Patents
Literature
3476results about "Random number generators" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
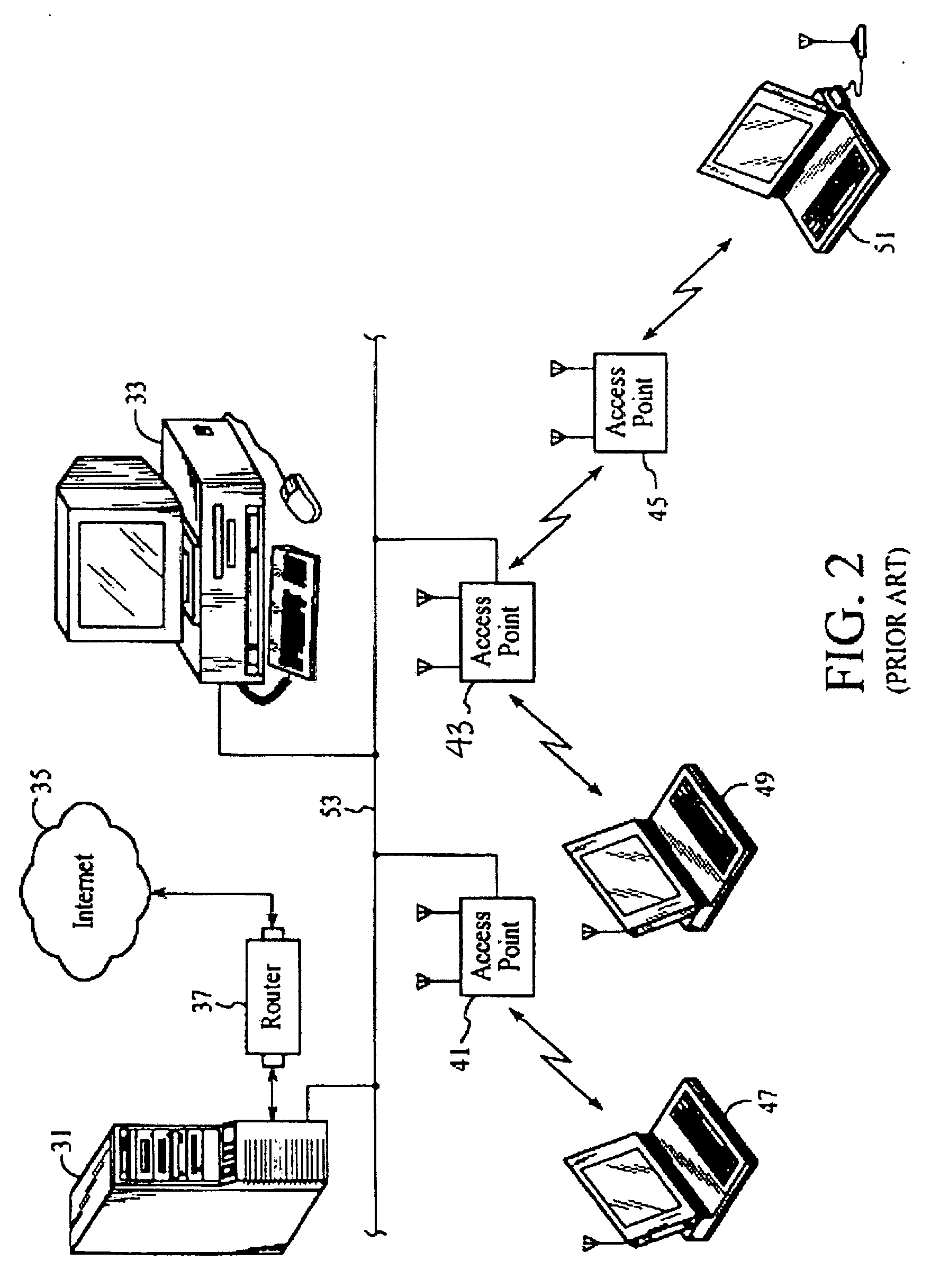
Administration of protection of data accessible by a mobile device
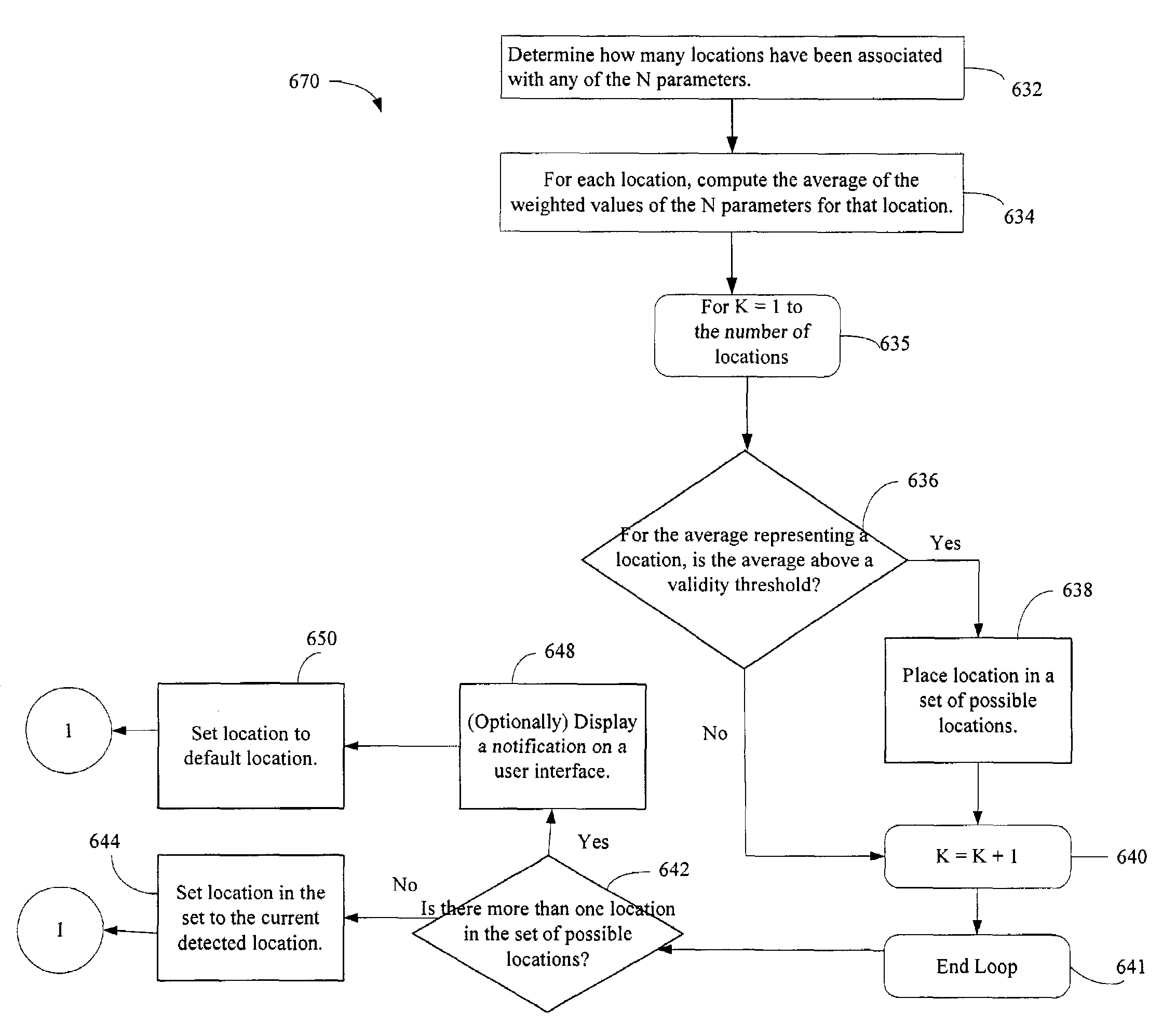
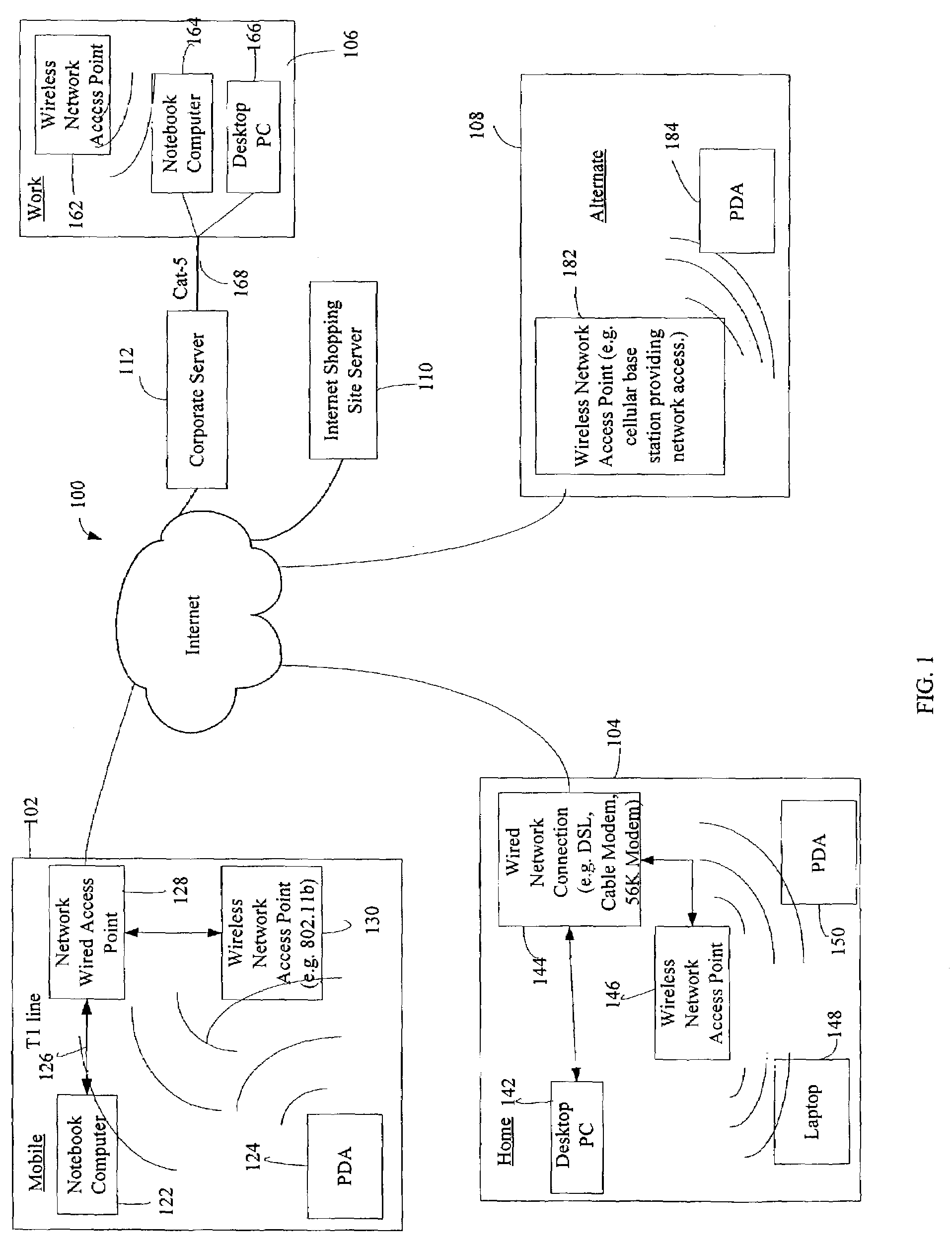
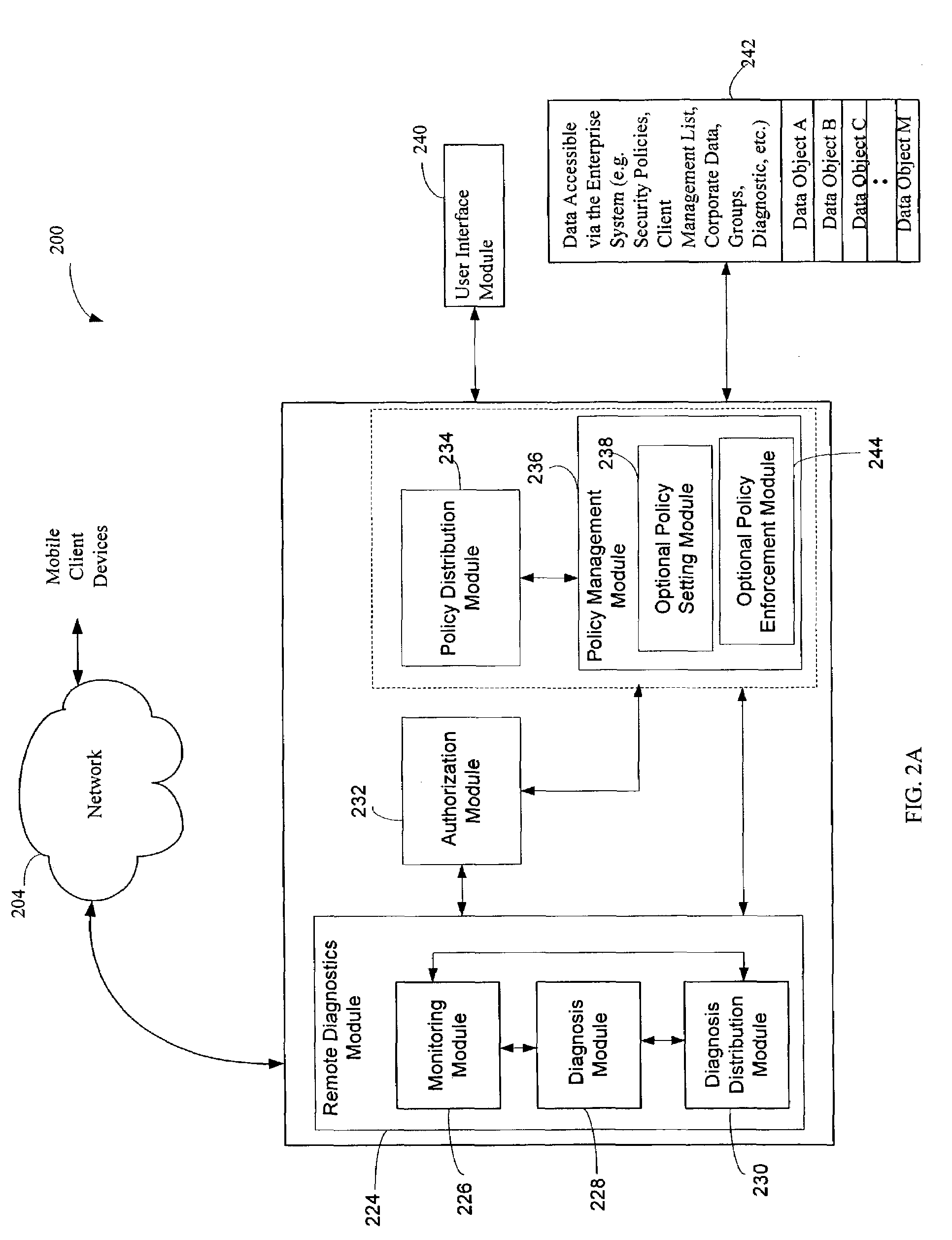
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
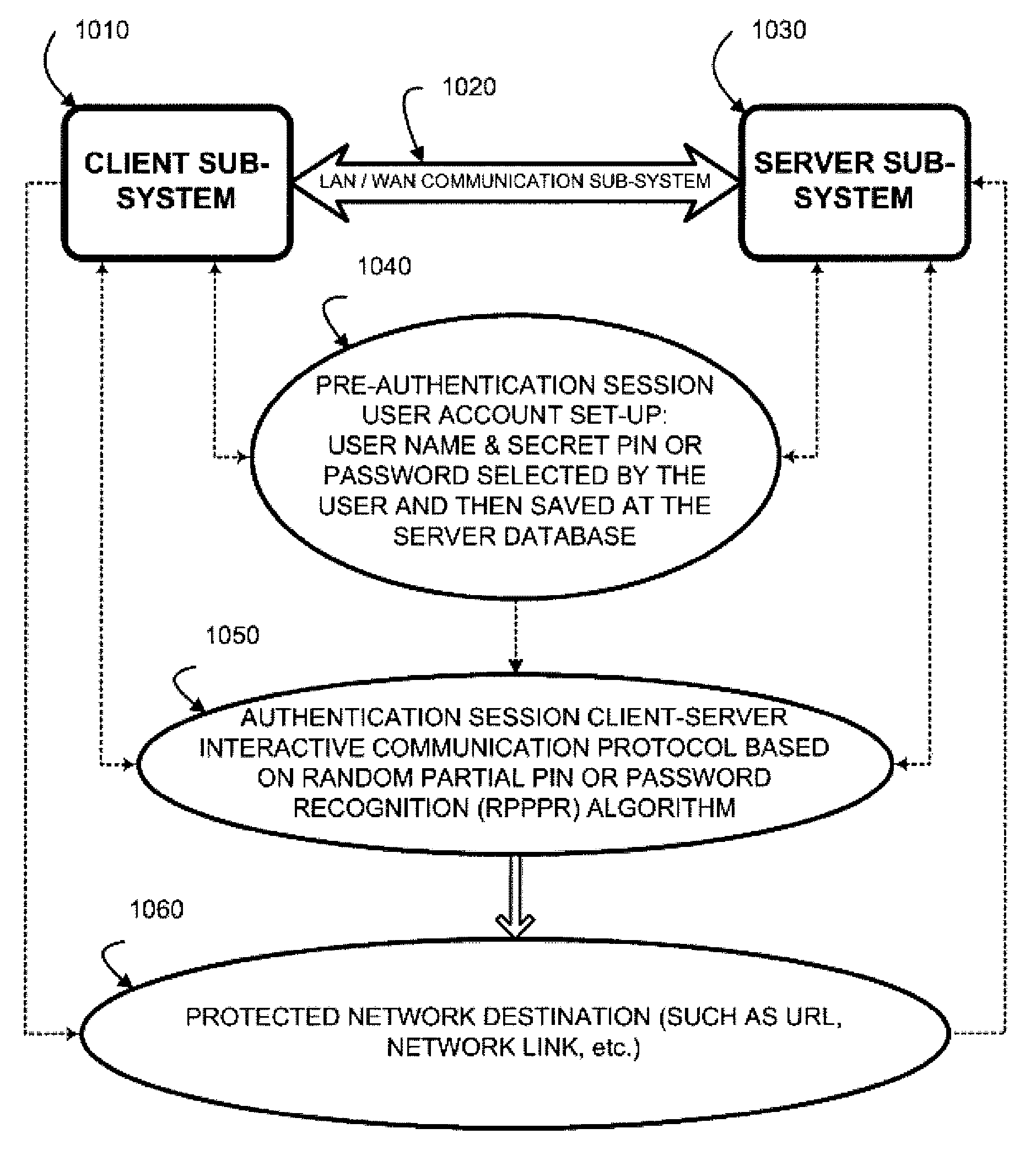
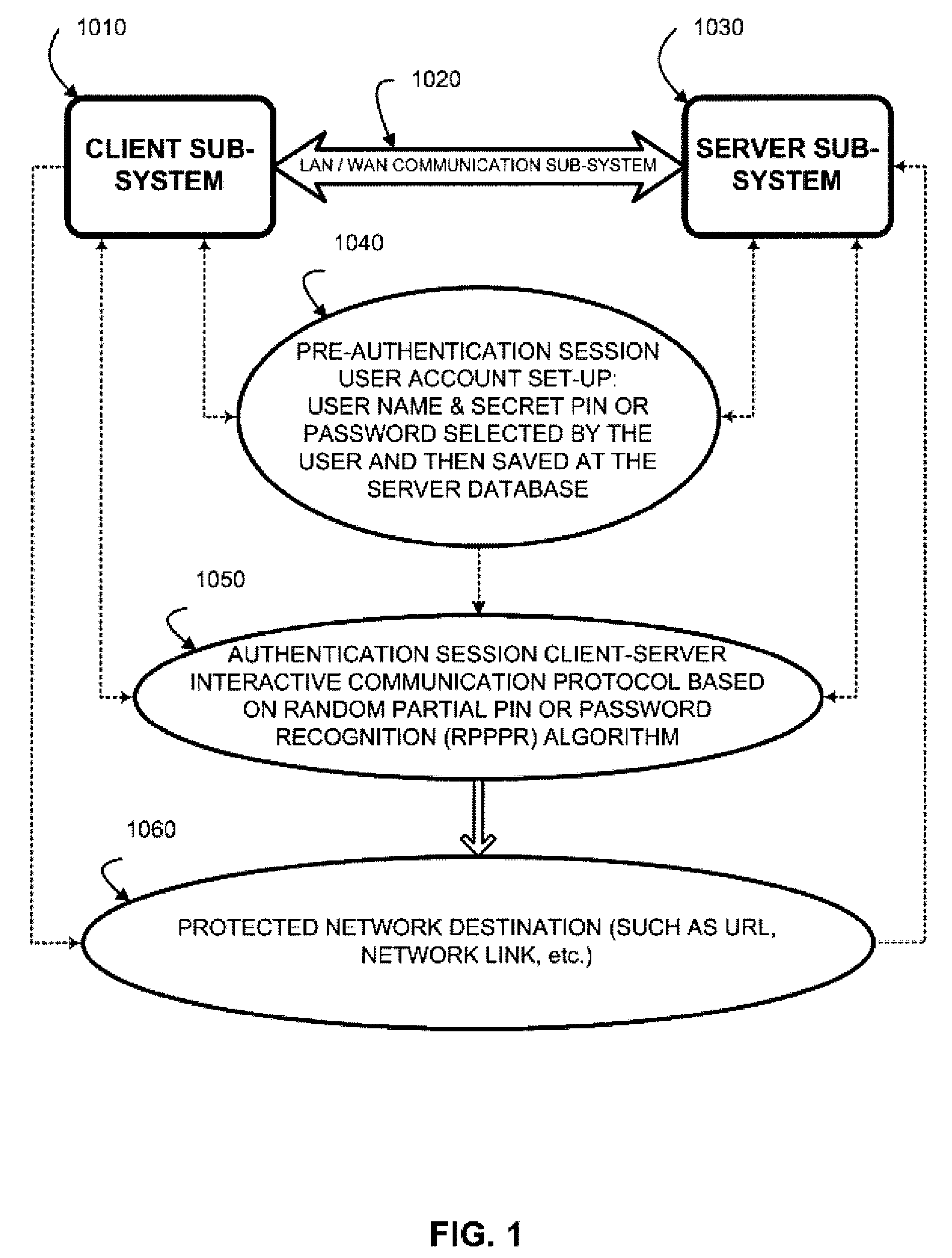
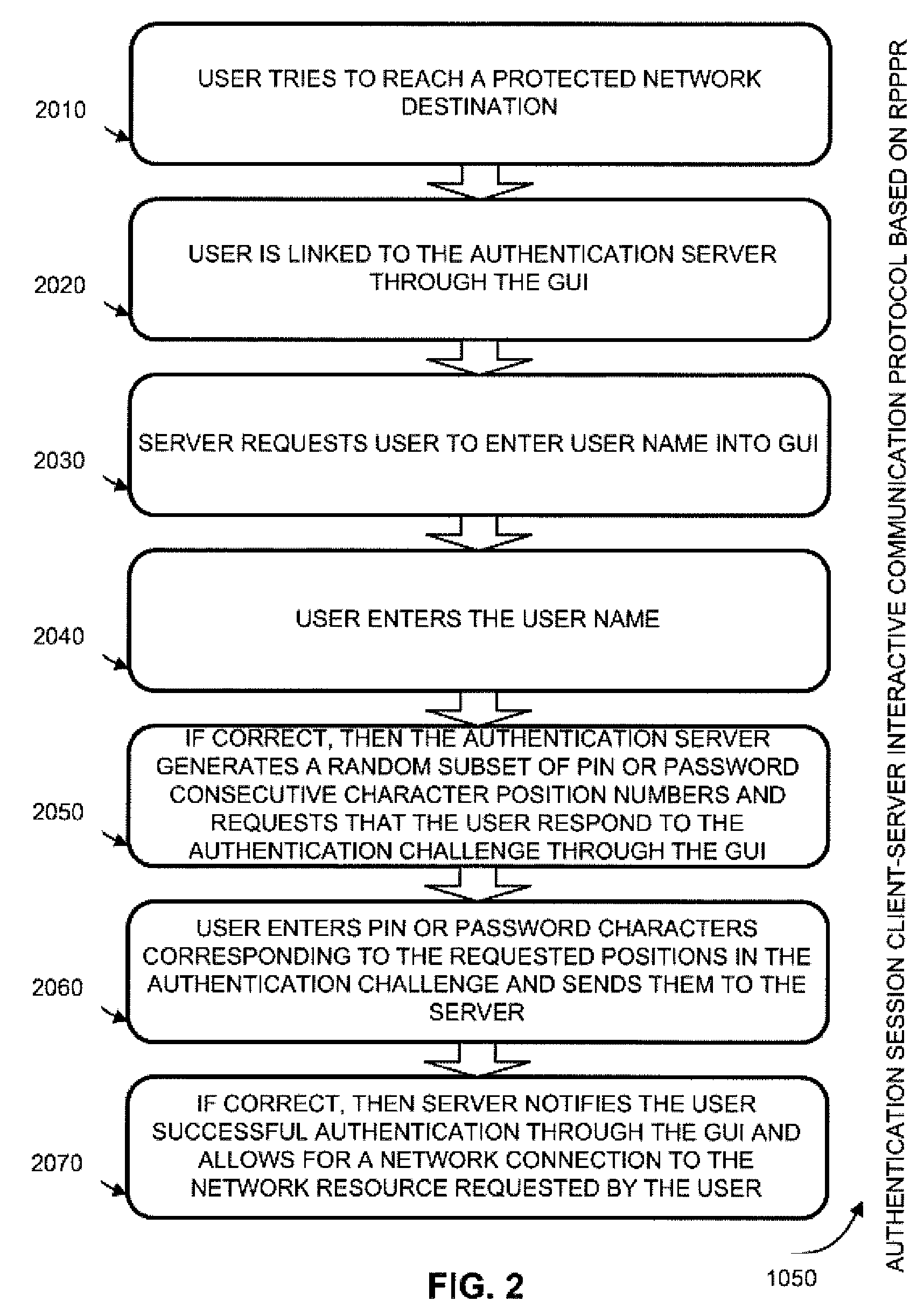
Two-channel challenge-response authentication method in random partial shared secret recognition system
ActiveUS20080098464A1Random number generatorsUser identity/authority verificationClient-sideServer-side
Random partial shared secret recognition is combined with using more than one communication channel between server-side resources and two logical or physical client-side data processing machines. After a first security tier, a first communication channel is opened to a first data processing machine on the client side. The session proceeds by delivering an authentication challenge, identifying a random subset of an authentication credential, to a second data processing machine on the client side using a second communication channel. Next, the user enters an authentication response in the first data processing machine, based on a random subset of the authentication credential. The authentication response is returned to the server side on the first communication channel for matching. The authentication credential can be a one-session-only credential delivered to the user for one session, or a static credential used many times.
Owner:AUTHERNATIVE INC
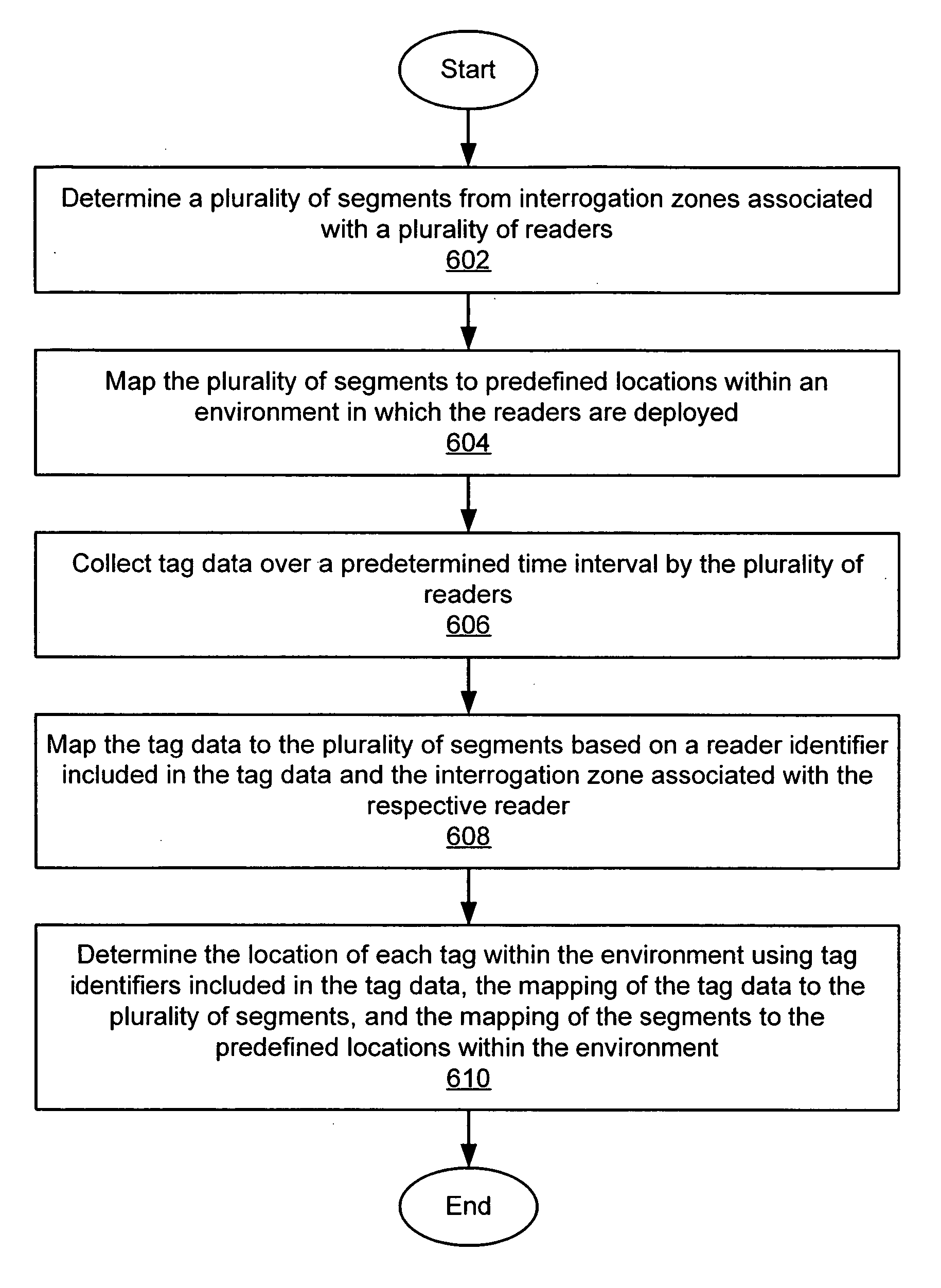
Location virtualization in an RFID system
ActiveUS20060170565A1Improve reliabilityRandom number generatorsFrequency-division multiplex detailsVirtualizationRadio frequency
A system and method of determining locations of one or more RFID tags within an RFID environment. The system includes a plurality of RFID readers, each operative to transmit and receive RF signals for scanning a tag disposed within an RF coverage region associated with the reader, and for receiving tag data in response to the scanning of the tag. A plurality of sub-locations is determined within the environment, each corresponding to at least a portion of at least one of a plurality of RF coverage regions associated with the readers. The sub-locations are mapped to a plurality of predefined locations within the environment. A reader scans a tag, and receives tag scan data from the tag in response to the scanning of the tag. The tag scan data includes a tag identifier associated with the scanned tag. The tag scan data is mapped to the sub-locations based on the RF coverage region associated with the reader. The location of the scanned tag is then determined with reference to the predefined locations within the environment, based on the tag identifier included in the tag scan data, the mapping of the tag scan data to the sub-locations, and the mapping of the sub-locations to the predefined locations.
