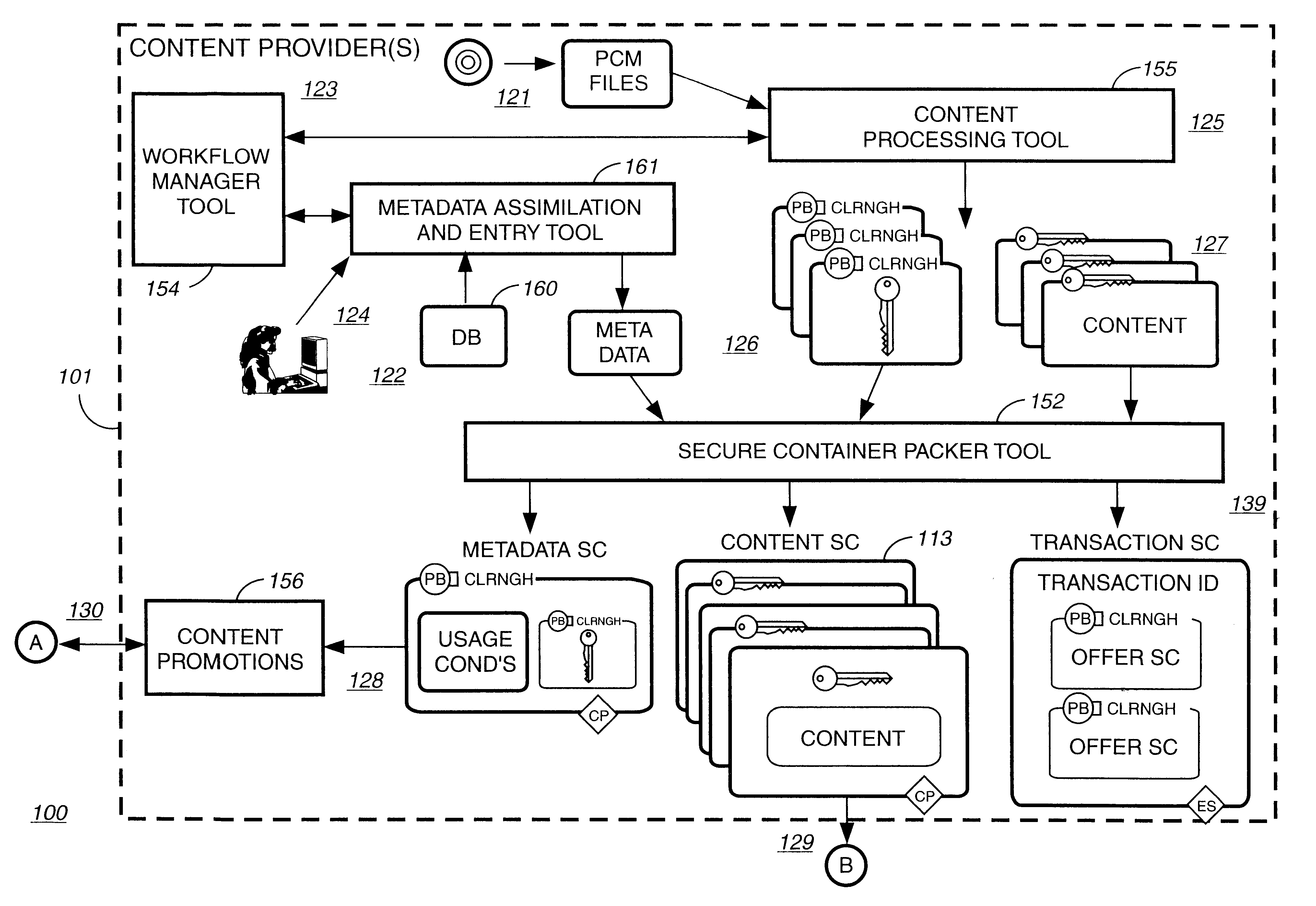
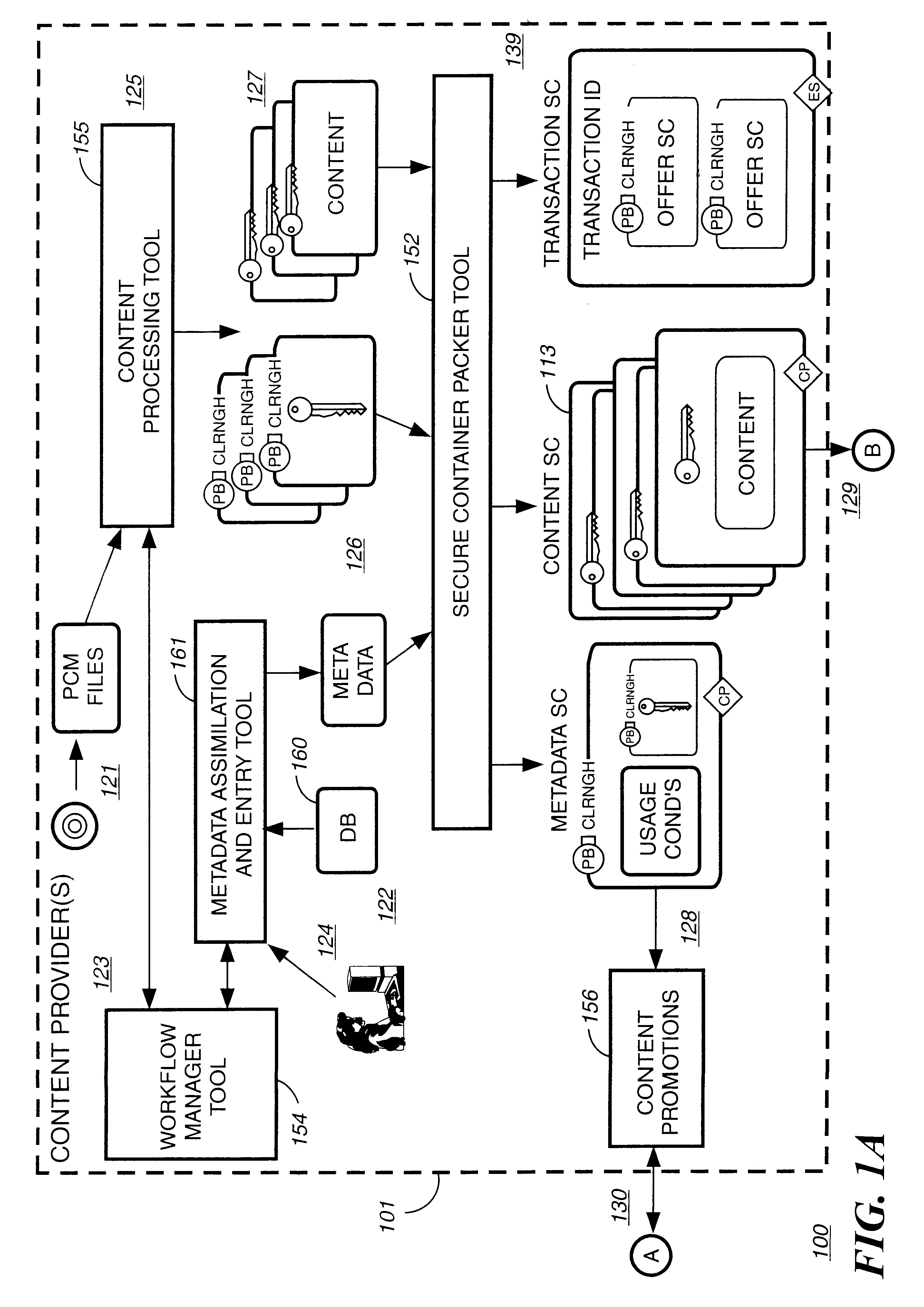
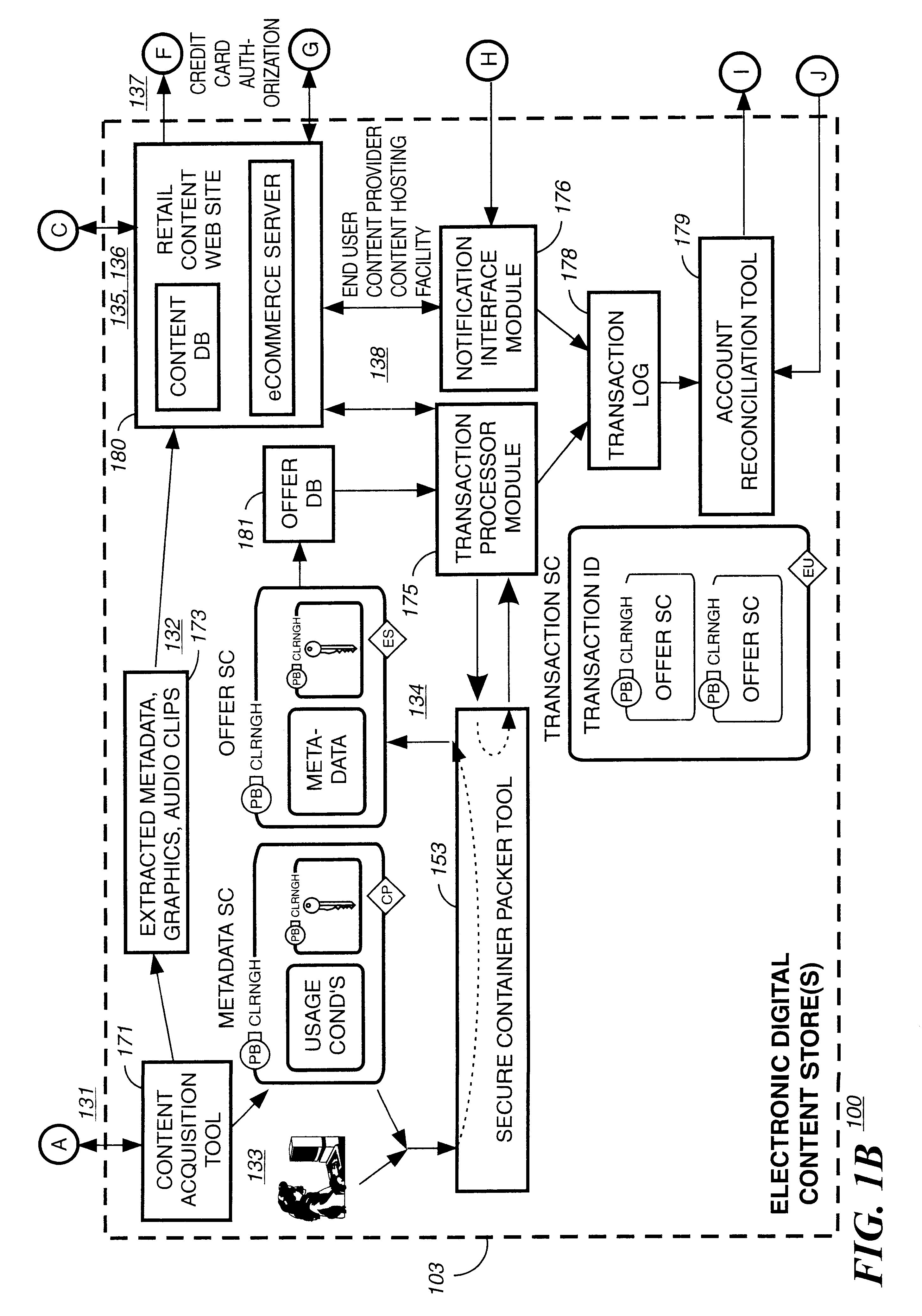
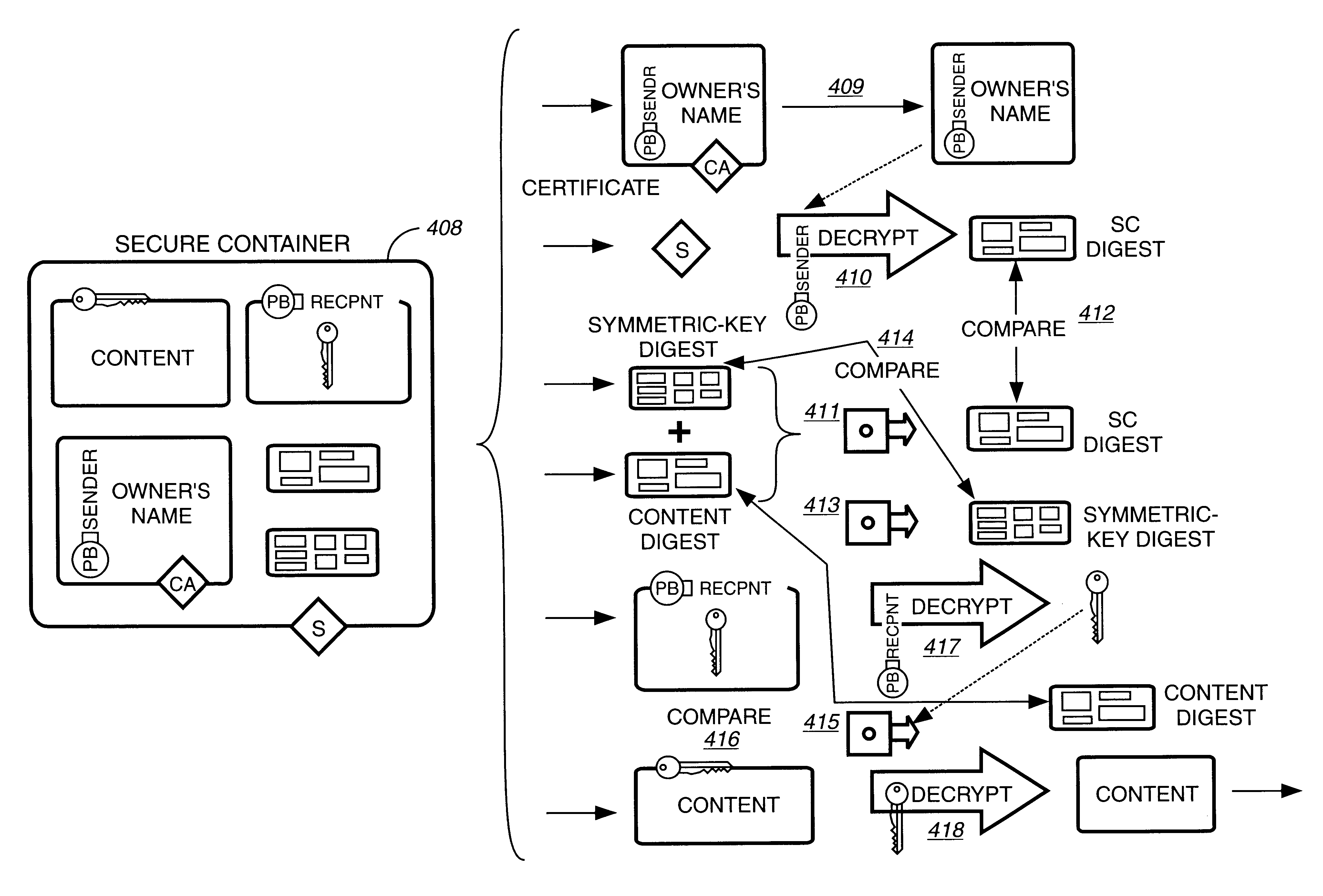
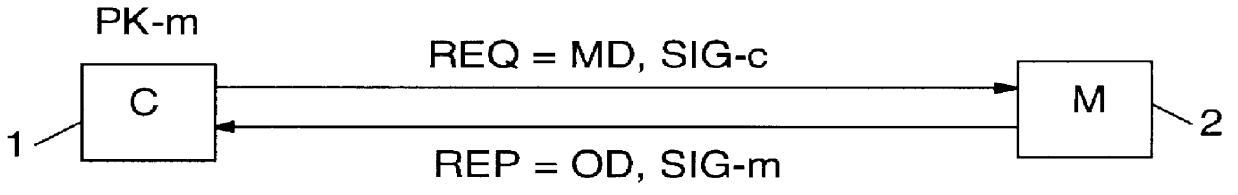Patents
Literature
8875results about "Payment protocols" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
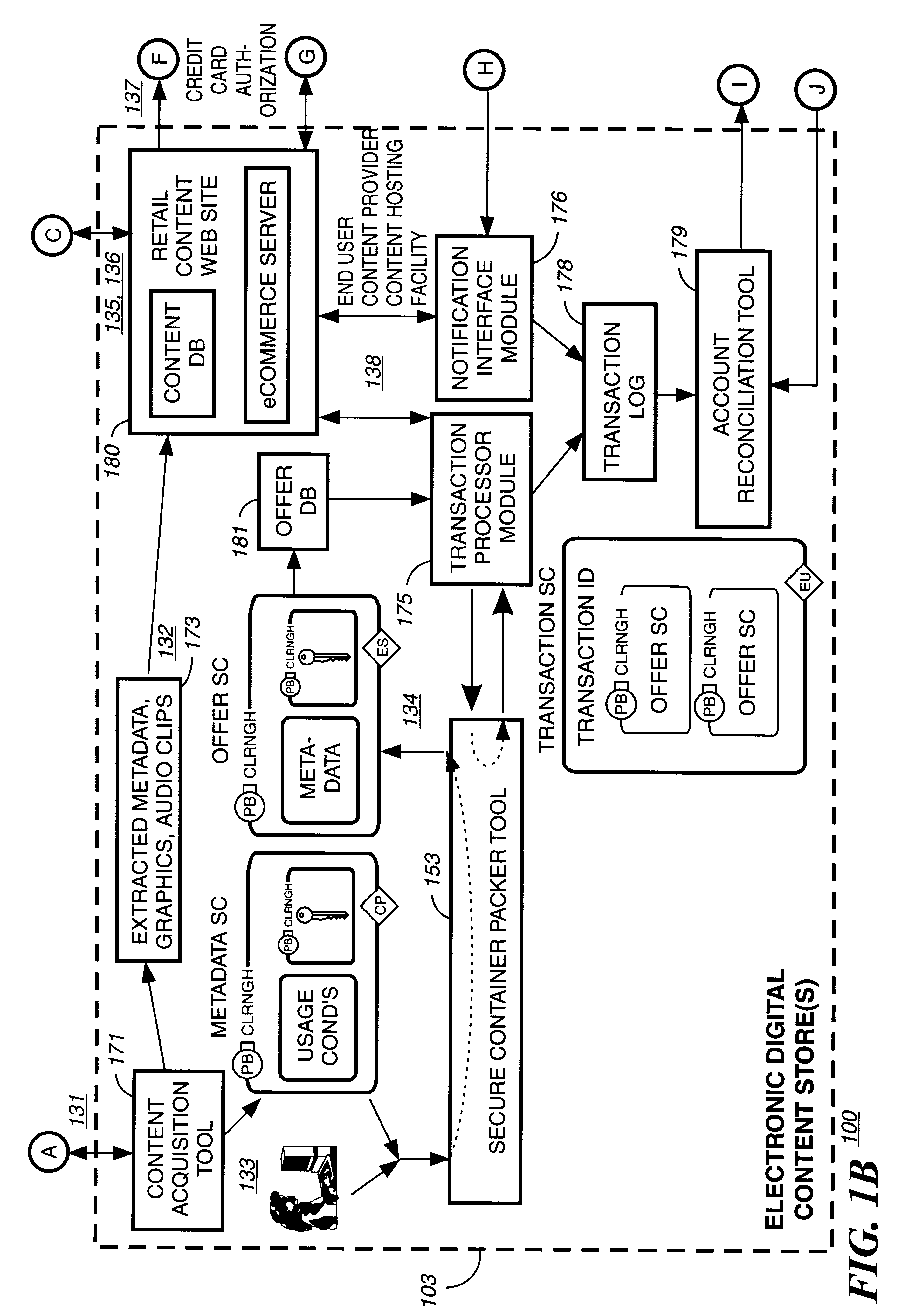
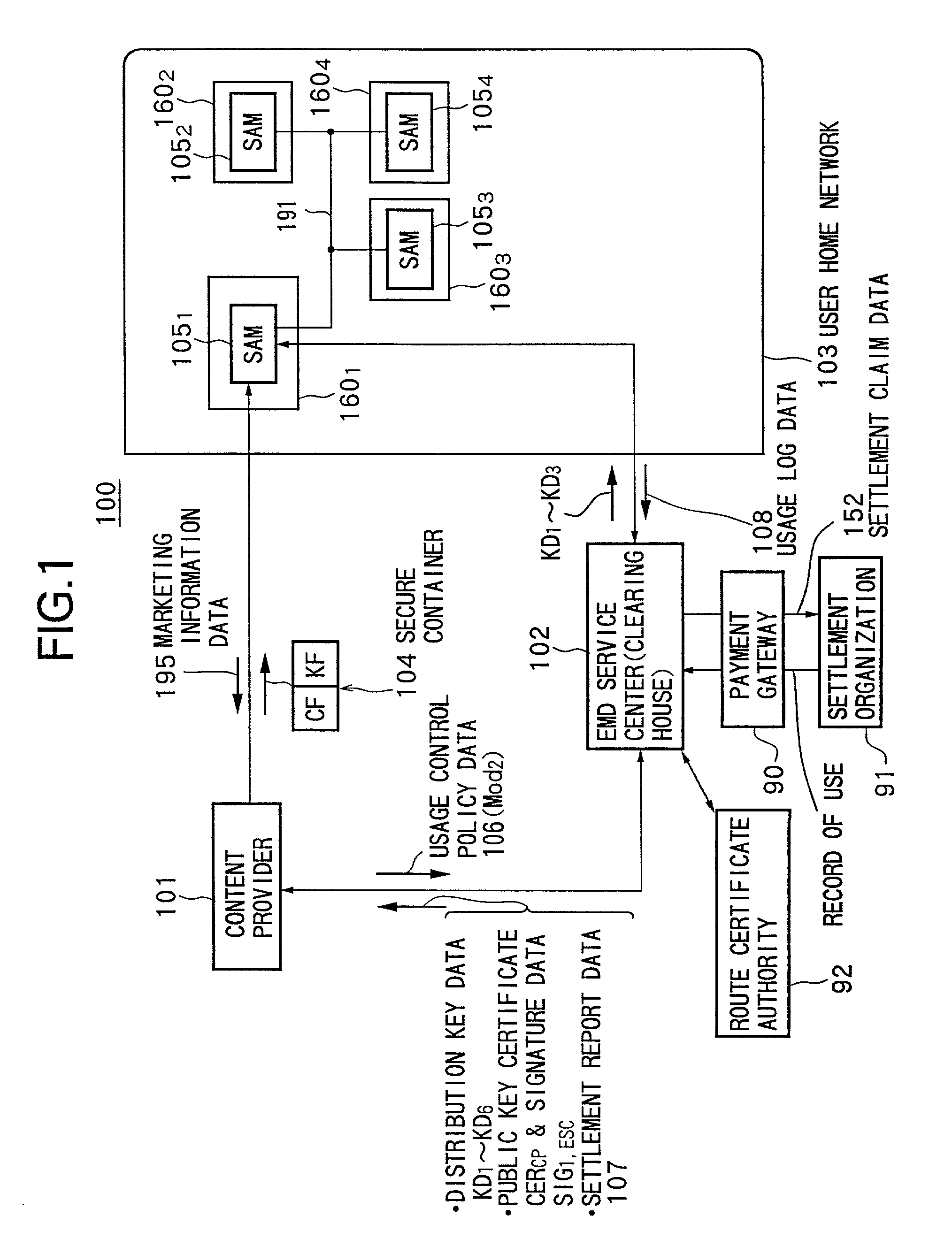
Electronic content delivery system
InactiveUS6226618B1Key distribution for secure communicationDigital data processing detailsDelivery systemSystem safety
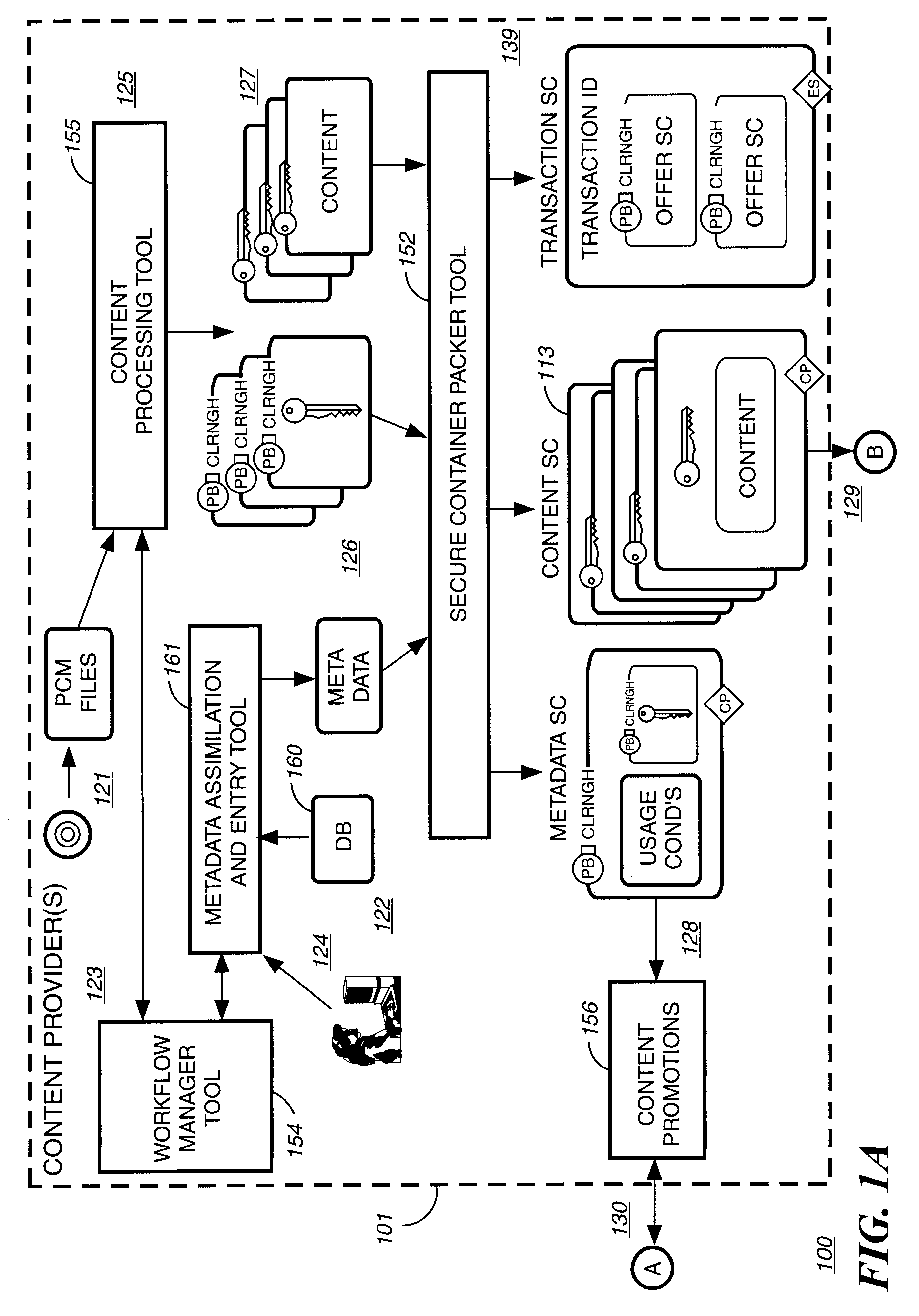
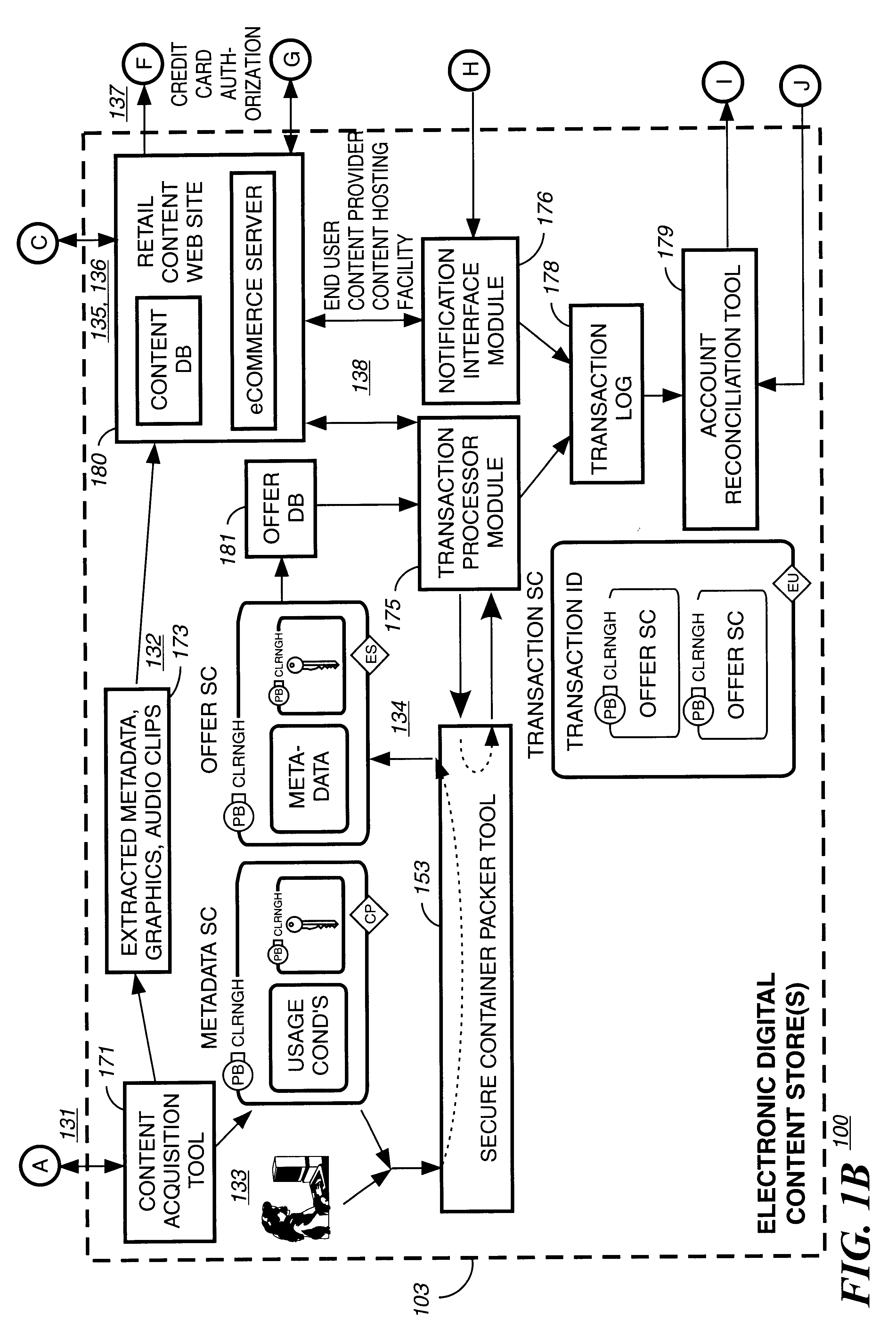
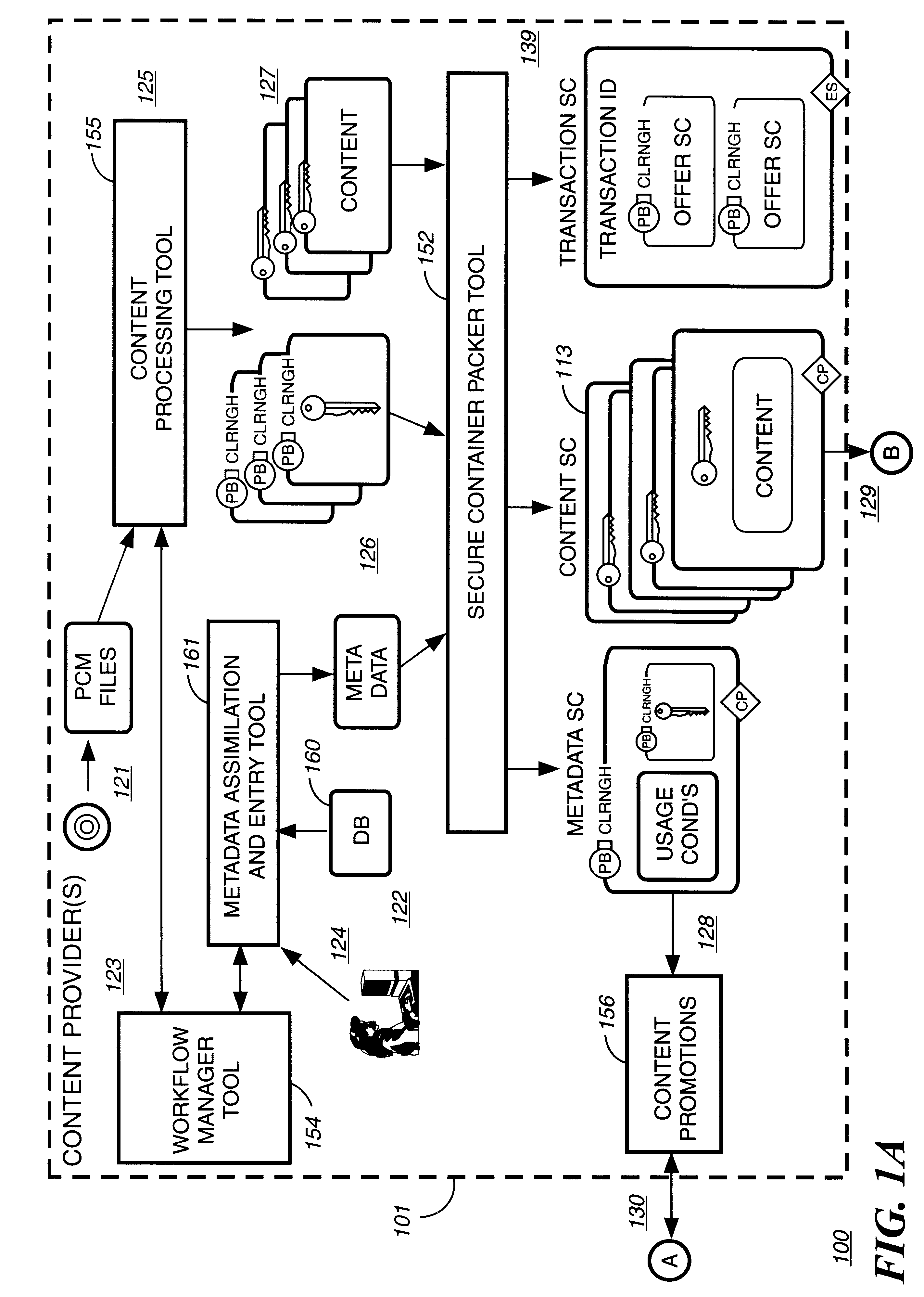
Disclosed is a method and apparatus of securely providing data to a user's system. The data is encrypted so as to only be decryptable by a data decrypting key, the data decrypting key being encrypted using a first public key, and the encrypted data being accessible to the user's system, the method comprising the steps of: transferring the encrypted data decrypting key to a clearing house that possesses a first private key, which corresponds to the first public key; decrypting the data decrypting key using the first private key; re-encrypting the data decrypting key using a second public key; transferring the re-encrypted data decrypting key to the user's system, the user's system possessing a second private key, which corresponds to the second public key; and decrypting the re-encrypted data decrypting key using the second private key.
Owner:LEVEL 3 COMM LLC
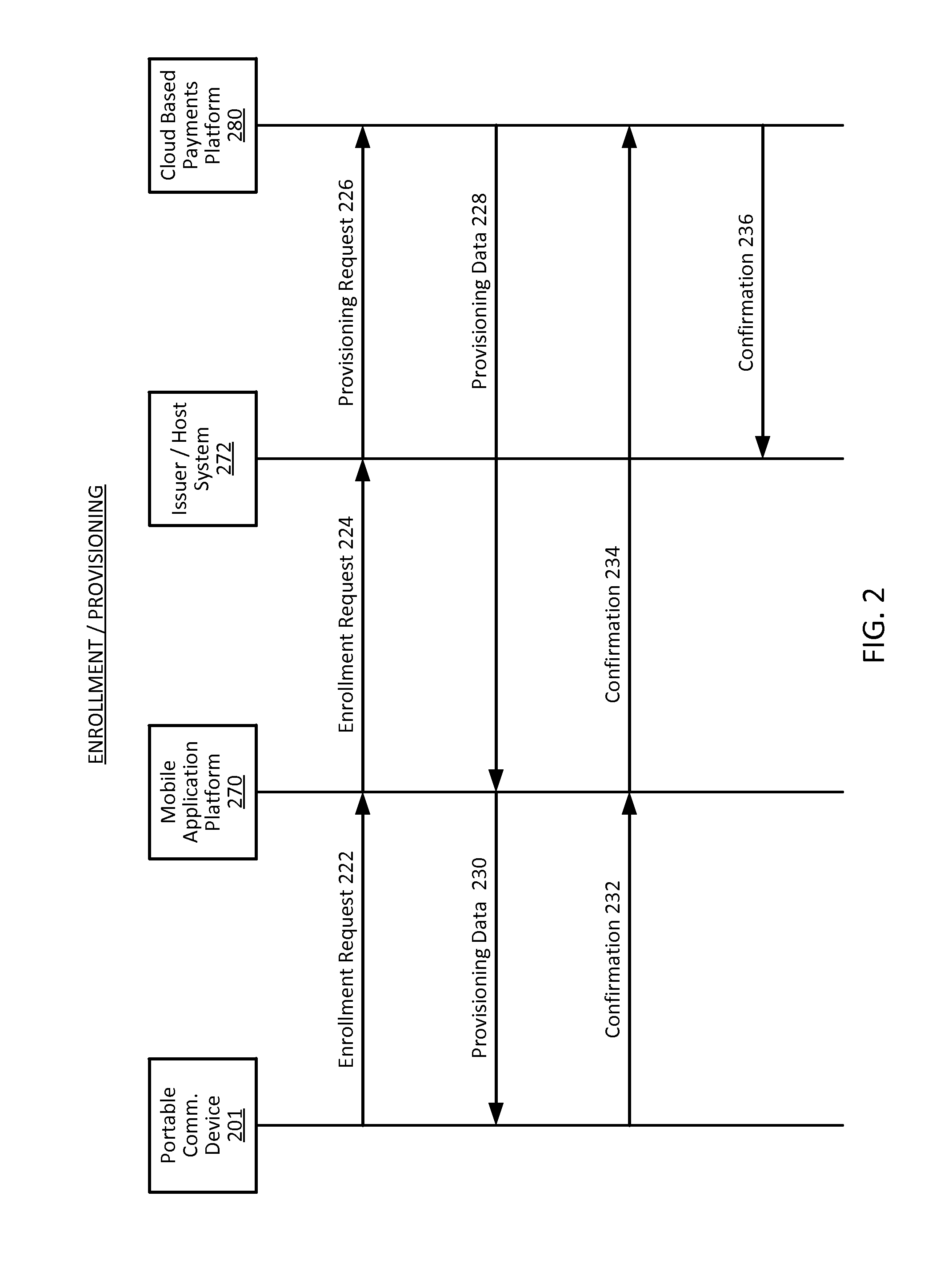
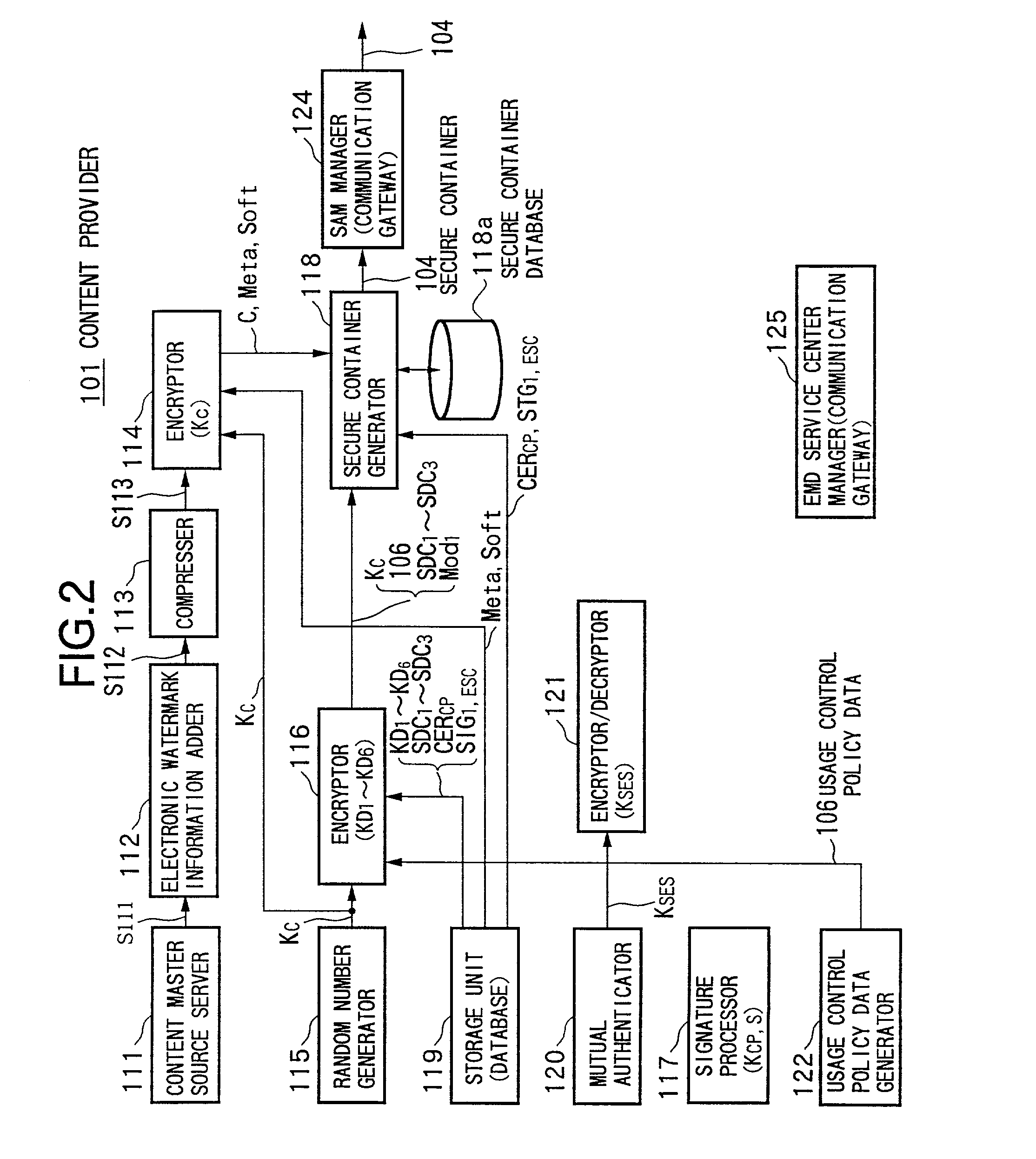
Automated method and apparatus to package digital content for electronic distribution using the identity of the source content
