Patents
Literature
892 results about "Protected area" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Protected areas or conservation areas are locations which receive protection because of their recognized natural, ecological or cultural values. There are several kinds of protected areas, which vary by level of protection depending on the enabling laws of each country or the regulations of the international organizations involved.
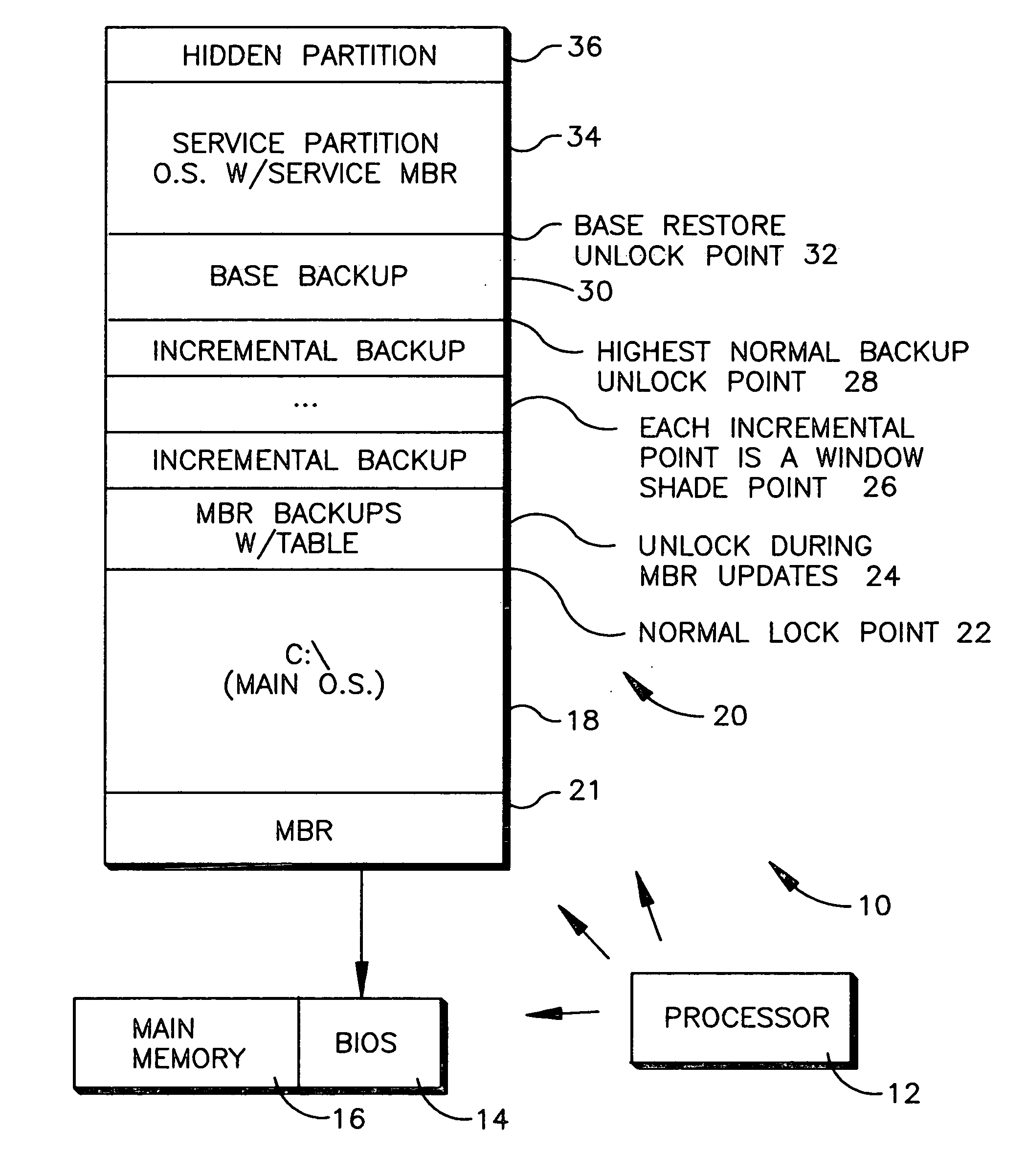
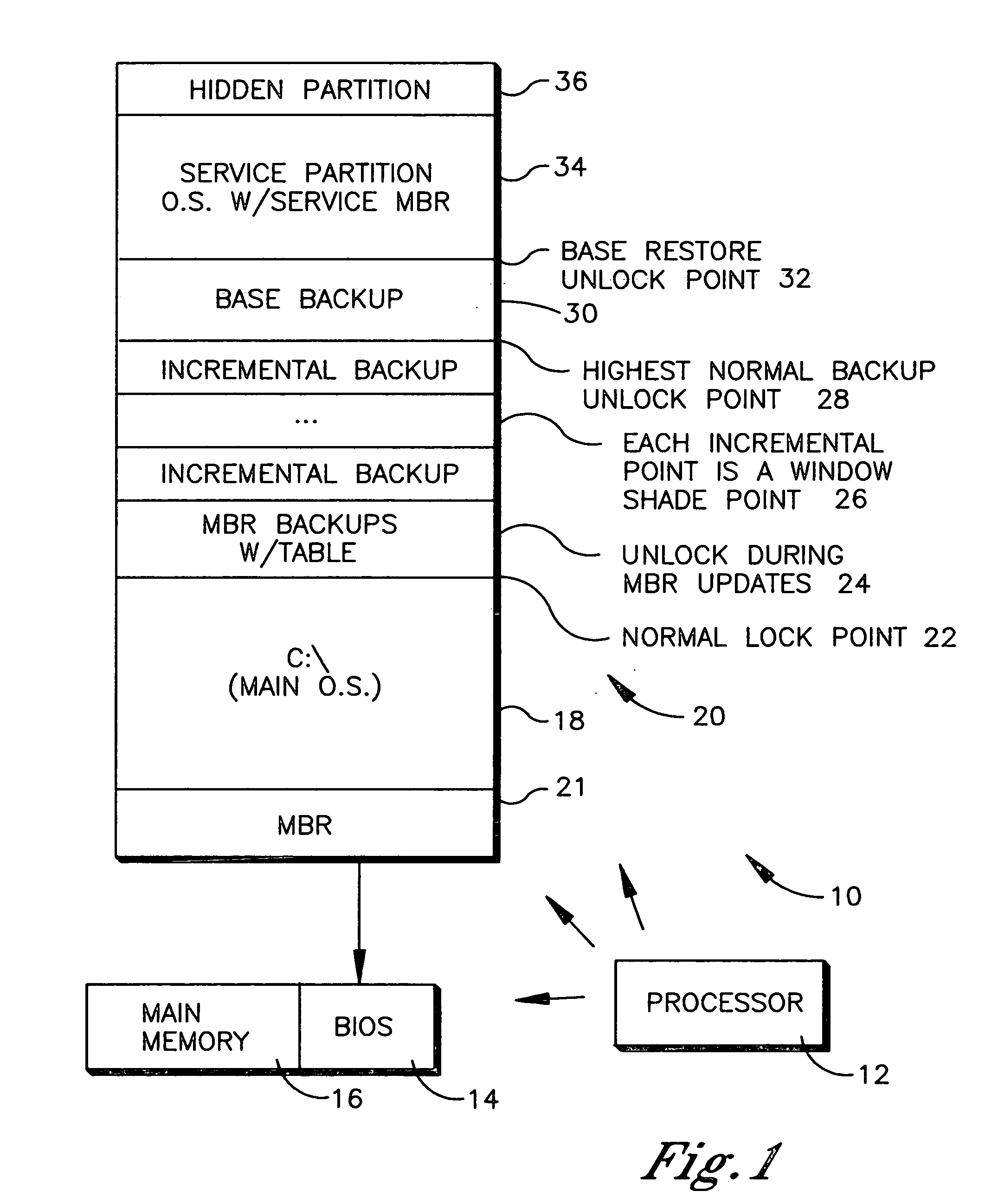
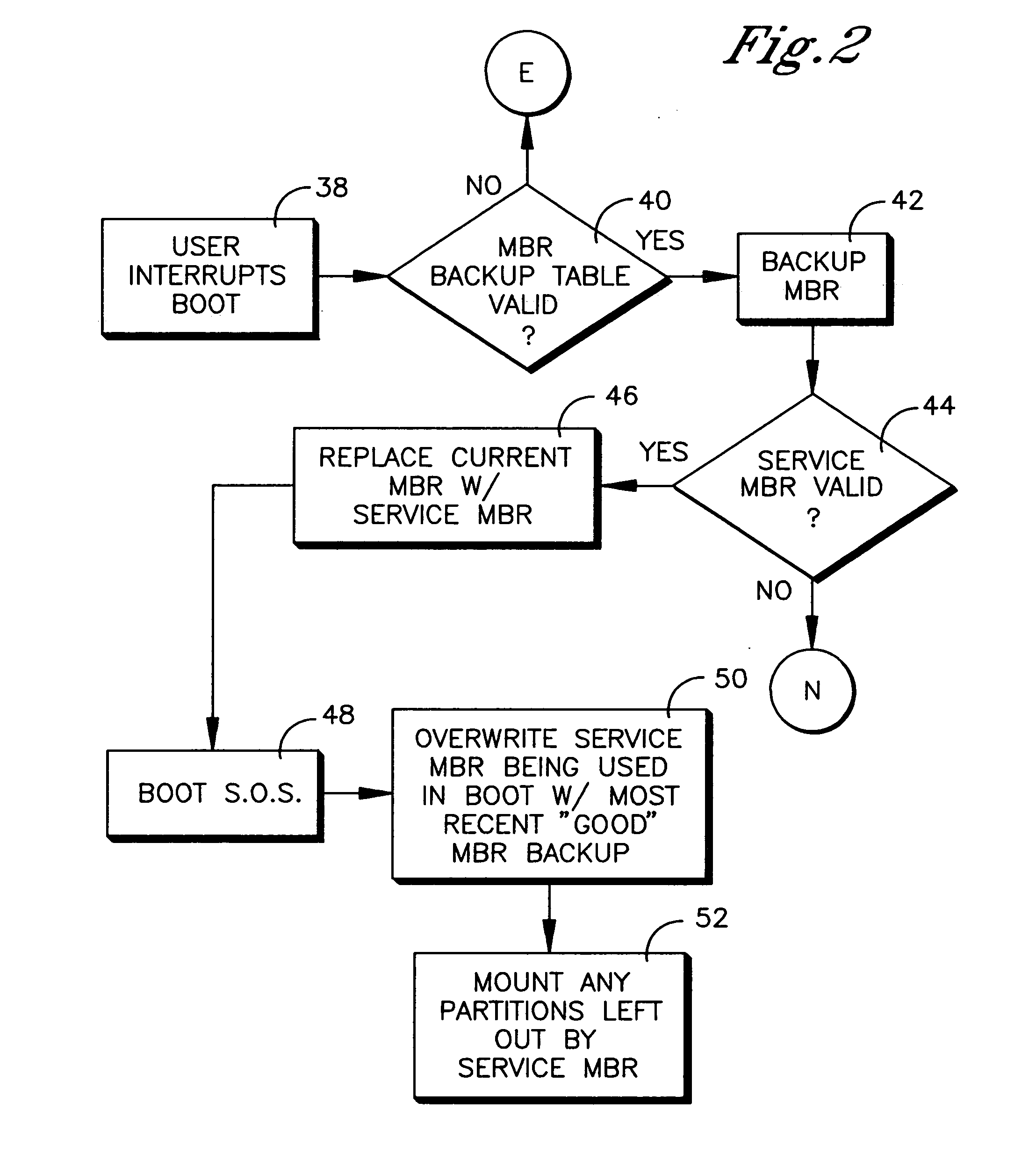
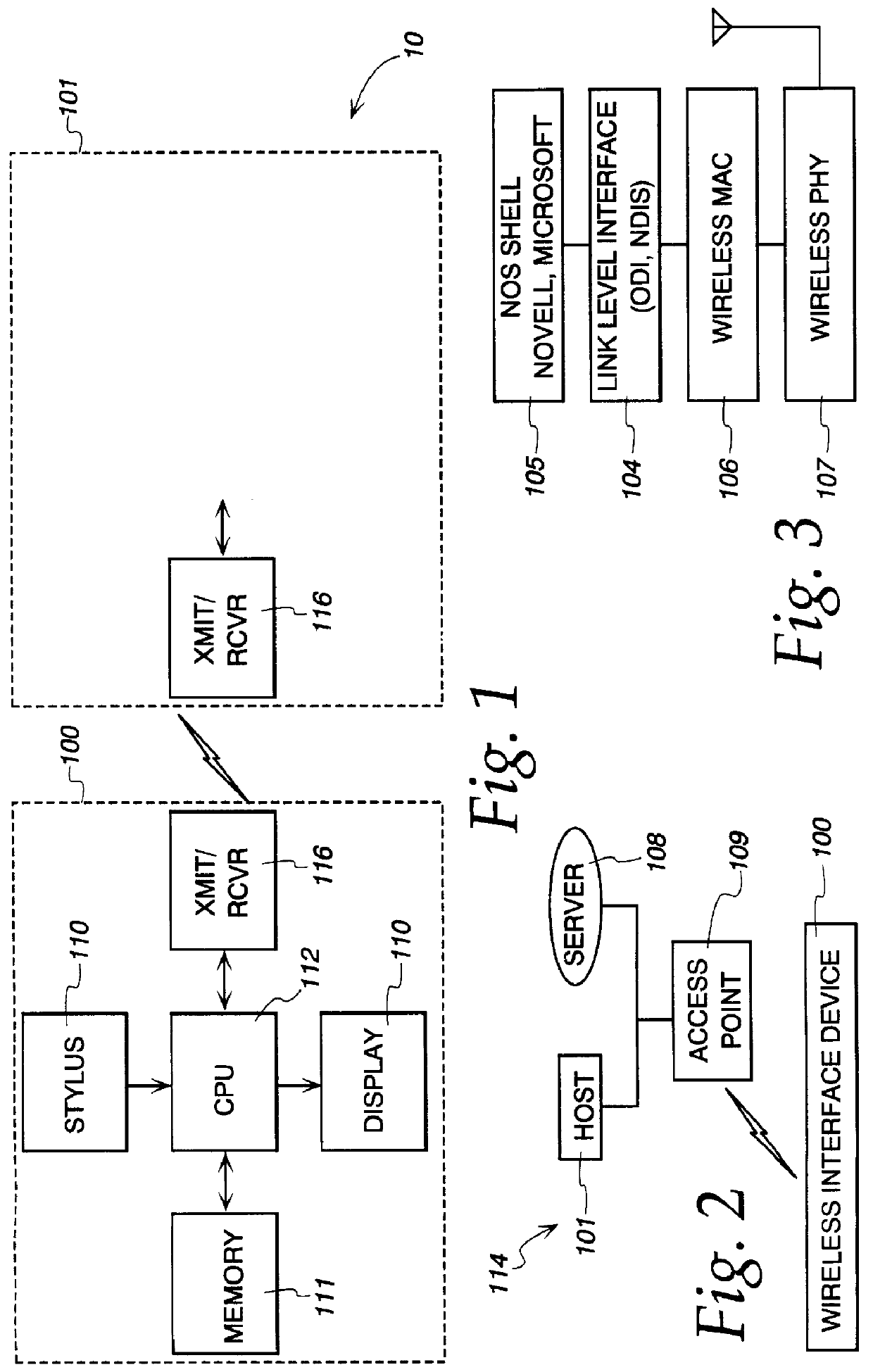
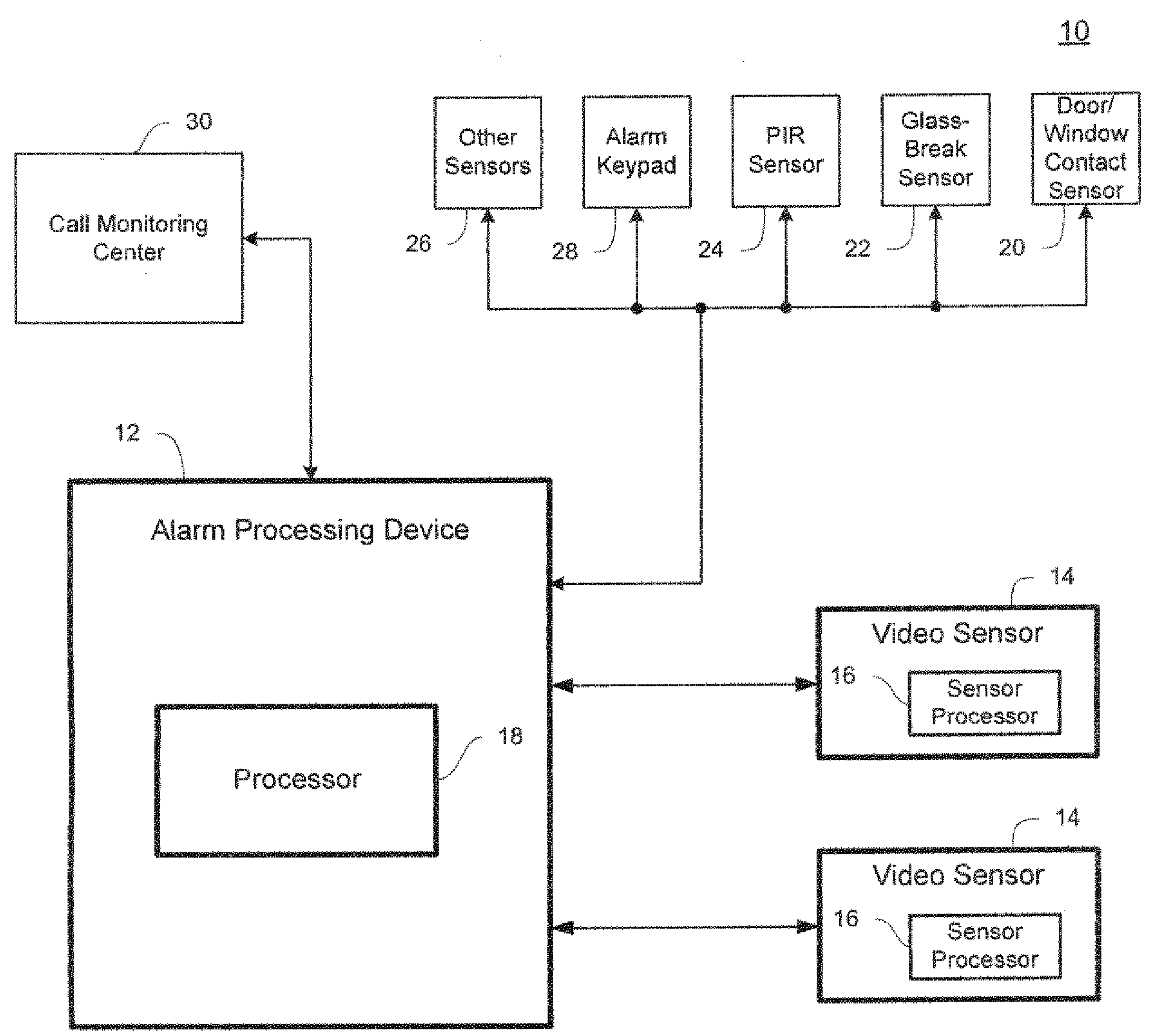
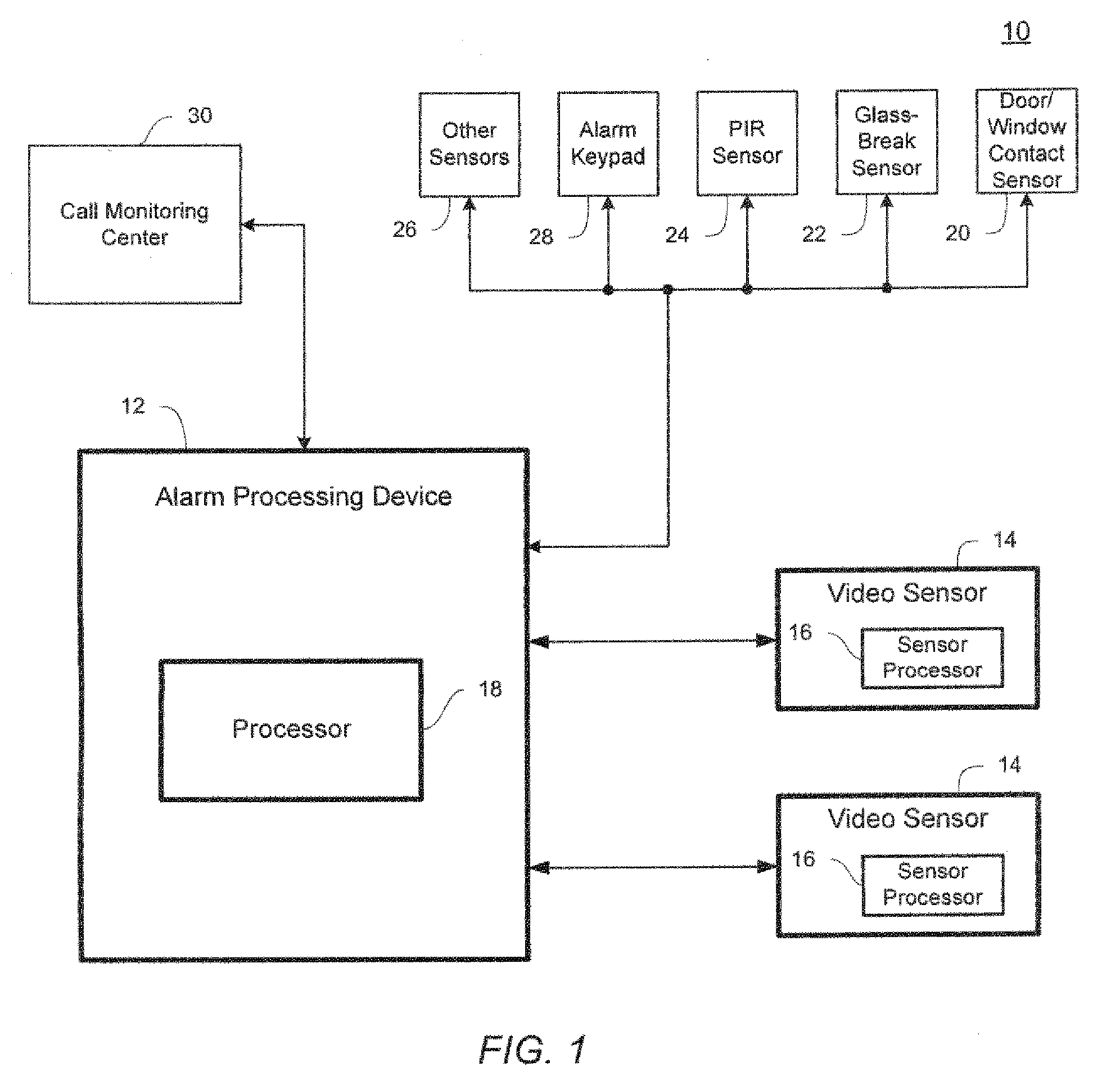
System and method for booting alternate MBR in event of virus attack
ActiveUS20080046781A1Digital computer detailsPlatform integrity maintainanceHard disc driveOperational system
In the event of a virally infected MBR on a hard disk drive that might prevent booting, a service MBR in a hidden protected area (HPA) can be used to boot a service O.S., and then the service MBR can be replaced with a previously backed-up MBR, also in the HPA, to mount any missing partitions.
