Patents
Literature
140 results about "User protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
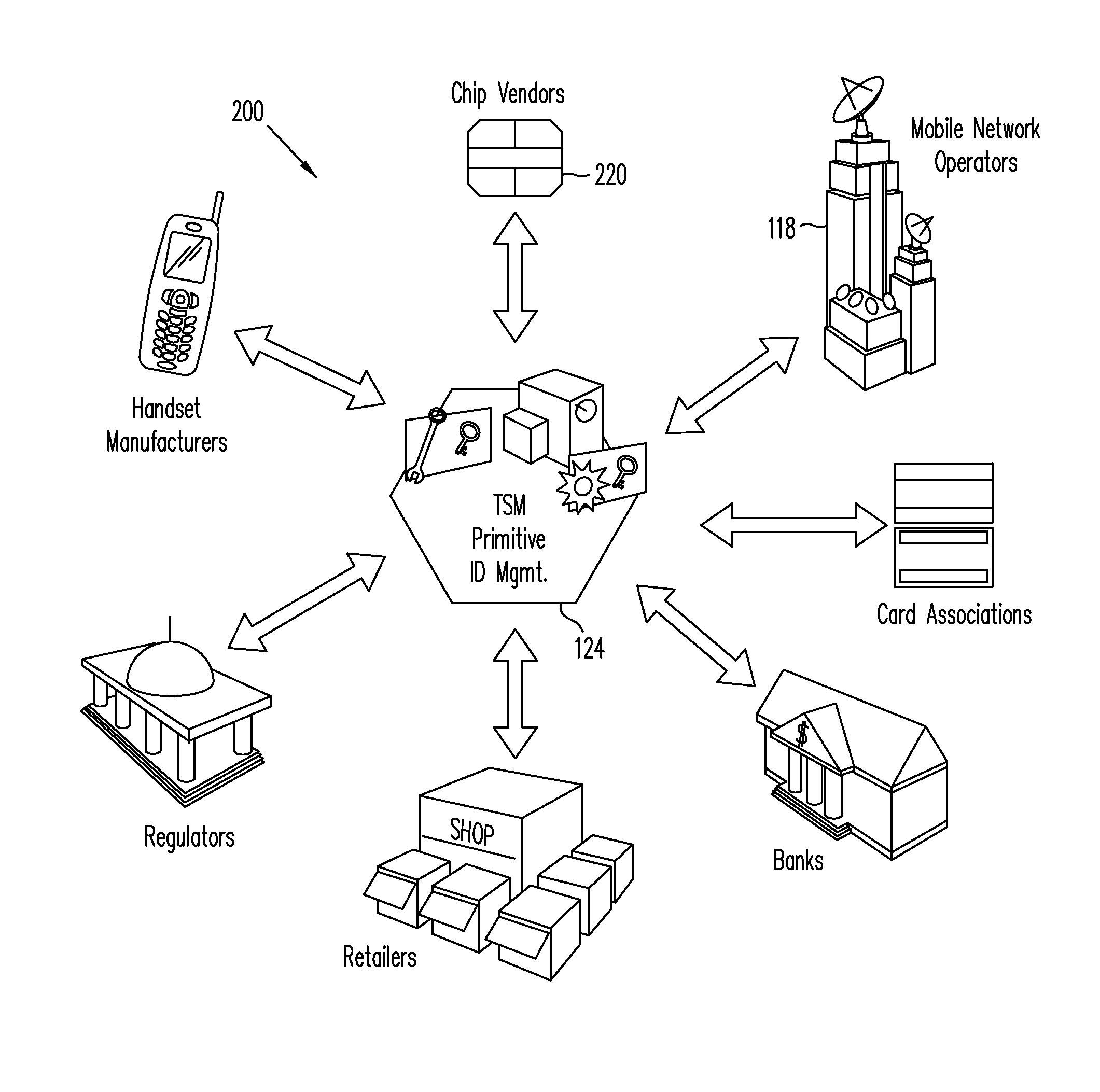
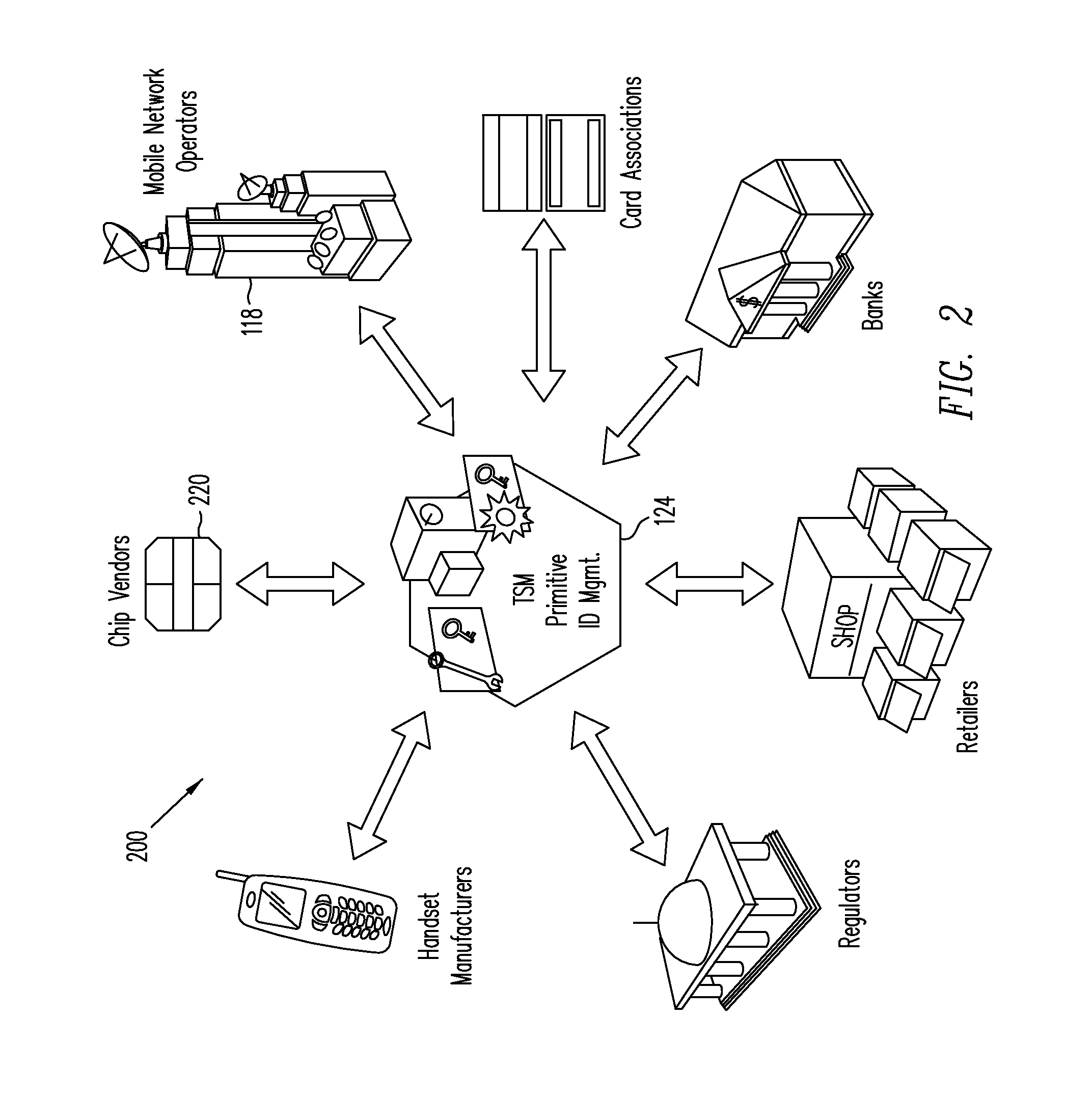
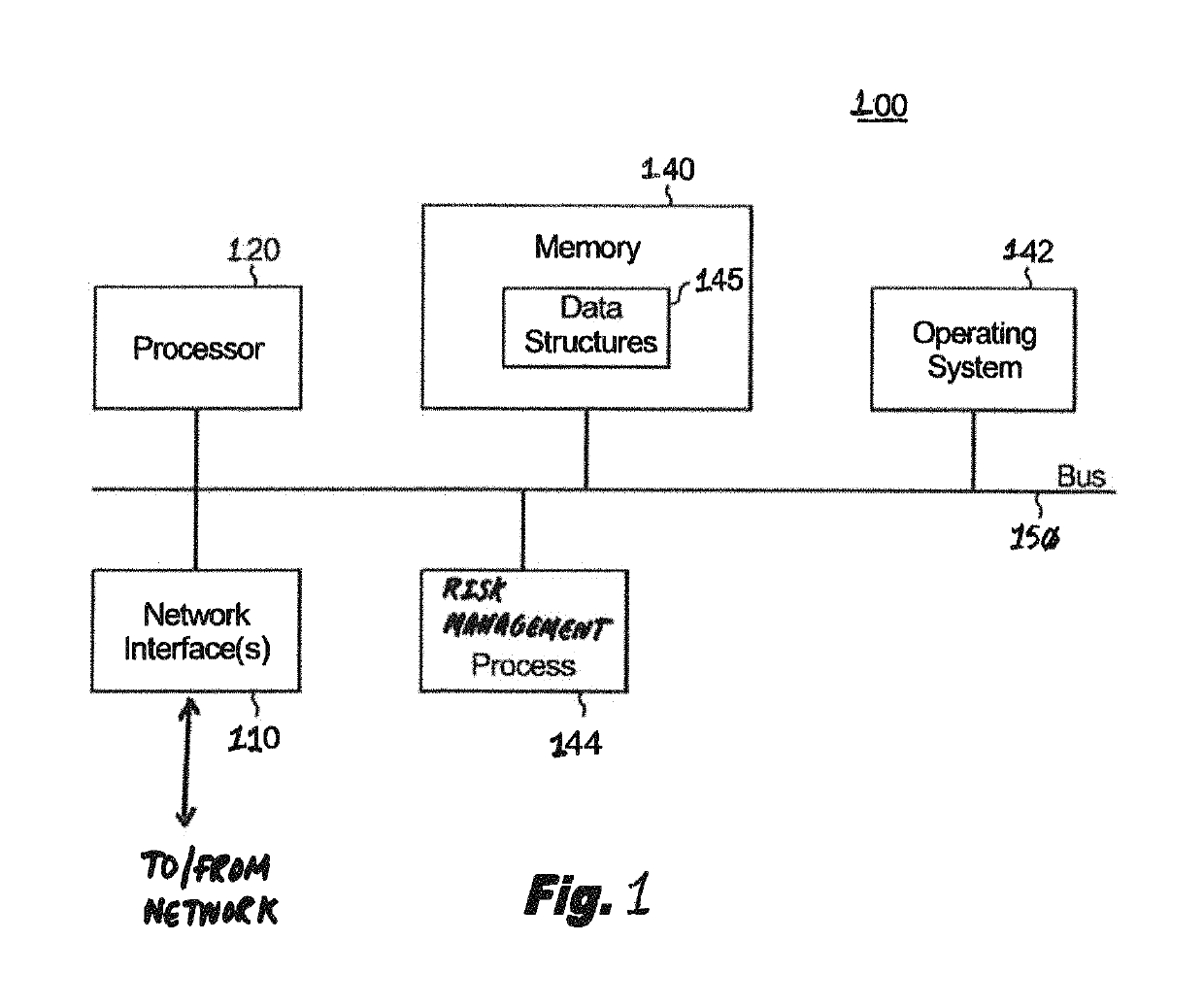
Trusted Integrity Manager (TIM)
A system for use with a trusted service manager (TSM) and a mobile device having a subscriber unique identifying data, according to one embodiment, includes: a server in which the server validates an application against the unique and identifying data of the mobile device and provides the validated application for the mobile device; and a secure element (SE) acting as a client in which the SE is present in the mobile device as client; the validated application from the server is installed in the SE; and the SE is adapted to execute the validated application to perform a service process. The service process includes enablement of payment functions on the mobile device, in which enablement of payment functions includes: providing secure communication between the mobile device and the server; secure provisioning of a payment instrument on the mobile device, wherein authentication and verification for the payment instrument on the mobile device is provided by the server; and binding the payment instruments and the validated application to the mobile device to provide a strong ID management for enhanced user protection and system security and integrity.
Owner:PAYPAL INC
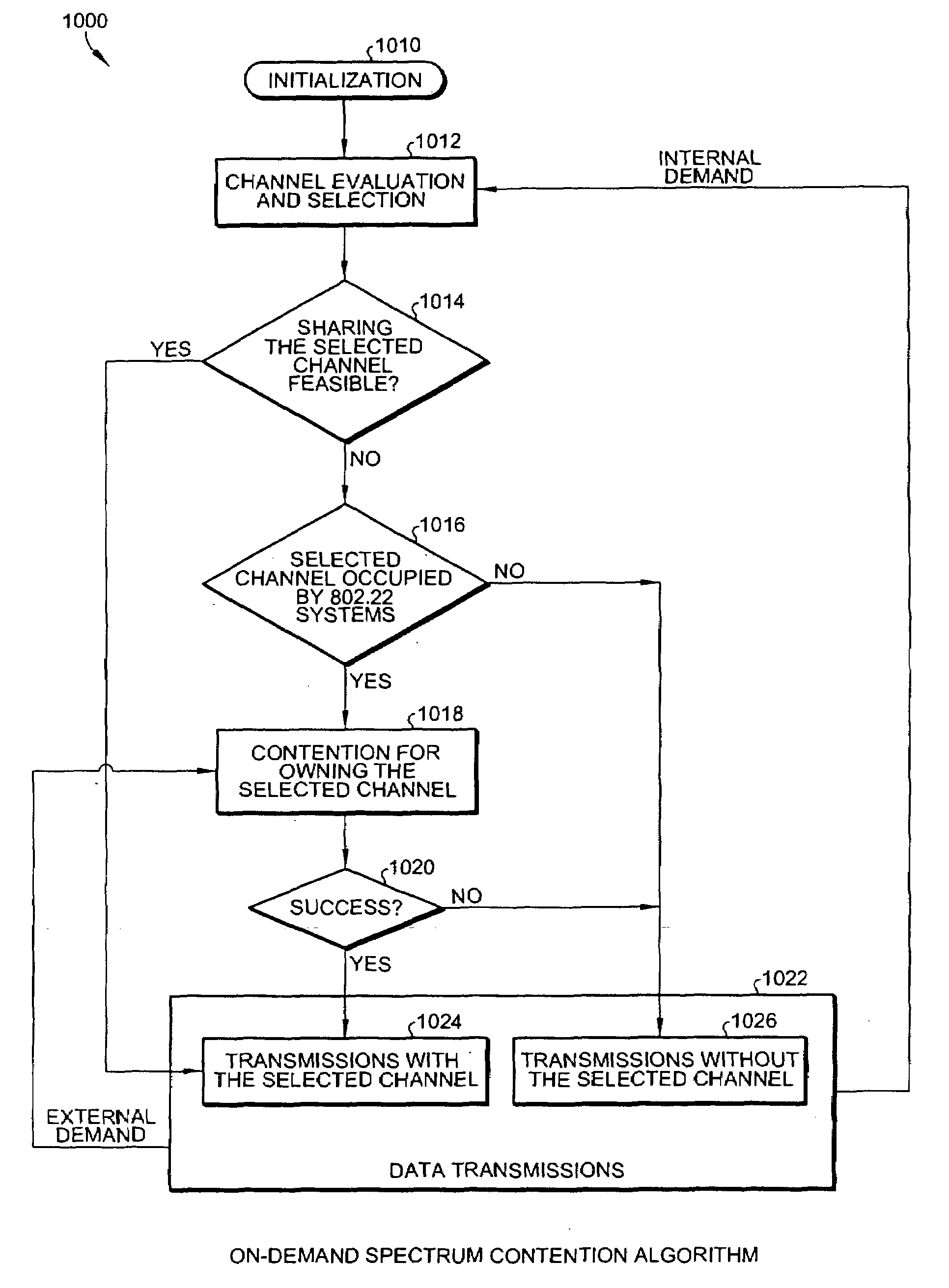
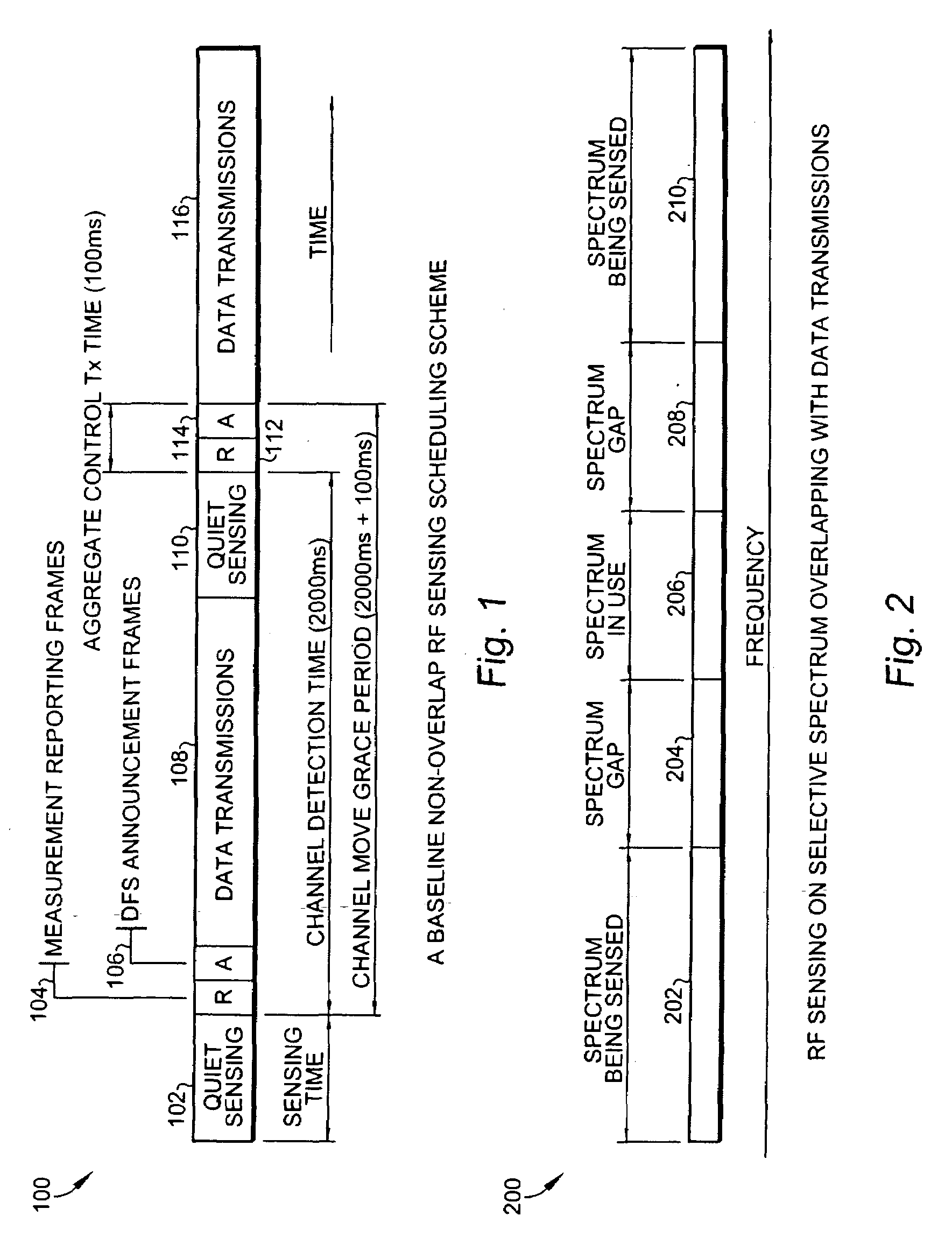
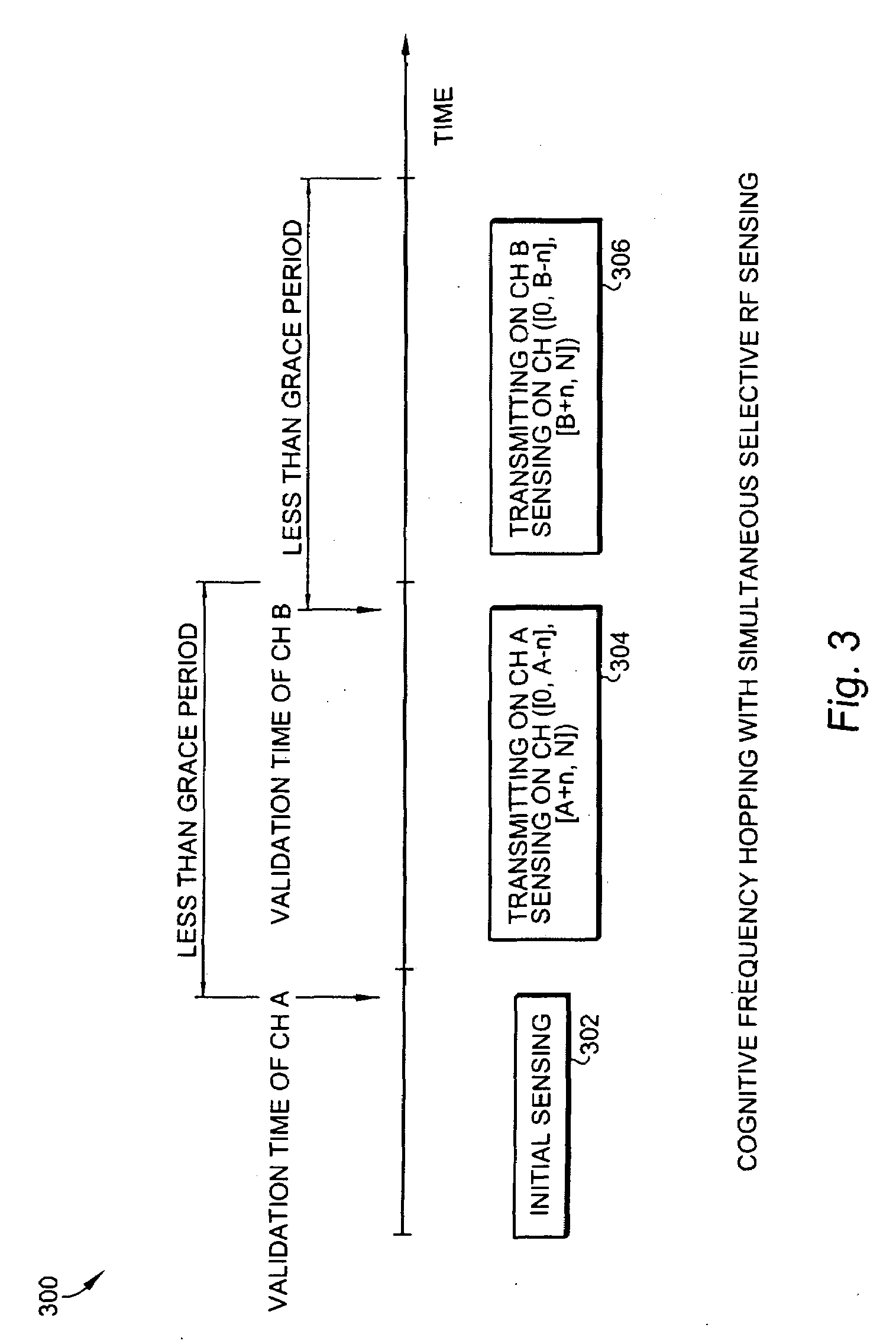
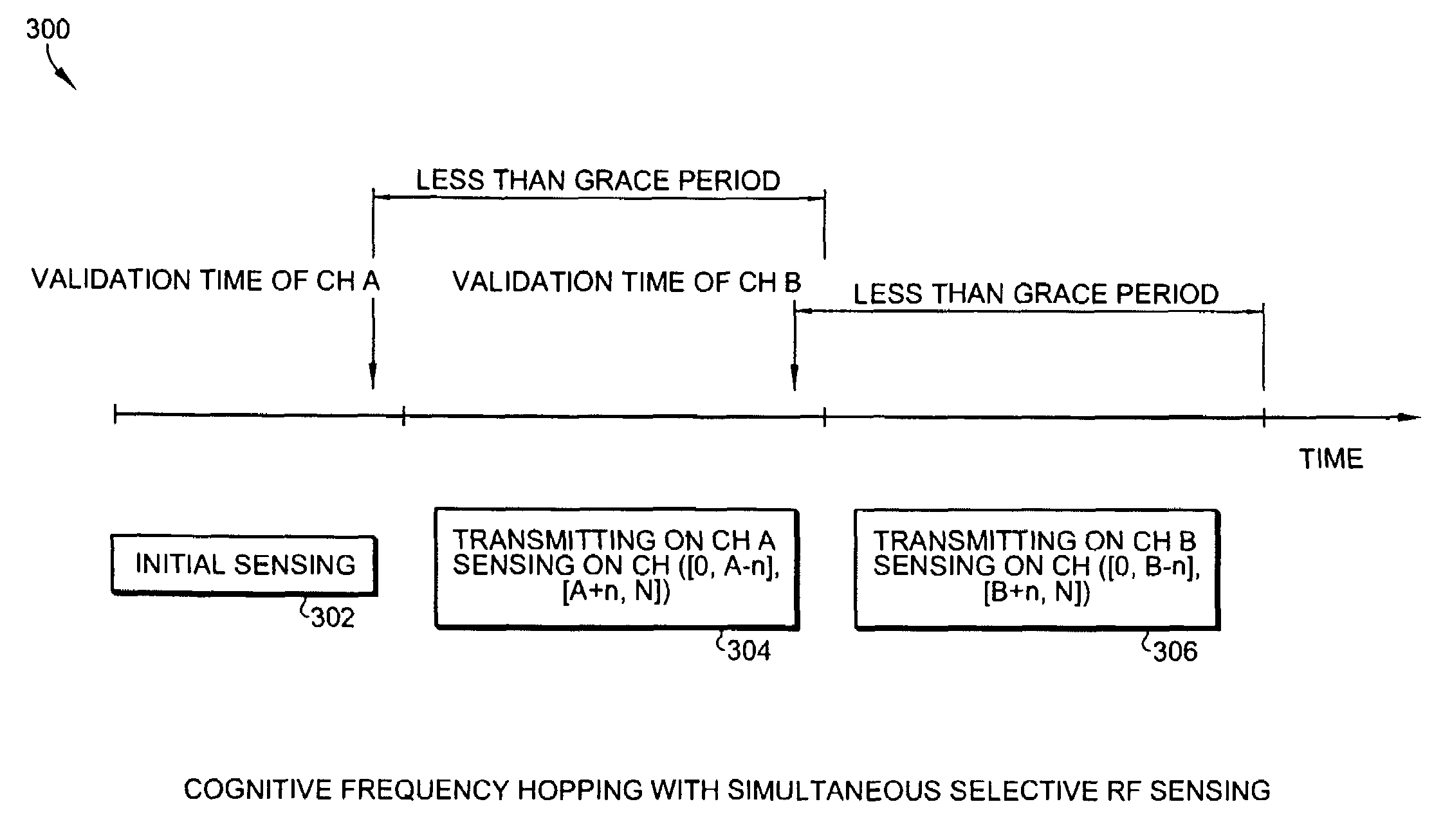
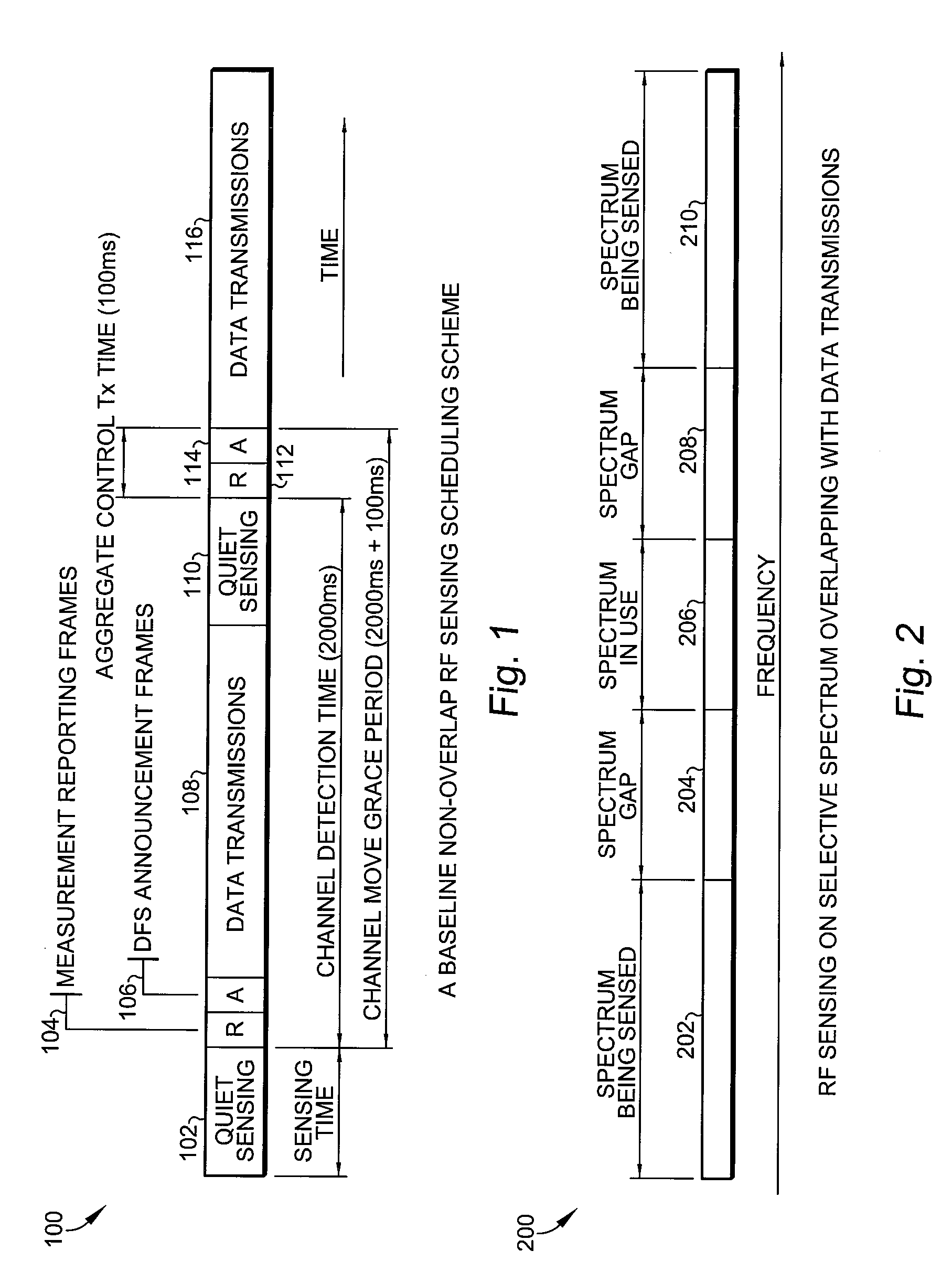
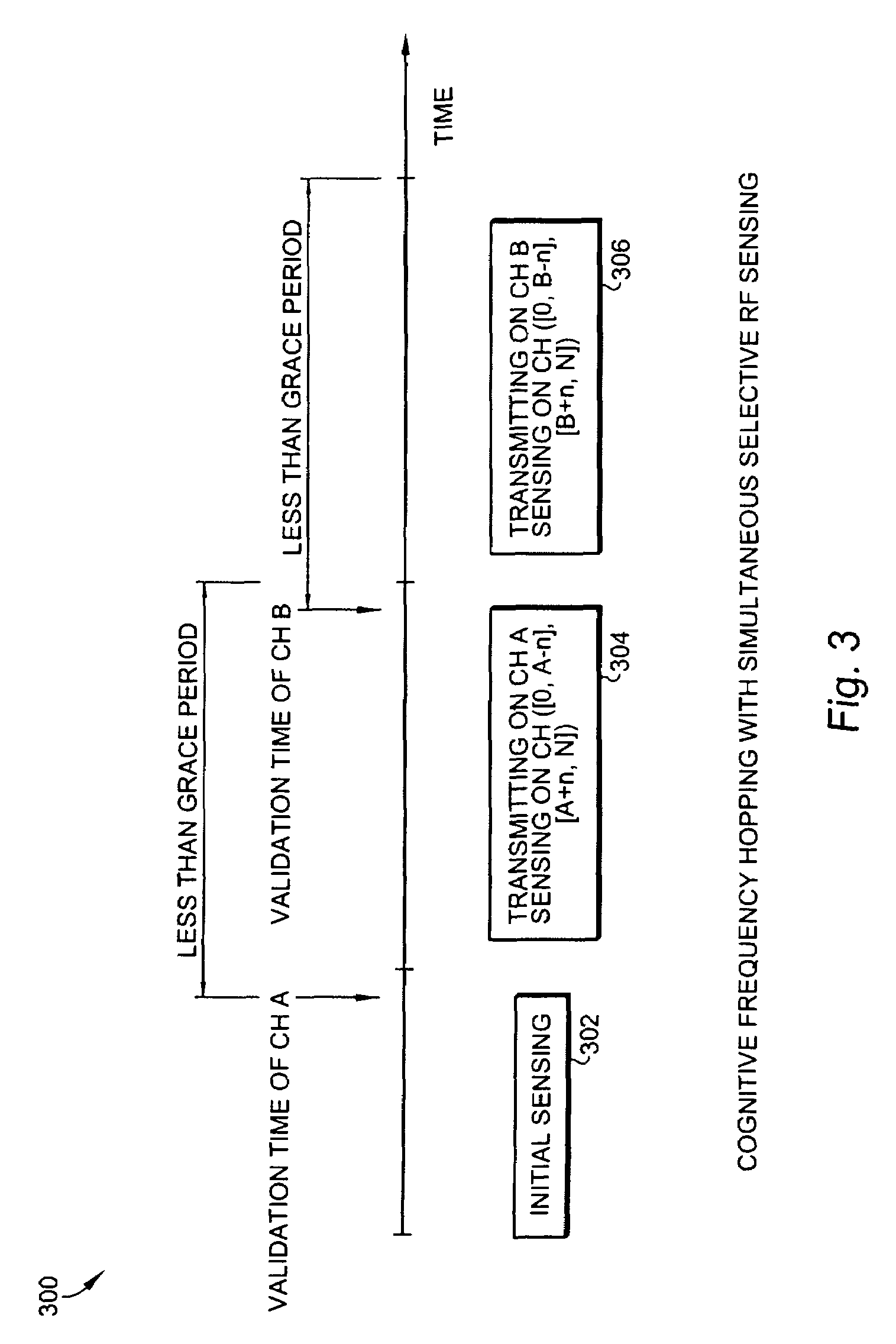
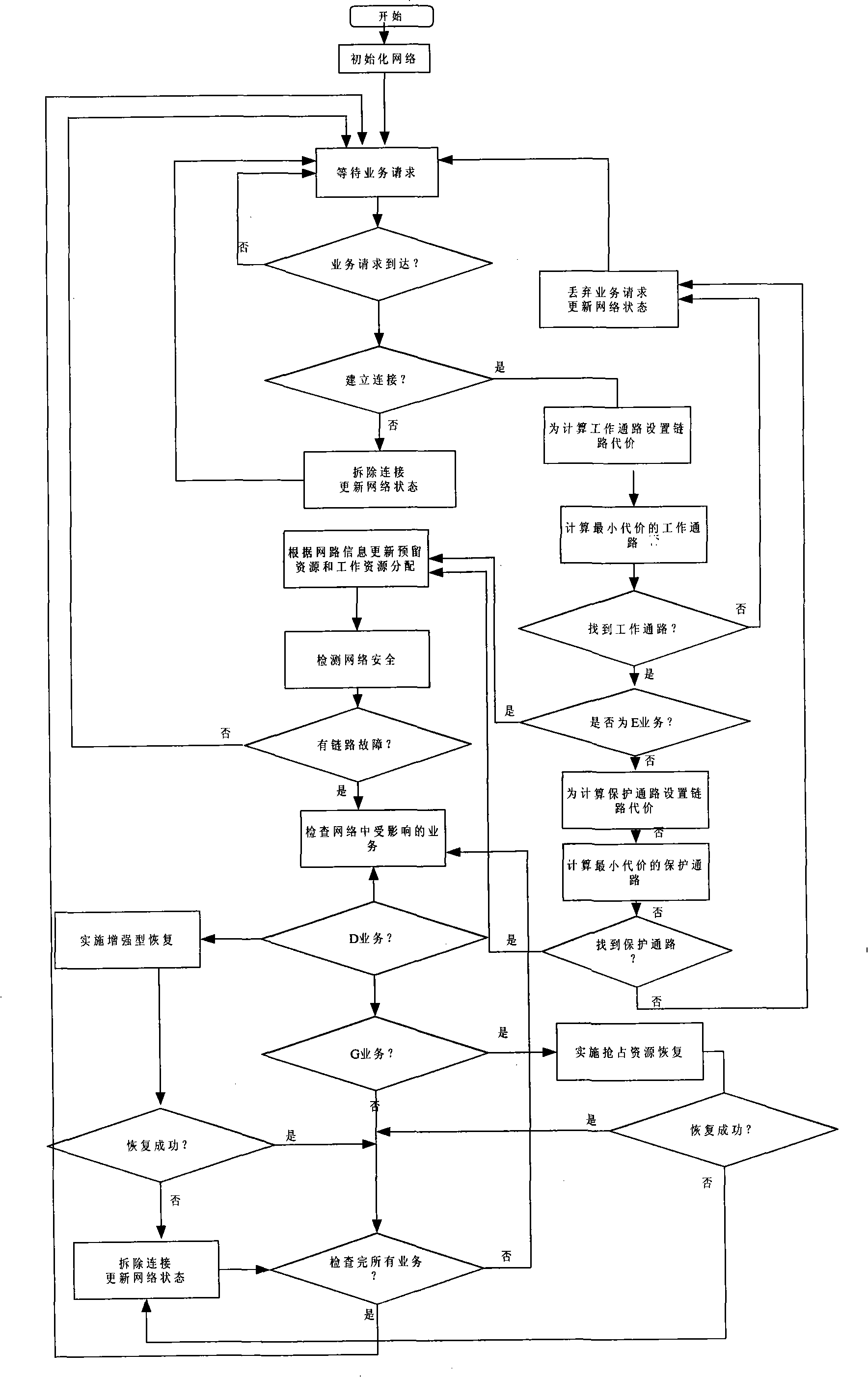
Methods of RF sensing control and dynamic frequency selection control for cognitive radio based dynamic spectrum access network systems-cognitive dynamic frequency hopping
ActiveUS20080090581A1Improve protectionError preventionTransmission systemsAccess networkFrequency spectrum
This invention relates to cognitive radio based wireless communications of dynamic spectrum access networks, and more particularly to a method of addressing radio frequency sensing control and dynamic frequency selection control. A method called Cognitive Dynamic Frequency Hopping that is based on the selective Simultaneous Sensing and Data Transmissions is described. The Cognitive Dynamic Frequency Hopping method is further facilitated by a collision avoidance technique. The described method satisfies both reliable and timely RF sensing for guaranteeing licensed user protection, and QoS satisfaction for services of the dynamic spectrum access systems.
Owner:STMICROELECTRONICS SRL
Personal safety device, method and article
ActiveUS20180005503A1Control with pedestrian guidance indicatorGarmentsControl circuitUser protection
Owner:KAINDL ROBERT
Fairness-based power and channel joint allocation method for cognitive radio system
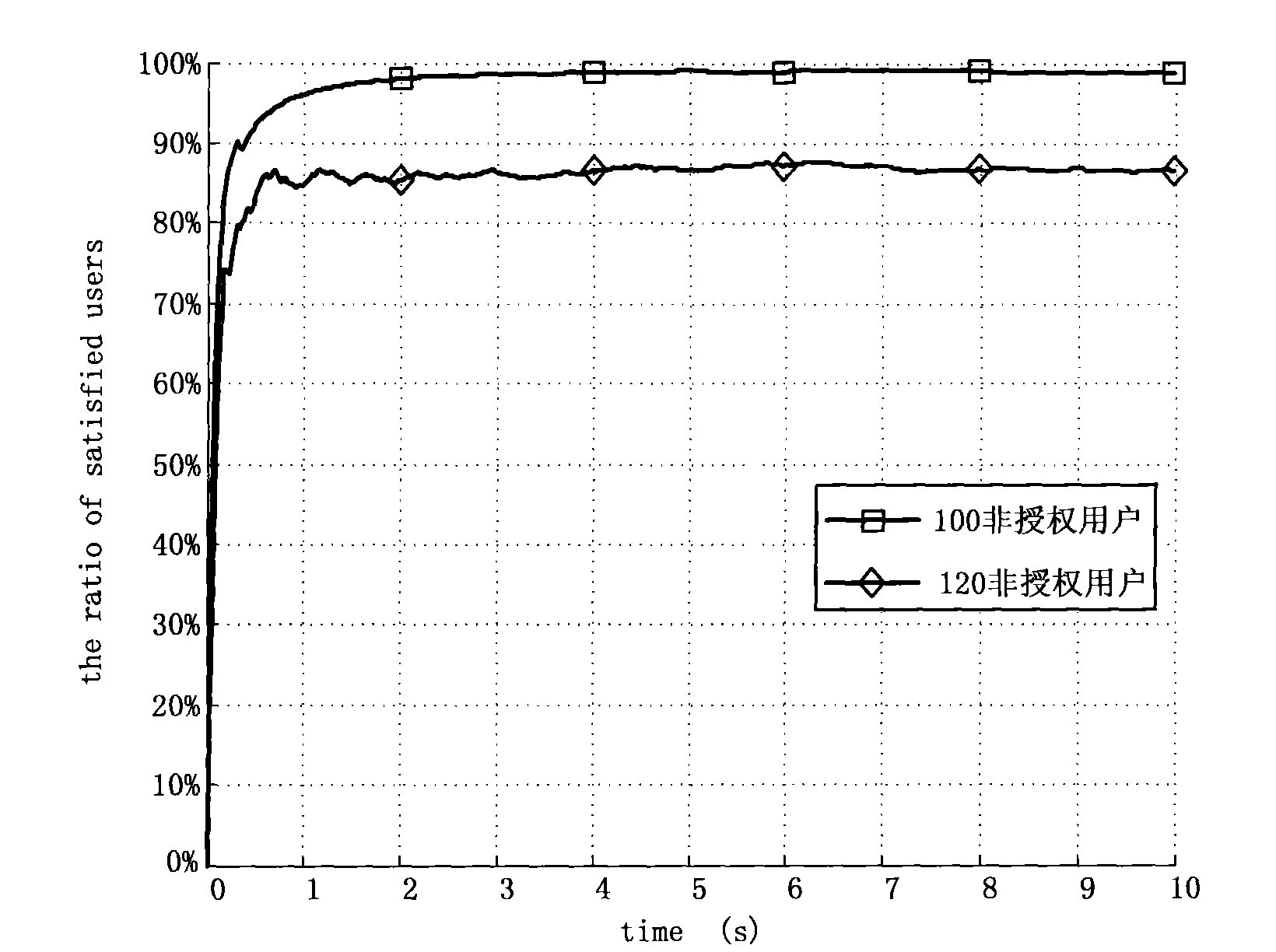
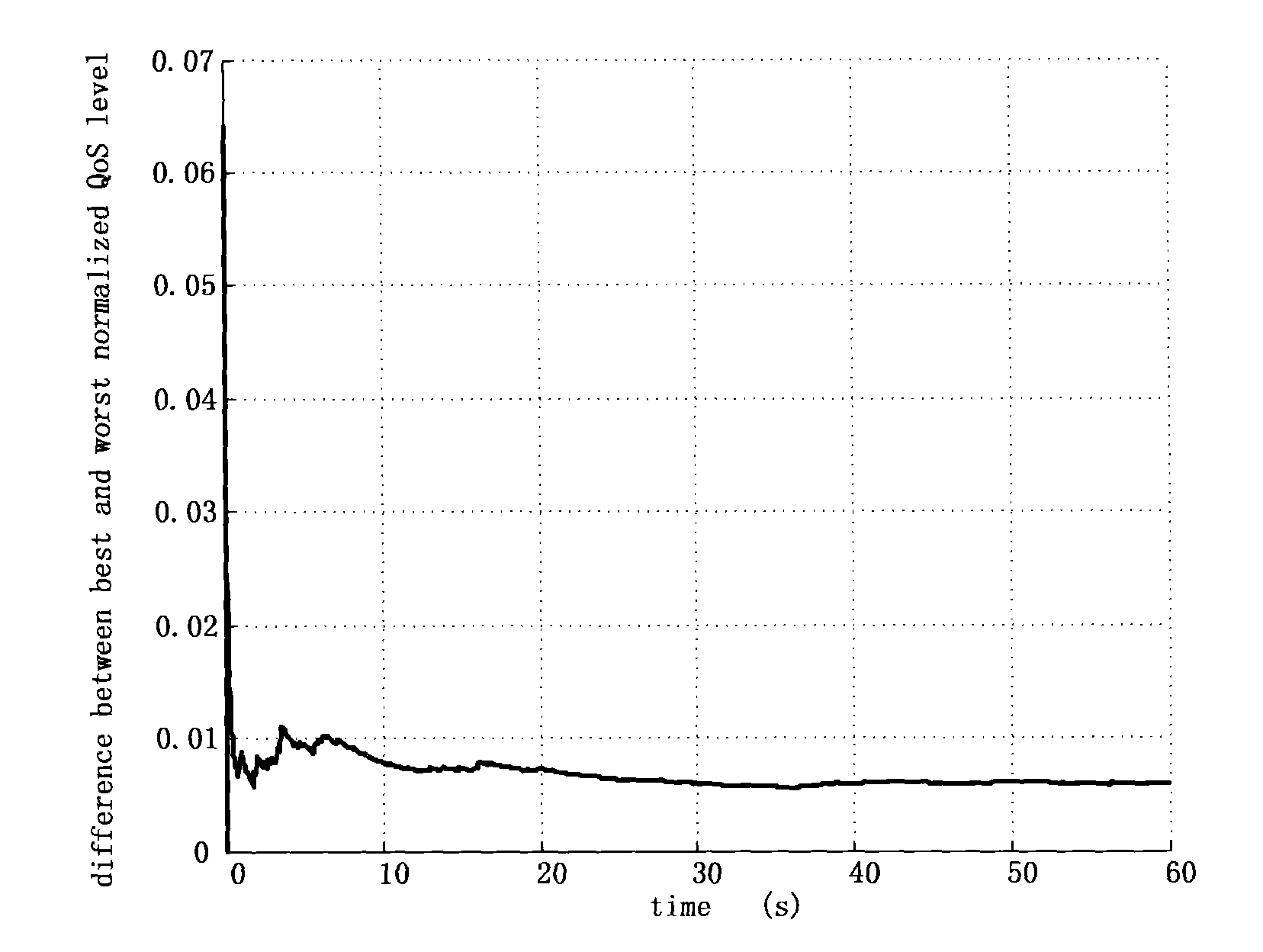
InactiveCN101626604AHigh QoS support levelImprove fairnessPower managementEnergy efficient ICTQuality of serviceMathematical definition
