Patents
Literature
122results about How to "Avoid illegal acquisition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
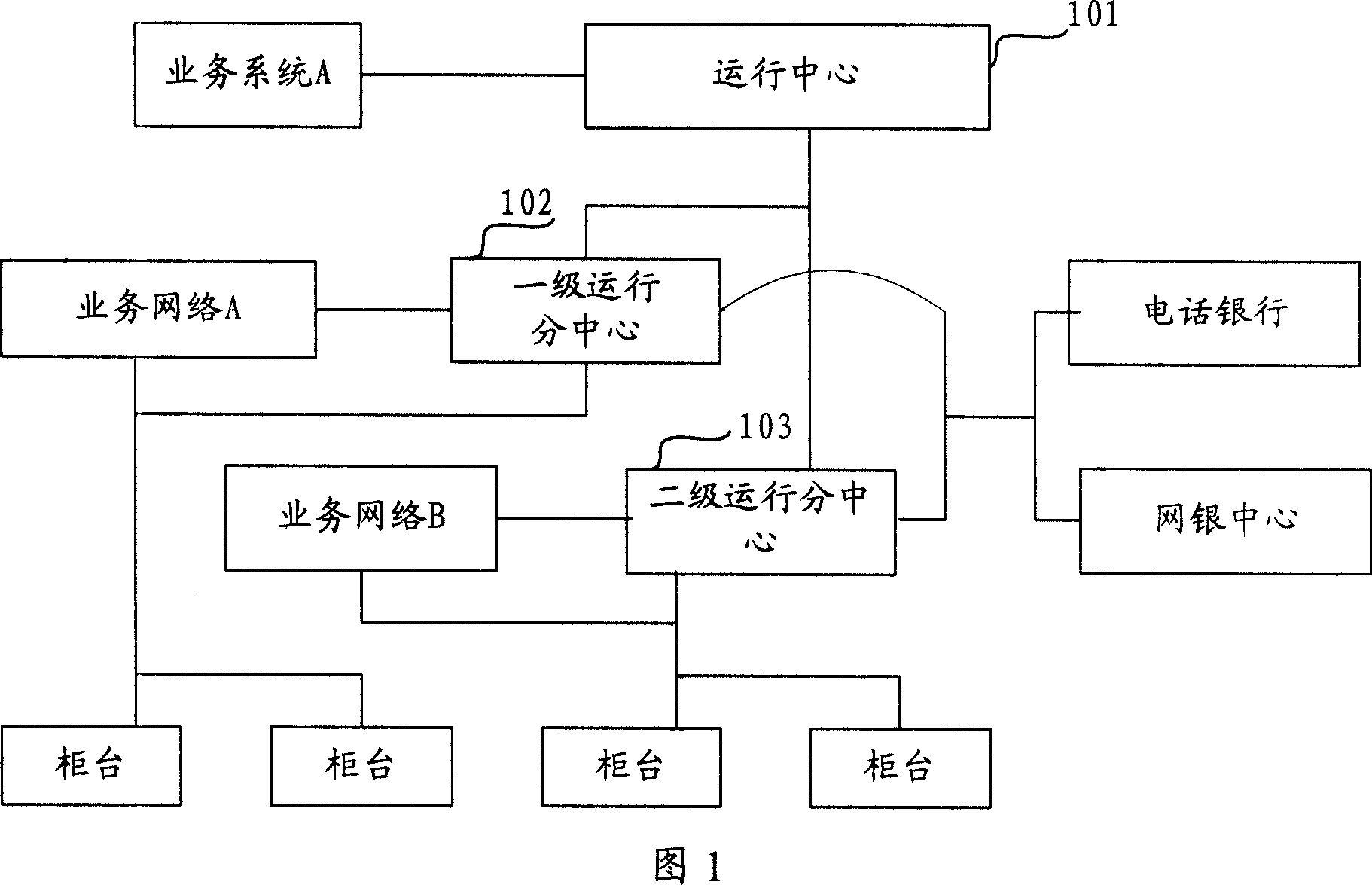
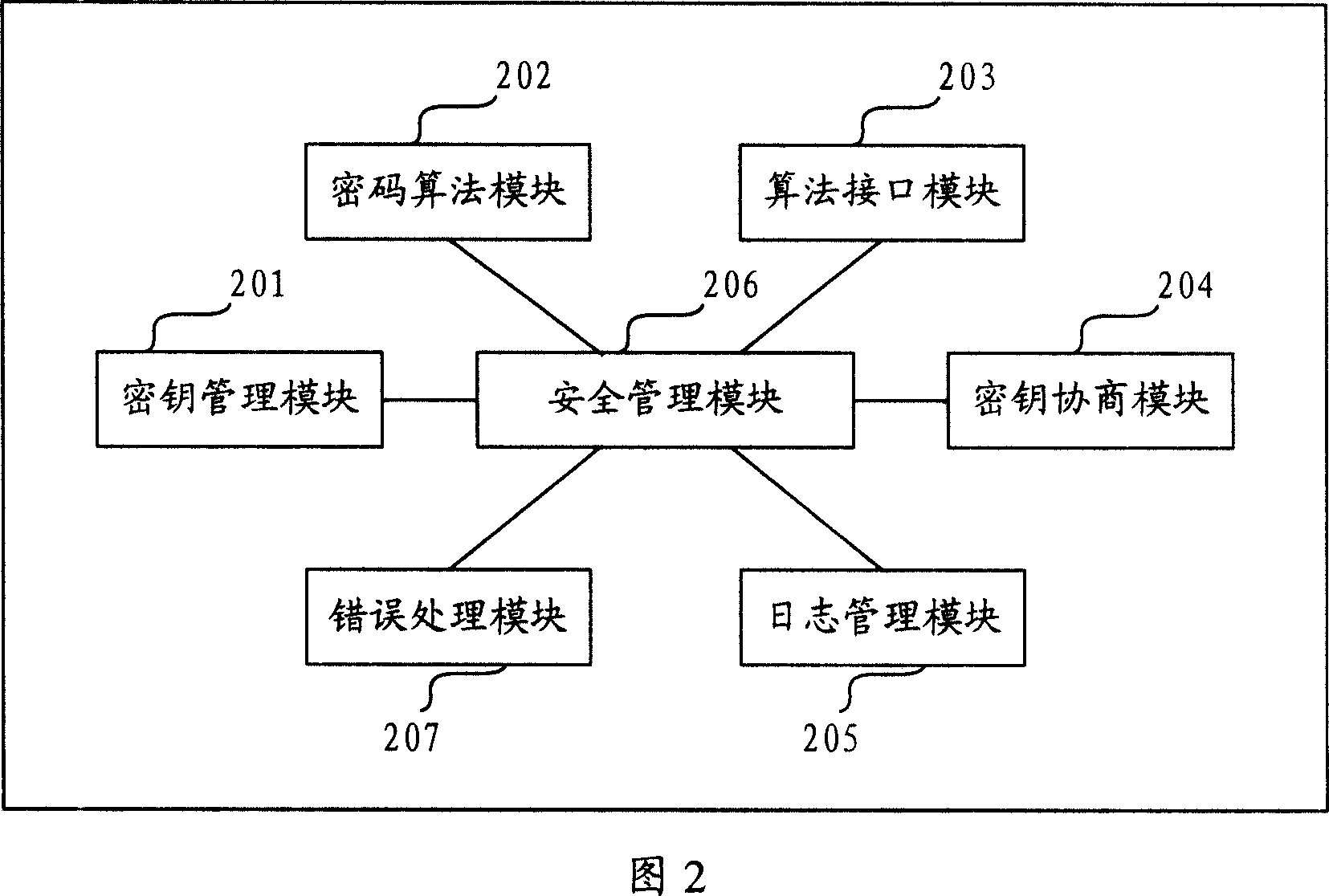
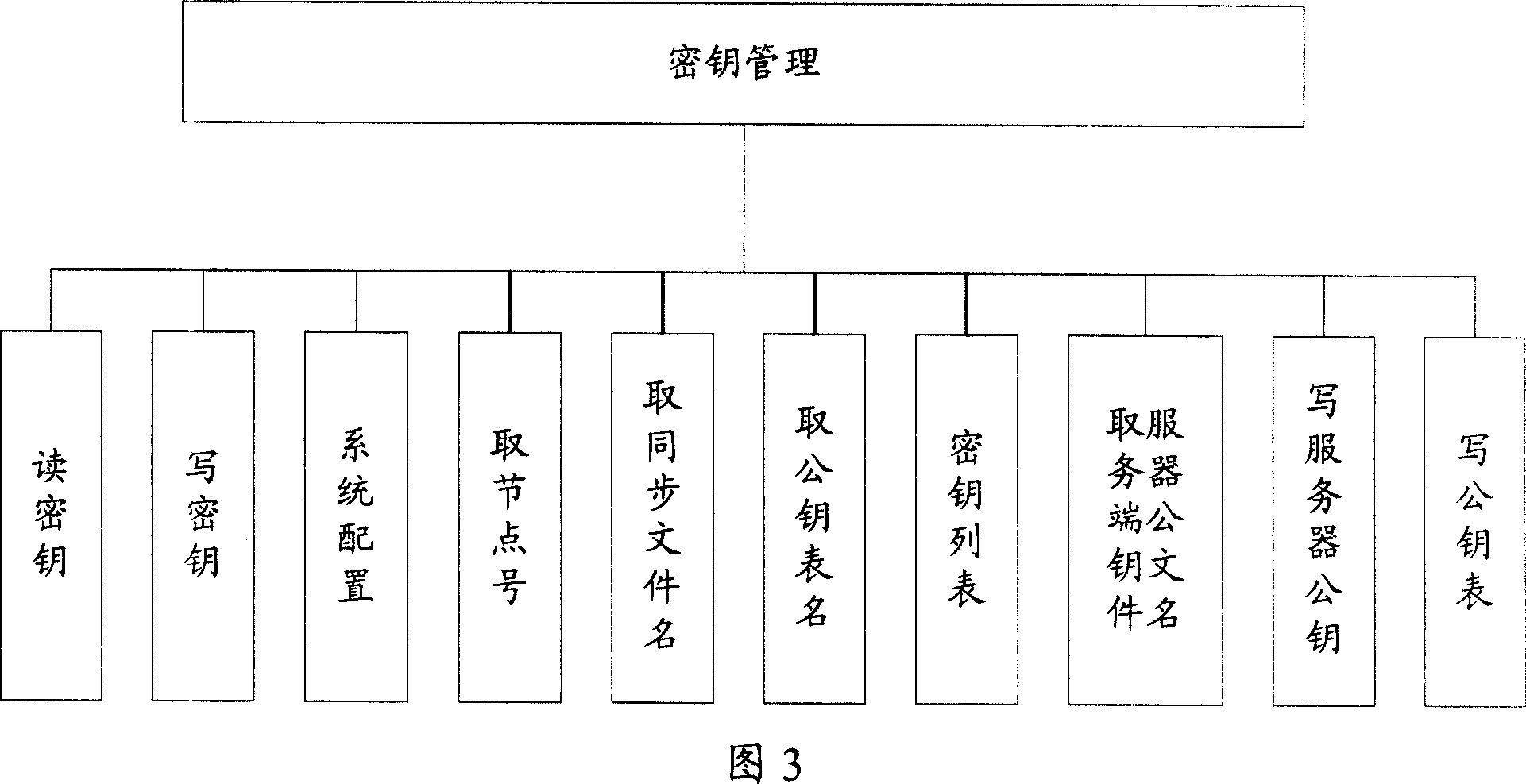
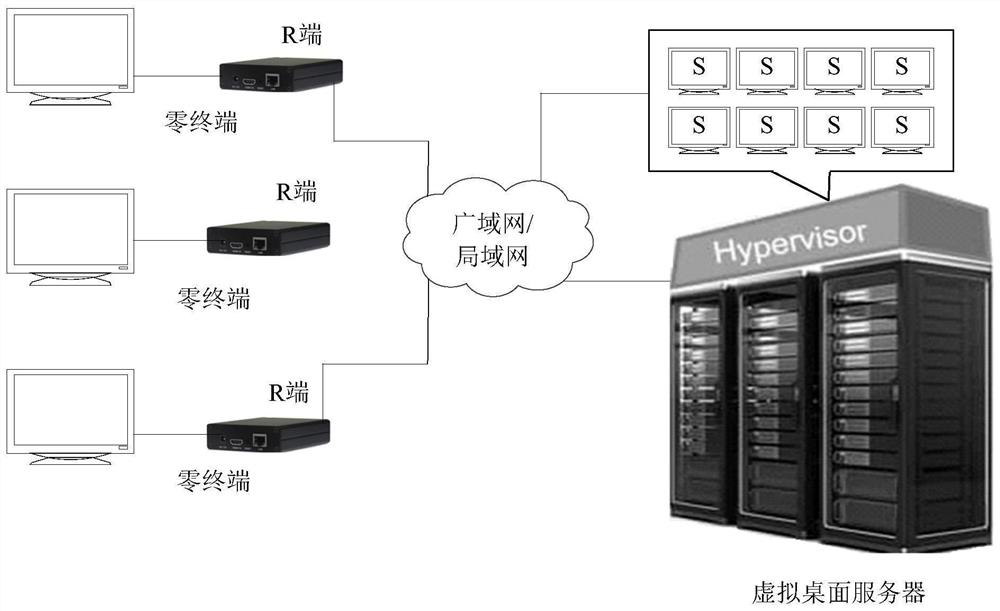
Information security control system
InactiveCN101043335AImplement encrypted transmissionAvoid illegal acquisitionUser identity/authority verificationError processingConfidentiality
The invention provides a control system for the information safety to solve the safe problems existed in the business system, and prevent the important data from leakage and illegal interpolation. The system includes: key management module, key negotiation module, code interface module, log management module, security management module and mistake processing module. The control system for the information safety provided by the invention can combine with the business system closely, and it is classified following the business system on the structure design, the business logic of every hierarchy has the corresponding security control to protect the every aspects of business, and the business safety technical measures cover the every aspect of business system that includes data transmission, data storage, database, files, logs and operation certification and so on, and it can assure the confidentiality, integrality, anti-aggression, usability, anti-repudiation, ID identify and authority control of business system.
Owner:CHINA CONSTRUCTION BANK
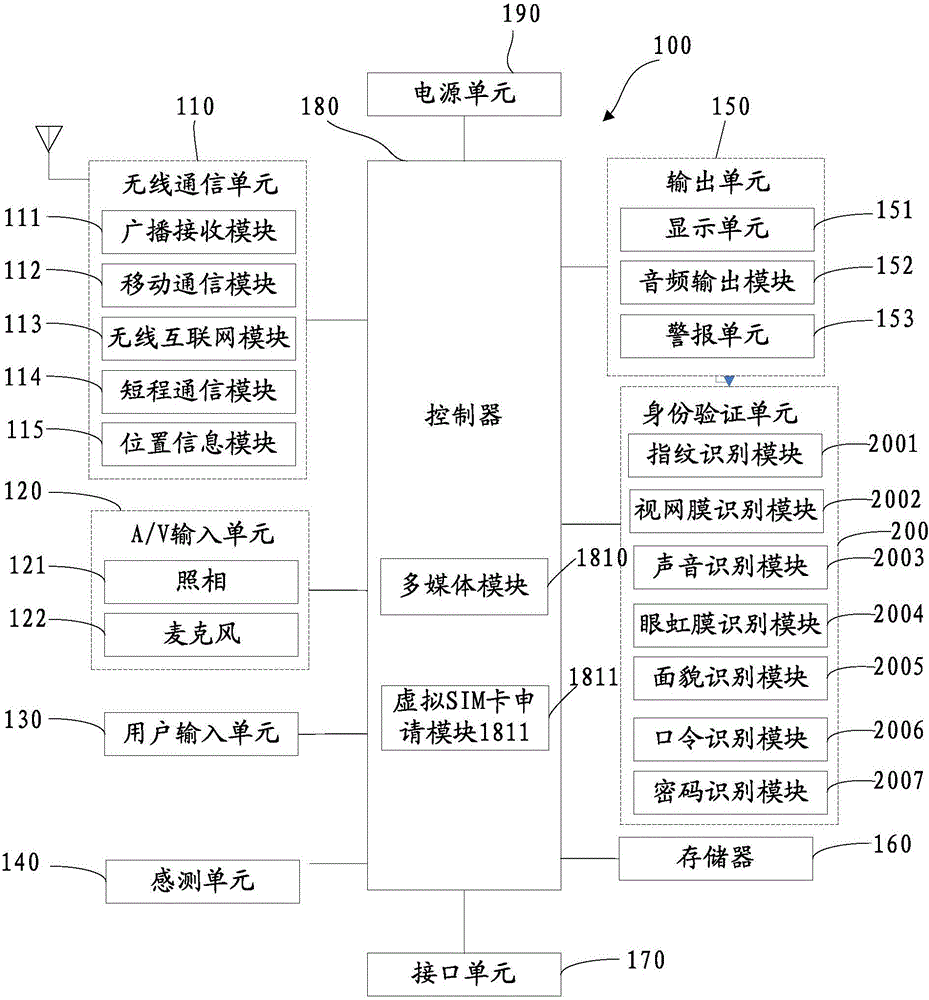
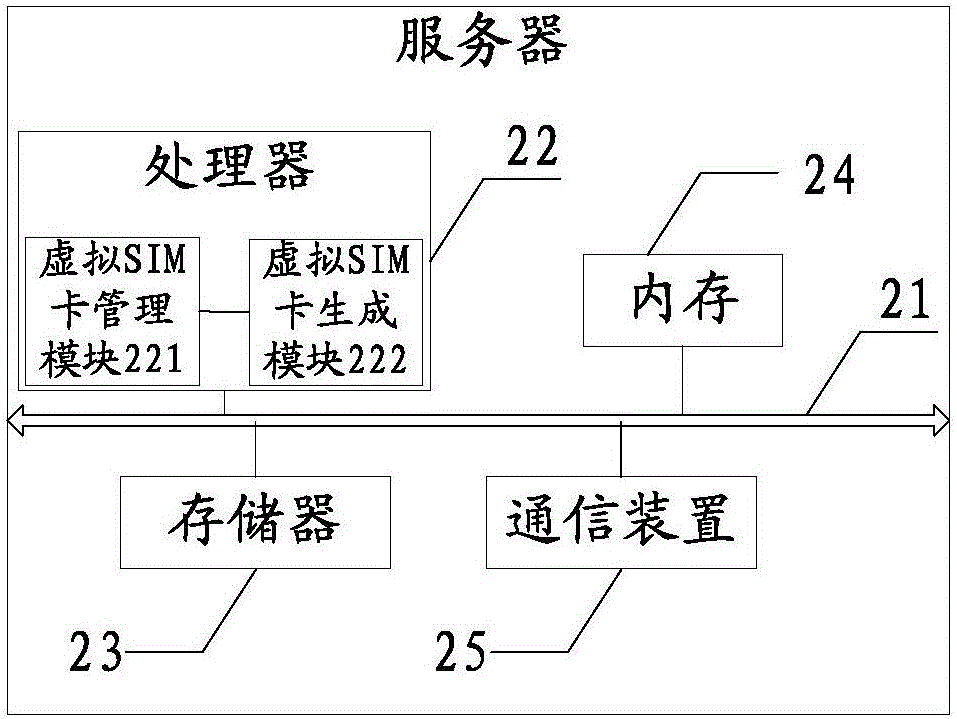
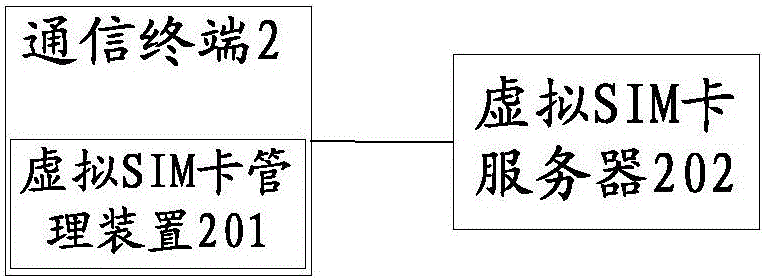
Virtual SIM (Subscriber Identity Module) card management device, communication terminal, access control method and management method
ActiveCN105848134AImprove securityAvoid illegal acquisitionSecurity arrangementNetwork data managementCDMA Subscriber Identity ModuleSubscriber identity module
The invention discloses a virtual SIM (Subscriber Identity Module) card management device, a communication terminal, an access control method and a management method. According to the invention, a virtual SIM card management device of the communication terminal can sends user identity authentication information of a user to a virtual SIM card server when the virtual SIM card management device applies to the virtual SIM card server for a virtual SIM card, and the virtual SIM card server can use the user identity authentication information to act as an authentication condition for accessing to the virtual SIM card when generating the virtual SIM card, integrates the user identity authentication information on the generated virtual SIM card and sends the virtual SIM card to the virtual SIM card management device. The virtual SIM card management device detects that access is initiated for the virtual SIM card, and carries out identity authentication on a user initiating the access at present according to the user identity authentication information in the virtual SIM card. The user is allowed to access to the virtual SIM card only when passing authentication. Therefore, other illegal users can be prevented from illegally acquiring data of the virtual SIM card, thereby improving the security of the virtual SIM card, and avoiding losses caused to the users and operators by leakage of the virtual SIM card data as far as possible.
Owner:NUBIA TECHNOLOGY CO LTD
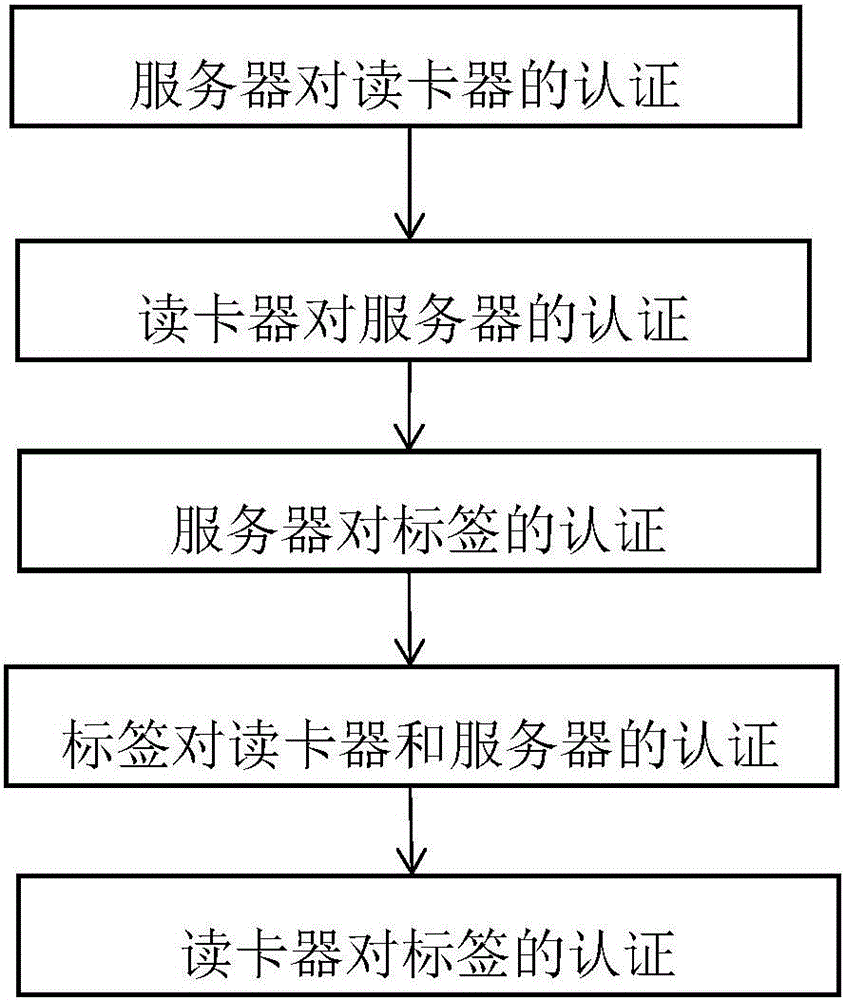
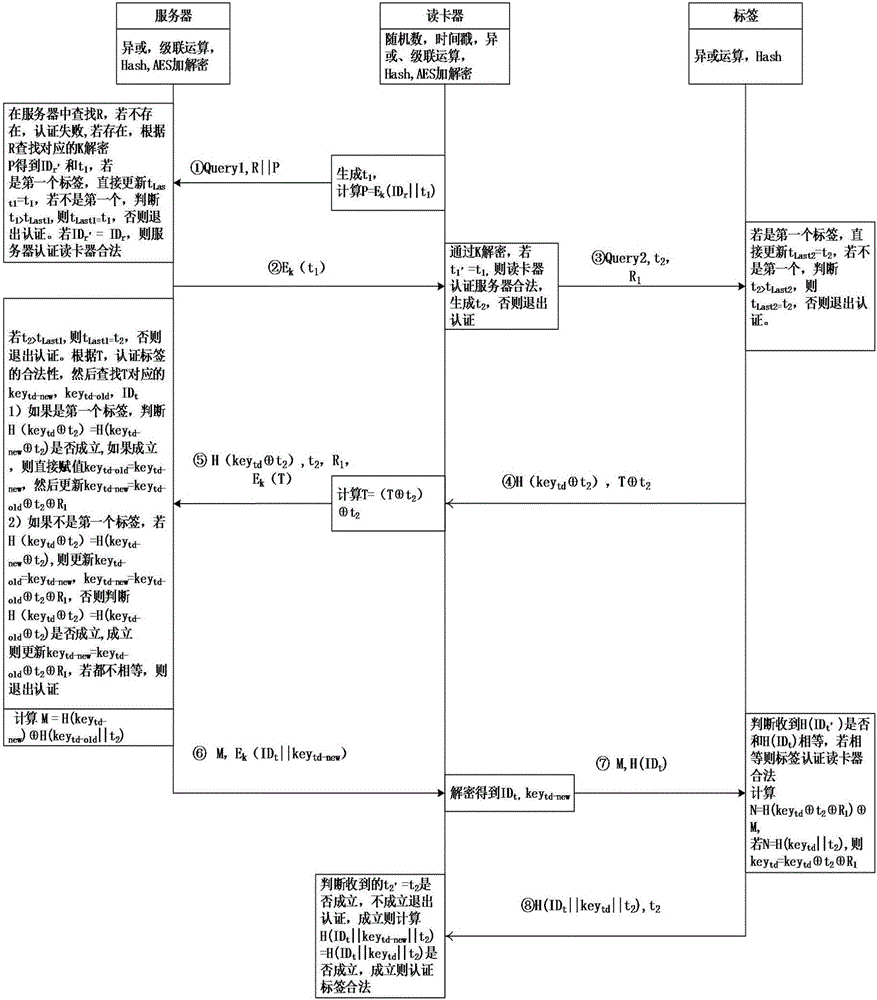
Mobile RFID system bidirectional authentication method and system
ActiveCN106712962APrevent eavesdroppingAvoid illegal acquisitionUser identity/authority verificationHash functionTimestamp
The invention discloses a mobile RFID system bidirectional authentication method, which comprises the steps of: step<1>, authentication on a card reader by means of a server; step<2>, authentication on the server by means of the card reader; step<3> authentication on a tag by means of the server; step<4>, authentication on the card reader and the server by means of the tag; and step<5>, authentication on the tag by means of the card reader. The mobile RFID system bidirectional authentication method introduces an updating mechanism of sharing a secret key by the server and the tag, introduces a timestamp, utilizes the unidirectional property of a Hash function and safety of AES encryption and decryption, realizes bidirectional security authentication among the server, the card reader and the tag, and satisfies the wireless and long-range communication between the card reader and the back-end server; and the tag adopts the simple Hash function and exclusive or calculation, and the cost of the tag side is reduced. The invention further discloses a system adopting the mobile RFID system bidirectional authentication method.
Owner:XIDIAN UNIV
Card reader and control method of card reader
ActiveUS20120002313A1Avoid illegal acquisitionIllegal acquisition can be preventedApparatus for flat record carriersConveying record carriersEngineeringElectrical and Electronics engineering
The present invention is to provide a card reader that can prevent the illegal acquisition of magnetic information recorded on a magnetic stripe, based on an output signal from a pre-head. More specifically described, in a card reader having a card insertion slot for guiding a magnetic card having a magnetic stripe to a transport passage and a pre-head arranged in the vicinity of the card insertion slot for detecting the presence of the magnetic stripe, the pre-head is equipped with a head portion having at least one pair of magnetic cores arranged to be opposite from each other having a magnetic gap between them and coils wound around a pair of the magnetic cores; and a signal different from that of the magnetic information recorded on the magnetic stripe is output from the pre-head.