Owner:LENOVO PC INT
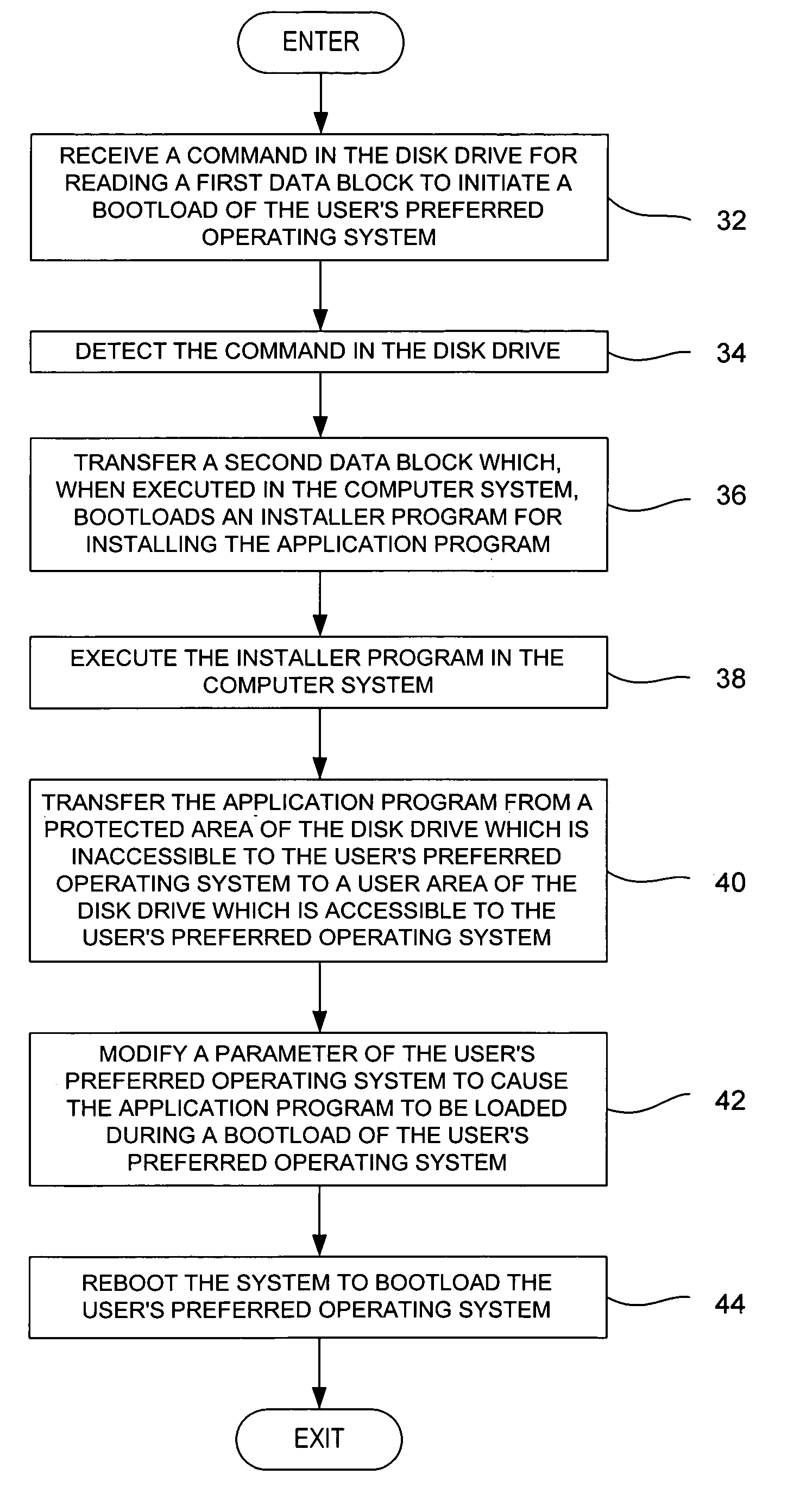
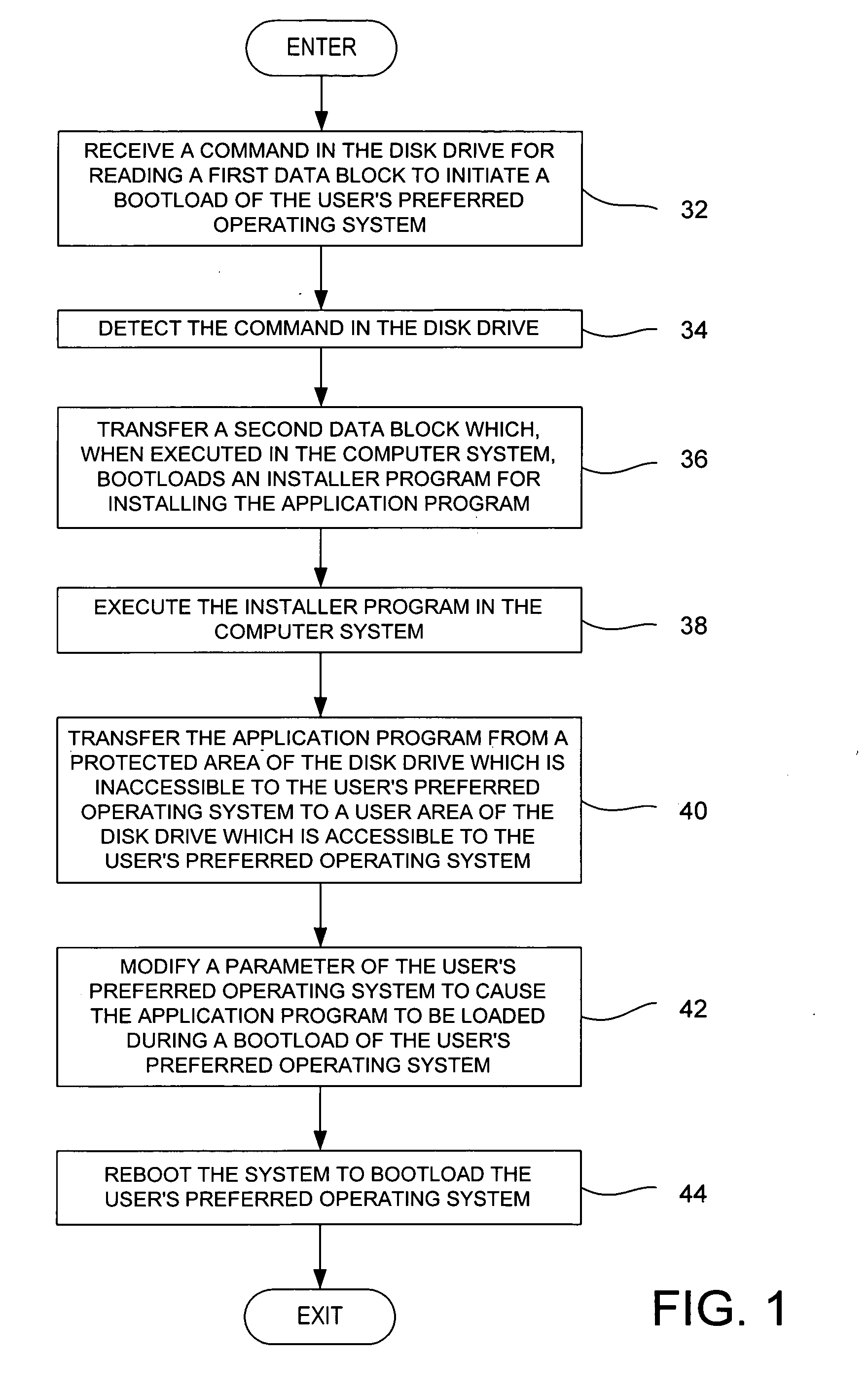
Method for installing an application program, to be executed during each bootload of a computer system for presenting a user with content options prior to conventional system startup presentation, without requiring a user's participation to install the program
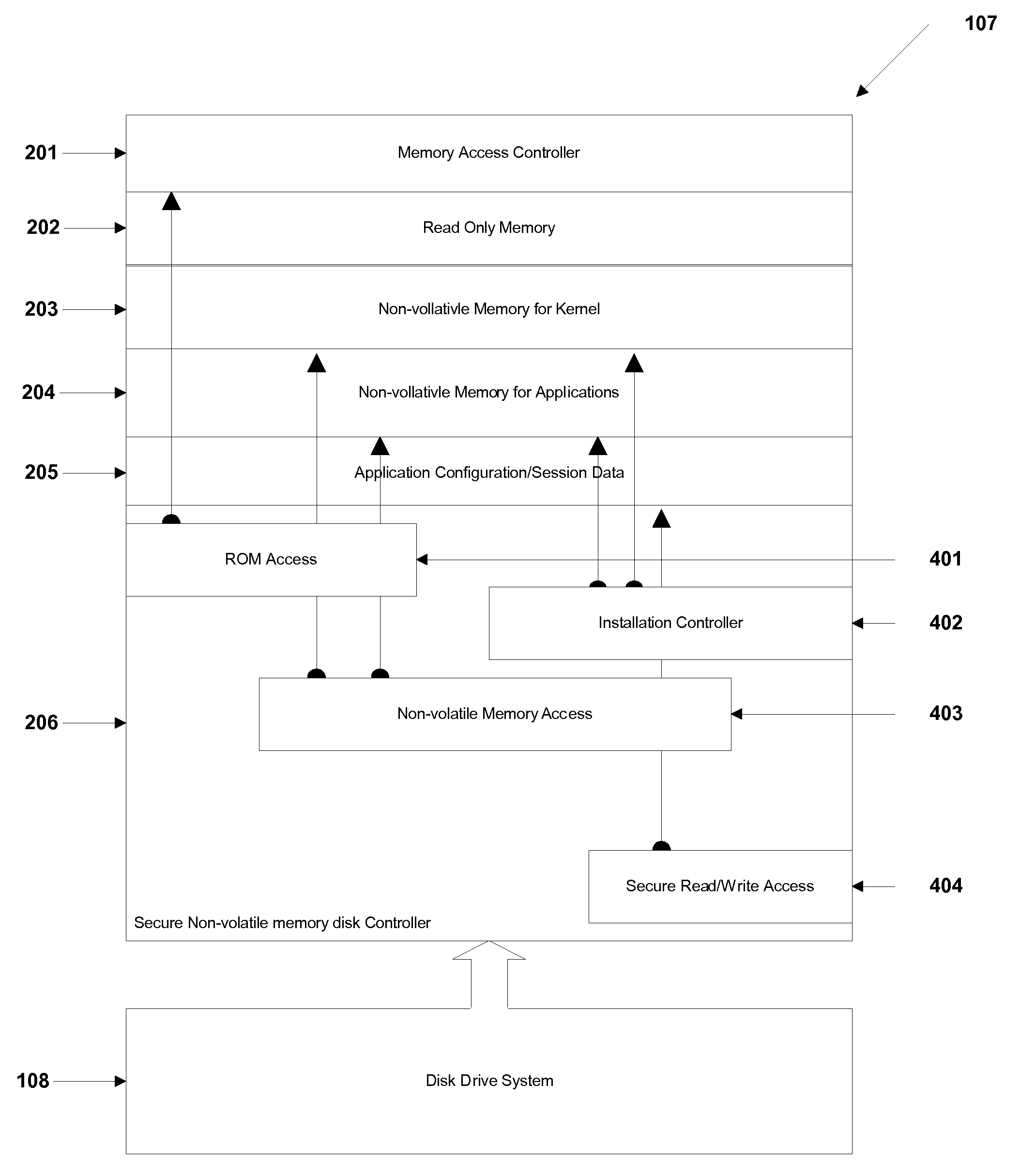
The present invention may be embodied in a method, performed in a computer system having a disk drive, for installing an application program for execution under a user's preferred operating system without requiring user intervention. A command is received by the disk drive for reading a first data block to initiate a bootload of the user's preferred operating system. The disk drive detects the command and transfers a second data block which bootloads an installer program for installing the application program. The installer program is executed in the computer system to transfer the application program from a protected area of the disk drive to a user area of the disk drive, to modify a parameter of the user's preferred operating system to cause the application program to be loaded during a bootload of the user's preferred operating system, and to reboot the system to bootload the user's preferred operating system.
Owner:WESTERN DIGITAL TECH INC
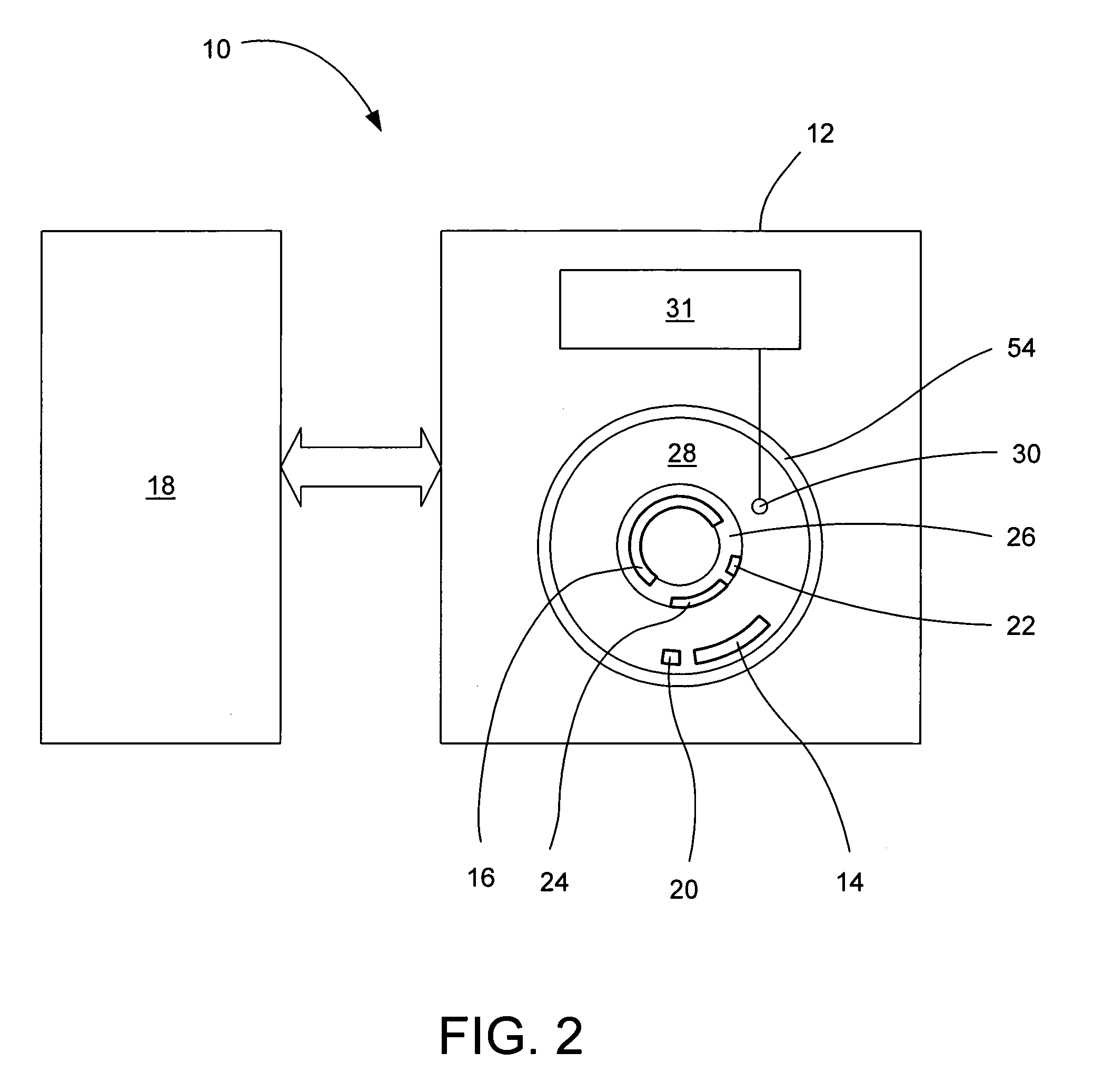
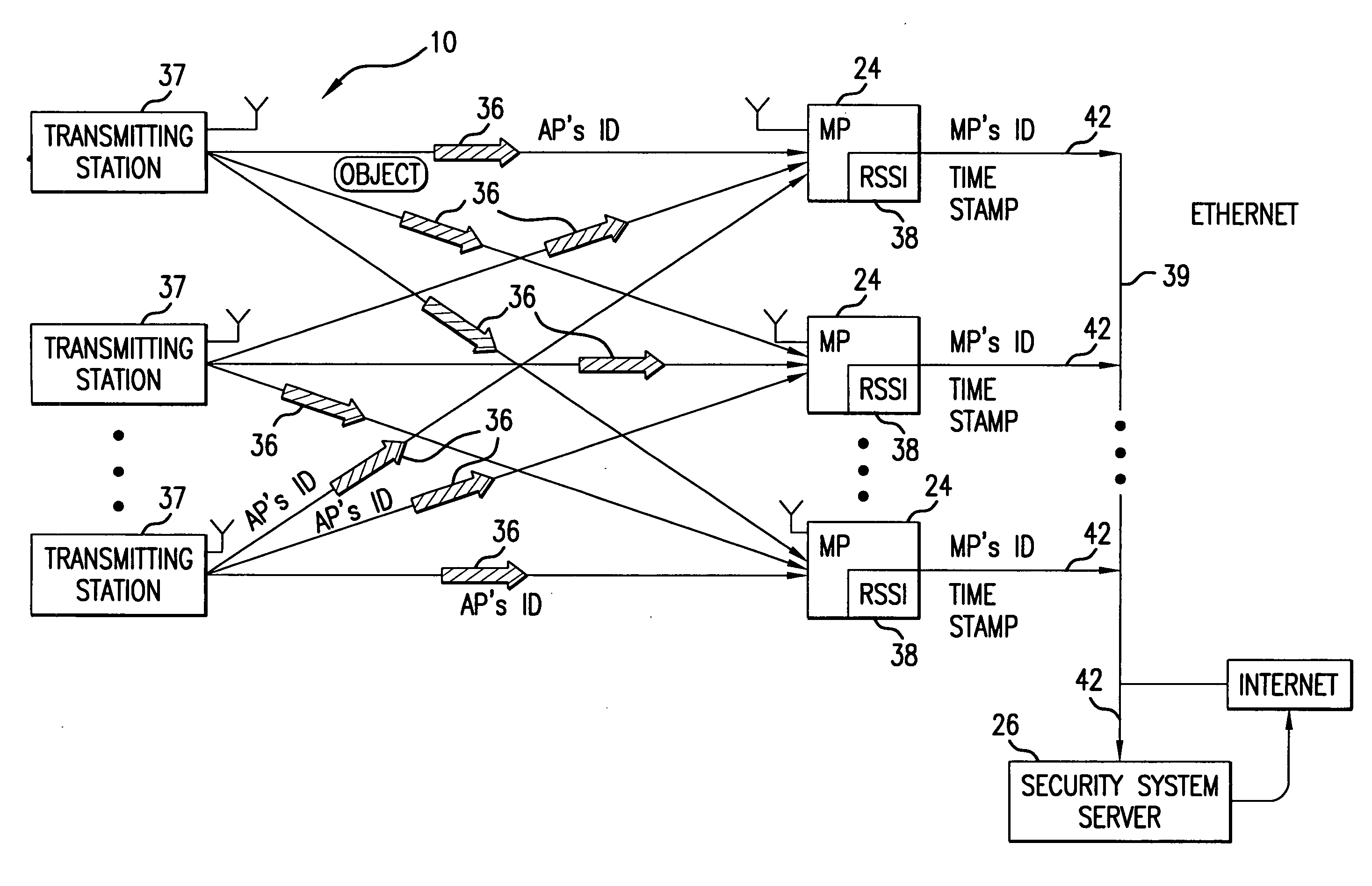
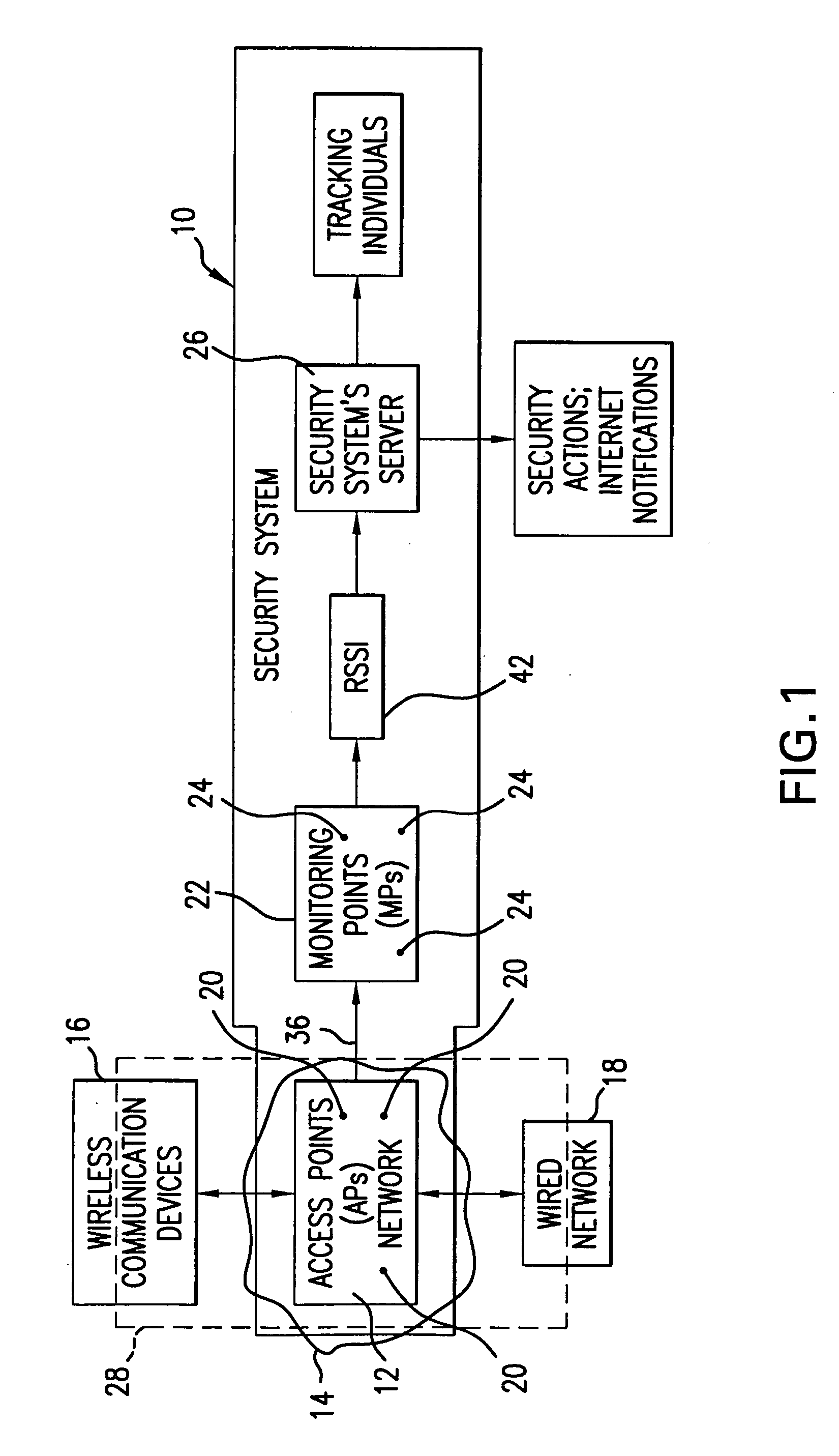
Method and system for providing physical security in an area of interest
InactiveUS20050055568A1Keep trackDigital data processing detailsHardware monitoringWi-FiPhysical security
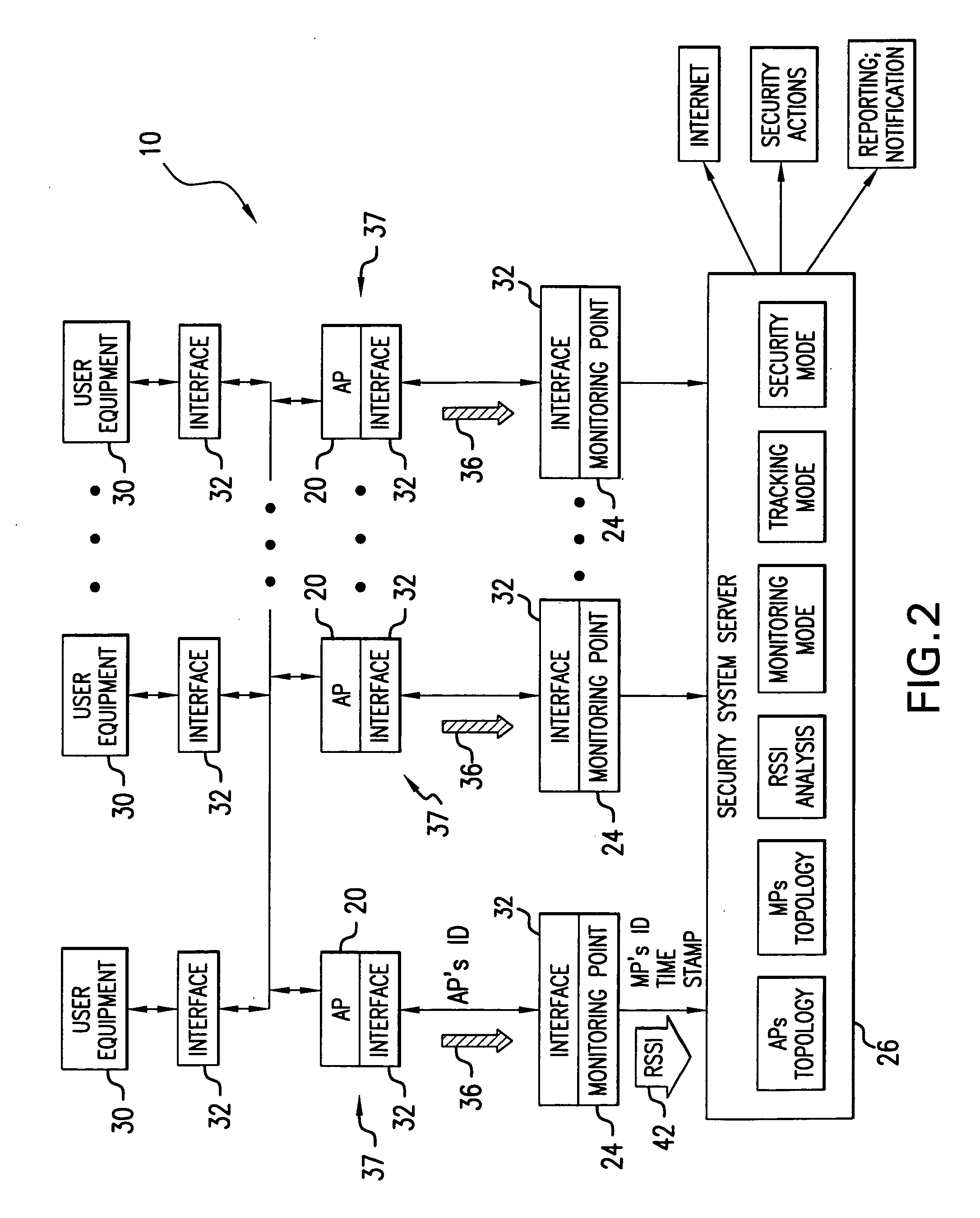
A system for detecting the presence of an intruder in a protected area utilizes a received signal strength indicator (RSSI) value of signals broadcast from transmitting stations deployed in the protected area. The system includes monitoring points for receiving broadcast signals, measuring the RSSI values of the received signals, and transmitting the measured RSSI values to a security system server. The security system server analyzes the RSSI values, and initiates security measures when the physical security of the protected area is violated which is detected when the measured RSSI values deviate from a predetermined strength of the broadcast signals. The security system also has the ability to track objects in the protected area and keep track of their movement in real time and report such movement. The system may be based on a Wi-Fi infrastructure in the protected area.
Owner:UNIV OF MARYLAND
System and method for detecting an intruder using impulse radio technology
Owner:HUMATICS CORP
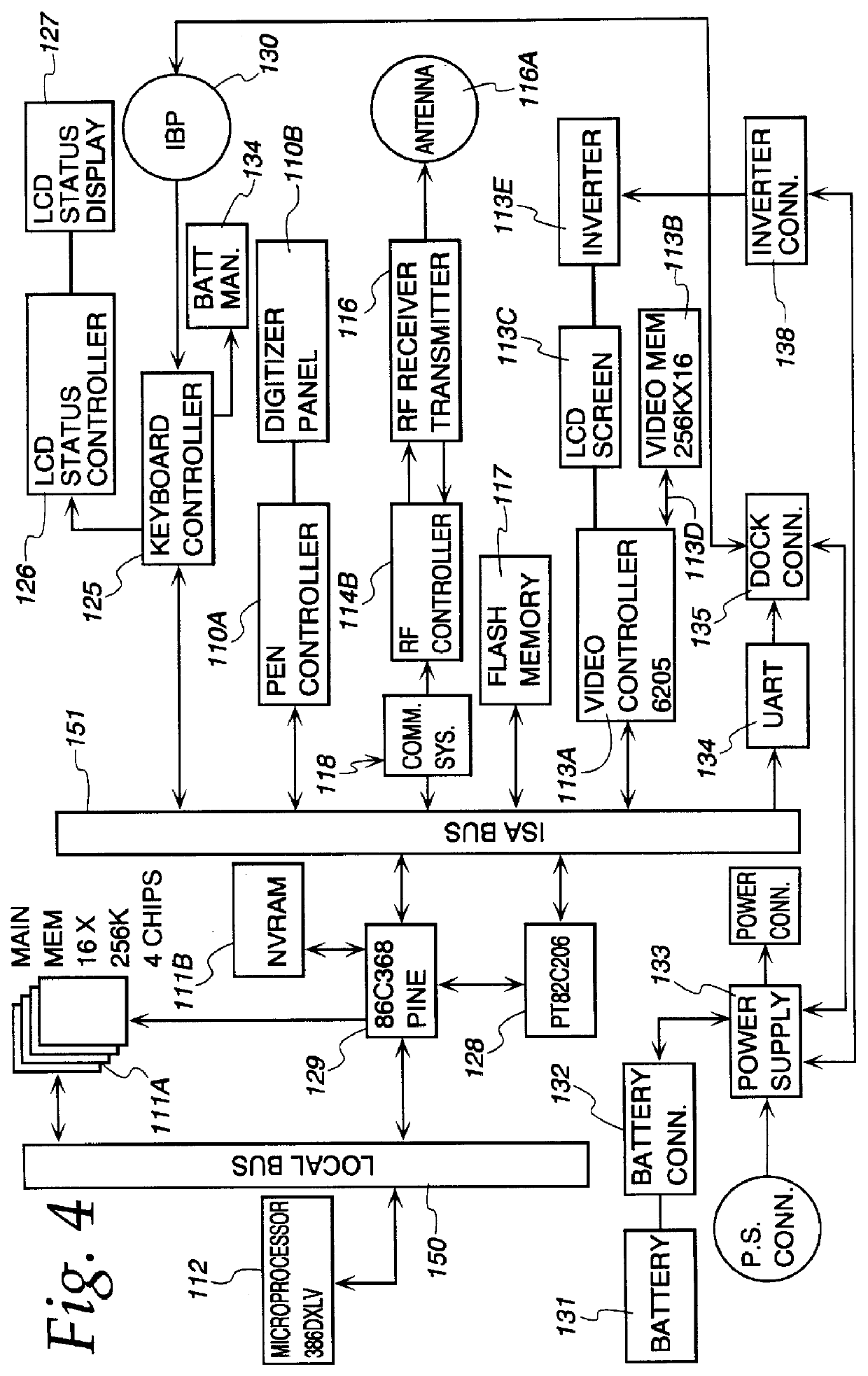
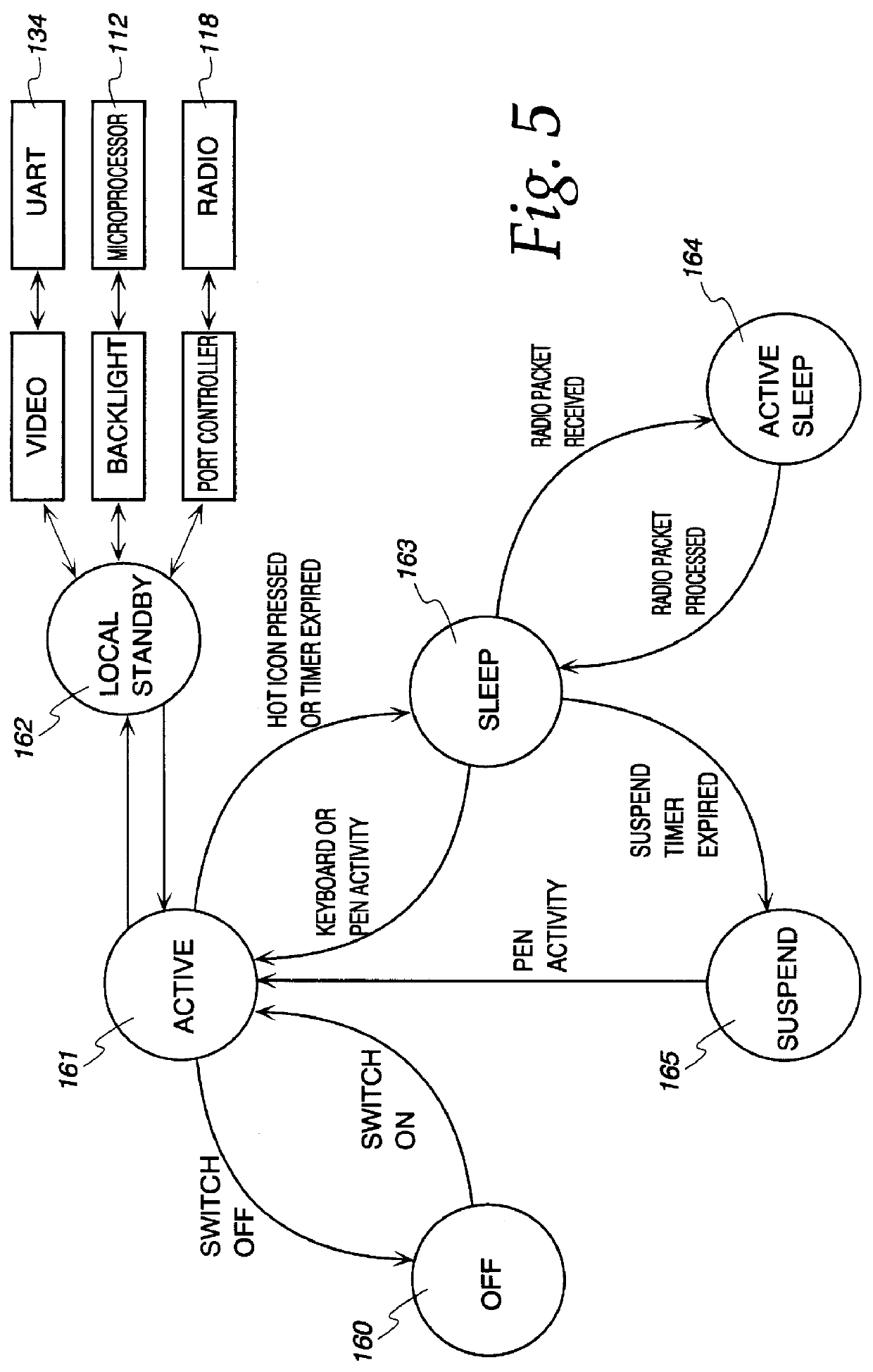
Method and system for rebooting a computer having corrupted memory using an external jumper
InactiveUS6018806AProgram loading/initiatingRedundant operation error correctionComputerized systemBIOS
A computer system includes a flash memory device for storing BIOS code. The BIOS code is stored in an unprotected area of the flash memory. A boot block, stored in a protected area of the flash memory, is used for rebooting the computer system in the event that the flash memory device becomes corrupted. During normal operation, the BIOS code is updated using a radio link. If the BIOS is corrupted while being updated, a recovery routine stored in the boot block is executed. The recovery routine permits the corrupted BIOS to be reprogrammed using a serial interface instead of the radio link.
