Patents
Literature
1330 results about "Quarantine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A quarantine is a restriction on the movement of people and goods which is intended to prevent the spread of disease or pests. It is often used in connection to disease and illness, preventing the movement of those who may have been exposed to a communicable disease, but do not have a confirmed medical diagnosis. The term is often used synonymously with medical isolation, in which those confirmed to be infected with a communicable disease are isolated from the healthy population.
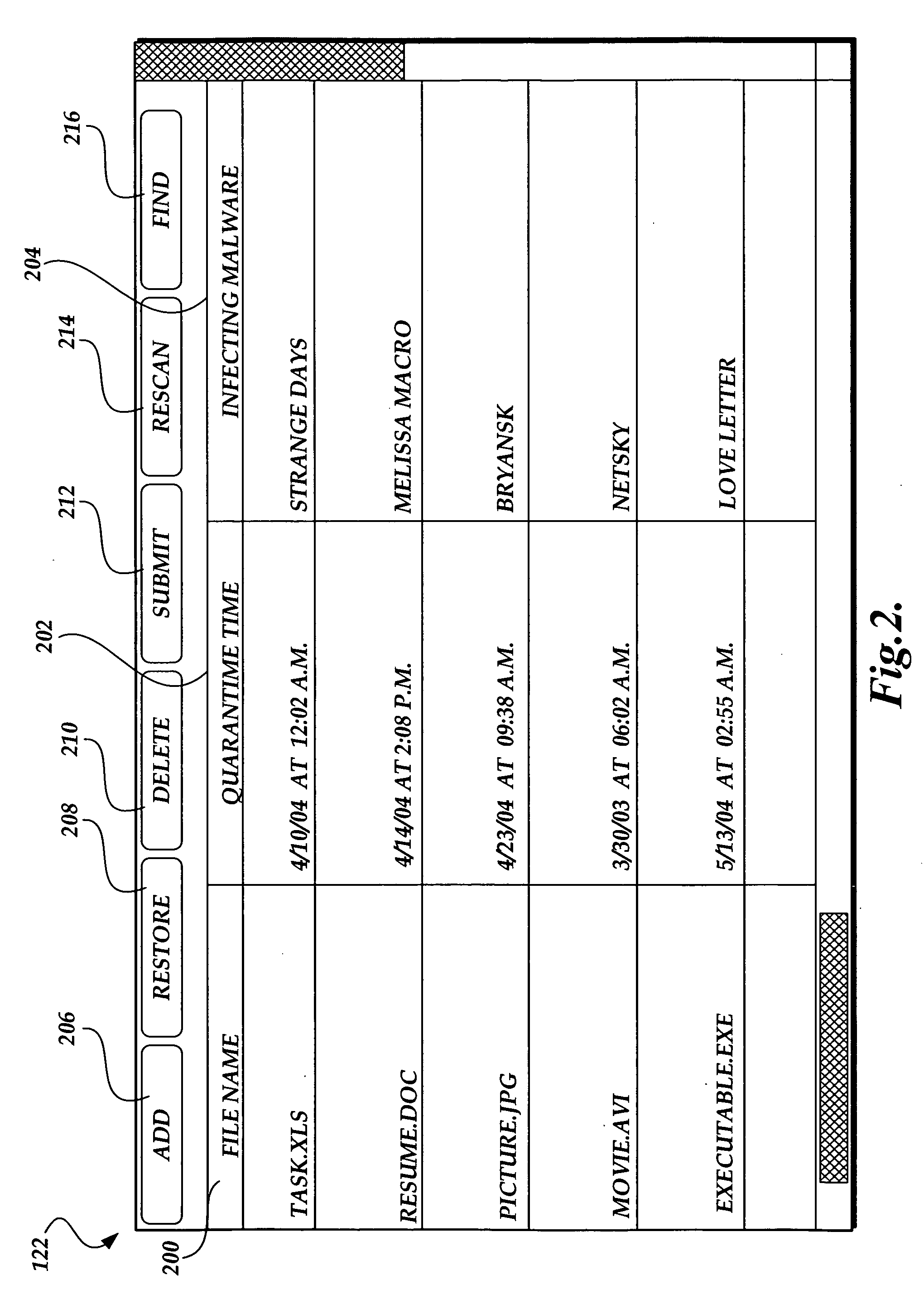
Delayed-delivery quarantining of network communications having suspicious contents
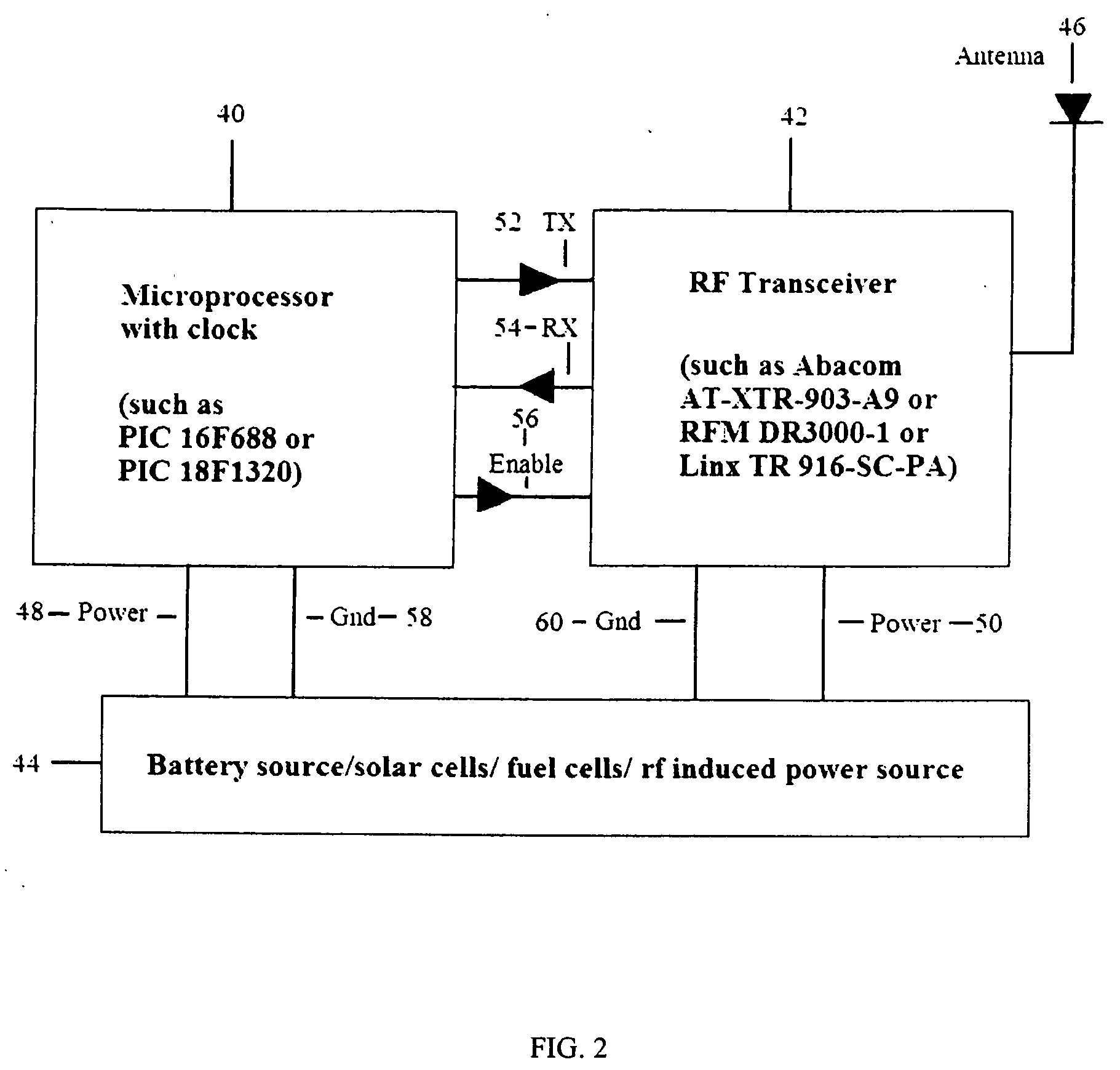
ActiveUS7080408B1Avoid spreadingAvoid damageMemory loss protectionError detection/correctionNetwork communicationQuarantine
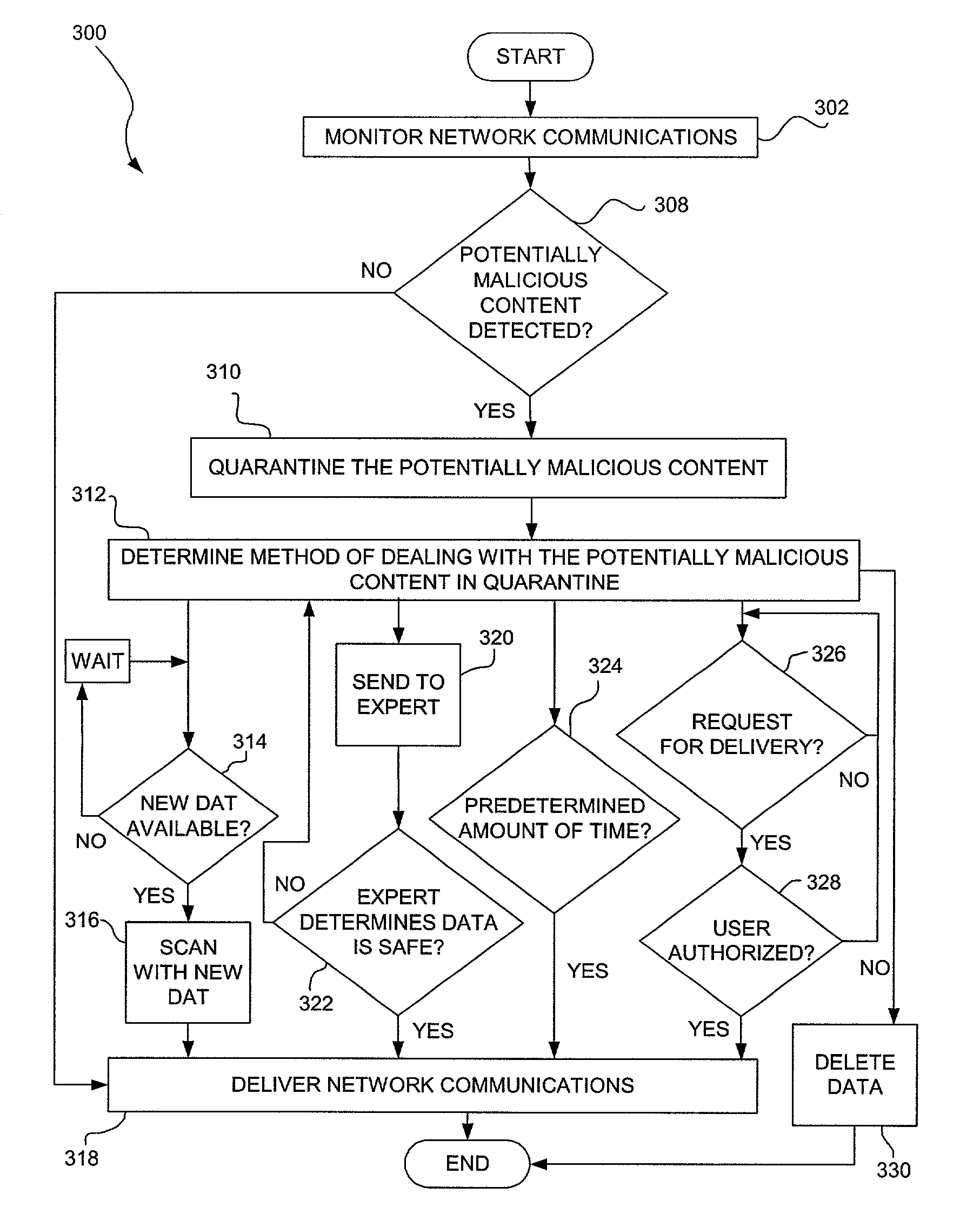
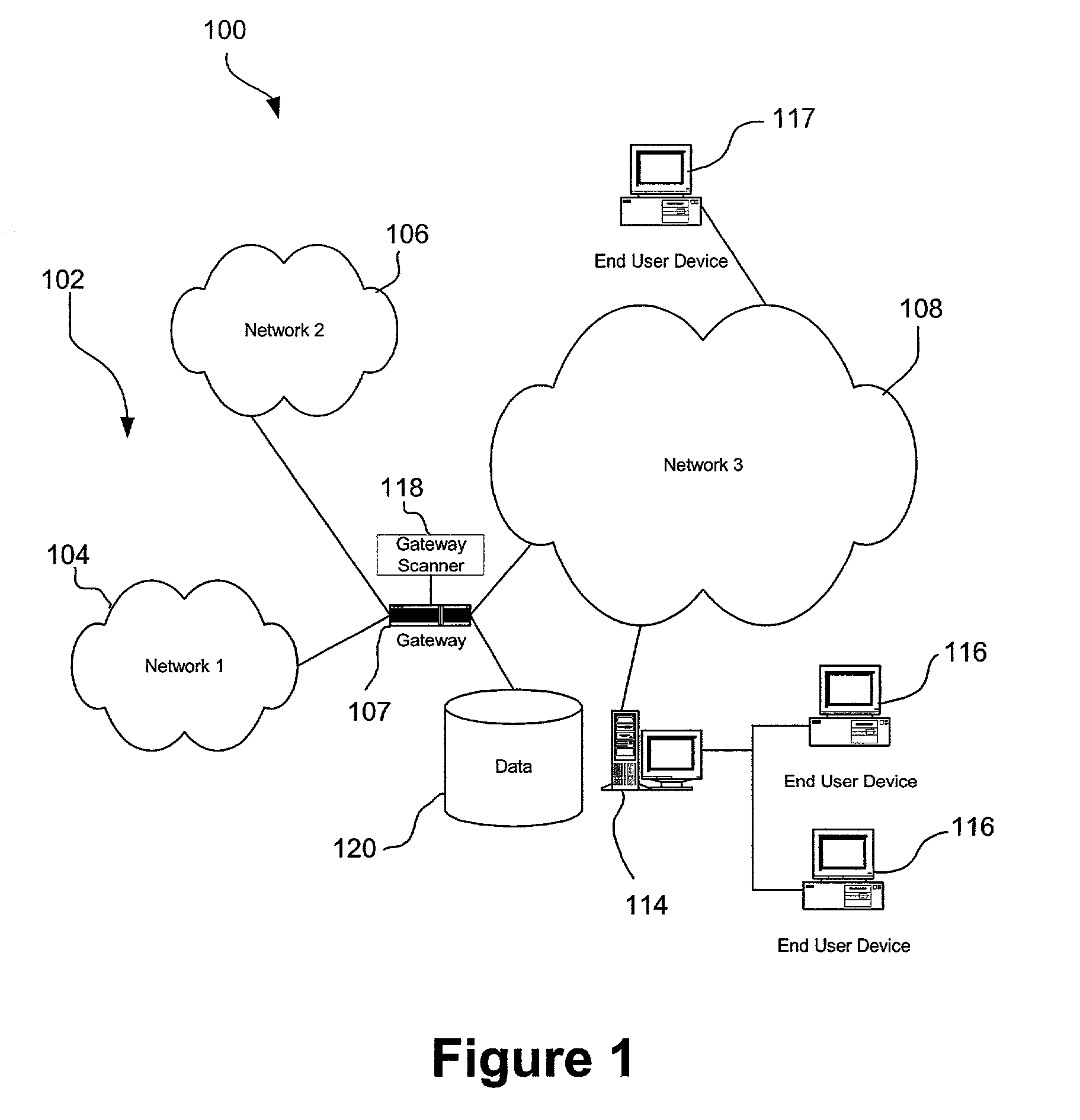
A system, method and computer program product are provided for network-based scanning for potentially malicious content. Incoming and / or outgoing network communications traveling over a network are monitored, preferably at a gateway. Potentially malicious content in the network communications is identified. The identified potentially malicious content of the network communications is quarantined to help prevent damage that could be caused if the content is indeed malicious. In one embodiment, a pattern for testing the potentially malicious content network communications for malicious code can be executed. The network communications are conditionally delivered over the network based on the testing. In other embodiments, the network communications are delivered over the network after a predetermined delay and / or upon receiving a user request to release the suspect content from quarantine.
Owner:MCAFEE LLC
Method for protecting a computer from suspicious objects
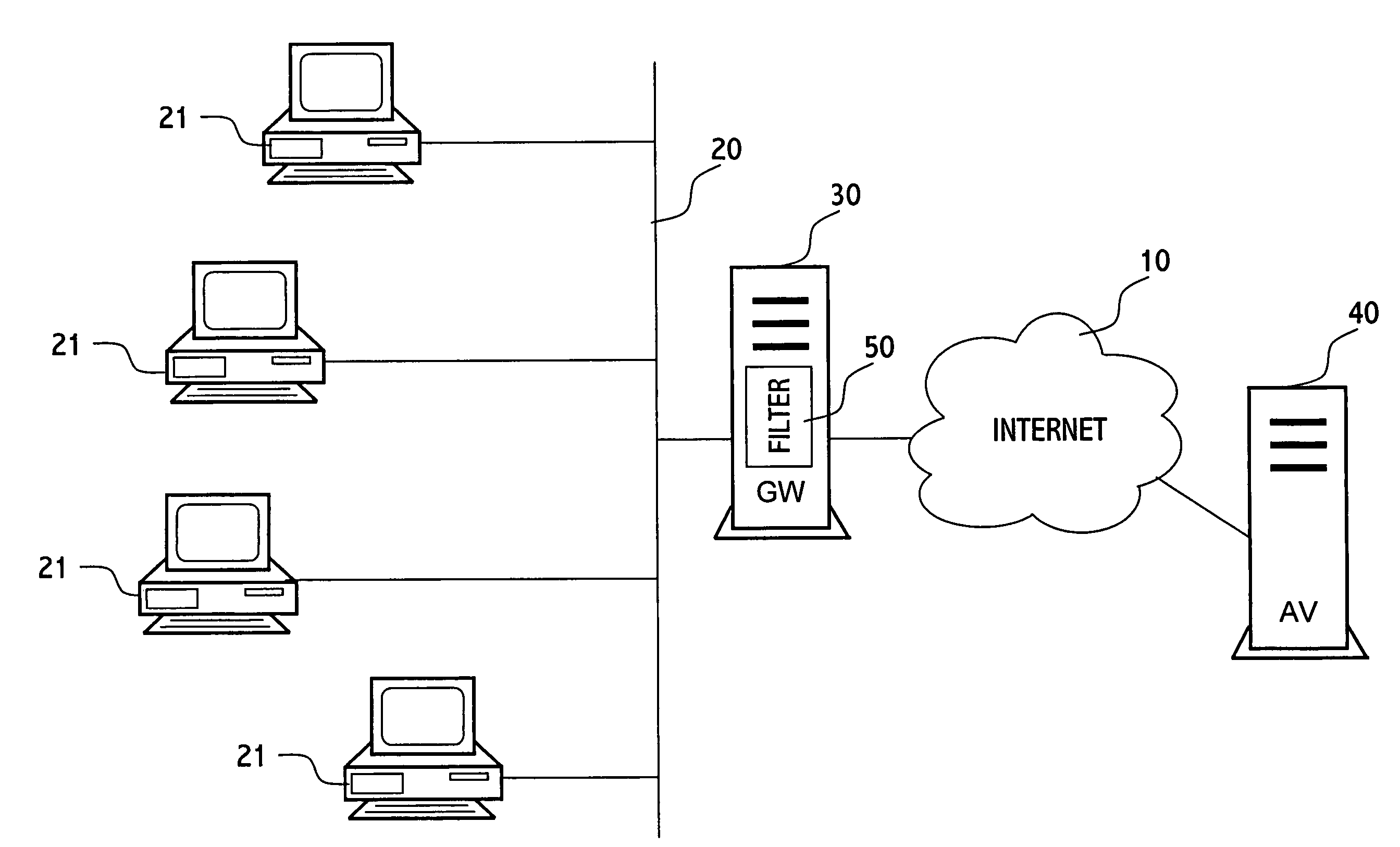
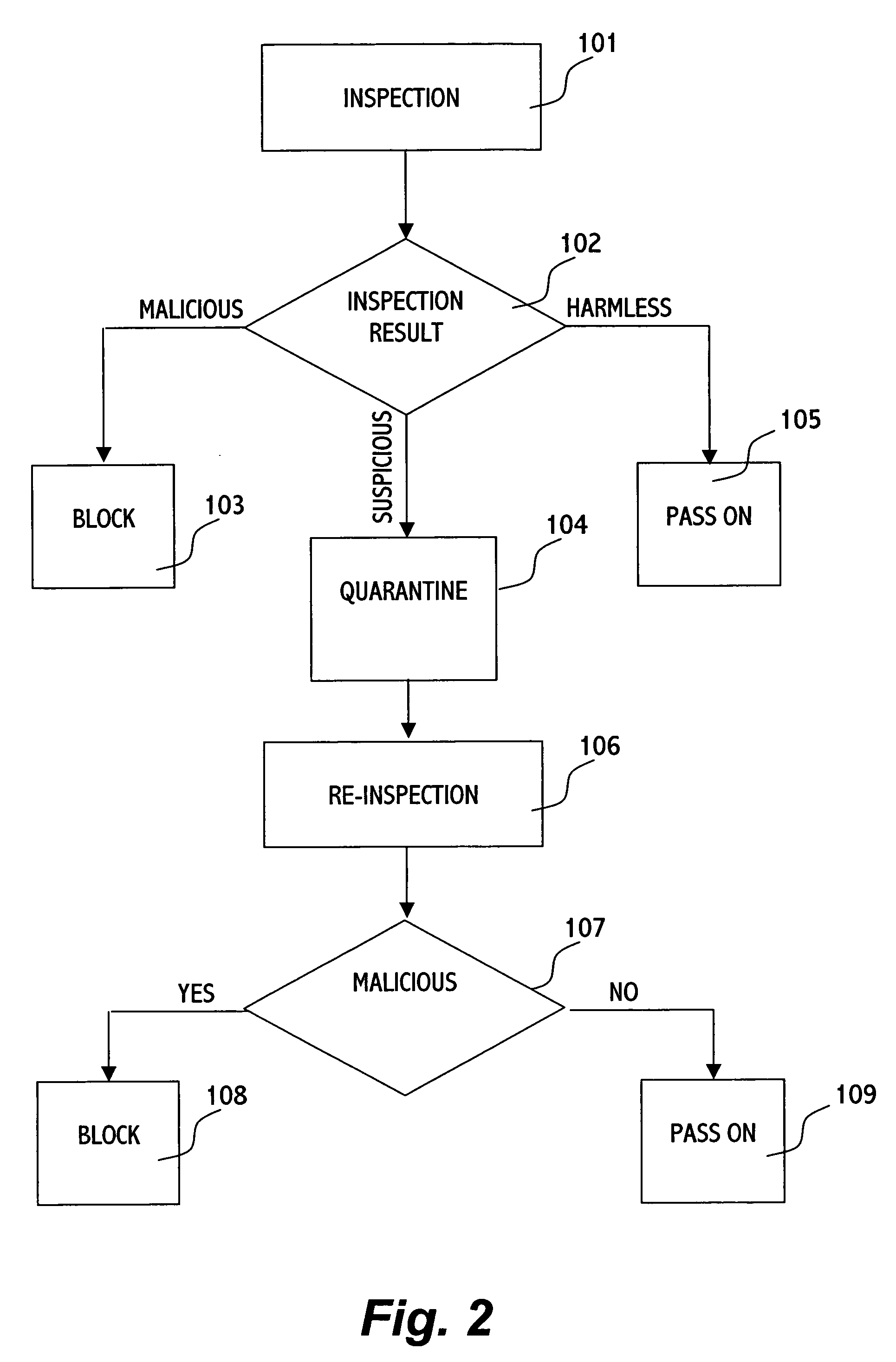
In an inspection facility (e.g. at a gateway server, at a proxy server, at a firewall to a network, at an entrance to a local area network or even at the user's computer) connected to an anti-virus center for updates, a method for protecting a computer from suspicious objects (e.g. a file, an executable, a Web page, an email message, etc.), the method comprising the steps of: inspecting an object; upon determining the object as suspicious, holding the object in quarantine (e.g. preventing from the object to be forwarded to its destination) for a time period, thereby enabling the inspection facility to be updated during the time period by the anti-virus center; upon ending of the time period, re-inspecting the object, thereby inspecting the object by updated inspection tests; and upon determining the object as malicious by the re-inspection, blocking the object, otherwise forwarding the object toward its destination.
Owner:ALADDIN KNOWLEDGE SYSTEMS
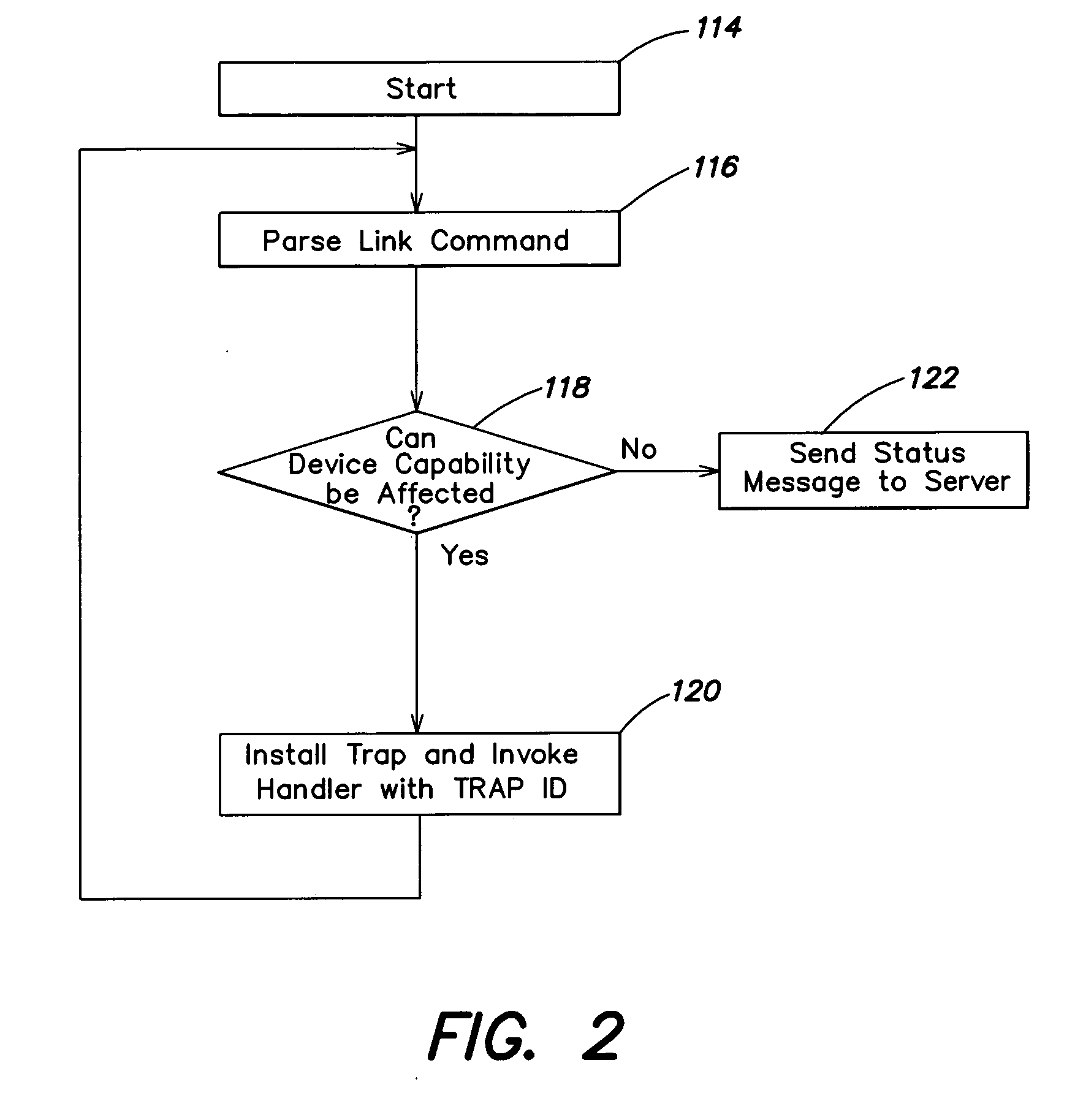
System and method for automatically altering device functionality
InactiveUS20070030539A1Avoid damagePrevent unauthorized accessMemory loss protectionError detection/correctionQuarantineEmbedded system
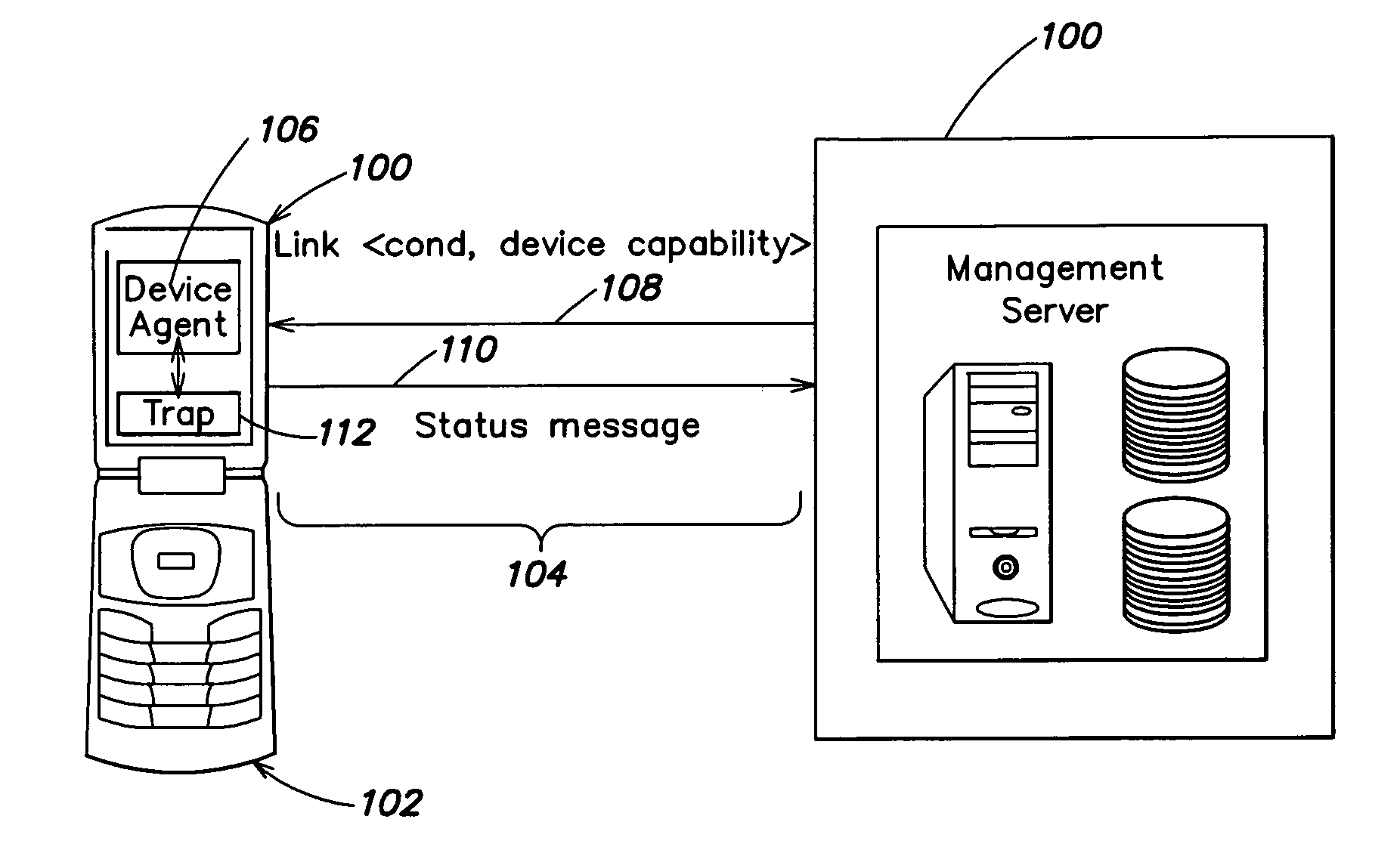
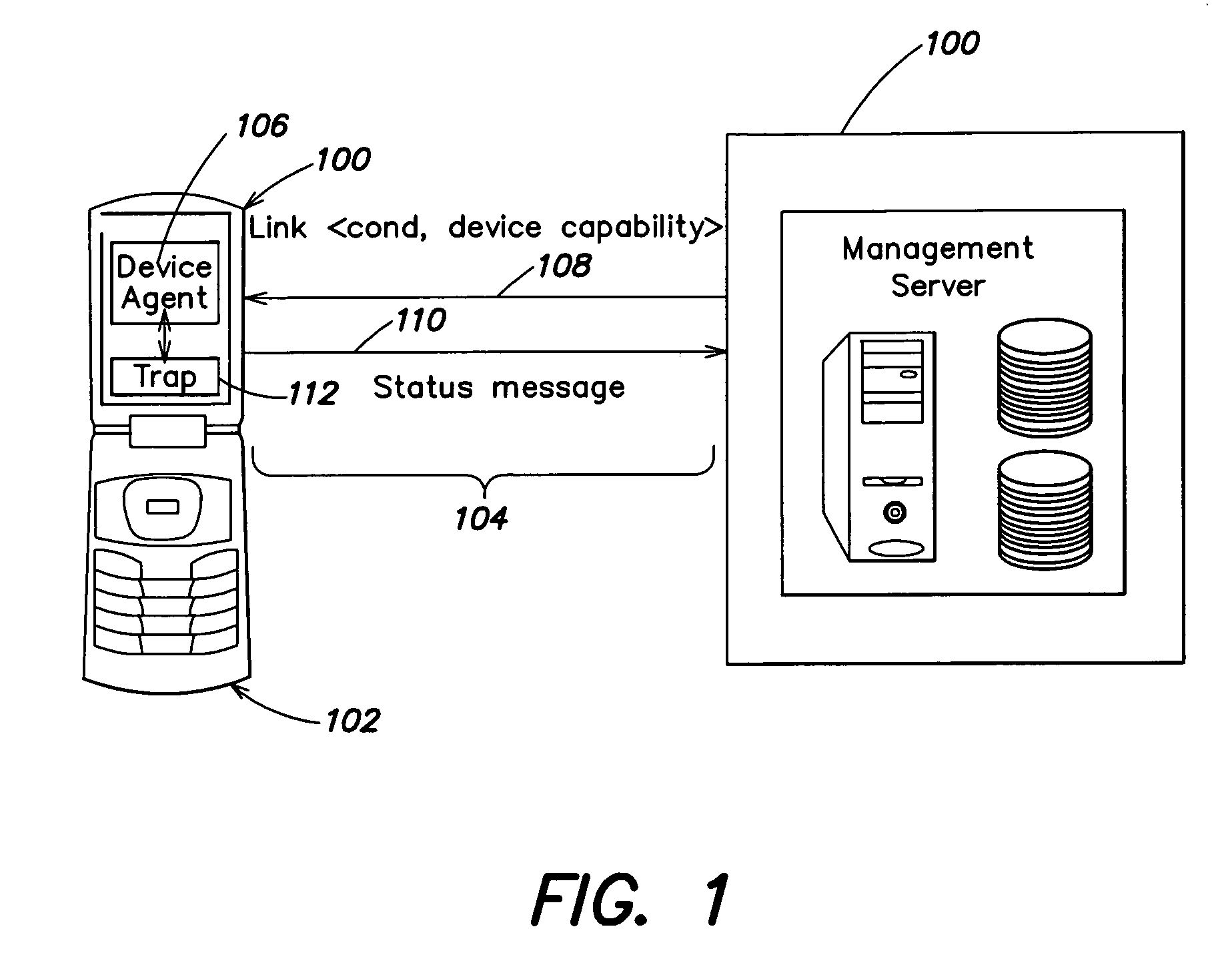
A system and method for automatically altering device functionality based on the occurrence of certain predetermined conditions. A link may be established between a device and a trusted server to provide an association between various conditions that may be detected at the device and actions that are to be taken on the device. In particular, software traps can be set up and linked to device functionality such that execution of the trap may automatically disable or enable certain device capabilities. Some aspects of the invention are directed to a system and method for remotely setting software traps for detecting software viruses and, upon execution of the traps, several methods for establishing a quarantine on infected devices.
