Patents
Literature
247results about How to "Prevent eavesdropping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Secure display
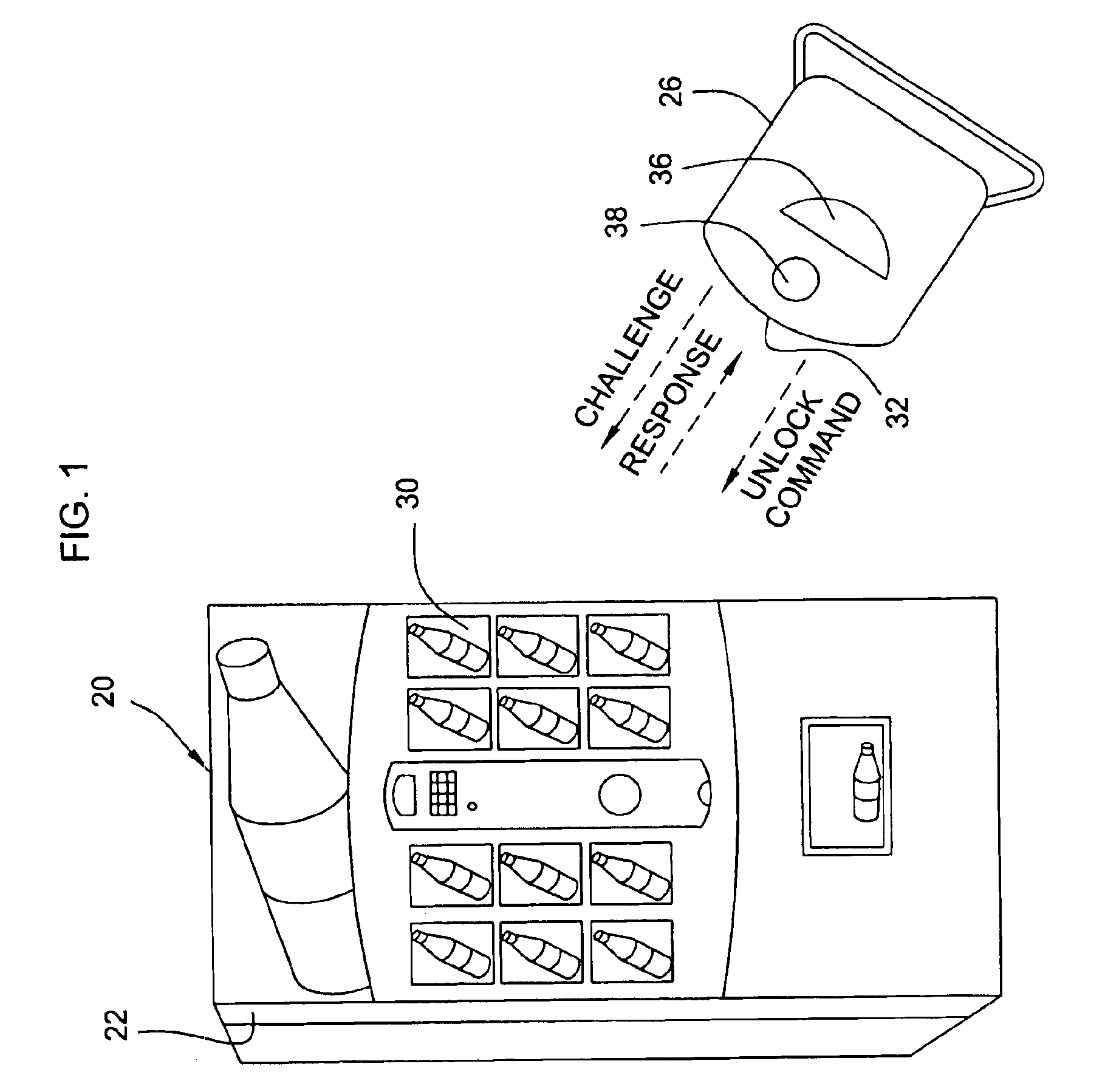
InactiveUS20130208103A1Facilitate communicationPrevent eavesdroppingDigital data processing detailsUnauthorized memory use protectionCommunication interfaceDisplay device
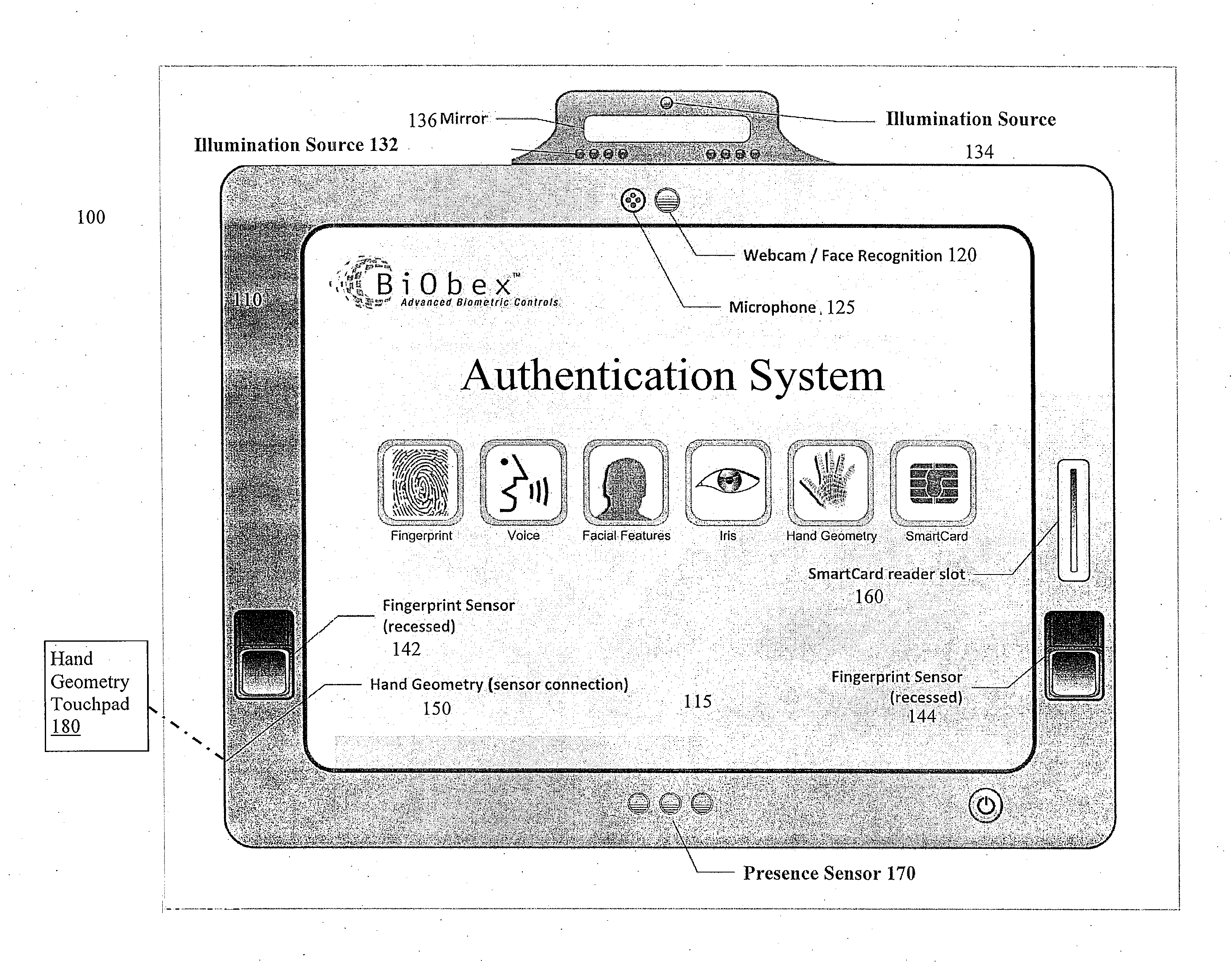
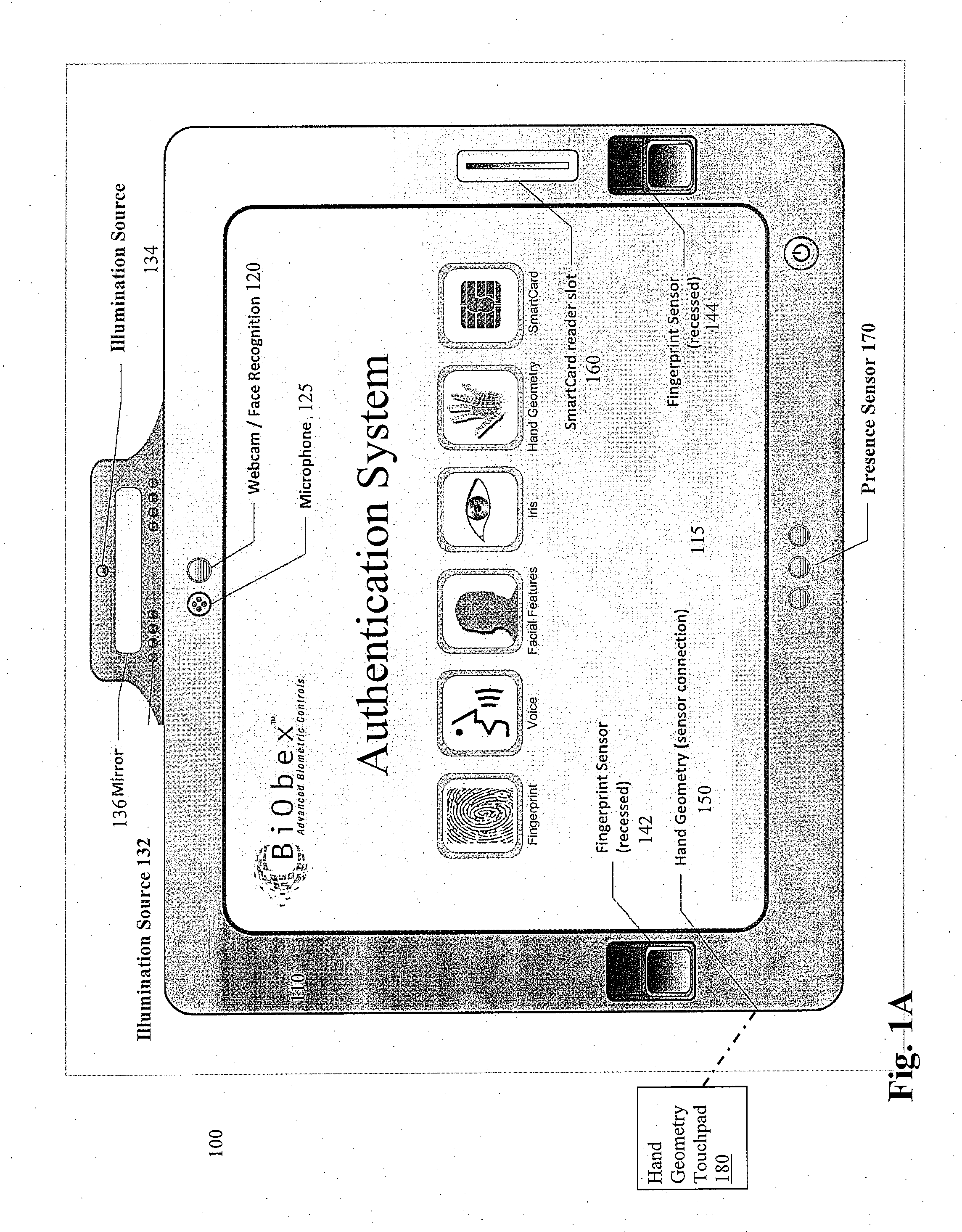
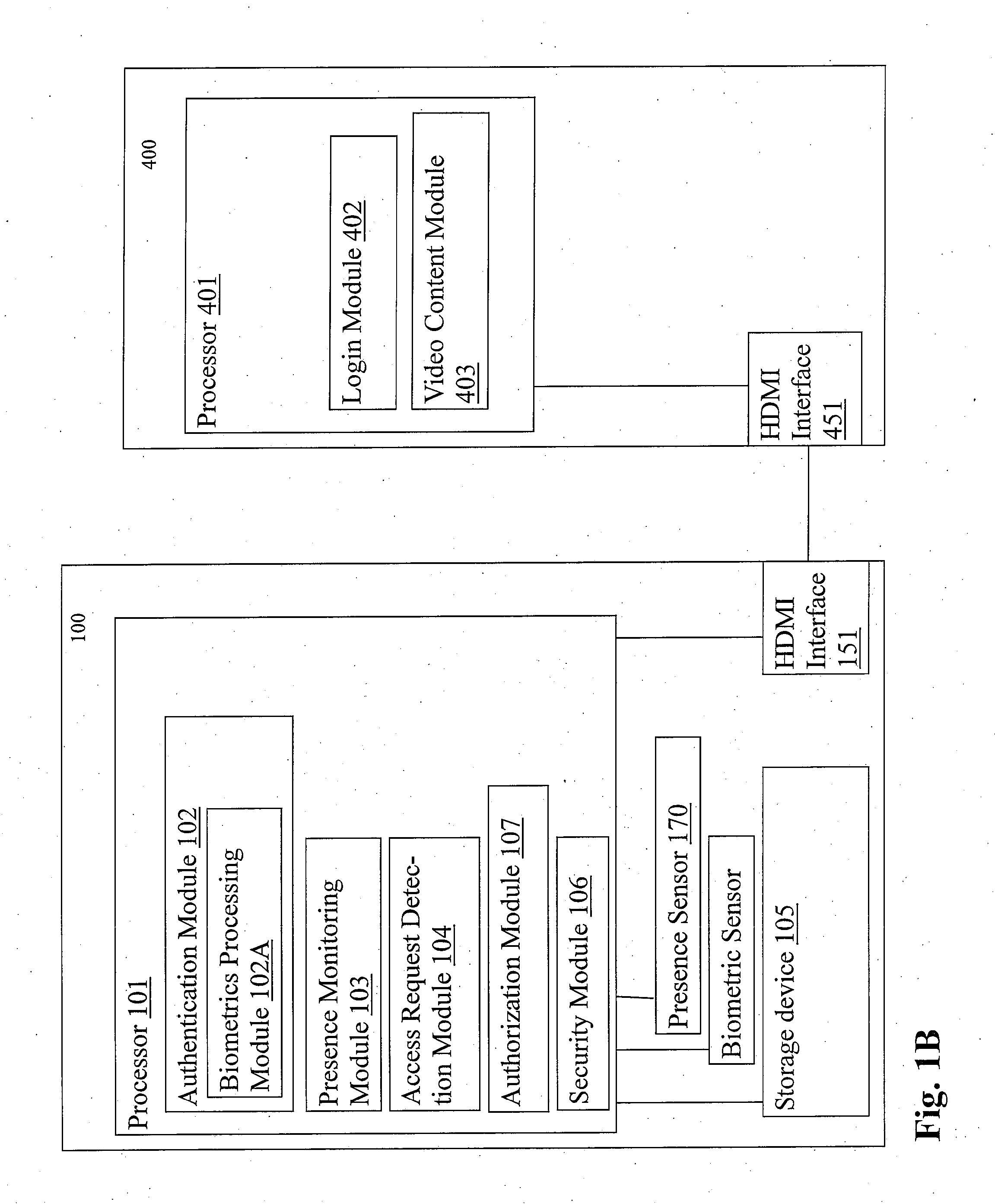
An electronic display is provided for facilitating authentication. The display may integrate one or more of a camera, microphone, fingerprint sensor, card reader, touch screen, and communication interface to collect biometric and other identification information to authenticate a user requesting access to the display. An integrated proximity or motion sensor may be used to track presence of the user. The user may be required to re-authenticate his identity after an absence from the display. The display may be a standalone device or may cooperate with an external computing device. The display may be configured to verify its identity to the external computing device. The display may be configured to perform its own authentication and authorization procedures before presenting content from an external device.
Owner:BIOBEX LLC
Secure memory having anti-wire tapping
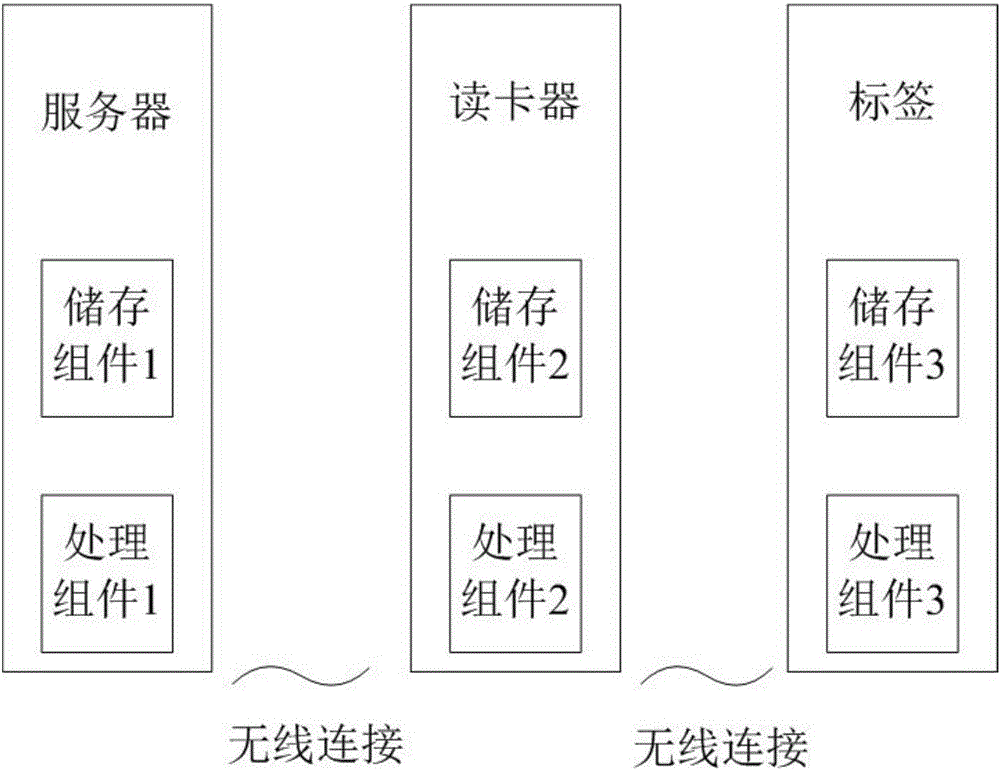
According to a first aspect of the present invention, cryptography without a dedicated microprocessor on the smart card is employed to provide authentication of both the smart card and the smart card reader, and wherein the cryptography provides only a preselected number of attempts at authentication, if not reset, before access to the smart card is denied permanently. According to a second aspect of the present invention, access to each the memory zones of the smart card may be individually provided by cryptography, passwords or both.