InactiveUS6345256B1Key distribution for secure communicationDigital data processing detailsDigital contentNumber content
A method to automatically retrieve data associated with content. An identifier is read that is stored on electronic readable medium storing content. The identifier is used to search a database for data associated with the content. Data that is associated with the content is retrieved as guided by the database. And the data retrieved is used to create a version of the content for electronic distribution. In accordance with another aspect of the invention, a computer readable medium is described to carry out the above method.
Owner:INT BUSINESS MASCH CORP
Method and apparatus to create encoded digital content
InactiveUS6263313B1Electrophonic musical instrumentsKey distribution for secure communicationDigital contentNumber content
Owner:LEVEL 3 COMM LLC
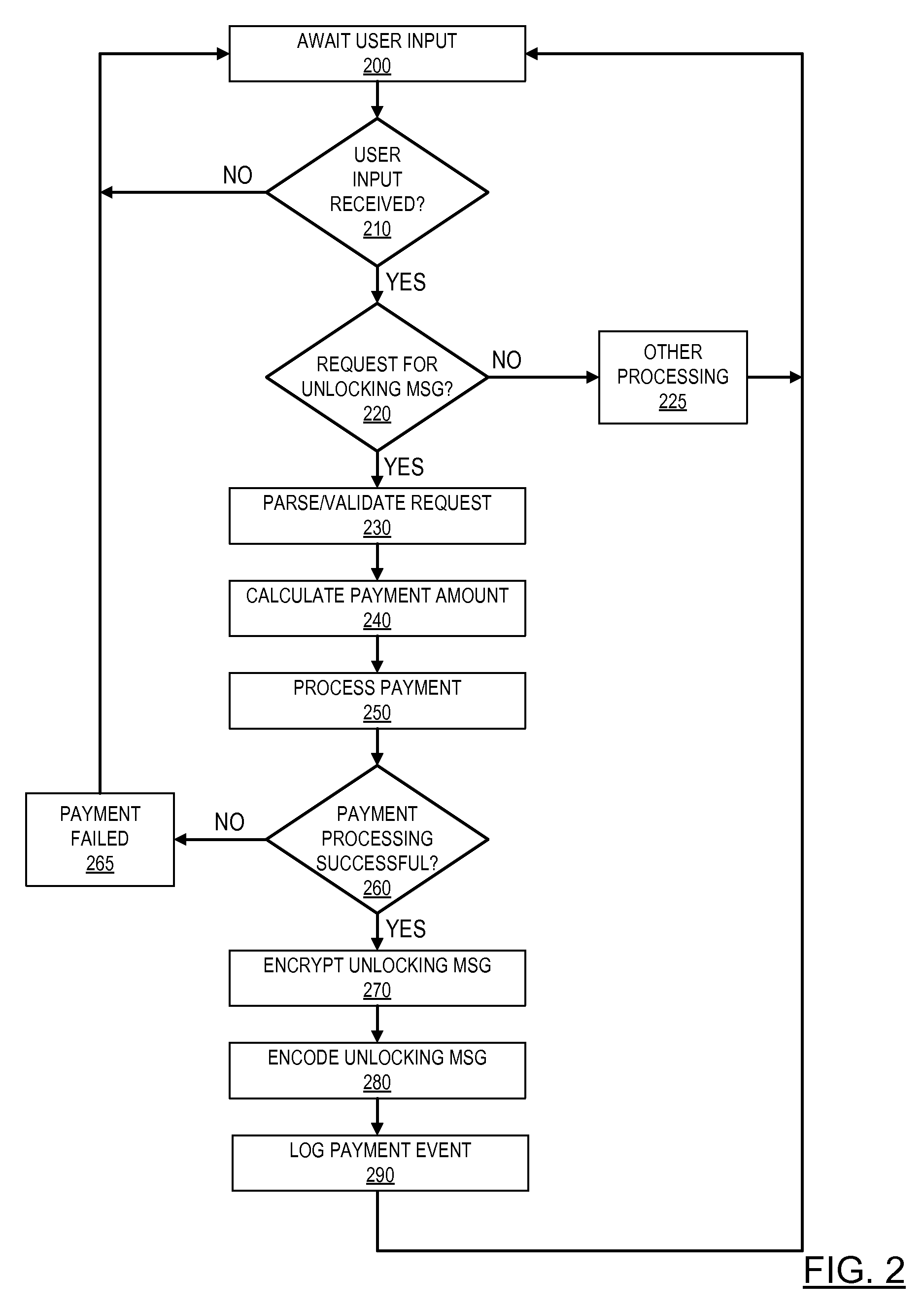
Pre-paid usage system for encoded information reading terminals
A fleet management system for managing a fleet of encoded information reading (EIR) terminals can comprise one or more computers, a fleet management software module, and a payment processing software module in communication with the fleet management software module. The fleet management software module can be configured, responsive to receiving a customer initiated request, to generate an unlocking message upon processing a payment by the payment processing software module. The unlocking message can be provided by a bar code to be read by an EIR terminal, or by a bit stream to be transferred to an EIR terminal via network. Each EIR terminal can be configured to perform not more than a pre-defined number of EIR operations responsive to receiving the unlocking message.