Owner:NEC CORP
Method, computer system and computer program product for executing a network supported business transaction
InactiveUS20060041670A1Improve security levelReliable decodingMultiple digital computer combinationsDigital data authenticationAuthorizationProtected area
The invention relates to a method for executing a network supported customer business transaction and a method for providing access to an access protected area of a server, in which in each case access to the access protected area in the server by the client terminal is granted when an access authorization is electronically activated.
Owner:BASF AG
Portable handheld electronic article surveillance and scanner device
ActiveUS7051943B2Credit registering devices actuationDynamo-electric converter controlHand heldBarcode
A handheld combined electronic article surveillance (EAS) and barcode scanner device. The device may be configured for wireless communication with a point of sale network so that is entirely portable within a protected area. The device may include a capacitor disposed in handle at a proximal end of the device and an antenna may be disposed at a distal end of the device. A base station may be provided for receiving the device.
Owner:SENSORMATIC ELECTRONICS CORP
Method and apparatus for constructing a set-top box to protect cryptographic capabilities
InactiveUS20050039212A1Improve securityEasy to switchCircuit security detailsPrinted circuit aspectsEpoxyX-ray
A construction arrangement for a small set-top box to protect cryptographic capabilities and prevent a digital program in clear from being able to be tapped as required by Digital Rights Management protocols. A first layer of sheet metal capable of blocking X-rays, is formed as a shallow pan to hold a set of printed circuit boards. A second layer has a thin epoxy based printed circuit material. A third layer has a printed circuit board with integrated components placed on top of the second layer. A fourth layer has a three layer thin printed circuit board with a first and second metallic layer and holes for large components, such as electrolytic capacitors. A black liquid thermosetting epoxy fills the interstices between the sheet metal layer and the second layer, and between the second layer and the third layer, and between the third layer and the fourth layer, thereby preventing access to exposed circuit trace carrying digital signals in the clear. A connection from the first metallic layer of the fourth printed circuit material layer to a sending circuit and a connection from the second metallic layer so that a short between these two layers sets off an indicator circuit that an attempt is made to enter the protected area.
Owner:AURORA NETWORKS
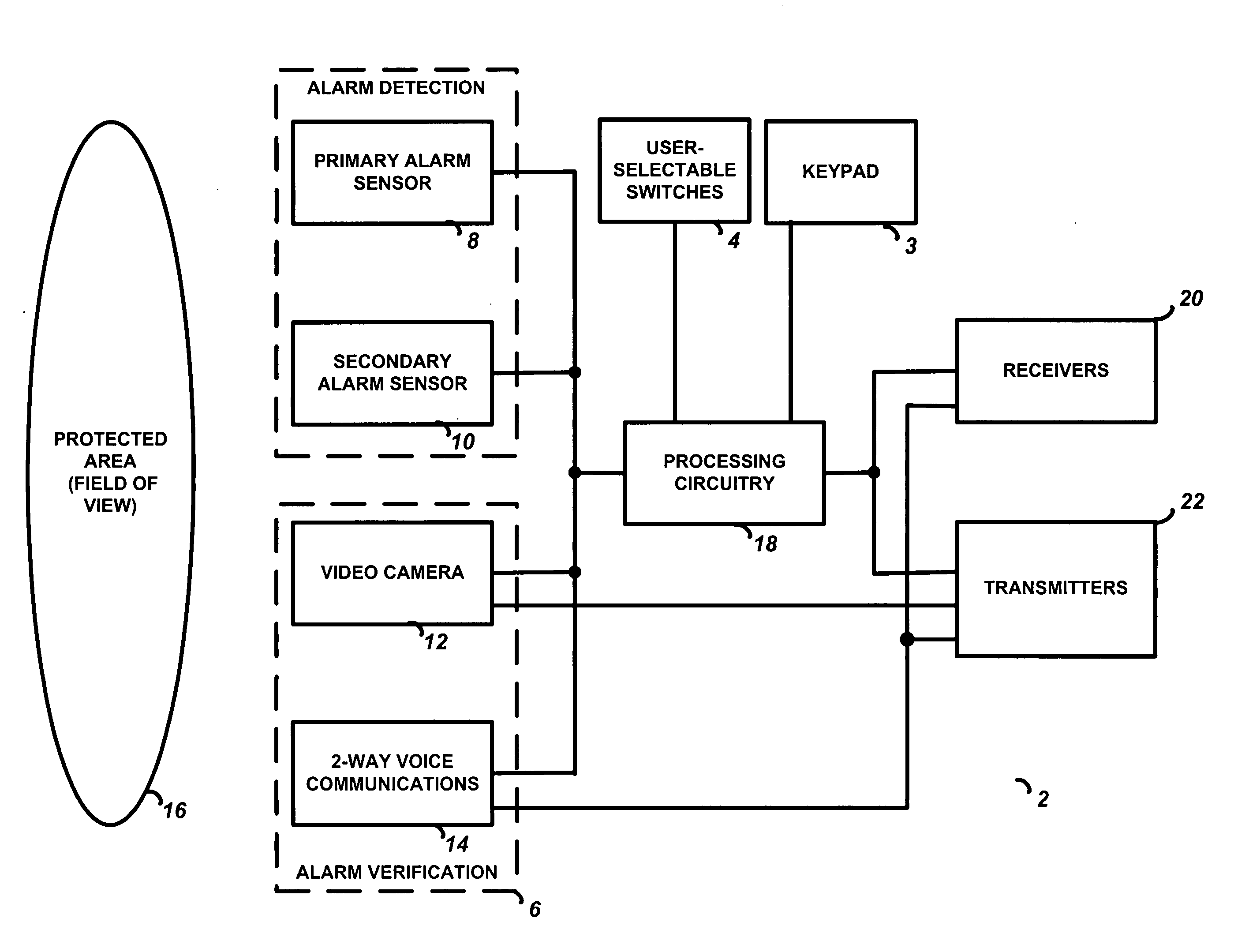
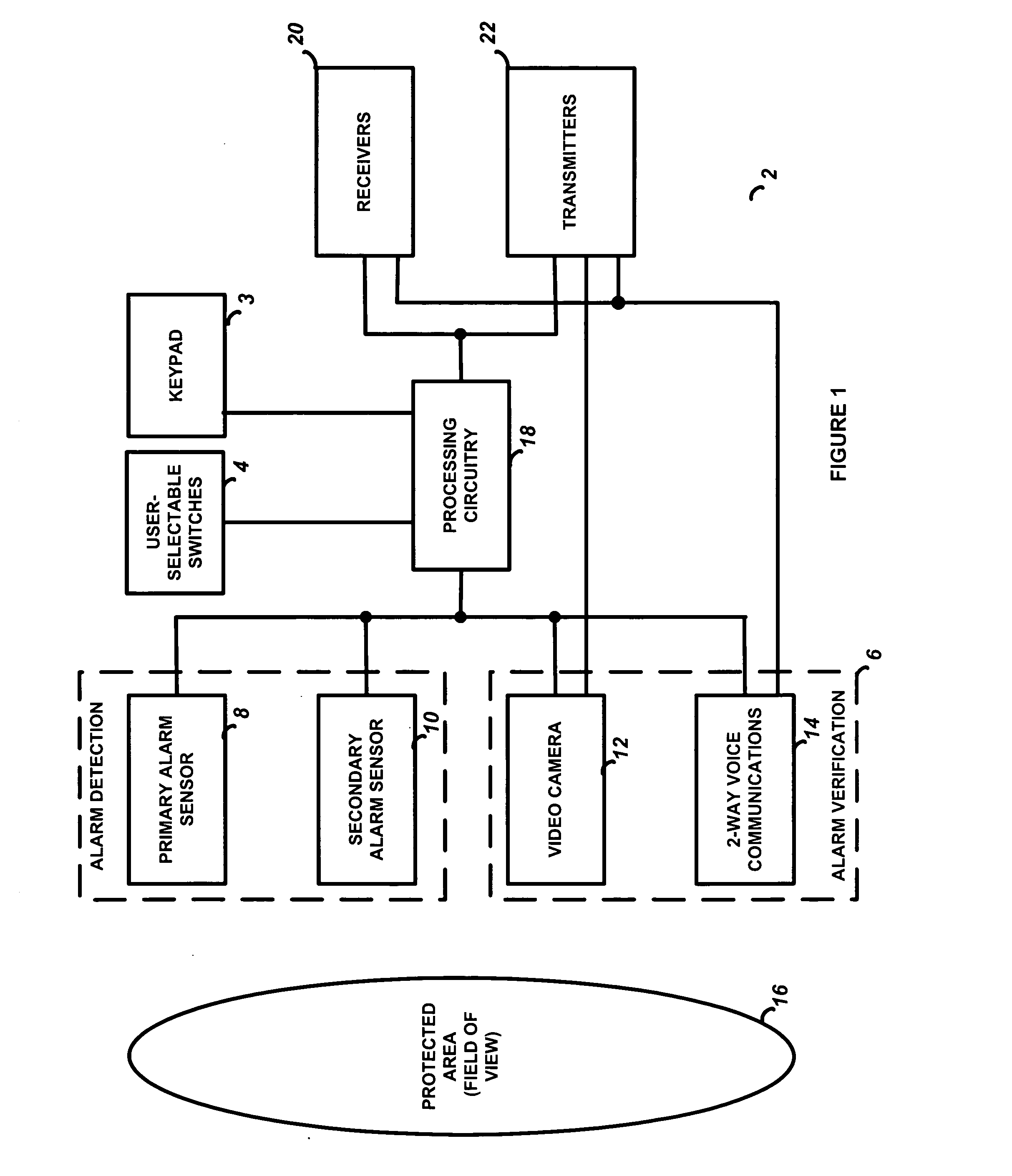
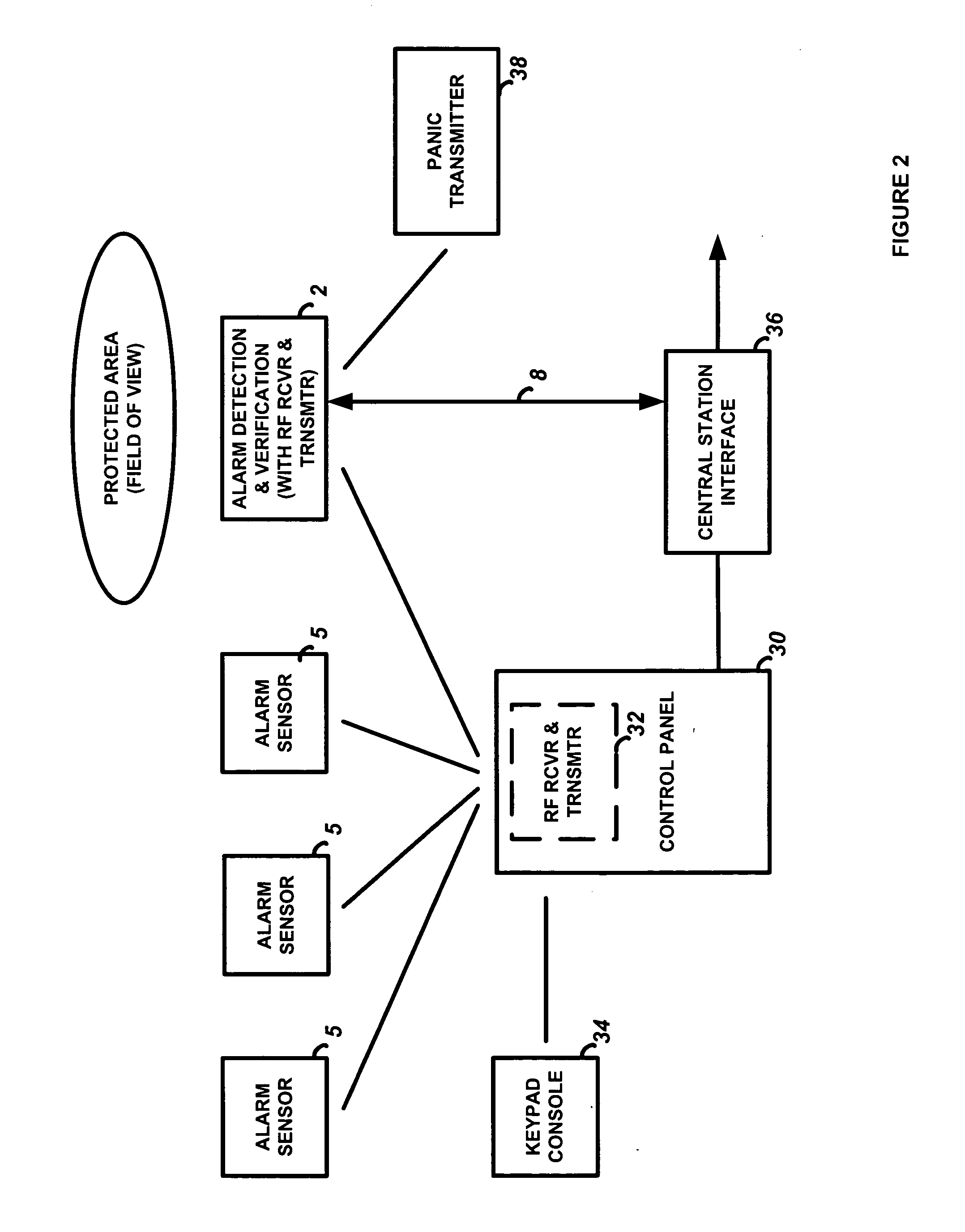
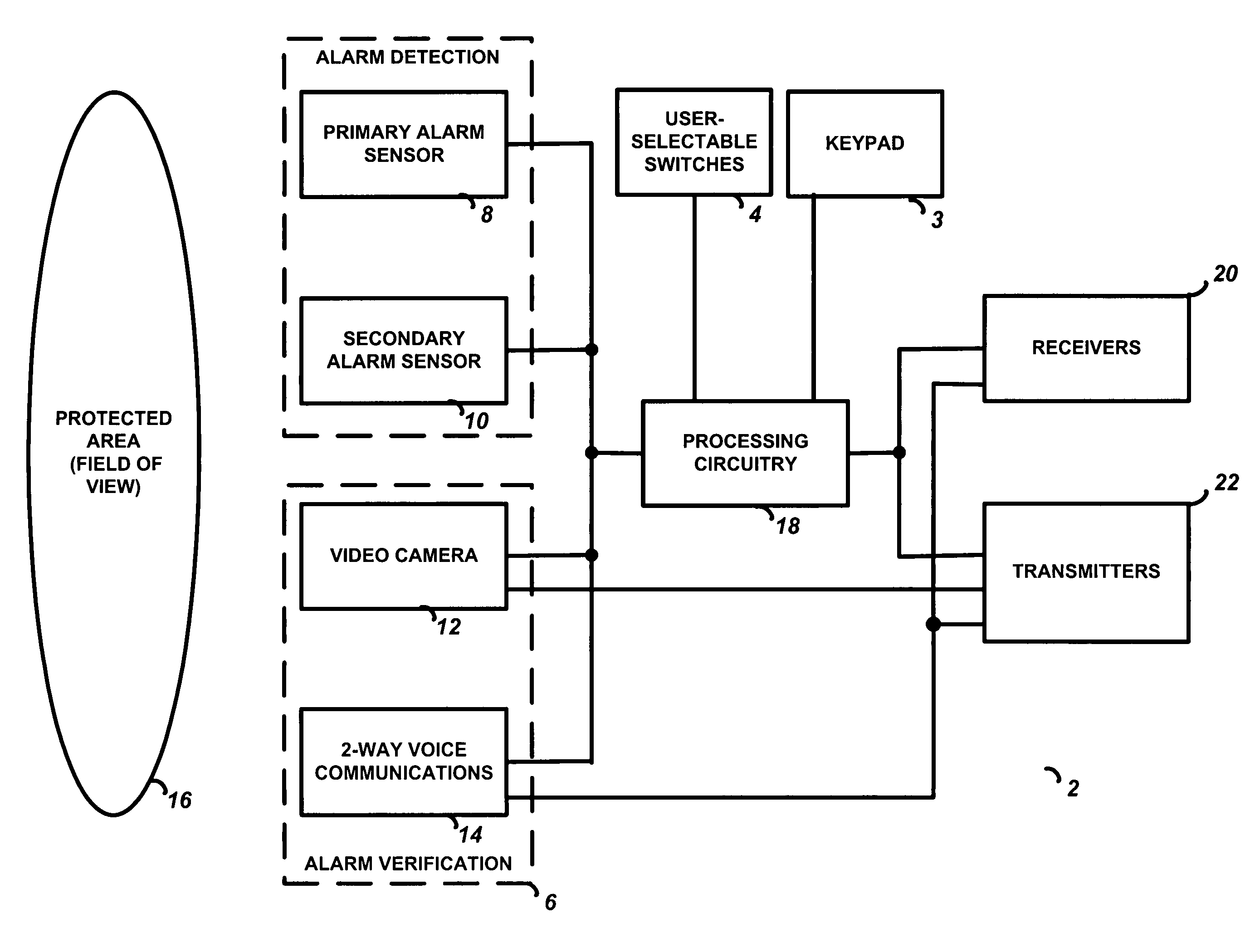
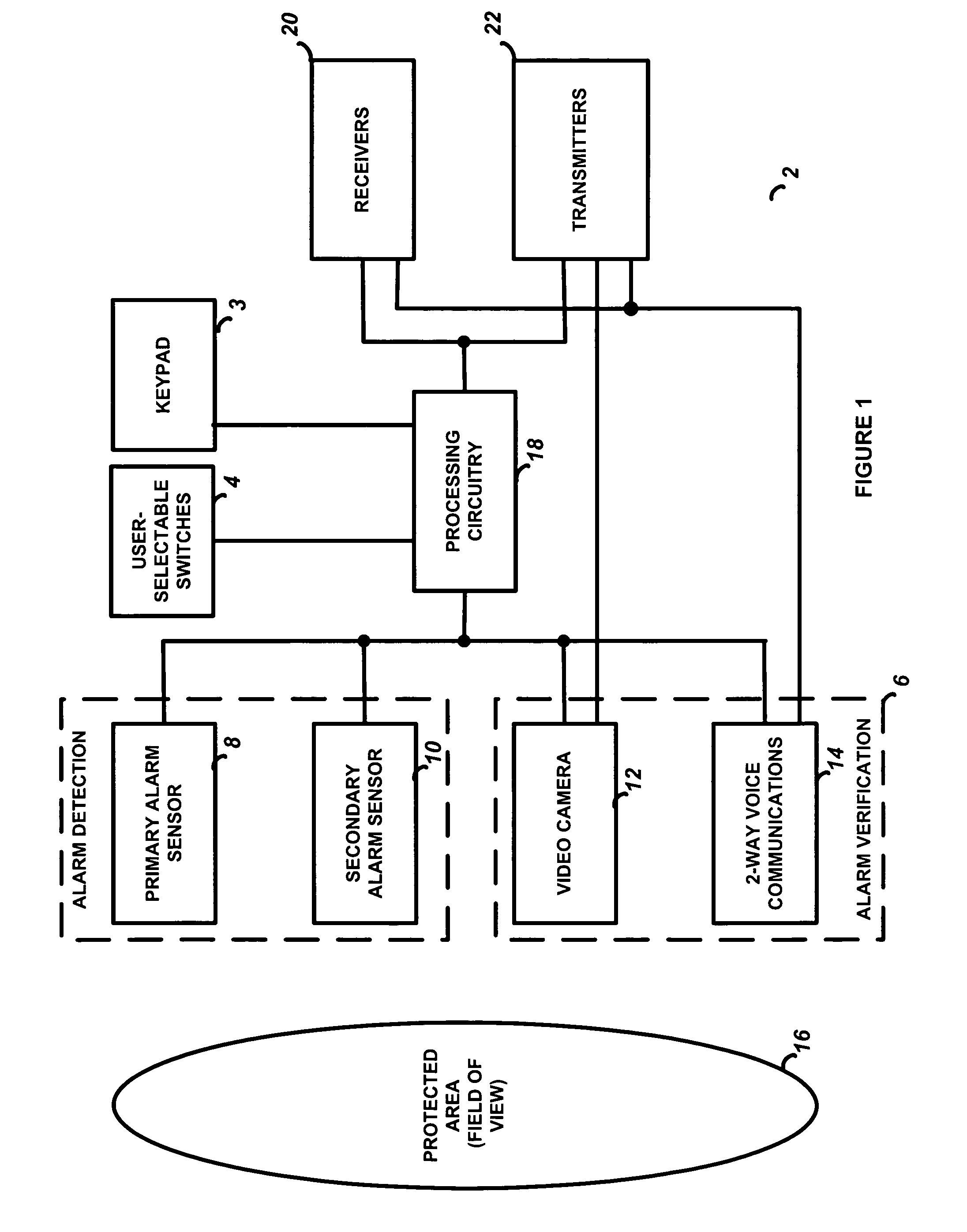
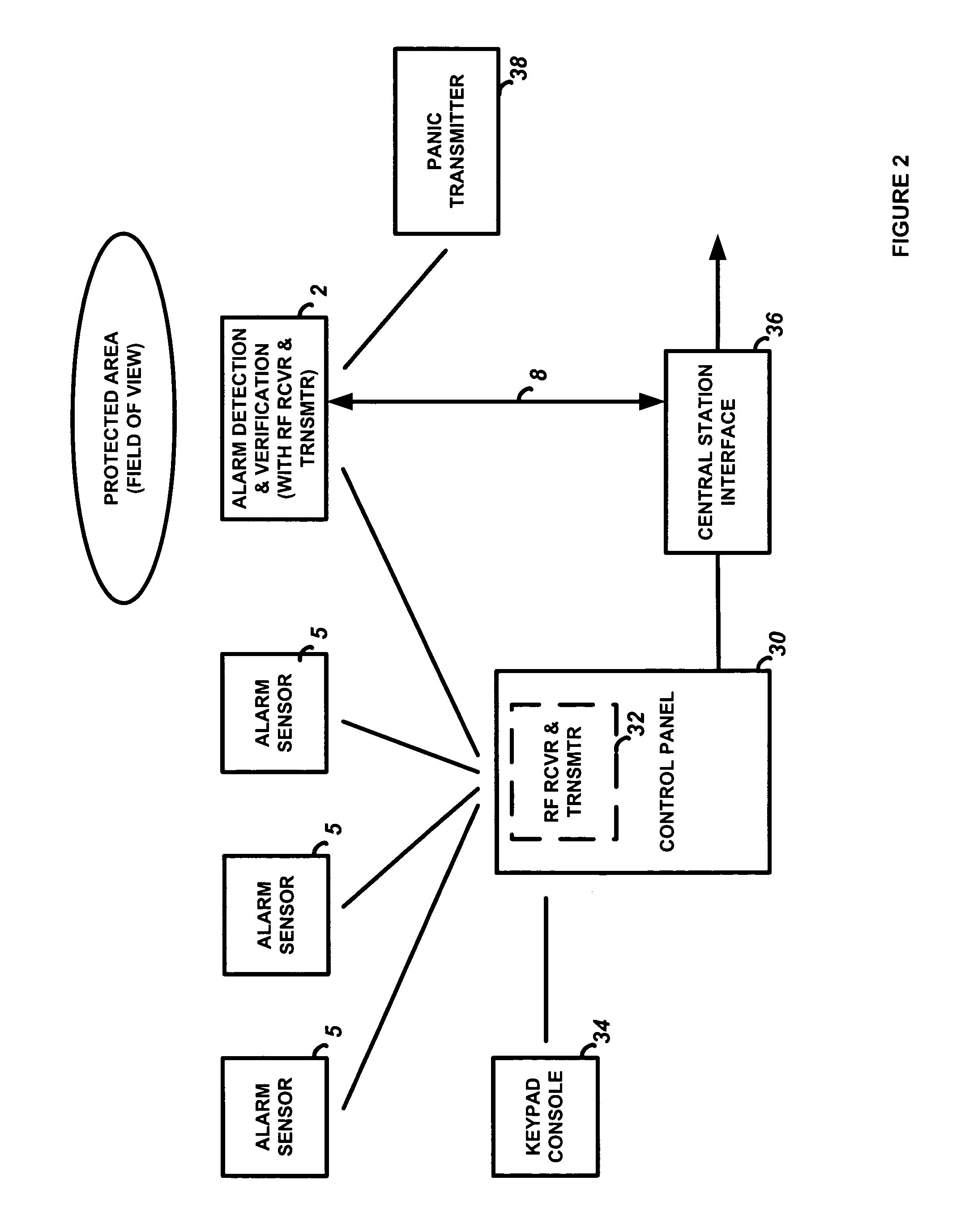
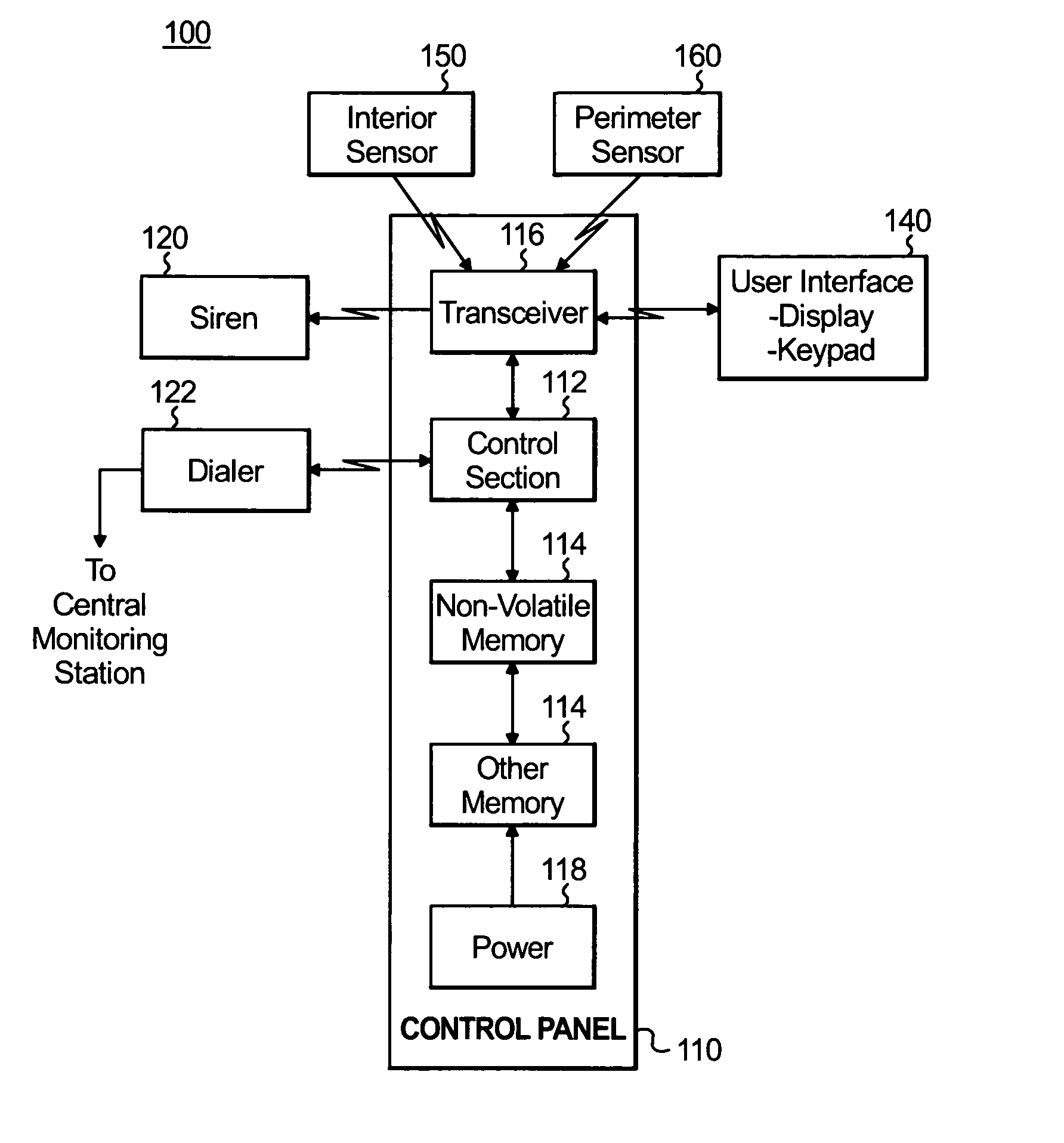
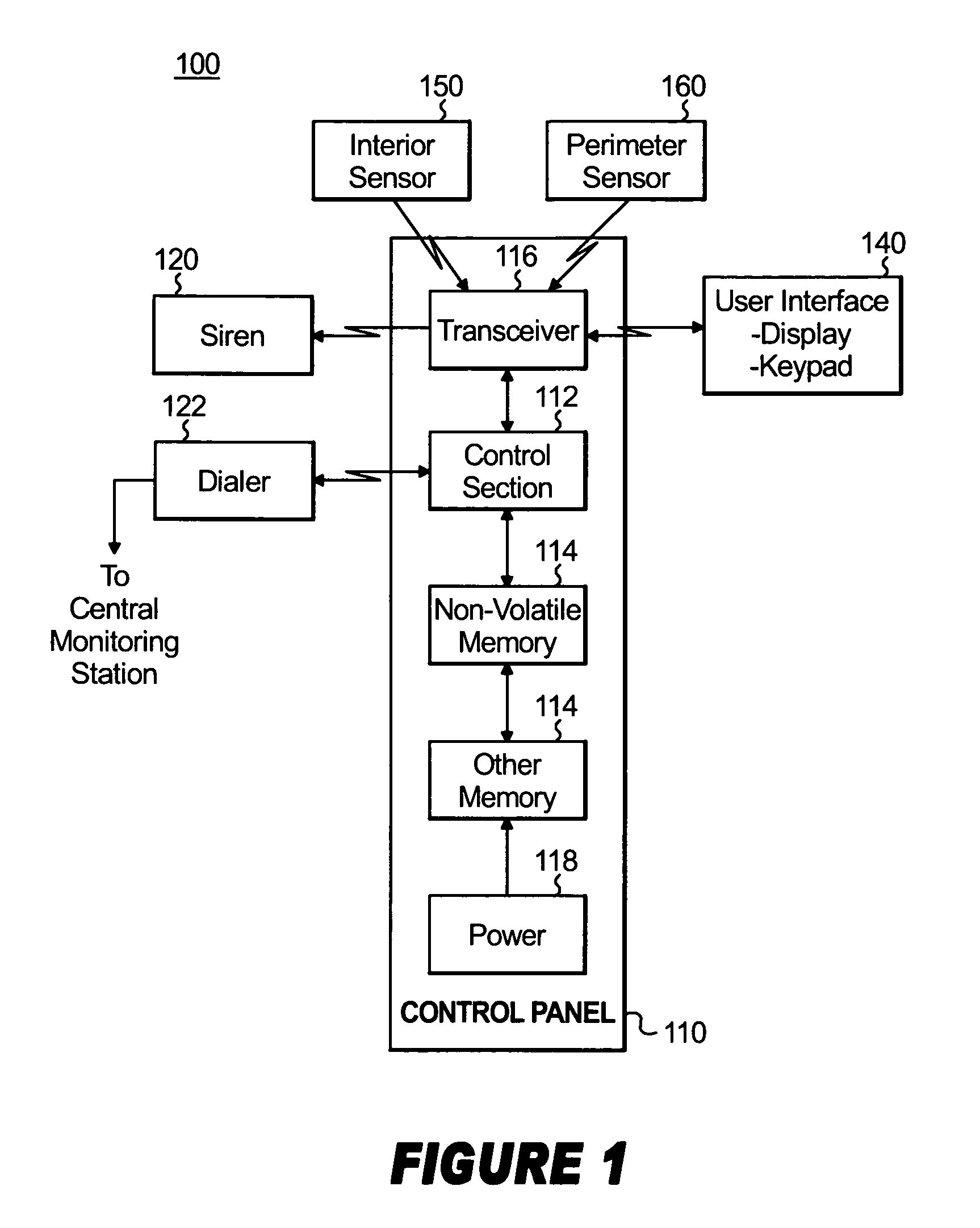
Integrated alarm detection and verification device
A security system device including a single housing including at least a primary alarm sensor, an alarm verification unit, and processing circuitry. The primary alarm sensor is adapted to monitor a primary protected area and to generate a primary alarm signal when the primary alarm sensor is triggered. The alarm verification unit selectively provides verification information (e.g. video and / or audio signals) from at least part of the primary protected area to a central station monitor. The processing circuitry is adapted to generate an alarm enable signal when the primary alarm signal is generated. On the occurrence of an alarm enable signal, the processing circuitry generates an alarm detected signal and causes the alarm detected signal to be transmitted to a central station monitor, enables operation of the alarm verification unit, and enables transmission of the verification information from the protected area to the central station monitor. A secondary alarm sensor may also be included within the housing, in which case the alarm enable signal is generated only on the triggering of both the primary and secondary alarm sensors. The primary alarm sensor may be adapted to cause the sensitivity of the secondary alarm sensor to be modified on the triggering of the primary alarm sensor.
