Patents
Literature
9050 results about "Authentication information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
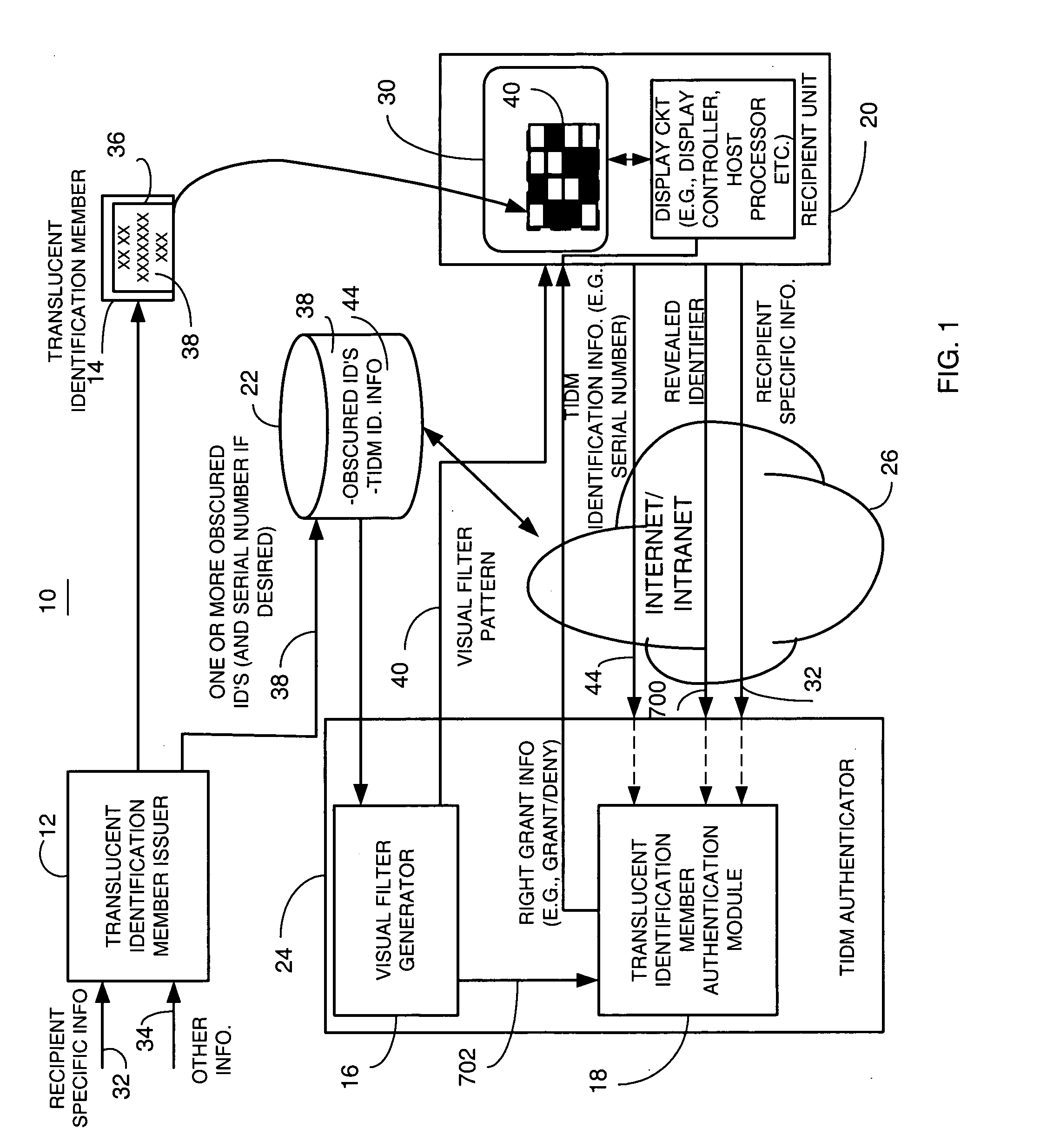
What is Authentication Authentication is the process whereby the system identifies legitimate users from unauthorized users. It is the process in which a user identifies his/her self to the system. How effective an authentication process is, is determined by the authentication protocols and mechanisms being used.
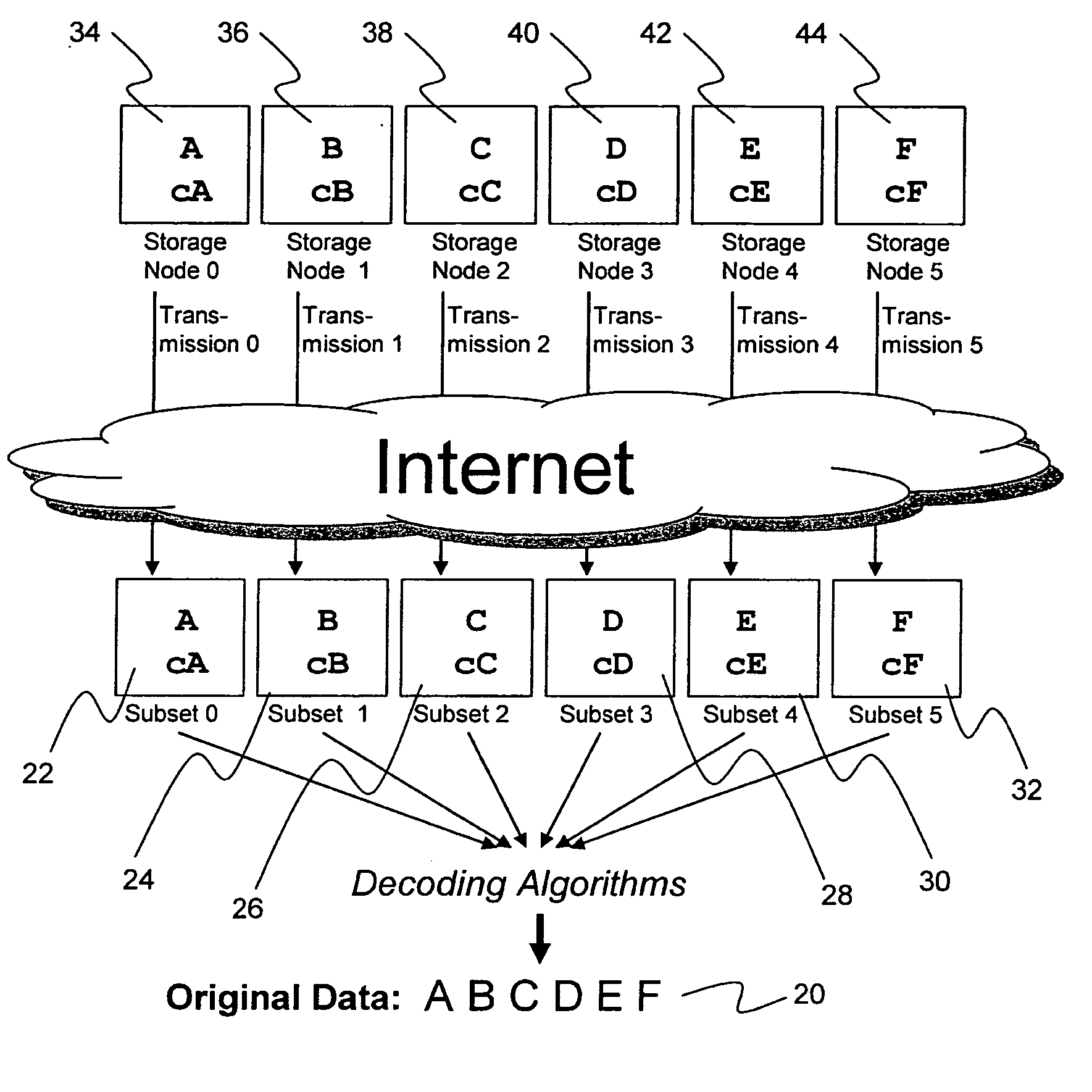
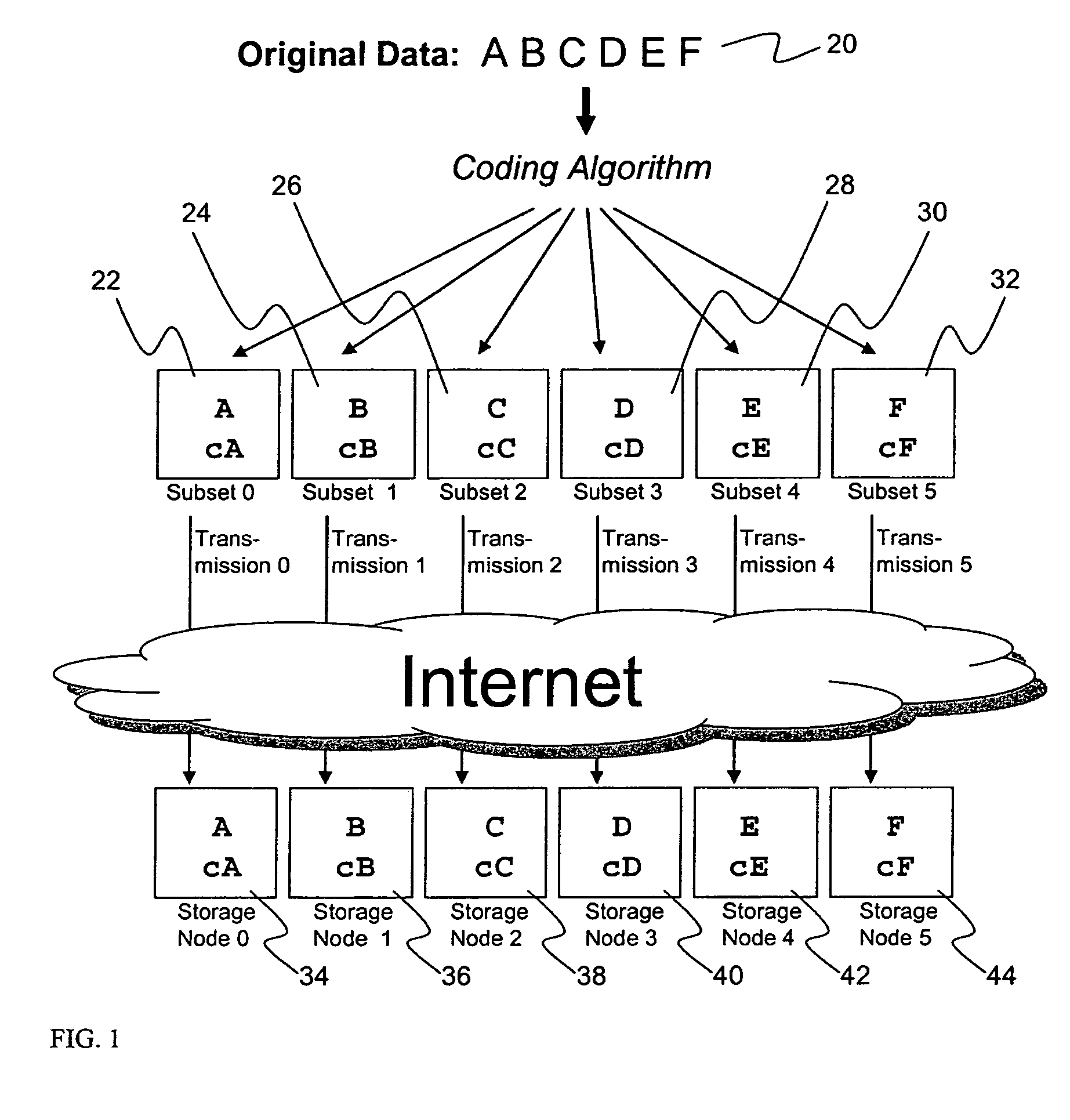
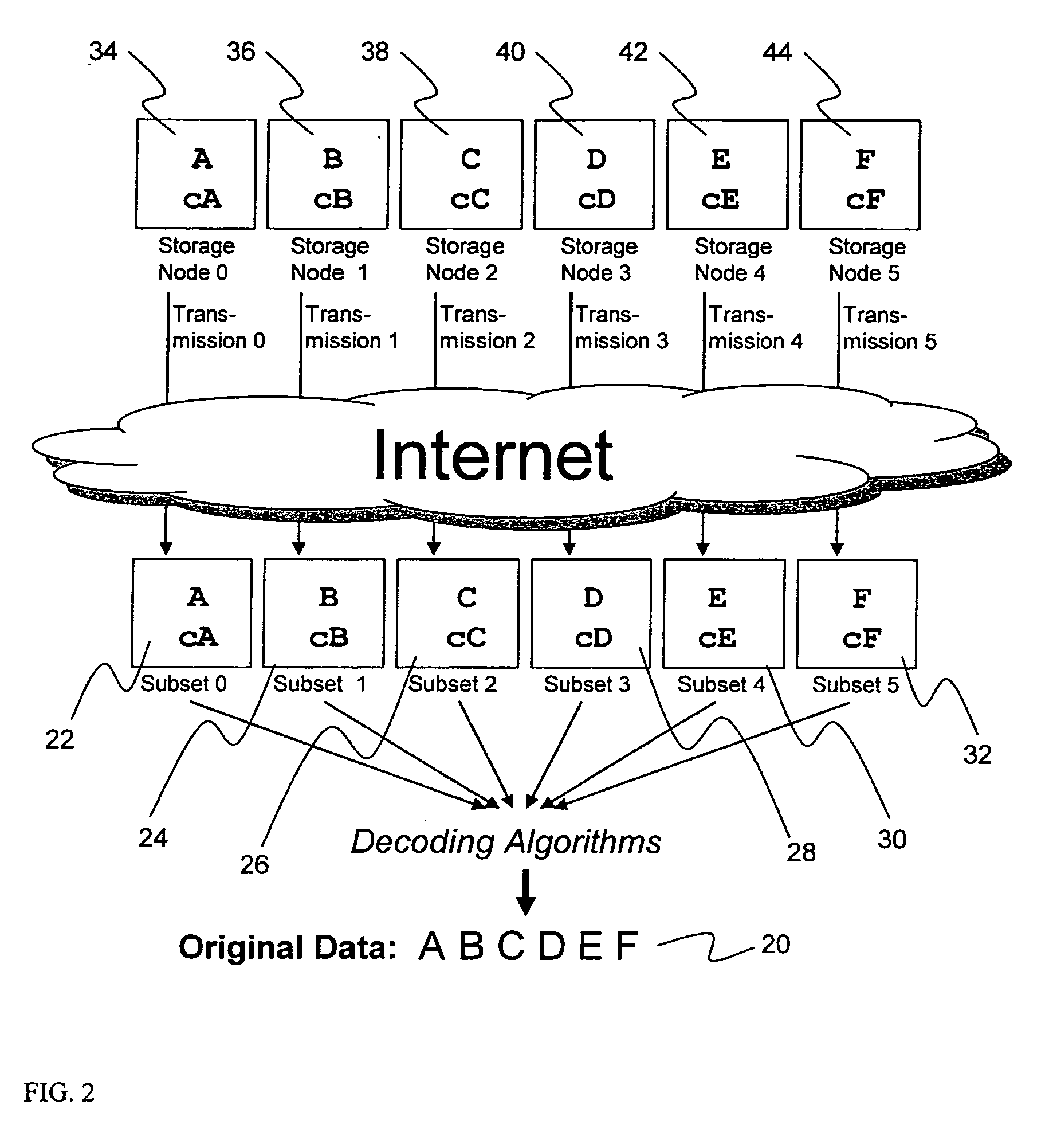
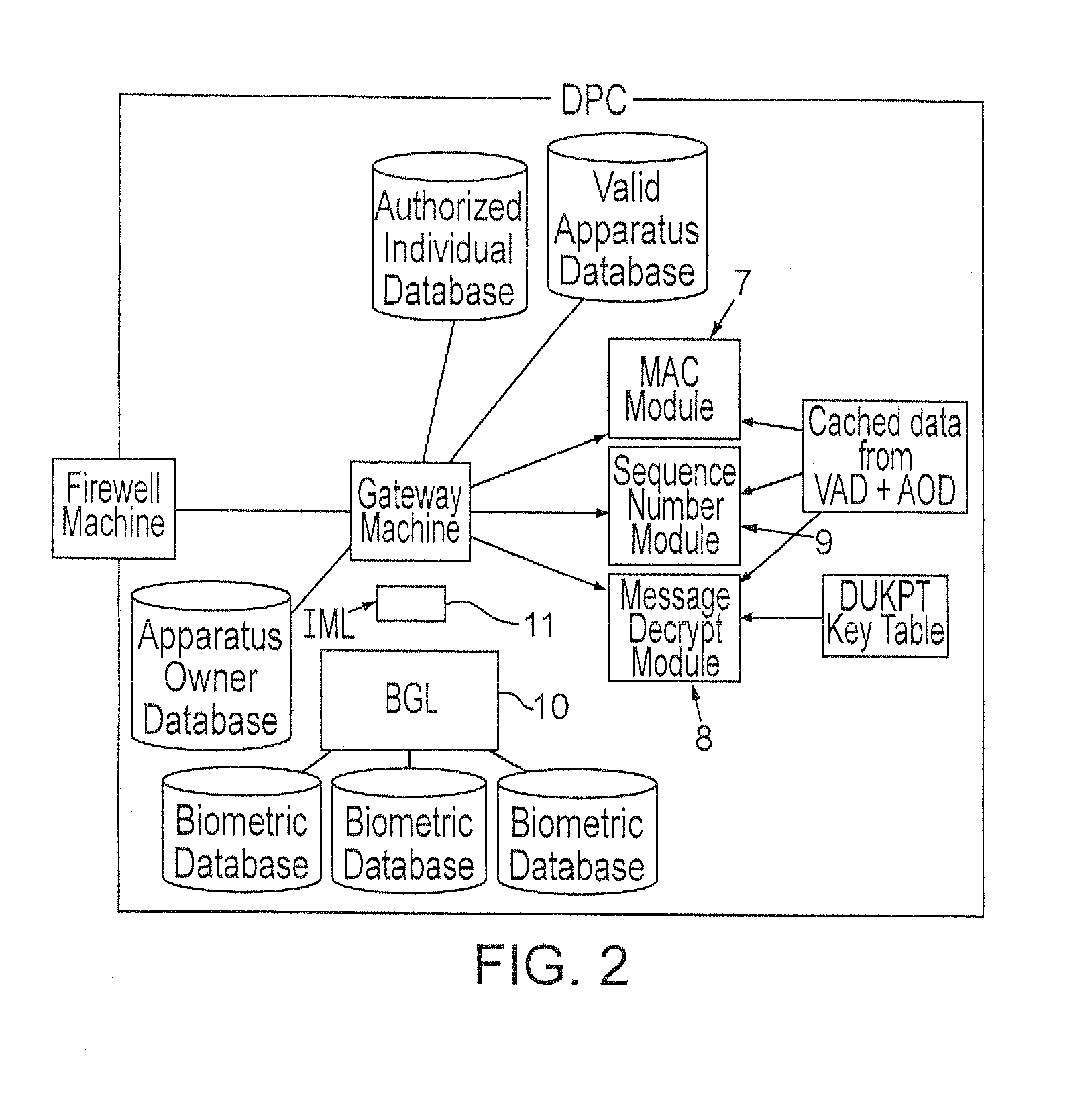
Metadata management system for an information dispersed storage system
ActiveUS20070079083A1Less usableImprove privacyComputer security arrangementsMemory systemsInformation dispersalMetadata management
Briefly, the present invention relates to an information dispersal sytem in which original data to be stored is separated into a number of data “slices” in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate storage devices as a way of increasing privacy and security. In accordance with an important aspect of the invention, a metadata management system stores and indexes user files across all of the storage nodes. A number of applications run on the servers supporting these storage nodes and are responsible for controlling the metadata. Metadata is the information about the data, the data slices or data subsets and the way in which these data subsets are dispersed among different storage nodes running over the network. As used herein, metadata includes data source names, their size, last modification date, authentication information etc. This information is required to keep track of dispersed data subsets among all the nodes in the system. Every time new data subsets are stored and old ones are removed from the storage nodes, the metadata is updated. In accordance with an important aspect of the invention, the metadata management system stores metadata for dispersed data where: The dispersed data is in several pieces. The metadata is in a separate dataspace from the dispersed data. Accordingly, the metadata management system is able to manage the metadata in a manner that is computationally efficient relative to known systems in order to enable broad use of the invention using the types of computers generally used by businesses, consumers and other organizations currently.