Owner:SANKYO SEIKI MFG CO LTD
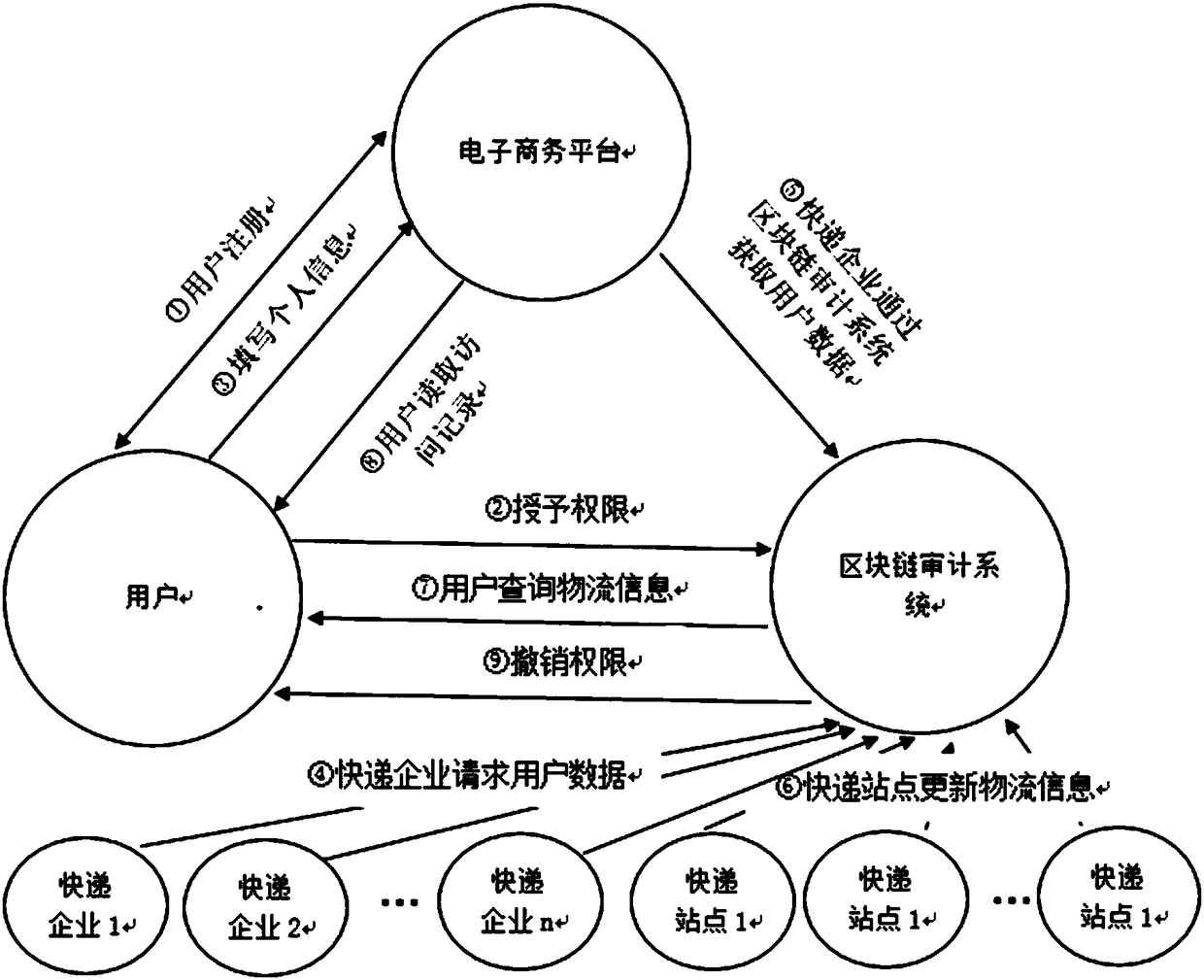
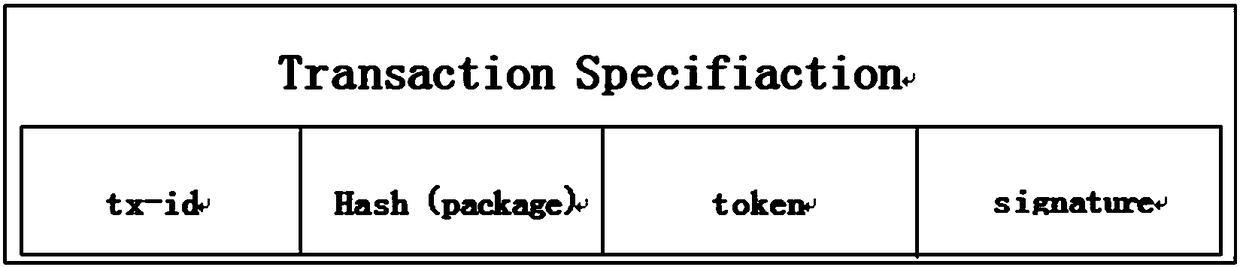
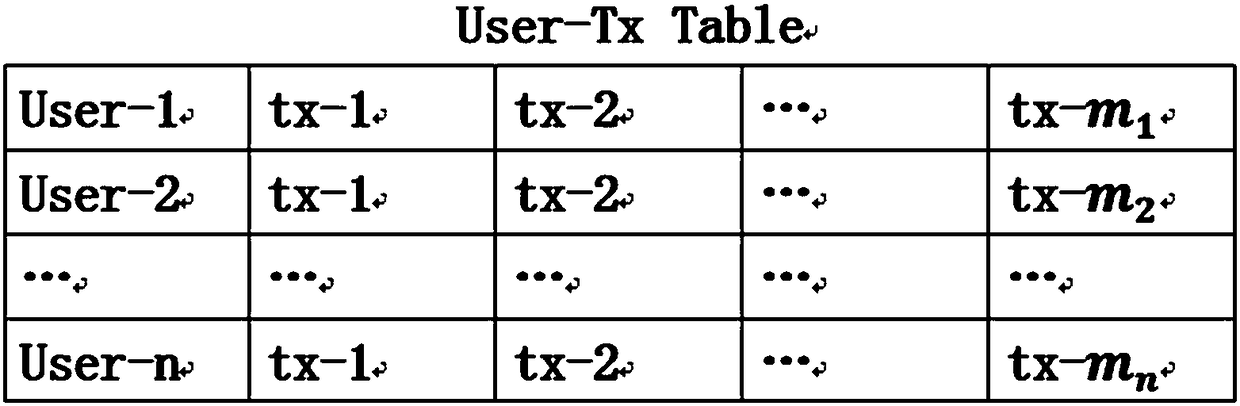
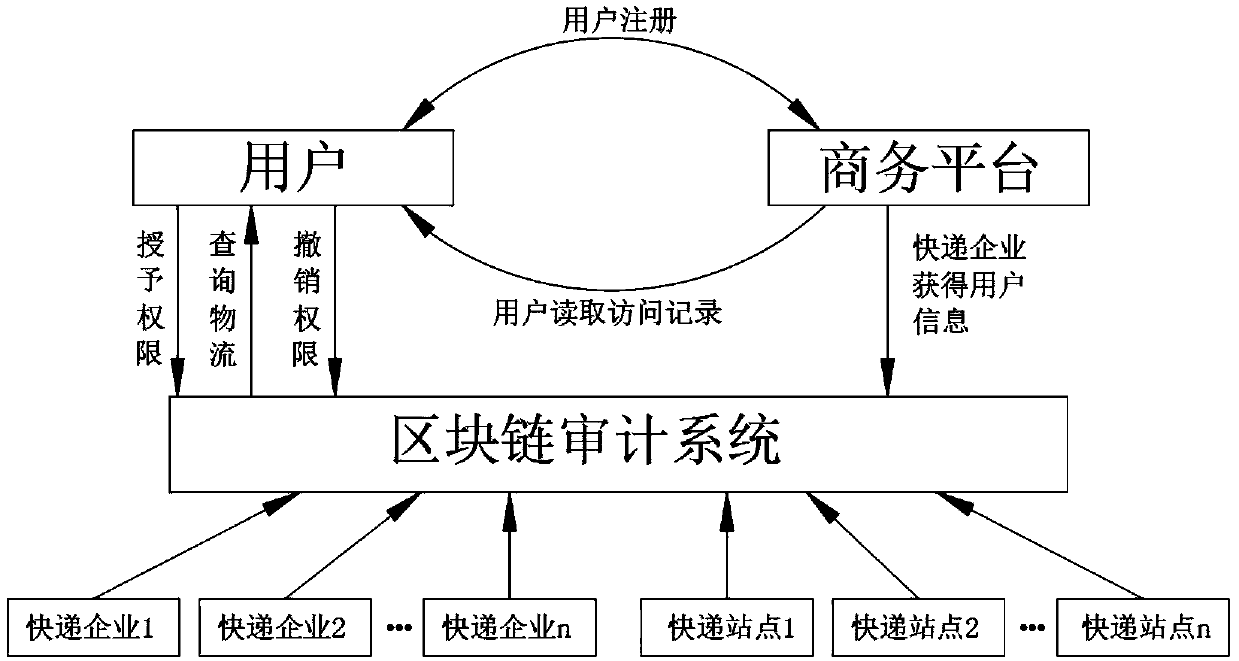
Express delivery information privacy protection system based on blockchain, and protection method thereof
ActiveCN108614974AEnhancing Operational ComplianceAvoid illegal acquisitionDigital data protectionDigital data authenticationPlaintextLogistics management
The invention discloses an express delivery information privacy protection system based on a blockchain, and a protection method thereof. The method records all operational motions of an express delivery enterprise for user data through a blockchain auditing platform, the operation compliance of the express delivery enterprise is enhanced, and the express delivery enterprise can be effectively prevented from illegally obtaining personal information. Meanwhile, a user can read a user data visitor record through an authorization record recorded in the blockchain, the access permission of the express delivery enterprise for the user data is revoked, and the sense of control of the user for personal data is enhanced. In addition, a ciphertext express waybill is used for replacing a plaintext express waybill, so that a possibility that the user data is leaked in each link of an express delivery business process can be lowered. An express delivery package logistics tracking scheme based on the blockchain can assist the user in checking the logistics situation of the express delivery package at any time in a blockchain system, and logistics information which can not be tampered on the blockchain can provide proof-providing information for disputes including delivery losing claims and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
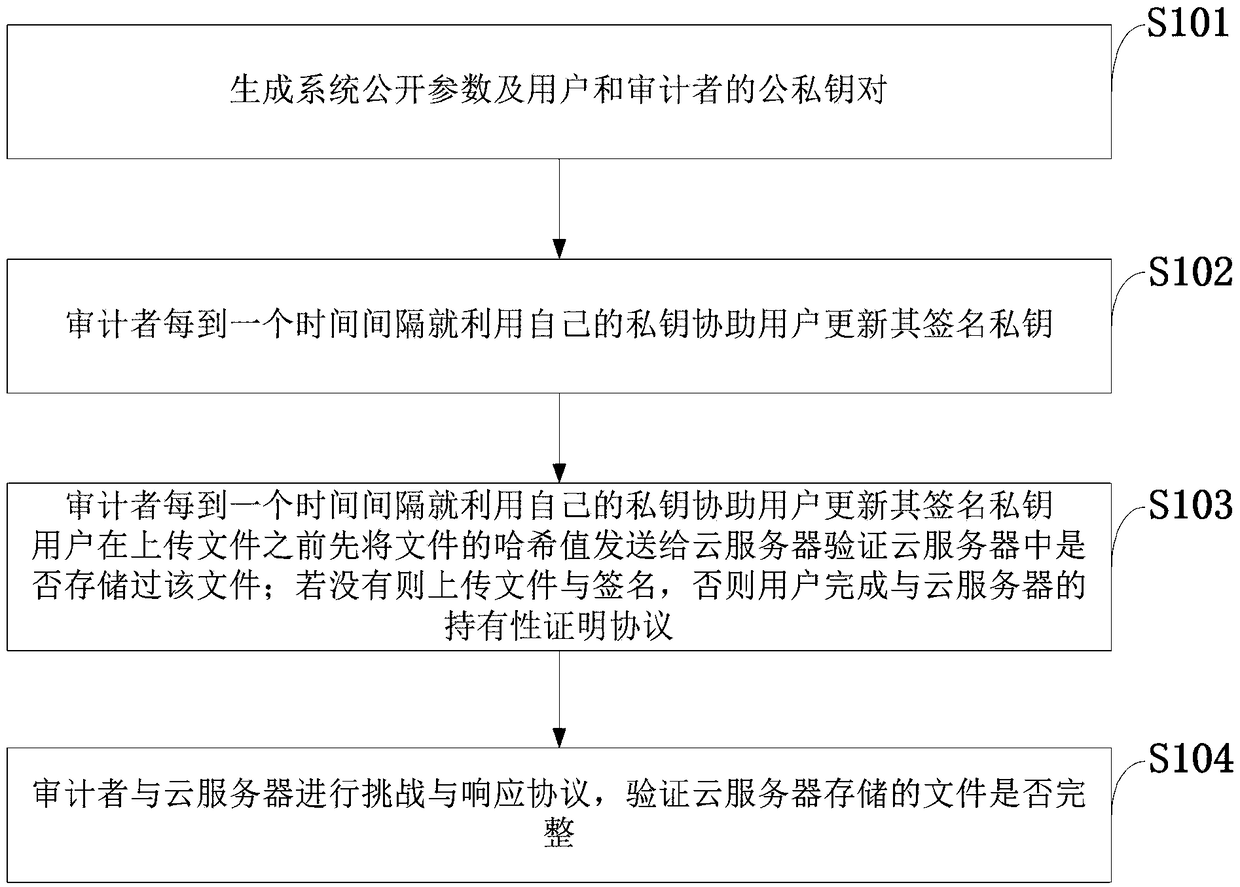
Method and system for supporting dense data deduplication and integrity verification
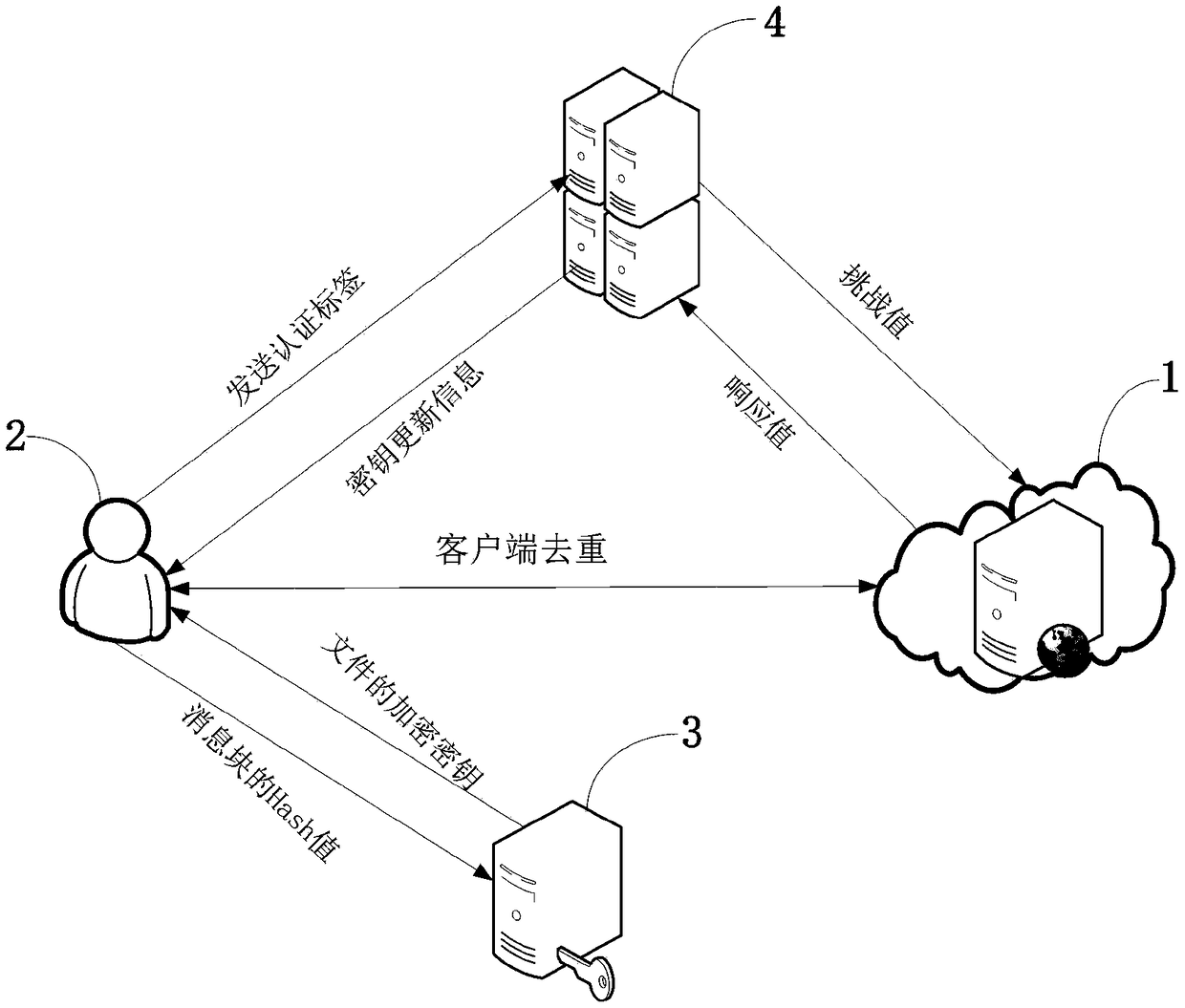
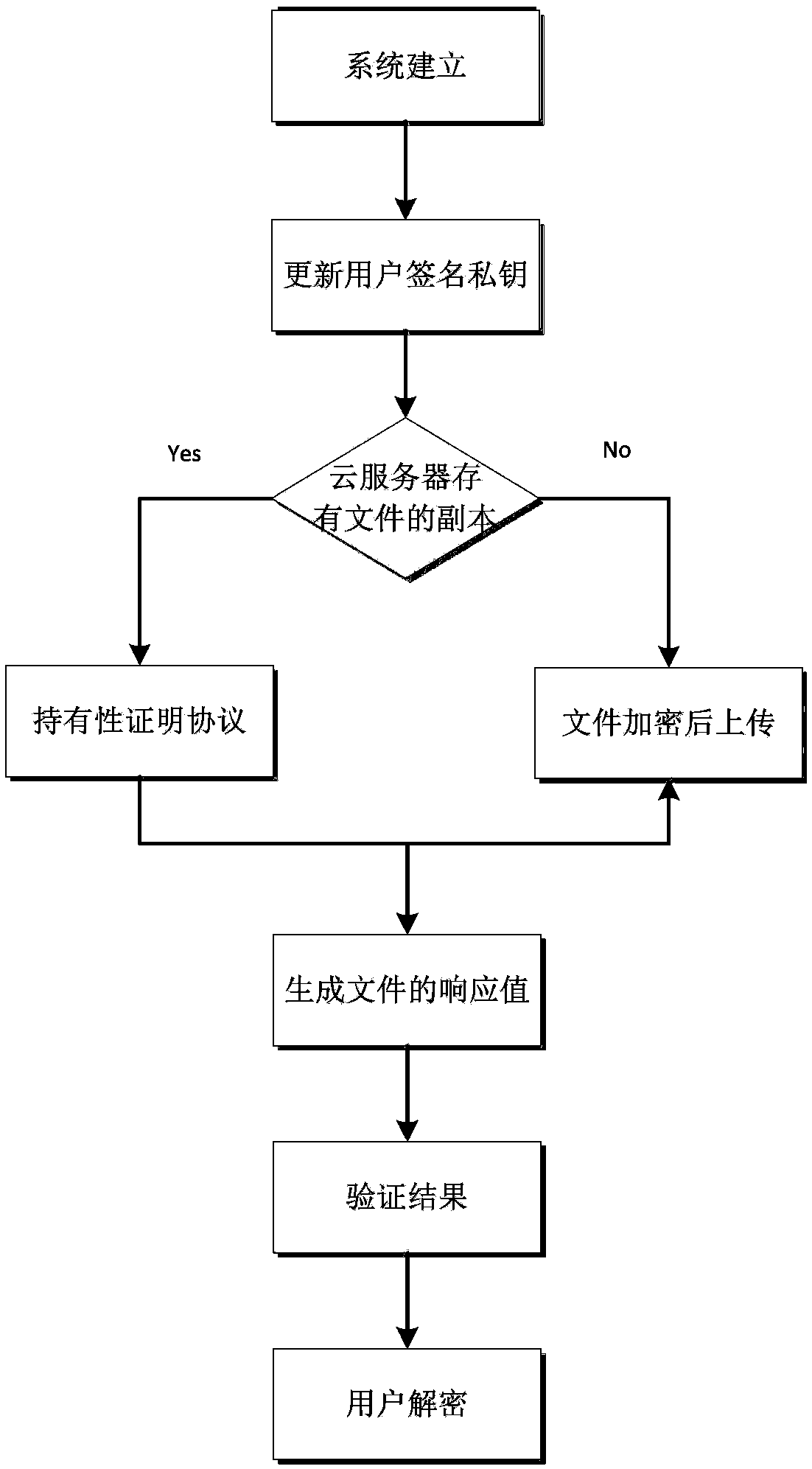
InactiveCN109286490AAchieve leakageEnsure safetyKey distribution for secure communicationUser identity/authority verificationClient-sideCurrent time
The invention belongs to a communication technology, and discloses a method and system for supporting dense data deduplication and integrity verification. In each time period, the user's signature private key is a product of two parts, the first part is an update message generated by an auditor according to his private key, and the second part is calculated by the user's private key and the current time period; the signature private key of any time period needs to be generated jointly by the user and the auditor; and in the data deduplication, the client deduplication of the file is implemented by using a Bloom filter. The invention utilizes the Bloom filter to implement the client deduplication of the file, and does not need to perform secondary uploading when the cloud server has alreadystored the same file, and prevents the malicious user from illegally obtaining the file through the fake certificate value while the malicious user does not possess the file. During the challenge andresponse process, the cloud server picks up a part of the message block of the file for verification, and the auditor cannot obtain the file through the response value sent by the cloud server.
Owner:XIDIAN UNIV
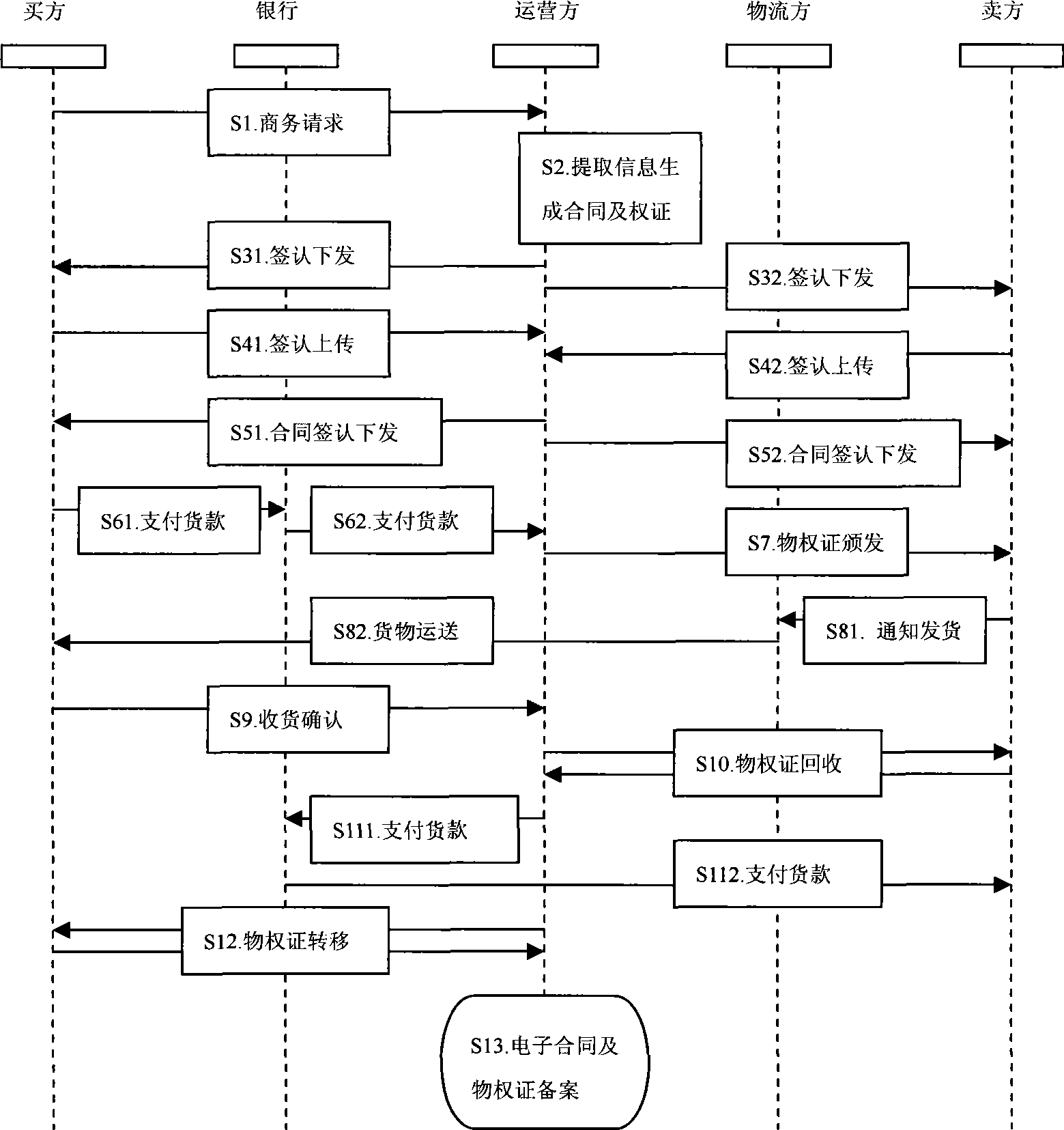
Electronic contract operation system based on digital property right certificate
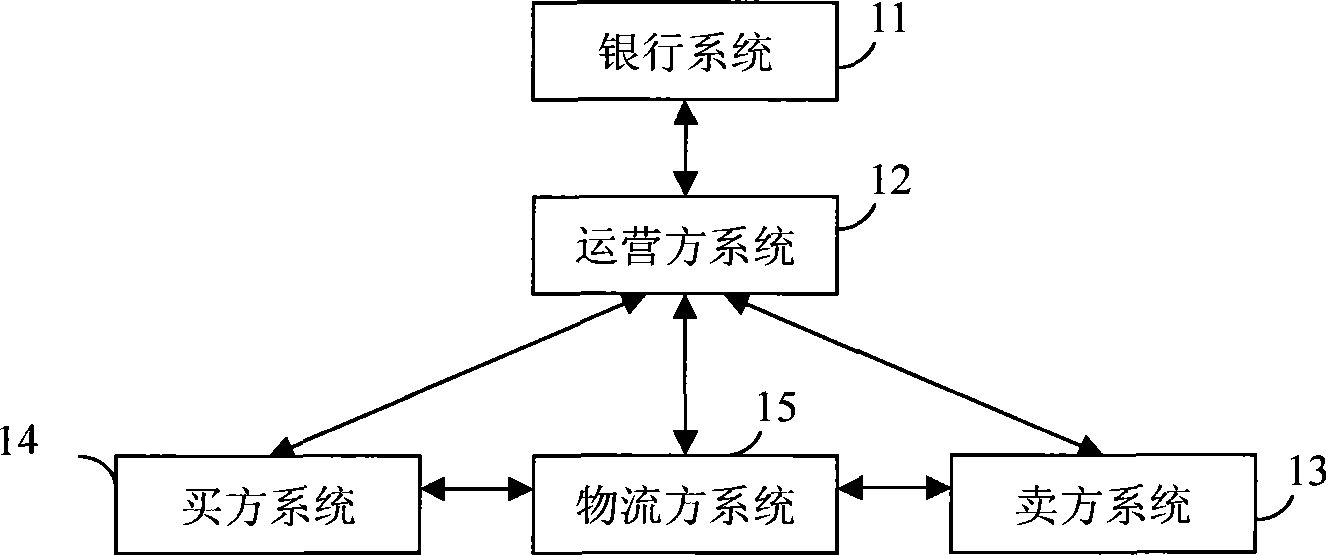
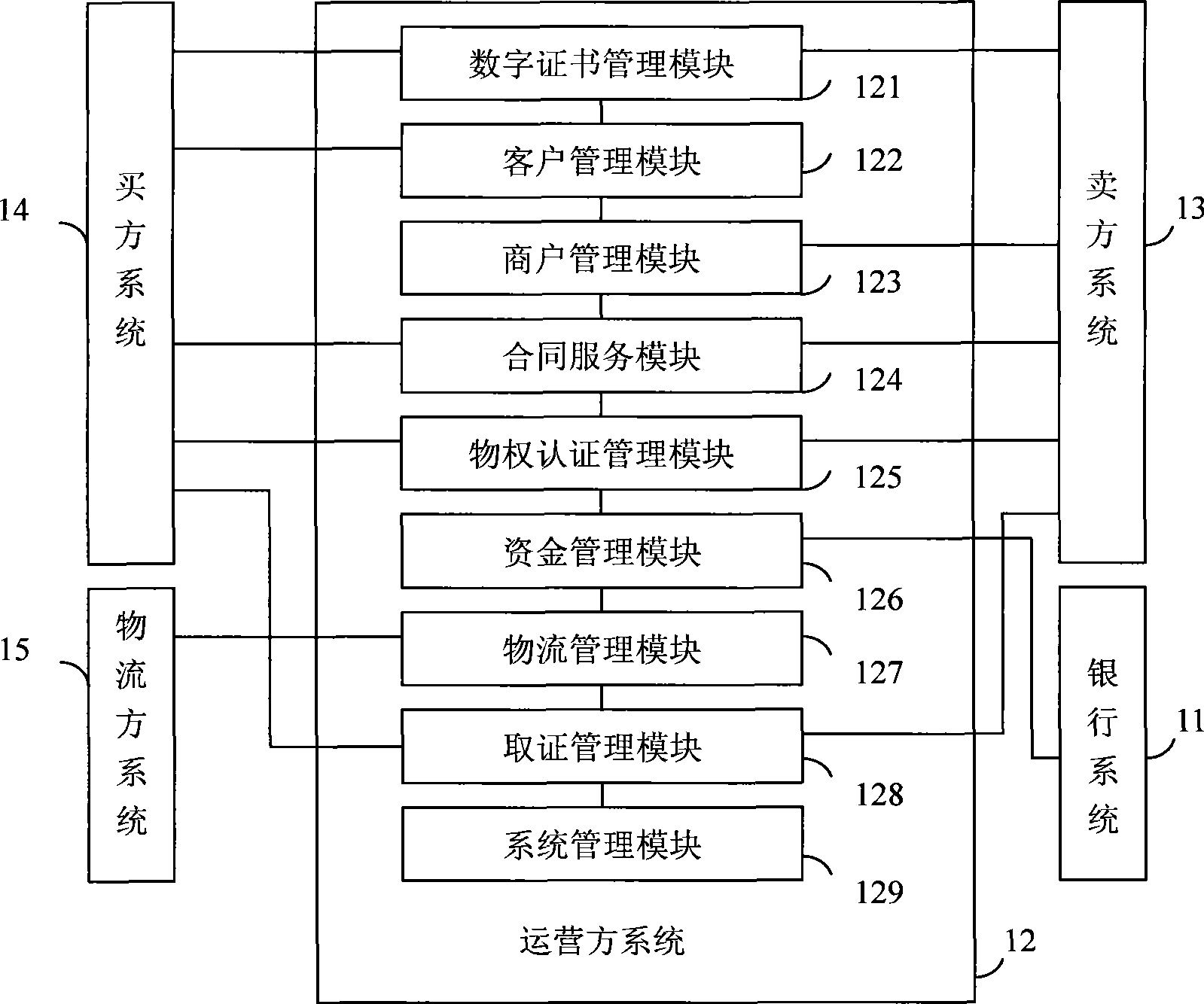
InactiveCN101510288AClear attributionMitigating the Defects of Judicial Evidence CollectionCommerceLogistics managementElectronic contracts
The invention discloses an electronic contract operation system based on digital real right certificate, which is characterized by consisting of a bank system used in money management, an operator system which carries out acknowledgement, management and supervision to an electronic contract, a buyer system which serves as the subject and the sponsor of the electronic contract, a logistics party system which provides goods delivery and a seller system which serves as the object of the electronic contract and the supplier of goods. In the operation process of the electronic contract, a digital real right certificate is introduced for the first time; and as the digital real right certificate is provided with an exclusive real right number, the change record of goods debtor-creditor relationship and the digital signatures of a buyer, a seller and an operator in the whole electronic transaction process, the debtor-creditor relationship between the buyer and the seller can be marked exclusively and the whole process of tracking and supervision on the ownership of goods real right relationship in the electronic contract transaction process is provided by the generation, issuing, revocation and transferring of the real right certificate so that the ownership of the debtor-creditor relationship in the electronic transaction is defined.