The invention provides a fairness-based power and channel joint allocation method for a cognitive radio system, belongs to the technical field of wireless communication, and in particular relates to power and channel joint allocation used in the cognitive radio system. The invention relates to the power and channel joint allocation method which can meet the requirements of unauthorized users on quality of service (QoS), ensure the fairness and protect the authorized users at the same time. According to different QoS requirements of the unauthorized users, a mathematical definition on the fairness is given. Simultaneously, in order to reduce arithmetic cost and shorten the allocation period, the method divides the whole allocation process into two stages; the first stage is called as the crude allocation, at the stage, the protection of the authorized users is taken as premises, and the maximum resource which can be utilized by each non-authorized user is obtained according to the QoS requirements of the non-authorized users and the fairness; and the second stage is called as the fine allocation, at the stage, a plurality of non-authorized users independently complete the tasks, which can be serially and simultaneously completed by the authorized users, so that the complexity is reduced, the quick power and frequency spectrum allocation can be conveniently realized so as to adapt to the quick time varying characteristics of available frequency spectrum resources in the cognitive radio system, and all authorized users can independently determine the final utilizable resources.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
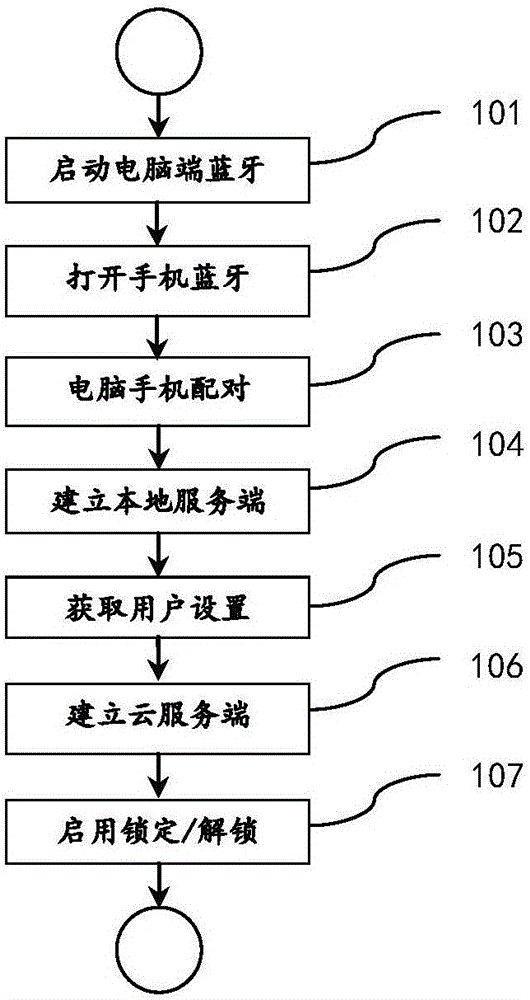
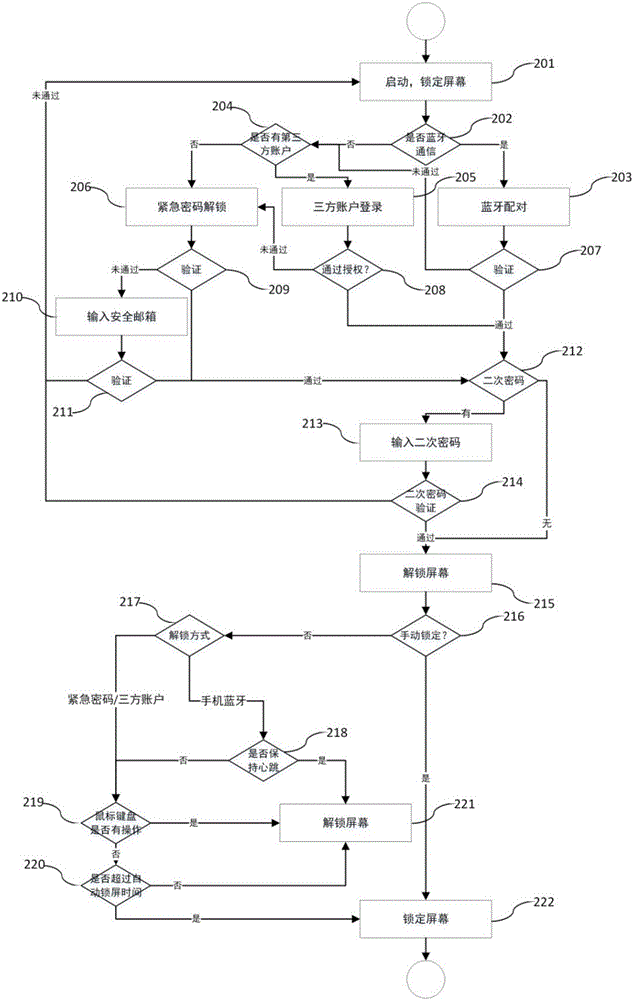
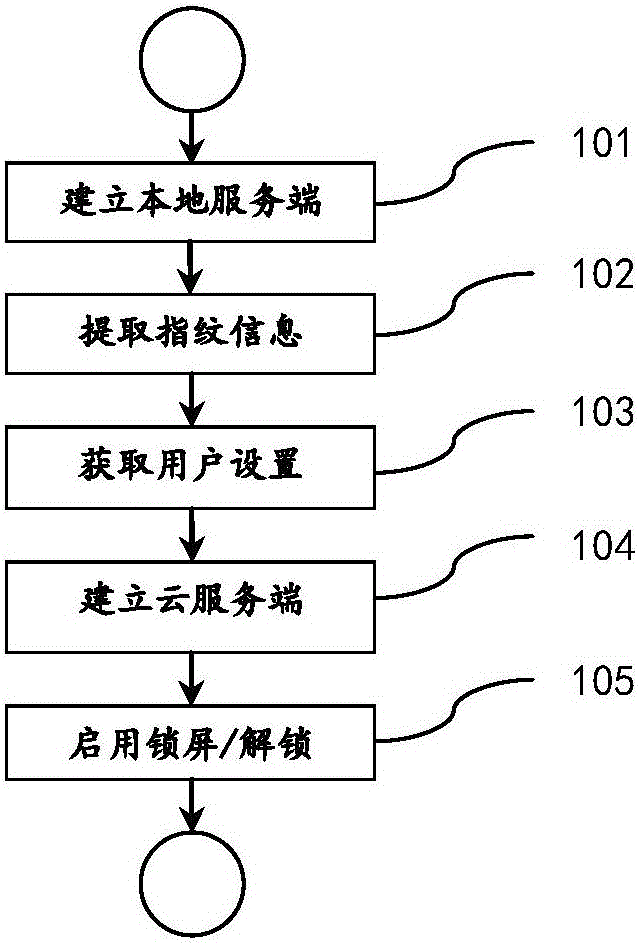
Method for locking/unlocking computer screen based on Bluetooth
InactiveCN105893802ACompatible securityCompatible requirementsNear-field transmissionDigital data authenticationPersonal computerProtected mode
The invention discloses a method for locking / unlocking a computer screen based on Bluetooth. The method includes the following steps that 101, Bluetooth at the computer end is started; 102, mobile phone Bluetooth is started; 103, a computer and a mobile phone are matched; 104, a local service end is established; 105, user setting is obtained; 106, a cloud service end is established; 107, locking / unlocking is started. The method has the advantages that portable Bluetooth equipment (such as a smart phone with a Bluetooth function) is used as a key for locking / unlocking the screen of a personal computer; user protection of multiple layers of secondary verification and an emergency mode are increased to provide a safer and more convenient unlocking technology and an identity verification method; a system active protection mode is adopted, protection is set to be automatic according to the used scene and hidden to the bottom layer which cannot be perceived by a user, and silent protection is achieved.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
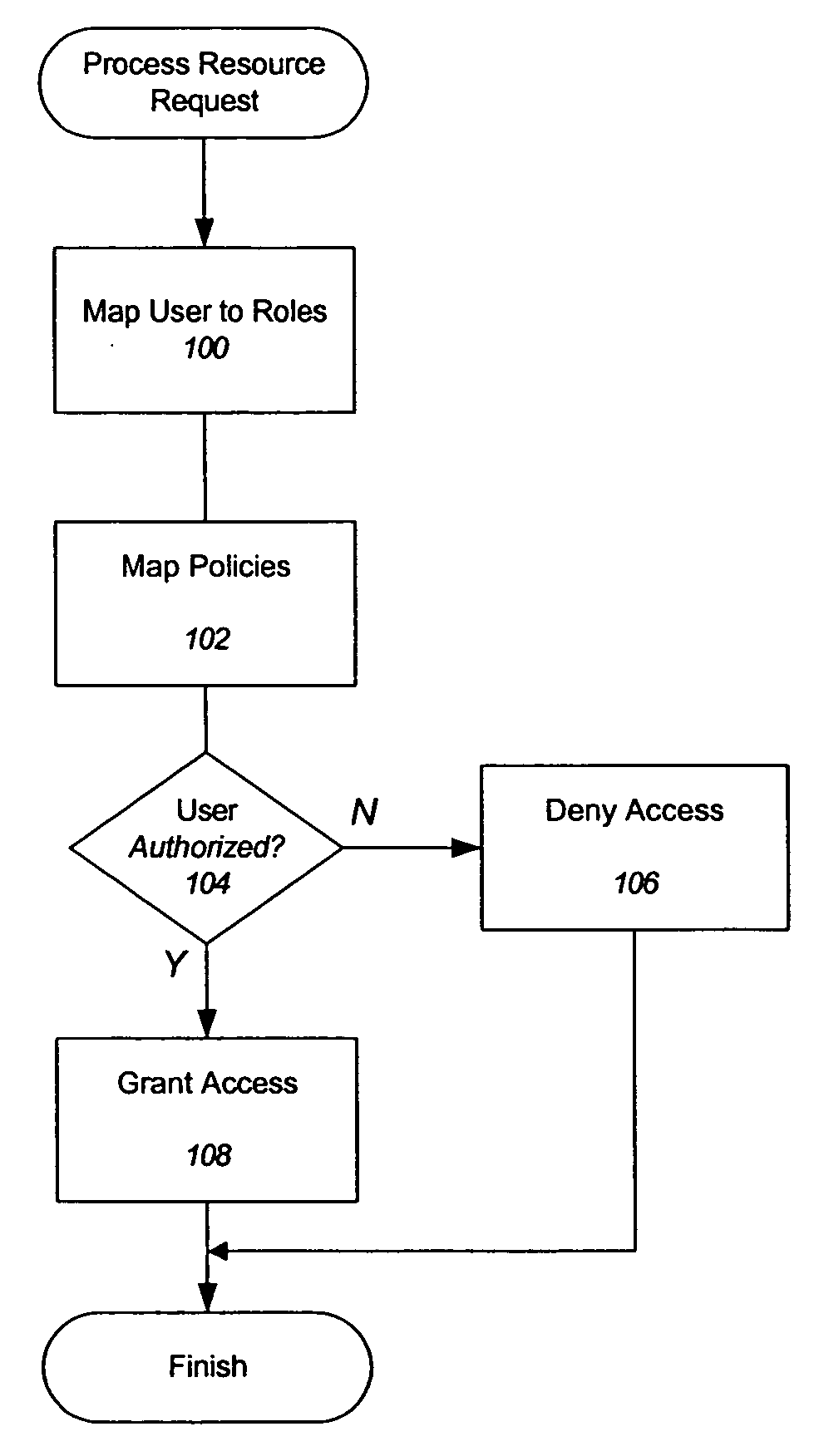
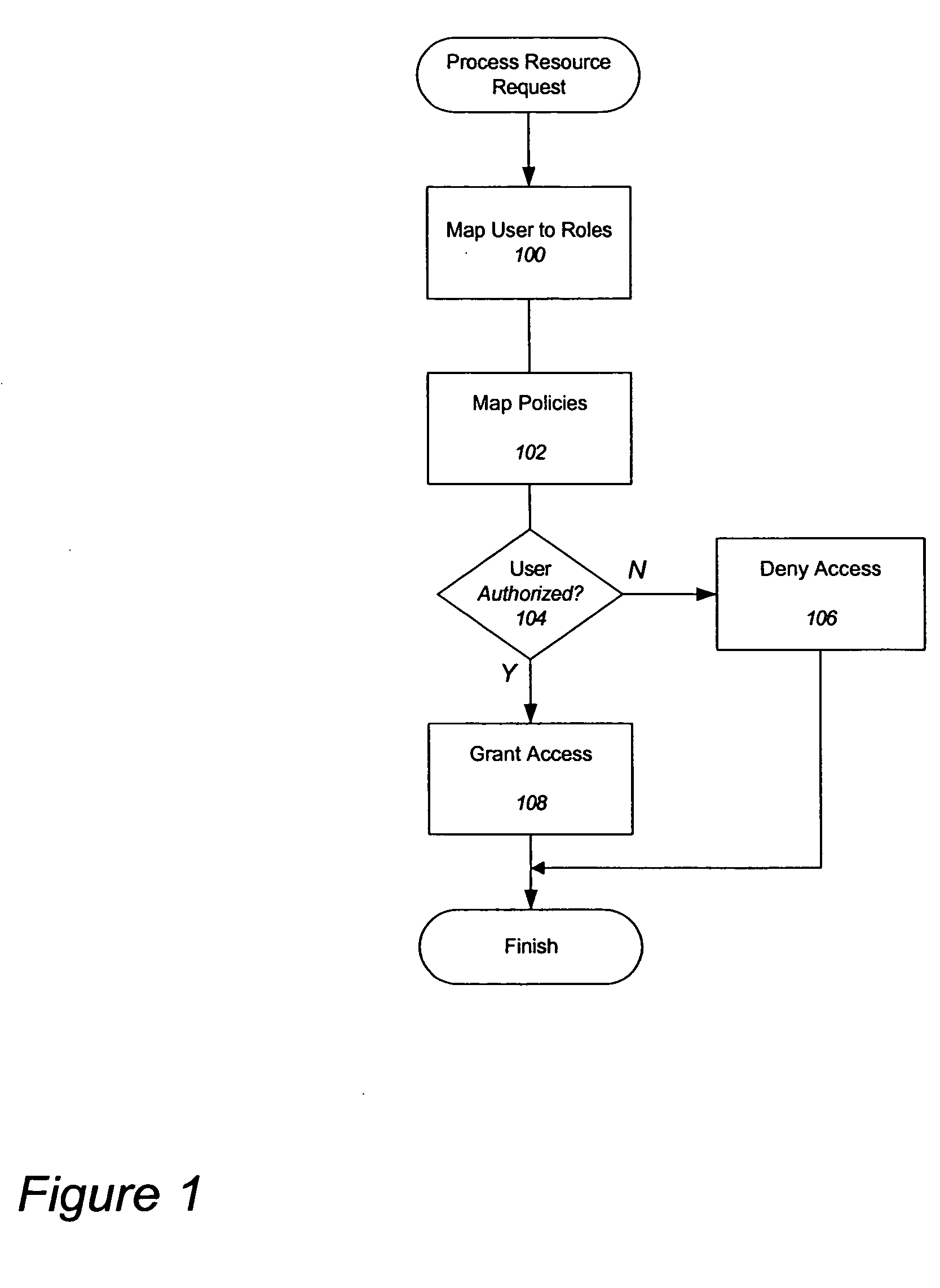
Delegated administration for a distributed security system
ActiveUS20050081063A1Digital data processing detailsHardware monitoringInformation dispersalDelegated administration
A system and method comprising the steps of, delegating a capability from a first user to a second user, propagating information that includes evidence of the delegation to a plurality of security service modules, wherein each one of the plurality of security service modules is capable of protecting one or more resources, providing the evidence to a first security service module belonging to the plurality of security service modules, enforcing the delegation when the second user attempts to access a resource in the one or more resources wherein the resource is protected by the first security service module, and wherein the enforcement is carried out by the first security service module.
