Patents
Literature
4201 results about "System safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The system safety concept calls for a risk management strategy based on identification, analysis of hazards and application of remedial controls using a systems-based approach. This is different from traditional safety strategies which rely on control of conditions and causes of an accident based either on the epidemiological analysis or as a result of investigation of individual past accidents. The concept of system safety is useful in demonstrating adequacy of technologies when difficulties are faced with probabilistic risk analysis. The underlying principle is one of synergy: a whole is more than sum of its parts. Systems-based approach to safety requires the application of scientific, technical and managerial skills to hazard identification, hazard analysis, and elimination, control, or management of hazards throughout the life-cycle of a system, program, project or an activity or a product. "Hazop" is one of several techniques available for identification of hazards.
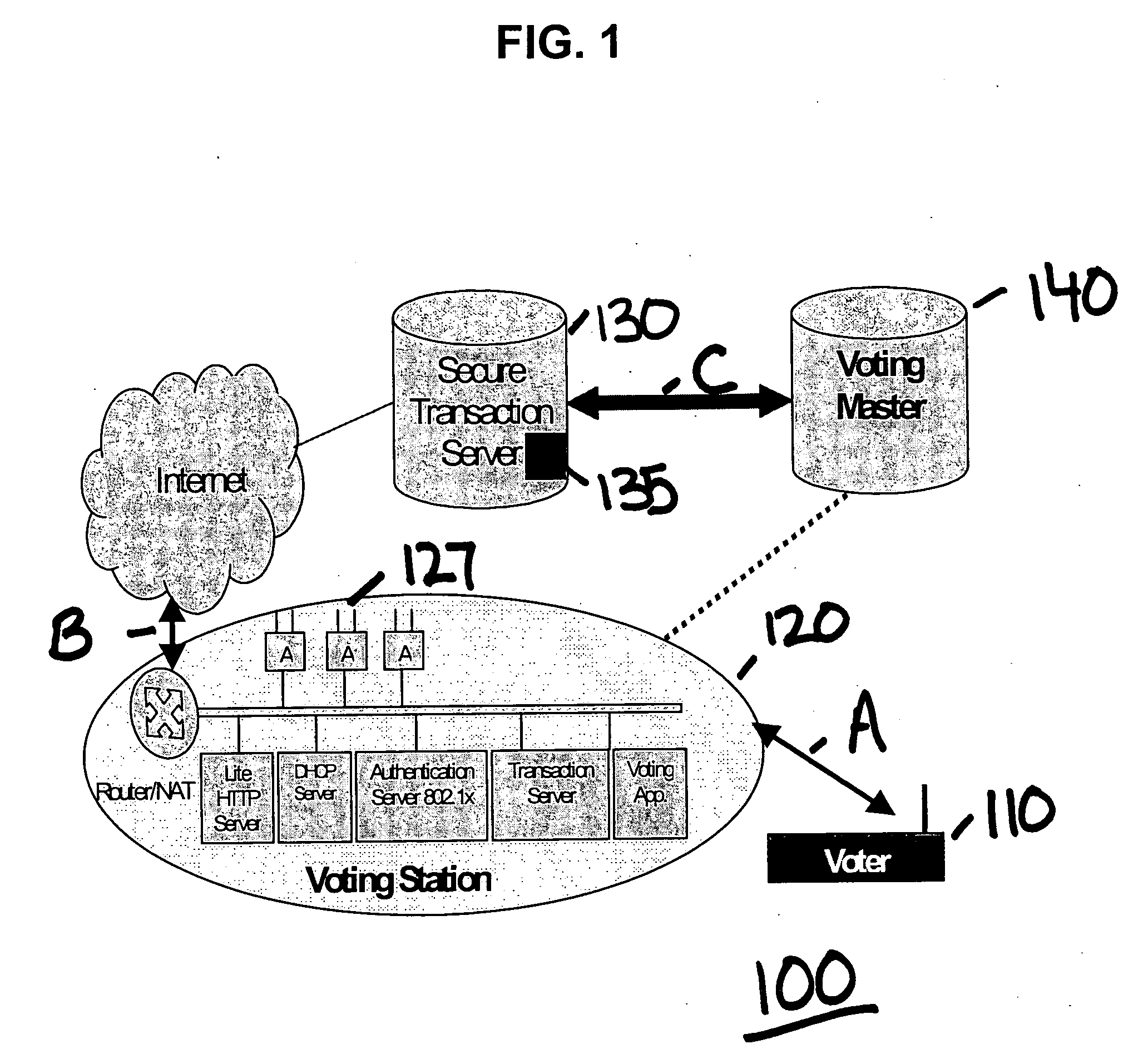
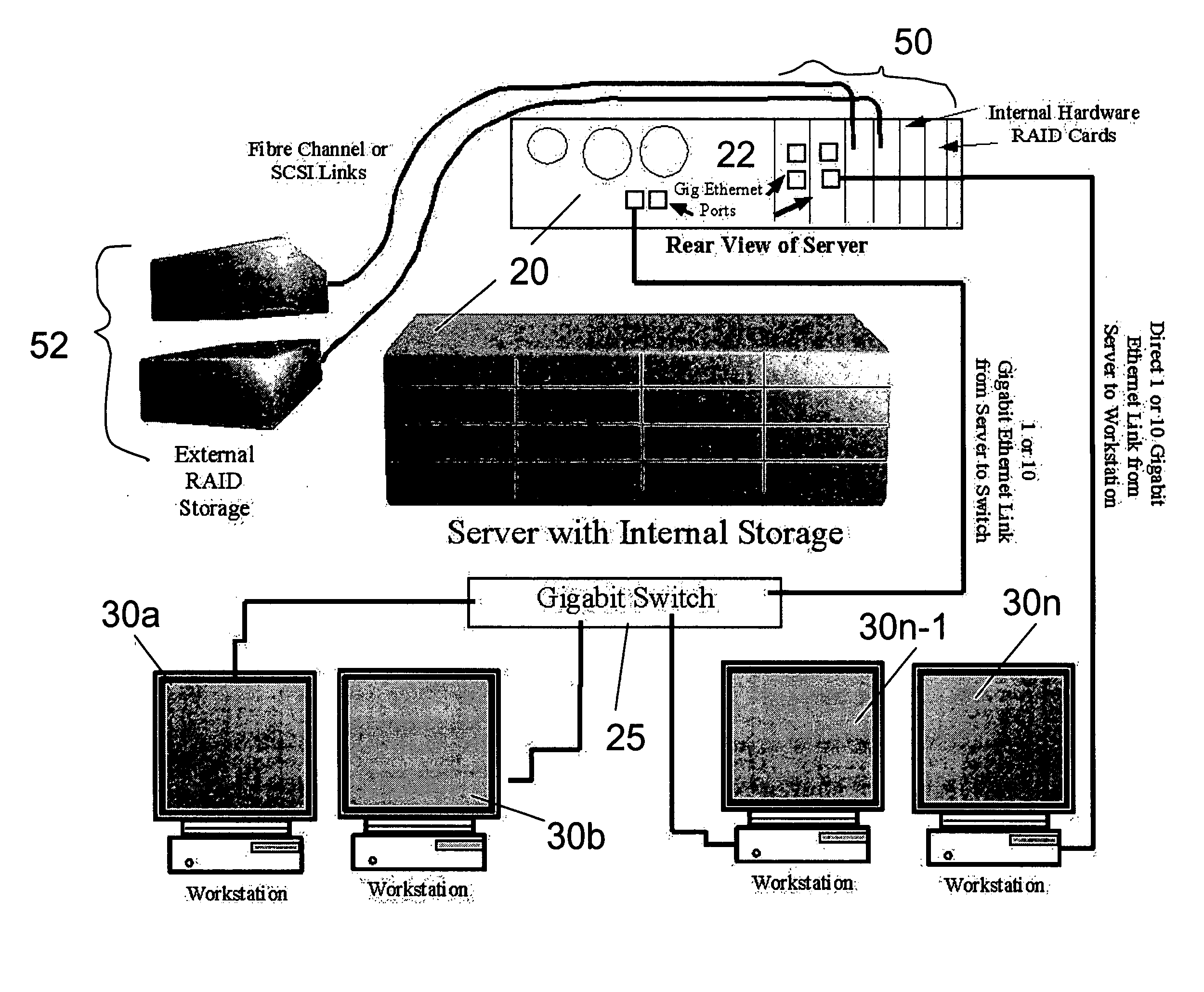
Electronic content delivery system
InactiveUS6226618B1Key distribution for secure communicationDigital data processing detailsDelivery systemSystem safety
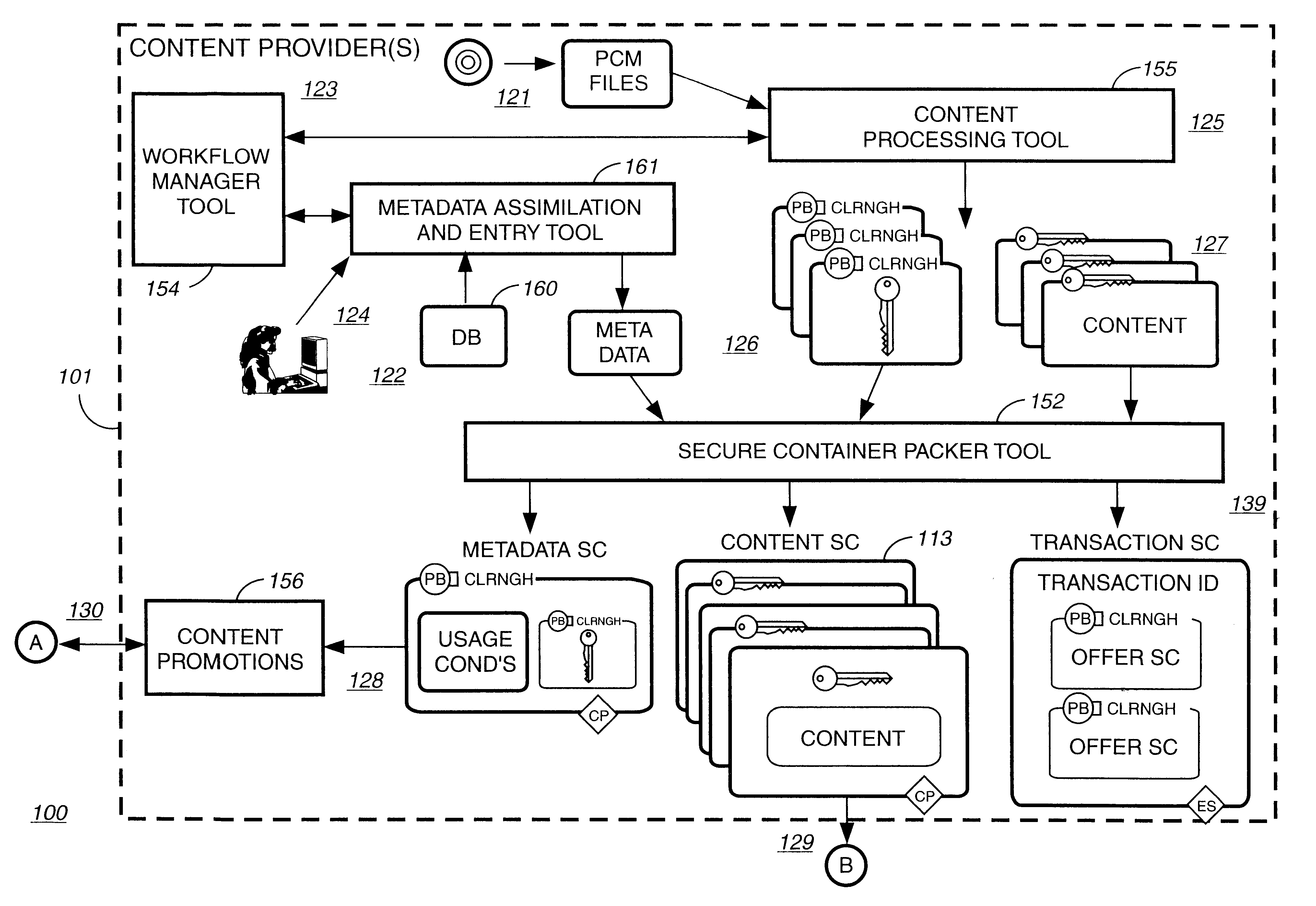
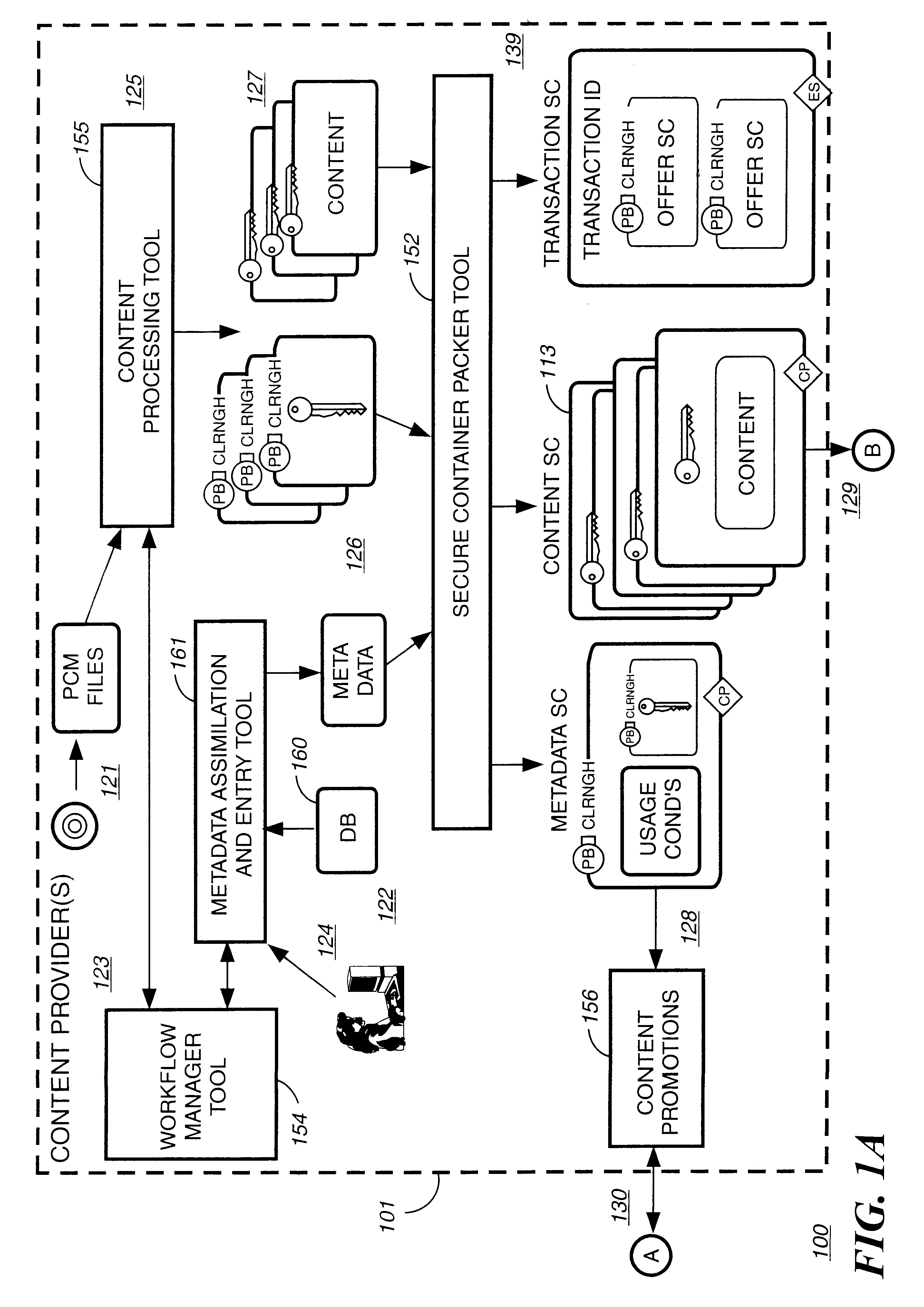
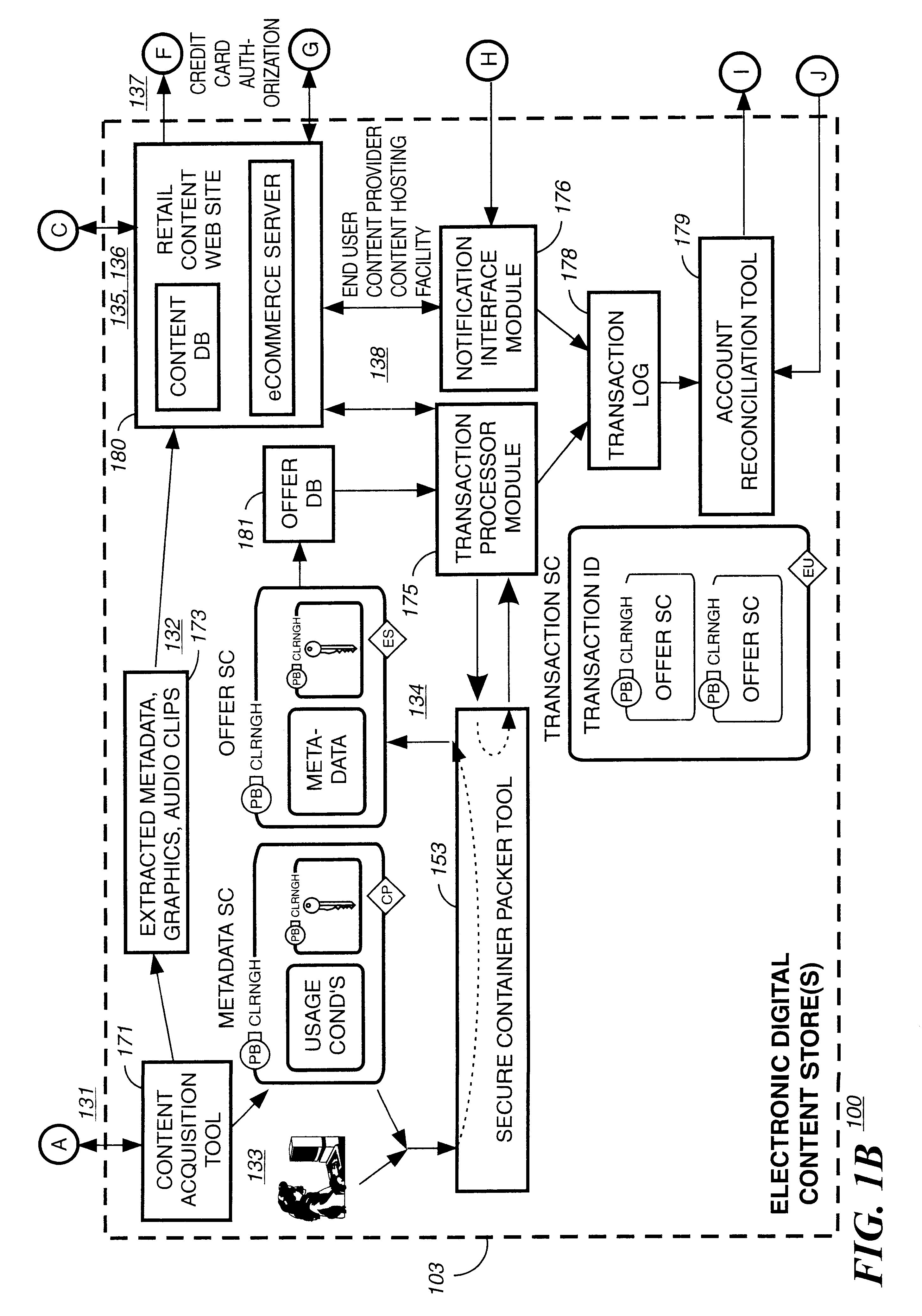
Disclosed is a method and apparatus of securely providing data to a user's system. The data is encrypted so as to only be decryptable by a data decrypting key, the data decrypting key being encrypted using a first public key, and the encrypted data being accessible to the user's system, the method comprising the steps of: transferring the encrypted data decrypting key to a clearing house that possesses a first private key, which corresponds to the first public key; decrypting the data decrypting key using the first private key; re-encrypting the data decrypting key using a second public key; transferring the re-encrypted data decrypting key to the user's system, the user's system possessing a second private key, which corresponds to the second public key; and decrypting the re-encrypted data decrypting key using the second private key.
Owner:LEVEL 3 COMM LLC
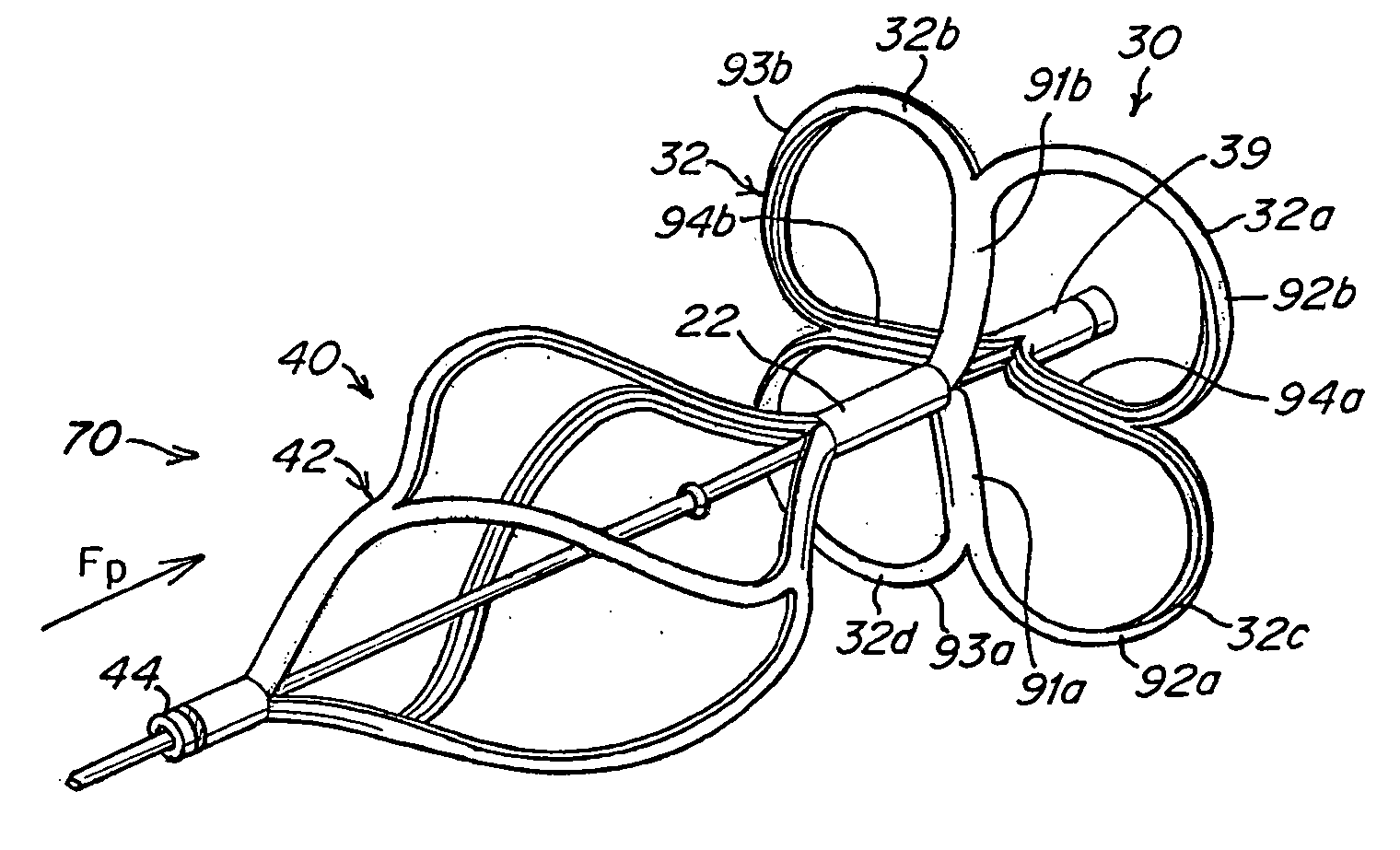
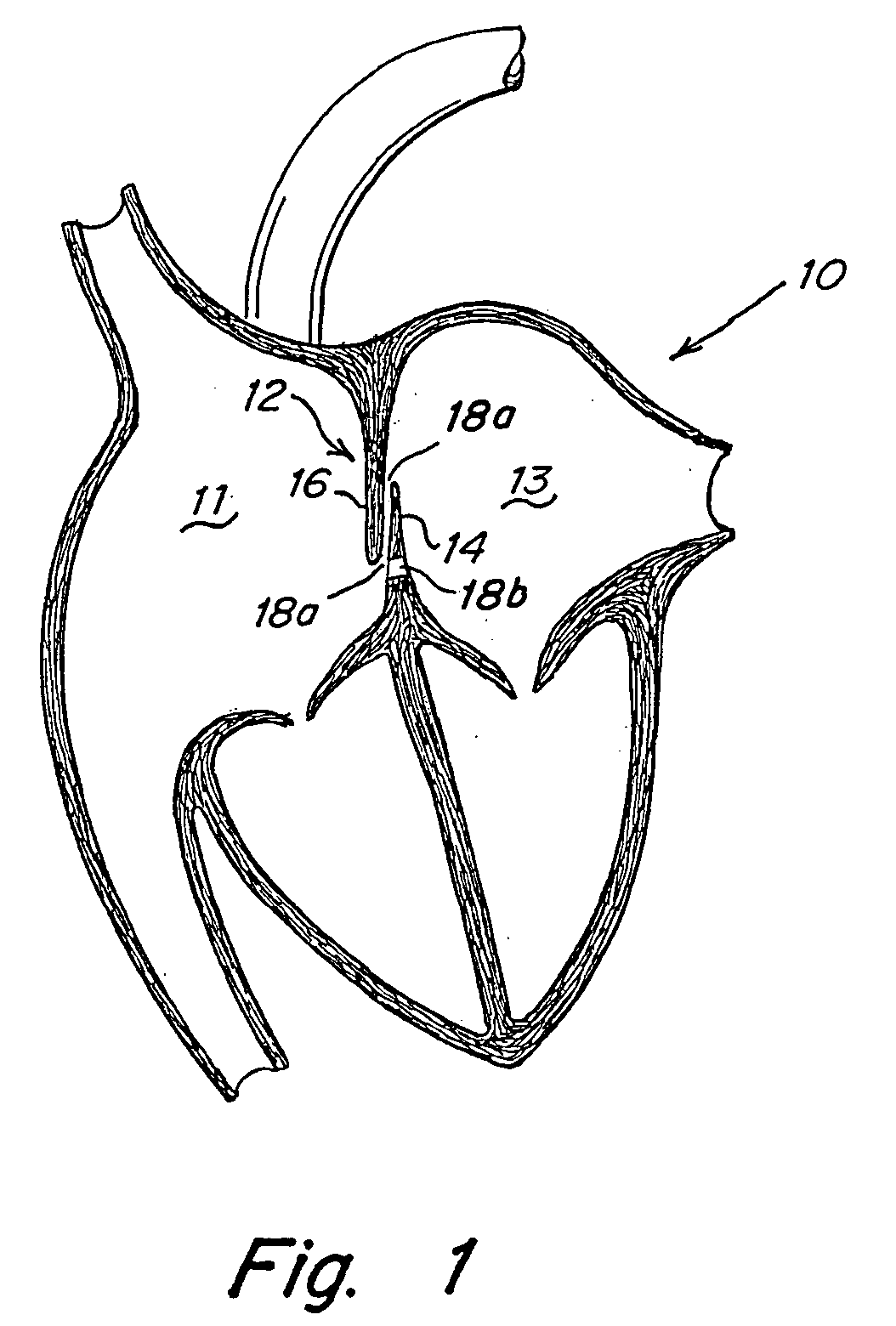
Occluder device double securement system for delivery/recovery of such occluder device
Devices, delivery systems and delivery techniques for an occlusion device for the closure of physical anomalies, such as an atrial septal defect, a patent foramen ovale (PFO), and other septal and vascular defects are described. The devices, delivery systems and delivery techniques relate particularly to, but are not limited to, a patent foramen ovale (PFO) occluder made from a polymer tube. Specifically, a petal-shaped occluder with a catch system is provided within a delivery sheath. In certain embodiments, the delivery system includes a first securement system for securing a first end of the occluder and a second securement system for securing a second end of the occluder to a delivery catheter and a delivery wire contained in the delivery system. The securement enable the deployment (and retrieval) of the device. The securement systems enable pushing and pulling of respective ends of the occluder to expand and contract the device by varying its axial length. In one aspect, the first securement system employs a threaded connection and the second securement system employs a suture connection. In another aspect, the first securement system employs a threaded connection and the second securement system employs a collet finger connection. The securement systems are detached when the device has been properly positioned. The securement systems can be manipulated by control systems provided in the control portion of the delivery system.