Owner:ATMEL CORP
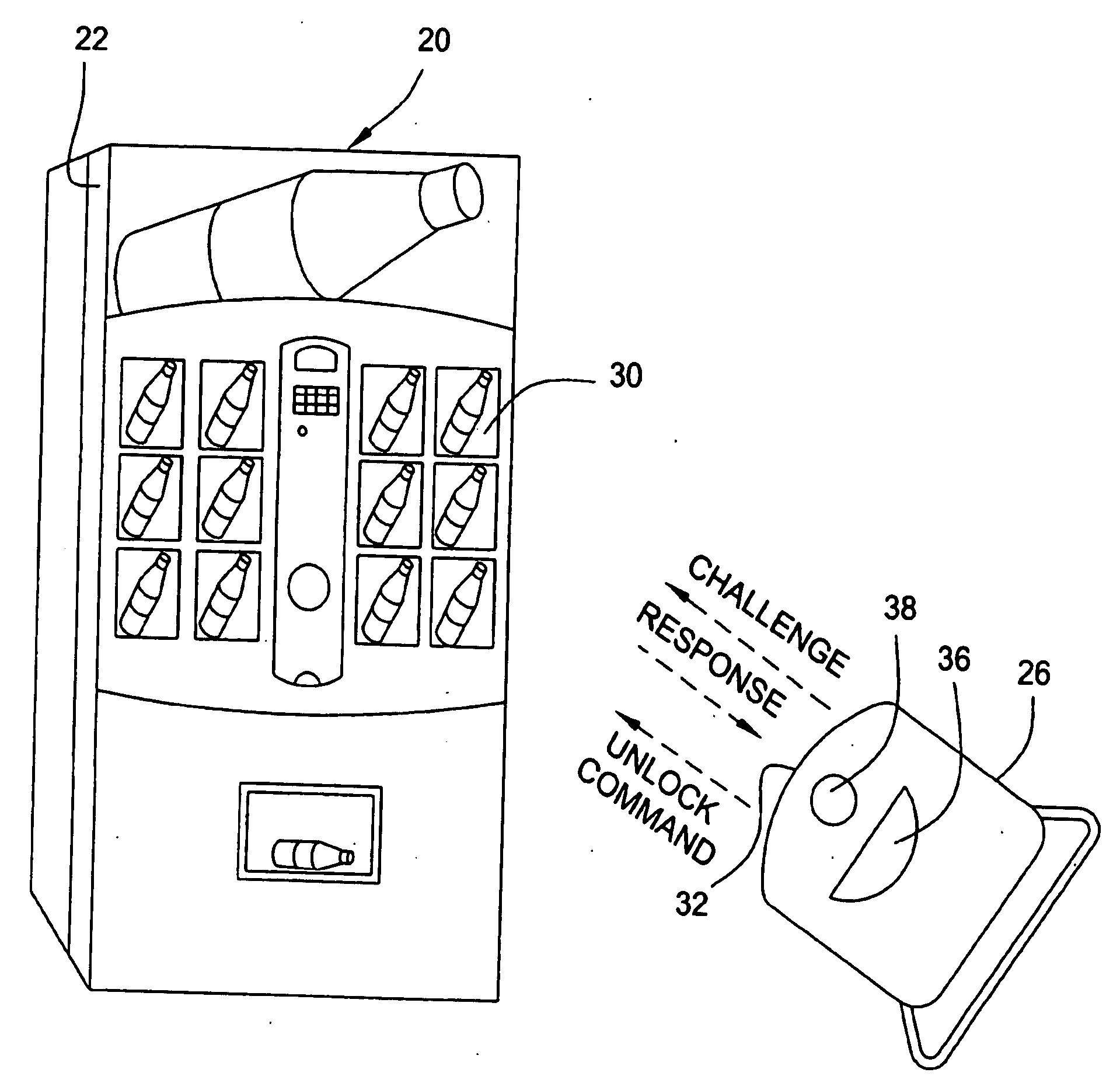
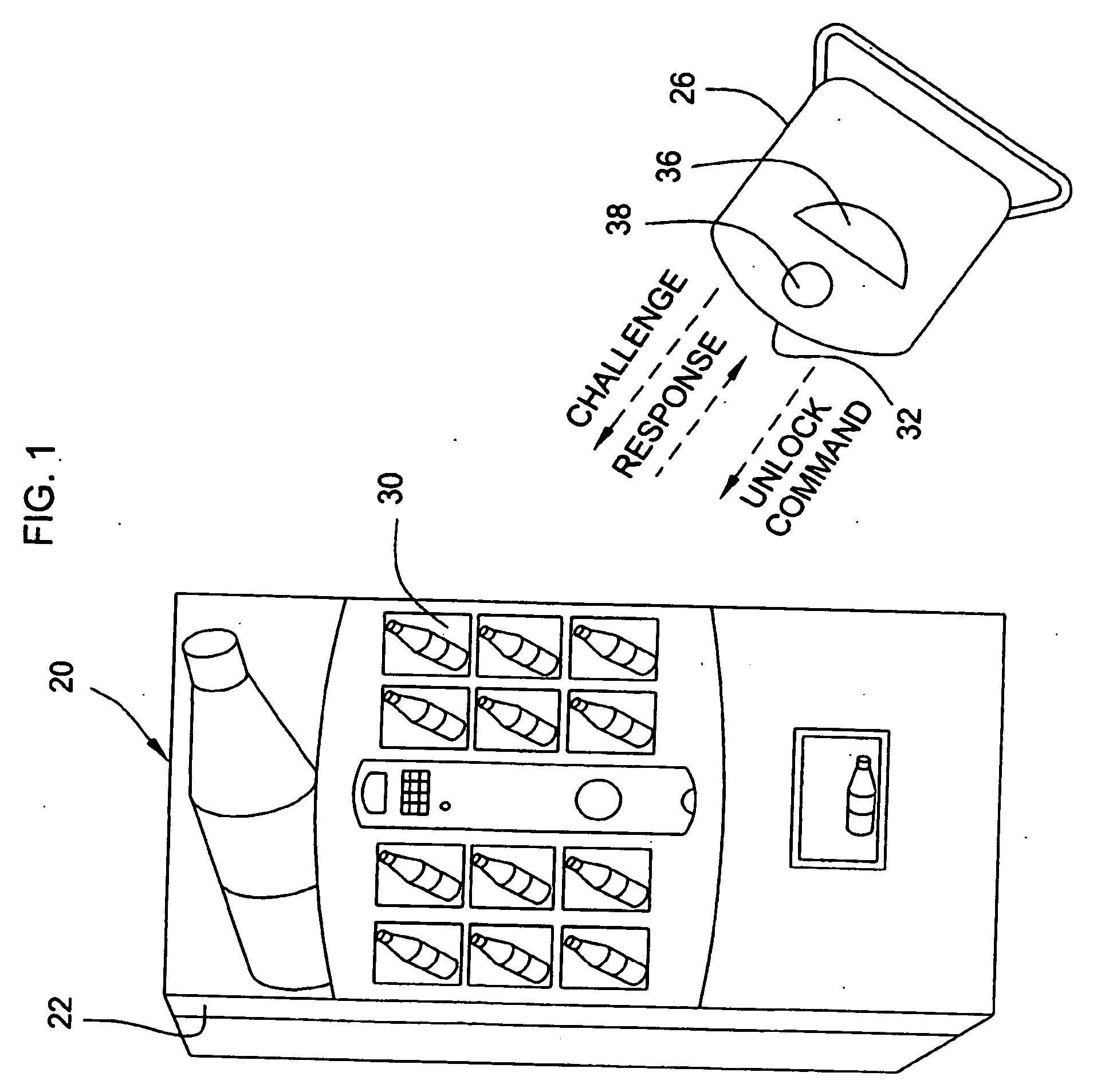
Vending machines with field-programmable locks
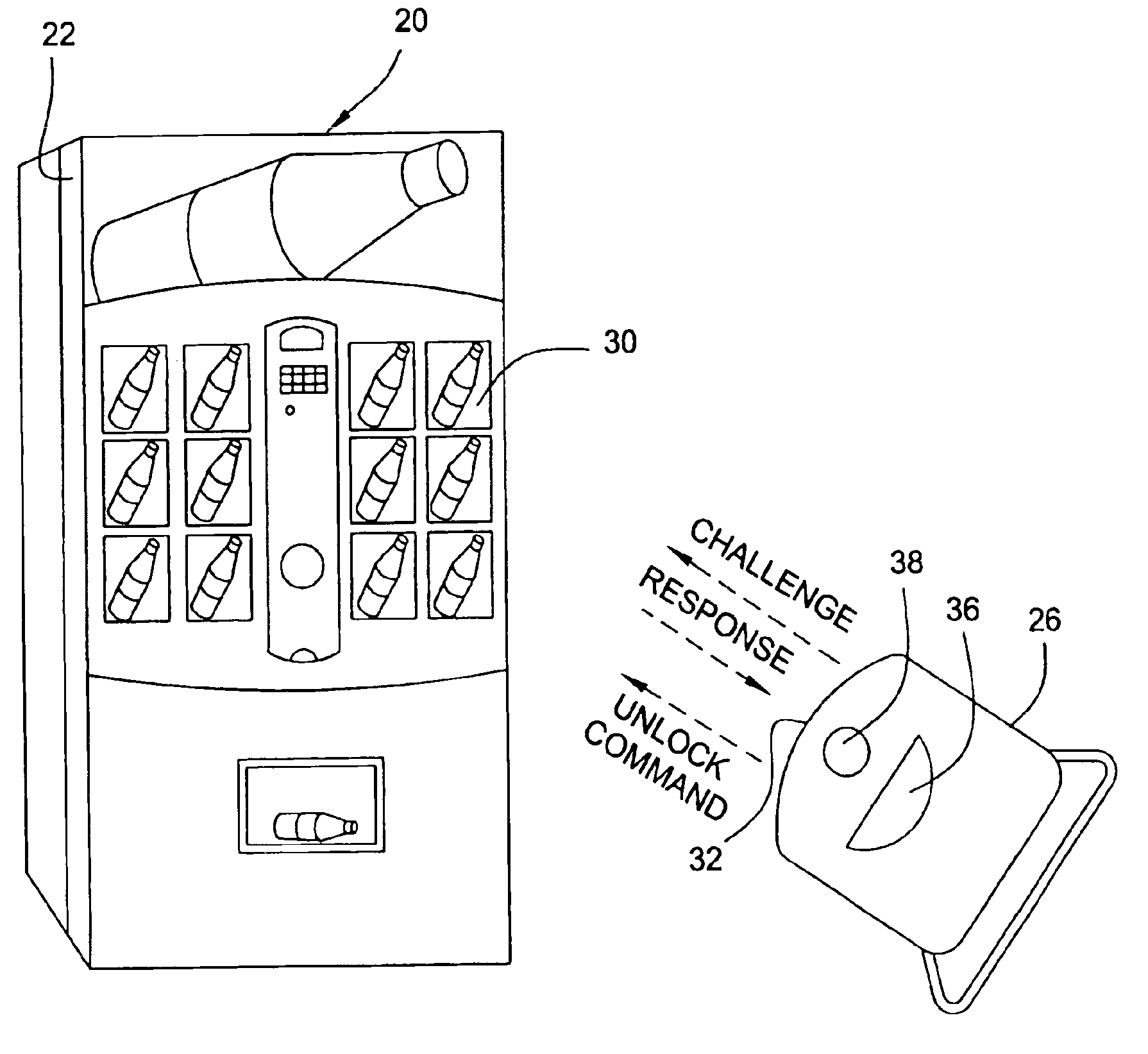
InactiveUS6900720B2Easily and inexpensively programmedImprove the level ofFrequency-division multiplex detailsDigital data processing detailsBiological activationHome based
Owner:MICRO ENHANCED TECH
Method for preventing IP address from leakage
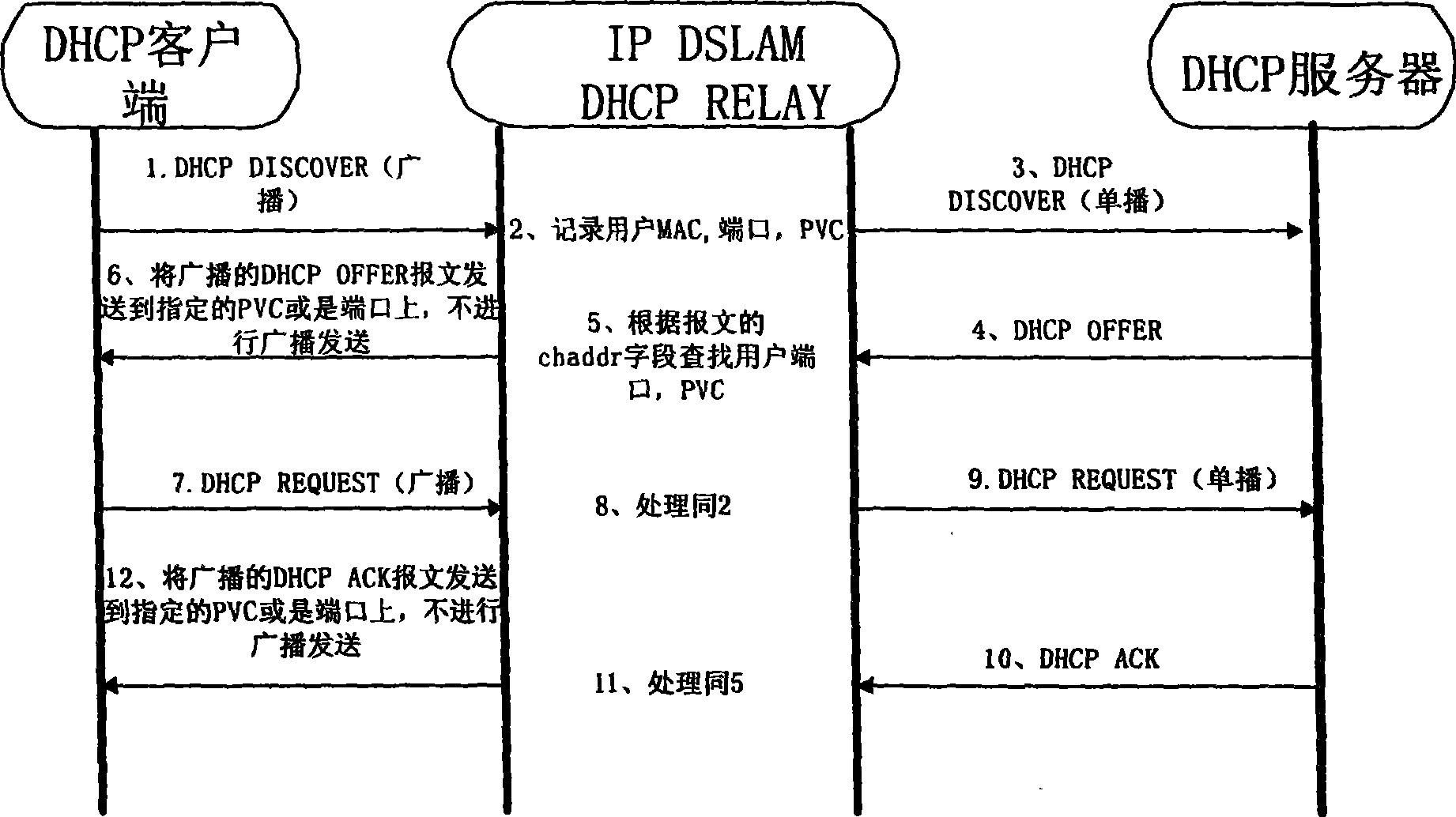
The invention discloses a method for preventing an IP address from being leaked, which comprises the following steps: recording a user port address for sending a message after a DHCP Relay acquires the DHCP message transmitted by a DHCP client; searching the MAC address of the DHCP client from the client hardware address field of the message; establishing corresponding relation between the MAC address and the user port address; searching the MAC address by using the DHCP Relay according to a client hardware address field in a response message after the response message transmitted by a DHCP server is received; searching the corresponding user port address according to the corresponding relation between the MAC address and the user port address; and then directly sending the response message to a user port determined by the user port address. The technical scheme provided by the invention effectively prevents the interception of a user, enhances the application safety of a DHCP protocol, simultaneously reduces the broadcast message transmission of a two-layer network, and saving the network bandwidth resources.
Owner:HUAWEI TECH CO LTD
Method and system for remote storing processing of data
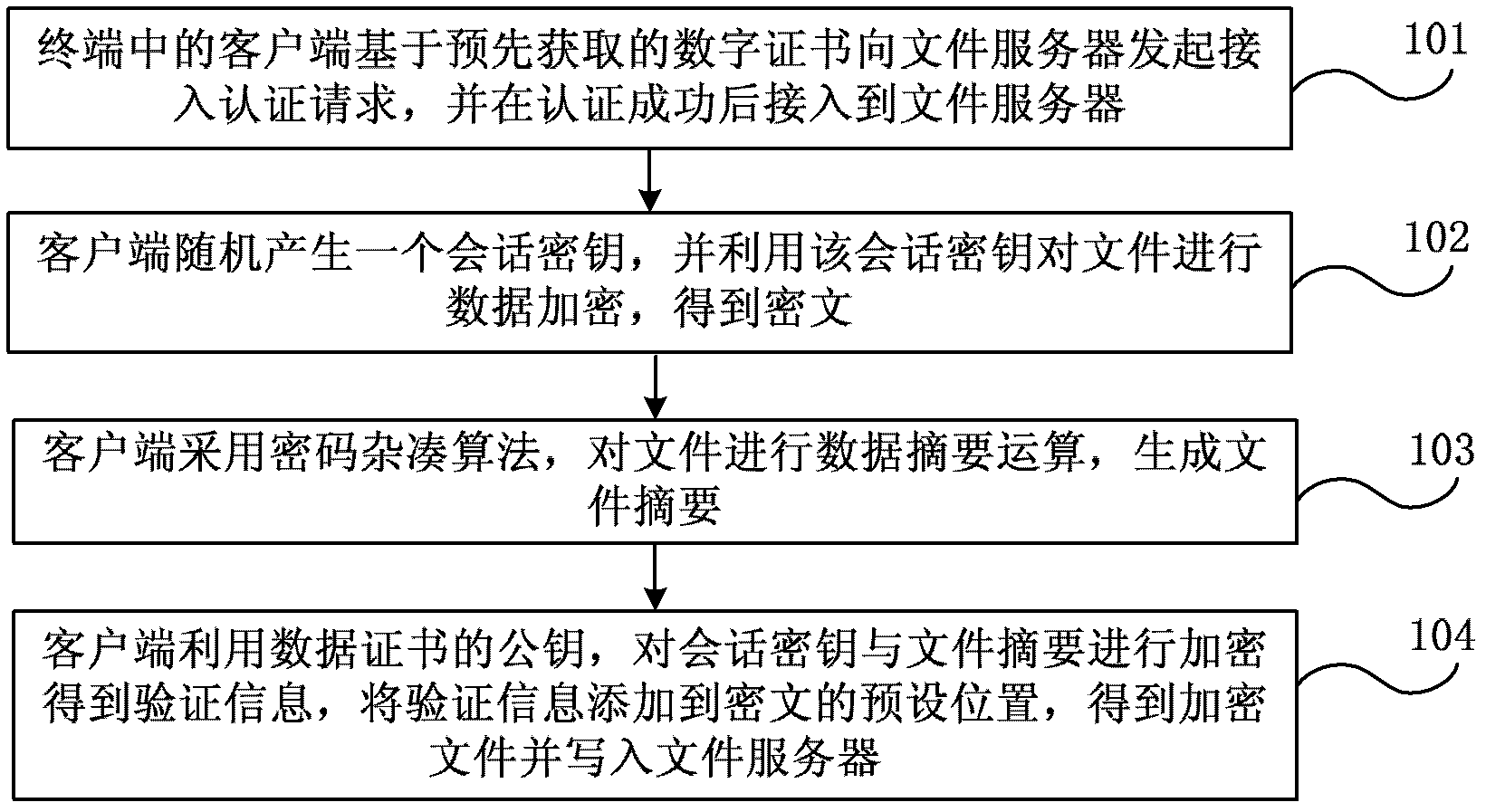
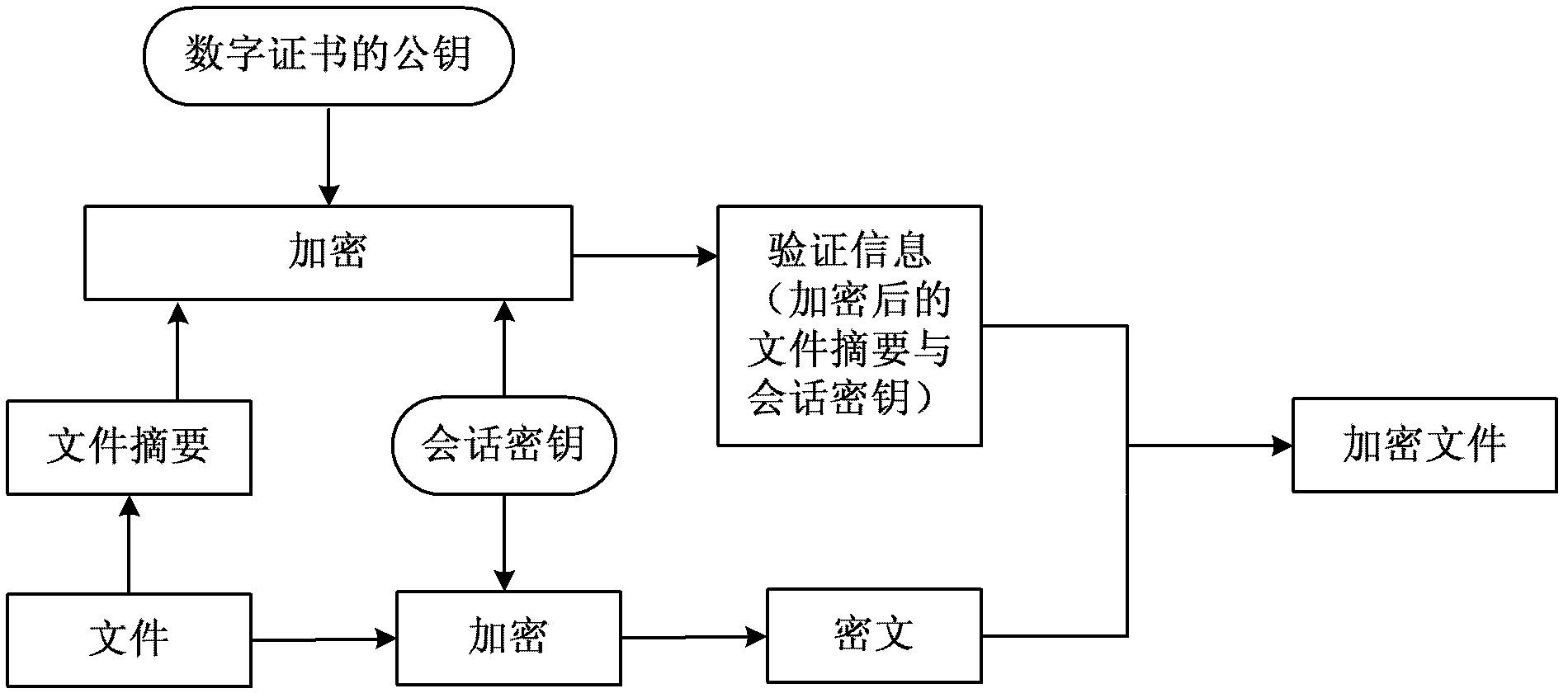
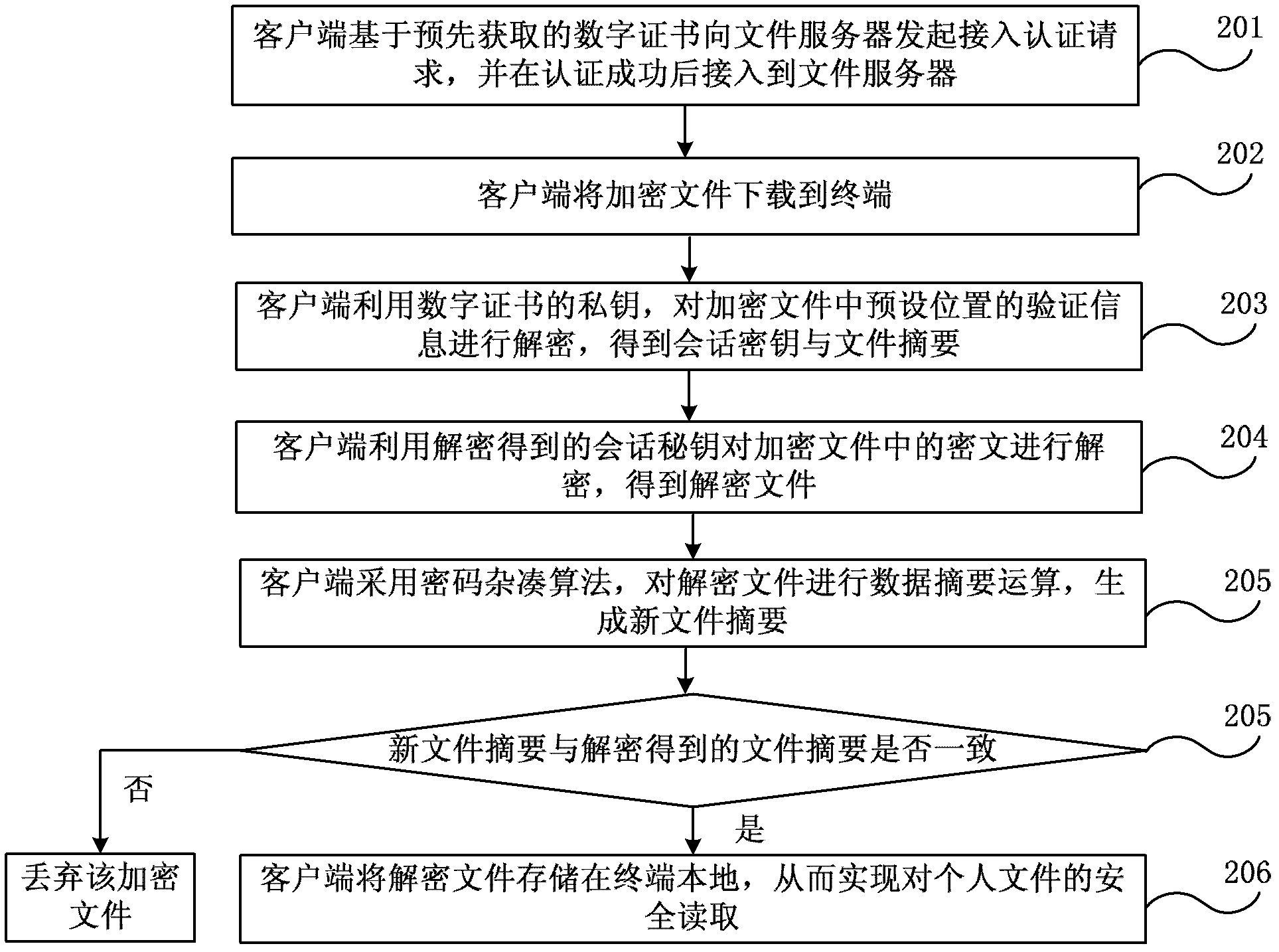
The utility model discloses a method and a system for remote storing processing of data. The method comprises that when a terminal uploads files stored locally to a file server of a network side, a client of the terminal initiates an access authentication request to the file server based on a digital certificate which is acquired in advance, the client accesses the file server after successful authentication, the client generates a dialog key randomly and conducts data encryption to files through the dialog key, a cyphertext is obtained, the client conducts data abstracting mathematical operation by using a cryptographic hash algorithm, the file summary is generated, the client conducts the encryption to the dialog key and the file summary by using a common key of the data certificate, authentication information is obtained, the authentication information is added to a preset position of the cyphertext, and an encryption file is obtained and written to the file server. By the aid of the method and the system, file data of a user is prevented from eavesdropping and stealing illegally during remote store, and the safety of data remote store is improved.
Owner:CHINA TELECOM CORP LTD
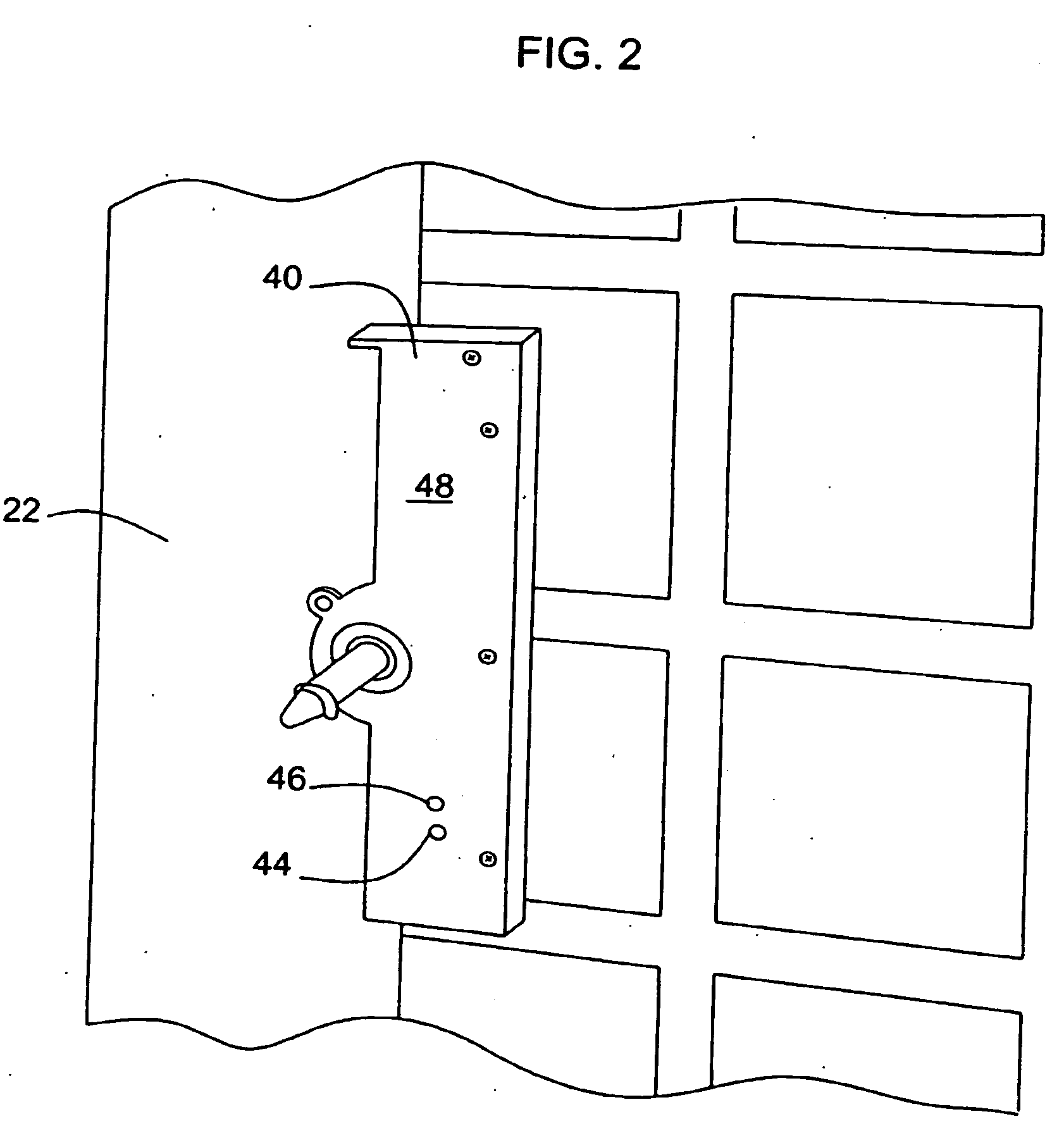
Vending machines with field-programmable electronic locks
InactiveUS20070096867A1Easily and inexpensively programmedImprove the level ofElectric signal transmission systemsMultiple keys/algorithms usageService personnelBiological activation
A vending machine uses a field-programmable electronic lock that learns a key code from a corresponding electronic key. The electronic lock has a learning process activation device that is accessible when the door of the vending machine is in the open position. Using the learning process activation device, a service person activates the electronic lock to perform a key code learning operation, in which the electronic lock receives a key code transmitted from an electronic key and stores the key code in a non-volatile memory for future access control of the vending machine. Data encryption is employed in the communications between the key and the lock to ensure the security of the communications. A communication device installed in the vending machine for communicating with a home base computer allows the operation of the electronic lock to be remotely controlled for access control and auditing purposes.