Owner:ORACLE INT CORP
Camera protective system and method
InactiveUS20120081537A1Engineering safety devicesColor television detailsProtection systemReal time transmission
A user protection system, a machine including a user protection system, and a method of protecting a user of a machine are disclosed. In an embodiment, a user protection system is provided including at least one camera directed to a protected area of the machine; a computing device operably coupled to the at least one camera, a program product stored in a memory of the computing device which when executed, analyzes at least one image of the protected area captured by the camera and transmitted in real time to the computing device, and a relay coupling operably connecting the computing device with a shut-off control on the machine, wherein, in a case in which at least a part of a user is detected at least partially within the protected area, the computing device transmits a command causing the machine to stop.
Owner:GENERAL ELECTRIC CO
Helmet testing equipment and methodology
ActiveUS20190086309A1Simple methodEasy to collectMaterial strength using single impulsive forceHelmetsEngineeringHead model
A method for testing a helmet for effectiveness of user protection includes moving a load along a predetermined path, supporting a target body at an impact location in the predetermined path, the target body including a head model and a helmet disposed on the head model, and impacting the target body with a force generated by the moving of the load. The impacting of the target body entails contacting the target body with an impactor free to move perpendicularly and tangentially relative to a surface of the target body. The supporting of the target body is at least reduced, if not eliminated, before or during the impact of the impactor with the target body at the location. Forces generated are automatically measured or sensed during the impact of the impactor with the target body at the location.
Owner:BRANDT RICHARD A
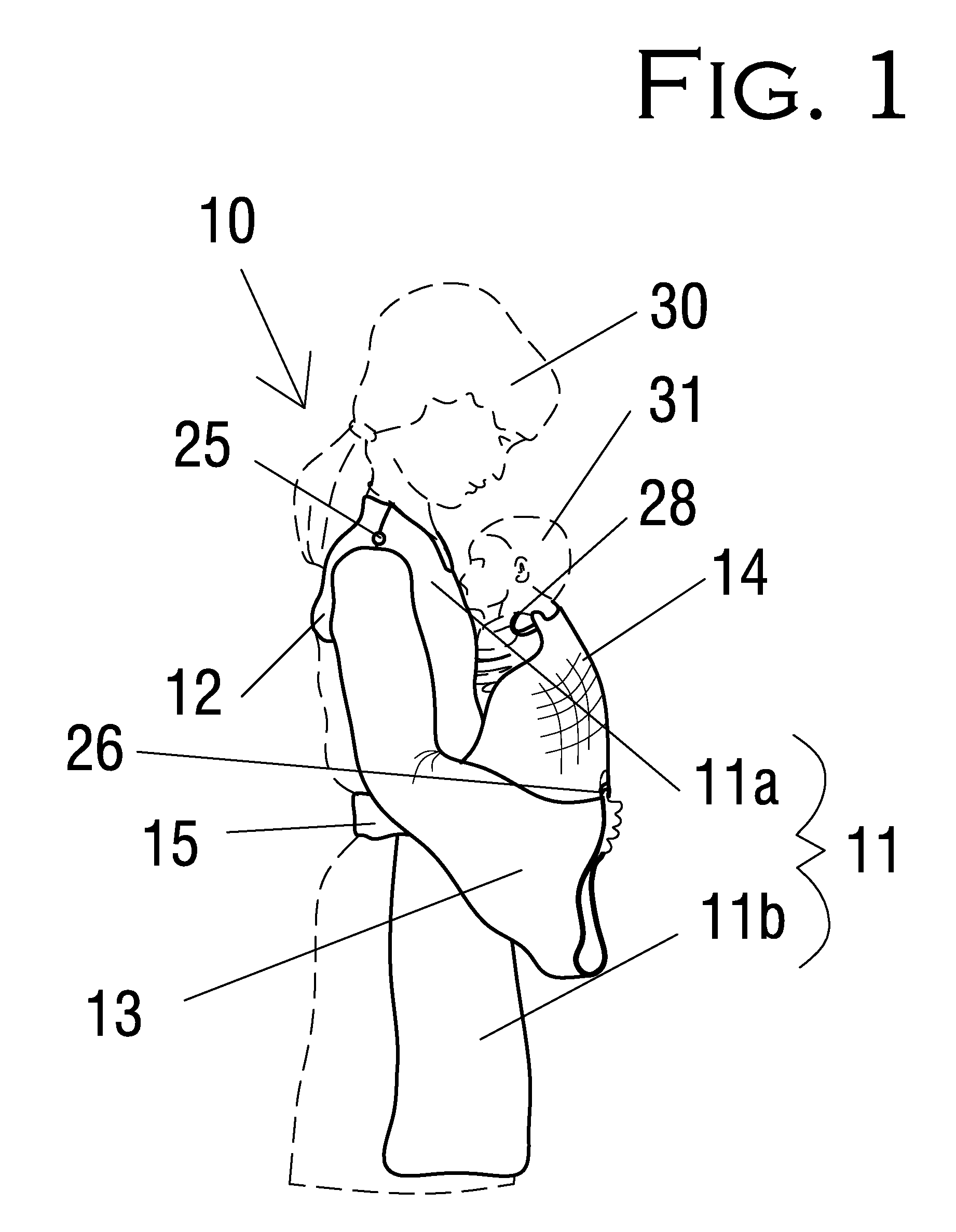
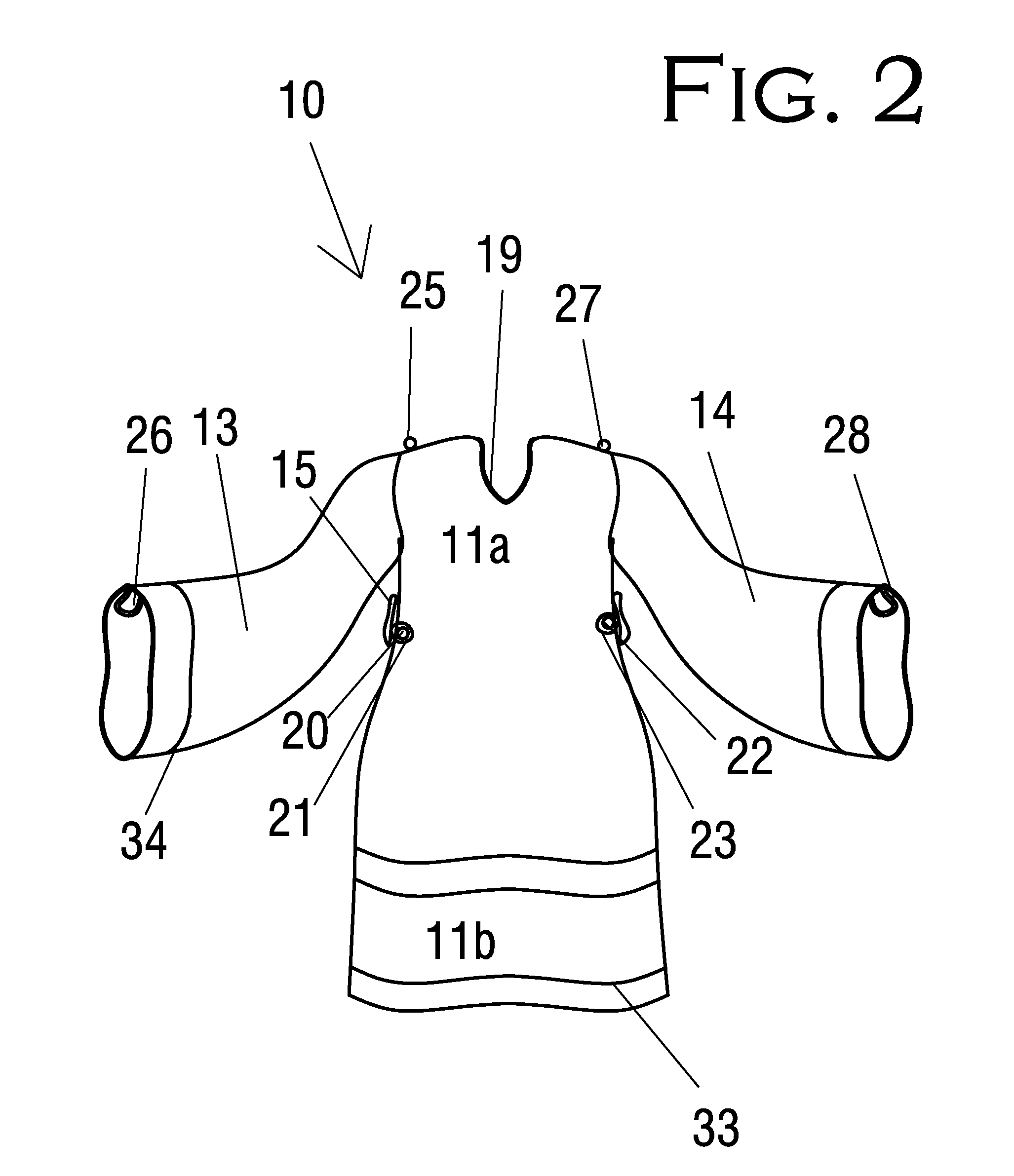
Combination user protection and baby safety towel
InactiveUS7634818B1Improve convenienceImprove securityBaby linensProtective garmentUser protectionEngineering
A combination user protector and baby safety towel is provided including a long front fabric member, a short back fabric member, two long sleeve fabric members, a belt fabric member, complementary belt-attachment members, and complementary sleeve-securing button and loop members. The front and sleeve fabric members are a soft, absorbent fabric.Each sleeve is positionable. The loop engages the button to retract the sleeve for washing the baby. The sleeve is held extended for drying the baby by insertion of the user's thumb into the loop.The combination user protector and baby safety towel allows the user to draw a wet baby out of a bath and immediately and conveniently wrap and dry the baby in the extended sleeve fabric members while cuddling the baby on the front fabric member. Thus safety and convenience are increased while the user's clothing is protected from wetness.