Owner:ODIN SOFTWARE INC +1
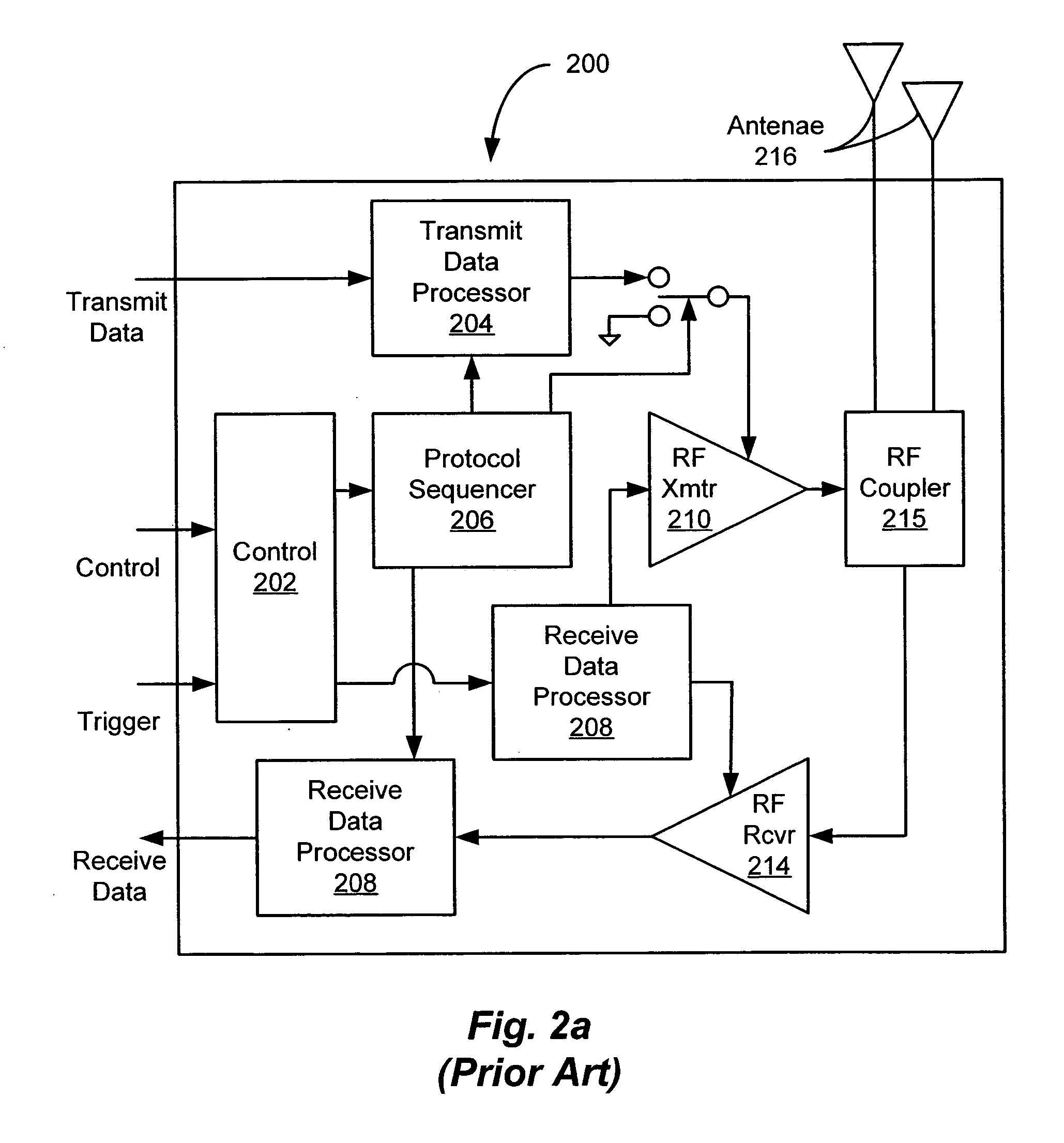
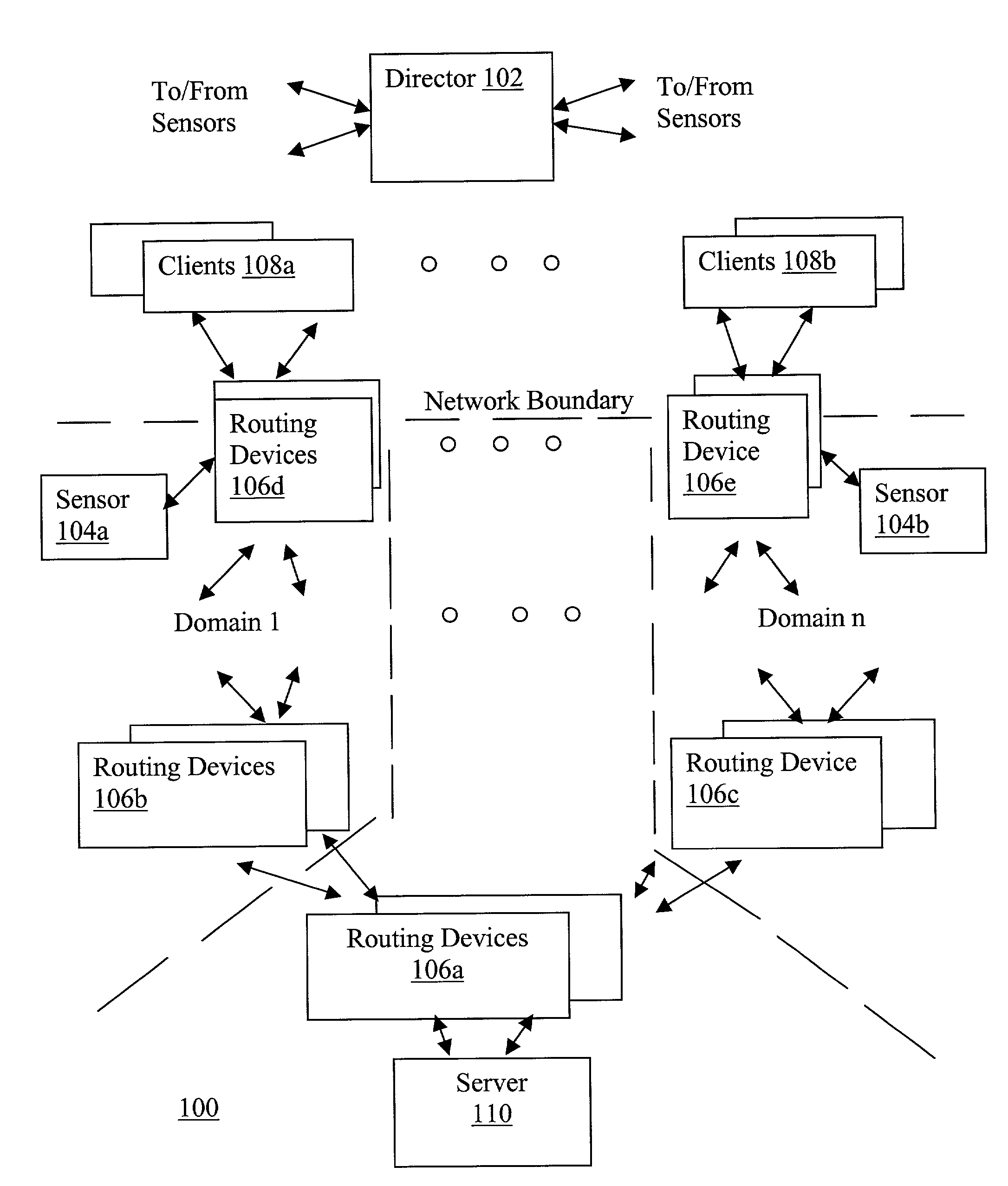
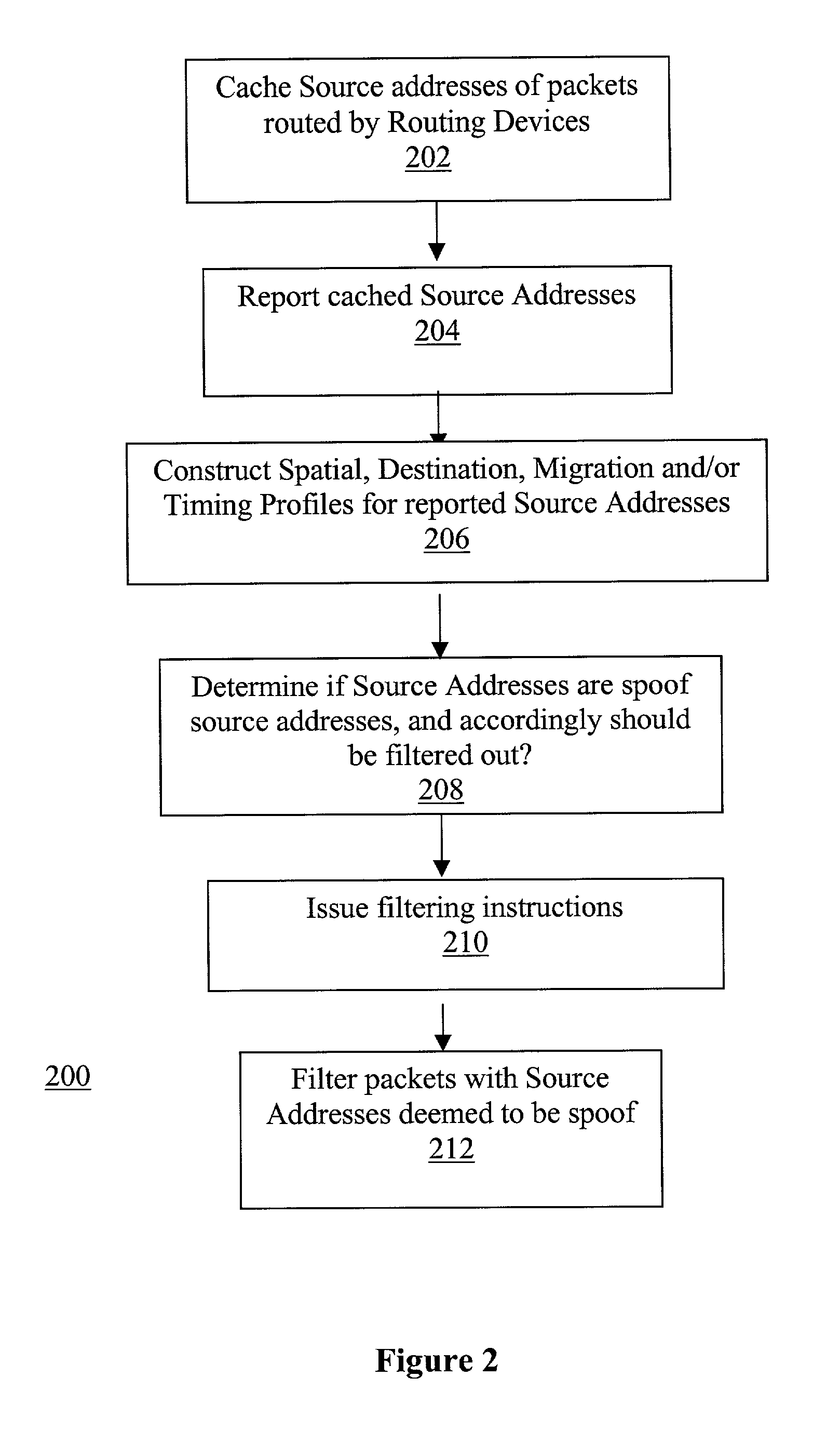
Network traffic regulation including consistency based detection and filtering of packets with spoof source addresses
InactiveUS7444404B2Ensuring quality of serviceEnsure qualityRandom number generatorsUser identity/authority verificationTraffic capacityReporting source
A director is provided to receive source address instances of packets routed through routing devices of a network. The director determines whether any of the reported source address instances are to be deemed as spoof source address instances. The director further determines where filtering actions are to be deployed to filter out packets having certain source addresses deemed to be spoof instances. The director makes its determinations based at least in part on a selected one of a number of consistency measures. The consistency measures may include but are not limited to spatial consistency, destination consistency, migration consistency, and temporary consistency. The consistency measures are evaluated using spatial, destination source address range, migration and timing S / D / M / T distribution profiles of the reported source addresses. In some embodiments, the determinations are based further in view of reference S / D / M / T distribution profiles, which may be an exemplary S / D / M / T distribution profile of a typical non-spoof source address or a historical S / D / M / T distribution profile of the source address.
Owner:ARBOR NETWORKS
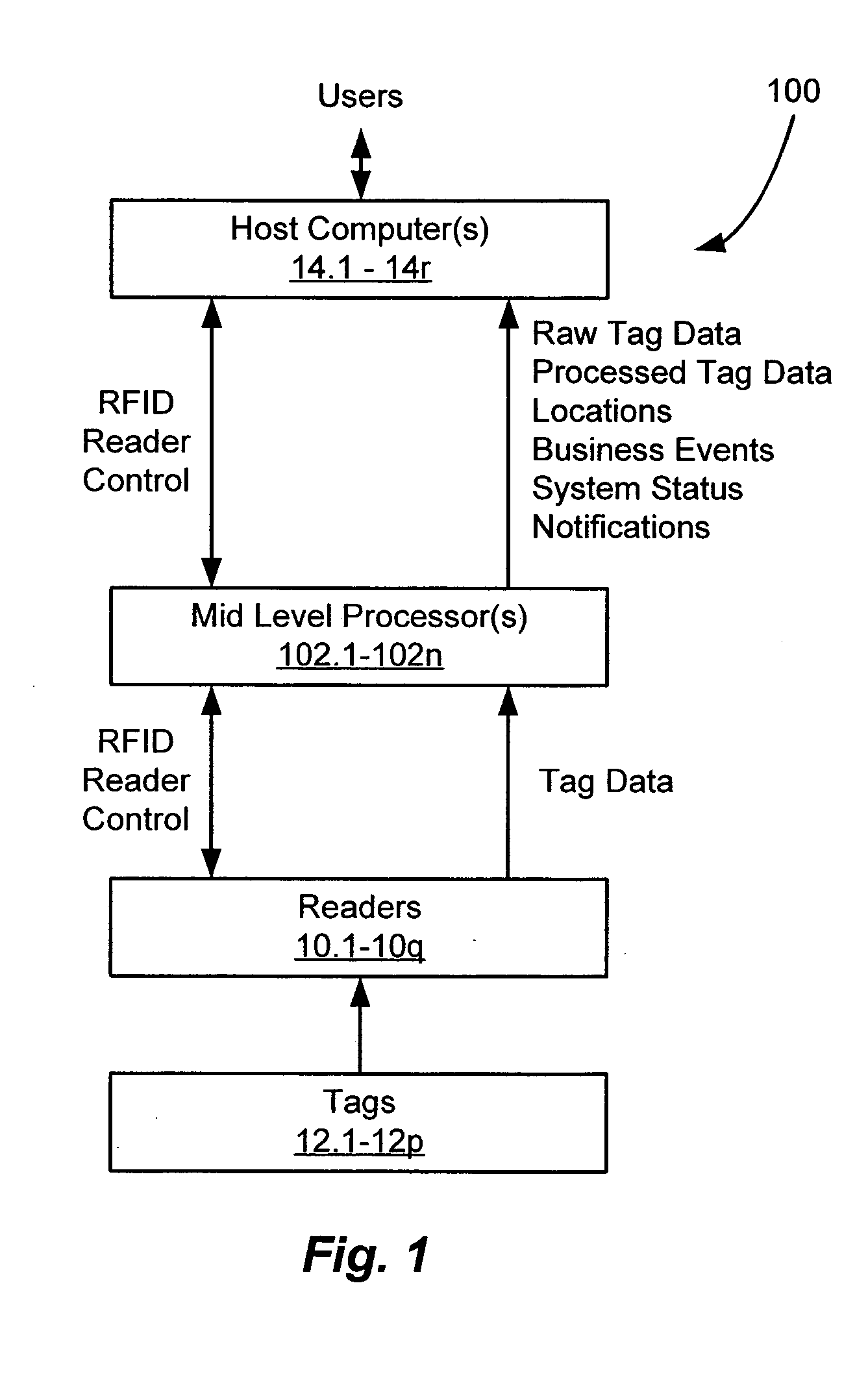
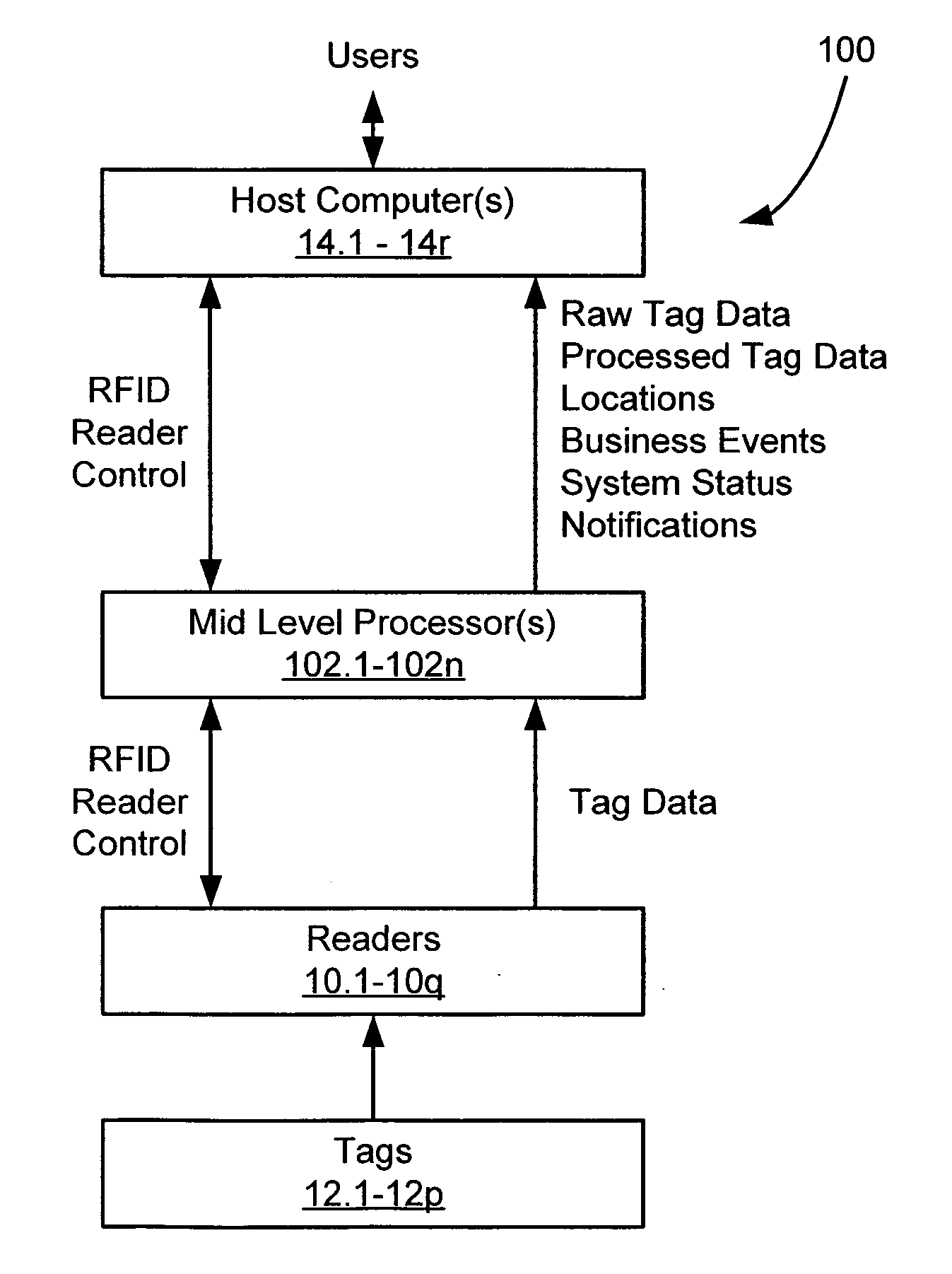
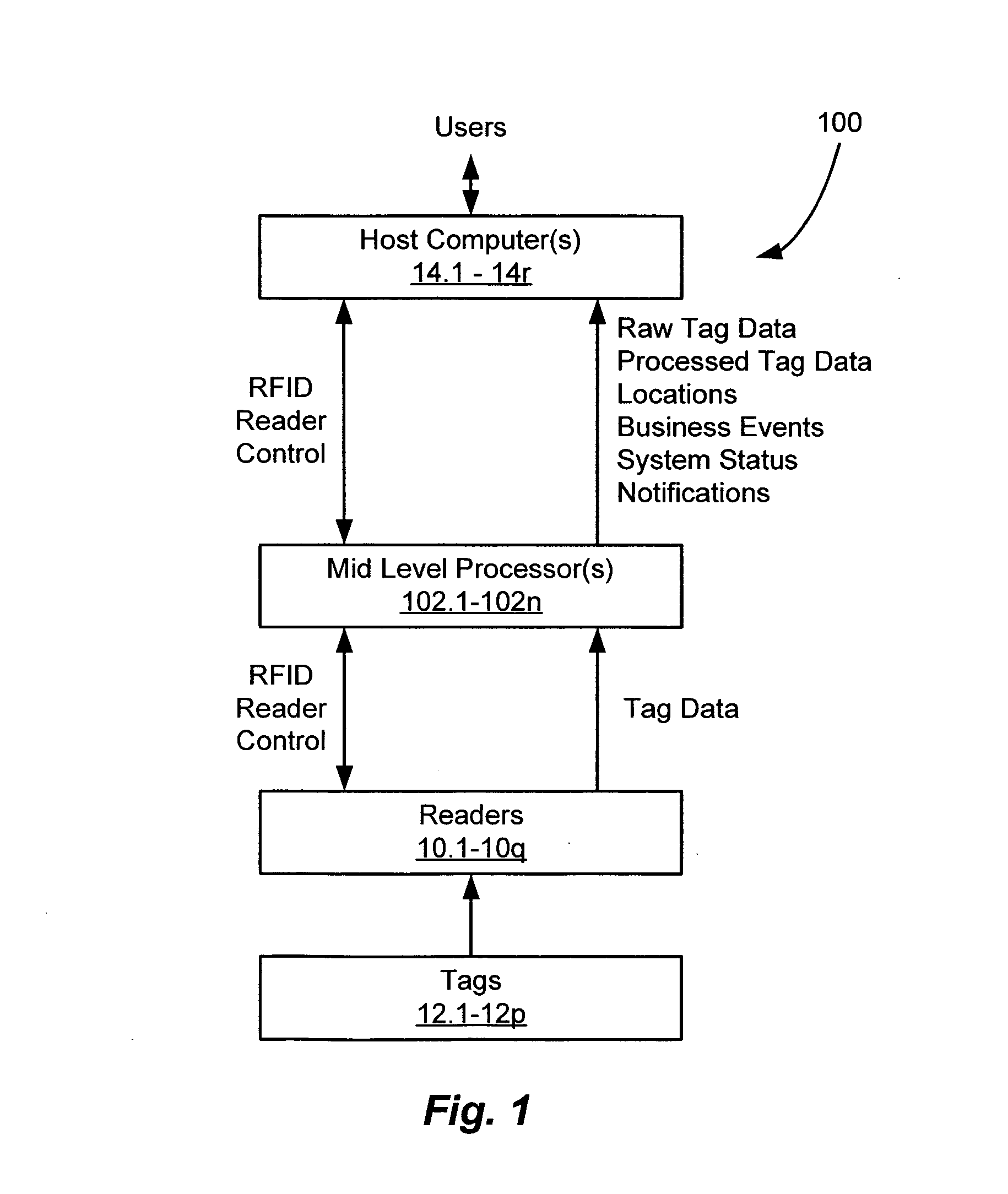
RFID tag data acquisition system
ActiveUS20060022801A1Easy accessRandom number generatorsMemory record carrier reading problemsData acquisitionComputer science
An architecture of an RFID system that facilitates the accessing of RFID tag data within an RFID environment. The architecture includes a plurality of RFID readers, each reader being operative to transmit a first RF signal for scanning at least one RFID tag disposed within an RF coverage region associated with the reader, and to receive at least one second RF signal including tag data in response to the scanning of the tag. The architecture further includes at least one host computer operative to execute at least one client application, and at least one controller / processor communicably coupled to the plurality of readers and the at least one host computer. The controller / processor is operative to control operation of the plurality of readers, to process the tag data received by the plurality of readers, and to provide the processed tag data to the at least one host computer for use by the at least one client application executing thereon.
Owner:QUAKE GLOBAL +1
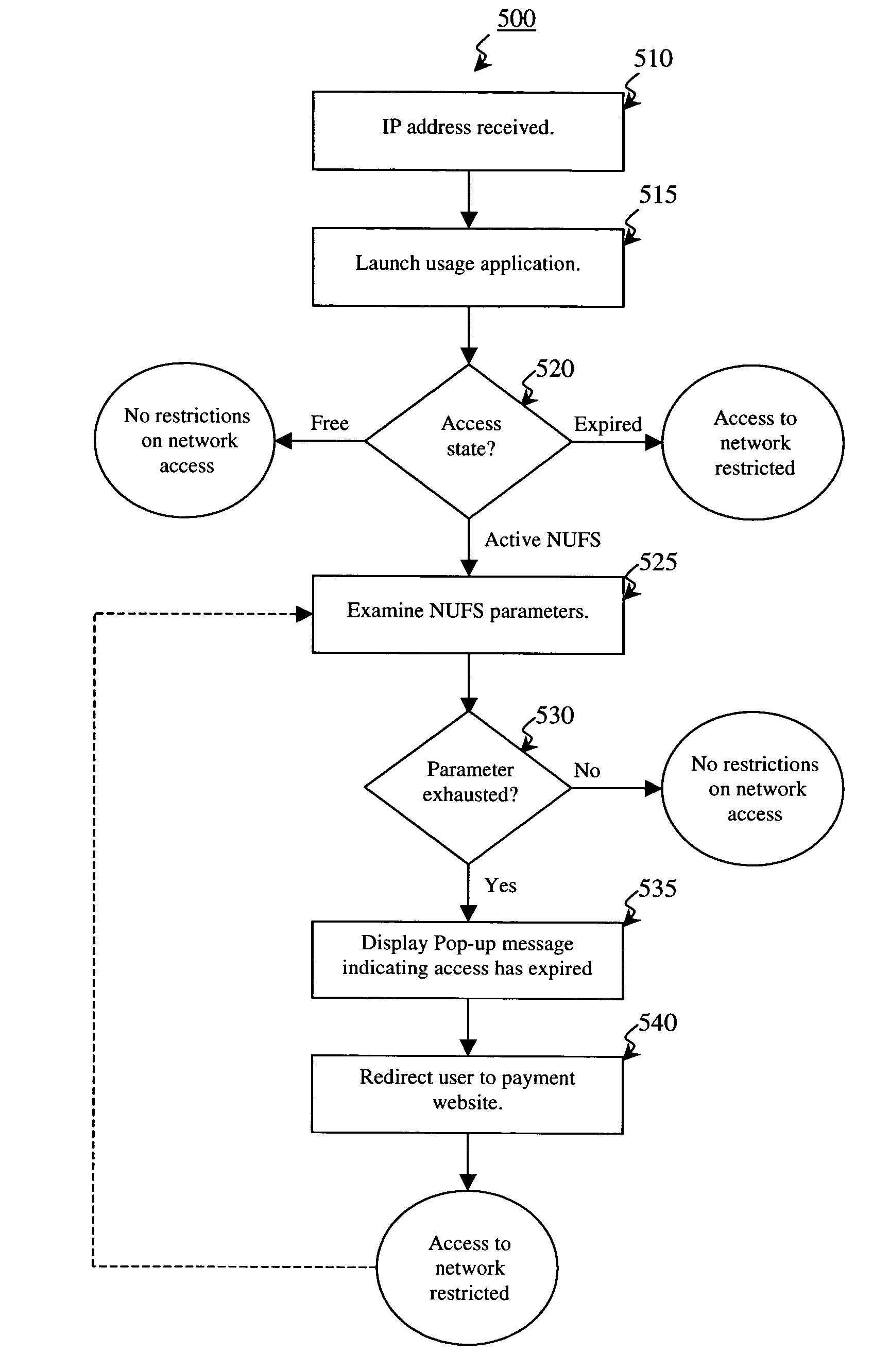
Self-managed network access using localized access management
ActiveUS7574731B2Provide usageAvoid modificationRandom number generatorsUser identity/authority verificationProgram planningBack end server
The invention provides a method and system for locally tracking network usage and enforcing usage plans at a client device. In an embodiment of the invention, a unique physical key, or token, is installed at a client device of one or more networks. The key comprises a usage application and one or more access parameters designated the conditions and / or limits of a particular network usage plan. Upon initial connection to the network, the usage application grants or denies access to the network based on an analysis of the current values of the access parameters. Therefore, network usage tracking and enforcement is made simple and automatic without requiring any back-end servers on the network while still providing ultimate flexibility in changing billing plans for any number of users at any time.
Owner:KOOLSPAN
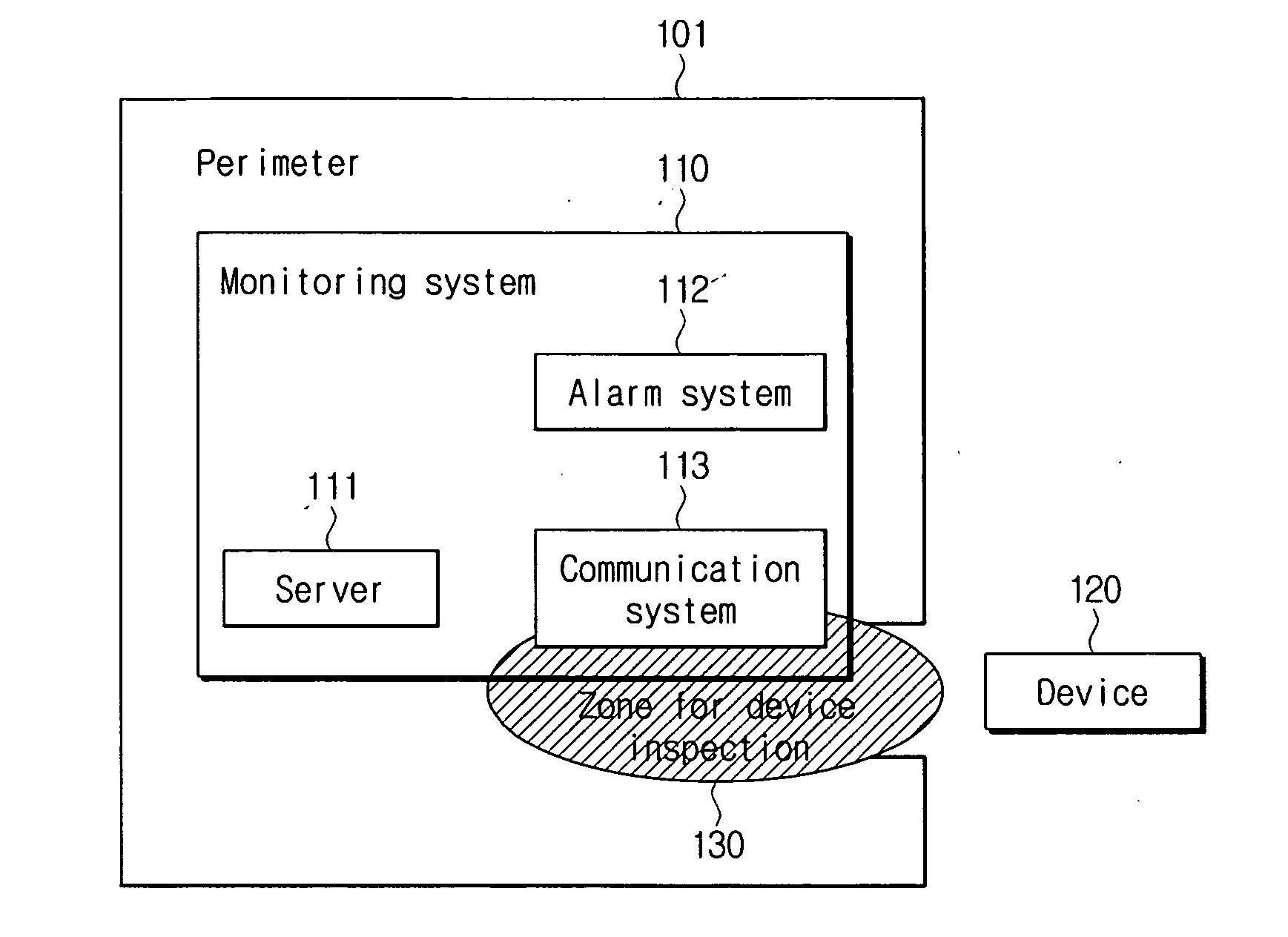
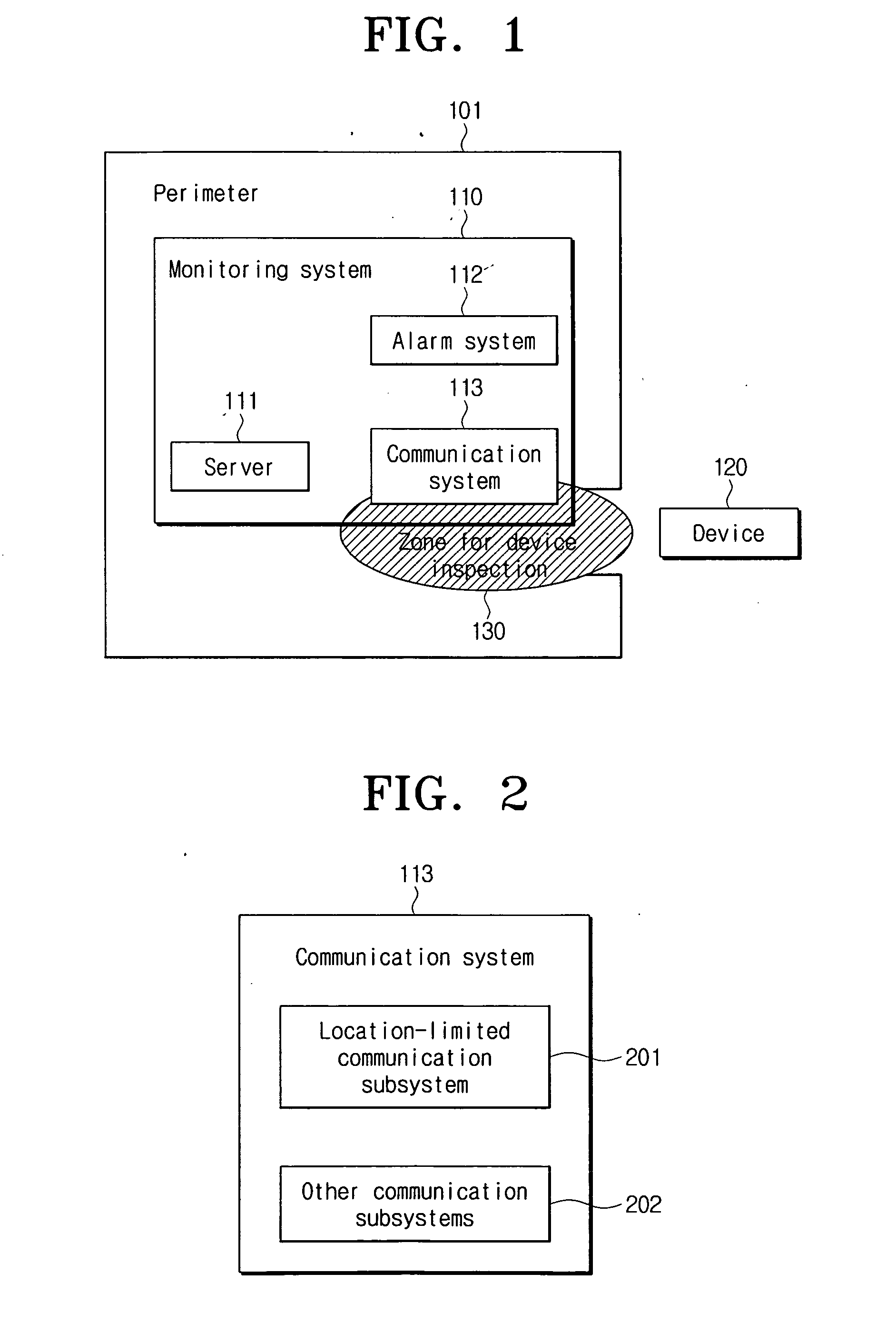
Device function restricting method and system in specific perimeters
ActiveUS20070101426A1Facilitating information leakageGood informationRandom number generatorsData taking preventionCommunications systemMonitoring system
An apparatus and method for restricting the functions of a device are provided. A restriction monitoring system includes a communication system that provides a location-limited communication channel that detects whether a device entering a perimeter is in an area for device inspection, a server that provides a credential and a security policy to the device and receives a report on whether the device violates the security policy through the location-limited communication channel, and an alarm system which triggers a security alarm when the device violates the security policy.
