Patents
Literature
33results about How to "Protect trade secrets" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
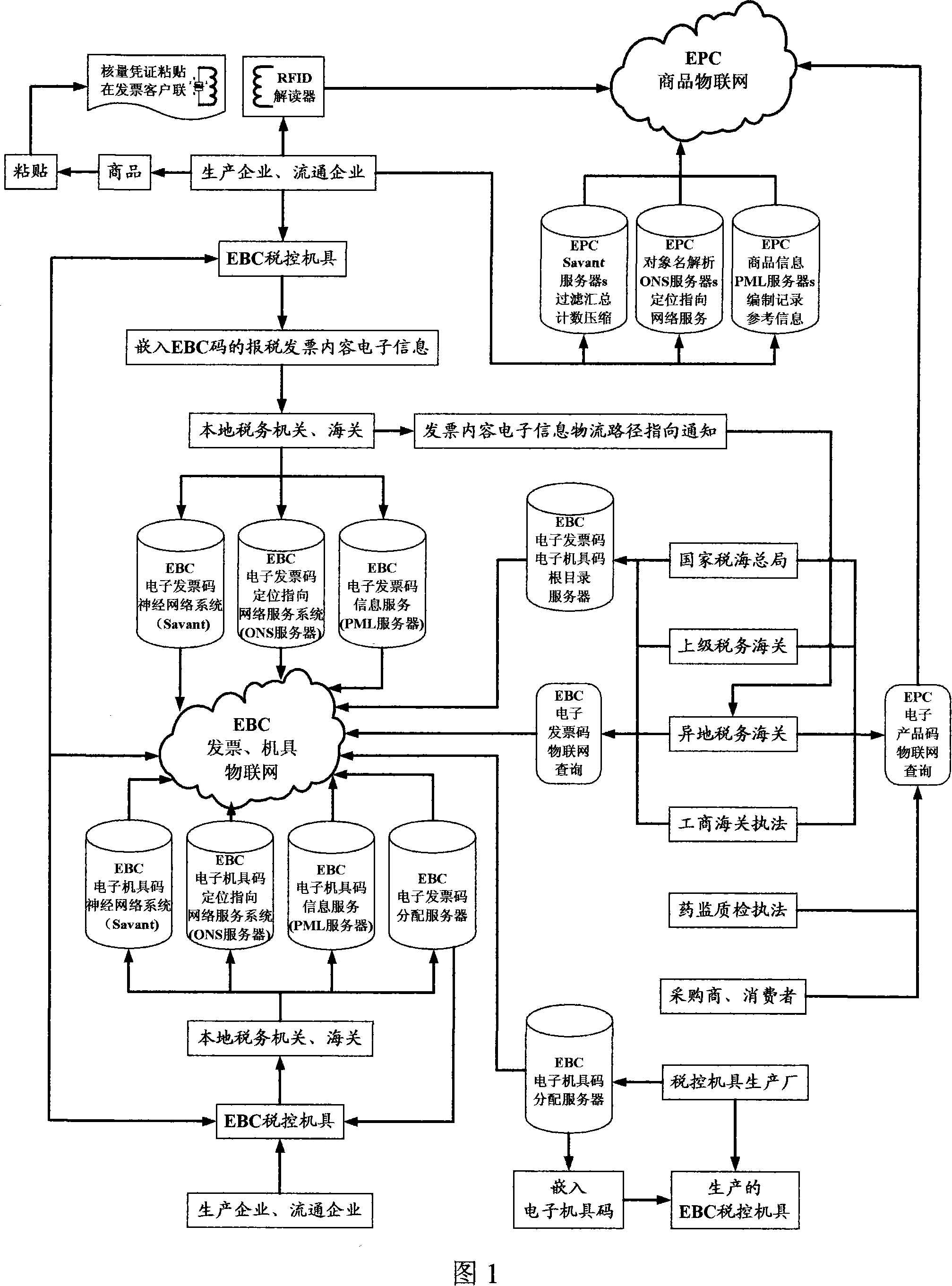
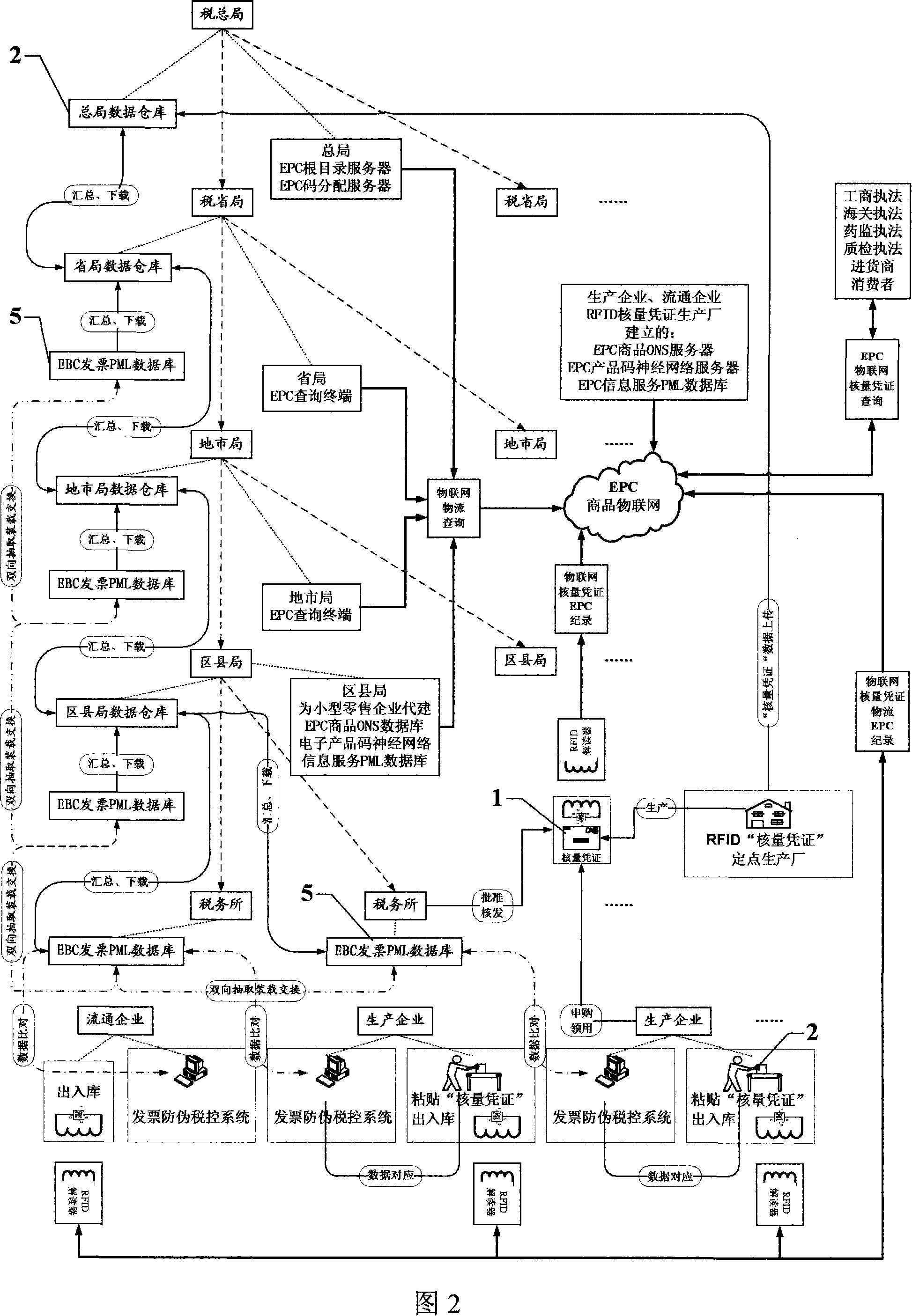
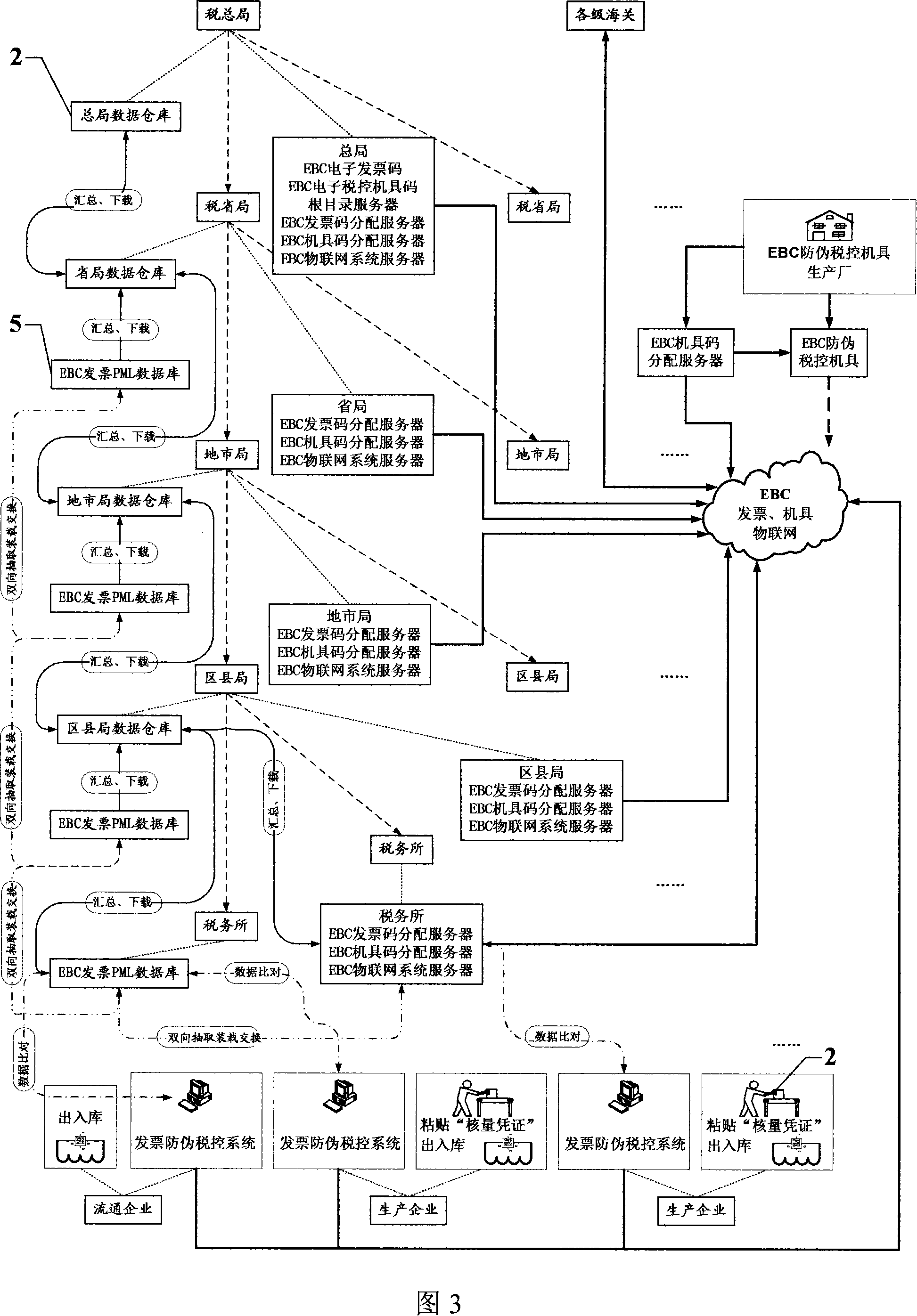
'Data great tracking' tax controlling system and tax controlling terminal based on EPC, EBC article internet
Construct and operation of a large-scale tracking tax control system for circulation tax verification amount and note control, note verification and tax control and data, based on EPC and EBC goods web, as well as a relevant tax control terminal. State Administration of Taxation provides an EPC code root directory DNS server; production enterprises and merchandising enterprises establish EPC code allocation servers, EPC system Savant servers, ONS servers and PML databases, in order to construct a commodity goods web based on EPC; State Administration of Taxation comprises an EBC code root directory DNS server and an EBC code allocation server; different levels of tax administrations and customs are composed of EBC system Savant servers, ONS databases and PML databases, so as to construct a nationwide goods web for EBC electronic invoices, machines and tools; as for all product arrangement RFID verification amount vouchers, the system utilizes RFID decoders to record commodity primary information and goods flow path information; all the enterprises utilize EBC tax control machines and tools to add EBC codes into invoice contents electronic data, and instaneously transmit to downstream tax administrations for comprehensive comparison; all market law enforcement agencies and purchasers and consumers can use EPC interpreters to verify commodity RFIDs, in order to form a powerful tax control system that covers everywhere.
Owner:SICHUAN ZHENGDAOTIANHE INFORMATION TECH
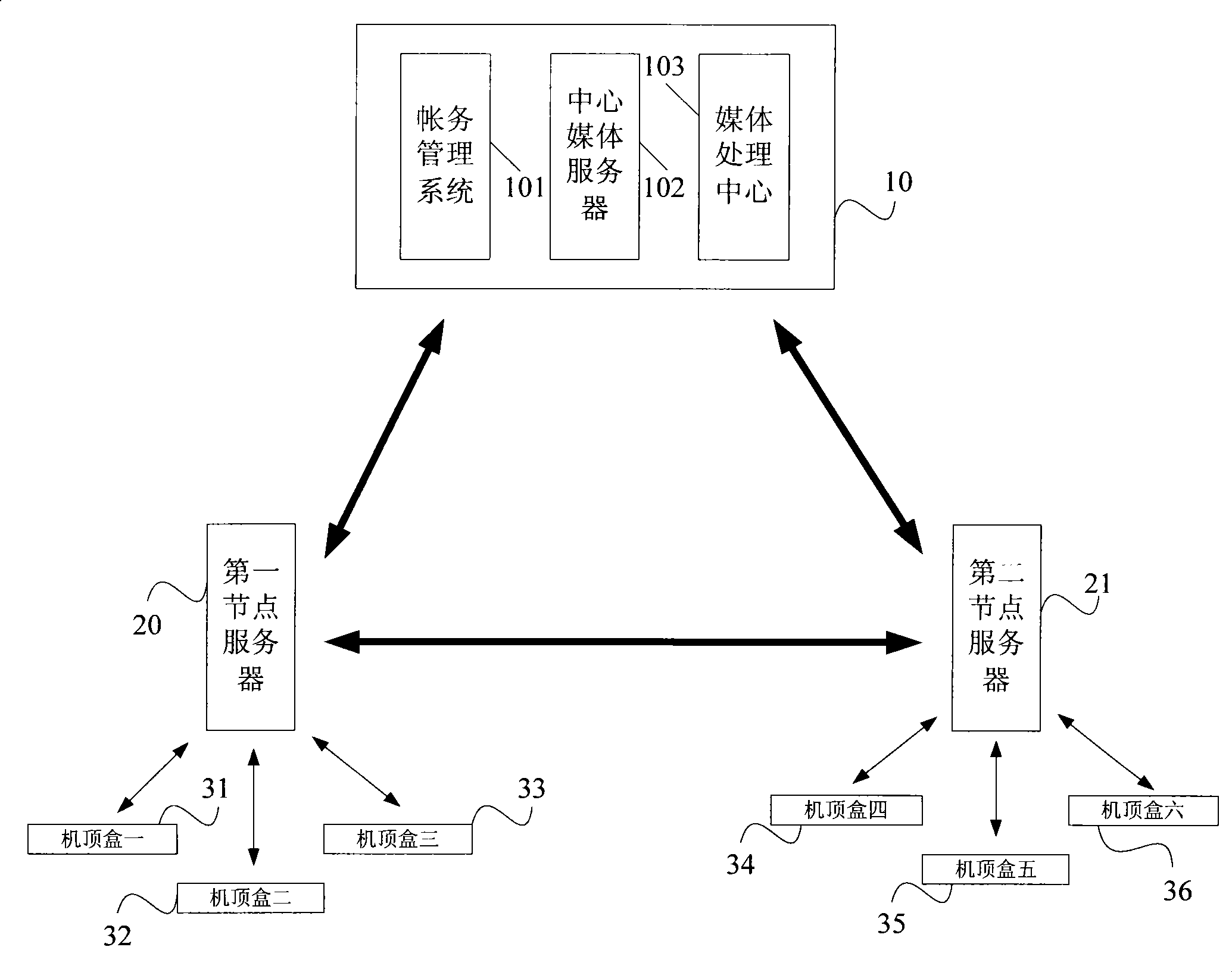
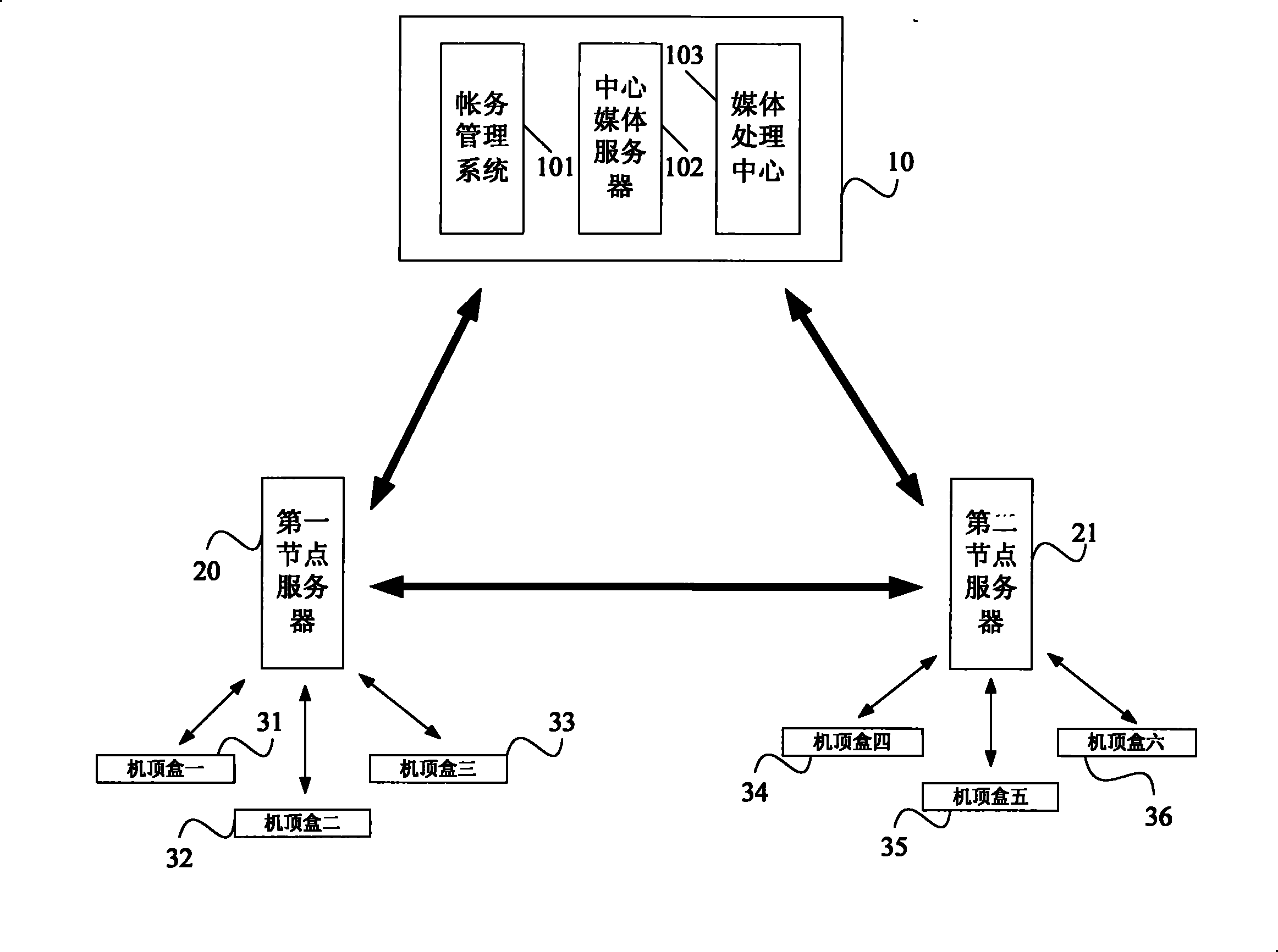
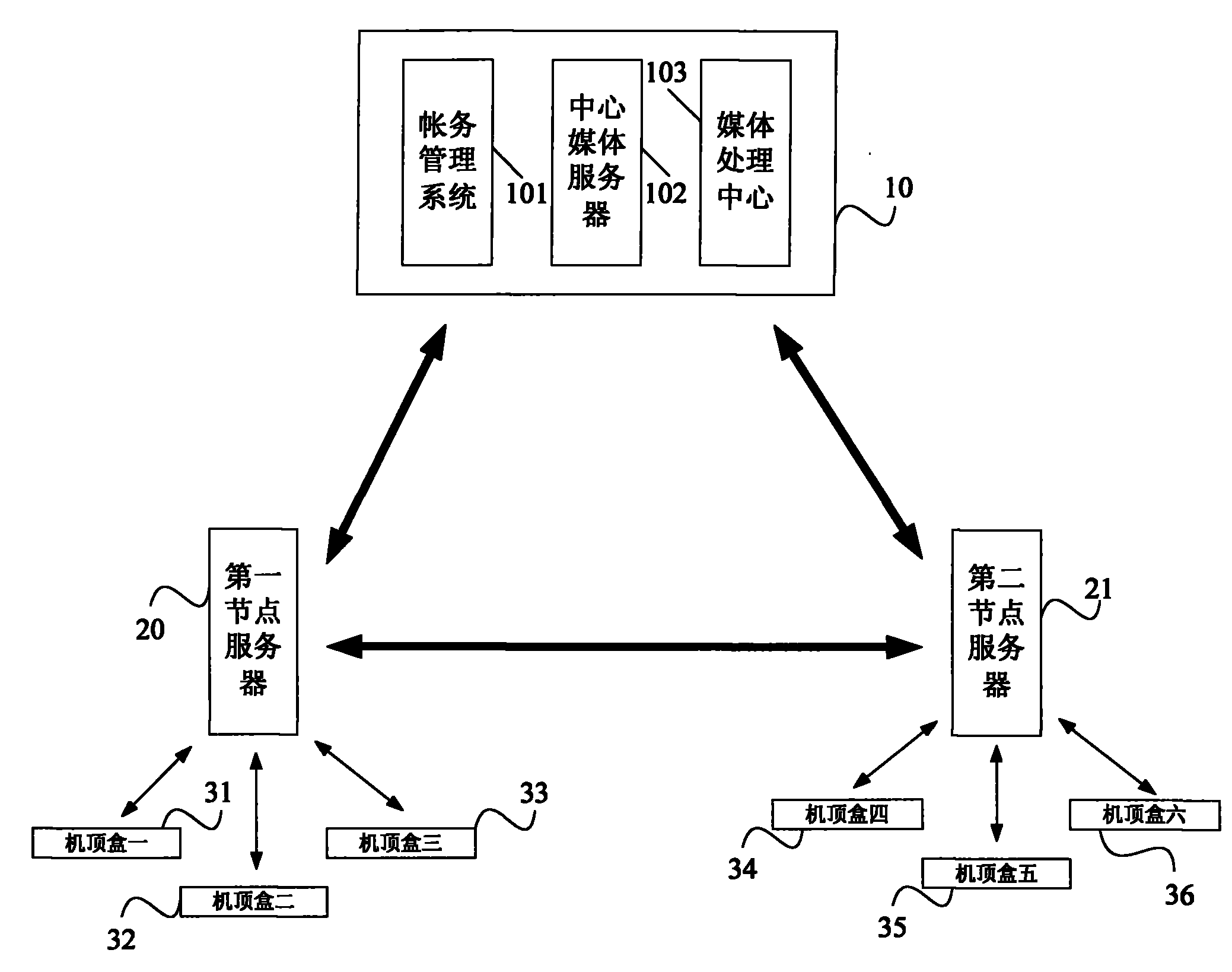
Playing on demand system for video
ActiveCN101453624ARealize network operationEasy to distributeTwo-way working systemsCommunity orComputer science
The invention discloses a (hotel, community or family) video-on-demand system. The video-on-demand system comprises a center server, a node server and a user terminal, wherein the center server is used for storing video information; the node server is used for establishing communication with the center server through a network so as to obtain at least one part of the video information and generating a programme list according to the video information; the user terminal is used for reading the programme list and displaying the programme list through display equipment; and when a user orders a corresponding programme, the user sends a video-on-demand request to the node server, reads corresponding decoded video information and plays the information through the display equipment. In the video-on-demand system, as each (hotel, community or family) node server is connected with the center server through the wide area network, thereby realizing network operation of the whole video-on-demand system. The video-on-demand system can carry out programme distribution and management through the network, thereby making the distribution and management operation simple and feasible and also improving efficiency.
