Patents
Literature
1516 results about "Anti virus" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
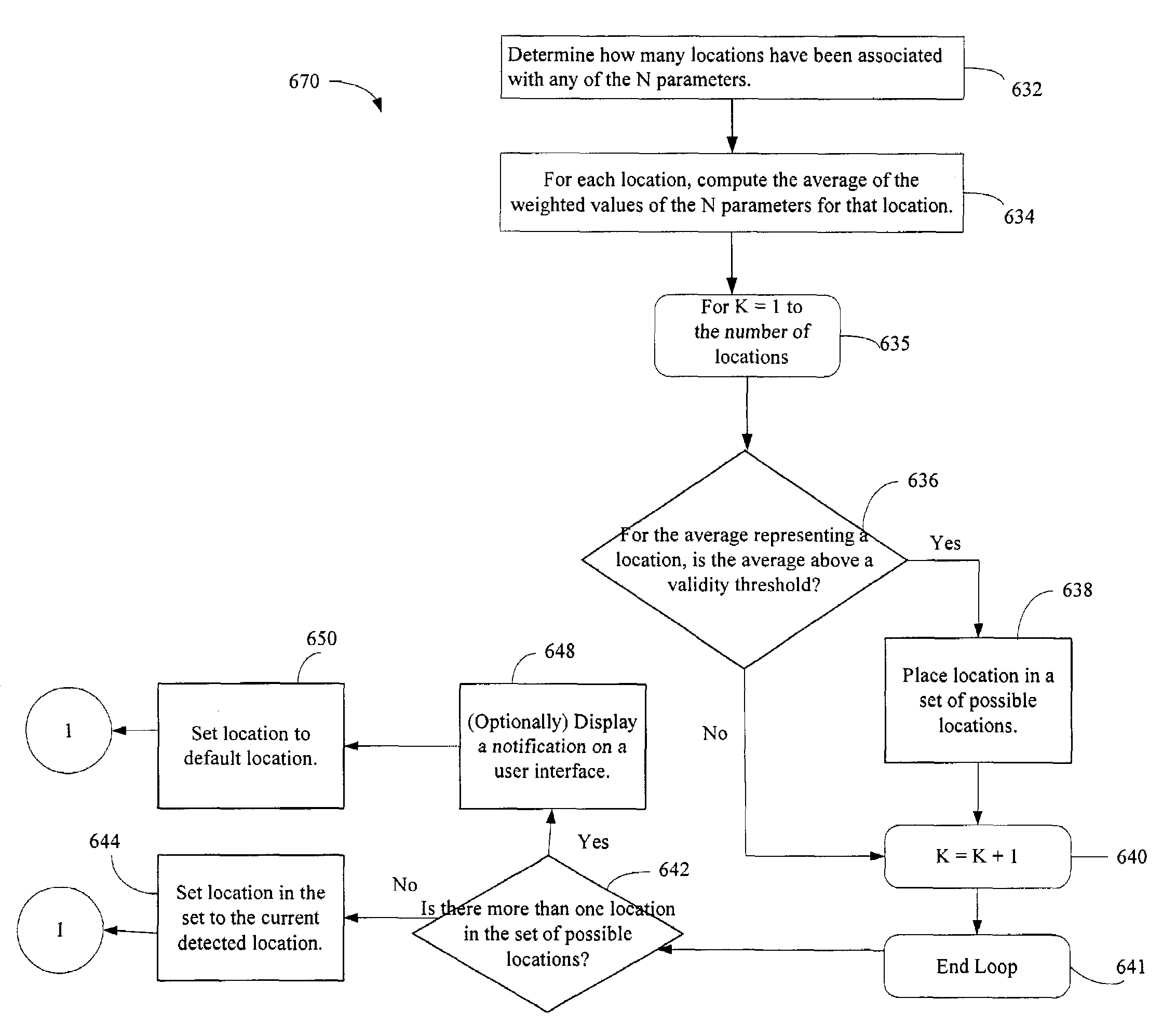
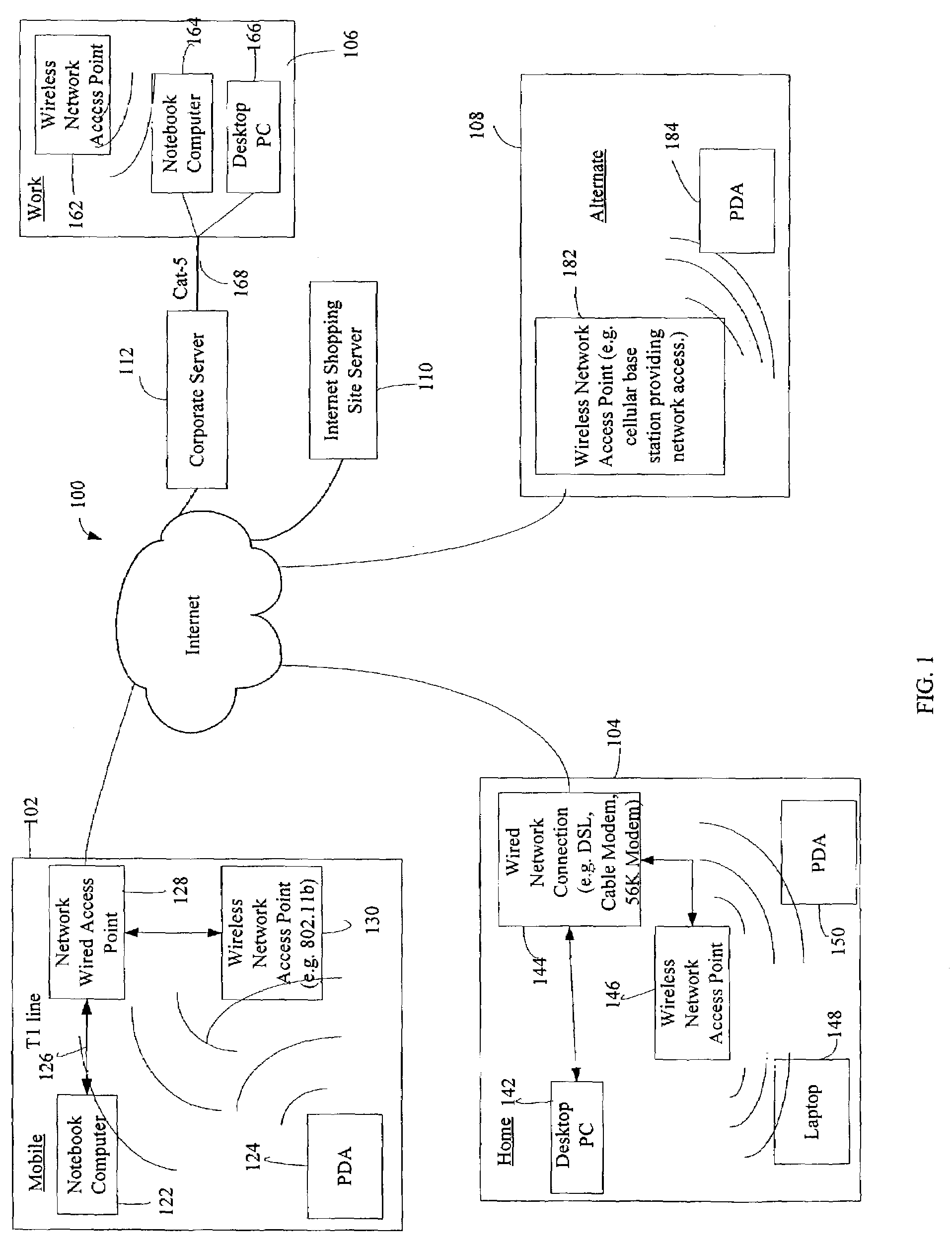
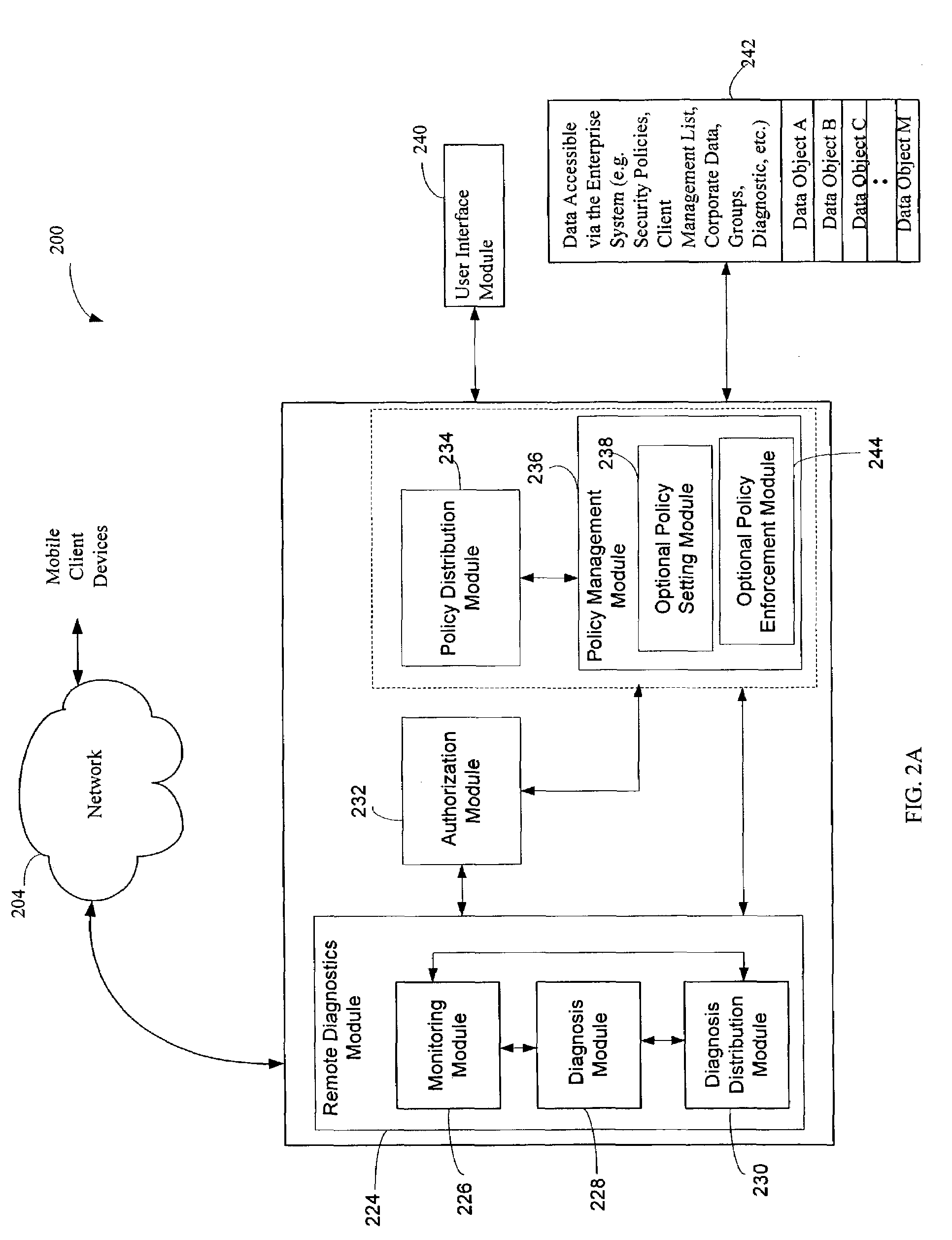
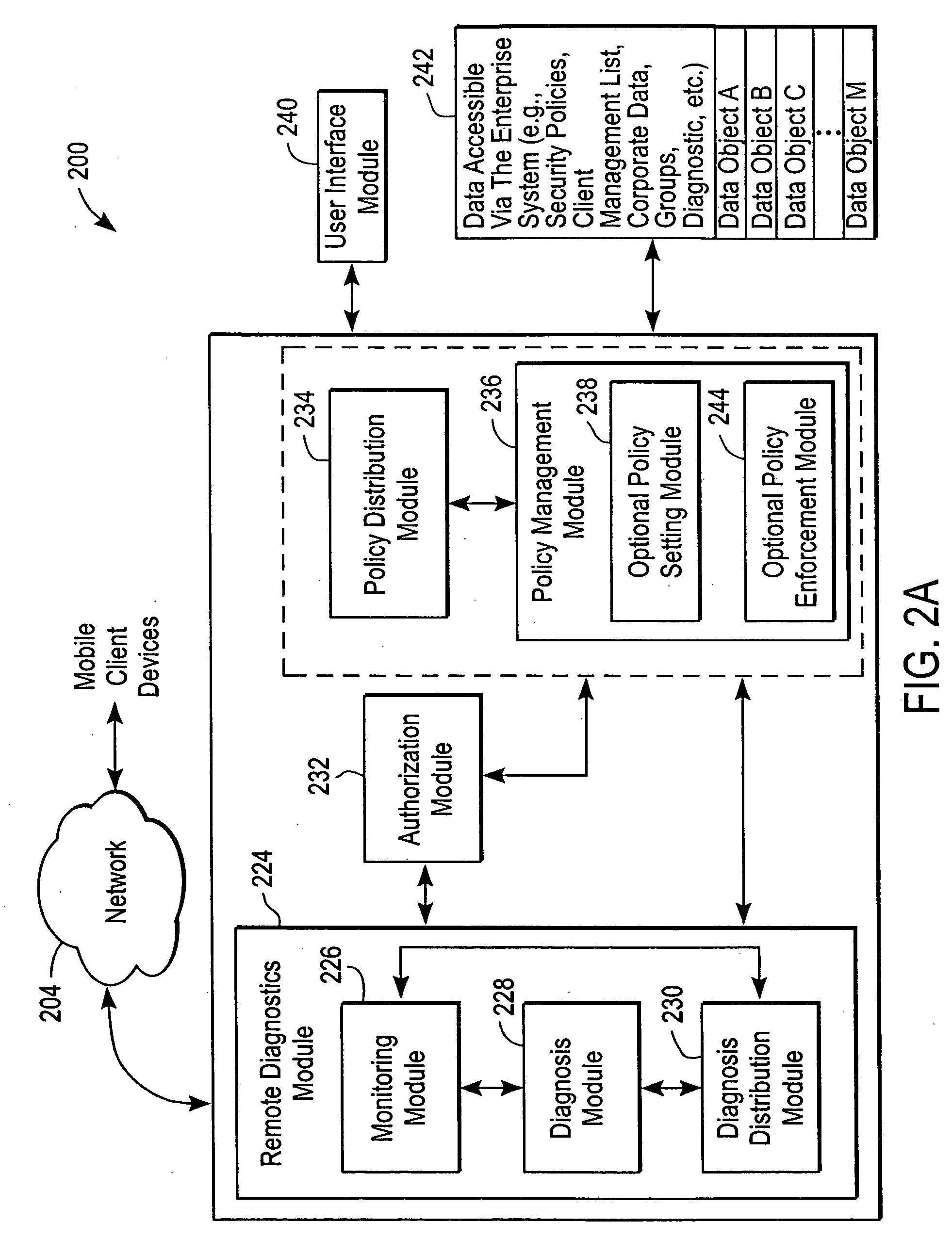
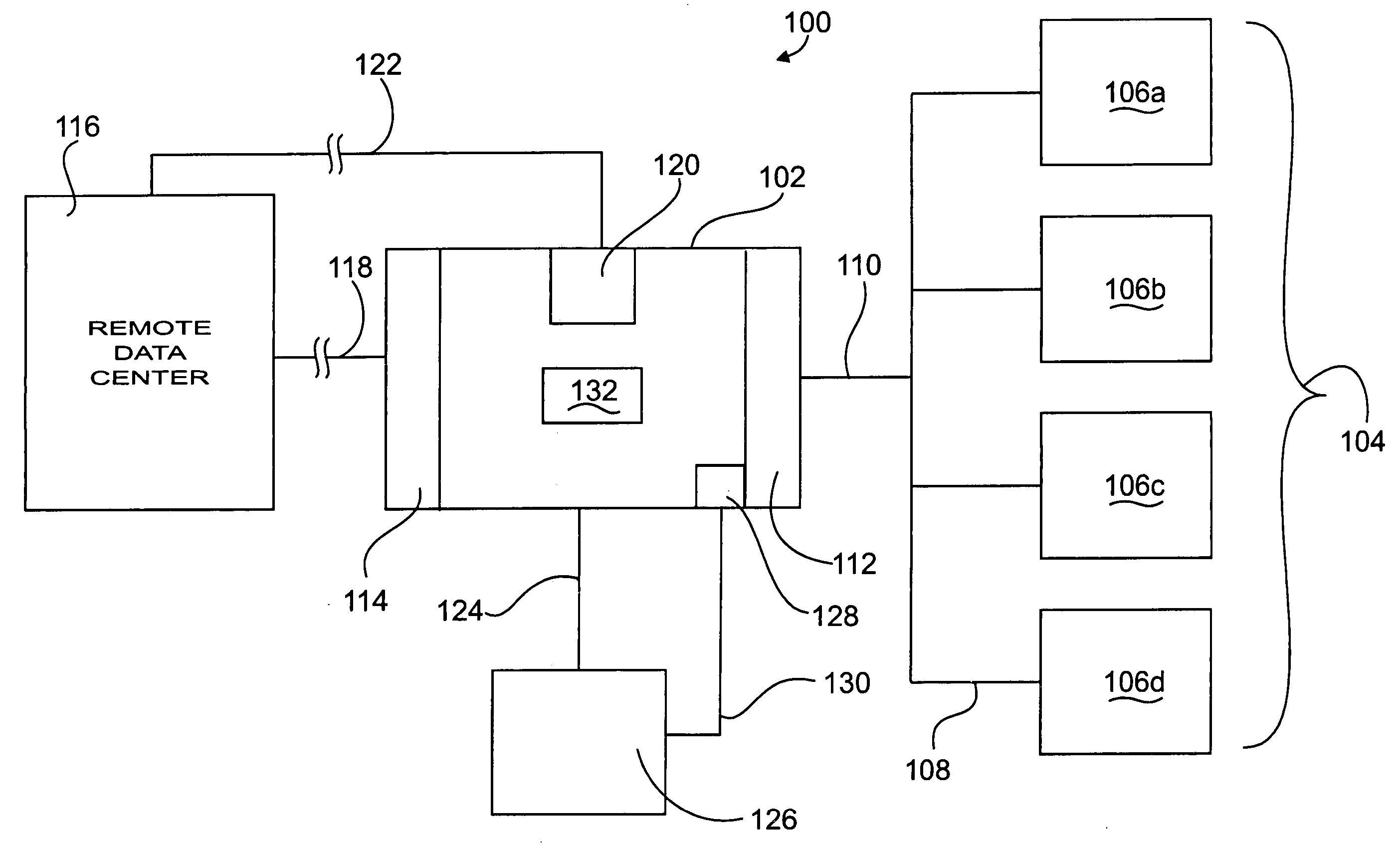
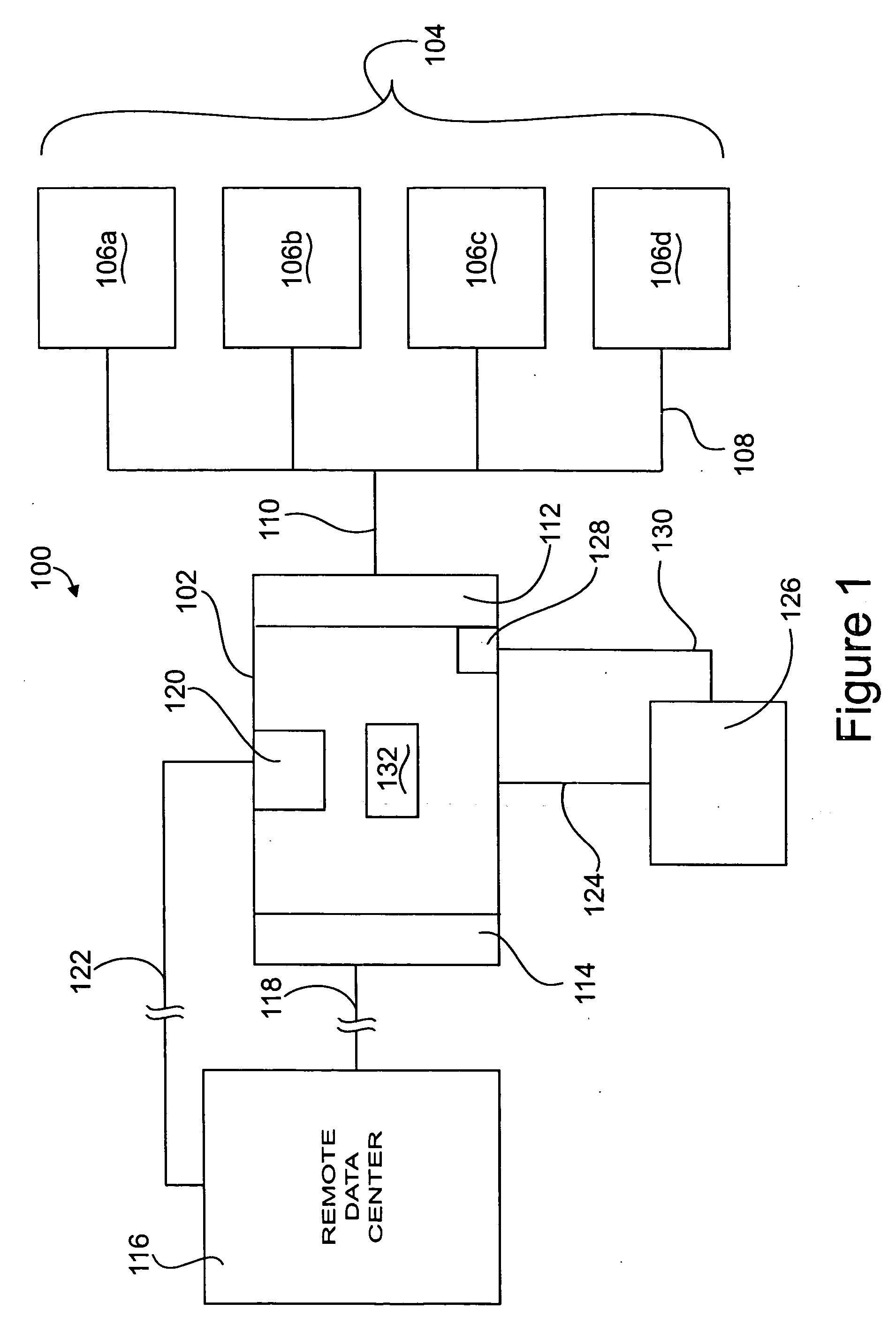
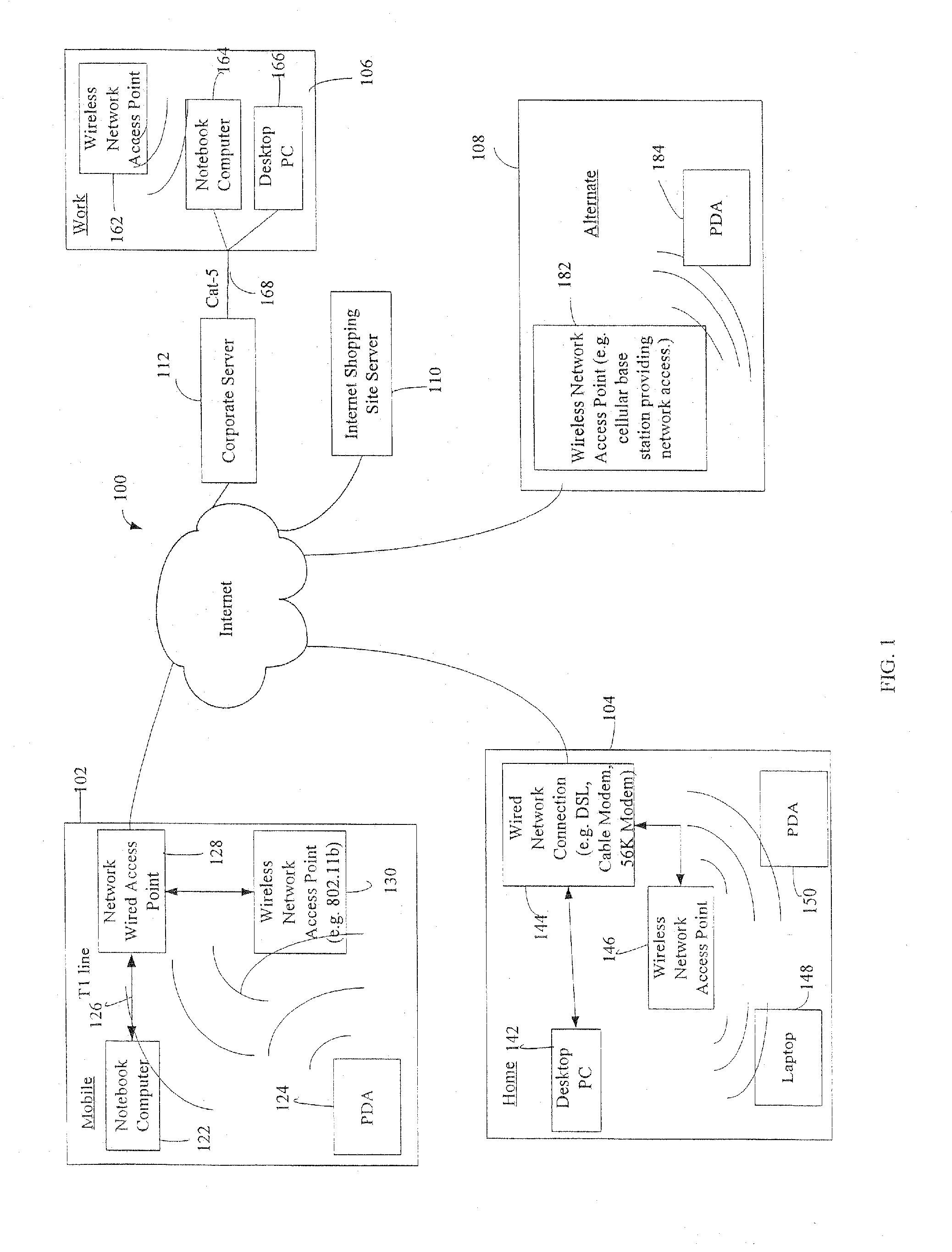
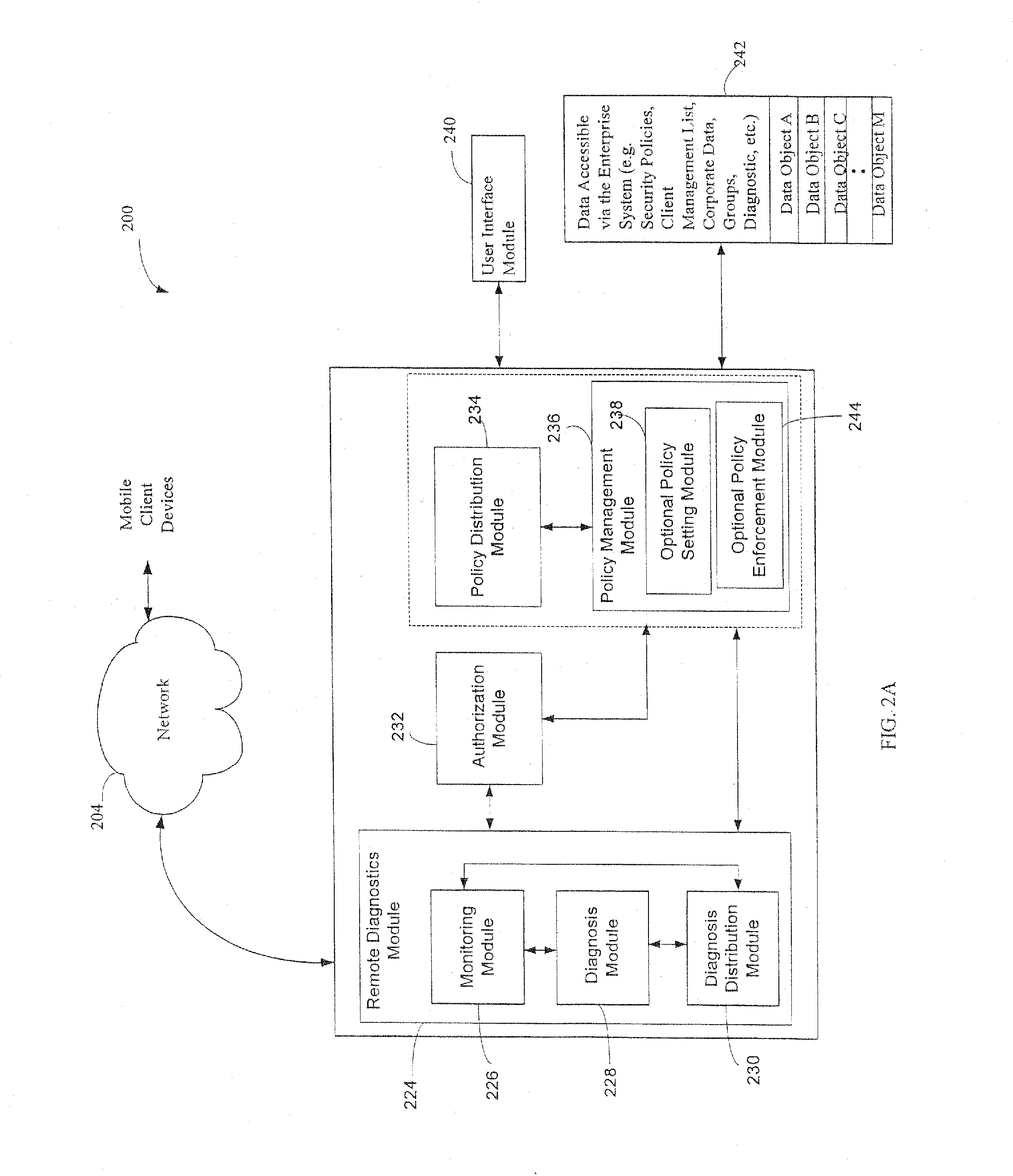
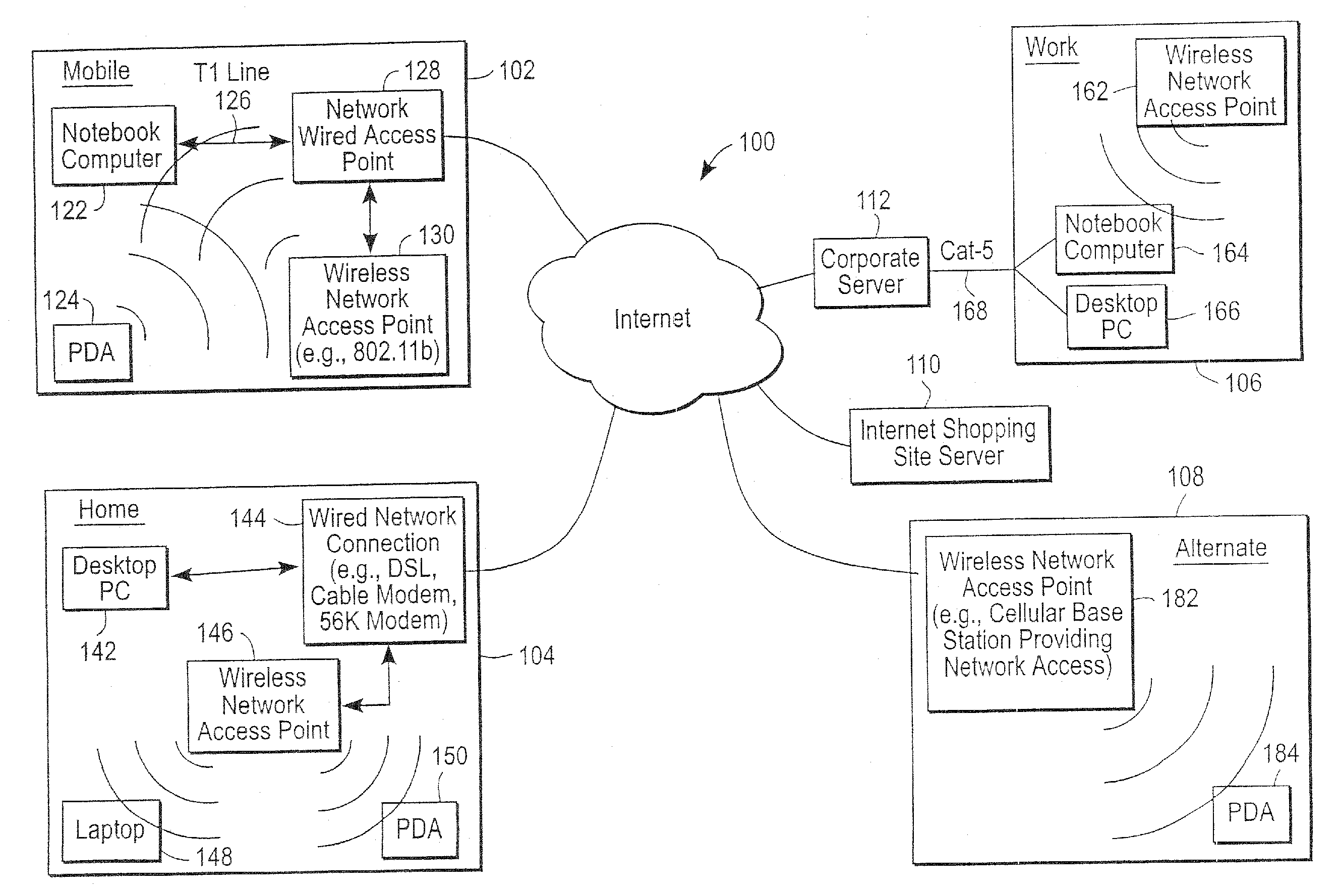
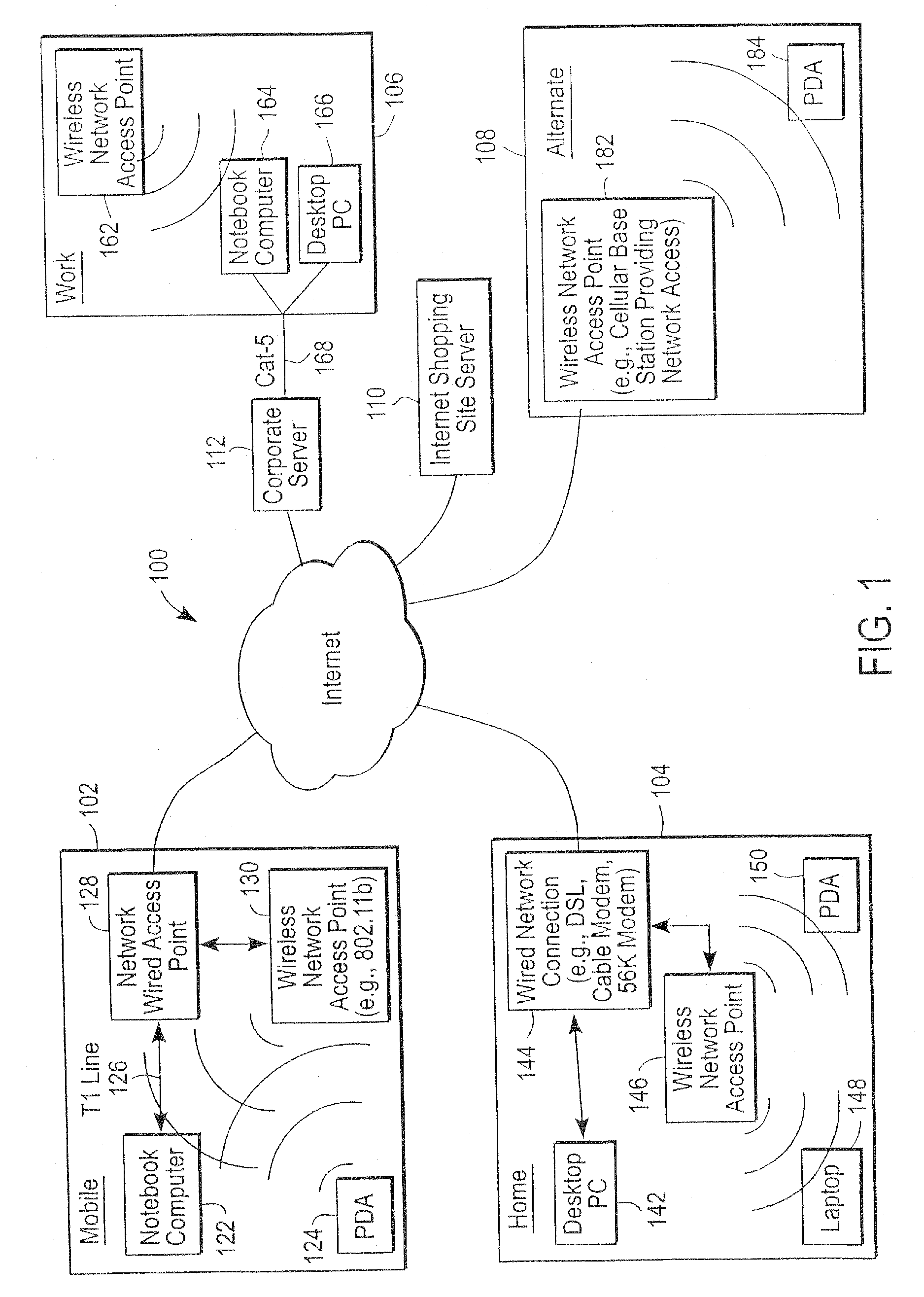
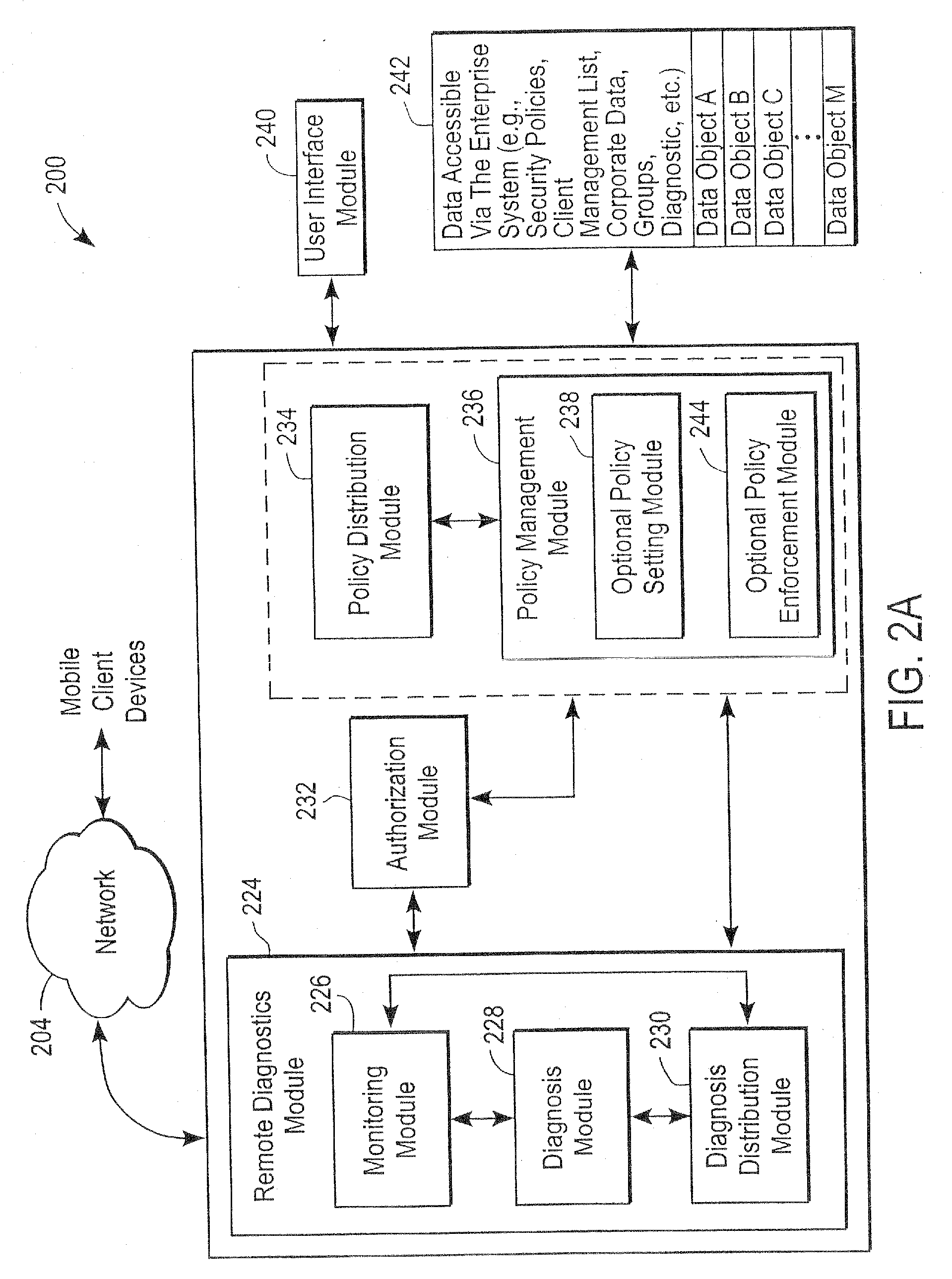
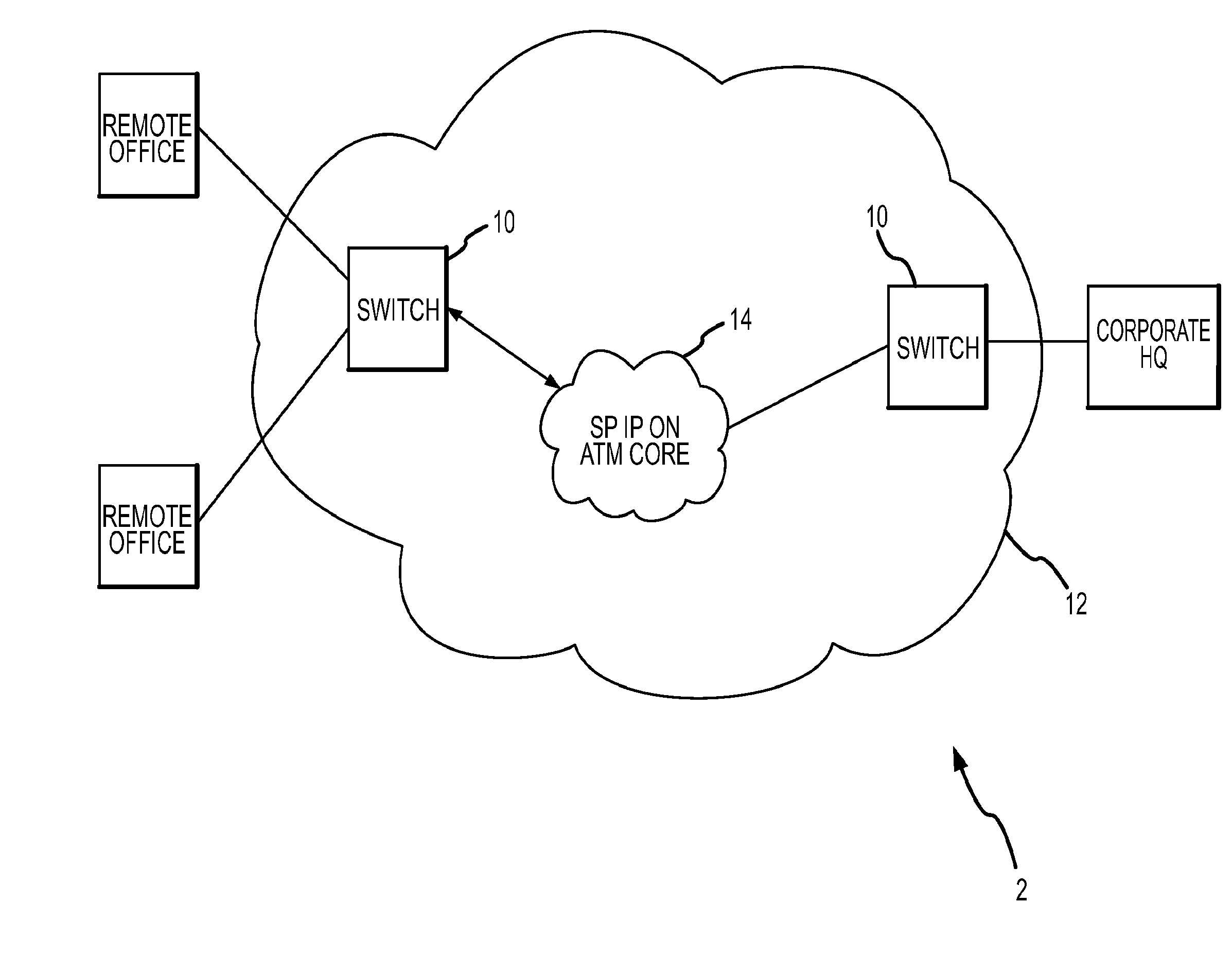
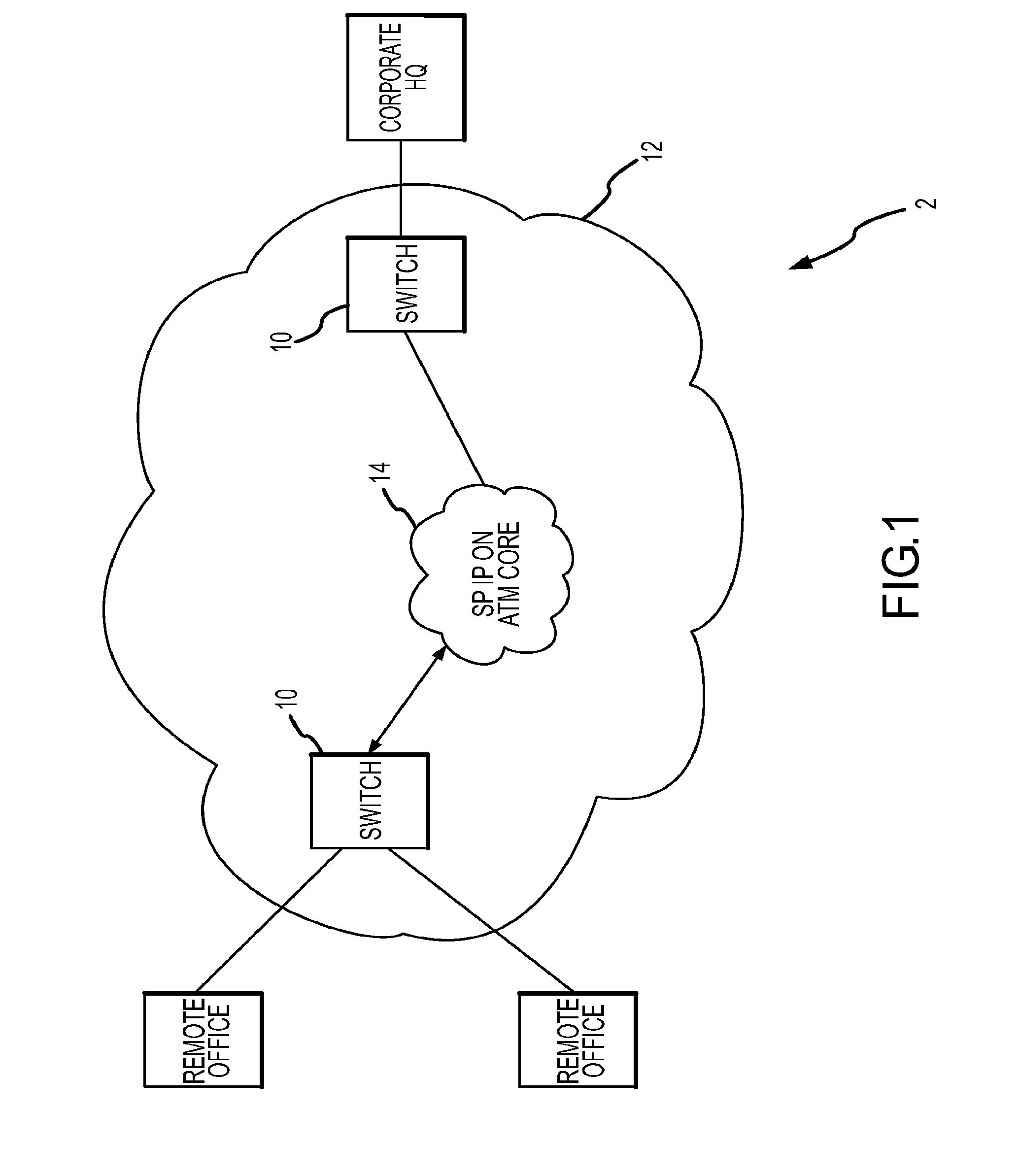
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
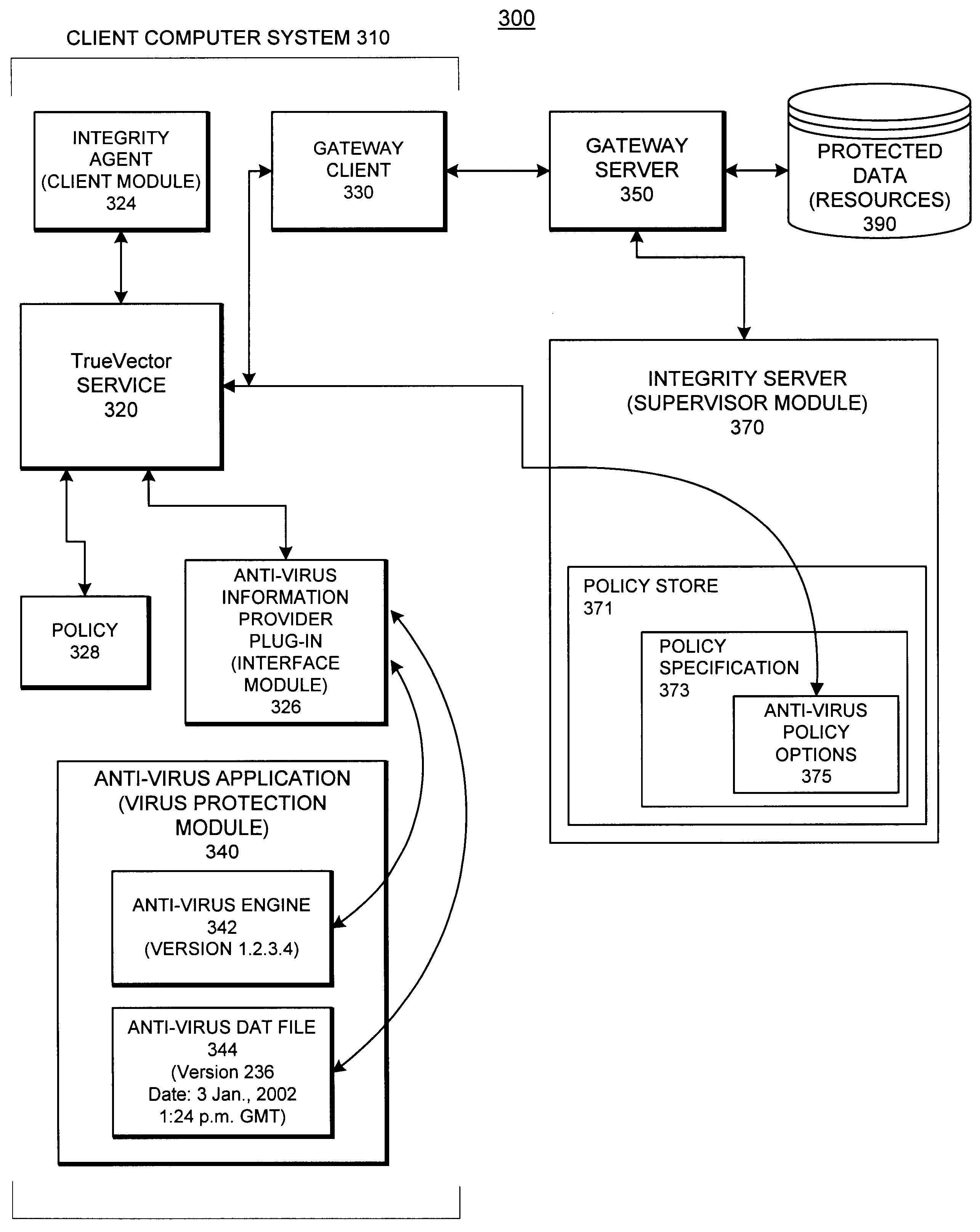
System and methods providing anti-virus cooperative enforcement
InactiveUS6873988B2Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
System and methods providing anti-virus cooperative enforcement
InactiveUS20030055994A1Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
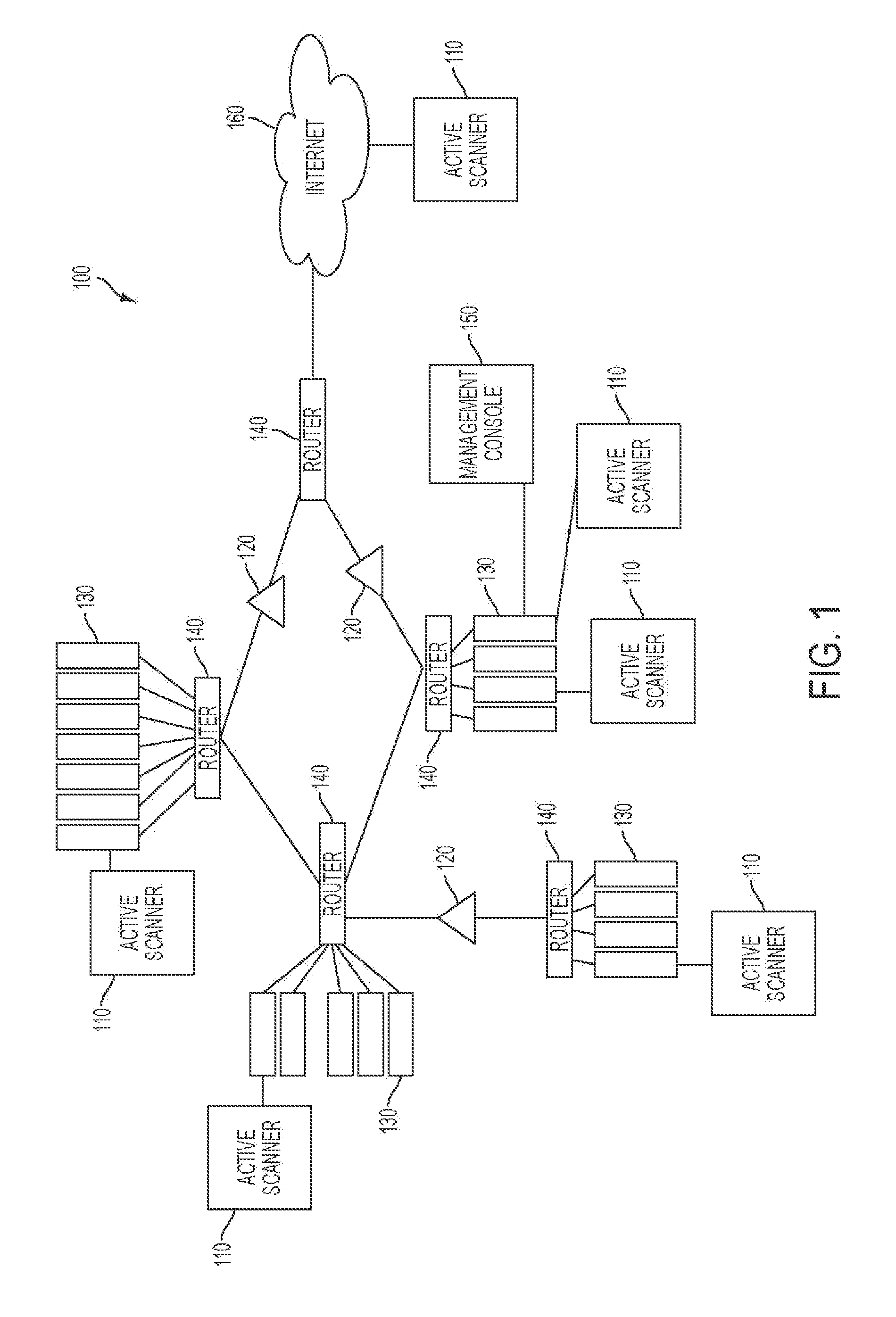
Apparatus and method for remotely monitoring a computer network
InactiveUS20060031476A1Easy to provideMinimize the possibilityDigital computer detailsTransmissionAnti virusPrivate network
There is provided an apparatus for remotely monitoring a computer network. Monitoring is performed using an inside out approach from behind firewalls and other security devices. The monitoring appliance is shipped to a client site preconfigured and typically requires no technically trained person for installation. Collected network data is periodically transmitted to a remote monitoring facility where it is recorded and analyzed. Both the monitoring appliance and the remote center maintain the configuration data. Typically, no client data is transmitted to the remote monitoring site. If the monitoring appliance fails, a completely configured replacement may be shipped to the site and easily installed. The monitoring appliance is optionally equipped to provide network services. Services such as web hosting, file server, print server, virtual private network (VPN), shared Internet access, web content filtering, anti-virus, spam e-mail elimination, and IP telephony services as well as other such services may be easily provided.
Owner:MATHES MARVIN LEE +1
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
