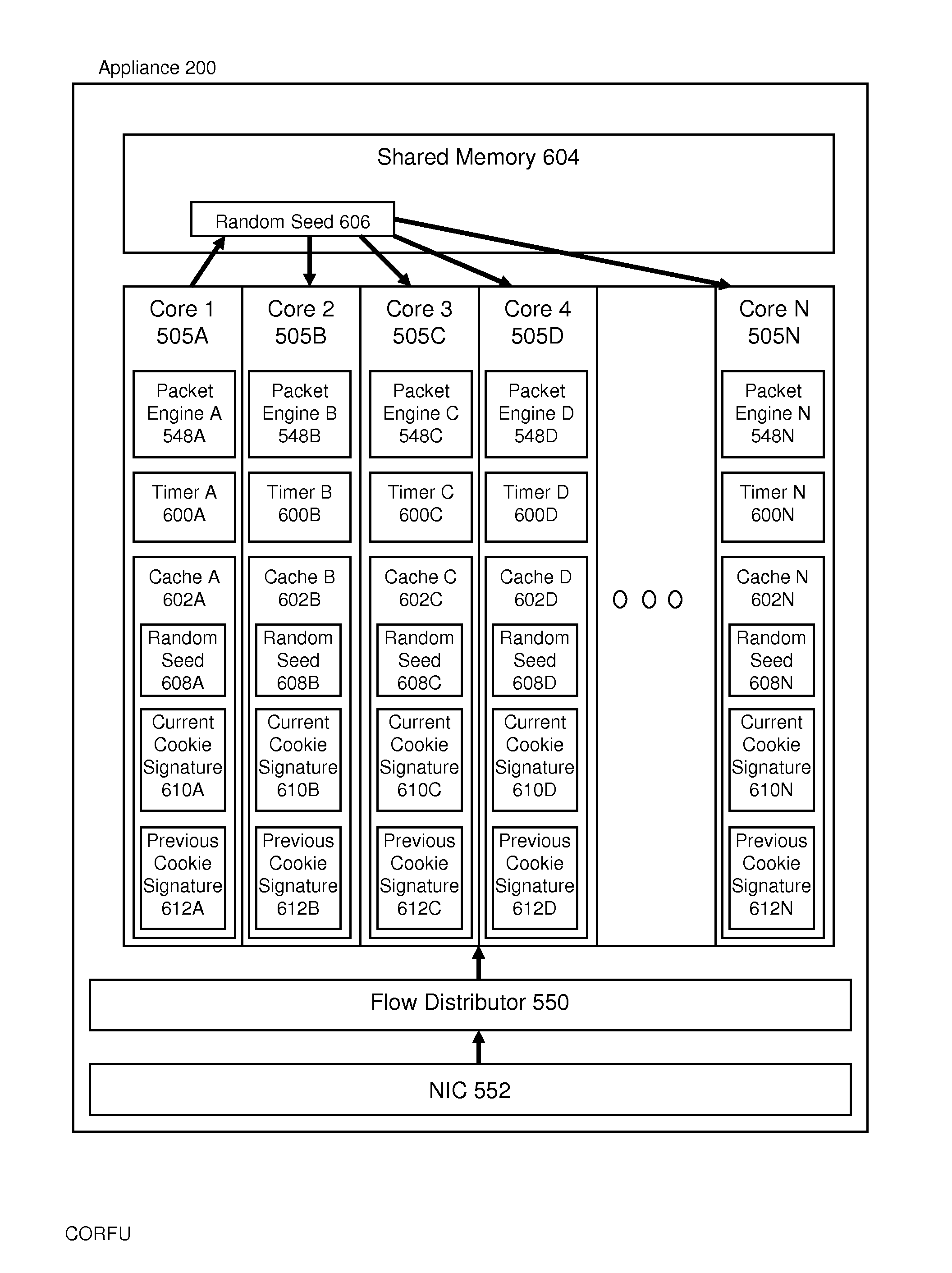
Systems and methods for generating and managing cookie signatures for prevention of HTTP denial of service in multi-core system
The present application is directed towards systems and methods for generating and maintaining cookie consistency for security protection across a plurality of cores in a multi-core system. A packet processing engine executing on one core designated as a primary packet processing engine generates and maintains a global random seed. The global random seed may be used as an initial seed for creation of cookie signatures by each of a plurality of packet processing engines executing on a plurality of cores of the multi-core system using a deterministic pseudo-random number generation function such that each core creates an identical set of cookie signatures.
Owner:CITRIX SYST INC
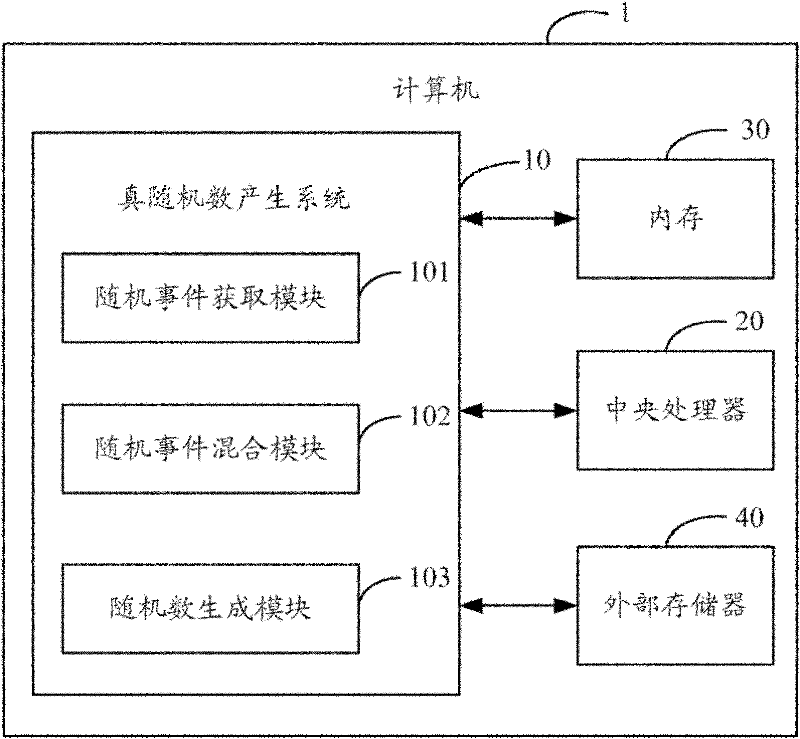
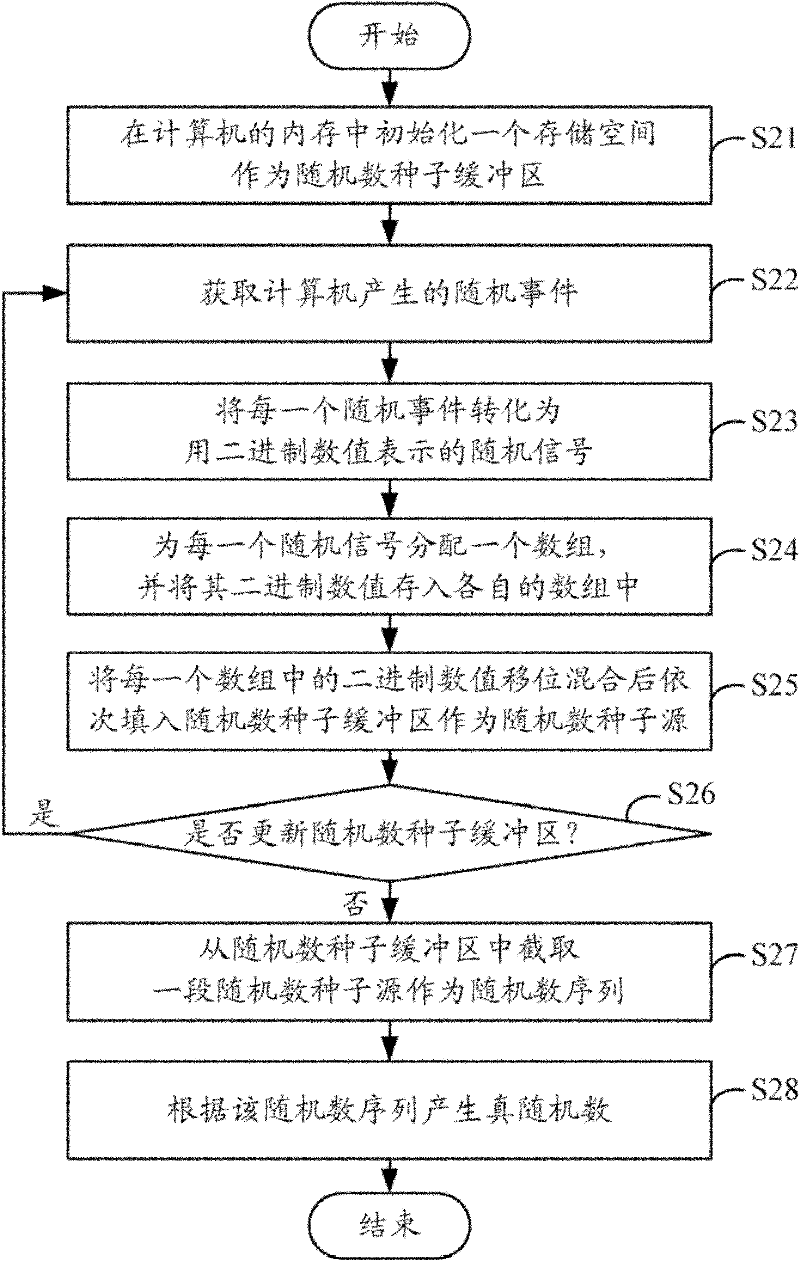
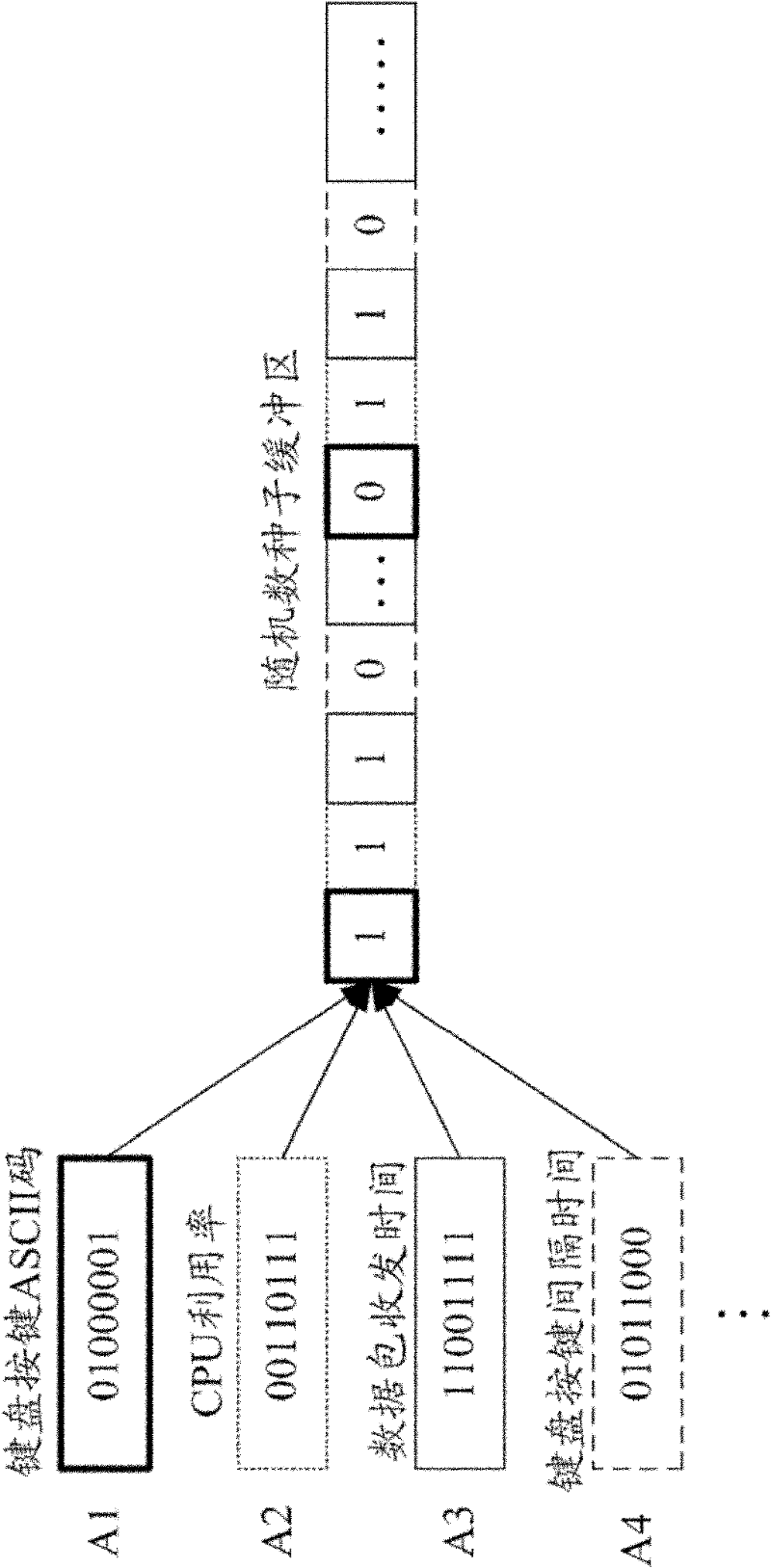
True random number generating system and method
The invention discloses a true random number generating system and a true random number generating method. The method comprises the following steps: initializing a storage space in the internal memory of a computer as a random number seed buffering region; acquiring a random event generated by the computer; converting each random event into a random signal represented by a binary number; allocating an array to each random signal, and storing the binary numbers of the random events into the arrays allocated to the random signals respectively; shifting and mixing the binary numbers in each array and filling the binary numbers into the random number seed buffering region in turn to generate a random number source; intercepting a section of random number seed source from the random number seed buffering region as a random number sequence; and generating true random numbers according to the random number seed sequence. When the system and the method are implemented, the random events generated by the computer in an operation process are used as the seeds and source of the random numbers to generate true random numbers, so the randomness is high.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
