Patents
Literature
425 results about "Active security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
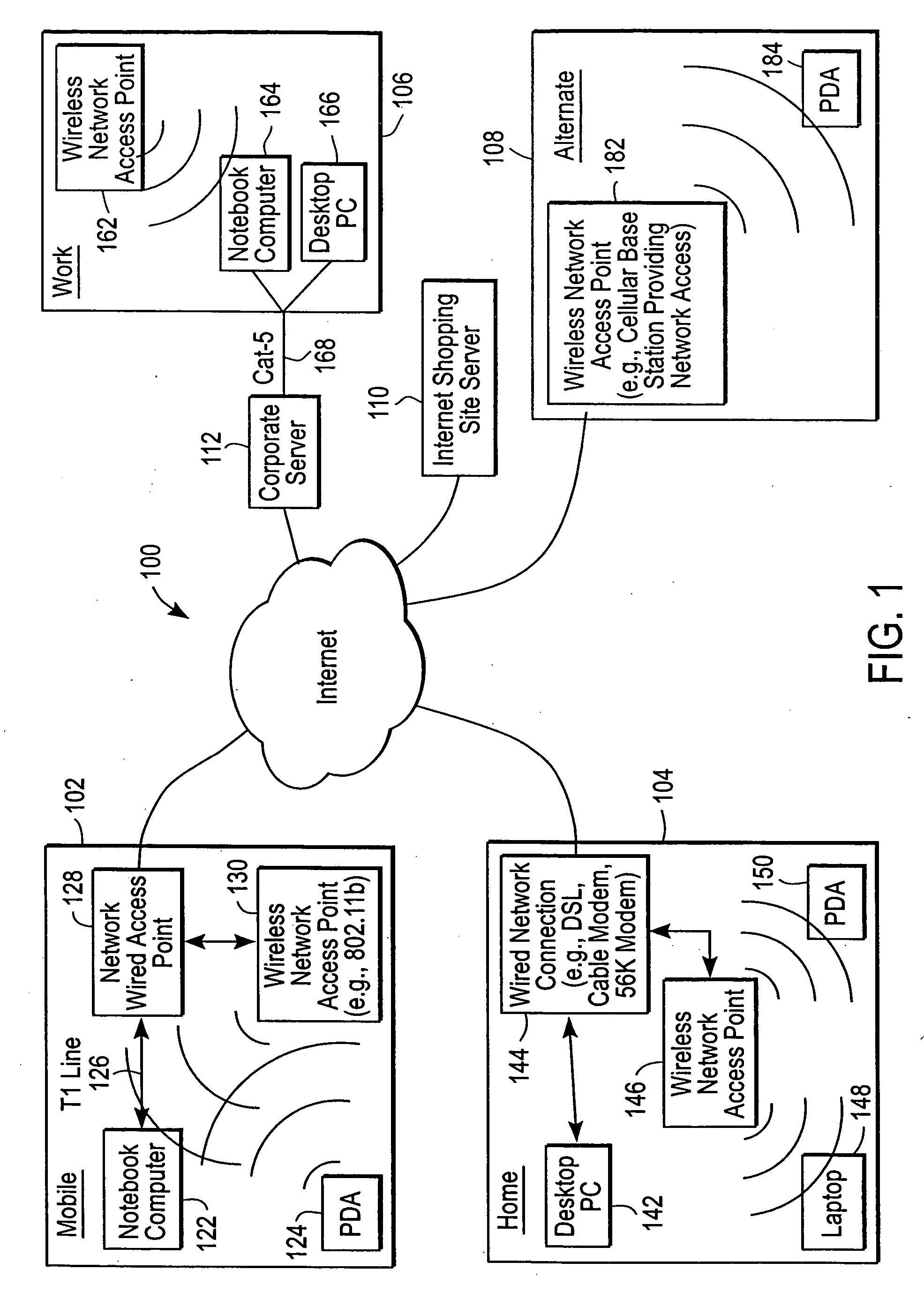
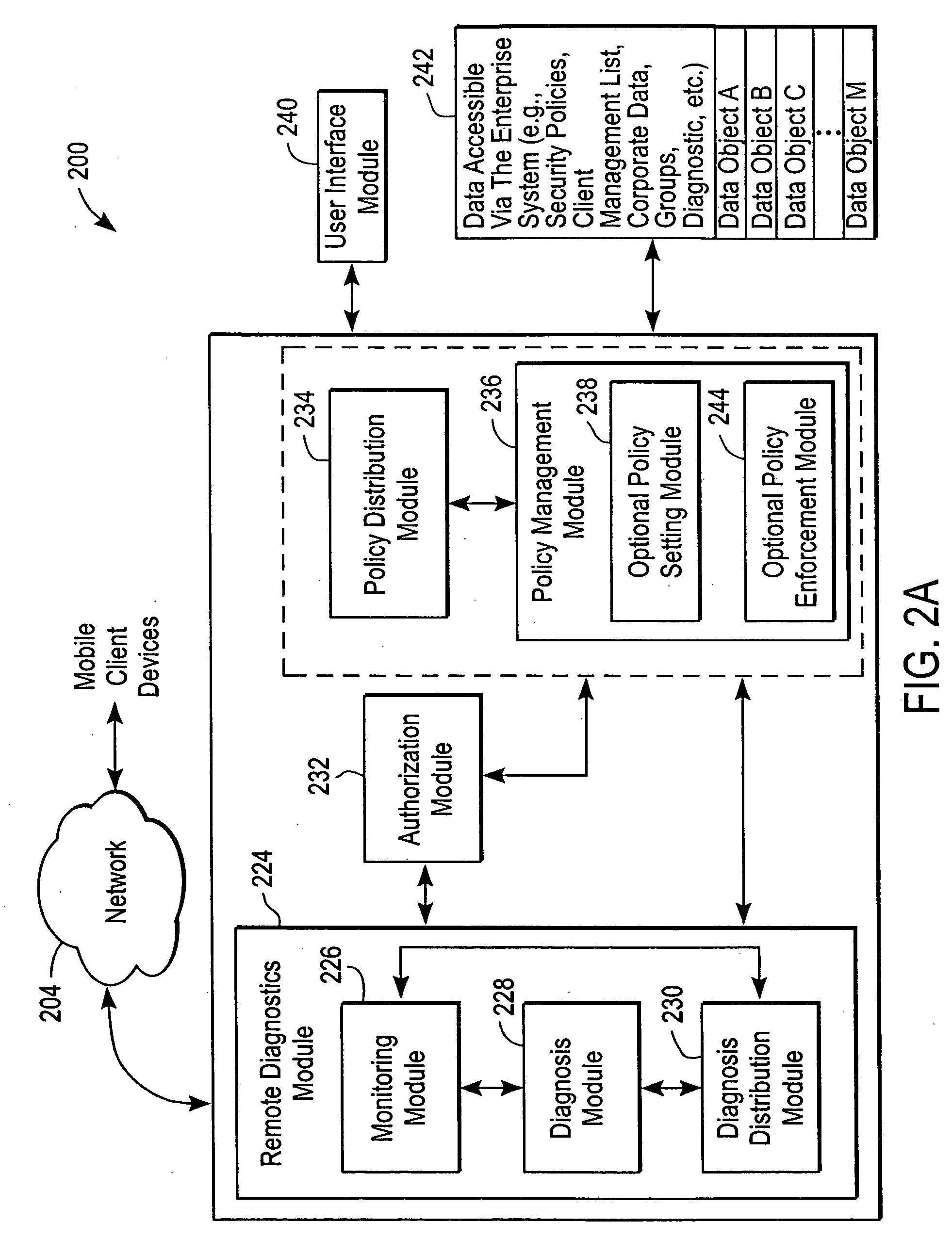
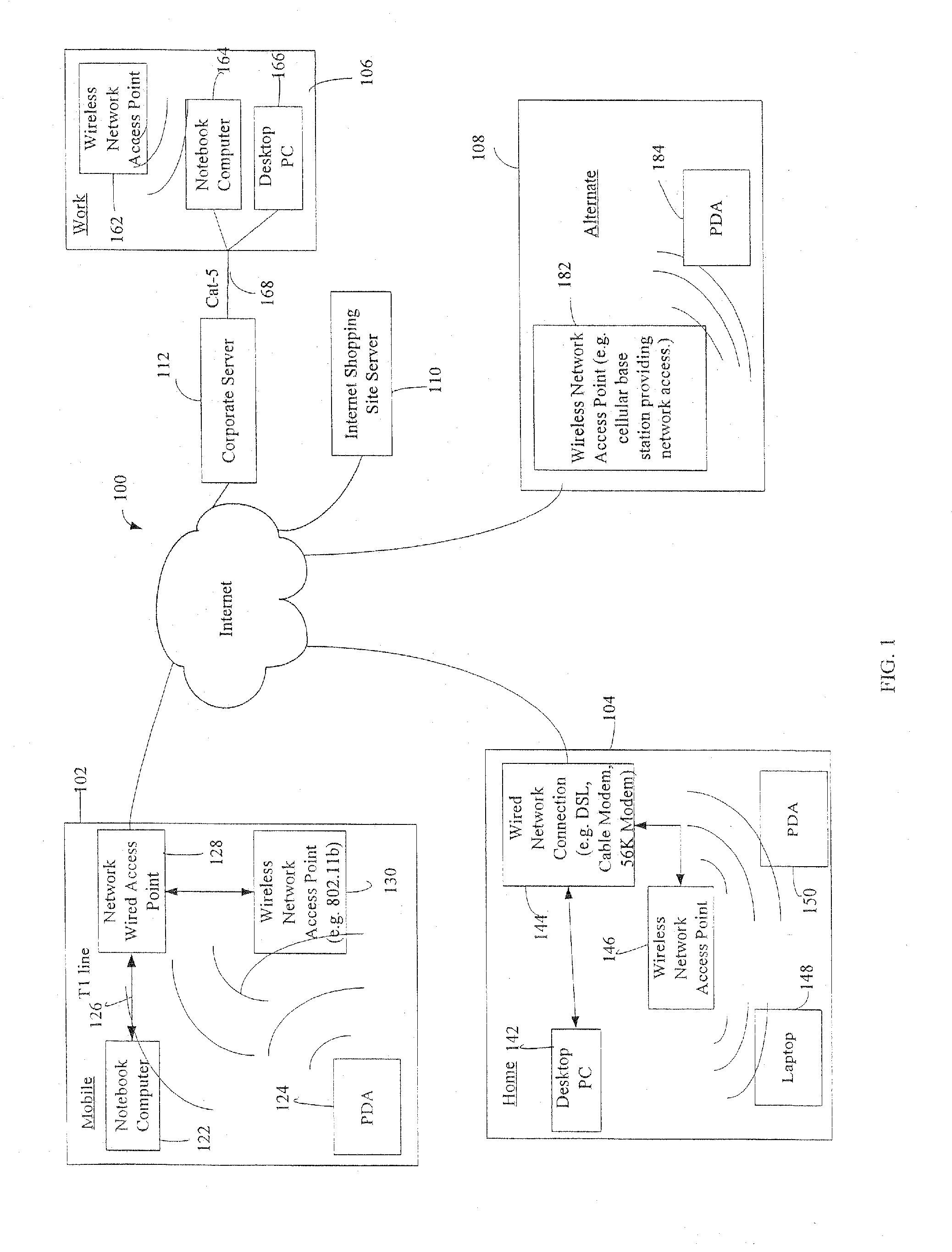
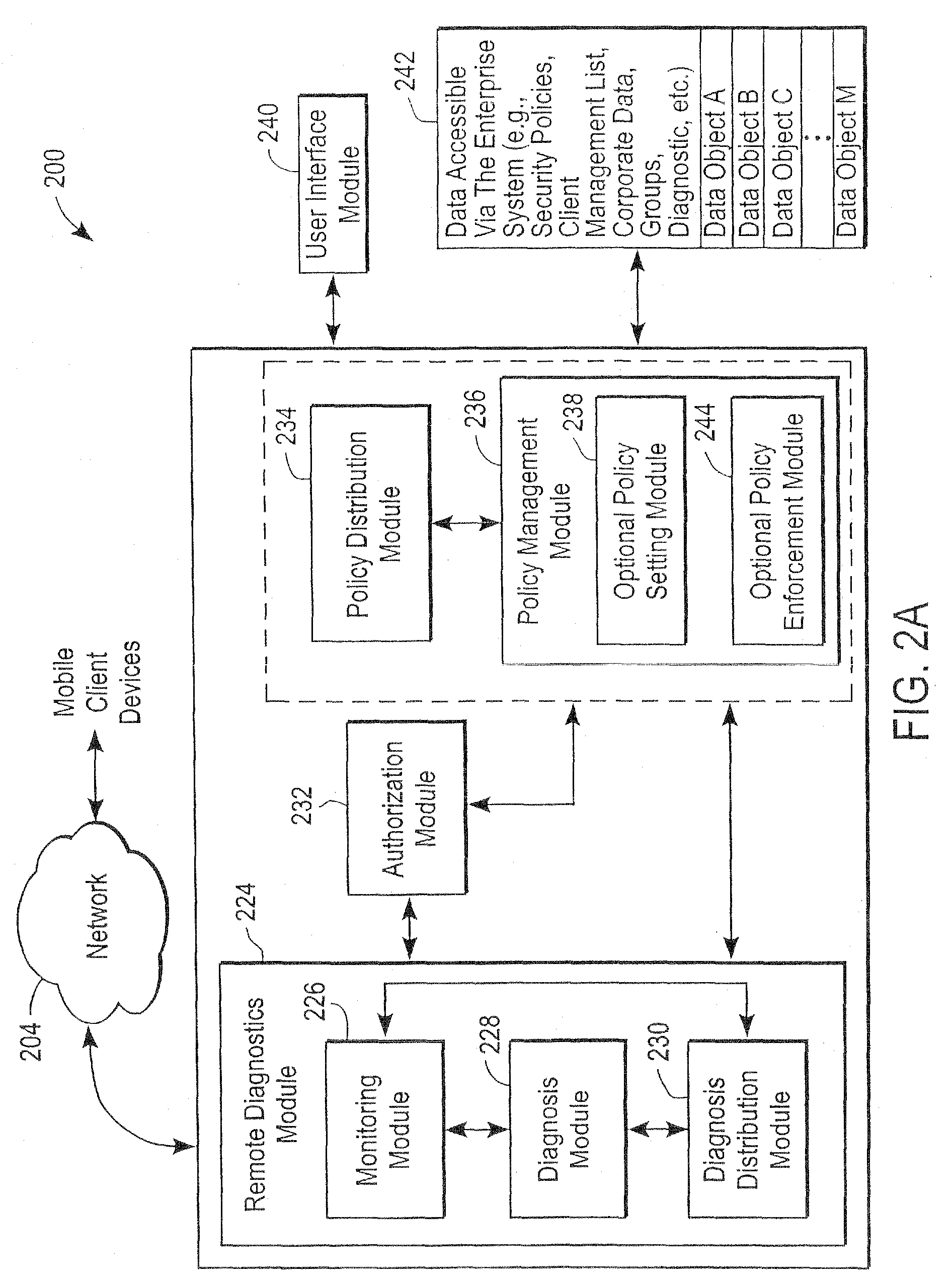
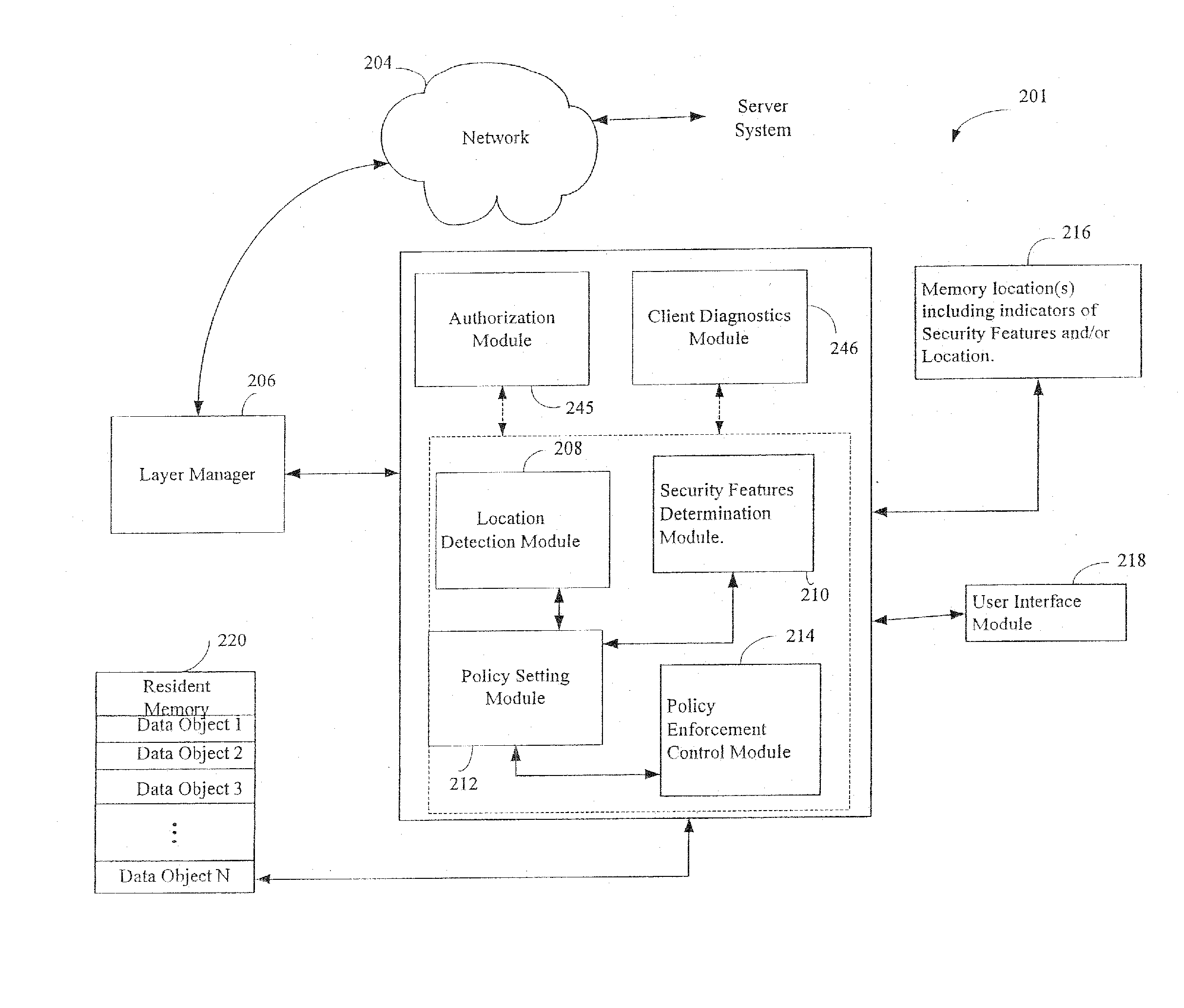
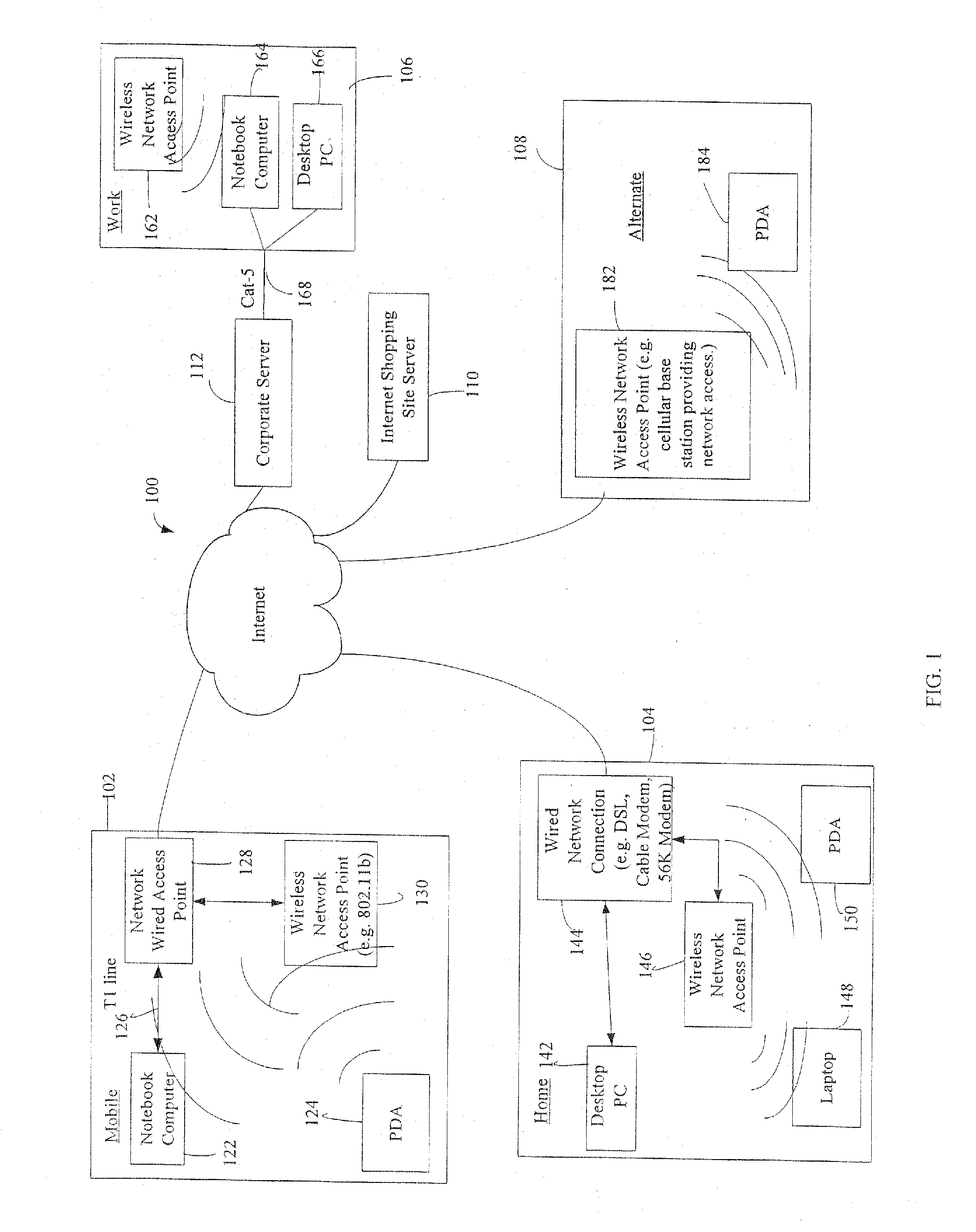
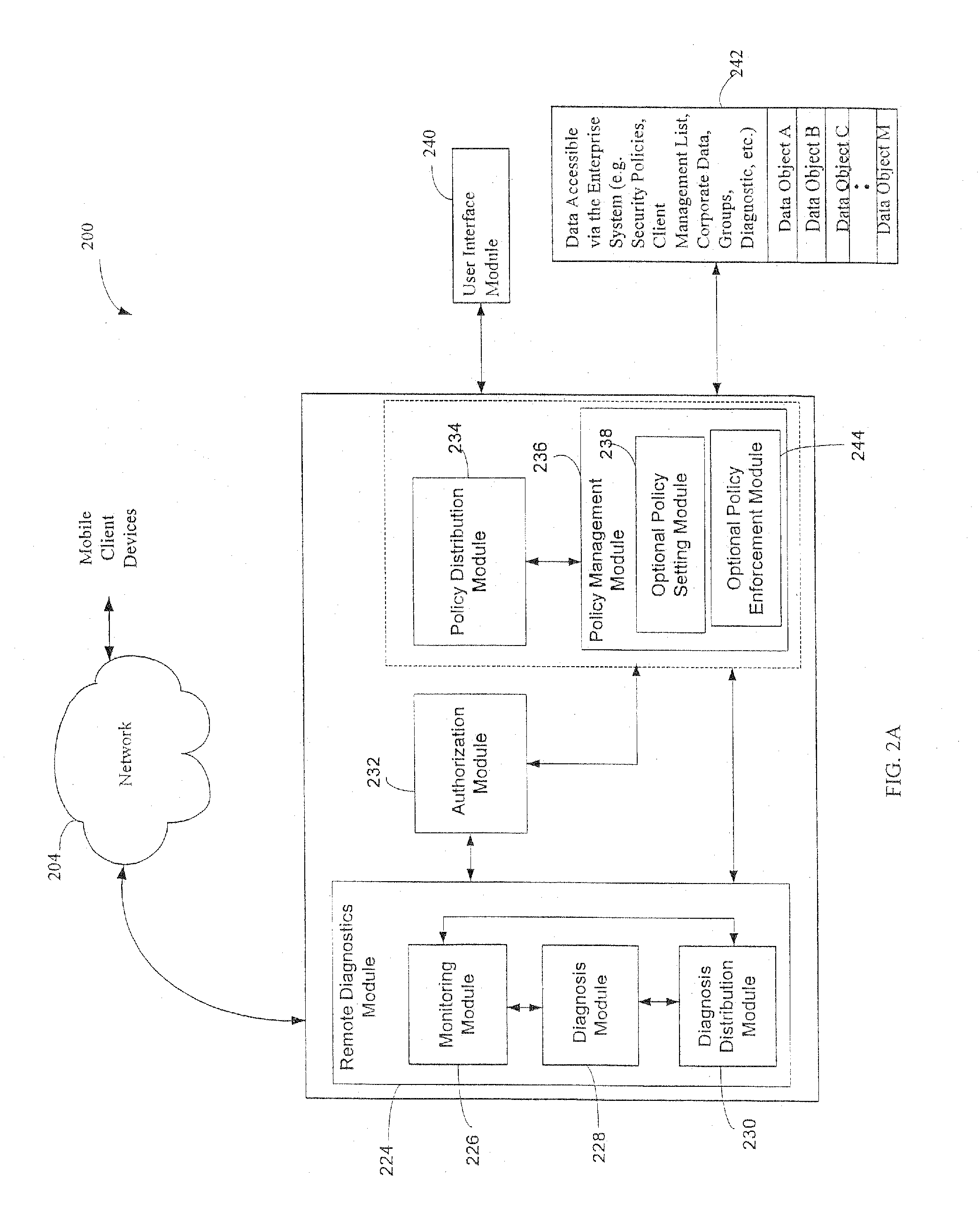
Administration of protection of data accessible by a mobile device
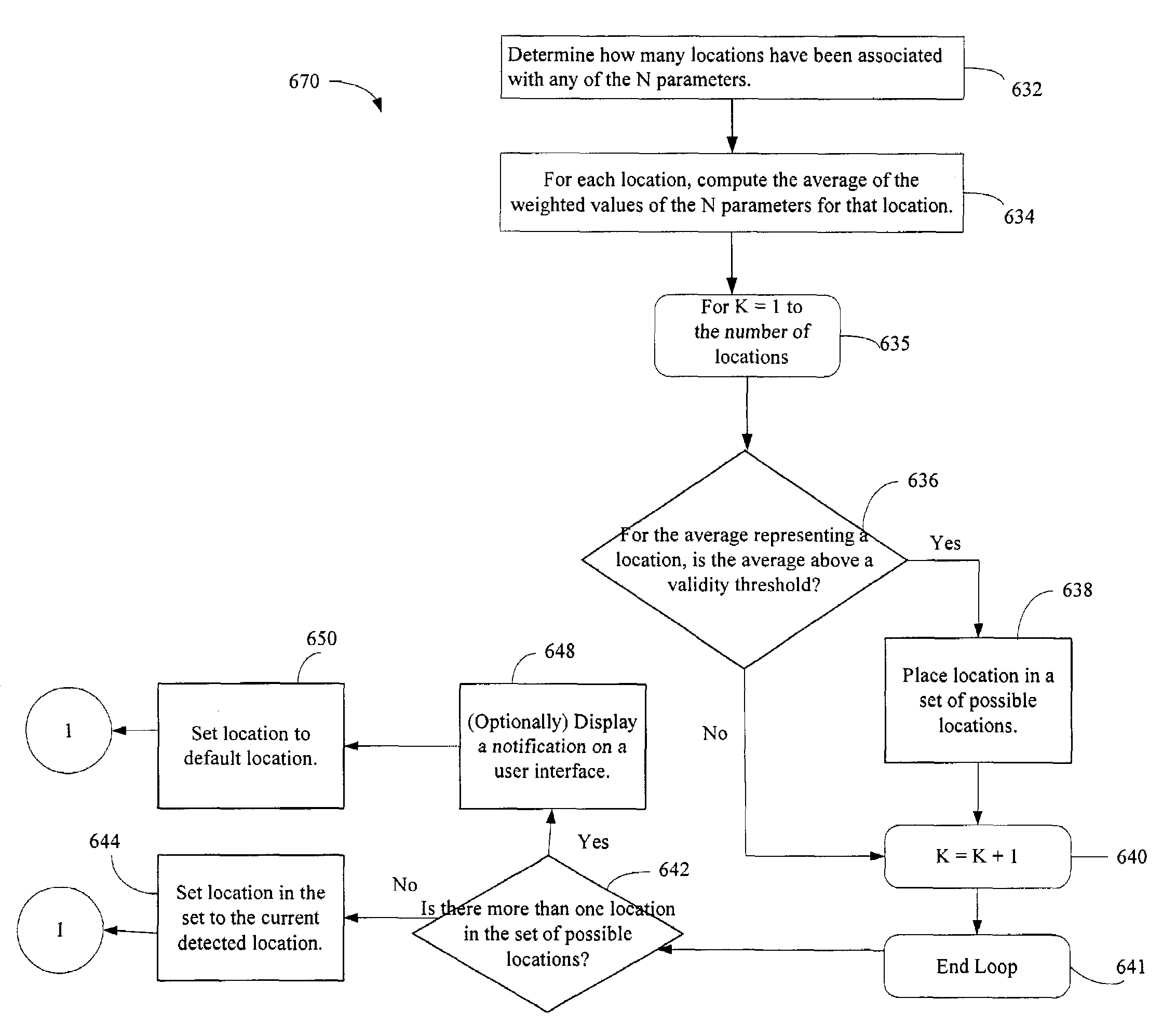
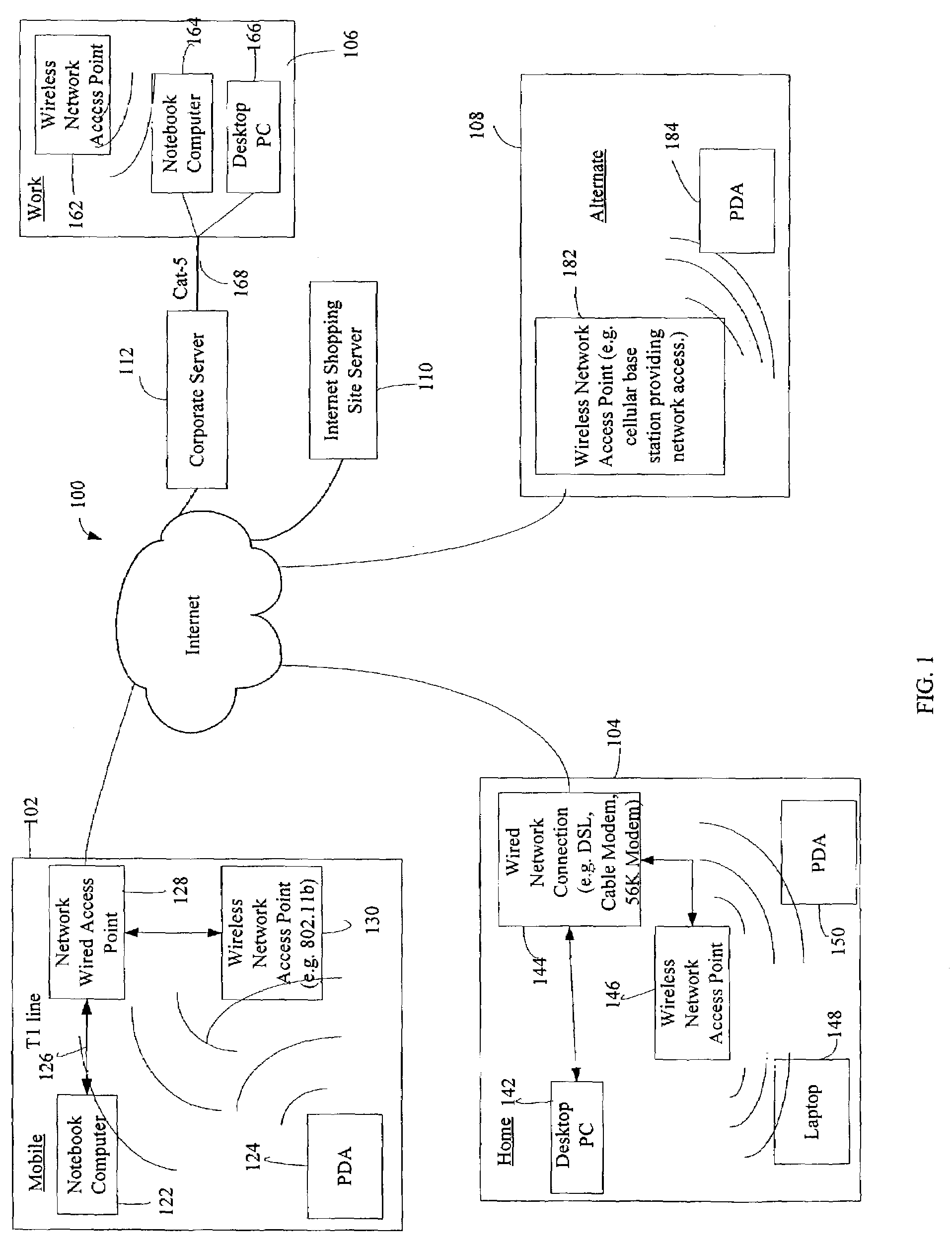
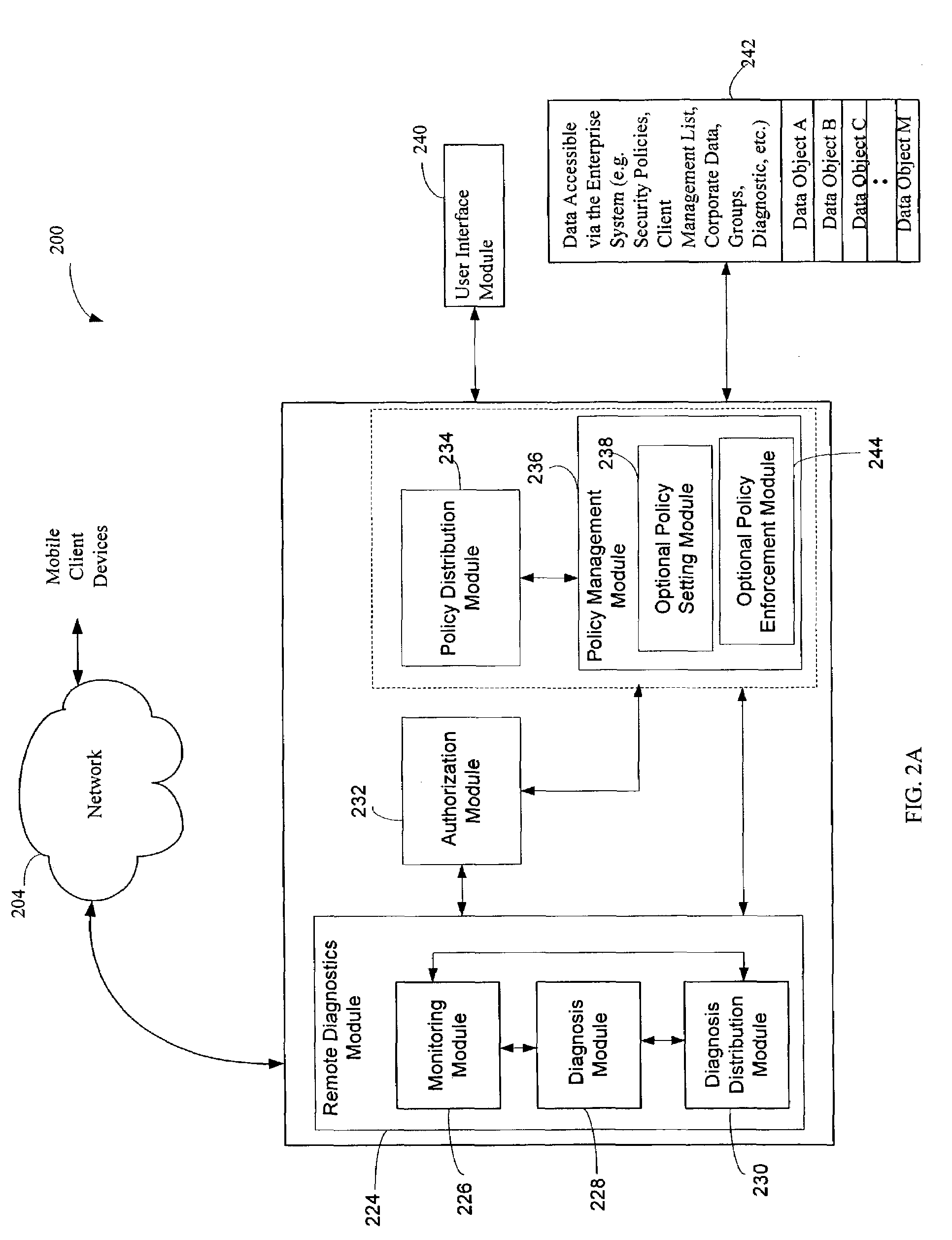
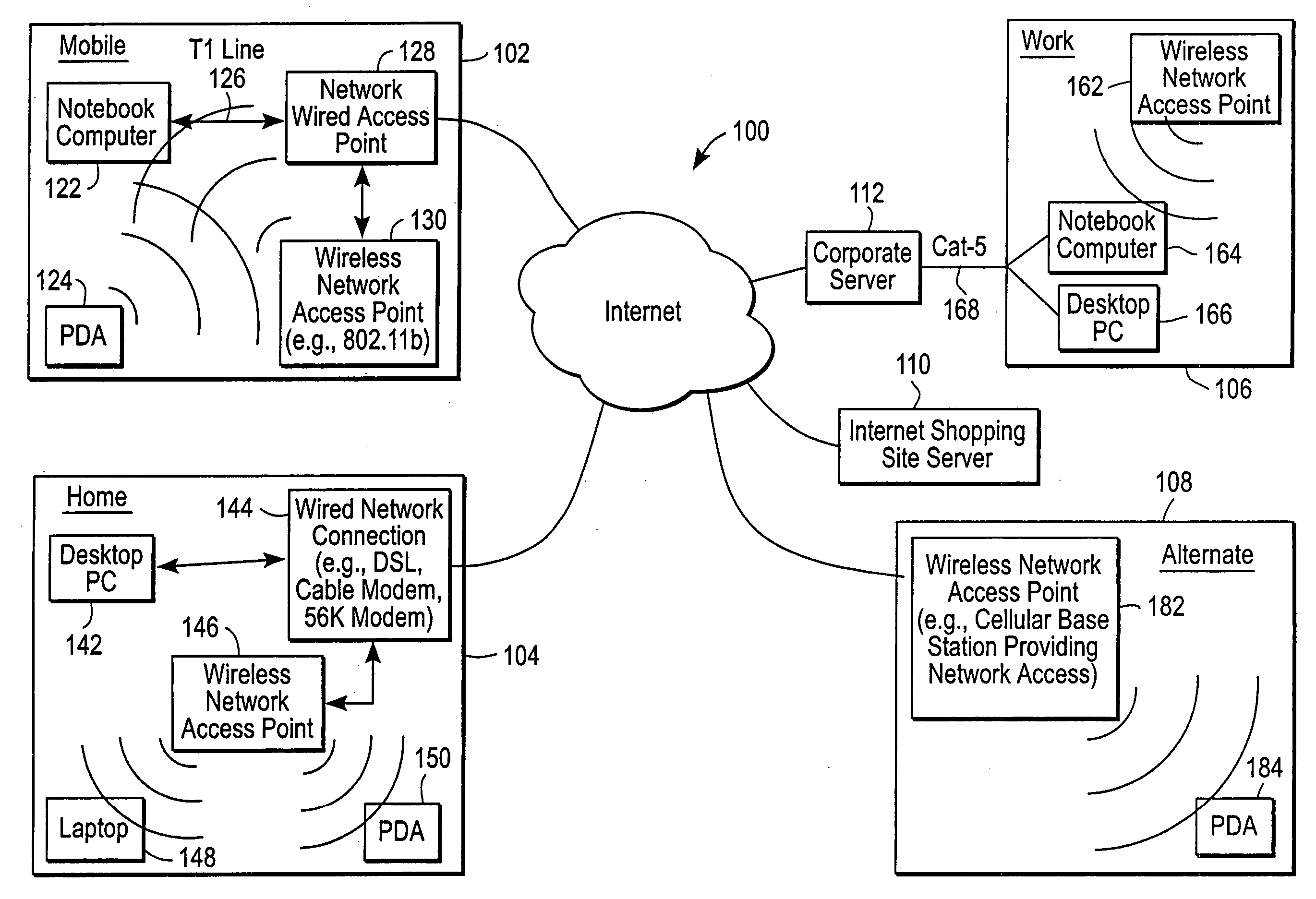
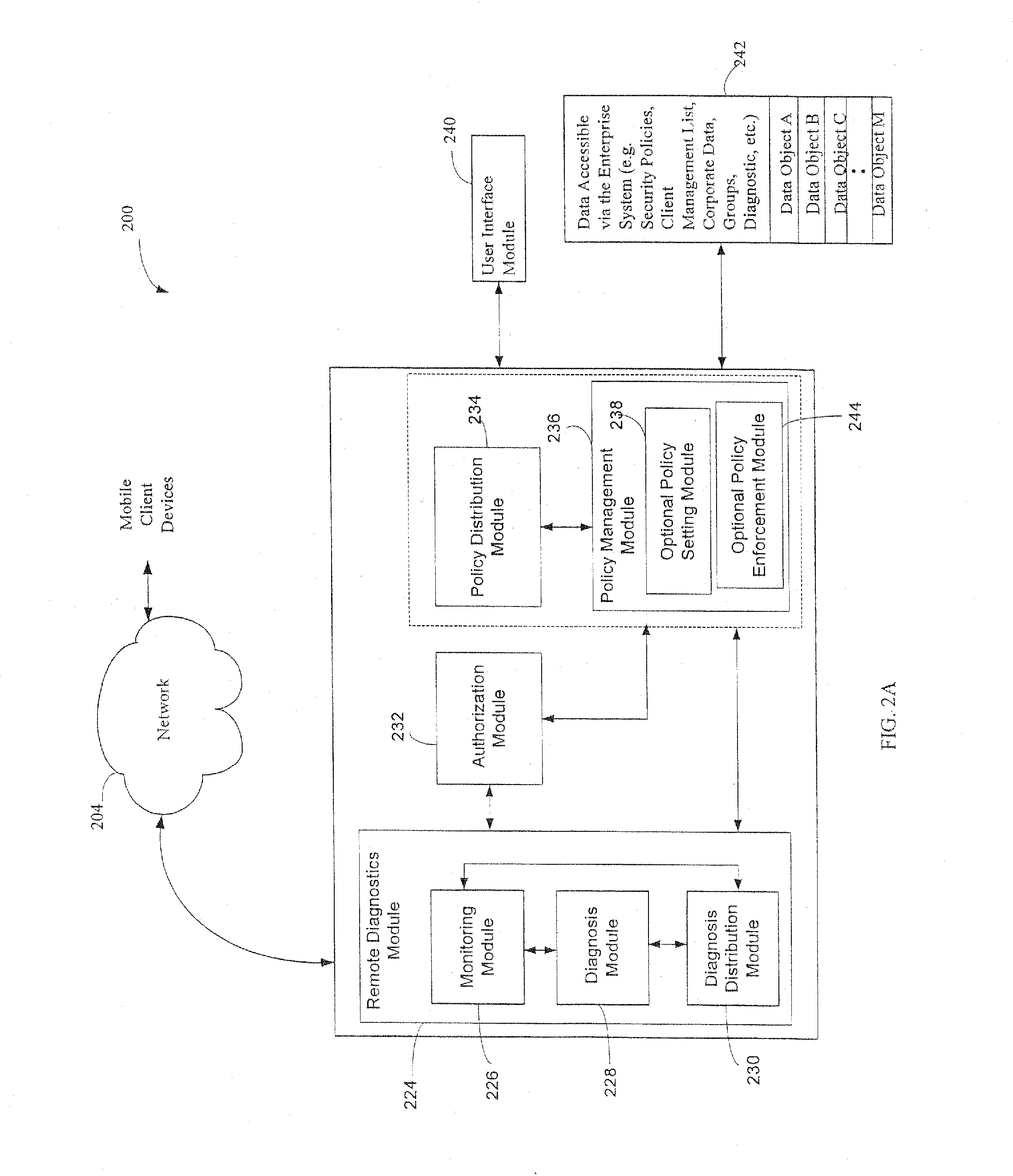
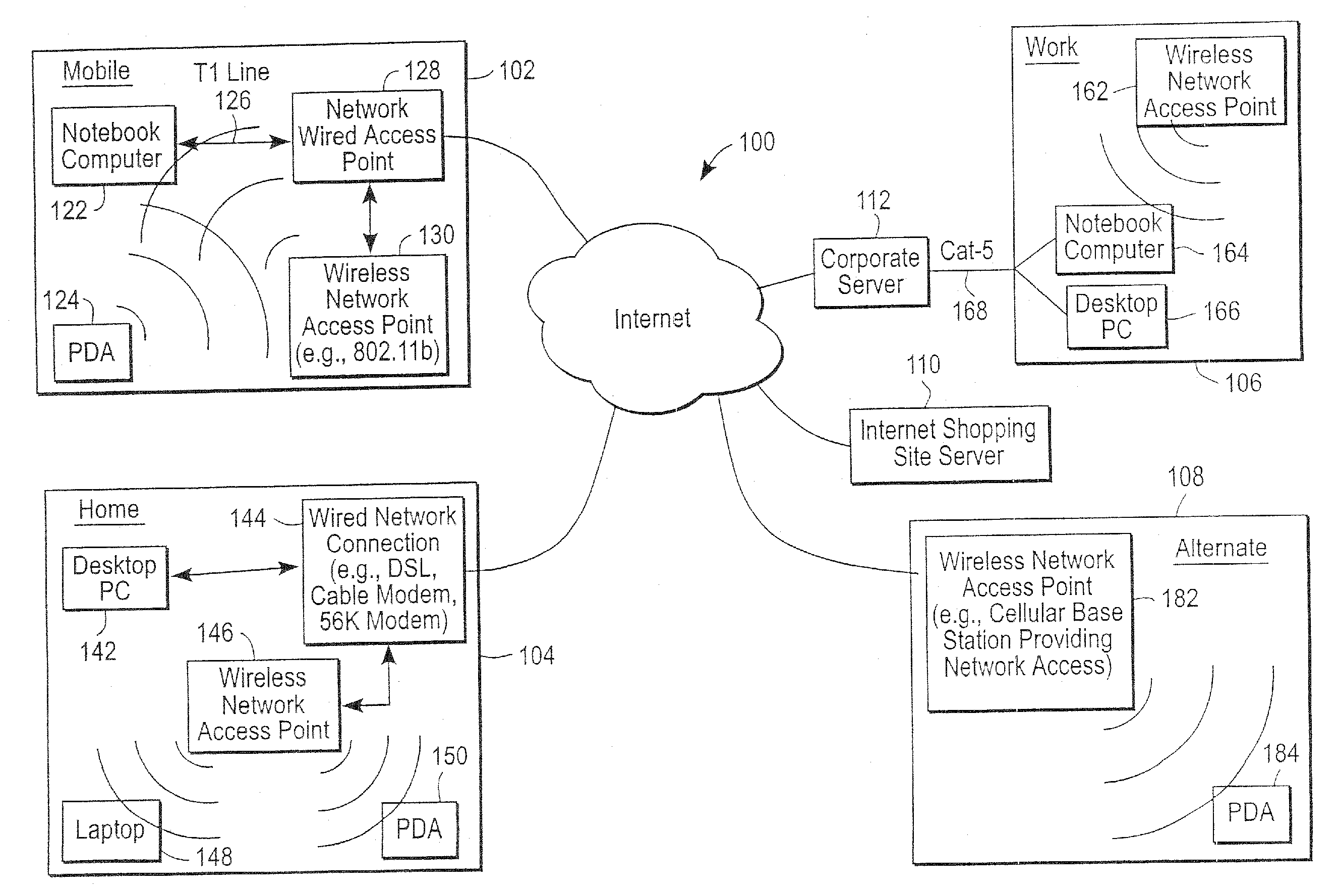
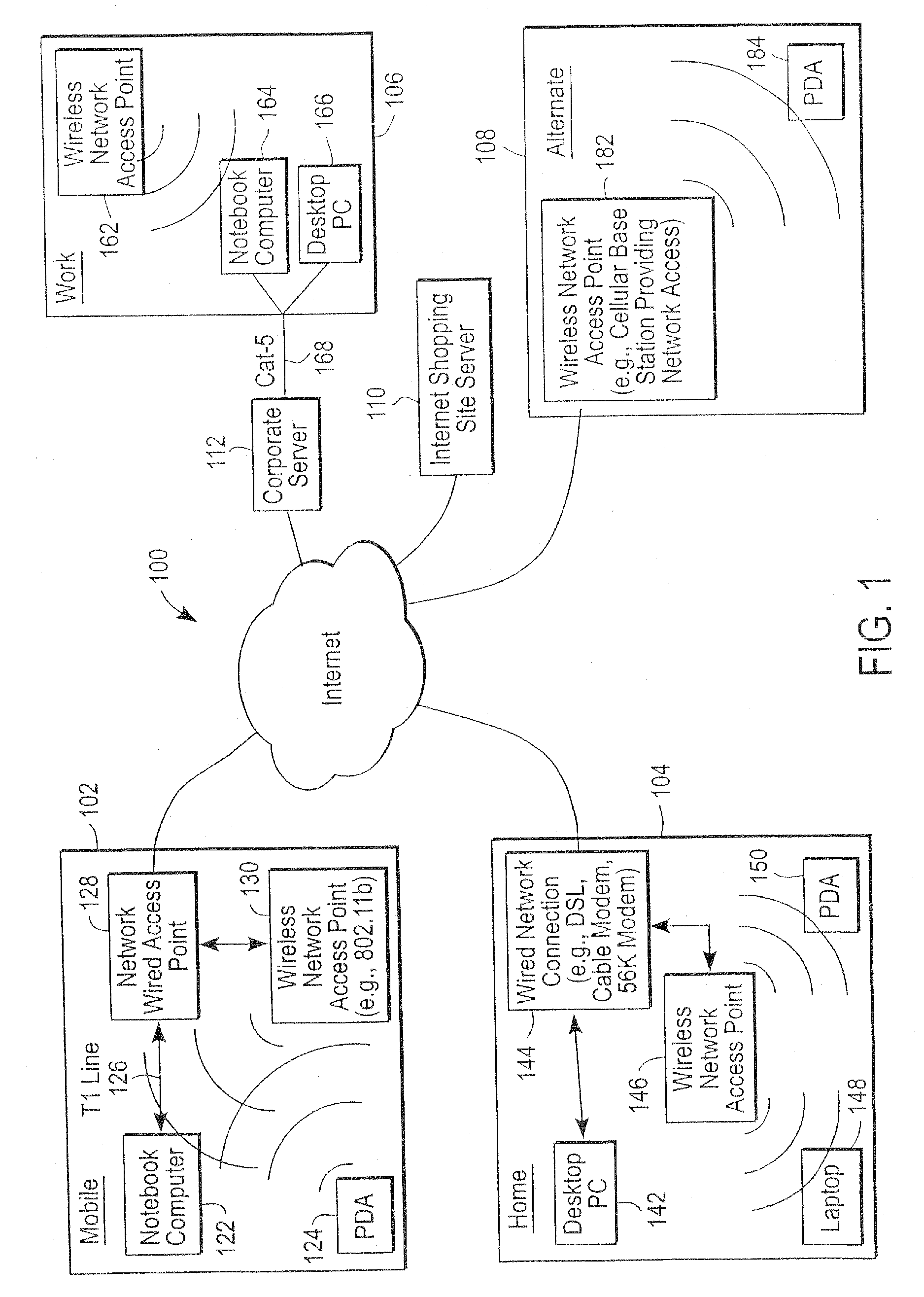
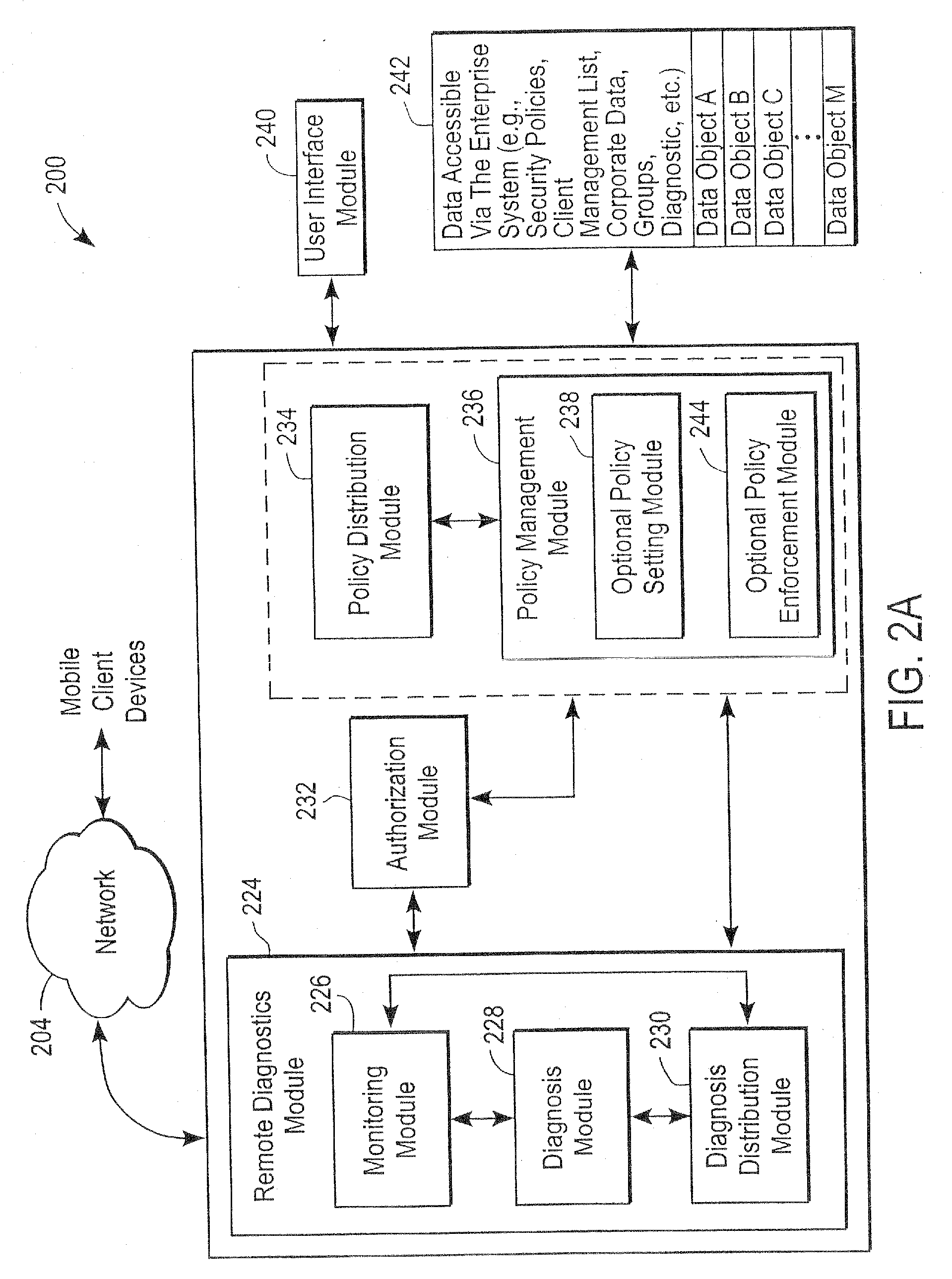
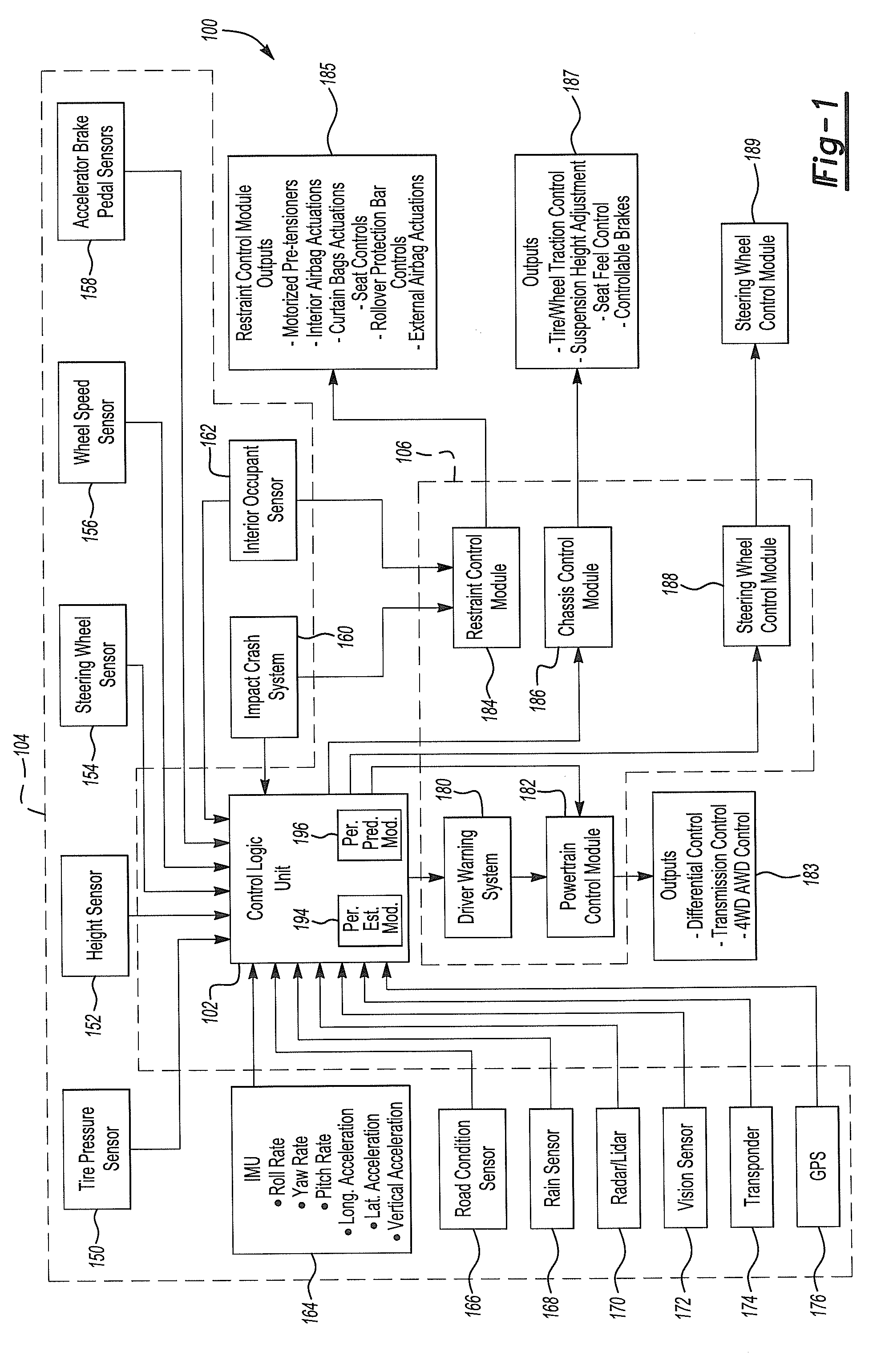
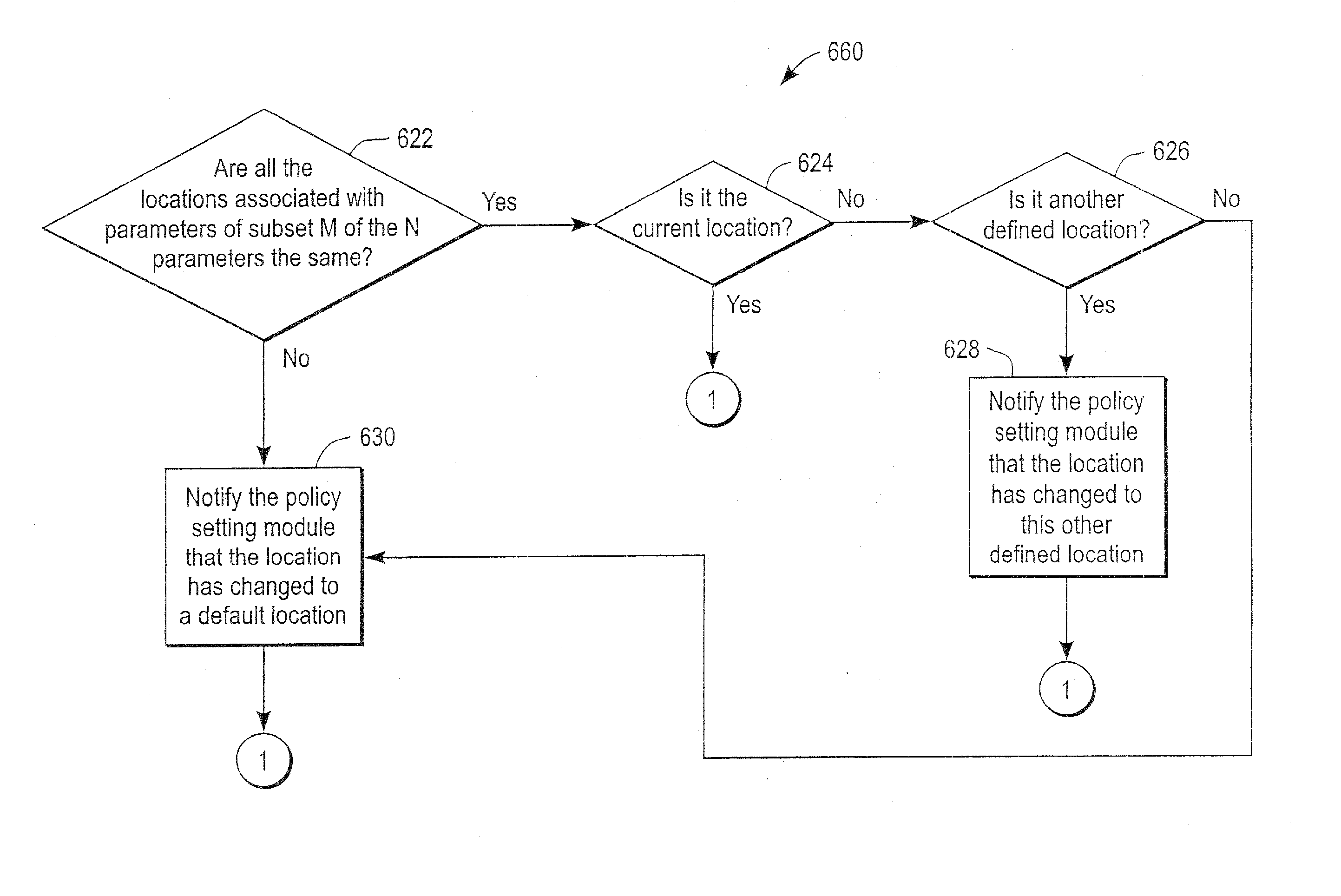
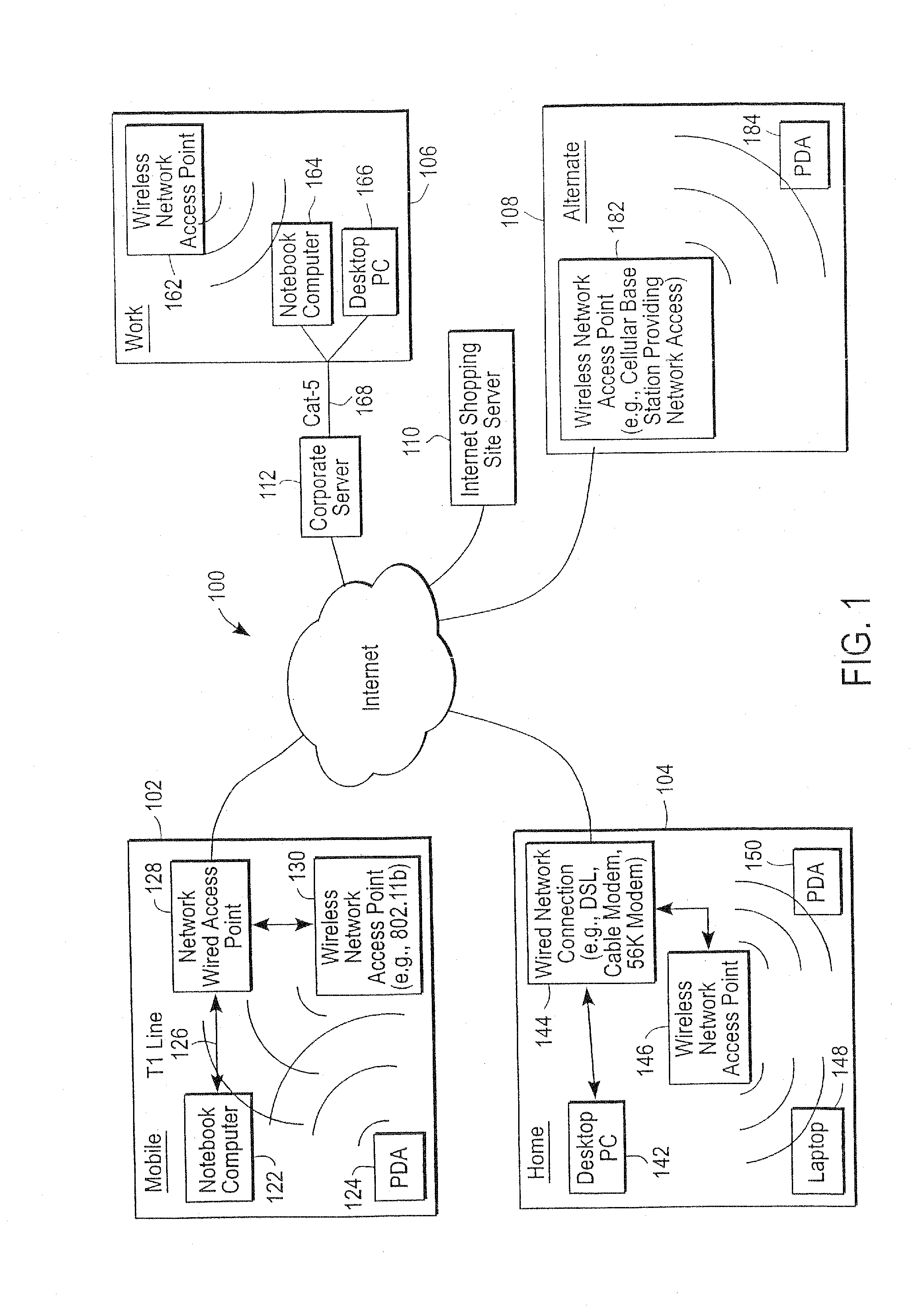
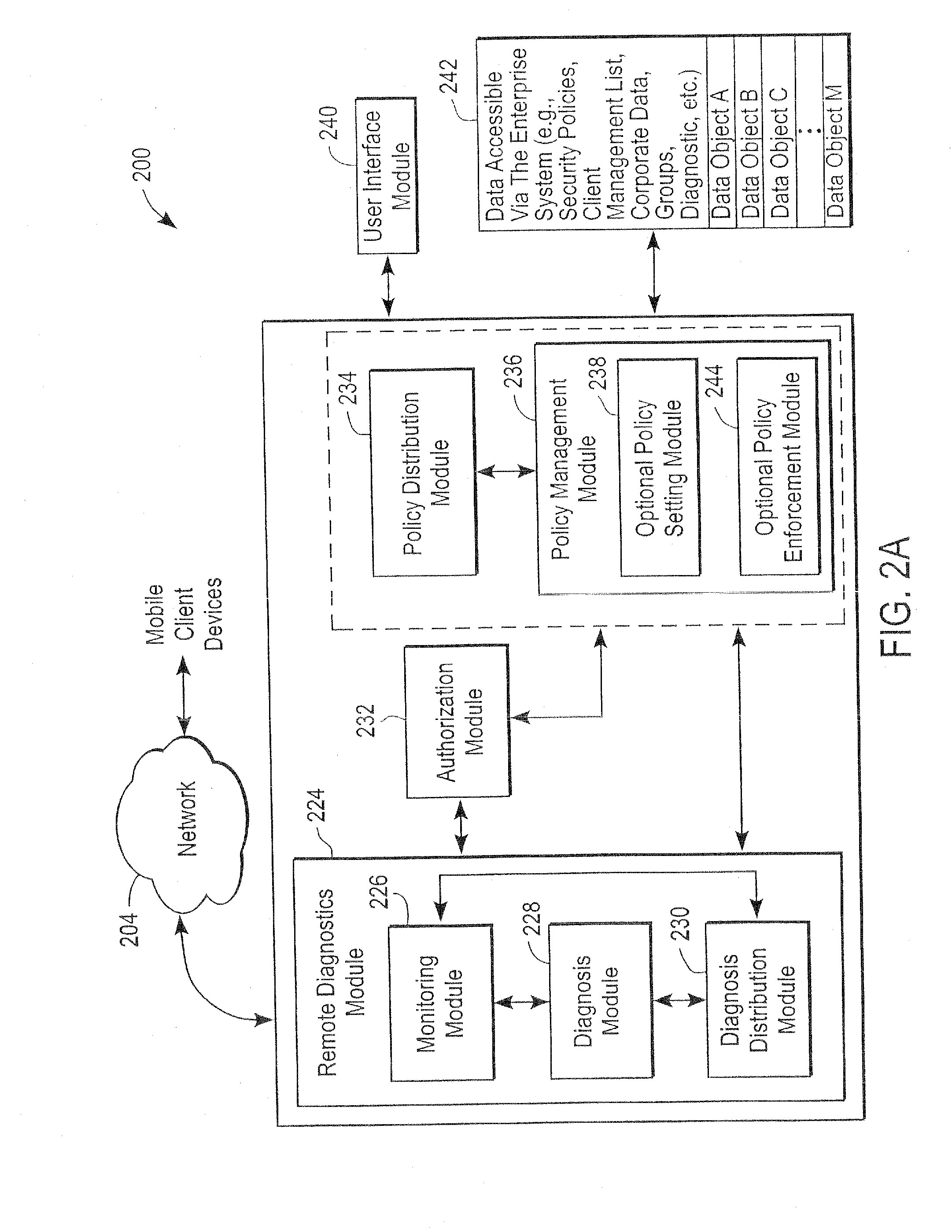
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
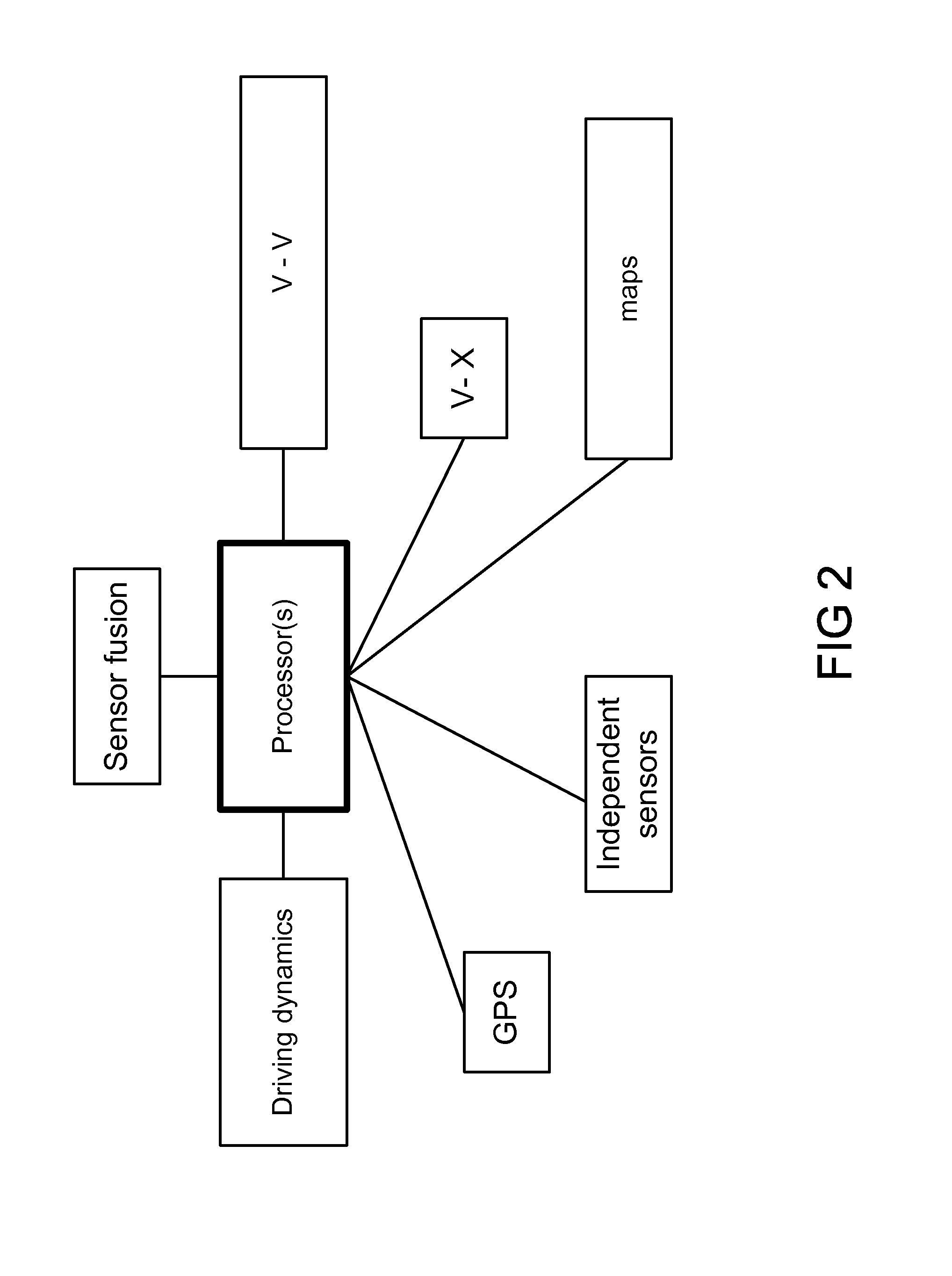
System and method for road side equipment of interest selection for active safety applications
ActiveUS20140358324A1Road vehicles traffic controlDigital data processing detailsActive safetyTraffic signal
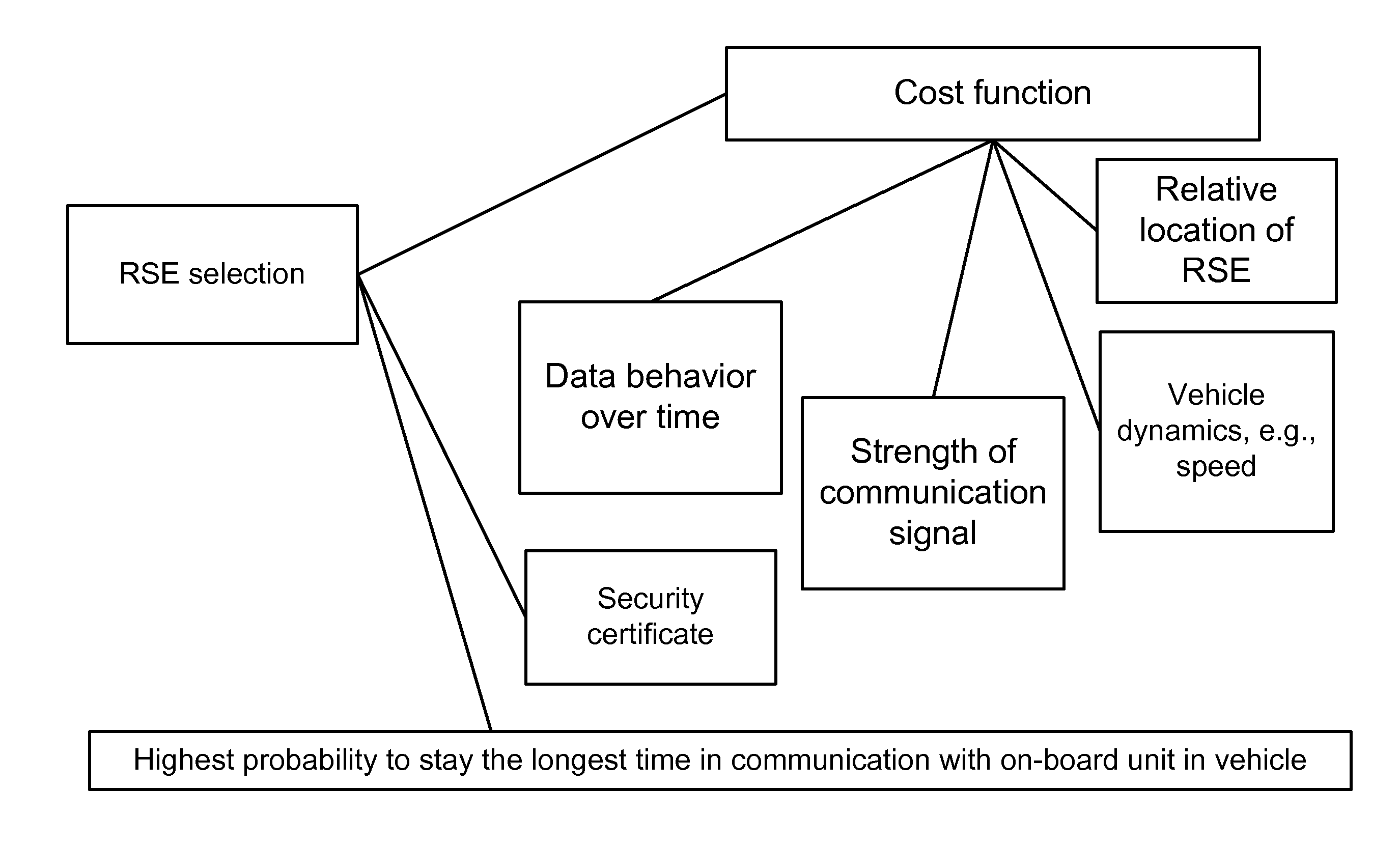
In one example, we describe a method and infrastructure for DSRC V2X (vehicle to infrastructure plus vehicle) system. In one example, some of connected vehicle applications require data from infrastructure road side equipment (RSE). Examples of such applications are road intersection safety application which mostly requires map and traffic signal phase data to perform the appropriate threat assessment. The examples given cover different dimensions of the above issue: (1) It provides methods of RSE of interest selection based solely on the derived relative geometric data between the host vehicle and