Owner:QINGDAO TONGXIN INNOVATION LAB TECH CO LTD
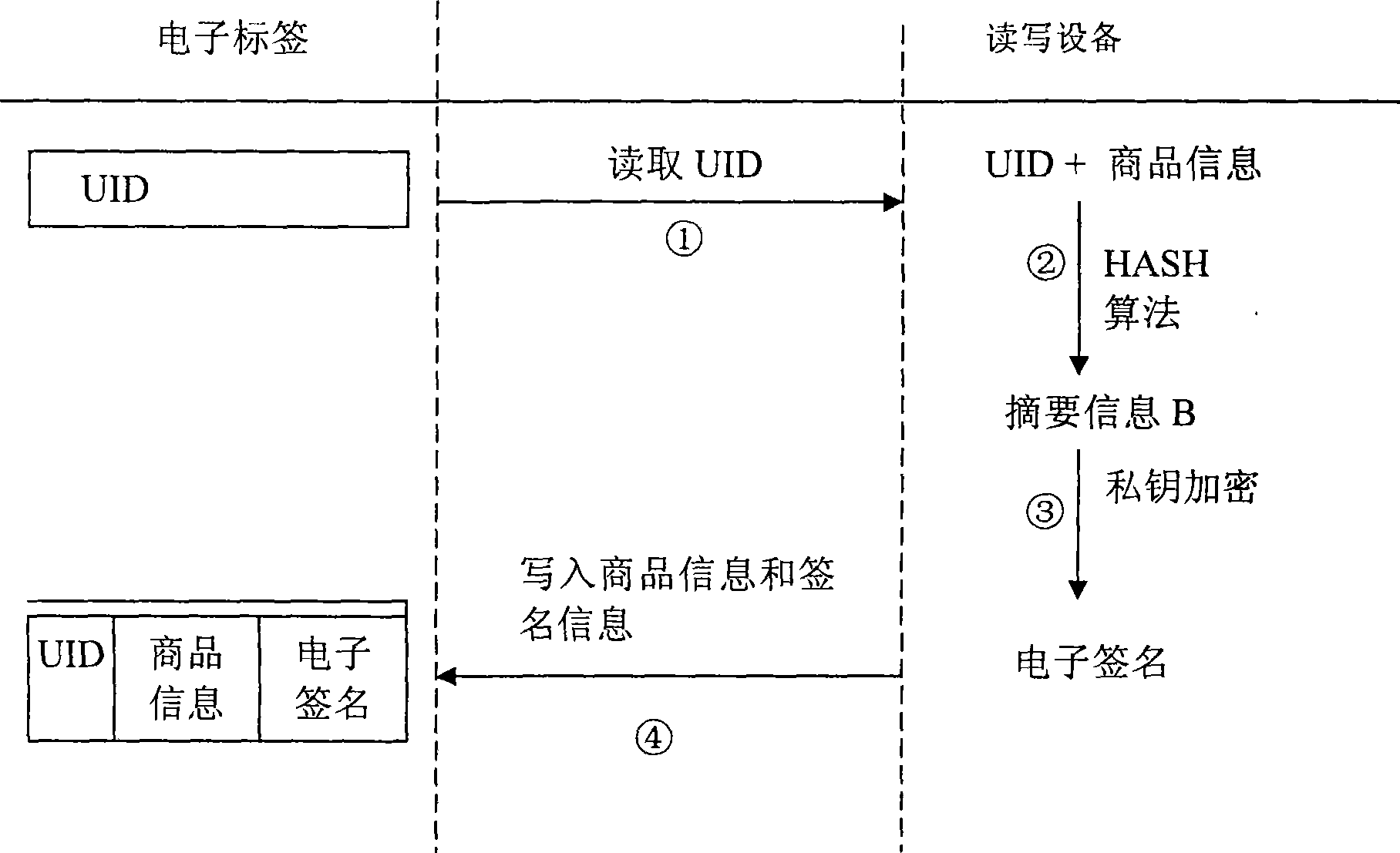
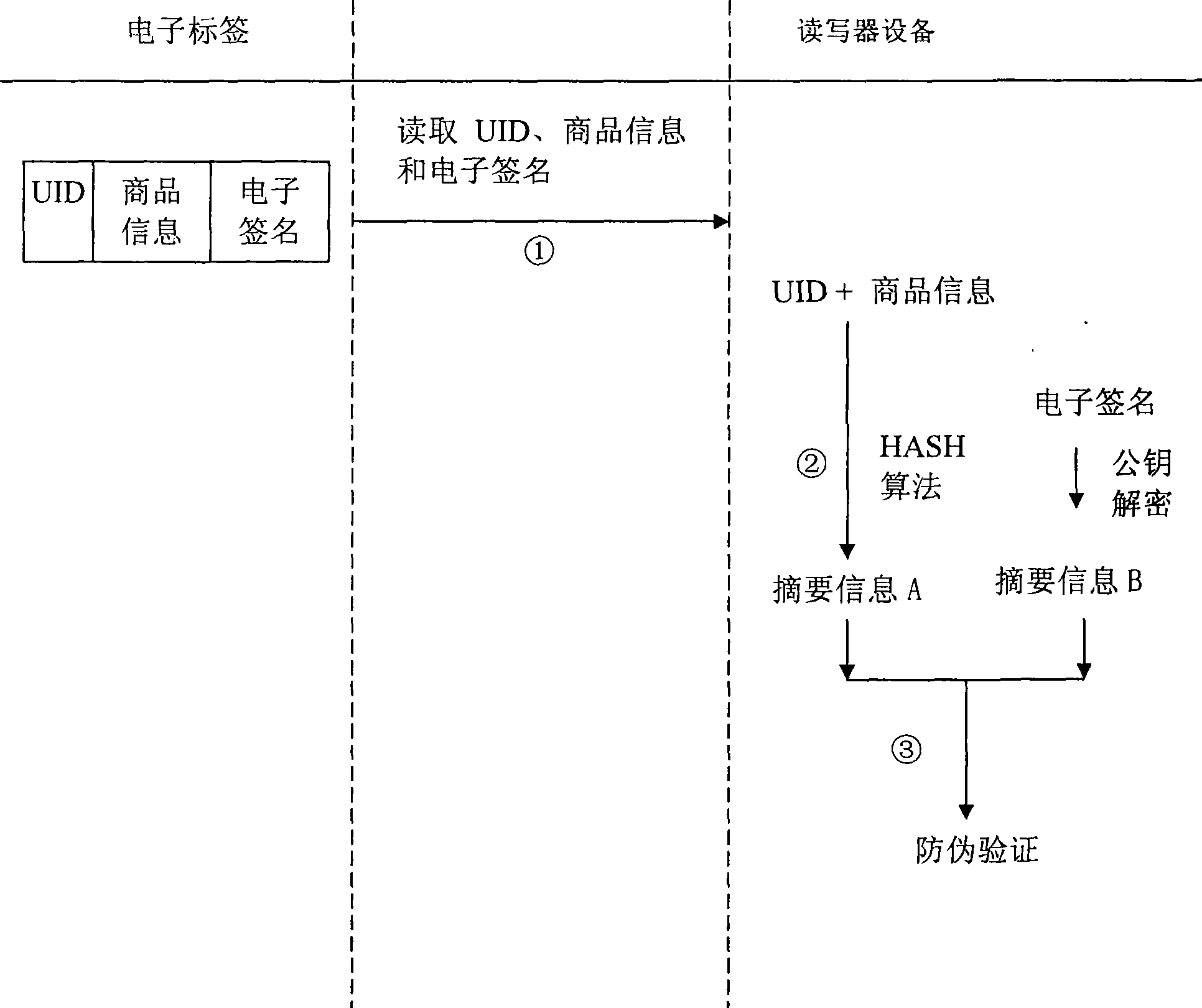
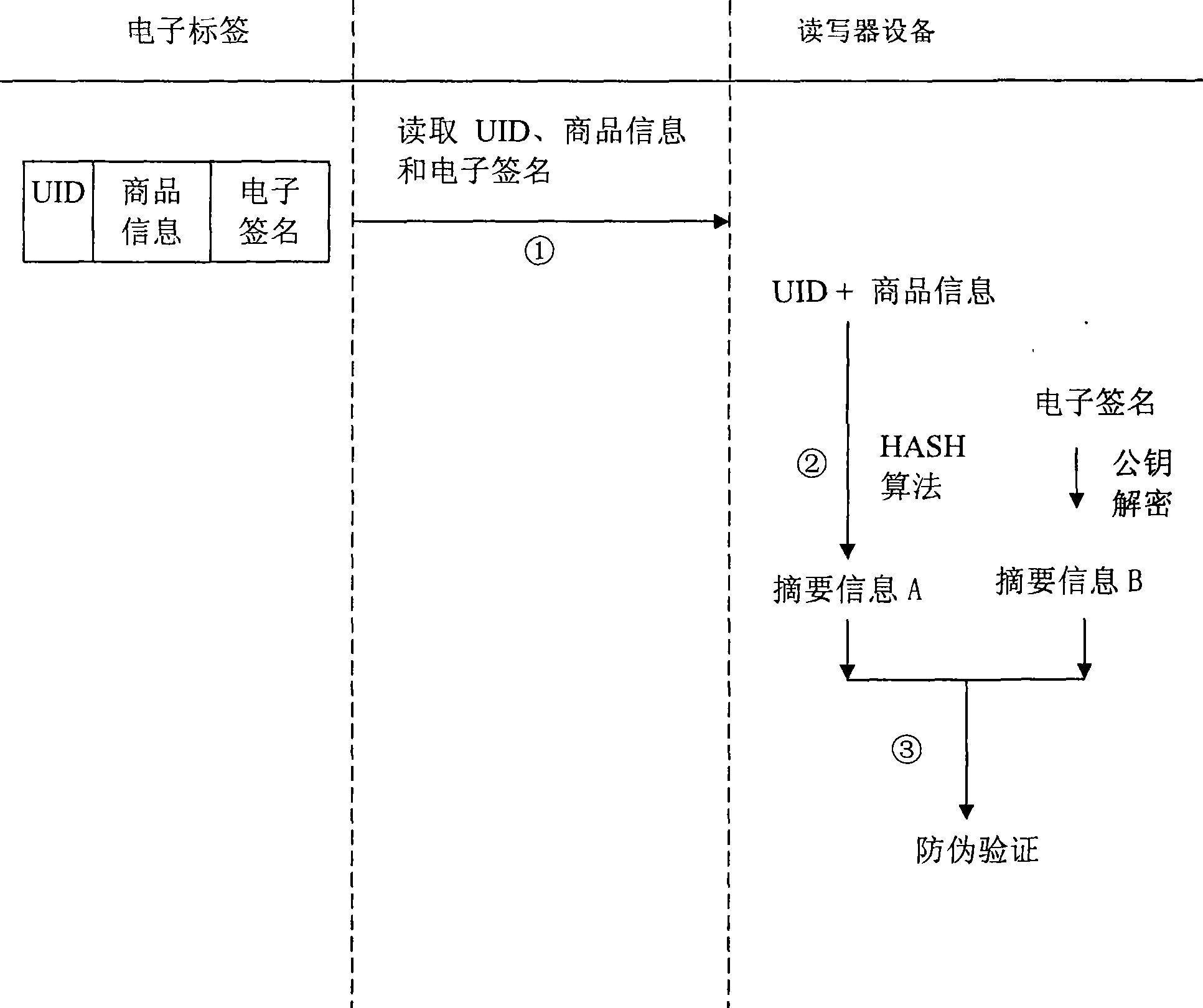
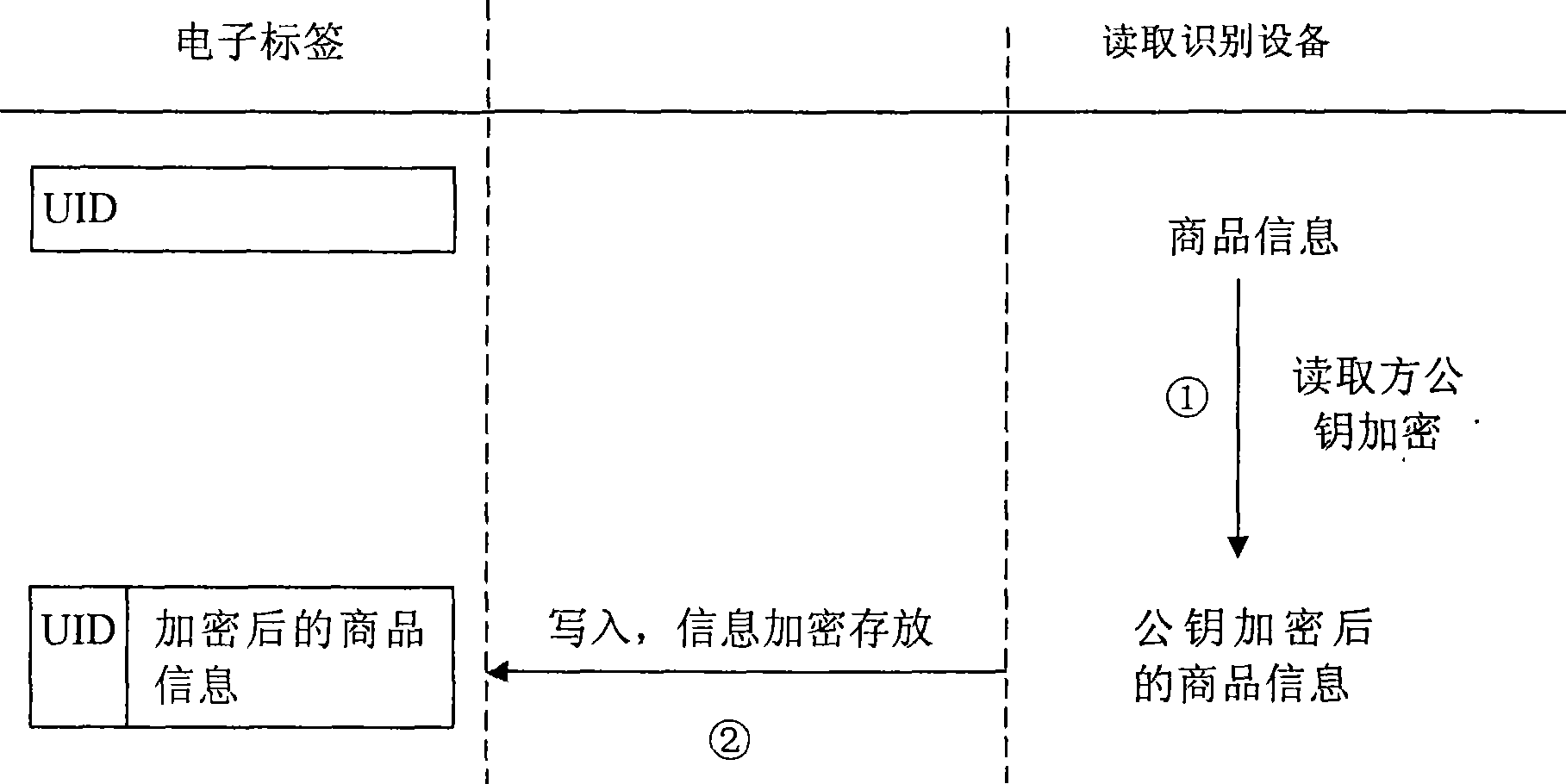
Electronic label security system
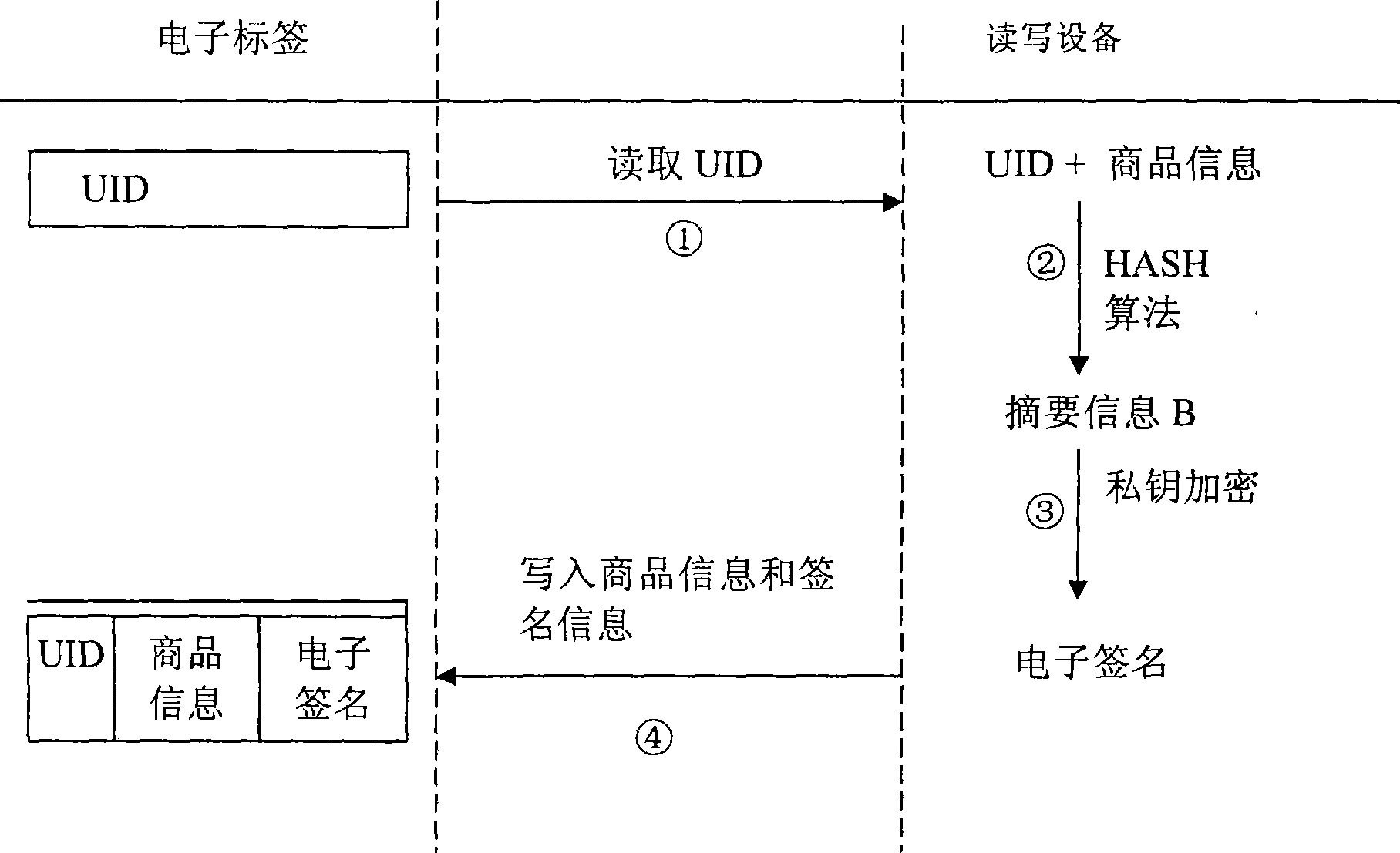
ActiveCN101369306AProtect trade secretsConvenient verificationSensing record carriersIdentification deviceSecurity system
The invention provides an electronic label safety system of performing true or false identification. The electronic label safety system includes a label and a reading identification device, wherein storage media are included on the electronic label and have unique identification UID, and information of the commodities are written on the electronic label. A private key is used to encrypt UID of the label and information of the commodities, to obtain the electronic label. The identification equipment is read for the UID of the label, the information of the commodities and the electronic signature. A public key is used to decrypt the electronic signature to obtain the UID of the label, wherein the anti-counterfeiting identification is not passed.