Owner:MFORMATION +1
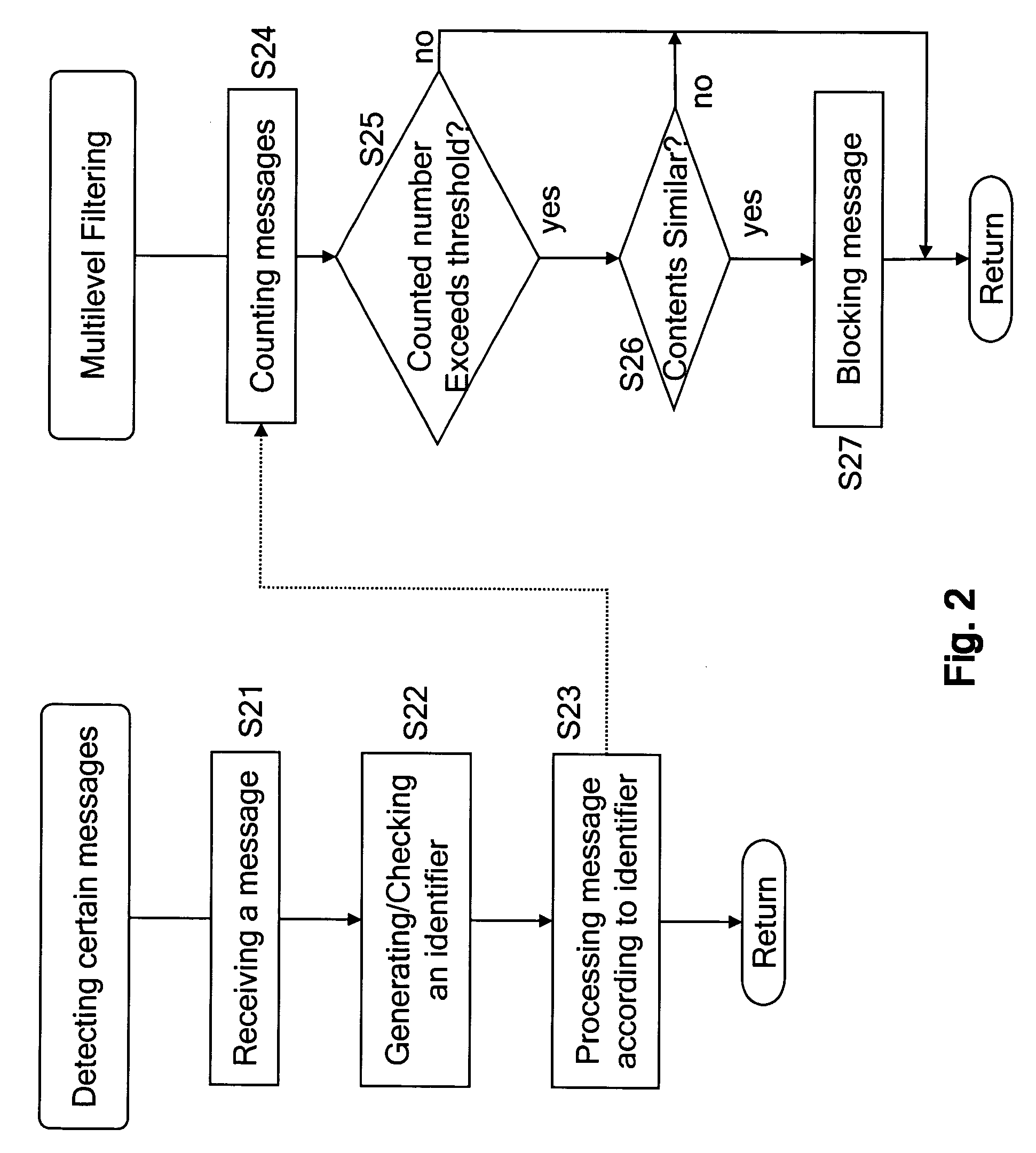
Messaging spam detection
InactiveUS20060026242A1Multiple digital computer combinationsData switching networksEmail addressTelecommunications
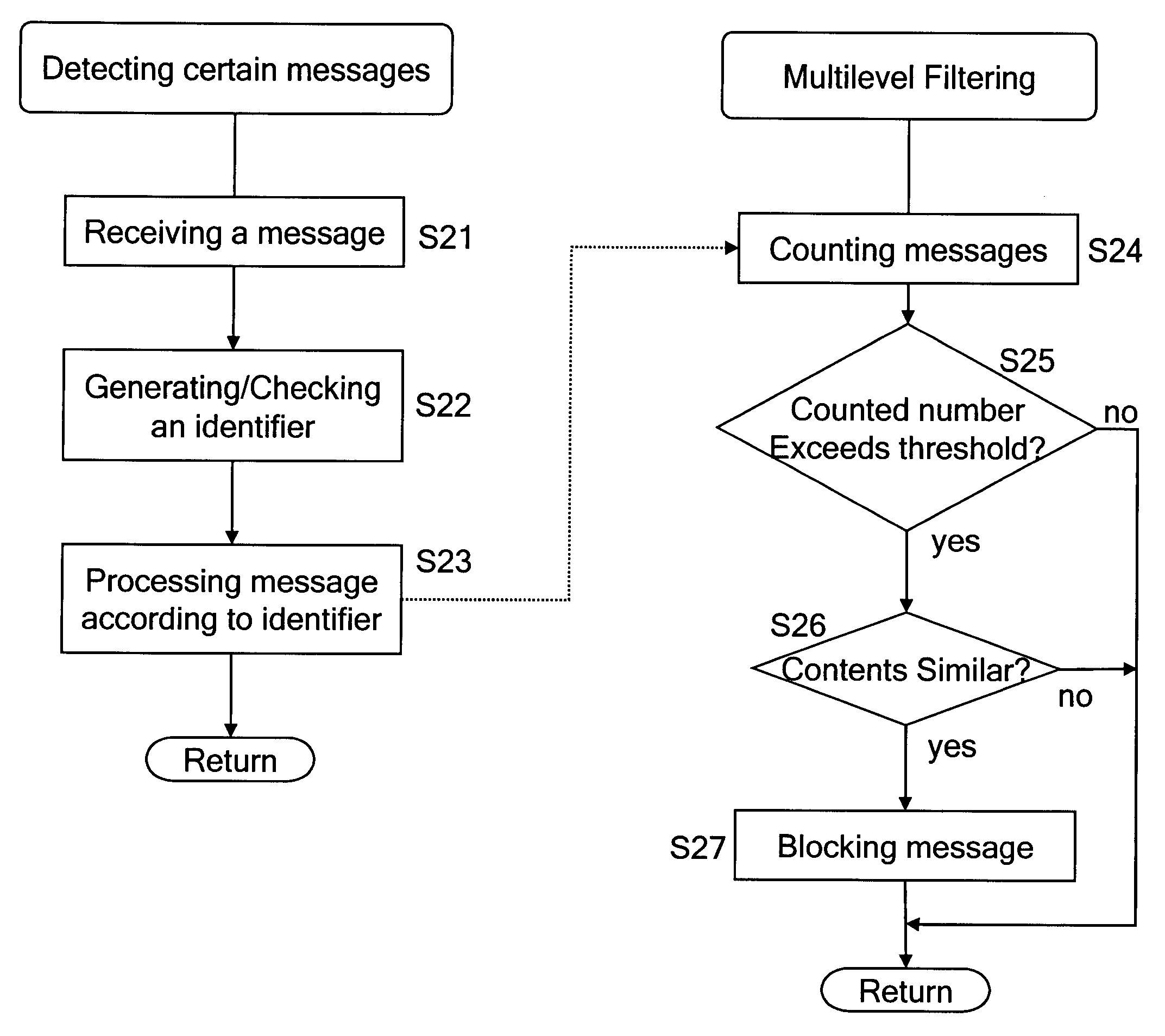
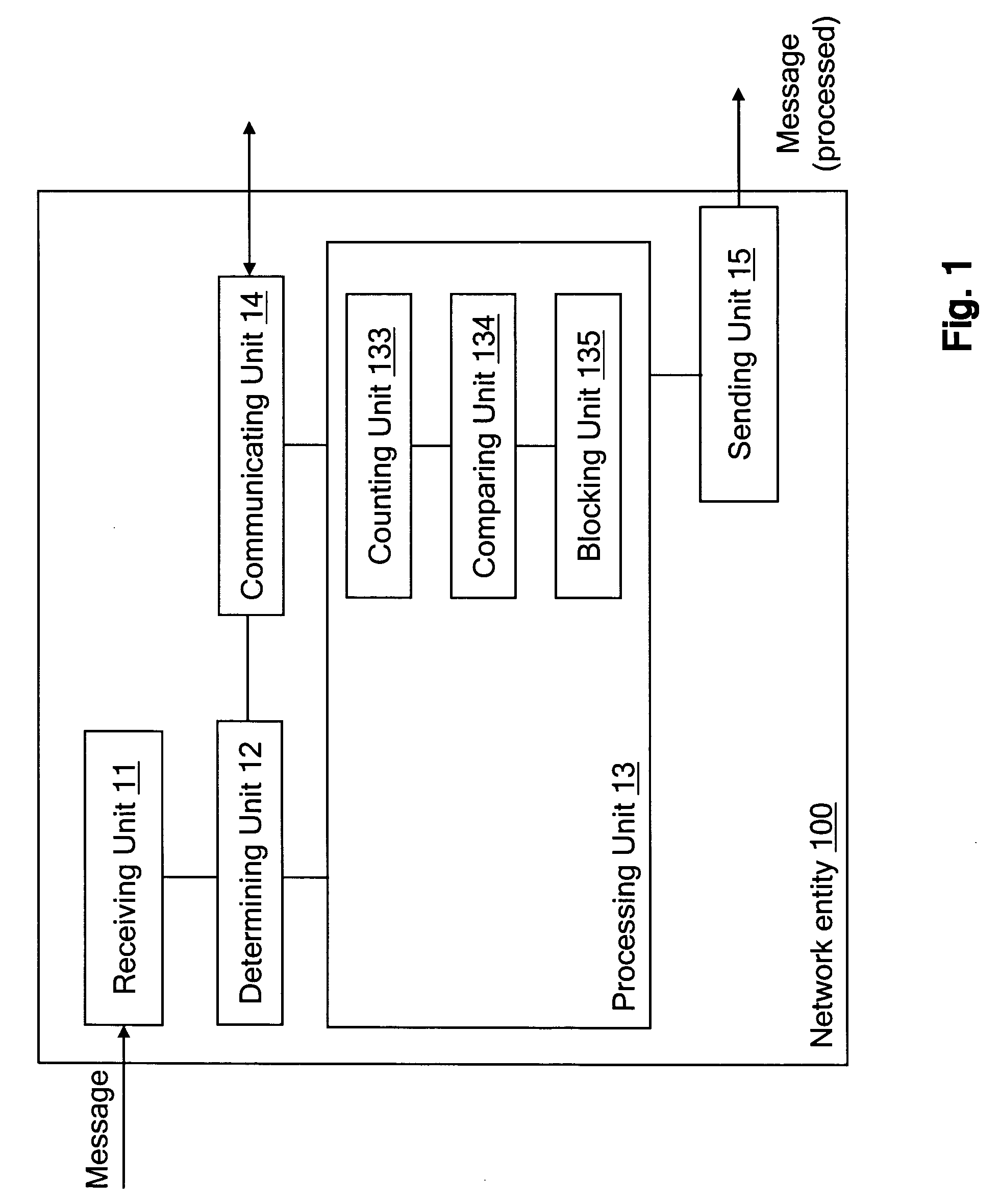
Detecting unsolicited messages (spam) by aggregating information across multiple recipients and / or across the same or differing messaging protocols. Multiple messages are analyzed to detect a call to action pattern that specifies a target communication address with which the recipients are requested to communicate, such as an email address, an Internet address, a telephone number, and the like. Once a frequency threshold of messages containing the call to action pattern is reached, subsequent messages are temporarily quarantined for evaluation by a human operator. If the human determines that the messages are not spam, the human can release the quarantined messages, and indicate that future messages with the call to action pattern are not to be delayed. Conversely, if the human determines that the messages are spam, the human can delete the messages in quarantine, and indicate that all future messages with that call to action pattern are to be deleted automatically.
Owner:WIRELESS SERVICES CORP
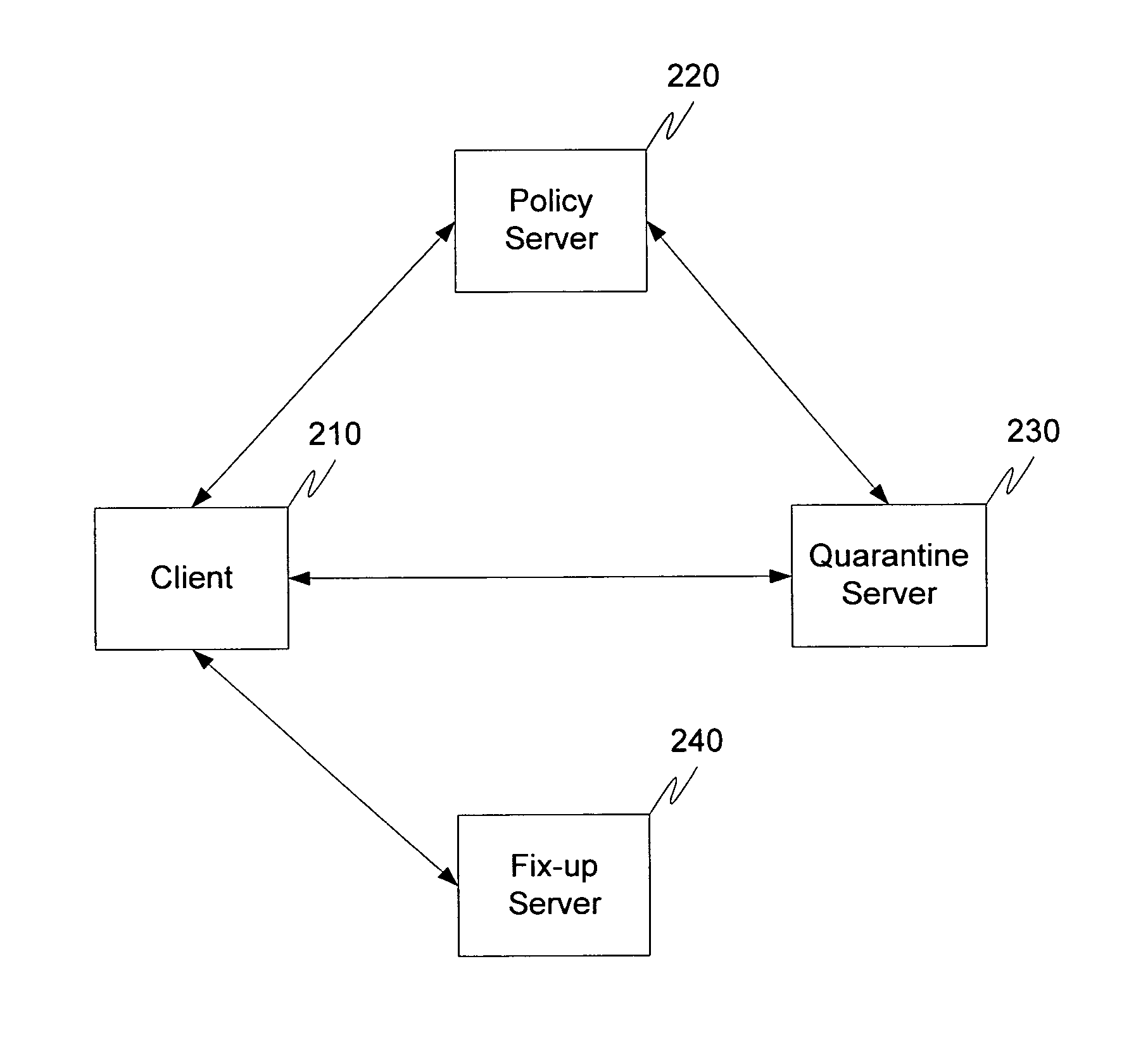
System and methods for providing network quarantine
InactiveUS20050131997A1Network resource is limitedMemory loss protectionDigital data processing detailsAccess networkSecure state
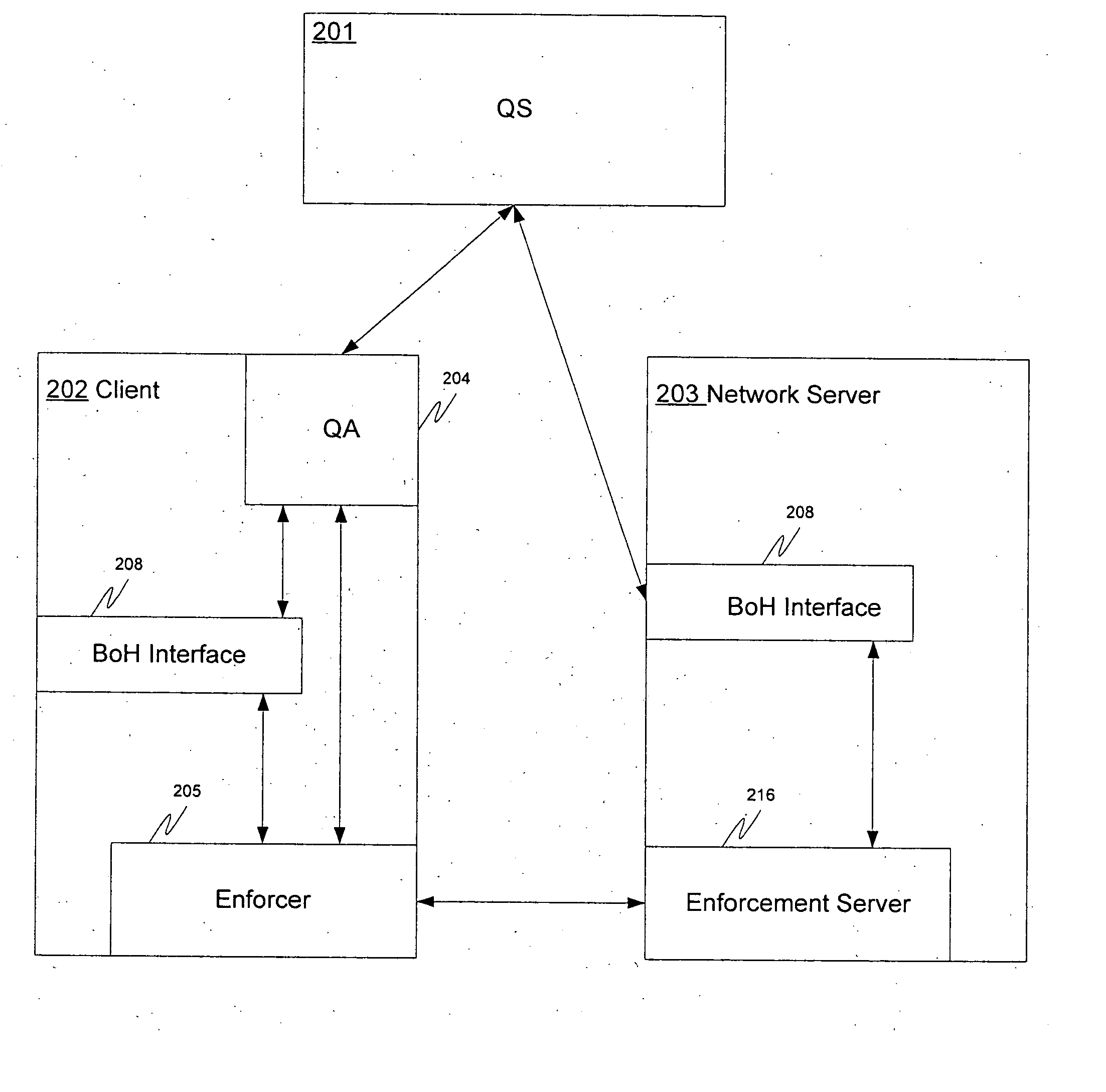
A system and method for ensuring that machines having invalid or corrupt states are restricted from accessing network resources are provided. A quarantine server located on a trusted machine in a network provides a bill of health to a quarantine agent located on a client computer that wishes to gain access to network resources administered by an organization. The quarantine agent requests bill of health from the quarantine server, and receives a manifest of checks that the client computer must perform. The quarantine agent then sends a status report on the checks back to the quarantine server. If the client computer is in a valid security state, the bill of health is issued to the client. If the client computer is in an invalid state, the client is directed to install the appropriate software / patches to achieve a valid state. When a client requests the use of network resources from a network administrator, the network administrator requests the client's bill of health. If the bill of health is valid, the client is admitted to the network. If the bill of health is invalid, or if the client does not have a quarantine agent, the client is placed in quarantine, in which the only network resources accessible to the client are those necessary to install the quarantine agent and requisite software / patches to achieve a valid state.