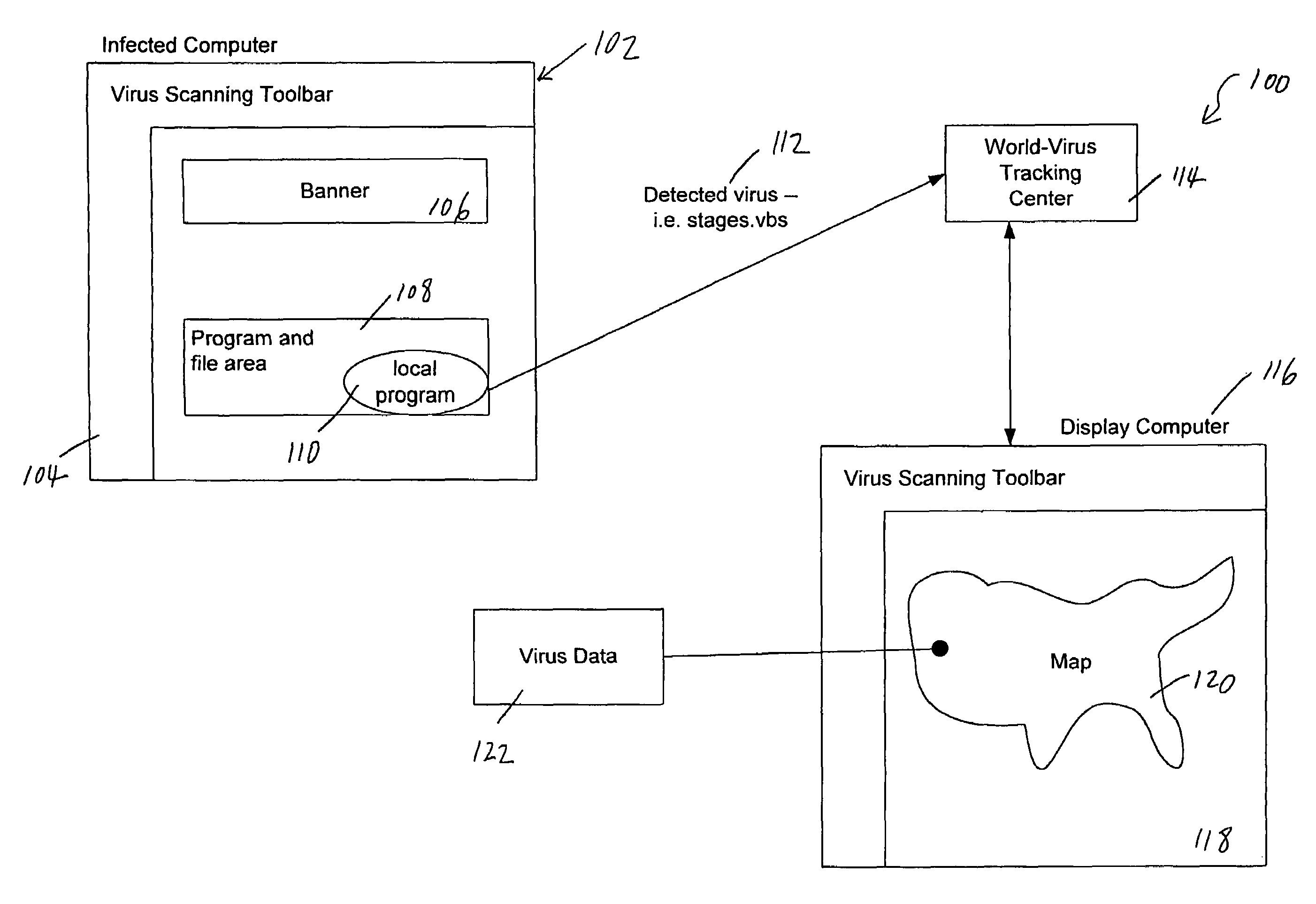
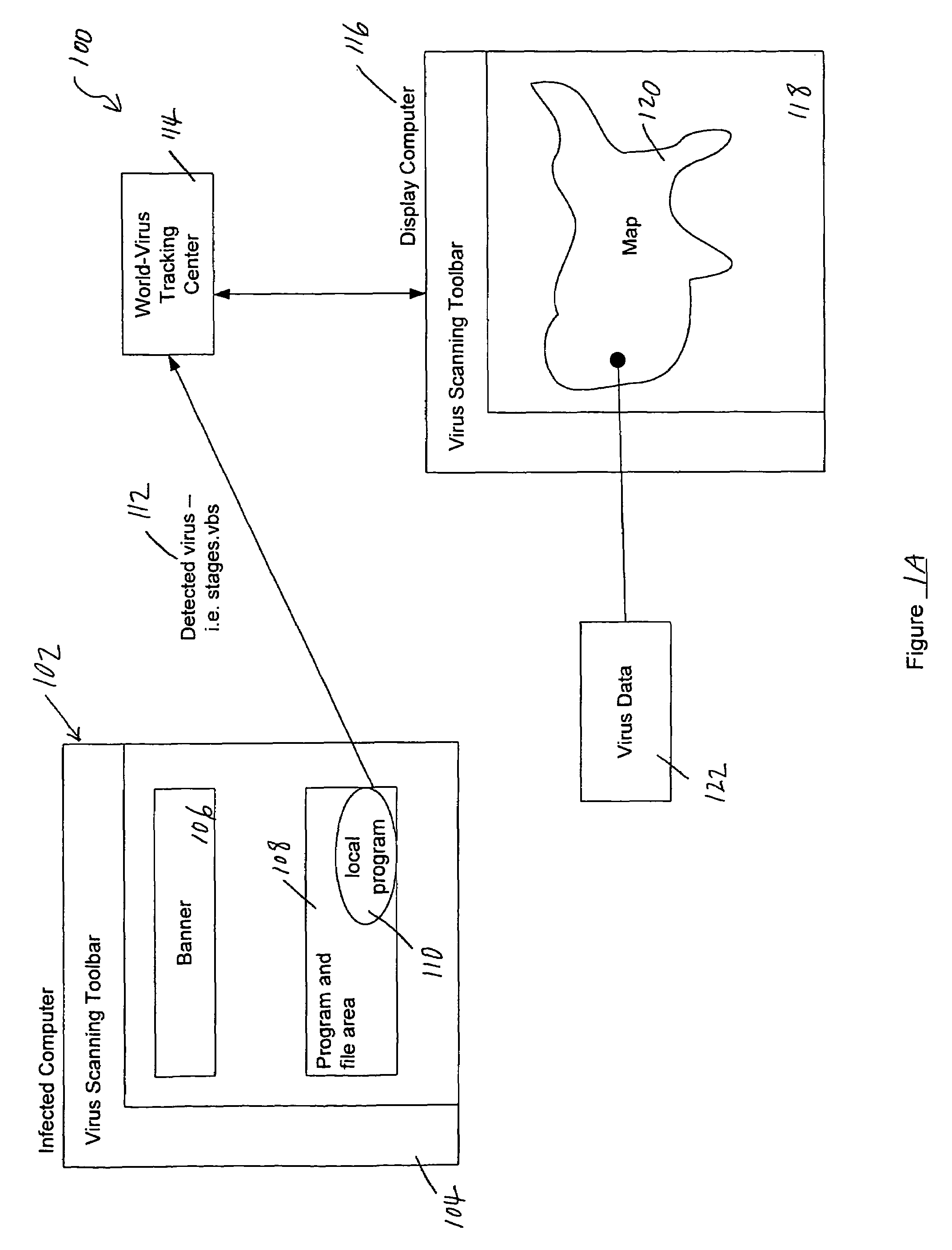
Tracking and reporting of computer virus information
An apparatus and method for providing real-time tracking of virus information as reported from various computers on a distributed computer network. Each client computer on the distributed network contacts an anti-virus scanning site. The site provides a small program or applet that resides in temporary memory of the client computer. The client-user invokes the scan with supplied pattern updates for detecting recent viruses. When the scan has been completed, the user is prompted to supply a country of origin. The name of the virus, its frequency of occurrence, and the country are forwarded as a virus scan log to a virus tracking server, which receives the virus information and thereafter stores it in a database server, which is used to further calculate virus trace display information. A tracking user contacts the virus tracking server and receives map information, which traces the virus activity. The maps show, according to user preference, the names of the viruses encountered in each country, and their frequencies of occurrence.
Owner:TREND MICRO INC
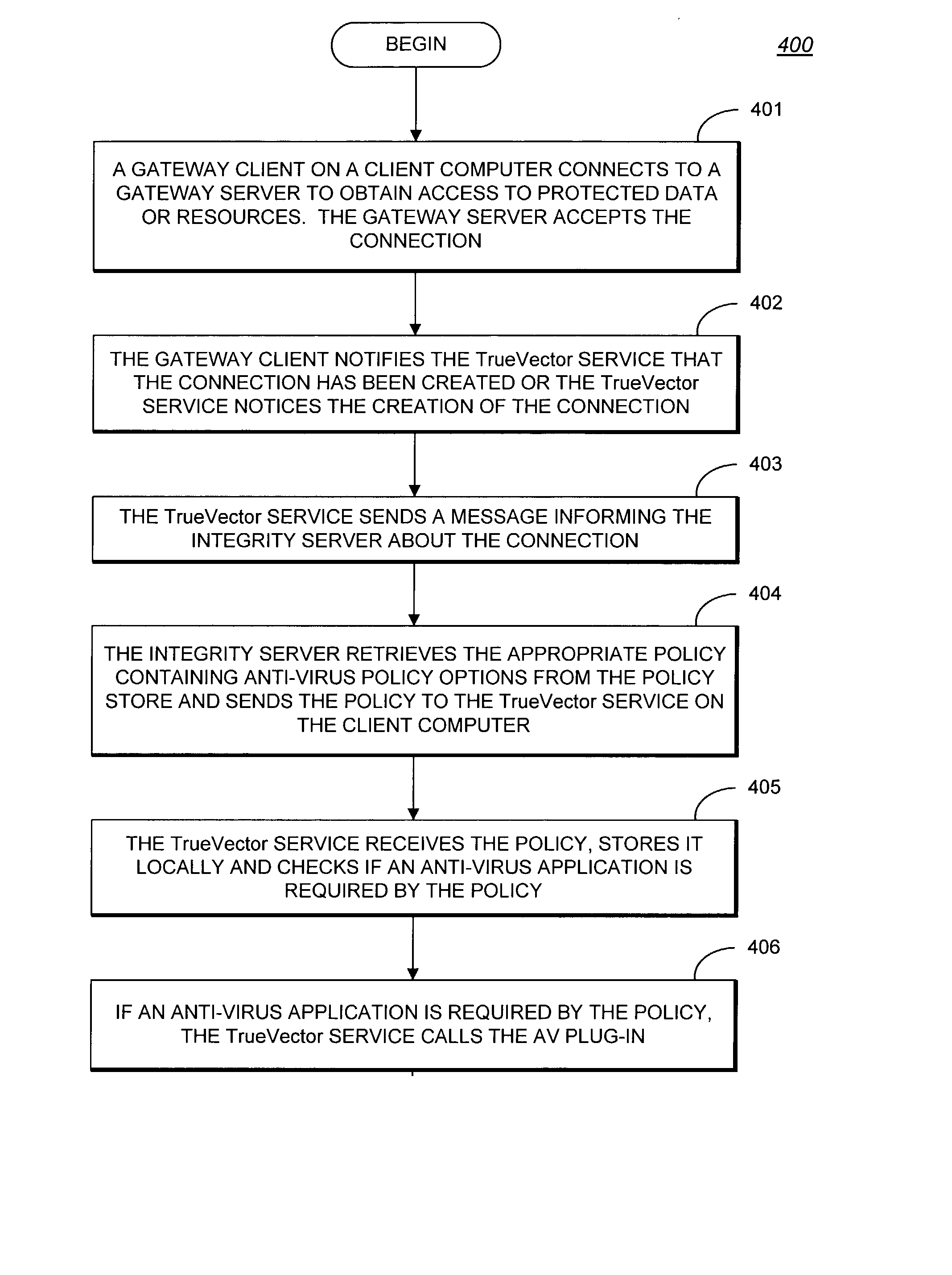
Method for protecting a computer from suspicious objects
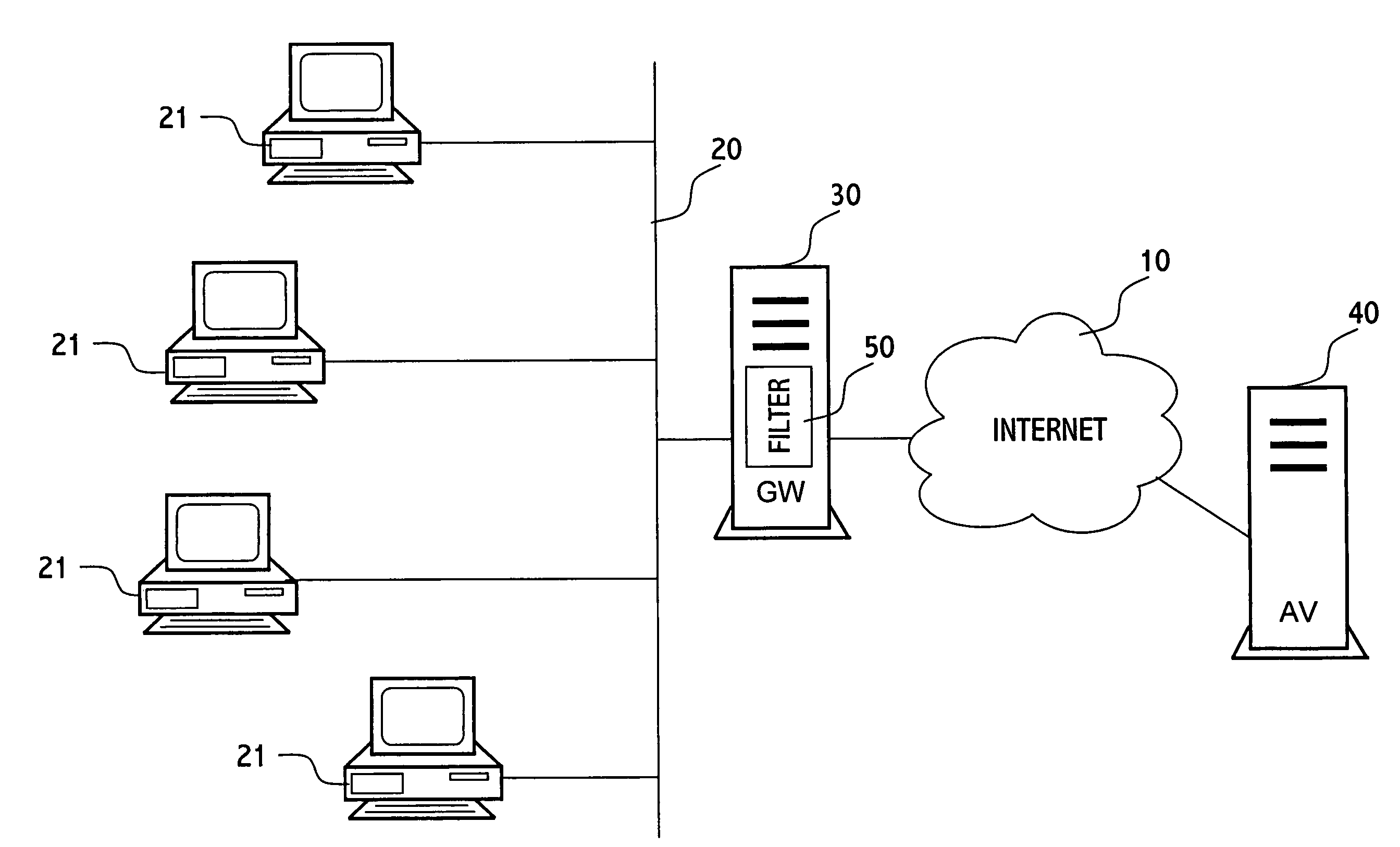
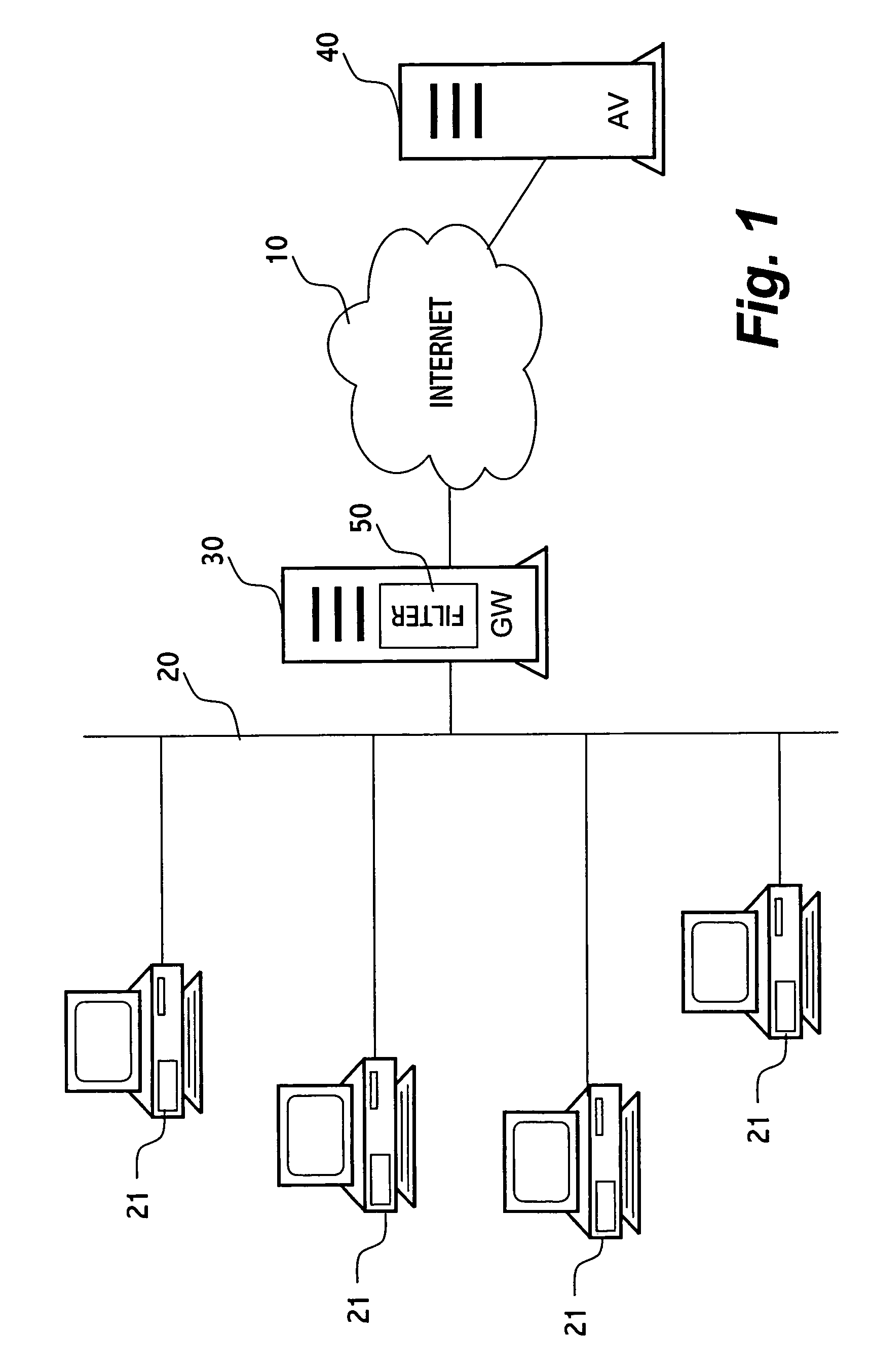
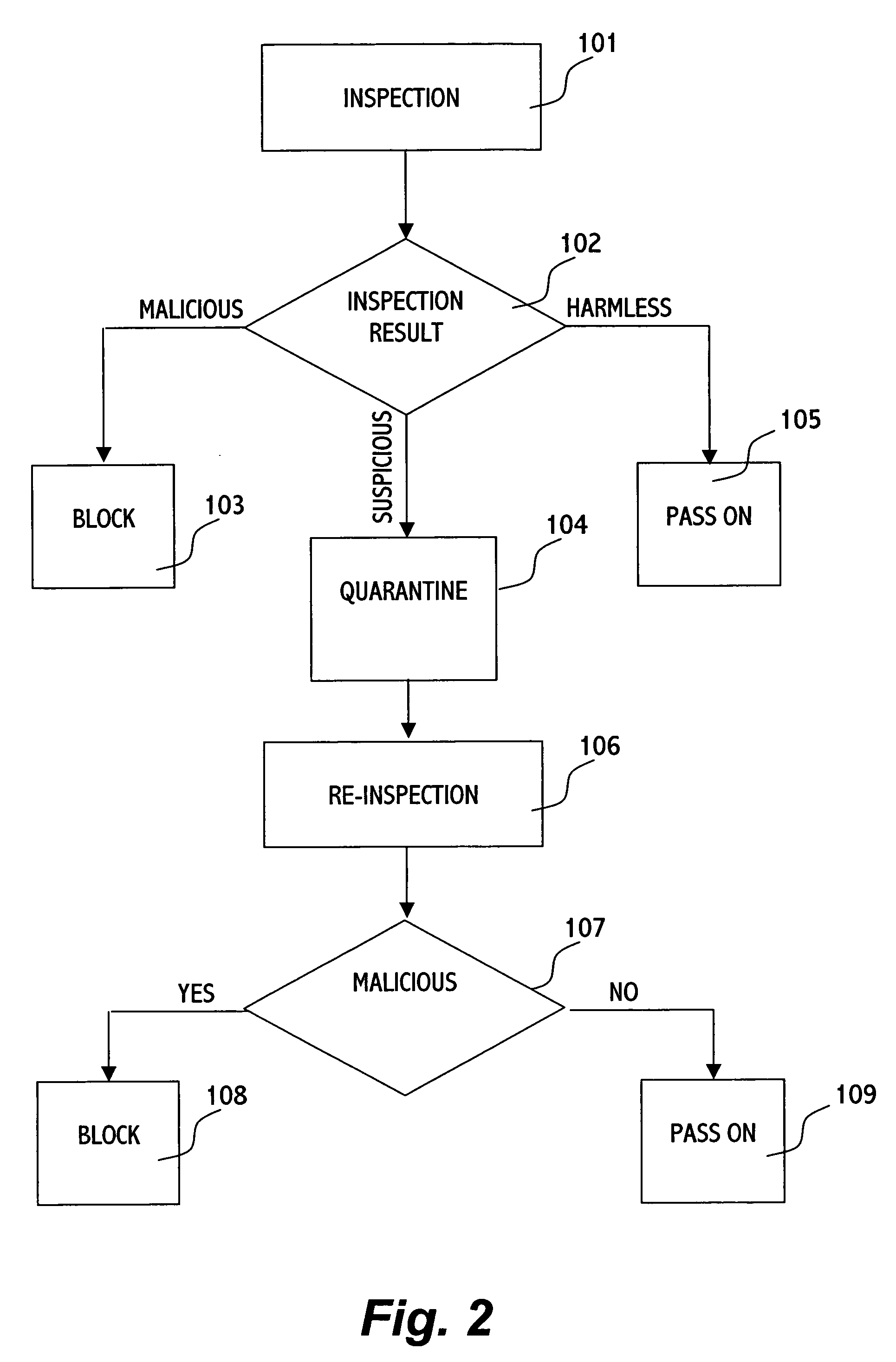
In an inspection facility (e.g. at a gateway server, at a proxy server, at a firewall to a network, at an entrance to a local area network or even at the user's computer) connected to an anti-virus center for updates, a method for protecting a computer from suspicious objects (e.g. a file, an executable, a Web page, an email message, etc.), the method comprising the steps of: inspecting an object; upon determining the object as suspicious, holding the object in quarantine (e.g. preventing from the object to be forwarded to its destination) for a time period, thereby enabling the inspection facility to be updated during the time period by the anti-virus center; upon ending of the time period, re-inspecting the object, thereby inspecting the object by updated inspection tests; and upon determining the object as malicious by the re-inspection, blocking the object, otherwise forwarding the object toward its destination.