Owner:METROLOGIC INSTR
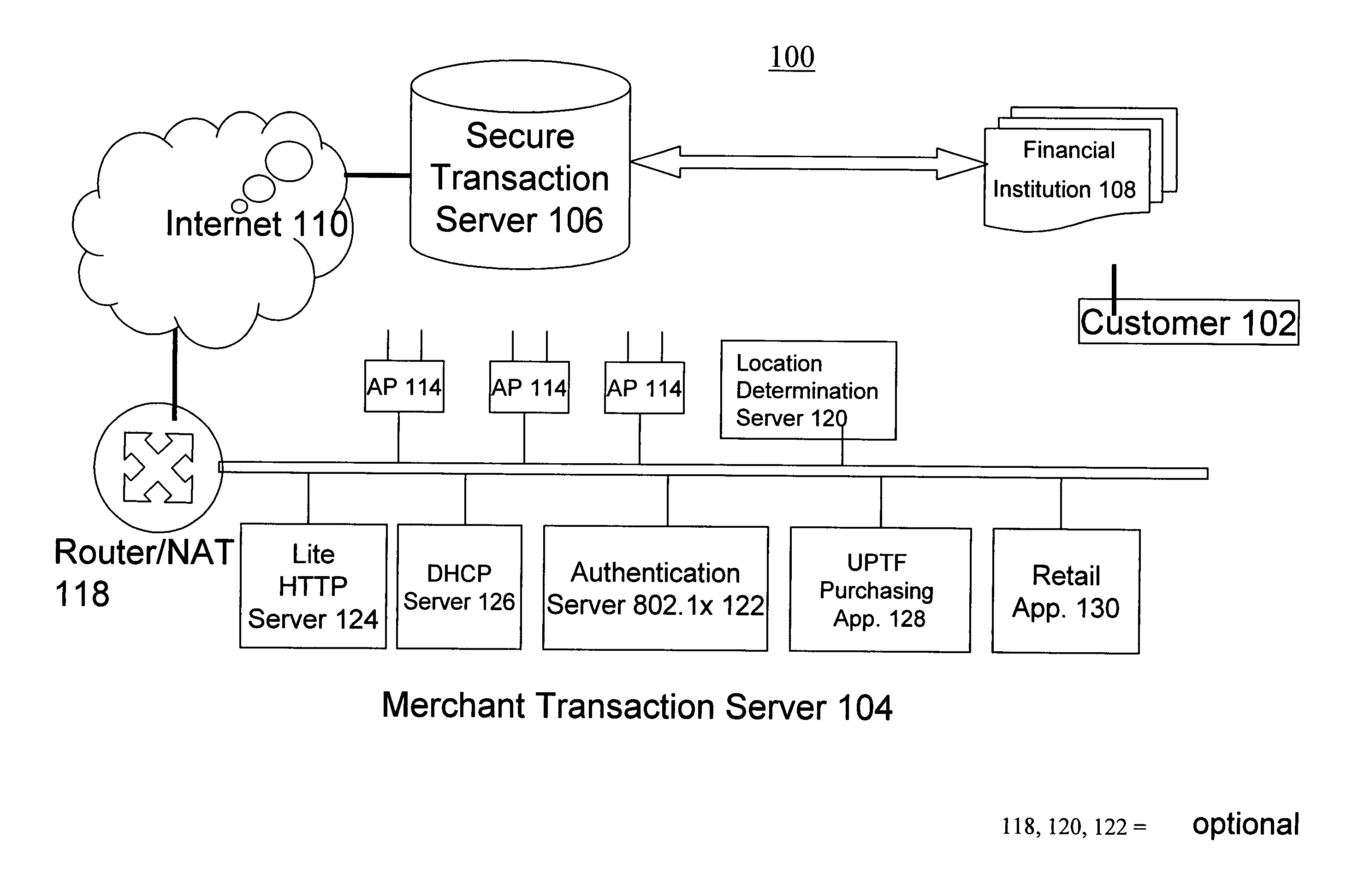
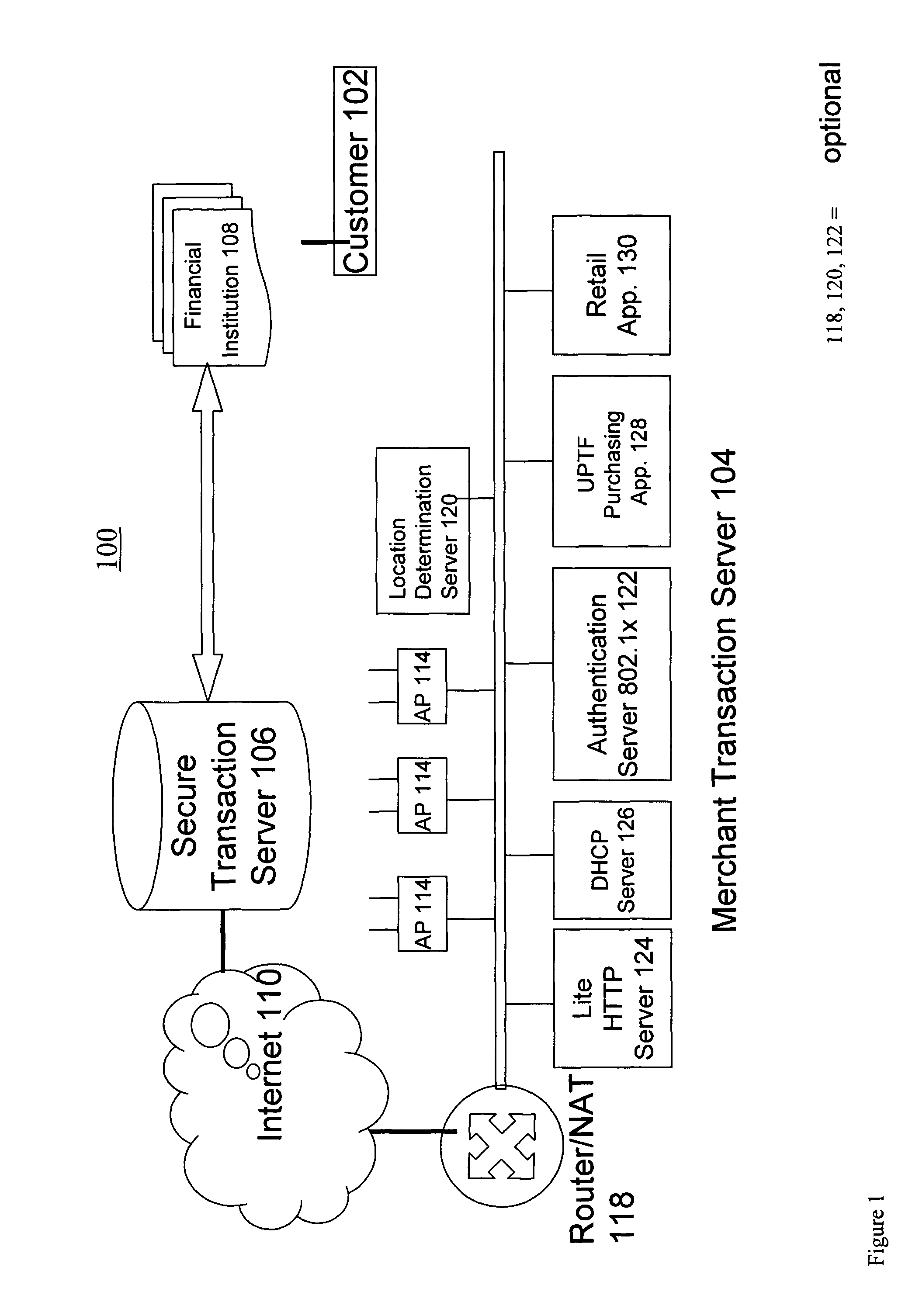
System and method for establishing eletronic business systems for supporting communications servuces commerce
ActiveUS20060059107A1Easy to addEasy to liftPayment protocolsBilling/invoicingEnterprise application integrationSupporting system
Owner:NETCRACKER TECH SOLUTIONS
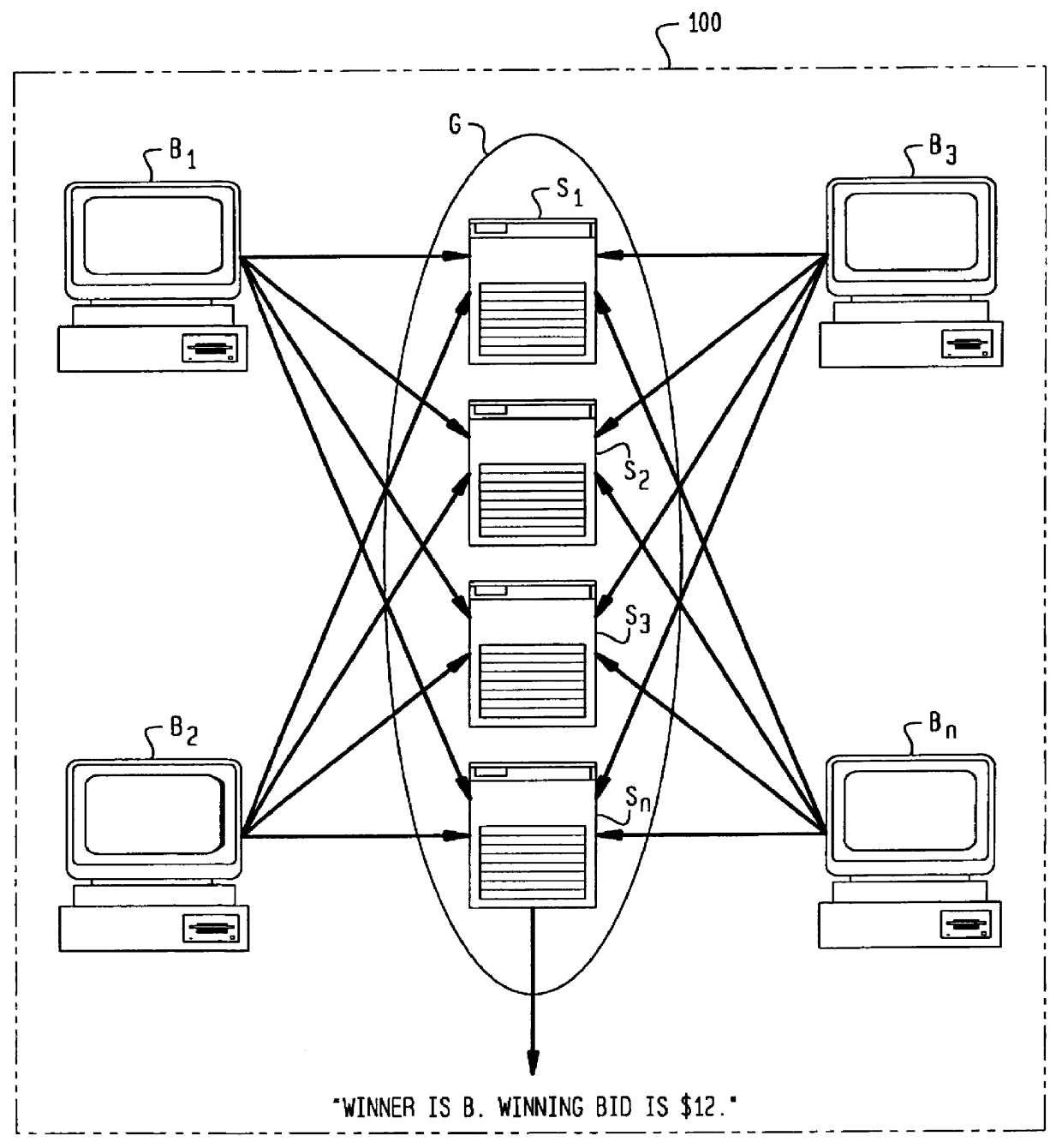
Secure auction systems
InactiveUS6055518AEasy to rebuildFinanceUser identity/authority verificationFinancial transactionMonetary value
The apparatus and method of the present invention provide secure auction service for use in a network having servers and bidding terminals. The auction service makes transactions among servers and bidding terminals subject to a distributed protocol. The distributed protocol distributes submitted bids among the multiple servers, closes a bidding period, verifies validity of monetary value of each submitted bid by utilizing said distributed protocol and determines a winning bidder.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Limited-use keys and cryptograms
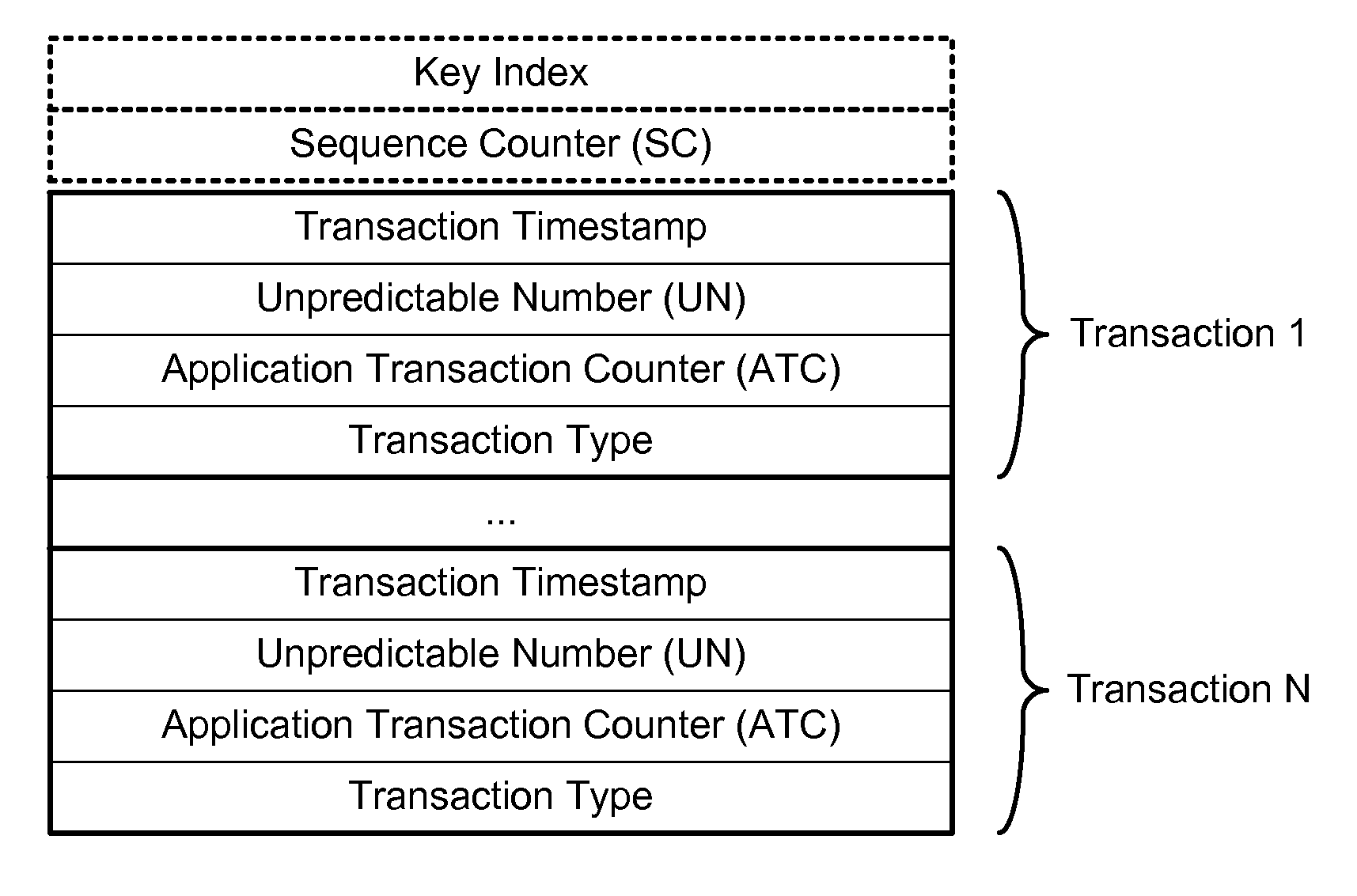
ActiveUS20150178724A1Promote generationImprove securityMultiple keys/algorithms usageCryptography processingCryptogramCommunication device
Techniques for enhancing the security of a communication device when conducting a transaction using the communication device may include encrypting account information with a first encryption key to generate a second encryption key, and encrypting key index information using the second key to generate a limited-use key (LUK). The key index information may include a key index having information pertaining to generation of the LUK. The LUK and the key index can be provided to the communication device to facilitate generation of a transaction cryptogram for a transaction conducted using the communication device, and the transaction can be authorized based on the transaction cryptogram generated from the LUK.
Owner:VISA INT SERVICE ASSOC
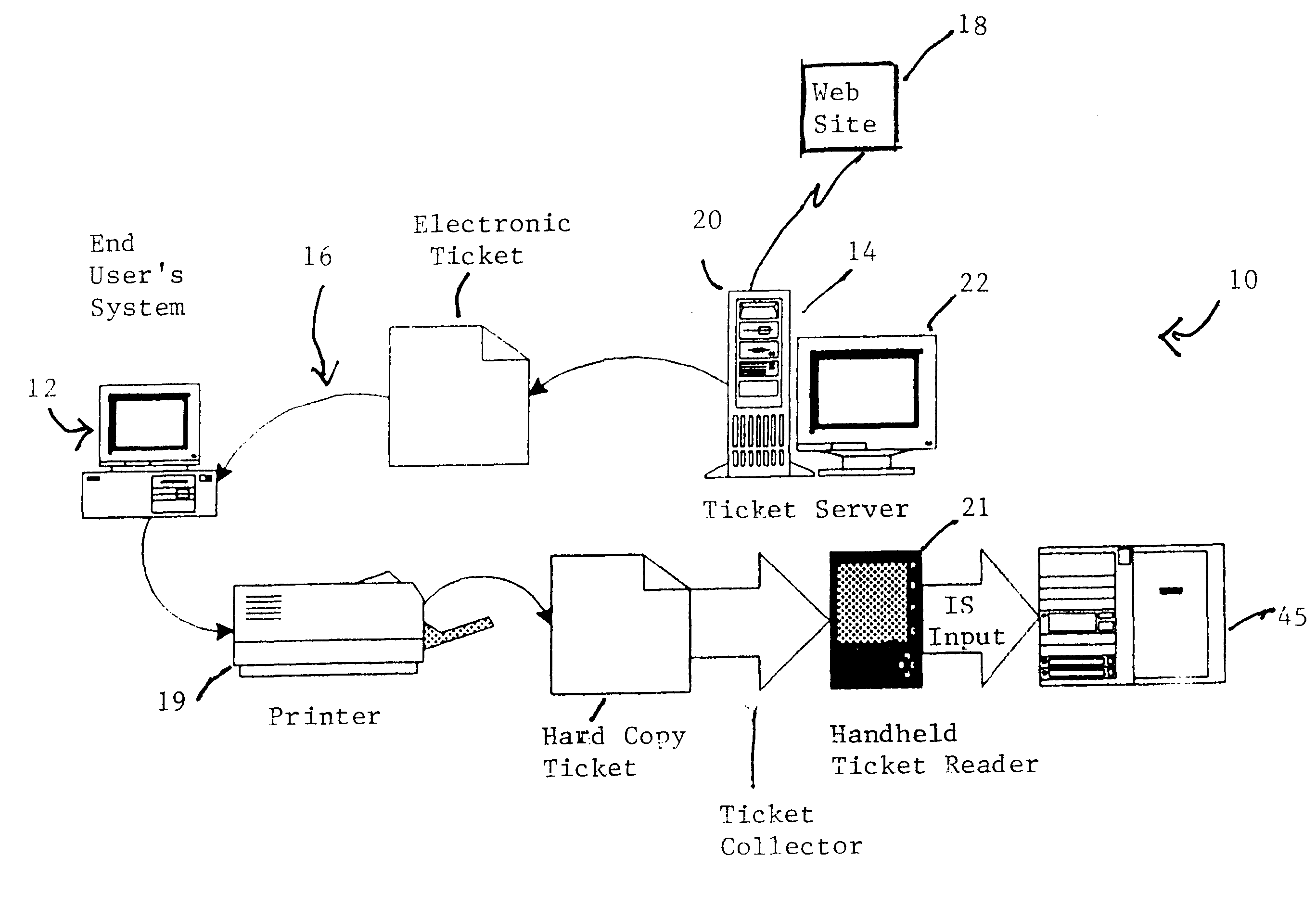
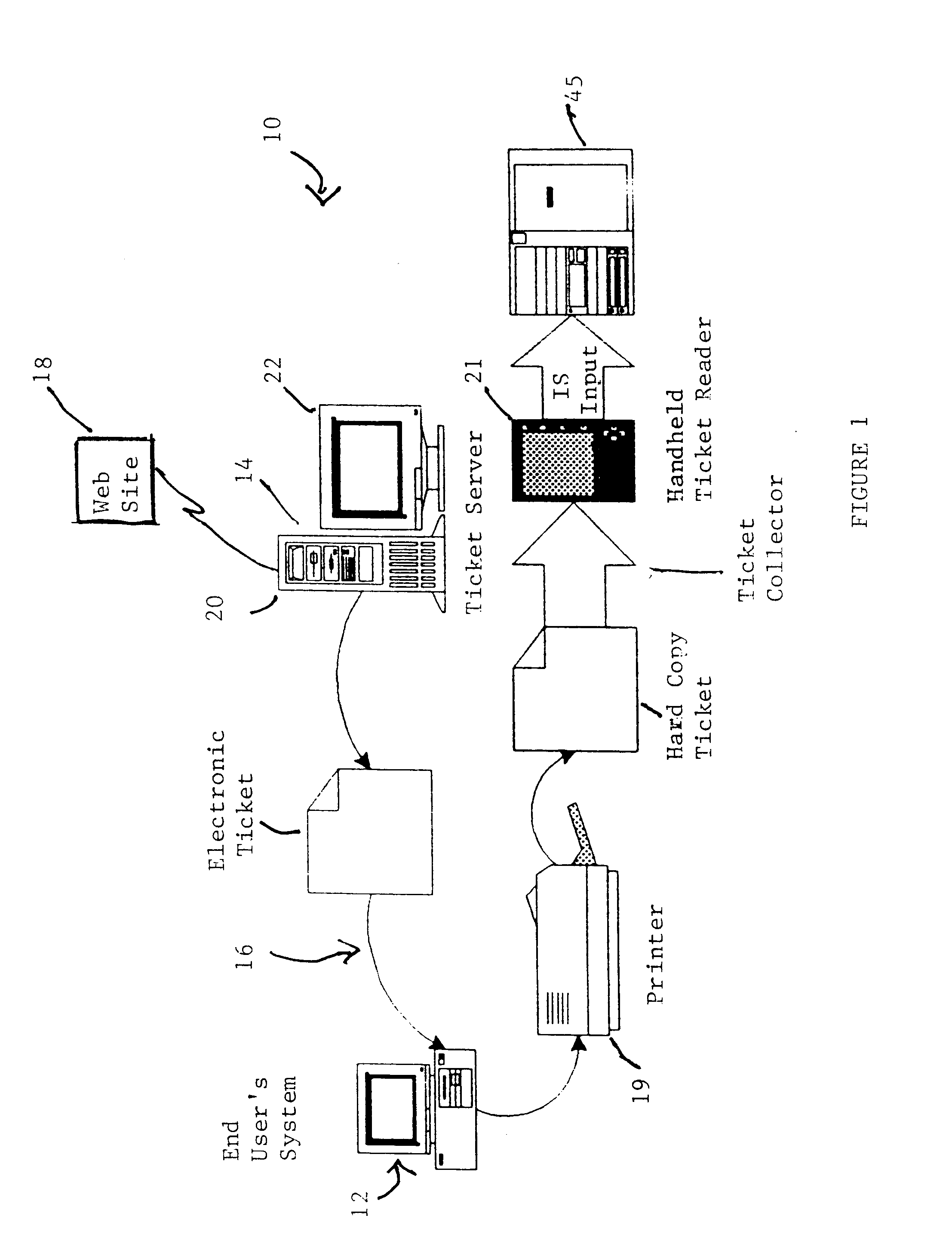
Cryptographic encoded ticket issuing and collection system for remote purchasers
InactiveUS6223166B1Prevent ticket fraudTicket-issuing apparatusElectrical apparatusCollection systemInformation networks
A cryptographic encoded, ticket issuing and collection system for real-time purchase of tickets by purchasers at remote user stations in an information network that includes a plurality of remote user stations coupled to a server in an information network, e.g., the Internet, for purchase of services, products, or tickets to an event. An operator of the remote user station selects a ticket for purchase to an event using standard protocols of information network. An electronic ticket is transmitted to the operator and includes a cypher code created using a public key cryptography system. The operator displays the electronic ticket for verification purposes and proceeds to print out the ticket at the station. The ticket is presented to a ticket collector whereupon the ticket is scanned by a portable terminal for decoding the cypher code using a public key reloaded into the terminal by the producers of the event. The decoded cypher code is compared against the event description stored in the portable terminal and if equal, the ticket is accepted for admission to the event. The ticket information is stored in the portable terminal and subsequently uploaded to the information system to check for duplicate tickets.
Owner:IBM CORP
Promotion system including an ic-card memory for obtaining and tracking a plurality of transactions
An apparatus is provided for tracking individual user consumer transactions which provides the user with an eraseable, re-writeable, visual format display while avoiding retrieval of data from an outside source.
Owner:VISIBLE RESULTS GRP LTD
Framework and system for purchasing of goods and services
InactiveUS7801826B2Risk minimizationReducing credit card fraudComputer security arrangementsPayment protocolsThird partyPurchasing
A system for conducting an agreement between two parties relying on a trusted a third party includes a first party generating a first view of the agreement and transmitting the first view of the agreement to the third party, a second party independently generating a second view of the agreement and transmitting the second view of the agreement to the third party, a wireless network connecting the first party and the second party, and a wired or wireless network connecting the second party to the third party. The trusted third party, receives the first view of the agreement and the second view of the agreement, verifies conditions including that the identities of the parties that transmitted the agreements and that the independent views of the agreement are consistent with each other, and takes action to execute the agreement if the conditions are satisfied.