Owner:MICROSOFT TECH LICENSING LLC
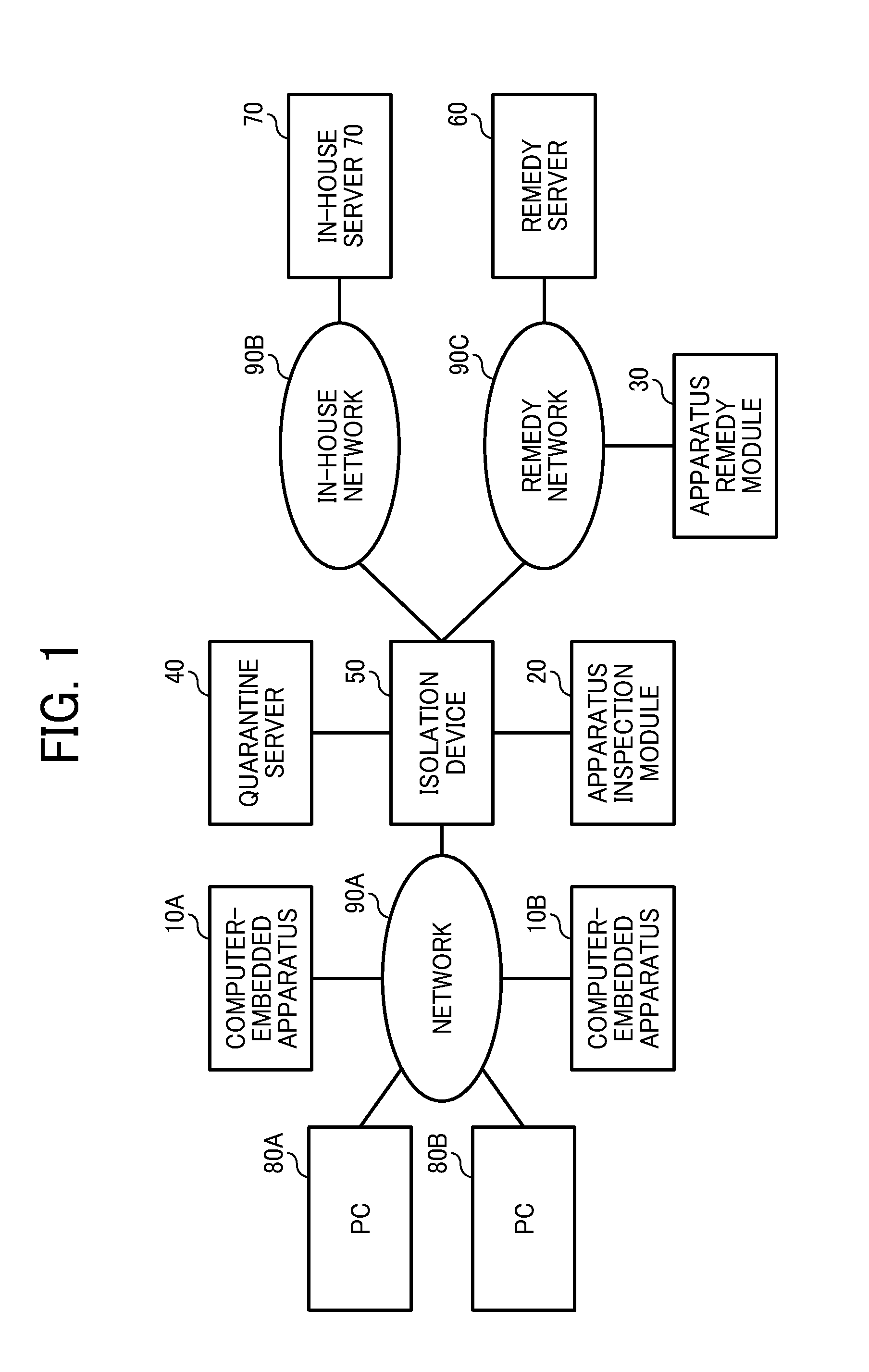
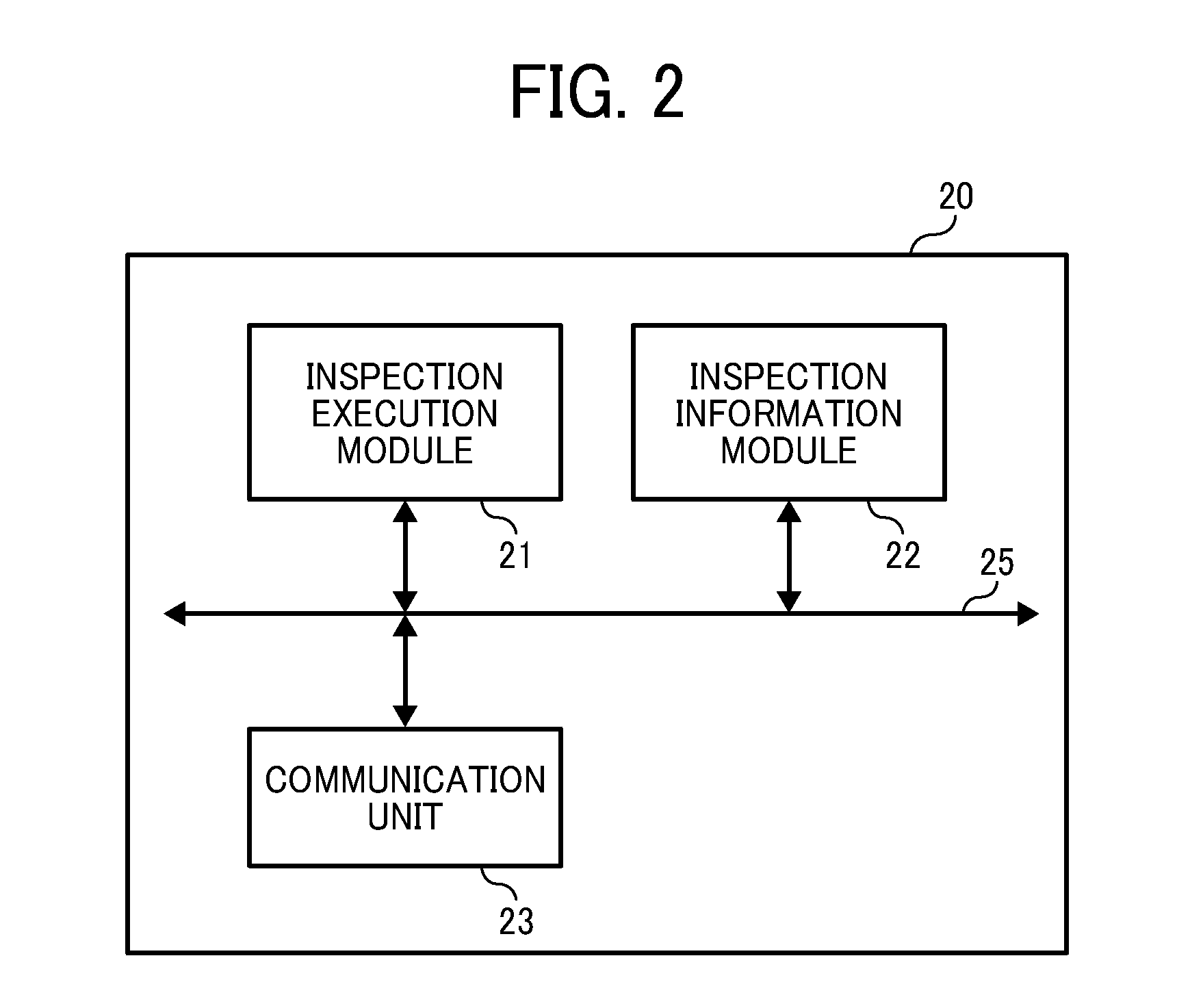
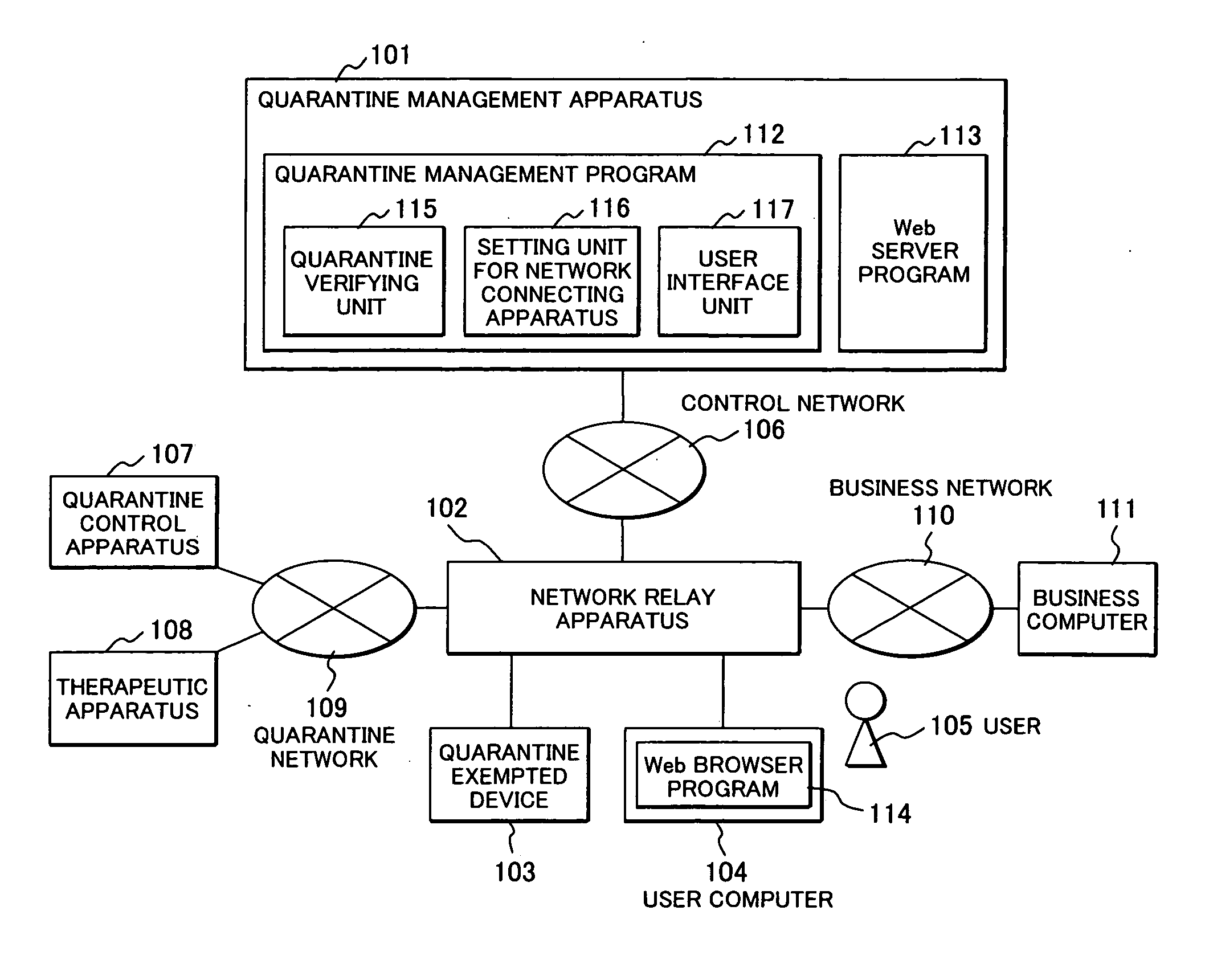
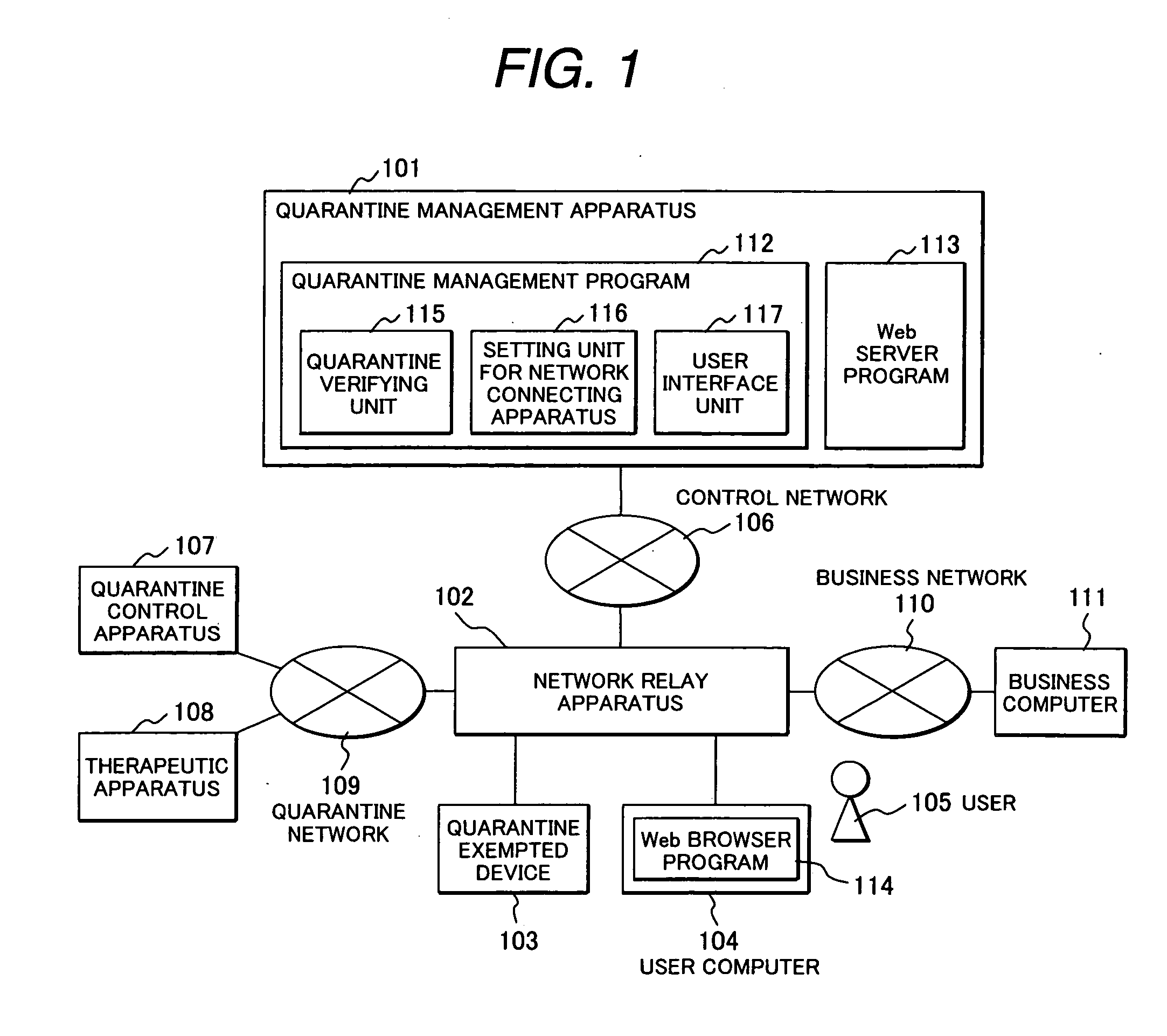
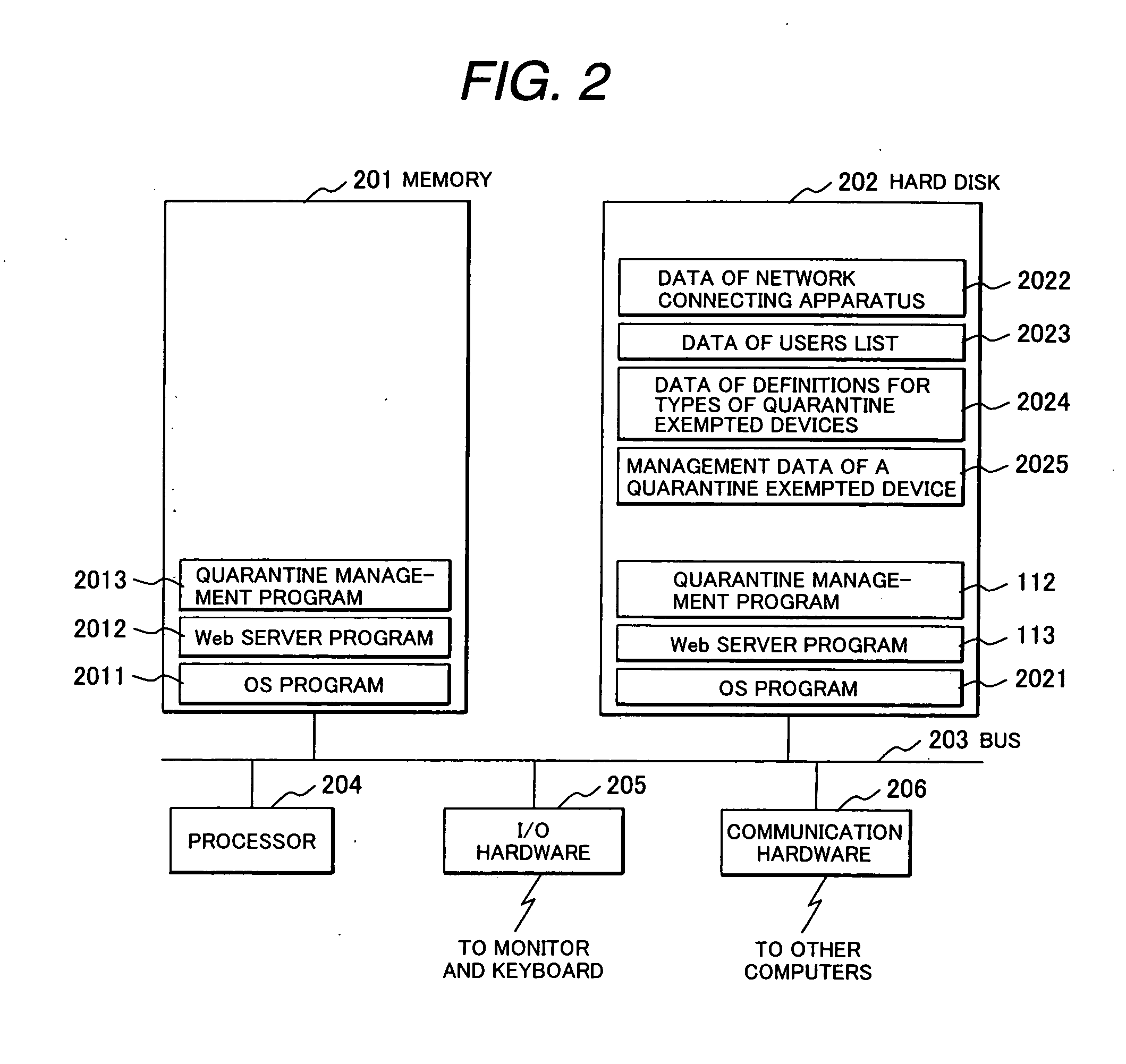
Quarantine network system and quarantine client
A quarantine network system includes a quarantine control apparatus and a quarantine client connectable with each other. The quarantine control apparatus includes a receiving unit to receive verification information of the quarantine client, an identification unit to identify a security policy that the quarantine client is required to conform to, and an inspection request unit to transmit an inspection request to the quarantine client, requesting the quarantine client to inspect conformance / non-conformance to the identified security policy. The quarantine client includes a receiver to receive the inspection request from the quarantine control apparatus, a storage unit storable inspection information to inspect conformance / non-conformance to the security policy, a reading unit to read out the inspection information from the storage unit, an inspection unit to inspect the quarantine client using the read-out inspection information, and an inspection result reporting unit to transmit an inspection result to the quarantine control apparatus.
Owner:RICOH KK
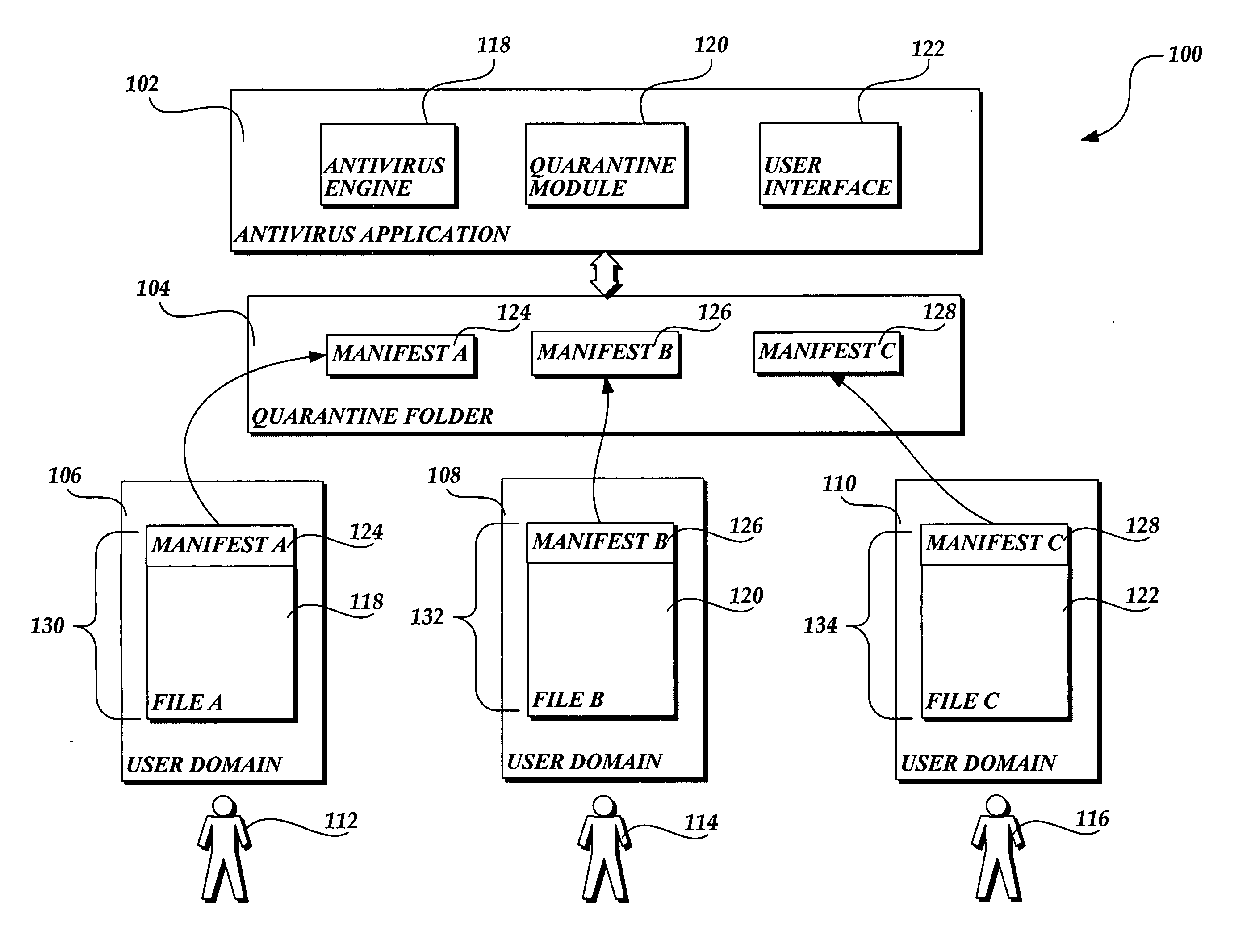
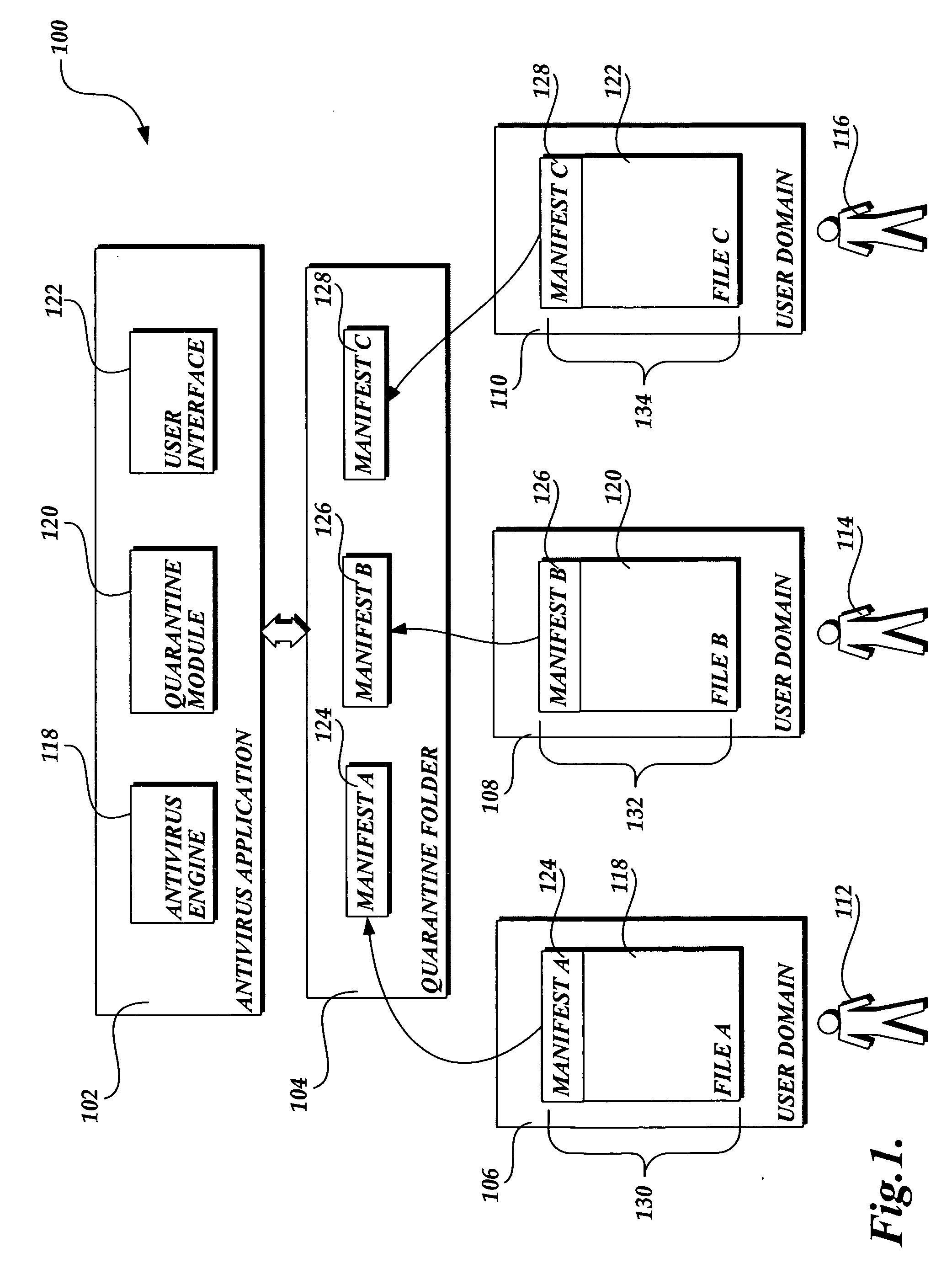
Privacy friendly malware quarantines
The present invention provides a system, method, and computer-readable medium for quarantining a file. Embodiments of the present invention are included in antivirus software that maintains a user interface. From the user interface, a user may issue a command to quarantine a file or the quarantine process may be initiated automatically by the antivirus software after malware is identified. When a file is marked for quarantine, aspects of the present invention encode file data with a function that is reversible. Then a set of metadata is identified that describes attributes of the file including any heightened security features that are used to limit access to the file. The metadata is moved to a quarantine folder, while the encoded file remains at the same location in the file system. As a result, the encoded file maintains the same file attributes as the original, non-quarantined file, including any heightened security features.
Owner:MICROSOFT TECH LICENSING LLC
System and methods for providing network quarantine using IPsec
A system and method for ensuring that machines having invalid or corrupt states are restricted from accessing host resources are provided. A quarantine agent (QA) located on a client machine acquires statements of health from a plurality of quarantine policy clients. The QA packages the statements and provides the package to a quarantine enforcement client (QEC). The QEC sends the package to a quarantine Health Certificate Server (HCS) with a request for a health certificate. If the client provided valid statements of health, the HCS grants the client health certificate that may be used in IPsec session negotiation.
Owner:MICROSOFT TECH LICENSING LLC
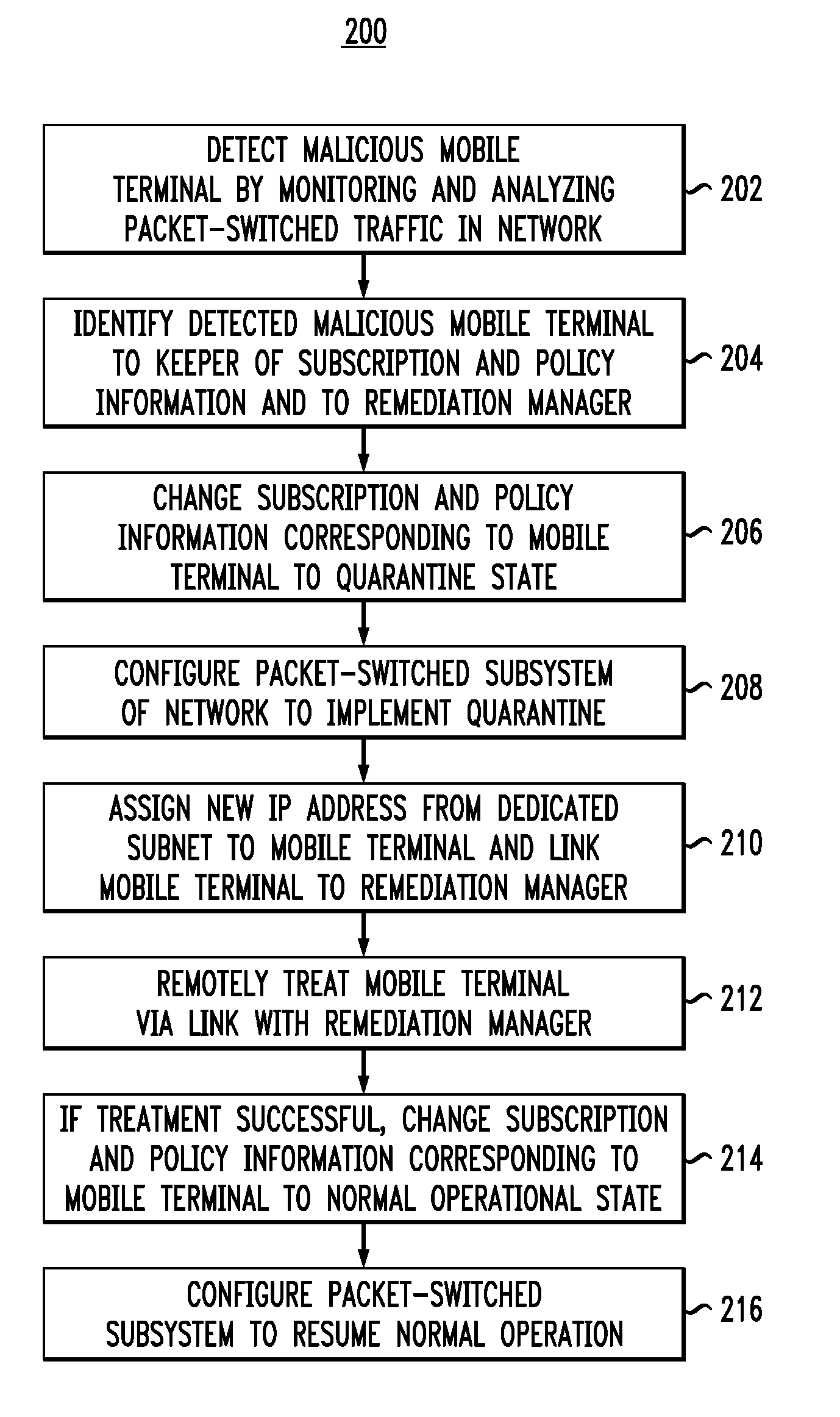
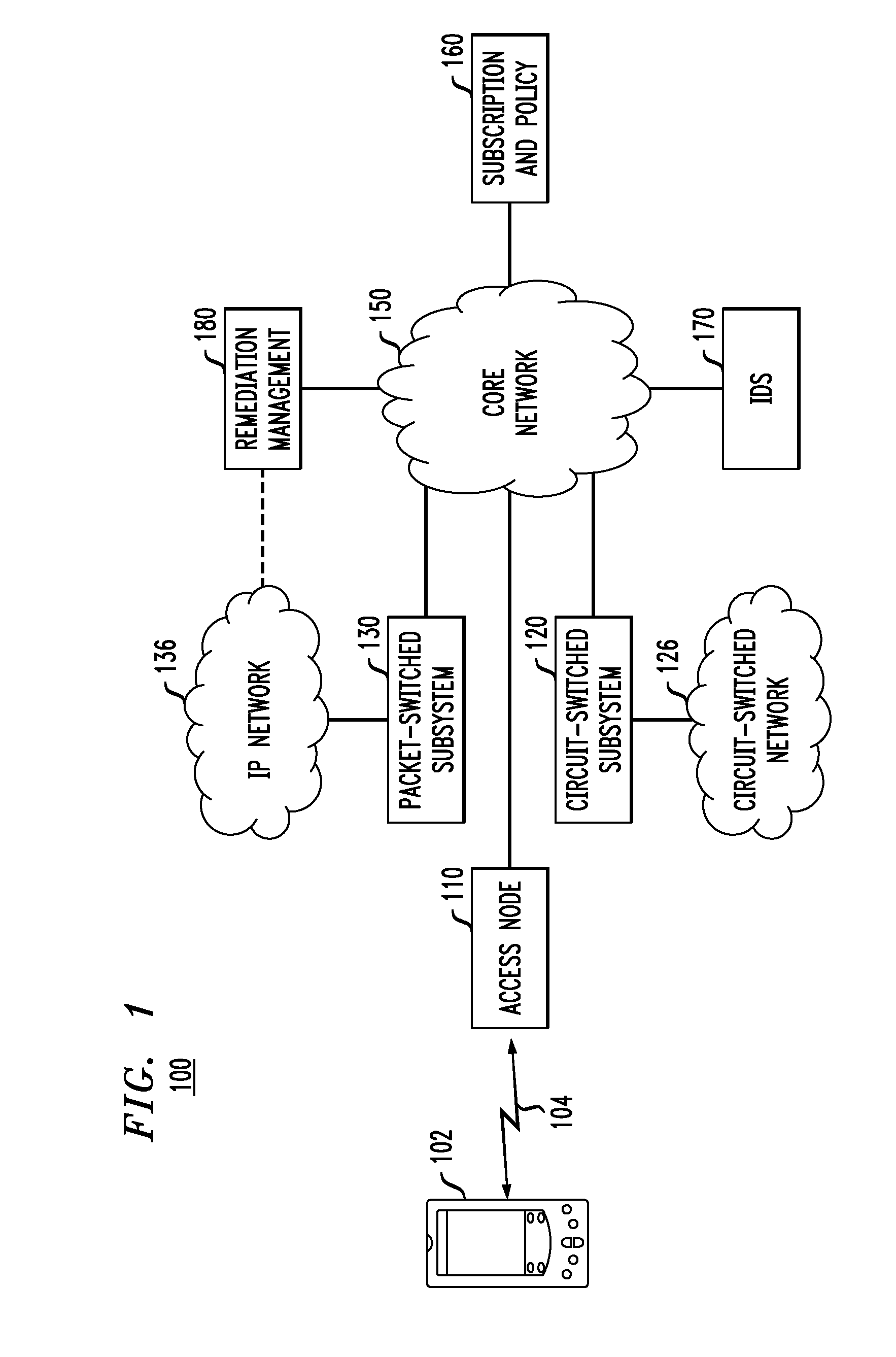
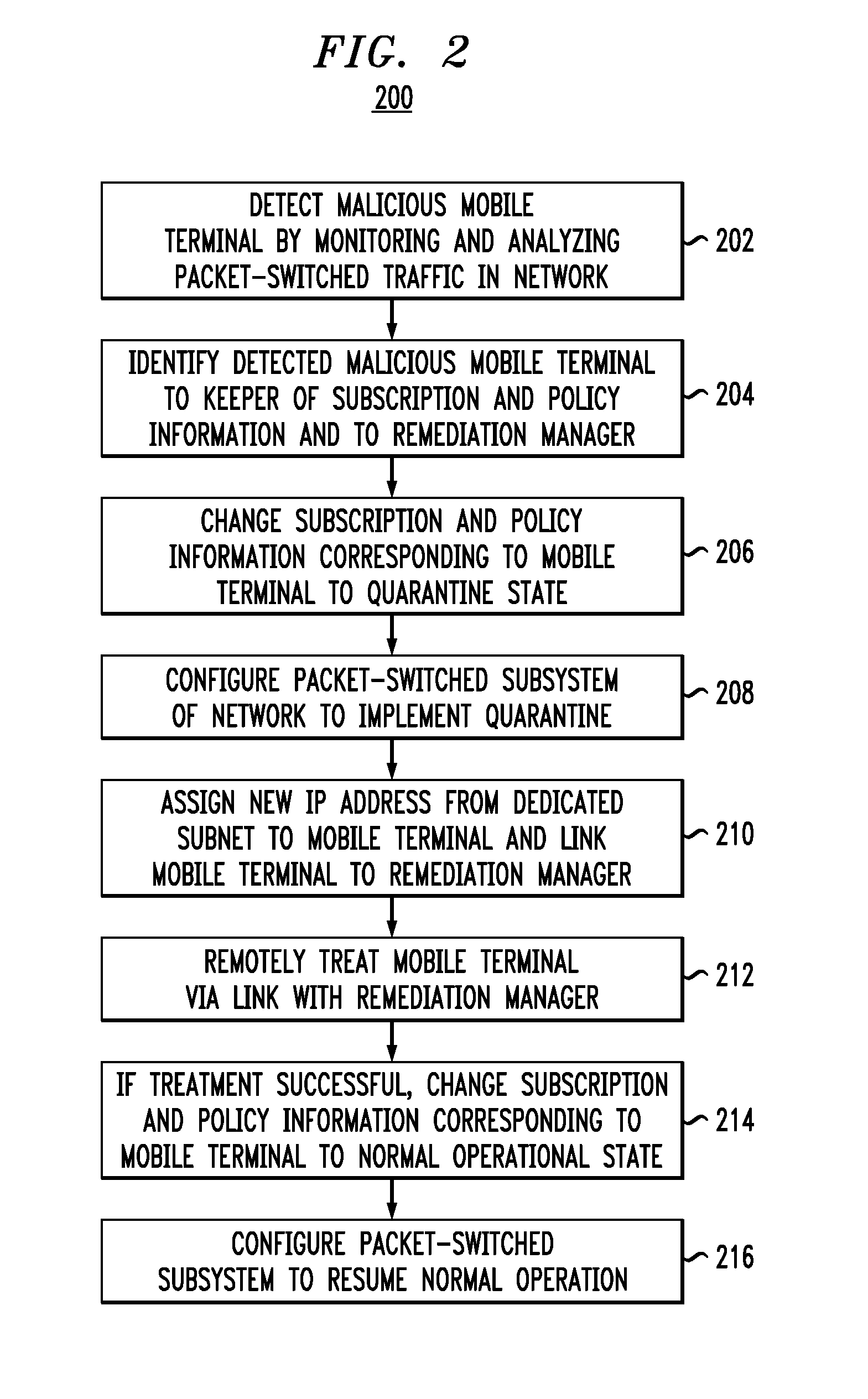
Treatment of malicious devices in a mobile-communications network
ActiveUS20110314542A1Memory loss protectionDigital data processing detailsOperational systemQuarantine
A method of remotely treating malicious mobile terminals connected to a mobile communications network. In one embodiment, when a malicious mobile terminal is detected by the intrusion-detection services of the network, the network changes the subscriber profile associated with the mobile terminal to operate the latter in a quarantine mode. The packet-switched subsystem of the network then links the quarantined mobile terminal to a remediation manager. The remediation manager remotely treats the mobile terminal, e.g., to repair or reinstall any corrupted software, terminate any active malicious processes, delete or quarantine any malware, and restore the operating system, configuration, and / or memory of the mobile terminal to a clean operational state. After the treatment, the network reverts the subscriber profile back to the initial state and removes the mobile terminal from the quarantine.
Owner:RPX CORP
System and methods for providing network quarantine
InactiveUS20050267954A1Digital computer detailsData switching by path configurationAccess networkQuarantine
A system and method for ensuring that machines having invalid or corrupt states are restricted from accessing network resources are provided. A quarantine coordination client (QCC) located on a client machine acquires statements of health from a plurality of quarantine policy clients. The QCC packages the statements and provides the package to a quarantine enforcement client (QEC). The QEC sends the package to a quarantine enforcement server (QES) with a request for network access. The QES passes the package to a quarantine coordination server (QCS) that disassembles the package and passes the individual statements of health to corresponding quarantine policy servers (QPS). The QPSs validate the statements of health and inform the QCS of the result. If the client provided valid statements of health, the QES grants the client access to the network.