Owner:SAMSUNG ELECTRONICS CO LTD
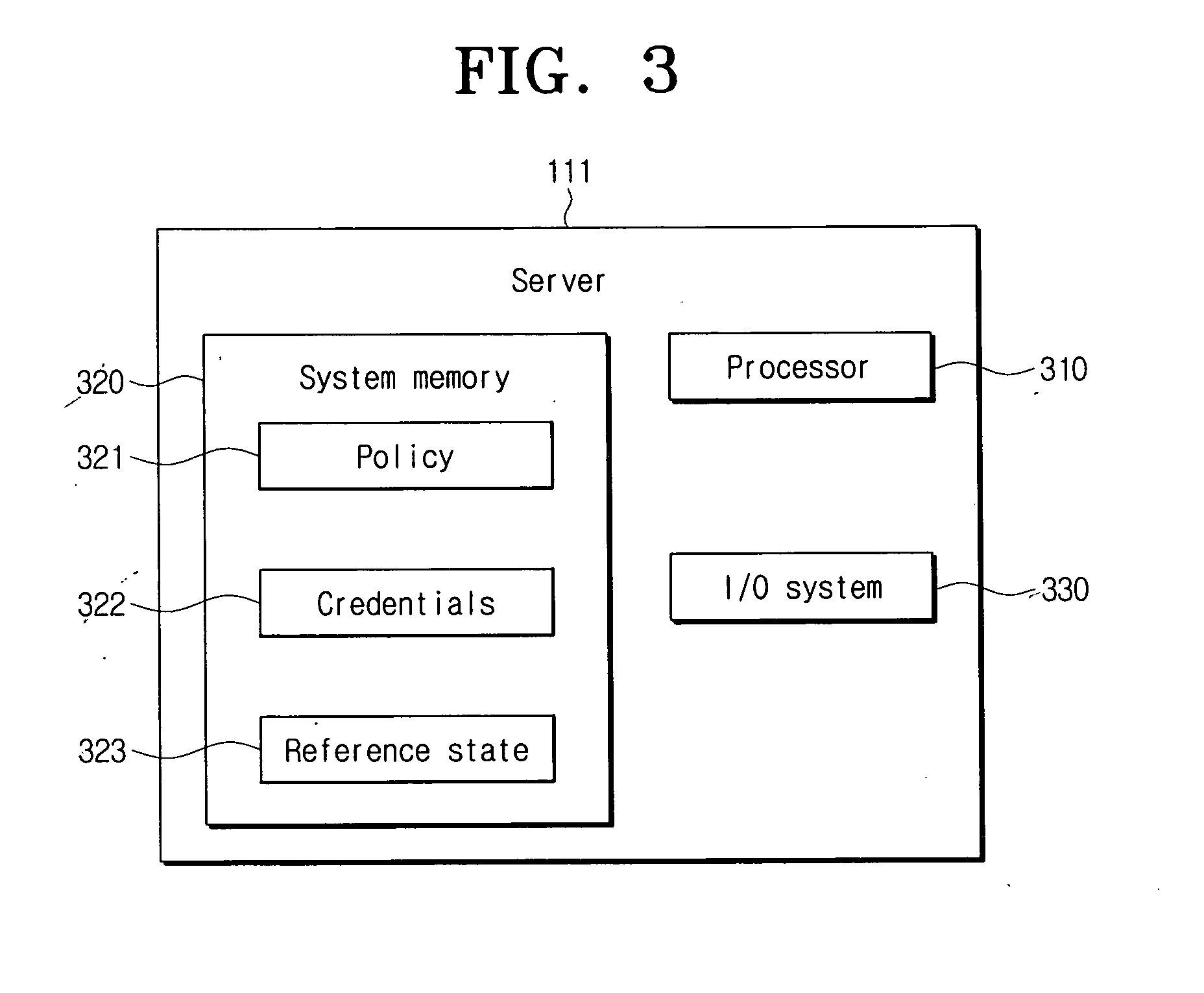
System and method for secure network connectivity
InactiveUS20070101405A1Accurate protectionConnection securityRandom number generatorsMemory loss protectionSecurity checkRemote computer
A system and method to ensure that a remote computer making a VPN connection complies with network security policies. Server-driven security checks may be configured to verify compliance with each access level before access is granted at that level. The security checks may be selected based at least according to the information received from the remote computer. After the server determines that the remote computer complies with the security policy for the requested access level, the server may pass a token to the remote computer, or may grant VPN access to the remote computer. If the remote computer does not comply with the security policy associated with the requested access level but is in compliance with a security policy corresponding to a lower access level, the server may grant the remote computer access to the lower access level.
Owner:BARCLAYS CAPITAL INC
High performance microprocessor having variable speed system clock
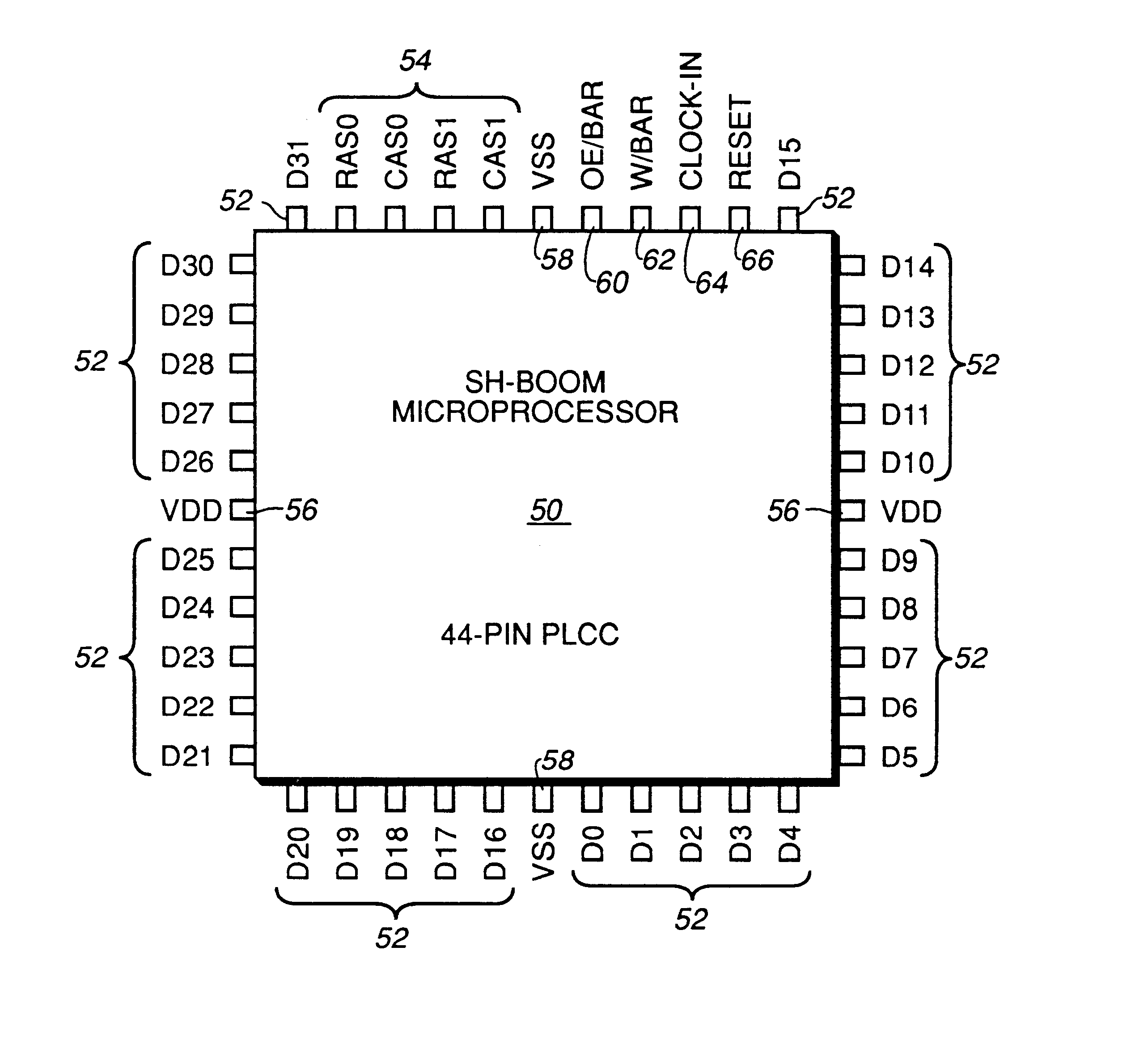
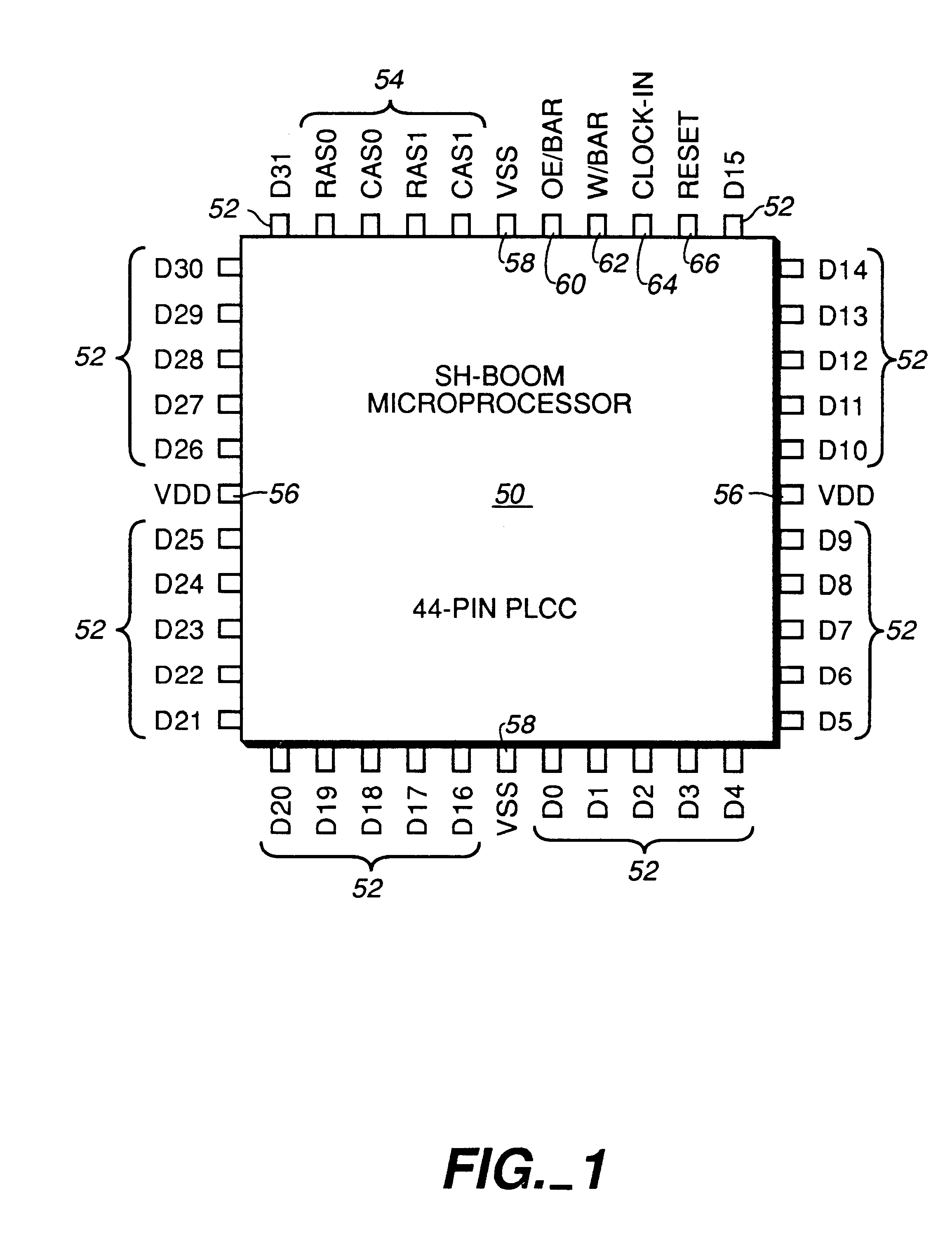
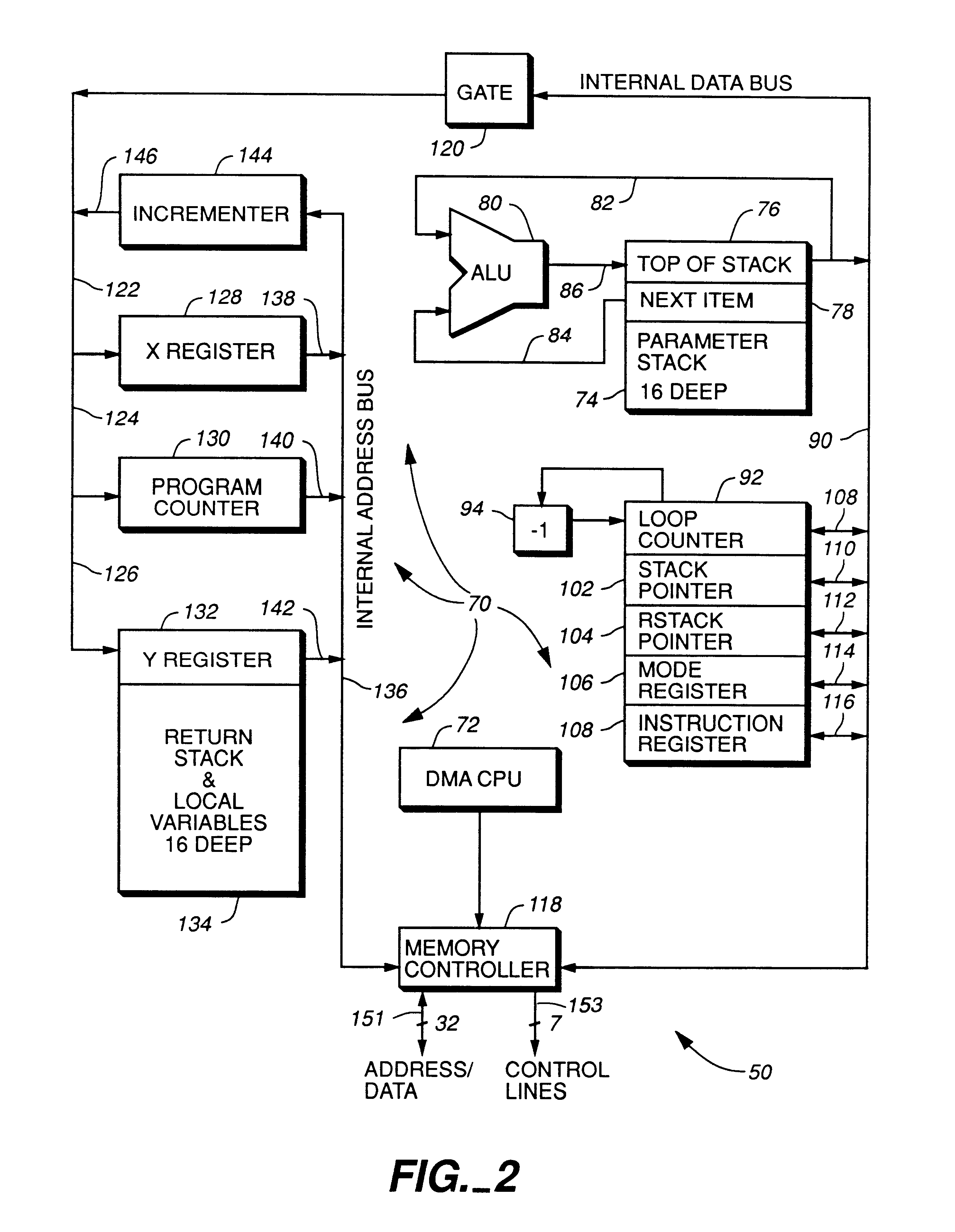
InactiveUS6598148B1Improve performanceWithout sacrificing microprocessor speedRandom number generatorsInstruction analysisComputer architectureStatic random-access memory
A microprocessor integrated circuit including a processing unit disposed upon an integrated circuit substrate is disclosed herein. The processing unit is designed to operate in accordance with a predefined sequence of program instructions stored within an instruction register. A memory, capable of storing information provided by the processing unit and occupying a larger area of the integrated circuit substrate than the processing unit, is also provided within the microprocessor integrated circuit. The memory may be implemented using, for example dynamic or static random-access memory. A variable output frequency system clock, such as generated by a ring oscillator, is also disposed on the integrated circuit substrate.
Owner:MOORE CHARLES H TTE UTD 03 21 2006 THE EQUINOX TRUST
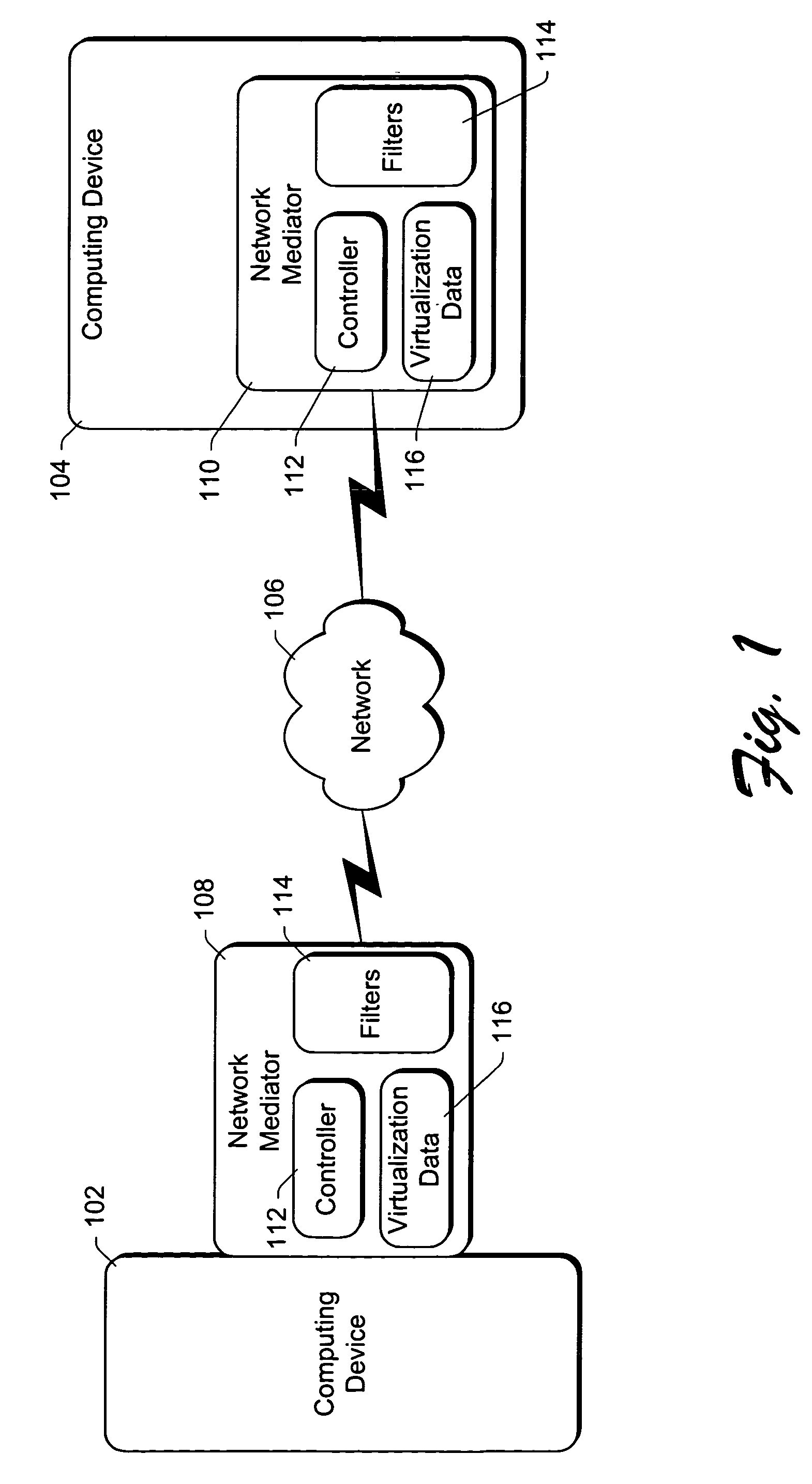
Using packet filters and network virtualization to restrict network communications
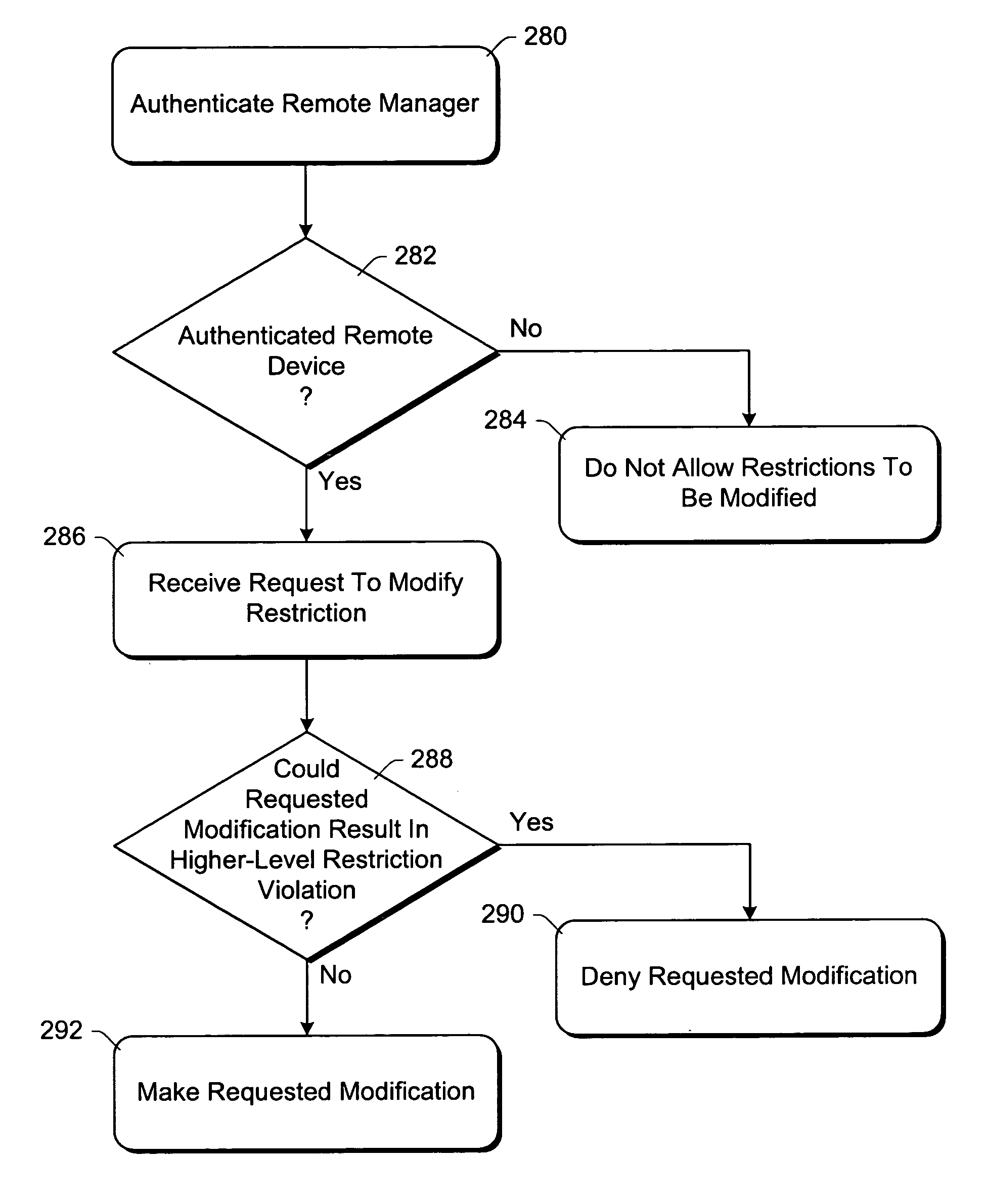
InactiveUS7093288B1Communication be restrictRandom number generatorsCharacter and pattern recognitionNetwork packetNetwork addressing
A network mediator corresponding to a computing device uses packet filters to restrict network communications. The network mediator includes a set of one or more filters, each filter having parameters that are compared to corresponding parameters of a data packet to be passed through the network mediator. The network mediator determines whether to allow the data packet through based on whether the data packet parameters match any filter parameters. The set of filters can be modified by a remote device, but cannot be modified by the computing device whose communications are being restricted. When a data packet is sent from the computing device, the data packet will include the virtual address which is changed to the network address by the network mediator prior to forwarding the packet on the network, and vice versa. By virtualizing the addresses, the computing device is restricted in accessing other devices over the network.
Owner:MICROSOFT TECH LICENSING LLC
Method, apparatus and article for computational sequence generation and playing card distribution
A computationally generated playing card sequence (e.g., pseudo-random, non pseudo-random, or partially pseudo-random) allows shuffled distribution of playing cards. Playing cards may be organized into card holders by at least one or a rank and a suit, and retrieved in the computationally generated order. Alternatively, playing cards may be organized into card holders in order of a computationally generated sequence, and retrieve as necessary. Unreadable playing cards may be automatically removed from play.
Owner:BALLY GAMING INC +1
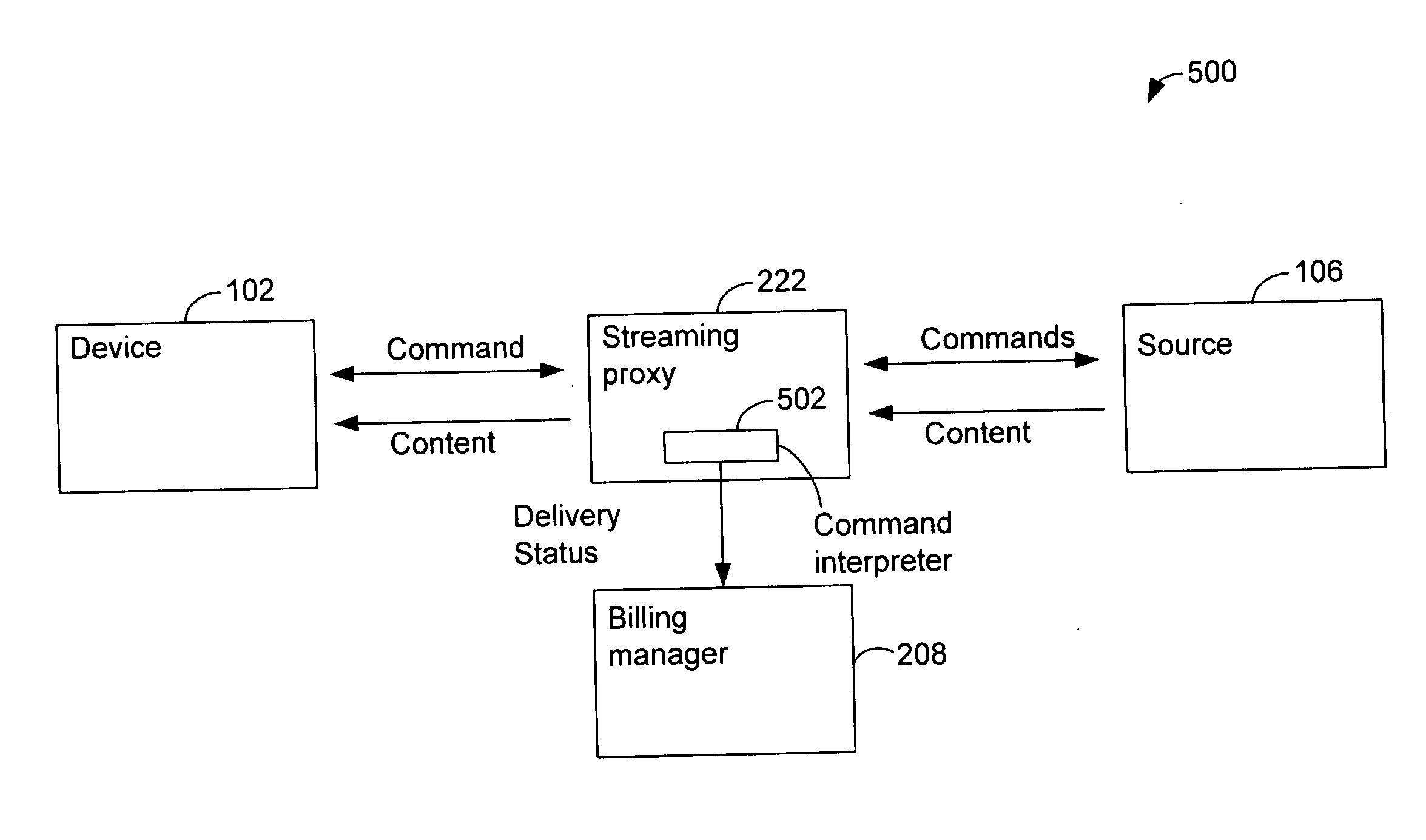
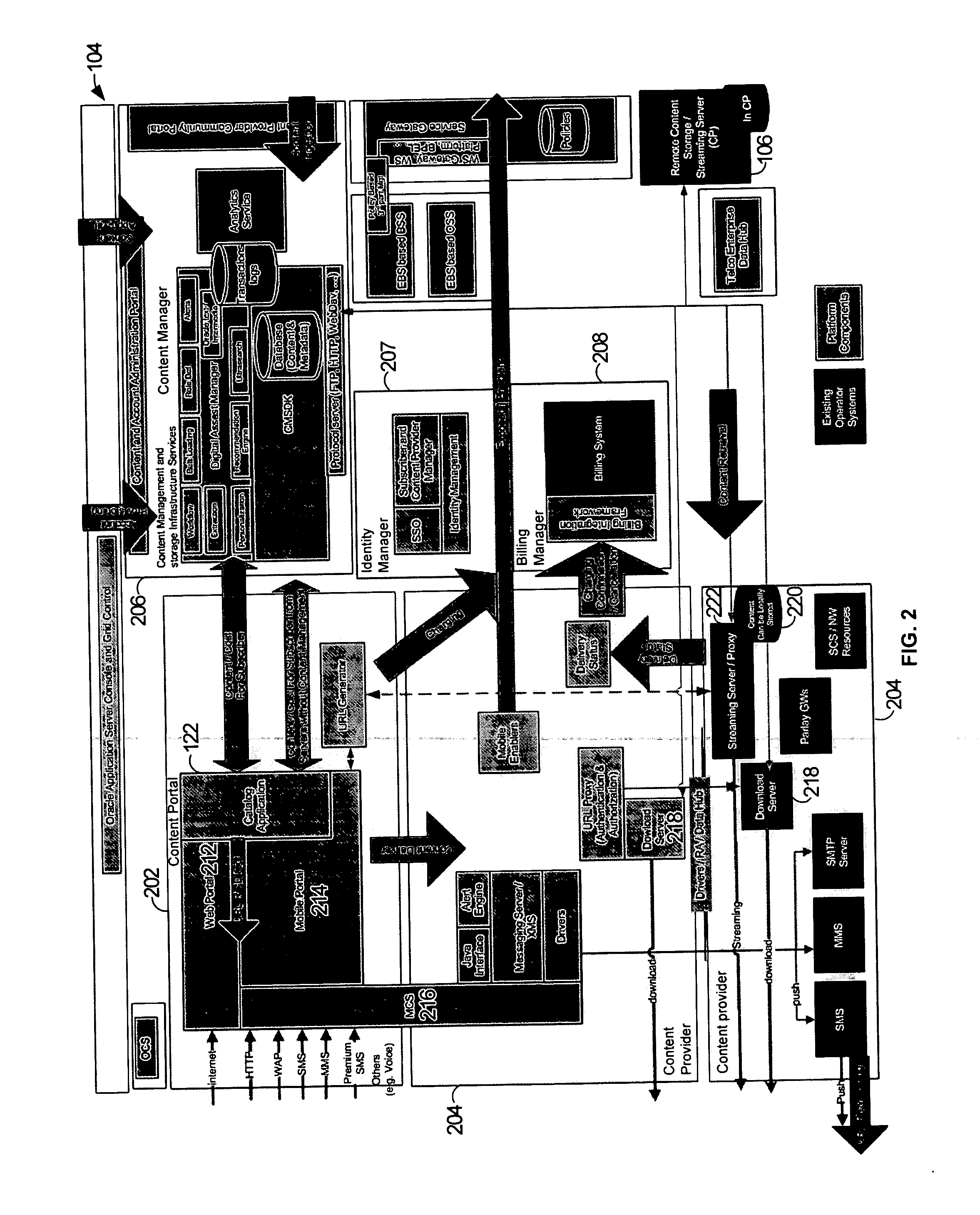
Platform and service for management and multi-channel delivery of multi-types of contents
ActiveUS20060272028A1Random number generatorsUser identity/authority verificationIdentity managementContent management
A platform for managing delivery of content originating from one or more content providers to users is provided. The platform includes a portal that is configured to support access through a plurality of access channels configured to receive requests through one or more access channels. A request for content is received from an access device through an access channel. An identity management module is configured to determine a user associated with the message. A content manager is configured to manage content for delivery through the plurality of access channels and configured to determine eligible content for the user. A billing module is configured to process billing for the user and content provider based on the content provided to the user. The content manager is then configured to deliver the requested content to the user's access device through the access channel.