Owner:PCMS HOLDINGS INC
Method and system for storage and retrieval of blockchain blocks using galois fields
A method and system for storage and retrieval of blockchains with Galois Fields. One or more blocks for a blockchain are securely stored and retrieved with a modified Galois Fields on a cloud or peer-to-peer (P2P) communications network. The modified Galois Field provides at least additional layers for security and privacy for blockchains. The blocks and blockchains are securely stored and retrieved for cryptocurrency transactions including, but not limited to, BITCOIN transactions and other cryptocurrency transactions.
Owner:LESAVICH STEPHEN +1
Secured transaction system and method
InactiveUS20130254117A1Reduce riskEasy to optimizePayment protocolsInternet privacyEncryption decryption
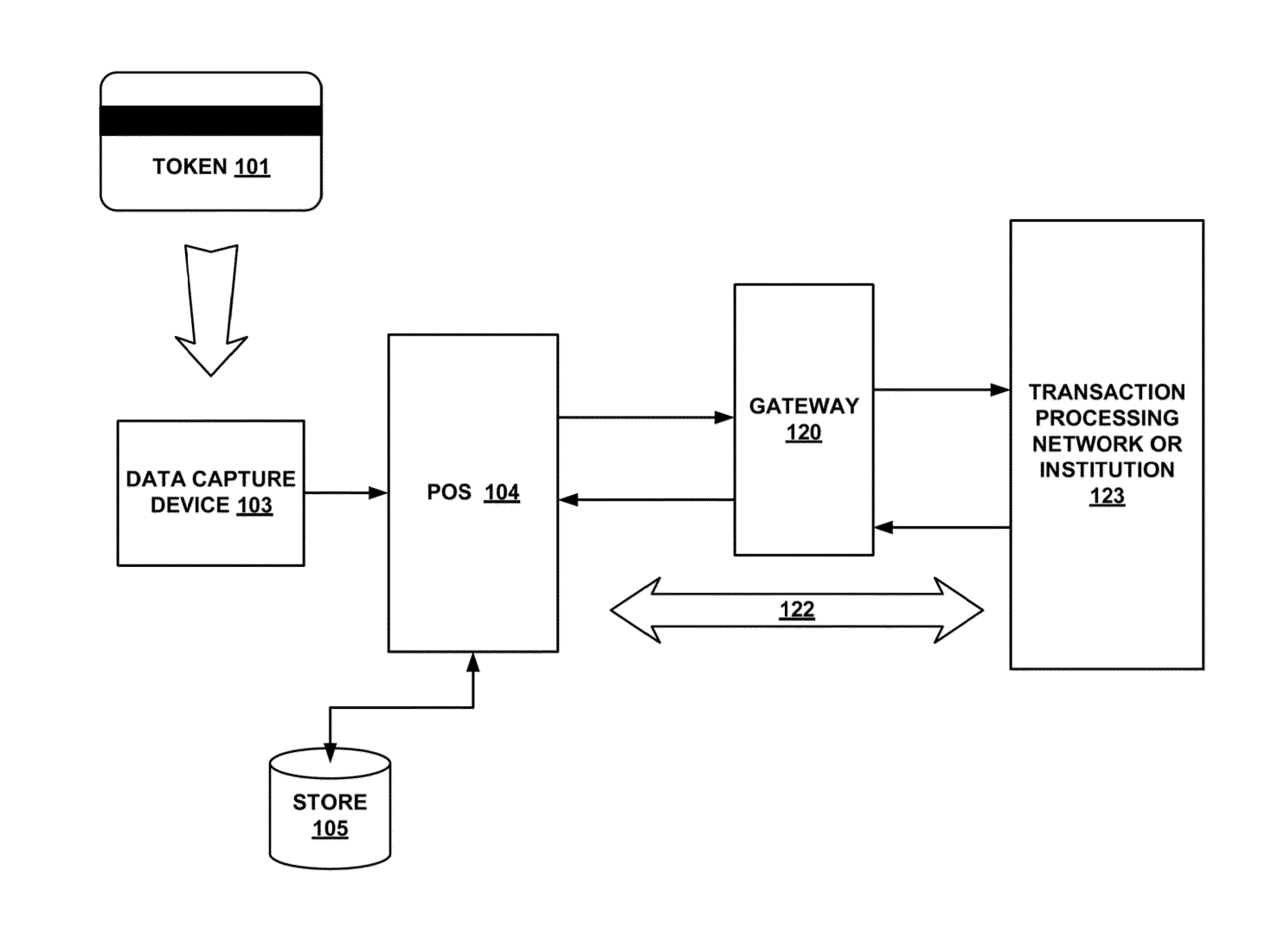
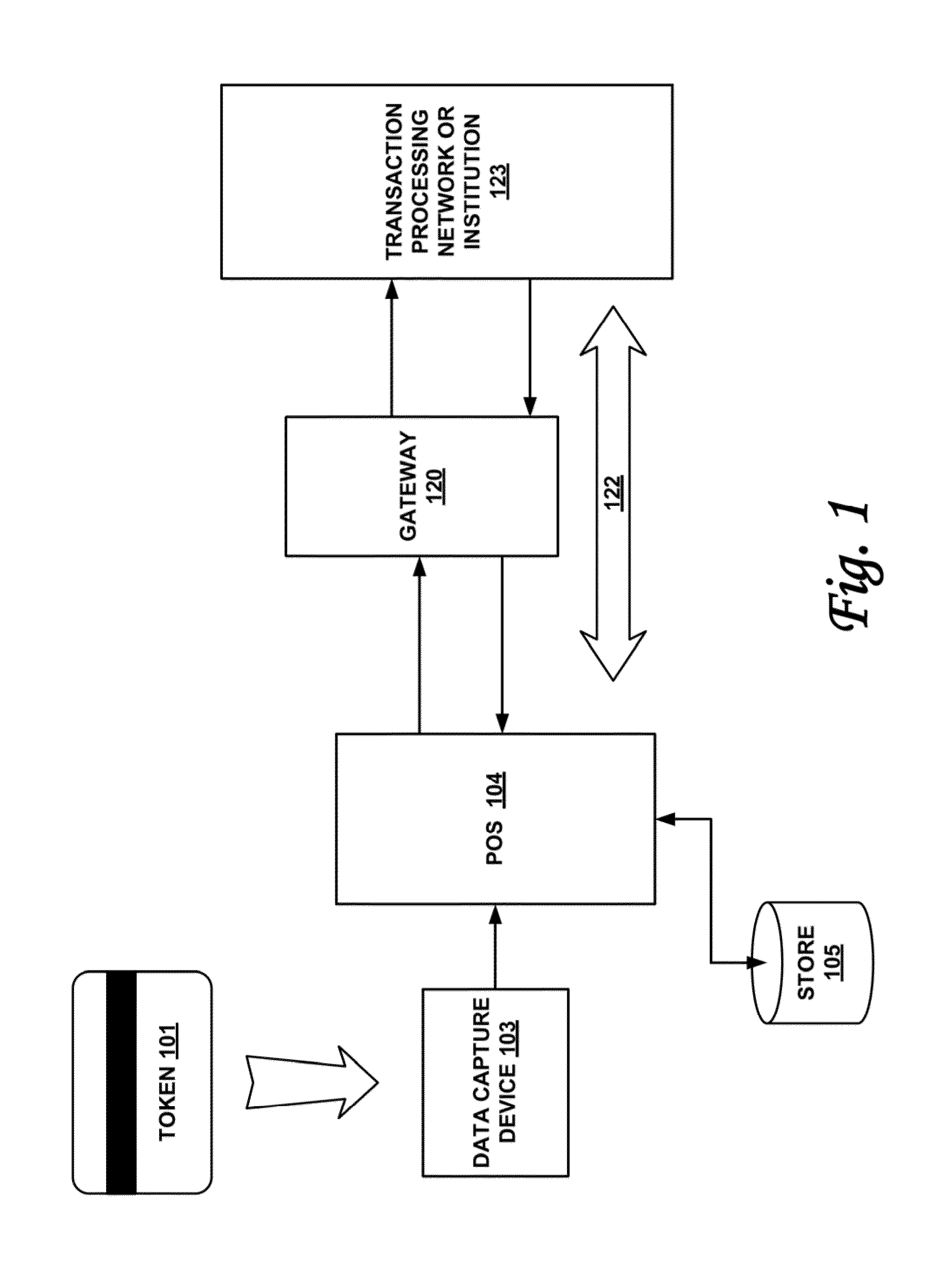
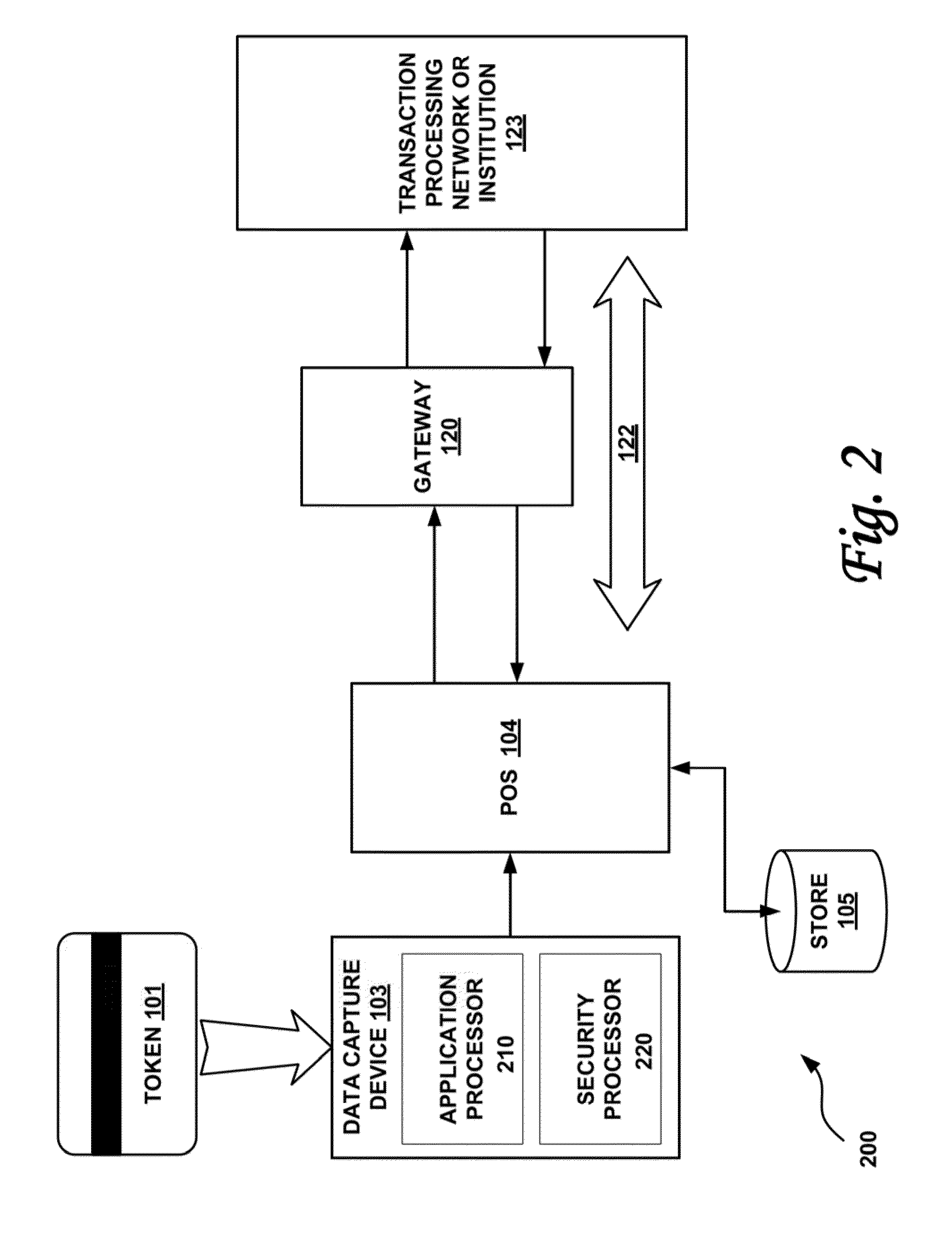
Systems and methods for performing financial transactions are provided. In one embodiment, the invention provides for method for bank card transactions, including: reading the token information at the point of swipe for traditional and non-traditional POS platforms; performing a low-security task on the token information using a first microprocessor, wherein the non-security task includes one or more tasks from the group of encryption determination, encryption-decryption request, key management, token information delivery, or transactional data delivery; and performing a security-related task on the token information using a second microprocessor based on a request from the first microprocessor, wherein the security-related task includes one or more tasks from the group of token information authentication, token information decryption, or token information encryption. Formatting the encrypted information such that it is compatible with the format of the current POS system.
Owner:VON MUELLER CLAY W +1
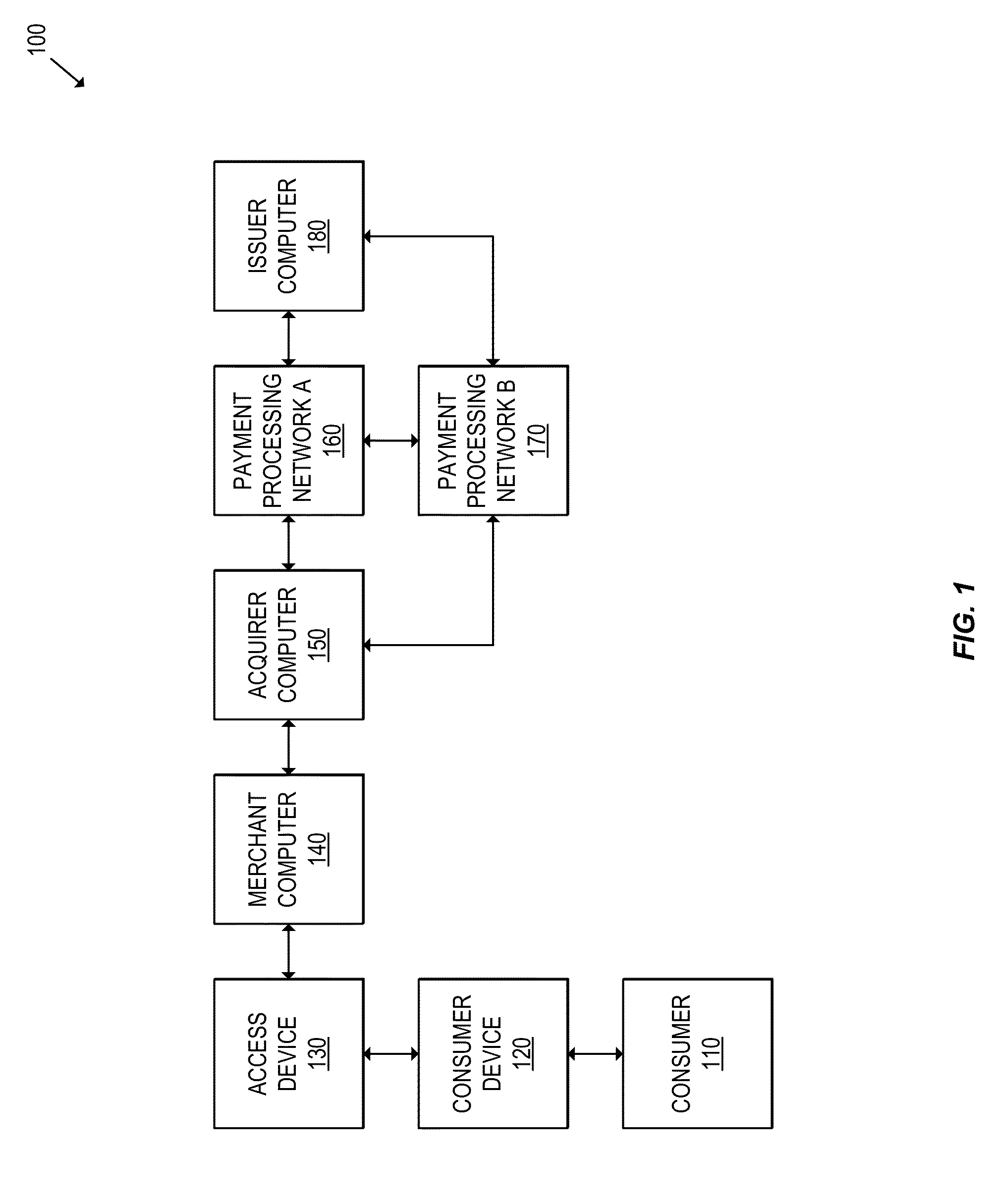
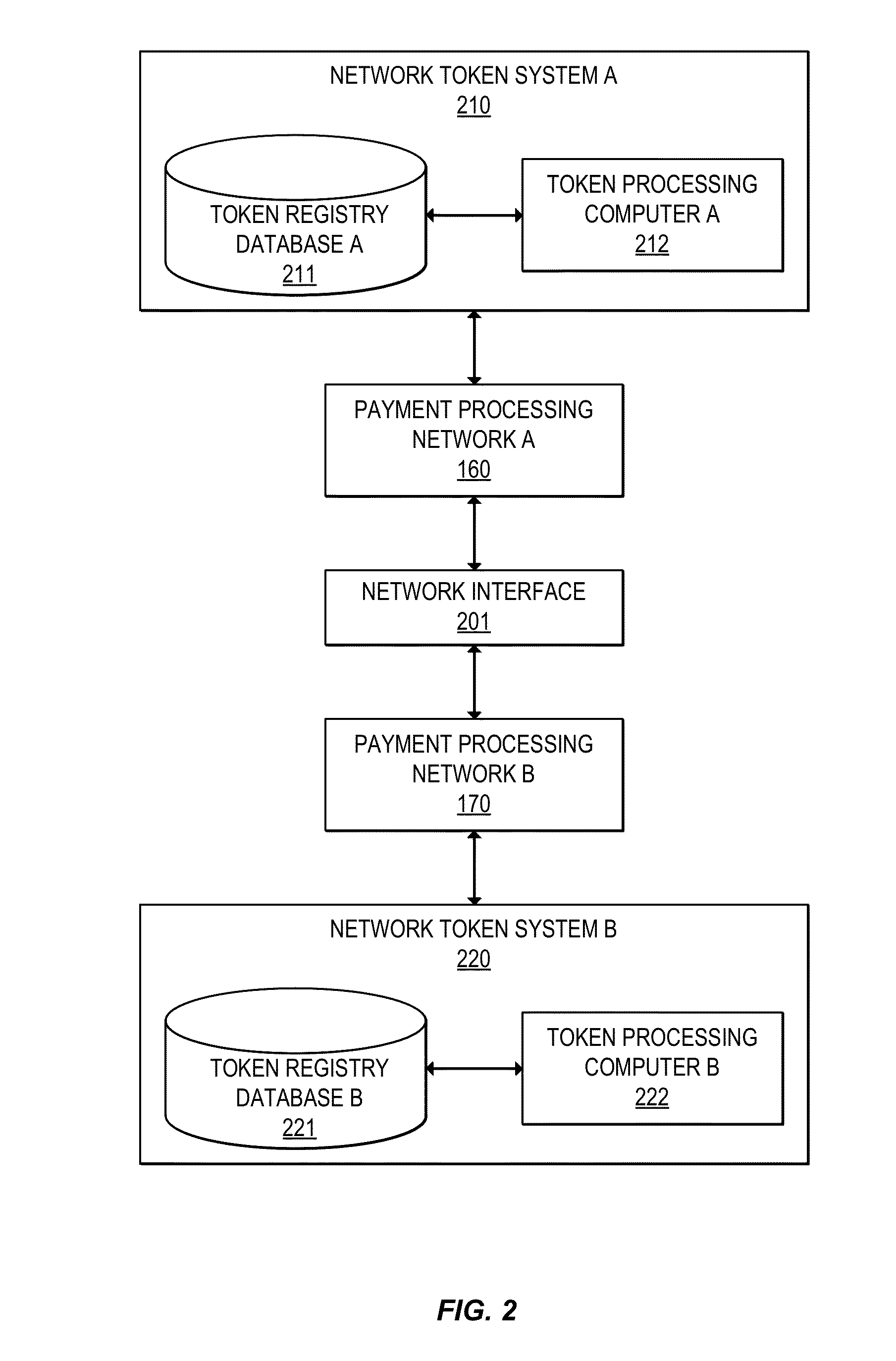
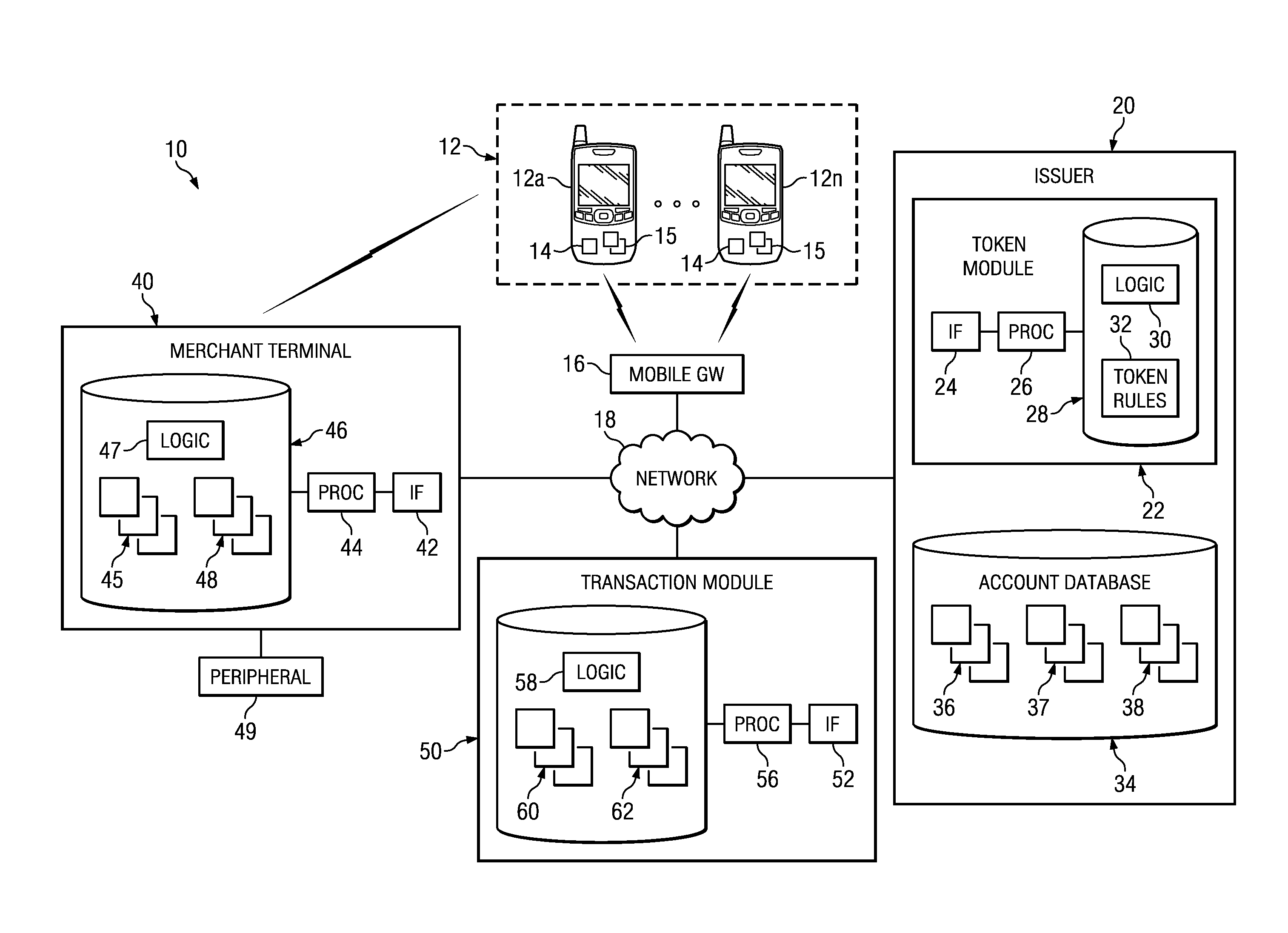
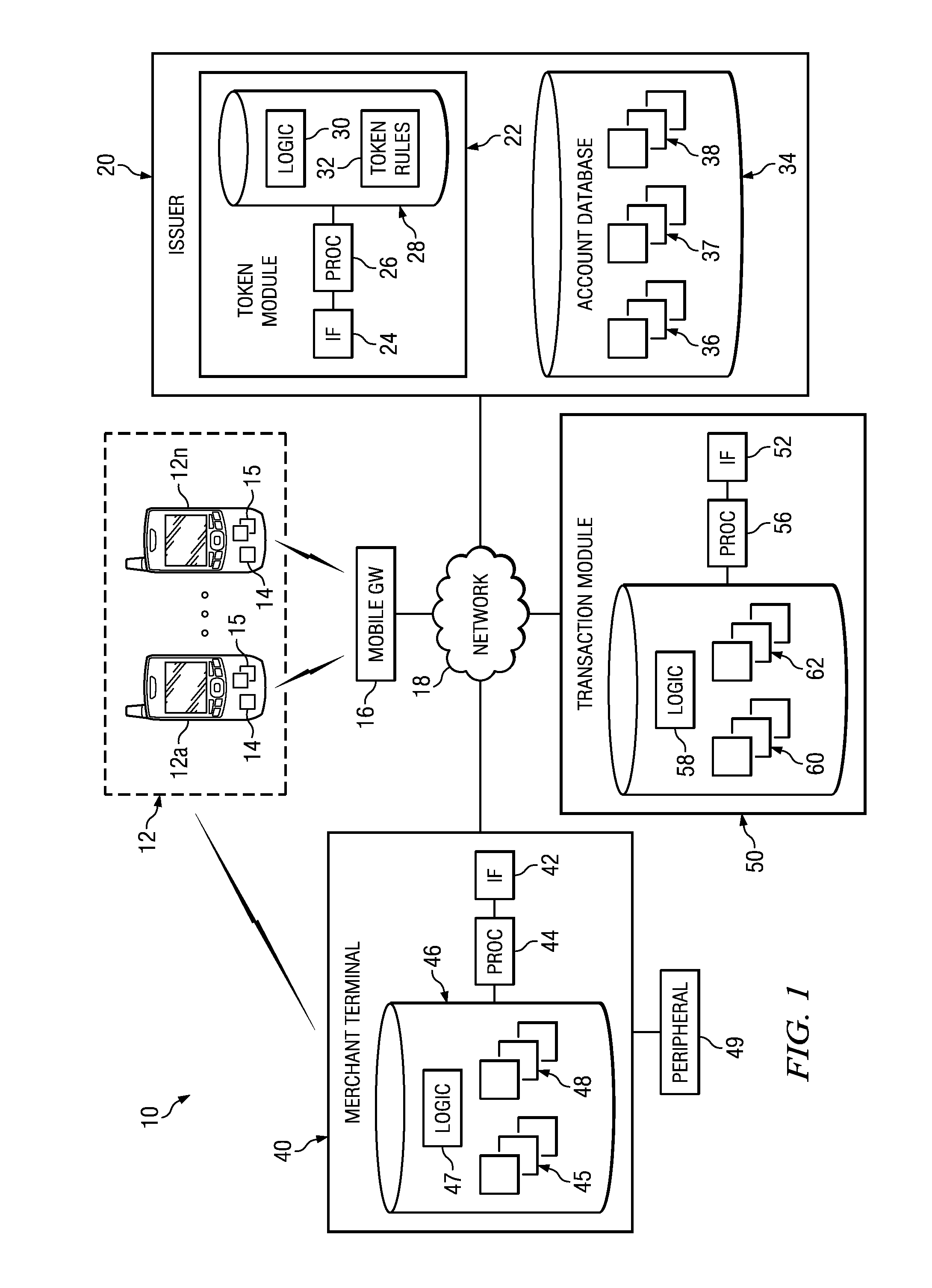
Multi-network tokenization processing
Systems, apparatuses, and methods are provided for enabling a transaction using a token associated with a first payment network to be conducted using a second payment network. When a transaction using a token is submitted to a payment network, the payment network can determine the payment network associated with the token. If the token is associated with a second payment network, a token verification request including the token can be sent to the second payment network. The second payment network can then return a token verification response including a primary account identifier such as a primary account number (PAN) corresponding to the token and a validation result. The transaction may then be processed using the primary account identifier.