Owner:MICROSOFT TECH LICENSING LLC
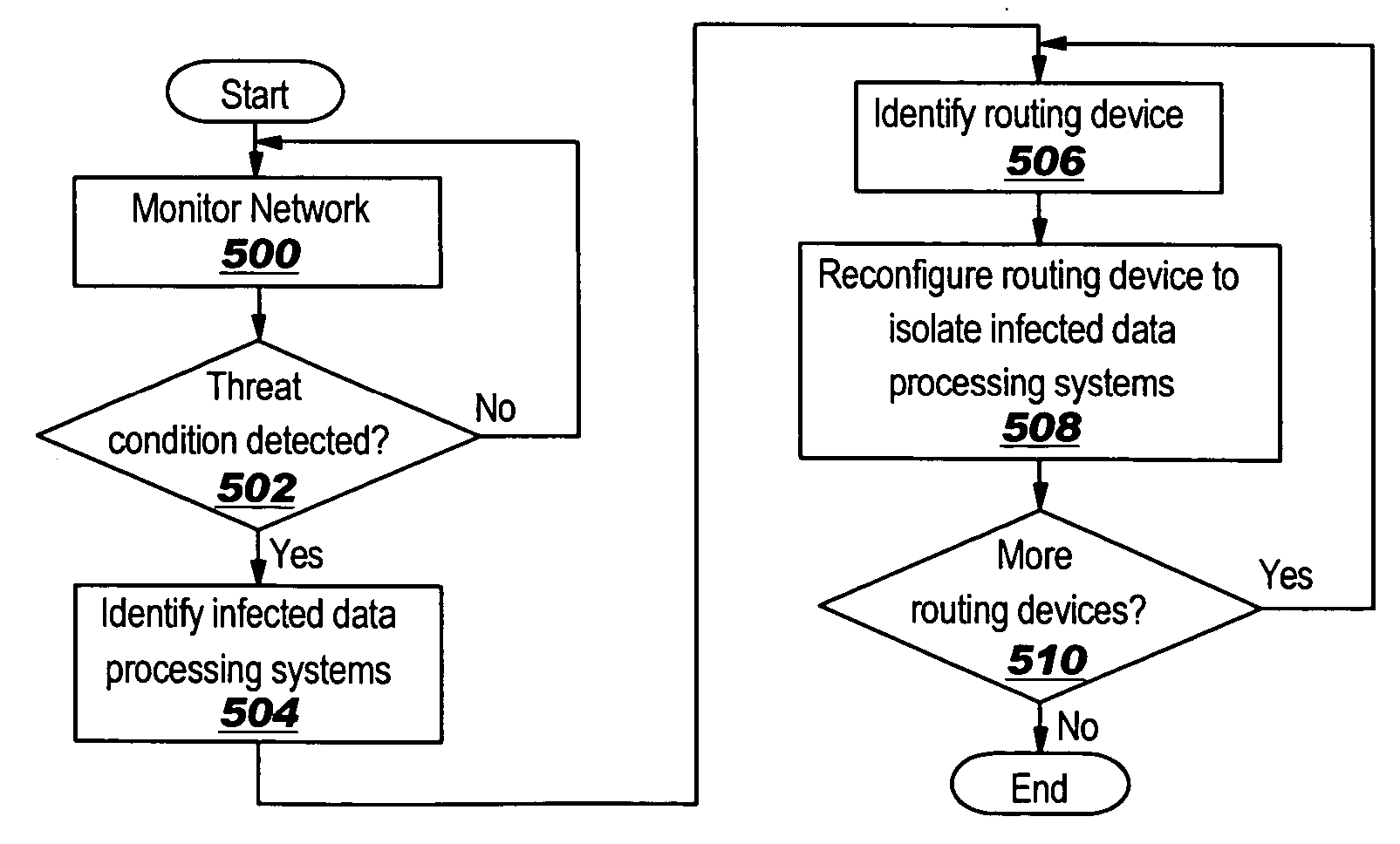
System for dynamic network reconfiguration and quarantine in response to threat conditions
InactiveUS20050278784A1Memory loss protectionError detection/correctionData processing systemQuarantine
A method, apparatus, and computer instructions for responding to a threat condition within the network data processing system. A threat condition within the network data processing system is detected. At least one routing device is dynamically reconfigured within the network data processing system to isolate or segregate one or more infected data processing systems within the network data processing system. This dynamic reconfiguration occurs in response to the threat condition being detected.
Owner:IBM CORP
Non-invasive radial artery blood pressure waveform measuring apparatus system and uses thereof
InactiveUS20060195035A1Accurate blood pressureOvercome difficultiesEvaluation of blood vesselsCatheterRR intervalRadiology
The invention relates to a non-invasive apparatus system for measuring radial artery blood pressure waveform, and its uses in heart rate variability measurement, autonomic nervous system measurement, personal identification, respiratory cycle and cough monitoring, home quarantine, and hospital quarantine thereof.
Owner:SUN DEHCHUAN
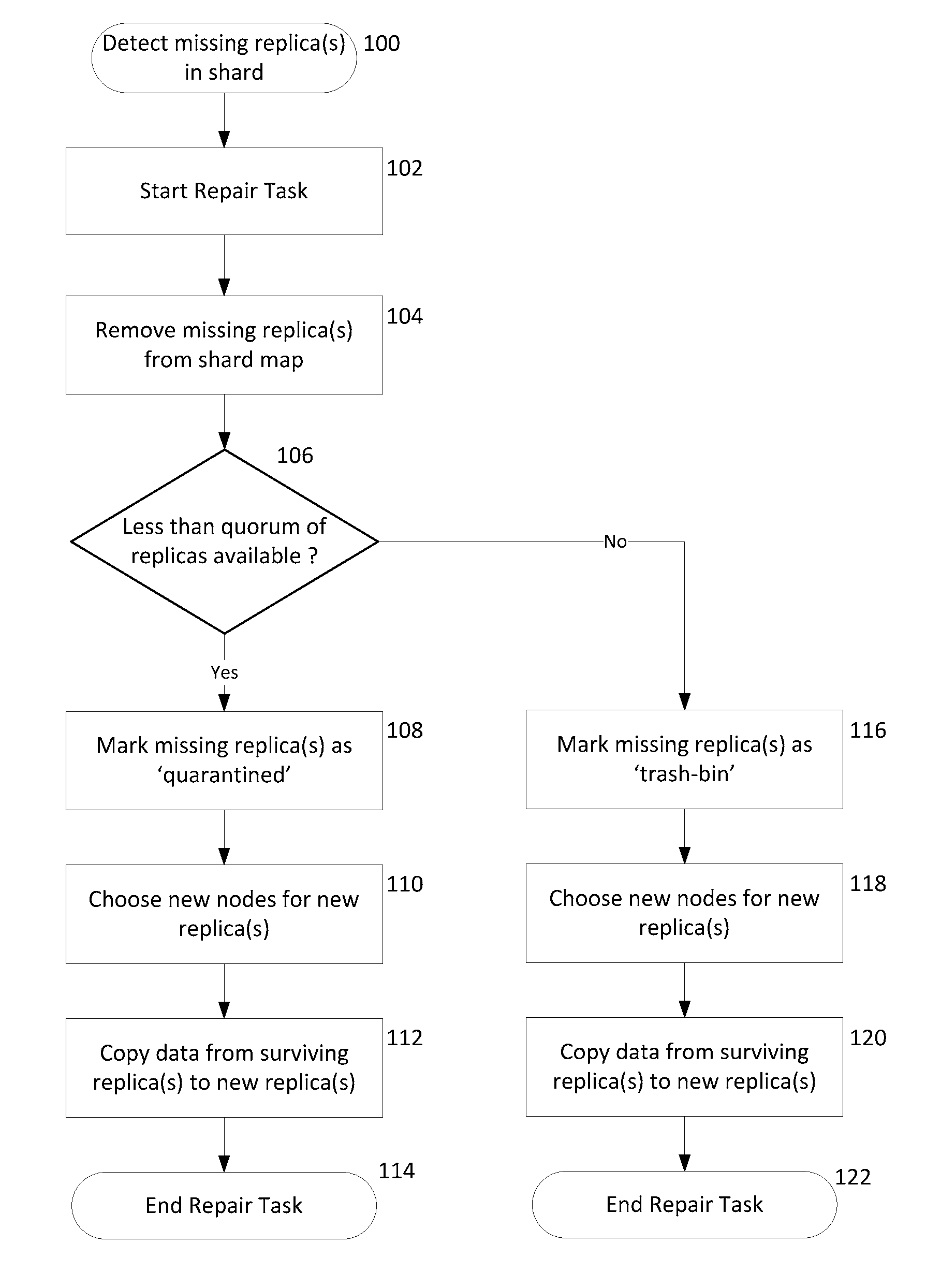
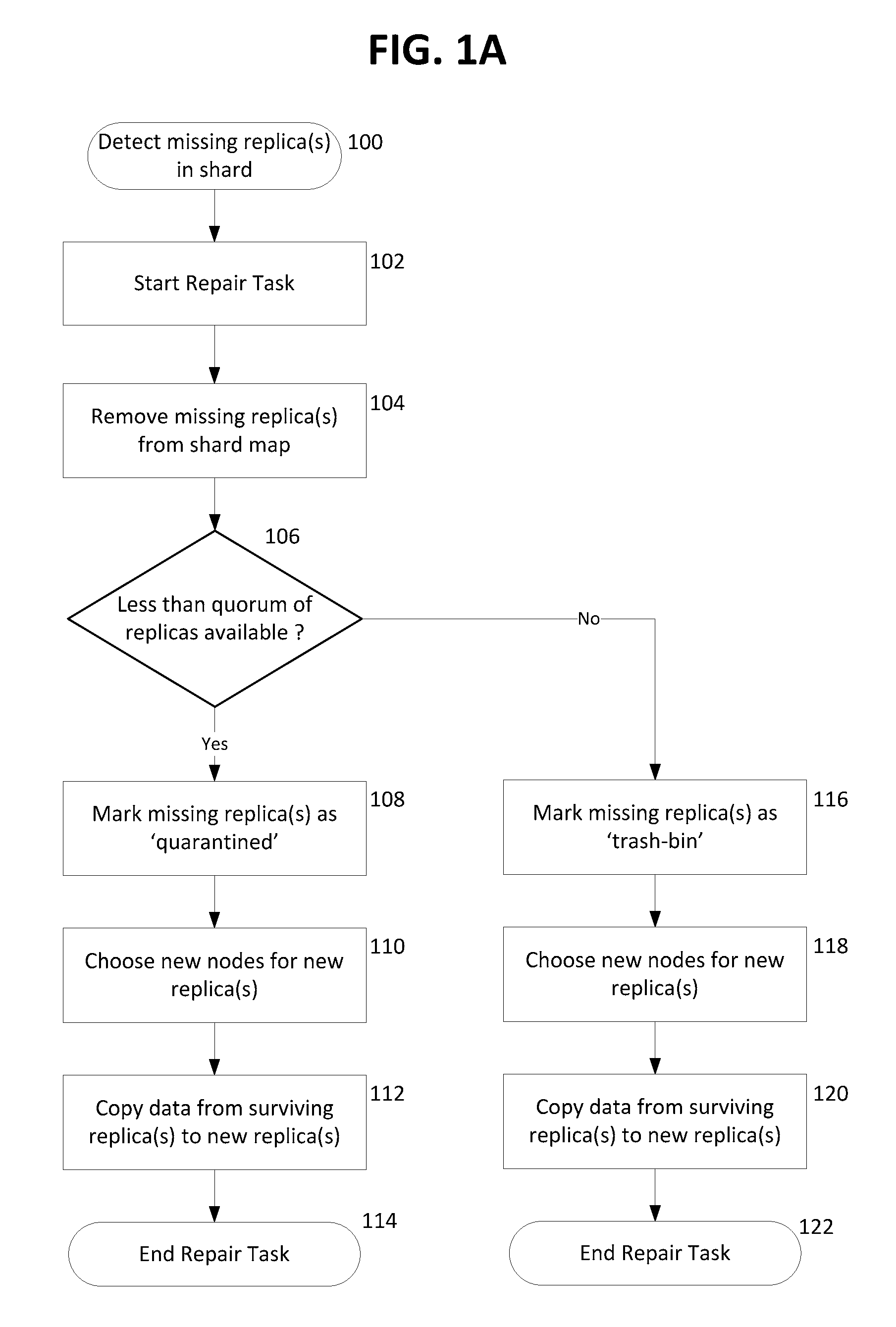
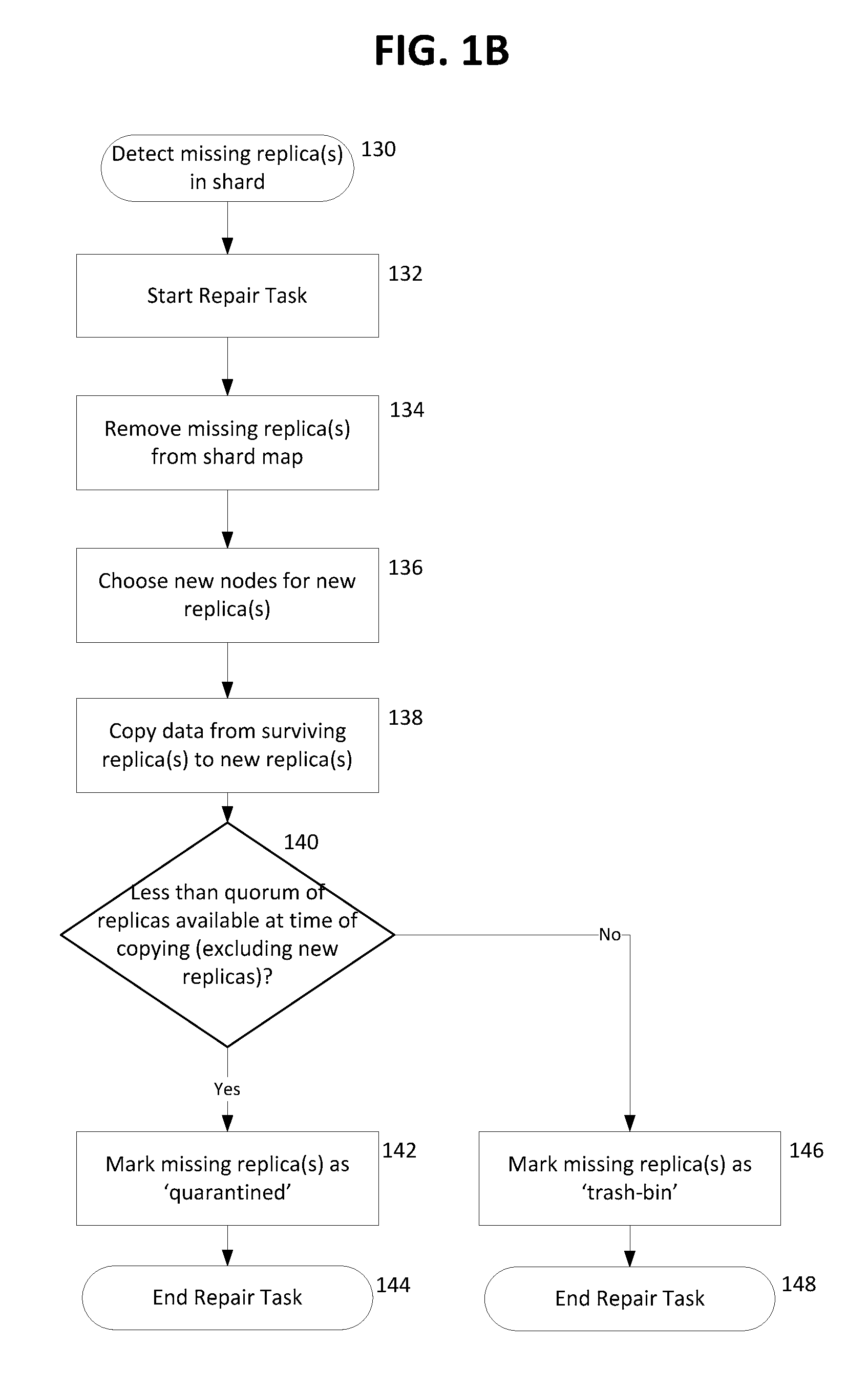
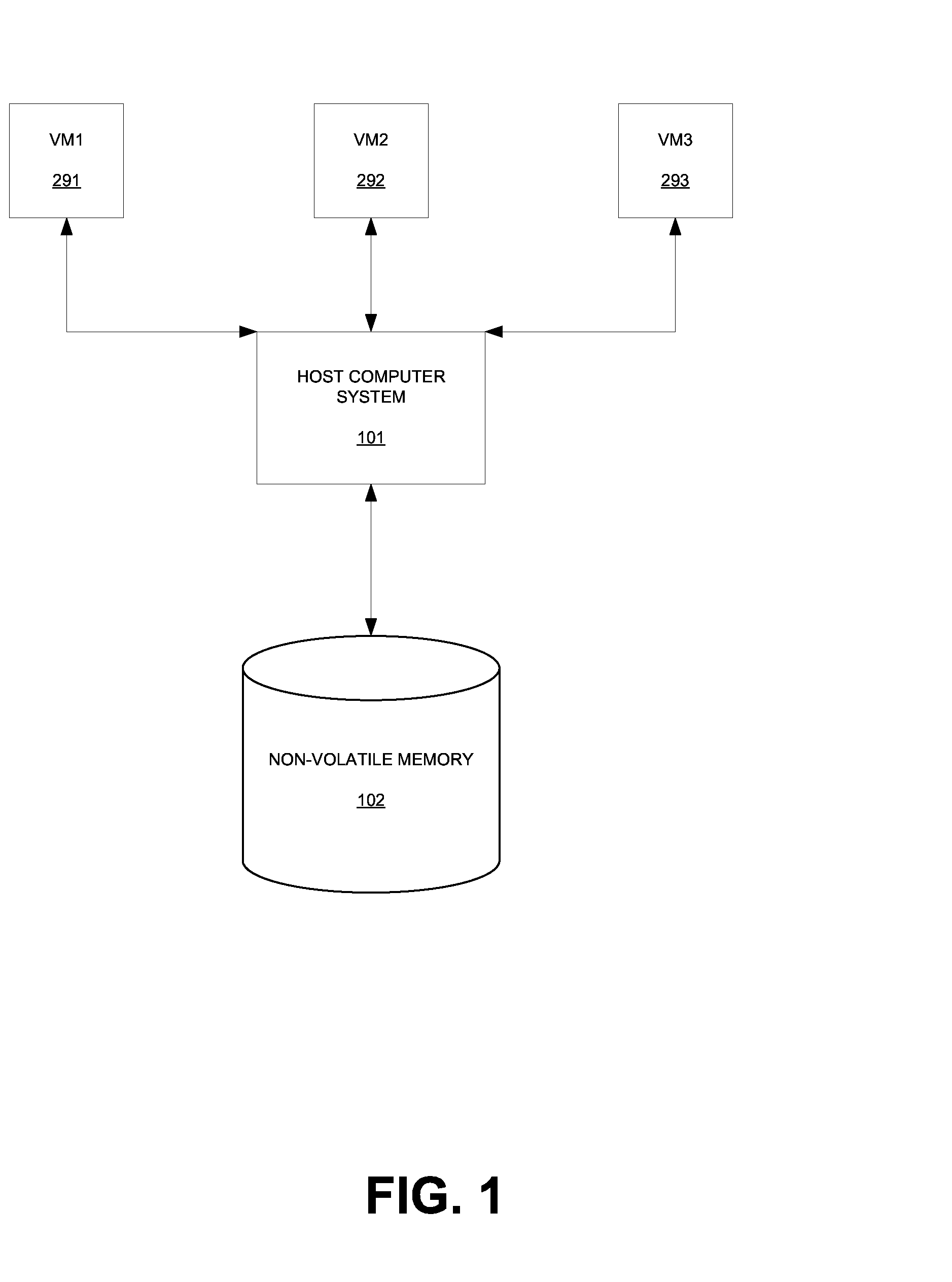
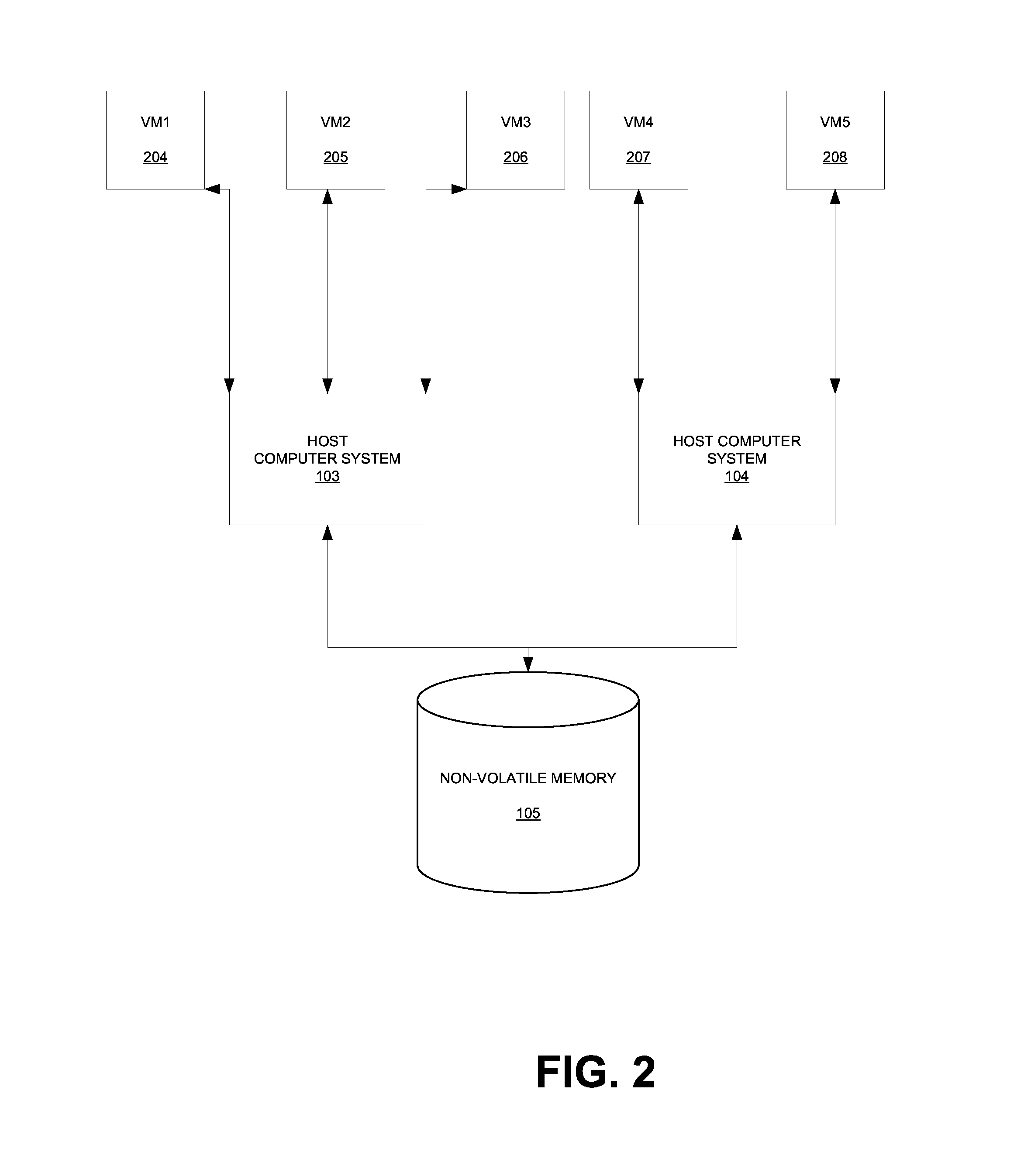
Quarantine and repair of replicas in a quorum-based data storage system
ActiveUS20150278324A1Digital data processing detailsDatabase distribution/replicationFault toleranceQuarantine
A data storage system with quorum-based commits sometimes experiences replica failure, due to unavailability of a replica-hosting node, for example. In embodiments described herein, such failed replicas can be quarantined rather than deleted, and subsequently such quarantines can be recovered. The teachings hereof provide data storage with improved fault-tolerance, resiliency, and data availability.
Owner:AKAMAI TECH INC
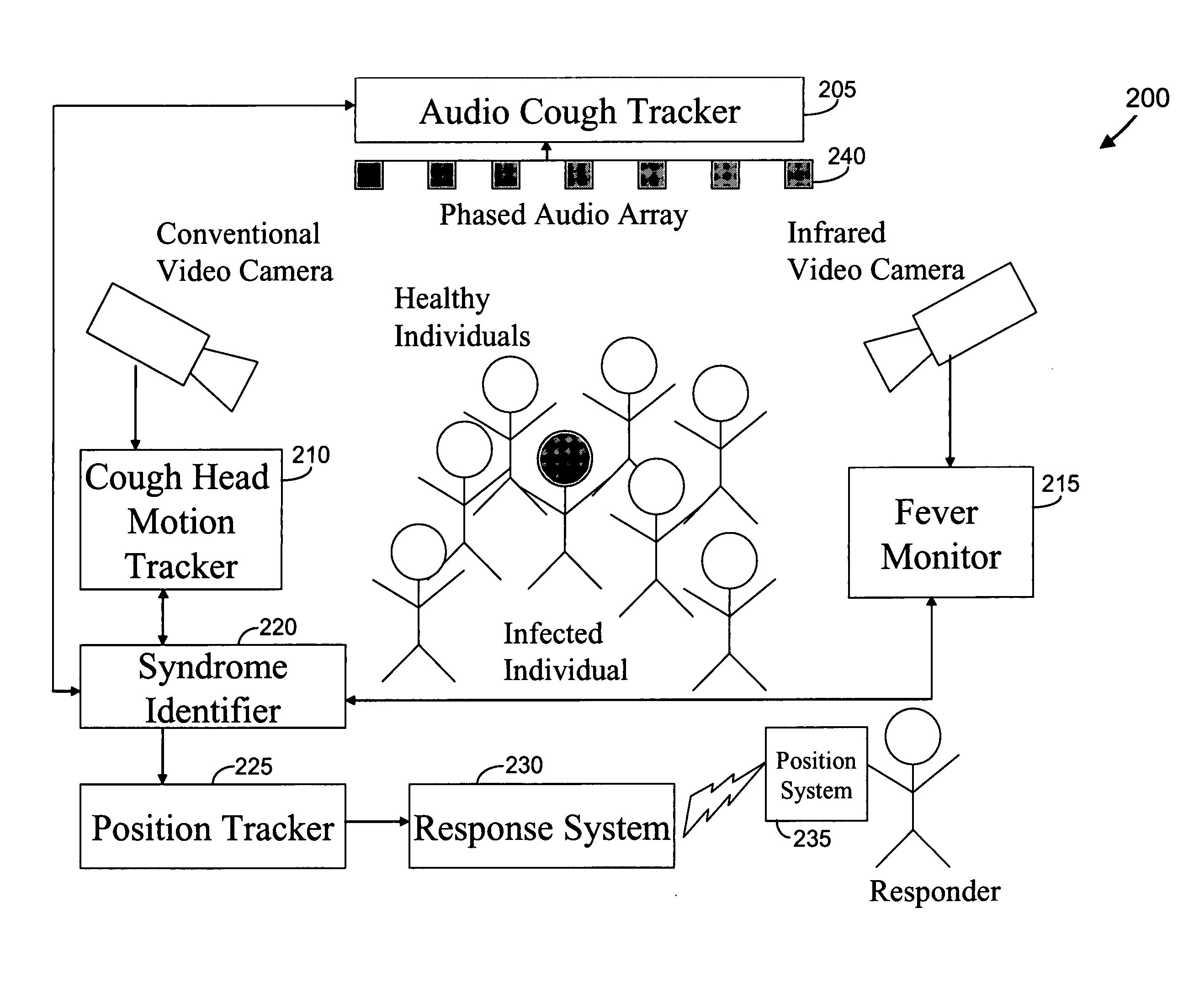
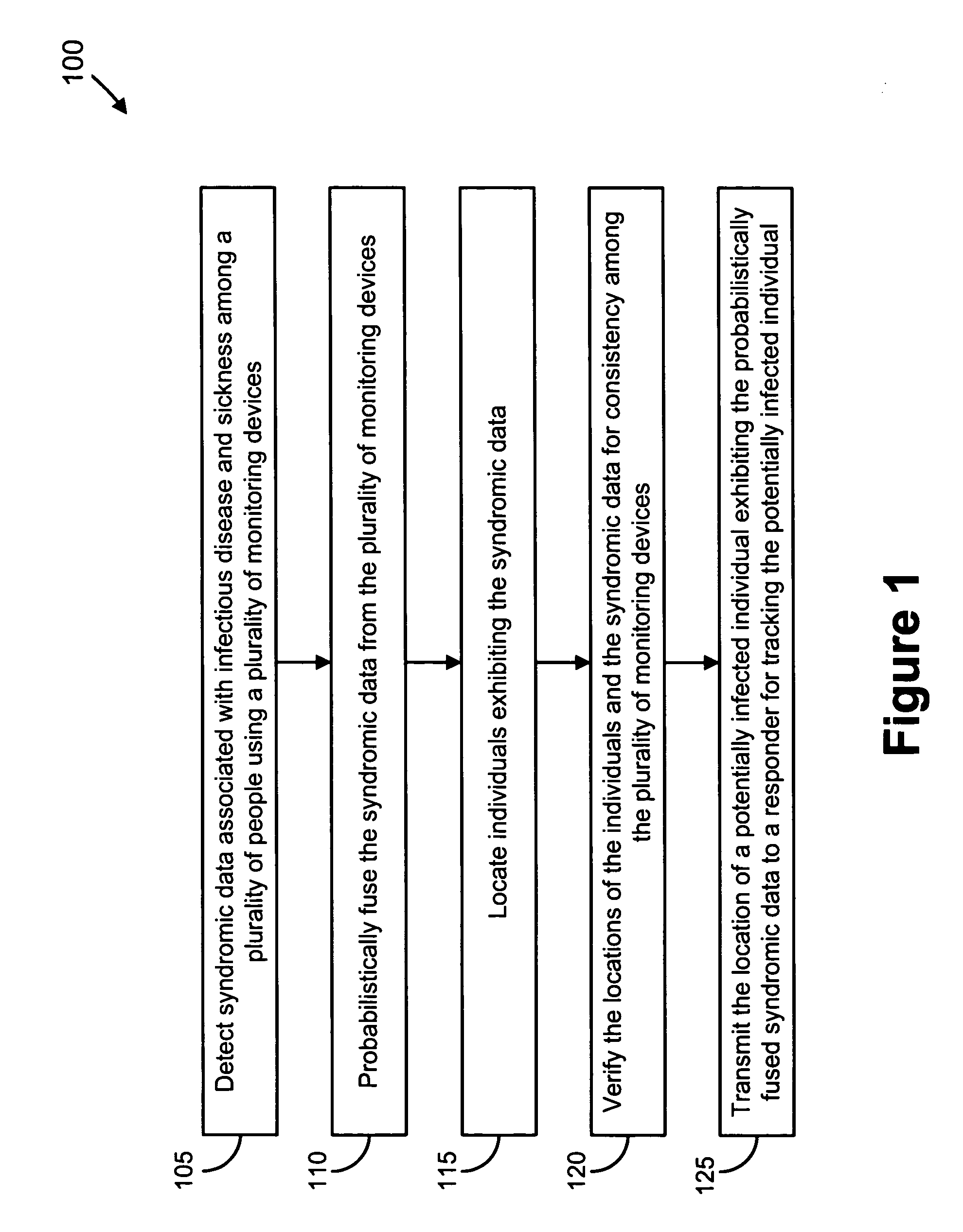
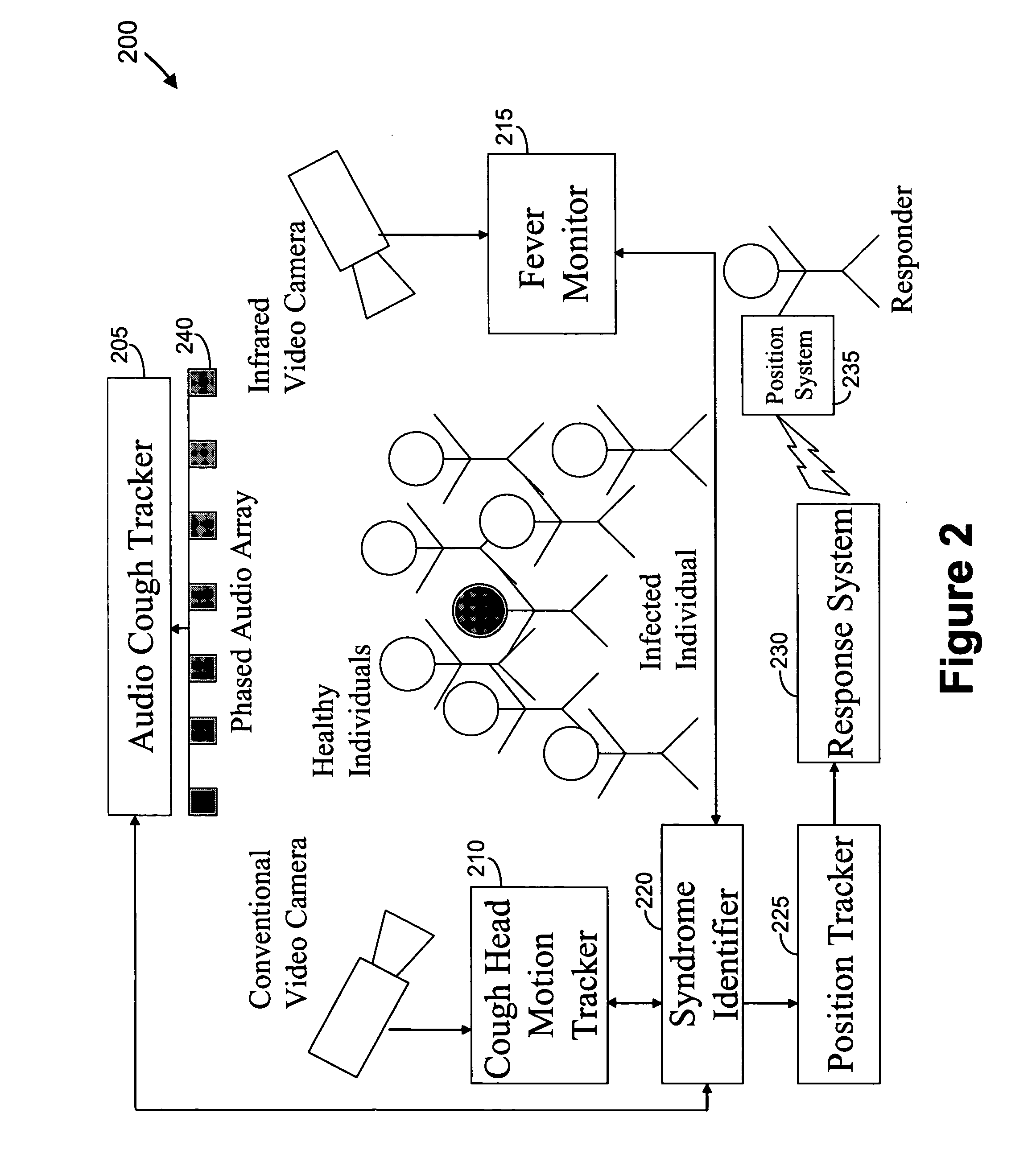
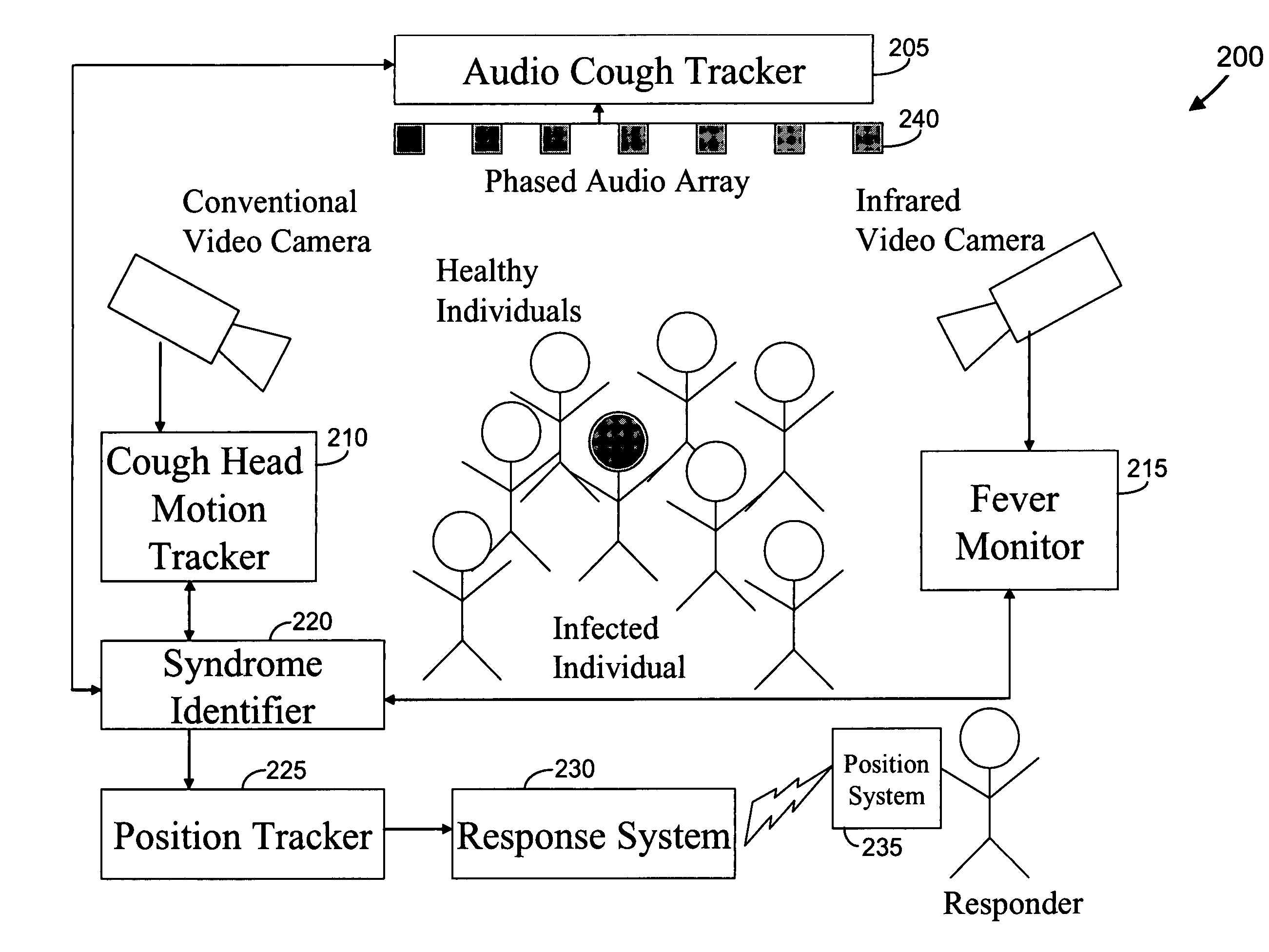
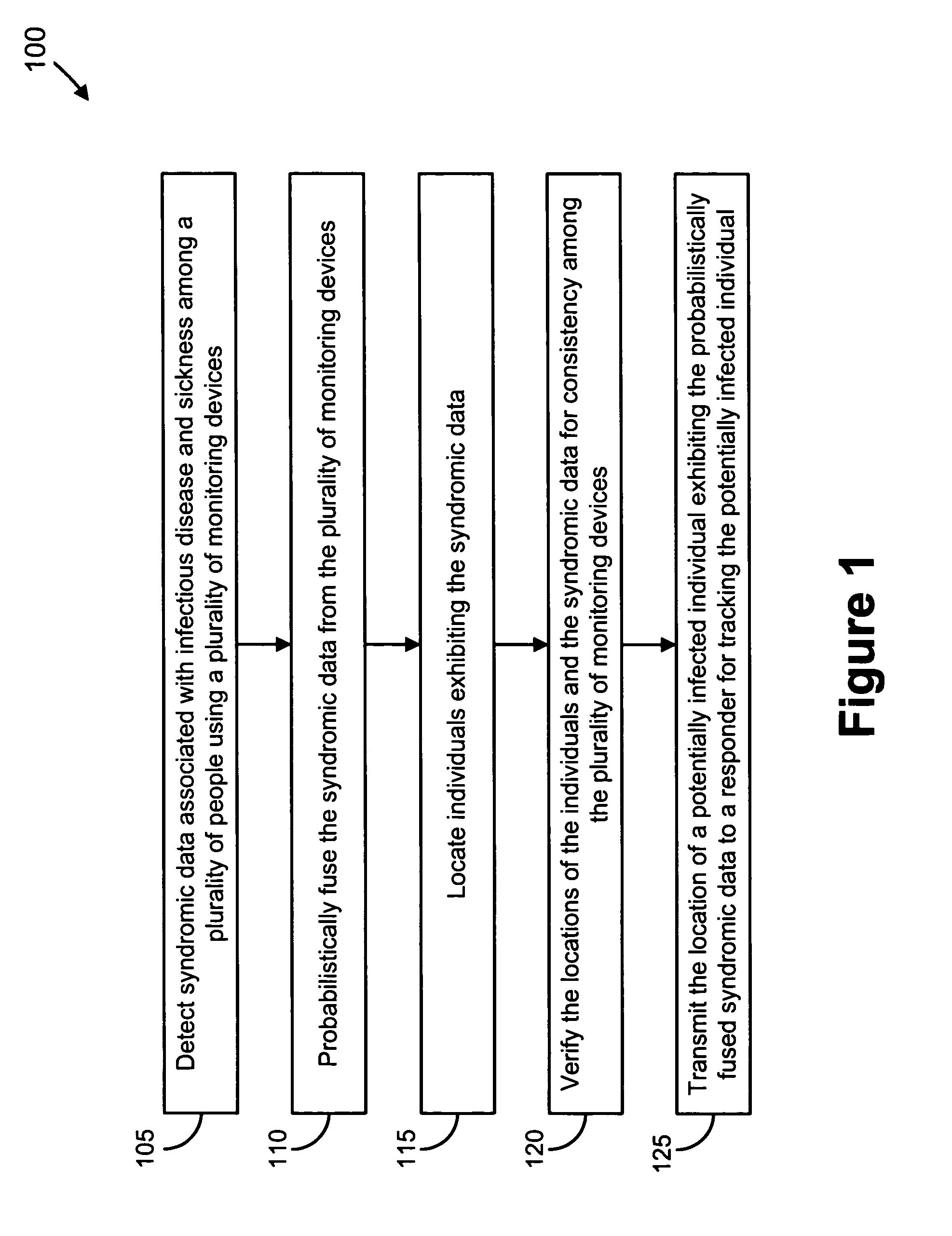
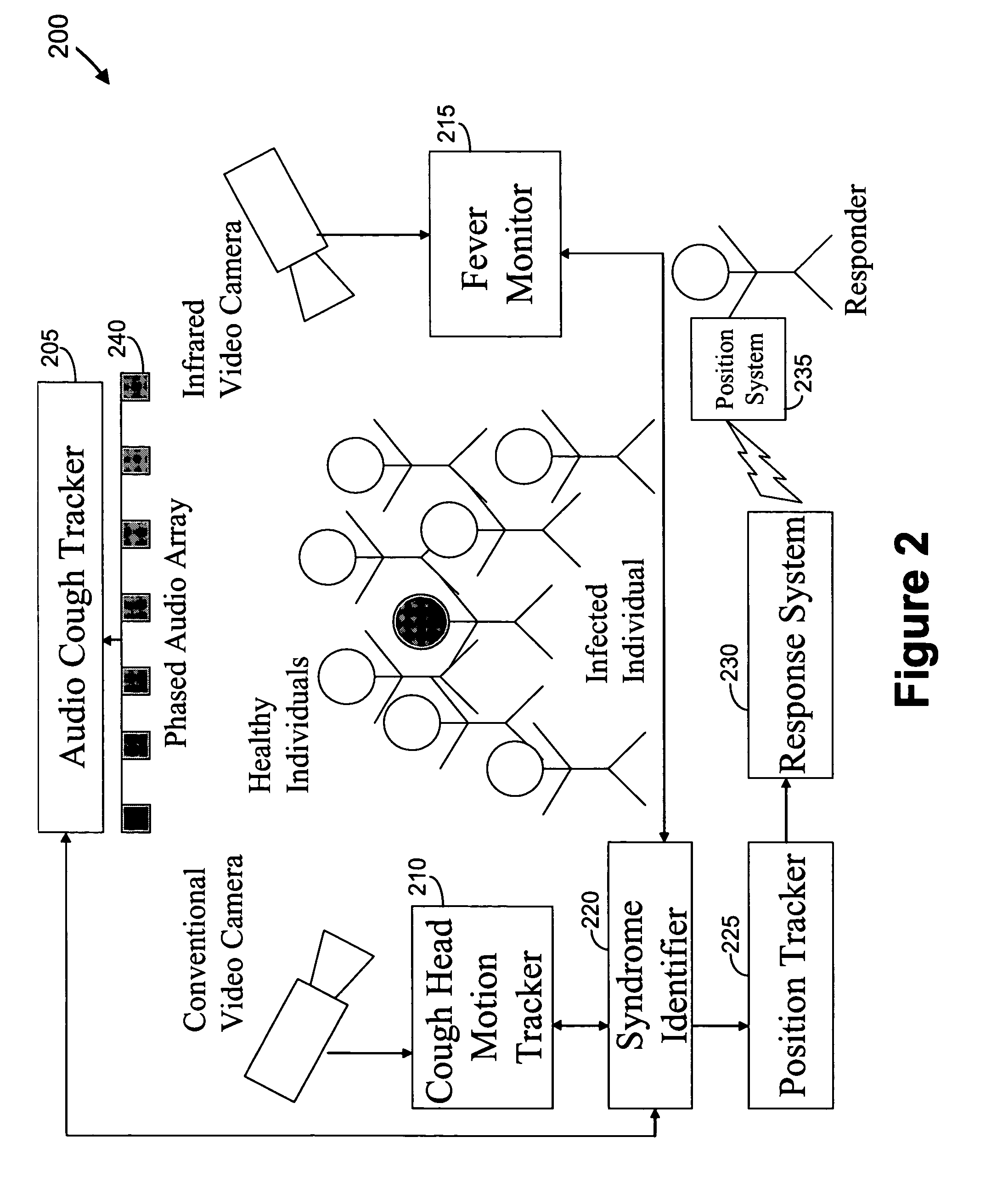
Video and audio monitoring for syndromic surveillance for infectious diseases
We present, in exemplary embodiments of the present invention, novel systems and methods for syndromic surveillance that can automatically monitor symptoms that may be associated with the early presentation of a syndrome (e.g., fever, coughing, sneezing, runny nose, sniffling, rashes). Although not so limited, the novel surveillance systems described herein can be placed in common areas occupied by a crowd of people, in accordance with local and national laws applicable to such surveillance. Common areas may include public areas (e.g., an airport, train station, sports arena) and private areas (e.g., a doctor's waiting room). The monitored symptoms may be transmitted to a responder (e.g., a person, an information system) outside of the surveillance system, such that the responder can take appropriate action to identifying, treat and quarantine potentially infected individuals, as necessary.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
