Patents
Literature
66 results about "Gate-keeper" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
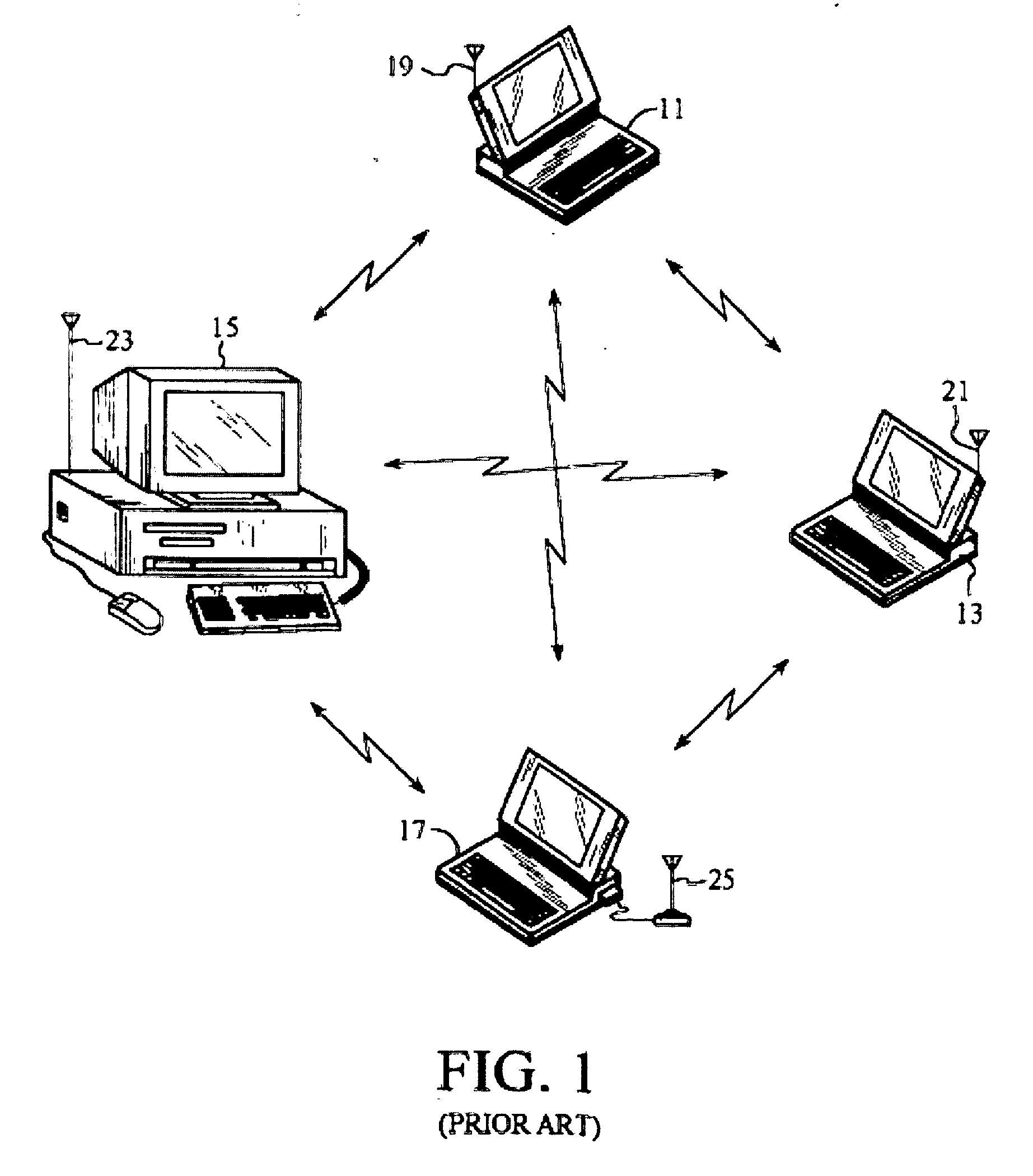
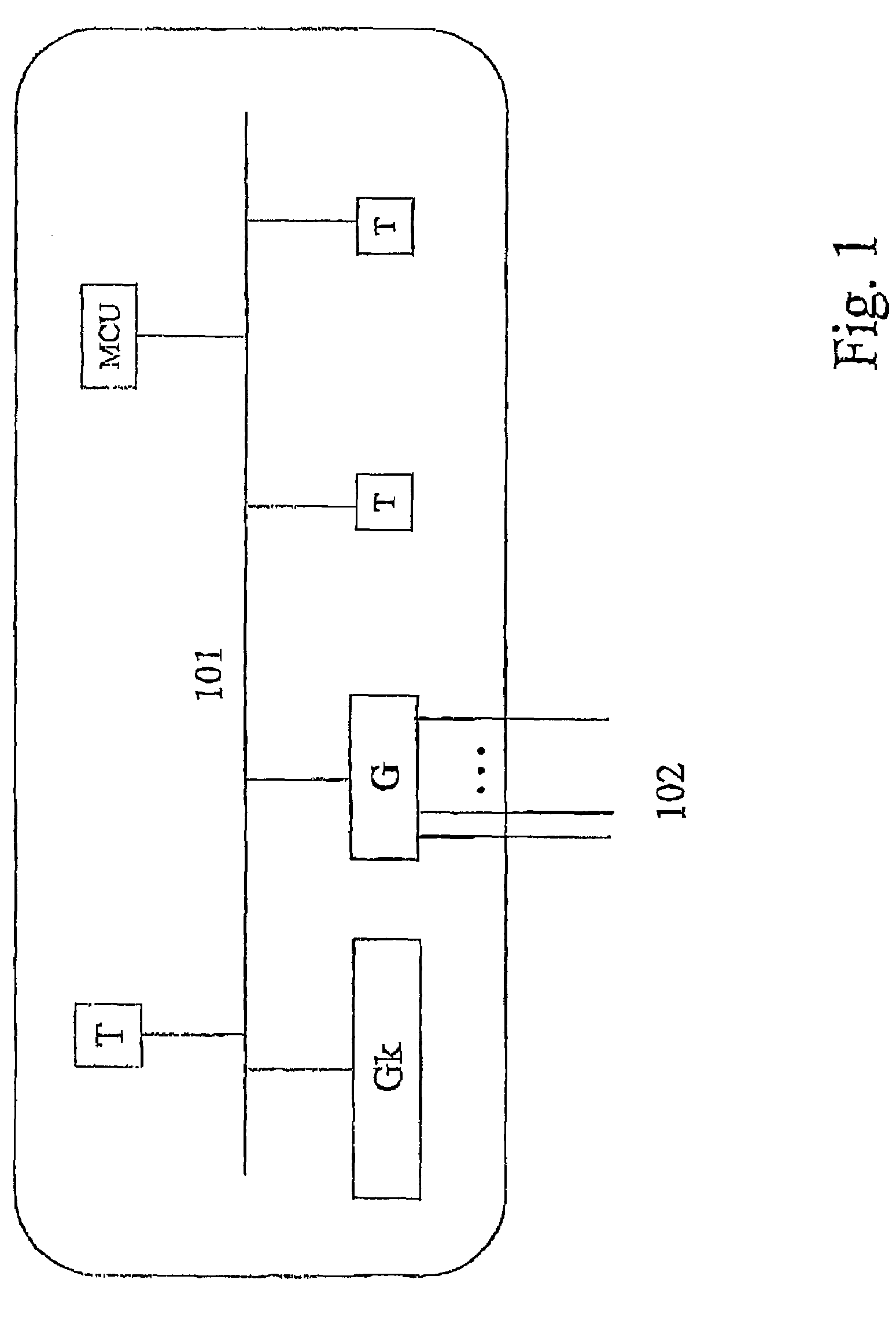
System for distributed network authentication and access control
InactiveUS7185360B1Facilitate wireless accessEasy accessError preventionFrequency-division multiplex detailsWeb authenticationGate-keeper
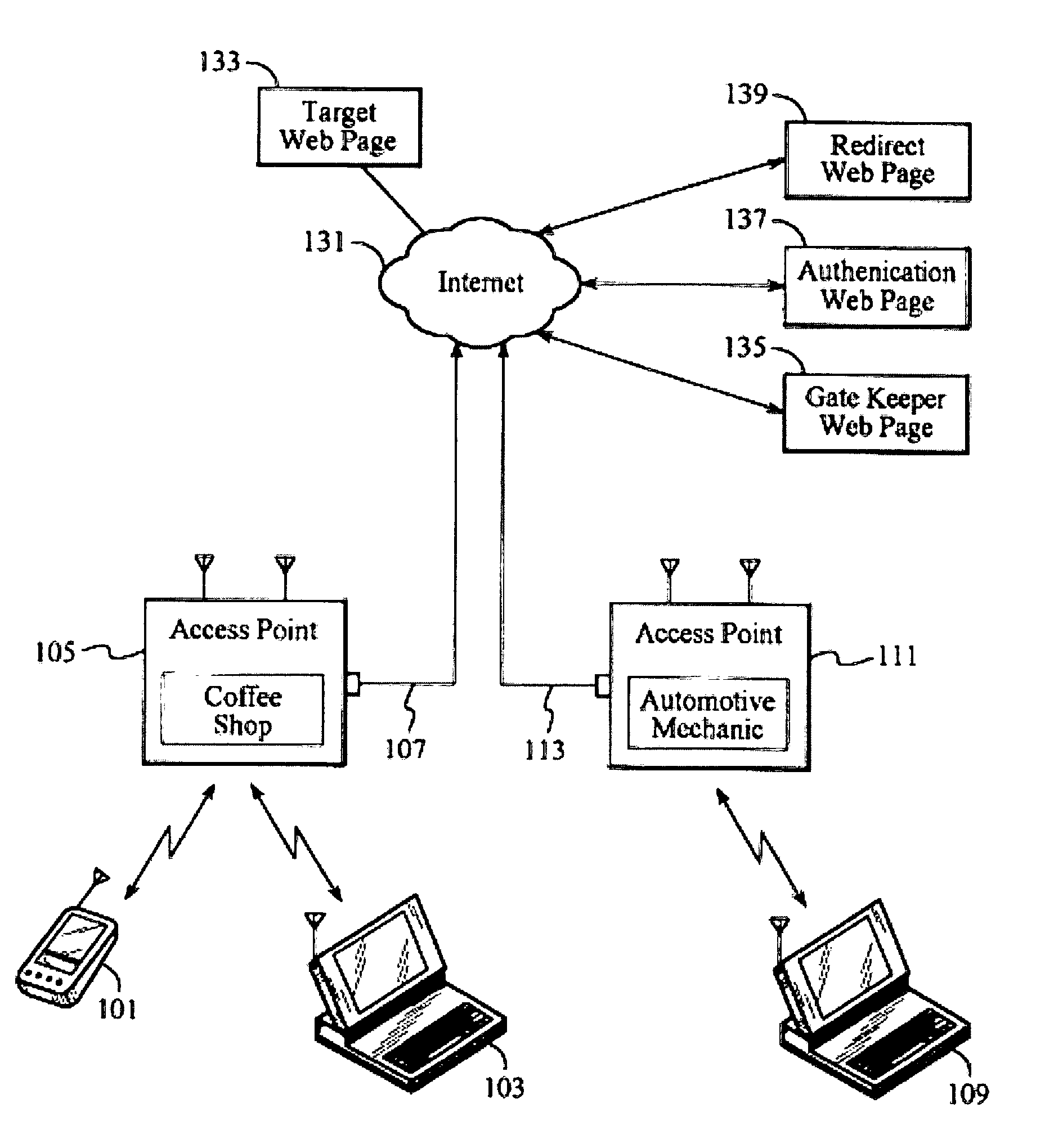
A user gains access to a private network by connecting to a network, either through a hardwired or wireless connection, and then initiates an Internet access request targeting any website. If the user is not already authorized for Internet access, then the user is sent to a first predetermined website that points the user to an authentication server accessible via the Internet. The authentication server sends the user an HTTP form pages requesting authentication information. When the user responds, a network monitoring device within the private network alters the form page to include the user's hardware address and an encoded ID based on the network's location. The authentication server forwards this data to a gate keeper server, which authenticates the new user and transmits an unblock message along with another encoded ID based on the network's location and the user's hardware address.
Owner:HEREUARE COMMUNICATIOINS
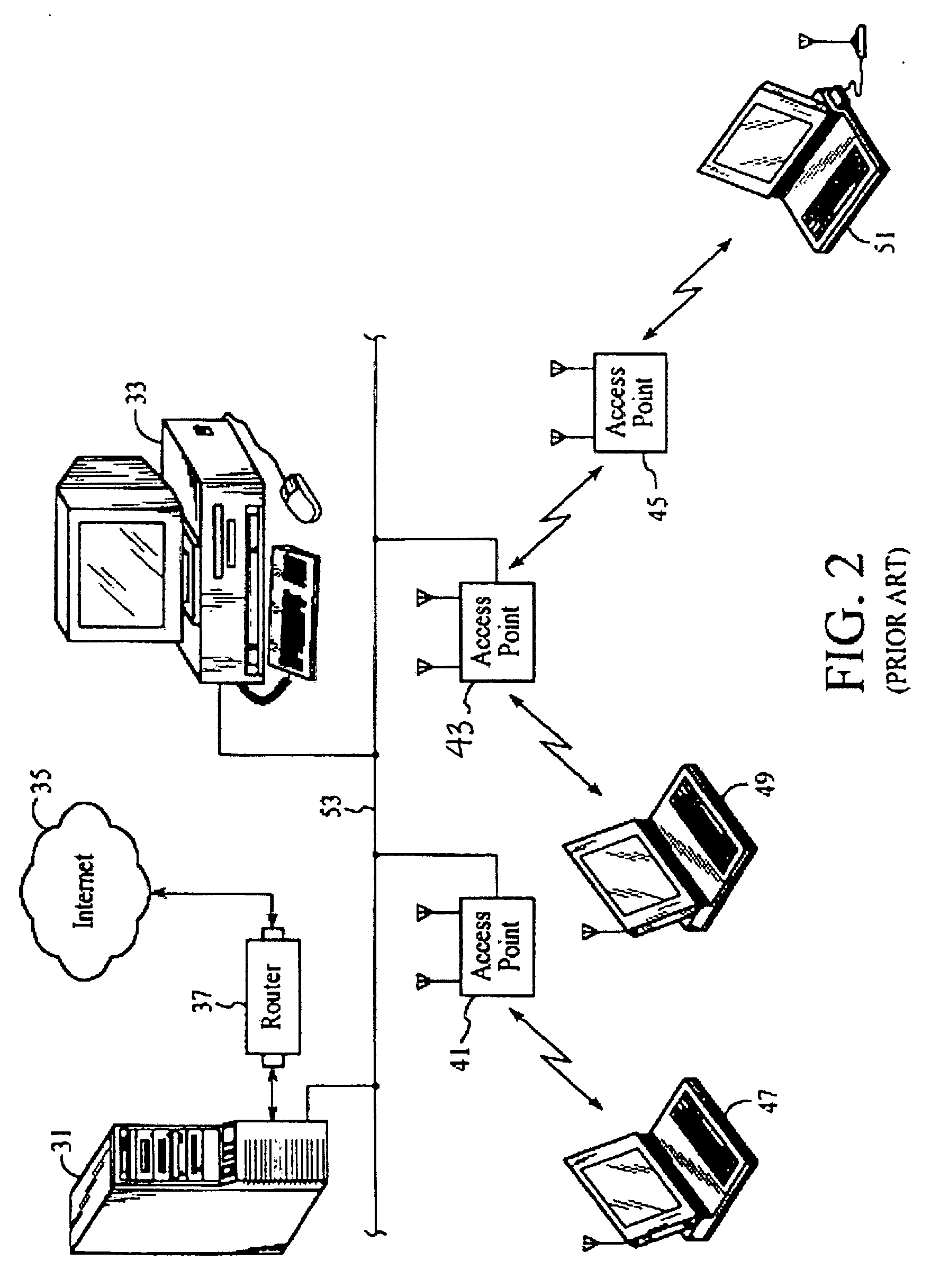
System and Method for Distributed Network Authentication and Access Control
InactiveUS20070124802A1Easy accessReduce difficultyRandom number generatorsUser identity/authority verificationWeb siteWeb authentication
A user gains access to a private network by connecting to a network, either through a hardwired or wireless connection, and then initiates an Internet access request targeting any website. If the user is not already authorized for Internet access, then the user is sent to a first predetermined website that points the user to an authentication server accessible via the Internet. The authentication server sends the user an HTTP form pages requesting authentication information. When the user responds, a network monitoring device within the private network alters the form page to include the user's hardware address and an encoded ID based on the network's location. The authentication server forwards this data to a gate keeper server, which authenticates the new user and transmits an unblock message along with another encoded ID based on the network's location and the user's hardware address.