Owner:WL GORE & ASSOC INC
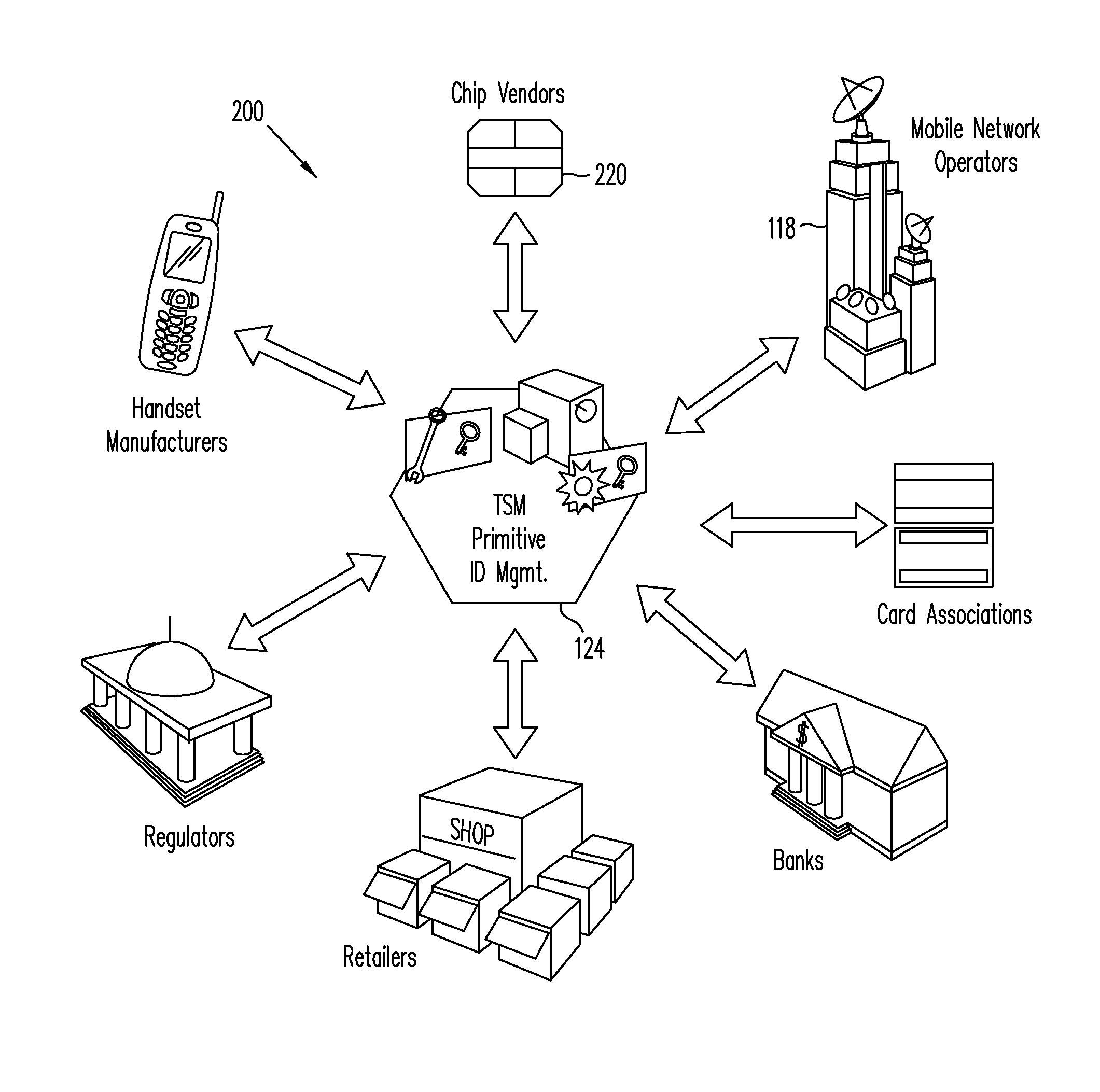
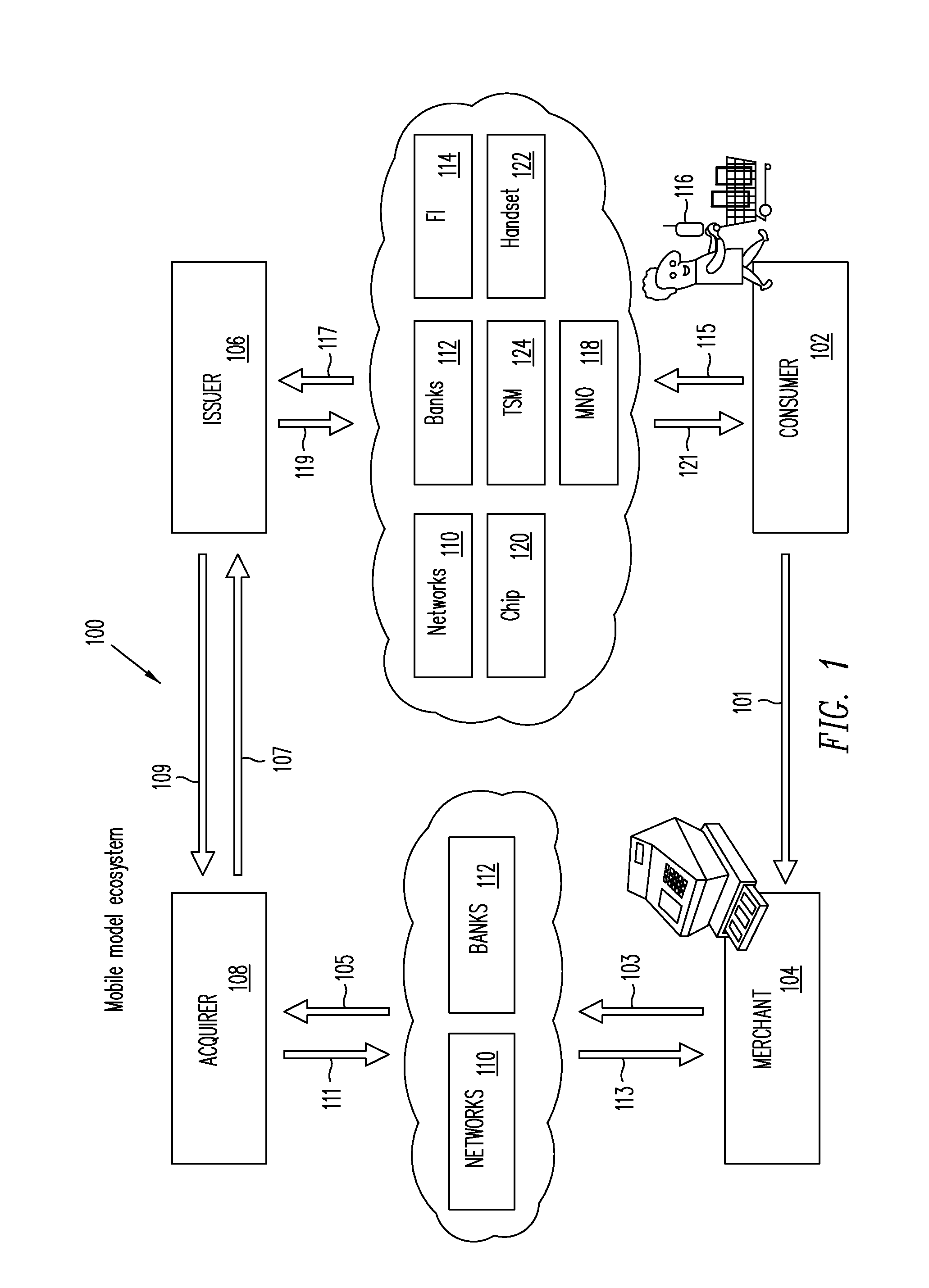
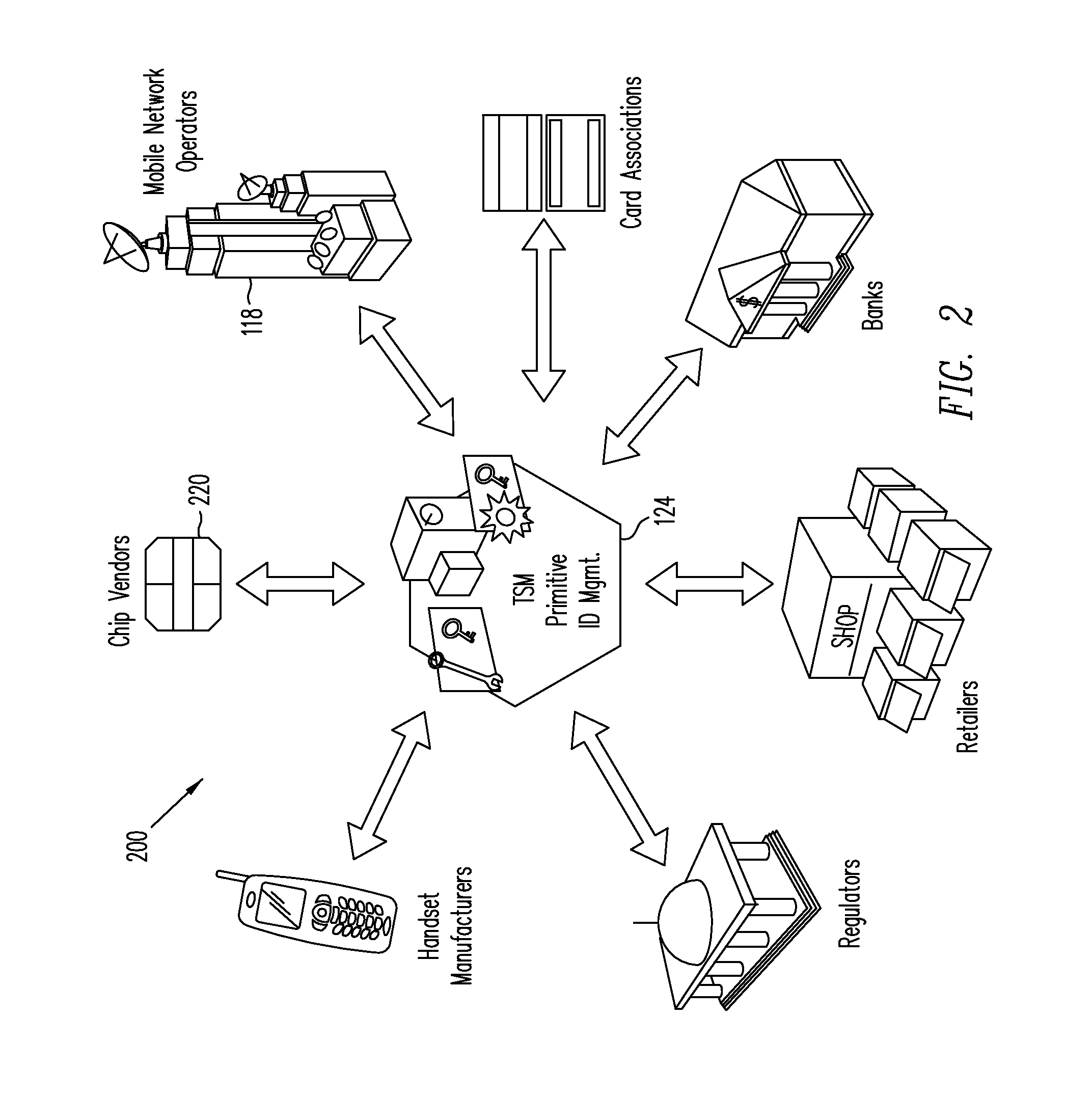
Trusted Integrity Manager (TIM)
A system for use with a trusted service manager (TSM) and a mobile device having a subscriber unique identifying data, according to one embodiment, includes: a server in which the server validates an application against the unique and identifying data of the mobile device and provides the validated application for the mobile device; and a secure element (SE) acting as a client in which the SE is present in the mobile device as client; the validated application from the server is installed in the SE; and the SE is adapted to execute the validated application to perform a service process. The service process includes enablement of payment functions on the mobile device, in which enablement of payment functions includes: providing secure communication between the mobile device and the server; secure provisioning of a payment instrument on the mobile device, wherein authentication and verification for the payment instrument on the mobile device is provided by the server; and binding the payment instruments and the validated application to the mobile device to provide a strong ID management for enhanced user protection and system security and integrity.
Owner:PAYPAL INC
Encryption in a secure computerized gaming system
InactiveUS7043641B1Straightforward and easy to manageUser identity/authority verificationUnauthorized memory use protectionHash functionDigital signature
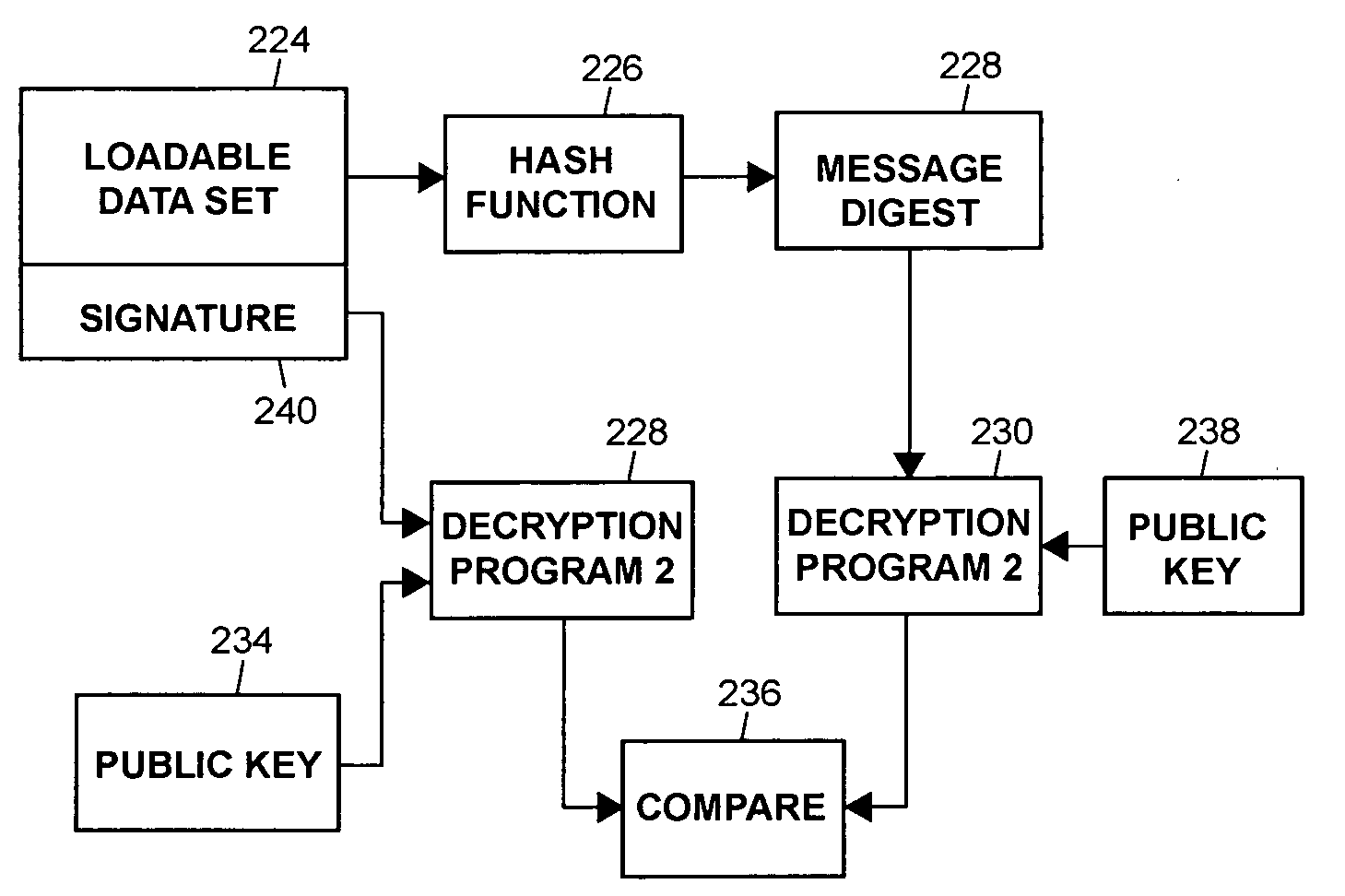
An architecture and method for a gaming-specific platform are disclosed that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. These and other functions make use of encryption, including digital signatures and hash functions as well as other encryption methods.
Owner:IGT
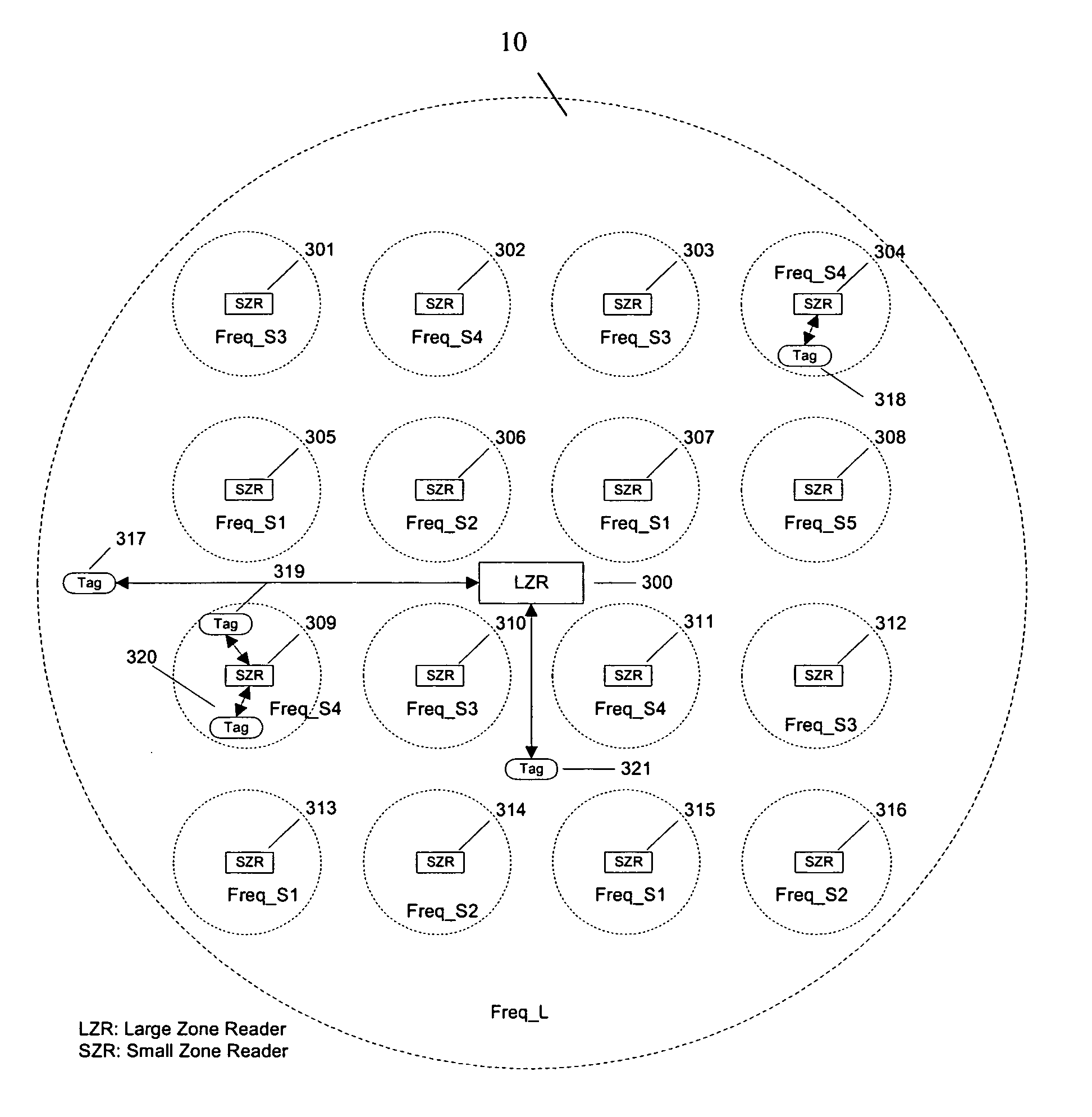
Method and system of using active RFID tags to provide a reliable and secure RFID system
InactiveUS20050093679A1Increase the areaMinimal interferenceFrequency-division multiplex detailsMemory record carrier reading problemsComputer scienceEmbedded system
The system of the present invention includes a large-zone RFID reader, a plurality of small-zone RFID readers, and a plurality of RFID tags. The large-zone RFID reader covers areas which are not covered by the small-zone RFID readers. The output power of the small-zone RFID readers is controlled by the large-zone RFID reader based on RFID tag operation patterns of the small-zone RFID readers. The system reliability is improved by a method that uses reliable RFID tags, RFID reader beacon signals, and RFID tag's repetitive transmitting signals to detect tag failures. The system security is provided by a method that uses integrated crypto engines in both the RFID tags and RFID readers.
Owner:ZAI LI CHENG RICHARD +1
Authentication in a secure computerized gaming system
InactiveUS20030203756A1Data processing applicationsUser identity/authority verificationComputer hardwareData set
The present invention provides an architecture and method for a gaming-specific platform that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments of the invention provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The invention provides these and other functions by encrypting a random number, storing the encrypted random number, and hashing the random number and a casino game data set to provide a first bit string, and storing the first bit string.
Owner:IGT
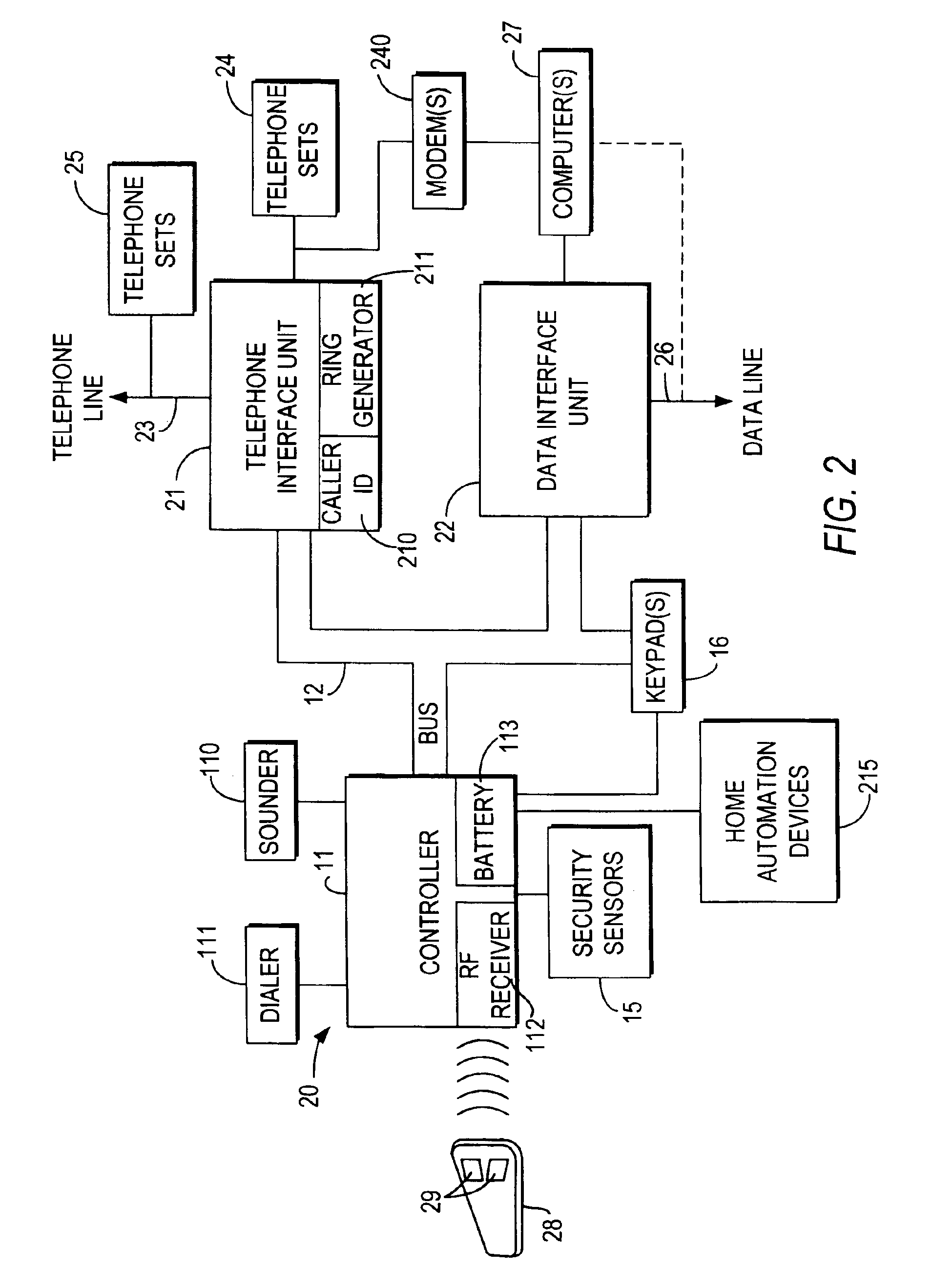
Integrated security and communications system with secure communications link
InactiveUS6928148B2Minimize the numberImprove securitySpecial service for subscribersCalled number recording/indicationData interfaceSecurity system
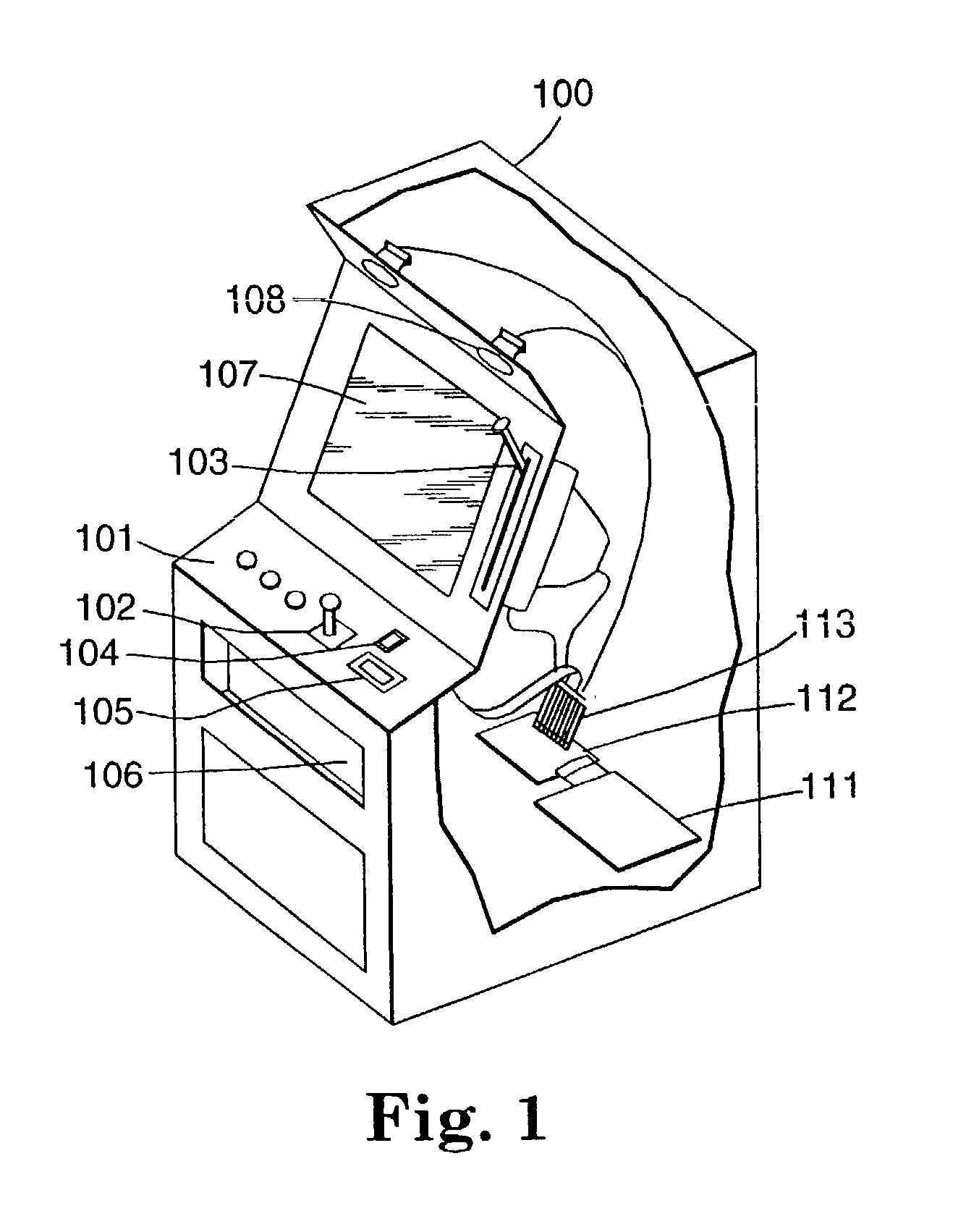
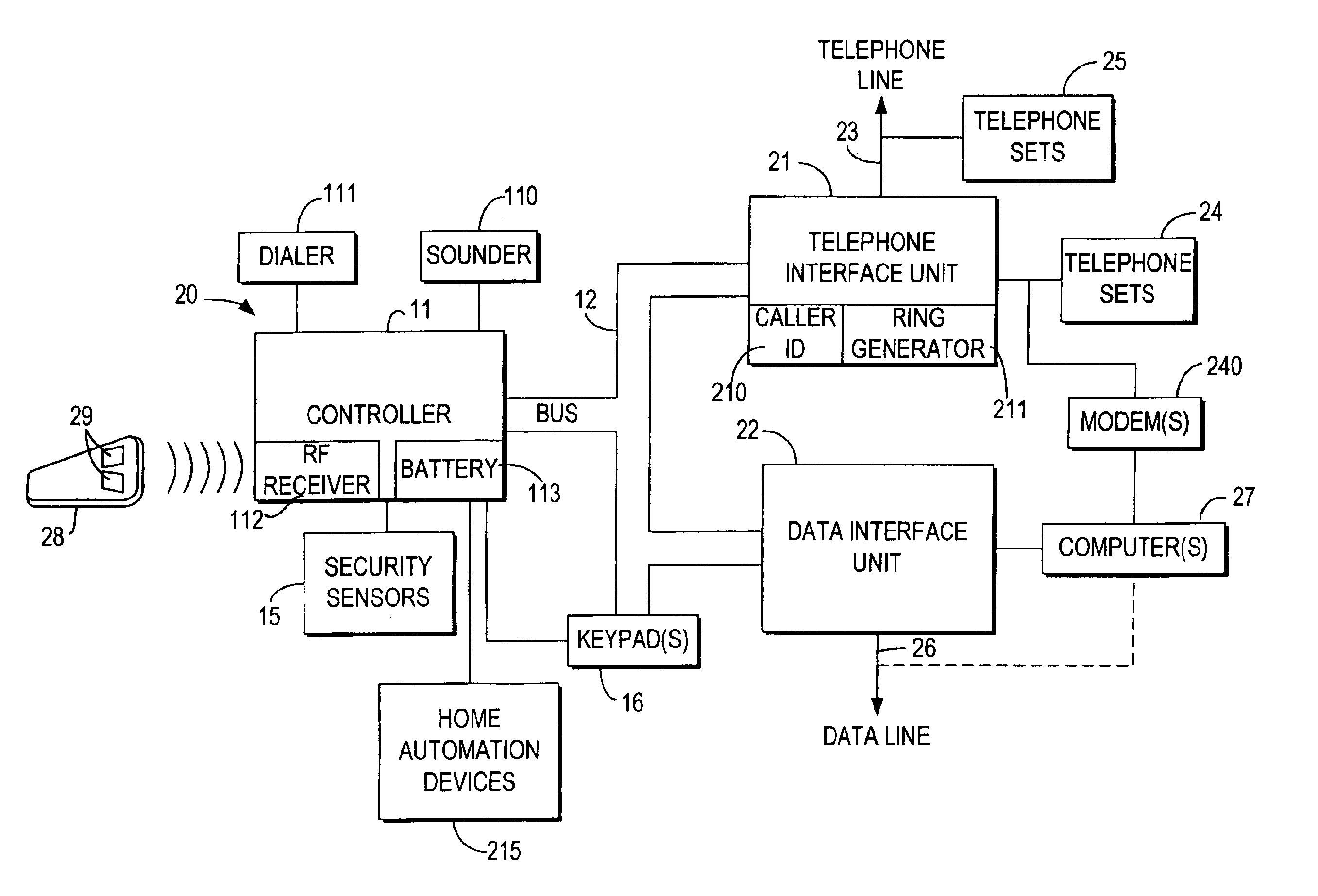
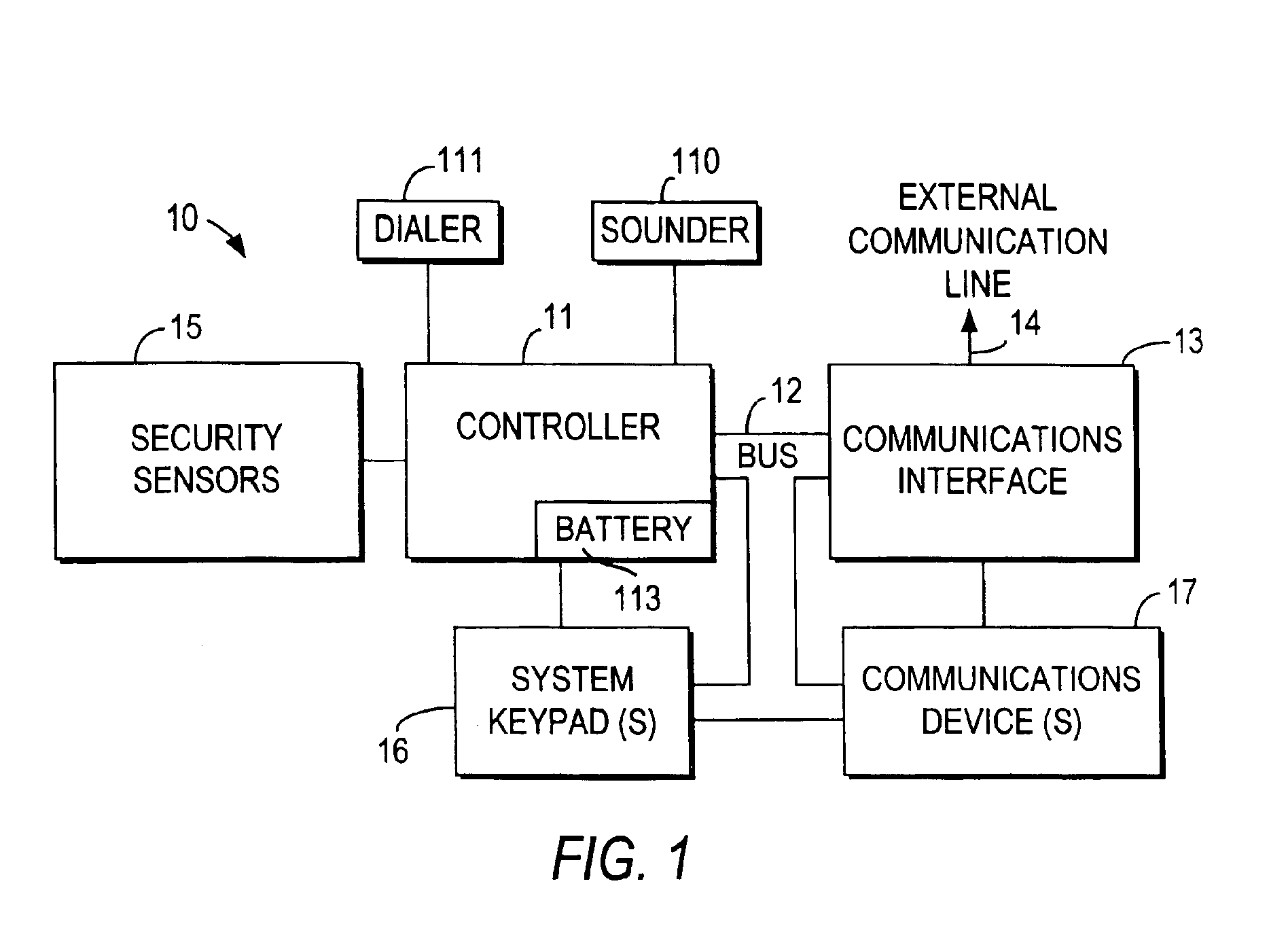
An integrated security and communications system combines a security system to either or both of a telephone system interface and a data interface. Users have access to voice-mail or other PBX-type telephone functions, many or all of which can be accessed not only at telephone sets, but also at keypads of the security system. Data functions such as electronic mail and possible partial or full World Wide Web access may also be provided at the keypads, as well as at connected personal computers or computer terminals. The system keypads may be enhanced to better accommodate some of the added functions. A central communications station could be used to maintain secure, shared private key encrypted communications with each premises system, using a redirector arrangement or relay to allow each premises system to communicate securely with a central monitoring station and with other systems. The secure communications system could be used without a security system to allow secure computer-to-computer communications.