Owner:ADEMCO INC
Method for managing keys and/or rights objects
ActiveUS20070116287A1Facilitate key managementPrecise positioningDigital data processing detailsAnalogue secracy/subscription systemsDatabaseMarine navigation
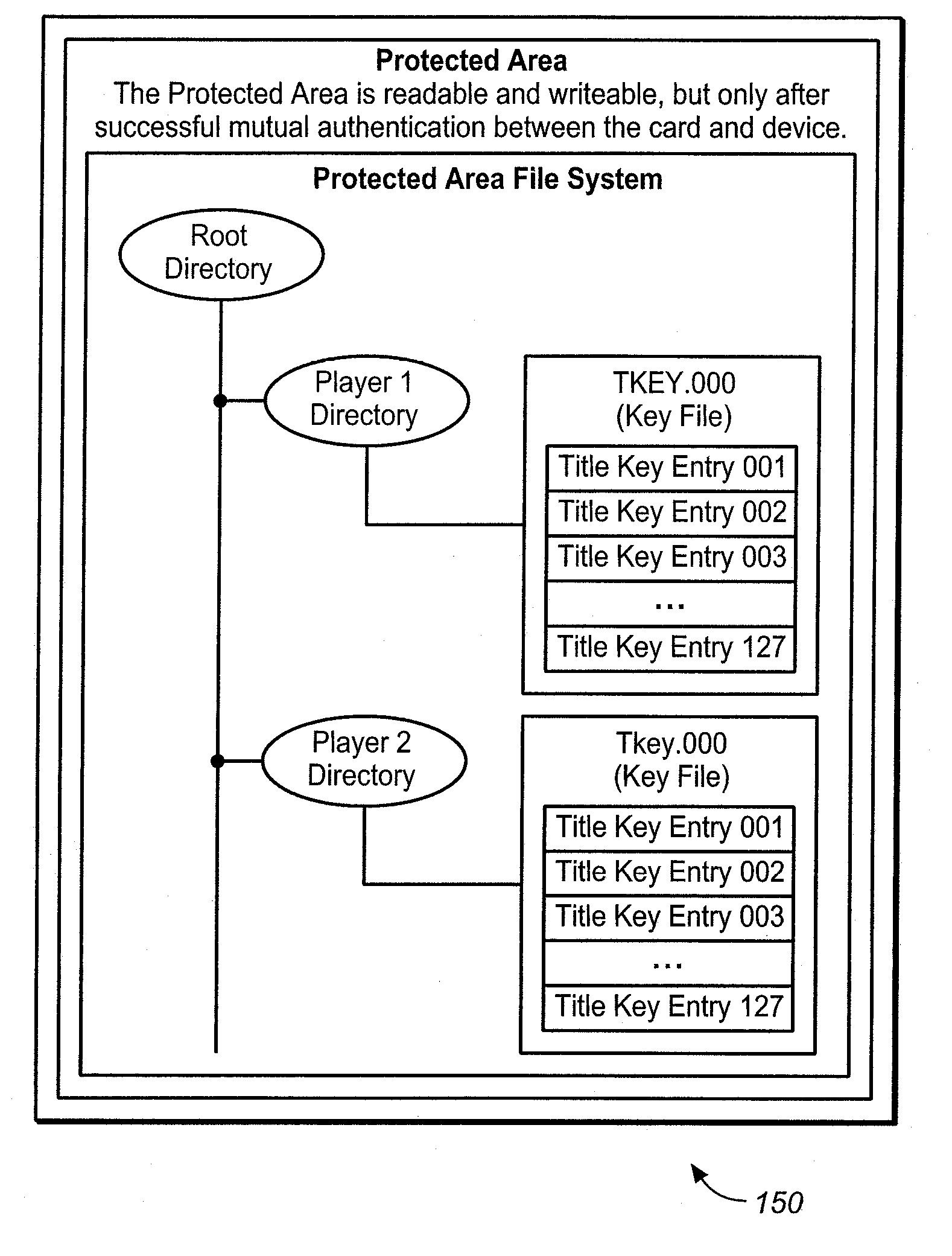
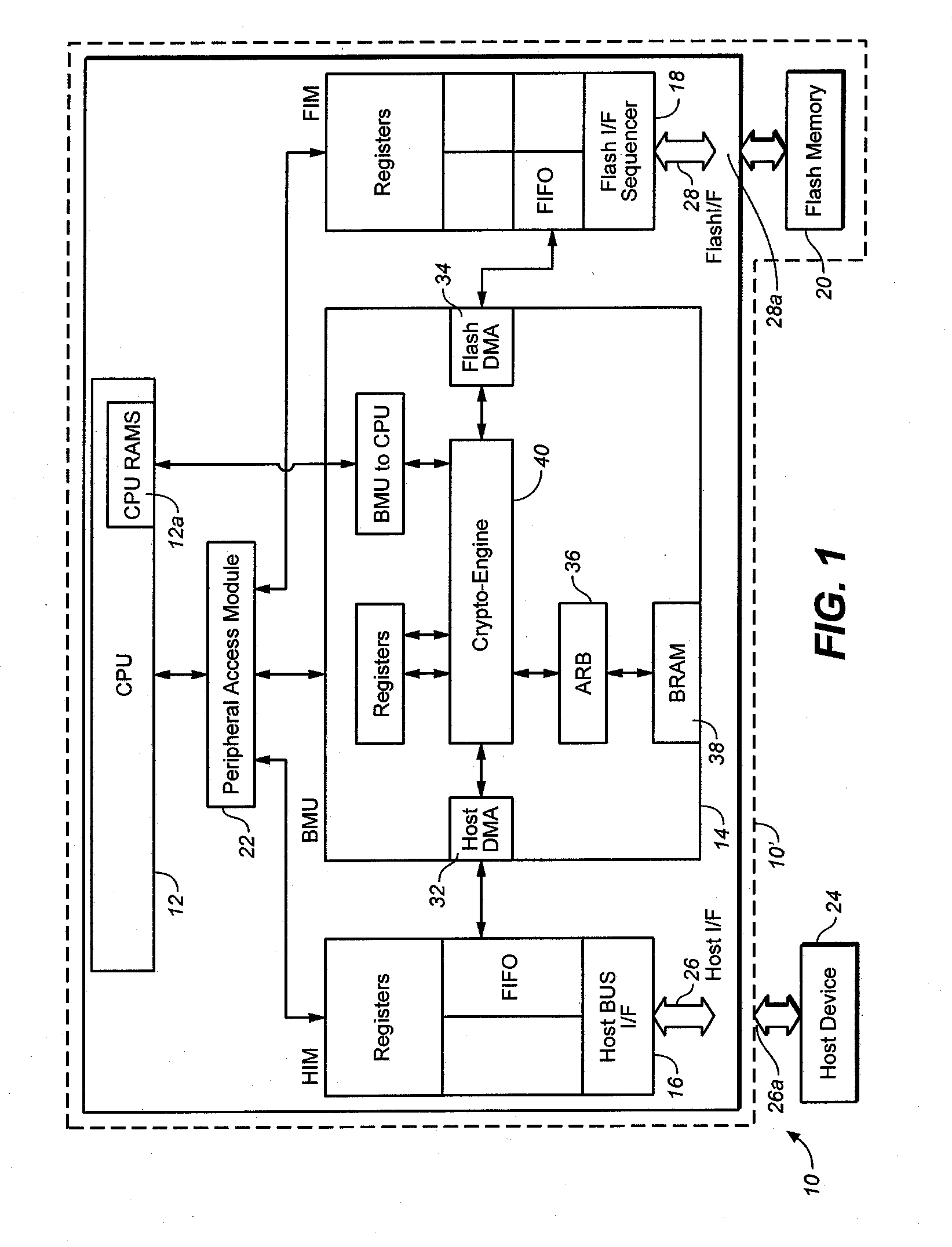
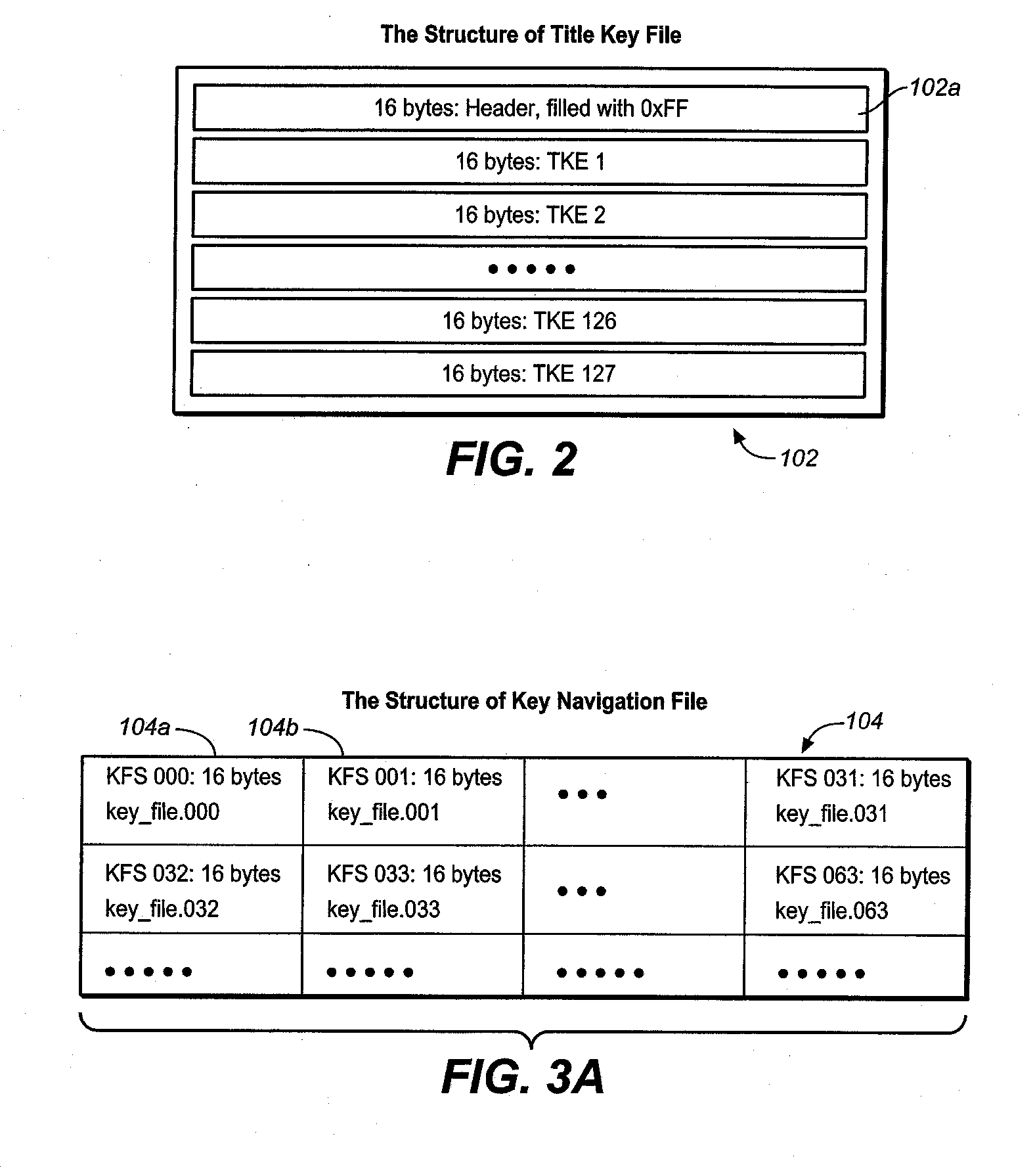
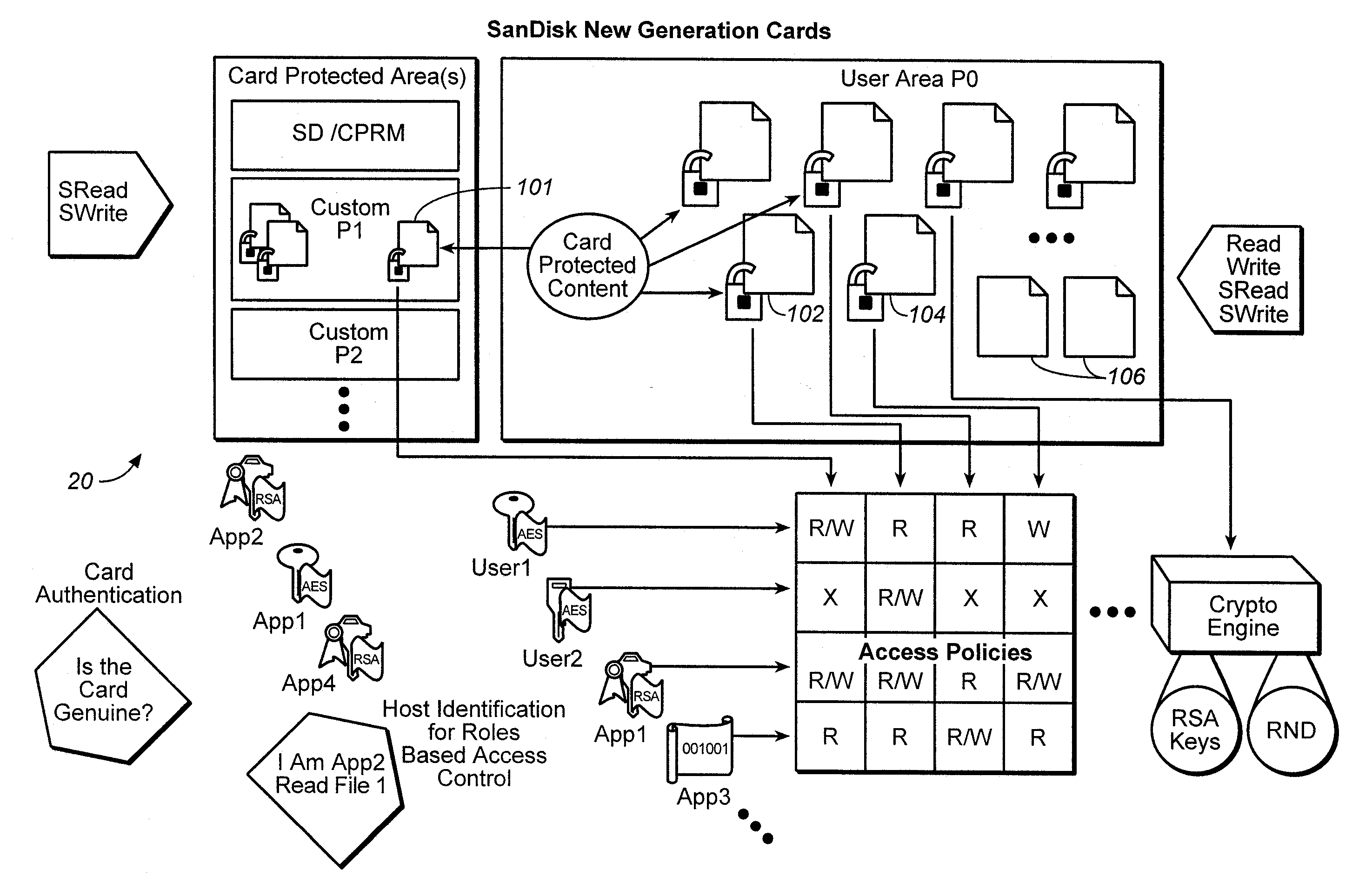
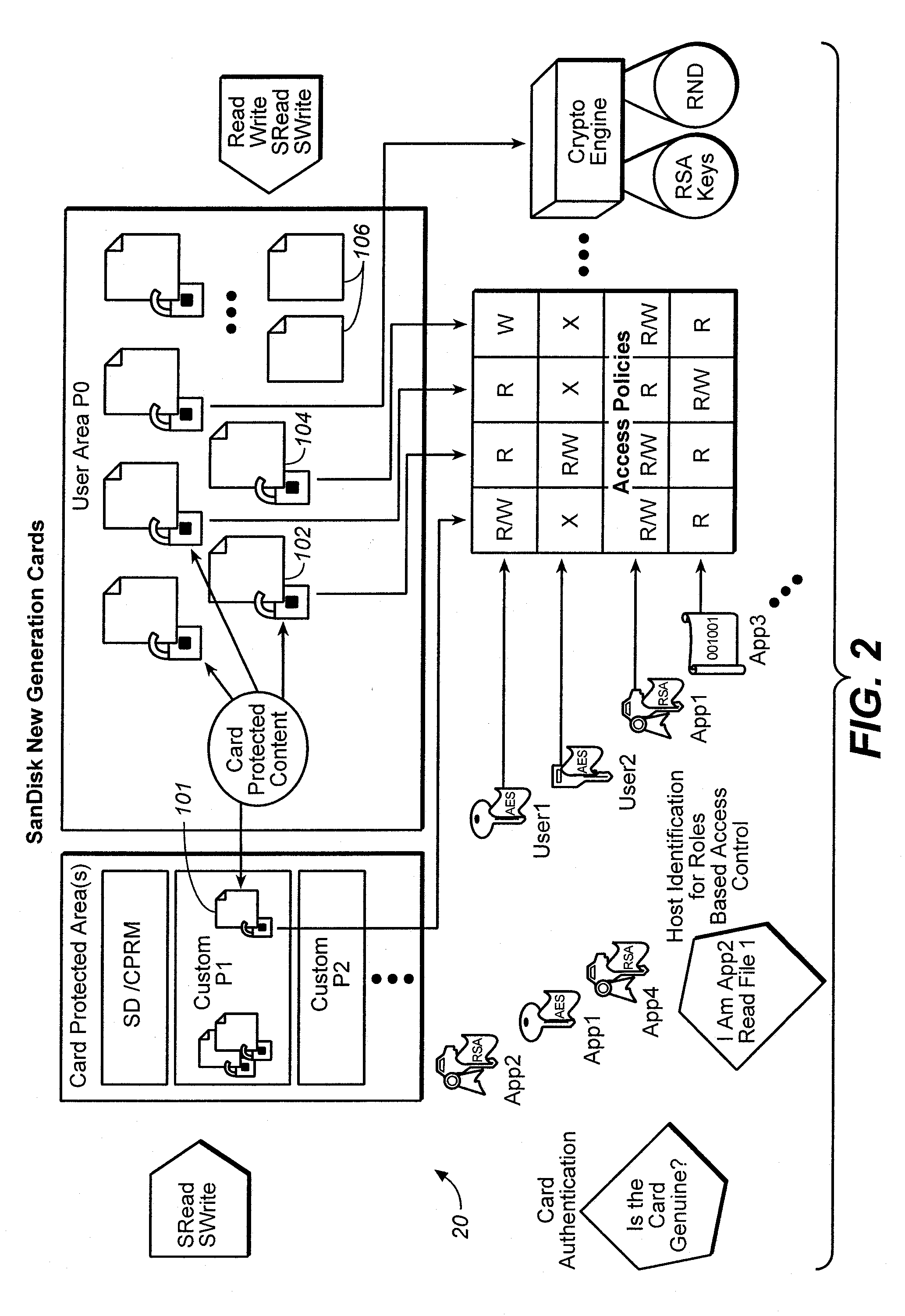
One or more rights objects (RO) files may be used for storing RO's preferably in the protected area available only to authenticated users. A RO navigation file is stored preferably in an unprotected public area containing status bits, where each status bit identifies whether a location in a RO file contains a valid RO or not. Preferably, there is a one-to-one correspondence between the location for a RO in a RO file and a location in the RO navigation file for the status bit which identifies whether its corresponding location in the RO file contains a valid RO or not. Whether a particular location in a RO file contains a valid RO or not can be found by checking its corresponding status bit in the RO navigation file. By finding out whether a particular location in a RO file contains a valid RO or not in this manner, it is possible to delete ROs without having to go through an authentication process. The process of finding an empty slot in the RO file for storing a new RO is also simplified. This greatly increases the efficiency of RO management. A similar system may be used for management of content encryption / encryption keys for protecting content files.
Owner:SANDISK TECH LLC
Computer network security system employing portable storage device
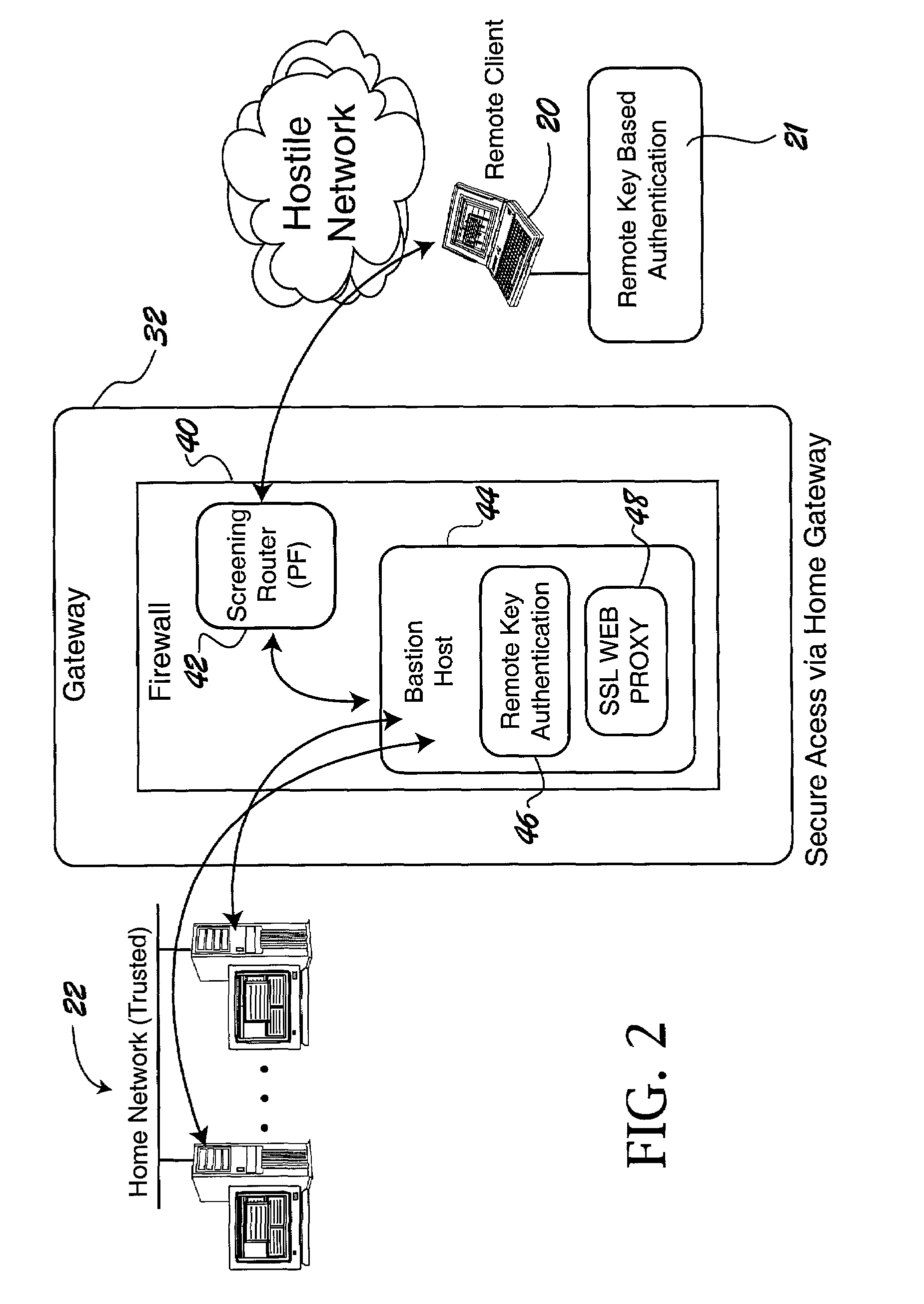
ActiveUS7228438B2Easy to useRaise security concernsUser identity/authority verificationUnauthorized memory use protectionUniform resource locatorClient machine
The trusted computer network is protected behind a gateway that includes a bastion host and screening router which blocks all URLs associated with the trusted network. The bastion host includes a remote client authentication mechanism and web proxy component that verifies and translates incoming URL requests from authenticated remote clients. Authentication is performed using one-time passwords that are stored on a portable storage device. The user configures the portable storage device by operating configuration software from the protected side of the gateway. The portable storage device also stores plug-in software to enable the client computer to properly retrieve the one-time password and exchange authentication messages with the bastion host. Further security is obtained by basing the one-time password on an encrypted version of the user's PIN. A symmetric key used to encrypt the PIN is stored in a protected area within the portable storage device.