Owner:DENISON WILLIAM D +2
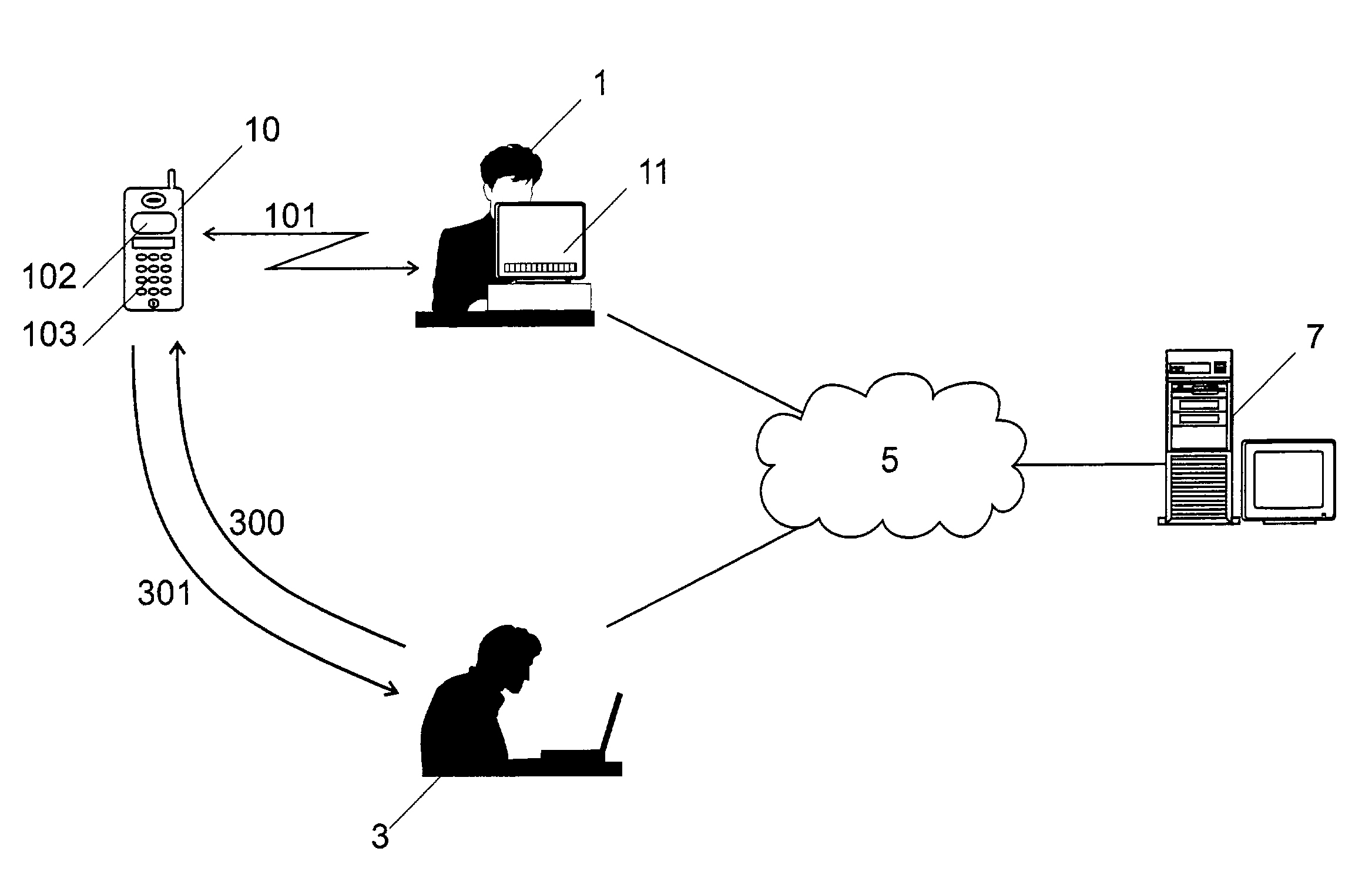
Method for securing communications between a terminal and an additional user equipment
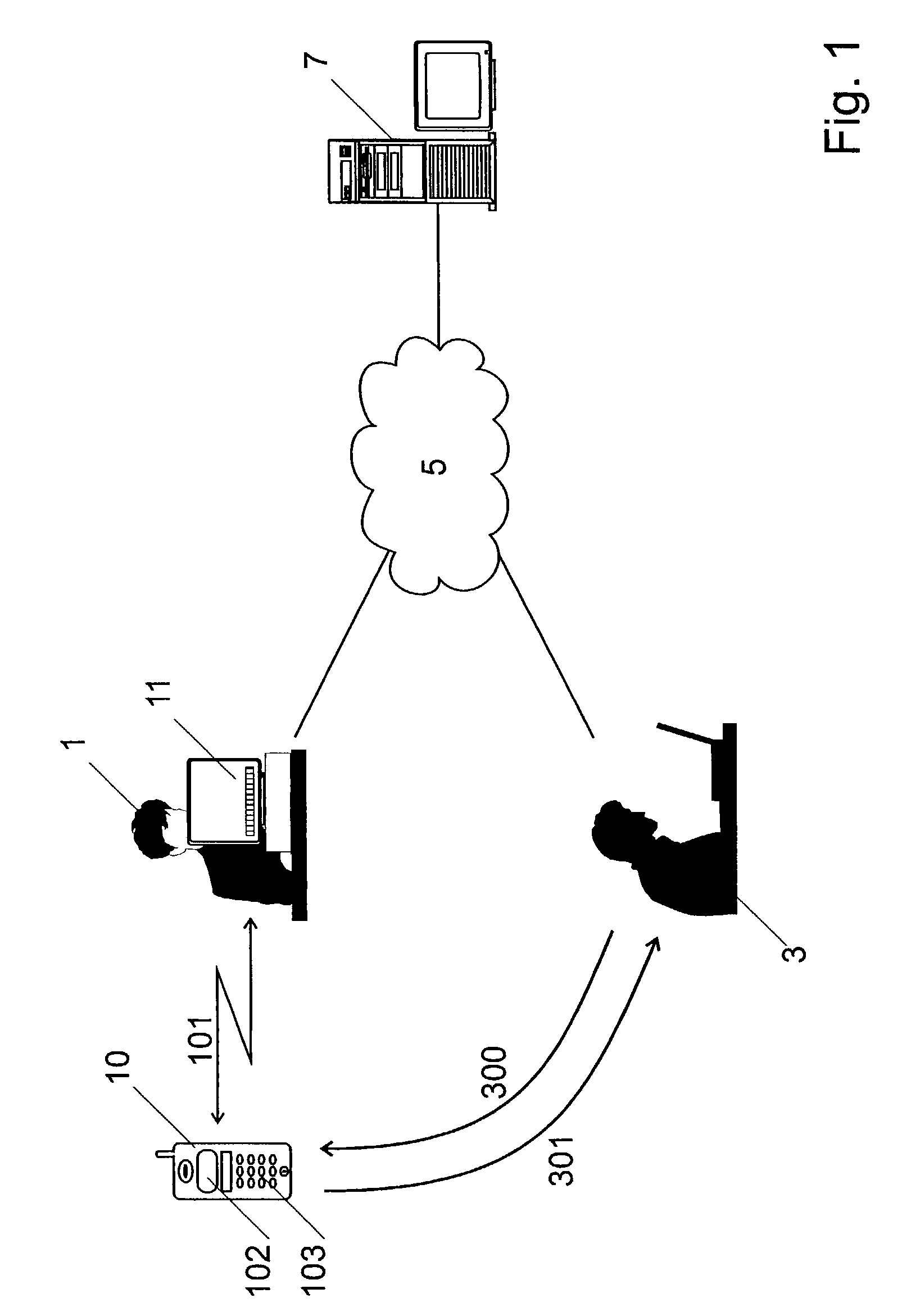
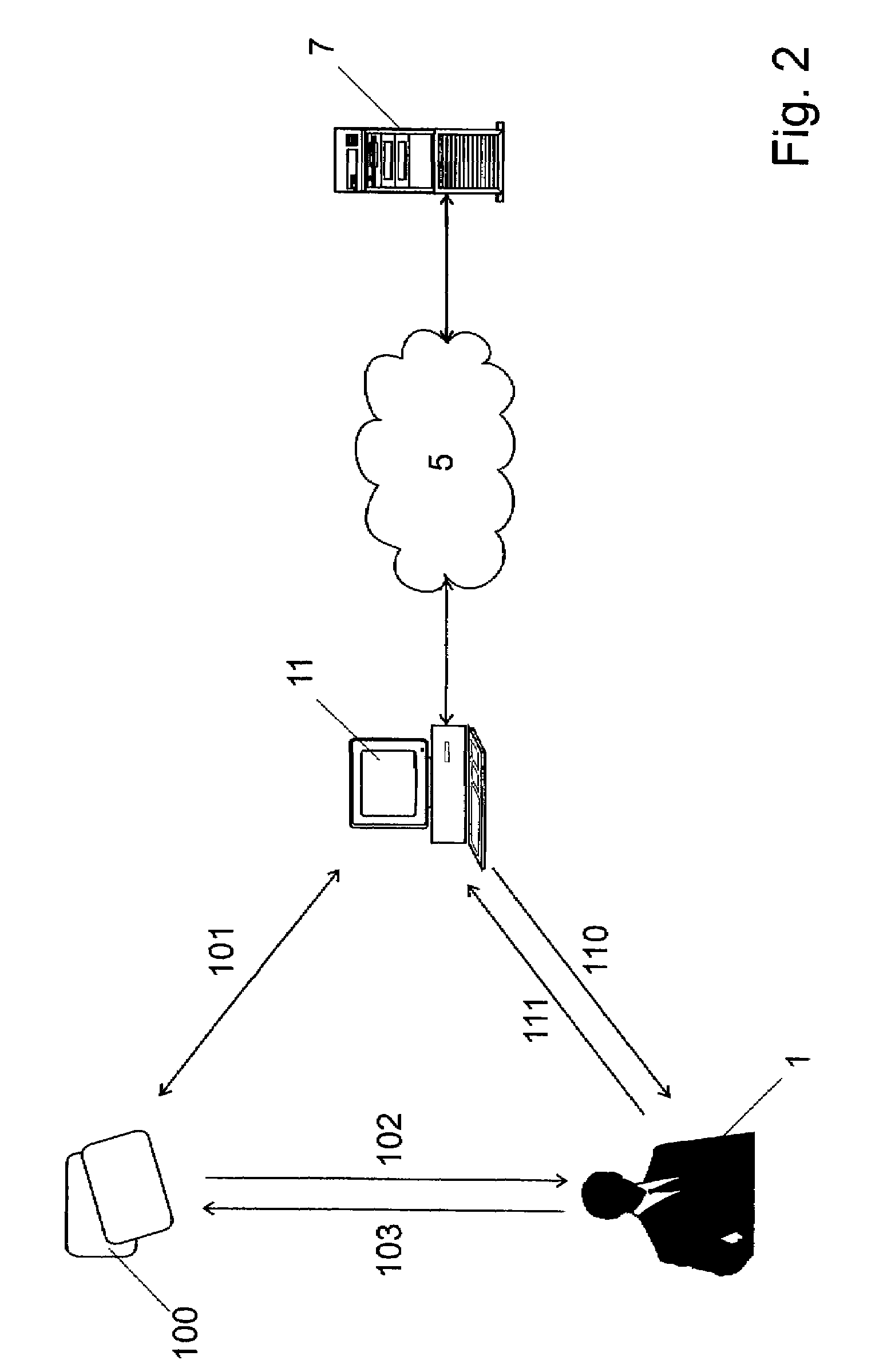
InactiveUS7409552B2Prevent eavesdroppingShort distance wireless communication capabilityKey distribution for secure communicationUser identity/authority verificationSecure communicationShortest distance
Method for securing a session over a radio or infrared wireless link (101) between a terminal (11) and a mobile equipment (10), said session being secured with a SIM card (100) in said mobile equipment (10). The terminal (11) and the mobile equipment (10) both comprise a display and a keyboard or keypad and can be mutually connected through said short distance wireless link (101). The method comprises the following steps:generating a secret in one of said terminals or said smart cards,displaying this secret on the display of said terminal (11) or said user equipment (10),entering said secret or the hash value of said secret on the input means of the other one of said terminals (11) or user equipments (10),using said shared secret for securing at least a part of said session over said short distance wireless link (101).
Owner:ZAMA INNOVATIONS LLC
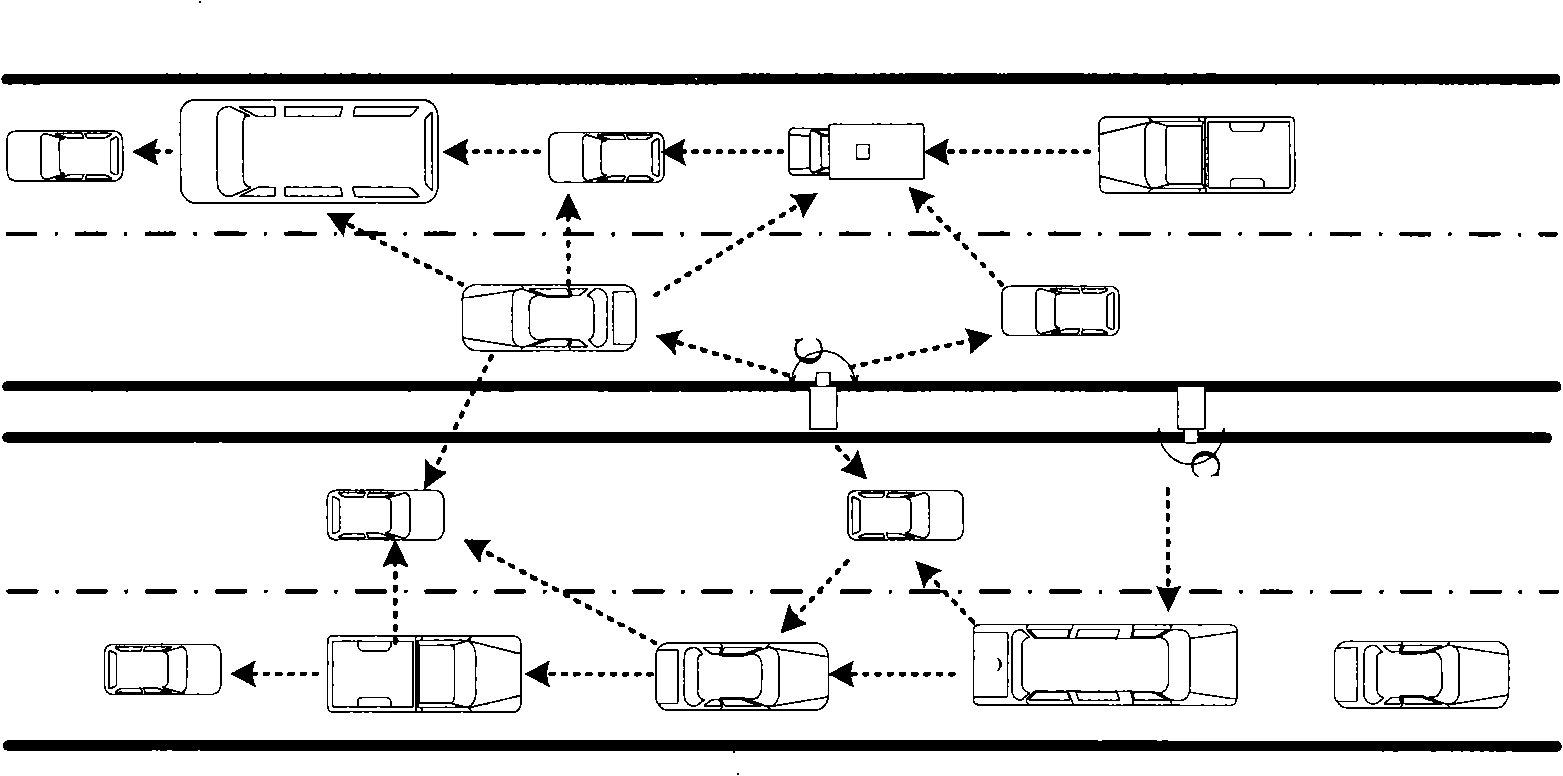
A secure communication method between nodes in vehicular network
InactiveCN101262333APrevent counterfeitingImprove security strengthKey distribution for secure communicationParticular environment based servicesKey exchangeSecure communication
The invention discloses a safe communication method between nodes in a vehicular network. The method provides a disperse trust and security system based on elliptic curves. Before communicating, communication nodes are two-way indentified by a (t, n) threshold authentication proposal to prevent hostile nodes from personating legal nodes and t-1 members in a network from counterfeiting certificates. Meanwhile, a key exchange based on password authentication is carried out to ensure that all conventioneers consult about a key by a safe approach, and therefore, a strong session key is generated to provide message discrimination, confidentiality and integrality for communication nodes in a vehicular network. The method of the invention adopts an elliptic curve encryption scheme and the (t, n) threshold authentication proposal, thereby being characterized by small calculated amount, low complexity, high safety, small key space, high speed, needing no authentic certificate authority and having great application value in vehicular networks.
Owner:SHANGHAI UNIV
Smart grid information transmission safety protection device and safety protection method
ActiveCN107483444AEasy to deployReduce maintenance costsUser identity/authority verificationPlaintextInformation transmission
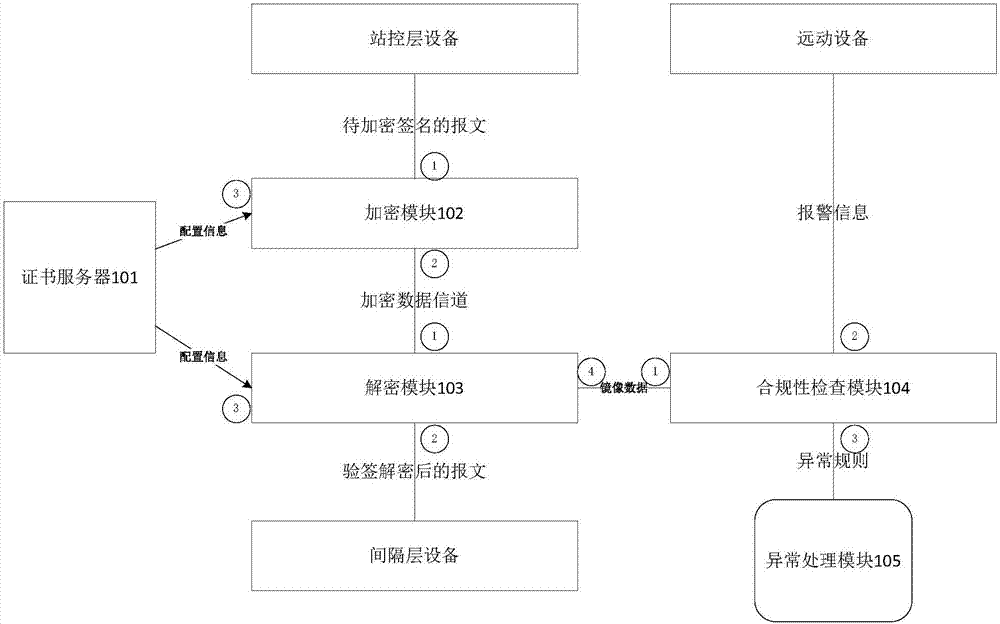
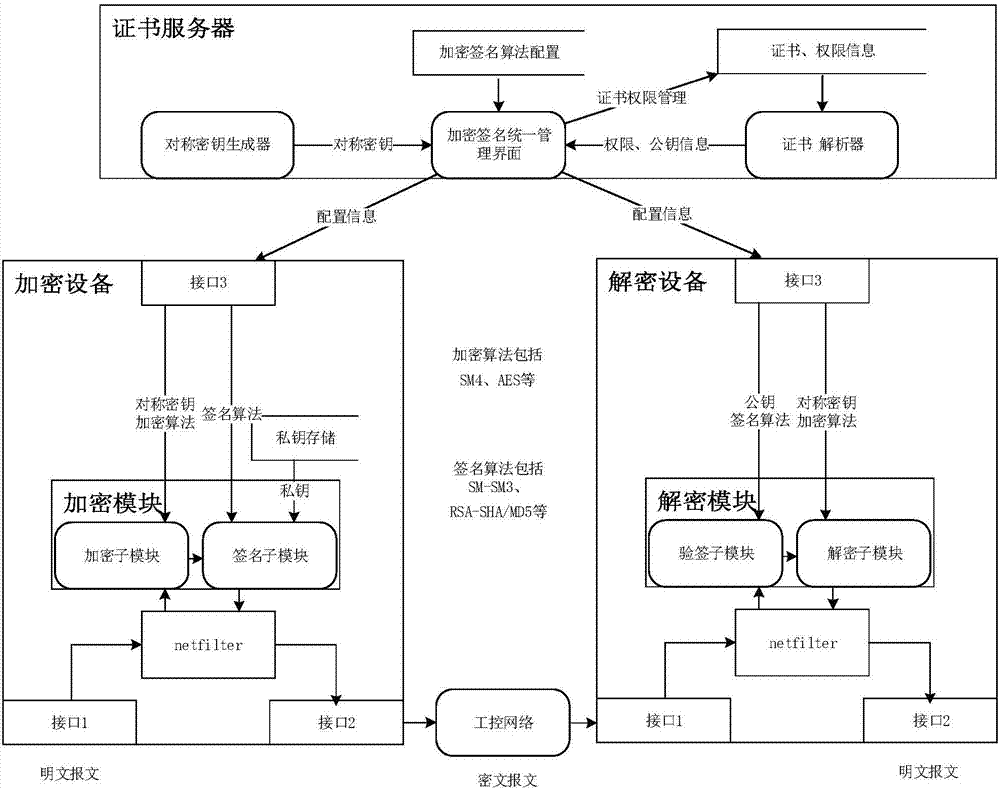
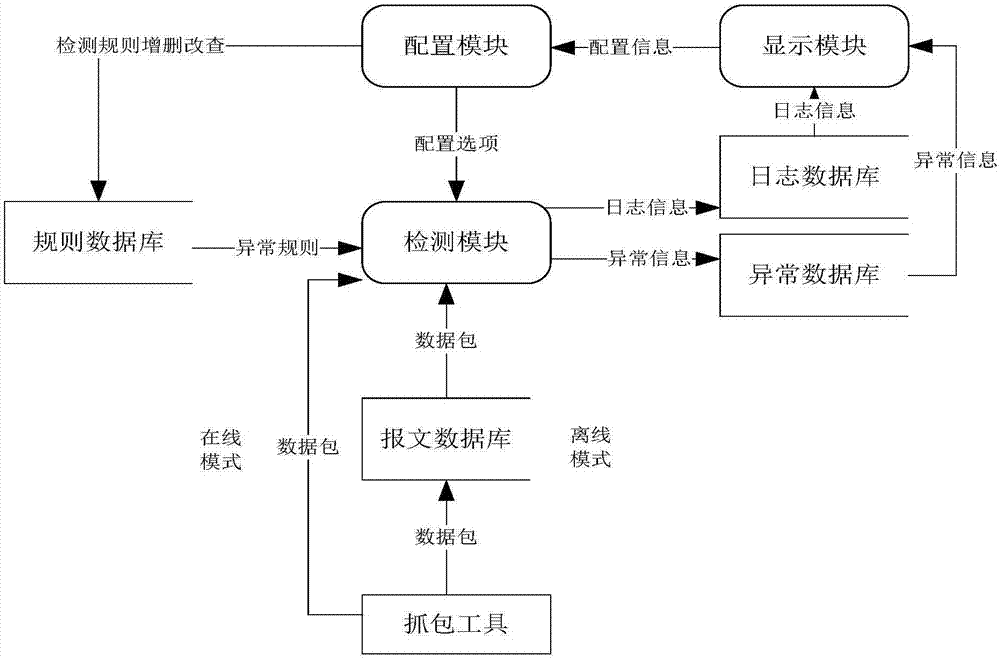
The invention discloses a smart grid information transmission safety protection device and a safety protection method, which relate to the technical field of smart grid information transmission safety. The device comprises a certificate server, an encryption and decryption module, a compliance check module and an exception handling module, wherein the encryption and decryption module is wholly serially connected between a station level and a bay level for carrying out encryption signature and signature verification decryption functions on original transparently-transmitted data; the compliance check module grabs a plaintext data packet in an offline or online mode and submits the plaintext data packet to the detection module for compliance check, and as for a compliance message, an analysis result is stored to a log database in a log format; and exception information is independently stored in an exception database through the exception handling module, and an administrator is notified. In the case of permissible delay in the smart grid, the encryption and decryption module together protects the internal information of the smart grid, behaviors that the internal data are tampered and destructed in the case of transmission are resisted, and the safety of the grid is further improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
Method of secure communication based on commercial cipher algorithm
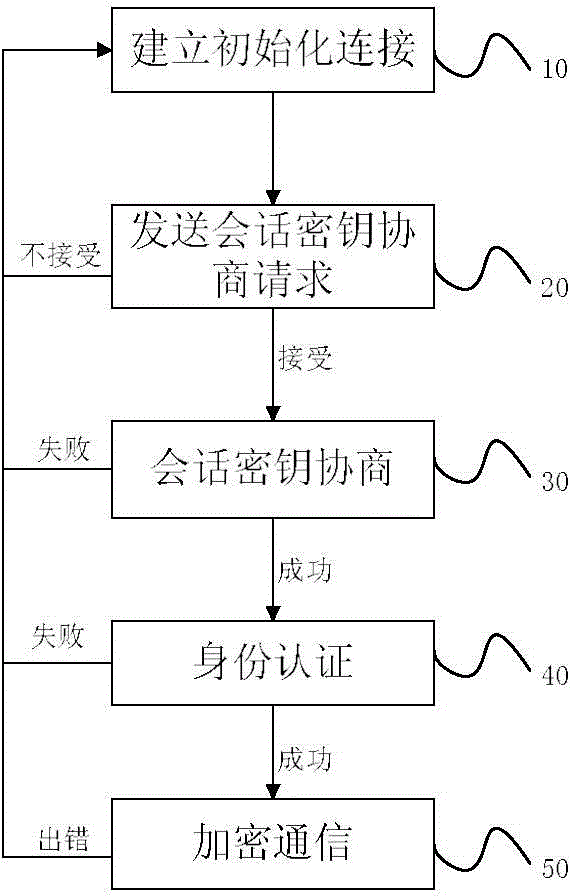
ActiveCN104158653APrevent eavesdroppingEnsure safetyKey distribution for secure communicationData transmissionSecure communication
The invention discloses a method of secure communication based on a commercial cipher algorithm. The method comprises the following steps: step 10, initializing connection between a client and a server is established; step 20, the client sends a session key negotiation request; step 30, the client and the server carry out session key negotiation; step 40, the client sends client device information for identity authentication; and step 50, the client and the server communicate in an encrypted way. According to the method of secure communication based on a commercial cipher encryption and decryption technology, key negotiation of a key exchange algorithm, a data encryption algorithm and a data integrity check algorithm is adopted to enable the client and the server to carry out bidirectional authentication and determine the session key, and a secure channel is established to prevent data eavesdropping, tampering and destruction and replay attack insertion in the data transmission process and ensure the security of data transmission. The method of the invention does not rely on a network access mode, can be implemented on any basic network, and can realize end-to-end security protection.