Owner:PURE STORAGE
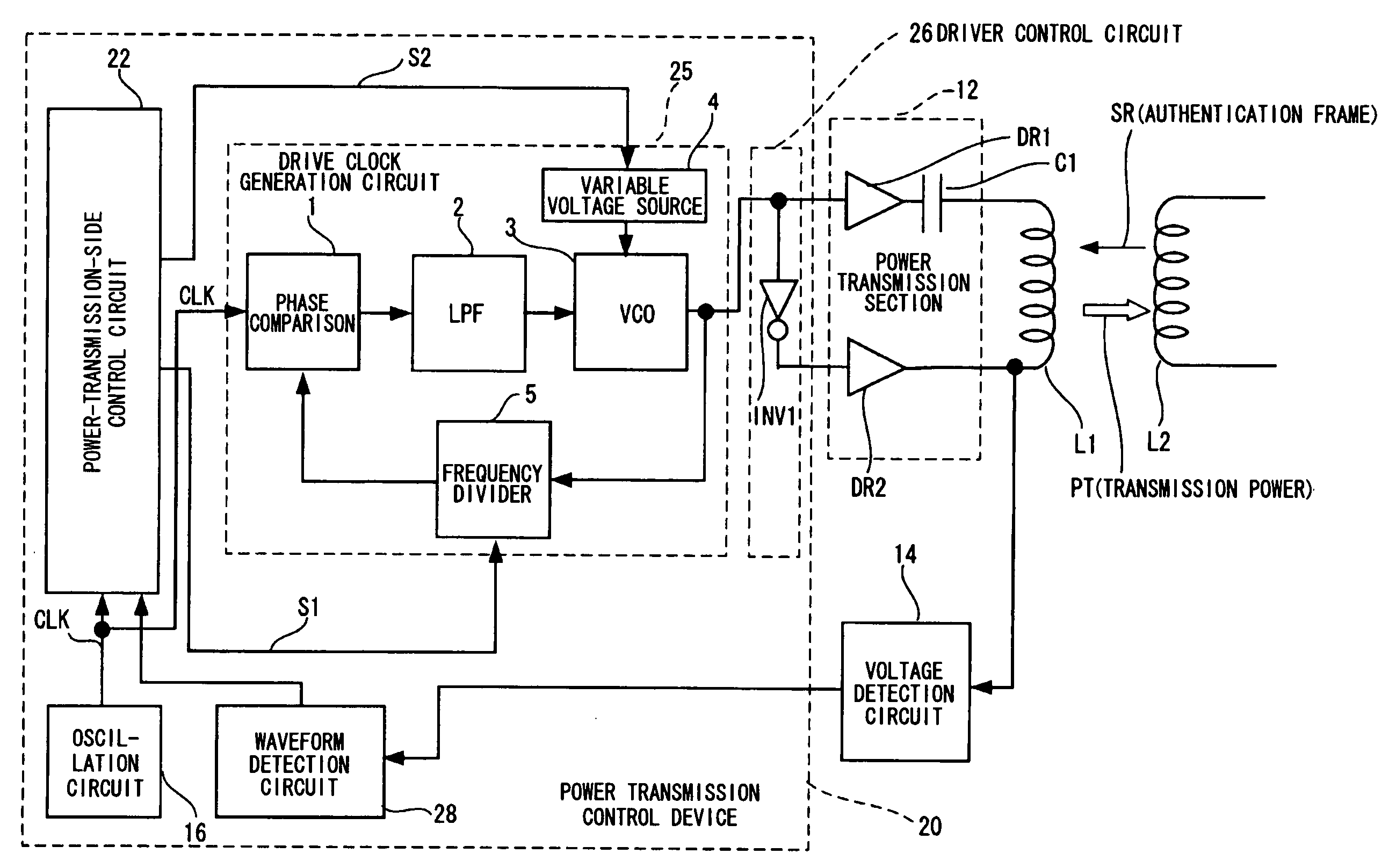
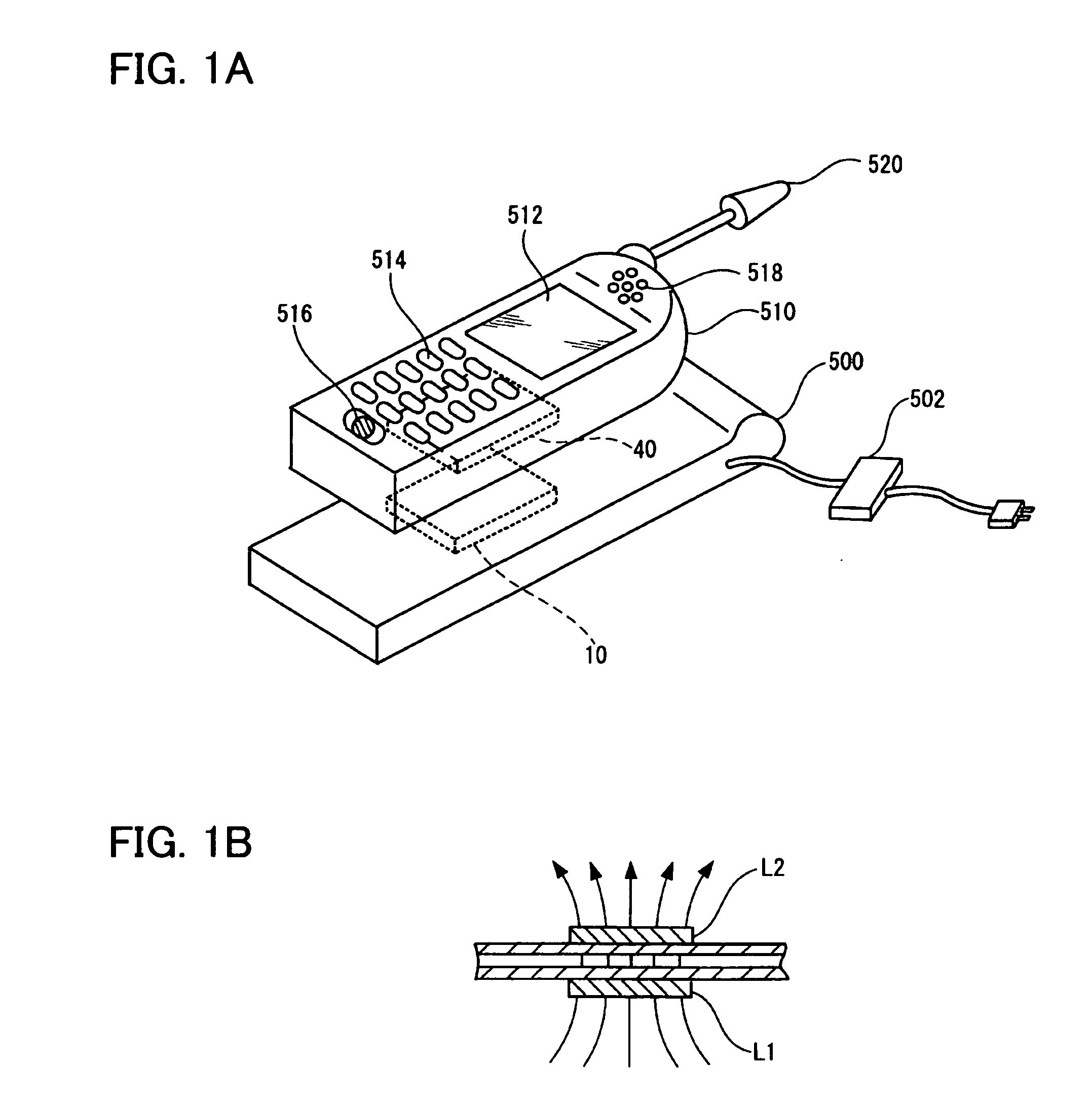
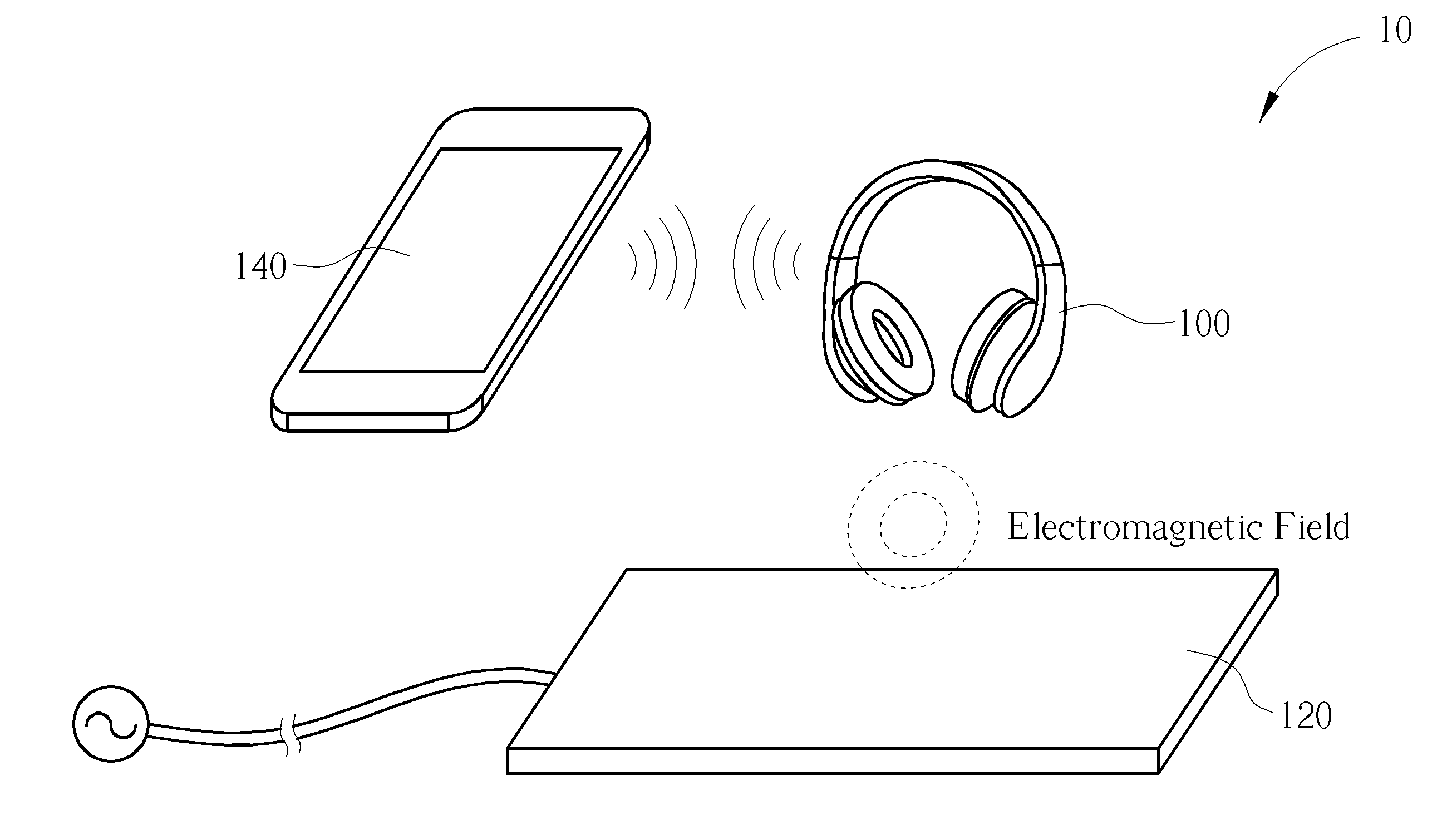
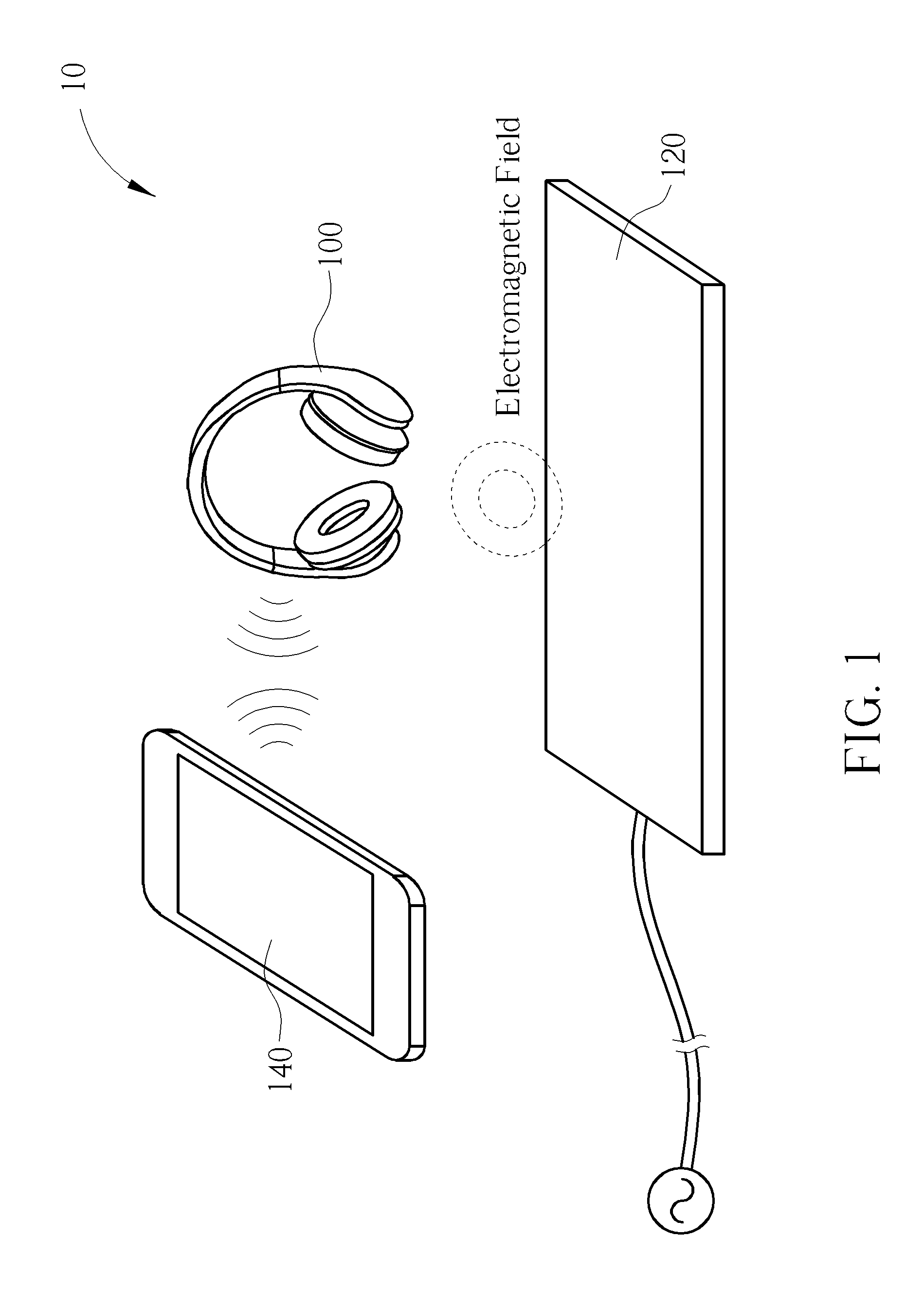
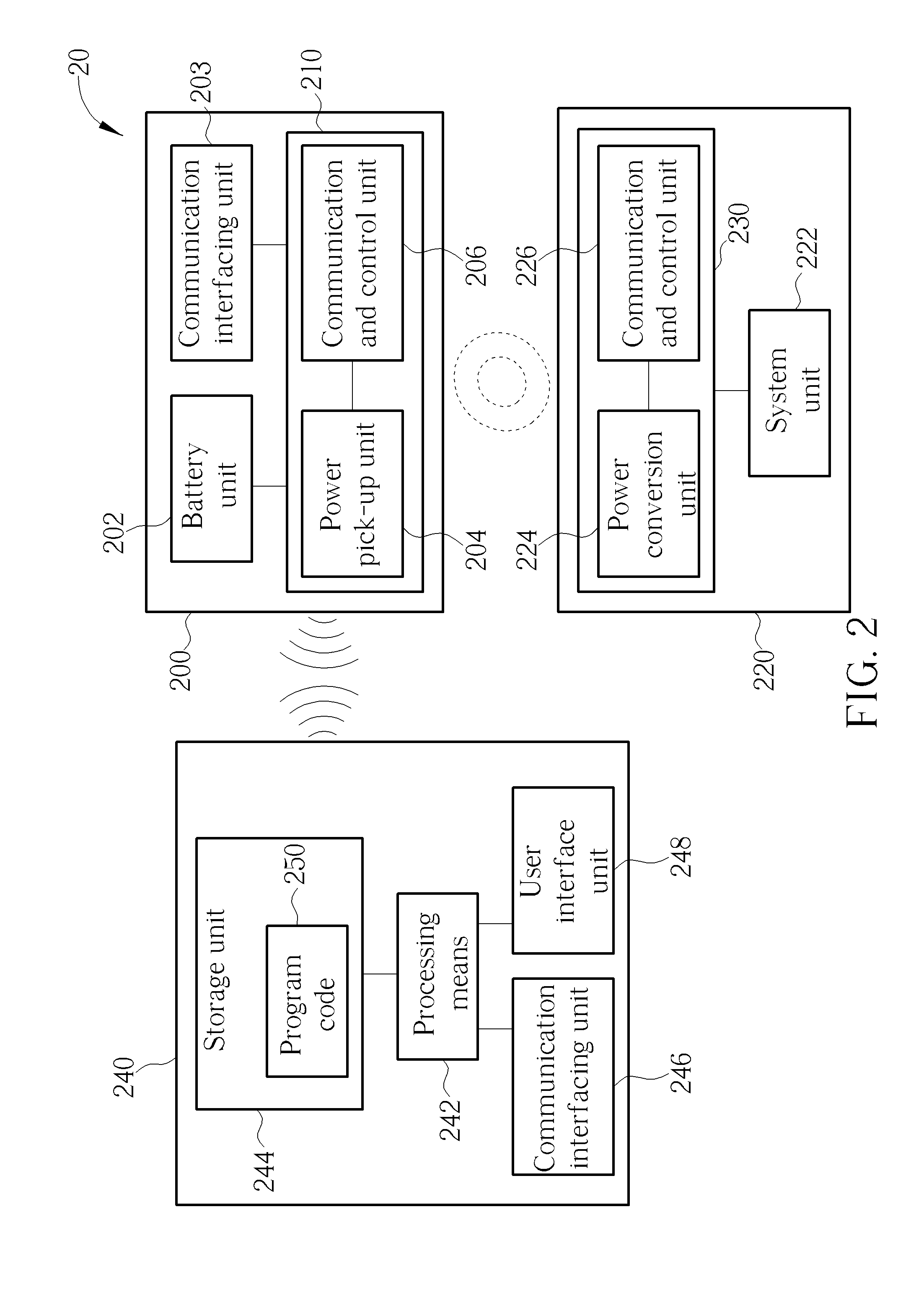
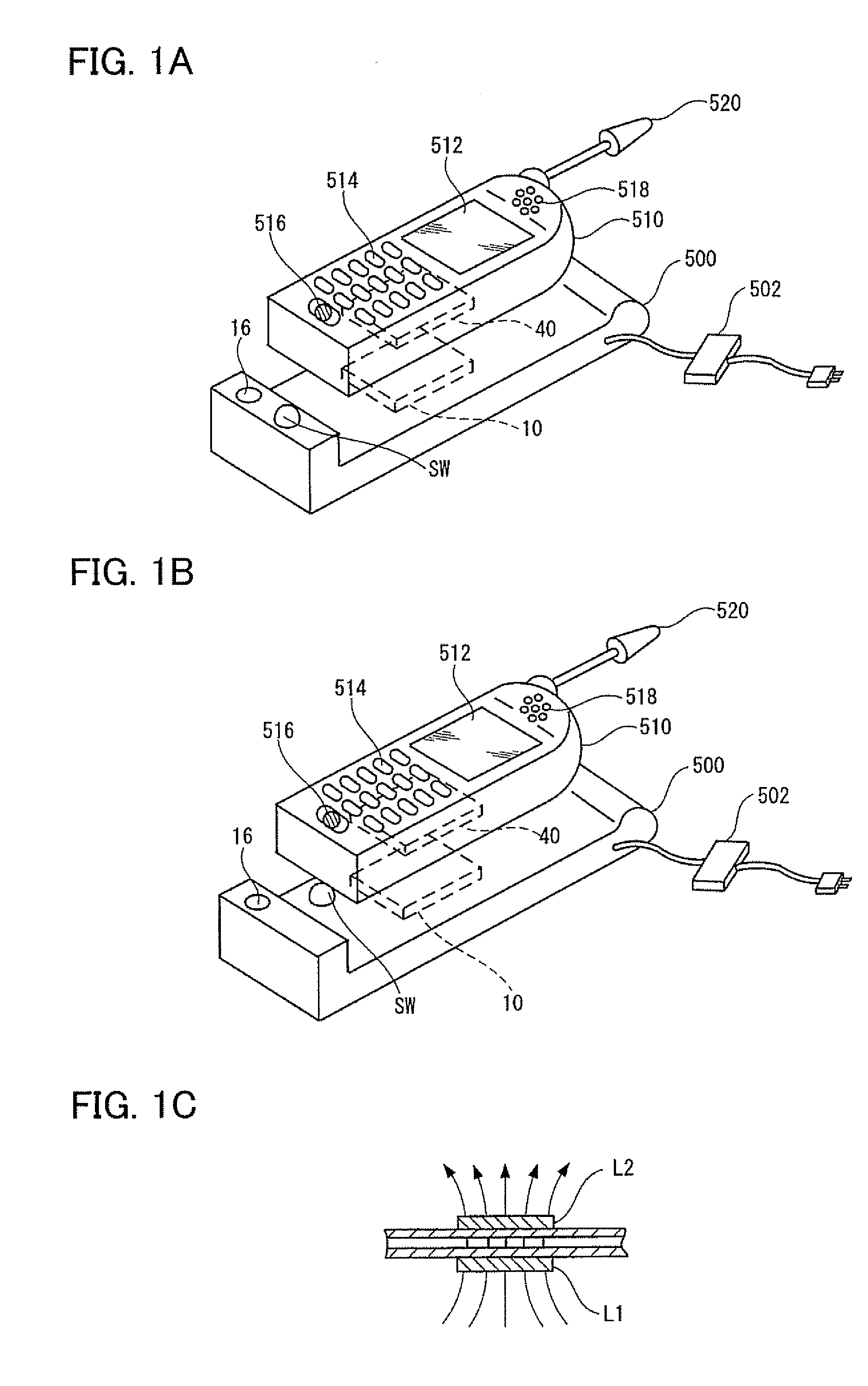
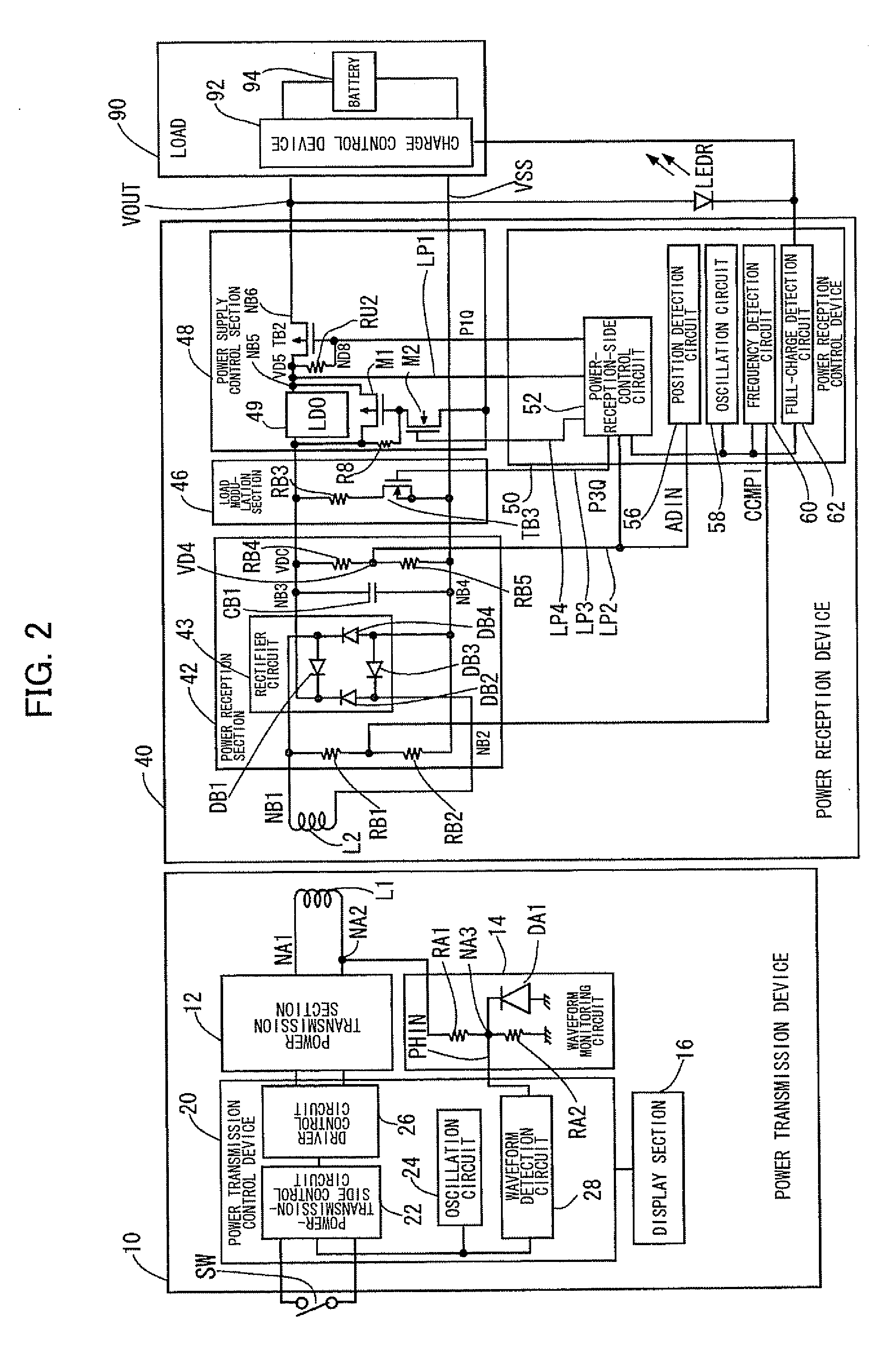
Power transmission control device, power reception control device, non-contact power transmission system, power transmission device, power reception device, and electronic instrument
ActiveUS20080197802A1Circuit authenticationInterconnection arrangementsElectric power transmissionResonance
A power reception device transmits authentication information (e.g., start code, manufacturer ID, product ID, rated power information, and resonance characteristic information) to a power transmission device before starting normal power transmission by a non-contact power transmission system. The power transmission device performs instrument authentication based on the received authentication information, and regulates the maximum transmission power is regulated to conform to a power-reception-device side rated power. The power transmission device then performs normal power transmission.
Owner:SEIKO EPSON CORP +1
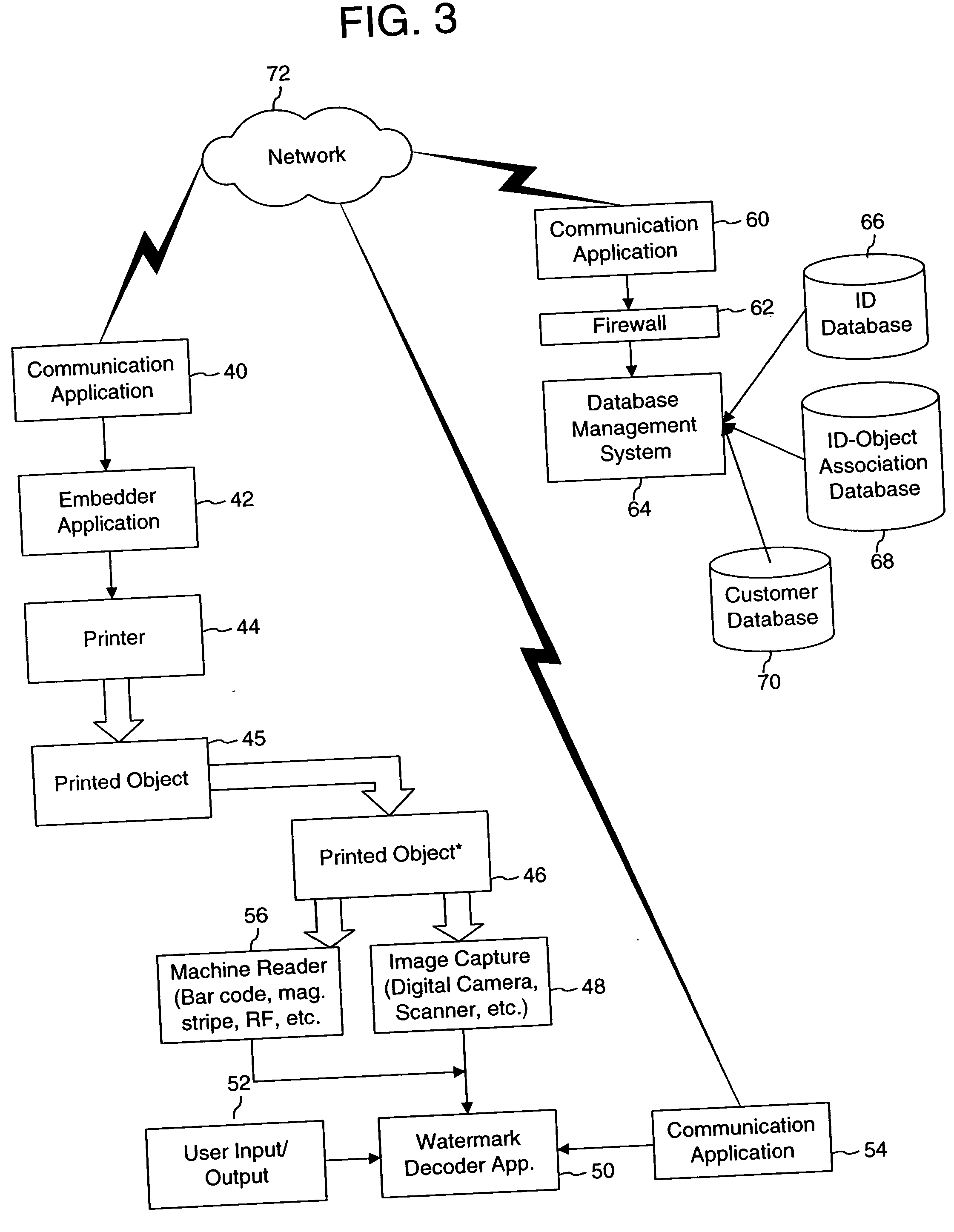
Digital authentication with digital and analog documents
InactiveUS20040153649A1More dataCompact formDigitally marking record carriersDigital data processing detailsAuthentication information
The disclosure describes systems for creating and authenticating printed objects using authentication information. Techniques for incorporating authentication information into digital representations of objects and using the authentication information to authenticate the objects are also provided.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
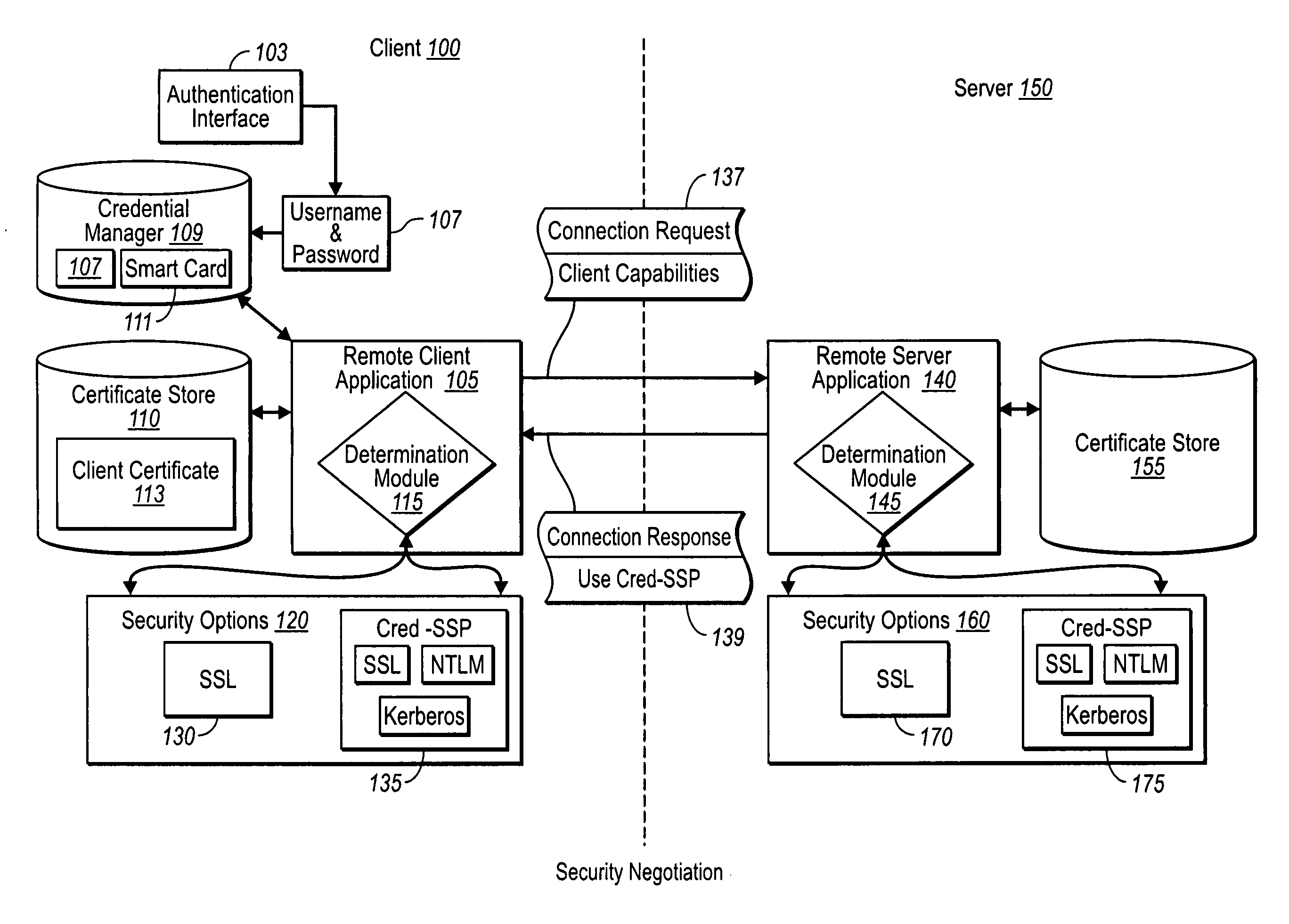
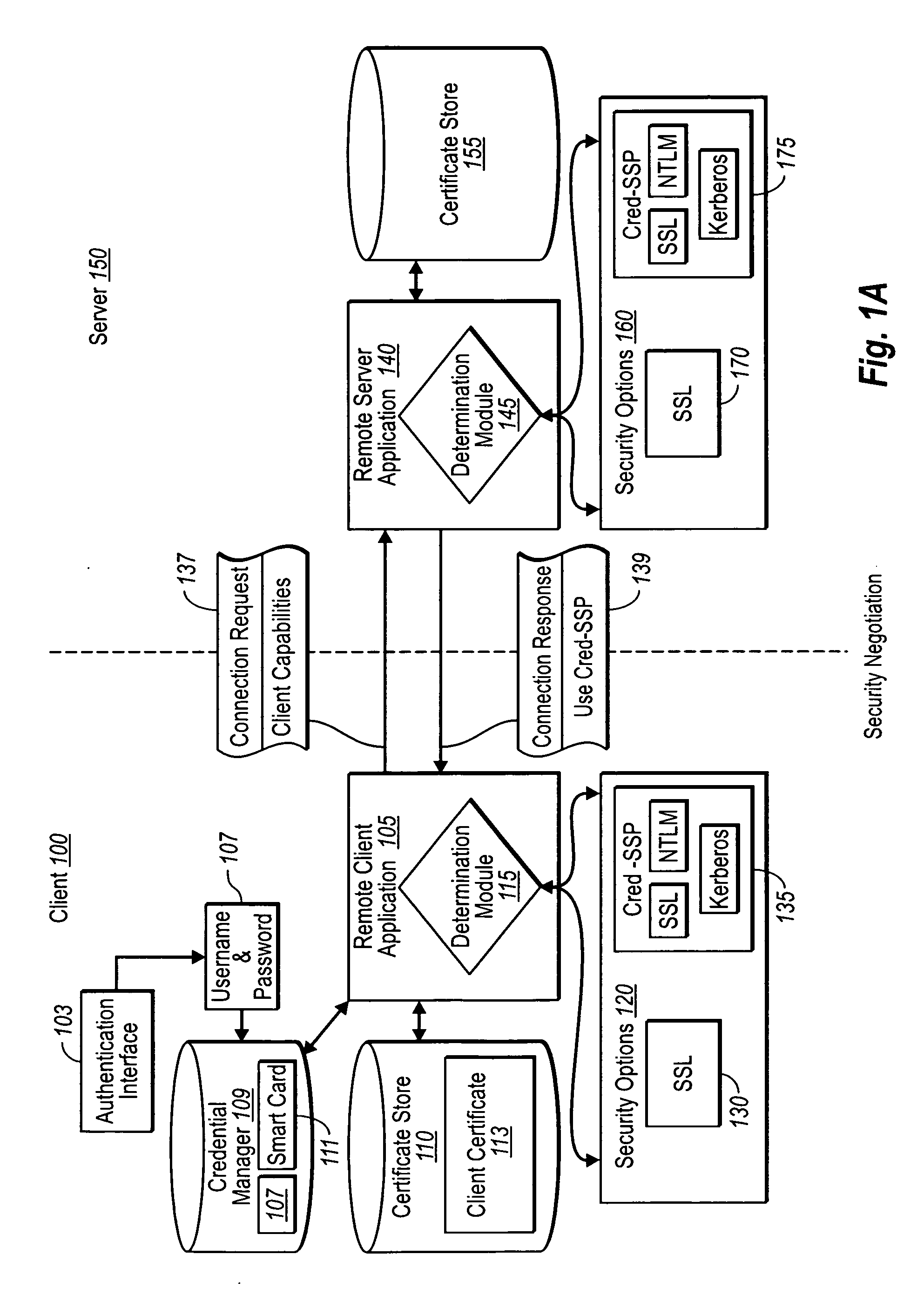
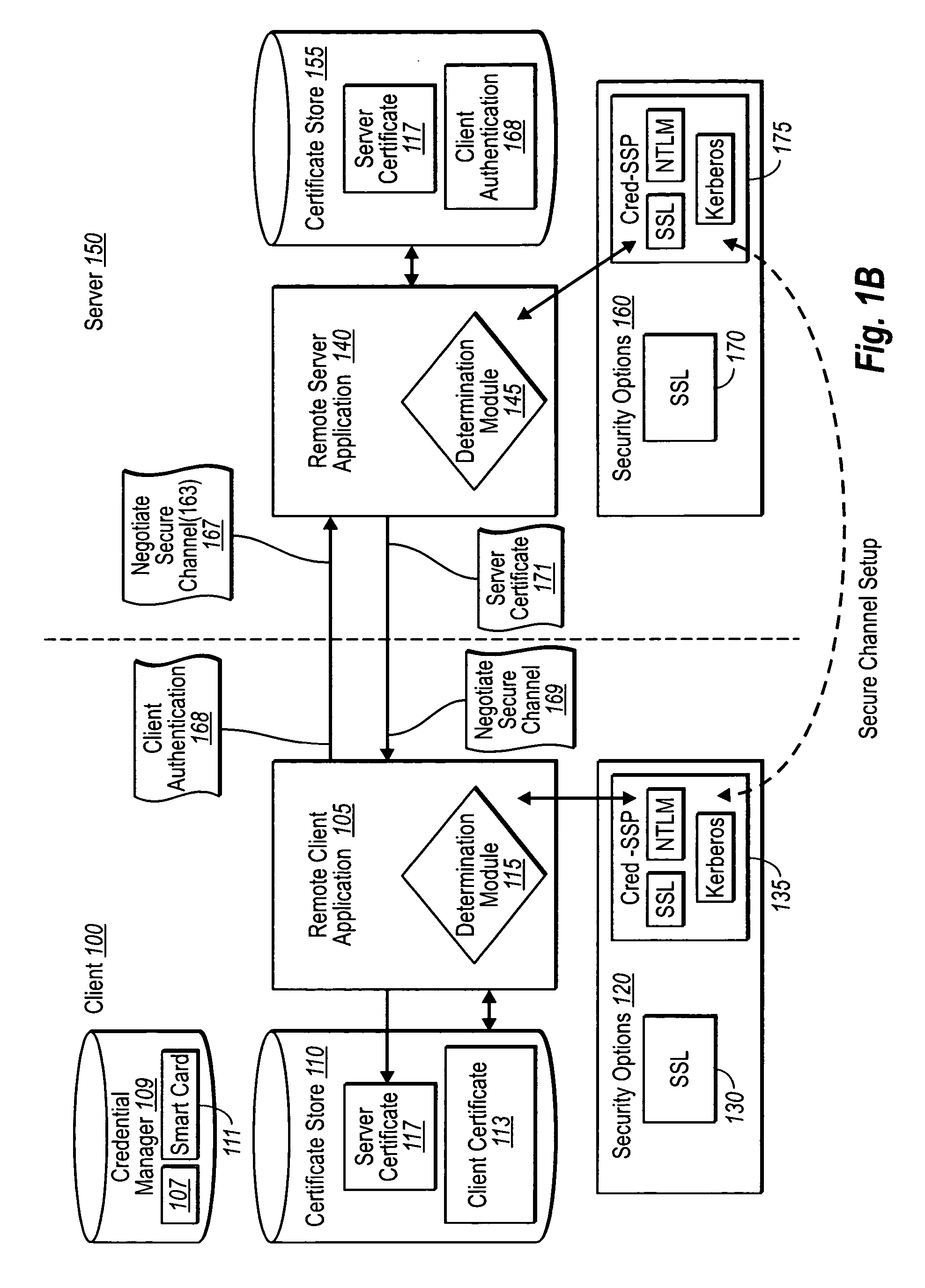
Creating secure interactive connections with remote resources
ActiveUS20070061878A1Easy to adaptDigital data processing detailsUser identity/authority verificationSecure communicationClient-side
Implementations of the present invention efficiently establish secure connections between a client and server, at least in part by authenticating the client and server early on in the connection setup phases. A client initiating a connection with a server identifies the secure communication protocols enabled at the client, and identifies these protocols in a connection request it sends to the server. The server processes the message and responds with a communication protocol it deems appropriate for the connection. The client and server then exchange appropriate authentication information, and then establish a connection session that implements the chosen communication protocol, and encrypts messages using the negotiated communication protocol. Additional implementations relate to reestablishing dropped connections behind virtual Internet Protocol addresses, without necessarily having to recommit much connection resource overhead.