Owner:VISA INT SERVICE ASSOC
Cryptocurrency Virtual Wallet System and Method
InactiveUS20150324789A1Prevent unauthorized accessConvenient transactionCryptography processingPayment protocolsComputer hardwareUser device
The present disclosure describes a method in which an encrypted request to transfer a requested amount of cryptocurrency from a user address to a destination address is received. The request includes a destination address, a requested amount, a user device encryption key, and biometric data. A partially signed transaction to transfer a requested amount of cryptocurrency from the user address to the destination address is also received. The partially signed transaction is cryptographically signed and a multi-signed transaction is broadcast to a cryptocurrency network to transfer the requested amount of cryptocurrency from the user address to the destination address.
Owner:TOKENIZE INC
Secure online commerce transactions
A method of enabling electronic commerce transactions is provided by a service, the service giving to users a disposable credit card or other indicia of credit for a particular transaction or amount. The service receives registration information from the user and authorizes the user. The service establishes an account for the user and issues a disposable (one use) credit card number to the user which has the same format as a permanent credit card number, is acceptable to the user and the institution with whom the user is transacting business. The system incorporates various security features.
Owner:ACEINC PTY LTD
Secure Remote Payment Transaction Processing Using a Secure Element
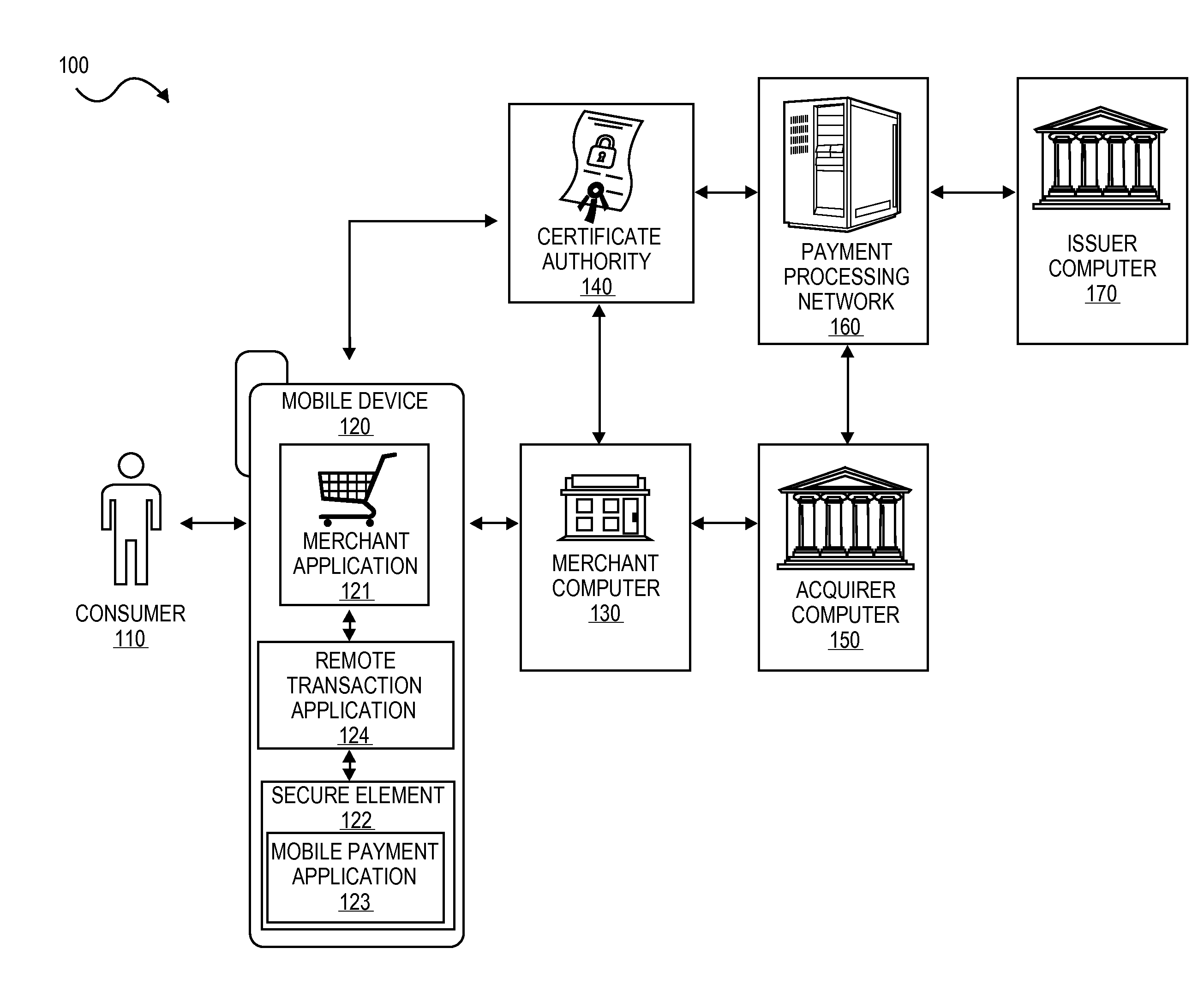
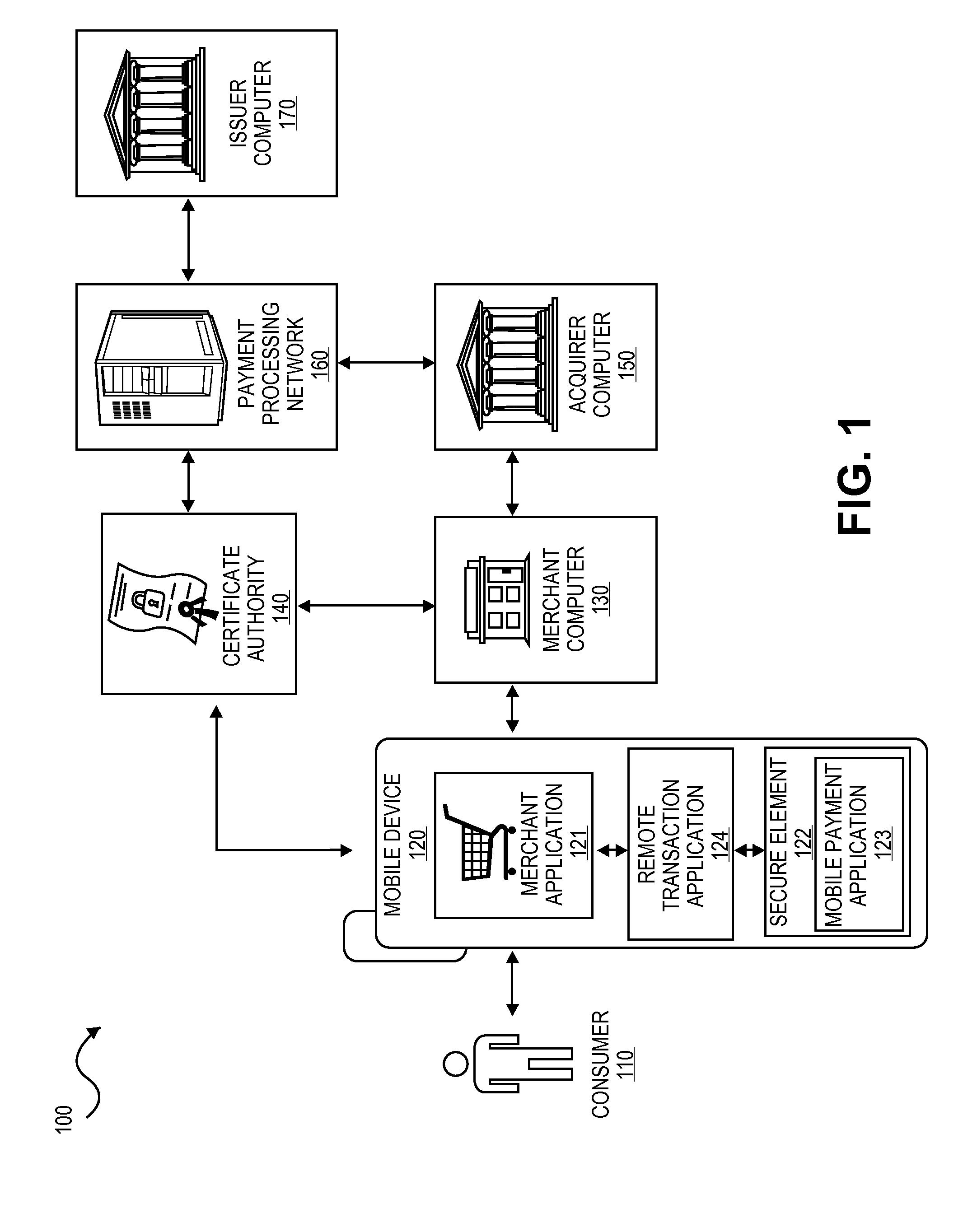
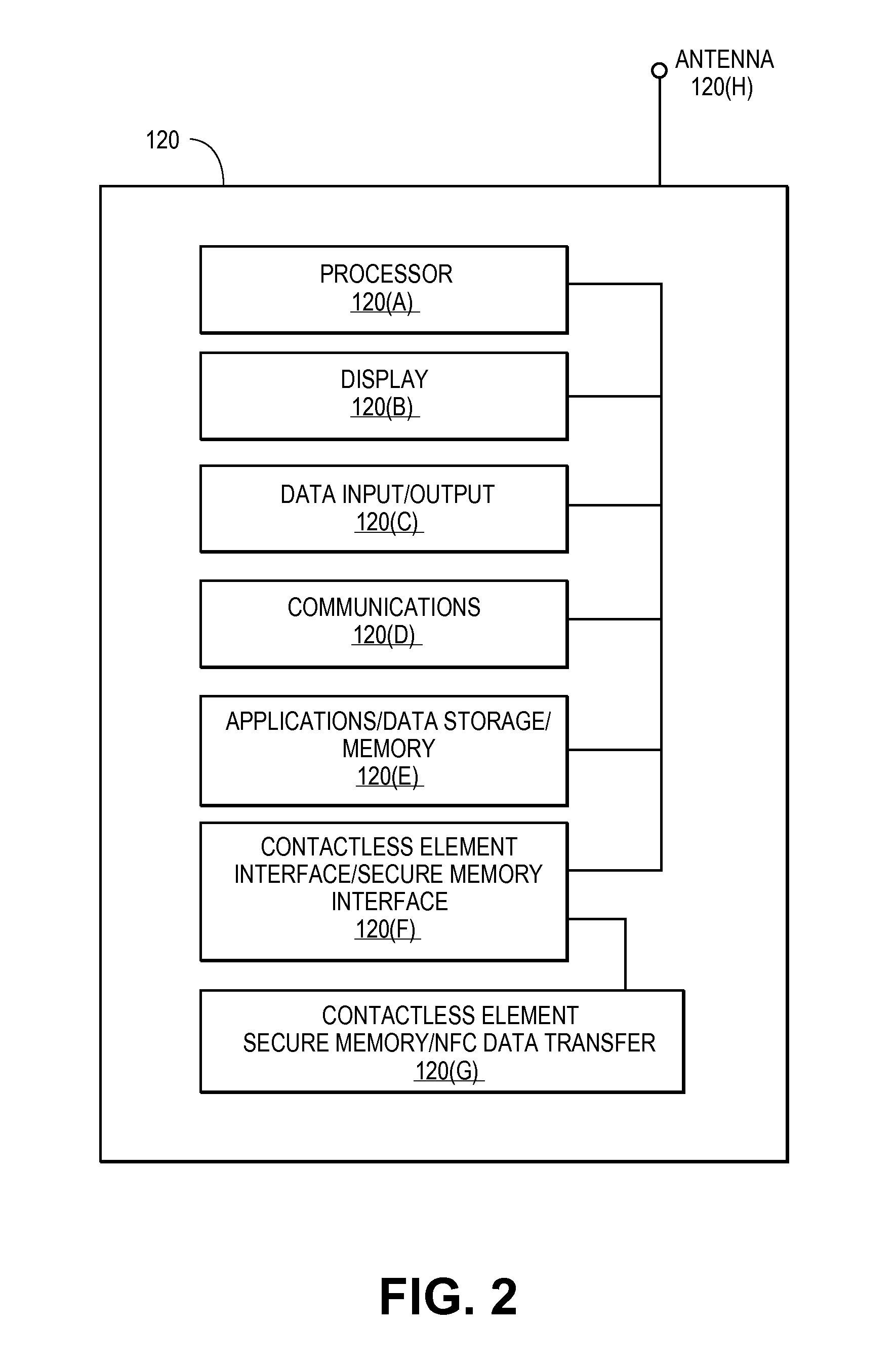
ActiveUS20150052064A1Improve security levelImprove securityPayment protocolsSecuring communicationPayment transactionTransaction data
Embodiments of the present invention are directed to methods, apparatuses, computer readable media and systems for securely processing remote transactions. One embodiment of the invention is directed to a method of processing a remote transaction initiated by a mobile device. The method comprises receiving, by a mobile payment application on a secure memory of the mobile device, transaction data from a transaction processor application on the mobile device. The method further comprises validating that the transaction processor application is authentic and in response to validating the transaction processor application, providing encrypted payment credentials to the transaction processor application. The transaction processor application further initiates a payment transaction with a transaction processor server computer using the encrypted payment credentials.
Owner:VISA INT SERVICE ASSOC
System and Method for Block-Chain Verification of Goods
A method for block-chain verification of goods includes obtaining, by a first computing device, a first address. The method includes exporting, by the first computing device, the first address to a first code affixed to a first product. The method includes filing, by the first computing device, a first crypto-currency transaction to the first address, at a transaction register. The method includes receiving, by a second computing device, from a code scanner, the first address, scanned from the first code affixed to the first product. The method includes verifying, by the second computing device, the first crypto-currency transaction at the transaction register, using the first address. The method includes identifying, by the second computing device, based on the verification, that the first product is authentic.
Owner:THE FILING CABINET
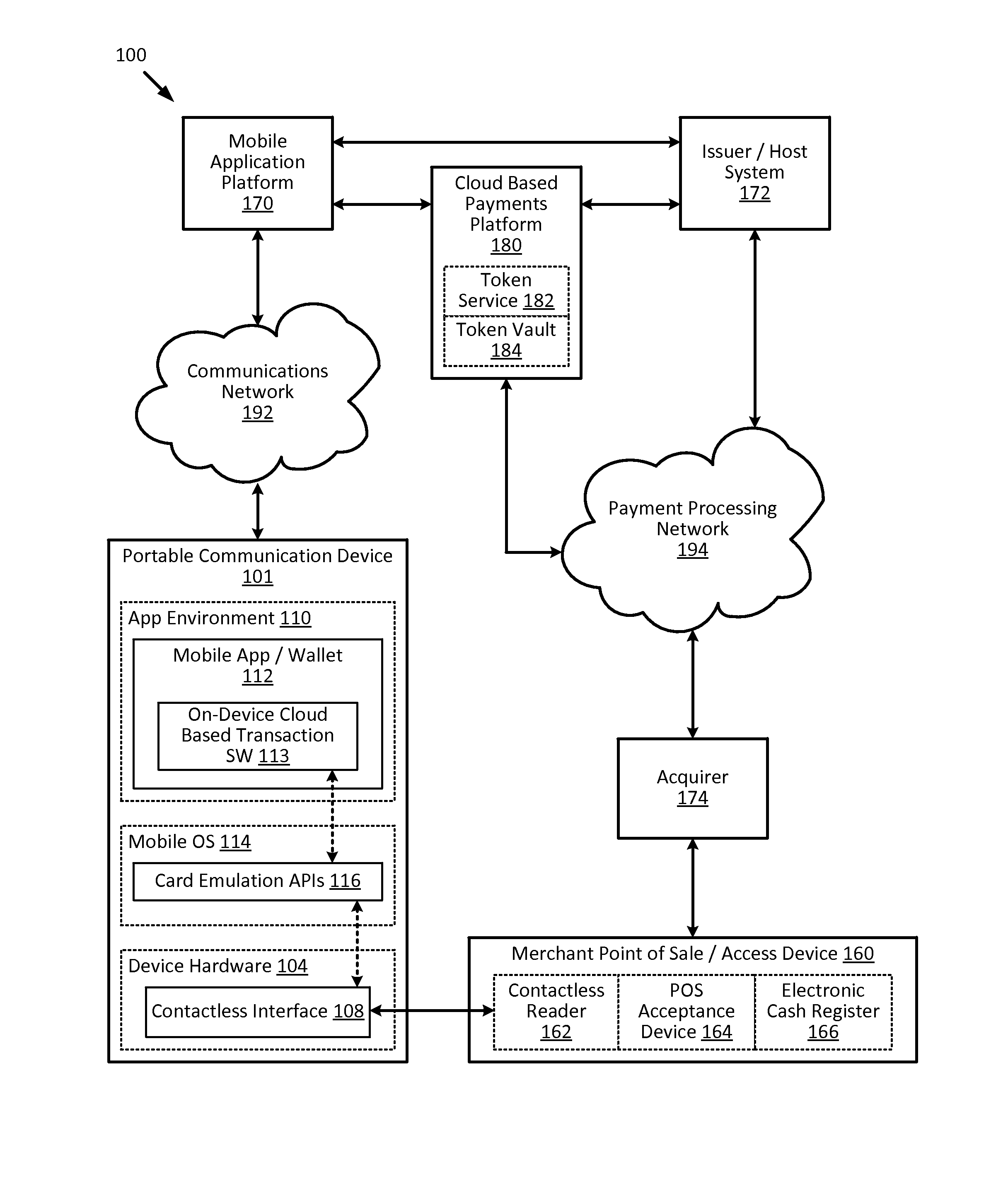
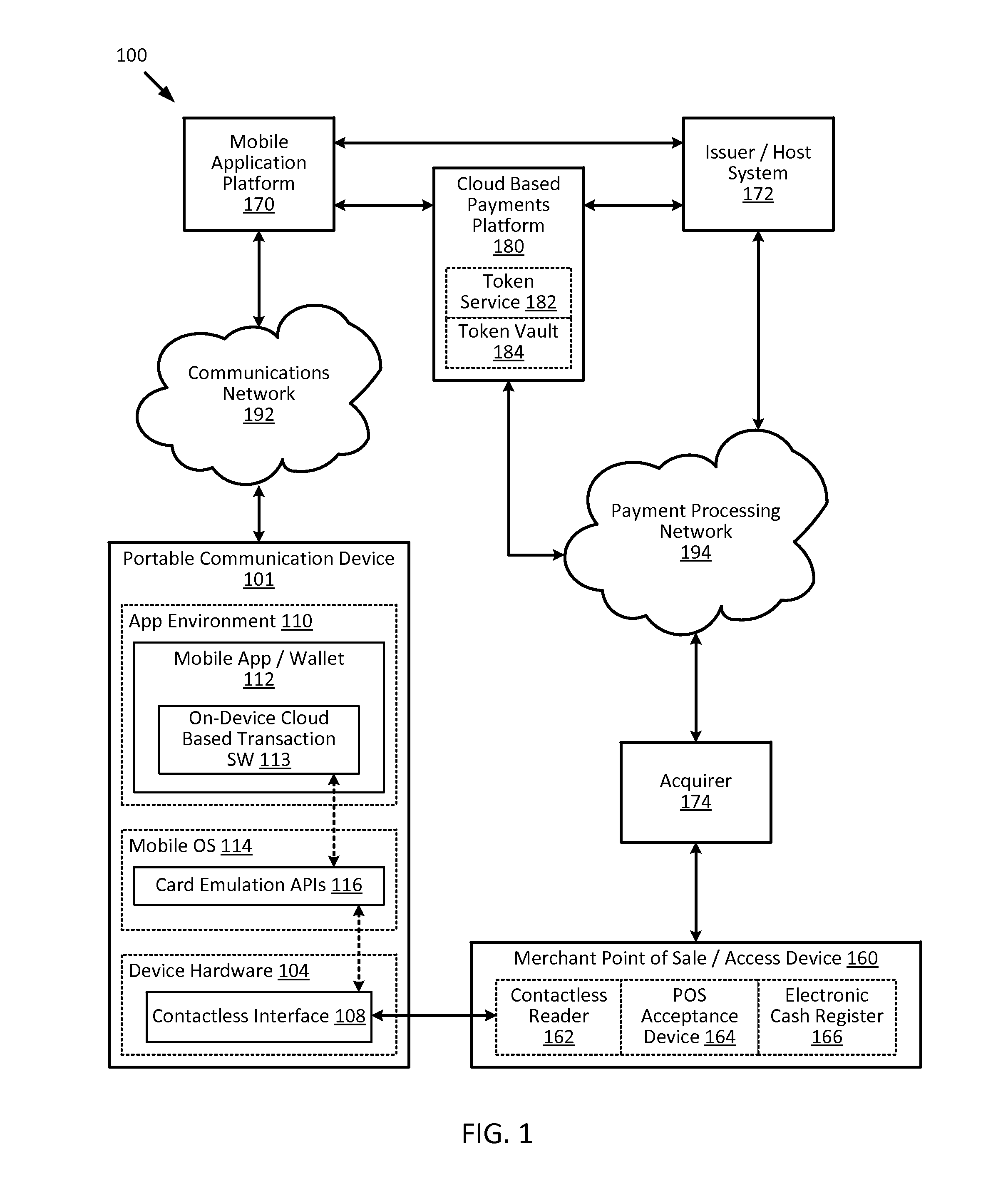
Cloud-based transactions methods and systems
ActiveUS20150180836A1Promote generationImprove securityKey distribution for secure communicationMultiple keys/algorithms usageCryptogramDatabase
Techniques for enhancing the security of a communication device when conducting a transaction using the communication device may include using a limited-use key (LUK) to generate a transaction cryptogram, and sending a token instead of a real account identifier and the transaction cryptogram to an access device to conduct the transaction. The LUK may be associated with a set of one or more limited-use thresholds that limits usage of the LUK, and the transaction can be authorized based on at least whether usage of the LUK has exceeded the set of one or more limited-use thresholds.
