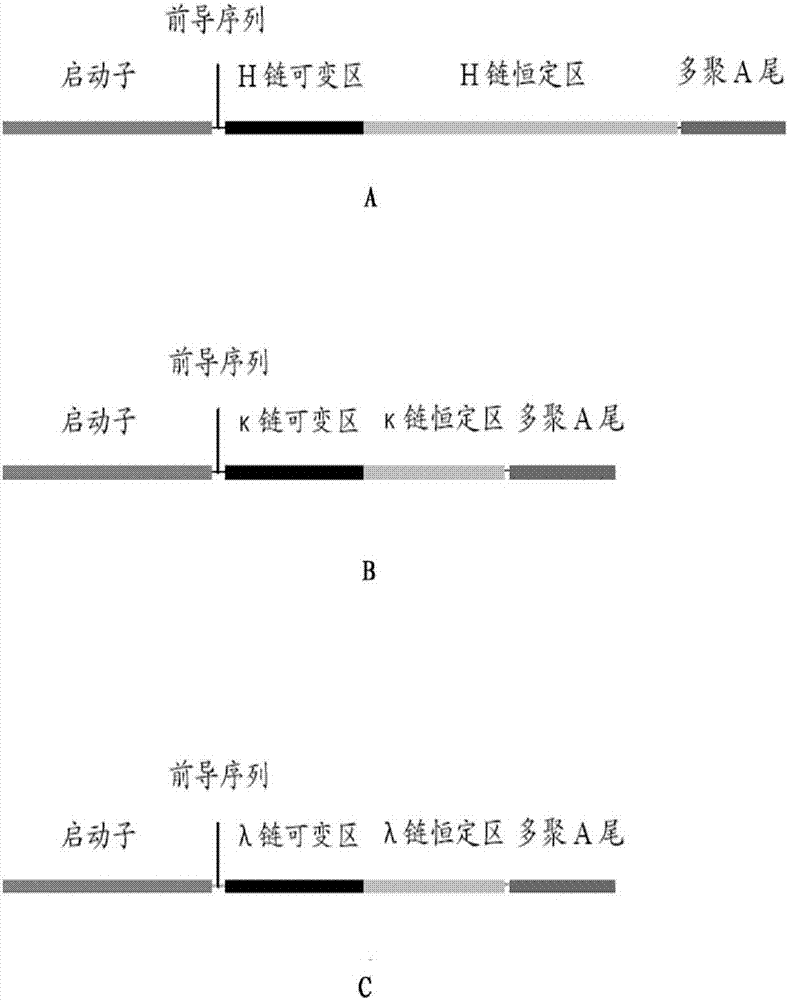
Patents
Literature
178 results about "Virus attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
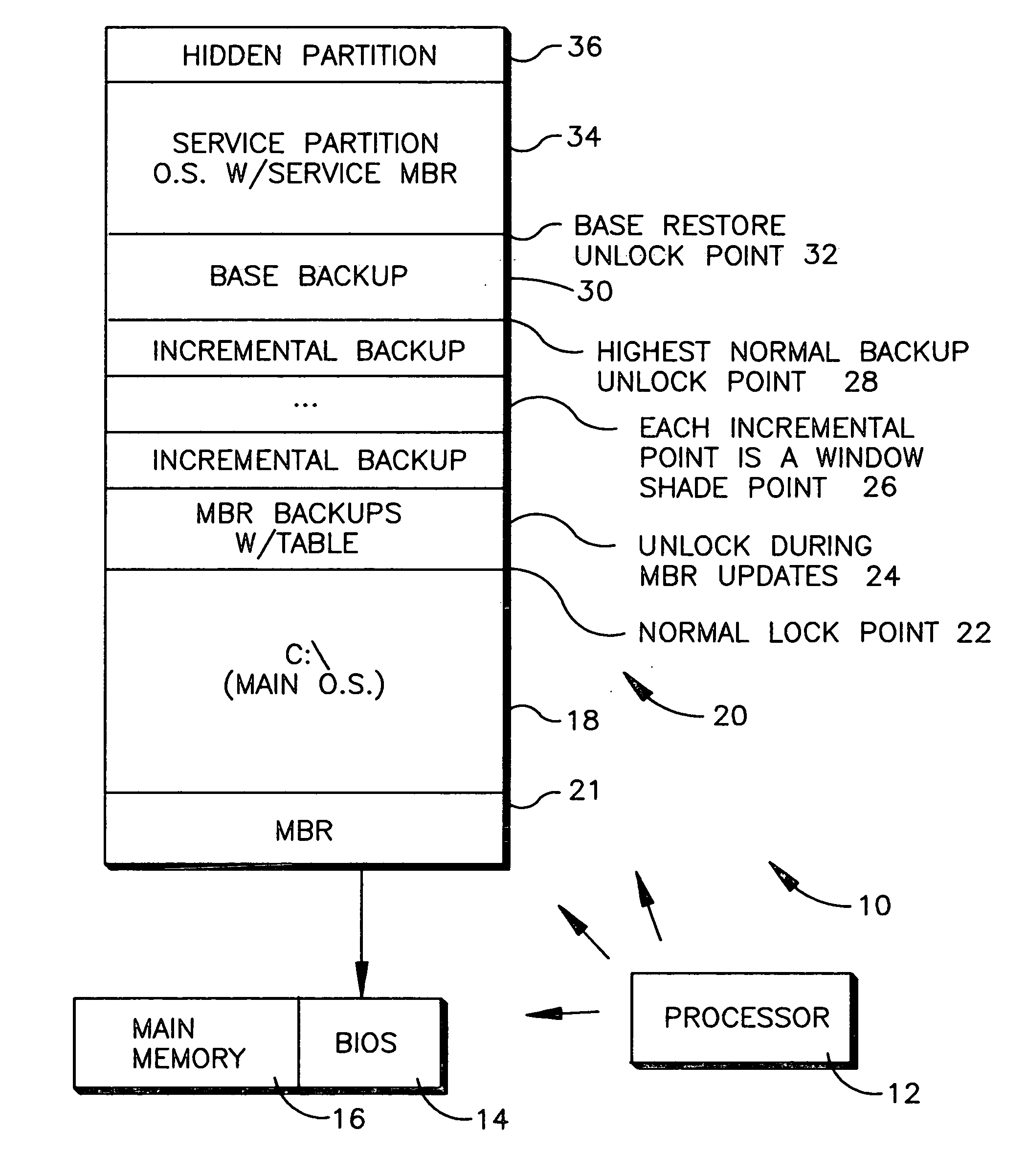
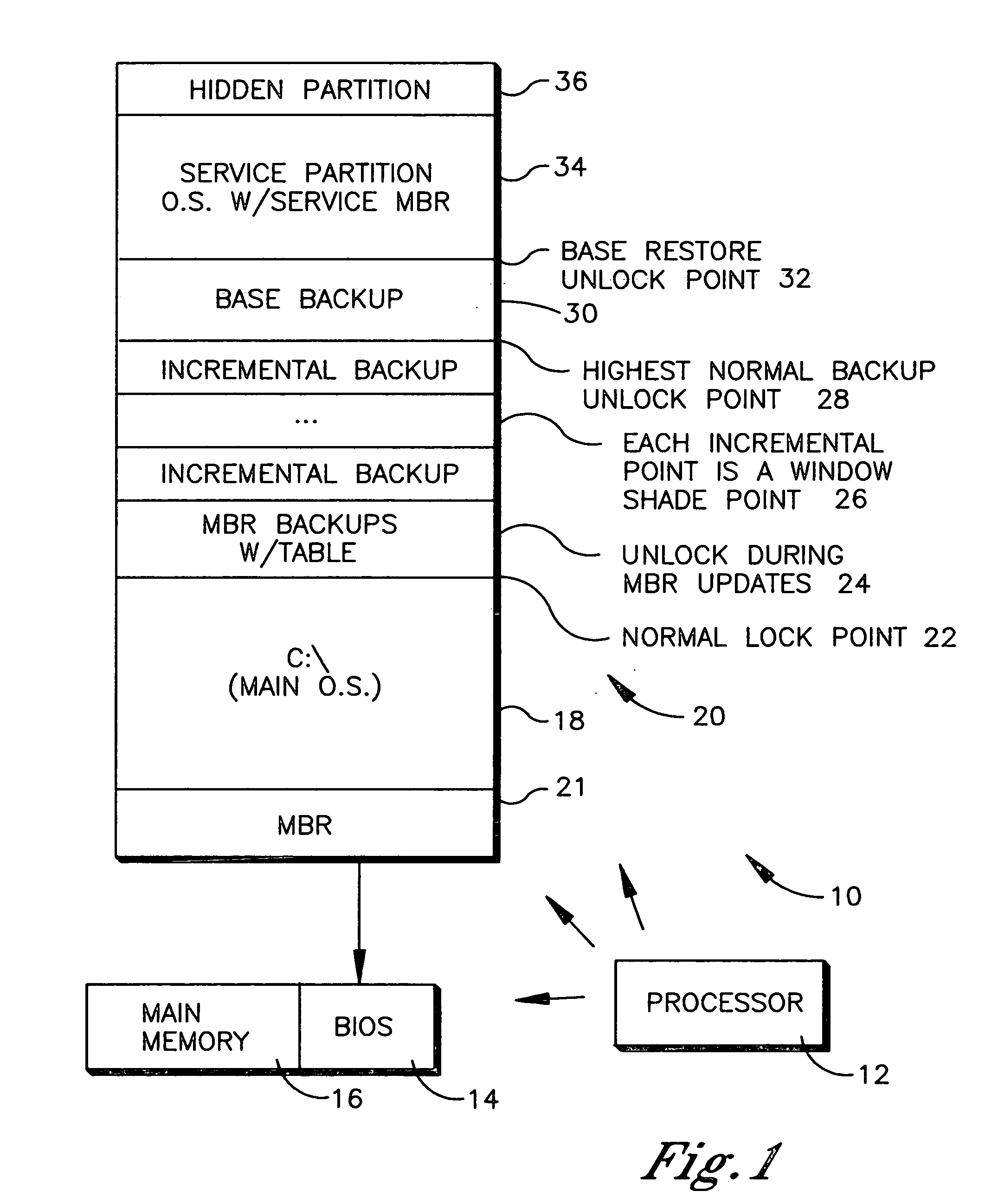
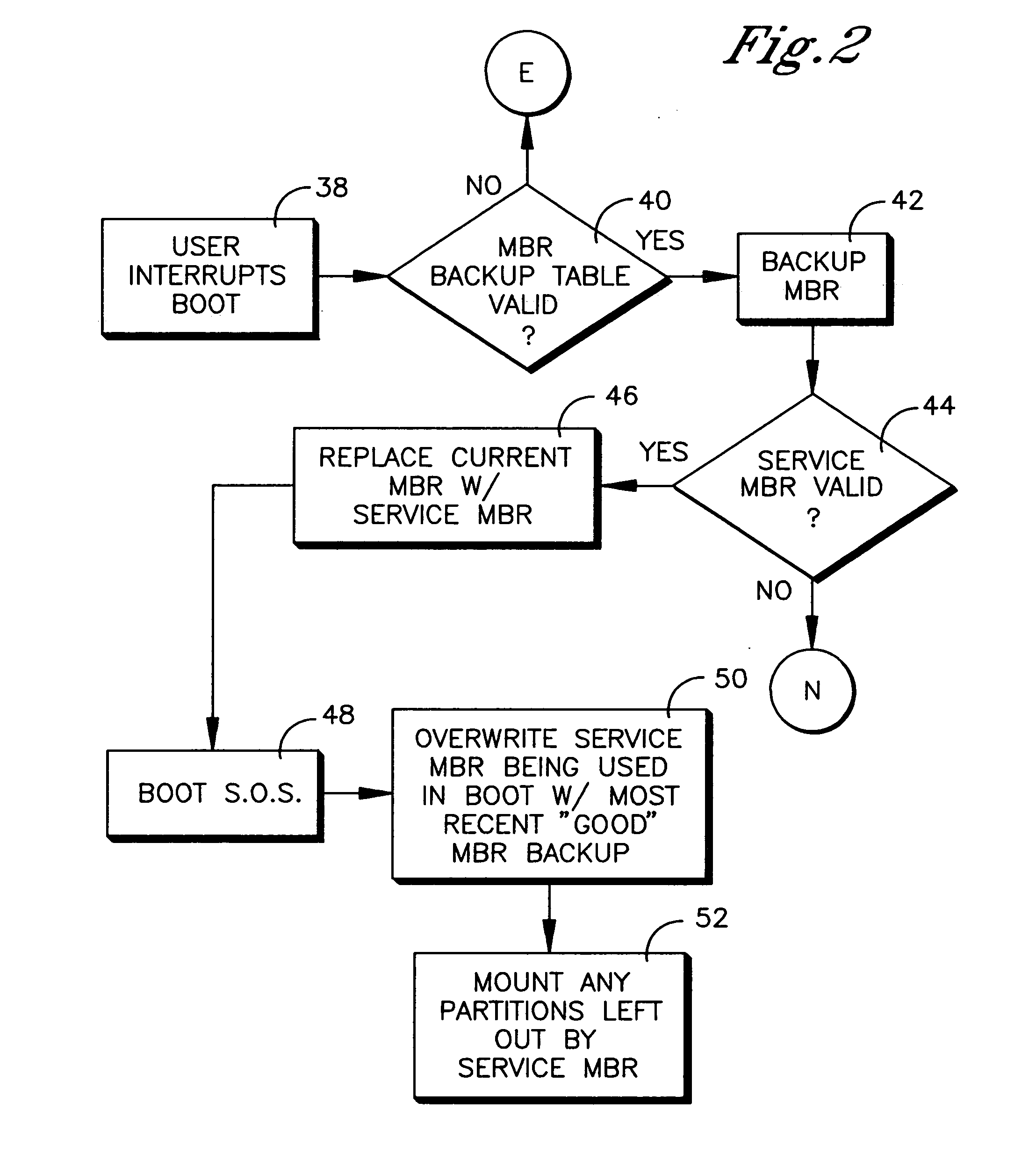
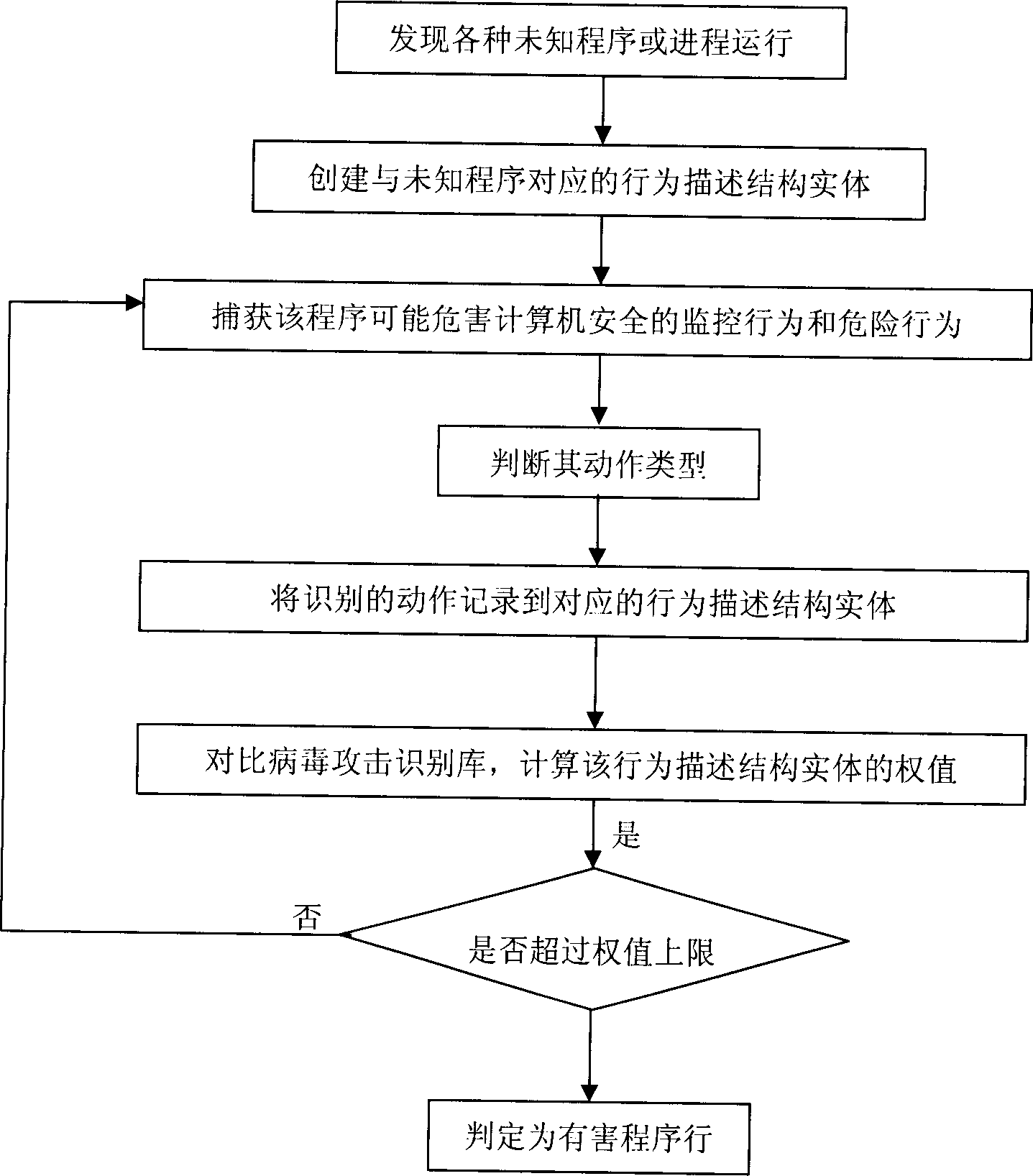
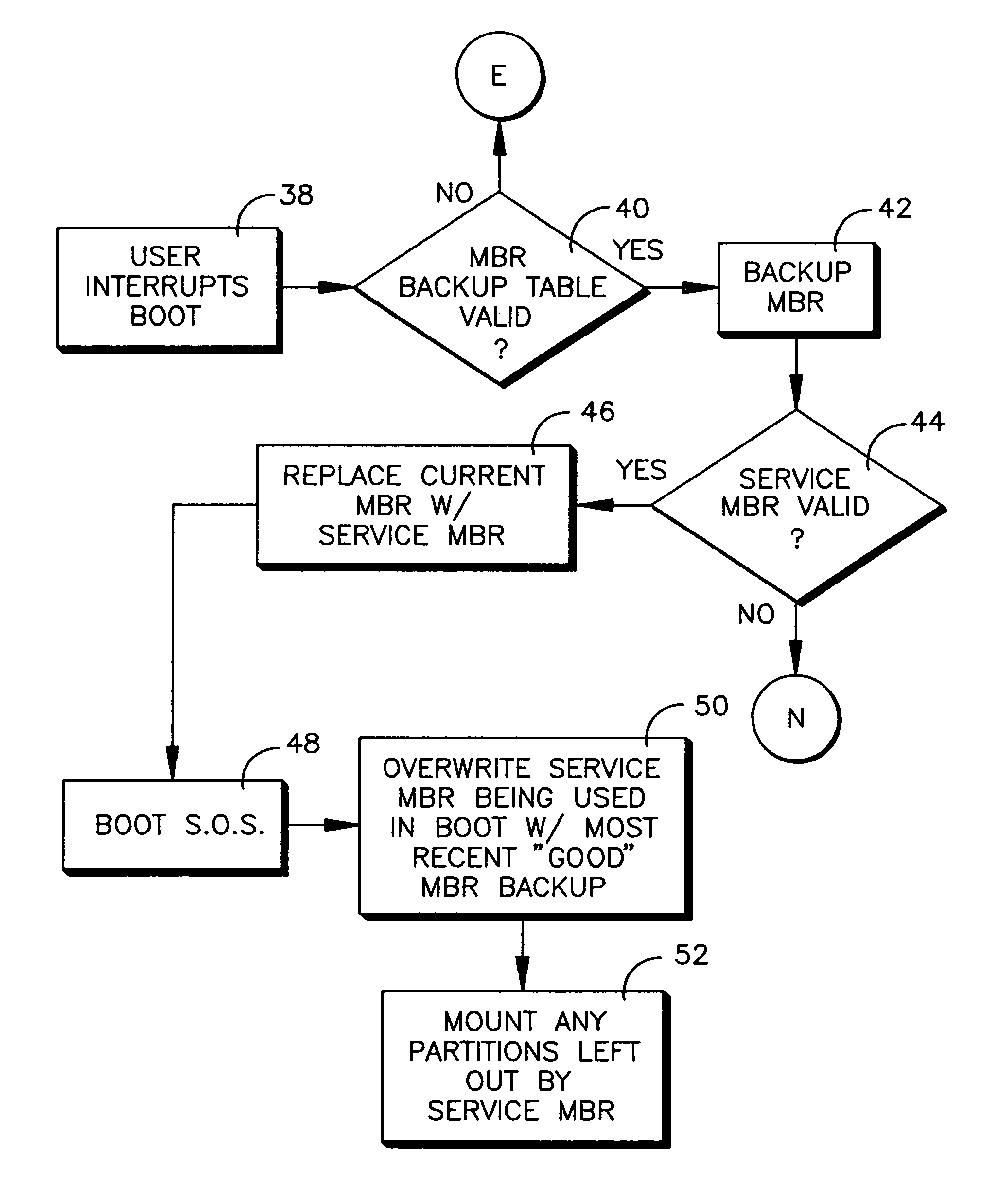
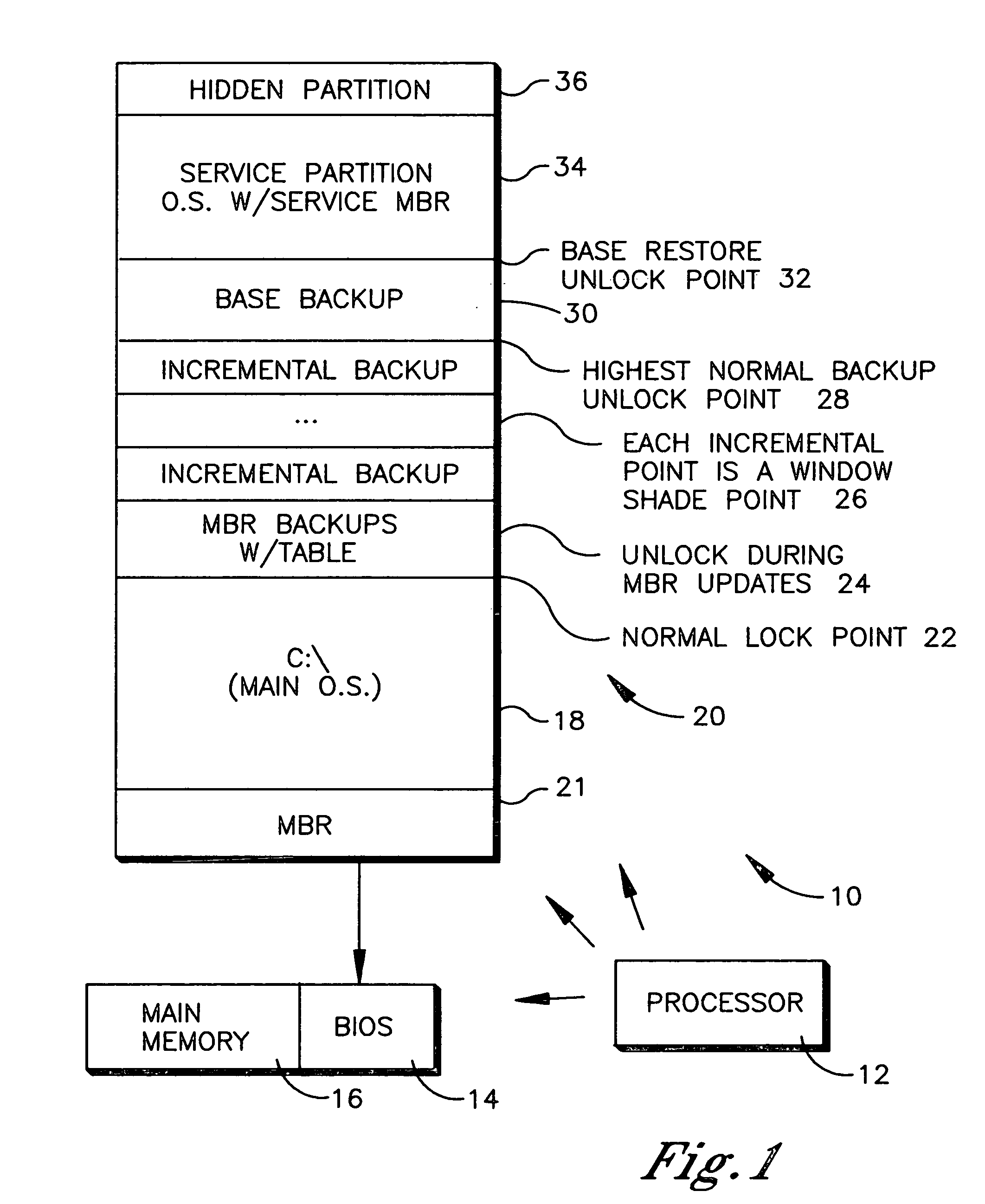
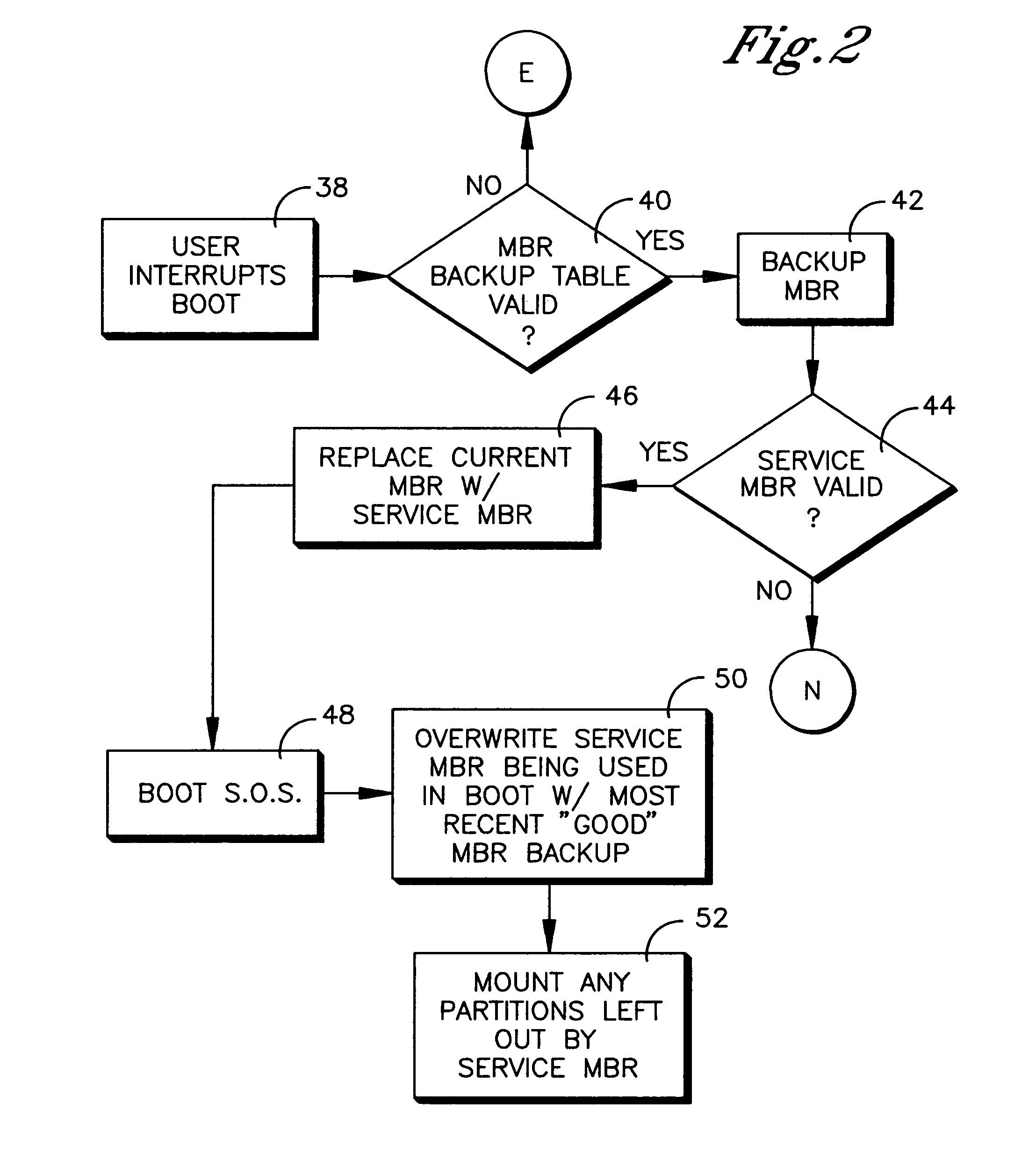
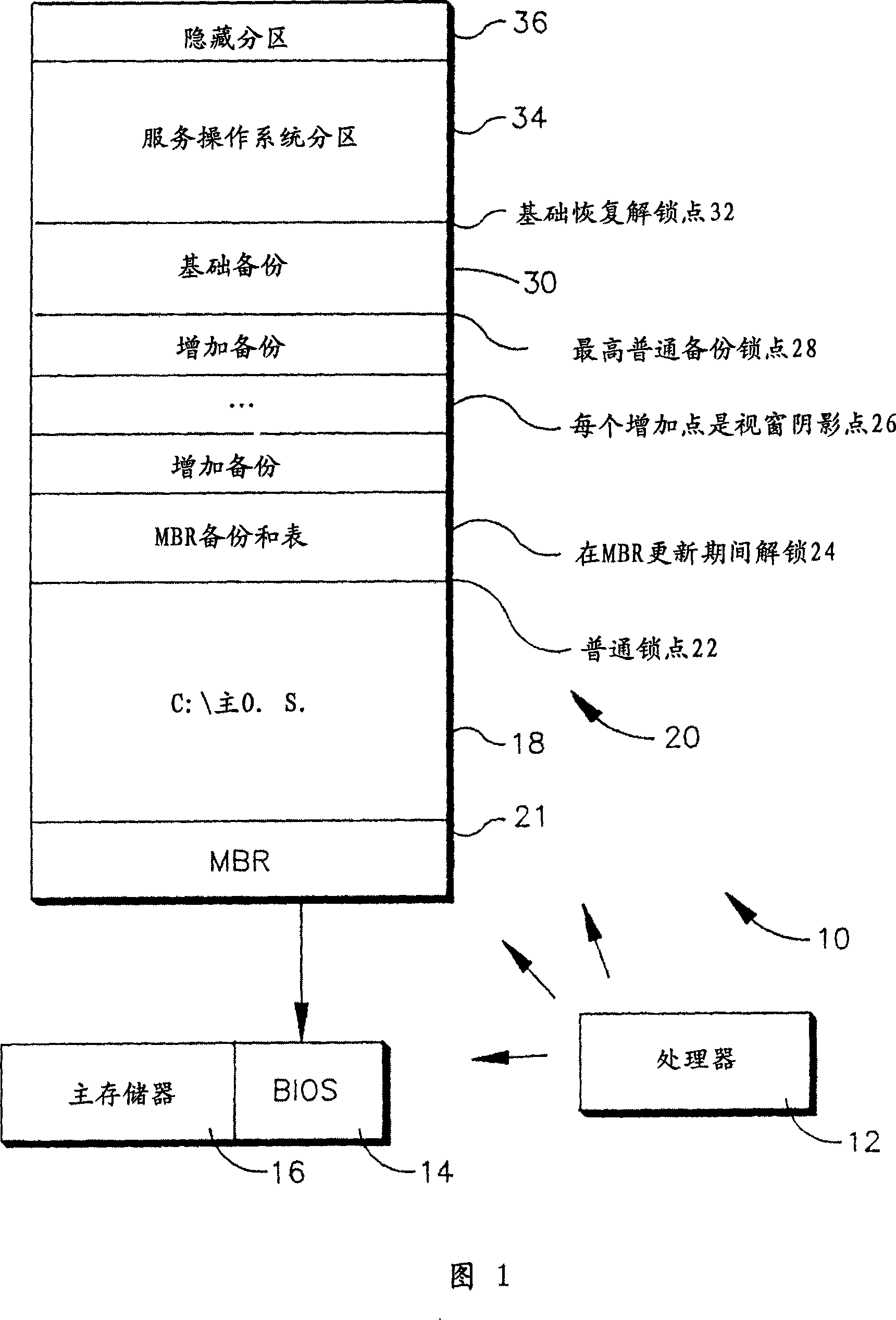
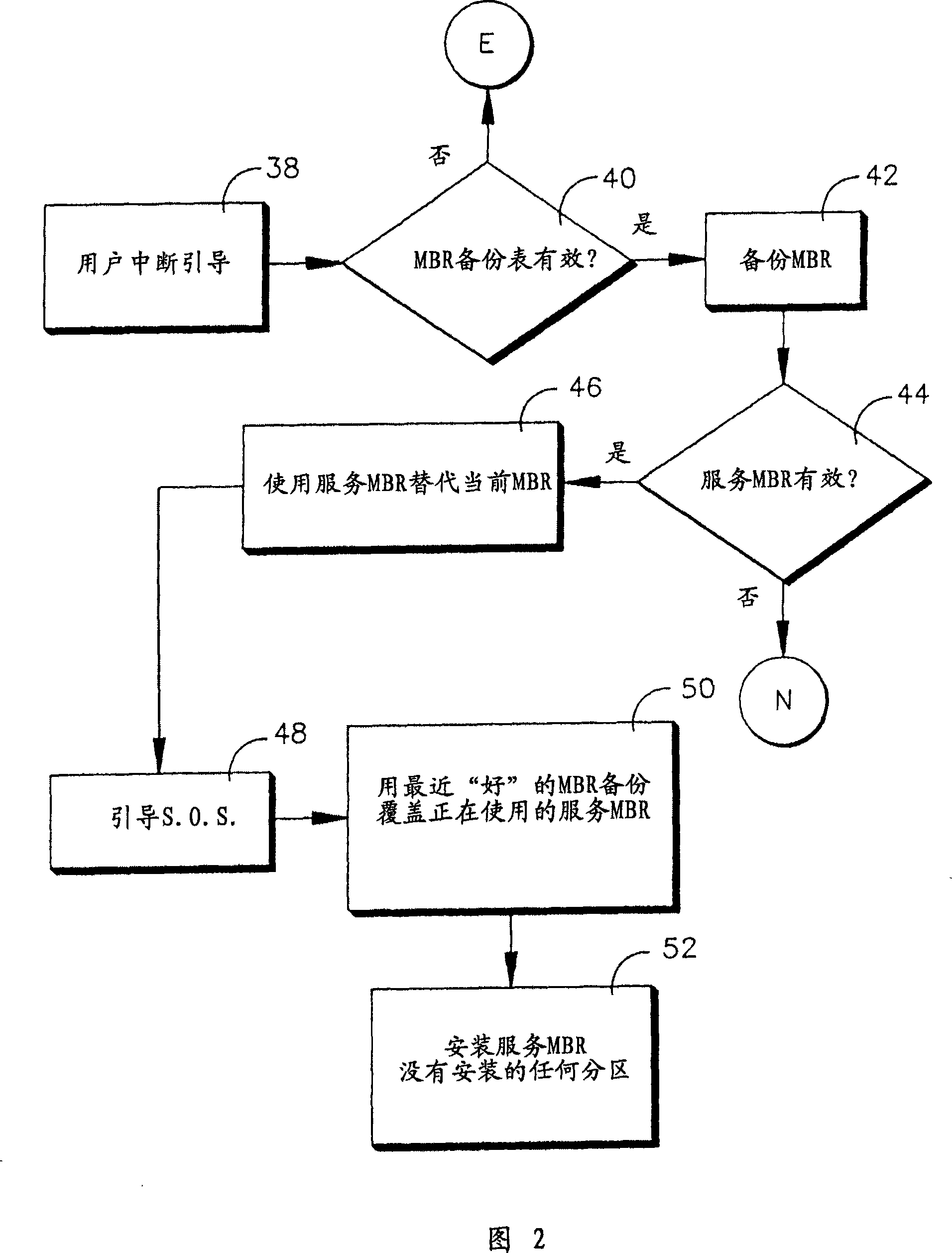
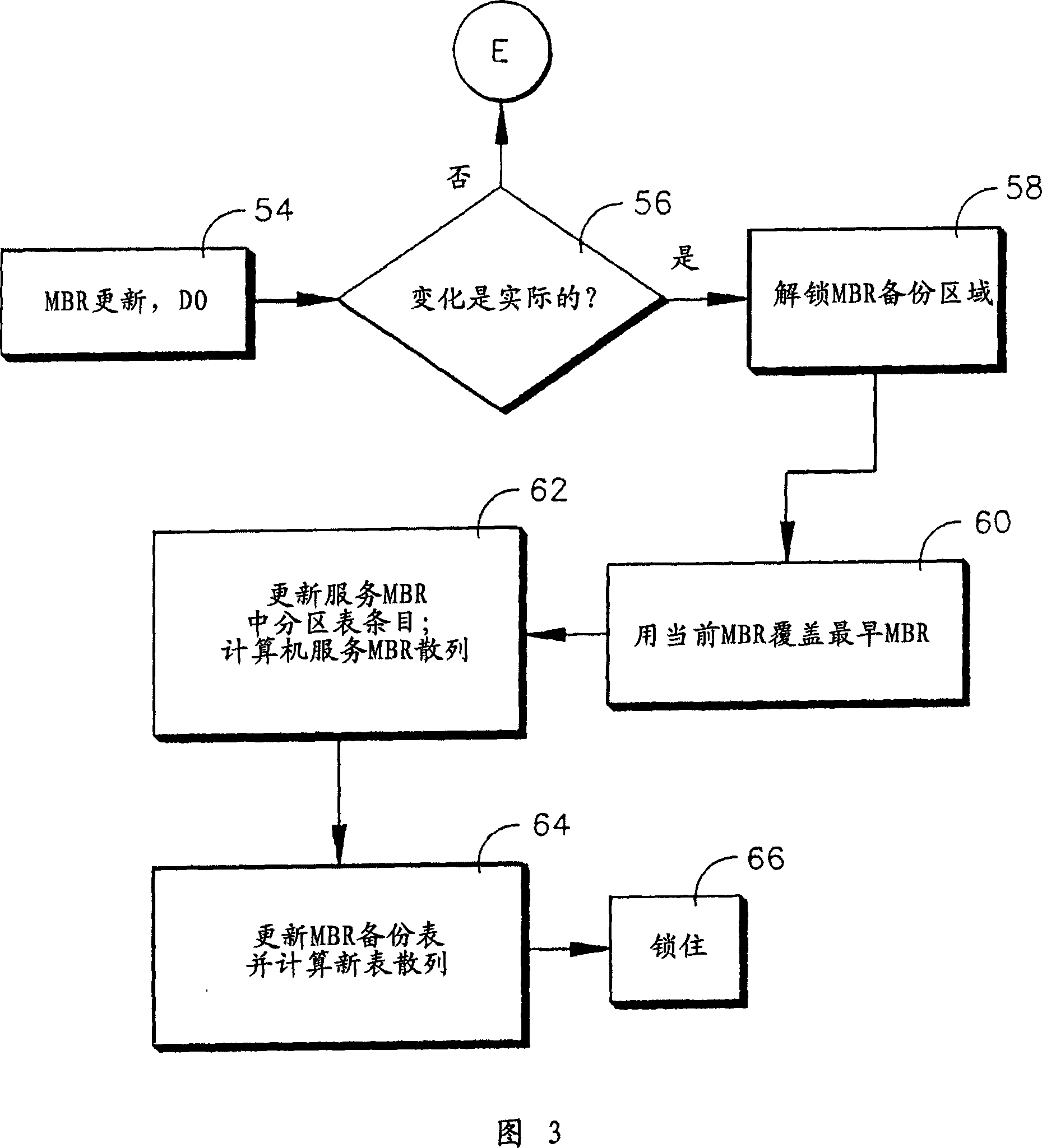
System and method for booting alternate MBR in event of virus attack
ActiveUS20080046781A1Digital computer detailsPlatform integrity maintainanceHard disc driveOperational system
In the event of a virally infected MBR on a hard disk drive that might prevent booting, a service MBR in a hidden protected area (HPA) can be used to boot a service O.S., and then the service MBR can be replaced with a previously backed-up MBR, also in the HPA, to mount any missing partitions.
Owner:LENOVO PC INT
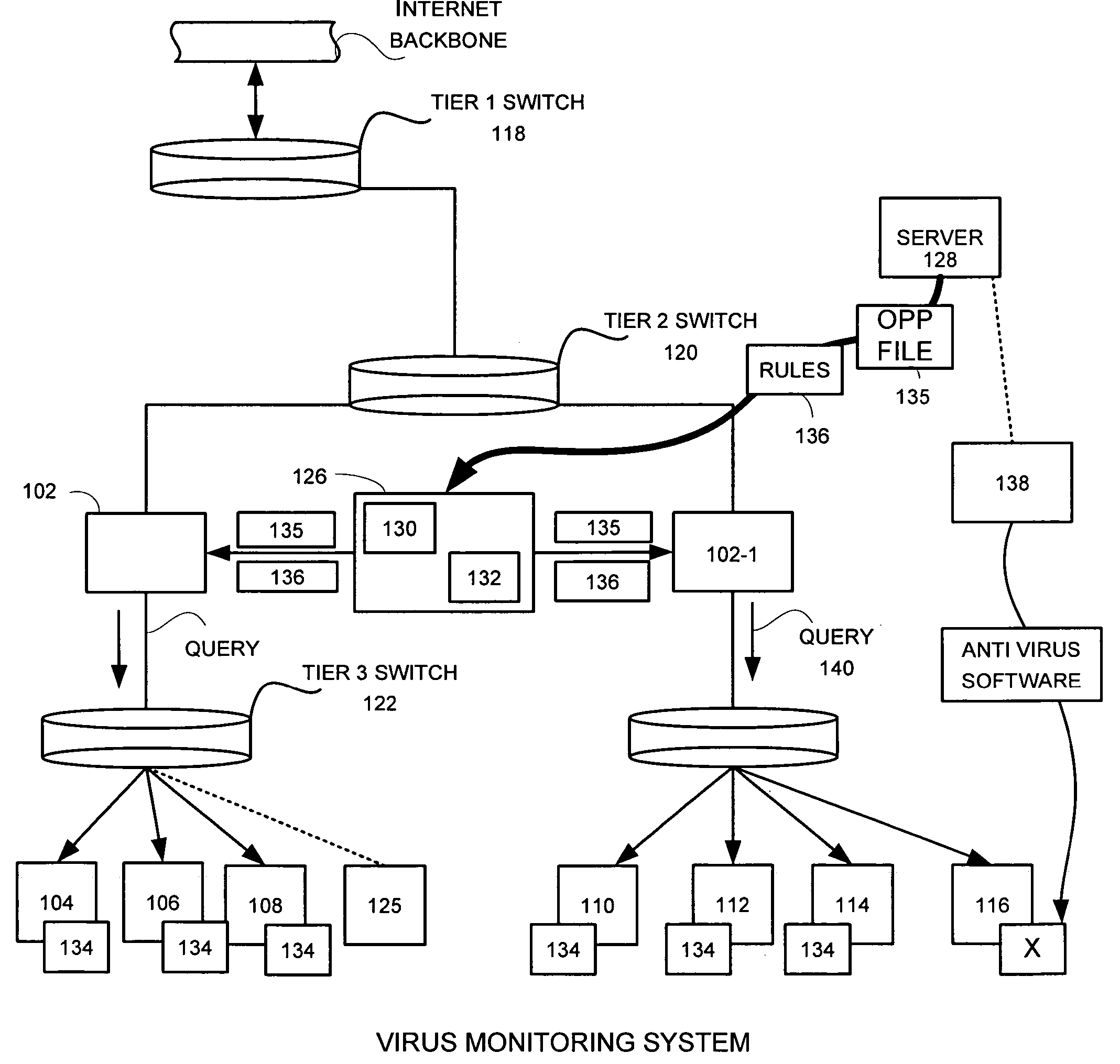
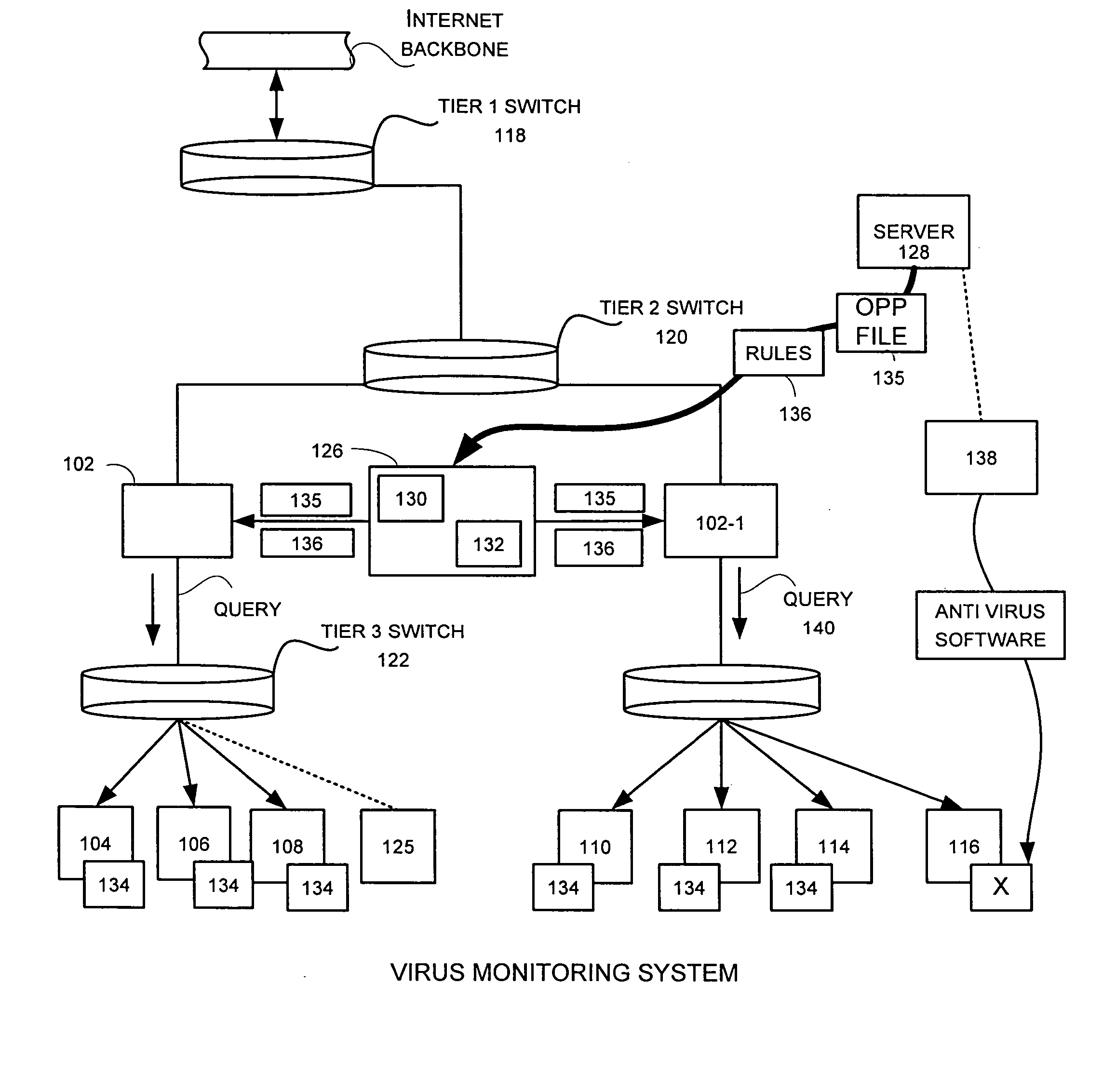
Virus monitor and methods of use thereof
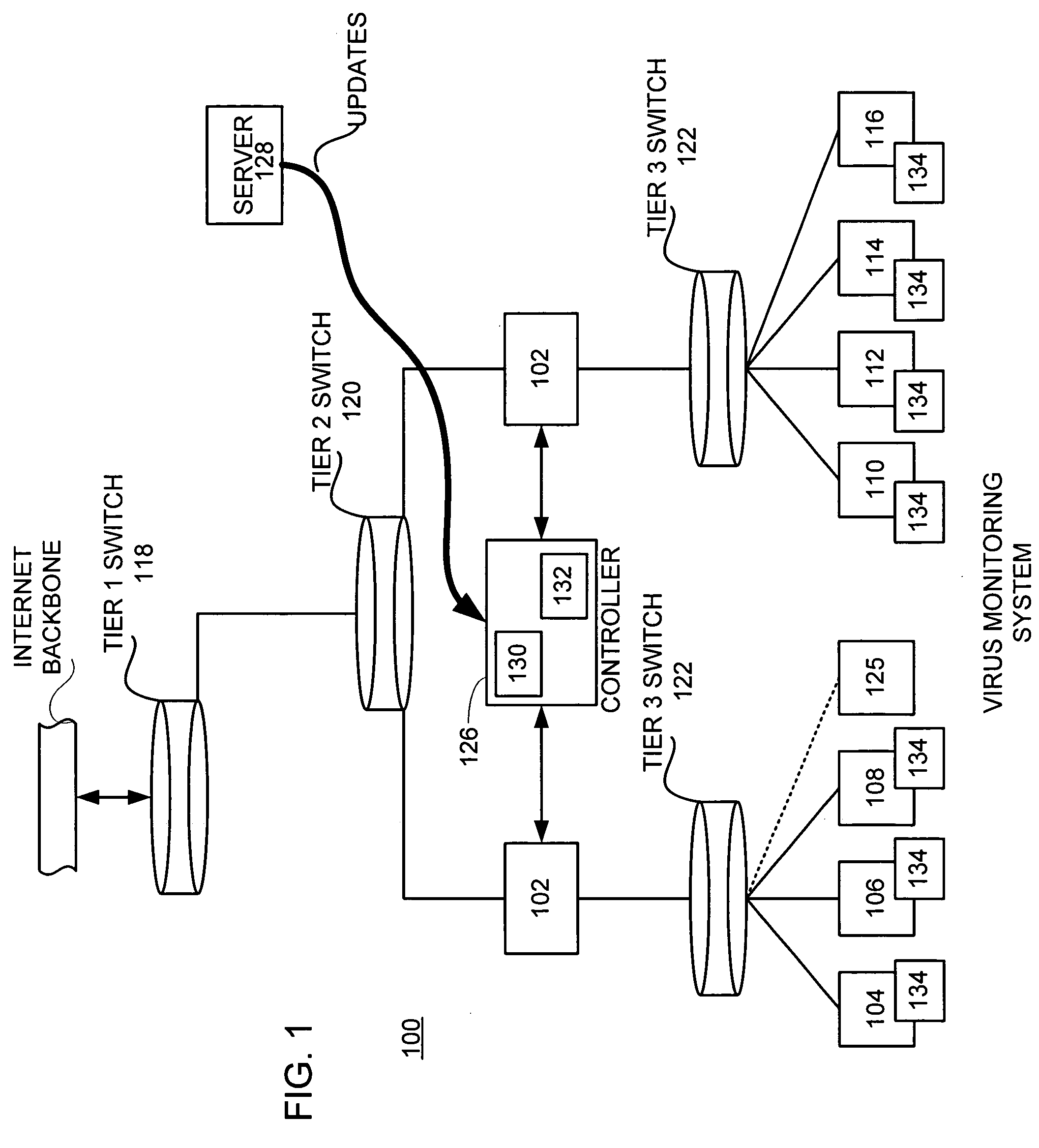
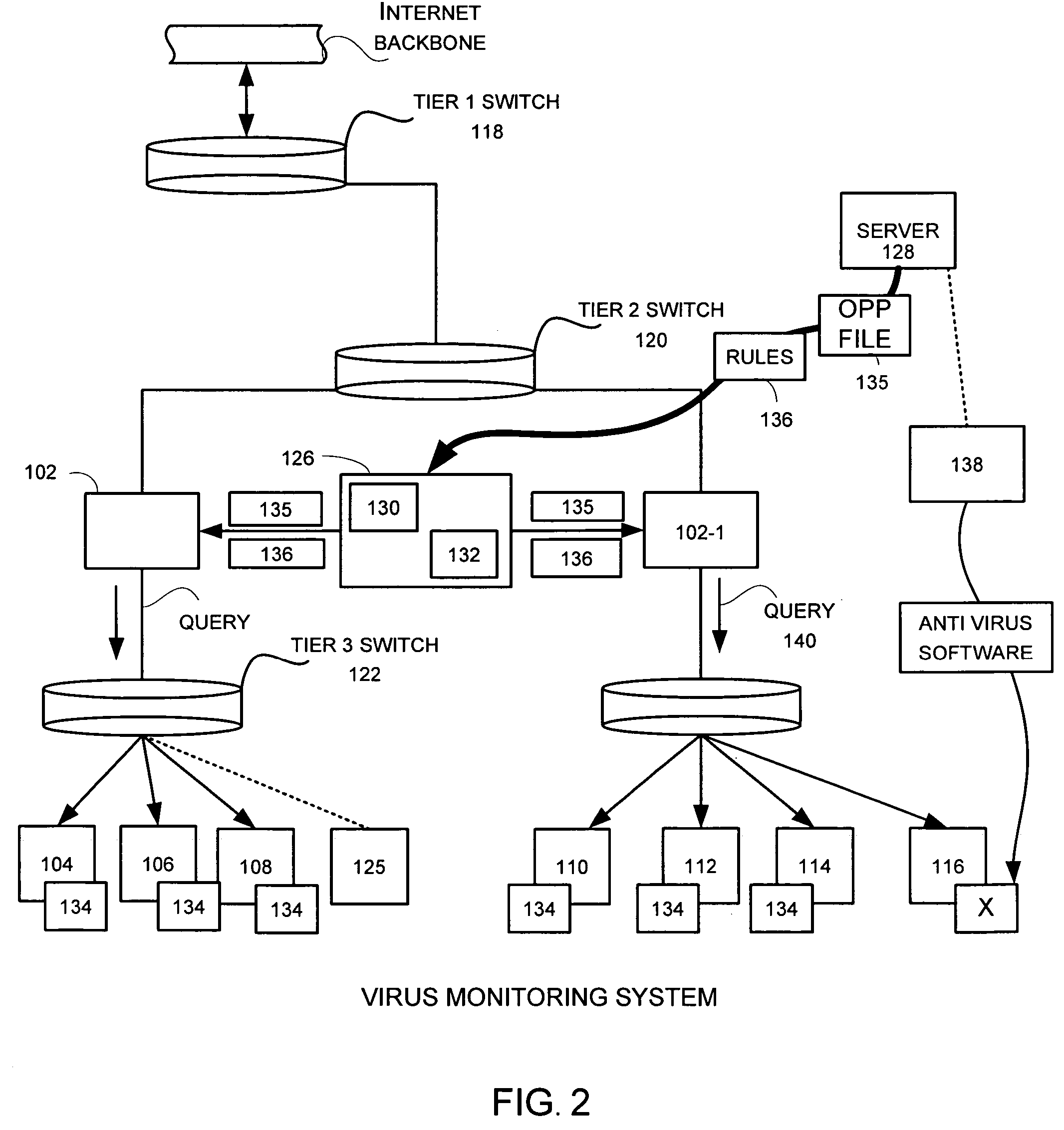
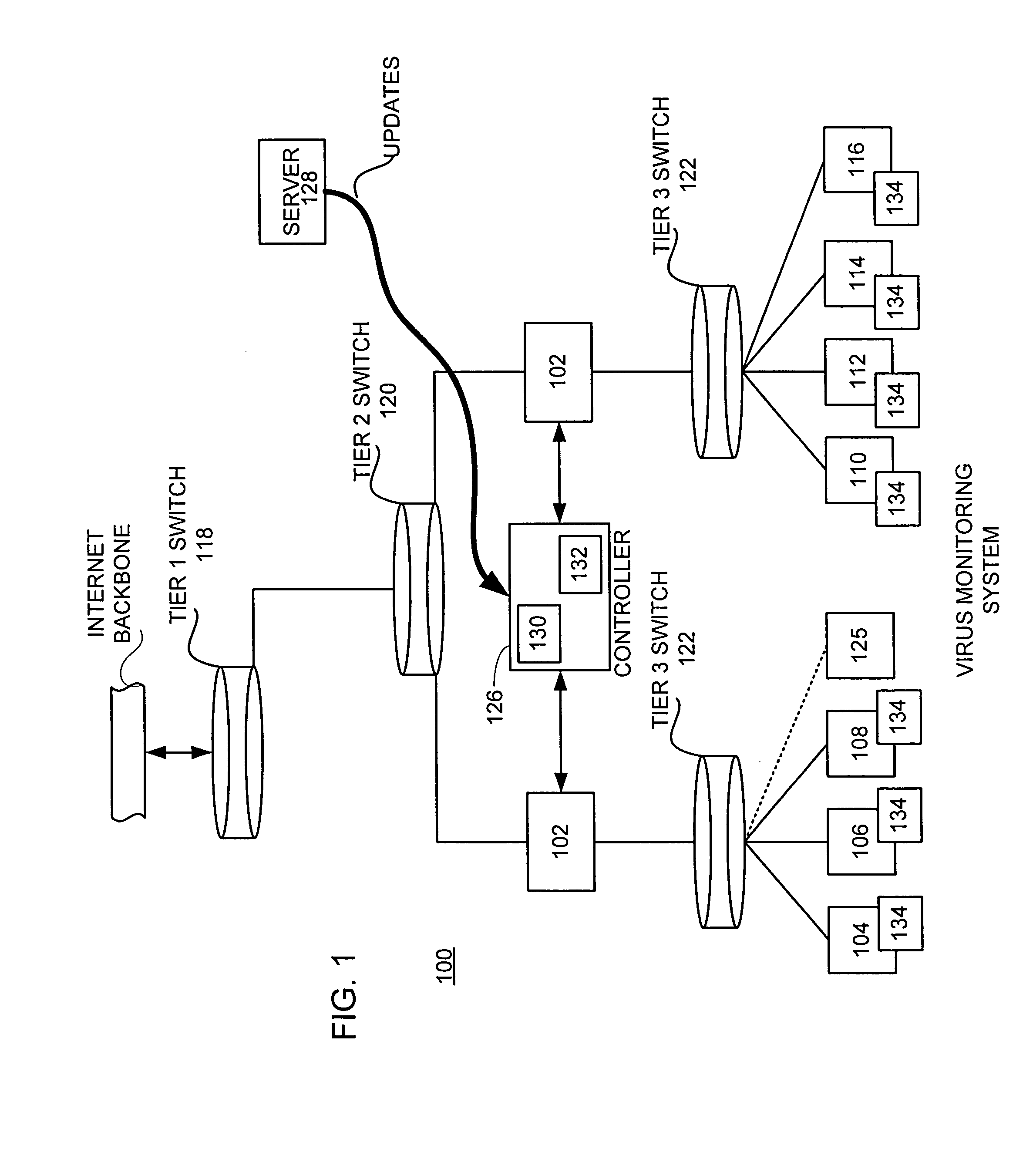
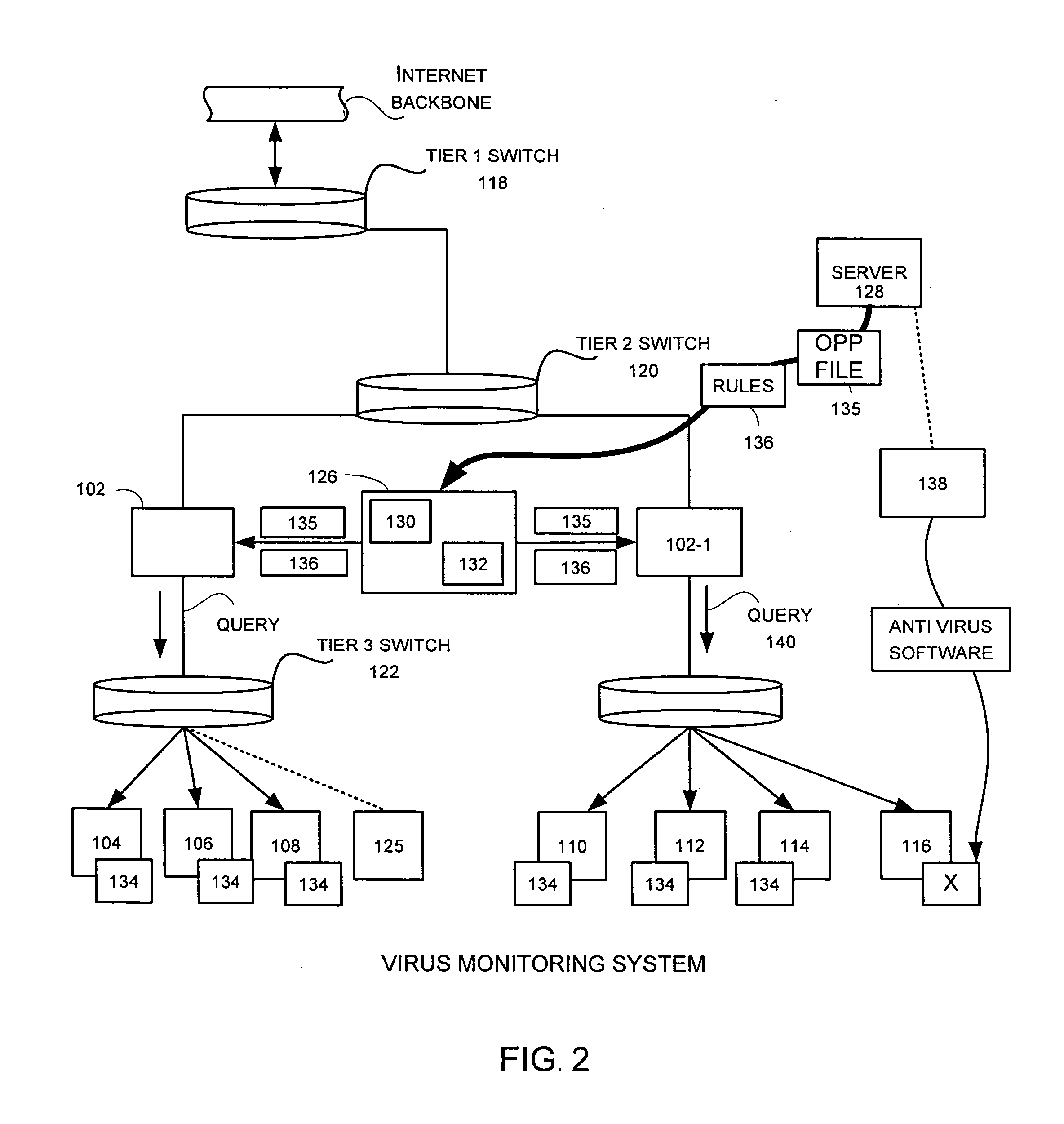
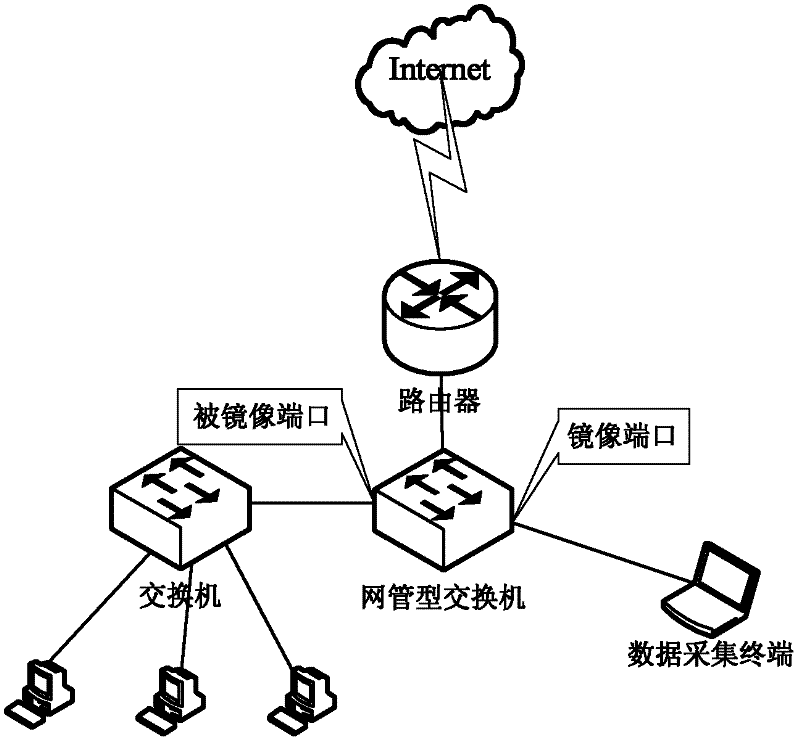
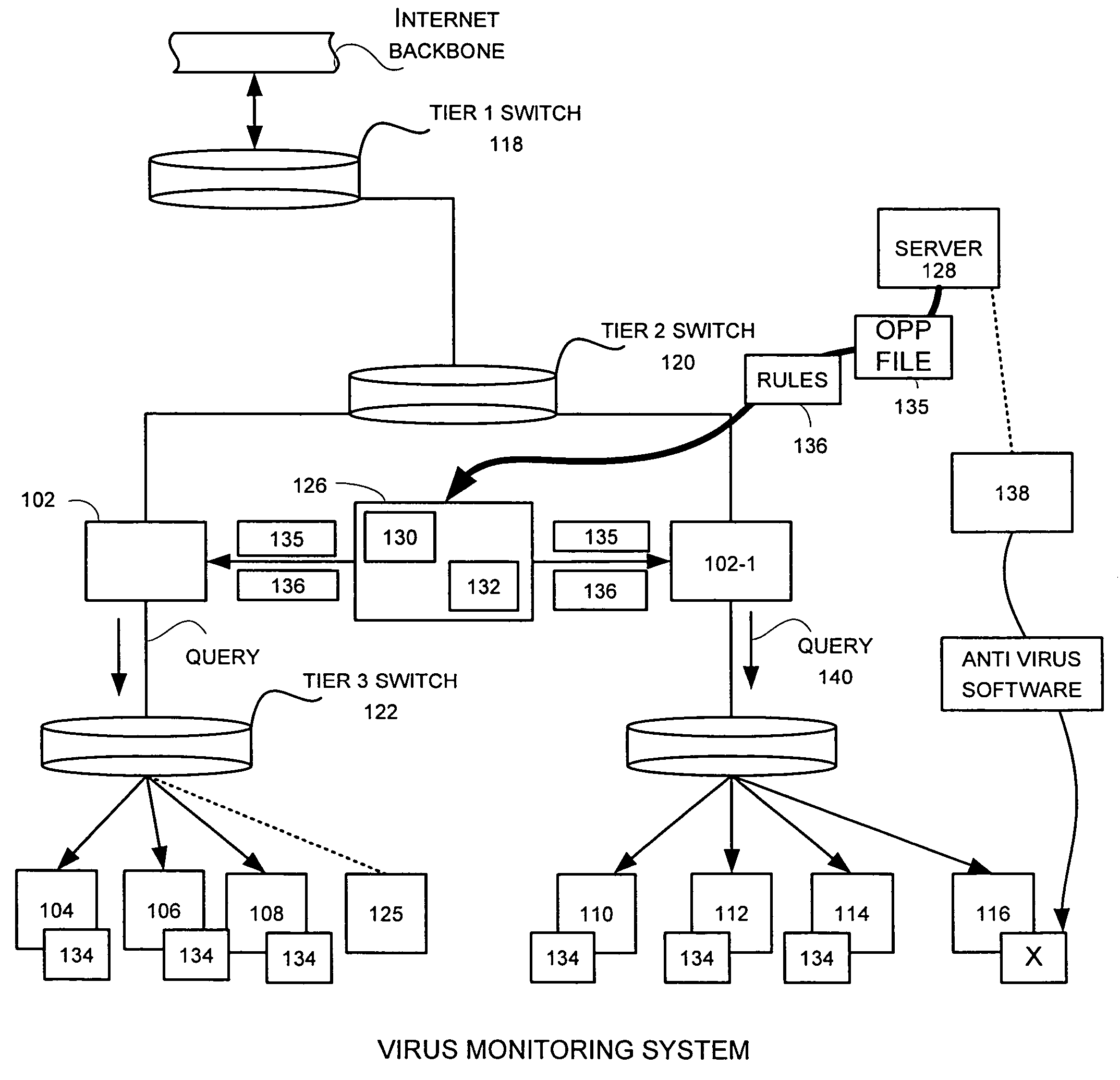
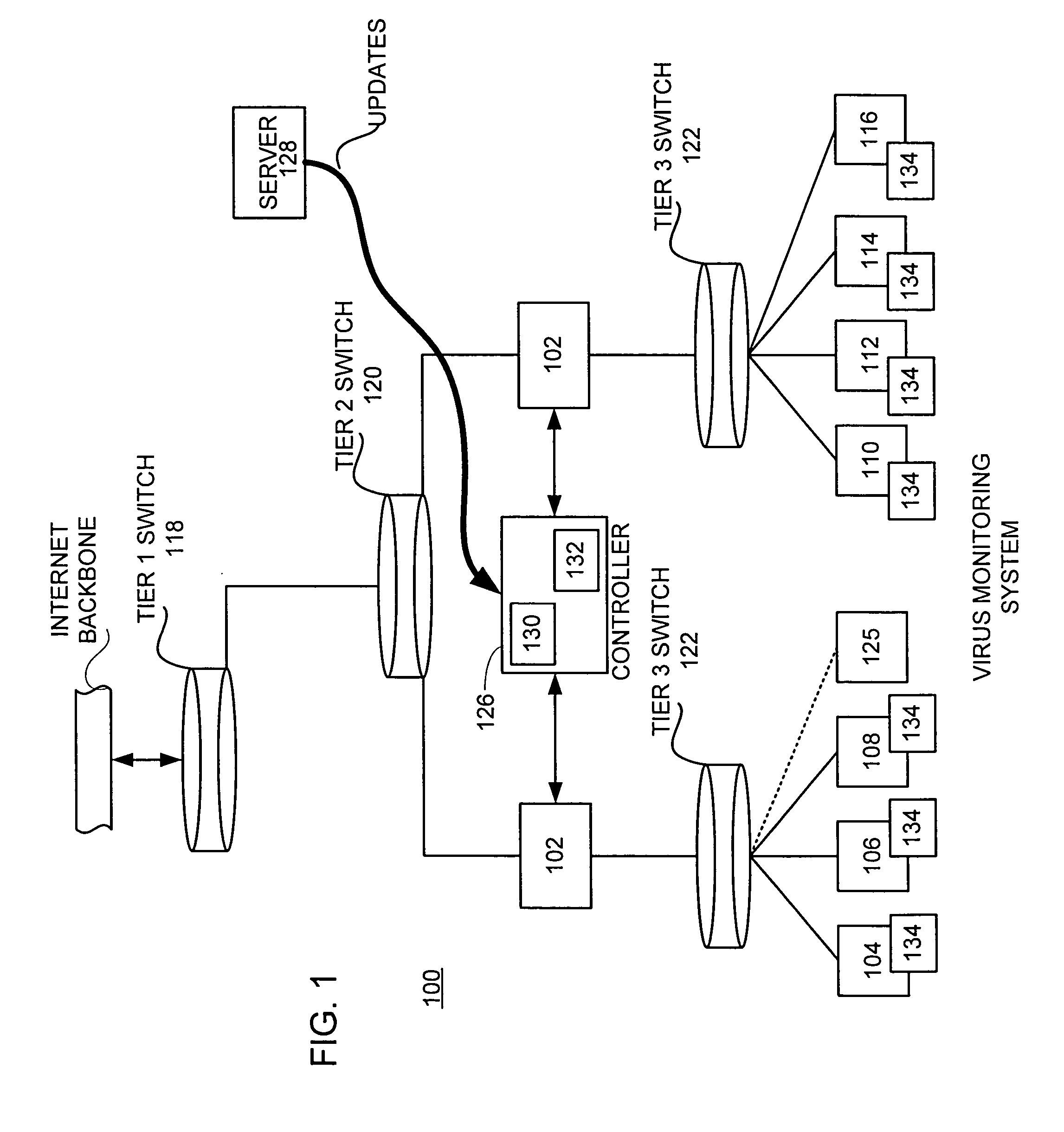
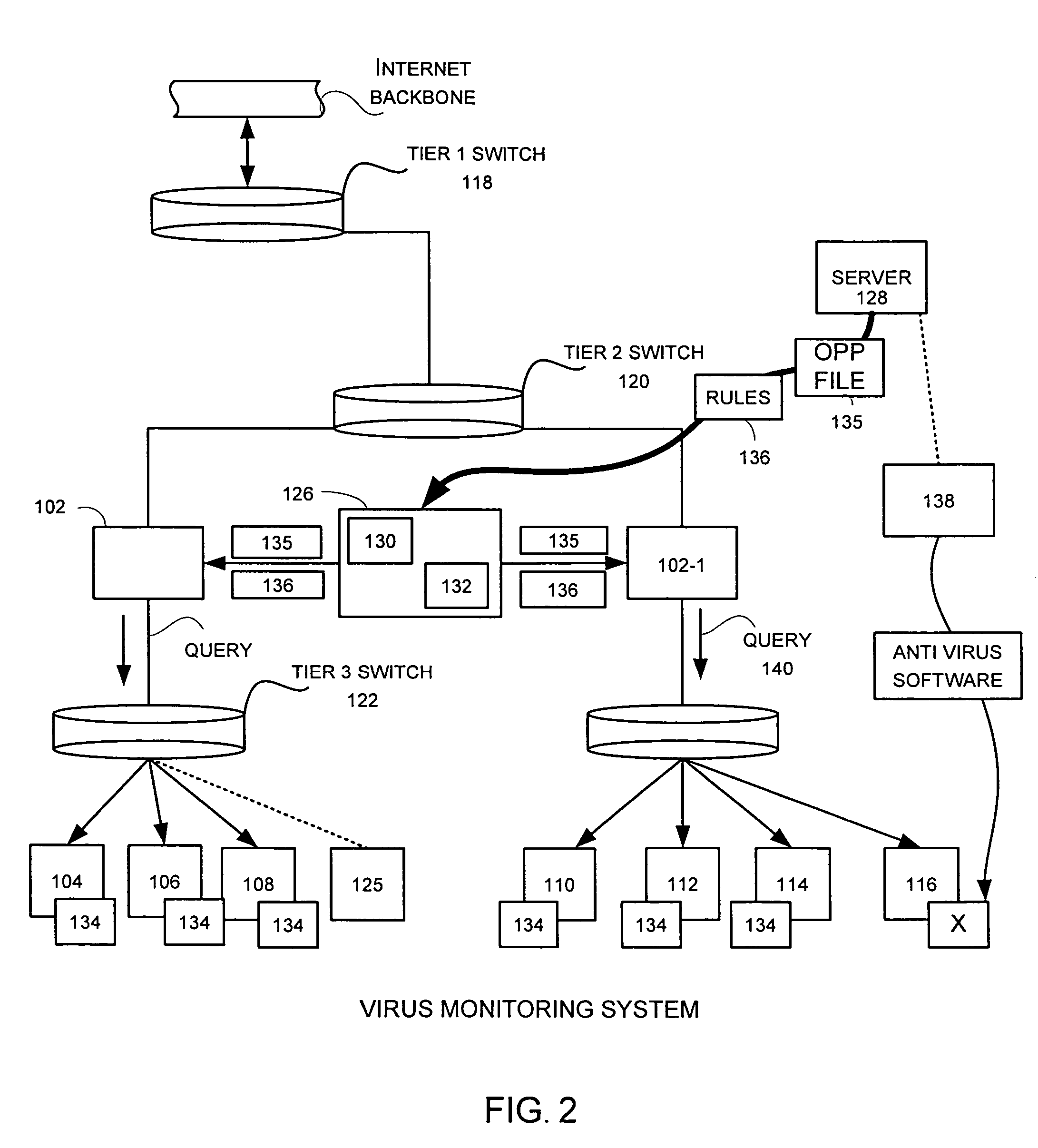
