Patents
Literature
43 results about "Trade secret" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A trade secret is a type of intellectual property in the form of a formula, practice, process, design, instrument, pattern, commercial method, or compilation of information that is not generally known or reasonably ascertainable by others, and by which a person or company can obtain an economic advantage over competitors. In some jurisdictions, such secrets are referred to as confidential information.
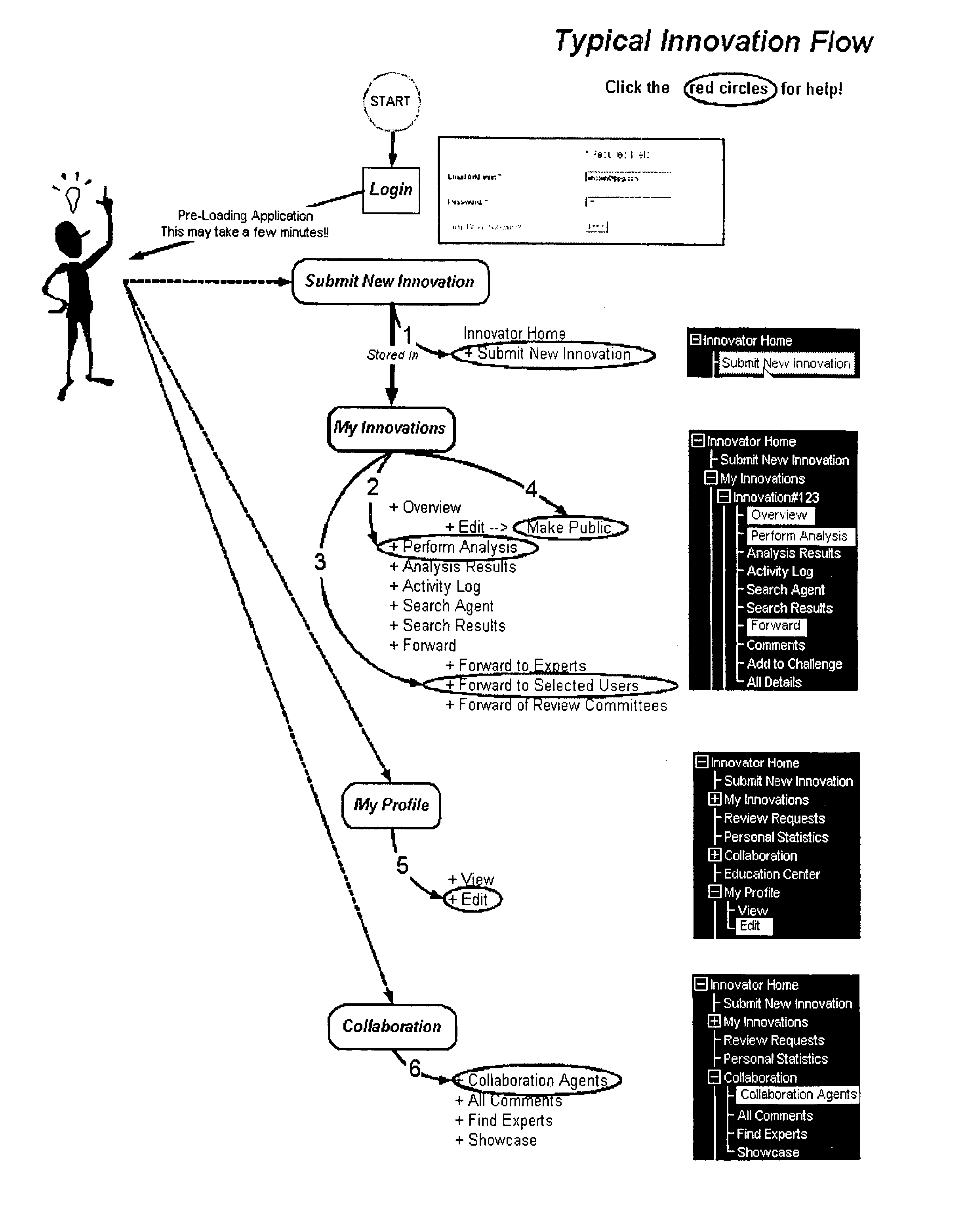
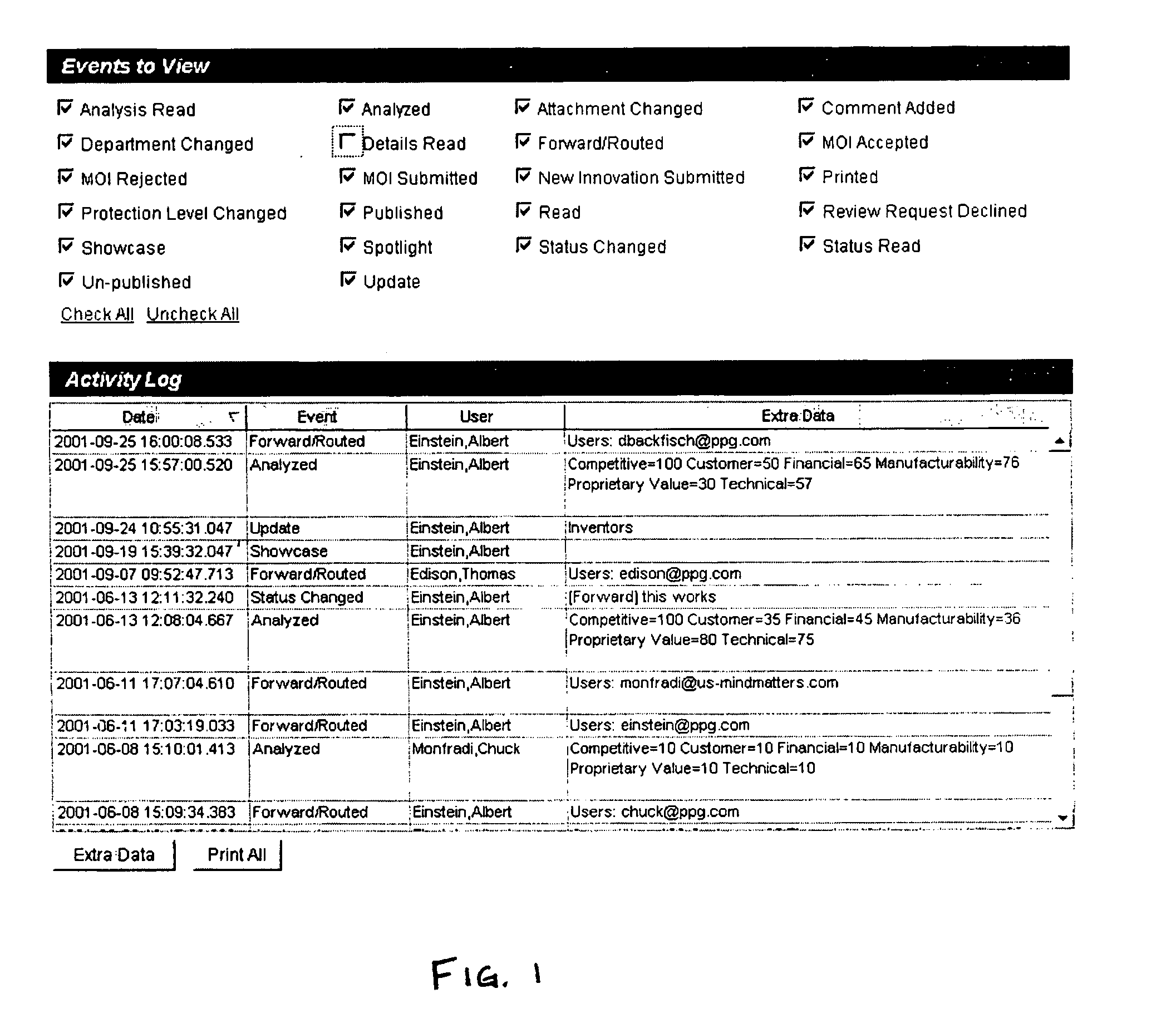
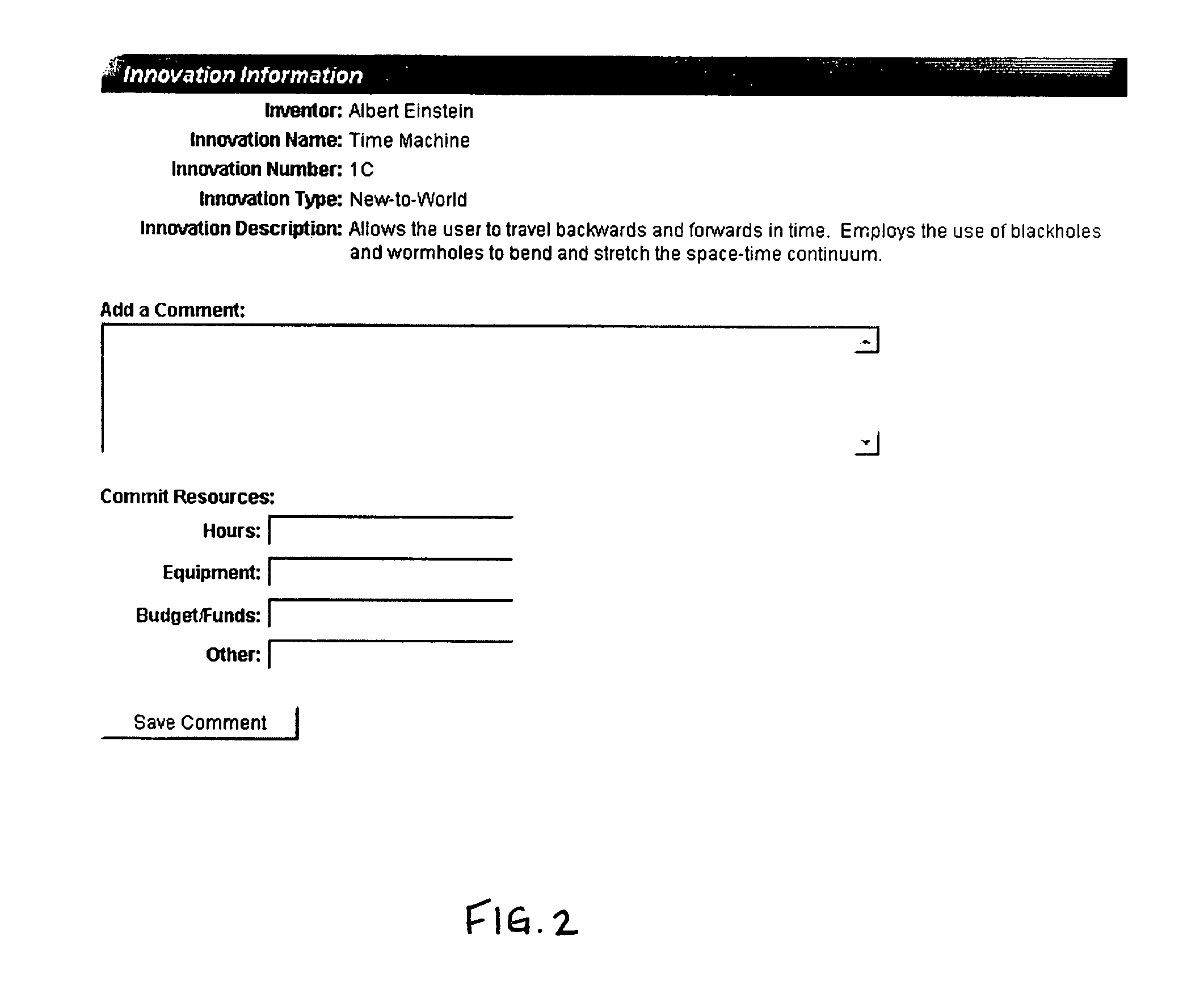
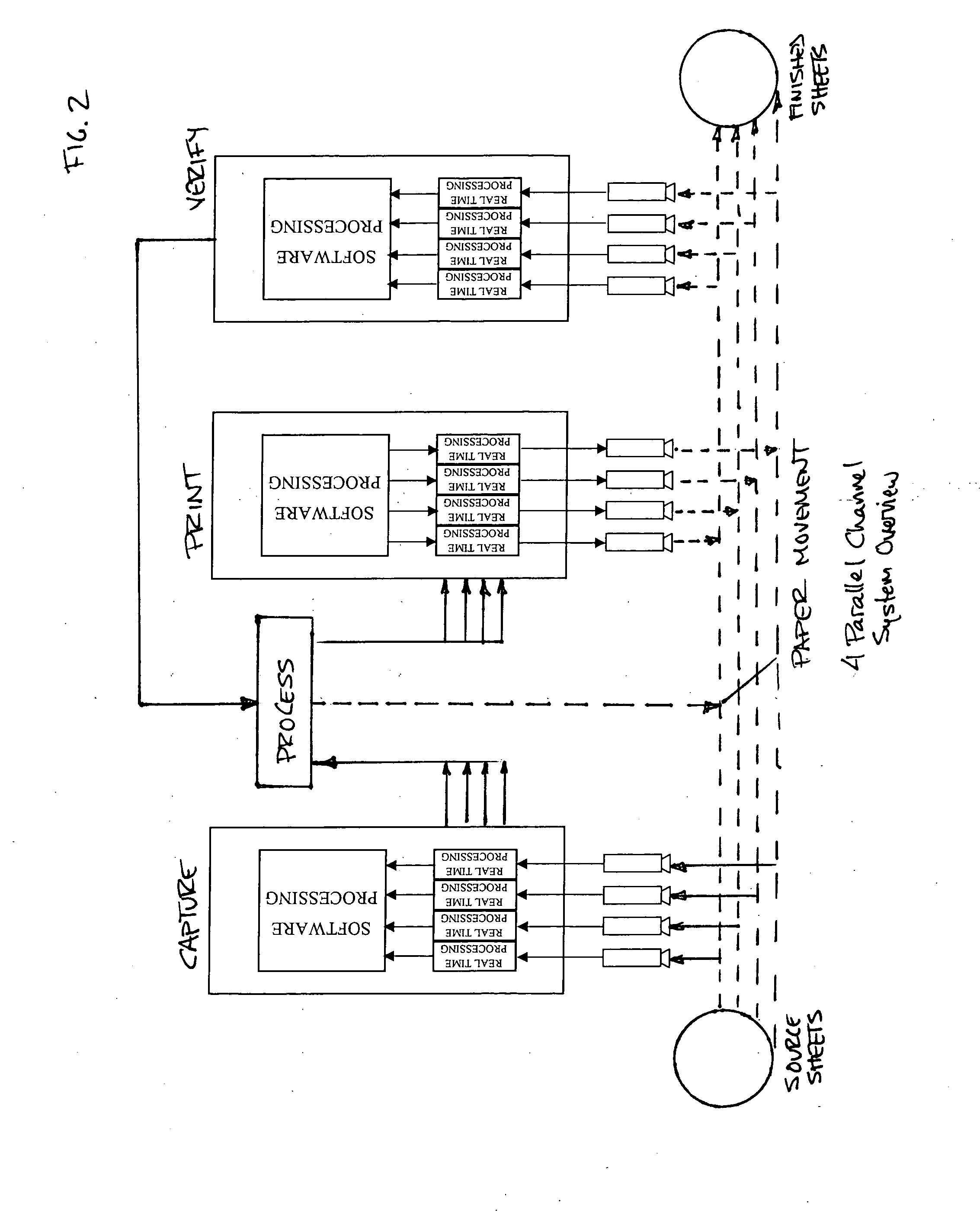
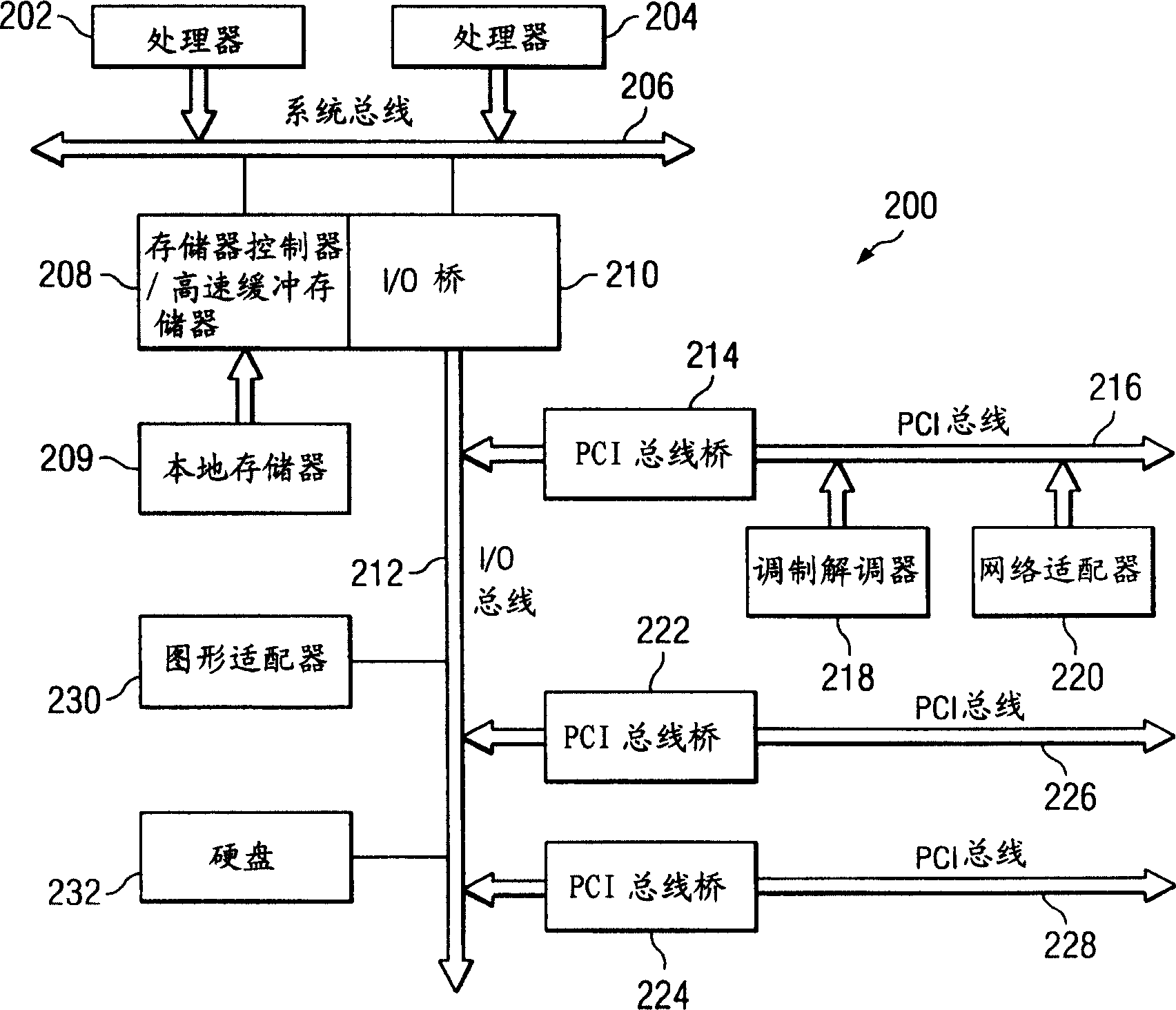
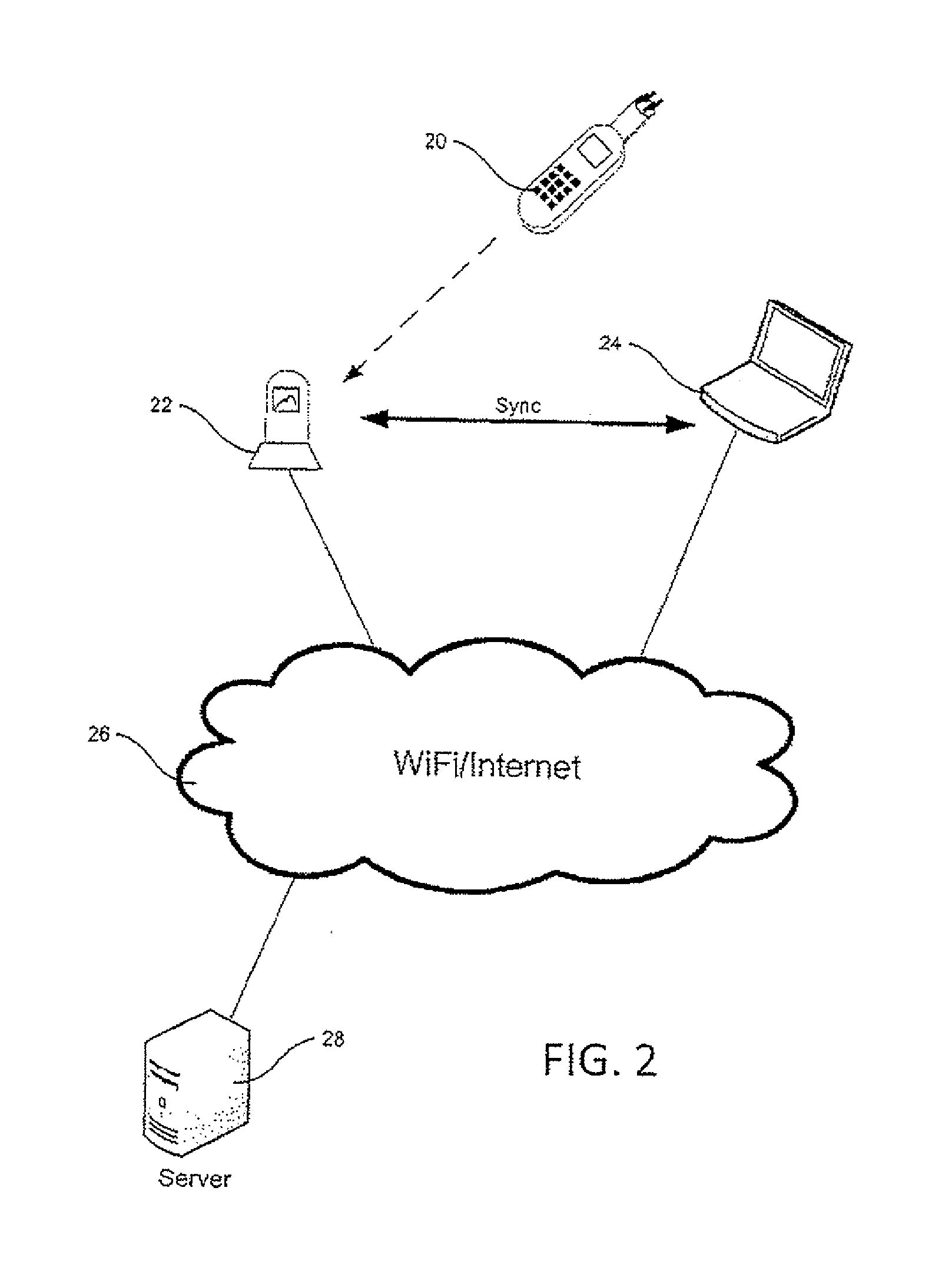
System for automating and managing an IP environment
InactiveUS20040073443A1Shorten the timeEasy to browseOffice automationResourcesReal-time dataLibrary science
A system for streamlining the process of creating, preserving and protecting proprietary assets. The system identifies, classifies, compiles, tracks and routes real-time data automatically on a continuous basis, and provides instant access to stored database information, such as trade secret archives, patent filings, computed valuations, user information and a variety of detailed reports. An employee has instant access to her latest innovations and proprietary materials, and constant supervision over them.