Owner:CHENGDU GUICHUANG TECH
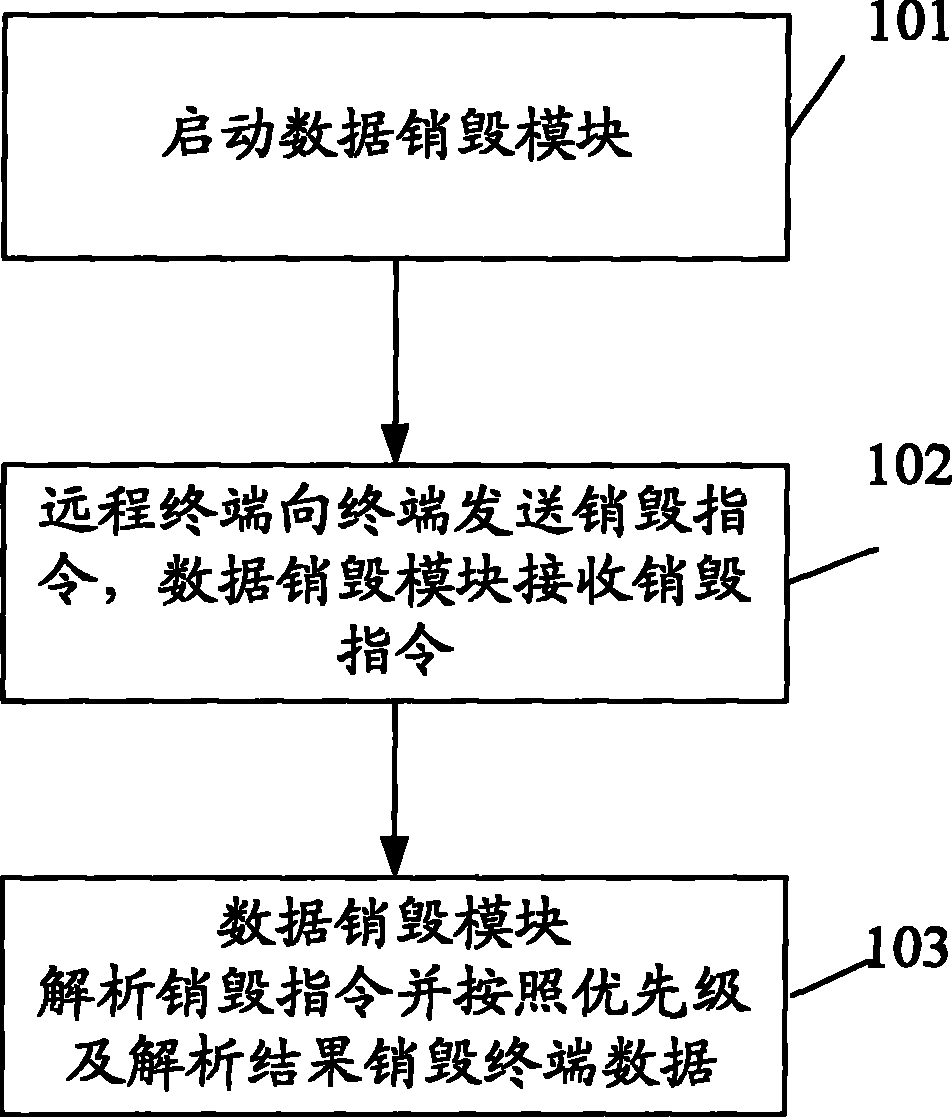
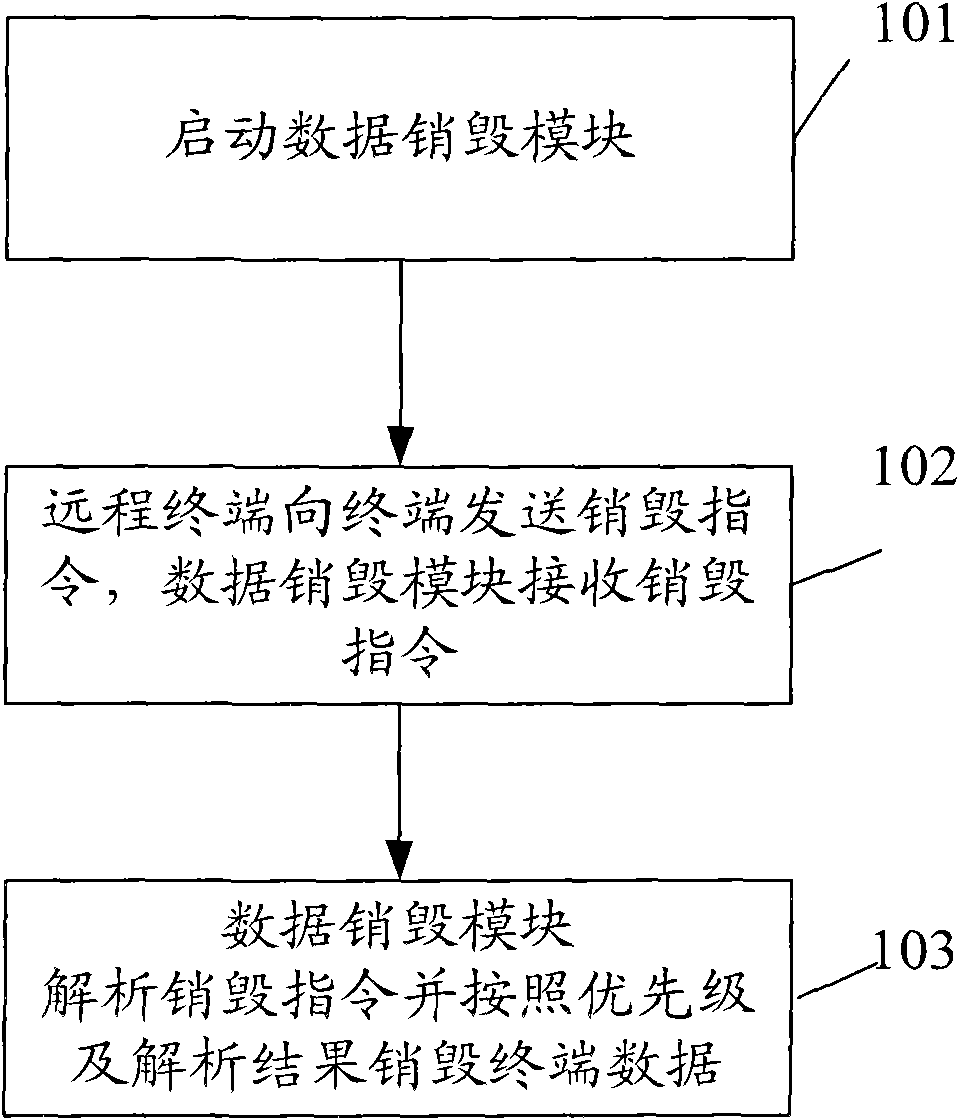
Method and device for destroying terminal data
InactiveCN101815128AEasy and quick to destroyPrevent leakageUser identity/authority verificationSubstation equipmentComputer hardware
Owner:ZTE CORP
Authorization method, device and system for user resources
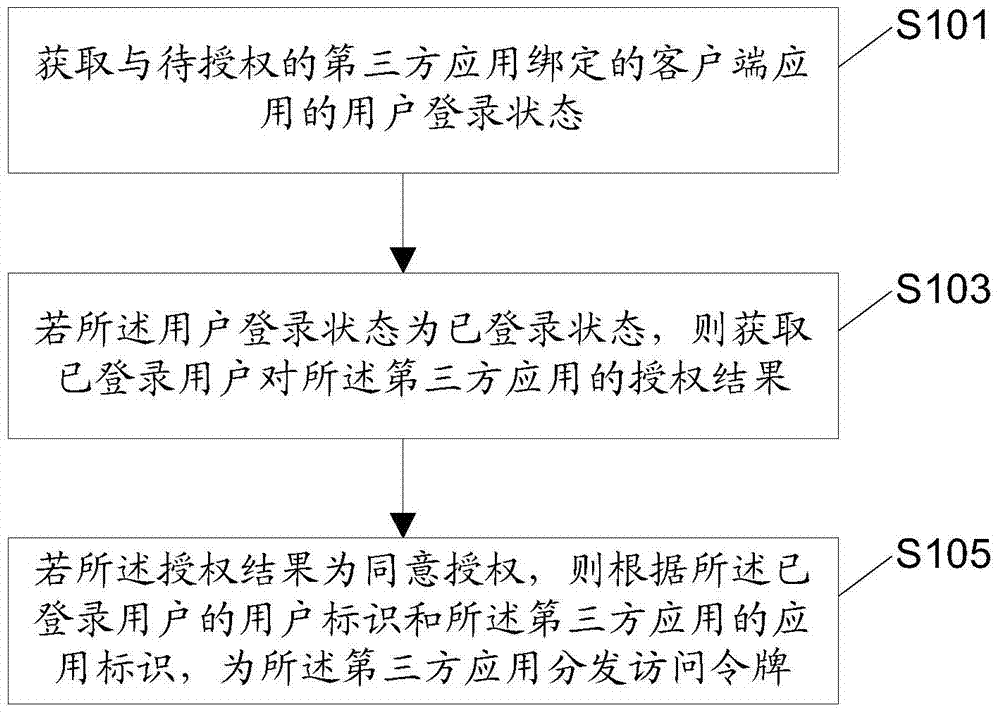
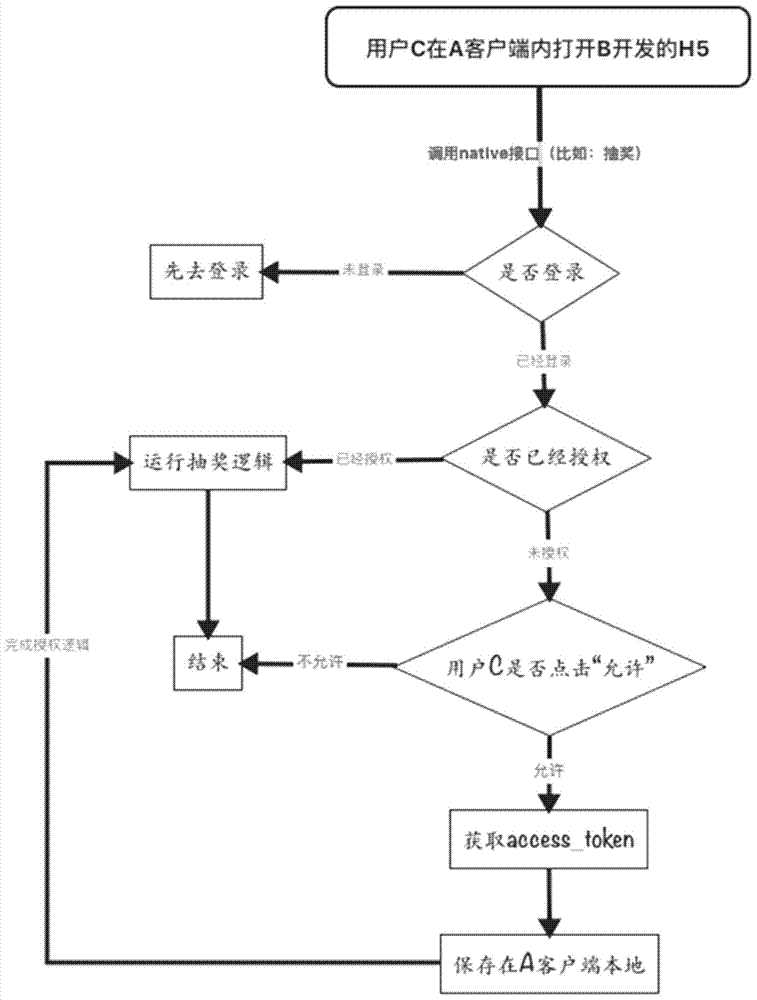
The application discloses an authorization method, device and system for user resources, a method and device for processing an authorization request, electronic equipment, and an authorization system for the user resources. The authorization method for the user resources comprises the following steps: obtaining the user login state of a client application that is bound to a third-party application to be authorized; if the user login state is a logged-in state, obtaining the authorization result of the logged-in user to the third-party application; if the authorization result is to agree authorization, distributing access tokens to the third-party application according to the user identity of the logged-in user and the application identifier of the third-party application. By adopting the method disclosed by the application, the 302 hop of the Http is not needed, the account information of the user can be prevented from being illegally obtained by phishing sites, and thus the effect of increasing the security and saving the network traffic can be achieved.
Owner:ALIBABA GRP HLDG LTD
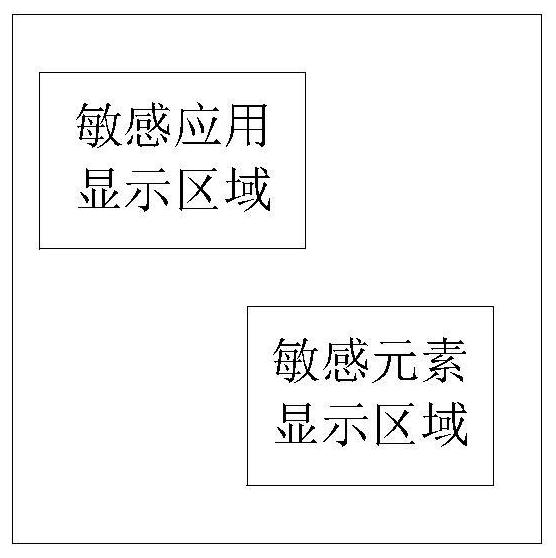
Anti-candid image processing method and device, terminal and storage medium
InactiveCN111711794AAvoid illegal acquisitionEasy to useDigital data protectionInternal/peripheral component protectionImaging processingRadiology
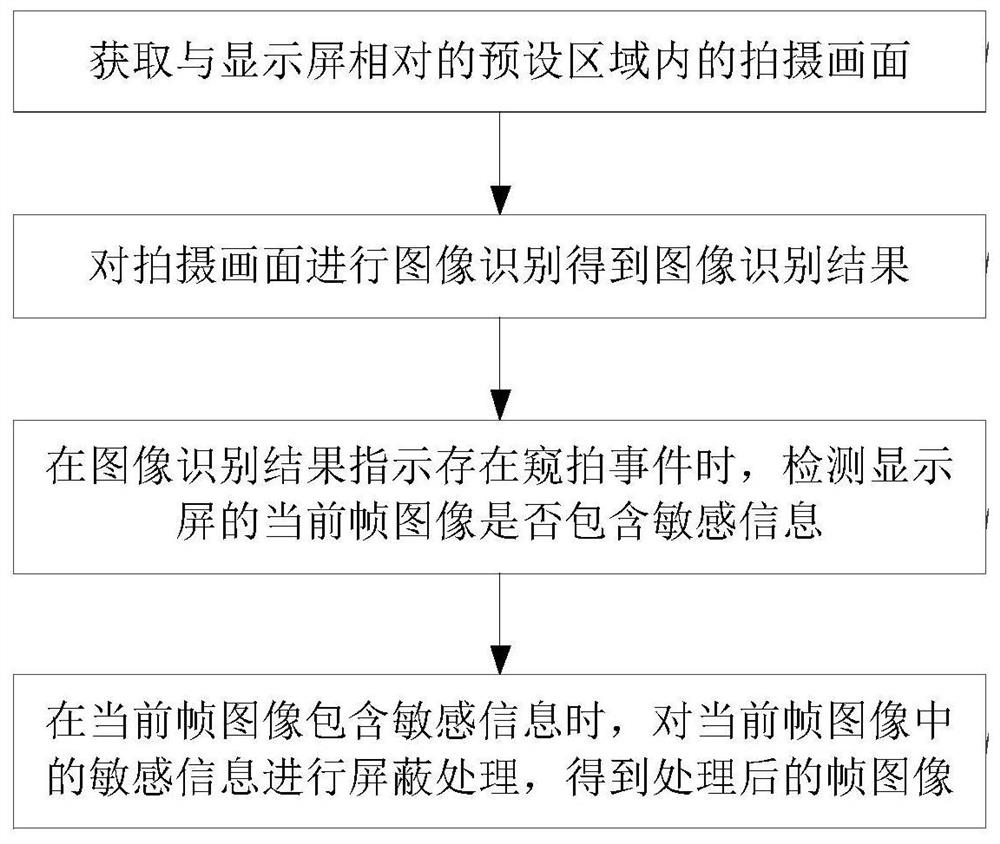
The invention discloses an anti-candid image processing method and device, a terminal and a storage medium. The method comprises the following steps: acquiring a shot image in a preset area opposite to a display screen; performing image recognition on the shot image to obtain an image recognition result; when the image recognition result indicates that a peeping and candid shooting event exists, detecting whether the current frame image of the display screen contains sensitive information or not; and when the current frame image contains the sensitive information, performing shielding processing on an area where the sensitive information in the current frame image is located to obtain a processed frame image. Only the display area of the sensitive information is shielded, and a display area of non-sensitive information is normally displayed. Important information can be effectively prevented from being illegally acquired by others, bad use feeling brought to a user due to sudden replacement of a display image or direct screen locking can be avoided, and user experience is improved.
Owner:上海辰珅科技有限公司
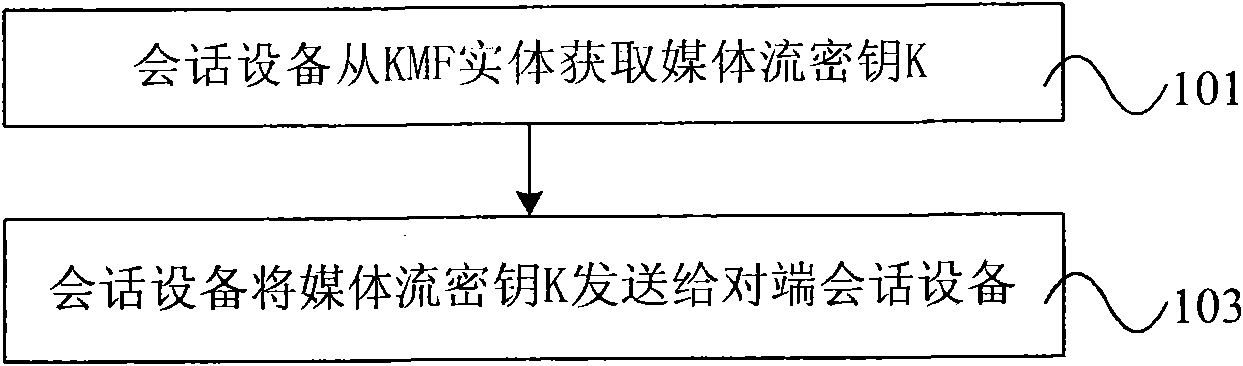
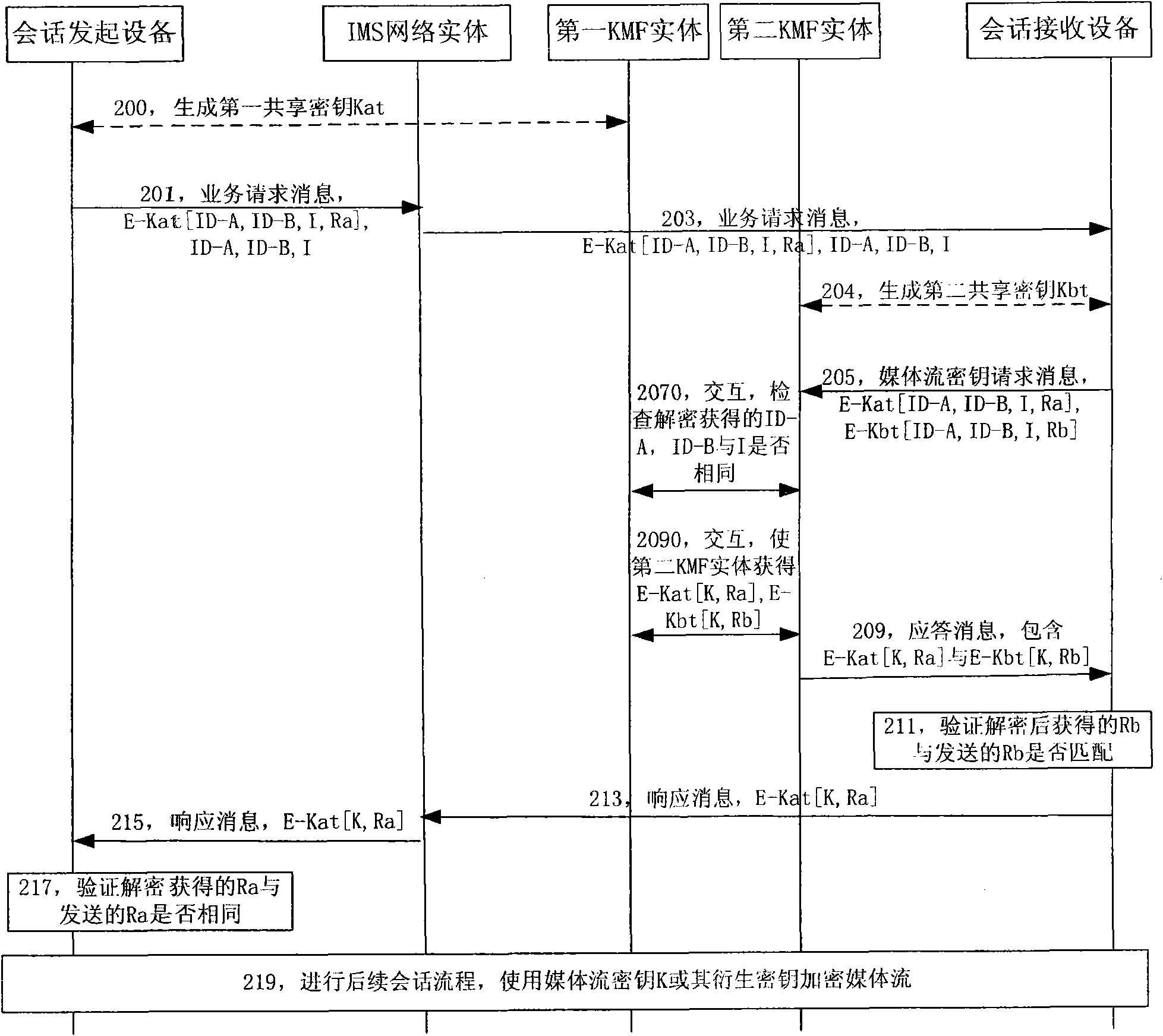
Method for acquiring media stream key, session equipment and key management function entity
The embodiment of the invention discloses a method for acquiring a media stream key, session equipment and a key management function entity, wherein the method for acquiring the media stream key comprises the following steps: using the session equipment to acquire the media stream key from a KMF entity; and using the session equipment to send the media stream key to the session equipment at the opposite end. The embodiment of the invention can increase the security of the media stream transmitted by session starting equipment and session receiving equipment in the session process.