A network level virus monitoring system capable of monitoring a flow of network traffic in any of a number of inspection modes depending upon the particular needs of a system administrator. The monitoring provides an early warning of a virus attack thereby facilitating quarantine procedures directed at containing a virus outbreak. By providing such an early warning, the network virus monitor reduces the number of computers ultimately affected by the virus attack resulting in a concomitant reduction in both the cost of repair to the system and the amount of downtime. In this way, the inventive network virus monitor provides a great improvement in system uptime and reduction in system losses.
Owner:TREND MICRO INC
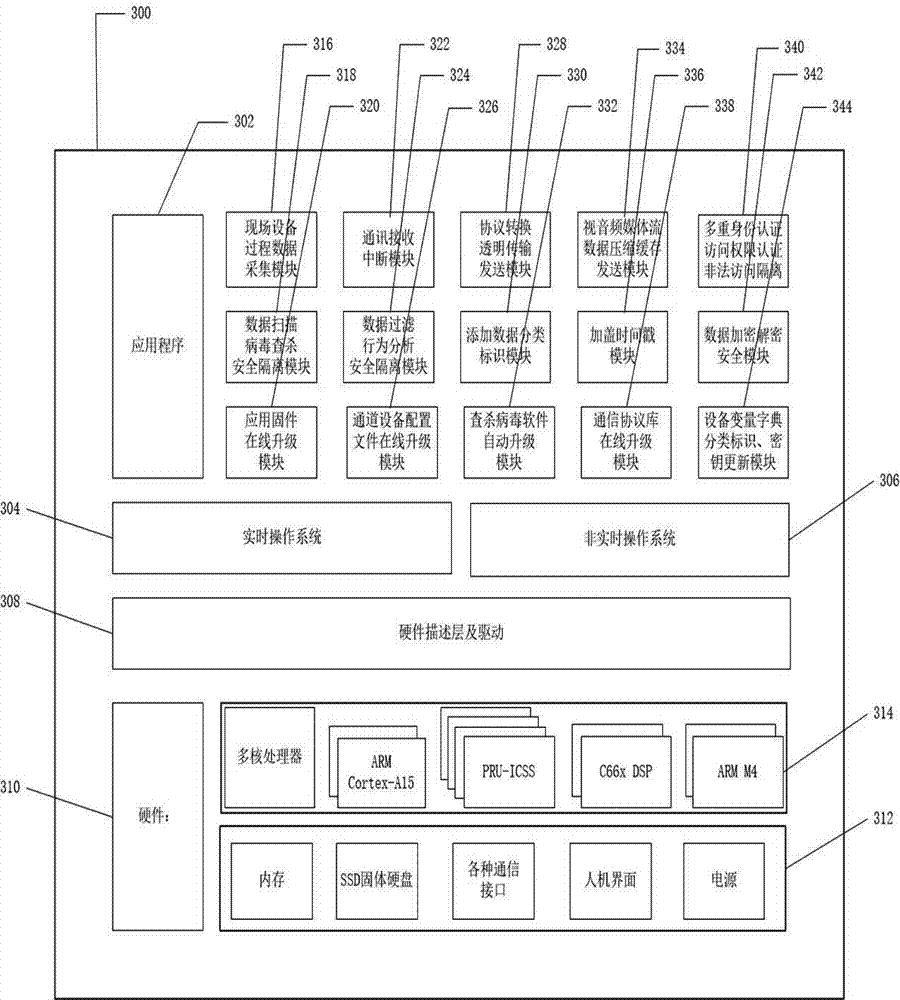
Intelligent industrial security cloud gateway equipment system and method
InactiveCN107040459AUser identity/authority verificationNetwork connectionsData centerSecurity authentication
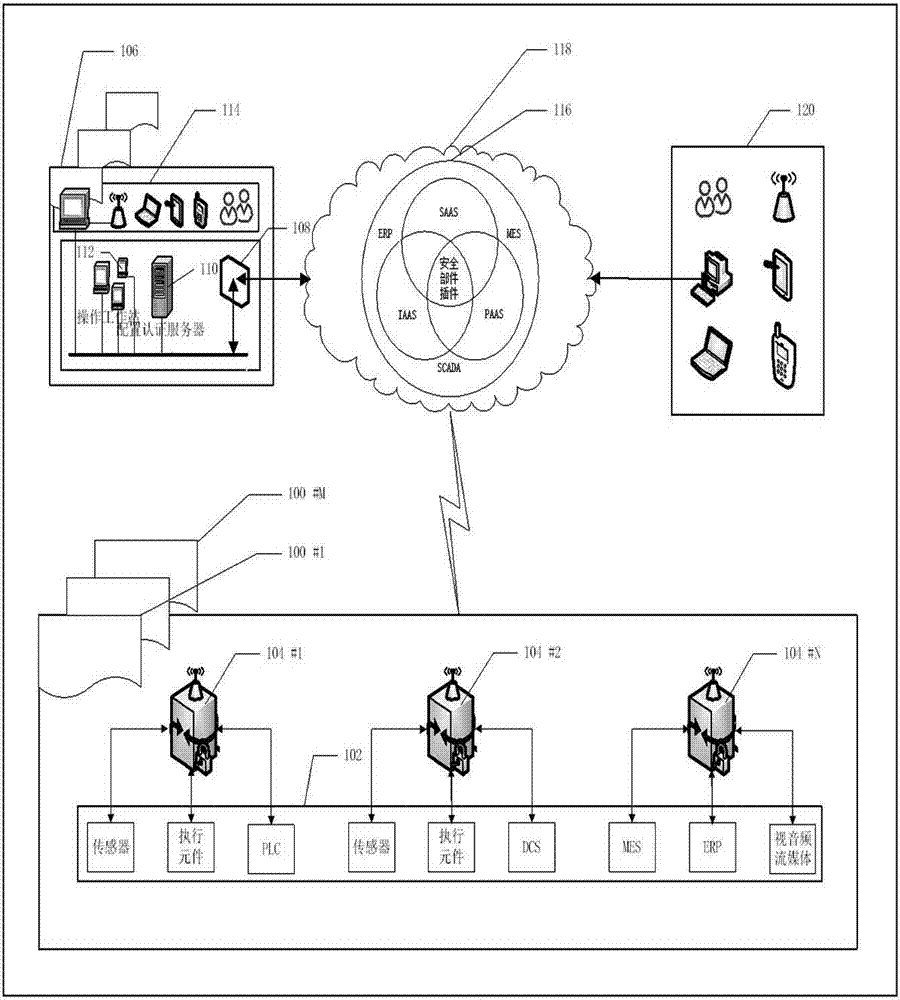
The invention discloses an intelligent industrial security cloud gateway equipment system and method. The industrial cloud security gateway equipment and method is characterized in that upper cloud data is encrypted and added with data classification identifiers and time stamps, and decryption, security scanning and multiple security authentication access control are carried out on data on downlink intelligent equipment, so that interconnection, protocol conversion, and multi-directional transparent and real-time transmission among cloud equipment, enterprise datacenter equipment and various intelligent equipment on an industrial field can be achieved. An intelligent industrial cloud security gateway is embedded intelligent equipment comprising various serial ports, communication interfaces for a field bus and field intelligent equipment such as the industrial Ethernet, communication interfaces for wireless mobile communication and wired Internet cloud equipment, wireless or