Owner:GABRICK JOHN J +1
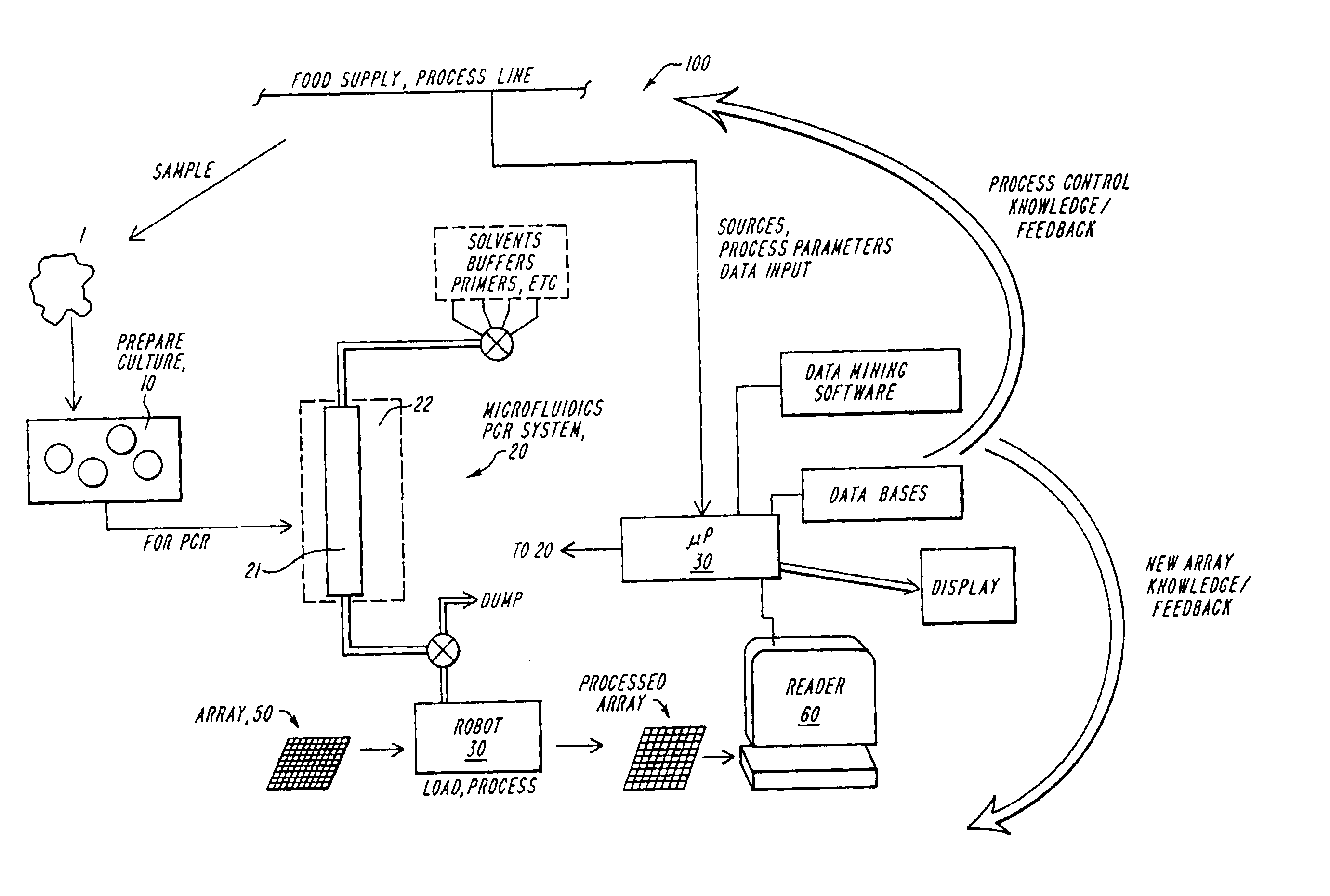
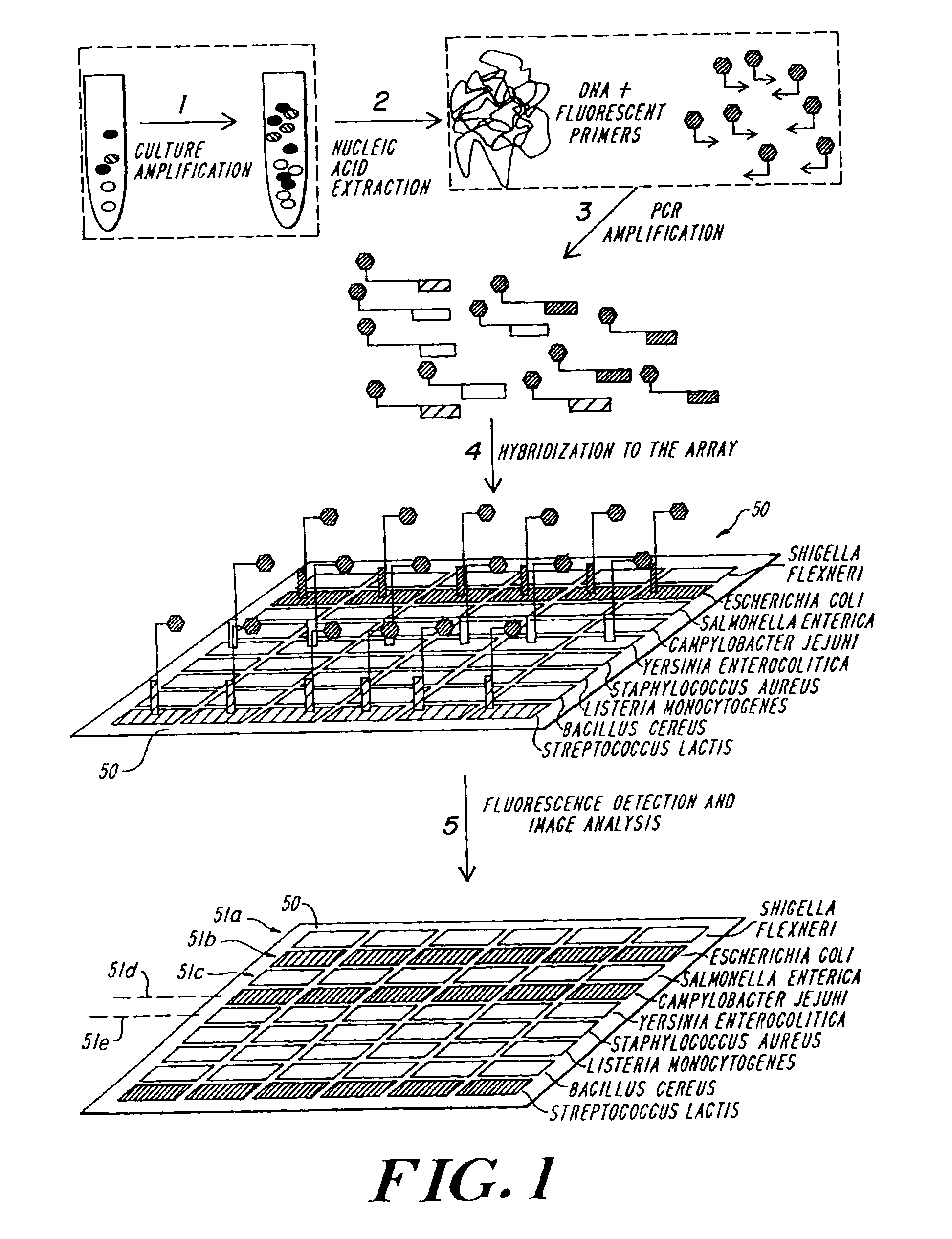
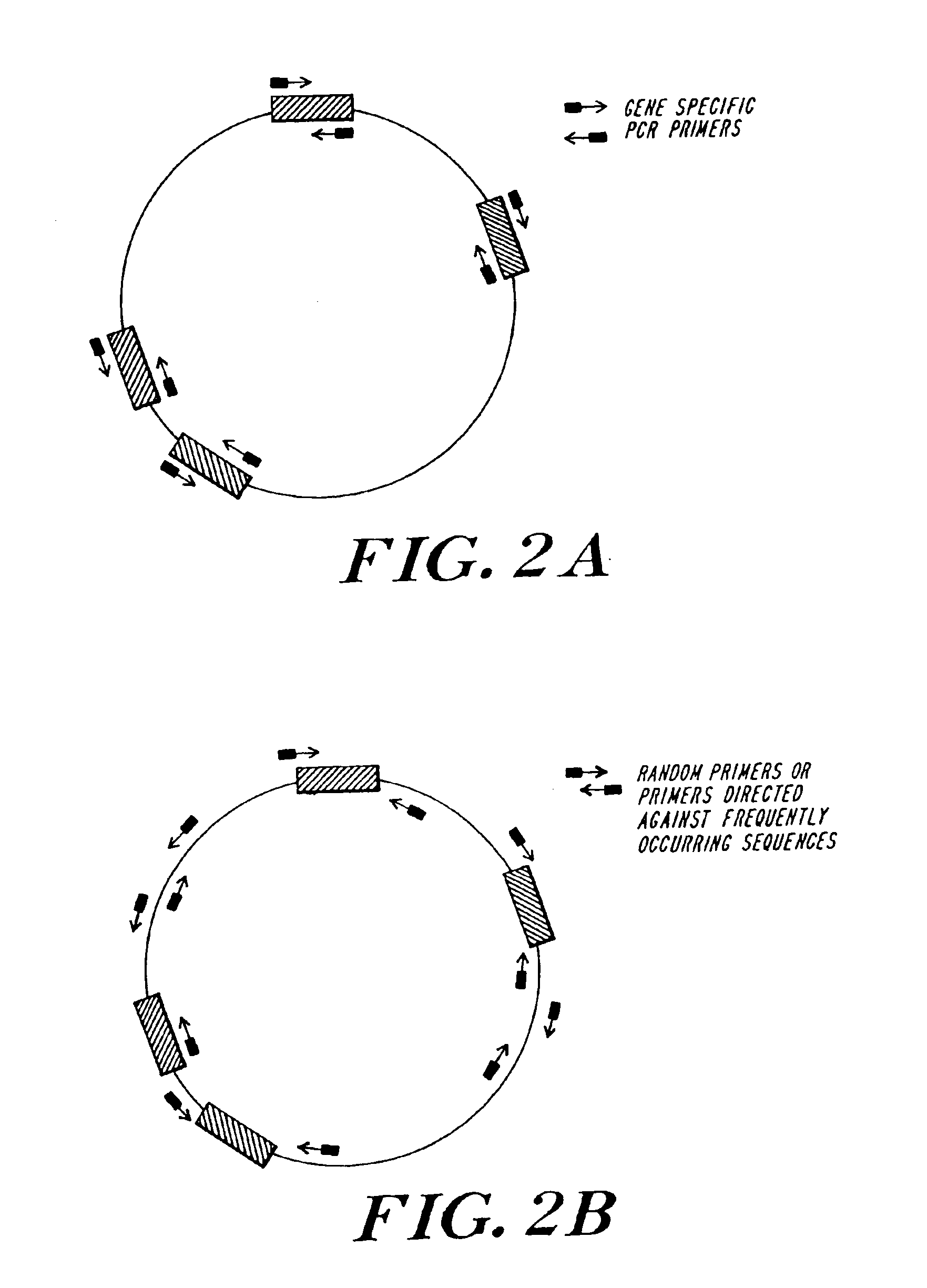
Multispecies food testing and characterization organoleptic properties
InactiveUS6878517B1High sensitivityThe testing process is simpleBioreactor/fermenter combinationsBiological substance pretreatmentsAdditive ingredientOrganism
A testing system useful for food products employs a multispecies testing array to test for presence or amount of a plurality of organisms in a sample by detecting plural characteristic sequences for each of plural organisms to form a multispecies distribution output or microbial profile, and this is processed or used in conjunction with data mining or other processing to provide trend, warning or other data. The processor correlates and stores information relating to taste, smell, texture, processing conditions, quality or source of a component or ingredient, potential pathogenicity or other factor, with correlations on a multidimensional space yielding new preconditions or warning indications, and providing a mechanism for specialization of the species distribution data for specific products, as well as for incorporation or development of process changes and company trade secrets.
Owner:CONAGRA FOODS
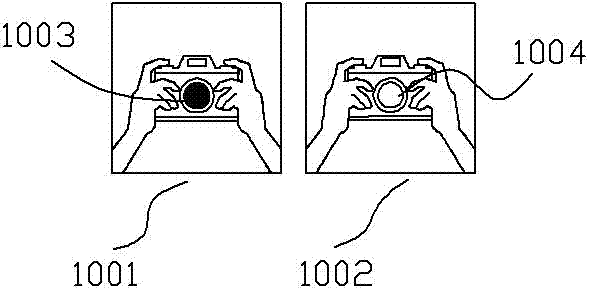
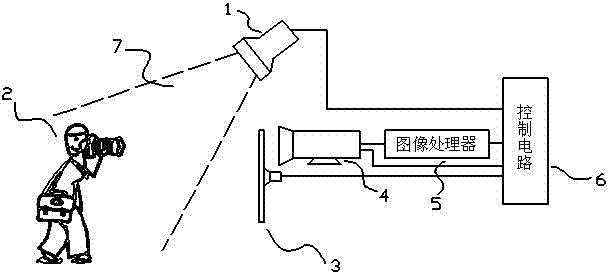
Device and method of automatically recognizing candid camera
InactiveCN106998422APrevent illegal filming in timeRecover damagesTelevision system detailsColor television detailsComputer visionControl circuit
The invention discloses a device and a method of automatically recognizing a candid camera. The device comprises a lighting source, a filter switcher, an image pickup device, an image processor and a control circuit, wherein the lighting source emits visible light and infrared light to irradiate on a to-be-detected area; the filter switcher can switch filters in turn to the front end of the image pickup device to enable the image pickup device to acquire visible light and infrared light images; the image processor compares a brightness difference between the infrared light image and the visible light image and a threshold, and whether a candid camera exists is judged; and the control circuit sends a control instruction to the above parts according to a self-stored program. Through the device and the method of the invention, an illegal photographing behavior can be recognized in an unattended and real-time mode, and the safety of the privacy of people and trade secrets can be effectively protected.
Owner:陈征
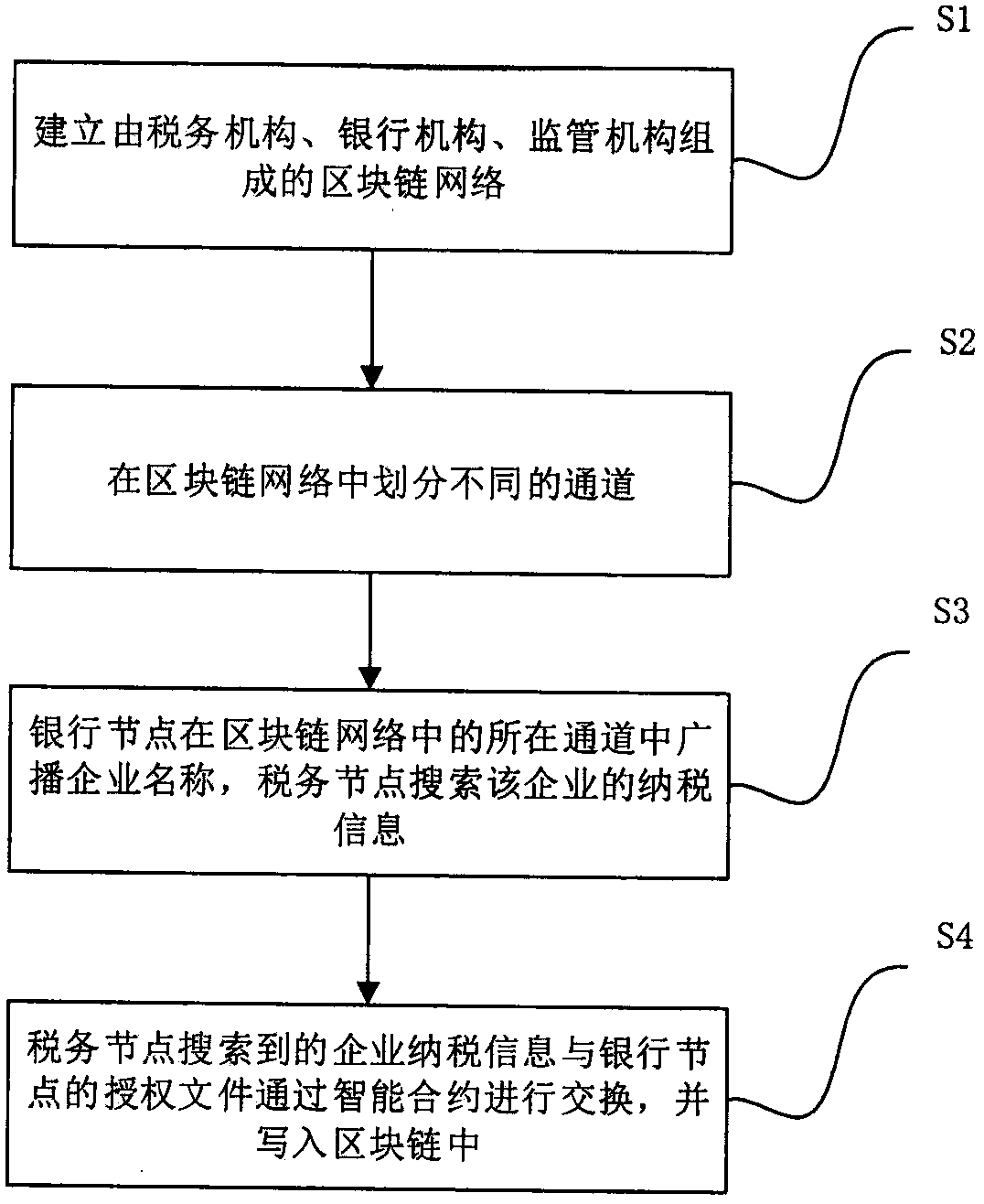
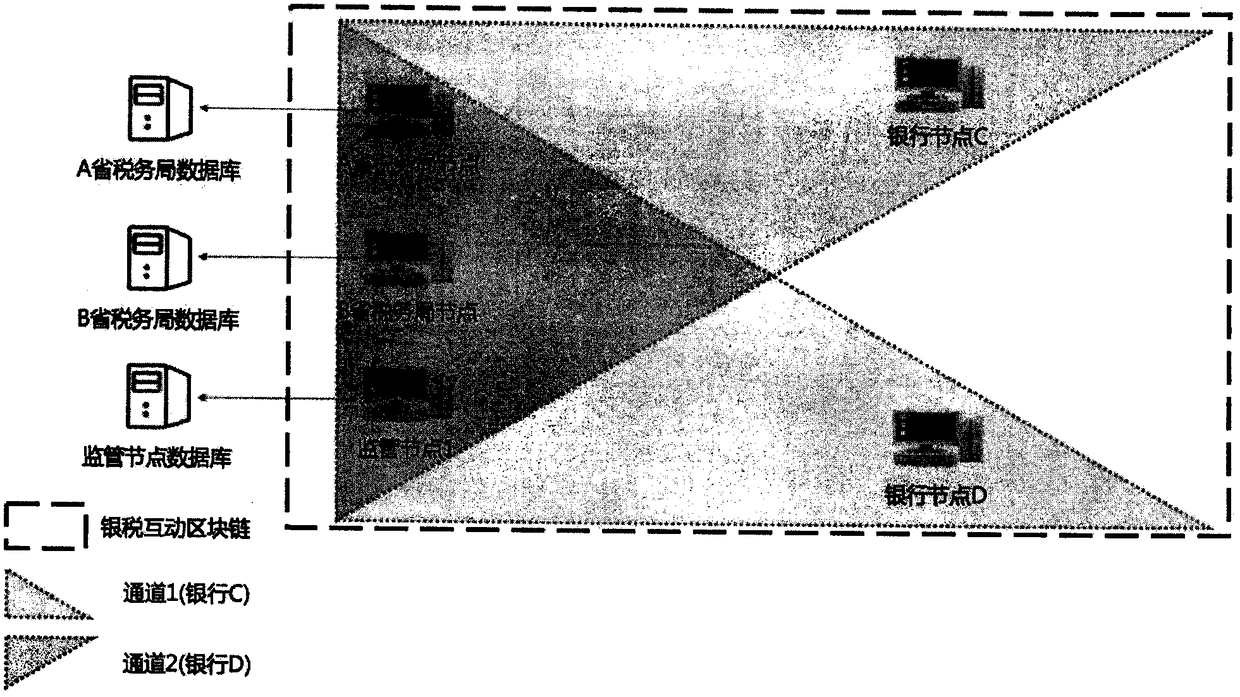
Bank-and-taxation interaction system construction method based on blockchain
InactiveCN108615185AProtect trade secretsAchieve preservationFinanceInteraction systemsComputer science
The invention discloses a bank-and-taxation interaction system construction method based on blockchain. The blockchain is used as a technical support. A supervision mechanism, a tax bureau and banks are used as nodes for being added into a blockchain network, thereby realizing storing and no-tampering of all bank request records by the bank-and-taxation interaction system. Furthermore, according to the method, through dividing different banks into different channels in the blockchain, the banks are isolated, thereby realizing a purpose of protecting business secrets of the banks.