Owner:HUAWEI TECH CO LTD
Recording medium processing apparatus
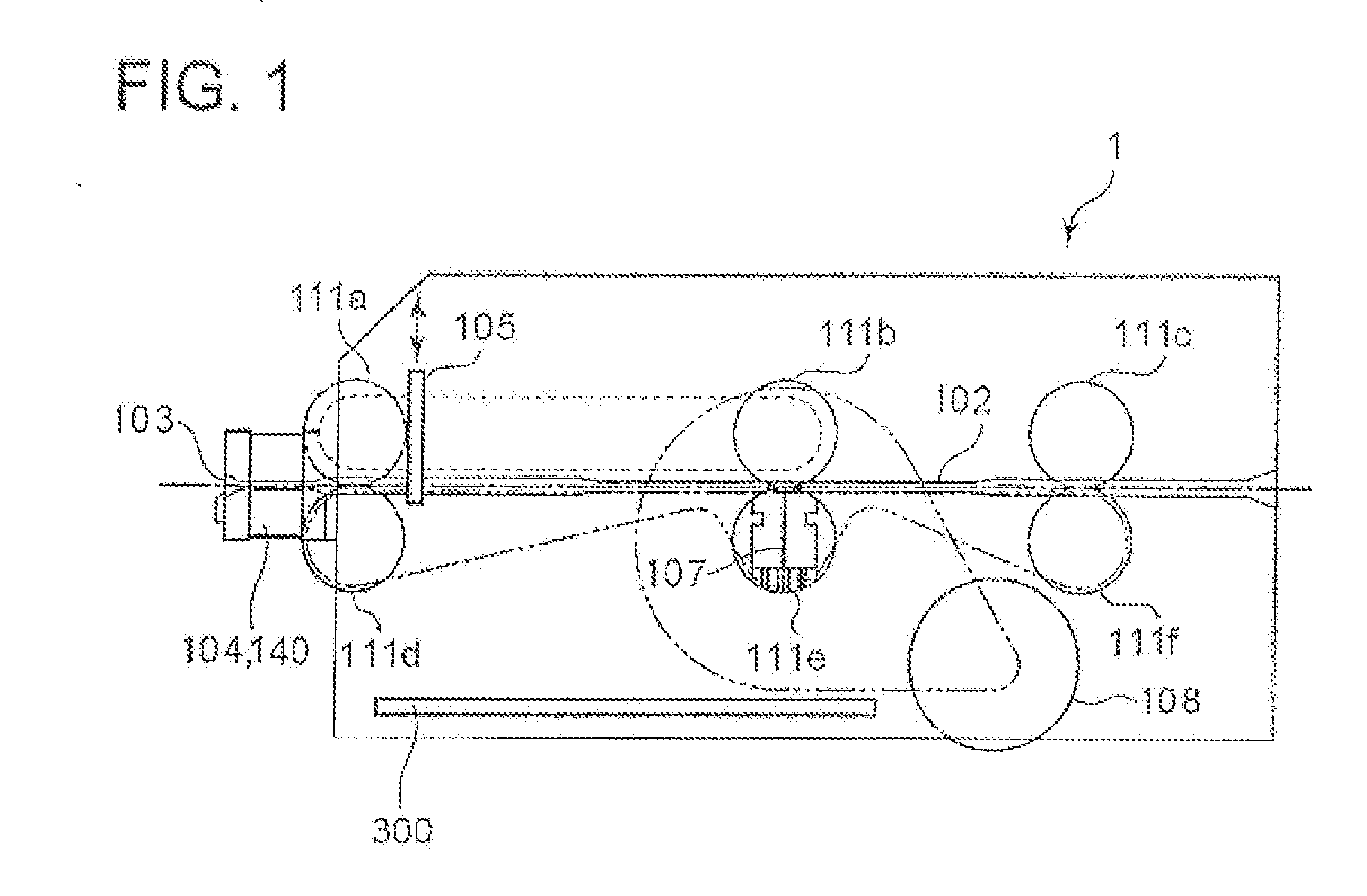
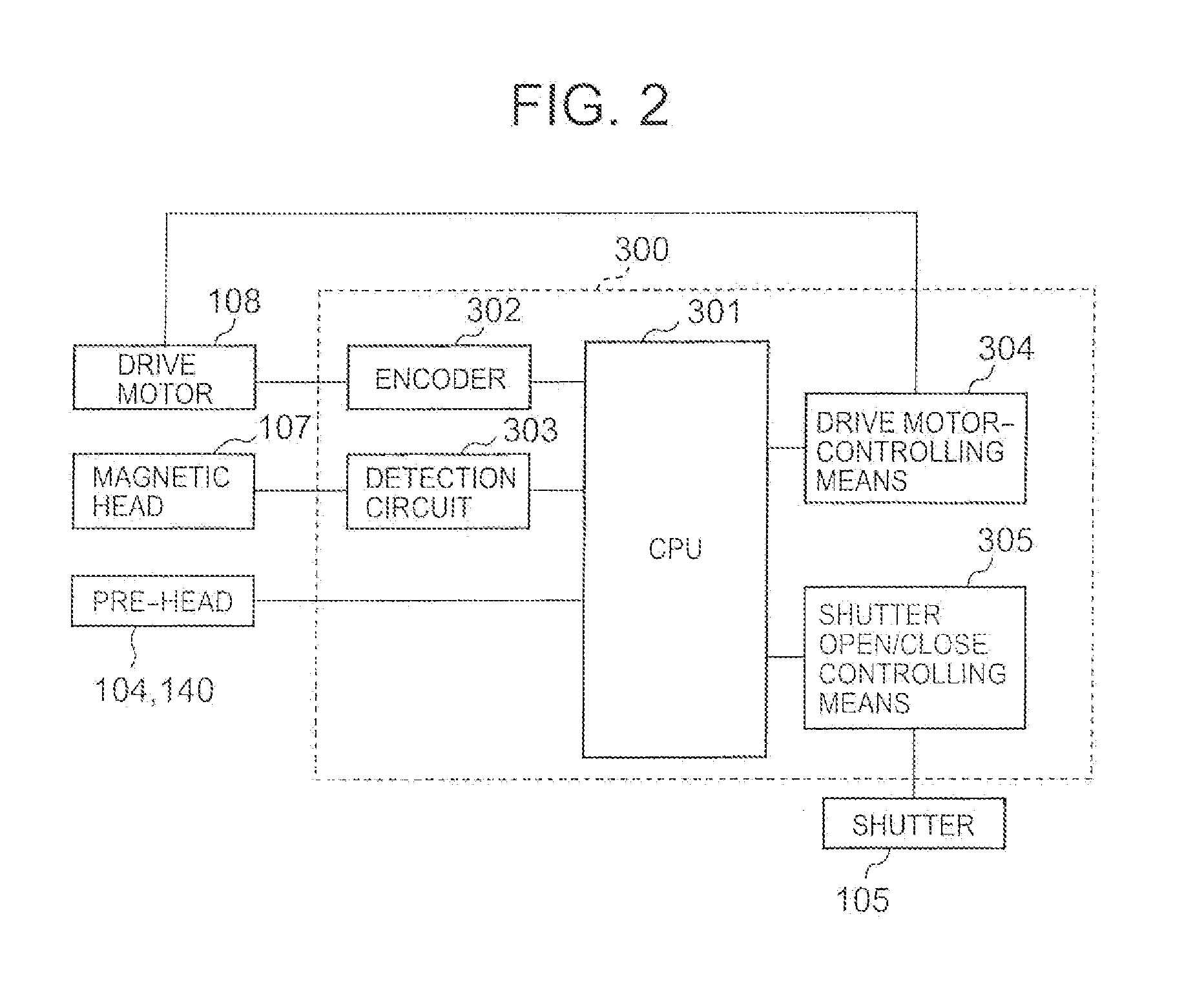
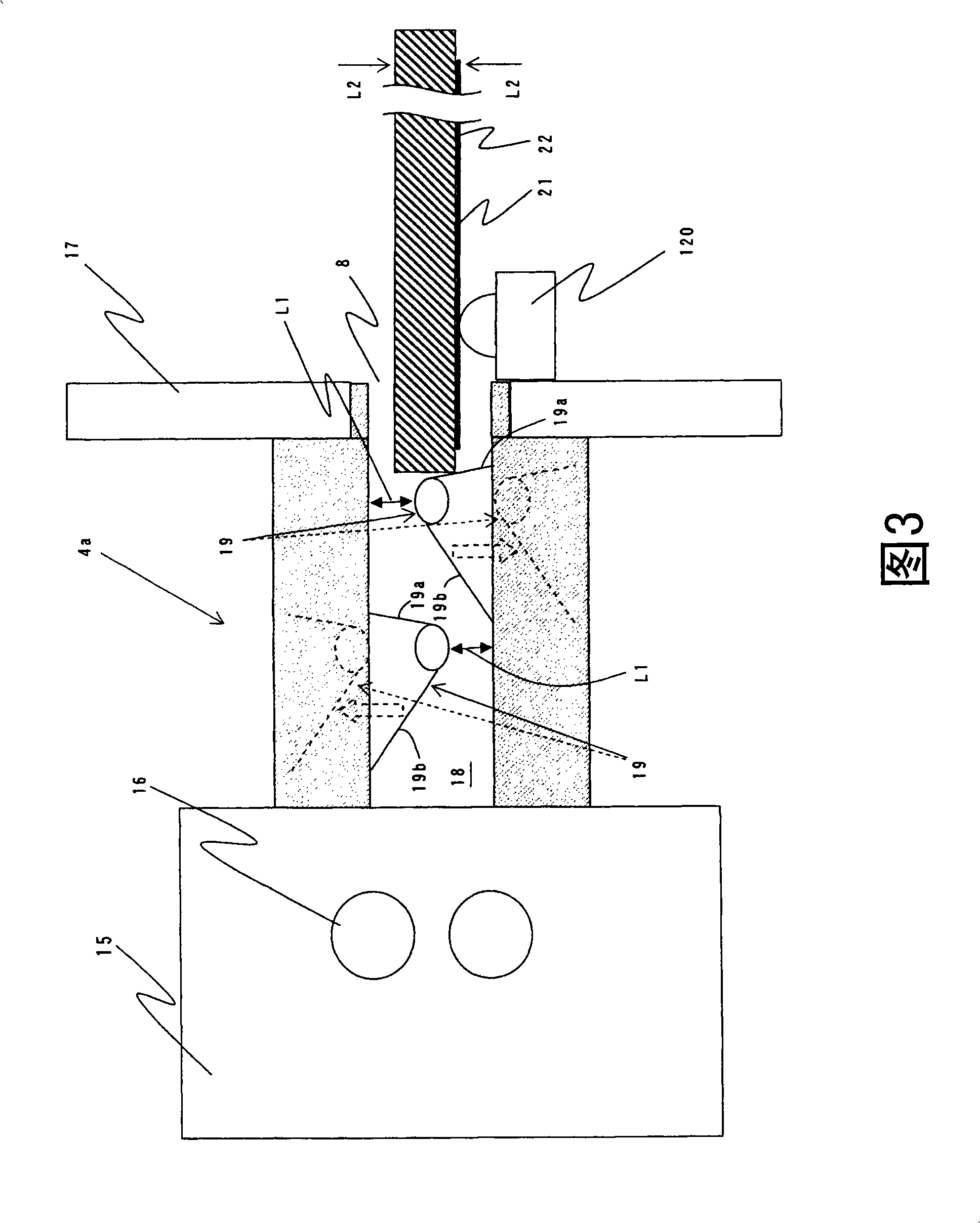
InactiveCN101329794AAvoid illegal acquisitionSkimming preventionComplete banking machinesConveying record carriersComputer hardwareRecording media
The object of the present invention is to provide a record medium processing device (4a) which can effectively prevent data based on side recording from unlawfully being obtained by simple structure when an operator inserts a card (21) without especially notice. A card mechanism (4a) for accepting the card (21) insertion and processing the inserted card (21) comprises a card inserting port (8) for accepting the card (21) and a conveying path (18) from the card inserting port (8) to the inner part of the device. The inner part of the conveying path (18) is equipped with processes (19) which is collided with the card (21) inserted from the card inserting port (8).
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
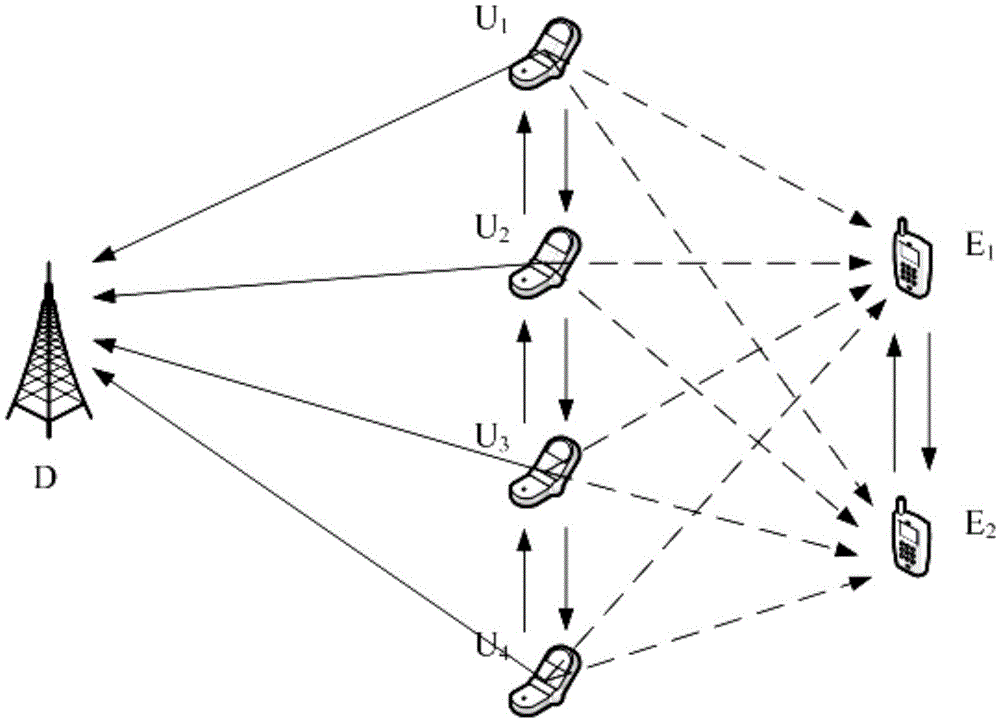
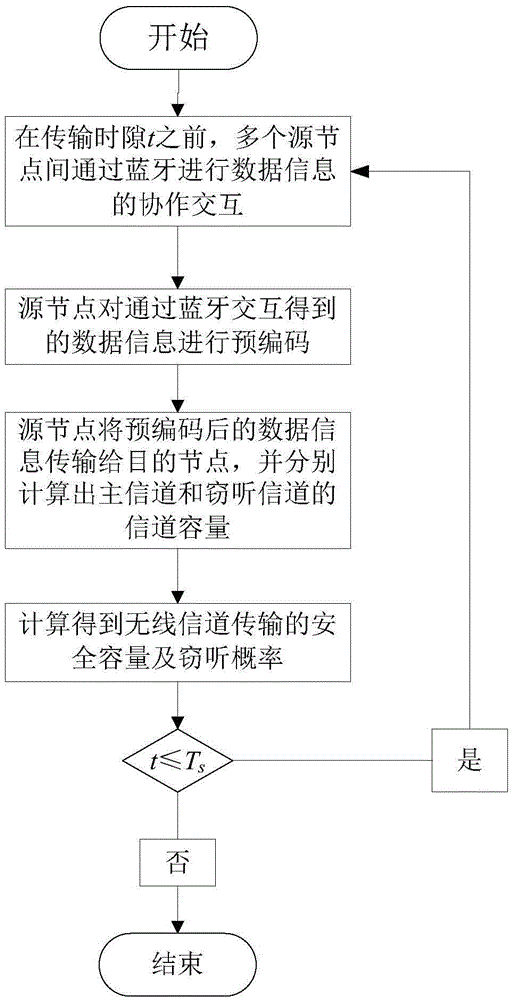
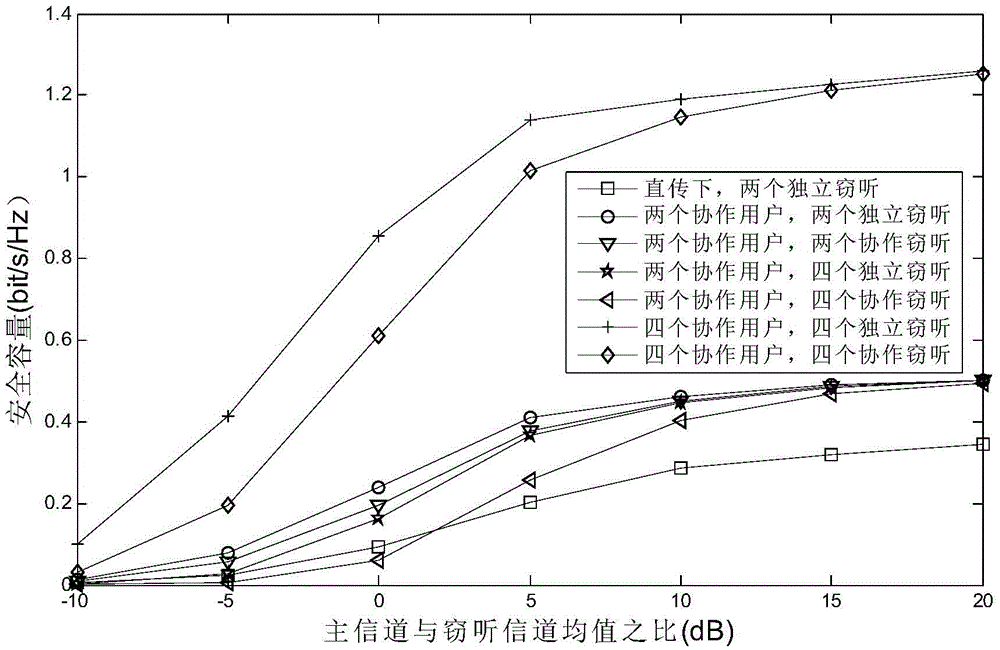
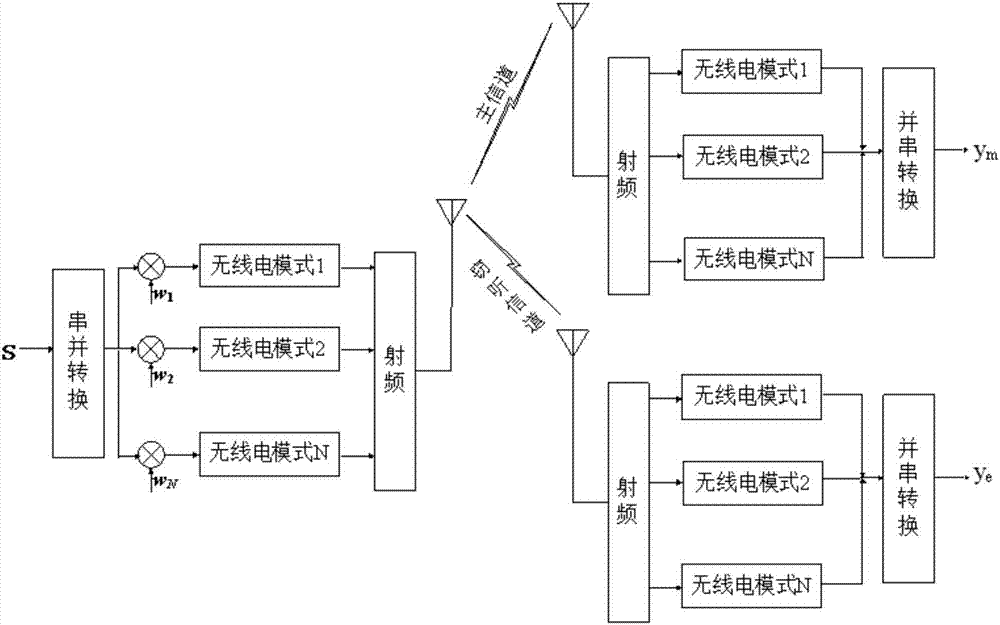
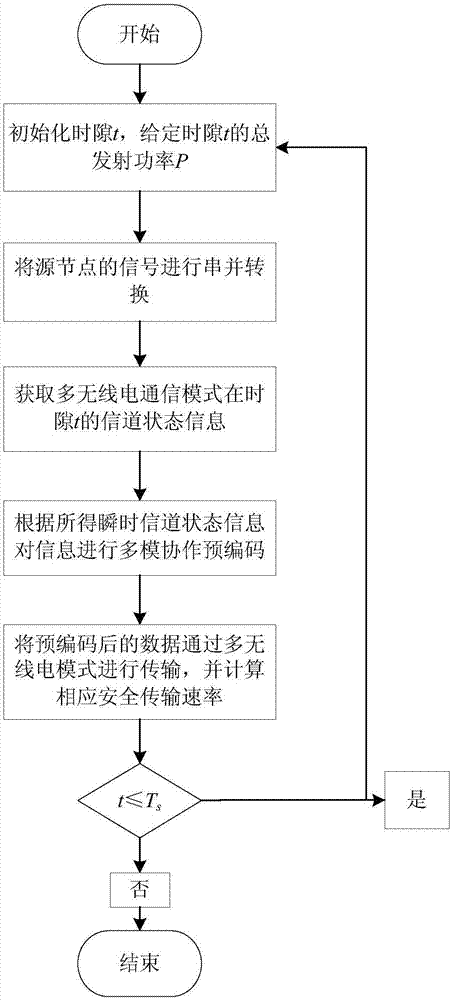
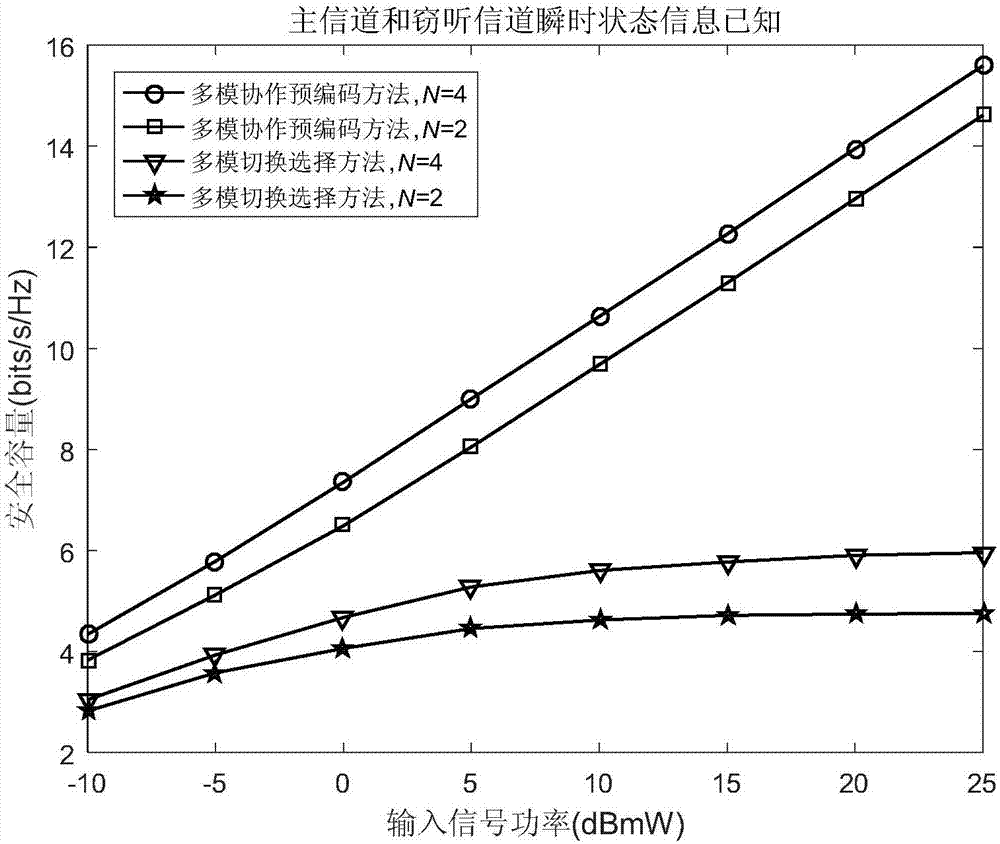
Wireless anti-eavesdropping communication method based on cooperation of multiple source nodes
ActiveCN105657700AAvoid illegal acquisitionIncrease safety capacityWireless commuication servicesTransmissionPrecodingTelecommunications
The invention discloses a wireless anti-eavesdropping communication method based on cooperation of multiple source nodes. The method includes the steps that data interaction is conducted on all the source modes in a Bluetooth mode, so that all the source nodes synchronously transmit the same data information to a target node; according to main channel state information, all the source nodes conduct precoding on the data information to be transmitted; all the source nodes synchronously transmit respective precoded information to the target node, then the target node and an eavesdropping node calculate capacity of the main channel and capacity of an eavesdropping channel respectively, and safety capacity and eavesdropping probability of wireless channel transmission are obtained further. In the mode of cooperation and precoding of the source nodes, the safety capacity of wireless transmission is remarkably improved, and the eavesdropping probability of wireless transmission is effectively reduced, which is beneficial for solving the safety problem caused by multiple eavesdropping nodes existing in an actual wireless communication scene.