the RSE's, in addition to some of the host vehicle data, such as heading. (2) It provides methods of RSE of interest selection when detailed map data is communicated or when some generic map data is available. (3) It provides methods of RSE of interest selection when other vehicles data is available. Other variations and cases are also given.
Owner:HARMAN INT IND INC
Active safety system
InactiveUS20080147277A1Minimize damageEasily damagedDigital data processing detailsPedestrian/occupant safety arrangementActive safetyControl system
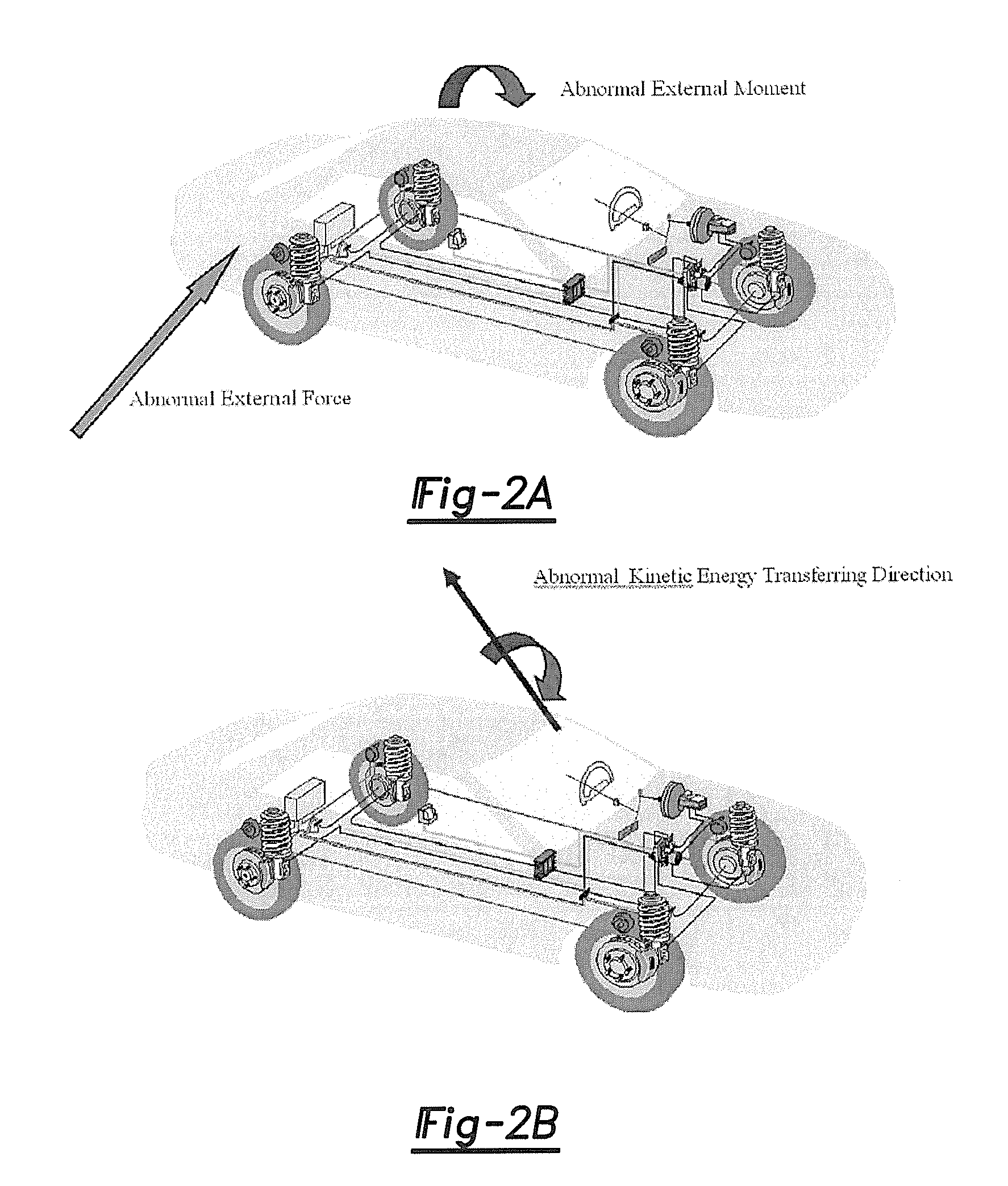
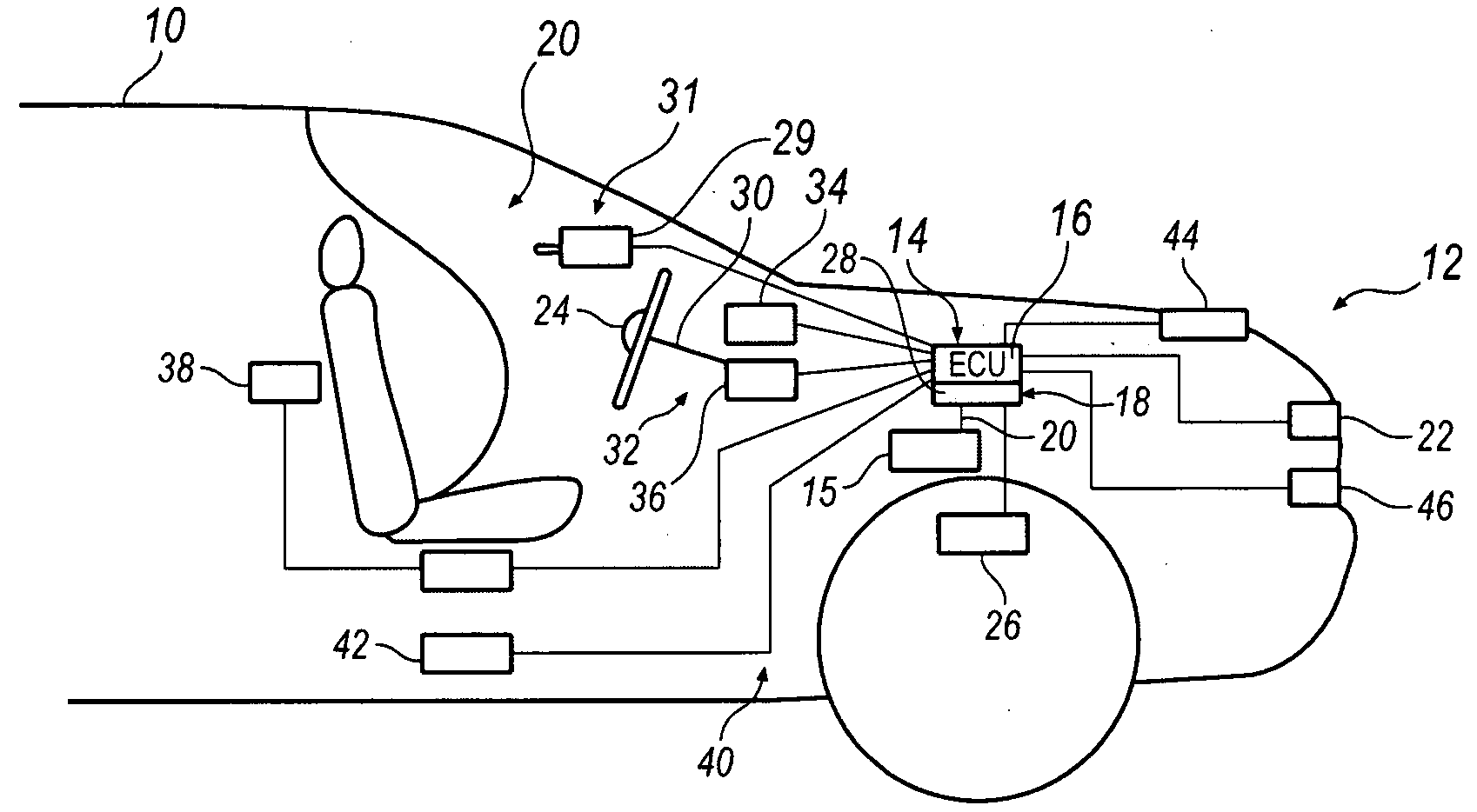
According to one embodiment, an active safety control system for a driver of a vehicle is provided when the vehicle is in a first perturbed state. The system generally includes a plurality of sensors, an actuation system and a controller. The plurality of sensors are operable to generate signals which indicate that the vehicle is in the first perturbed state. The actuation system is adapted to change driving conditions of the vehicle. The controller is configured to selectively control the actuation system in response to the signals without driver intervention to change the driving conditions of the vehicle to regain control of the vehicle after the vehicle has entered the first perturbed state.
Owner:FORD GLOBAL TECH LLC
System and method for road side equipment of interest selection for active safety applications
ActiveUS8954205B2Digital data processing detailsRoad vehicles traffic controlActive safetyTraffic signal
In one example, we describe a method and infrastructure for DSRC V2X (vehicle to infrastructure plus vehicle) system. In one example, some of connected vehicle applications require data from infrastructure road side equipment (RSE). Examples of such applications are road intersection safety application which mostly requires map and traffic