Owner:MICROSOFT TECH LICENSING LLC
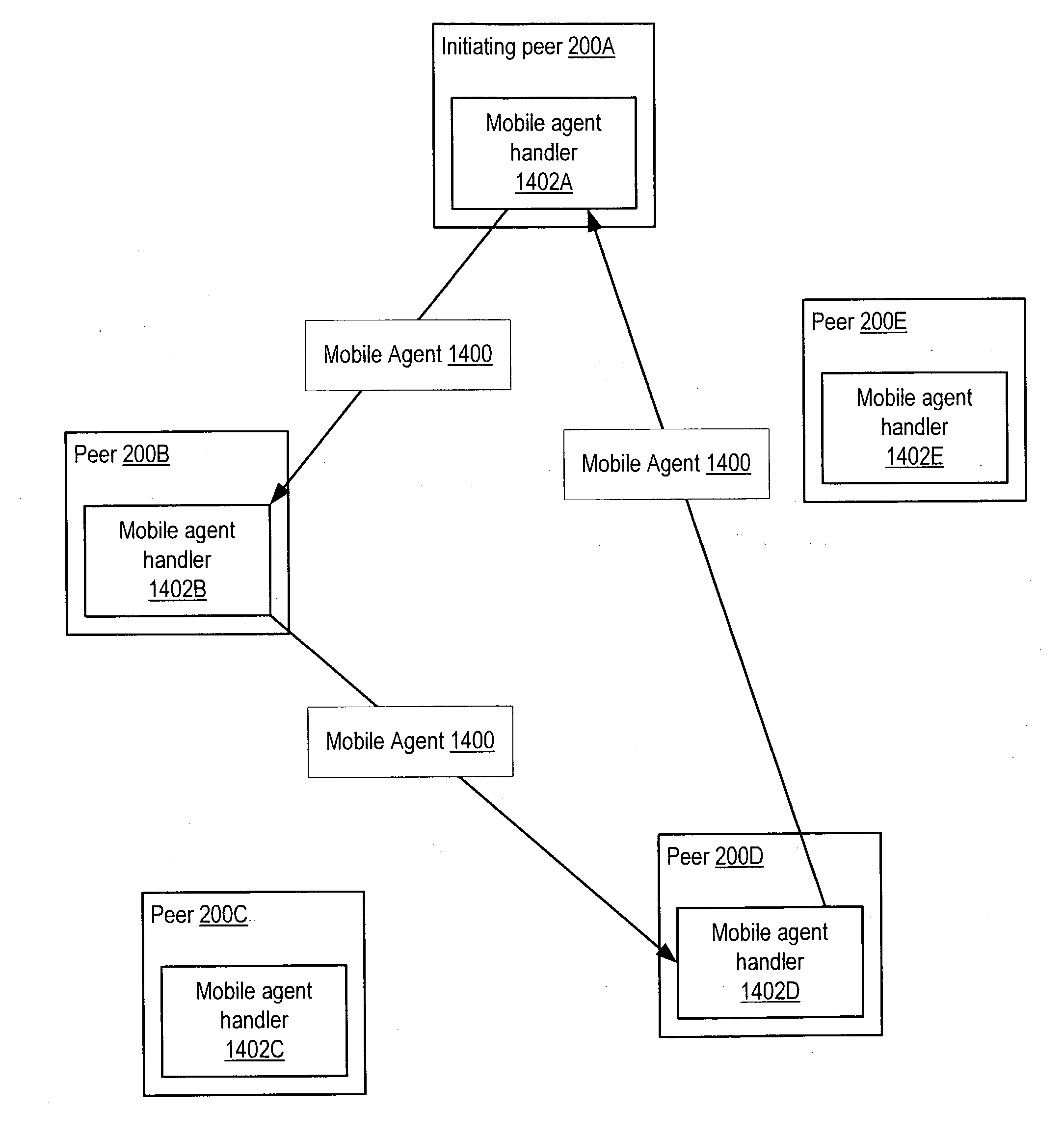
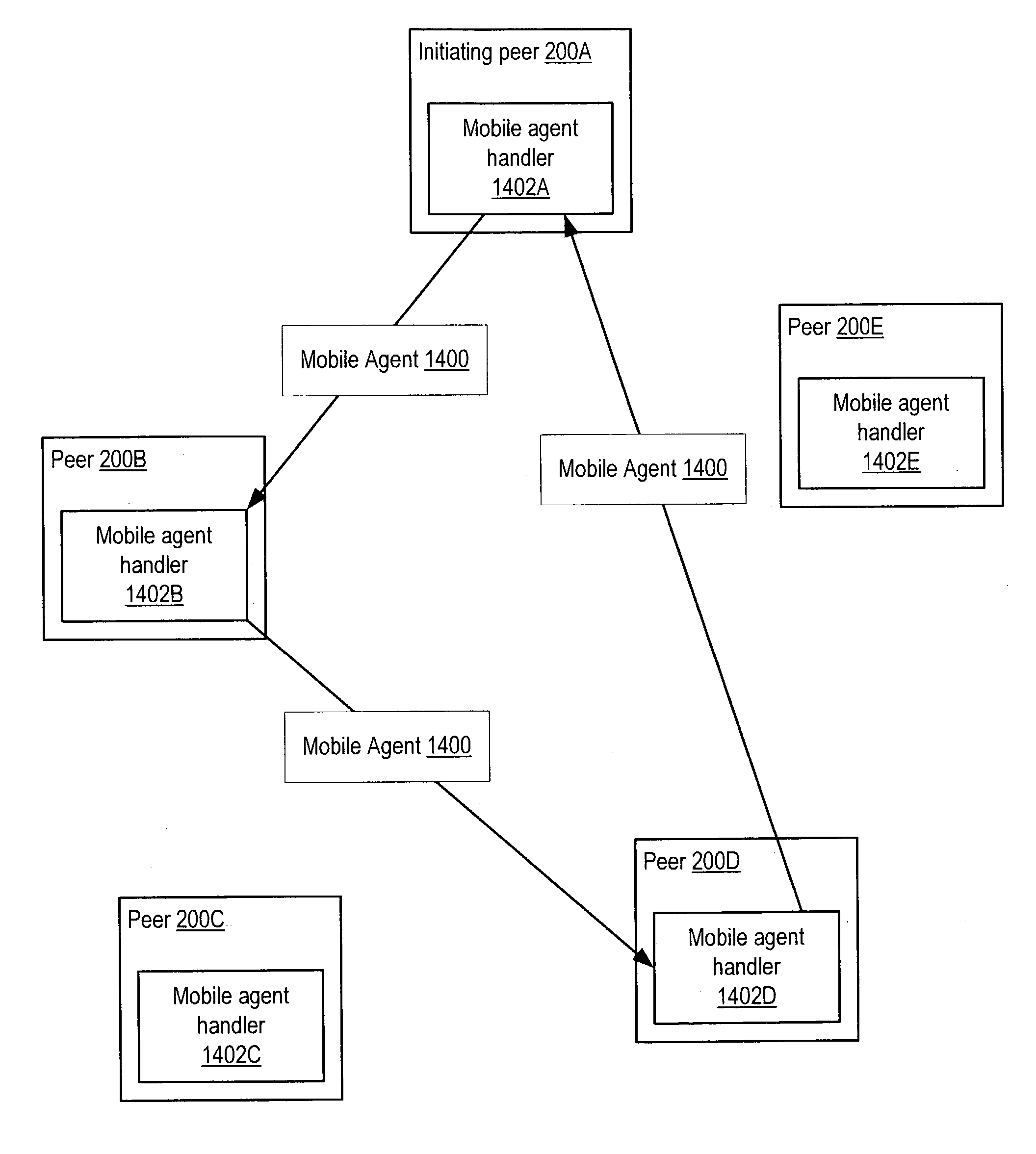
Managing distribution of content using mobile agents in peer-topeer networks
Embodiments of a system and method for using mobile agents for managing distribution of content in peer-to-peer networks. An initiating peer node may launch a mobile agent including an itinerary of a group of peer nodes configured to receive and share content from a distributor. The mobile agent may visit the peer nodes on the itinerary to search for and collect information on distributor content stored on the visited peer nodes. The mobile agent may return the payload to the initiating peer node after completing the itinerary. In one embodiment, the mobile agent may include authentication information, and each visited peer node may access the authentication information to verify the mobile agent as authorized by the distributor. The initiating peer node may examine the information provided by the mobile agent to detect unauthorized copies of the distributor content.
Owner:ORACLE INT CORP
Method and apparatus for providing authentication using policy-controlled authentication articles and techniques
A method and apparatus provides first or second factor authentication by providing selectability of a plurality of second factor authentication policies associated with a second factor authentication article. The first or second factor authentication article includes authentication information, such as a plurality of data elements in different cells or locations on the authentication article, which can be located by using corresponding location information. The method and apparatus provides second factor authentication based on the first or second factor authentication article by enforcing at least one of the plurality of selected authentication policies.
Owner:ENTRUST
Managing distribution of content using mobile agents in peer-topeer networks
Embodiments of a system and method for using mobile agents for managing distribution of content in peer-to-peer networks. An initiating peer node may launch a mobile agent including an itinerary of a group of peer nodes configured to receive and share content from a distributor. The mobile agent may visit the peer nodes on the itinerary to search for and collect information on distributor content stored on the visited peer nodes. The mobile agent may return the payload to the initiating peer node after completing the itinerary. In one embodiment, the mobile agent may include authentication information, and each visited peer node may access the authentication information to verify the mobile agent as authorized by the distributor. The initiating peer node may examine the information provided by the mobile agent to detect unauthorized copies of the distributor content.
Owner:ORACLE INT CORP
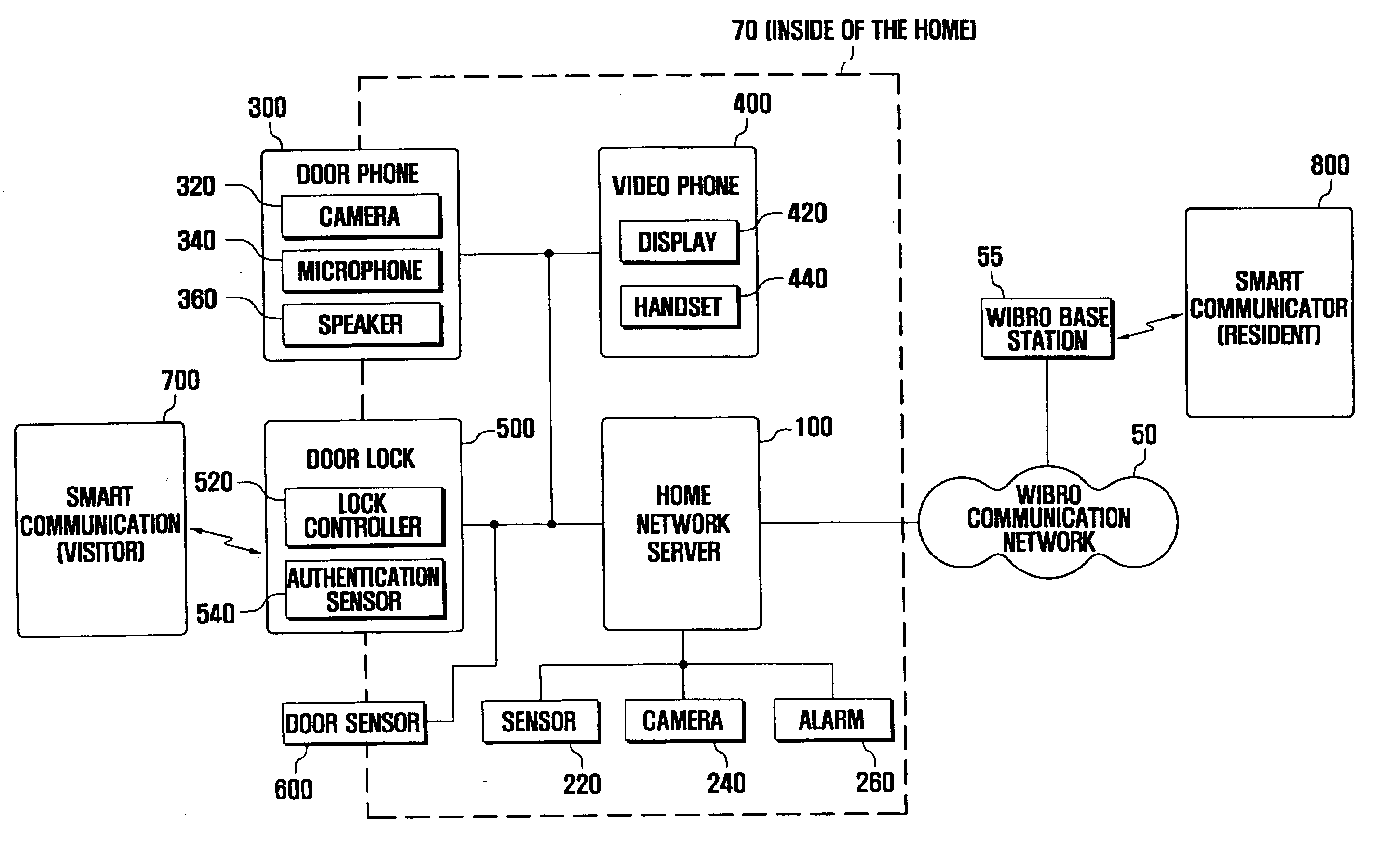
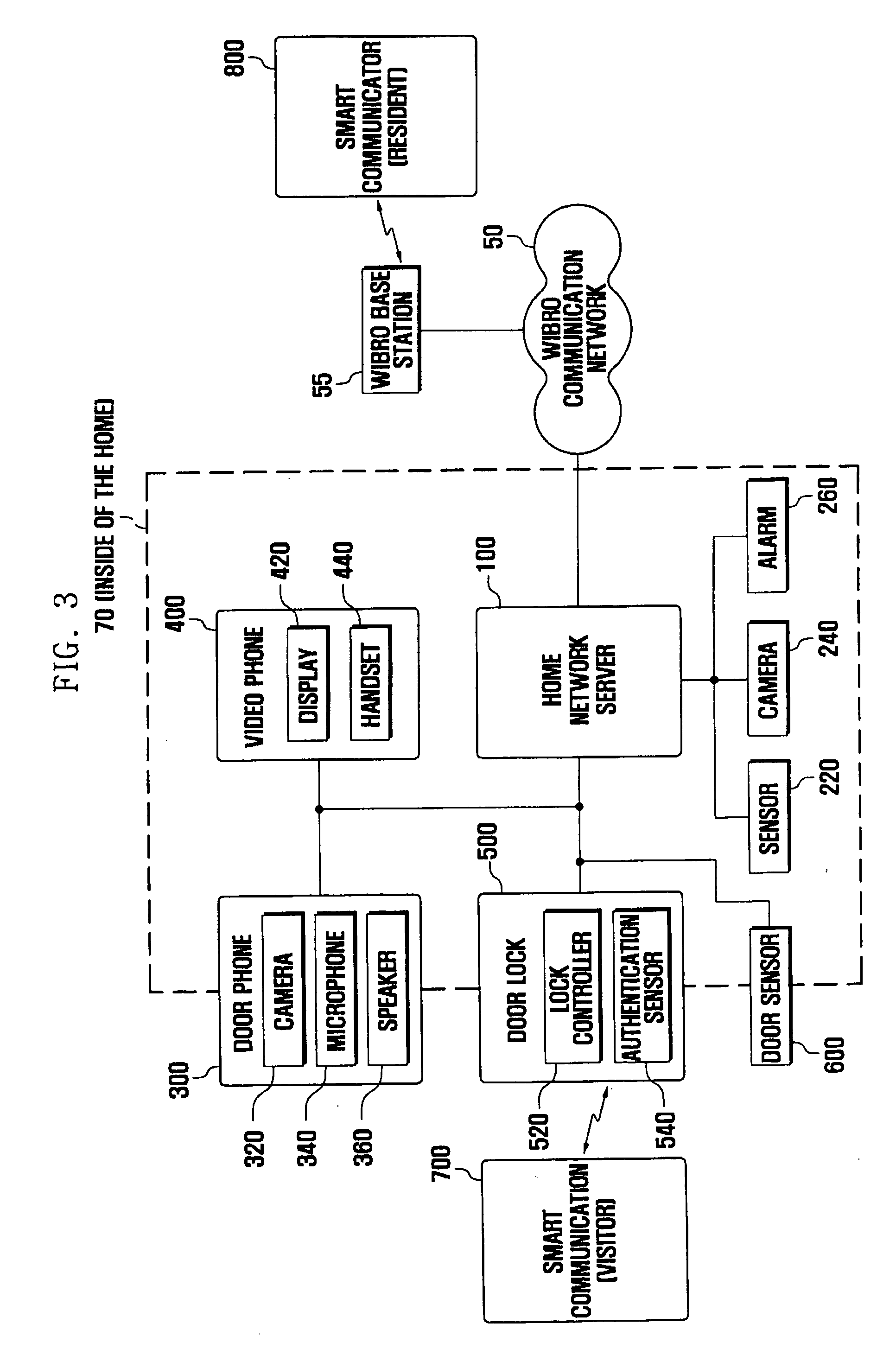
Access authentication system and method using smart communicator
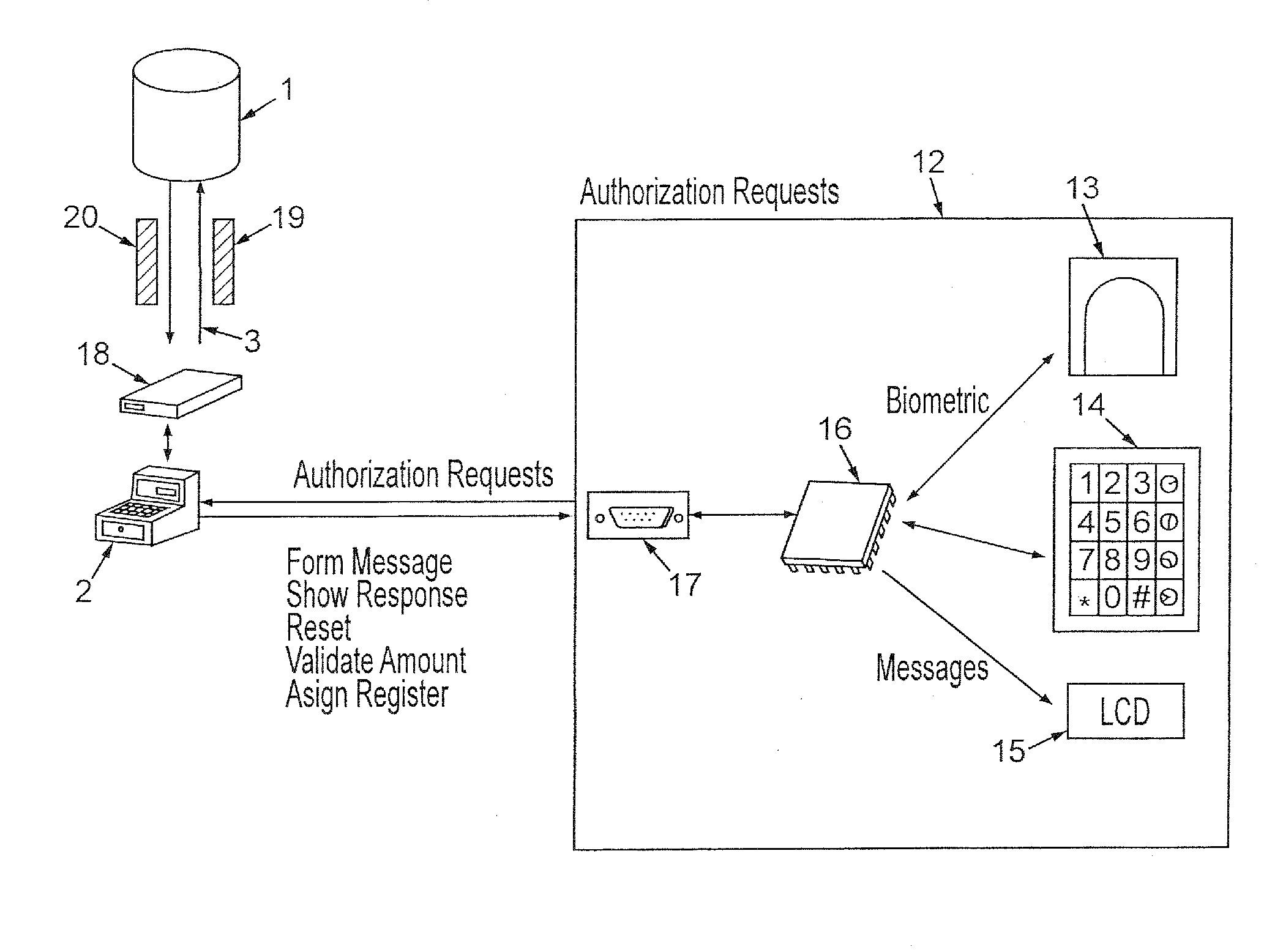
ActiveUS20070216764A1Electric signal transmission systemsMultiple keys/algorithms usageCommunication controlAuthentication system
Disclosed is an intelligent access authentication system and method. The intelligent access authentication system includes a door lock that can be locked and released in a predetermined manner, a door phone for communicating with the visitor; a smart communicator which configures access approval levels of expected visitors and access authentication information for each access approval level, communicates with the visitor, and controls the door lock, and a home network server which stores the access approval levels of expected visitors and access authentication information for each access approval level received from the smart communicator, checks the access approval level of the visitor attempting to release the door lock by referring to previously stored information, and transmits a door lock operating command to the door lock according to the access approval level of the visitor. In the present invention, the resident can check the visitor and control the door lock to be released according to the access approval level of the visitor, even at a remote location.