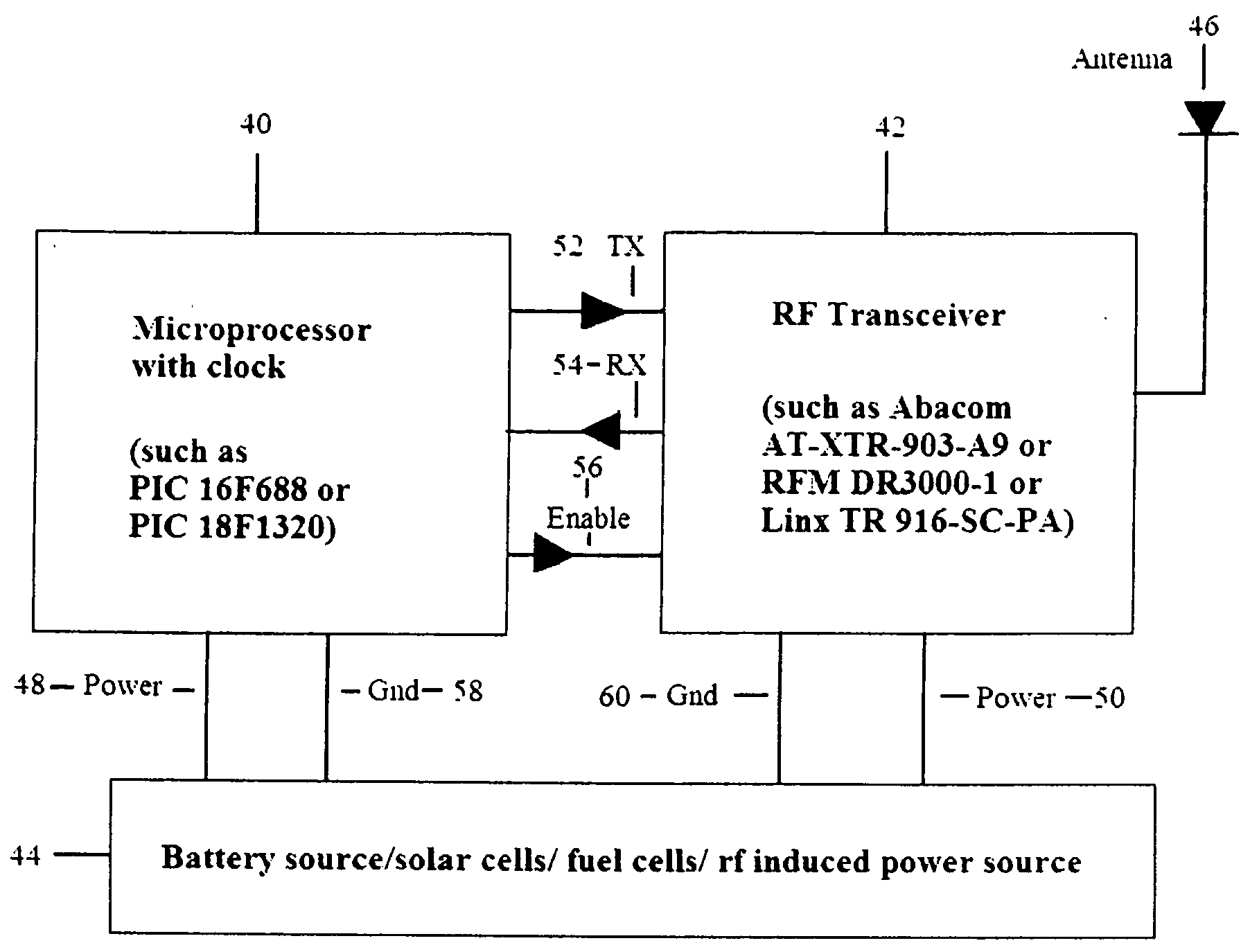
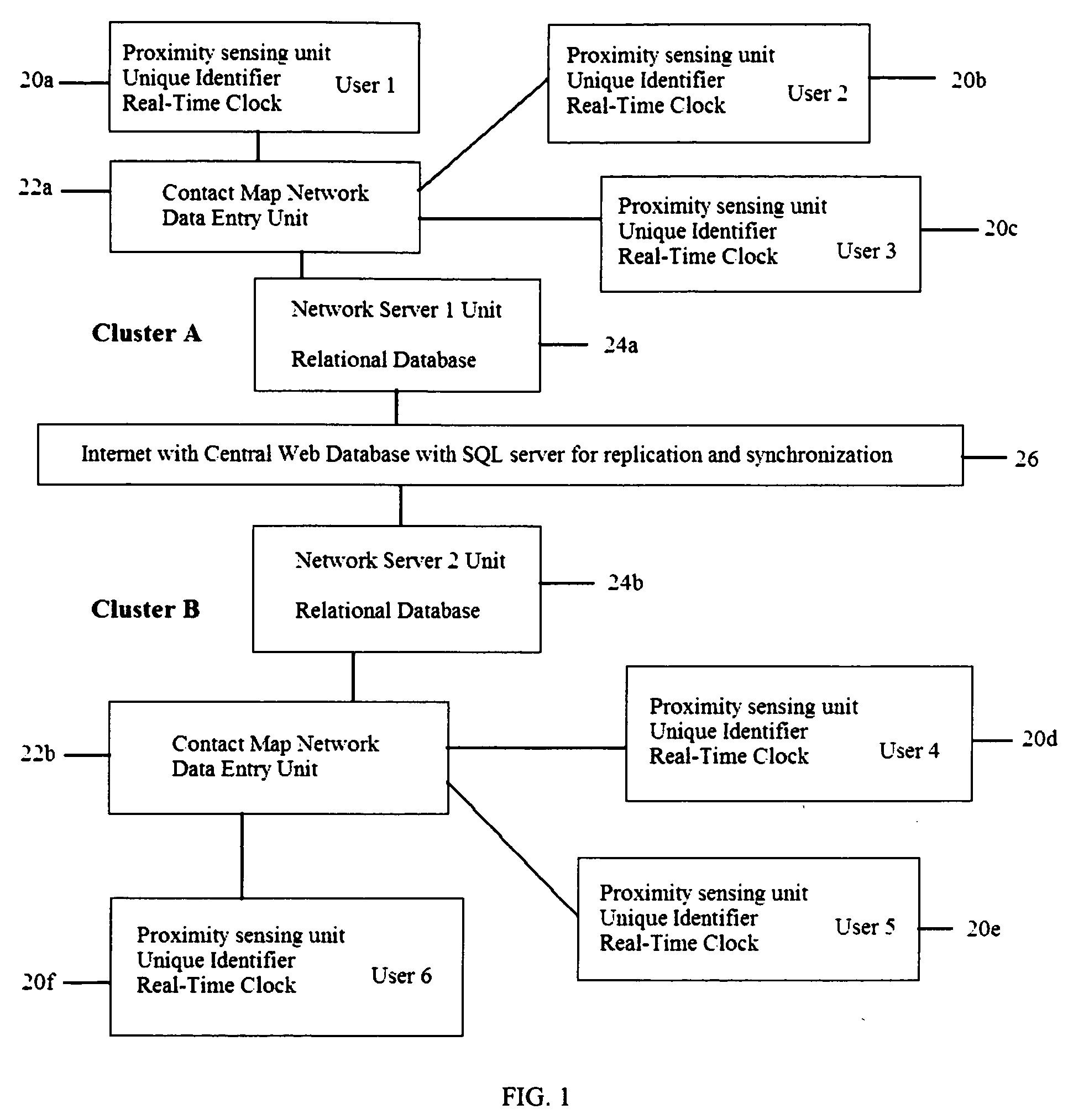
System and method for creating a proximity map of plurality of living beings and objects
A proximity network map defines who and what objects have come in contact of each other including location and time. This map selects the list people who have come in contact with known infected people based on contagious disease epidemiology criteria to control its spread, or to prevent radiation poisoning, limit bio-chemicals exposure, etc. These people then undergo testing and quarantine procedures. It monitors hygiene practices and reduces nosocomial infections in hospitals and mitigates the pandemic flu threat by controlling contamination. It controls people interaction, information flow in a high security environment, control crime or gang activities. Each person or object carrying a proximity-sensing unit with unique ID records all units it encountered over a period of time. This information is stored with time stamp in a relational database and transferred to network servers. The databases are then replication throughout via a central web database server for retrieval and analysis.
Owner:WONG CHON MENG
Biological toxin detection system for mailed materials
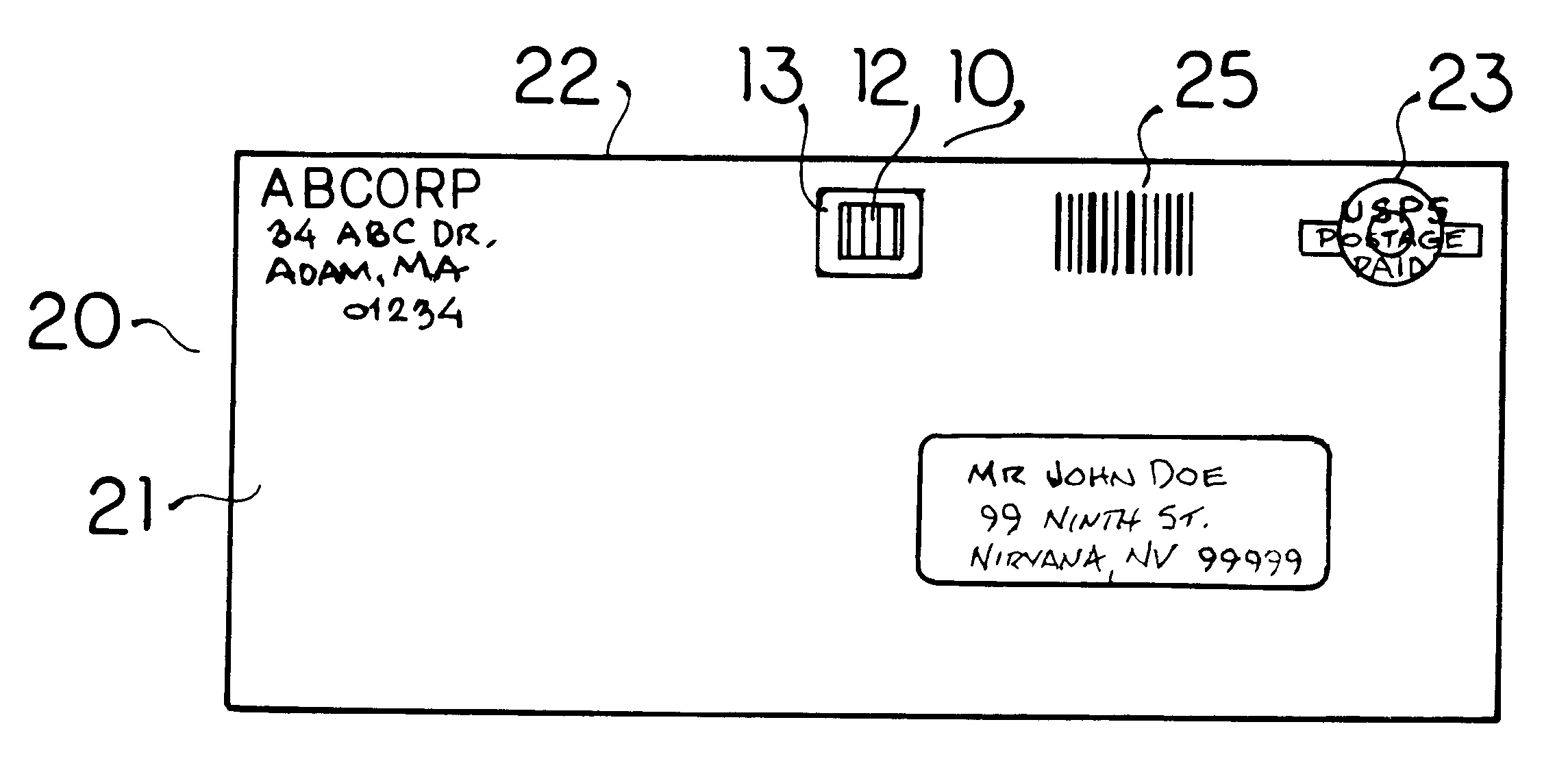
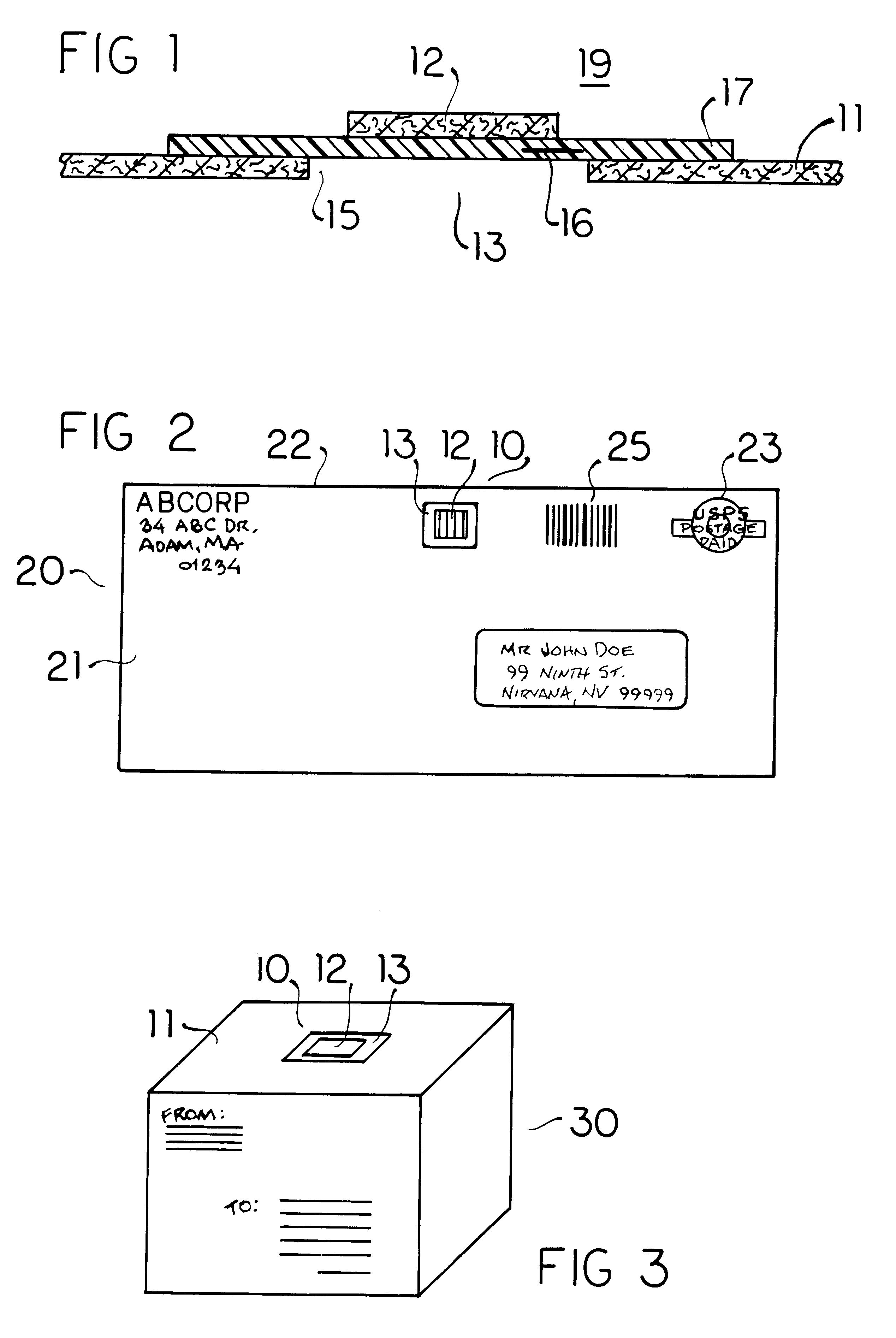
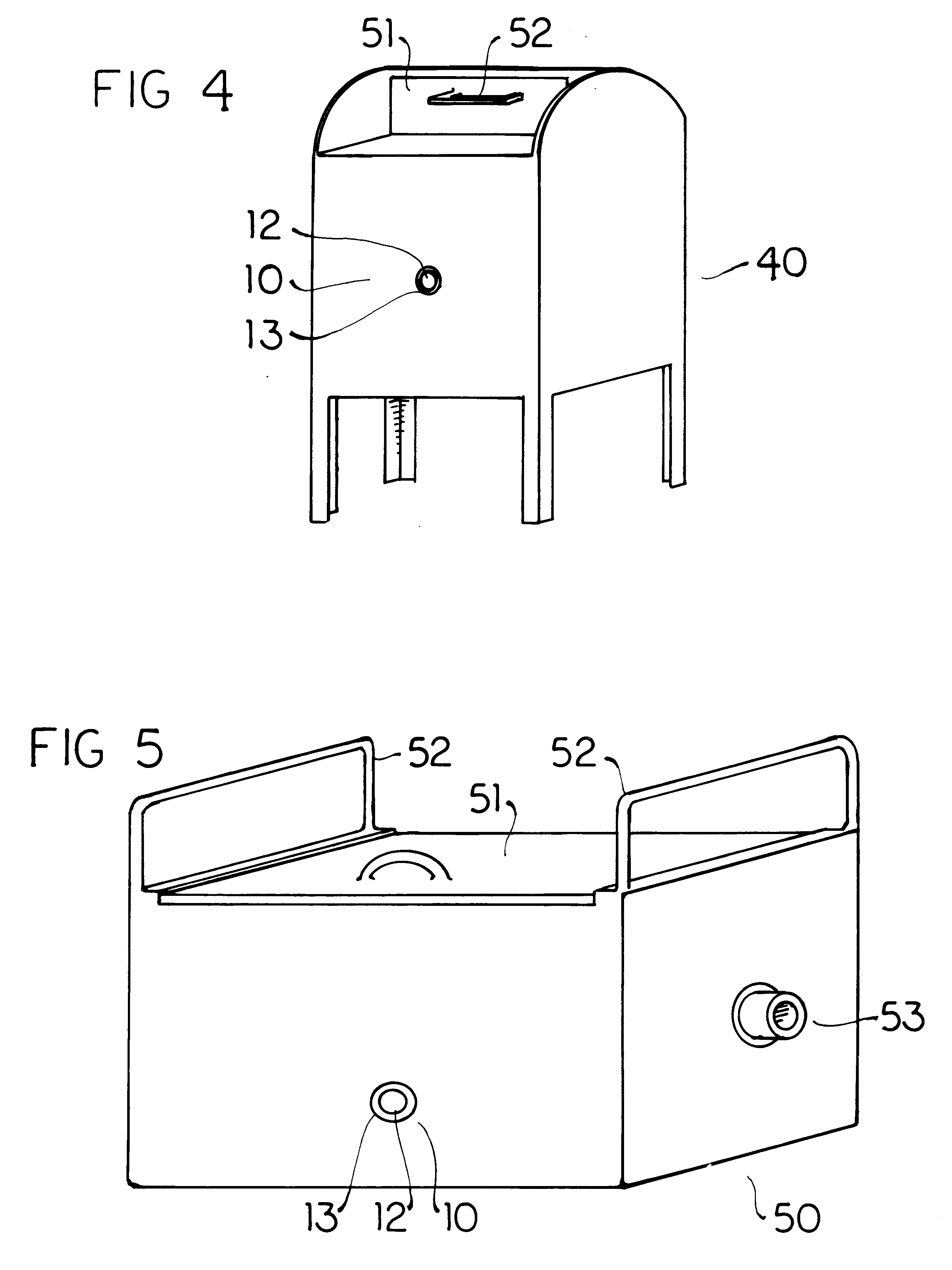
InactiveUS6524846B1Easy to manufactureReadily adheres to paperBioreactor/fermenter combinationsBiological substance pretreatmentsPorous substrateQuarantine
Envelopes and other containers intended for mail transportation possess a biological agent / toxin indicator operative upon the interior in detection of volatile bases including gaseous amines released from bacterial biological agents including Bacillus antracis, i.e. anthrax. The biological agent indicator has an acidic acid-base indicator compound that irreversibly changes color when neutralized by volatile bases. The compound is applied in liquid form to an appropriately porous substrate. A polymeric matrix is specifically suggested for this substrate. Irreversible indication of the presence of volatile bases including amines produced by live bacterial agents as toxins at temperate ambient conditions down to below freezing is provided. An indicator compound having a pH of 2-5 is recommended. Halogenated xanthene, sulphonated azo, and sulphonated hydroxy-functional triphenylmethane dyes are suggested. The presence of toxins produced by live bacterial biological agents within a package or container upon which the indicator is mounted is indicated by a slowly reversible color change. Primary public use envelopes and collection containers, secondary transportation and stationary quarantine enclosures, and articles worn inside a room with mail and when handling mail including a badge and gloves are specifically suggested.