Owner:ALADDIN KNOWLEDGE SYSTEMS
Virus detection and removal system and method for network-based systems
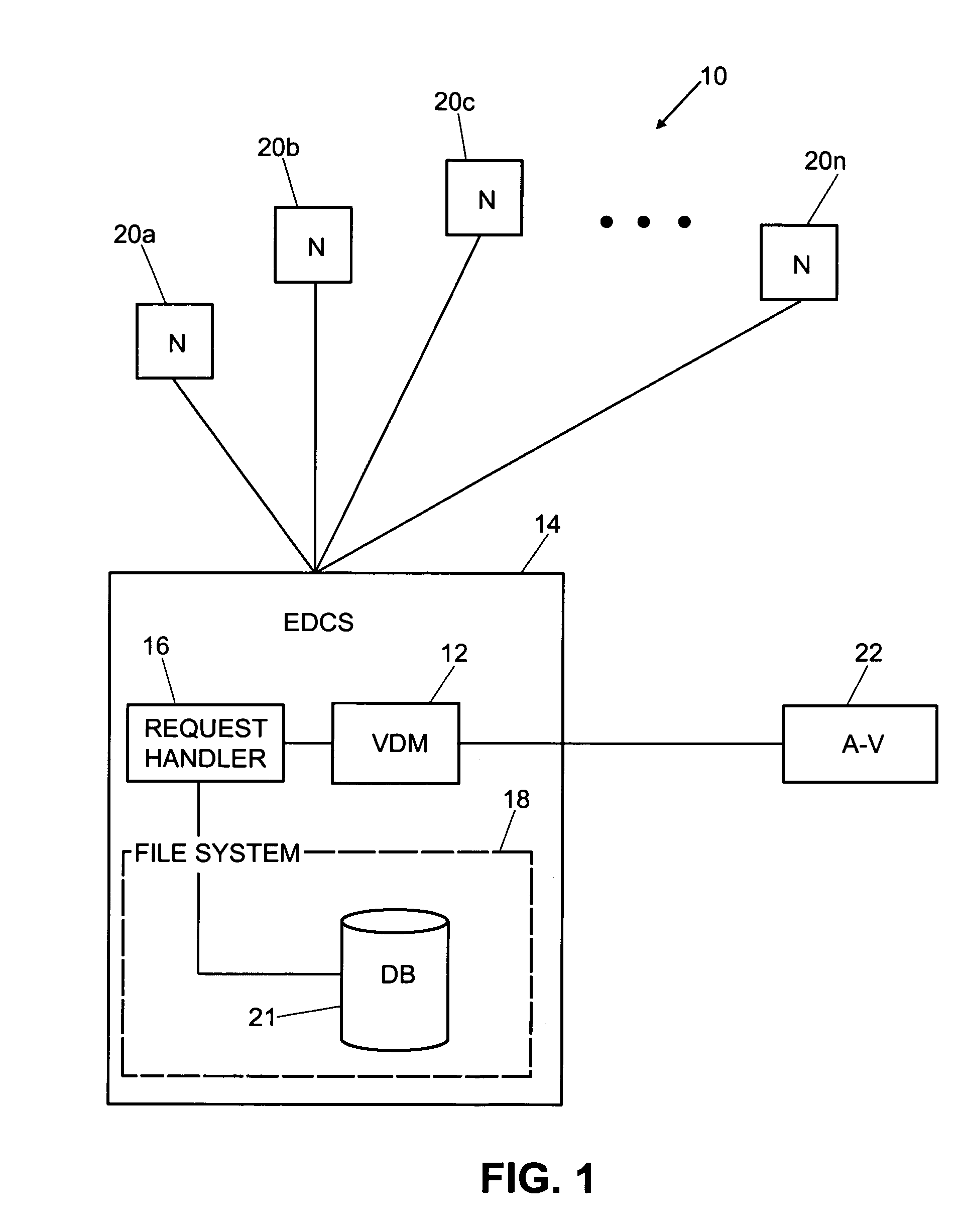
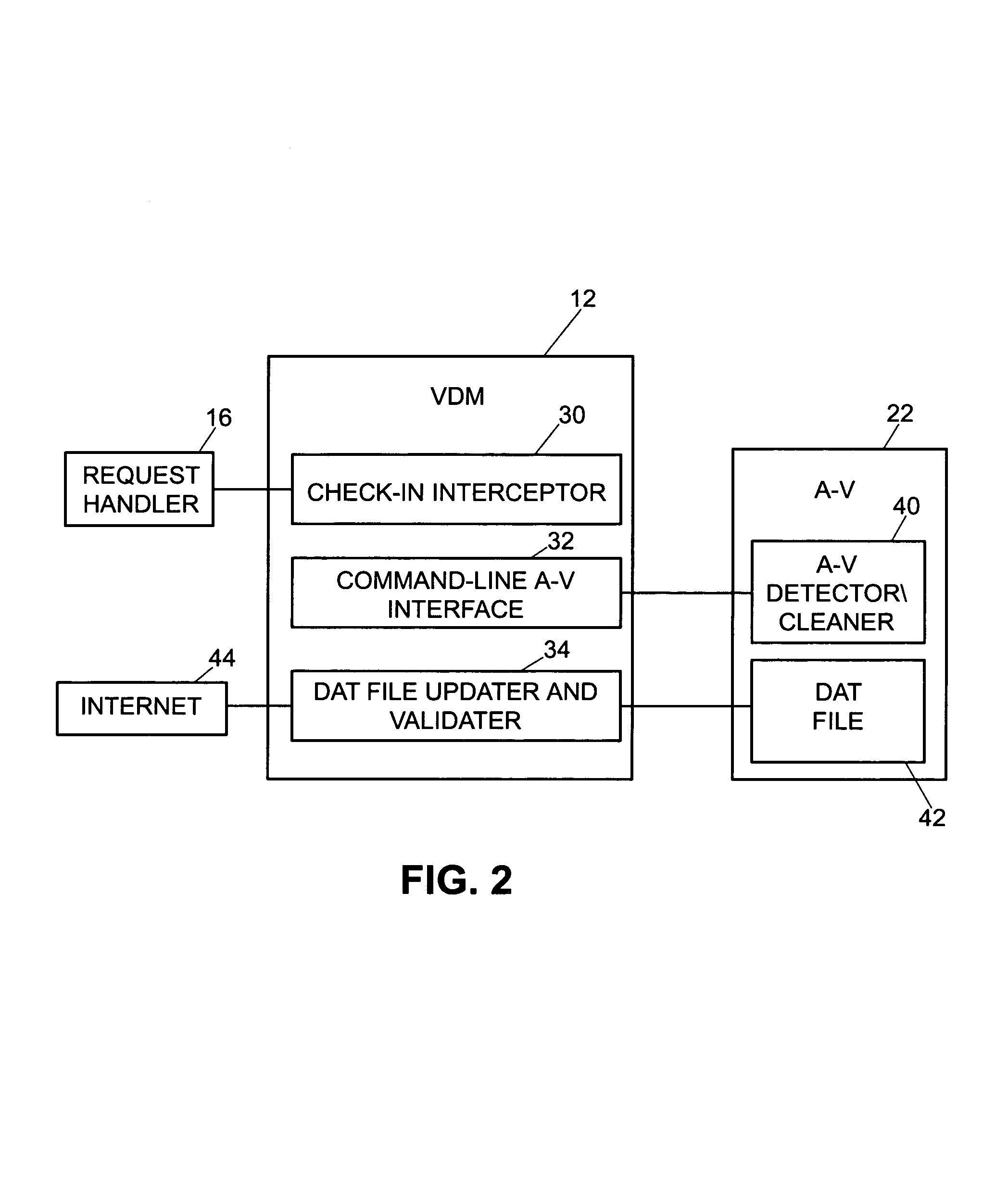
InactiveUS7080407B1Memory loss protectionUnauthorized memory use protectionElectronic documentAnti virus
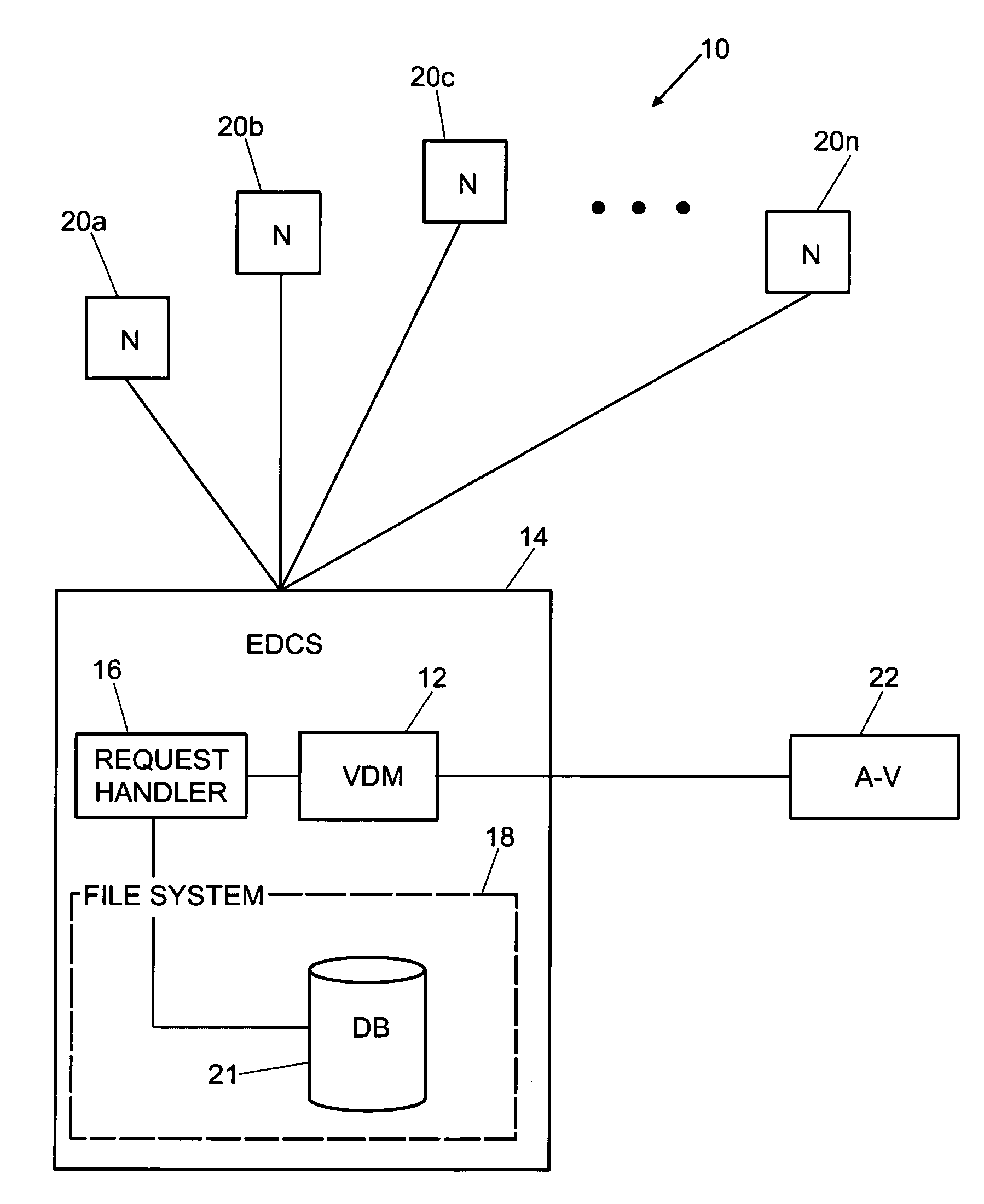
An enhanced virus detection monitoring (VDM) system and method suitable for use with network systems, and in particular electronic document control systems (EDCS) is disclosed. The VDM system intercepts files and documents before they are made available to other users (“check-in”) and inspects the files / documents for virus infection. If a virus infection is found in a file or document, the VDM system invokes anti-virus software to disinfect the file or document. Once the virus has been removed from the file or document, the file (or document) is then made available to other users of the system. If the virus cannot be removed, the file (or document) is not allowed to be checked-in.
Owner:CISCO TECH INC
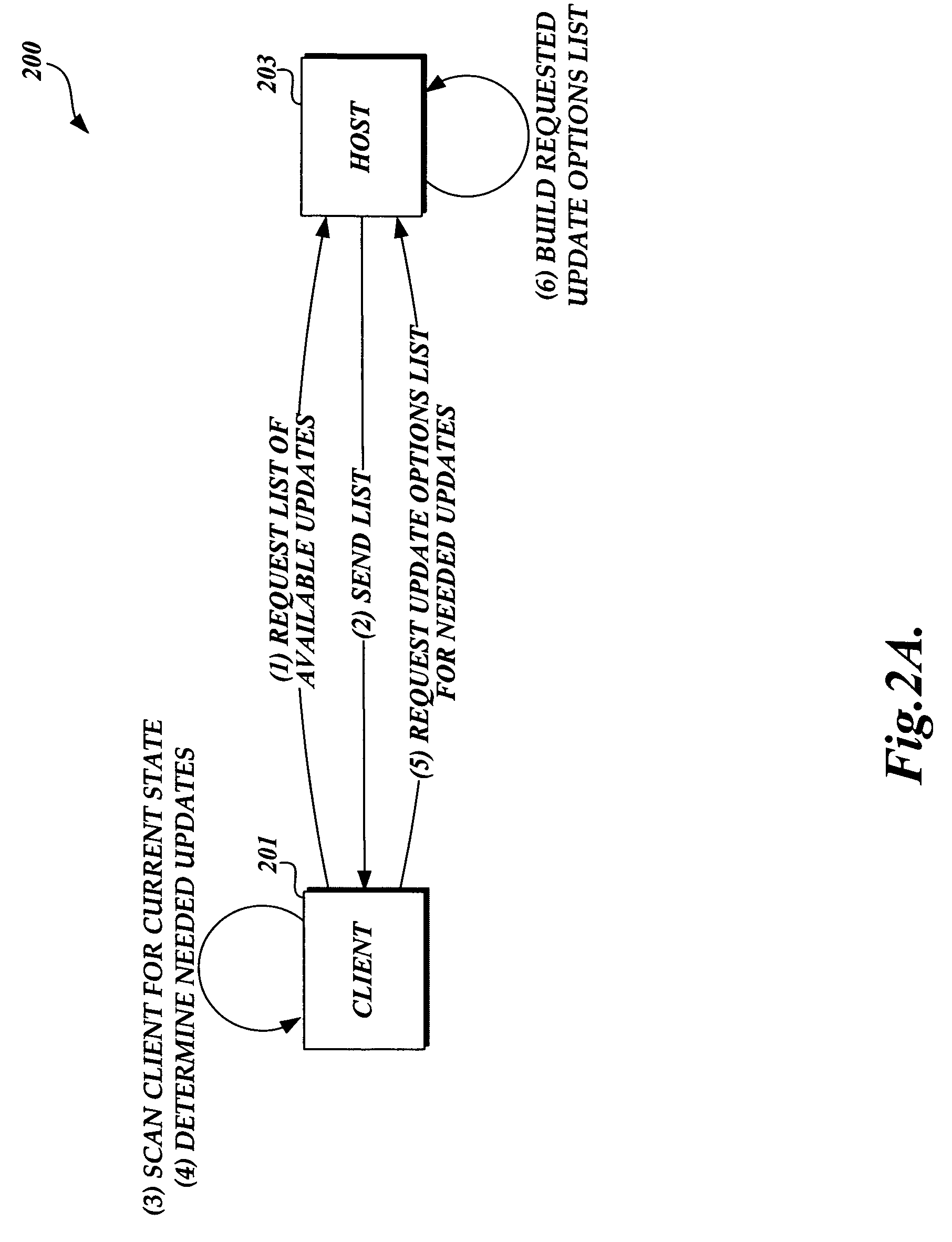
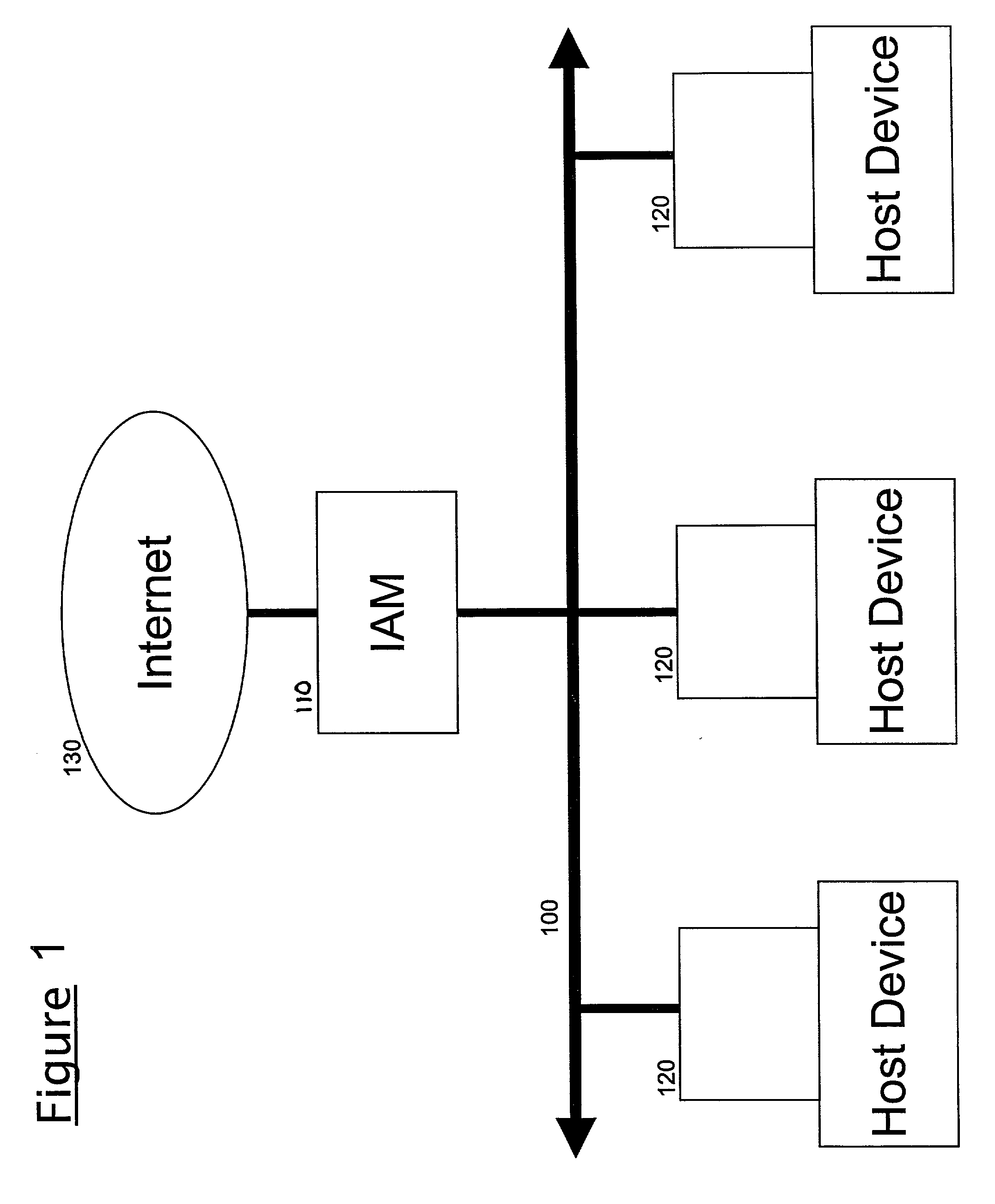
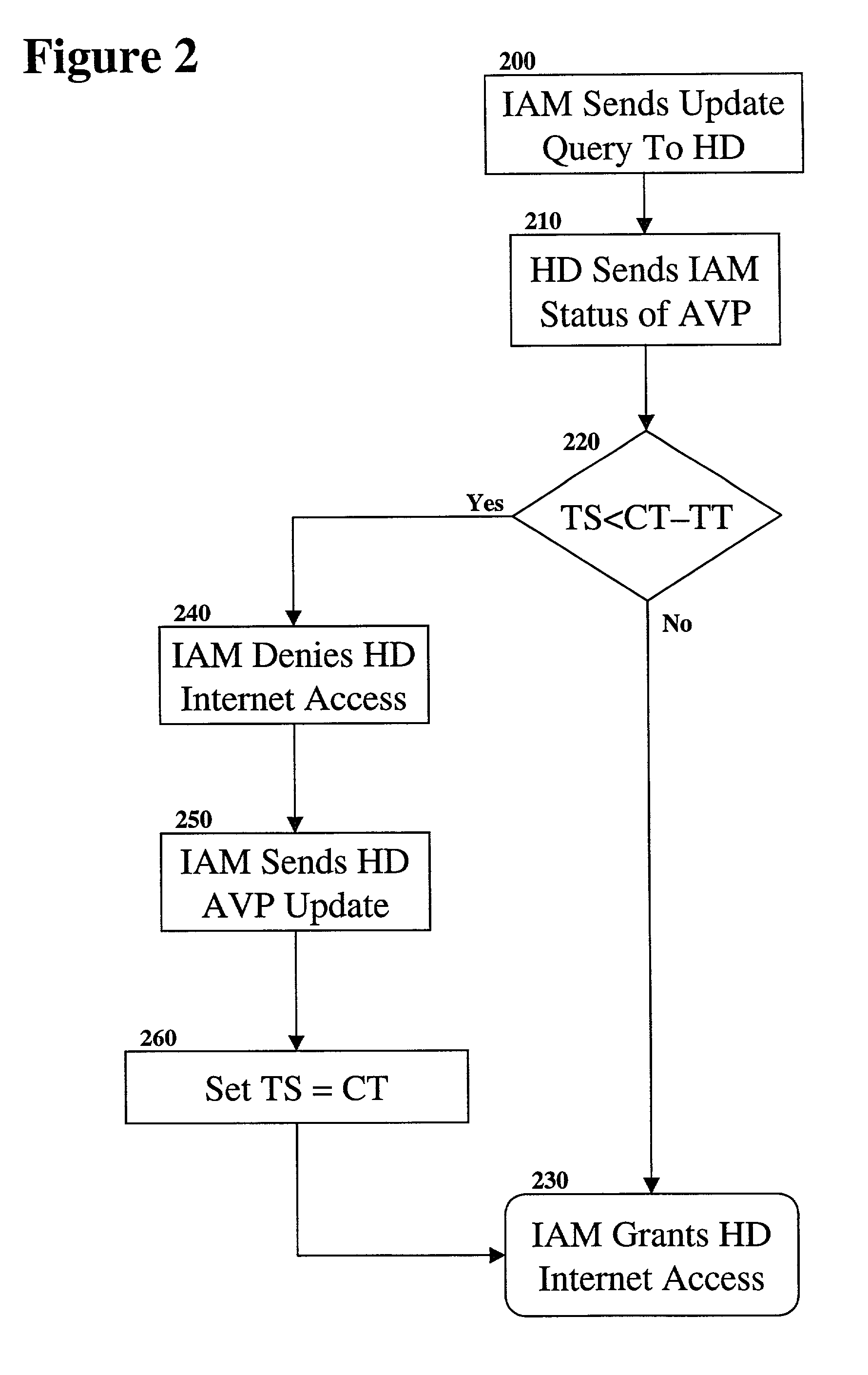
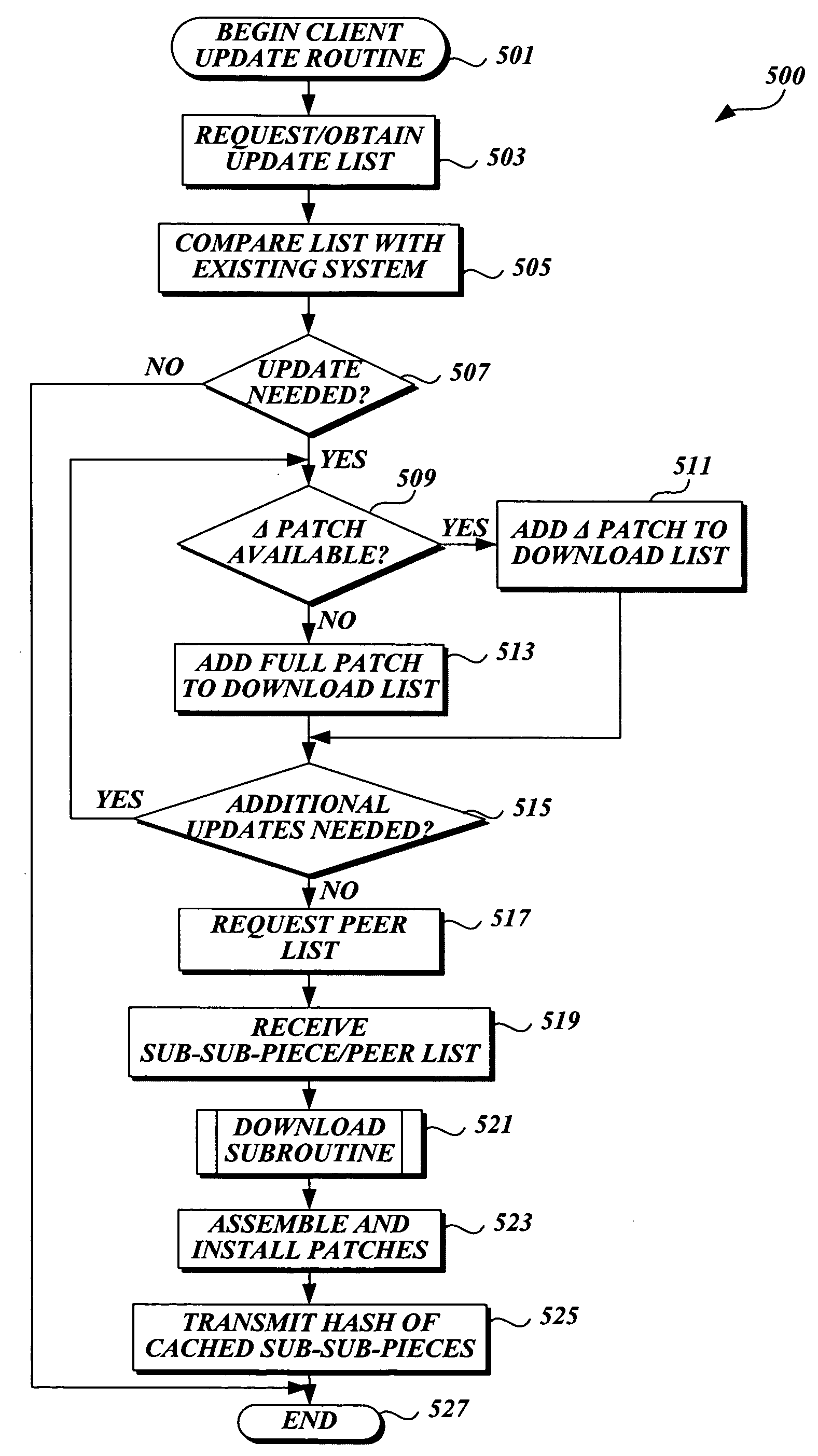
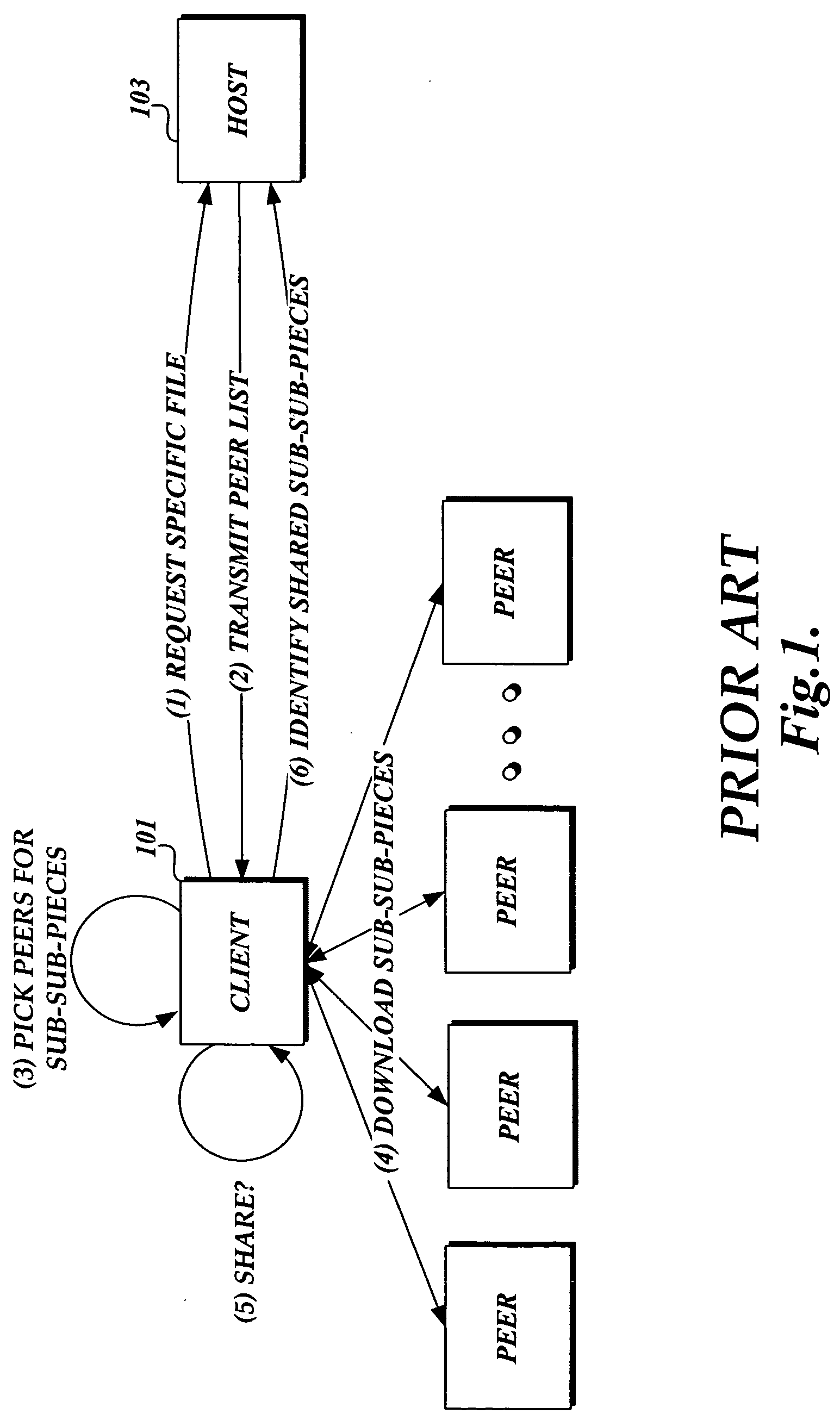
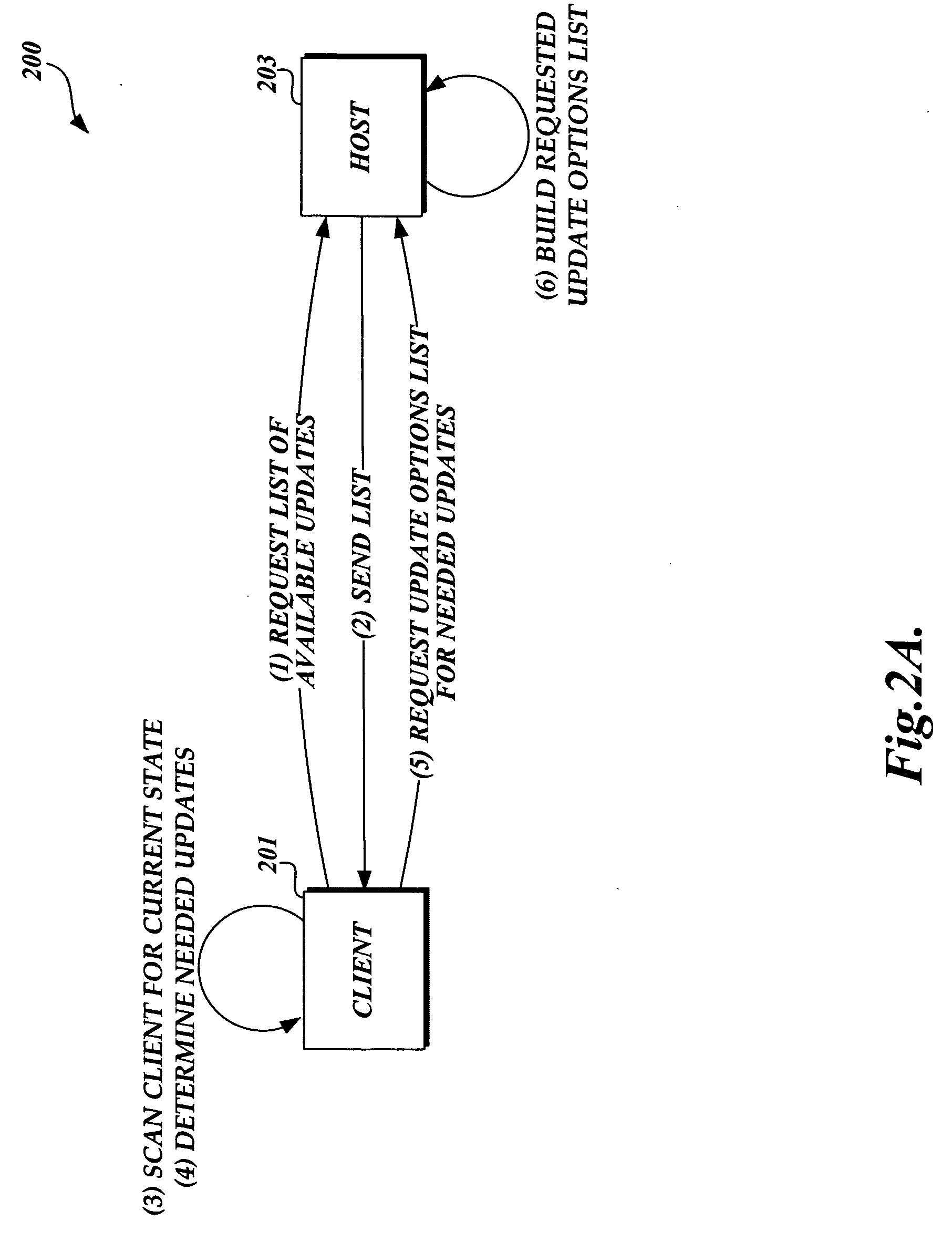
Method and system for downloading updates
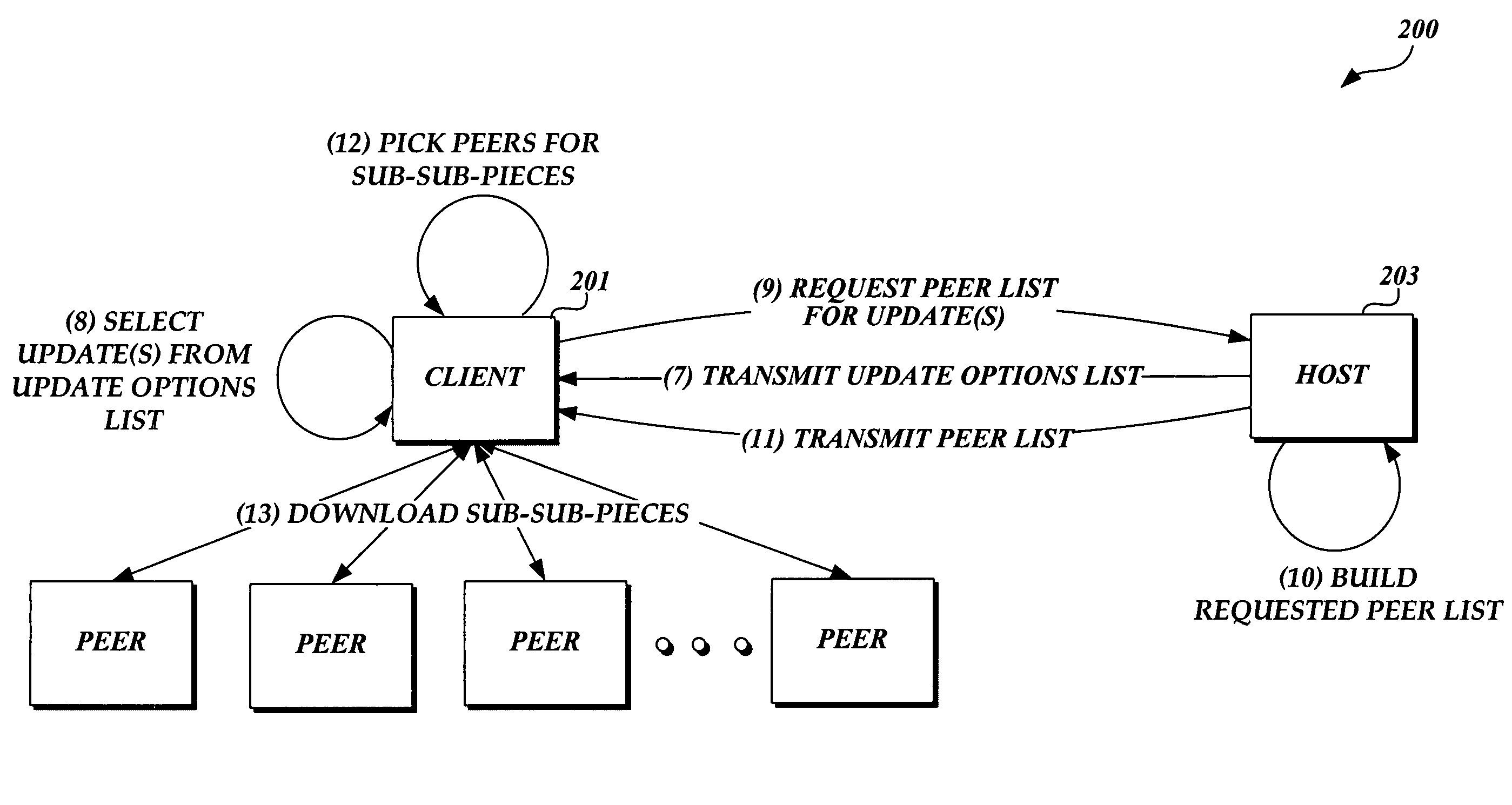
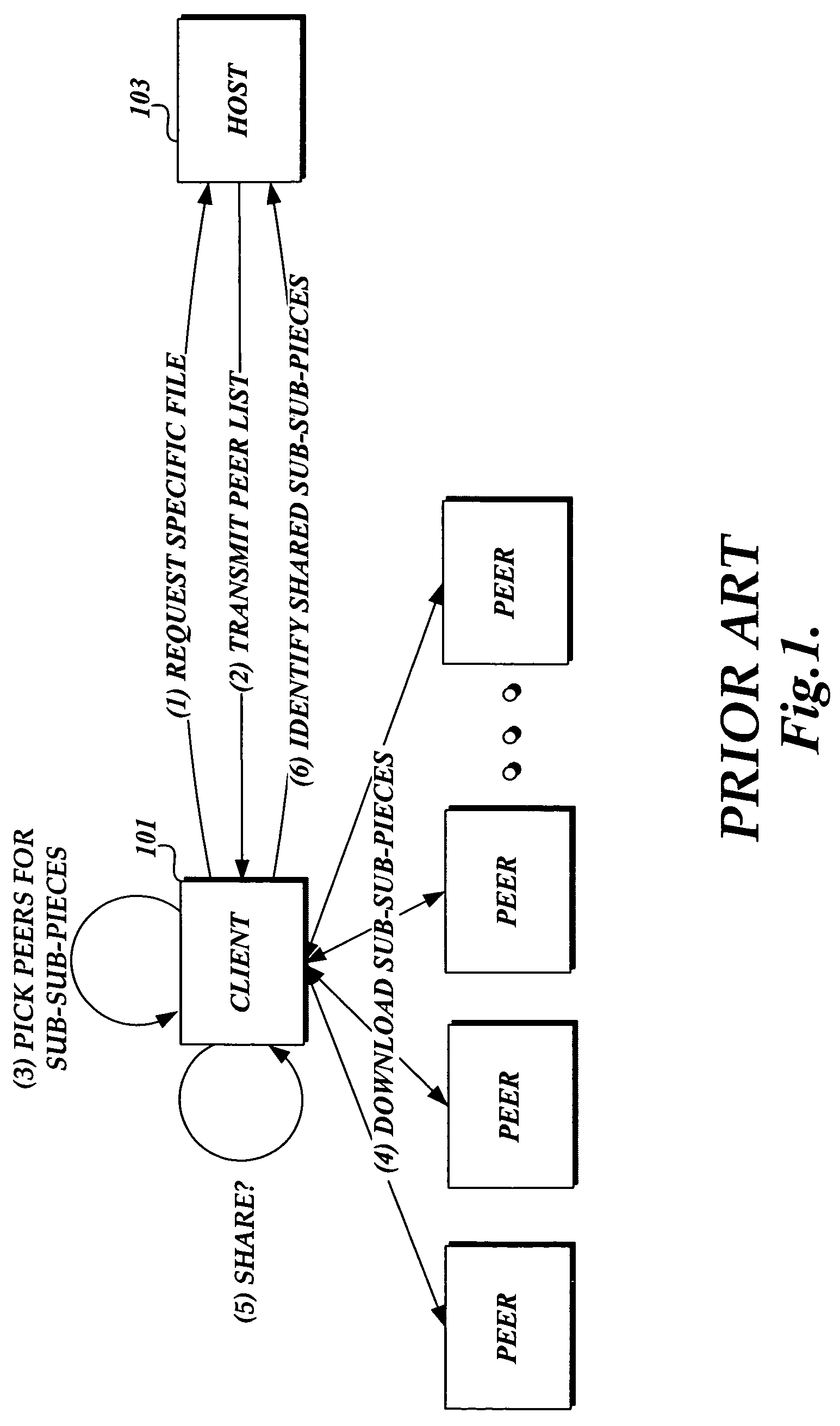
ActiveUS7716660B2Minimize timeReduce the amount requiredSoftware maintainance/managementMultiple digital computer combinationsAnti virusSoftware update
Embodiments of the present invention provide the ability for a software provider to distribute software updates to several different recipients utilizing a peer-to-peer environment. The invention described herein may be used to update any type of software, including, but not limited to, operating software, programming software, anti-virus software, database software, etc. The use of a peer-to-peer environment with added security provides the ability to minimize download time for each peer and also reduce the amount of egress bandwidth that must be provided by the software provider to enable recipients (peers) to obtain the update.
Owner:MICROSOFT TECH LICENSING LLC
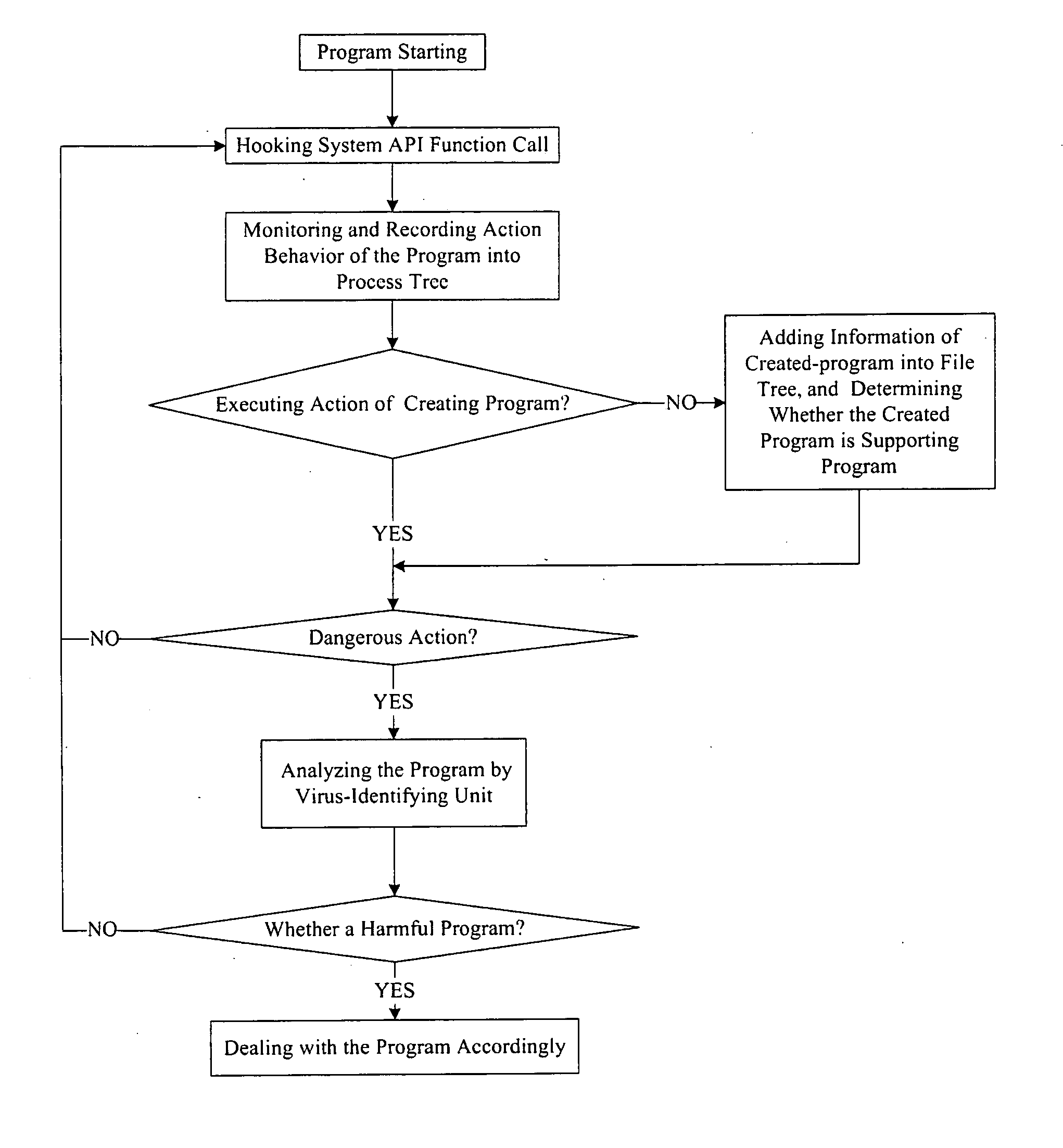
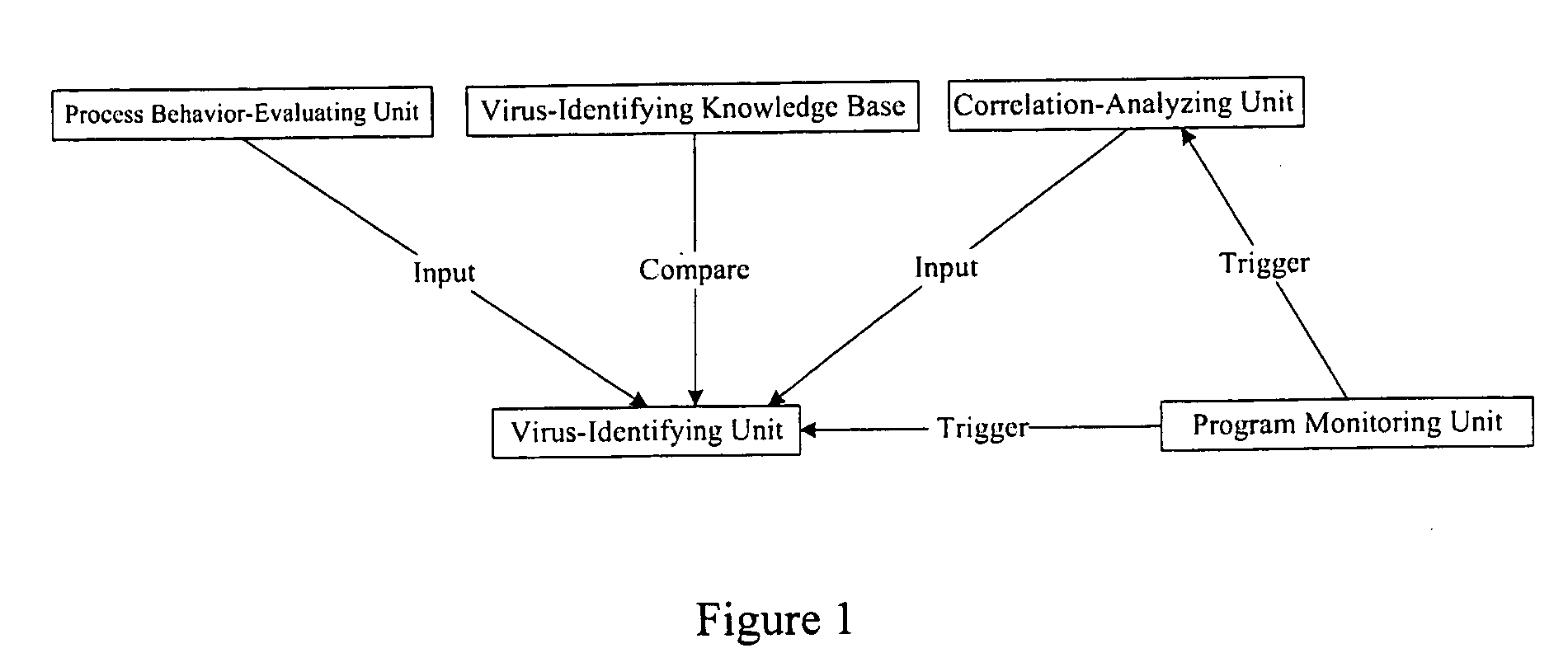
Antivirus protection system and method for computers
InactiveUS20080066179A1Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorProgram behavior