Owner:HEREUARE COMMUNICATIOINS
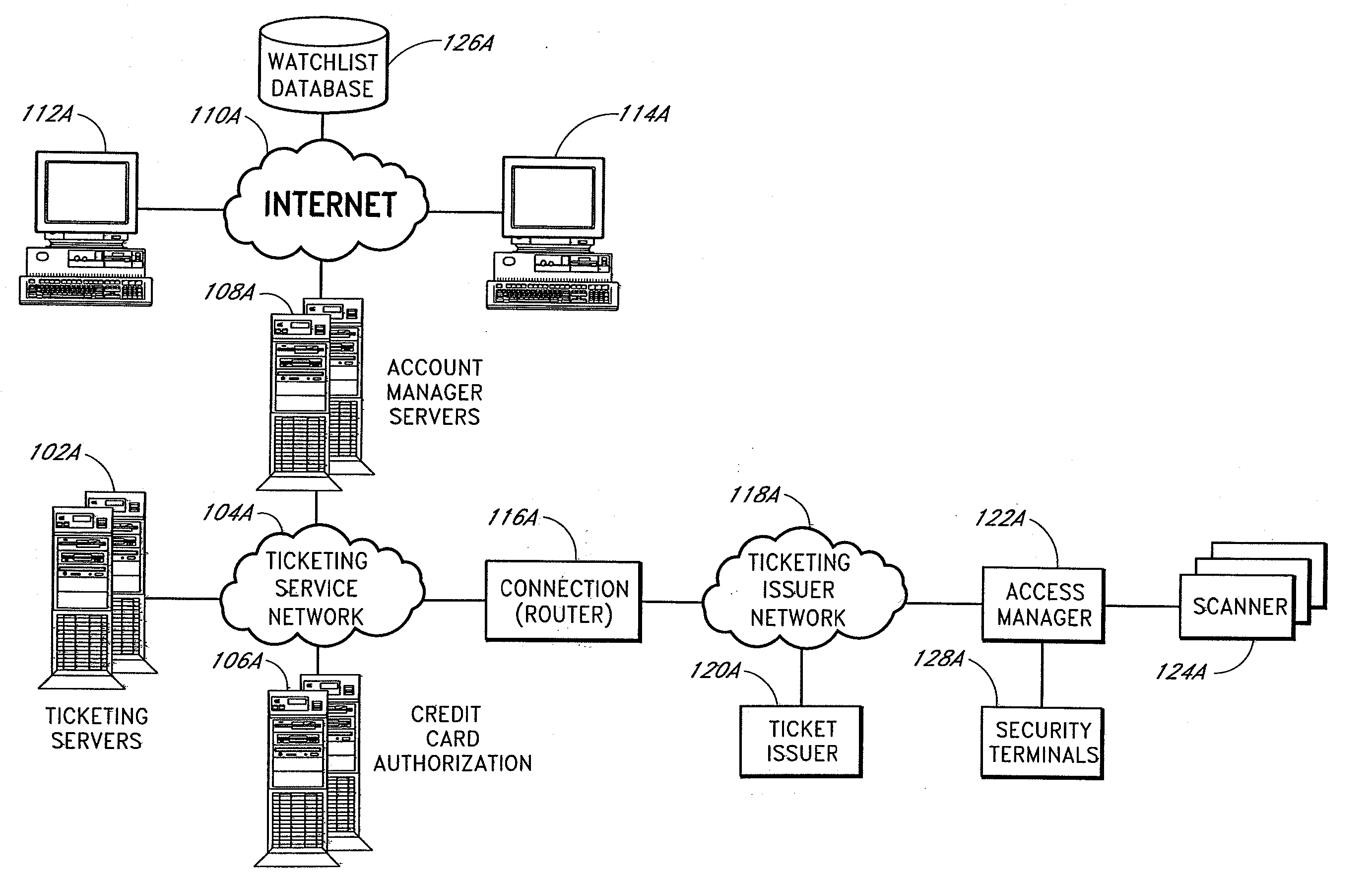
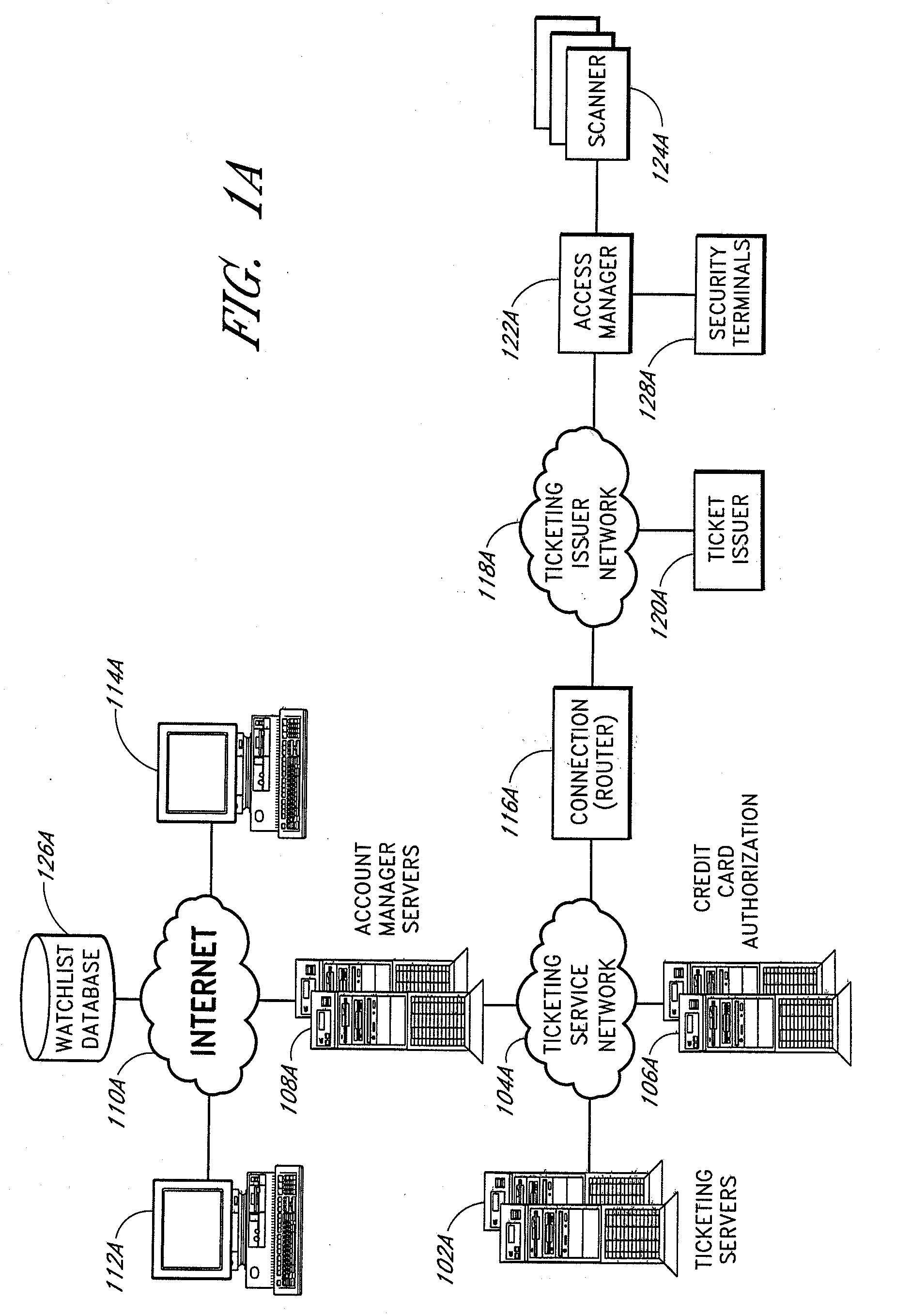
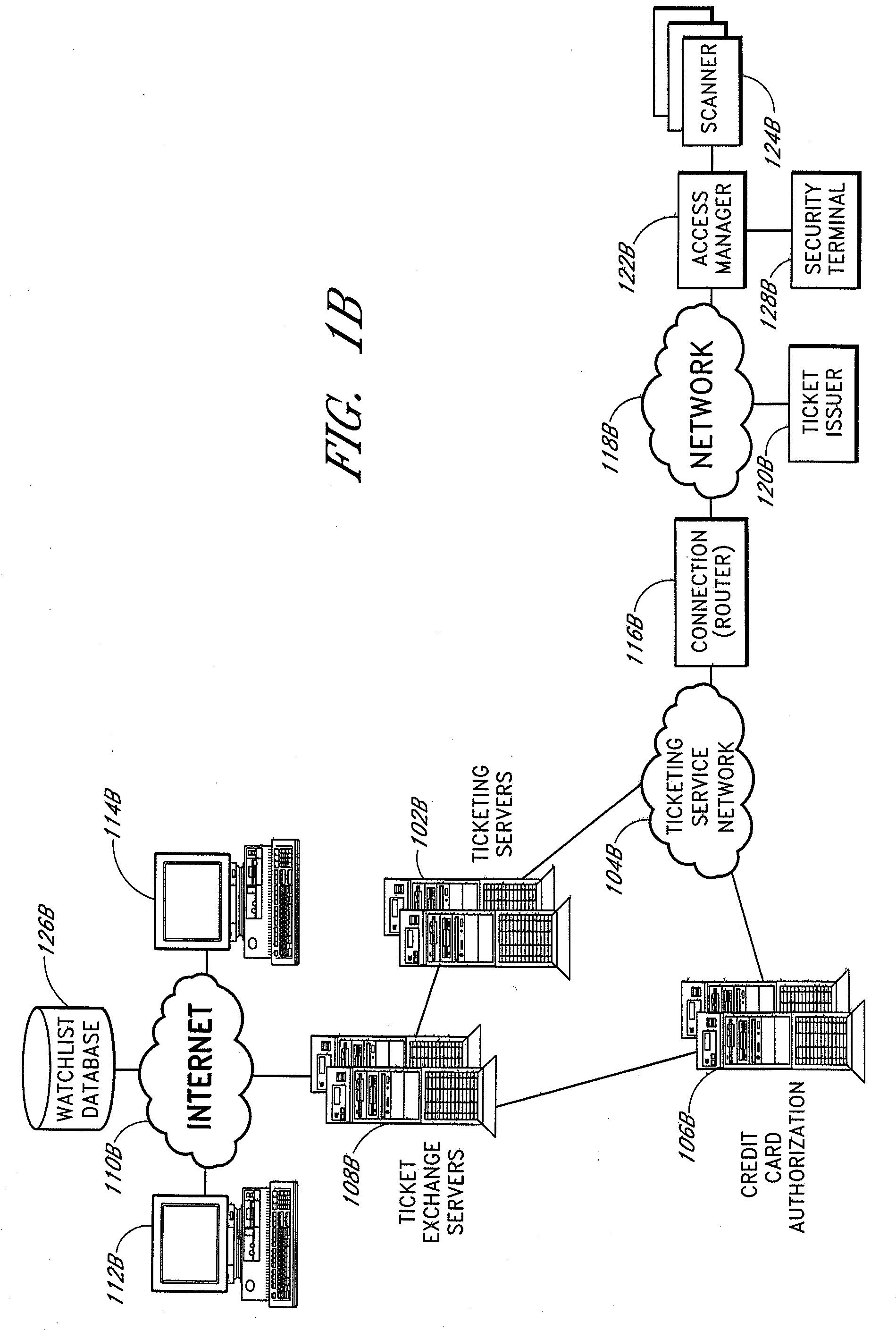
Apparatus for access control and processing
ActiveUS20070276944A1Electric signal transmission systemsTicket-issuing apparatusGate-keeperControl system
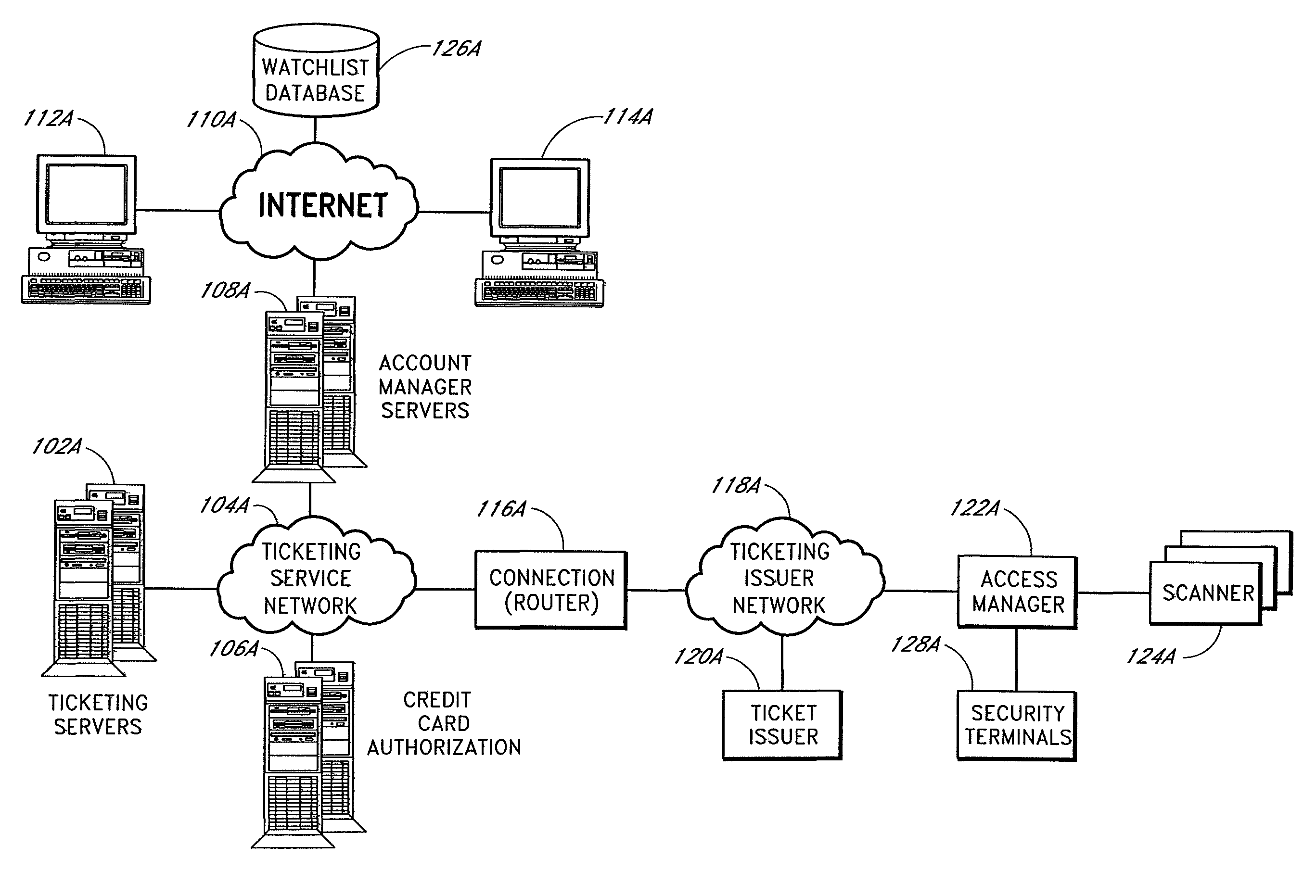
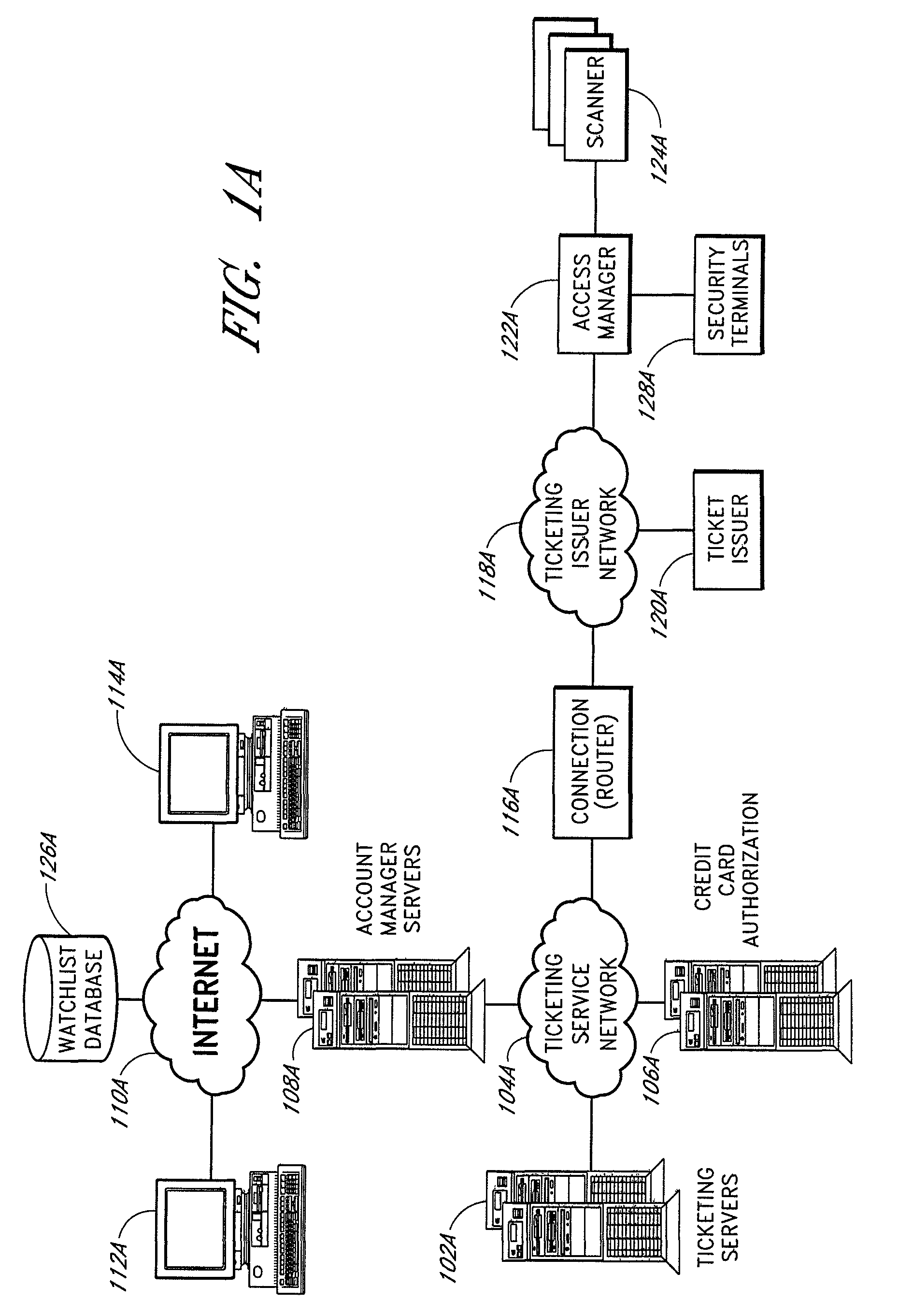
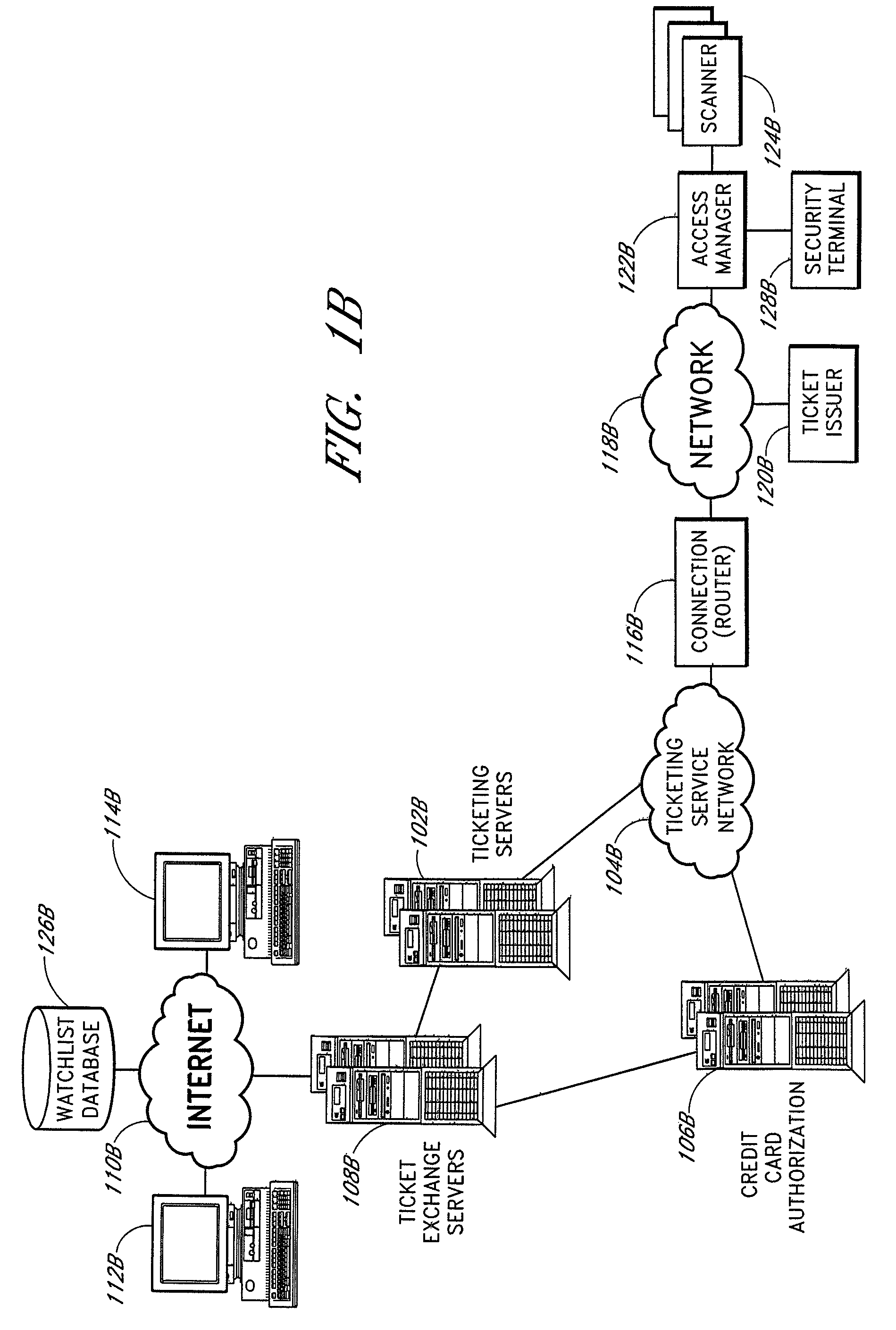
The present invention relates to methods and systems for providing secure access control to a facility. An access control system comprises a scanner located adjacent to a venue entrance. A computer system is coupled to the scanner. The computer system is configured to receive a coded user identification data scanned from an admission ticket from a ticket bearer via the scanner, decode the coded user identification data, and transmit the decoded user identification to a terminal for display to a gate keeper so that the gate keeper can determine whether the ticket bearer is to be admitted. An optional turnstile is coupled to the computer system, wherein the computer system enables the turnstile rotation.
Owner:LIVE NATION ENTERTAINEMENT INC
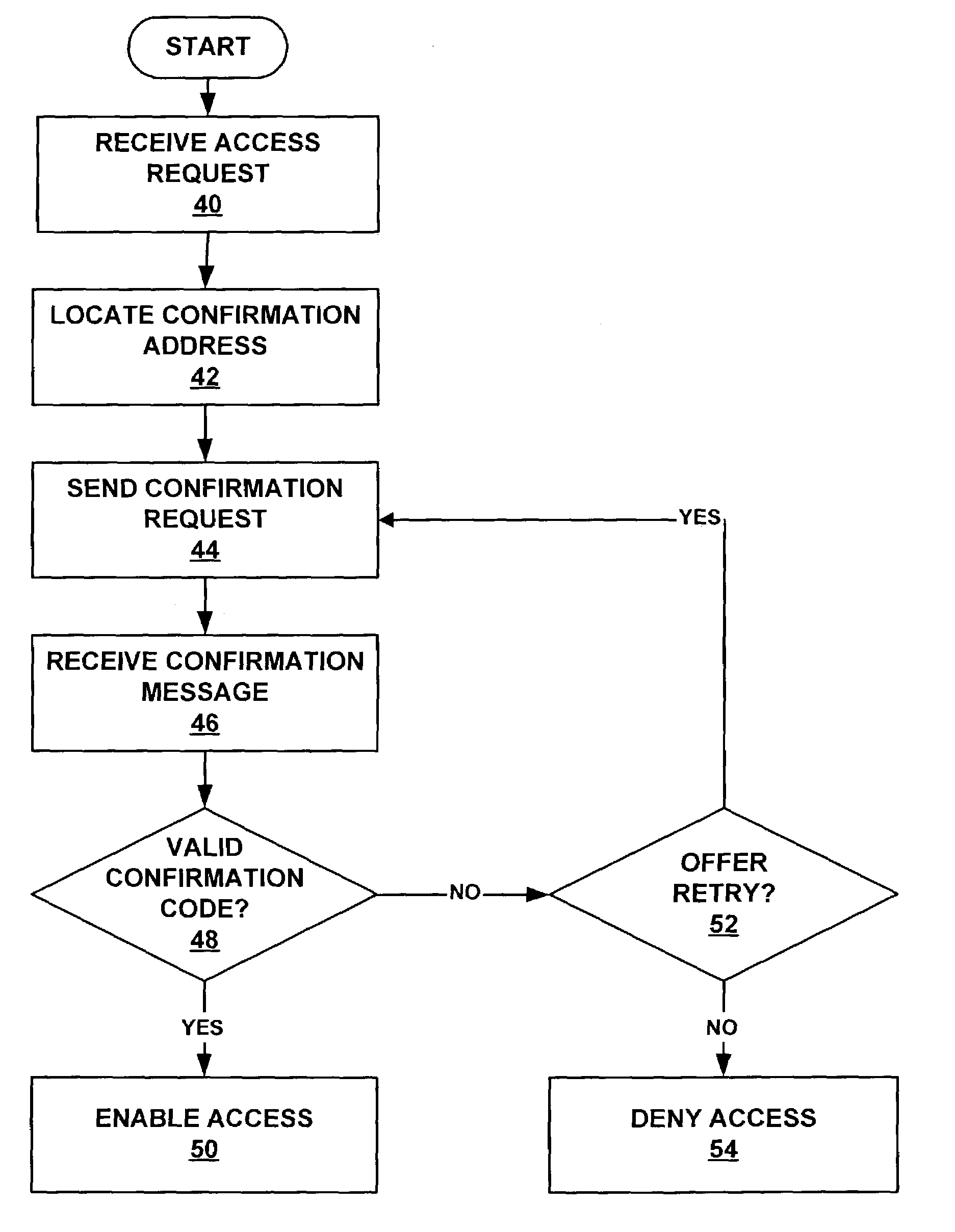
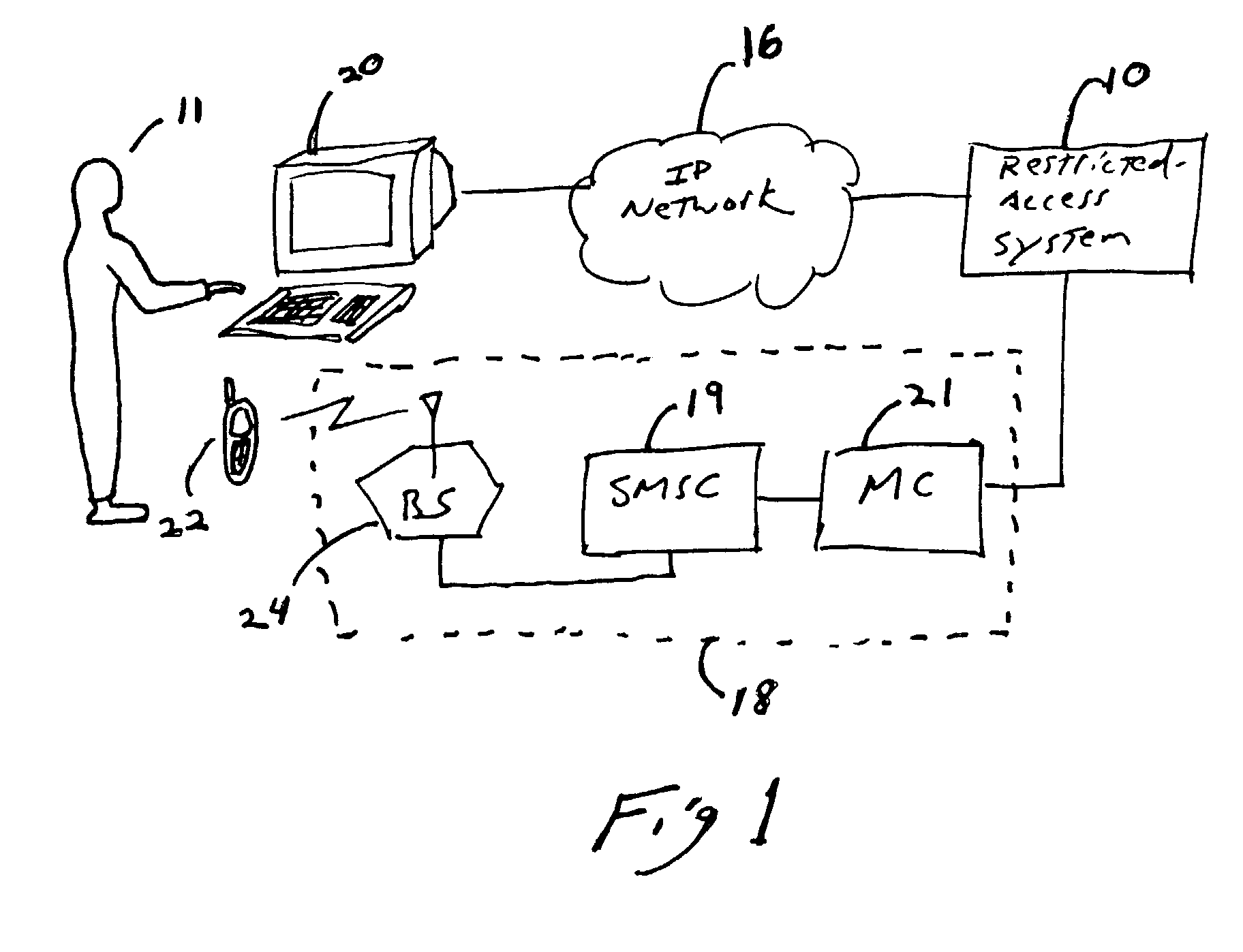
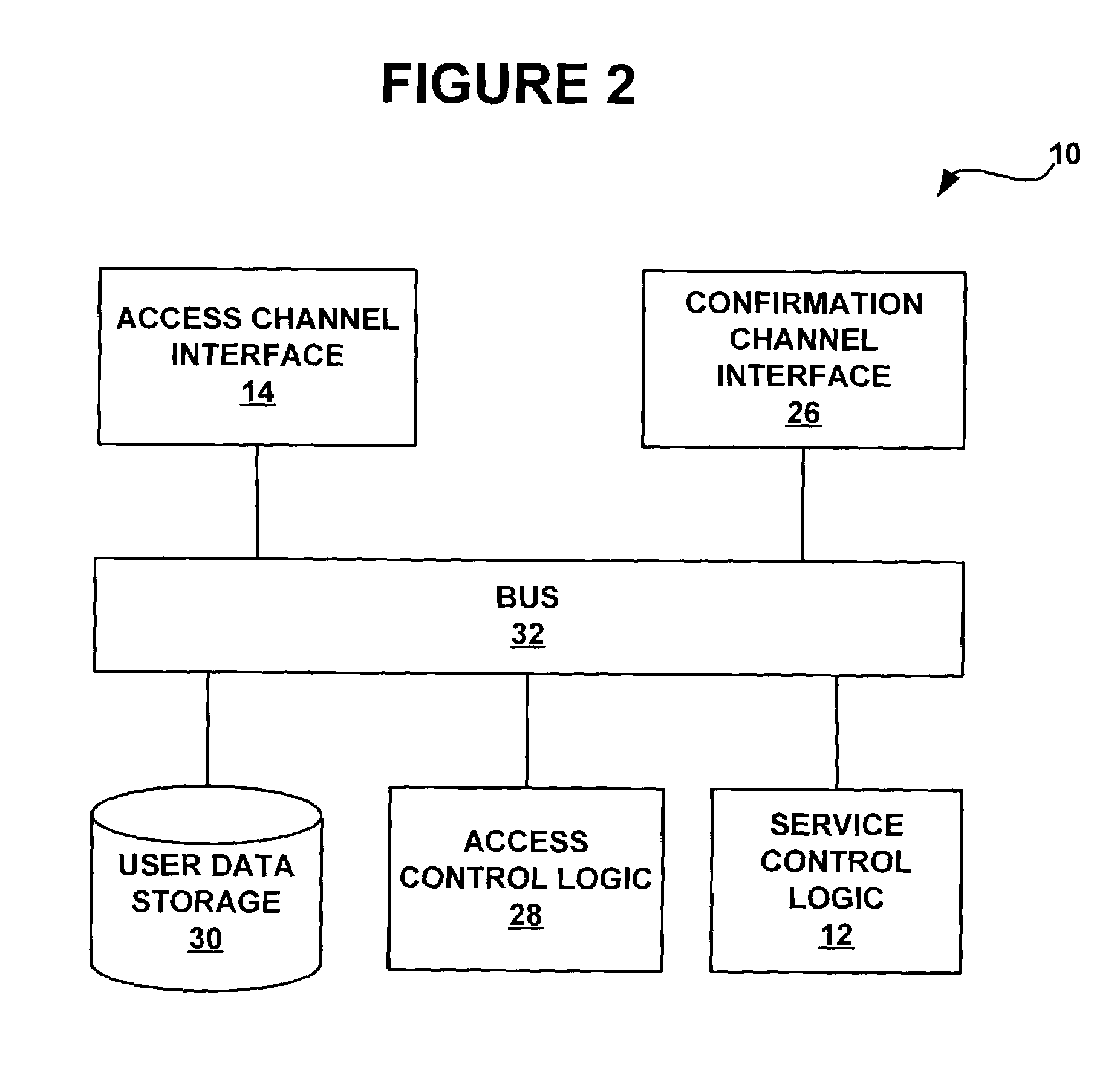
Method and system for multi-network authorization and authentication
ActiveUS7142840B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunication interfaceText messaging
A system for authenticating and / or authorizing users of a service includes one communication interface with an access communication channel and another communication interface with a confirmation communication channel. Requests for a user to access a service are received over the access communication channel, and confirmation codes for the user are received over a trusted confirmation channel, such as an SMS text messaging system. Confirmation codes may be received from the user requesting access to the service or by a third party acting as a gatekeeper to the service. The system tests the validity of received confirmation codes, and enables the user to access the service if a valid confirmation code is received.