Owner:北京罗格数据科技有限公司
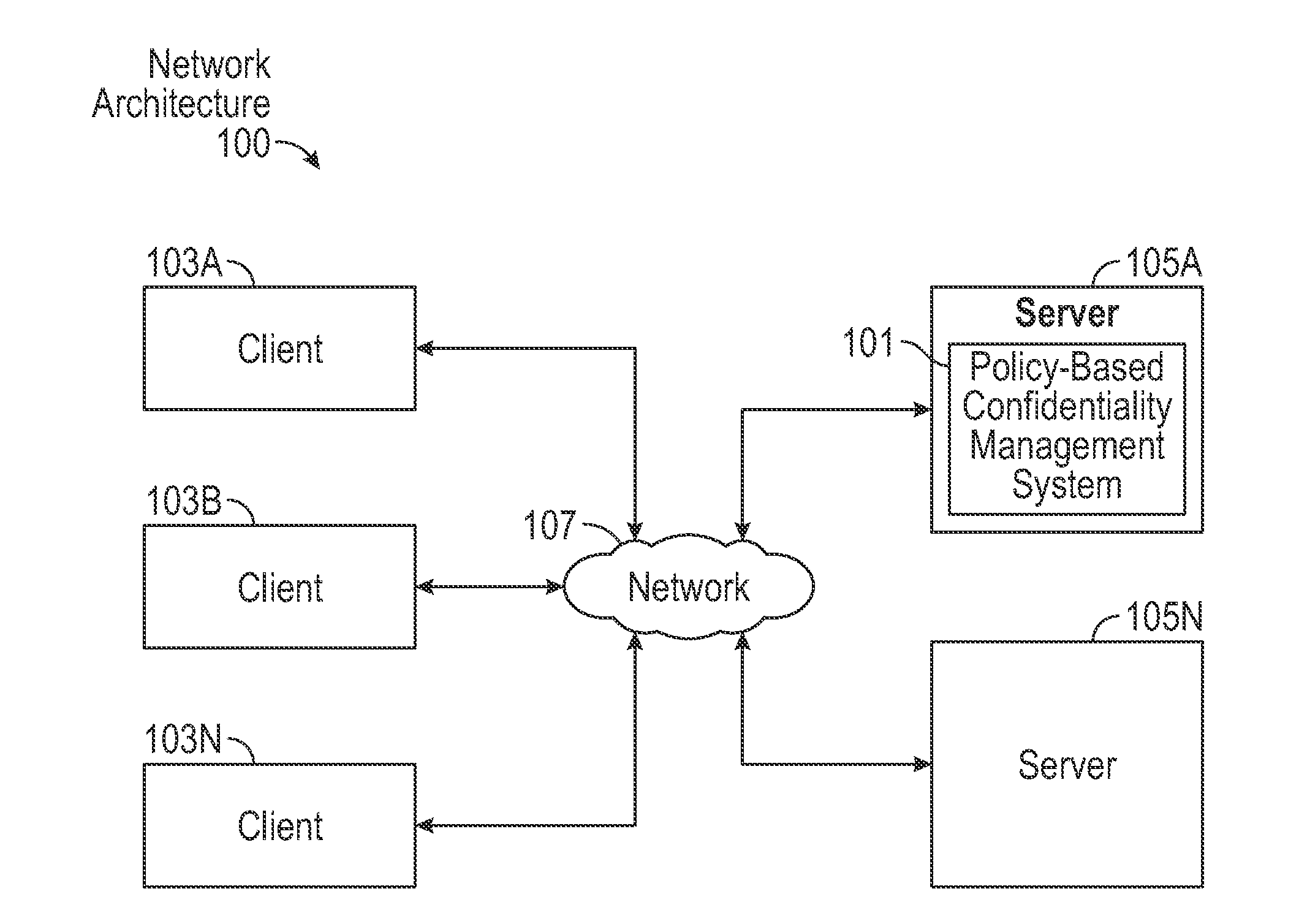
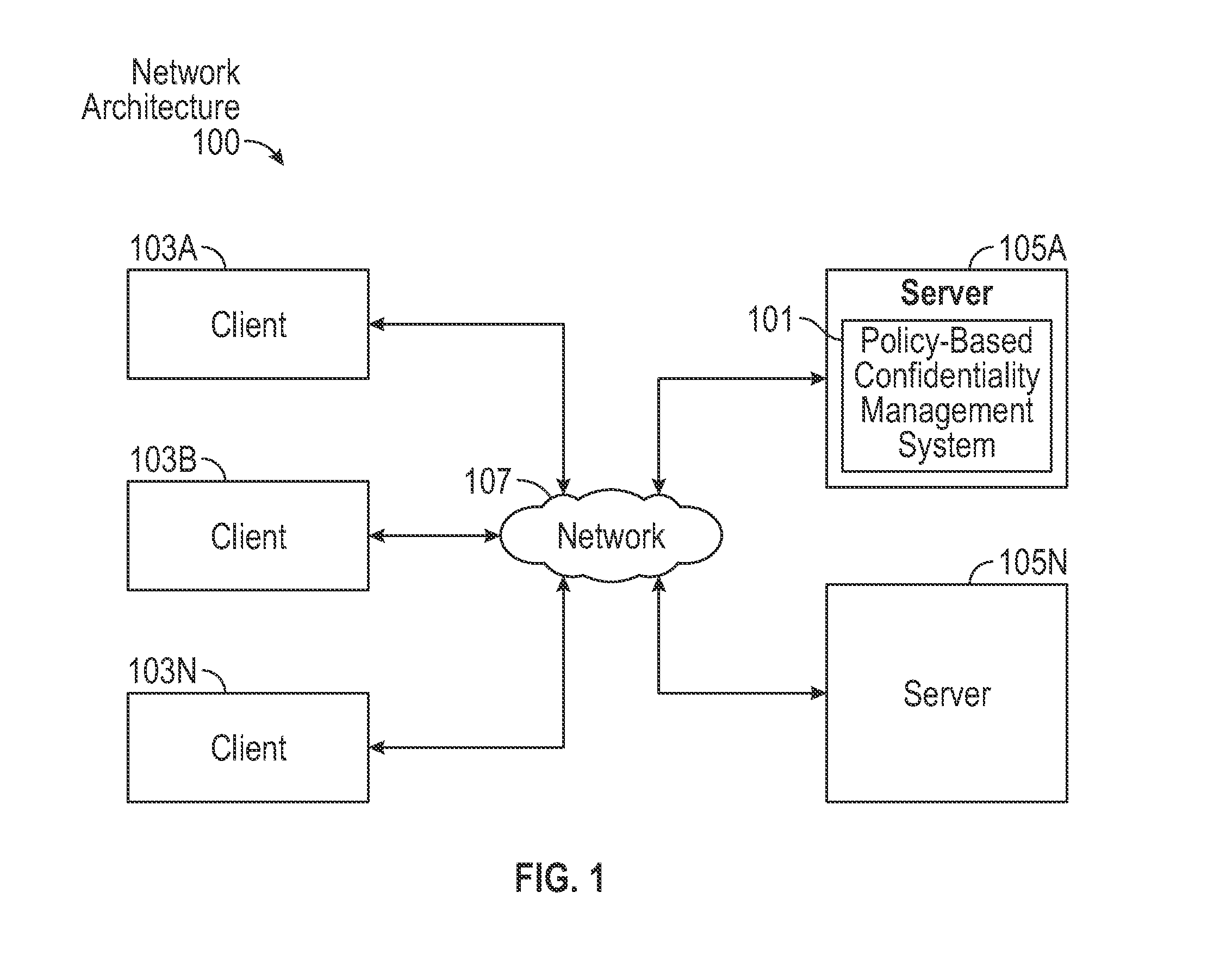
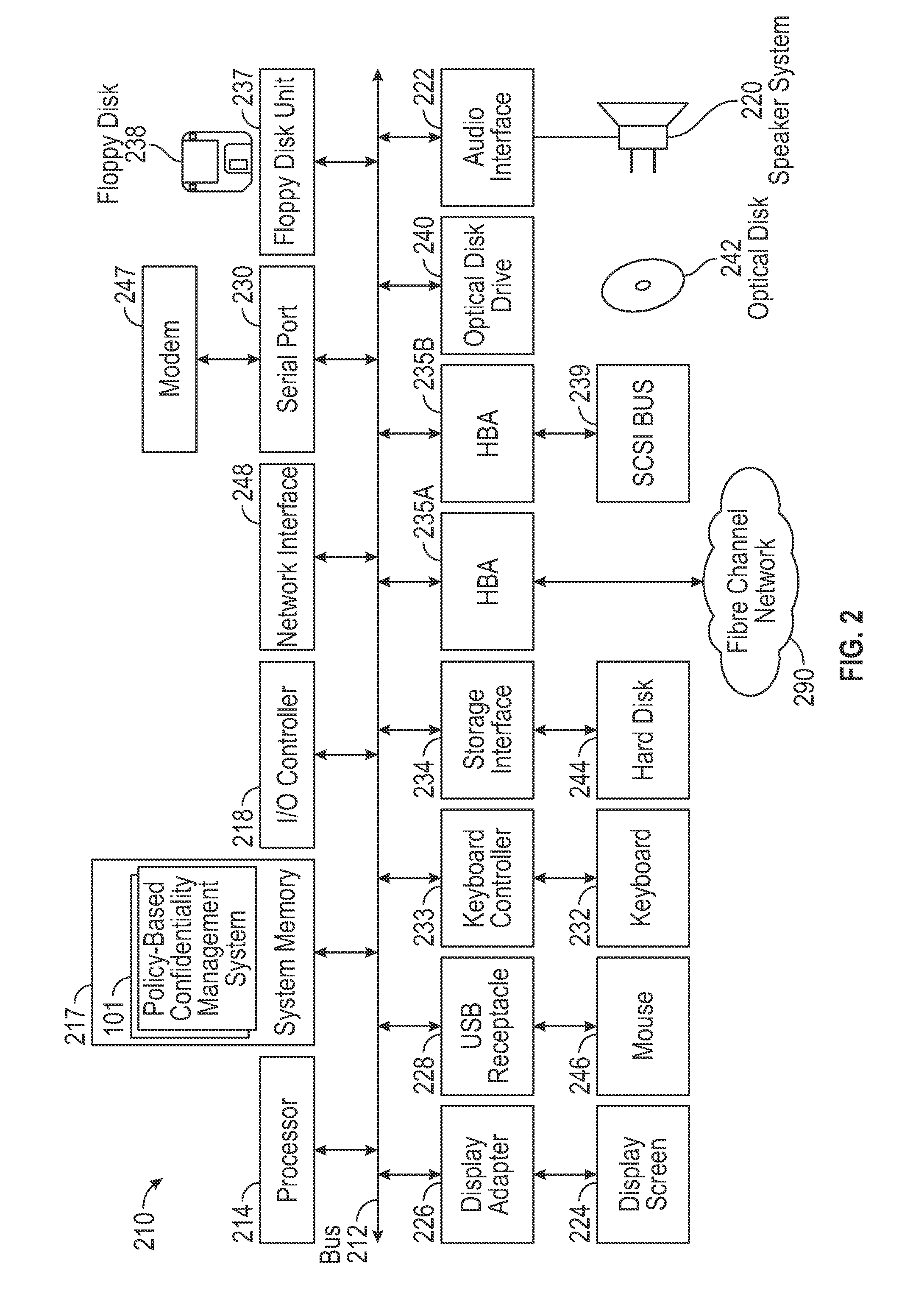
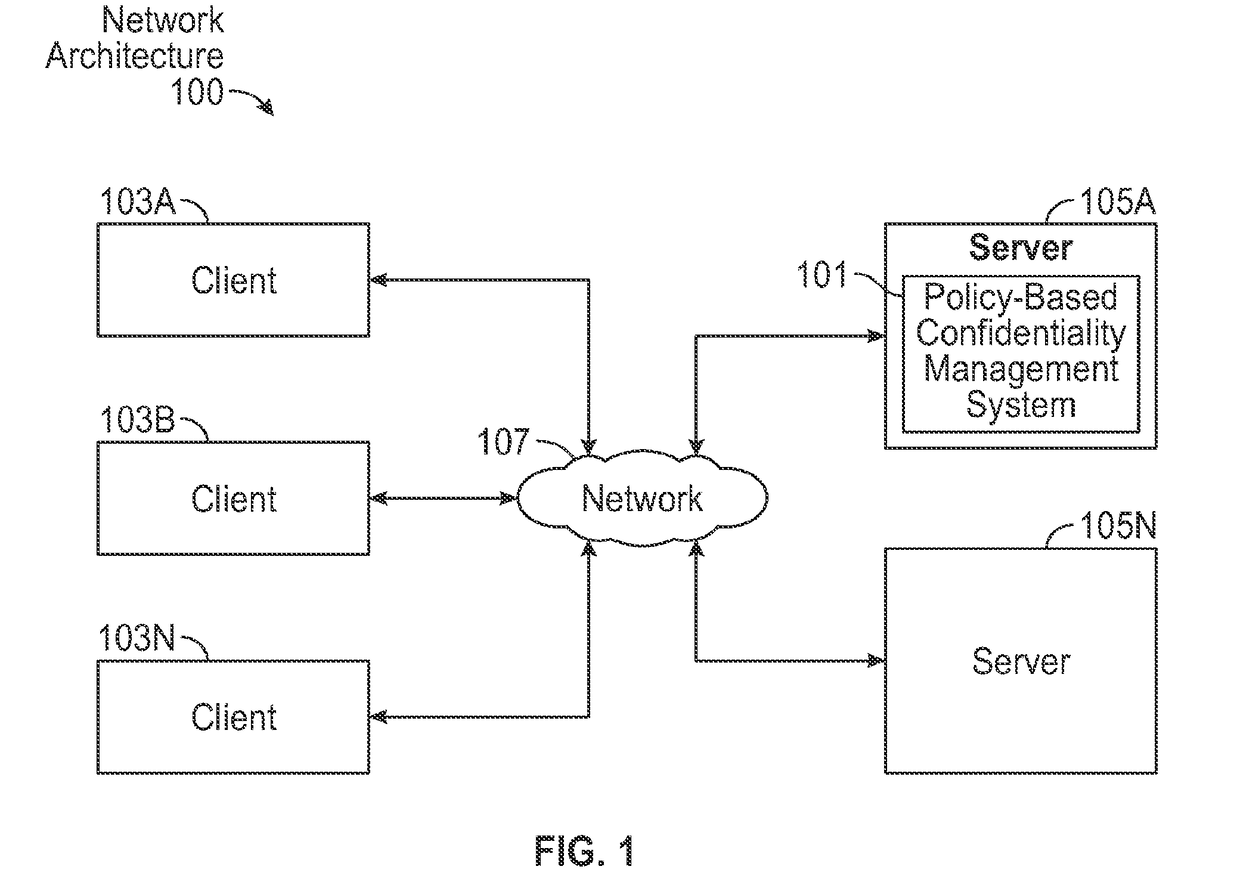
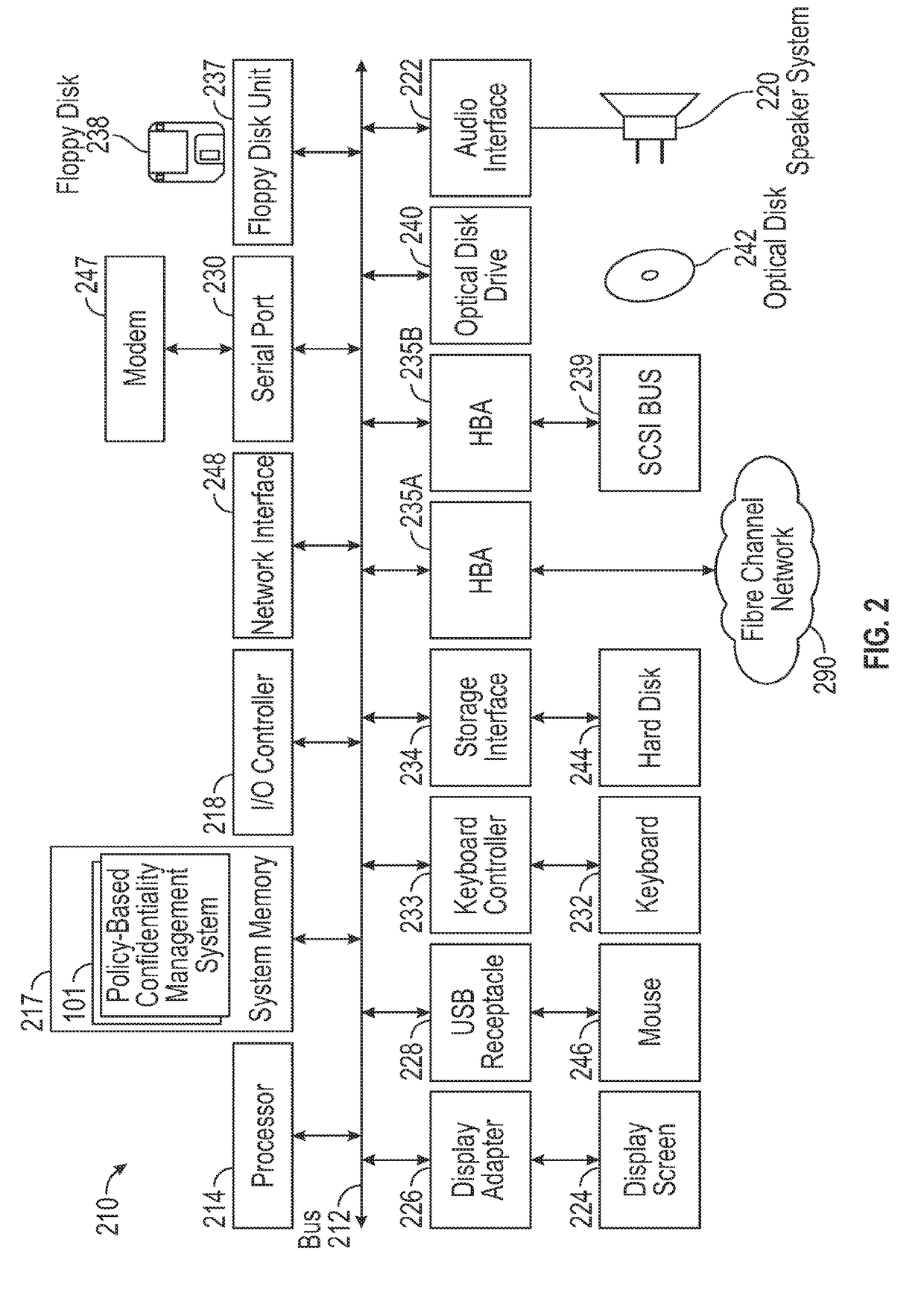
System and Method for Policy-Based Confidentiality Management
InactiveUS20150026760A1Without creating productivity barrierSimple processDigital data protectionTransmissionInternet privacyConfidentiality
A system and method for policy-based confidentiality management provides comprehensive, fluid management of information security and ethical walls. It streamlines processes for securing confidential information without creating productivity barriers, provides interfaces to securely support processes of each major audience in a professional service organization across multiple systems and allows a Risk Team to create policy types for different scenarios and identify systems affected by the policies. It supports standard policy types and those for lateral hires, ITAR, data privacy, price sensitivity, trade secrets, and conflicts of interest and provides two-stage review to prevent incorrect policy application. User interfaces allow granting, denying, and requesting access. Reports sort information governance policies by user / group, client / engagement, or policy type. The system prevents both service desk and other professionals from violating risk management policies in the first place and provides a common user experience, whether a wall has an information barrier or is confidential.
Owner:LIPMAN KEITH
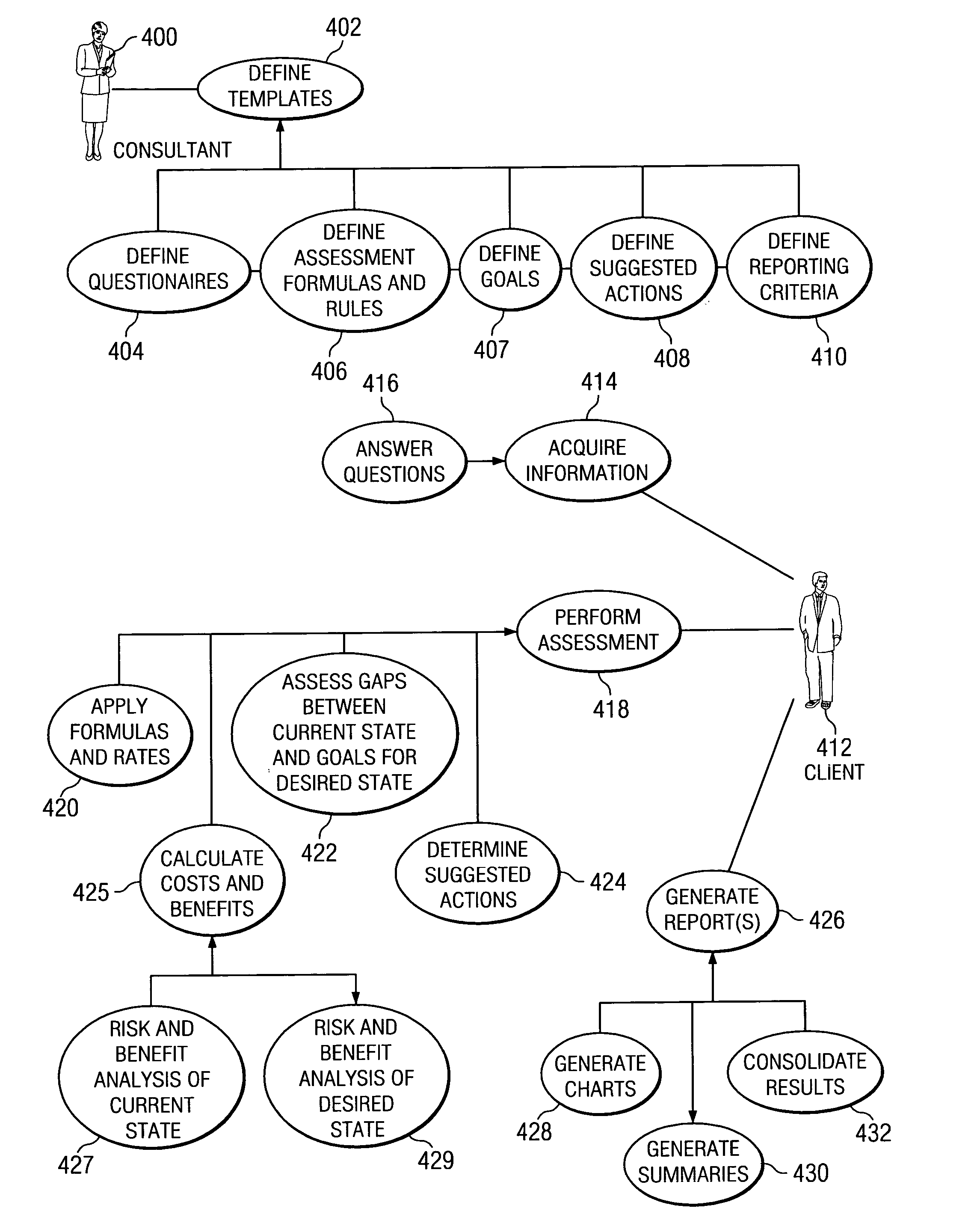
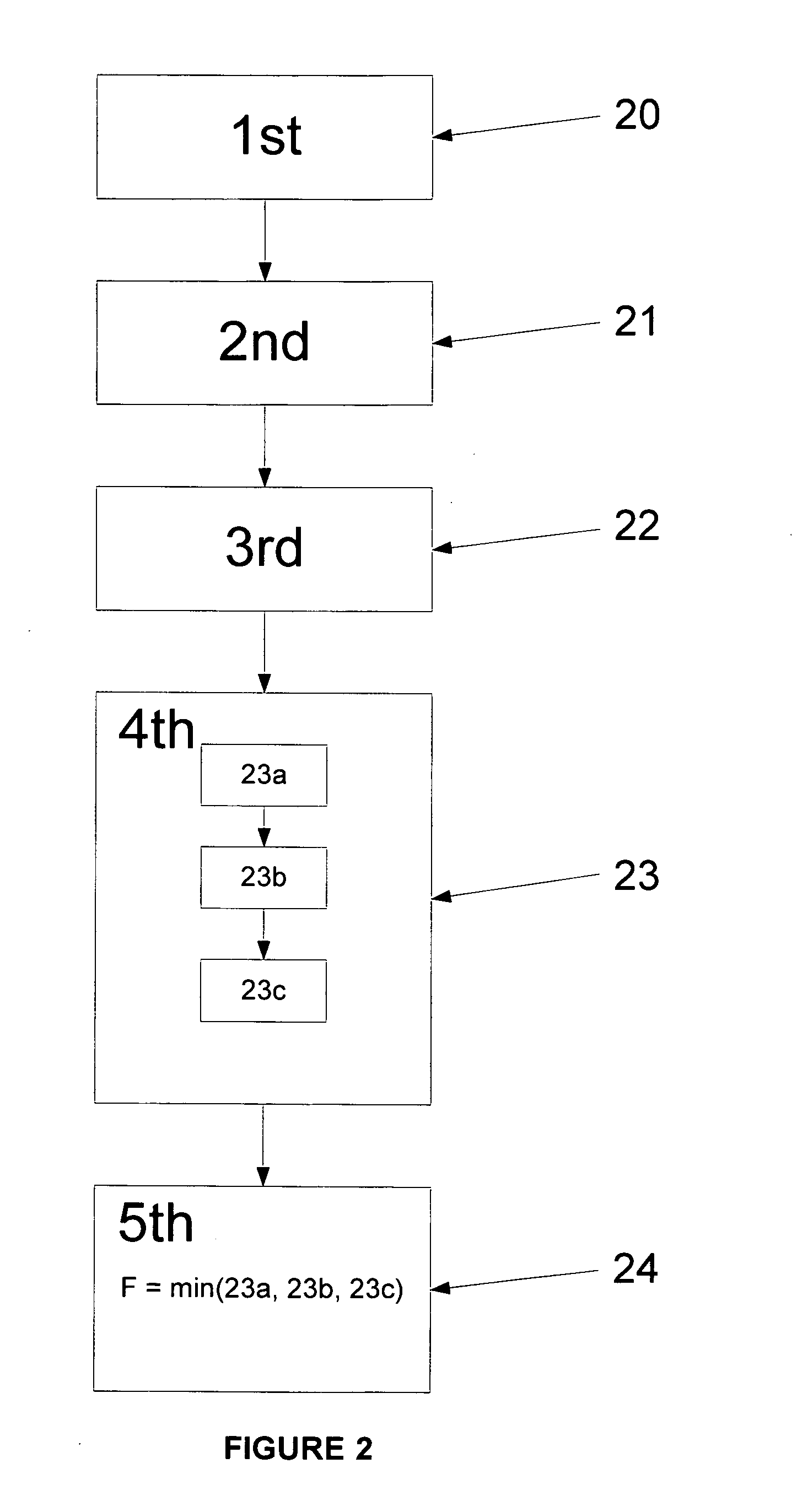
Consulting assessment environment
A method, apparatus, and computer program product for providing a consulting assessment environment. Consultants may use the environment to define templates that encode questionnaires and domain knowledge regarding business practices, as well as reporting criteria to specify the content and format of the assessment results. Consultants or their clients may use the environment to automate the process of performing assessments and generating reports from those assessments. These assessments may analyze the current state of the business, compare the business's current state with desired states or with best practices, and perform risk / benefit and / or cost / benefit analyses, according to the specifications made in the templates on a real-time basis for producing immediate assessment results and actions. An information hiding feature is provided to allow sensitive domain knowledge encoded within the templates, such as trade secrets, to be made inaccessible to clients.