signal phase data to perform the appropriate threat assessment. The examples given cover different dimensions of the above issue: (1) It provides methods of RSE of interest selection based solely on the derived relative geometric data between the host vehicle and the RSE's, in addition to some of the host vehicle data, such as heading. (2) It provides methods of RSE of interest selection when detailed map data is communicated or when some generic map data is available. (3) It provides methods of RSE of interest selection when other vehicles data is available. Other variations and cases are also given.
Owner:HARMAN INT IND INC
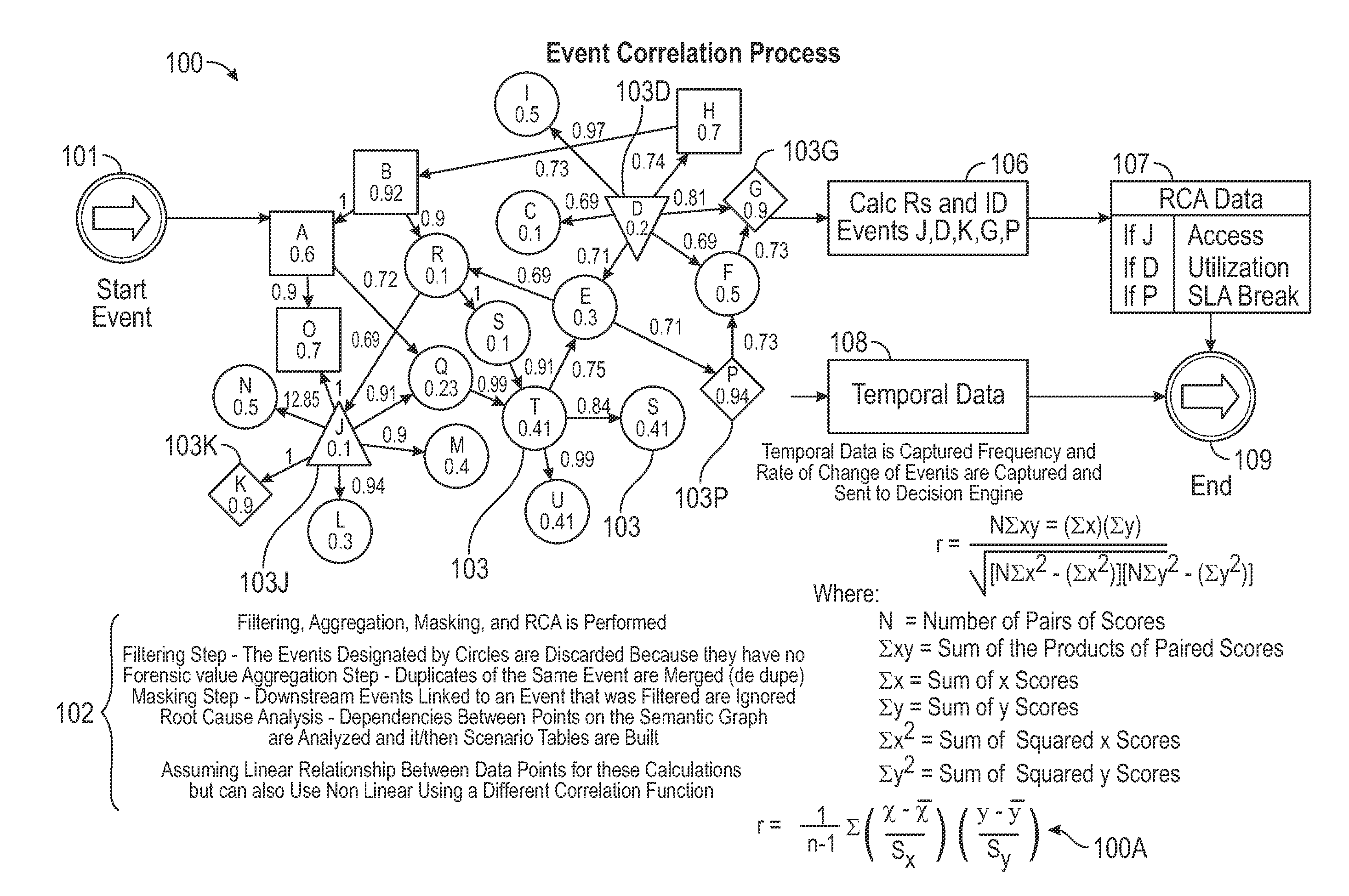
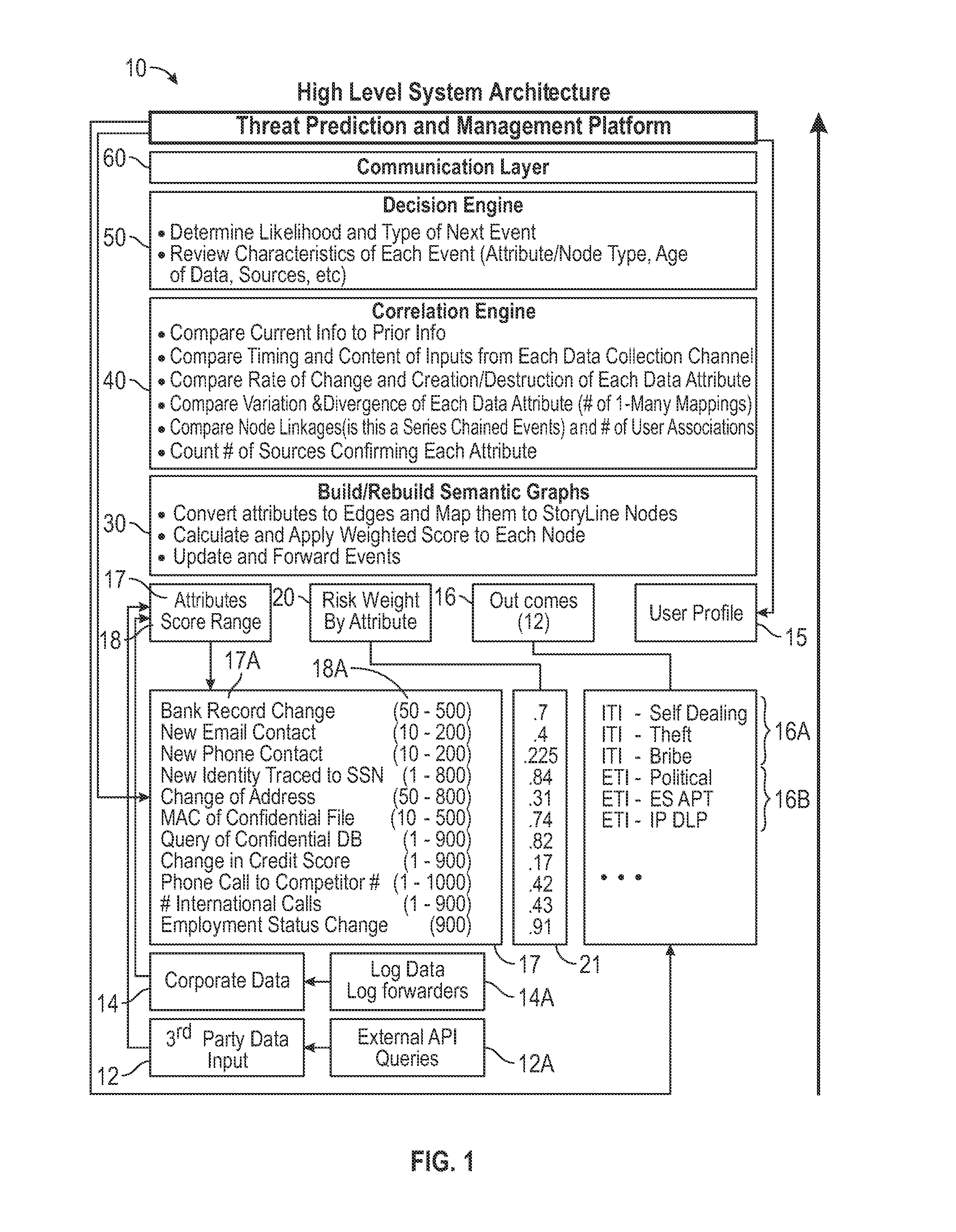
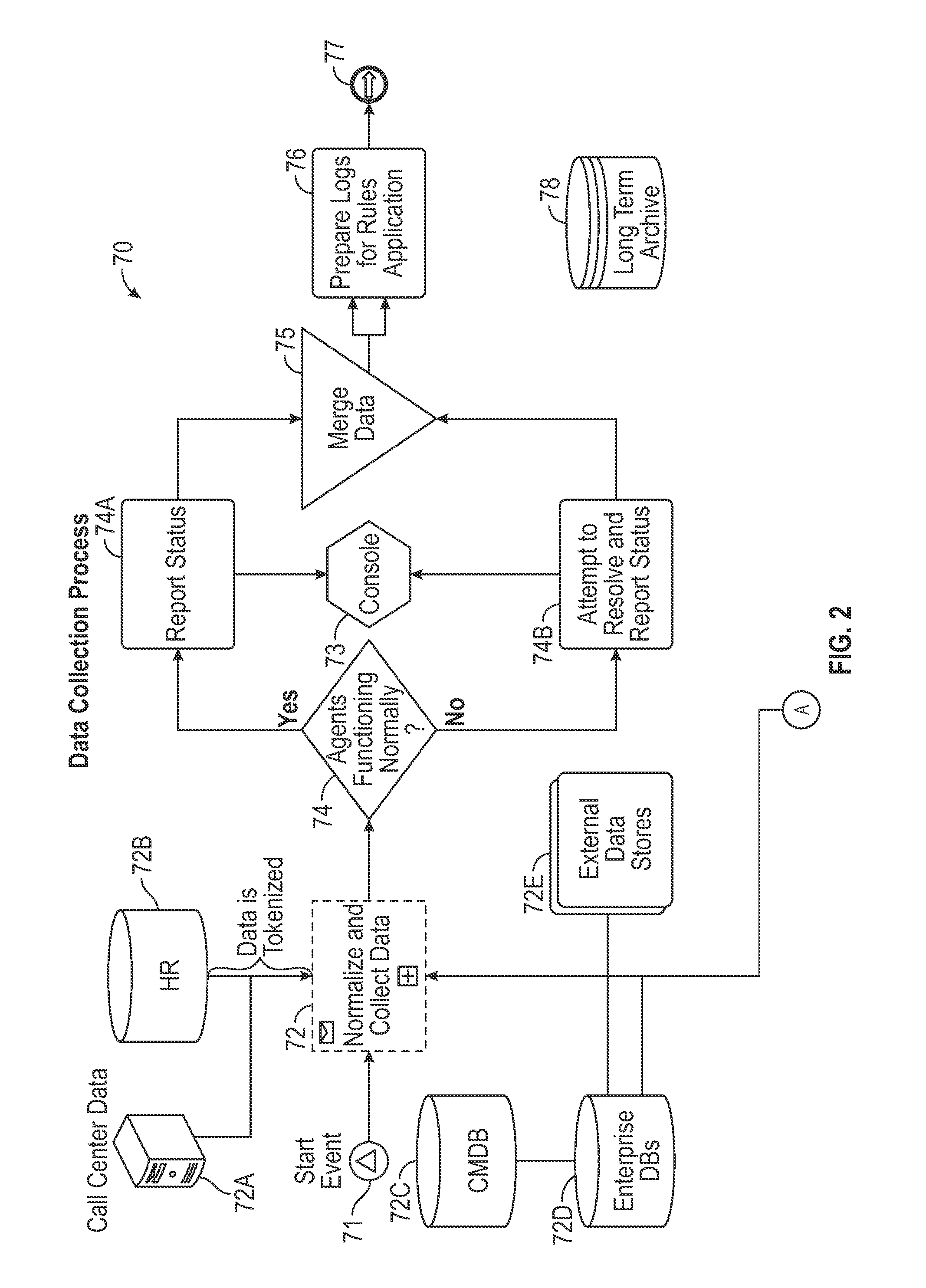
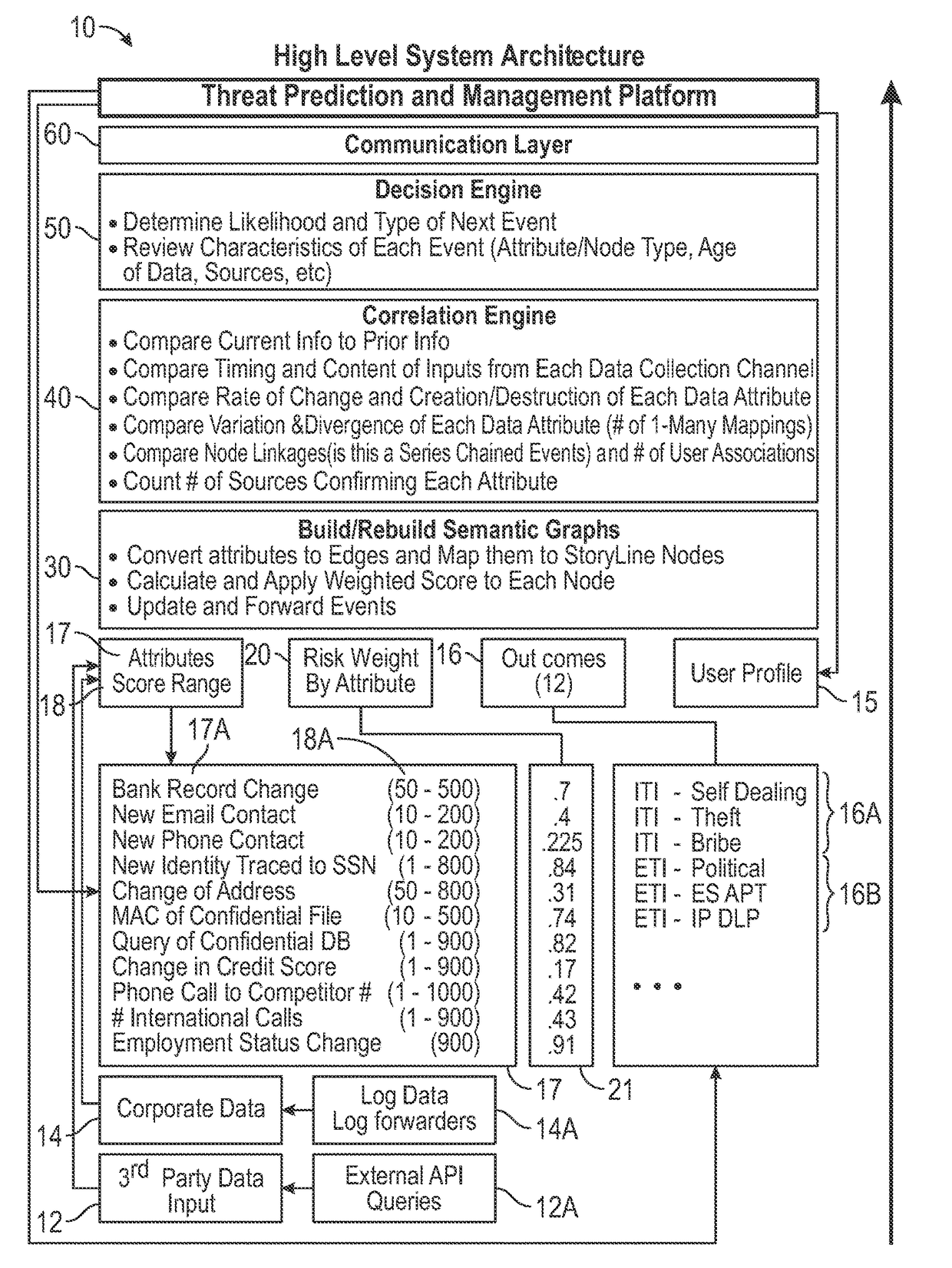
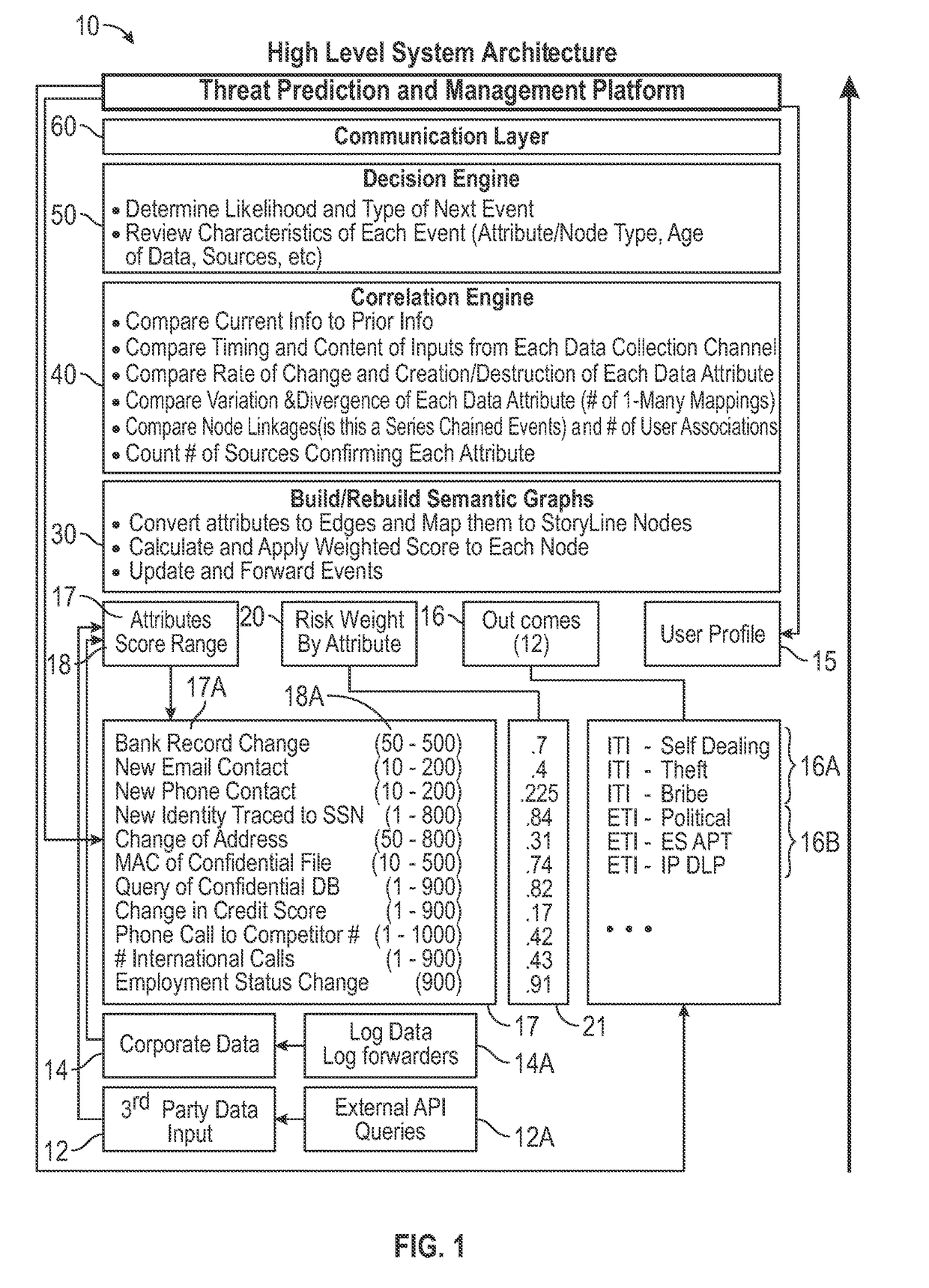
System and Method for Predicting Impending Cyber Security Events Using Multi Channel Behavioral Analysis in a Distributed Computing Environment
InactiveUS20160028758A1Parts stableImprove throughputDigital data information retrievalMemory loss protectionEarly warning systemBehavioral analytics
Multi channel distributed behavioral analysis architecture provides a software solution to the major operational challenges faced with providing an early warning system for impending cyber security events. Most cyber security events are premeditated. However, many current cyber security defense technologies only address the real-time detection of a software vulnerability, the presence of malware (known or unknown “zero day”), anomalies from pre-established data points, or the signature of an active security event. The system and method of the multi channel distributed behavioral analysis architecture introduces a technique which provides the data collection, assessment, and alerting ability prior to the occurrence of an event based on threat actor behavior.