Owner:ADEMCO INC
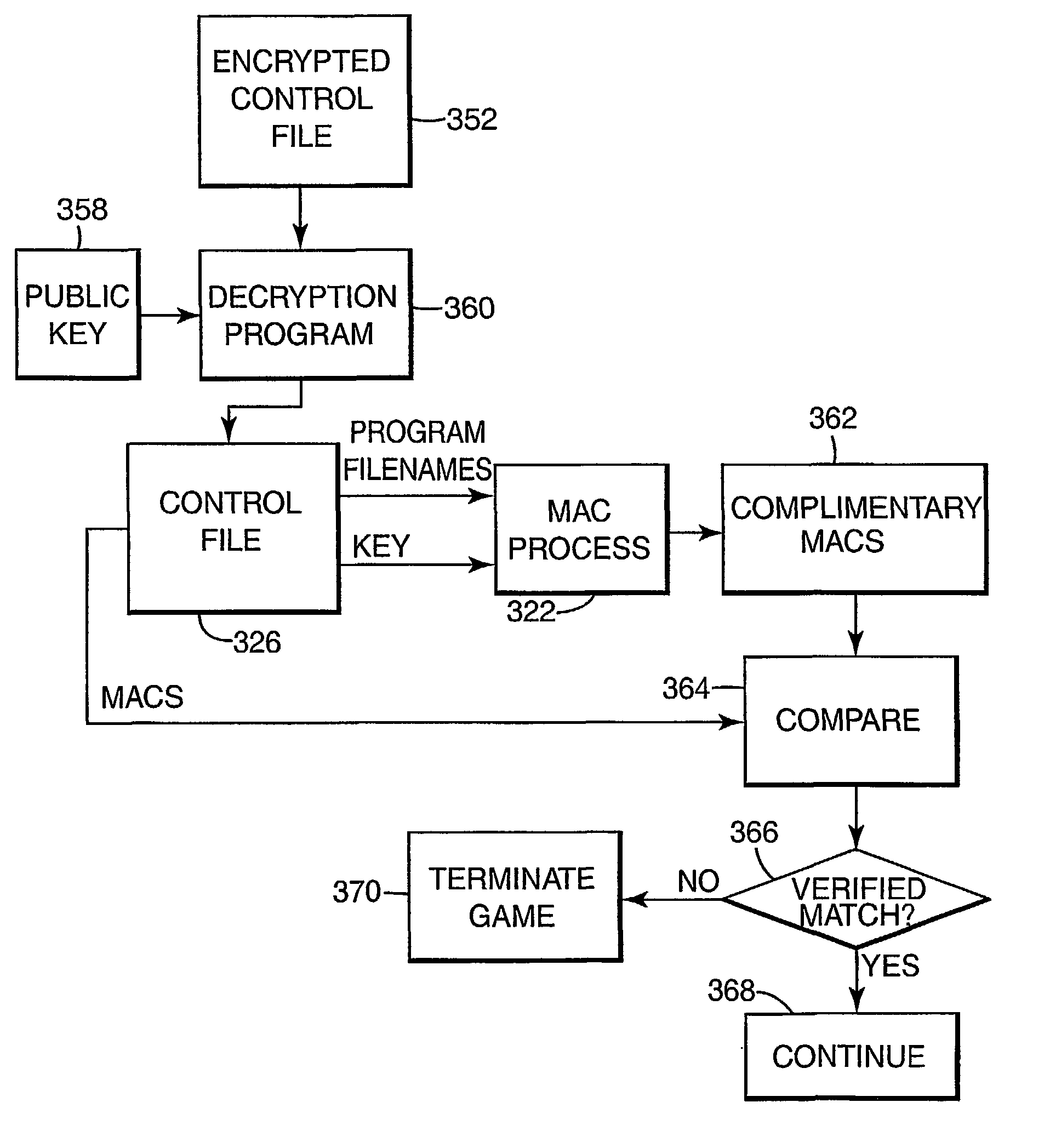
Encryption in a secure computerized gaming system
InactiveUS7203841B2Straightforward and easy to manageUser identity/authority verificationUnauthorized memory use protectionComputer hardwareHash function
The present invention provides an architecture and method for a gaming-specific platform that features secure storage (354) and verification (366) of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments of the invention provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The invention provides these and other functions by use of encryption (216), including digital signatures (220) and hash functions (210) as well as other encryption methods.
Owner:IGT
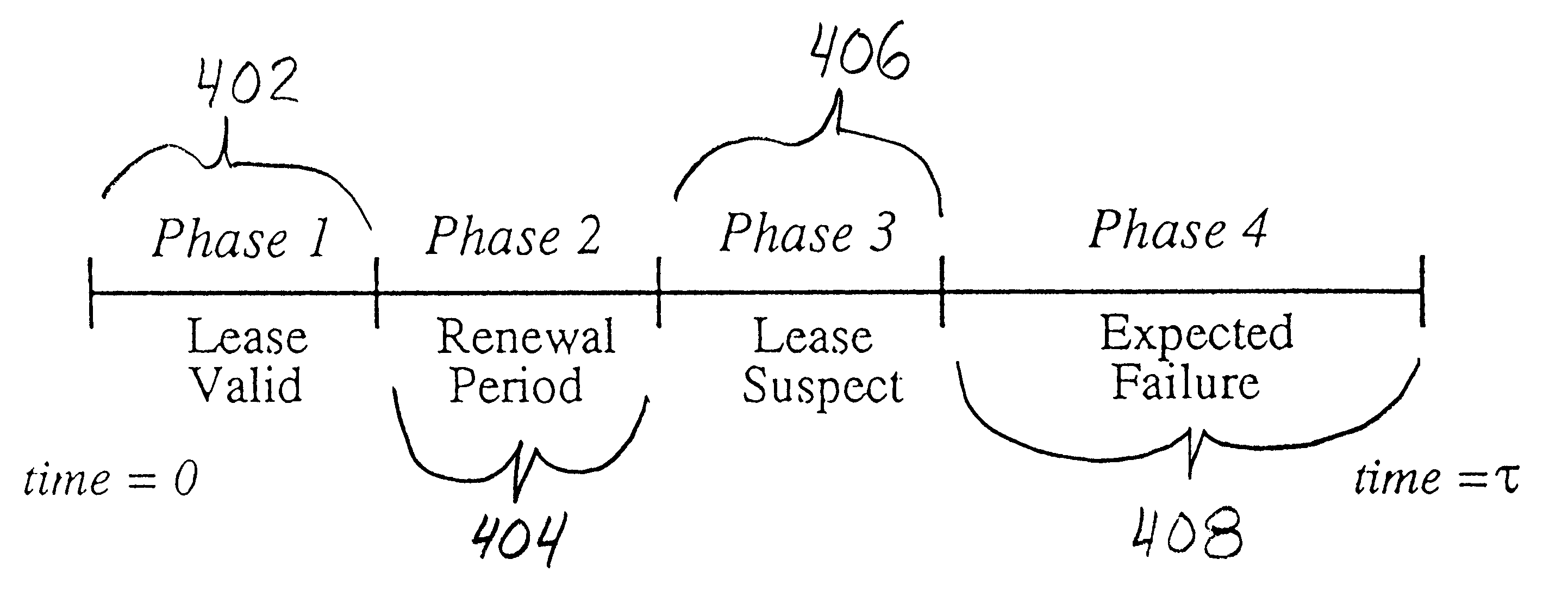
Lease based safety protocol for distributed system with multiple networks
InactiveUS6775703B1Memory adressing/allocation/relocationMultiple digital computer combinationsDirty dataClient-side
A system, method, and computer program product for a lease-based timeout scheme that addresses fencing's shortcomings. Unlike fencing, this scheme (or protocol) enables an isolated computer to realize it is disconnected from the distributed system and write its dirty data out to storage before its locks are stolen. In accordance with the invention, data consistency during a partition in a distributed system is ensured by establishing a lease based protocol between in the distributed system wherein a client can hold a lease with a server. The lease represents a contract between a client and a server in which the server promises to respect the client for a period of time. The server respects the contract even when it detects a partition between the client and itself.
Owner:IBM CORP
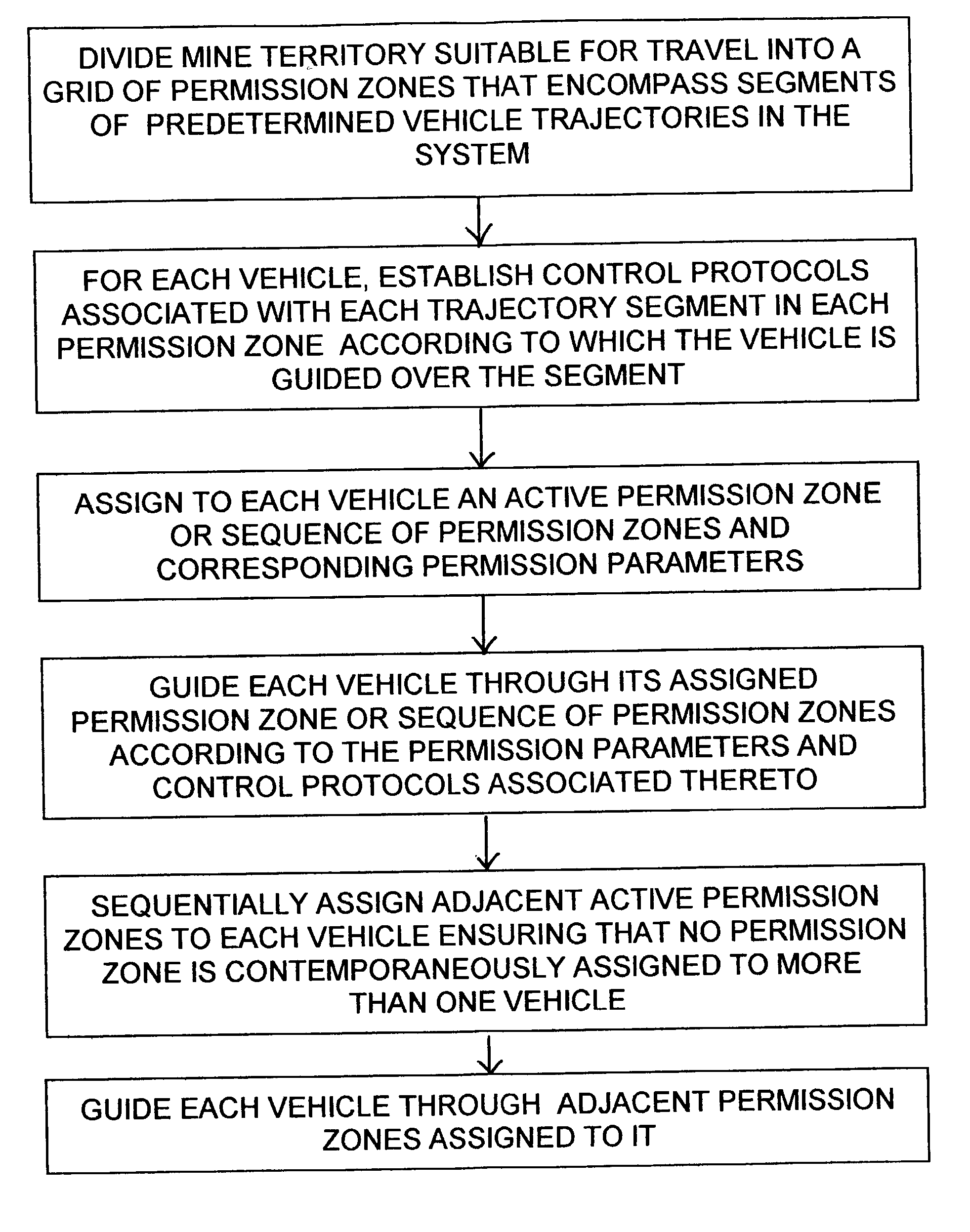
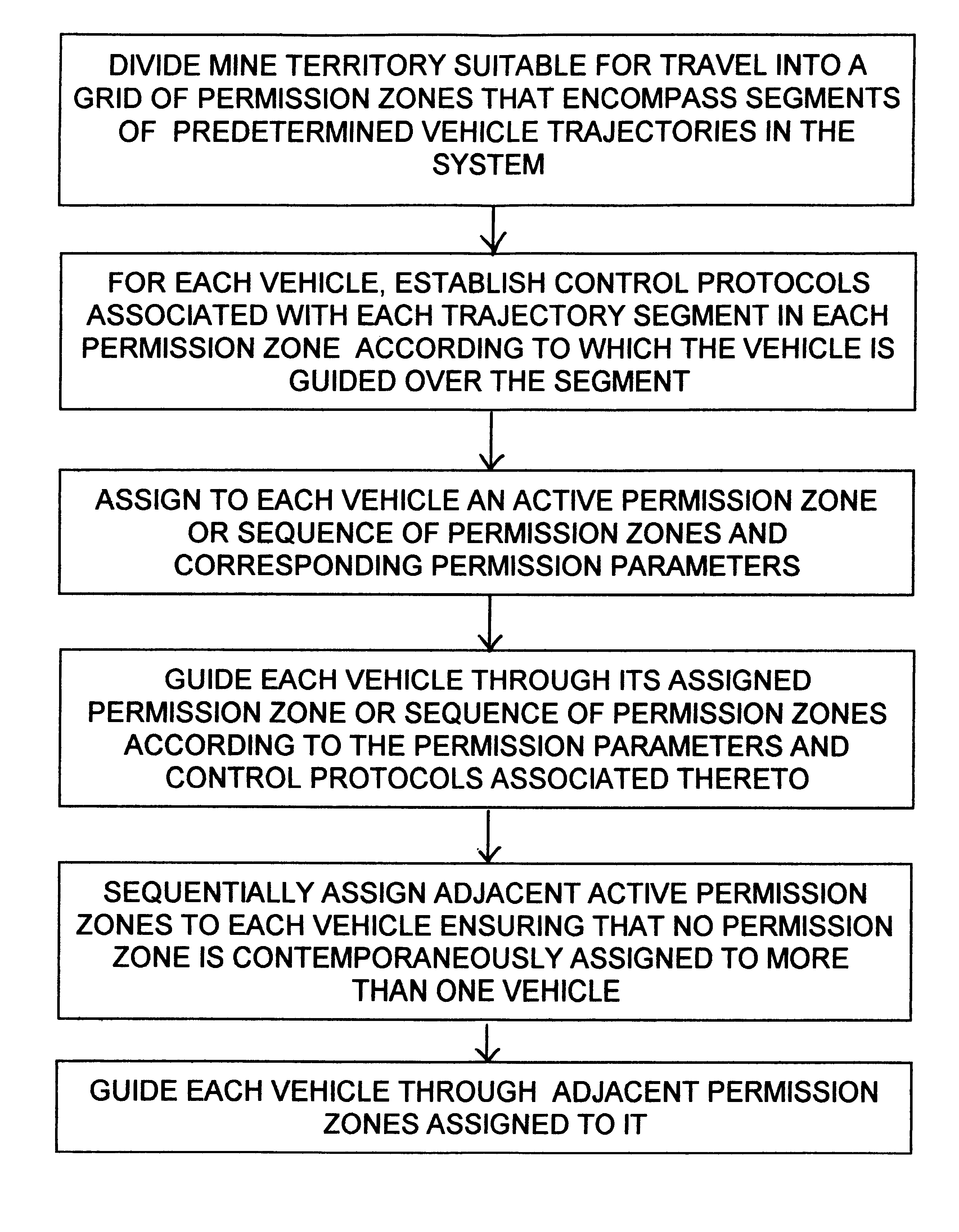
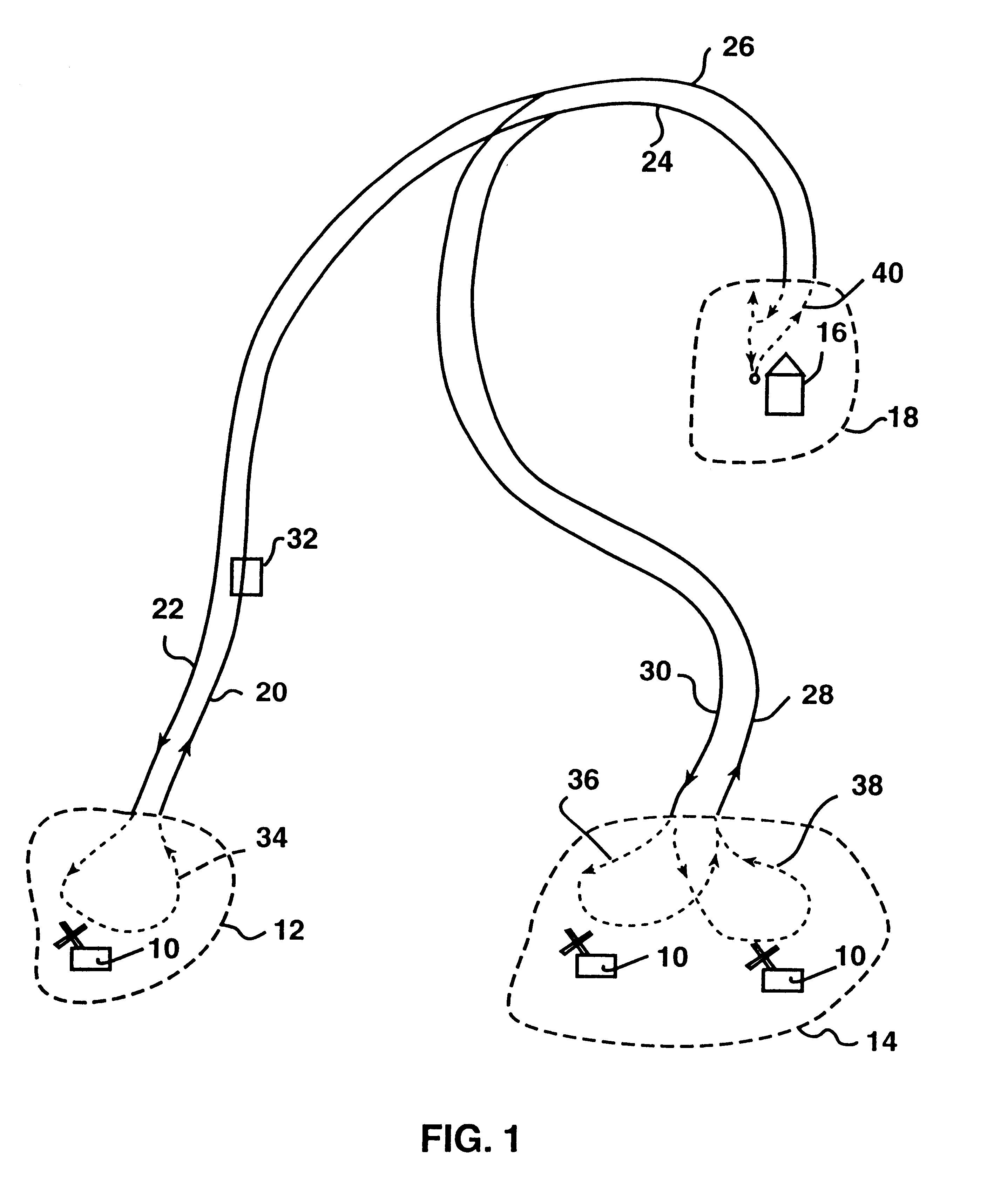
Permission system for controlling interaction between autonomous vehicles in mining operation
InactiveUS20020143461A1Minimize ruttingAnalogue computers for vehiclesAnalogue computers for trafficSystem safetyGuidance system
A supervisory safety-control system is implemented by dividing a mine's territory into zones of free operation ("permission zones") wherein a vehicle is allowed to move according to predetermined permission parameters but unhindered by other system constraints. Traffic of autonomous vehicles in each permission zone is controlled by the supervisory system in conjunction with and in addition to conventional safety constraints associated with the guidance system that effects the vehicle's tracking of predetermined trajectories. Permission zones are assigned and activated using criteria that ensure the vehicle will remain entirely within active zones so long as the vehicle acts within such predetermined permission parameters. Each permission zone is also associated with a maximum velocity profile that overrides guidance-system safety controls, if necessary, and ensures stoppage of the vehicle at the end of the permission zone.
Owner:MODULAR MINING SYSTEMS
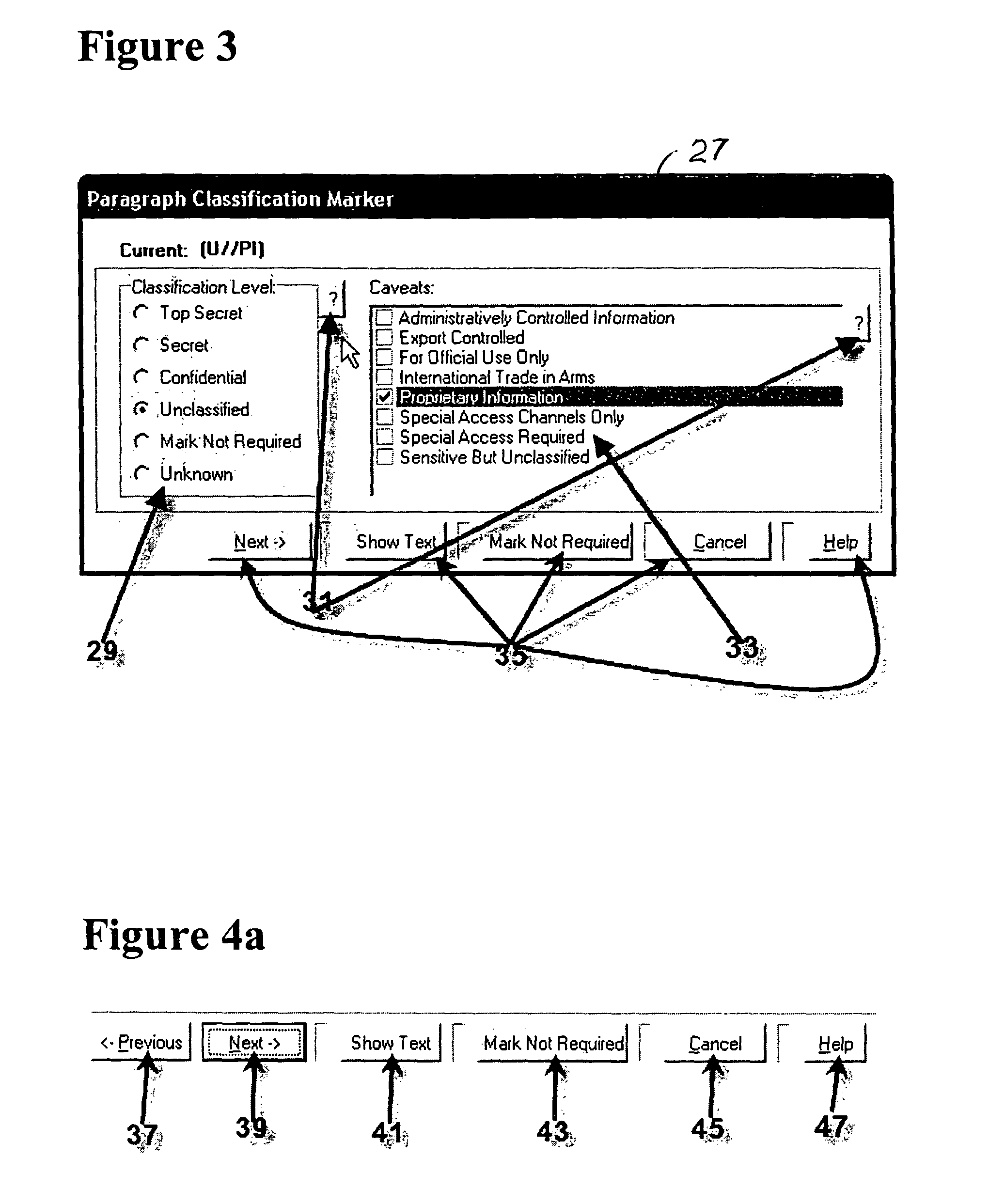
Method for providing customized and automated security assistance, a document marking regime, and central tracking and control for sensitive or classified documents in electronic format
ActiveUS7958147B1Guarantee capacityPositive determinationDigital data information retrievalDigital data processing detailsOff the shelfDocumentation procedure
A software engine runs in a compatible mode with off-the-shelf word processors, e-mail programs and presentation development software and other document development software. The software engine is used for the security classification of sensitive or national security classified information in electronic and resultant hard copy document formats. The software engine ensures that the individual considers all informational portions of a document, that appropriate document marks are employed, that document marks in their electronic format are persistent and that all necessary information, such as classification guides, standards and security regulations, provided by the organization to classify information is at hand and immediately available. In addition to the document sensitivity or classification determination and marking support, the software engine tracks and controls documents and the electronic media storing documents. It also provides warnings and alarms, ad hoc document security analysis and reporting capability to system security administrators with respect to document or network events or captured information that may be indicative of risk to the information requiring protection. The software also provides the ability for an organization to centrally establish and control a security classification or sensitivity marking hierarchy for automated security classification support.
Owner:TURNER JAMES LUKE +1
Authentication in a secure computerized gaming system
InactiveUS6962530B2Straightforward and easy to manageData processing applicationsUser identity/authority verificationComputer hardwareData set
An architecture and method for a gaming-specific platform are disclosed that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and do so in a manner that is straightforward and easy to manage. Some embodiments provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The disclosed embodiments provides these and other functions by encrypting a random number, storing the encrypted random number, and hashing the random number and a casino game data set to provide a first bit string, and storing the first bit string.