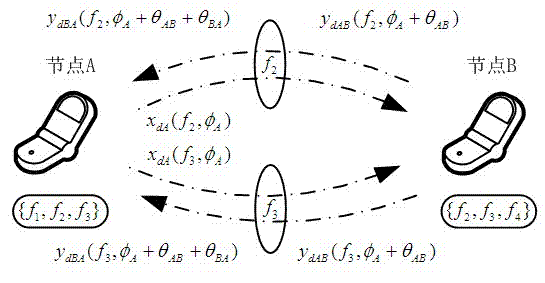
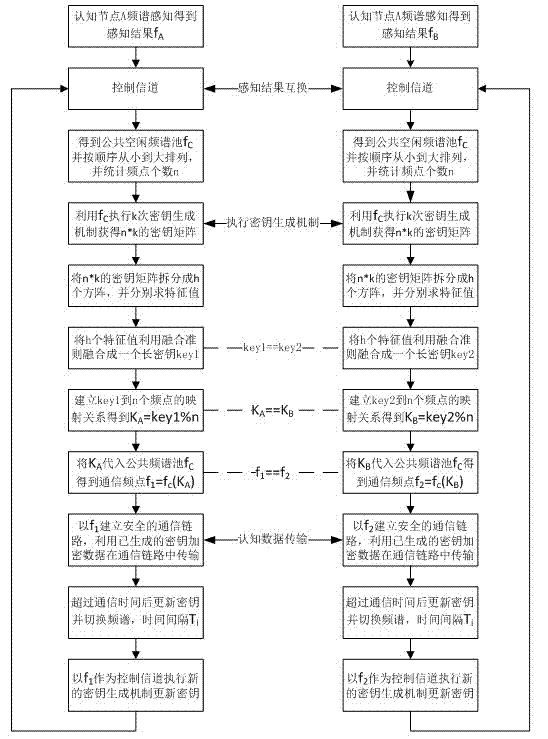
Communication key generation method and secure channel selection method for cognitive radio system
ActiveCN102833736AImprove match rateIncrease spawn rateSecurity arrangementCommunications securityComputer hardware
The invention discloses a communication key generation method and a secure channel selection method for a cognitive radio system, and belongs to the field of secure communication and information security in radio communication. A common available channel set is established according to a local spectrum pool of received and transmitted nodes, the quantity of channels of the channel set is at least equal to one, beacon signals with random initial phases are received and transmitted multiple times by the aid of channels which are sequentially selected from the available channel set, and phases of the received signals are detected and utilized for generating a random key element matrix according to reciprocity of wireless transmission characteristics of the same channels within a coherent time and differentiation of wireless transmission characteristics of different channels, and finally communication keys are acquired by fusion processing of the matrix. The communication keys are used for encrypting transmitted information and are also used as random seeds for selecting secure communication channels. The communication key generation method and the secure channel selection method have the advantages that interaction of the communication keys among the received and transmitted nodes through the channels is omitted, hidden dangers such as wiretapping, tampering and saturation attack from attackers can be eliminated, and commutation security of the cognitive radio system can be guaranteed.