Owner:ZITOVAULT
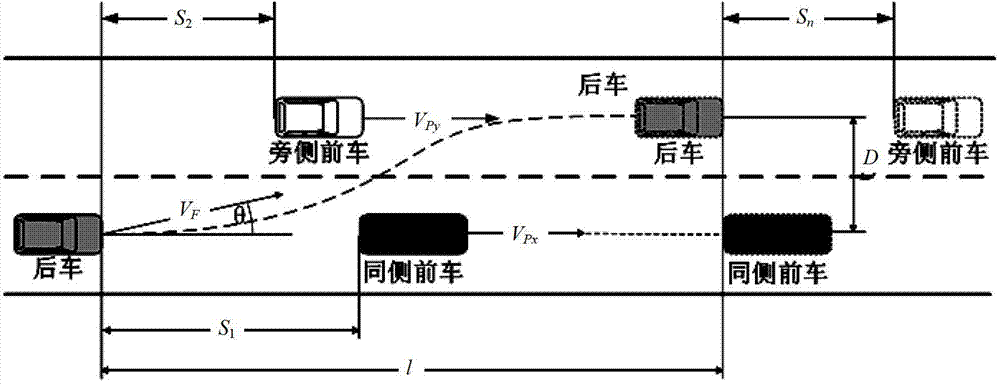
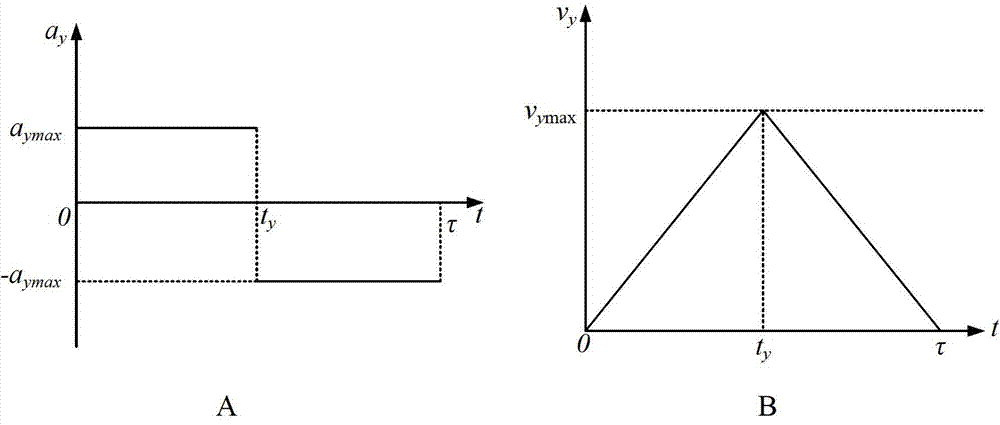
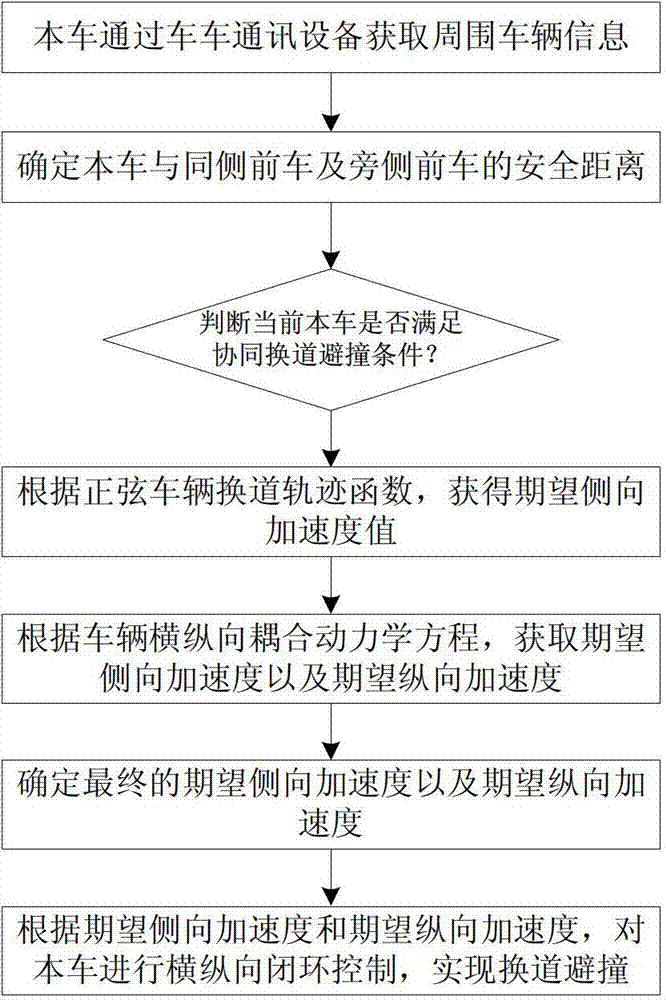
Active-lane-changing collision-avoidance control method and device based on vehicle-vehicle coordination
ActiveCN103496366AEnsure safetyAvoid security issuesExternal condition input parametersActive safetyRear-end collision
The invention provides an active-lane-changing collision-avoidance control method and device based on vehicle-vehicle coordination and belongs to the technical field of intelligent traffic / automobile active safety control. The active-lane-changing collision-avoidance control device comprises a vehicle-vehicle communication unit, a distance measuring sensor, a three-axis acceleration sensor, a vehicle speed sensor, an electronic control unit, an ESP control unit, a driver auxiliary operation unit, a tail lamp control unit and a vehicle inner warning unit. According to the active-lane-changing collision-avoidance control method, surrounding vehicle information is obtained through the vehicle-vehicle communication unit, the safety distance between a vehicle and a front vehicle on the same lane and the safety distance between the vehicle and a front vehicle on the side lane are determined; then, whether the vehicle meets the coordinated lane-changing collision-avoidance requirement is judged, if yes, the expectant lateral and the longitudinal acceleration of the vehicle is calculated, and control over the direction and the speed of the vehicle are conducted, and if not, lane-changing danger warning is conducted. By the adoption of the active-lane-changing collision-avoidance control method and device based on vehicle-vehicle coordination, active-lane-changing collision-avoidance control is achieved, driver safety accidents caused by emergency brake and rear-end collision accidents caused by emergency brake can be avoided, manual operation errors are avoided, and the safety of driving the vehicle is guaranteed.
Owner:北京踏歌智行科技有限公司
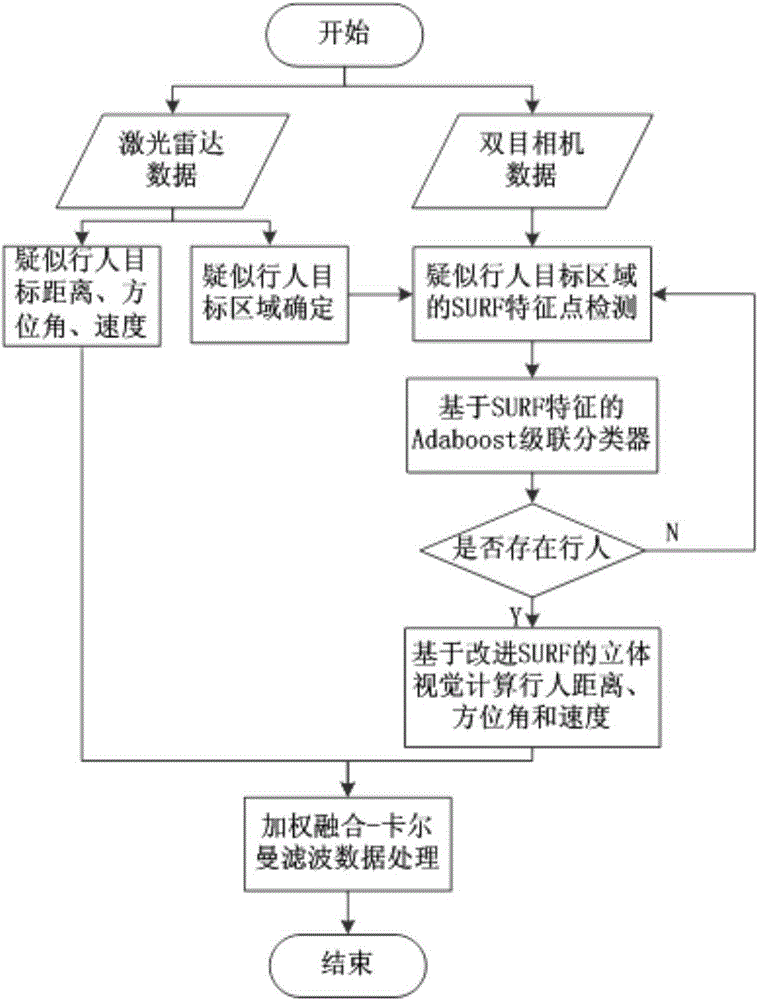
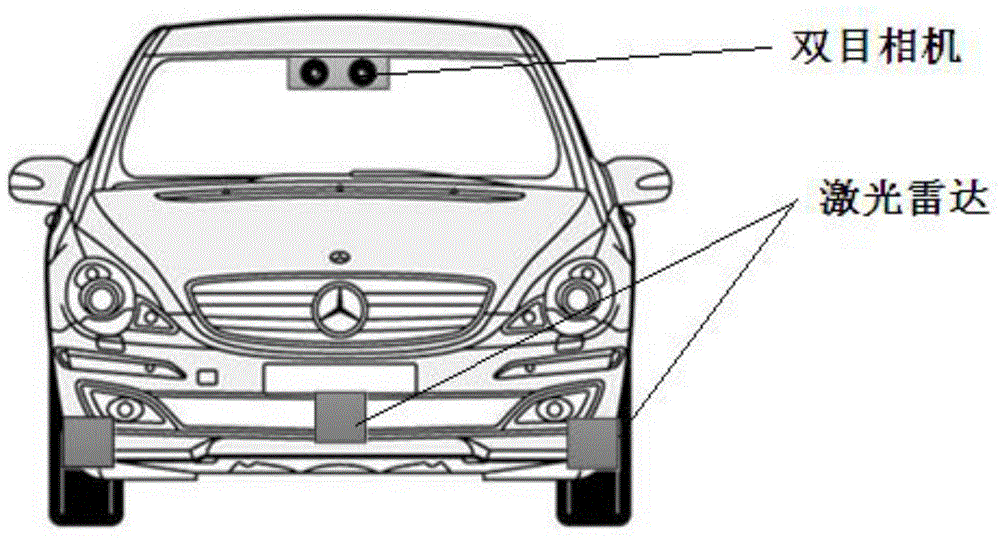
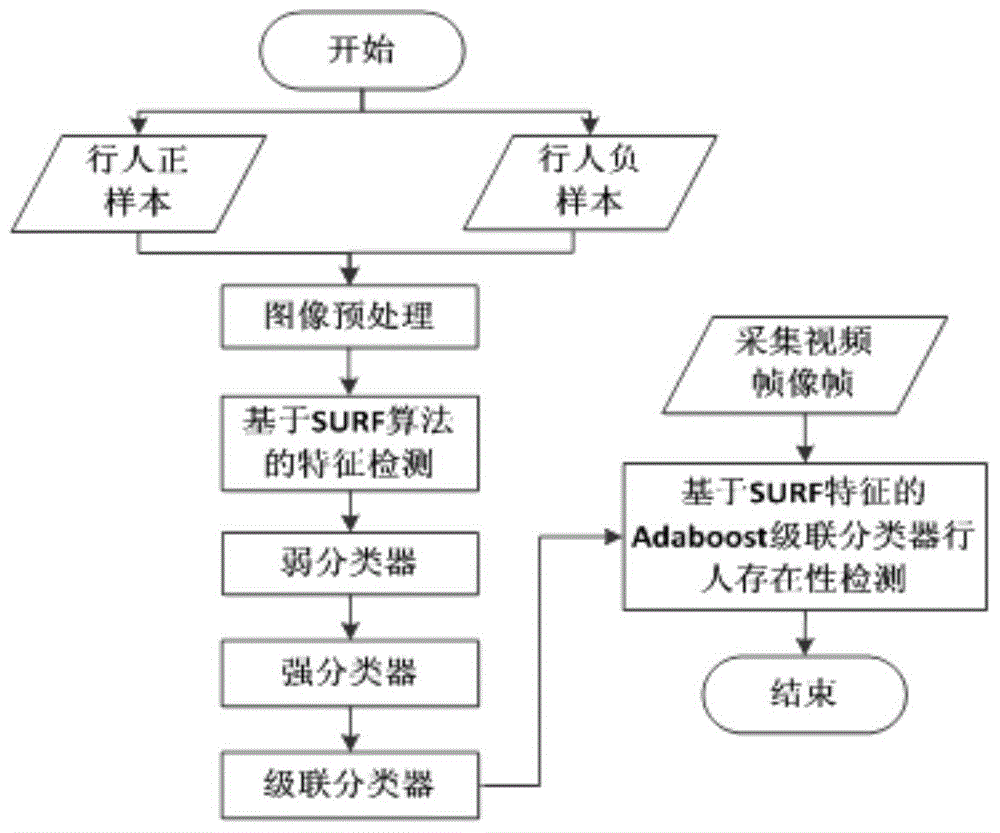
Detection method and system, based on laser radar and binocular camera, for pedestrian in front of vehicle
ActiveCN104573646AHigh measurement accuracyThe data is accurate and completeCharacter and pattern recognitionActive safetyVisual perception
The invention belongs to the field vehicle active safety, and particularly discloses a detection method and system, based on laser radar and binocular camera, for a pedestrian in front of vehicle. The method comprises the following steps: collection data of the front of the vehicle through the laser radar and the binocular camera; respectively processing the data collected by the laser radar and the binocular camera, so as to obtain the distance, azimuth angle and speed value of the pedestrian relative to the vehicle; correcting the information of the pedestrian through a Kalman filter. The method comprehensively utilizes a stereoscopic vision technology and a remote sensing technology, integrates laser radar and binocular camera information, is high in measurement accuracy and pedestrian detection accuracy, and can effectively reduce the occurrence rate of traffic accidents.
Owner:CHANGAN UNIV
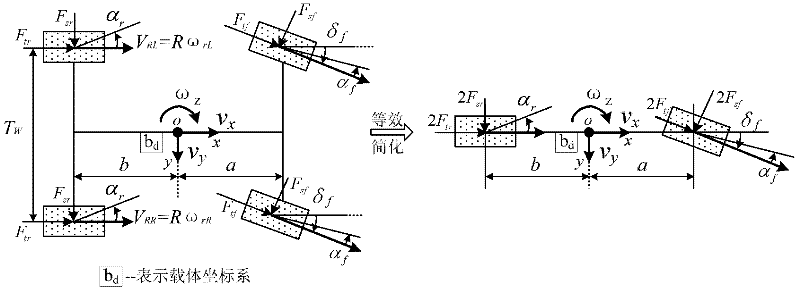
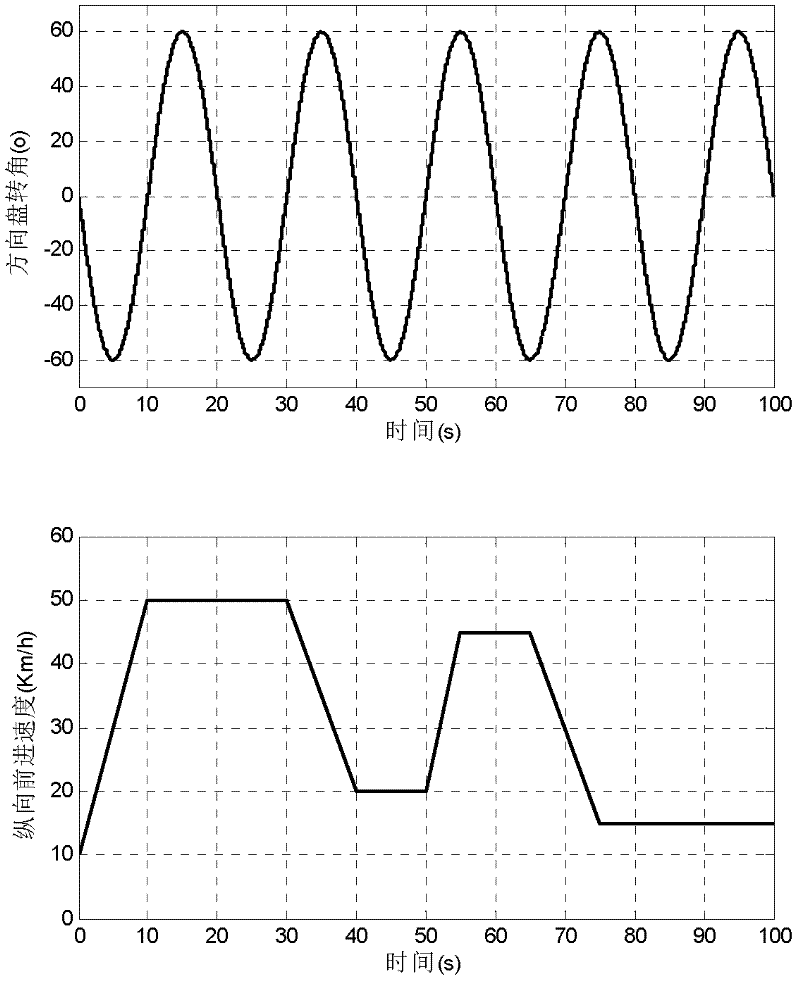
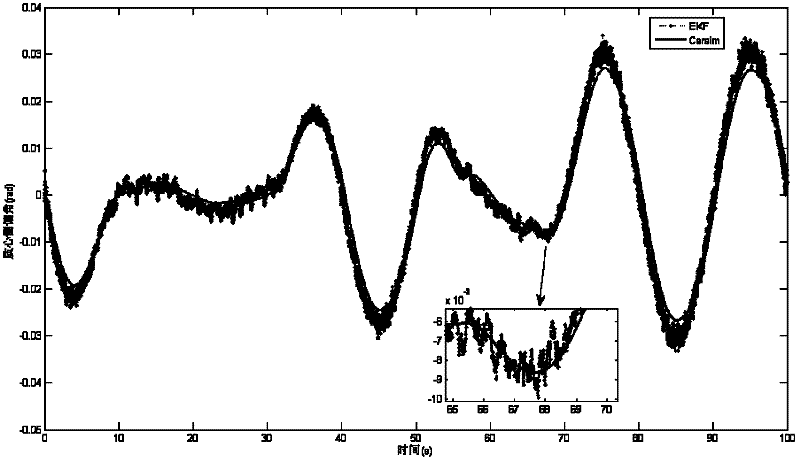
Vehicle operating state estimation method based on improved extended Kalman filter
A vehicle operating state estimation method based on improved extended Kalman filter includes using the improved extended Kalman filter algorithm for properly modeling to acquire operating state information such as longitudinal forward speed, yaw velocity, lateral speed, side slip angle and the like of a vehicle in a higher maneuvering operating state, wherein the information can be used for relevant control of vehicle active safety. The vehicle operating state estimation method based on improved extended Kalman filter has the advantages of high precision, low cost, high instantaneity and the like.