Owner:IGT
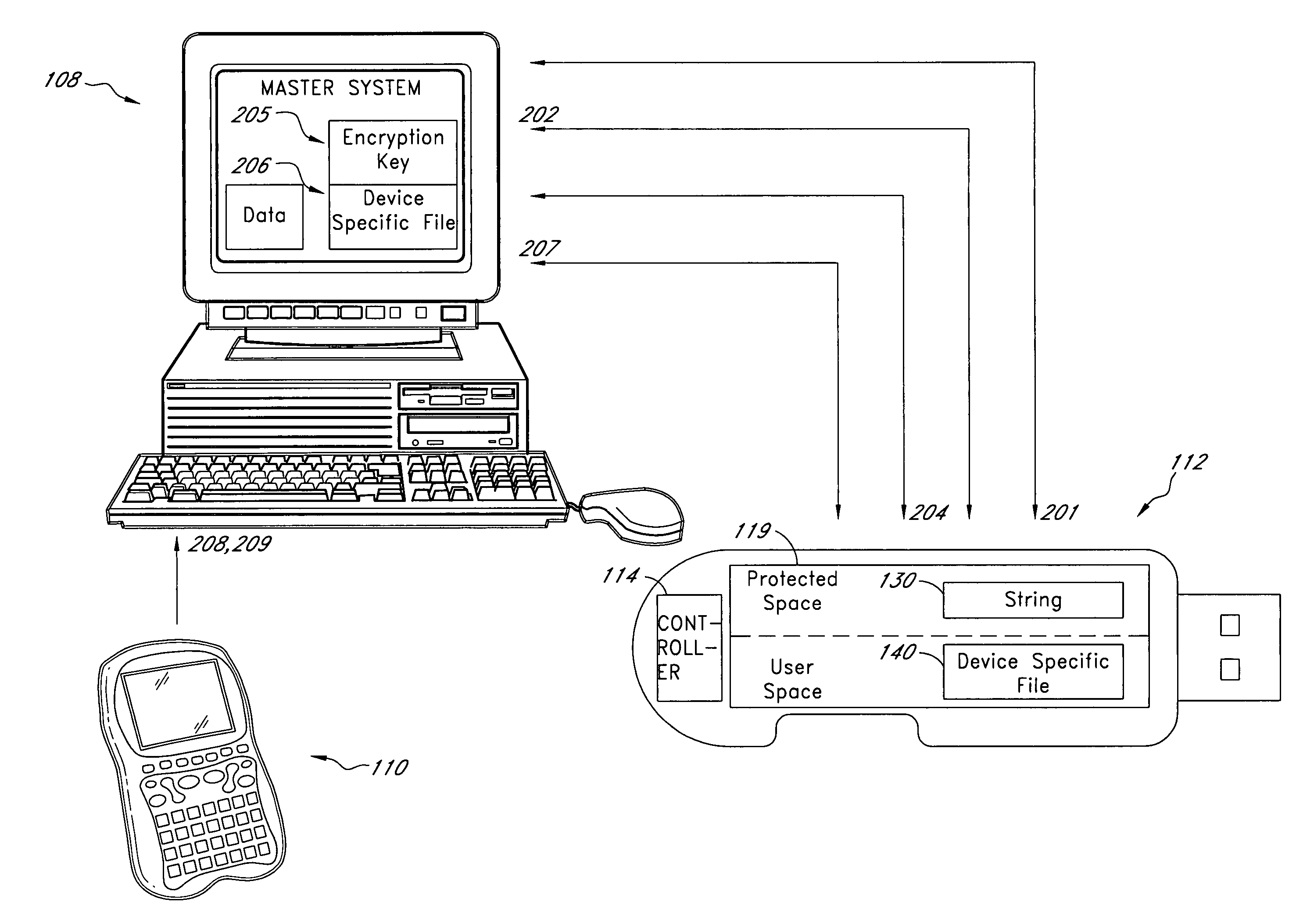
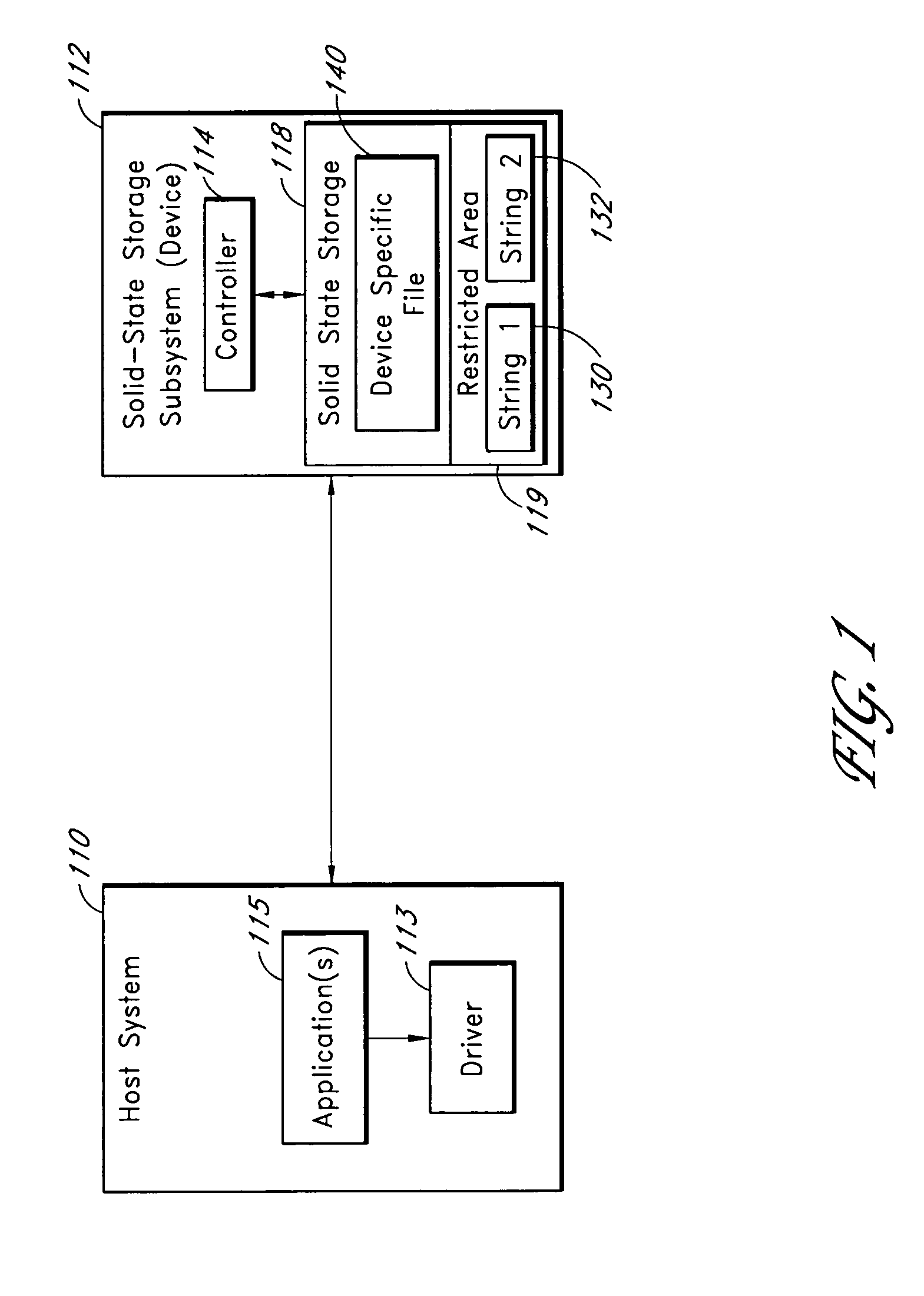
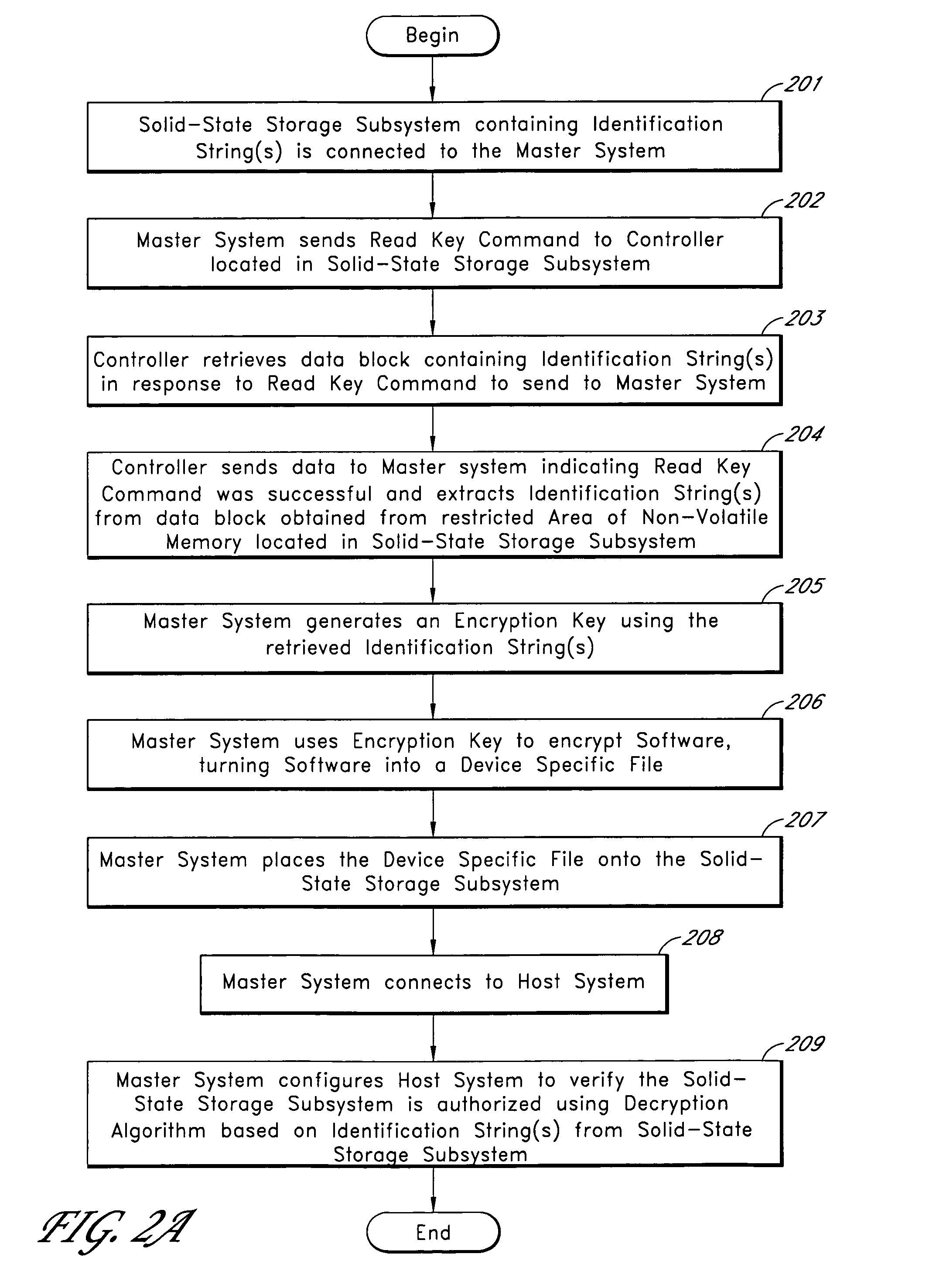
Solid-state storage subsystem security solution
ActiveUS8108692B1Unauthorized memory use protectionHardware monitoringSolid-state storageSecurity solution
A solid-state storage subsystem, such as a non-volatile memory card or drive, includes a main memory area that is accessible via standard memory access commands (such as ATA commands), and a restricted memory area that is accessible only via one or more non-standard commands. The restricted memory area stores information used to control access to, and / or use of, information stored in the main memory area. As one example, the restricted area may store one or more identifiers, such as a unique subsystem identifier, needed to decrypt an executable or data file stored in the main memory area. A host software component is configured to retrieve the information from the subsystem's restricted memory area, and to use the information to control access to and / or use of the information in the main memory area.
Owner:WESTERN DIGITAL TECH INC
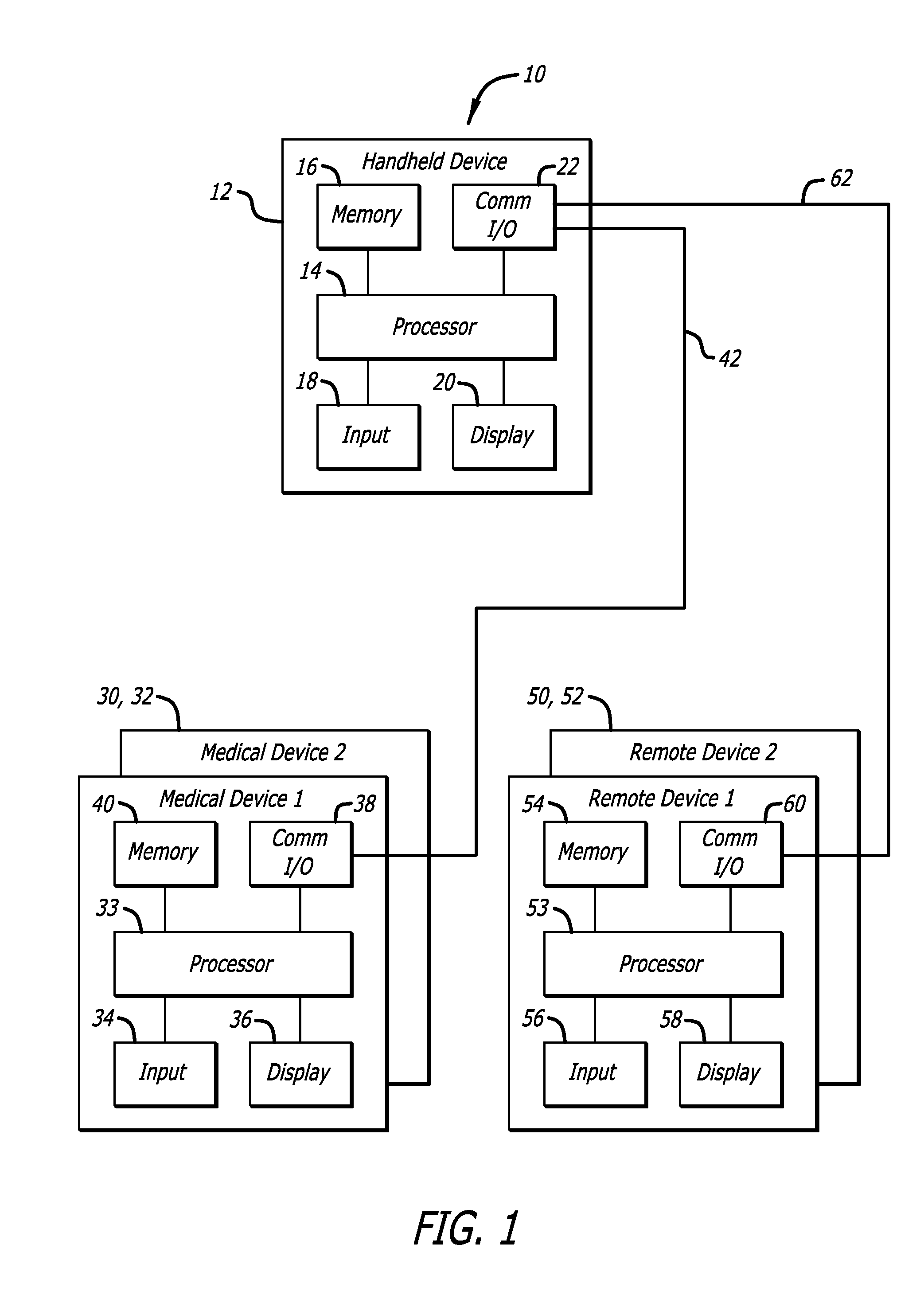
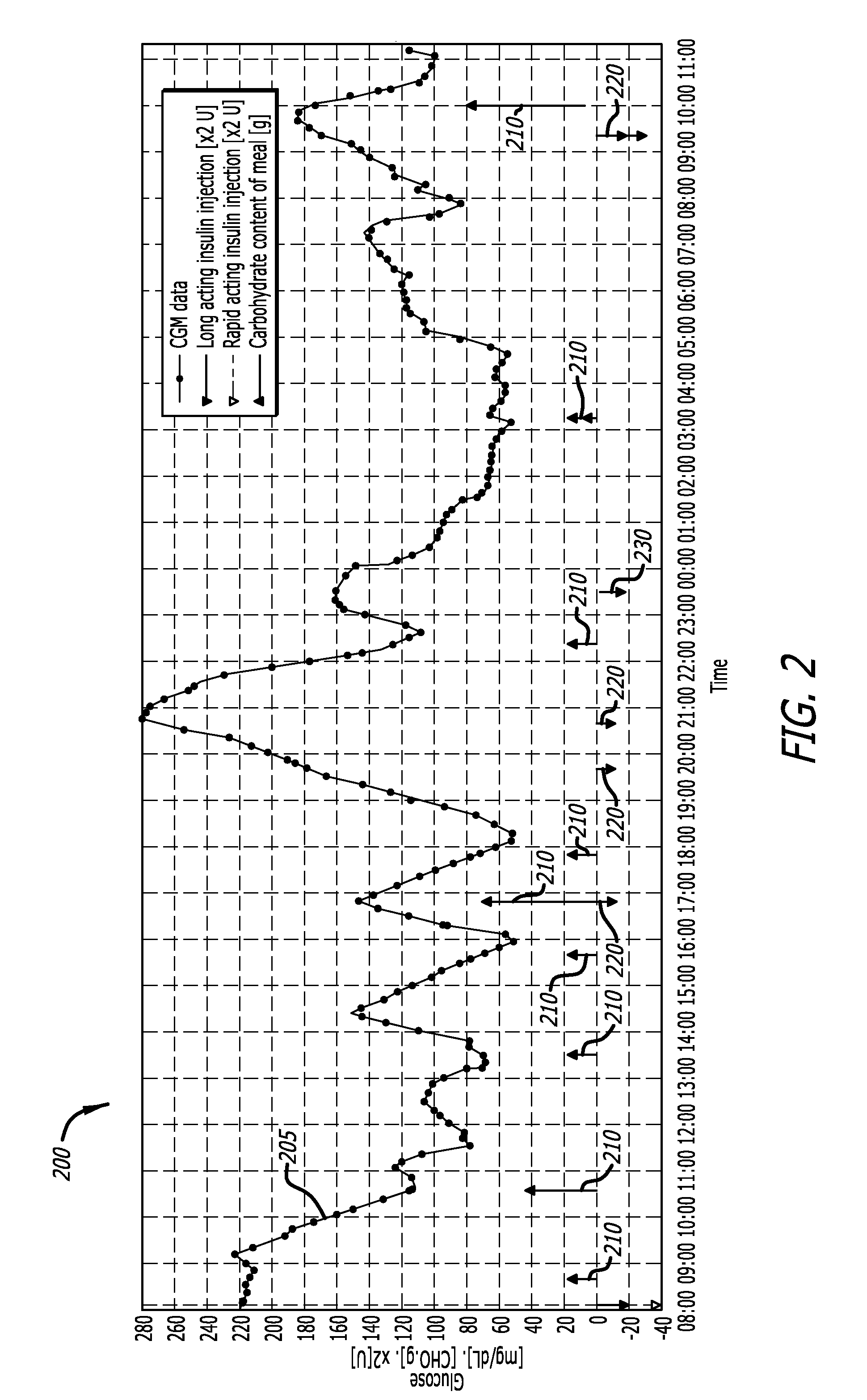
Safety features for integrated insulin delivery system
ActiveUS20100298765A1Preventing hypoglycemiaLimited hyperglycemiaDrug and medicationsMedical devicesGlucose sensorsHypoglycemia
Safety features are applied to an integrated insulin delivery system to enhance safety while accounting for glucose sensor bias and calibration errors. One safety feature includes comparisons of calibrations of the sensor to nominal sensitivity and taking action, such as limiting insulin delivery or taking a further calibration of the sensor. In another feature, an automatic resumption of a basal delivery rate is programmed into the delivery device to avoid the possibility of complete loss of delivery of insulin in the event that communication with the delivery device is disrupted. Other features include steps taken to avoid hypoglycemia in the event that the sensor is negatively biased.
Owner:ABBOTT DIABETES CARE INC
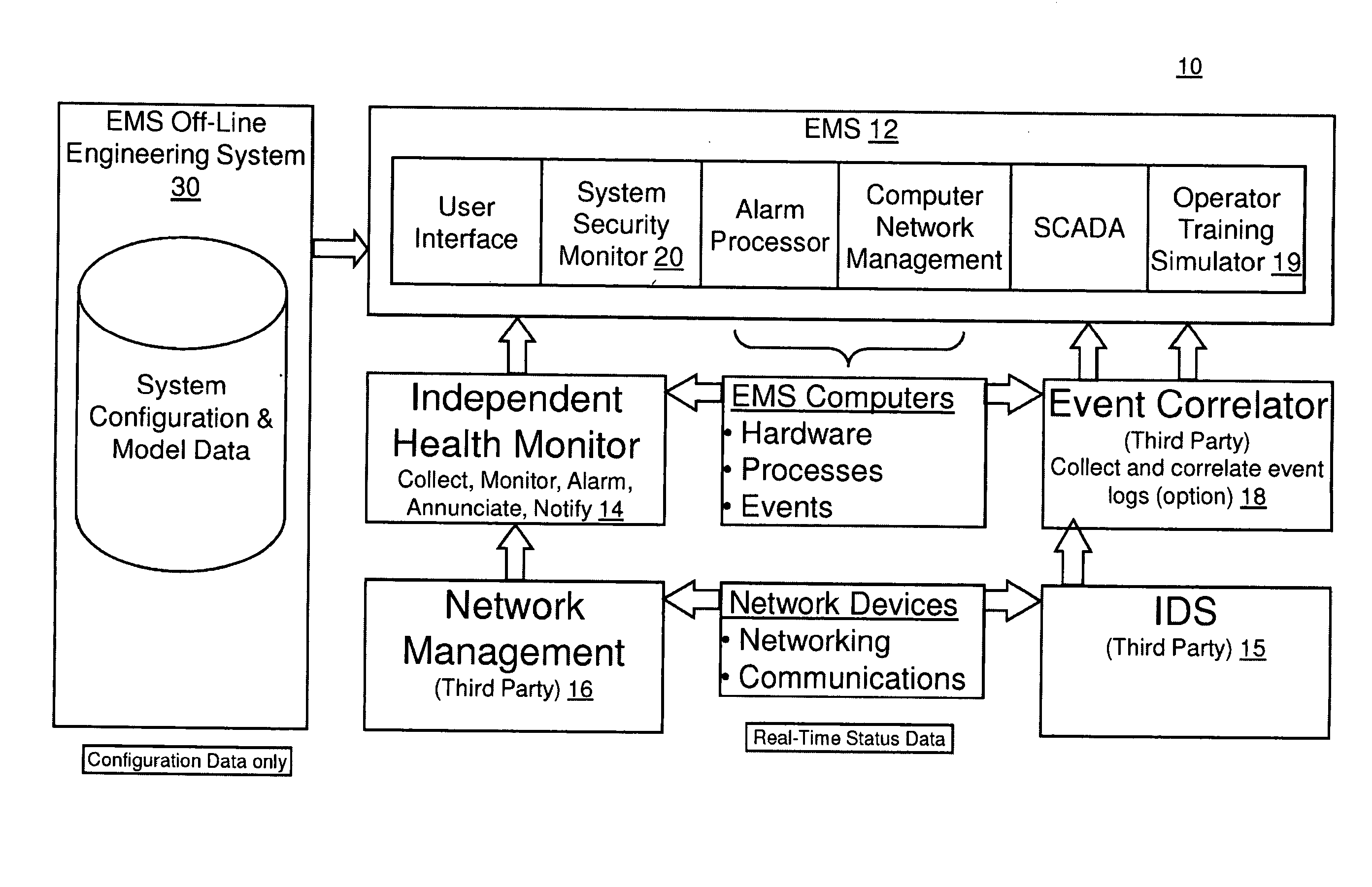
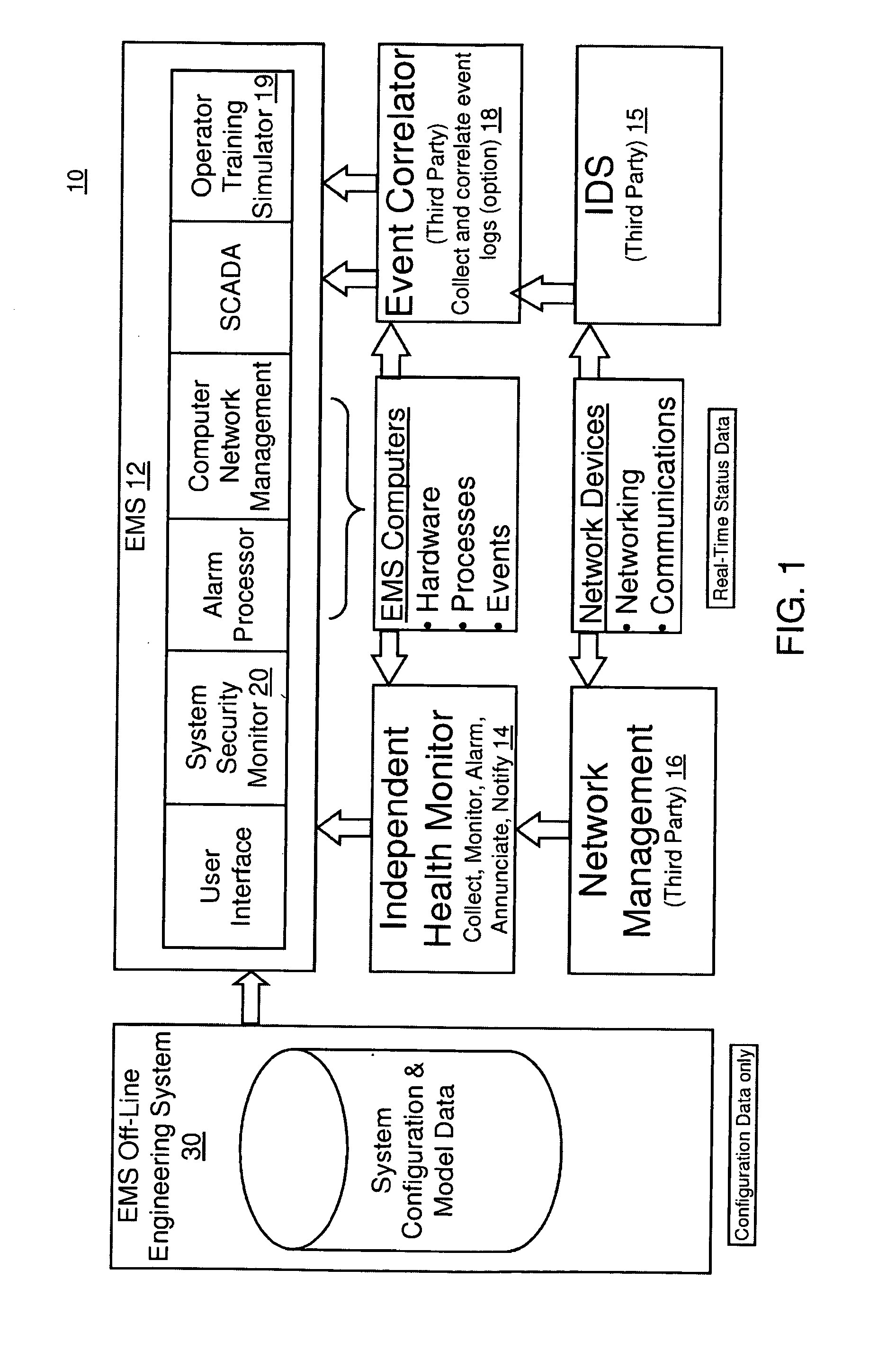
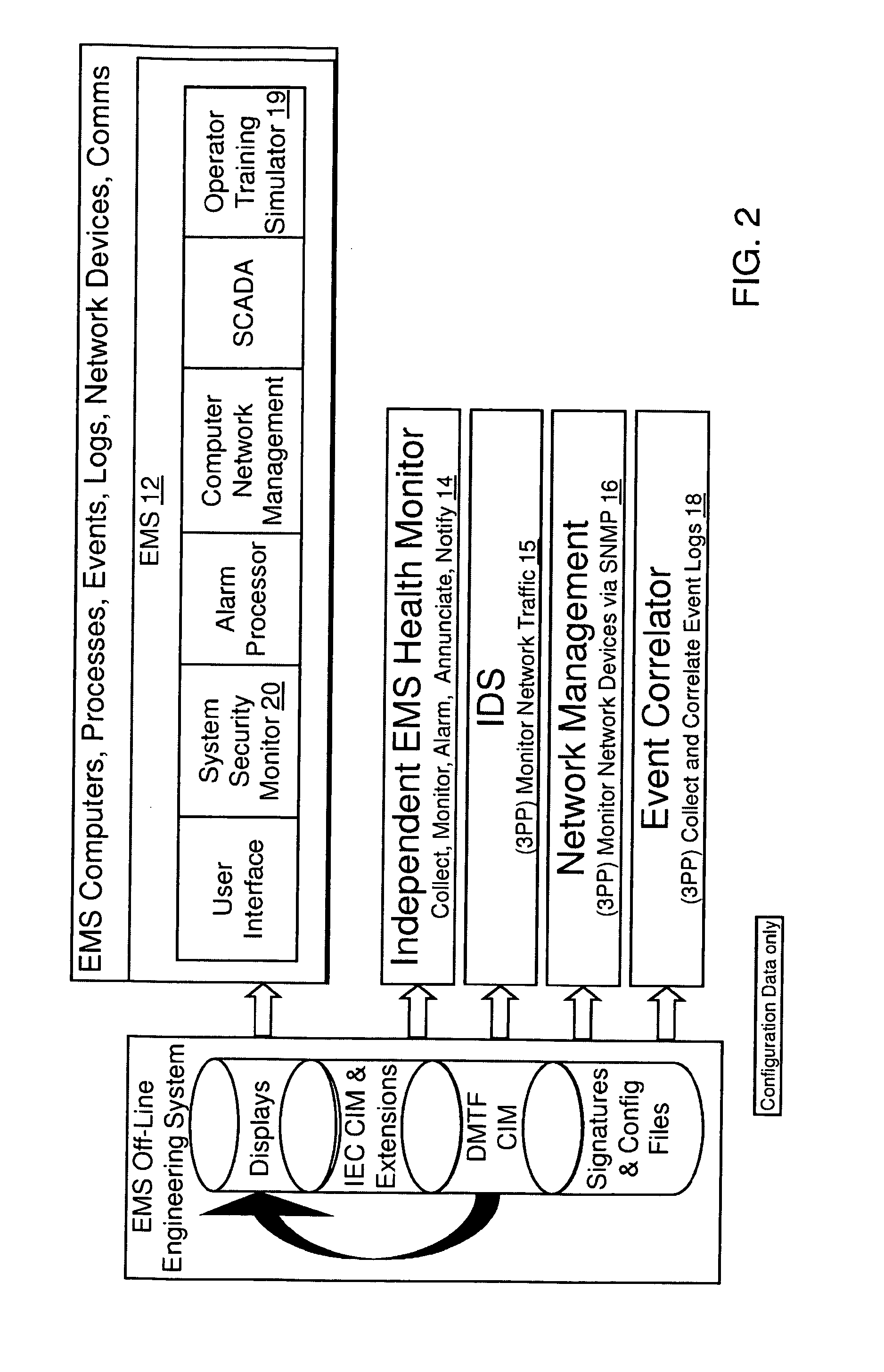
Method and system for cyber security management of industrial control systems
ActiveUS20110039237A1Low chanceFull accessMemory loss protectionError detection/correctionCommand and controlData acquisition
A method and system for cyber security management of Supervisory Control And Data Acquisition (SCADA) systems is provided to enhance situational awareness and cyber security management for industrial control systems. A centralized System Security Manager (SSM) is integrated into a SCADA to collect security related data for the industrial control system and an integrated command and control user interface displays security related data, a system security level, and interfaces with a user to allows for changing of system security settings for the industrial control system based on the security related data collected and manages changes in operational state of the SCADA based on the security level to restrict use of system interfaces and system accesses.