Owner:SOVEREIGN PEAK VENTURES LLC
System and method for intrusion detection using a time domain radar array
InactiveUS20080165046A1High resolutionImprove performanceRadio wave reradiation/reflectionTime domainUltra-wideband
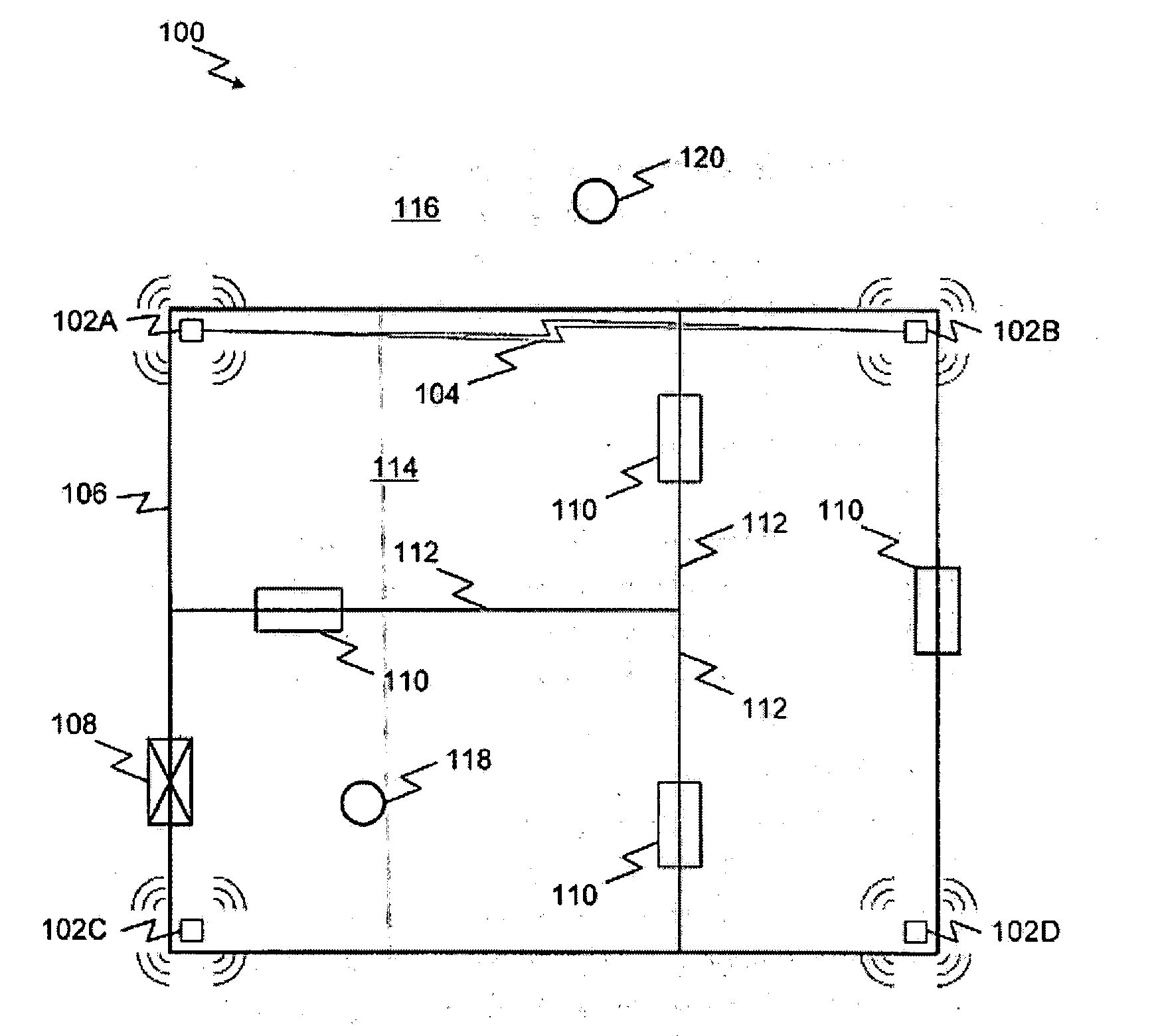
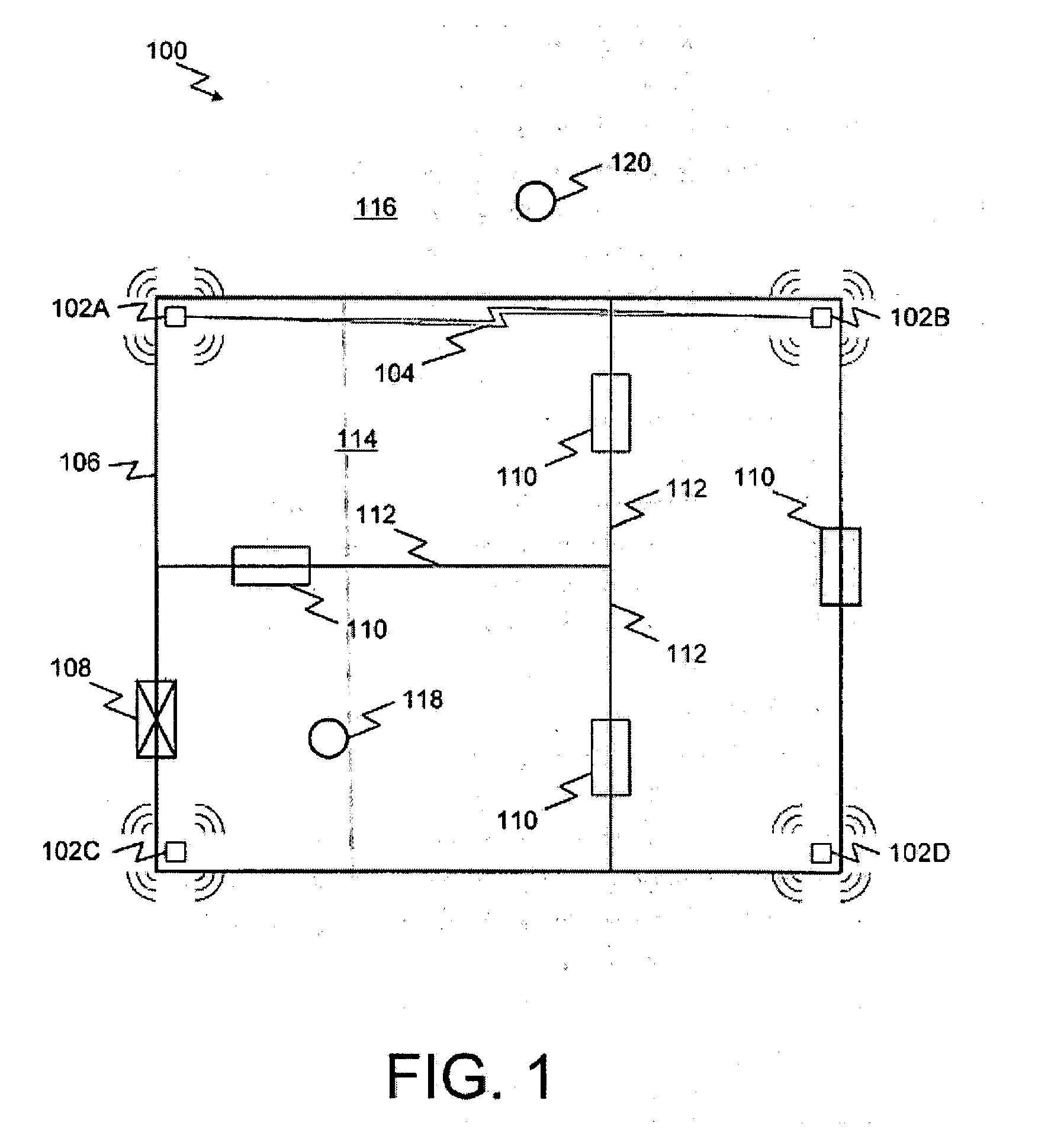
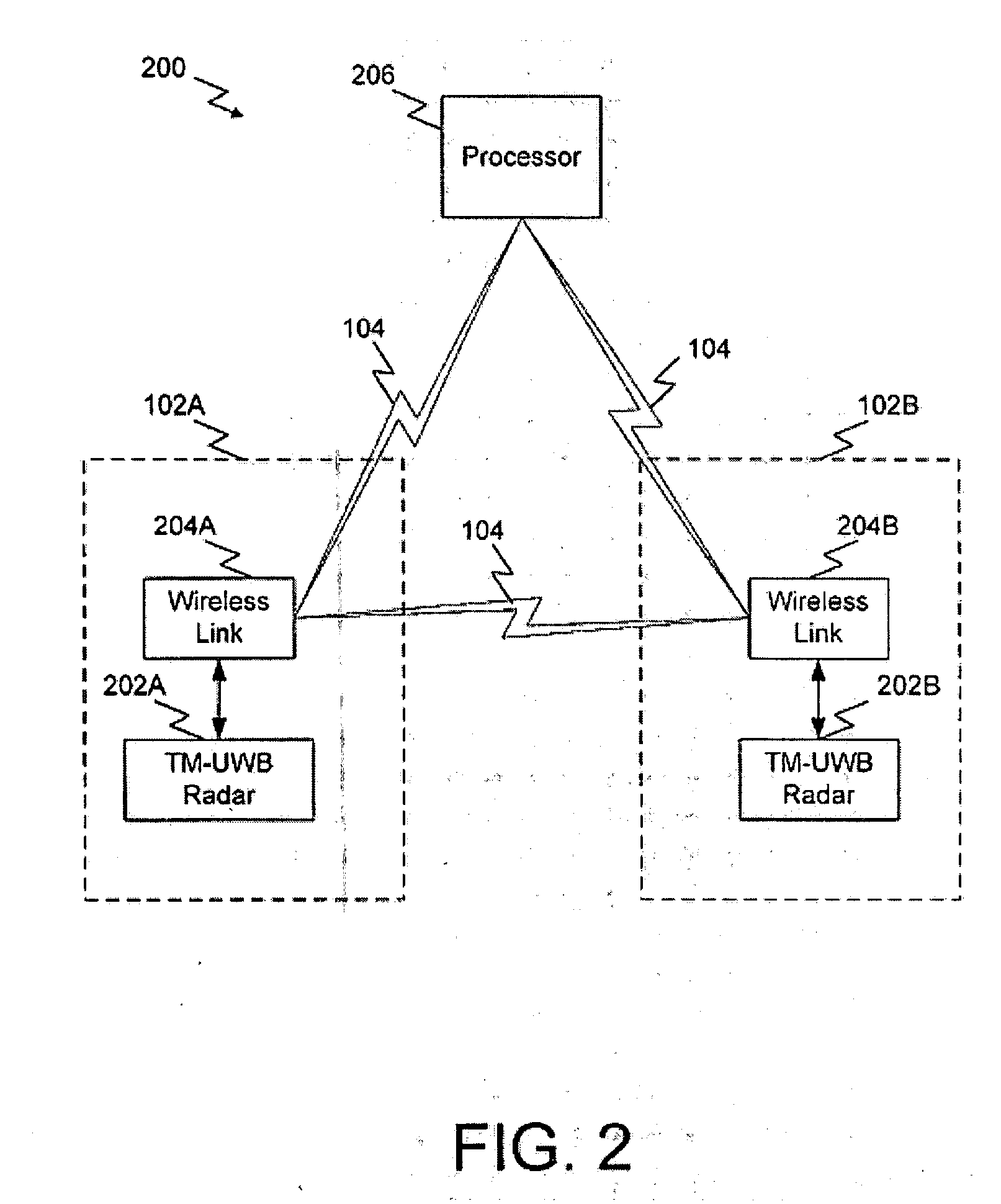
A system and method for highly selective intrusion detection using a sparse array of ultra wideband (UWB) radars. Two or more UWB radars are arranged in a sparse array around an area to be protected. Each UWB radar transmits ultra wideband pulses that illuminate the area to be protected. Signal return data is processed to determine, among other things, whether an alarm condition has been triggered. High resolution radar images are formed that give an accurate picture of the area to be protected. This image is used to detect motion in a highly selective manner and to track moving objects within the protected area. Motion can be distinguished based on criteria appropriate to the environment in which the intrusion detection system operates.
Owner:HUMATICS CORP
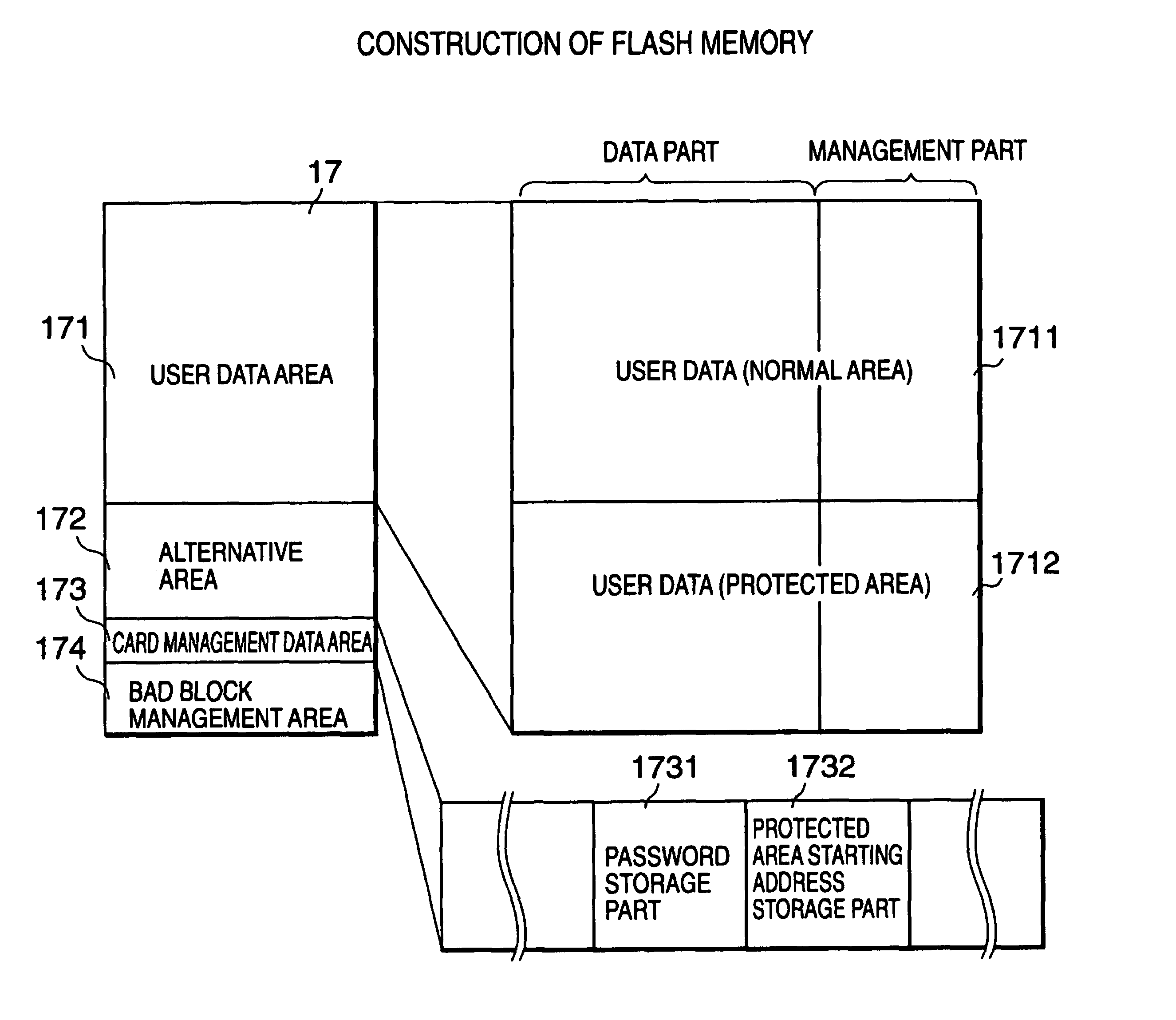
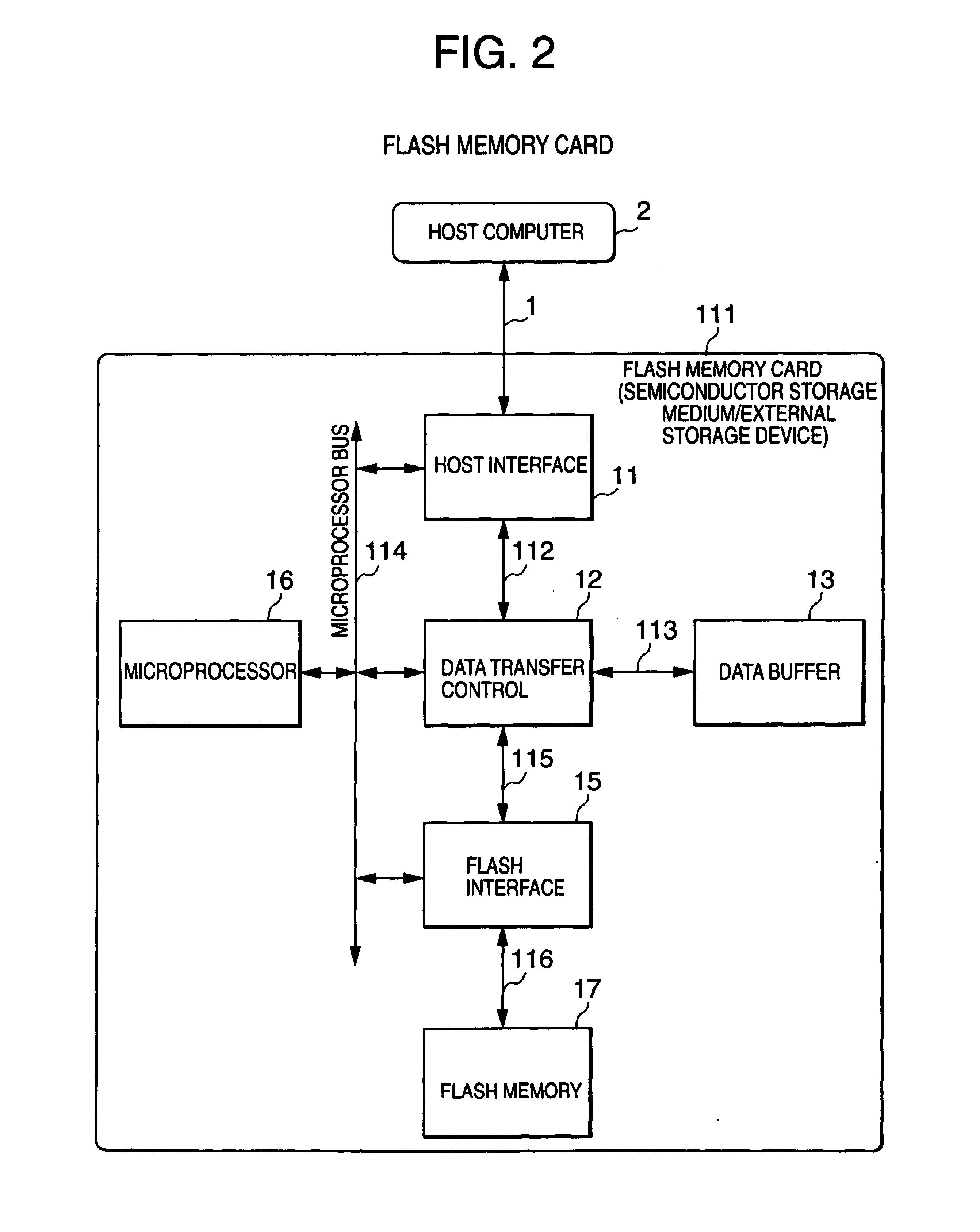
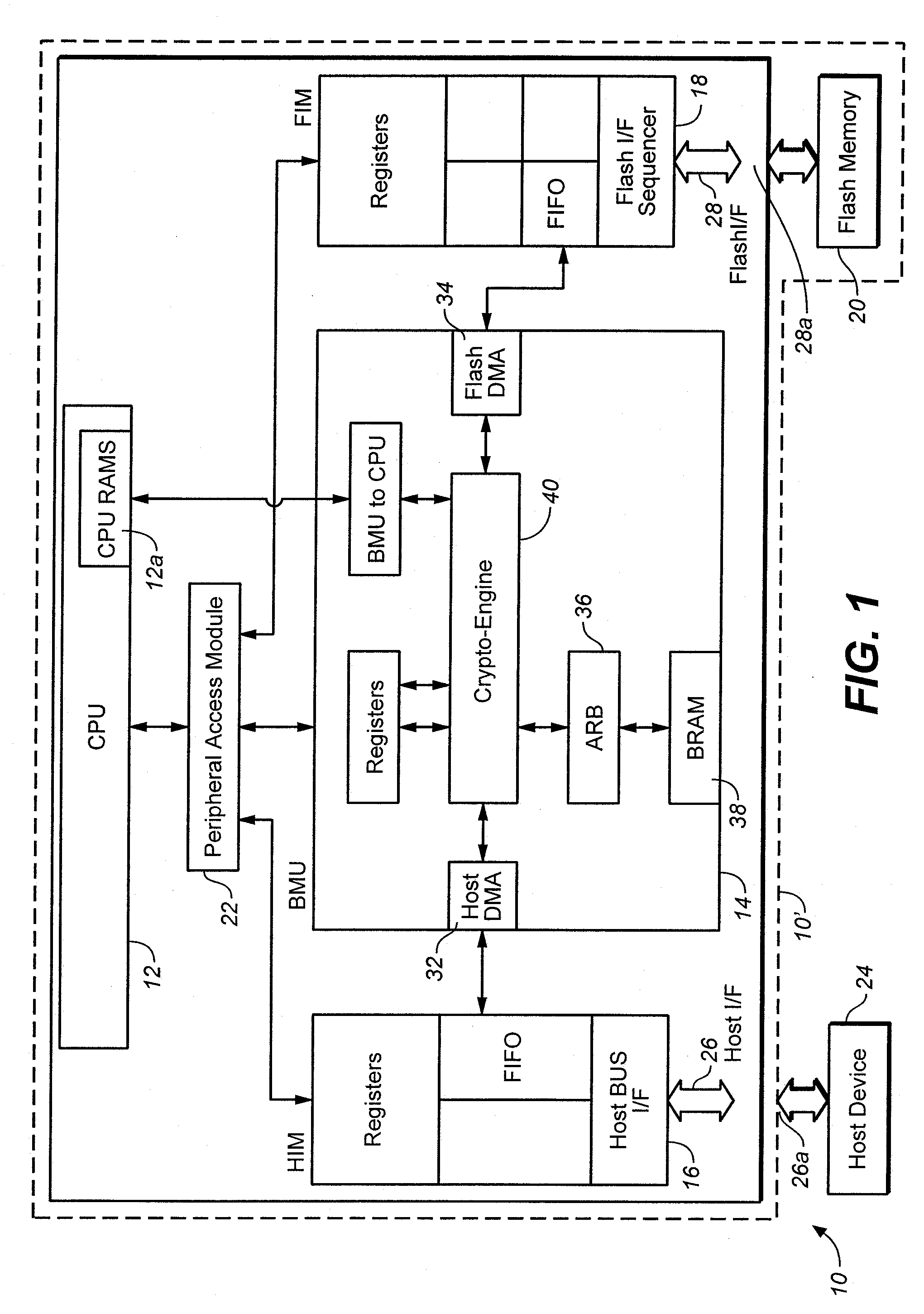
External storage device using non-volatile semiconductor memory
InactiveUS7054990B1Improve usabilityLimited accessRead-only memoriesUnauthorized memory use protectionExternal storagePassword
The external storage device according to the present invention which uses a non-volatile semiconductor memory such as a flash memory is provided with plural areas which store user data, and restricts access to the user data from a host computer and also dynamically changes an area an access to which is to be restricted. Accordingly, the ease of use of the external storage device for the host computer is improved. Specifically, the interior of the flash memory is divided into a normal area not protected by a password or the like and a protected area protected by a password or the like. A microprocessor controls accesses to the normal area and the protected area in accordance with a command from the host computer. In addition, the host computer can access the protected area after passing through authentication using a password. Moreover, the host computer changes information indicative of the location of the protected area, thereby dynamically changing the protection area.