Owner:SPRINT SPECTRUM LLC
System and method for secure content sharing and synchronization
ActiveUS20130097687A1Easy accessCustomer relationshipDigital data information retrievalContent distributionGate-keeper
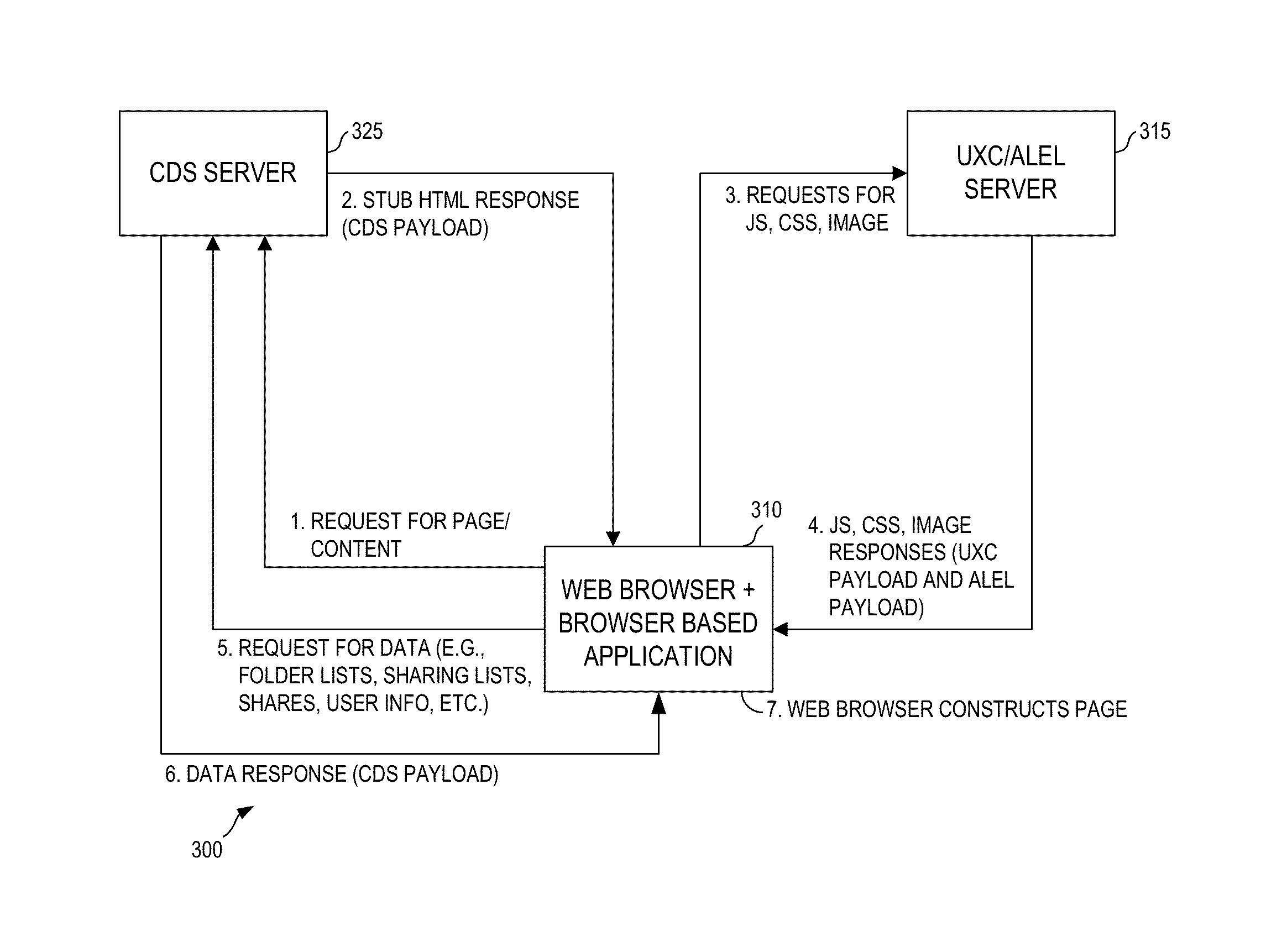
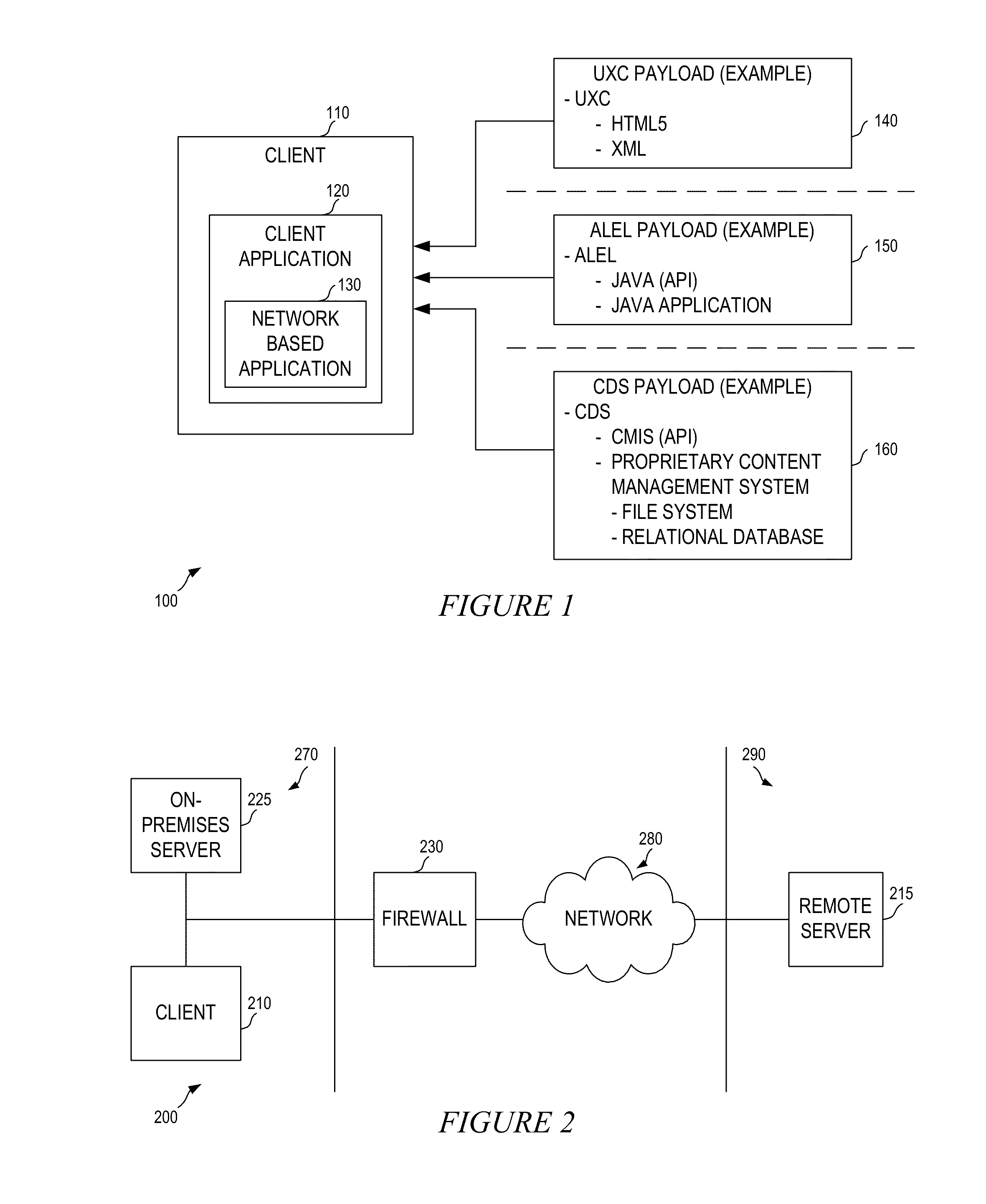
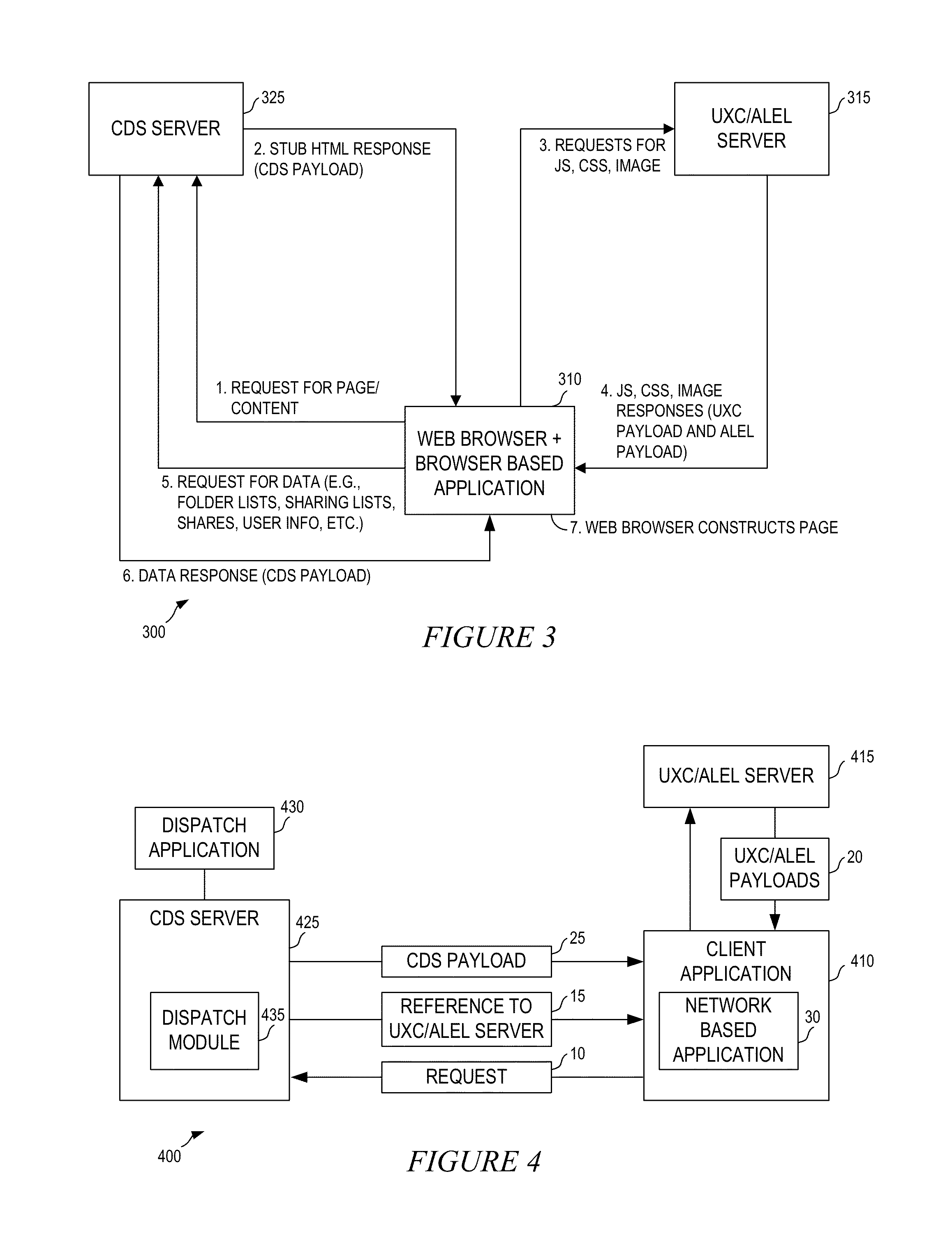
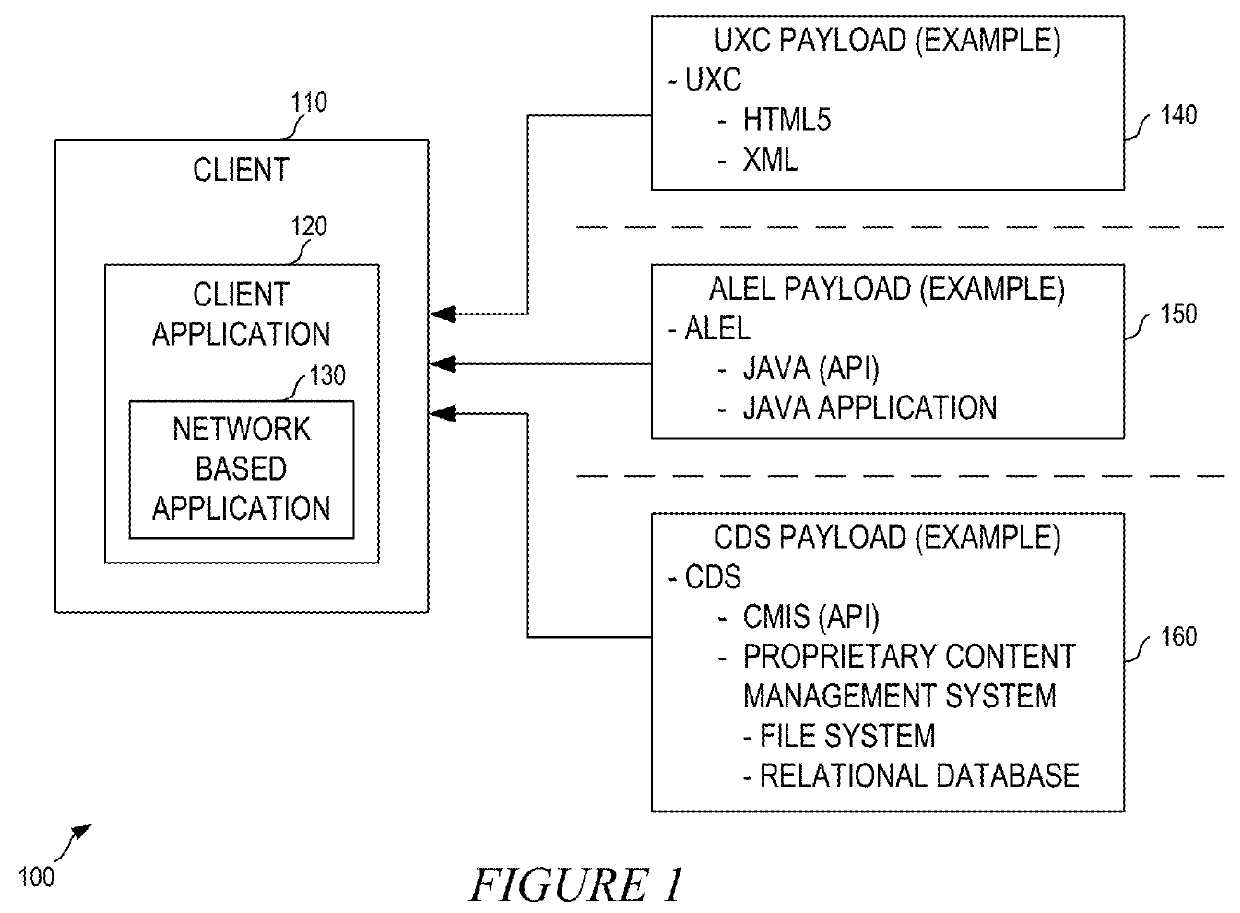
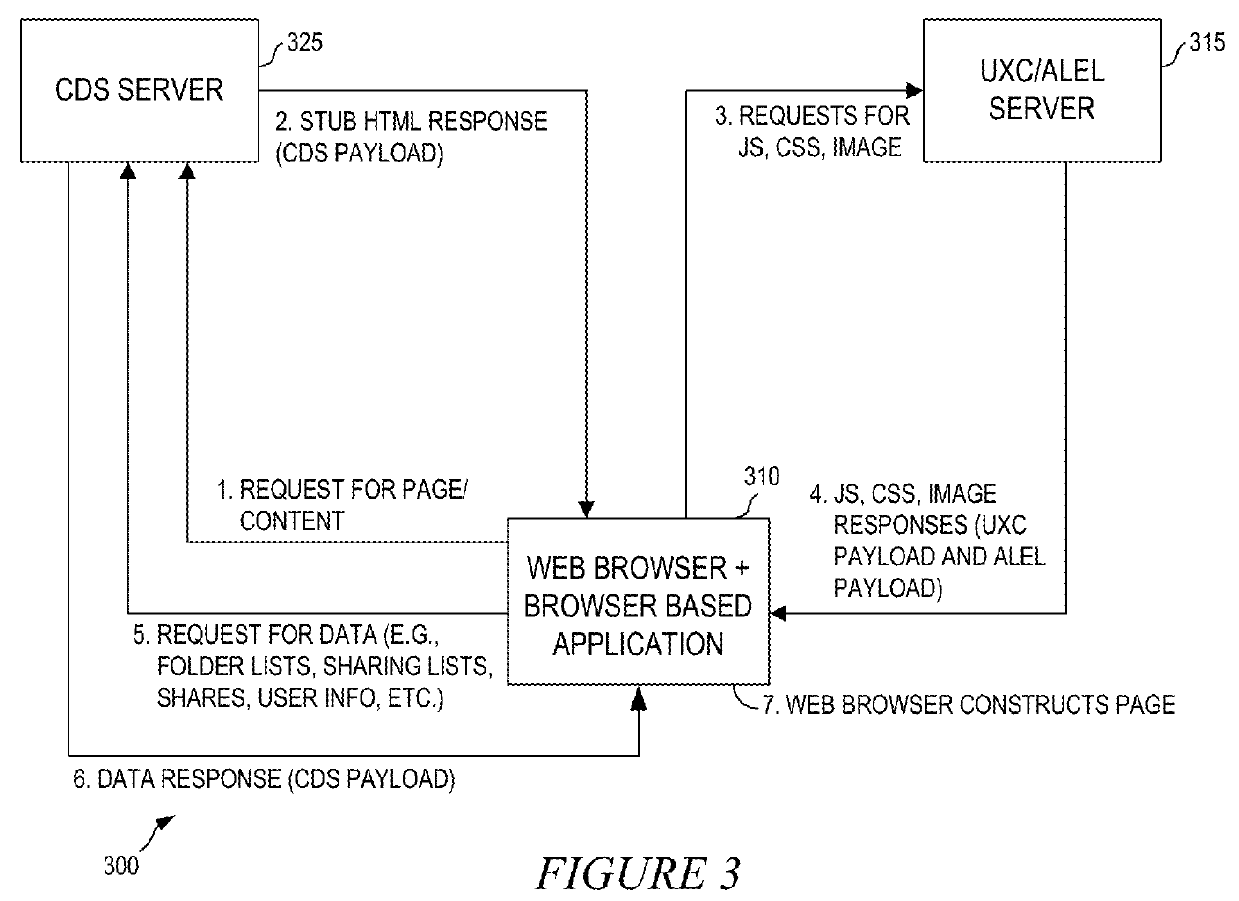
A flexible content sharing system may comprise a network based application built on a client device using information from dissociated user experience component (UXC), application logic and execution layer (ALEL), and content distribution system (CDS) payloads. An ALEL engine may communicate a request from the network based application to a CDS module. The CDS module may interface the ALEL engine and a CDS server. The ALEL engine can act as a gate keeper and securely communicates requests from client devices to the CDS server. The CDS server is configured to manage and alert the ALEL of any enterprise policies that may be applicable to the client devices connected to the ALEL engine which, in turn, notifies the client devices to comply with the enterprise policies. The CDS server may synchronize any change made to the content by any of the client devices running network based applications.
Owner:OPEN TEXT SA ULC
Apparatus for access control and processing
ActiveUS8294549B2Electric signal transmission systemsTicket-issuing apparatusGate-keeperControl system
Owner:LIVE NATION ENTERTAINEMENT INC
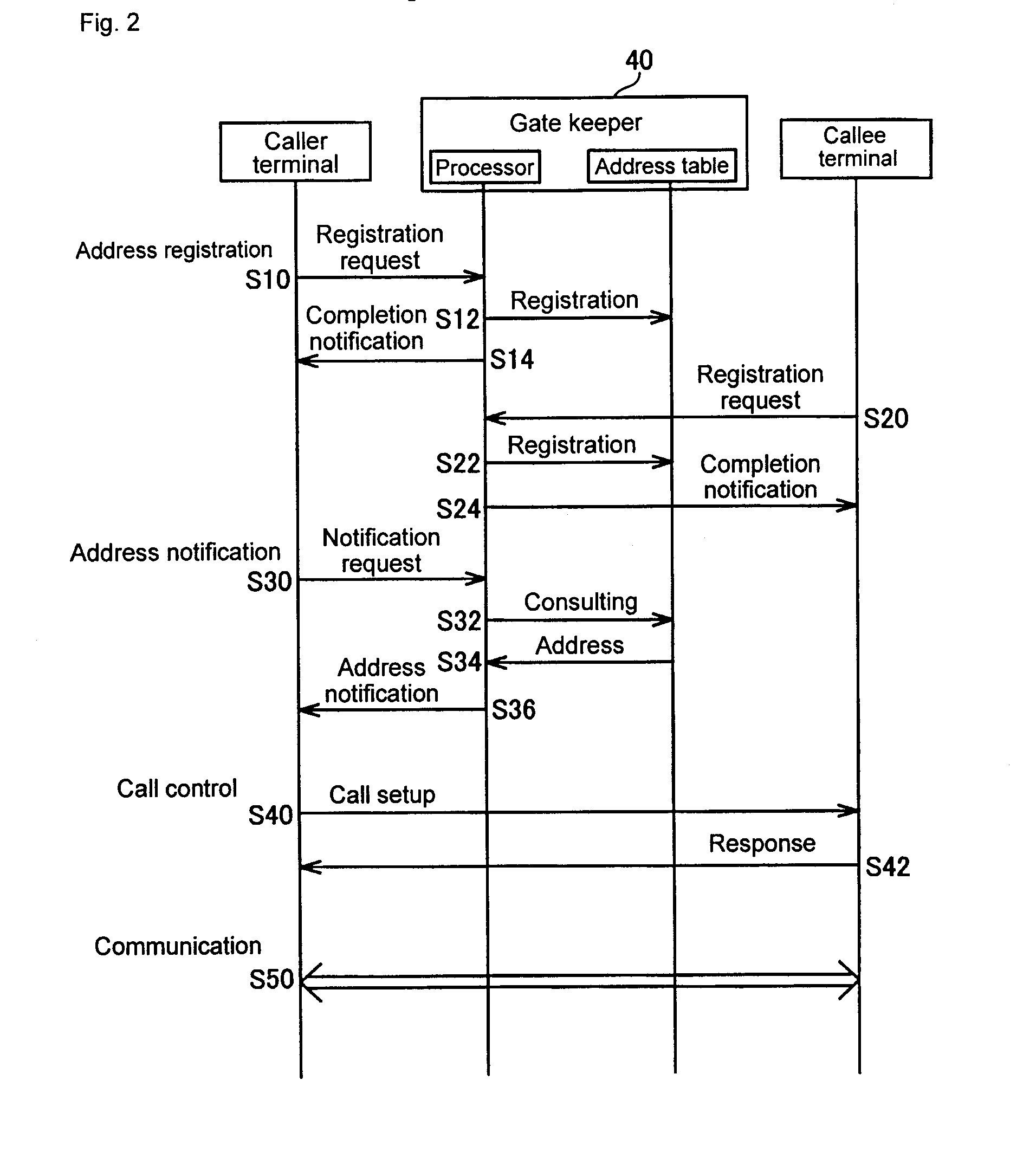
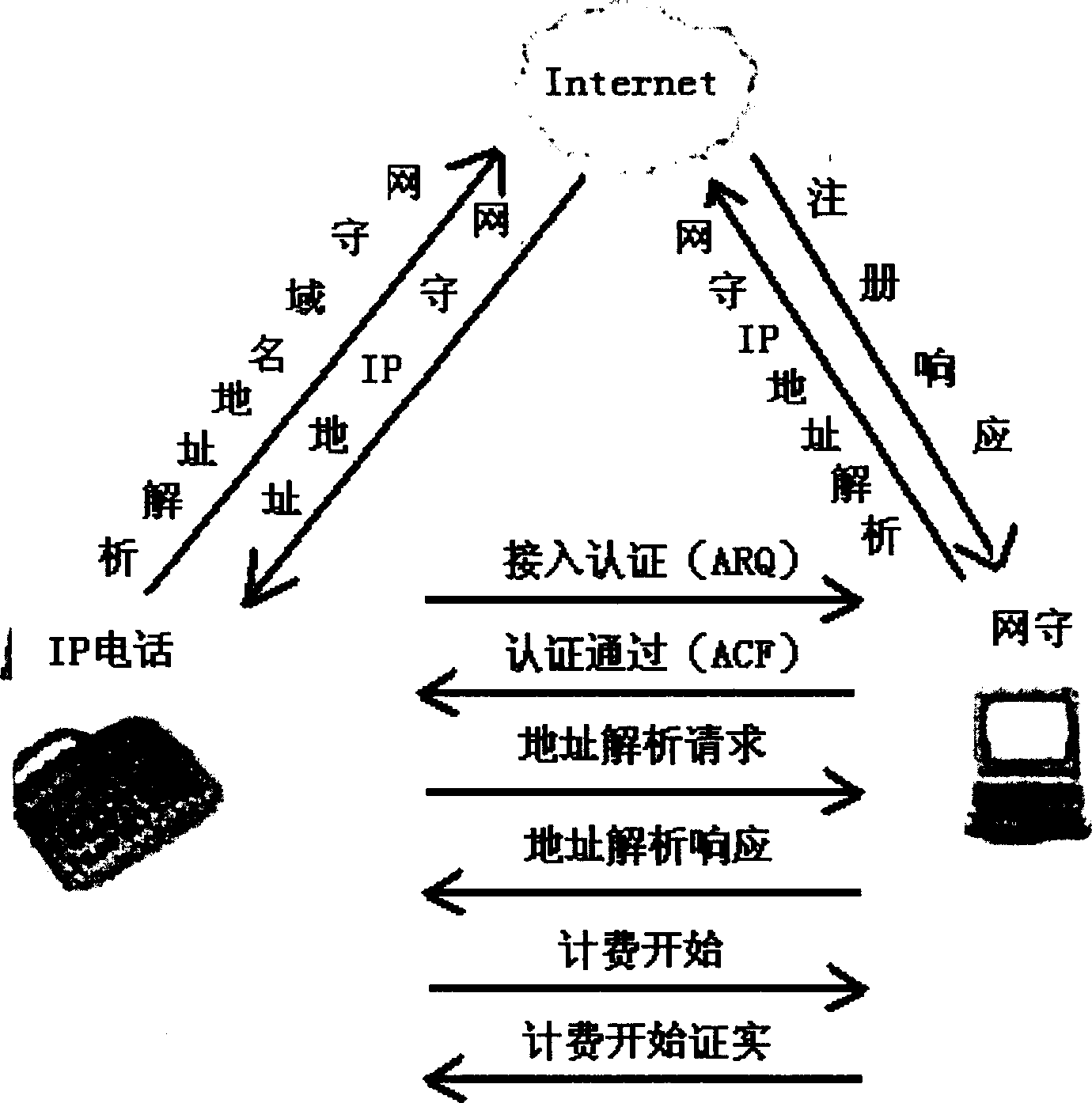
Address Resolution Device, Address Resolution Method, And Communication System Including The Same
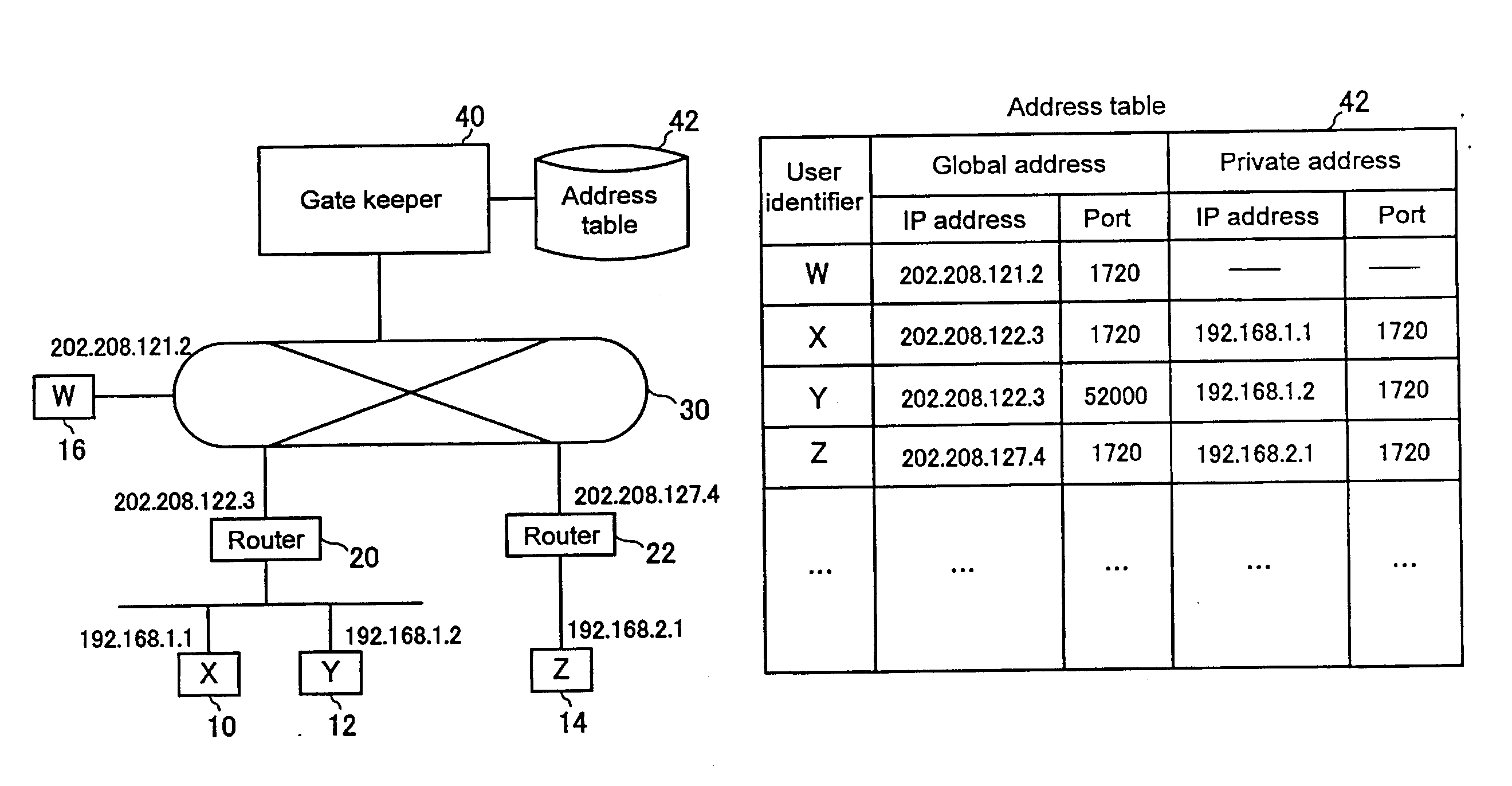
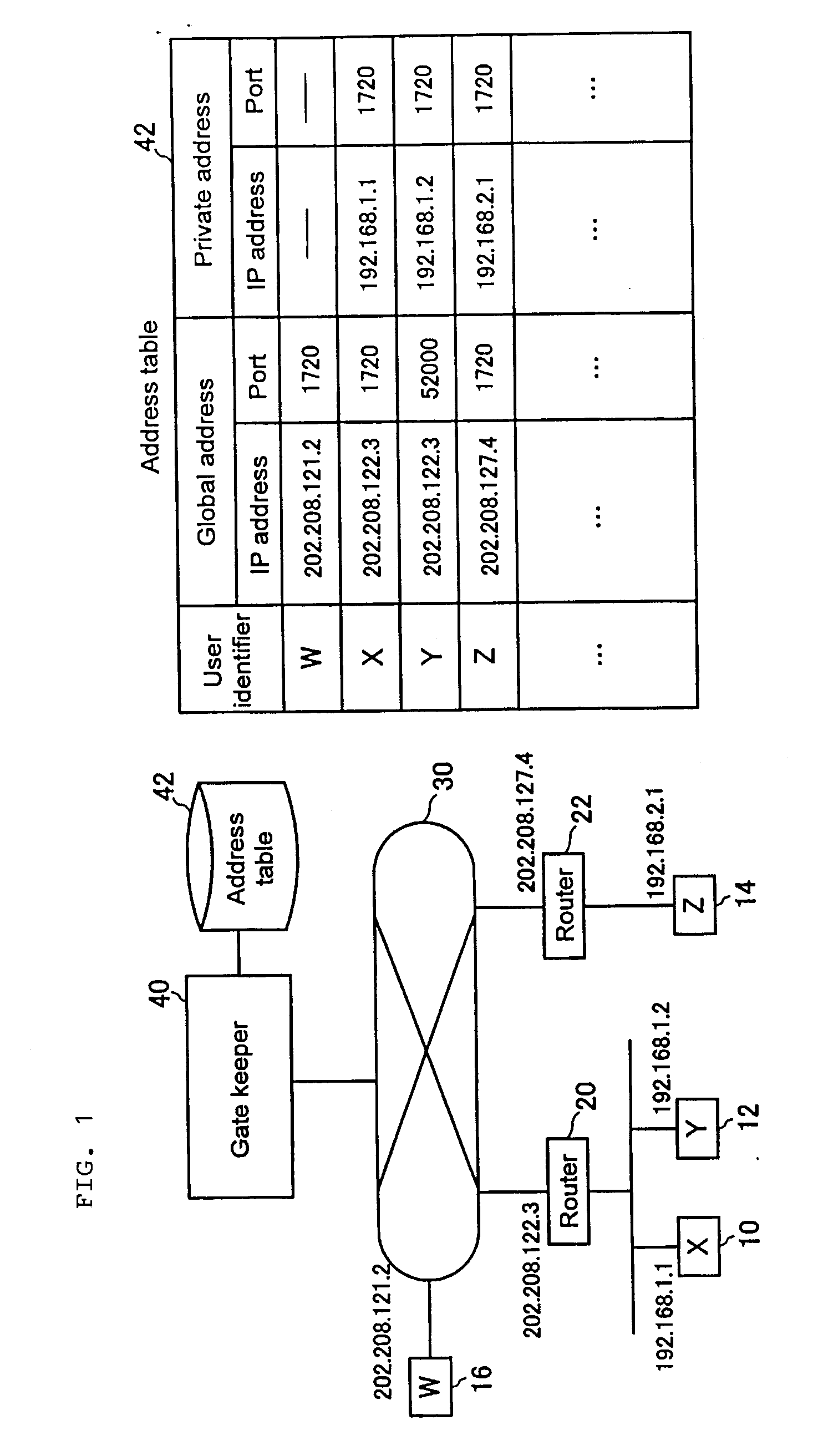
An address resolution device includes a gate keeper having an address table with which global addresses, private addresses, and grouping IDs can be registered. During address registration, the gate keeper registers the address of a communication packet into the global addresses, the address assigned to the terminal into the private addresses, and if available, a Grouping ID into grouping IDs. During address notification, the gate keeper consults the address table to notify the caller terminal of the callee terminal private address when the callee terminal and the caller terminal have the same Grouping ID or when they have the same global address. Otherwise, the gate keeper notifies the caller terminal of the callee terminal global address.