The example embodiments herein relate to an antivirus protection system and method for computers based on program behavior analysis. The antivirus protection system may comprise: a Process Behavior-Evaluating Unit for identifying the programs existing in the user's computers and classifying them into normal programs and suspect programs; a Program-Monitoring Unit for monitoring and recording the actions and / or behaviors of programs; a Correlation-Analyzing Unit for creating correlative trees and analyzing the correlations of actions and / or behaviors of programs, the correlative trees comprising a process tree and a file tree; a Virus-Identifying Knowledge Base, comprising a Program-Behavior Knowledge Base and a Database of Attack-Identifying Rules; a Virus-Identifying Unit for comparing captured actions and / or behaviors to the information in the Virus-Identifying Knowledge Base to determine whether the program is a virus program. With the techniques of certain example embodiments, it may be possible to increase efficiency and reduce the need to upgrade virus codes after viruses become active, while also effectively blocking unknown viruses, Trojans, etc.
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
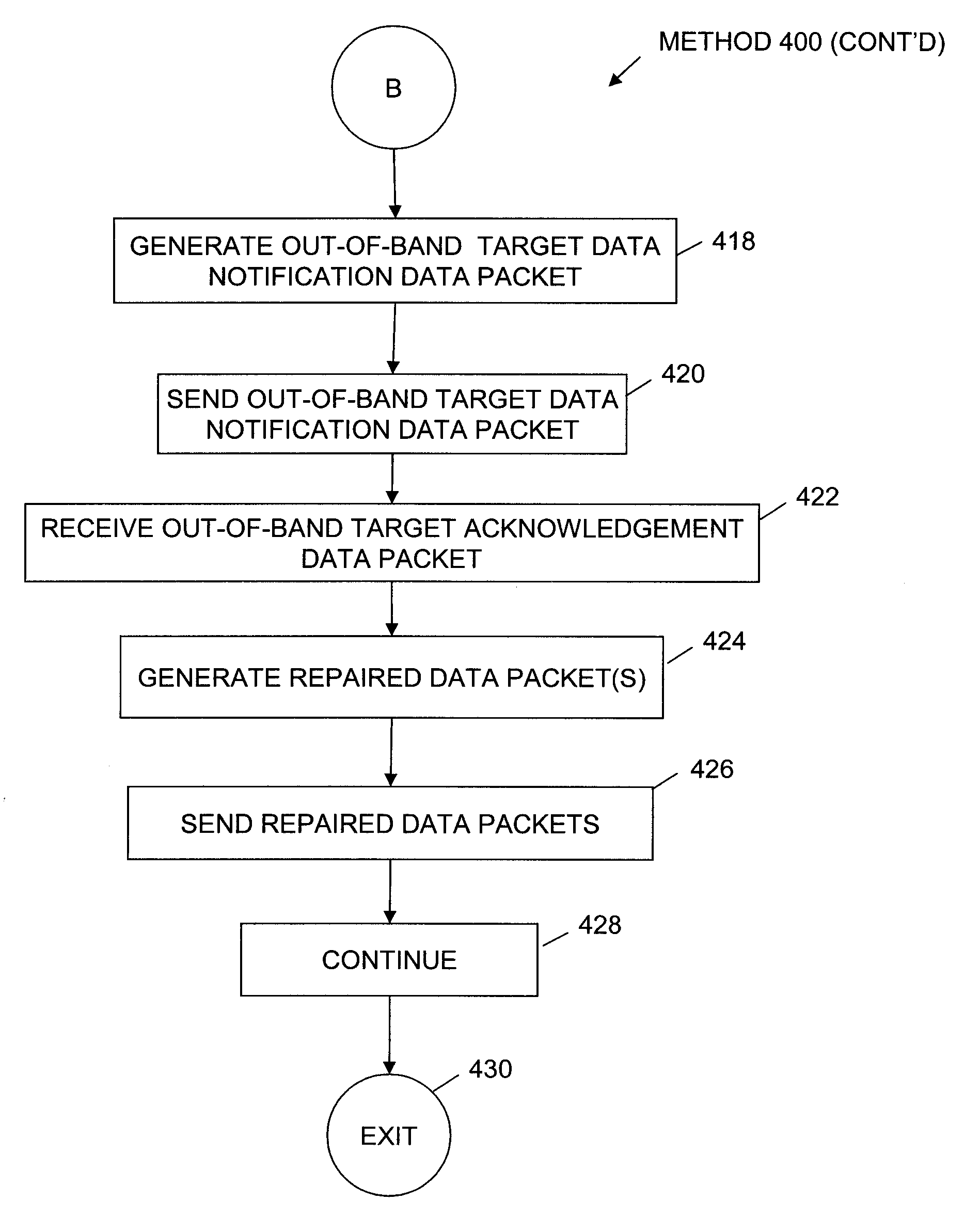
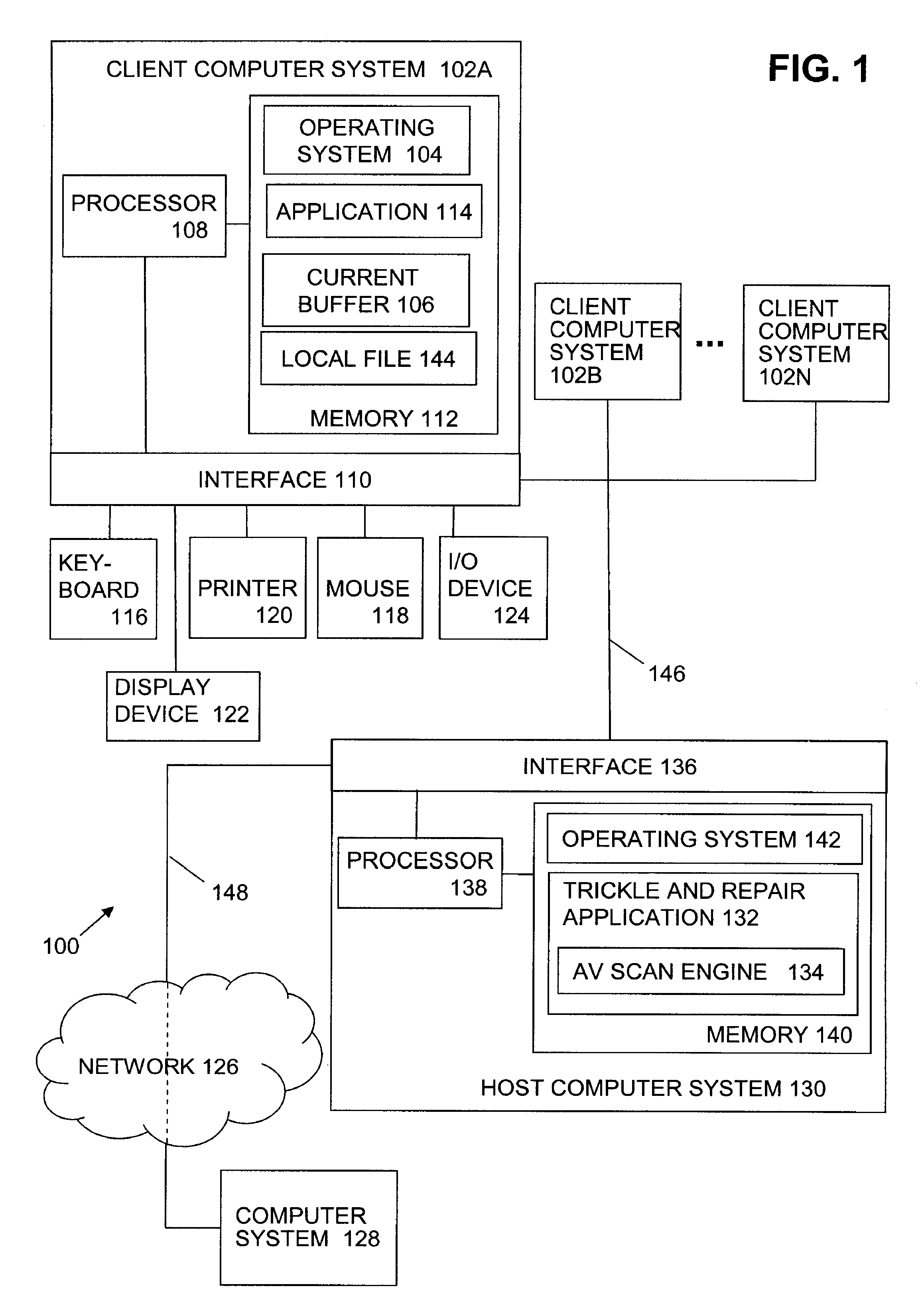
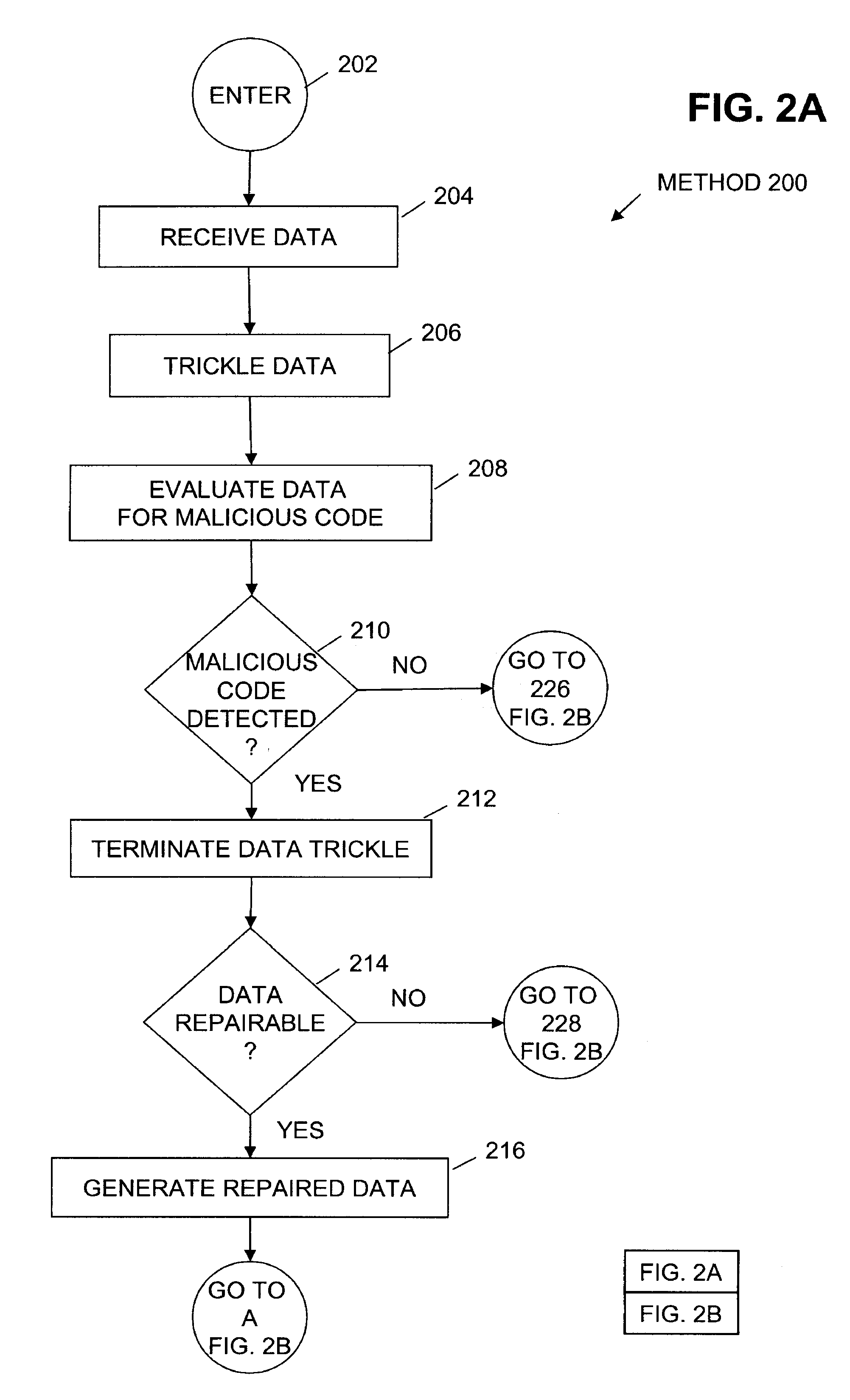
Method to trickle and repair resources scanned using anti-virus technologies on a security gateway
ActiveUS7930750B1Small amountMemory loss protectionError detection/correctionAnti virusComputer hardware
In one embodiment, a trickle and repair application receives data from a sending computer system and trickles the data to a target computer system over an in-band communication channel. The received data is evaluated for the presence of malicious code. When malicious code is detected in the data, trickling of the data is terminated. If the infected data is repairable, the data is repaired and an out-of-band target data notification is generated and sent to the target computer system. In one embodiment, receipt of the out-of-band target data notification causes the target computer system to flush the current buffer and any local files containing the trickled data. The target computer system returns an out-of-band target acknowledgement to the trickle and repair application and the repaired data is sent to the target computer system.