wired local area network interfaces for Bluetooth, broadband and the like, an Ethernet switch, a GPS module, and embedded software. The intelligent industrial cloud security gateway can systematically prevent user data leakage and network virus attacks, is core equipment of a secure and reliable intelligent industrial cloud service system, and can serve intelligent industrial manufacturing.
Owner:高岩
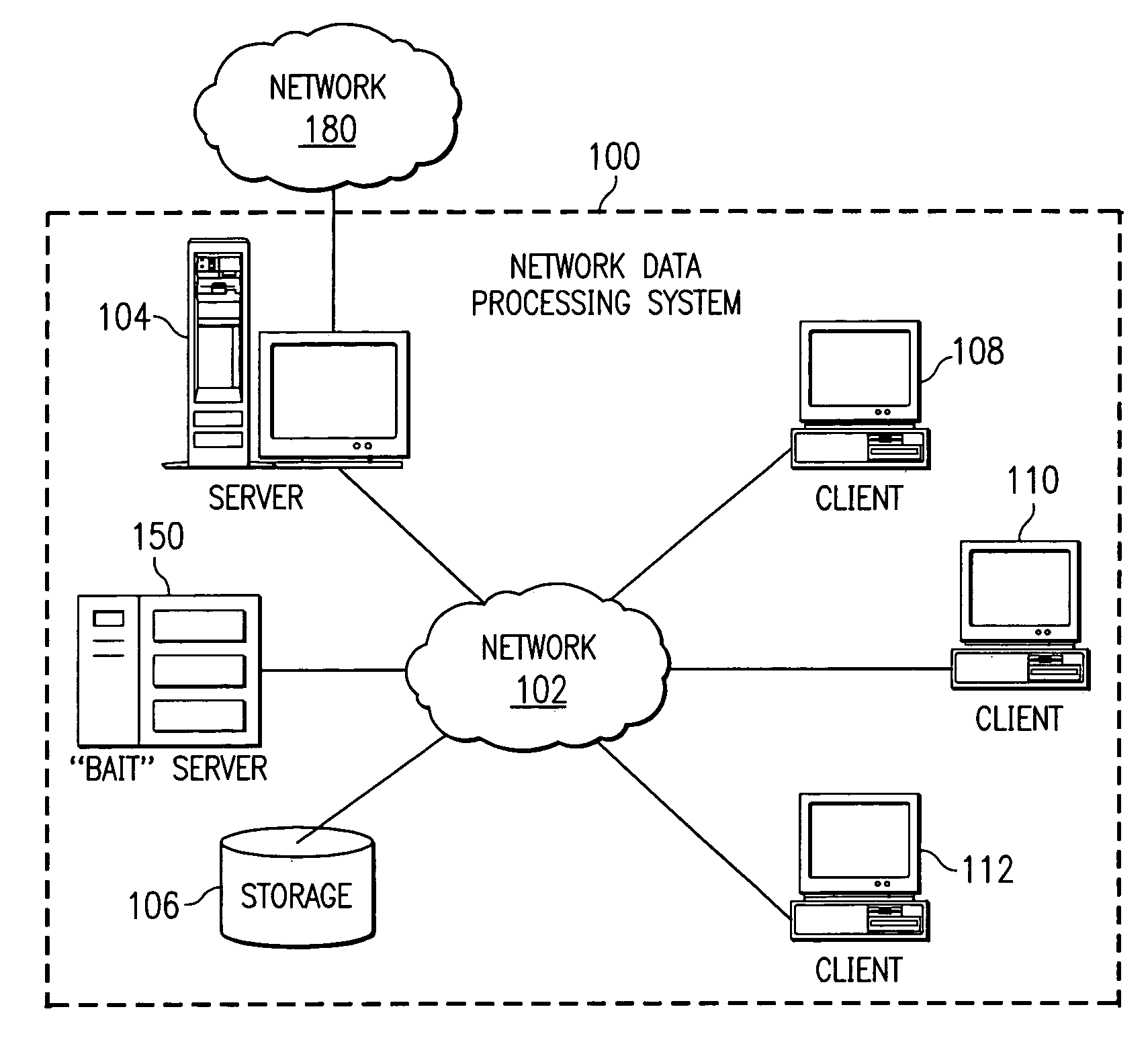
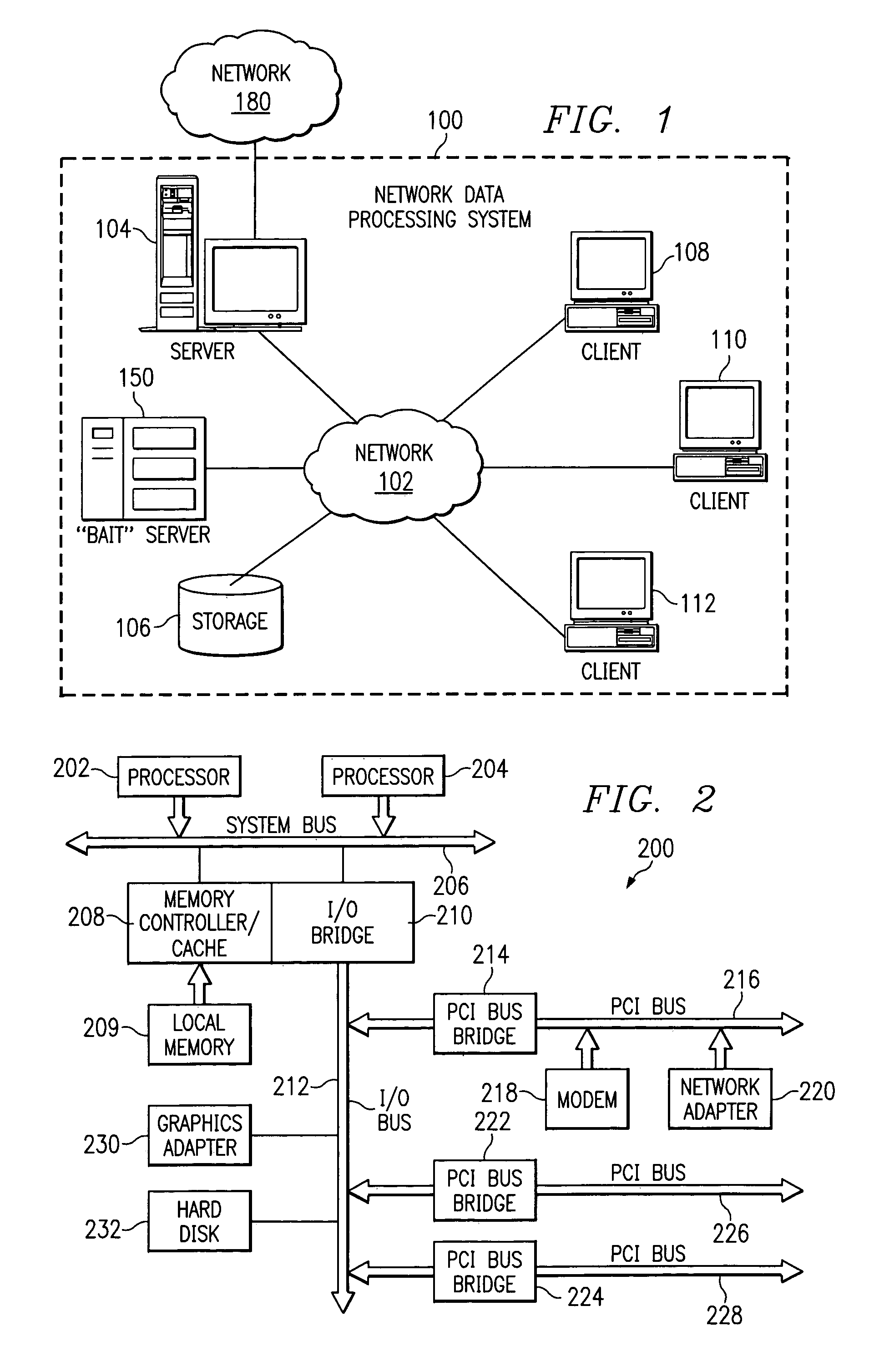
Method and apparatus for the detection, notification, and elimination of certain computer viruses on a network using a promiscuous system as bait
A method, computer program product, and network data processing system for identifying, locating, and deleting viruses is provided. In one embodiment, the network data processing system includes a local server, several client data processing systems, and a bait server. The address of the bait server is not published to the clients. Thus, any attempt to access the bait server would indicate the presence of a virus on the client attempting access. The bait server monitors itself and, responsive to an attempt from a client to access the bait server, broadcasts an indication that a virus attack is underway to all devices within the network. The bait server then ignores all further access requests by the offending client until it receives an indication that the offending client has been disinfected and directs the local server to disconnect the offending client(s) from the network. The bait server also notifies the local server and / or a network administrator of the problem and the identity of the offending client allowing appropriate action to be initiated to disinfect the offending client.