Owner:GINGANET CORP
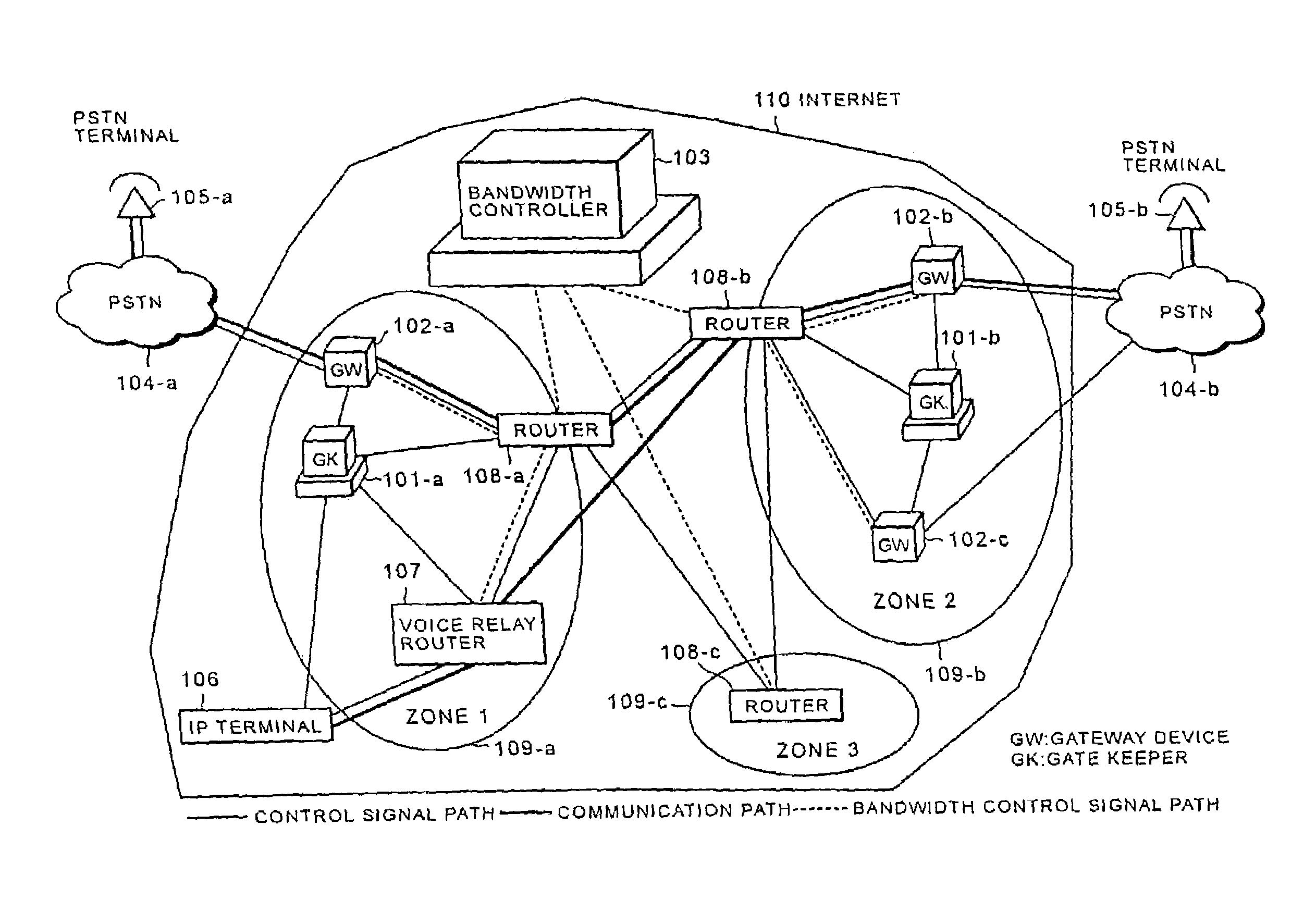
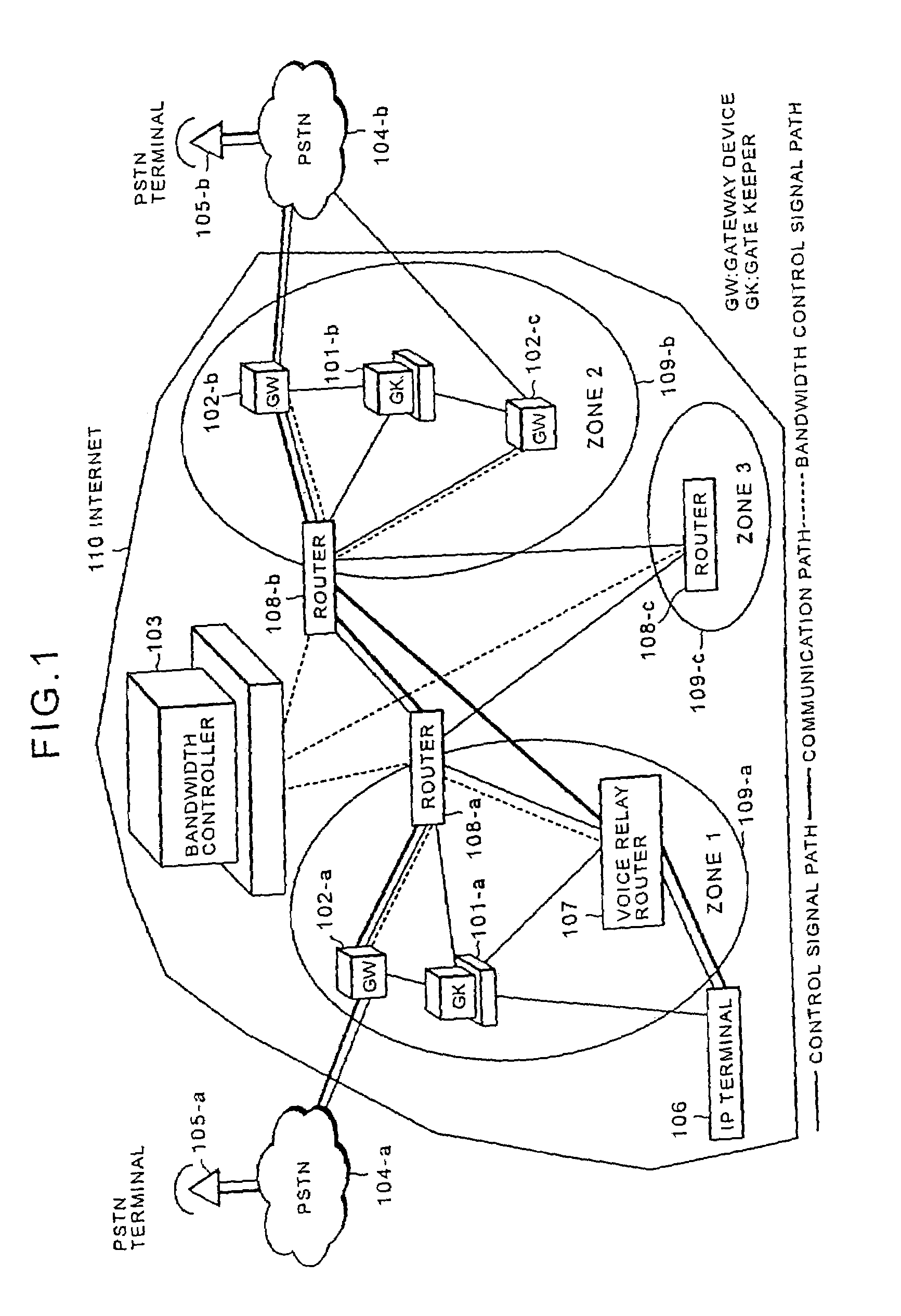
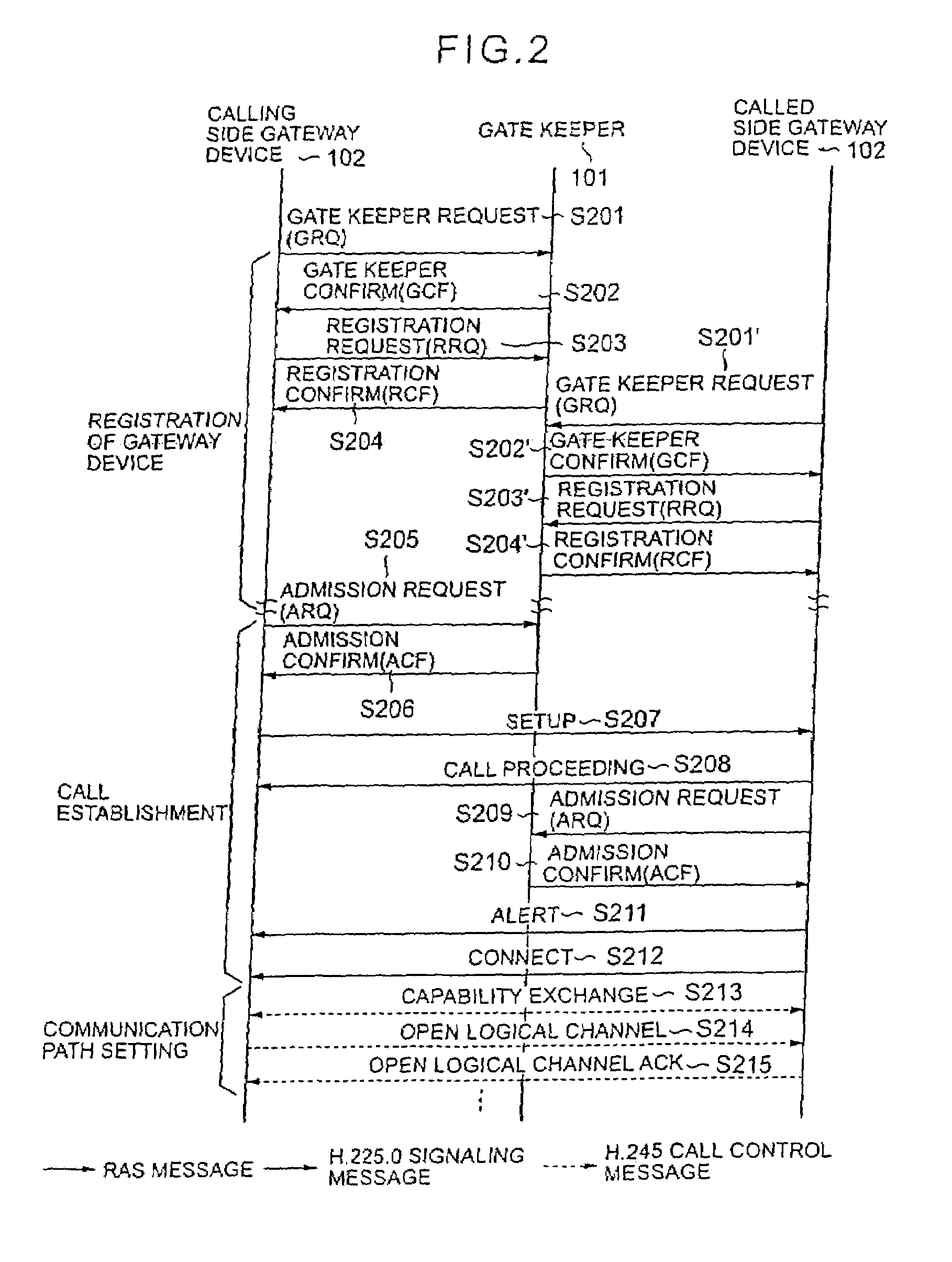
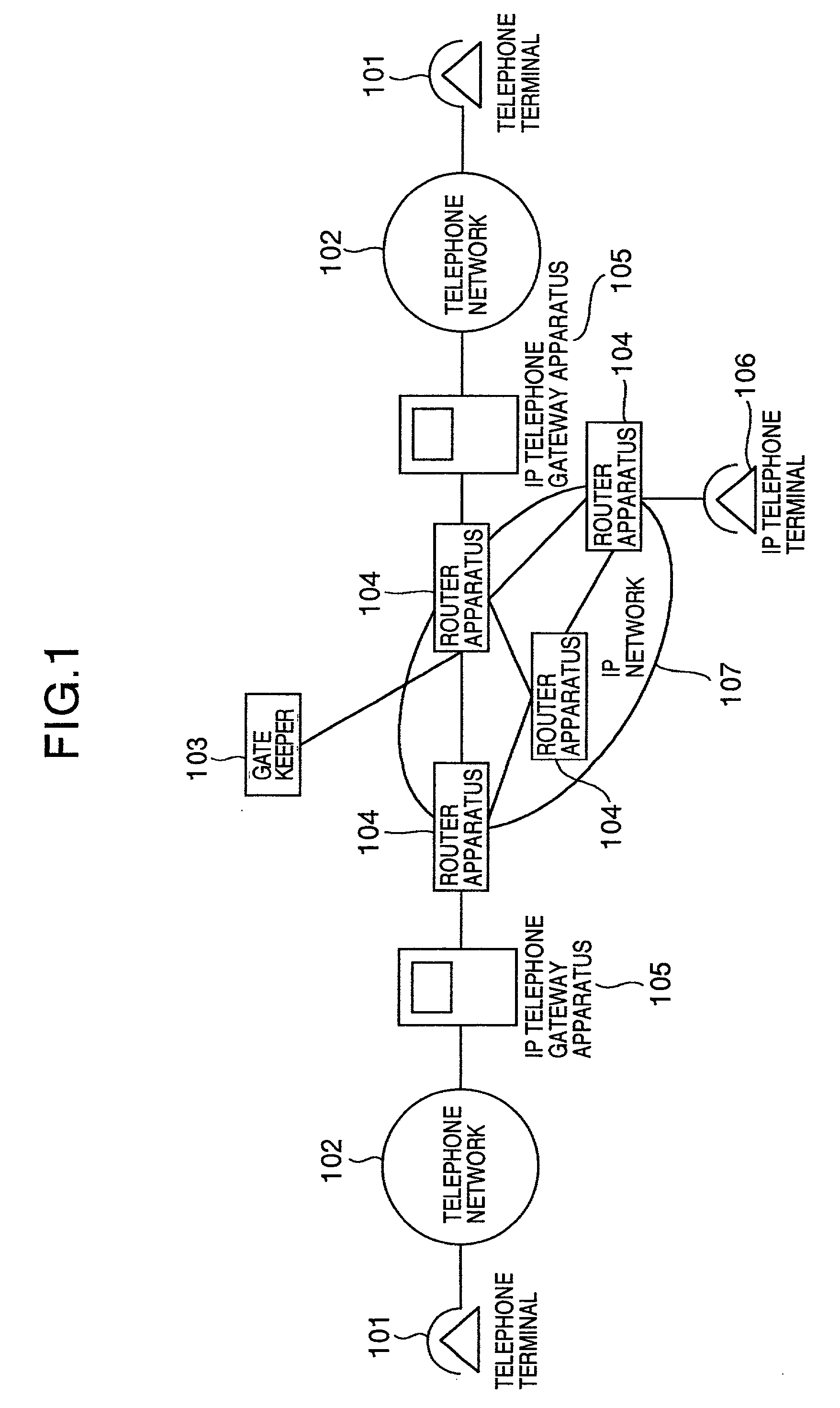
Internet telephone connection method, bandwidth controller and gate keeper
InactiveUS7272134B2Improve reliabilityFlexibly variationInterconnection arrangementsTelevision system scanning detailsCommunication qualityGate-keeper
In an Internet telephone connection method, a communication bandwidth is managed by using a bandwidth controller, gateway devices and voice relay routers to monitor communication quality under bandwidth reservation. A communication path under bandwidth reservation is preferentially selected by using gate keepers and the voice relay routers, and the connection of the Internet telephone is performed. A problematic device is prohibited from being selected as a connection-destination device at the time of a call setup and the problem restoration is monitored by using the gate keepers and the gateway devices. Further, a device having invalid attribute information is prohibited from being selected as a connection-destination device at the time of call-setup, and the restoration of the attribute information is notified to the overall network. Accordingly, the reservation of the communication bandwidth can be performed under the control of the overall network, fixed communication quality can be maintained and reliability can be enhanced.
Owner:HITACHI LTD
Gate keeper
InactiveUS20050071509A1Increase contactEfficiently provideSpecial service for subscribersGraded-service arrangementsGate-keeperMultimedia
Owner:THRYV INC
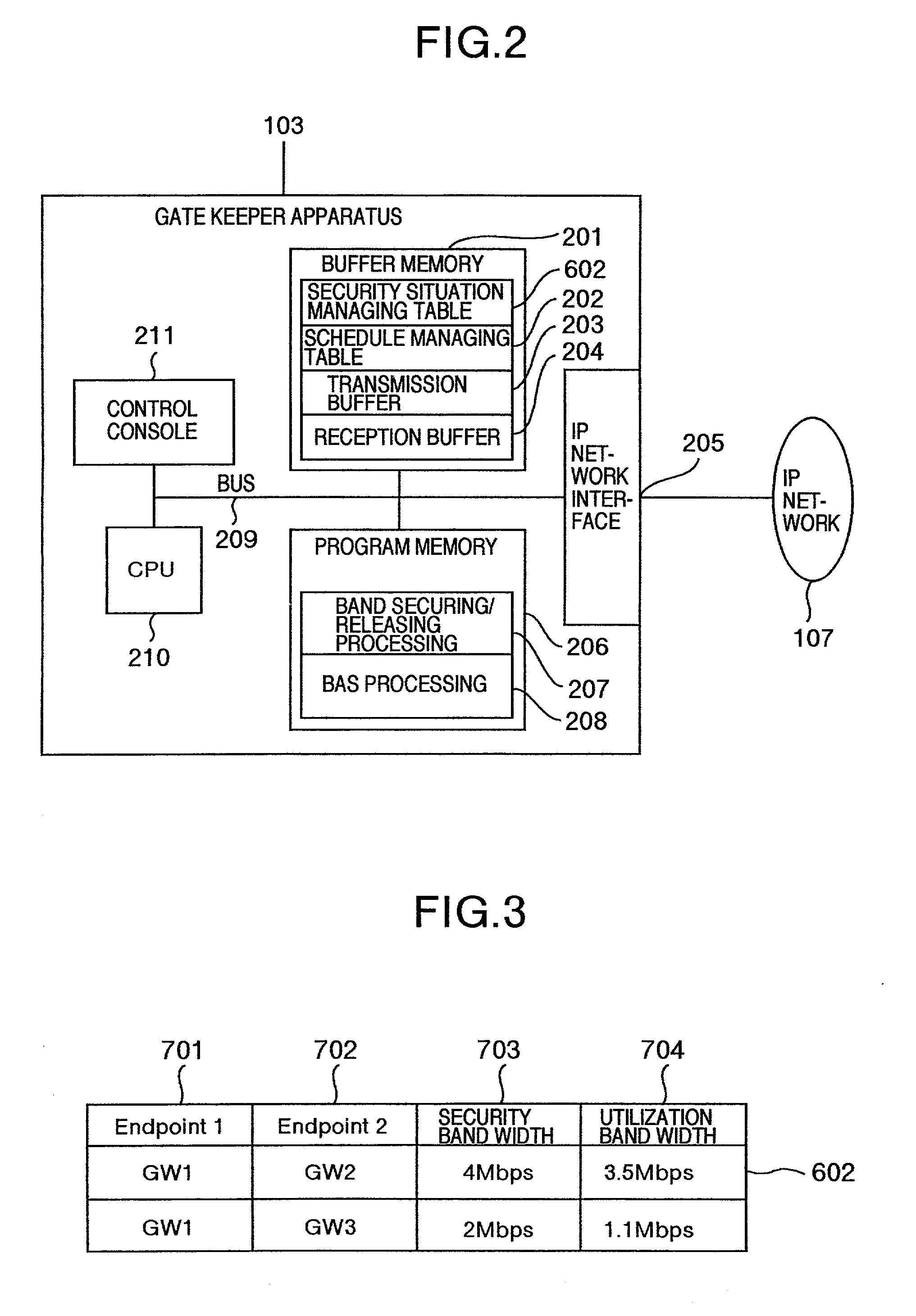
Method of requesting security and release of communication band
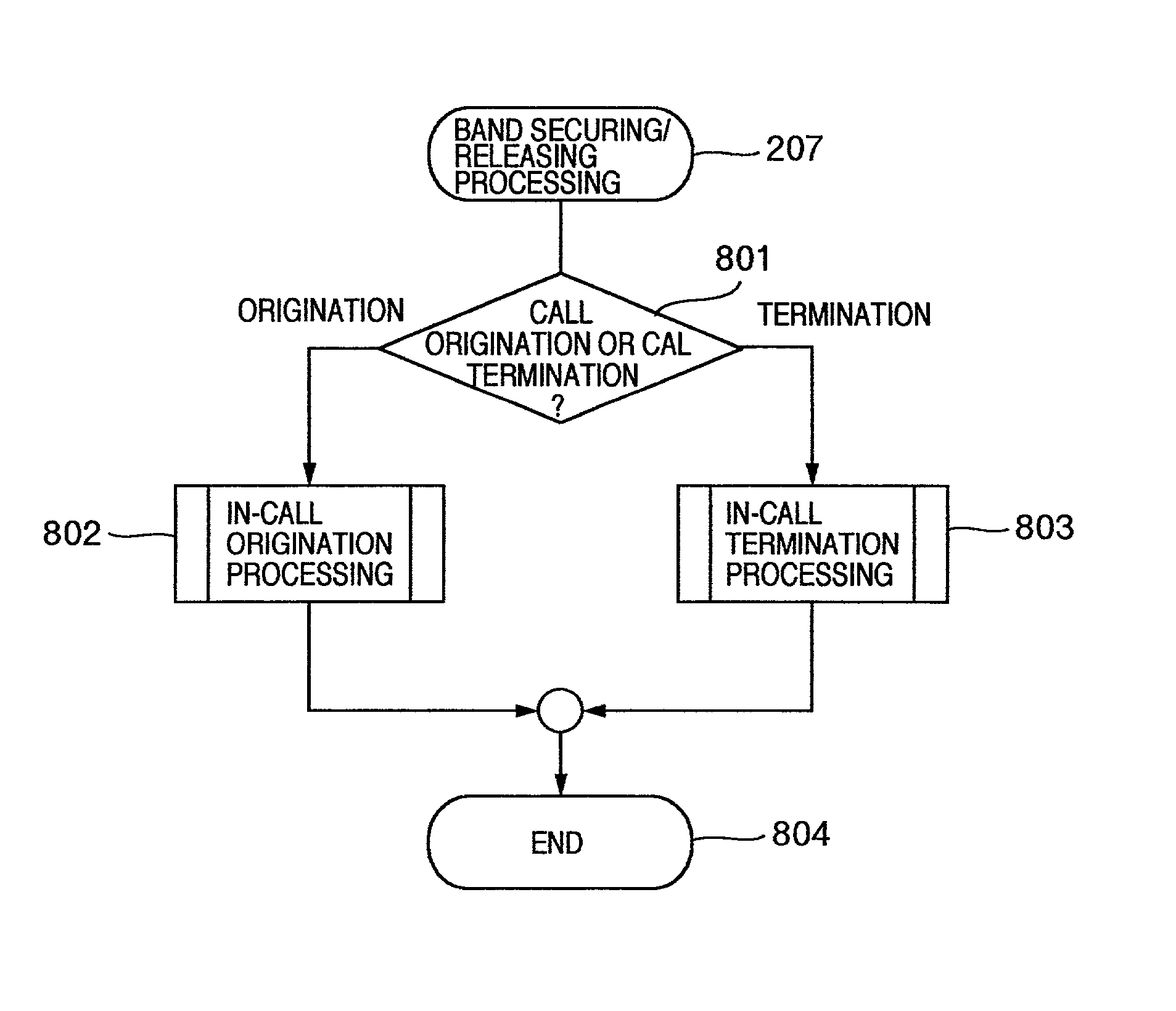
InactiveUS20020176406A1Interconnection arrangementsData switching by path configurationGate-keeperComputer science
By adopting a method of requesting a band for each plurality of calls, or a method of requesting a band independently of origination or termination of a call, a method of reducing the frequency of origination of a call is provided. A first aspect may provide that a gate keeper requests security and release of a band not every call, but collectively for a plurality of calls, and the security and the release of a band are requested at frequency less than that of origination or termination of calls. A second aspect may provide that an estimated value of a time series change in necessary band is previously set in a gate keeper, and security and release of a band required for communication are requested depending on a time, but independently of origination and termination of a call.
Owner:HITACHI LTD
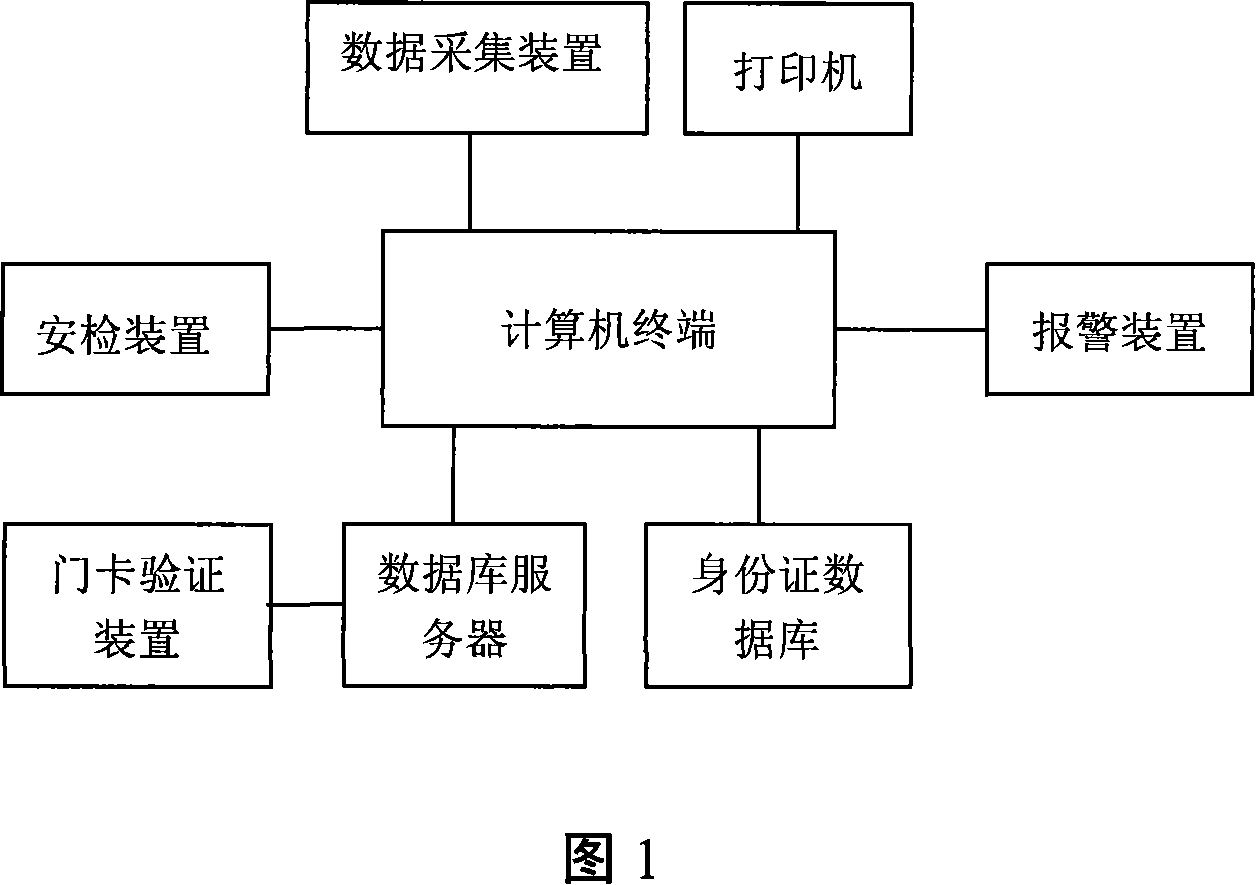
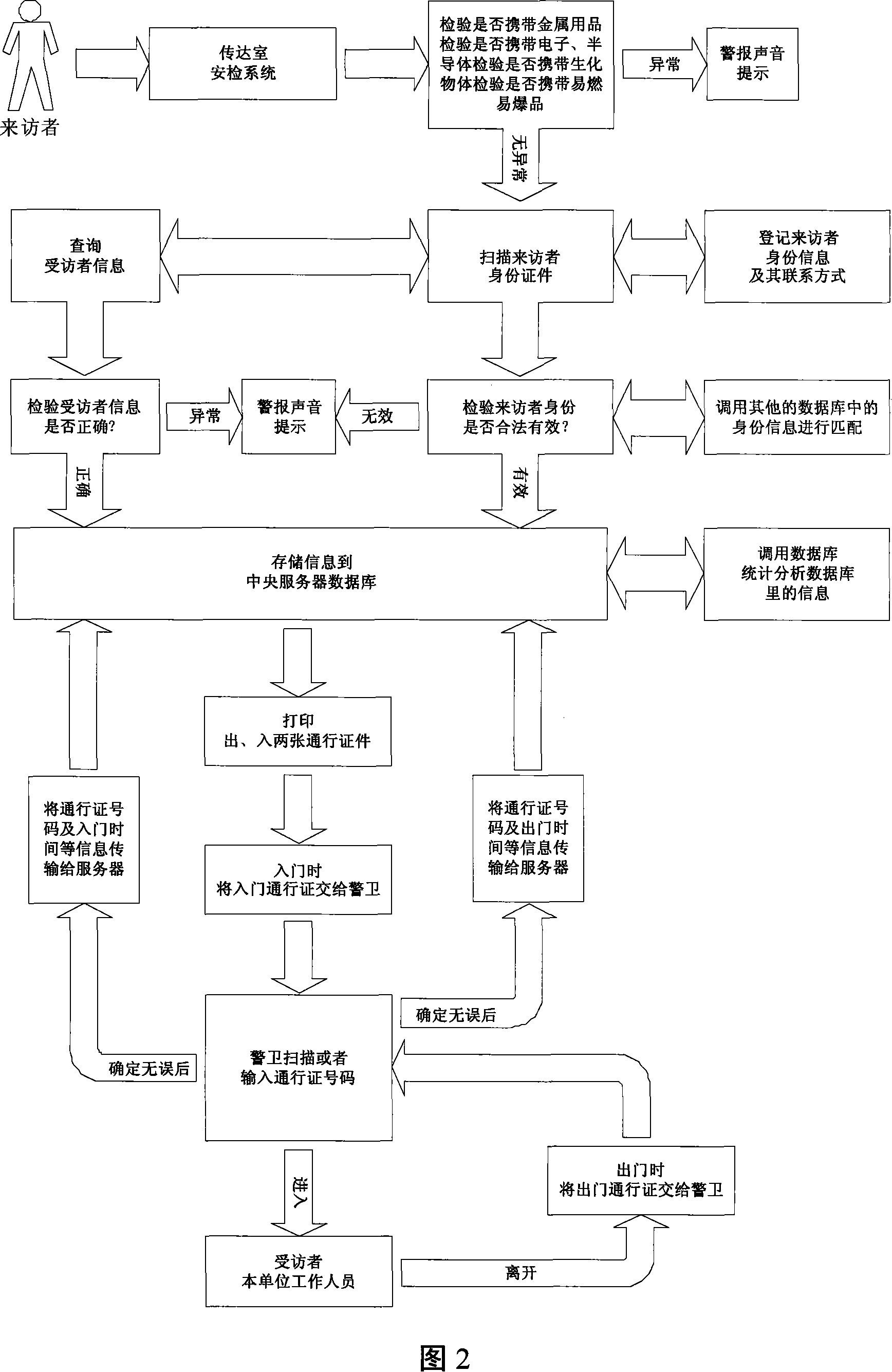
An electronic guard defense system and method
InactiveCN101216960AImprove securityHigh popularityIndividual entry/exit registersInformation processingGate-keeper
The invention relates to an electronic gate keeper security system and a method thereof. The system comprises a data acquisition device for acquiring certificate information of a visitor and sending the information to an information processing terminal; the information processing terminal connected with a printer, carrying out data communication with a database server or an identification card database server, calling corresponding data to match according to the certificate information, and starting the printer to output and print a gate card certificate with a number mark; the database server for storing the certificate information of the visitor; and a gate card verification device for acquiring the number mark of the gate card certificate, and sending the number mark to the database server to be stored. The method can verify whether the certificate information of the visitor is correct. The system and the method in the invention are adopted to verify the effective certificate information of the visitor, and matching detection is carried out via an available database (local database or remote network database) so as to implement security conveniently and safely.