Owner:TWITTER INC
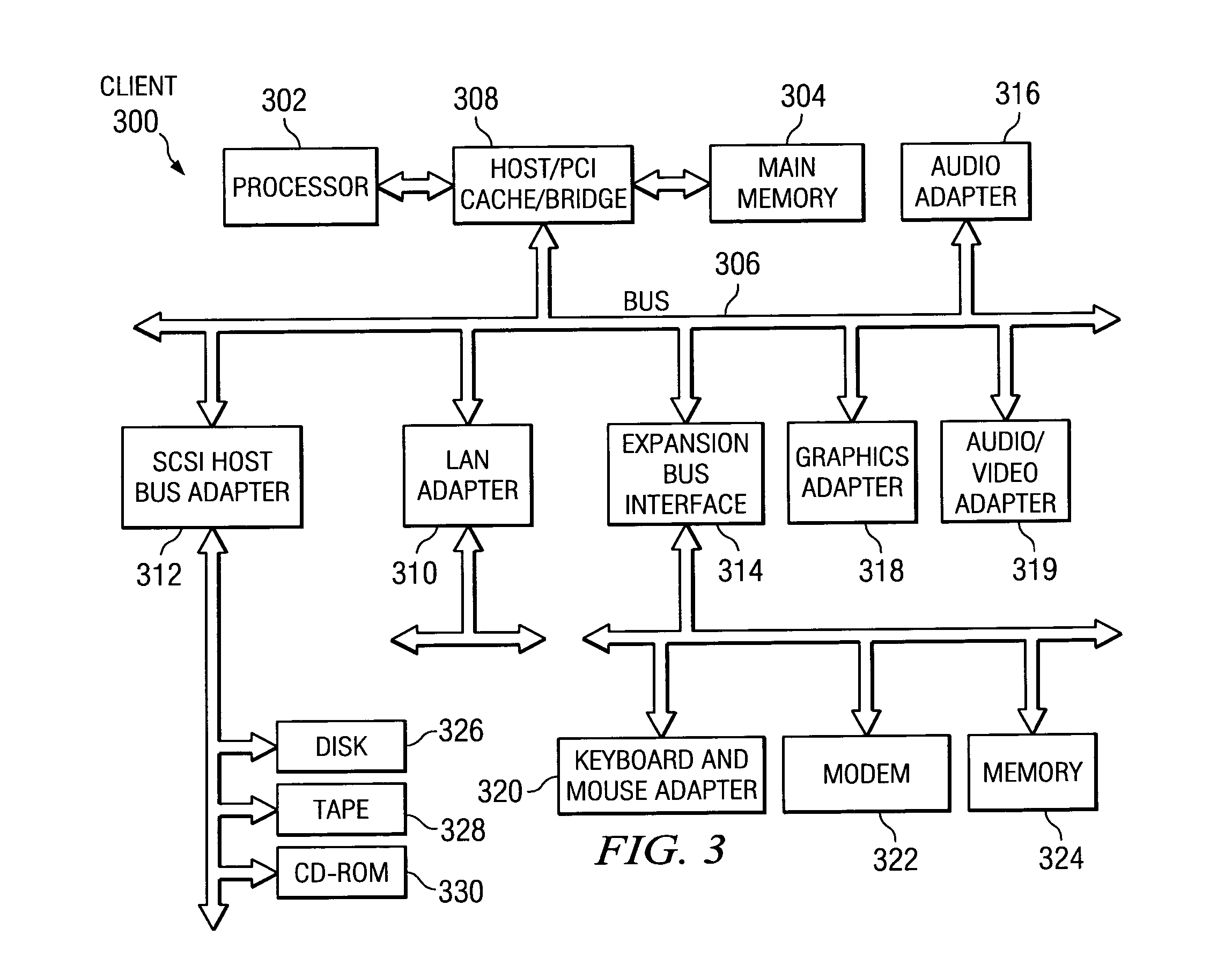
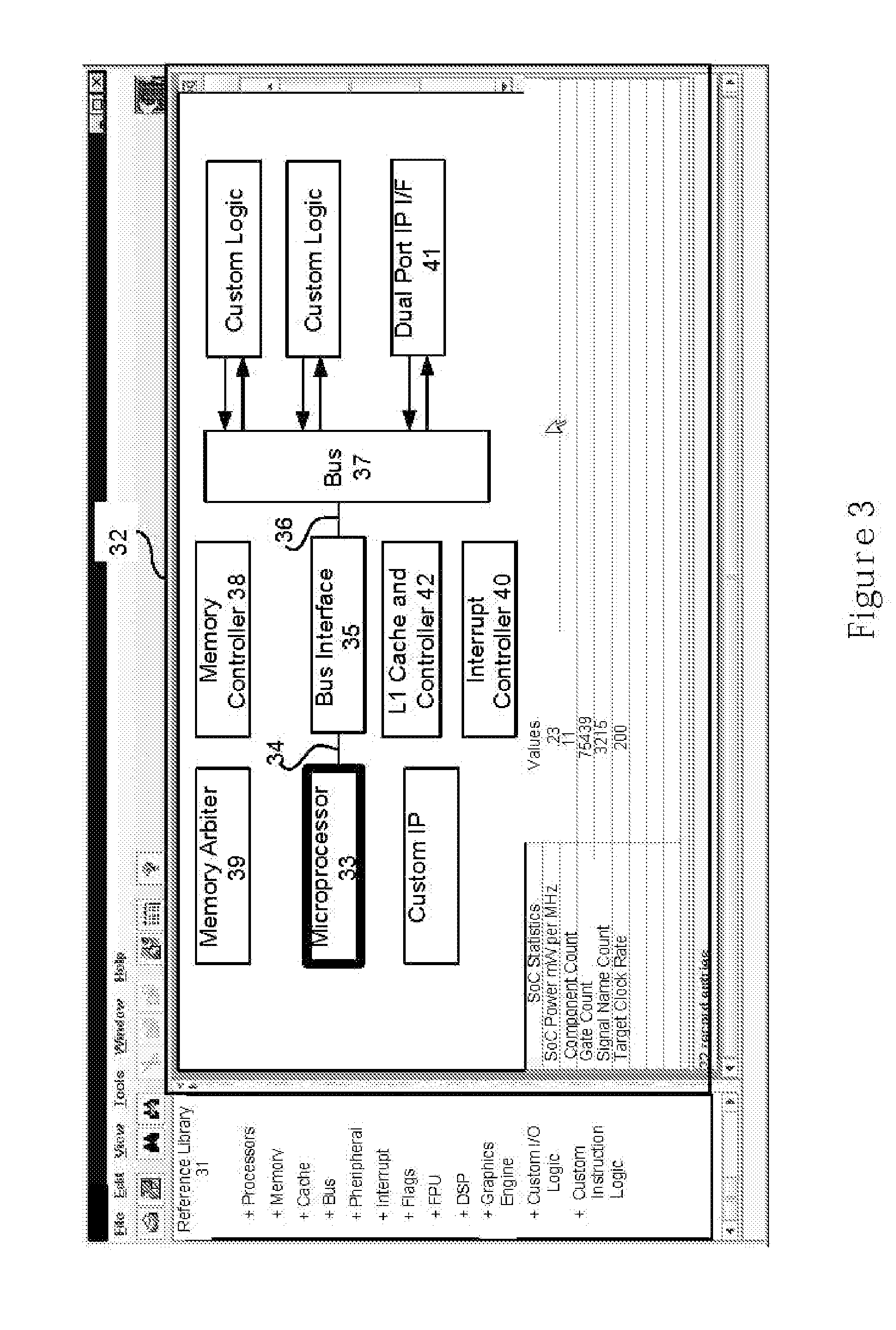
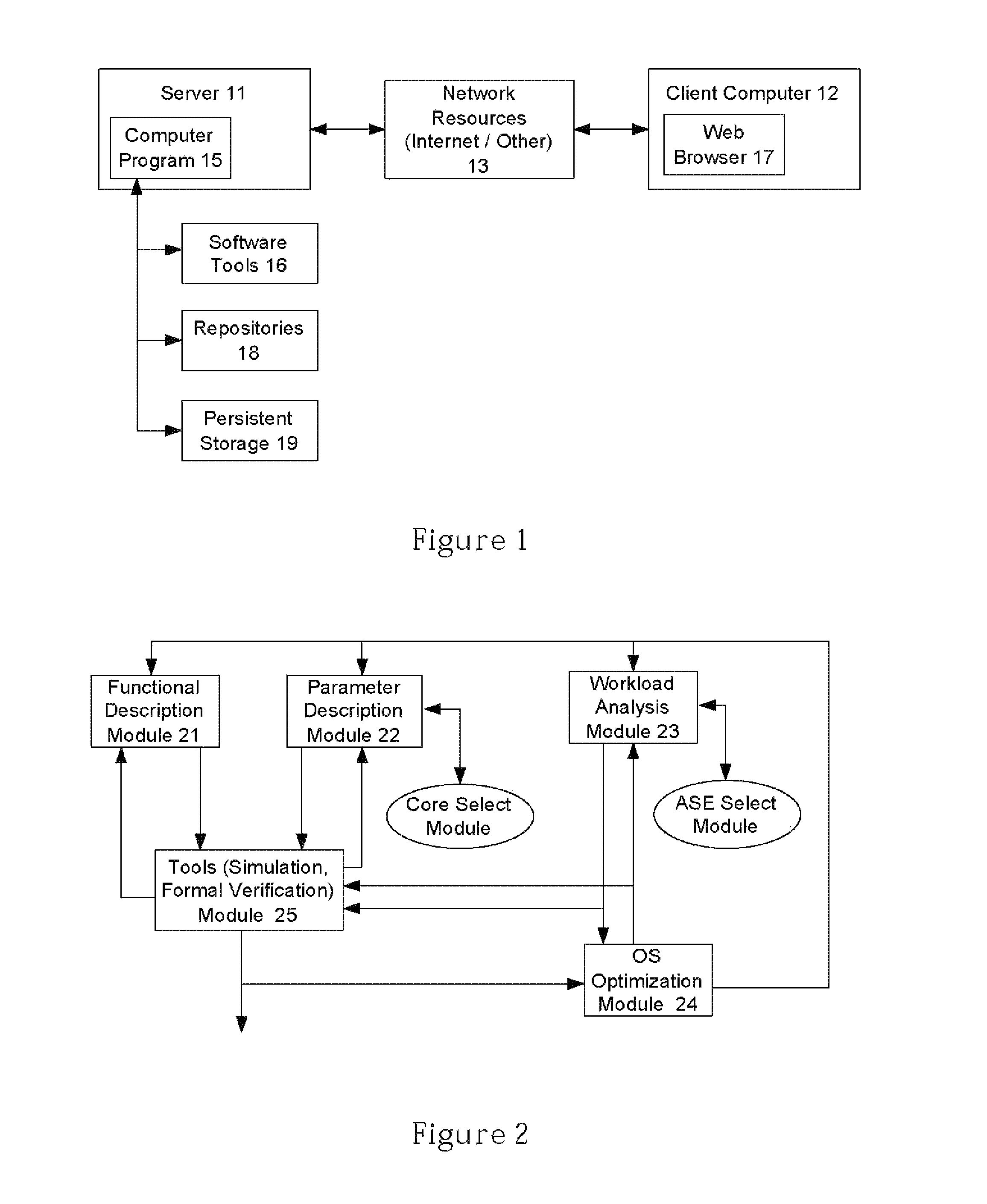
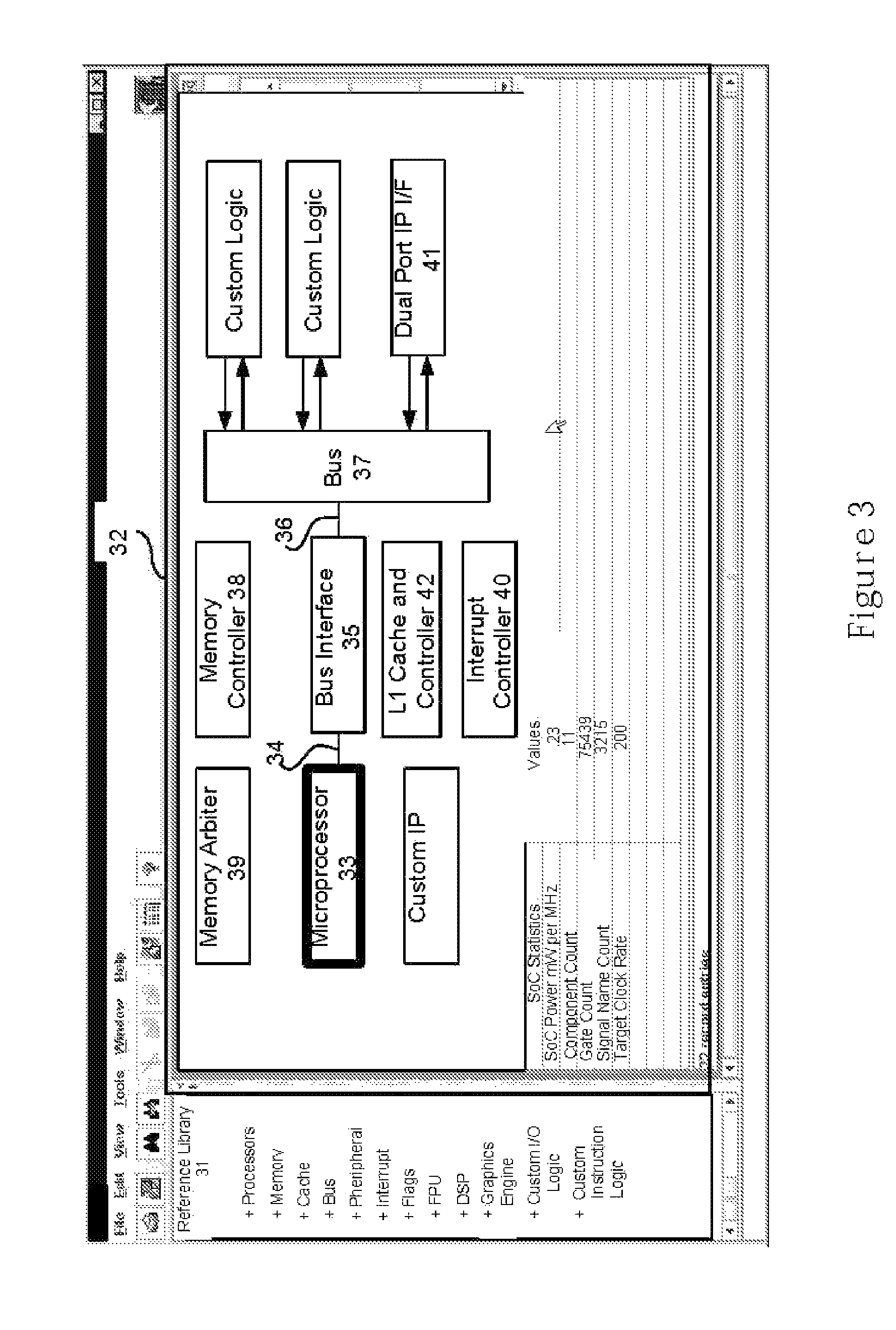
Protecting Trade Secrets During the Design and Configuration of an Integrated Circuit Semiconductor Design
ActiveUS20080222589A1Computer programmed simultaneously with data introductionCAD circuit designGraphicsComputer architecture
A system and method for facilitating the design process of an integrated circuits (IC) is described. The system and method utilizes a plurality of repositories, rules engines and design and verification tools to analyze the workload and automatically produce a hardened GDSII description or other representation of the IC. Synthesizable RTL is securely maintained on a server in a data center while providing designers graphical access to customizable IP block by way of a network portal.
Owner:ARM FINANCE OVERSEAS LTD
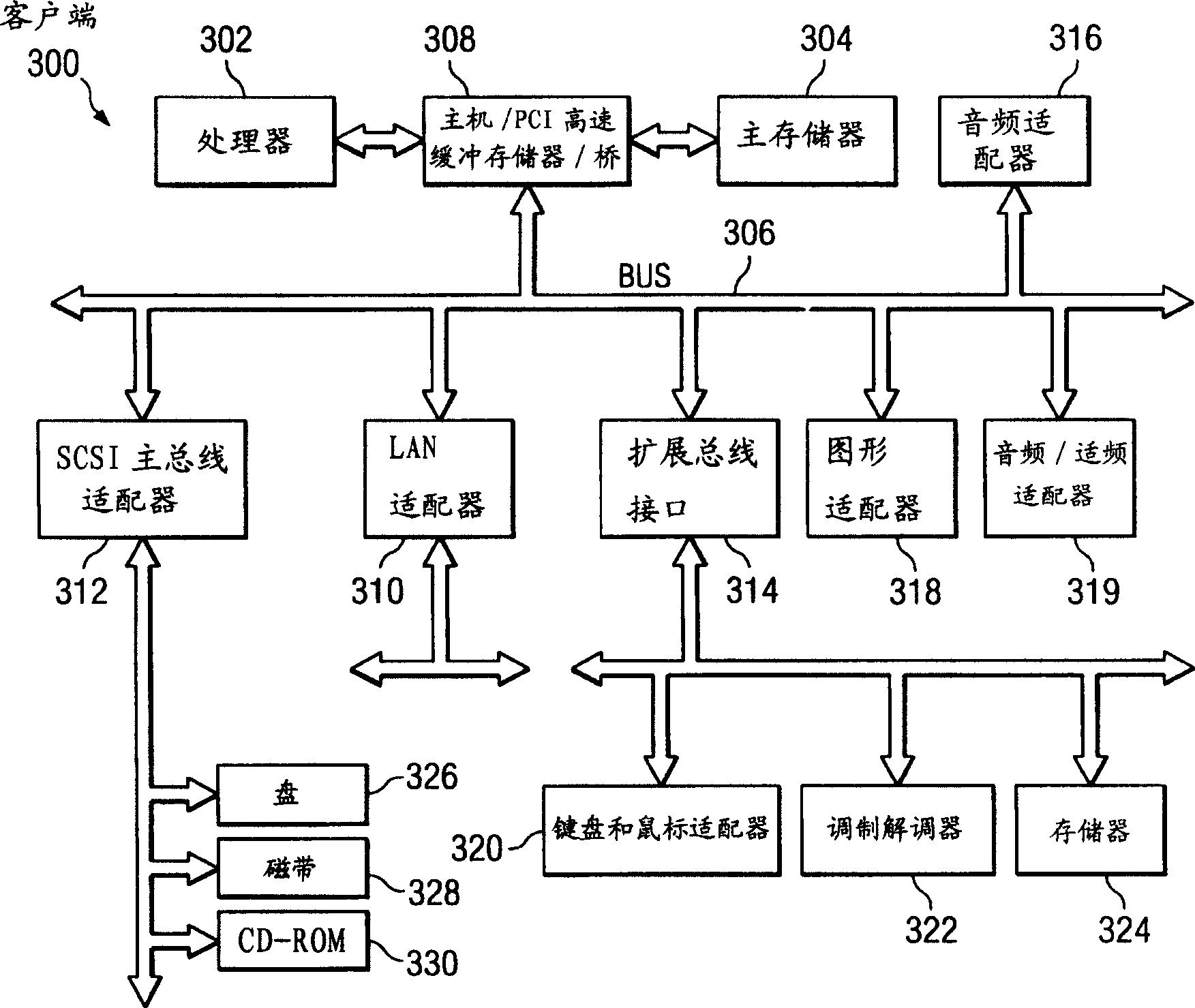
Scalable transaction system for a network environment
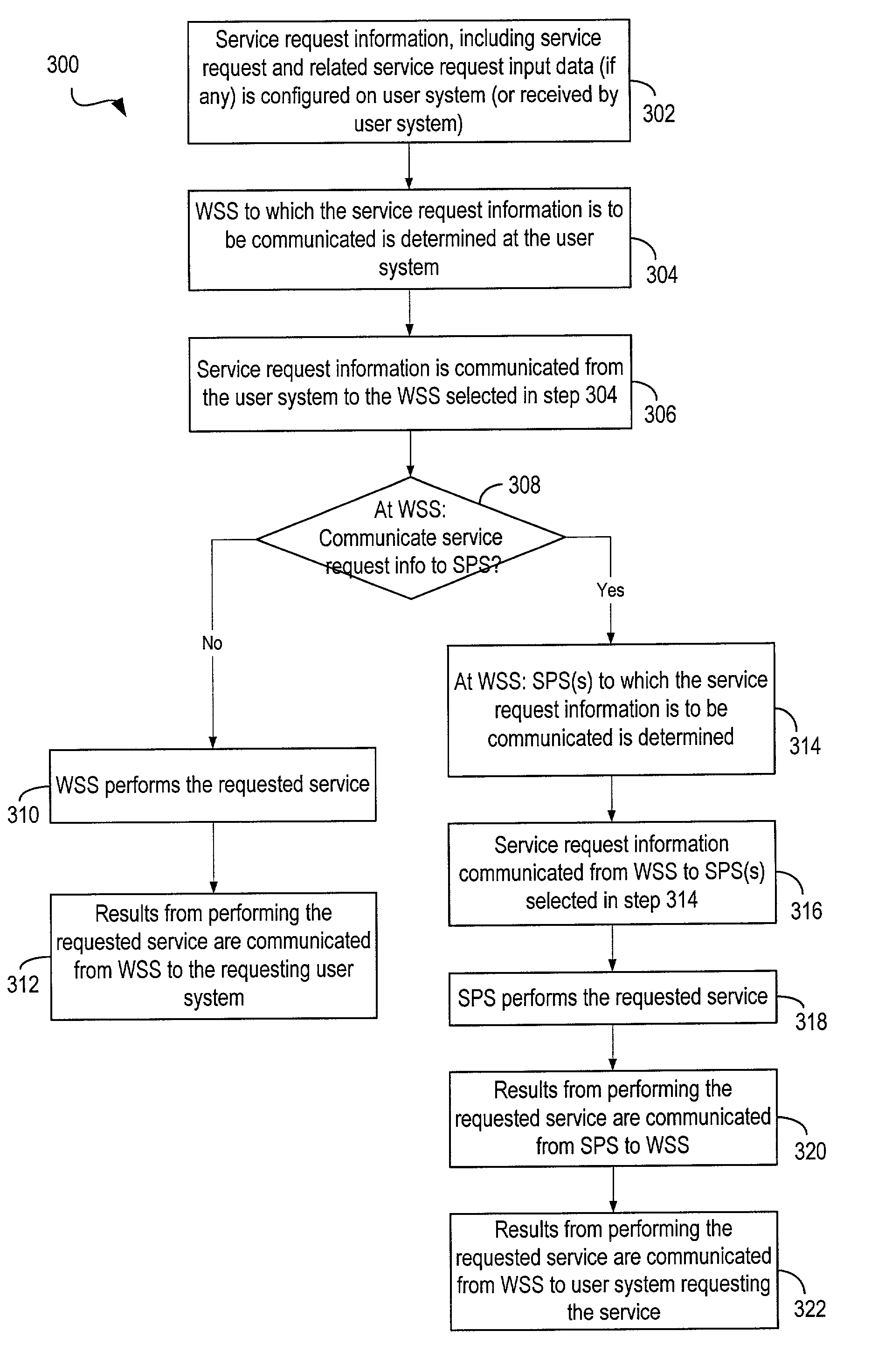
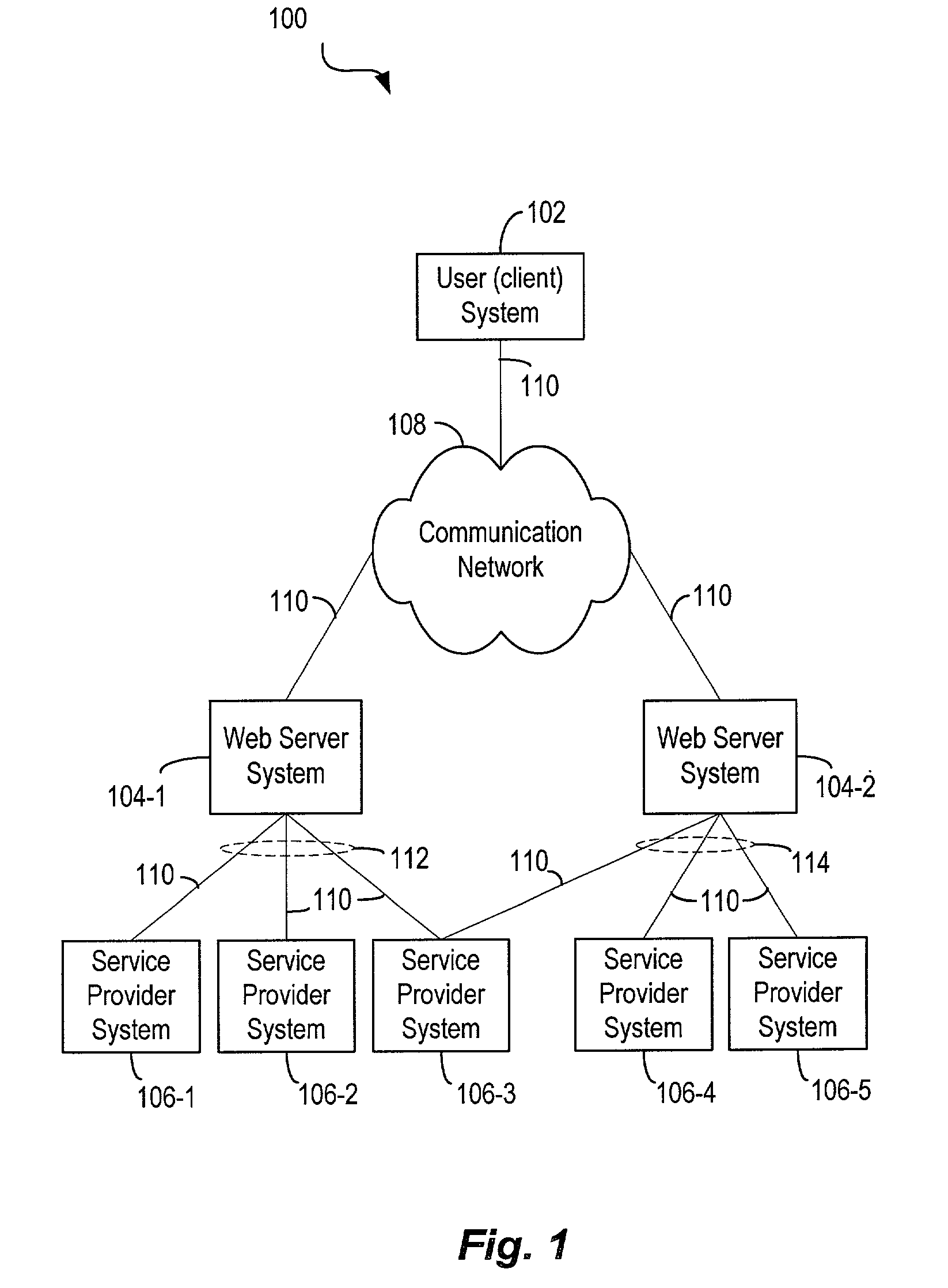
ActiveUS6947977B1Multiple digital computer combinationsElectronic credentialsService providerWeb environment
Techniques for performing services in a secure and scalable manner in a network environment. Code modules and data used for performing a service and that contain proprietary, confidential, or trade secret information, are stored and executed by service provider systems that are not exposed to user systems used to configure the service requests. The techniques are scalable as the number of service provider systems performing the services can be scaled, either up or down, in proportion to the demand for the services.