Owner:贾晓丽
Method and circuit for generating random numbers, and computer program product therefor
ActiveUS20070140485A1Improve securityRandom number generatorsSecuring communicationRandom seedNumber generator
A random number generator uses the output of a true random generator to alter the behavior of a pseudo-random number generator. The alteration is performed by a mixing logic that builds a random seed for the pseudo-random number generator and includes a generator of an alteration signal, the generation of which exploits the random instant of arrival of the bits outgoing from the true random generator. The alteration signal is obtained by processing the seed by means of the pseudo-random sequence.
Owner:TELECOM ITALIA SPA
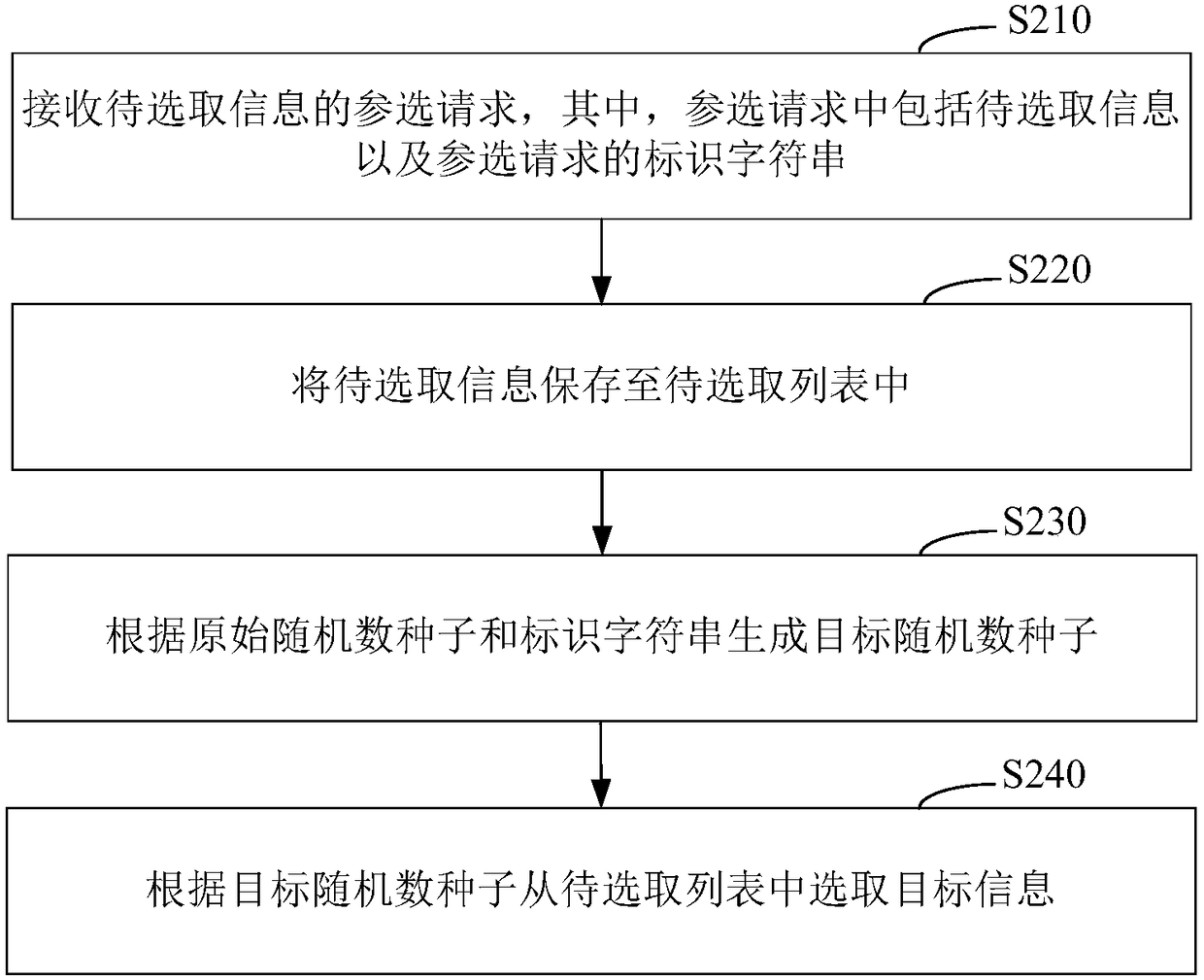
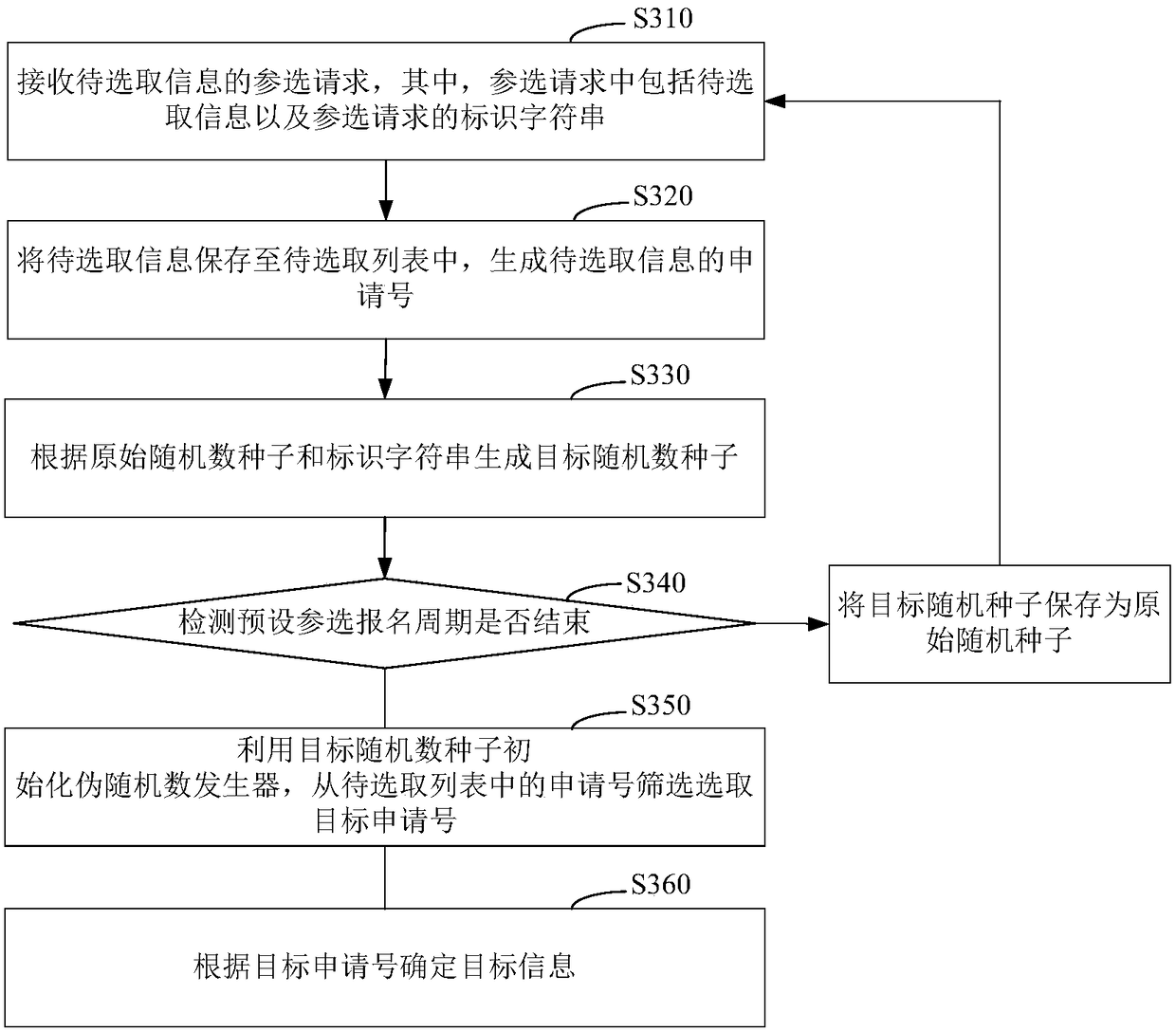
Target information selecting method, apparatus, computer equipment and storage medium
ActiveCN108648323AIncrease randomnessImprove fairnessLottery apparatusObjective informationRandom seed
The invention relates to a target information selecting method, an apparatus, computer equipment and a storage medium. The method comprises the following steps: receiving an election request of to-be-selected information, wherein the election request comprises the to-be-selected information and identification string of the election request; storing the to-be-selected information to a to-be-selected list, generating a target random seed number according to an original random seed number and the identification string, and selecting the target information according to the target random seed number from the to-be-selected list. The updating of the target random seed number is related to the election request of the to-be-selected information, the target random seed number is not determined by less information, randomness of the target random seed number is greatly increased, the possibility of any artificial interference on lottery result is reduced, the randomness of the target informationselected according to the target random seed number is greatly increased, and the fairness for selecting the target information is increased.