Owner:广东南方信息安全产业基地有限公司
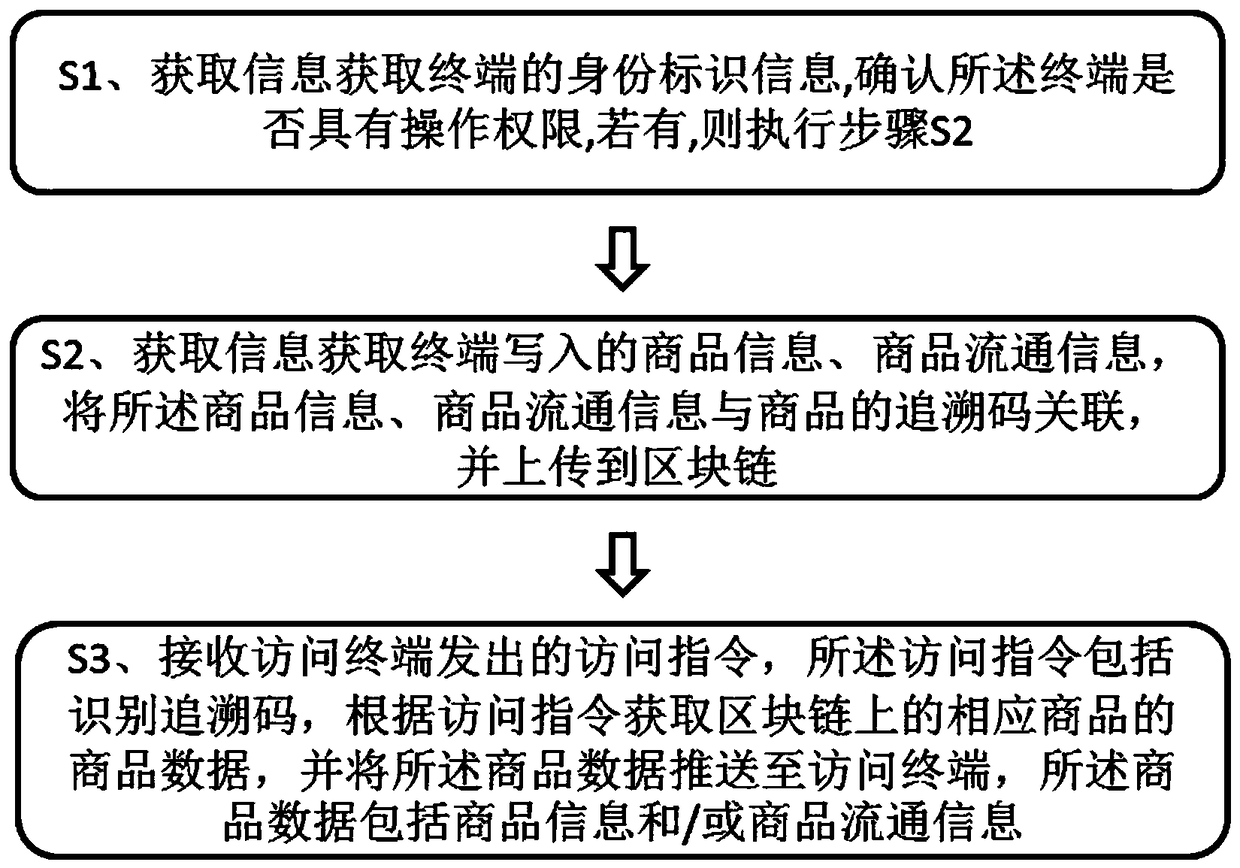
Commodity anti-counterfeiting traceability system, method, device and storage medium
InactiveCN109360000AGuarantee authenticity and reliabilityPremium shopping experienceCo-operative working arrangementsCommerceBlockchainInternet of Things
Owner:SF TECH
Pharmaceutical information tamper-proof traceability management system based on mobile block chain
PendingCN109325775ARealize visualizationEnsure transparencyCo-operative working arrangementsCommerceTamper resistanceBarcode
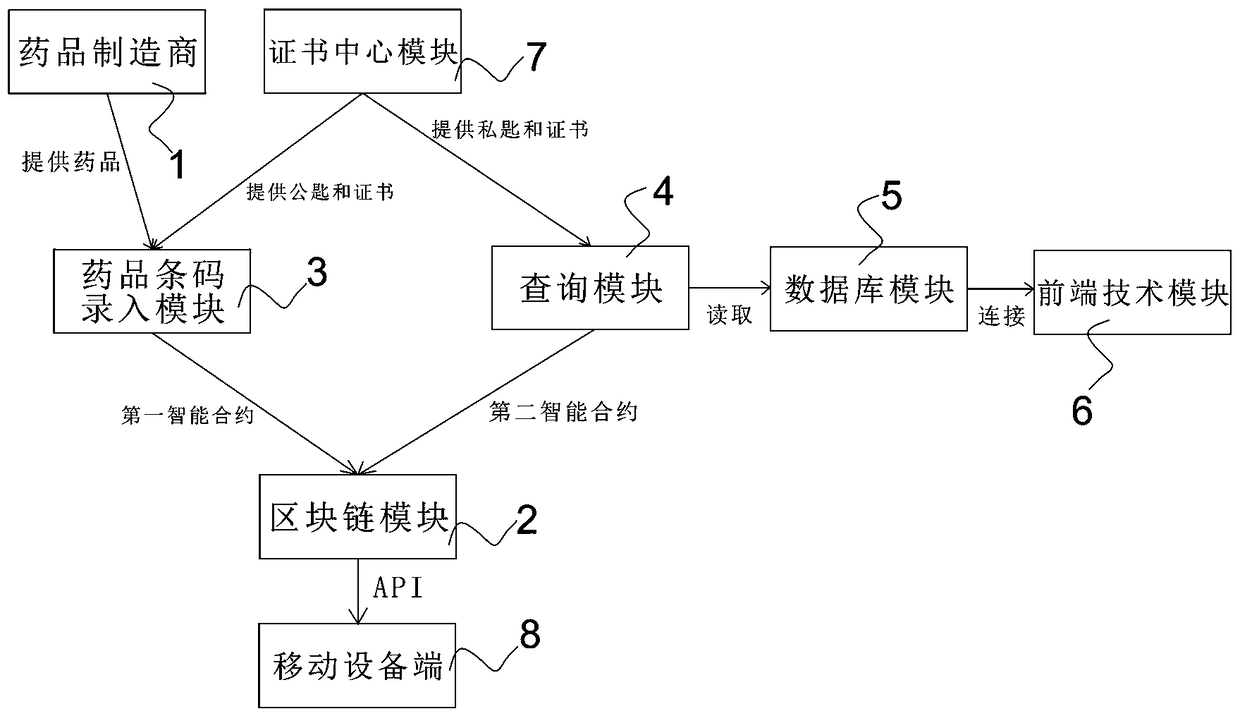
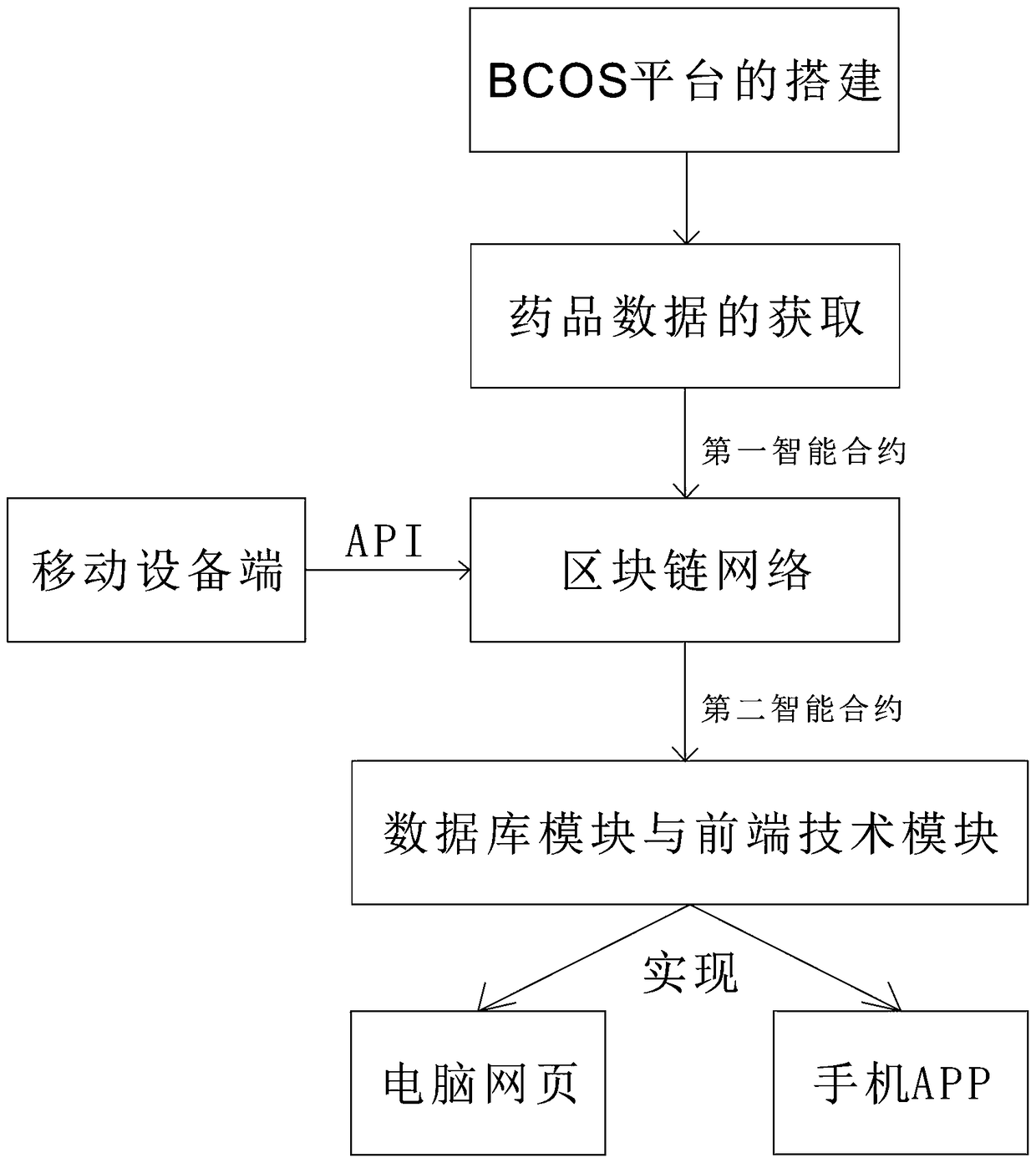
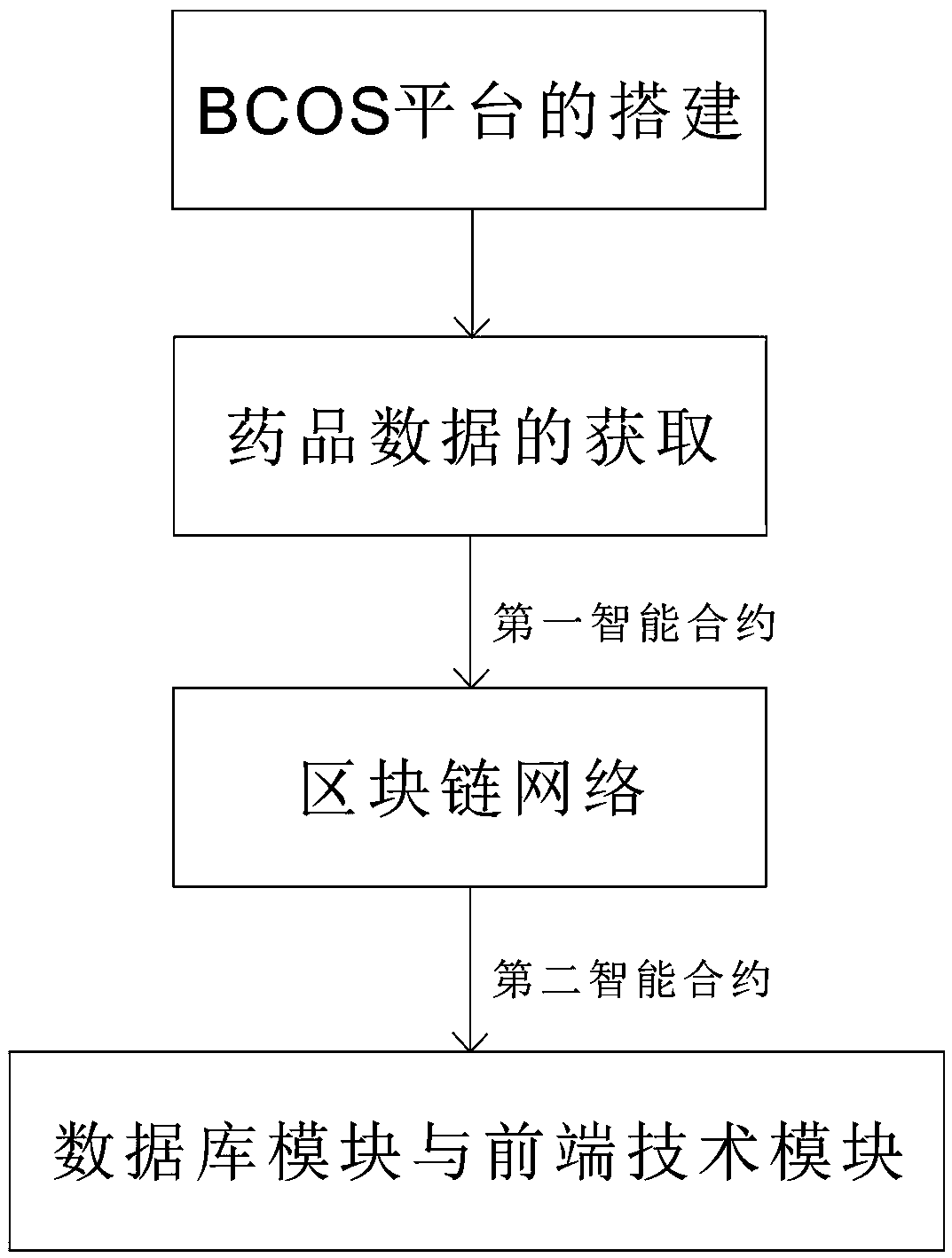
The invention relates to a pharmaceutical information tamper-proof traceability management system based on a mobile block chain, characterized by comprising a block chain module, a pharmaceutical barcode input module, a query module, a certificate center module, a mobile device terminal for connecting the block chain module through a mobile block chain API, a database module for reading and storing data and a front-end technical module for realizing data visualization. The pharmaceutical bar code input module encrypts the privacy data of the drug and the enterprise through the public key andstores the read bar code data into the block chain module through the first intelligent contract, and the query module reads the privacy and public data in the block chain module through the private key and the second intelligent contract. The invention realizes the tracking of the drug supply chain and the visualization of the data, and guarantees the transparency of the drug supply chain. The mobile block chain API not only enables the mobile device to participate in the network governance and transaction information verification as a node in the block chain network, but also can access thedata on the storage chain, thereby improving the convenience.
Owner:GUANGDONG POLYTECHNIC NORMAL UNIV
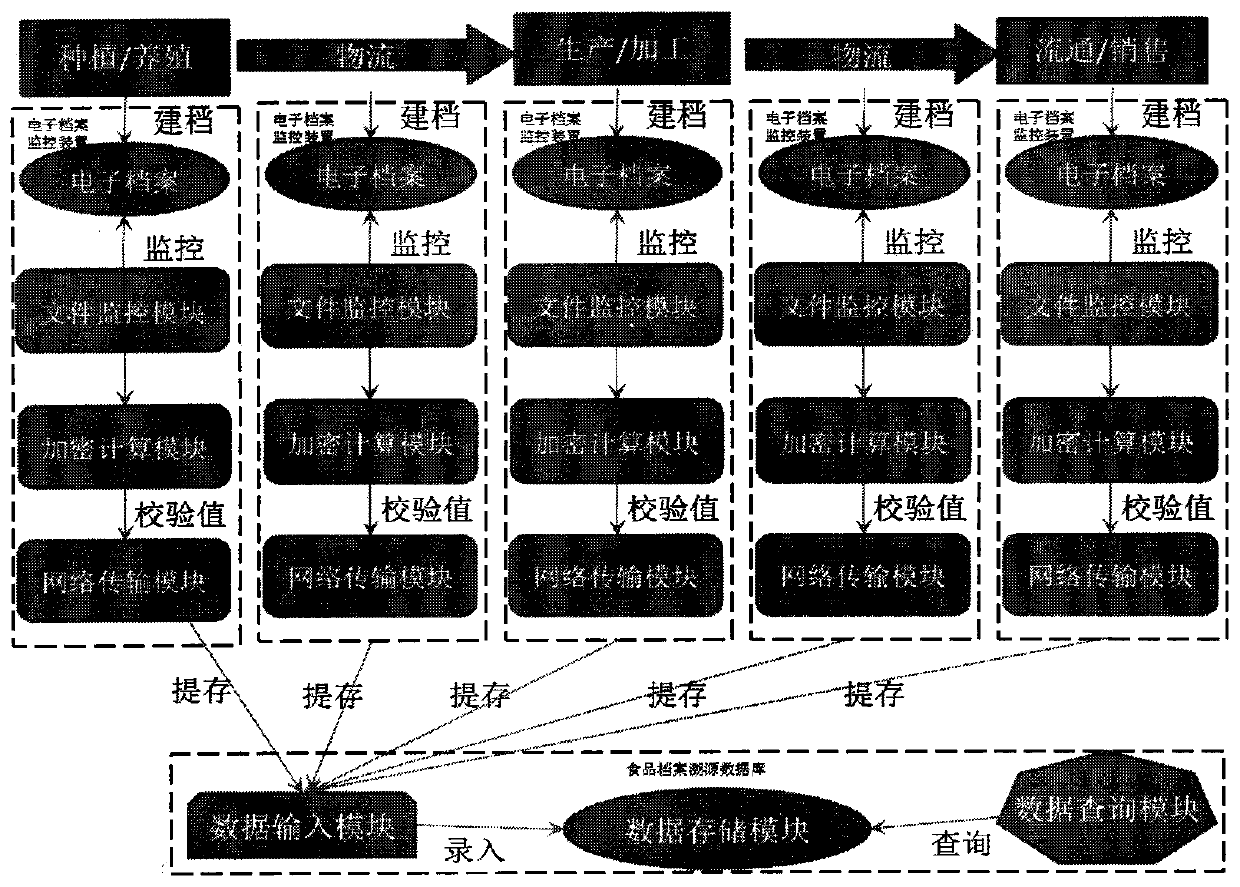
Food safety traceability system capable of preventing archive from being tampered
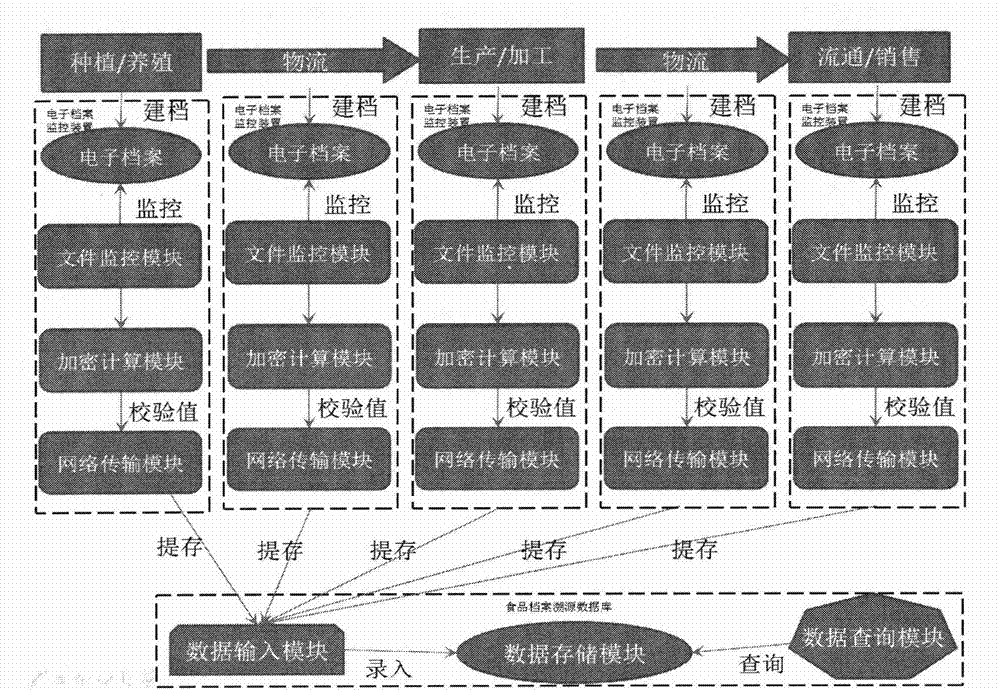
Provided is a food safety traceability system capable of preventing archive from being tampered. The food safety traceability system comprises a food archive database and a monitoring device. The monitoring device comprises an encryption module, an information sending module and a file monitoring module. The encryption module calculates integrity checking information of electronic archives and transmits the integrity checking information to an information reception module of the food archive database through the information sending module; and the file monitoring module is set to carry out monitoring on archive file establishing, modifying and deleting operation. A processing module comprises a storage module, wherein the storage module is for storing names of monitoring food and food motoring steps as well as identification information of the monitoring food; and an identification identifying module, wherein the identification identifying module is for identifying identification information of food main bodies. The food archive database also comprises a data input module, a data storage module and a data query module for querying integrity checking information of the electronic archive files.