Owner:CA TECH INC
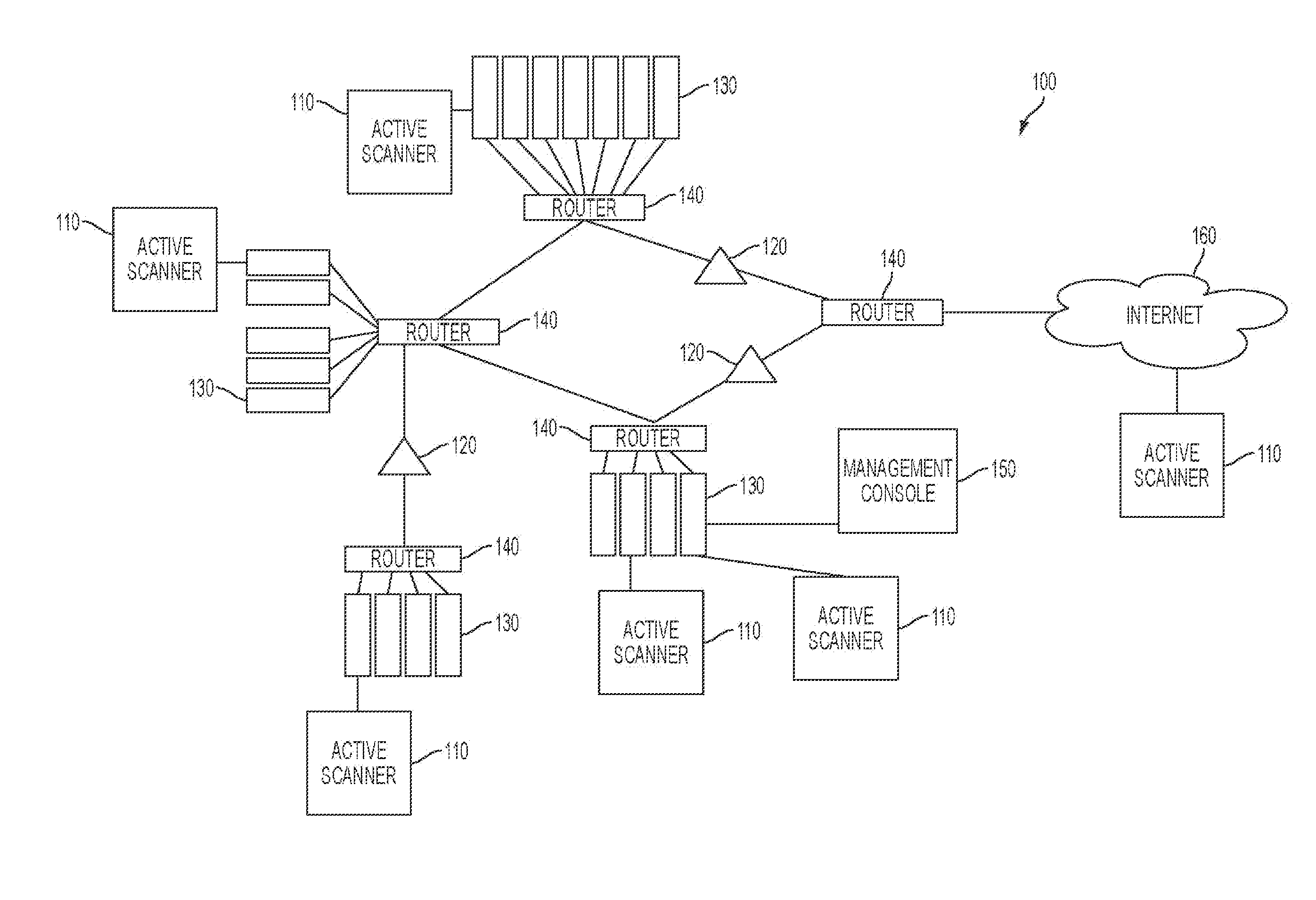
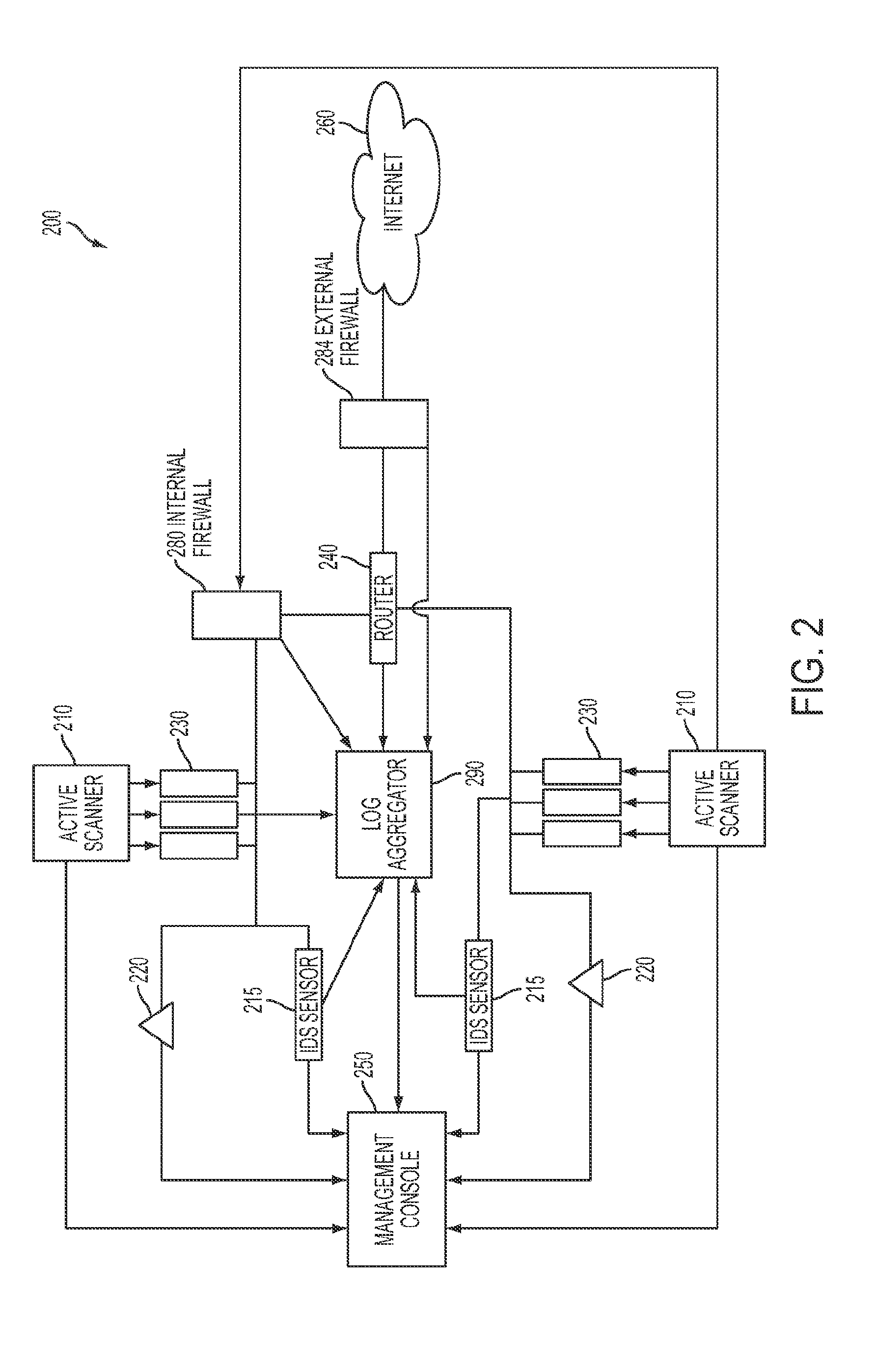
System and method for strategic Anti-malware monitoring
ActiveUS20140013434A1Mitigate and manage governanceMitigate and manage and riskMemory loss protectionError detection/correctionAnti virusFile system
The system and method described herein may leverage active network scanning and passive network monitoring to provide strategic anti-malware monitoring in a network. In particular, the system and method described herein may remotely connect to managed hosts in a network to compute hashes or other signatures associated with processes running thereon and suspicious files hosted thereon, wherein the hashes may communicated to a cloud database that aggregates all known virus or malware signatures that various anti-virus vendors have catalogued to detect malware infections without requiring the hosts to have a local or resident anti-virus agent. Furthermore, running processes and file system activity may be monitored in the network to further detect malware infections. Additionally, the network scanning and network monitoring may be used to detect hosts that may potentially be participating in an active botnet or hosting botnet content and audit anti-virus strategies deployed in the network.
Owner:TENABLE INC
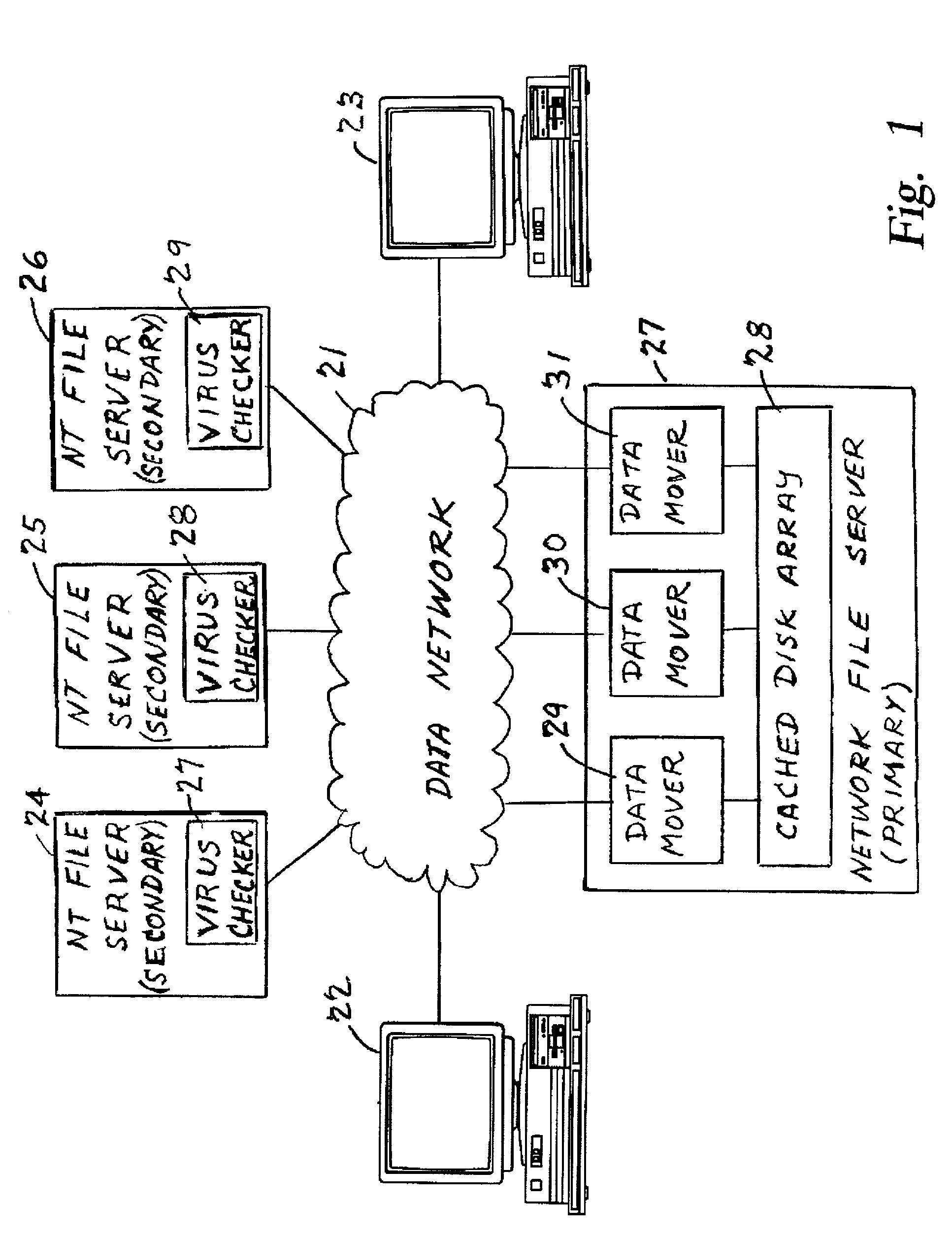
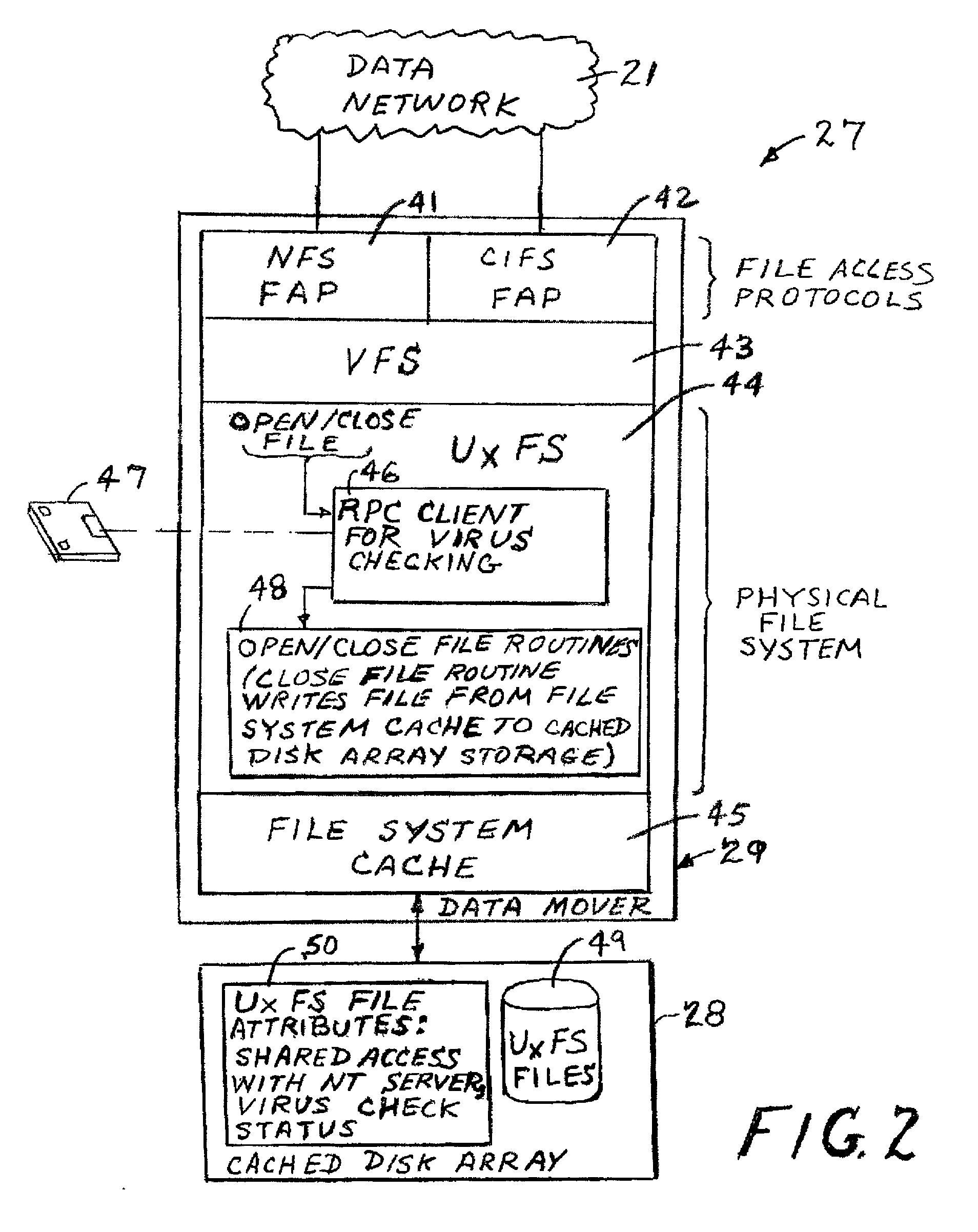
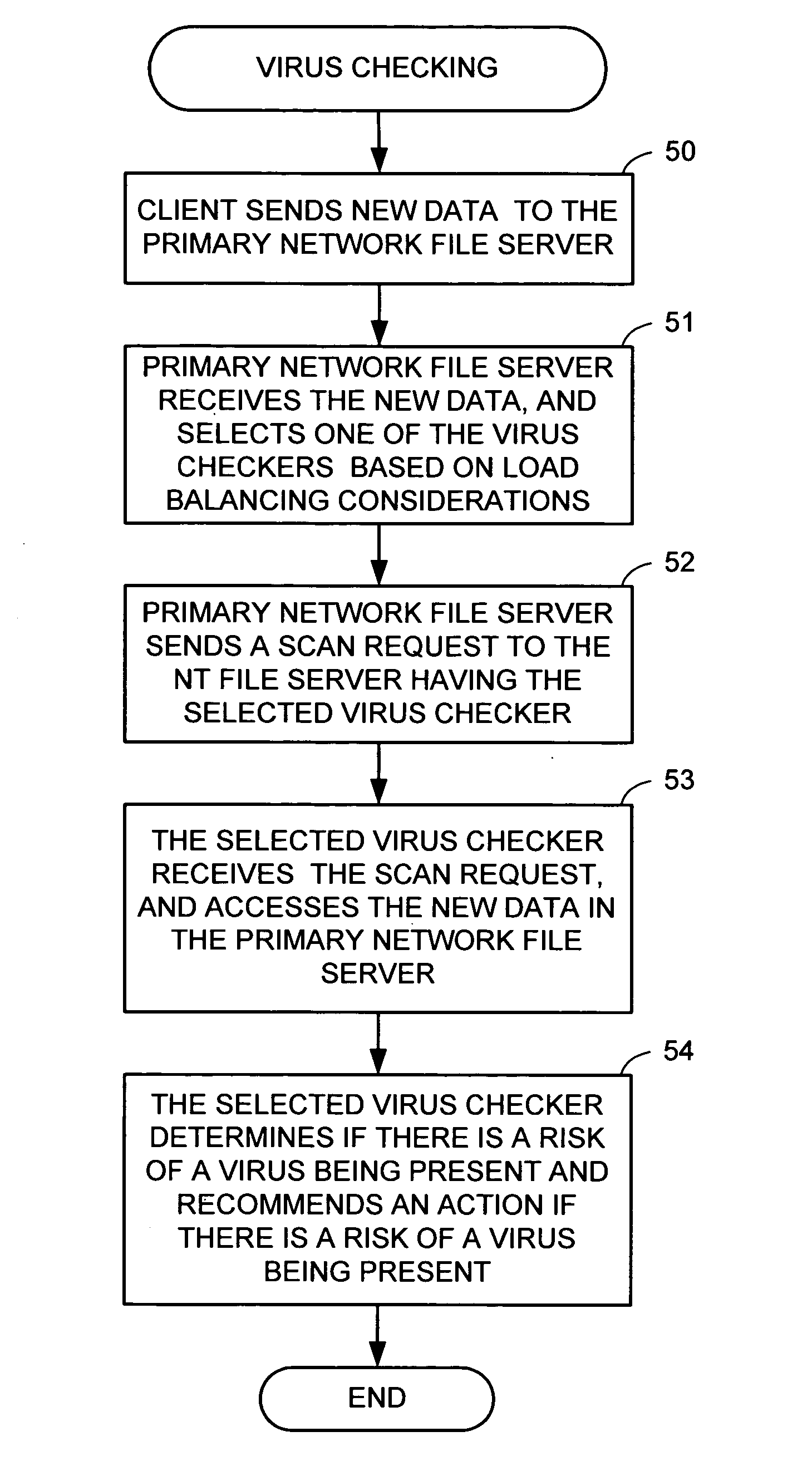
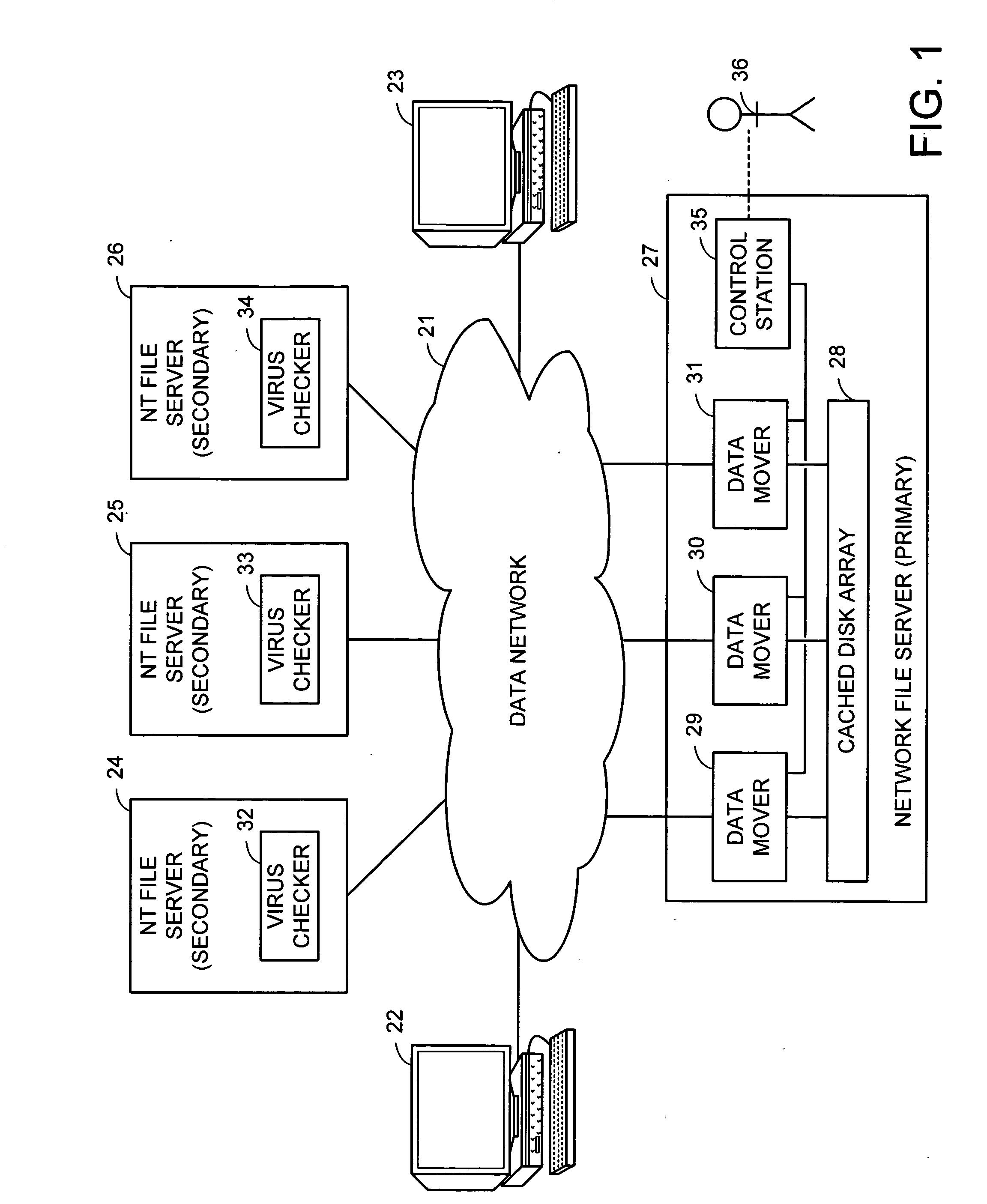
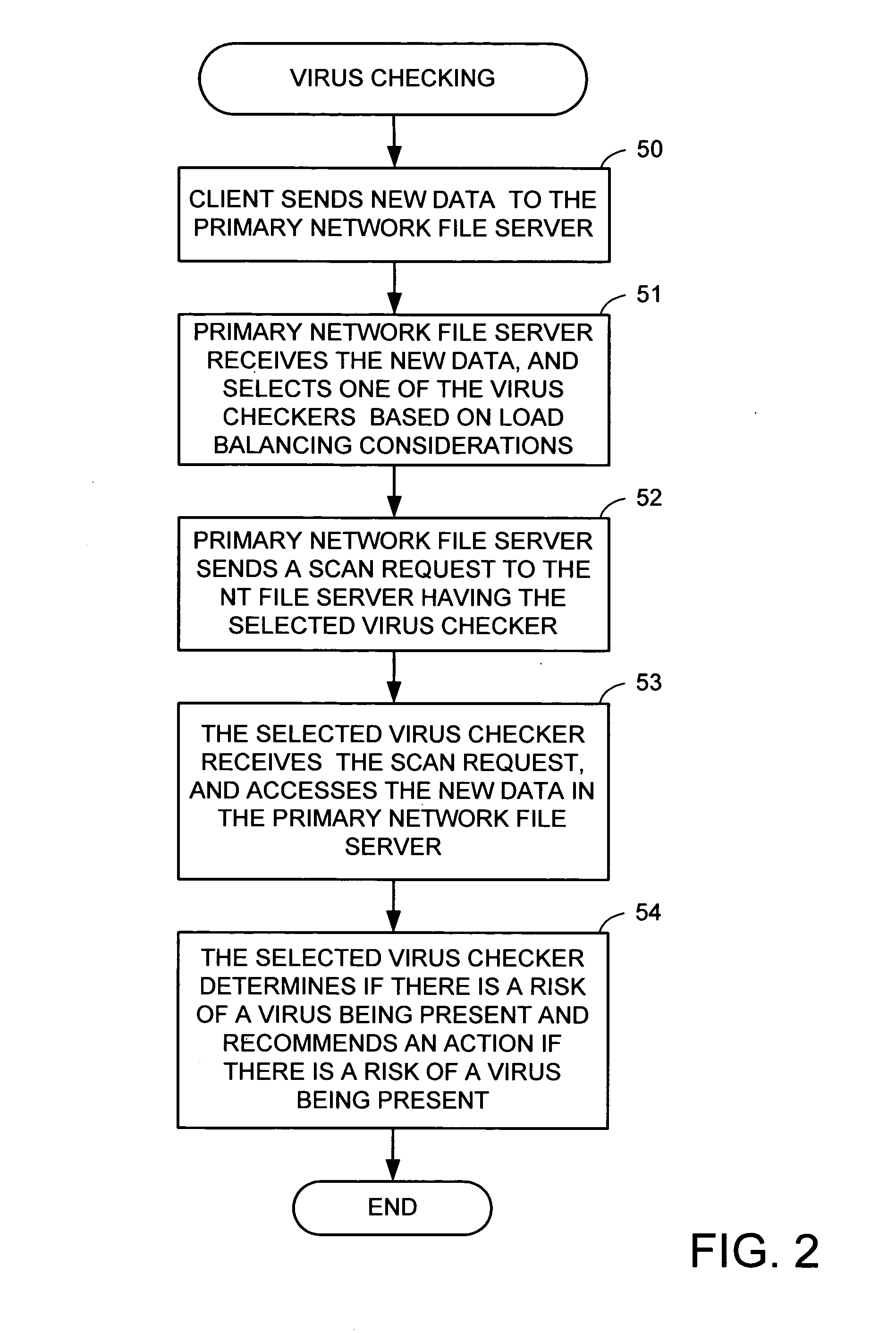
Using a virus checker in one file server to check for viruses in another file server
ActiveUS20020129277A1Memory loss protectionUnauthorized memory use protectionAnti virusRandom access memory
When a network client accesses a file in a network file server, the network file server invokes a conventional virus checker program in an NT file server to transfer pertinent file data from the network file server to random access memory in the NT file server to perform an anti-virus scan. Users may interact with the virus checker program in the usual fashion, to select file types to check, and actions to perform when a virus is detected. This method eliminates the need for porting the virus checker program to the network file server, and avoids maintenance problems when the virus checker program is updated or upgraded. Moreover, a kernel mode driver in the NT file server may provide an indirect interface to the virus checker program for initiating an anti-virus scan. Therefore, the driver supports a wide variety of virus checker programs and ensures continued operation when the virus checker program is upgraded.
Owner:EMC IP HLDG CO LLC
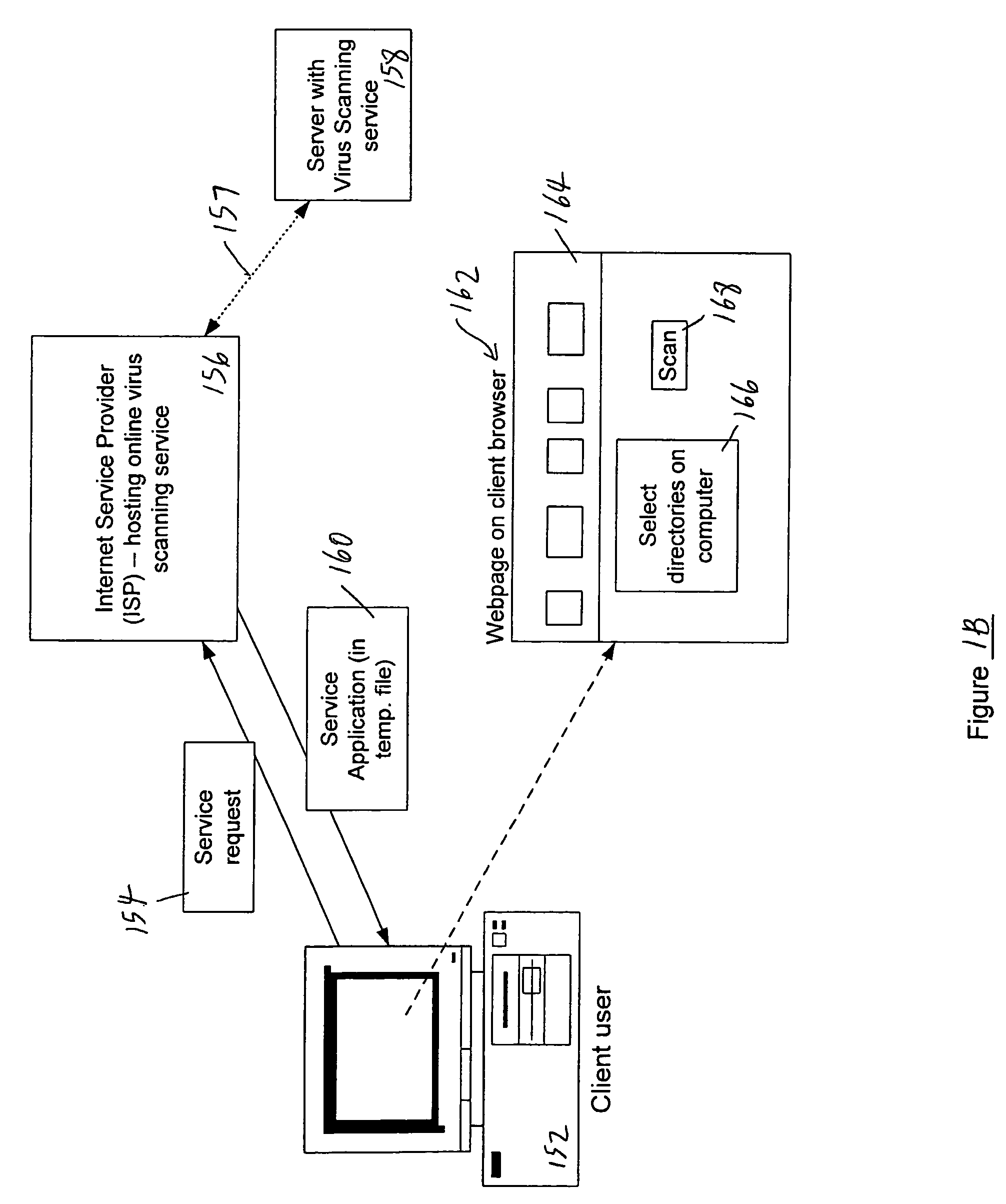
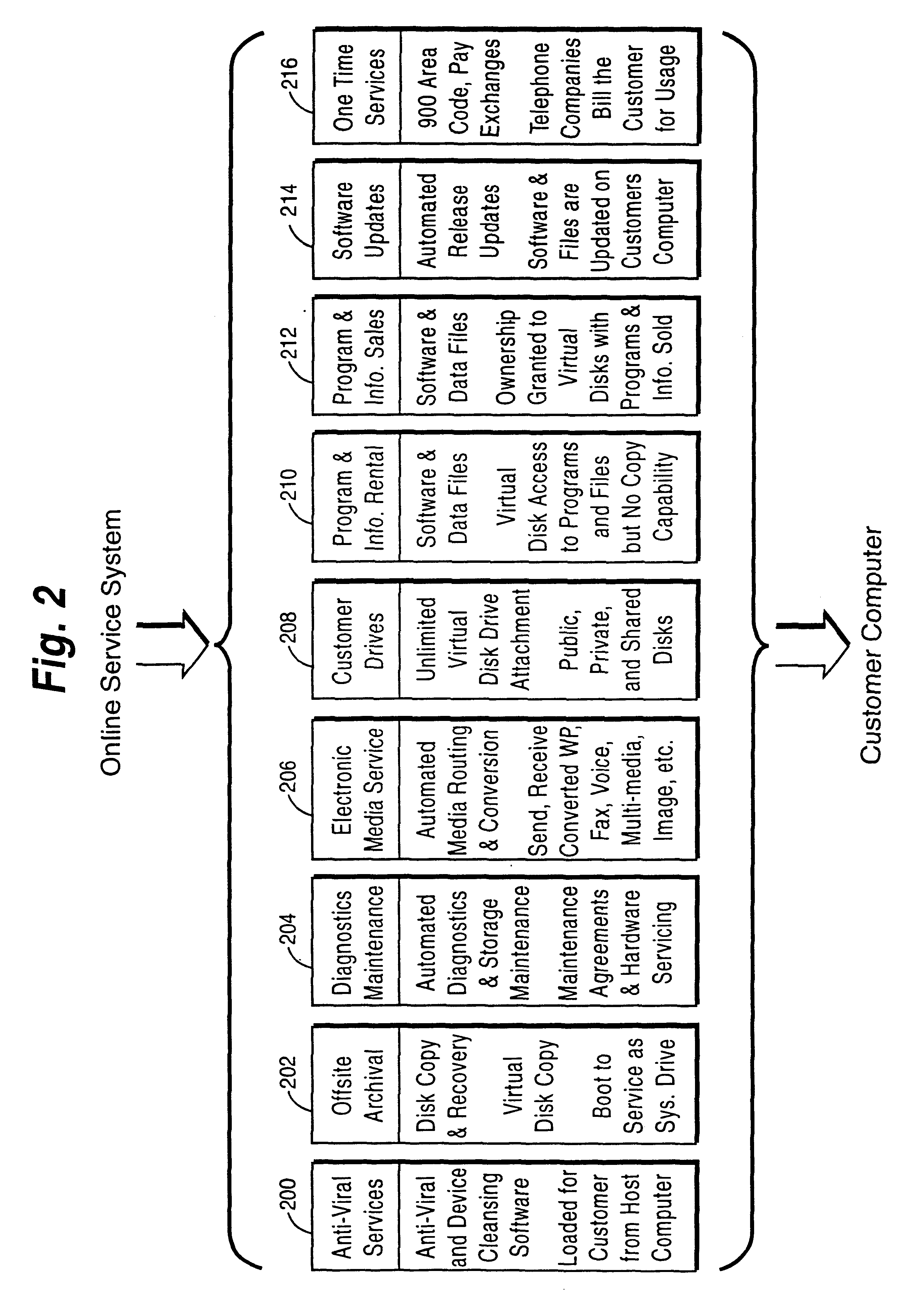
Online computer services including help desk, anti-virus and/or application service features
InactiveUS6327579B1Guaranteed uptimeRelieving userFinanceResource allocationAnti virusTelecommunications link
A customer computer connects to an online service provider by phone, Internet, or other telecommunications link. The link gives the customer access to additional processing and storage resources such as virtual storage, processing power and / or additional software or data through interaction between the customer computer and an online service provider computer over the link. The additional resources made available to the customer computer enhance the customers' local needs through access to virtual storage, a more powerful processor of similar type for program execution, and / or online support services such as software rental, software sales, release update services, anti-viral services, data backup and recovery services, diagnostic services and / or repair services.