Owner:LENOVO PC INT
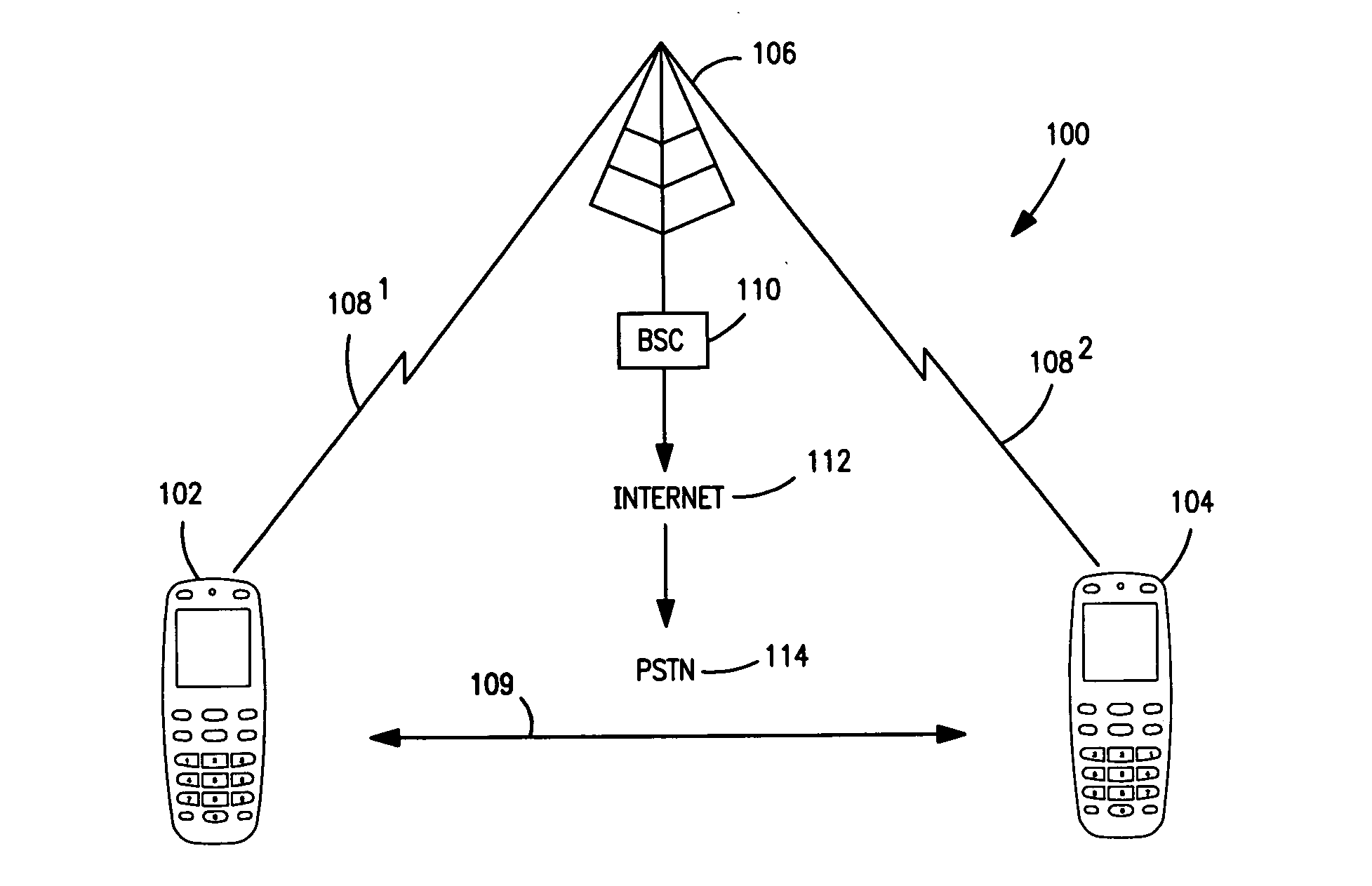
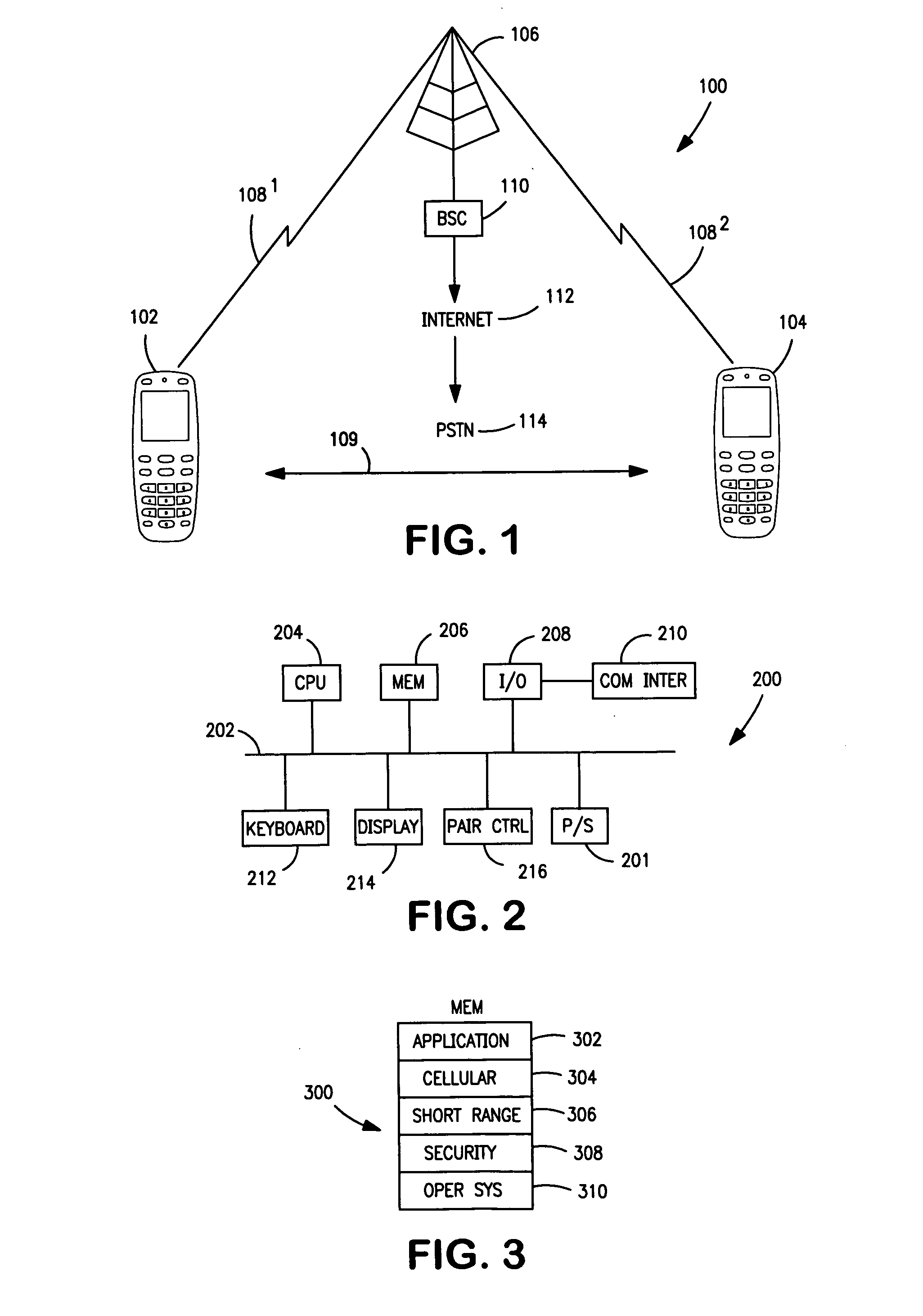
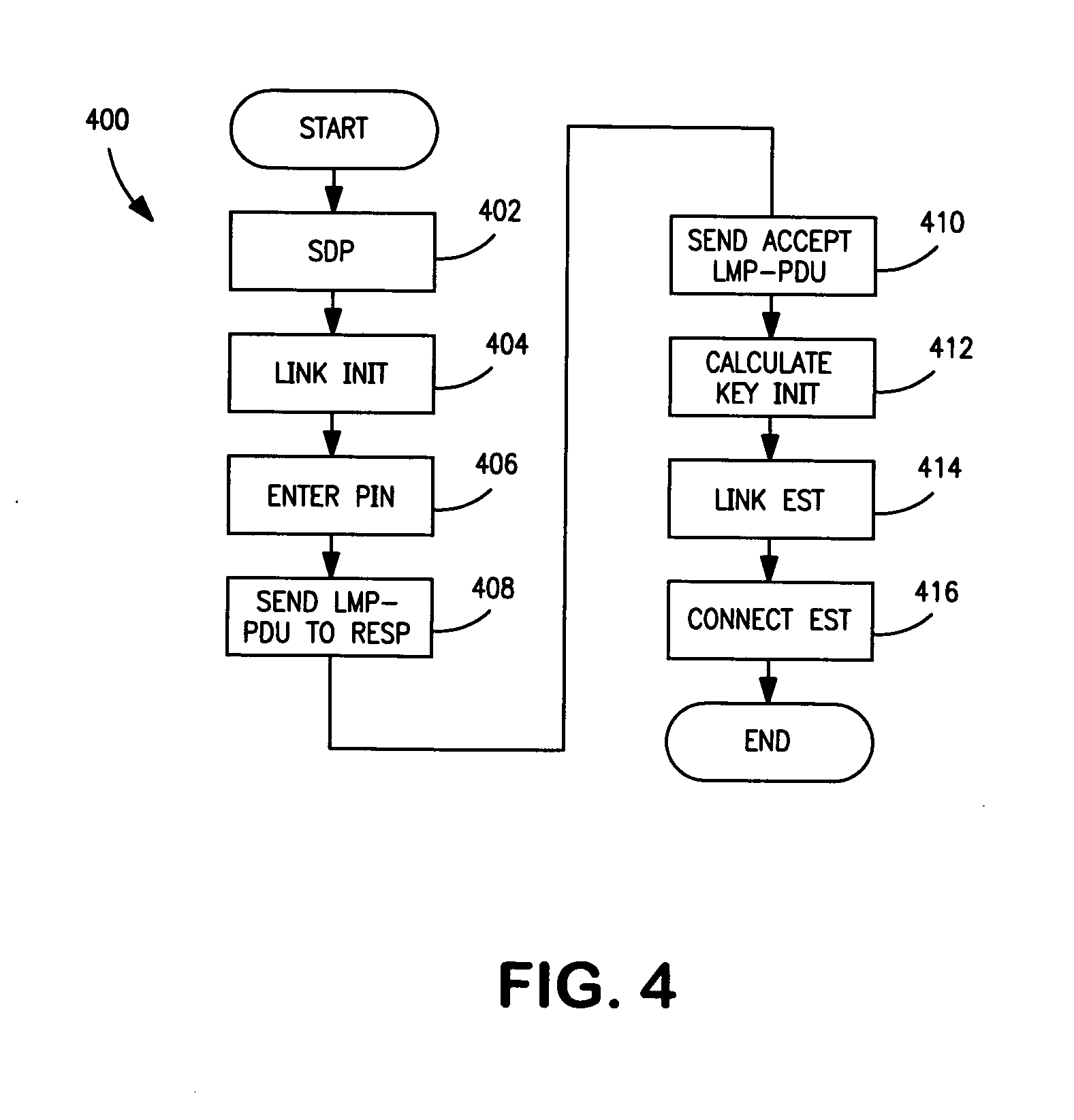
Restricting and preventing pairing attempts from virus attack and malicious software
A method, device and system restrict and prevent virus attack and malicious software to a wireless communication device from a pairing attempt by another wireless communications device. A switch is included in a transmission path coupling a first device to a second device, wherein the second device is attempting to pair with first wireless communications device. A detector coupled to the transmission path, detects an address of the second wireless communications device in a pairing communication protocol between the first and second devices. A counter coupled to the detector counts the pairing attempts of the second device. A compare circuit compares the pairing attempts to a selected number N. The compare circuit signals the switch to open when the number of attempts equals or exceeds the number N, breaking the connection, thereby preventing the first device from receiving virus attacks and malicious software.
Owner:NOKIA TECHNOLOGLES OY
Network traffic management by a virus/worm monitor in a distributed network
InactiveUS20050050334A1Unauthorized memory use protectionHardware monitoringDowntimeInternet traffic
A network level virus monitoring system capable of monitoring a flow of network traffic in any of a number of inspection modes depending upon the particular needs of a system administrator. The system includes a network virus sensor self registration module coupled to a network virus / worm sensor arranged to automatically self register the associated network virus / worm sensor. The monitoring provides an early warning of a virus attack thereby facilitating quarantine procedures directed at containing a virus outbreak. By providing such an early warning, the network virus monitor reduces the number of computers ultimately affected by the virus attack resulting in a concomitant reduction in both the cost of repair to the system and the amount of downtime. In this way, the inventive network virus monitor provides a great improvement in system uptime and reduction in system losses.
Owner:TREND MICRO INC
Traffic classification method and device based on transport layer characteristics
InactiveCN102271090AImplement classificationTraffic Classification ImplementationData switching networksData streamTransport layer
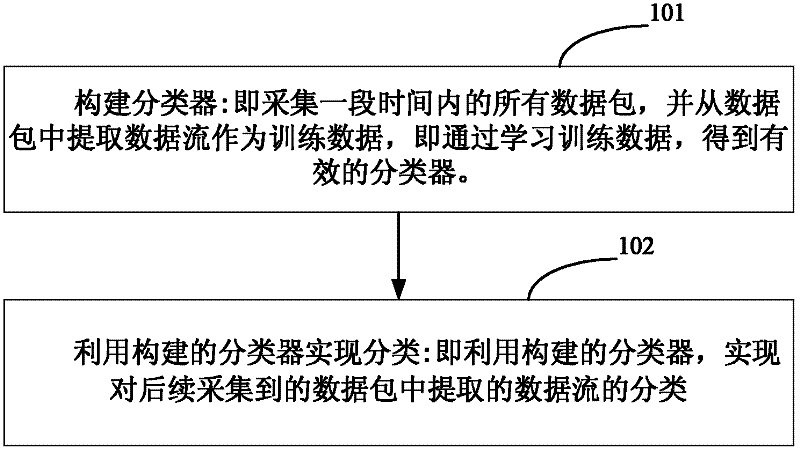
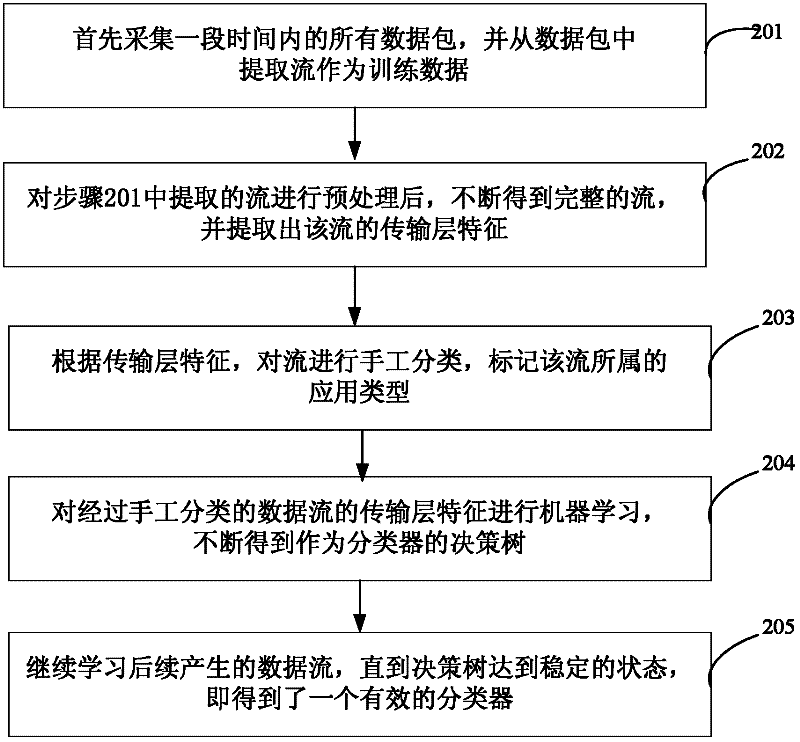
The invention relates to the technical field of Internet application, in particular to a transport-layer-characteristic-based traffic classification method for the Internet application. The method comprises the following steps of: acquiring a data packet which serves as training data, and constructing a classifier by utilizing transport layer characteristics of a data stream extracted from the data packet; and classifying the data stream extracted from a subsequently acquired data packet by utilizing the constructed classifier. The application type of the stream can be identified only by extracting the transport layer characteristics of the stream without knowing load contents such as a port number, a characteristic field and the like of the data packet. The privacy of a user is uninvolved, and a dynamic-port-number-based or encrypted stream can be identified by the technology. Moreover, the method is highly accurate and integral, novel application can be identified and the user can be prompted to check suspected virus attack streams.
Owner:四川智联科创科技有限公司
Automatic registration of a virus/worm monitor in a distributed network
A network level virus monitoring system capable of monitoring a flow of network traffic in any of a number of inspection modes depending upon the particular needs of a system administrator. The system includes a network virus sensor self registration module coupled to a network virus / worm sensor arranged to automatically self register the associated network virus / worm sensor. The monitoring provides an early warning of a virus attack thereby facilitating quarantine procedures directed at containing a virus outbreak. By providing such an early warning, the network virus monitor reduces the number of computers ultimately affected by the virus attack resulting in a concomitant reduction in both the cost of repair to the system and the amount of downtime. In this way, the inventive network virus monitor provides a great improvement in system uptime and reduction in system losses.
Owner:TREND MICRO INC
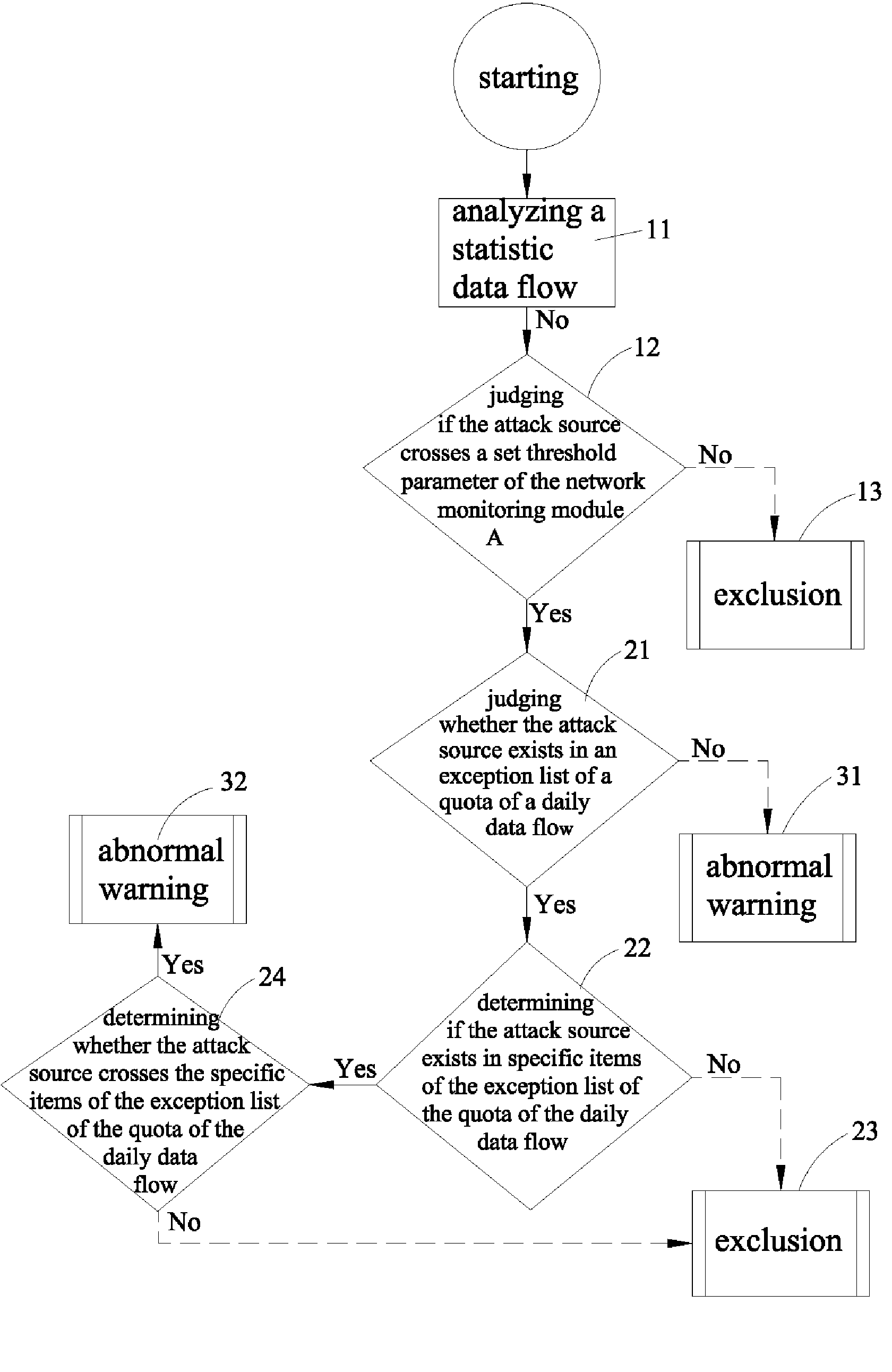
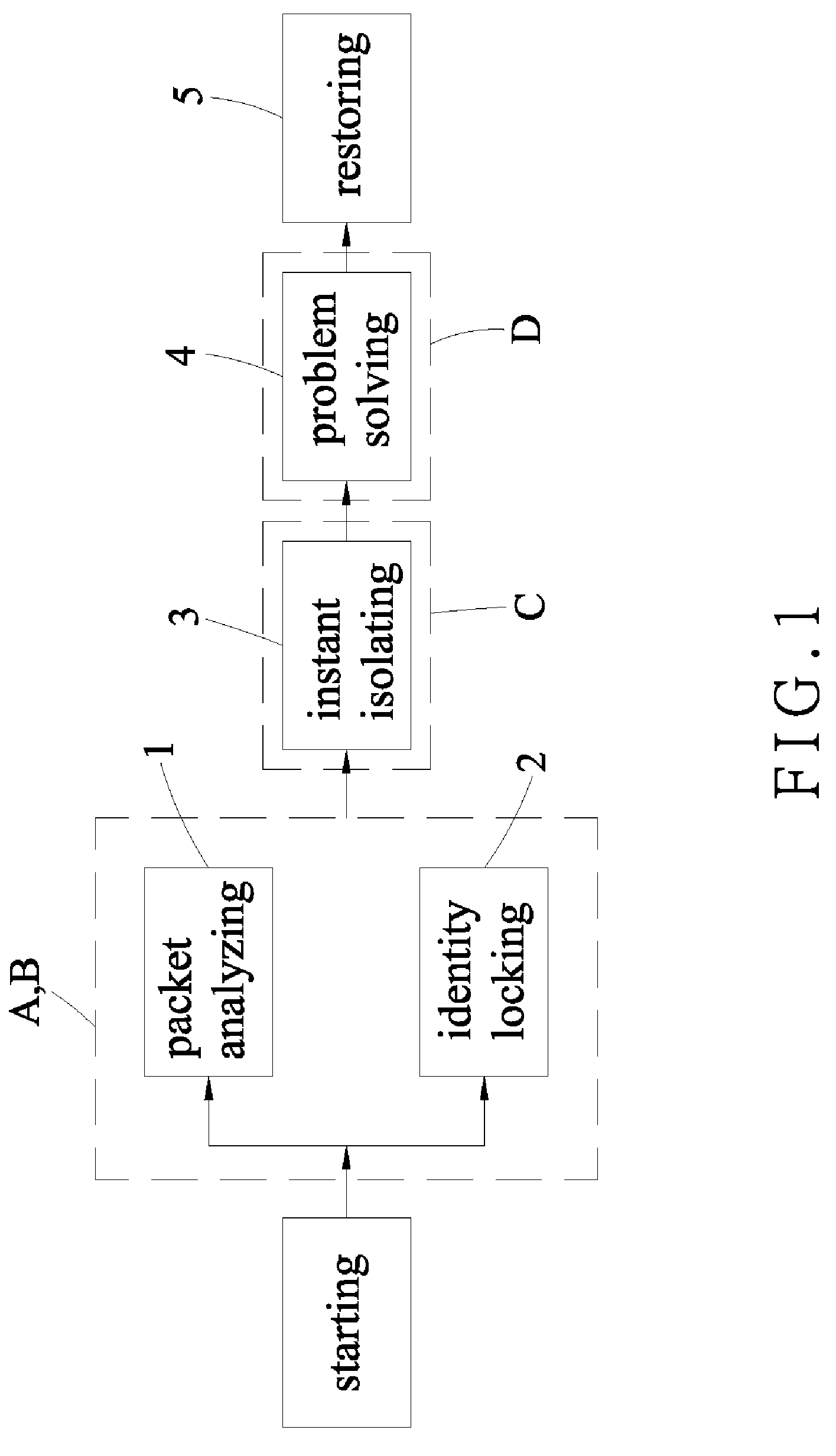
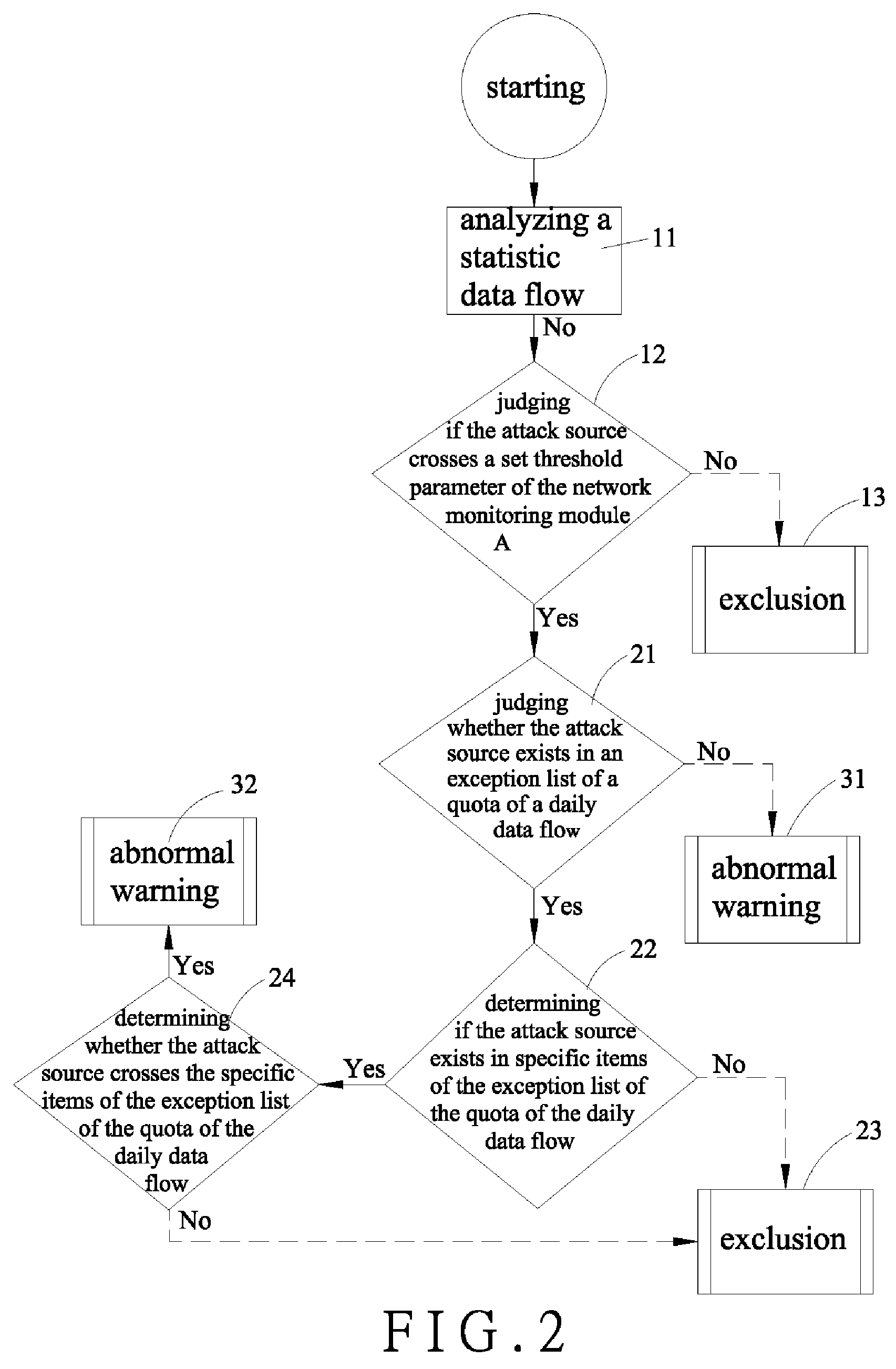
Method for analyzing abnormal network behaviors and isolating computer virus attacks
InactiveUS20080196103A1Reduce search timeMemory loss protectionUnauthorized memory use protectionNetwork behaviorOnline identity
A method for analyzing abnormal network behaviors and isolating computer virus attacks comprises network equipments controlled by an automatic program so as to have a serious of processes of a packet analyzing, an identity locking and an instant isolating. By using a network monitoring module or / and a network identity module involved in the automatic program to simultaneously deal with the processes of the packet analyzing and the identity locking, and then by using an automatic locking module also involved in the automatic program to execute the process of the instant isolating, the viruses are appropriately isolated and then antivirus softwares scan the infected computer so as to have a problem solving, thereby obtaining a restoring.