Owner:北京华电天益信息科技有限公司
Virtualized technology-based data anti-disclosure system
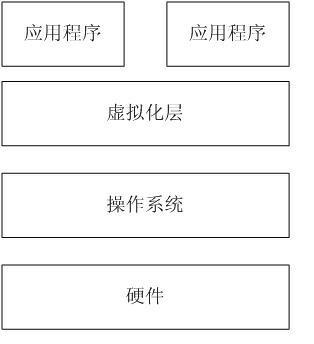
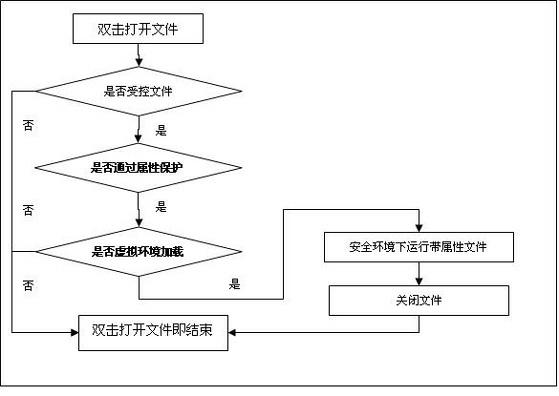
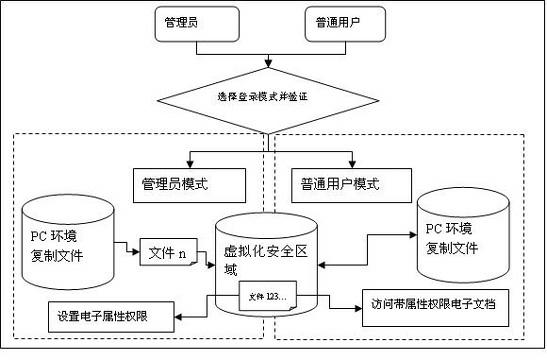
InactiveCN102254117AMeet individual requirementsPrevent Active DisclosureDigital data protectionVirtualizationSystem call
The invention relates to a virtualized technology-based data anti-disclosure system, which is characterized in that: the data anti-disclosure system is realized by constructing virtualized operating environment in a work station by utilizing the virtualized technology on the basis of an operating system and redirecting the input / output calling, system calling and the calling of a dynamic library of the host operating system; and the data anti-disclosure system consists of a management module, a driving redirection module, monitoring module, a log auditing module and a data encryption / decipherment module. The data anti-disclosure system has the advantage that a data anti-disclosure protective method for preventing unauthorized users from wiretapping, breaking and copying and propagating confidential data illegally by ensuring that limited users only can access key data under the virtual safety environment and the physical storage of the key data is also concentrated in virtual storage space which is subjected to encrypting protection simultaneously is provided.
Owner:李鹏 +1
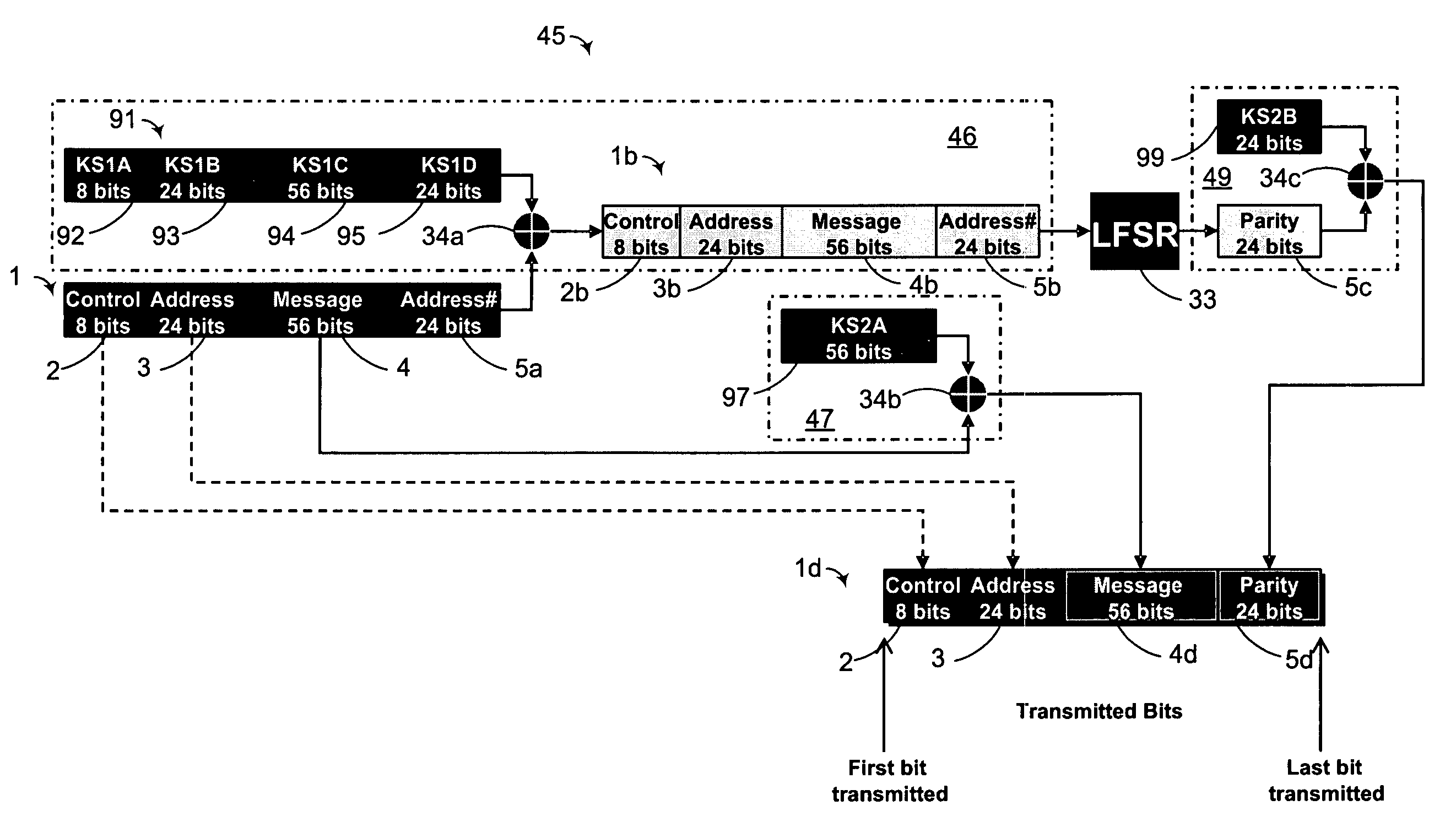
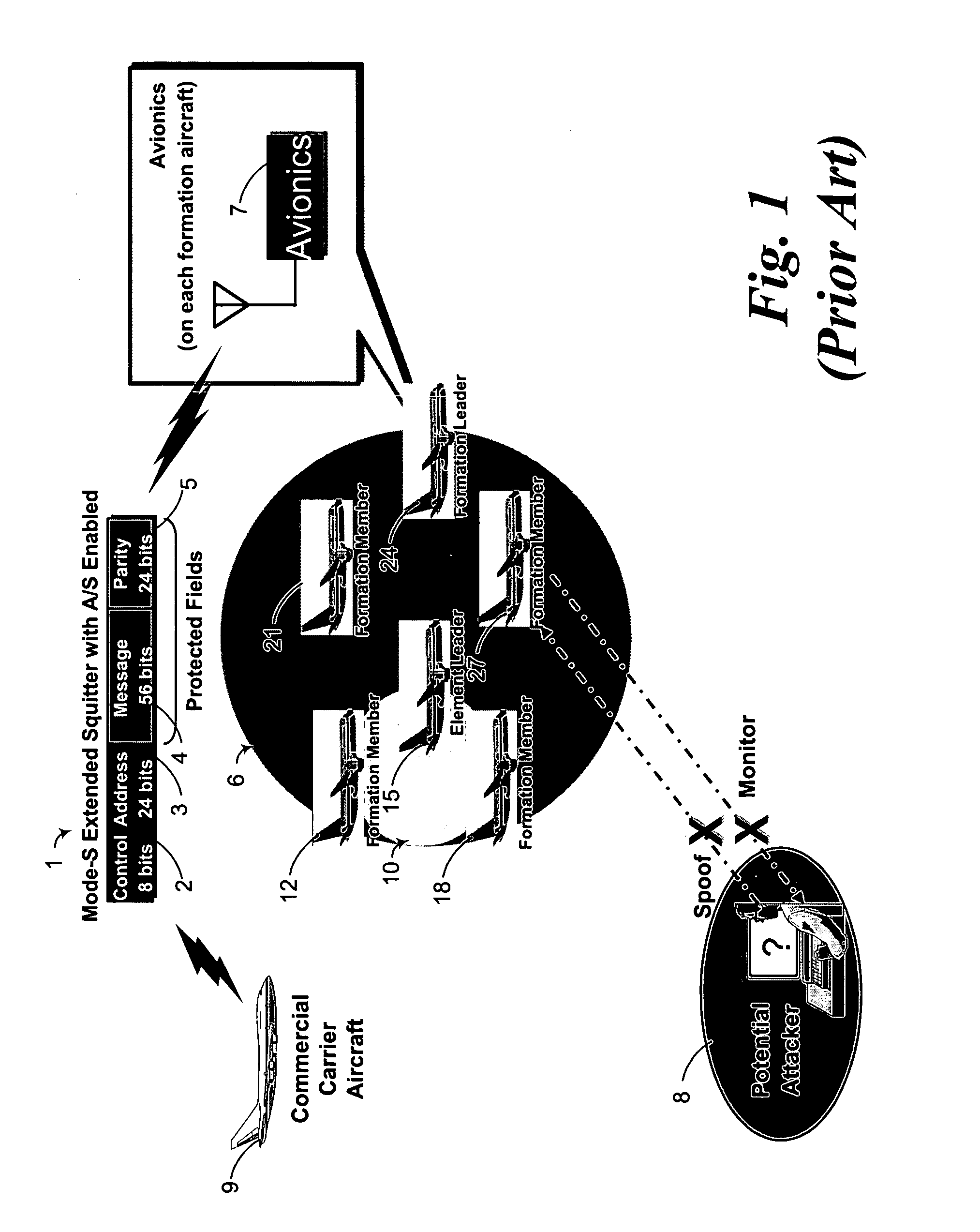
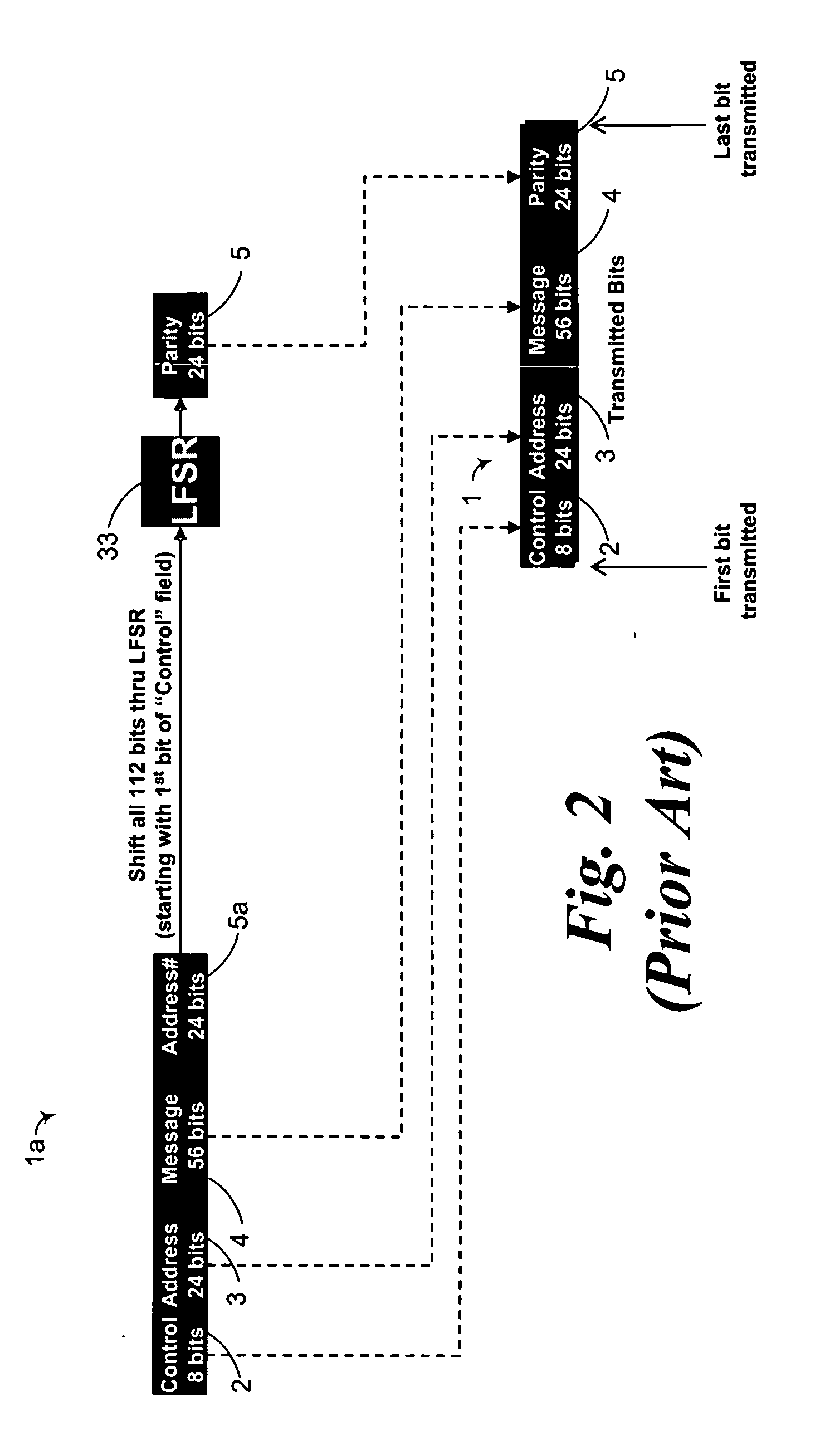
Information security for aeronautical surveillance systems
ActiveUS20060008087A1Prevent eavesdroppingRapid identificationDirection finders using radio wavesSecret communicationSquitterAviation
Owner:HONEYWELL INT INC
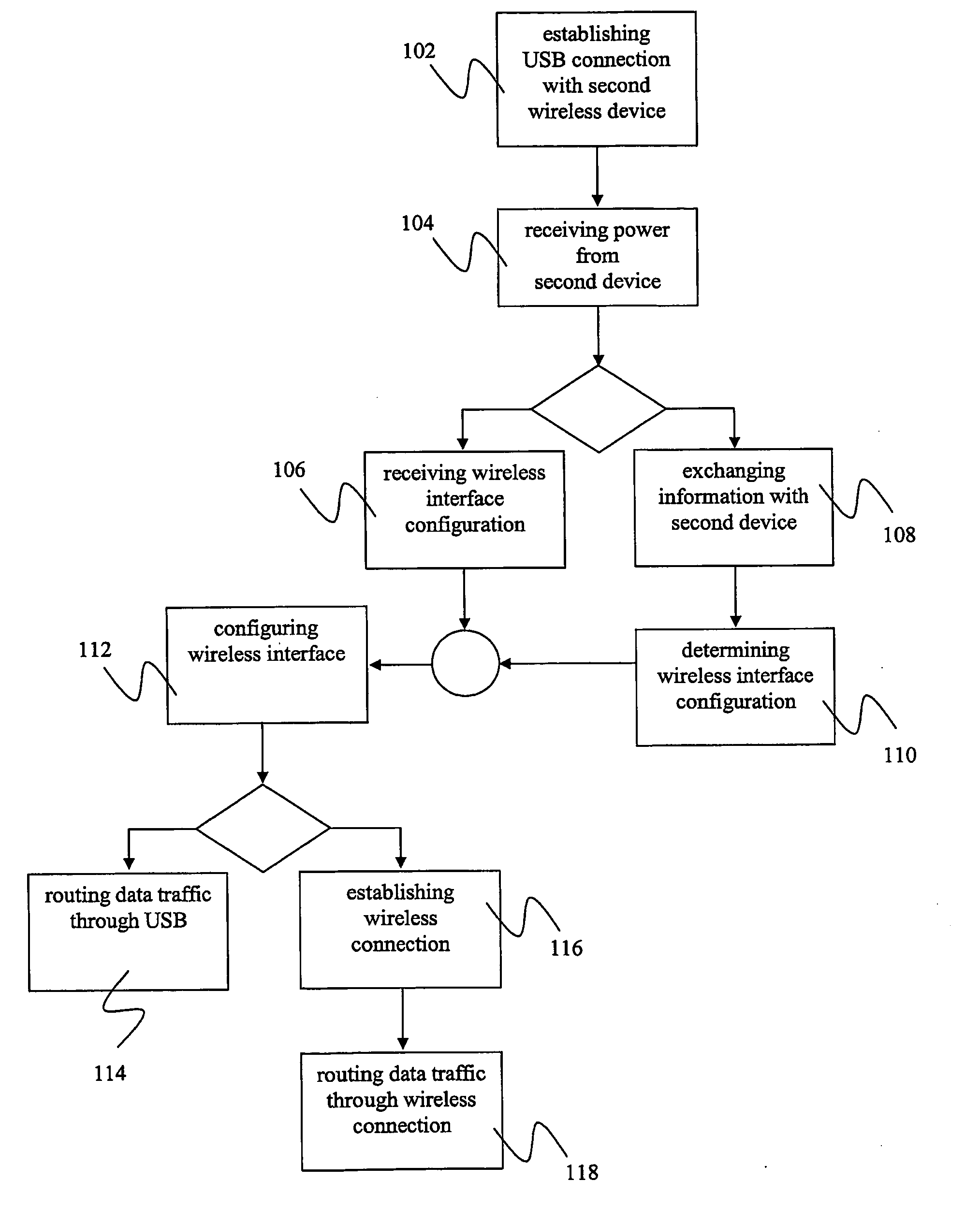
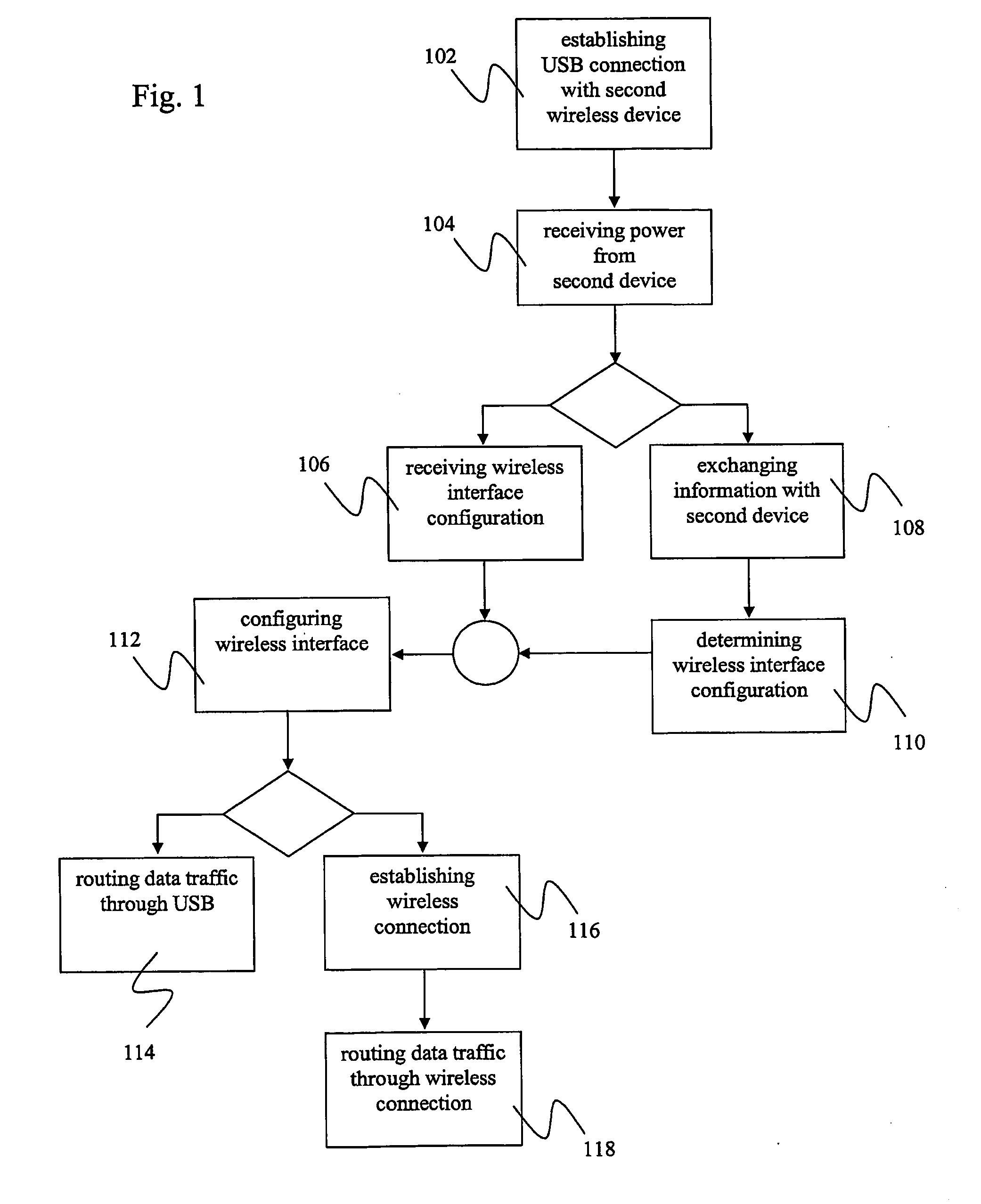
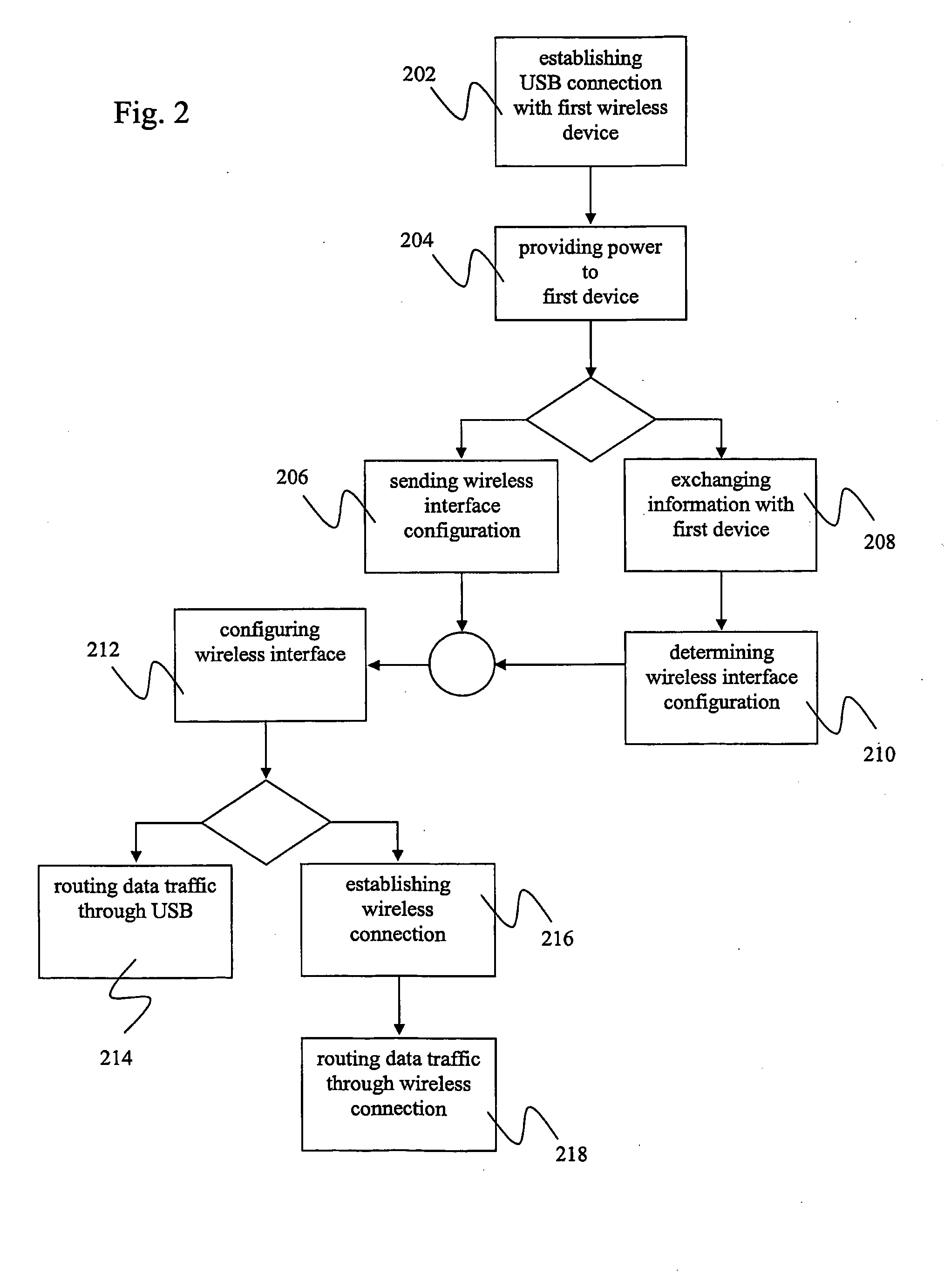
Methods and Devices for Wire-Based Configuration of Wireless Devices
ActiveUS20100128632A1Simple and easy configurationImprove securityDigital data processing detailsData switching by path configurationUSBElectronic equipment
The invention relates to a method for configuring a wireless interface of a first electronic device, comprising establishing a wired Universal Serial Bus (USB) connection with a second electronic device having a wireless interface; negotiating, via said USB connection, a configuration for said wireless interface with said second electronic device, said configuration enabling a wireless connection between said first and said second electronic device; and configuring said wireless interface of said first electronic device according to said configuration.