Owner:VISA INT SERVICE ASSOC
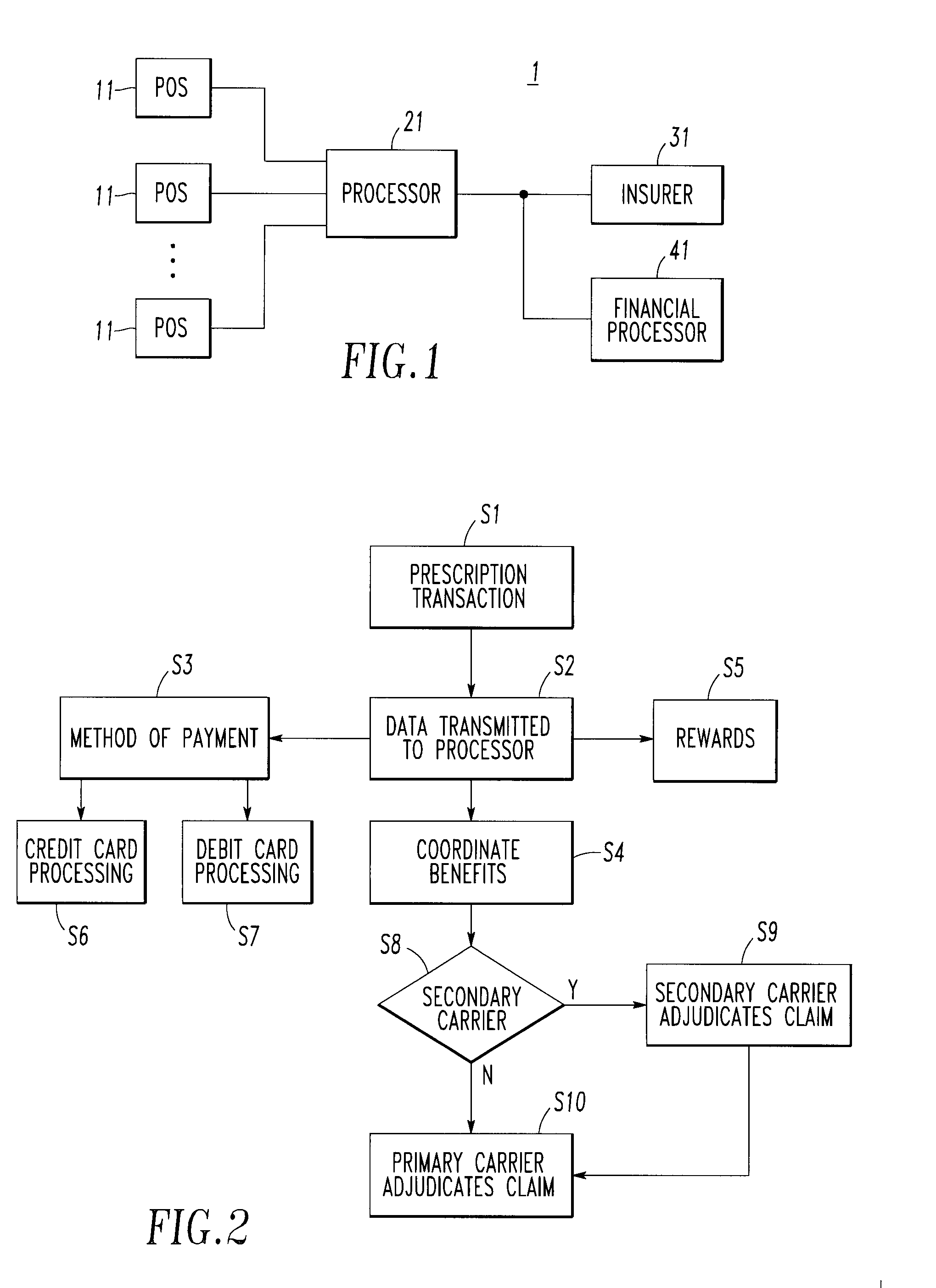
Integrated pharmaceutical accounts management system and method
InactiveUS20020002495A1Facilitate real-time adjudicationEasy to processHand manipulated computer devicesDrug and medicationsData warehouseDrug interaction
<heading lvl="0">Abstract of Disclosure< / heading> An integrated suite of services for consumers, service providers and manufacturers in the pharmaceutical industry is disclosed. The present invention utilizes one or more of the NCPDP standard formats and adopts the switch for an integrated system of, for example, instant adjudication of prescriptions, consumer data warehousing and / or incentive rewards for the consumer. A participating consumer with one card, can instantly purchase pharmaceuticals and charge the transaction to a credit card and earn and apply savings dollars redeemable for pharmaceutical purchases. For a participating service provider, instant adjudication and instant validation of consumer eligibility can be performed. Moreover, a service provider may receive messages related to the patient's medications. Significantly, data is recorded for consumers even when consumers make the pharmaceutical purchase with cash. The system includes a unique card issued to participating consumers. The card is adapted to encode conventional credit or debit card information specific to the participating consumer so that the consumer can consummate a transaction for the purchase of pharmaceuticals without possession of an additional credit card. The system further includes a host processor coupled to the point of sale at the service provider through a leased line or public switch network or the like. When a customer performs a pharmaceutical transaction at the point of sale of the service provider, the host processor coordinates any benefits and data with other prescription benefit management systems through messages transmitted and received from any primary or secondary carrier systems. The host processor further is adapted to facilitate real-time adjudication of claims and checks for any dangerous drug-to-drug interactions. The host processor additionally facilitates any financial processing including the accumulation and redemption of any bonus dollars earned by the consumer. Furthermore, since the card used by the consumer can be encoded with credit or debit card information, the host processor determines the desired payment method and performs the actual financial transaction. Even if the transaction at the point of sale is a cash purchase, the consumer may desire to use his unique card for the accrual of bonus dollars. Therefore, data concerning the transaction (i.e., pharmacy number, prescription number, etc.) can be recorded even for transactions conducted with cash.
Owner:NPAX
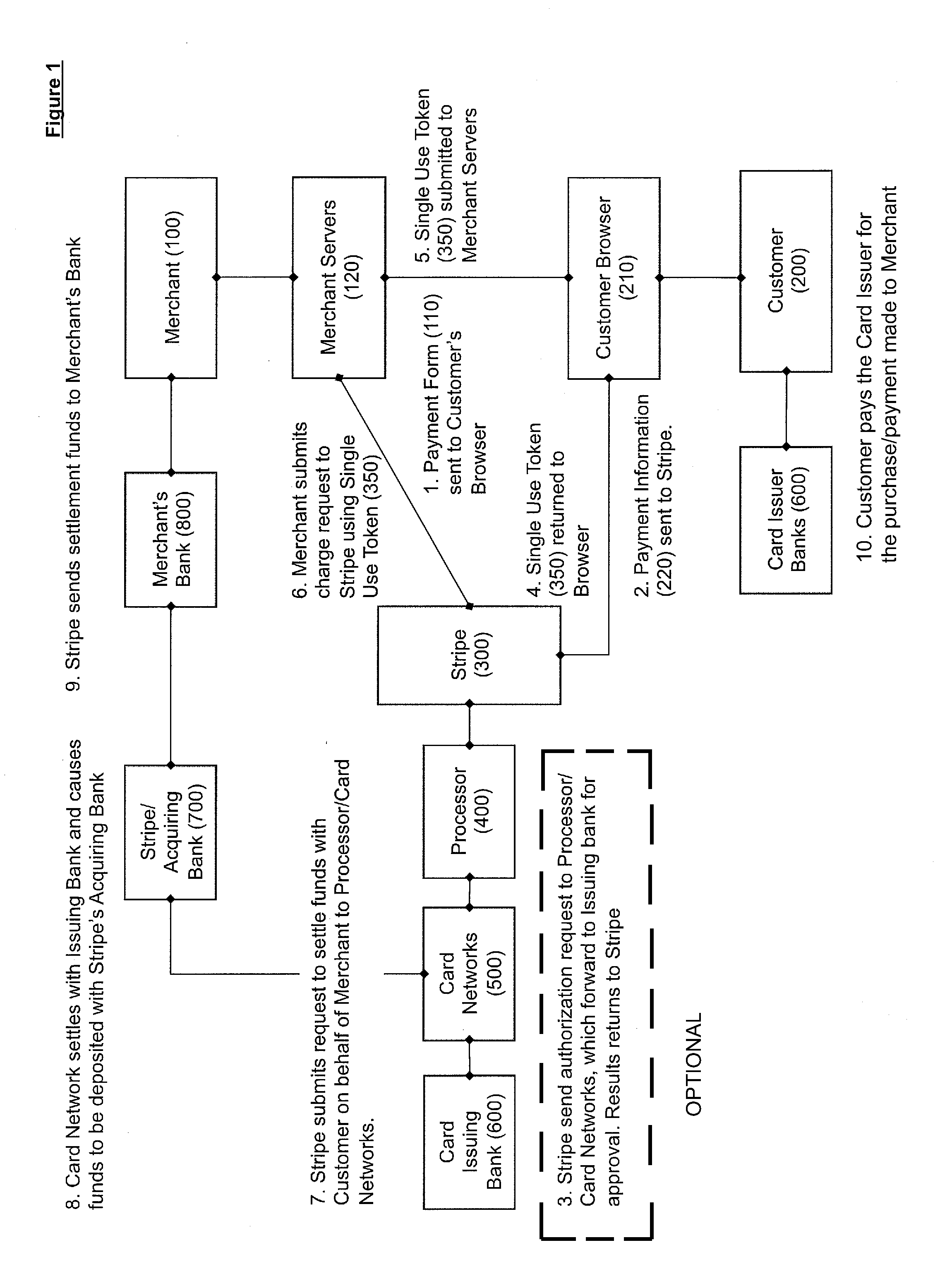
Method for conducting a transaction between a merchant site and a customer's electronic device without exposing payment information to a server-side application of the merchant site
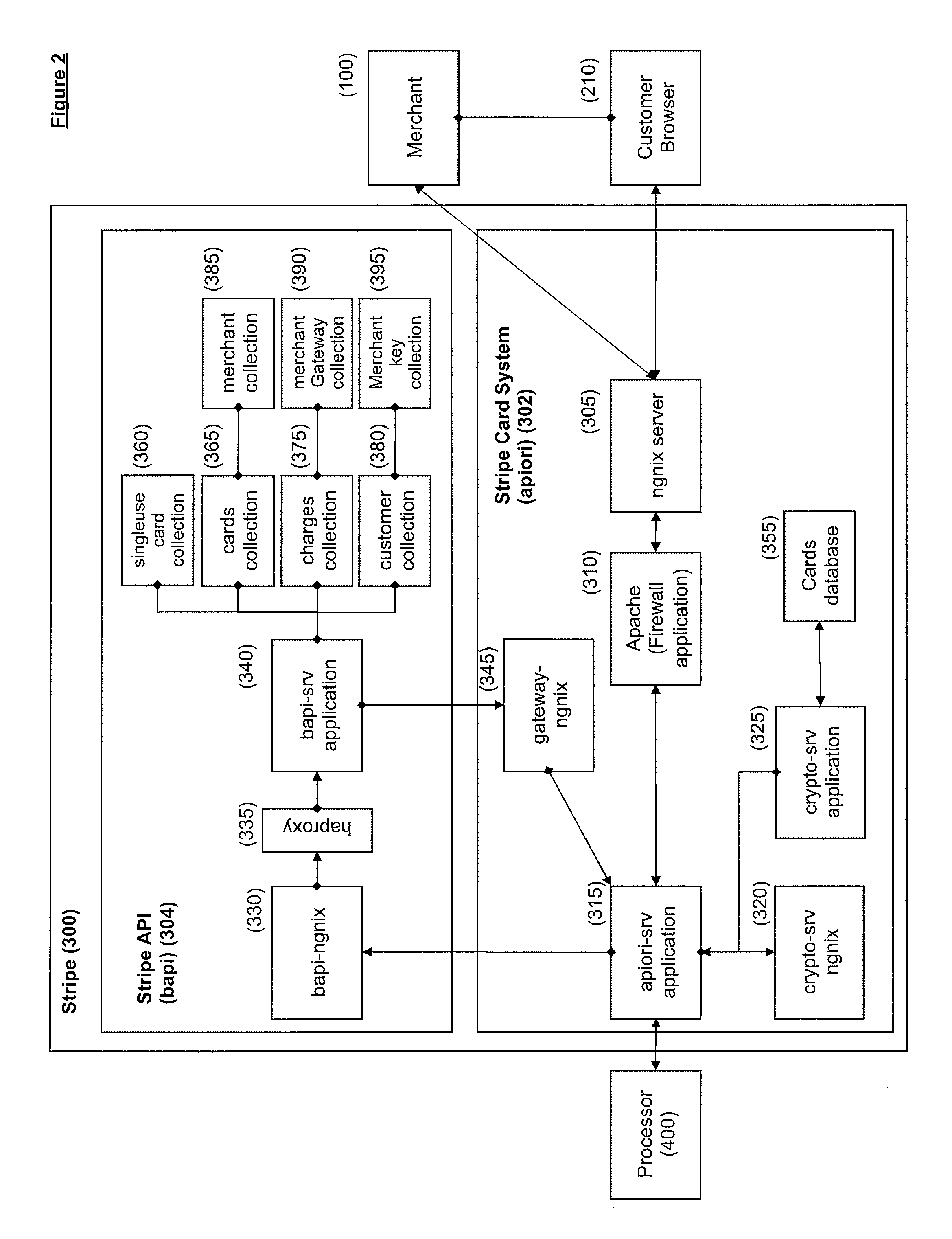
A transaction is conducted between a merchant site and a customer's electronic device using a payment processor. The merchant site is associated with a client-side application and a server-side application. The client-side application executes on the customer's electronic device. The client-side application electronically sends payment information retrieved from the customer's electronic device to the payment processor. The client-side application does not send the payment information to the server-side application. The payment processor creates a token from the payment information sent by the client-side application. The token functions as a proxy for the payment information. The payment processor electronically sends the token to the client-side application. The client-side application electronically sends the token to the server-side application for use by the server-side application in conducting the transaction. The payment information can thus be used by the server-side application via the token without the server-side application being exposed to the payment information.
Owner:STRIPE INC
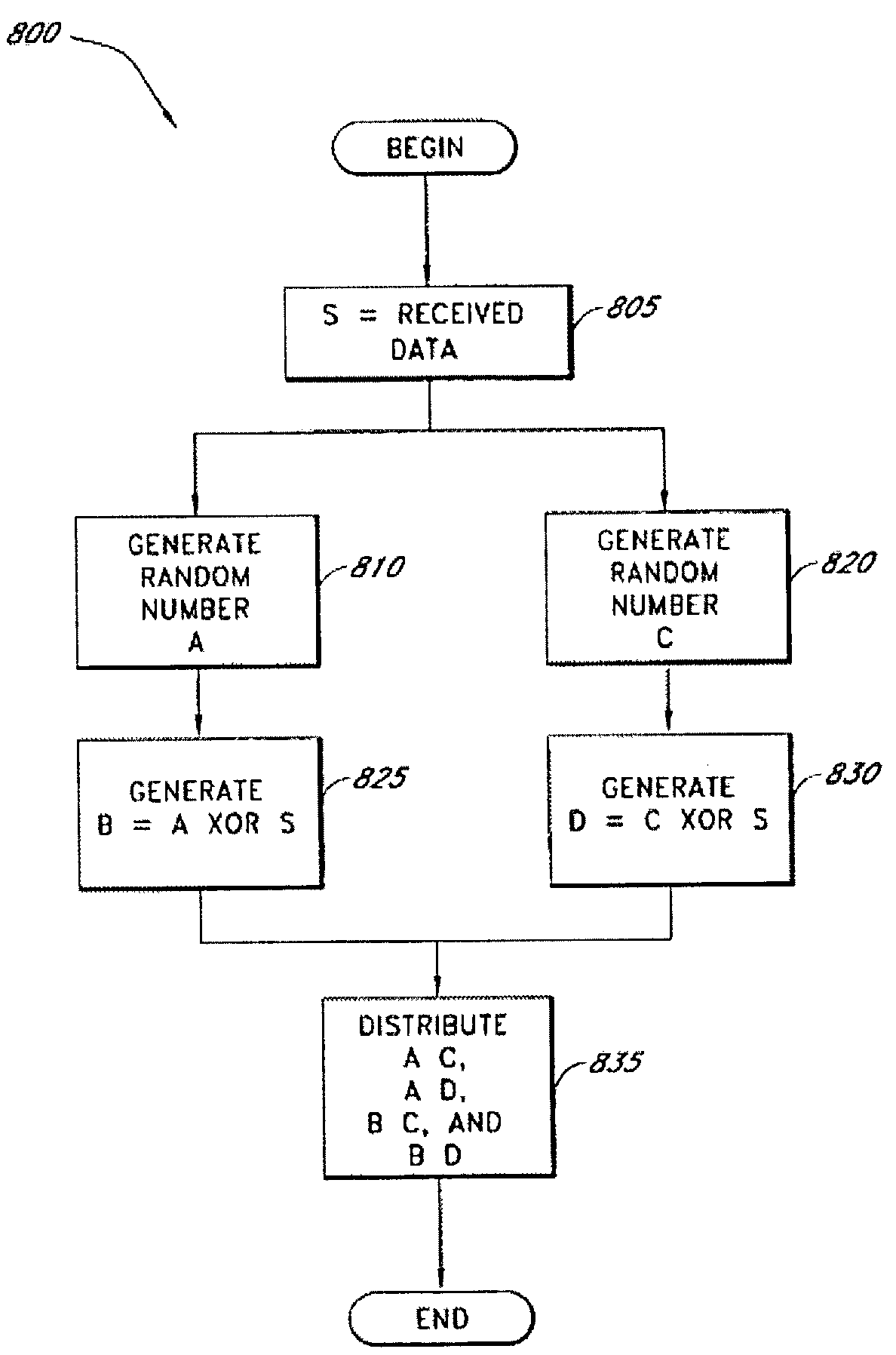
Secure data parser method and system
InactiveUS7391865B2Minimal compute resourceAvoid the needDigital data processing detailsUser identity/authority verificationGovernmental agencyVariospora
The present invention provides a method and system for securing sensitive data from unauthorized access or use. The method and system of the present invention is useful in a wide variety of settings, including commercial settings generally available to the public which may be extremely large or small with respect to the number of users. The method and system of the present invention is also useful in a more private setting, such as with a corporation or governmental agency, as well as between corporation, governmental agencies or any other entity.
Owner:SECURITY FIRST INNOVATIONS LLC
Token verification using limited use certificates
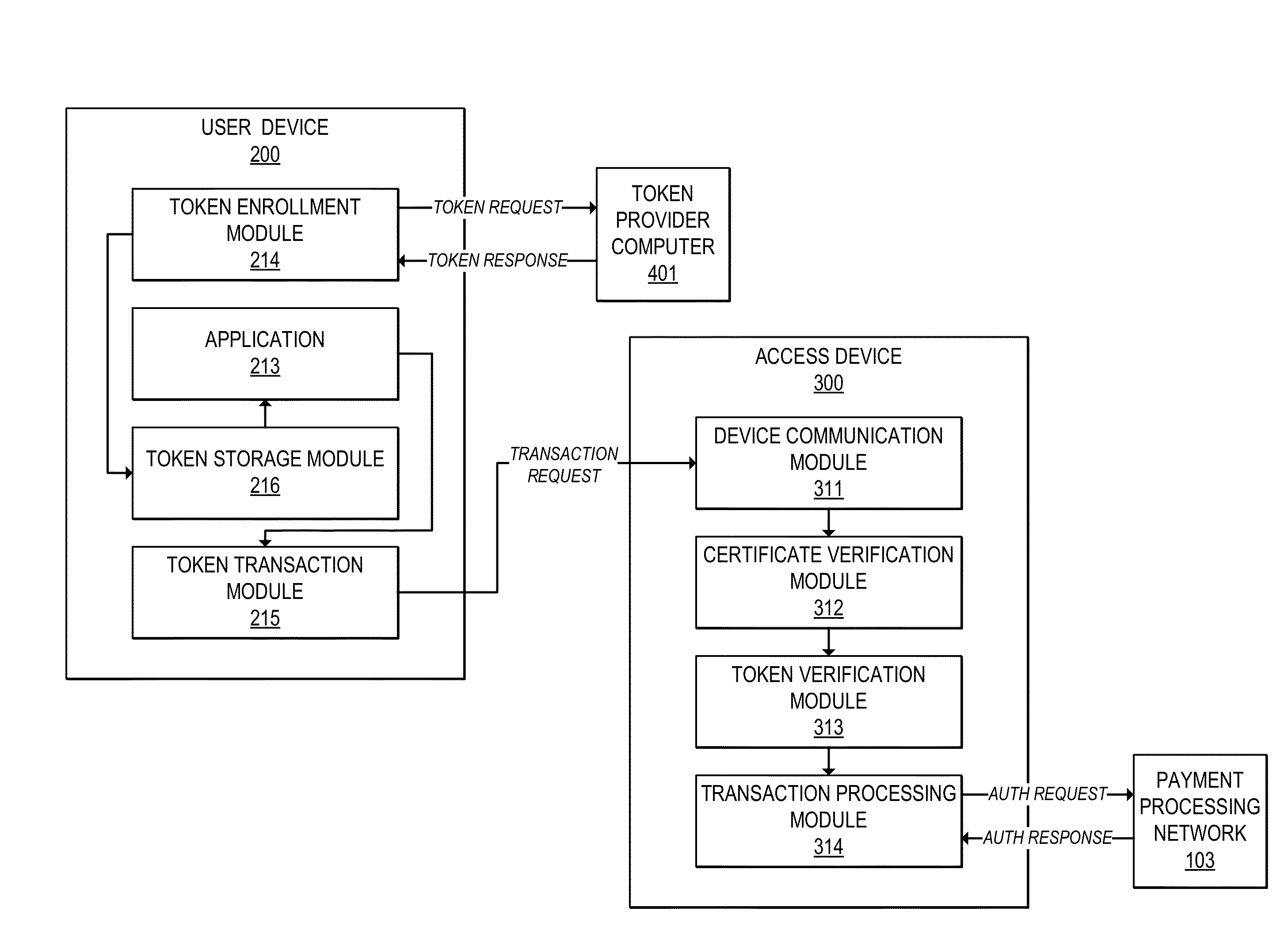
InactiveUS20150220917A1User identity/authority verificationPayment protocolsUser deviceDigital signature
Methods, devices, and systems are provided for verifying tokens using limited-use certificates. For example, a user device can send a token request to a token provider computer, and receive in response a token and a token certificate associated with the token. The token certificate may include, for example, a hash of the token and a digital signature by the token provider computer or another trusted entity. The user device can provide the token and the token certificate to an access device. The access device can verify the token using the token certificate, and verify the token certificate using a digital signature. In some cases, the token and token certificate may be verified offline. The access device can then conduct a transaction using the token.
Owner:VISA INT SERVICE ASSOC
Data providing system, device, and method
InactiveUS7073073B1Reduce loadKey distribution for secure communicationDigital data processing detailsData storingData store
Owner:SONY CORP
Mobile transactions using authorized tokens
InactiveUS20140025581A1Disadvantages can be reduced eliminatedTransactions be reduced eliminatedPayment protocolsComputer securityMobile station
Conducting mobile transactions comprises determining, using a processor, whether a network is available to facilitate a mobile transaction. An interface, communicatively coupled to the processor, receives an encrypted token from a mobile device without using the network if the network is not available. The processor is further operable to process the encrypted token to complete the mobile transaction.
Owner:BANK OF AMERICA CORP
Method and system for storage and retrieval of blockchain blocks using galois fields
A method and system for storage and retrieval of blockchains with Galois Fields. One or more blocks for a blockchain are securely stored and retrieved with a modified Galois Fields on a cloud or peer-to-peer (P2P) communications network. The modified Galois Field provides at least additional layers for security and privacy for blockchains. The blocks and blockchains are securely stored and retrieved for cryptocurrency transactions including, but not limited to, BITCOIN transactions and other cryptocurrency transactions.