Owner:ORACLE INT CORP
Authorization infrastructure based on public key cryptography
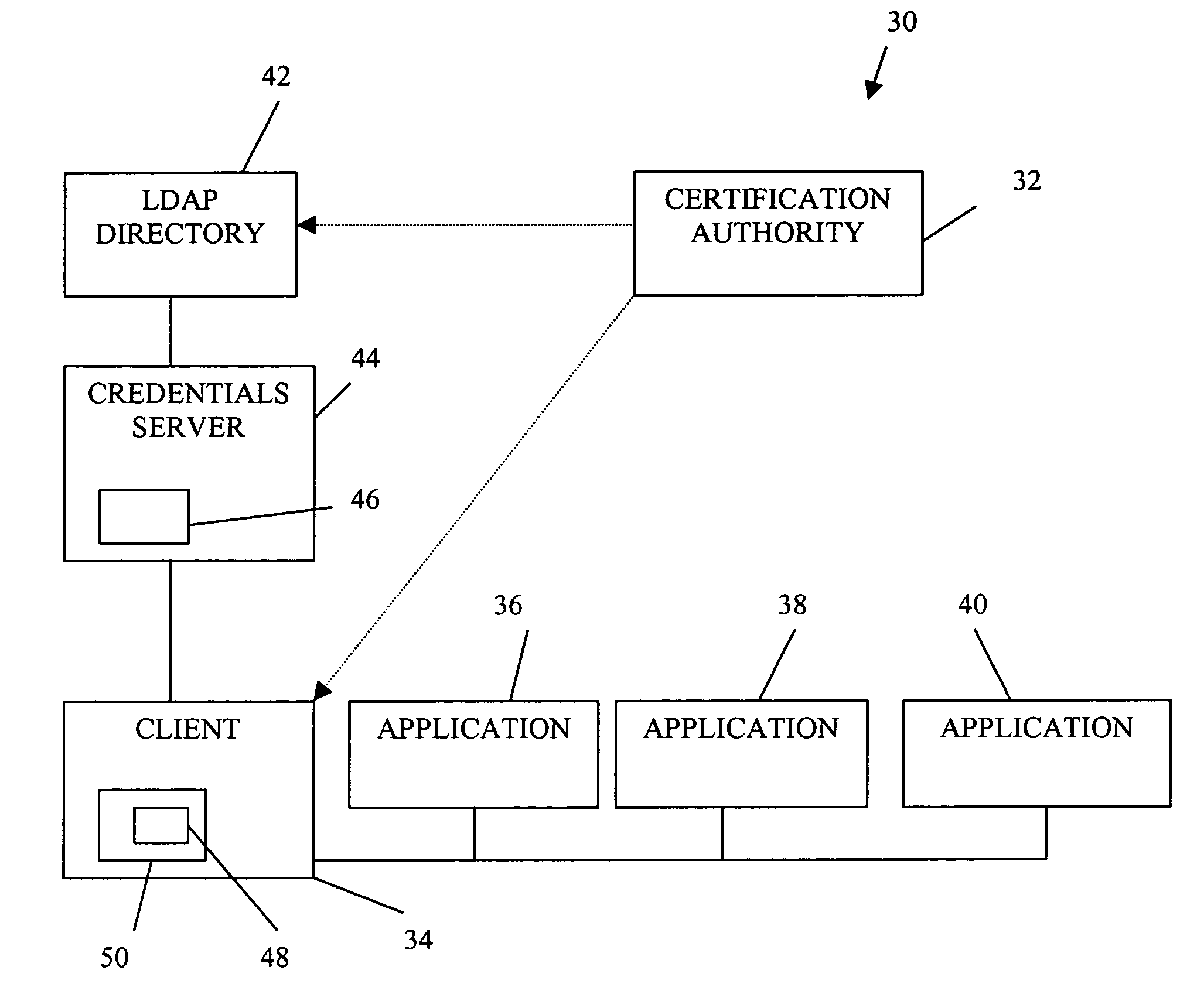
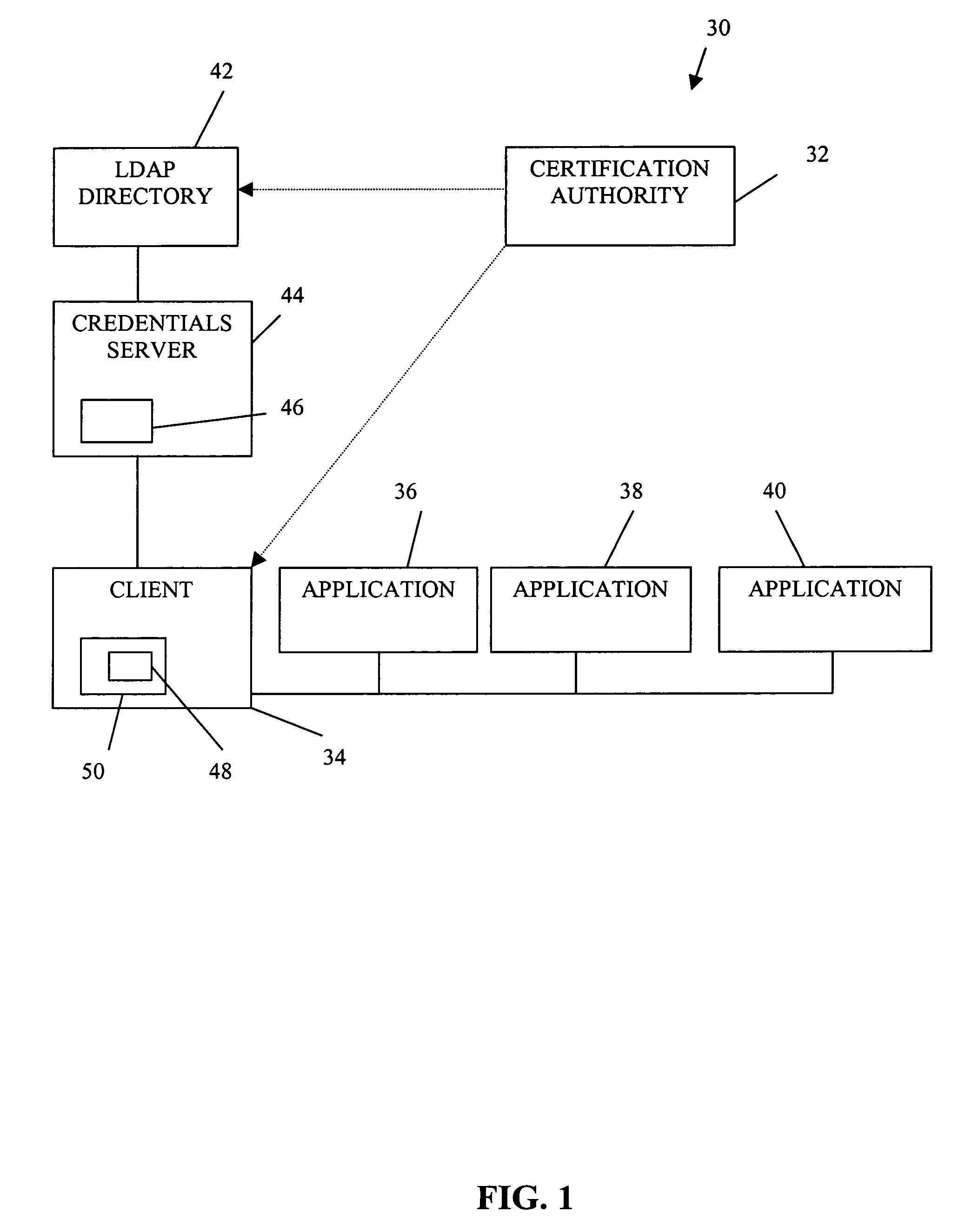
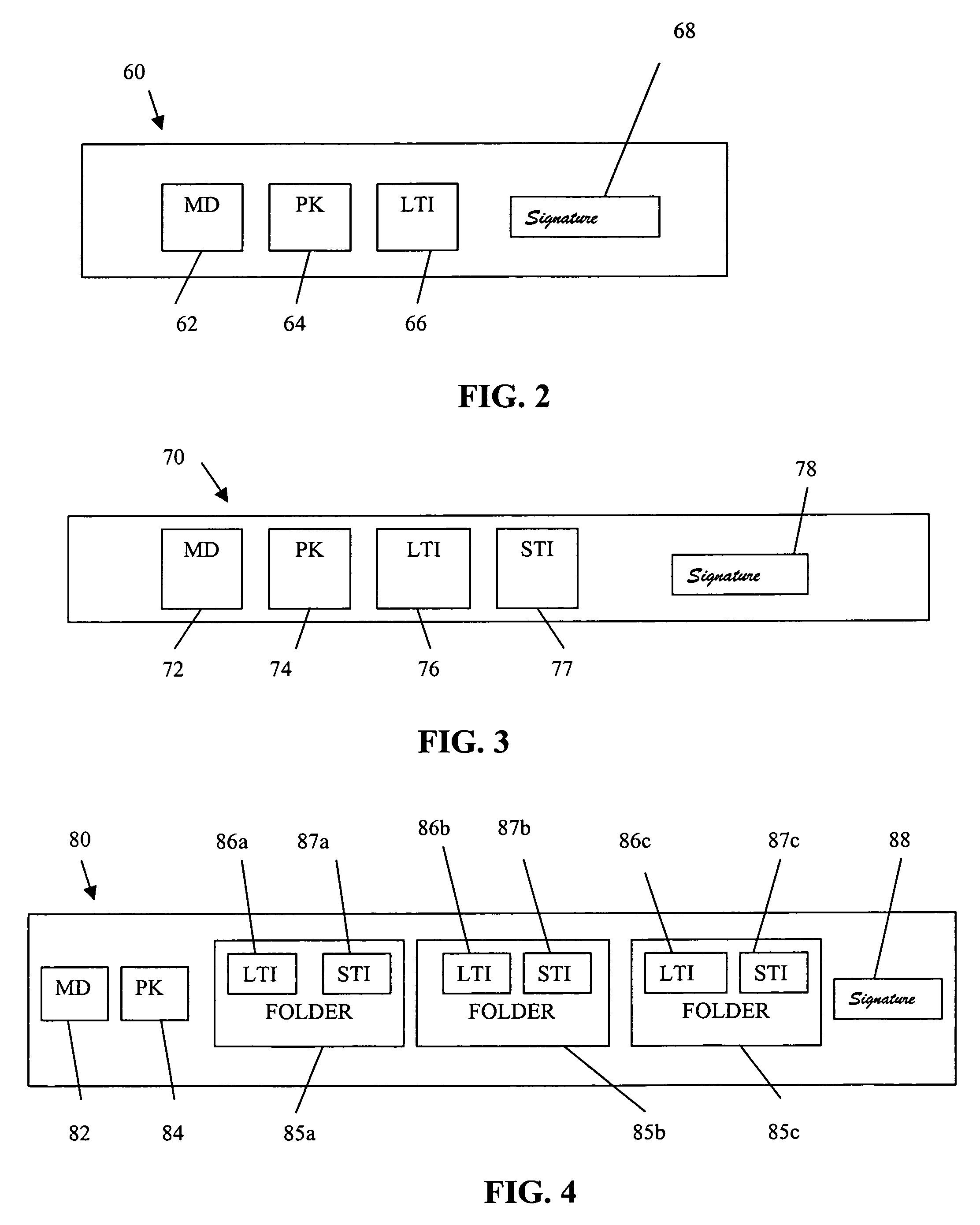
InactiveUS7340600B1Random number generatorsUser identity/authority verificationRoot certificateClient-side
A public key authorization infrastructure includes a client program accessible by a user and an application program. A certificate authority issues a long-term certificate that binds a public key of the user to long-term identification information related to the user. A directory stores the issued long-term certificate and short-term authorization information related to the user. A credentials server issues a short-term certificate to the client. The short-term certificate binds the public key to the long-term identification information and to the short-term authorization information. The client presents the short-term certificate to the application program for authorization and demonstrates that the user has knowledge of a private key corresponding to the public key in the short-term certificate. The short-term certificate includes an expiration date, and is not subject to revocation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
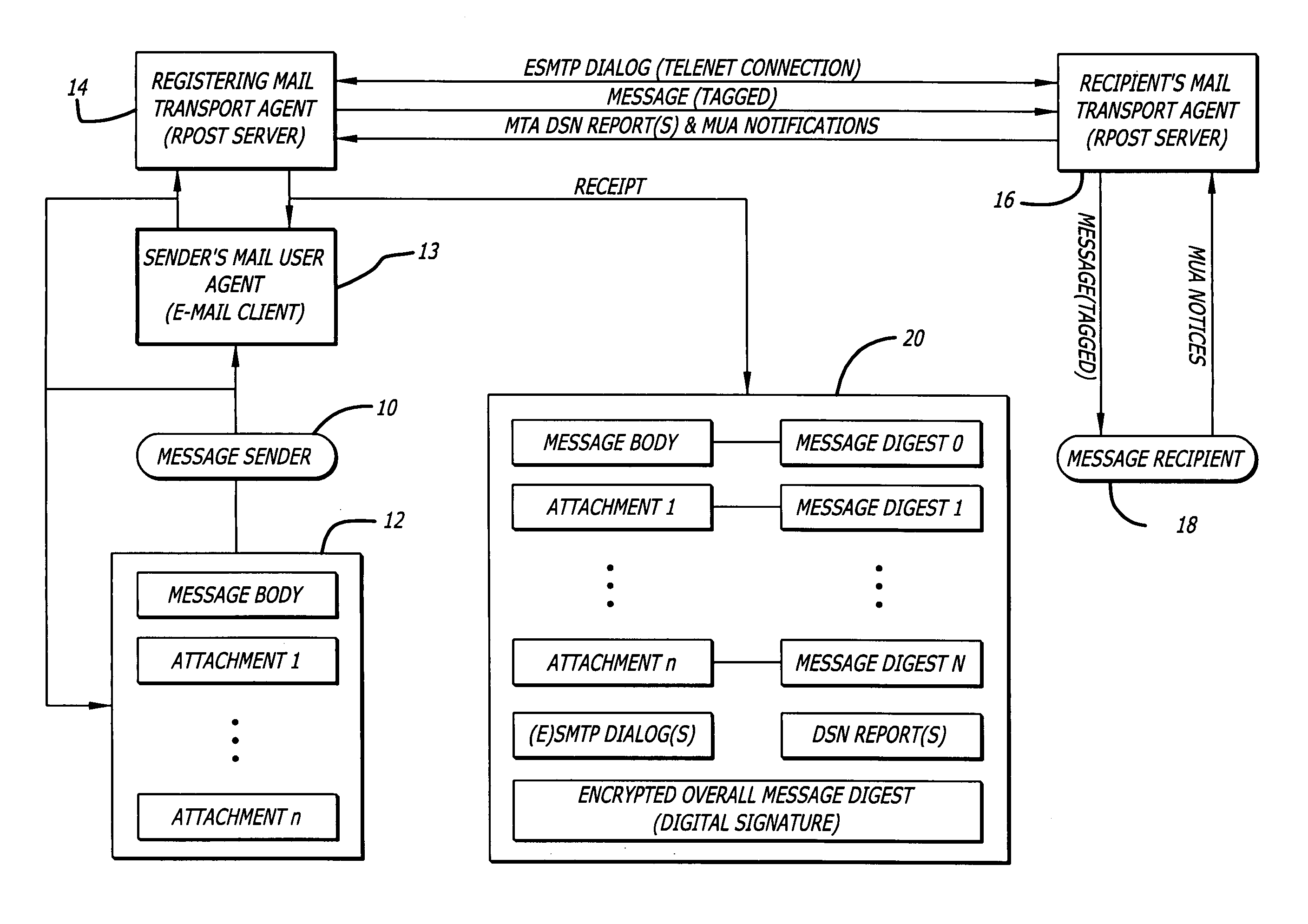
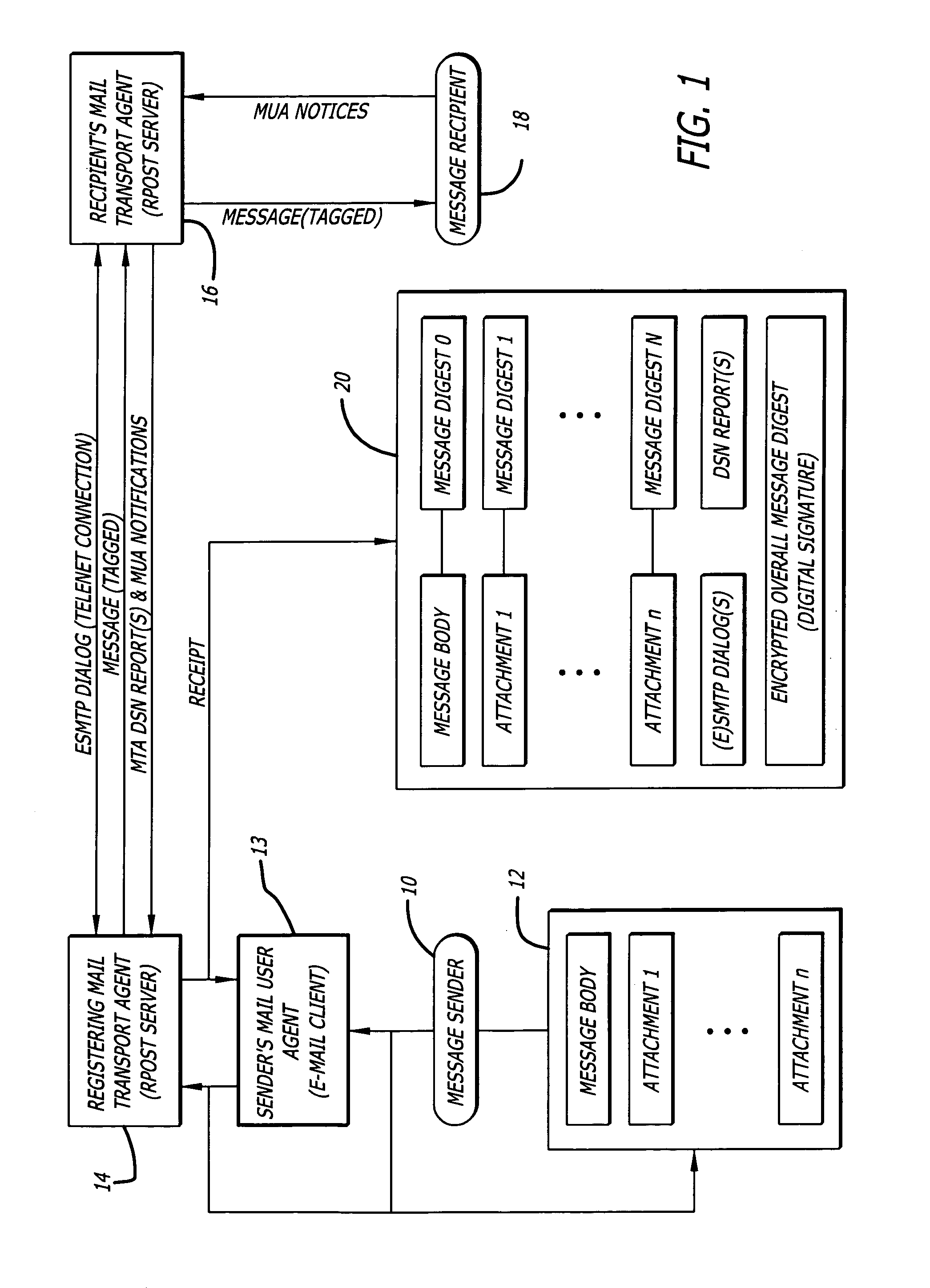
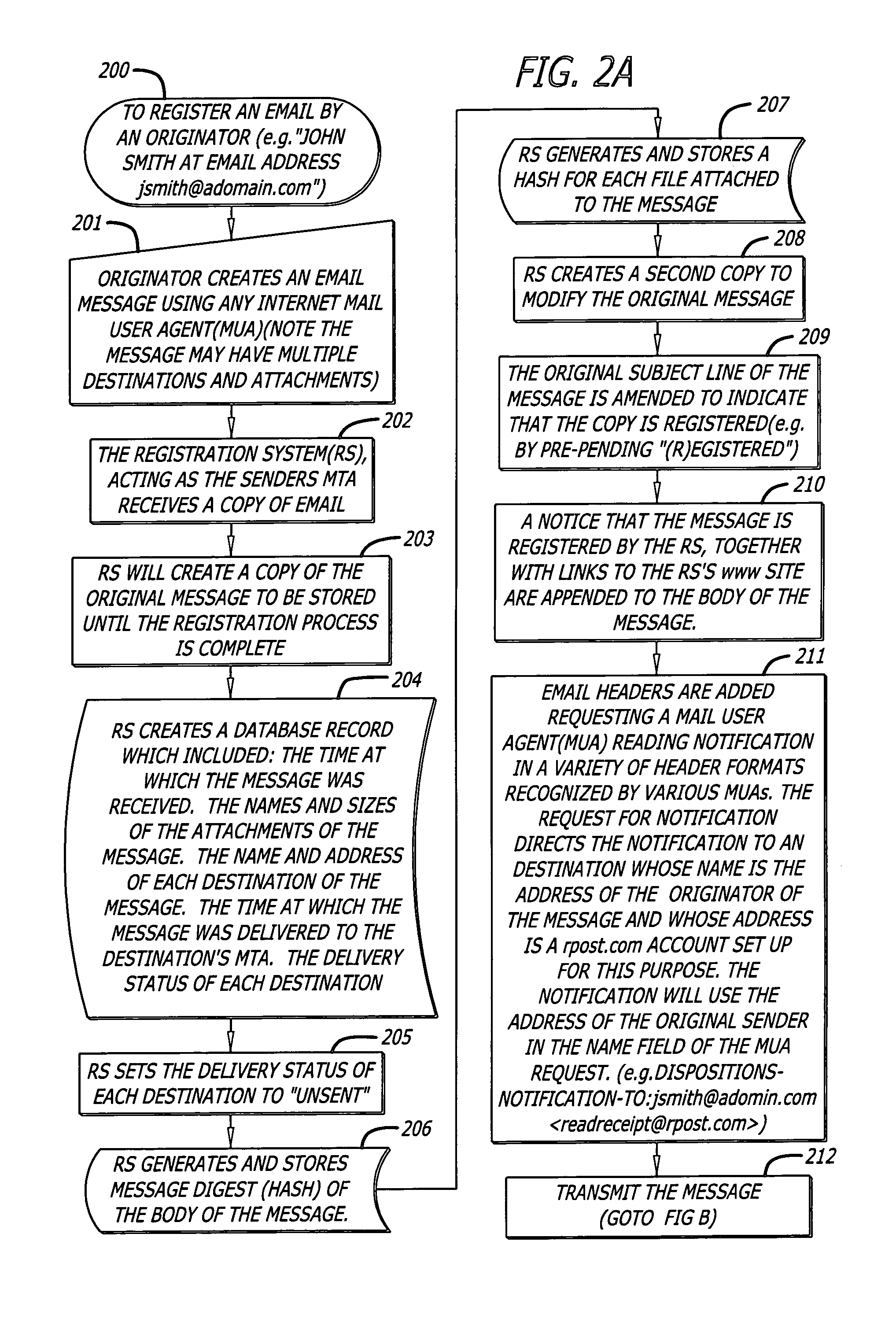
System and method for verifying delivery and integrity of electronic messages
InactiveUS7240199B2Key distribution for secure communicationRandom number generatorsDigital signatureElectronic messaging
A server receives a message from a sender and transmits the message to a recipient. The server normally transmits the message in a first path to the recipient. When the sender indicates at a particular position in the message that the message is registered, the server transmits the message in a second path to the recipient. The sender can also provide additional indications in the message to have the server handle the message in other special ways not normally provided by the server. After learning from the recipient or the recipient's agent that the message was successfully received, the server creates, and forwards to the sender, an electronic receipt. The receipt includes at least one, and preferably all, of the message and any attachments, a delivery success / failure table listing the receipts, and the receipt times, of the message by the recipient's specific agents, and the failure of other agents of the recipient to receive the message and a an encrypted hash of the message and attachments subsequently. By verifying that the digital signature on the sender's receipt matches the digital receipt at the server, the server can verify, without retaining the message, that the receipt is genuine and that the message is accurate.
Owner:RPOST COMM
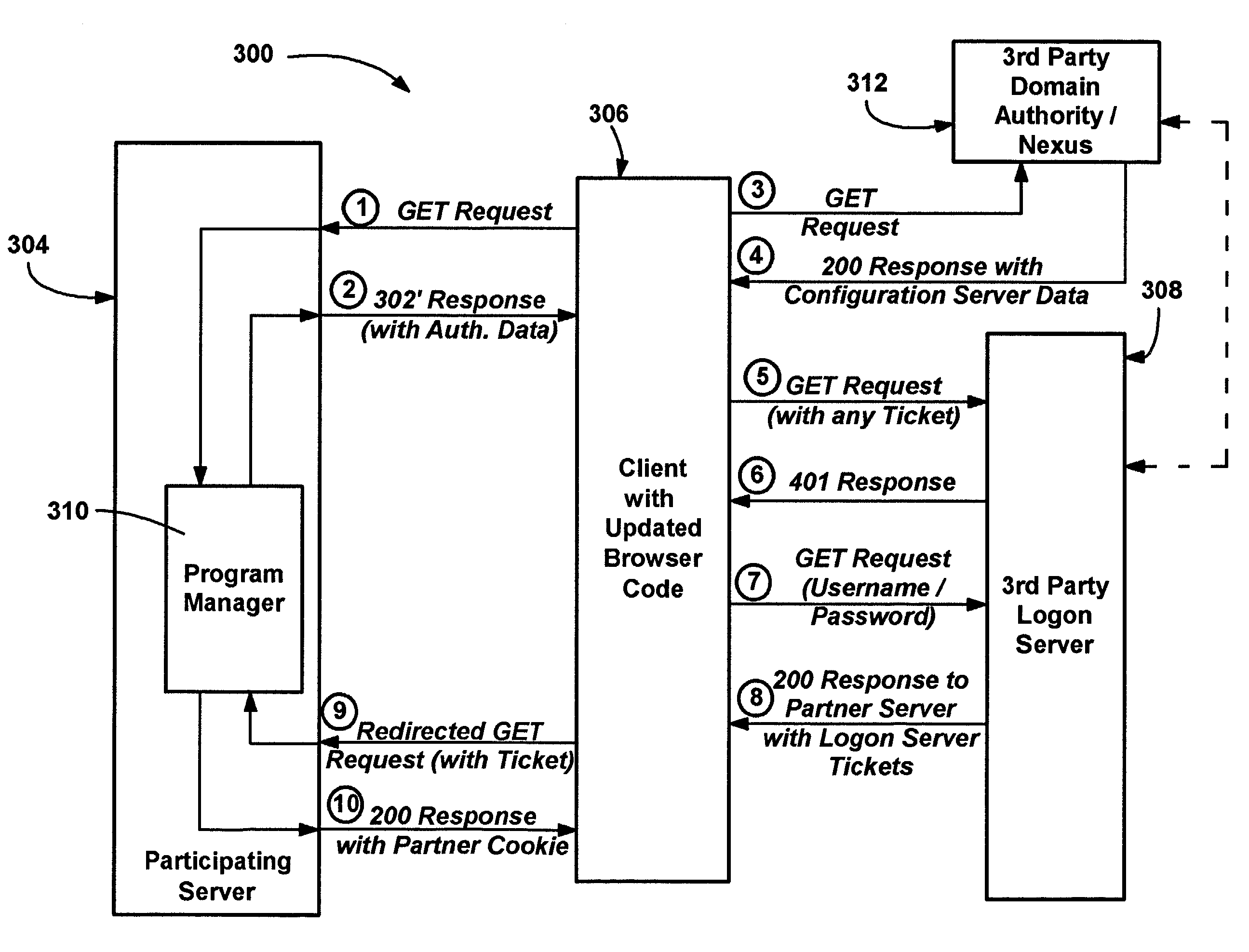
Method and system of integrating third party authentication into internet browser code
InactiveUS7191467B1Random number generatorsUser identity/authority verificationThird partyThe Internet
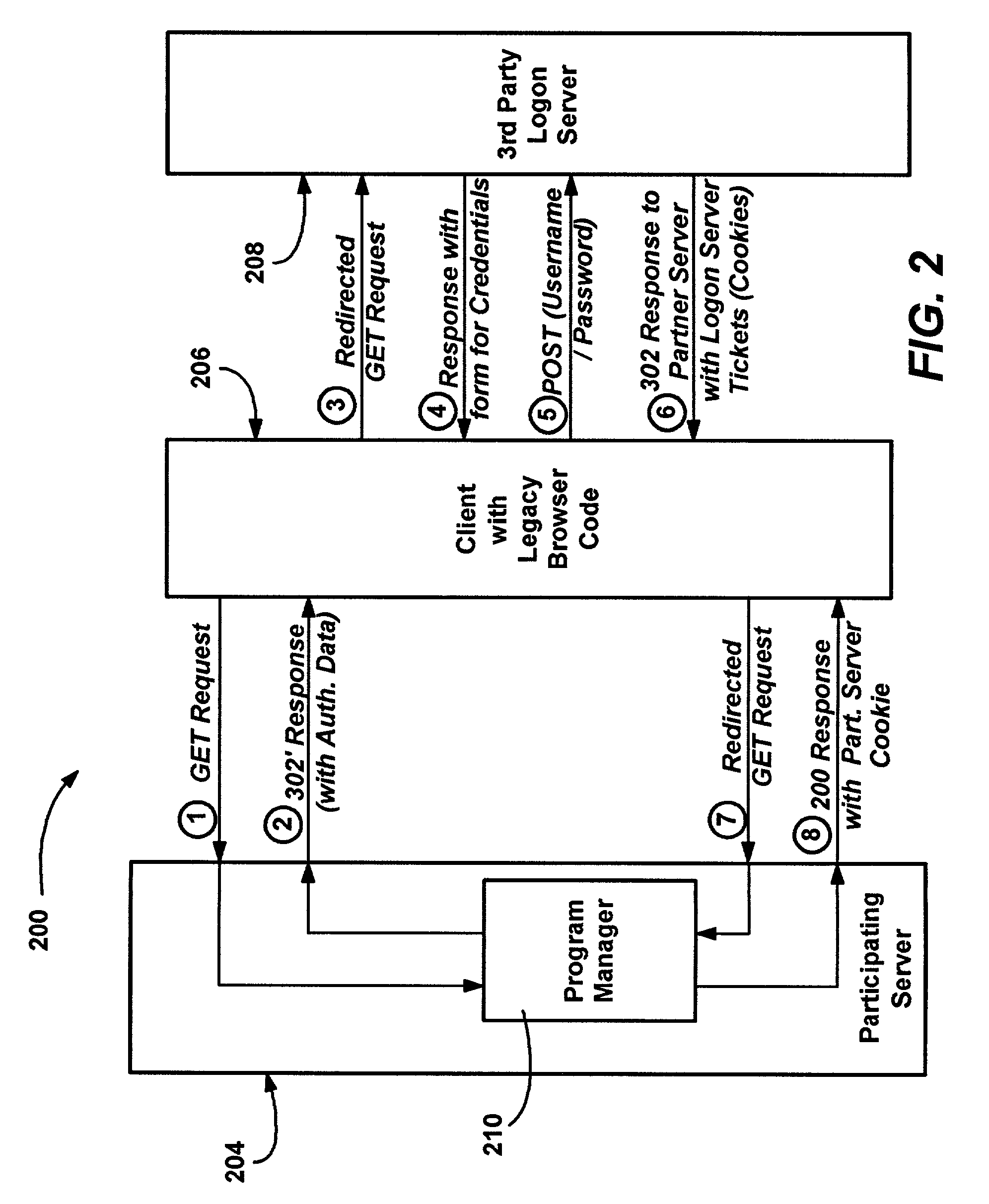
A method and system for using an Internet client's local authentication mechanism in systems having updated browser code, so as to enable third party authentication according to an authentication scheme specified by a participating server on clients with updated browser code, while not breaking clients with legacy browser code. A redirect response from a server has authentication data added thereto such that updated browser code can detect the data's presence and enable the use of local security mechanisms for authentication purposes with the server-specified authentication scheme, including local credential entry for verification at a third party login server. At the same time, if such a redirect response is received by prior browser code, the added data is ignored while conventional redirection occurs, such that third party authentication may be performed via redirection to a third party's Internet page that provides a form for credential entry.