Owner:ROBINSON JR WILLIAM L
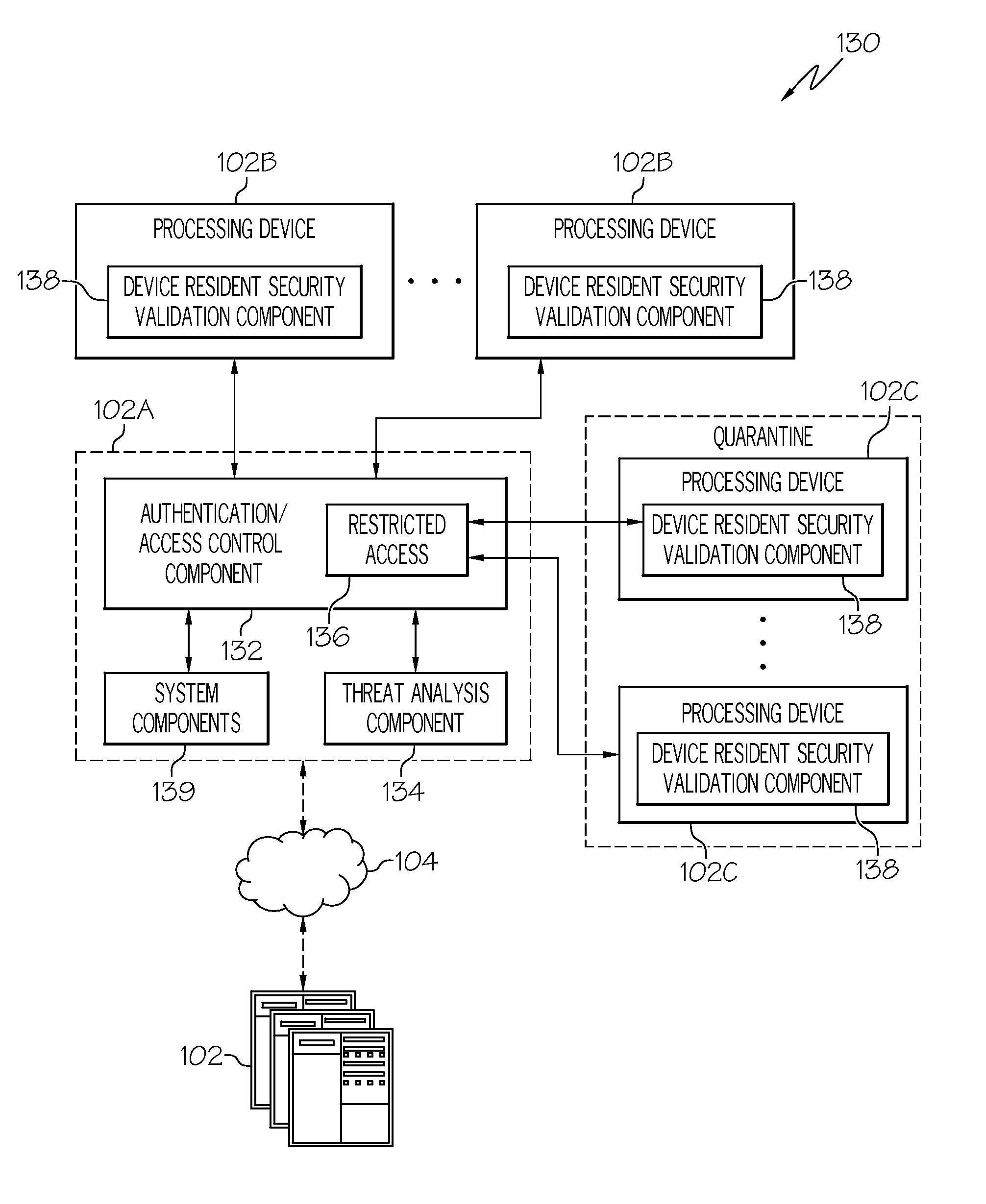
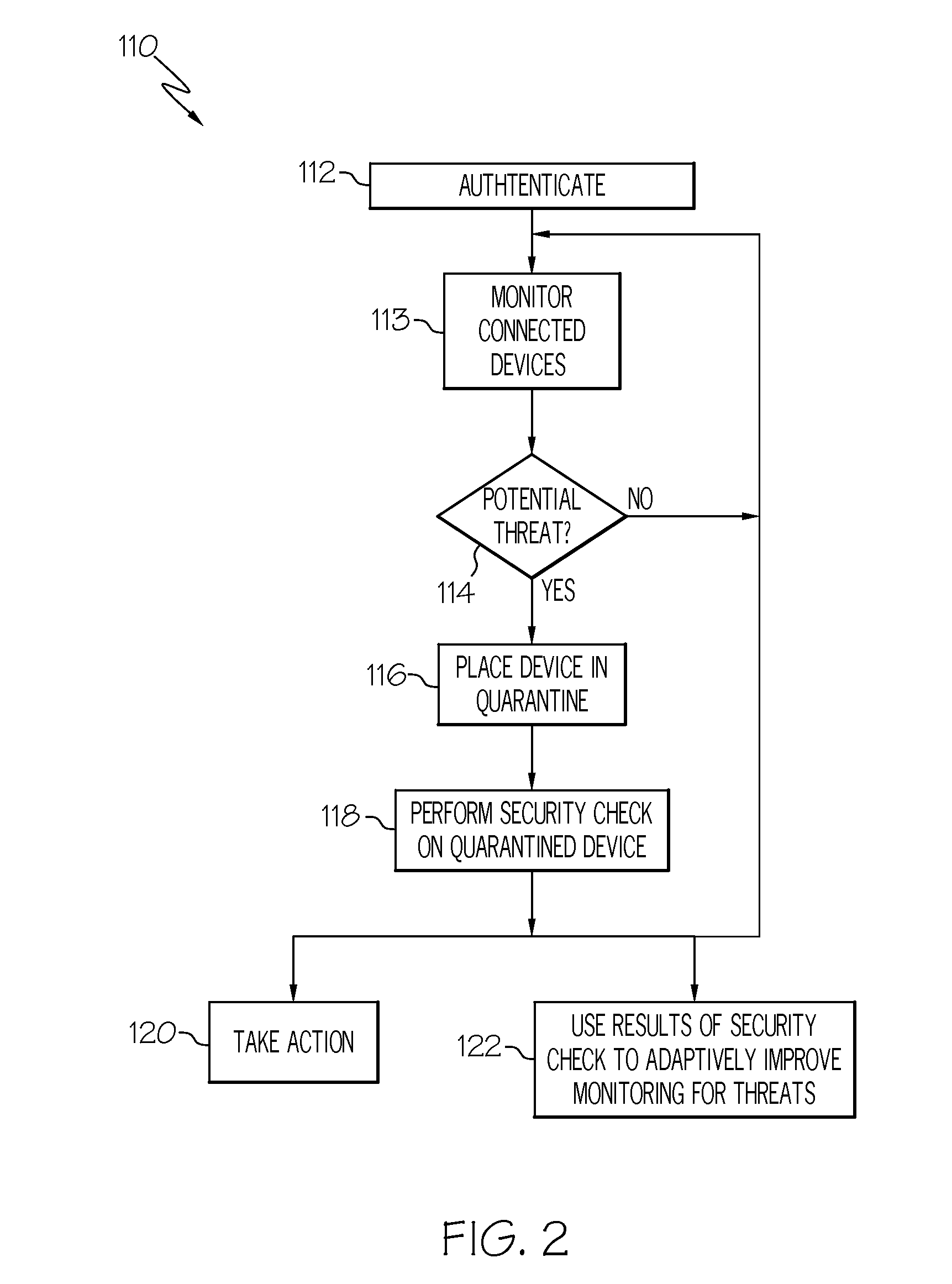
Adaptive Autonomic Threat Detection and Quarantine
InactiveUS20090064334A1Memory loss protectionUnauthorized memory use protectionTraffic capacityQuarantine
Autonomic threat detection is performed by collecting traffic samples of traffic patterns associated with a networked device having a device resident validation module. A threat analysis system is used to recognize a pattern of traffic indicative of a compromised device based at least in part upon the traffic samples. If the samples indicate a compromised device, the device is quarantined and a security check is performed on the device. The security check may include requesting data from the corresponding device resident validation module to determine if the device is compromised, analyzing data from the device resident validation module of the quarantined device and taking an action based upon analysis of the data. At least one of the data from the device resident validation module of the quarantined device or the traffic samples is utilized to autonomically train the threat analysis system to identify compromised devices.
Owner:IBM CORP
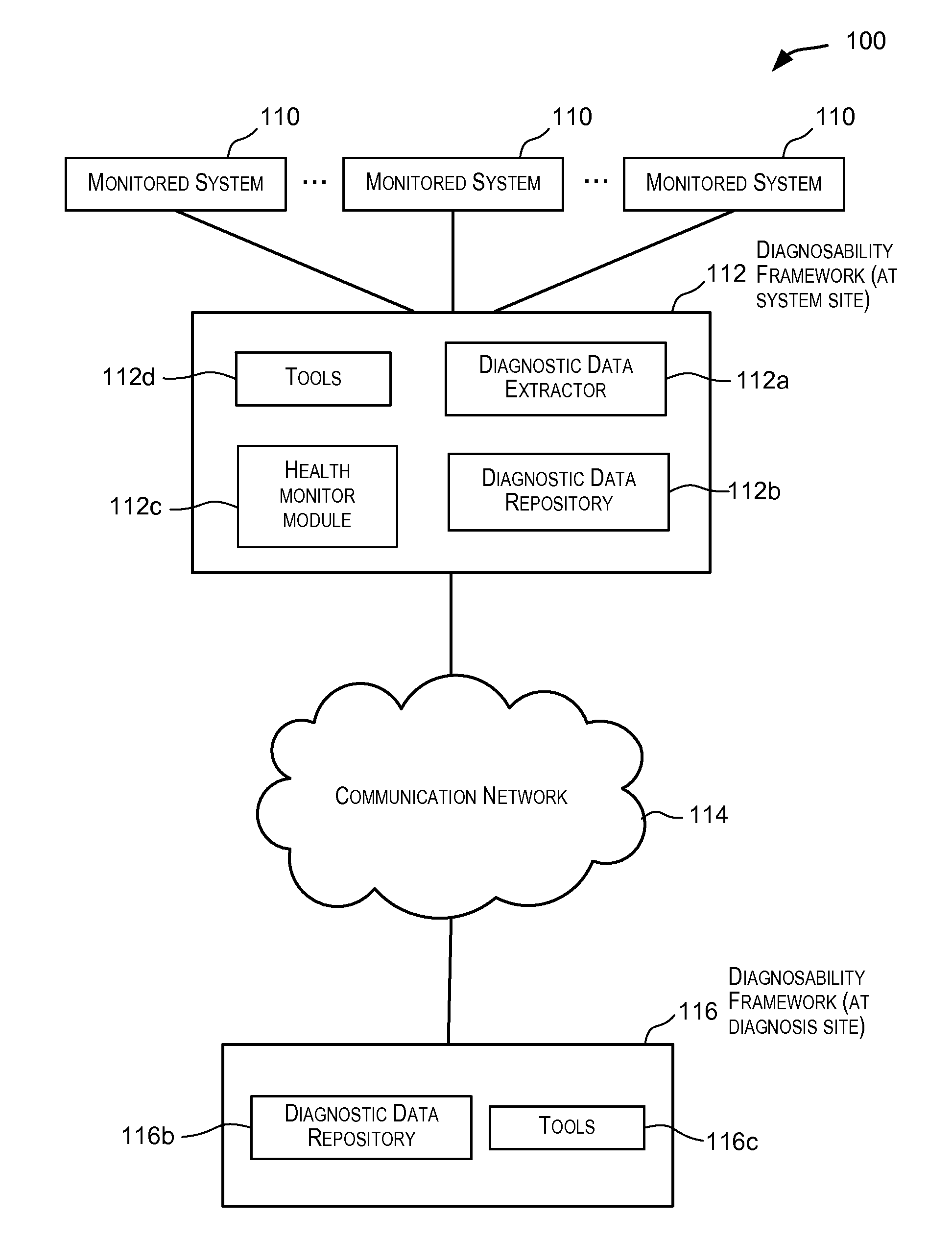
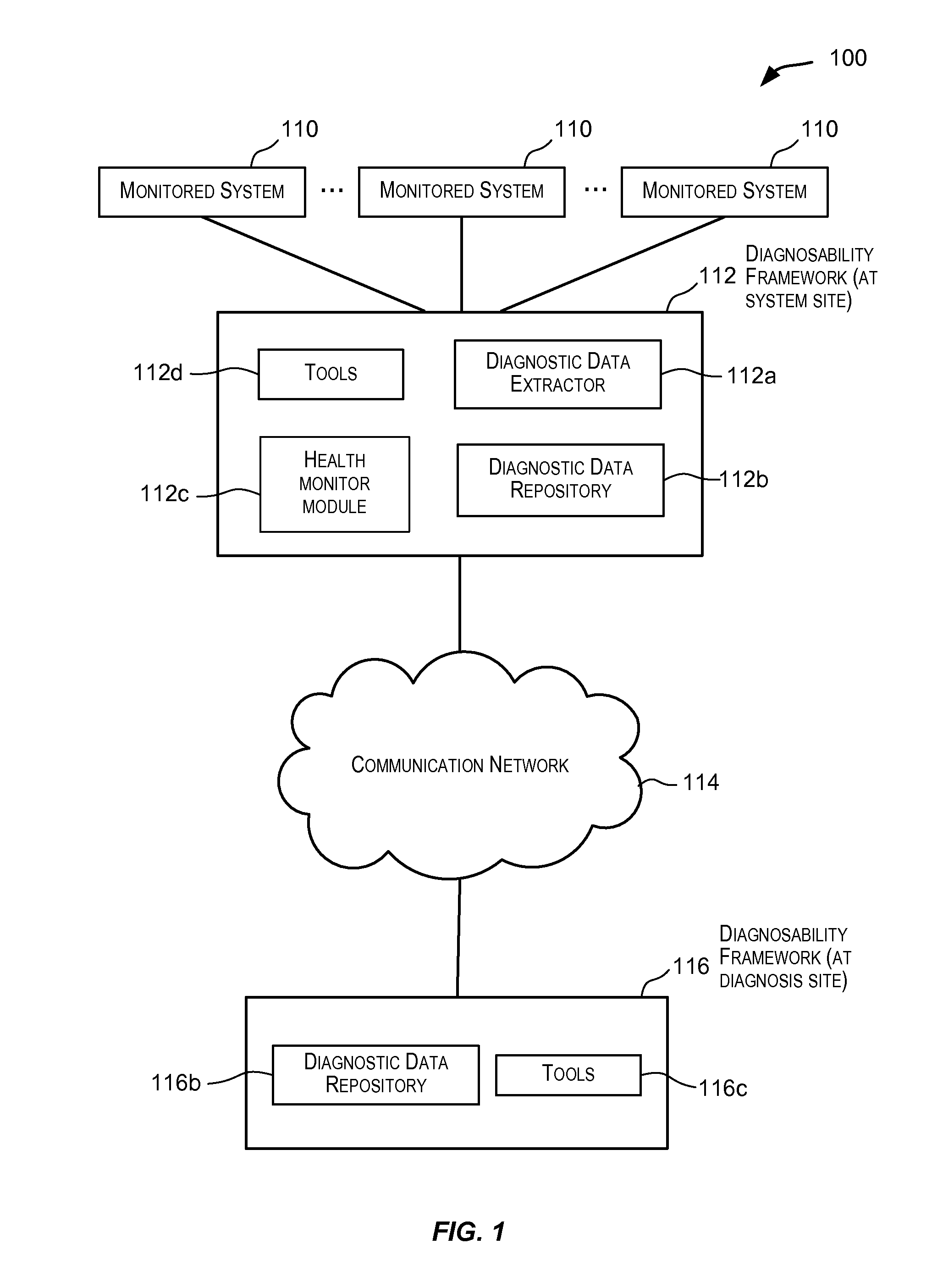
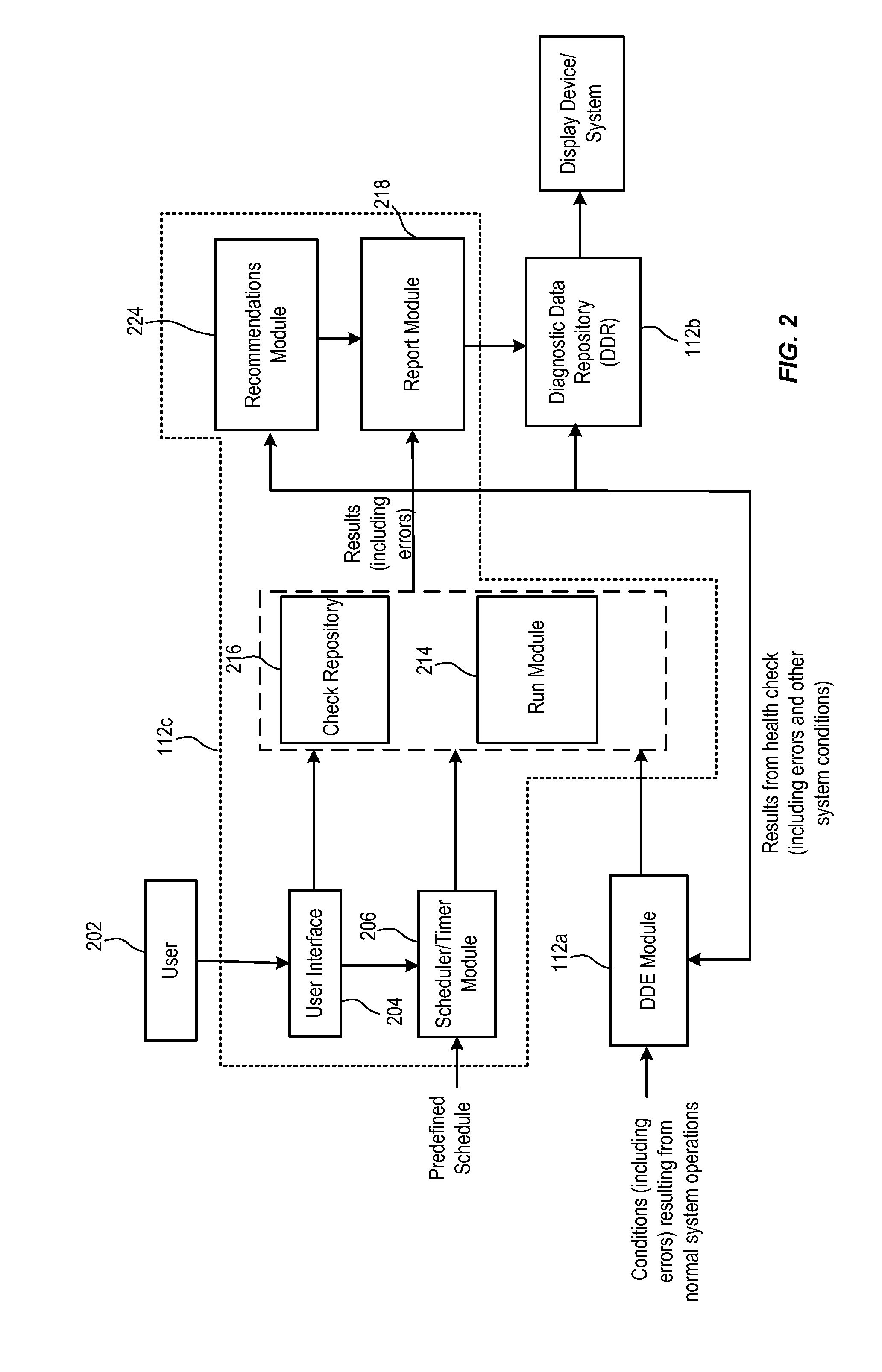
Health monitor
ActiveUS20090106605A1Easy diagnosisLimit/quarantine the damages caused by the detected conditionsError detection/correctionTransmissionMedicineMonitoring system
Techniques for proactively and reactively running diagnostic functions. These diagnostic functions help to improve diagnostics of conditions detected in a monitored system and to limit / quarantine the damages caused by the detected conditions. In one embodiment, a health monitor infrastructure is provided that is configured to perform one or more health checks in a monitored system for diagnosing and / or gathering information related to the system. The one or more health checks may be invoked pro-actively on a scheduled basis, reactively in response to a condition detected in the system, or may even be invoked manually by a user such as a system administrator.
Owner:ORACLE INT CORP
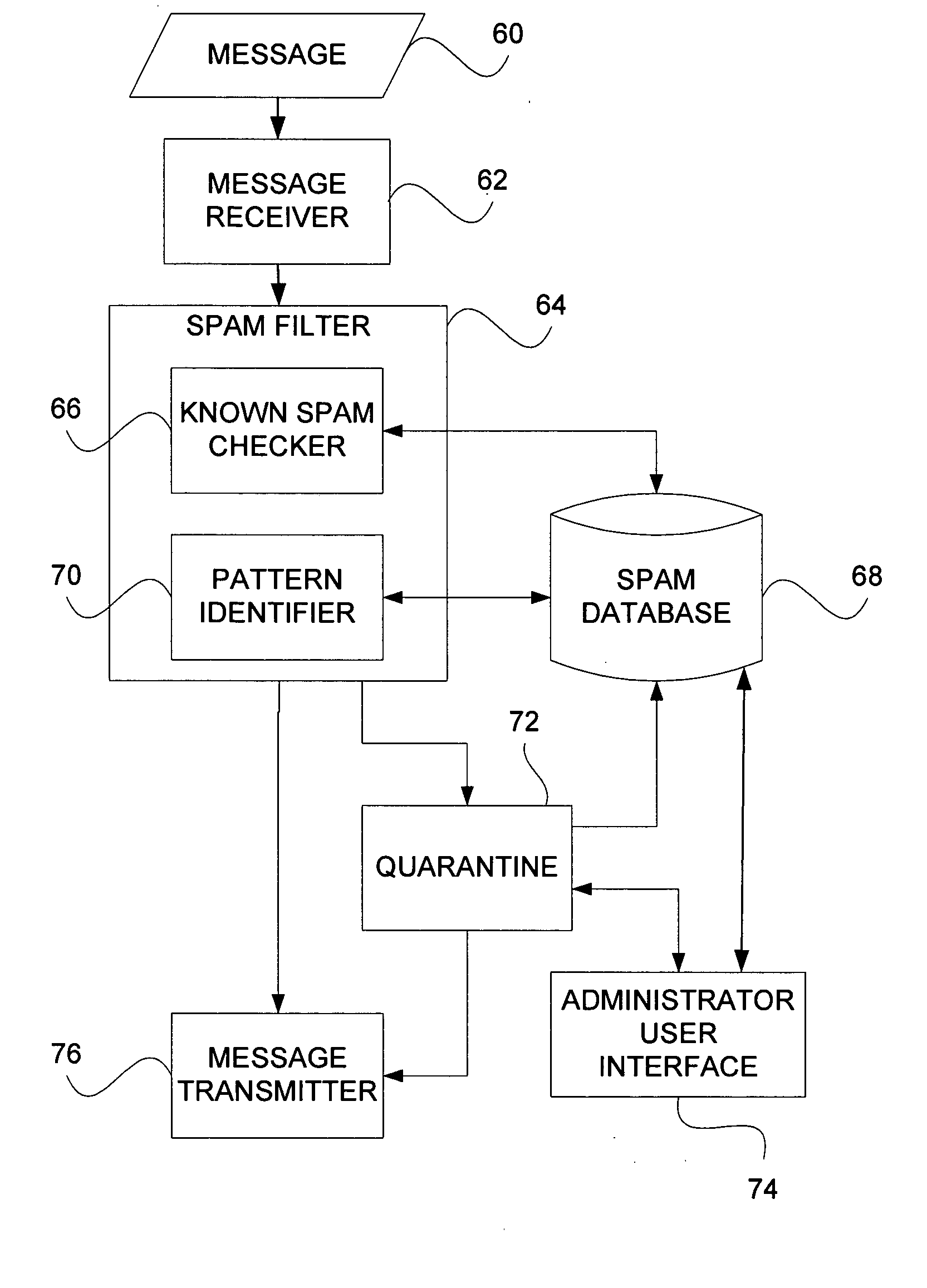
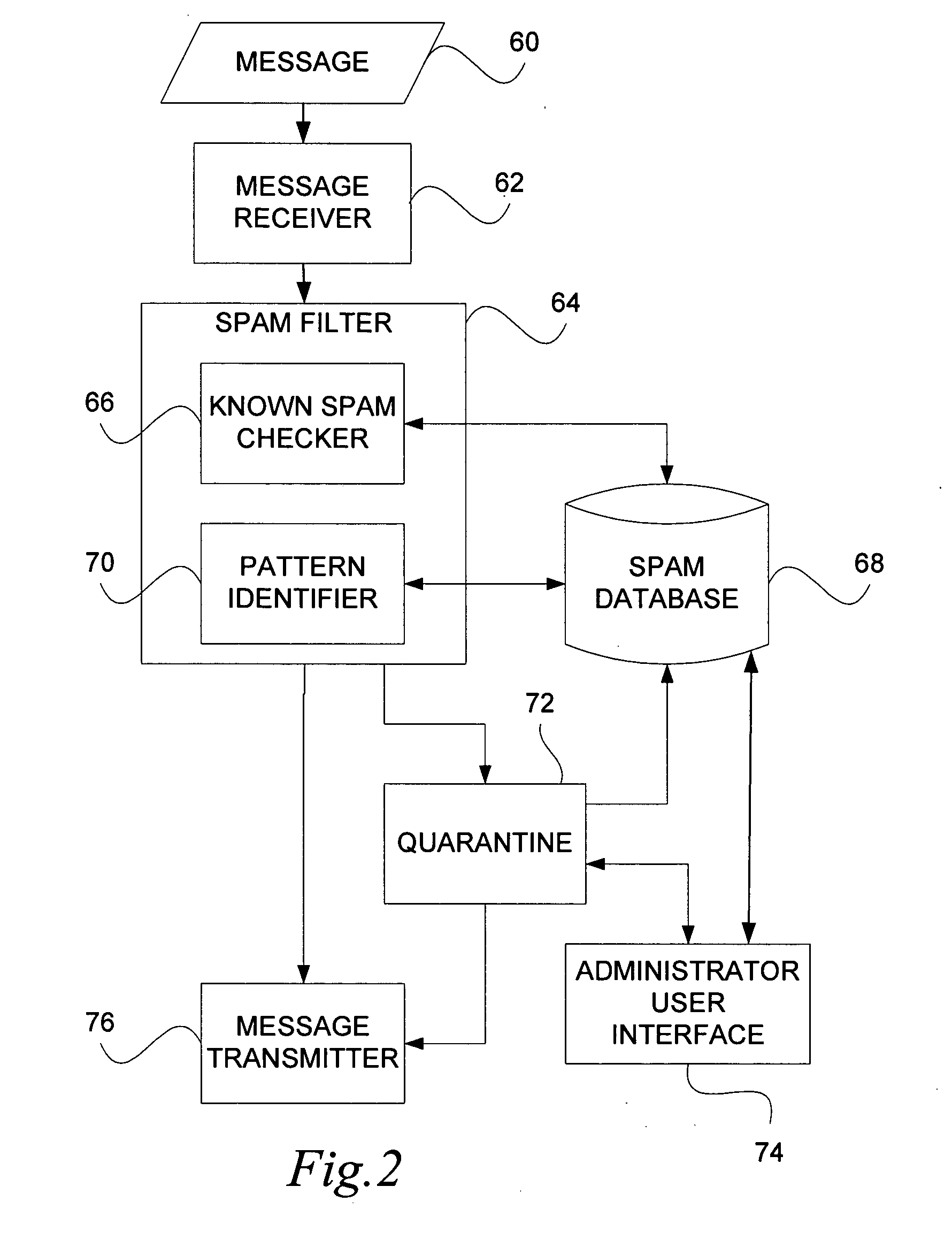
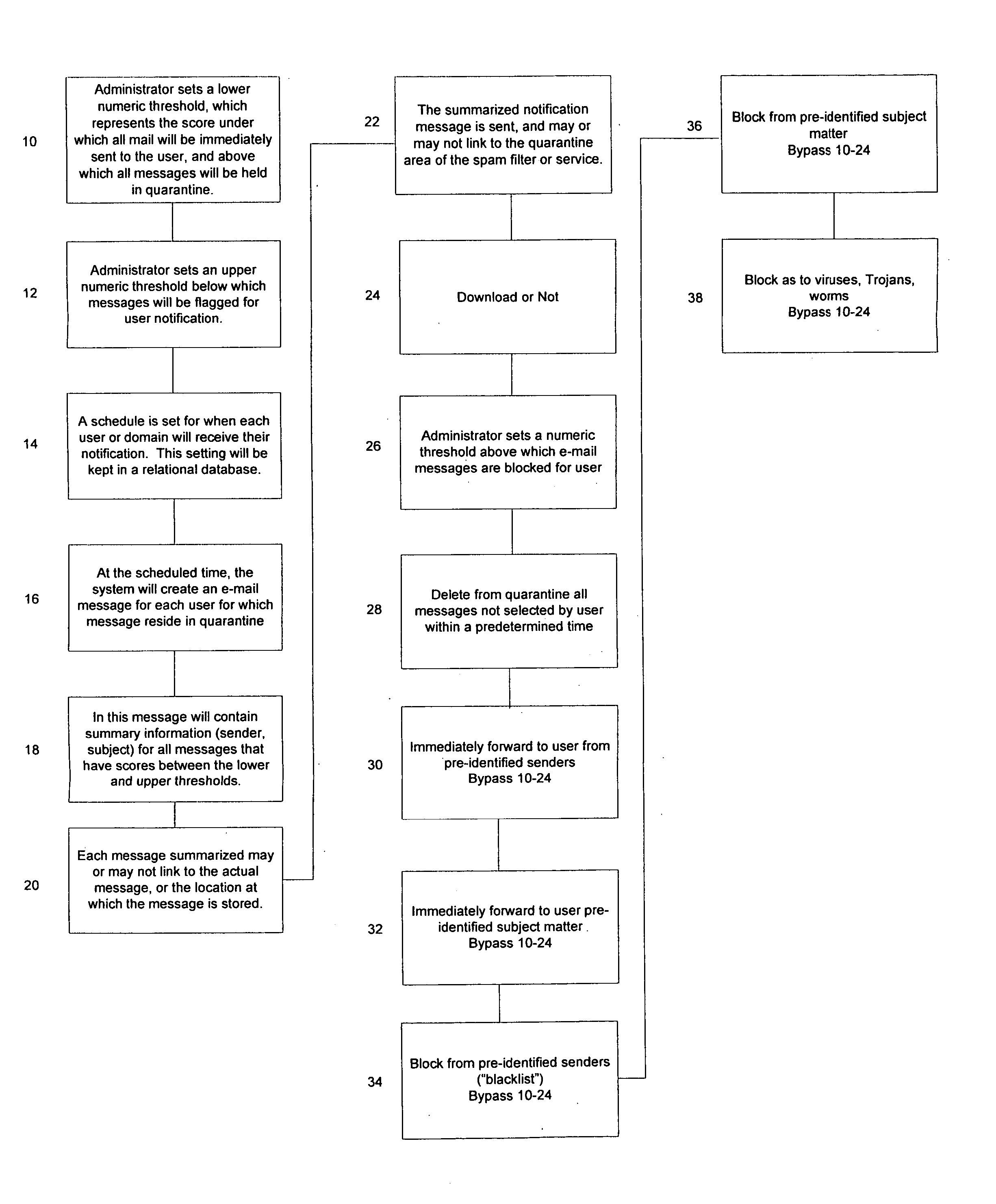
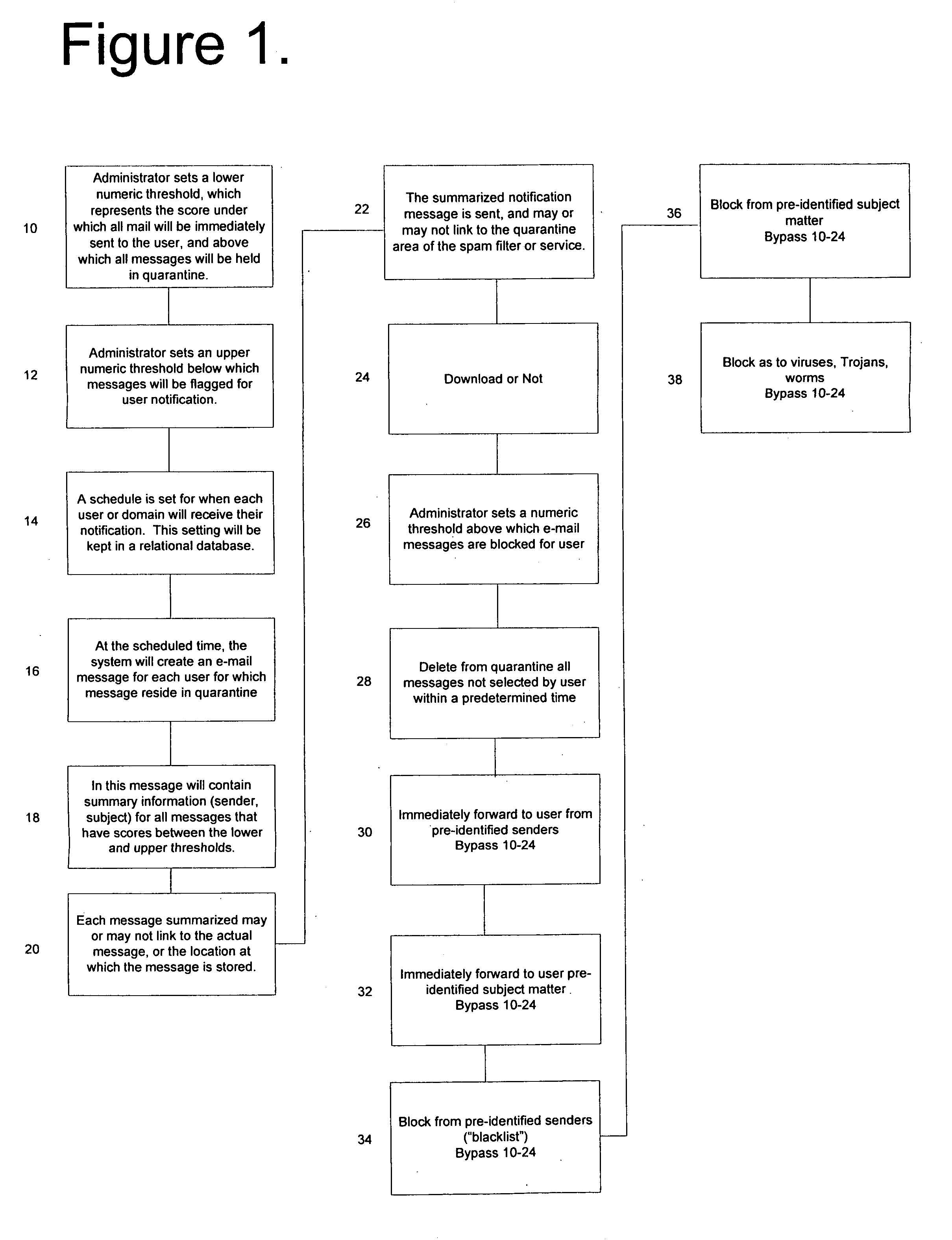
Notification and summarization of E-mail messages held in SPAM quarantine
InactiveUS20050210116A1Easy to manageReduce the amount requiredUser identity/authority verificationUnauthorized memory use protectionSpammingQuarantine
“False positives” of valid E-mail messages are avoided according to a method which creates a numeric score that represents the probability that the message in question is valid, and then quarantines the message in an area separate from the intended message recipient user's primary in-box for scheduled notification to the user of the presence of possible valid messages for selection.