Owner:HUAWEI TECH CO LTD
Method and apparatus for facilitating communication in a content centric network
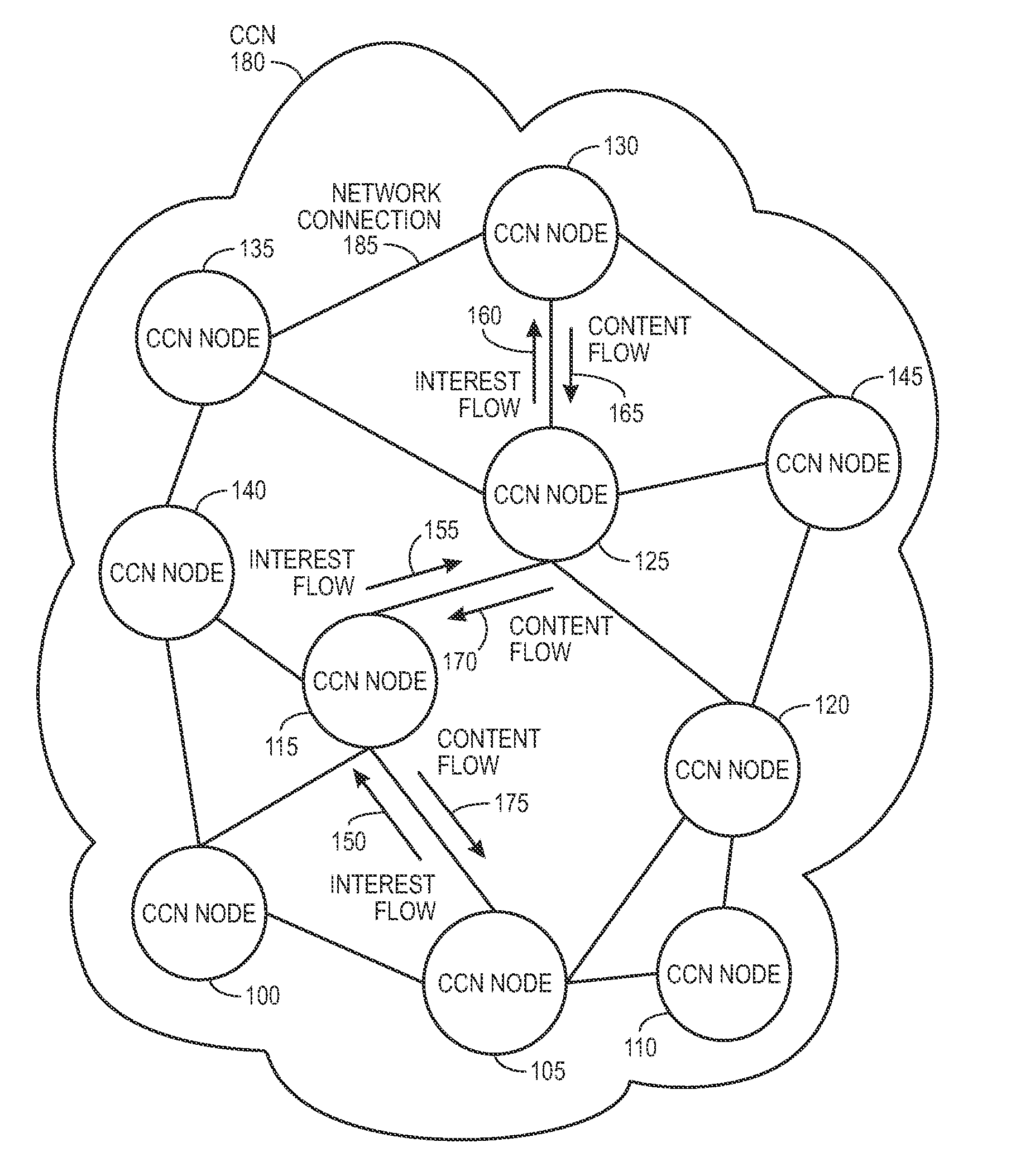
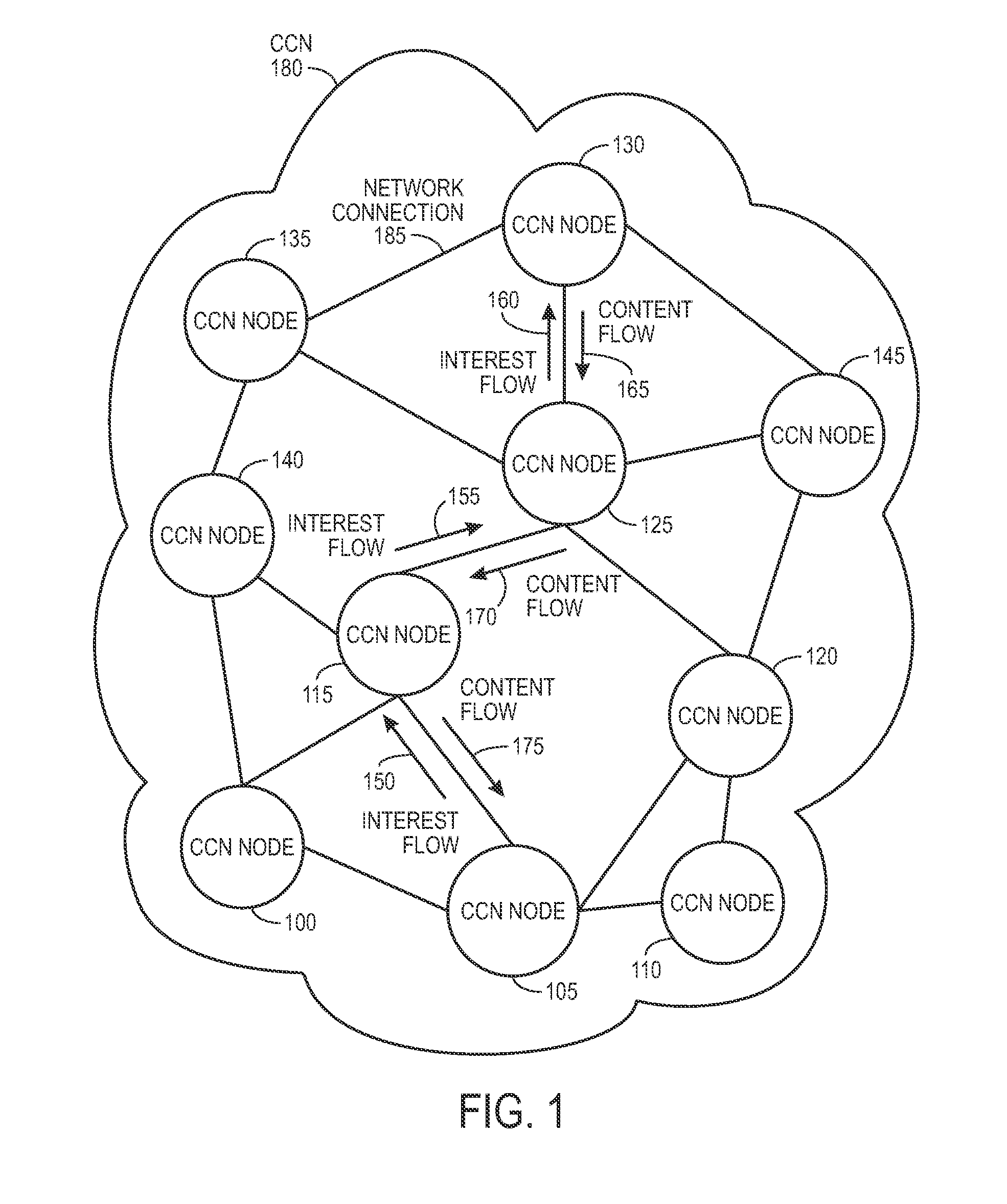
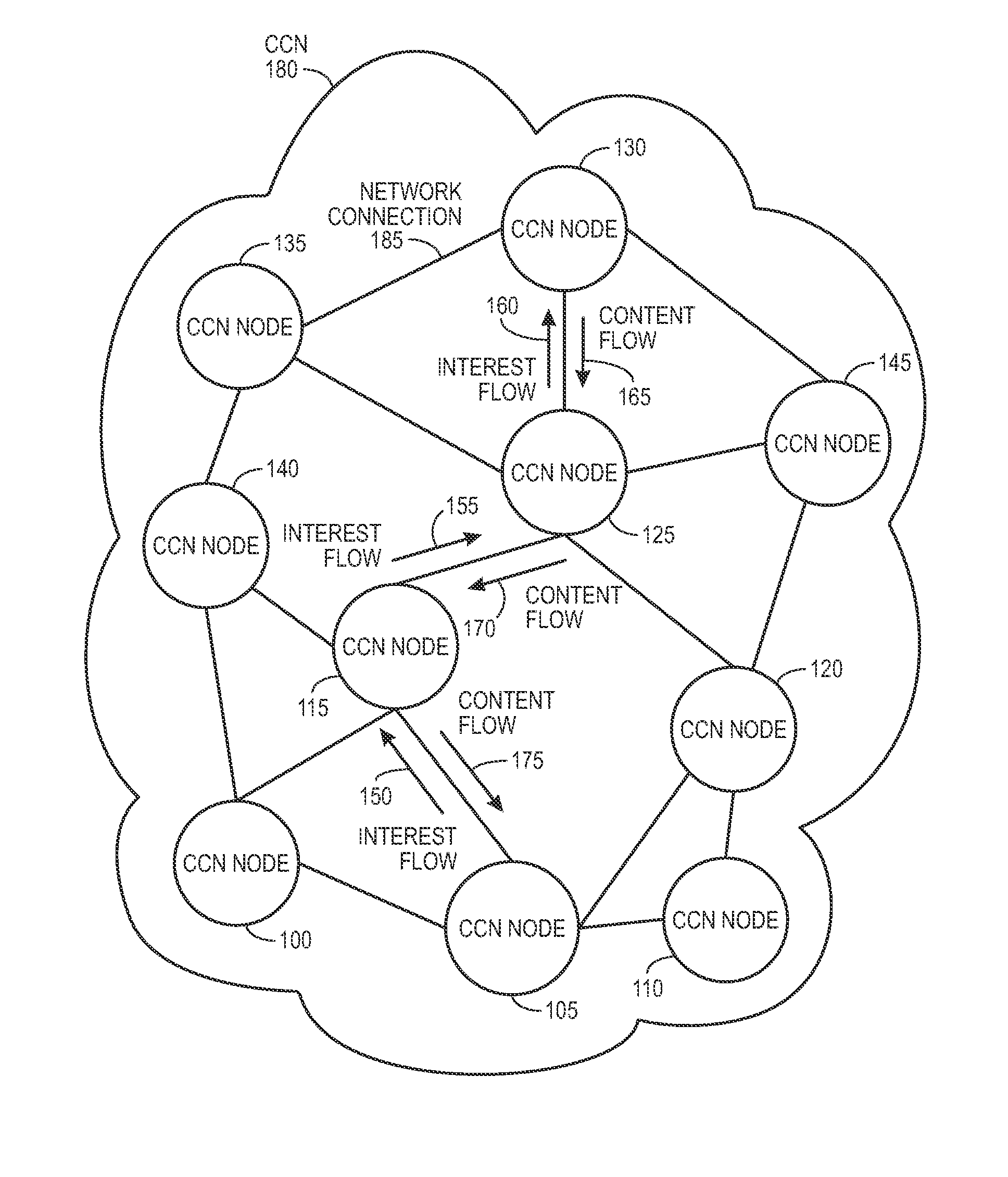
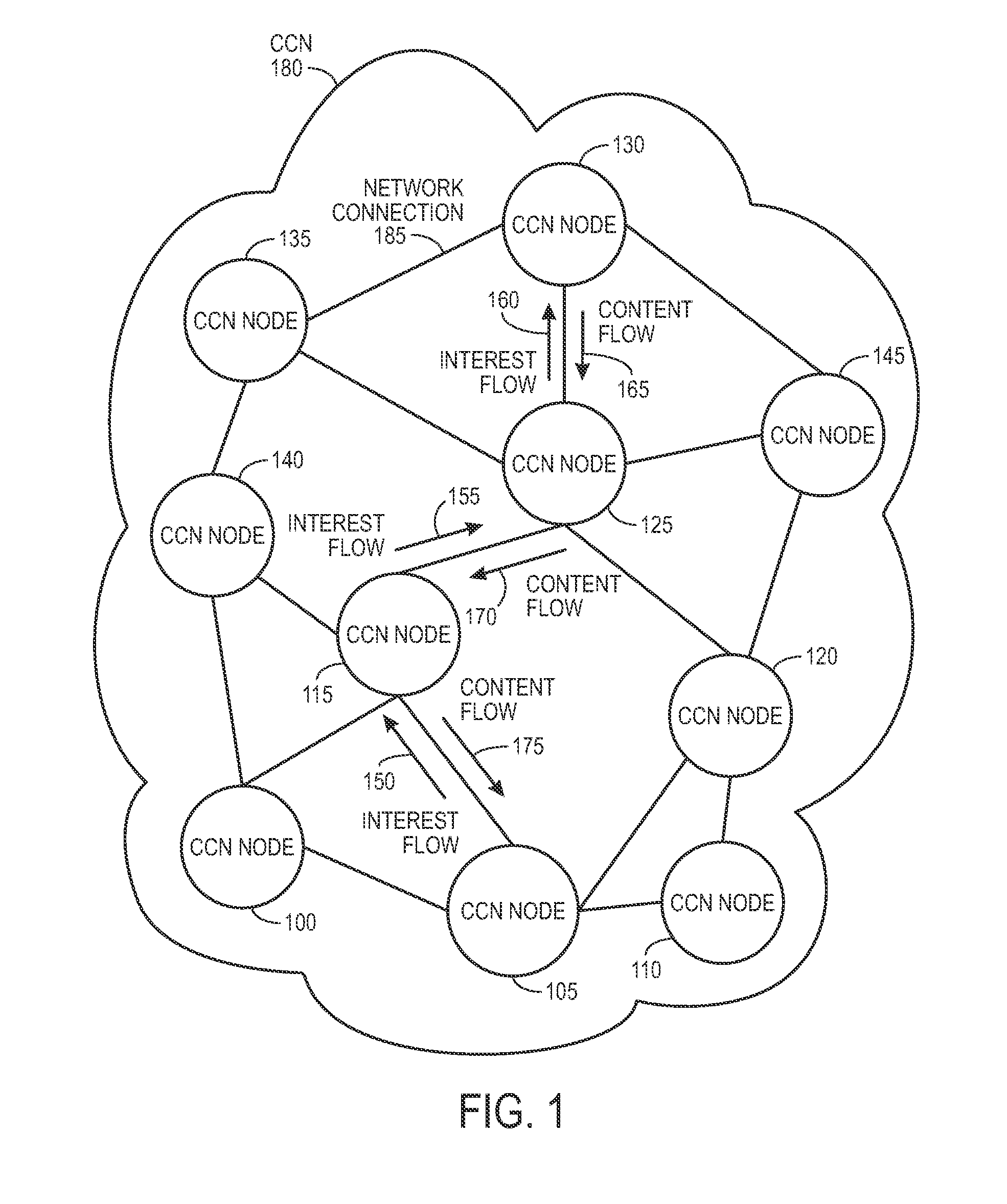
ActiveUS20090287835A1Easy flow controlMultiple digital computer combinationsTransmissionContent centricWorld Wide Web
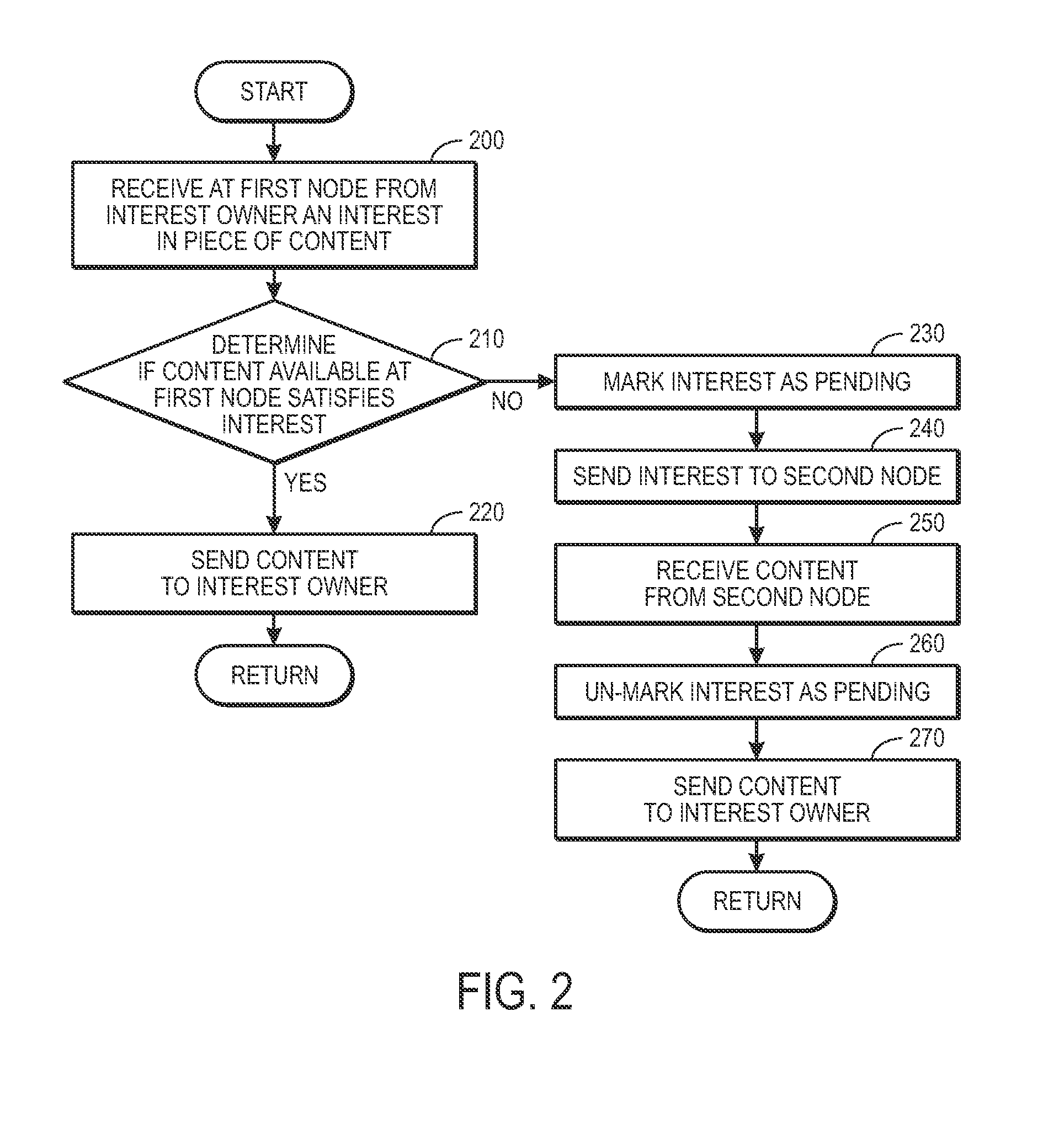
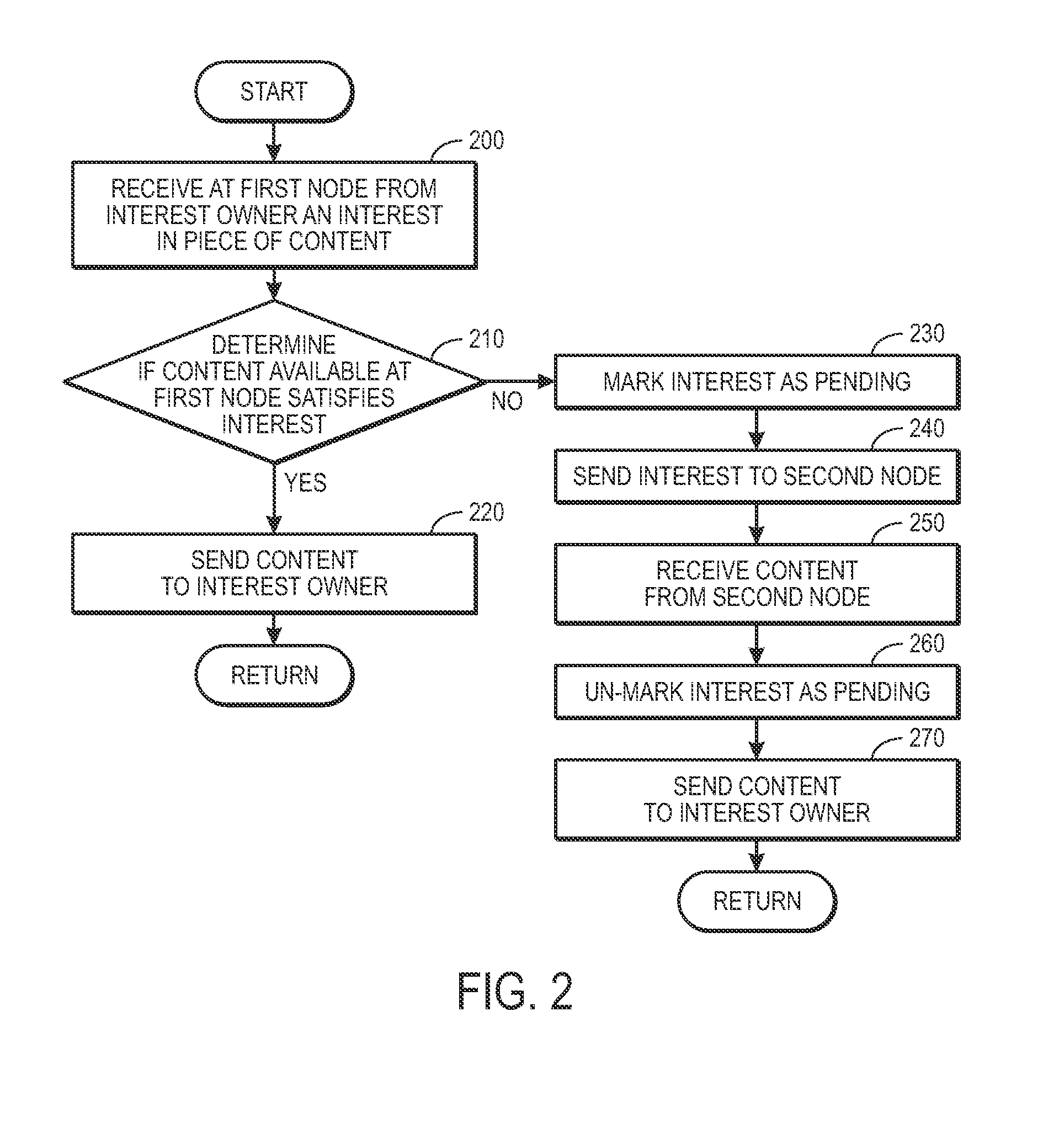
One embodiment of the present invention provides a system for facilitating communication in a content centric network (CCN). During operation, the system receives at a first node from an interest owner an interest in a piece of content. The interest indicates a structured name for the content. Furthermore, the name is unique and persistent with respect to the content, and where the name includes authentication information for the content. Next, the system determines whether content available at the first node satisfies the interest. If so, the system sends the content to the interest owner. Otherwise, the system marks the interest as pending, and forwards the interest to a second node in the network based on the interest. After receiving content from the second node in response to the forwarded interest, the system un-marks the interest as pending and sends the content to the interest owner.