Owner:刘品新 +1
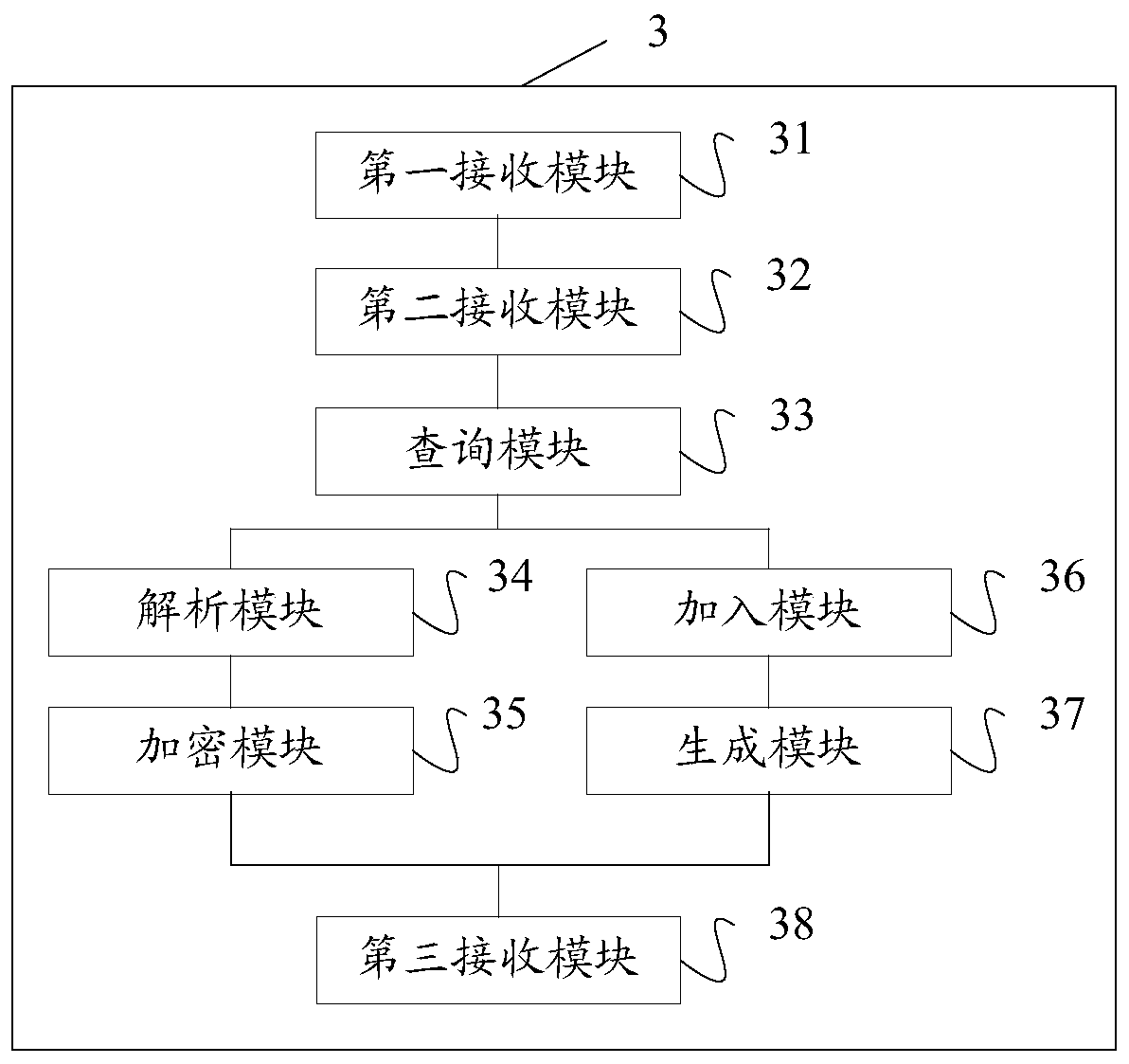
Data query system and method, storage medium and terminal
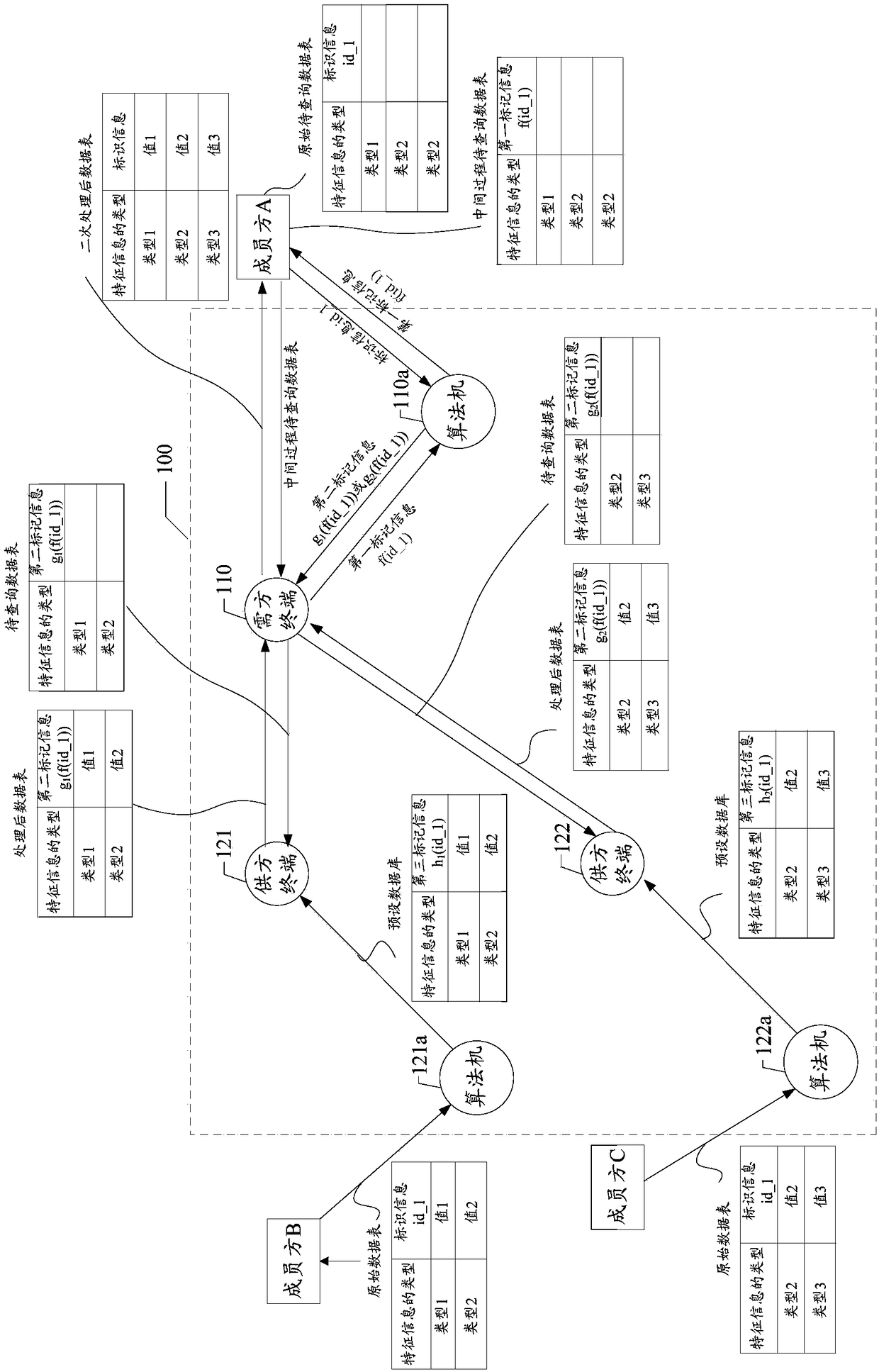
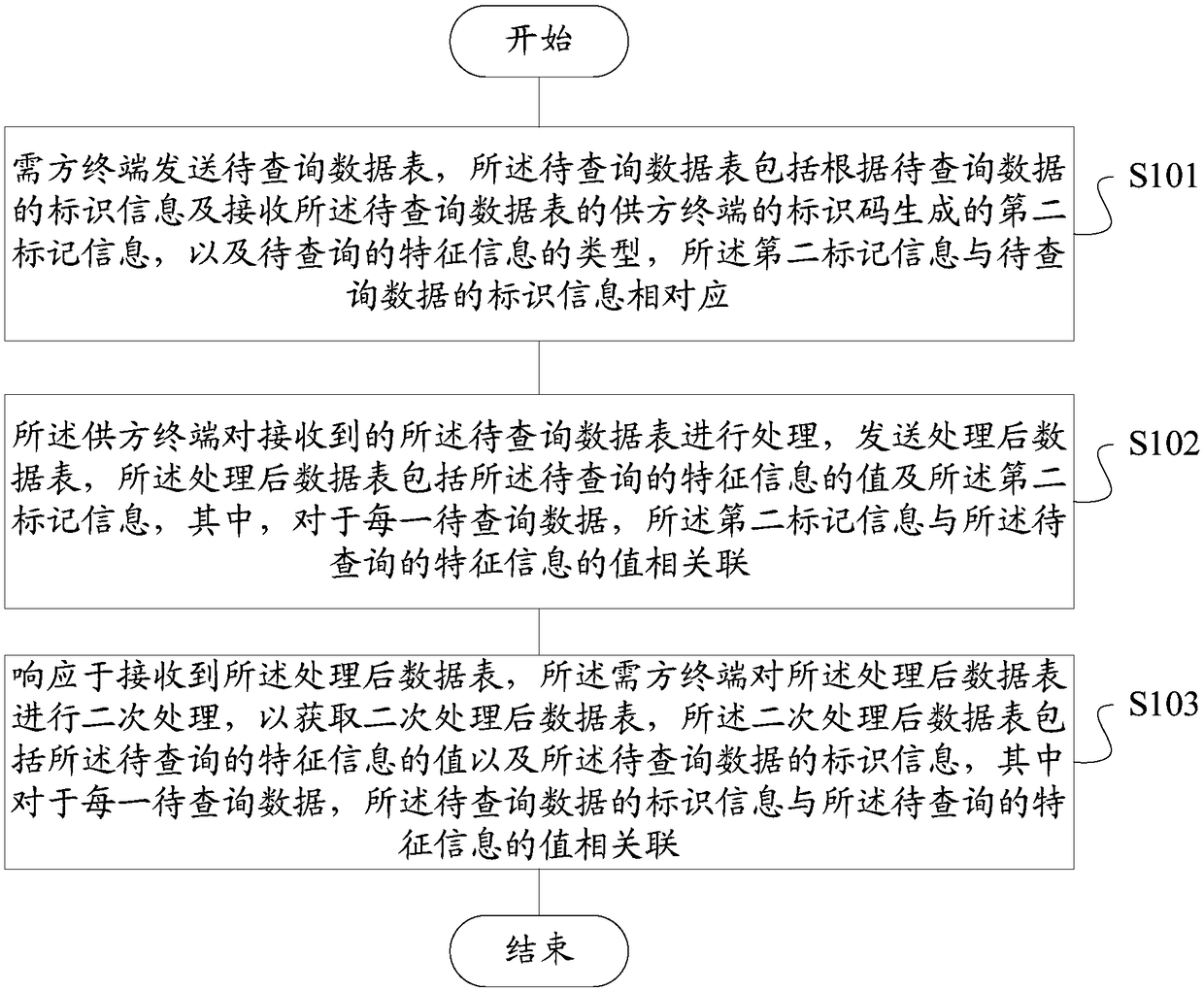
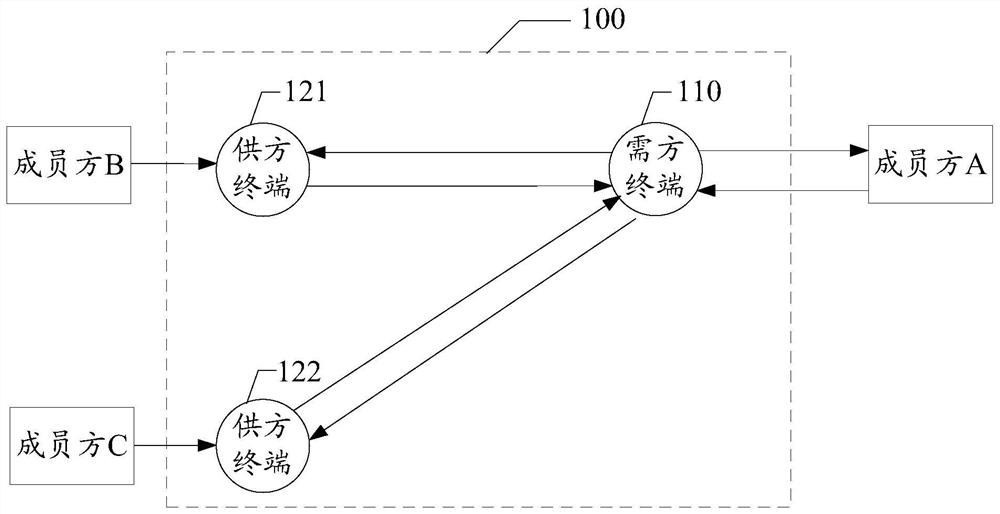
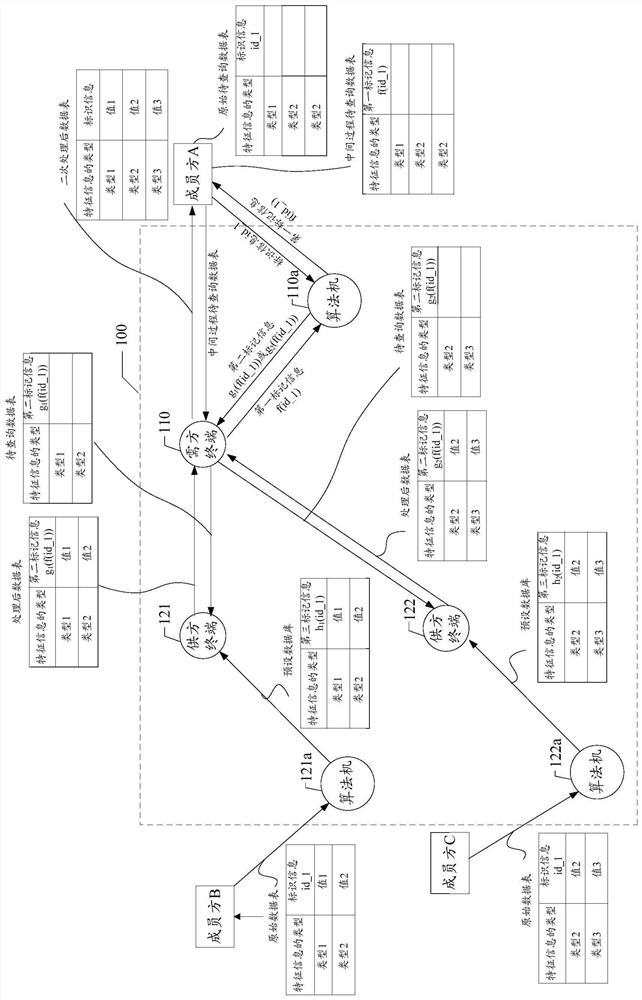
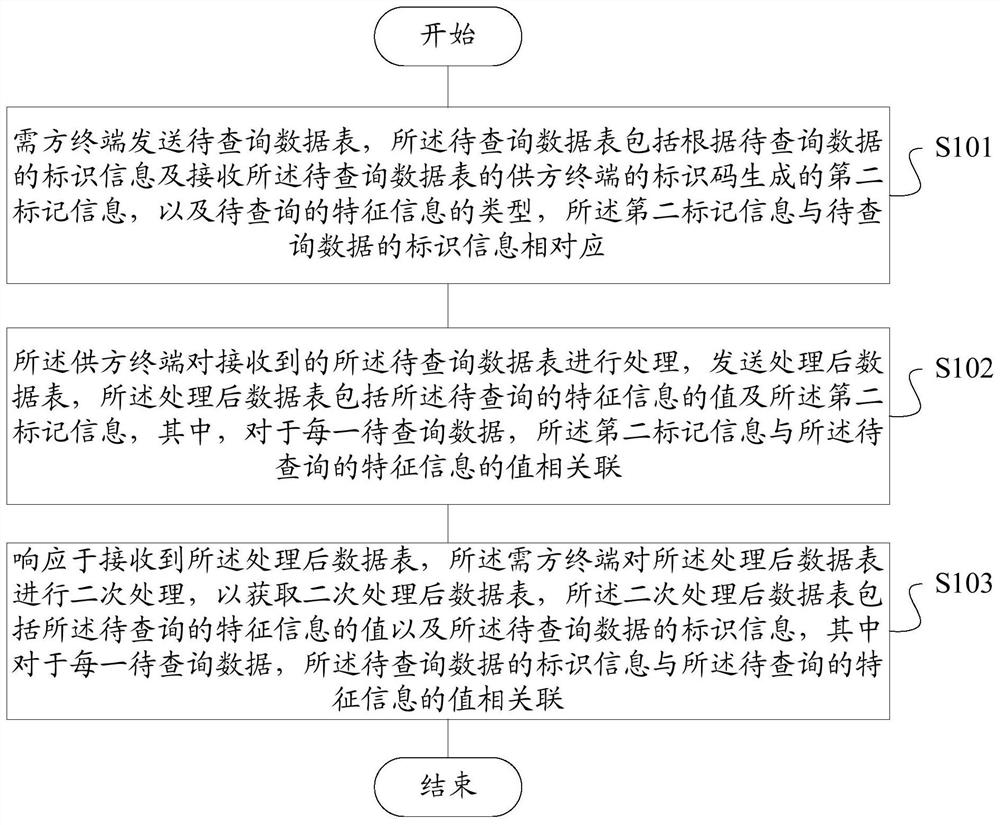
ActiveCN108268799AGuaranteed privacyProtect trade secretsDigital data protectionComputer terminalData query
The invention discloses a data query system and method, a storage medium and a terminal. The system comprises a demander terminal and a supplier terminal. The demander terminal sends a to-be-queried data table, wherein the to-be-queried data table comprises second marker information generated according to identifier information of to-be-queried data and an identifier code of the supplier terminalreceiving the to-be-queried data table, and the type of to-be-queried feature information. The supplier terminal processes the received to-be-queried data table and sends the processed data table, wherein the processed data table comprises the value of the to-be-queried feature information and the second marker information; and in response to operation of receiving the processed data table, the demander terminal performs secondary processing on the processed data table to obtain a data table subjected to secondary processing, wherein the data table subjected to the secondary processing comprises the value of the to-be-queried feature information and the identifier information of the to-be-queried data. Through the scheme provided by the invention, sensitive information can be effectively isolated during data query, so that the privacy of personal privacy information is guaranteed and the leakage risk is lowered.
Owner:上海数据发展科技有限责任公司
Method and apparatus for multilevel transaction based on block chain
Owner:上海专精特新金融信息服务有限公司 +1
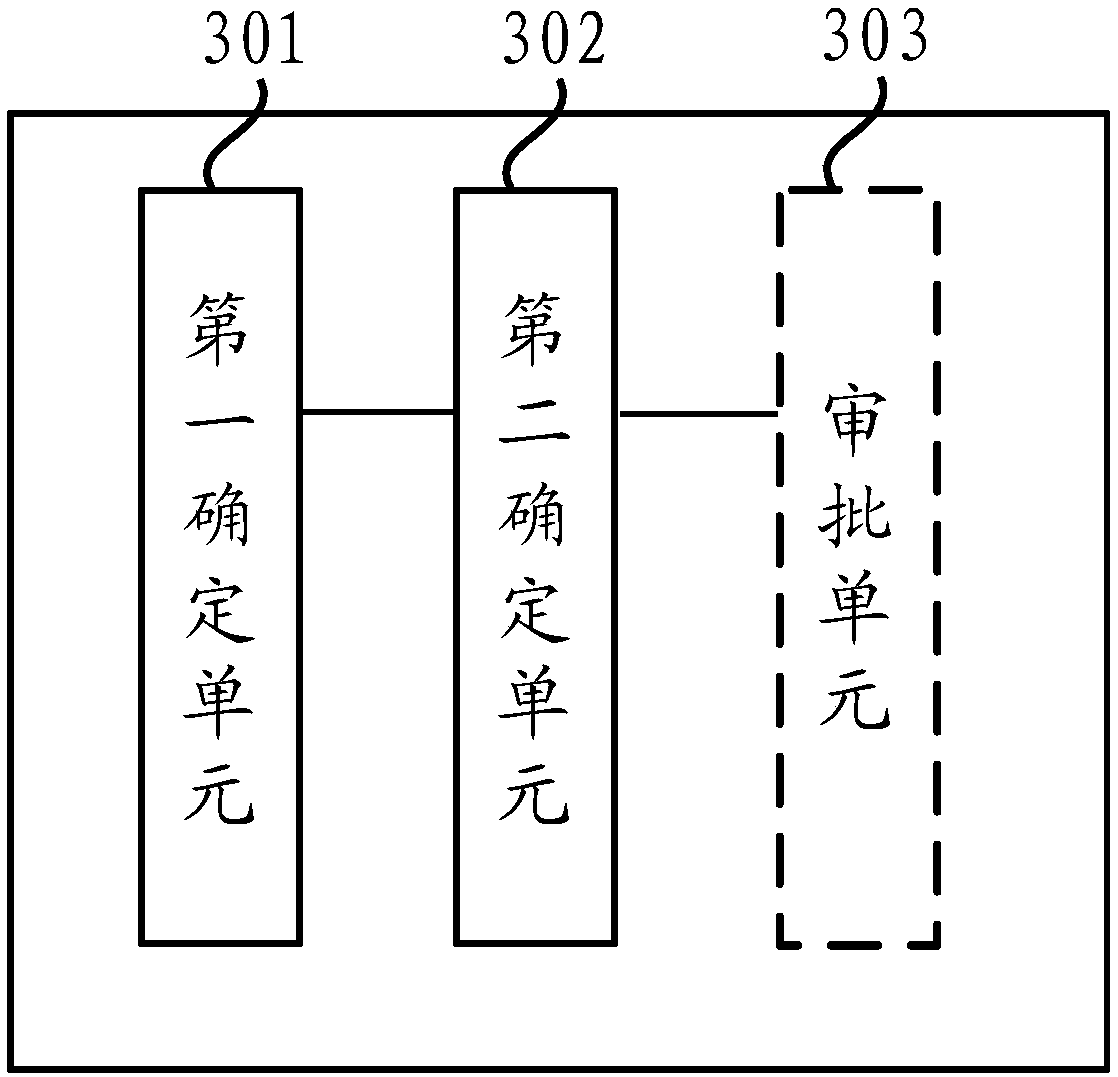
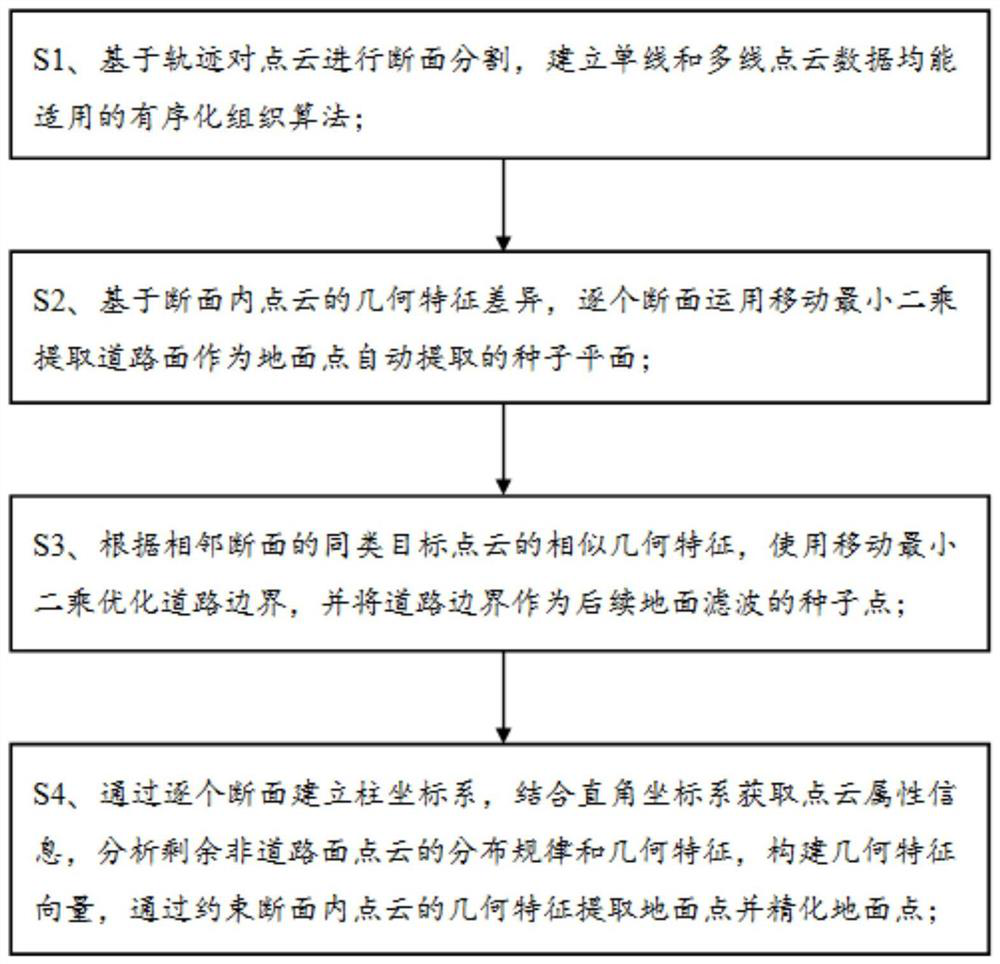
Vehicle-mounted point cloud ground point extraction method and storage medium
ActiveCN114119998APrevent extractionAccurate extractionImage enhancementImage analysisAlgorithmMobile lidar
The invention relates to the technical field of mobile laser radar data processing, in particular to a vehicle-mounted point cloud ground point extraction method and a storage medium, and the method comprises the steps: S1, carrying out the section segmentation of a point cloud based on a track, and building an ordering organization algorithm which can be suitable for single-line and multi-line point cloud data; s2, on the basis of geometric feature differences of point clouds in the sections, road surfaces are extracted from the sections one by one by applying a moving least square method to serve as seed planes for automatic extraction of ground points; s3, according to similar geometric features of similar target point clouds of adjacent sections, optimizing a road boundary by using a moving least square method, and taking the road boundary as a seed point of subsequent ground filtering; and S4, establishing a cylindrical coordinate system section by section, analyzing the distribution rule and geometric features of the remaining non-road surface point clouds, and extracting and refining ground points by constraining the geometric features of the point clouds in the sections. According to the invention, the technical problems of low precision, slow speed and poor applicability of the vehicle-mounted LiDAR point cloud ground point extraction method are solved.