Owner:MICROSOFT TECH LICENSING LLC
Authentication apparatus and method for use in vehicle
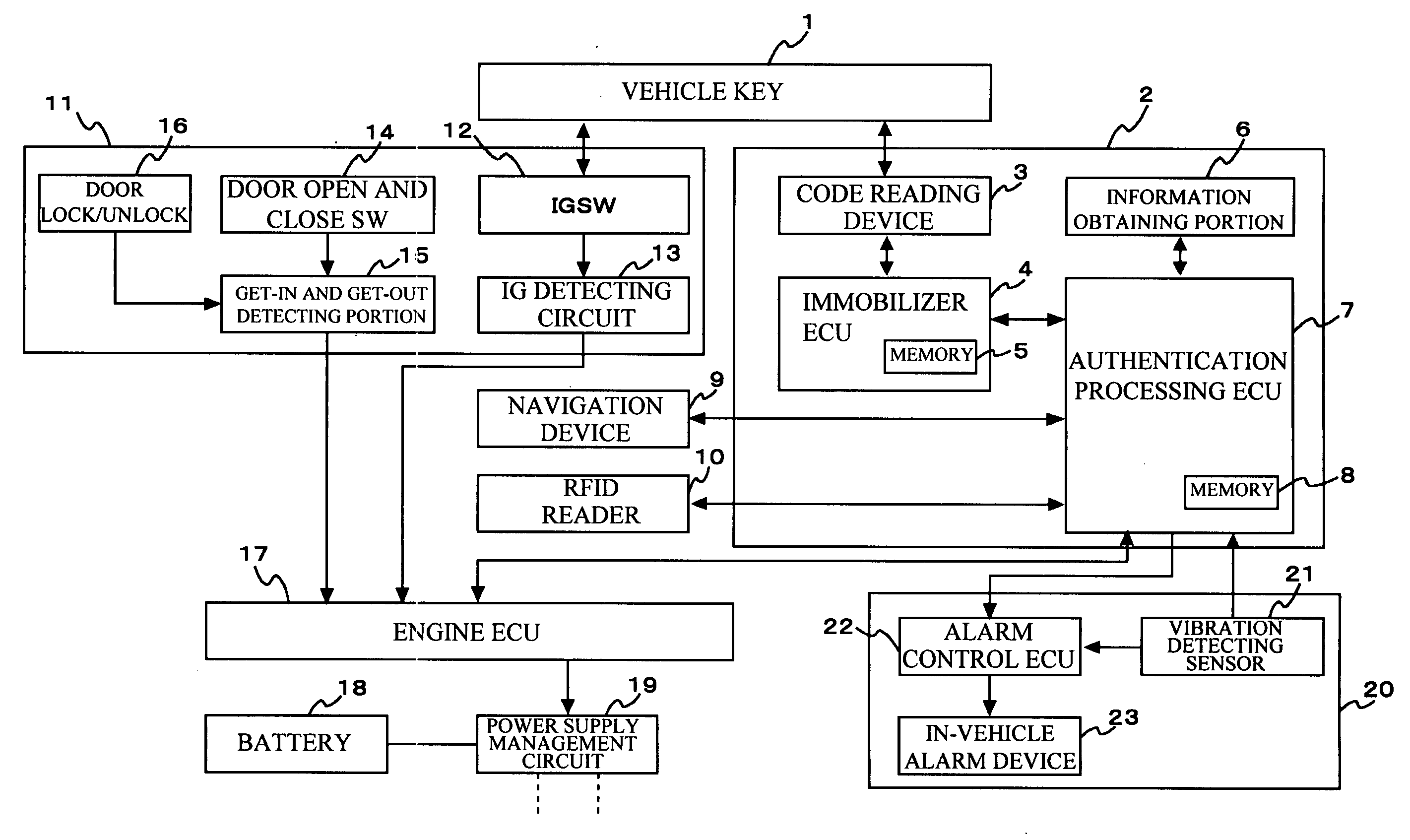
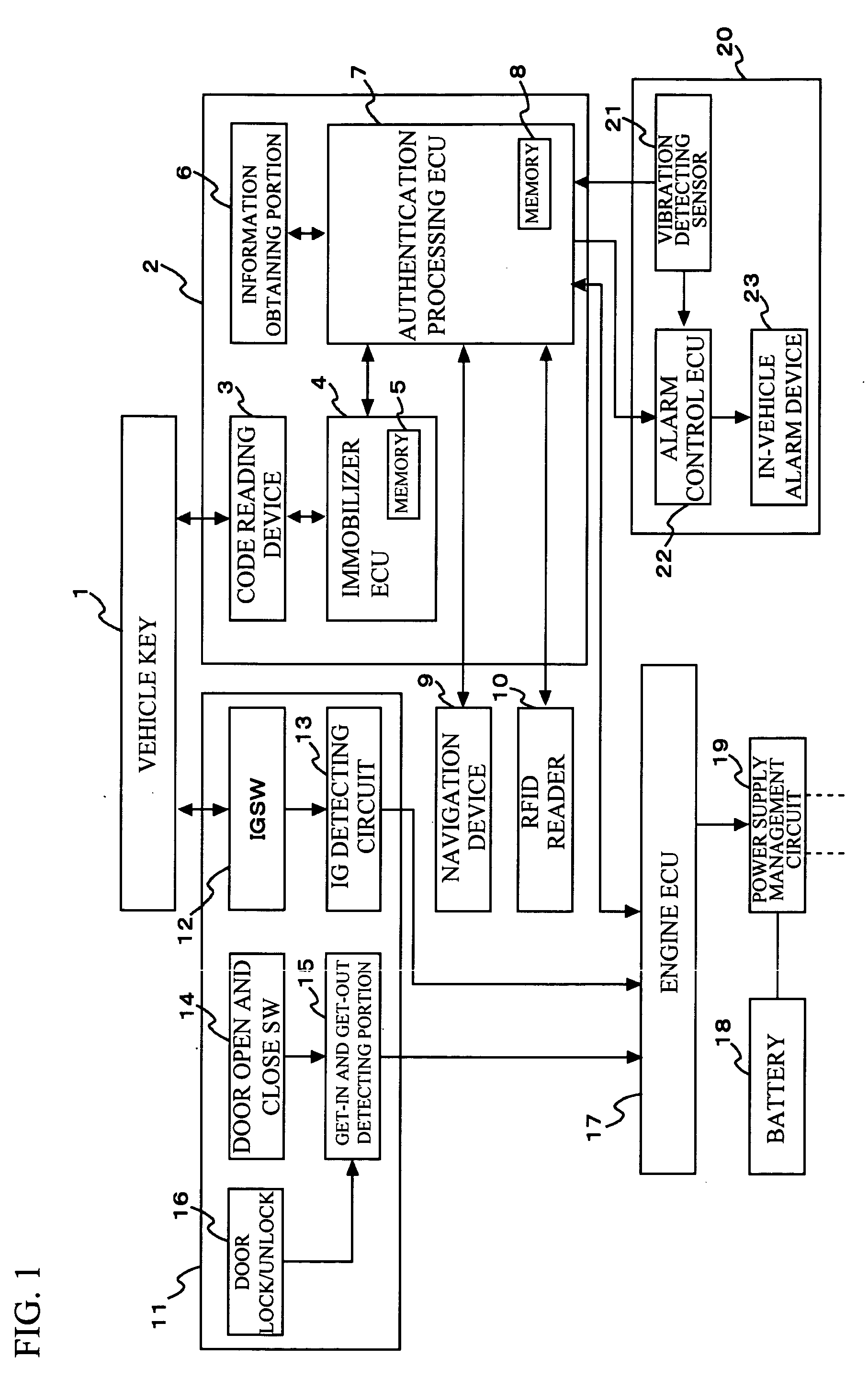
InactiveUS20070124599A1Increasing authentication levelReduce certification timeRandom number generatorsAnti-theft devicesComputer hardwareRisk level
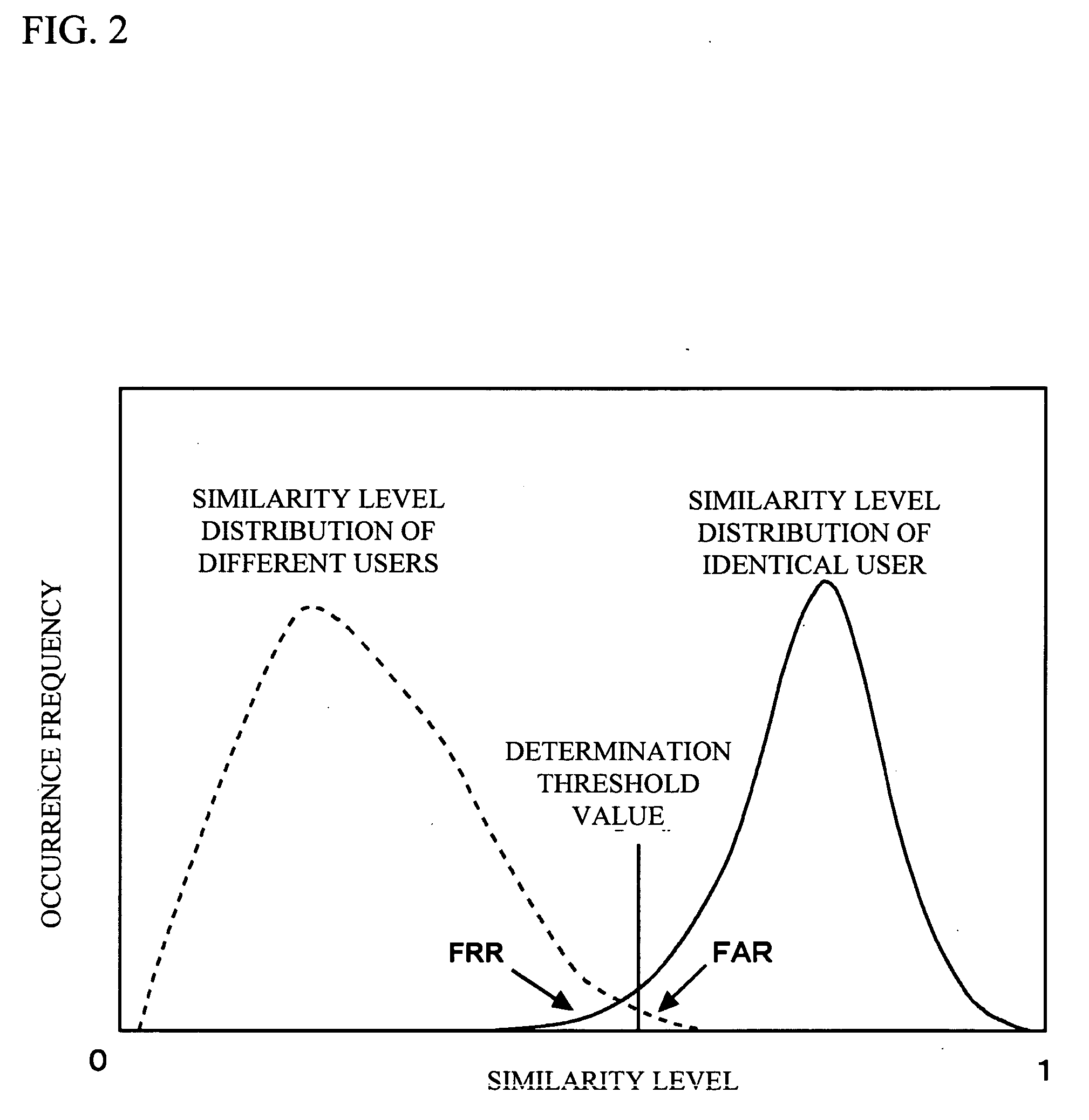
An authentication method for use in a vehicle includes identifying validity by use of identification information stored, detecting an unauthorized use risk level predicted by a state of a vehicle, changing an authentication level according to an identification result and the unauthorized use risk level at the time of processing a biometric authentication, calculating a matching level between first biometric characteristic information of a vehicle passenger and second biometric characteristic information stored, and comparing the matching level calculated and an authentication level to output an authentication result at the time of processing the biometric authentication.
Owner:FUJITSU GENERAL LTD
Systems and methods for distributing and securing data
ActiveUS20080137857A1Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
Apparatus and method for generating a pool of seeds for a central determination gaming system
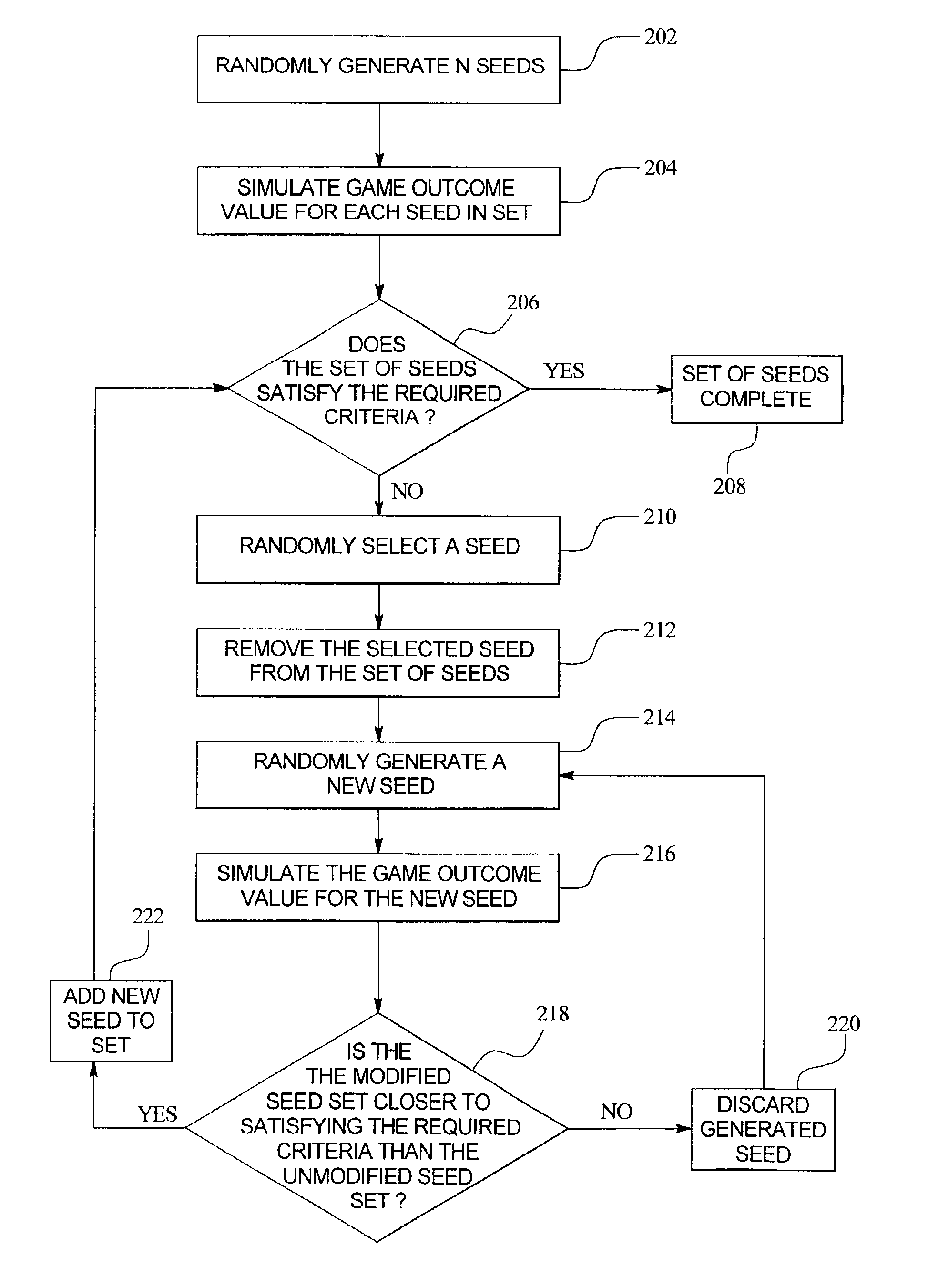
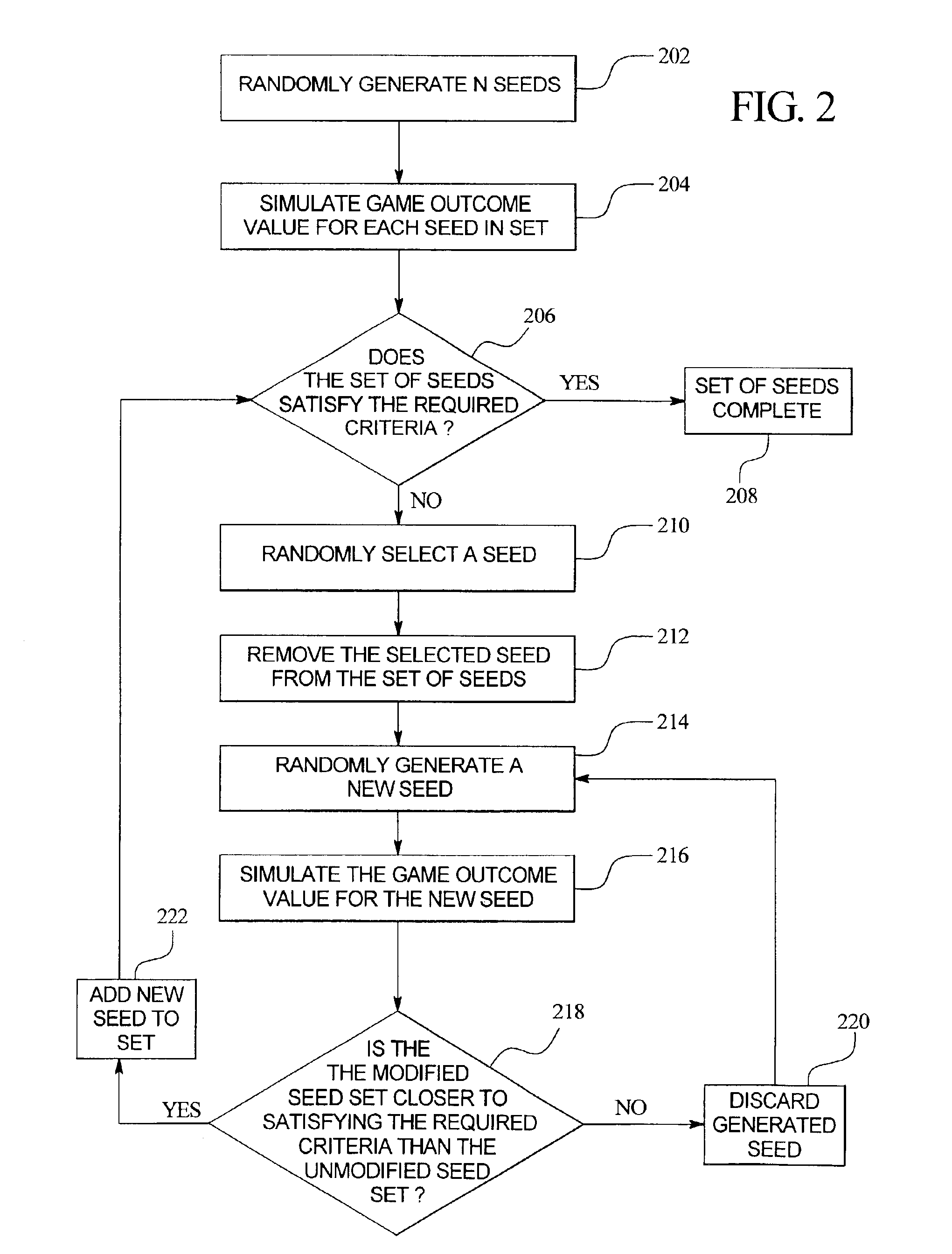
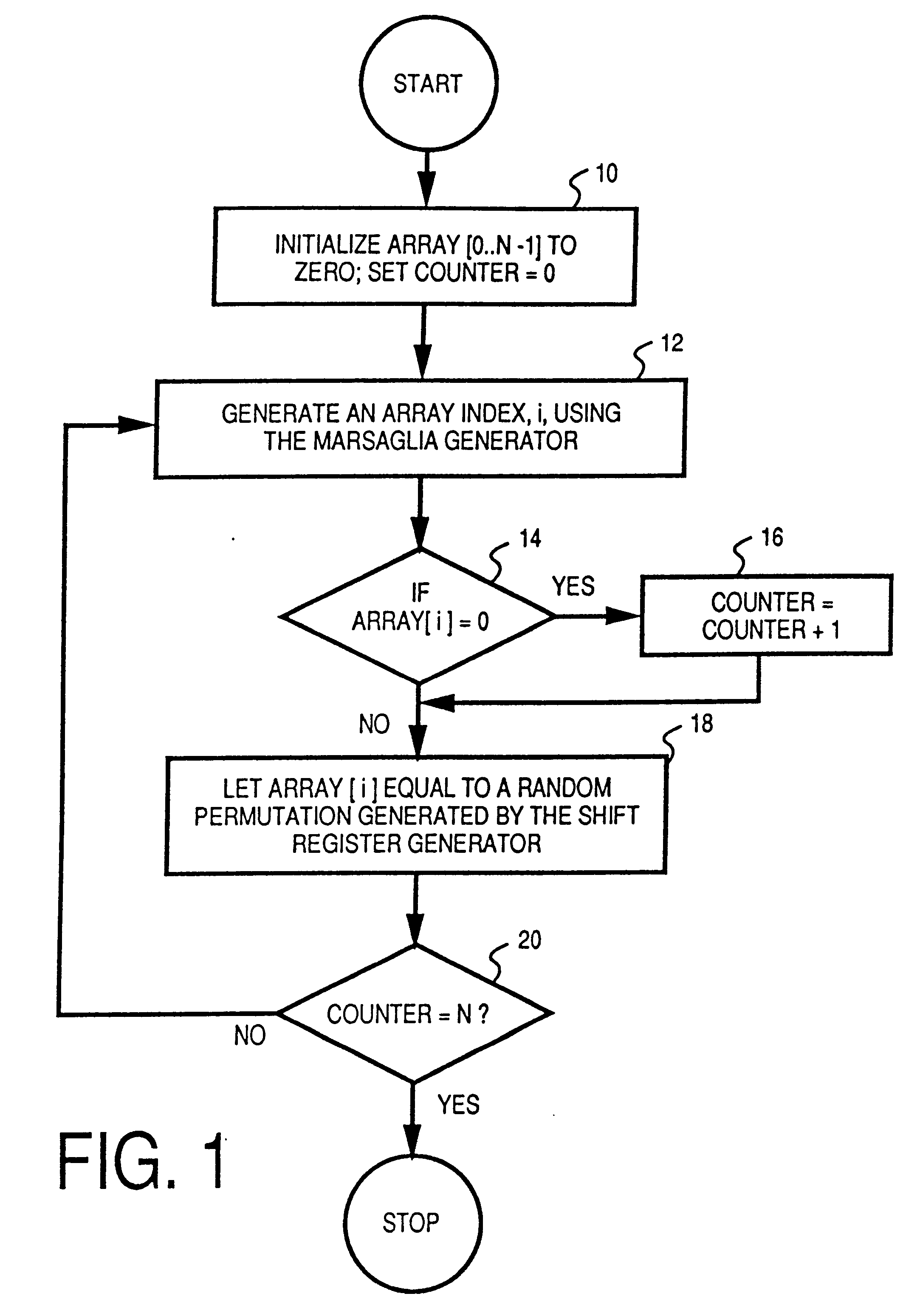
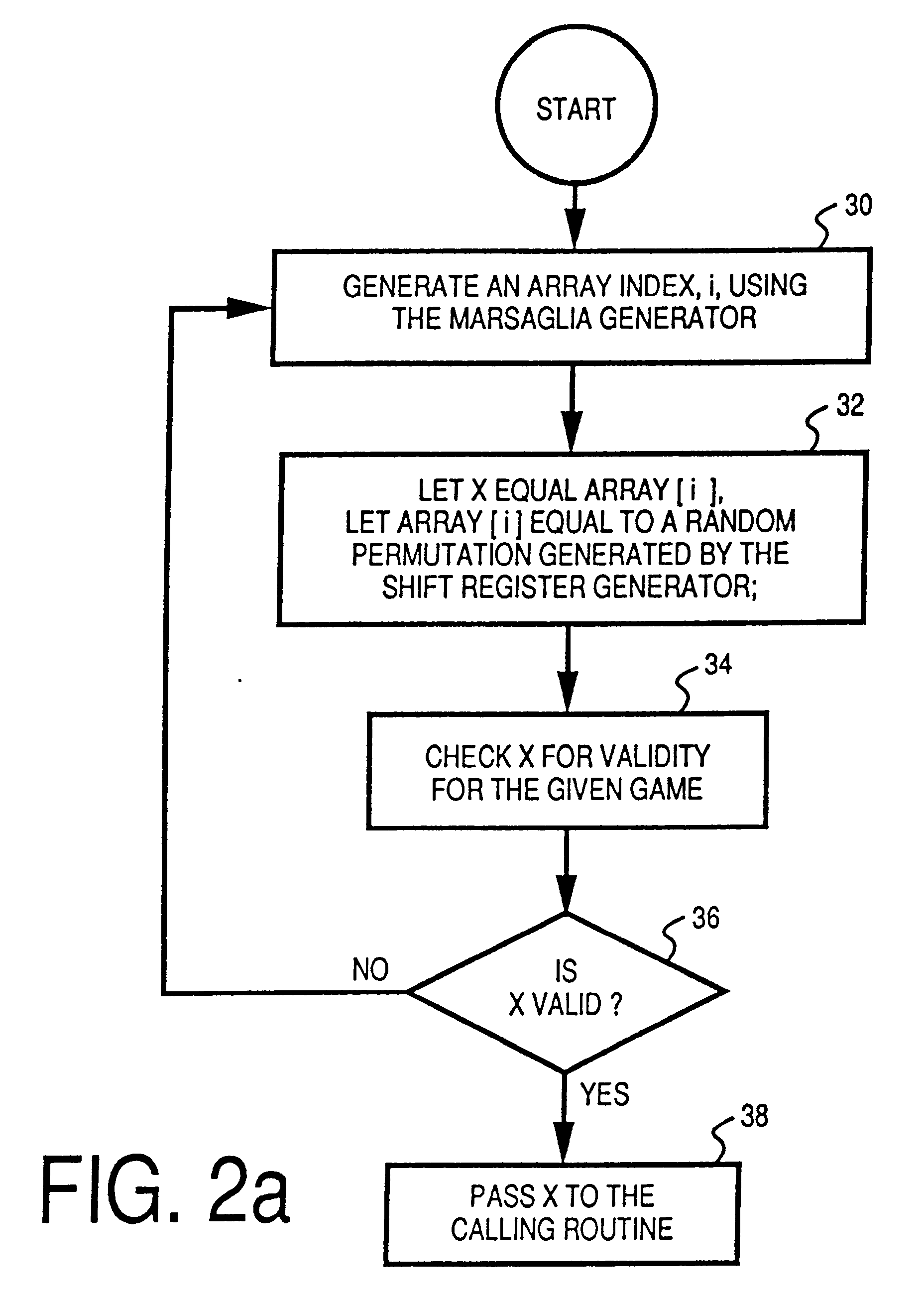
InactiveUS6866584B2Random number generatorsApparatus for meter-controlled dispensingRandom Number SeedComputer science
An apparatus and method for generating one or more pools or sets of seeds for use in a central determination gaming system. In one embodiment of the present invention, a processor of the apparatus or seed generator randomly generates a predetermined number of random number seeds. After the predetermined number of seeds are generated, the processor simulates the game outcome value that each generated seed ultimately determines. Having simulated a game outcome value for each generated seed, the processor determines if the set of seeds satisfies a required condition or criteria. If the required conditions or criteria are satisfied, the set is complete and ready for use in a central determination gaming system. If the required conditions or criteria are not satisfied, the processor modifies the generated set of seeds until the required conditions or criteria are satisfied.
Owner:IGT
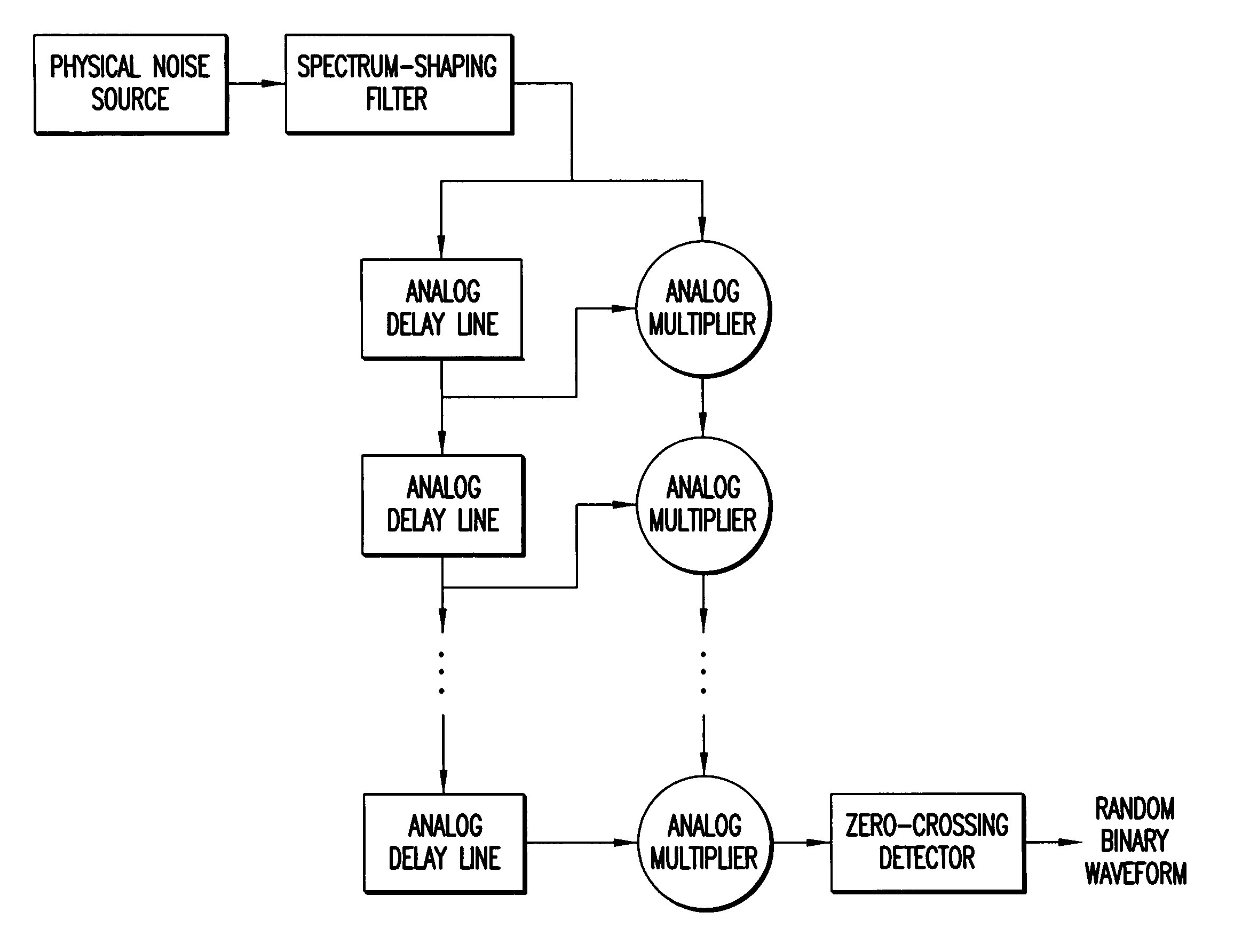
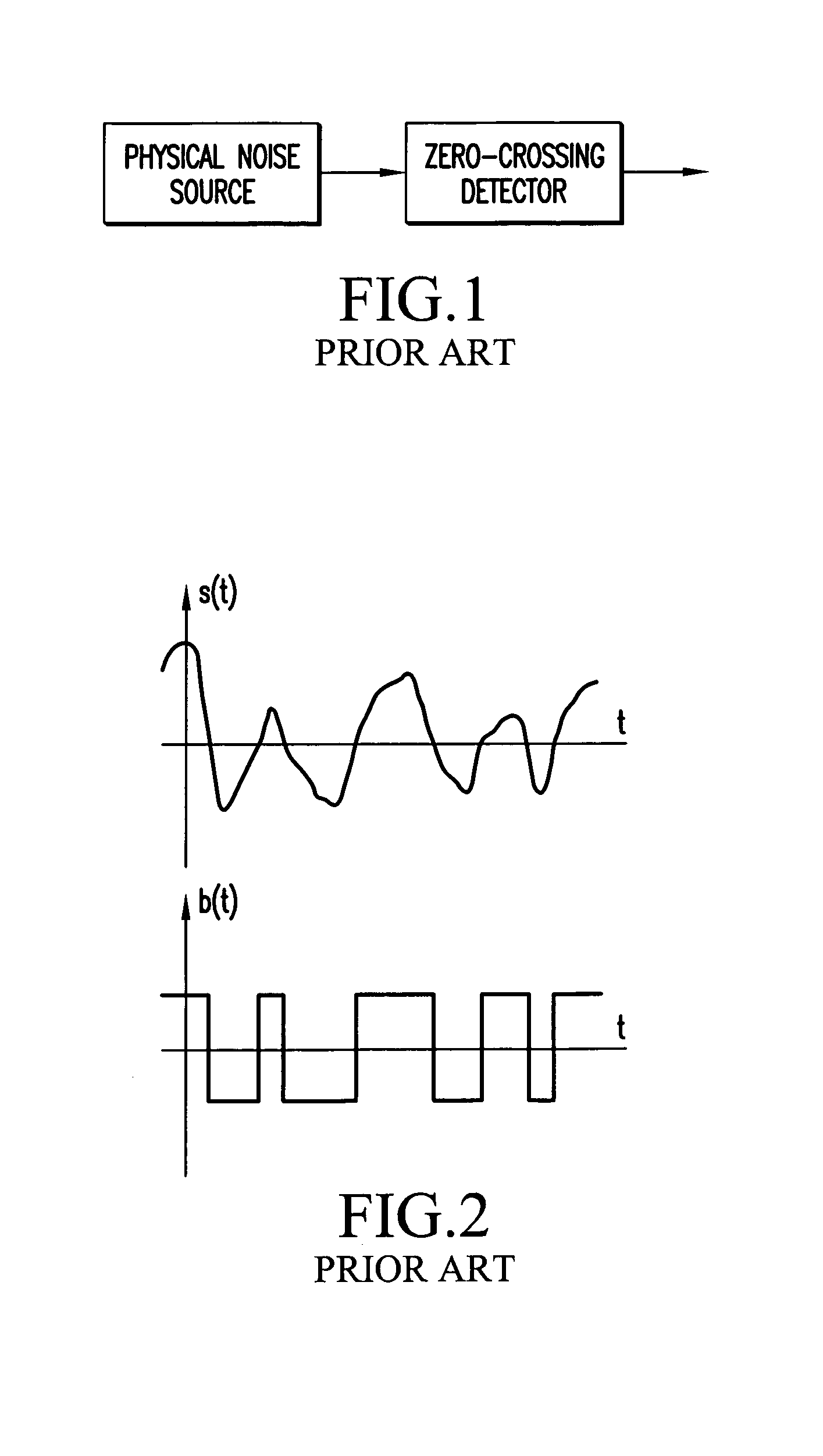
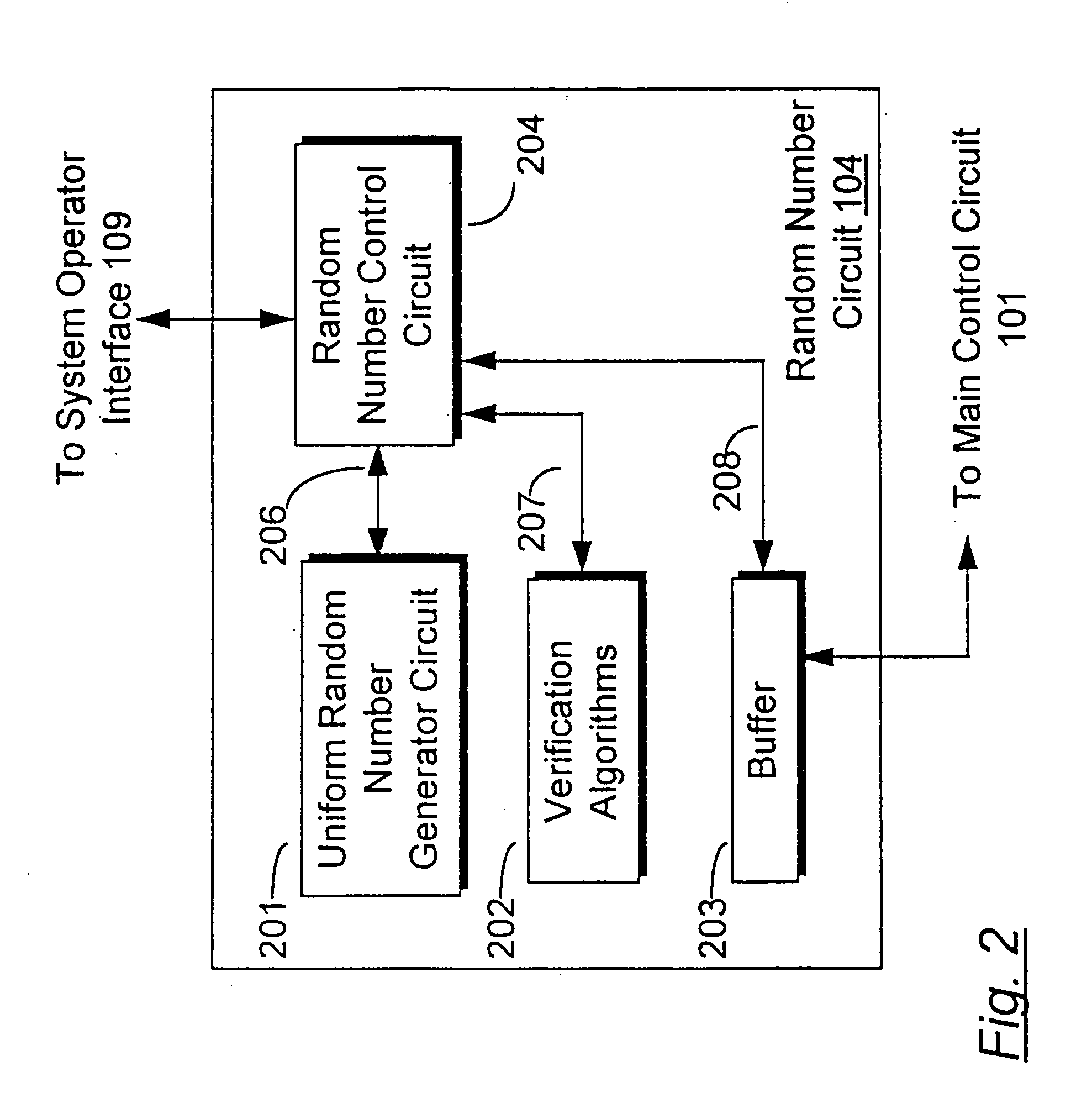
Random number generator
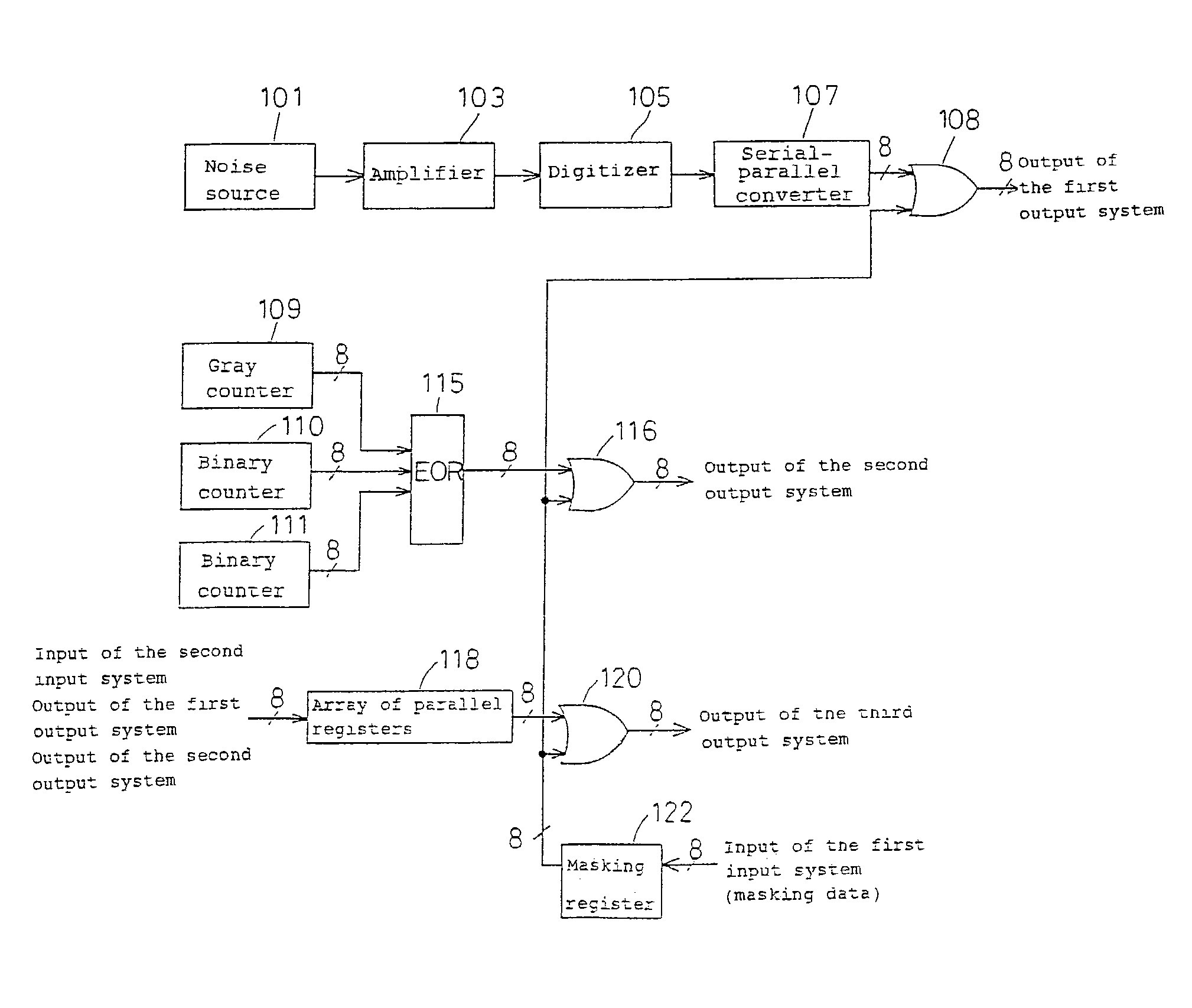
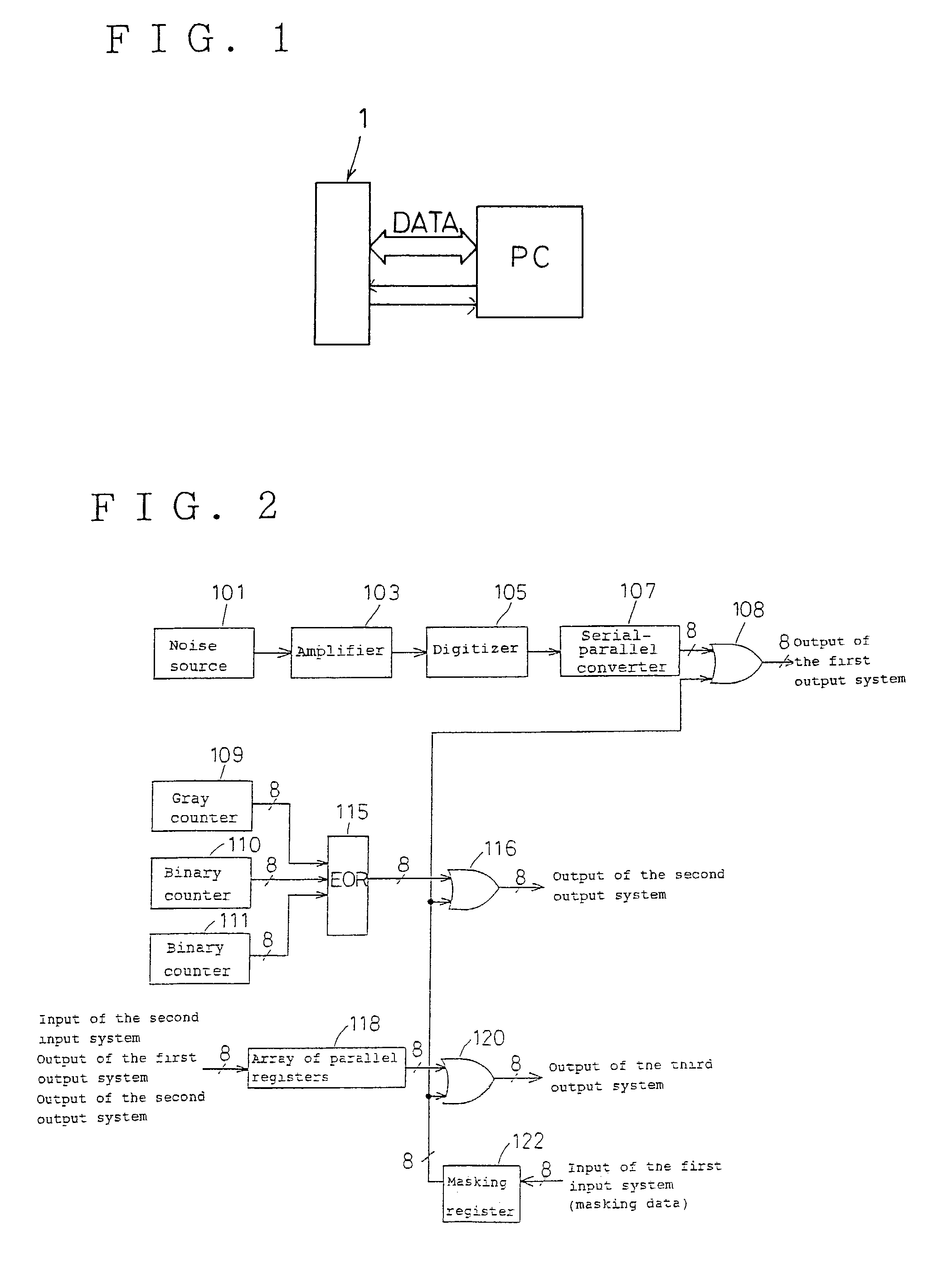
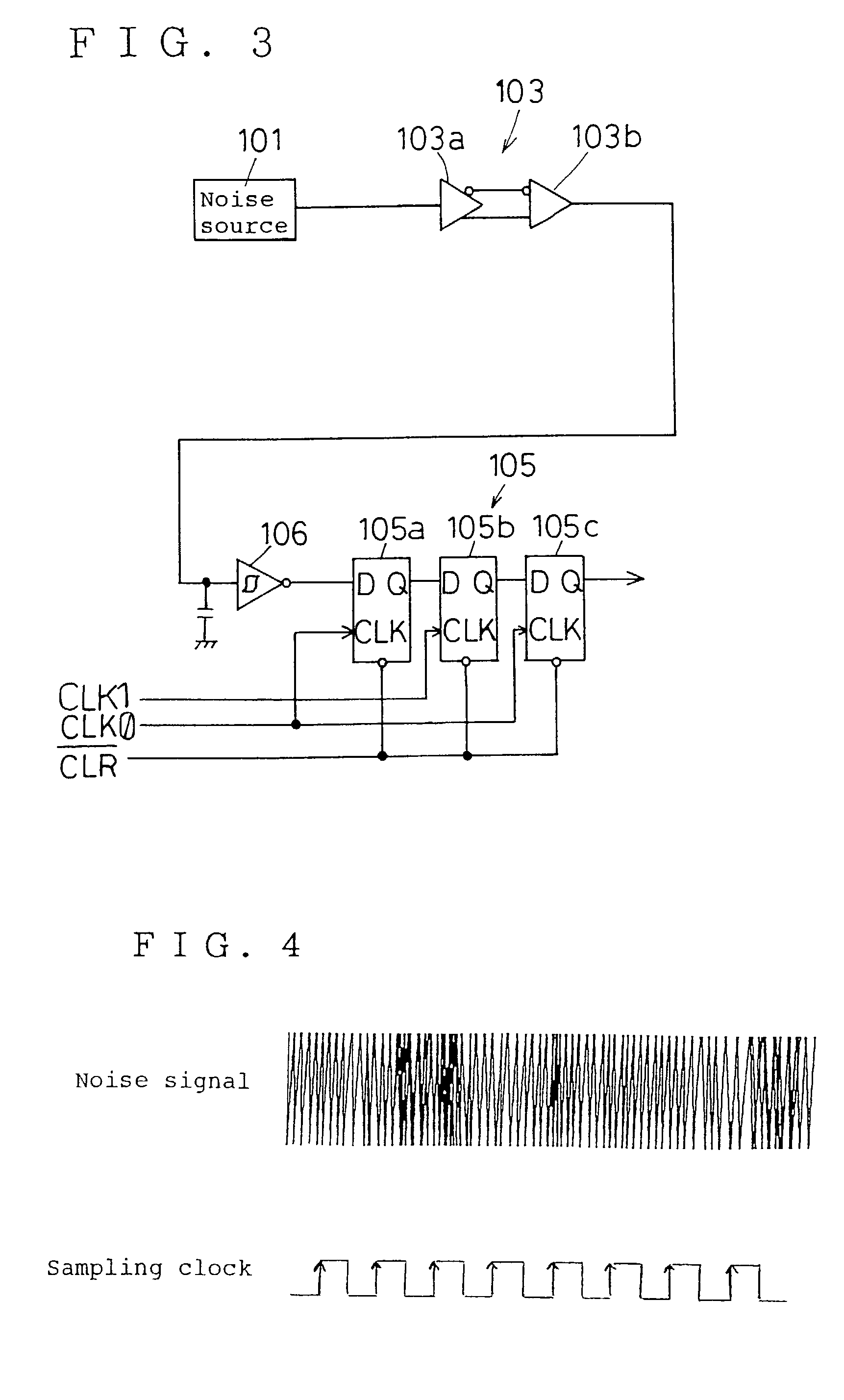
InactiveUS7124157B2Promote generationStable structureRandom number generatorsDigital function generatorsAudio power amplifierNumber generator
A random number generator having a simple construction which generates physical random numbers necessary for encryption. The random number generator has an amplifier to amplify noise signals generated from a noise source and digitizer to digitize the amplified noise signals. The digitizer includes a serial register.
Owner:HMI