Owner:CISCO TECH INC
Apparatus, method and article for authentication, security and control of power storage devices, such as batteries
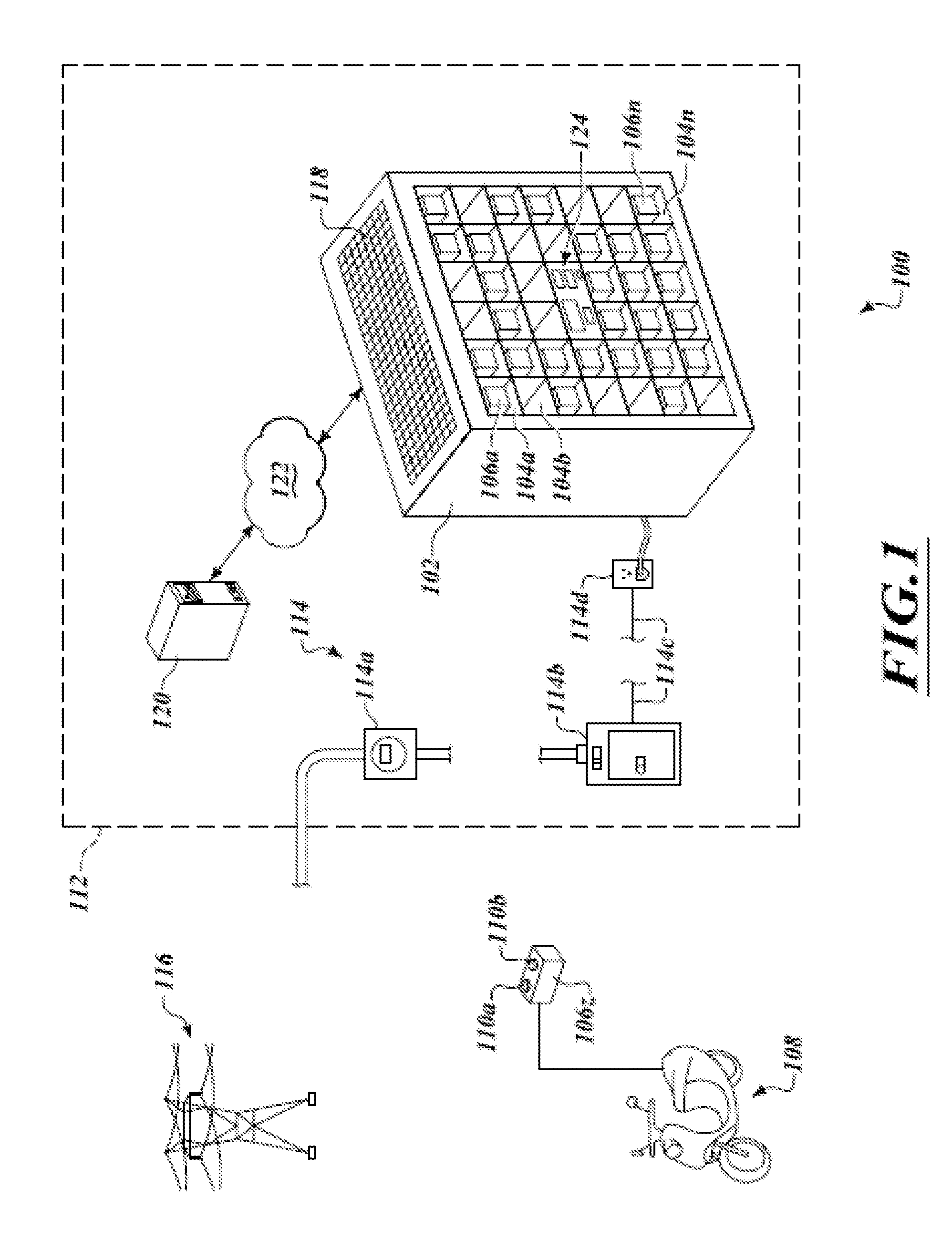
ActiveUS20130026973A1Limited rangeLong recharging timeRegistering/indicating working of vehiclesCoin-freed apparatusSupercapacitorEngineering
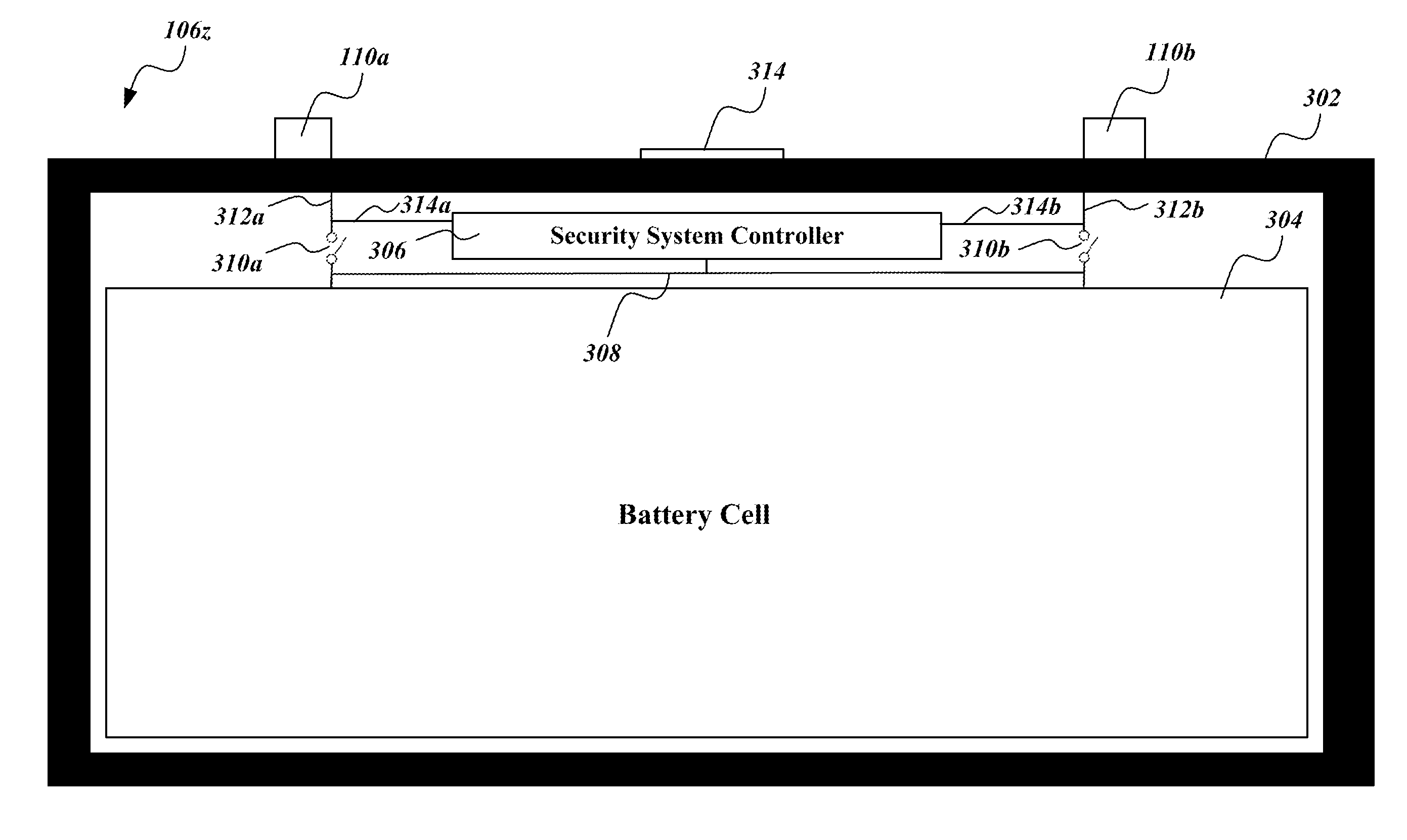
A network of collection, charging and distribution machines collect, charge and distribute portable electrical energy storage devices (e.g., batteries, supercapacitors or ultracapacitors). To charge, the machines employ electrical current from an external source, such as the electrical grid or an electrical service of an installation location. By default, each portable electrical energy storage device is disabled from accepting a charge unless it receives authentication information from an authorized collection, charging and distribution machine, other authorized charging device, or other authorized device that transmits the authentication credentials. Also, by default, each portable electrical energy storage device is disabled from releasing energy unless it receives authentication information from an external device to which it will provide power, such as a vehicle or other authorization device.
Owner:GOGORO
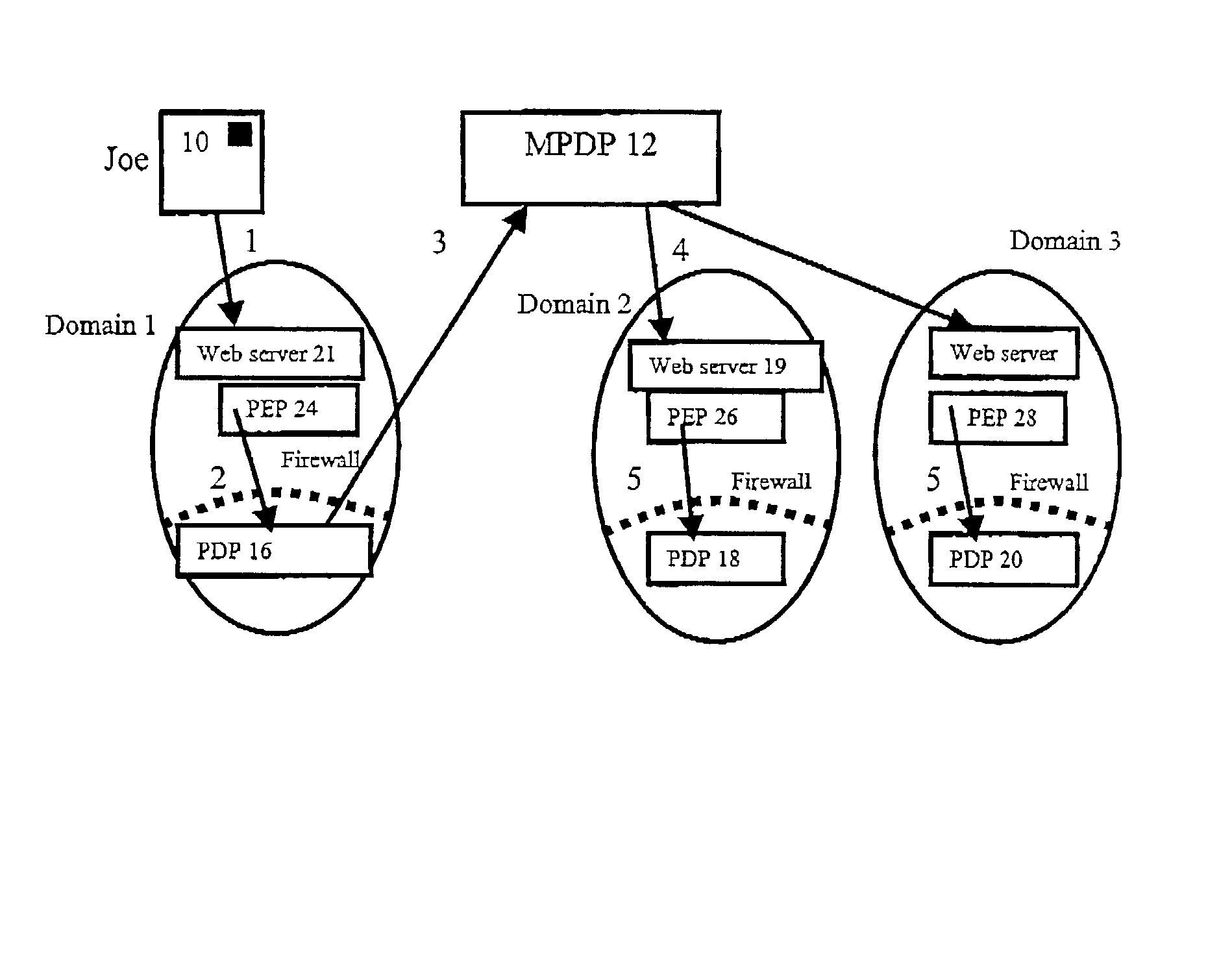
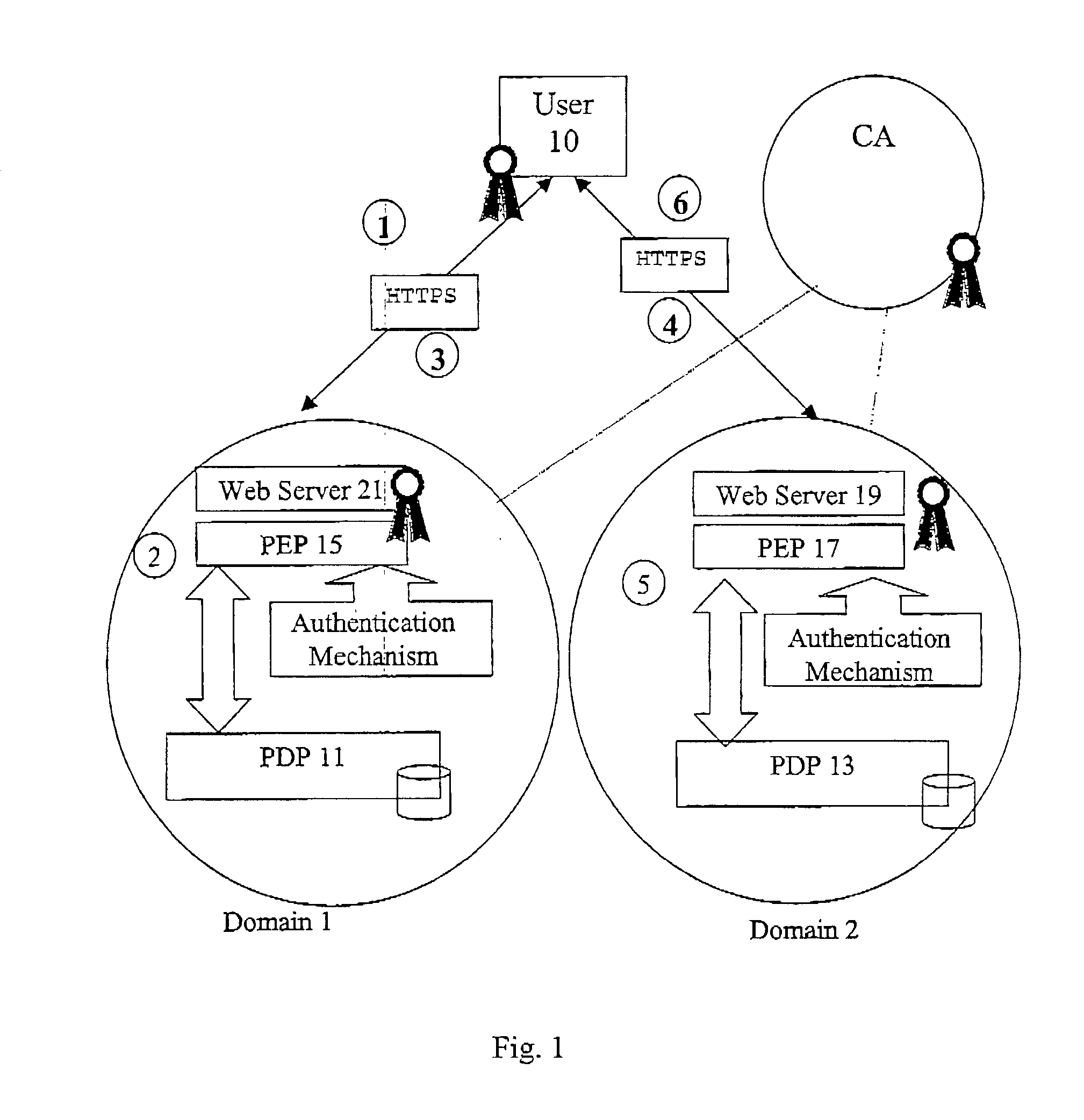
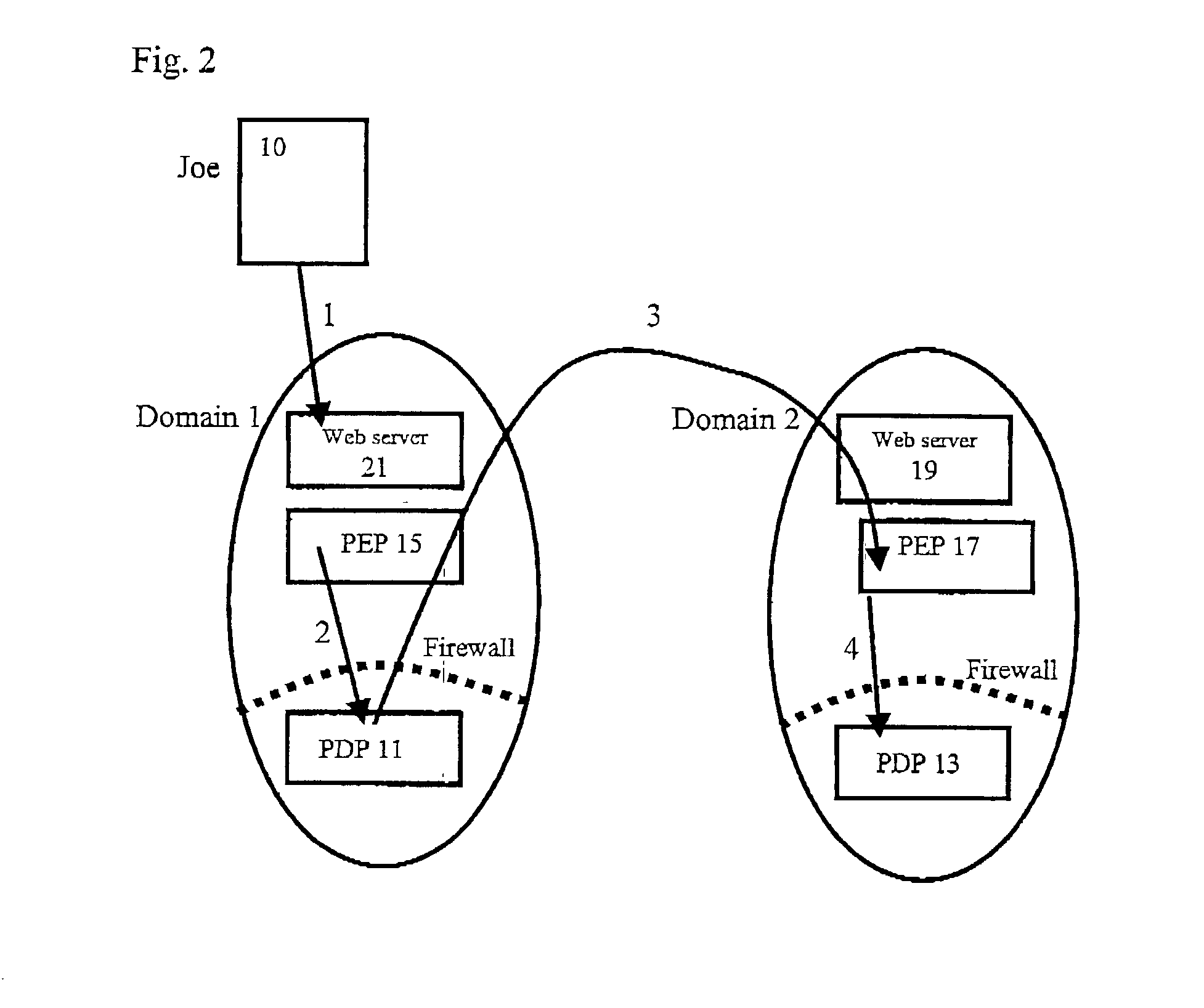
Multi-domain authorization and authentication
ActiveUS20030023880A1Special data processing applicationsSecuring communicationPolicy decisionAuthorization
A method of multi-domain authorisation / authentication on a computer network comprises: a user making a request to a policy enforcement point of a computer for access to information on the computer; providing a location address for a user's authorisation and / or authentication information, a policy decision point of the service on the computer network then verifying the authorisation / authentication information; and the user being given access by the PEP to the information or the service requested, if the request is accepted, wherein the user's authorisation / authentication and / or further information is located on a meta policy decision point (MPDP).
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
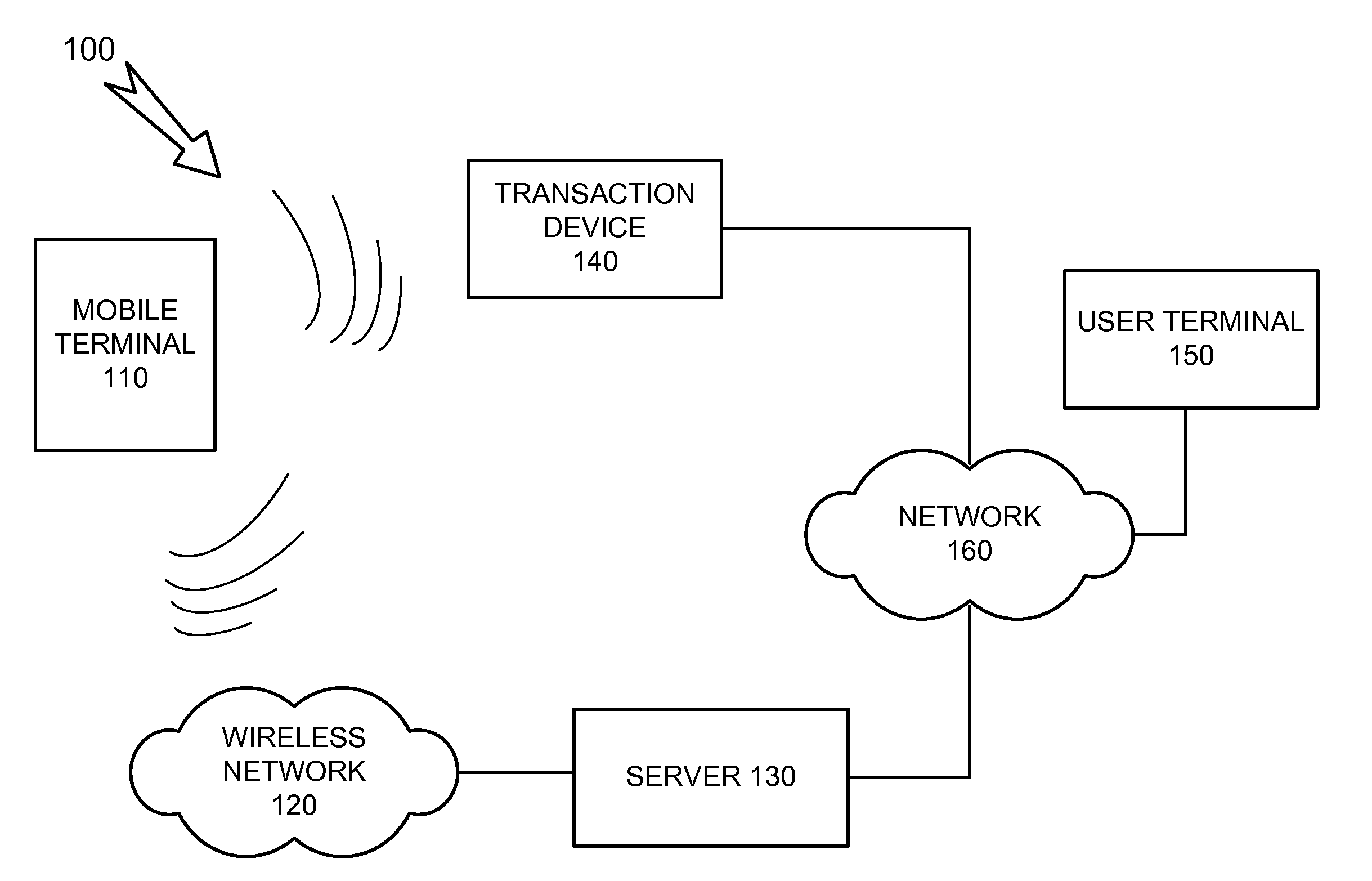
Virtual wallet
A managed service may include first logic to receive authentication information from a user terminal on behalf of a user, and receive user information on behalf of the user when the user terminal is authenticated via the authentication information. The first logic may send a portion of the user information to a mobile wallet application operating on a mobile terminal related to the user, and may receive updated user information from the mobile terminal, where the updated user information identifies a change to the portion of the user information, the change based on an operation performed via the mobile terminal on behalf of the user. The managed service may include second logic to store the user information in a server virtual wallet application on behalf of the user, retrieve the portion of the user information from the server virtual wallet application for the sending, and store the updated user information in the server virtual wallet application.
Owner:VERIZON PATENT & LICENSING INC
Method of Handling Wireless Charging Authentication
A method of handling wireless charging authentication for an electronic device of a wireless charging system includes sending a first message to a controller of the wireless charging system to notify the controller that an authentication is required by a wireless charger of the wireless charging system; receiving a second message including authentication information from the controller; and sending a third message including the authentication information to the wireless charger, in order to satisfy the authentication.