Owner:NOKIA TECHNOLOGLES OY
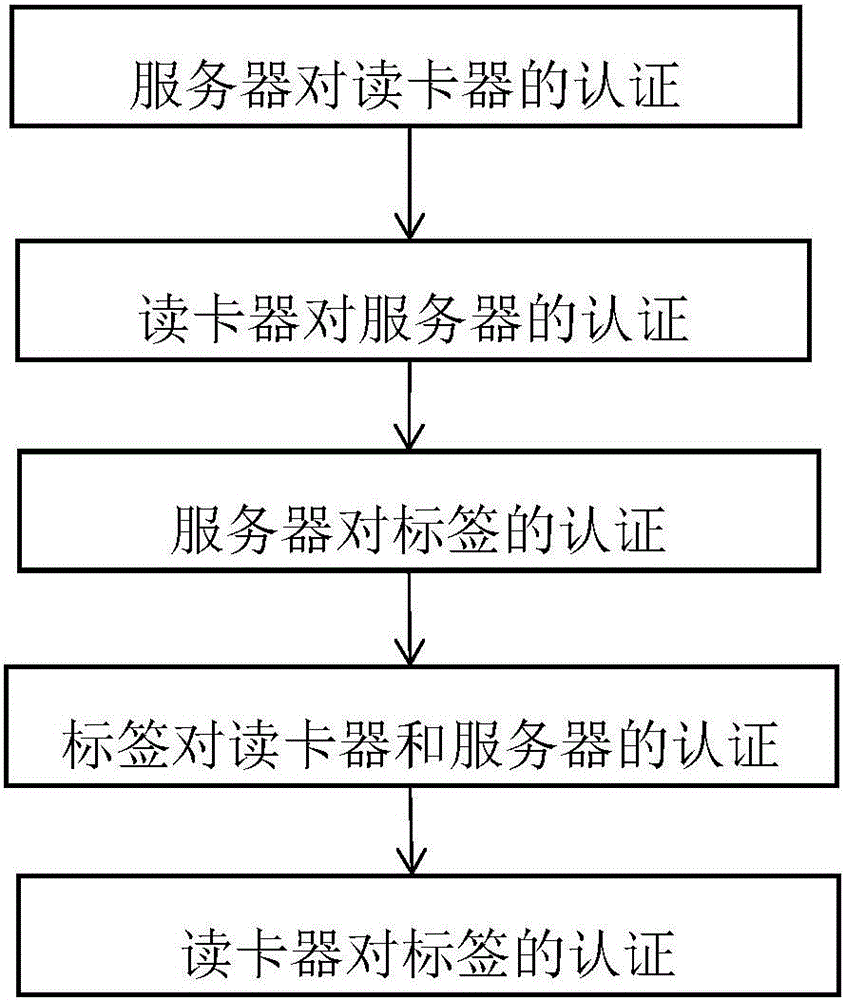
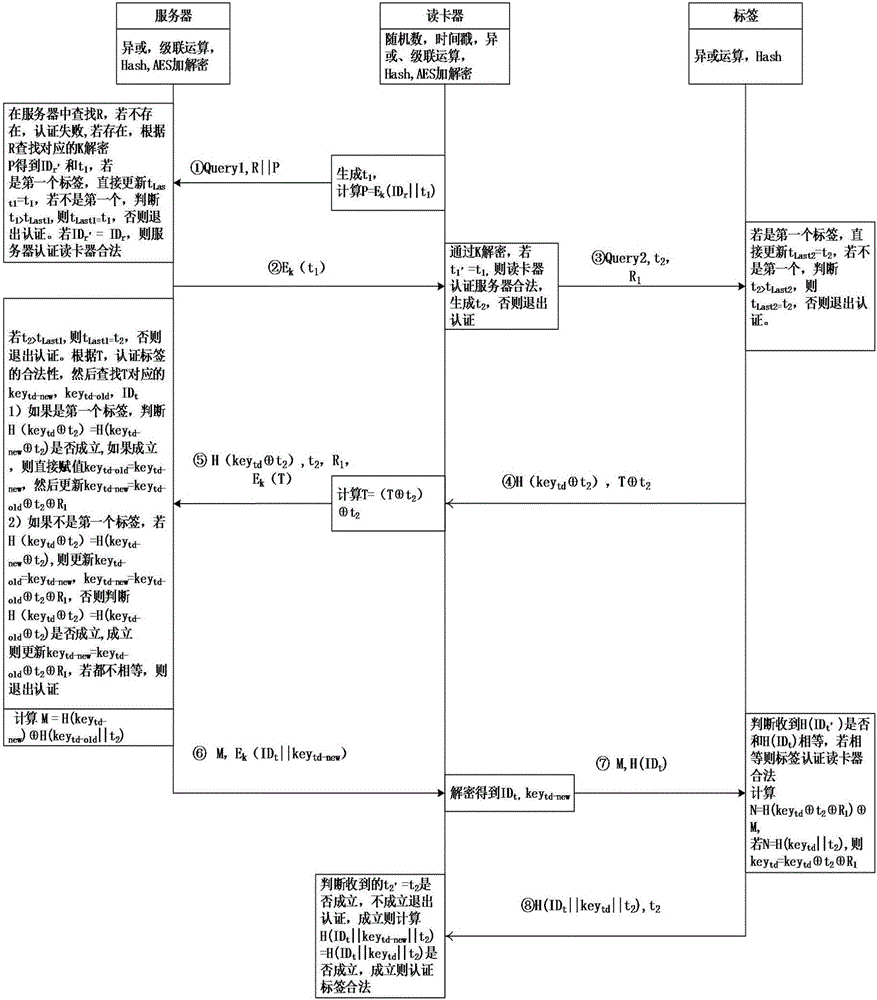
Mobile RFID system bidirectional authentication method and system
ActiveCN106712962APrevent eavesdroppingAvoid illegal acquisitionUser identity/authority verificationHash functionTimestamp
The invention discloses a mobile RFID system bidirectional authentication method, which comprises the steps of: step<1>, authentication on a card reader by means of a server; step<2>, authentication on the server by means of the card reader; step<3> authentication on a tag by means of the server; step<4>, authentication on the card reader and the server by means of the tag; and step<5>, authentication on the tag by means of the card reader. The mobile RFID system bidirectional authentication method introduces an updating mechanism of sharing a secret key by the server and the tag, introduces a timestamp, utilizes the unidirectional property of a Hash function and safety of AES encryption and decryption, realizes bidirectional security authentication among the server, the card reader and the tag, and satisfies the wireless and long-range communication between the card reader and the back-end server; and the tag adopts the simple Hash function and exclusive or calculation, and the cost of the tag side is reduced. The invention further discloses a system adopting the mobile RFID system bidirectional authentication method.
Owner:XIDIAN UNIV
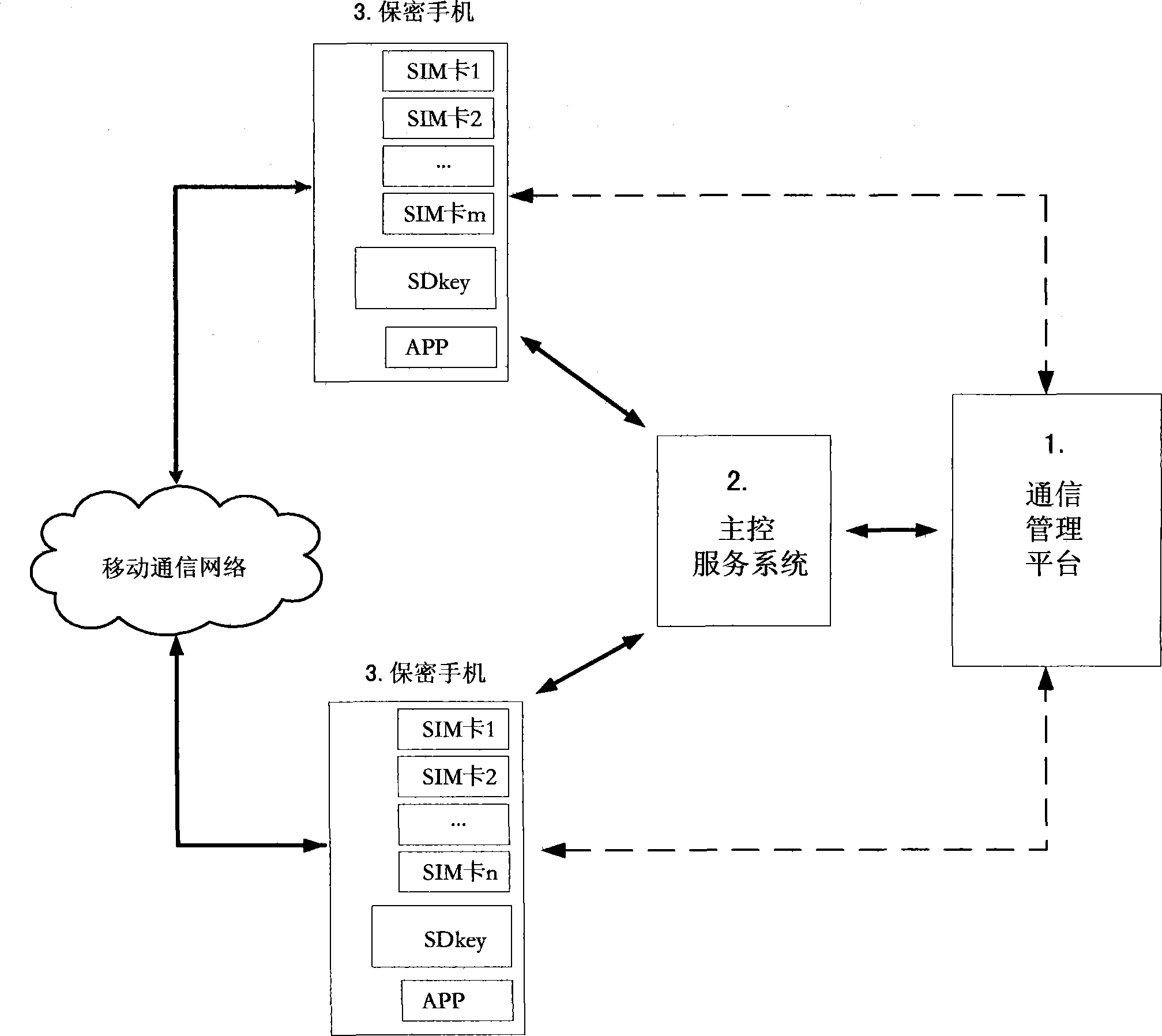
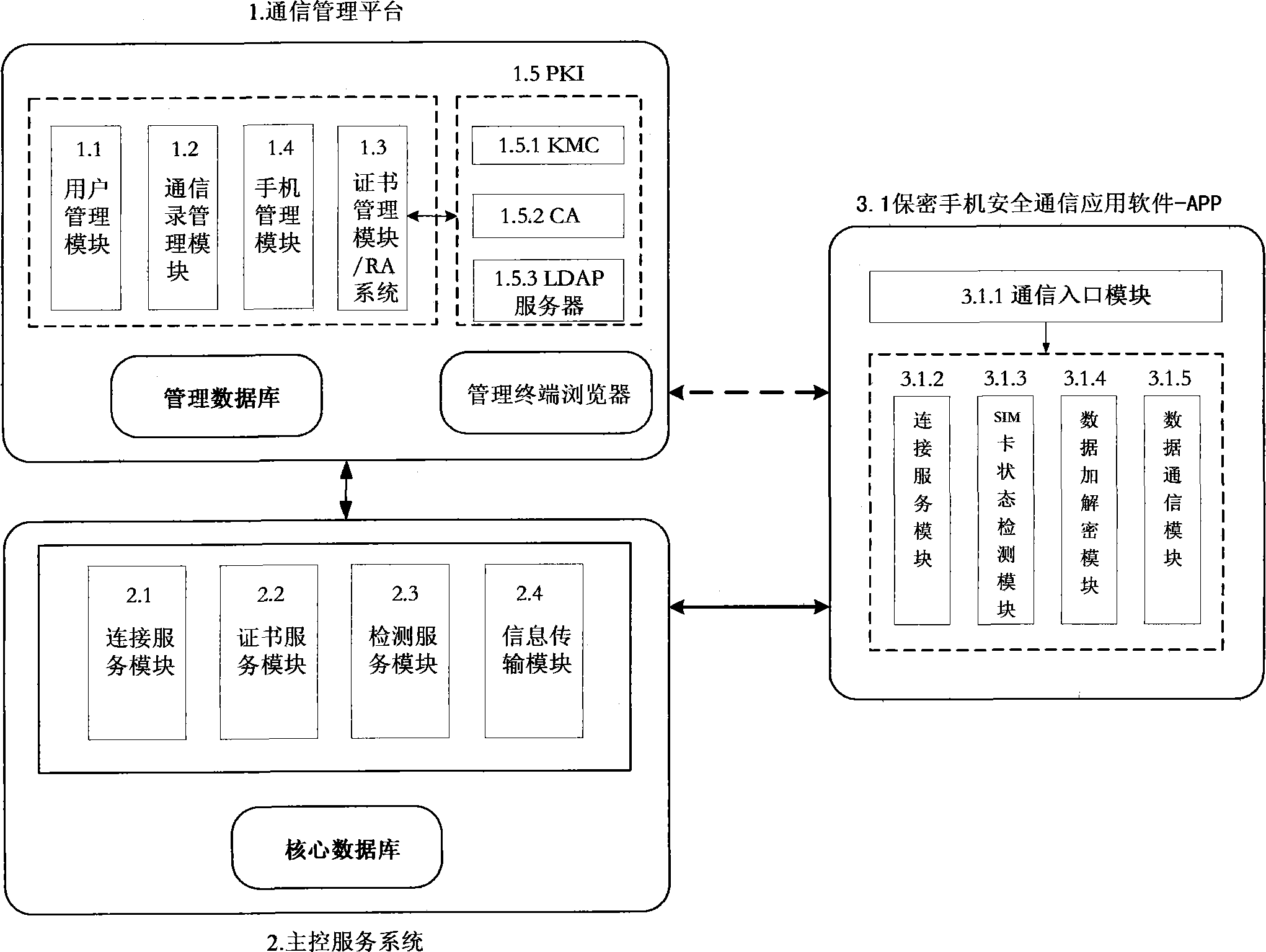
Secrete communication system and method for smart phone
ActiveCN104333455APrevent illegal eavesdroppingPrevent eavesdroppingUser identity/authority verificationSecurity arrangementCiphertextEavesdropping
The invention belongs to the technical field of information safety, in particular to secrete communication of a smart phone. According to the technical scheme, a secrete communication system for the smart phone comprises a communication management platform (1), a main control service system (3) and a plurality of secrete mobile phones (3). Compared with the technology and method for the other secrete mobile phones, the secrete communication system and method use an encryption crushing technology and a recombination decryption technology to transmit complete communication information through x mobile communication signal channels, and each mobile communication signal path transmits one part of cipher-text fragments of a voice data unit or a short message; people cannot restore the complete cipher-text not to mention the plain text of the voice or the plain text of the short message through eavesdropping any one of the mobile communication signal channels, and therefore, the illegal eavesdropping on the mobile communication network is effectively avoided; the voice data or short message encryption, decryption and crushing recombination are performed in a customized SD key in the secrete mobile phone, and the rogue program eavesdropping to the secrete mobile phone terminal can be effectively avoided.