Owner:SOUTHEAST UNIV
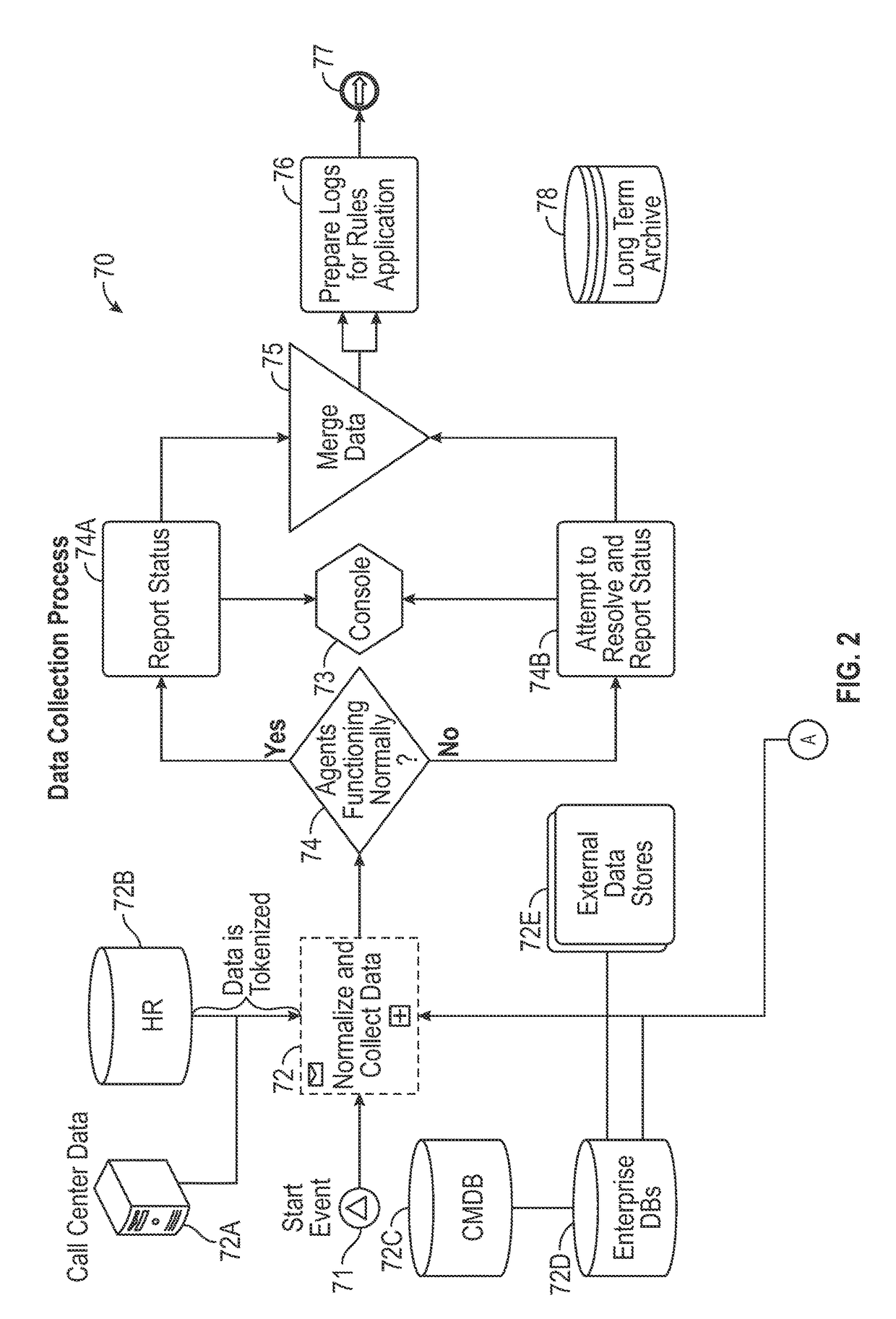
Method and system for improving computer network security
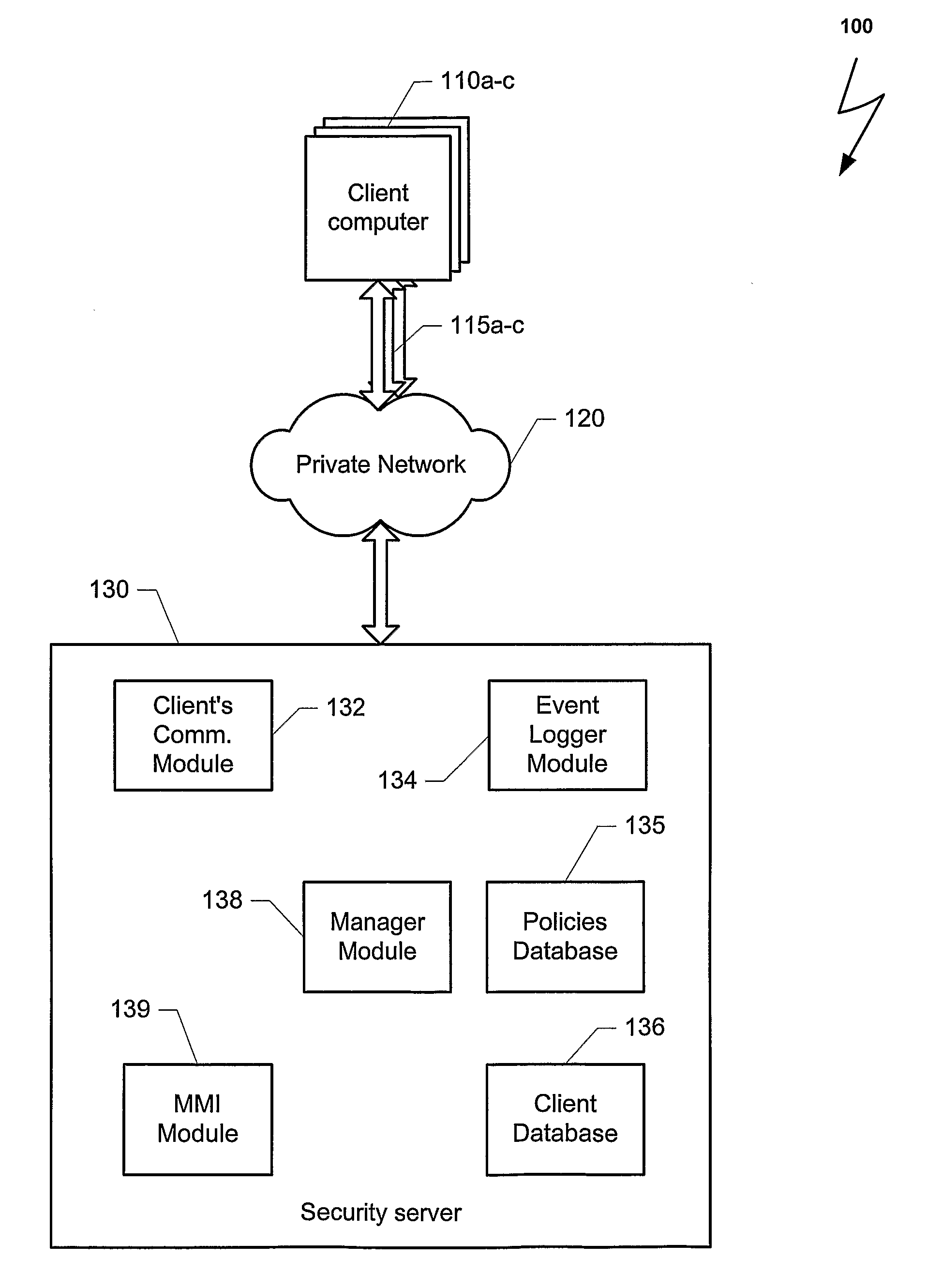
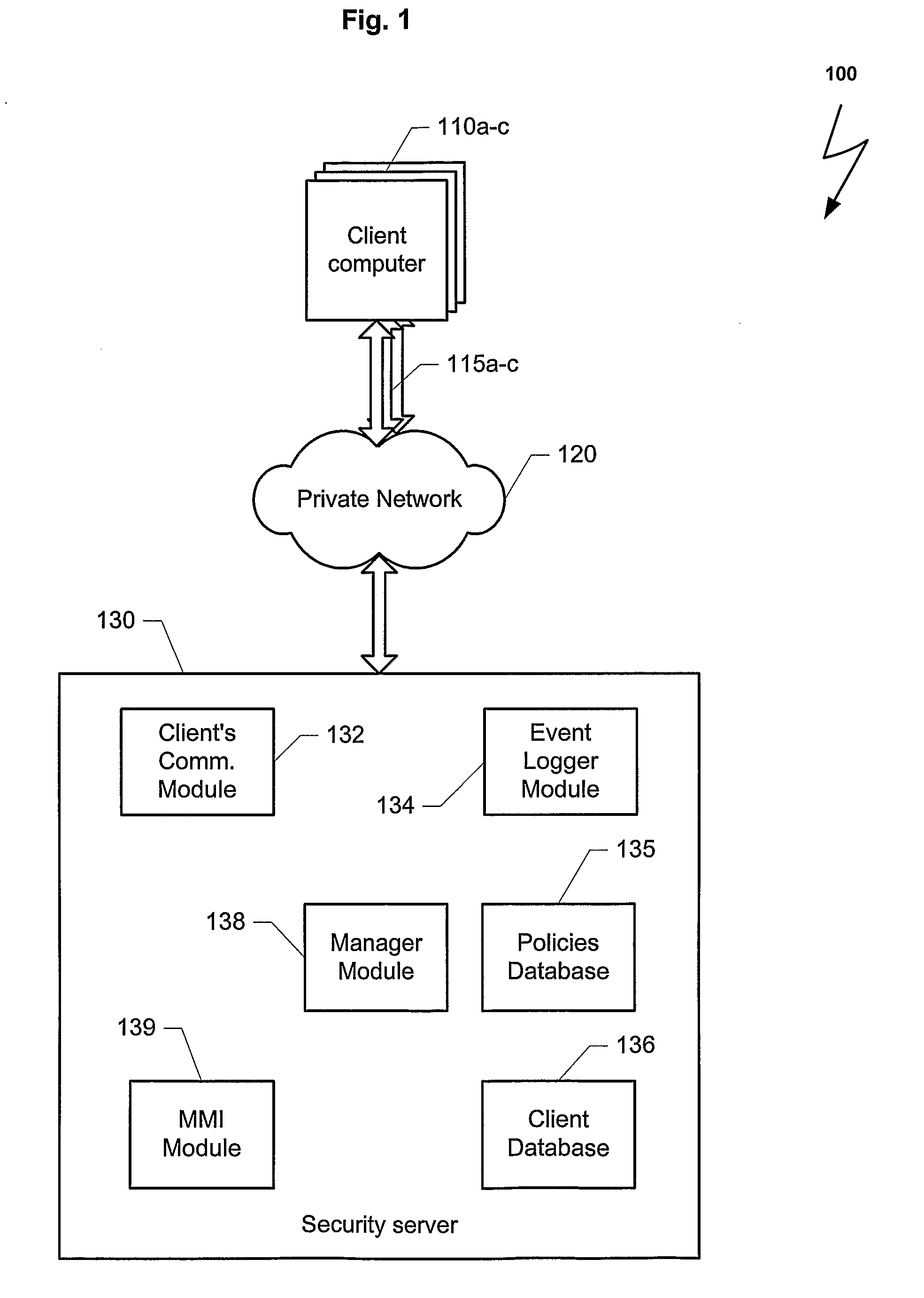
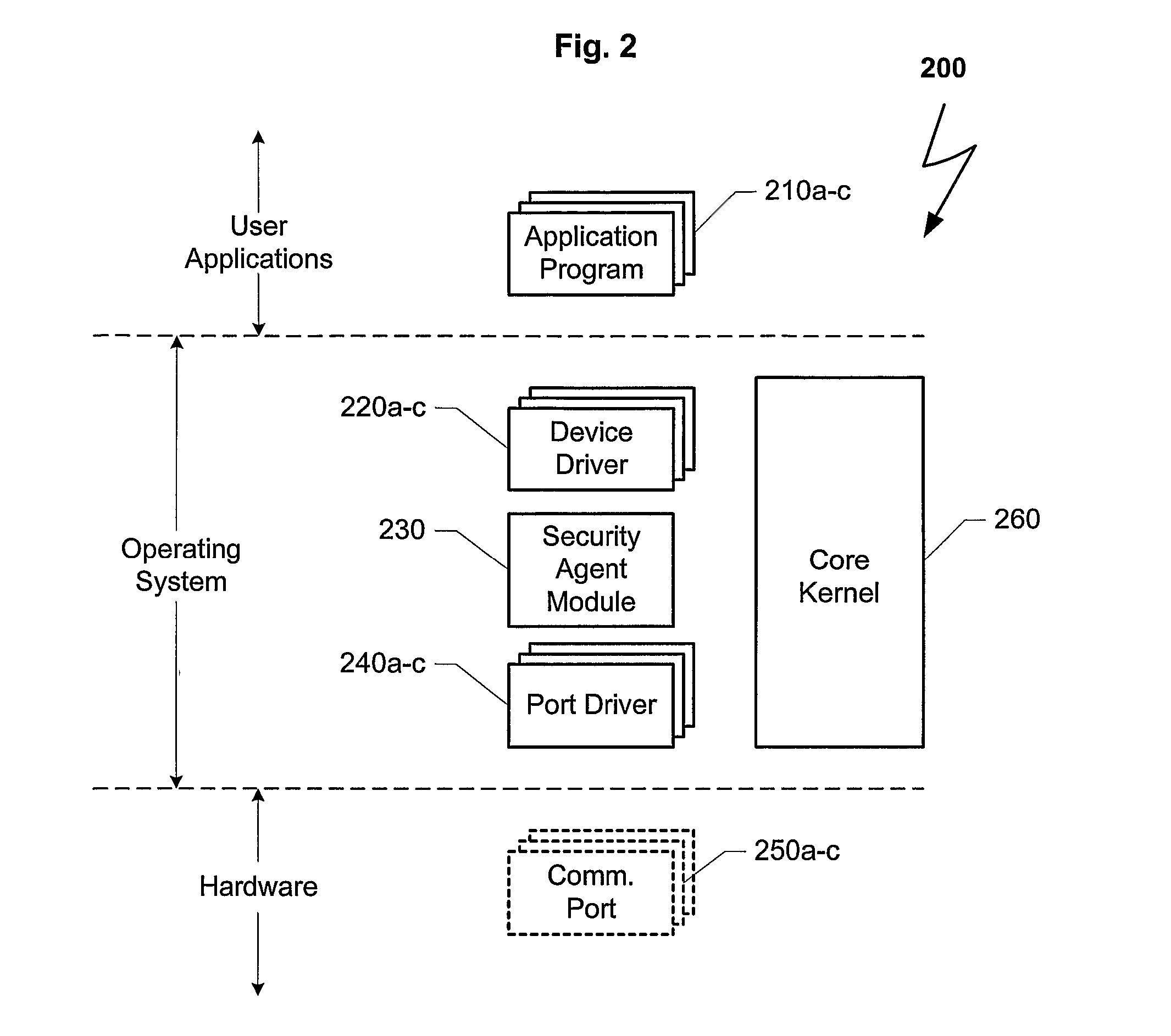
Computers connected to a private network are monitored and controlled through the use of a client agent that operates in association with the computer and a server client that establishing security parameters, privileges and authorizations for the computer. The invention can prevent access to certain devices according to an active security policy. Any activity of the computer, such as a request to transfer data to an external device, access a particular file, etc. is monitored and controlled by the client agent. No operations or procedures are allowed by the computer inconsistent with the active security policy. The security policy may be set by the administrator of the private network according to the user rights and position in the organization
Owner:SUPERCOM IP LLC
Administration of protection of data accessible by a mobile device
InactiveUS20080046965A1Multiple digital computer combinationsDigital data authenticationAnti virusClient-side
Owner:APPLE INC
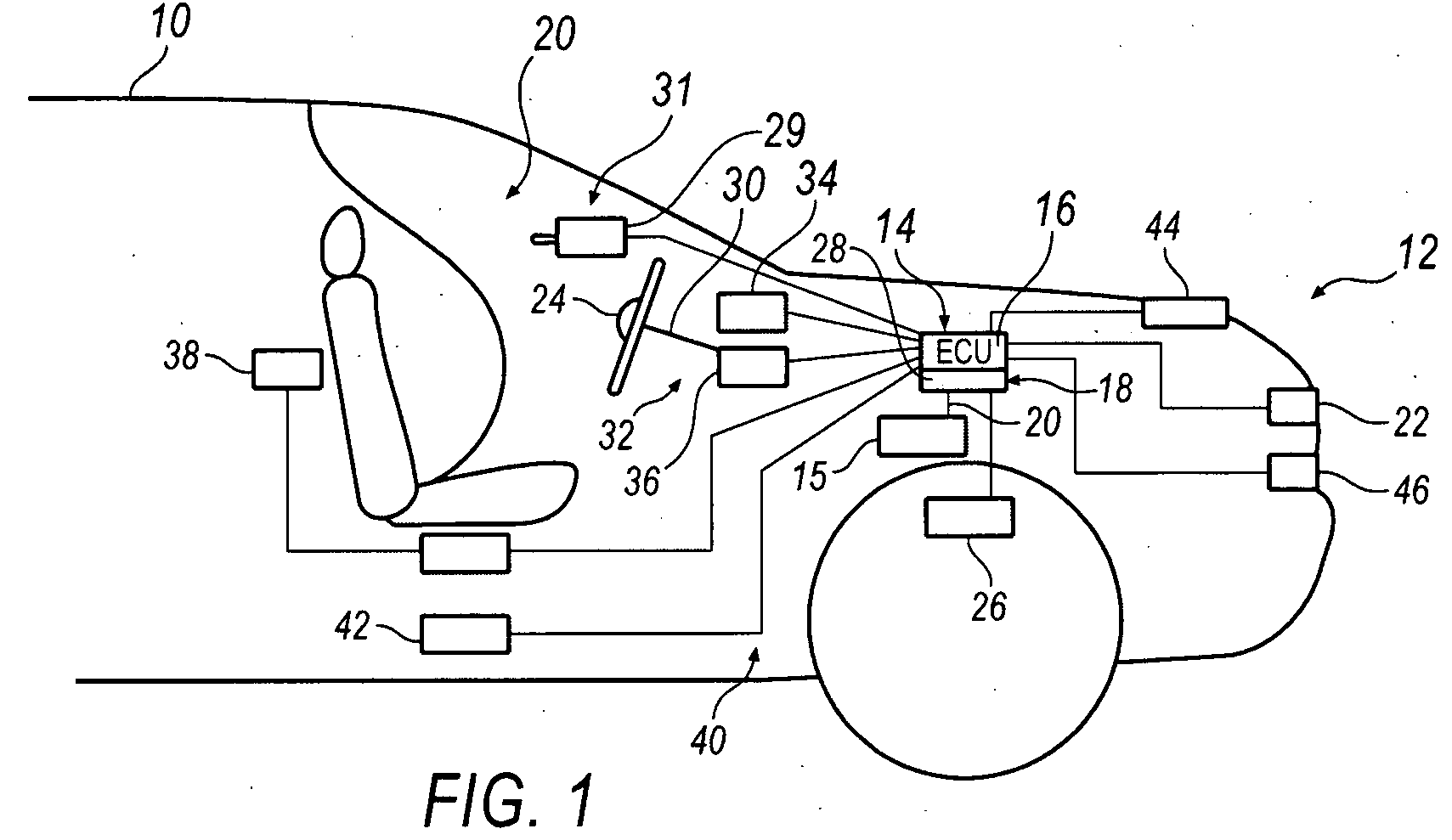
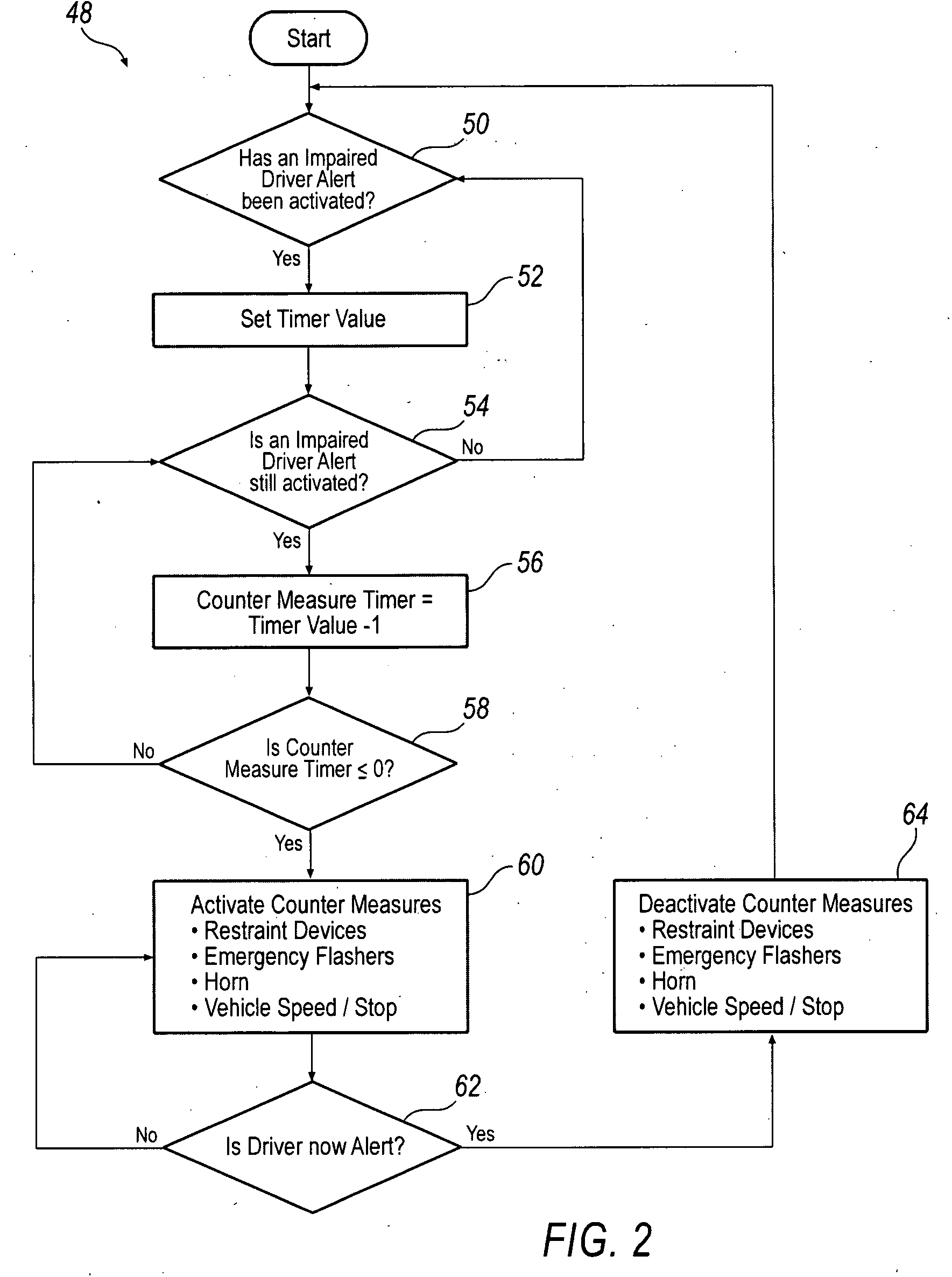
System and method for implementing active safety counter measures for an impaired driver
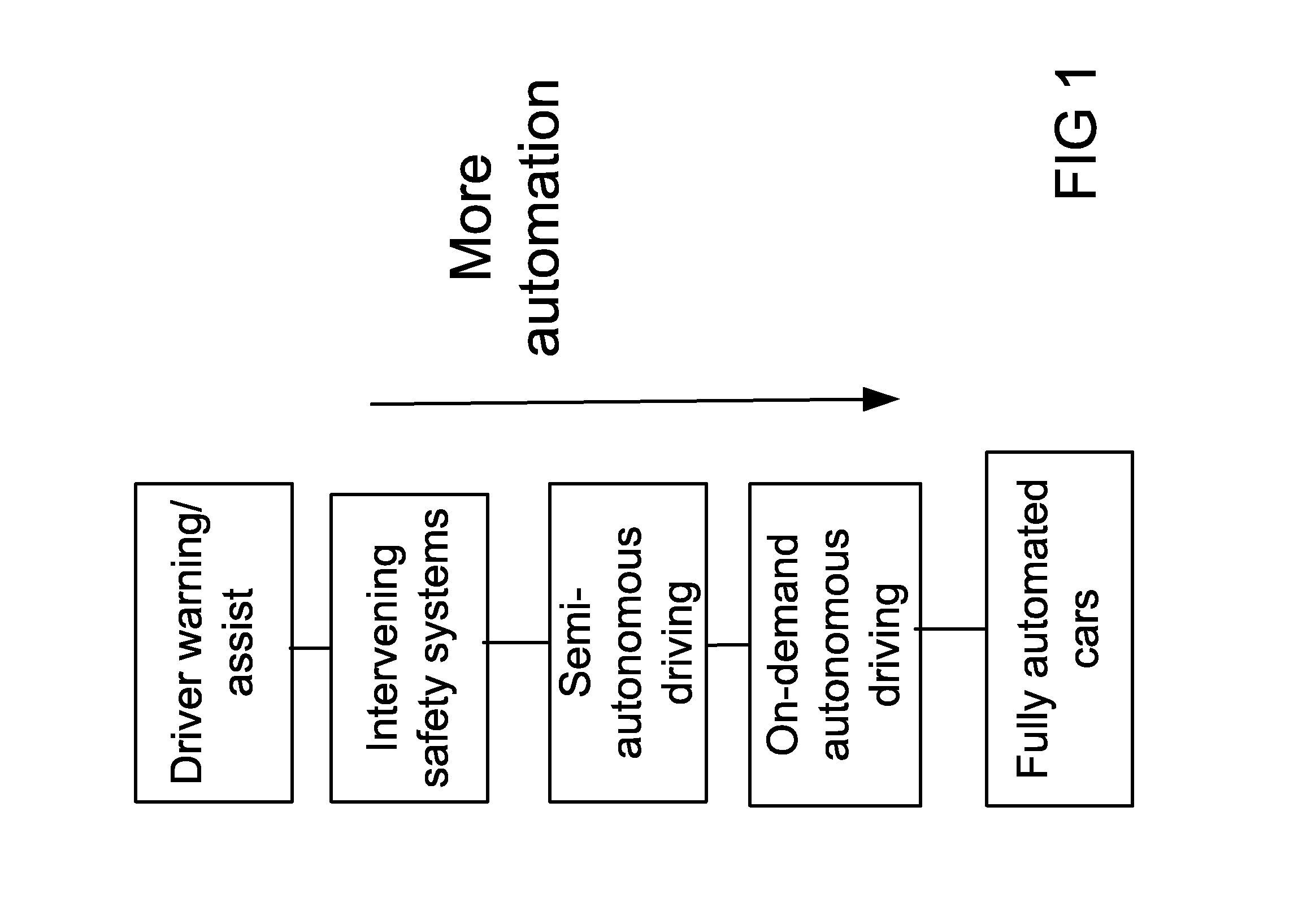
Various methods and systems are disclosed for implementing active safety countermeasures in vehicles when it is determined that the driver is impaired.
Owner:FORD GLOBAL TECH LLC
Sensor alignment process and tools for active safety vehicle applications
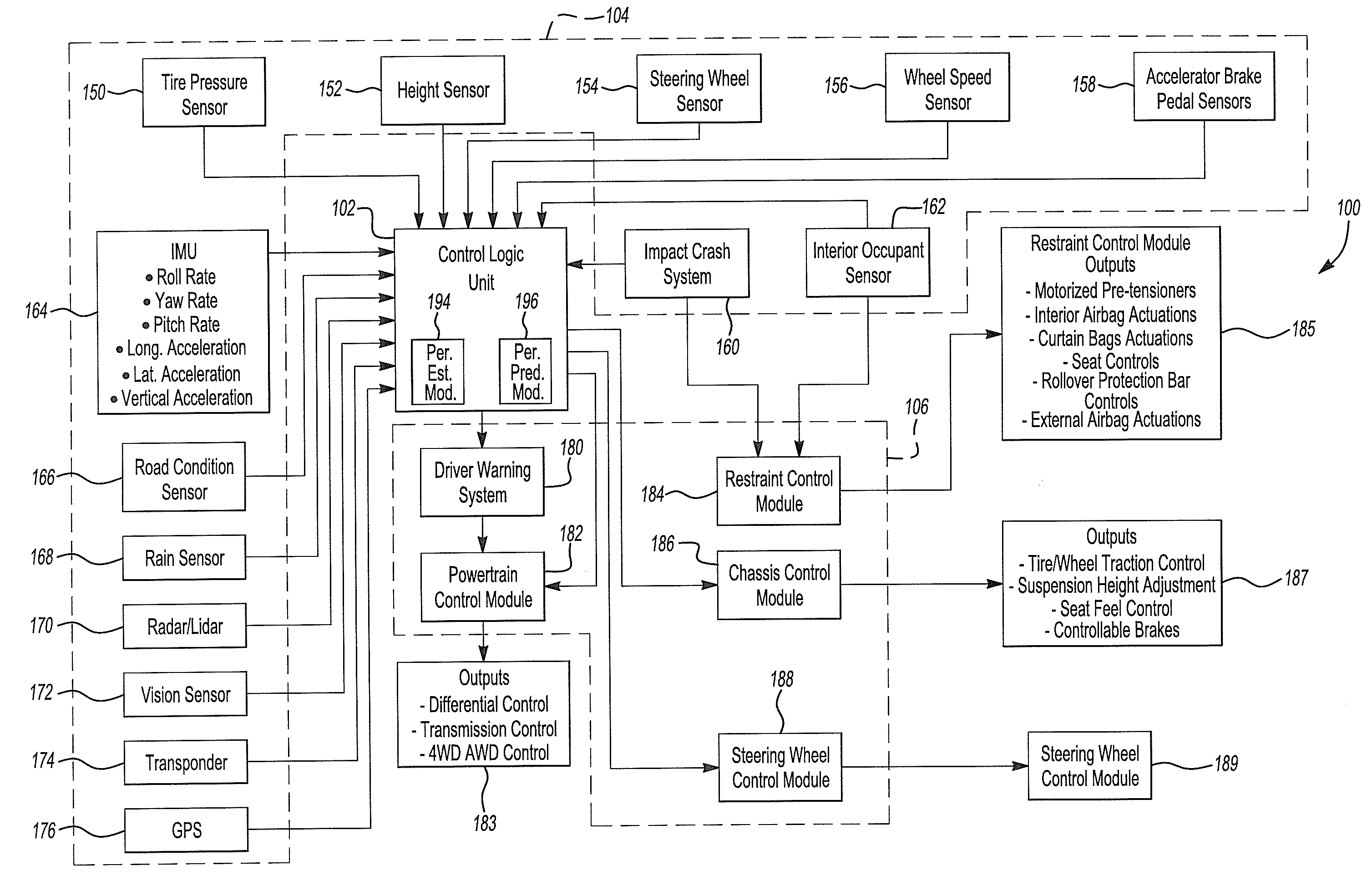
A method and tools for virtually aligning object detection sensors on a vehicle without having to physically adjust the sensors. A sensor misalignment condition is detected during normal driving of a host vehicle by comparing different sensor readings to each other. At a vehicle service facility, the host vehicle is placed in an alignment target fixture, and alignment of all object detection sensors is compared to ground truth to determine alignment calibration parameters. Alignment calibration can be further refined by driving the host vehicle in a controlled environment following a leading vehicle. Final alignment calibration parameters are authorized and stored in system memory, and applications which use object detection data henceforth adjust the sensor readings according to the calibration parameters.
Owner:GM GLOBAL TECH OPERATIONS LLC
Novel sensor alignment process and tools for active safety vehicle applications
InactiveUS20120290169A1Vehicle testingRegistering/indicating working of vehiclesGround truthActive safety
A method and tools for virtually aligning object detection sensors on a vehicle without having to physically adjust the sensors. A sensor misalignment condition is detected during normal driving of a host vehicle by comparing different sensor readings to each other. At a vehicle service facility, the host vehicle is placed in an alignment target fixture, and alignment of all object detection sensors is compared to ground truth to determine alignment calibration parameters. Alignment calibration can be further refined by driving the host vehicle in a controlled environment following a leading vehicle. Final alignment calibration parameters are authorized and stored in system memory, and applications which use object detection data henceforth adjust the sensor readings according to the calibration parameters.
Owner:GM GLOBAL TECH OPERATIONS LLC
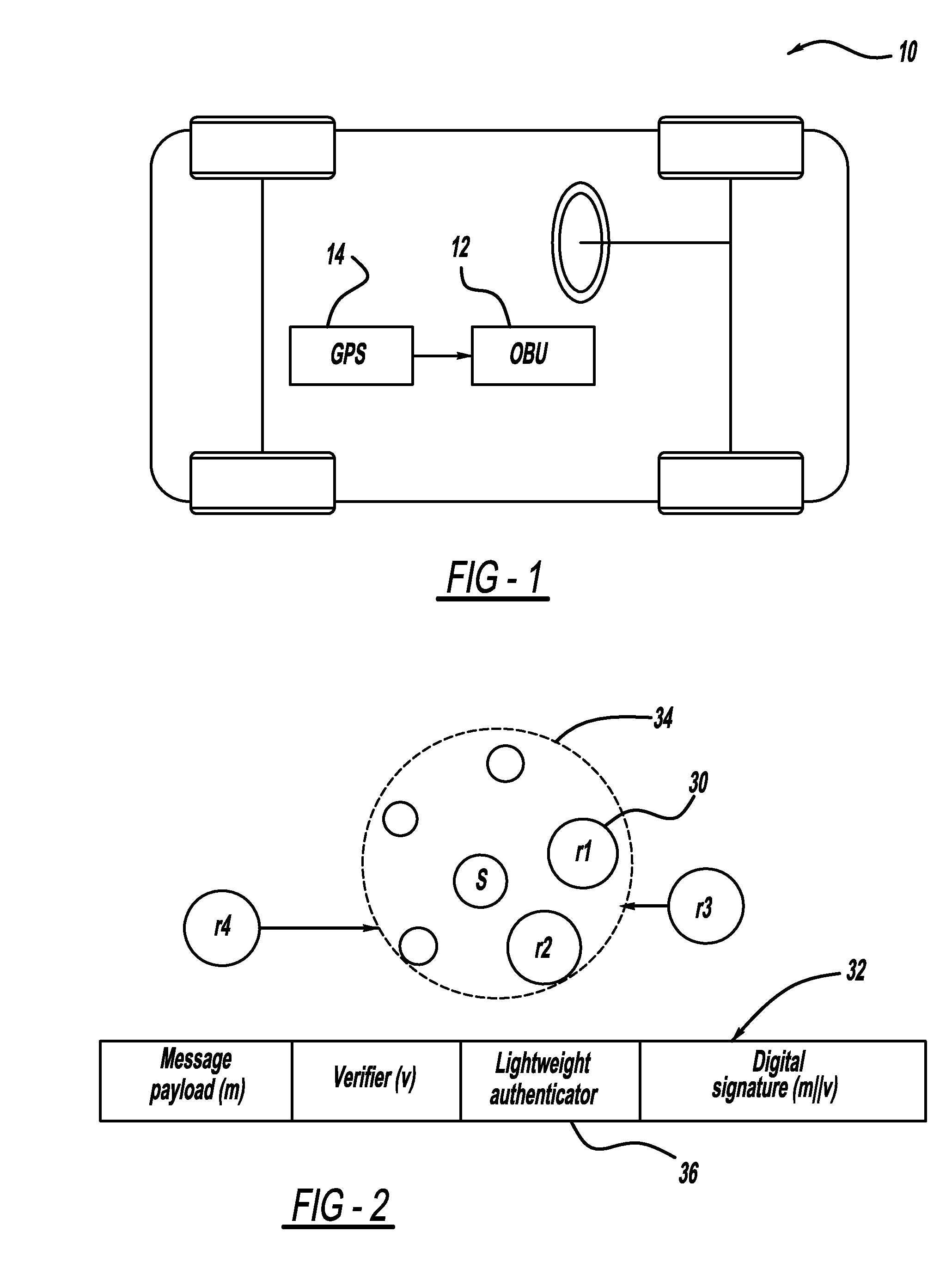
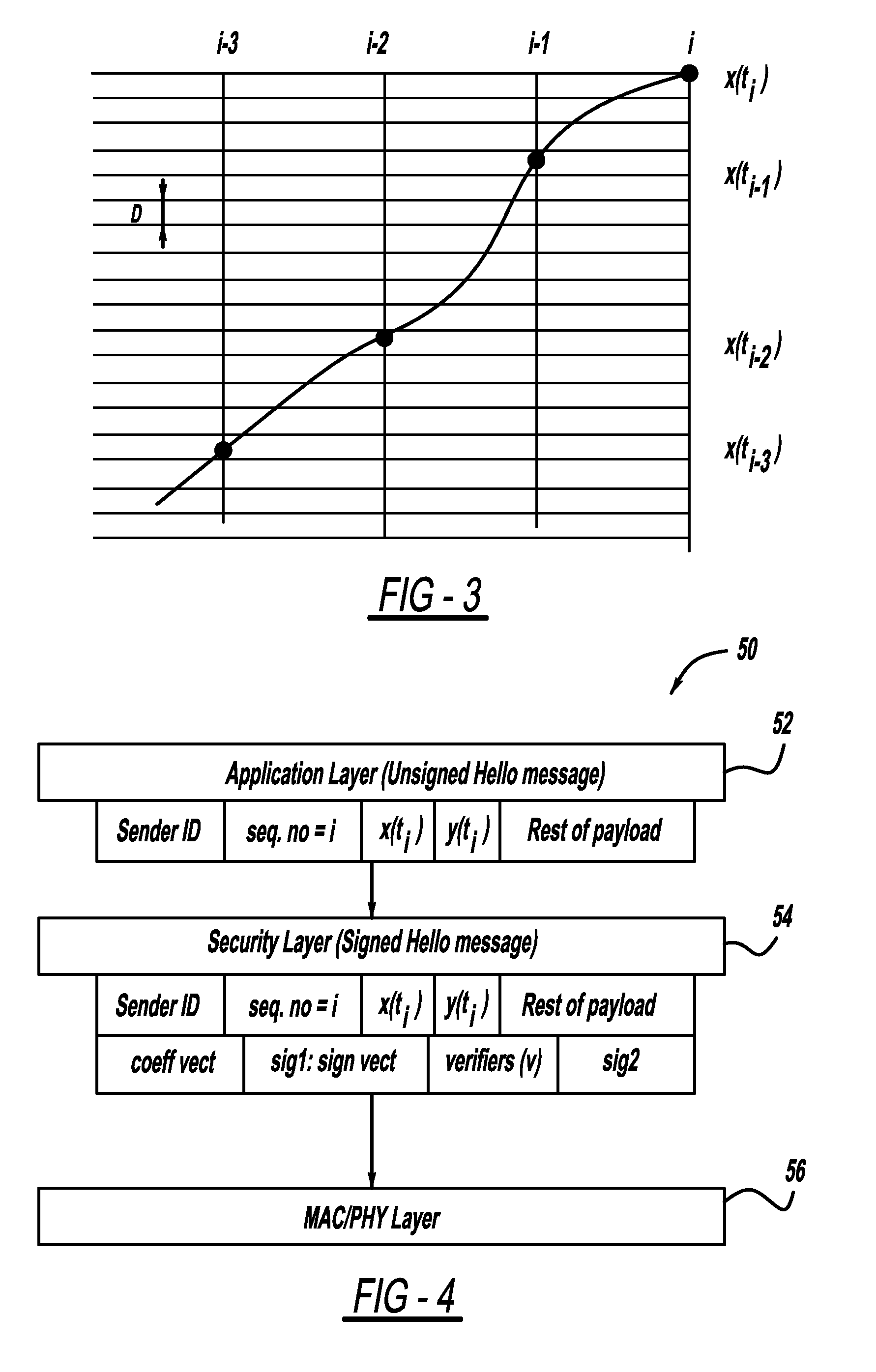
Lightweight geographic trajectory authentication via one-time signatures
InactiveUS20090254754A1User identity/authority verificationAnti-collision systemsActive safetyCommunications system
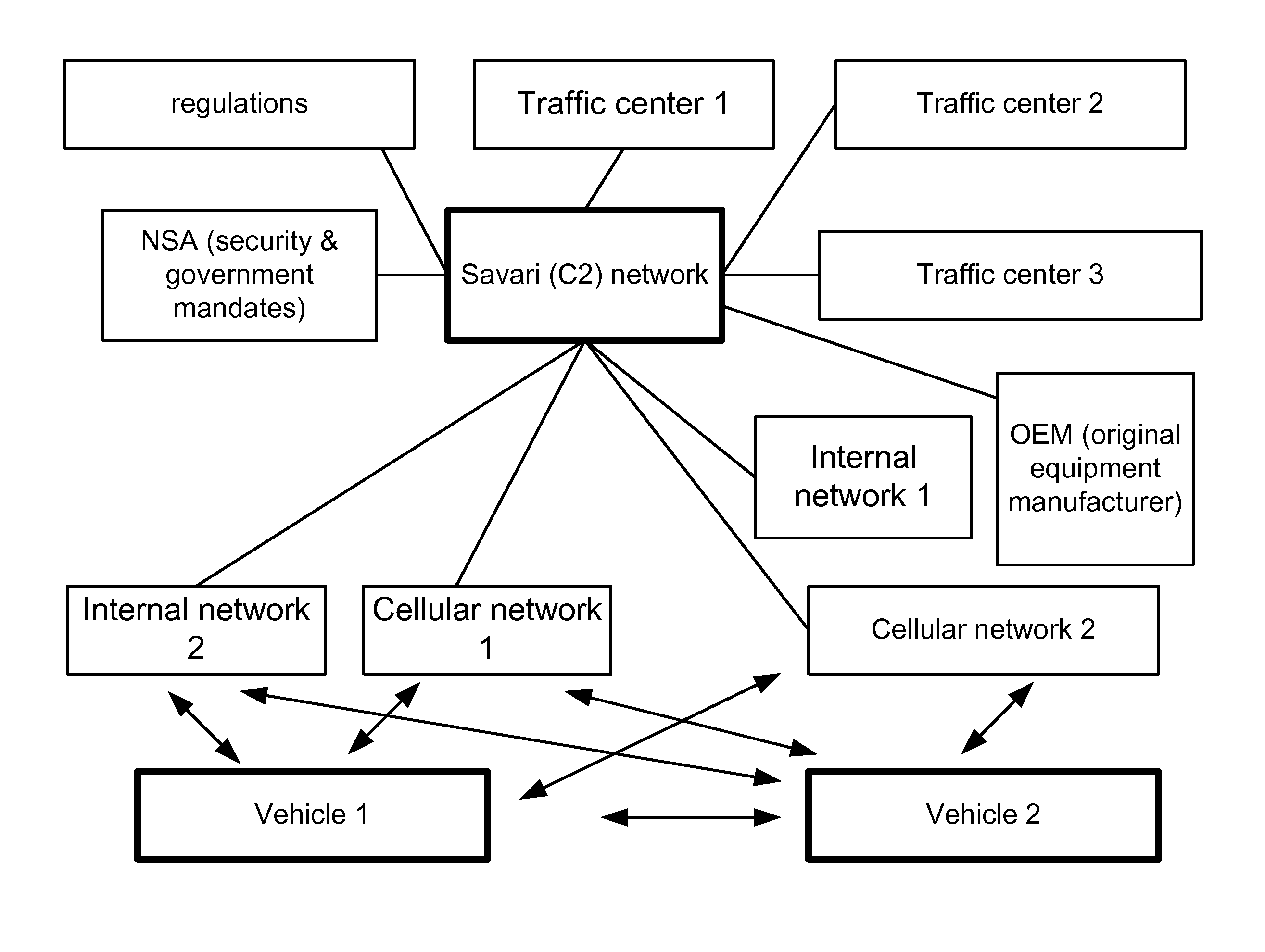
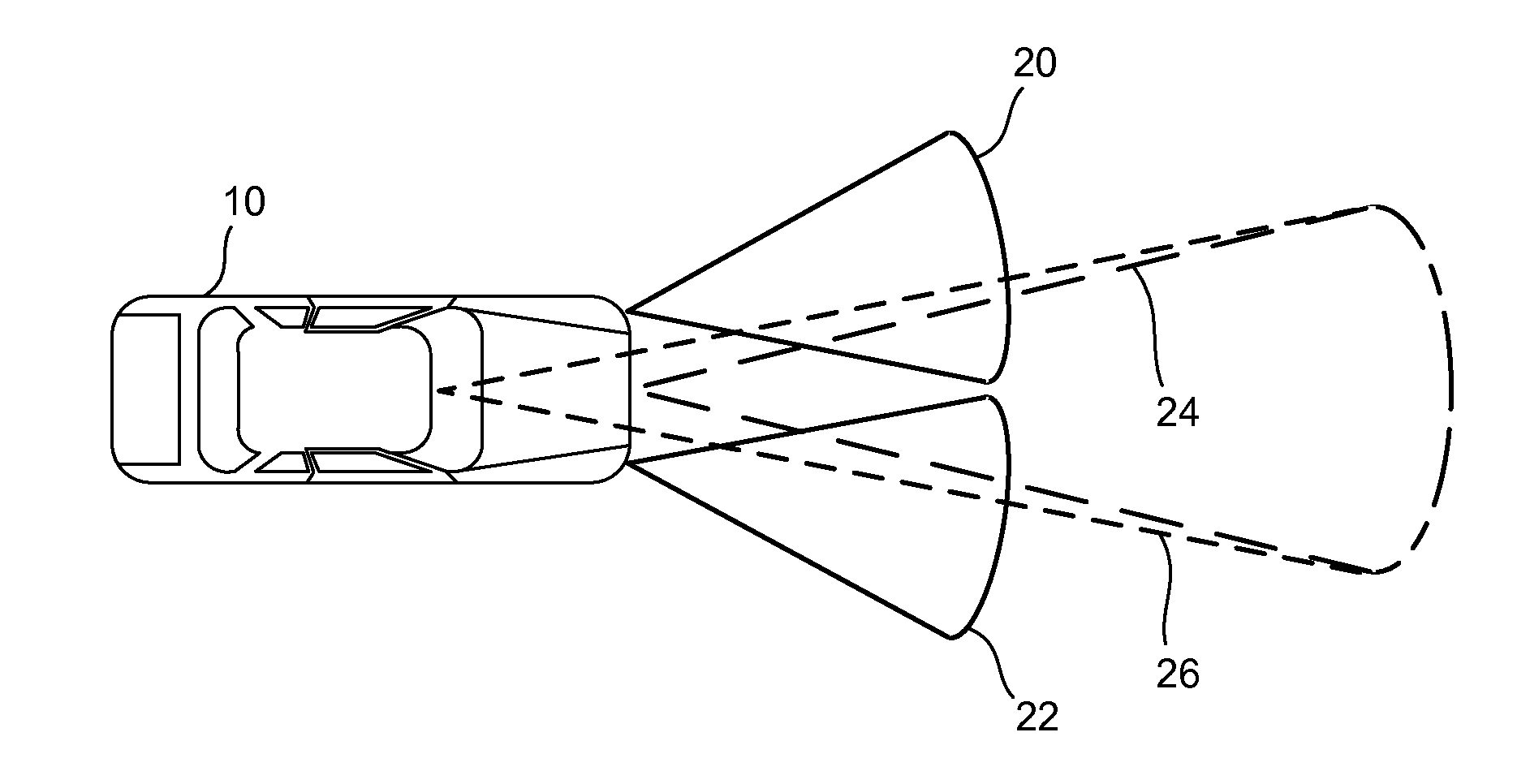
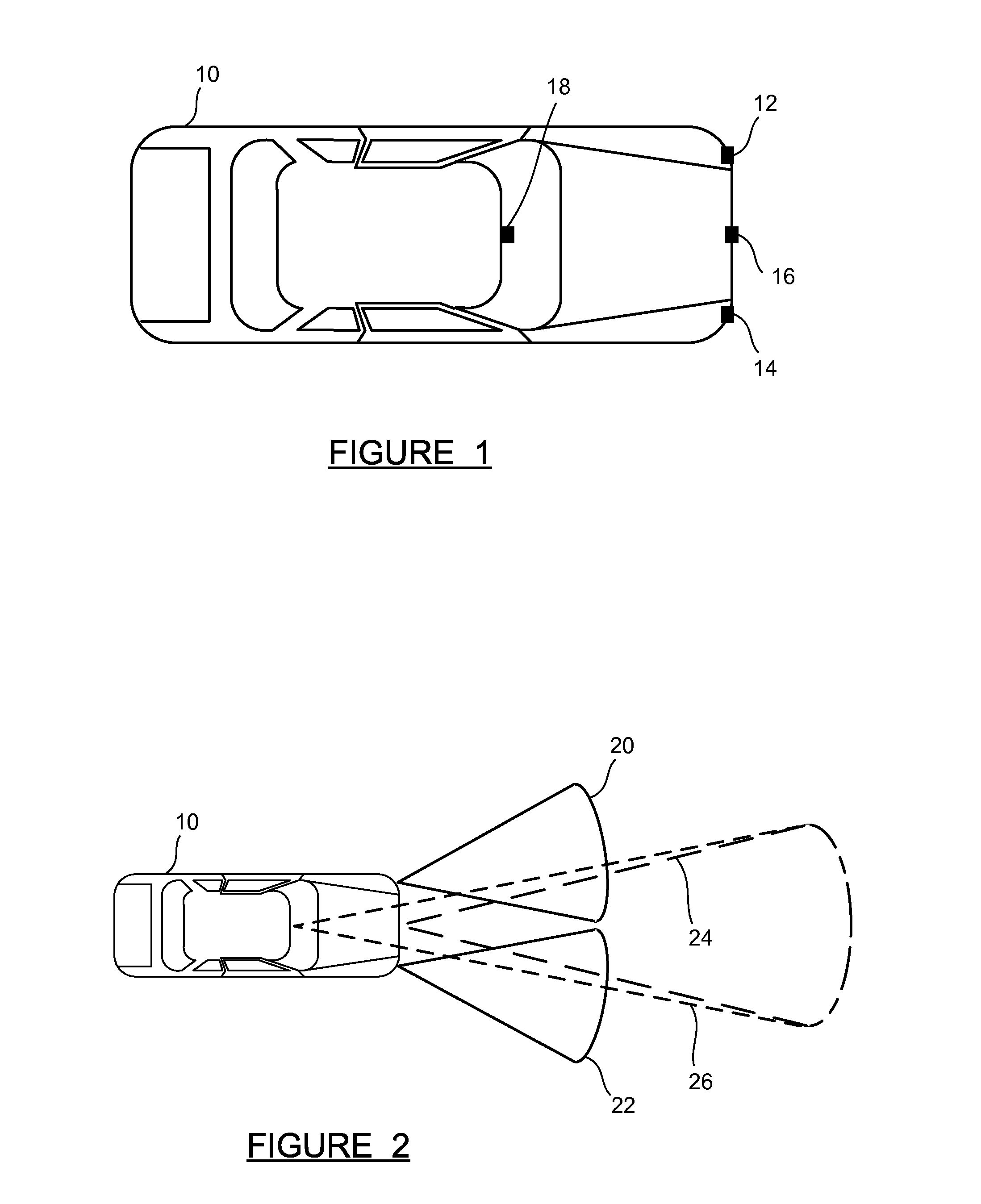
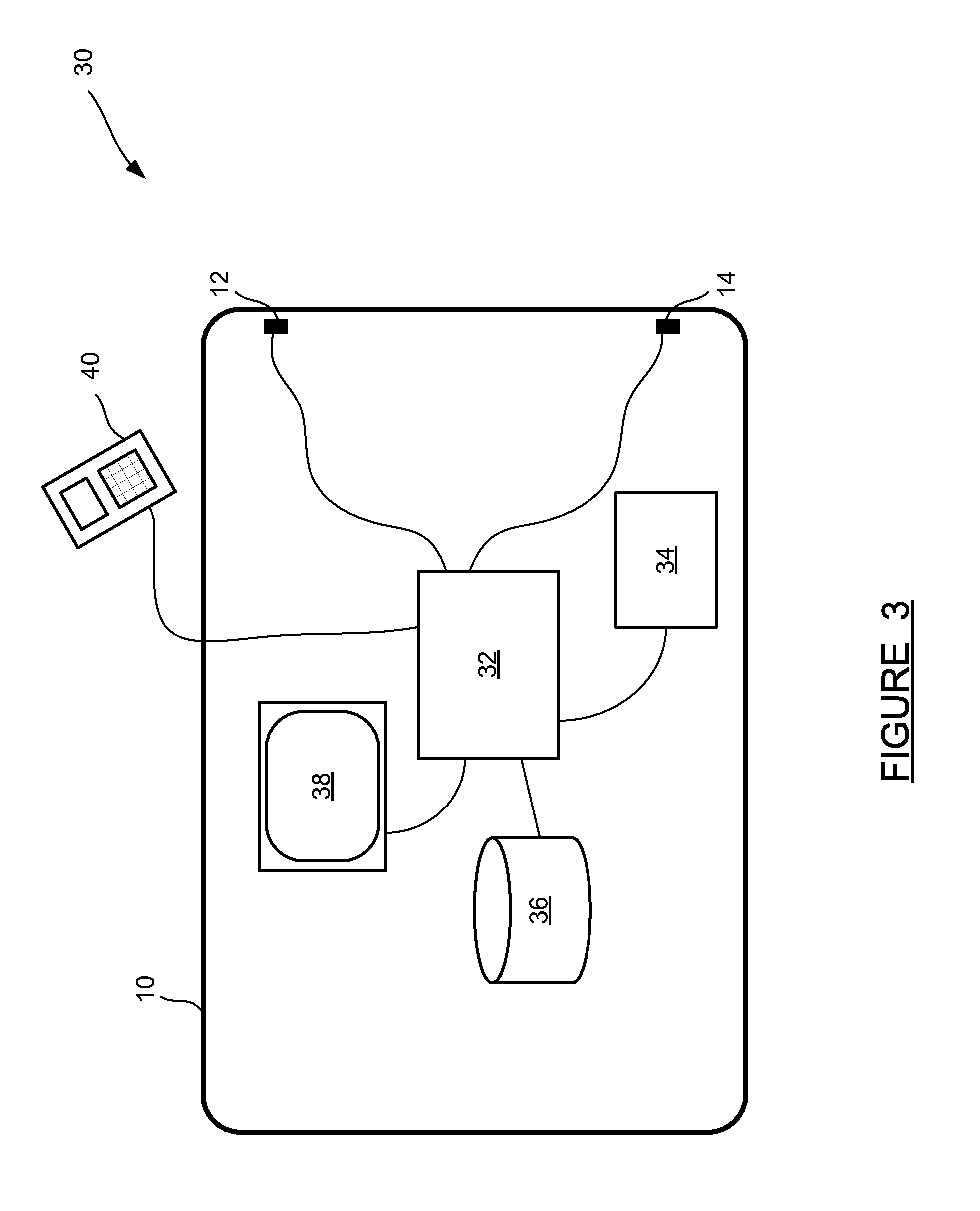
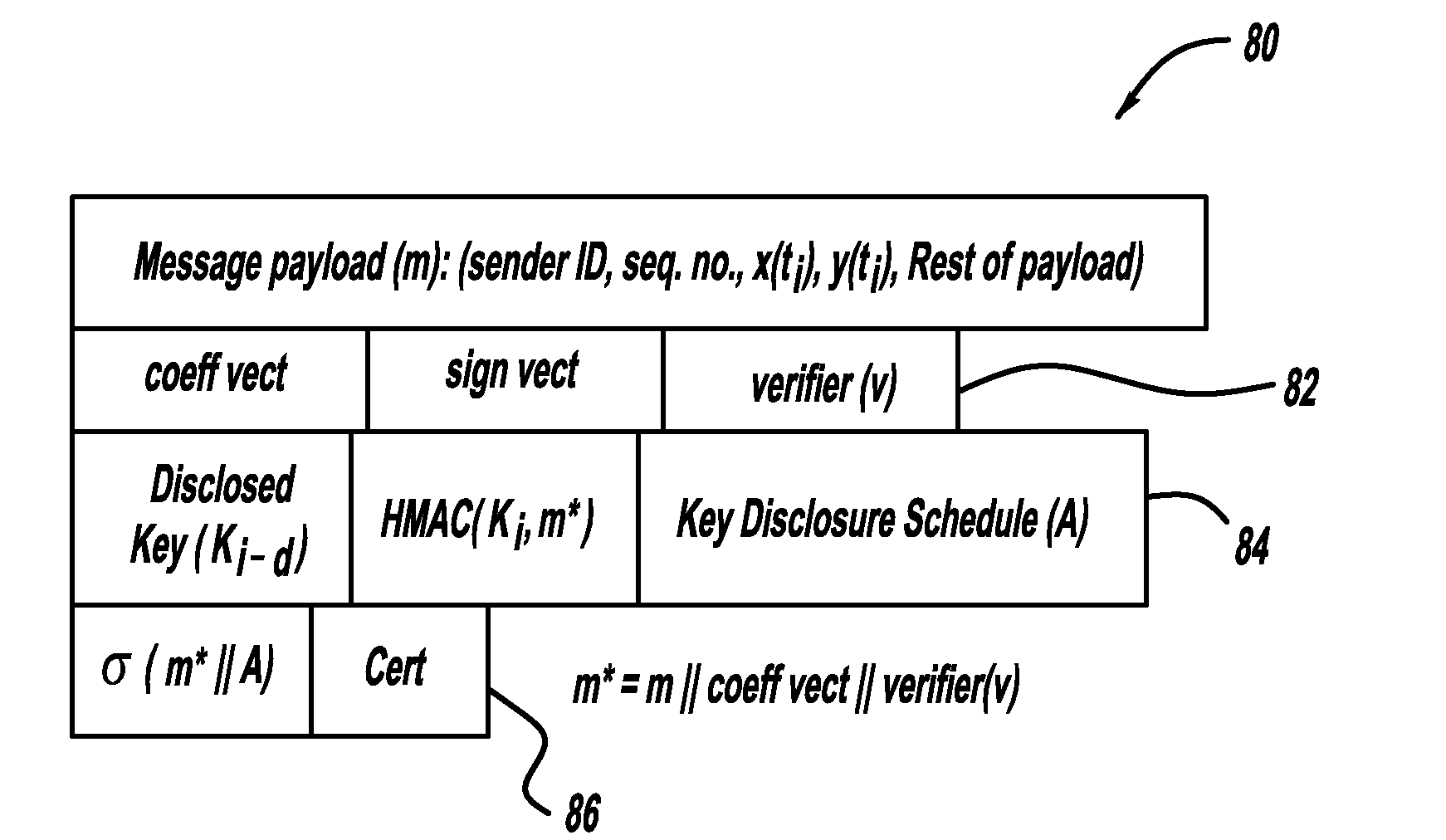