Owner:HTC CORP
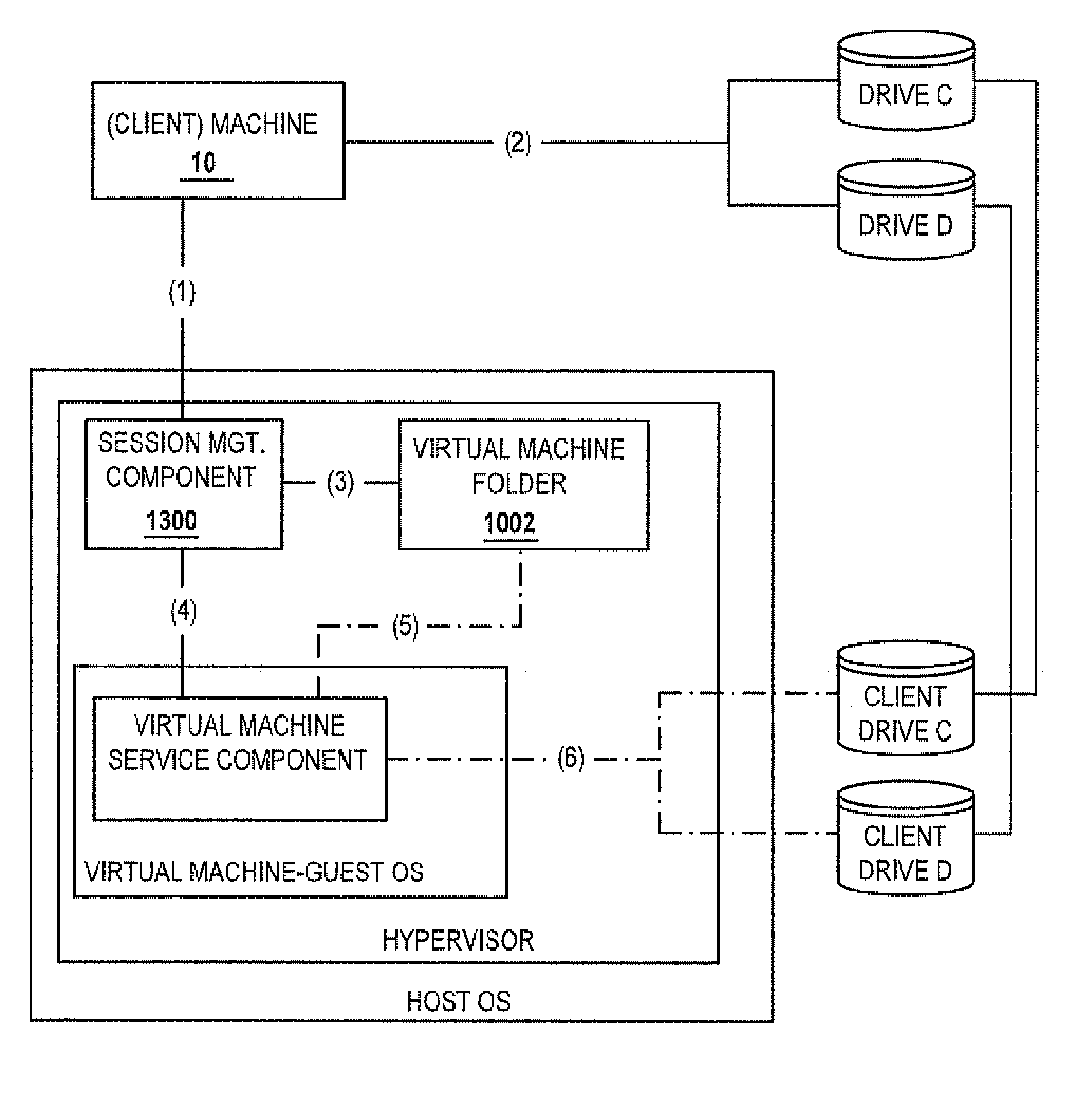
Methods and systems for providing remote access to a computing environment provided by a virtual machine
ActiveUS20070180449A1Low costReduce difficultyDigital data information retrievalInterprogram communicationVirtualizationOperational system
A method for providing remote access to a computer environment provided by a virtual machine includes the step of receiving authentication information associated with a user of a client machine. Based on the received authentication information, a computer environment provided by a virtualized operating system and already associated with the user is identified. A connection is established between the client machine and the identified computing environment
Owner:CITRIX SYST INC
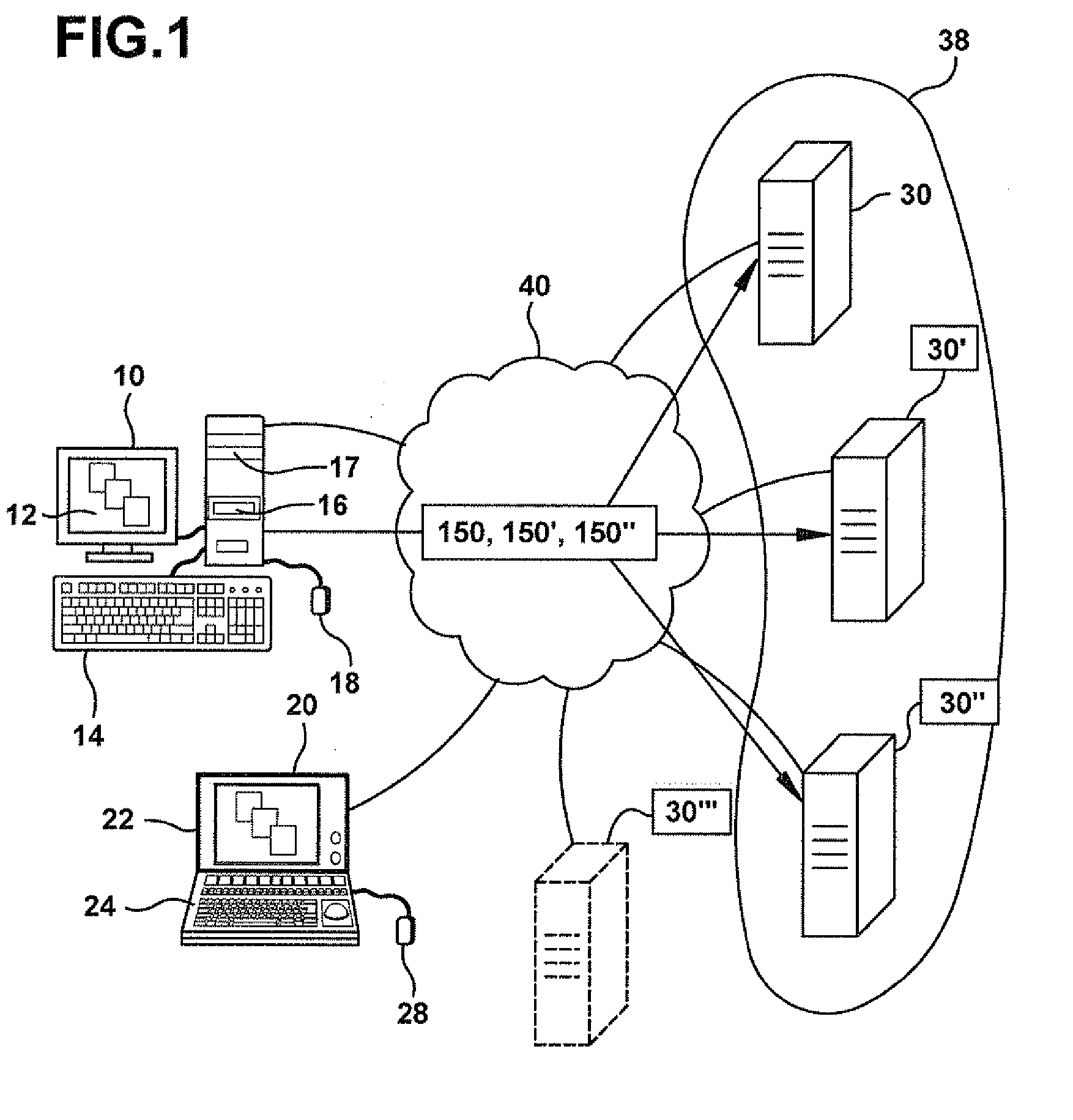
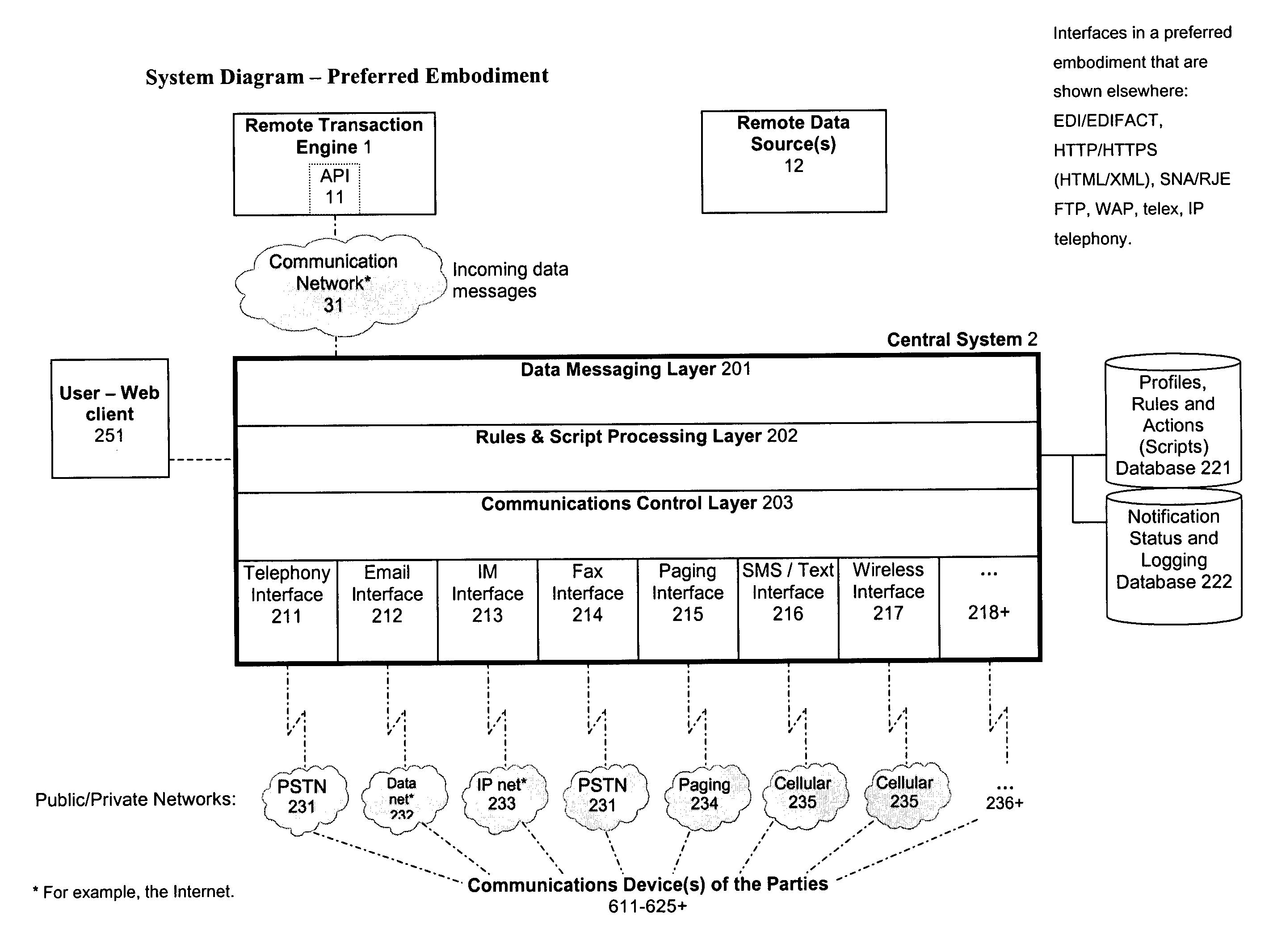
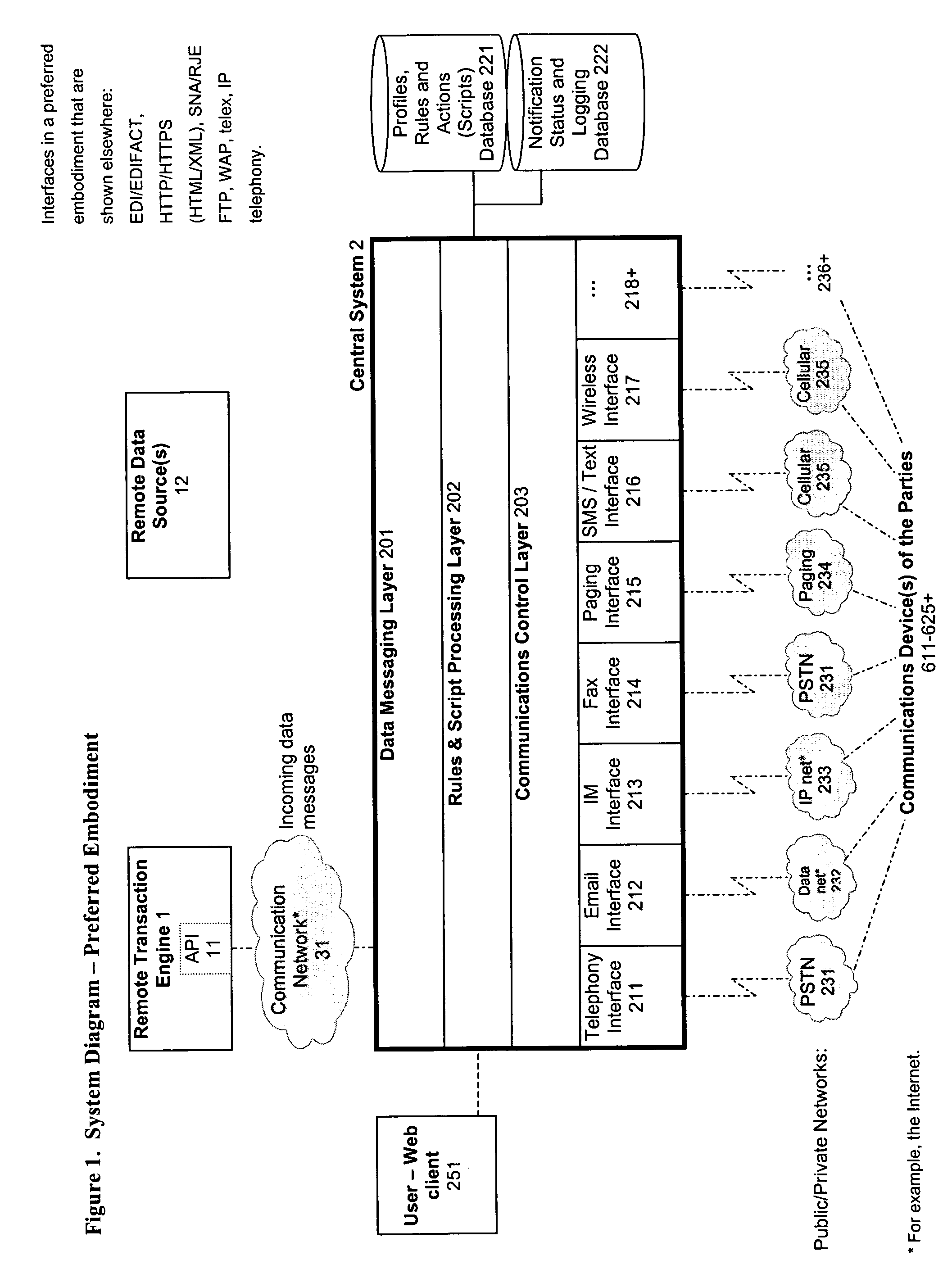
System and method for verification, authentication, and notification of a transaction
ActiveUS20040078340A1Increase valueFinanceBuying/selling/leasing transactionsTelecommunications linkSocial Security number
A system and method for verifying, authenticating, and providing notification of a transaction, such as a commercial or financial transaction, with and / or to at least one party identified as engaging in the transaction and / or identified as having a potential interest in the transaction or type of transaction, are provided. A central system accepts information regarding a transaction, including information about at least one party identified as engaging in the transaction, such as by a credit account number or Social Security number or merchant account number, and / or identified as having a potential interest in the transaction. Based on the information regarding the transaction and any supplemental information the central system determines, the central system communicates with and / or to at least one party and / or additional or alternative parties, via at least one communications device or system having a communications address, such as a telephone number or Short Message Service address, predetermined as belonging to the at least one party and / or additional or alternative parties. Via said communications, at least one party having an interest or a potential interest in the transaction may be notified of it, and may further be enabled or required to supply additional verifying or authenticating information to the central system. If the transaction was initiated or engaged in via a communications link, such as via the Internet, said communications preferably occur over at least one different communications link and / or protocol, such as via a wireless voice network. The central system may then compute a result based on the outcomes of said communications, and may then transmit the result to the user and / or to a second system or device.
Owner:ST ISIDORE RES
Communication device and communication method
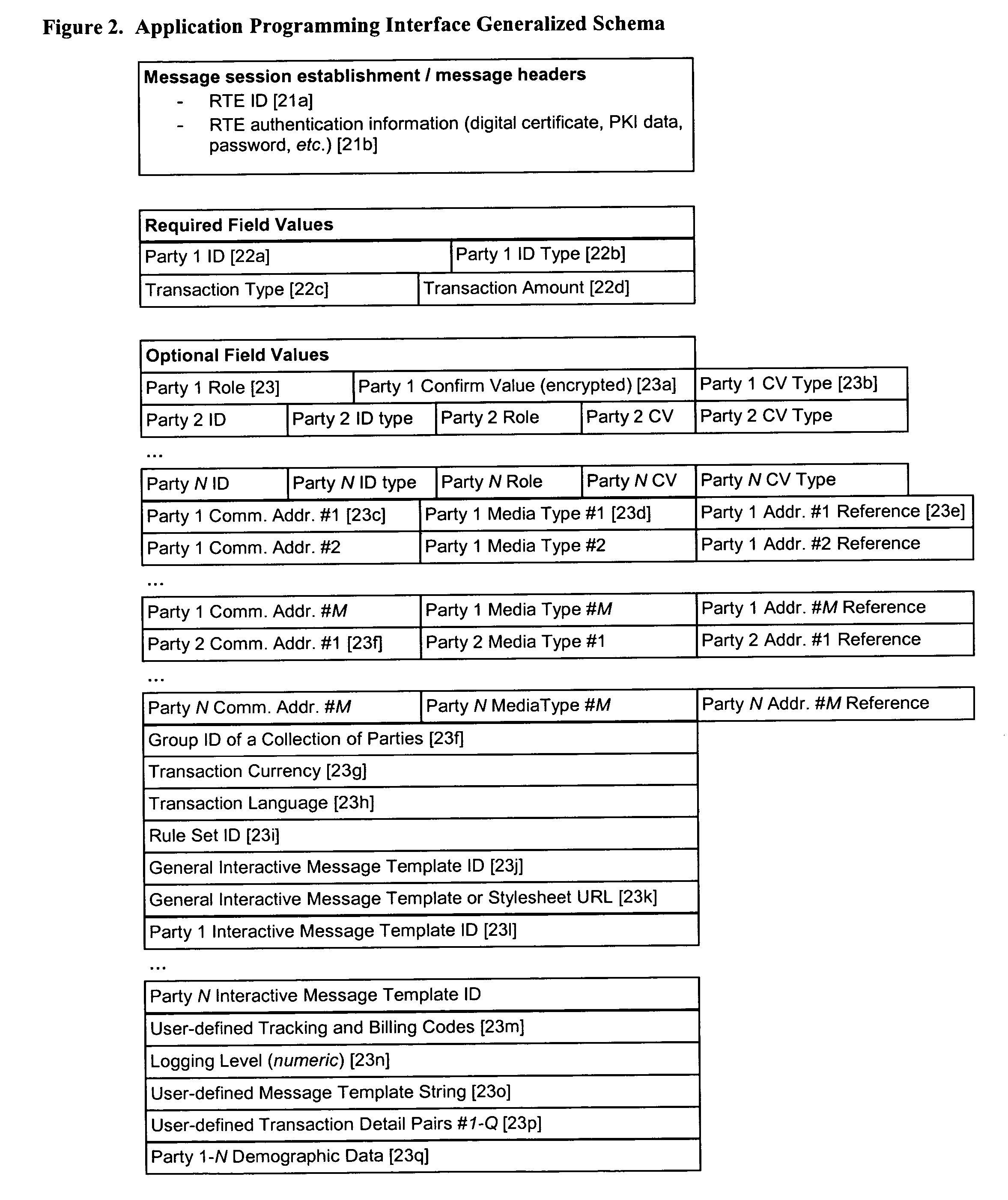
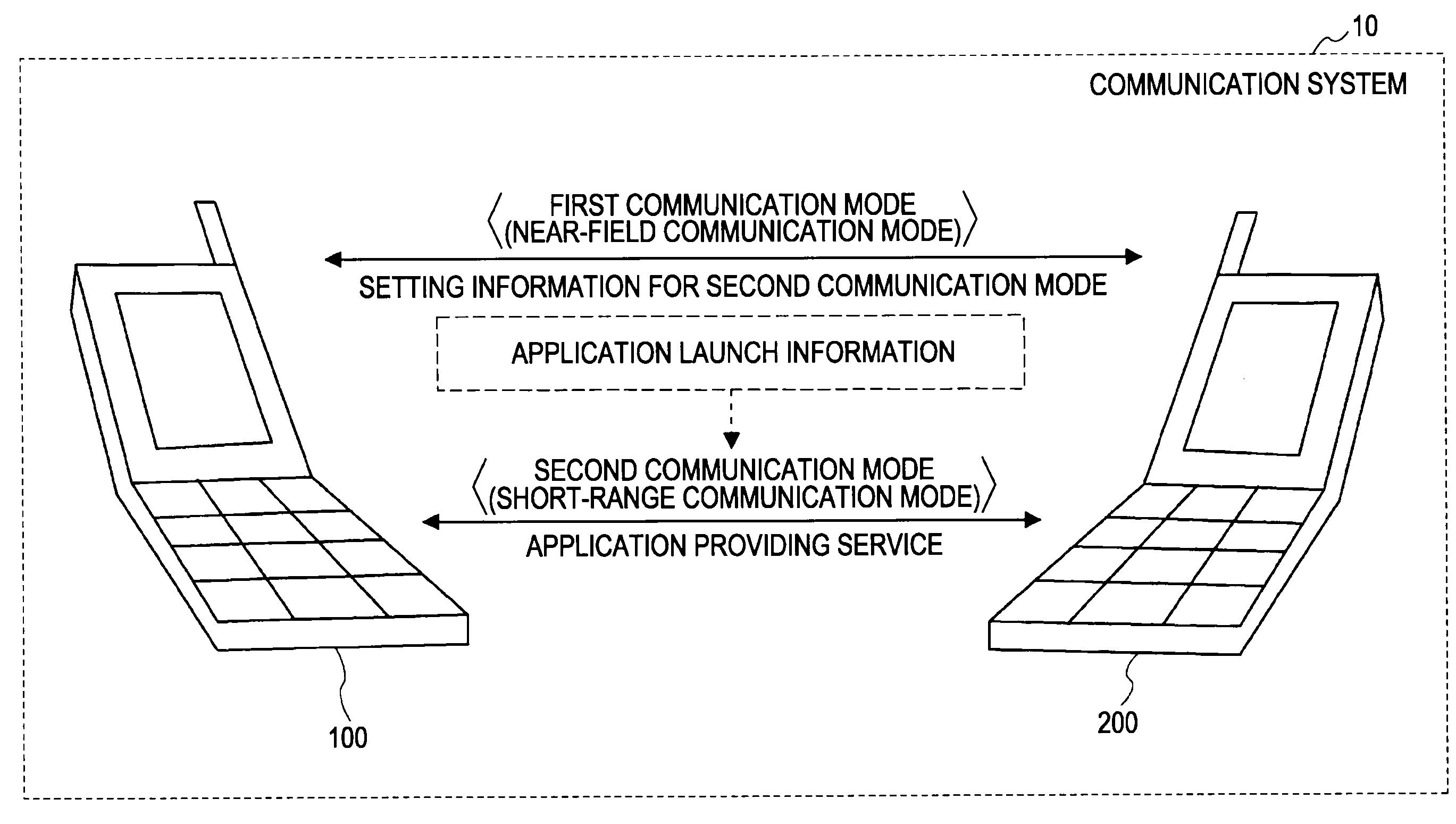
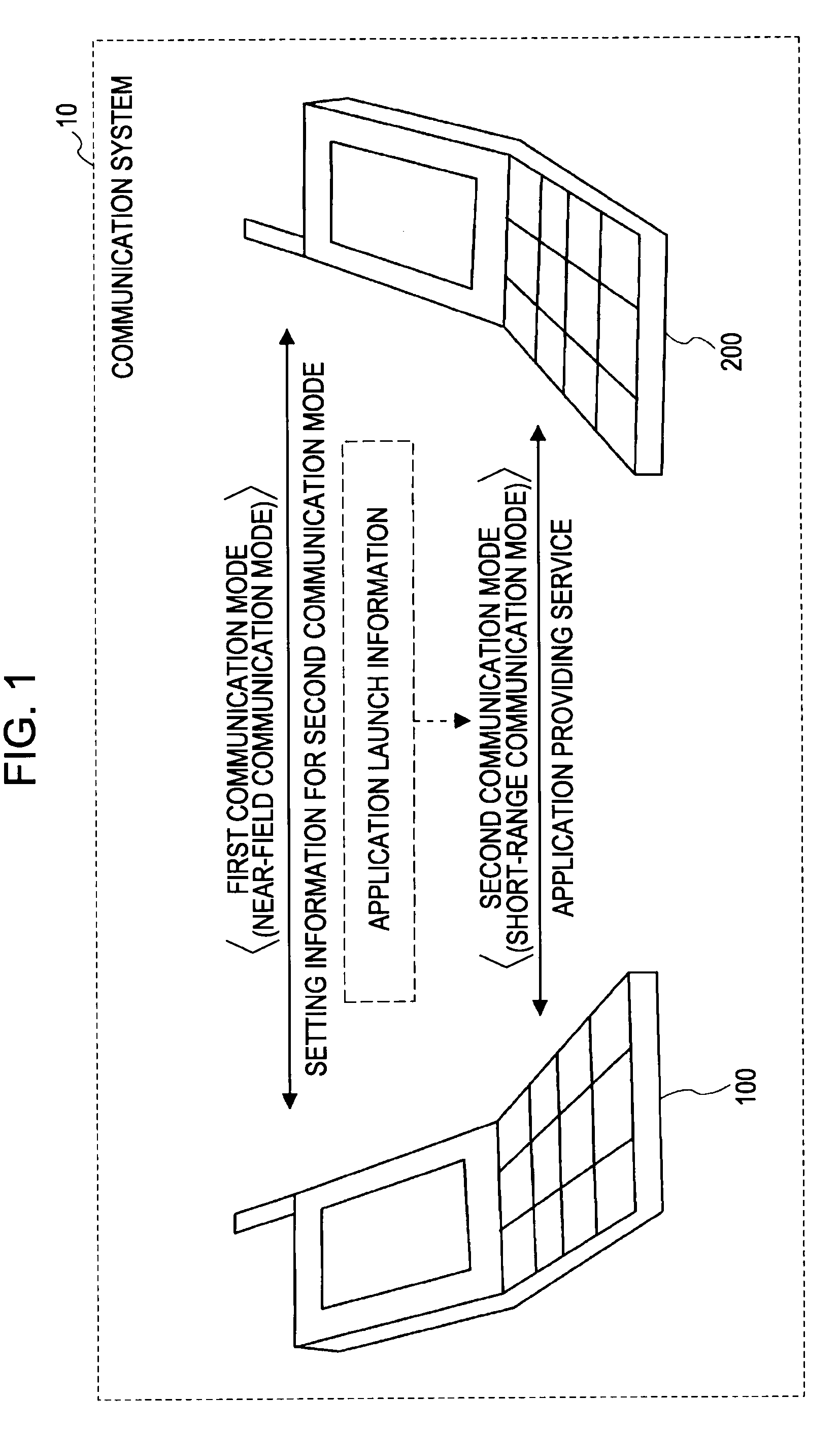
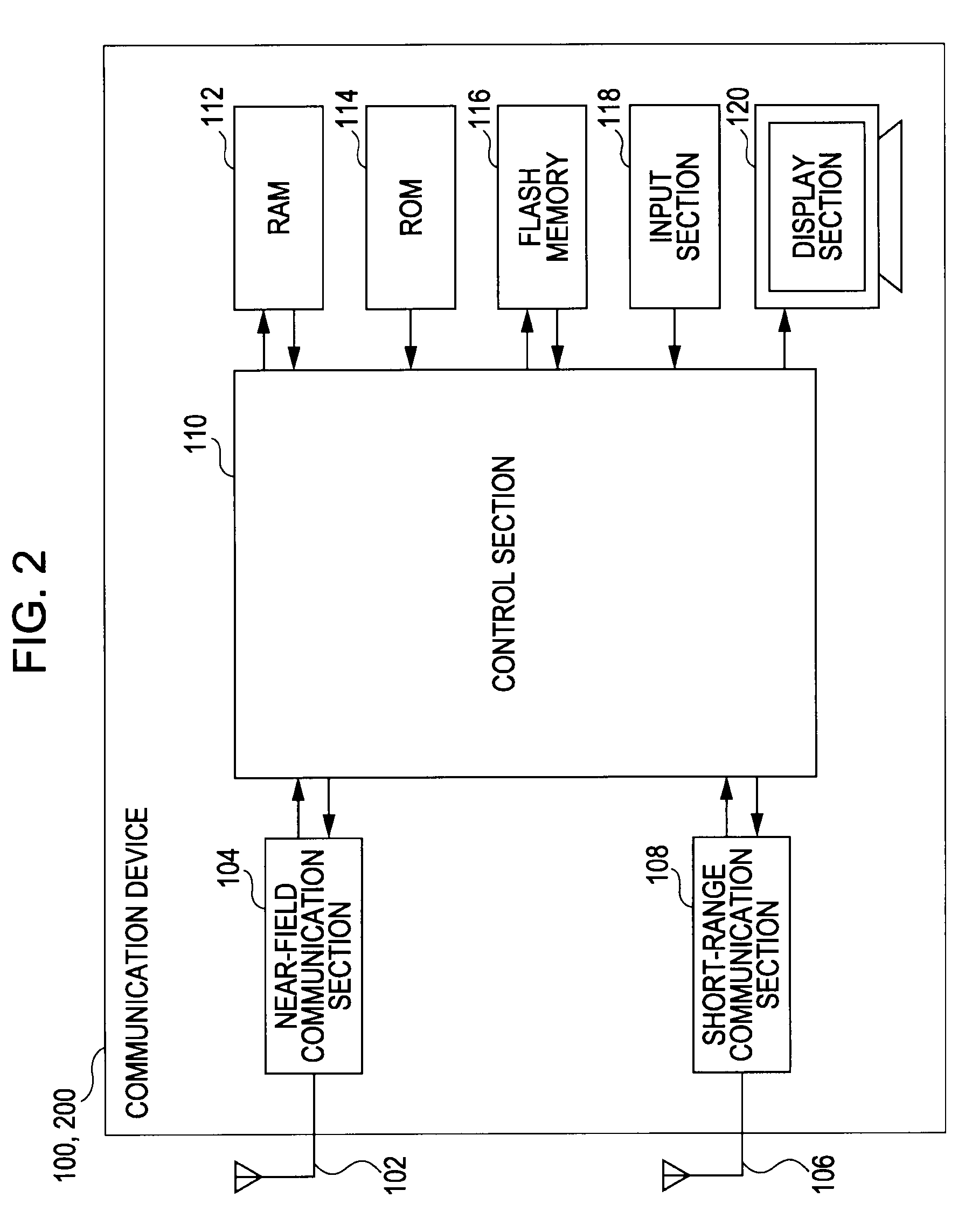
InactiveUS20090227282A1Reduce the amount requiredShort timeServices signallingFrequency-division multiplexExecution controlCommunication control
A communication device has a first communication section that supports a first communication mode having a low communication rate and a second communication section that supports a second communication mode having a higher communication rate than the first communication mode. The communication device includes a packet generation section and a communication control section. The packet generation section generates a first portion containing authentication information used for connection authentication for the second communication mode and a second portion other than the first portion. The communication control section performs control to cause the first communication section to transmit the first portion and to cause the second communication section to transmit the second portion after the connection authentication succeeds using the authentication information contained in the first portion.