Owner:SIEMENS AG
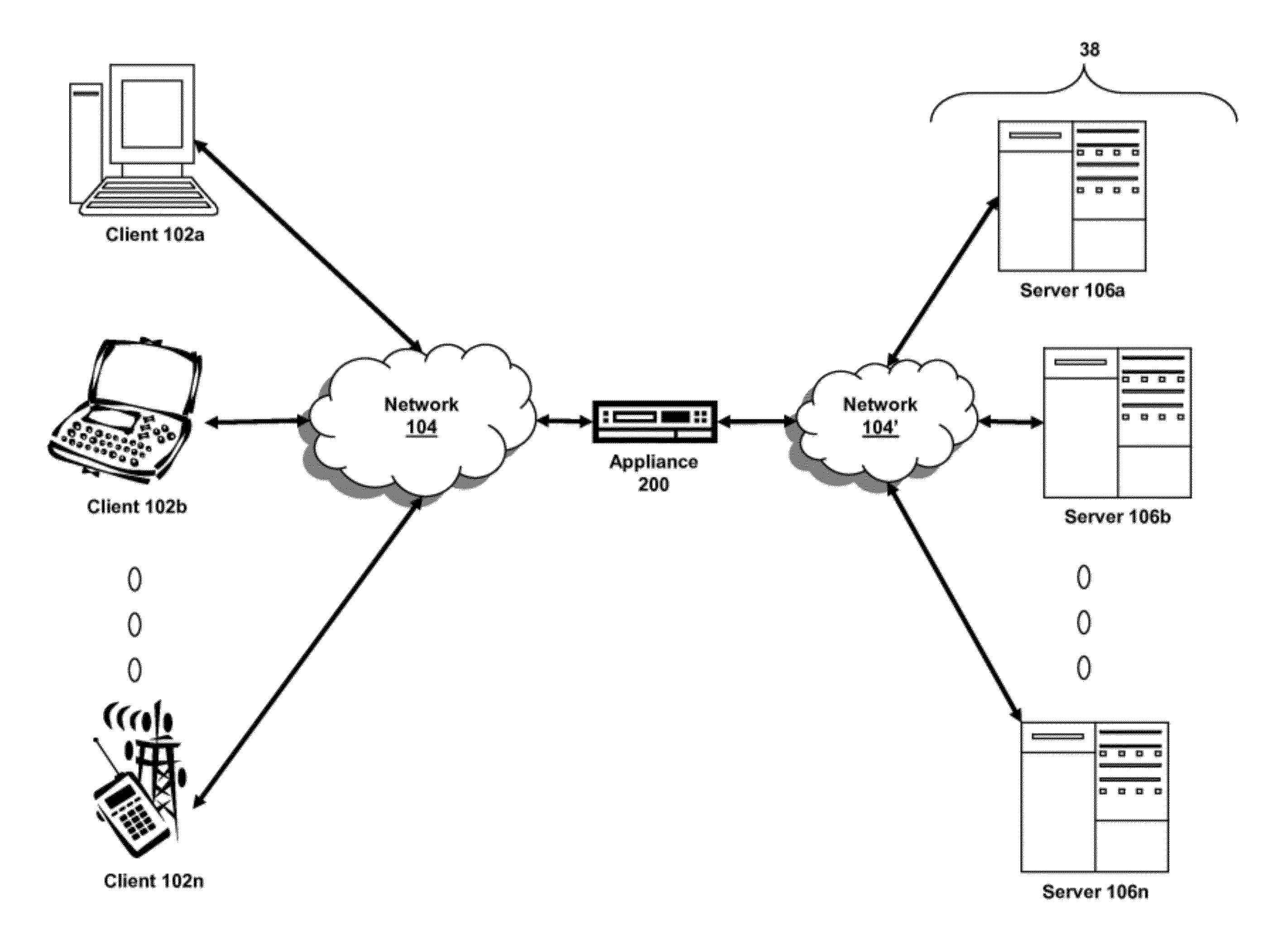
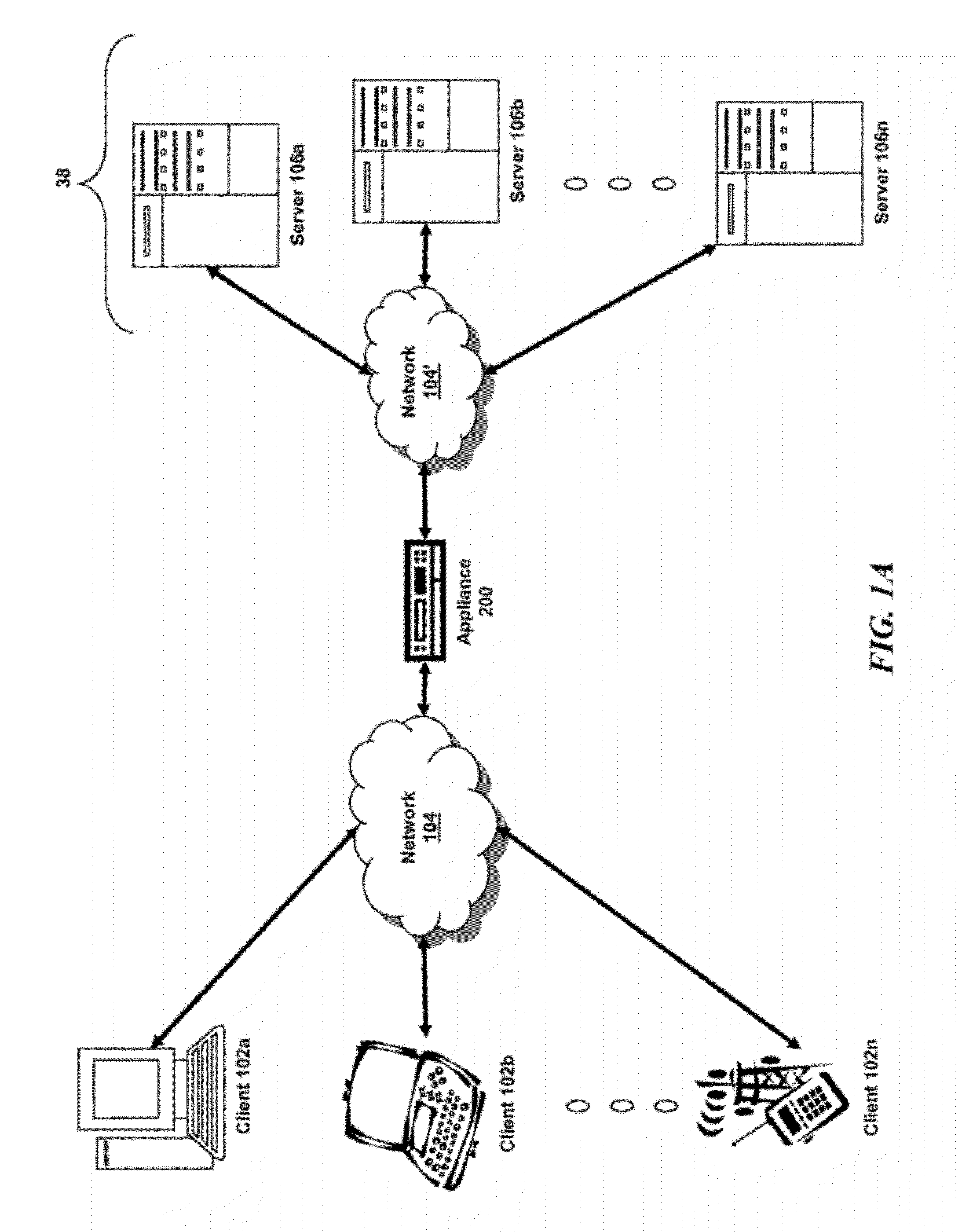
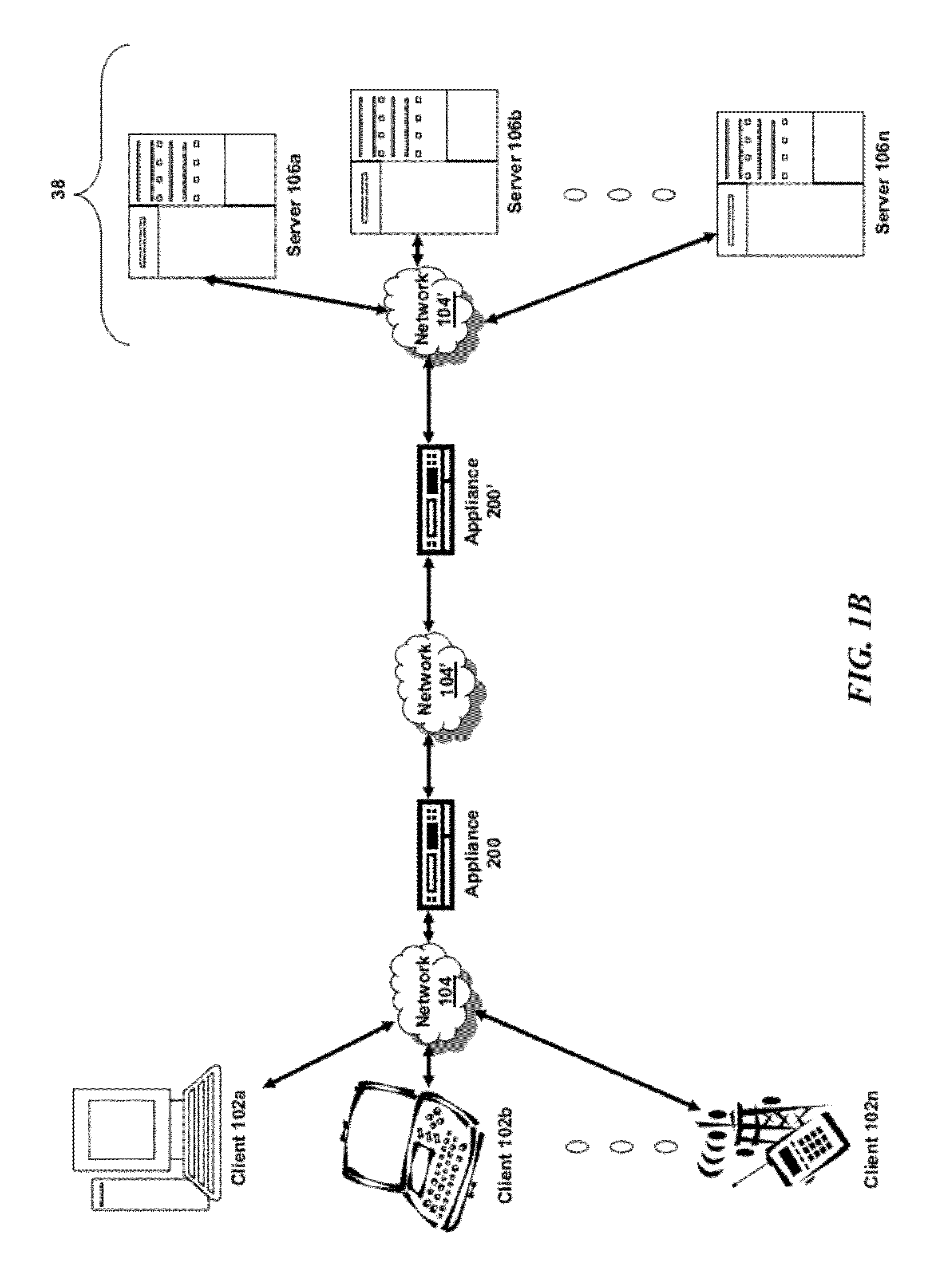
Systems and methods for managing domain name system security (dnssec)
ActiveUS20120117621A1Digital data processing detailsComputer security arrangementsDomain nameComputer network
The present invention is directed towards systems and methods for providing multiple modes of a zone for DNSSEC by an intermediary device. The method includes providing, by a device intermediary to a plurality of clients and a plurality of servers, a plurality of modes of a zone for Domain Name Service. The device receives a selection of a first mode of the zone of the plurality of modes of the zone. The device receives information identifying to enable DNS Security for the selected first mode. The device establishes the zone for DNS in accordance with the selected first mode and with DNS Security enabled.
Owner:CITRIX SYST INC
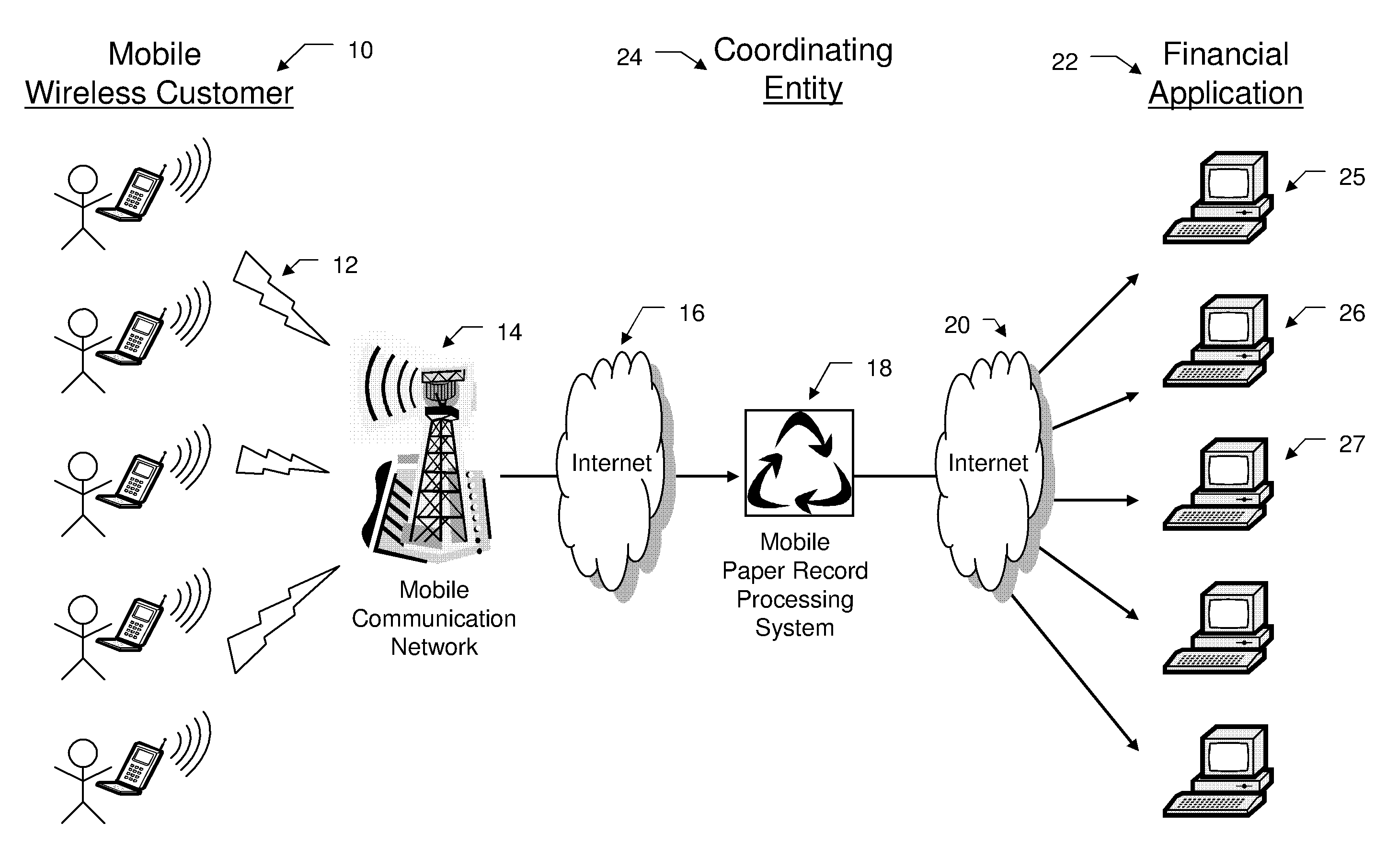
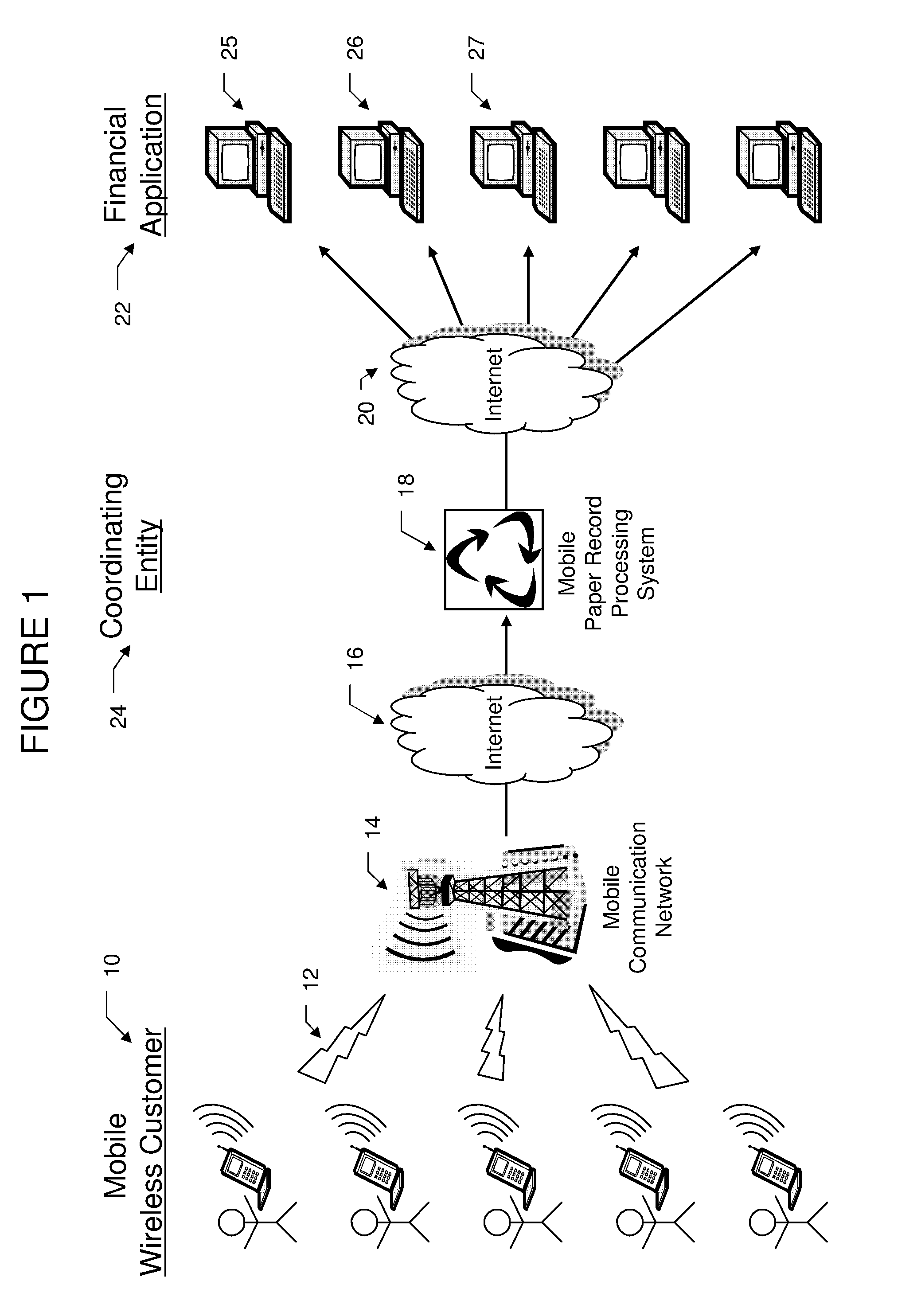
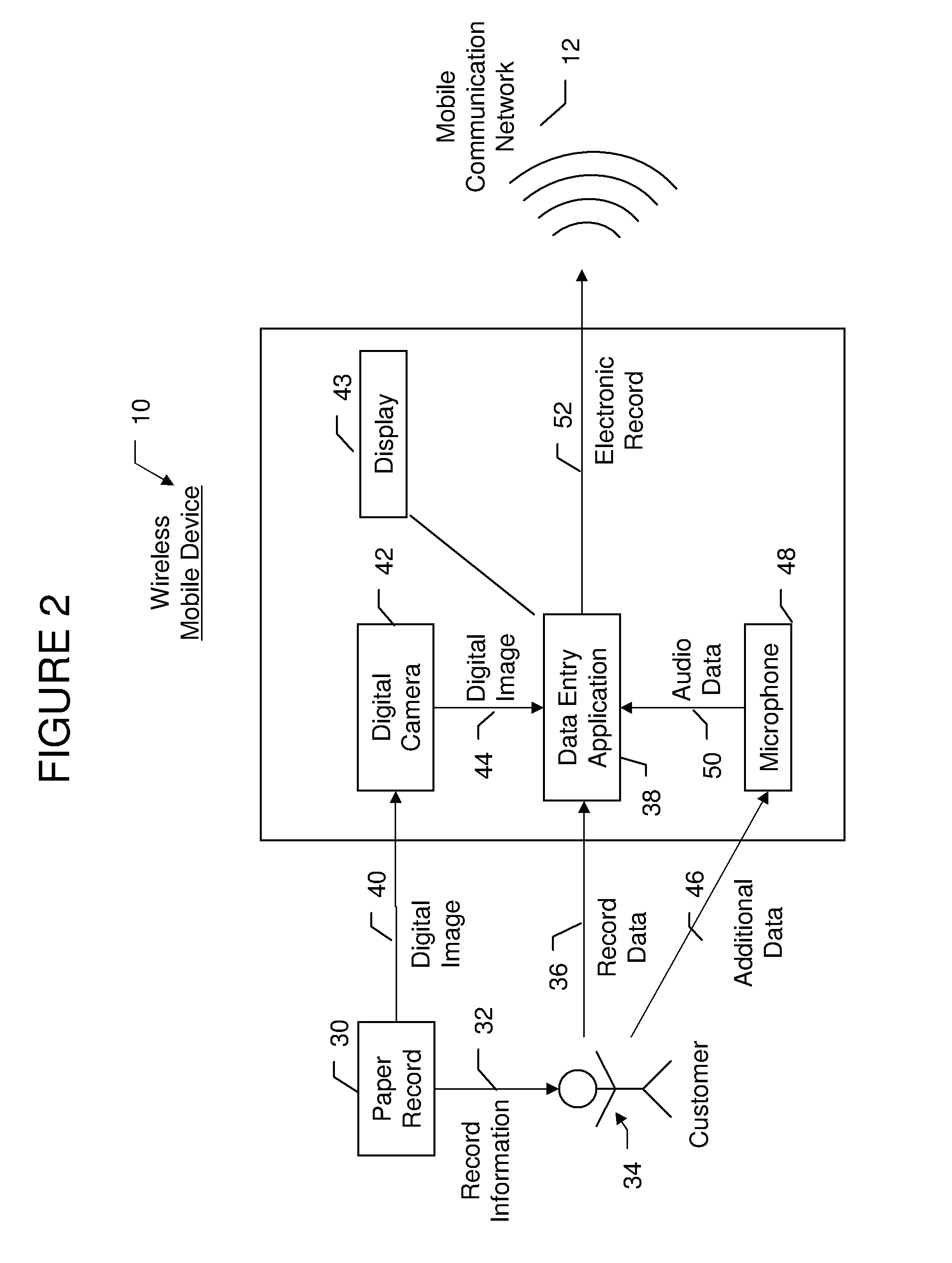
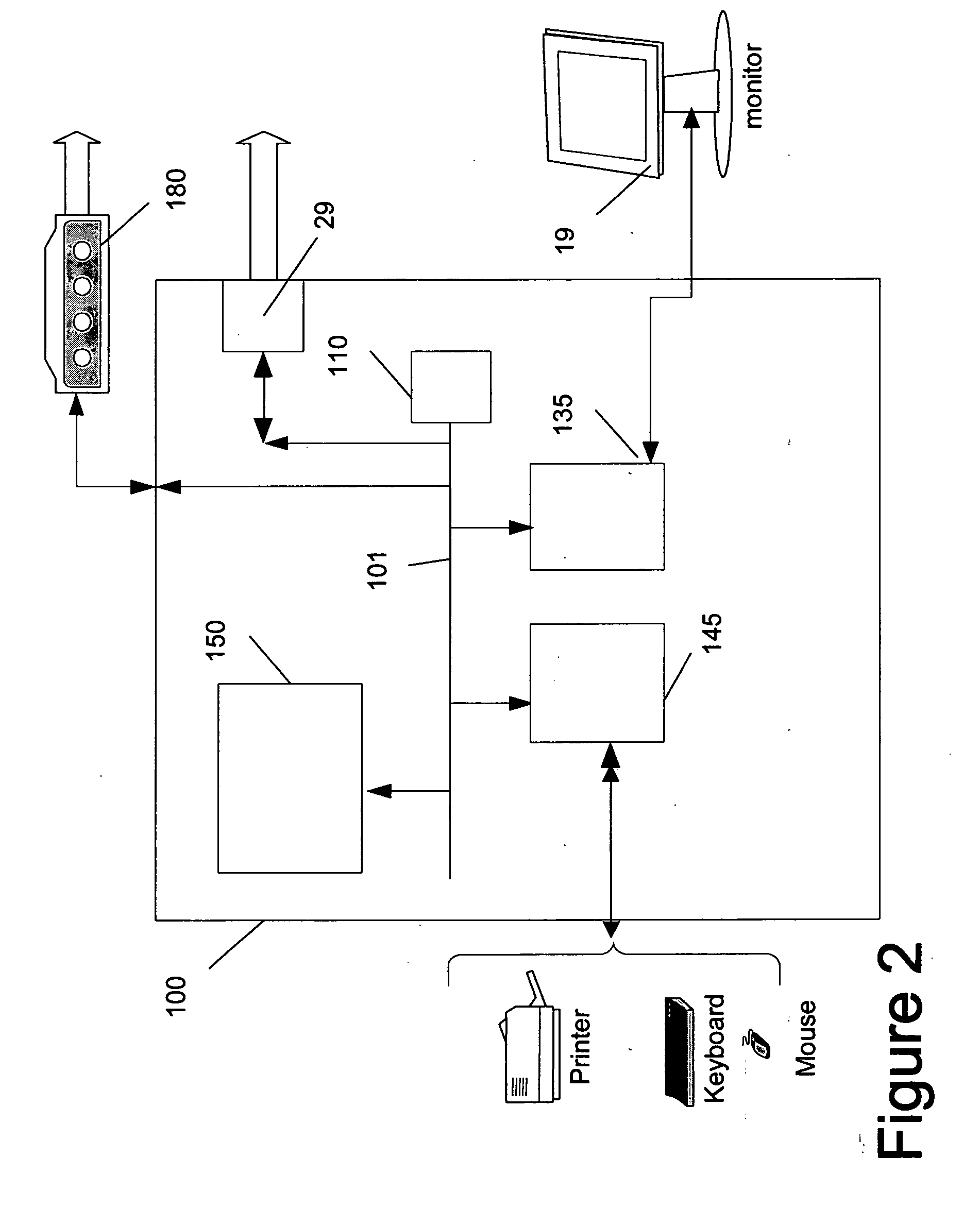
Mobile paper record processing system
InactiveUS6991158B2The process is convenient and fastMonitor progressComplete banking machinesFinanceWireless transmissionComputer graphics (images)
A method is disclosed for electronically capturing and storing paper records for accounting purposes using a mobile handheld device with an integrated digital camera or scanner. This method involves digitalizing a paper receipt with a digital camera or scanner, manually entering accounting data into a form presented on the display of a handheld device and performing a wireless transmission of the digital image of the paper record together with the entered information to a record storing system. The storing system securely stores the digital image of the record for future references and transmits manual entered record data to an accounting application using existing telecommunication or data networks.
Owner:MUNTE RALF MAXIMILIAN
Permission system for controlling interaction between autonomous vehicles in mining operation
InactiveUS6799100B2Analogue computers for vehiclesAnalogue computers for trafficGuidance systemControl system
A supervisory safety-control system is implemented by dividing a mine's territory into zones of free operation ("permission zones") wherein a vehicle is allowed to move according to predetermined permission parameters but unhindered by other system constraints. Traffic of autonomous vehicles in each permission zone is controlled by the supervisory system in conjunction with and in addition to conventional safety constraints associated with the guidance system that effects the vehicle's tracking of predetermined trajectories. Permission zones are assigned and activated using criteria that ensure the vehicle will remain entirely within active zones so long as the vehicle acts within such predetermined permission parameters. Each permission zone is also associated with a maximum velocity profile that overrides guidance-system safety controls, if necessary, and ensures stoppage of the vehicle at the end of the permission zone.
Owner:MODULAR MINING SYSTEMS
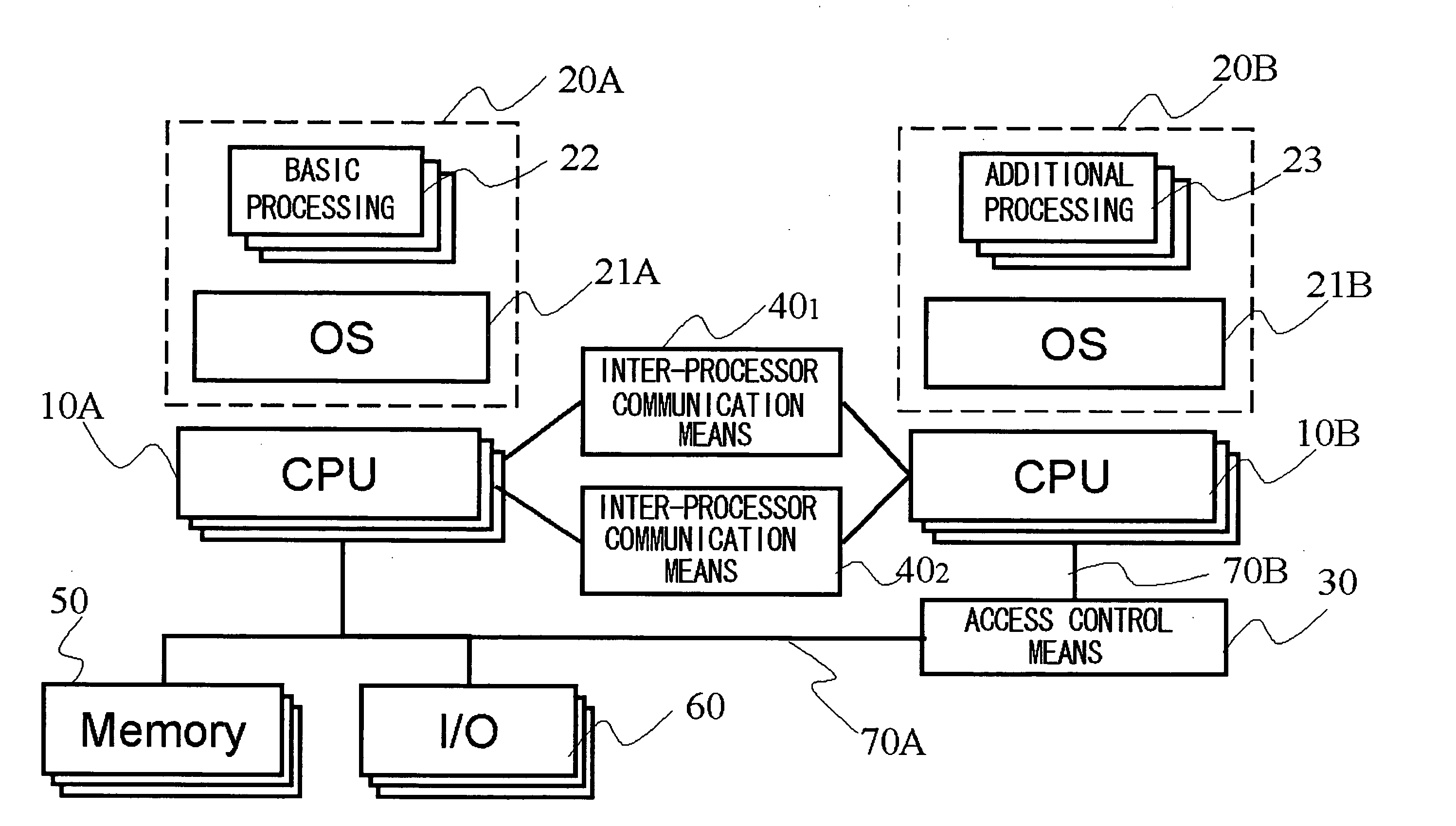
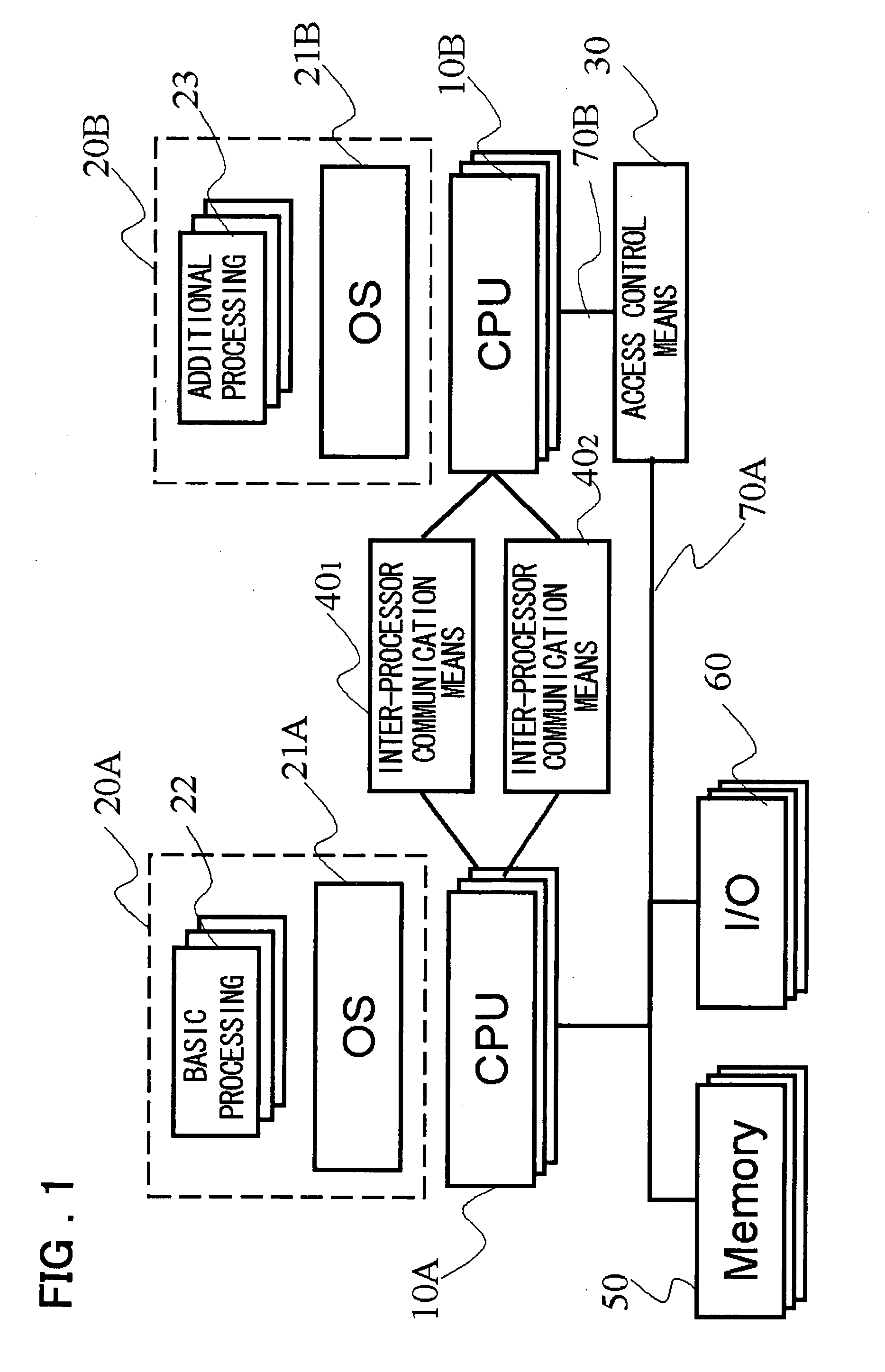
Information Communication Device and Program Execution Environment Control Method
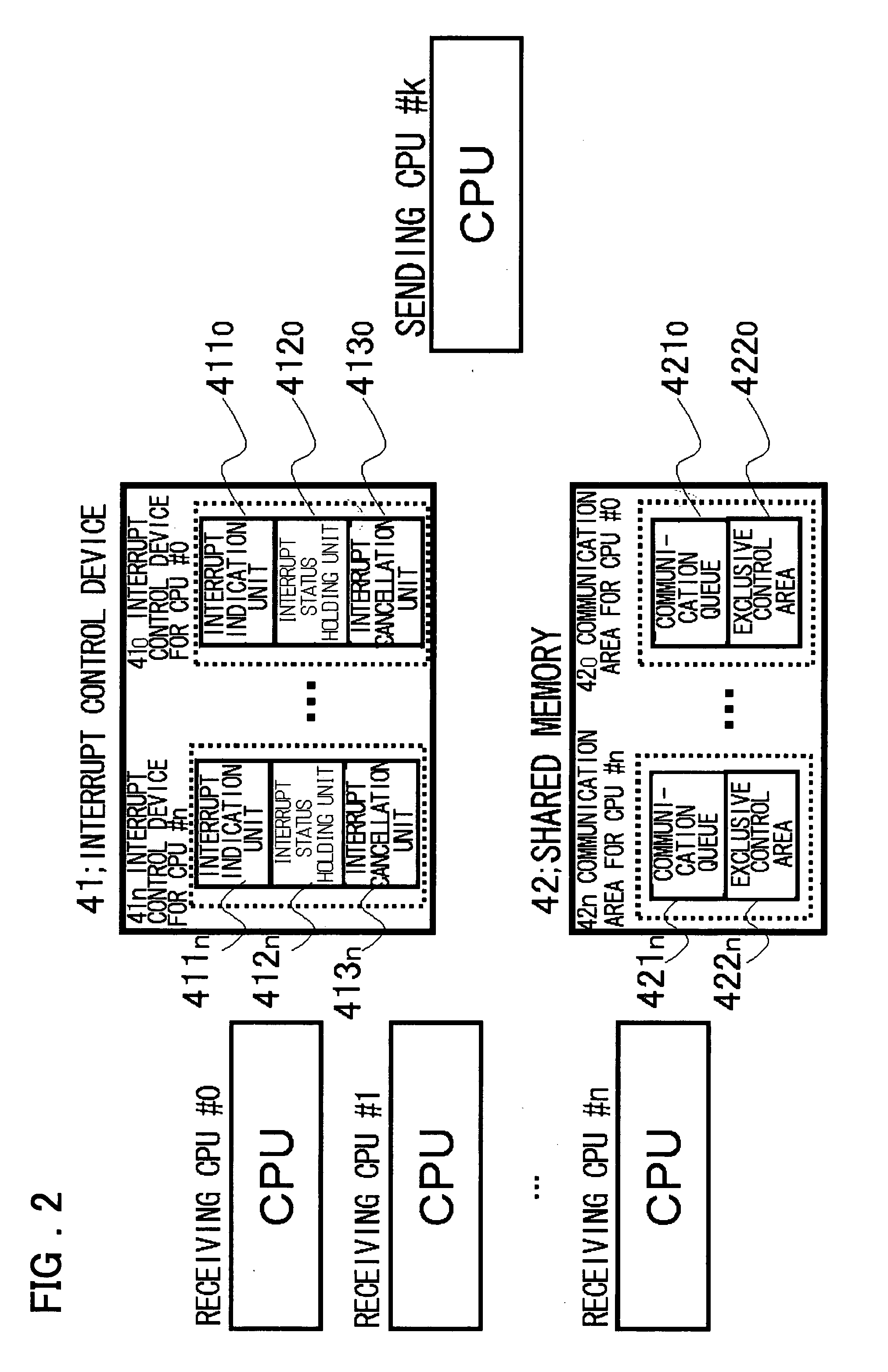
ActiveUS20080005794A1Ensure safetyHigh speed machiningResource allocationMemory loss protectionInterprocessor communicationCommunication device
A device and a method are provided for increasing processing speed and for ensuring system security when an application or a driver is added. The device includes a first CPU group 10A that executes software 20A composed of basic processing 22 and an OS 21A; a second CPU group 10B that executes software 20B composed of additional processing 23 and OS 21B corresponding to the additional processing, inter-processor communication means 40, and 402 used for communication between the first CPU 10A and the second CPU 10B, and access control means 30 that controls access made by the second CPU 10B to a memory 50 and / or an input / output device 60.