Owner:RENESAS ELECTRONICS CORP
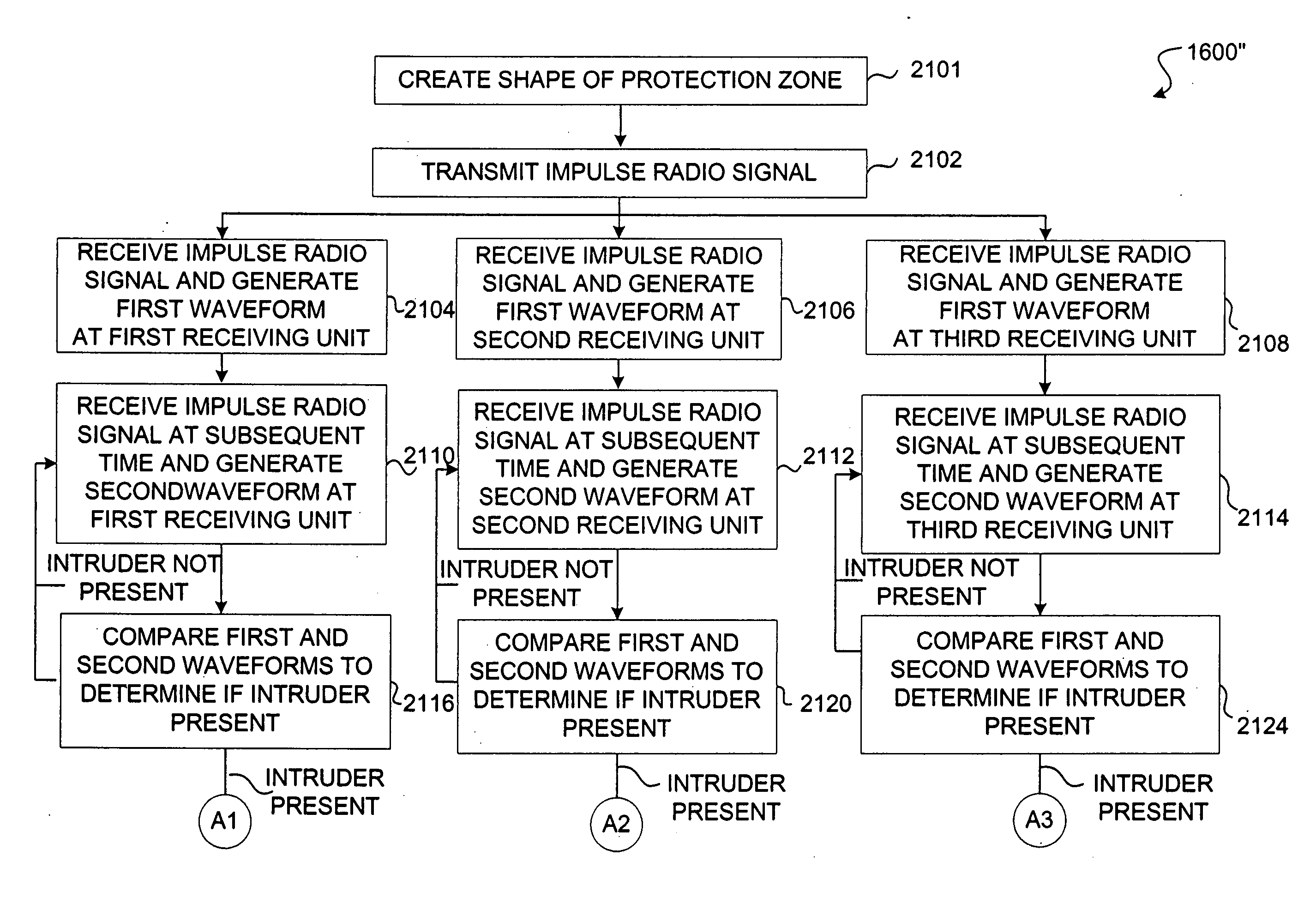
System and method for detecting an intruder using impulse radio technology
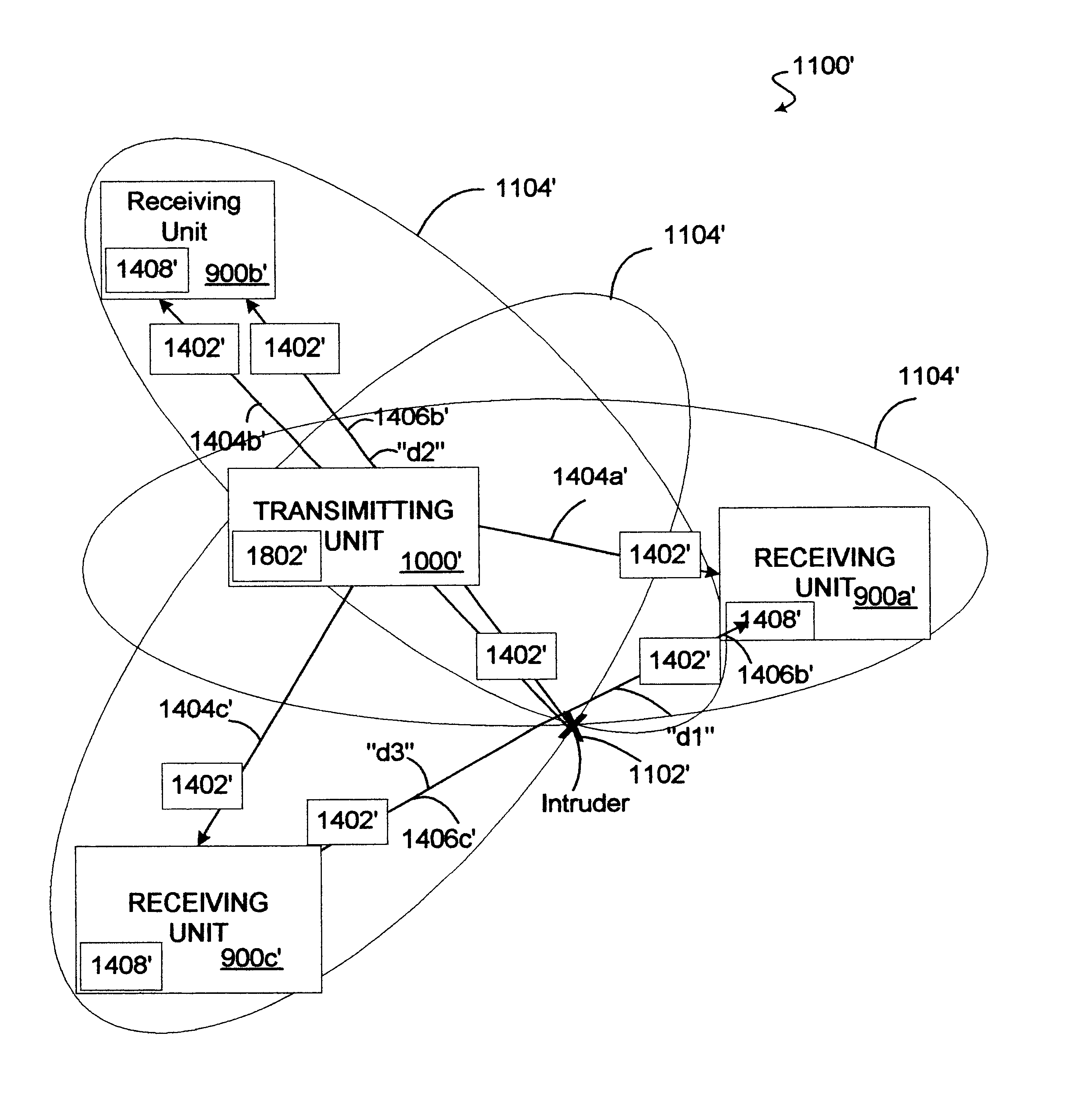
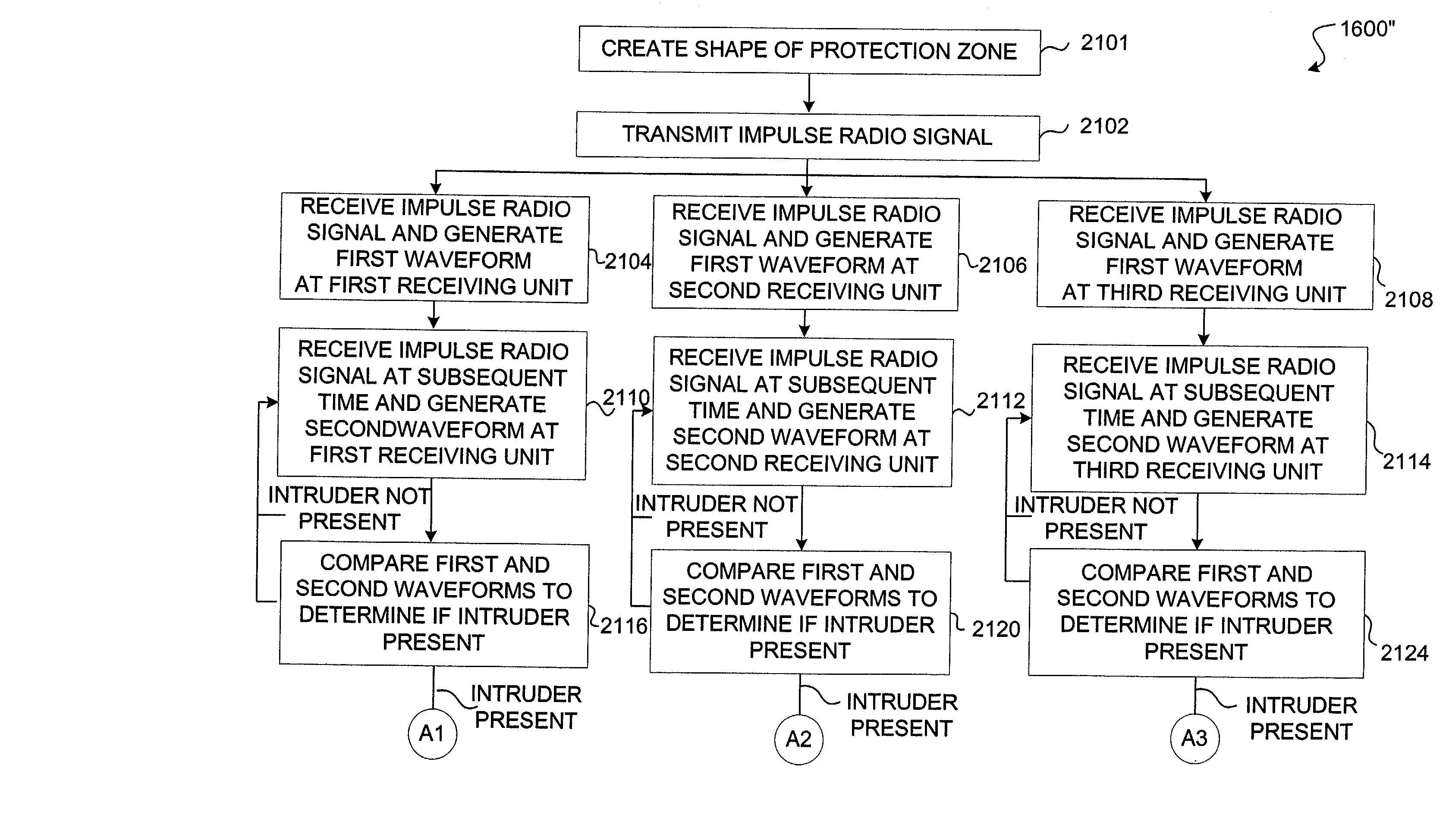
An intrusion detection system and method are provided that can utilize impulse radio technology to detect when an intruder has entered a protection zone. In addition, the intrusion detection system and method can utilize impulse radio technology to determine a location of the intruder within the protection zone and also track the movement of the intruder within the protection zone. Moreover, the intrusion detection system and method can utilize impulse radio technology to create a specially shaped protection zone before trying to detect when and where the intruder has penetrated and moved within the protection zone.
Owner:HUMATICS CORP
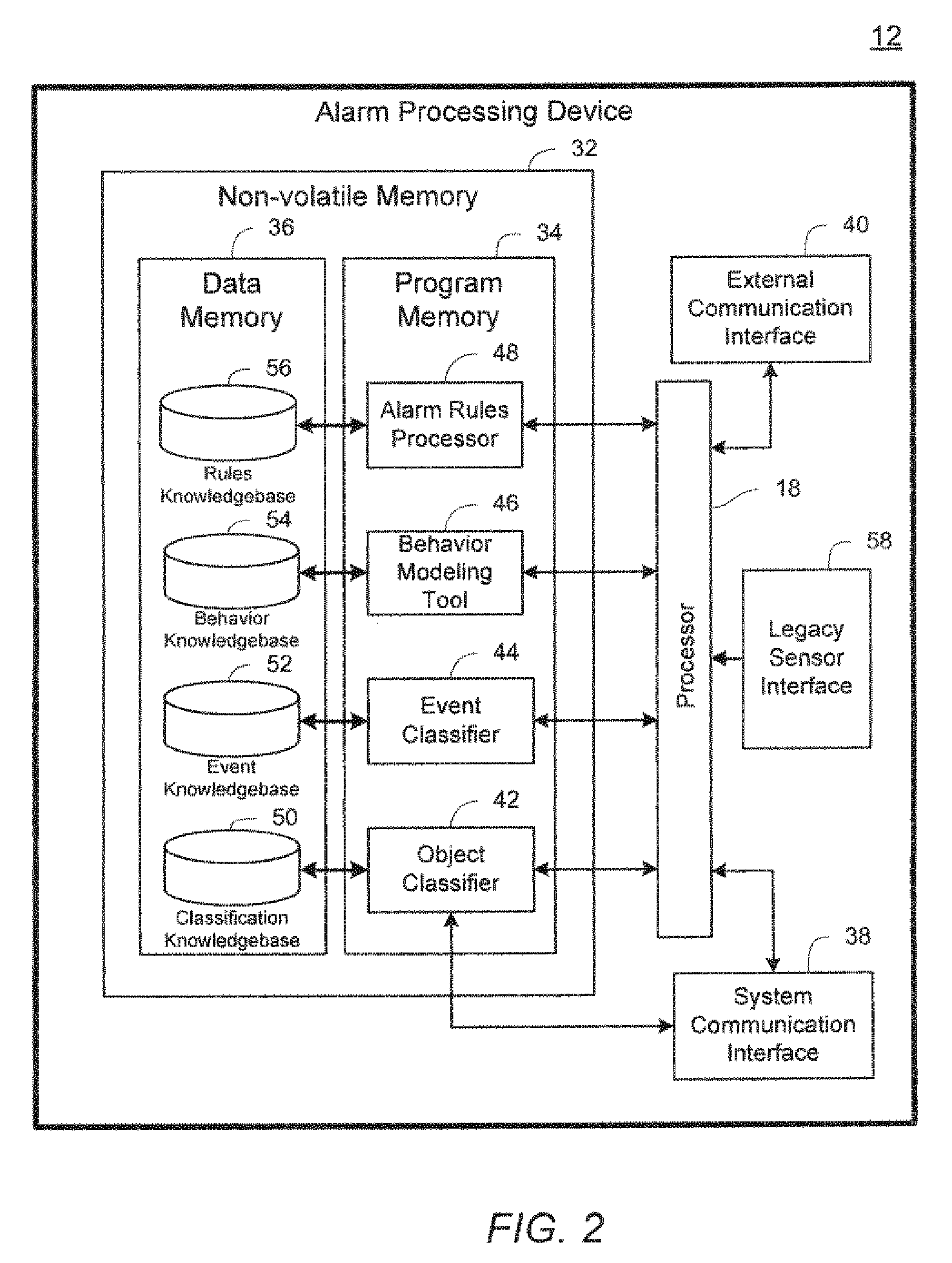
Video sensor and alarm system and method with object and event classification
InactiveUS20090195382A1Low bandwidth communicationReduce communicationElectric testing/monitoringCharacter and pattern recognitionData setVideo sensors
A method and system detects an intrusion into a protected area. Image data is captured and processed to create a reduced image dataset having a lower dimensionality than the captured image data. The reduced image dataset is transmitted to a centralized alarm processing device where the reduced image dataset is evaluated to determine an alarm condition.
Owner:SENSORMATIC ELECTRONICS CORP
Mail receptacle with delivery indicator
The “Mail Receptacle with Delivery Indicator” is a device which will allow the user of the unit to visually detect the presence of mail without opening the unit, or even approaching said unit directly. There are several possible embodiments of said device, including but not limited to a unit which can be placed at the roadside in rural areas for delivery of mail, a unit which can be mounted on the outside wall of a house for delivery of mail in urban areas, a smaller unit, possibly assembled in groups, which could be used for multiple dwellings such as apartment complexes, a special unit to be placed inside a wall locker in a school, factory, or any other location in which wall lockers are used, or a decorative unit which could be placed on a desk or table to be used for personal or interoffice communication. The unit may also include a recording means which would allow a verbal message for the user of the mailbox to be recorded and played back at the convenience of the user. The unit may also include a security mechanism which prevents unauthorized persons from having access to mail within the unit. The unit may also include a protected area for displaying the name and / or house number of the user, providing easier identification of the proper unit for someone delivering mail.
Owner:NEFF RICHARD DEAN
Integrated alarm detection and verification device
A security system device including a single housing including at least a primary alarm sensor, an alarm verification unit, and processing circuitry. The primary alarm sensor is adapted to monitor a primary protected area and to generate a primary alarm signal when the primary alarm sensor is triggered. The alarm verification unit selectively provides verification information (e.g. video and / or audio signals) from at least part of the primary protected area to a central station monitor. The processing circuitry is adapted to generate an alarm enable signal when the primary alarm signal is generated. On the occurrence of an alarm enable signal, the processing circuitry generates an alarm detected signal and causes the alarm detected signal to be transmitted to a central station monitor, enables operation of the alarm verification unit, and enables transmission of the verification information from the protected area to the central station monitor. A secondary alarm sensor may also be included within the housing, in which case the alarm enable signal is generated only on the triggering of both the primary and secondary alarm sensors. The primary alarm sensor may be adapted to cause the sensitivity of the secondary alarm sensor to be modified on the triggering of the primary alarm sensor.
Owner:ADEMCO INC
Protecting areas of skin proximate hair or nails from hair colors/ dyes and other contaminants
InactiveUS20070277331A1Protect the skinSelective and uniform deliveryCosmetic preparationsCationic surface-active compoundsHair dyesProtection sex
The present invention provides for selective and uniform delivery of compositions to protect certain targeted areas: (1) skin proximate colorable or dyeable hair from staining by hair colors or hair dyes; or (2) skin proximate nails against nail skin contaminants which may include hair color or hair dyes. Embodiments of products of the present invention may comprise the protective composition and a device for selective and uniform delivery of the composition to the targeted area of the skin. Products may also comprise a protective composition having a solid or semisolid consistency which is formed to enable selective and uniform delivery of the composition to the targeted area of the skin. Products may also comprise: (a) a hair color or hair dyeing kit comprising the protective composition and one or more hair color or hair dyeing components; or (b) a nail cosmetic kit comprising the protective composition and one or more nail cosmetic components.
Owner:INGENUITY ADVISORS
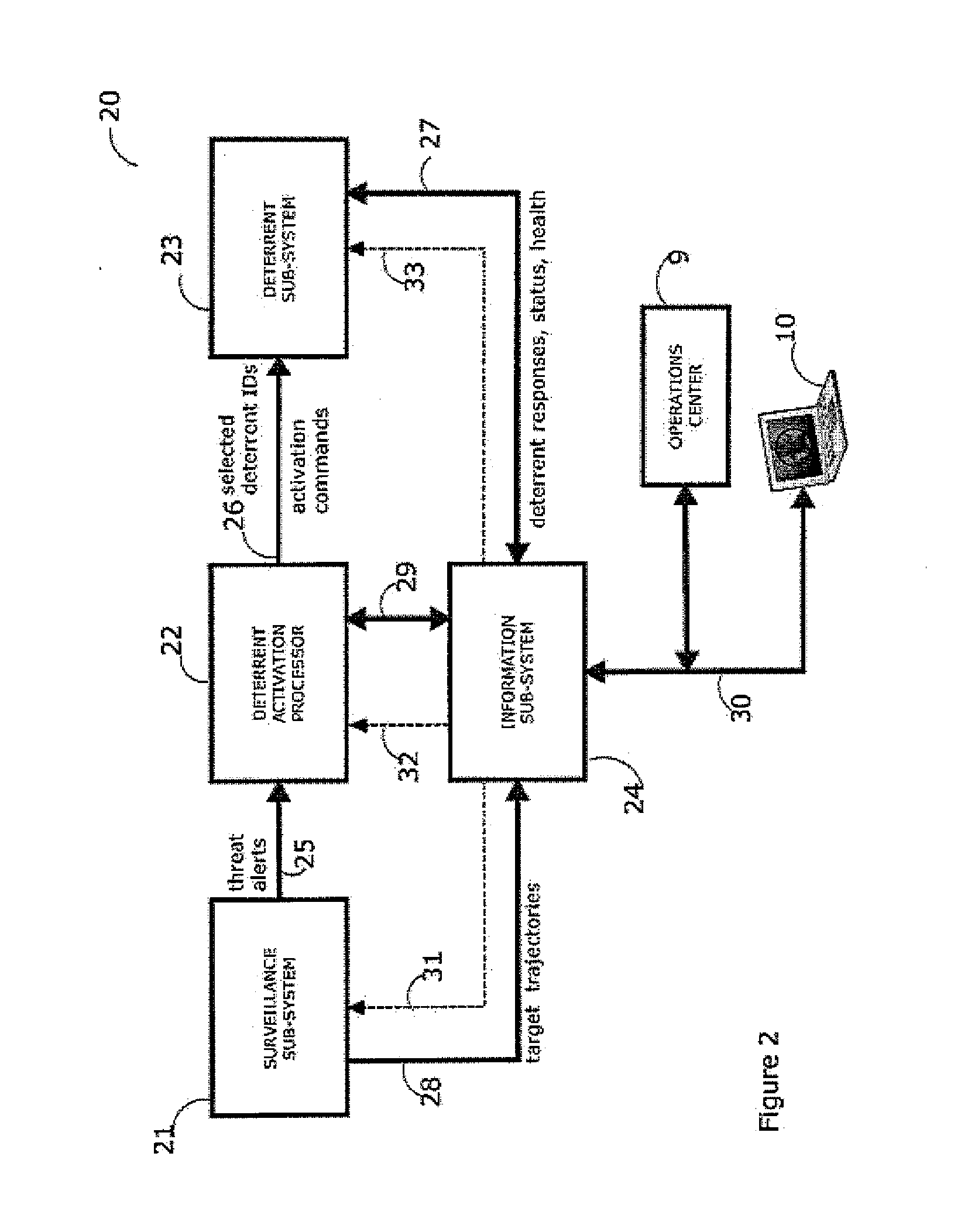
Device & method for smart, non-habituating, automatic bird deterrent system
ActiveUS20130098309A1Improve intelligenceMore automated capabilityAnimal huntingAnimal repellantsWide areaAnalysis data
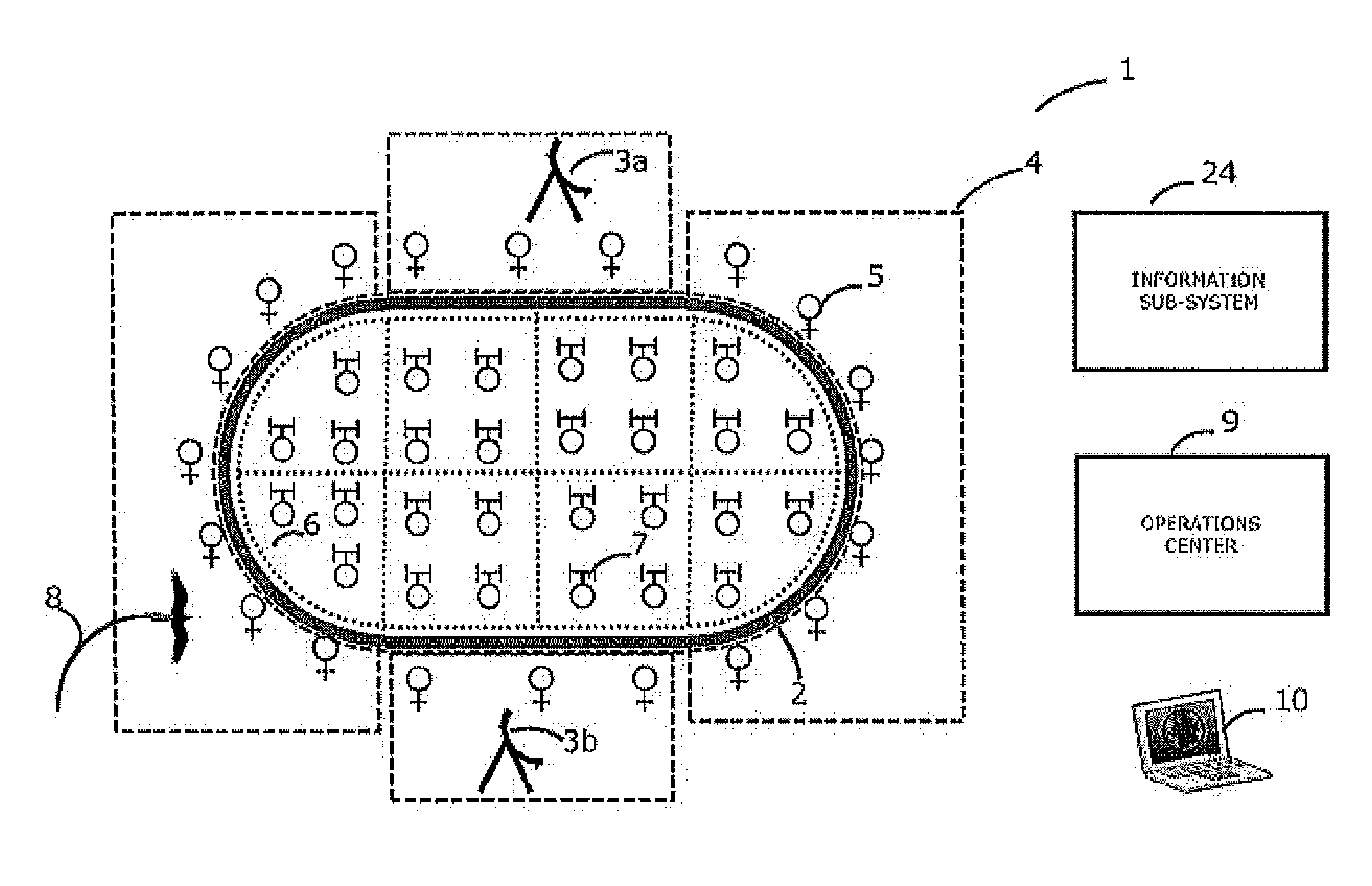
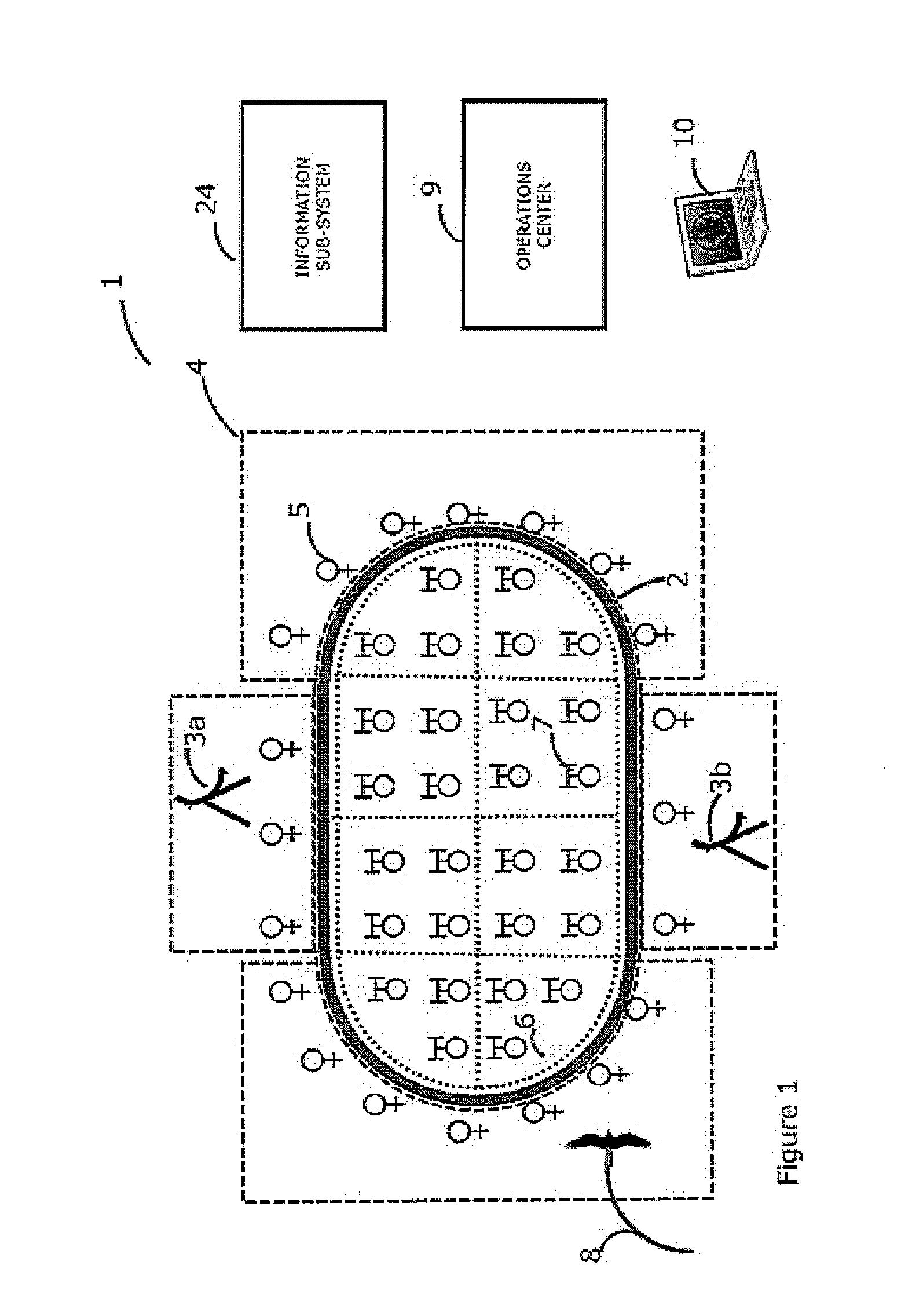
Operation of a bird deterrent system includes i. measurement of bird habituation to activation of deterrent devices; ii. reduction of habituation through increased selectivity in activating deterrents only for birds posing a threat to or threatened by a protected area, and in particular, those within threat altitudes; iii. provision of analytical data in support of safety management systems, risk management, etc.; iv. integrated, wide-area radar coverage with multiple virtual intrusion zones providing multiple lines of defense around and over very large protected areas.