Owner:SONY CORP
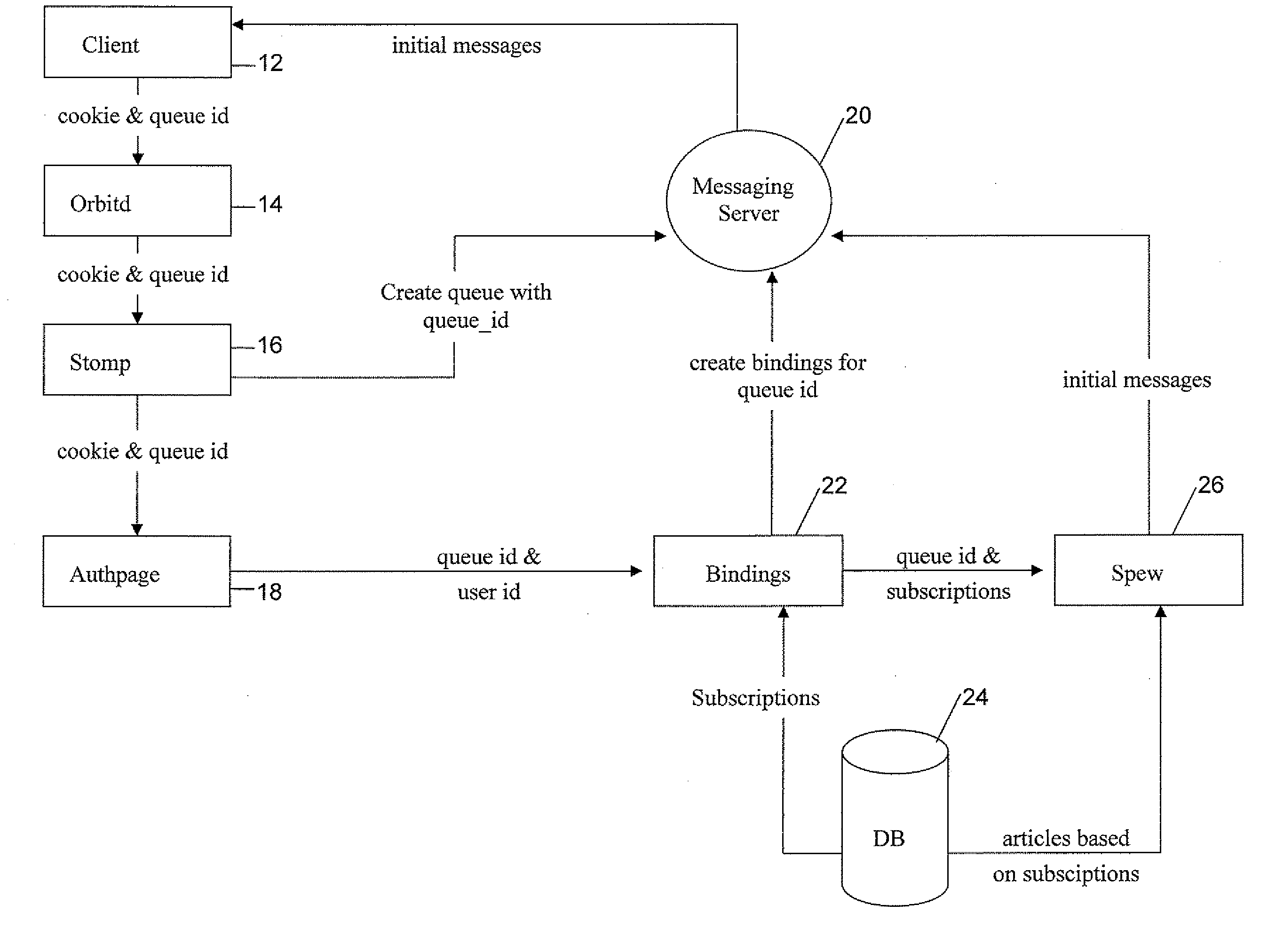
System and method for localized and/or topic-driven content distribution for mobile devices
A computer-implemented method for delivering targeted advertising in an asynchronous messaging-based social networking platform, the system comprising: providing a messaging server configured to managed asynchronous message delivery to a plurality of users, wherein a message comprises: a content title; a timestamp; a profile id, wherein the profile id is a unique identifier associated with a publisher of the message; and a message; providing a user authentication database configured to store and manage user authentication information for the plurality of users; maintaining a plurality of bindings configured to associate at least one user of the system with at least one other user of the system; storing an articles database configured to store messages within the system; identifying a plurality of publishers wherein each publisher posts a plurality of messages within the system; determining a plurality of channels; for each channel, associating a plurality of the publishers with the channel; and providing advertising within the system.
Owner:TRIBUNE INTERACTIVE
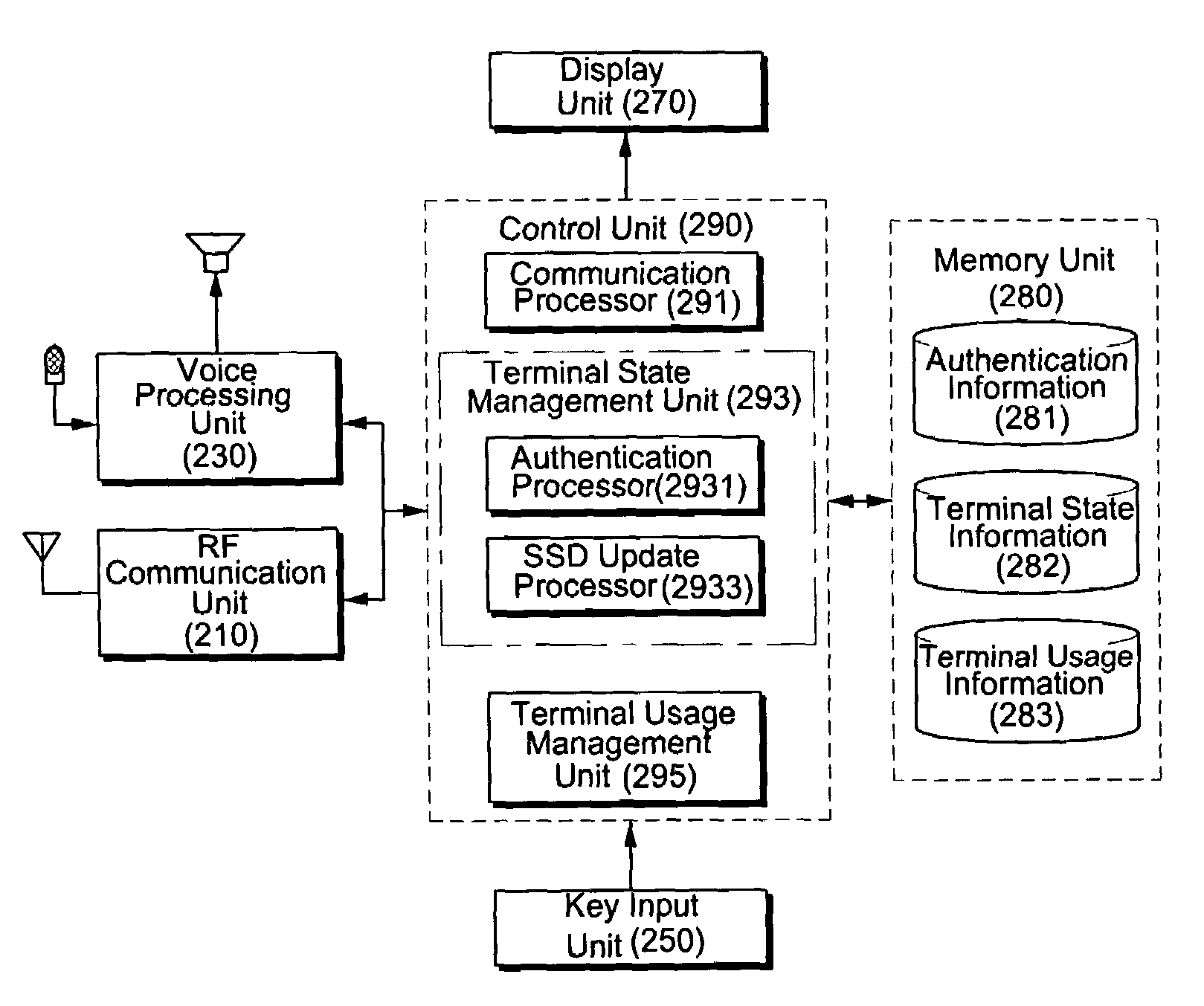
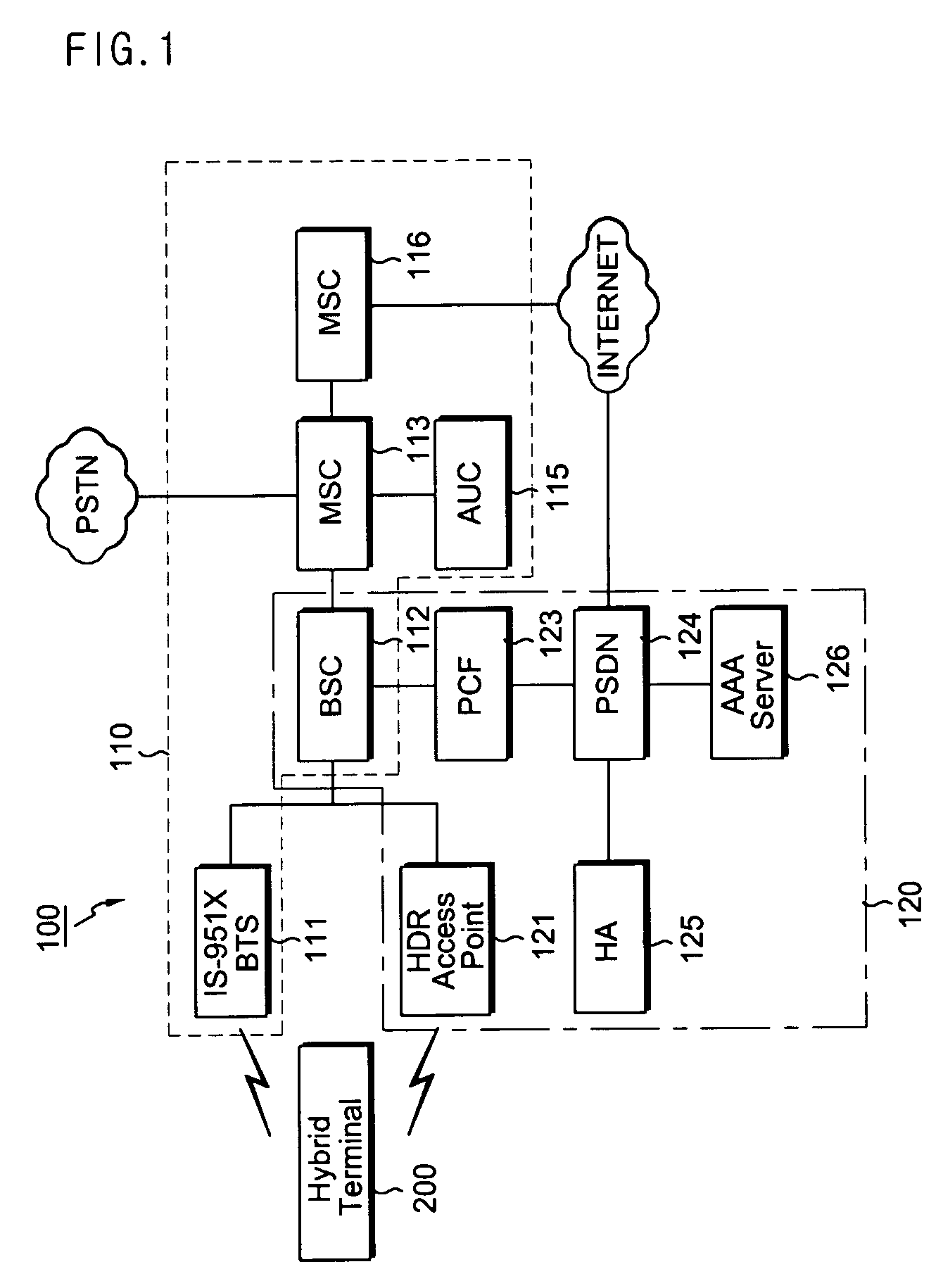
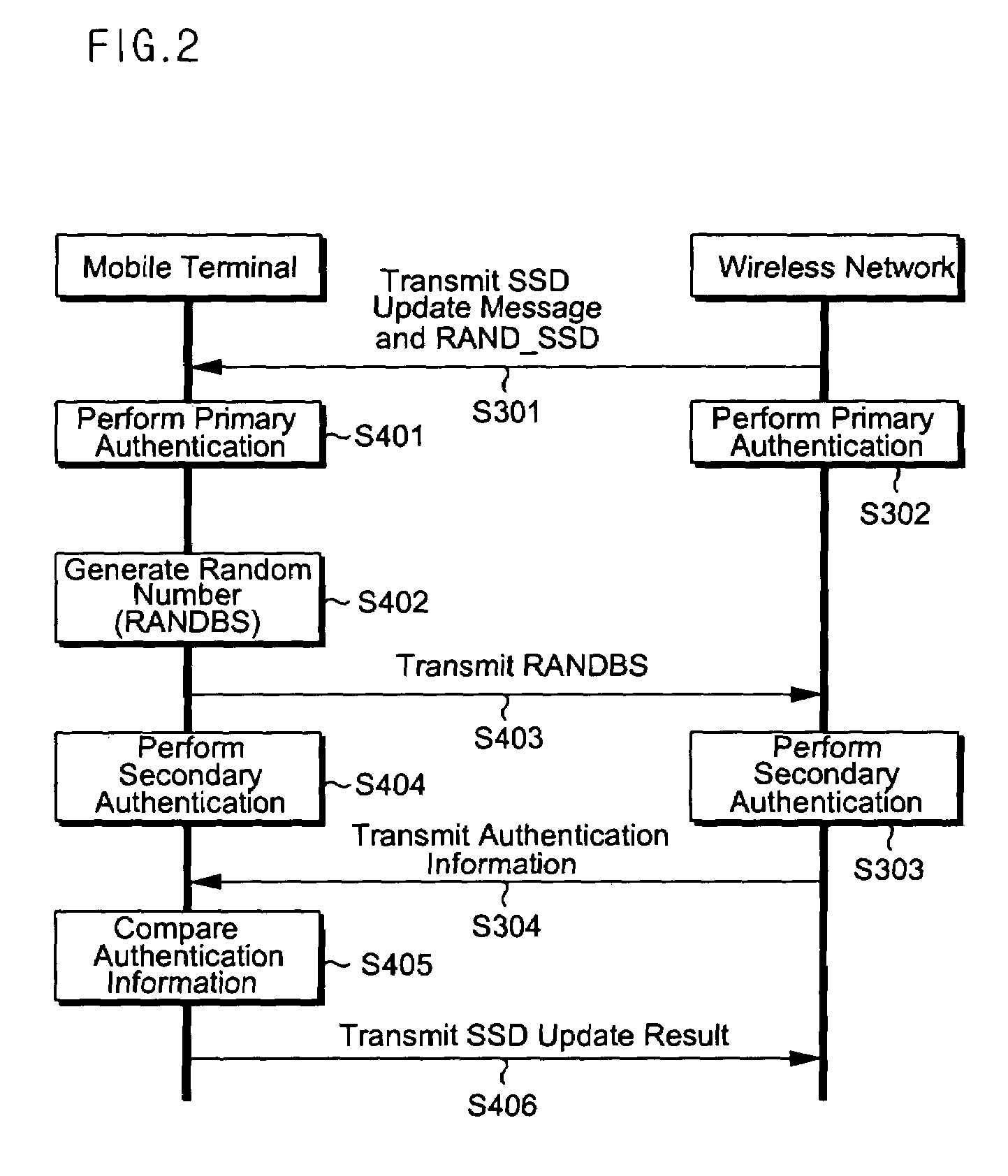
Mobile communication terminal, wireless data service authentication server, system for automatically blocking voice call connection, and method of processing various messages in mobile communication terminal
ActiveUS7418257B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTime informationWireless data services
Disclosed is a technology for preventing a legitimate terminal's user from being damaged due to the fraudulent usage of a cloned terminal. A mobile communication terminal transmits authentication information containing terminal usage time information to a wireless network according to a voice call connection procedure, and performs a voice call release process upon receiving an authentication failure message from the wireless network in response to the authentication information.
Owner:PANTECH CORP
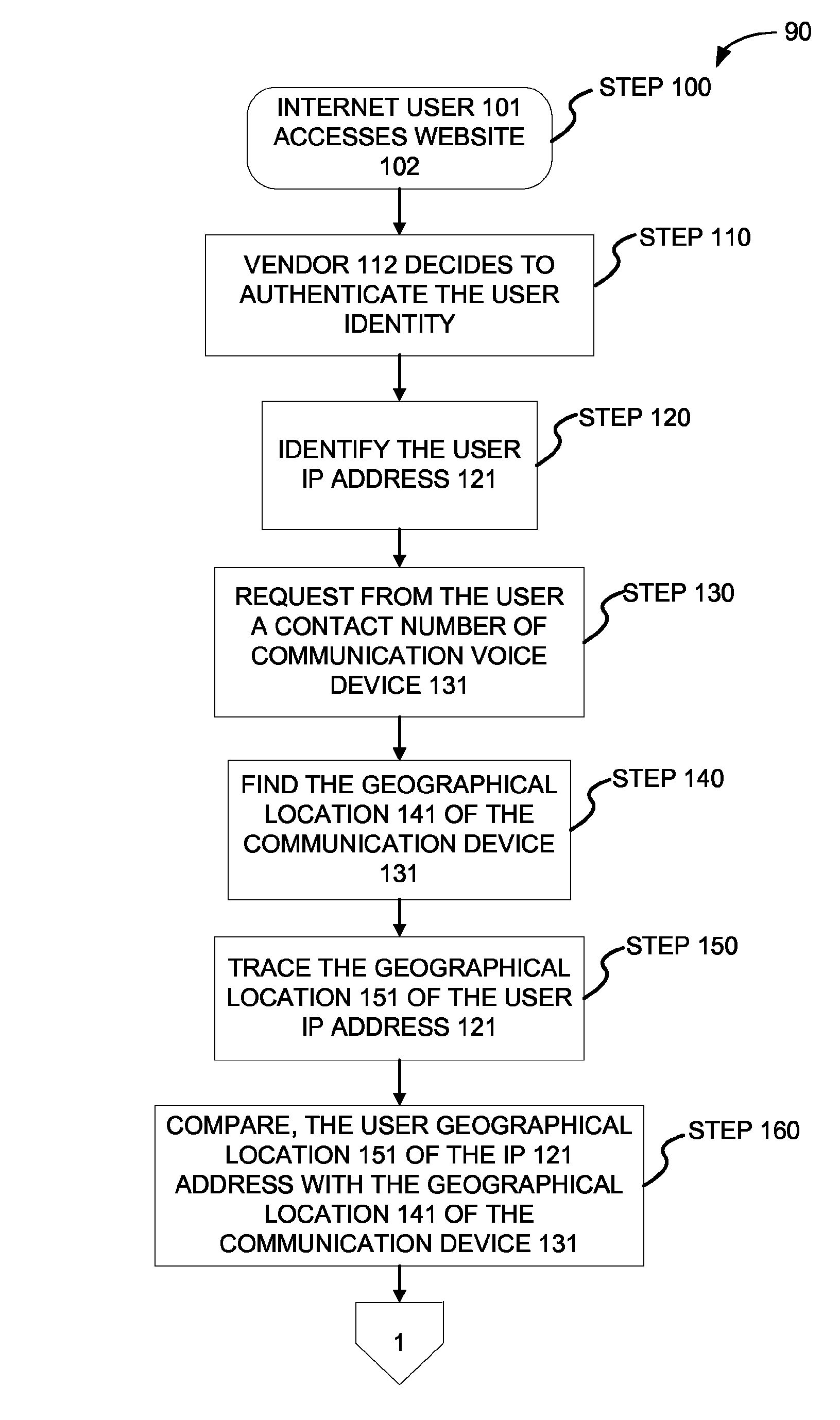
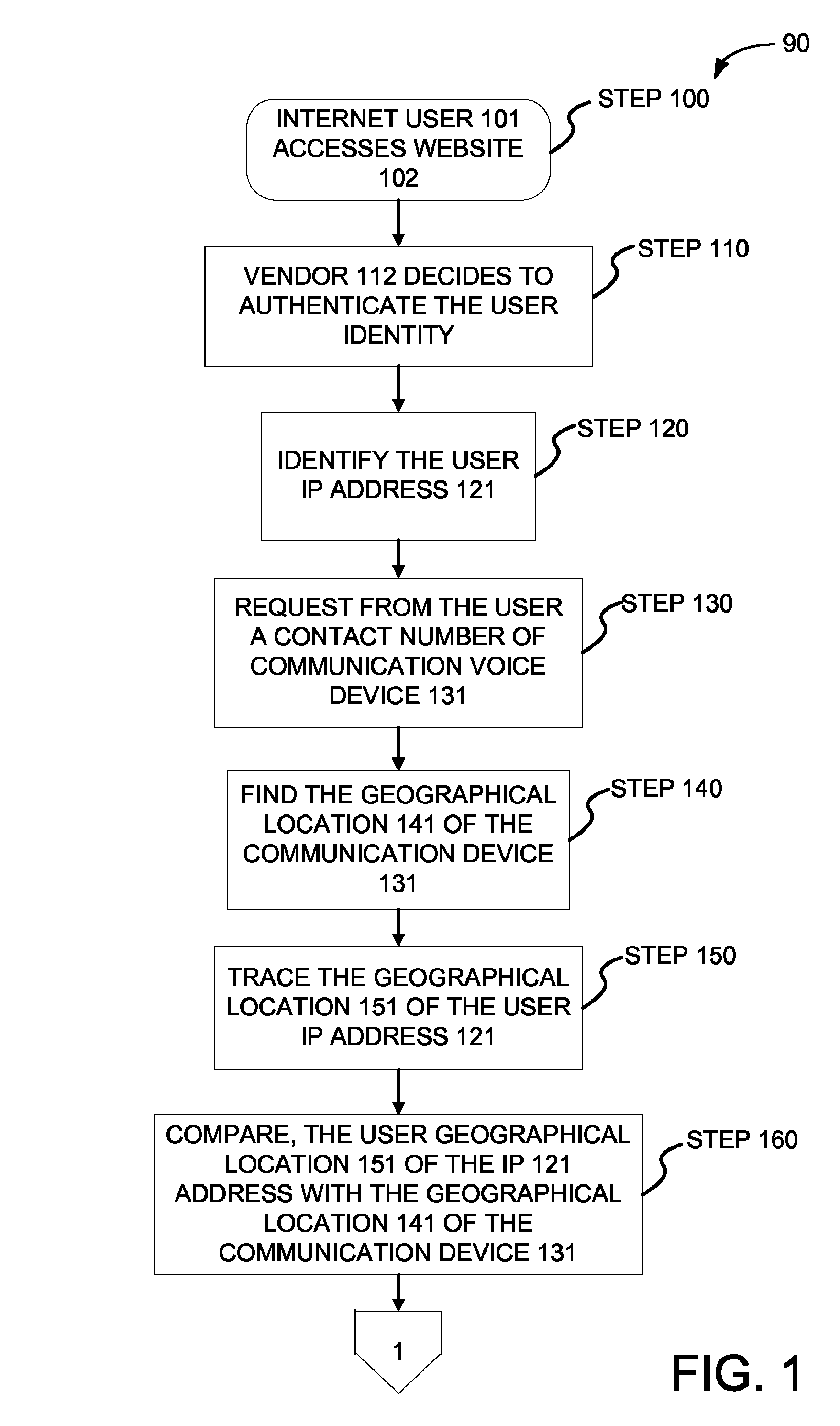
Method and system for authenticating internet user identity
InactiveUS8656458B2Lower potentialDigital data processing detailsSpecial service for subscribersIp addressInternet users
Owner:HEFFEZ GUY
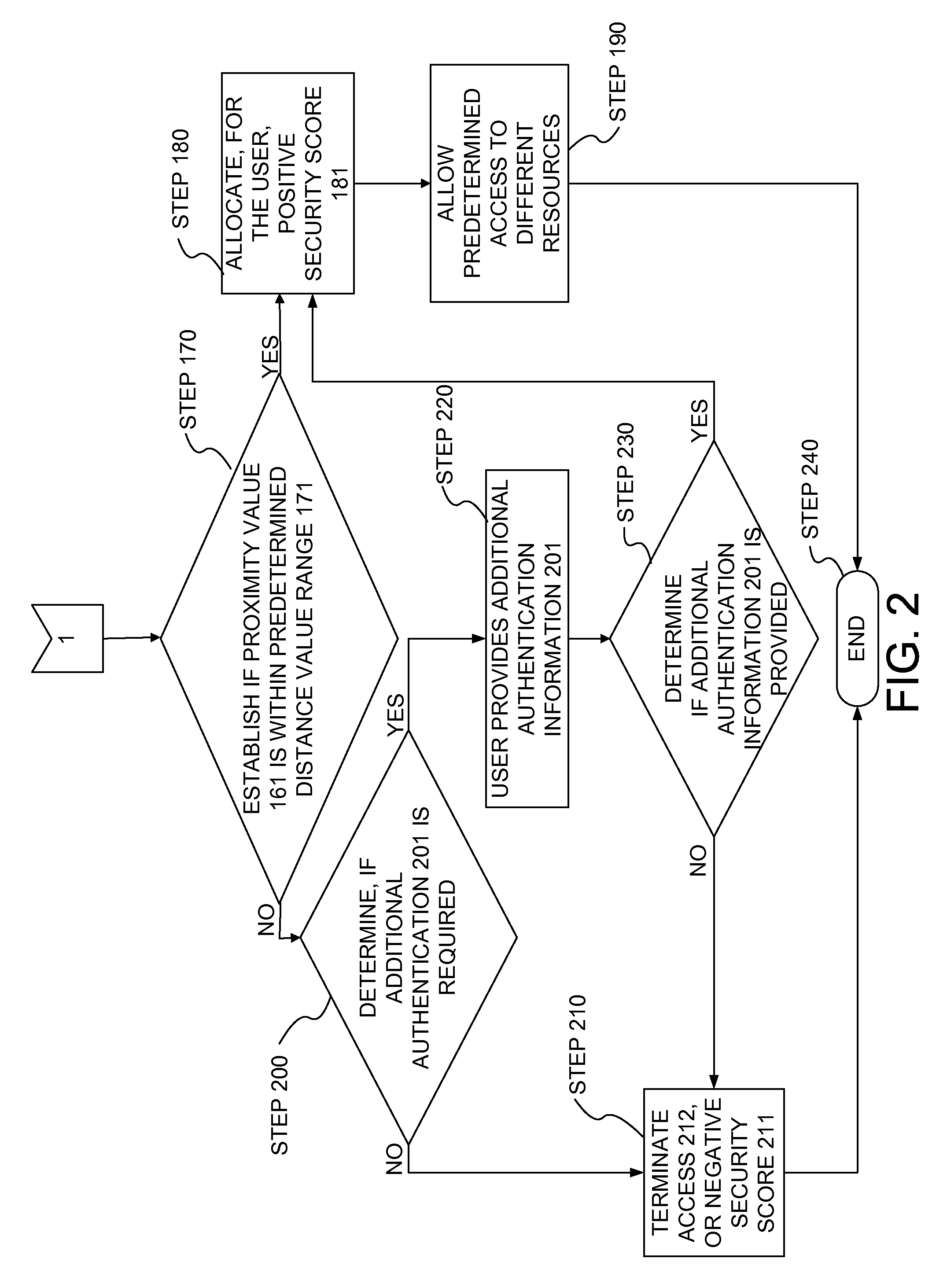
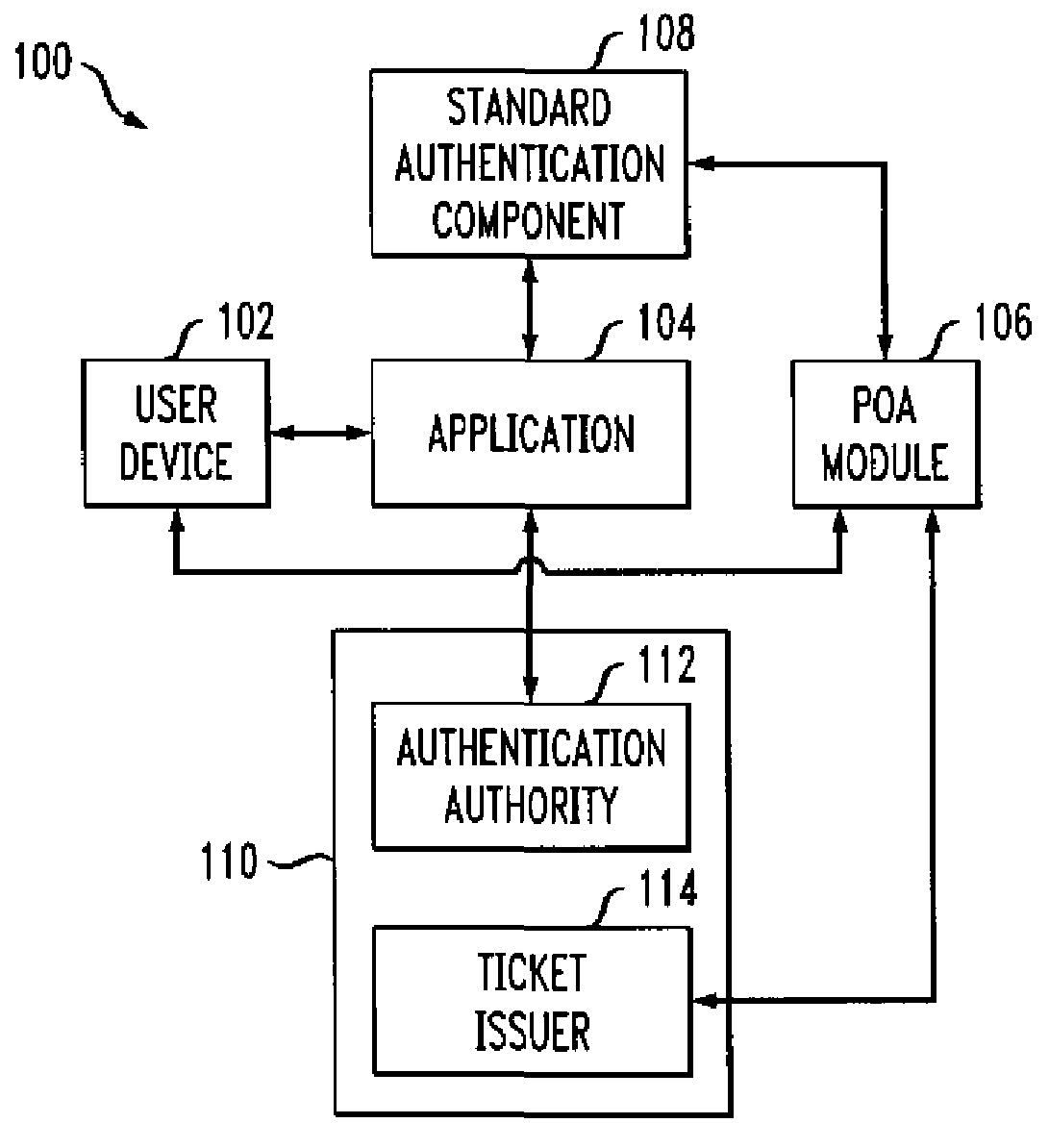
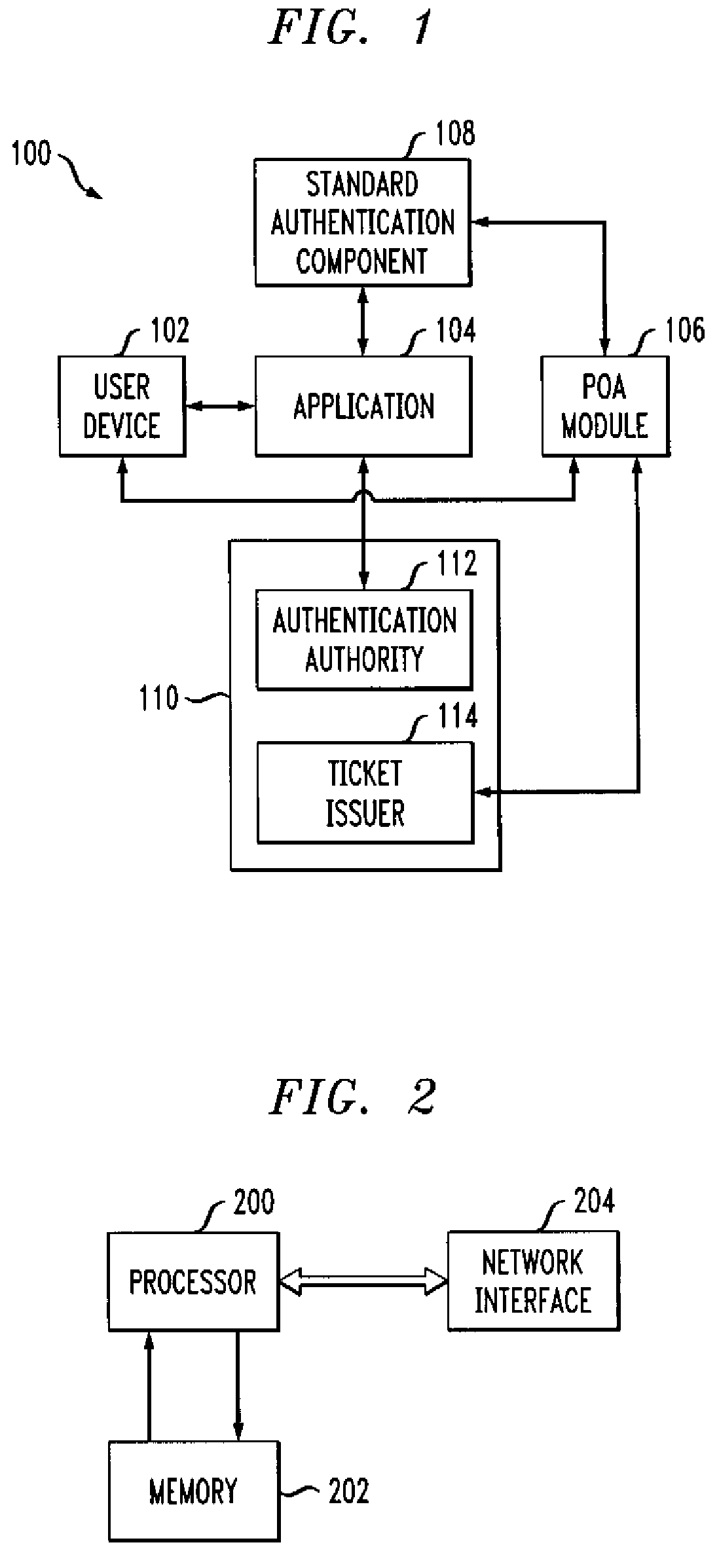
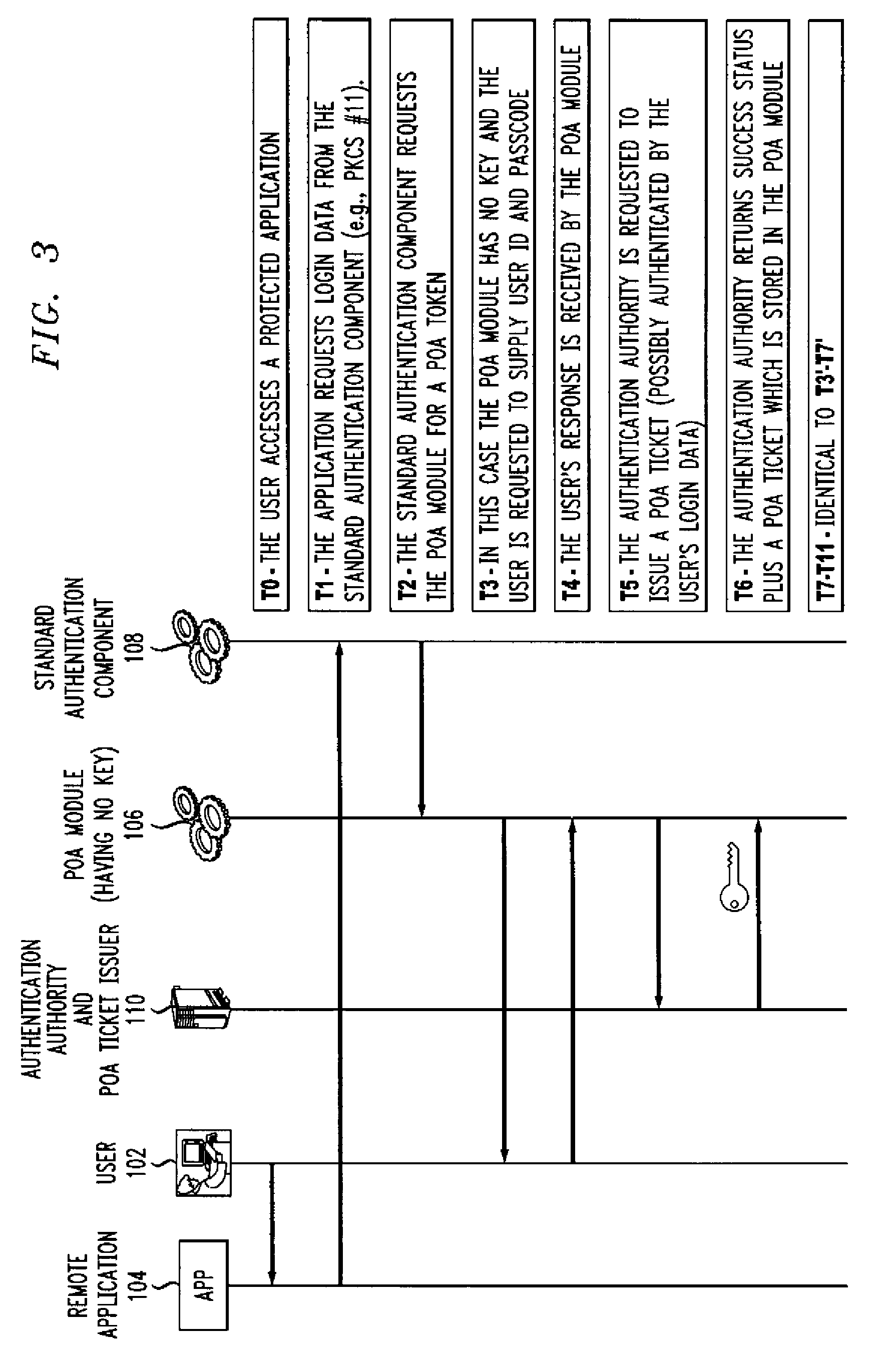
Authentication method and apparatus utilizing proof-of-authentication module
ActiveUS7562221B2Unauthorised/fraudulent call preventionDigital data processing detailsComputer hardwareValidation methods
A single sign-on technique allows multiple accesses to one or more applications or other resources using a proof-of-authentication module operating in conjunction with a standard authentication component. The application or other resource issues an authentication information request to the standard authentication component responsive to an access request from the user. The application or other resource receives, responsive to the authentication information request, a proof-of-authentication value from the standard authentication component, and authenticates the user based on the proof-of-authentication value. The standard authentication component interacts with the proof-of-authentication module to obtain the proof-of-authentication value. The proof-of-authentication module is configured to generate multiple proof-of-authentication values for authentication of respective access requests of the user.