Owner:广州市申迪计算机系统有限公司
Method for real-time team coordination with unrealiable communications between team members
ActiveUS7162199B1Special service provision for substationMultiplex system selection arrangementsBurst transmissionRandom seed
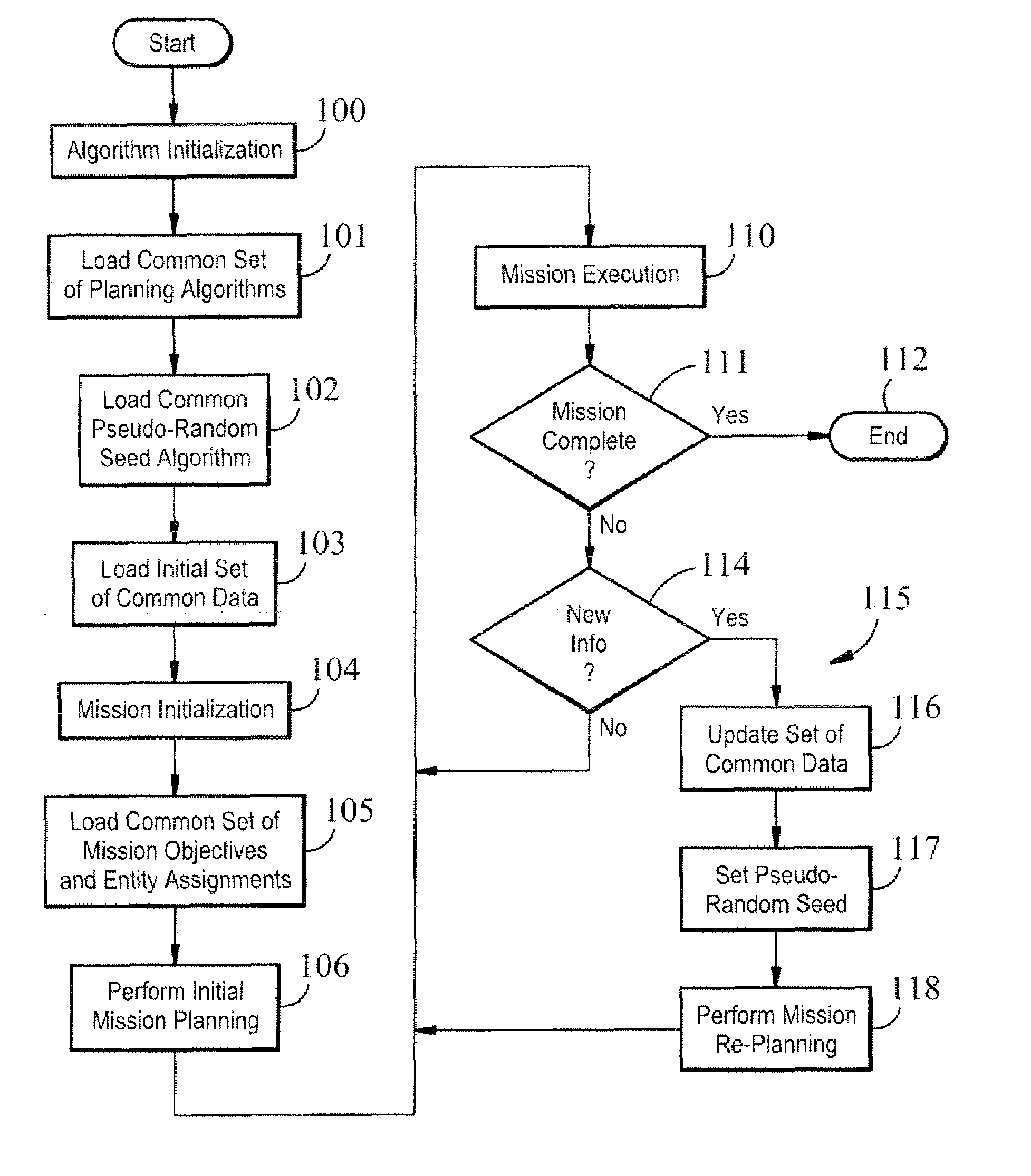
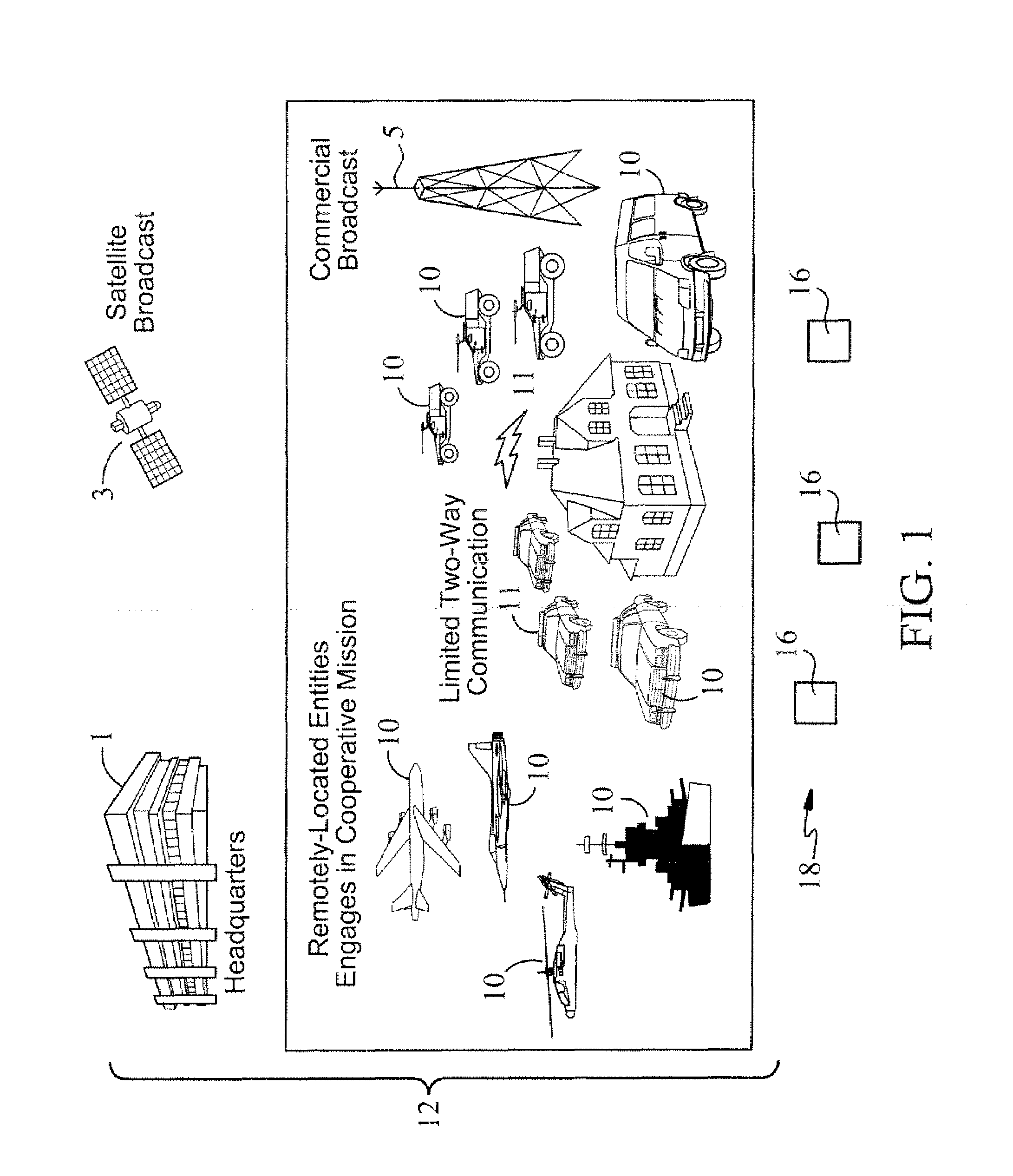
A system and method of coordinating team members, each team member having a mission processor, in real time for continued coordinated operation in the absence of reliable communications between team members. Prior to a mission, each team member is provided with common programs and data for a mission, the data including identity of programs and data supplied to other team members and providing to each team member a pseudo random seed for use in conjunction with random functions. Each team member is provided with an initial set of conditions, whereby each team member performs deterministically to generate a same plan for itself and each of the other team members. Each team member monitors for a transmission event and responds to a transmission event by generating a re-planning operation, whereby each team member will produce a coordinated replan for itself and each other team member, whereby the team members remain coordinated. The monitoring can be detecting the presence or absence of a scheduled transmission from a team member, or receiving a transmission from a broadcast source, or receiving a transmission directed to team members from a headquarters, or receiving a commercial satellite broadcast, or maintaining a receiver for receiving a burst transmission from another team member or receiving a transmission indicative of a condition as reported by a team member.