Owner:BEIJING CHERILEAD TECH
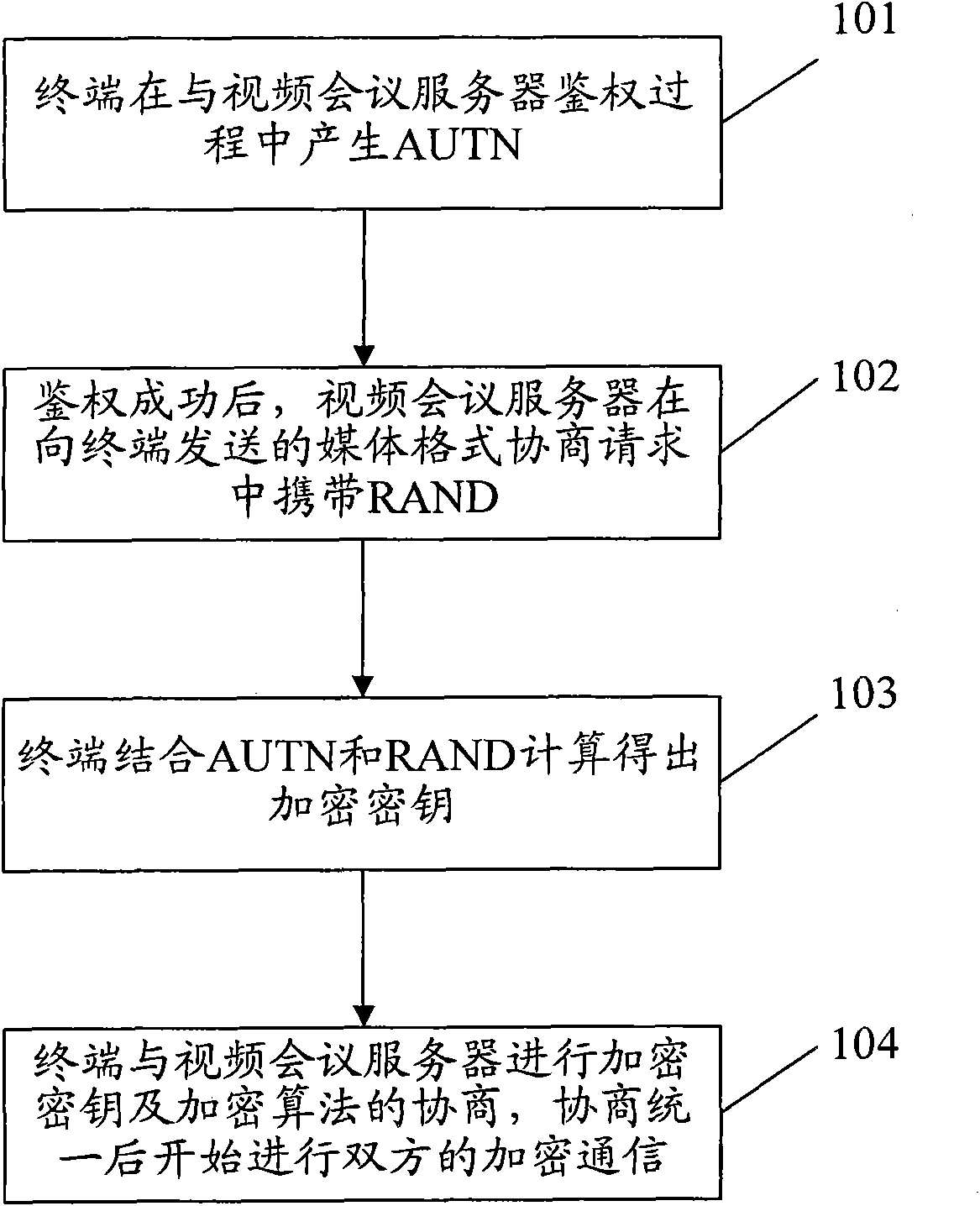
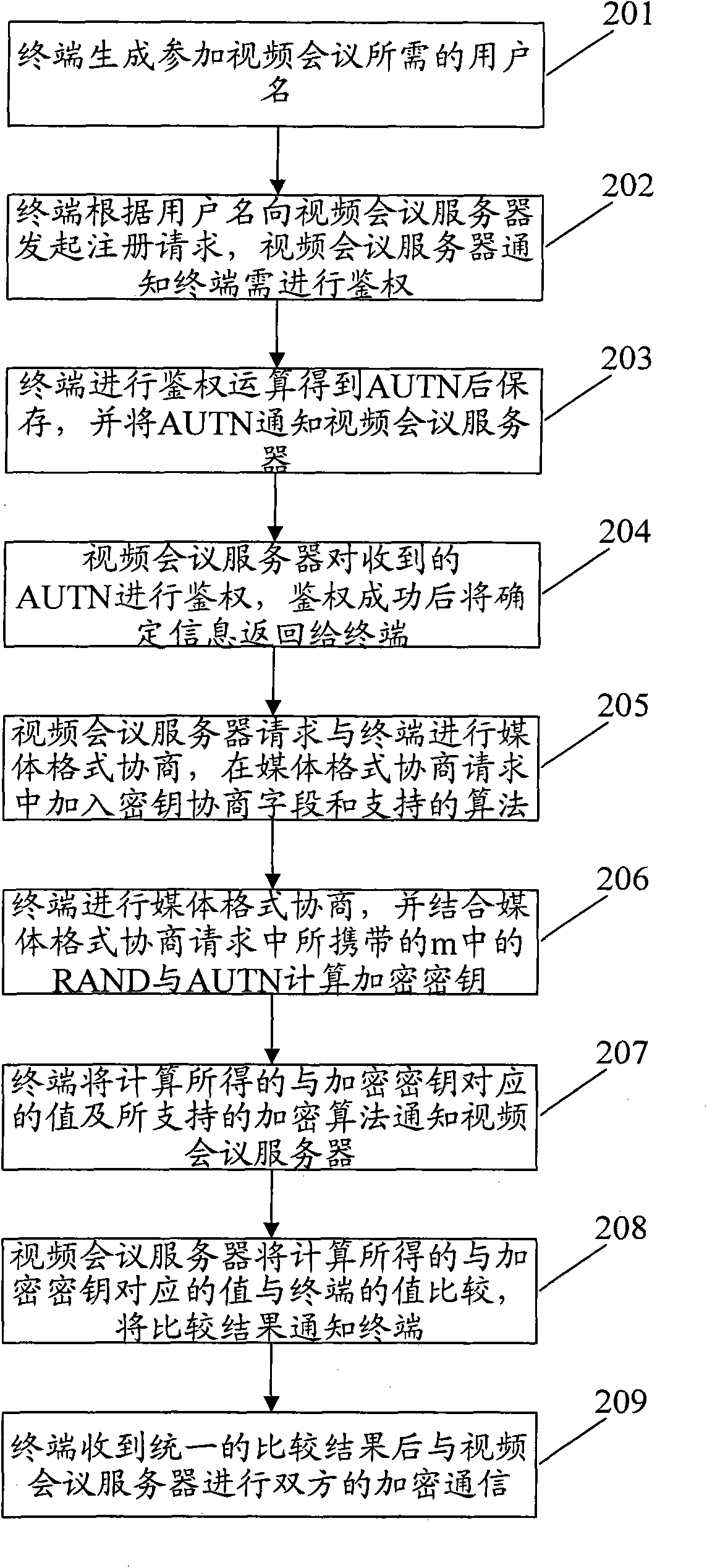
Method and system of terminal for encrypting videoconference data
ActiveCN101635823AEnsure confidential transmissionPrevent eavesdroppingTelevision conference systemsUser identity/authority verificationEavesdroppingWeb authentication
The invention discloses a method of a terminal for encrypting videoconference data, which comprises the following steps: generating a network authentication token (AUTN) by a terminal in authentication with a videoconference server; carrying random passwords (RAND) by the videoconference server in media format negotiation requests sent to the terminal after the authentication is succeeded; calculating an encryption key by the terminal by combining the AUTN and the RAND; carrying out negotiation of encryption key and encryption calculation with the videoconference server; and carrying out encryption communication between the two parties after the negotiation is unified. The invention also discloses a system of a terminal for encrypting videoconference data. The method and the system can be used for encrypting videoconference data and ensuring the confidential transmission of the videoconference data. Because user names registered in each terminal are different in a videoconference, encryption keys generated by each terminal are different. In the communication between a terminal and a server, the invention can effectively prevent a third party from eavesdropping.
Owner:ZTE CORP
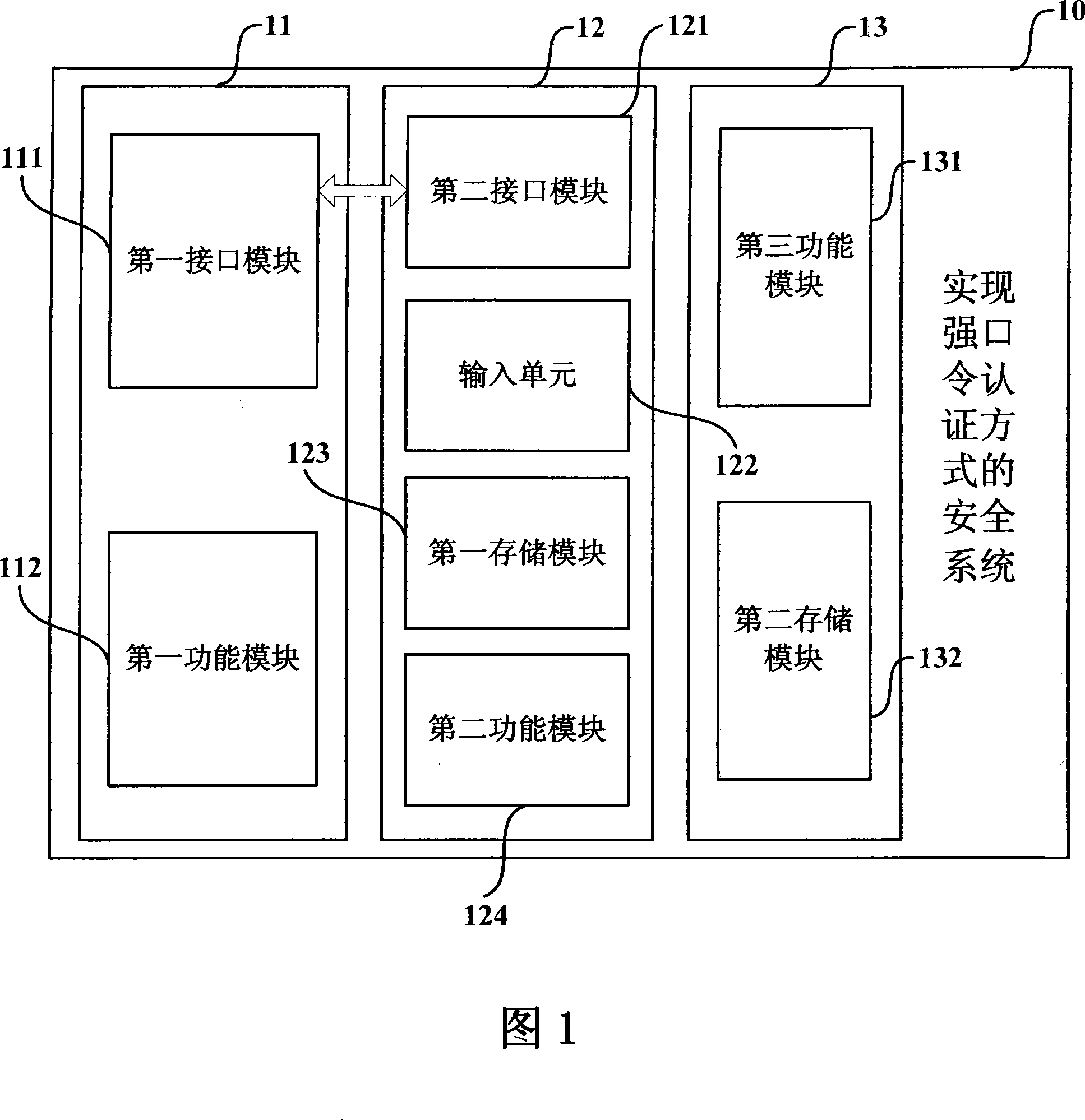
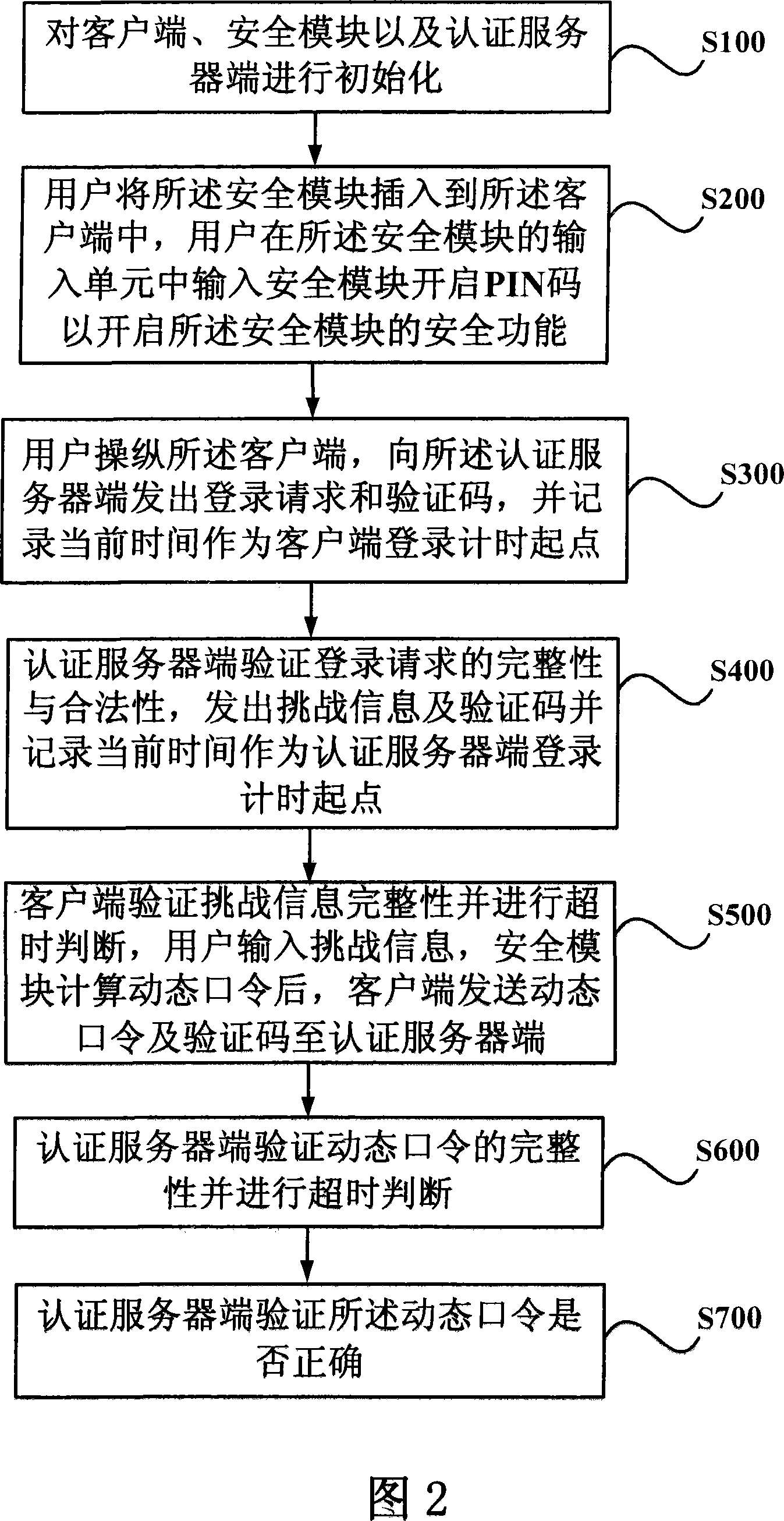
A secure system and method for realizing powerful password authentication mode
ActiveCN101188495APrevent snoopingPrevent eavesdroppingSecuring communicationMan-in-the-middle attackPassword
The invention relates to the field of password authentication and discloses a security system and method that realizes the pattern of strong password authentication so as to resolves such problems in the prior password authentication pattern as the password being easily pried and attacked. The invention uses a security module for password authentication, and imports the user password into the security module instead of a host machine keyboard, adopts the random number with sufficient length as a user password, and the user password is not directly sent onto the network when logging in, and the dynamical information about the transmitted password is once for all, thereby being free from the attacks by various passwords. At the same time, the invention adopts a challenge / reply mechanism and a time synchronization mechanism, and combines the security function property of the security module, helping the method to prevent the counterfeit of a server and the assaults of a middleman apart from the fight against password assaults.
Owner:BEIJING SINOSUN TECH
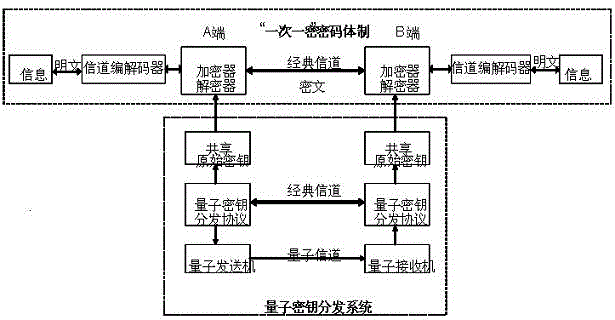
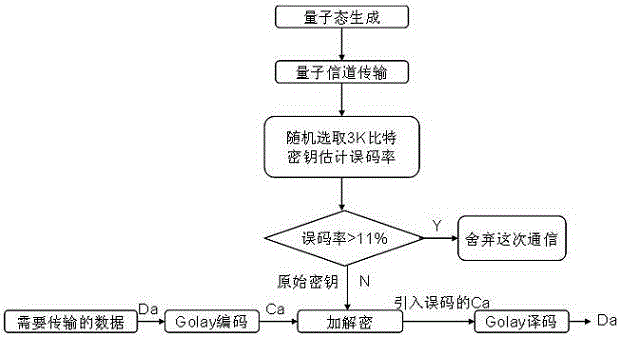
Security data communication achieving method based on quantum key distribution
InactiveCN104468097AReduce lossIncrease spawn rateKey distribution for secure communicationError preventionComputer hardwareKey distribution
The invention discloses a security data communication achieving method based on quantum key distribution. In traditional data communication based on quasi single-photon source quantum key distribution, a large number of quantum bits will be consumed in the data reconciliation process, and quantum key distribution efficiency is low. According to the security data communication achieving method based on quantum key distribution, a new quantum security communication model is built, the data reconciliation process is omitted, original key error codes are equivalent to channel error codes, and data secrecy transmission is achieved by exchanging the encryption and decryption sequence and the channel coding frequency. Dolay coding with the high error correcting capability is adopted for channel coding, original keys are used for encrypting and decrypting the coded data in a one-time pad mode, Dolay decoding is carried out on the decrypted data with error codes, and verification is carried out in an experiment system. Research results show that the quantum key distribution process is simplified, the key security is enhanced, computing and communication resources are saved, the key generating rate is improved, and a new idea is provided for quantum key distribution.
Owner:PLA UNIV OF SCI & TECH
Method and system for generating safety key bound with device
ActiveCN101931953APrevent eavesdroppingPrevent tamperingNetwork traffic/resource managementSecurity arrangementEngineeringSecurity parameter
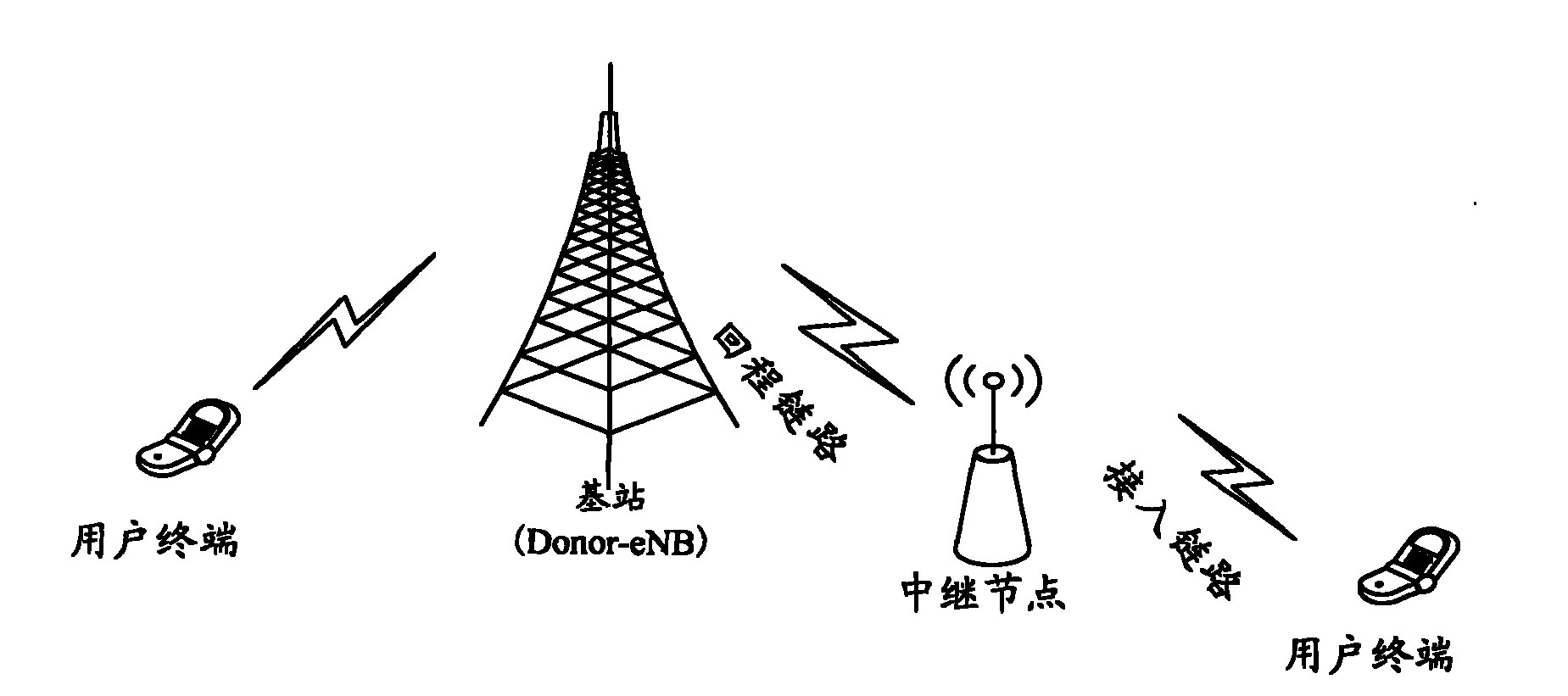
The invention discloses a method and a system for generating a safety key bound with a device. The method comprises the following steps of: a network side and a relay node (RN) reach an agreement on the user safety key and device-dependent safety parameters; and the network side notifies the RN to generate the safety key bound with the device, and the RN generates the safety key bound with the device and responds to the network side according to the user safety key and device-dependent safety parameters. Through the method and the system, the safety key bound with the device is generated, an attracter is prevented from wiretapping and falsifying communication data by using illegal equipment, and the safety of the communication data between the RN and the network side is ensured.
