Transaction security method, acceptance device and submission software
A transaction confidentiality and transaction technology, applied in the fields of software and information security, electronics, communications, and finance, it can solve the problems of discounted effects, difficult implementation, too mechanical physical barriers, etc., to achieve easy popularization and application, and unlimited social and economic benefits. , Improve the effect of security and confidentiality functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
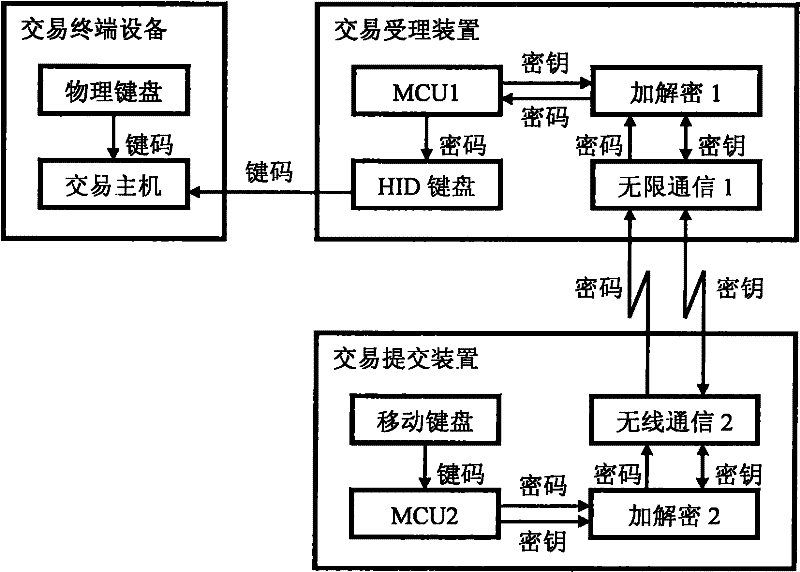
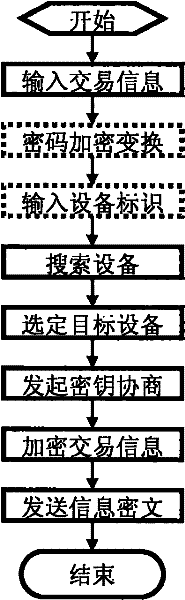
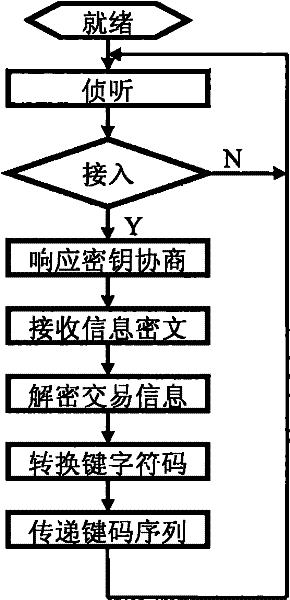
[0026] For an embodiment of the invention, see figure 1 . First design the transaction acceptance device, in which MCU1 uses 8051 compatible processor chip, HID keyboard is realized by CY7C63803 controller chip, encryption and decryption 1 functional unit is realized by 8051 processor firmware programming, and wireless communication 1 is realized by a Bluetooth communication module. The transaction accepting device constituted in this way itself is passive, and the power cord of the USB is used as an external power supply to take power directly. On the one hand, the 8051 processor is connected with CY7C63803 by two IO pins, and its firmware programming realizes the I2C bus sending function; on the other hand, it is connected with the Bluetooth communication module by a standard serial port. Use CY7C63803 controller endpoint 0 as the default control endpoint to implement HID and USB protocols, configure endpoint 1 as a HID keyboard (low speed, interrupt mode), program its firm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com