Owner:LIN CHAO YU +2
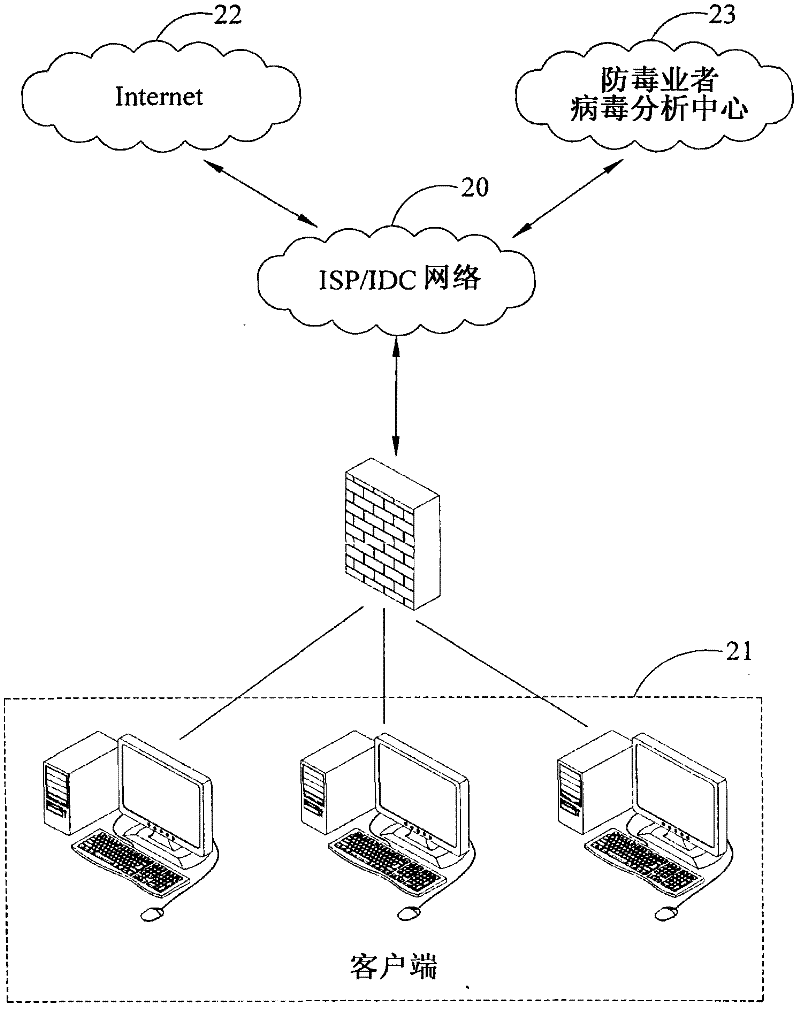
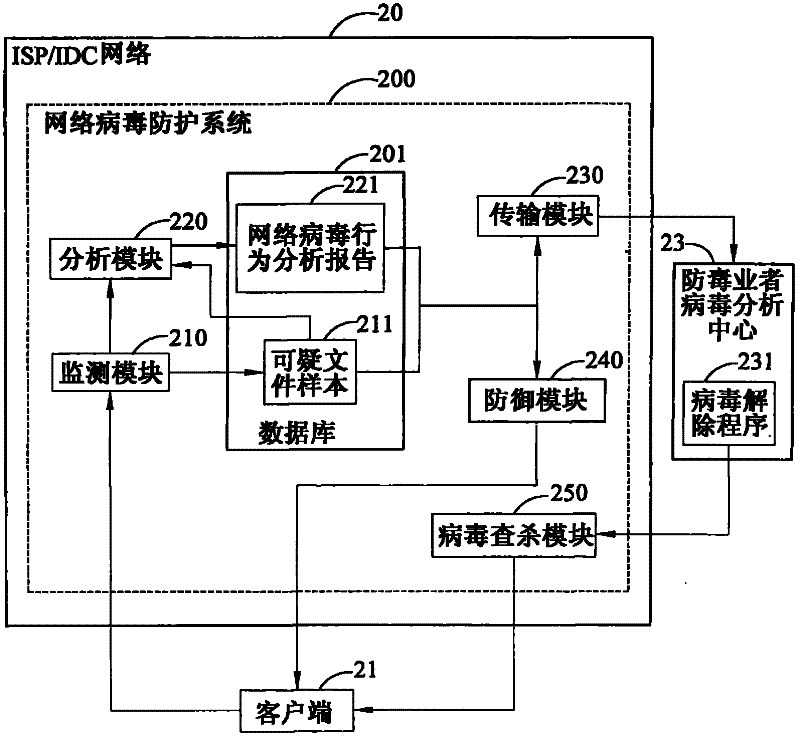
Method and system for defending network virus
InactiveCN102457495AImprove success efficiencyReduce the risk of virus attackTransmissionNetwork communicationClient-side
The invention relates to a method and a system for defending a network virus. The network virus is a botnet virus or a target attacking virus with pertinence to a virus attacking object. The method comprises the following steps: analyzing a network flow of a client and capturing a suspicious file sample when an existing suspicious file is confirmed while detecting the flow of the client during a process of obtaining a network communication service by the client; analyzing if the botnet virus or virus action thereof exists; generating an analysis report for the botnet virus action; transmitting the suspicious file sample and the analysis report to an antivirus operator so as to create a virus removing program; and meanwhile, supplying a network antivirus service to an infected client according to the analysis report and searching and killing the virus after receiving the virus removing program which is sent back. According to the method, when the client which is infected by the virus is detected, defending measures can be taken in real time, thereby efficiently preventing virus diffusion, preventing the infected client from automatically connecting to a malicious website for performing virus variation, and efficiently reducing the risk of the client suffering in a virus attack.
Owner:CHUNGHWA TELECOM CO LTD
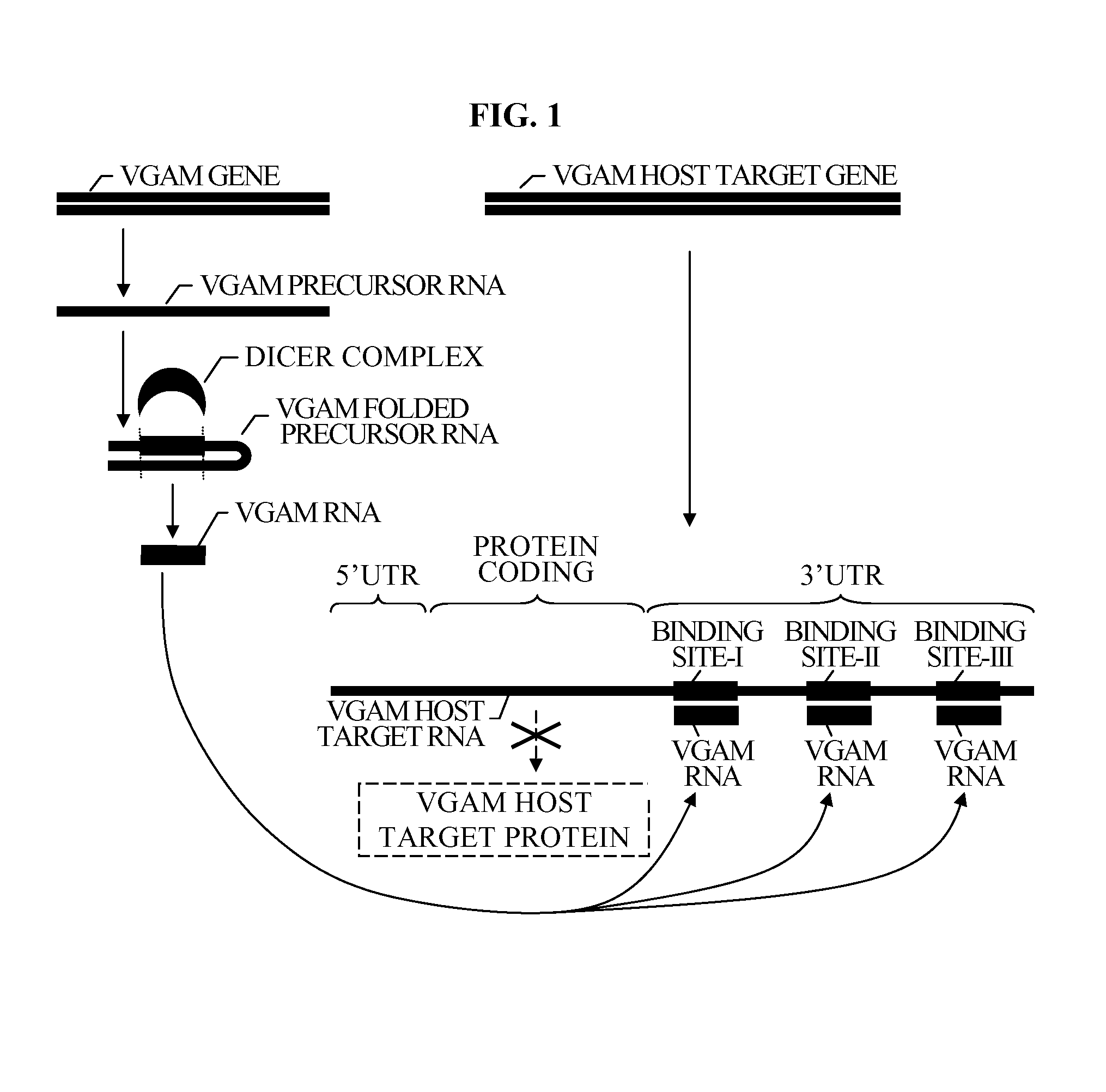
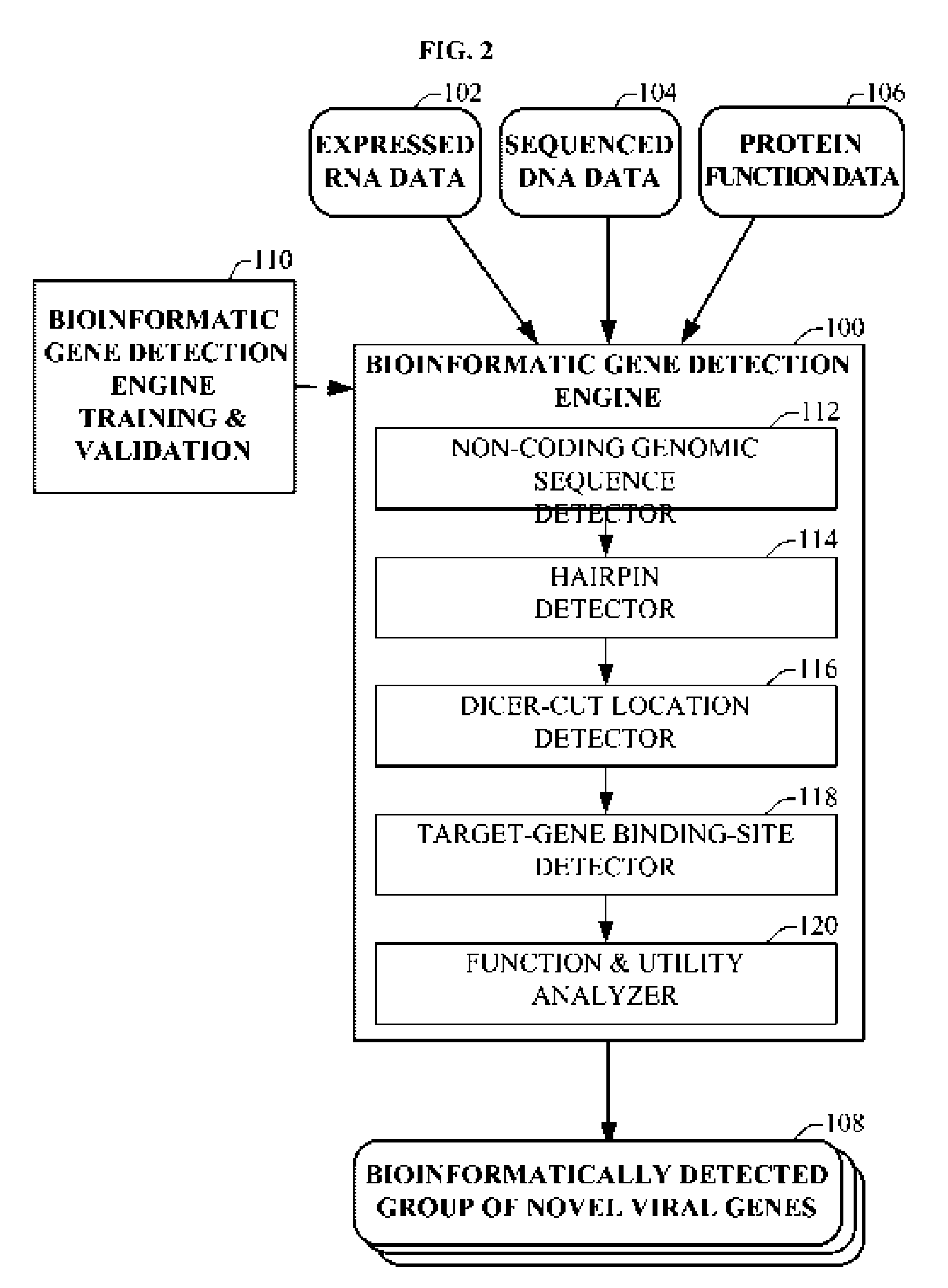
Bioinformatically detectable human herpesvirus 5 regulatory gene
ActiveUS7696334B1Preventing and treating viral diseasesSugar derivativesMicrobiological testing/measurementOperonVirus attack
The present invention relates to a group of novel viral RNA regulatory genes, here identified as “viral genomic address messenger genes” or “VGAM genes”, and as “genomic record” or “GR” genes. VGAM genes selectively inhibit translation of known host target genes, and are believed to represent a novel pervasive viral attack mechanism. GR genes encode an operon-like cluster of VGAM genes. VGAM and viral GR genes may therefore be useful in diagnosing, preventing and treating viral disease. Several nucleic acid molecules are provided respectively encoding several VGAM genes, as are vectors and probes, both comprising the nucleic acid molecules, and methods and systems for detecting VGAM genes, and for counteracting their activity.
Owner:ROSETTA GENOMICS
Lactobacillus plantarum, method for fermenting and preparing bacteriocin of Lactobacillus plantarum, and application of Lactobacillus plantarum and bacteriocin
The invention provides a new Lactobacillus plantarum bacterial strain YJG which was preserved in the China General Microbiological Culture Collection Center (CGNCC) with the collection number of CGMCC No. 2994 on march, 30th, 2009. The Lactobacillus plantarum bacterial strain YJG can produce broad-spectrum bacteriostatic activity bacteriocin with high yield, and can express bacteriostasis for staphylococcus aureus, salmonella and E.coli of gram-negative bacterium, L. plantarum, L.brevis, Streptococcus and Bacillus of gram-positive bacterium, and the like. A virus attacking tests with high dosage proves that the Lactobacillus plantarum bacterial strain YJG is safe to animal bodies. The Lactobacillus plantarum bacterial strain YJG and a zymophyte liquid thereof can be used for preparing additives of green animal feeds, and the bacteriocin of the Lactobacillus plantarum bacterial strain YJG can be used for preparing green biological veterinary drugs, environmental-friendly biopreservatives, biocontrol drugs and the like.
Owner:CHINA AGRI UNIV
Device and method for mobile telephone system recovery
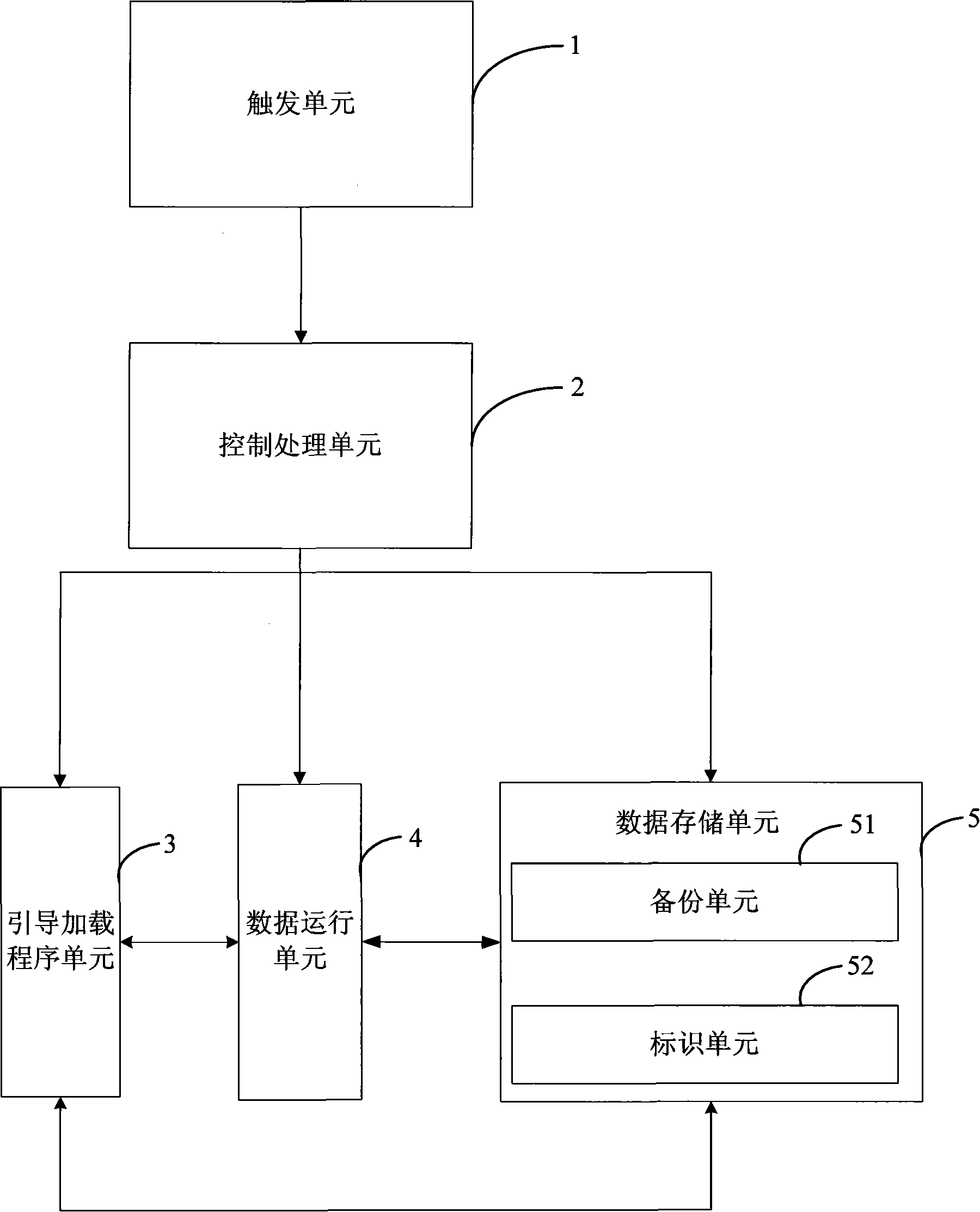
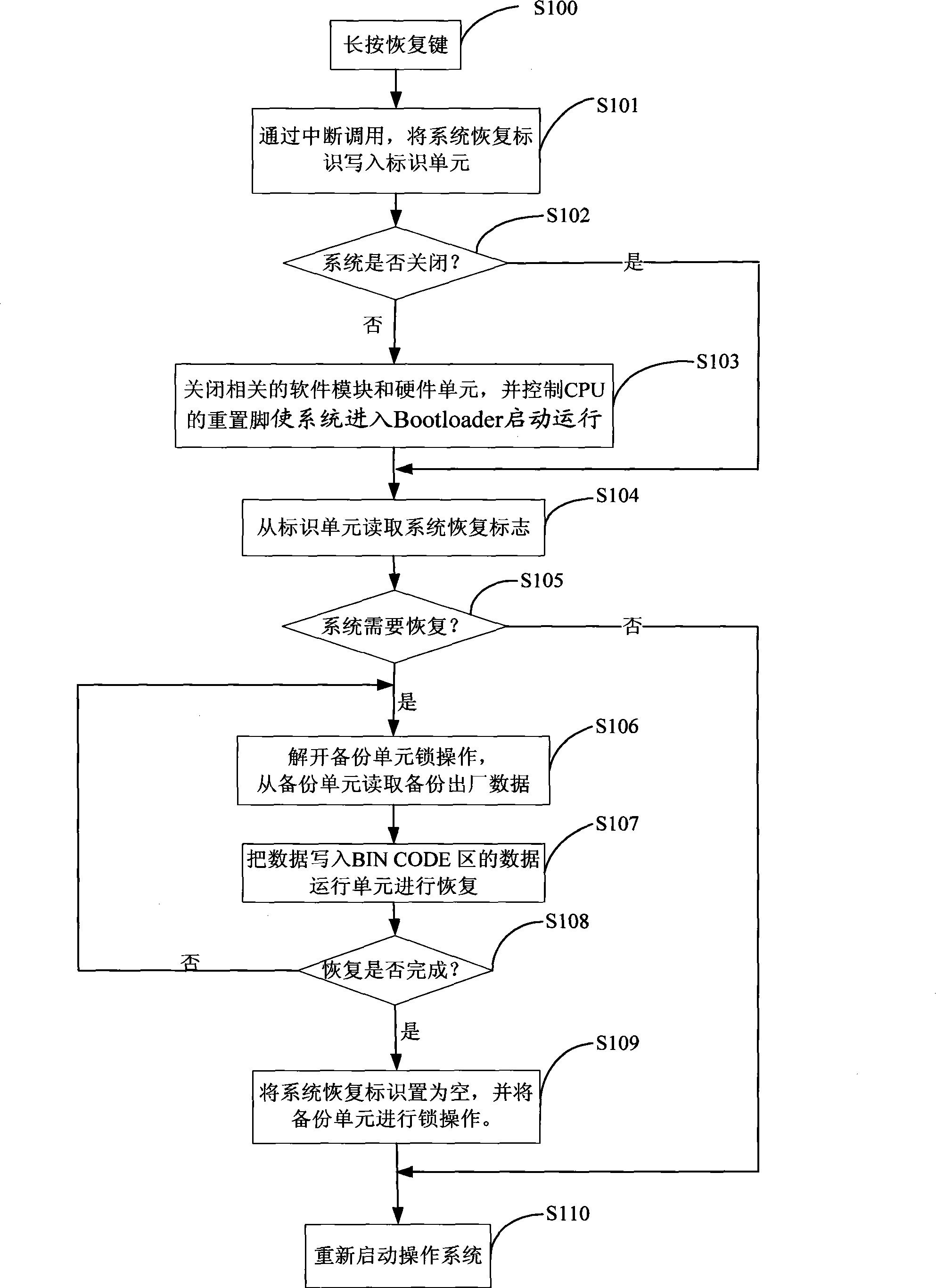
InactiveCN101251813AReduce maintenance costsImprove usabilityRadio/inductive link selection arrangementsProgram loading/initiatingData operationsSystem recovery
The invention provides a mobile phone system recovery device which comprises a trigger unit, a program conducting and loading unit, a data storage unit, a data operation unit and a control processing unit. After the control processing unit receives a system recovery instruction sent by the trigger unit, the data in the data storage unit is written to the data operation unit for carrying out system recovery operation; a program in the program conducting and loading unit is transferred to complete the initialization and reboot of the system. The invention also provides a mobile phone system recovery method. When the mobile phone meets virus attack or certain special situations which cause that a mobile phone system is damaged and can not normally operate, the embodiment of the invention is implemented and a user can recover the initial system in time without needing other auxiliary equipment, thereby effectively reducing the maintenance cost of the mobile phone and improving the accessibility of the system.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Mobile phone virtus examining and protecting method and system based on base station
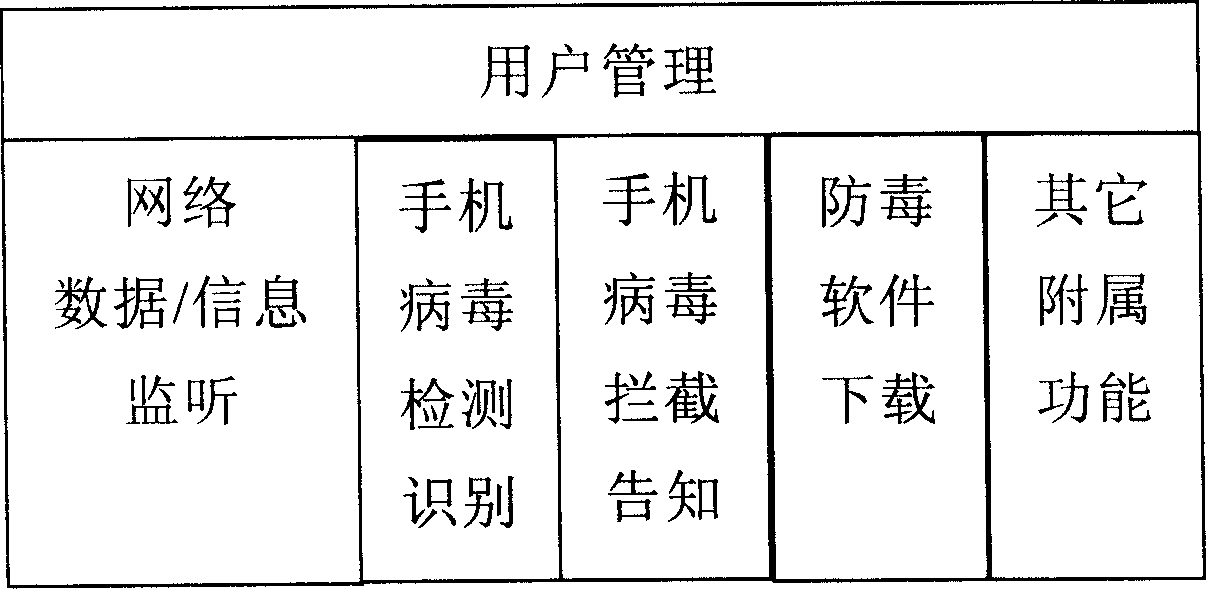
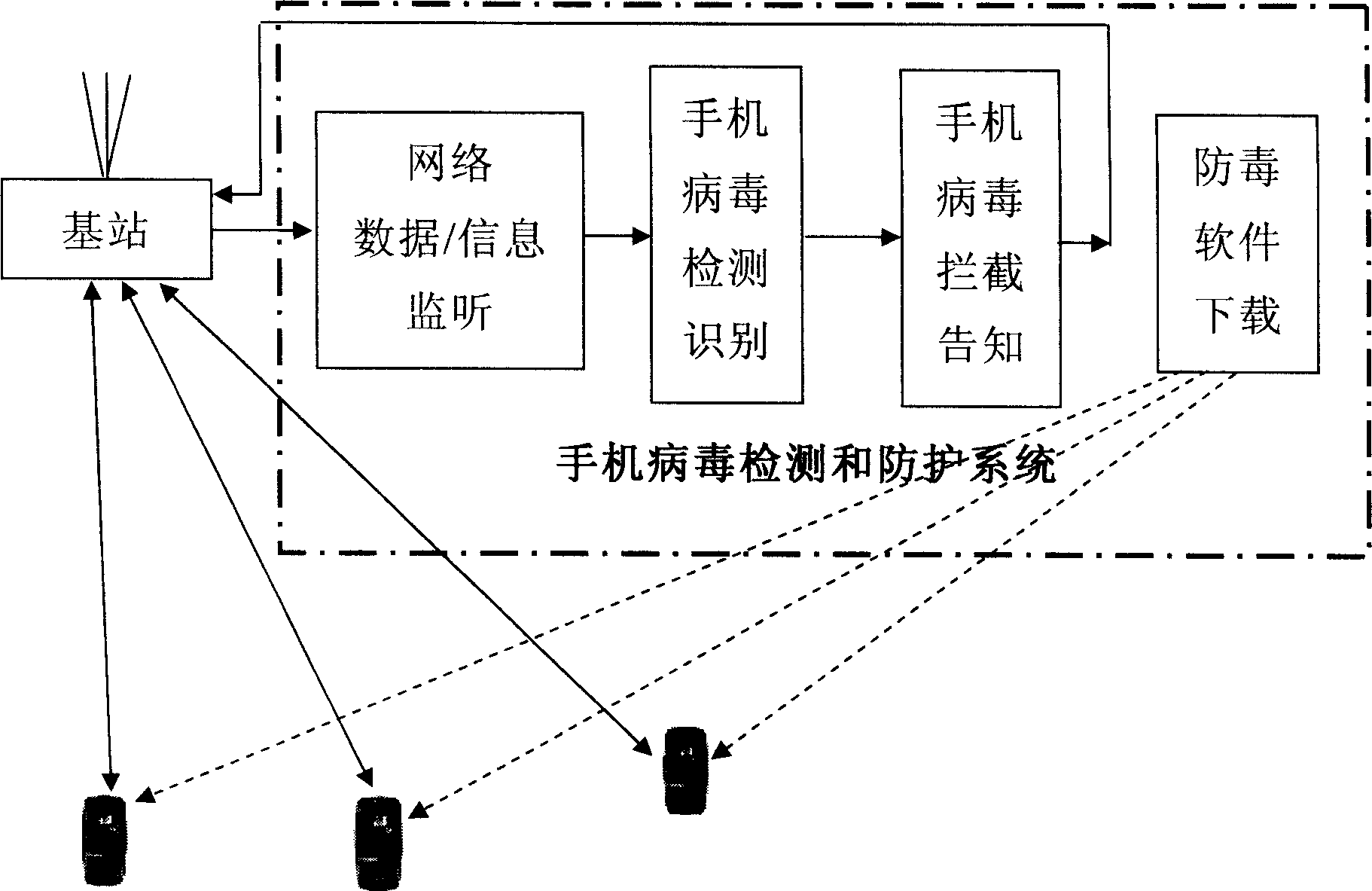
InactiveCN1889773AExpand business scopeInfringement of legitimate interestsRadio/inductive link selection arrangementsTransmissionThe InternetMobile phone
A detecting and protecting method of mobile phone virus based on base station includes utilizing server of base station to carry out detection and protection of mobile phone virus for cutting off propagation path of mobile phone virus, enabling mobile phone to directly download antivirus software without computer an Internet for effectively protecting mobile phone from virus attack under any condition.