Owner:TRUJILLO LESTHER +1
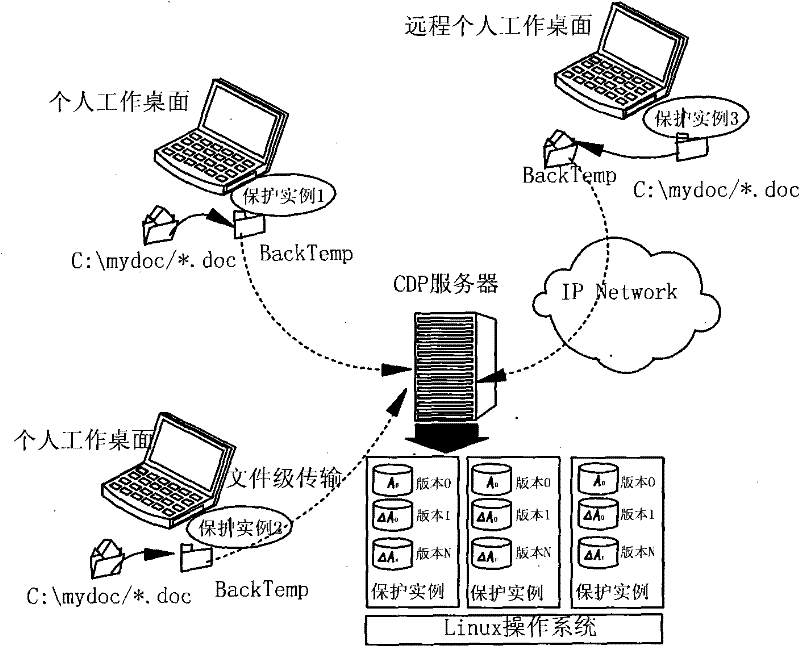
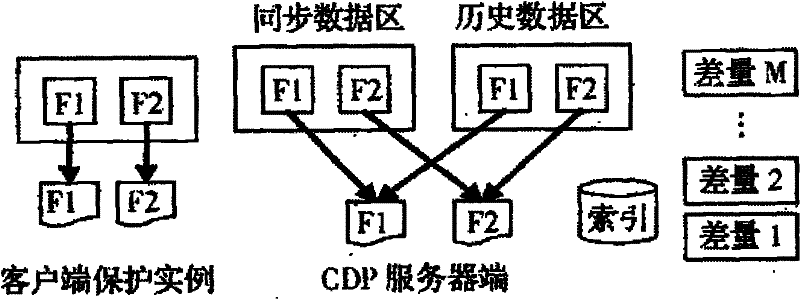
Continuous data protection method based on centralized storage
InactiveCN101751474AReduce storage spaceEasy to recordSpecial data processing applicationsOperational systemGNU/Linux
The invention provides a continuous data protection method based on centralized storage; difference algorithm is adopted to carry on difference transmission of files in data transmission process, the file changes are recorded through the combination of mirror and difference for storage, the system operates in Linux operating system, the user protected data and the metadata information are directly stored in the file system of the server, the system creates a metadata directory, a storage protection instance list and user information content for each user, also includes a soft link pointing at an physical data storage space, the time data storage space allocates an independent directory, logic volume and a partition for different user groups, and subsequently creates correspondingly directories for the users, a directory as the subdirectory of the user directory is created for each protection instance for protecting all versions of difference data of the protection instance; the invention is an important component part of project chunk level and file level continuous data protection system and helps obtain good benefits in part of enterprise key data protection services.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
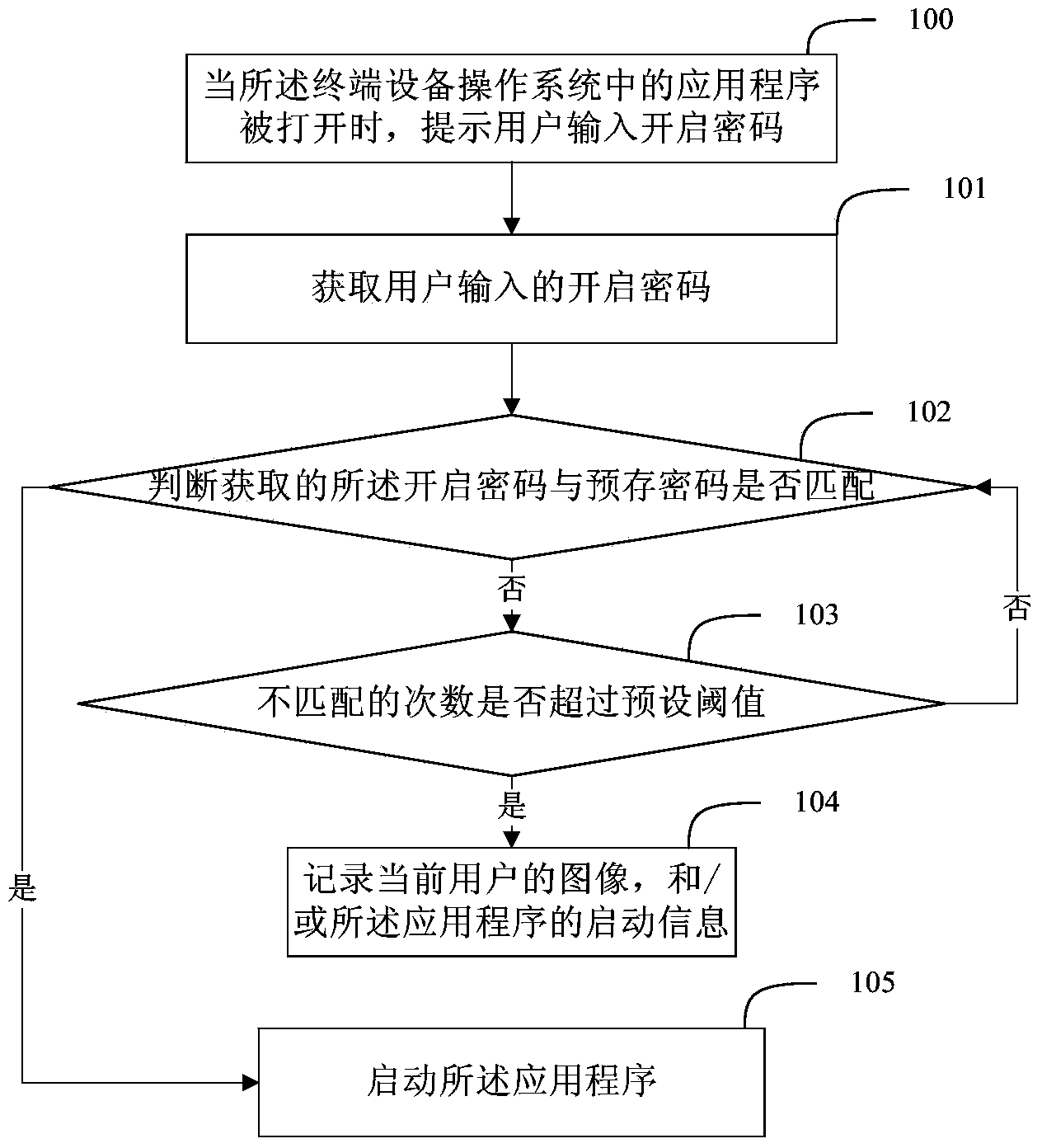
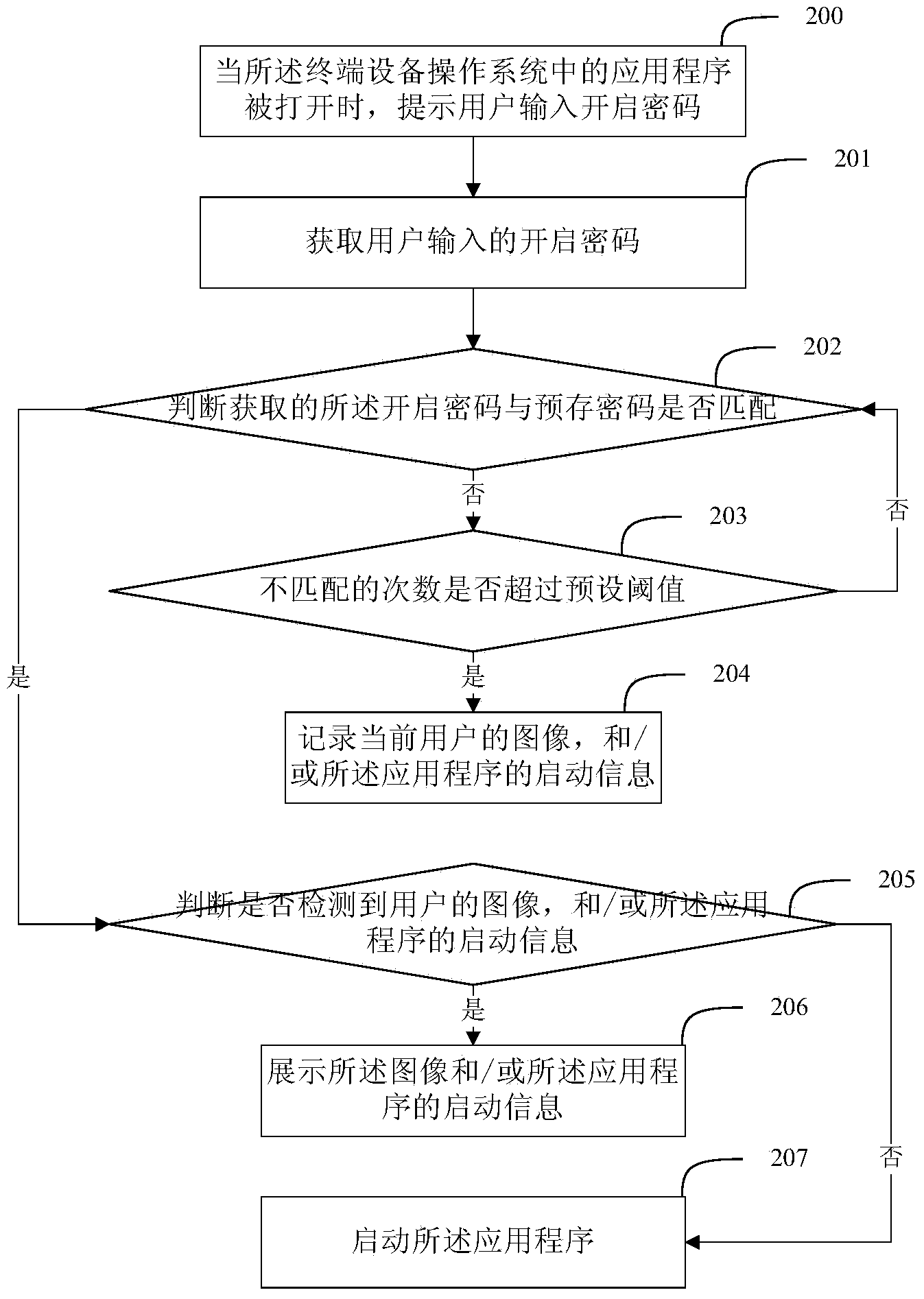
Method and device for application program safety management for terminal equipment, and terminal
ActiveCN104268453ADigital data authenticationPlatform integrity maintainanceOperational systemPassword
The embodiment of the invention discloses a method for application program safety management for terminal equipment. The method comprises the following steps of: when an application program in the operation system of the terminal equipment is opened, prompting a user to input a start password; acquiring the start password input by the user; judging whether the acquired start password is matched with a pre-stored password; if so, then starting the application program; or else, when the mismatching times exceeds a preset threshold value, then recording the current image of the user, and / or the start information of the application program. The embodiment of the invention discloses a device for application program safety management for terminal equipment, and a terminal. Through implementation for the technical scheme of the invention, the application program protected by the user, in the operation system of the terminal equipment can be monitored and recorded, thus the user can know who illegally operates the own privacy application.
Owner:KENIU NETWORK TECH BEIJING
Methods of RF sensing control and dynamic frequency selection control for cognitive radio based dynamic spectrum access network systems-cognitive dynamic frequency hopping
Owner:STMICROELECTRONICS SRL
Multi-failure protection method for multiple service levels in WDM network
InactiveCN101262298AAddressing the need for protectionMultiple fault protection satisfiesWavelength-division multiplex systemsFault recovery arrangementsGrade of serviceResource utilization
The invention relates to a protection method with a plurality of service grades for multiple faults in WDM networks, pertaining to the technical field of optical network communication. The method comprises the steps as follows: step one: connections of different grades are established for service requests arrived, that is, working accesses and accesses for protection are established; step two: for service connections conveying data in the networks, when failed links occur, the service grade is judged, different protection methods are executed to services of different grades, and enhanced recovery is executed to the service of the highest grade. The method of the invention meets the requirements for different protections raised by users in case of multilink faults in the WDM optical networks. EDSP takes into consideration of an enhanced recovery mechanism for load balancing, protection of resource sharing and resource recycling, so as to improve resource utilization rate and reduce blocking probability; effective multiple faults protection is also provided, and the requirement for services of diamond grade (highly reliable protection for multiple faults (three faults and more)), platinum grade (single fault being 100 percent protected) and economic grade (no protection) are met.
Owner:NORTHEASTERN UNIV
Acoustic signal level limiter
ActiveUS7200238B1Avoid crossingFlexible designSubstation equipmentDifferential amplifiersUltrasound attenuationCommunications system
An acoustic signal level limiter provides a telephone handset / headset user protection against loud audible signals generated within a communications system. The acoustic signal limiter comprises an acoustic signal level attenuation circuit and at least one acoustic signal level relay circuit. Once activated, the acoustic signal level attenuation circuit creates an attenuation network that attenuates an electrical acoustic signal transmitted through the communications system. Acoustic signal level relay circuits are activated to further attenuate the electrical acoustical signal to prevent the acoustic signal level attenuation circuit from operating in a deep saturation mode and provide further hearing safety for the telephone headset / handset user. A fuse in series and “Zener Zap” shunting transistor diodes provide assured higher signal level protection.
Owner:PLANTRONICS
Self-sealing protection filter port
ActiveUS20050102986A1Reduces and prevents entryImprove securityCombination devicesAuxillary pretreatmentEngineeringVALVE PORT
A self-sealing protection filter port for gas masks prevents contamination of the inner-environment of the mask during exchange of filters and therefore increases safety. A biased valve closes the air inlet to the port when the protection filter is not installed. As a new filter is inserted, the valve is forced open, allowing filtered air to flow through the air inlet to the user. The protection filter engages the filter port using a retaining element. The self-sealing protection filter in a protection mask having an internal close-biased valve is installed in the standard protection filter port of the mask.