Owner:OL SECURITY LIABILITY CO
Protecting trade secrets during the design and configuration of an integrated circuit semiconductor design
ActiveUS7774723B2Computer programmed simultaneously with data introductionCAD circuit designGraphicsComputer architecture
Owner:ARM FINANCE OVERSEAS LTD
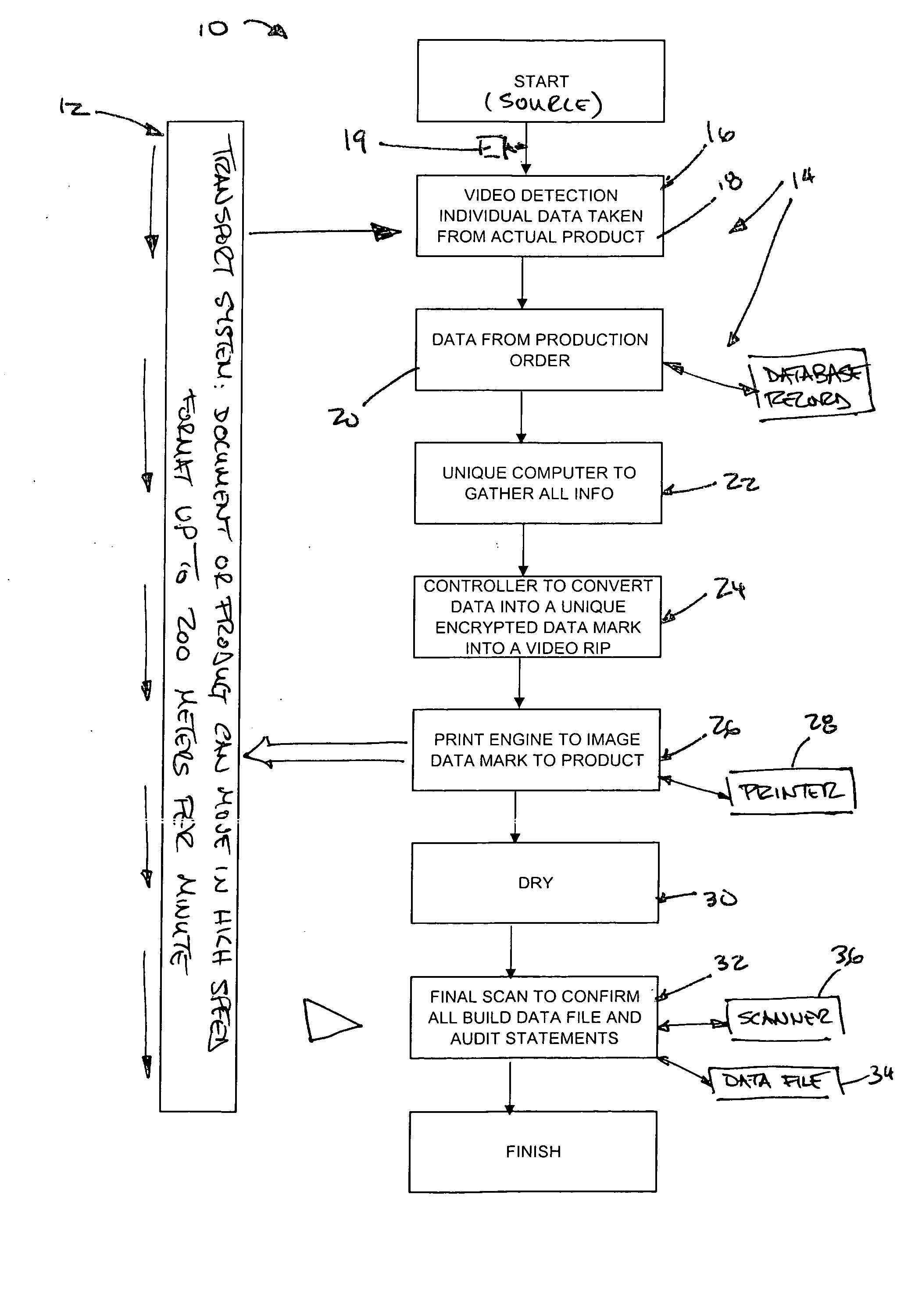
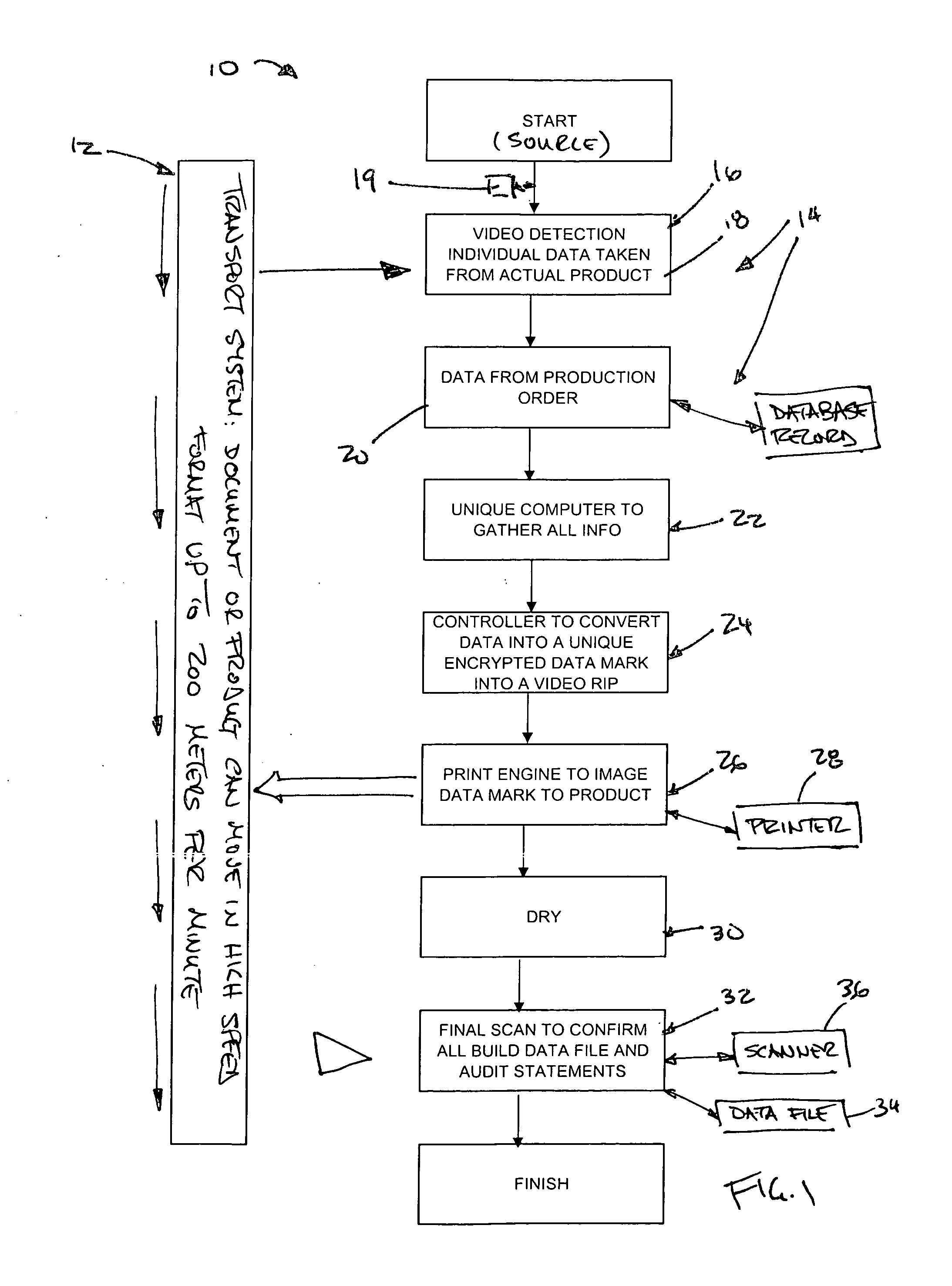
Real-time auditing of covert data marks
A system and method is provided for the real time auditing of covert data marks. Specific information relating to a product or document is entered into an information cell or shell from a product data file. A high definition, high resolution, high speed inline video system is provided to take specific details from the individual product or document, which details are added to the data cell or shell. Details are then inspected, quality checked, matched in the event there are multiple identifiers (e.g., currency would normally carry two matching sequential numbers), and verified to the product order. This cell or shell is passed to the special design computer / controller through a high speed electronic interface. Information entering the computer / controller is once again verified and matched to the original data as well as the product or document. The cell or shell is converted into a specially created 2-dimensional bar code which is encrypted by the computer / controller and then transformed into a video rip. This video rip is sent to high quality / high resolution production print engines. The encrypted 2-dimensional bar code is imaged directly to the product or document as it is carried past the print imaging engines. The ink also is specially designed and manufactured for this system and process. It is an invisible ink which is unique, durable, permanent and not available commercially (covered under trade secrets). These special inks are well suited for delivery using inkjet technology to efficiently make well formed invisible images at slow to high speed production schemes. The product or document is then sent instantly into a drying scheme (this can be air, forced air, heat, UV Dryer, depending on the printing system selected). After drying there is a final scanning. This scanning equipment is the same scanner design which will be used in the field so that each product or document will be verified with the actual scanning device and programs which will be used in the field. From this final scanning of the 2-dimensional data bar code, a final audited product or document profile is created, as is a database which will be the point of reference in the infrastructure during the life of the product or document. Each time any product or document is scanned at a transaction point, the database will be updated, either in real-time or downloaded from a data collection scanning device. This will build a complete history from the point of manufacture to the moment it is removed from service.
Owner:COVERT SECURITY SOLUTIONS
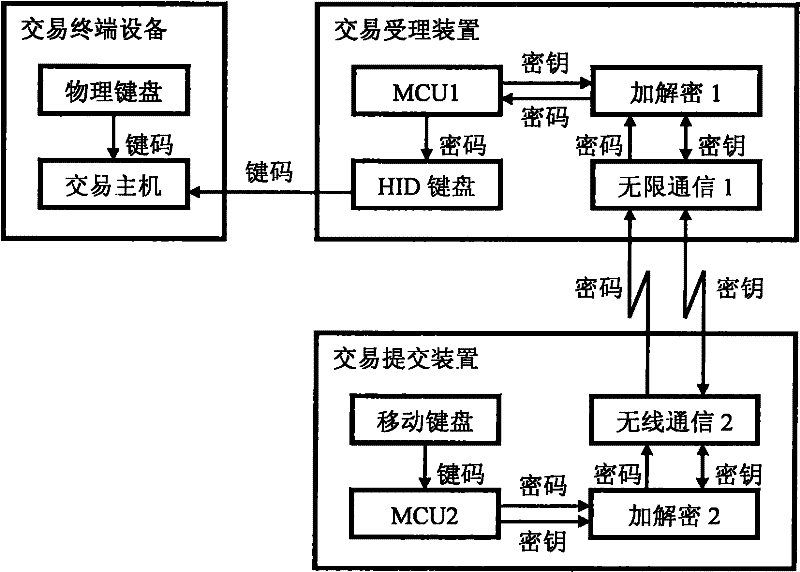
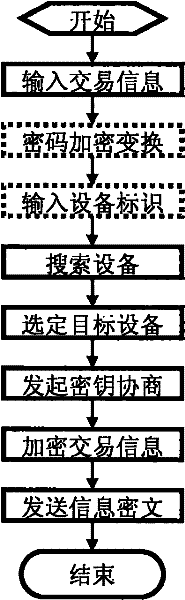
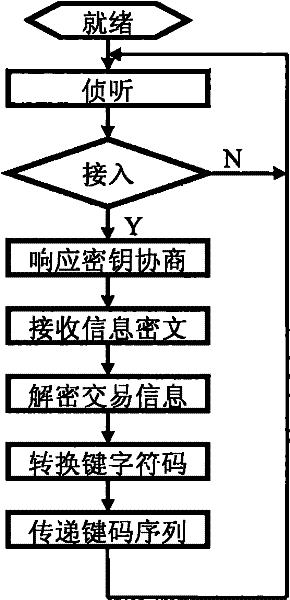
Transaction security method, acceptance device and submission software
InactiveCN102262760AProtect account password securityImprove security and confidentiality functionsPayment architectureKey exchangeBluetooth
A transaction confidentiality method, acceptance device and submission software relate to the technical fields of finance, electronics, communication, software and information security. Trading institutions, especially banks' trading terminal equipment (such as ATM, POS) are equipped with wireless transaction acceptance devices. Customers use mobile phones to input transaction information (password and / or amount), and use short-range wireless communication (such as Bluetooth) to establish a confidential channel to send and submit; transaction acceptance The device is configured to automatically identify the HID keyboard, convert the transaction information to generate a key character code sequence, and transmit the simulated keyboard keys to the host of the transaction terminal device, which is equivalent to inputting from a physical keyboard; the key negotiation process bilaterally generates and exchanges random keys, and the transaction acceptance device Randomly generate or transform the exported key, and finally use it to encrypt and decrypt transaction information; limit the valid value range of the character code of the verification key, and shield and not pass invalid character codes; the mobile phone submission software also encrypts and transforms to prevent peeping, effectively protecting the account password; device system No changes to business processes are required.
Owner:杨筑平
Computer and office equipment provided with device with functions of preventing secret photography and preventing eavesdropping
InactiveCN102663307AMeet different needsAvoid influenceInternal/peripheral component protectionParalemminEavesdropping
The invention discloses computer and office equipment provided with a device with the functions of preventing secret photography and preventing eavesdropping, which relates to equipment, such as a notebook computer, a desktop computer, a pen based computer, a palm computer, relevant office equipment and the like. The computer and office equipment with the device with the functions of preventing secret photography and preventing eavesdropping comprises a casing of the computer and office equipment, a power supply circuit and a functional circuit. The computer and office equipment with the device with the functions of preventing secret photography and preventing eavesdropping is characterized in that a device system with the functions of preventing secret photography and preventing eavesdropping is arranged in the computer and office equipment, and the device system with the functions of preventing secret photography and preventing eavesdropping is connected with a mainboard of the computer and office equipment. By adding the warning system with the functions of preventing secret photography and preventing eavesdropping according to the computer and office equipment, the condition whether secret photography equipment and a detectaphone work at the periphery of a user or not can be automatically monitored, the information of reminding is also sent out to the user in time, and the influence of illegal secret photography equipment and an illegal detectaphone to the work and the life of people in the work and the life nowadays is solved. Meanwhile, the behavior of a competitor adopting some underhand means to carry out secret photography and eavesdropping so as to obtain the privacy of other people or the trade secret of an enterprise is effectively prohibited.
Owner:崔华
Method and system for managing commercial secret based on block chain negotiation encryption
ActiveCN109361654AImprove experienceReduce the risk of leaking secretsFinanceCharacter and pattern recognitionComputer scienceEncryption
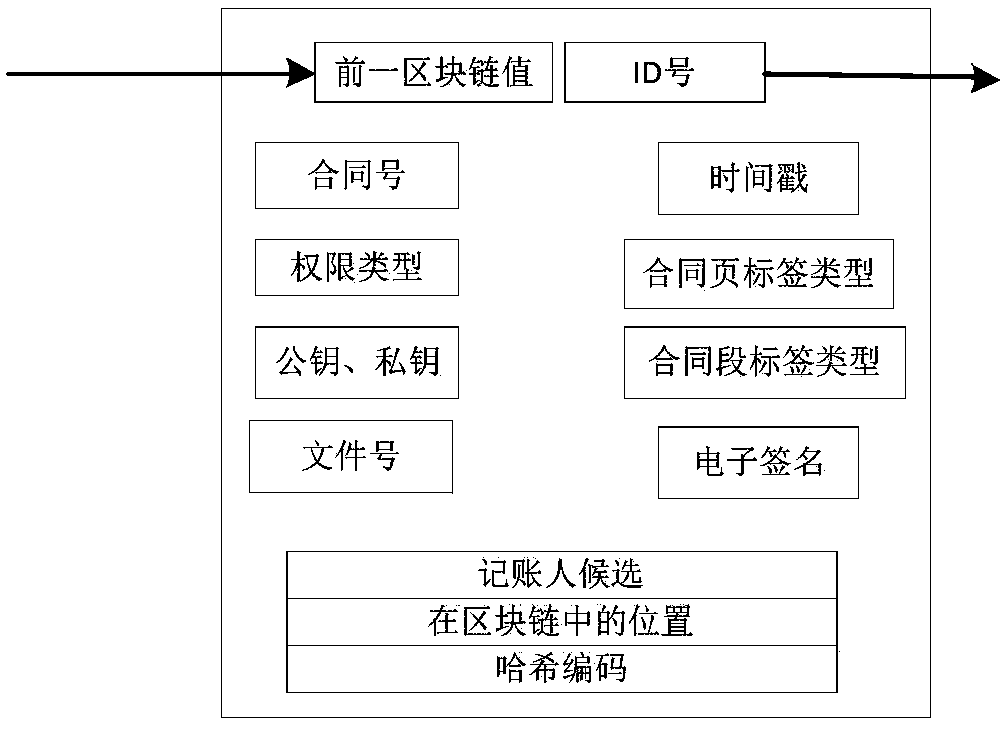
The invention relates to a method and a system for managing commercial secret based on block chain negotiation encryption. A plurality of company legal persons and natural persons with different levels inside the company form N nodes; each time a contract is successfully signed, a record is constructed and a new block is formed; the block comprises a contract page label type and a contract sectiontype; the block also comprises a two-dimensional code generating module; when different nodes check, corresponding two-dimensional codes are generated for obtaining corresponding contract informationaccording to difference of jurisdiction of the different nodes to check the block; the contract page and the contract section character image regions with normalized size are subjected to uniform gridding coverage; the contract page and the contract section character images are divided into a plurality of attribute regions, wherein each small attribute calculating grid is a sub-qualitative mapping cluster; and the two-dimensional code of a corresponding content is generated according to the query jurisdiction type and the attribute of the sub-qualitative mapping cluster. The method and the system for managing commercial secret based on block chain negotiation encryption in the invention realize a new management mode in the commercial secret field, thereby significantly reducing the risk of leakage of the commercial leakage in the related contract signing process and reducing the occurrence of error rate; moreover, the accuracy rate aspect is greatly enhanced; the management efficiencyin the commercial secret contract field is enhanced; and the user experience is enhanced.
Owner:广州市溢信科技股份有限公司
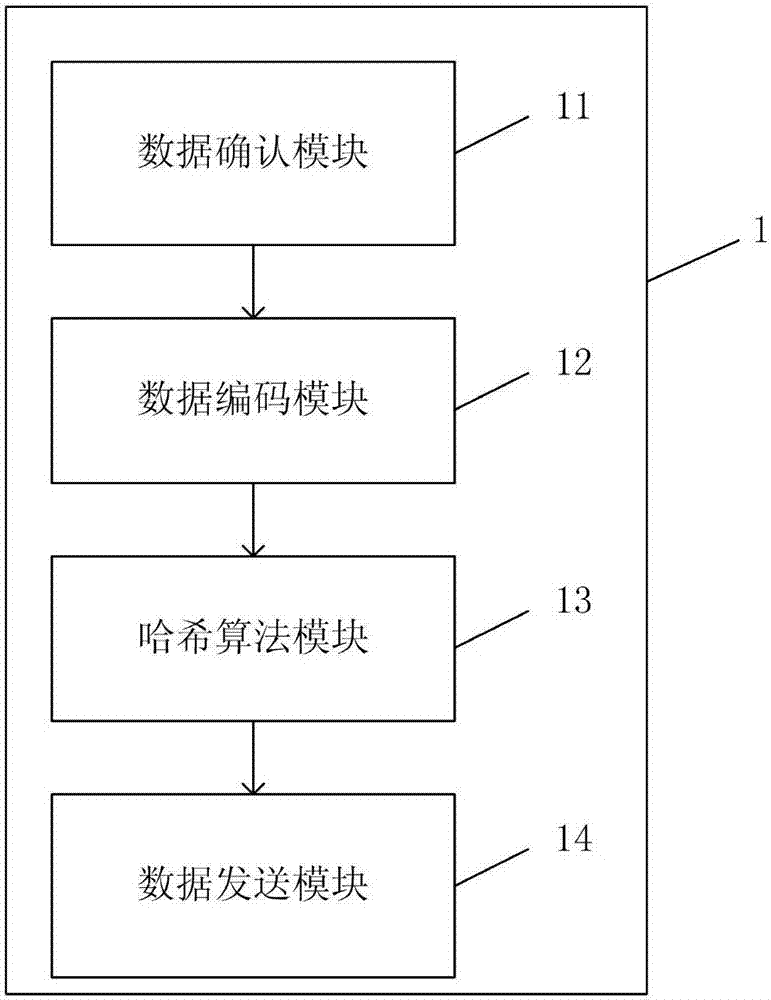
Data blind signature evidence preservation method and system based on multiple hash algorithms
ActiveCN107171787AGuaranteed privacyImprove reliabilityEncryption apparatus with shift registers/memoriesOriginal dataUser privacy
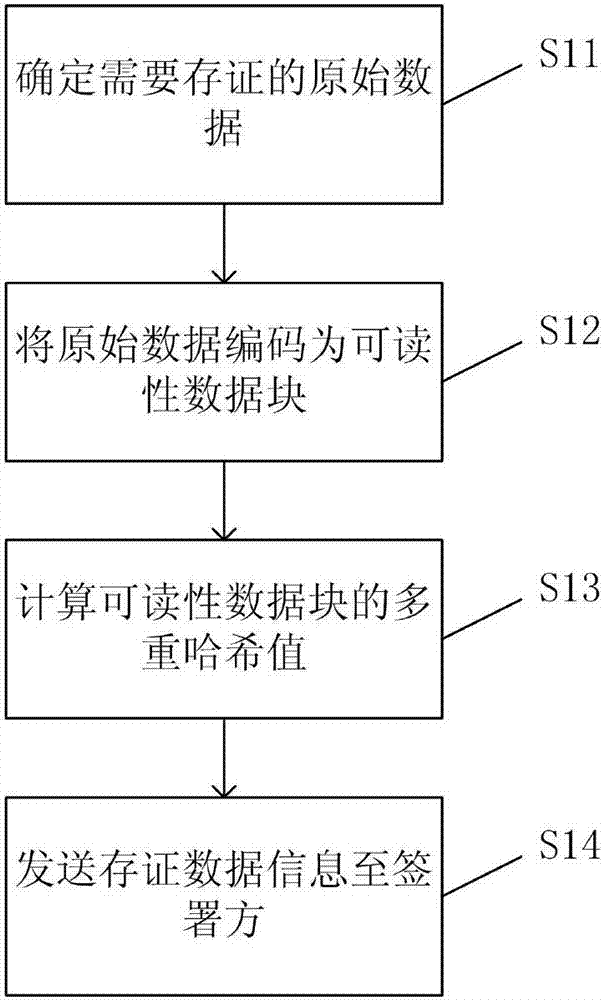
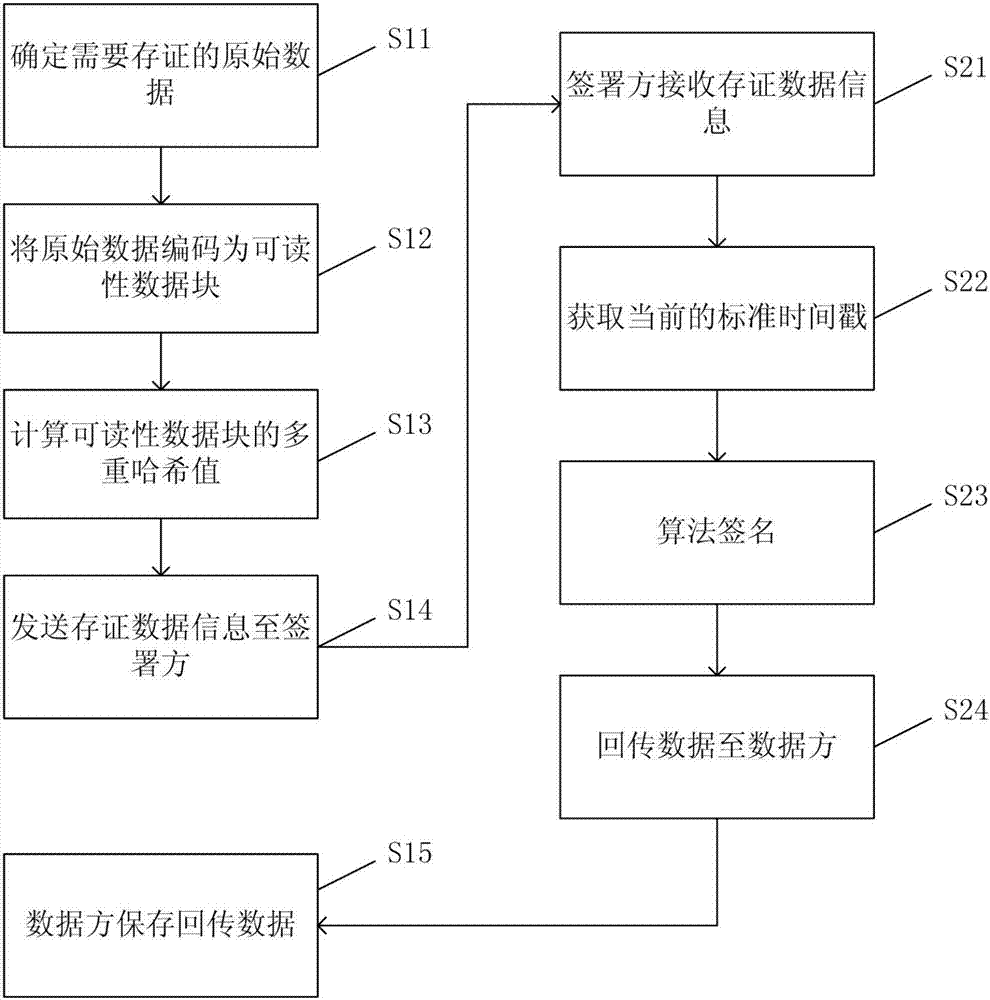
The invention provides a data blind signature evidence preservation method and system based on multiple hash algorithms. The data blind signature evidence preservation method based on the multiple hash algorithms comprises the following steps: determining raw data that needs to perform evidence preservation; encoding the raw data into a readable data block according to a format pre-negotiated with a signatory; enabling the readable data block to calculate a hash value of the readable data block according to a hash algorithm combination list pre-negotiated with the signatory to obtain a corresponding hash value list; and sending the identification number of the raw data, the size of the readable data block, the hash algorithm combination list and the hash value list to the signatory. According to the data blind signature evidence preservation method and system provided by the invention, the data side does not need to send the raw data to the signatory, and thus the user privacy and business secrets can be effectively protected; and moreover, the reliability of the system can be improved by adopting the multiple hash algorithms.
Owner:云瓣科技有限公司
System and method for distributed, policy-based confidentiality management
InactiveUS20170103231A1Without creating productivity barrierComprehensive managementDigital data protectionTransmissionConfidentialityControl system
A system and method for distributed policy-based confidentiality management provides comprehensive management of information security and ethical walls. It streamlines processes for securing confidential information without creating productivity barriers, provides interfaces to support processes of each major audience in a professional service enterprise across multiple systems and allows creation of enterprise policy types for different scenarios and systems affected by the policies. It supports standard policy types and those for lateral hires, ITAR, data privacy, price sensitivity, trade secrets, and conflicts of interest and provides two-stage review to prevent incorrect policy application. A distributed access control system provides user interfaces for granting, denying, and requesting access in a distributed fashion. Reports sort information governance policies by user / group, client / engagement, or policy type. The system prevents both service desk and other professionals from violating risk management policies at all while providing a common user experience.
Owner:LIPMAN KEITH
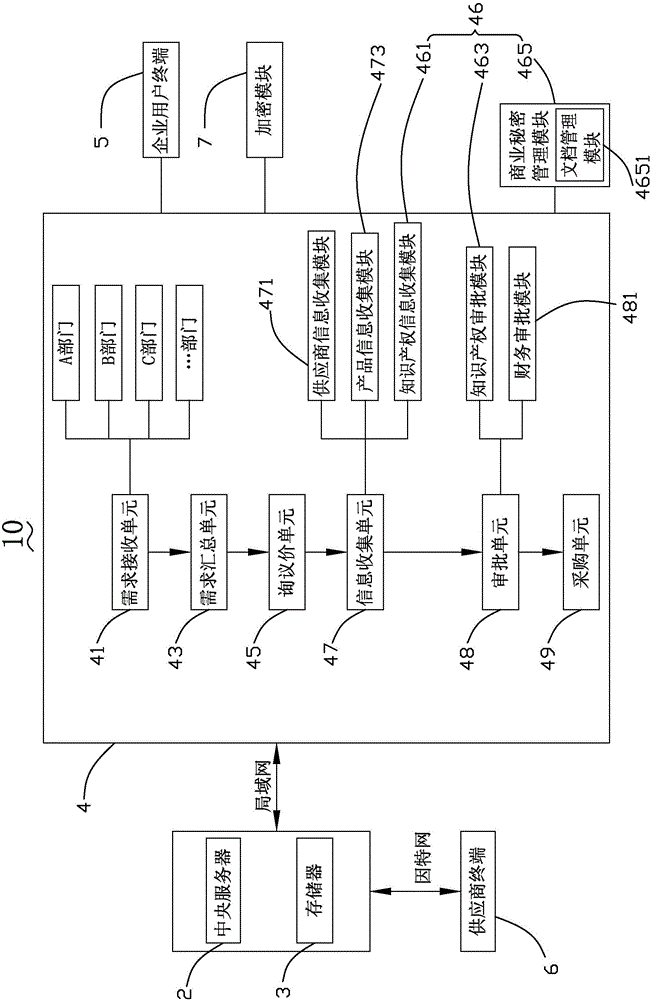
Enterprise procurement management system
InactiveCN105069579AOptimize management processEasy to manageResourcesIntellectual property managementIntelligent management
The present invention provides an enterprise procurement management system. The enterprise procurement management system comprises a central server, a storage, a procurement intelligent management system, an enterprise user terminal and a supplier terminal. The procurement intelligent management system is connected with the storage and the enterprise user terminal, the central server is connected with the procurement intelligent management system and the supplier terminal, wherein the procurement intelligent management system comprises an intellectual property management unit which includes an intellectual property information acquiring module, an intellectual property approval module and a business secret management module. By employing the intellectual property management unit of the enterprise procurement management system provided by the invention, the problem of scattered enterprise intellectual property management is solved, and the intellectual property management is integrated into the original management system of the enterprise, thereby optimizing the intellectual property management process and having the advantages of easy management and management centralization.