Owner:毛兴鹏
Monitoring electronic mail message digests
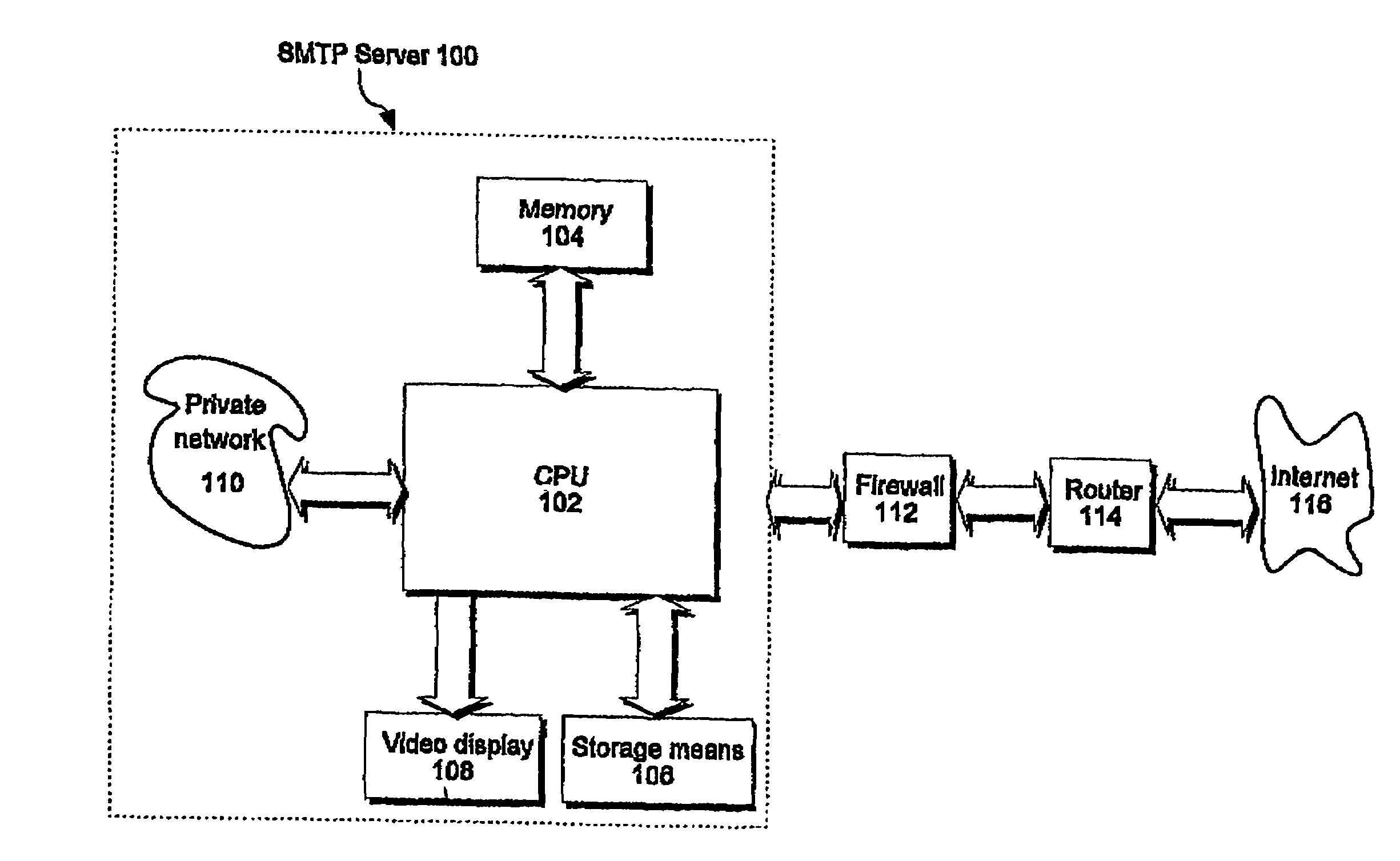
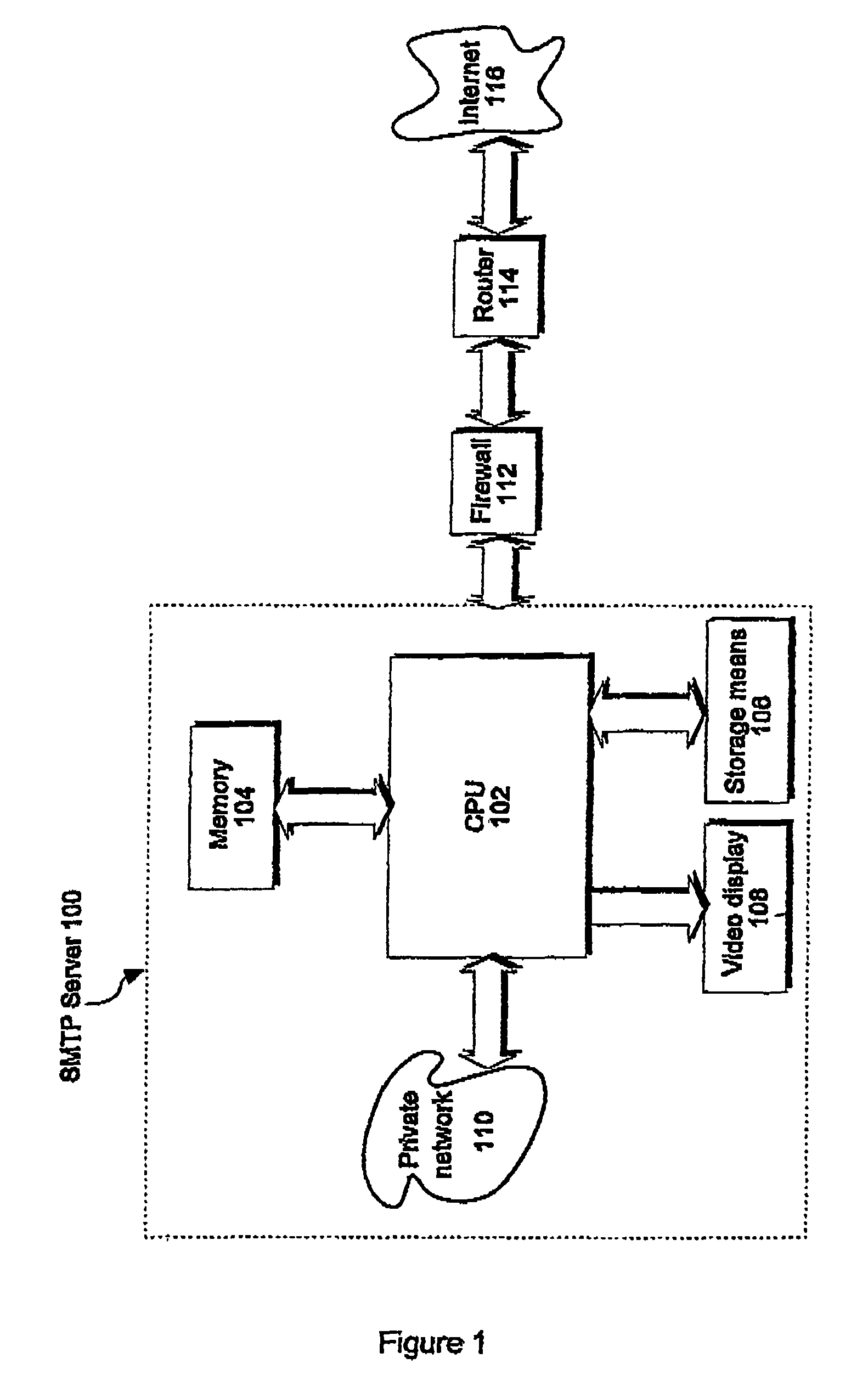
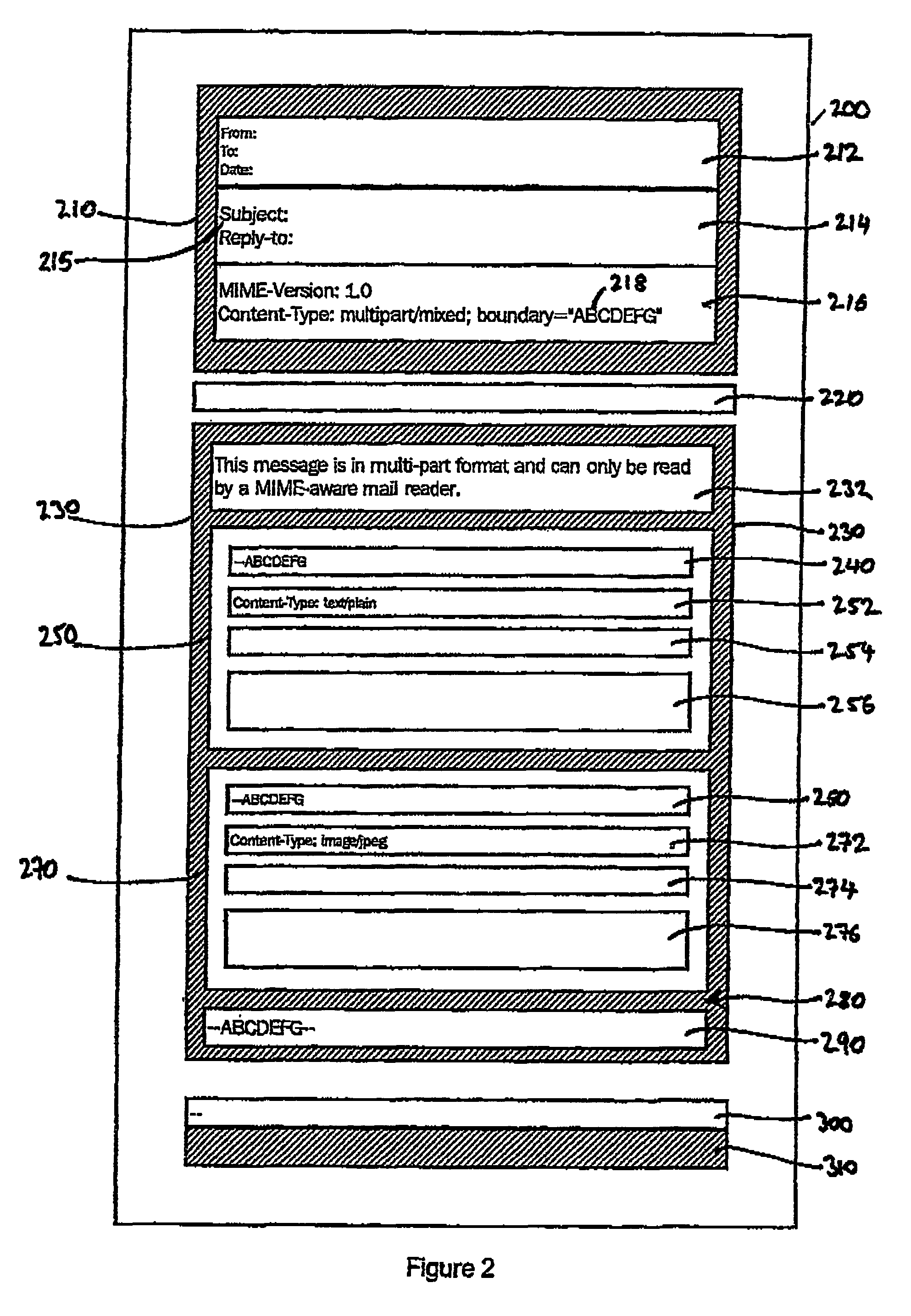
ActiveUS7801960B2Automatically and efficiently identifyingReduce data volumeData processing applicationsDigital data processing detailsTimestampThe Internet
A method for monitoring electronic mail messages, each mail message comprising header information and a main body, particularly for protection against virus attacks and unsolicited commercial email (UCE). The method comprises generating a summary digest of only the subject line and the message content of the main body, wherein the message content may comprise textual content and / or attached files. The generated summary digest is stored in a memory, and compared with existing summary digests stored in memory. If the number of matches exceeds a threshold value, an alert signal is raised and appropriate action initiated. A timestamp may be stored with each summary digest, together with sender / recipient details and the internet protocol (IP) address of origin, to aid detection of the originator of the message.
Owner:CLEARSWIFT
Method for distinguishing baleful program behavior
InactiveCN1801030AAccurate checkFree from attackDigital data processing detailsUnknown procedureProgram behavior
The invention discloses a specification method of harmful program based on the virus attack identification base of state movement set, which comprises the following steps: 1.1) monitoring and recording the movement behavior of unknown program; 1.2) integrating the recorded program to compare with the virus identification regular base; 1.3) judging the compared result whether the result is harmful program behavior; alarming or stopping the operation of program if yes; continuing operating and returning to the step 1.1) if not. The invention analyses the unknown program behavior without depending virus code, which improves the efficiency and precision.
Owner:MICROPOINT WISDOM (BEIJING) INFORMATION SECURITY TECH CO LTD
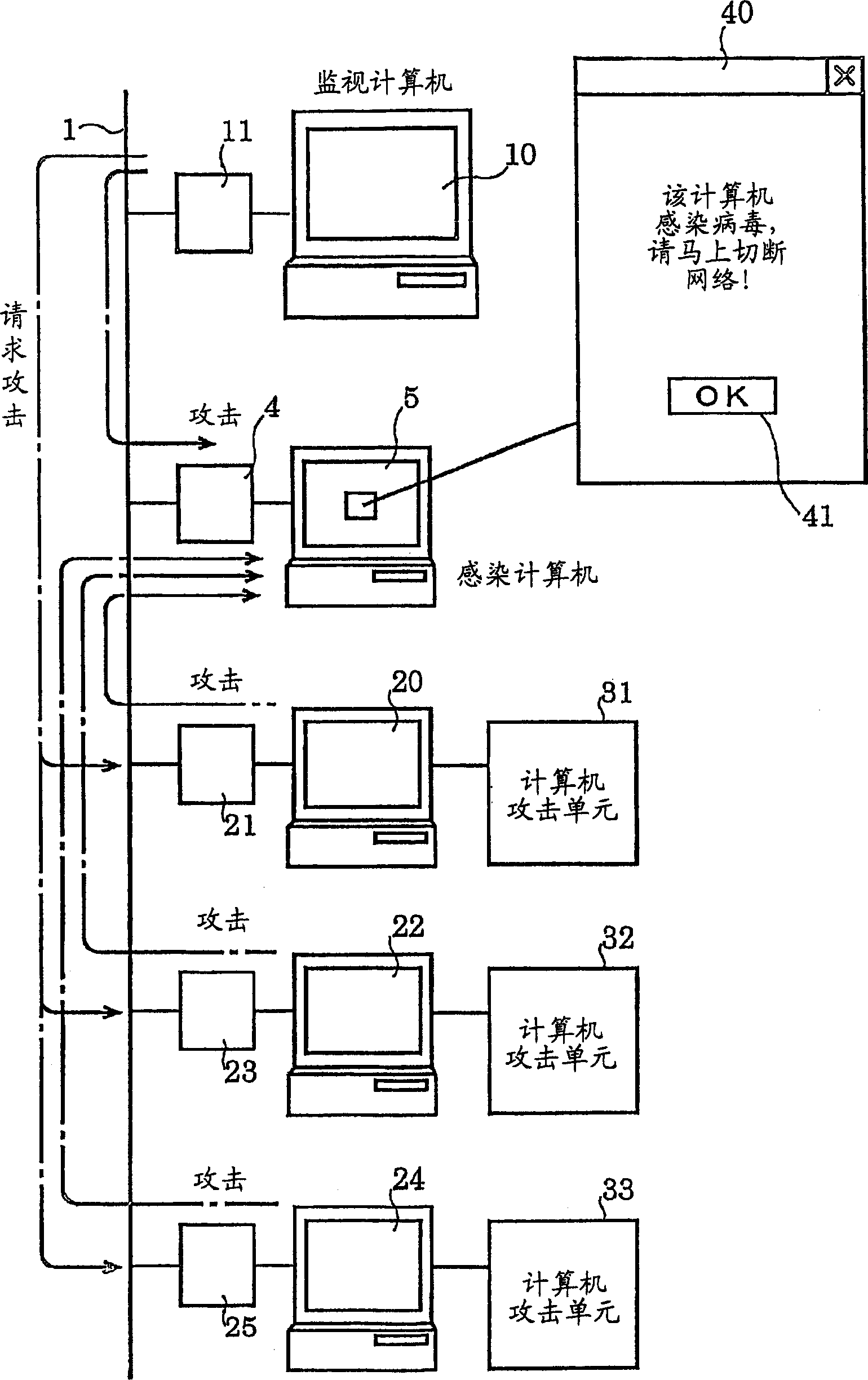
System and method for booting alternate MBR in event of virus attack
ActiveUS7757112B2Error detection/correctionDigital computer detailsHard disc driveOperational system
In the event of a virally infected MBR on a hard disk drive that might prevent booting, a service MBR in a hidden protected area (HPA) can be used to boot a service O.S., and then the service MBR can be replaced with a previously backed-up MBR, also in the HPA, to mount any missing partitions.
Owner:LENOVO PC INT
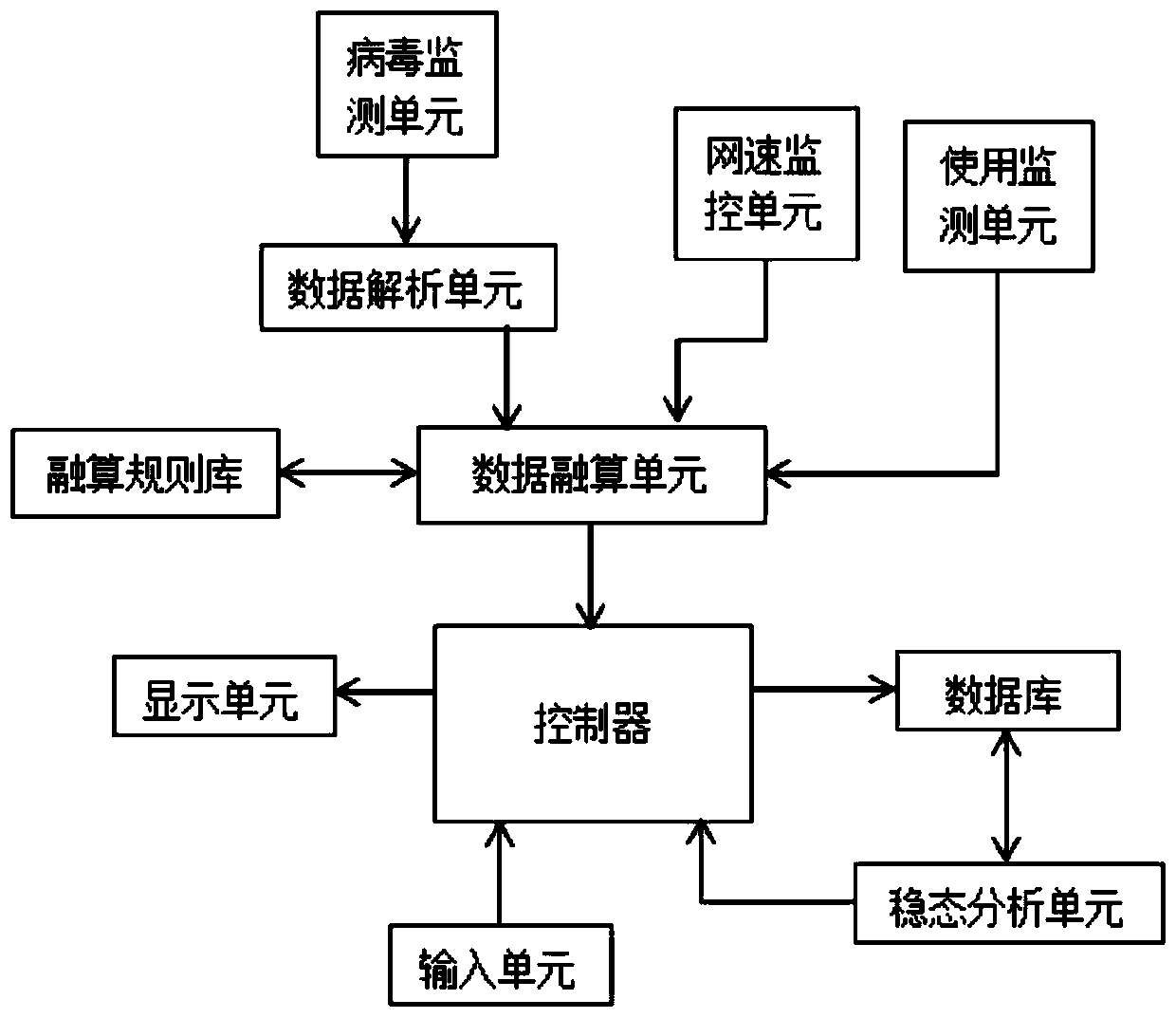
Industrial control system network security situation sensing system based on artificial intelligence
ActiveCN110716476AMonitor usage in real timePractical and convenientProgramme controlComputer controlThe InternetCell controller
The invention discloses an industrial control system network security situation sensing system based on artificial intelligence. The system comprises a virus monitoring unit, a data parsing unit, a data fusion and calculation unit, a fusion and calculation rule library, an Internet speed monitoring unit, a usage monitoring unit, a controller, a display unit, a database, an input unit and a steady-state analysis unit. In the system provided by the invention, a virus attack attacking the system is analyzed and judged through the virus monitoring unit and the data parsing unit; then, real-time Internet speed of a security network is monitored and analyzed through the Internet speed monitoring unit, and a steady-state valve group of the Internet speed is obtained; meanwhile, usage rate of a CPU is monitored in real time through the monitoring unit; then, comprehensive analysis is executed in combination with latest virus attack frequency, the steady-state valve group and the real-time usage rate, thus, an evaluation signal is obtained, and different evaluation signals are transmitted to the database for storage.
Owner:珠海市鸿瑞信息技术股份有限公司
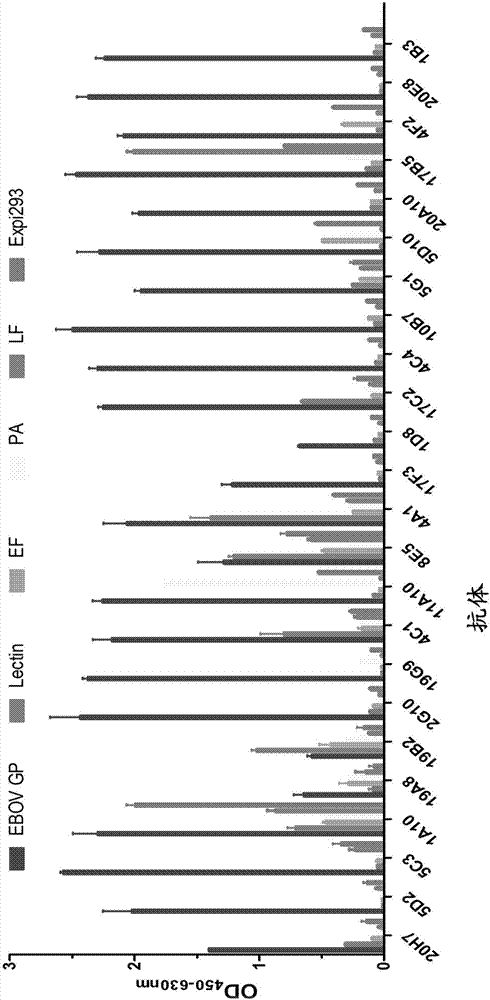
Monoclonal antibody of human anti-Ebola virus envelope glycoprotein, and application thereof
ActiveCN107033242AAct as an infectionHigh activityImmunoglobulins against virusesAntiviralsNPC1Glycan
The invention discloses a monoclonal antibody of a human anti-Ebola virus envelope glycoprotein GP. The antibody has a unique CDR region and has a unique action site. Computer simulation analysis and biological experiments confirm that the antibody acts on the NPC1 receptor binding region of the GP, and also acts on the glycan cap region of the GP, so the antibody plays a role in the anti-Ebola virus infection through the unique neutralizing mechanism formed by the combined action of the antibody on the two structural domains of the GP. The antibody has high antigen binding activity and neutralizing activity, can protect 50% of virus attacked cells just at dose of 0.3 [mu]g / ml, and has a protection rate reaching 100% at an antibody concentration of 100 [mu]g / ml, so the antibody provided by the invention has a wide application prospect in the preparation of Ebola virus disease treatment medicines.