Owner:LOCKHEED MARTIN CORP
Blockchain consensus method and device based on VRF and threshold signature
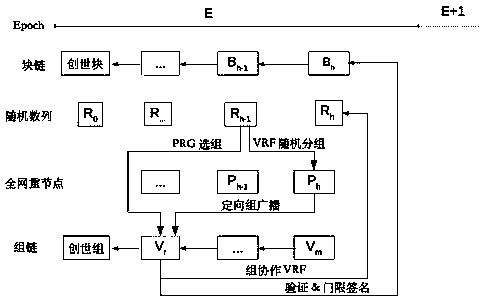
ActiveCN111090892AStrong communication skillsReduce data volumeDigital data protectionAlgorithmRandom seed
The invention discloses a block chain consensus method and device based on VRF and threshold signatures. The method comprises the steps: enabling a system to carry out the periodic random sampling ofa light node miner, forming a plurality of verification groups, enabling a random number of a former block to serve as a random seed of a PRG function, and determining a verification group at a current height through the generated random number; and the whole-network re-node performs VRF grouping according to the random number of the previous block, randomly selects a proposal group of the currentheight, and proposal parts give a plurality of candidate block proposal orientations to broadcast to a verification group of the current height. And the verification group at the current height completes candidate block verification through signature voting in a group cooperation mode without interaction, and achieves intra-group consensus in a threshold signature mode to broadcast to the outsideof the group. According to the method, the intra-group consensus is achieved through periodic random sampling and grouping and voting by utilizing non-interactive signatures, the data size can reachthe minimum, and an efficient, safe and decentralized blockchain consensus scheme is realized based on a VRF algorithm and a threshold signature (BLS) algorithm.
Owner:吕晟珉
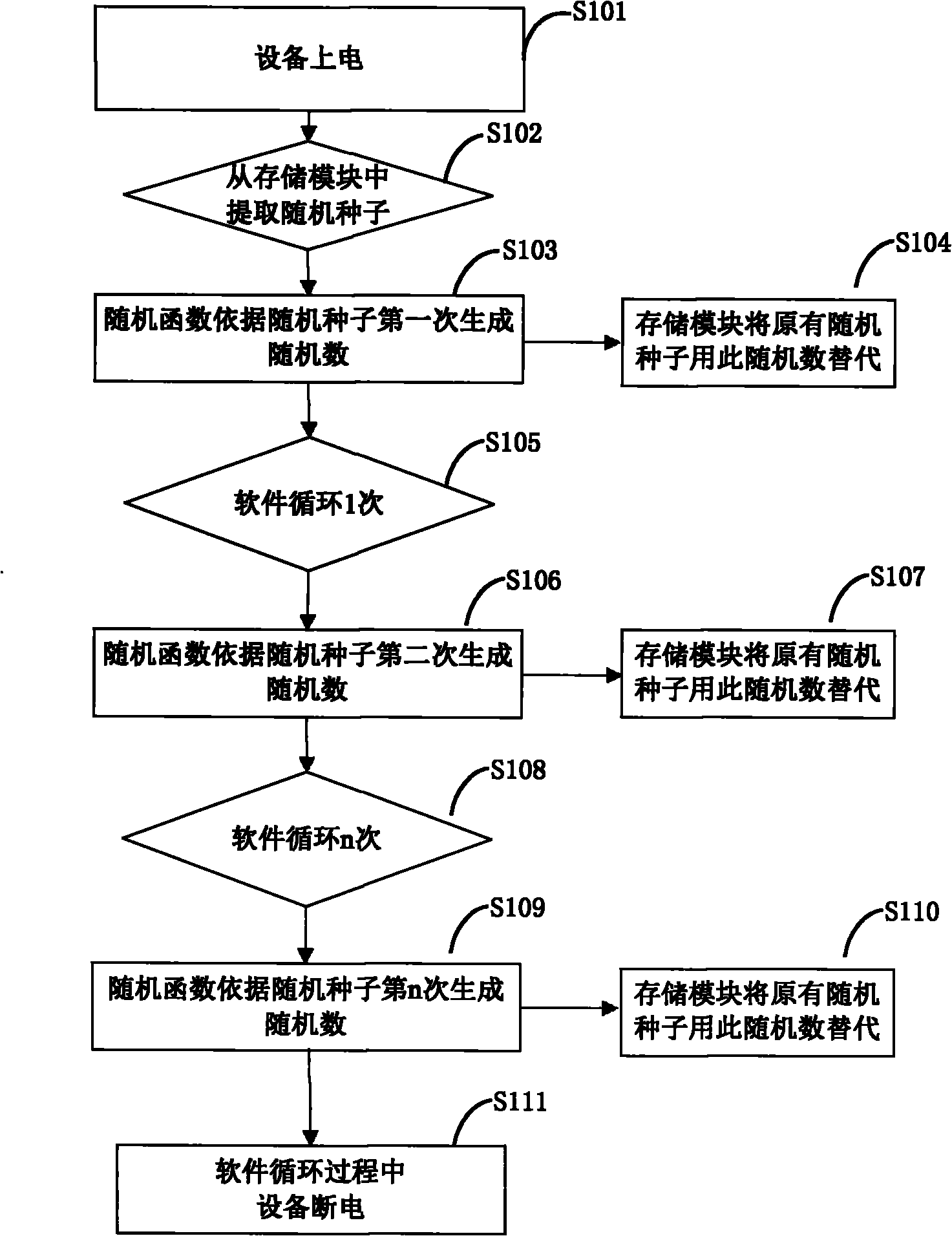
True random number generation method implemented by software
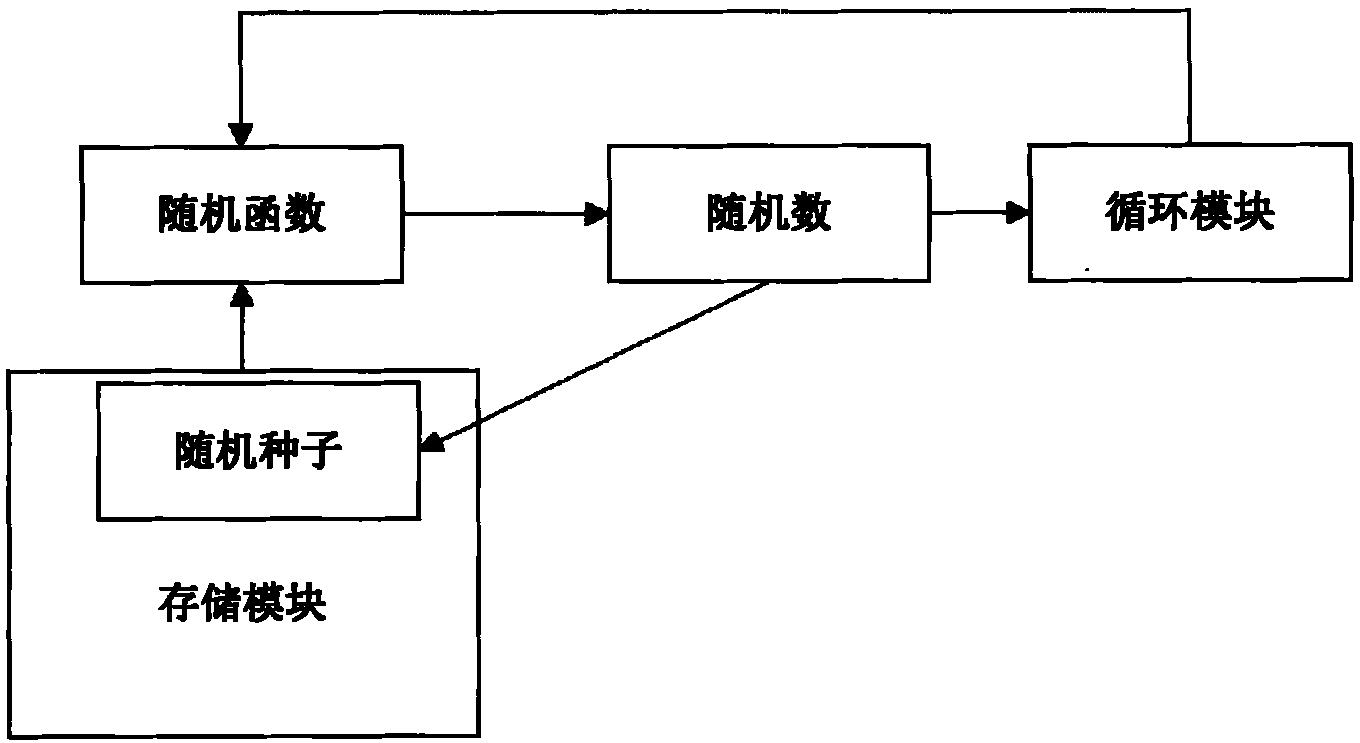
InactiveCN102063285ASolve the problem that only pseudo-random numbers can be generatedRandom number generatorsElectricityRandom seed
The invention discloses a true random number generation method implemented by software. The method comprises a pseudo random number generation module, a circulation module and a storage module. The pseudo random number module generates a pseudo random number according to a random seed stored in the storage module; the circulation module uninterruptedly generates new pseudo random numbers with the pseudo number through software circulation; and the storage module is used for storing the random numbers generated by the circulation module at fixed period. Due to uncertainty of power-on time of electronic equipment in final detection and using process of users, the true random number can be generated after the equipment is used for multiple times.