A system and method for a vehicle-to-vehicle communications system that provide active safety applications employing lightweight geographic authentication using one-time signatures. The system and method require each vehicle to construct a discretized representation of its trajectory, which captures its kinematical history to a tunable degree of accuracy and to a tunable extent in the past. This trajectory information is then signed using a one-time signature. Thus, with every periodic message, the sending vehicle transmits the usual application payload, a signed version of the trajectory as described, and the digital signature over all of the fields.
Owner:GM GLOBAL TECH OPERATIONS LLC
Lane line detection method based on monocular vision
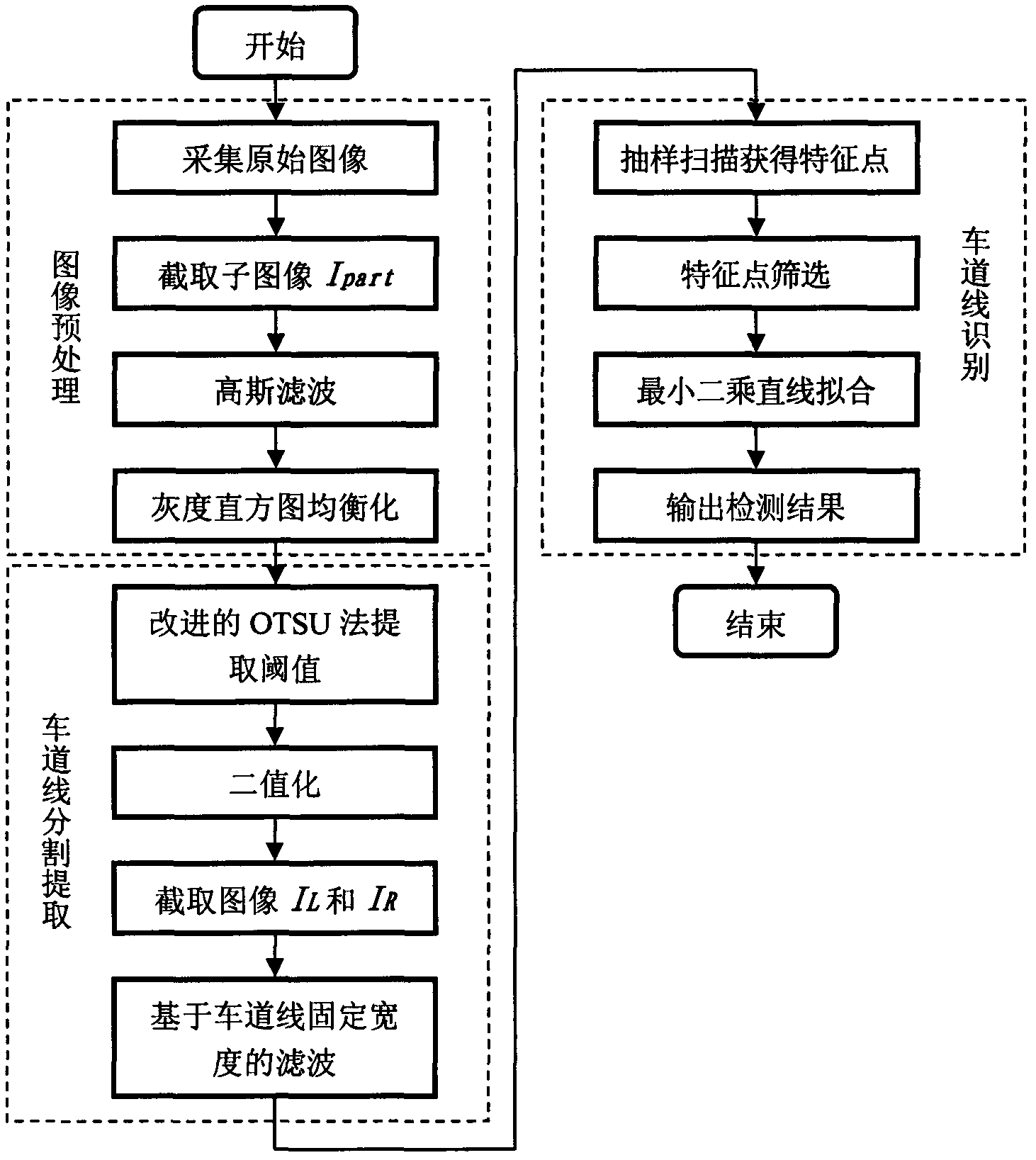
InactiveCN102629326AGood split extractionSmall amount of calculationCharacter and pattern recognitionActive safetyPattern recognition
The invention belongs to the technical field of vehicle active safety and relates to a lane line detection method based on monocular vision. The lane line detection method comprises the following steps: acquiring an original image of a road condition in front of a vehicle; intercepting subimages of boundary regions at the two sides, wherein the subimages include the original image; removing the high-frequency noise of the subimages and carrying out grey level histogram equalization and binaryzation; intercepting left and right lane line detection region images; filtering based on the fixed width range of a lane line according to the features of low grey value pavements at the two sides of the lane line; preliminarily determining feature points of the lane line in a sampling line scanning manner and screening; and carrying out lane detection. The lane line detection method has the characteristics of good real time and high reliability.
Owner:TIANJIN POLYTECHNIC UNIV
System and method for predicting impending cyber security events using multi channel behavioral analysis in a distributed computing environment
InactiveUS9602530B2Parts stableImprove throughputDigital data information retrievalPlatform integrity maintainanceEarly warning systemBehavioral analytics
Multi channel distributed behavioral analysis architecture provides a software solution to the major operational challenges faced with providing an early warning system for impending cyber security events. Most cyber security events are premeditated. However, many current cyber security defense technologies only address the real-time detection of a software vulnerability, the presence of malware (known or unknown “zero day”), anomalies from pre-established data points, or the signature of an active security event. The system and method of the multi channel distributed behavioral analysis architecture introduces a technique which provides the data collection, assessment, and alerting ability prior to the occurrence of an event based on threat actor behavior.
Owner:ZITOVAULT
Administration of protection of data accessible by a mobile device
InactiveUS20080077971A1Digital data processing detailsData switching by path configurationAnti virusEnterprise networking
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
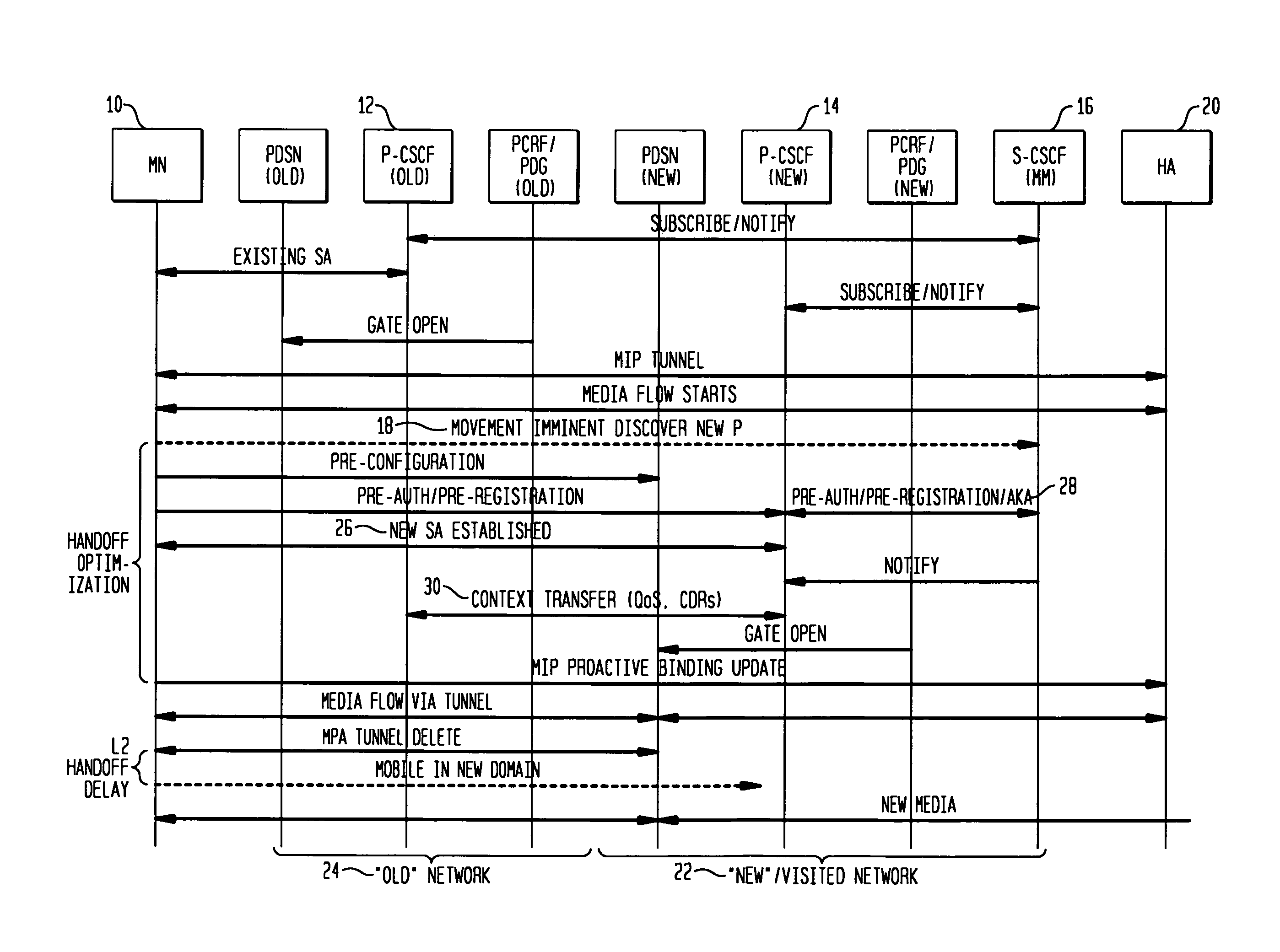
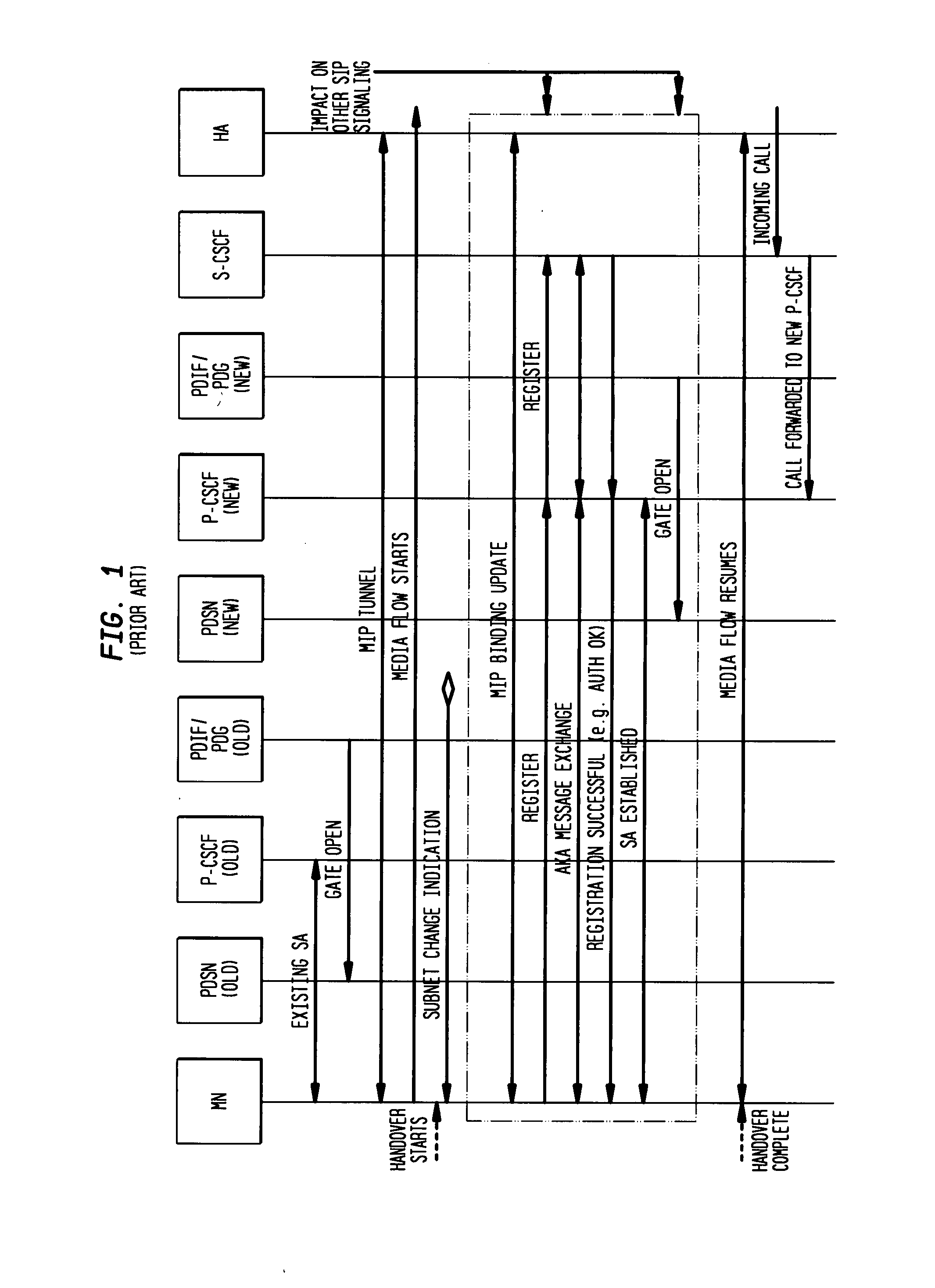
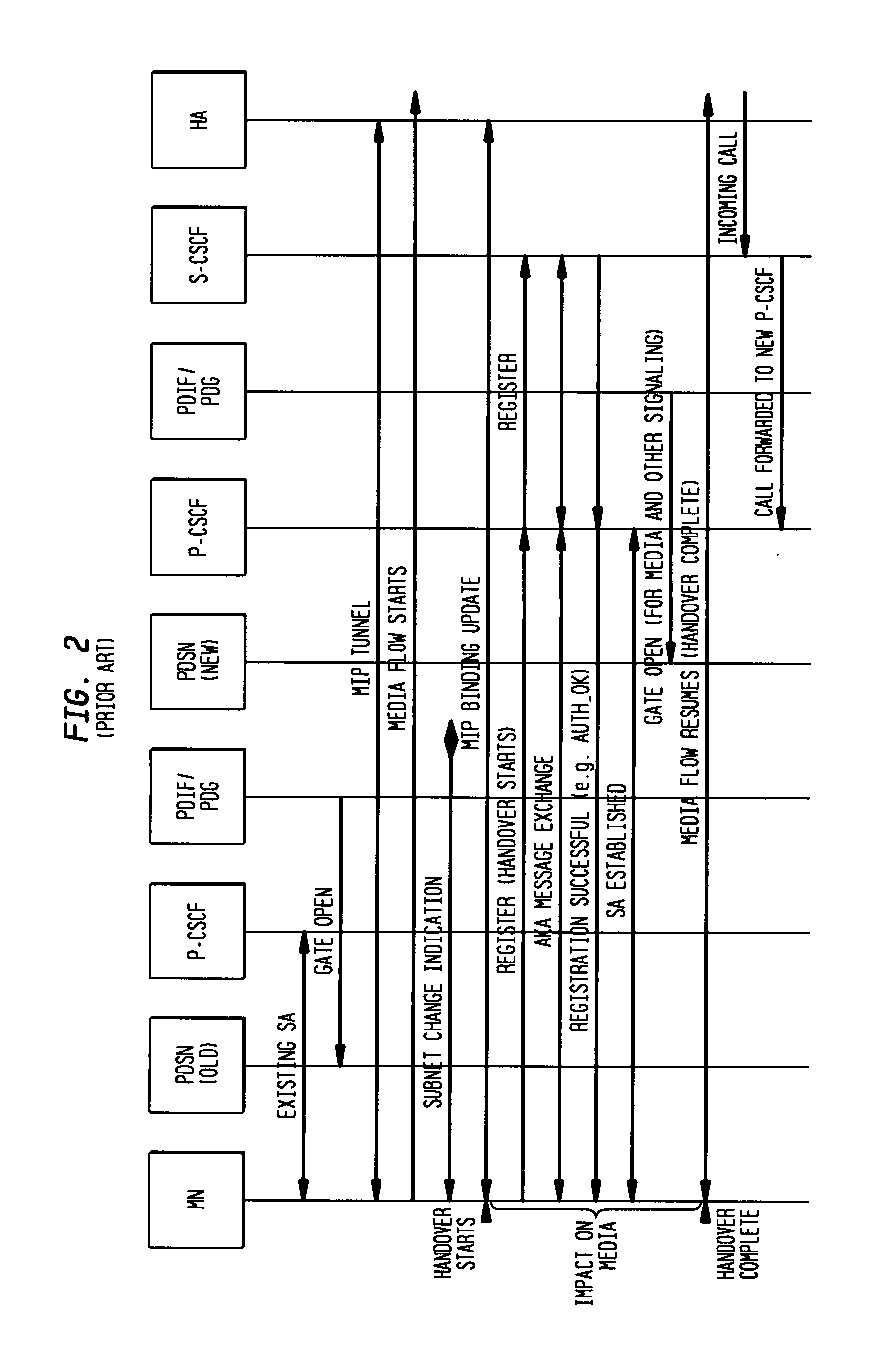
P-CSCF fast handoff for IMS/MMS architecture
ActiveUS20080069050A1Wireless network protocolsRadio/inductive link selection arrangementsSecurity associationPull technology
A mechanism by which handoff delay can be minimized while not compromising the IMS / MMD security and also protecting the media if required by certain applications is presented. One proactive method includes proactive authentication. Another proactive method includes proactive security association, such as transferring SA keys from old proxy to new proxy, or transferring keys through serving signal entities. Reactive methods include transferring SA keys from old proxy to new proxy, using either push or pull technology. Other reactive methods include transferring keys through serving signal entities using either push or pull technology.