Systems and methods for user access authentication based on network access point
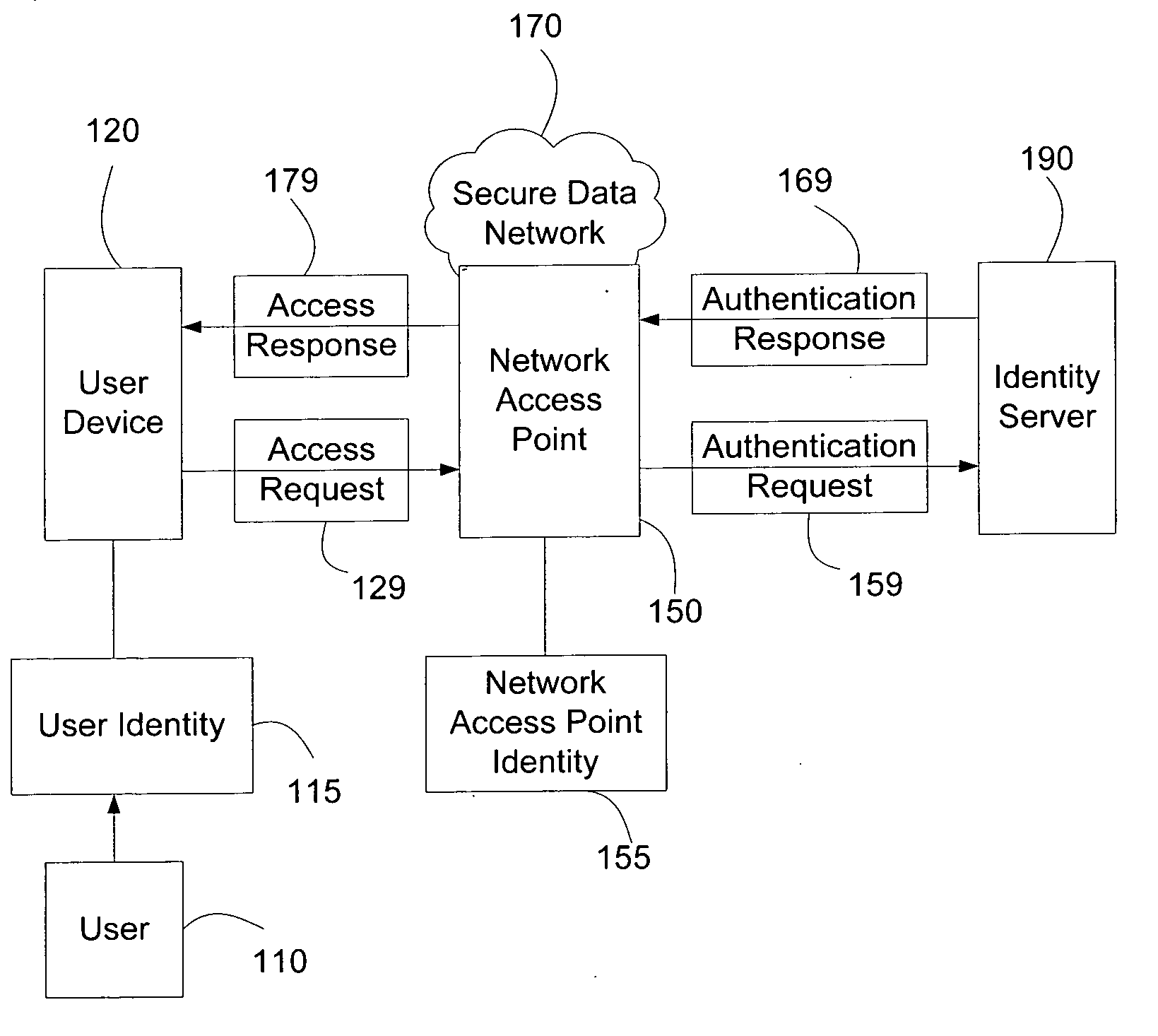
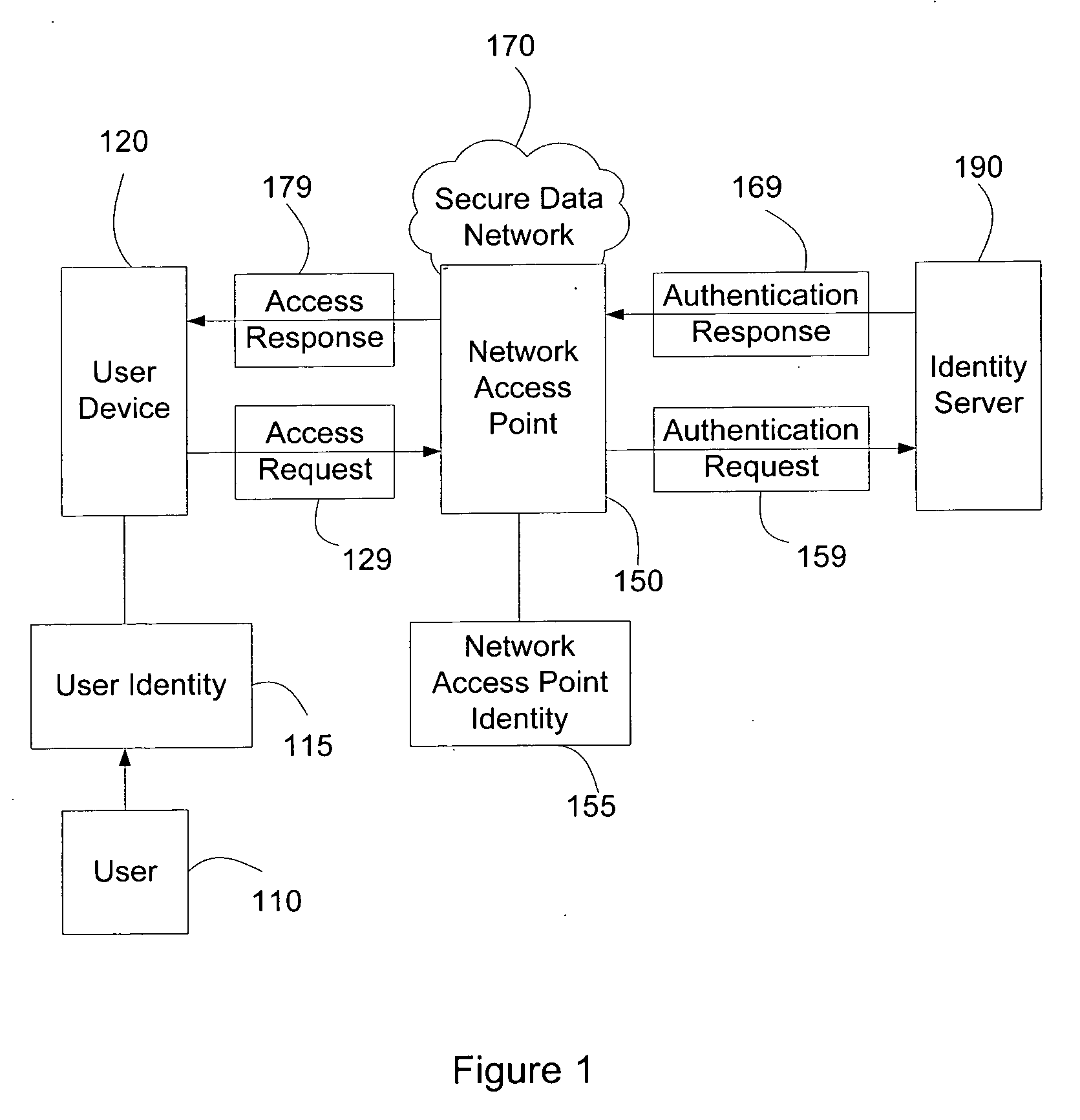
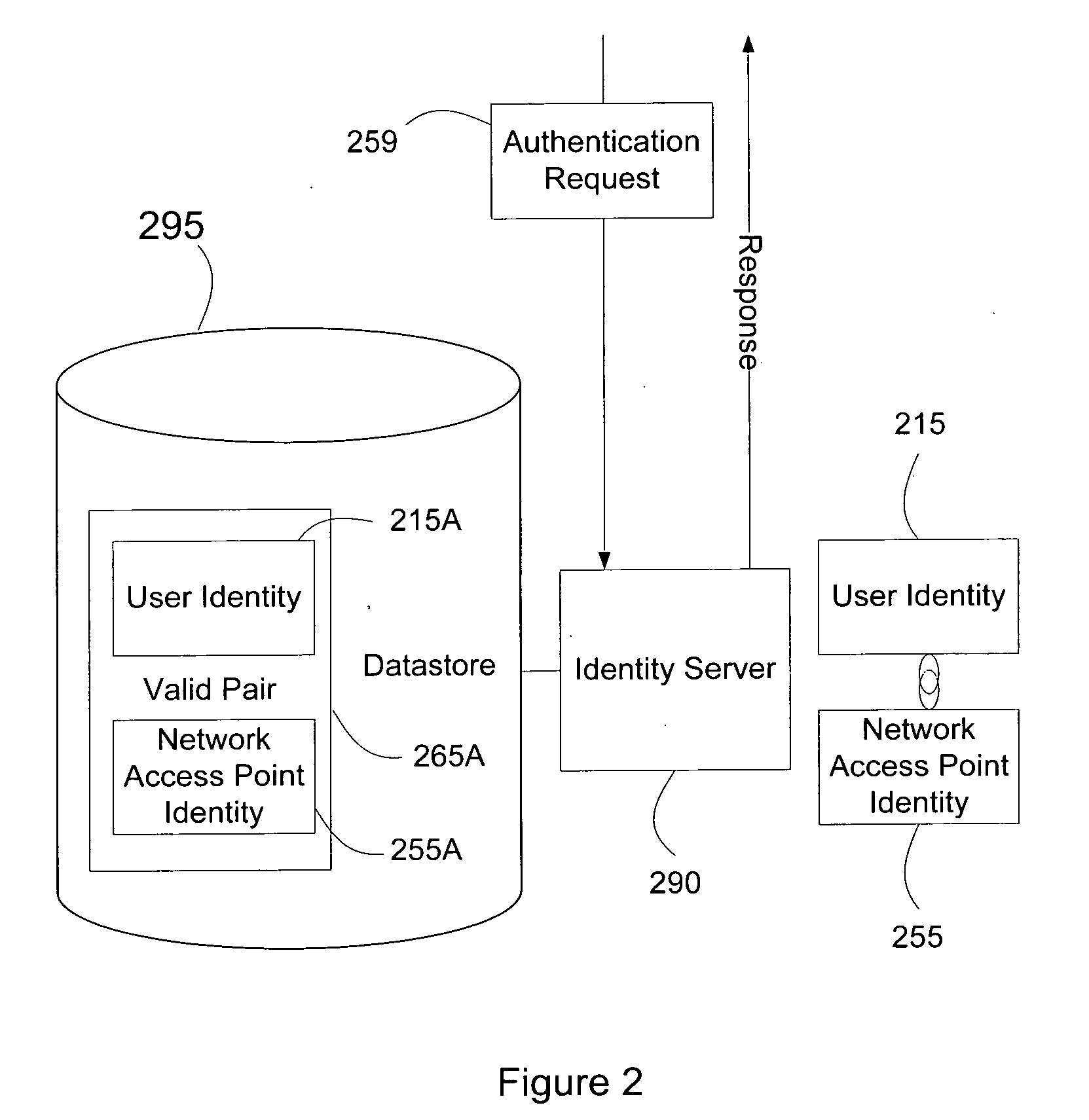
ActiveUS20070271598A1Random number generatorsUser identity/authority verificationTime informationAuthentication system
Systems and methods of authenticating user access based on an access point to a secure data network include a secure data network having a plurality of a network access points serving as entry points for a user to access the secure data network using a user device. The user is associated with a user identity, each network access point with a network access point identity. The user uses a user device to send an access request, requesting access to the secure data network, to the network access point, which then sends an authentication request to an identity server. The identity server processes the authentication request, by validating the combination of the user identity and the network access point identity, and responds with an authentication response, granting or denying access, as communicated to the user device via an access response. The secure data network may comprise an application level secure data network, in which the user uses the user device to request access to a network application. Furthermore, the identity server may validate the combined user identity and network access point identity data in conjunction with time information, access allowance data, and / or traffic volume data.
Owner:A10 NETWORKS
Method and apparatus for generating random signals
InactiveUS7145933B1Reduce probabilityRandom number generatorsTransmissionRandom intervalComputer science
Owner:MITSUBISHI ELECTRIC CORP
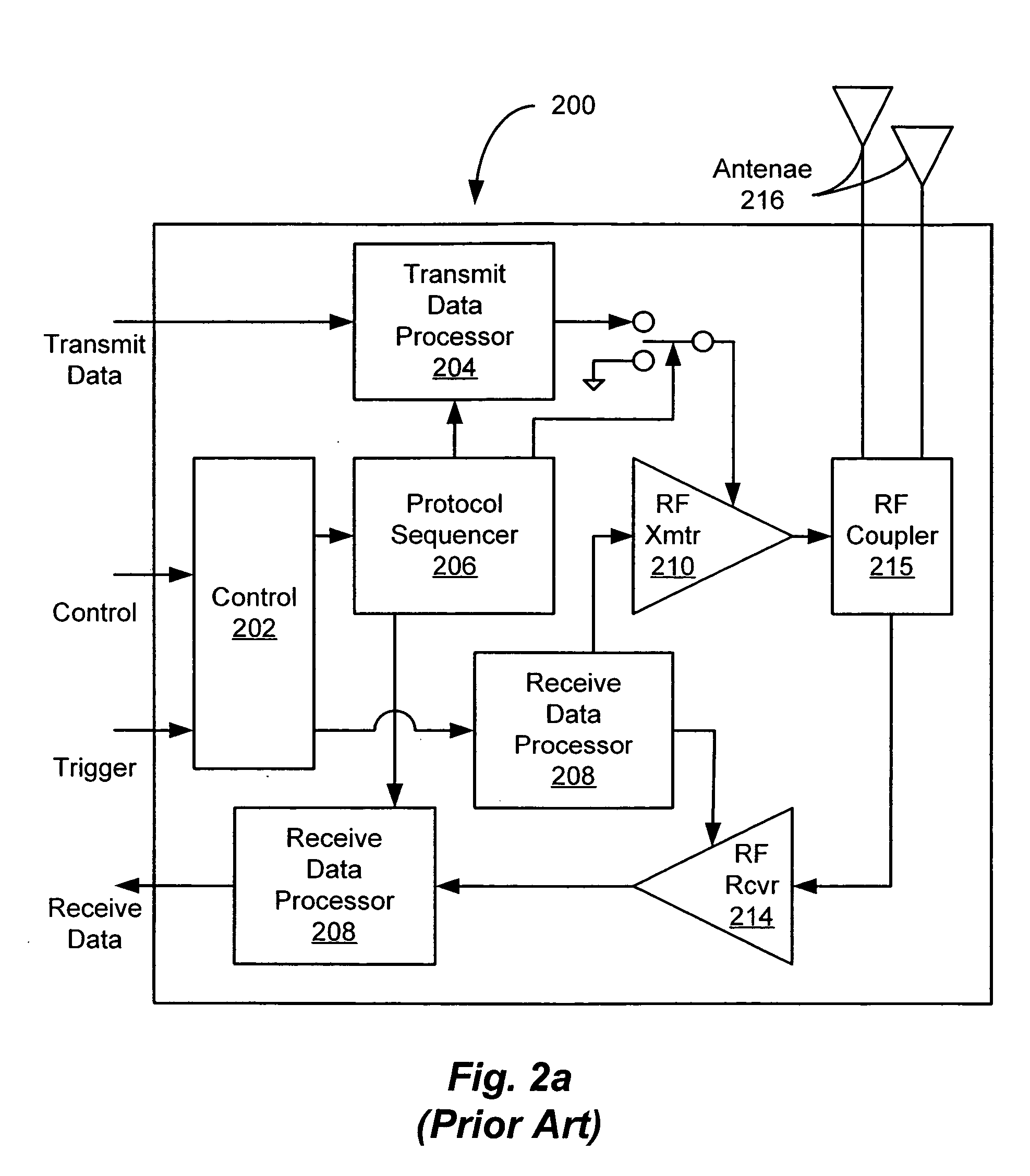
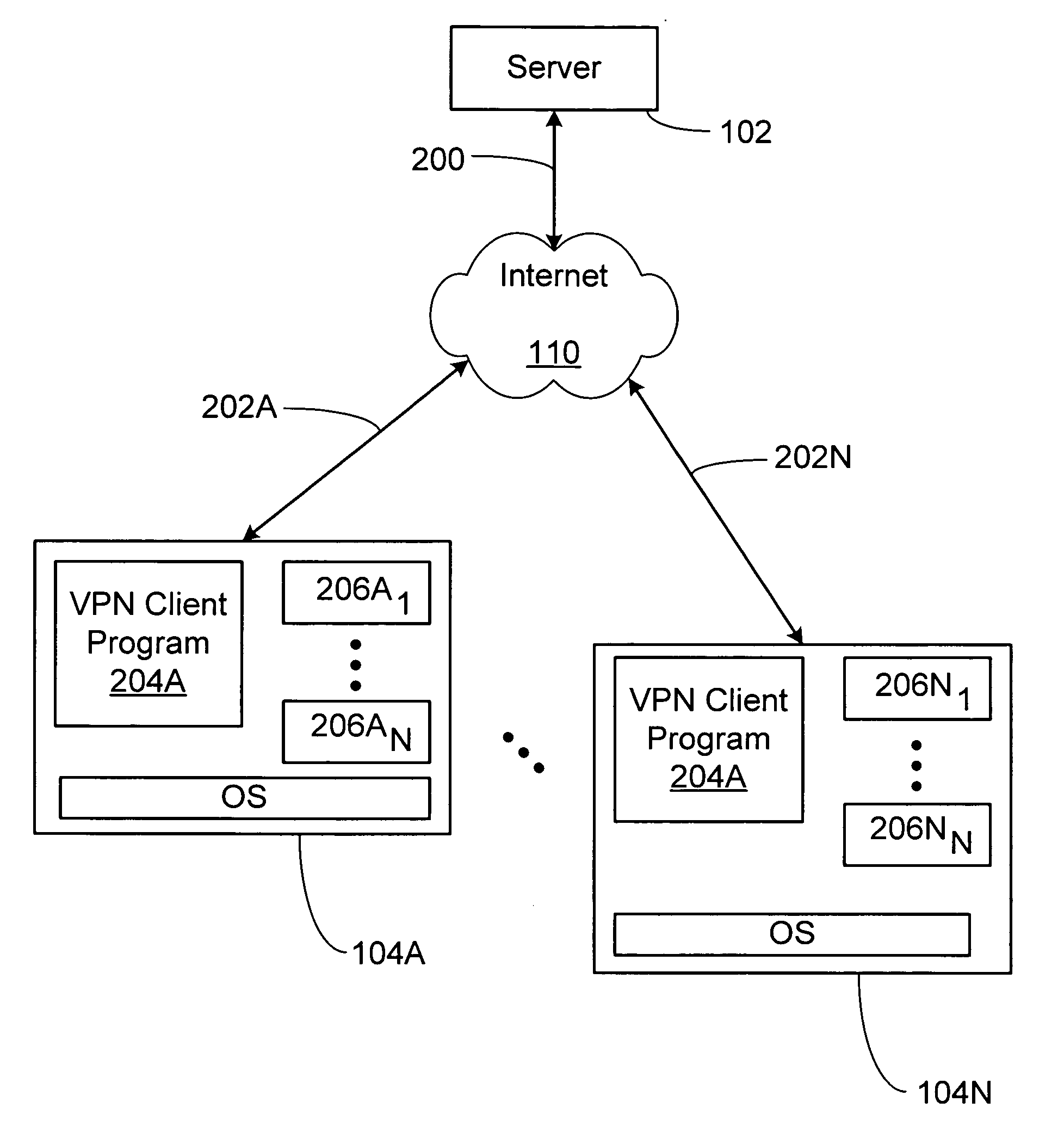
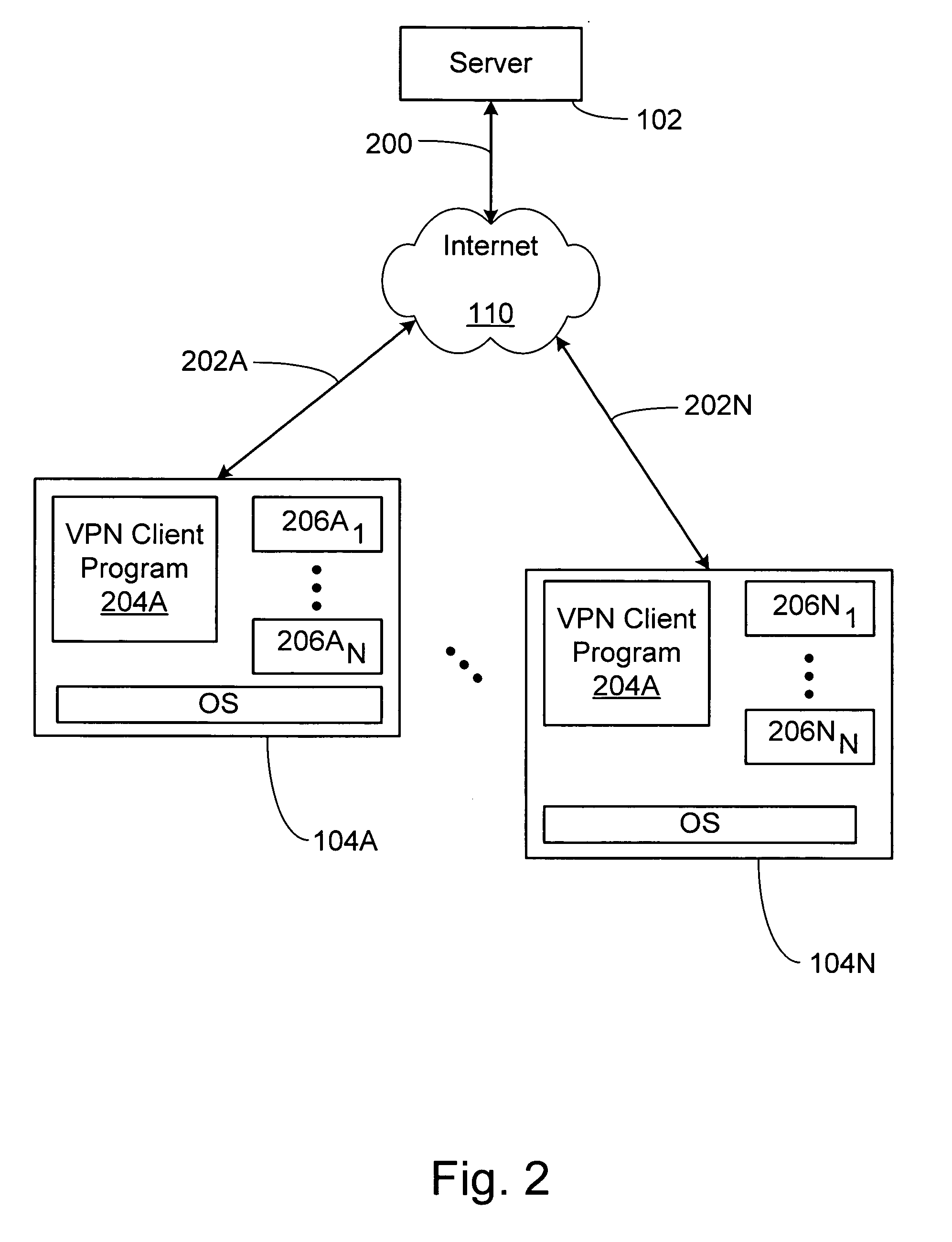
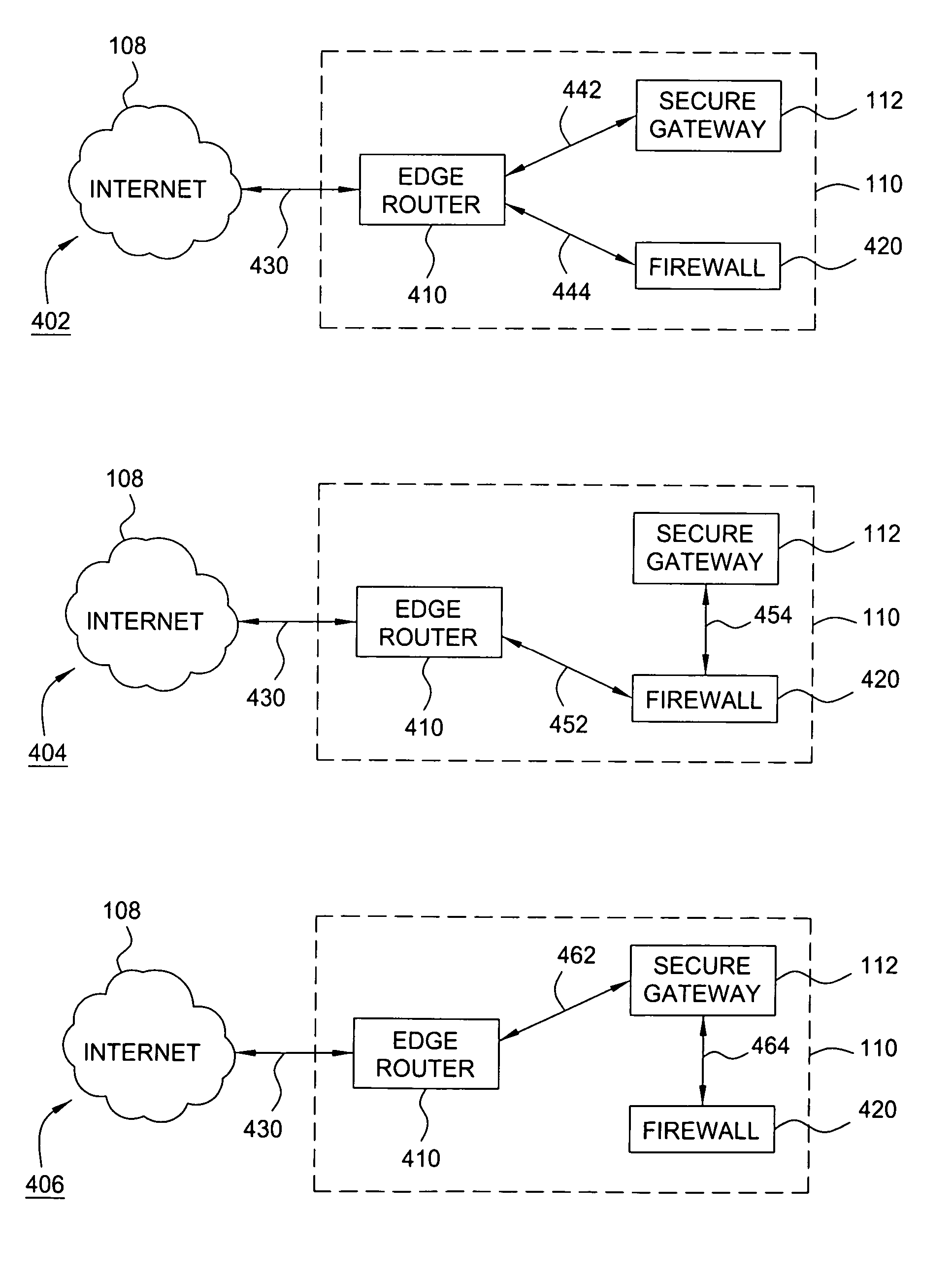
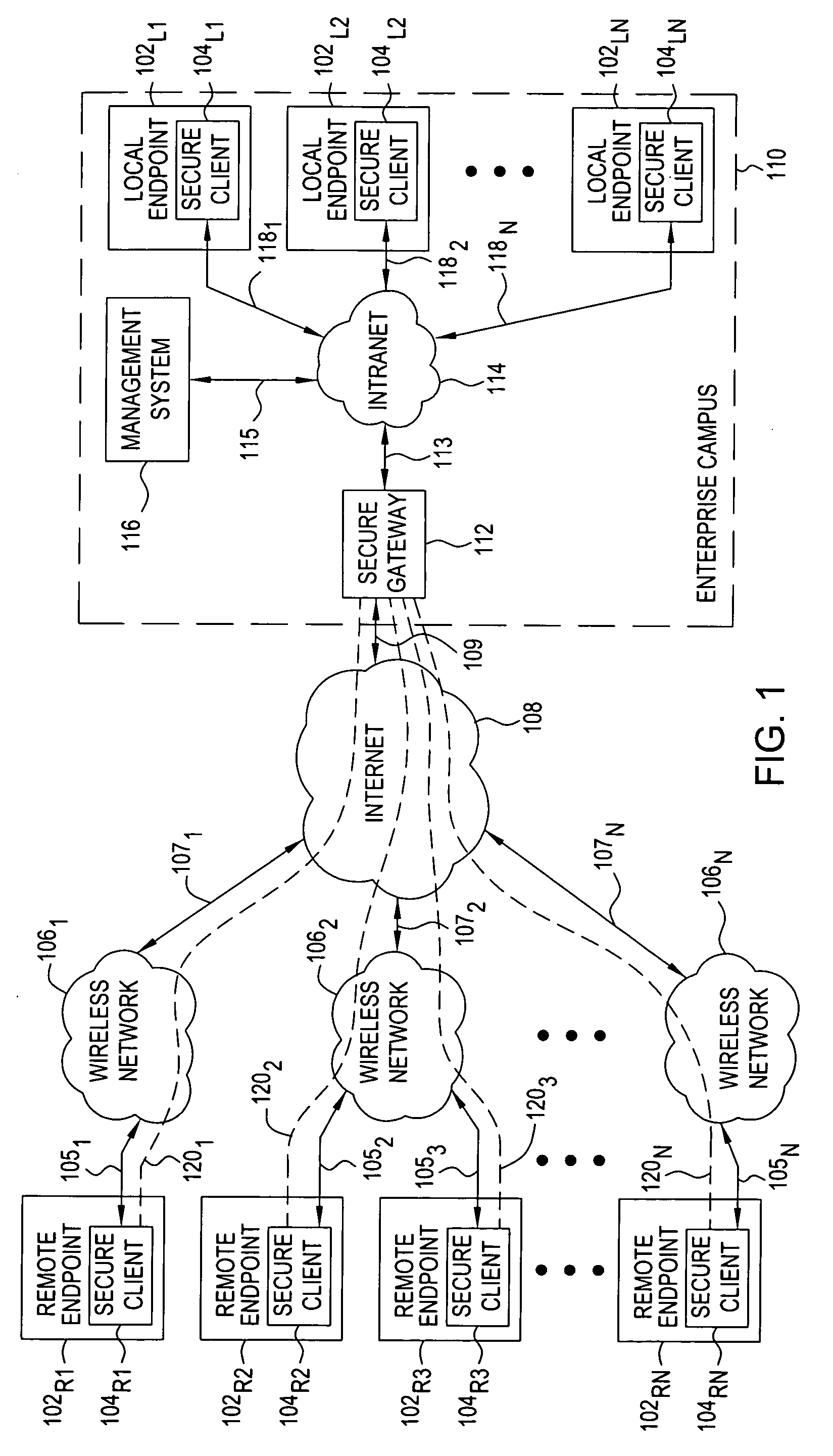
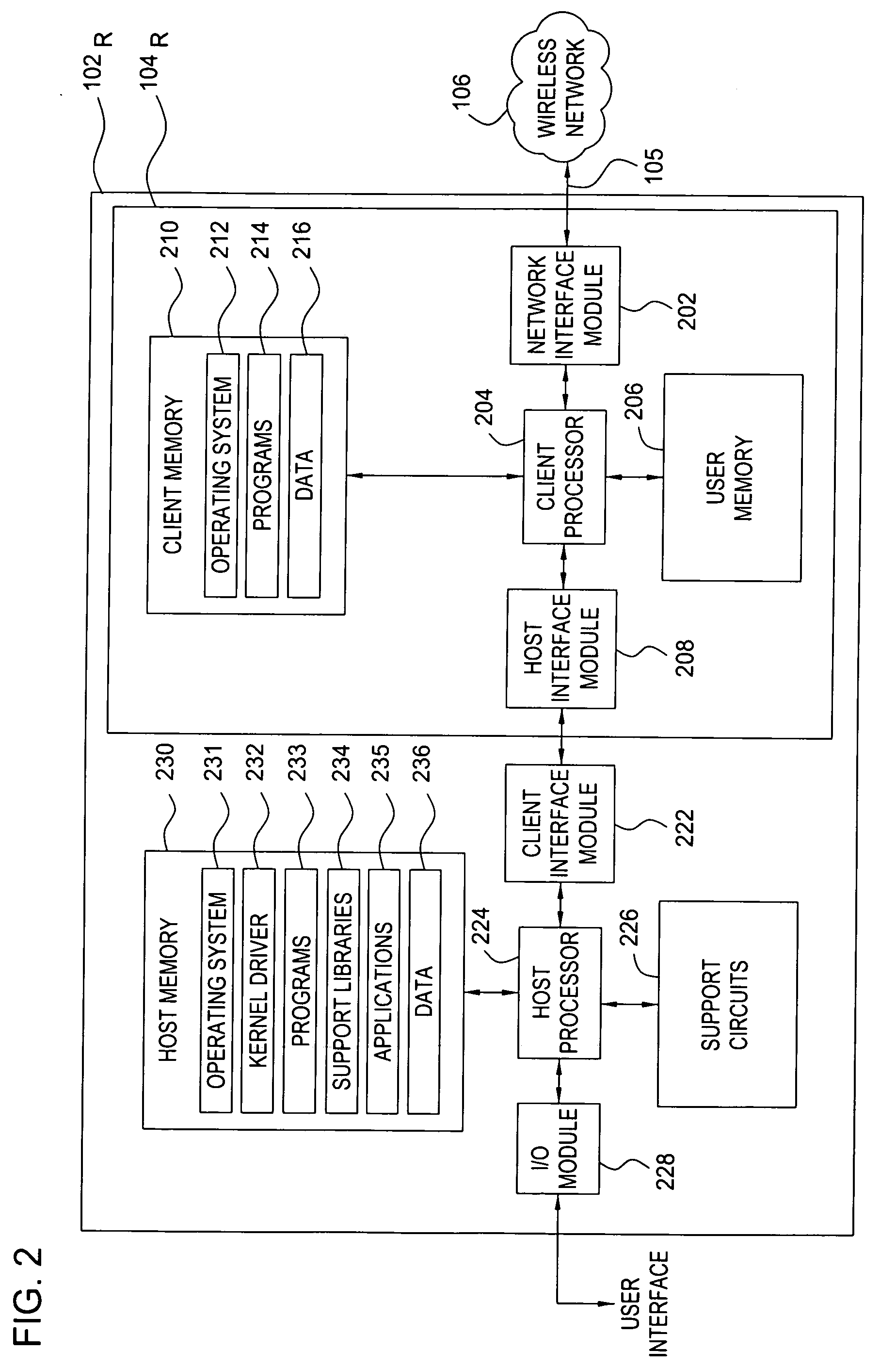
Method and apparatus for providing secure remote access to enterprise networks
ActiveUS20070130457A1Random number generatorsUser identity/authority verificationNetwork connectionNetwork interface
The invention includes a method and apparatus for providing secure remote access to enterprise networks. An apparatus includes a network interface module adapted for maintaining a secure network connection with a network device independent of a power state of a host computer associated with the apparatus a storage module for storing information associated with the secure connection, and a processor coupled to the network interface and the memory where the processor is adapted for automatically initiating the secure connection without user interaction.
Owner:ALCATEL LUCENT SAS
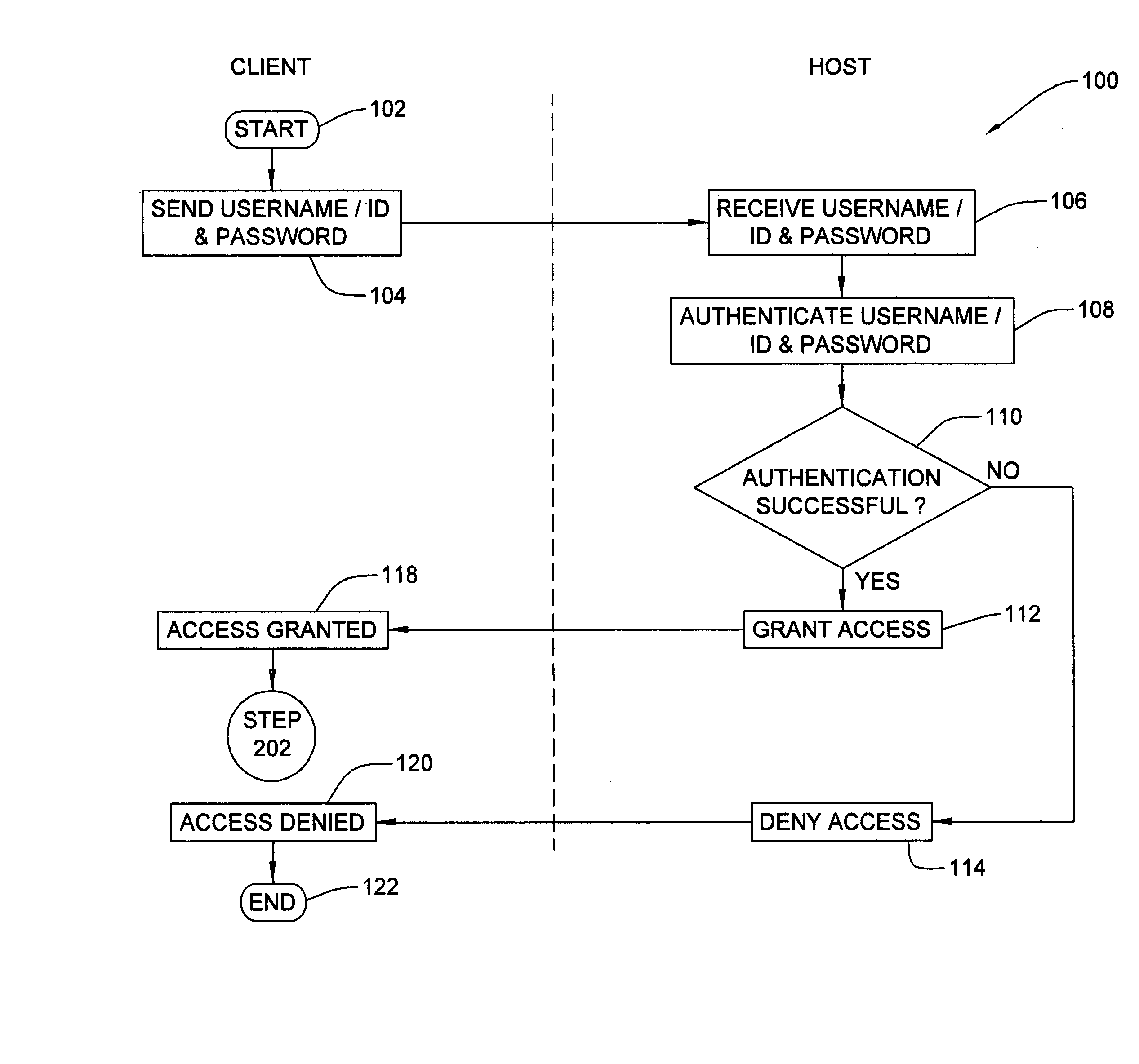
System and Method for Distributed Network Authentication and Access Control
InactiveUS20070124802A1Easy accessReduce difficultyRandom number generatorsUser identity/authority verificationWeb siteWeb authentication