Owner:LESAVICH STEPHEN +1
Methods for providing cardless payment
ActiveUS7099850B1Convenient and easy to rememberConvenient and/orPublic key for secure communicationPayment protocolsComputer hardwareThe Internet
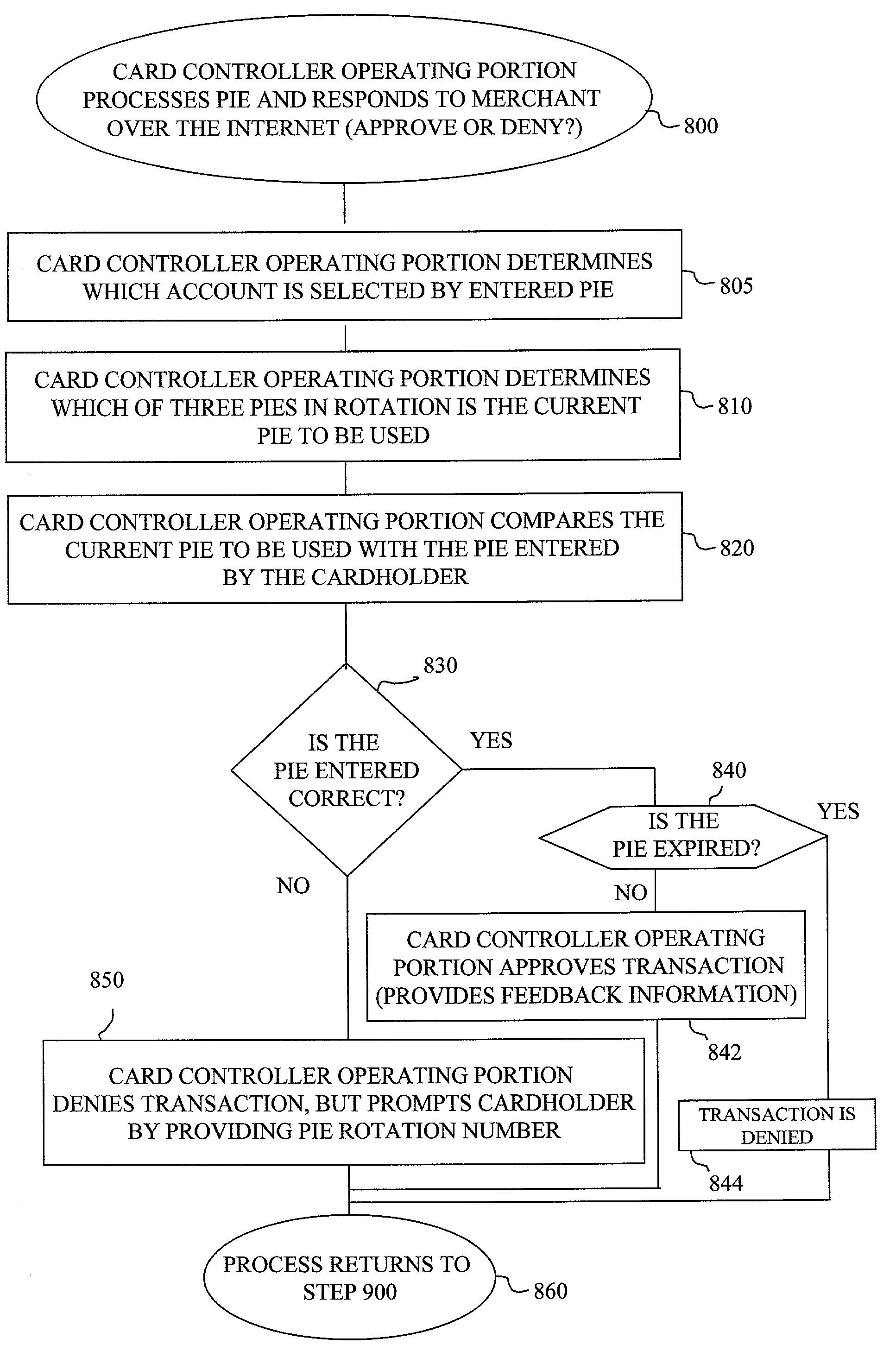
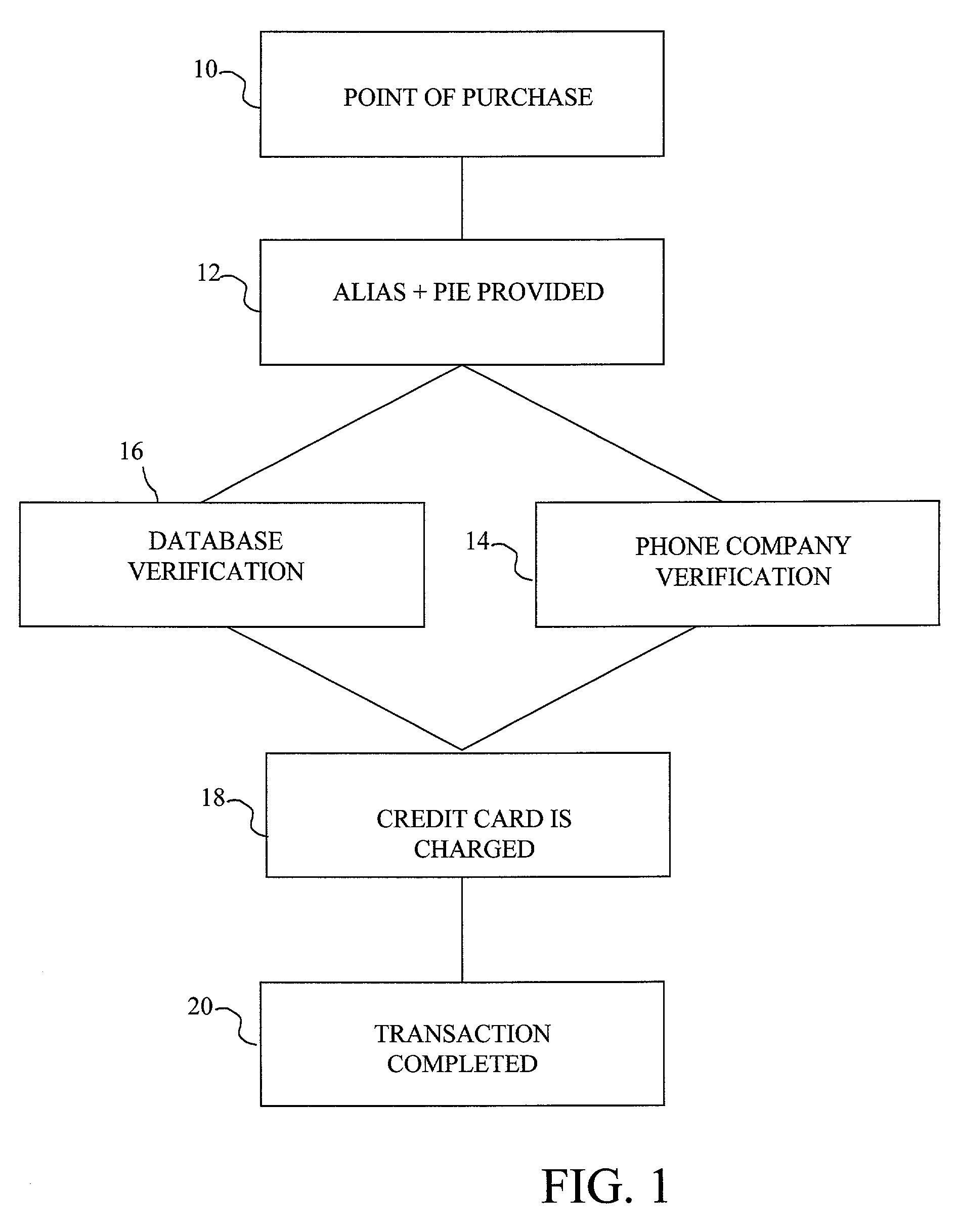
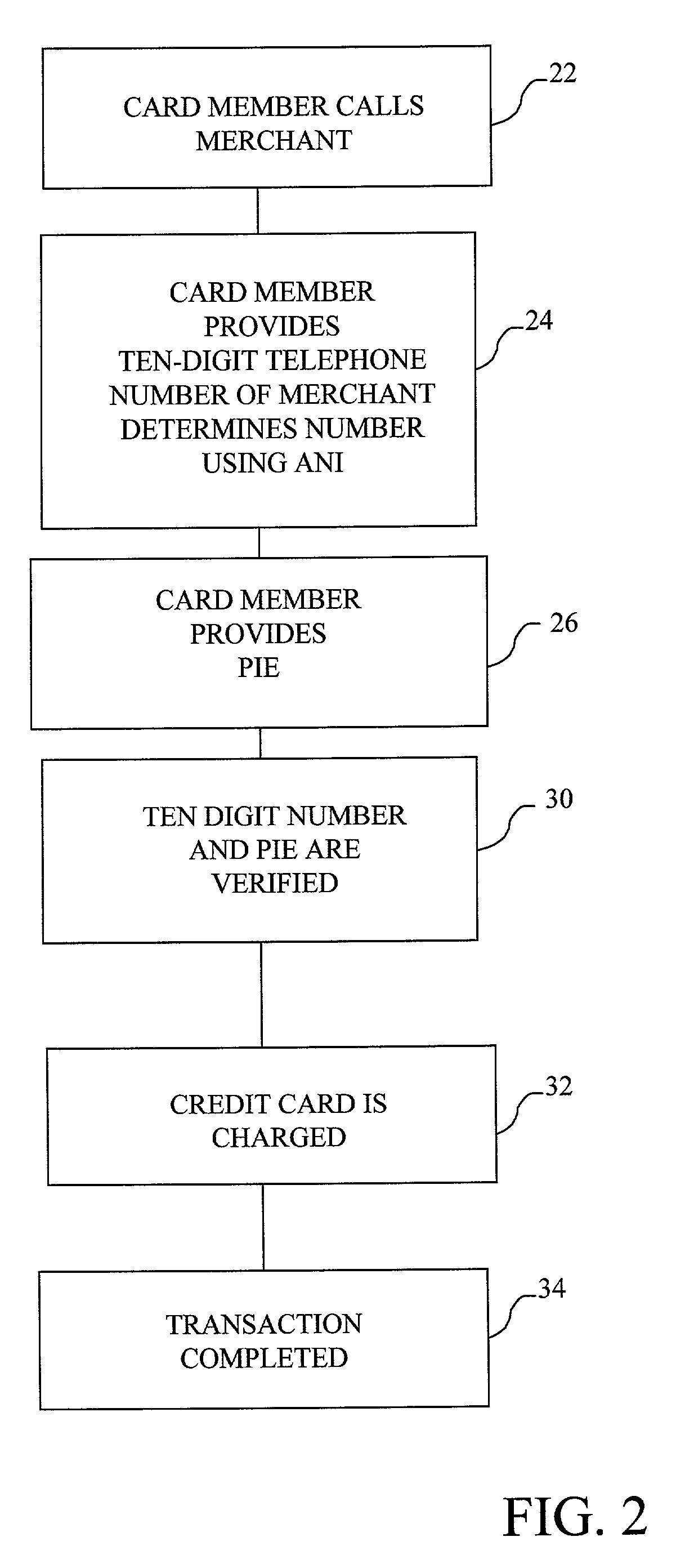
The method and system of the invention provide a variety of techniques for using a selected alias and a selected personal identification entry (PIE) in conjunction with use of a transaction card, such as a credit card, debit card or stored value card, for example. A suitable number or other identification parameter is selected by the account-holder as an alias. The account-holder is then required to choose a PIE for security purposes. The alias is linked to the account-holder's credit card number via a database. When the account-holder enters into a transaction with a merchant, the physical card need not be present. The account-holder simply provides his or her alias and then the PIE. This can be done at any point of sale such as a store, catalog telephone order, or over the Internet. The alias and PIE are entered and authorization is returned from the credit card company.
Owner:JPMORGAN CHASE BANK NA
Secure anonymous information exchange in a network
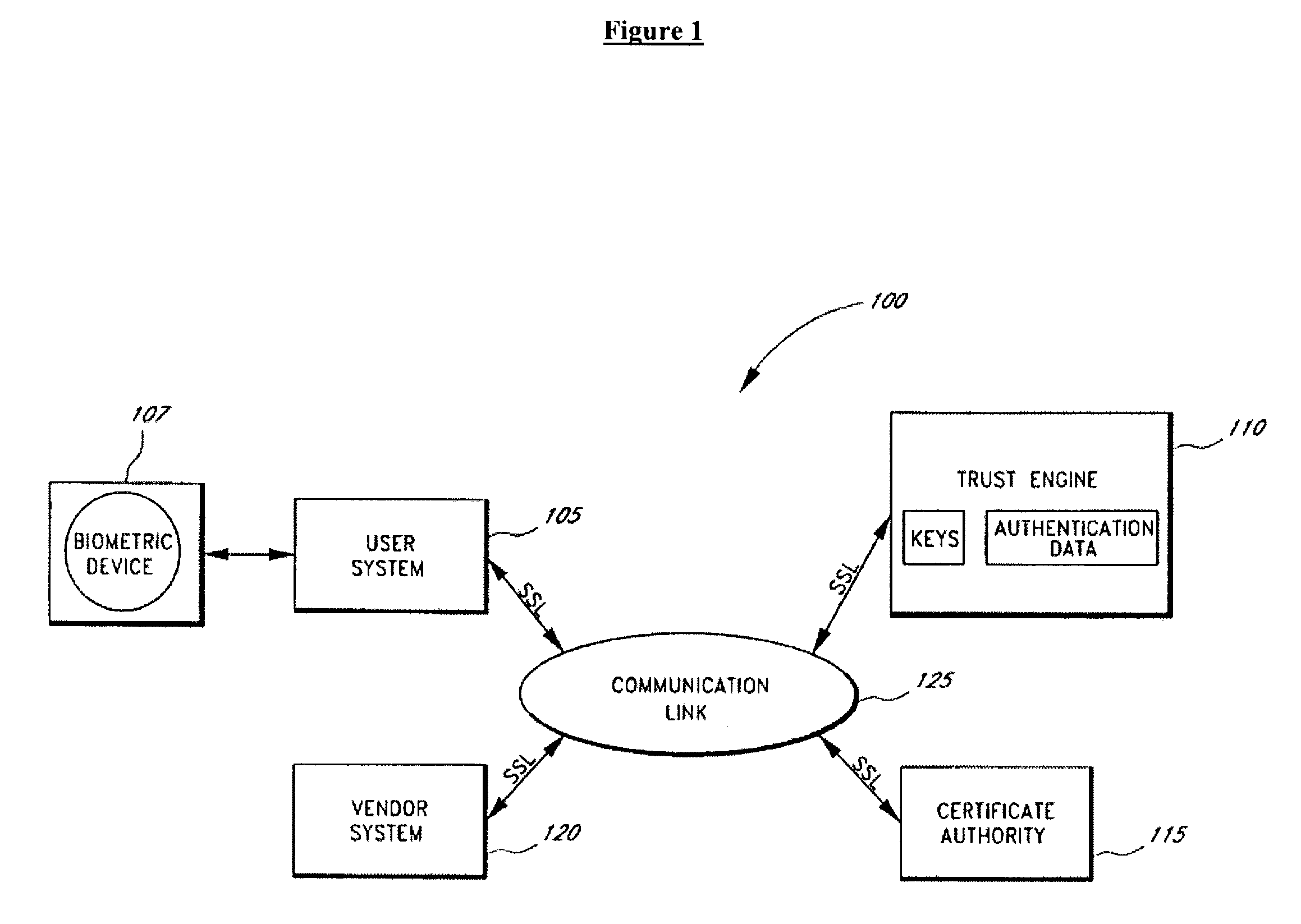
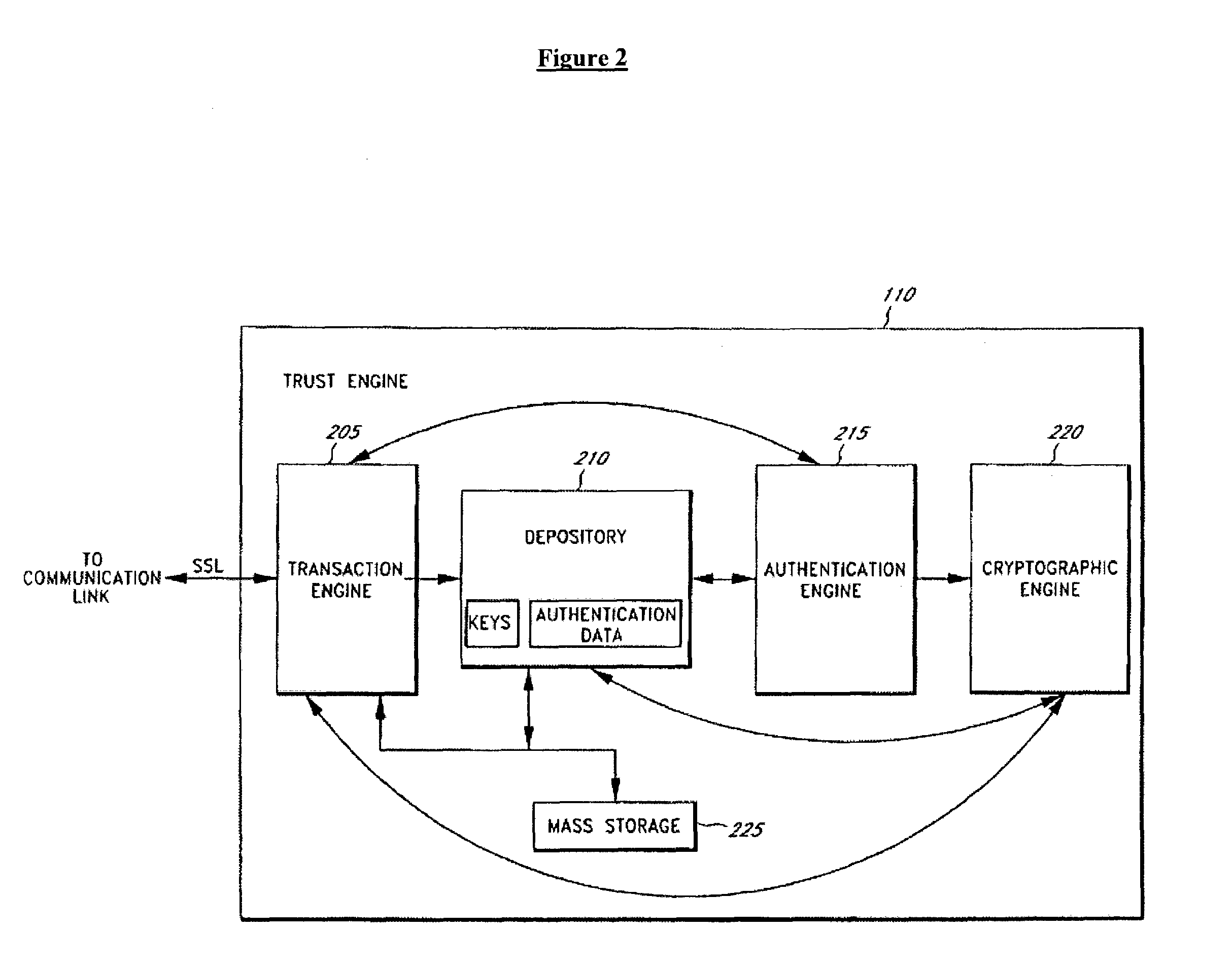
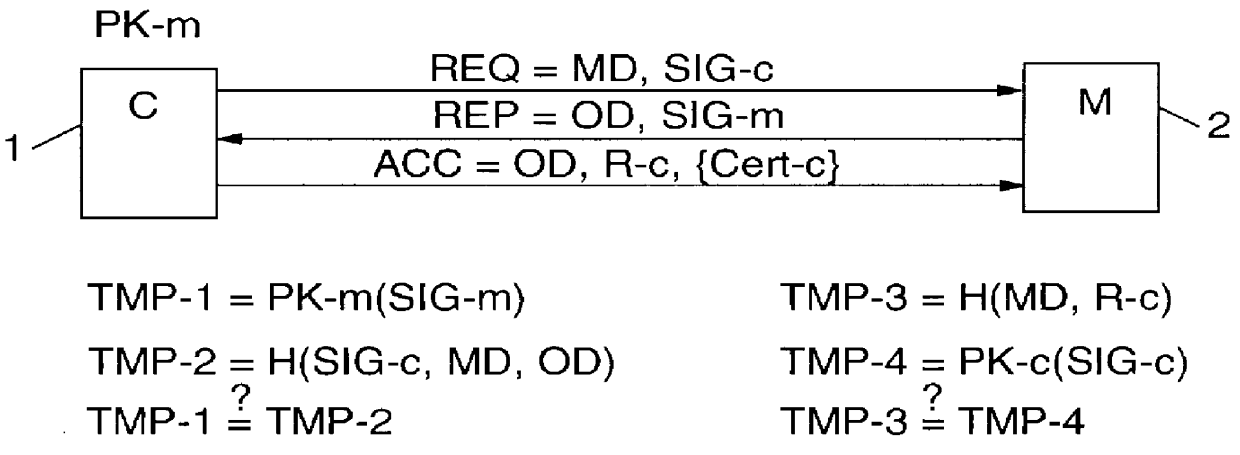
InactiveUS6061789AMinimize additional effort and expenditureUser identity/authority verificationDigital data protectionSystems designData set
PCT No. PCT / IB96 / 00025 Sec. 371 Date Jul. 2, 1998 Sec. 102(e) Date Jul. 2, 1998 PCT Filed Jan. 12, 1996 PCT Pub. No. WO97 / 25801 PCT Pub. Date Jul. 17, 1997Computer network management for electronic commerce requires technical implementations of business processes. The process addressed here is a technical method for a communication in which two or more parties legitimately want to communicate anonymously, often before discussing a deal or closing a business, e.g. for anonymous bidding or auctioning in electronic commerce. Essentially, the invention is a method, described by a protocol, for safely exchanging data in a network that provides a public key infrastructure and an anonymous communication possibility between network users. It consists of a sequence of steps in which both sender (e.g. customer) and addressee (e.g. merchant) compose data sets (i.e., requests and replies) that are based on received data and / or prior knowledge. The data sets are enciphered to provide anonymity, and digitally signed to provide proof of the partner. The invention is also a system designed to implement the invented method.