Owner:CHANGSHA LUZHI INFORMATION TECH
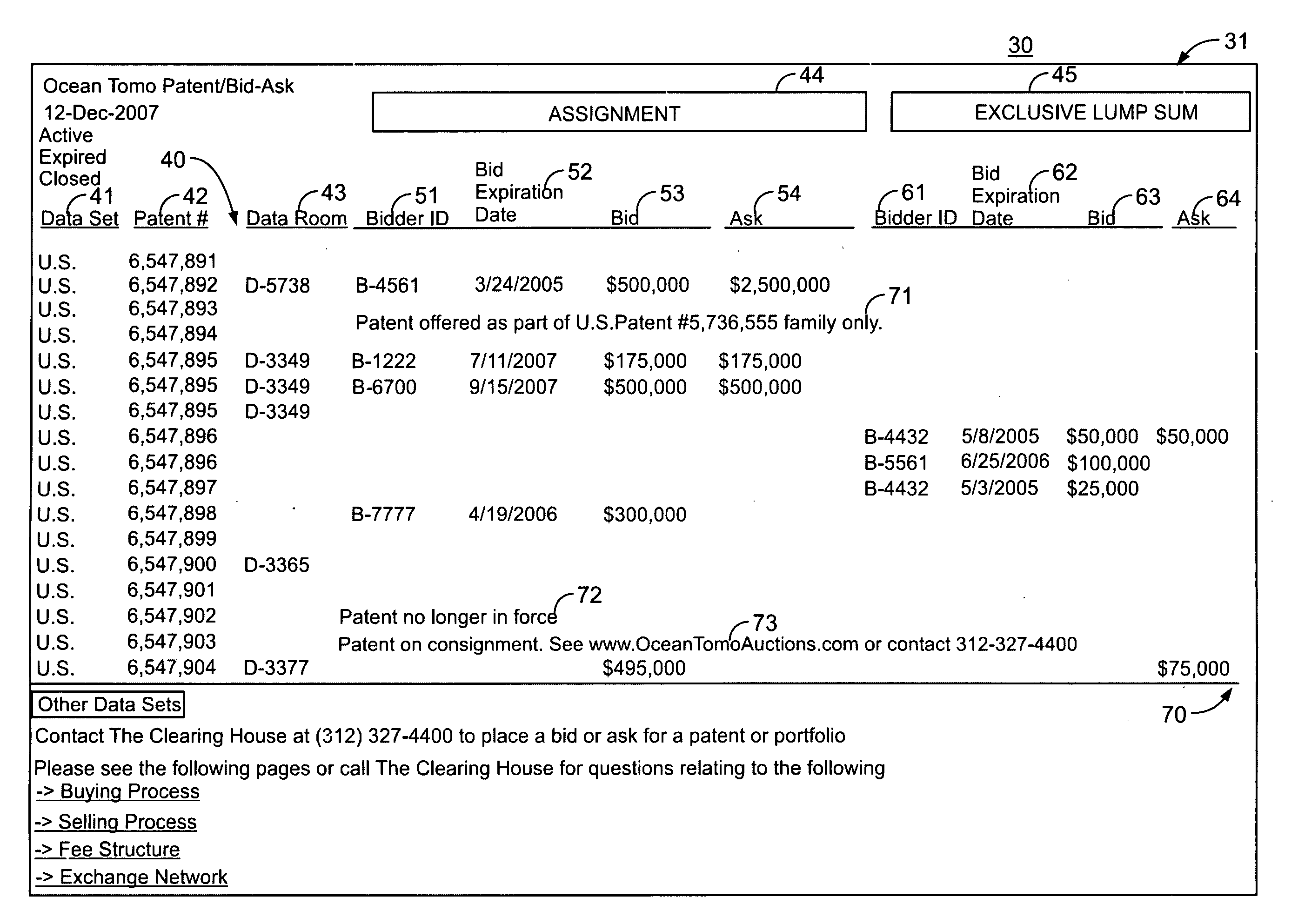
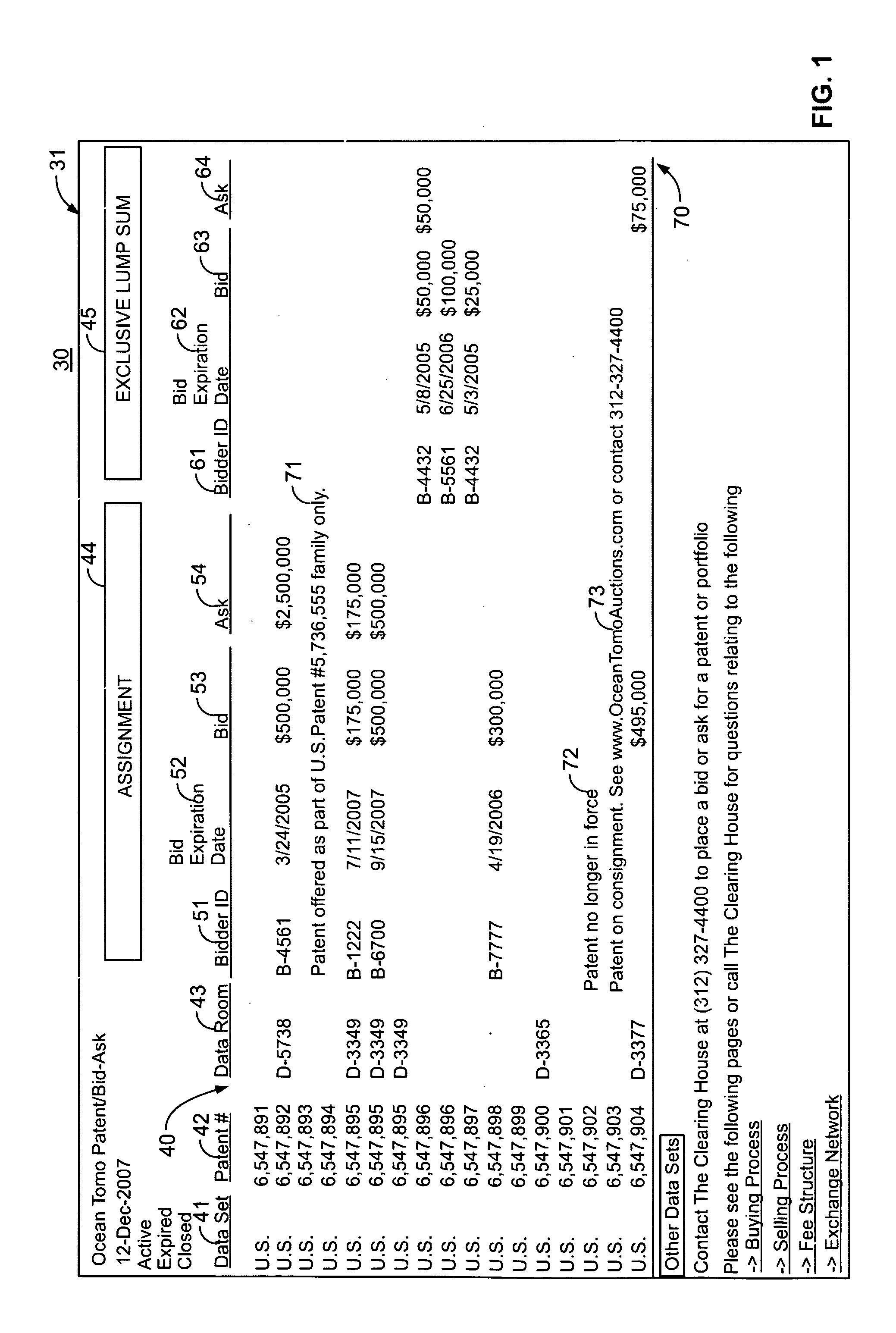
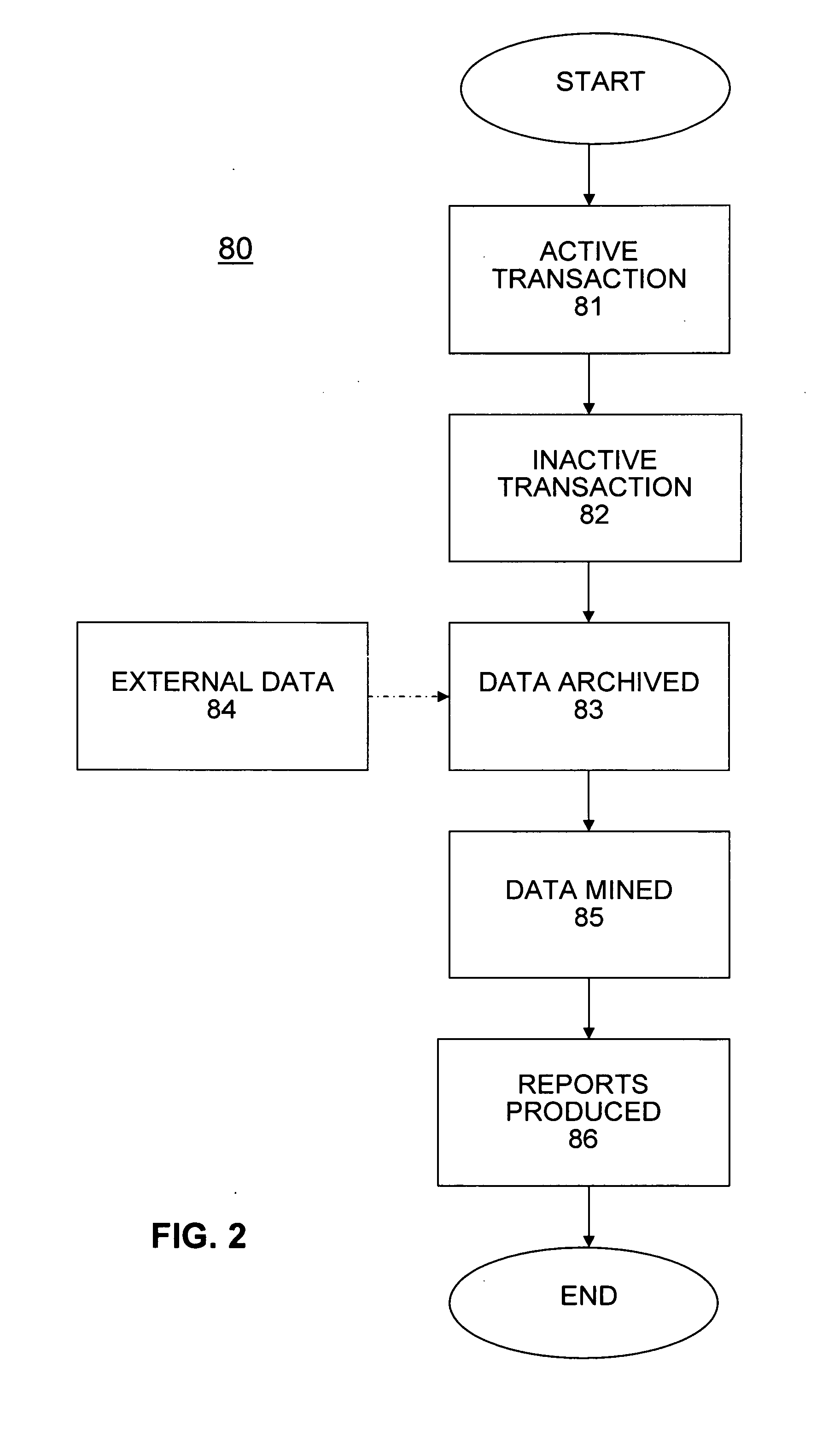
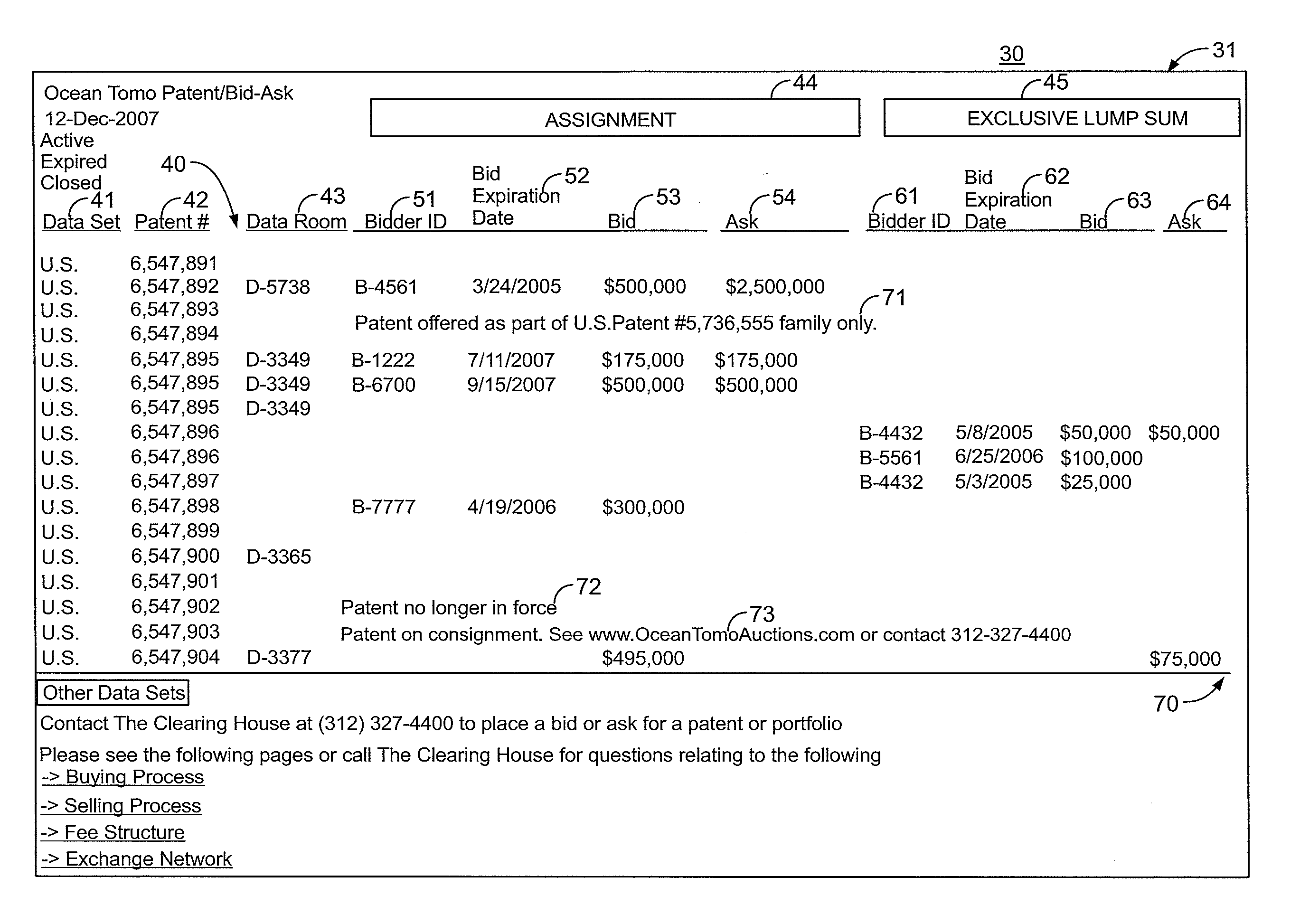
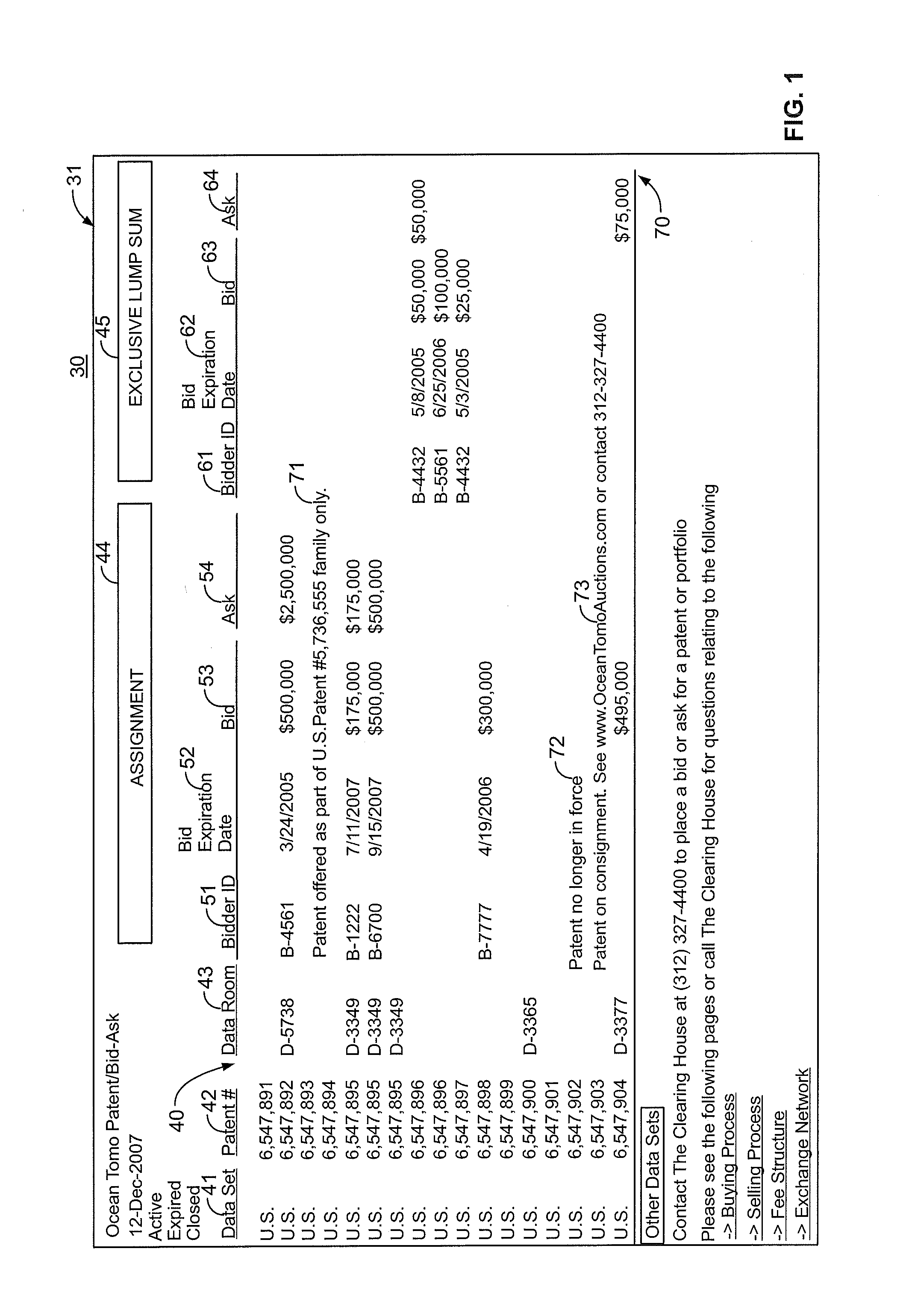
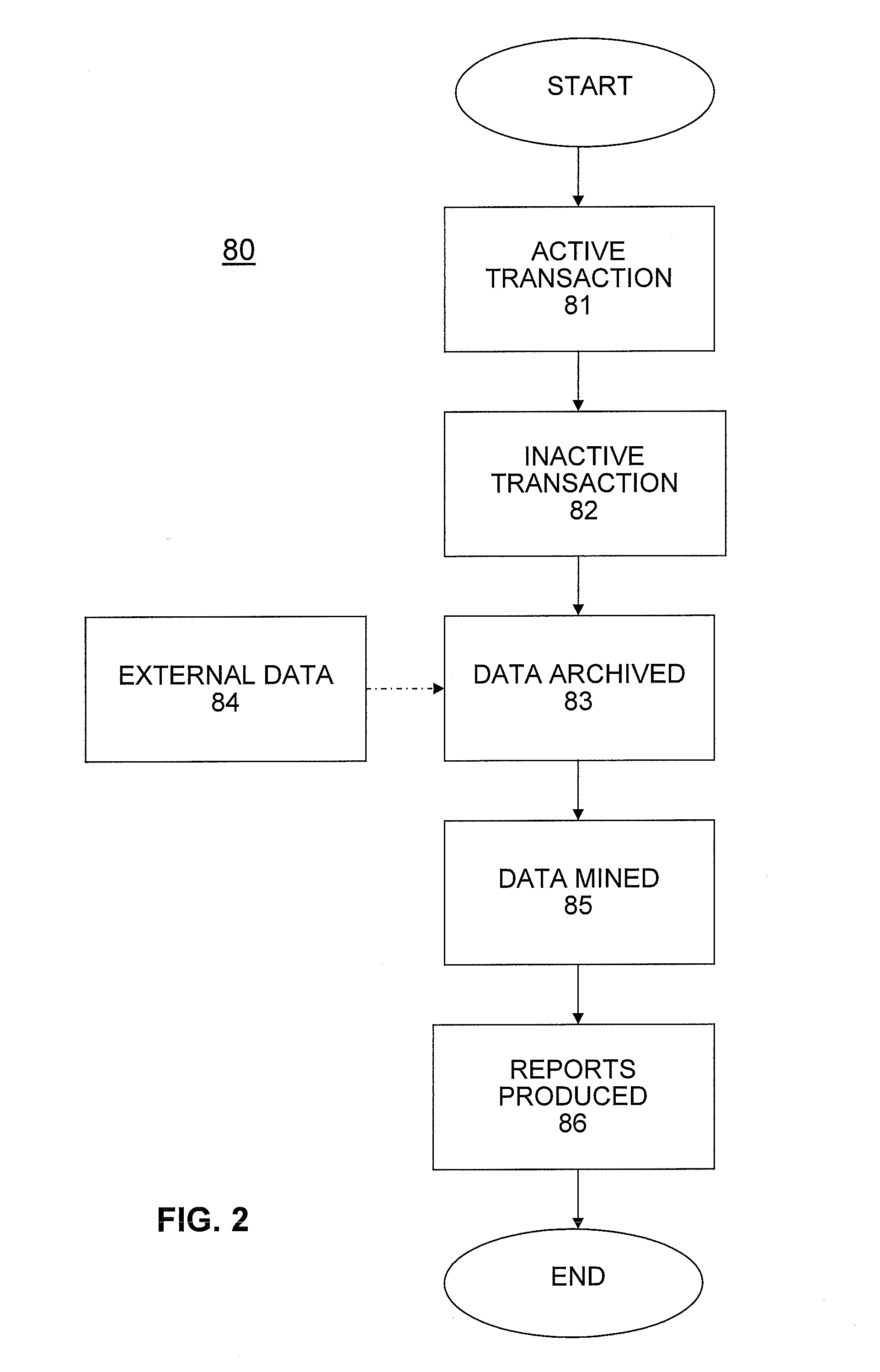
System and methods for valuing and trading intangible properties and instruments
PendingUS20110320333A1Facilitated diligenceLack of liquidityFinanceCommerceExchange networkTrademark
A system and methods providing an exchange network for valuing and trading of intangible instruments, such as one or more rights to an intangible property including a given intellectual property (patents, copyrights, trademarks, trade dress, trade secrets and / or the rights of publicity). The system and methods permits a party to access a database of the intangible instruments including data relating to identifying value of the instrument. The system and methods permits a party to perform due diligence on the intangible instrument and, as a result, to formulate a bidding strategy for the intangible instrument that the bidder believes is appropriate. If the bidder and the owner reach agreement on the price, a transaction for the intangible instrument is executed between the parties.