Owner:CHENGDU UNIVERSITY OF TECHNOLOGY
Hierarchical simulation method for three-dimensional chip power supply ground network
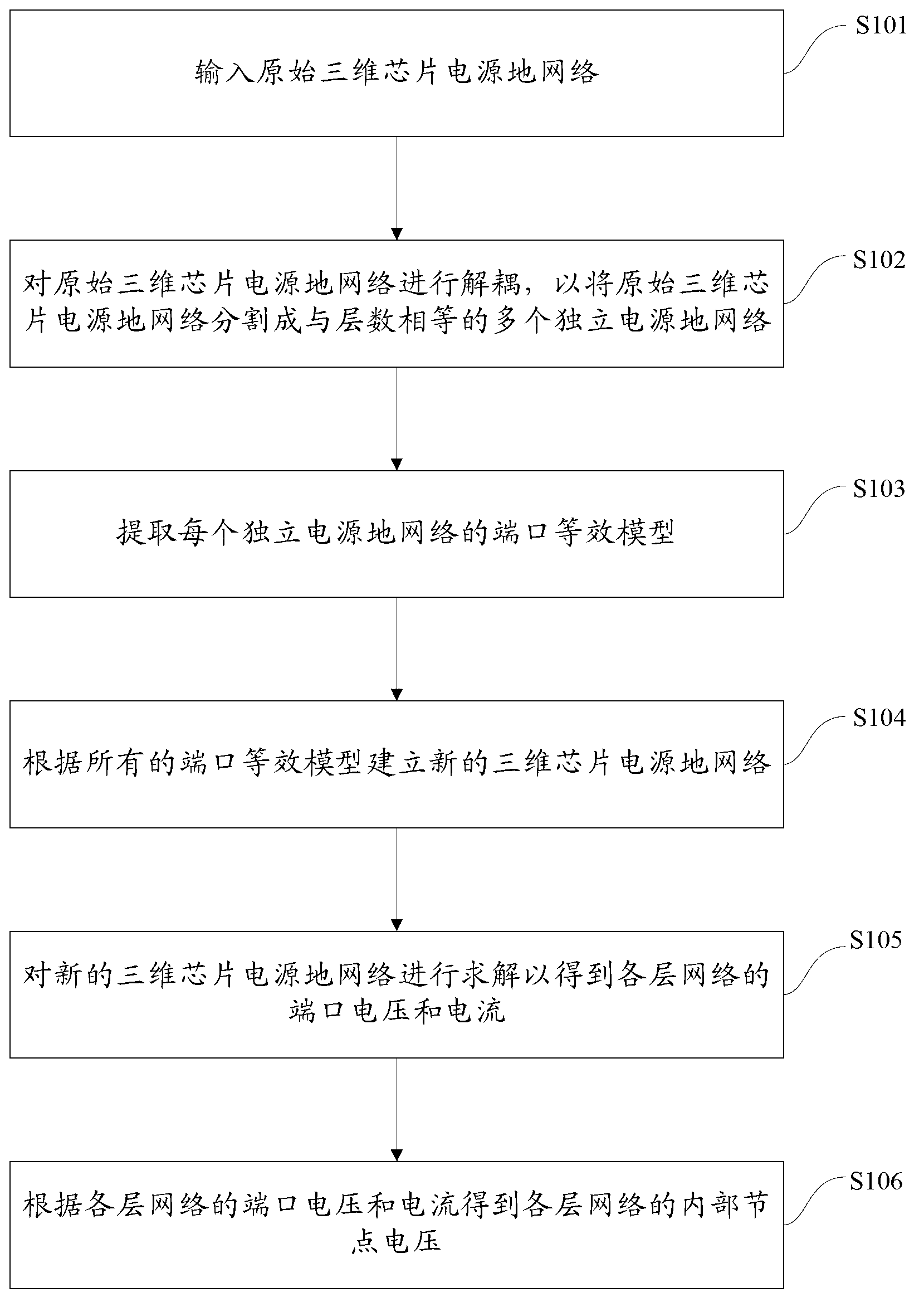
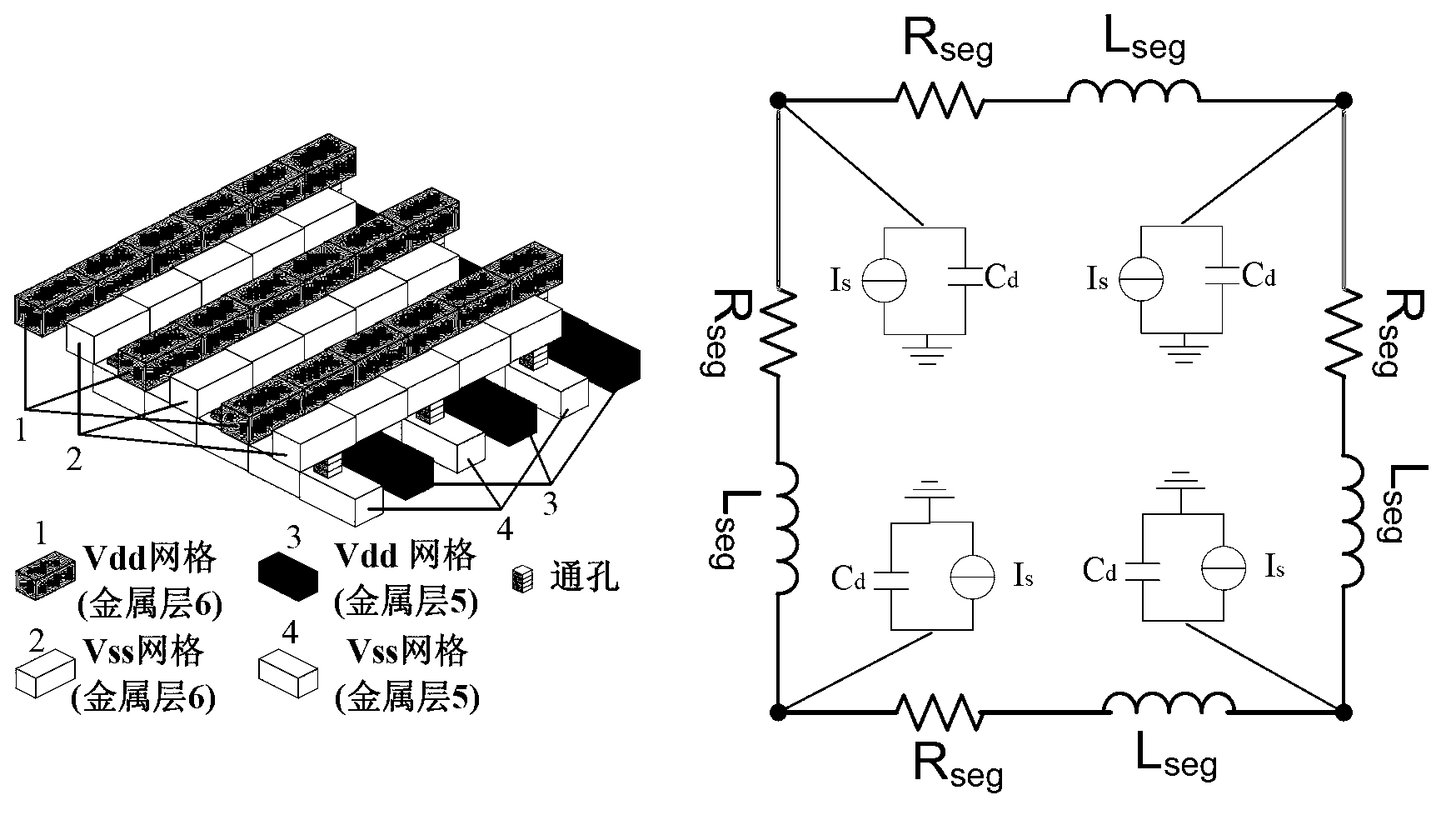
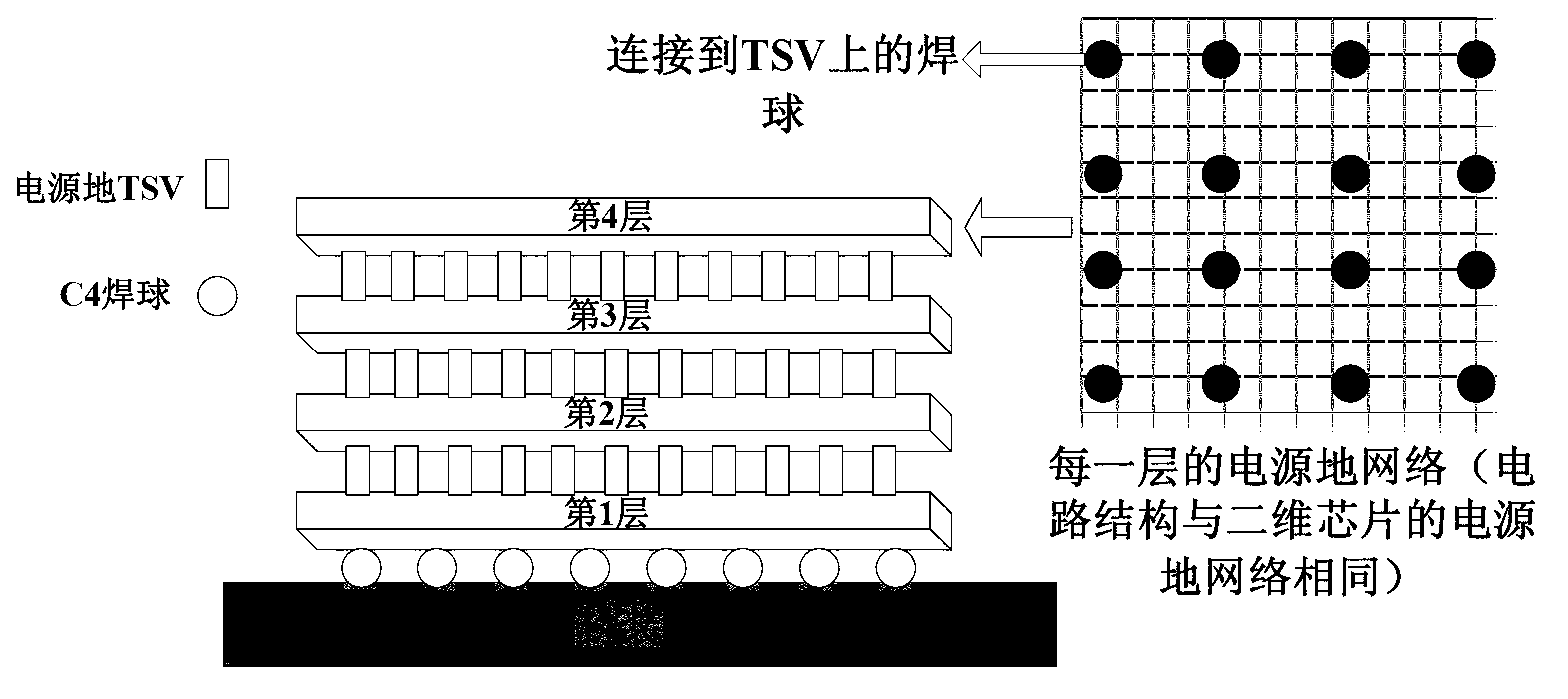
InactiveCN103310070AReduce complexityGuaranteed electrical characteristicsSpecial data processing applicationsEngineeringThree-dimensional integrated circuit
The invention provides a hierarchical simulation method for a three-dimensional chip power supply ground network. The method comprises the following steps: inputting an original three-dimensional chip power supply ground network; decoupling the original three-dimensional chip power supply ground network so as to divide the original three-dimensional chip power supply ground network into a plurality of independent power supply ground networks with the number as same as the layer number; extracting a port equivalent model of each independent power supply ground network; establishing a new three-dimensional chip power supply ground network according to all the port equivalent models; solving the new three-dimensional chip power supply ground network to obtain port voltage and current of each layer of network; obtaining the internal node voltage of each layer of network according to the port voltage and current of each layer of network. According to the method provided by the invention, simulating calculation can be performed on each layer in parallel, so that the calculating efficiency is improved and the simulating complexity is reduced.
Owner:TSINGHUA UNIV
System and method for controlling using right of each function of electronic device
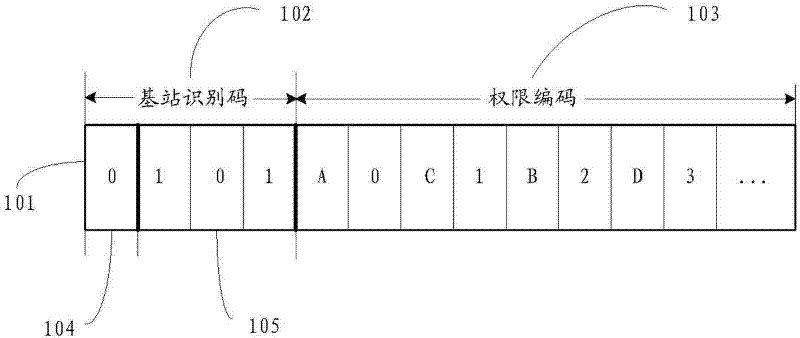
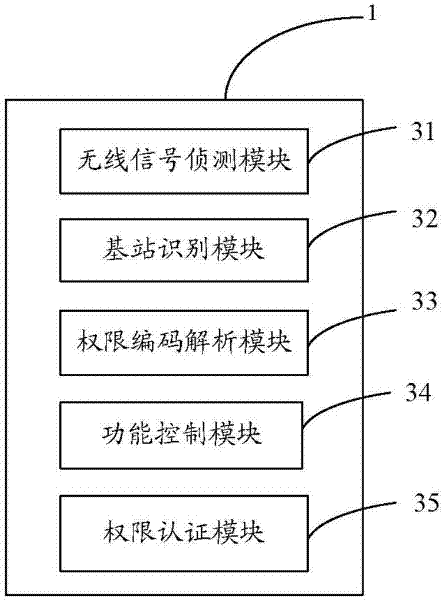
InactiveCN102547488AProtect trade secretsNo need for manual controlTelemetry/telecontrol selection arrangementsControl systemComputer science
Provided is a method for controlling using right of each function of an electronic device. The method includes the following steps: detecting a wireless signal sent by a base station; judging whether the base station is a preset base station based on an identification code of the wireless signal; receiving user information input by a user, then determining whether the user information exists in using right level information on a server or not, recording using right level of different users by the using right level information, and obtaining the using right level corresponding to the user information from the using right level information if the user information exists in the using right level information; obtaining functions identified by the using right level from the using right code of the wireless signal based on the obtained using right level, and controlling the functions with the level identification in the electronic device to be available. The invention further provides a system for controlling the using right of each function of the electronic device, which is capable of automatically controlling the using right of each function of the electronic device according to the area where the electronic device is located.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
A data distribution system and distribution method
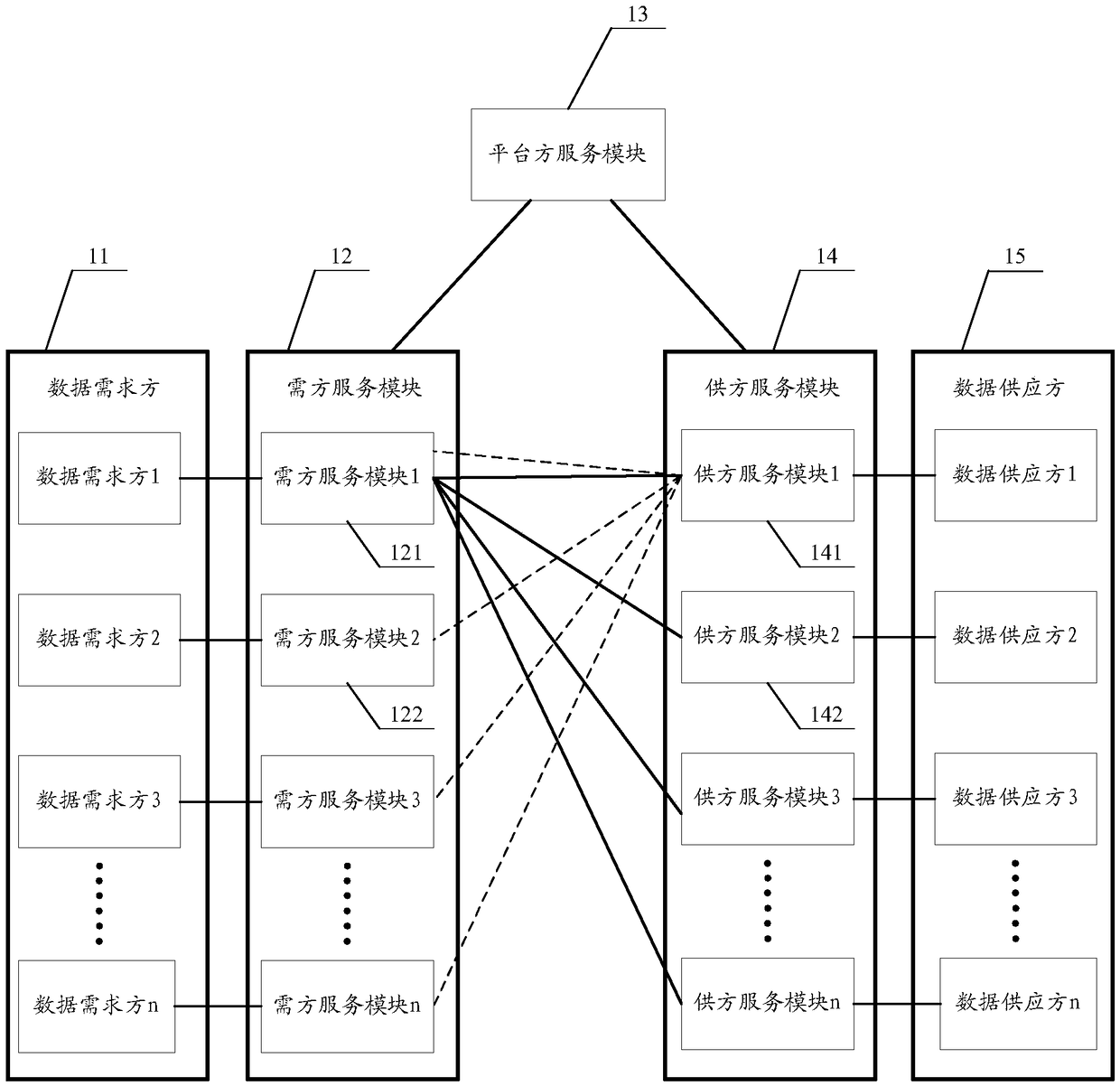
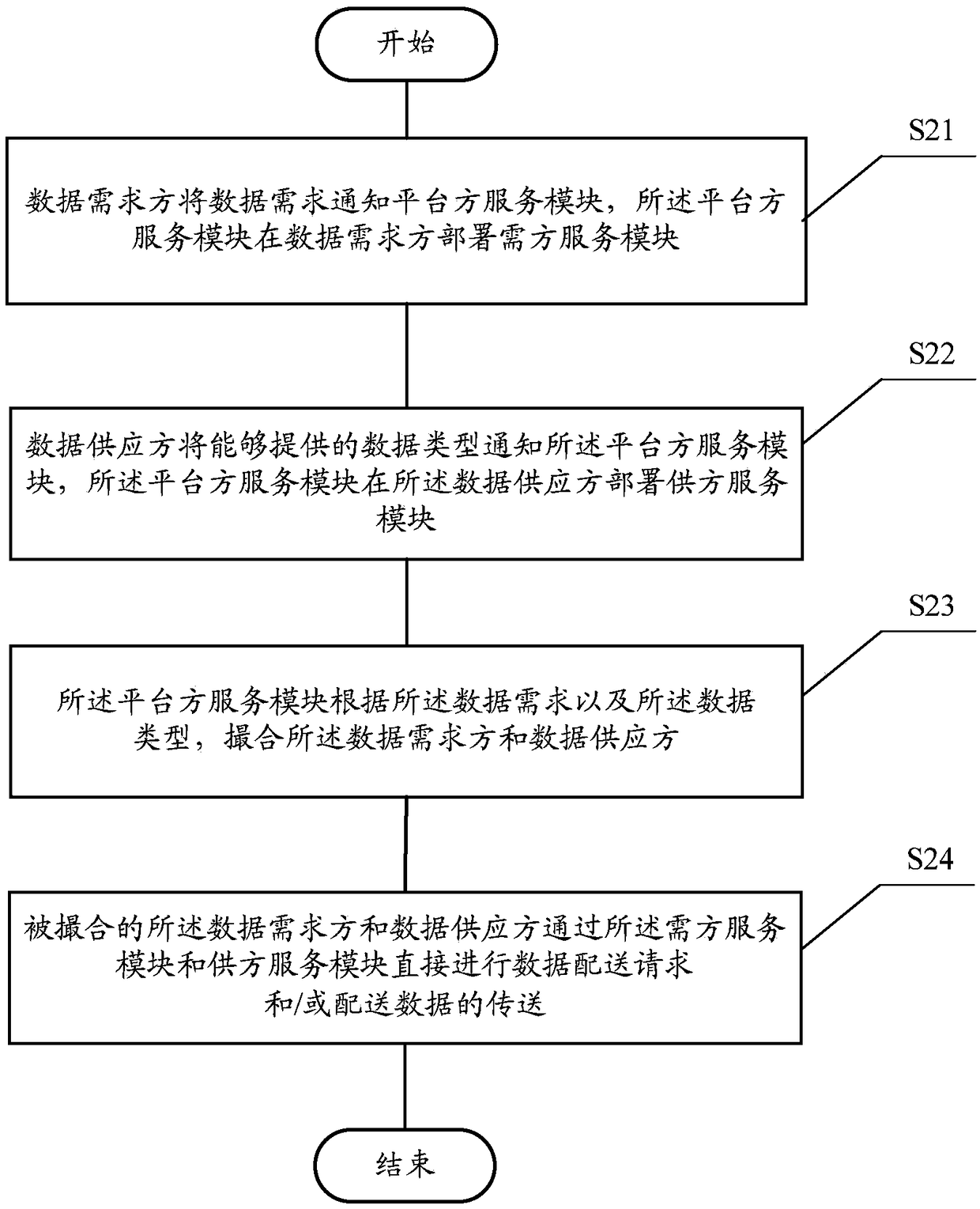
InactiveCN109034683AEnsure safetyImprove efficiencySoftware designLogisticsDistribution systemThird party
The invention relates to a data distribution system and distribution method. The data distribution system comprises a plurality of demander service modules, a plurality of supplier service modules anda platform service module. The demander service modules are arranged on the data demander; the supplier service modules are arranged at the data supplier; the platform service module is adapted to determine the data demand of the data demander and the data type that the data supplier can provide according to the notification of the data demander and the data supplier, and to match the data demander and the data supplier according to the data demand and the data type; the matched data demander and the data supplier directly carry out data distribution request and / or transmission of distribution data through the demander service module and the supplier service module. The technical proposal of the invention enables the data distribution request and the distribution data not to be touched bya third party in the transmission process, and effectively ensures the safety of the data transaction.