Owner:ACCIPITER RADAR TECH
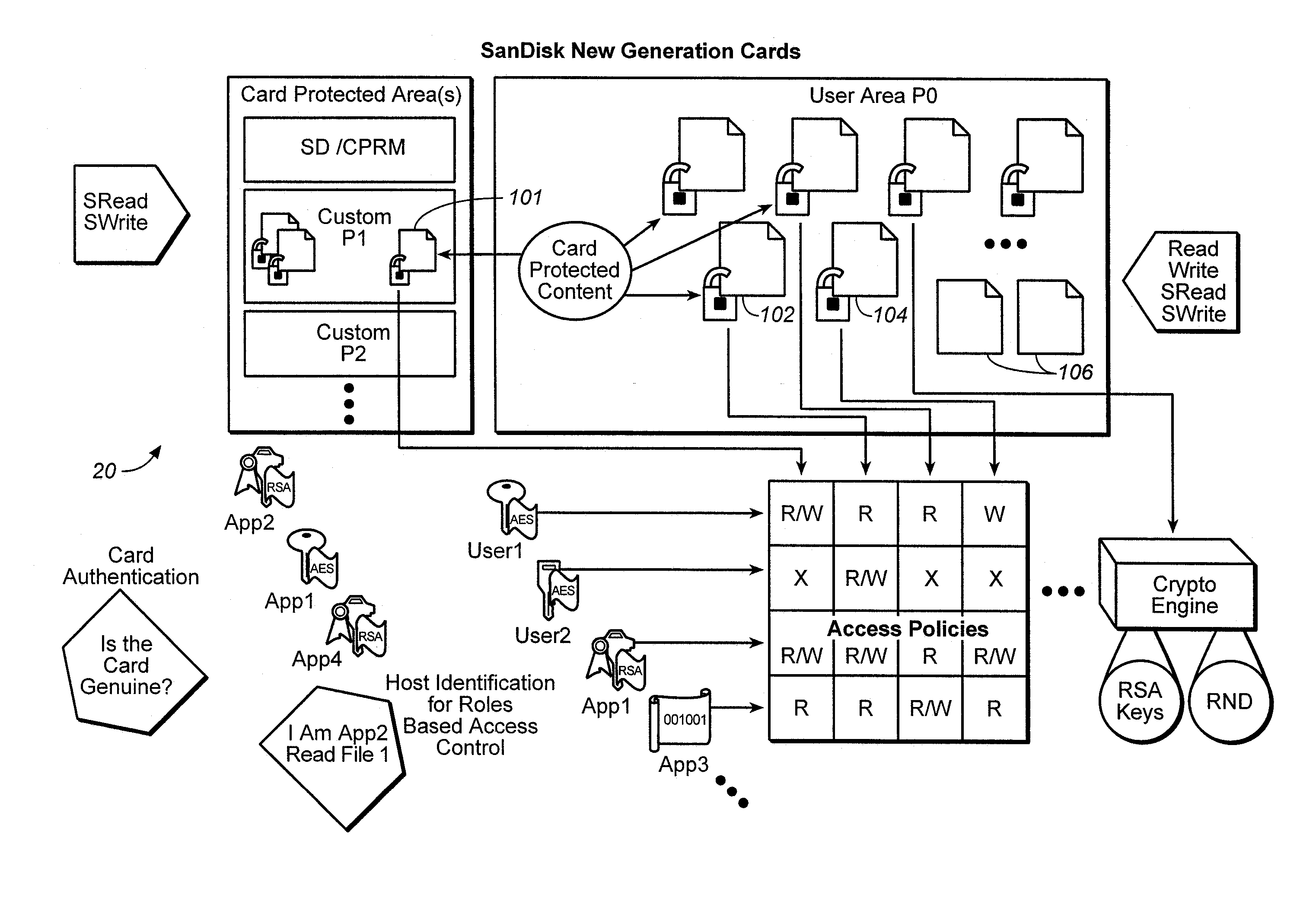
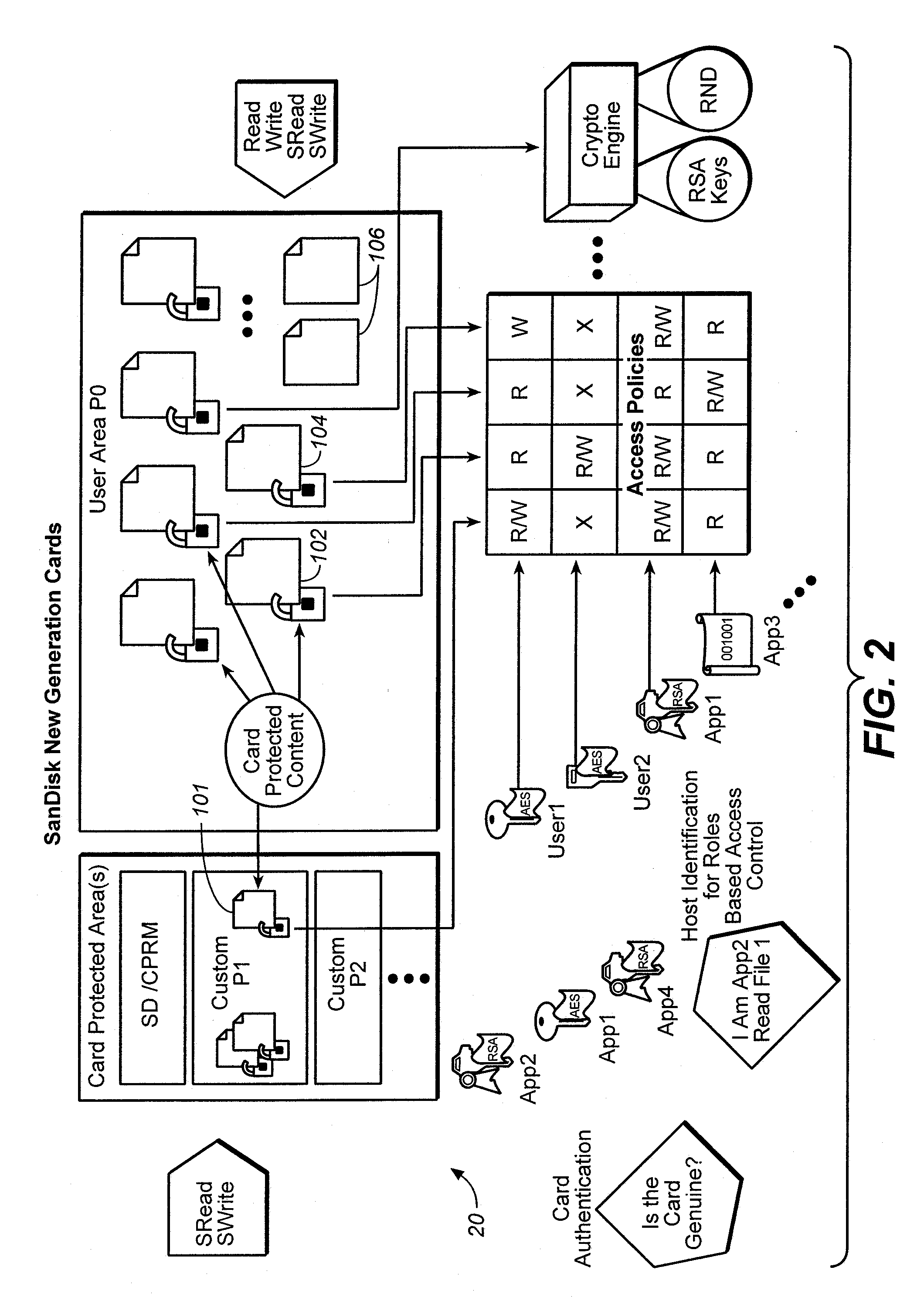
Method for versatile content control with partitioning
ActiveUS20060242065A1Improve versatilityData processing applicationsDigital data processing detailsPasswordMusic player
In some mobile storage devices, content protection is afforded by dividing the memory into separate areas where access to protected areas requires prior authentication. While such feature does provide some protection, it does not protect against a user who obtained a password by illicit means. Thus, another aspect of the invention is based on the recognition that a mechanism or structure may be provided to divide a memory into partitions and so that at least some data in the partitions can be encrypted with a key, so that in addition to authentication that is required for accessing some of the partitions, access to one or more keys may be required to decrypt the encrypted data in such partitions. In some applications, it may be more convenient to the user to be able to log in the memory system using one application, and then be able to use different applications to access protected content without having to log in again. In such event, all of the content that the user wishes to access in this manner may be associated with a first account, so that all such content can be accessed via different applications (e.g. music player, email, cellular communication etc.) without having to log in multiple times. Then a different set of authentication information may then be used for logging in to access protected content that is in an account different from the first account, even where the different accounts are for the same user or entity.
Owner:SANDISK TECH LLC
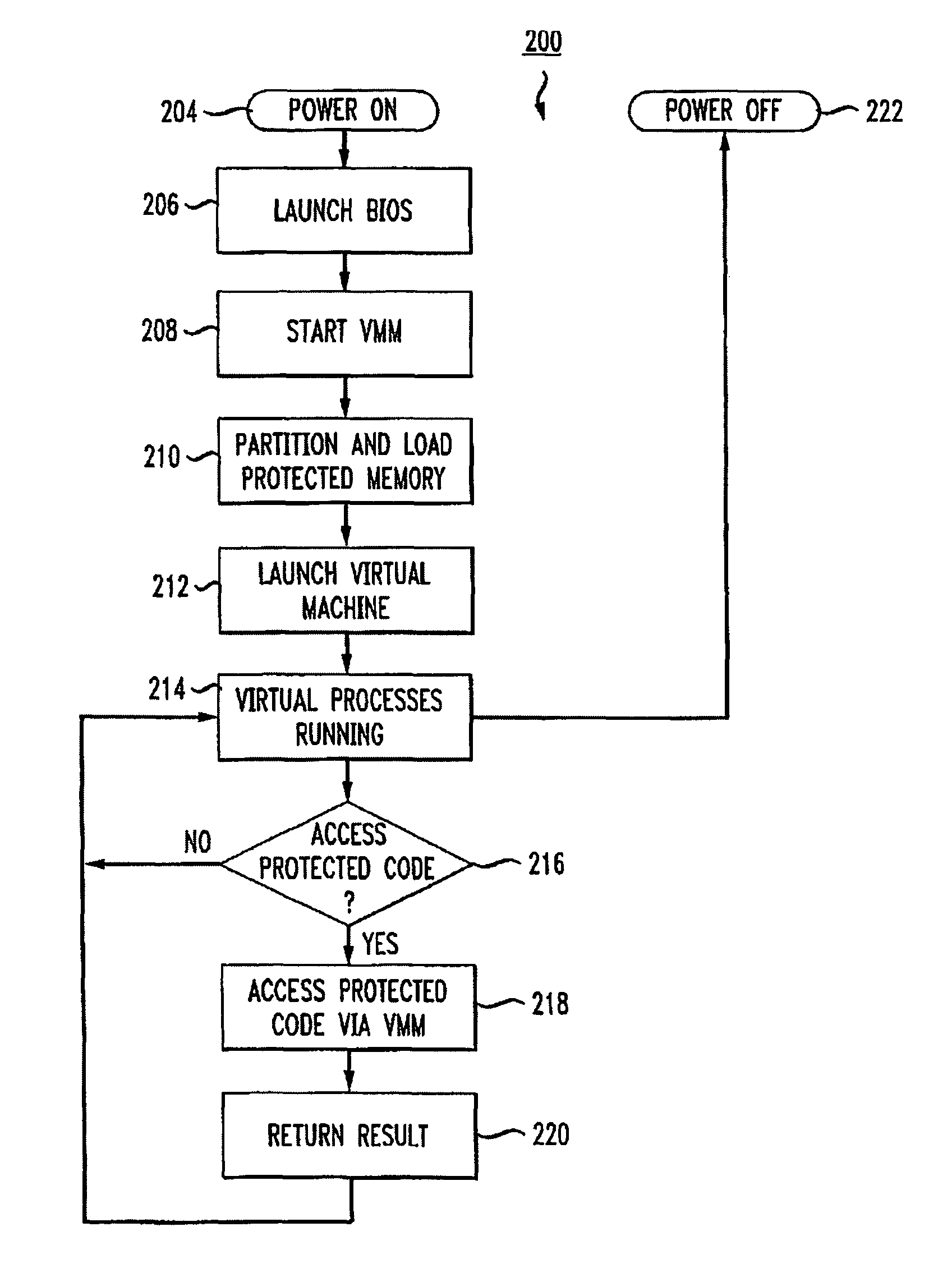
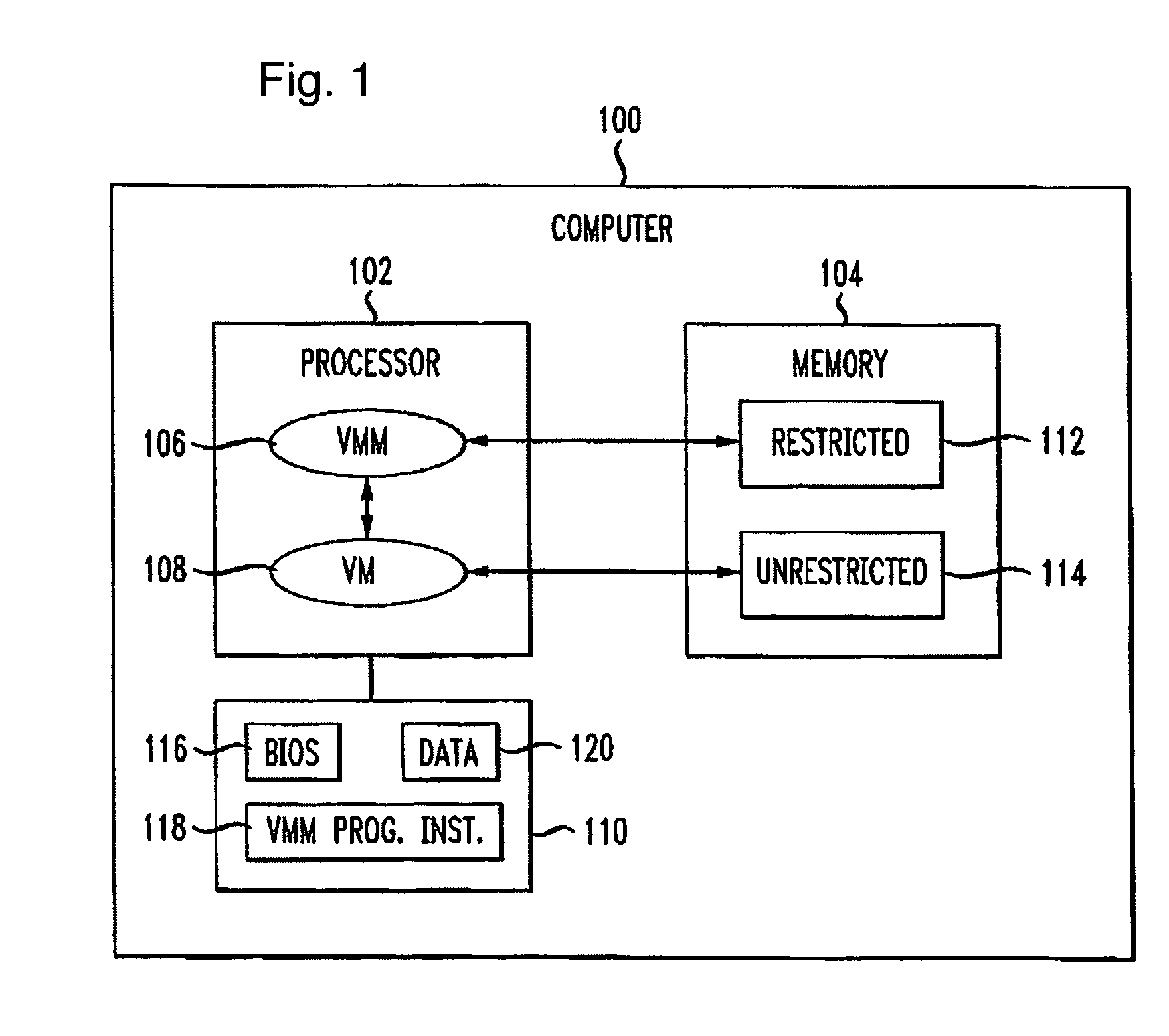
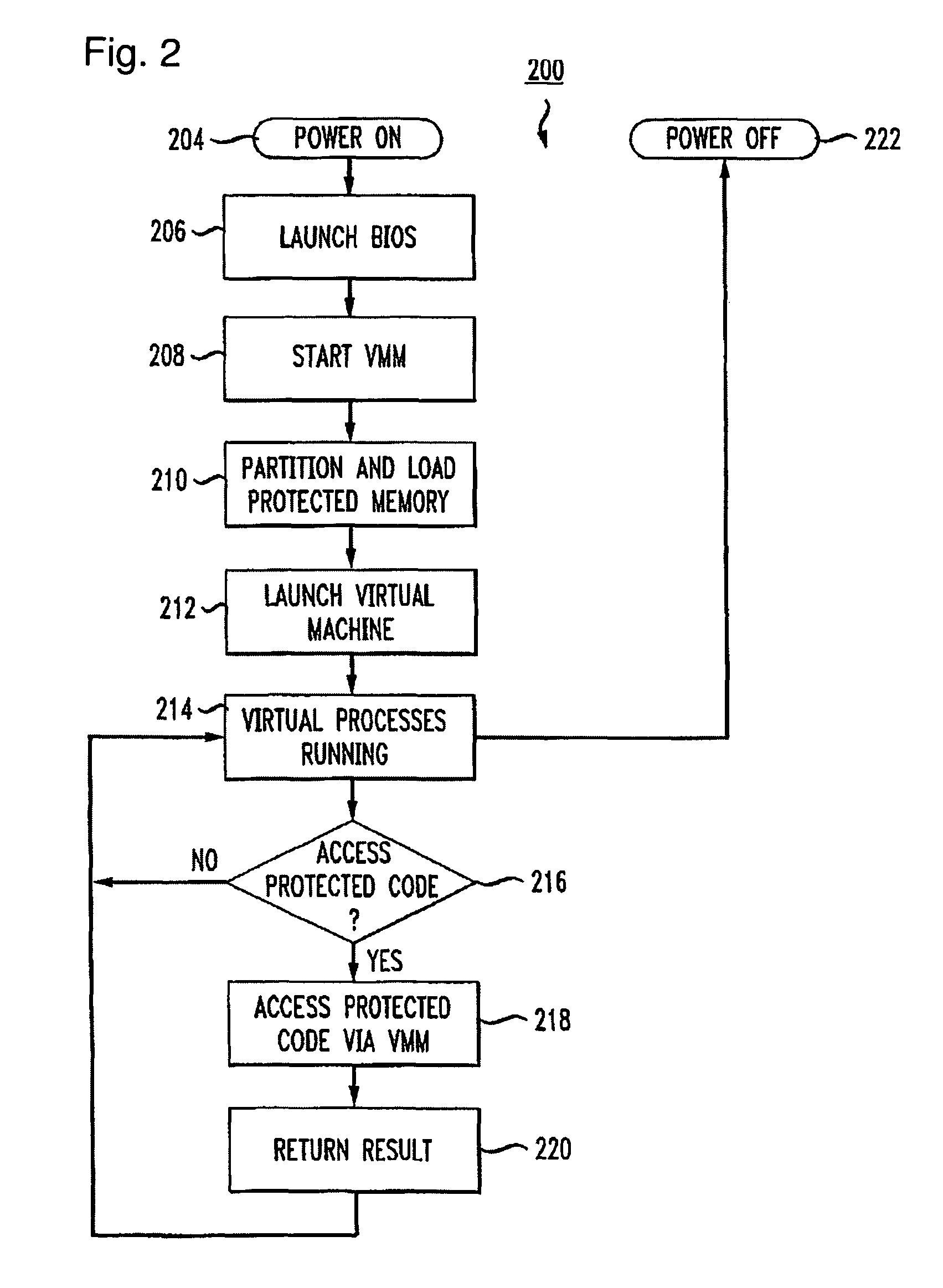
Virtualization-based security apparatuses, methods, and systems
InactiveUS8156298B1Avoid disadvantagesAvoid problemsMemory architecture accessing/allocationComputer security arrangementsOperational systemProtection mechanism
Apparatuses, devices, and methods for protecting content on a computer are disclosed that employ a novel hypervisor configured to segregate, or partition, hardware resources or portions thereof into protected and unprotected areas and devices. The partitioning, effectively hides protected hardware resources, such as the BIOS device, etc., from operating systems running on the computer. The hypervisor controls access resources into the protected area and limits the manner in which the operating systems on the computer can access the protected resources and content. The hypervisor can be configured to physically partition entire hardware resource or to employ virtualization technology to partition hardware resources, such as memory devices, into protected and unprotected areas that are virtually partitioned. The hypervisor of the present invention provides a new concept in employing anti-forensic techniques to bring about a protection mechanism that prevents unauthorized users including remote attackers who have obtained administrative access from accessing, reverse engineering, or otherwise exposing content protected. The content can generally be anything that can be maintained in a computer including data, algorithms, code, information and processes in general, etc., such as personal, sensitive, confidential and proprietary information and algorithms, and cryptographic keys.
Owner:NULLRING
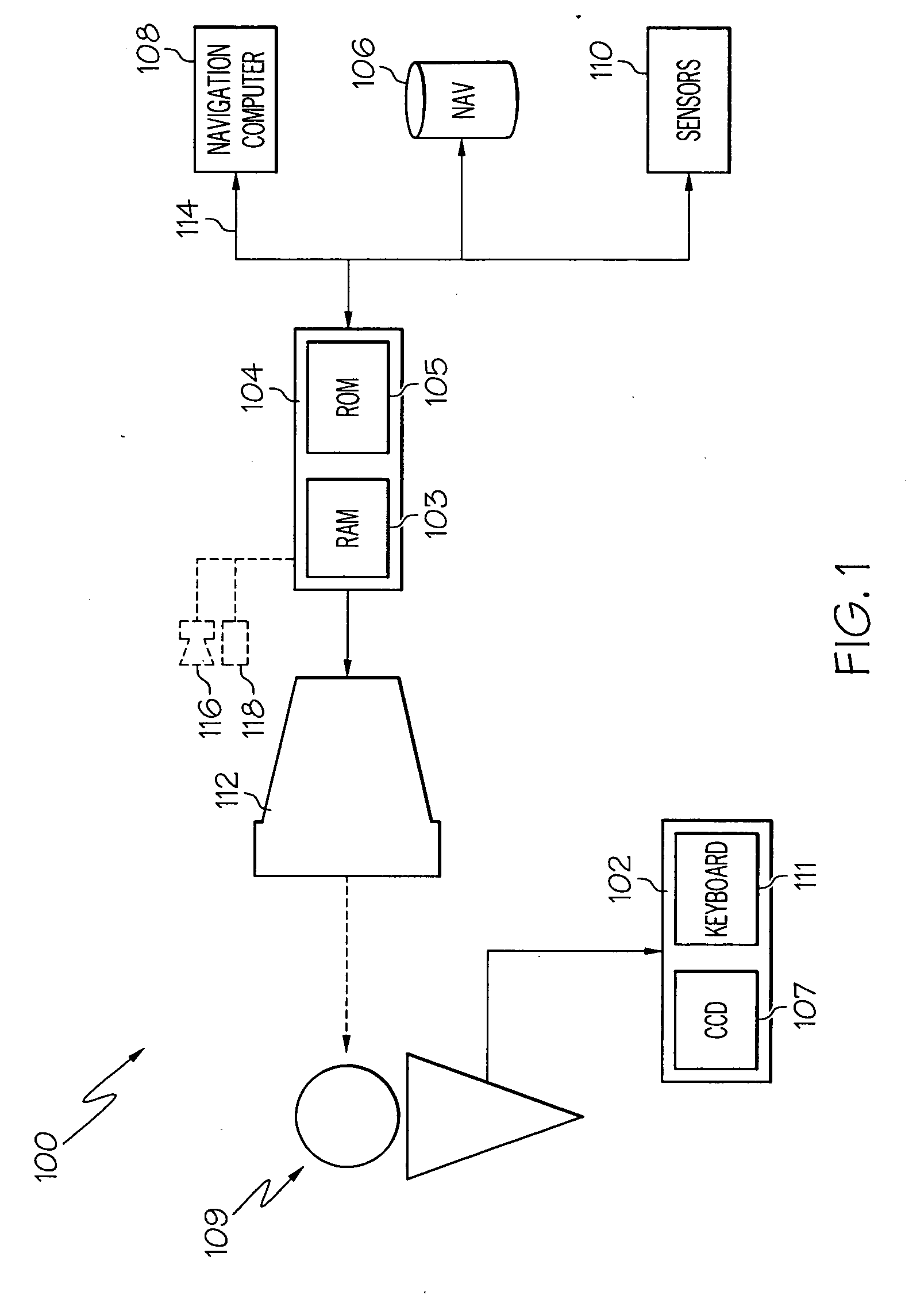
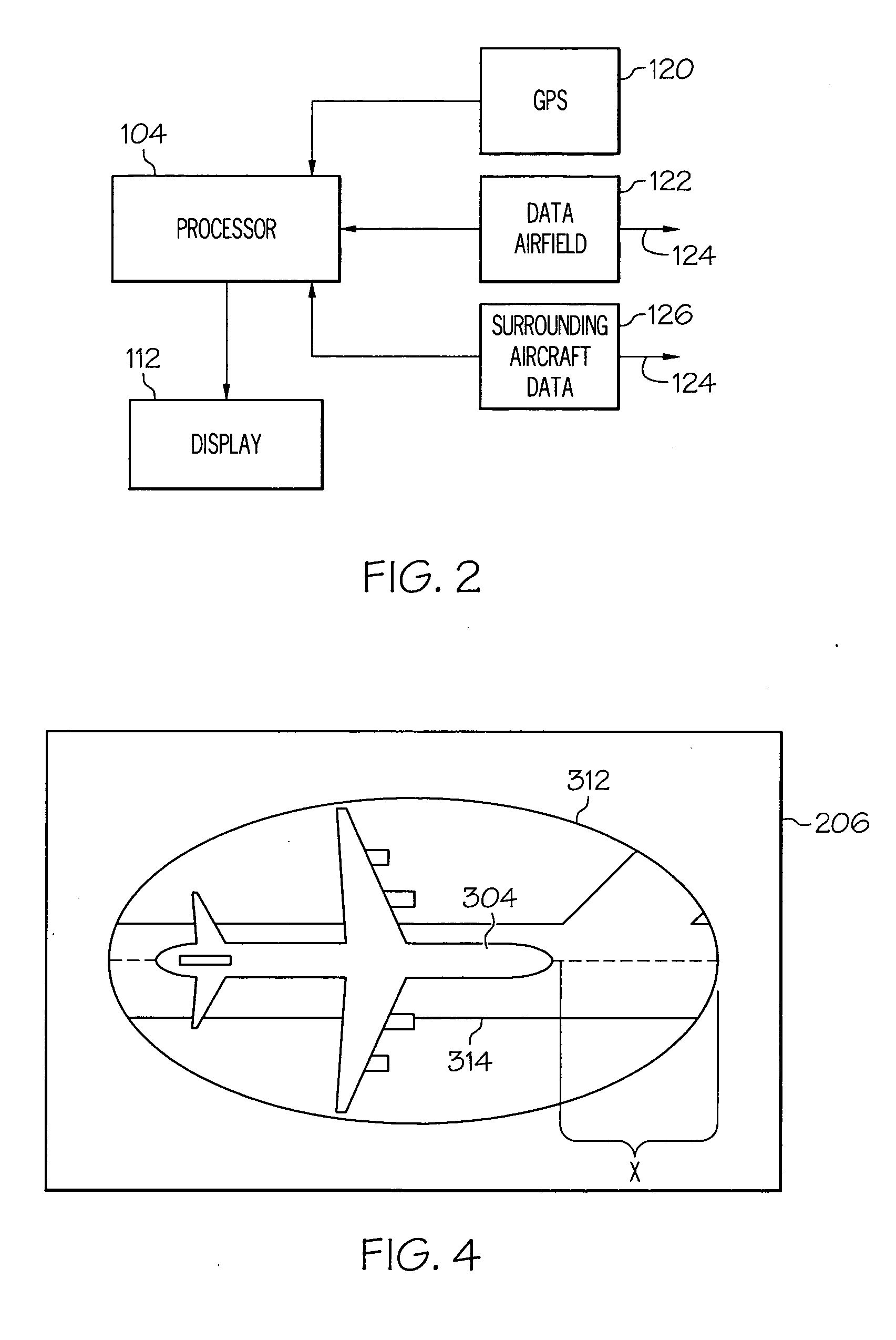
Ground incursion avoidance system and display
An airborne processor is linked to a ground-based, vehicle based, or satellite-based supplier of approaching aircraft data and / or terrain data, including airfield structures. The processor also has access to the aircraft's state, e.g. position, speed, intended route, aircraft dimensional data, or the like. Algorithms within the processor calculate a zone of protection about the aircraft in light of aircraft type, turning radius, and other identifying data. The processor combines the present and estimated future positions of the aircraft with the approaching aircraft and / or airfield structure data, and creates an alert to the crew if a threat of a ground incursion is detected. The display provides a visual of the zone of protection about the aircraft, and approaching aircraft and / or airfield structure to draw the attention of the crew to the threat.
Owner:HONEYWELL INT INC
Method of reducing false alarms during auto-arm
A method for reducing false alarms for a security system when the security system is programmed to automatically arm the security system. The method reduces false alarms by preventing the security system to auto-arm the system in away mode based upon certain detected events within the premises. The method comprise the steps of determining if a current time equals or is within a predetermined detection period, judging whether at least one of a plurality of motion sensors have detected an event within a protected area during the predetermined detection period, determining if a premises exit signal has been generated within a predetermined period from said detected movement, generating an automatic arm adjustment signal based upon said detected event and the premises edit signal; and executing a modification to the programmed automatic arm based upon the automatic arm adjustment signal. The method will also notify the owner that the auto-arm mode failed.
Owner:ADEMCO INC
Versatile content control with partitioning
InactiveUS20060242066A1Easy to optimizeImprove versatilityData processing applicationsInternal/peripheral component protectionPasswordMusic player
In some mobile storage devices, content protection is afforded by dividing the memory into separate areas where access to protected areas requires prior authentication. While such feature does provide some protection, it does not protect against a user who obtained a password by illicit means. Thus, another aspect of the invention is based on the recognition that a mechanism or structure may be provided to divide a memory into partitions and so that at least some data in the partitions can be encrypted with a key, so that in addition to authentication that is required for accessing some of the partitions, access to one or more keys may be required to decrypt the encrypted data in such partitions. In some applications, it may be more convenient to the user to be able to log in the memory system using one application, and then be able to use different applications to access protected content without having to log in again. In such event, all of the content that the user wishes to access in this manner may be associated with a first account, so that all such content can be accessed via different applications (e.g. music player, email, cellular communication etc.) without having to log in multiple times. Then a different set of authentication information may then be used for logging in to access protected content that is in an account different from the first account, even where the different accounts are for the same user or entity.