Owner:NEC CORP
Personnel and vehicle identification system using three factors of authentication
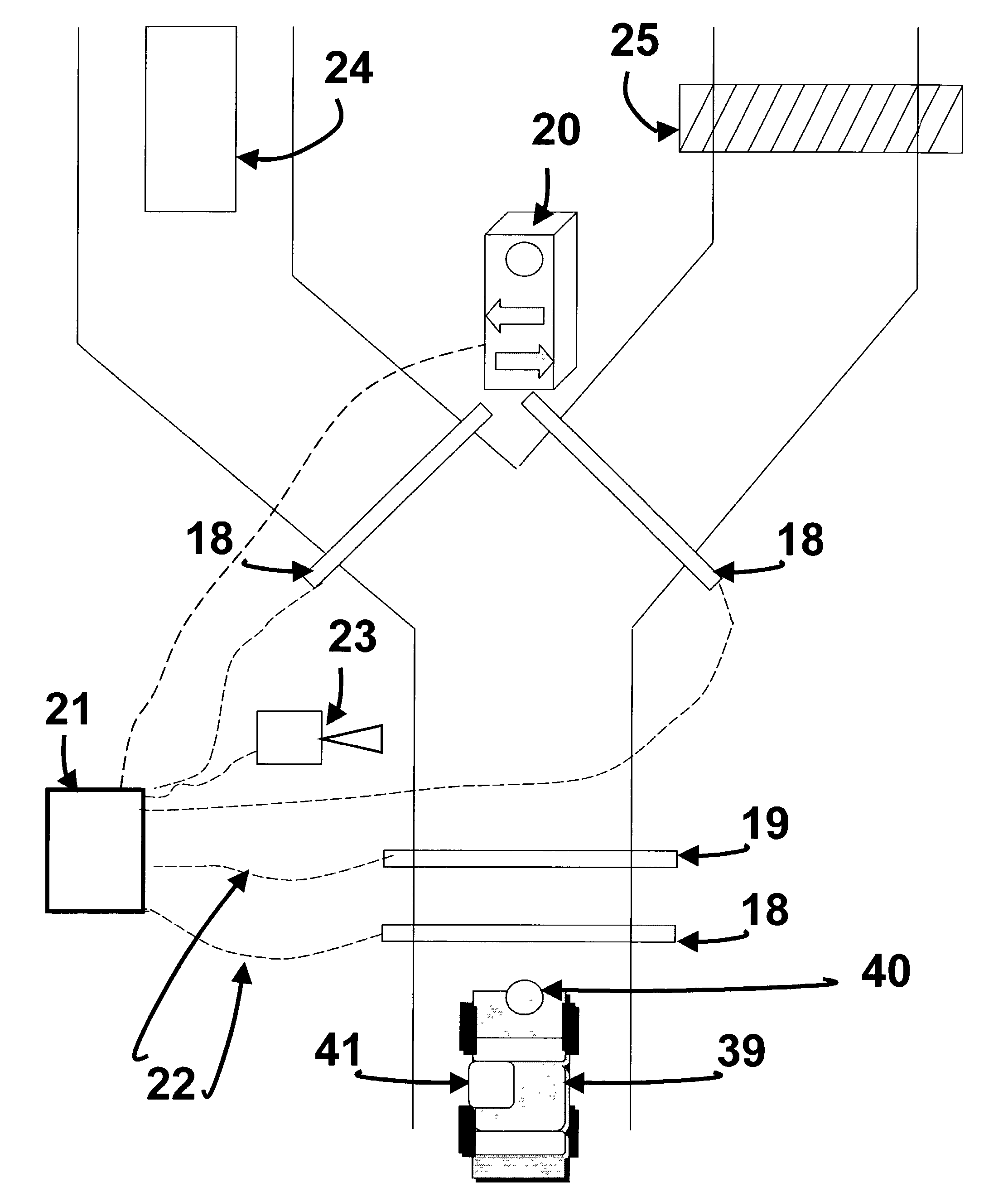
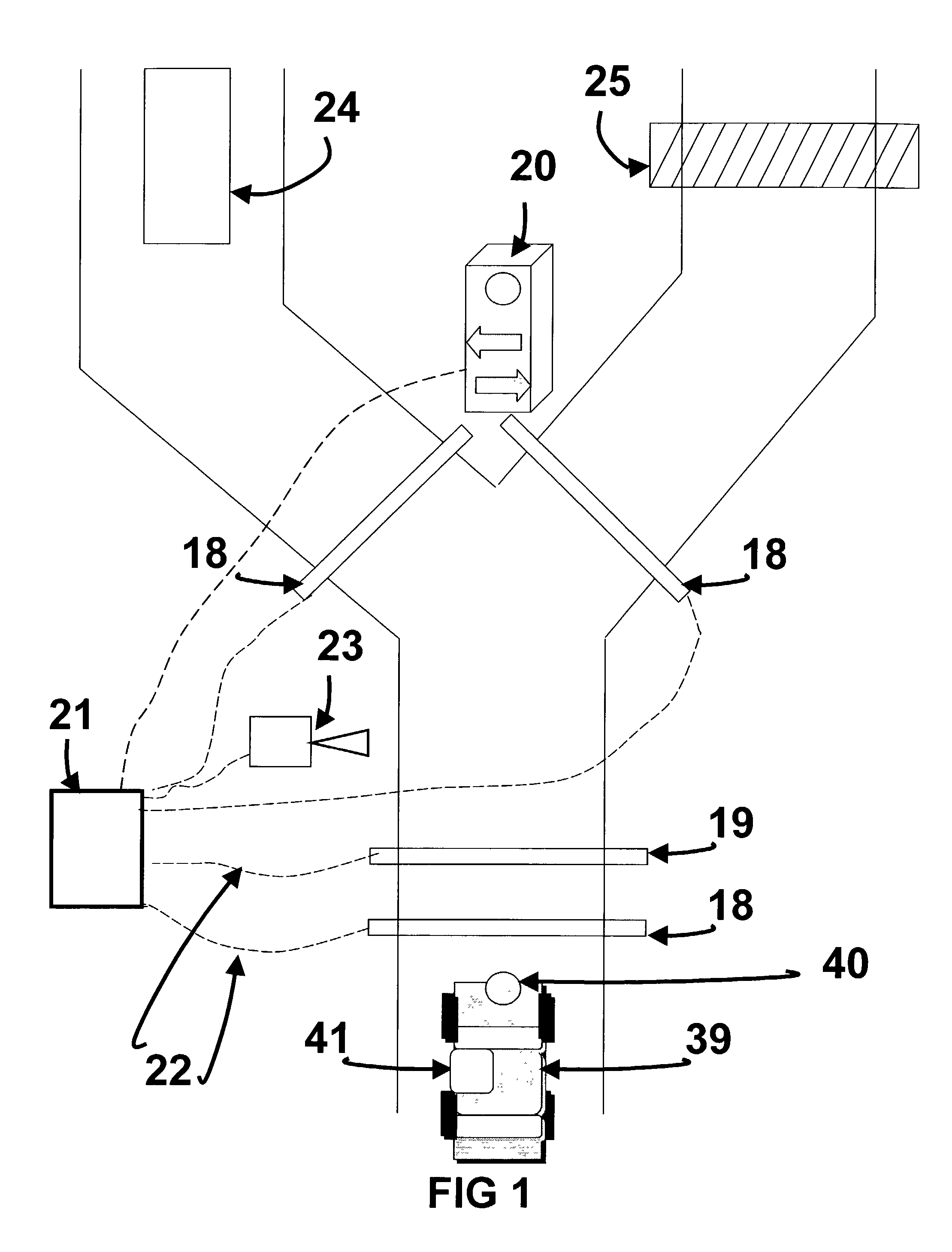
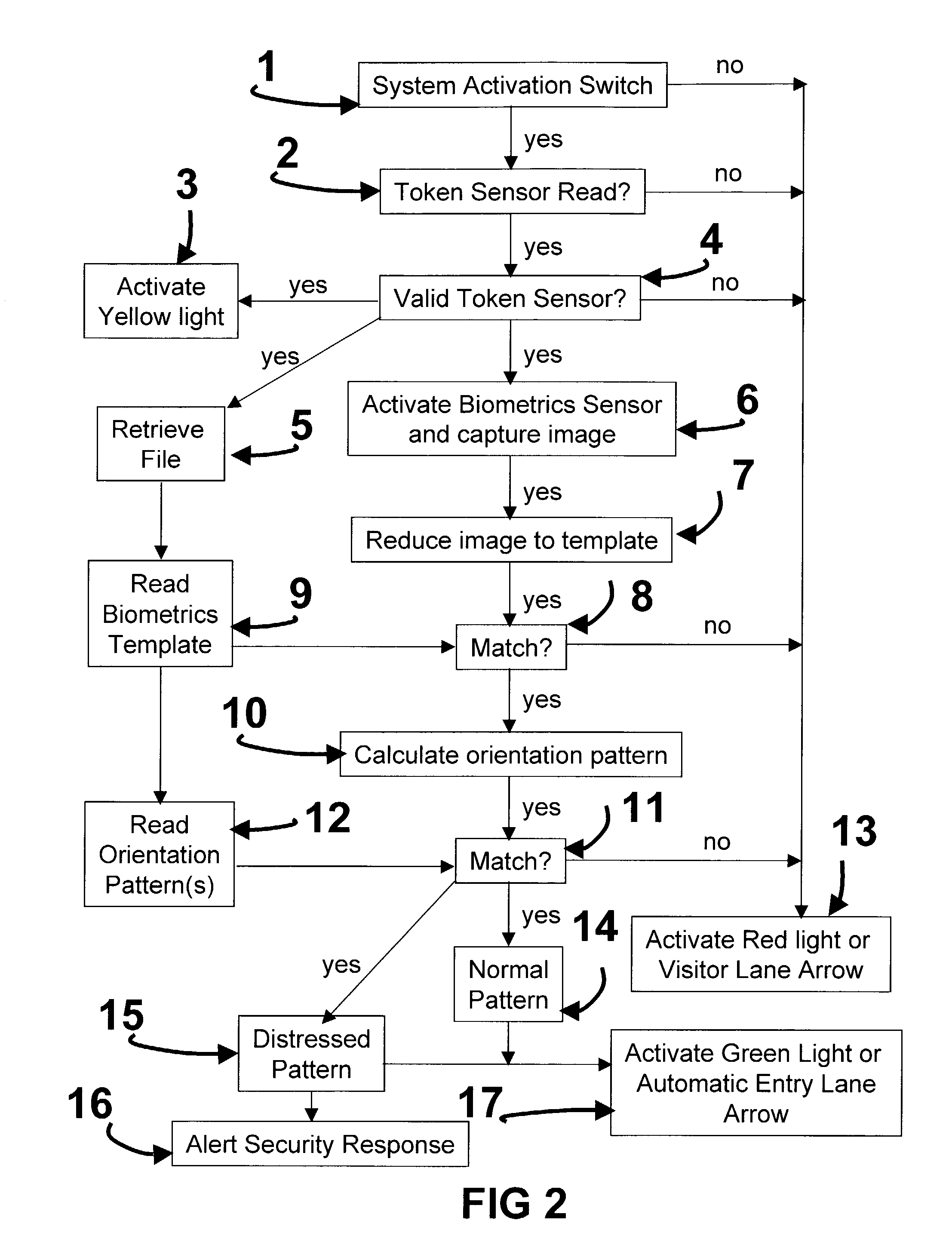
InactiveUS20040002894A1Electric signal transmission systemsTicket-issuing apparatusCombined useBarcode
The Personnel And Vehicle Identification System Using Three Factors of Authentication (PAVIS-3) invention is a novel approach that combines the three authentication factors using contactless token, contactless biometric, and the unique position of said biometric presented by a person to allow rapid authentication and access to a base or building. This invention has the real potential to reduce manpower at base gates, building, and greatly improve system security. A vehicle with a contactless token such as an RFID, proximity chip, or barcode, approaches an entry lane at a base, the contactless token is read, verified, (first factor) queuing the individual's file with a biometric template and personal identification position. The biometric image is taken, reduced to a template, compared with the template in the database and if matched (second factor) the body position is examined to see if it matches the personal identification position (third factor) as a normal or covert distressed signal. If normal the vehicle is given a green light, if any match fails the vehicle is directed to the visitor's lane.
Owner:THE RIGHT PROBLEM
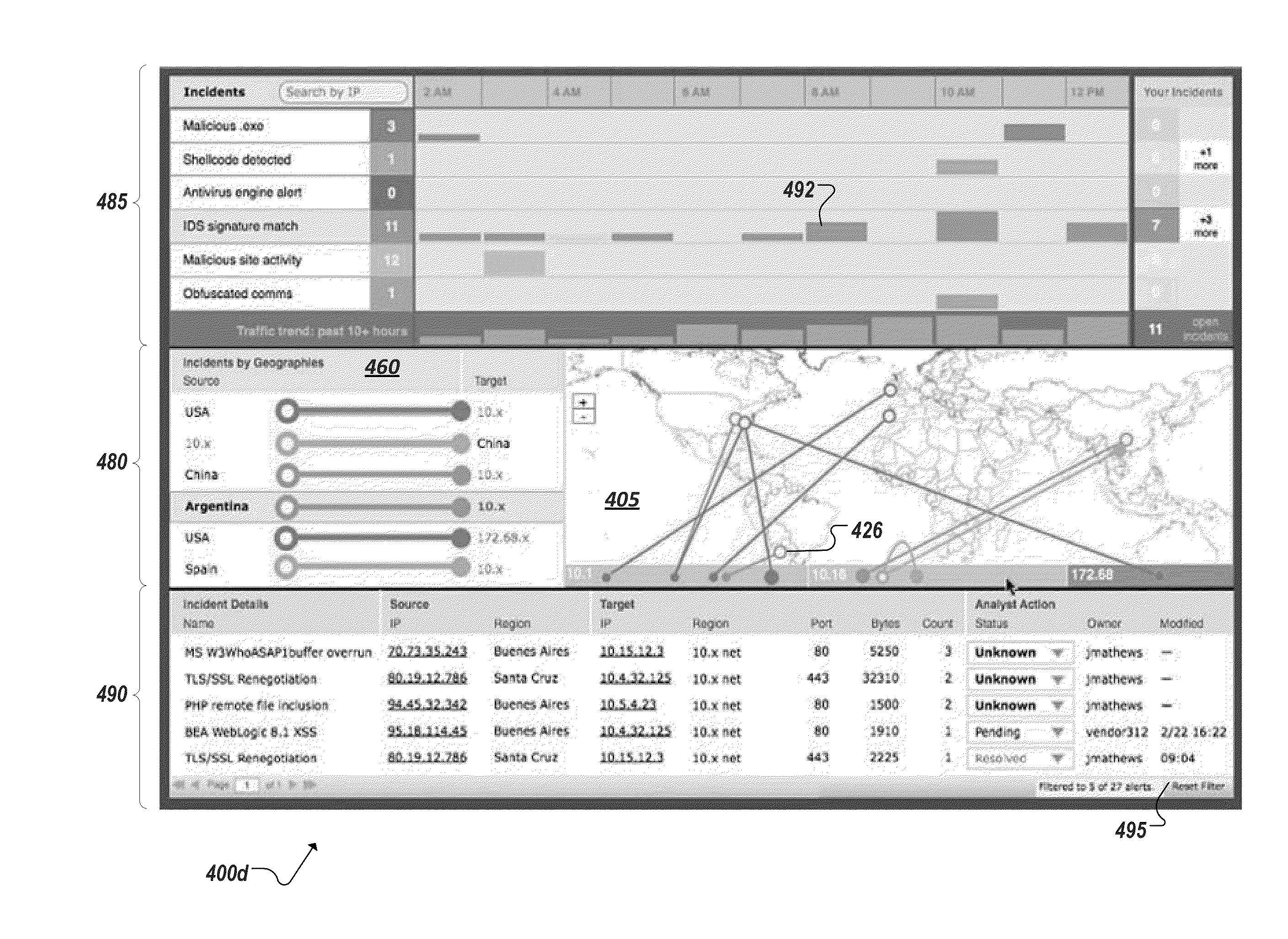
Geo-mapping system security events
A particular security event is identified that has been detected as targeting a particular computing device included in a particular computing system. A particular grouping of assets in a plurality of asset groupings within the particular computing system is identified as including the particular computing device. A source of the particular security event is also identified and at least one of a geographic location and a grouping of assets in the plurality of asset groupings is associated with the identified source. Data is generated that is adapted to cause a presentation of a graphical representation of the particular security event on a display device, the graphical representation including a first graphical element representing the particular computing device as included in the particular grouping of assets and a second graphical element representing the source associated with the at least one of a geographic location and a grouping of assets.
Owner:MCAFEE LLC
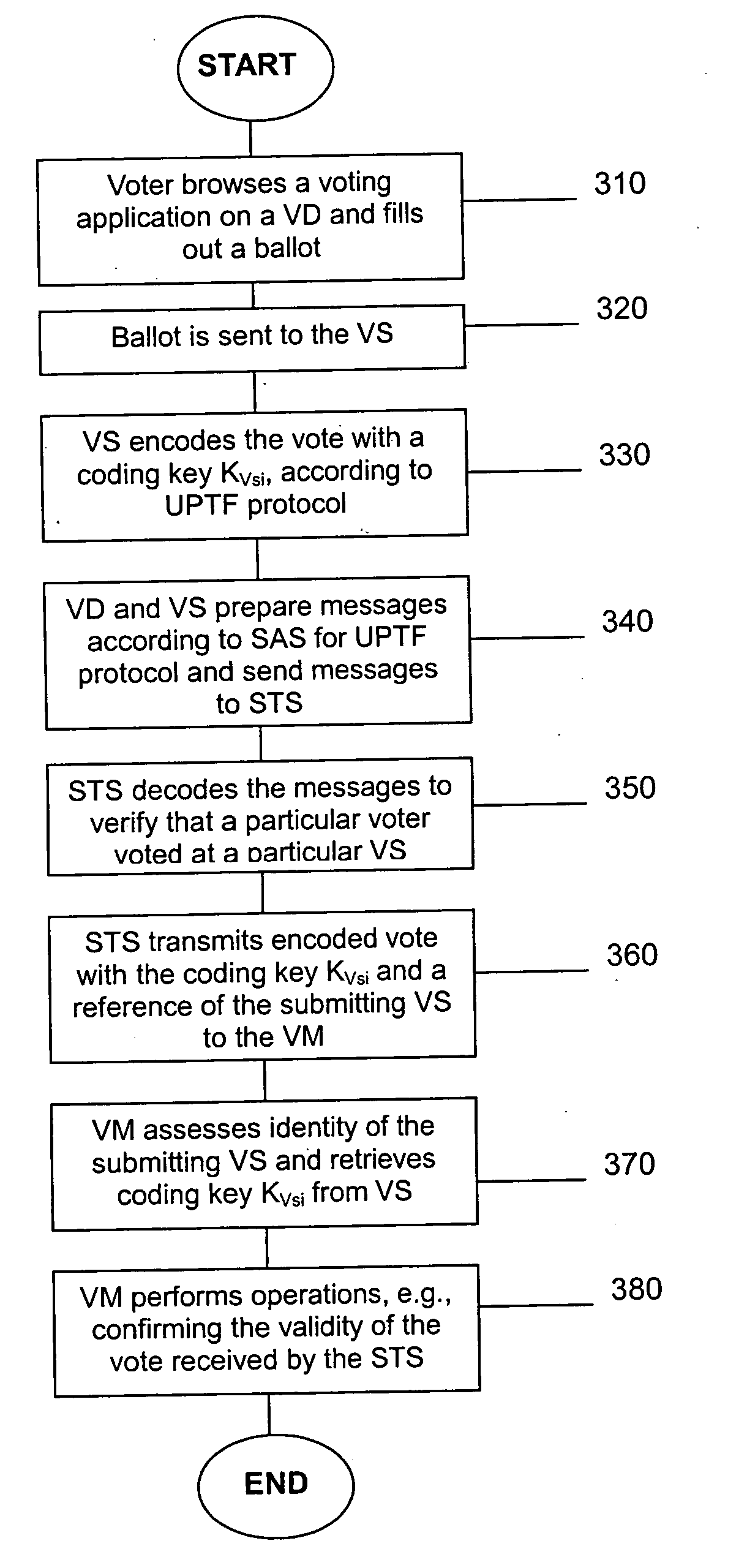
Opinion registering application for a universal pervasive transaction framework
InactiveUS20050203966A1Digital data processing detailsUser identity/authority verificationUser inputAnonymity
A computer-based system securely transmitting and authenticating a transaction input by a user while retaining the anonymity of the user with respect to content of the transaction, including a device encoding the content of the transaction input by the user with a key known only to another device, encoding other portions of the transaction with another key known only to a secure transaction server, and sending the encoded content of the transaction and the encoded other portions of the transaction to the secure transaction server to authenticate an identity of the user of the device, wherein the secure transaction server decodes the other portions of the transaction and sends the encoded content of the transaction to the another device to be finally decoded.
Owner:PCMS HOLDINGS INC
Method and system for preventing identity theft and increasing security on all systems
The present invention provides a method and system for preventing identity theft and increasing security on systems. Some embodiments include receiving, into a computer system, a request to perform an electronic transaction for an identified human user at a remote location; accessing, by the system, a set of authentication criteria of the identified user; retrieving, into the system, a plurality of real-time authentication parameters relevant to the user and to the transaction; and comparing, by the system, the plurality authentication criteria to the accessed set of authentication parameters of the user and either authorizing an action to complete the electronic transaction or not. Some embodiments include displaying, on a first personal electronic device of the user, an indication of the real-time alert of the request to perform the electronic transaction; and eliciting and receiving a real-time authorization indication from the user using the first personal electronic device of the user.
Owner:CANNON ROYCE E
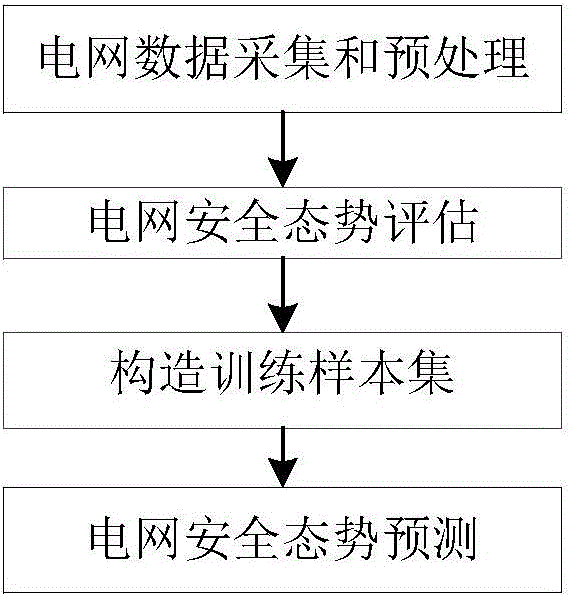
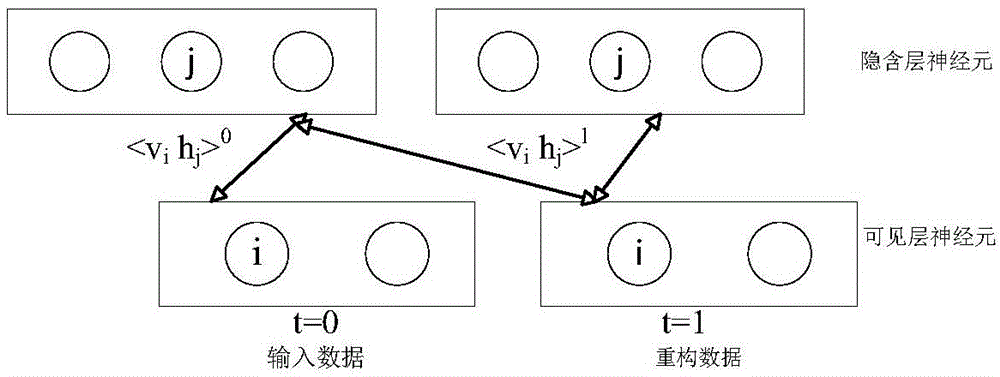
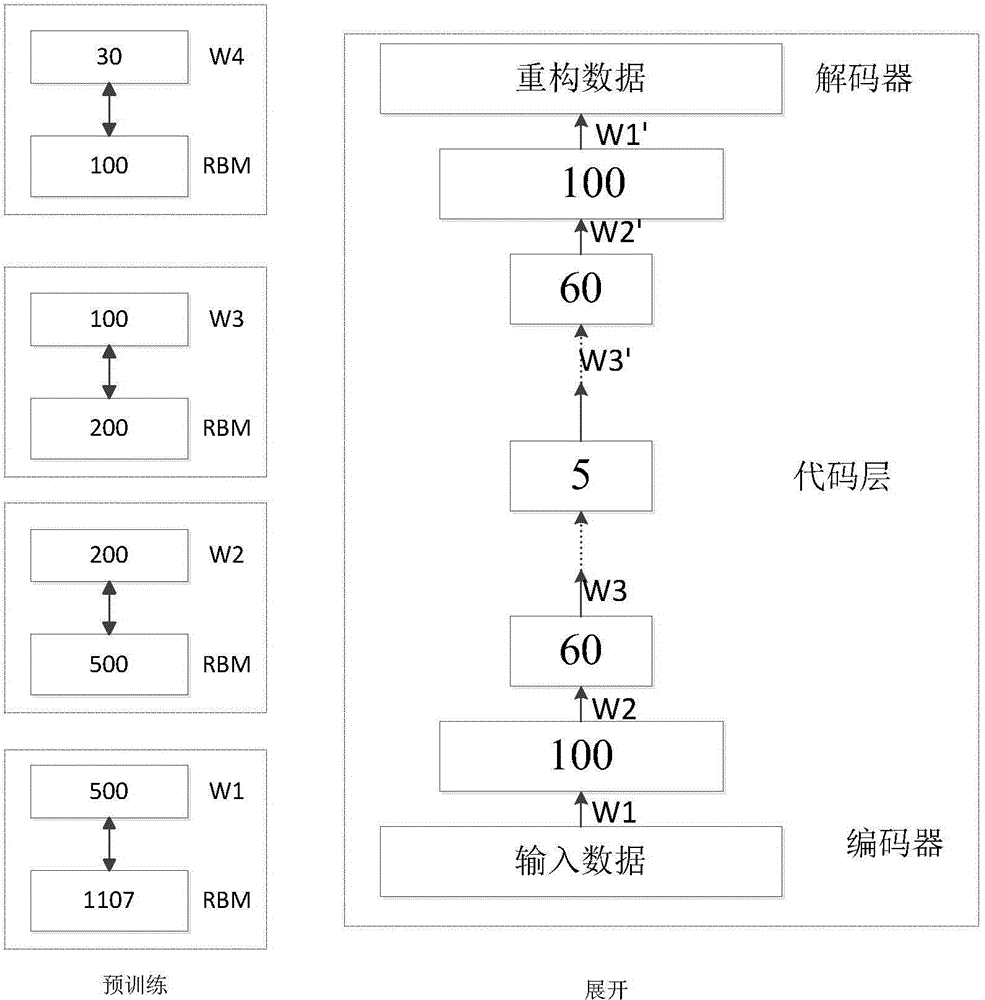
Power grid security situation predicting method based on improved deep learning model
InactiveCN104794534AFast predictionStrong non-linear mapping abilityForecastingDeep belief networkMulti input
The invention discloses a power grid security situation predicting method based on an improved deep learning model and belongs to the technical field of power system safety. The power grid security situation predicting method includes: performing power grid security situation evaluation through power grid data collection and preprocessing; aiming at the characteristic that indicator data of power grid security situation evaluation are high in relevance and dimension, providing an improved self-coding network method to lower dimension of the indicator data, and utilizing a data sample after dimension reduction and a power grid security situation value corresponding to a next time monitoring point; adopting an improved deep belief network to build a deep learning situation predicting model with multi-input and multi-output for power grid security situation prediction. By the power grid security situation predicting method, speed and accuracy of power grid security situation prediction can be improved effectively.