Owner:上海数据发展科技有限责任公司
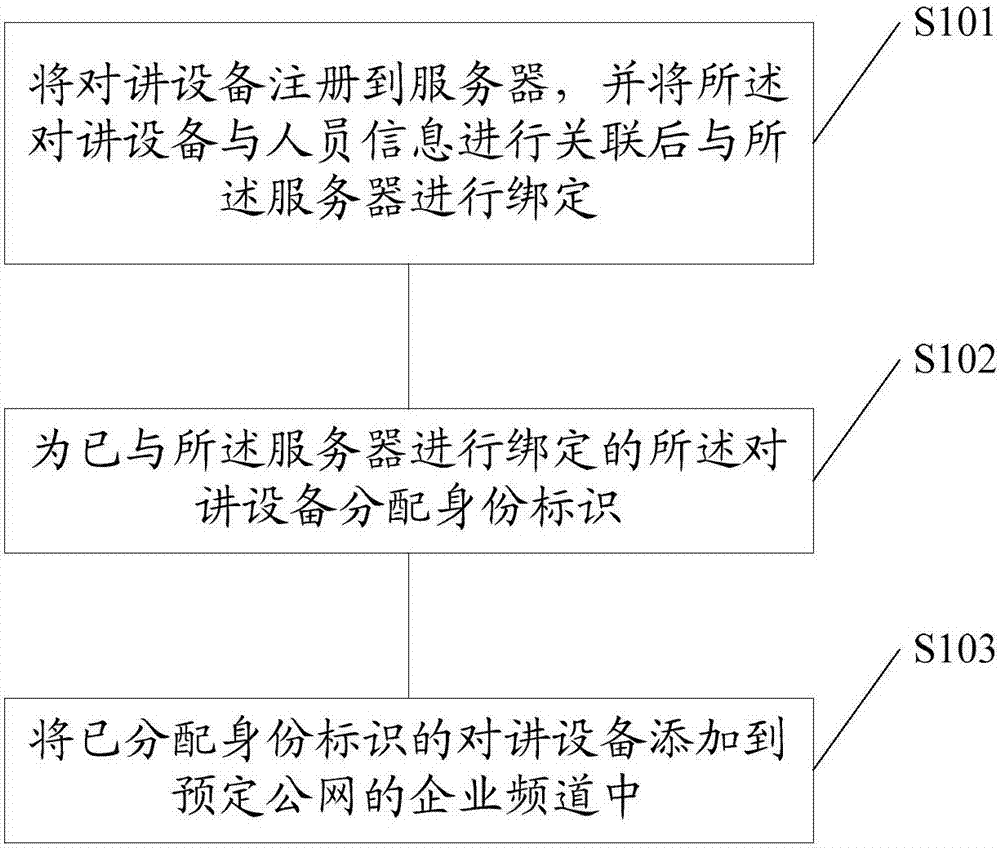
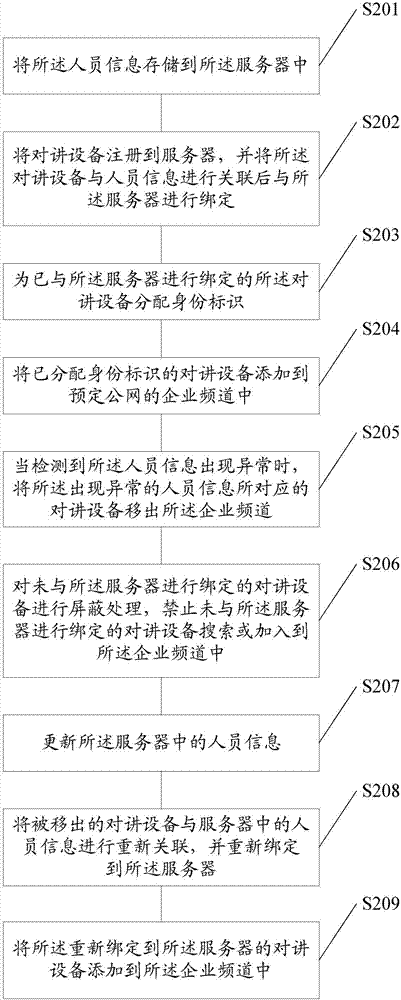
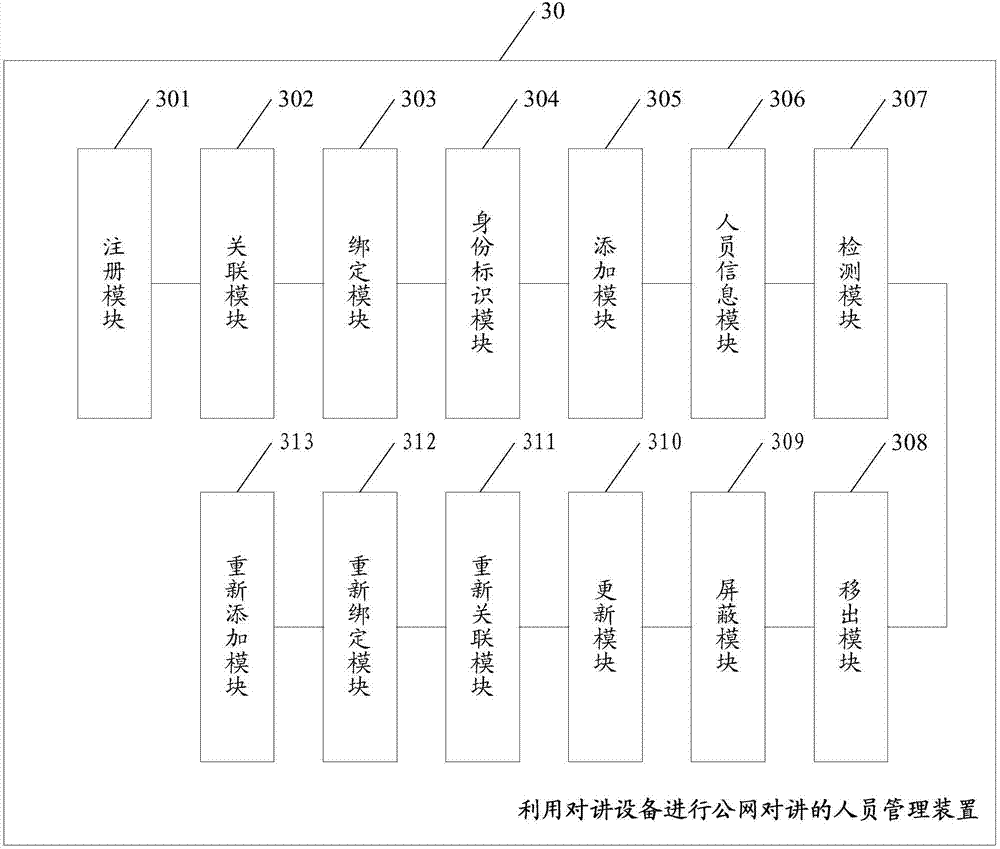
Personnel management method and device for utilizing talkback equipment to carry out public network talkback
InactiveCN107086982AImprove experienceProtect trade secretsTransmissionTelecommunicationsPublic network
Embodiments of the invention disclose a personnel management method for utilizing talkback equipment to carry out public network talkback. The method comprises the following steps of registering the talkback equipment to a server, associating the talkback equipment with personnel information and binding the talkback equipment with the server; distributing an identifier to the talkback equipment bound with the server; and adding the talkback equipment distributed with the identifier into an enterprise channel of a predetermined public network. The embodiments of the invention also disclose a personnel management device for utilizing the talkback equipment to carry out public network talkback. According to the method and the device, the talkback and the management are carried out in the enterprise channel in the usage scenarios of an enterprise, so that the user experience is improved while the trade secret of a company is protected.
Owner:LAUNCH TECH CO LTD
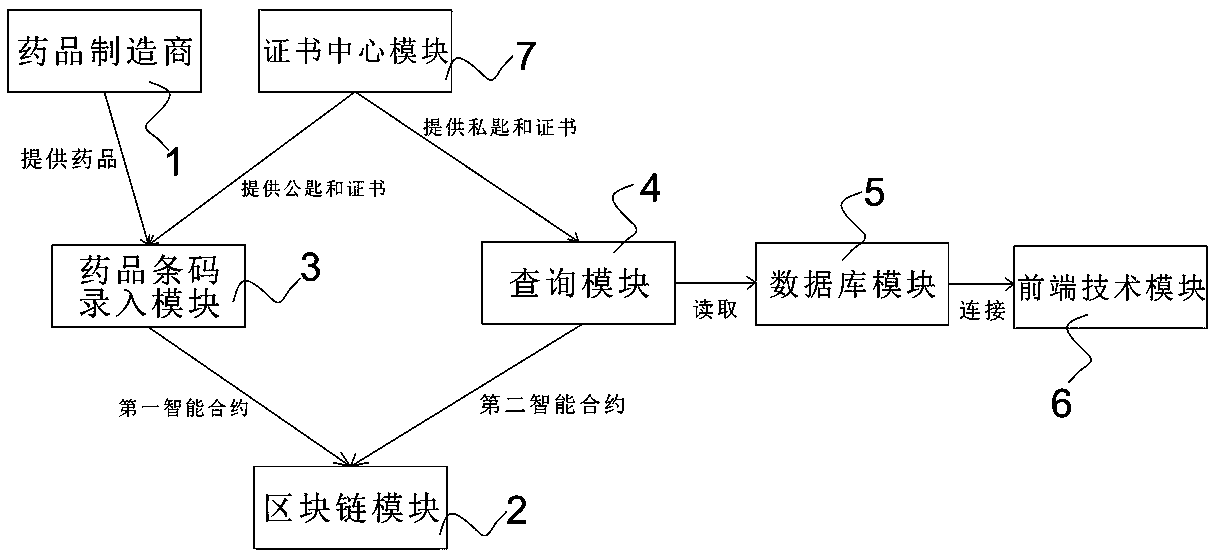
A tamper-proof traceability management system for pharmaceutical information based on block chain
The invention relates to a drug information tamper-proof traceability management system based on block chain, characterized in that it comprises a block chain module, a drug bar code input module forreading the drug bar code, a query module for querying drug information data, a database module for reading and storing the data queried by the inquiry module into a database, a front-end technical module for visualizing the data in the database module, and a certificate center module for providing a public key and a certificate to a drug bar code input module and a private key and a certificate to the inquiry module; The drug bar code input module encrypts the privacy data of the drug and the enterprise through the public key and stores the read bar code data into the block chain module through the first intelligent contract. The query module reads the privacy data and the public data in the block chain module through the private key and the second intelligent contract. The invention realizes the tracking of the drug supply chain and the visualization of the information data, and ensures the transparency of the whole drug supply chain.
Owner:GUANGDONG POLYTECHNIC NORMAL UNIV
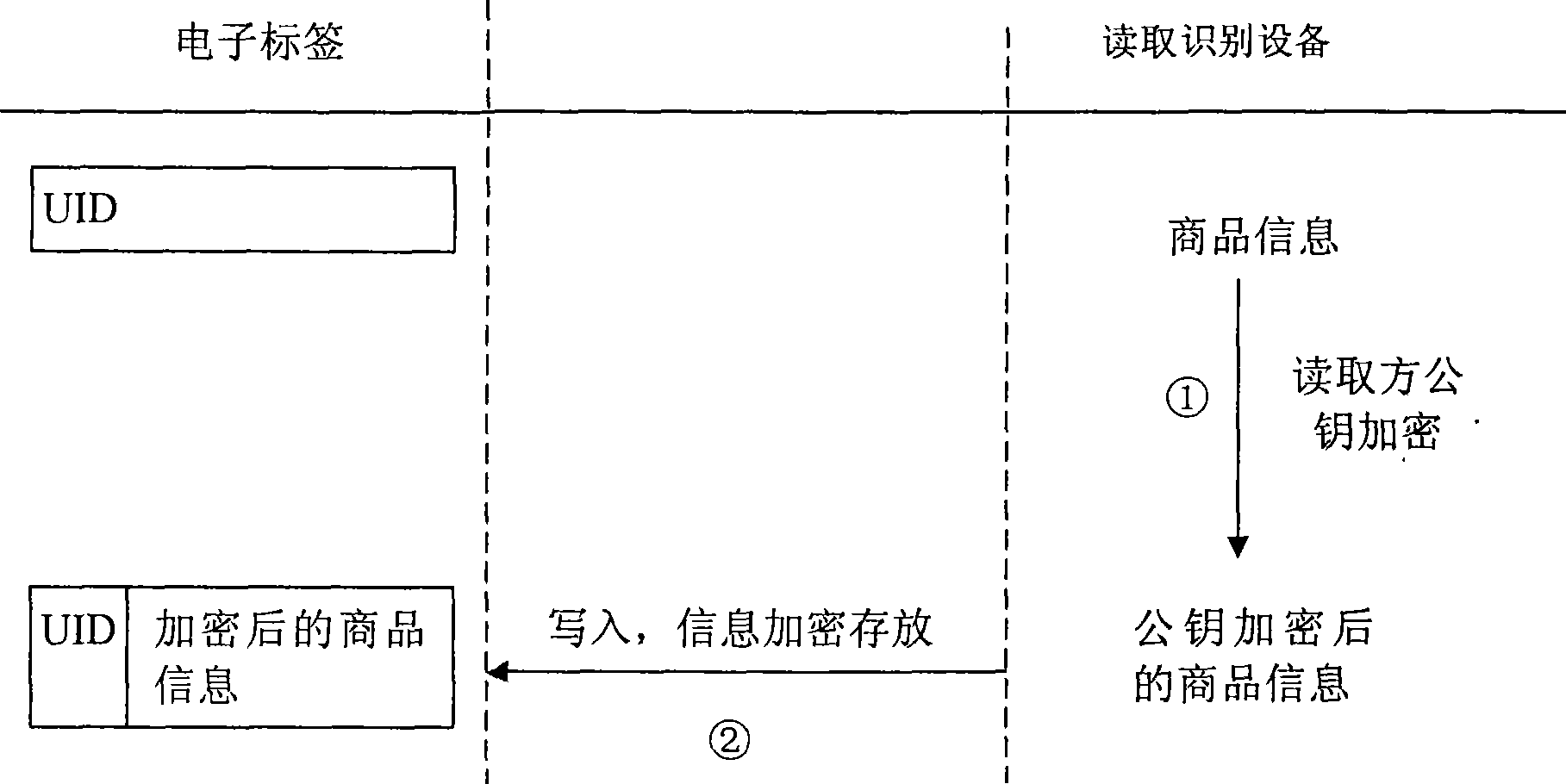
Method and system for protecting radio frequency identification label data
InactiveCN103136552AProtection securityMinor changesCo-operative working arrangementsRecord carriers used with machinesRadio frequencyData needs
The invention discloses a method and a system for protecting radio frequency identification label data. The method comprises manufacturing an encryption card and a corresponding decryption card; transmitting data needed to be written in a radio frequency identification label and label identification to an integrated circuit (IC) card reader which is provided with the encryption card to encrypt to generate enciphered data, and utilizing a radio frequency identification device (RFID) reader to write the enciphered data into the radio frequency identification label; utilizing the RFID reader to read the enciphered data in the radio frequency identification label, transmitting the enciphered data to an IC card reader which is provided with the decryption card to decrypt to generate decryption data. The method and the system for protecting the radio frequency identification label data protect the safety of the data of the radio frequency identification label. The IC card technology is used, a prior RFID application system is changed little, and compatibility is high. On the base of the prior RFID system, only the cost of an IC card system is increased, and the cost is low.
Owner:中国航天科工集团第二研究院七0六所 +1
Data circulation method, device and system, storage medium and server
InactiveCN110457937APrevent leakageImprove securityDigital data protectionPayment protocolsConfidentialityDatabase
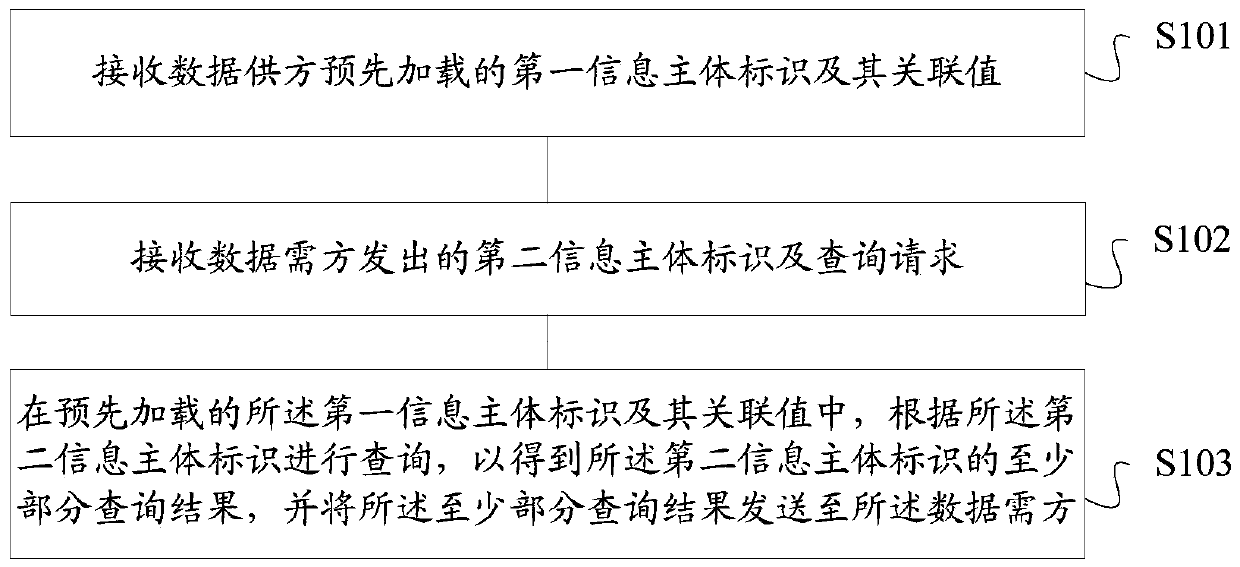
The invention discloses a data circulation method, device and system, a storage medium and a server. The method comprises the following steps: receiving a first information main body identifier and anassociated value thereof pre-loaded by a data supplier; receiving a second information main body identifier and a query request sent by a data demander; and performing querying according to the second information main body identifier in the pre-loaded first information main body identifier and the associated value thereof to obtain at least part of a query result of the second information main body identifier, and sending the at least part of the query result to the data demander. Leakage of commercial confidentiality of a data demander can be effectively avoided.
Owner:上海数据发展科技有限责任公司
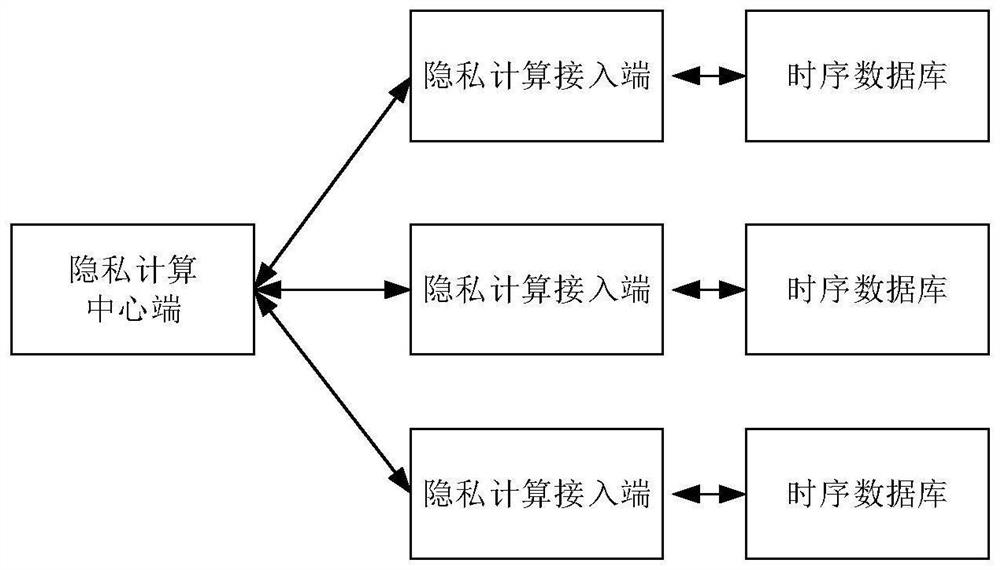
Privacy calculation system and method for total driving duration of online car-hailing driver and application
PendingCN114722093AProtect trade secretsProtect private dataDigital data information retrievalSpecial data processing applicationsComputing systemsData bank
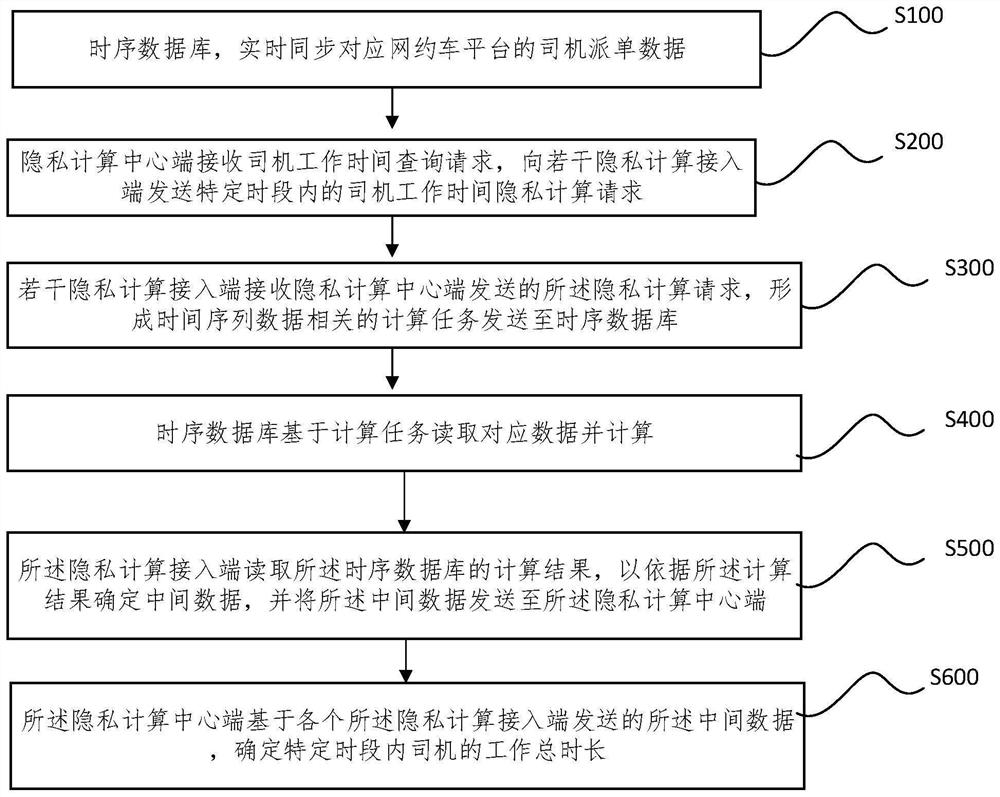
According to the privacy calculation system and method for the total driving duration of the online car-hailing driver and the application, a time sequence database is used for synchronizing driver order dispatching data corresponding to an online car-hailing platform in real time; the privacy computing center end receives a driver working time query request; the plurality of privacy computing access ends are used for receiving the privacy computing request sent by the privacy computing center end, forming a computing task and sending the computing task to the time sequence database; the time sequence database is used for reading corresponding data based on the calculation task and calculating; the privacy computing access end reads a computing result of the time sequence database; a calculation result is sent to a privacy calculation center end; and the privacy calculation center end accumulates the calculation results sent by the privacy calculation access ends to obtain the total working time length of the driver in the specific time period. According to the invention, the calculation of the total driving duration of the cross-platform online car-hailing driver is realized, and the privacy data and the commercial secret of the online car-hailing company are protected through privacy calculation.