Owner:SANDISK TECH LLC
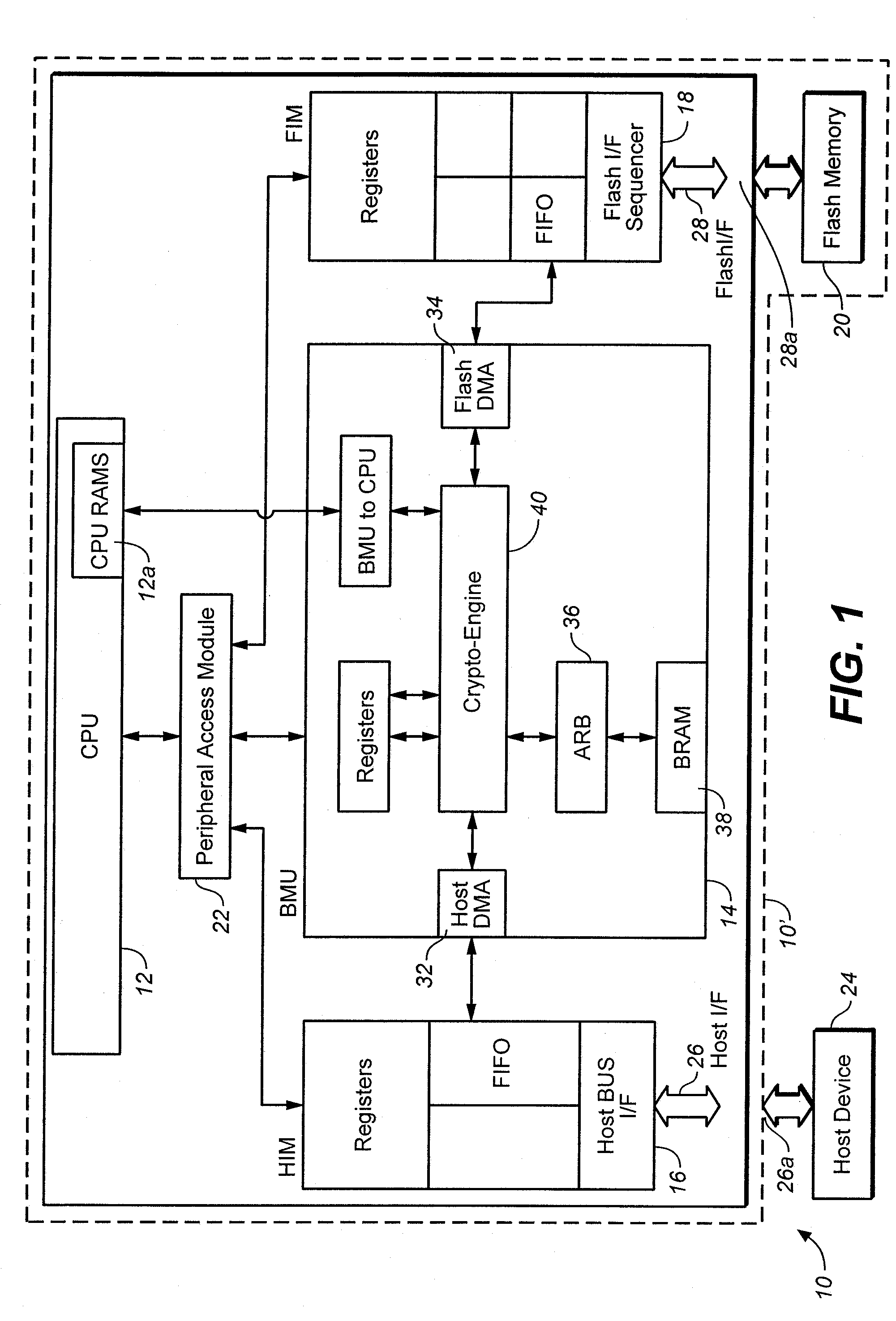
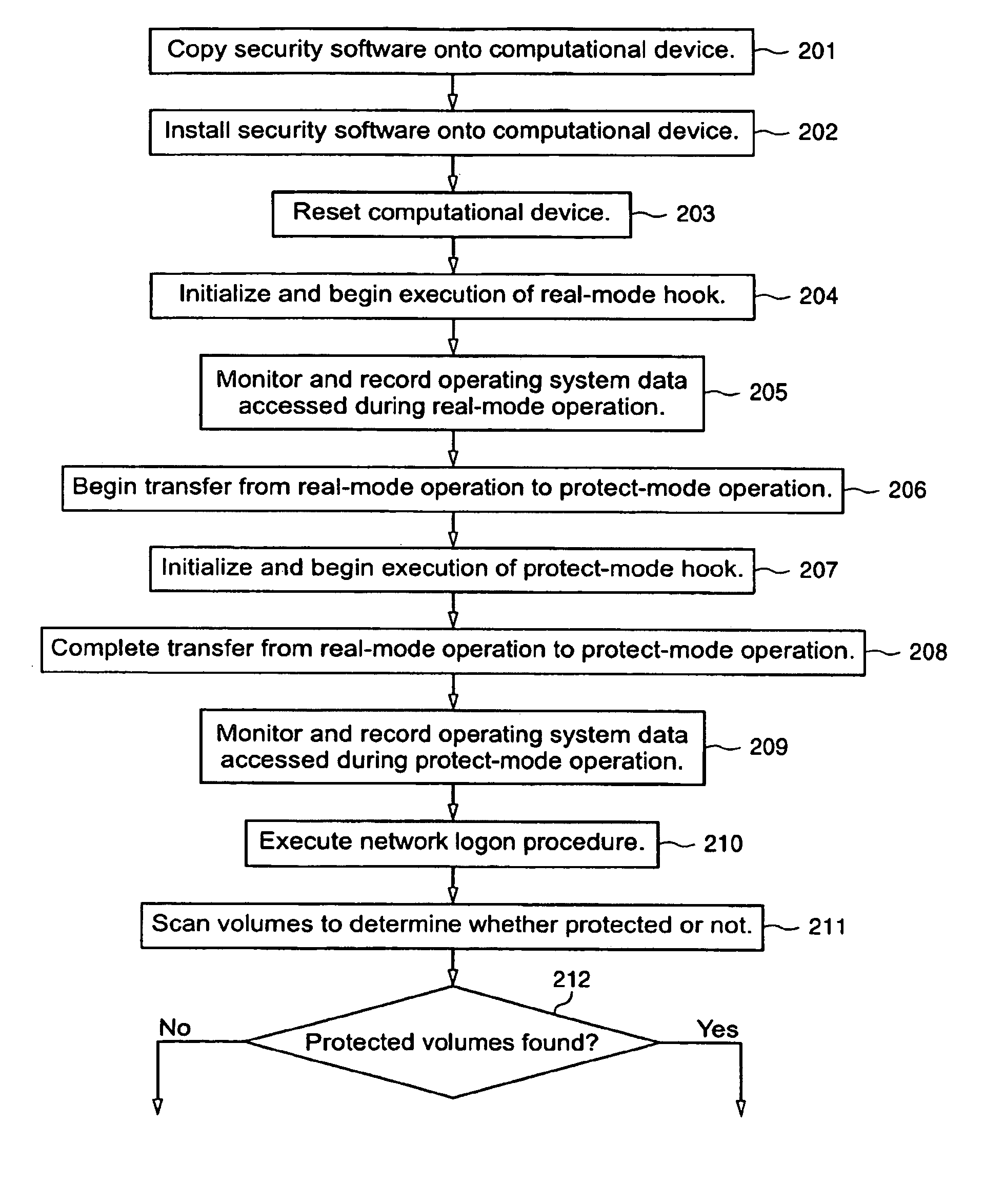
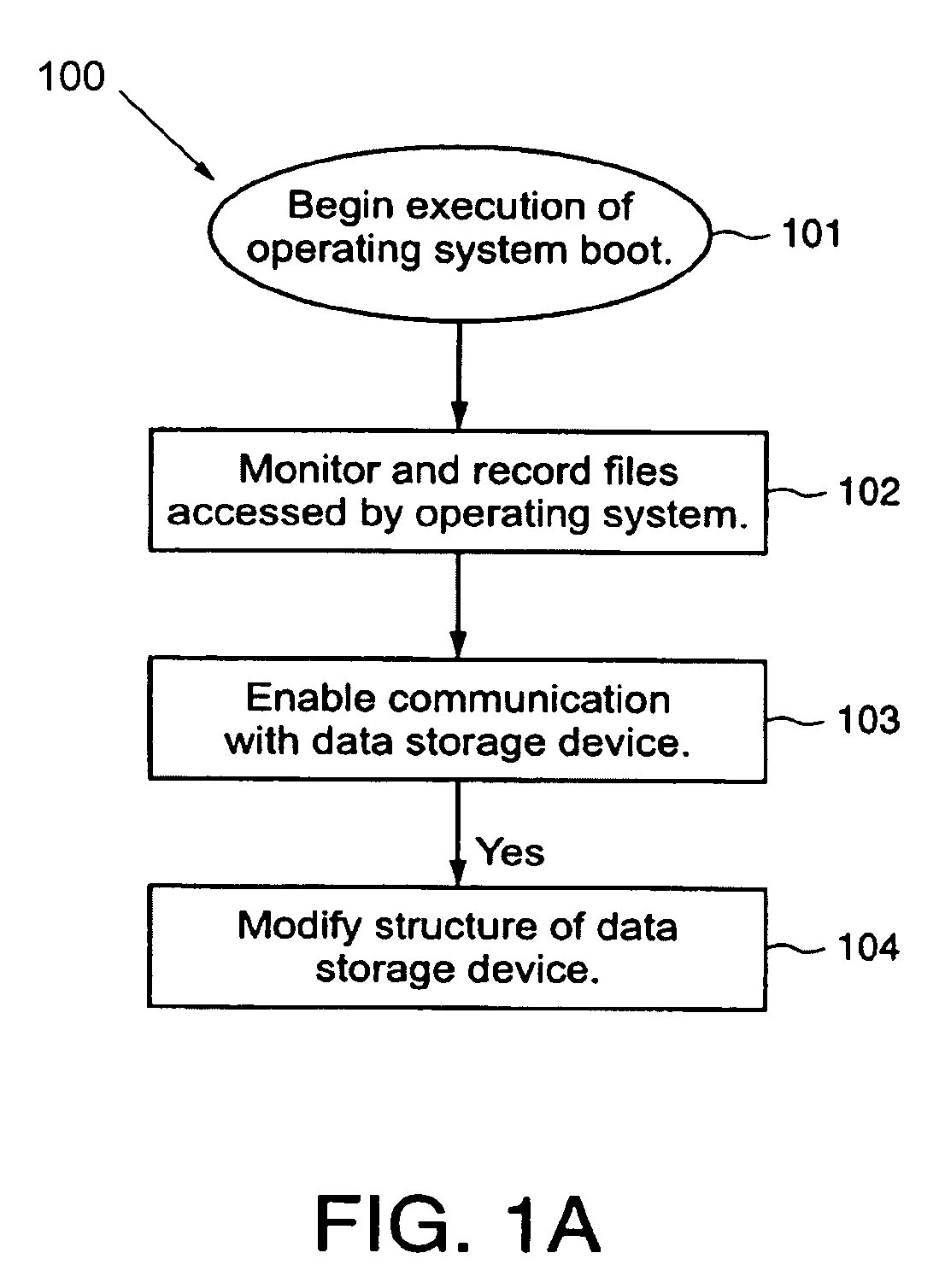
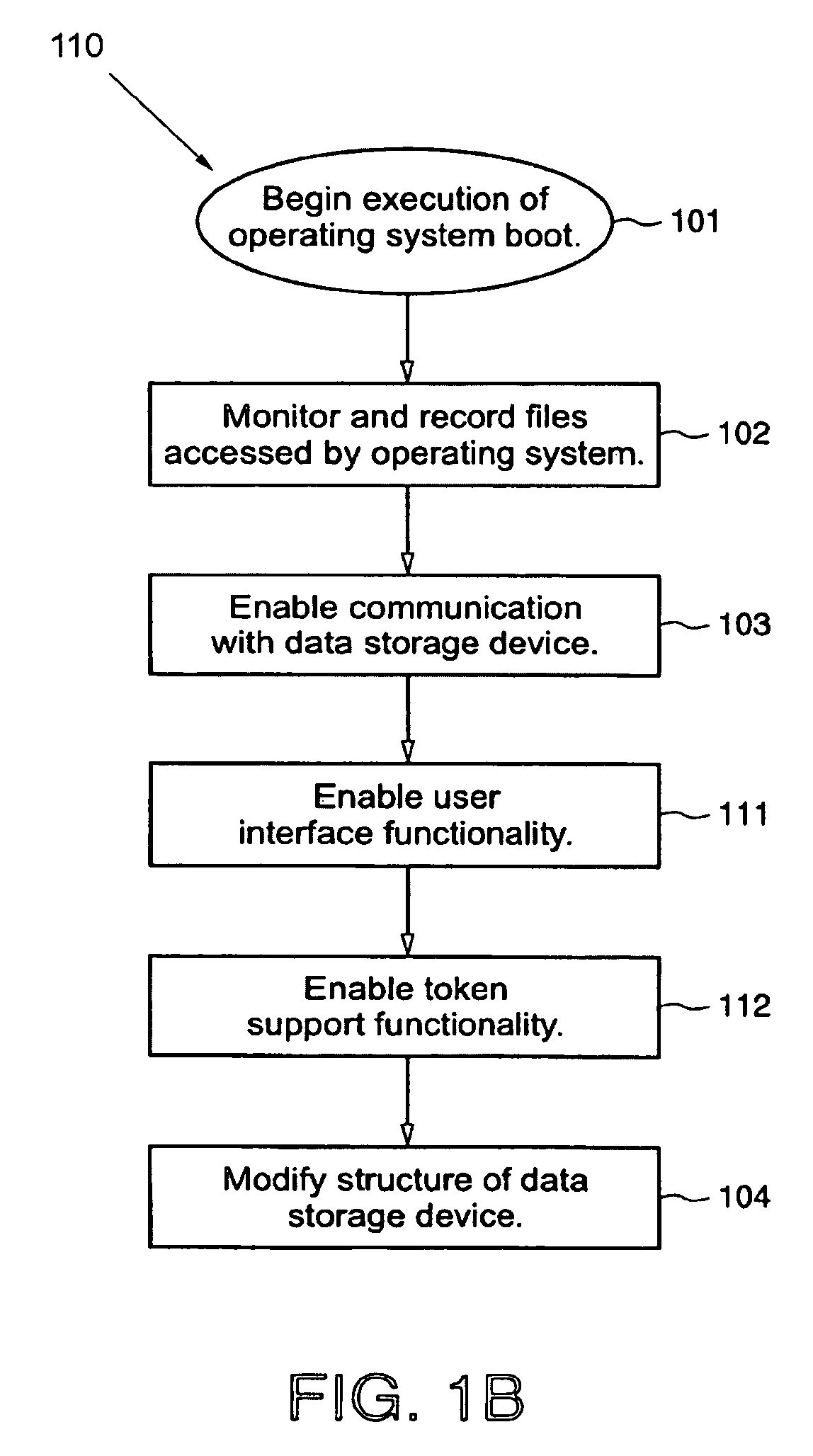
Protected volume on a data storage device with dual operating systems and configurable access and encryption controls
InactiveUS7757100B2Avoid decryptionAvoid accessUser identity/authority verificationDigital computer detailsOperational systemData storing
A method provides a protected region of a data storage device associated with a computational device, where data in the protected region is primarily protected by preventing access without proper access authorization. The method comprises the steps of providing, in an unprotected region of the data storage device, a first operating system and associated operating system data; monitoring operating system data accessed by the computational device until a predetermined functionality becomes available; storing, in the protected region, the monitored operating system data; providing, in the protected region, a second operating system; transferring control of the computational device from the first operating system to the second operating system; storing data in the protected region; and preventing access to the stored data in the protected region without access authorization. In a further embodiment of the method, the second operating system optionally provides a second level of security by preventing decryption of data stored in the protected region without decryption authorization.
Owner:SPEX TECH
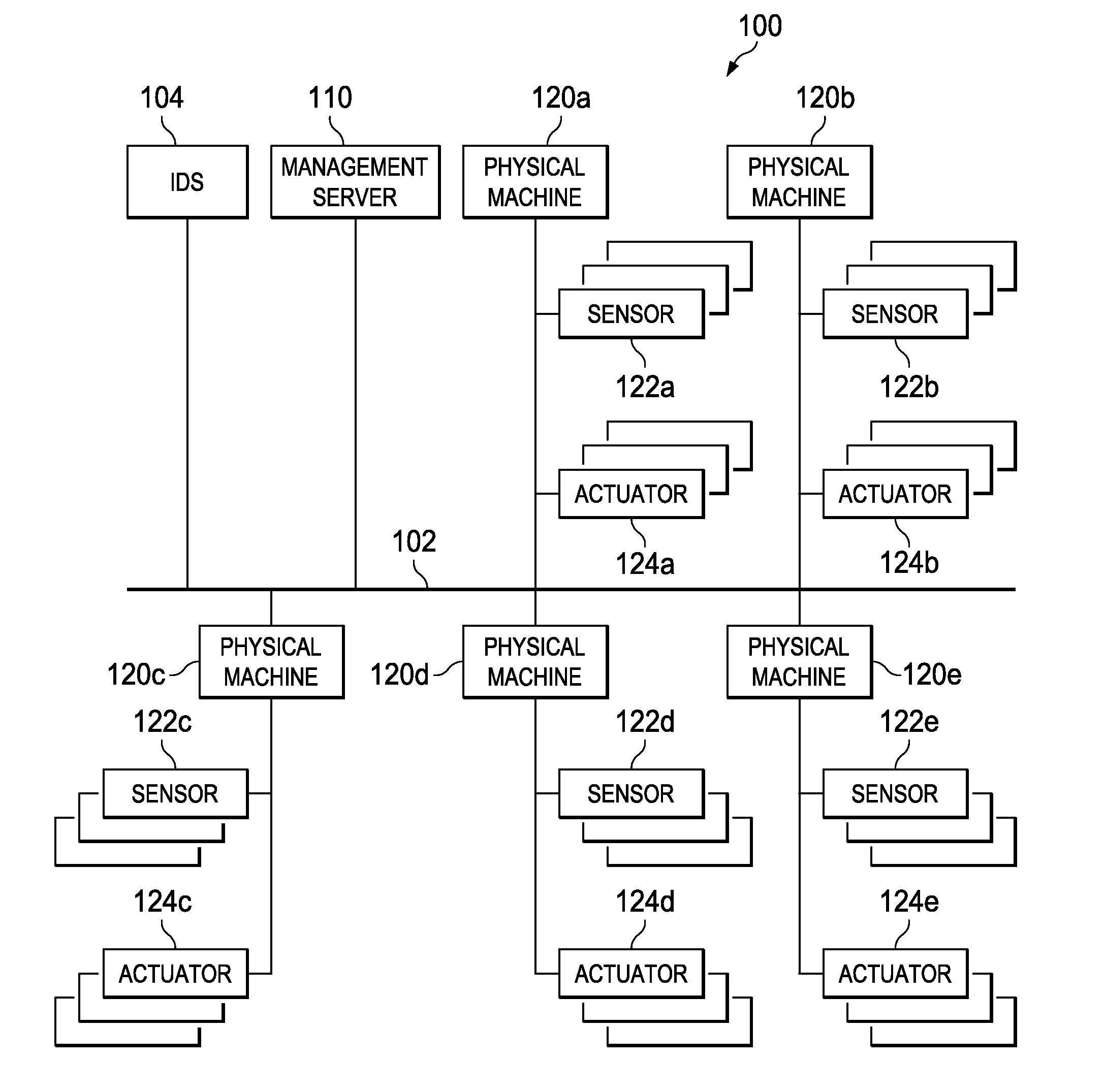
Abnormality Detection for Isolating a Control System
InactiveUS20120209411A1Restoring connectionReduce monitoring loadProgramme controlSafety arrangmentsControl systemEngineering
A mechanism is provided for effectively detecting an abnormality occurring in a control system and isolating the control system in which abnormality is acknowledged. The mechanism receives, from one or more control systems in the plurality of control systems, respective abnormality notifications for respective counter control systems to be monitored by the plurality of control systems. The mechanism adds up abnormality notifications transmitted from respective monitoring sections of the plurality of control systems so as to evaluate the reputation of a control system suspected to have an abnormality. The mechanism causes a protected area for operating the control system suspected to have an abnormality to restrict outbound traffic from at least the inside of the protected area, when an indication is identified that the control system is abnormal according to criteria from a result of the evaluation.
Owner:IBM CORP
Intruder detector system
An intruder detection system for detecting the presence of an intruder in a protected area. A light beam, preferably from a laser, is reflected from a target, which is a potential intruder. The time period required for the beam to return to a light detector, as well as the intensity of the reflected light, is recorded. The system includes a computer and software for analyzing the measurements of distance and intensity of reflected light. The algorithm for detecting the presence of an intruder is based on changes in the measured distance and / or intensity of reflected light from initial measurements made during a "learning" period. The system tacks targets using data collected in consecutive searches of the area to be protected. Preferably, an alarm is sounded and / or a video camera is slaved to the system.
Owner:LASER GUARD
Intelligent asset protection system
InactiveUS20090212920A1Accurately determine its locationAccurate locationMultiplex system selection arrangementsLocks for portable objectsTelecommunicationsPassword
An intelligent asset protection system is claimed and disclosed which features a plurality of devices are used to protect a retail establishment by radiating and detecting into a protection zone to identify transponders within a given area. These devices that radiate and detect are typically located in the ceiling or above the area that is desired to be monitored and create a cone shaped interrogation field which expands as it is broadcast downward into the monitored area. In communication with the RAD units, the system uses transponders capable of storing information which includes passwords and unique identifiers as well as information about the object to which the transponder is attached. The transponder is capable of responding to a RAD unit and broadcasting information to it which may include the information stored on the transponder. The transponder in some embodiments will have a battery located on board, but the transponder will remain in an inactive sleep mode until a RAD unit contacts it with a radiated
Owner:YANG XIAO HUI
System and method for detecting an intruder using impulse radio technology
Owner:HUMATICS CORP
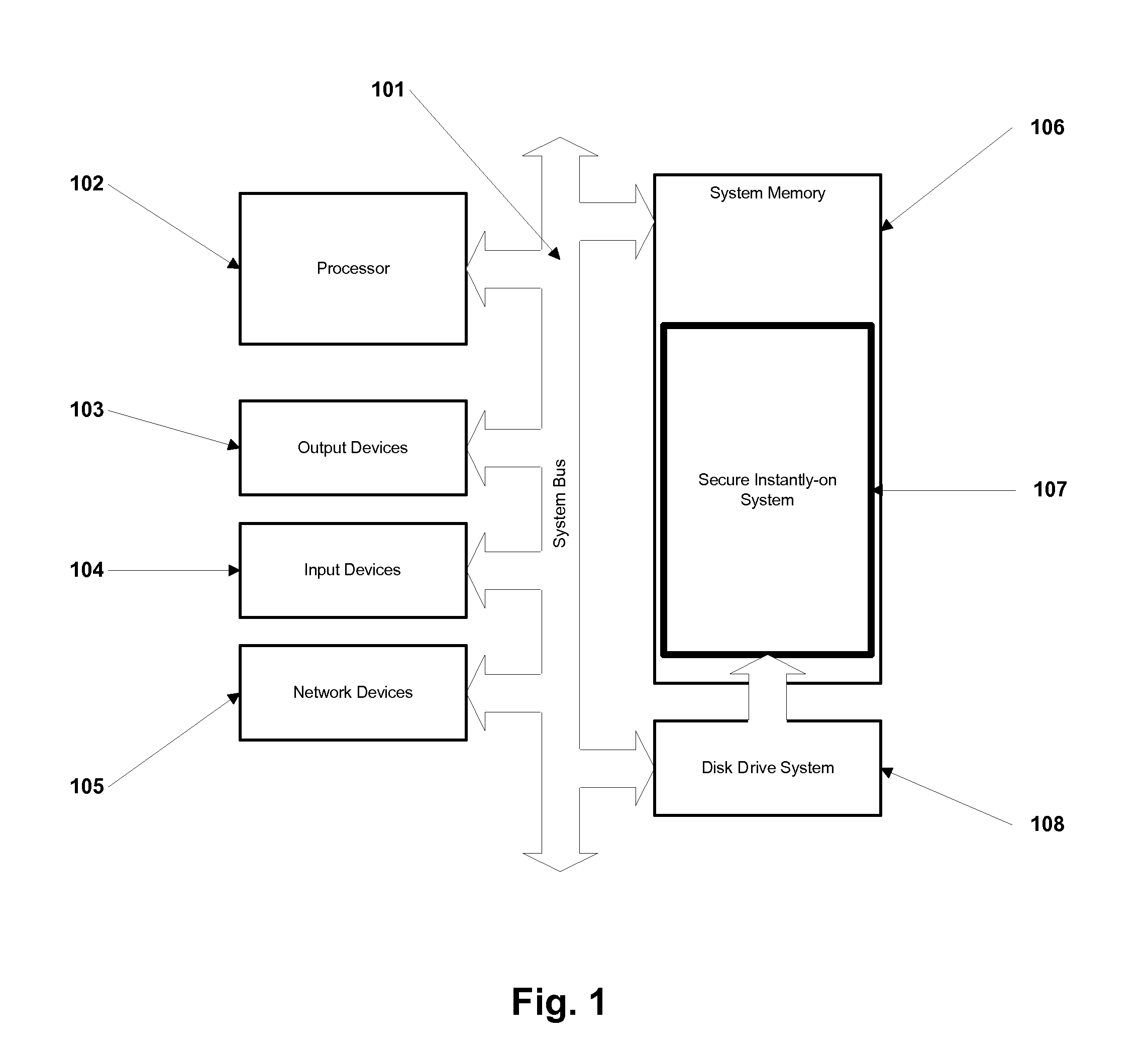
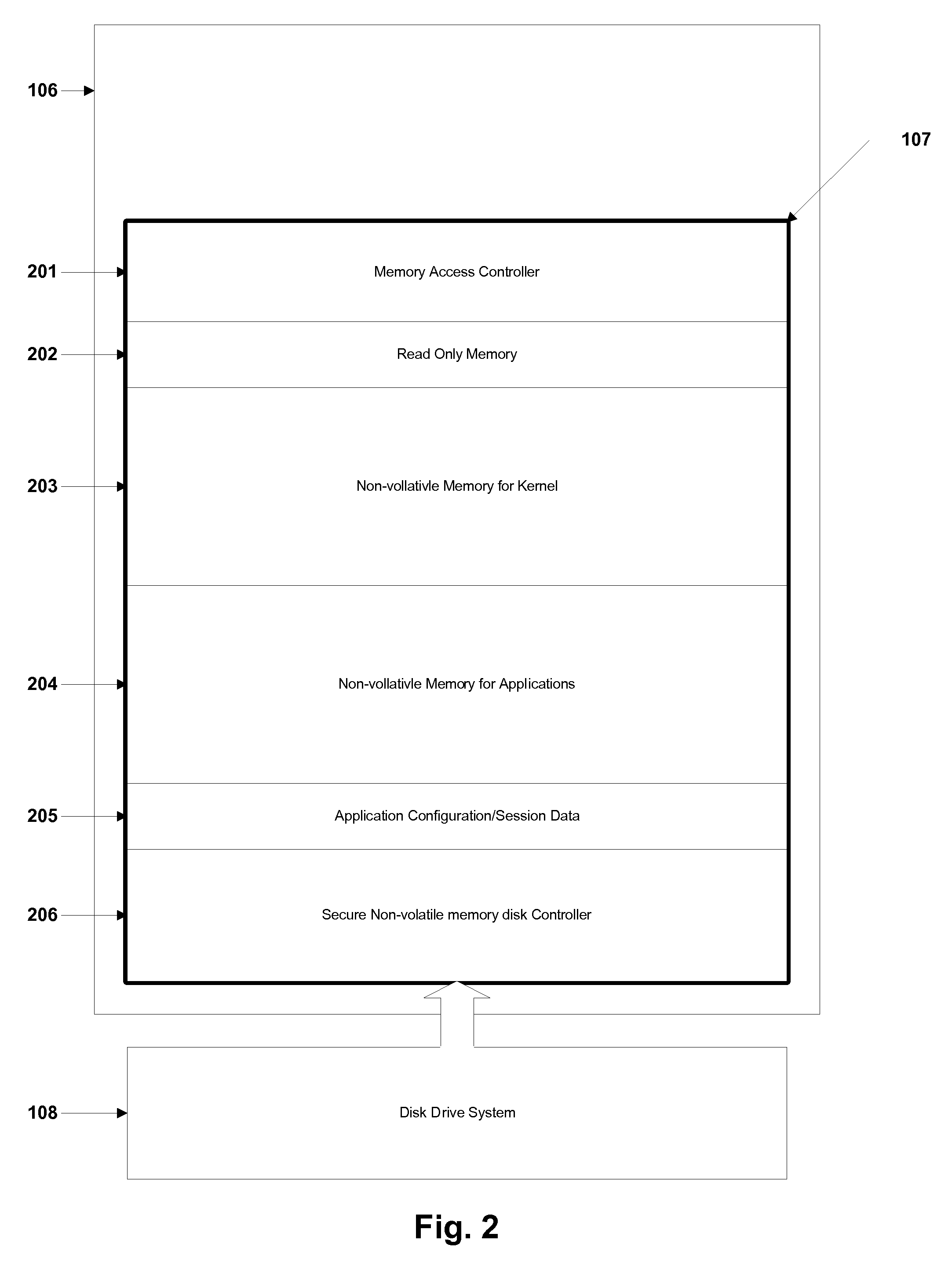
Method and Apparatus for Secure Instantly-On Computer System
ActiveUS20100058041A1Memory architecture accessing/allocationMultiple keys/algorithms usageOperational systemComputerized system
A method and apparatus for an instantly-on computer system is presented. A computer that incorporates fast non-volatile primary memory for storing the operating system, resulting in an instant-on or instant-booting of the computer. Large parts of the operating system code and application code are stored in non-volatile write-protectable areas that cannot be modified by malicious sources, resulting in a secure computer. It solves the problem from typical computers having to load the operating system and applications from a slow device such as the hard disk to the main memory. This loading is avoided by permanently housing the operating system in a non-volatile main memory. The system also solves the problem of corruption of operating system areas from malicious sources. The memory contains writeable and write-protected areas and a memory controller controls the access to the various regions of the memory.
Owner:CEREMORPHIC INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com