Owner:EMC CORP +6
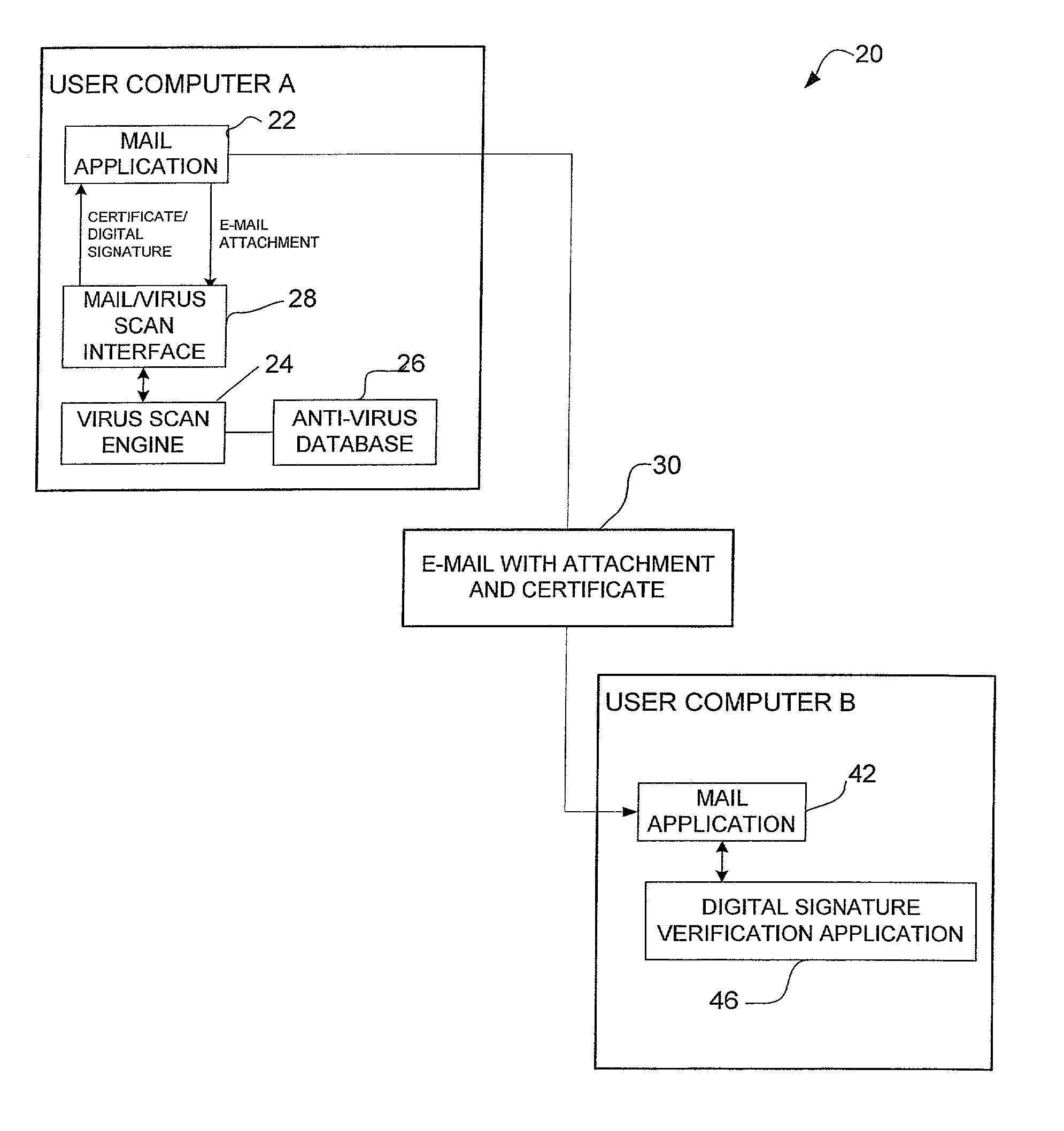
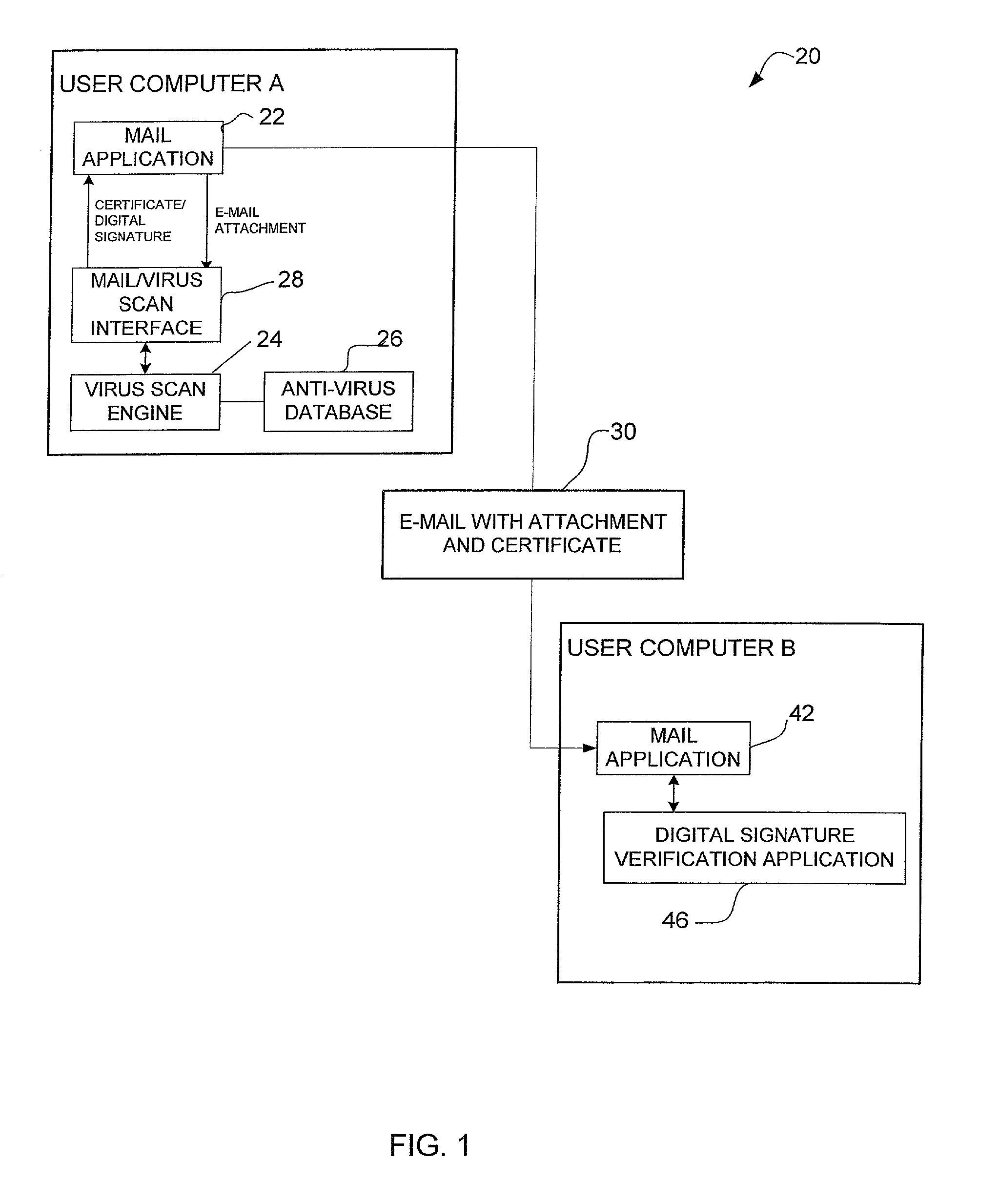
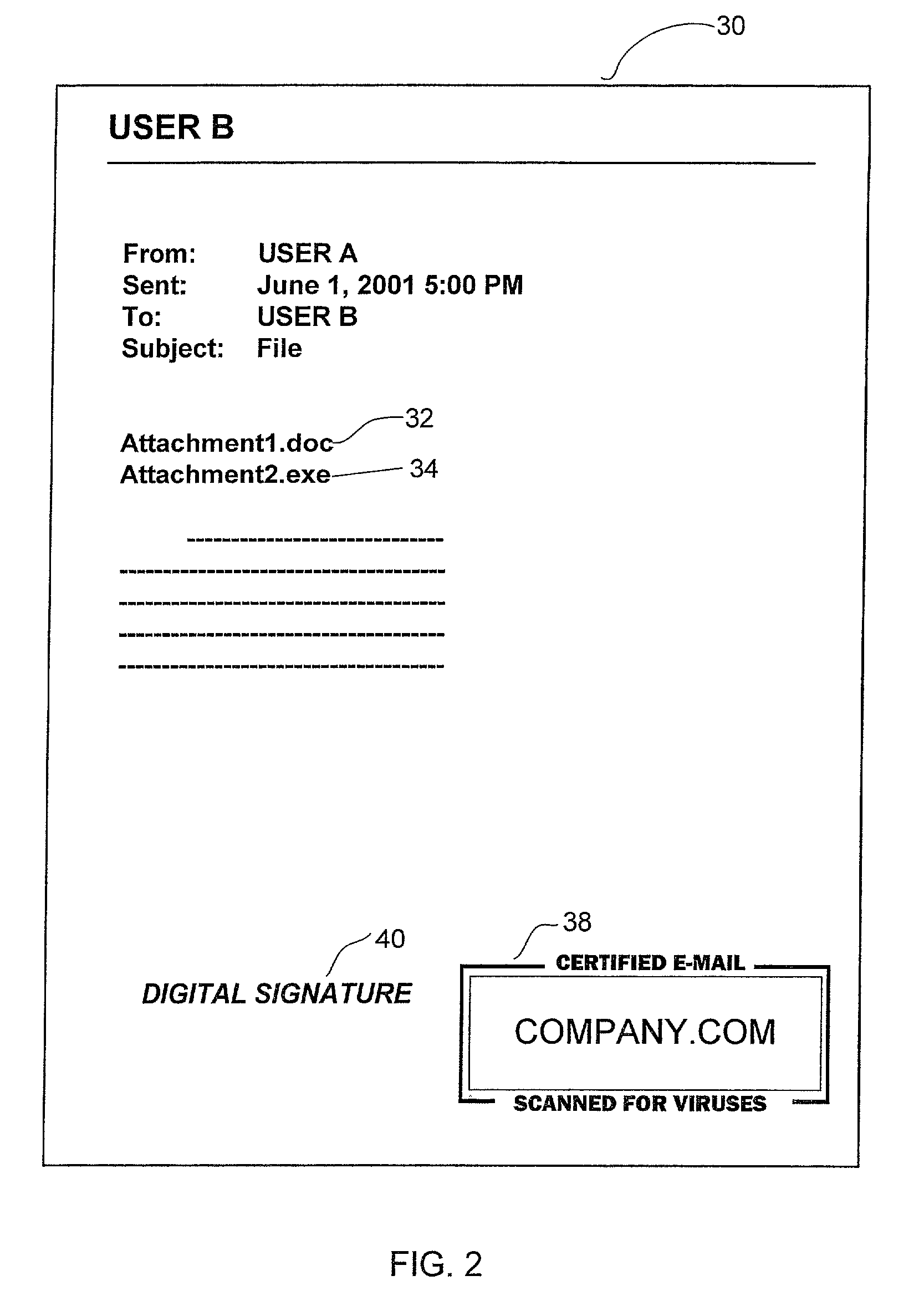
System and method for certifying that data received over a computer network has been checked for viruses
A method for certifying that data sent from a computer is free from viruses identified by an anti-virus database. The method includes scanning data for viruses before it is sent from the computer and attaching a certificate identifying the data as being scanned for viruses if no viruses are found during scanning. The data is sent with the certificate from the computer to a recipient computer. A method for certifying that content available on a host site is free from viruses is also disclosed.
Owner:MCAFEE LLC
System and method for network virus protection
A system and method for virus protection of computers on a local area network (LAN) is disclosed. The LAN's anti-virus policy is programmed into the firewall, or other Internet access module, which applies that policy to the client computers on the LAN. This policy might include the frequency with which the anti-virus software is updated and the number of versions that the software is permitted to be out of date. Any client computer not meeting the policy is not permitted to access the Internet. The firewall can also update out of date client computers to make them compliant with the policy.
Owner:QUEST SOFTWARE INC
Method and system for downloading updates
ActiveUS20060130037A1Minimizing download timeReduce the amount requiredSoftware maintainance/managementMultiple digital computer combinationsAnti virusSoftware update
Embodiments of the present invention provide the ability for a software provider to distribute software updates to several different recipients utilizing a peer-to-peer environment. The invention described herein may be used to update any type of software, including, but not limited to, operating software, programming software, anti-virus software, database software, etc. The use of a peer-to-peer environment with added security provides the ability to minimize download time for each peer and also reduce the amount of egress bandwidth that must be provided by the software provider to enable recipients (peers) to obtain the update.
Owner:MICROSOFT TECH LICENSING LLC
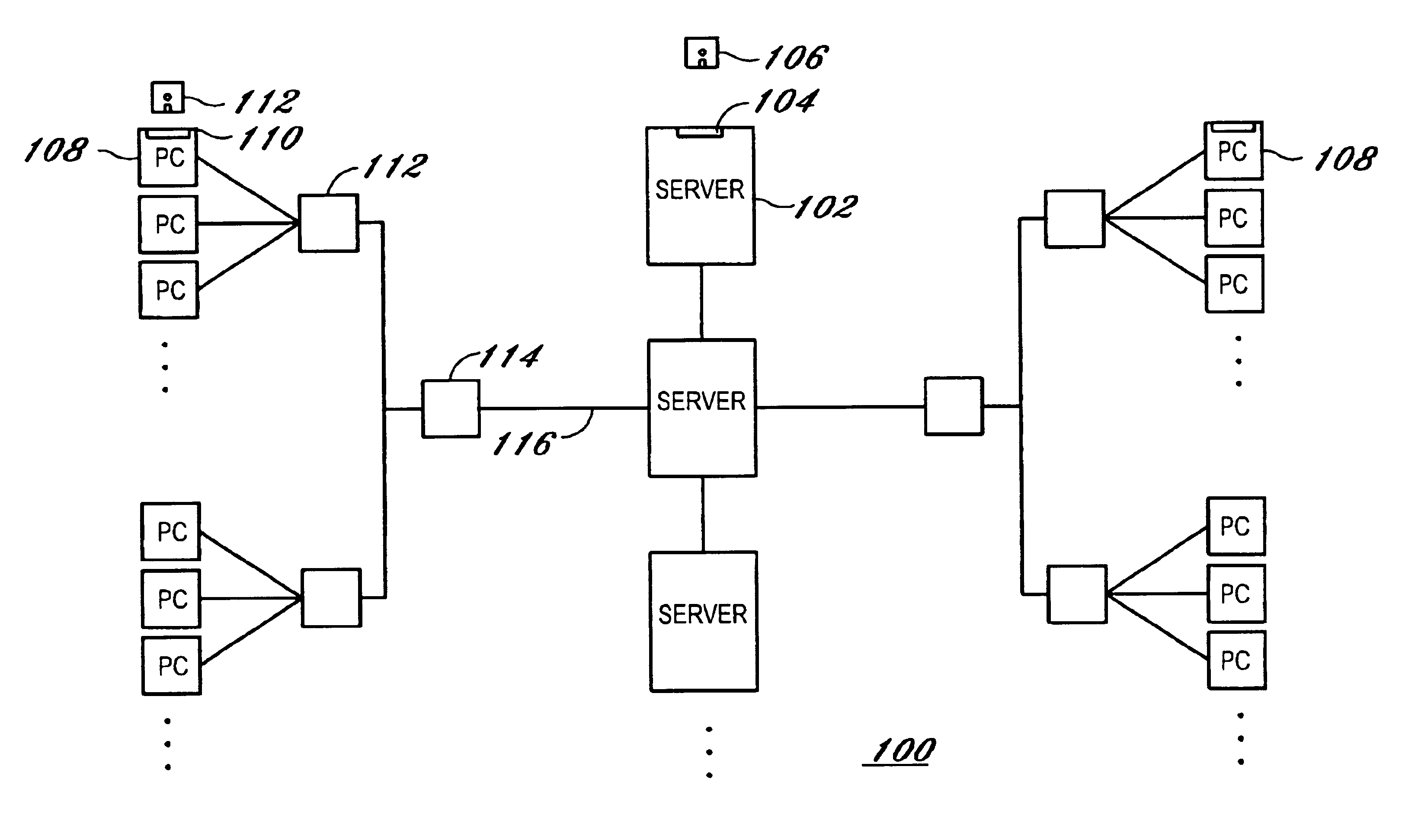
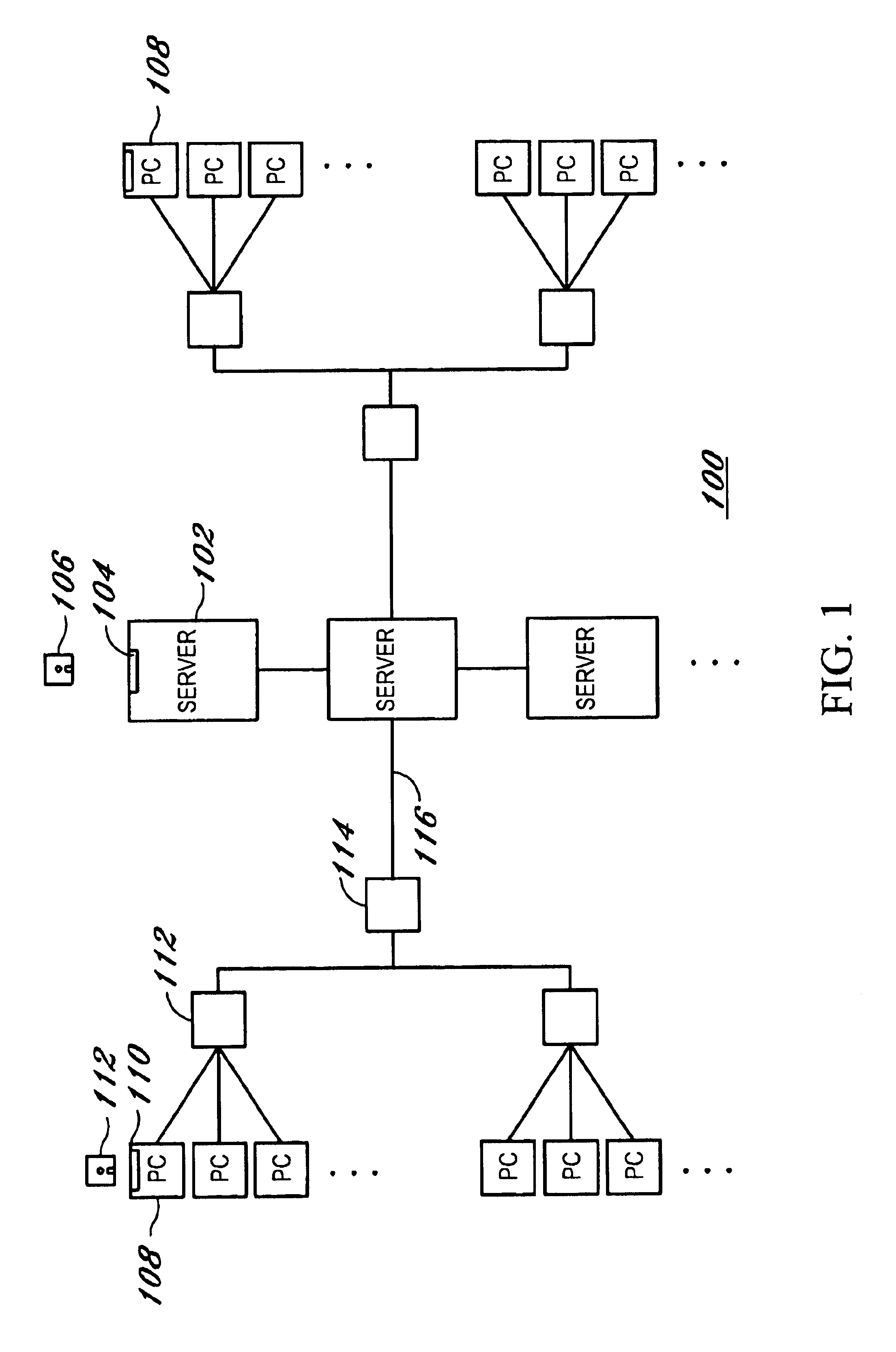
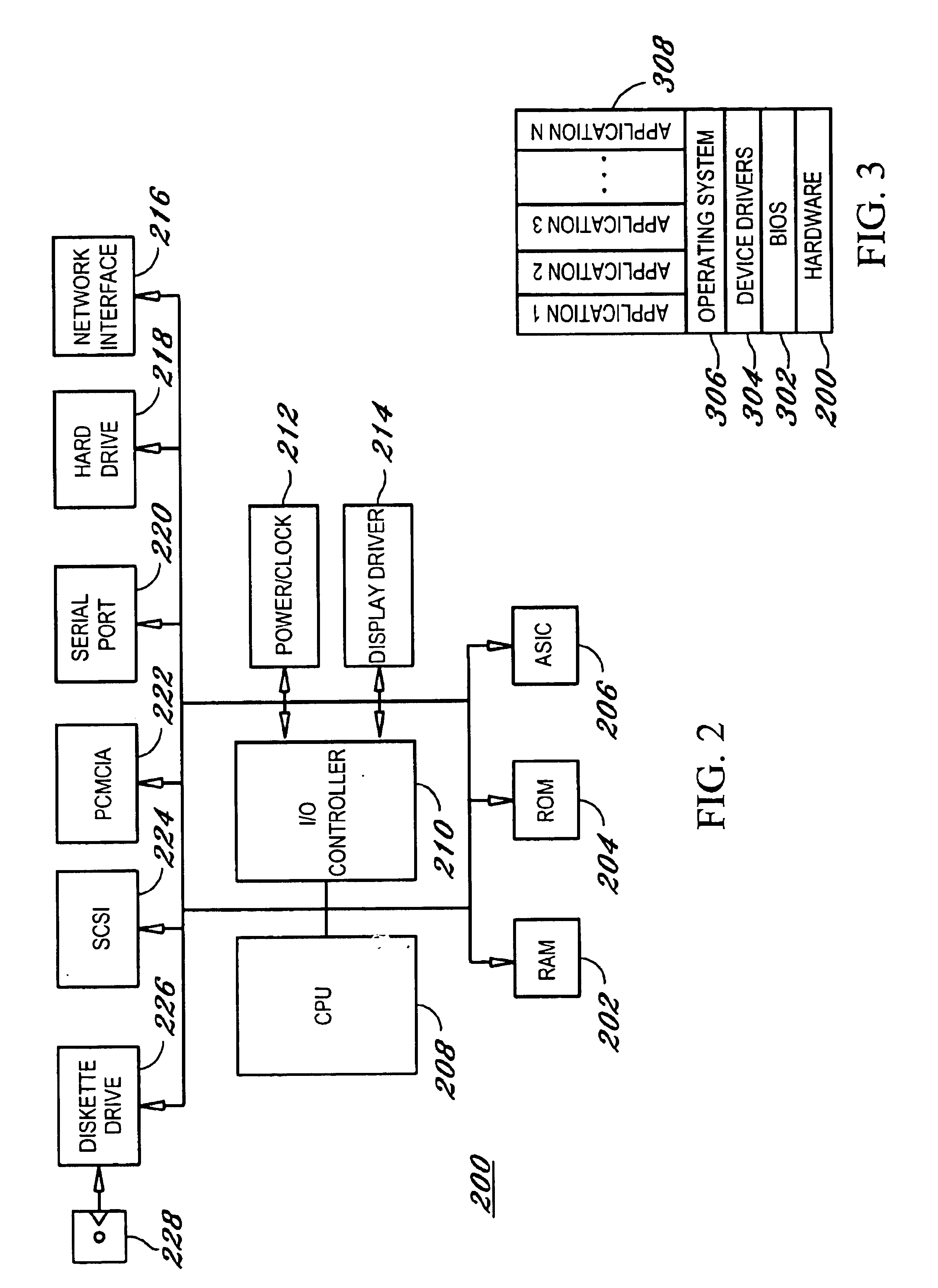
Method and apparatus to manage network client logon scripts using a graphical management and administration tool
A GUI (Graphical User Interface) Manager is used by a network administrator to fill-in predefined templates. The administrator does not need to compile, debug or write a single line of scripting code. The GUI manager has a “select the box” and “point and click” and “fill-in the blank” approach for selecting computer settings. The predefined configuration and / or template(s) are used by a logon script program on a client system to manage the configuration of resources on at least one client. There are three levels of resources that can be managed. The first type of resource is an operating system. The second type of resource is an application resource. And the third type of resource is to redirect a resource on the client to a resource on a network such as a drive letter mapping. Resources include configurations from the group of configuration settings consisting of drive mappings, shell folders, printer deployment, proxy server access, application paths, service packs, anti-virus updates, policies and automatic mail profile creation. In another embodiment, validation logic is used on the clients' system during the execution of an application program that takes the template and applies the defined configuration settings in the template to the clients' system so as to automatically configure at least one configuration setting for a user if the combination of one or more predefined conditions for a selected group, a selected operating system and a selected connection method are met. In still another embodiment, an interpretive engine is used on the client's system to permit the administration of client resources with a template while also allowing network administrators to build their own custom logon scripts.
Owner:QUEST SOFTWARE INC
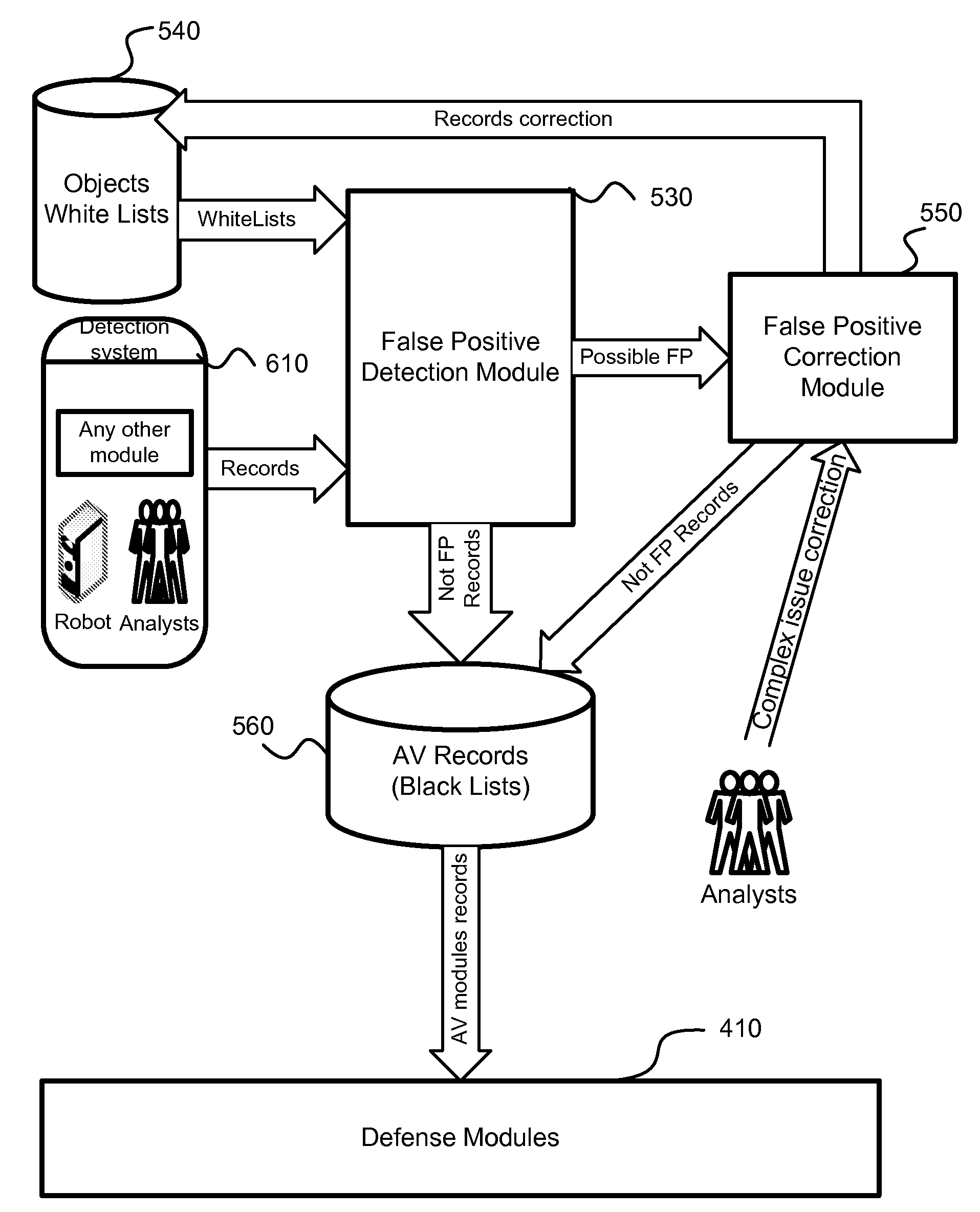
Detection and minimization of false positives in anti-malware processing
ActiveUS7640589B1Eliminate disadvantagesMemory loss protectionError detection/correctionAnti virusMalware
A system, method and computer program product for detection of false positives occurring during execution of anti-malware applications. The detection and correction of the false positives is implemented in two phases, before creation of new anti-virus databases (i.e., malware black lists) or before creation of new white lists, and after the anti-virus databases or new white lists are created and new false positives are detected. The system calculates a probability of detection of a certain potential malware object. Based on this probability, the system decides to either correct a white list (i.e., a collection of known clean objects) or update a black list (i.e., a collection of known malware objects). A process is separated into a several steps: creation and update (or correction) of white lists; creation and update of black lists; detection of collisions between these lists and correction of black lists or white lists based on the detected collisions.
Owner:AO KASPERSKY LAB
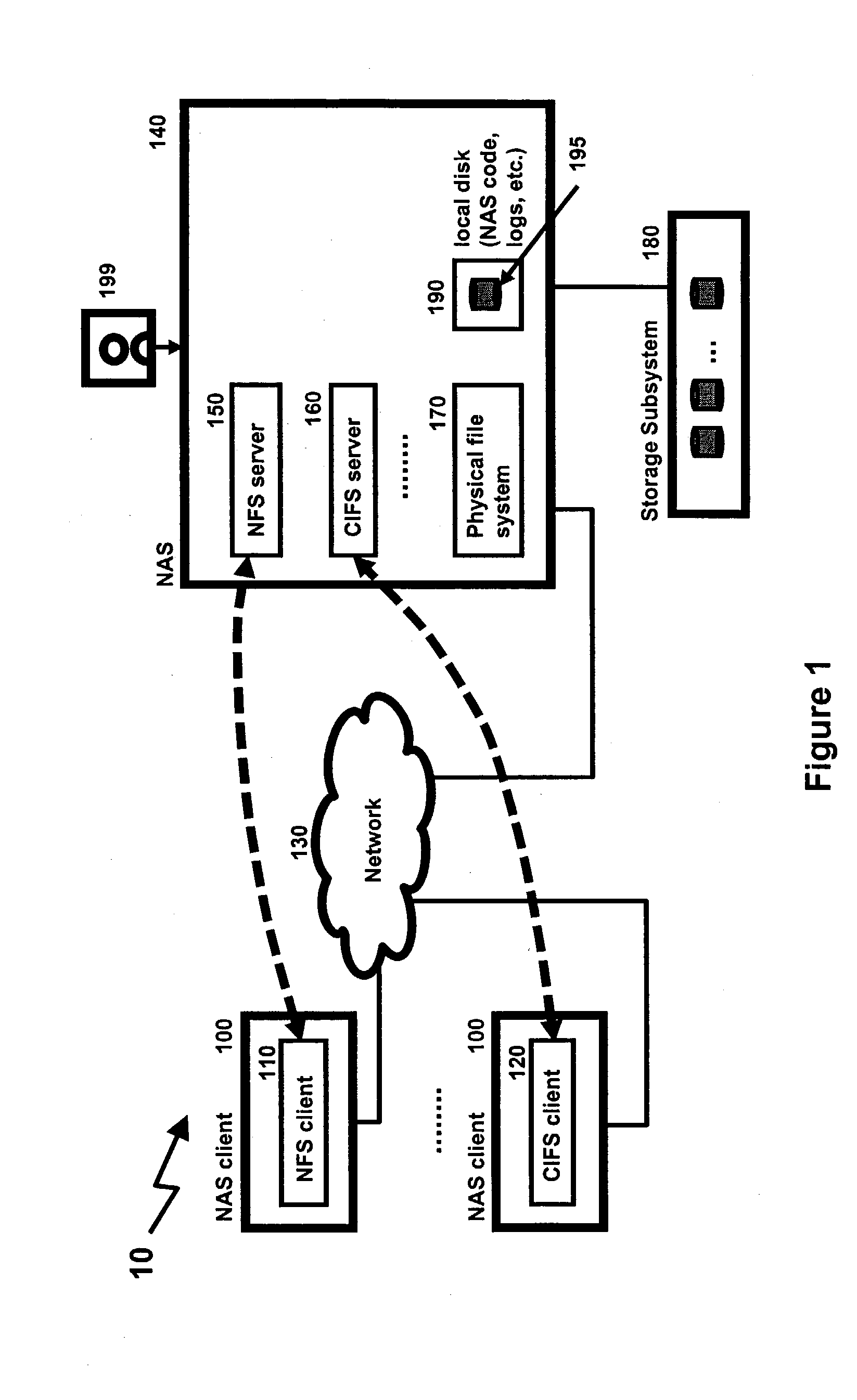
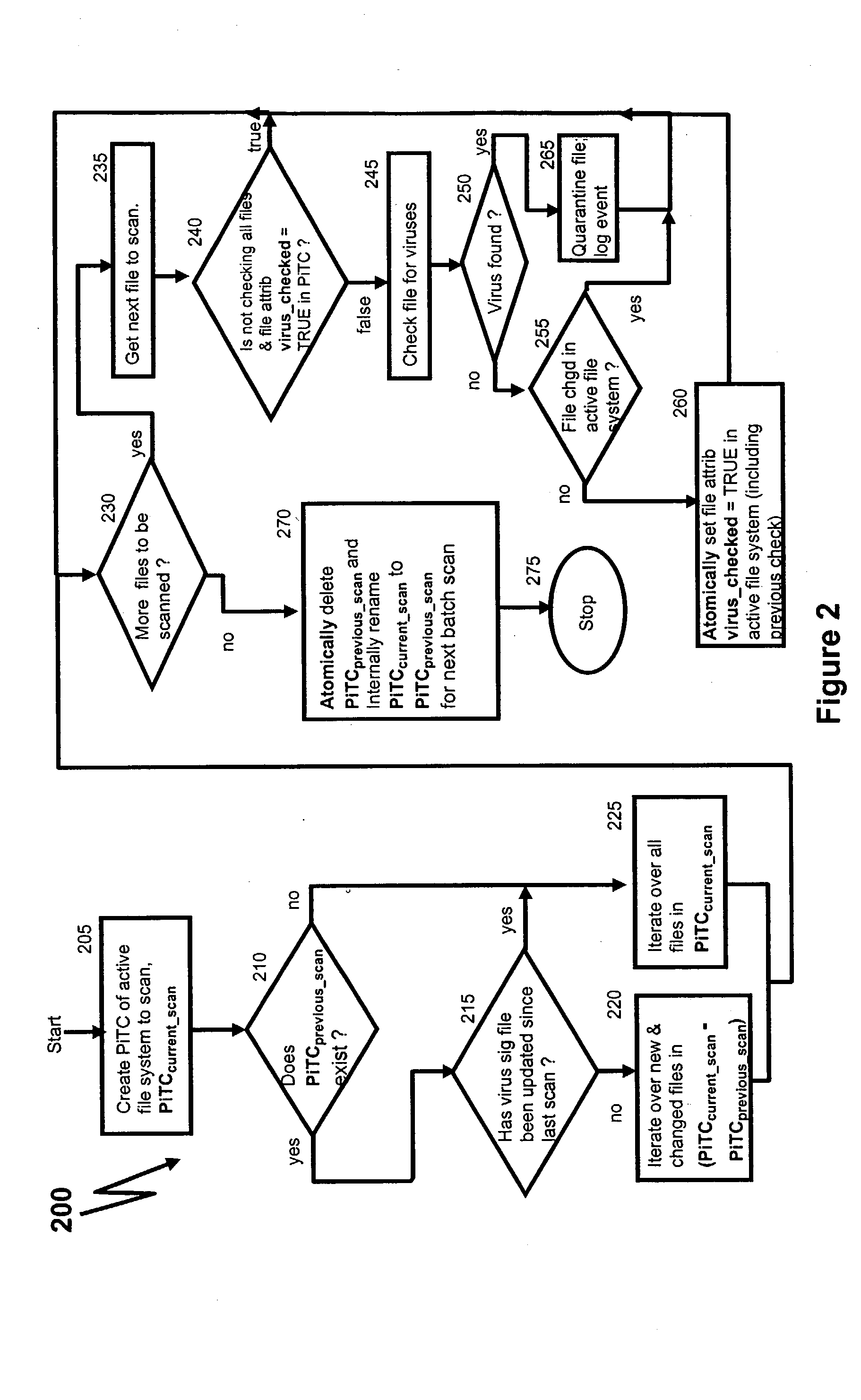
Running anti-virus software on a network attached storage device
InactiveUS20040158730A1Memory loss protectionUnauthorized memory use protectionAnti virusFile system
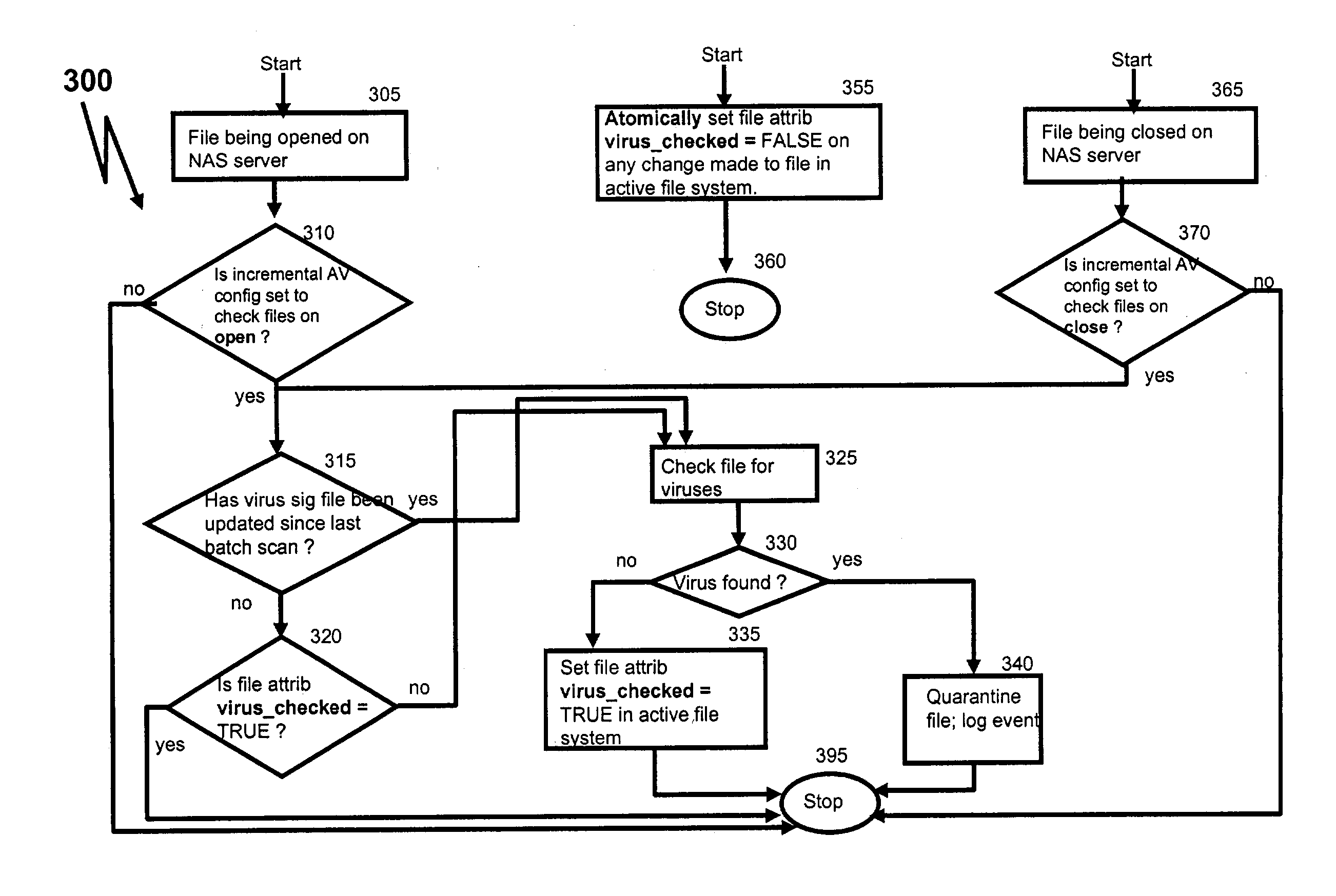
There is provided a method for running anti-virus software for a file system that is accessible by a client through a server. The method includes (a) creating a current point-in-time copy (PiTC) of the file system, (b) determining whether a file in the file system is changed, based on a difference between the current PiTC and an earlier PiTC of the file system, and (c) determining whether the file is to be examined by the anti-virus software, based on whether the file is changed.