Owner:倍奥锐(北京)科技有限公司
Inventory allocation with tradeoff between fairness and maximal value of remaining inventory
A method of balancing advertisement inventory allocation includes constructing a flow network of nodes having impressions connected to contracts through corresponding arcs such as to satisfy demand requests of the contracts; normalizing an impression value of each node to a predetermined cost range; setting a cost of each arc to each corresponding normalized value; iteratively performing a plurality of times: (a) sampling the nodes or the arcs to create sample nodes and arcs, each time starting from a different random seed; (b) optimally allocating impressions from the sample nodes to the contracts with a minimum-cost network flow algorithm; (c) separately allocating impressions from sample arcs of lowest cost before allocating those from sample arcs of higher cost; averaging allocations from iterations (b) to create a first allocation; averaging allocations from iterations (c) to produce a second allocation; and computing a weighted solution of the first and second allocations.
Owner:OATH INC
Variable probability bidirectional rapidly-exploring random tree improved path planning algorithm
InactiveCN108762270AAvoid collisionImprove search speedPosition/course control in two dimensionsVehiclesPath lengthAlgorithm
The invention relates to a variable probability bidirectional rapidly-exploring random tree improved path planning algorithm. Firstly, when importing a state space map, state space preprocessing needsto be performed according to the setting of the vehicle volume, and the state space edge is extended and protected to prevent the node from excessively approaching the state space edge to cause a collision. Secondly, a variable probability target selection strategy based on the node environment is adopted to accelerate the convergence speed. Finally, the bent part in the generated path is removedwhile the straight part in the generated path is retained, that is, whether connection lines between the first node as the start and the subsequent nodes have an obstacle is judged, the redundant nodes are deleted, the path is optimized, and the number of turns and the total path length during the driving of the trolley are reduced. The variable probability optimization algorithm is achieved based on the original bidirectional RRT algorithm, and the target pointing method is used to improve the search speed and reduce the calculation amount. At the same time, the path length and the number ofnodes are reduced, and the passability is ensured.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
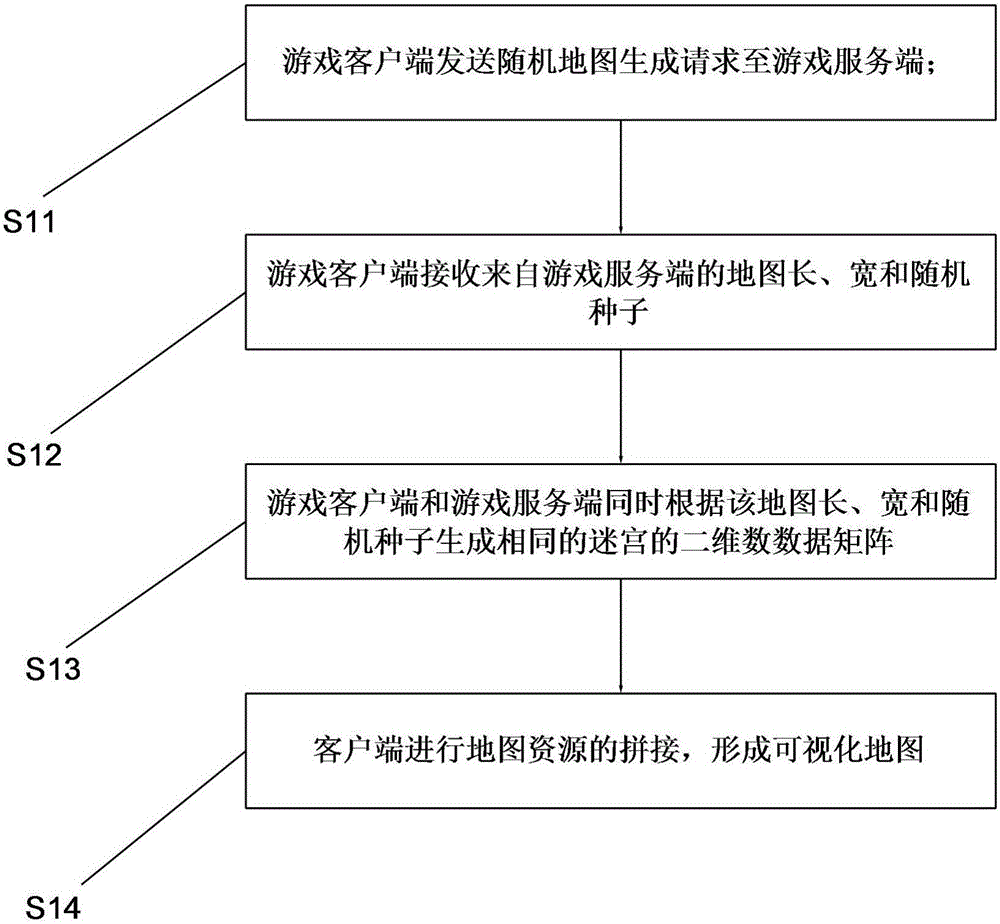
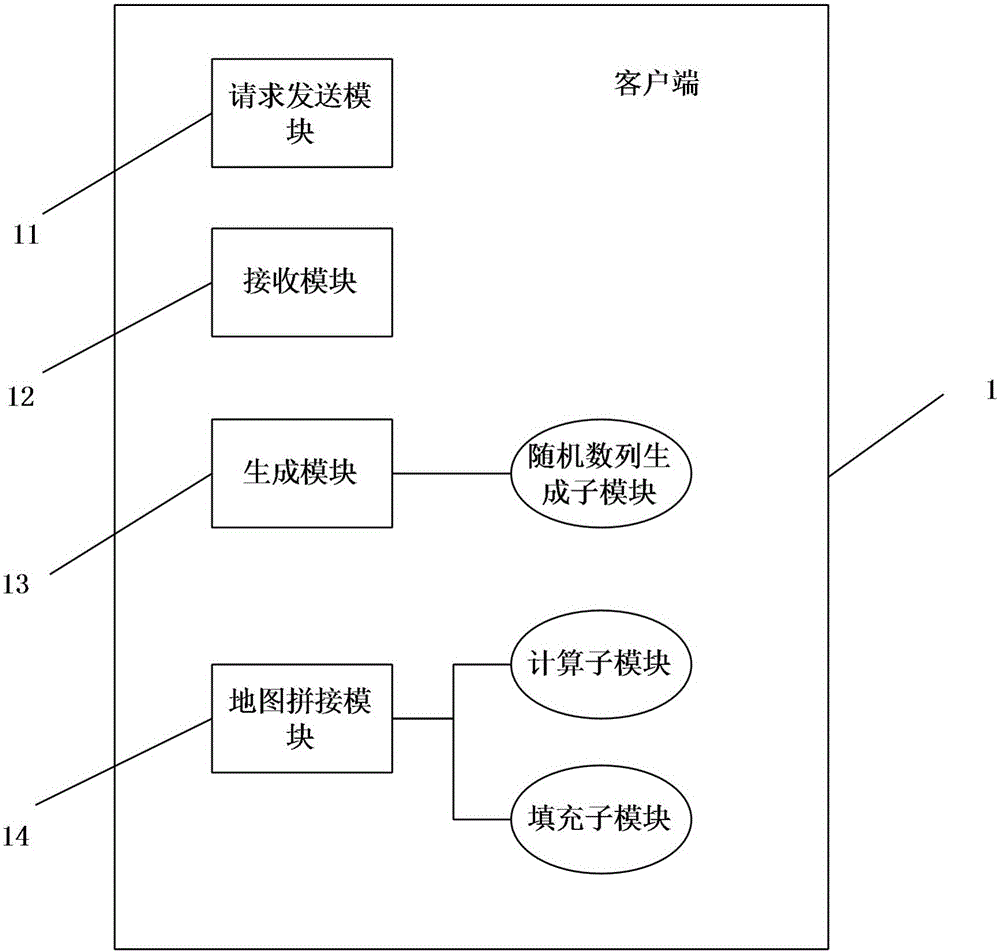
Random map generation method, client, server and system
The invention relates to a random map generation method. The method comprises following steps: a game client sends a random map generation request to a game server; the game client receives map lengths, widths and random seeds of the game server; the game client and the game server generate same two-dimensional data matrixes of labyrinths according to map lengths, widths and random seeds. Compared with the prior art, the random map generation method has following beneficial effects: by transferring seed parameters through the server, the mode for generating same random maps through the server and the client is adopted so that data amount of transmission is reduced and transmission time is greatly shortened; as for generated maps, visible maps can be spliced with natural effect by taking a resources splicing method; and the invention further provides a client used for realizing the above method, a server map generation system and a client map splicing system.