Owner:NANJING UNIV OF POSTS & TELECOMM
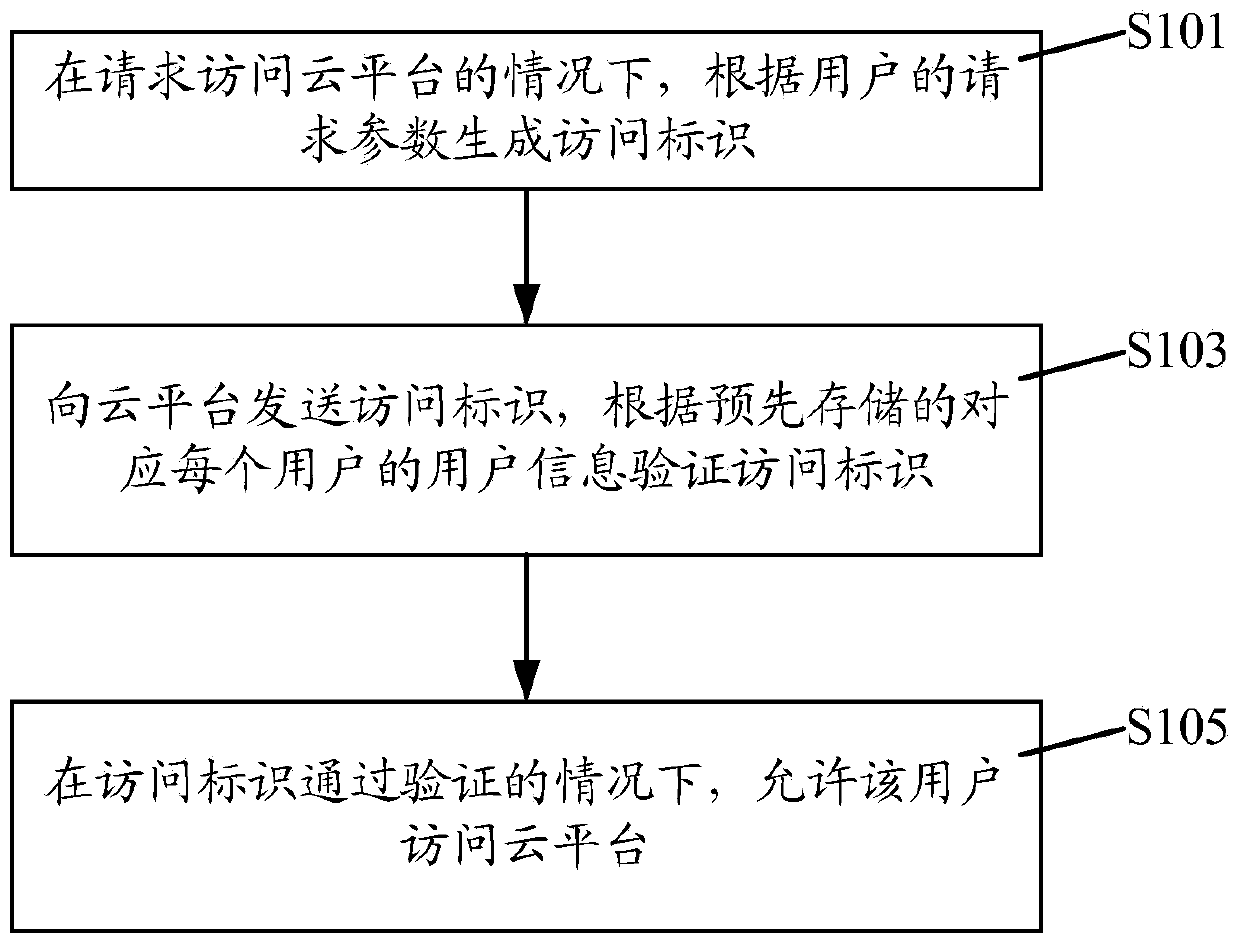
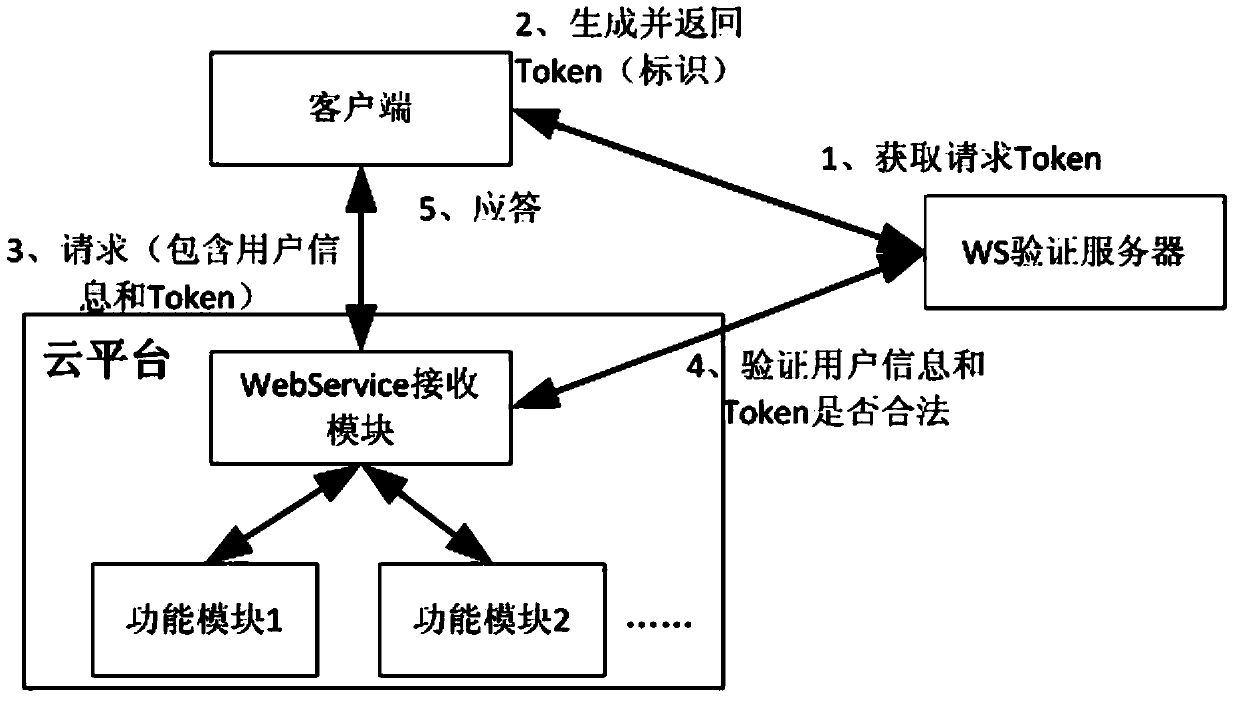
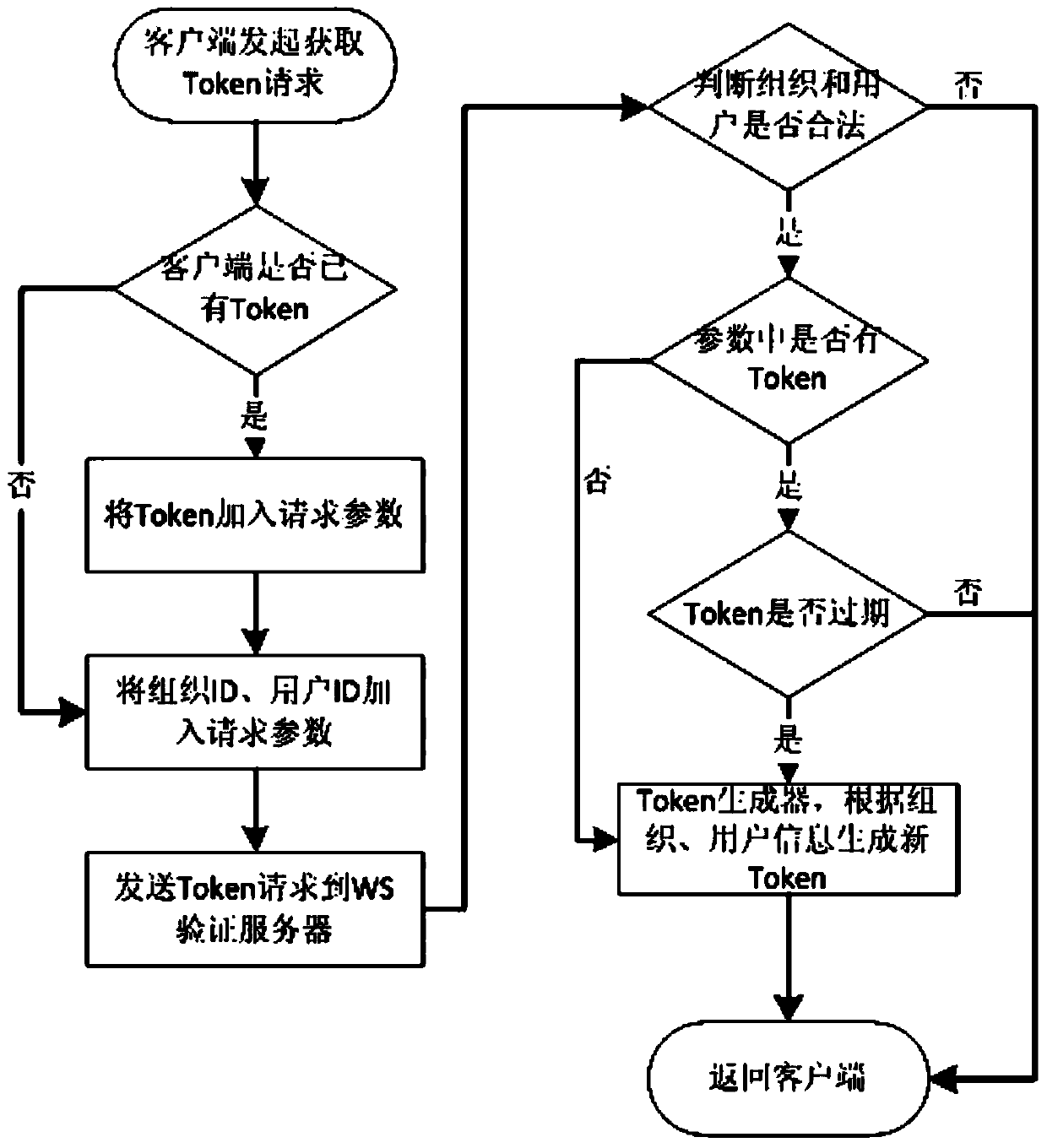
Cloud platform access method and device
ActiveCN103747076AHigh security mechanismAvoid malicious accessDigital data protectionTransmissionAccess methodUser information
The invention discloses a cloud platform access method and a cloud platform access device, wherein the cloud platform access method comprises the following steps that under the condition of requesting to access a cloud platform, access marks are generated according to the request parameters of users; the access marks are sent to the cloud platform, and are verified according to the pre-stored user information corresponding to each user; under the condition that the access marks pass the verification, the users are allowed to access the cloud platform. The cloud platform access method and the cloud platform access device have the advantages that access marks are generated according to the request parameters of the users, in addition, the access marks are verified through the pre-stored user information, and the effect of allowing the users to access the cloud platform only under the condition that the access marks pass the verification is ensured, so the safety mechanism of the cloud platform is effectively improved, the malignant access of illegal users to the cloud platform is avoided, and the resource waste of the cloud platform is reduced.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
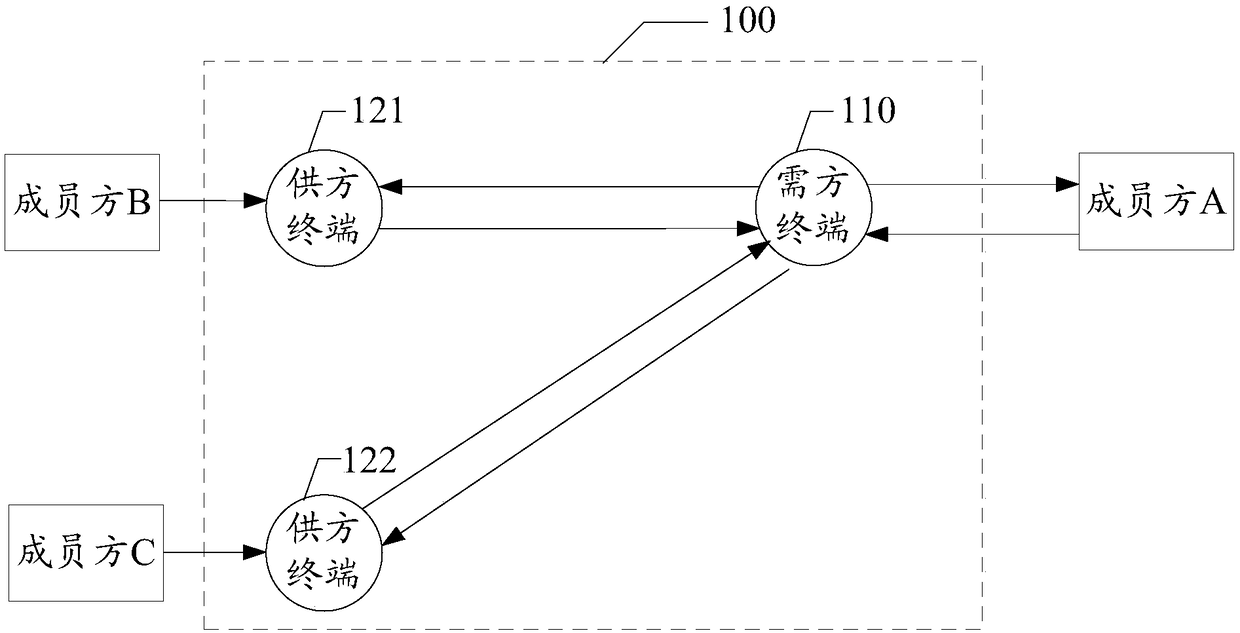
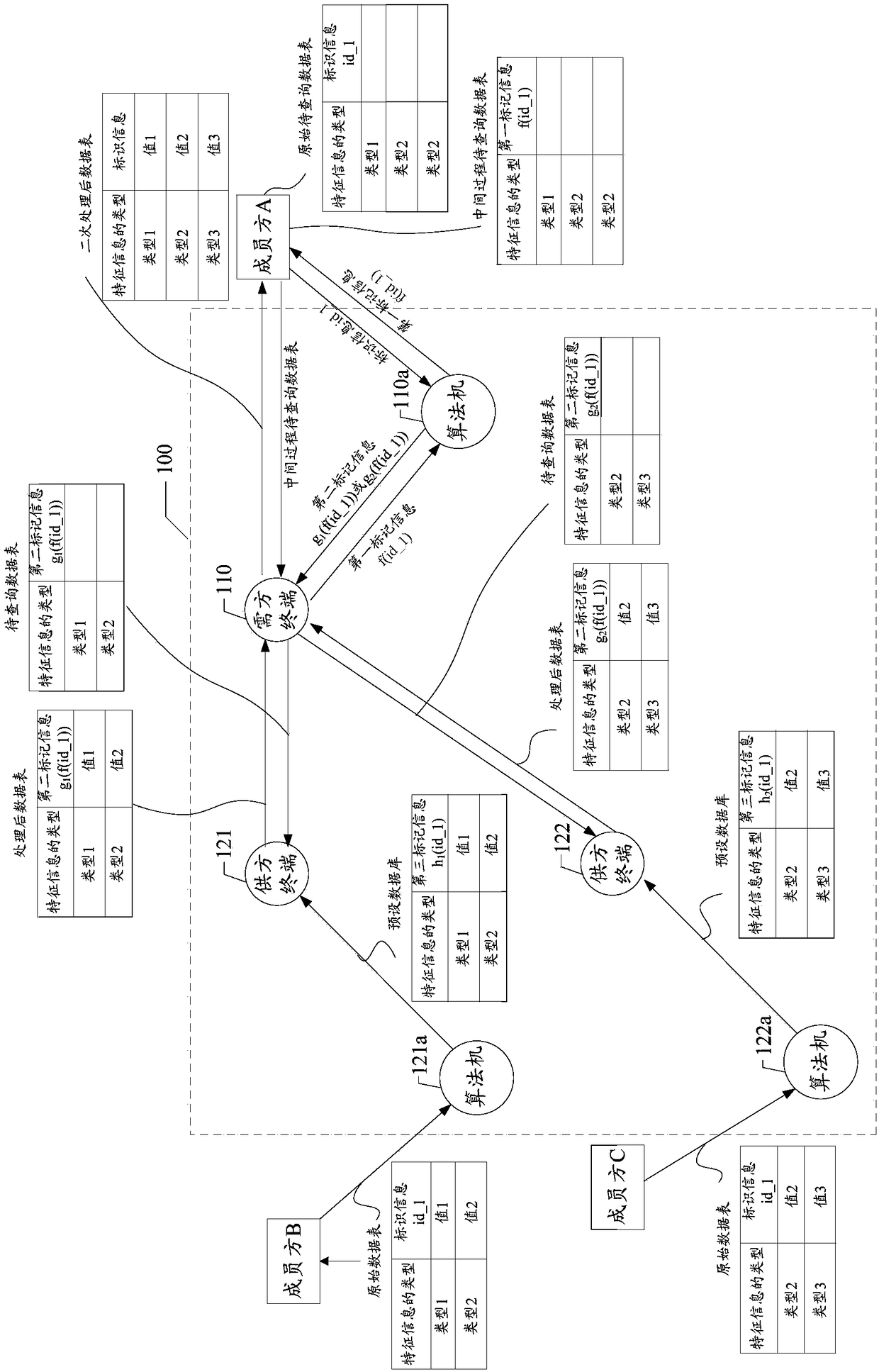
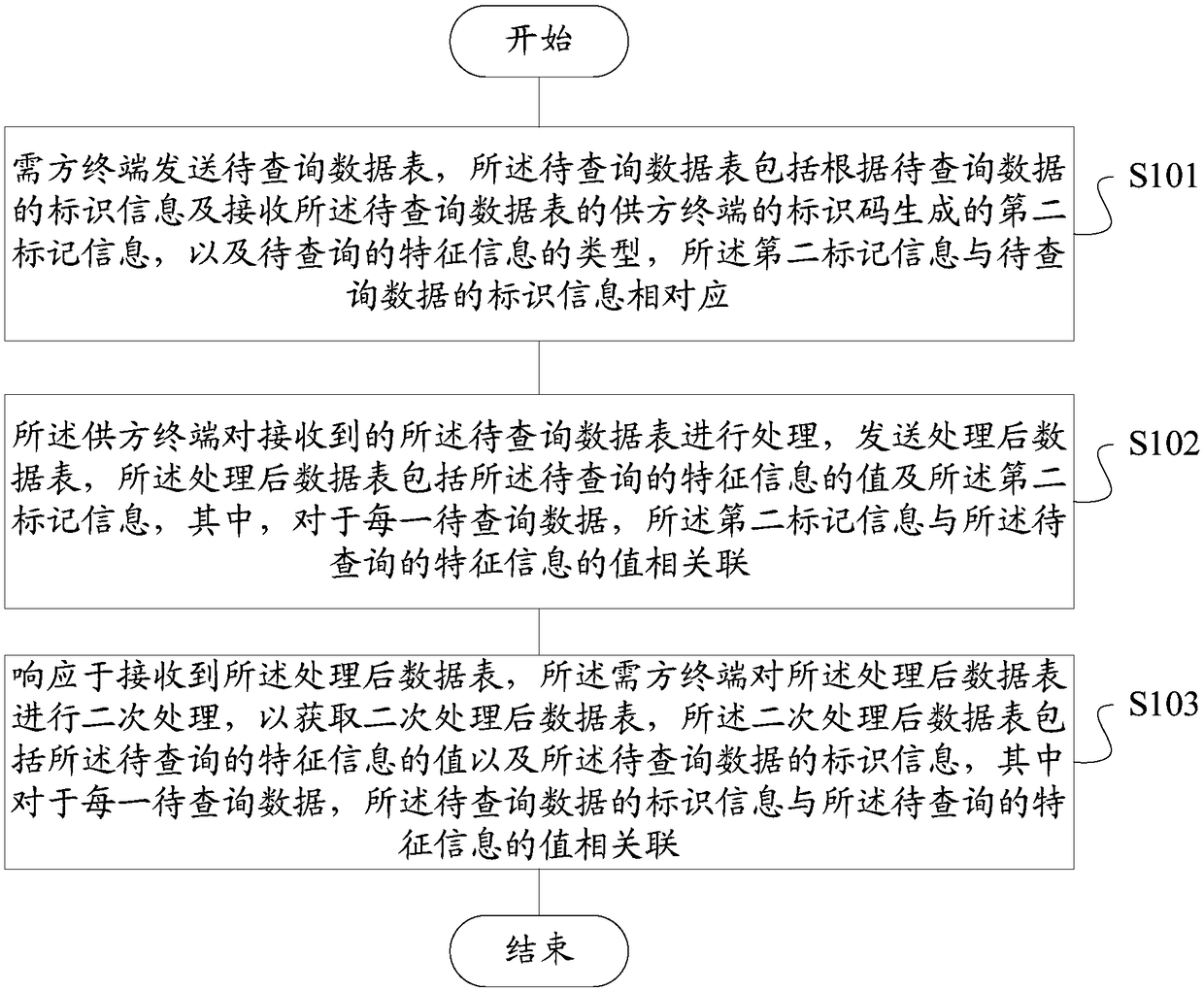
Data query system and method, storage medium and terminal
ActiveCN108268799AGuaranteed privacyProtect trade secretsDigital data protectionComputer terminalData query
The invention discloses a data query system and method, a storage medium and a terminal. The system comprises a demander terminal and a supplier terminal. The demander terminal sends a to-be-queried data table, wherein the to-be-queried data table comprises second marker information generated according to identifier information of to-be-queried data and an identifier code of the supplier terminalreceiving the to-be-queried data table, and the type of to-be-queried feature information. The supplier terminal processes the received to-be-queried data table and sends the processed data table, wherein the processed data table comprises the value of the to-be-queried feature information and the second marker information; and in response to operation of receiving the processed data table, the demander terminal performs secondary processing on the processed data table to obtain a data table subjected to secondary processing, wherein the data table subjected to the secondary processing comprises the value of the to-be-queried feature information and the identifier information of the to-be-queried data. Through the scheme provided by the invention, sensitive information can be effectively isolated during data query, so that the privacy of personal privacy information is guaranteed and the leakage risk is lowered.
Owner:上海数据发展科技有限责任公司
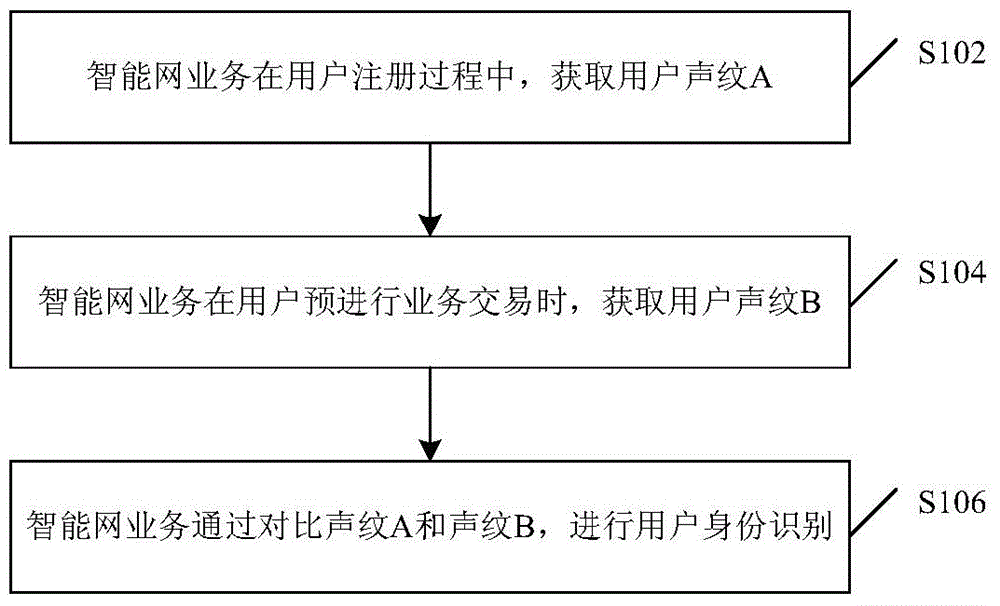
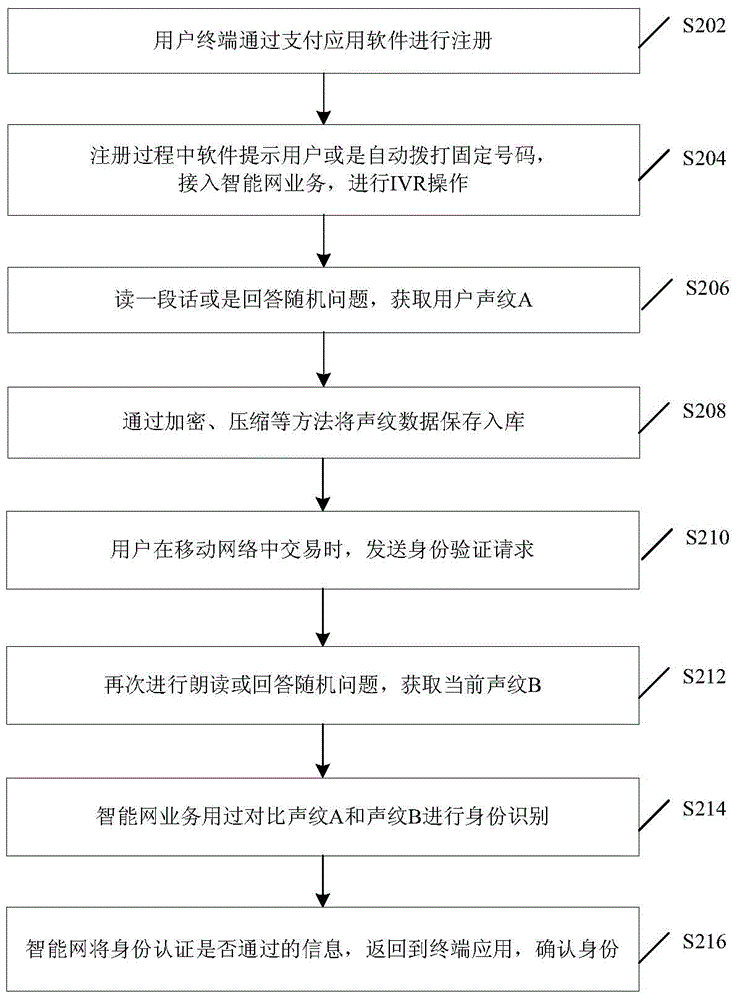
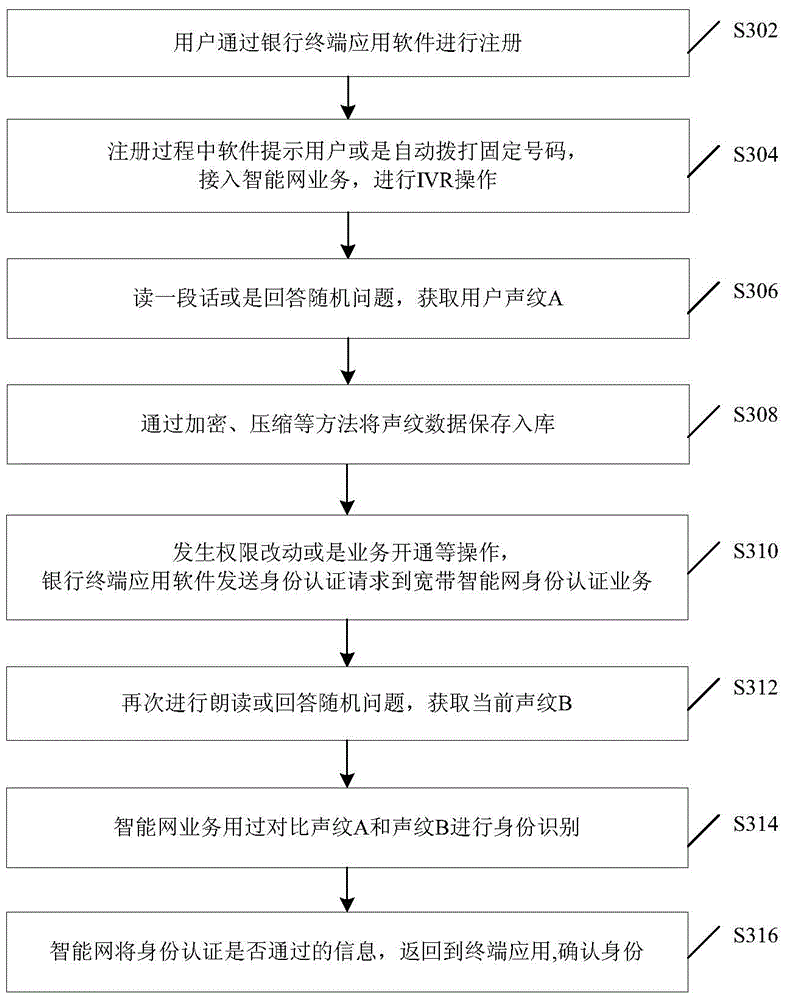
Identity identifying method and device
InactiveCN105096954AAvoid illegal acquisitionSolve problems with efficient and reliable control implementation methodsInterconnection arrangementsSpeech analysisIdentity recognitionData acquisition
Disclosed are an identity recognition method and apparatus, and a storage medium. The method is applied to an intelligent network, and comprises: obtaining a user voiceprint A during registration of a user; obtaining a user voiceprint B when the user intends to perform a business transaction; and recognizing an identity of the user by comparing the voiceprint A with the voiceprint B. By using a service of performing identity recognition through a voiceprint based on a broadband intelligent network, the problem in the prior art that a voiceprint recognition technology lacks an efficient and reliable control implementation method in the mobile payment field is solved. Control and data collection from a terminal to a server can be effectively implemented by using a call, and an operator's intelligent service and the terminal's transactional APP software are combined, so that a phishing website and viruses are prevented from illegally obtaining user information, thereby providing a reliable identity authentication environment for high-value transactions in the mobile Internet. In addition, more reliable and unique identity authentication is provided through the voiceprint recognition.
