Communication key generation method and secure channel selection method for cognitive radio system
A cognitive radio and communication key technology, applied in the field of secure channel selection, can solve the problems of low randomness and inappropriateness, and achieve the effects of realizing secure channel selection and data secure communication, preventing eavesdropping, and high generation rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] All features disclosed in this specification, or steps in all methods or processes disclosed, may be combined in any manner, except for mutually exclusive features and / or steps.
[0025] Any feature disclosed in this specification (including any appended claims, abstract and drawings), unless expressly stated otherwise, may be replaced by alternative features which are equivalent or serve a similar purpose. That is, unless expressly stated otherwise, each feature is one example only of a series of equivalent or similar features.
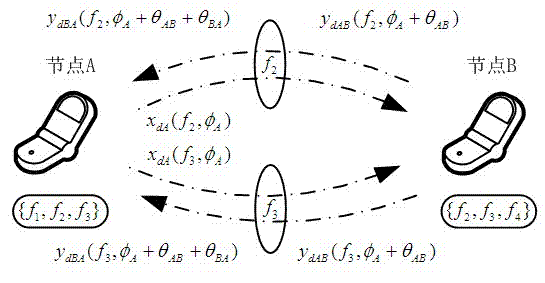
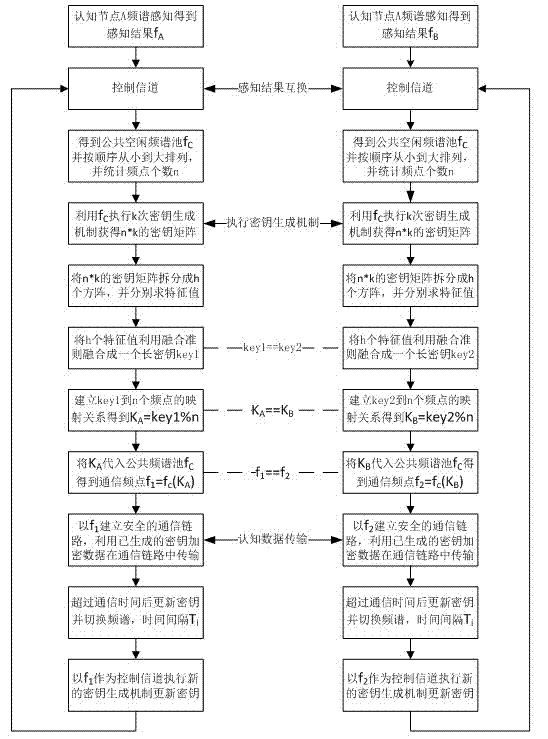
[0026] For attached figure 1 In the shown cognitive radio system communication key generation model, the communication key generation steps are as follows:
[0027] Step 1. According to the node A with nodeB The local spectrum pool selection constructs the public available channel set C ={ f 2 , f 3}, the number of channels in the set N =2, select a channel from the public available channel set f 2 ,node A Use this channel to send th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com