Owner:SAMSON RONALD W
System and methods for providing network quarantine
A client quarantine agent requests bill of health from a quarantine server, and receives a manifest of checks that the client computer must perform. The quarantine agent then sends a status report on the checks back to the quarantine server. If the client computer is in a valid security state, the bill of health is issued to the client. If the client computer is in an invalid state, the client is directed to install the appropriate software / patches to achieve a valid state. When a client requests the use of network resources from a network administrator, the network administrator requests the client's bill of health. If the bill of health is valid, the client is admitted to the network. If the bill of health is invalid, the client is placed in quarantine.
Owner:MICROSOFT TECH LICENSING LLC
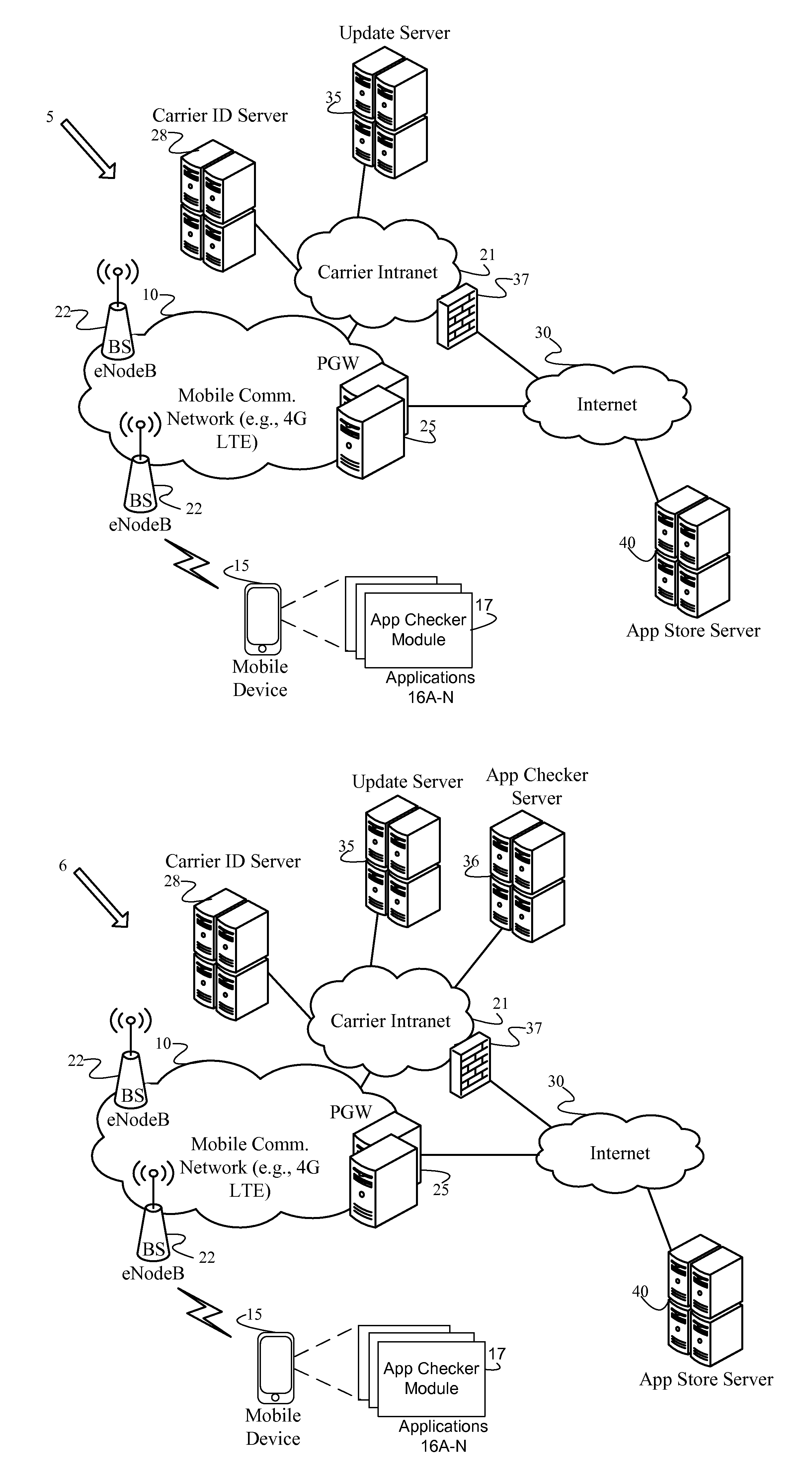
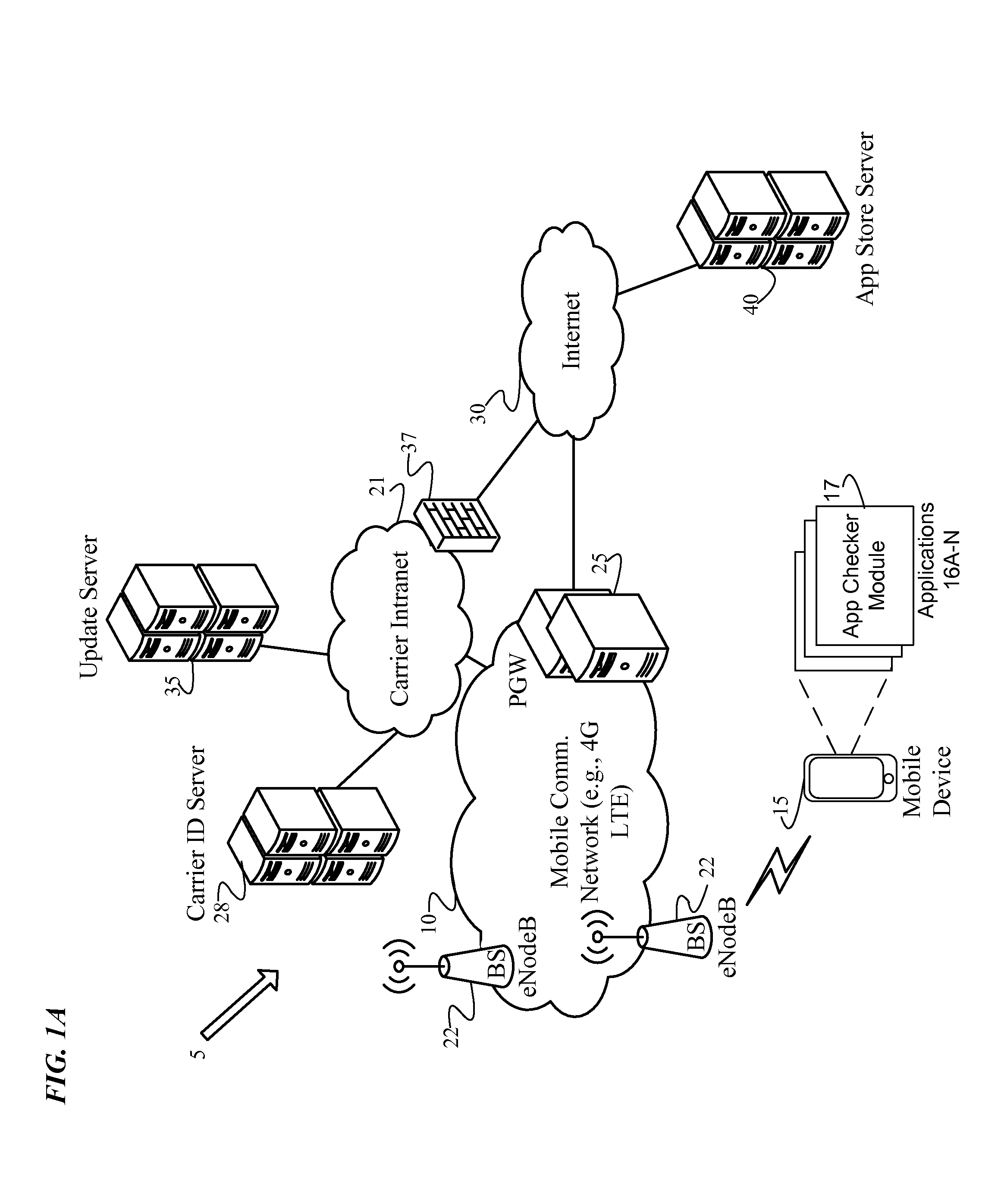
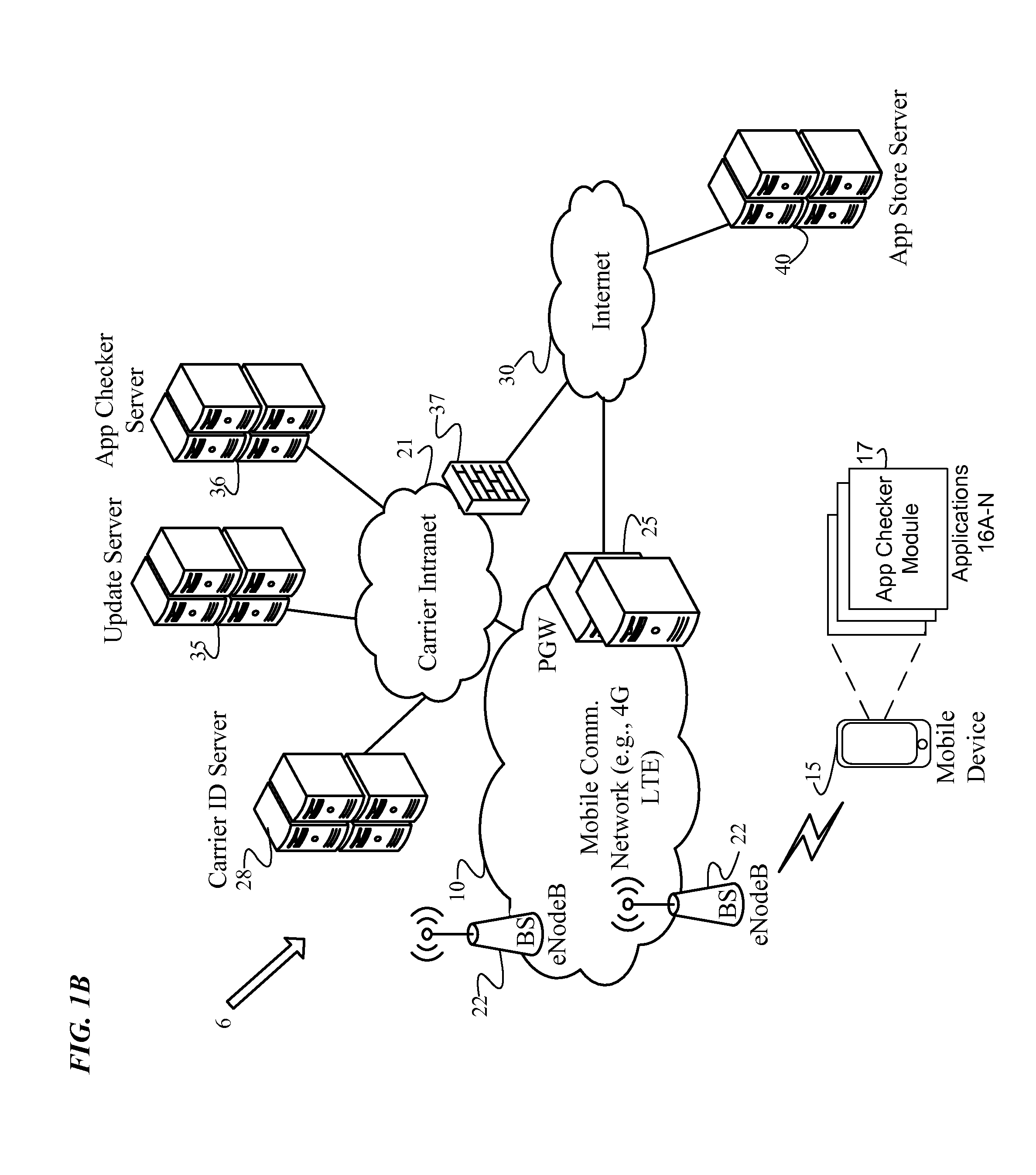
Identification and isolation of incompatible applications during a platform update
An Application (“App”) Checker identifies and isolates incompatible applications on a mobile device during a software platform update. After receiving a target platform version number from an Update Server, the App Checker generates a list of installed applications on the mobile device. Next, the App Checker sends a request to an App Store Server or Update Server for an application catalog of applications compatible with the target platform version. Upon receiving the application catalog indicating compatibility status of applications relative to the target platform version, the App Checker iteratively compares the installed application list with the application catalog to identify whether or not each installed application is compatible with the target platform. The App Checker then populates an application quarantine or removal database to identify each incompatible application to isolate incompatible applications, and quarantines or removes the incompatible applications. Finally, the mobile device is upgraded to the target platform version.
Owner:VERIZON PATENT & LICENSING INC
Method for device quarantine and quarantine network system
InactiveUS20070118567A1Avoid connectionMemory loss protectionError detection/correctionDevice typeNetwork connection
A network quarantine management system eliminates registration or updating work of a quarantine-exempted device and prevents a fraudulent device from abusing authorized network information registered as a quarantine-exempted device and from impersonation. when a quarantine management system detects network connection of a new device, the system judges the type (printer, NAS, etc.) of the device by port scanning. The system enables the device to communicate with another device coupled to a business network without an inspection for connecting the device to the business network, if the newly coupled device is judged to be of an authorized type. The device type judgment is conducted whenever a connection is made and is repeatedly conducted after establishment of the connection to check that the type is of an authorized type and, if the type is found to be an unauthorized type, the device is isolated for inspection.
Owner:HITACHI LTD
Providing security for network subscribers
InactiveUS20060211406A1Avoid receivingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer networkQuarantine
Messages are marked on the basis of whether they are originated in a home network or in a foreign network. Messages originated in the foreign network may be subjected to further filtering and may be put to ‘quarantine’ for further checking.
Owner:NOKIA SOLUTIONS & NETWORKS OY
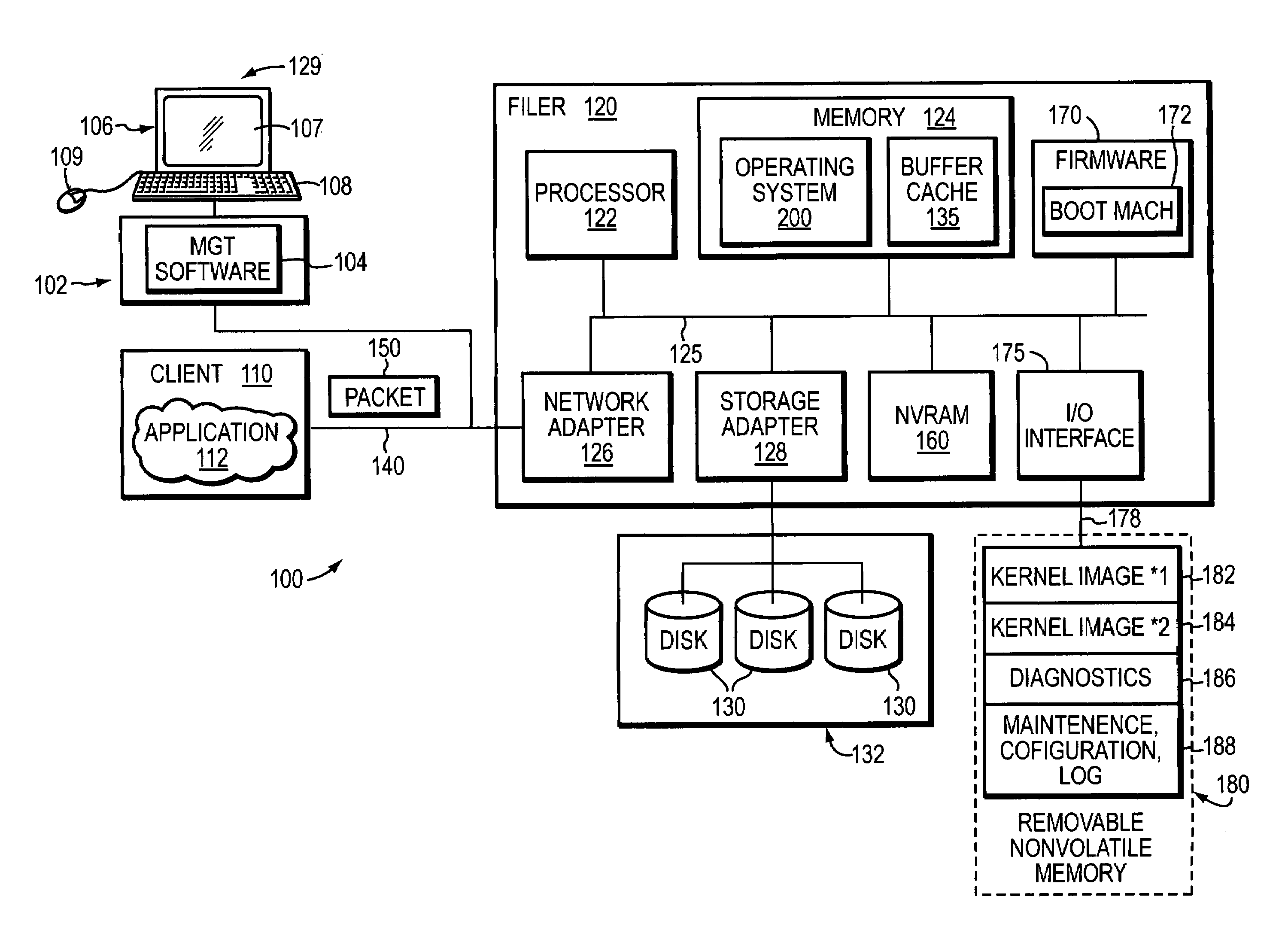
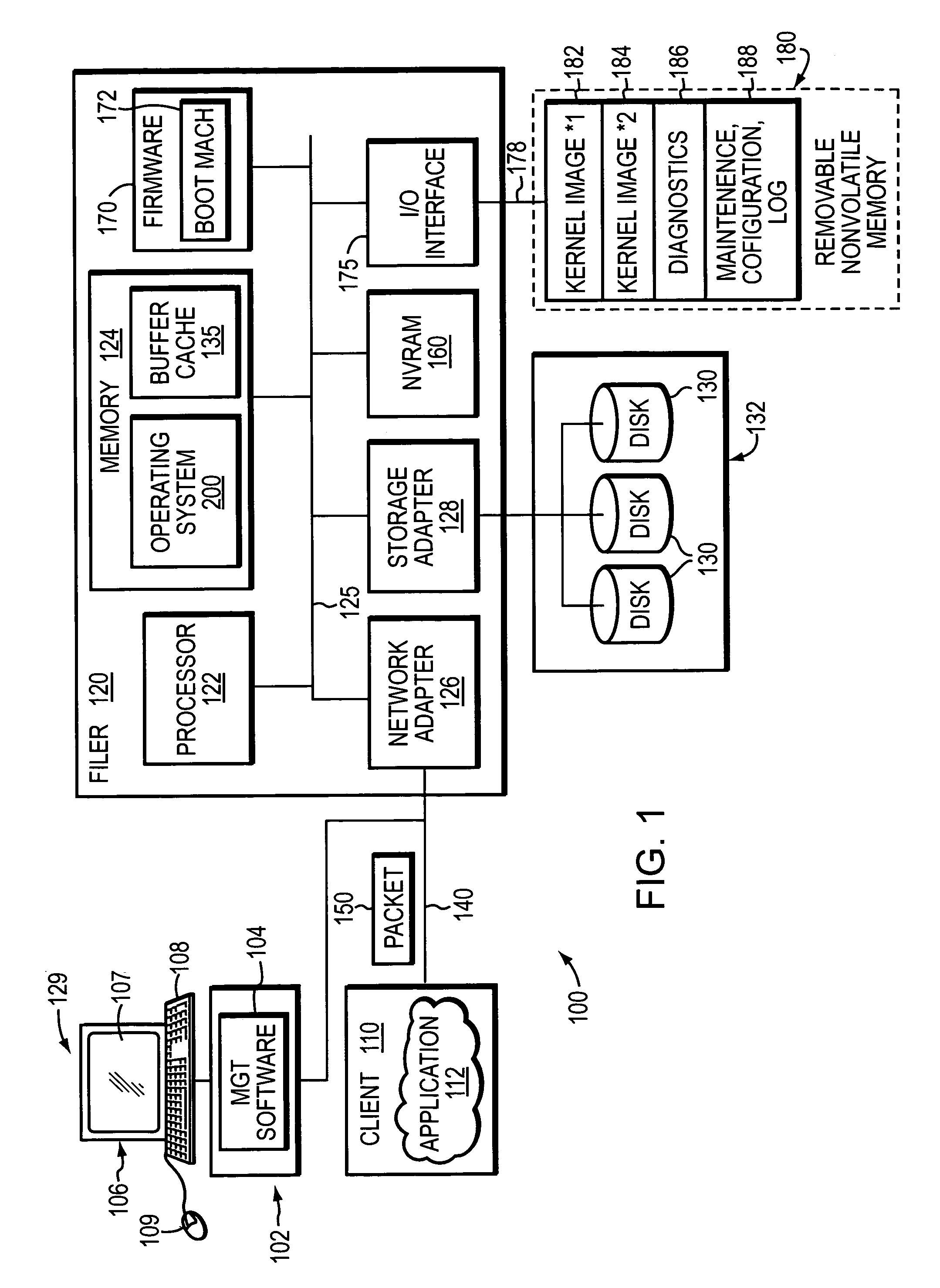
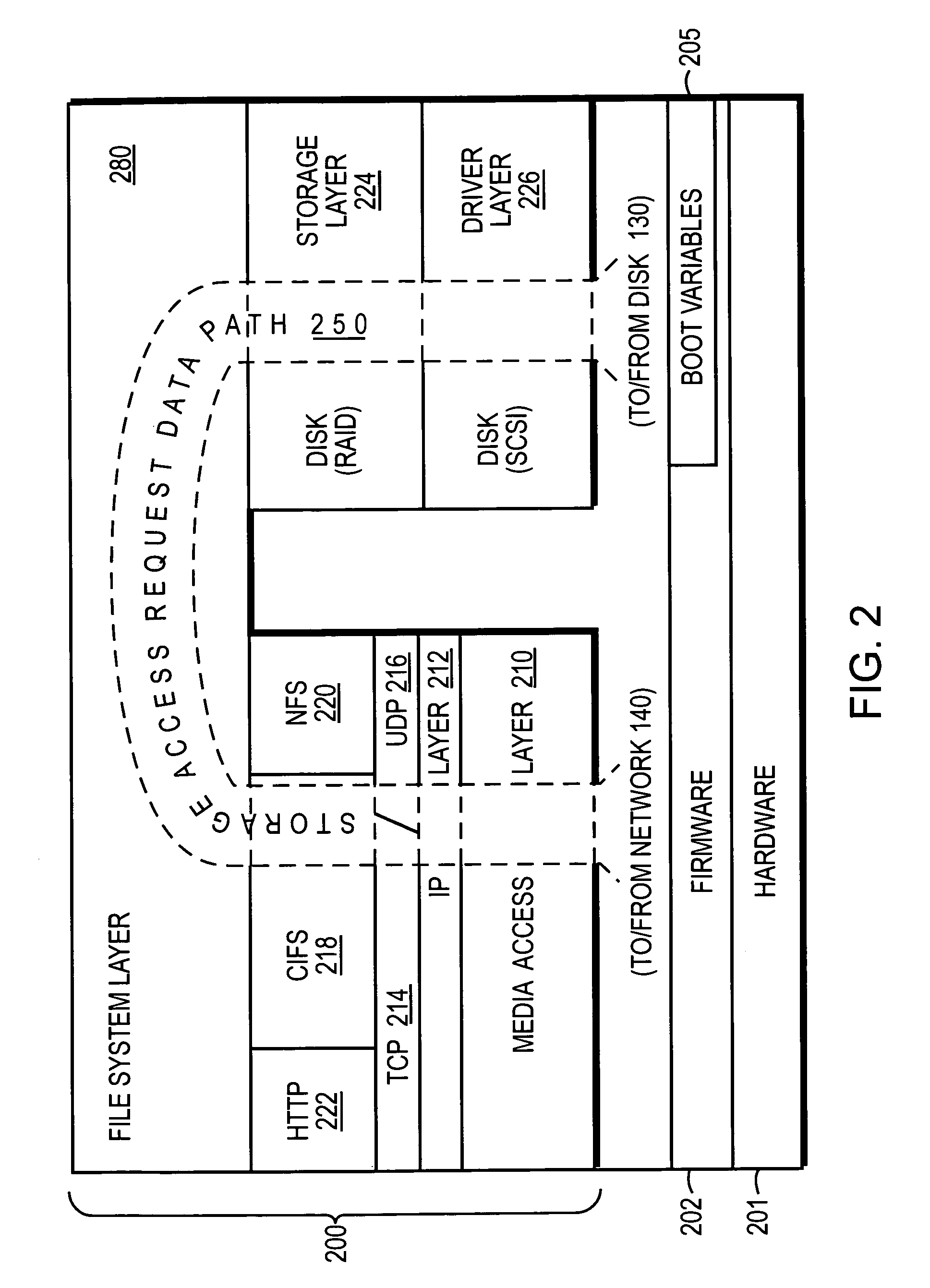
Method and system to quarantine system software and configuration
ActiveUS7562208B1Enhanced couplingEasy to splitError detection/correctionDigital computer detailsOperational systemPersonal computer
The present invention provides a system and method to quarantine in the storage operating system and configuration information in which the storage operating system is stored in a designated partition on a removable nonvolatile memory device, such as a compact flash or a personal computer (PC) card that is interfaced with a motherboard of a filer system server. By providing for separate partitions, a failure or error arising during an upgrade to the storage operating system will not corrupt the other partitions.
Owner:NETWORK APPLIANCE INC
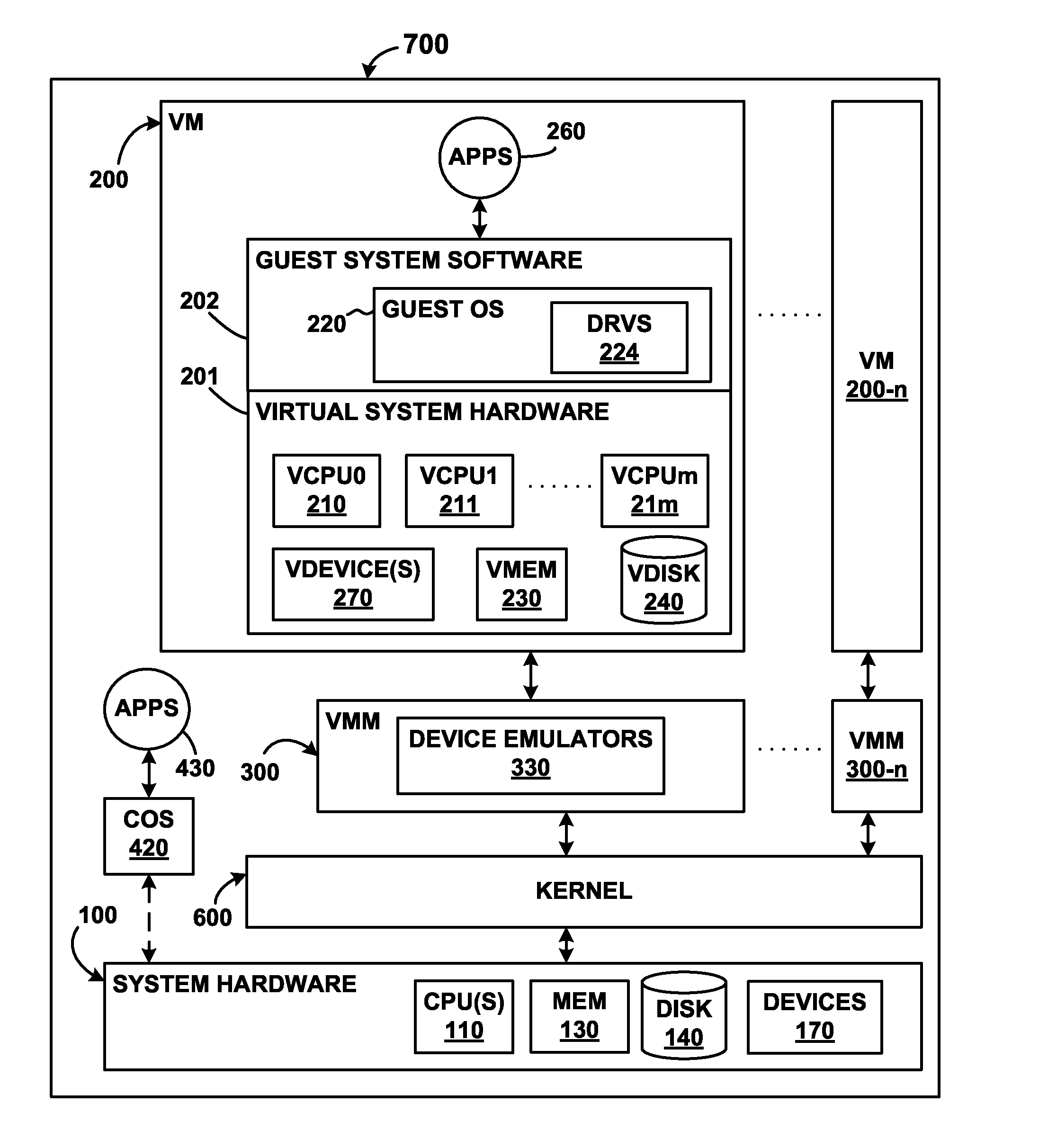
Offloading operations to a replicate virtual machine
A method for detecting malicious code within a first virtual machine comprising creating a snapshot of the first virtual machine and transferring the snapshot to a second machine. A scan operation is run on the snapshot using resources of the second machine. In response to detecting malicious code during the scan operation, action is taken at the first virtual machine to address the detection of the malicious code. Thus, the action in response to detecting the malicious code may include placing the first virtual machine in quarantine.