Owner:ZTE CORP
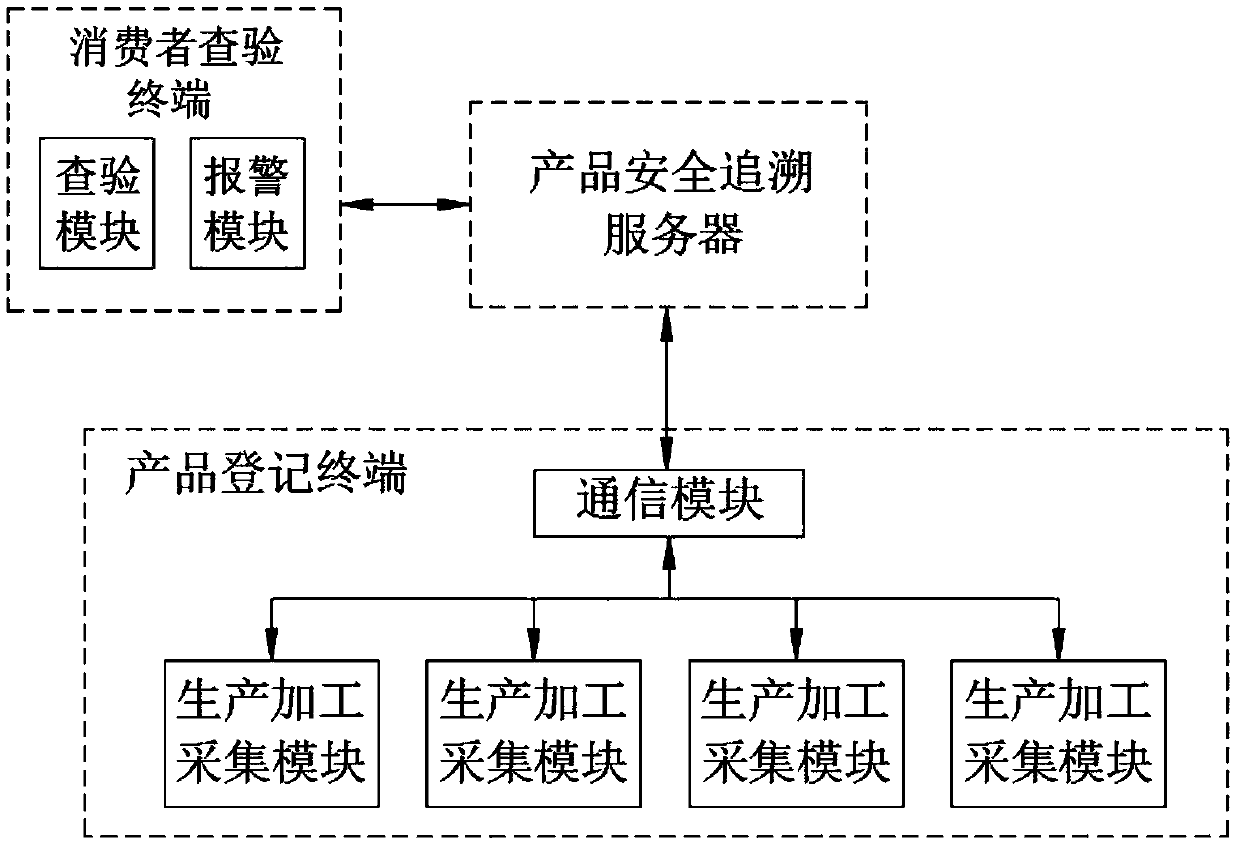
A tamper-proofing product quality safety tracing system and method based on blockchain encryption
PendingCN109685534AProtect interestsEasy to distinguishPayment protocolsCommerceElectricityTamper resistance
The invention discloses a tamper-proofing product quality safety traceability system based on blockchain encryption, comprising a protection system, a product registration terminal and a product safety traceability server which are connected, and the product registration terminal is connected with the product safety traceability server and is used for sending various data of a product to the product safety traceability server; Wherein the product registration terminal comprises a communication module, and a production and processing acquisition module, a logistics distribution acquisition module and a product sales acquisition module which are electrically connected with the communication module, and the communication module is connected with the product safety tracing server. According tothe invention, all related data are recorded in the block chain; In the blockchain auditing system, all the blocks are encrypted and stored in each node, so that anyone cannot tamper product information, and when the quality problem of the product occurs, all the information is traced and can be followed, real and credible, the production and distribution process is monitored more seriously, andthe legitimate interests of consumers are ensured.
Owner:江苏哩咕信息科技有限公司
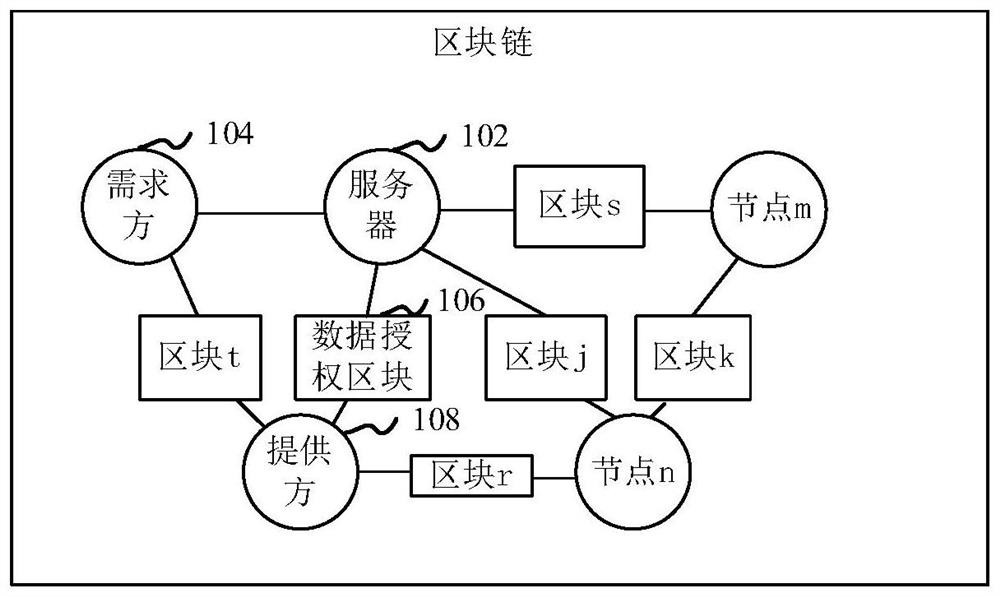
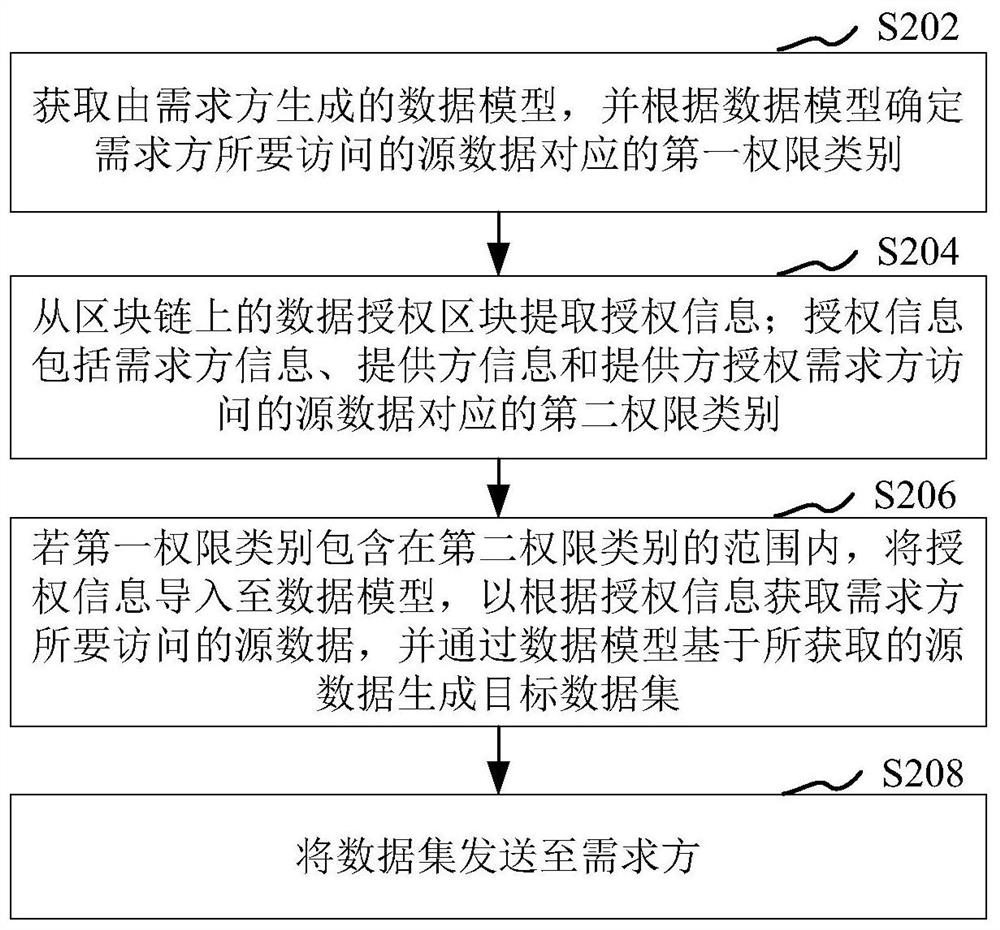
Data acquisition method and device based on blockchain, computer equipment and storage medium
ActiveCN111885153AAvoid illegal acquisitionEnsure safetySecuring communicationData setData acquisition
The invention relates to a data acquisition method and device based on blockchain, computer equipment and a storage medium. The method comprises the steps: obtaining a data model generated by a demandside, and determining a first permission category corresponding to source data to be accessed by the demand side according to the data model; extracting authorization information from a data authorization block on the blockchain, wherein the authorization information comprises demander information, provider information and a second authority category corresponding to source data accessed by the demander authorized by the provider; if the first permission category is included in the range of the second permission category, importing the authorization information into the data model to obtain source data to be accessed by the demander according to the authorization information, and generating a target data set based on the obtained source data through the data model; and sending the targetdata set to the demand side. By adopting the method, the security in the data acquisition process can be improved.
Owner:DONGGUAN MENGDA INDAL INVESTMENT
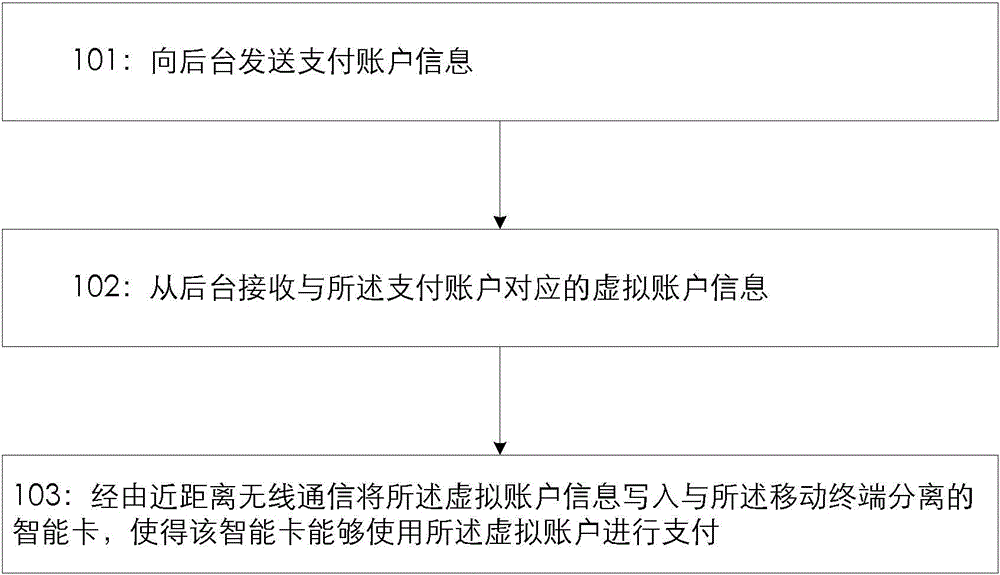
Method and device for carrying out payment by using mobile terminal
InactiveCN105590202AReduce the hassle of carrying peripheralsReduce use costPayment architecturePaymentShortest distance
The invention provides a method for carrying out payment by using a mobile terminal. The method comprises the steps of sending payment account information to a background, receiving virtual account information corresponding to the payment account information from the background, and writing the virtual account information into a smart card separated from the mobile terminal via short-distance wireless communication, so that the smart card can carry out payment by using a virtual account.
Owner:CHINA UNIONPAY
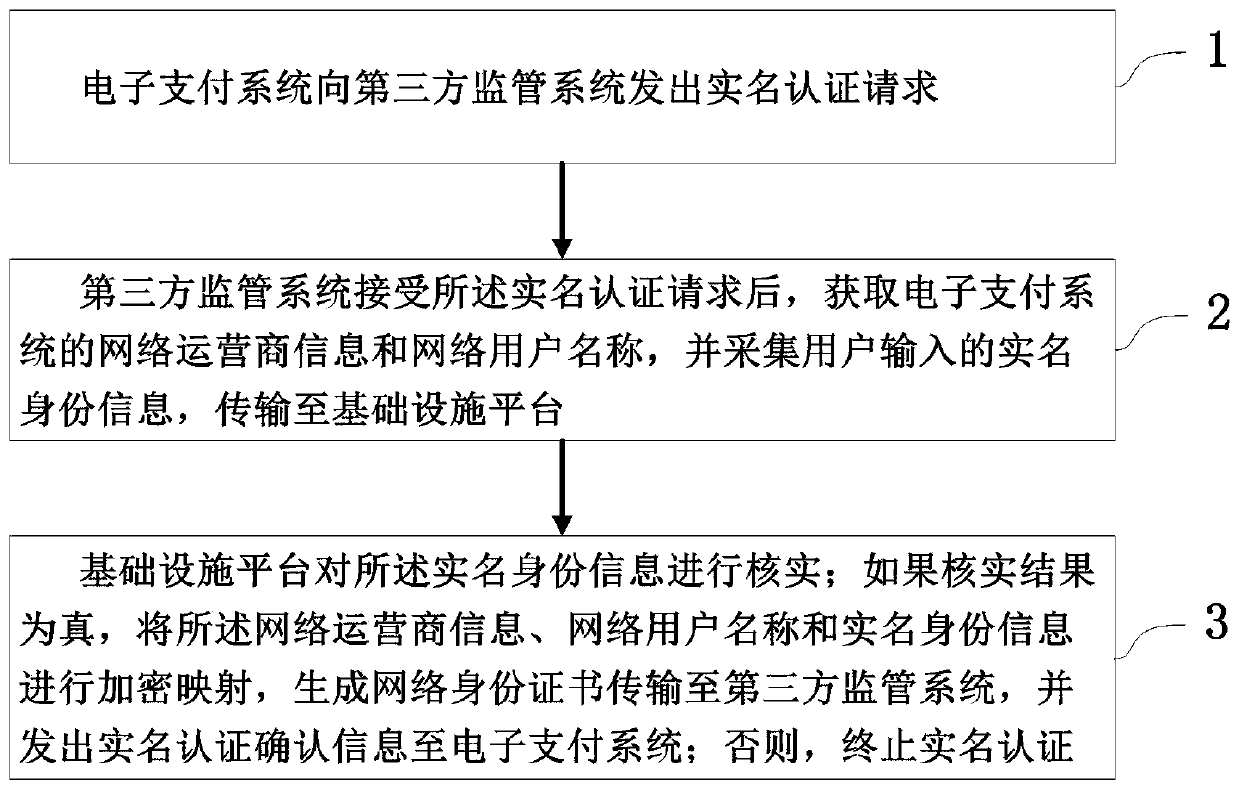
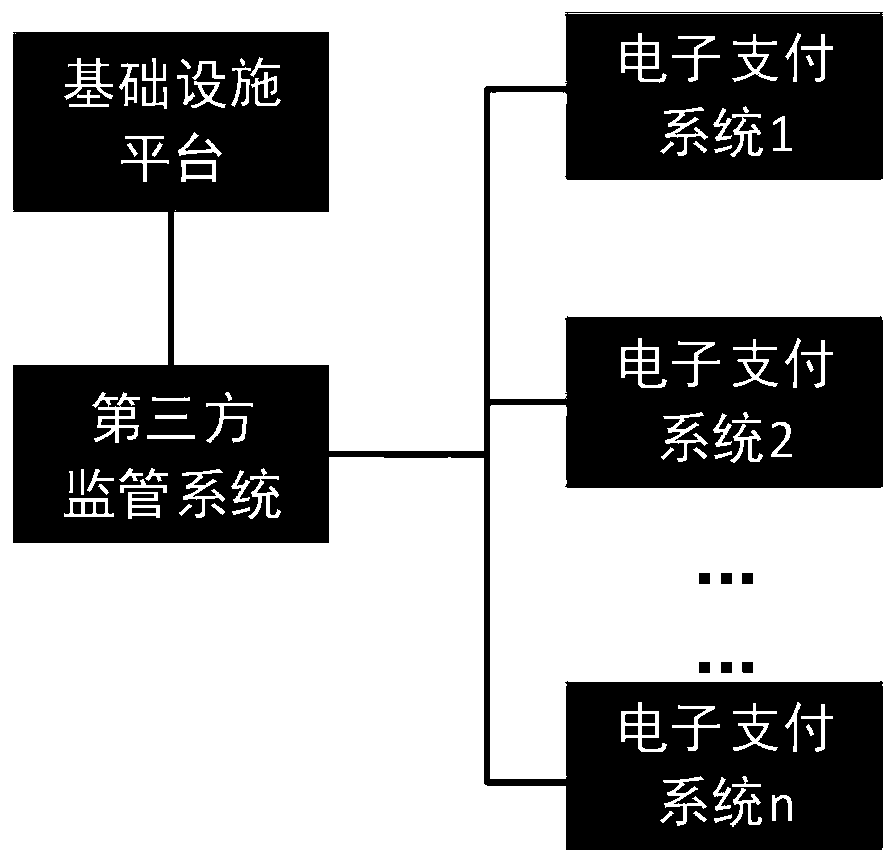
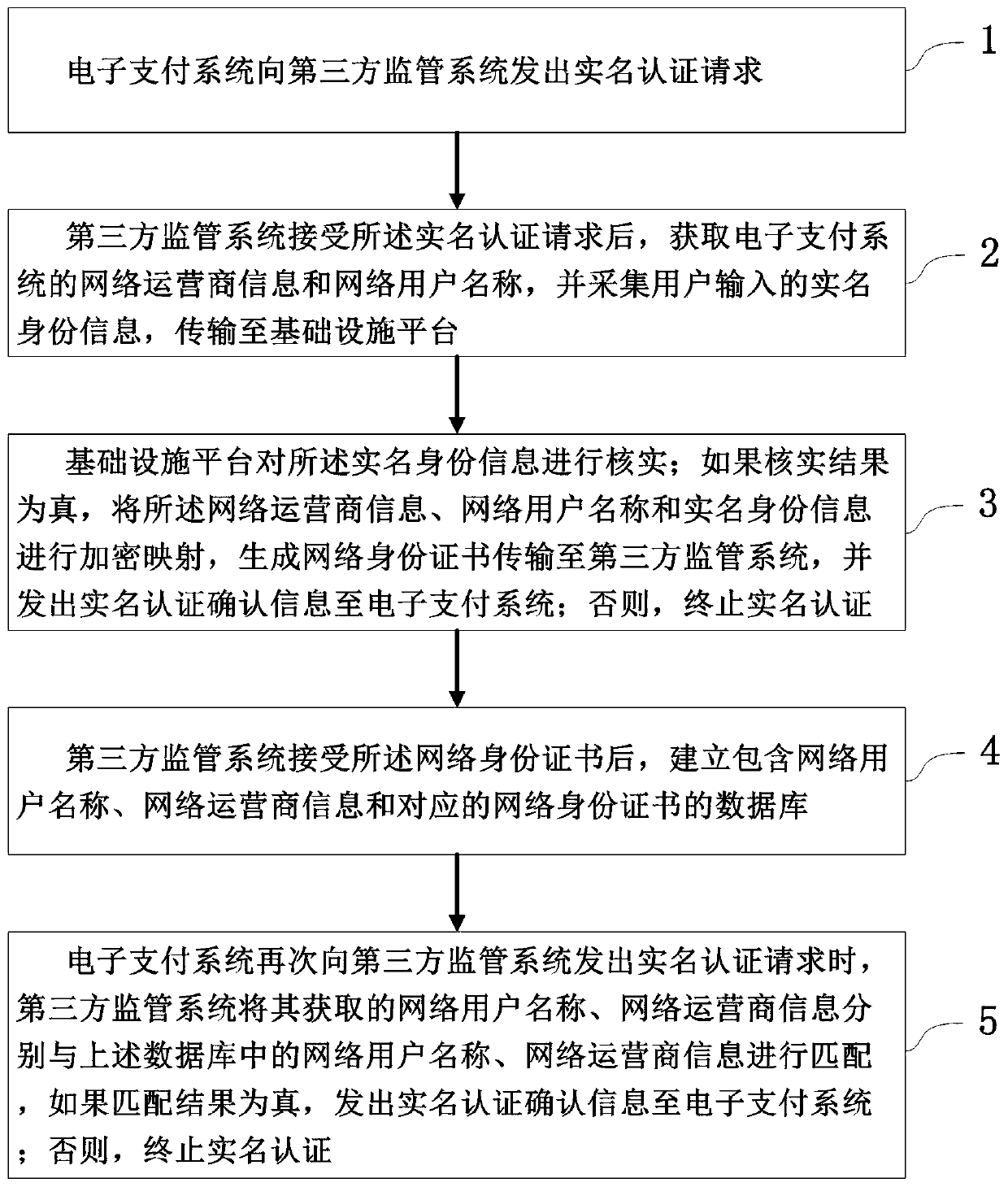
User identity real-name authentication method of an electronic payment system
ActiveCN109829722AGuaranteed operational safetyEffective protectionProtocol authorisationThird partyInformation security
The invention relates to a user identity real-name authentication method of an electronic payment system, belongs to the technical field of network information security, and solves the problem that real-name authentication is unsafe and unreliable in the prior art. The method comprises the following steps that an electronic payment system sends a real-name authentication request to a third-party supervision system; After receiving the real-name authentication request, the third-party supervision system acquires network operator information and a network user name of the electronic payment system, acquires user real-name identity information and transmits the user real-name identity information to the infrastructure platform; The infrastructure platform verifies the real-name identity information; If the verification result is true, performing encryption mapping on the network operator information, the network user name and the real-name identity information, generating a network identity certificate, transmitting the network identity certificate to a third-party supervision system, and sending real-name authentication confirmation information to an electronic payment system; Otherwise, the real-name authentication is terminated. According to the method, a third-party supervision system is combined with a network identity certificate, so that the privacy of a user is protected,and the person and the certificate are the same.