A user gains access to a private network by connecting to a network, either through a hardwired or wireless connection, and then initiates an Internet access request targeting any website. If the user is not already authorized for Internet access, then the user is sent to a first predetermined website that points the user to an authentication server accessible via the Internet. The authentication server sends the user an HTTP form pages requesting authentication information. When the user responds, a network monitoring device within the private network alters the form page to include the user's hardware address and an encoded ID based on the network's location. The authentication server forwards this data to a gate keeper server, which authenticates the new user and transmits an unblock message along with another encoded ID based on the network's location and the user's hardware address.
Owner:HEREUARE COMMUNICATIOINS
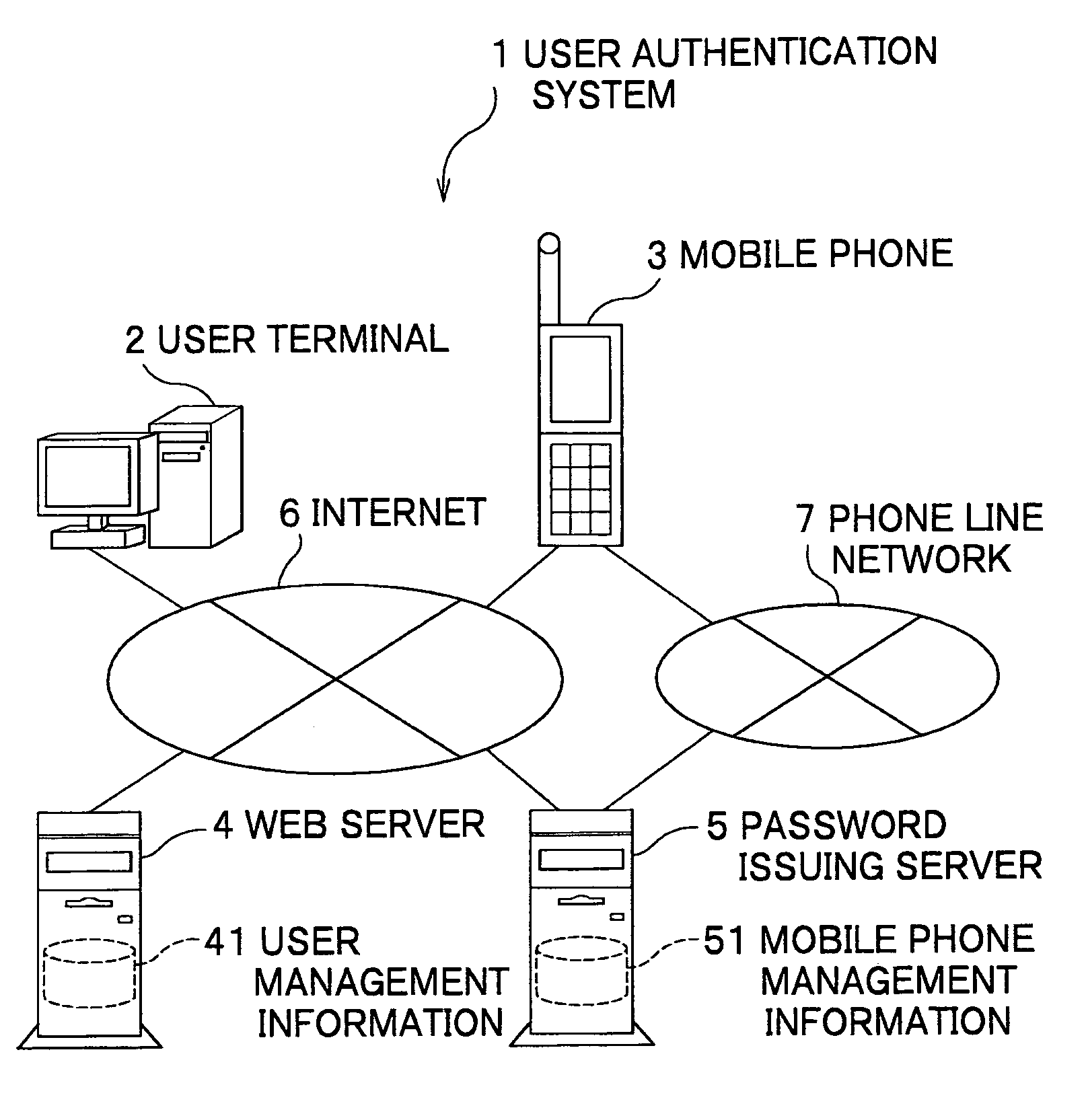
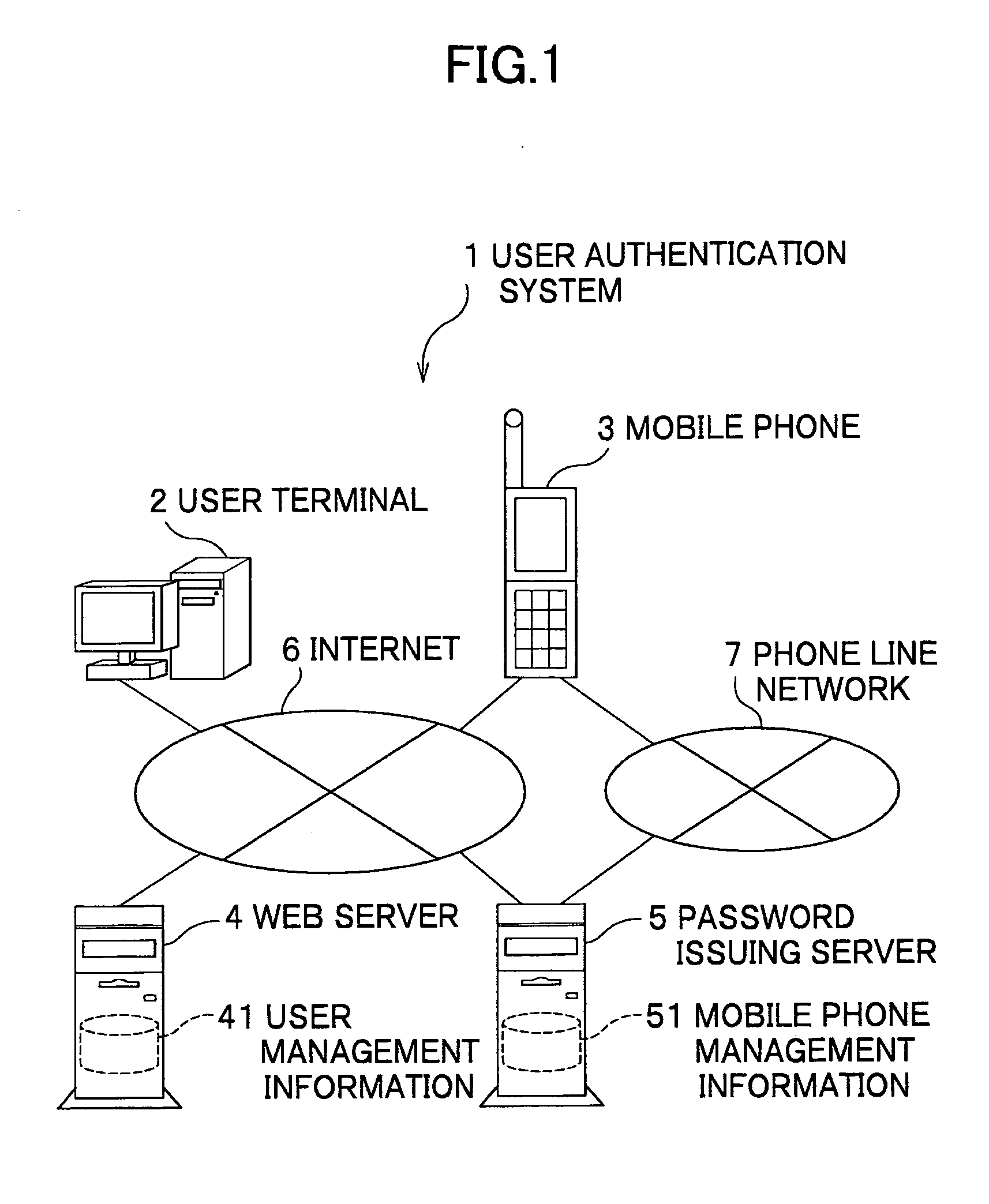
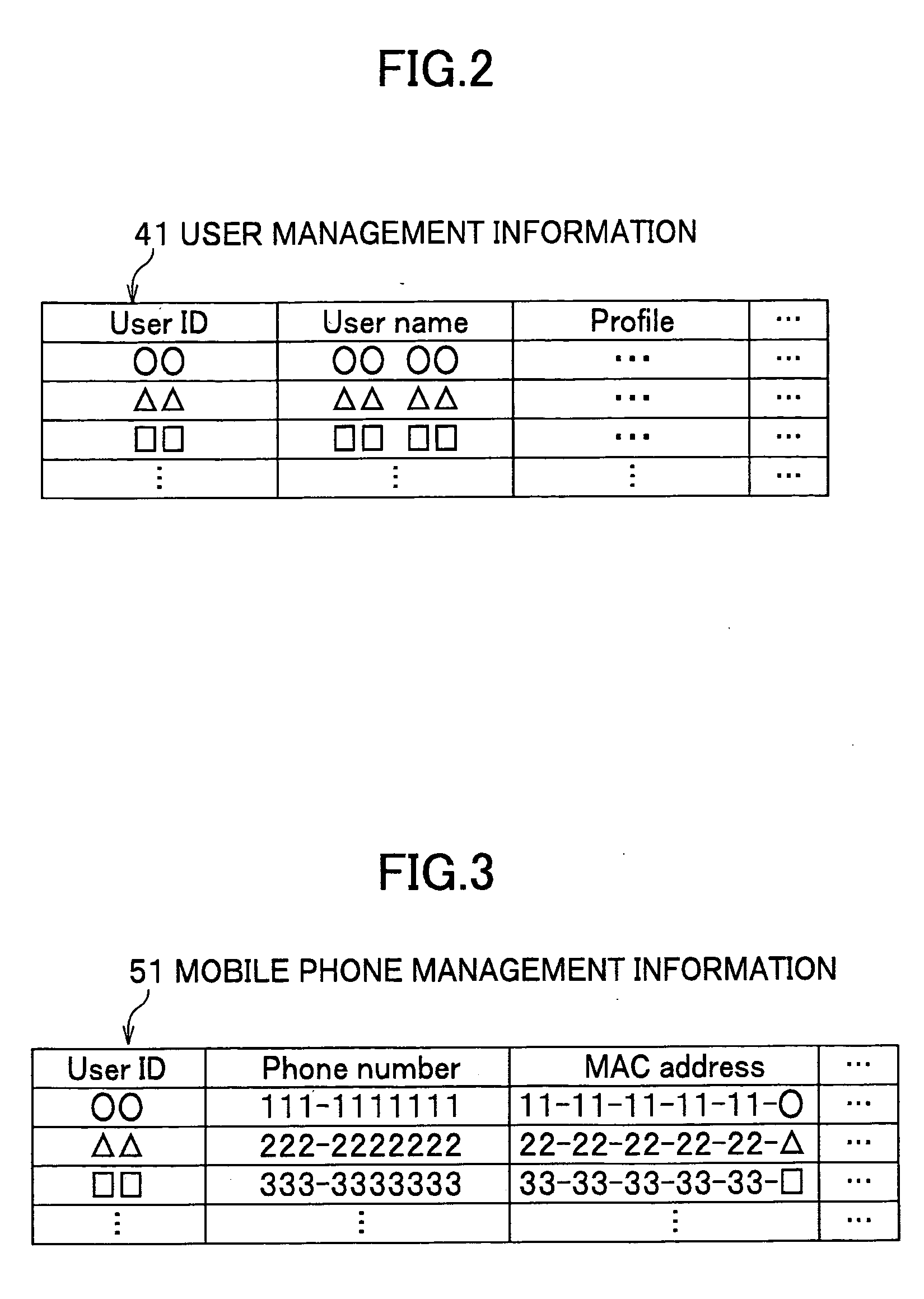
User authentication system and user authentication method
InactiveUS20070079135A1Acutation objectsRandom number generatorsService provisionUser authentication
A user authentication system capable of maintaining high-level security and of reducing a user's load of operations necessary for login is provided. The user authentication system includes a user terminal, a mobile phone, a password issuing unit, and a service providing unit. When a user accesses the system via the user terminal, the service providing unit encodes connection information of the password issuing unit into a code, and sends the encoded code to the user terminal. The mobile phone decodes the code displayed on the user terminal, and accesses the password issuing unit using the connection information. The password issuing unit generates a one-time password, and sends the one-time password to the service providing unit and also to the mobile phone. The user terminal sends the one-time password displayed on the mobile phone and user identification information to the service providing unit. When the service providing unit determines that the two one-time passwords each sent from the user terminal and the password issuing unit are identical, the service providing unit permits the access of the user via the user terminal.
Owner:FORVAL TECH
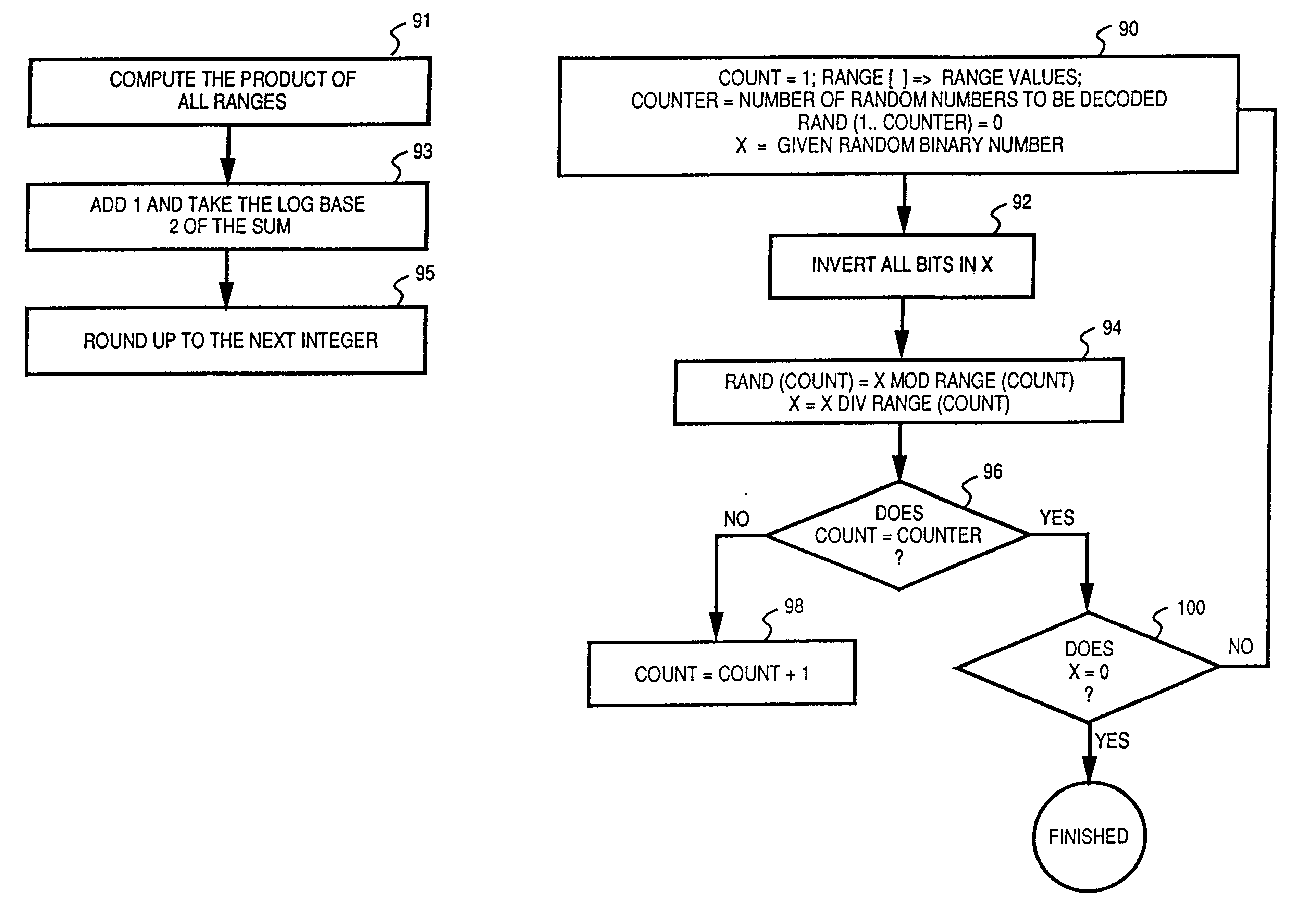
Random number generator for electronic applications
InactiveUS6193607B1Fast executionLottery apparatusRandom number generatorsGeneration processNumber generator
A method and apparatus for generating random numbers for use in electronic applications is disclosed. A given sequence of random binary numbers of a certain length can be decoded into several random numbers for a specific application. The upper range values of the random numbers to be decoded determine the number of bits required for the generation of the these random numbers. In the decoding process, the given random binary number divides a range value to generate a remainder and a quotient. The quotient becomes the new random binary number for the generation of other random numbers while the remainder is the generated random number. The process then repeats to generate other random numbers. At the end of the generation process, the last quotient determines the validity of the generated random numbers.