Owner:李天
Method of unifying accounts of intelligent network users
InactiveCN1453958AMetering/charging/biilling arrangementsData switching by path configurationGate-keeperThe Internet
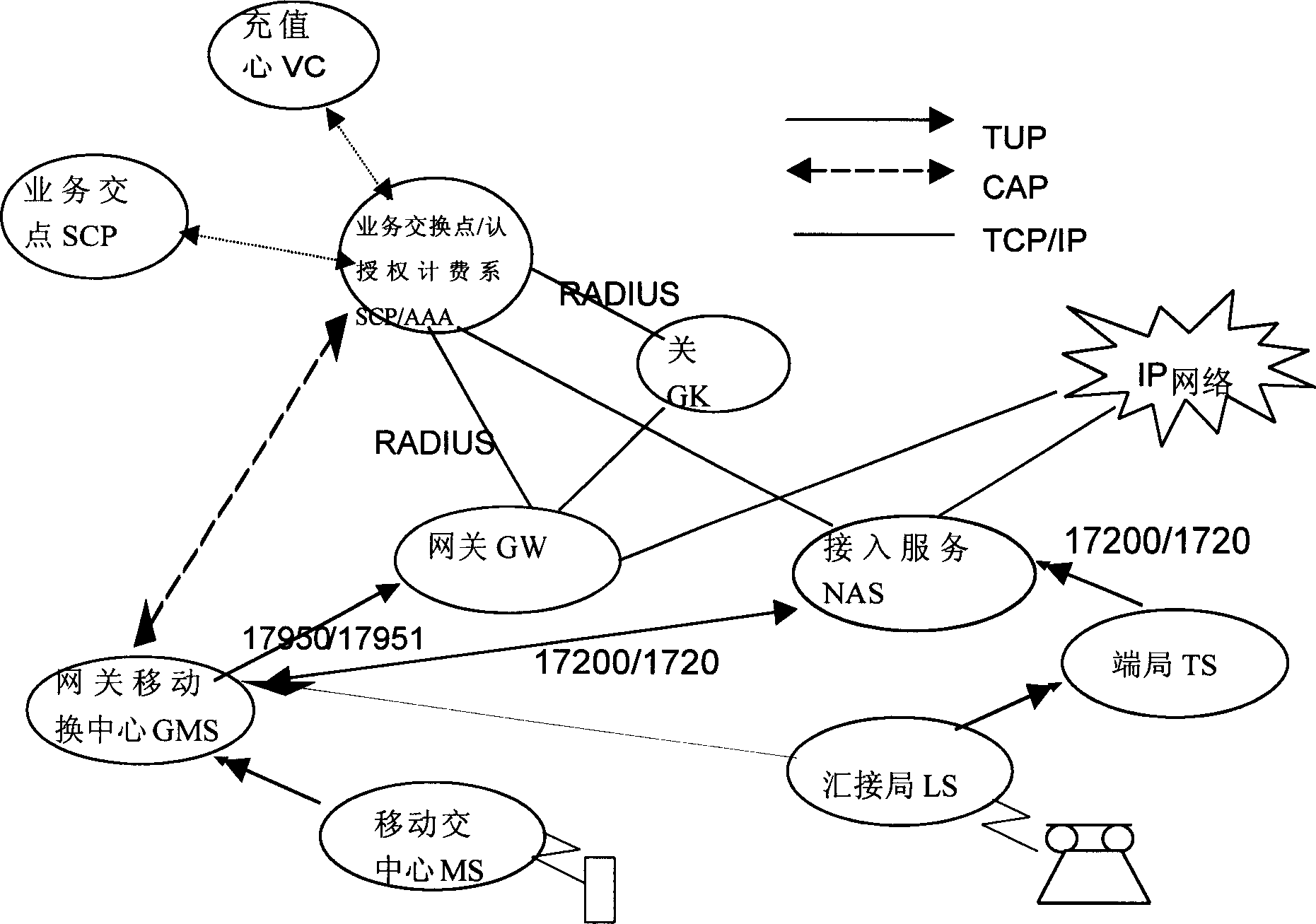
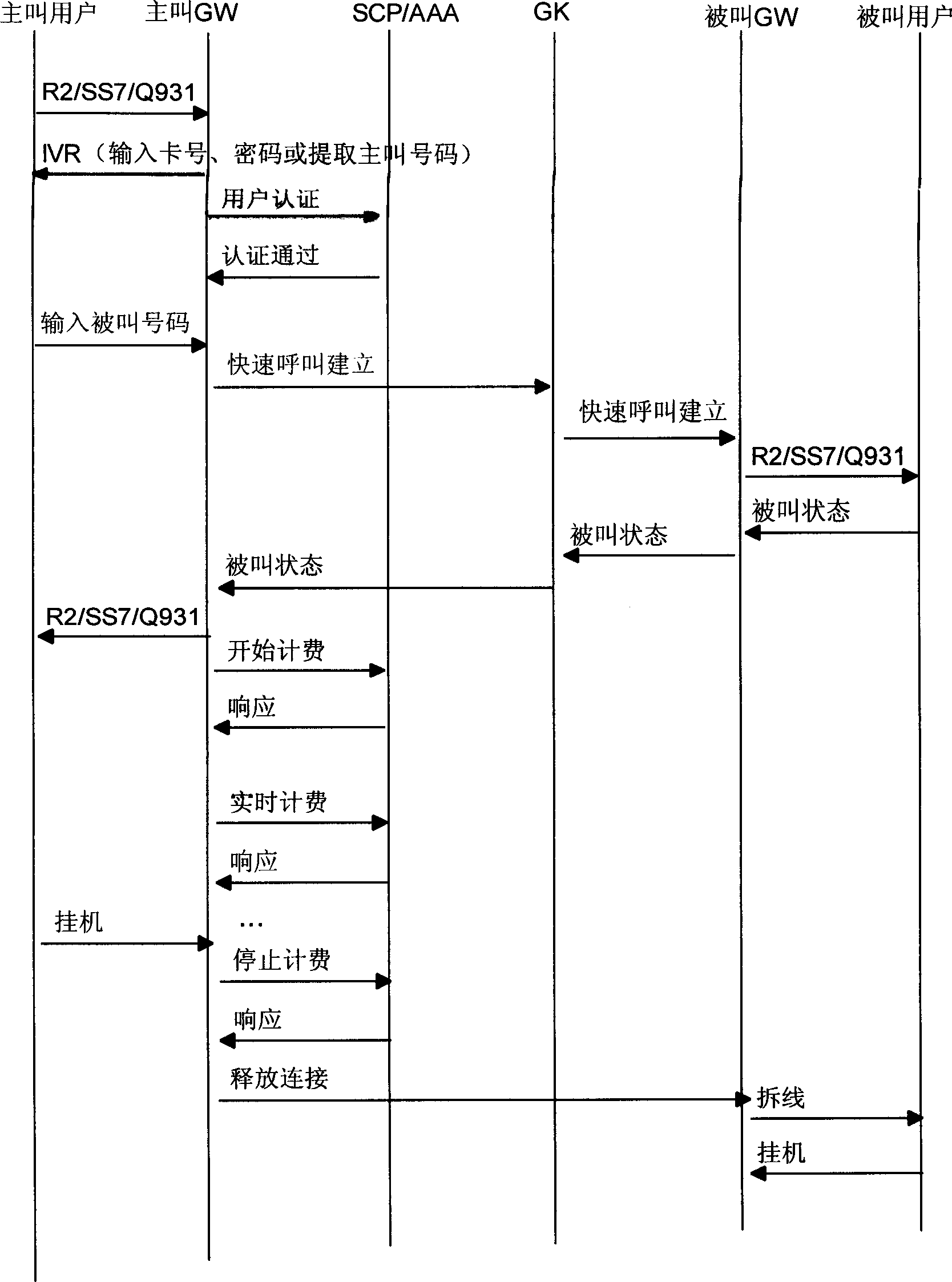
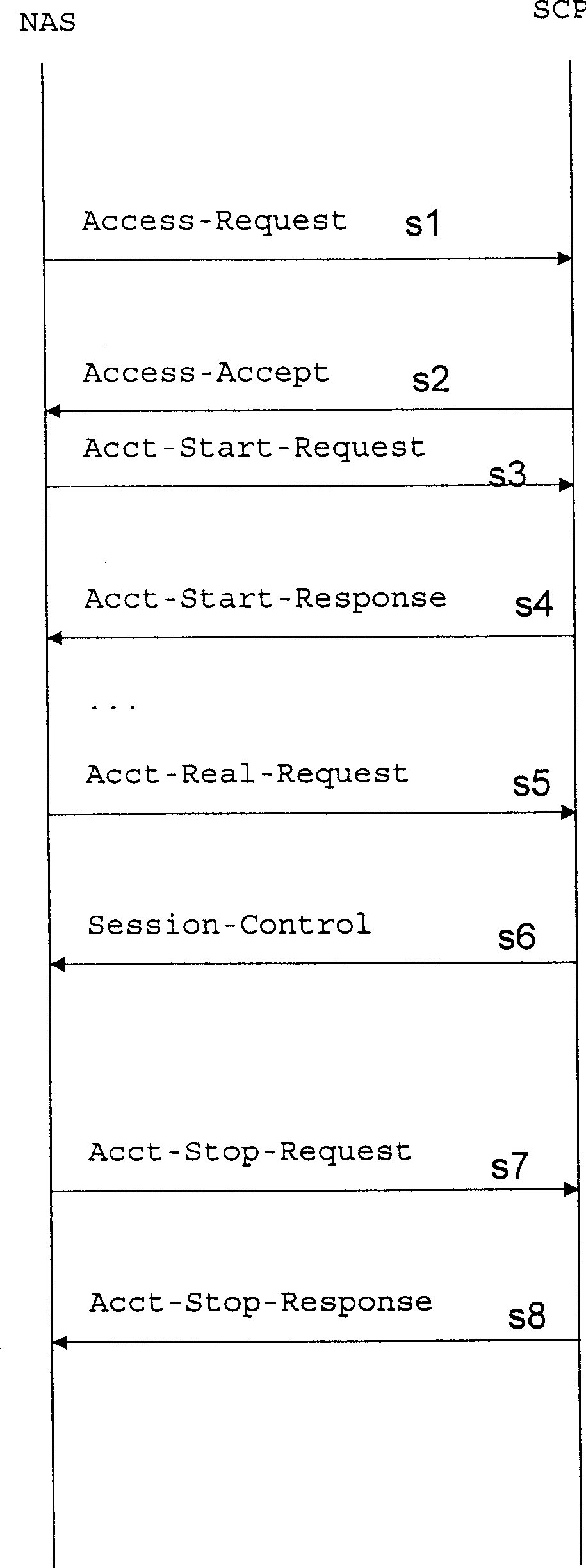
The method includes distributing unified account to at least one user of intelligent network, binding several phones with the said unified account and deducting its cost on real time from the unifiedaccount when bound phone is used through service of the intelligent network. The steps of calling IP phone with bound stationary phone are as: connecting access number of IP phone, realizing voice interaction and information collection by main gateway, applying authentication and charge through RADIUS protocol to the intelligent netowrk and then send them to gate keeper as well as finishing control of IP phone route by the gate keeper. The bound stationary phone can be also on the Internet network by using server through RADIUS protocol.
Owner:HUAWEI TECH CO LTD
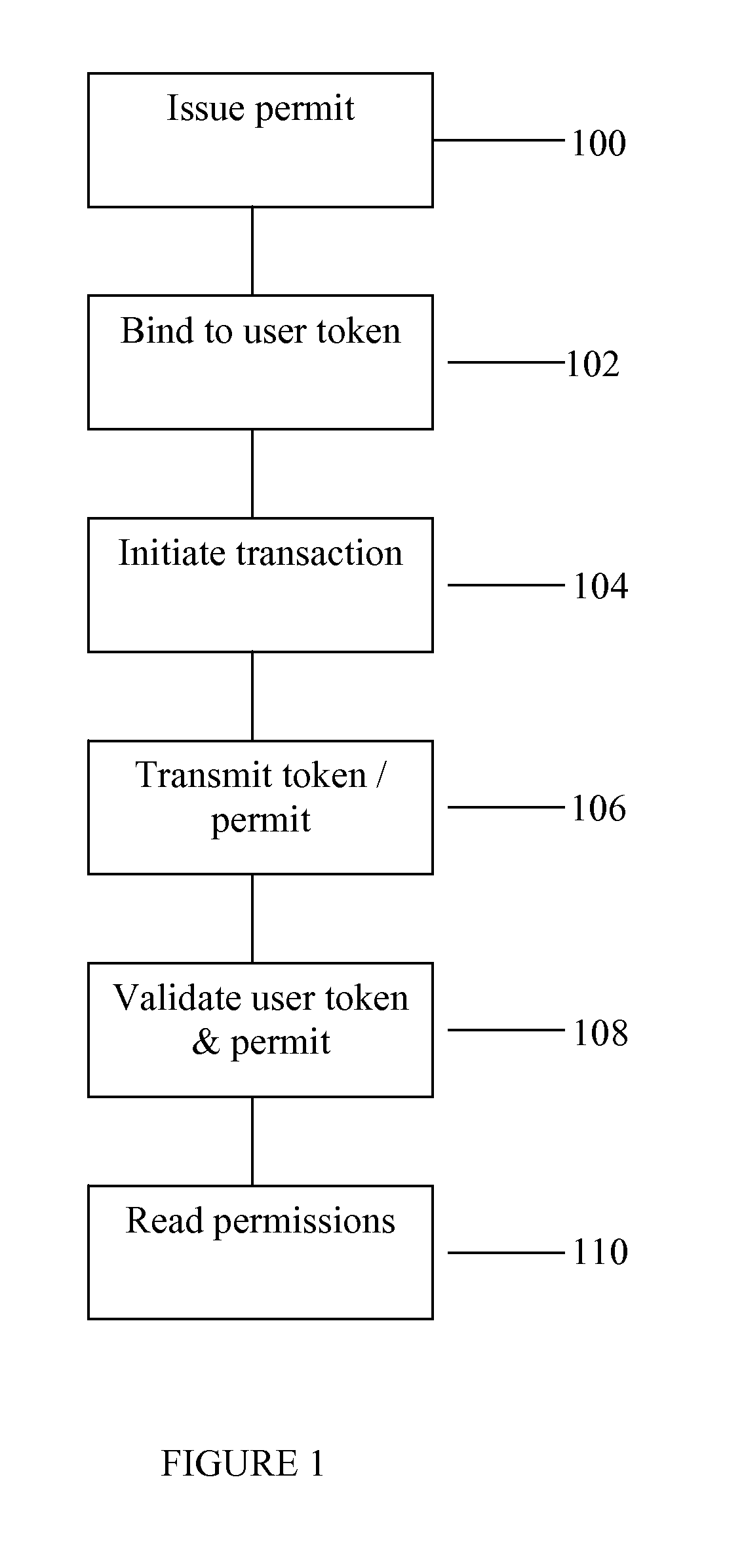
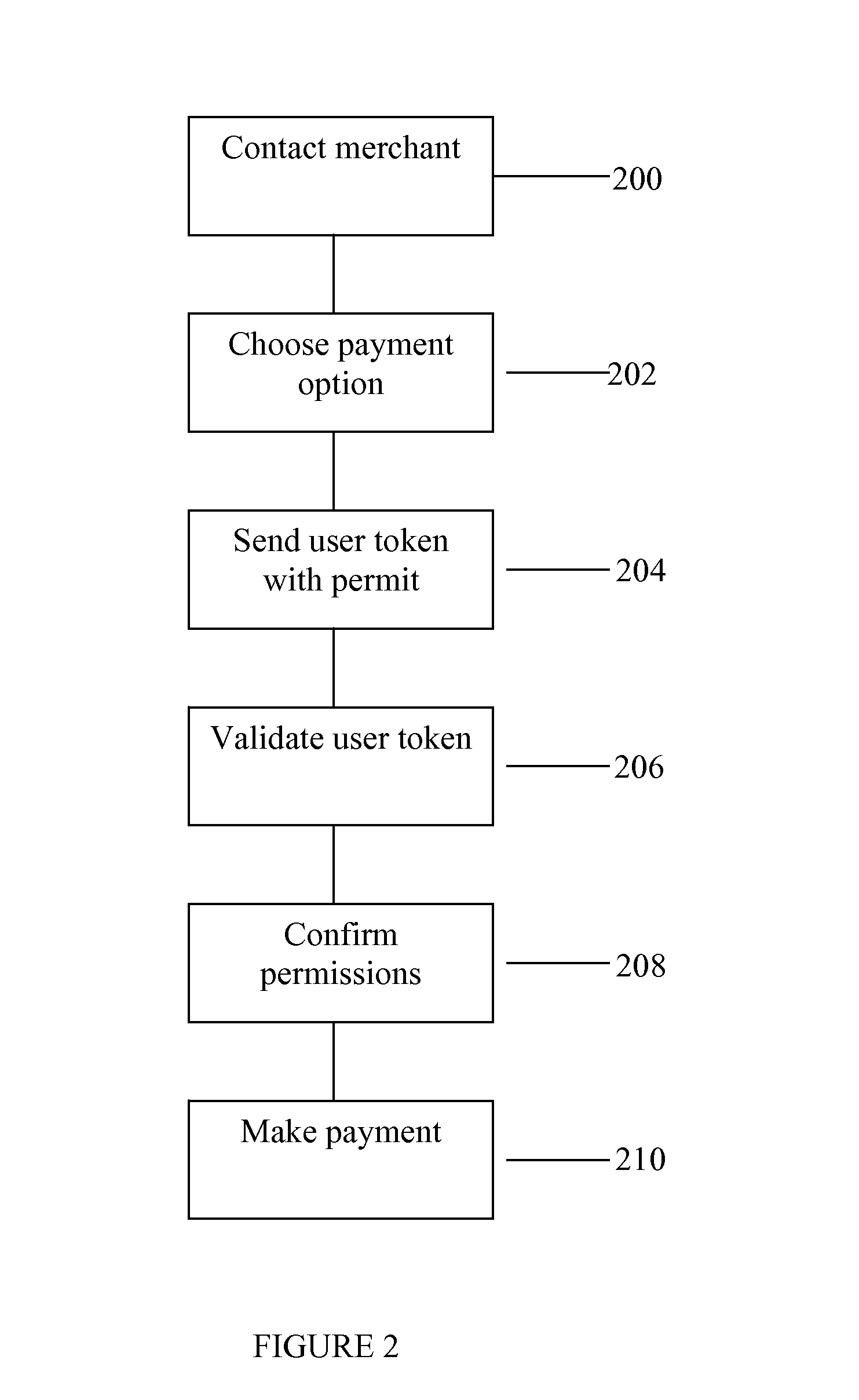
System and method for handling permits for user authentication tokens
ActiveUS8549602B2Valid verificationDigital data processing detailsUser identity/authority verificationDigital signatureInternet privacy
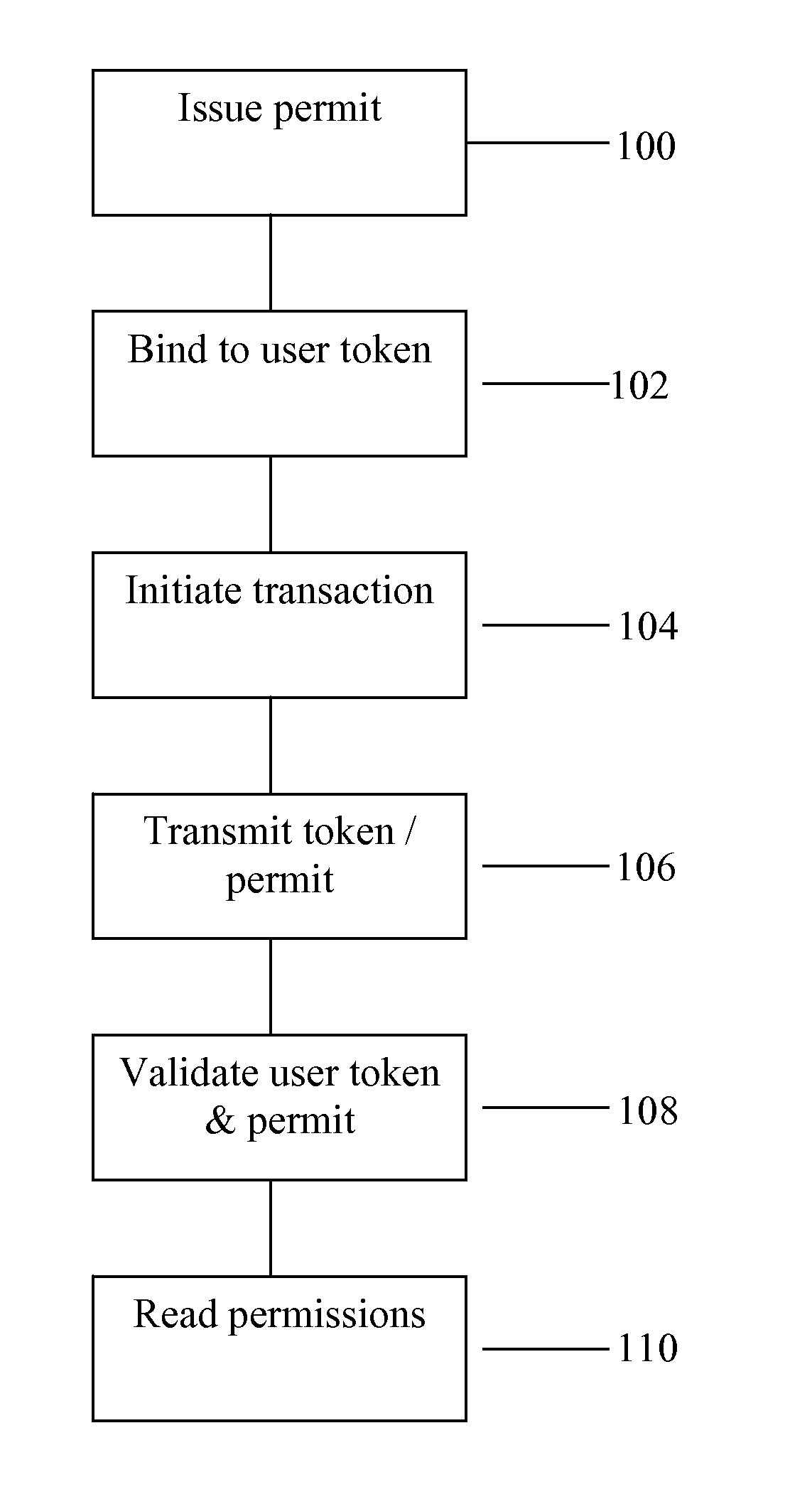
The invention consists of a method of handling permits, comprising the steps of: (a) providing a user with a user permit linked to a user authentication token, the user permit defining permissions granted to the user and the user token containing identity authentication information for the user; (b) presenting the user token to a gatekeeper to confirm the user's identity; (c) validating the user permit based on the permit issuer's digital signature; and, (d) granting the user access based on said permissions within the user permit.
Owner:IQVIA INC
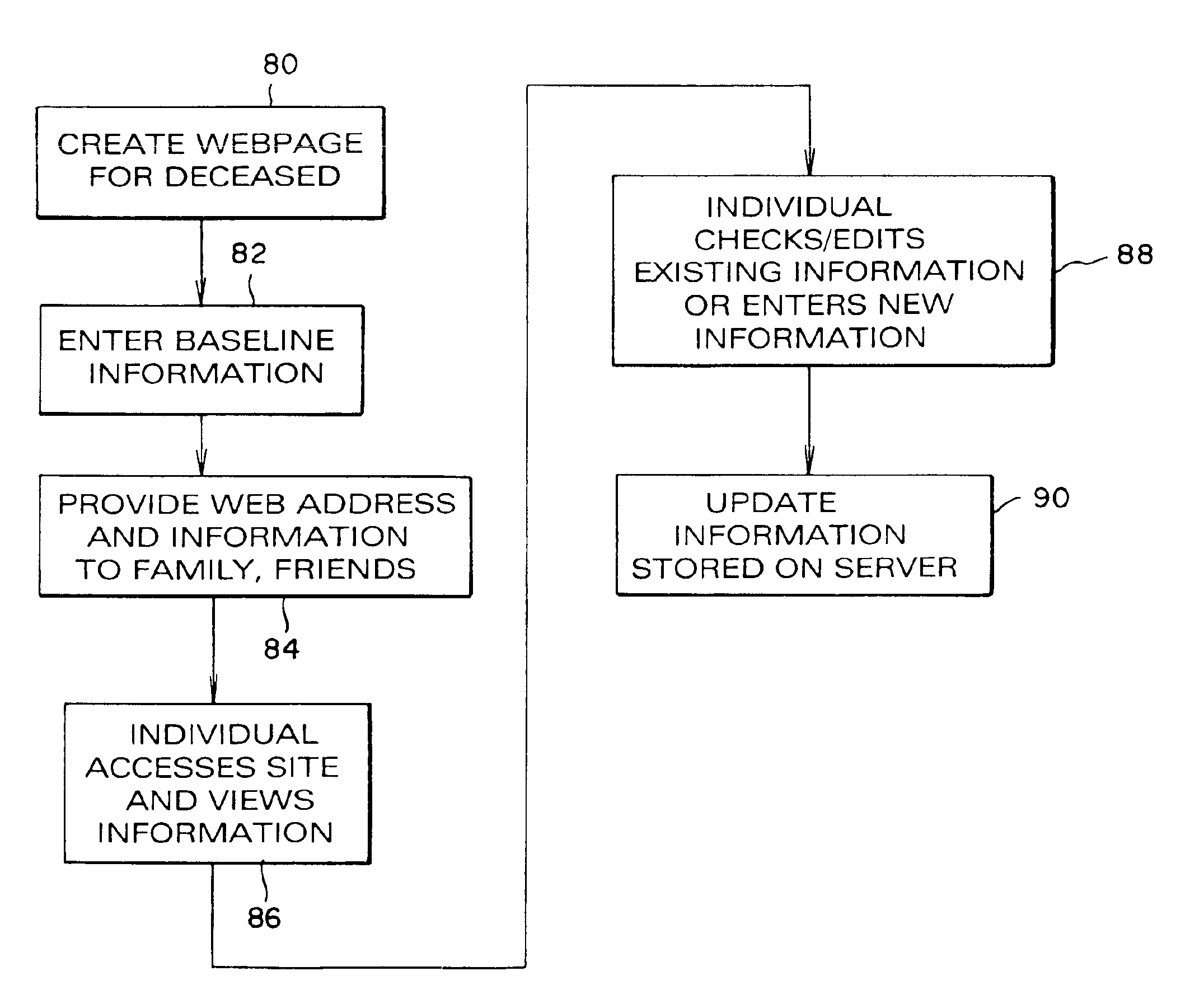
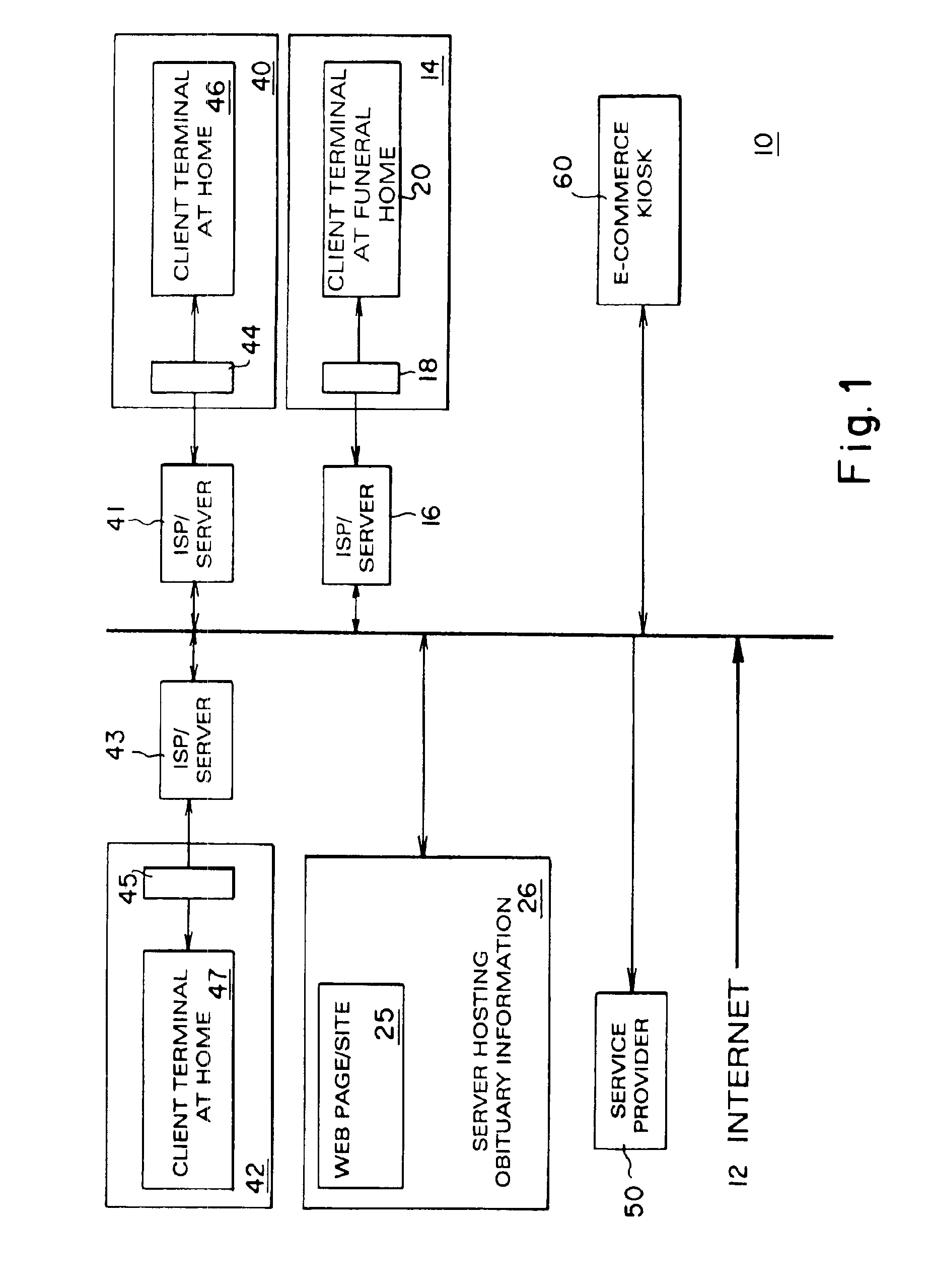
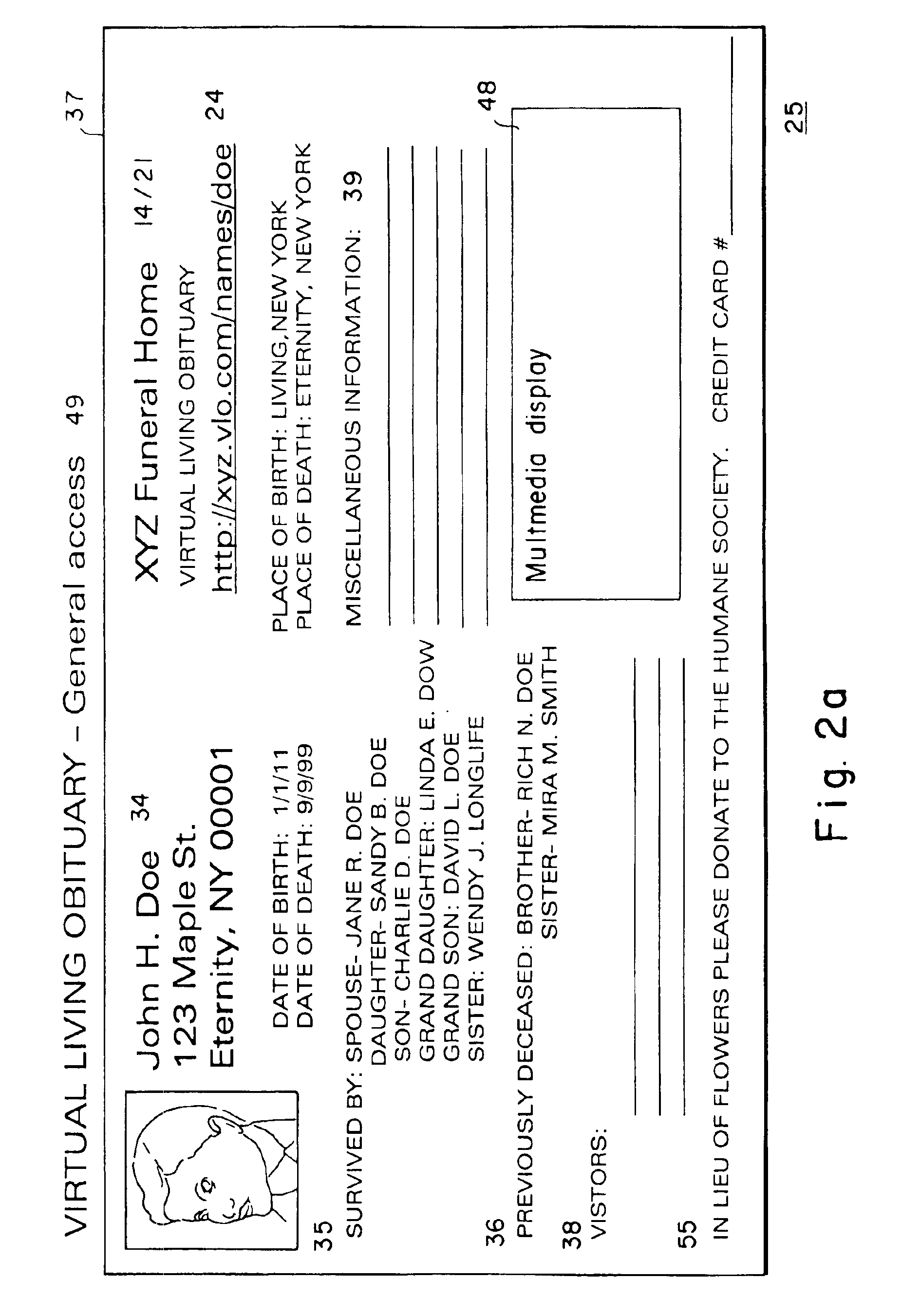
Method and system for capturing memories of deceased individuals
InactiveUS6947921B2Multiple digital computer combinationsOffice automationDistributed memoryComputer software
A method, system, and computer software product for capturing and distributing memories of a deceased individual. An electronic storage memory database is provided having controls for allowing selective entry of information into said database with respect to said selected individual. Individuals can be pre-authorization for accessing said database for viewing or entering of data into the database with respect to a deceased individual. Also a gatekeeper can be designated for providing editorial control over entry of said data.