Owner:GOOGLE LLC
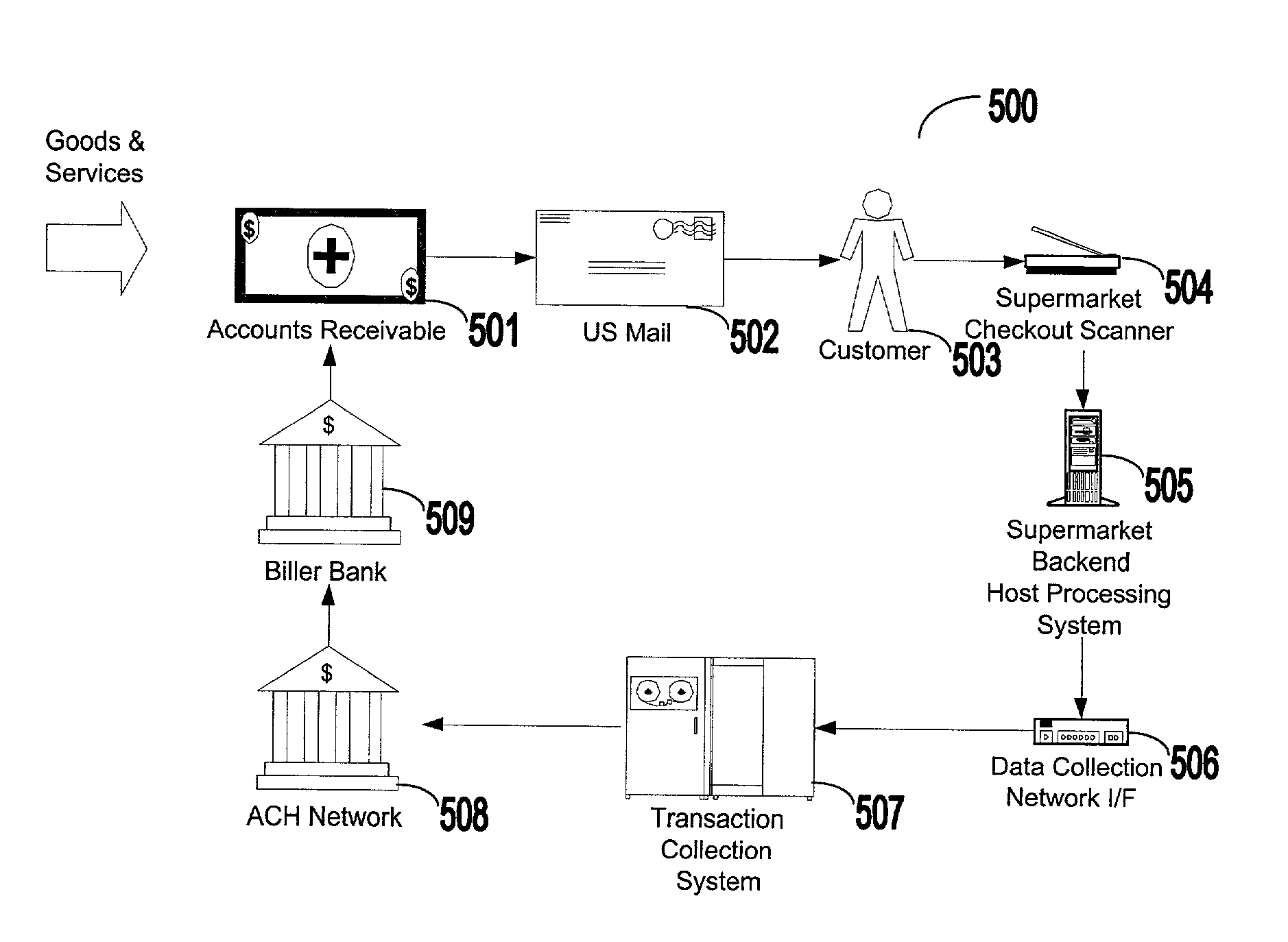
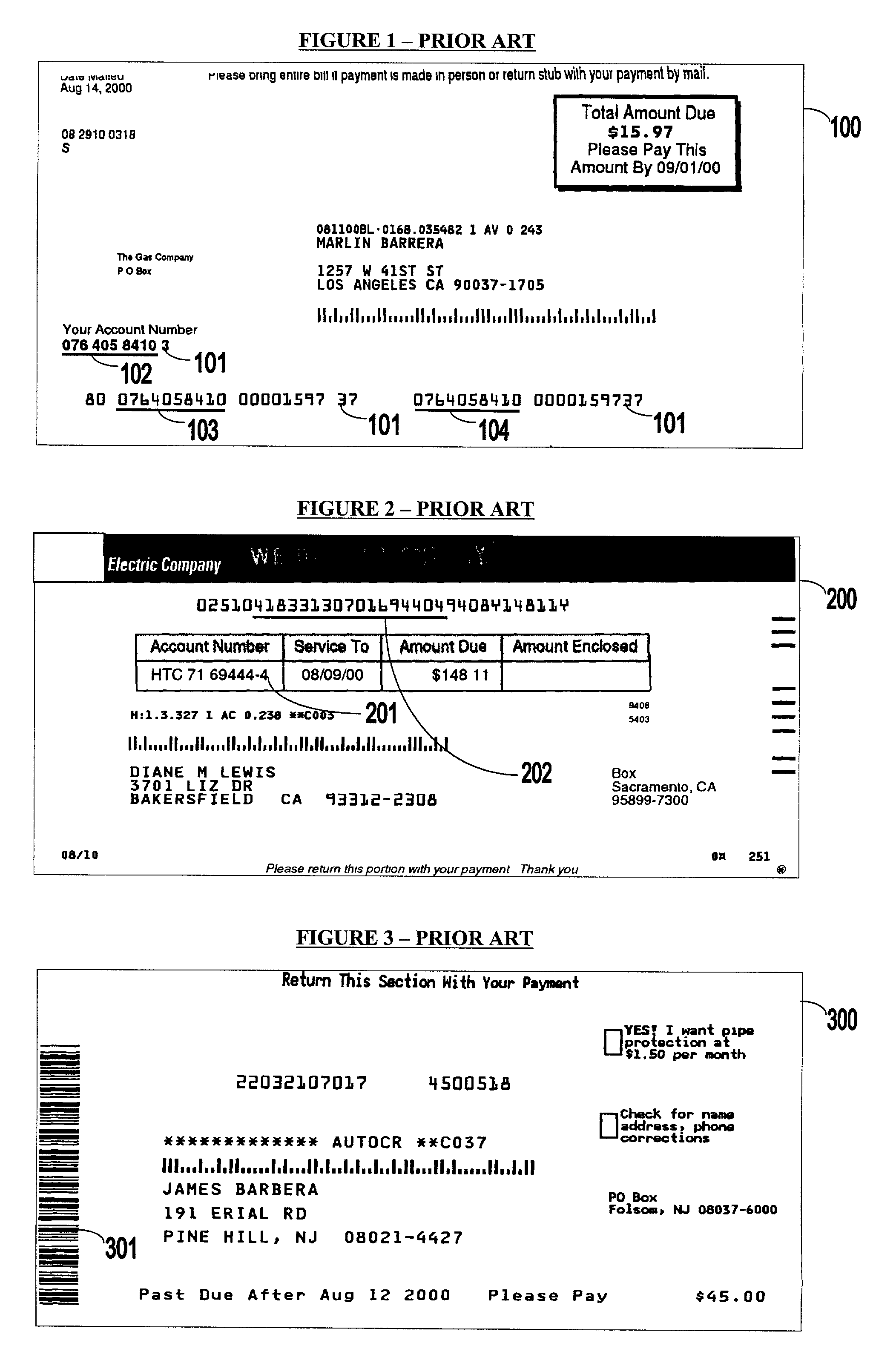
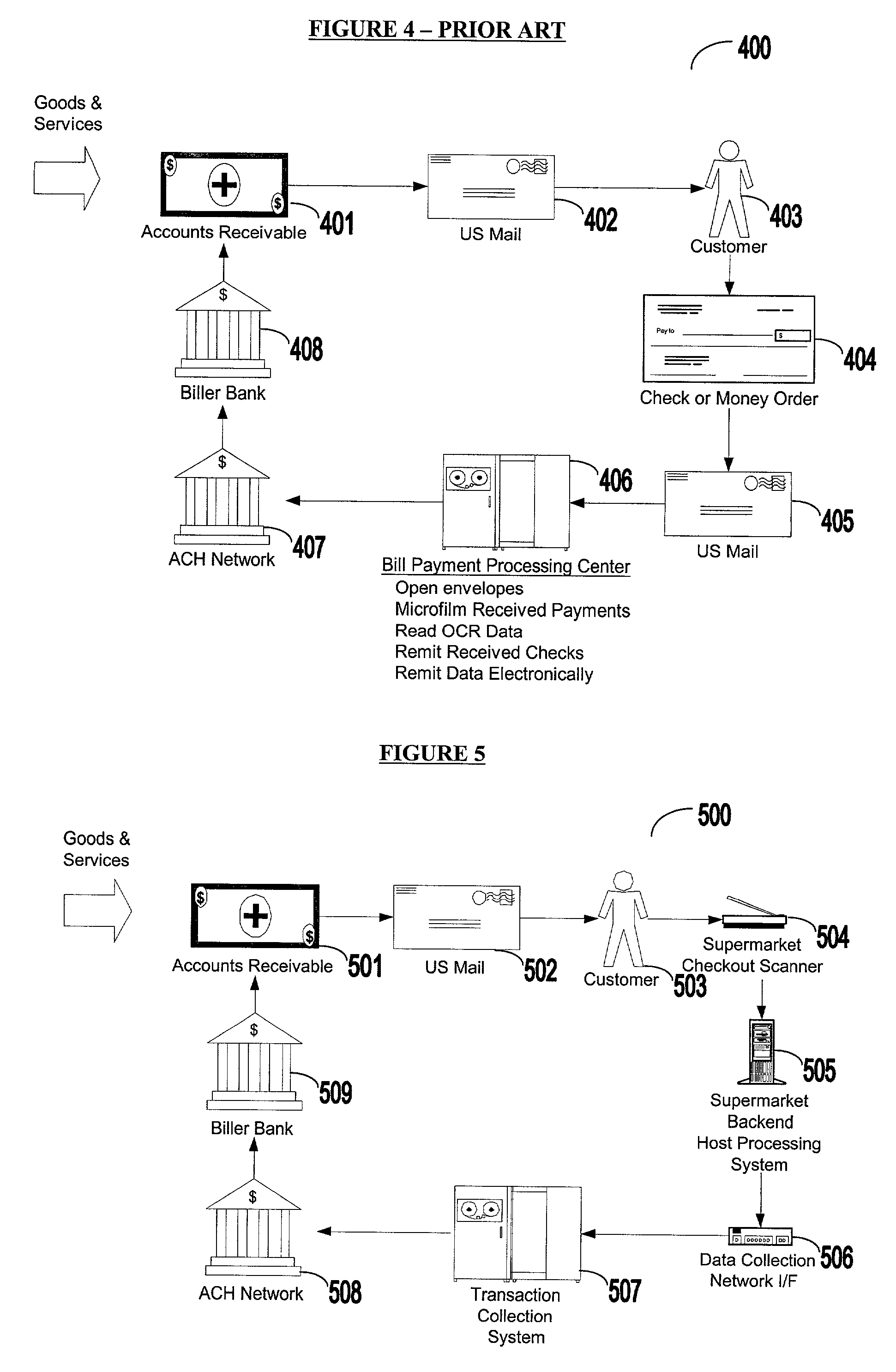
Bar coded bill payment system and method
InactiveUS6993507B2Cost-free profit marginPay their bills more efficientlyComplete banking machinesFinanceThird partyInvoice
Owner:PAYSCAN AMERICA
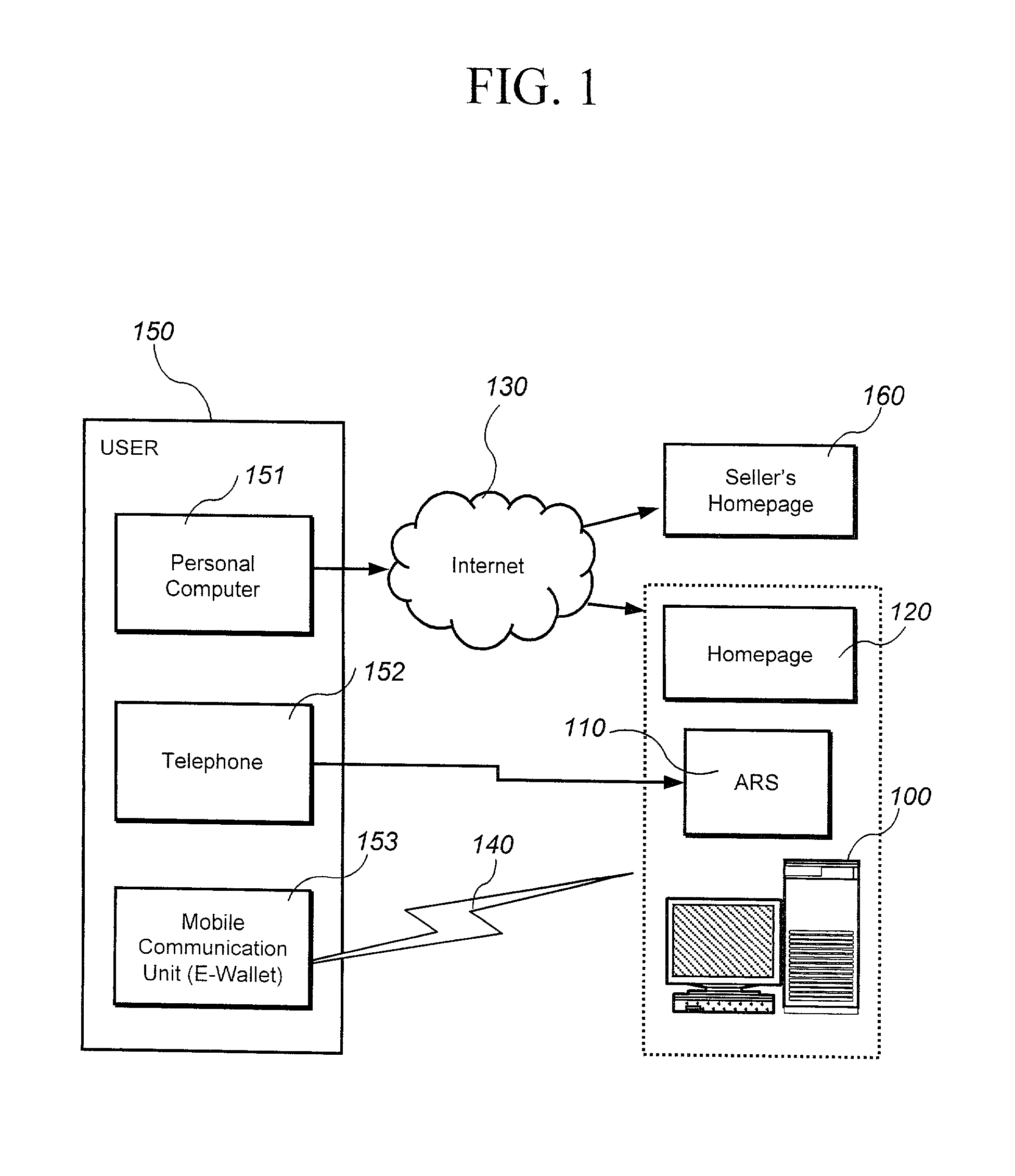
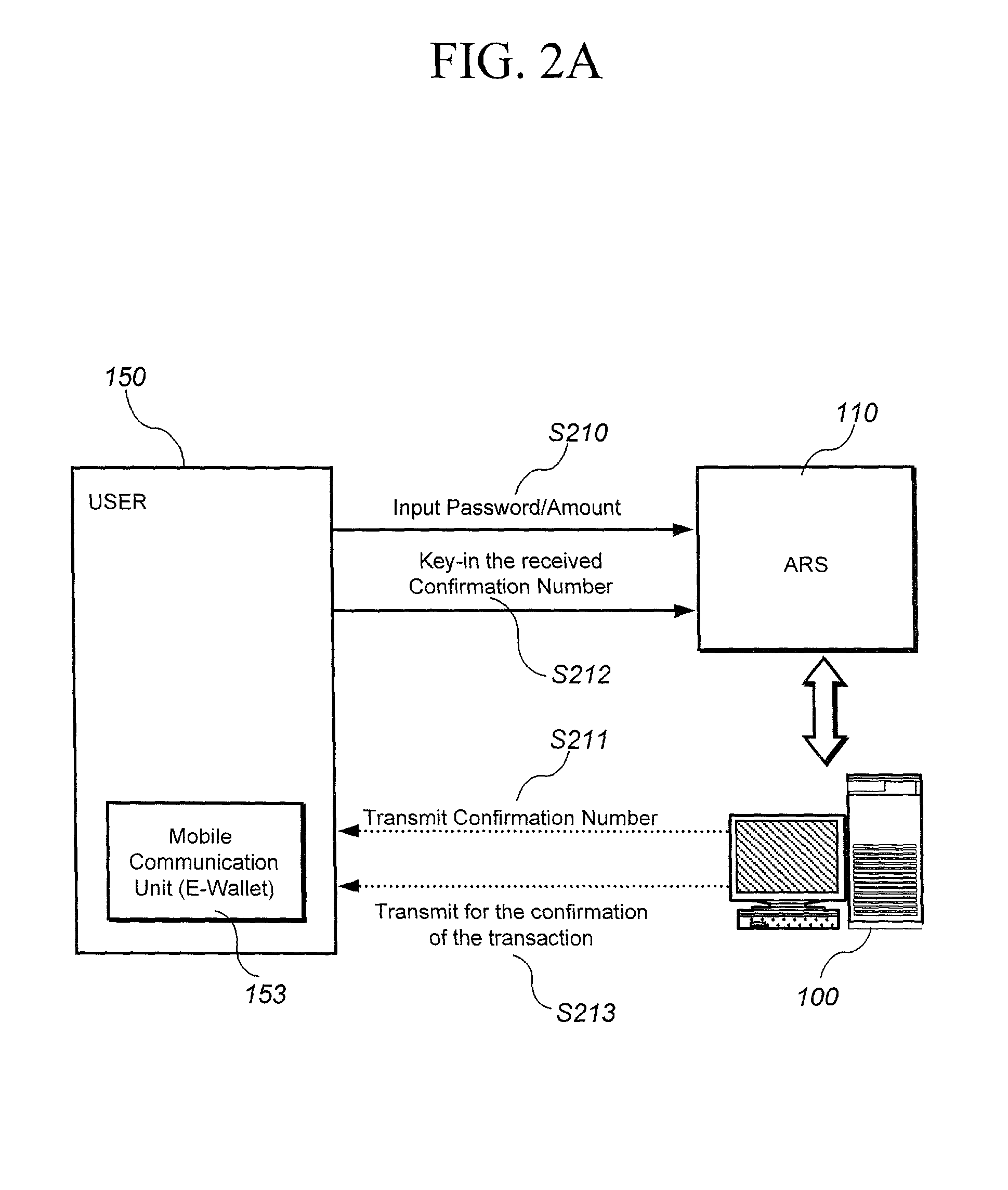
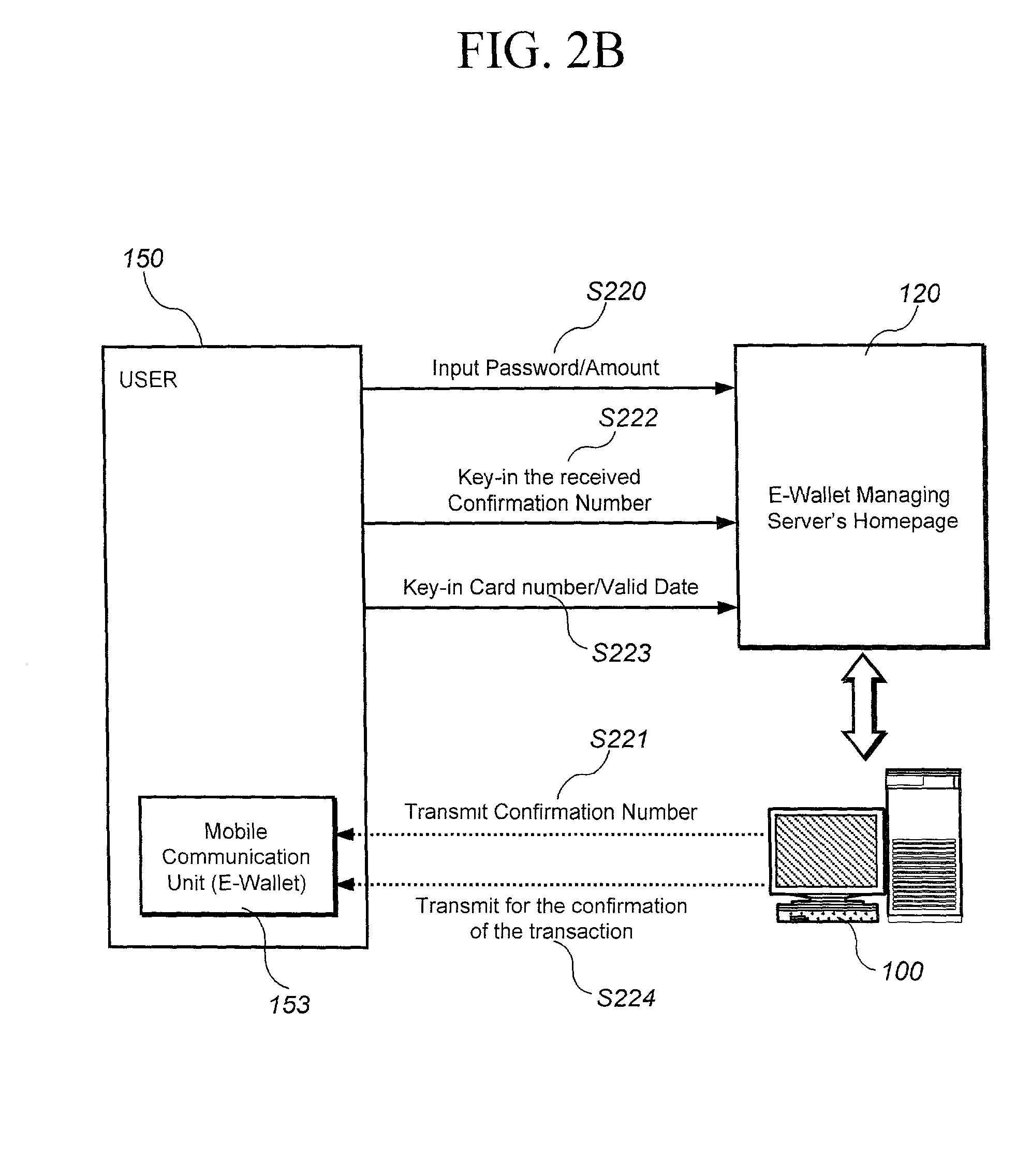
Method and system for transaction of electronic money with a mobile communication unit as an electronic wallet
InactiveUS20010007983A1Performed conveniently and safelyFinancePayment protocolsCommunication unitComputer science
A electronic monetary system comprising a mobile communication unit as an electronic wallet for transactions including electronic payments, money transfer, and recharging the electronic account. The security of the electronic transactions is confirmed by circulating a confirmation number through a loop formed by an E-wallet managing server through the wireless network to the mobile communication unit of the user.
Owner:INFOHUB
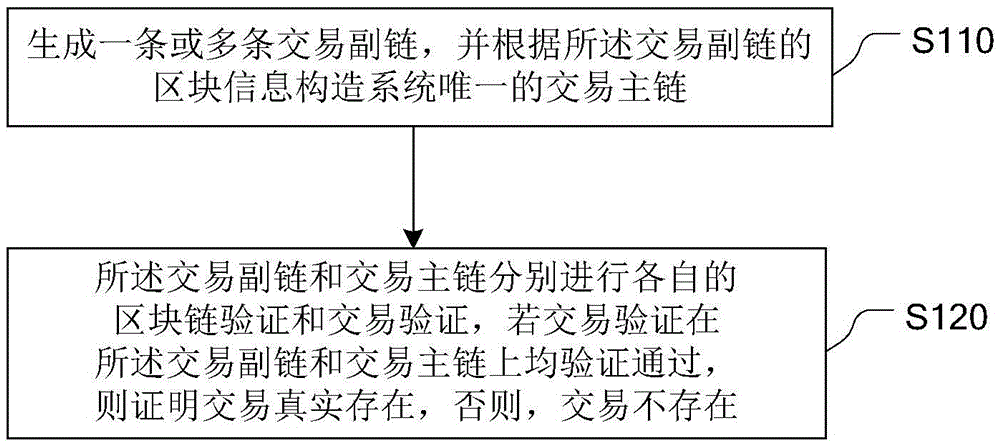
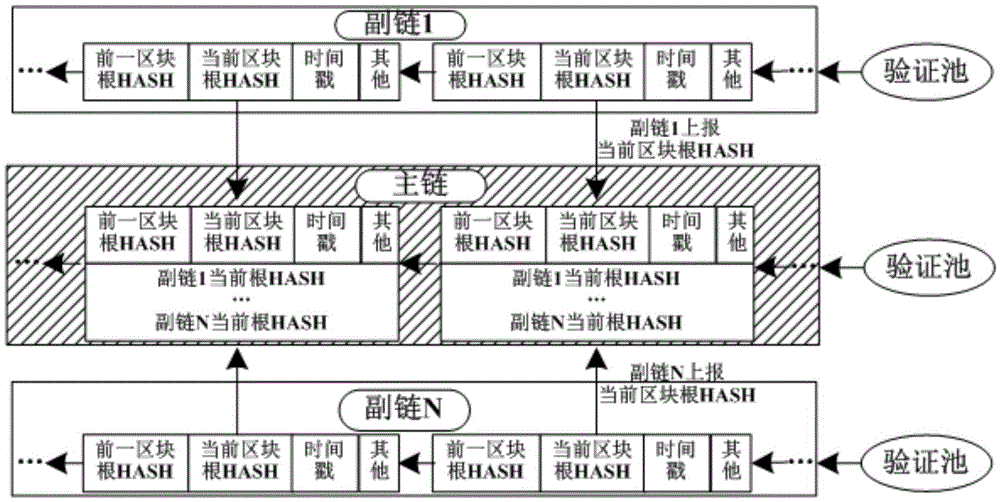
Distributed shared general ledger construction method of block chain
ActiveCN105488675AAvoid the risk of being destroyedFast updatePayment protocolsBuying/selling/leasing transactionsCredit noteThe Internet
The invention relates to the digital transaction in assets on the Internet, and provides a distributed shared general ledger construction method of a block chain. The method comprises the following steps: generating one or a plurality of transaction auxiliary chains, and constructing a unique transaction main chain of a system according to the block information of the transaction auxiliary chains; and causing the transaction auxiliary chains and the transaction main chain to independently carry out respective block chain verification and transaction verification, if the transaction verification is qualified on both the transaction auxiliary chains and the transaction main chain, proving that the transaction actually exists, and otherwise, proving that the transaction does not exist. The distributed shared general ledger construction method of the block chain supports the transaction in assets of various businesses, wherein the transaction in assets comprises the transaction of non-monetary assets in the block chain, such as credit notes, intelligent properties, discount coupons, bonds and the like, and meanwhile, the distributed shared general ledger construction method supports transfer among different business assets. In addition, the update of key functions can be carried out on the transaction auxiliary chains, so that update speed can be improved, and a risk that the transaction main chain is broken can be avoided.
Owner:BUBI BEIJING NETWORK TECH CO LTD
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com