Owner:STATE GRID SHANDONG ELECTRIC POWER
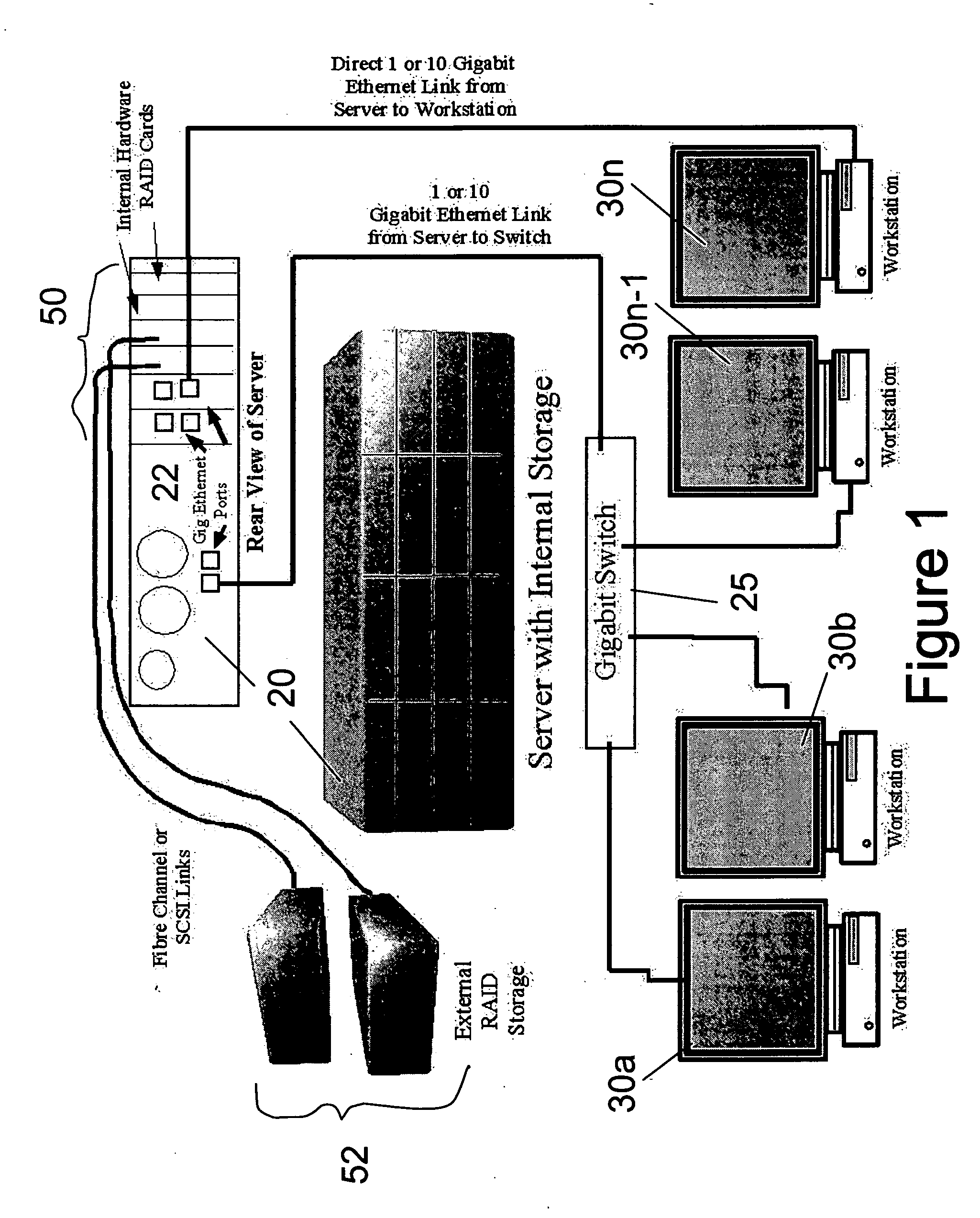
Novel media file access and storage solution for multi-workstation/multi-platform non-linear video editing systems
ActiveUS20060184673A1Digital data processing detailsElectronic editing digitised analogue information signalsSymbolic linkMulti platform
Owner:EDITSHARE LLC
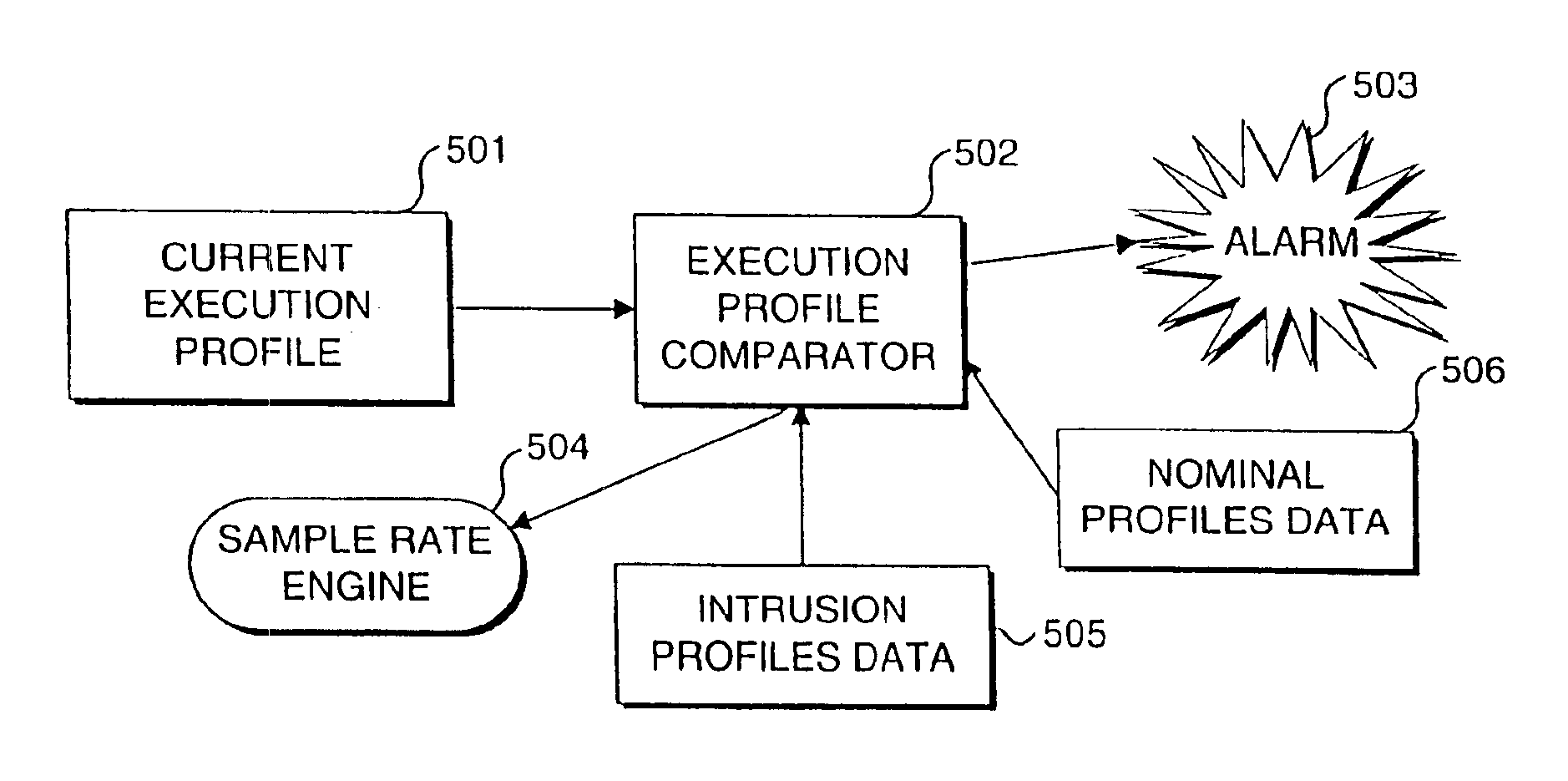
Method of and system for detecting an anomalous operation of a computer system
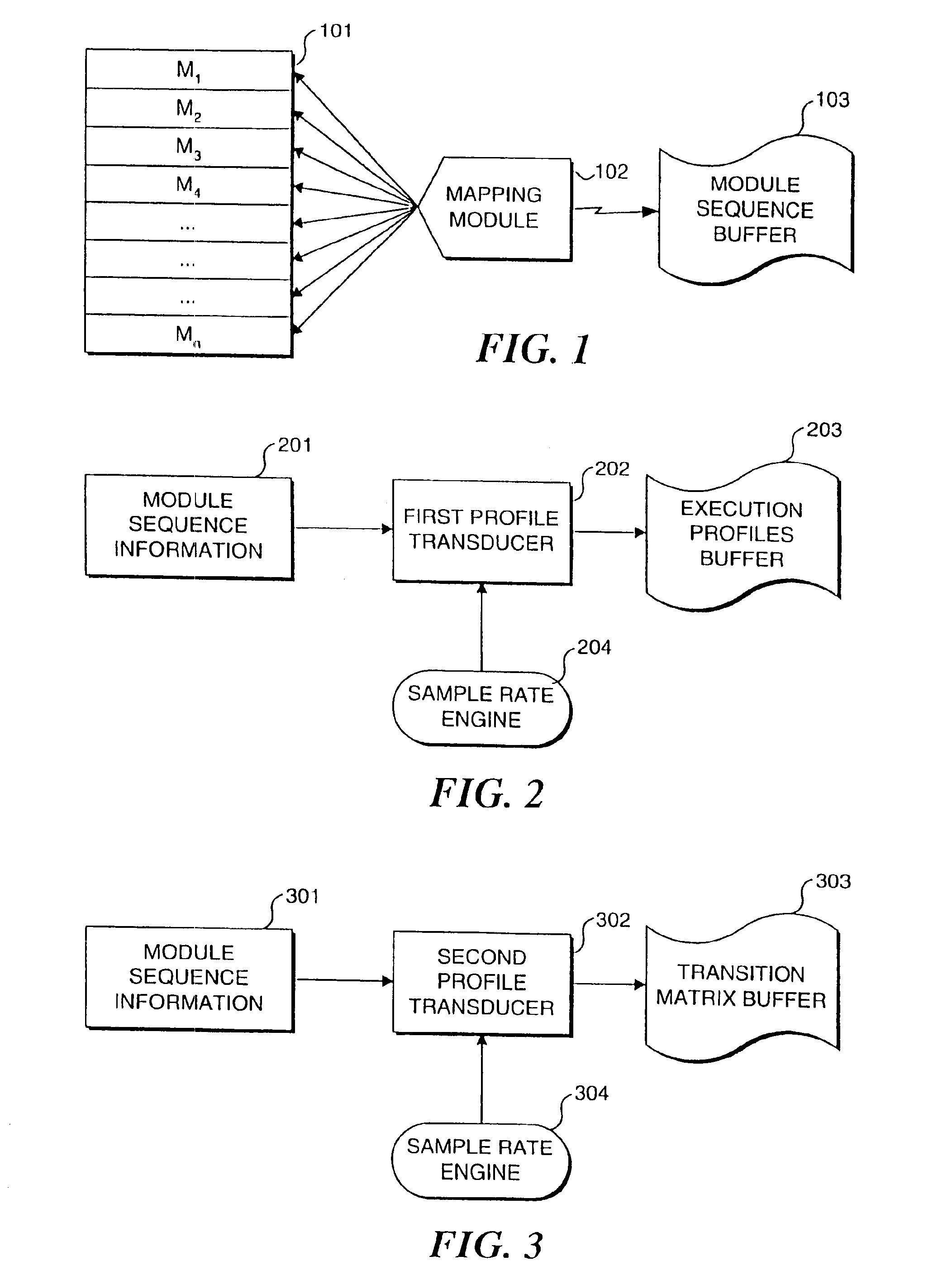
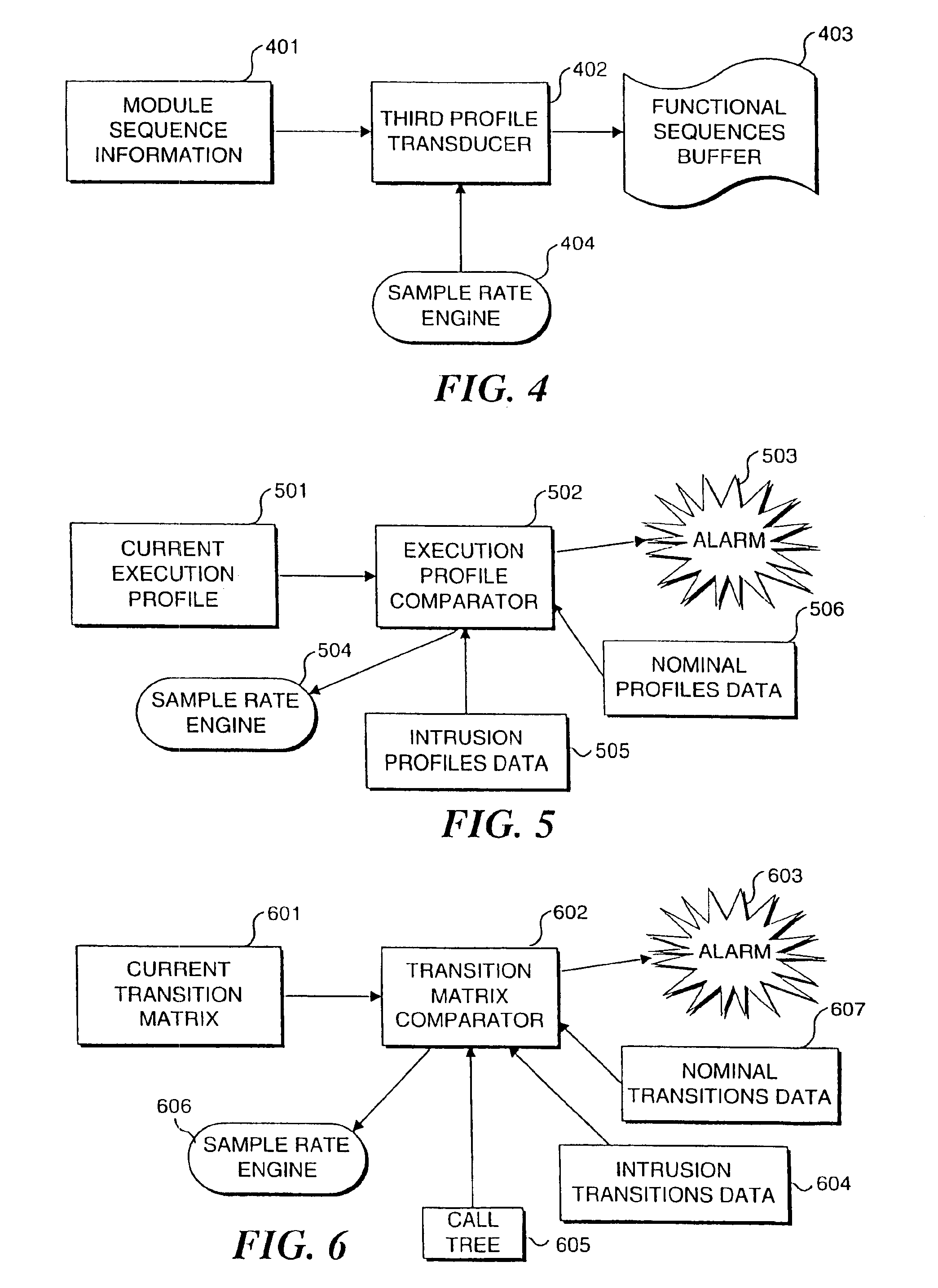
InactiveUS6963983B2Memory loss protectionDigital data processing detailsSoftware systemTheoretical computer science
A real-time approach for detecting aberrant modes of system behavior induced by abnormal and unauthorized system activities that are indicative of an intrusive, undesired access of the system. This detection methodology is based on behavioral information obtained from a suitably instrumented computer program as it is executing. The theoretical foundation for the present invention is founded on a study of the internal behavior of the software system. As a software system is executing, it expresses a set of its many functionalities as sequential events. Each of these functionalities has a characteristic set of modules that is executed to implement the functionality. These module sets execute with clearly defined and measurable execution profiles, which change as the executed functionalities change. Over time, the normal behavior of the system will be defined by the boundary of the profiles. An attempt to violate the security of the system will result in behavior that is outside the normal activity of the system and thus result in a perturbation of the system in a manner outside the scope of the normal profiles. Such violations are detected by an analysis and comparison of the profiles generated from an instrumented software system against a set of known intrusion profiles and a varying criterion level of potential new intrusion events.
Owner:STRATACLOUD
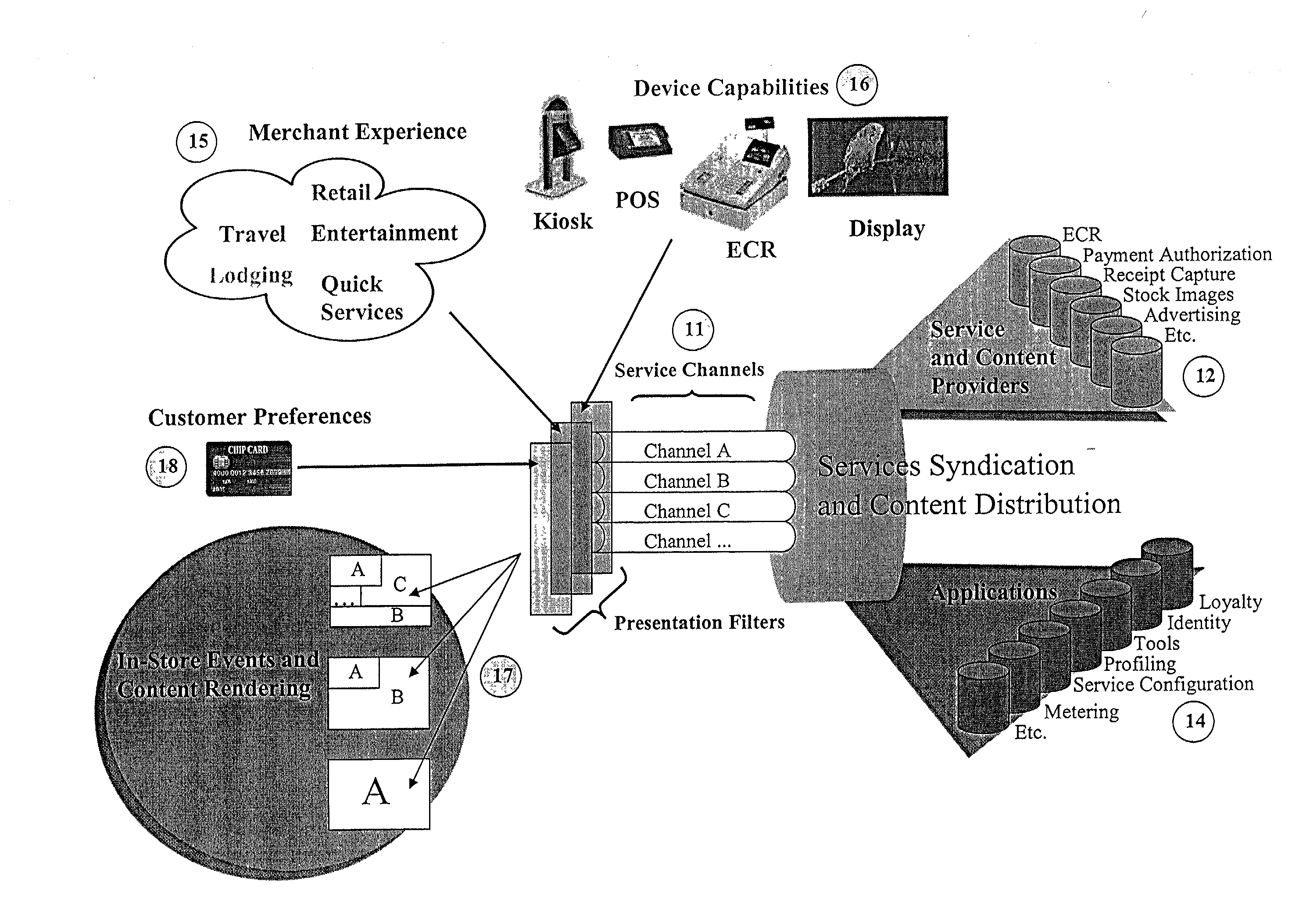
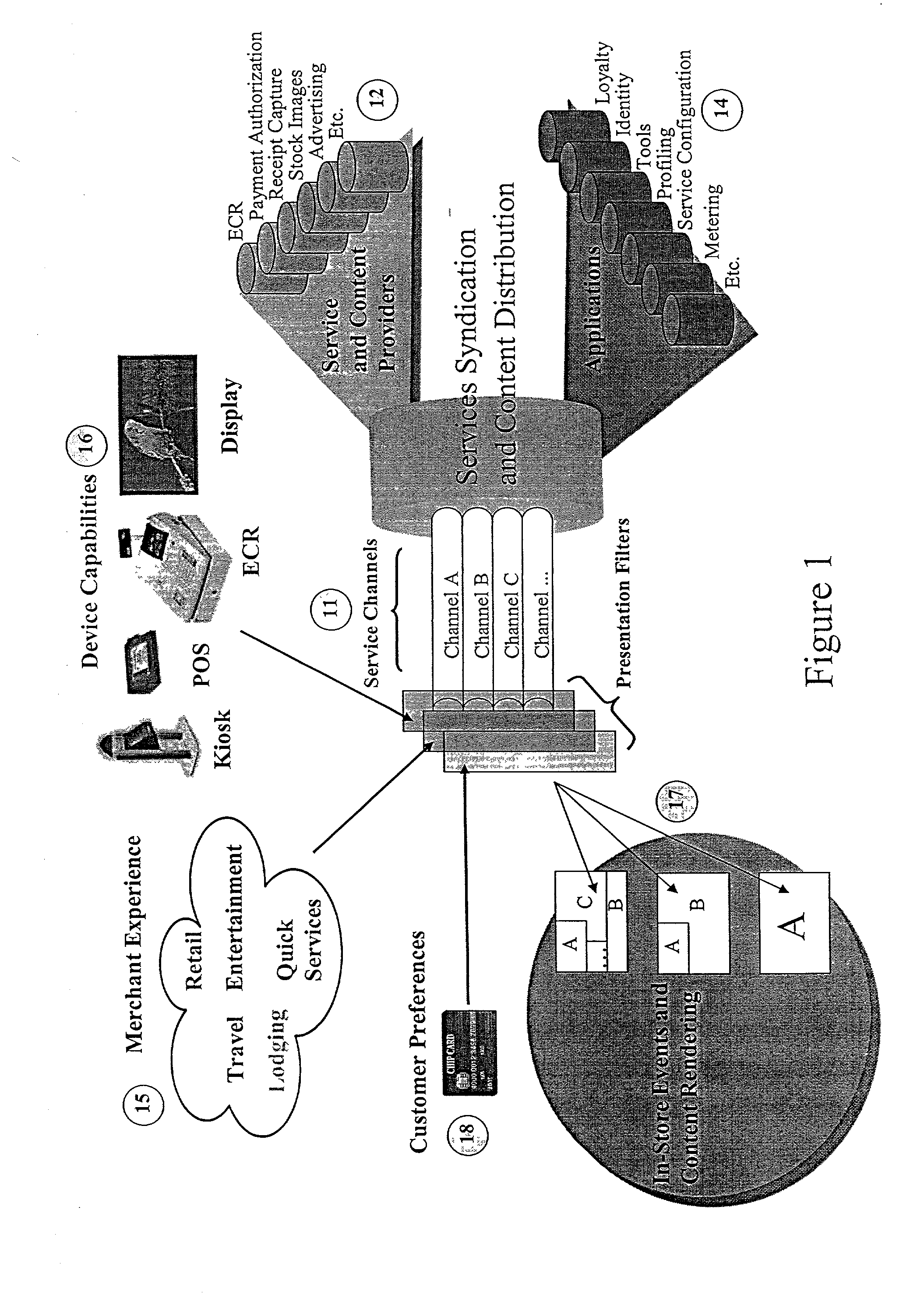
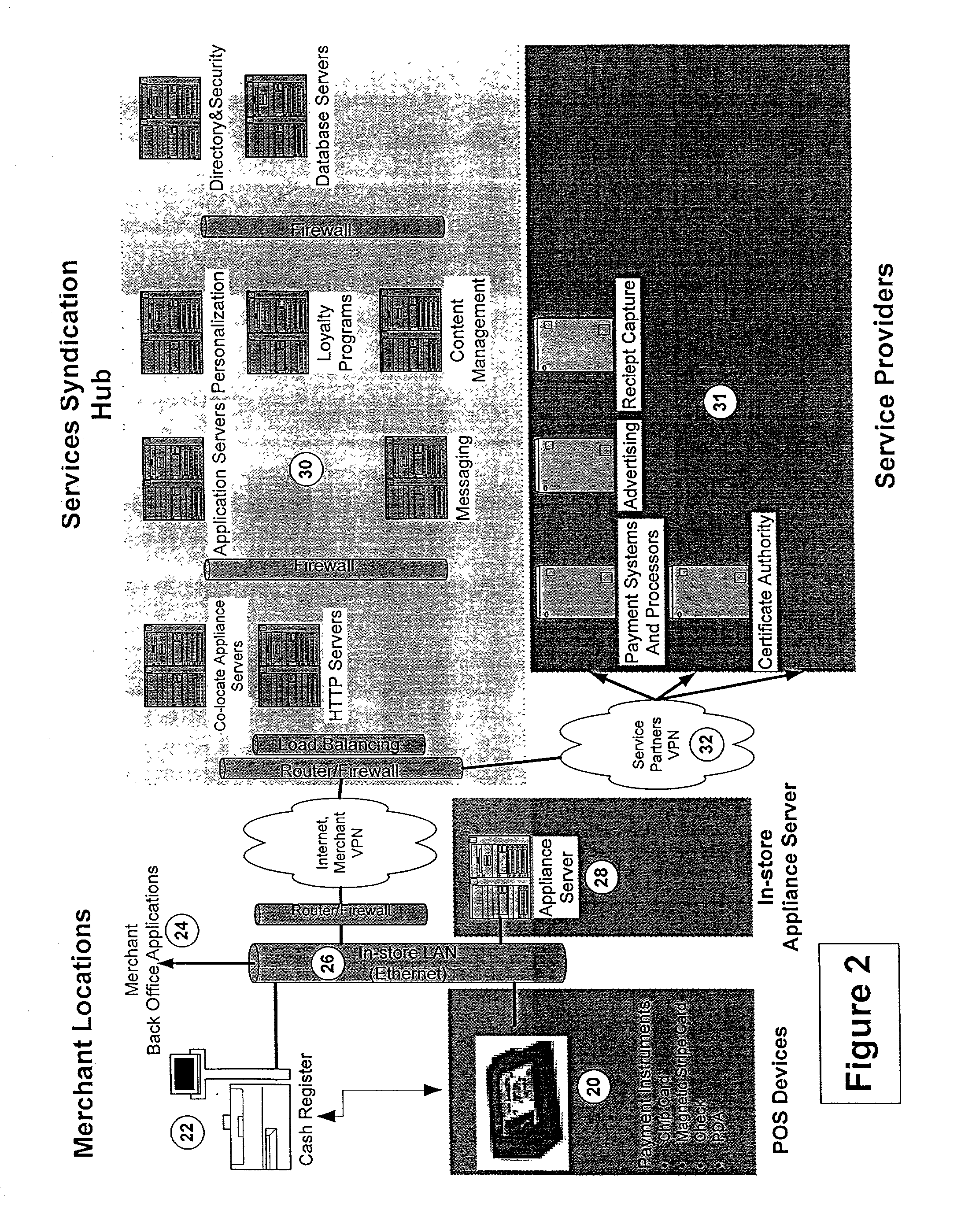
Method and system for providing multiple services via a point-of-sale portal architecture
ActiveUS20080195465A1Hand manipulated computer devicesPayment protocolsDialog managementSystems management
A secure point-of-sale (POS) portal architecture for delivering multiple services is provided. According to one exemplary aspect of the architecture, a number of services offered by various parties are integrated for delivery to merchants. The parties offering the services include, for example, payment processors and merchant acquirers and other external value-added service providers. The integrated services, in turn, are offered to merchants and / or their respective customers via one or more POS devices and its supporting system infrastructure at the merchant locations. The integrated services include, for example, acceptance of multiple payment instruments, payment processing, user dialog management, sales promotion and customer support, loyalty programs, back office processing, receipt capture, employee training, risk management, dispute resolution, system security, system administration etc. Moreover, these integrated services may be customized based on a merchant's particular requirements to provide a specific environment for delivering these services.