Owner:OCEAN TOMO
RFID-based efficient tracking and tracing method with privacy protection feature
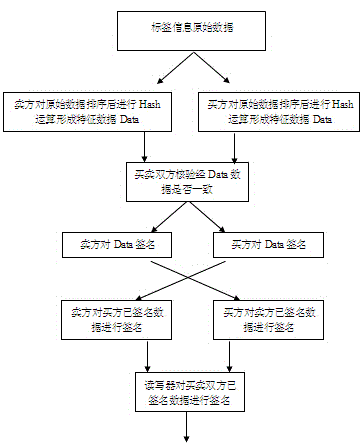
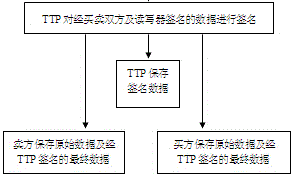
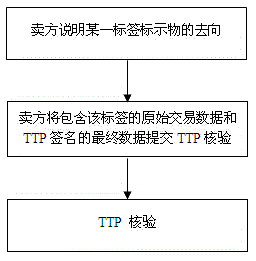
Provided is an RFID-based efficient tracking and tracing method with a privacy protection feature. According to the method, an item is labeled with an RFID tag, and the item is tracked and traced through the ID number of the RFID tag. First, a trusted third party TTP is established, and a user and equipment used thereby register in the TTP. After one transaction between a buyer and a seller, both parties of transaction and the TTP digitally sign the abstract of the ID of the tag and the information of the item labeled with the tag, both parties of transaction store original transaction data and the abstract signed by all the parties, and the TTP records the abstract signed by all the parties. When tracking (tracing) is needed, the seller (buyer) gives the original data and the data signed by the TTP as a proof to the TTP, and the TTP checks whether the abstract calculated according to the original data is consistent with the abstract recorded by the TTP and signed by all the parties so as to determine the whereabouts or source of the item. According to the method, transaction detail data is not stored in the TTP, so that the privacy and business secrets are well protected, and higher processing efficiency is achieved.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
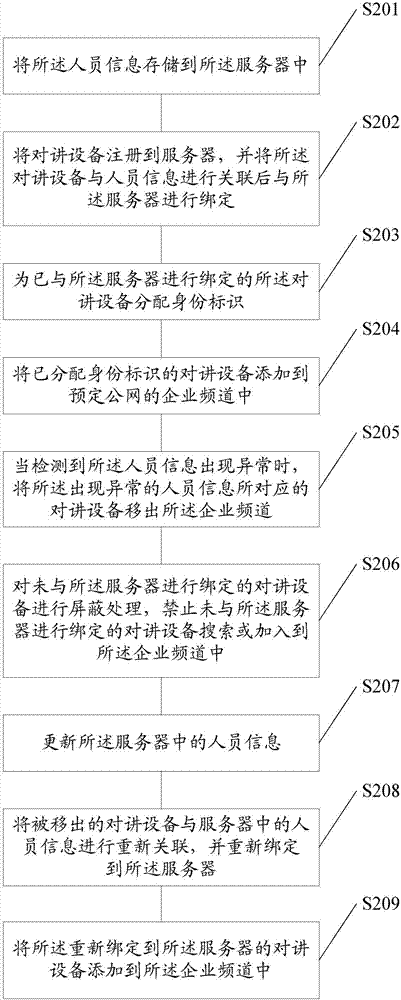
Personnel management method and device for utilizing talkback equipment to carry out public network talkback
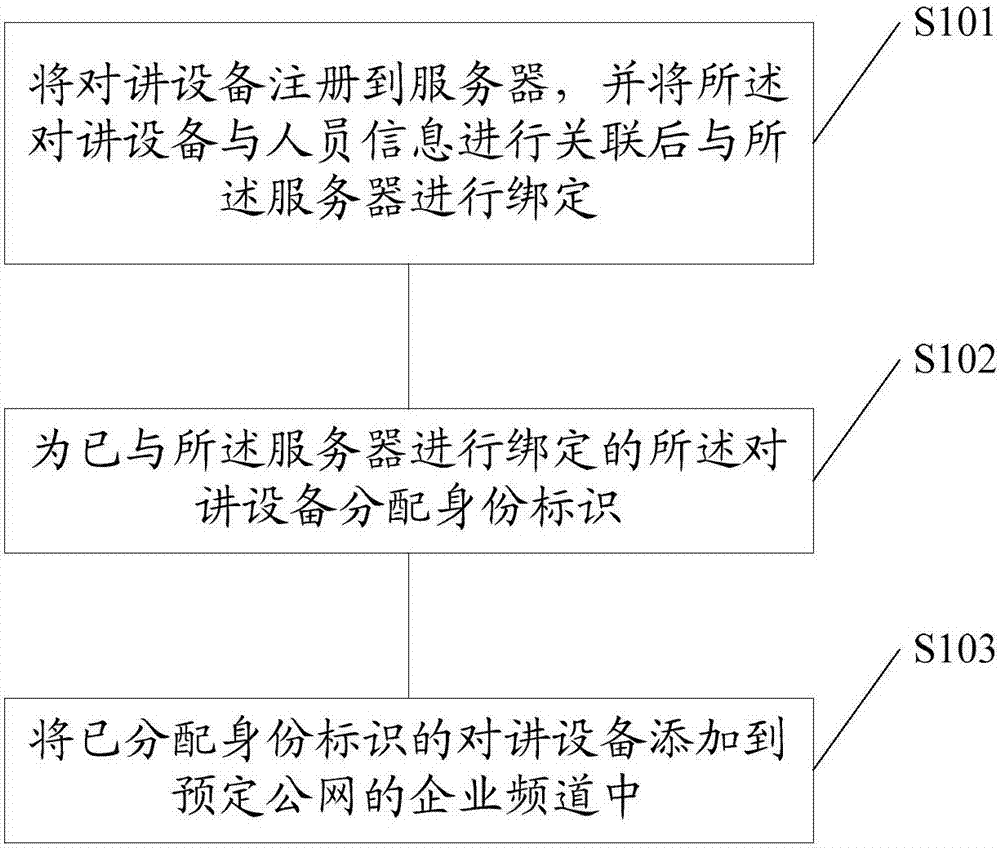
InactiveCN107086982AImprove experienceProtect trade secretsTransmissionTelecommunicationsPublic network
Embodiments of the invention disclose a personnel management method for utilizing talkback equipment to carry out public network talkback. The method comprises the following steps of registering the talkback equipment to a server, associating the talkback equipment with personnel information and binding the talkback equipment with the server; distributing an identifier to the talkback equipment bound with the server; and adding the talkback equipment distributed with the identifier into an enterprise channel of a predetermined public network. The embodiments of the invention also disclose a personnel management device for utilizing the talkback equipment to carry out public network talkback. According to the method and the device, the talkback and the management are carried out in the enterprise channel in the usage scenarios of an enterprise, so that the user experience is improved while the trade secret of a company is protected.
Owner:LAUNCH TECH CO LTD
Document on-line preview method based on commercial secret protection system
InactiveCN105825139AStrong scalabilityAdd supportDigital data protectionProgram/content distribution protectionDocumentation procedureDocument format
The present invention provides a document on-line preview method based on a commercial secret protection system. The document on-line preview method comprises the steps of (1) converting a first file format of a document into a second file format; (2) adding commercial secret signs and document watermark to the document; (3) converting the second file format of the document into a third file format, and adding edit protection attribute to the document to restrict the preview document of the third file format from being loaded by an editing tool of the third file format; and (4) storing the preview document of the third file format into a resource directory to permit access of a Web terminal. The document on-line preview method has the beneficial effects that the document on-line preview method can be used in a common PC server even a virtual machine, and supports common document formats of enterprises, the demand of enterprise office personnel on document preview effects can be satisfied, and commercial secret documents can be effectively controlled by the enterprises, thereby facilitating direct preview of the documents by the enterprise office personnel.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Data encryption technology-based trade secret sending method
ActiveCN109302282ARealize secure encrypted transmissionKey distribution for secure communicationPlaintextInformation transmission
The invention provides a data encryption technology-based trade secret sending method. Firstly, for the further secure sending of trade secrets, two trade secret sending parties are made to acquire the same local key by using a DH algorithm, the outside only can acquire a public key and cannot acquire private keys of the two parties or crack the local key in the process, and therefore first-levelprotection is provided for information sending; secondly, the two information sending parties set their own plaintext code sorting schemes, and second-level protection is set; finally, new plaintext code are encrypted on the basis of an AES encryption algorithm by utilizing the local key, and third-level protection is set, and then secure encryption transmission of data between the two trade information transmission parties is achieved; and meanwhile the AES encryption algorithm is extremely efficient on the data encryption transmission aspect and provides a guarantee for real-time and efficient transmission of ciphertext information. The secure and efficient multiple algorithm-combined data encryption technology-based trade secret sending method in which the two communication parties customize the encryption scheme is provided.
Owner:ZHEJIANG UNIV OF TECH
System and methods for valuing and trading intangible properties and instruments
InactiveUS20140358764A1Raise the possibilityMore commercially satisfyingFinanceCommerceExchange networkTrademark
A system and methods providing an exchange network for valuing and trading of intangible instruments, such as one or more rights to an intangible property including a given intellectual property (patents, copyrights, trademarks, trade dress, trade secrets and / or the rights of publicity). The system and methods permits a party to access a database of the intangible instruments including data relating to identifying value of the instrument. The system and methods permits a party to perform due diligence on the intangible instrument and, as a result, to formulate a bidding strategy for the intangible instrument that the bidder believes is appropriate. If the bidder and the owner reach agreement on the price, a transaction for the intangible instrument is executed between the parties.
Owner:OCEAN TOMO
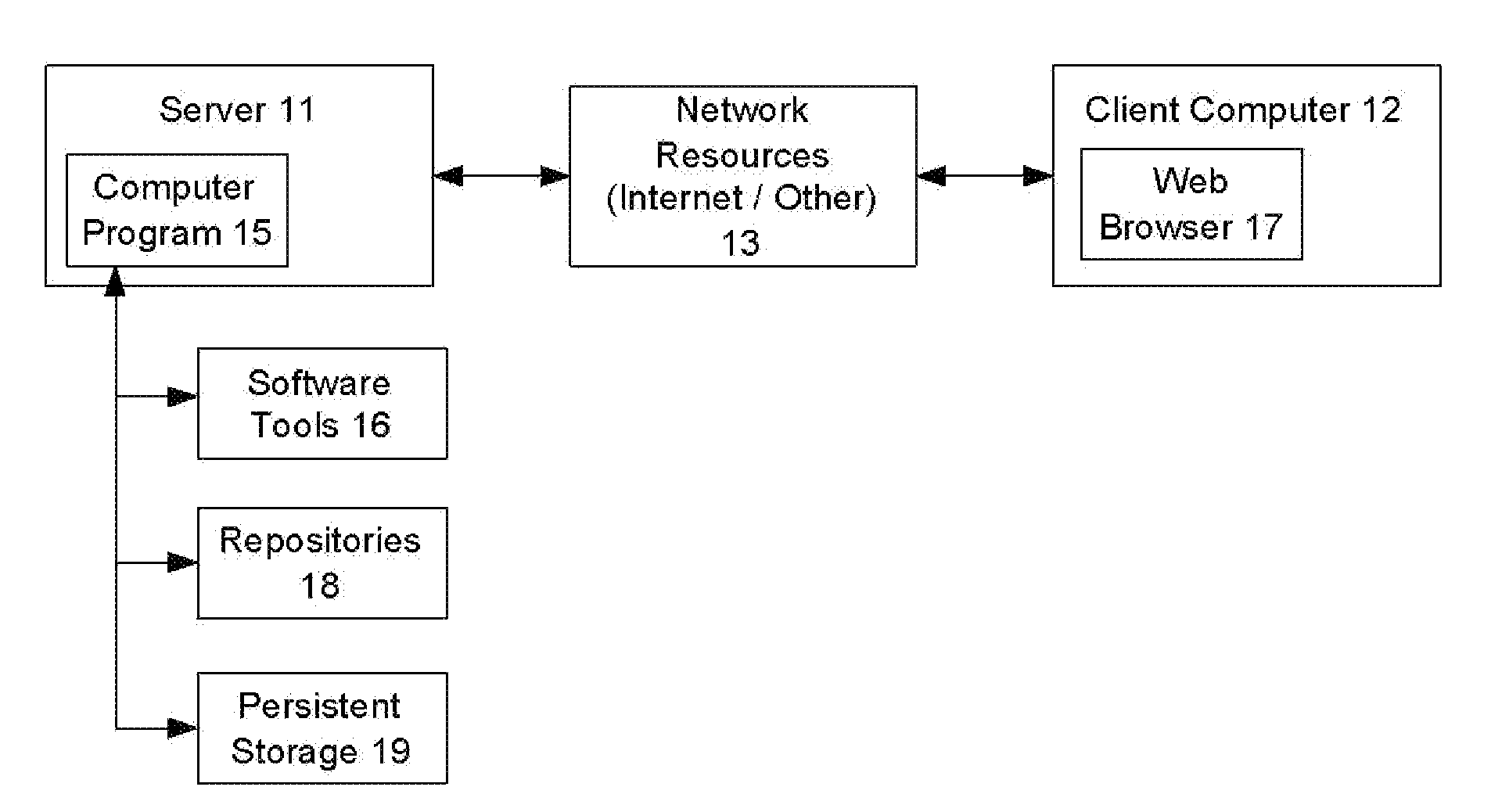
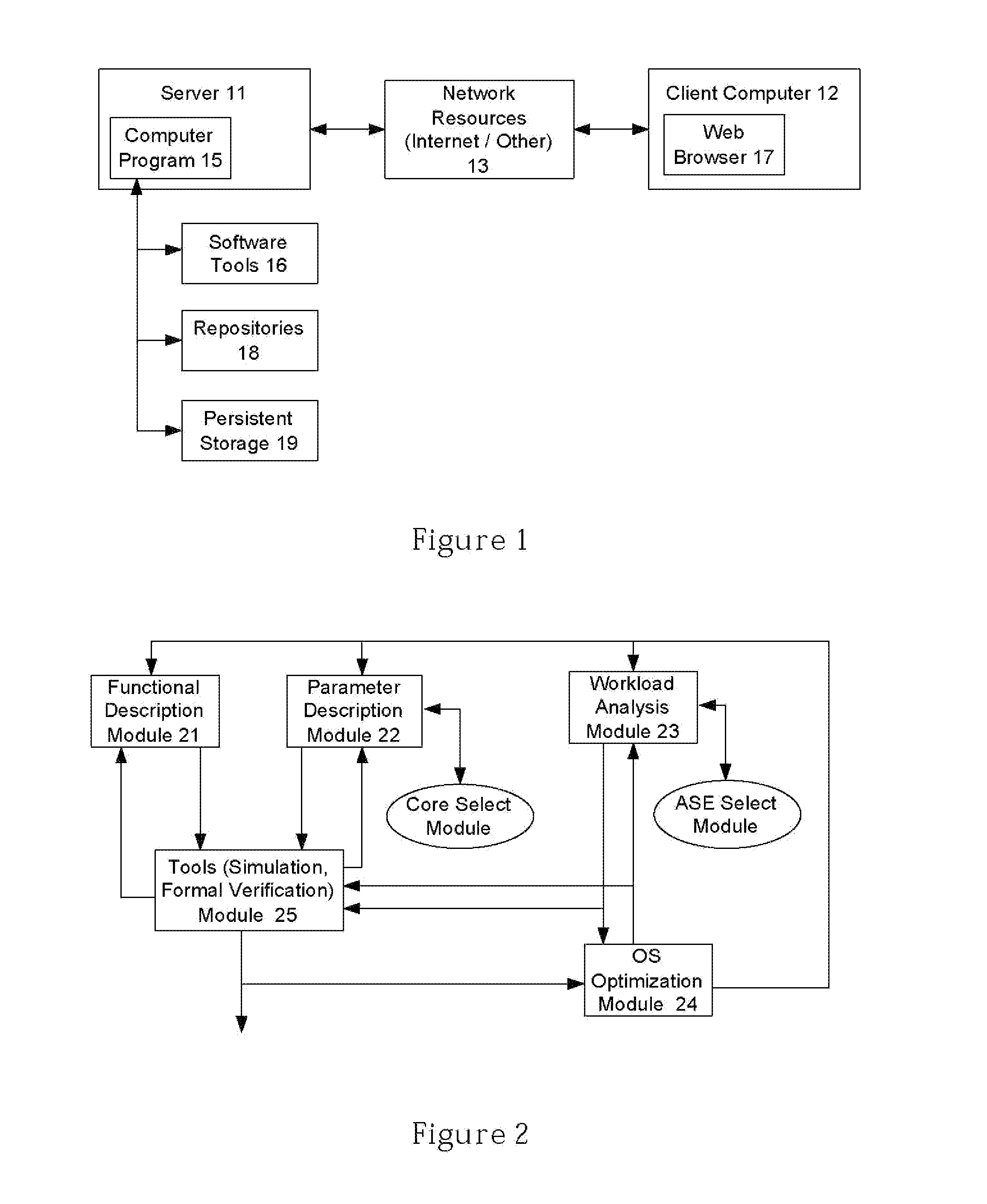
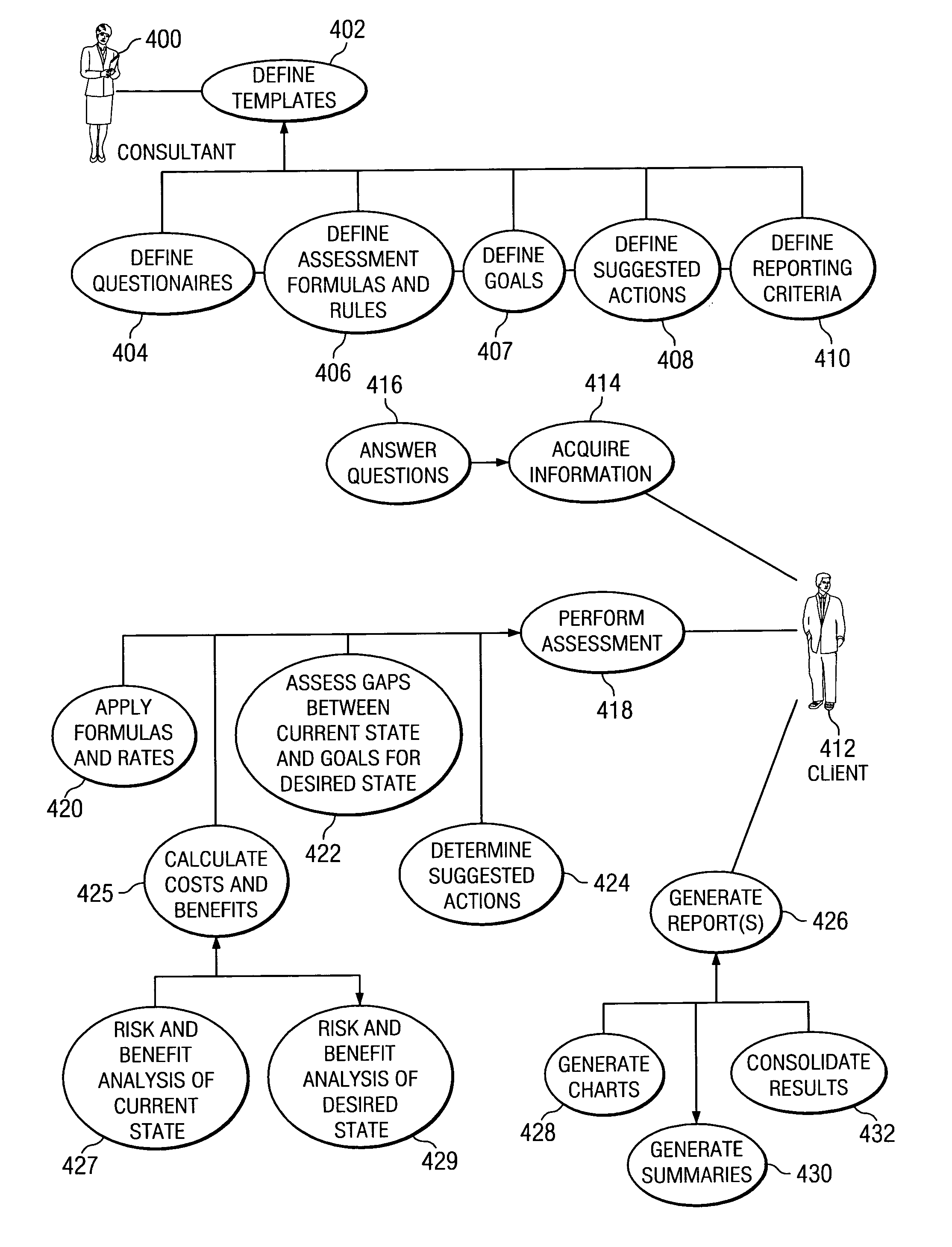
Consulting assessment environment
A method, apparatus, and computer program product for providing a consulting assessment environment. Consultants may use the environment to define templates that encode questionnaires and domain knowledge regarding business practices, as well as reporting criteria to specify the content and format of the assessment results. Consultants or their clients may use the environment to automate the process of performing assessments and generating reports from those assessments. These assessments may analyze the current state of the business, compare the business's current state with desired states or with best practices, and perform risk / benefit and / or cost / benefit analyses, according to the specifications made in the templates on a real-time basis for producing immediate assessment results and actions. An information hiding feature is provided to allow sensitive domain knowledge encoded within the templates, such as trade secrets, to be made inaccessible to clients.
Owner:INT BUSINESS MASCH CORP
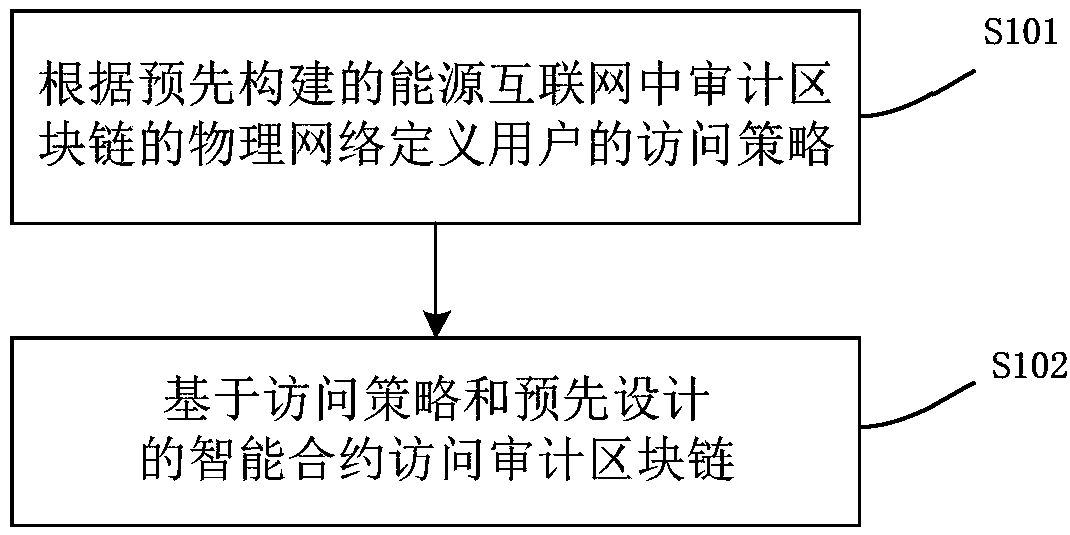
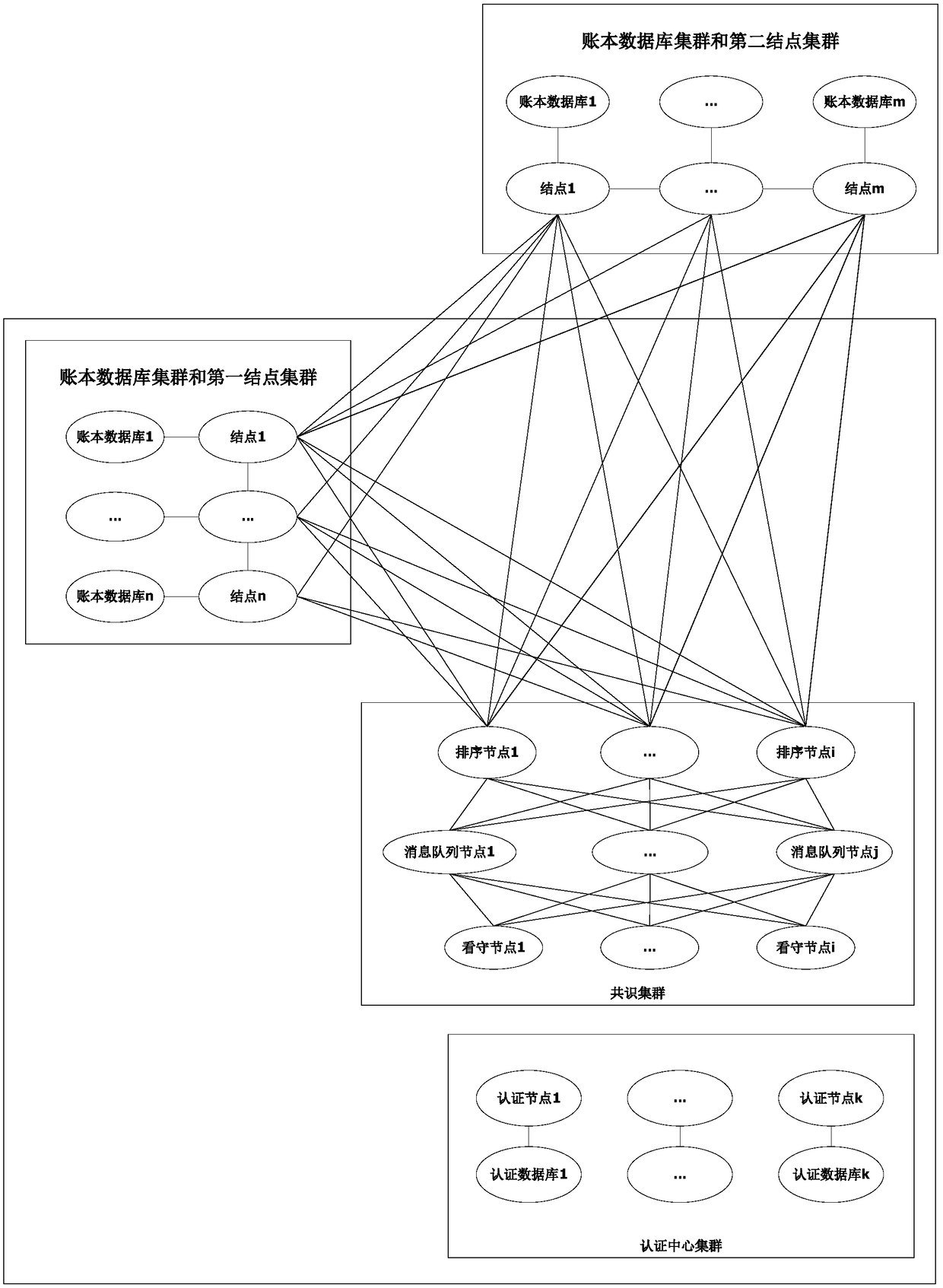
A design method and device of an audit block chain in an energy internet
ActiveCN109344658AGuaranteed uptimePrevent tamperingFinanceDigital data protectionData validationTransaction data
The invention provides a design method and device of an audit block chain in an energy network. The method comprises the steps of firstly defining the access policy according to the physical network of the pre-constructed audit block chain in the energy Internet; then using the access policy and the pre-designed smart contract to access the audit block chain, and pre-designing the smart contract based on the transaction business process of the energy Internet. The invention ensures the stable operation of the audit network, prevents the transaction data from being tampered with, and can realize the cross service across industries and regions. The technical proposal provided by the invention can ensure that the private secret data and the trade secret data cannot be tampered with, the transaction process can be traced, the audit service with public credibility is provided to the transaction organization and the supervision organization, and the safety of the energy internet transactionis ensured. The method provides the two-way accounting books, traces the flow of energy and financial assets, monitors illegal transactions in energy and financial assets, provides data validation services, confirms the integrity and validity of data, and provides data screening services to ensure the truthfulness and reliability of transaction reporting, clearing and settlement of confidential data.