Owner:INST OF BIOENG ACAD OF MILITARY MEDICAL SCI OF THE CHINESE
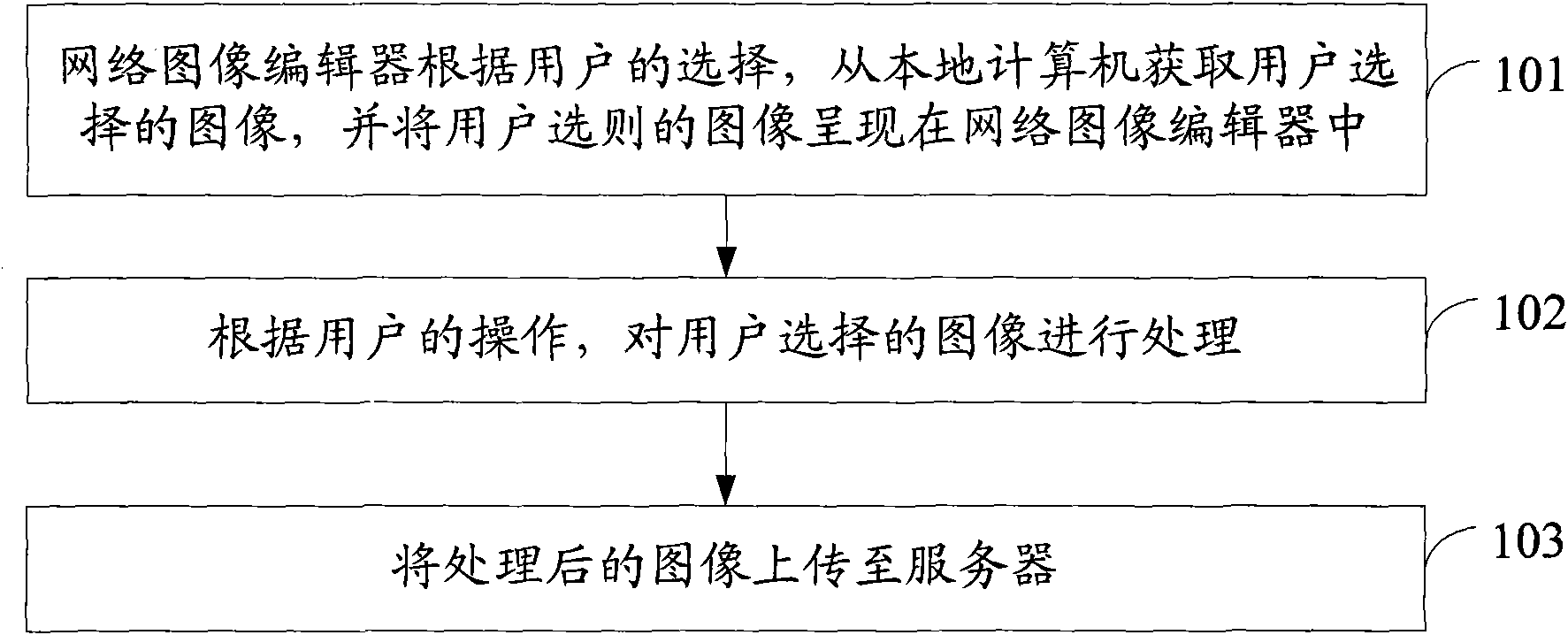
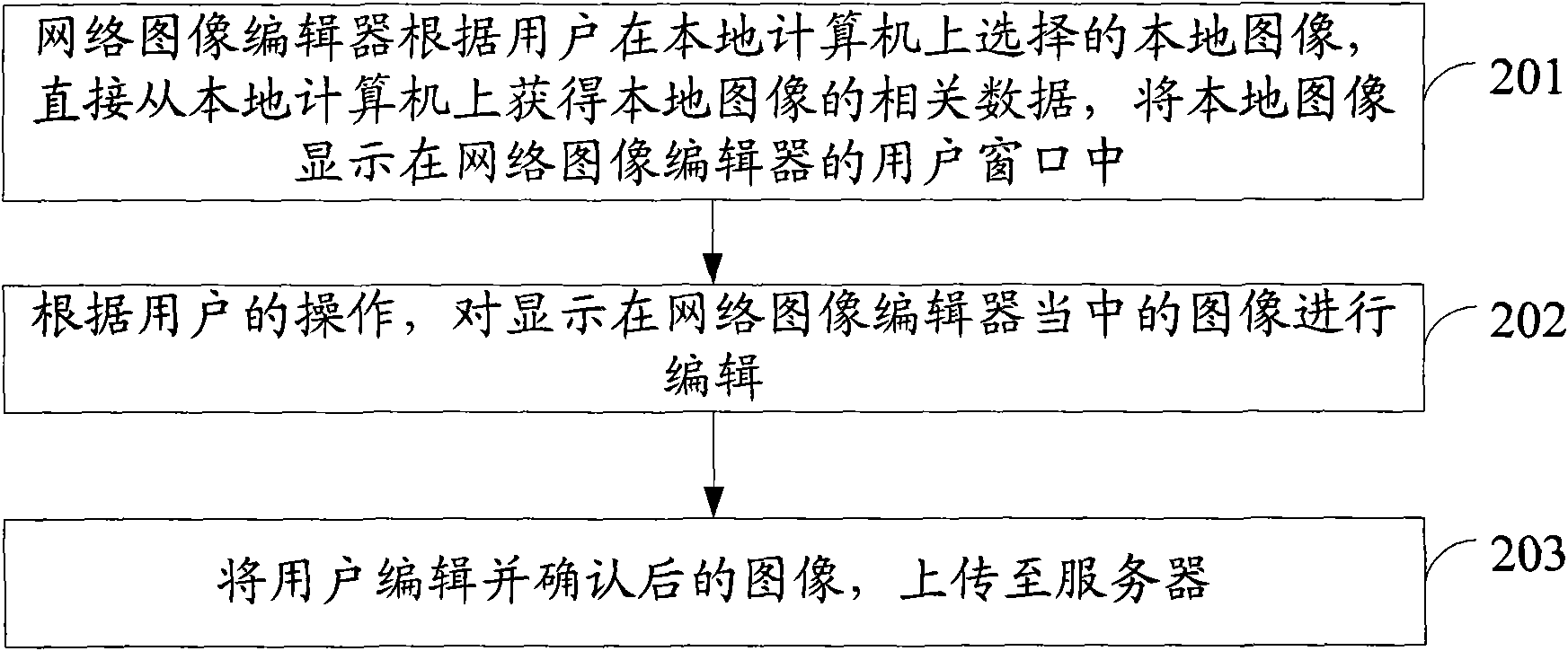
An image processing method and device
InactiveCN101551915ASave storage resourcesWill not be attackedSpecial data processing applicationsEditing/combining figures or textImaging processingProcess module
The invention discloses a kind of image processing method and device. The described method includes: web image editor based on the user's choice, to obtain the image selected by the user from the local computer, and present the selected image in the web image editor; process the selected image according to the user's operations; and upload the processed image to the server. The described device includes: access module, display module, processing module and uploading module. The invention directly reads the local image through the network image editor and edits the image and then uploads the confirmed image to the server which does not need to upload files to the server and download and may save network resources and server storage resources. At the same time, it can also ensure that the local computer will not be under virus attack during the process of reading the local image.
Owner:TENCENT DIGITAL TIANJIN
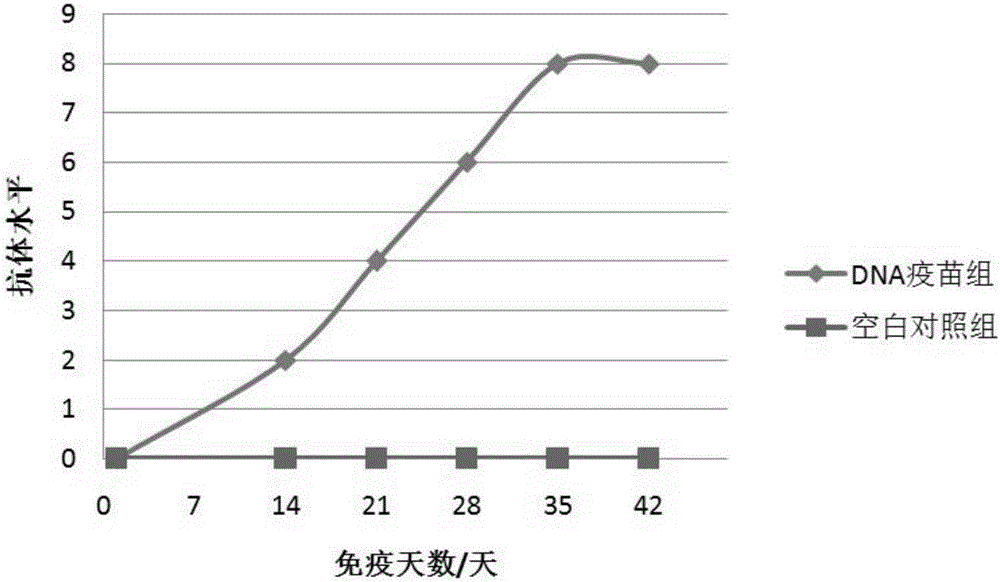
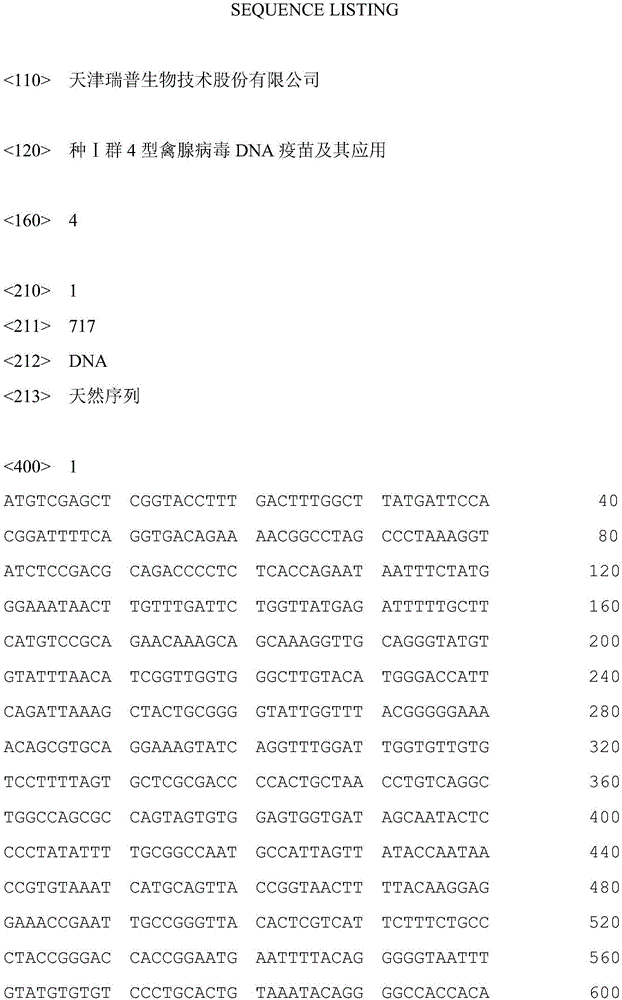
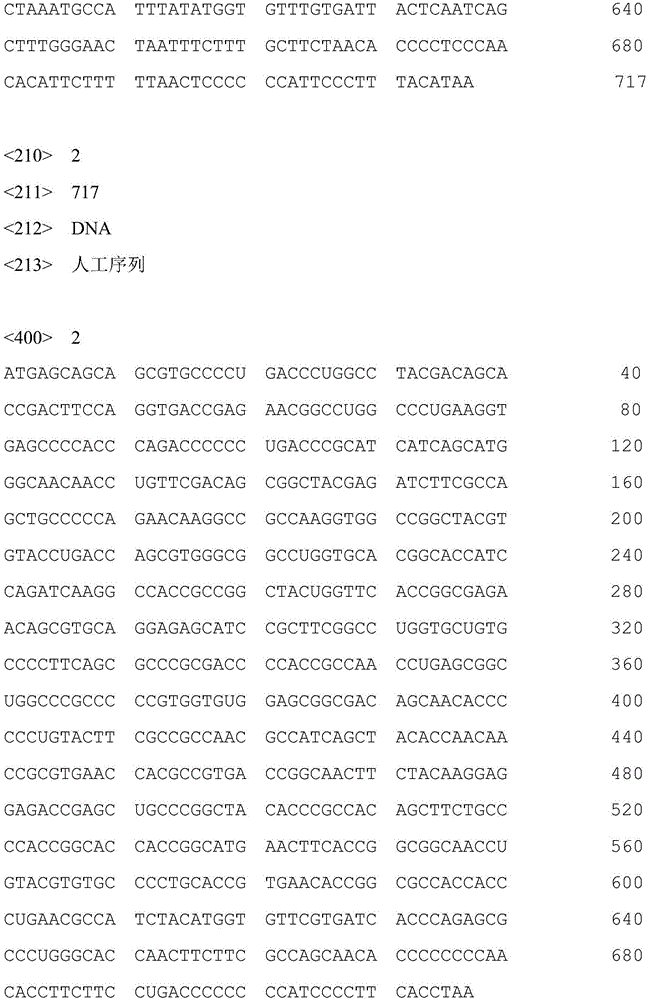
I-group 4-type fowl adenovirus DNA vaccine and application thereof
InactiveCN106729694AEffective immune protectionGood prospects for commercial developmentDigestive systemAntiviralsFiberRecombinant vaccines
The invention provides an I-group 4-type fowl adenovirus DNA vaccine and application thereof. According to the technical scheme, based on experimental means, research finds and shows that fiber protrusions have good immunity prototypes, in this way, with 4-type fowl adenovirus fibrous protein C-terminal genes being antigen substances, codon optimization is carried out on the basis of a natural sequence, an eukaryotic expression vector pCAGGS is cloned, and the DNA vaccine pCAGoptiFAV4C is constructed. According to the researched fowl adenovirus NDA vaccine, a method of gene engineering fermentation is adopted for preparing antigens, and therefore the I-group 4-type fowl adenovirus DNA vaccine is low in cost, pure in antigen and safe to use. By the utilization of a serology method and an immunity virus attack method, the immunity effect of the vaccine is evaluated. The result shows that the vaccine can provide effective immune protection for fowl, and has good commercial development prospects. Compared with a traditional vaccine, the DNA vaccine achieves the safety of subunit vaccines and inactivated vaccines, and also has the features of simultaneous induction of humoral immunity and cellular immune response, wherein the features only belong to attenuated vaccines or recombinant vaccines.
Owner:TIANJIN RINGPU BIO TECH
System and method for guiding standby MBR during virus attack
InactiveCN101046752AEasy to understandError detection/correctionPlatform integrity maintainanceHard disc driveVirus
Owner:LENOVO (SINGAPORE) PTE LTD
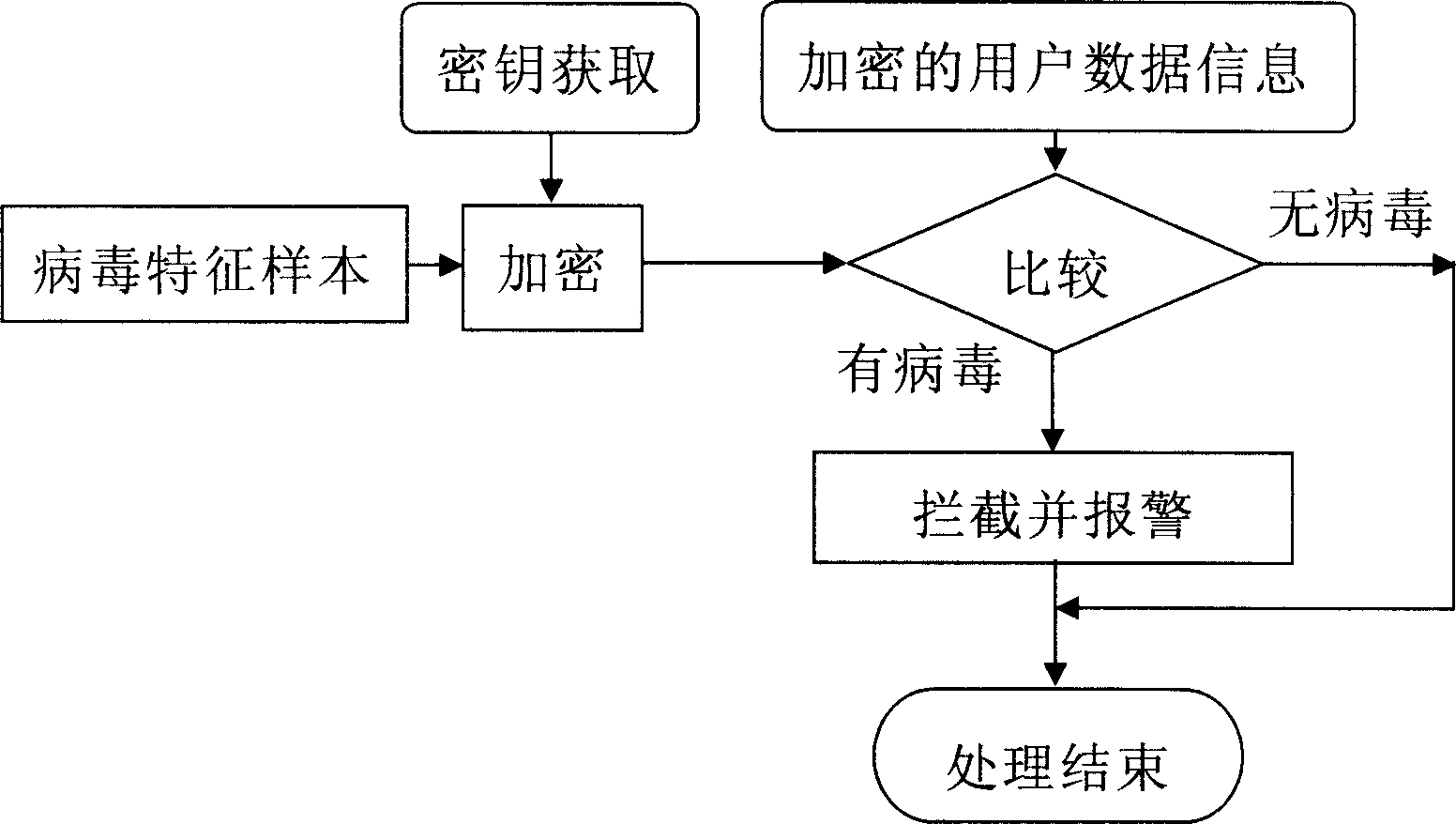
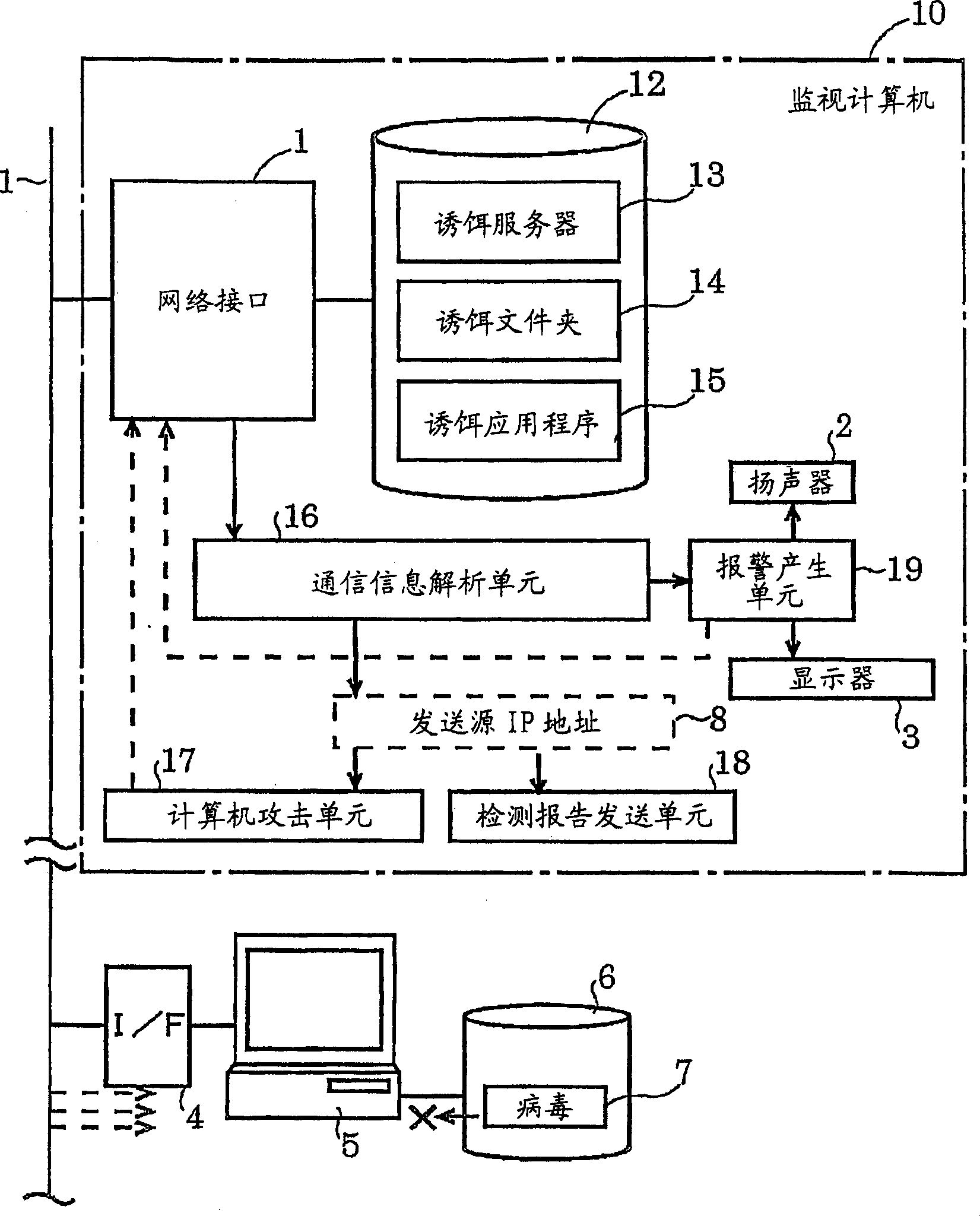
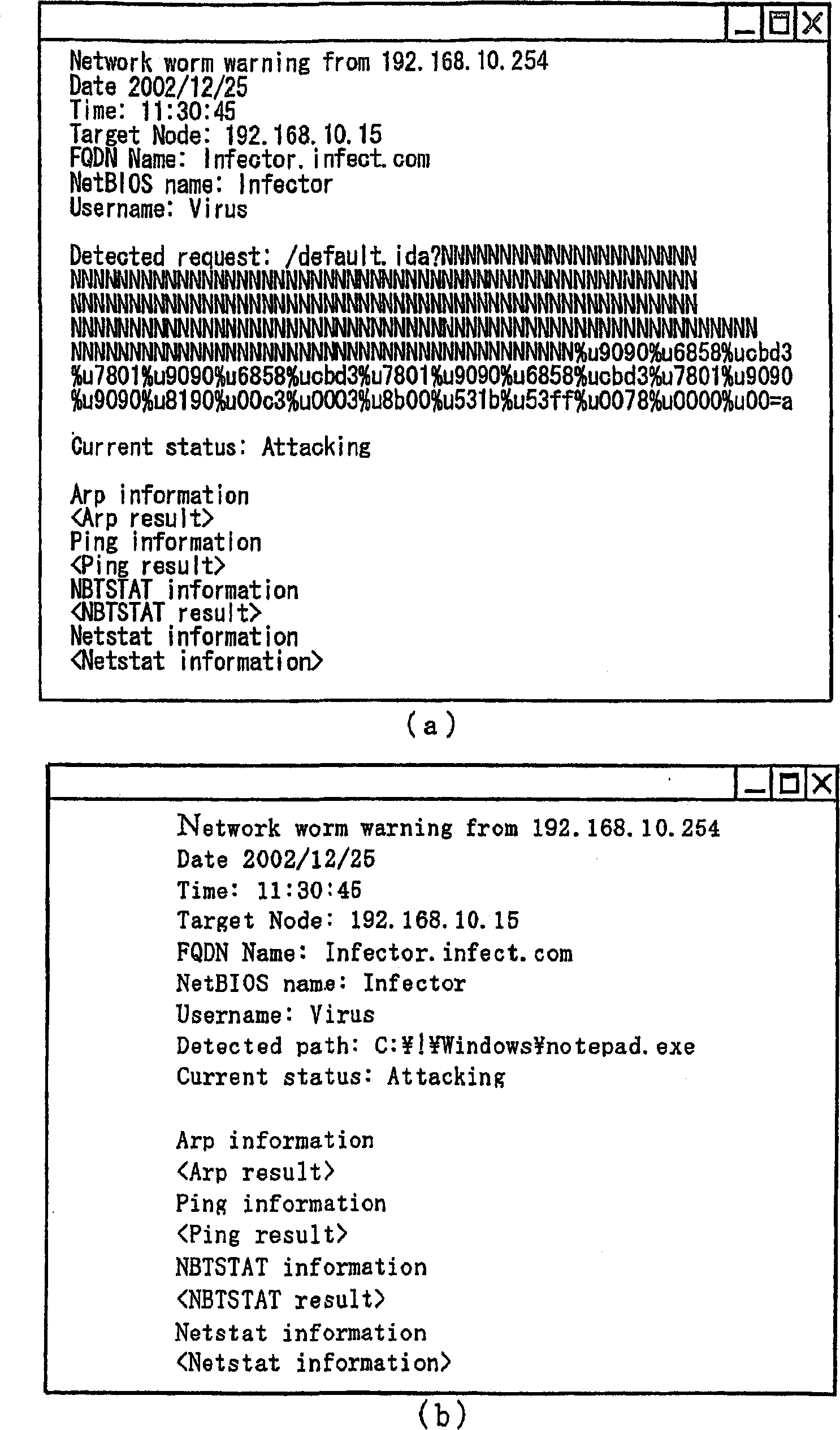
Method and system for preventing virus infection
InactiveCN1761939ATechnology to stop damage from spreadingProgram control using stored programsDigital computer detailsInformation analysisCountermeasure
There is disclosed a system for detecting virus infection in a network and preventing the virus infection. Decoy means (13, 14, 15) accessible via the network (1) are arranged on a storage device (12). The system includes: communication information analysis means (16) for detecting virus intrusion into the decoy means (13, 14, 15) and upon detection of the virus intrusion, detecting a computer as a source of the virus from the communication information acquired upon the virus intrusion; and computer attack means (17) for performing virus attack process to the virus source computer for suppressing action of the virus via the network. Attack of the computer attack means (17) by a monitoring computer (10) is continued until a computer (5) infected with virus is identified and the virus is removed by an administrator.
Owner:SEIKO EPSON CORP
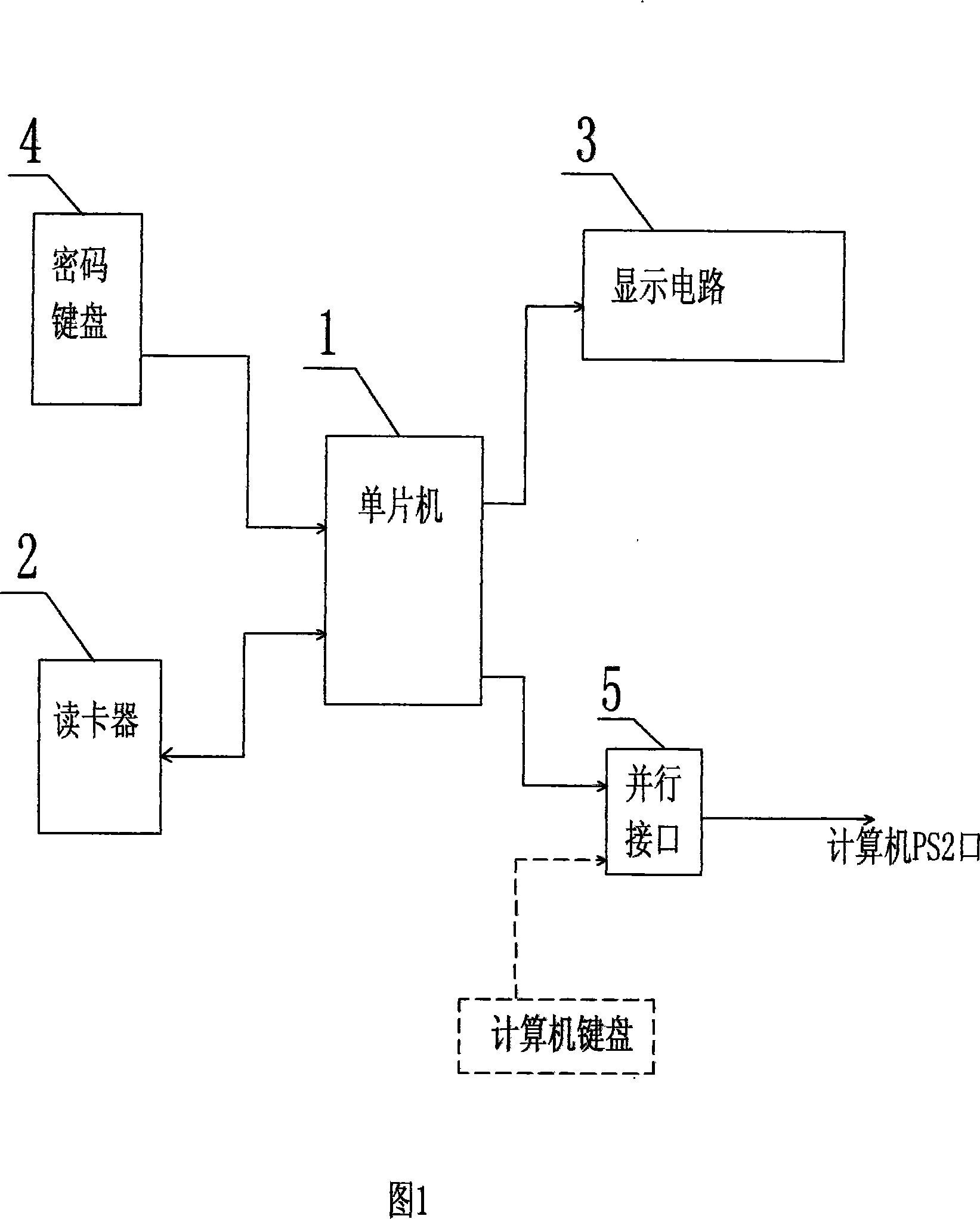
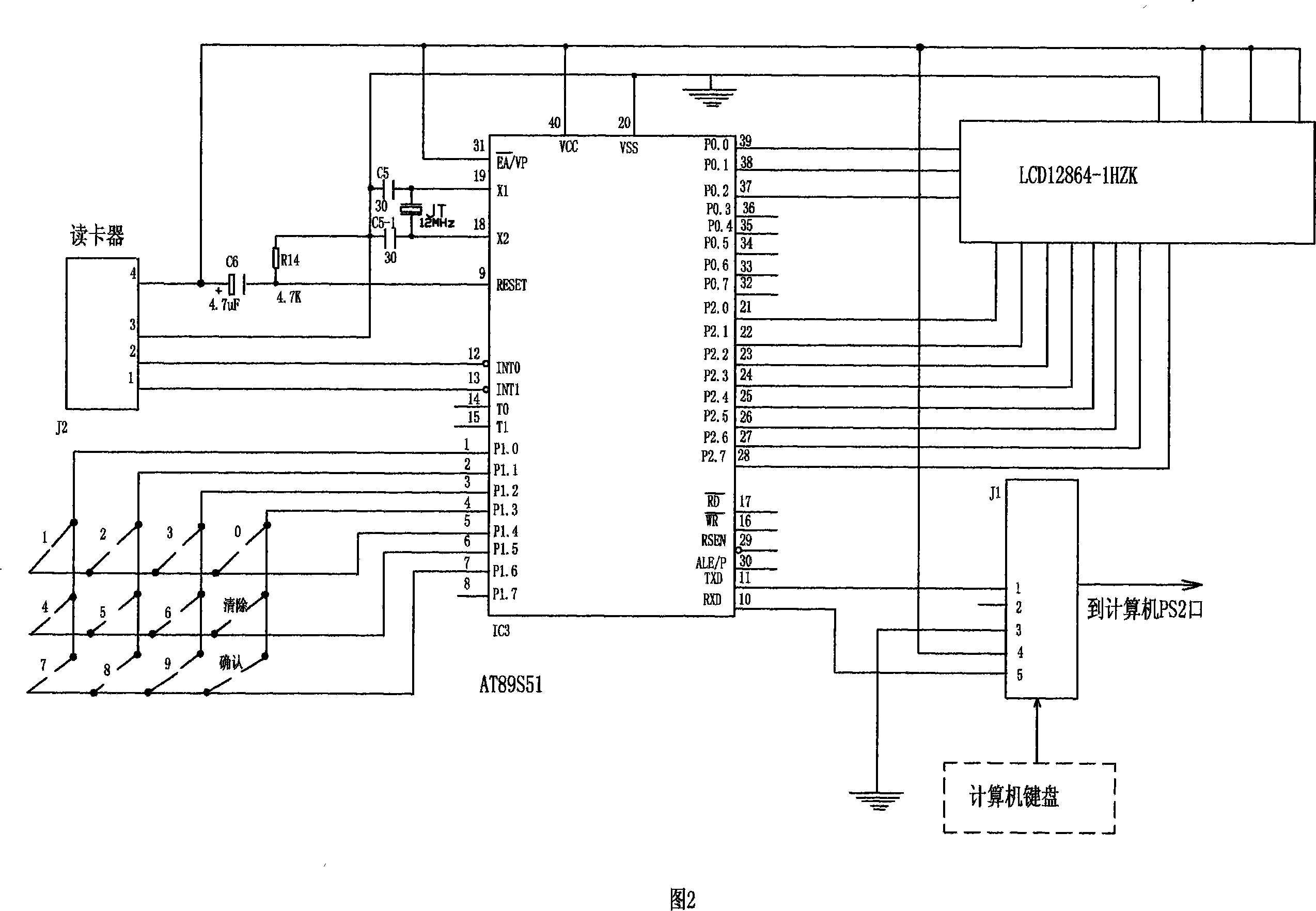
Method and device for encrypting network user password
InactiveCN101098223AEnsure safetyEasy to carrySynchronising transmission/receiving encryption devicesMicrocontrollerPassword
A method for encrypting network user password and a relative device, belong to computer network application safety technique field, for effectively protecting personal password from virus attack. The inventive method comprises that (1), operator sends user memory card and user password with private key in a server database to user, (2), when user accesses, server provides a random encrypted code when requests user to input password, (3), user inserts the memory card into an encrypt device, to input user password and the random encrypt code, to process private password encrypt via the encrypt device, to obtain a new encrypt password to be input into computer, (4), the server receives the private key stored in the database to decrypt data, compares user password and the random encrypt code to pass the password check or not. The encrypt device comprises a single chip, a card reader, and a display screen. The invention can protect personal password via encrypt in computer network.