Owner:ZTE CORP
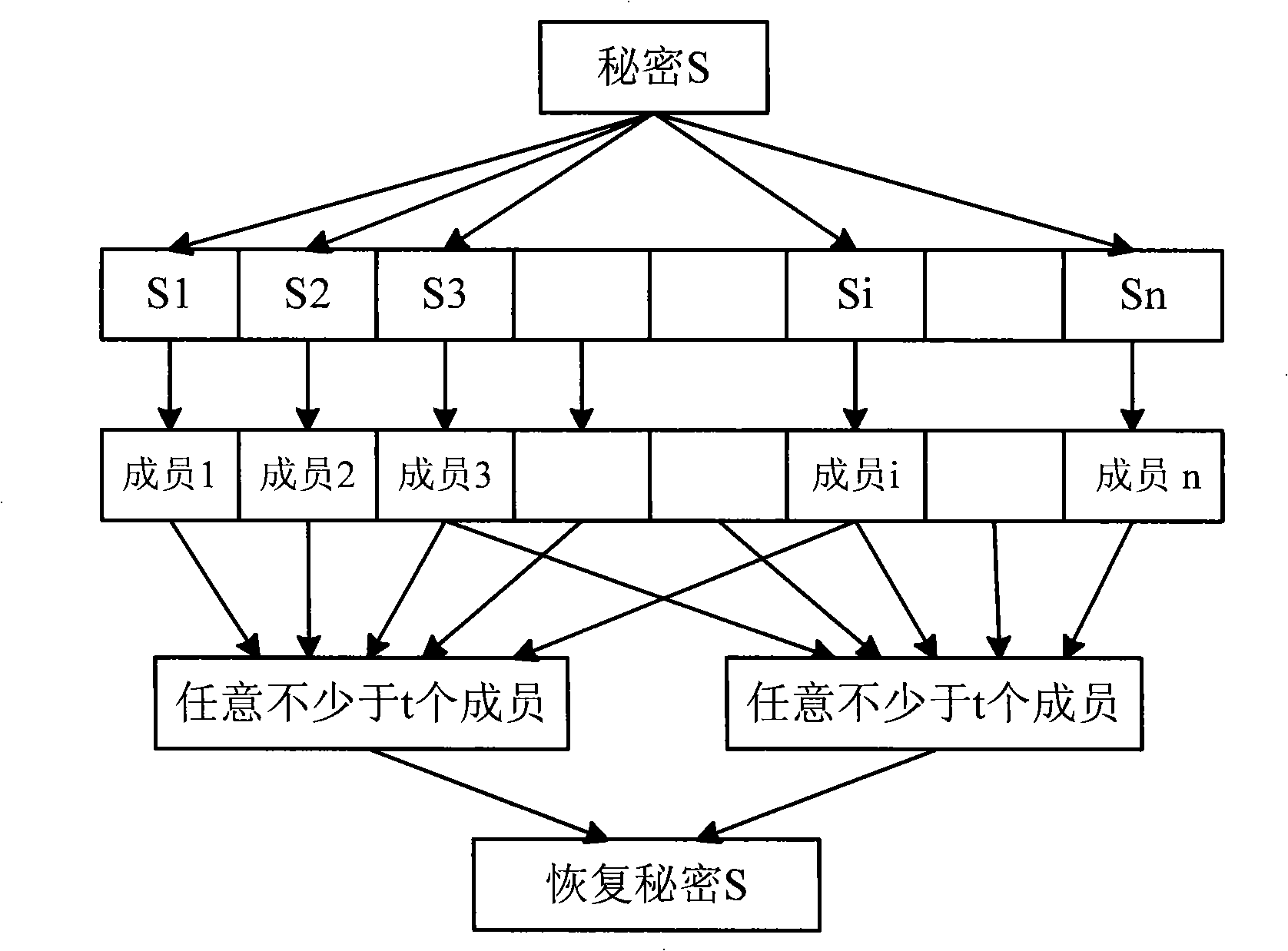
Allocation and management method of the secrete key in the sensor network
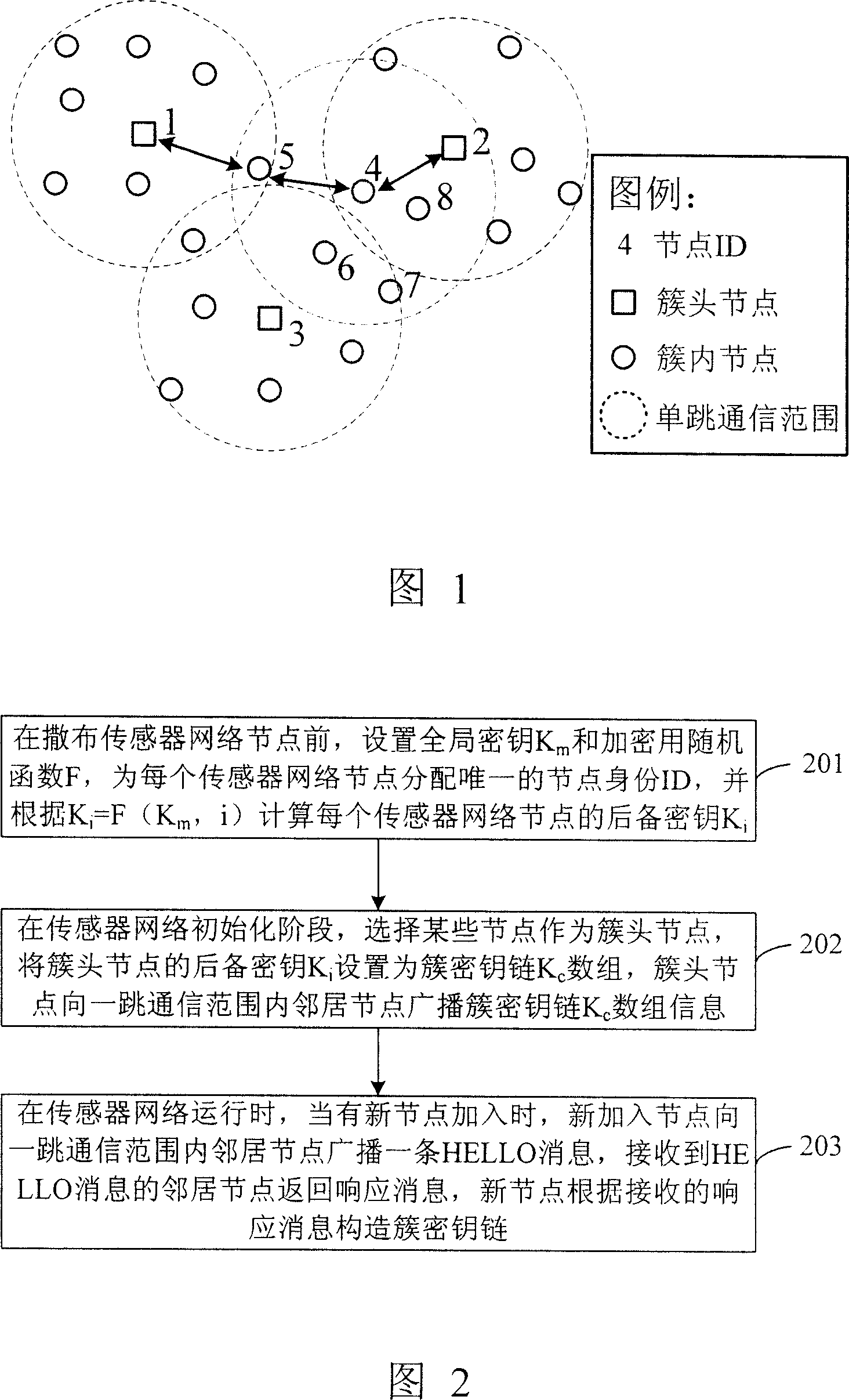
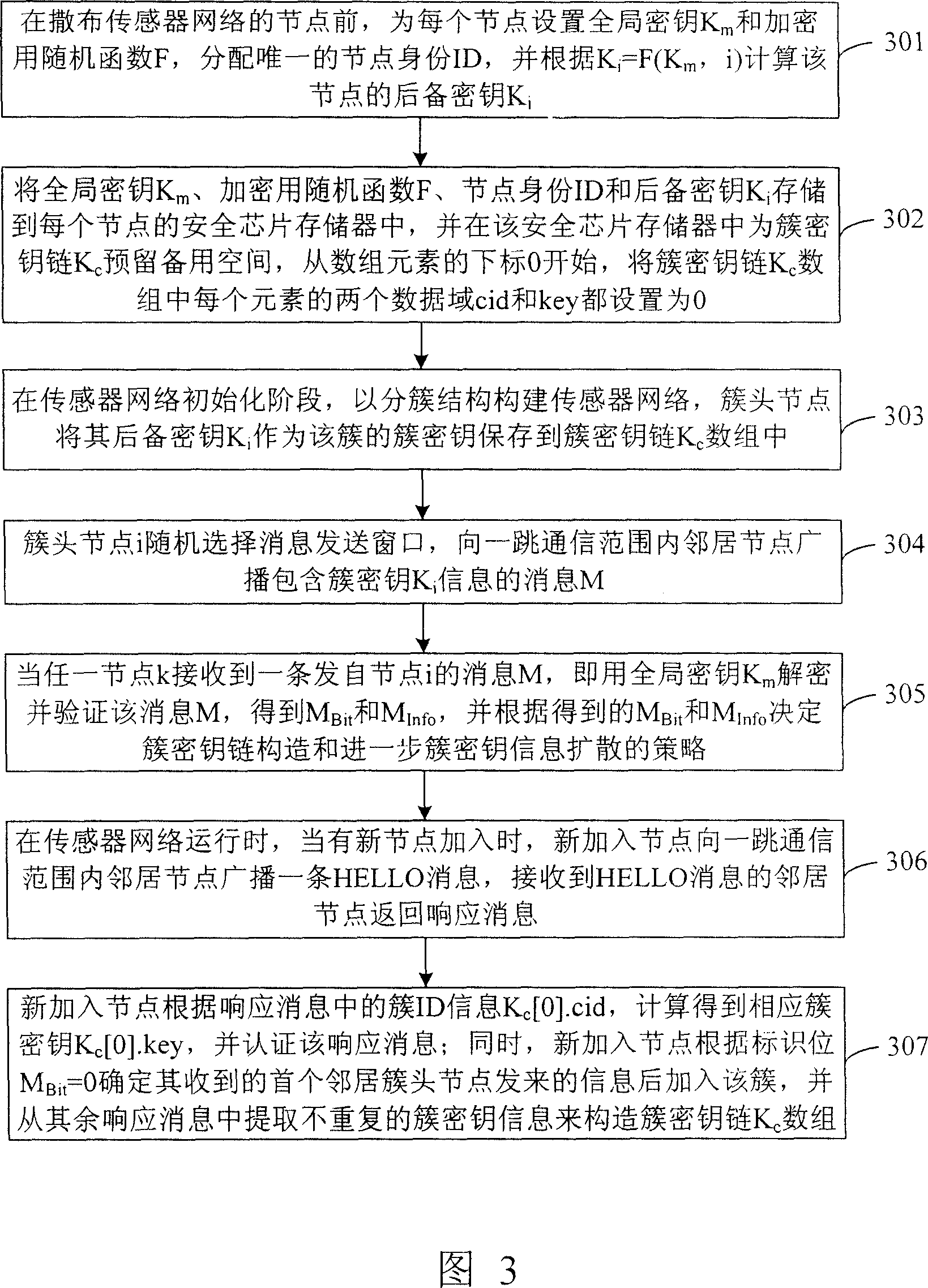
InactiveCN1996833AEnable secure communicationPrevent eavesdroppingKey distribution for secure communicationData switching by path configurationData setArray data structure
This invention discloses one method to align and manage in sensor network, which comprises the following steps: a, before distributing sensor network points to set whole key Km and coded random function F for each point with only identification and to compute point backup key Kid; b, in sensor initiating phase, establishing sensor network by cluster structure as cluster code key data set; c, in sensor operation, when there is new points, adding new communication range of HELLO information.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Bluetooth master and slave devices and method for establishing safety channel between same
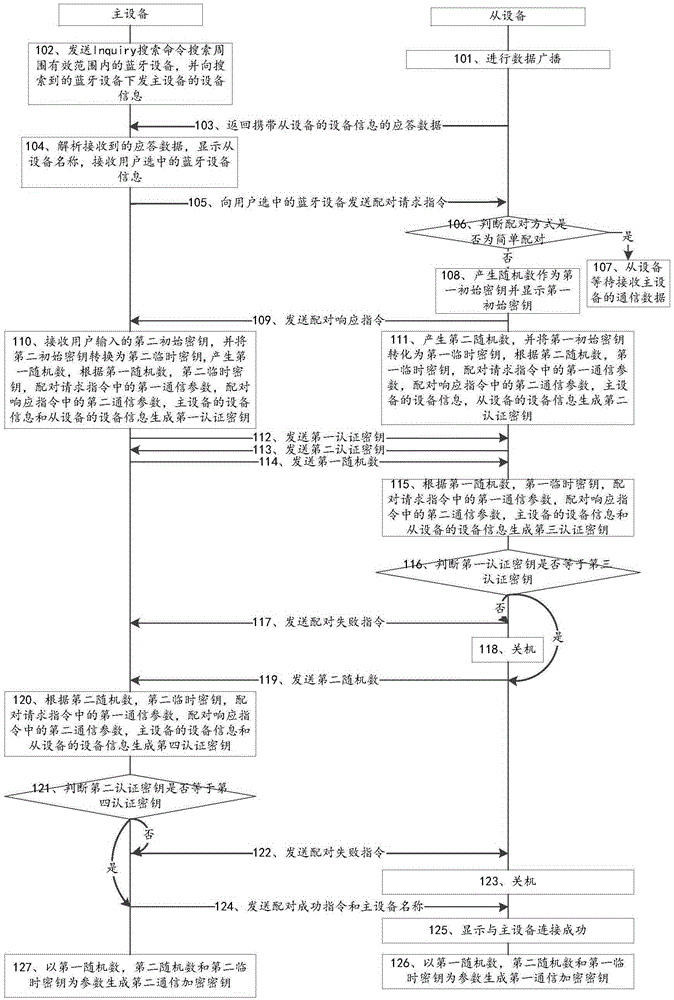
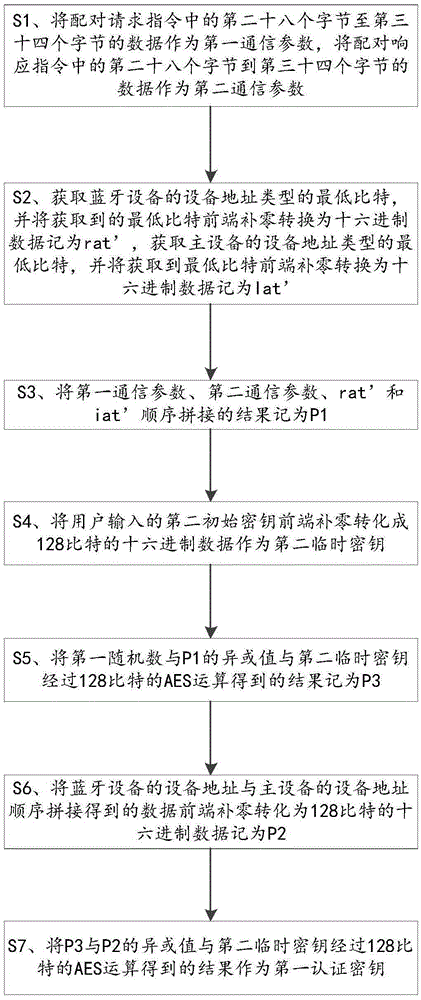
ActiveCN105430605AAchieve connectionPrevent Malicious ConnectionsConnection managementWireless commuication servicesSecure channelBluetooth
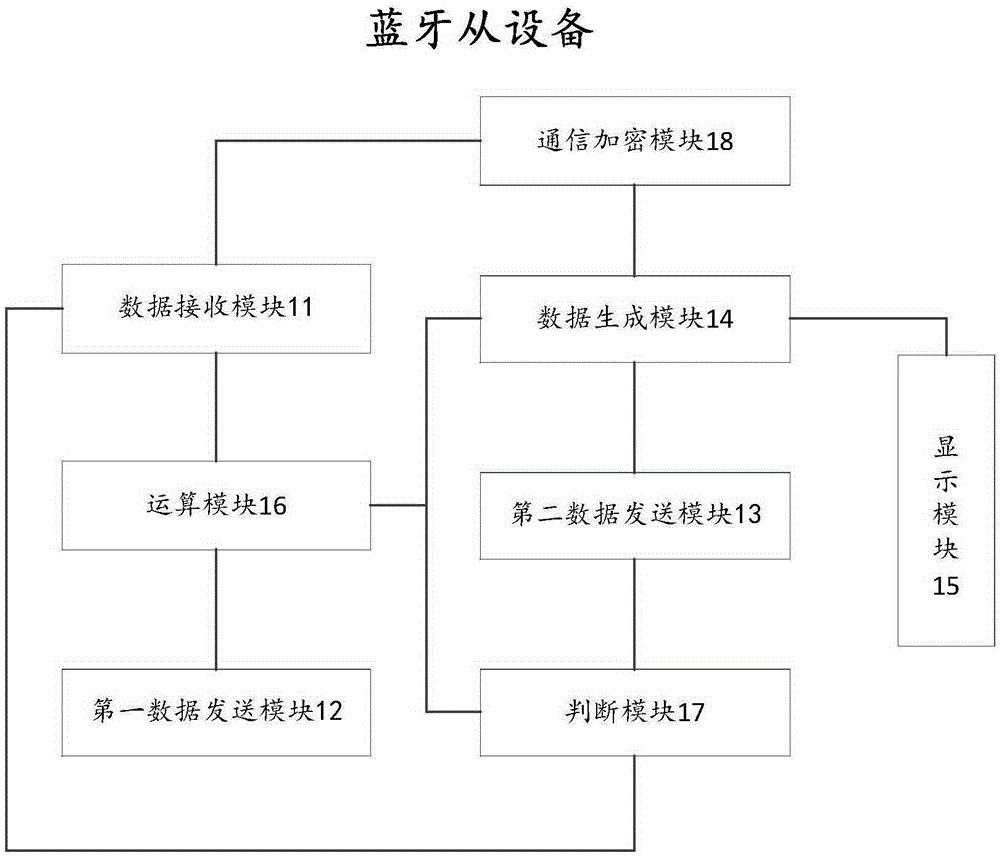
The invention discloses Bluetooth master and slave devices and a method for establishing a safety channel between the same, and belongs to the field of information safety. The method comprises: both the Bluetooth devices exchange respective device information; according to the device information, a connection is established between the Bluetooth devices; both the Bluetooth devices exchange and verify respective authentication keys generated according to a same algorithm; and after authentication is successful, both the Bluetooth devices generate communication encryption keys according to a same algorithm, so that the safety channel is established between the Bluetooth devices. The Bluetooth slave device comprises a data receiving module, a first data sending module, a second data sending module, a data generation module, an operation module, a judgment module, a communication encryption module and a display module; the Bluetooth master device comprises a data receiving module, a data sending module, a data generation module, an operation module, a judgment module, a communication encryption module and an input module. The connection between the Bluetooth devices by verification codes is achieved, and the malicious connection of other devices is prevented.
Owner:FEITIAN TECHNOLOGIES
Method for realizing self surrogate function for mobile node
ActiveCN1589060ASafe roamingPrevent eavesdroppingRadio/inductive link selection arrangementsTransmissionEncryption decryptionComputer science
A method for making a mobile nod to realize self agent function is camed out by getting a legal configuration transmit address after panning in the expanding network domain then starting the register rule: certifying to the base domain management entity and informing it the acquired configuration transmit address, getting the ARP agent to the base domain network host to automatically respond the access request of the upper layer protocol stock and determine the path communicated with its host setting up a background service frame to integrate the ciphering and deciphering module and tunnel module and enter into the frame carrying out tunnel packaging and de-packaging operation data, negotiating on dynamic session cipher key and ciphering and de-ciphering user actual transmission data done before dellvery.
Owner:CHINA IWNCOMM
Safe fire-fighting equipment inspection method
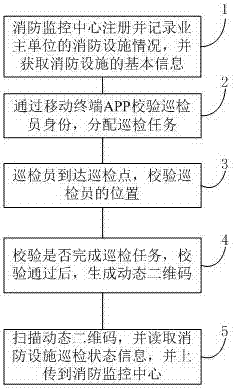
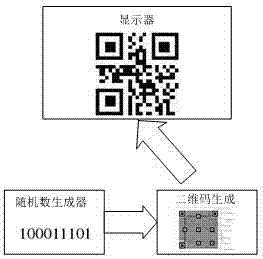
InactiveCN107393048ANon-reproducibleRestraint behaviorChecking time patrolsData processing applicationsValidation methodsComputer terminal
The invention discloses a safe fire-fighting equipment inspection method. The method comprises steps as follows: step 1: fire-fighting equipment is registered through a fire-fighting equipment management platform of the fire-fighting monitoring center; step 2: the identity of an inspector is verified through a mobile terminal APP and the inspector receives allocated inspection tasks and inspection standards; step 3: the inspector arrives in the inspection location, the position of the inspector is verified, and the fire-fighting equipment is inspected according to the inspection standards; step 4: whether the inspection tasks are completed is verified, and a dynamic QR code is generated by a safe inspection QR code generator after verification passes; step 5, the dynamic QR code is scanned, and the inspection state information of the fire-fighting equipment is read and uploaded to the fire-fighting equipment management platform of the fire-fighting monitoring center. According to the safe fire-fighting equipment inspection method, accidents such as damage to the system by an illegal person disguised as an inspector, irresponsible behavior of the inspector for inspection, fake inspection behavior and the like are avoided by verifying the legal identity of the inspector, the position of the inspection location and the inspection process; transmission safety is guaranteed and eavesdropping and tampering attack are prevented by establishing safety communication.
Owner:北京富邦智慧物联科技有限公司
Strong discrimination method of enciphered mode by public key cryptographic algorithm
InactiveCN1658553APrevent eavesdroppingEasy to managePublic key for secure communicationUser identity/authority verificationCommunications securityRelevant information
This invention discloses a strong distinguishing method adopting open code key calculation encryption mode. The process is:found wireless chain-channel, the identifier sends the identification request to the user, and return the identification information to the server, the server find the user open code key and the information integrality code key from the database to found the dialog with the user, the server and the user produce the random numbers, encode the open code key for each other, decode the code key through the identifier, compare self random number with the random number changed by the opposite side and judge whether the identification is successful. Repeat this process for three times, and the server and the user calculate the whole identification and exchange integrality value through encoding and decoding code key and the information integrality code key and the relative information. The identifier judges whether the identification is successful, decides whether the user can get into the network and realizes the online communication of users and the broadcasting of the base station. The strong points are that it realizes the insurance of the identification of the user and the server and the safety of the communication.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
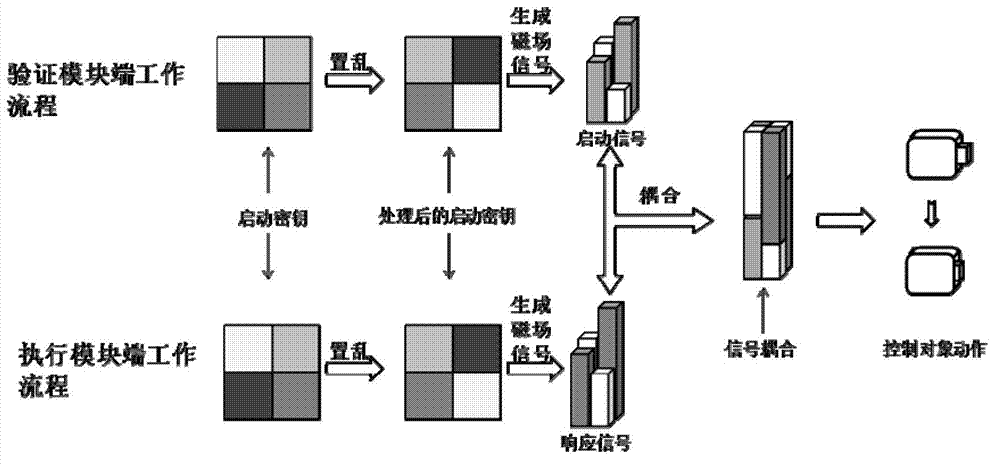
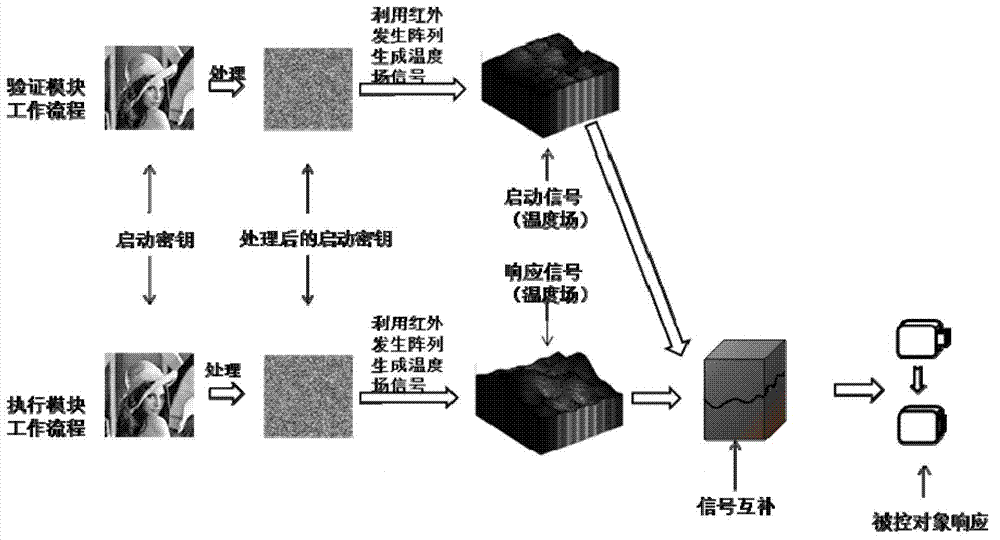
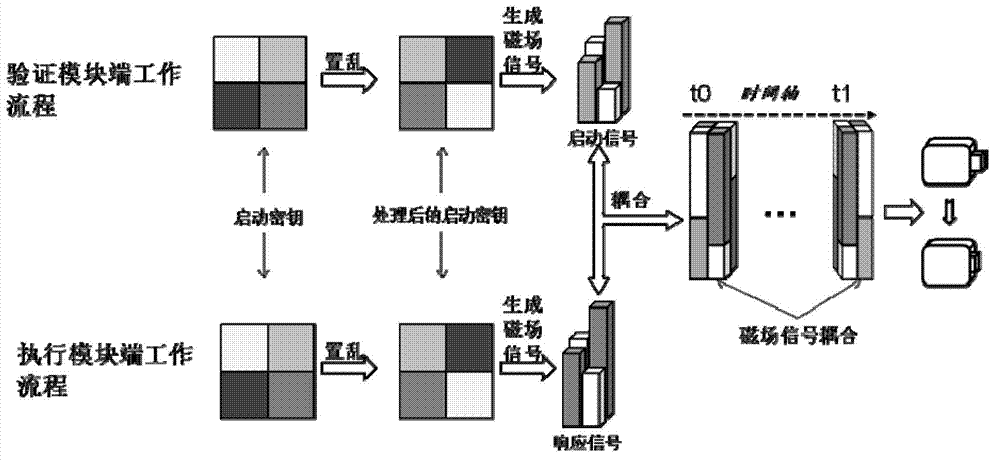
Start-up system and start-up method based on dynamic human body characteristic recognition
ActiveCN103310510ALow costImprove securityIndividual entry/exit registersExclusive orComputer module
The invention provides a start-up system based on dynamic human body characteristic recognition. The start-up system comprises two functional modules including an identification module and an execution module, wherein the identification module is used for identifying a user identity through carrying out dynamic human body characteristic information verification on a user; information interaction is carried out between the identification module and the execution module in a traditional wireless communication manner or an inductive communication manner; the execution module receives a start-up signal sent by the identification module and executes the corresponding start-up movement; all functions of the identification module can be realized on a mobile intelligent terminal; the inductive communication is realized by coupling, complementation and the like of various signals; meanwhile, various field signals in a communication process can be subjected to physical encryption so that the communication safety is guaranteed. The system disclosed by the invention takes the mobile intelligent terminal as main equipment, is strong in safety and convenient to use; the system is particularly suitable for starting up various types of equipment which is private and exclusive or needs authorization permission.