Owner:XINGTANG TELECOMM TECH CO LTD +1
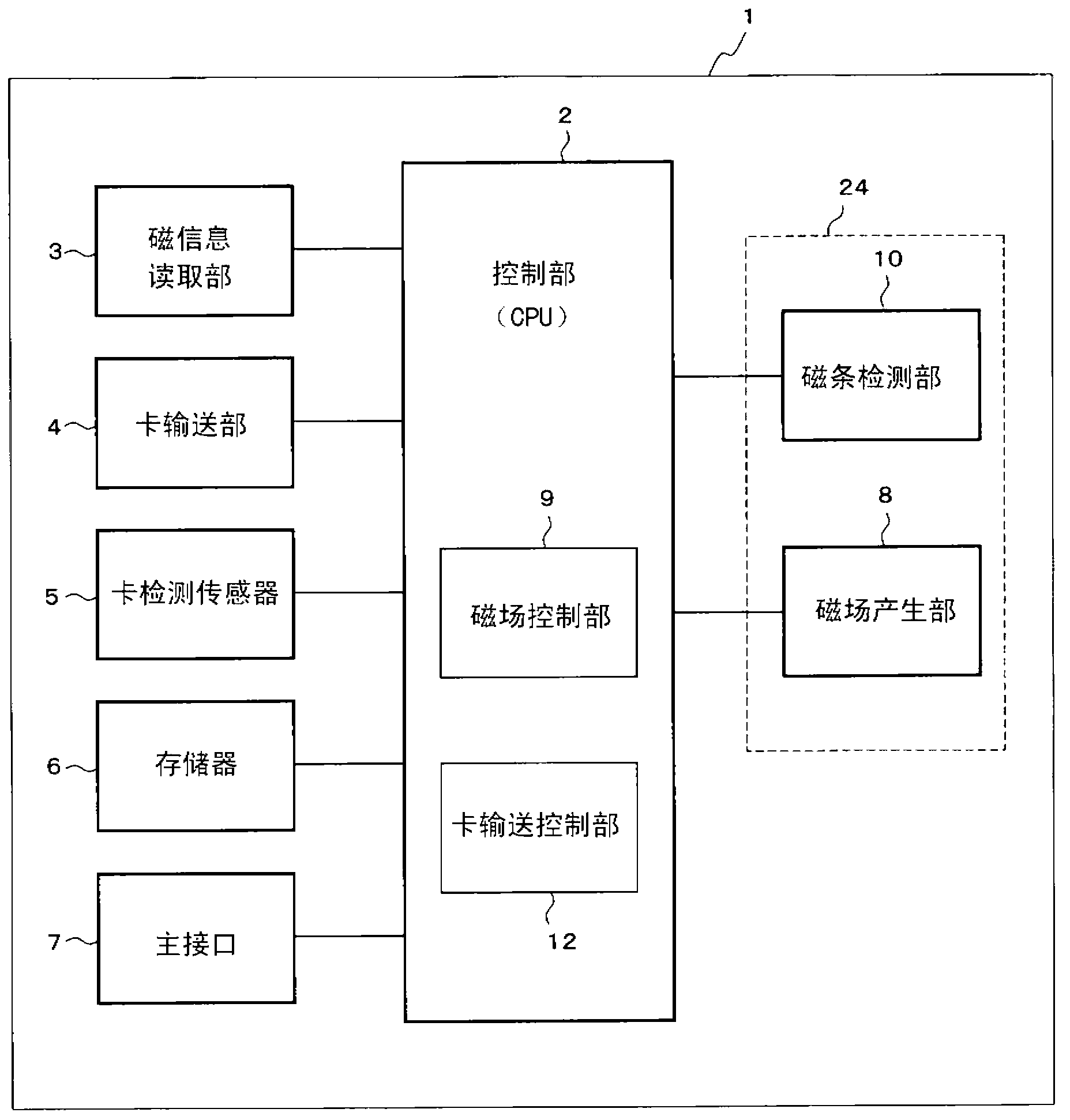
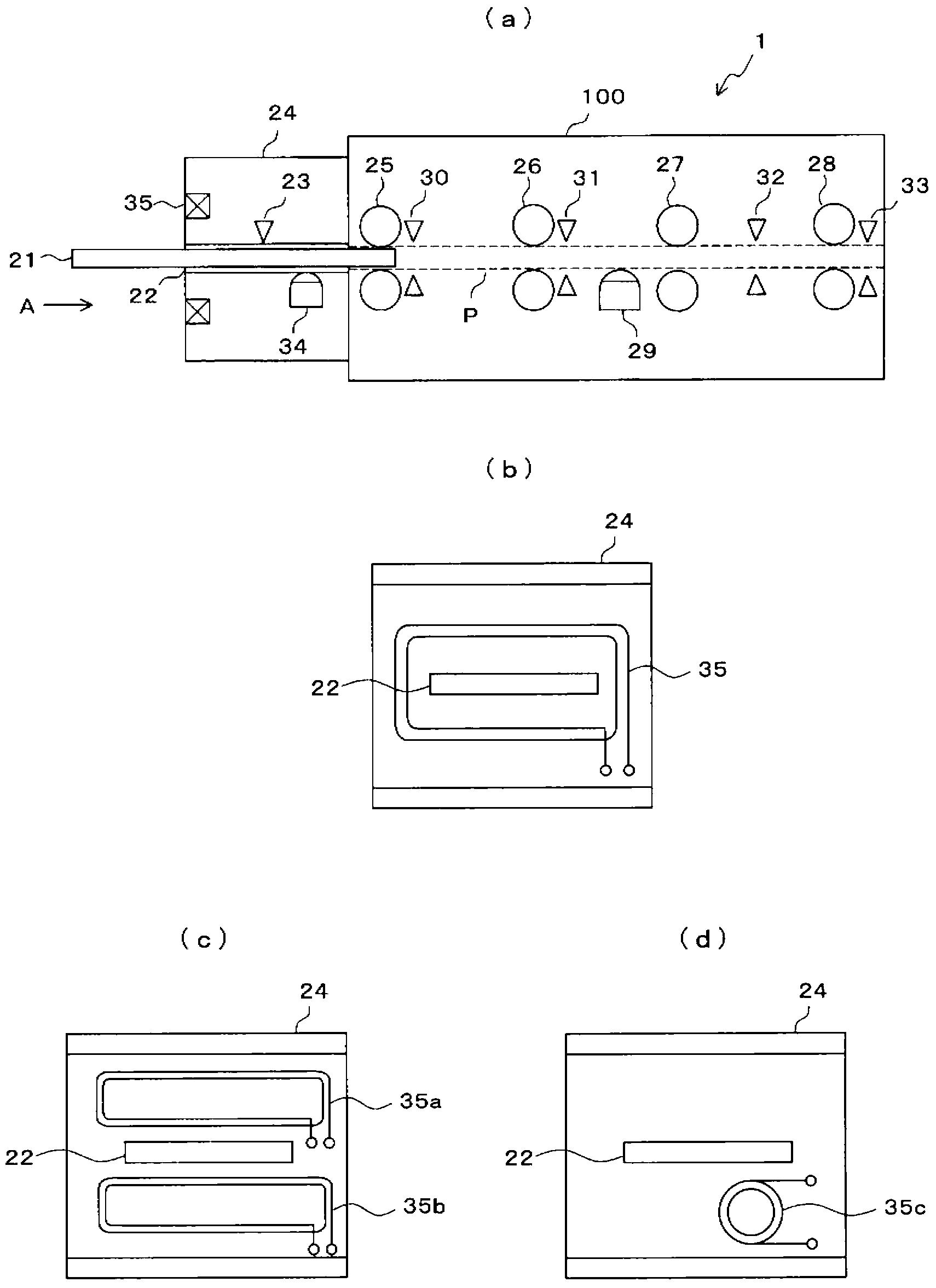
Apparatus for reading magnetic recording medium
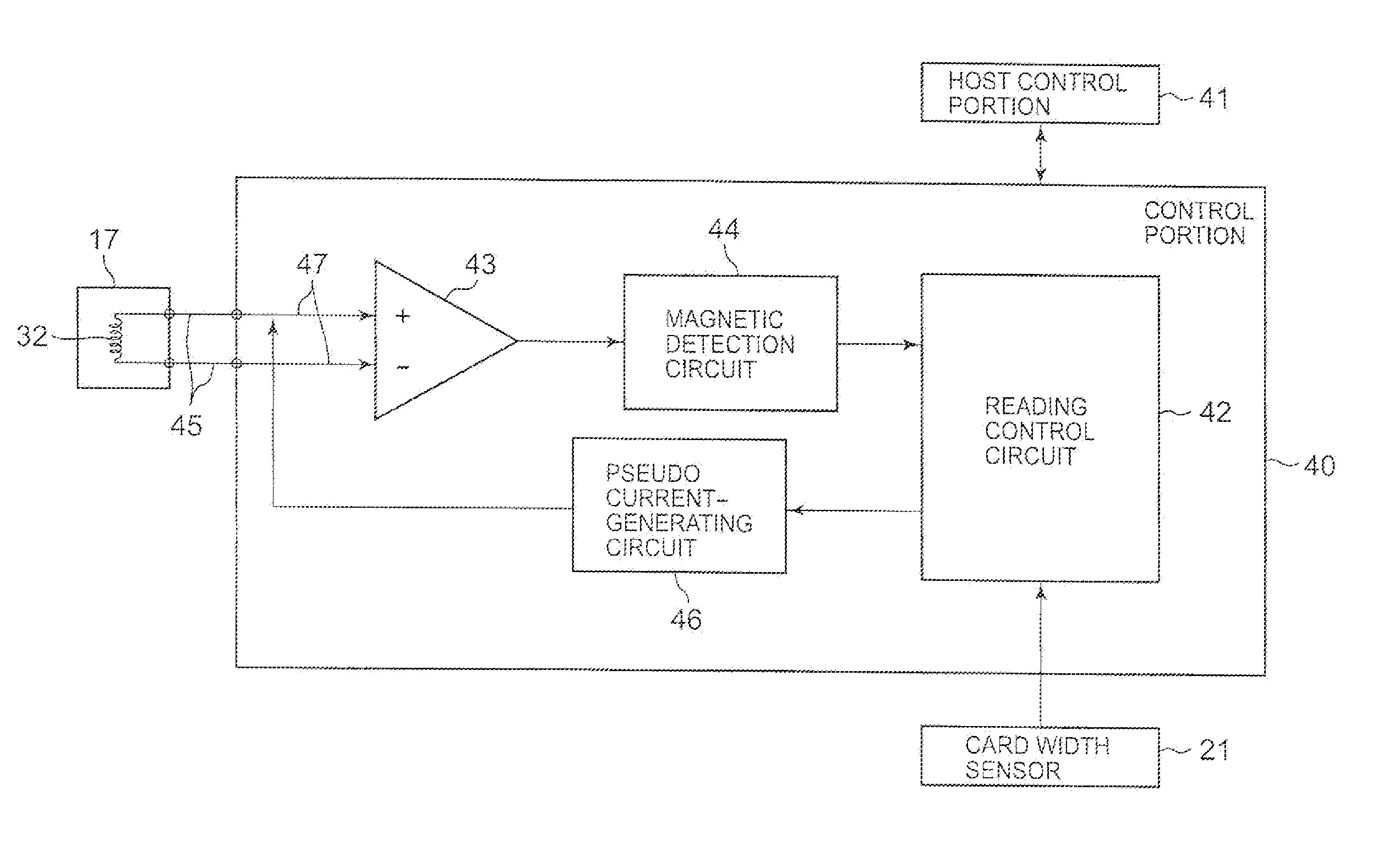
ActiveCN103210402AAvoid illegal acquisitionComplete banking machinesCoin countersOriginal dataEngineering
A loop antenna (35) for generating a jamming magnetic field is provided near an insertion hole (22) into which a magnetic card (21) is to be inserted, and the jamming magnetic field is applied to a magnetic head (34). When the loop antenna (35) is generating a jamming magnetic field, and a magnetic card (21) is inserted into the insertion hole (22), a magnetic-stripe detection unit (10) outputs a detection signal with which just an evaluation of whether or not data is recorded within a magnetic stripe (21a) of the magnetic card (21) can be executed. With such a configuration, original data can be prevented from being obtained illegitimately, even when an illegitimate reading apparatus is connected to the magnetic-stripe detection unit (10) with lead wires.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
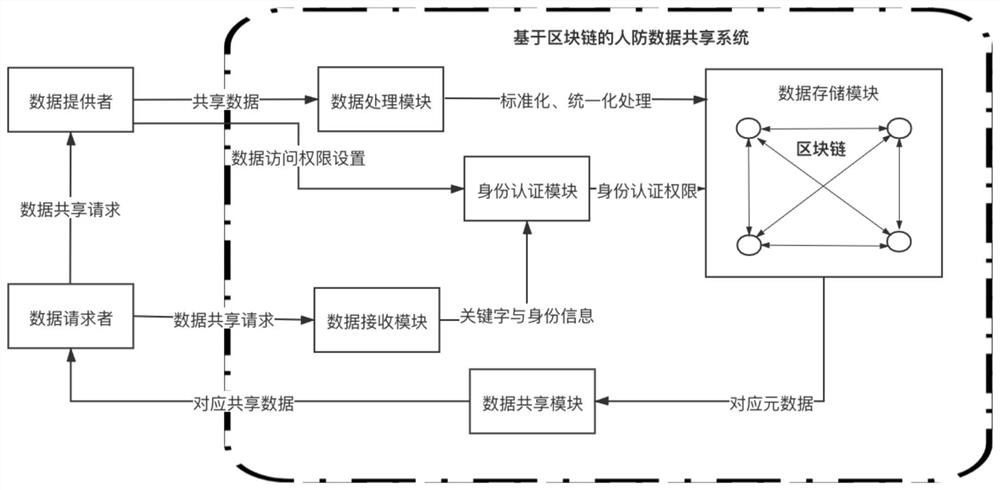
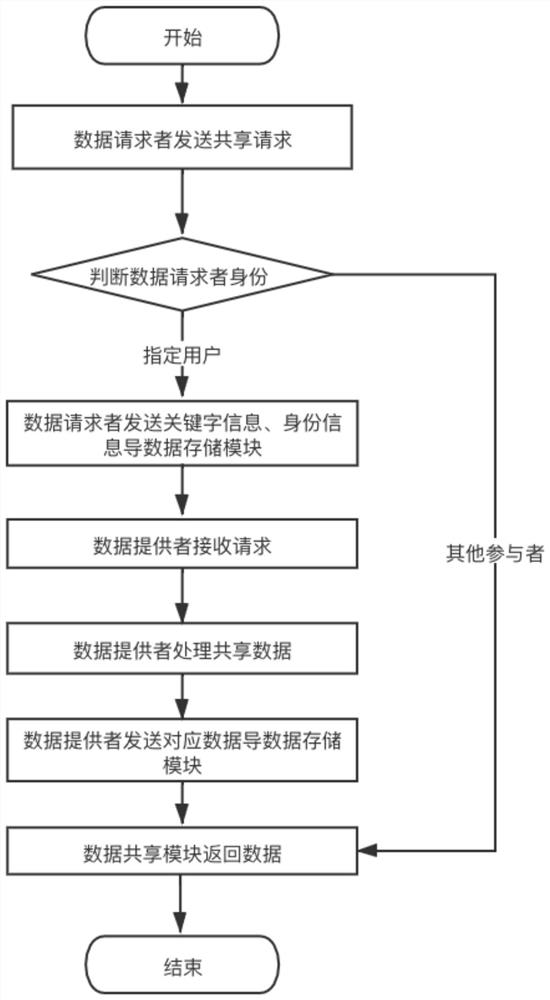
Civil air defense data sharing system and method based on block chain
ActiveCN112511599AEnsure safetyGuaranteed privacyEncryption apparatus with shift registers/memoriesUser identity/authority verificationData providerCiphertext
The invention discloses a civil air defense data sharing system and method based on a block chain, and the system comprises a data receiving module which is used for receiving keywords and identity information transmitted by a data requester, and receiving shared data of a data provider; a data processing module, used for standardizing and unifying the shared data sent by the data provider, and sending the processed structured data ciphertext and keyword index to the data storage module; a data storage module, used for storing the structured data ciphertext and the keyword index; an identity authentication module, used for carrying out identity authentication on the identity information sent by the data requester; and a data sharing module, used for matching the corresponding data in the data storage module according to the identity authentication result and the keyword and sharing the data to the data requester. According to the invention, data can be prevented from being illegally acquired, used and tampered, and data sharing and secret-related data protection are realized.
Owner:NANJING LES INFORMATION TECH
Mobile phone off-line authentication method
ActiveCN104753918APrevent offline authenticationFew linksTransmissionSecurity arrangementCiphertextKey generation
The invention discloses a mobile phone off-line authentication method. A SD card is inserted in the mobile phone of the user, symmetric cryptographic algorithm is adopted for establishing encryption system and combined symmetric key generation algorithm is adopted for real time generating symmetric key, change is generated at every time for real time updating and effectively managing the key; in each user mobile phone, key seed corresponding to friend circle user is beforehand encrypted into the ciphertext and stored for ensuring storage safety of key seed of the friend circle user, and user identity information center is established on network, the key seeds of all users are encrypted into the ciphertext and stored in the user identity information center for ensuring the storage safety of key seeds of all users, and the safety downloading of the key seeds of friend circle users of mobile phone end is also ensured, thus the off-line authentication between the mobile phone and the user can be realized.
Owner:胡祥义
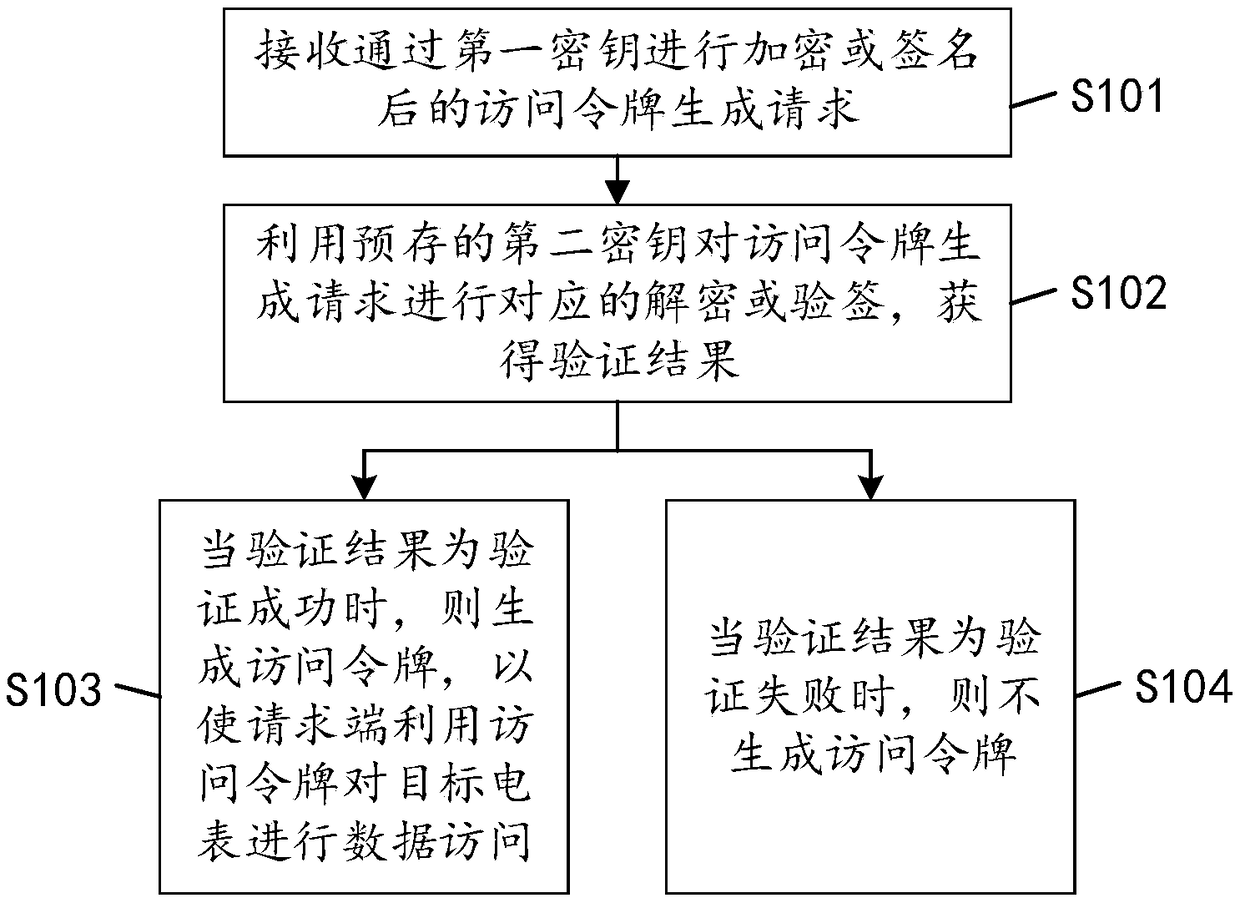
Electric meter data accessing method, device, equipment and readable storage medium
InactiveCN109150528AImprove securitySafeguard the public interestKey distribution for secure communicationPublic key for secure communicationThird partyEncryption
The invention discloses an electric meter data accessing method. The method comprises the following steps: receiving an access token generation request after encryption or signature by a first key; decrypting or verifying the access token generation request by using a pre-stored second key to obtain a verification result; when the authentication result is successful, generating an access token sothat the requesting end accesses the data of the target electric meter by using the access token; preventing generation of an access token generated when the authentication result is an authenticationfailure. The technical proposal provided by the embodiment of the invention greatly improves the safety of the meter data, can effectively avoid a third party from illegally obtaining an access token, and thus ensures the public interest. The invention also discloses an electric meter data accessing device, equipment and a storage medium, which have corresponding technical effects.
Owner:HEXING ELECTRICAL +2
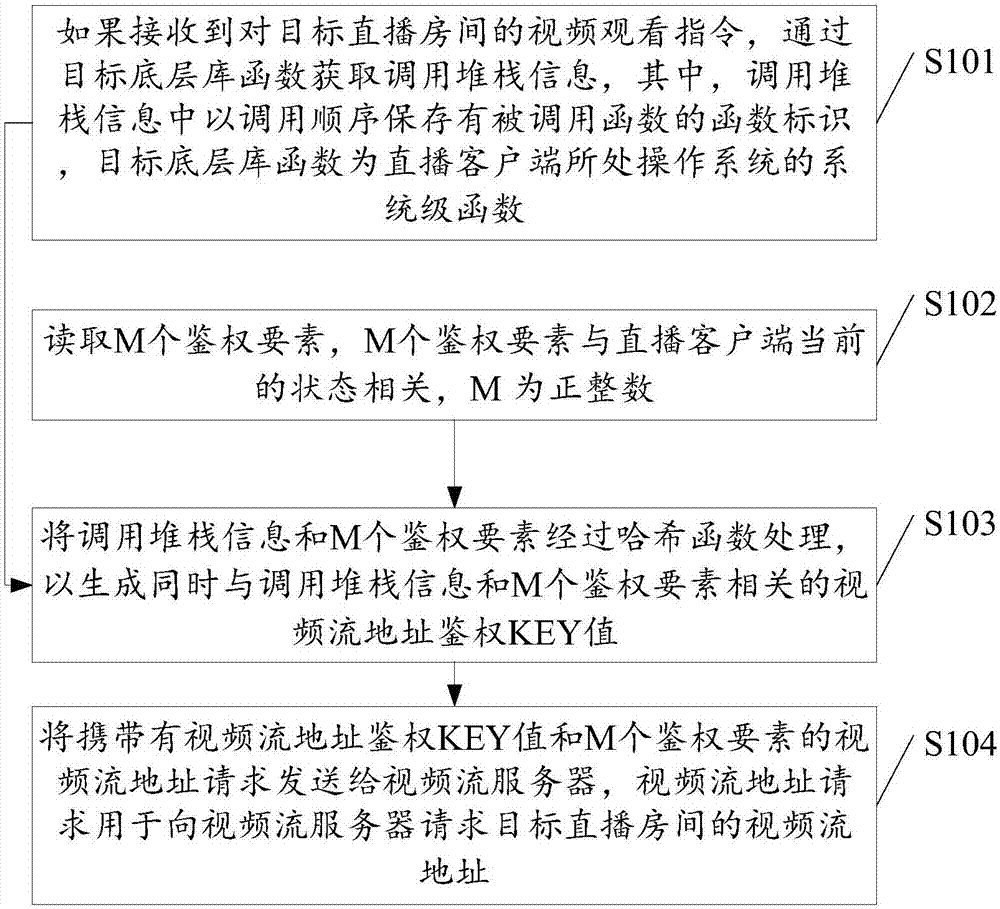
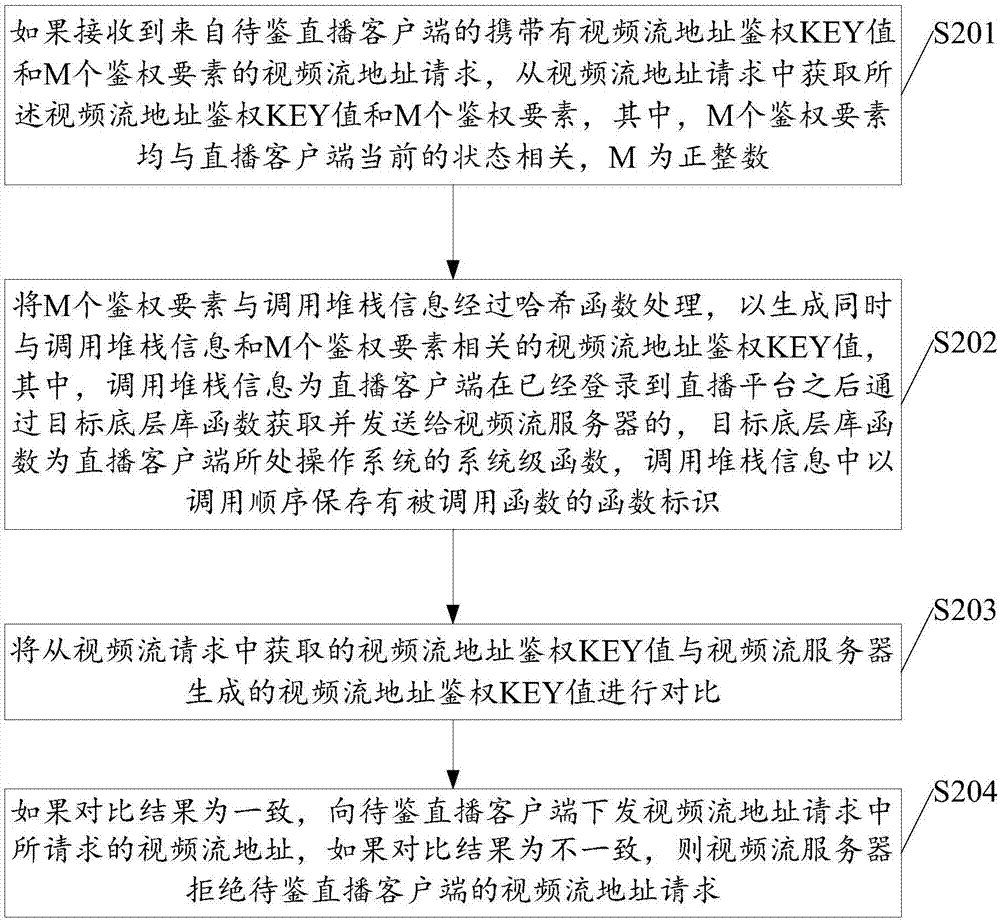
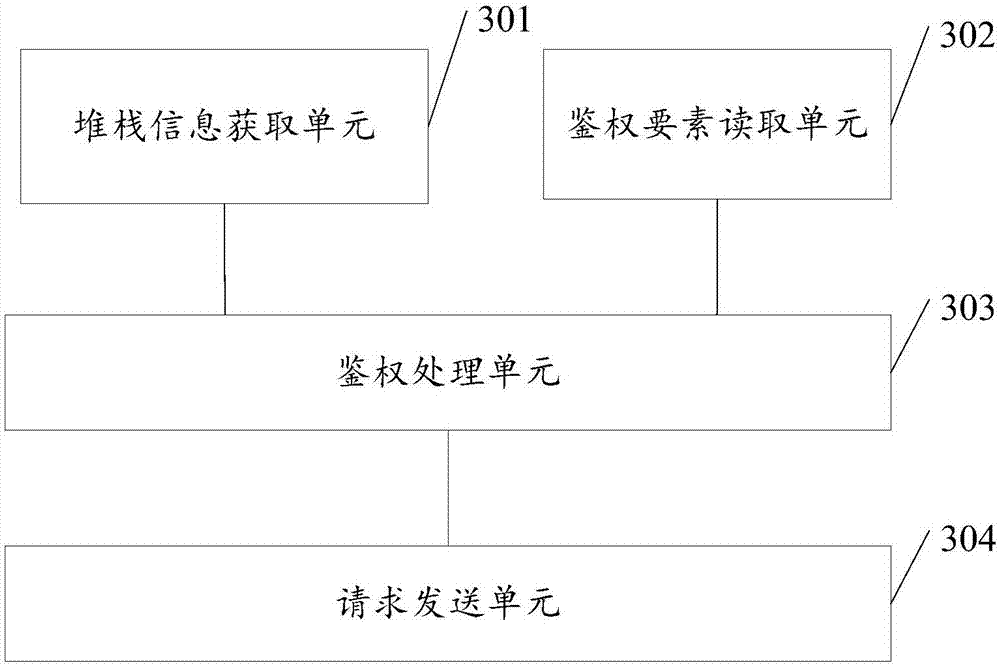
Video streaming address authentication method and device
ActiveCN107333151AAvoid illegal acquisitionImprove reliabilitySelective content distributionCall stackHash function
The invention discloses a video streaming address authentication method and device, and is applied to the field of network live broadcasting. The method comprises the steps of: if receiving a video viewing instruction for a target live broadcasting room, acquiring call stack information by a target bottom layer library function, wherein a function identifier of a called function is stored in the call stack information, and the target bottom layer library function is a system-level function of an operation system where a live broadcasting client is positioned; reading M authentication elements, wherein the M authentication elements are related to a current state of the live broadcasting client; processing the call stack information and the M authentication elements by an Hash function so as to generate a video streaming address authentication KEY value simultaneously related to the call stack information and the M authentication elements; and sending a video streaming address request carrying the video streaming address authentication KEY value and M authentication elements to a video streaming server, wherein the video streaming address request is used for requesting the video streaming server for a video streaming address of the target live broadcasting room. The video streaming address authentication method and device disclosed by the invention solve the problem of low safety of existing video streaming address authentication.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