Owner:IBM CORP
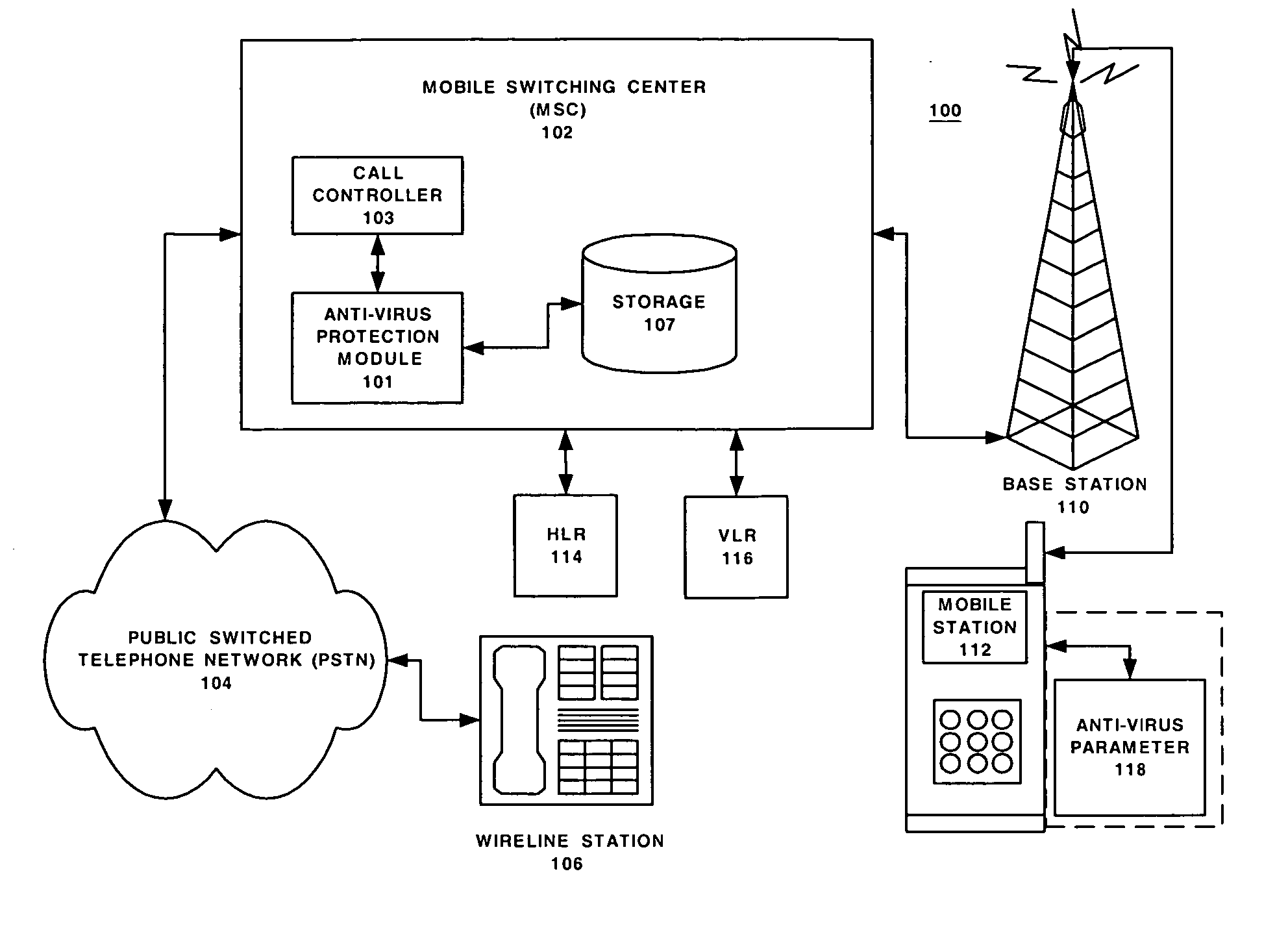
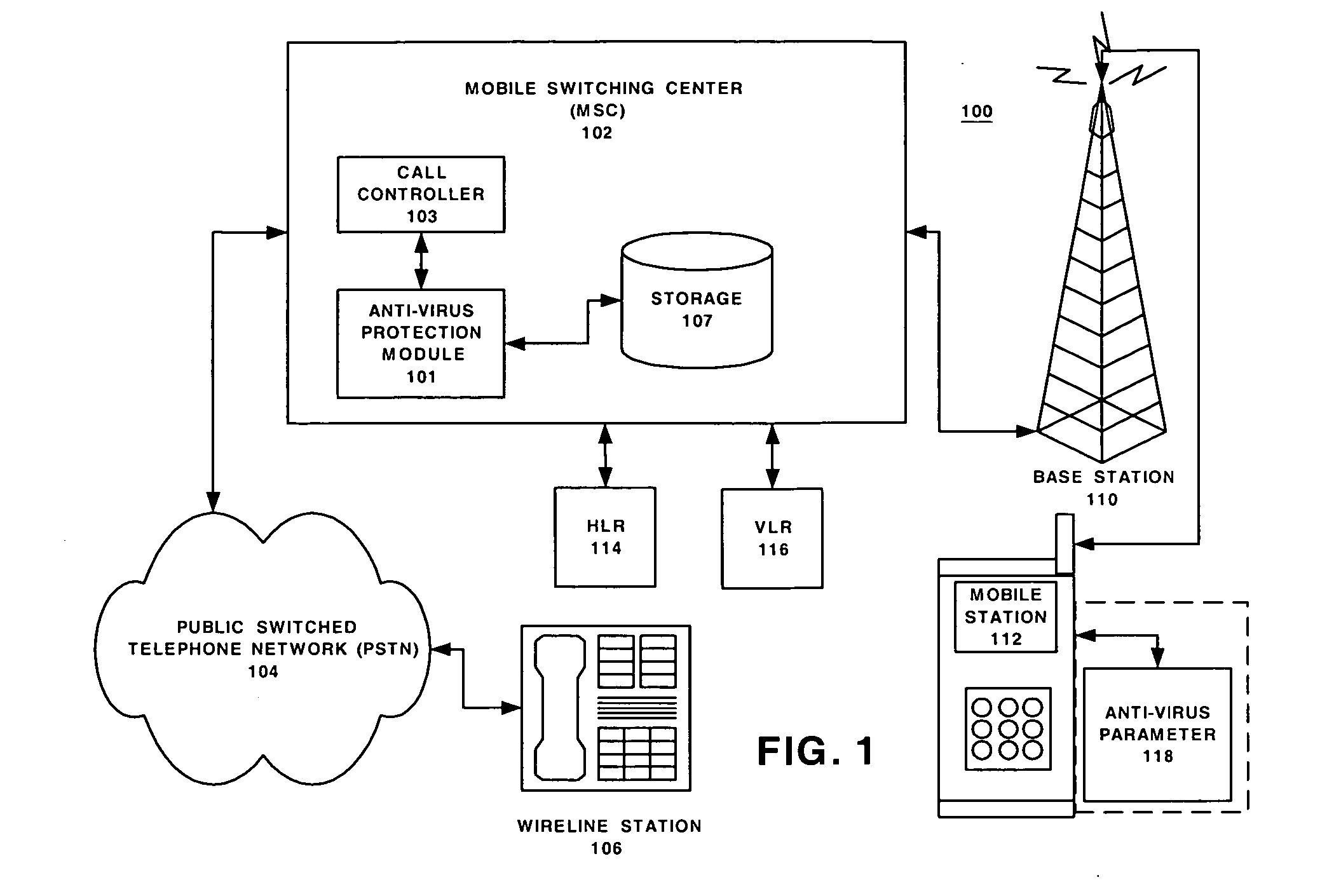
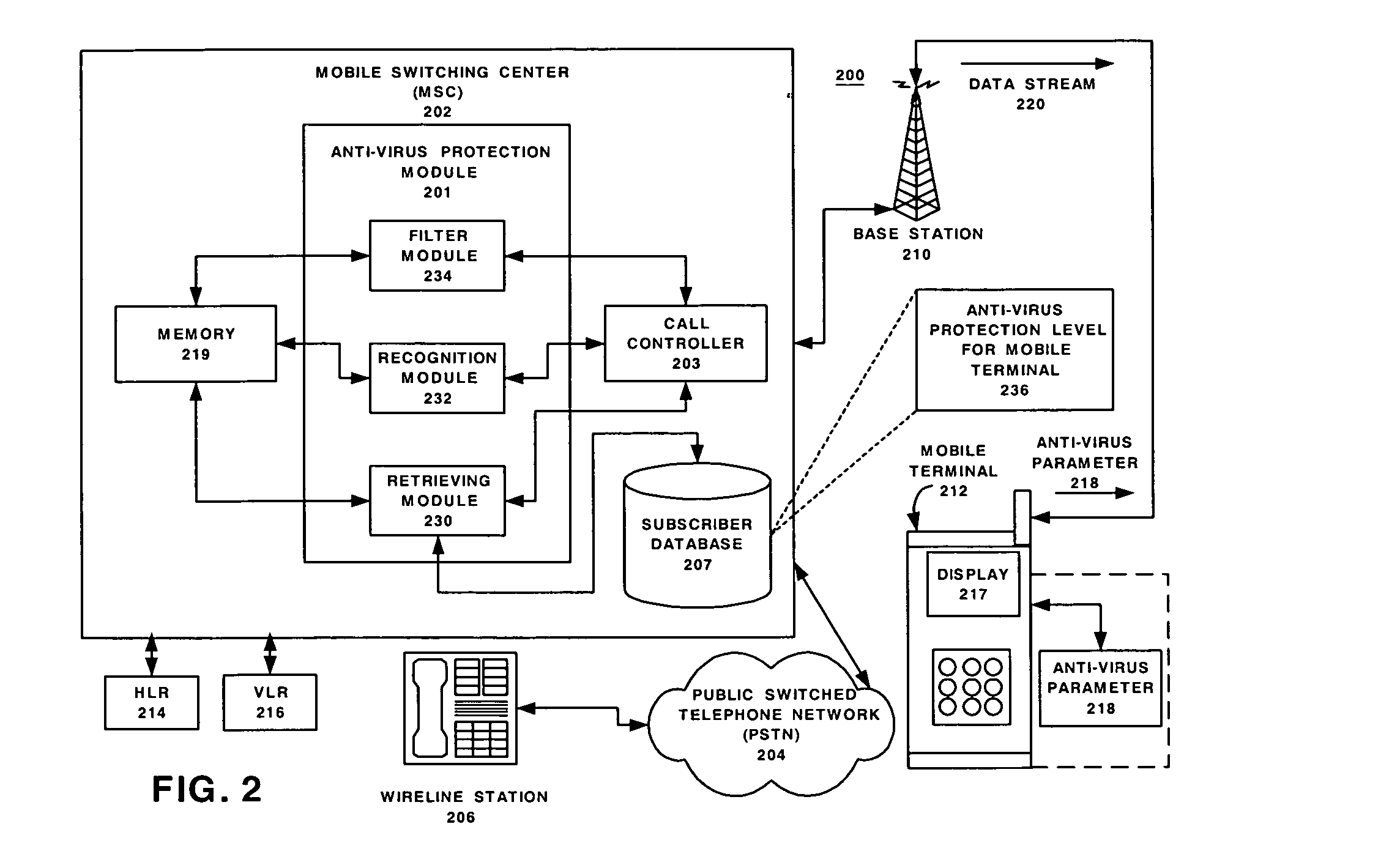
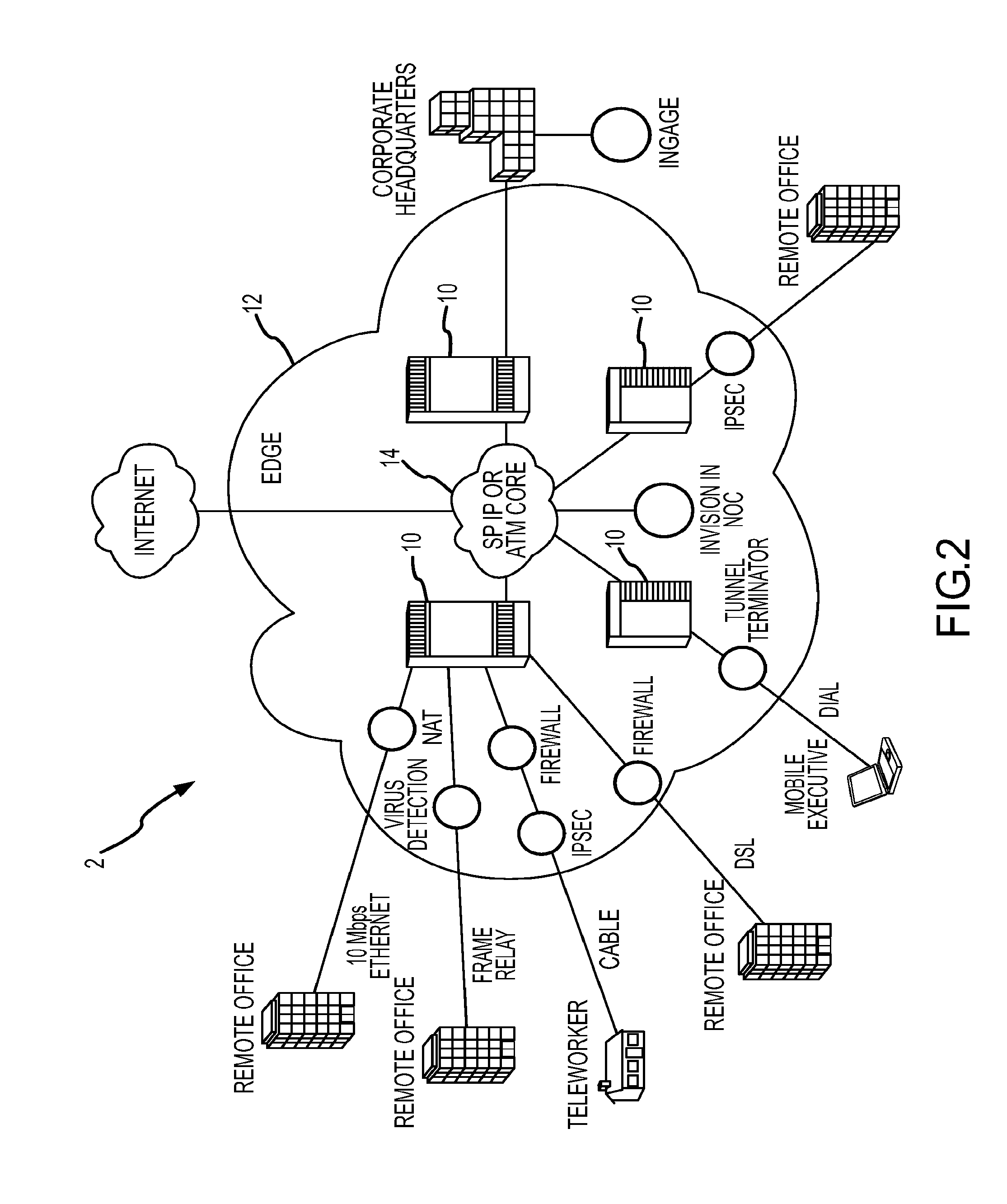
Network support for mobile handset anti-virus protection
InactiveUS20050138395A1Easy to understandMemory loss protectionUnauthorised/fraudulent call preventionAnti virusData stream
Embodiments of the method and system provide network support for automatic anti-virus protection by a telecommunication network for mobile terminals. The method may have the steps of: storing in the telecommunication network at least one anti-virus protection level for at least one mobile terminal; initiating, by the telecommunication network, a call setup for a call associated with the mobile terminal, the call having a data stream; using, by the communication network, the at least one anti-virus protection level to recognize a virus in the data stream intended for the mobile handset; and filtering, by the network, the recognized virus from the data stream before the data stream arrives at the mobile terminal. The system implements the method.
Owner:ALCATEL-LUCENT USA INC +1
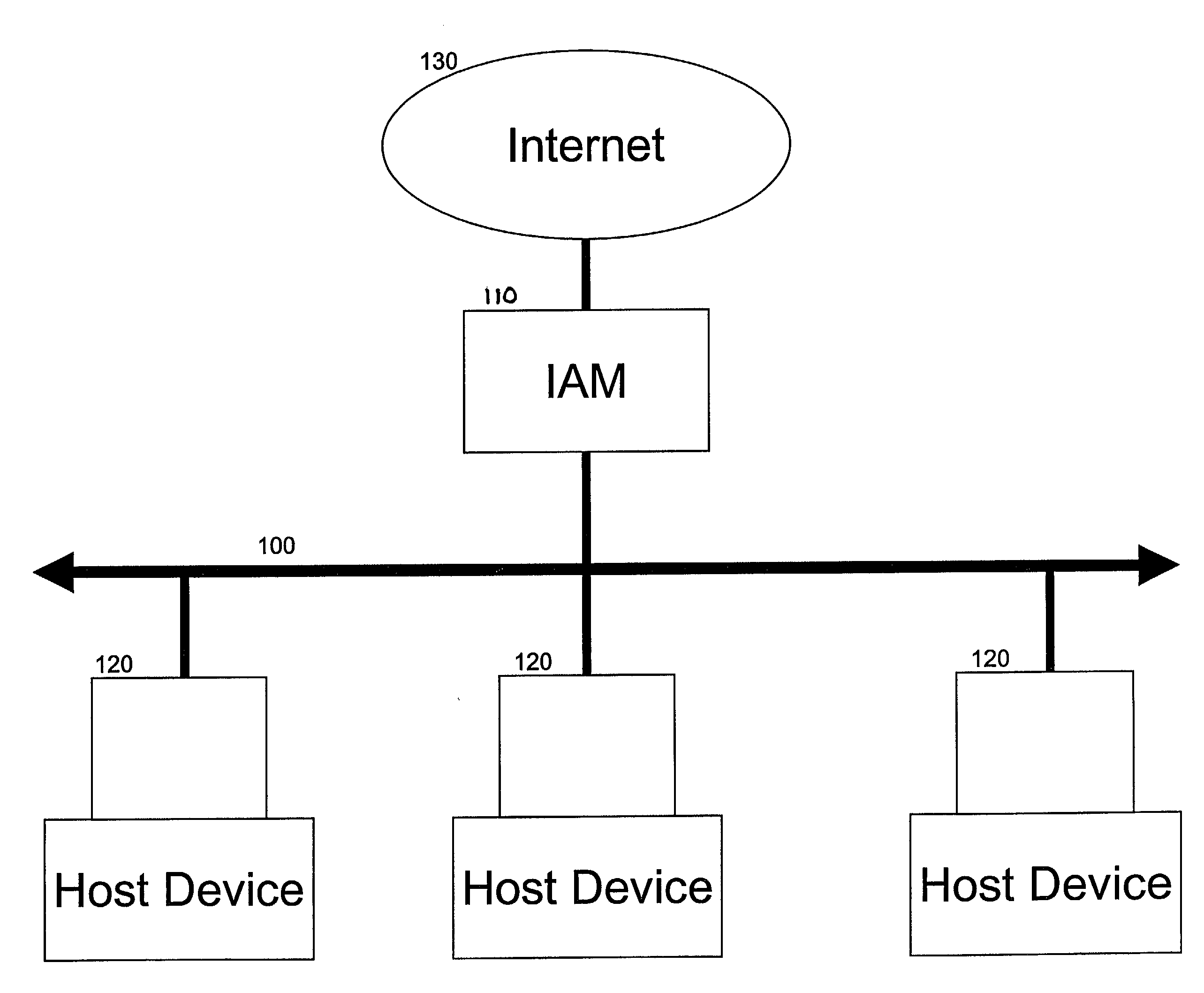
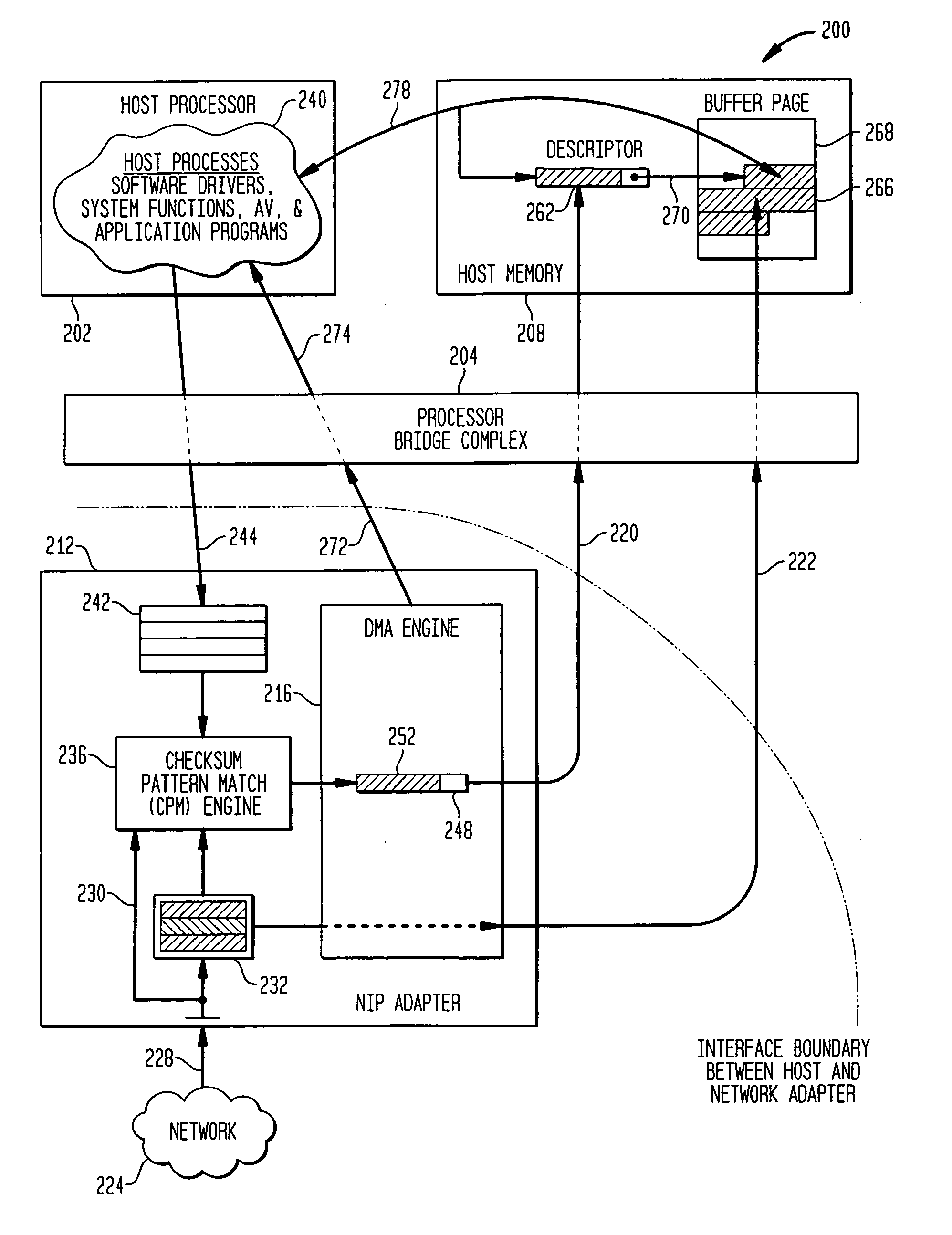
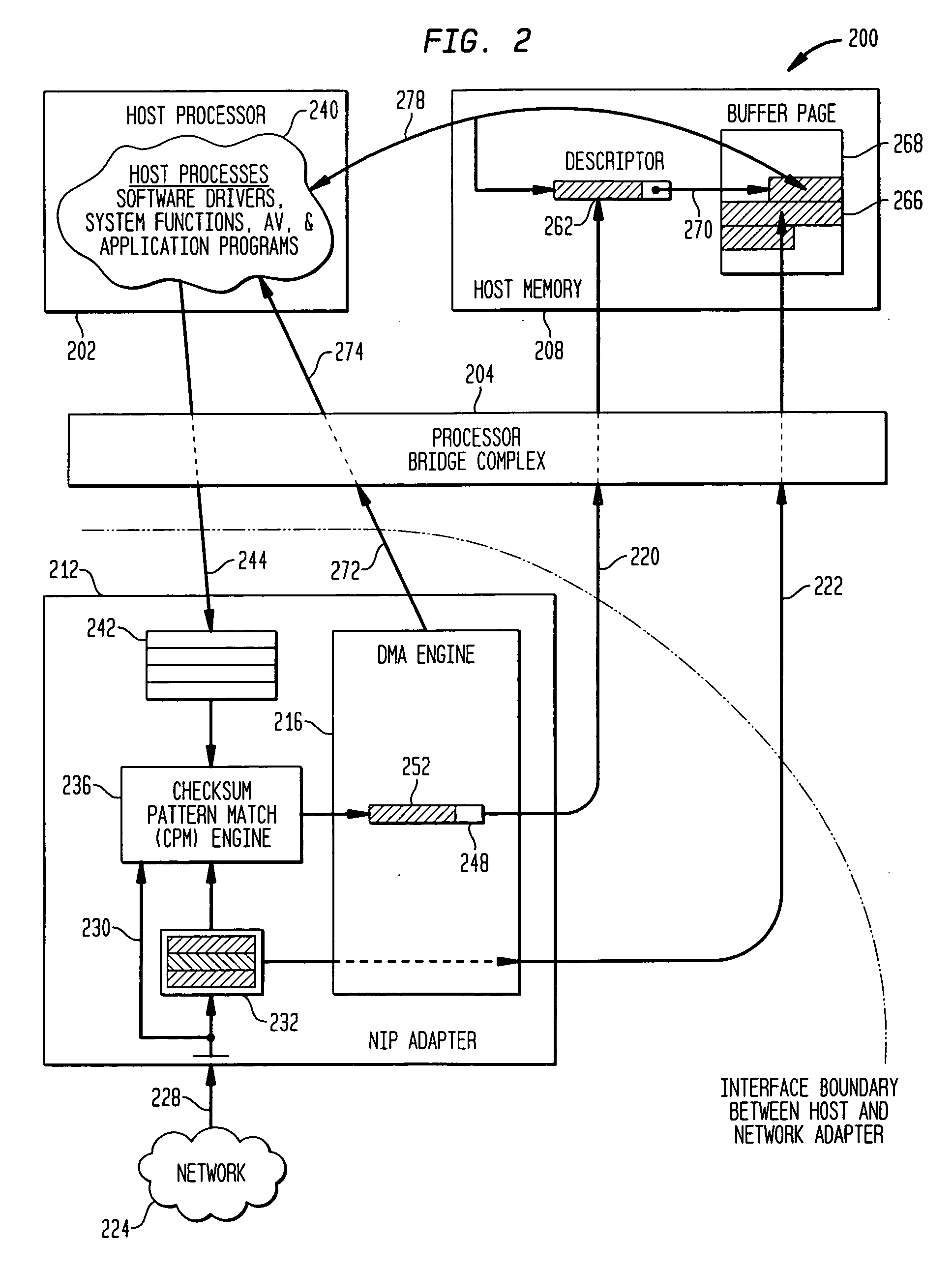
Methods and apparatus for interface adapter integrated virus protection
A virus detection mechanism is described in which virus detection is provided by a network integrated protection (NIP) adapter. The NIP adapter checks incoming media data prior to it being activated by a computing device. The NIP adapter operates independently of a host processor to receive information packets from a network. This attribute of independence allows NIP anti-virus (AV) techniques to be “always on” scanning incoming messages and data transfers. By being independent of but closely coupled to the host processor, complex detection techniques, such as using check summing or pattern matching, can be efficiently implemented on the NIP adapter without involving central processor resources and time consuming mass storage accesses. The NIP adapter may be further enhanced with a unique fading memory (FM) facility to allow for a flexible and economical implementation of polymorphic virus detection.
Owner:AVAGO TECH INT SALES PTE LTD
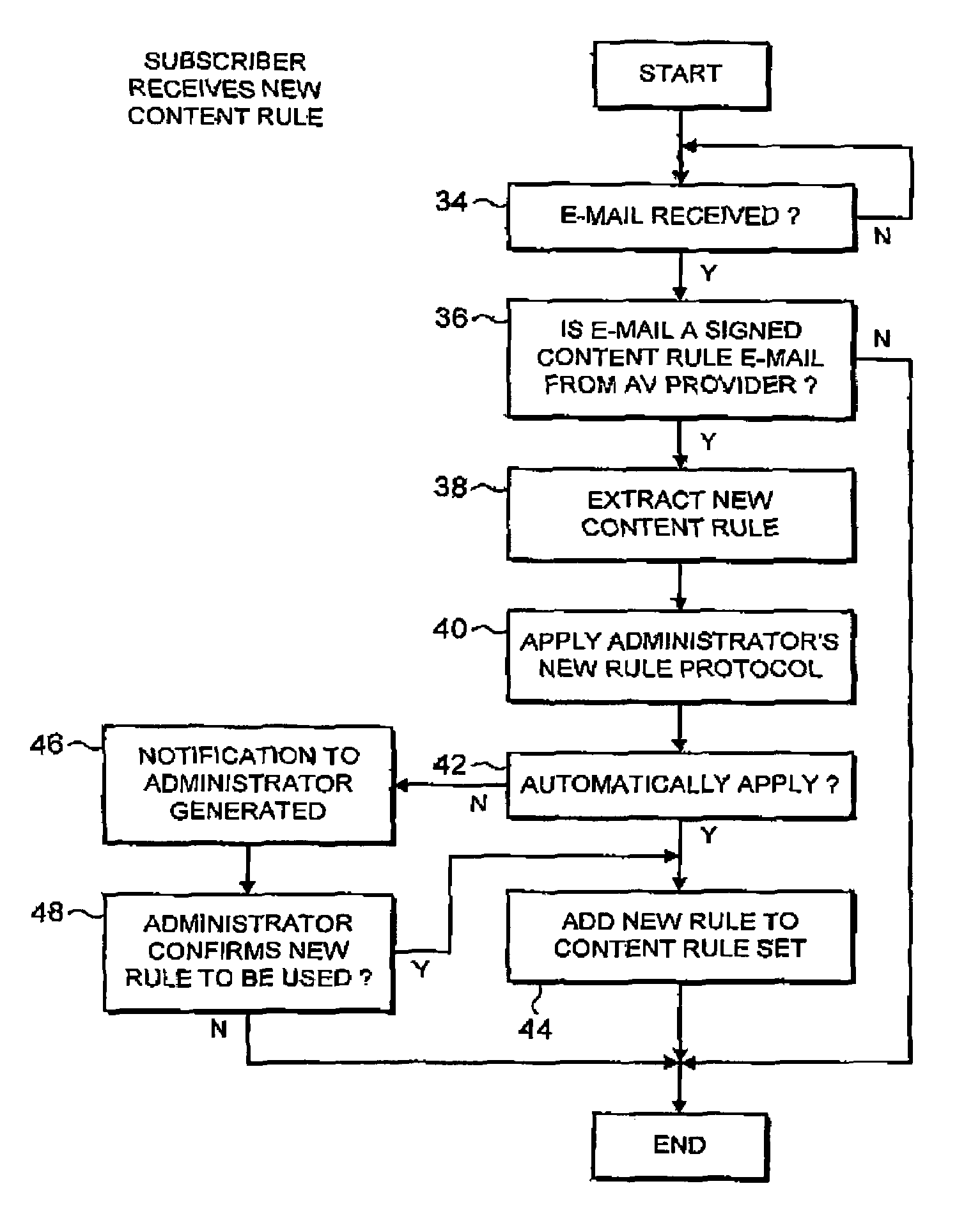
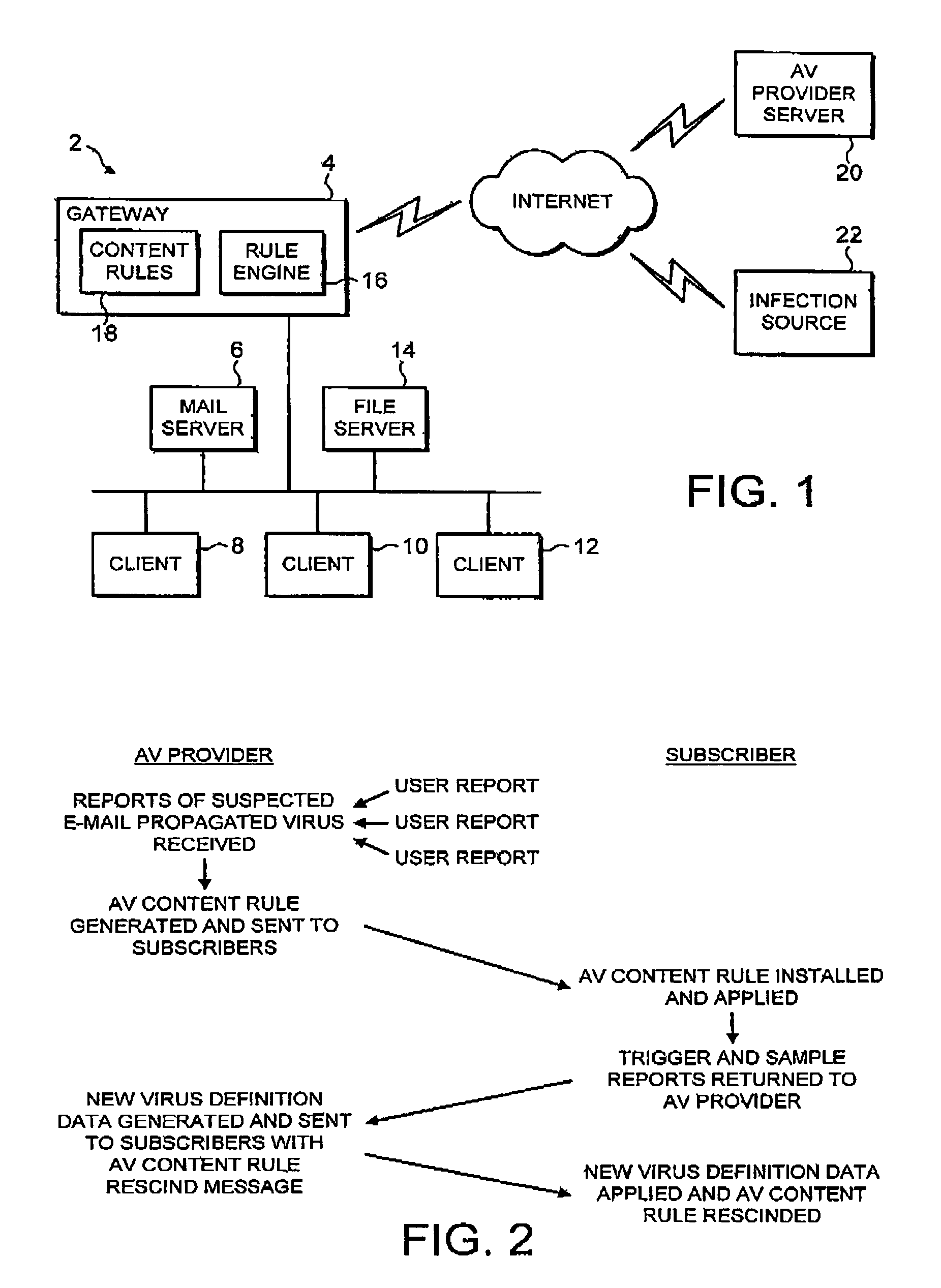
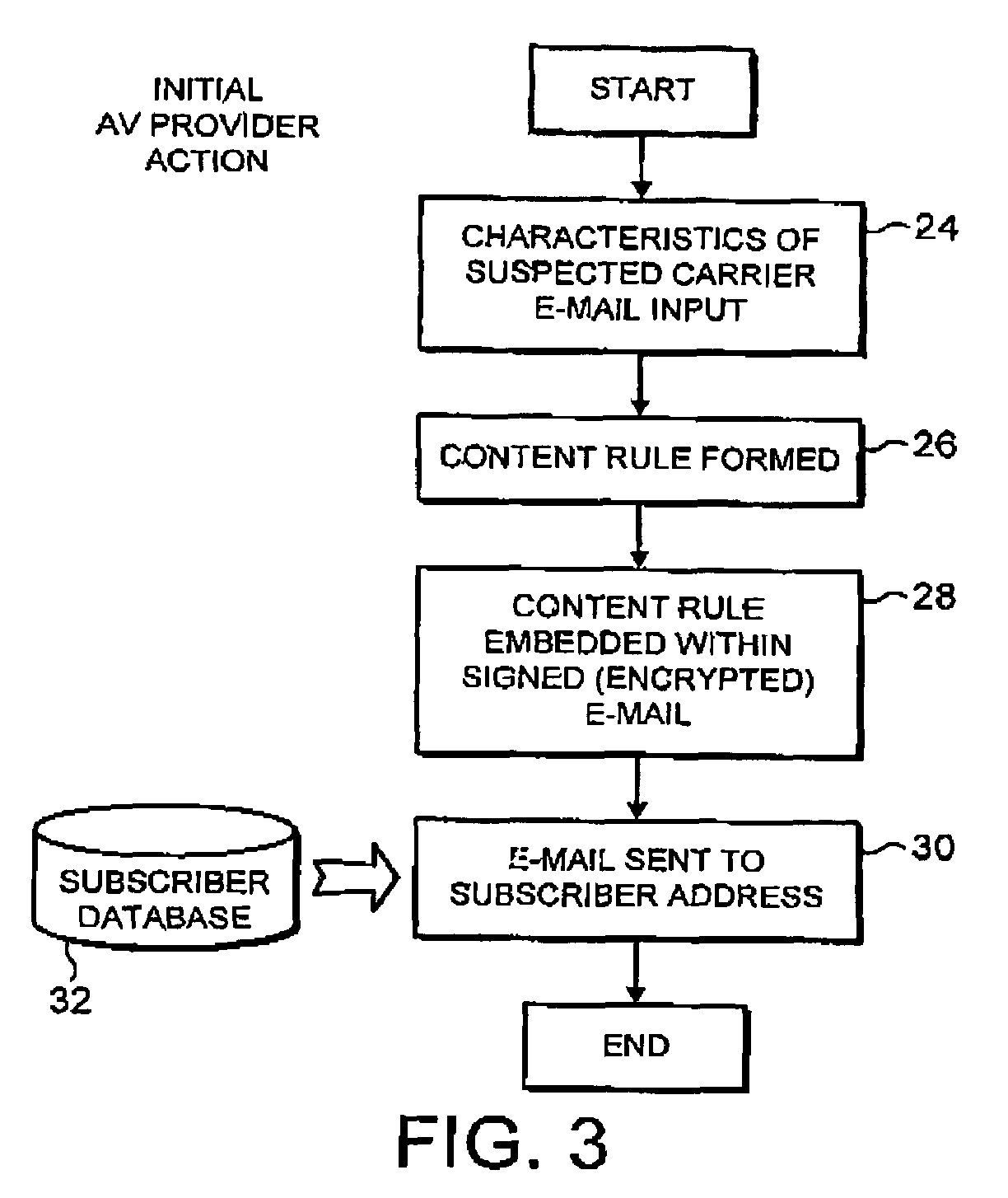
Detecting malware carried by an e-mail message
ActiveUS7237008B1Improve distributionRapidly and efficiently deployedUnauthorized memory use protectionHardware monitoringAnti virusMalware
An anti-virus system provider distributes an e-mail identifying content filtering rule seeking to identify e-mail messages suspected of containing an item of malware from a central source (20) to users (2). This distribution may be by an e-mail message itself which is appropriately signed and encrypted. At the user system (2), the received e-mail identifying content filtering rule is extracted from the e-mail message and added to the content filtering rules (18) being applied within that user system. In this way, malware which is distributed by e-mail may be identified by characteristics of its carrier e-mail rather than characteristics of the malware itself which not yet have been properly analyzed or the mechanisms for detecting such characteristics of the malware itself not yet put in place.