Owner:ZHEJIANG UNIV
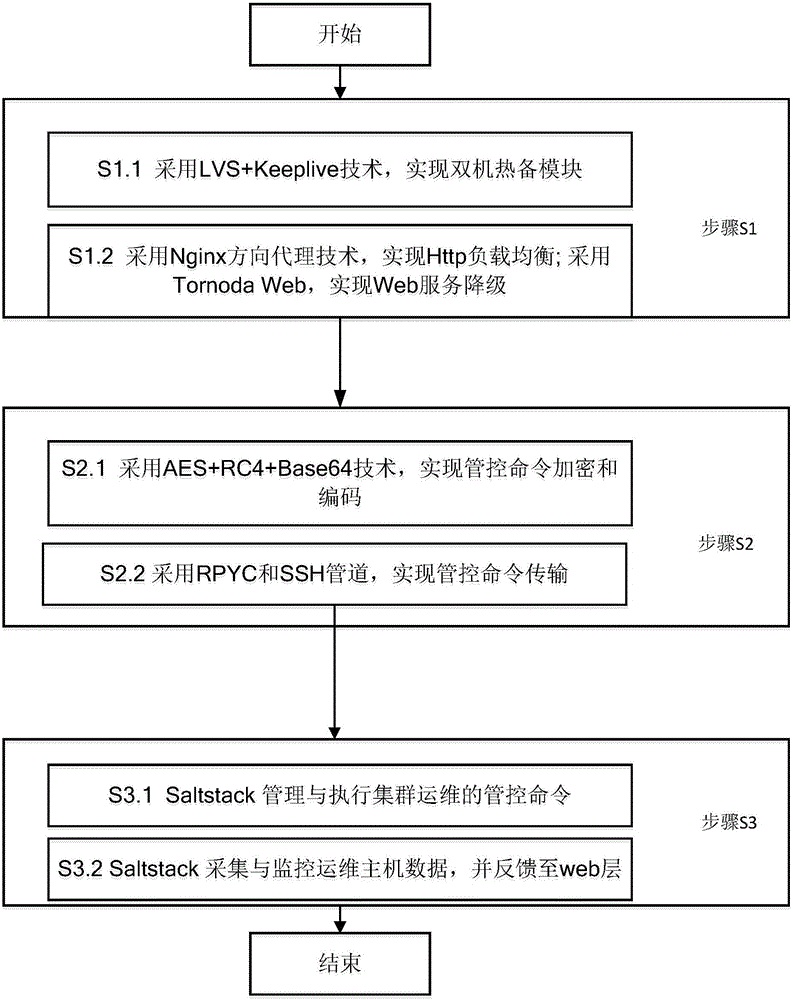
High-reliability cluster operation and maintenance management method
InactiveCN106100894ASupport manual hot switchingSupport automatic failoverData switching networksFault toleranceControl layer
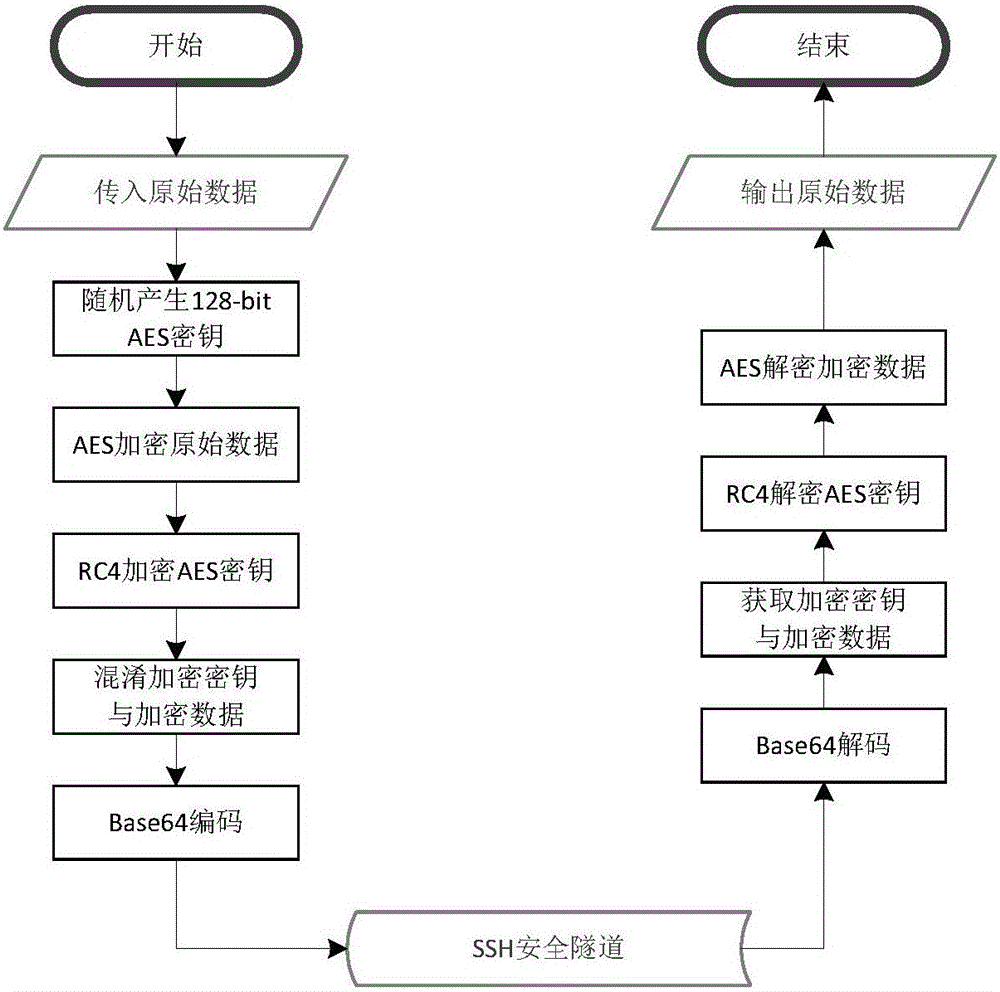
The invention discloses a high-reliability cluster operation and maintenance management platform method. Specifically, the method comprises (1), a high-reliability cluster control command web access and http form scheduling release step of establishing a cluster operation and maintenance web management platform, wherein remote management and visual management of a cluster are realized, and reliability of cluster operation and maintenance web management is realized from an access layer, a scheduling layer and a central control layer through adoption of a load balance technology and redundancy and fault-tolerance technologies; (2), a high-reliability cluster control command transmission and issuing step of in a data transmission process, encrypting transmission data and an AES key by employing AES and RC4 algorithms, carrying out base 64 coding on encrypted data, and transmitting the coded data through an ssh tunnel, thereby realizing data reliability of the cluster operation and maintenance management; and (3), a high-reliability cluster control command performance and feedback step of establishing an expandable cluster operation and maintenance central operation and maintenance control system, wherein various configuration management frames and a user customized configuration frame are supported, and central control reliability of the cluster operation and maintenance management is realized.
Owner:SOUTH CHINA UNIV OF TECH
Ultrasonic active sound attenuation anti-eavesdrop and anti-wiretapping device, and anti-eavesdrop and anti-wiretapping method using the device
InactiveCN105047191AProtection against eavesdropping or wiretappingImprove securitySound producing devicesCarrier signalVIT signals
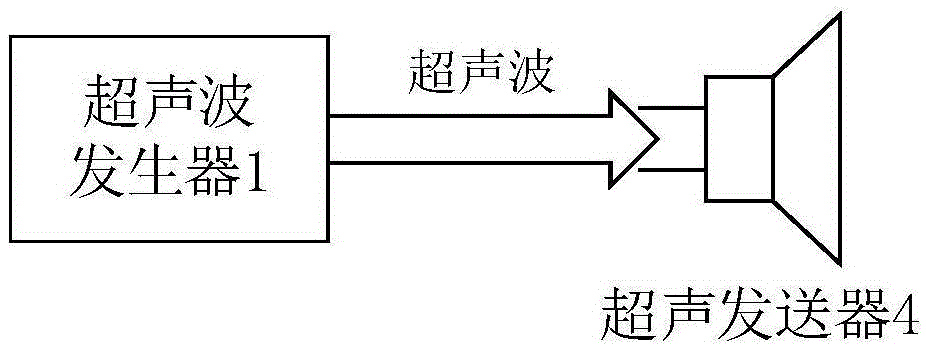
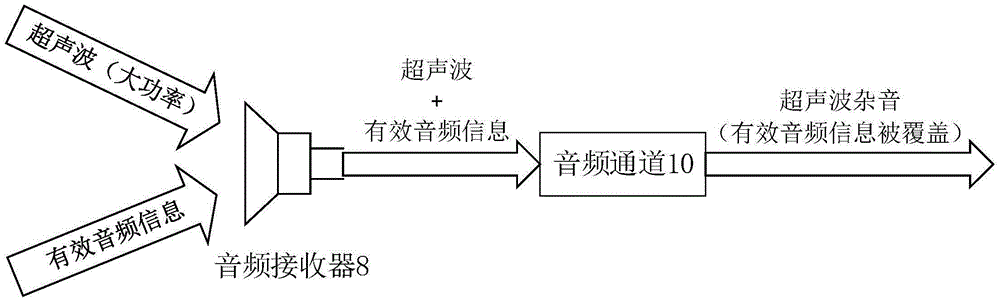
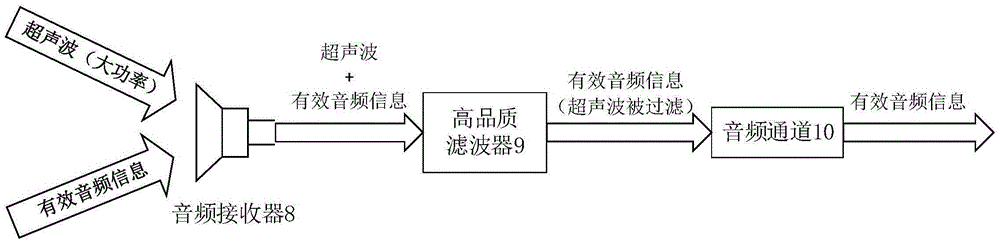
The invention claims an ultrasonic active sound attenuation anti-eavesdrop and anti-wiretapping device, and an anti-eavesdrop and anti-wiretapping method using the device. The device comprises an ultrasonic generator which is used for generating ultrasonic signals, a valid audio frequency information gatherer which is used for gathering valid audio frequency information which may be eavesdropped and wiretapped, an inverter which is connected with the valid audio frequency information gatherer for performing backward processing of the valid audio frequency information and forming active sound attenuation interference audio frequency information, a modulator which can modulate the active noise reduction interference audio frequency information by taking the ultrasonic signals as carrier waves so as to form modulated ultrasonic signals, and an ultrasonic transmitter which is connected with the modulator for transmitting the modulated ultrasonic signals. The ultrasonic active sound attenuation anti-eavesdrop and anti-wiretapping device of the invention can interfere various types of eavesdropping and wiretapping devices in the prior art effectively, thus effectively preventing eavesdropping or wiretapping of conference information or military content, and improving safety of the information.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Safe communication method and device
ActiveCN105307163AEnsure safe executionPrevent eavesdroppingSecurity arrangementSecure communicationSecure channel
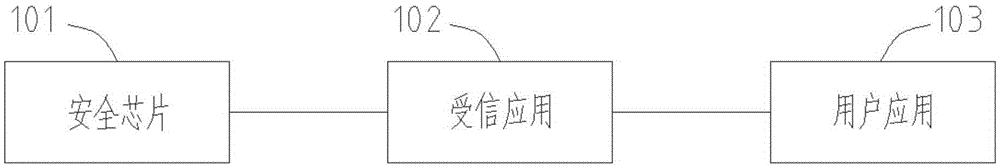
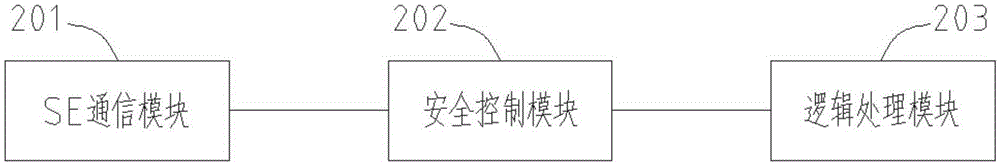
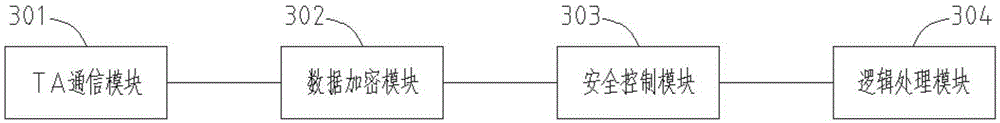
The invention provides a safe communication method and device. The method comprises steps of performing basic information authentication, external authentication and secondary authentication on a security chip and a trusted application, so as to establish a connection between the security chip and the trusted application; performing basic information authentication, external authentication and secondary authentication on the trusted application and a user application, so as to establish a connection between the trusted application and the user application; and establishing a logic connection between the security chip and the user application. A safe channel is established before business communication, and all data communicated in the safe channel is encrypted and transmitted, so that the data in the link is not transparent any longer. The method can effectively prevent interception, guarantees the business to be executed safely, needs no external equipment, and increases user experience.
Owner:HENGBAO
Secret data transmission protection method based on isomorphism of asymmetrical encryption algorithm
InactiveCN101808089AReduce system overheadPrevent eavesdroppingPublic key for secure communicationUser identity/authority verificationData transmissionClient-side
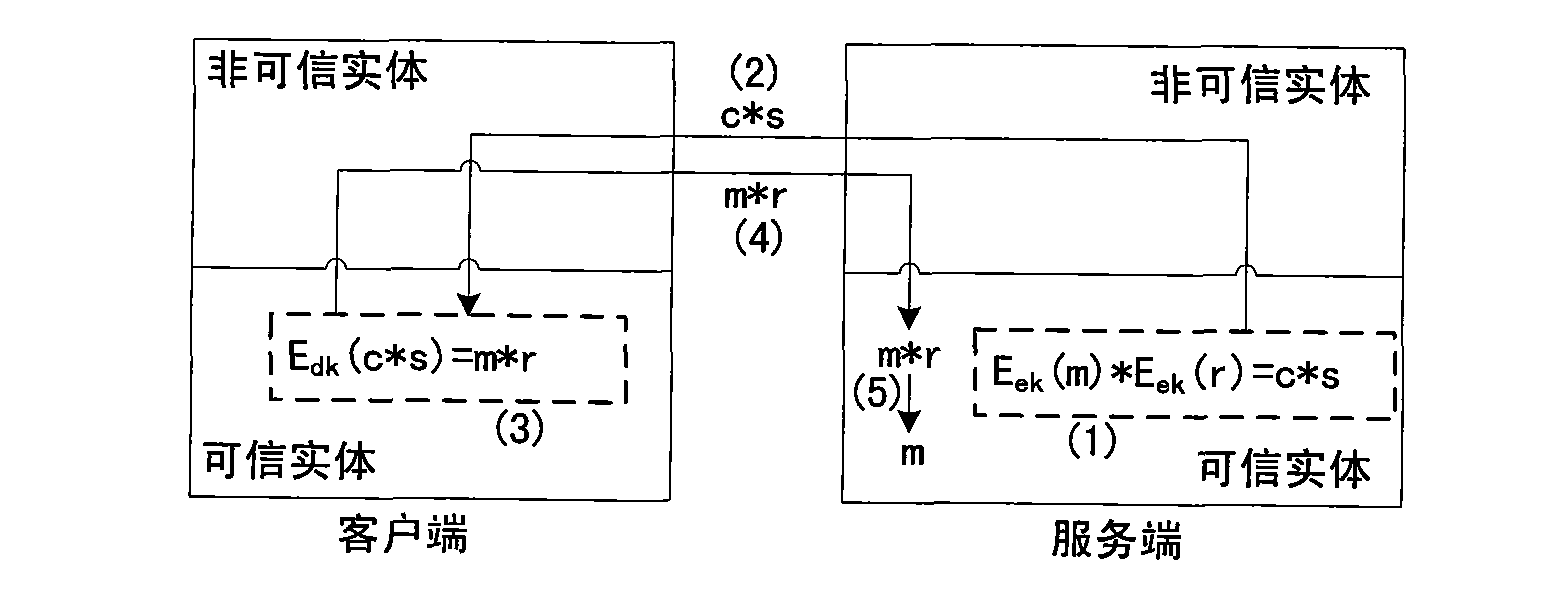
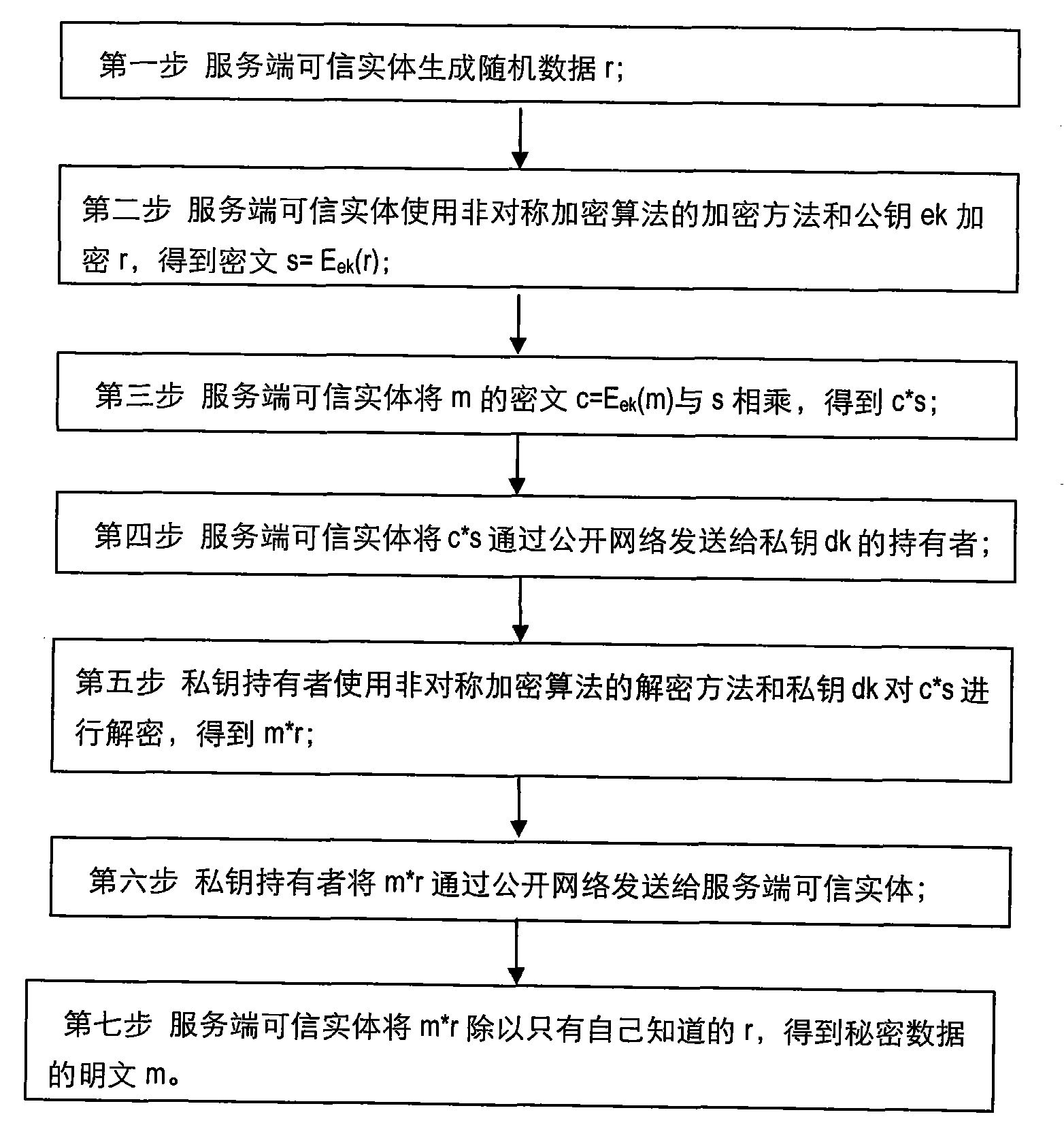
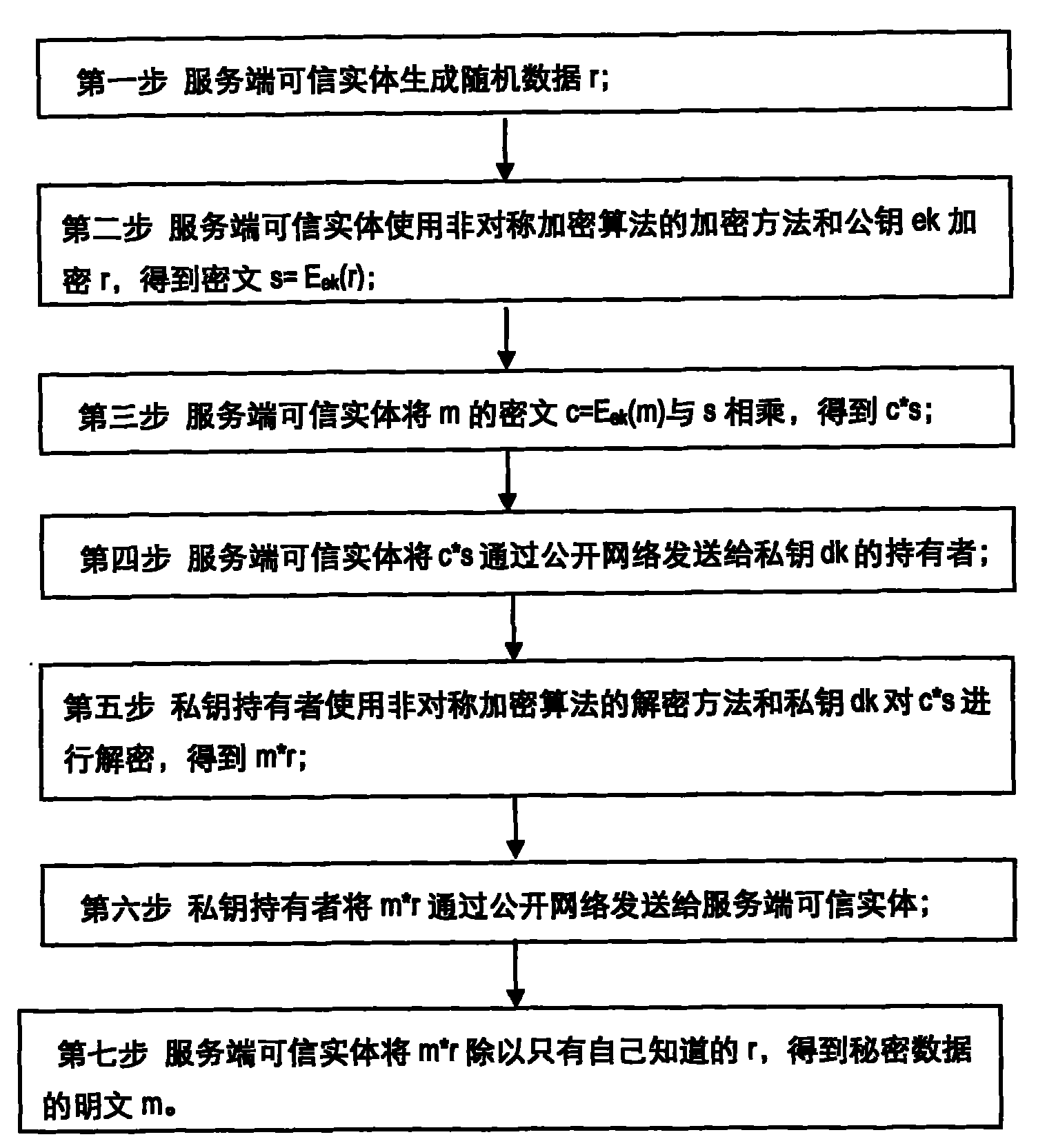
The invention discloses a secret data transmission protection method based on the isomorphism of an asymmetrical encryption algorithm and aims to provide a protection method which has low cost, high efficiency and high safety and is used for the whole processes from decryption to transmission of secret data. A server trusted entity firstly selects a random number r, fakes a cipher text c of secret data, and sends the result to a client trusted entity through a public network; the client trusted entity decrypts the data and returns the result to the server trusted entity through the public network; and the server trusted entity restores a plain text m of the secret data from the result according to the isomorphism of the asymmetrical encryption algorithm. The invention solves the problem of safety when the secret data are transferred in non-trusted clients, open networks and server non-trusted user spaces, and does not need additional identity authentication, thereby reducing the cost.
Owner:NAT UNIV OF DEFENSE TECH
Intelligent submarine cable with invisibly implanted sensing fiber in cable core insulating layer
The invention discloses an intelligent submarine cable with an invisibly implanted sensing fiber in a cable core insulating layer. The intelligent submarine cable comprises a cable core, a sensing fiber and an outer armor strengthening protective layer. The cable core comprises an insulating sheath. The insulating sheath is divided into an inner insulating layer and an outer insulating layer. The sensing fiber is invisibly implanted between the inner insulating layer and the outer insulating layer. The sensing fiber wraps the inner insulating layer with appropriate pitch and is wound and bound through gauze bundling. The sensing fiber which is invisibly implanted in the insulating sheath is used with a suitable detection instrument and system to carry out distributed online monitoring on the position movement of the cable and shape strain of bending, torsion and the like of the cable body, and sensitively detect the information of water sound, seismic waves, boat approaching, anchor hooking and the like within a certain range from the submarine cable. Due to the fact that the sensing fiber is invisibly implanted in the cable core insulating layer and is adhered with the insulating layer, the behavior of cable core stripping can be timely identified, and communication fiber intercepting is effectively prevented. The anti-intercepting intelligent submarine cable integrates communication and sensing.
Owner:江苏通光海洋光电科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com