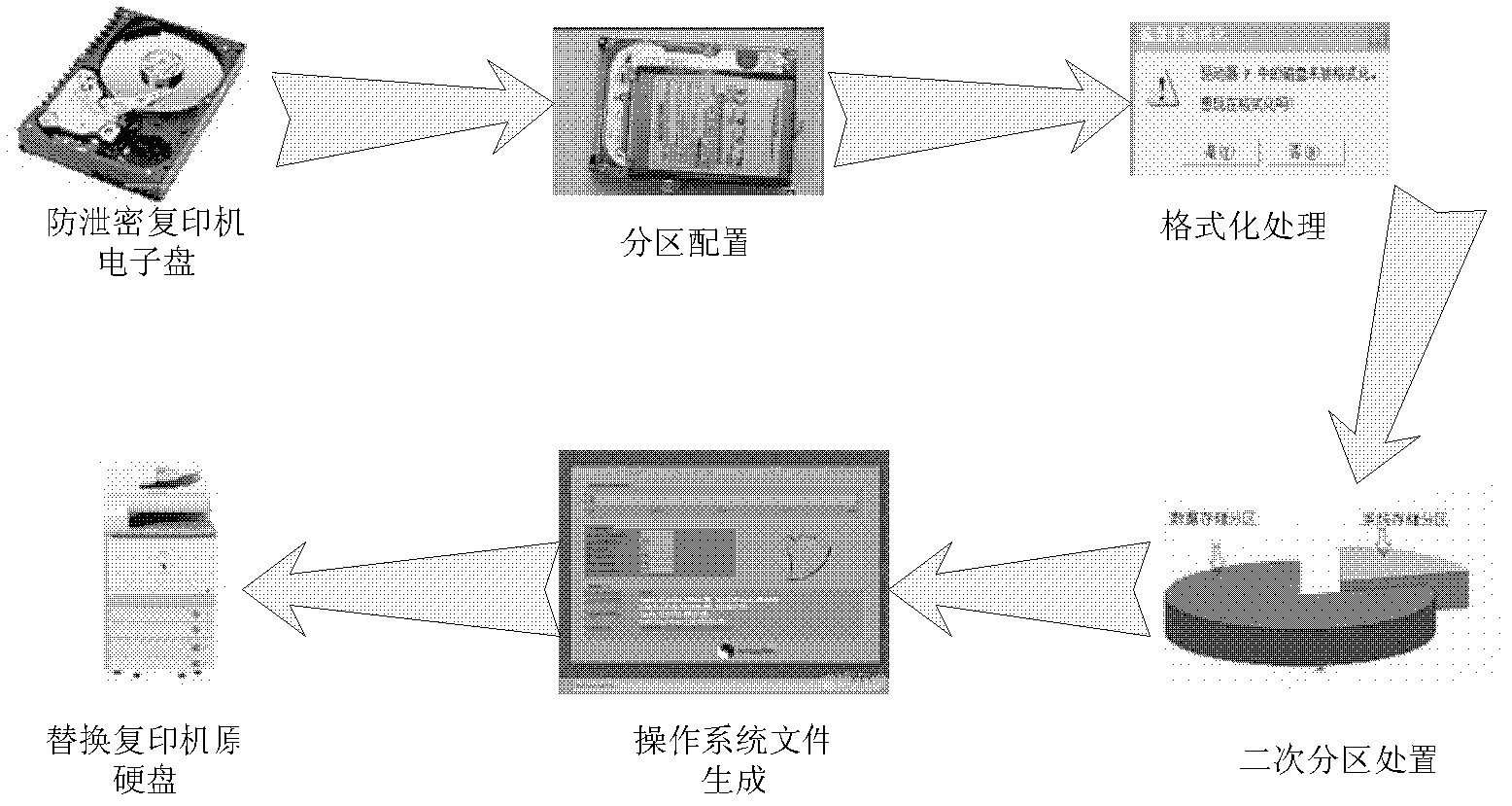
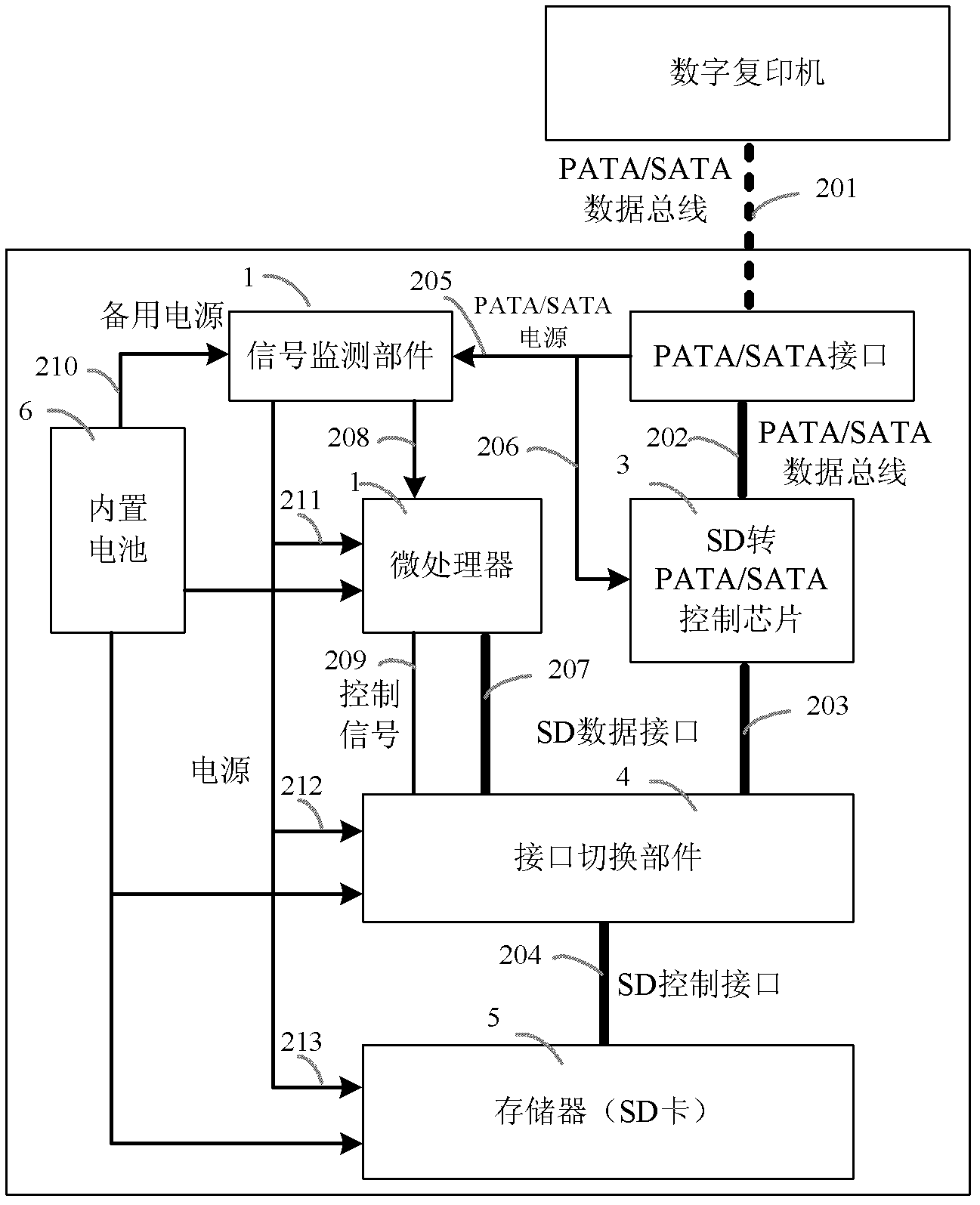
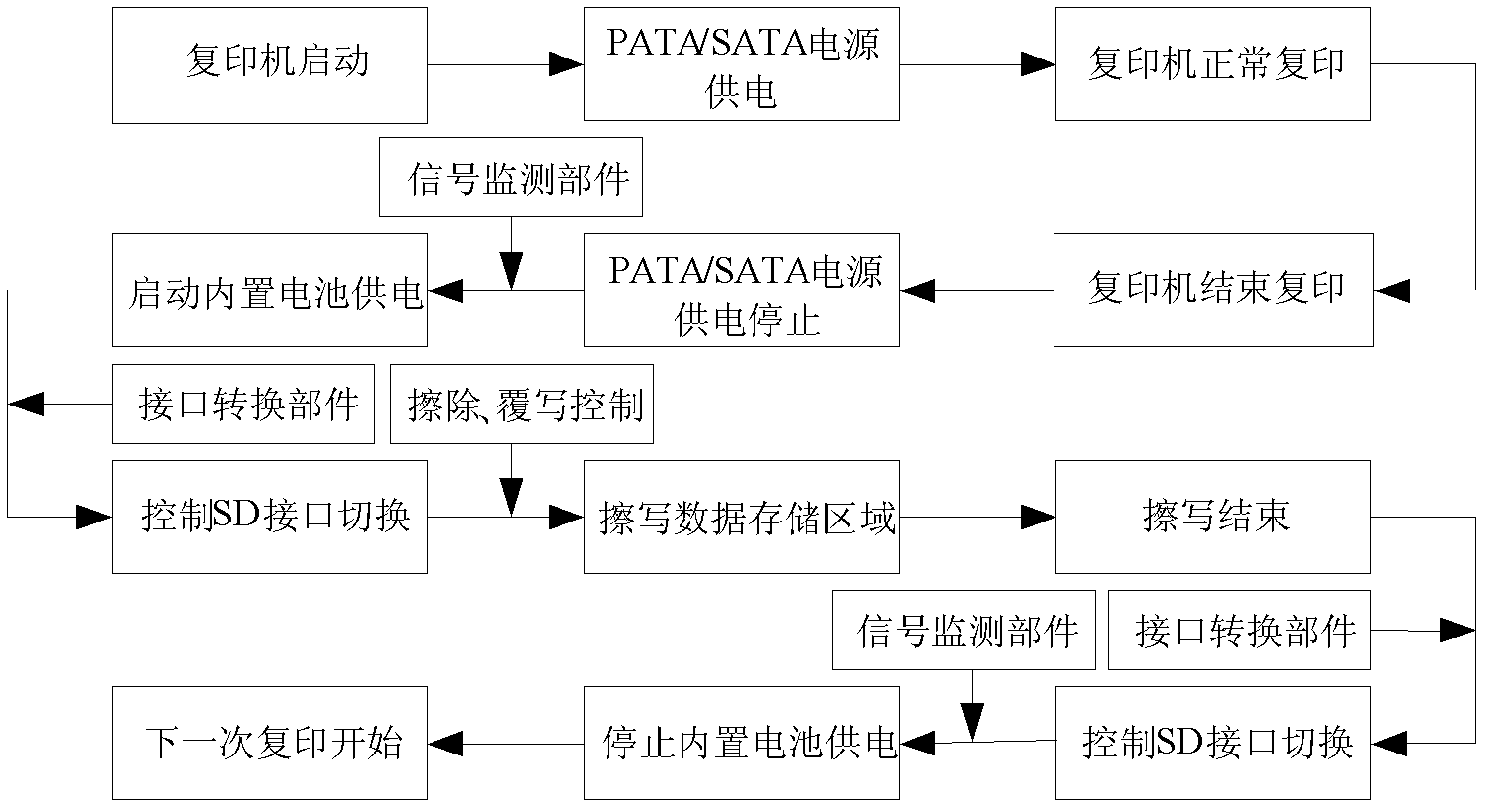
Anti-disclosure copier safety electronic disc
ActiveCN102436424AAvoid illegal acquisitionTo achieve the purpose of security and confidentialityUnauthorized memory use protectionSignal monitoringMicroprocessor
The invention discloses an anti-disclosure copier safety electronic disc, which comprises a signal monitoring component, a microprocessor, a built-in battery and a memorizer. The signal monitoring component is connected with an external power supply, the built-in battery, the microprocessor and the memorizer and used for detecting a power supply of the electronic disc. When the external power supply works normally, the signal monitoring component leads the memorizer to work normally; and when the external power supply is cut off, the built-in power supply is switched to supply power, and the microprocessor is started and operated to perform erasing and copying operation on a data storage protection unit of the memorizer. The microprocessor is used for achieving erasing and copying operation of the data storage protection unit of the memorizer, the built-in battery is used for supplying power to each component of the electronic disc, and the memorizer is used for storing copied data. The anti-disclosure copier safety electronic disc can protect copier data from being stolen.
Owner:中国人民解放军总参谋部第五十五研究所
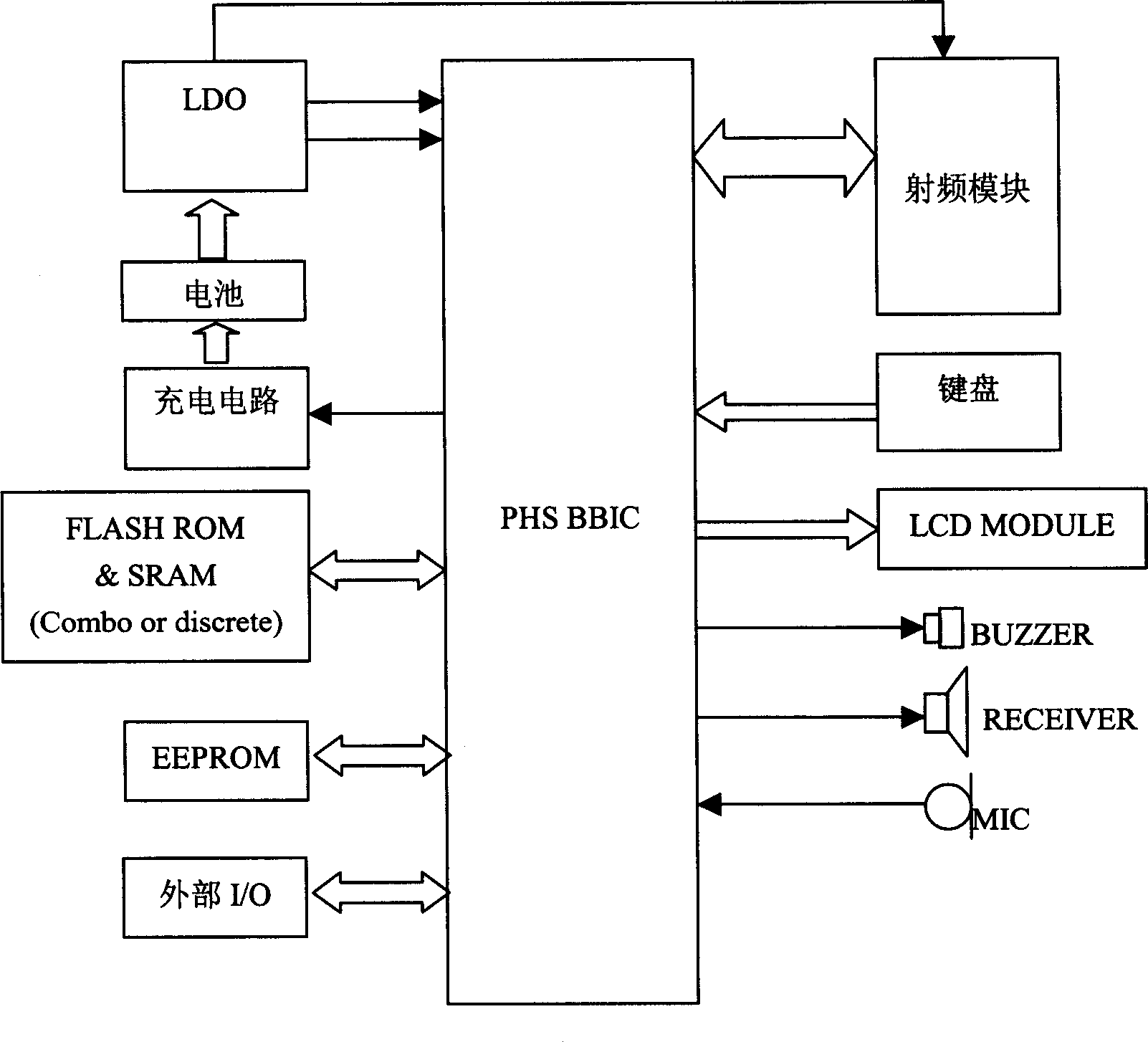
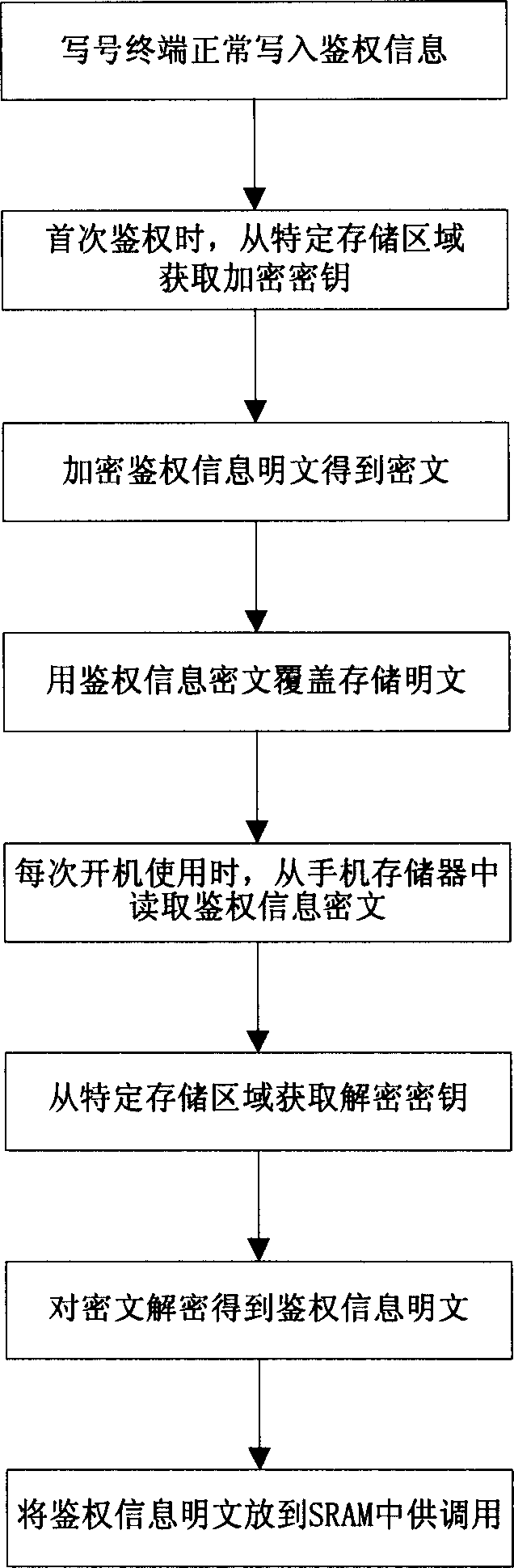
Protection of authentication information of PHS mobile telephone
InactiveCN1553729AEffective protectionGuaranteed not to leakUser identity/authority verificationRadio/inductive link selection arrangementsPlaintextCiphertext
A method for protecting authentication information stored in PHS mobile phone includes following steps: 1) the write terminal writes the authentication information into the memory of mobile phone at normal procedure; 2) the PHS mobile phone makes encryption for the plaintext of authentication information as making first authentication, and replaces the information plaintext by cryptograph of authentication information; 3) makes decryption, when the PHS mobile phone starts up, makes decryption operation for the authentication cryptograph. When making encryption and decryption, an encryption key and a decryption key in key pair that is only corresponding to a certain chip in mobile phone are used. The method can be farthest compatible with current write phone number method of PHS mobile phone, and can prevent the authentication information from illegally stealing.
Owner:ZTE CORP
Merchandiser and method of controlling game thereof
ActiveUS20140045565A1Play gameAvoid illegal acquisitionApparatus for meter-controlled dispensingVideo gamesEngineering
A merchandiser and a method of controlling a game thereof are disclosed. The merchandiser includes prize cartridges that have transparent partitions among which prizes are contained, drive parts that move the respective prize cartridges, a gaming device that executes a game provided for each of identification numbers of the prize cartridges, and a controller that controls the drive part so that the prize of the prize cartridge is dropped to a prize discharge part according to a result of playing the game. Thereby, since a designated prize can be acquired according to the result of playing a game, an interest in the game can be increased.
Owner:ANDAMIRO
Physical layer secure communication method based on multi-radio cooperative precoding
ActiveCN106953819AImprove securityAvoid illegal acquisitionTransmitter/receiver shaping networksSecurity arrangementData informationEavesdropping
The invention discloses a physical layer secure communication method based on multi-radio cooperative precoding, which is suitable for secure information transmission between a user terminal and a base station in a heterogeneous wireless network. In the heterogeneous wireless network environment, the user terminal fully utilizes the multi-radio access technology to realize the cooperative secure information transmission between different communication modes. The physical layer secure communication method considers two situations that instantaneous channel state information of an eavesdropping channel between a source node and an eavesdropping node is known and unknown separately, preprocesses a source node signal by means of multi-mode cooperative precoding, and transmits data information after precoding to a destination node. Compared with the traditional multi-mode switching selection method, the multi-mode cooperative method provided by the invention significantly improves the secure transmission rate of wireless transmission, and is conductive to solving the security problem caused by the eavesdropping node existing in the multi-mode communication scene.
Owner:NANJING UNIV OF POSTS & TELECOMM
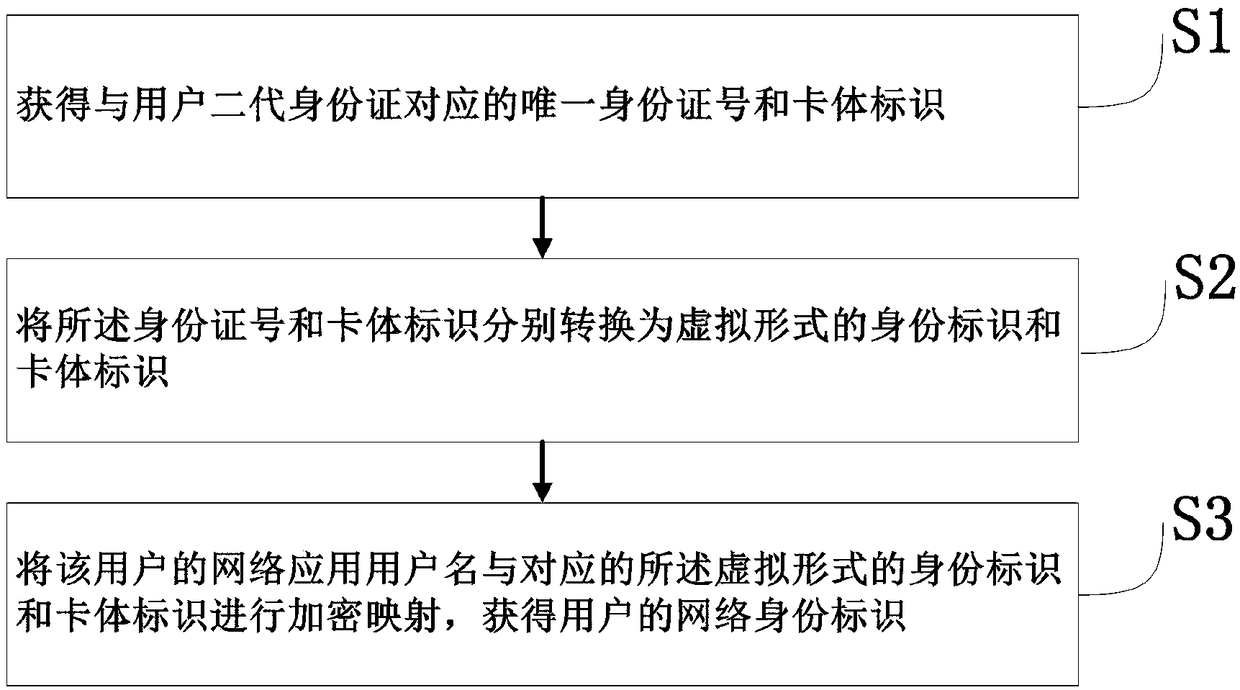
A method for generating and protecting real-name system network identity
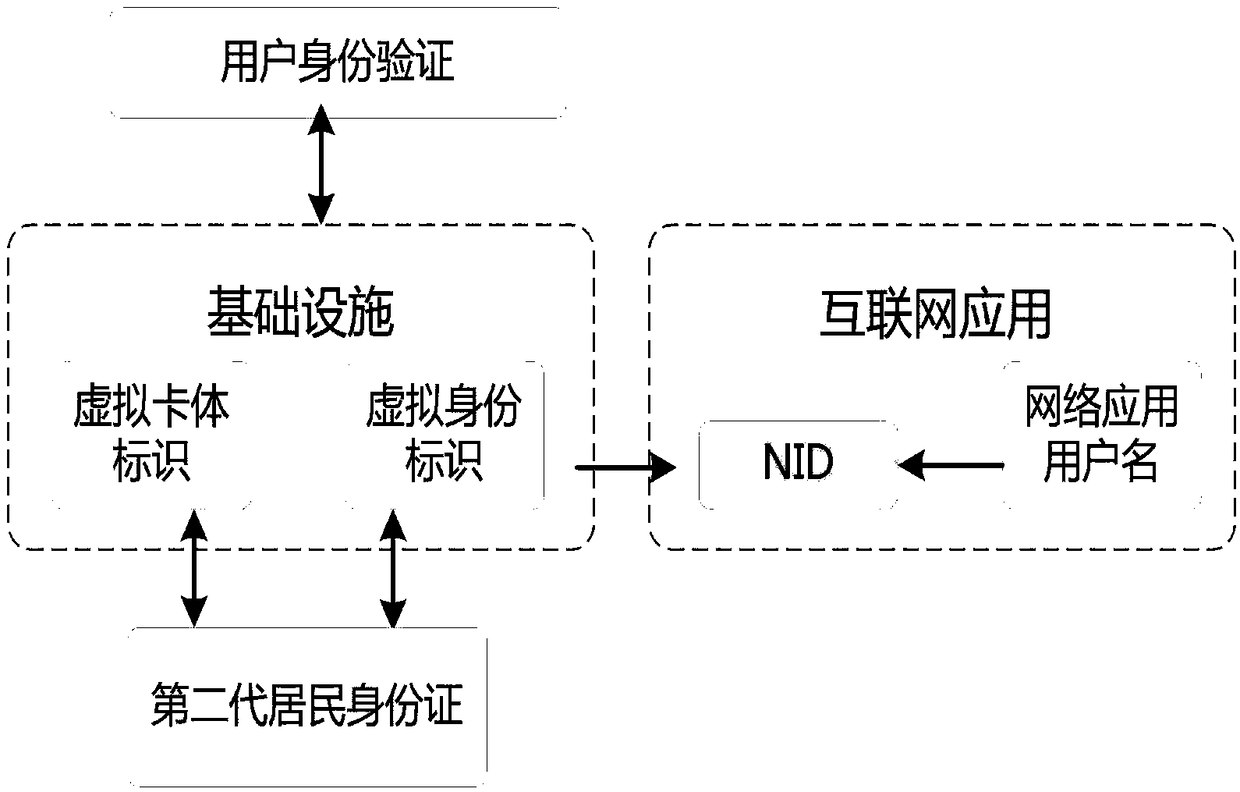
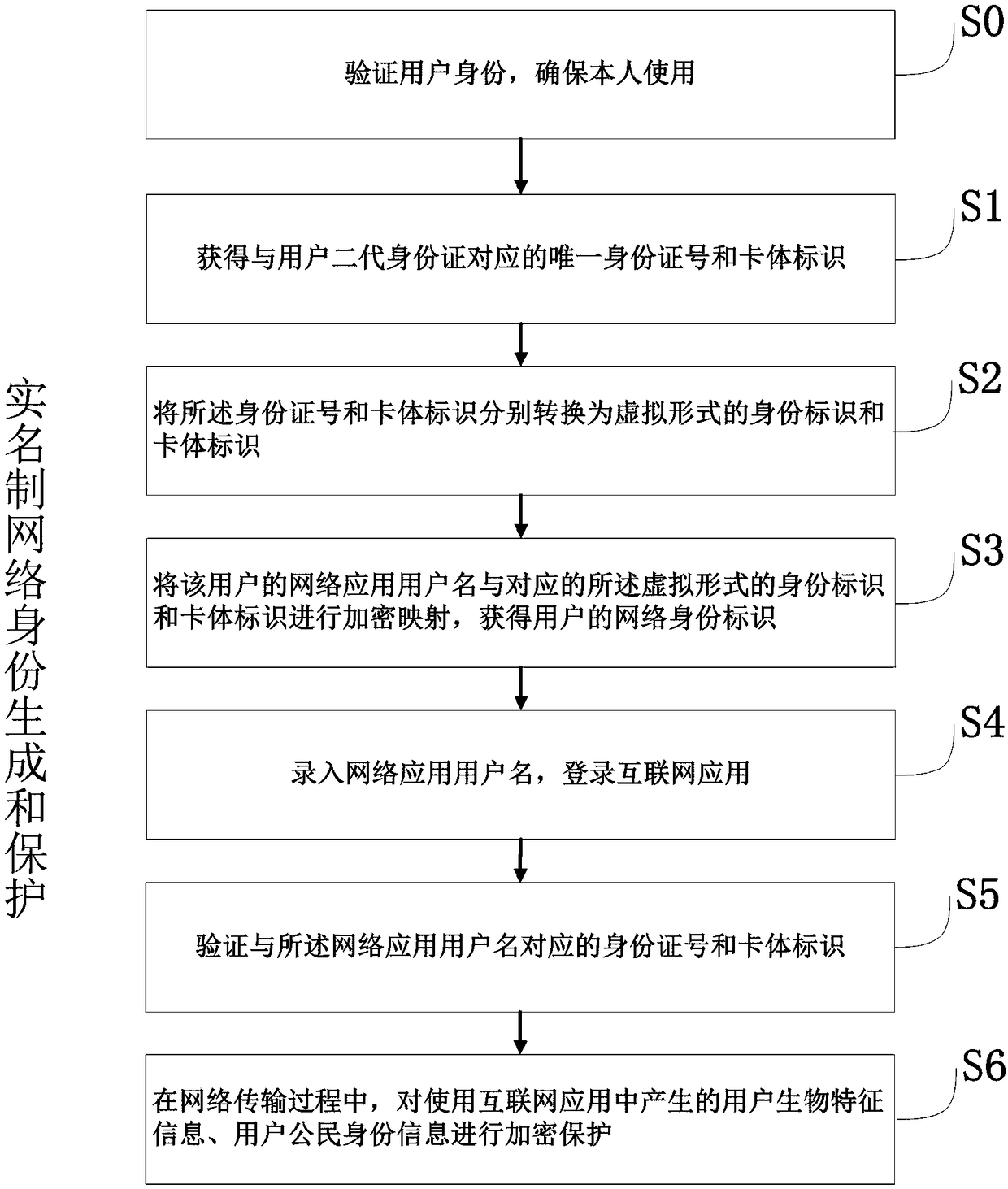
ActiveCN109067702AEnsure safetyGuaranteed confidentialityPublic key for secure communicationInformation securityOnline identity
The invention relates to a method for generating and protecting a real-name system network identity, belonging to the technical field of information security, which solves the problem in the prior artthat the identity of a person and a witness cannot be truly realized, and the personal privacy of a user is not effectively protected. The invention discloses the method for generating and protectingthe real-name system network identity, which is based on the civic identity information of a user and the user name of a network application registered in an Internet application to carry out encryption mapping, can obtain a unique network identity mark, and realizes the identity of a person and a certificate on the Internet. Because the network identity is non-restorable, non-extrapolable, and only corresponds to a unique user, the user's identity information and use security are protected to some extent. At the same time, in the process of network transmission, the user's biometric information and citizenship information involved in the use of Internet applications are also encrypted to protect personal privacy from leakage. The invention not only facilitates the real name system of network identity, but also effectively protects personal privacy.
Owner:XINGTANG TELECOMM TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com