Owner:李江
Mink viral enteritis and canine distemper binary living vaccine as well as preparation method and application thereof
The invention discloses a mink viral enteritis and canine distemper binary living vaccine as well as a preparation method and application thereof. The effective components of the binary living vaccine comprise a mink viral enteritis virus (MEV) antigen and a canine distemper virus (CDV) antigen, wherein the MEV antigen is a JLM strain and has the collection number of CGMCC No. 9904, and the CDV antigen is a JTM strain and has the collection number of CGMCC No. 9905. Researches on the humoral immunity, the immunizing and virus attacking protection level and the pathologic change show that the JLM strain and the JTM strain are free from mutual immunity interference. The safety and effect of the binary living vaccine are researched further accordingly, and the research result shows that the binary living vaccine is safe to use and is not lower than the unitary living vaccine in effect.
Owner:华威特(江苏)生物制药有限公司
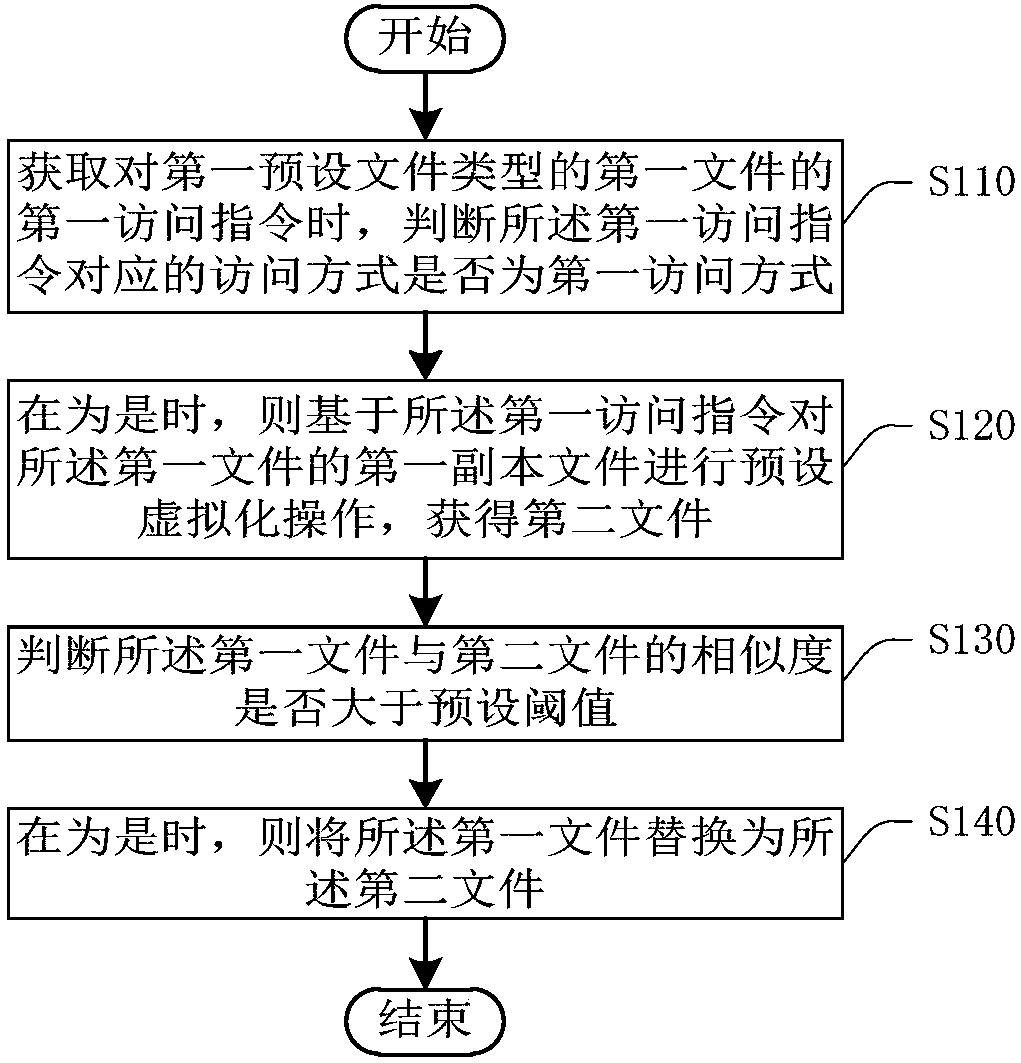
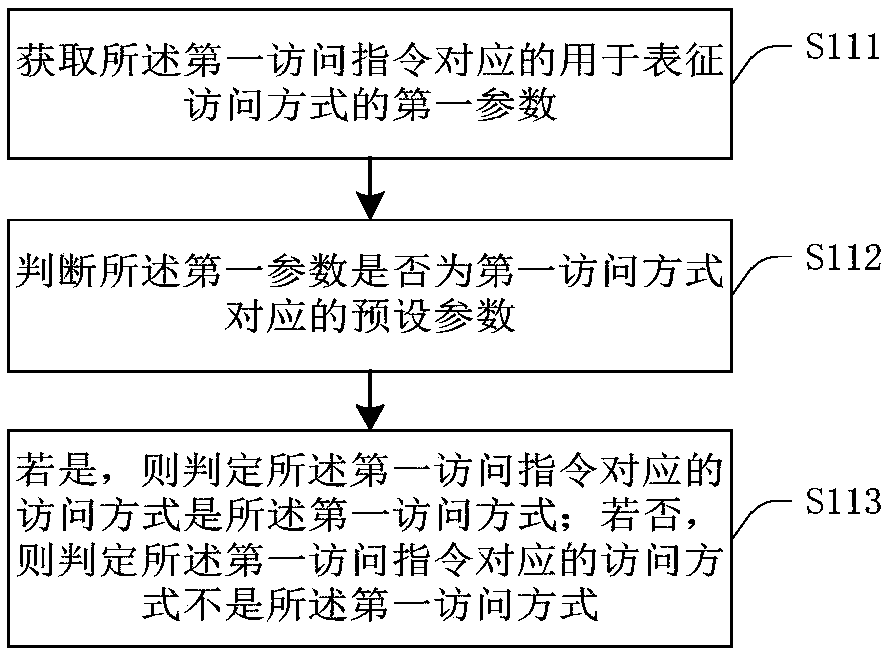
File protection method and device
ActiveCN107871089ARealize active protectionSettle the lossDigital data protectionVirtualizationRansomware
The invention provides a file protection method and device, and relates to the technical field of computers. The file protection method comprises the following steps of: when a first access instruction for a first file in a first preset file type is obtained, judging whether an access manner corresponding to the first access instruction is a first access manner or not; when the judging result is positive, carrying out a preset virtualization operation on a first copy file of the first file on the basis of the firs access instruction so as to obtain a second file; judging whether a similarity between the first file and the second file is greater than a preset threshold value or not; and when the similarity is greater than the preset threshold value, replacing the first file by the second file. Aiming at the manner of attacking files by ransomware, the file protection method is capable of defensing behaviors and features of the ransomware in an active manner, so as to prevent the ransomware from attacking the files in an encryption form and the like, and avoid the loss caused by virus attack.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
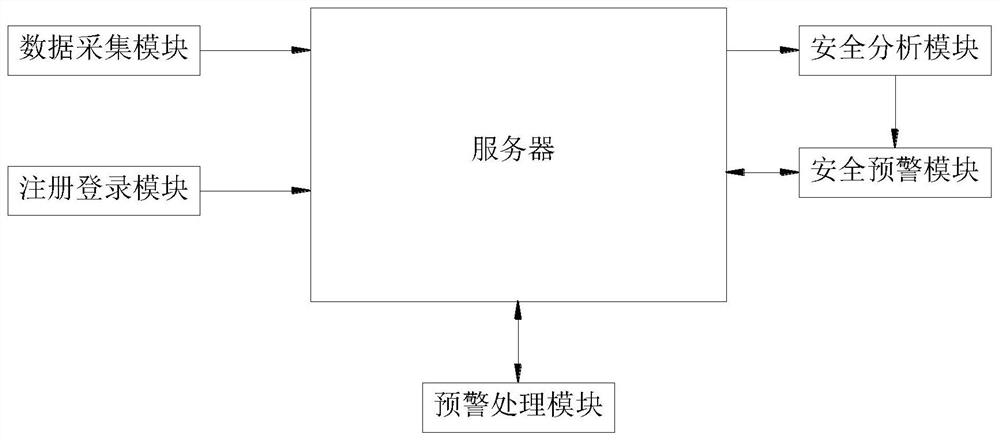
System construction method and device for industrial control system safety detection and early warning
The invention discloses a system construction method and device for industrial control system safety detection and early warning. The system is used for solving the problems that an existing industrial control system safety detection system cannot carry out safety analysis and early warning according to the temperature information of the industrial control equipment, the time when the industrial control equipment is attacked by an virus and the total number of times, and the early warning industrial control equipment cannot be reasonably distributed to corresponding technicians for early warning processing. A data acquisition module acquires industrial control information of industrial control equipment in an industrial control system and sends the industrial control information to a server; a safety analysis module performs safety analysis on the industrial control information; a safety early warning module carries out early warning processing on the industrial control early warning instruction, the industrial control temperature early warning instruction, the industrial control temperature attack early warning instruction and the industrial control attack early warning instruction, carries out safety analysis on industrial control equipment in the industrial control system and reasonably distributes the information to corresponding selected early warning personnel for processing, thereby improving the in-time early warning processing in the industrial control equipment.
Owner:贵州航天云网科技有限公司
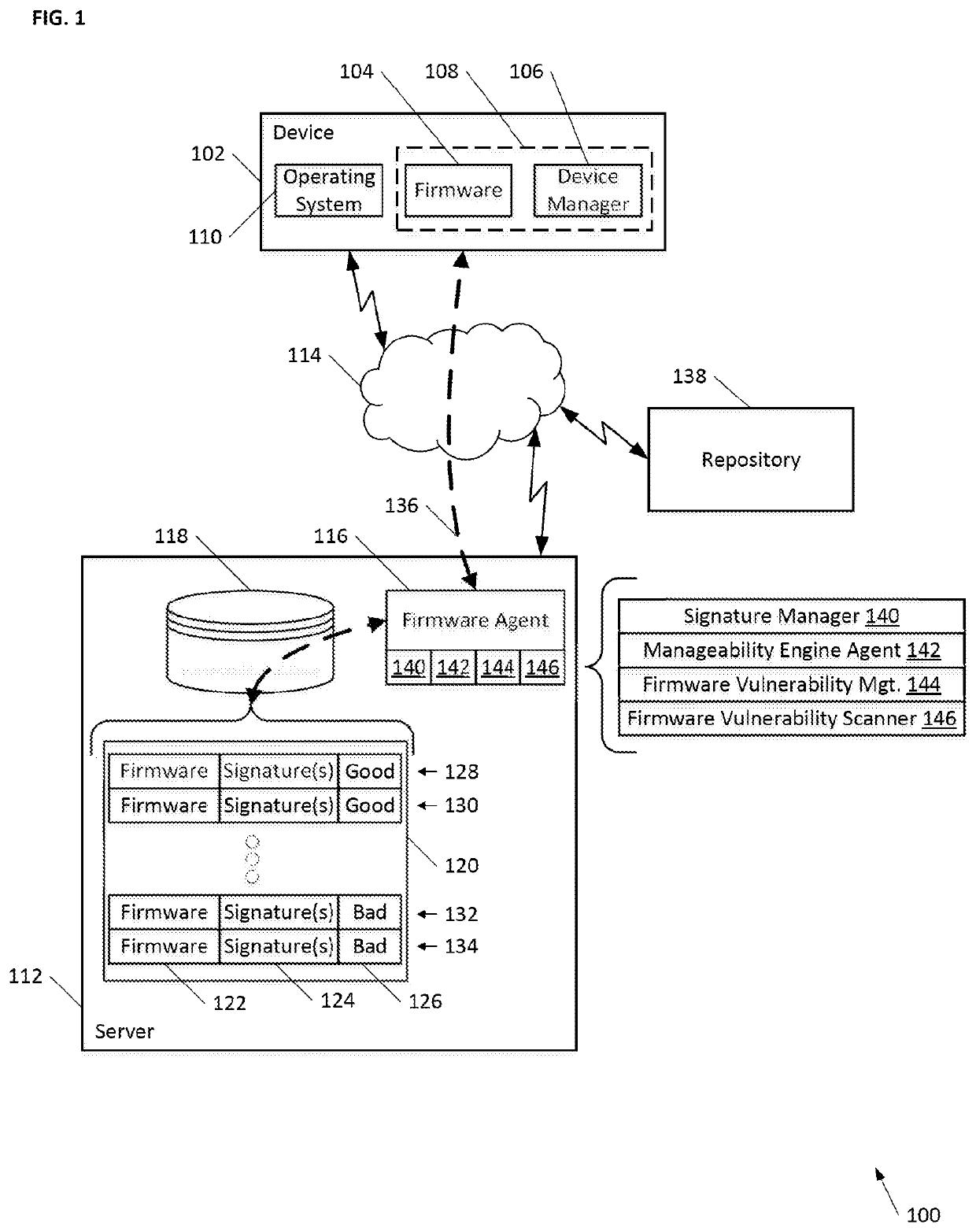
Manageability engine and automatic firmware validation
Malicious attacks have moved from higher level virus attacks on software and data files operating on a device, to subverting the firmware underlying the device, where the firmware will compromise operation of the device even after attempts to remove the virus, unwanted programs, or other activity due to the subversion. If the firmware is compromised then even a clean reinstall of all software and / or services on the device may only result in a clean device that is then subsequently compromised again. Although device manufacturers may update a firmware to remove the vulnerability, there remains a problem in getting users to actually perform the update. To facilitate device security, a database or databases of firmware may be maintained where their status of vulnerable (bad) or not (good) is maintained and various options are presented for scanning firmware for vulnerabilities, out of band or manually, and pulling / pushing updates as desired to automatically update a device or prompt a user for updating. Updates may be mandatory per a policy and / or controlled by user preference. Looking for vulnerabilities may be device driven, or managed by an external entity. As new vulnerabilities are discovered, existing firmware may be checked for the vulnerability, and if found, devices having vulnerable firmware may be updated. New firmware may be recorded in the database(s) and the database(s) periodically scanned for vulnerabilities.
Owner:ZIMMER VINCENT J +1
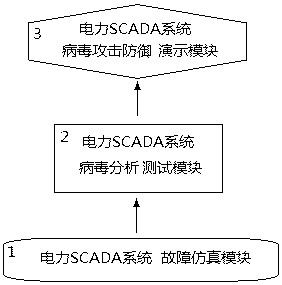
Virus analysis testing bed of electric SCADA (Supervisory Control And Data Acquisition) system
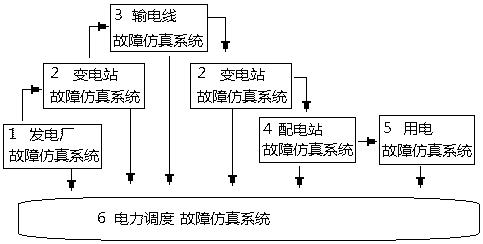
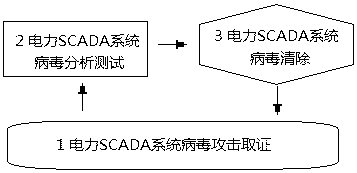
ActiveCN105678040ADesign optimisation/simulationPlatform integrity maintainanceSCADAData acquisition
The invention discloses a design device and a design method of a virus analysis testing bed of an electric SCADA (Supervisory Control And Data Acquisition) system, and belongs to the technical field of safety and intrusion detection of industrial control systems. The device comprises an electric SCADA system fault simulation module, an electric SCADA system virus analyzing and testing module and an electric SCADA system virus attack defense demonstration module. The design method comprises the following steps: under an electric SCADA system fault simulation condition, simulating fault information of power generation, power transformation, power transportation, power distribution, power utilization and power dispatching to acquire a field state of attacking the electric system by viruses, so as to realize virus attacking evidence obtaining of the electric SCADA system; and analyzing, testing and cleaning viruses, and dynamically demonstrating a virus attacking and defending process of the electric SCADA system. Compared with an existing electric system virus detection simulation device, the testing bed can be used for systematically simulating the environment of the whole electric SCADA system, can be used for detecting and analyzing the viruses attacking the electric SCADA system and also has dynamical demonstration functions of attacking and defending.
Owner:SHANGHAI YUNJIAN INFORMATION TECH CO LTD
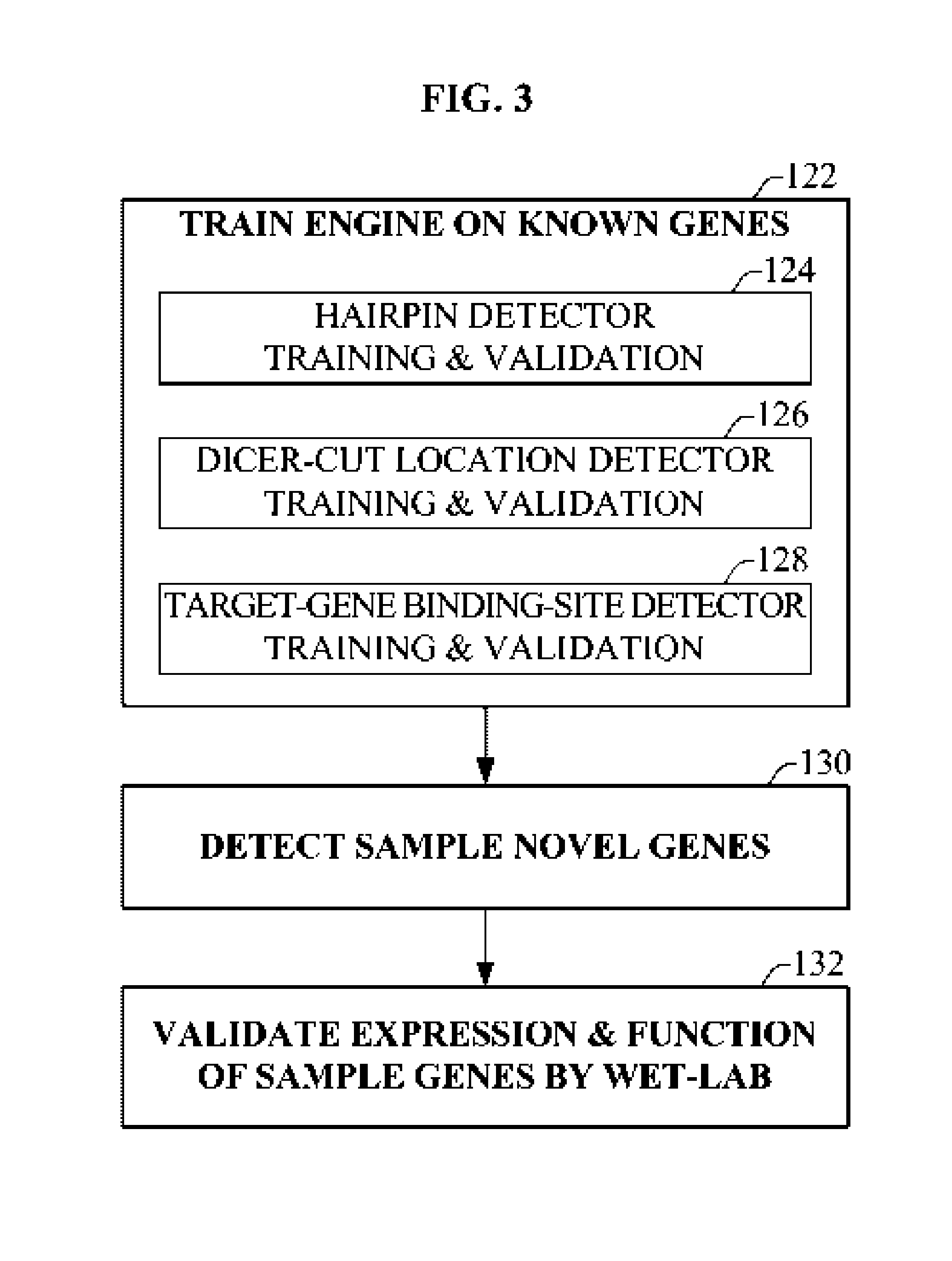
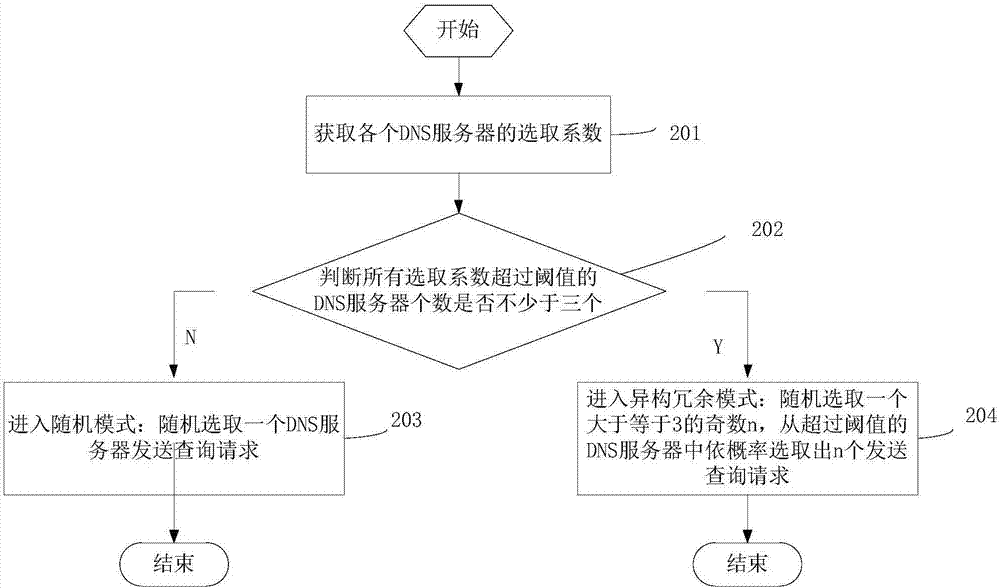
Mimic security method and device for recursive DNS server
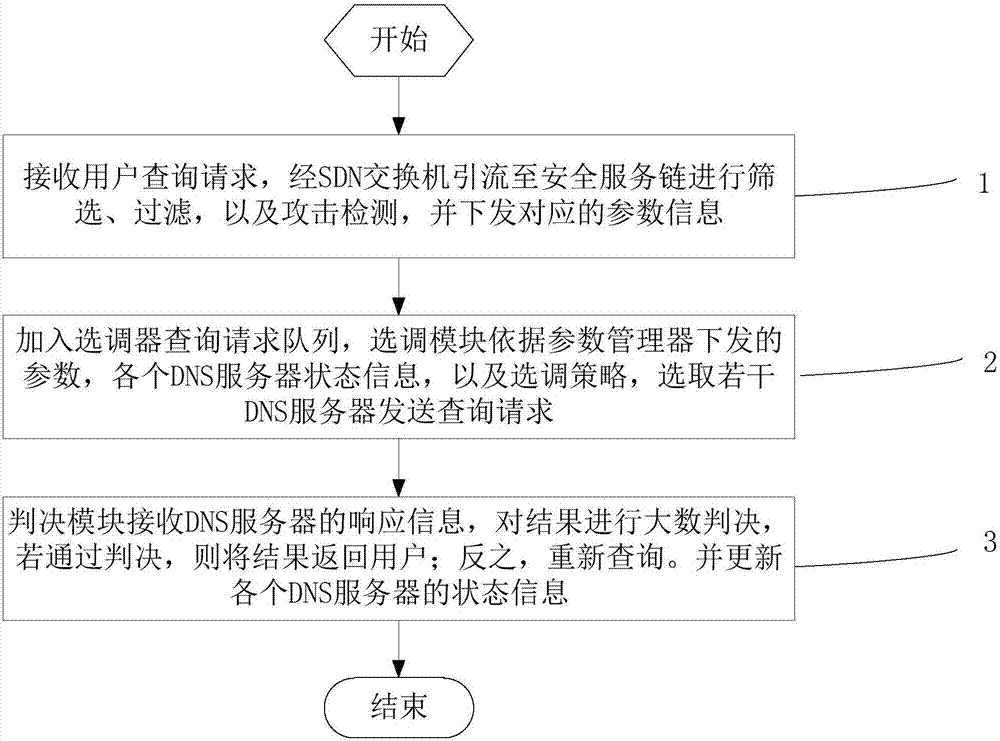
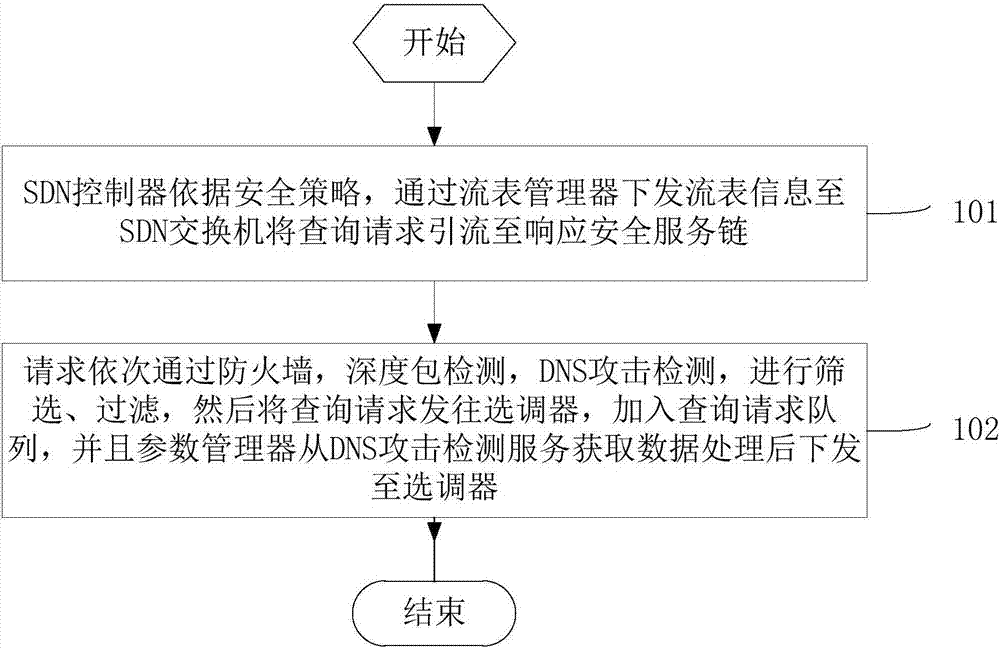
ActiveCN106961422ASolve attacks such as cache poisoningGuaranteed reliabilityTransmissionComputer networkMajority decision
The invention discloses a mimic security method and a device for a recursive DNS server, overcoming the security threatening problem of the recursive DNS server. The method comprises the following steps: 1) receiving the inquiry requests of users; guiding the inquiry requests through a DNS switch to a security service chain where screening, filtering and attack detecting are performed to the requests; and obtaining the attack detecting data by a parameter manager followed by the delivering of corresponding parameter information to a transferring device; 2) for each inquiry request in the request queue of the transferring device, selecting by the transferring device a plurality of inquiry requests by the DNS server according to the parameter manager delivered parameters, the state information of various DNS servers and the transferring strategy; and 3) receiving the responding information of the DNS servers by a determining module; making the majority decision to the result; and updating the state information of the various servers in the DNS server pool. The method and the device of the invention solve the virus attacks to the cache of a recursive server without the modification of the DNS protocol or DNS inquiry responding procedure.
Owner:THE PLA INFORMATION ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com