Owner:MCAFEE LLC
On-access and on-demand distributed virus scanning
On-demand and on-access anti-virus scan requests are distributed over a plurality of virus checkers for on-demand anti-virus scanning concurrent with on-access anti-virus scanning. For example, the on-demand requests are grouped into chunks of multiple requests, and the on-demand and on-access requests are combined in a queue. Scanning for requests from a prior chunk are completed before distributing the requests for a next chunk. To give priority to the on-access requests, the on-demand requests are not placed on the queue unless the number of requests on the queue is less than a threshold. An on-access request is placed on the queue in response to a request for user access to the file. On-demand requests are produced in response to a request from a system administrator for anti-virus scanning of the files in a specified file system.
Owner:EMC IP HLDG CO LLC
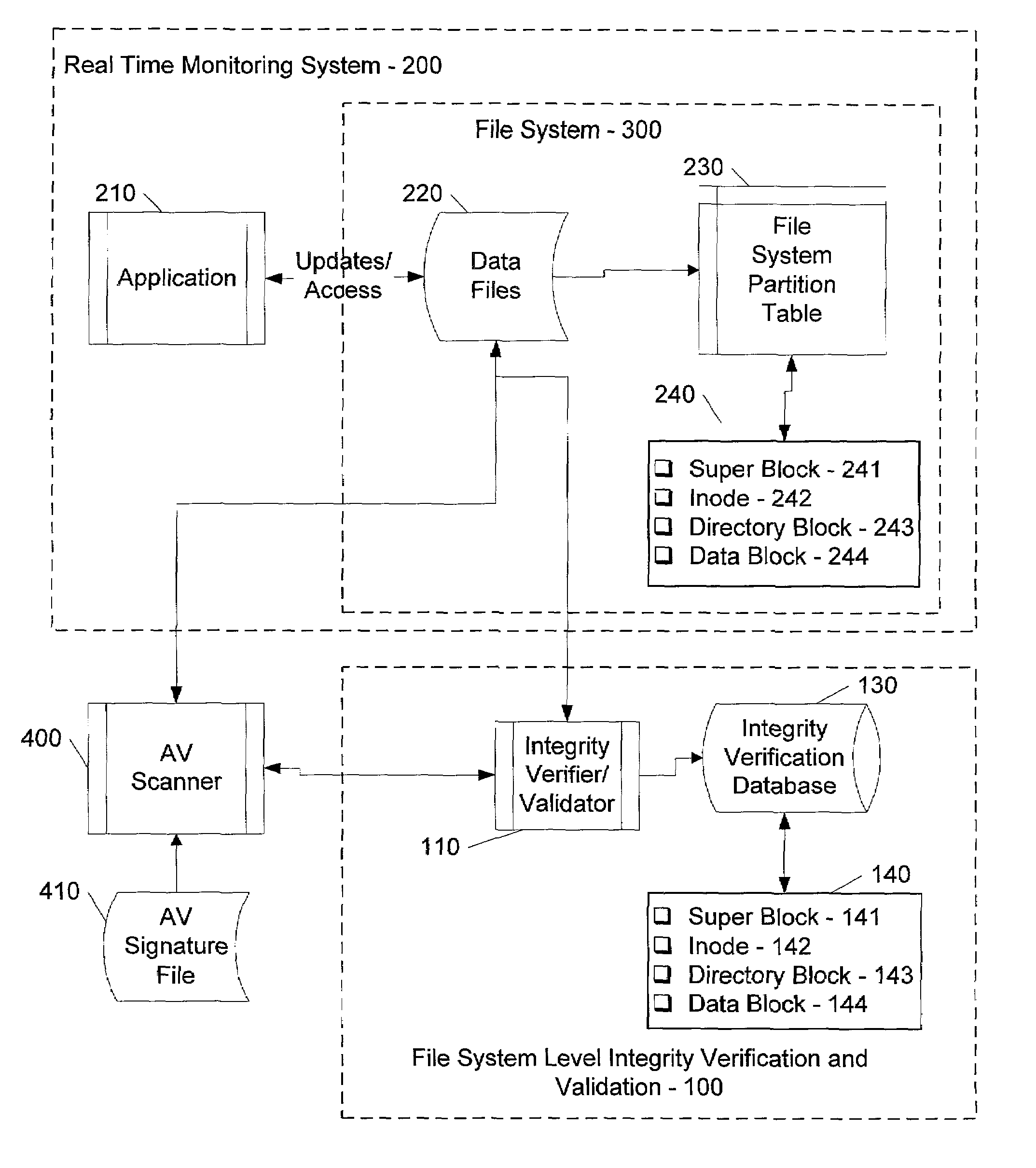
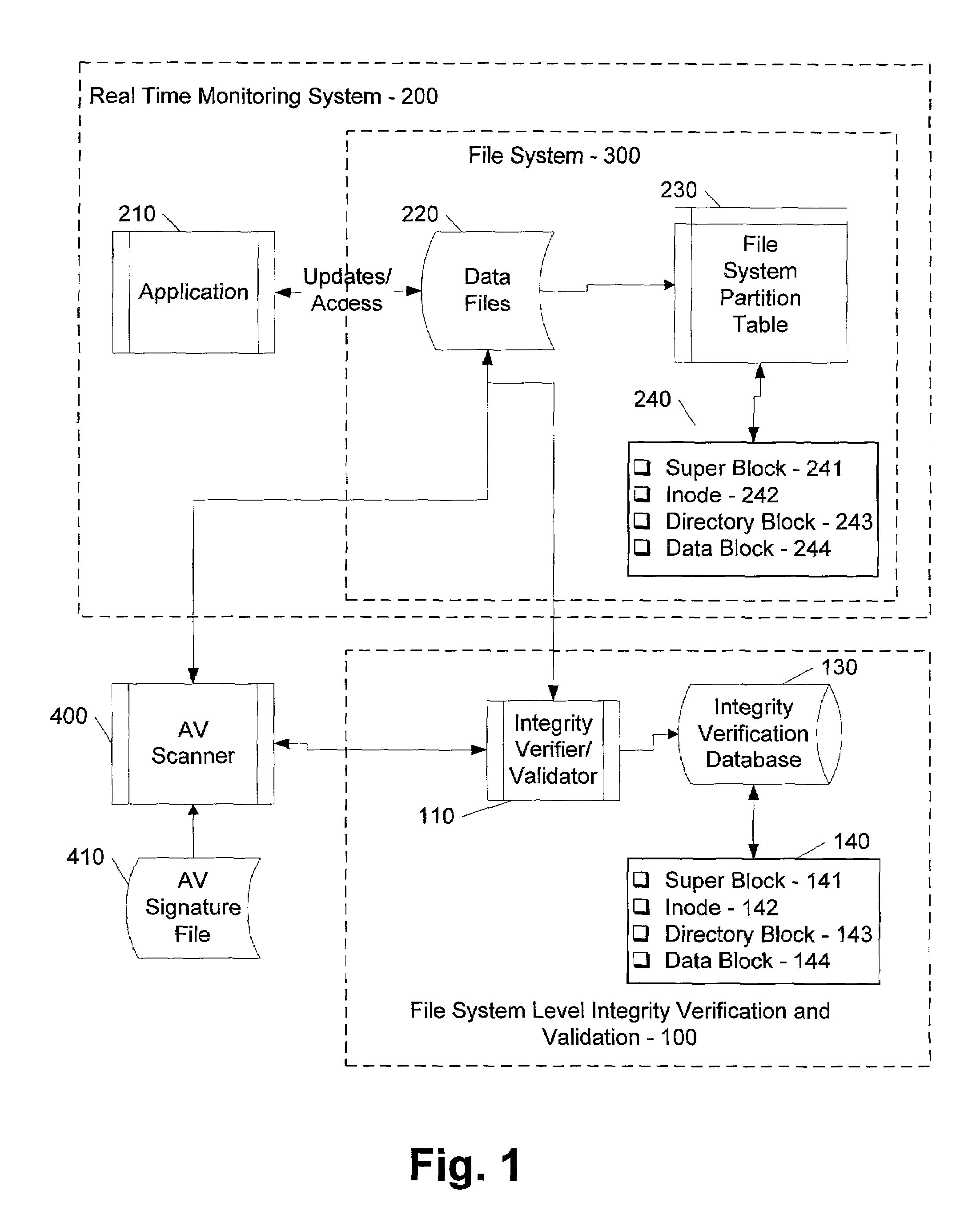
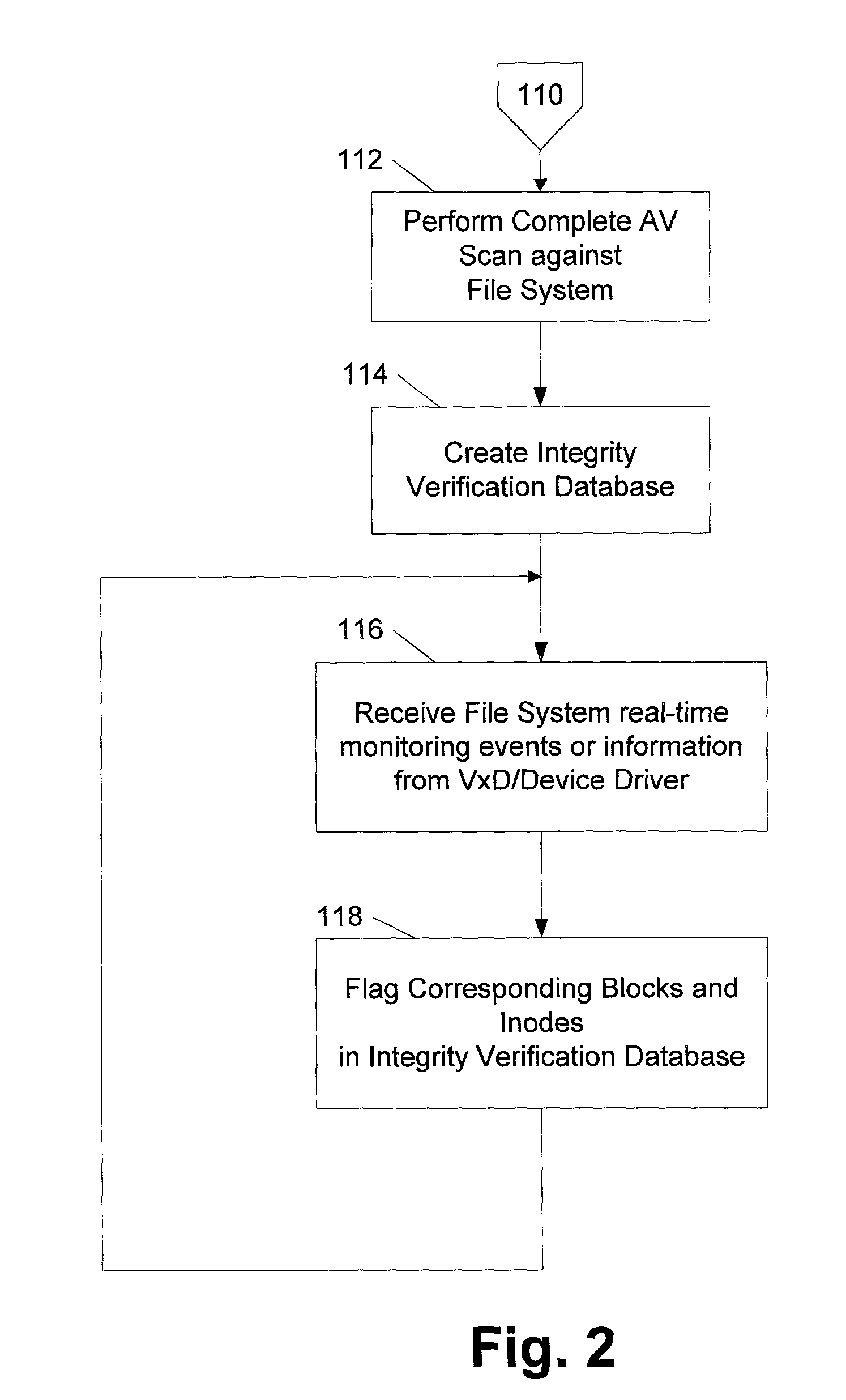
File system level integrity verification and validation
ActiveUS7069594B1Preventing rescanningGood level of efficiencyMemory loss protectionError detection/correctionAnti virusInode
An integrity verifier and validator is provided in which an initial anti-virus scan is performed against an entire file system to verify the integrity of the file system and create a corresponding file system level integrity verification database of known scanned regions of the file system. The database contains a copy of the file system's partition table referencing the range of occupied inodes and directory blocks. When new or updated content is written to the file system the integrity of the corresponding occupied inodes and directory blocks is no longer assured, and the integrity verifier flags them on the database for rescanning. Subsequent attempts to rescan any portion of the file system triggers the integrity validator to scan the database to validate whether that portion of the file system falls within any of the occupied inodes or directory blocks that have been flagged for rescanning. If they are not flagged, then rescanning of that portion of the file system is unnecessary as the integrity of at least that portion is assured. However, if they are flagged, then the anti-virus software rescans that portion of the file system for the presence of viruses.
Owner:MCAFEE LLC
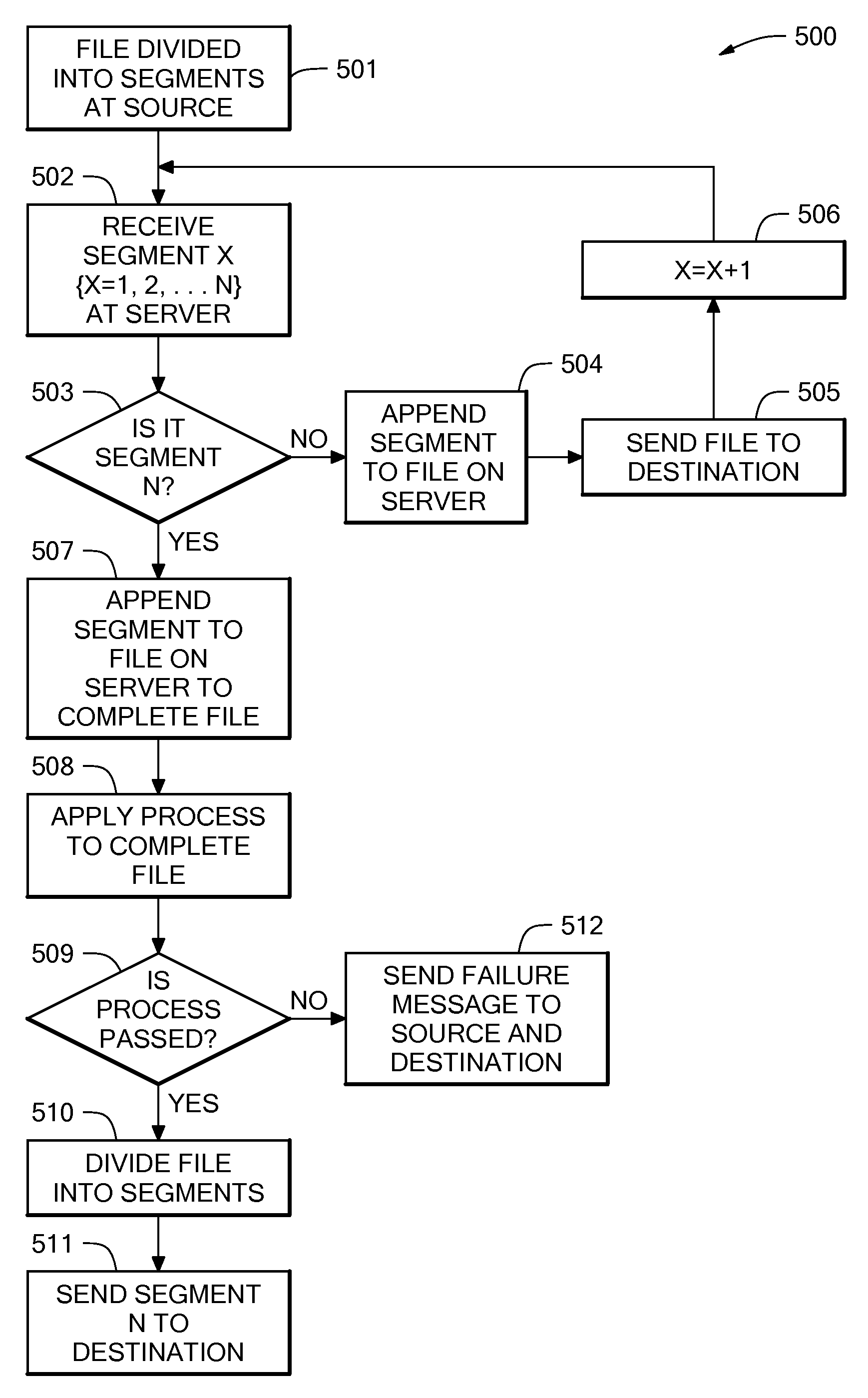
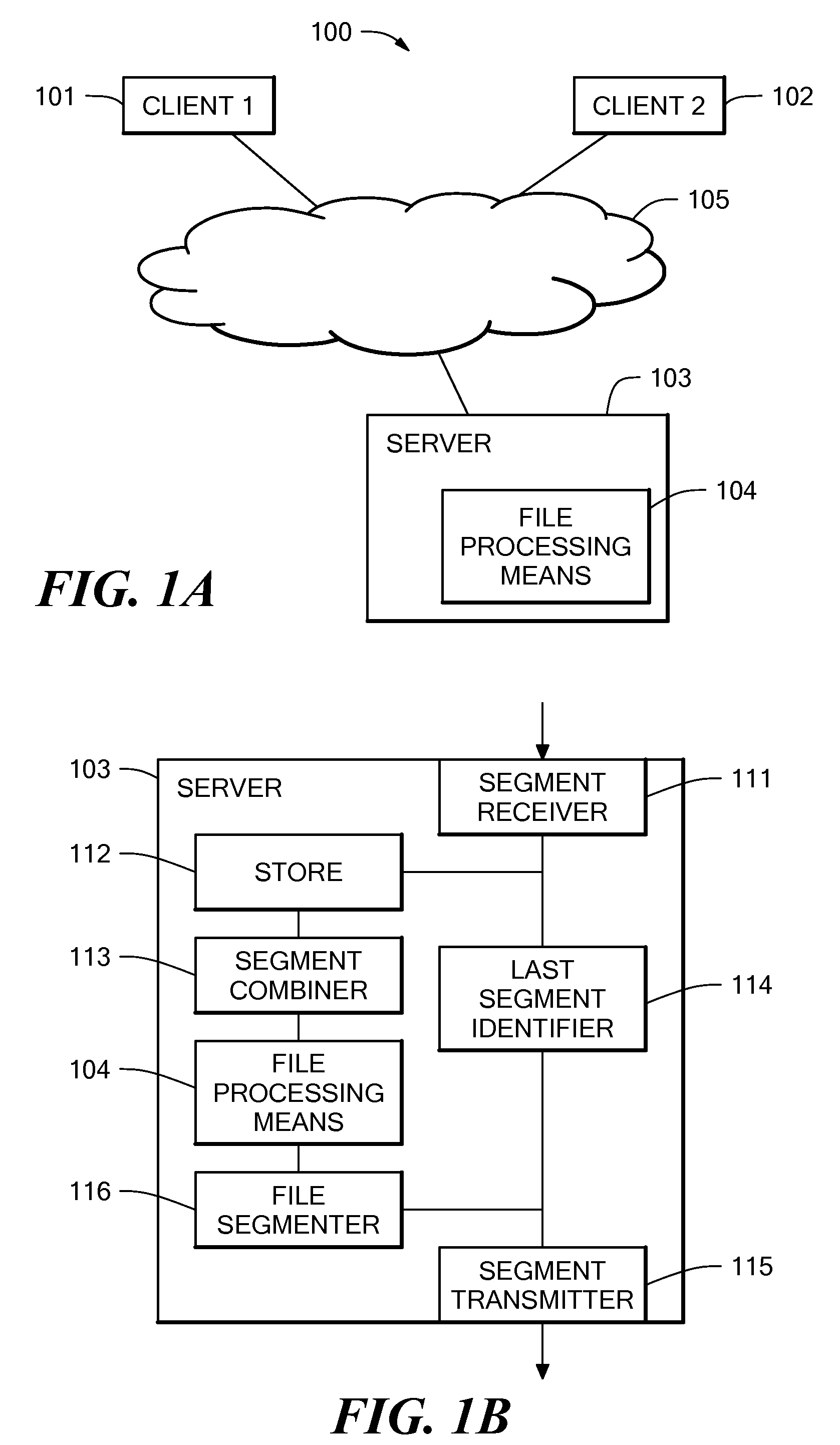
Method and system for file transfer
ActiveUS20080040503A1Reduce transmission delayMultiple digital computer combinationsTransmissionAnti virusConfidentiality
A method and system for file transfer are provided in which a file is transferred between a source client and a destination client via a middle server. The server receives segments of a file from the source client and stores the segments of the file as they are received. The server also forwards the segments of the file to a destination client as they are received, with the exception of one segment. The server combines the segments to form the whole file and applies a process to the whole file. The process may be for example an authorisation process such as an anti-virus check, a confidentiality check, or a content validity check. If the file passes the process, the remaining excepted segment is forwarded to the destination client.
Owner:IBM CORP
Service processing switch
Methods and systems for providing IP services in an integrated fashion are provided. According to one embodiment, a system includes a switch fabric and a line interface / network module, multiple virtual routing engines (VREs) and a virtual services engine (VSE) coupled with the switch fabric. The line interface / network module receives packets, steers ingress packets to a selected VRE and transmits egress packets according to their relative priority. VREs determines if a packet associated with a packet flow requires processing by the VSE by performing flow-based packet classification on the packet and evaluating forwarding state information associated with previously stored flow learning results. The VSE includes a central processing unit configured to perform firewall processing, Uniform Resource Locator (URL) filtering and anti-virus processing. If the packet is determined to require processing by the VSE, then the packet is steered to the VSE for firewall, URL filtering and / or anti-virus processing.
Owner:FORTINET
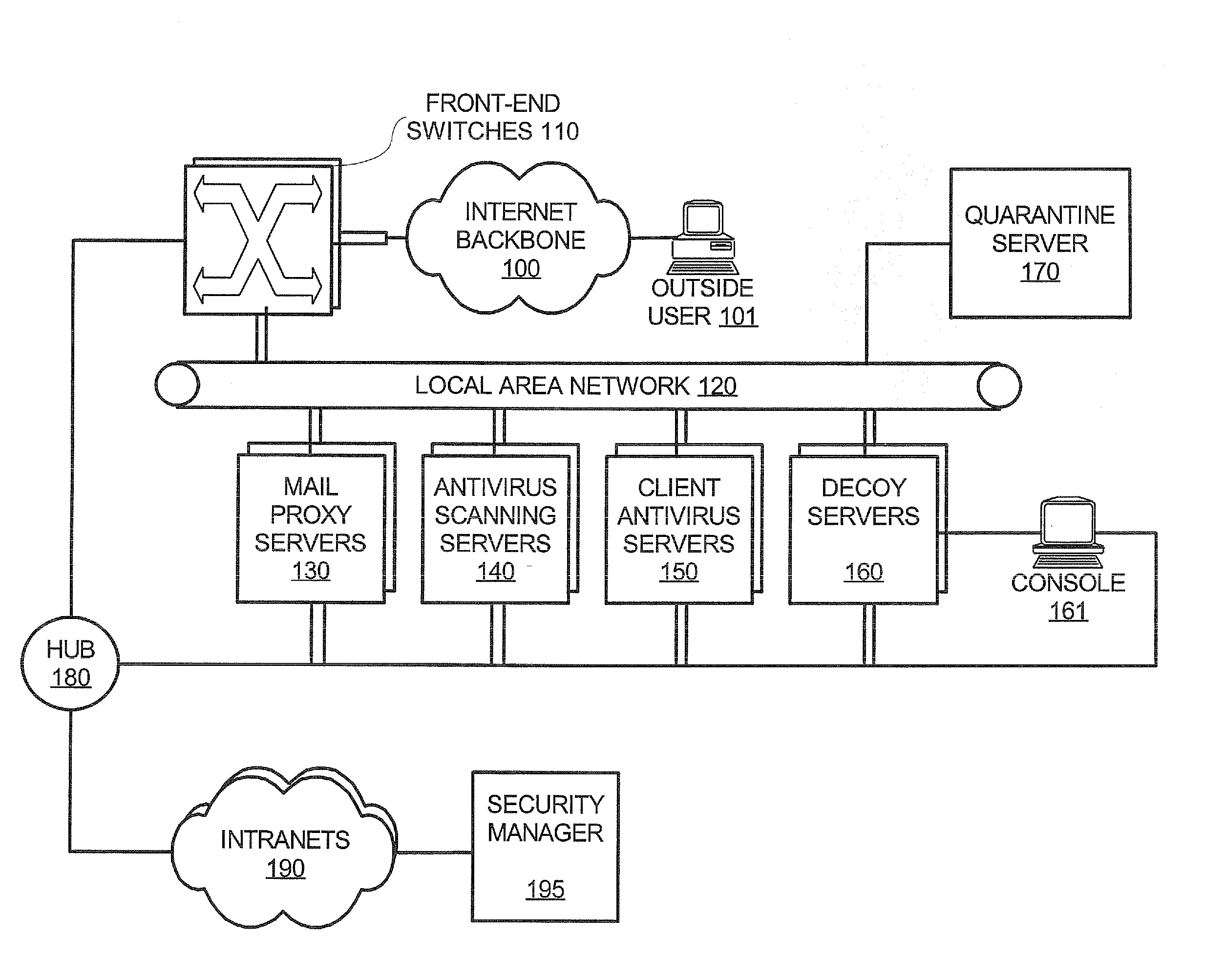
Network security architecture
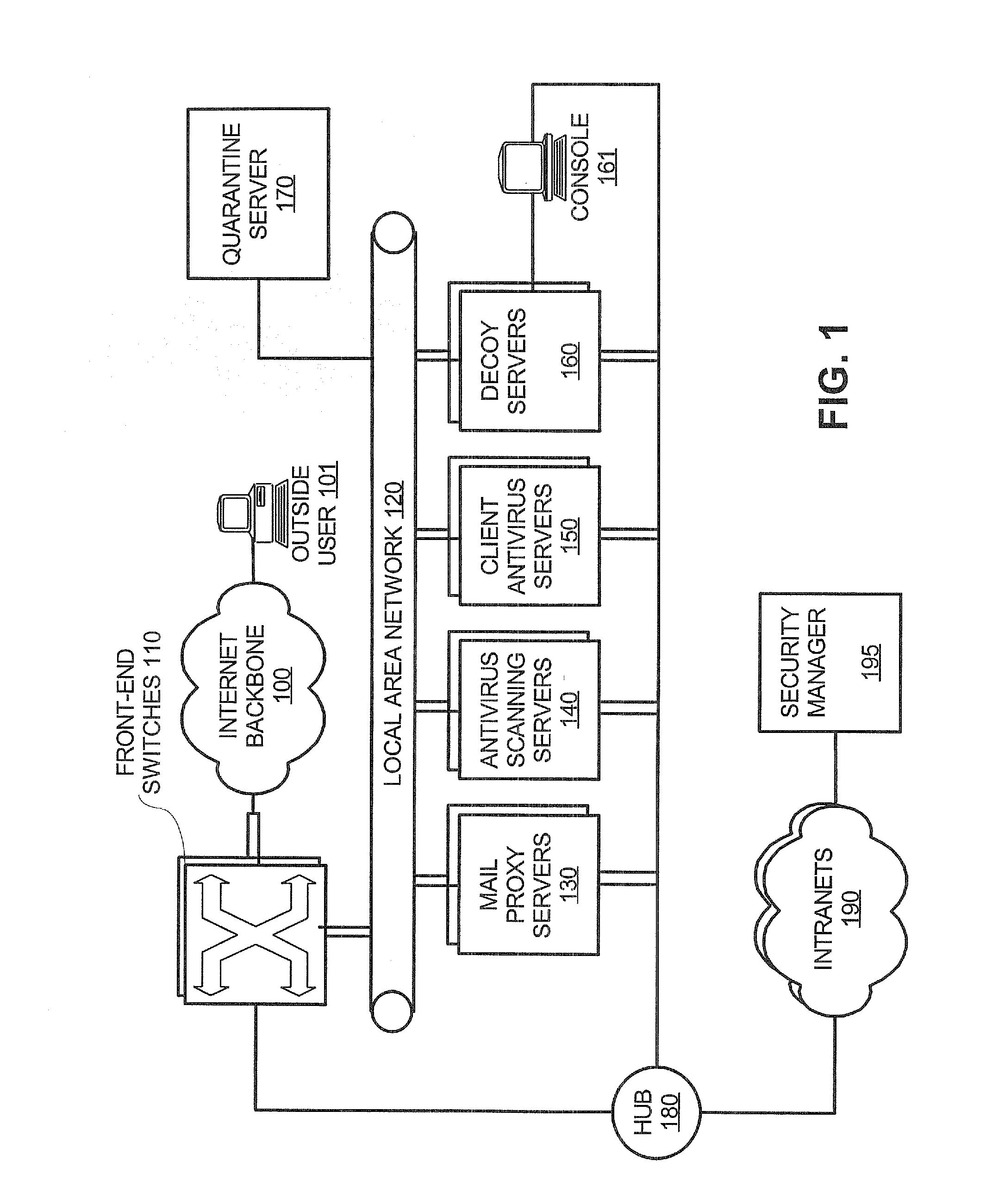
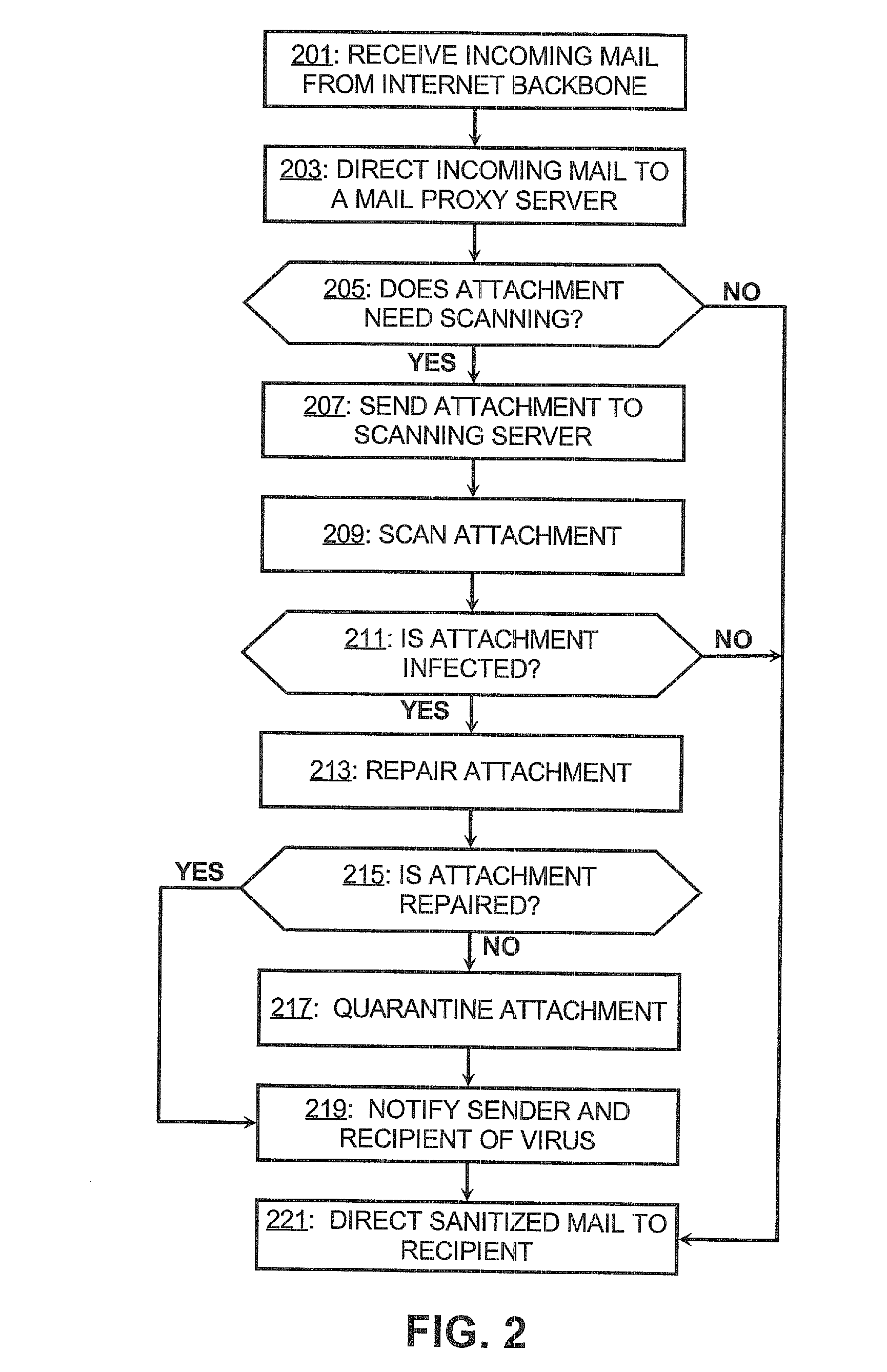
InactiveUS20120005756A1Memory loss protectionUnauthorized memory use protectionAnti virusInternet privacy
A network security system is deployed between an internet backbone and intranets that belong to subscribing organizations. The system includes a scanning system that scans incoming electronic mail for malicious code and an anti-virus server for downloading anti-virus code to clients on the intranets. A switch is provided for directing incoming electronic mail from the internet backbone to the scanning system so that the electronic mail can be scanned. In one embodiment, a decoy server is also provided for masquerading as a legitimate server and logging suspicious activity from communications received from the internet backbone.
Owner:VERIZON PATENT & LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com