Owner:GUANGZHOU DUOYI NETWORK TECH
Methods and devices for selectively encrypting and decrypting data
ActiveCN102012993AWithout sacrificing protection strengthFast encryption and decryptionComputer security arrangementsSecuring communicationComputer hardwarePlaintext
Owner:BIGKNOW (BEIJING) DATA TECH CO LTD
Data storage method, query method and device, storage medium and computer equipment
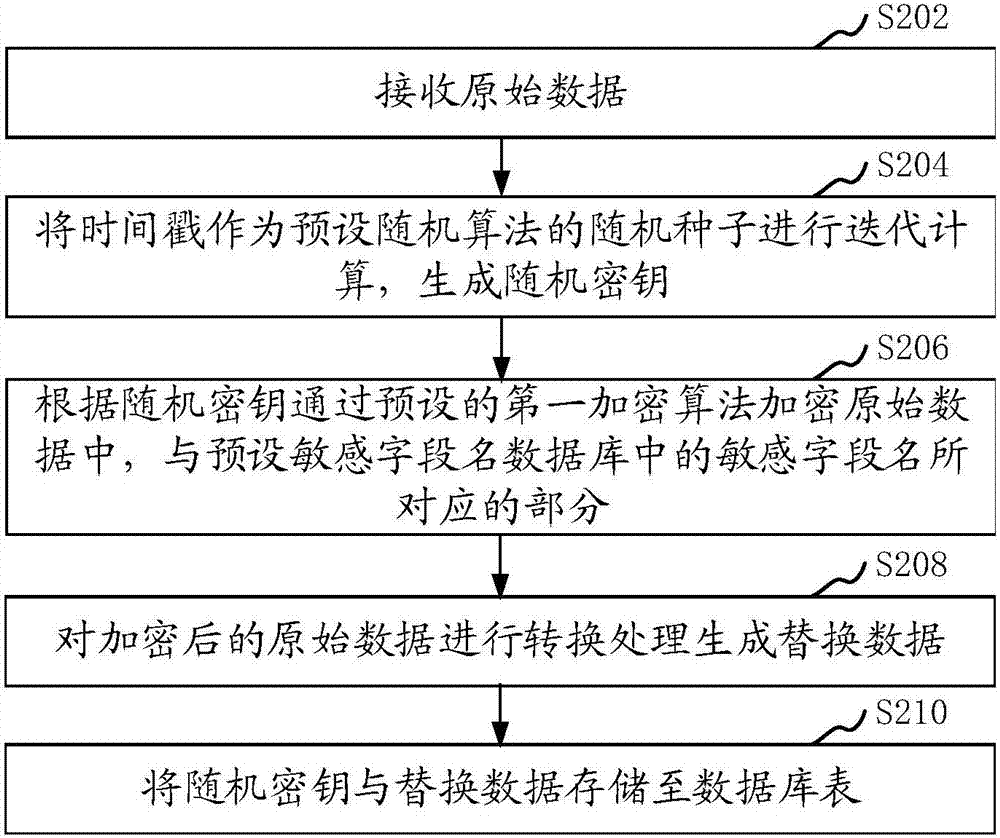
ActiveCN108009440AImprove securityIncrease the difficultyDigital data protectionTimestampStochastic algorithms
The invention relates to a data storage method and device, a storage medium and computer equipment. The method comprises the following steps: receiving original data which comprises timestamp; carrying out iterative computation by taking the timestamp as a random seed of a preset random algorithm to generate a random secret key; encrypting portions, which correspond to sensitive field names in a preset sensitive field name database, in the original data by a preset first encryption algorithm according to the random secret key; carrying out transformation treatment on the encrypted original data to generate replacement data; and storing the random secret key and the replacement data to a database table. By the data storage method and device, the storage medium and the computer equipment, safety of data storage is improved.
Owner:重庆金融资产交易所有限责任公司
Optical disk device and data randomizing method for optical disk drive
InactiveUS20060248427A1Reduction in format efficiencyIncrease the number ofError preventionTransmission systemsComputer hardwareCompact disc