Owner:IMMEDIATE RESPONSE TECH +1
Method and device for detecting health state of human eyes and mobile terminal
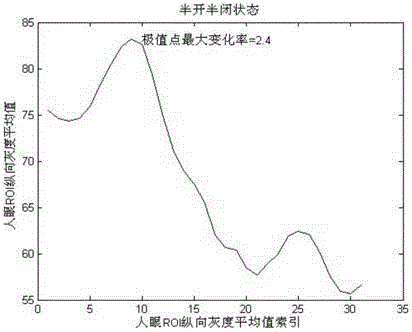
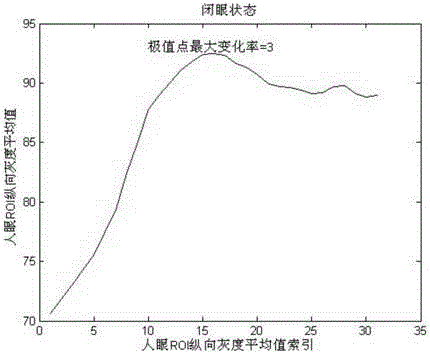
ActiveCN105022981AProtect eyesightInput/output for user-computer interactionCharacter and pattern recognitionComputer scienceVisual acuity
Owner:ZTE CORP
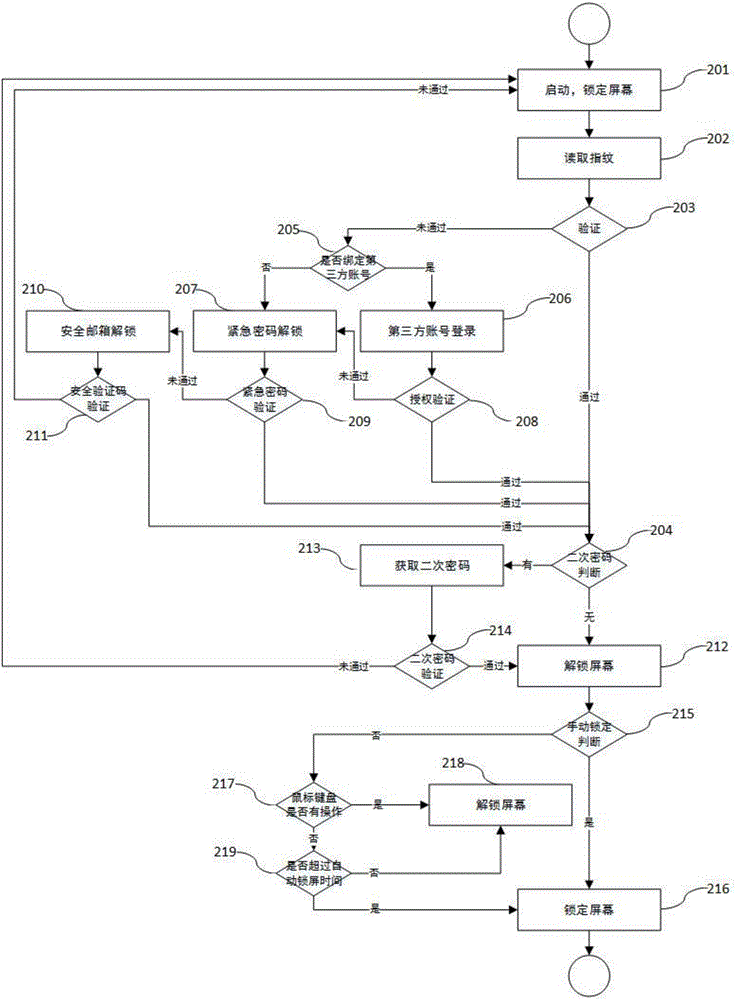
Method for locking or unlocking computer screen based on fingerprints
InactiveCN105809005ALow costNo lossInternal/peripheral component protectionDigital data authenticationPersonal computerProtected mode
The invention discloses a method for locking or unlocking a computer screen based on fingerprints. The method comprises the following steps of establishing a local server, extracting fingerprint information, obtaining user settings, establishing a cloud server and enabling screen to be locked or unlocked. The method for locking or unlocking the computer screen based on the fingerprints has the following advantages that the fingerprints serve as a key for locking or unlocking the screen of a personal computer, security is achieved, and the cost is low; multiple layers of secondary validation user protection and an emergency mode are added for providing a more secure and convenient unlocking technology and identity authentication method; an active system protection mode is adopted; according to a use scene, protection is set to be automatically hidden at the bottom layer which cannot be sensed by a user, and soundless protection is achieved.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
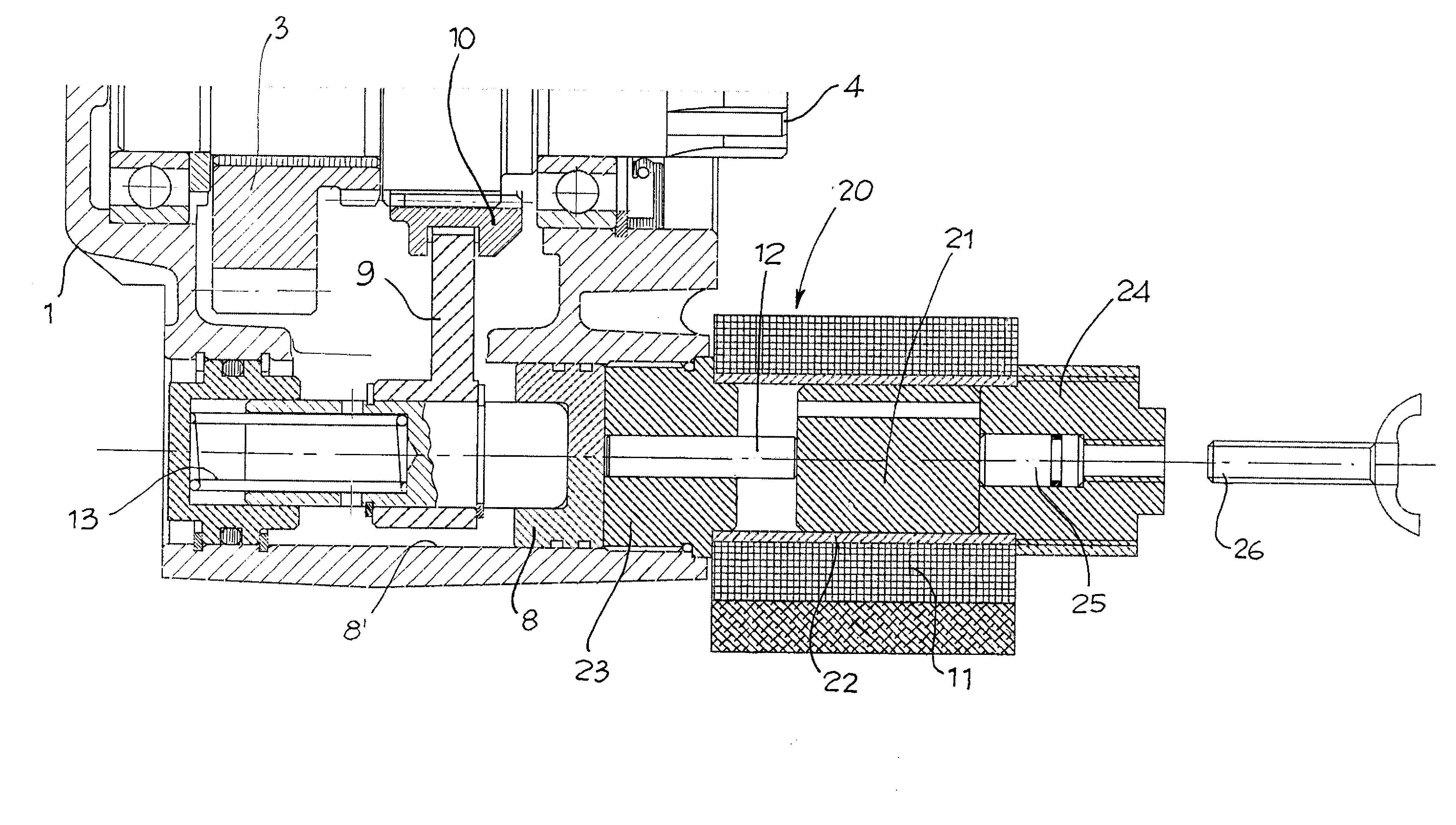
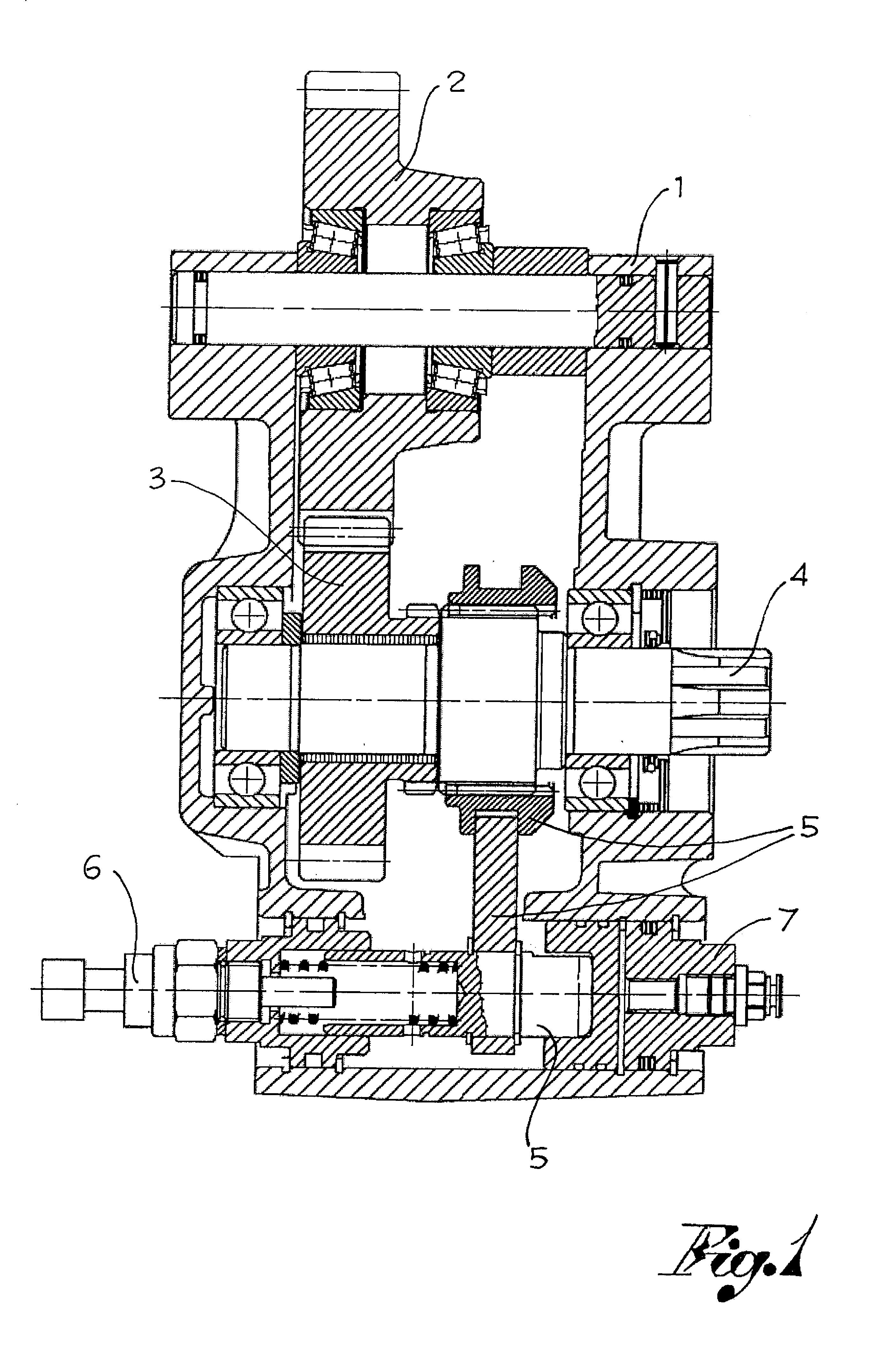
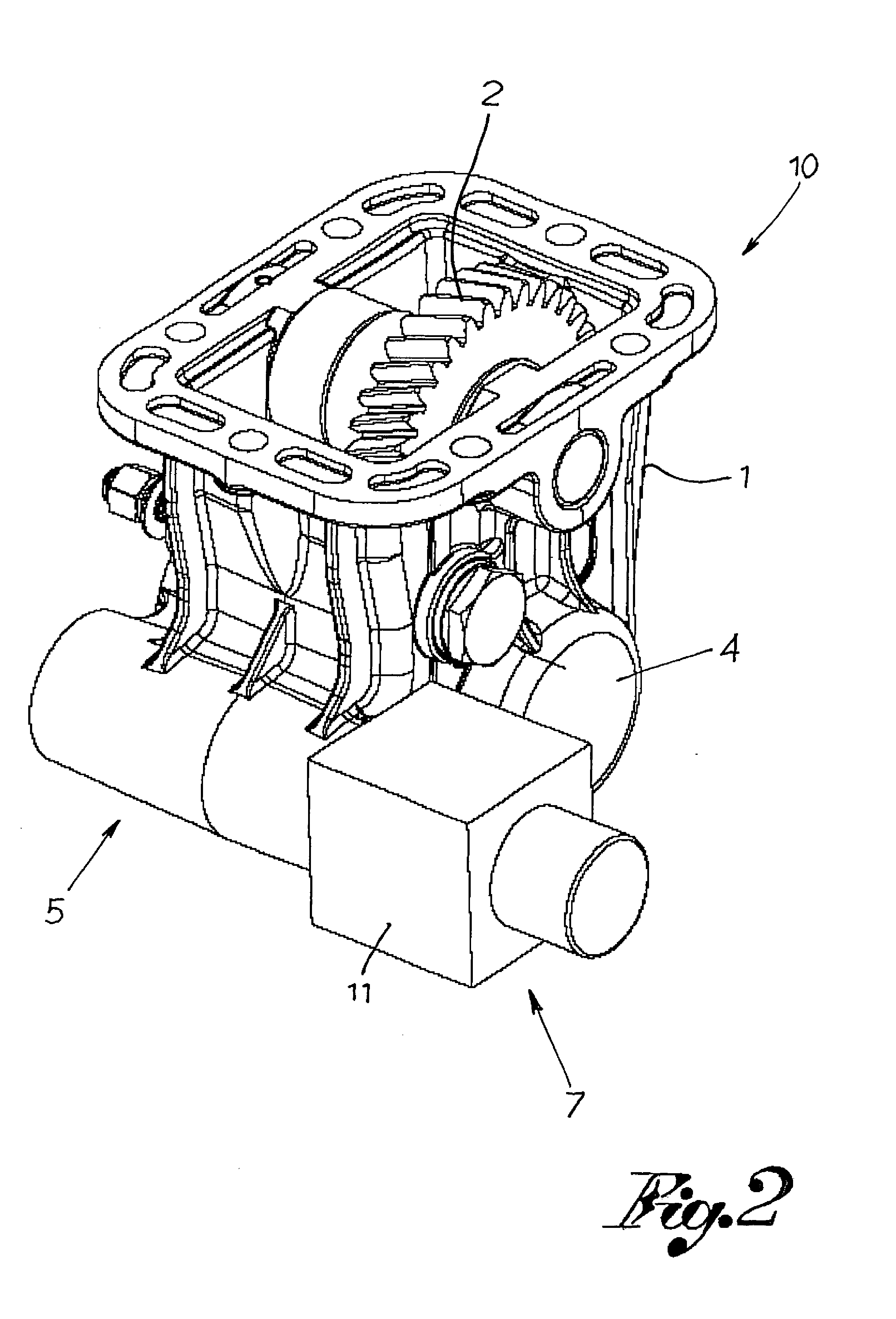
Solenoid Device for Engaging Power Takeoffs
ActiveUS20070135260A1Magnetically actuated clutchesGearing controlElectrical resistance and conductancePower flow
A device for engaging power takeoffs, primarily used to drive a load from the engine of a vehicle, has an electromagnet with a single winding of small size which is driven by a microprocessor system in PWM mode allowing to differentiate the current intensity of the engaging phase and of the phase of maintaining said engaging. The control system monitors, without the aid of external sensors, parameters such as electromagnet current, power supply and electromagnet voltage, electromagnet winding resistance, electromagnet winding inductance. From these parameters, the system is able to determine the engaging or unengaging position of the power takeoff, and it is able automatically to uncouple if the monitored parameters do not fall within the expected ranges, simultaneously notifying the user of the protective intervention.
Owner:O M F B S P A HYDRAULIC COMPONENTS
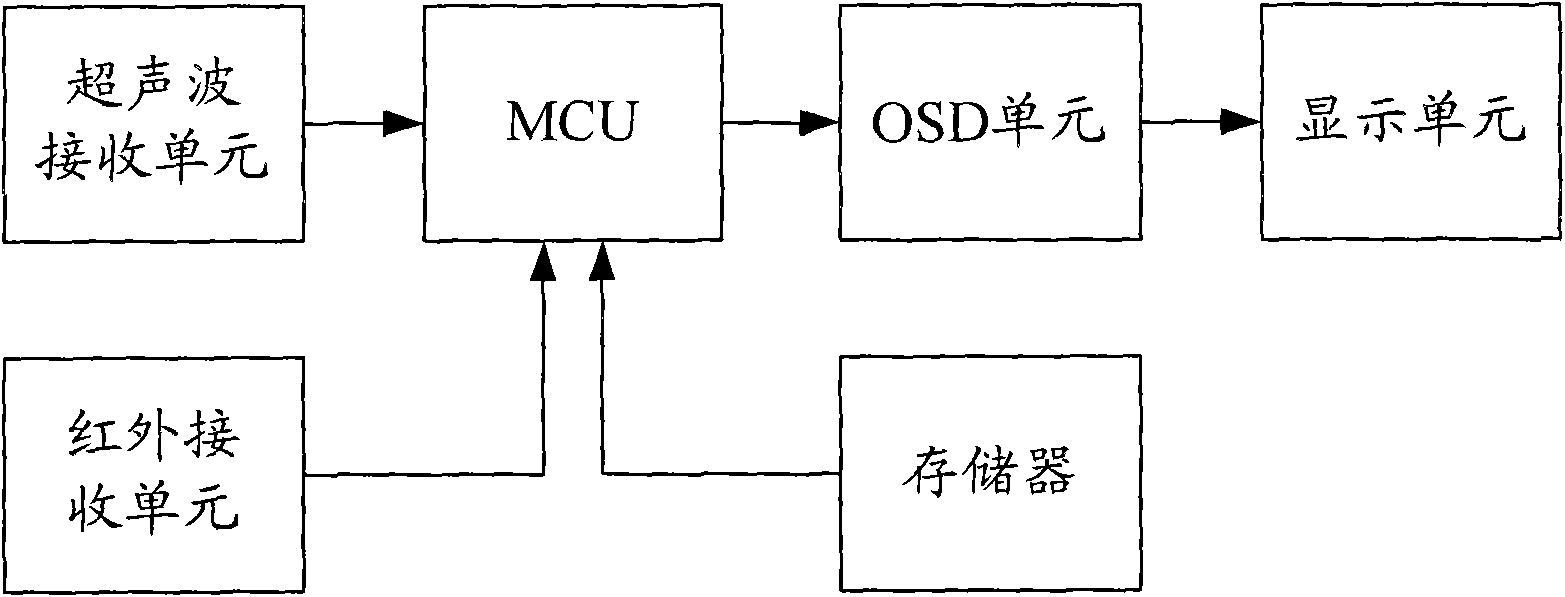
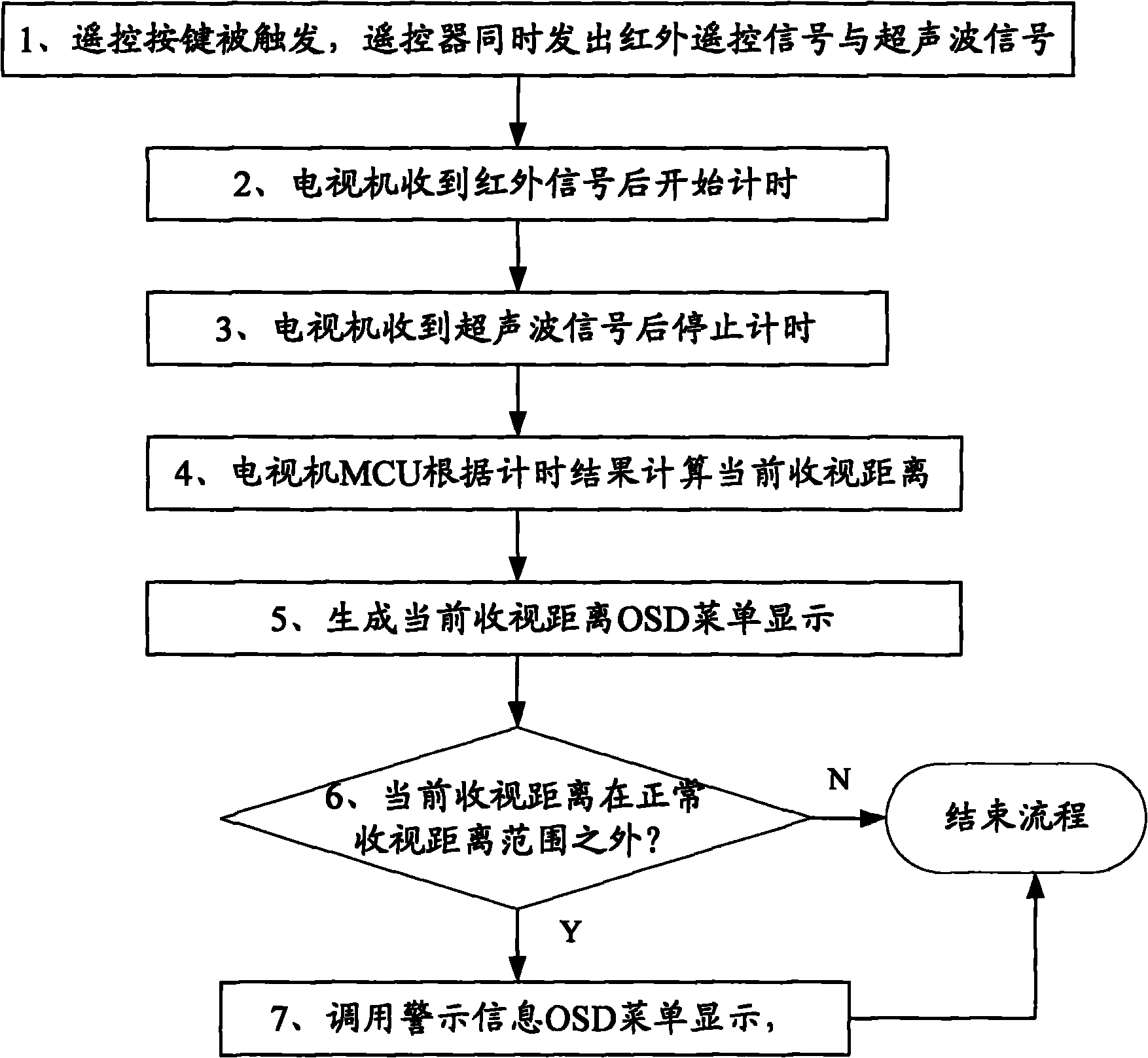
Television with viewing distance warning function and realizing method thereof
InactiveCN101931766AProtect eyesightTelevision system detailsColor television detailsTechnology of televisionComputer science
The invention is applicable to the technical field of televisions and provides a television with the viewing distance warning function and a realizing method thereof, and the method comprises the following steps: a) calculating the transmission time of an ultrasonic signal sent by a remote controller of the television; and b) calculating the current viewing distance according to the transmission time of the ultrasonic signal and the transmission speed, comparing the current viewing distance with the preset normal viewing distance, and calling warning information for display if the current viewing distance exceeds the range of the normal viewing distance. The technical scheme can carry out real-time monitoring on the current viewing distance of a user, emit the warning information when the viewing distance exceeds the preset range and further remind the user of protecting eyesight.
Owner:SHENZHEN TCL NEW-TECH CO LTD
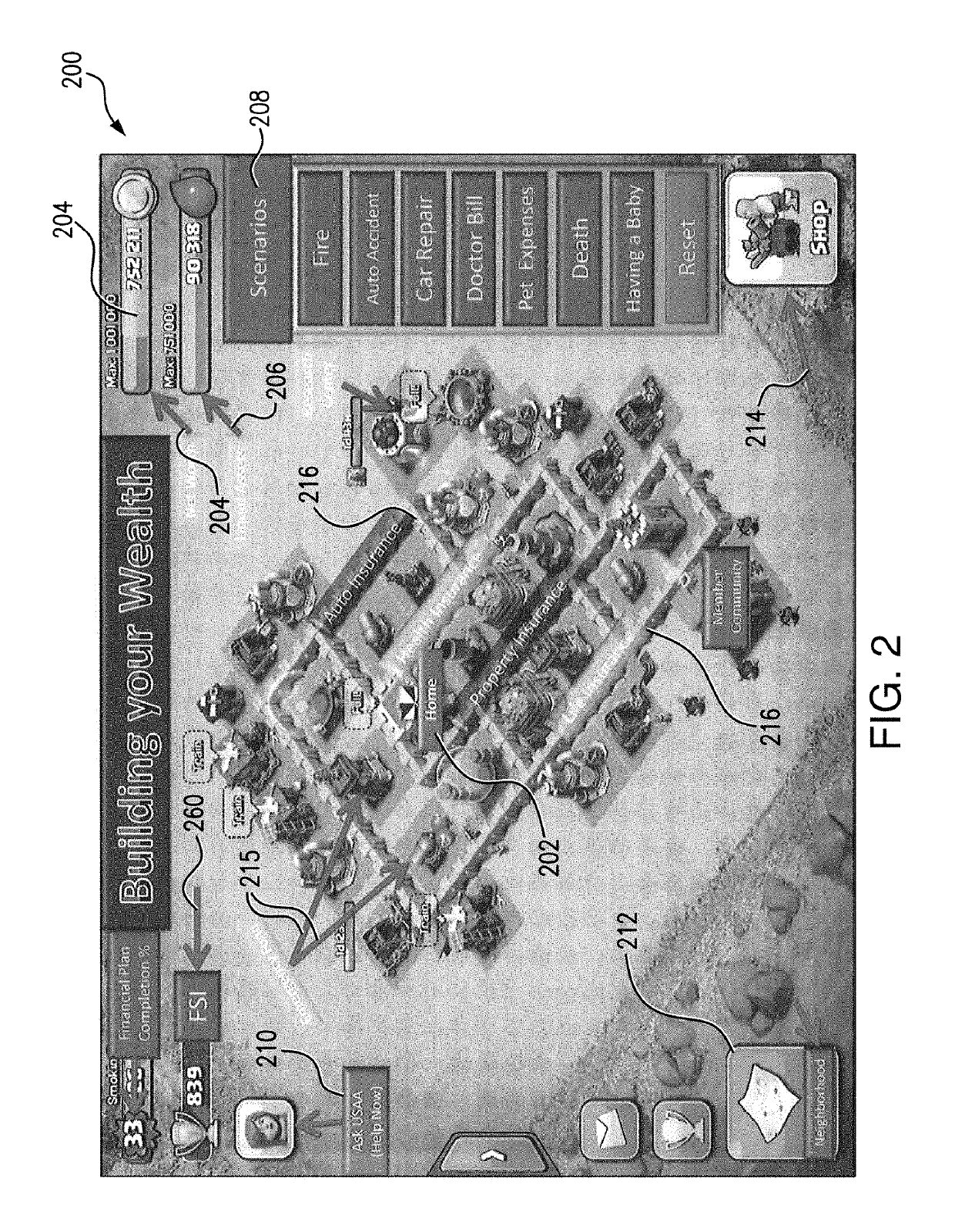
Techniques to visualize and gamify risk management services
Techniques for gamifying risk management services include associating a financial status of a user with a defensible position display element in a gameplay scenario, receiving risk management data regarding at least one risk management service secured by the user, associating the risk management service with at least one defensive display element in the gameplay scenario, and providing the defensible position display element and each defensive display element to a display to cause the display to visualize the defensible position display element protected by each defensive display element in the gameplay scenario.
Owner:USAA
Portable storage device
ActiveUS20090147460A1Conveniently disassembledLower assembly costsDigital data processing detailsSensing record carriersEngineeringElectrical and Electronics engineering
Owner:ADATA
Solenoid device for engaging power takeoffs
ActiveUS7461569B2Magnetically actuated clutchesGearing controlElectrical resistance and conductanceSolenoid valve
A device for engaging power takeoffs, primarily used to drive a load from the engine of a vehicle, has an electromagnet with a single winding of small size which is driven by a microprocessor system in PWM mode allowing to differentiate the current intensity of the engaging phase and of the phase of maintaining said engaging. The control system monitors, without the aid of external sensors, parameters such as electromagnet current, power supply and electromagnet voltage, electromagnet winding resistance, electromagnet winding inductance. From these parameters, the system is able to determine the engaging or unengaging position of the power takeoff, and it is able automatically to uncouple if the monitored parameters do not fall within the expected ranges, simultaneously notifying the user of the protective intervention.