Owner:CHINA ELECTRIC POWER RES INST +2
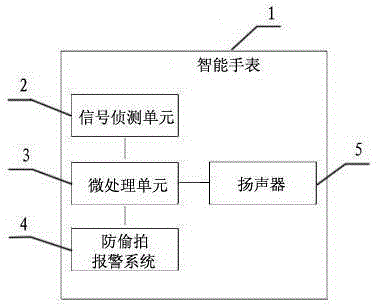
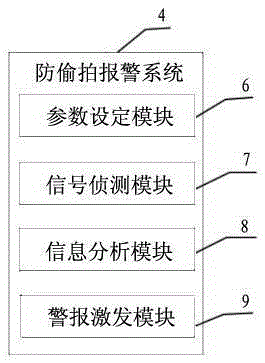
Intelligent watch with secret photography prevention system module
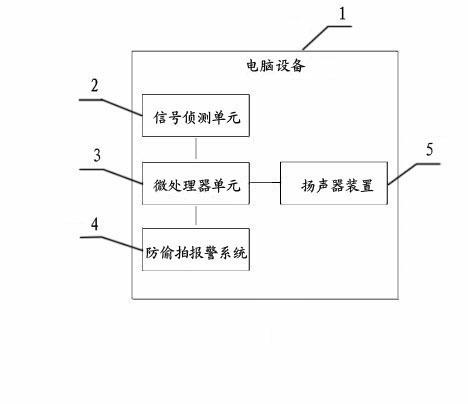
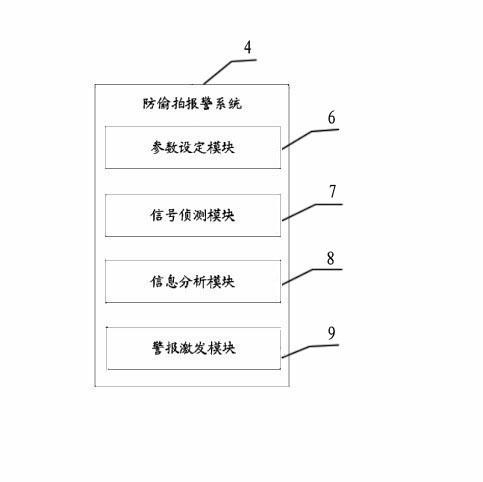
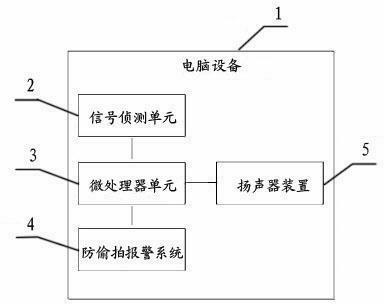
InactiveCN105334722ALow costFirmly connectedTime-pieces with integrated devicesAlarmsKey pressingComputer module
An intelligent watch with a secret photography prevention system module comprises an intelligent watch shell, an intelligent watch screen, function keys, an intelligent watch mainboard, a supply circuit and a function circuit. A battery protection circuit board and a rechargeable battery are arranged in the intelligent watch shell. The intelligent watch is characterized by being provided with the system module with the secret photography prevention function, wherein the system module is composed of a signal detection unit, a microprocessor unit, a secret photography prevention alarm system and a loudspeaker. The system module with the secret photography prevention function is arranged on the intelligent watch, can automatically detect whether secret photography devices exist on site, is high in sensitivity and can conduct sound-light alarming, and therefore influences of illegal secret photography devices on work and life of people in daily work and life are eliminated, unnecessary troubles are reduced, and bad behaviors that some people with ulterior motives conduct secrete photography by some underhand means to obtain privacy or trade secret of others are effectively prevented.
Owner:倪晓旺
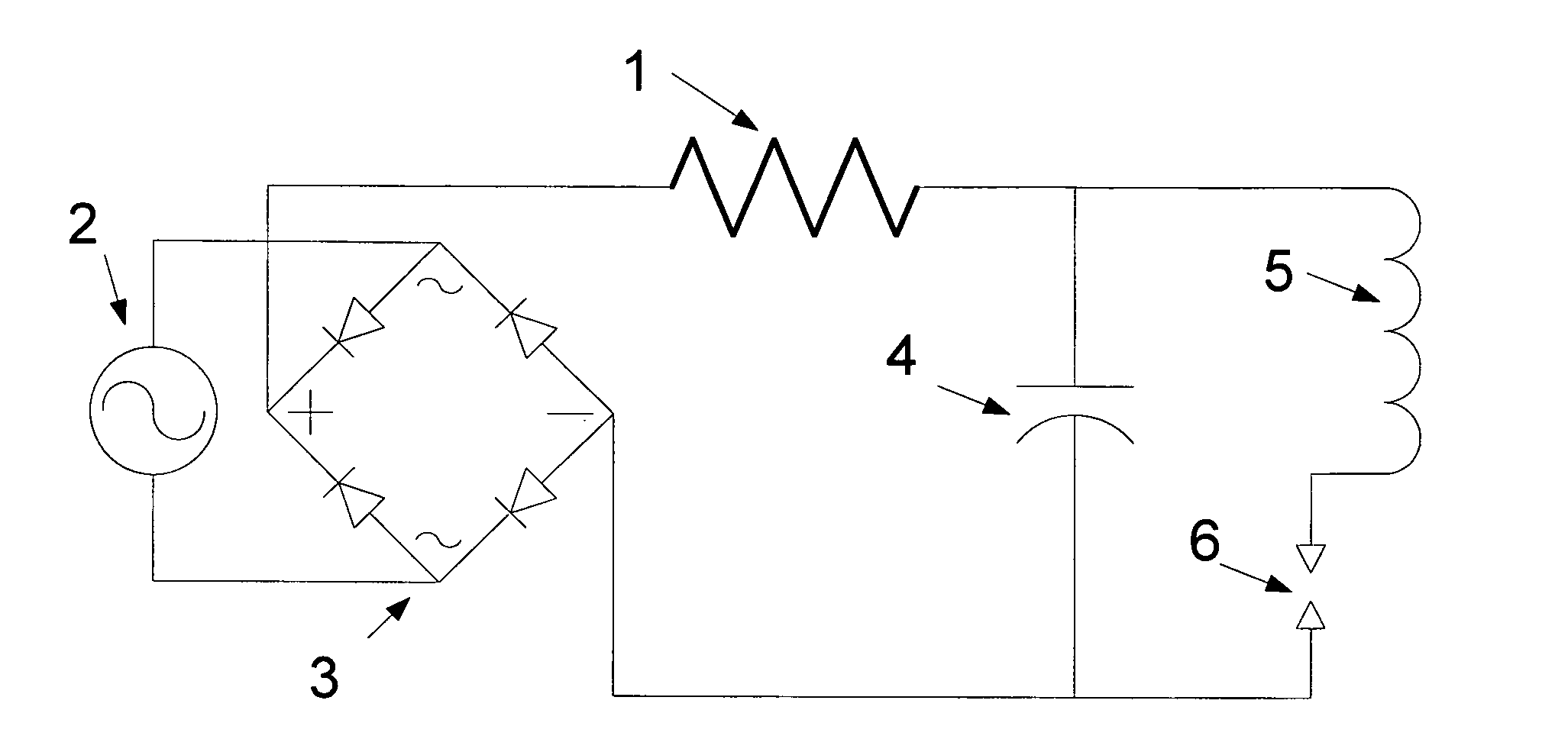
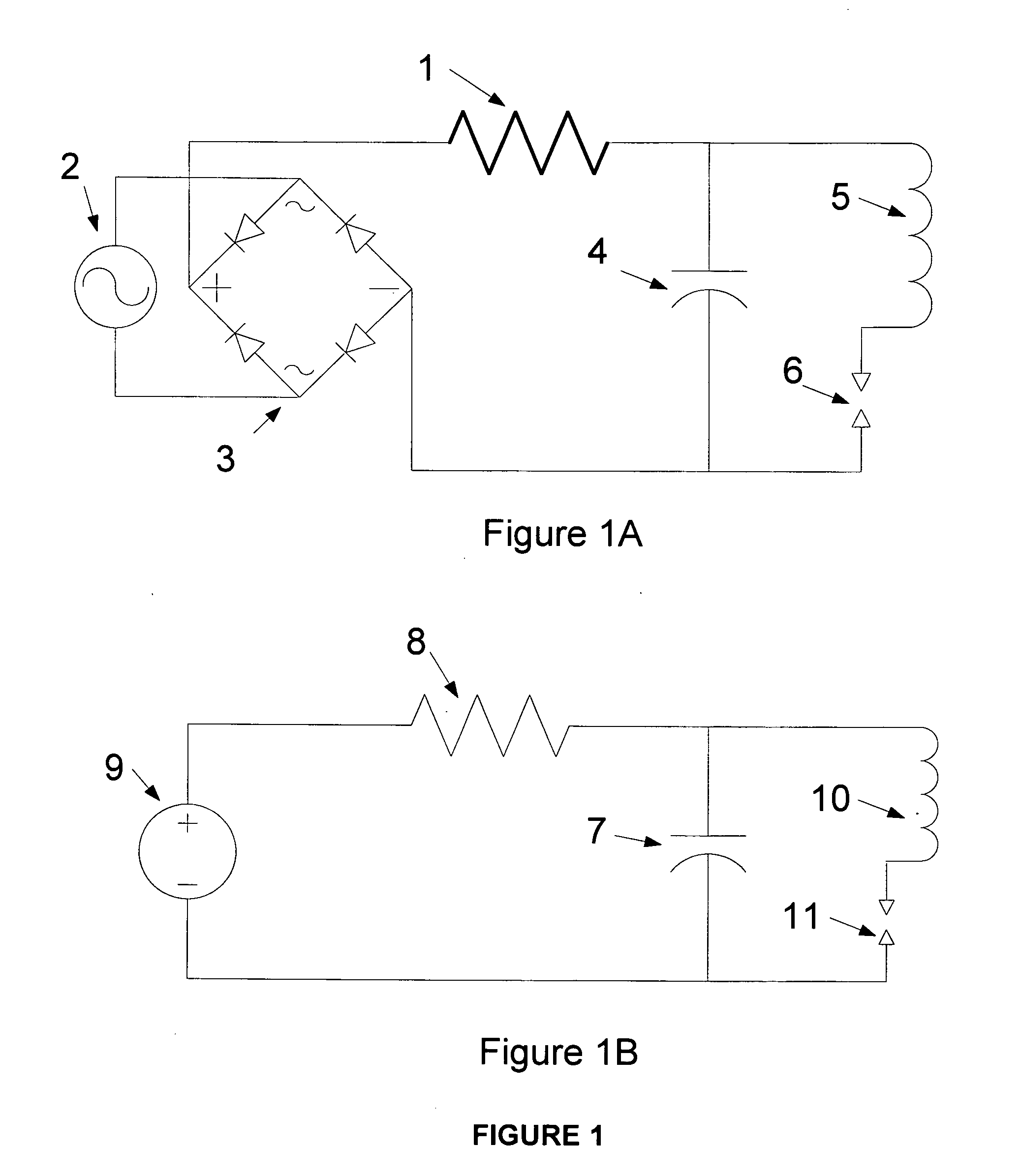
Method for selecting protective resistor value for a capacitor charging circuit which enables maximum energy transfer with minimal heat
InactiveUS20110115496A1Maximize efficiencyControl is neededMaterial thermal analysisFault locationEngineeringElectron
Electronic devices operate in an analog world and their circuitry is subject to non-linear environmental effects that can cause operational problems. Selecting components for a design for a capacitor-charging circuit that incorporates a current-limiting resistor and uses non-linear power supplies, either means having to test every possible combination of elements, and suffering a resultant ‘combinatorial explosion’ as complexity increases, or choosing to over-engineer against untested surprise failure points. Doing the latter in a cost-efficient manner through a min / max / log-set testing series also enables use of non-linear power supplies whose parameters are not known due to competitive or trade secret protective efforts by their manufacturers.
Owner:DAVIS JOHN MICHAEL +1
Anti-peeping lamp bank and display device
ActiveCN104566051AImprove privacyProtect personal privacyPlanar light sourcesPoint-like light sourceDisplay deviceEngineering
Owner:BOE TECH GRP CO LTD +1
Consulting assessment environment
A method, apparatus, and computer program product for providing a consulting assessment environment. Consultants may use the environment to define templates that encode questionnaires and domain knowledge regarding business practices, as well as reporting criteria to specify the content and format of the assessment results. Consultants or their clients may use the environment to automate the process of performing assessments and generating reports from those assessments. These assessments may analyze the current state of the business, compare the business's current state with desired states or with best practices, and perform risk / benefit and / or cost / benefit analyses, according to the specifications made in the templates on a real-time basis for producing immediate assessment results and actions. An information hiding feature is provided to allow sensitive domain knowledge encoded within the templates, such as trade secrets, to be made inaccessible to clients.
Owner:TWITTER INC
Whole Body Infrared Thermography Systems And Methods
InactiveUS20150216422A1Computer-assisted medical data acquisitionMedical automated diagnosisWhole bodyThermography
Disclosed herein is a method where a thermography device collects raw data that is forwarded to a server wherein the server runs the raw data through a database of signature parameters and generates a report. After the report is generated, the server notifies a technician that a report has been created and makes the report available online for the technician to login and retrieve. The separation of the measurement system and the analysis system allows some protection of trade secrets which are contained within the analysis software.
Owner:BEILIN DANIEL
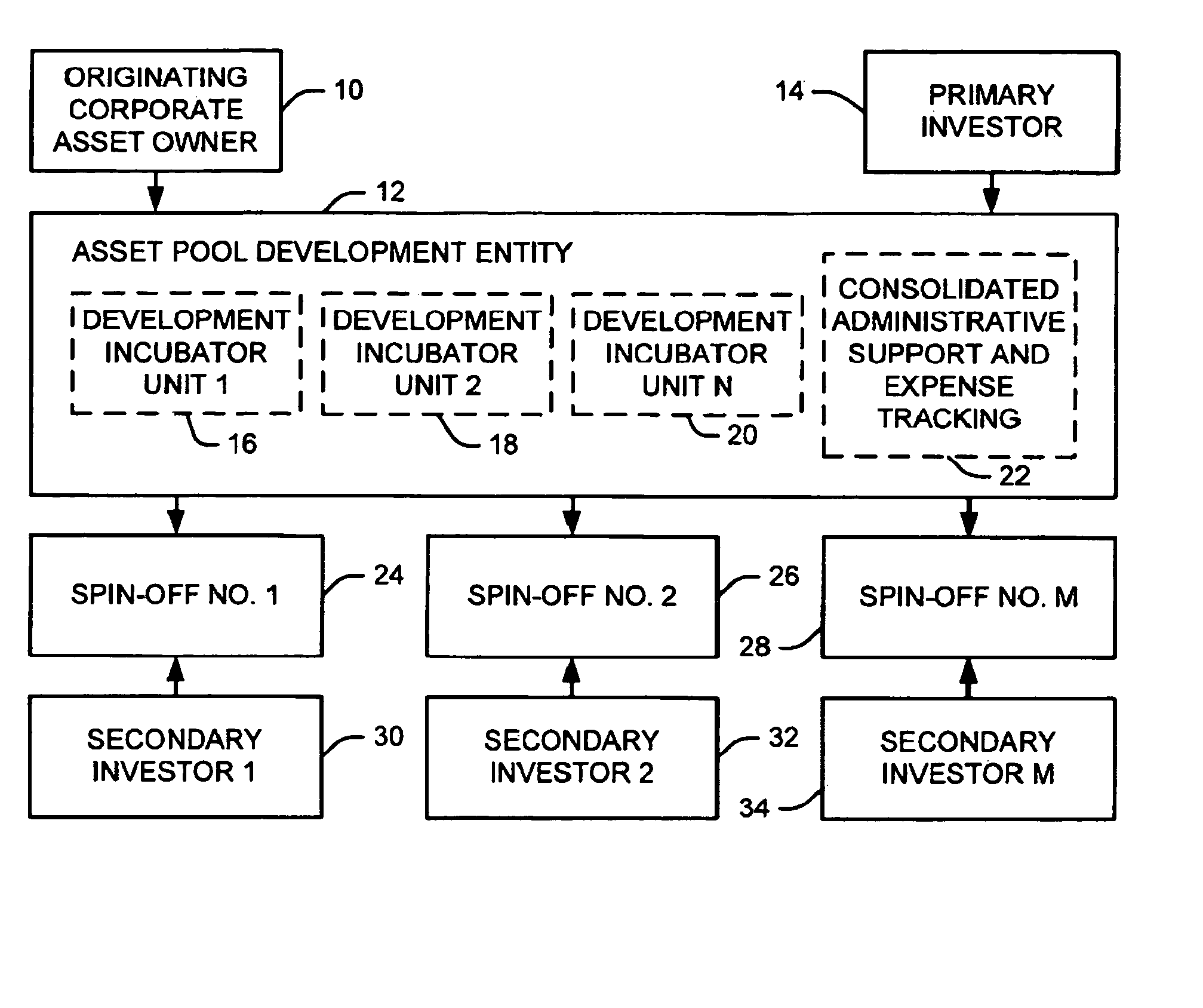
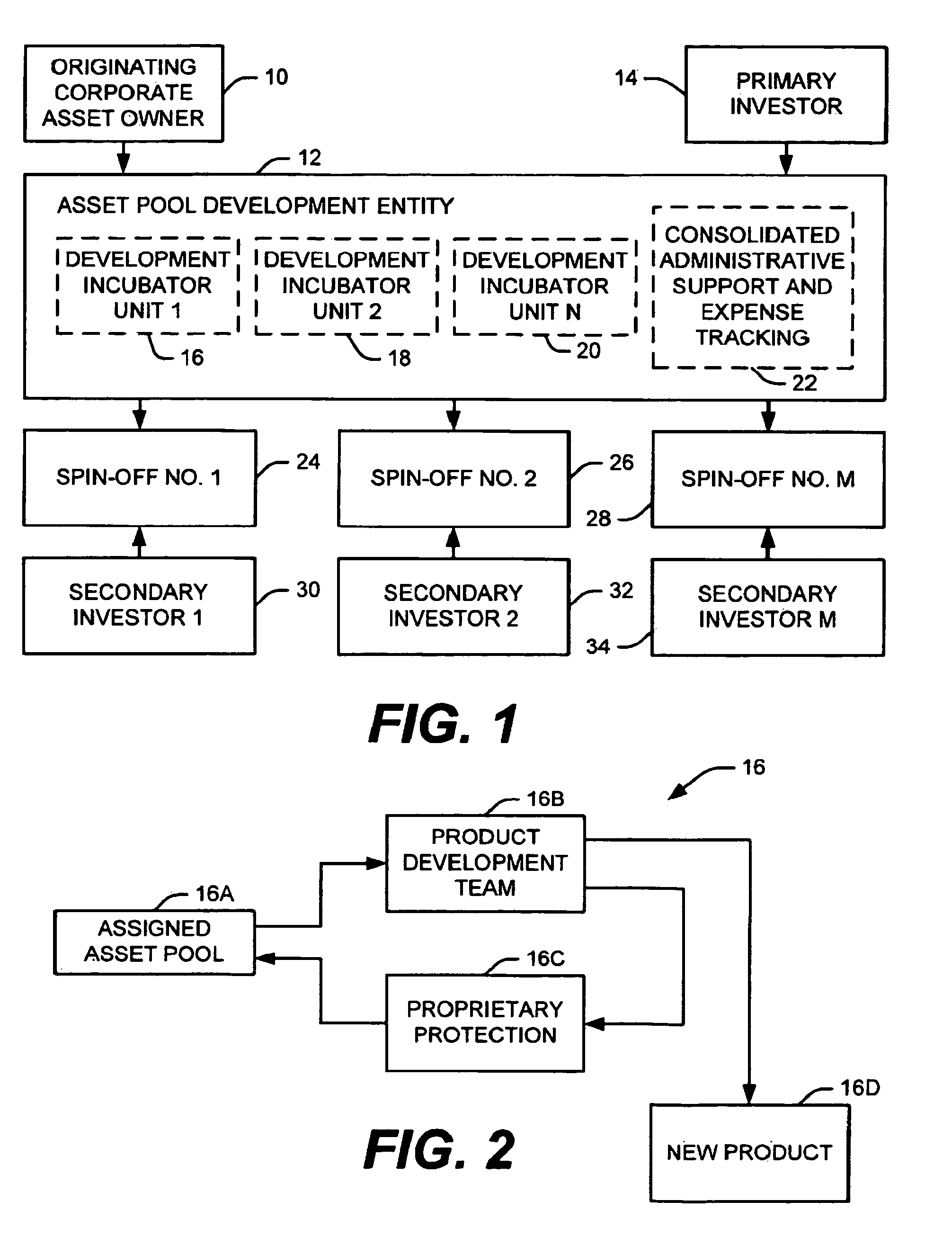
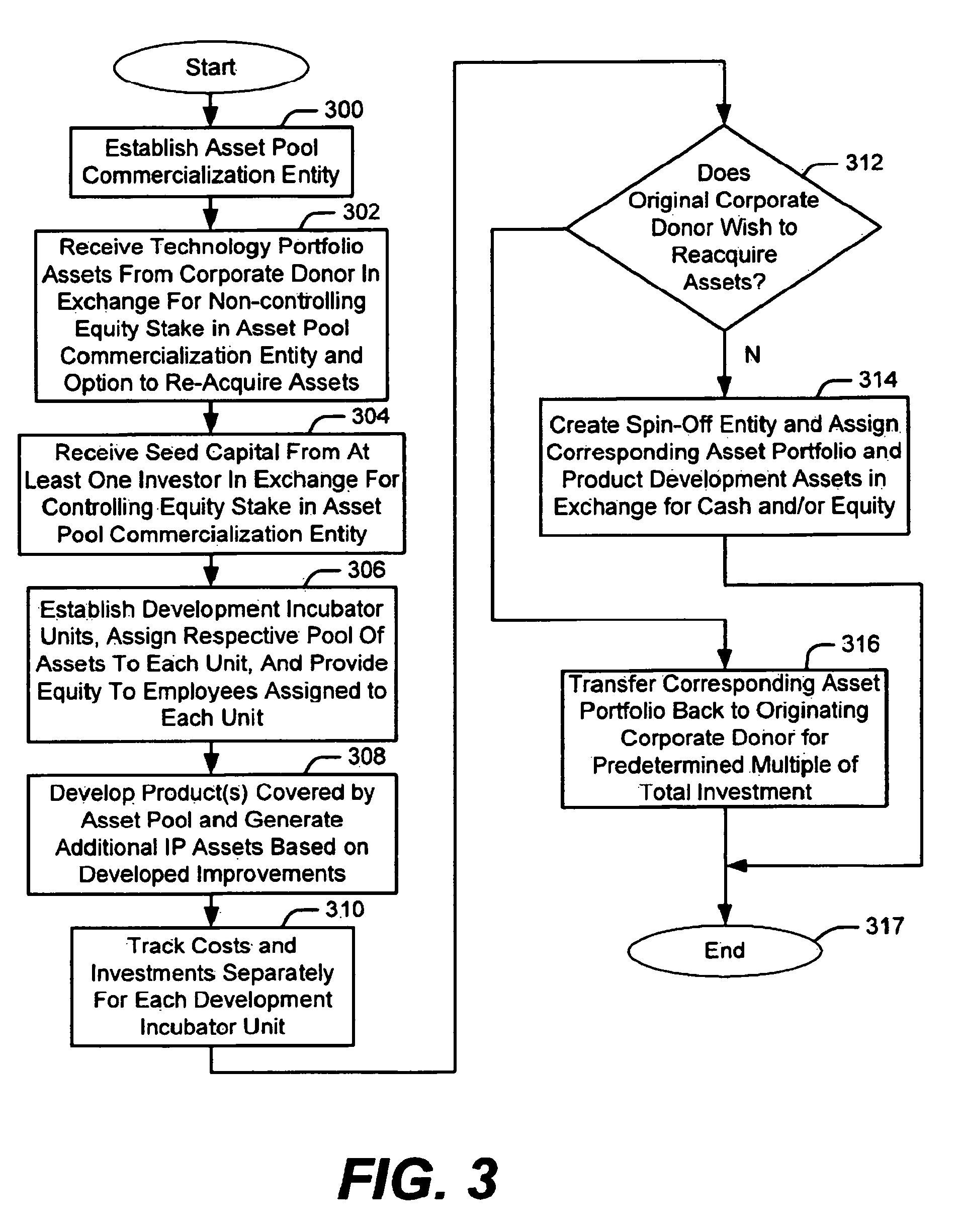
System and method for developing technology assets
An automated method for developing new products within a development entity, comprises receiving respective catalogs of technology assets, each including at least one of a patent, trade secret, know-how, documentation, prototypes, pre-production units, production samples, tooling, and demonstration frameworks. Each catalog corresponds to a discrete pool of technology assets having subject matter in common. The development entity also receives, from the originating owner, title to each pool in exchange for an equity interest in the development entity and an option to re-acquire the pool upon payment of a reacquisition fee to at least one primary investor. Further development of each technology asset pool is funded by at least one primary investor, who receives an equity interest in the development entity in exchange for its capital investments. Costs expended by the development entity to develop new product concepts corresponding to each asset pool are separately tracked. If the re-acquisition option is exercised, these costs form the basis for calculating the fee to be paid. If not, monetization is achieved by selling and / or licensing elements the enhanced technology asset pool to a spin-off entity funded by at least one secondary investor.
Owner:AVAYA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com