A random seed scramble for preventing the deterioration of a medium is applied to the next generation optical disk. A seed is stored to a BIS area. ID or an EDC is checked to hold interchangeability before and after scramble release. When no error is generated in data before the scramble release, it is recognized as an unscrambled disk. In contrast to this, when no error is generated in data after the scramble release, it is recognized as a scrambled disk. An information storing area showing an area to be rewritten by performing the scramble and an area to be rewritten without performing the scramble is arranged.
Owner:KATAYAMA YUKARI +7
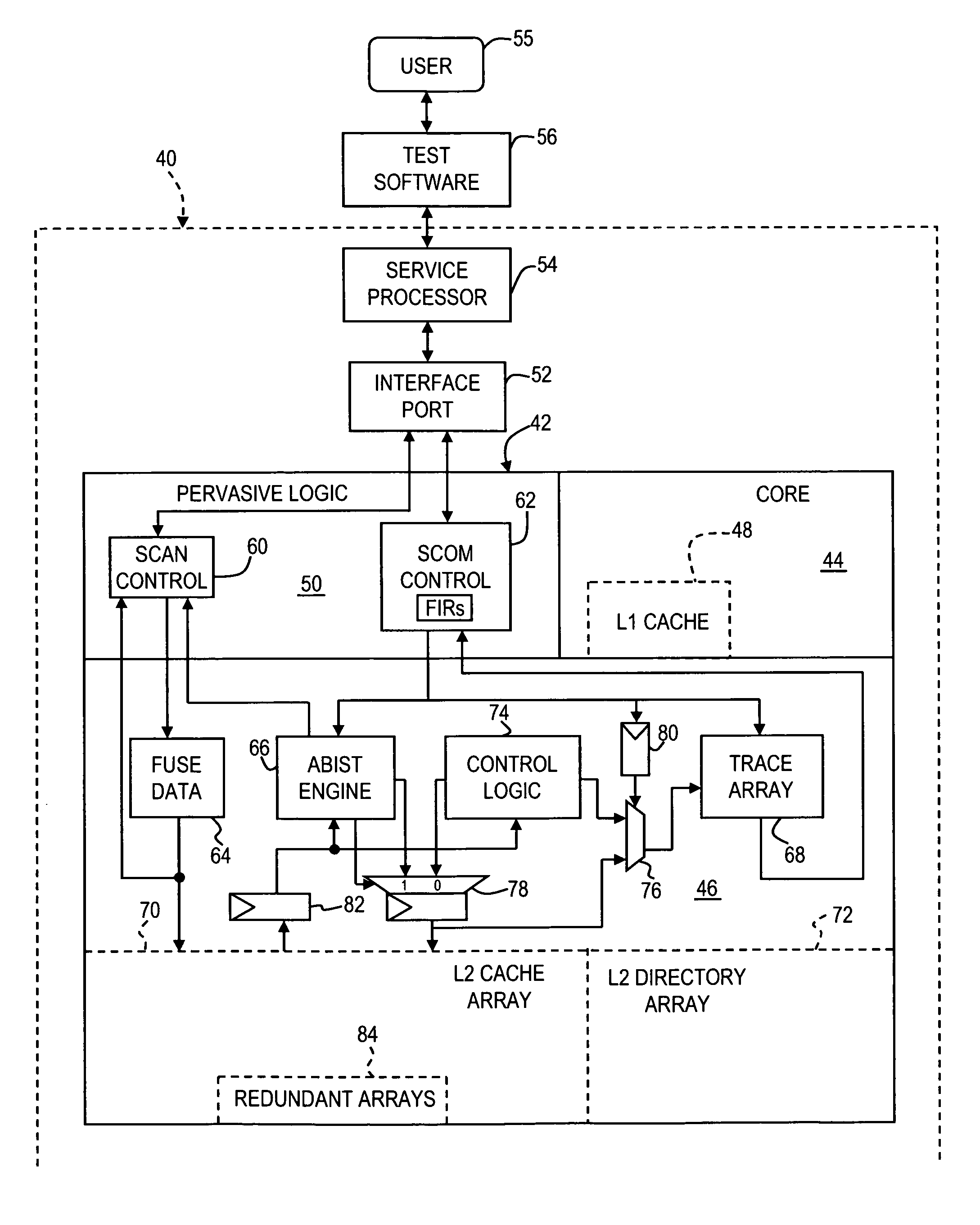
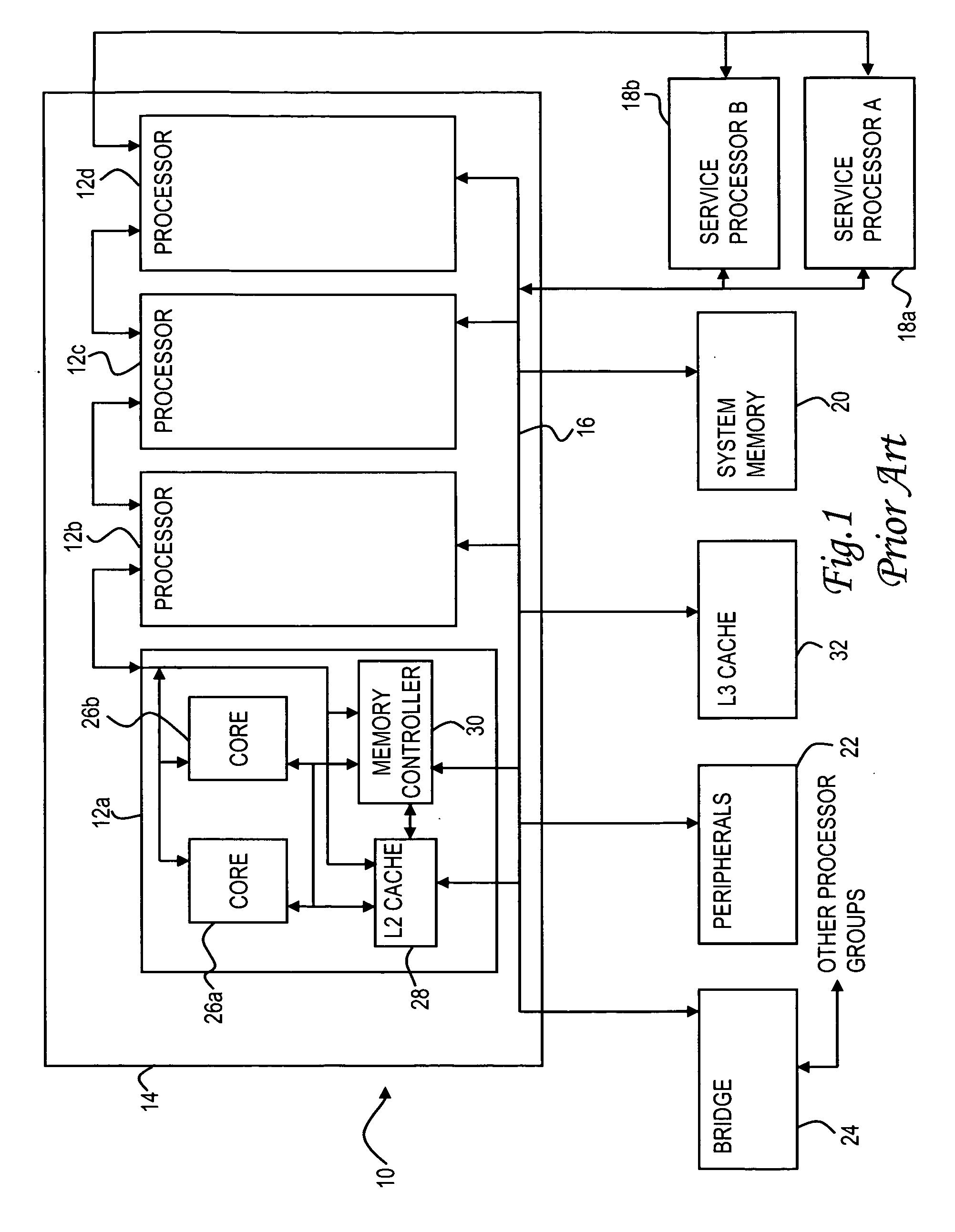
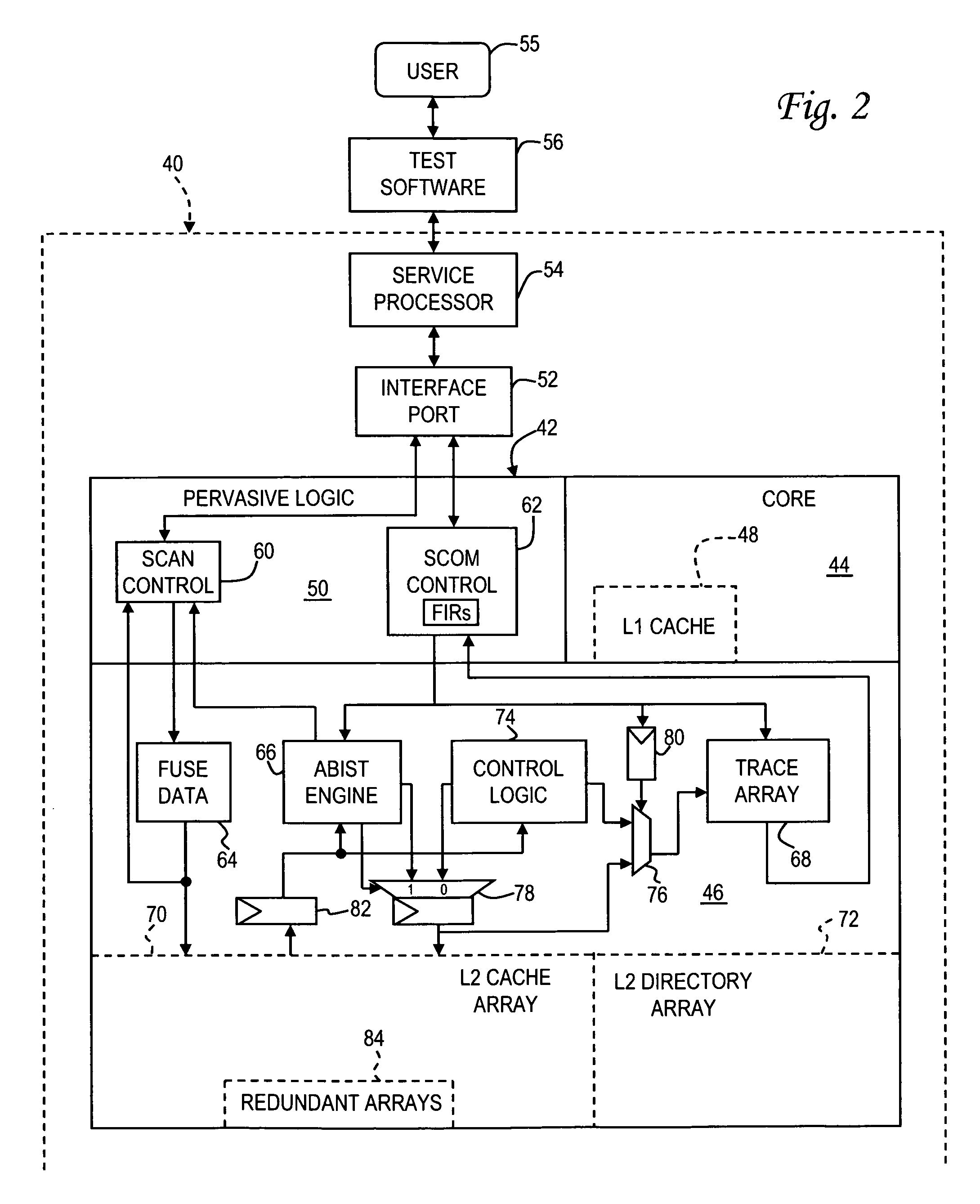
Method for cache correction using functional tests translated to fuse repair
A method of correcting defects in a storage array of a microprocessor, such as a cache memory, by operating the microprocessor to carry out a functional test procedure which utilizes cache memory, collecting fault data in a trace array during the functional test procedure, identifying a location of the defect in the cache memory using the fault data, and repairing the defect by setting a fuse to reroute access requests for the location to a redundant array. The fault data may include an error syndrome and a failing address. The functional test procedure creates random cache access sequences that cause varying loads of traffic in the cache memory using a test pattern based on a random seed. The functional test procedure may be carried out after completion of a nonfunctional, built-in self test of the microprocessor which sets some of the fuses.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com