Owner:TELCORDIA TECHNOLOGIES INC +1
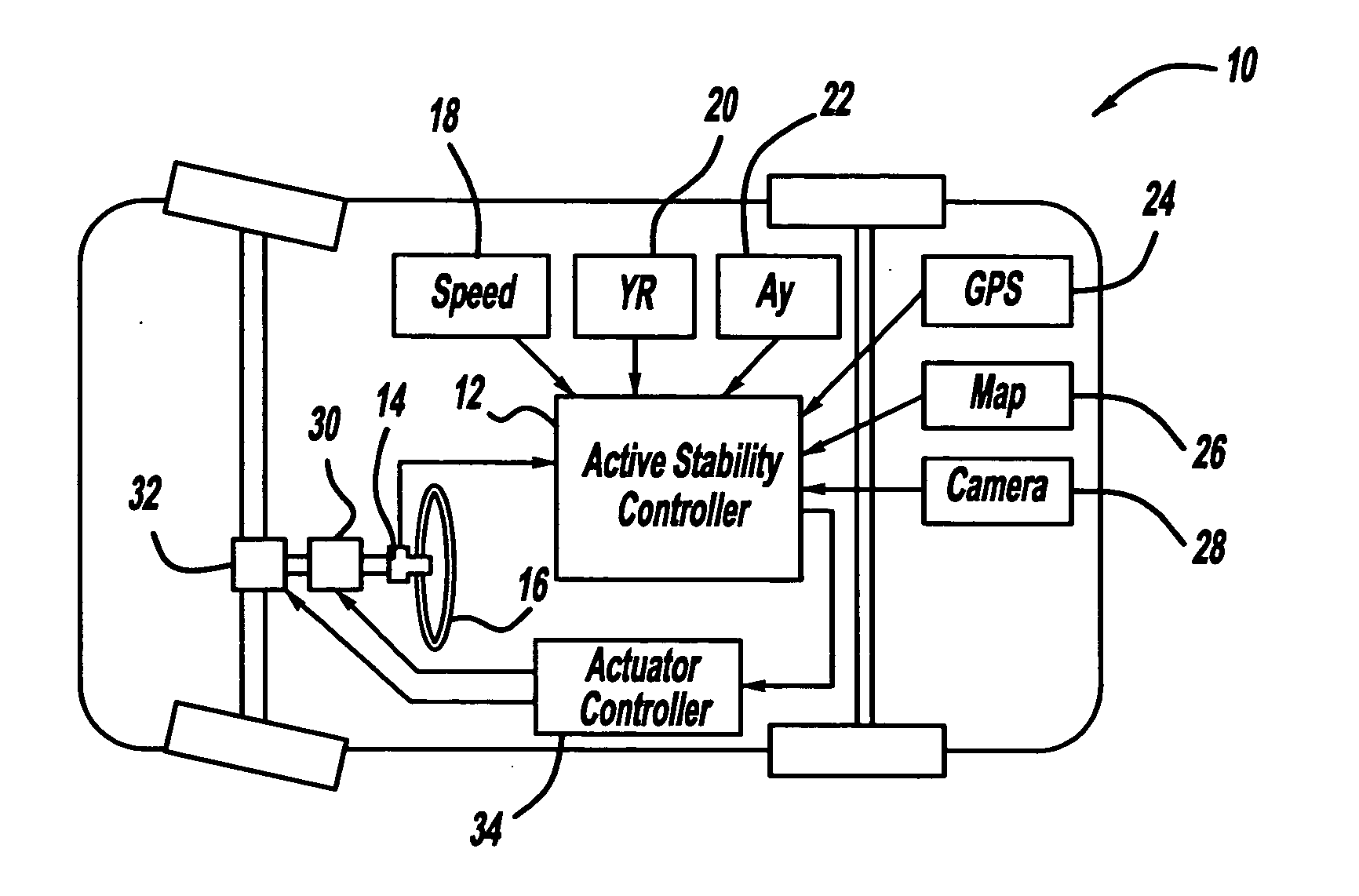
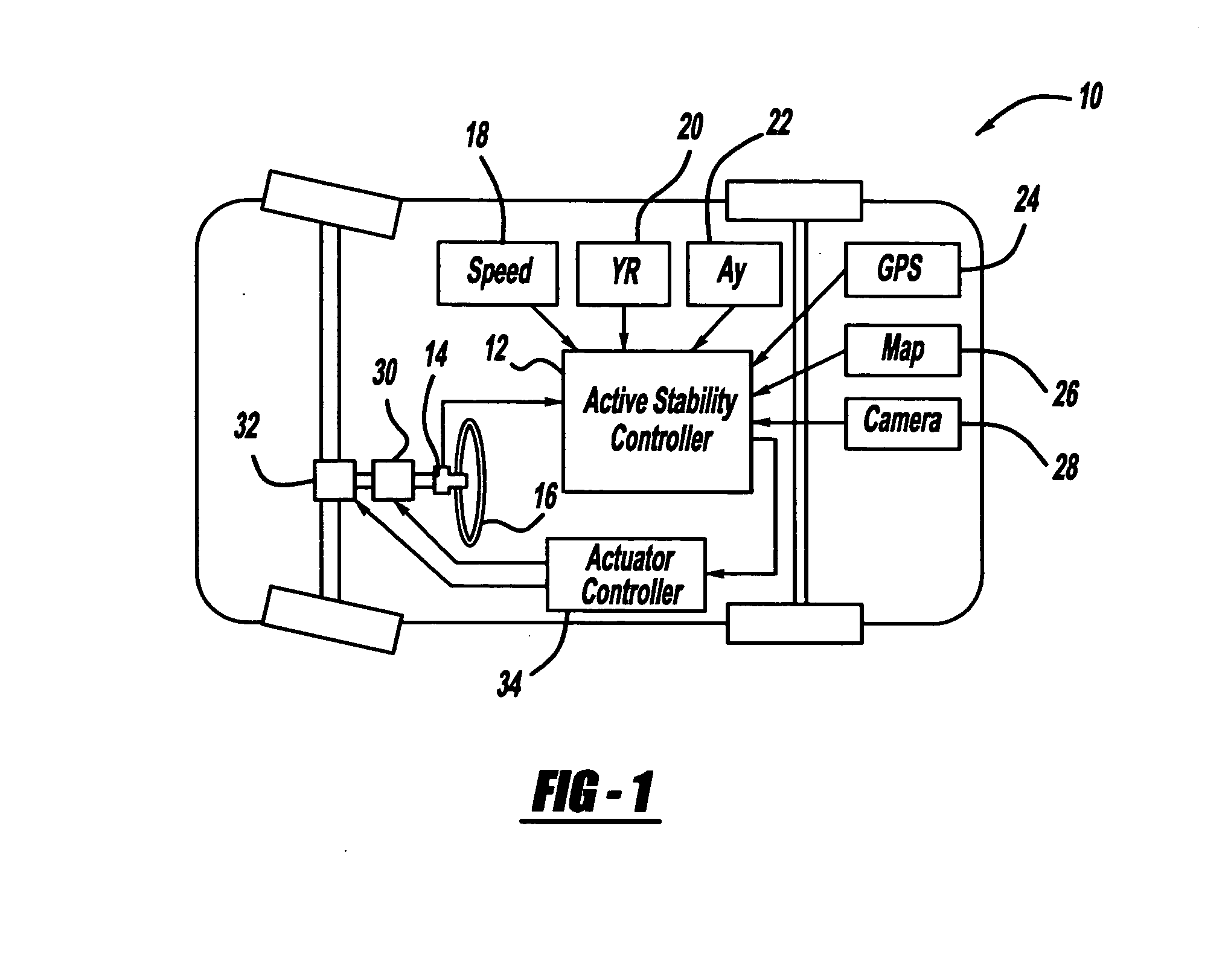
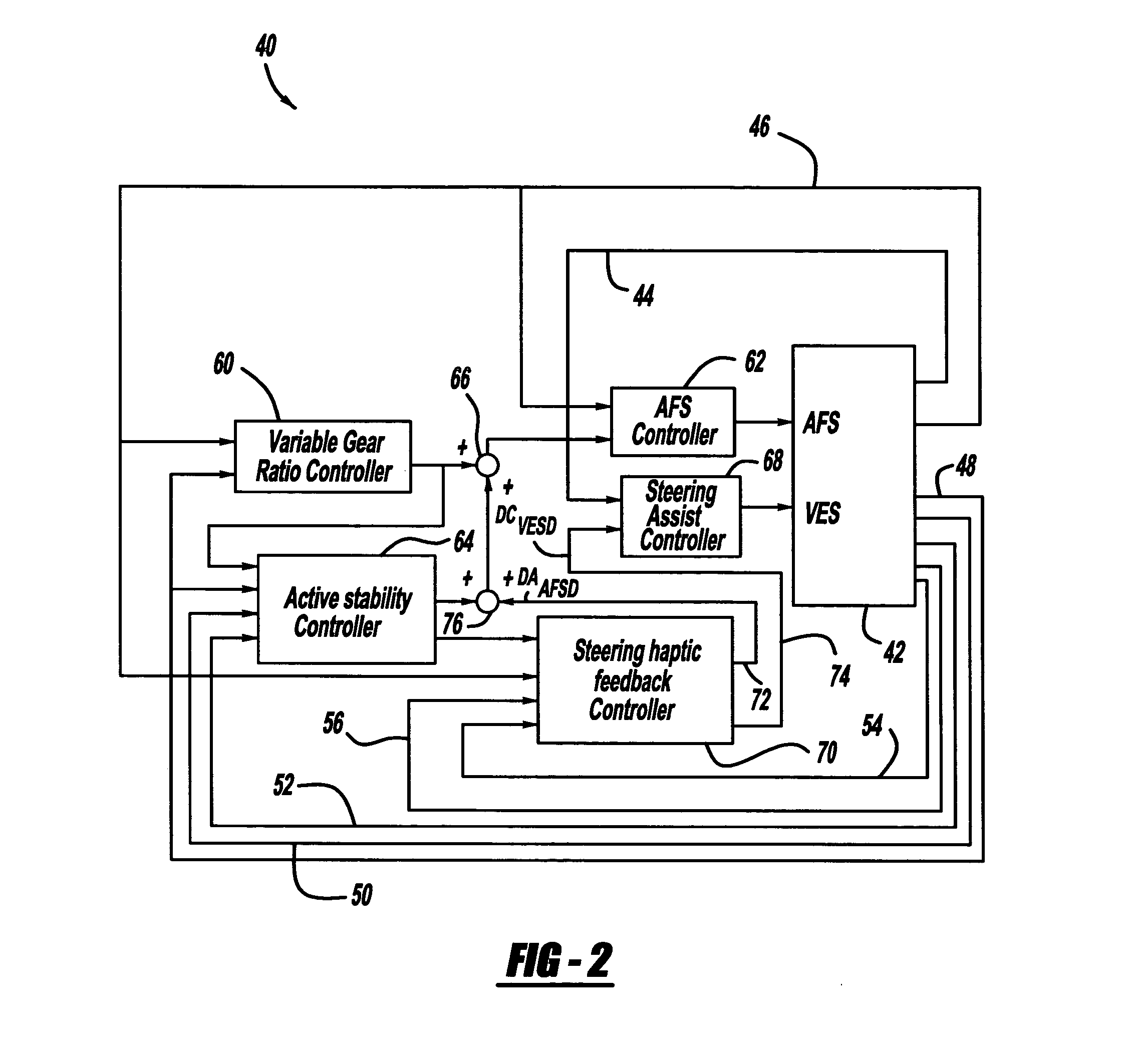
Steering haptic feedback system for vehicle active safety
InactiveUS20070299580A1Promote shakingIncrease volumeSteering initiationsDigital data processing detailsActive safetySteering wheel
A system and method that warn a vehicle driver by shaking or dithering the steering wheel that one or more active control systems on the vehicle is providing active control. The system includes an AFS actuator for providing a steering assist signal for stability control purposes, and a VES actuator for providing resistance against turning of the steering wheel. The system also includes a controller for causing the AFS actuator to shake the steering wheel if the active control is active and for causing the VES controller to apply and release tension to the steering wheel if the steering wheel is turned and the active control is active. The controller may increase the shaking of the steering wheel as the amount of the active control increases.
Owner:GM GLOBAL TECH OPERATIONS LLC
Stand-by safety chain monitoring and protecting device for wind power generation control system
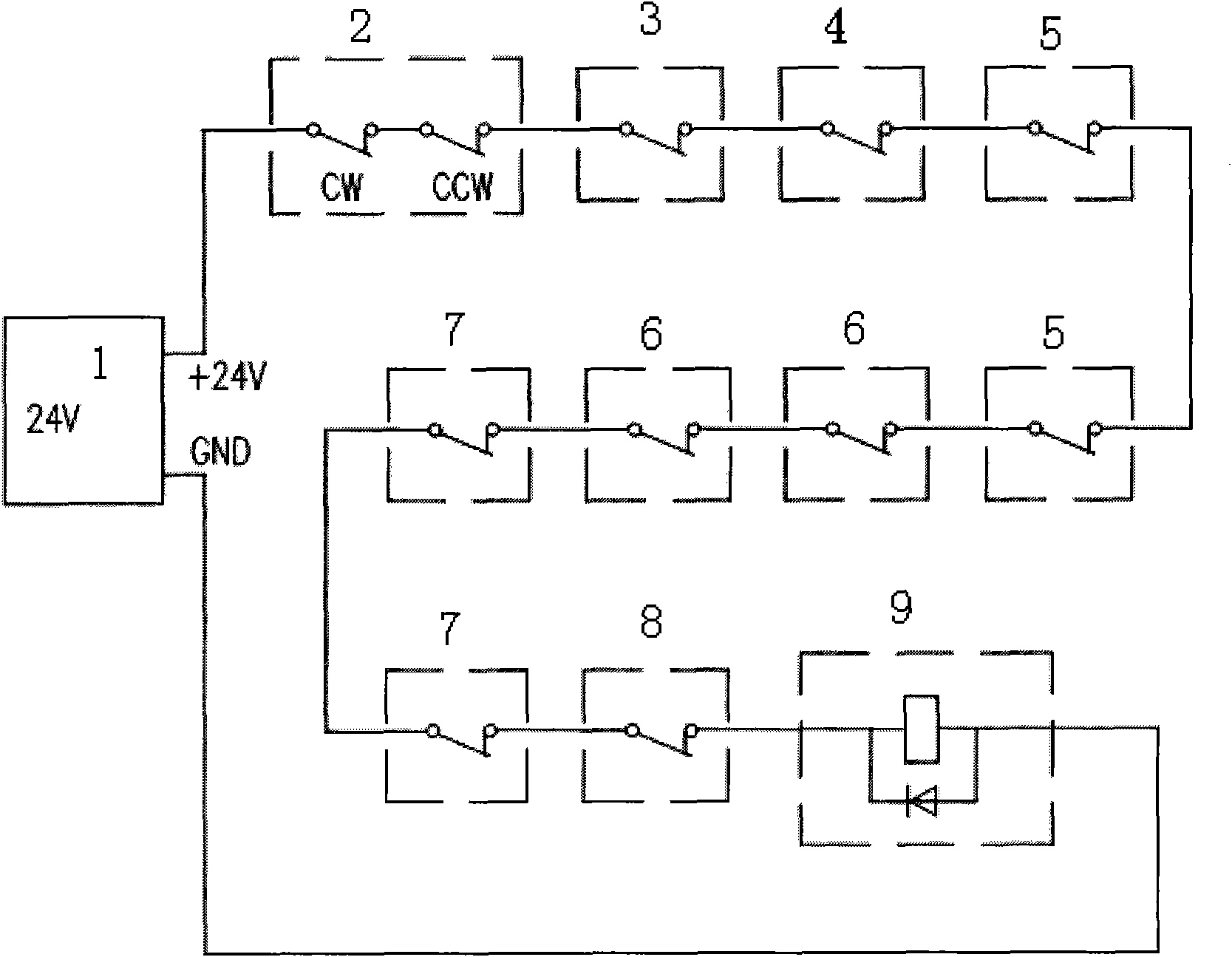
InactiveCN101776042AImprove protectionReduce connectionsWind motor controlMachines/enginesActive safetyControl system
The invention discloses a stand-by safety chain monitoring and protecting device for a wind power generation control system, comprising a power supply, a cable-twisting switch, an engine-room vibration protection switch, a grid protection switch, a converter protection switch, an engine room and tower support emergent stop button, a distributed heartbeat signal monitoring switch, a rotary speed protection switch and a safety chain relay, wherein the power supply generates power signals and is respectively connected in series with the cable-twisting switch, the engine-room vibration protection switch, the grid protection switch, the converter protection switch, the engine room and the tower support emergent stop button, the distributed heartbeat signal monitoring switch, the rotary speed protection switch and the safety chain relay. The monitoring and protecting device adopts an active safety design, runs independent of a PLC system and monitors relevant signals at real time; and when incidents endangering the safety of a machine set occur, the monitoring and protecting device actively controls a pitch system to realize full feathering, thereby achieving the safe shut-down of the machine set.
Owner:NANJING SCIYON AUTOMATION GRP
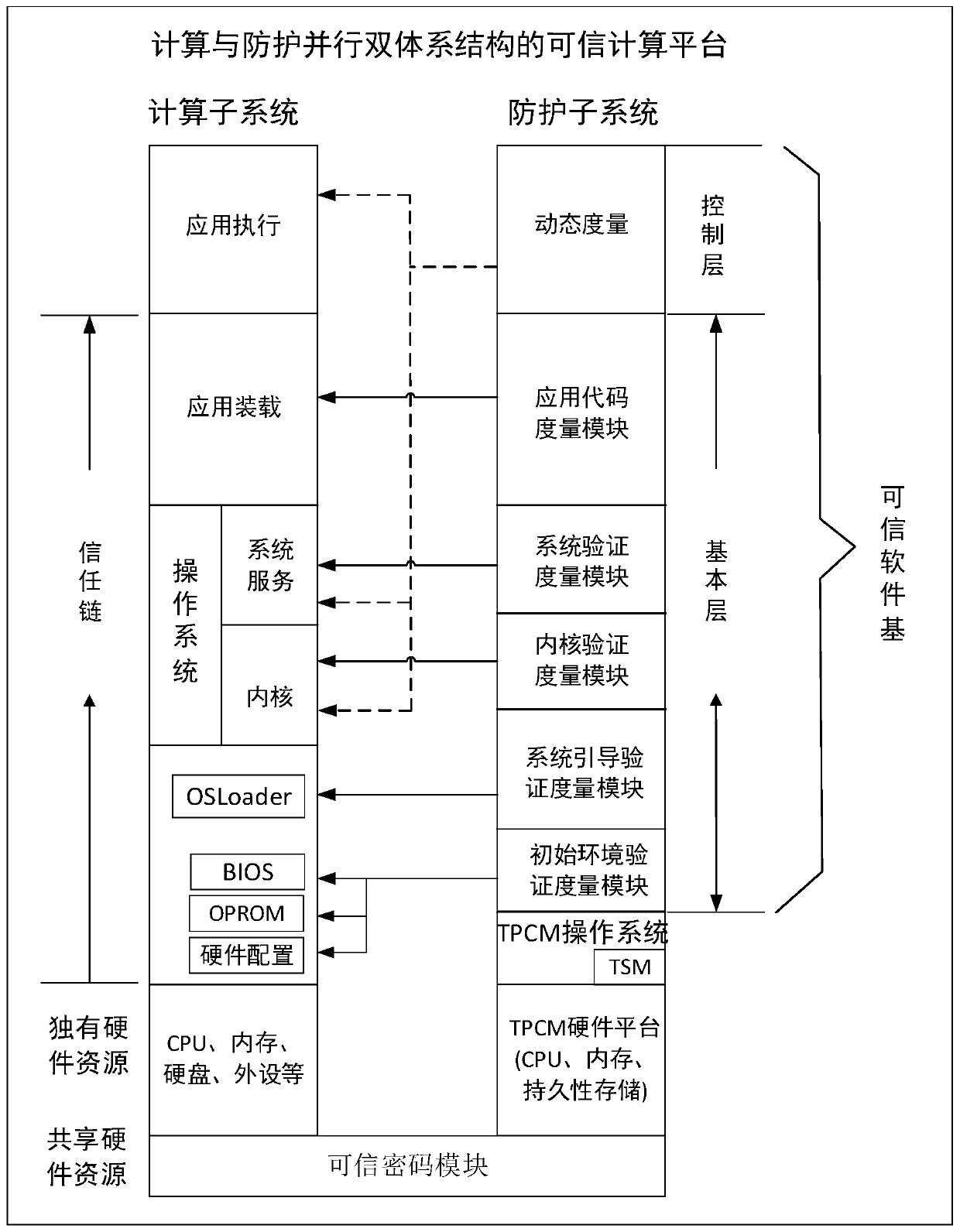
Trusted computing platform of a computing and protection parallel double-system structure
ActiveCN109871695AComputable, measurable and controllableRealize active security protectionPlatform integrity maintainanceActive safetyTrusted Computing
The invention discloses a trusted computing platform of a computing and protection parallel double-system structure. wherein the trusted computing platform comprises a computing subsystem and a protection subsystem which are parallel, the computing subsystem is used for completing a computing task, and the protection subsystem is used for carrying out active measurement and active control on the computing subsystem according to a trusted strategy through a trusted platform control module; And the protection subsystem is specifically used for respectively carrying out static measurement and dynamic measurement on the computing subsystem through the trusted software base. According to the trusted computing platform provided by the invention, active safety protection is realized while computing is realized through the computing subsystem and the protection subsystem which are parallel to each other. In addition to establishing a static trust chain which takes a trusted platform control module as a trust root for step-by-step measurement, a dynamic measurement mechanism based on a security trusted strategy is also designed, and active defense on the whole computer system in the starting and operating processes of the computer is realized.
Owner:北京自主可信科技有限公司
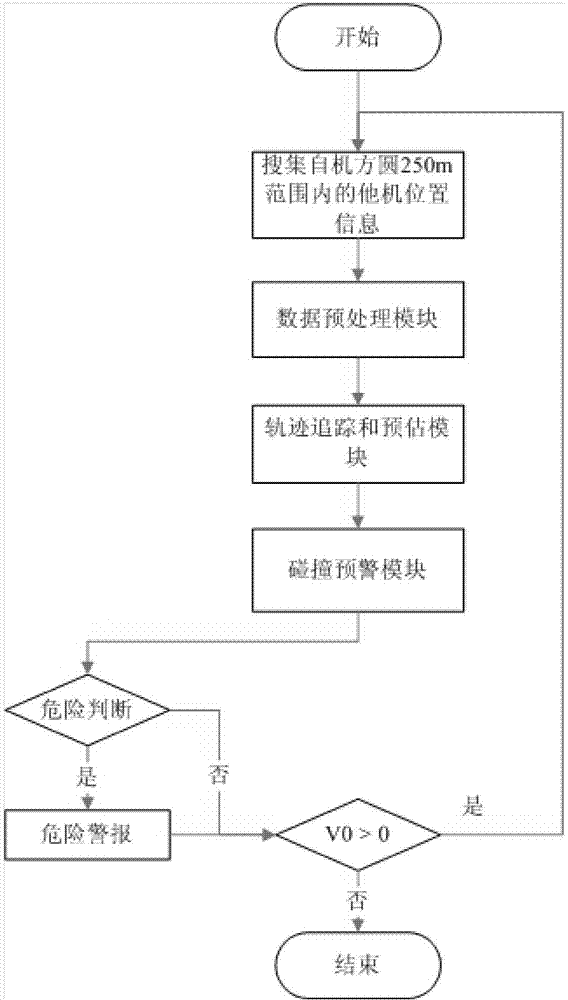
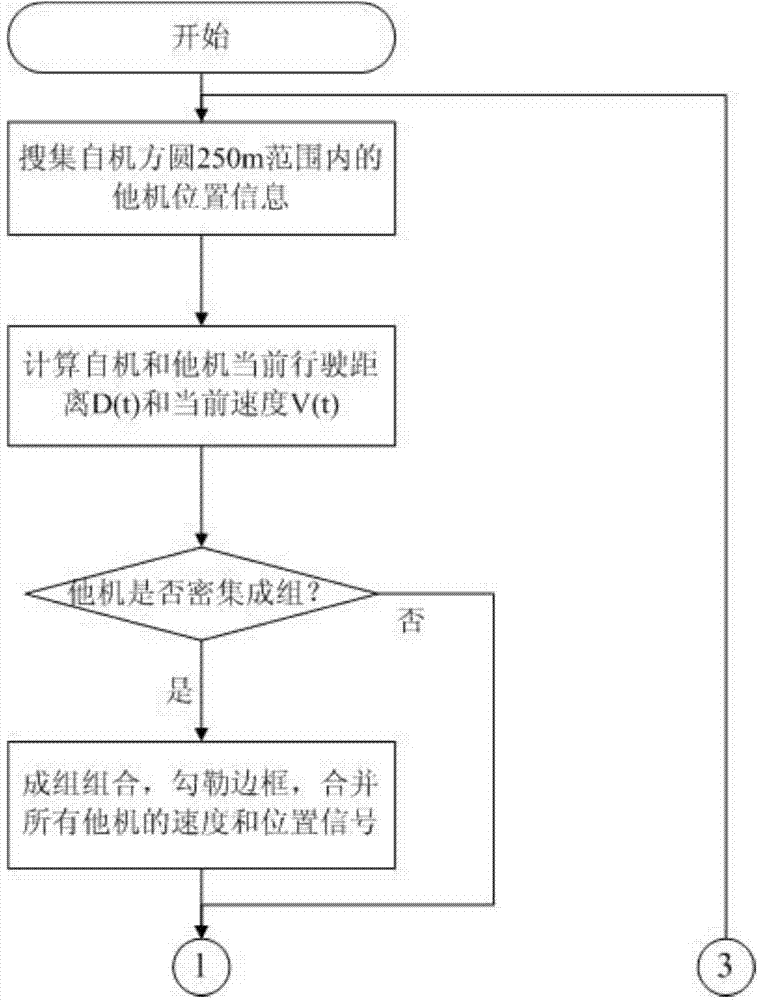
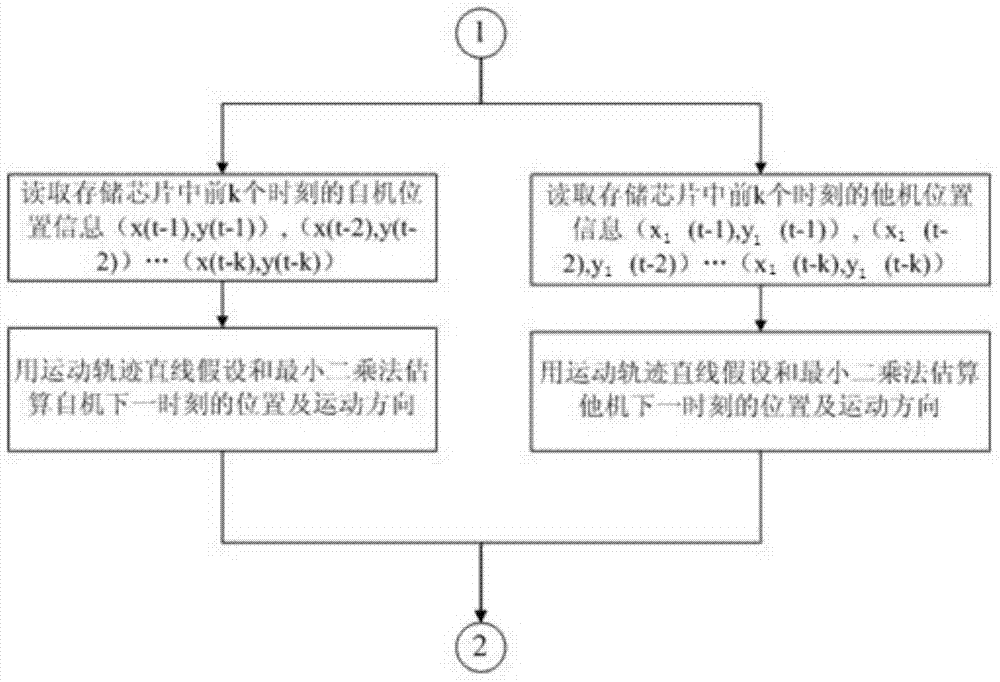
Active vehicle safety pre-warning method and safety pre-warning system with same applied
ActiveCN104269070ALow costDo not disclose personal privacyAnti-collision systemsActive safetyData pre-processing
The invention relates to the technical field of active vehicle safety control and the mobile internet, in particular to an active vehicle safety pre-warning method and a safety pre-warning system with the active vehicle safety pre-warning method applied. The safety pre-warning system comprises a mobile intelligent terminal, a wireless communication network and a satellite positioning system. The active vehicle safety pre-warning method includes the steps that a data preprocessing module, a line tracing and estimating module and a danger pre-warning module are installed on the mobile intelligent terminal, an own vehicle can judge whether a collision risk exists or not according to information of pedestrians and other vehicles within a target range, and a safety alarm is given if necessary. By ingenious utilization of popular smart phones, low-cost vehicles and pedestrians can enjoy protection of the active safety technology, individual privacy will not be leaked, and the active vehicle safety pre-warning method and the safety pre-warning system with the active vehicle safety pre-warning method applied are highly popular, low in cost and likely to be accepted by public.
Owner:DONGFENG MOTOR CORP HUBEI
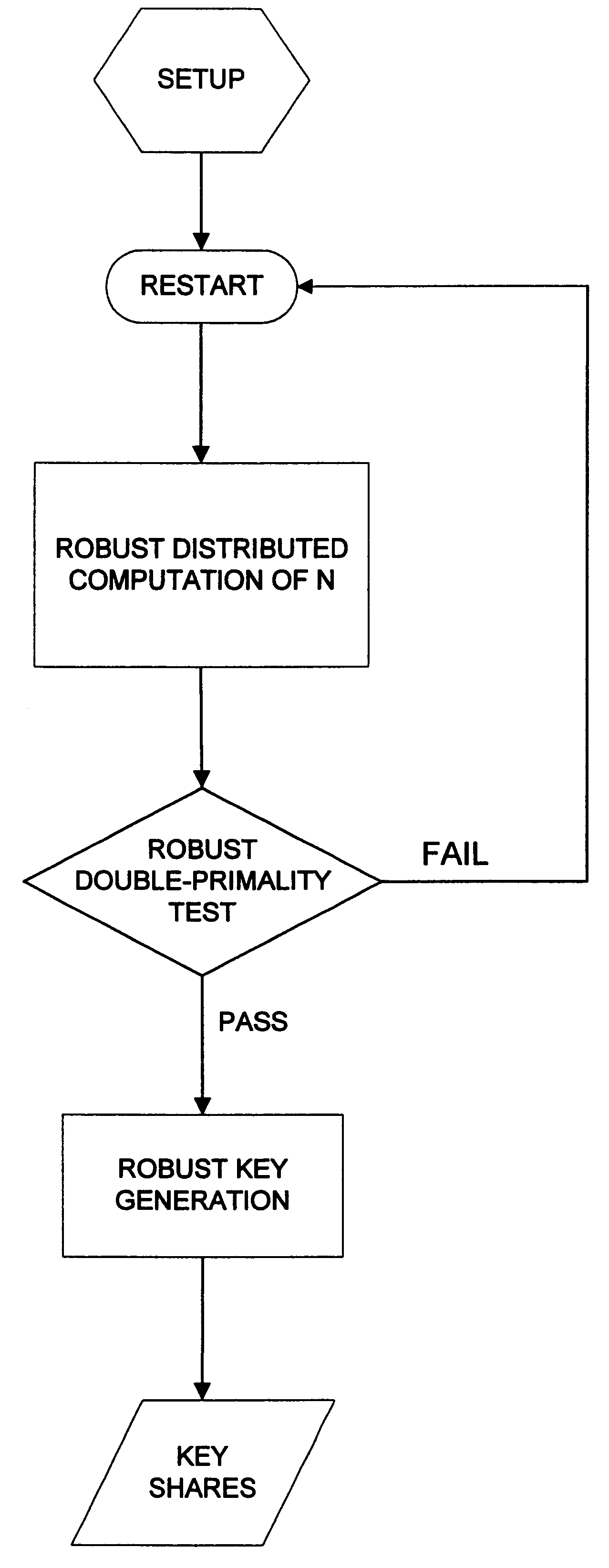
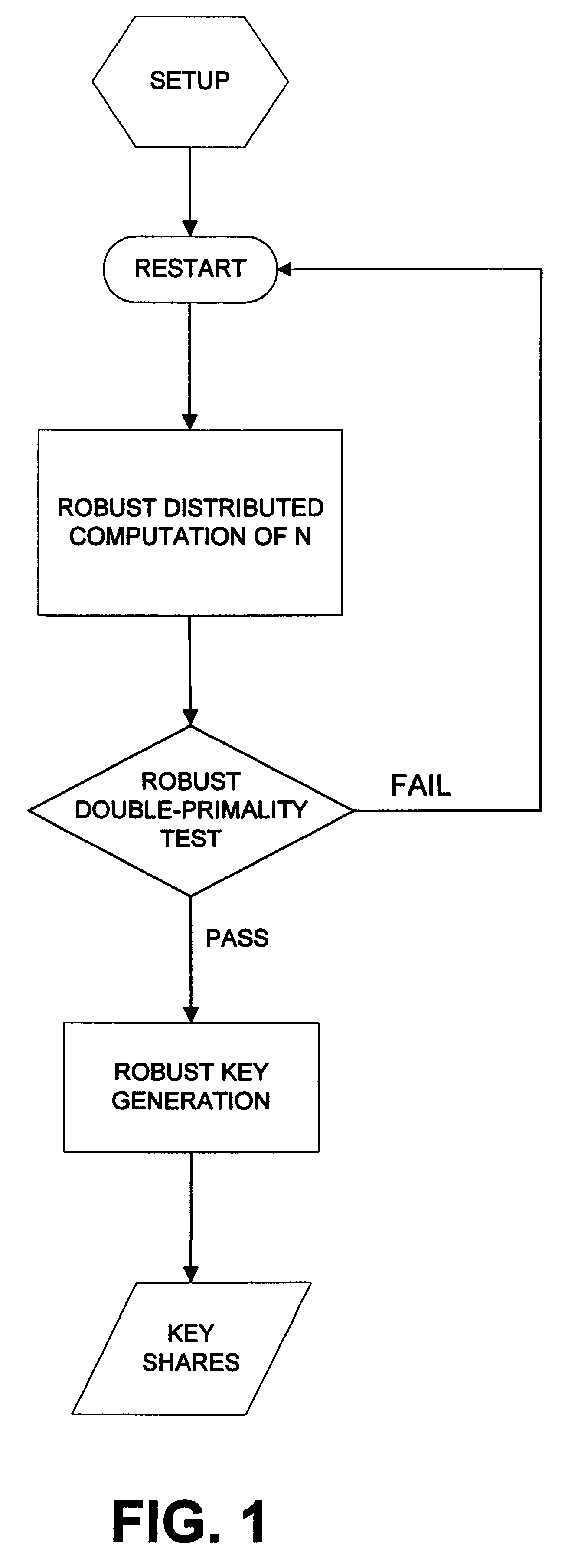
Robust efficient distributed RSA-key generation
InactiveUS6237097B1Reduce in quantityConfidenceKey distribution for secure communicationPublic key for secure communicationParallel computingEngineering
The invention provides for robust efficient distributed generation of RSA keys. An efficient protocol is one which is independent of the primality test "circuit size", while a robust protocol allows correct completion even in the presence of a minority of arbitrarily misbehaving malicious parties. The disclosed protocol is secure against any minority of malicious parties (which is optimal). The disclosed method is useful in establishing sensitive distributed cryptographic function sharing services (certification authorities, signature schemes with distributed trust, and key escrow authorities), as well as other applications besides RSA (namely: composite ElGamal, identification schemes, simultaneous bit exchange, etc.). The disclosed method can be combined with proactive function sharing techniques to establish the first efficient, optimal-resilience, robust and proactively-secure RSA-based distributed trust services where the key is never entrusted to a single entity (i.e., distributed trust totally "from scratch"). The disclosed method involves new efficient "robustness assurance techniques" which guarantee "correct computations" by mutually distrusting parties with malicious minority.