Owner:杭州锘崴信息科技有限公司
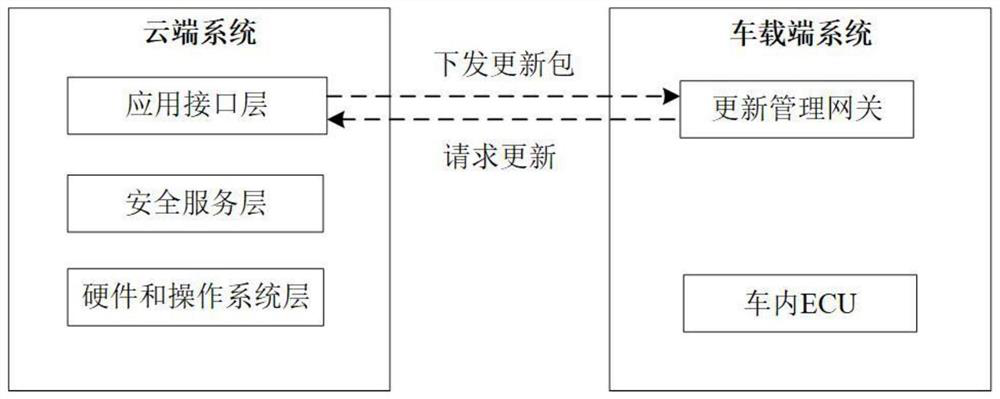
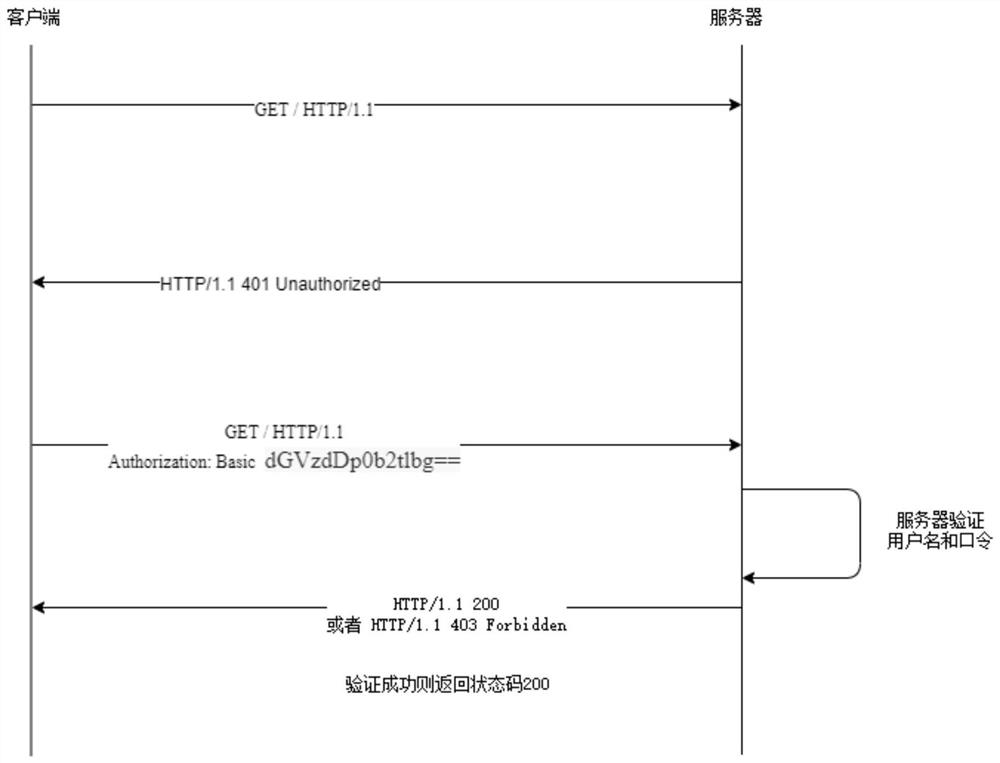
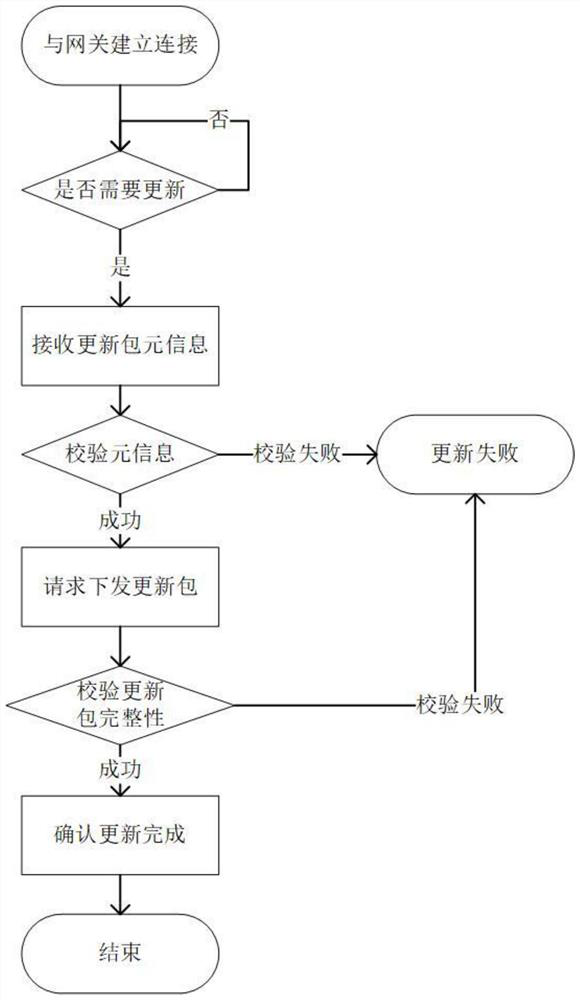
Networked automobile safety remote updating method based on bidirectional identity authentication
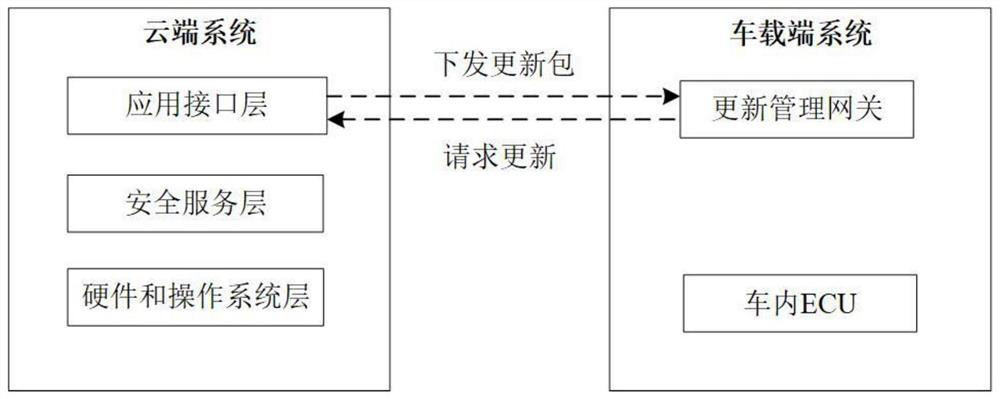
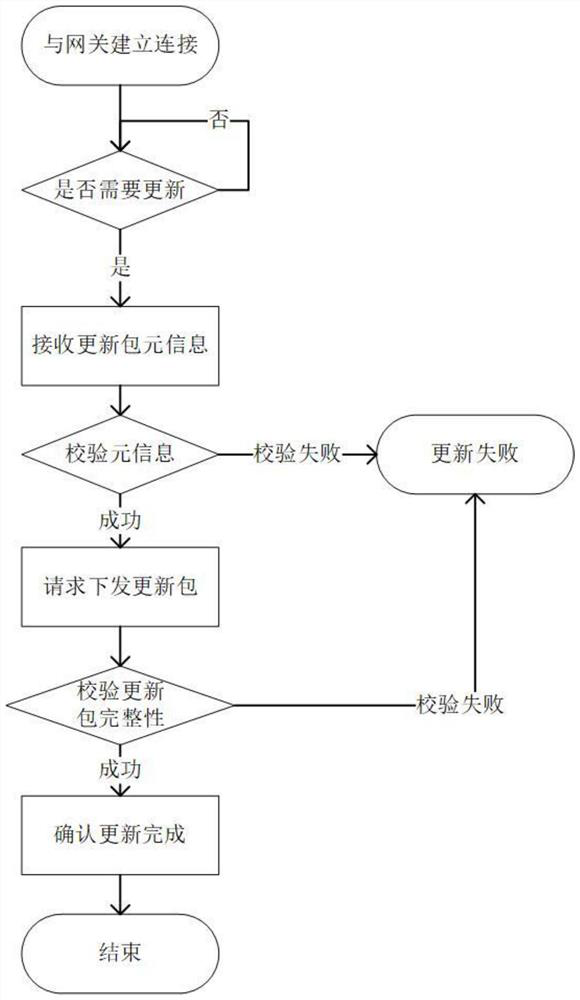
ActiveCN112713999AGuarantee authenticityProtect trade secretsVersion controlUser identity/authority verificationAutomotive systemsAutomotive software
The invention relates to the field of intelligent networked automobile information security, in particular to a networked automobile security remote updating method based on bidirectional identity authentication, which is applied to an automobile OTA system. The automobile OTA system comprises a cloud system and a vehicle-mounted terminal system; the cloud system comprises an OEM server and a software supplier server, and the vehicle-mounted terminal system comprises an updating gateway and an electronic control unit; the OEM server completes the identity authentication of the vehicle and issues the updating authority of each electronic control unit to the corresponding software supplier; the updating gateway acquires the software updating information from the OEM server, performs identity verification, and downloads software updating packages of different electronic control units (ECU) from the corresponding software supplier server after acquiring the identity password and the information of the software supplier; and the electronic control unit is used for installing and operating own software after acquiring the software update package. The method has the advantage that safety protection is carried out on the full life cycle of automobile software updating.
Owner:BEIHANG UNIV
Electronic label security system
ActiveCN101369306BProtect trade secretsConvenient verificationSensing record carriersIdentification deviceSecurity system
The invention provides an electronic label safety system of performing true or false identification. The electronic label safety system includes a label and a reading identification device, wherein storage media are included on the electronic label and have unique identification UID, and information of the commodities are written on the electronic label. A private key is used to encrypt UID of the label and information of the commodities, to obtain the electronic label. The identification equipment is read for the UID of the label, the information of the commodities and the electronic signature. A public key is used to decrypt the electronic signature to obtain the UID of the label, wherein the anti-counterfeiting identification is not passed.
Owner:广东南方信息安全产业基地有限公司
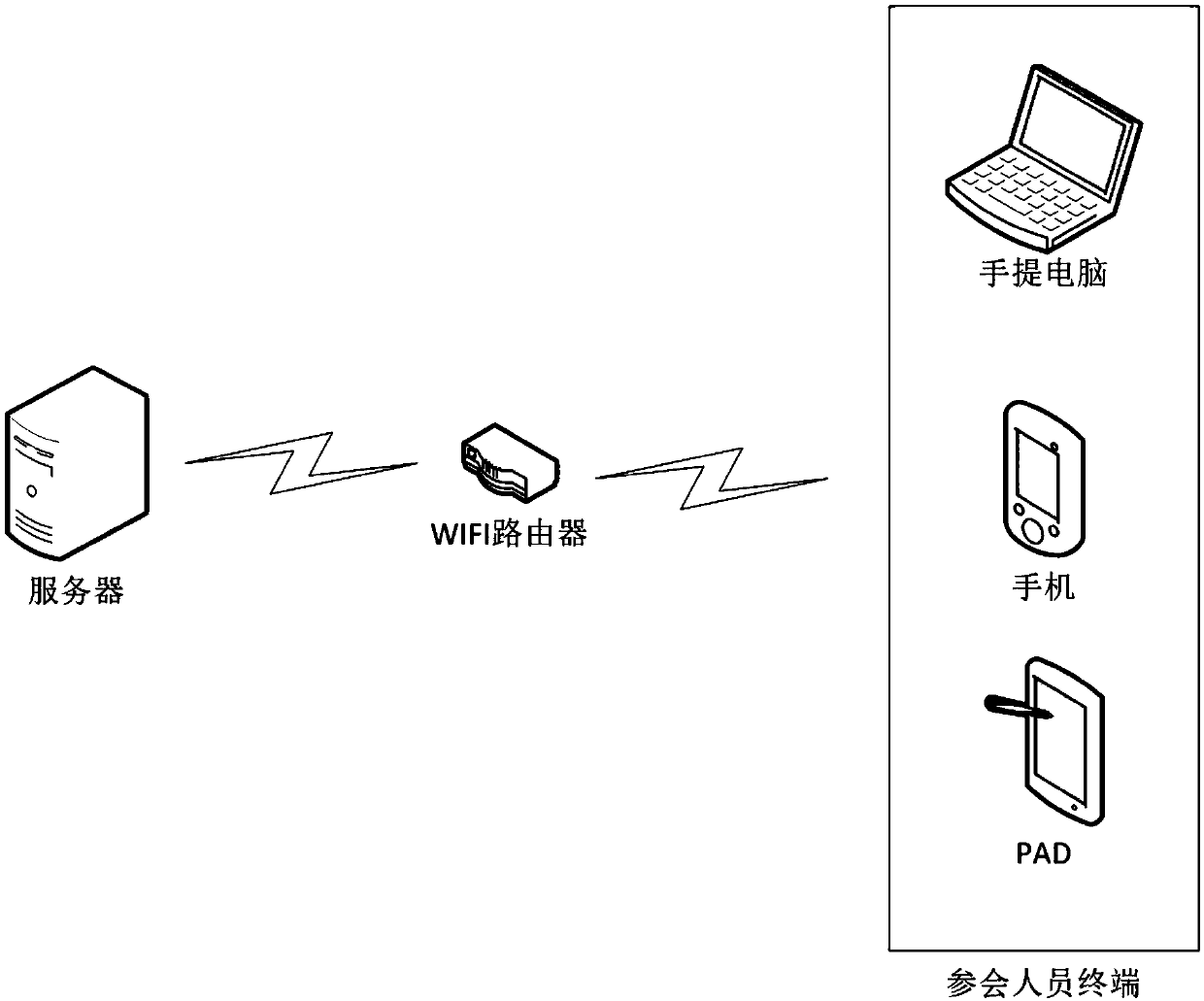
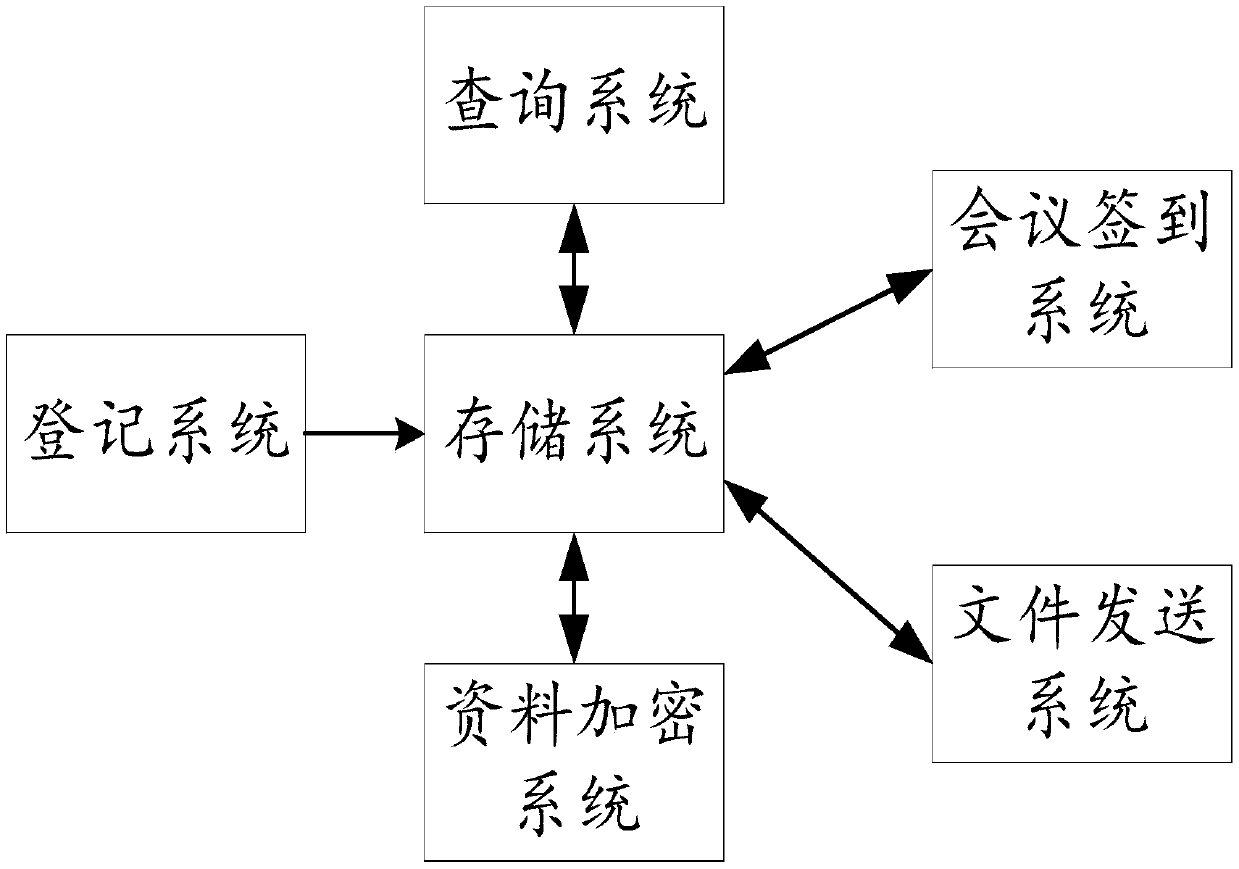
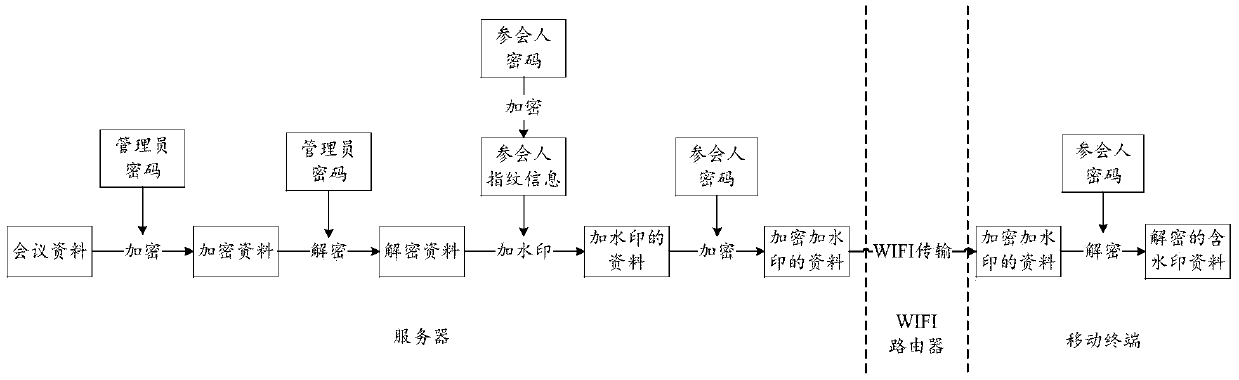
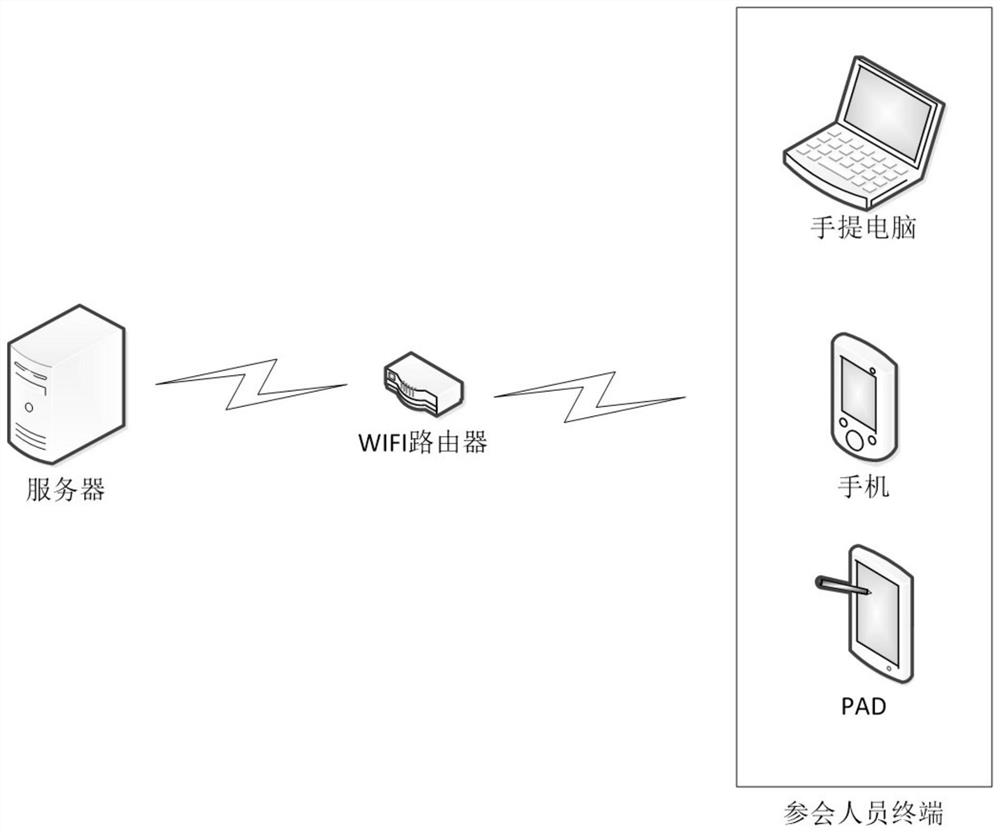
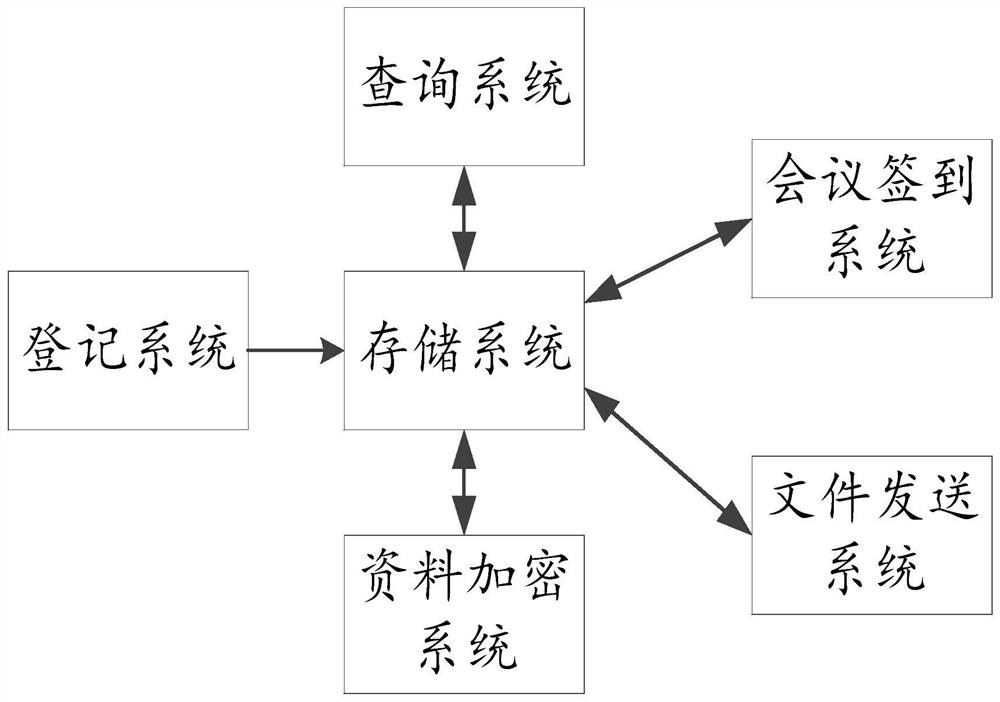
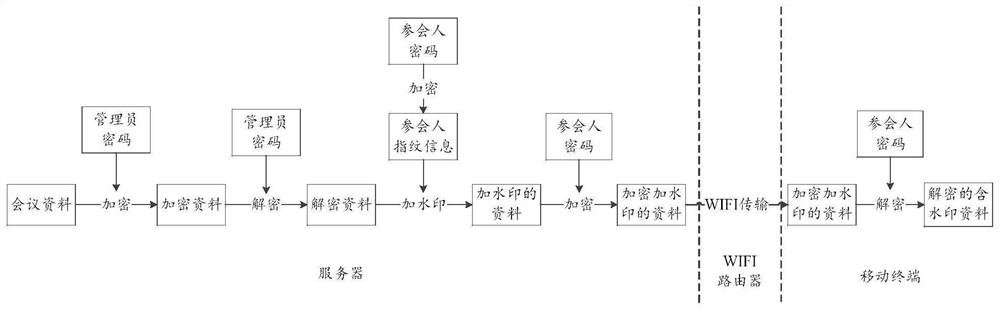
WIFI-based secrecy conference system
ActiveCN109561107AShorten the timeProtect trade secretsRegistering/indicating time of eventsTransmissionHuman–computer interactionEncryption
The invention provides a WIFI-based secrecy conference system, which mainly comprises a storage system, a conference sign-in system, a file sending system and a data secrecy system. The WIFI-based secrecy conference system enables participants to sign in for the conference and register the participation time by using WIF through the conference sign-in system so as to save the time of the participants; and the WIFI-based secrecy conference system can also record the late arrival, early departure and halfway departure of the participants according to the WIFI registration time, there is no needto arrange workers for field supervision which spends a lot of labor cost. In addition, the WIFI-based secrecy conference system avoids the circumstances that non-participants ask for the confidentialbusiness conference data and the like by means of face recognition and conference data encryption and watermarking through the file sending system and the data secrecy system, all participants to which the data belongs can be checked, and thus business secretes of enterprises are protected.