Owner:MONUMENT PEAK VENTURES LLC
Reliable data transmission method under unreliable network connection
InactiveCN101729562AImprove productivityImprove work efficiencyError preventionGate-keeperAutomatic transmission
The invention provides a reliable data transmission method under unreliable network connection to solve the problems that how to completely and reliably transmit data between networks under the condition of intermittent or occasional connection of the networks. The method comprises the following steps of network access proxy, network state judgment, automatic data transmission and automatic data cache. The method is applied to the government industry and large-scale group enterprises on a large scale, a user offline makes documents or submits data under the condition that a user is transitory online by dialing or a gate keeper automatically intermittently communicate with inner and outer nets, and the data is automatically transmitted by the method when the network is communicated. The method has the characteristics of simple operation and safe, effective data uploading, and excellent promotion and use value.
Owner:INSPUR COMMON SOFTWARE
Calling flow control method
InactiveCN1479512AConvenient and flexible through customized strategiesAchieve recoverySubscriber signalling identity devicesNetwork connectionsGate-keeperComputer science
Owner:ZTE CORP
Gate keeper
InactiveUS7886009B2Special service for subscribersMultiple digital computer combinationsGate-keeperMultimedia
Owner:THRYV INC
NAT traversing system and method for meeting television
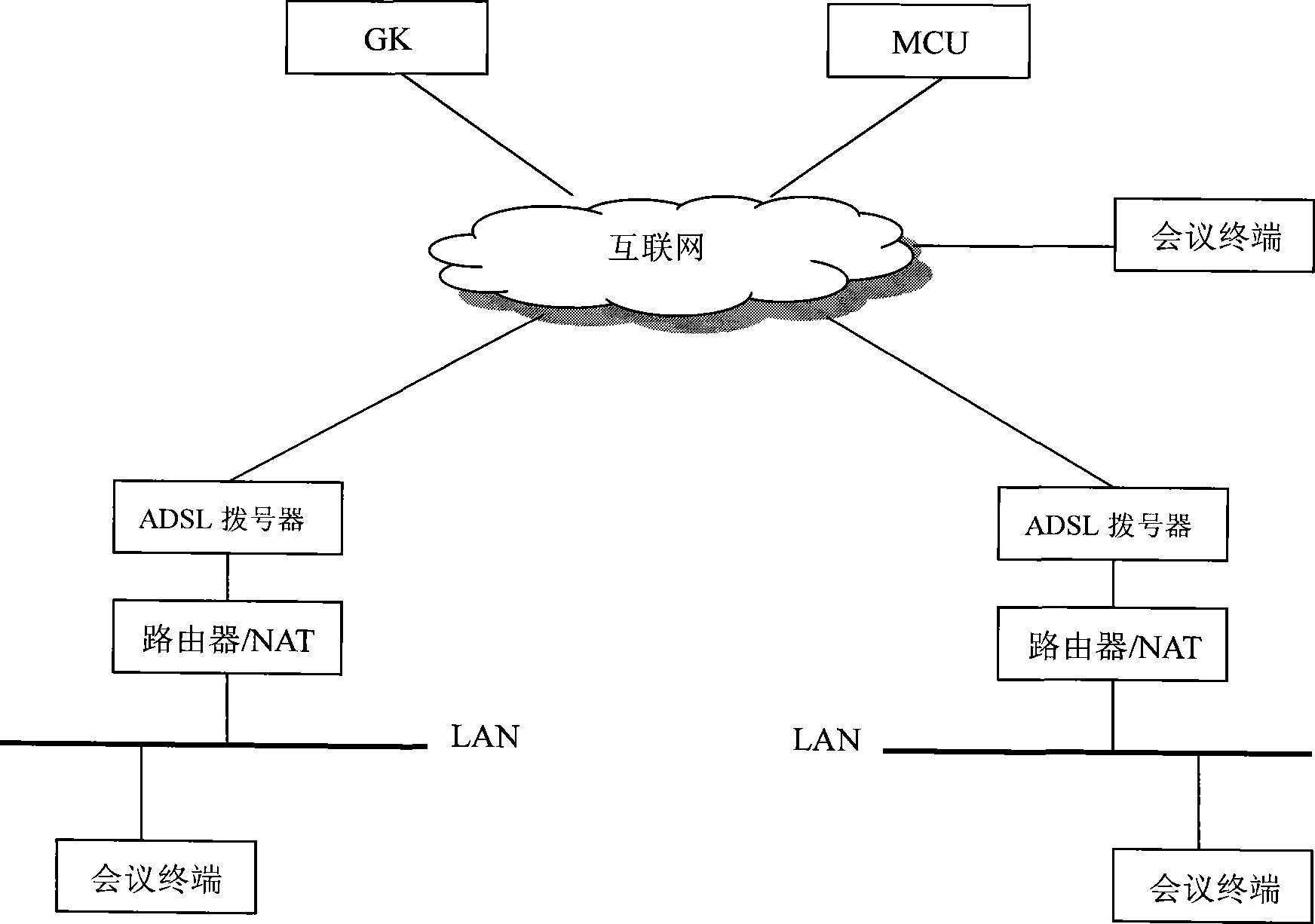
InactiveCN101459692AEfficient use ofRealize crossingTelevision conference systemsTwo-way working systemsGate-keeperIp address
The invention discloses an NAT crossing system of a conference TV, which comprises a communication control module and a plurality of conference terminals, wherein at least one of a plurality of conference terminals is located in an inner network, a plurality of conference terminals are connected with internet through a Router and an IP address obtaining unit, and the communication control module is connected with a plurality of conference terminals mutually through the internet. The NAT crossing system also comprises a gatekeeper which is connected with the internet, wherein the gatekeeper comprises an IP address analytical element which is used to analyze an outer network IP address corresponding to a registration request signal according to the registration request signal which is sent by the conference terminals in the inner network to the gate keeper. The invention also discloses an NAT crossing method of the conference TV. The system and the method can conveniently realize NAT crossing between the inner network and the outer network under the condition that the cost is not increased, and the system and the method are widely applied in various enterprise TV conferences.
Owner:深圳市迪威新软件技术有限公司 +1
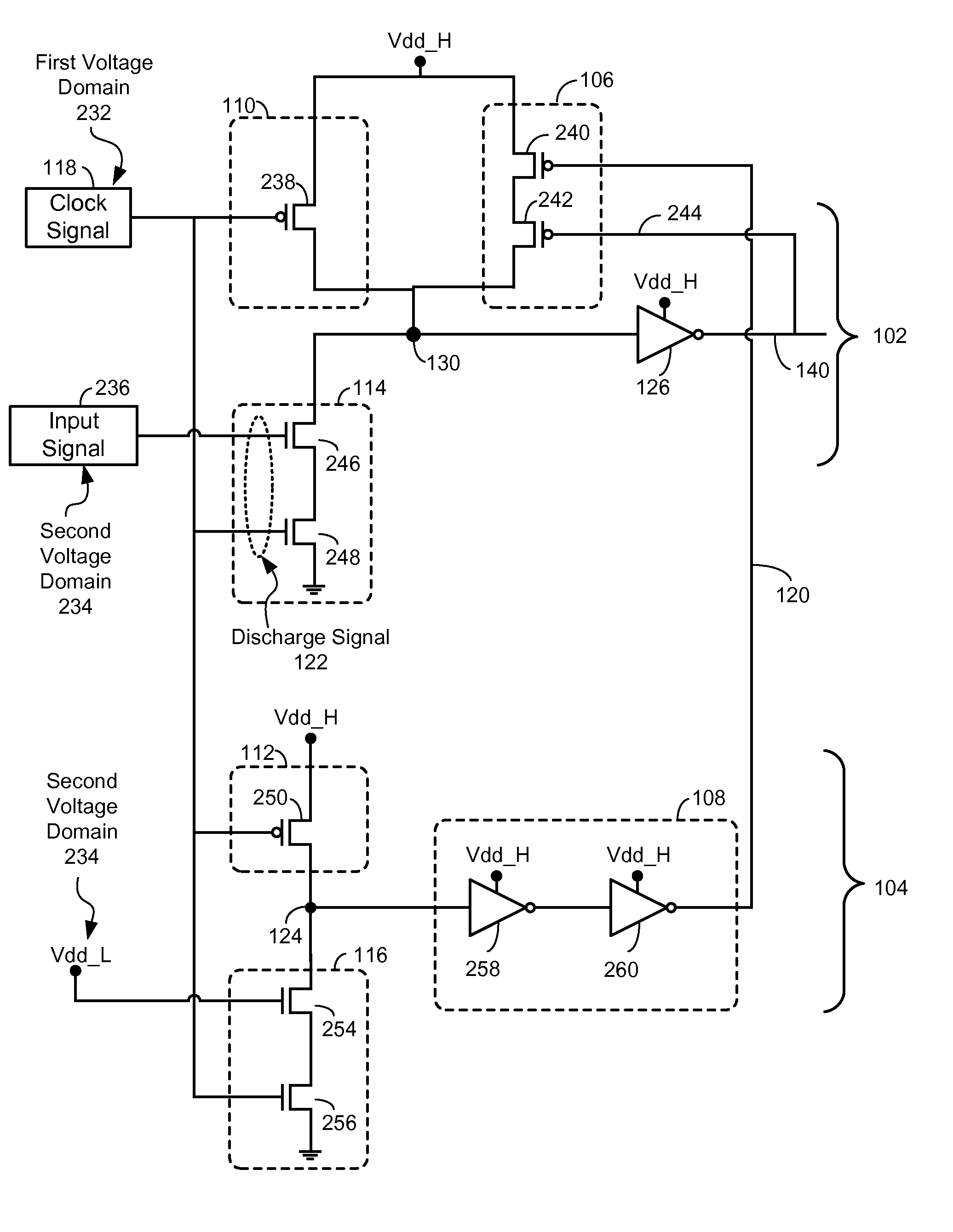
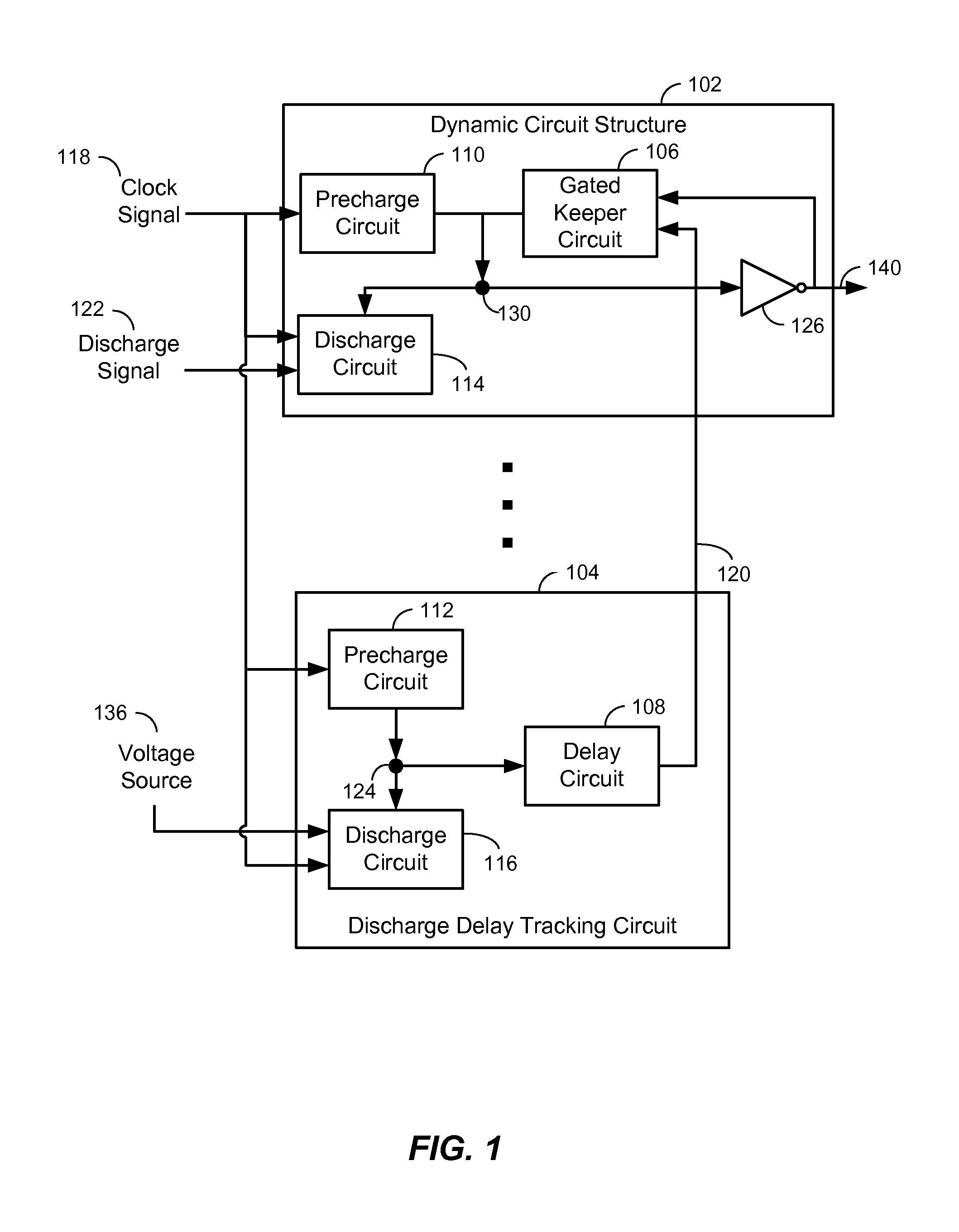
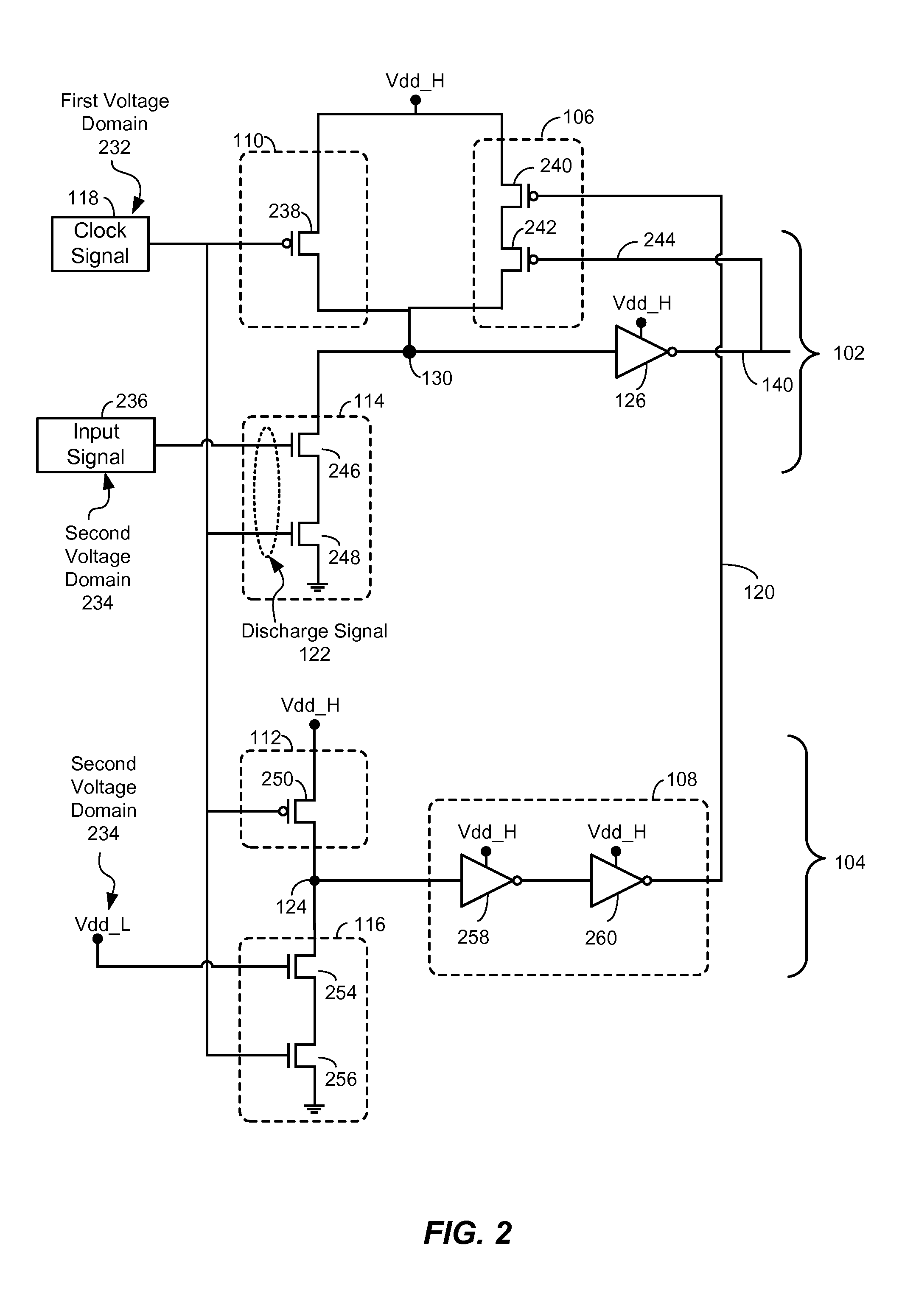
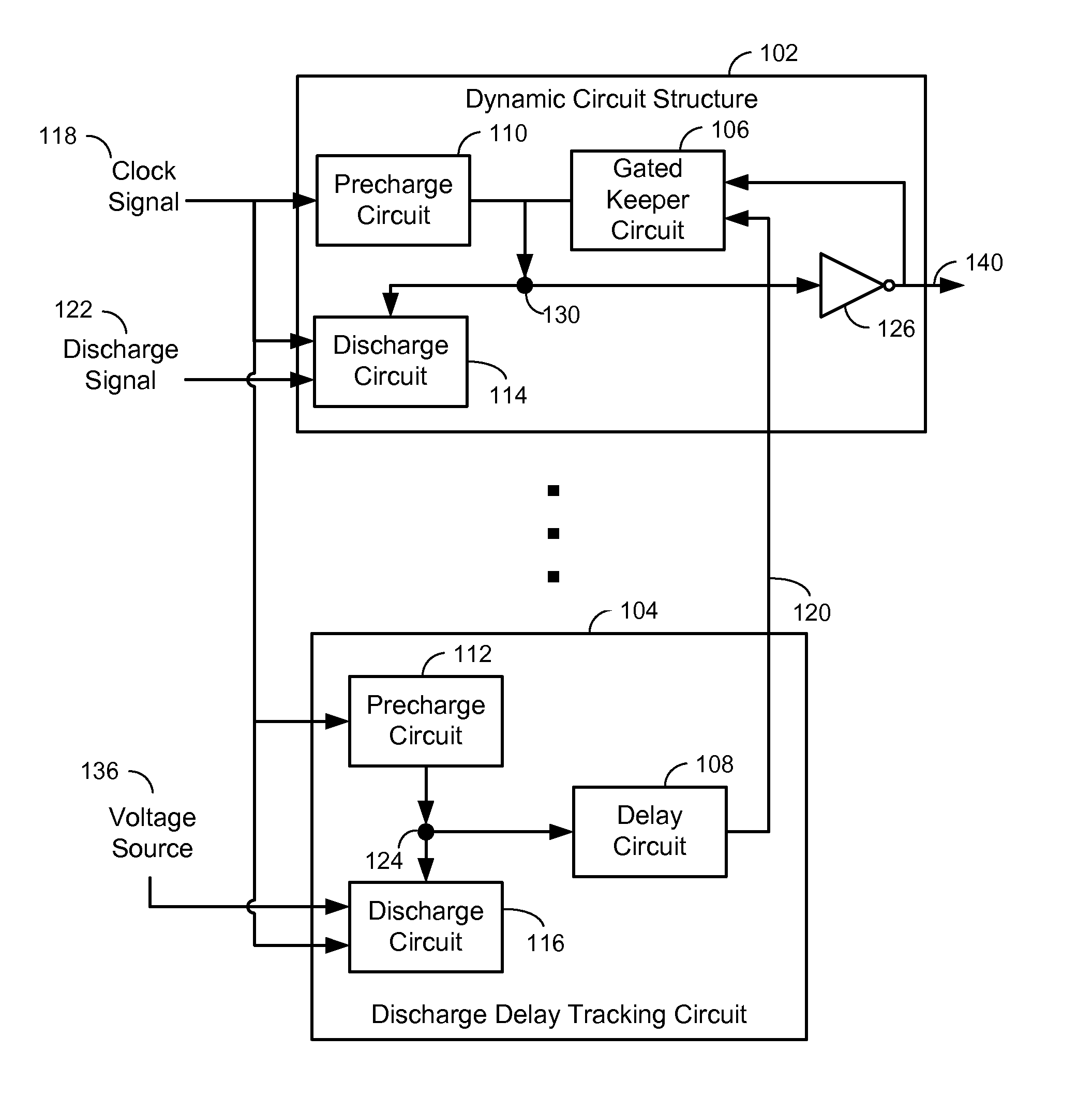
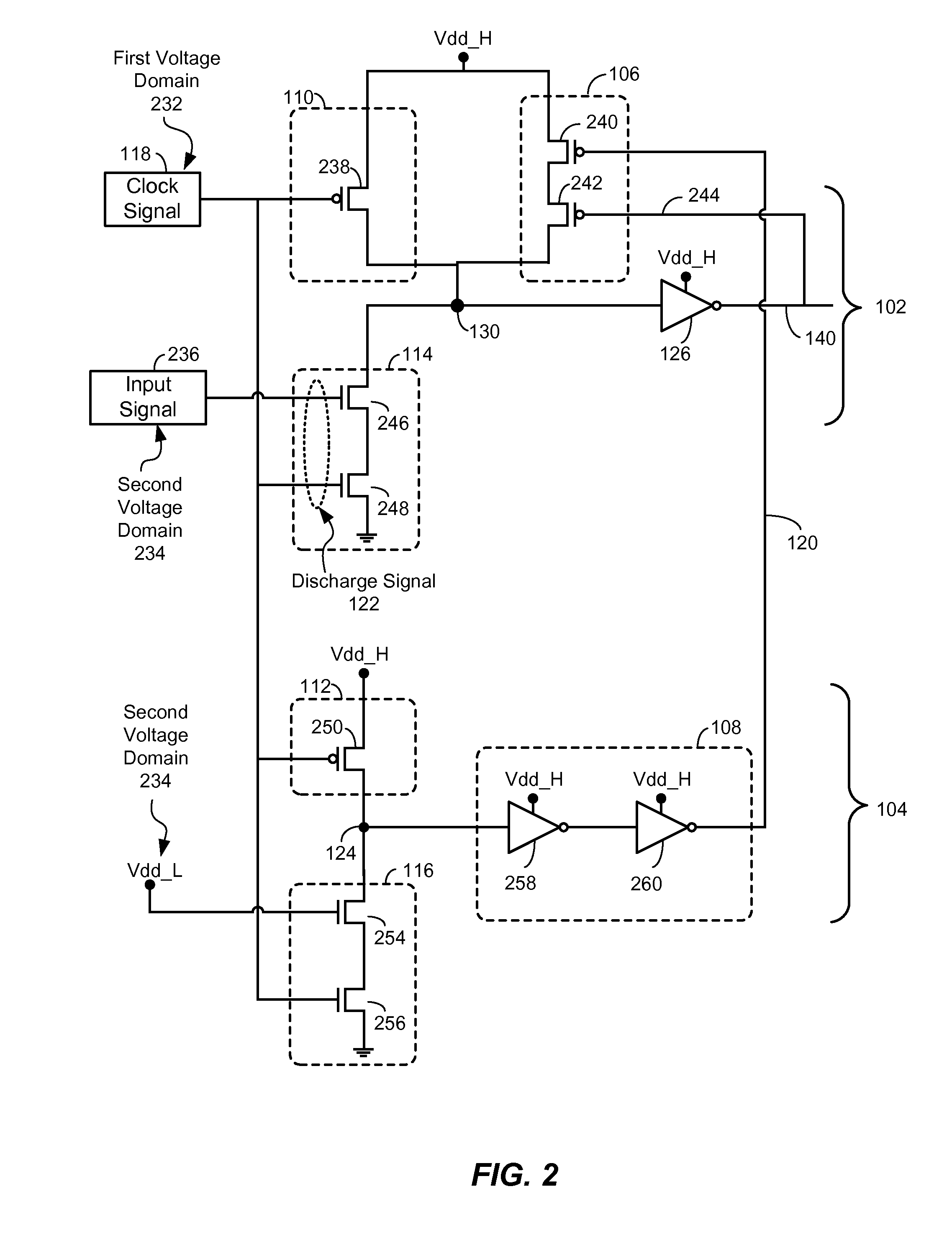
Voltage Level Shifter with Dynamic Circuit Structure having Discharge Delay Tracking
InactiveUS20110193609A1Reduce and eliminate effectPulse automatic controlElectronic switchingGate-keeperVoltage
Owner:QUALCOMM INC
Voltage level shifter with dynamic circuit structure having discharge delay tracking
ActiveUS7986165B1Reduces and eliminates effectReduce and eliminate effectLogic circuit coupling/interface arrangementsGate-keeperVoltage
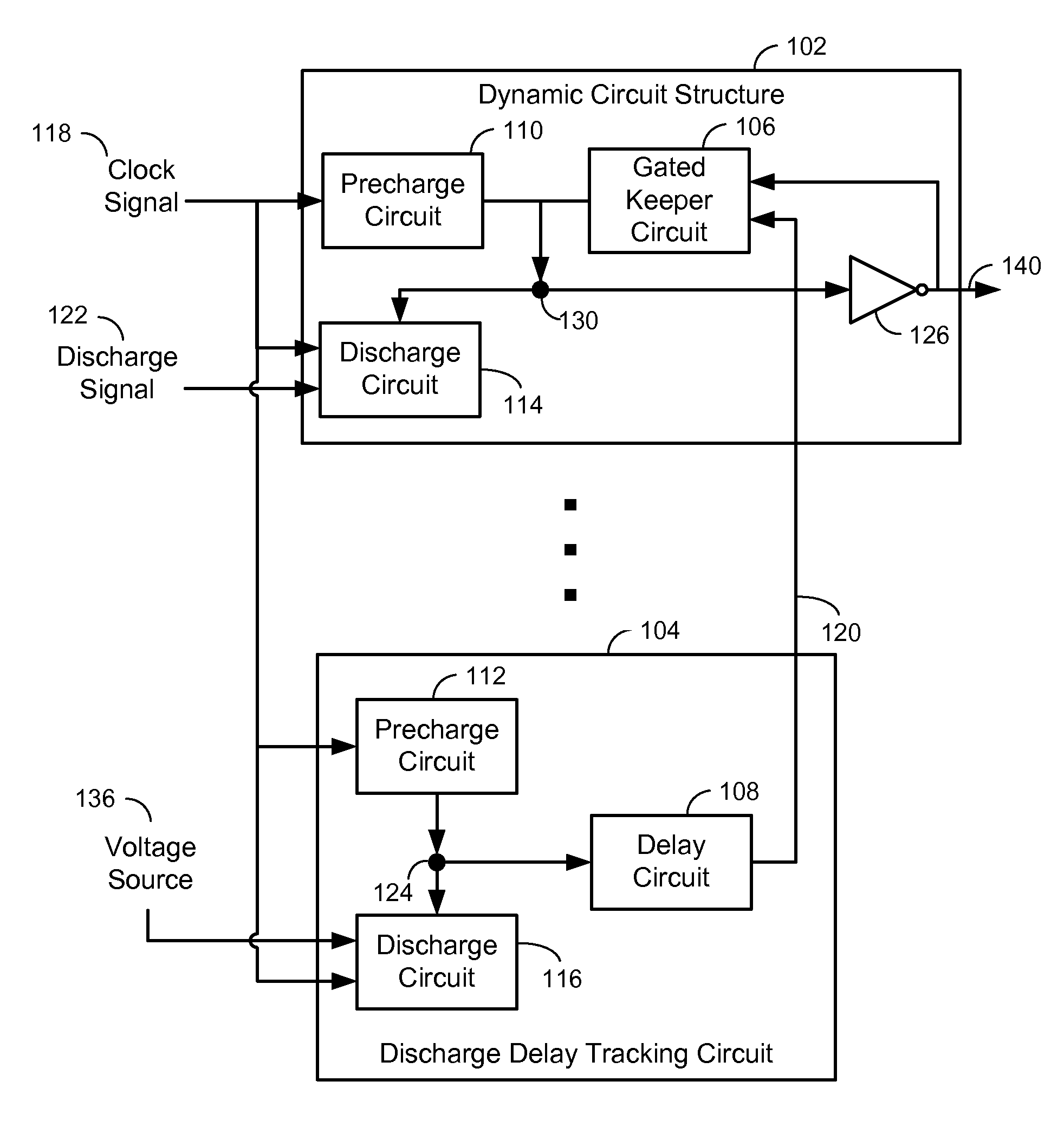
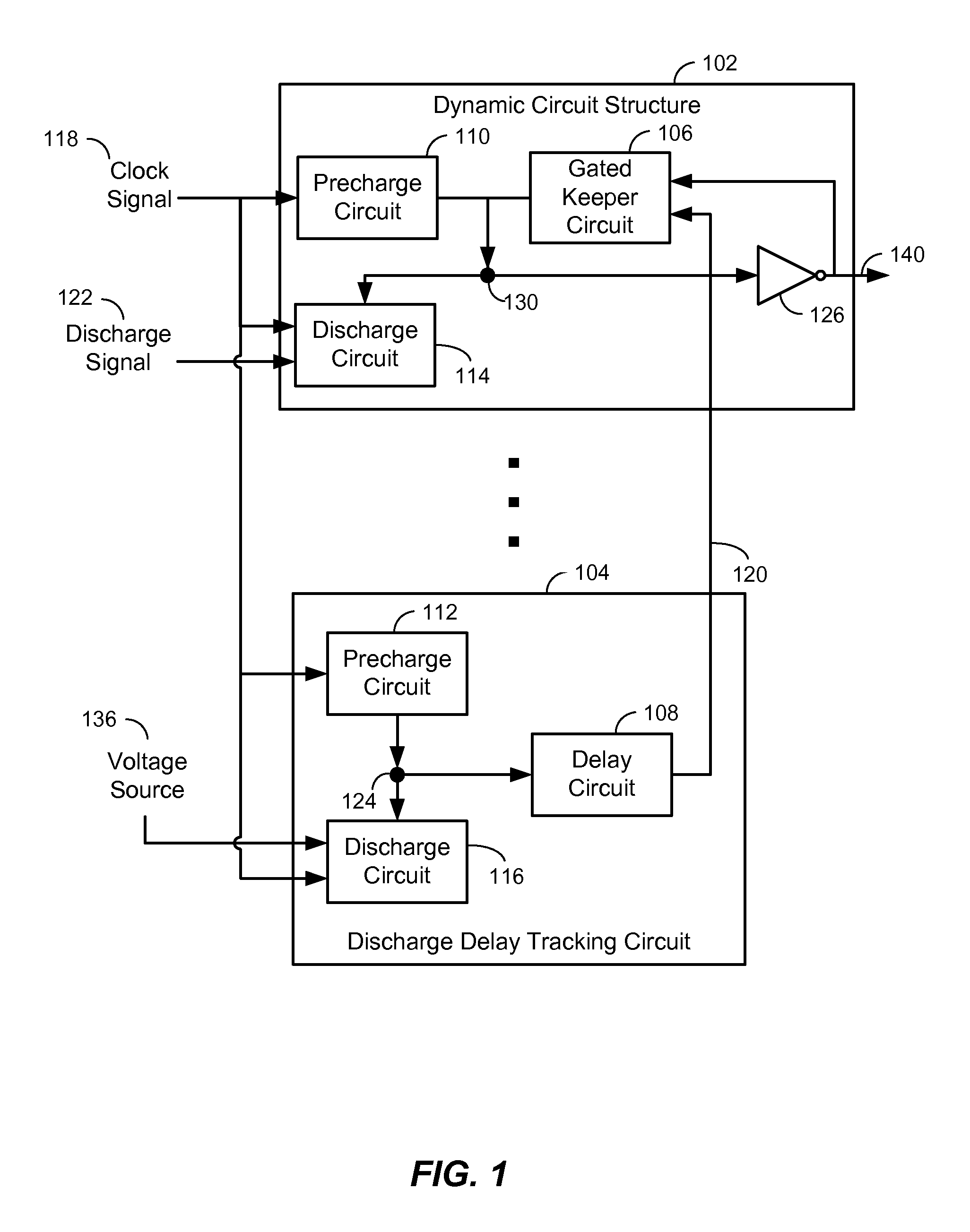
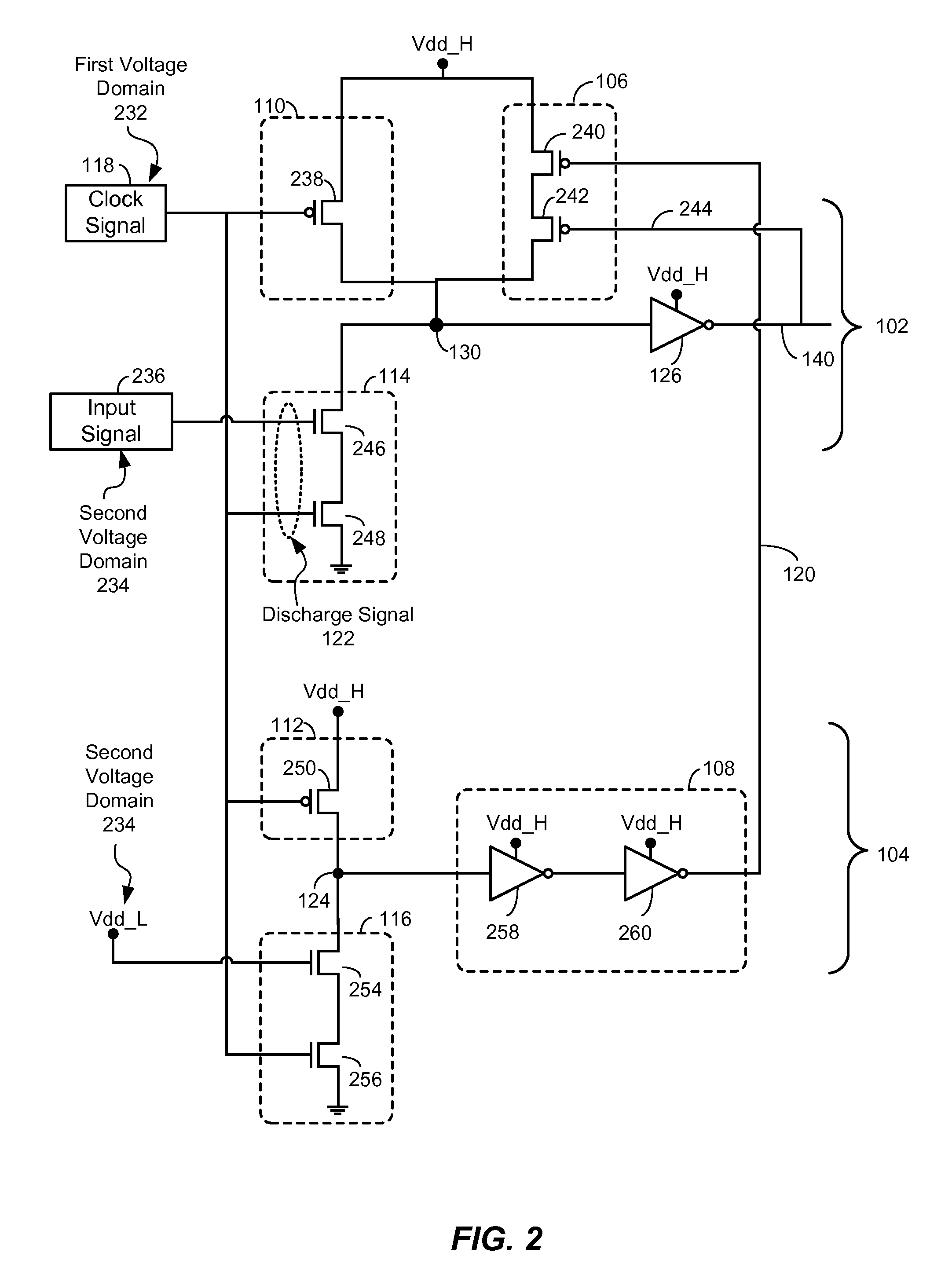
An apparatus is disclosed. In a particular embodiment, the apparatus includes a a dynamic circuit structure that includes a dynamic node coupling a precharge circuit, a discharge circuit, and a gated keeper circuit. The gated keeper circuit is enabled by a signal from a discharge delay tracking circuit.