Owner:IGT
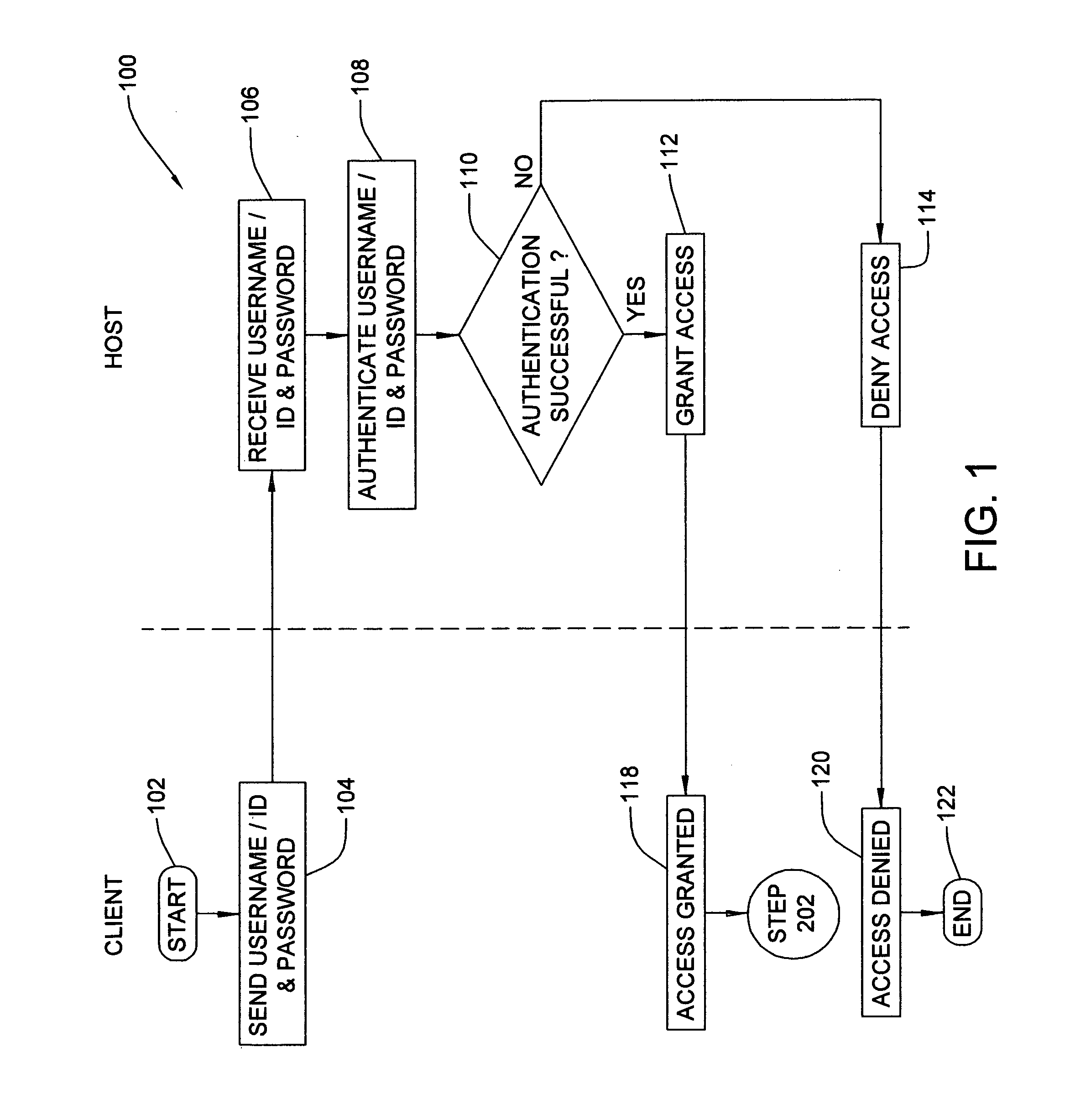
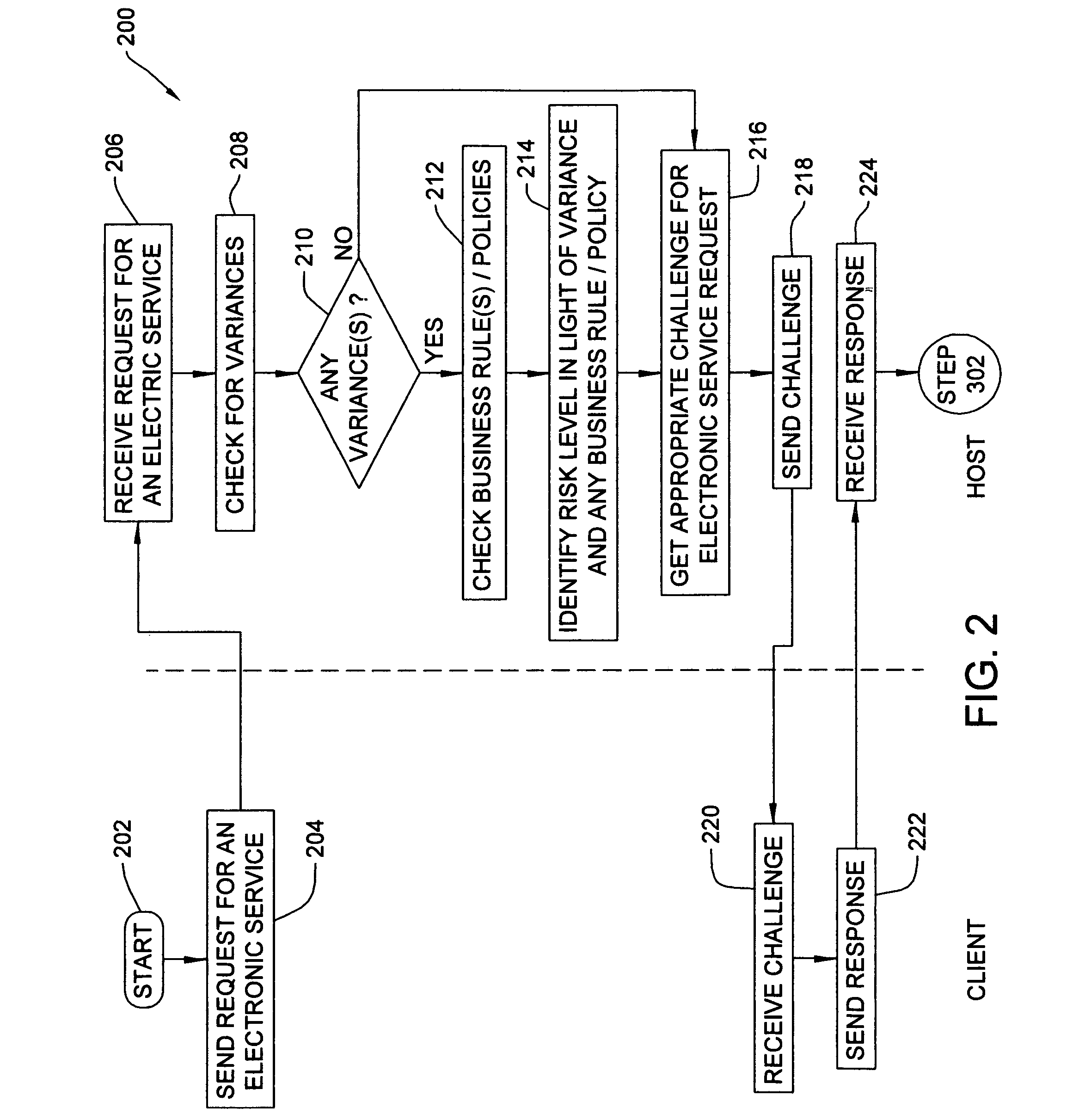
Method, system and program product for authenticating a user seeking to perform an electronic service request
InactiveUS20080066165A1Lower risk levelHigh riskDigital data information retrievalRandom number generatorsUser profileElectronic service
A method, system and program product for authenticating a user seeking to perform an electronic service request is provided. The method includes verifying user identity data received from a user requesting an electronic service, detecting whether or not any variances are found based on the set of user profile data associated with the user seeking to perform the electronic service requested, identifying the risk level for the electronic service based on whether or not any variances are found and any characteristics thereof, if any variances are found, applying one or more business policies or rules for handling any variances that are found. The method further includes issuing to the user, using a customer relationship management system, a challenge corresponding to the risk level identified for the electronic service requested, and authorizing the user to perform the electronic service requested only if a correct response is received to the challenge issued.
Owner:KYNDRYL INC
Method for control of gaming systems and for generating random numbers
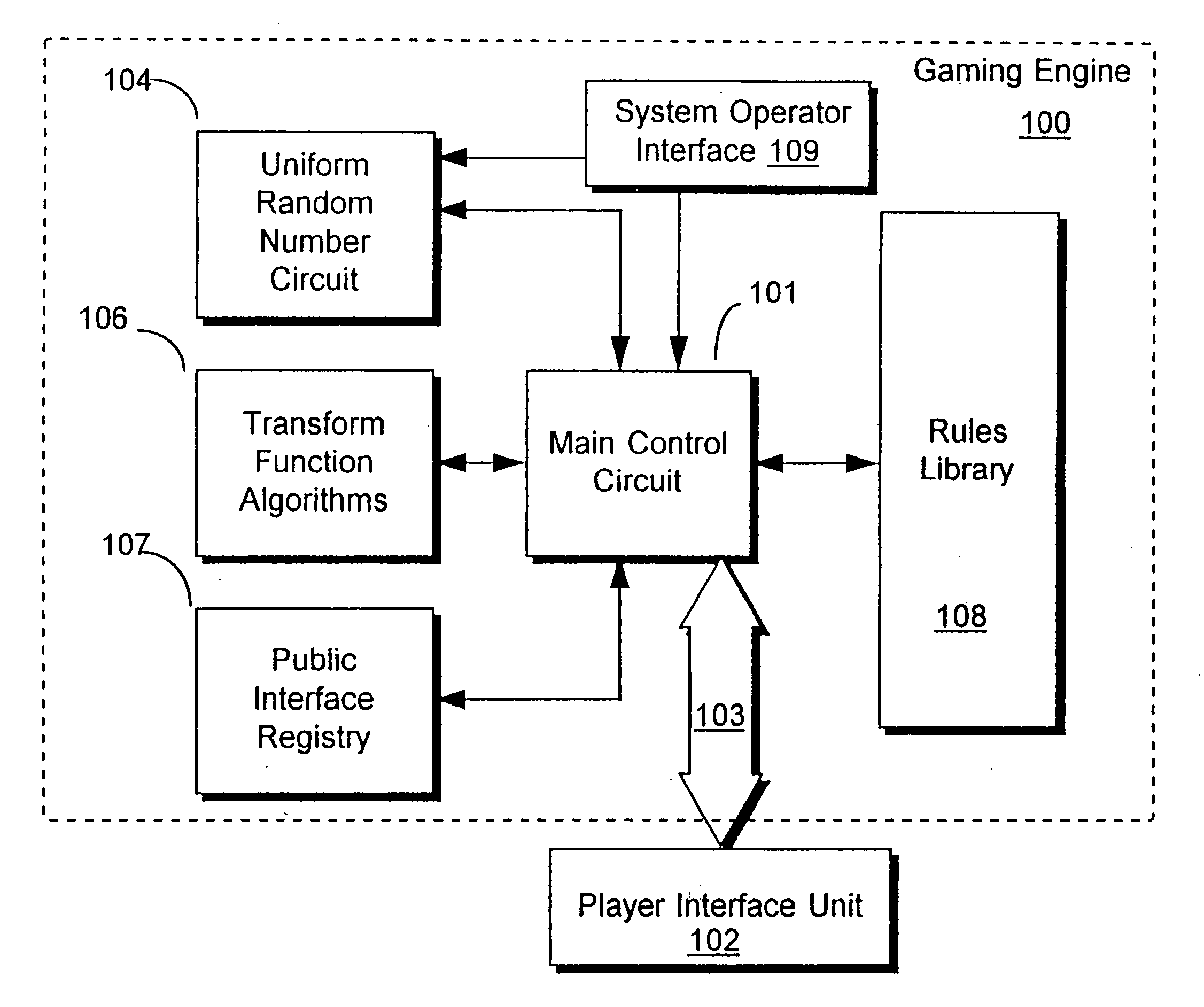
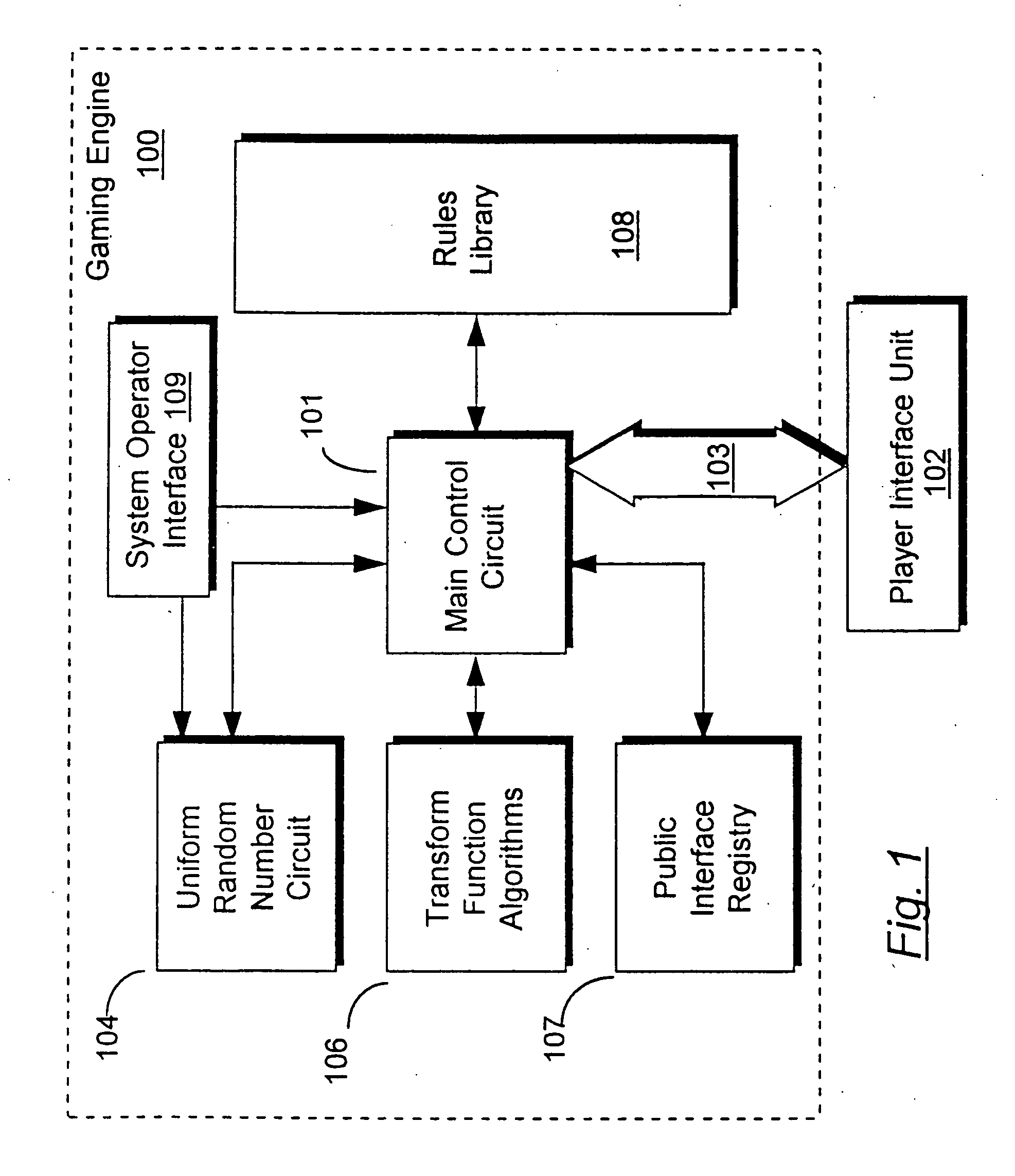
InactiveUS20060165235A1Convenient timeImprove efficiencyRandom number generatorsMultiple digital computer combinationsArray data structureNumber generator
An apparatus for implementing a game having a deterministic component and a non-deterministic component wherein a player uses the game through at least one player interface unit. Each player interface unit generates a player record indicating player-initiated events. A random number generator provides a series of pseudo-random numbers and a rules library stores indexed rules for one or more games. An interface registry stores mapping records where the mapping records are used to associate the player-initiated events to pre-selected rules in the rules library. A control means is coupled to the player interface to receive the output of the player interface unit, coupled to the interface registry, the rules library, and the random number generator. The control means processes the player record and returns an output record to the player interface unit where the output record is determined by executing the game's rules with reference to the pseudo-random numbers and predefined combinatorial algorithms for selecting sets of the pseudo-random numbers.
Owner:ZYNGA
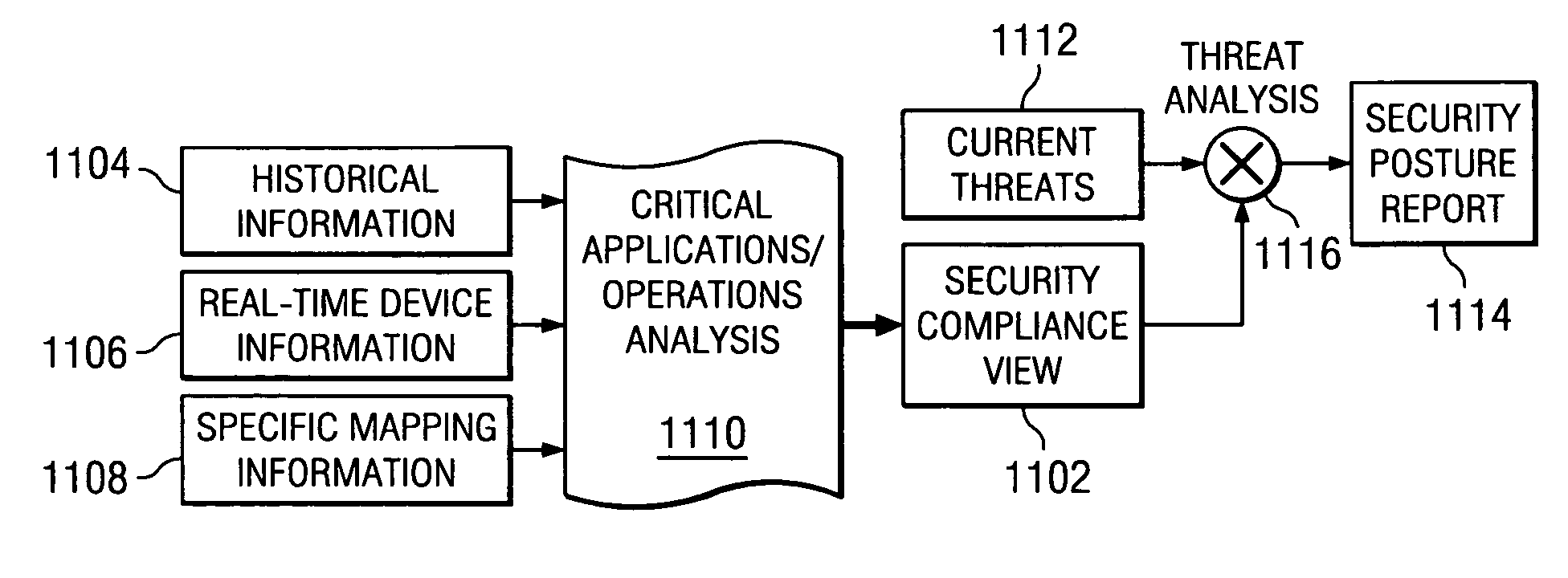
Method of assuring enterprise security standards compliance
ActiveUS20060156408A1Random number generatorsUser identity/authority verificationRisk impactSecurity compliance
A method, apparatus, and computer instructions for providing a current and complete security compliance view of an enterprise system. The present invention provides the ability to gain a real-time security posture and security compliance view of an enterprise and to assess the risk impact of known threats and attacks to continued business operations at various levels is provided. Responsive to a change to an enterprise environment, a request, or an external threat, an administrator loads or updates at least one of a Critical Application Operations database, a Historical database, an Access Control database, a Connectivity database, and a Threat database. Based on a comparison of information in the databases against similar security data elements from company or external policies, the administrator may generate a Security Compliance view of the enterprise. A Security Posture view may also be generated by comparing the Security Compliance view against data in the Threat database.
Owner:TWITTER INC
Modelling network to assess security properties
ActiveUS20070136788A1Random number generatorsUser identity/authority verificationRich modelReachability
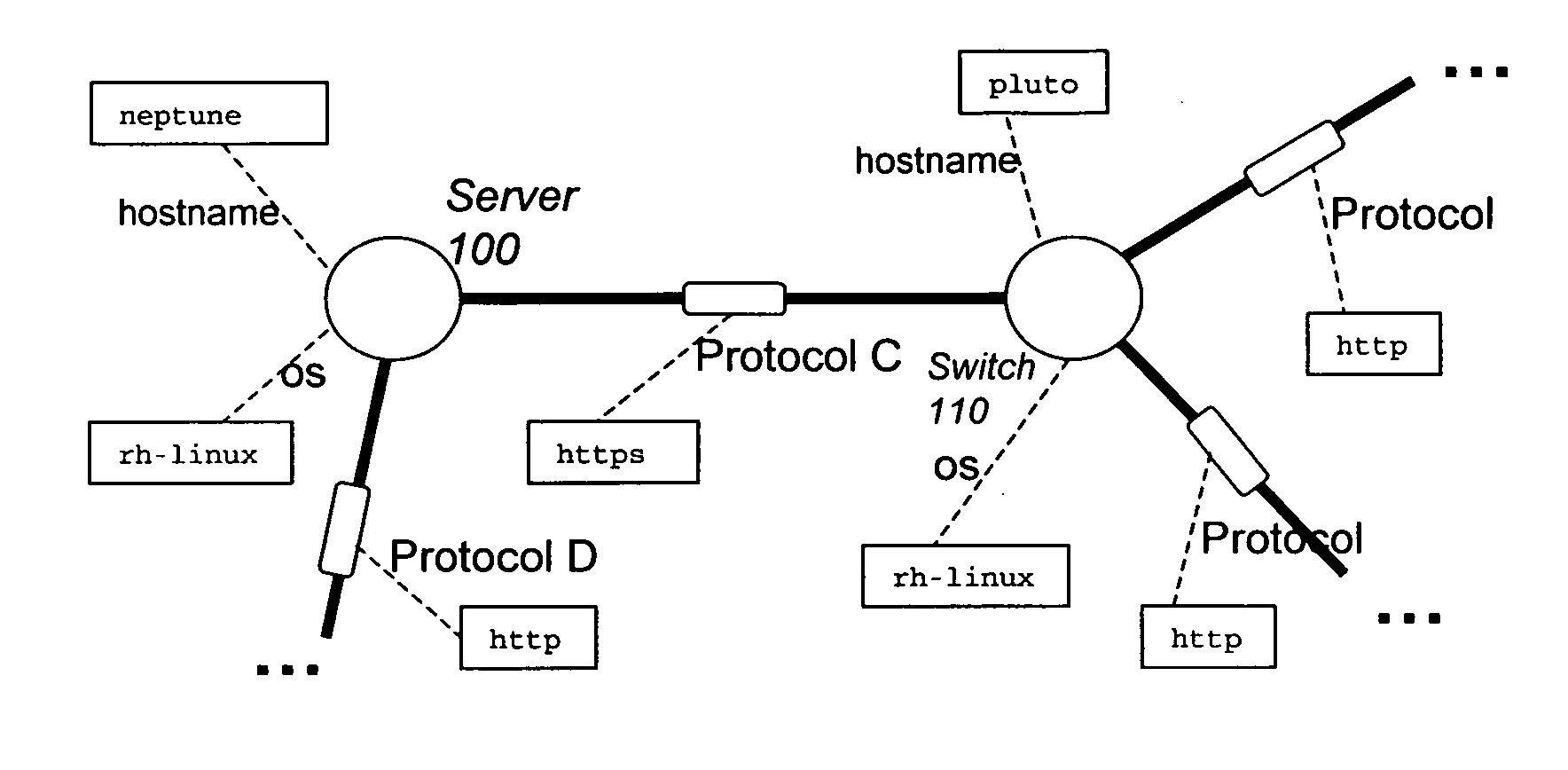
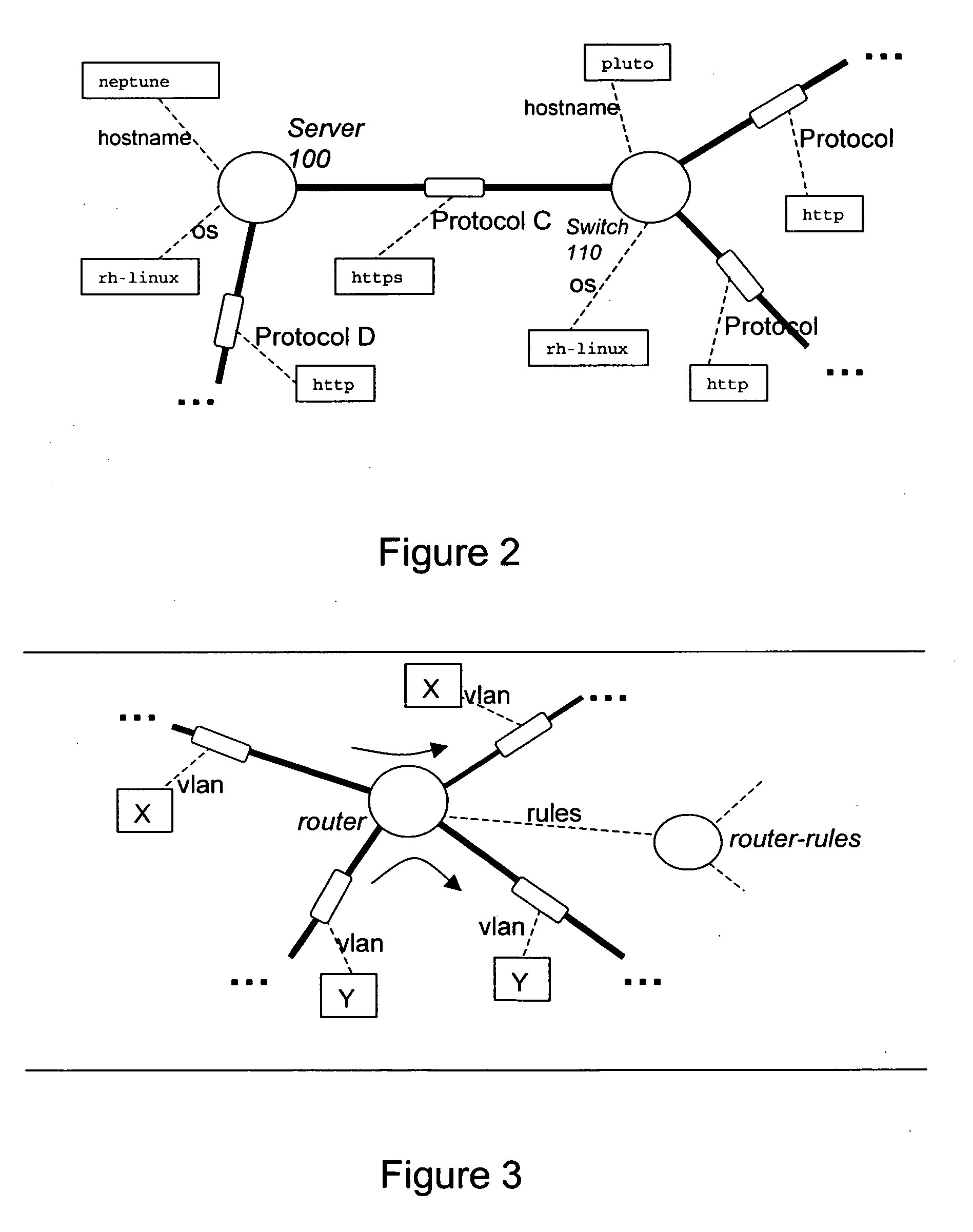
A method of assessing a network uses a model (450) having nodes (100, 110) to represent parts of the network infrastructure and the application services, and having links to represent how the nodes influence each other. Dependencies or effects of the application services are found by determining paths through the nodes and links of the model (530). Such assessment can be useful for design, test, operations, and diagnosis, and for assessment of which parts of the infrastructure are critical to given services, or which services are dependent on, or could have an effect on a given part of the infrastructure. The dependencies or effects can encompass reachability information. The use of a model having links and nodes can enable more efficient processing, to enable larger or richer models. What changes in the dependencies or effects result from a given change in the network can be determined (830).
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
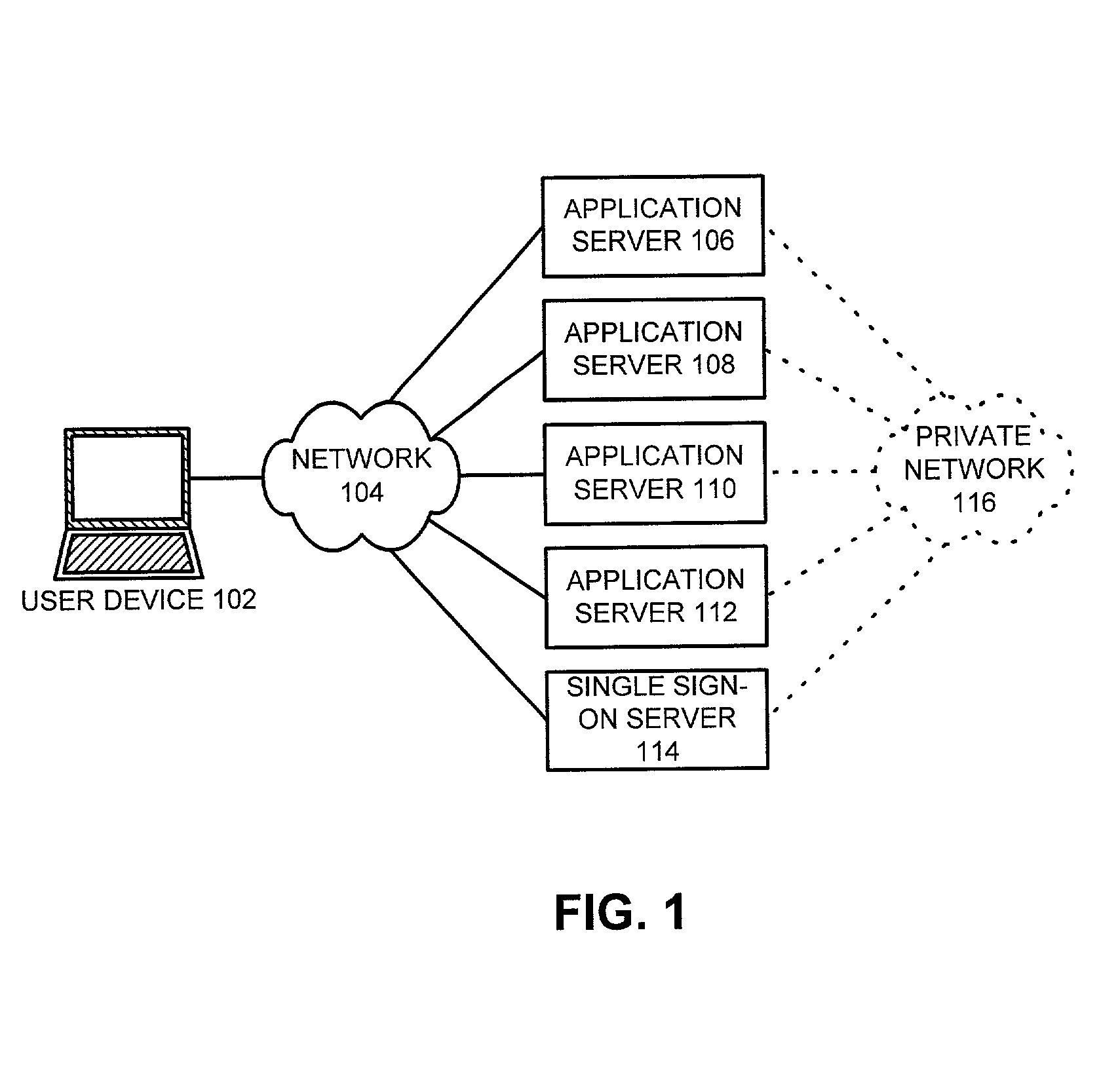
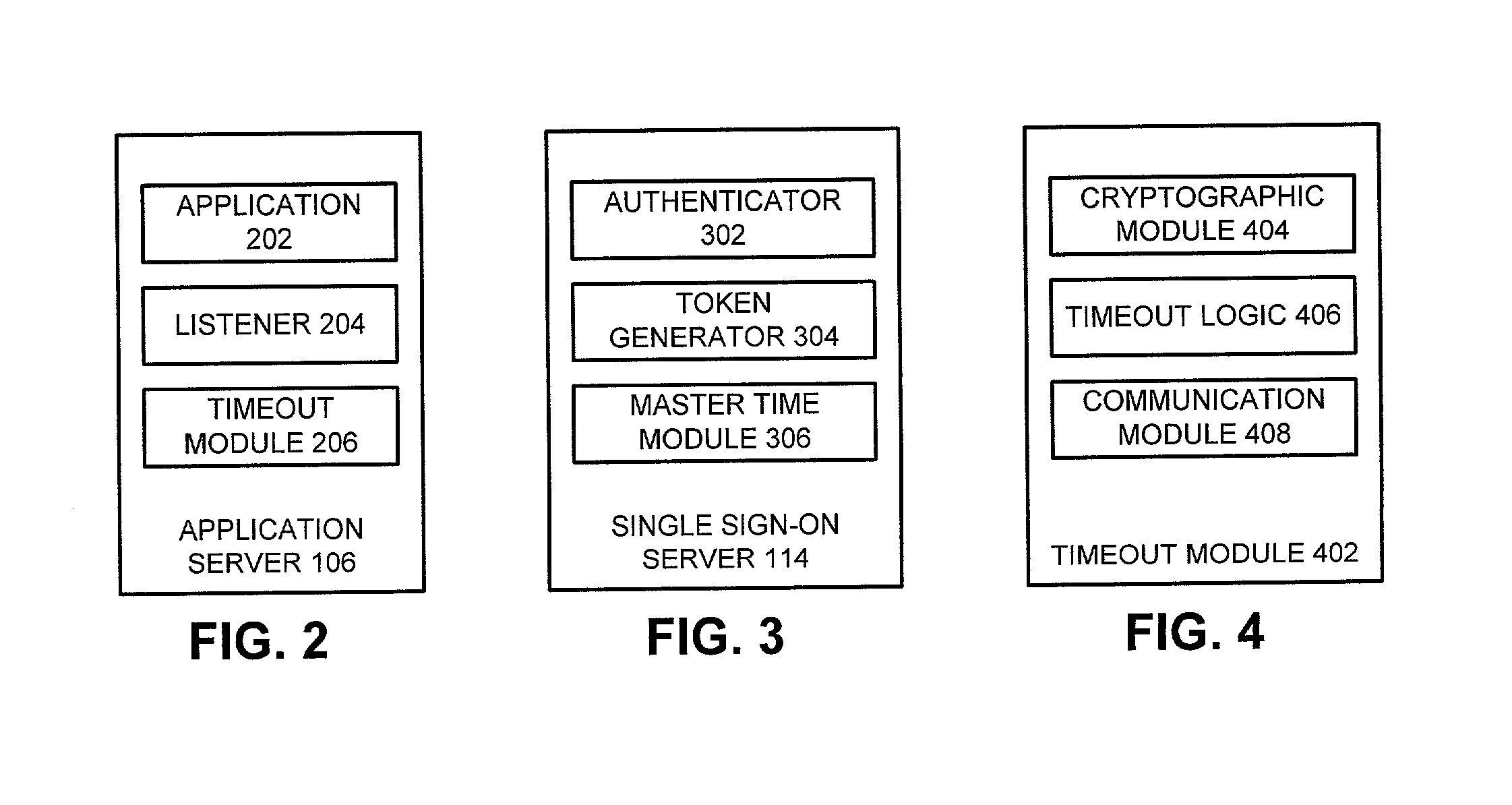
Method and apparatus to facilitate a global timeout in a distributed computing environment
ActiveUS7111323B1Facilitates global timeoutData processing applicationsRandom number generatorsUser deviceDistributed Computing Environment
One embodiment of the present invention provides a system to facilitate global timeout in a distributed computing environment. The system operates by receiving an access request from a user at an application within the distributed computing environment. The system determines if the distributed computing environment has issued an authentication to a user device through which the user accesses the application and also determines if the authentication has expired because of non-use for a specified period. This authentication is stored within a time-stamped token on the user-device. If the authentication has not been received or has expired, the system redirects the access request to a single sign-on server for the distributed computing environment requiring the user to reauthenticate with the distributed computing environment, otherwise the system grants the user access to the application.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com