Owner:CERTCO
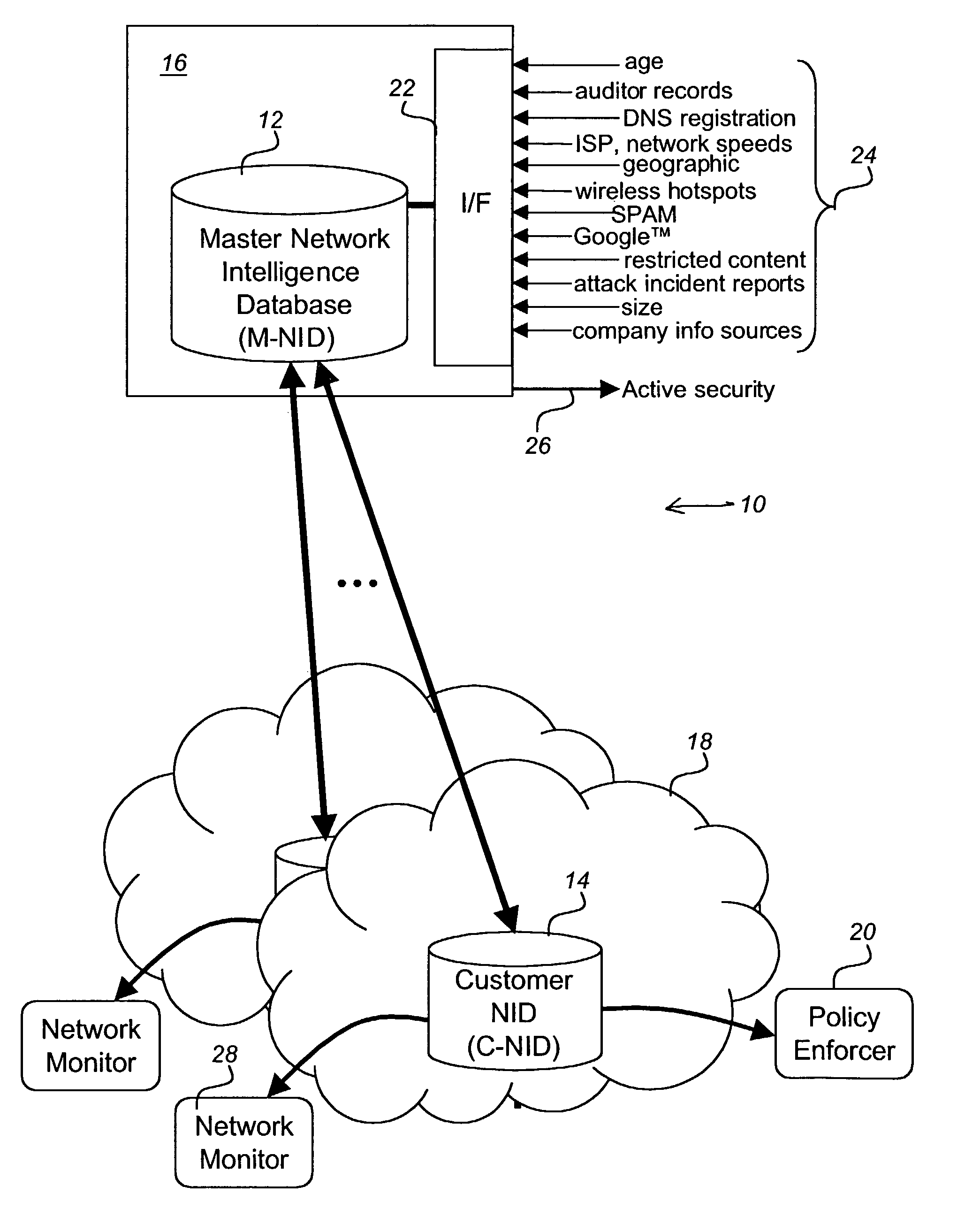
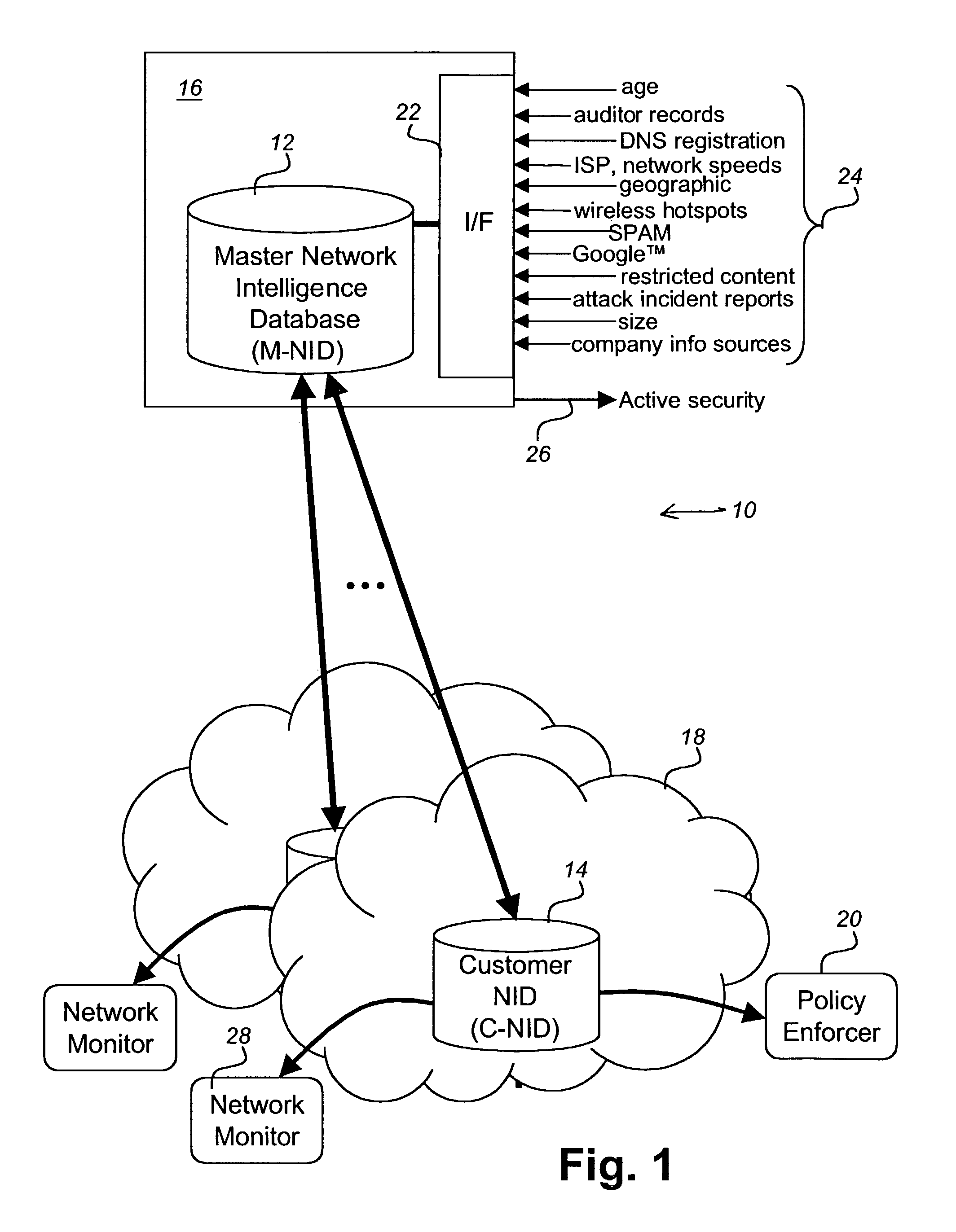
Network intelligence system
ActiveUS8024795B2Memory loss protectionDigital data processing detailsProxy serverSecurity information
A network security system takes an active approach to network security. This is accomplished by providing intelligence about other networks. A master network intelligence database is established that uses a plurality of network information agents for gathering information about networks and providing the information to the master network intelligence database. A customer network security system is then able to secure the customer network in dependence upon information received from the master network intelligence. Security information includes at least one of hostility level on the Internet, collected from numerous sites; security event history; spam levels; hosted services; public wireless; organization type; organization associations; peer ISPs; bandwidth connection to the Internet; active security measures; number of users on the network; age of the network; inappropriate content served; industry; geographic placement; open proxy servers; and contact information.
Owner:IBM CORP
On-vehicle information providing device
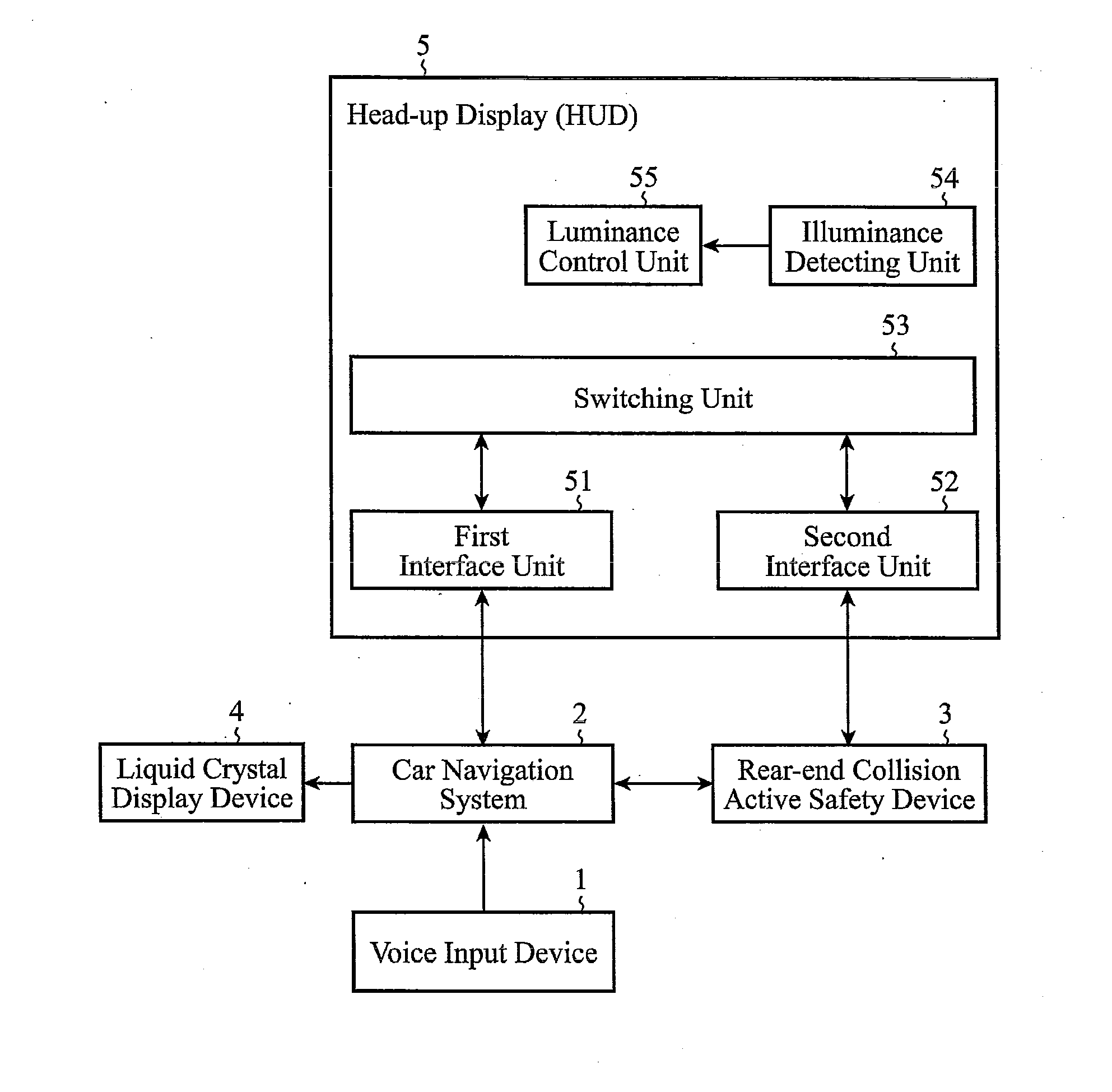
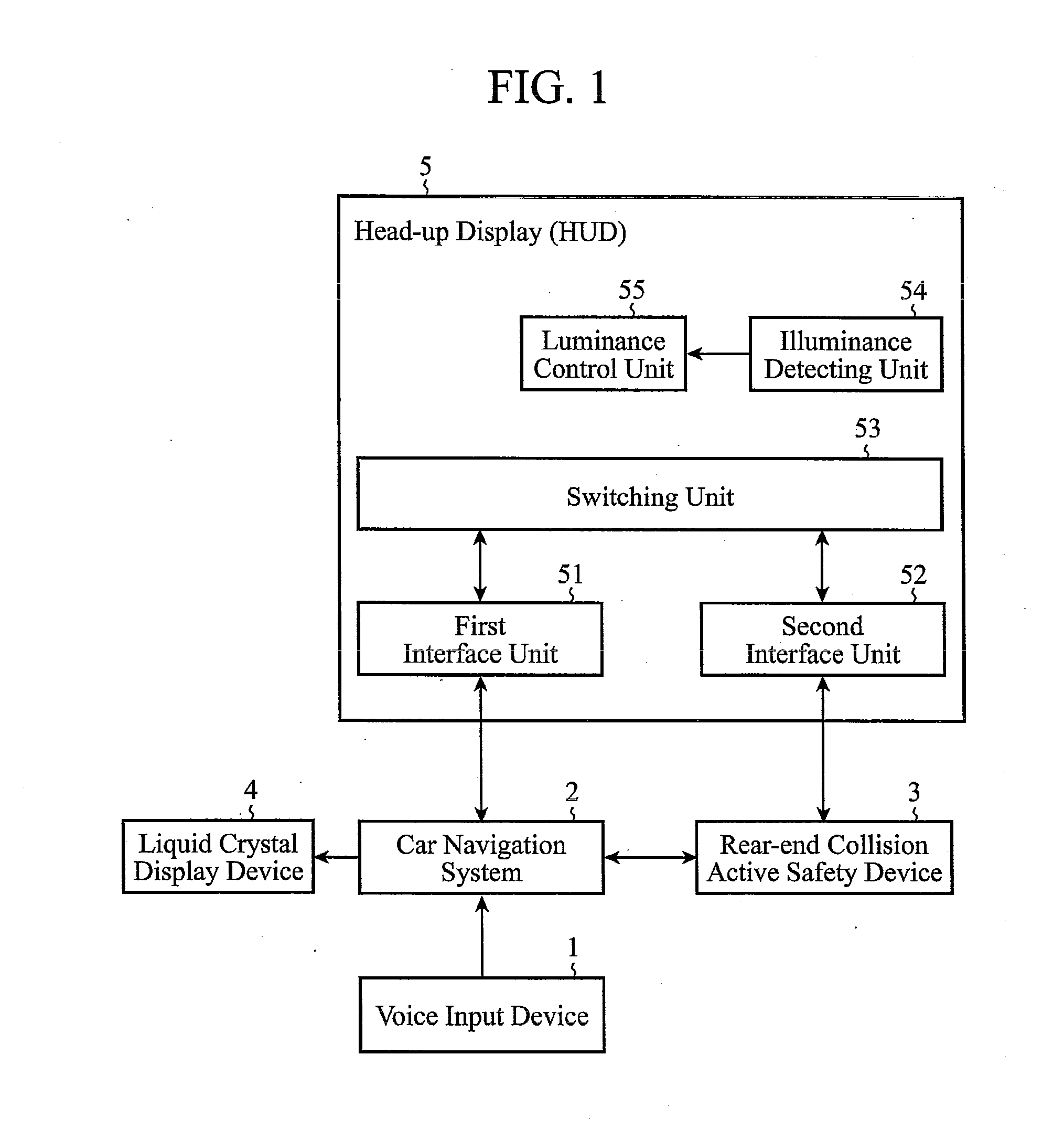
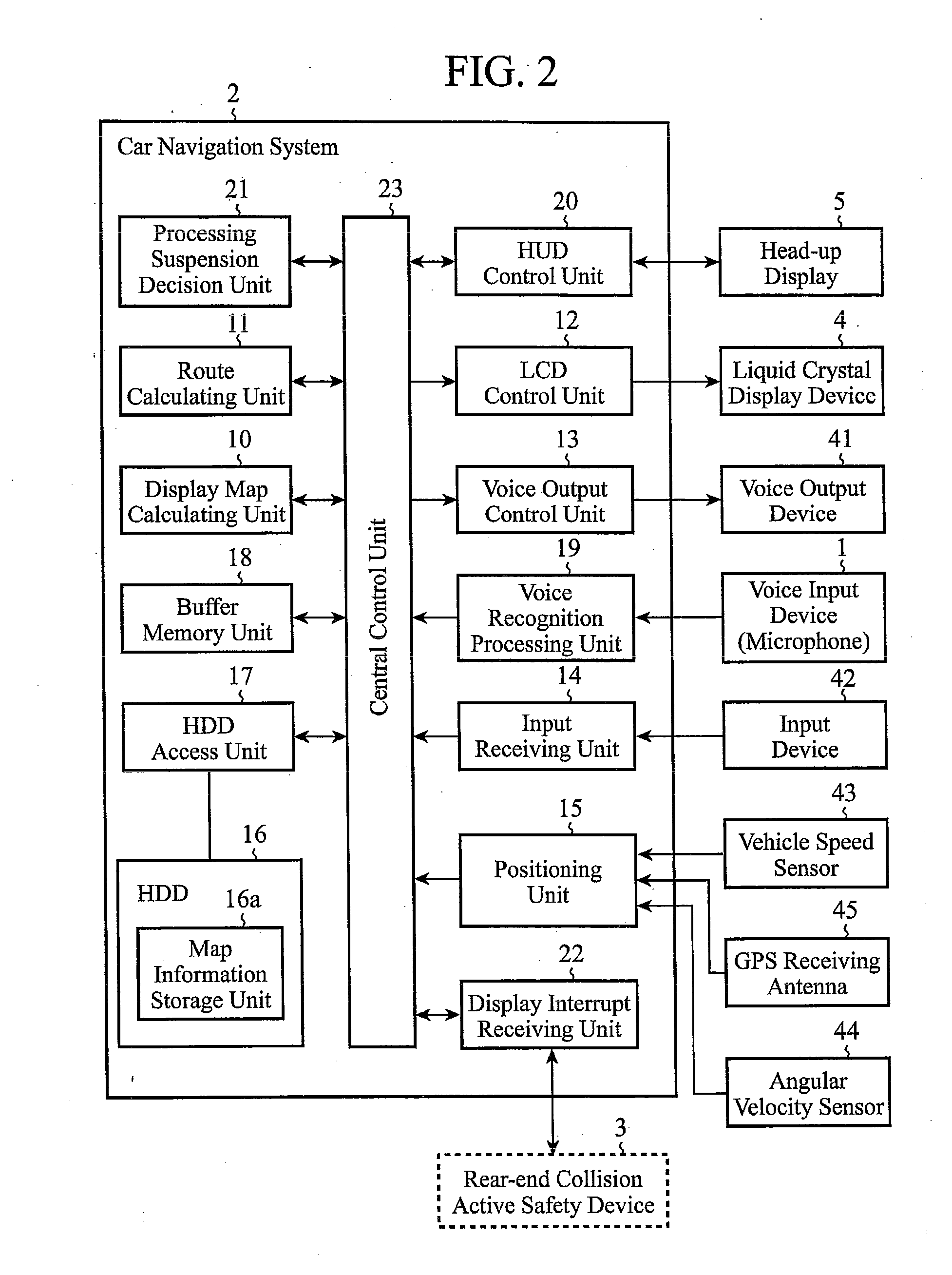
ActiveUS20100182140A1Reduce transferFast informationInstruments for road network navigationRoad vehicles traffic controlHead-up displayLiquid-crystal display
In an on-vehicle information providing device including an input device 1 for inputting information corresponding to operation, on-vehicle information equipment 2 for executing processing corresponding to the information input, an active safety system 3 for monitoring surrounding conditions of the vehicle and generating caution information, a liquid crystal display device 4 for displaying a processing result of the on-vehicle information equipment, and a head-up display (HUD) 5 for displaying the information delivered from the on-vehicle information equipment or from active safety system, the on-vehicle information equipment sends, if any display interrupt request is made from the active safety system during execution of the display processing onto the HUD, a display switching control request to the HUD by suspending the display processing, and the HUD switches from a state of displaying the information from the on-vehicle information equipment to a state of displaying the information from the active safety system in response to the display switching control request from the on-vehicle information equipment.
Owner:MITSUBISHI ELECTRIC CORP
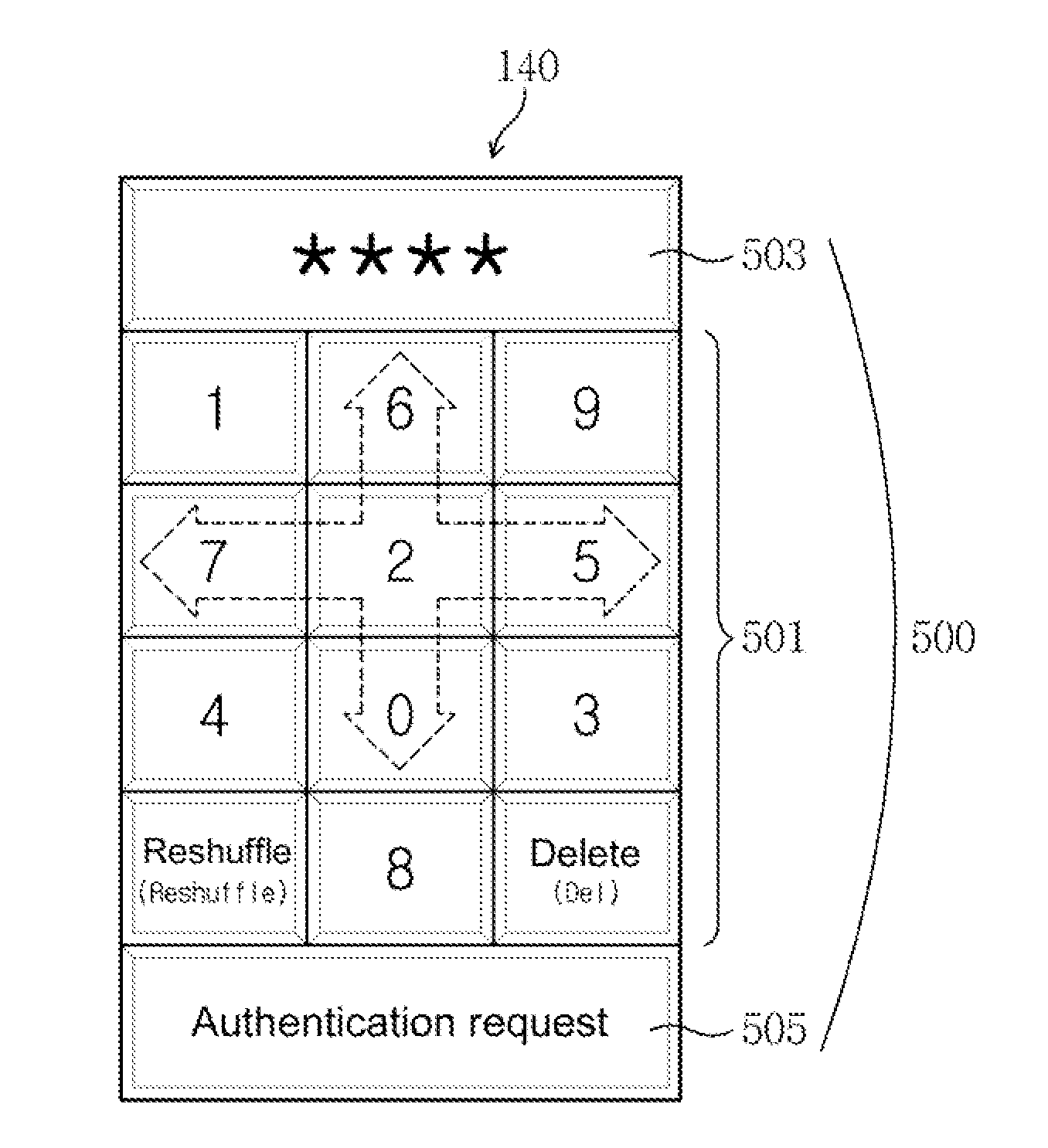
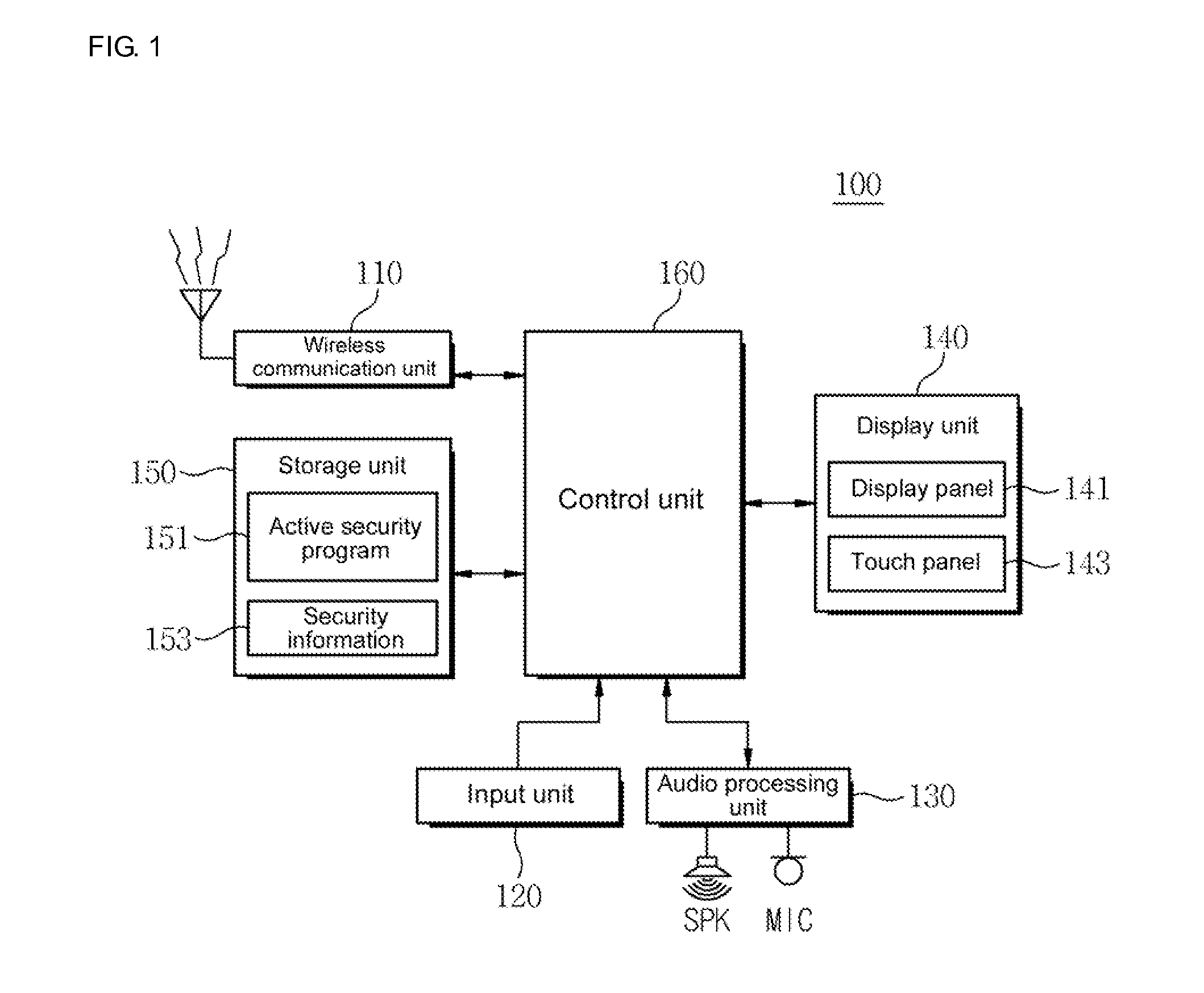
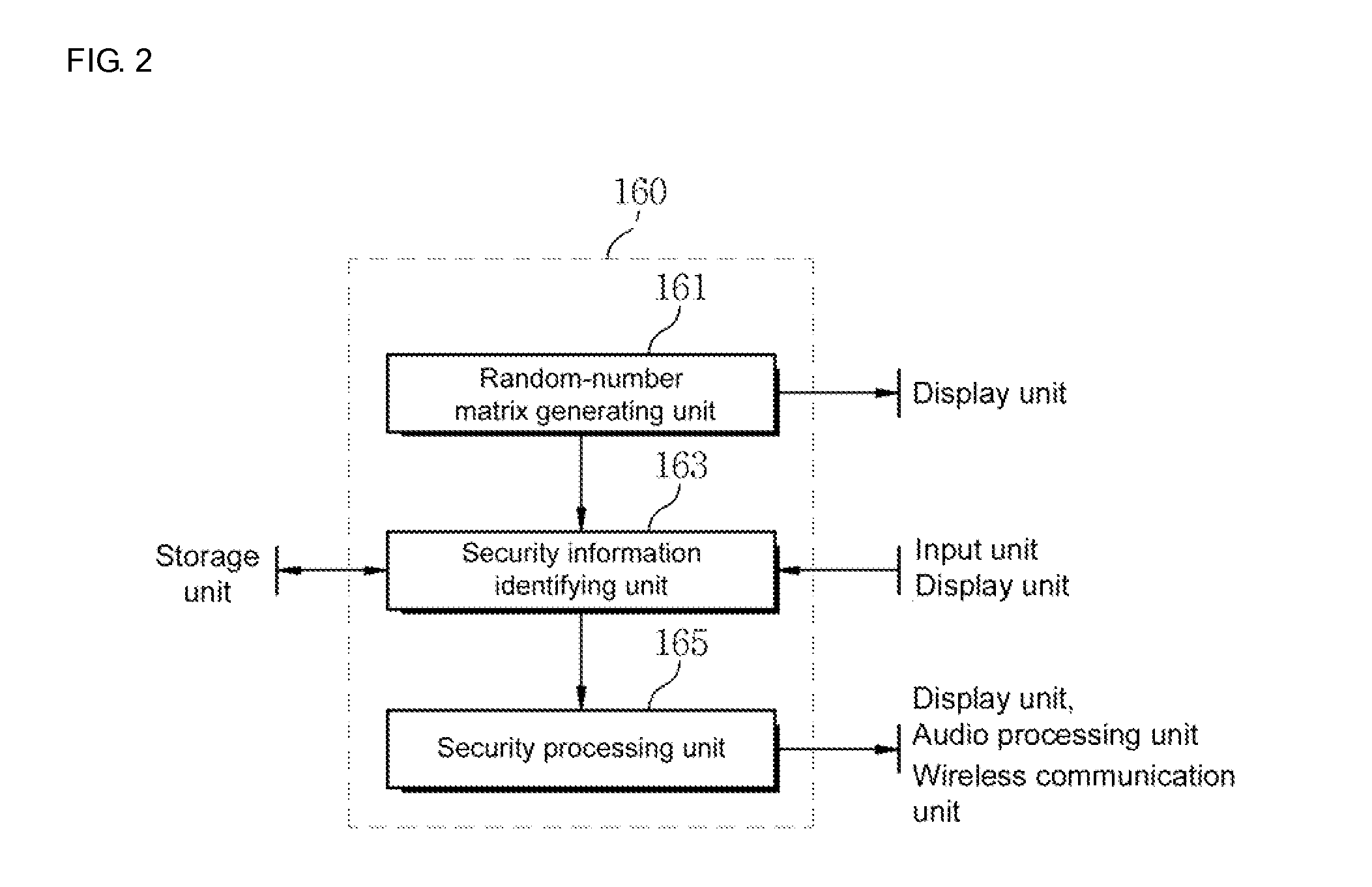
Method for providing active security authentication, and terminal and system supporting same
InactiveUS20130047238A1Avoid it happening againImprove securityMultiple keys/algorithms usageDigital data processing detailsComputer terminalSecurity authentication
Disclosed herein are a method for providing active security authentication, and a terminal and system for supporting the same. The terminal includes a storage unit, a display unit, an input unit and a control unit. The control unit arranges a plurality of keys through an arrangement of random numbers when a security execution condition is satisfied, outputs, to the display unit, a security authentication screen based on a random-number matrix in which at least some keys in key regions adjacent to an item key among the plurality of keys arranged by the arrangement of the random numbers are set to exception keys that a user must not press, and decide that the terminal is used for an illegal use when the exception keys are included in an input information generated through the input unit.
Owner:BLUE POPCON CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com