Owner:QUALCOMM INC
Method for, and a topology aware resource manager in an IP-telephony system
InactiveUS7606885B2Increase profitEffective resourcesDigital computer detailsNetwork connectionsGate-keeperResource information
A method and arrangement in a communications network. The object is to provide a way of handing recourse management issues and admission control within an IP telephony system. The object is achieved by a topology aware resource manager collecting routing information concerning the IP network, obtaining resource information concerning resources within the IP network, creating a resource map by combing the routing information and resource information, and performing recourse management issues and admission control within the system by the resource map and by interacting with a gatekeeper.
Owner:NETABOCKET
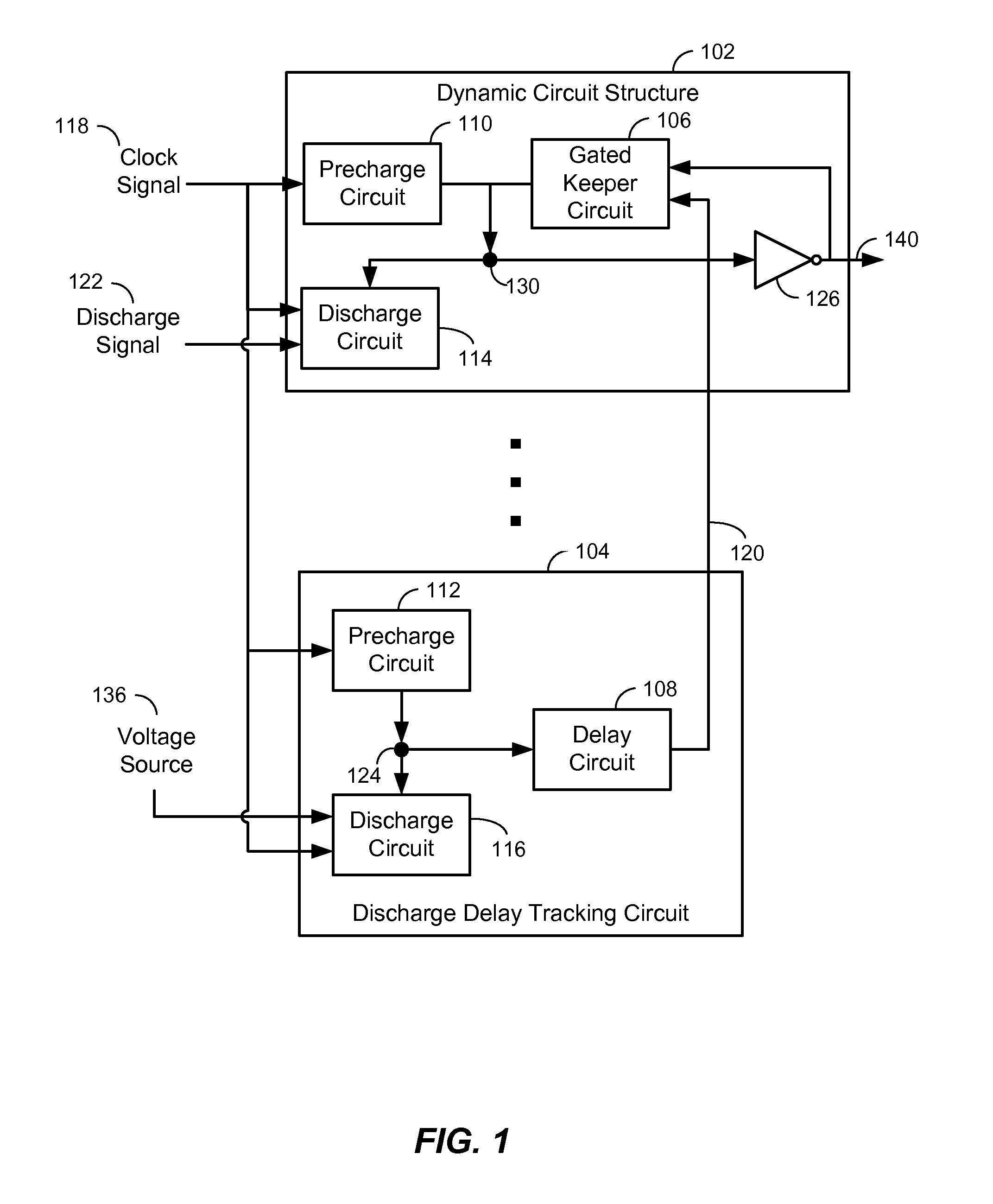
Voltage level shifter with dynamic circuit structure having discharge delay tracking
ActiveUS20110193592A1Reduce and eliminate effectDigital storageLogic circuit coupling/interface arrangementsGate-keeperEngineering
An apparatus is disclosed. In a particular embodiment, the apparatus includes a a dynamic circuit structure that includes a dynamic node coupling a precharge circuit, a discharge circuit, and a gated keeper circuit. The gated keeper circuit is enabled by a signal from a discharge delay tracking circuit.
Owner:QUALCOMM INC
Cross-gate keeper call processing method
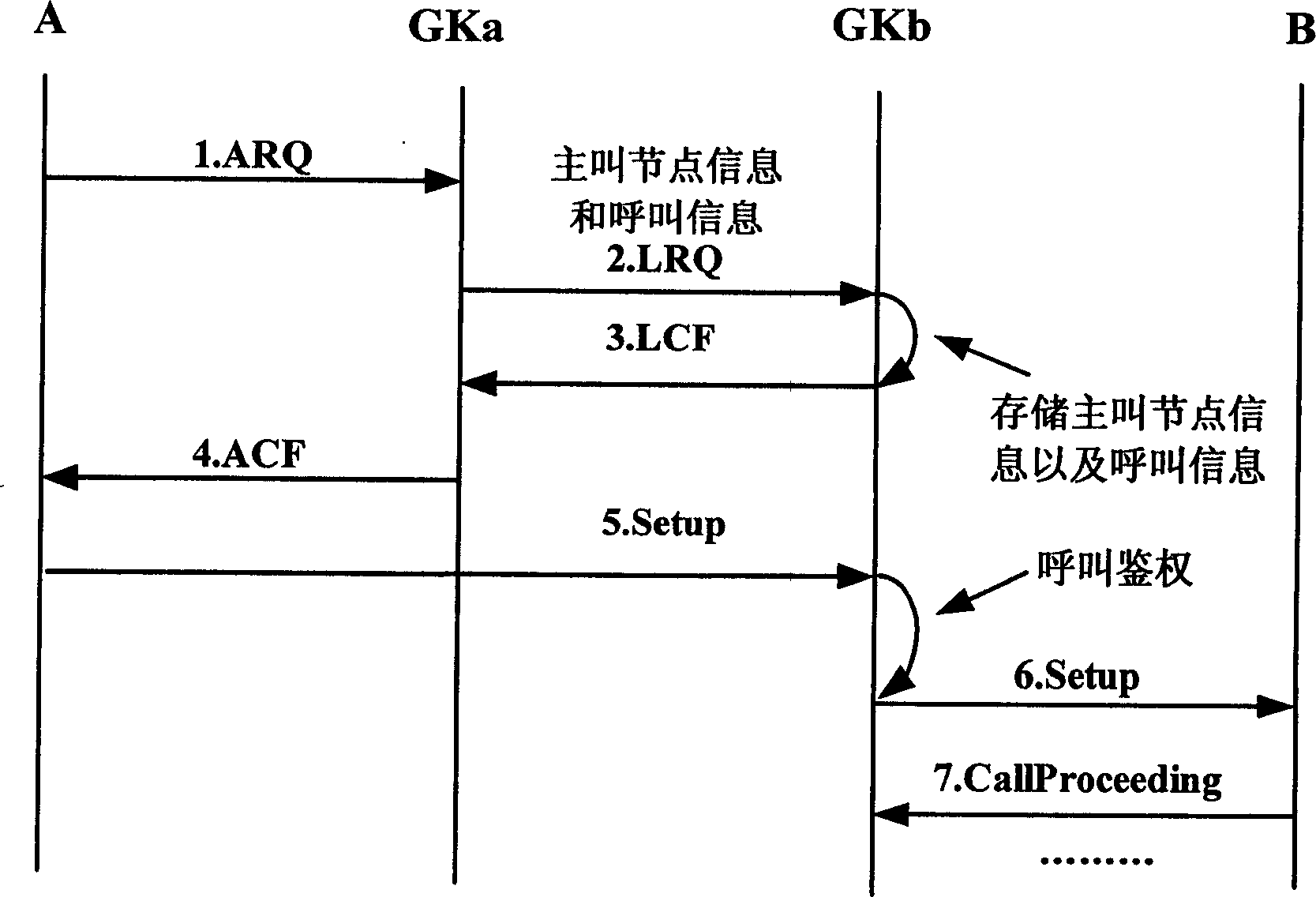
InactiveCN1859518AEasy maintenancePrevent illegal call accessInterconnection arrangementsTransmissionGate-keeperTelecommunications
The present invention discloses trans-gate keeper call processing method. It contains call side gate keeper receiving permission demand signaling, utilizing positioning demand signaling to transmit node information and / or calling information to called side gate keeper; after called side gate keeper receiving positioning demand signaling, storing said call side node information and / or calling information. Said invented method can make called side gate keeper obtaining call and called side node information, calling information and billing information; in trans- gate keeper calling procedure utilizing these information capable of realizing calling authentication and call charging etc, thereby raising system reliability and security.
Owner:HUAWEI TECH CO LTD
System and method for secure content sharing and synchronization
ActiveUS9338158B2Easy accessCustomer relationshipDigital data information retrievalContent distributionGate-keeper
Owner:OPEN TEXT SA ULC
System and method for data tracking and management
InactiveUS20060075025A1Ensure data integrityMultiprogramming arrangementsMultiple digital computer combinationsApplication computersCentral database
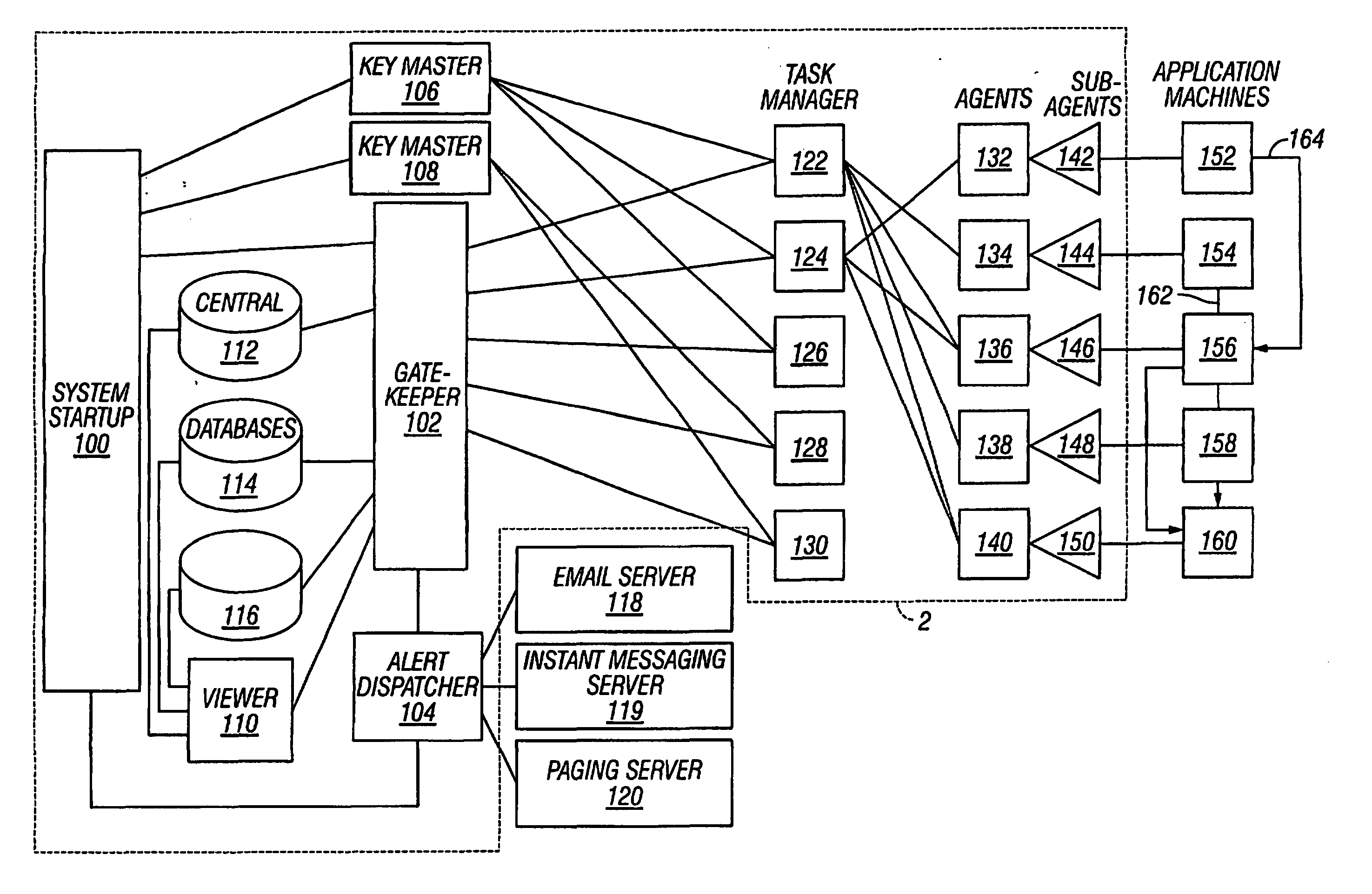
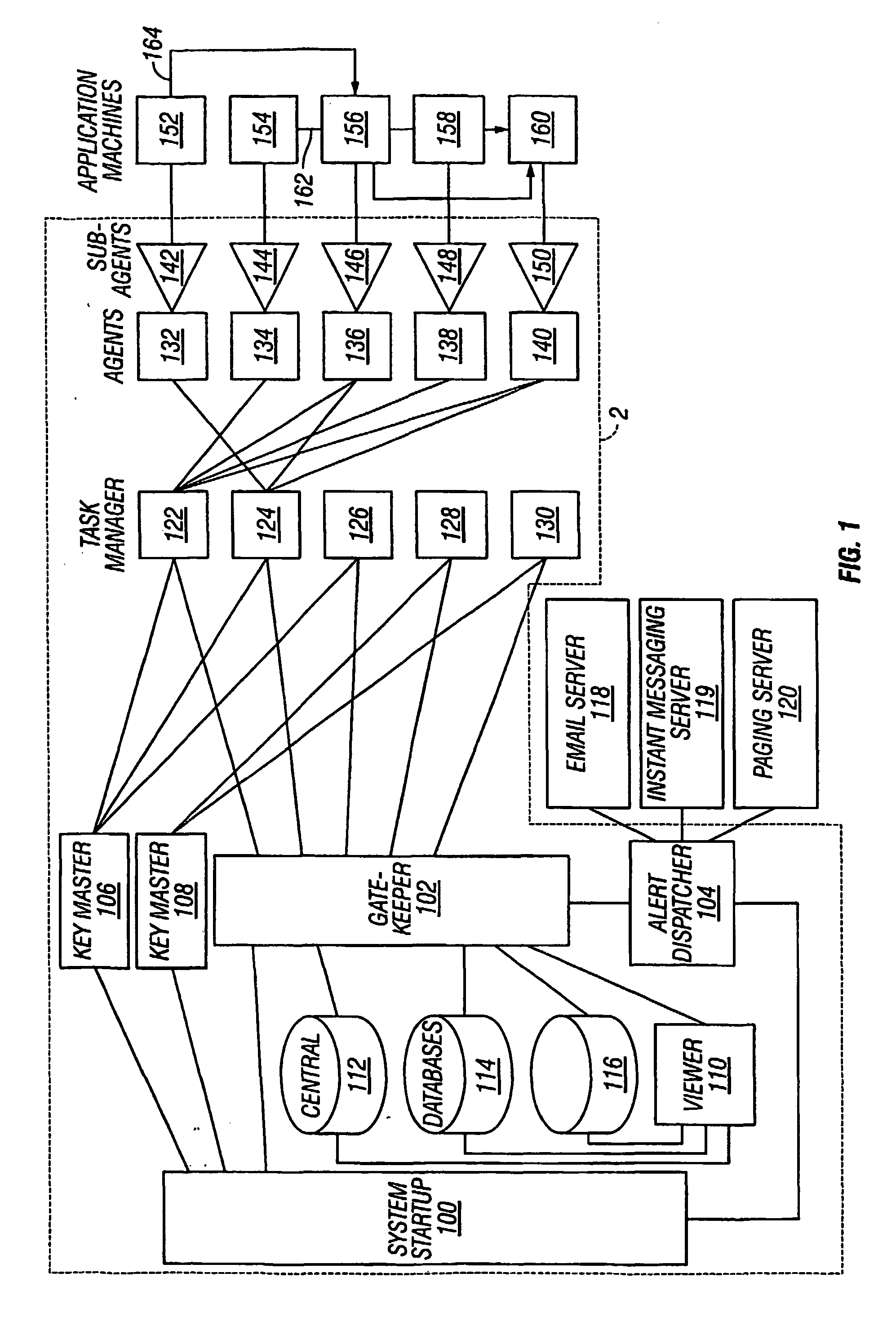
In one embodiment of the present invention's a system for tracking and managing data over a computer network including a plurality of application computers each operating a computer software application program is provided, comprising a key master (106, 108); a system startup module (100) connected to the key master (106, 108); a gatekeeper (102) connected to the system startup module (100); as task manager (122, 124, 126, 128's 130) connected to the key master (106, 108) and the gatekeeper (102); a central database (112, 114, 116) connected to the gatekeeper (102); a plurality of agents (132, 134, 136, 138, 140) connected to the task manager; a plurality of sub-agents (142, 144, 146, 148, 150) independently connected to the plurality of agents (132, 134, 136, 138, 140) and the plurality of application computers (152, 154,156, 158, 160); and an alert dispatcher (104) connected to the system startup module (100) and the gatekeeper (102).