Owner:O M F B S P A HYDRAULIC COMPONENTS
Card selection prompting method of multi-card terminal and multi-card mobile terminal
InactiveCN103369506AEasy to managePrivacy protectionNetwork data managementComputer hardwareUser protection
The invention is applicable to the technical field of communication, and provides a card selection prompting method of a multi-card terminal. The method comprises the steps of inquiring a communication event record of a mobile terminal with a communication opposite end when a trigger action of a communication event of the mobile terminal and the communication opposite end is detected, and displaying card selection prompt according to the communication event record. The invention also provides a multi-card mobile terminal for realizing the above method correspondingly. Therefore, a user is assisted to protect the privacy well, and the management and flexible use of the relation between a number and a contact by the user are strengthened.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Mobile device and eye-protection control method thereof
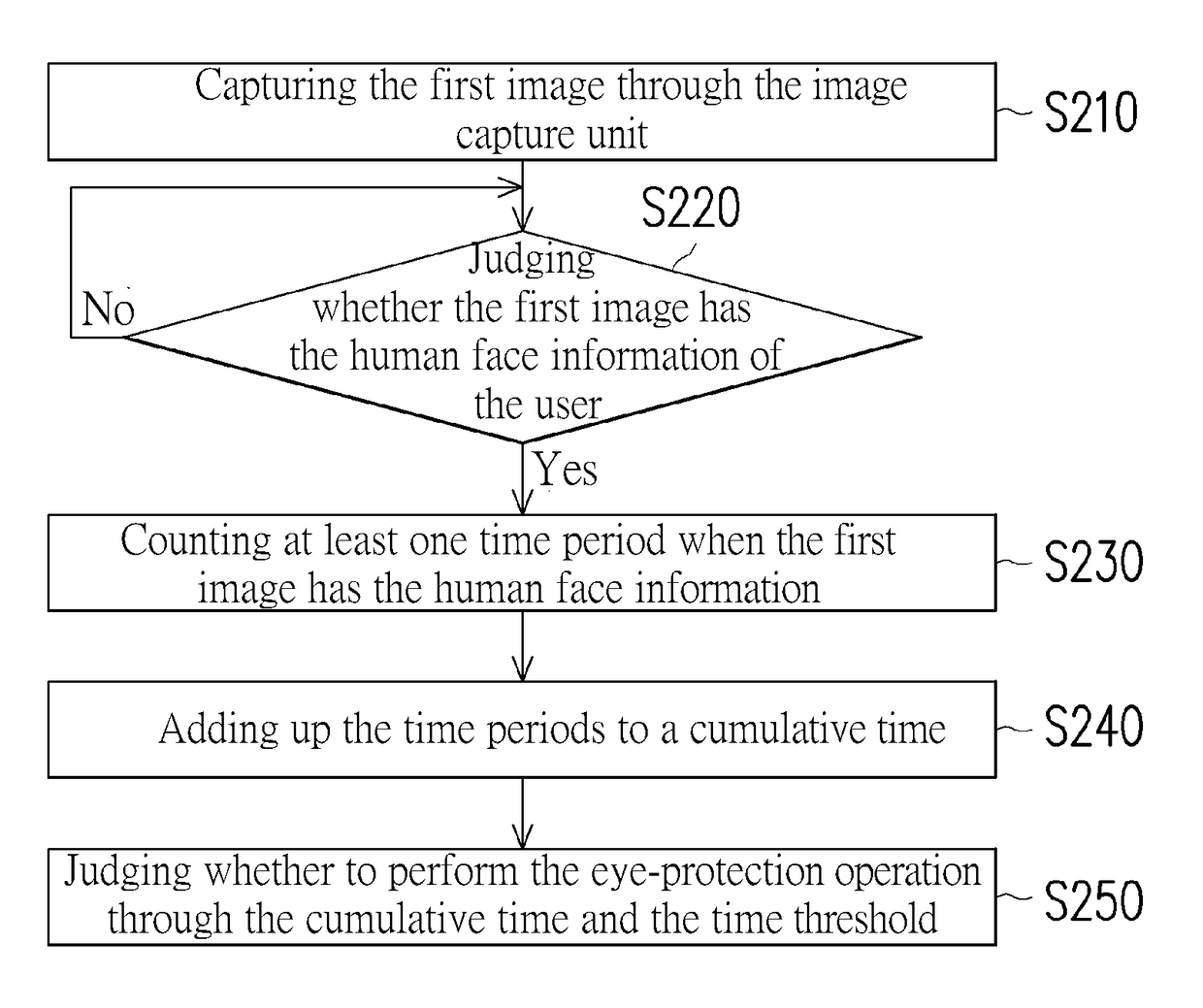
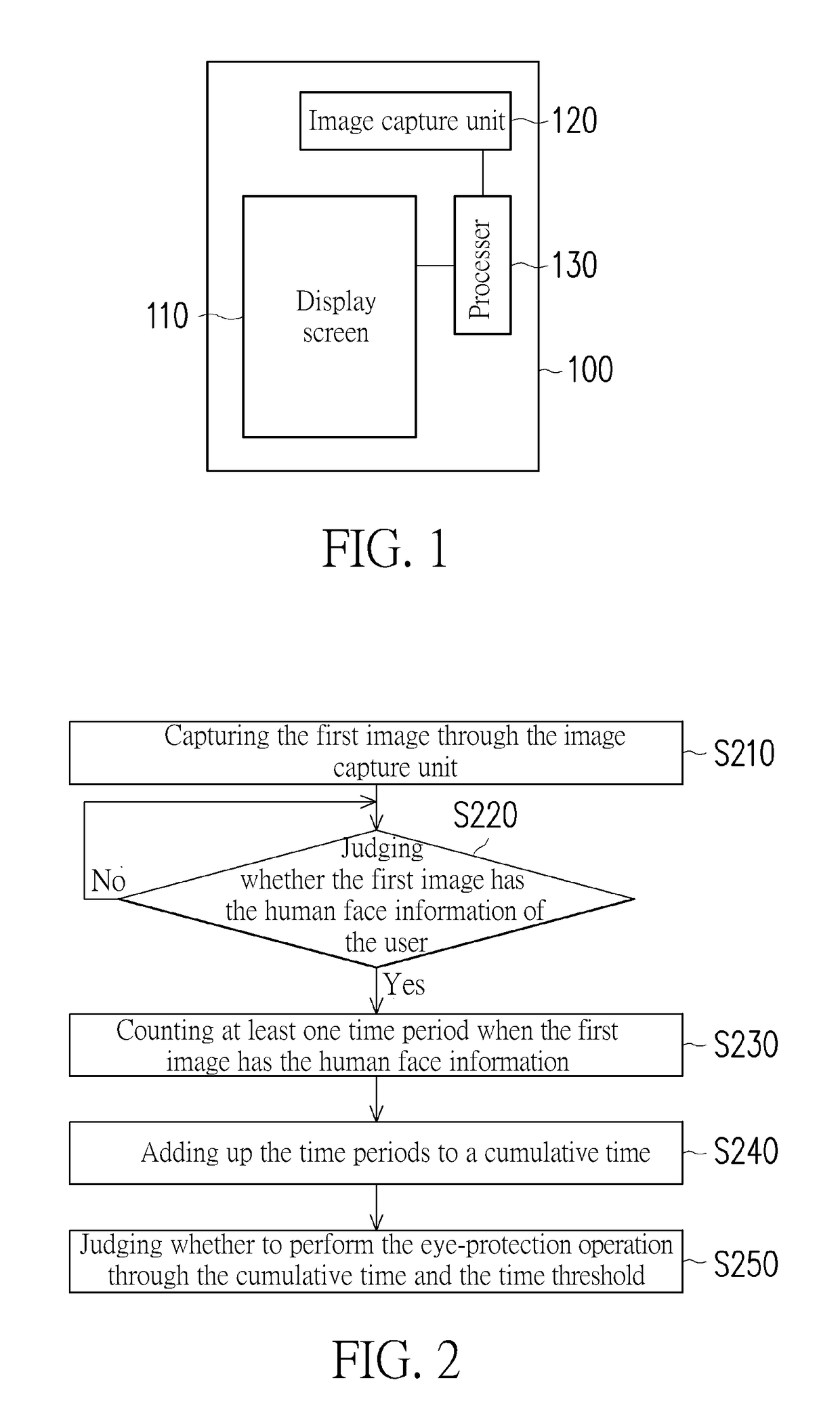
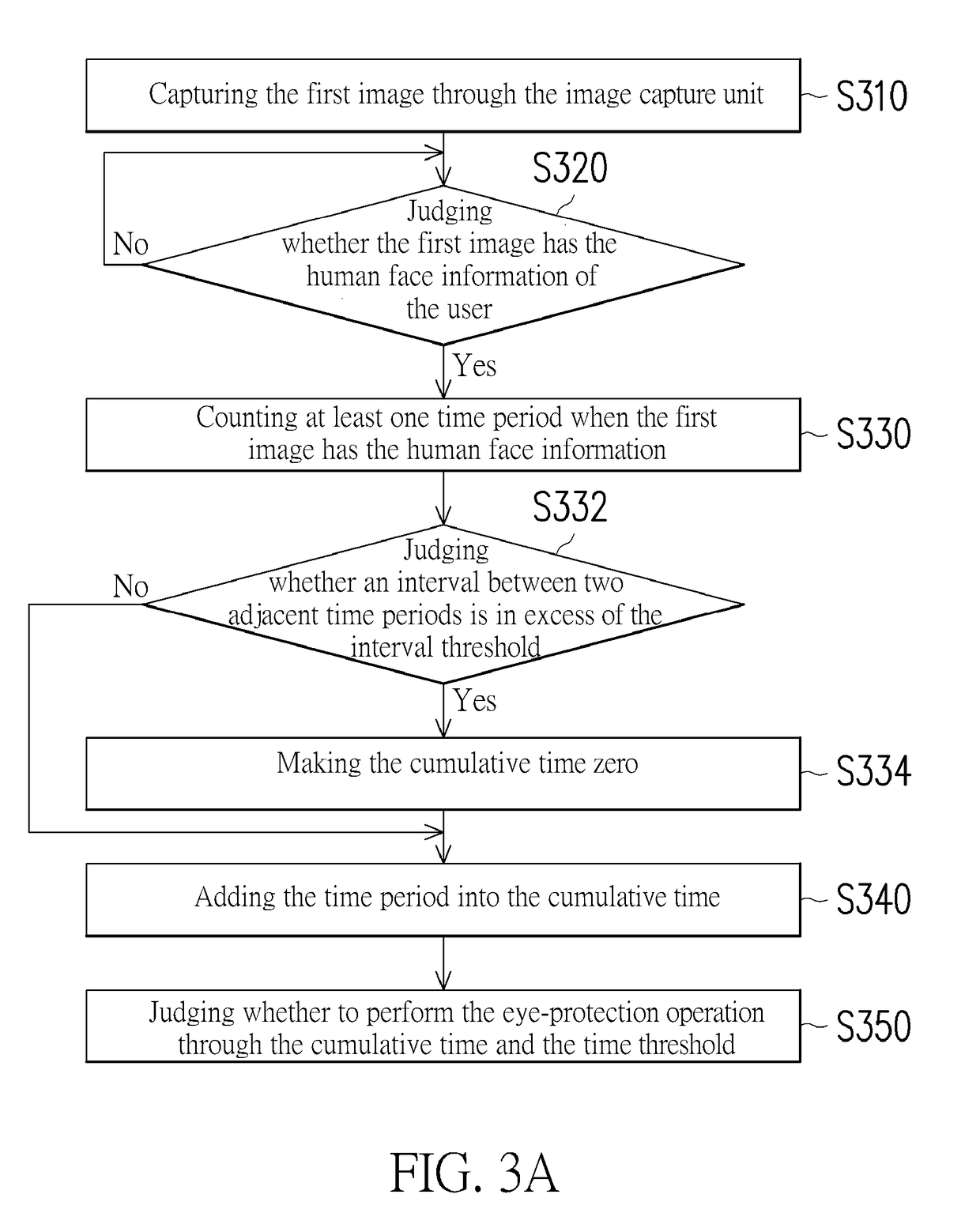
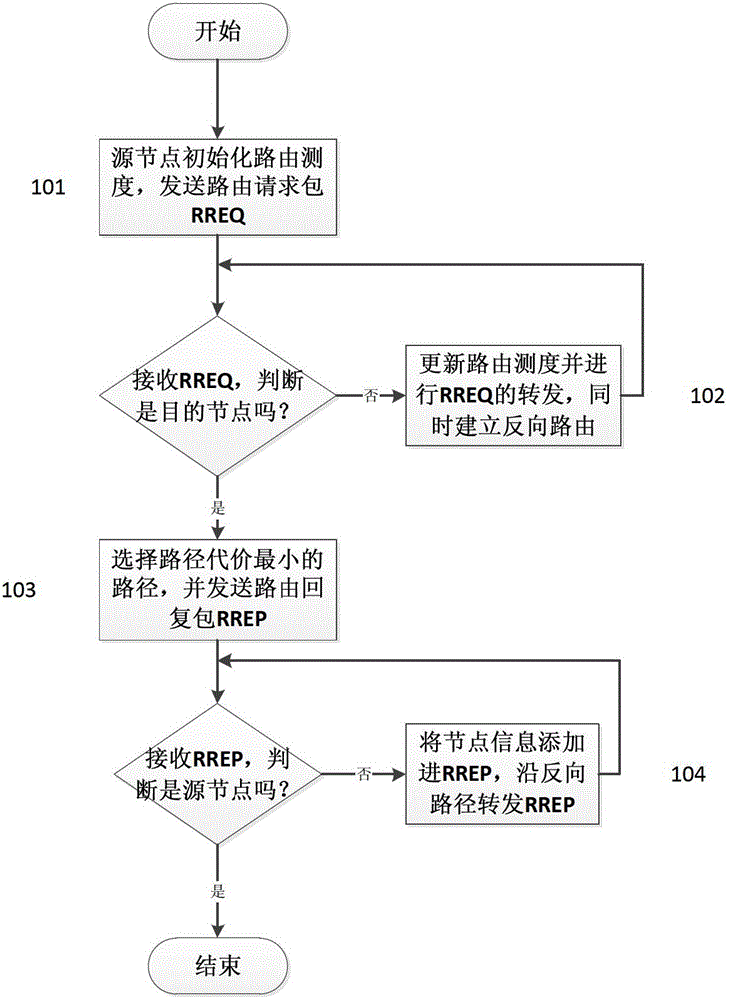
ActiveUS20170318227A1Avoid overuseInput/output for user-computer interactionTelevision system detailsFace detectionProtecting eye
A mobile device and an eye-protection control method thereof are provided. The mobile device includes a display screen, an image capture unit, and a processer. The display screen is for displaying information. The image capture unit is for capturing a first image. The processer is coupled to the image capture unit to obtain the first image. The processer performs a human face detection to the first image to judge whether the first image has a human face information of a user. The processer counts a plurality of time periods when the first image has the human face information and adds up the time periods to a cumulative time, and the processer judges whether to perform an eye-protection operation through the cumulative time and a time threshold. Accordingly, the mobile device can remind the user to protect eyes and avoid overuse of the eyes.
Owner:HANNSTOUCH SOLUTION
Display control method and device, electronic equipment and computer readable storage medium
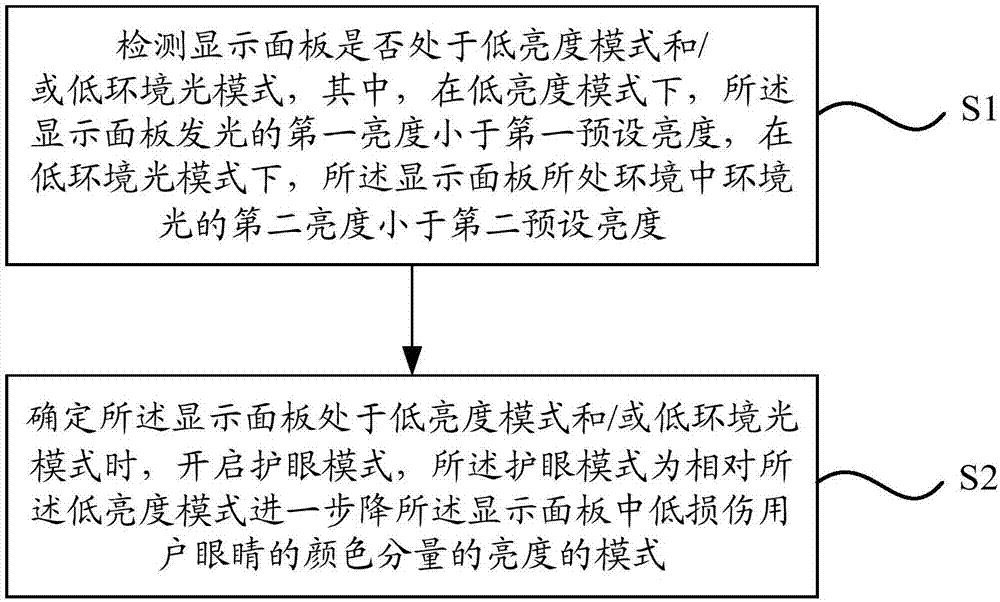
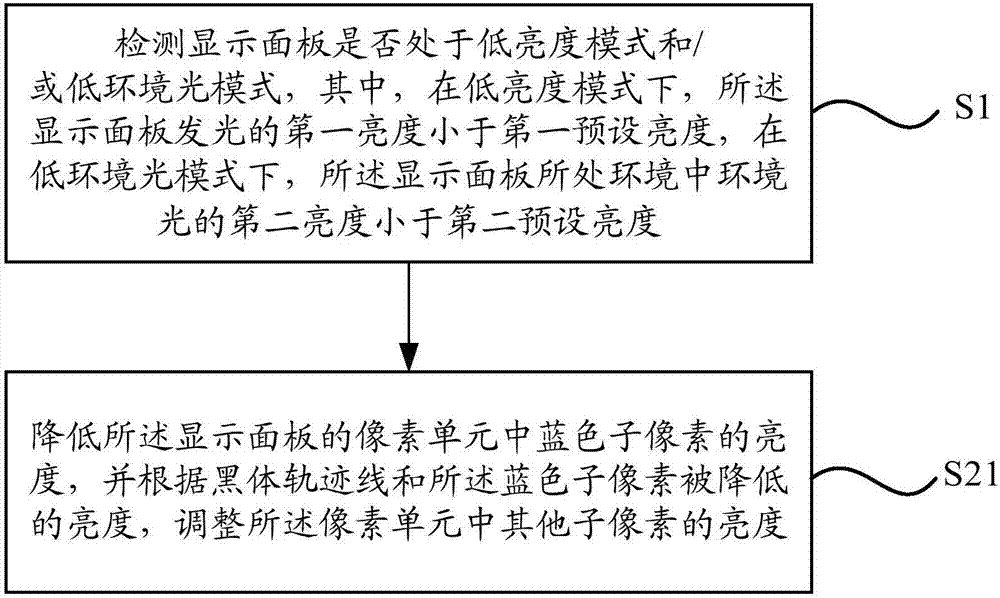
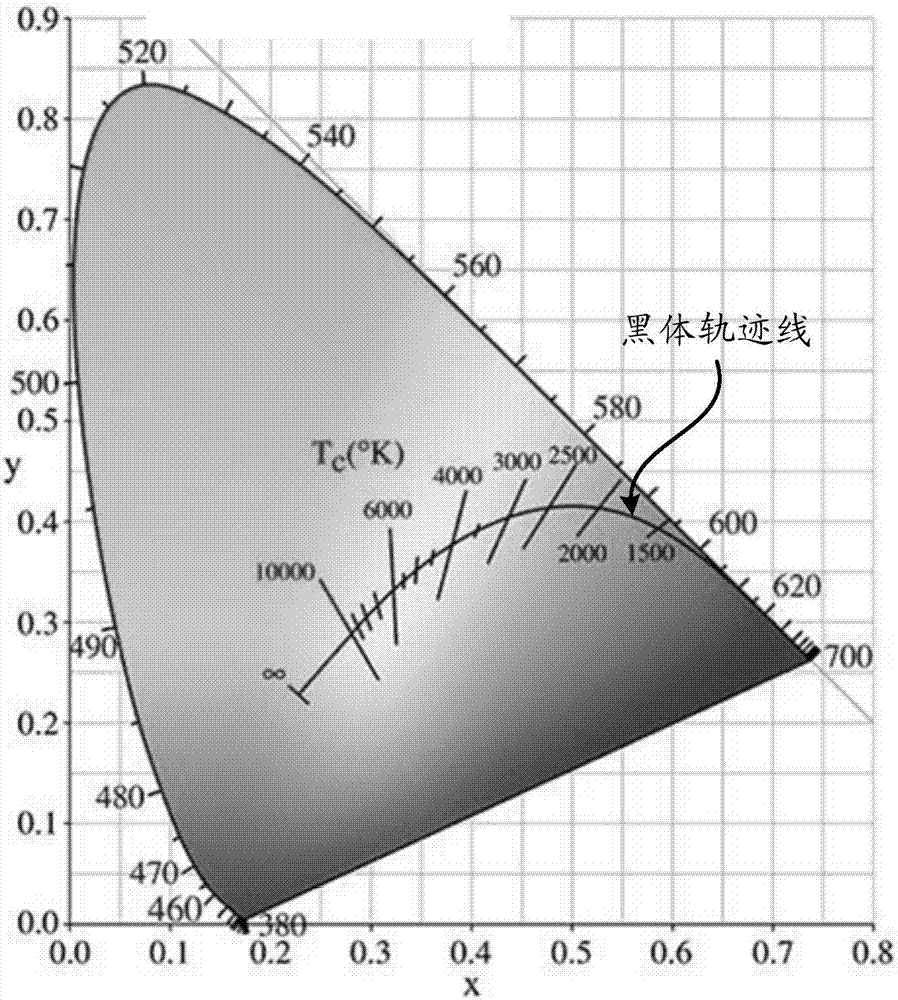