Owner:VISA USA INC (US)
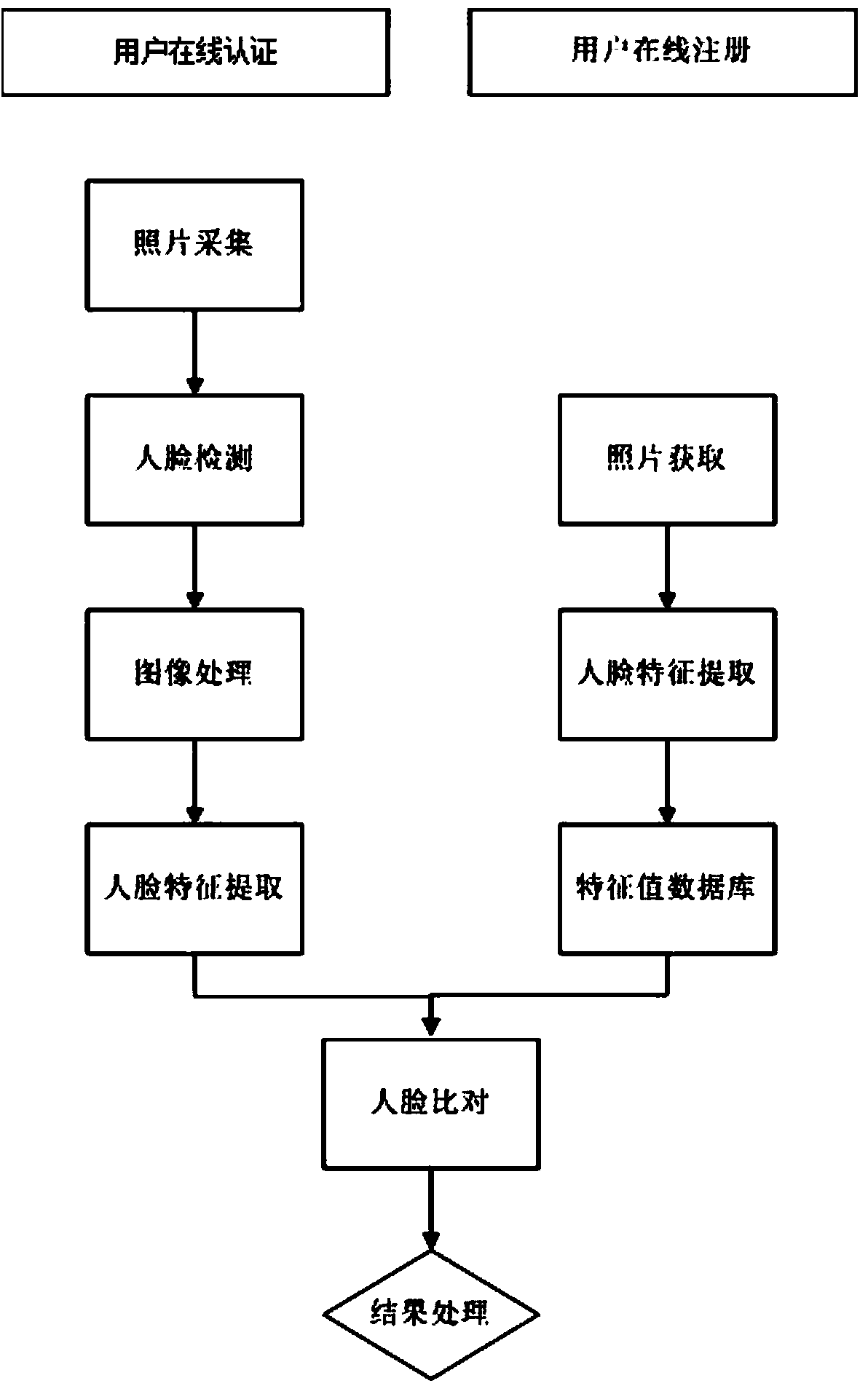
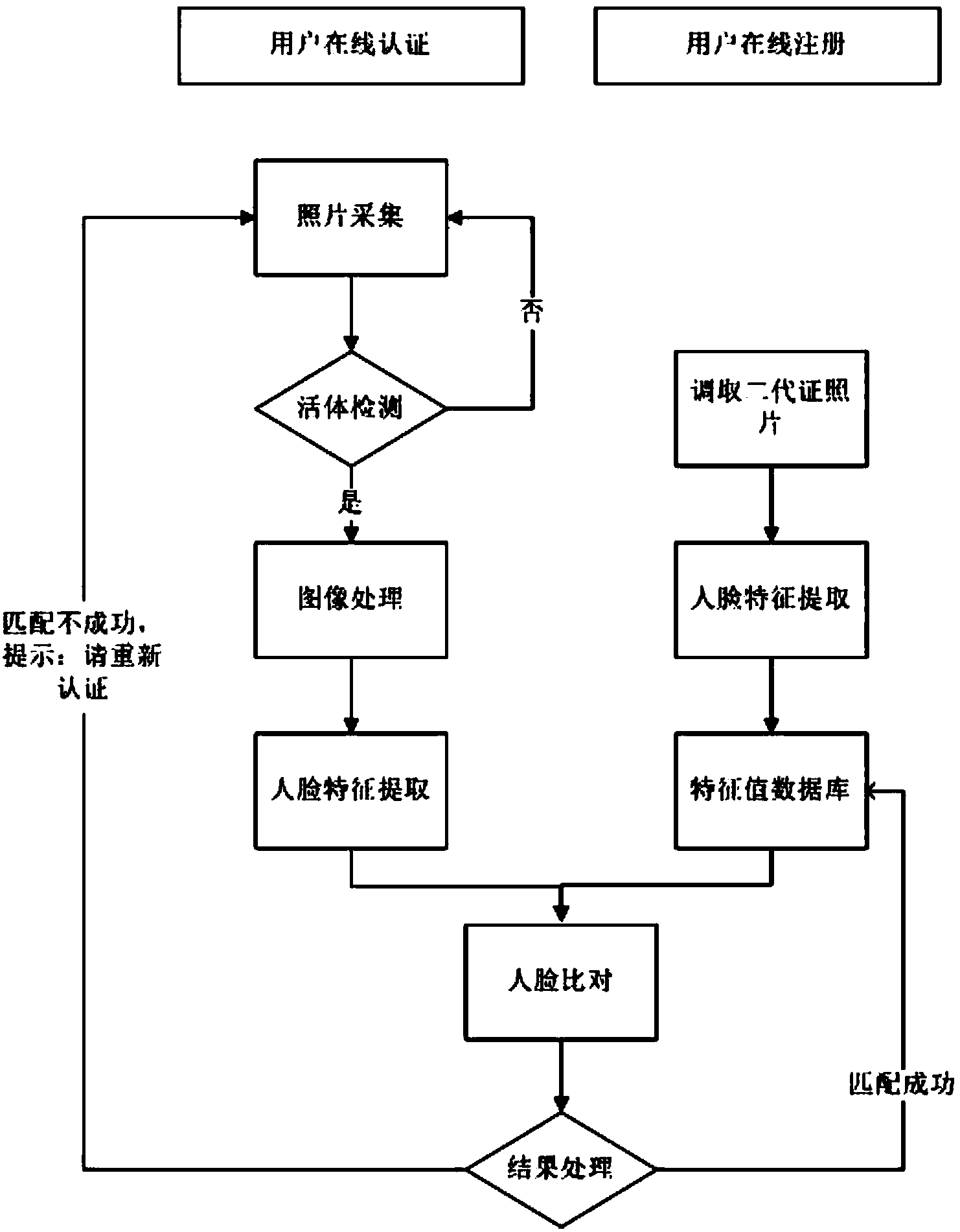
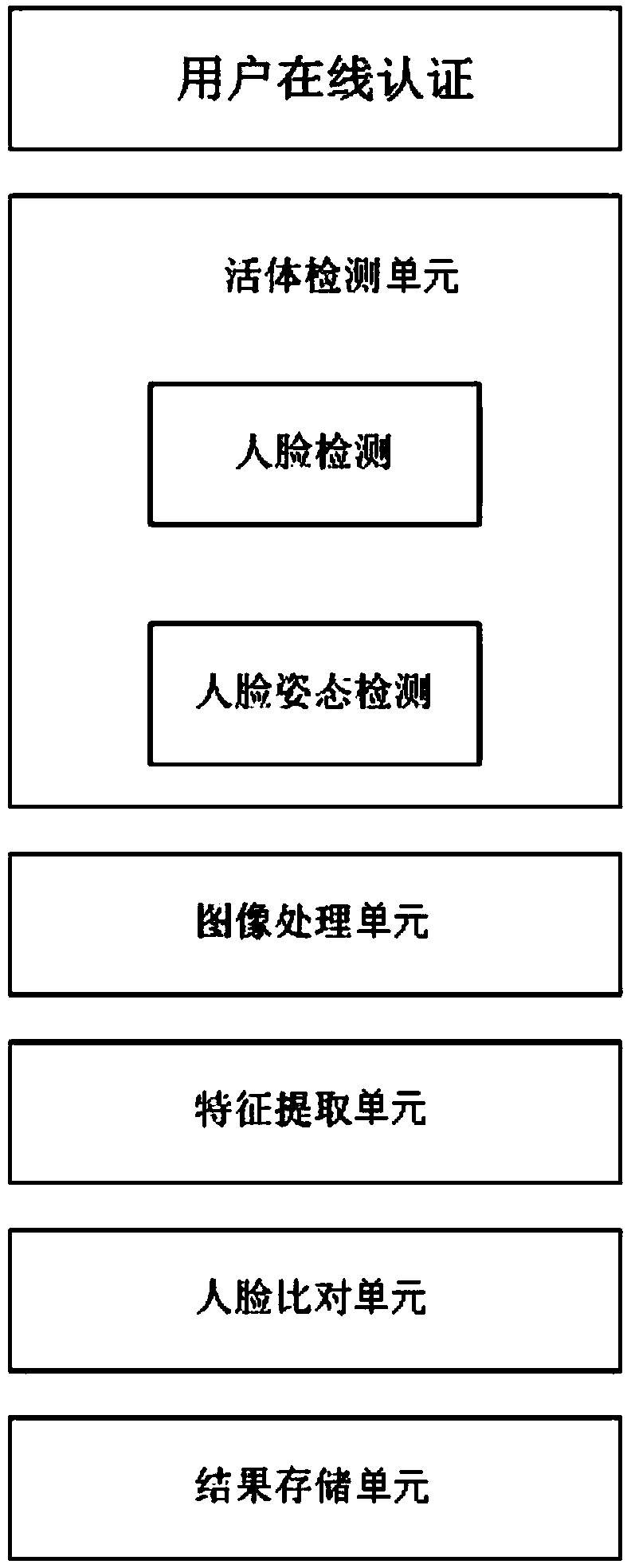
User online authentication method and system based on living body detection and face recognition
ActiveCN103593598AAvoid fraudulent authenticationImprove securityCharacter and pattern recognitionDigital data authenticationSystem safetyLiving body
The invention discloses a user online authentication method and system based on living body detection and face recognition. The method includes the user online registration step and the user online authentication step. The user online authentication step comprises the living body detection step, the image processing step, the feature value extraction step, the face comparison step and the result processing step. In the living body detection step, whether an authenticated user is a living body or not is determined and a face picture is acquired. In the image processing step, the collected face picture is processed. In the feature value extraction step, face part features of the processed face picture are extracted. In the face comparison step, extracted feature data of the collected face image are compared with corresponding face data in a user face feature value database, a threshold value is set, and when similarity exceeds the threshold value, the acquired result through matching is output. The user online authentication method and system can avoid authentication cheating through videos including faces, safety of the system is improved, recognition time can be shortened, and recognition accuracy is improved.
Owner:SHANGHAI JUNYU DIGITAL TECH
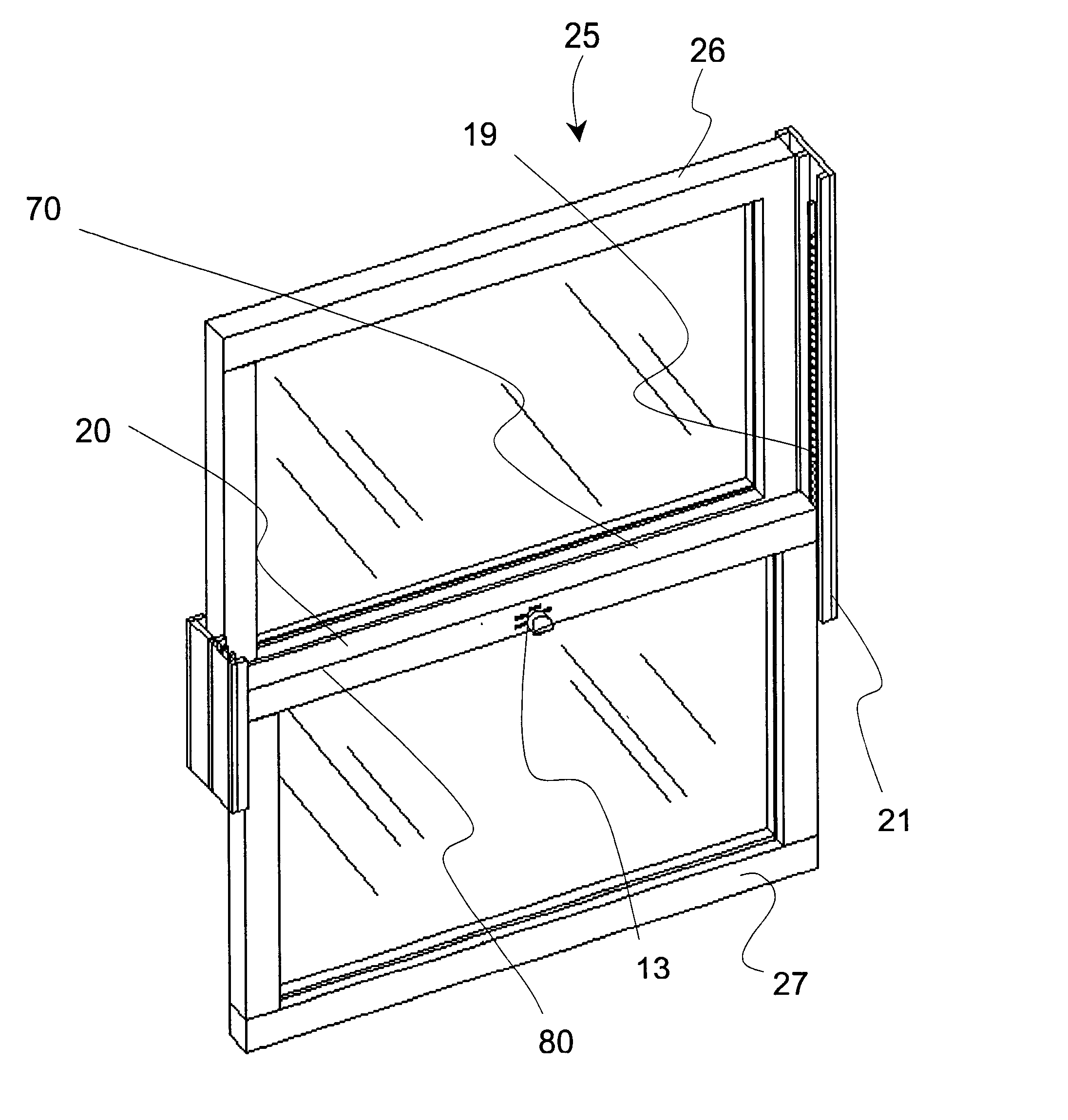
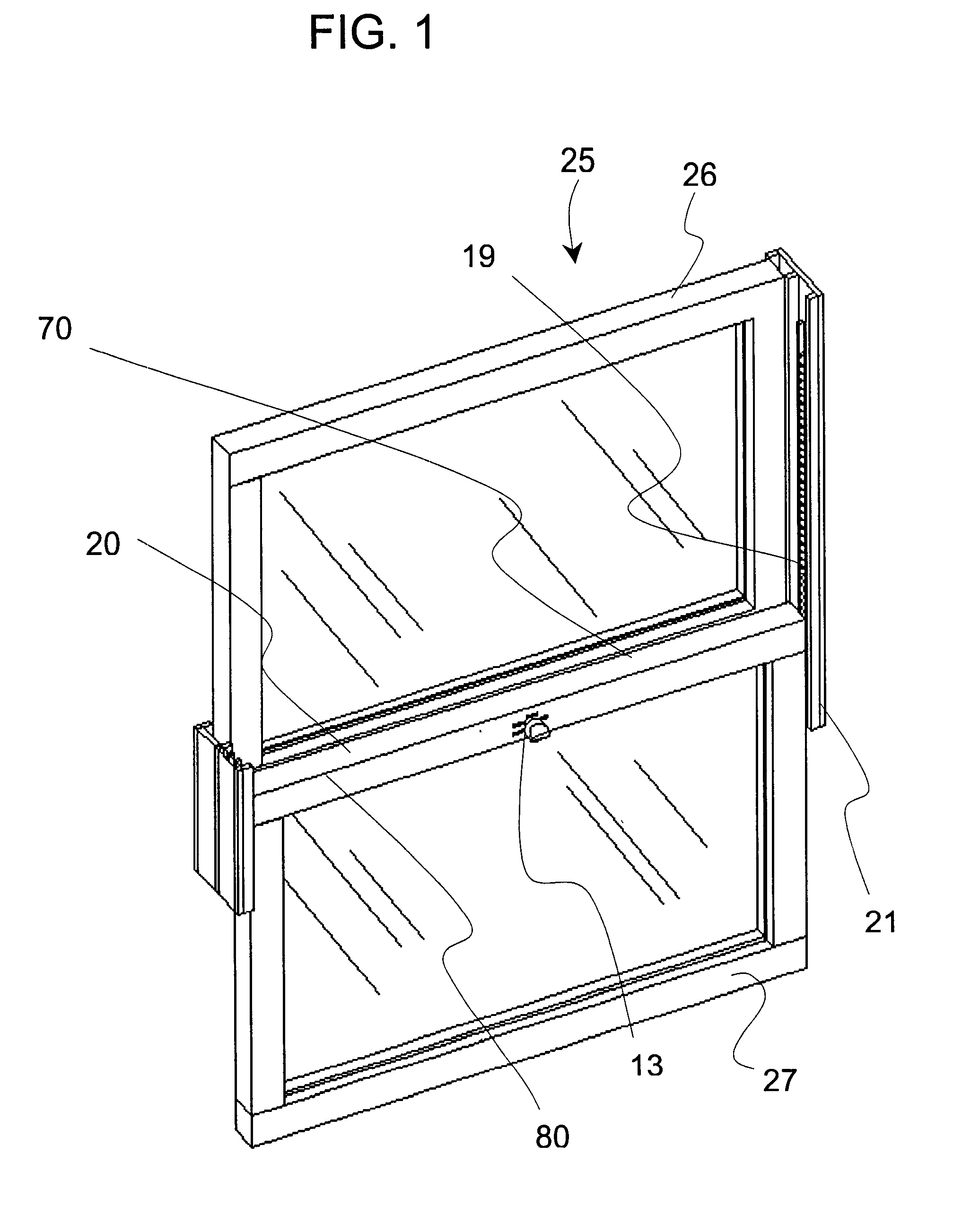
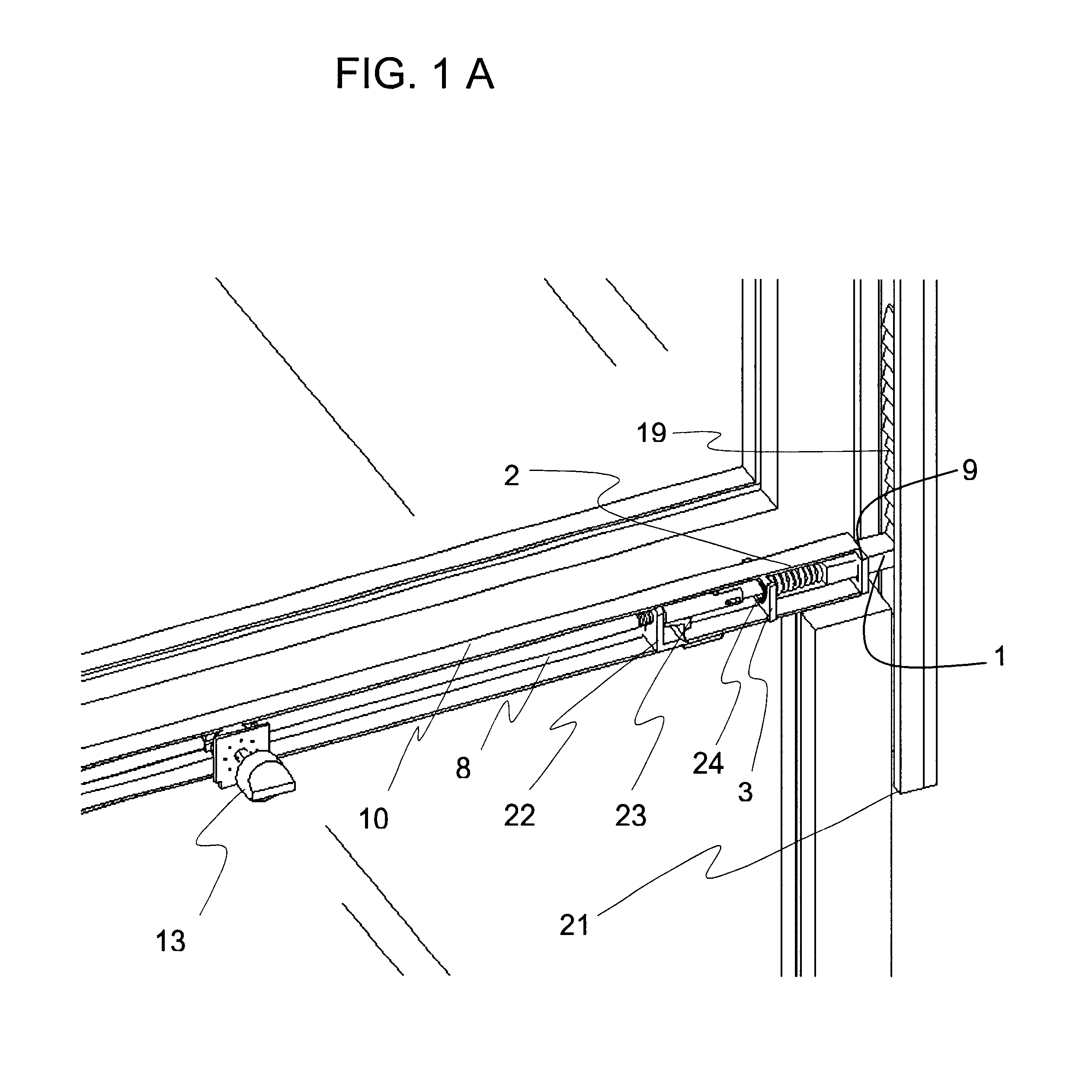
Window latch system
A sliding latch and locking mechanism, for windows and doors, whereby the latching mechanism provides a means for discrete position retention of a sliding window or door and provides an increased measure of security. The latching system combines four modes of operation i.e. lock, close only, raise (free sliding), and tilt to provide angular pivoting of window sash, that allow three levels of security, i.e. fully locked, close only with discrete positions maintained, and raise or lower without discrete positions maintained (free sliding). The latching system security levels are accomplished by means of a selector knob positioned to the desired mode of operation. Also, a mechanism is integrated to provide interlocking in the fully closed position with the upper or adjacent window or door sash.
Owner:ELLIOTT GORDON W
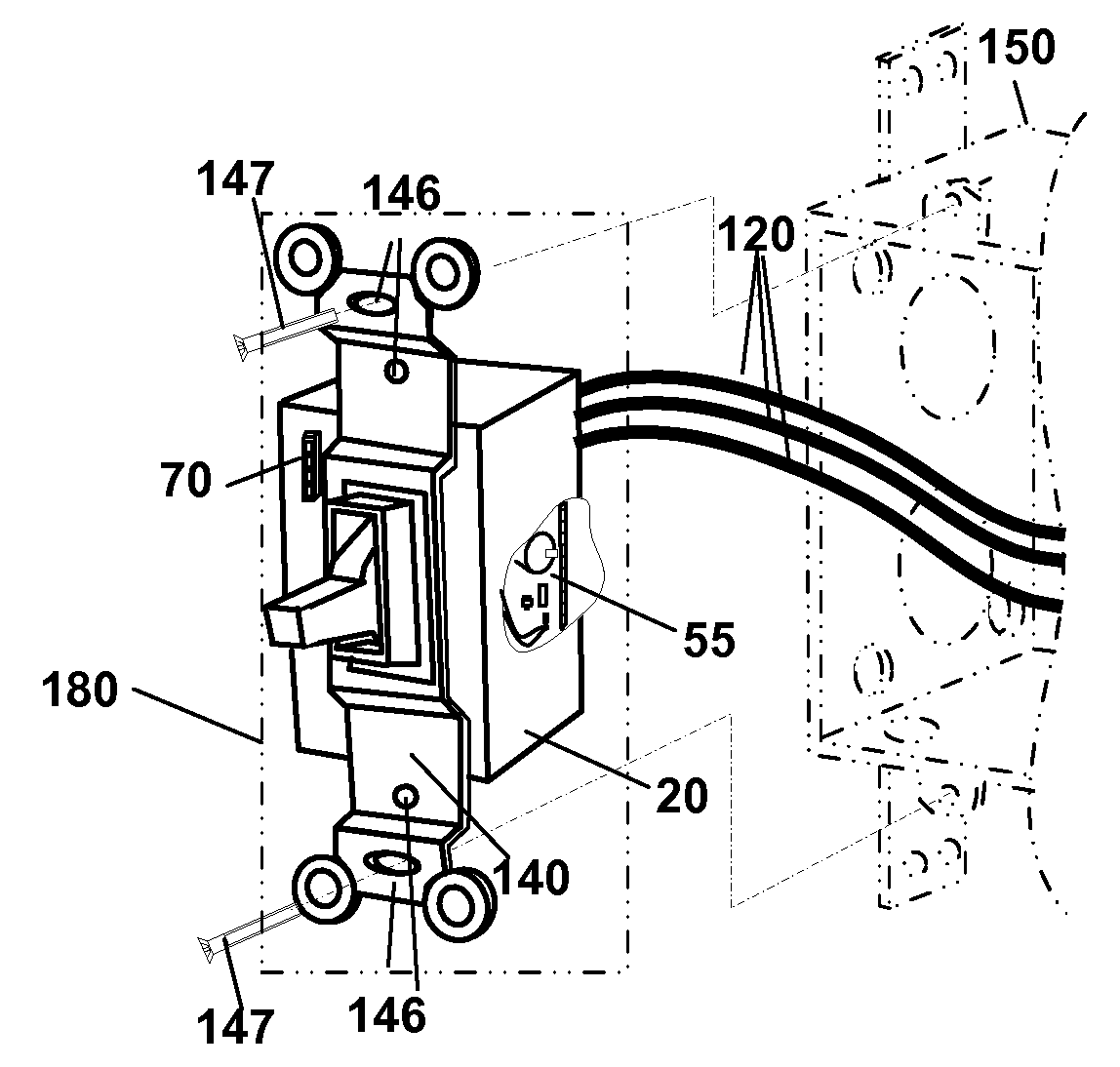
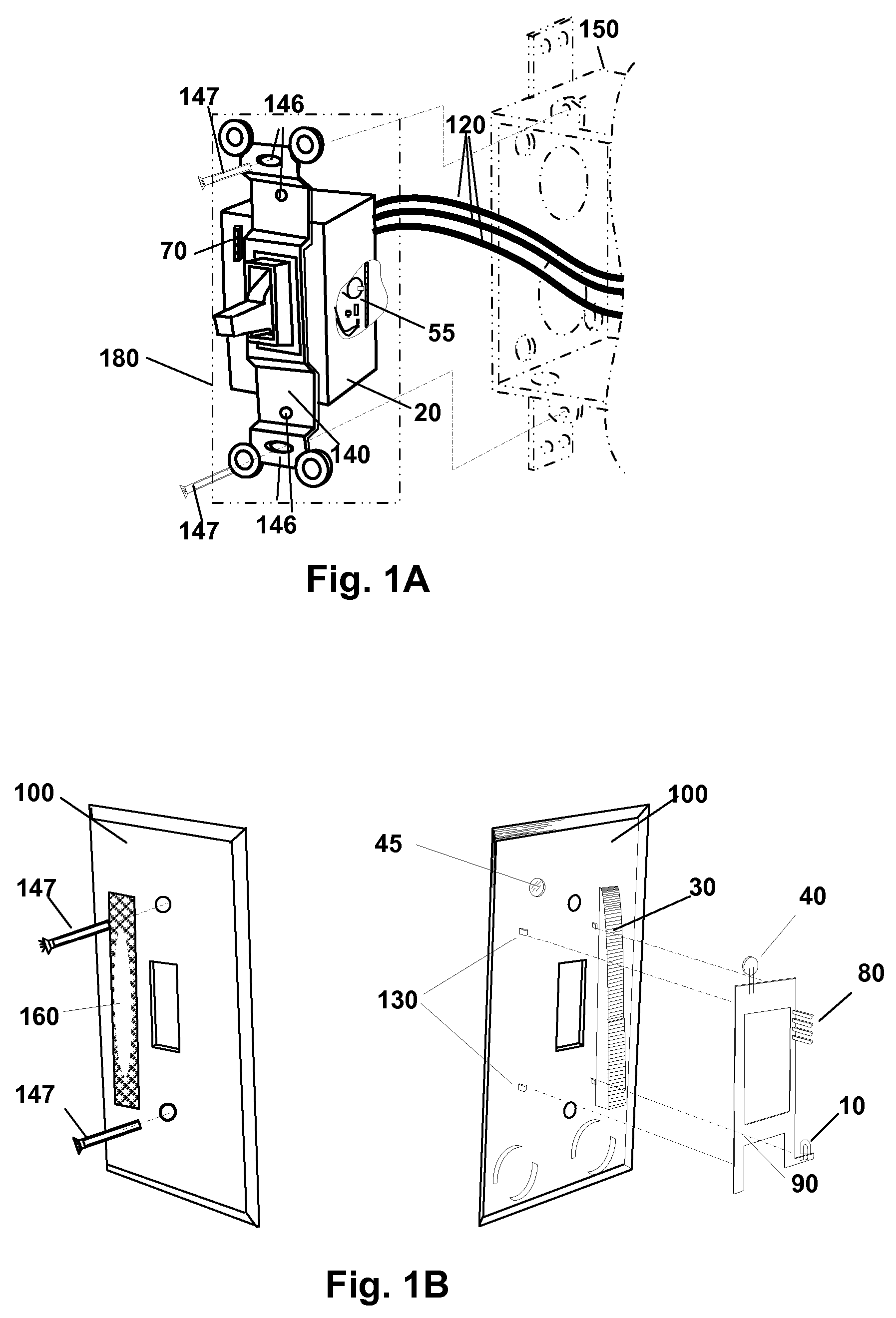
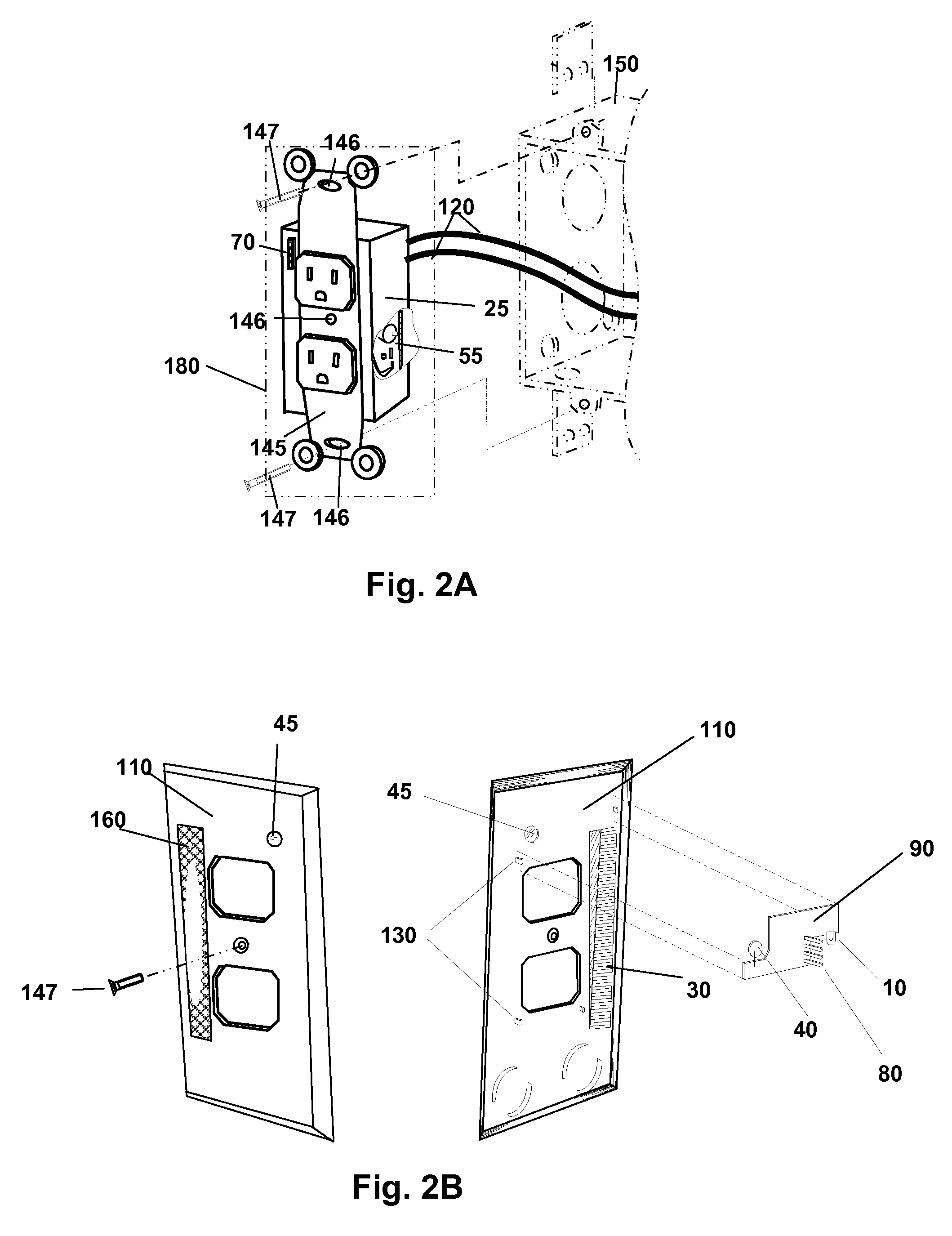
Concealed Safety Lighting and Alerting System
A concealed safety lighting and alerting system is described where a power failure light, night light, visual and audio alarm are integrated into an electric wiring device and its cover plate. An electric wiring device with built-in safety condition sensing is described. A cover plate with features for emitting light is also described. The electric wiring device contains a sensing circuit that provides a signal to control a system safety device that may be a safety lighting source, audible alarm source or both. The cover plate may contain a variety of components allowing the system designer to expand the functionality of the system while keeping design complexity low. The system is modularly designed to overcome space limitations found when combining the multiple safety functions and controls into an electric wiring device that fits into conventional electric work boxes.
Owner:BARTON ROBERT A
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com