Owner:ACCENX TECH
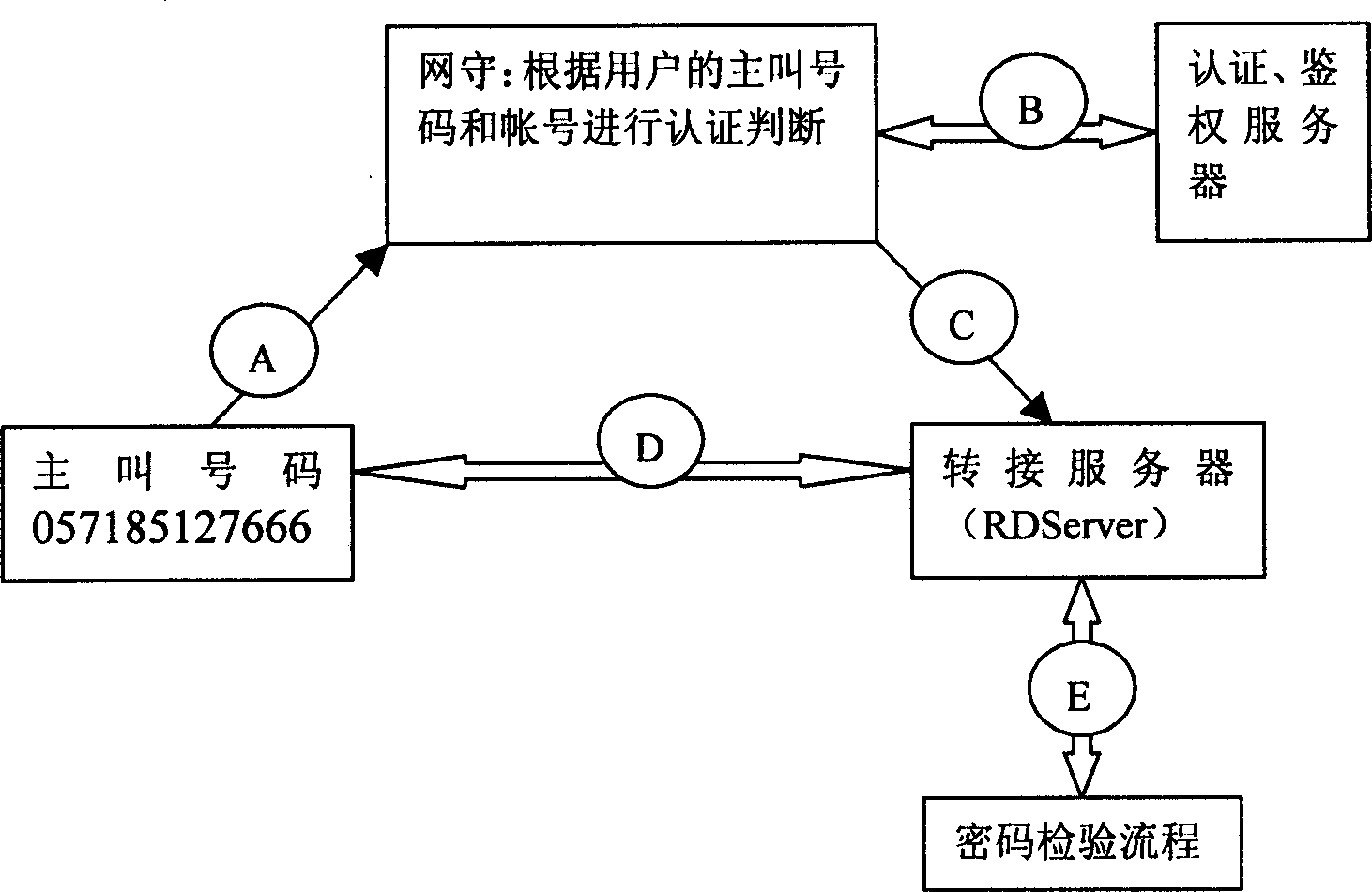
Authentication for dialing number and coding certification combination based on NGN communicating network
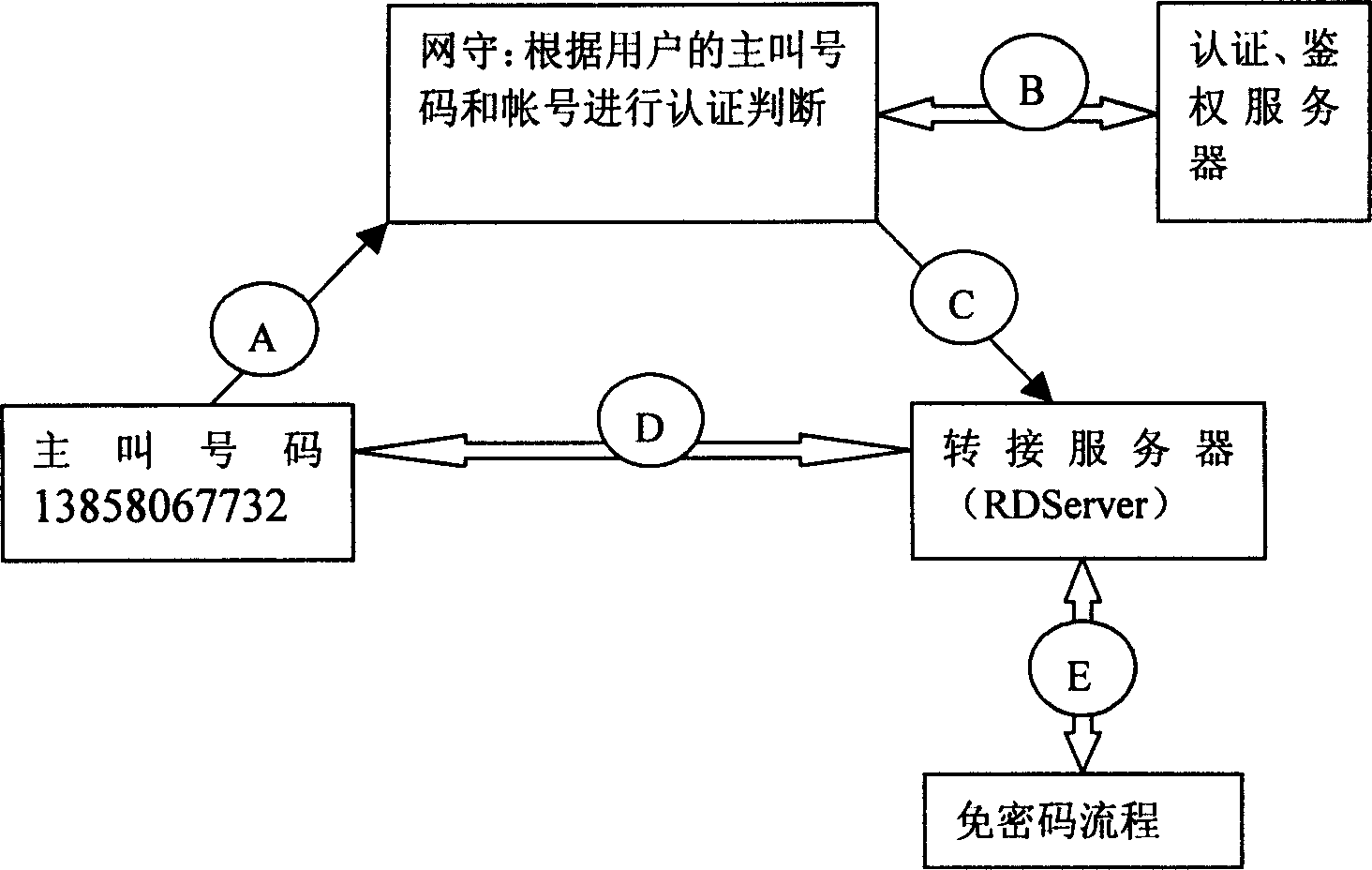
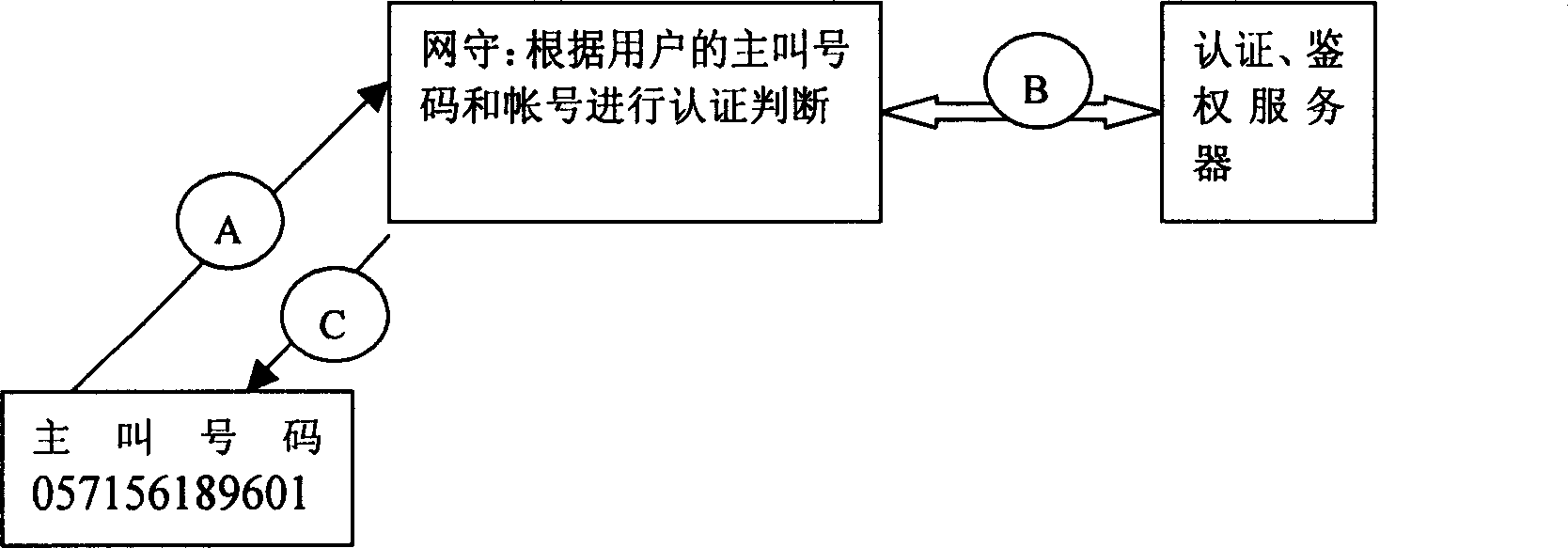
InactiveCN1713768AEasy to useReduce complexityRadio/inductive link selection arrangementsSecurity arrangementGate-keeperPassword
When user initiates a call, the gate keeper sends inquiry request to authentication system base on phone number of user. The authentication system decides if the calling number belongs to calling limitation, calling free password or binding calling. If the calling number is calling limitation number, directly clears down line. If calling number doesn't belongs to two kind of numbers above, with IVR function of switching server, prompts user to input password for checking. With the invention user can avoid complex password check process and directly enter calling procedure.
Owner:DAYANG TELECOMM HANGZHOU
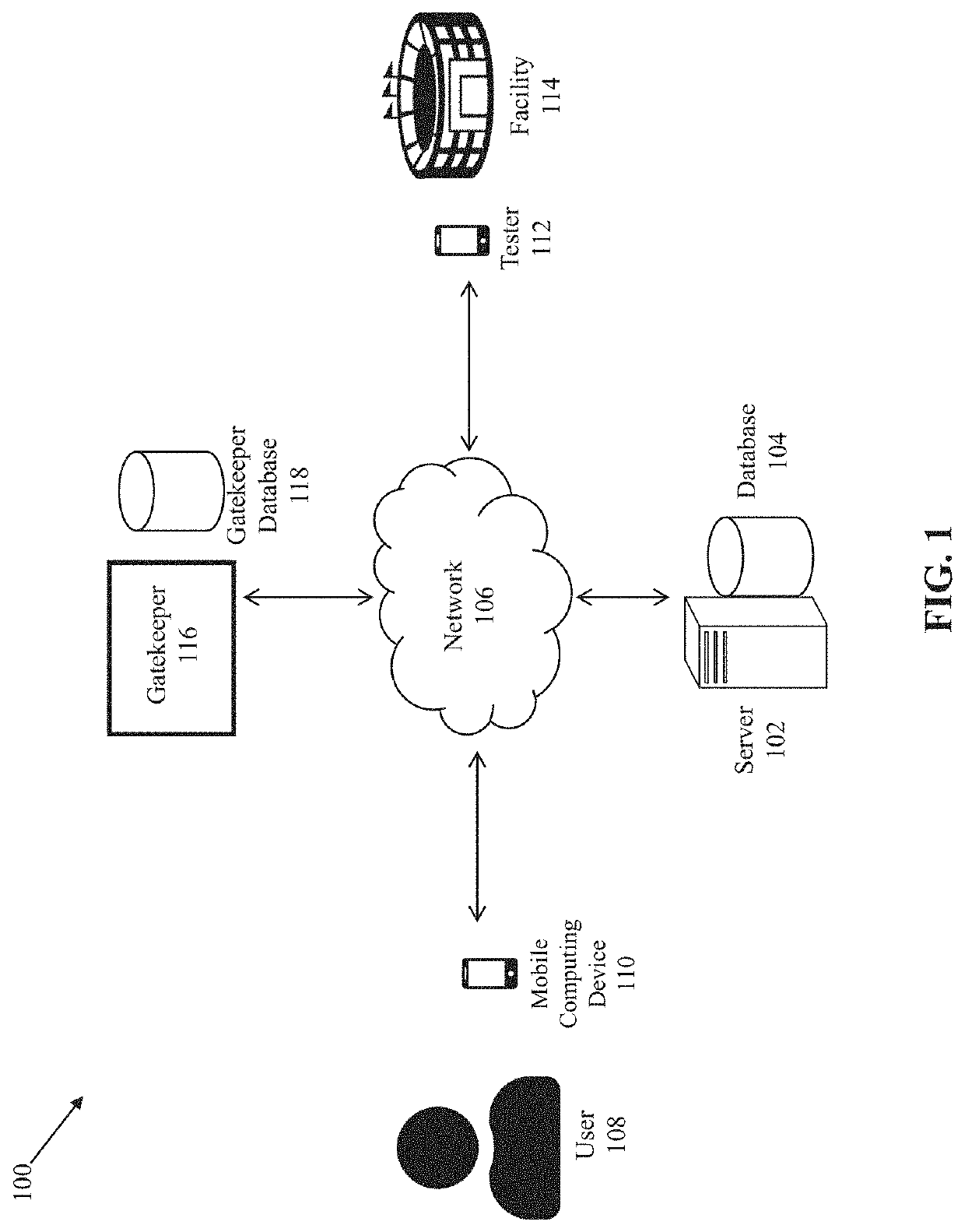
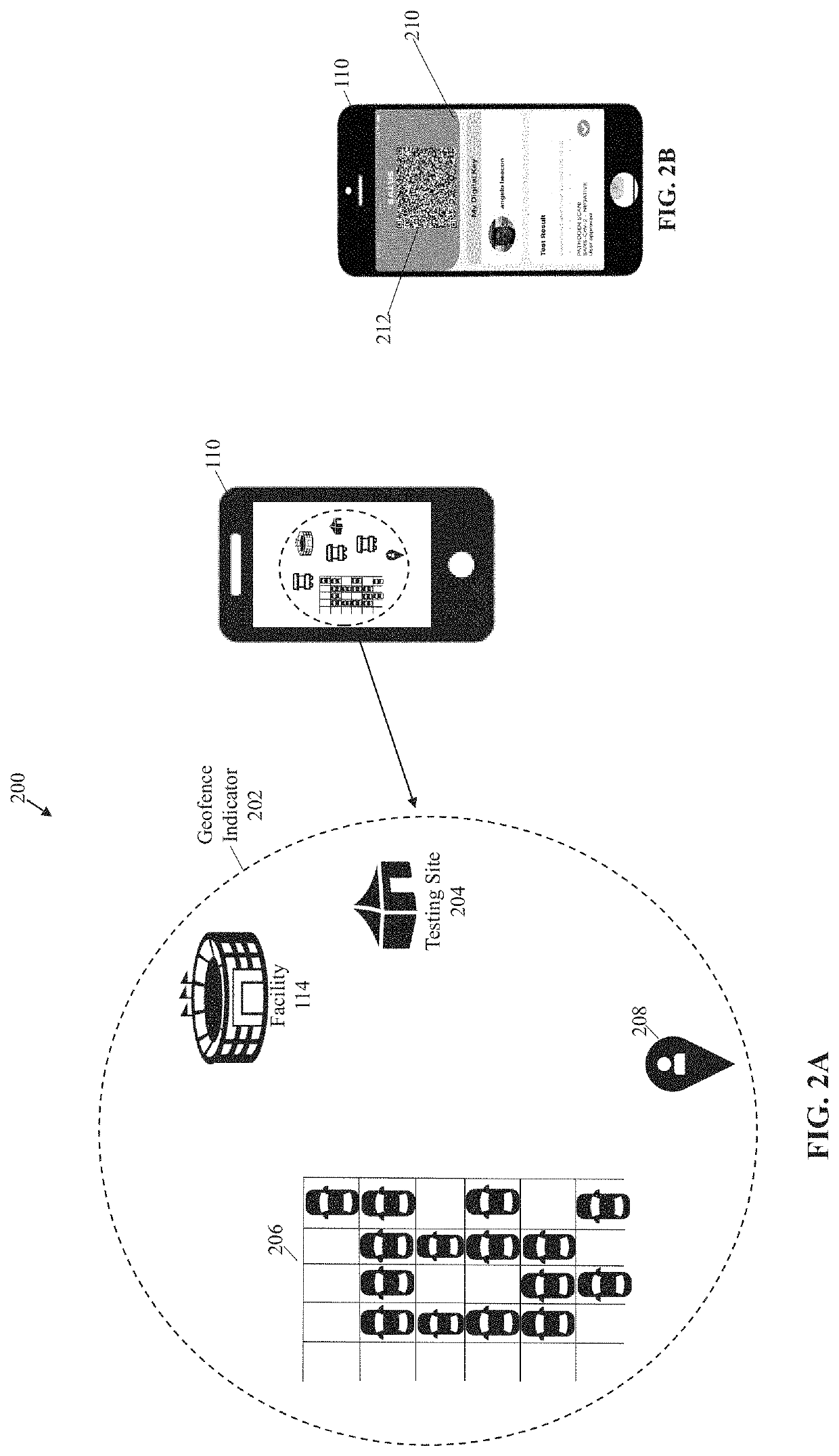
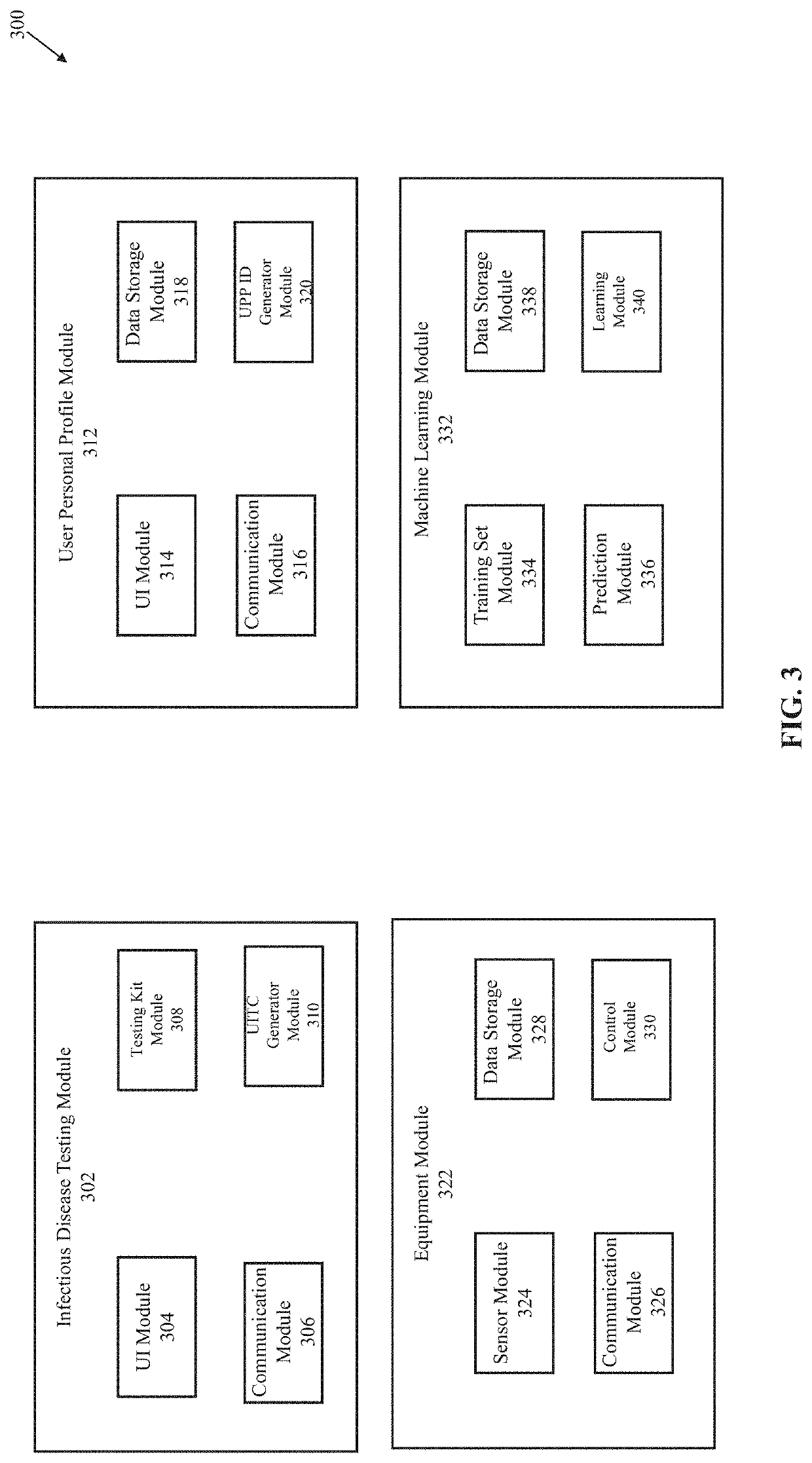
Systems and methods for managing infectious disease dissemination
ActiveUS11011003B1Effectively prevents disseminationEpidemiological alert systemsIndividual entry/exit registersGate-keeperSoftware engineering
System and method for infectious disease prevention includes transmitting, via a server, a facility credential associated with a facility configured to identify a user operating on an application deployed by server from a mobile computing device. The server receives a user identification test code (UITC) associated with a status of an infectious disease of the user. The server then generates a two-dimensional code associated with the facility credential based on the UITC. The server determines if the two-dimensional code is valid for permitting access to the facility based on the status of the infectious disease. Thereafter, the server activates the two-dimensional code on the mobile computing device for a predetermined period of time. A gatekeeper device responds to the two-dimensional code from the mobile computing device and then permits the user access to the facility within the predetermined period of time based on the facility credential and the two-dimensional code.
Owner:AAJ COMP SERVICES INC DBA OF OZ
Method and system for realizing video conference
InactiveCN101710960AEnsure independenceEnsure safetyTelevision conference systemsTwo-way working systemsGate-keeperRelevant information
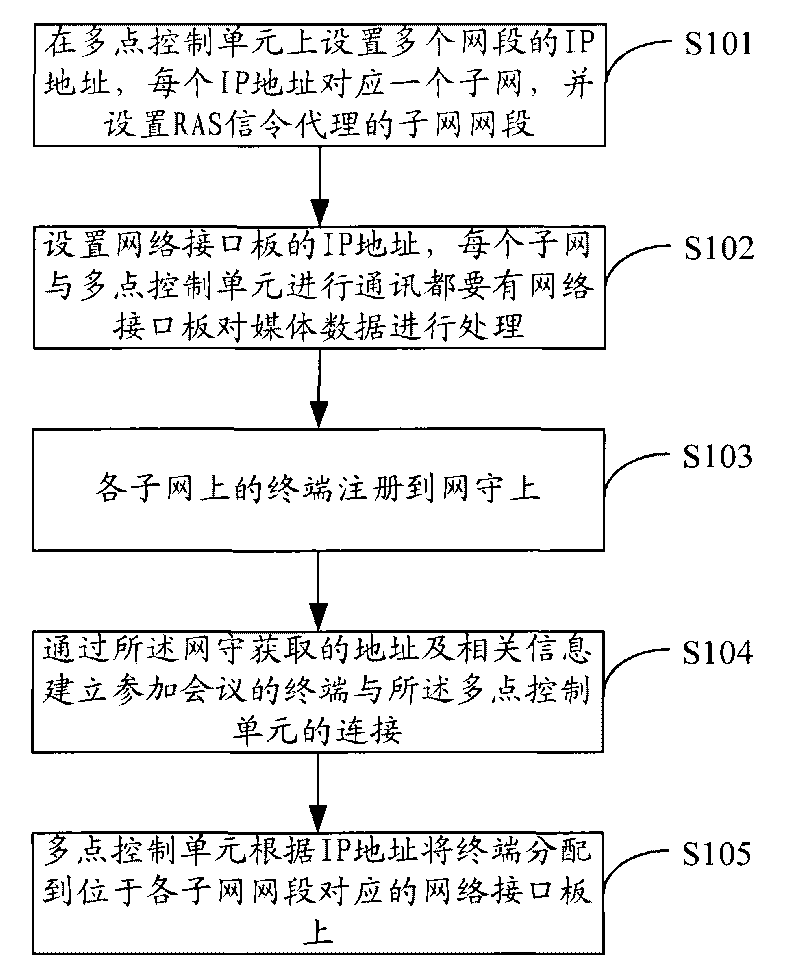
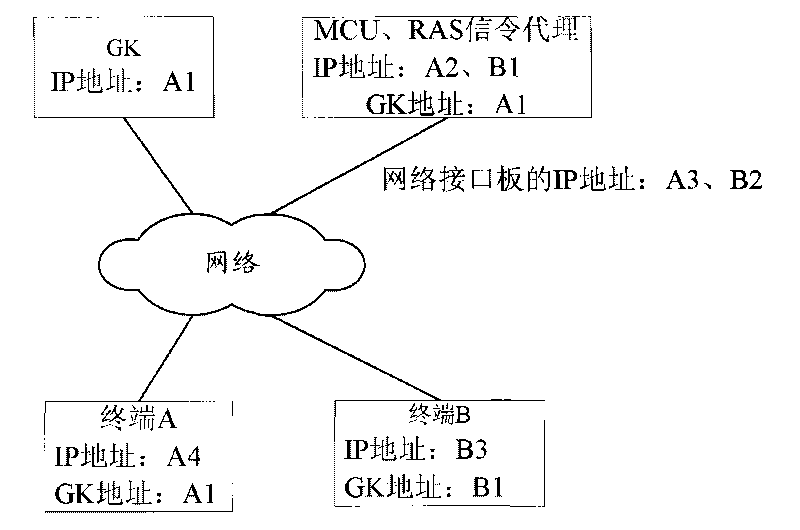
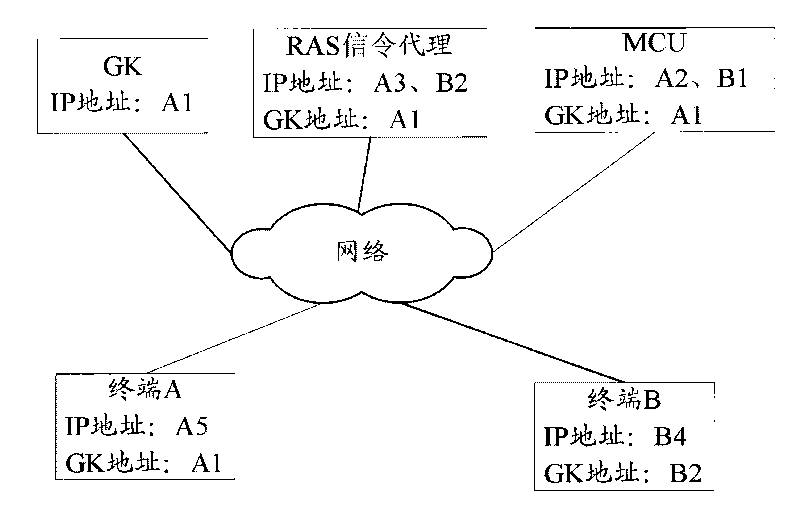
The invention is applicable to the field of video conference communication, and provides a method and a system for realizing video conference. The method comprises setting IP addresses of multi network segments on a multi control unit (MCU) with each IP address corresponding to one sub-network, and setting sub-network segments of RAS signaling agent; setting IP addresses of network interface boards which are used for processing media data when each sub-network communicates with the MCU; registering the terminal on each sub-network on a Gate Keeper (GK); establishing the connection between a terminal participating the conference and the MCU by the address and related information obtained by the GK; distributing the terminal participating the conference to the network interface boards corresponding to each sub-network segment by the MCU according to the IP address. The above method can realize pure IP video conference between sub-networks incapable of performing intercommunication on IP level under the precondition of ensuring independence between the sub-networks and unnecessary additional arrangement of special line.
Owner:ZTE CORP
Authentication system for networked computer applications
ActiveCN101421968AUser identity/authority verificationRecord carriers used with machinesApplication serverComputerized system
A system such as in a networked computer system comprising a user, an application server, a gatekeeper server and an authentication server. Communication within the system is managed by the gatekeeper server, wherein the user communicates with the authentication server and the application server through the gatekeeper server. Once the user has been initially authenticated by the authentication server, the user may request application services from a plurality of application servers within the networked computer system without having to be re-authenticated.
Owner:WELLS FARGO BANK NA
Network vice gate keep (GK) using non-static IP address technology
InactiveCN1430381ATelephonic communicationData switching by path configurationDomain nameGate-keeper
A techqniue to use non-static IP address by network speech gate keeper (GK) includes: registering domain name for gate keeper, logging-on real time JP address of gate keeper, analysing domain name addressing for terminal gate keeper. We can construct an independent operational VoIP system by using this technique under the condition without static IP address resource to enlarge the using range of VoIP system extensively.
Owner:风行互联(北京)科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com