PendingCN107122150AReduce color componentsAchieve protectionCathode-ray tube indicatorsDigital output to display deviceProtecting eyeComputer science
The invention relates to a display control method, which comprises the following steps that: detecting whether a display panel is under a low-luminance mode and / or a low-ambient-light mode or not; and when a determining result shows that the display panel is under the low-luminance mode and / or the low-ambient-light mode, starting an eye protection mode, wherein the eye protection mode is a mode that the luminance of a color component which damages user eyes in the display panel is further lowered relative to the low-luminance mode. According to the technical scheme of the method, under a situation that the display panel is under the low-luminance mode, the eye protection mode is automatically started to further lower the color component which damages the user eyes in the display panel, a user does not need to carry out a manual operation, the problem that eyes can not be effectively protected since most users who are not familiar with the function of the display panel can not search or found the above regulation is avoided, and a user protection range is greatly improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
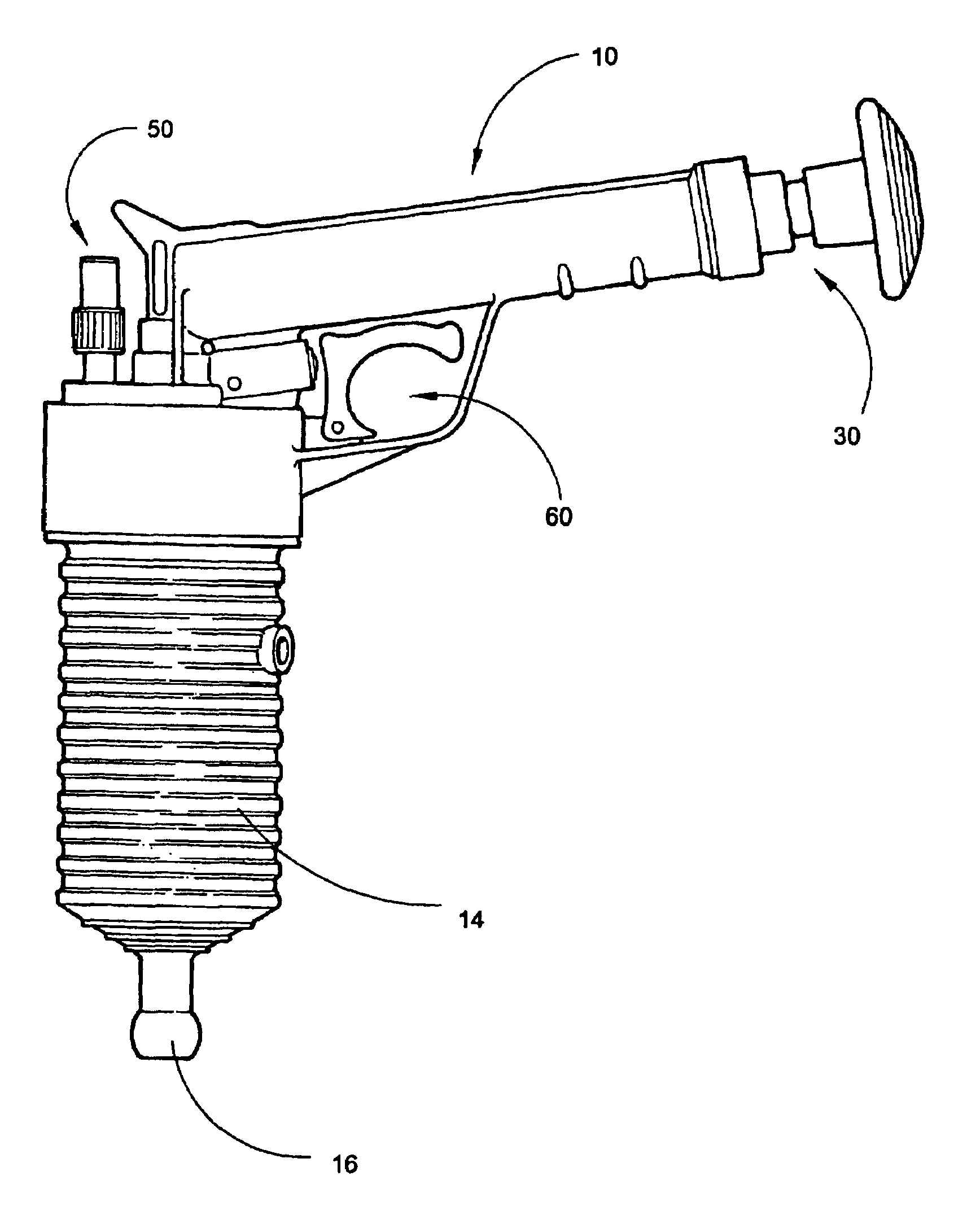
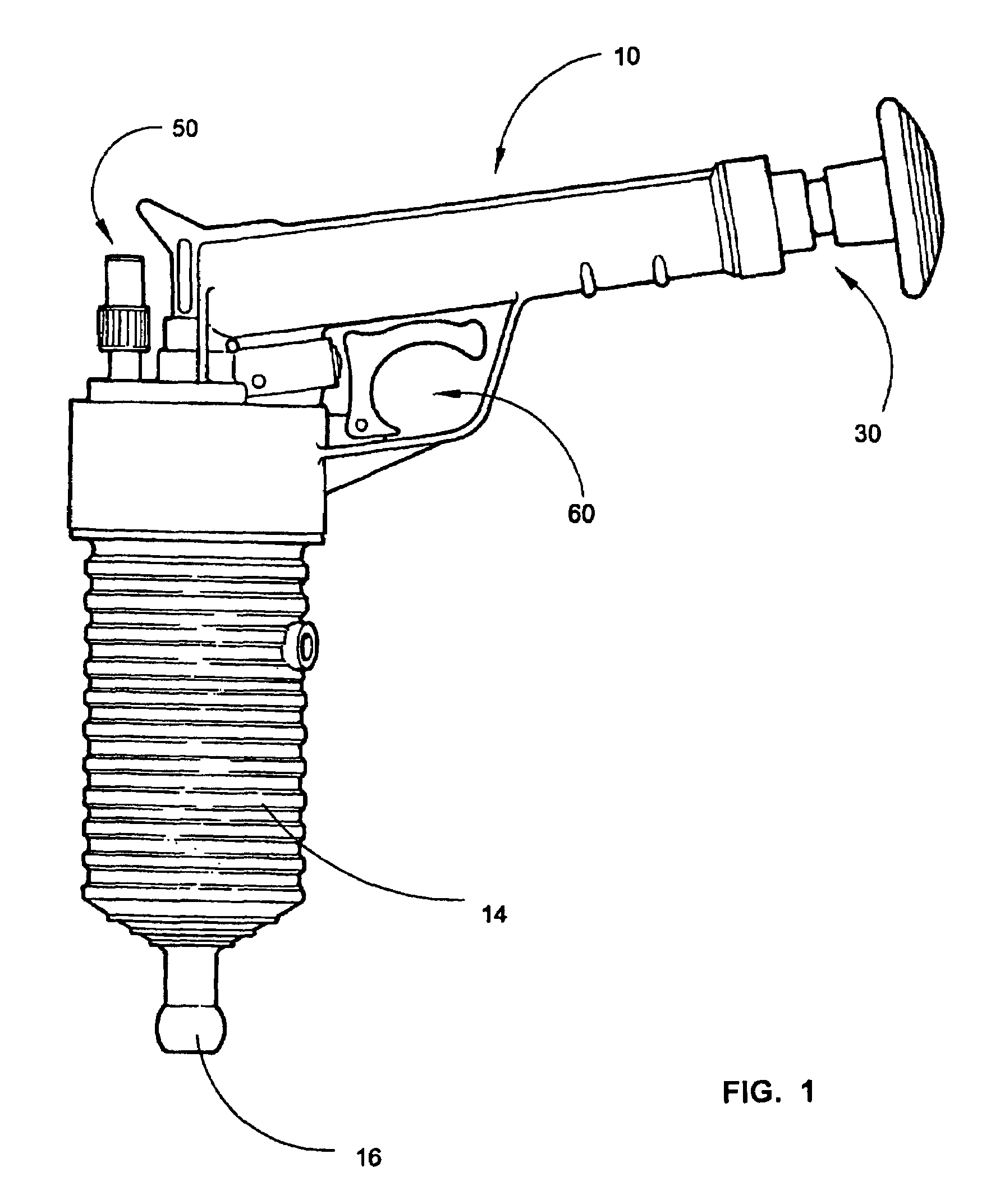
Self-contained handheld drain clearing compressed air device
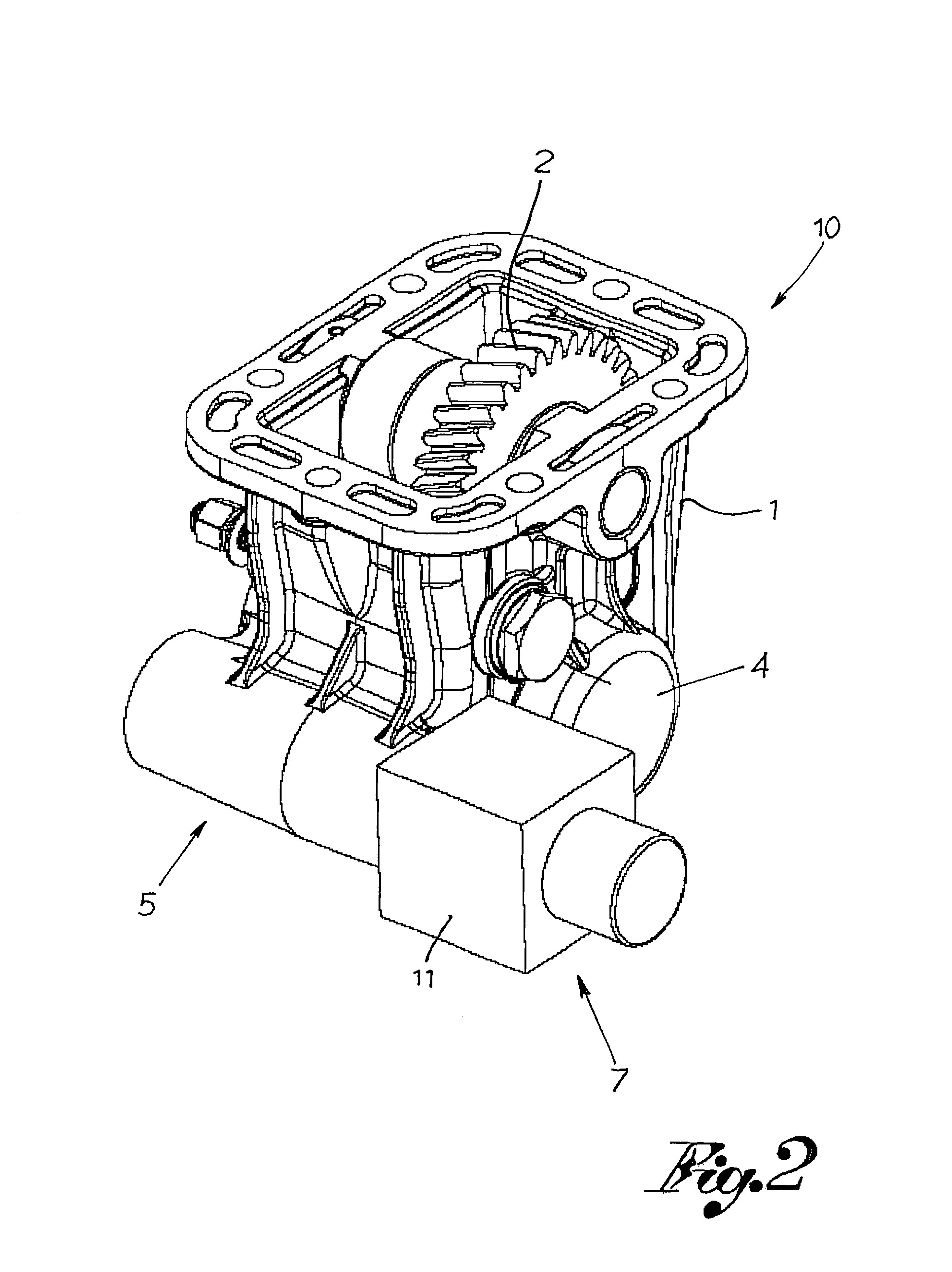
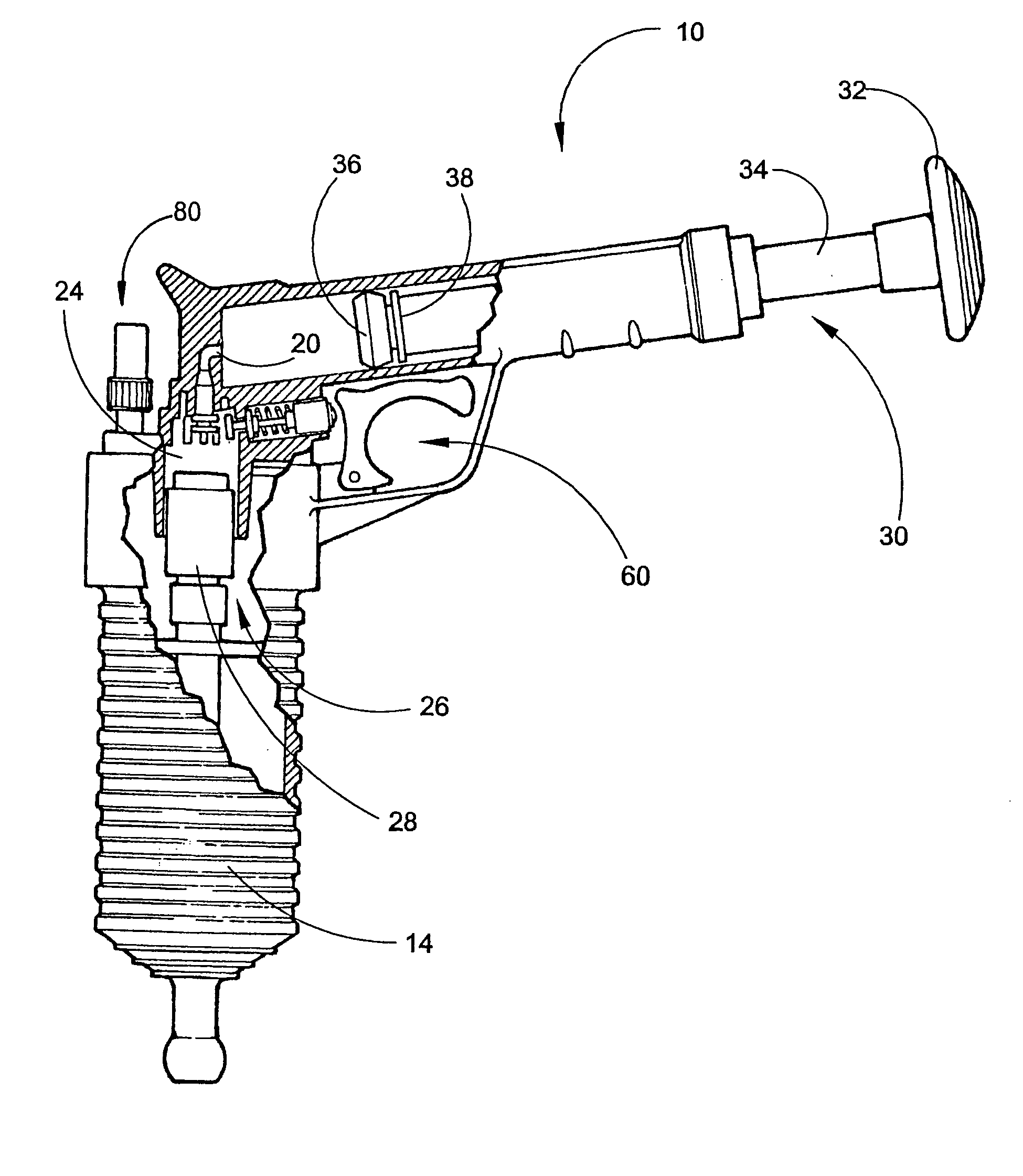
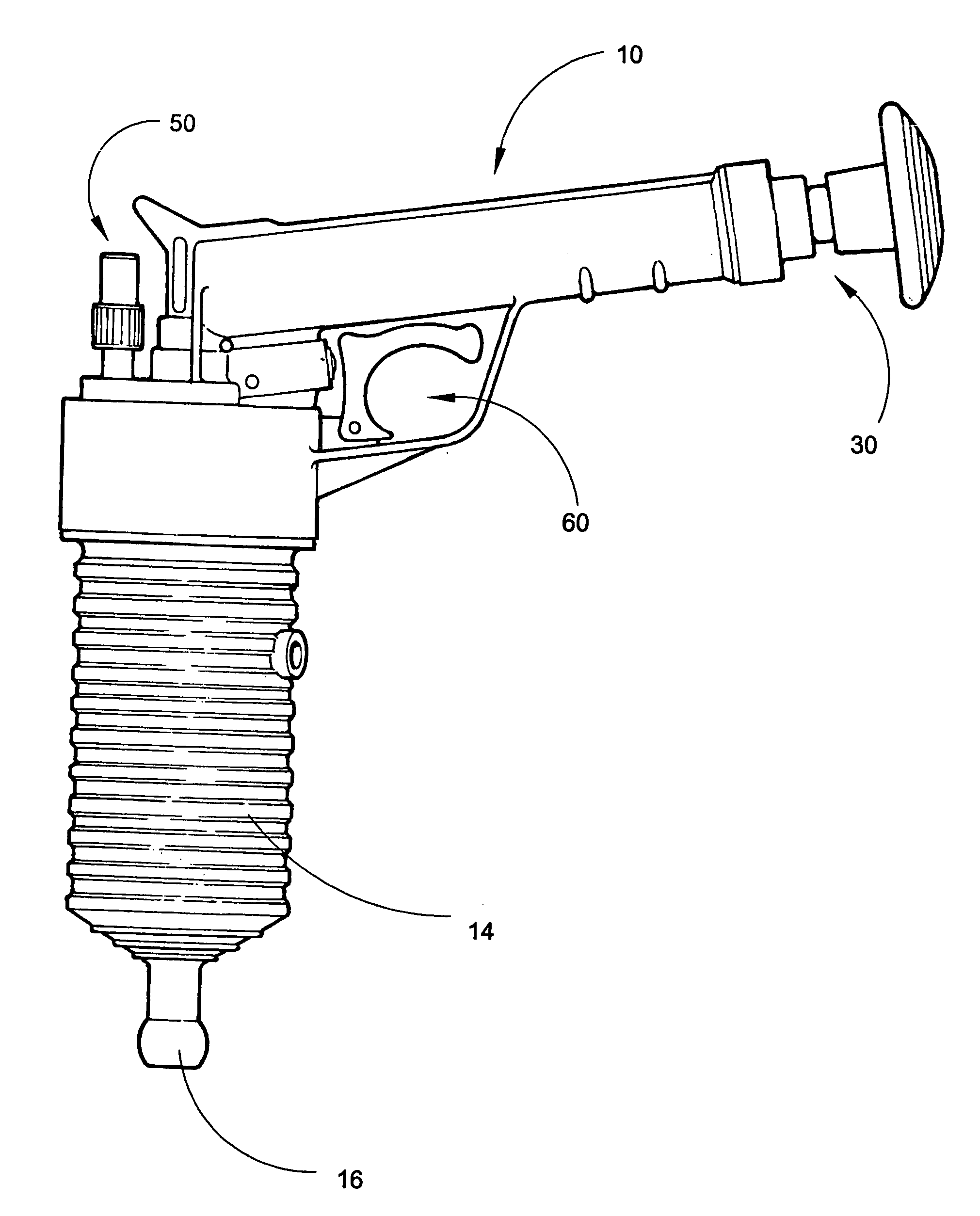
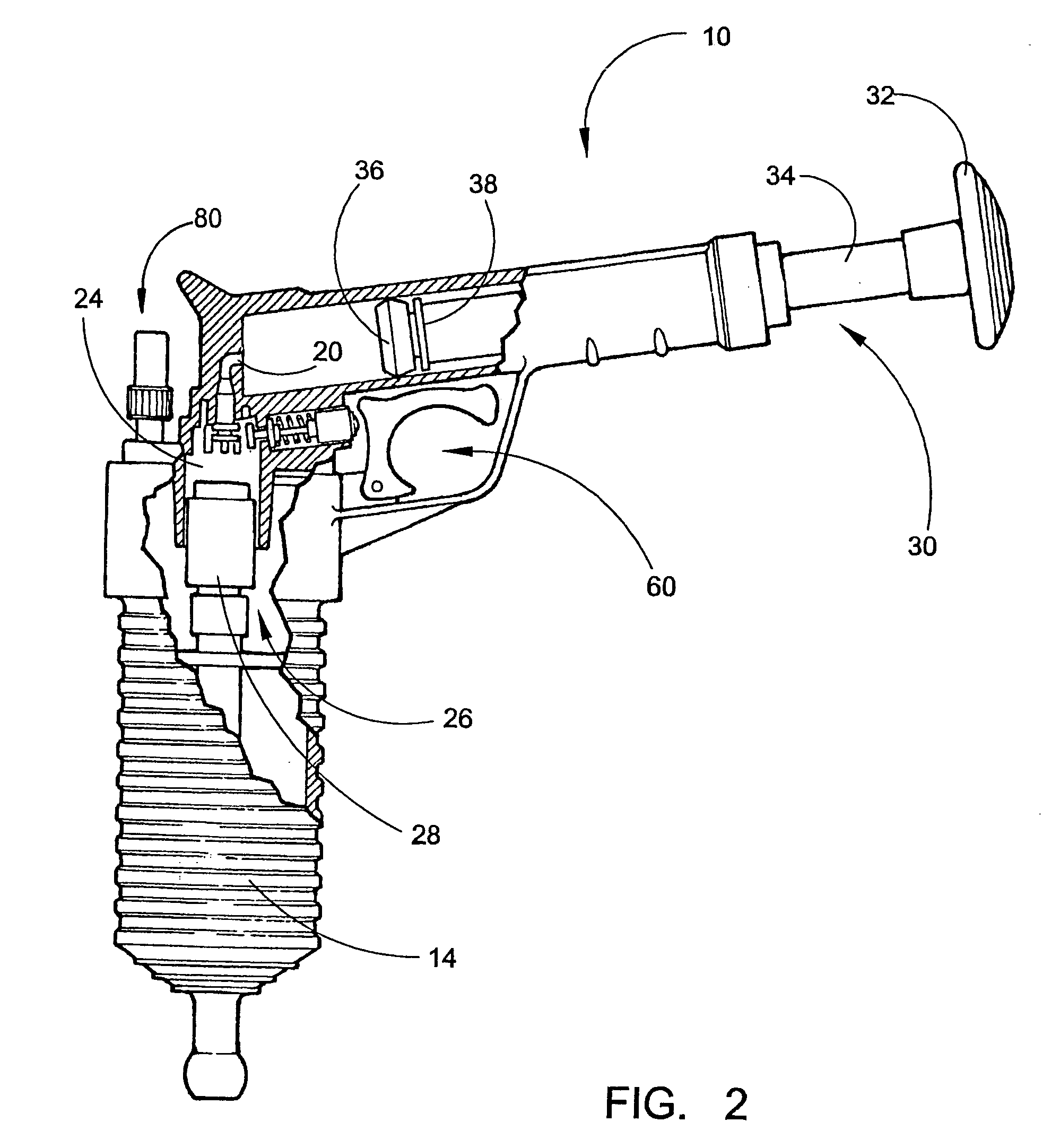
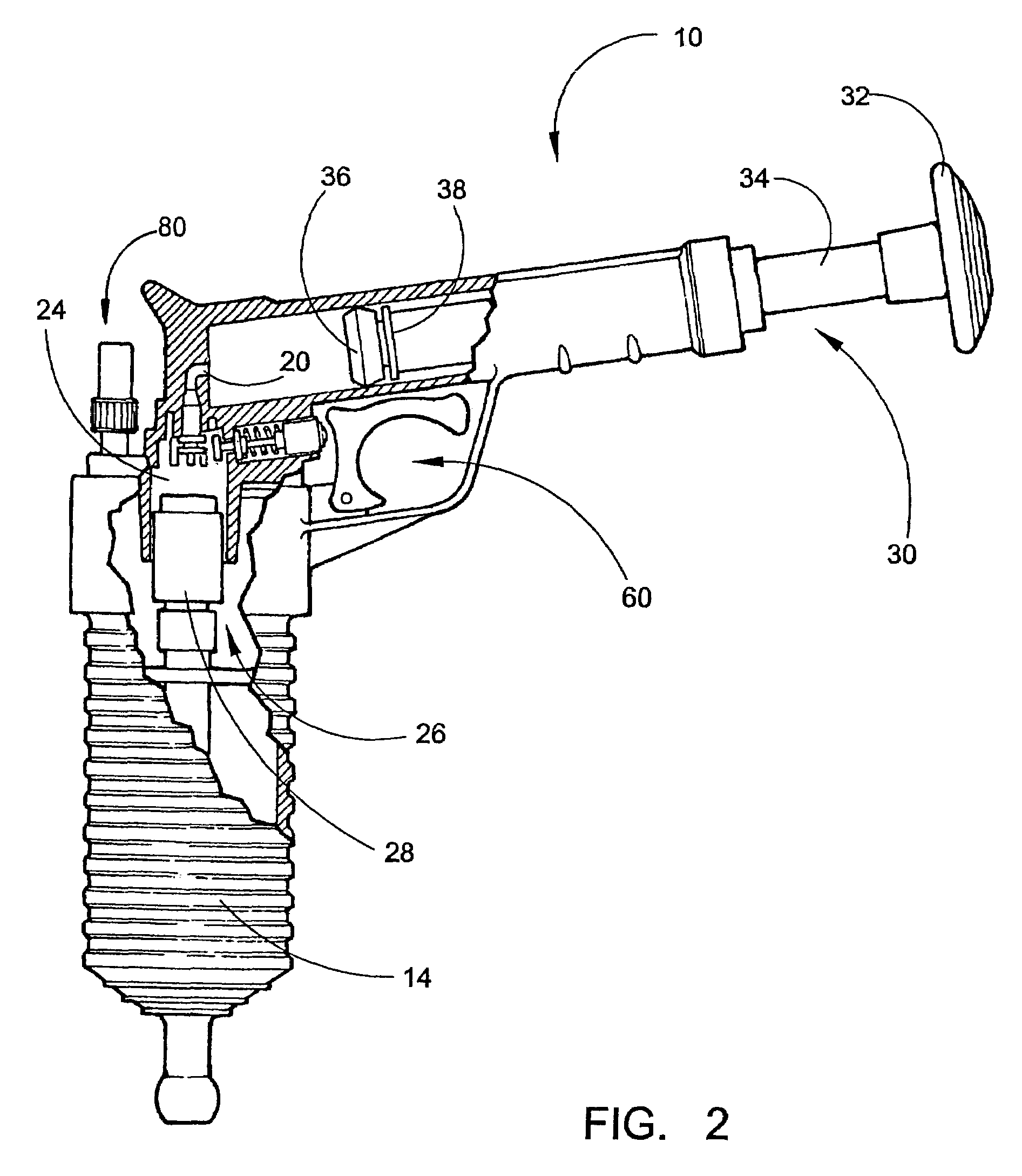
InactiveUS20060096060A1Low costQuick and efficientSuction cleanersHollow article cleaningInlet valveHand held
A self-contained handheld drain clearing device is provided that uses compressed air to unblock various household drains and pipes. The device comprises an upper body and a lower body. The upper body includes a cylindrical chamber for housing a manual pump. A one-way inlet valve allows compressed air to enter a collection chamber, from which it exits to a storage chamber through a small hole in a piston. A trigger component is located in the upper body of the device, as is a pressure release safety component included for user protection. The lower body of the device primarily serves as a storage area for compressed air, containing an upper end and a lower end. The upper end contains threads for joining the lower body with the upper body, while the lower end contains a fitting for receiving various drain-sealing adapters.