Owner:GUANGDONG POWER GRID CO LTD +1
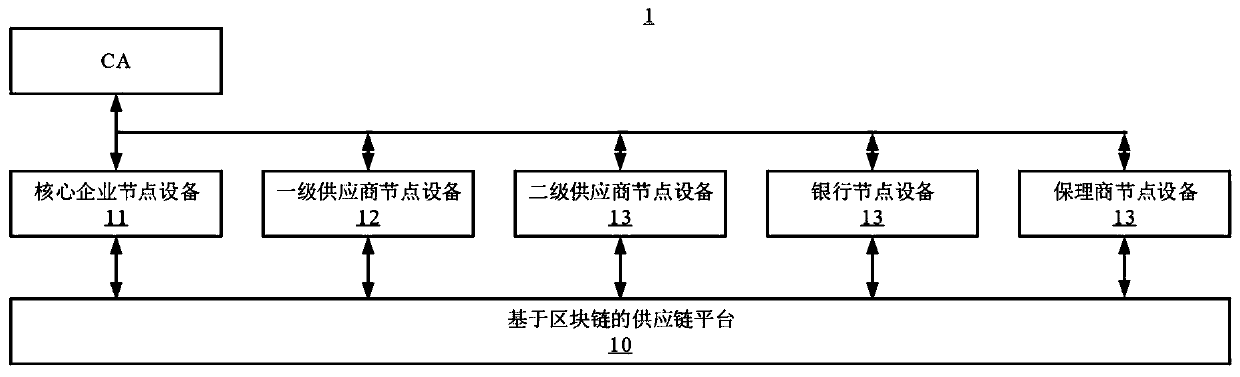
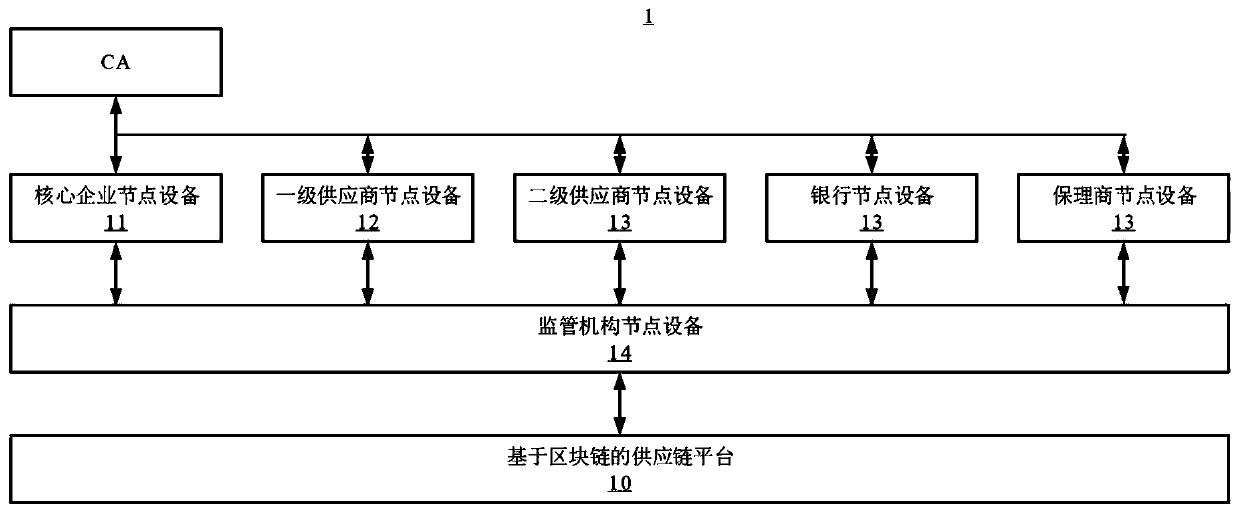
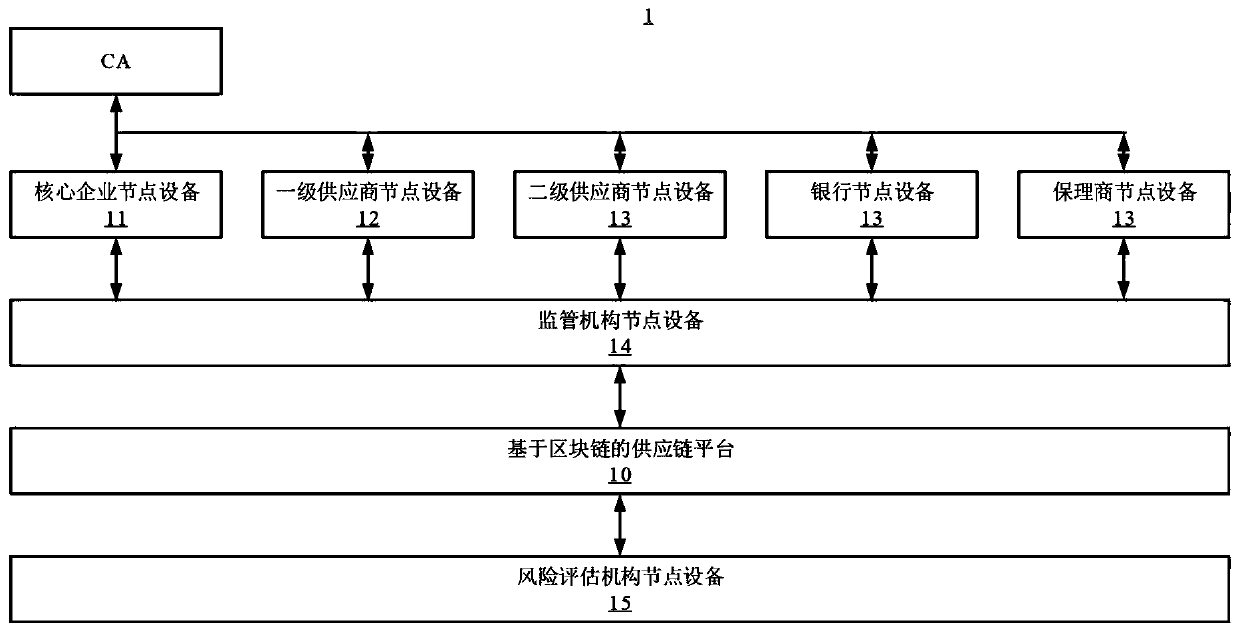
Supply chain transaction privacy protection system and method based on block chain and related equipment
PendingCN110992034AProtect trade secretsProtect entity business secretsPayment protocolsBlockchainPrivacy protection
The invention provides a supply chain transaction privacy protection system based on a block chain. The system comprises core enterprise node equipment used for encrypting payable amount committed bya core enterprise to a first-level supplier to obtain a confidential transaction, signing the confidential transaction and uploading signed transaction data to a supply chain platform based on the block chain; first-level supplier node equipment used for receiving the confidential transaction, decrypting the confidential transaction and outputting the decrypted confidential transaction to the first-level supplier; and a supply chain platform which is based on the block chain and is used for storing the transaction data. The invention further provides a supply chain transaction privacy protection method based on the block chain, block chain node equipment and a storage medium. According to the invention, the plaintext payable amount of the core enterprise can be encrypted into the confidential transaction and uploaded, only two transaction parties can decrypt the amount of money in the confidential transaction, and the transaction privacy is protected from being leaked.
Owner:SHENZHEN THUNDER NETWORK TECH +1
A method and system for protecting radio frequency identification tag data
InactiveCN103136552BProtection securityMinor changesCo-operative working arrangementsRecord carriers used with machinesData needsLabeled data
The invention discloses a method and a system for protecting radio frequency identification label data. The method comprises manufacturing an encryption card and a corresponding decryption card; transmitting data needed to be written in a radio frequency identification label and label identification to an integrated circuit (IC) card reader which is provided with the encryption card to encrypt to generate enciphered data, and utilizing a radio frequency identification device (RFID) reader to write the enciphered data into the radio frequency identification label; utilizing the RFID reader to read the enciphered data in the radio frequency identification label, transmitting the enciphered data to an IC card reader which is provided with the decryption card to decrypt to generate decryption data. The method and the system for protecting the radio frequency identification label data protect the safety of the data of the radio frequency identification label. The IC card technology is used, a prior RFID application system is changed little, and compatibility is high. On the base of the prior RFID system, only the cost of an IC card system is increased, and the cost is low.
Owner:中国航天科工集团第二研究院七0六所 +1
A secure remote update method for connected vehicles based on two-way identity authentication
ActiveCN112713999BGuarantee authenticityProtect trade secretsVersion controlUser identity/authority verificationAutomotive systemsAutomotive software
The present invention relates to the field of information security of intelligent networked automobiles. A method for remotely updating networked automobile security based on two-way identity authentication is applied to an automobile OTA system. The automobile OTA system includes a cloud system and a vehicle-mounted terminal system. The cloud system includes an OEM server and software. The supplier server, the vehicle-end system includes an update gateway and an electronic control unit; the OEM server completes the identity authentication of the vehicle and issues the update authority of each electronic control unit to the corresponding software supplier; the update gateway obtains software update information from the OEM server, And perform identity verification, after obtaining the identity password and the information of the software supplier, download the software update packages of different electronic control unit ECUs from the corresponding software supplier server; after the electronic control unit obtains the software update package, install its own software and Operation; the advantage of the present invention is: carry out safety protection to the whole life cycle of automobile software update.
Owner:BEIHANG UNIV
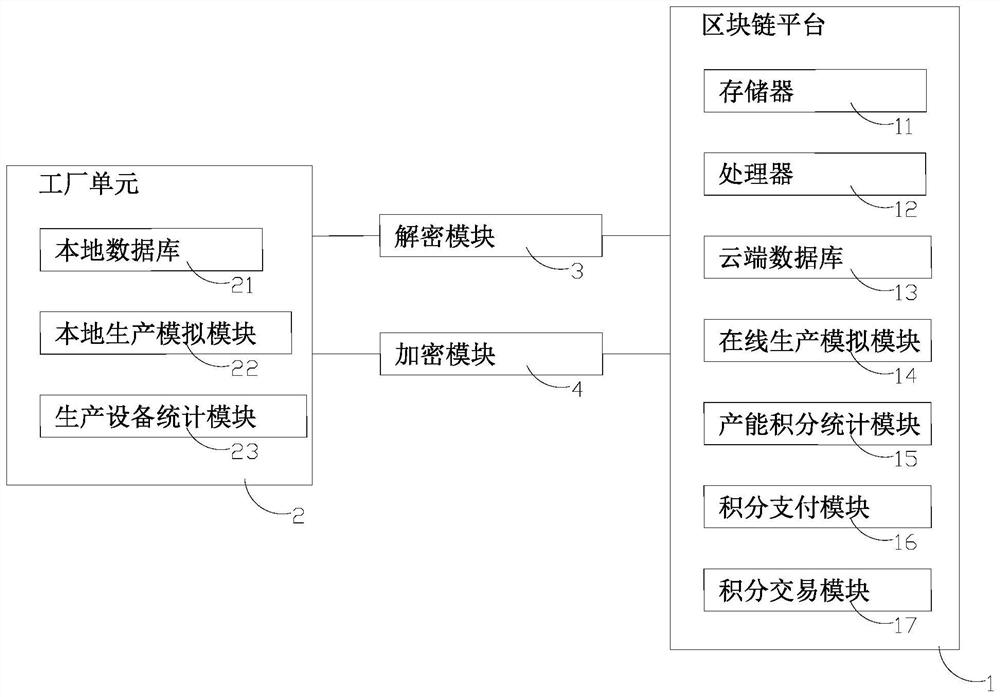
Intelligent manufacturing management method and system based on block chain
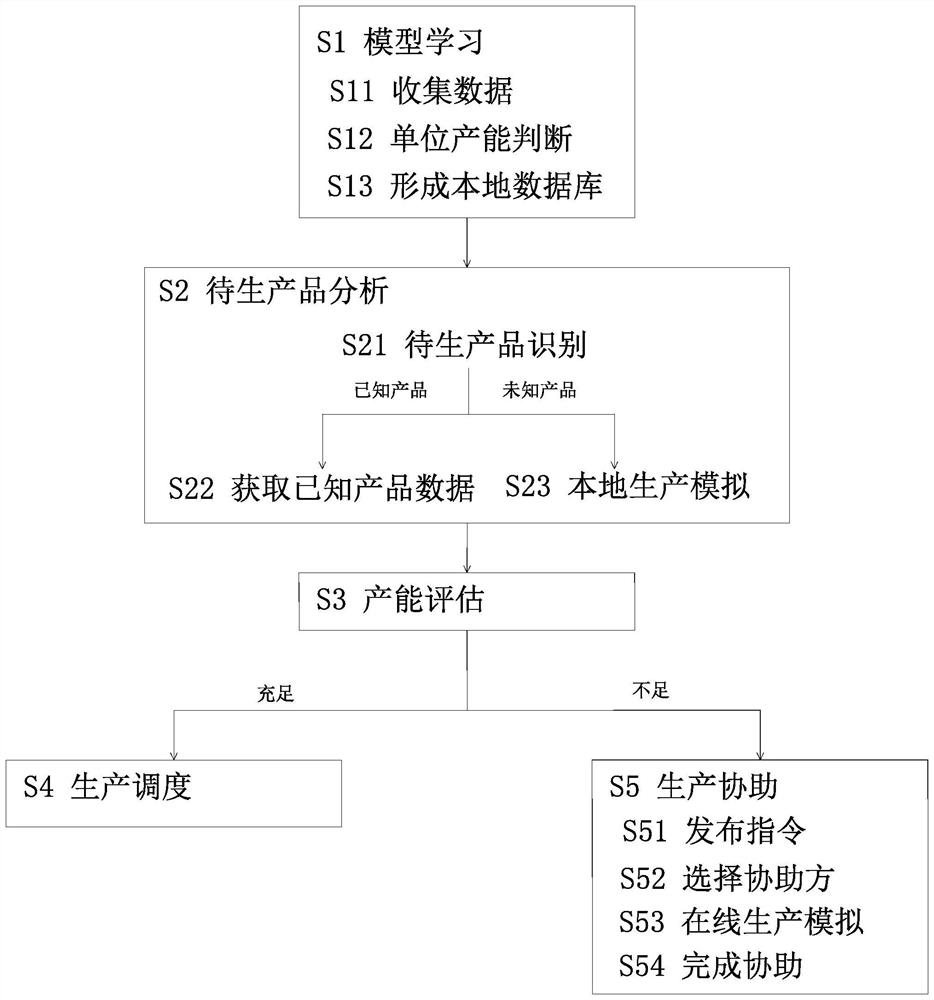
PendingCN114611904AReduce wasteAchieve collaborationDigital data protectionOffice automationPaymentFinancial transaction
The invention relates to an intelligent manufacturing management method based on a block chain, and the method comprises the steps: carrying out the model learning, and forming a local database; analyzing a to-be-generated product, and analyzing production information of the to-be-generated product; productivity evaluation; production scheduling is conducted, and if the capacity is sufficient, direct production is conducted; and production assistance: if the productivity is insufficient, issuing an assistance instruction to the platform, and carrying out productivity assistance work by other factories. Through production resource integration, waste of production resources is reduced, cooperation of production capacity among factories is achieved, and the utilization rate of the production resources is increased; production data are encrypted and stored on the platform, so that the commercial secret of a factory to be assisted is protected; by setting capacity points, avoiding traditional currency transactions, establishing a unified payment standard on the whole platform and comprehensively considering the production cost and the production qualification rate of the assisting factories, the problem of random pricing of production assistance of part of factories is avoided, and the uniformity of production assistance in the platform is improved.
Owner:顾静艳
A confidential conference system based on wifi
ActiveCN109561107BShorten the timeProtect trade secretsRegistering/indicating time of eventsTransmissionComputer networkEngineering
The application provides a WIFI-based confidential conference system, which mainly includes: a storage system, a conference sign-in system, a file sending system and a data security system. This application uses the conference sign-in system to allow participants to use WIFI to sign in to the meeting, register the time of the participants, and save the time of the participants; it can also record the late arrival, early leave, and midway departure of the participants according to the WIFI registration time, without the need to arrange work On-site supervision by personnel costs a lot of labor costs, and through the file sending system and data security system, face recognition, conference data encryption and watermarking methods are used to avoid non-participants from requesting confidential business conference materials, etc. All the personnel who belong to the participating materials can be checked to protect the company's business secrets.
Owner:GUANGDONG POWER GRID CO LTD +1
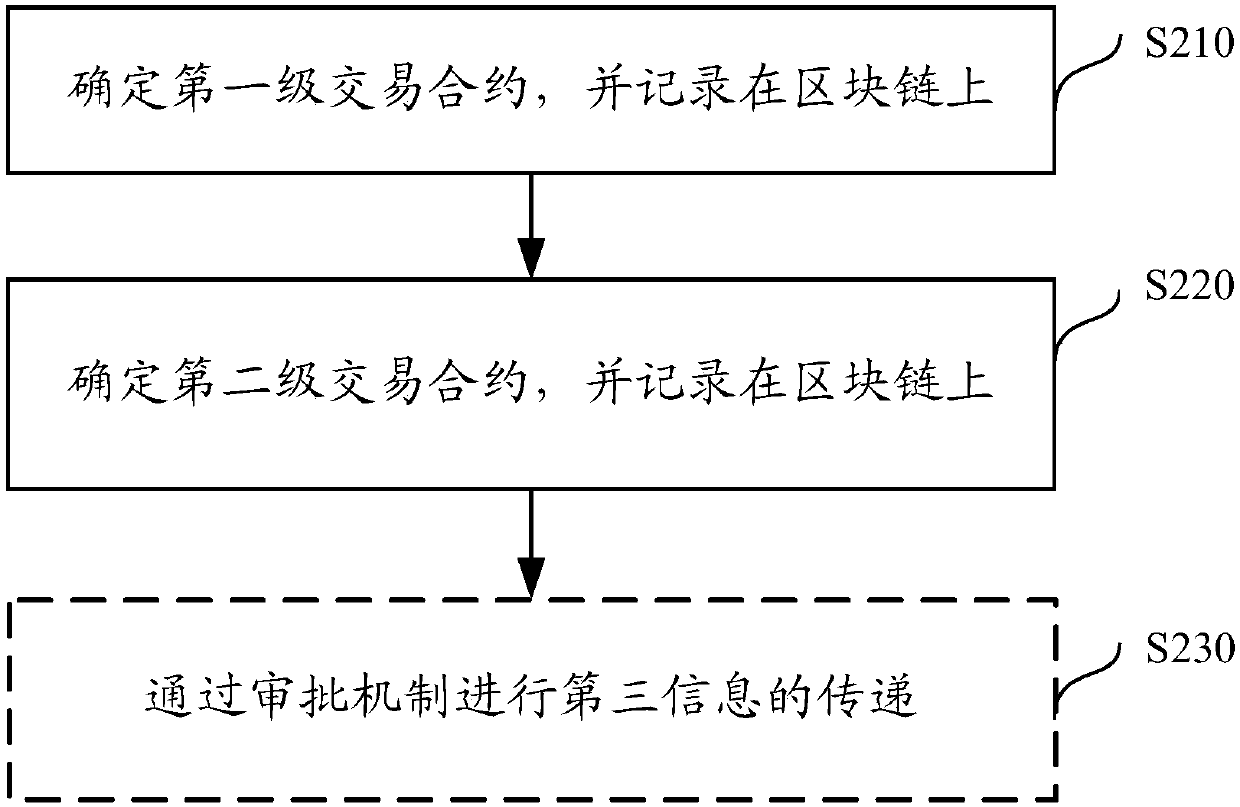
Method and device for multi-level transaction based on block chain
ActiveCN107590658BInvisible reductionInvisible to ensureProtocol authorisationFinancial transactionDatabase
Owner:上海专精特新金融信息服务有限公司 +1
Data query system and method, storage medium, terminal
ActiveCN108268799BGuaranteed privacyProtect trade secretsDigital data protectionDatasheetEngineering
The invention discloses a data query system and method, a storage medium and a terminal. The system comprises a demander terminal and a supplier terminal. The demander terminal sends a to-be-queried data table, wherein the to-be-queried data table comprises second marker information generated according to identifier information of to-be-queried data and an identifier code of the supplier terminalreceiving the to-be-queried data table, and the type of to-be-queried feature information. The supplier terminal processes the received to-be-queried data table and sends the processed data table, wherein the processed data table comprises the value of the to-be-queried feature information and the second marker information; and in response to operation of receiving the processed data table, the demander terminal performs secondary processing on the processed data table to obtain a data table subjected to secondary processing, wherein the data table subjected to the secondary processing comprises the value of the to-be-queried feature information and the identifier information of the to-be-queried data. Through the scheme provided by the invention, sensitive information can be effectively isolated during data query, so that the privacy of personal privacy information is guaranteed and the leakage risk is lowered.
Owner:上海数据发展科技有限责任公司
A tamper-proof file food safety traceability system
Provided is a food safety traceability system capable of preventing archive from being tampered. The food safety traceability system comprises a food archive database and a monitoring device. The monitoring device comprises an encryption module, an information sending module and a file monitoring module. The encryption module calculates integrity checking information of electronic archives and transmits the integrity checking information to an information reception module of the food archive database through the information sending module; and the file monitoring module is set to carry out monitoring on archive file establishing, modifying and deleting operation. A processing module comprises a storage module, wherein the storage module is for storing names of monitoring food and food motoring steps as well as identification information of the monitoring food; and an identification identifying module, wherein the identification identifying module is for identifying identification information of food main bodies. The food archive database also comprises a data input module, a data storage module and a data query module for querying integrity checking information of the electronic archive files.
Owner:刘品新 +1
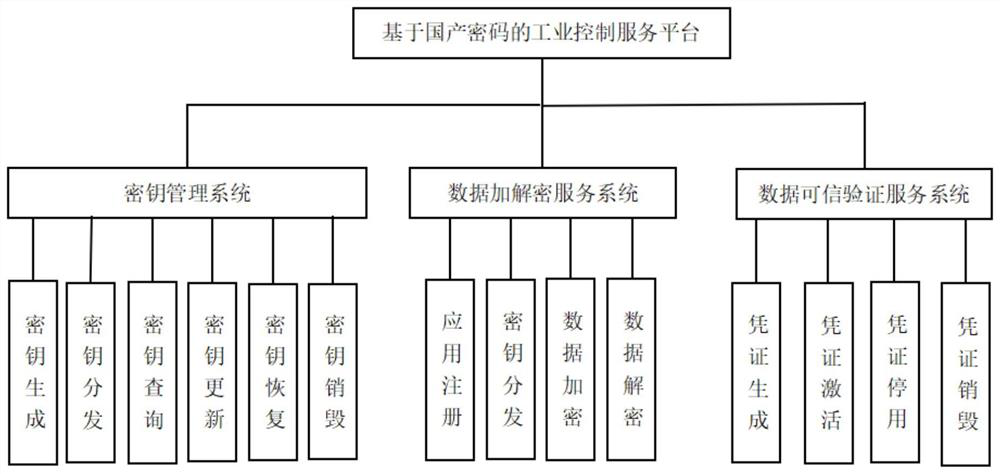
Industrial control service platform and method based on domestic password, and storage medium
PendingCN114785596AGuaranteed real-timeGuaranteed stabilityKey distribution for secure communicationDigital data protectionPasswordControl data
The invention relates to the technical field of industrial control encryption, in particular to an industrial control service platform and method based on a domestic password and a storage medium, and the platform comprises a key management system which is used for carrying out the unified management of keys; the data encryption and decryption system is used for being in butt joint with the industrial control system and encrypting the industrial control data in the transmission and storage process of the industrial control data; and the data credibility verification service system is used for carrying out authenticity verification on the industrial control data and generating a data voucher. According to the method, the security of the industrial control data is improved, the authenticity, reliability and authority of the industrial control data are ensured, and the technical problems of low security and poor generalizability of a domestic cryptographic algorithm are solved.
Owner:贵州爱信诺航天信息有限公司
Playing on demand system for video
ActiveCN101453624BRealize network operationImprove efficiencyTransmissionSelective content distributionCommunity orComputer terminal
The invention discloses a (hotel, community or family) video-on-demand system. The video-on-demand system comprises a center server, a node server and a user terminal, wherein the center server is used for storing video information; the node server is used for establishing communication with the center server through a network so as to obtain at least one part of the video information and generating a programme list according to the video information; the user terminal is used for reading the programme list and displaying the programme list through display equipment; and when a user orders a corresponding programme, the user sends a video-on-demand request to the node server, reads corresponding decoded video information and plays the information through the display equipment. In the video-on-demand system, as each (hotel, community or family) node server is connected with the center server through the wide area network, thereby realizing network operation of the whole video-on-demandsystem. The video-on-demand system can carry out programme distribution and management through the network, thereby making the distribution and management operation simple and feasible and also improving efficiency.
Owner:QINGDAO TONGXIN INNOVATION LAB TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com