Owner:VMWARE INC
Video and audio monitoring for syndromic surveillance for infectious diseases
We present, in exemplary embodiments of the present invention, novel systems and methods for syndromic surveillance that can automatically monitor symptoms that may be associated with the early presentation of a syndrome (e.g., fever, coughing, sneezing, runny nose, sniffling, rashes). Although not so limited, the novel surveillance systems described herein can be placed in common areas occupied by a crowd of people, in accordance with local and national laws applicable to such surveillance. Common areas may include public areas (e.g., an airport, train station, sports arena) and private areas (e.g., a doctor's waiting room). The monitored symptoms may be transmitted to a responder (e.g., a person, an information system) outside of the surveillance system, such that the responder can take appropriate action to identifying, treat and quarantine potentially infected individuals, as necessary.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
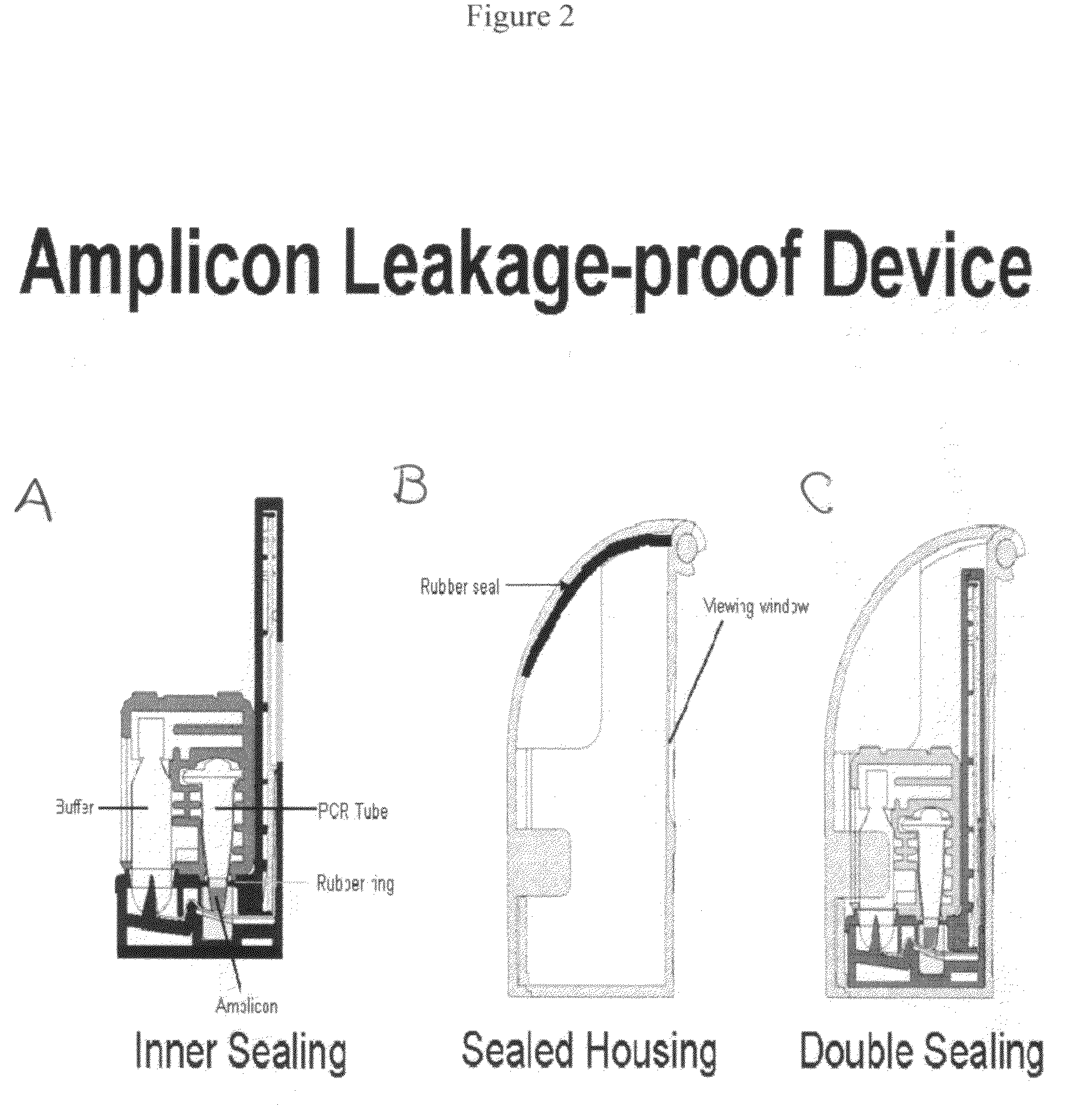
Enclosed unit for rapid detection of a target nucleic acid amplification product
ActiveUS20090181388A1Quick checkSimple and rapid in operationBioreactor/fermenter combinationsBiological substance pretreatmentsFood industryQuarantine
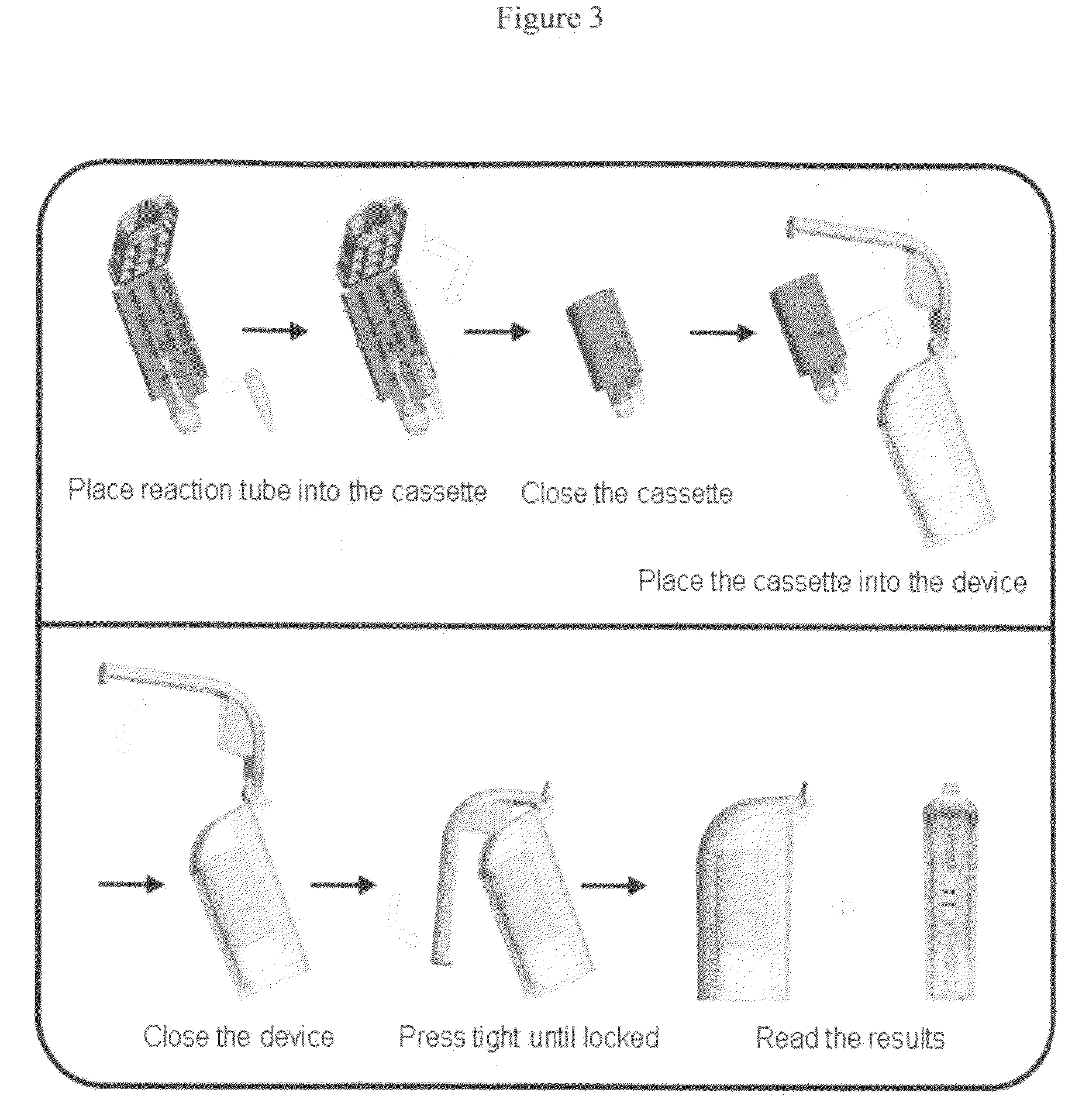
The invention relates to a method for rapid detection of a target nucleic acid amplification product while preventing cross-contamination between target nucleic acid amplification products and avoiding false positives, comprising the steps of: a) leaving the reaction tube unopened after the amplification reaction is finished, so as to prevent the target nucleic acid amplification product from leaking out and resulting in contamination; b) placing the unopened reaction tube inside an enclosed unit, making the target nucleic acid amplification product be transferred to a test strip from the reaction tube in a physically enclosed environment; c) performing detection in a visual read-out manner, and determining the result; d) discarding the enclosed unit in a safety place as a whole without opening it after the detection. The invention also relates to a totally enclosed unit for detecting a target nucleic acid amplification product, and still relates to applications of the totally enclosed rapid detection unit in detection of infectious pathogens, food industry, agriculture, livestock husbandry, customs quarantine control, and determination of DNA.
Owner:YOU QIMIN +3
No-iron treatment method for cotton shirt
ActiveCN101768869AAvoid yellowingGuaranteed flatnessHeating/cooling textile fabricsTextile treatment by spraying/projectingFiberQuarantine
The invention provides a no-iron treatment method for a cotton shirt, which can solve the problems of yellowing due to overhigh baking temperature and poor seam appearance due to seam shrinkage of the cotton shirt. The method comprises the following process flows: resin absorbing, pre-baking, pressing, baking and cooling, wherein a working solution comprises the following components in percentage by mass: 15 to 25 percent of resin, 1 to 2.5 percent of catalyst and 2 to 4 percent of fiber protective agent; and the pH value of the working solution is regulated to be between 4.5 to 5.0. The process can ensure that seams or pleats of collar, yoke, two sleeves, side seams, a left front panel, a right front panel, a left back panel, a right back panel and other parts of the shirt are flat and fitting, no bulge is generated after the shirt is washed, and all the appearance flatness of products and the appearance of the seams and the pleats are up to the 4.0 level of 'the No-iron Textiles Standard' published by the State Administration of Quality Supervision, Inspection and Quarantine, namely the testing index is higher than 'the No-iron Textiles Standard' by 0.5 to 1 level.
Owner:ZHEJIANG GIUSEPPE GARMENT
Rapid parallel nucleic acid detection method and system based on micro-fluidic chip
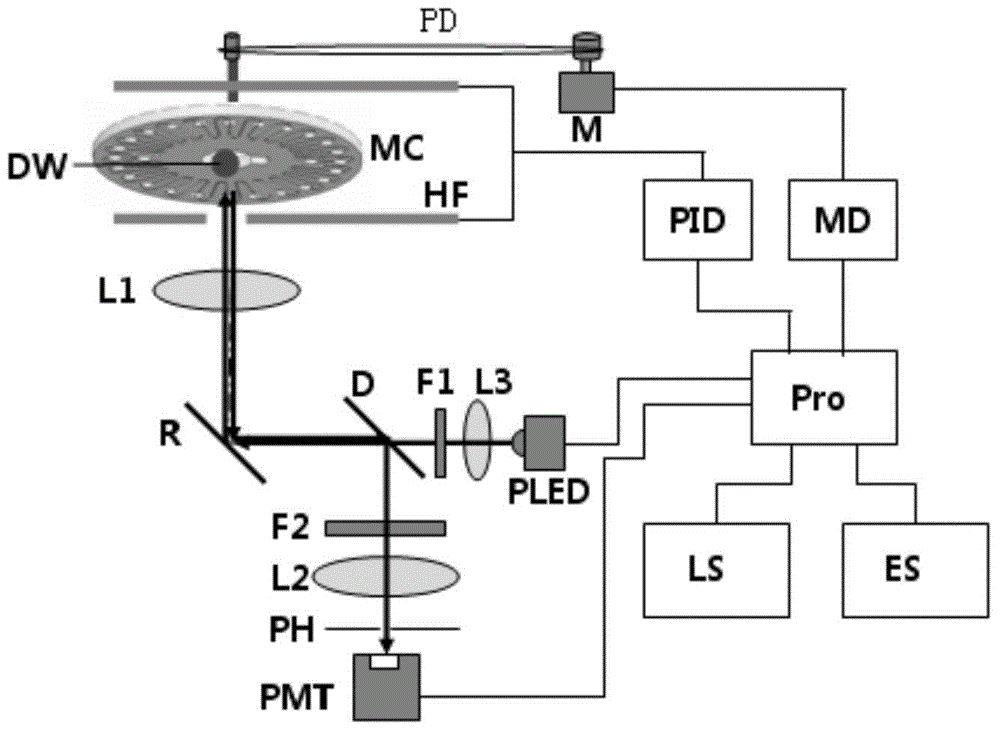
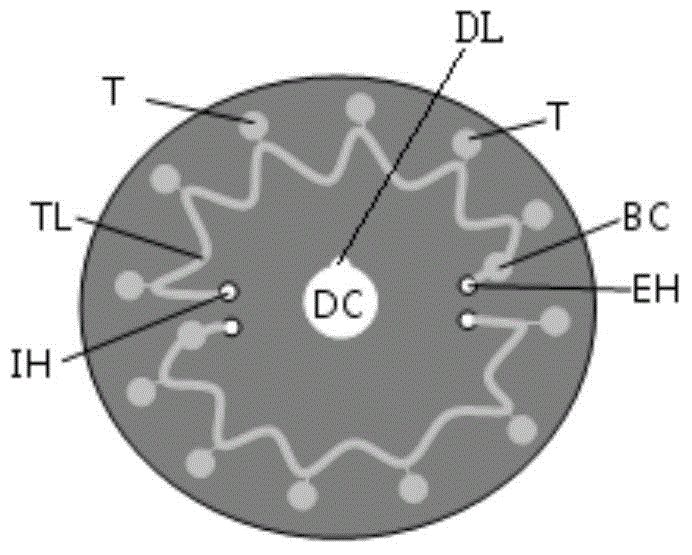
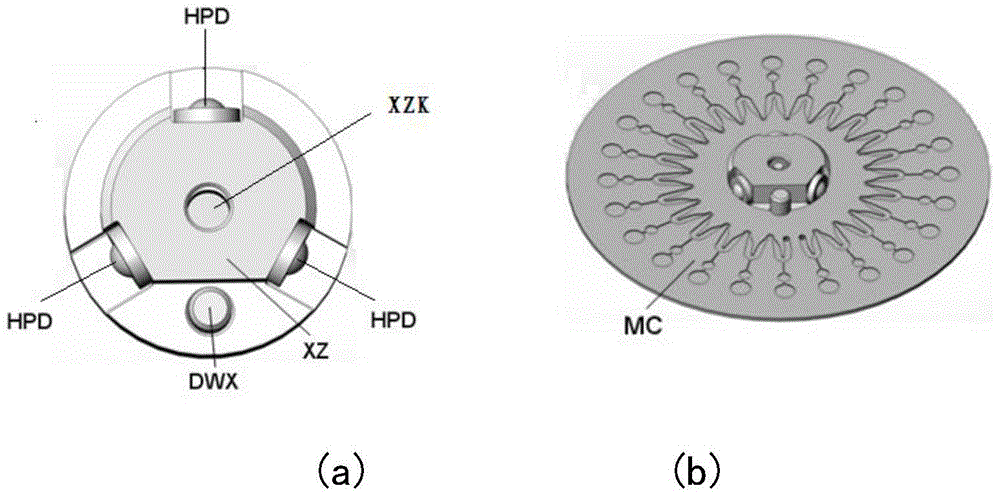
ActiveCN104630373AMeet automatic sampling requirementsUniform heating temperature fieldBioreactor/fermenter combinationsSequential/parallel process reactionsFluorescenceDisplay device
The invention relates to a rapid parallel nucleic acid detection method and system based on a micro-fluidic chip. The nucleic acid detection system comprises a micro-fluidic chip, a motor, exciting light, a double-focal-plane imaging lens set, a detector, a signal acquisition processor and a display; the micro-fluidic chip comprises at least one reaction channel; a heating film is arranged at the periphery of the micro-fluidic chip; a submillimeter air layer is maintained between the micro-fluidic chip and the heating film; and the micro-fluidic chip is irradiated by adopting the exciting light, so that a nucleic acid sample generates fluorescence under excitation of the exciting light, the fluorescence is gathered on the detector by virtue of the double-focal-plane imaging lens set so as to generate an analog signal, the detector transmits the generated analog signal to the signal acquisition processor so as to generate a real-time fluorescence detection signal, and the real-time fluorescence detection signal is displayed by the display. The method and the system disclosed by the invention can be applied to the fields of clinical pathogenic bacterium molecular diagnosis, food inspection and quarantine, food poisoning pathogenic bacterium detection, bacteriology classification and epidemiological investigation and have huge economical and social benefits.
Owner:CAPITALBIO CORP +2
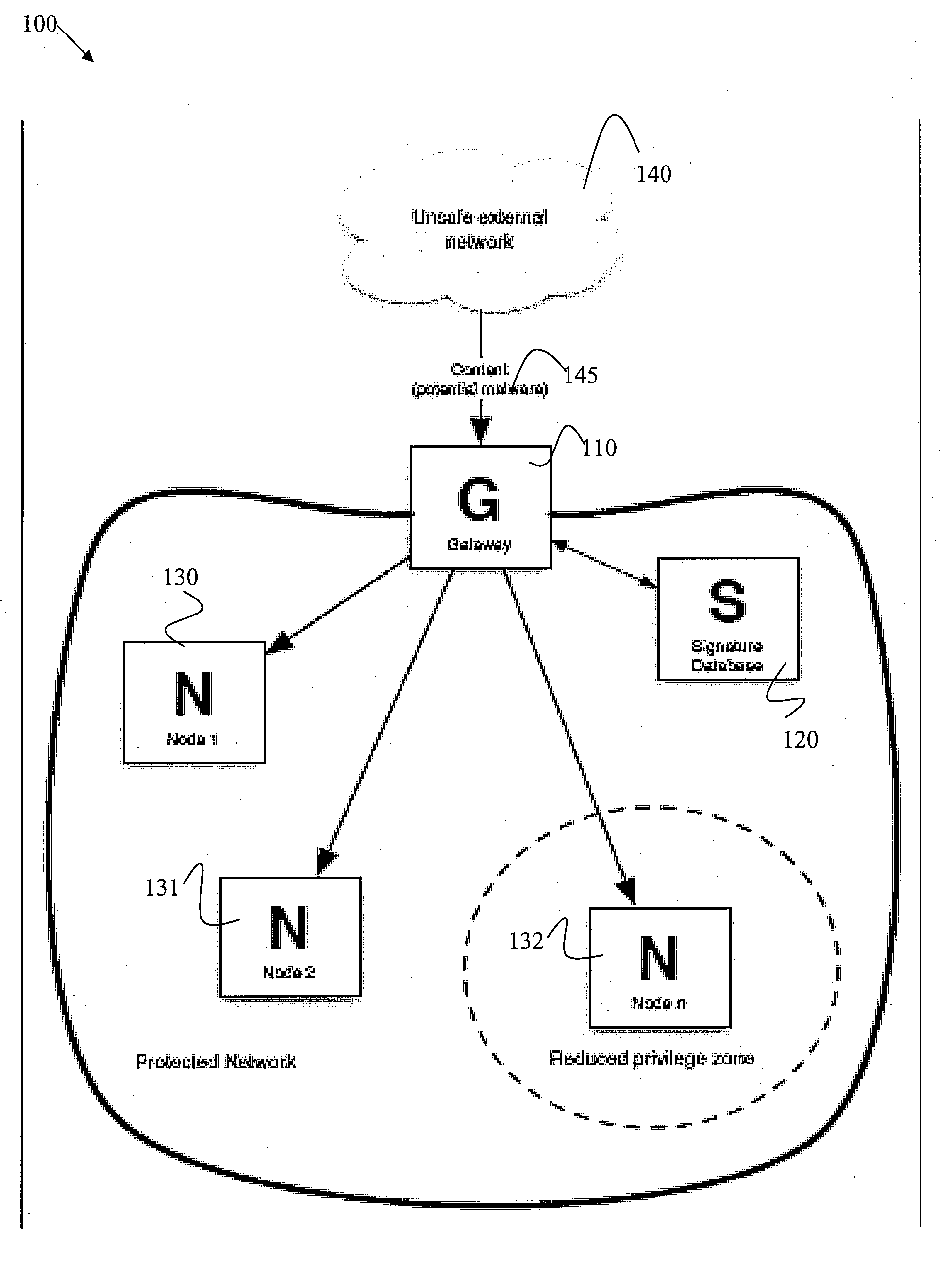
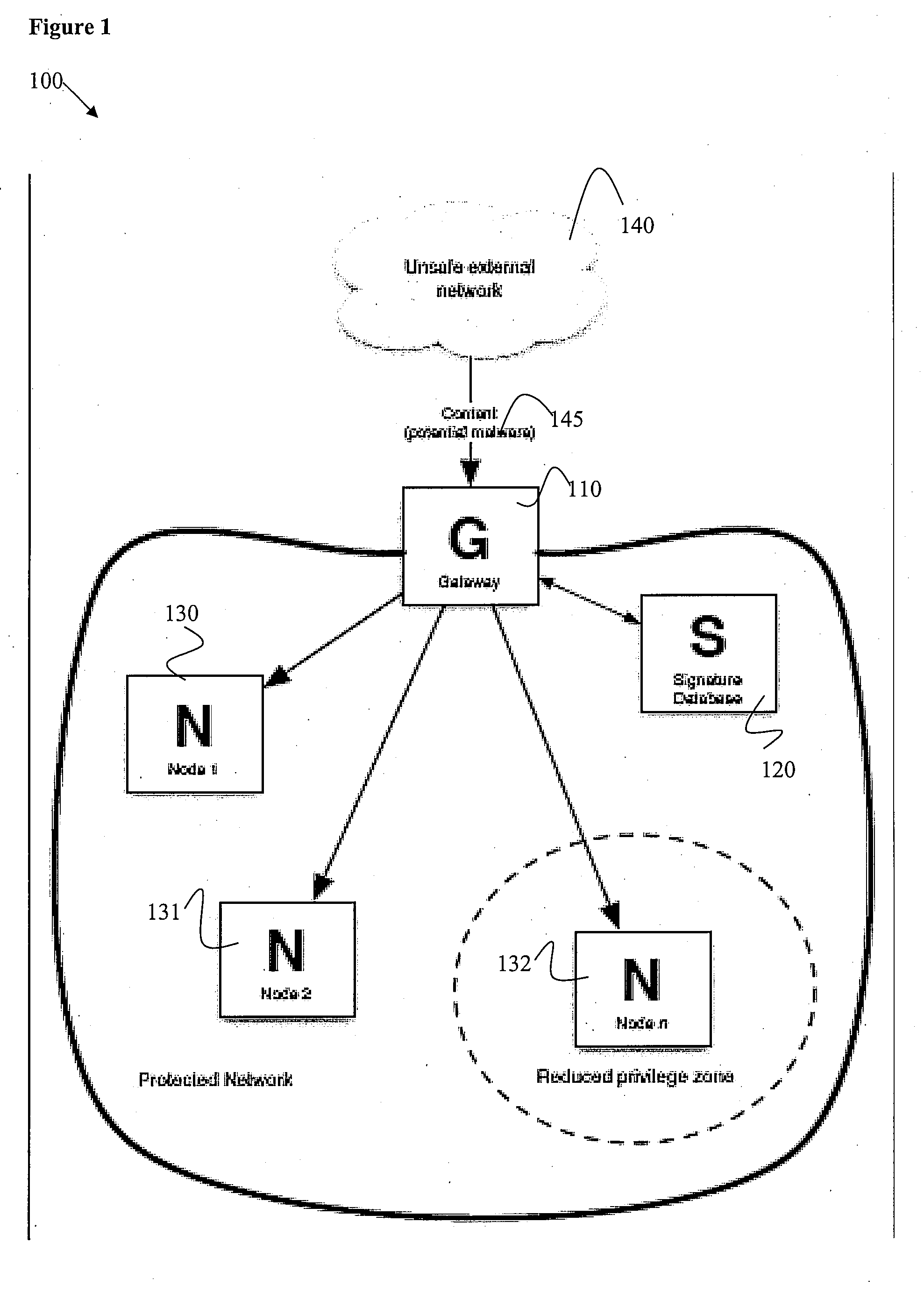
Method and System For Unsafe Content Tracking
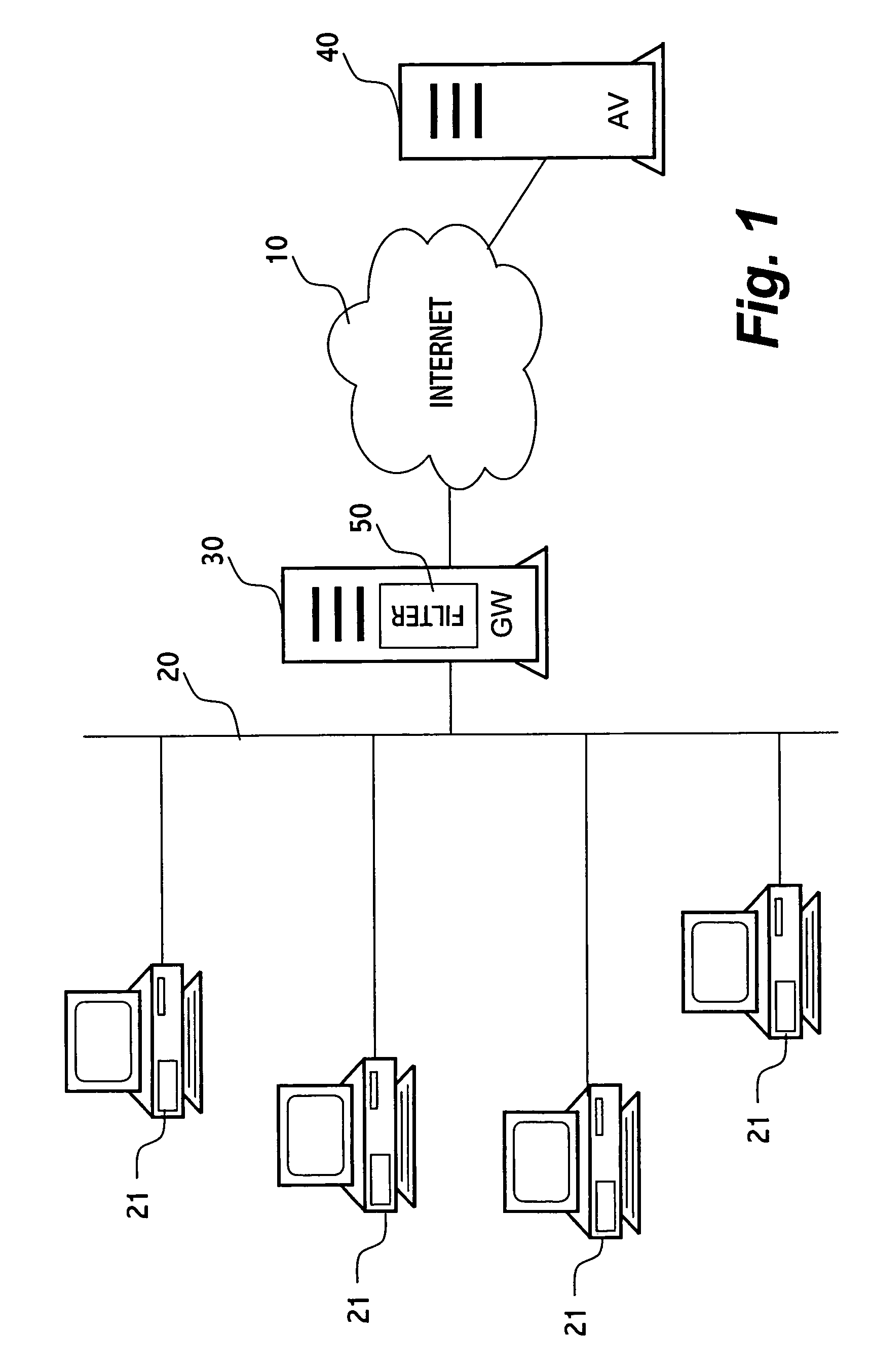
InactiveUS20080201722A1Reduce deliveryComputer security arrangementsInput/output processes for data processingQuarantineWorld Wide Web
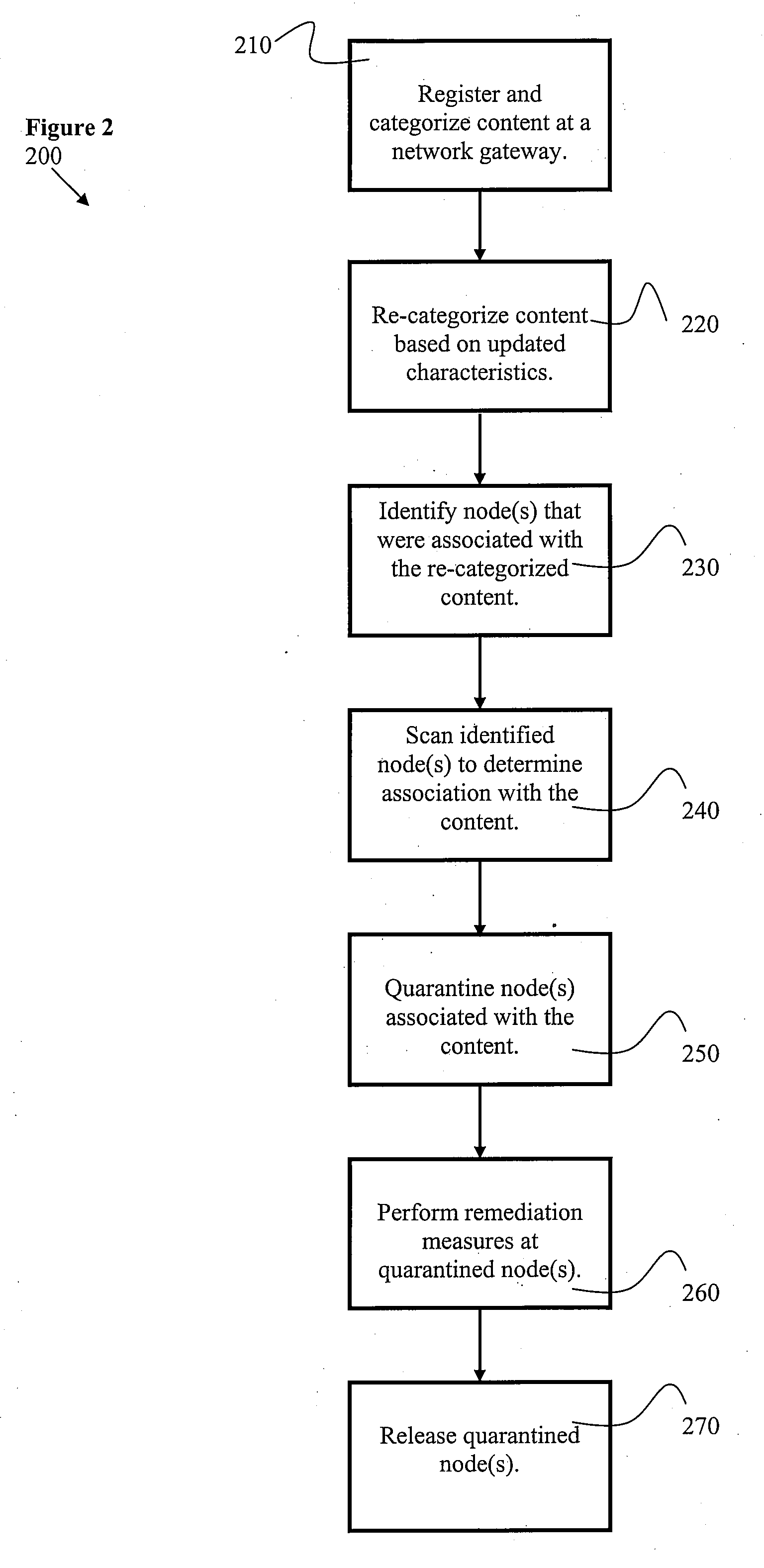
Certain embodiments of the present invention provide methods and systems for registering and categorizing content in a network. Certain embodiments provide a method for registering and categorizing content passing through a gateway in a network. The method includes registering content at a network gateway. Registering includes an initial categorization of the content according to at least one category based on at least one characteristic. The method also includes allowing delivery of the initially categorized content to at least one node based on the initial categorization. The method further includes re-categorizing the content based on additional information. Additionally, the method includes identifying, based on the at least one category and the re-categorized content, one or more nodes associated with the initially categorized content. Furthermore, the method may also include remediation of the node(s) associated with the re-categorized content and removal from quarantine or removal of restrictions on delivery of content.
Owner:SOPHOS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com