Owner:ZHANG YUN BING
Data protection for computer system
ActiveUS7210013B2Input/output to record carriersMemory loss protectionHard disc driveApplication software
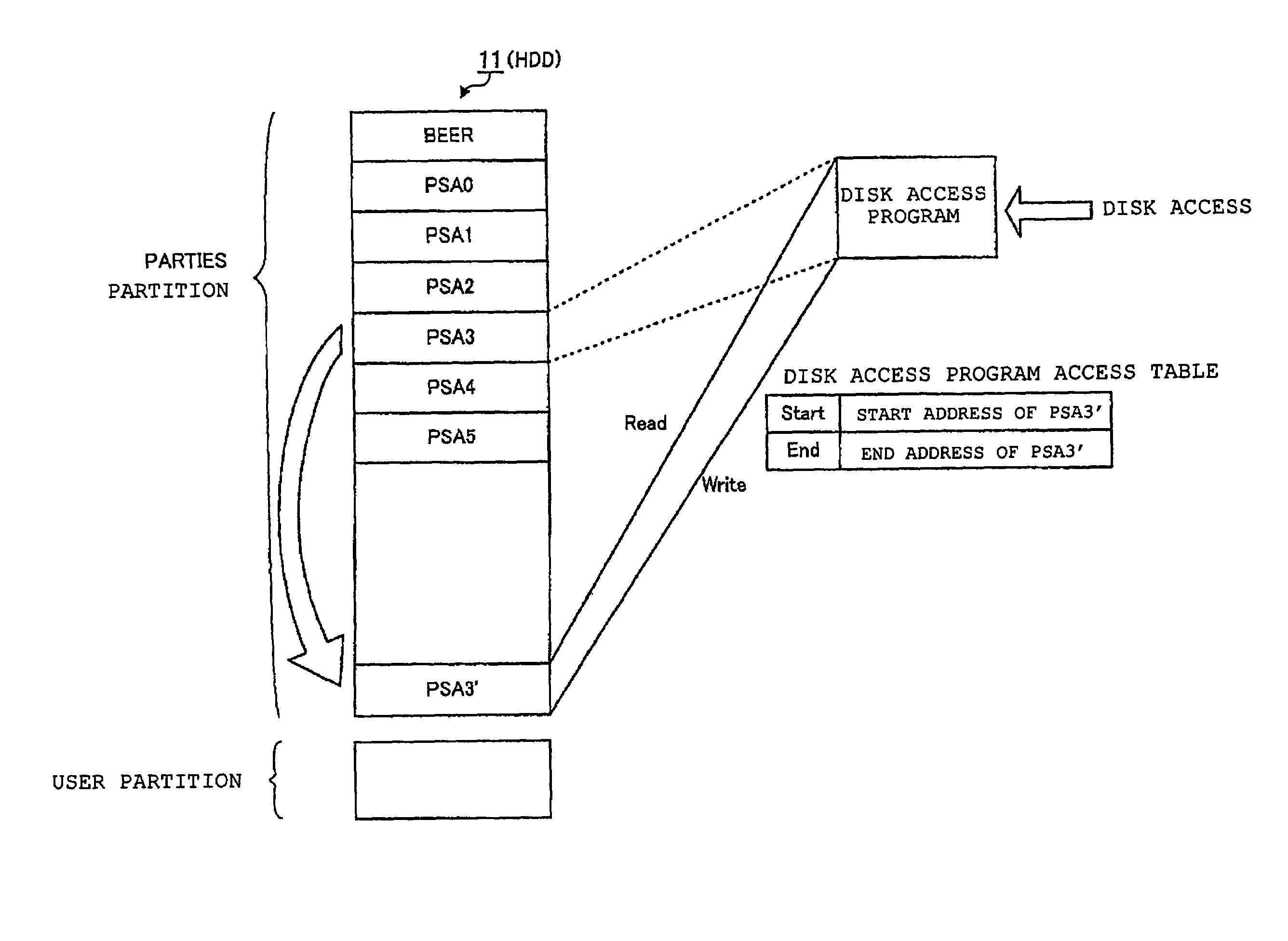
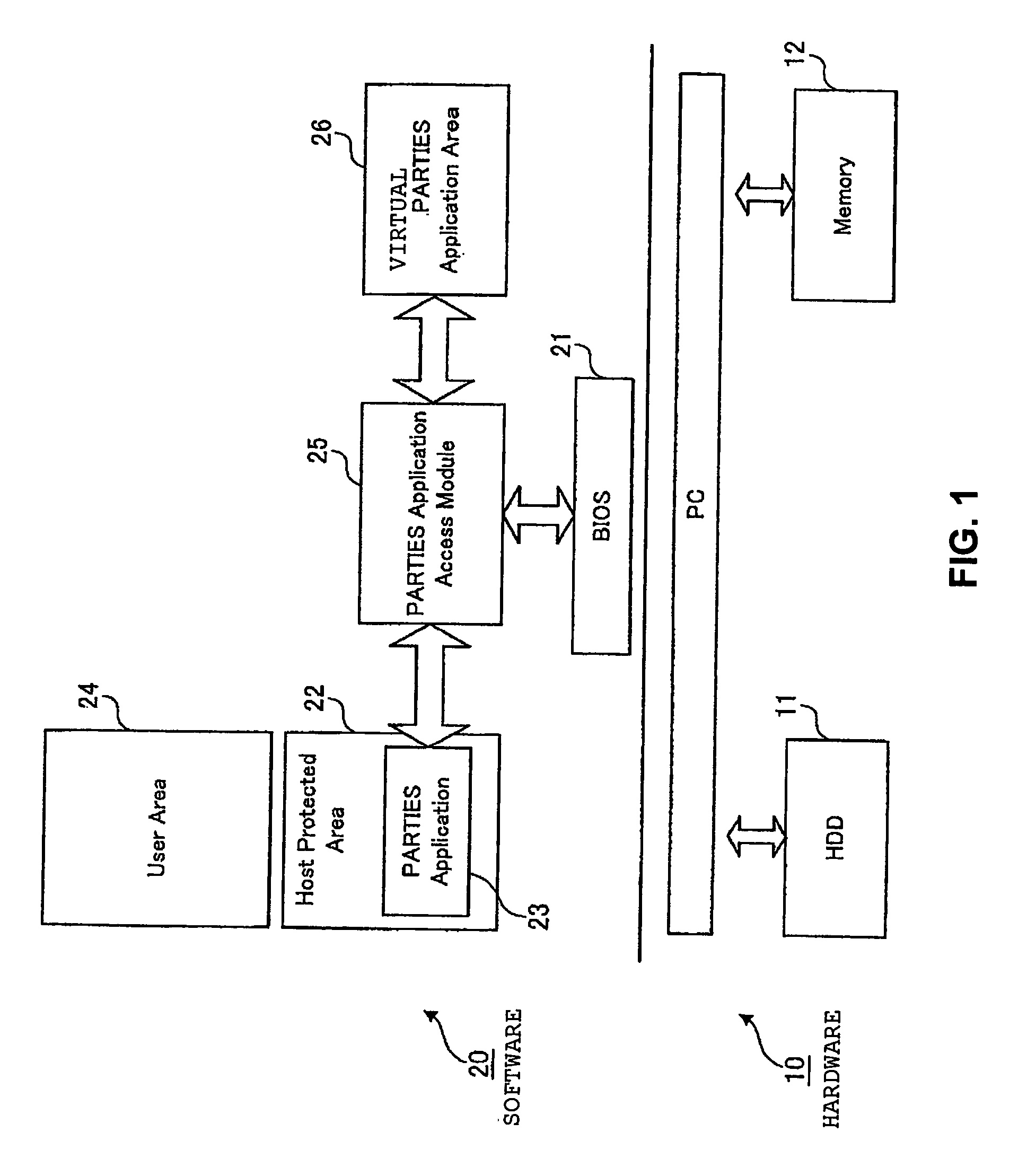
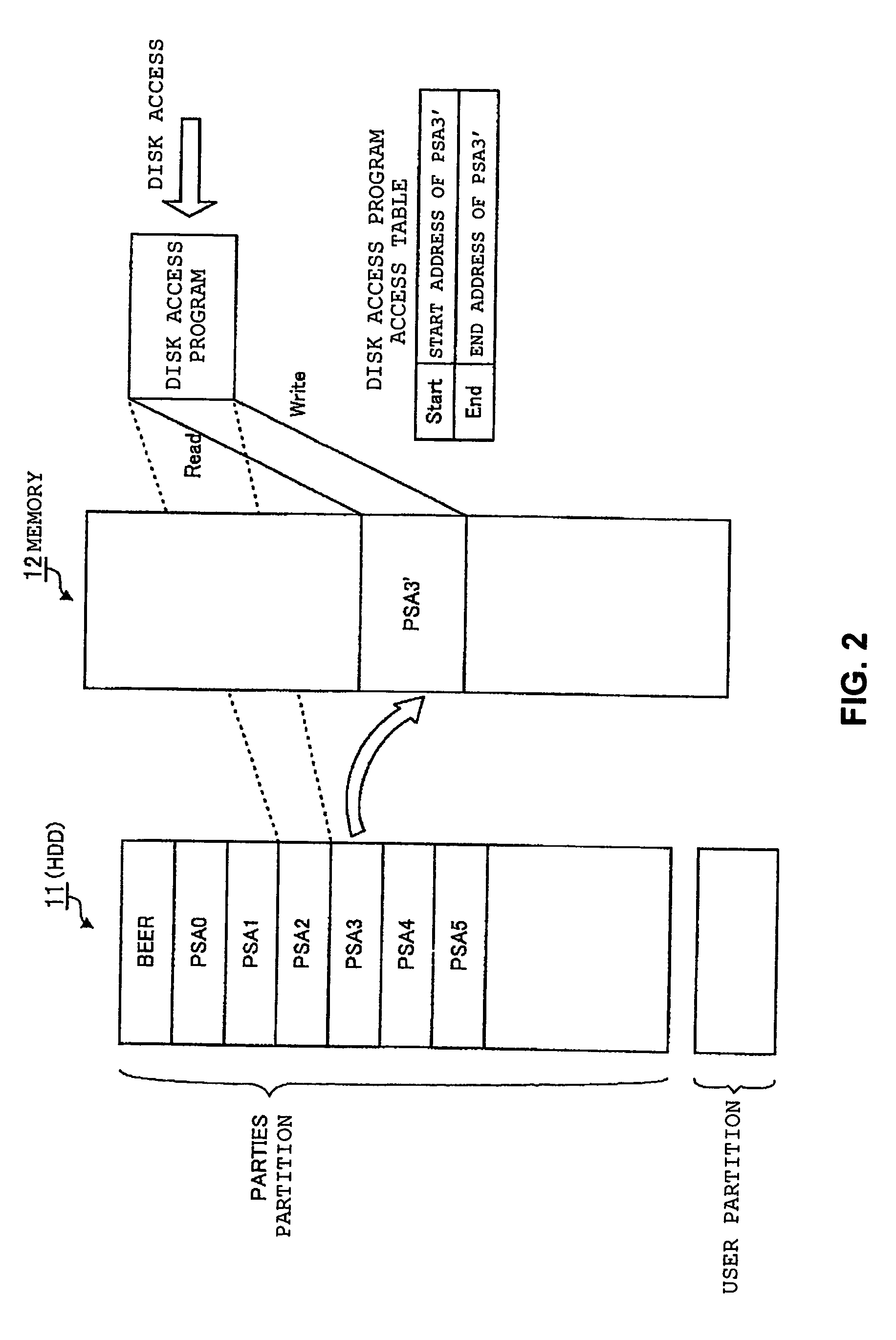
For a hard disk drive divided into a user area that is an area operating in a user environment, and a host protected area that is an area protected from a user, provided are: a basic input / output system which supports a boot from the host protected area as well as supports a validation, for a system vendor authentication, of a Protected Area Run Time Interface Extension Services application stored in the host protected area; and a Protected Area Run Time Interface Extension Services application access module which generates a virtual Protected Area Run Time Interface Extension Services application area by copying the Protected Area Run Time Interface Extension Services application onto an unoccupied area of a memory.
Owner:LENOVO PC INT
Personal live comment sending method and device
ActiveCN106101805AReduce display impactSelective content distributionPersonalizationTransparent display
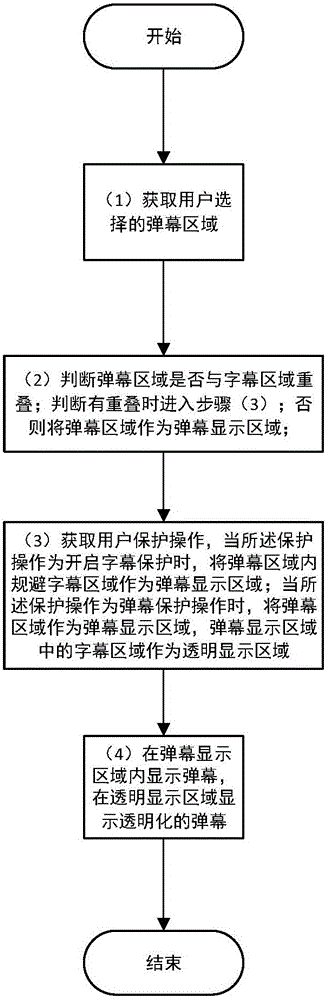
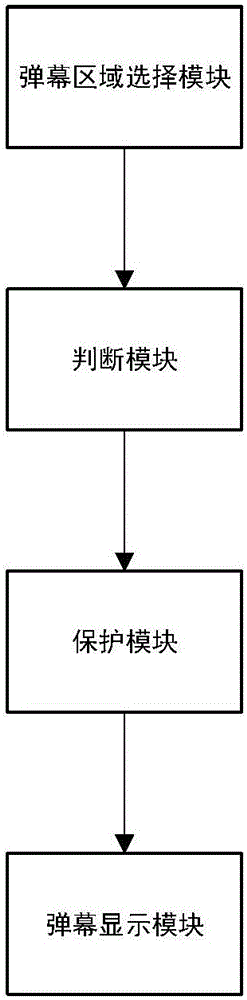
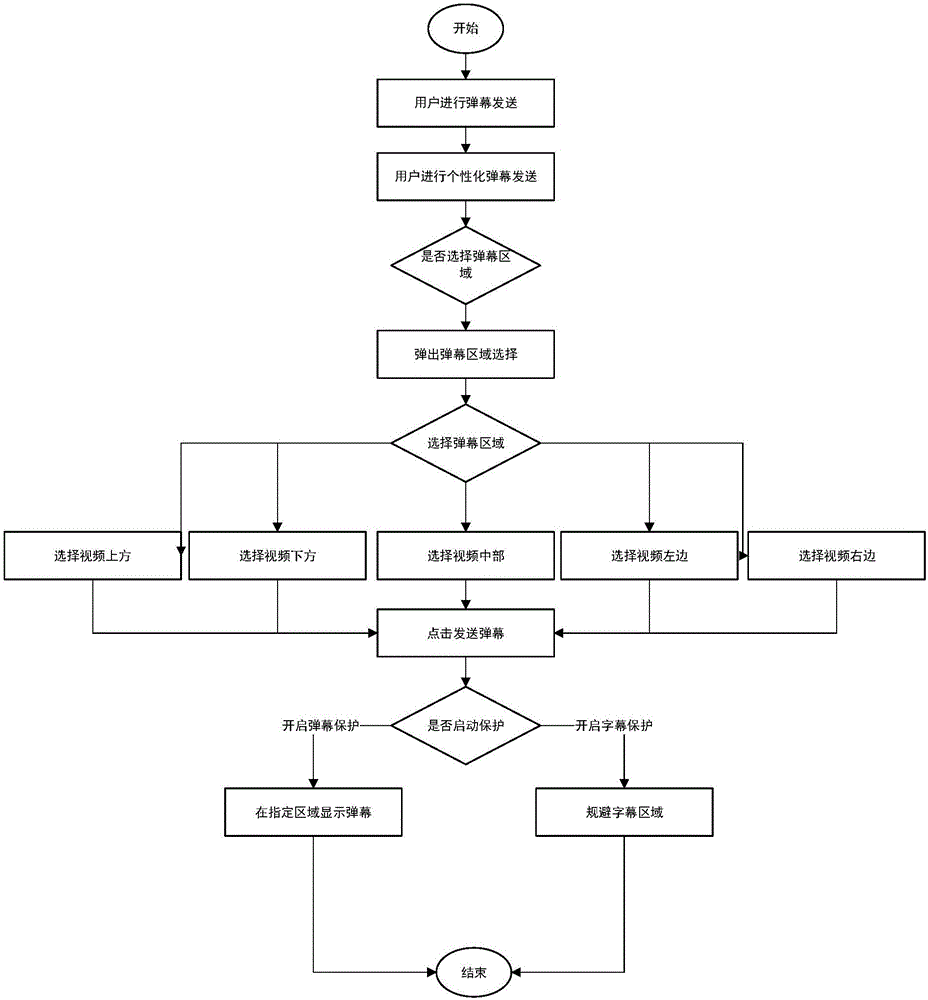
The invention discloses a personal live comment sending method and device. The method comprises the following steps: (1) acquiring a live comment area selected by a user; (2) judging whether the live comment area is overlapped with a subtitle area or not, if so, entering a step (3), and otherwise, using the live comment area as a live comment display area; (3) acquiring a user protection operation, using a subtitle avoiding area in the live comment area as the live comment display area when the protection operation is a subtitle protection enabling operation, and using the live comment area as the live comment display area and using the subtitle area in the live comment display area as a transparent display area when the protection operation is a live comment protection operation; and (4) displaying live comments in the live comment display area, and displaying transparent live comments in the transparent display area. The device comprises a live comment area selection module, a judging module, a protection module and a live comment display area. Through adoption of the personal live comment sending method and device, the live comment display area can be selected personally, so that the influence of the live comments on video display is lowered.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Routing and time slot distributing method on basis of main user protection in cognitive radio network
InactiveCN102724669AIncrease network capacityImprove throughputHigh level techniquesNetwork planningComputation complexitySocially distributed cognition
The invention discloses a routing and time slot distributing method on the basis of main user protection in a cognitive radio network for a distributive cognitive radio network. The method comprises the following steps of designing a reasonable chain measuring and routing information spreading mechanism to search a source-to-target node communication route for a secondary user in a network; and on the premise of not causing over interference to a main user, increasing flow of a throughput bottle-neck link in the route by using the time slot distributing method, so that the throughput of the secondary user in the network is improved. Through reasonable routing and time slot distribution, a primary user and the secondary user in the distributive cognitive radio network can use a frequency band authorized by the main user at the same time and over interference to the main user is not caused. Theoretical analysis and simulation result show that compared with the current routing algorithm, the method can reduce calculation complexity and efficiently increase the throughput of the secondary user simultaneously.
Owner:XI AN JIAOTONG UNIV
Self-contained handheld drain clearing compressed air device
A self-contained handheld drain clearing device is provided that uses compressed air to unblock various household drains and pipes. The device comprises an upper body and a lower body. The upper body includes a cylindrical chamber for housing a manual pump. A one-way inlet valve allows compressed air to enter a collection chamber, from which it exits to a storage chamber through a small hole in a piston. A trigger component is located in the upper body of the device, as is a pressure release safety component included for user protection. The lower body of the device primarily serves as a storage area for compressed air, containing an upper end and a lower end. The upper end contains threads for joining the lower body with the upper body, while the lower end contains a fitting for receiving various drain-sealing adapters.
Owner:ZHANG YUN BING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com