Owner:EMC IP HLDG CO LLC
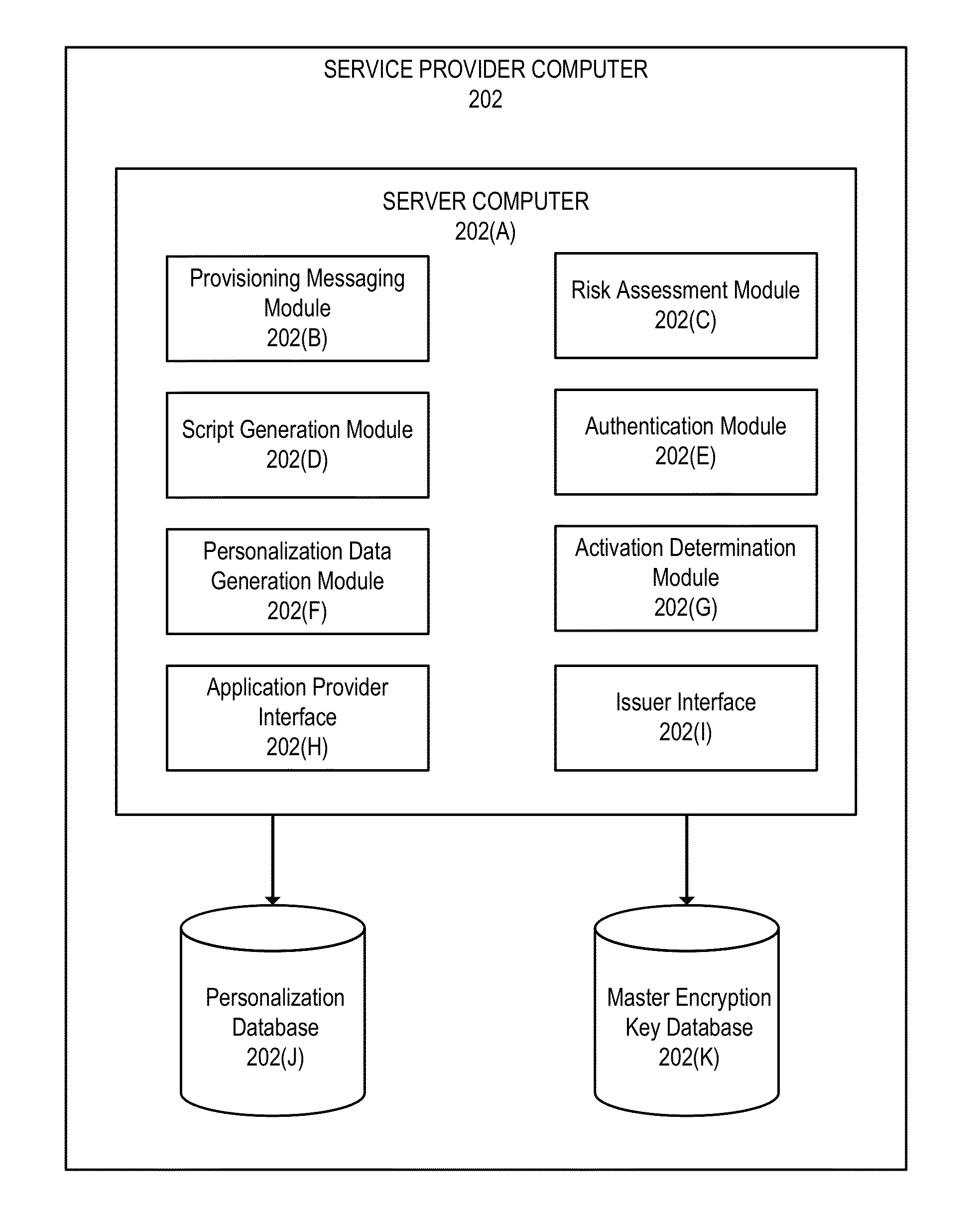
Device provisioning using partial personalization scripts
ActiveUS20140337236A1Efficient supplyFinanceProtocol authorisationPersonalizationUser authentication
Embodiments of the invention relate to systems and methods for efficiently provisioning mobile devices with personalization data. For some embodiments, a method is disclosed comprising receiving a request for provisioning comprising device information for a mobile device and user authentication information for a user, generating a partial personalization script, an activation script, and a deletion script using the device information, sending the partial personalization script, the activation script, and the deletion script to an application provider computer, wherein the application provider computer initiates execution of the partial personalization script on the mobile device, authenticating the user authentication information, and sending an activation message to the application provider computer, wherein the application provider computer initiates execution of the activation script.
Owner:VISA INT SERVICE ASSOC
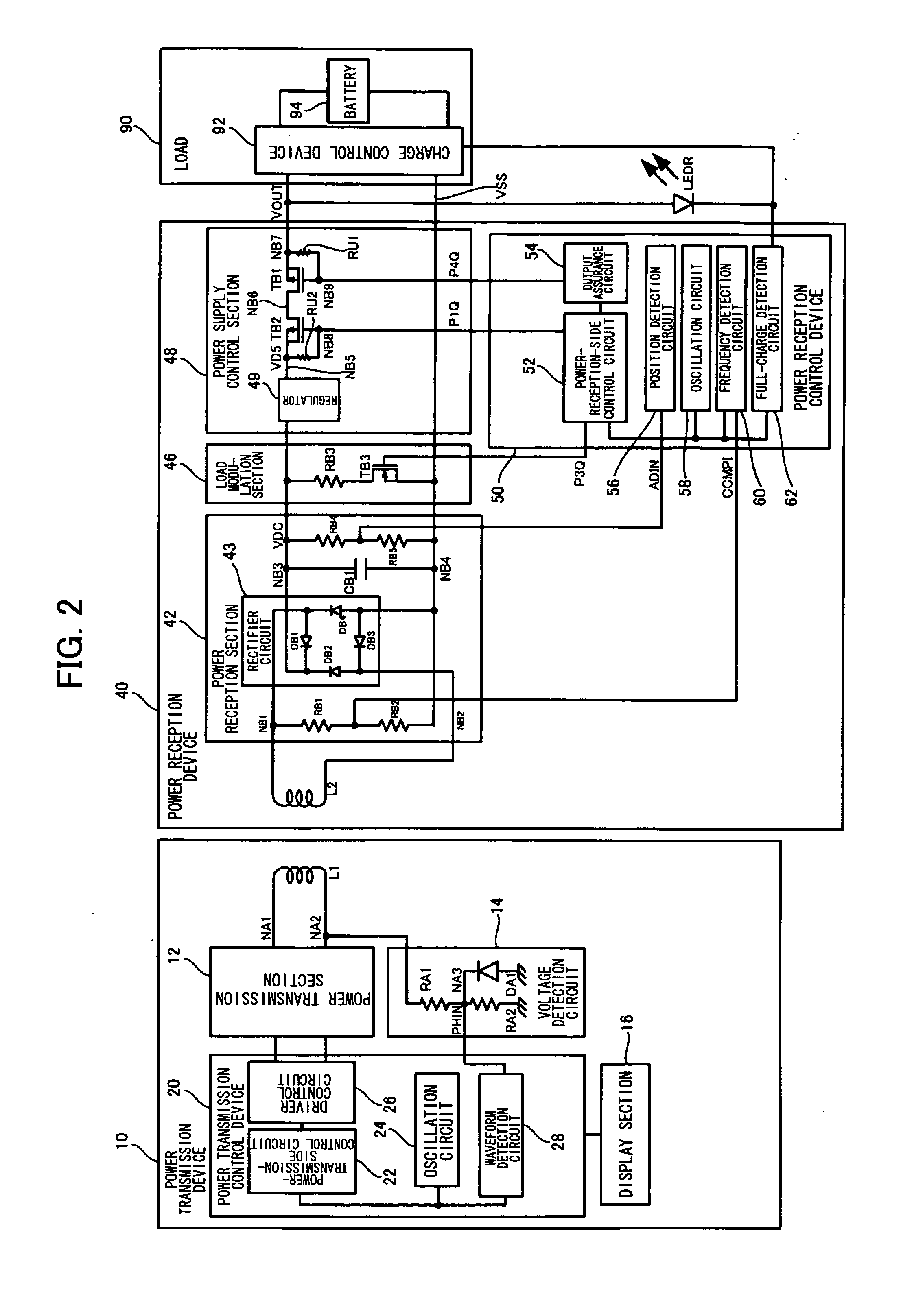
Power transmission control device, power transmission device, non-contact power transmission system, and electronic instrument
ActiveUS20090001932A1Low costSmall sizeCircuit authenticationNear-field transmissionElectric power transmissionDrivetrain
A power-transmission-side control circuit causes a power transmission device to perform temporary power transmission when a switch provided in a power-transmission-side instrument has been turned ON, and performs ID authentication based on ID authentication information. The power-transmission-side control circuit detects the presence or absence of a foreign object during normal power transmission by monitoring a change in induced voltage in a primary coil, causes the power transmission device to stop temporary power transmission when the ID authentication information from the power reception device has not been received within a given period of time, causes the power transmission device to stop temporary power transmission when the ID authentication has failed, and causes the power transmission device to stop normal power transmission when removal, a metal foreign object, a takeover state, or a full-charge state has been detected after normal power transmission has started.
Owner:SEIKO EPSON CORP
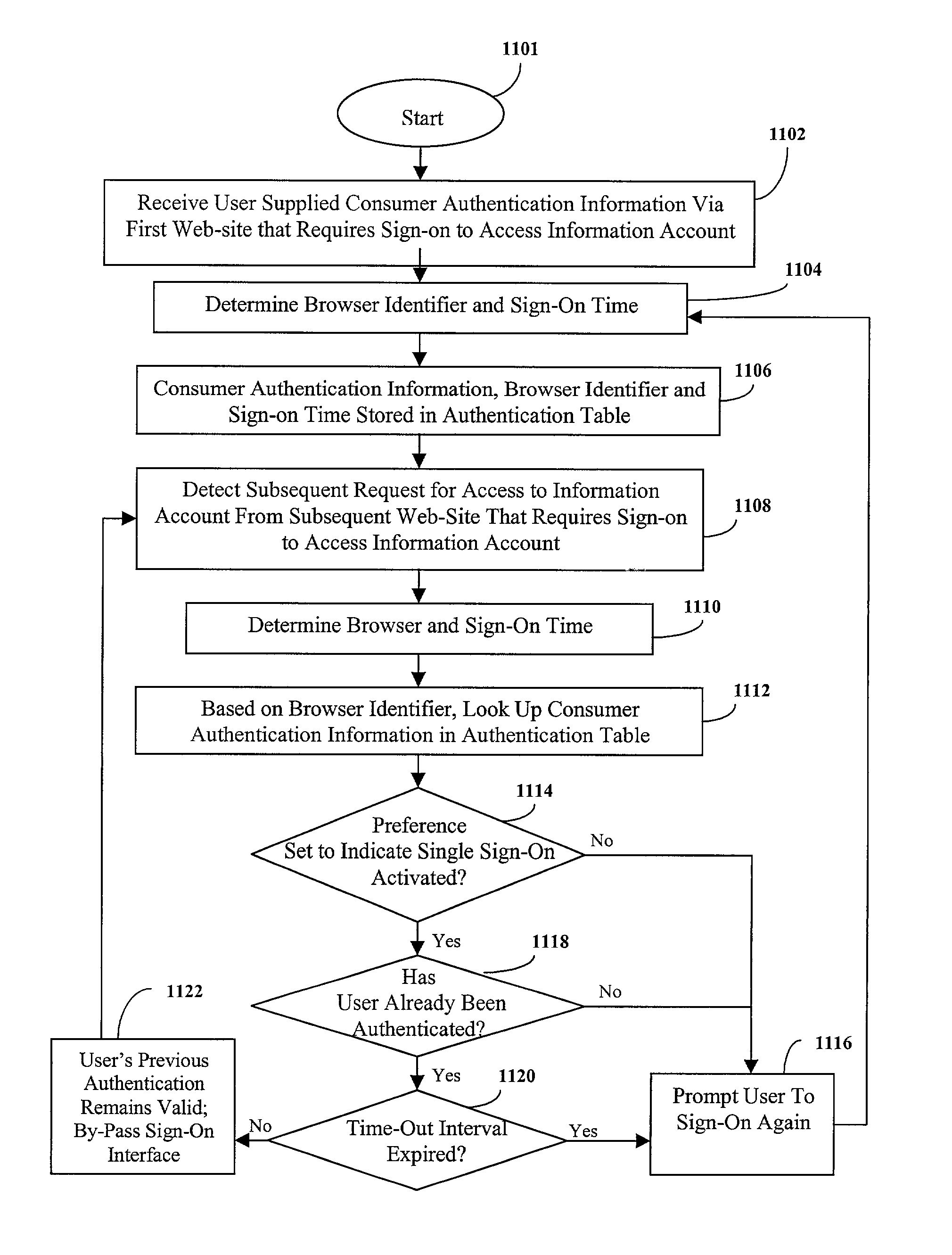
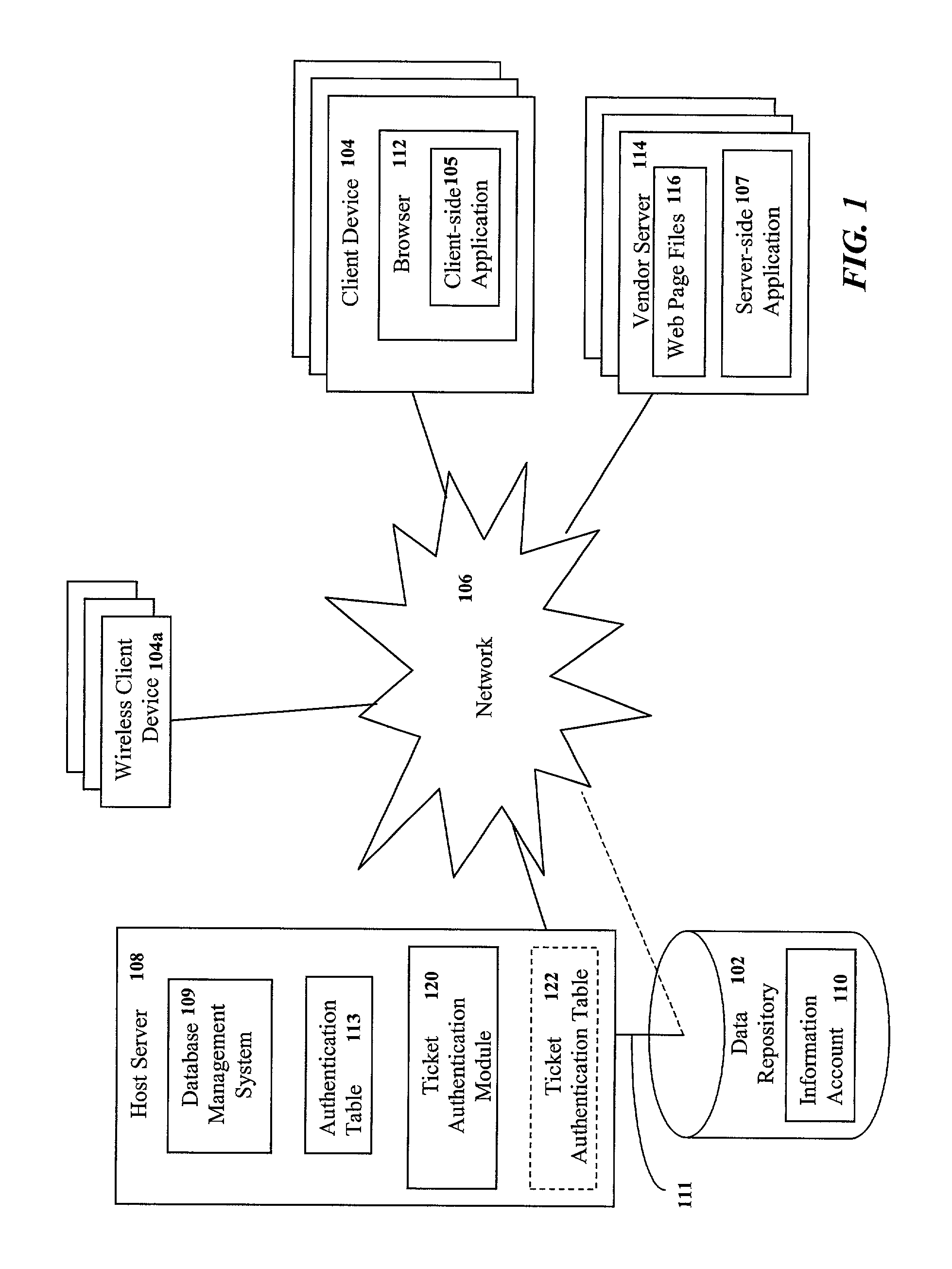
Consumer-controlled limited and constrained access to a centrally stored information account
Consumer authentication information is associated with an information account stored in a central database, such that access to the information account by the consumer is conditioned upon receipt and verification of the consumer authentication information. A temporary authorization may also be associated with the information account. The temporary authorization has consumer-defined attributes that define access privileges to be granted to a person who presents the temporary authorization along with a request for further access to the information account. The temporary authorization may be transmitted to the consumer for presentation to a third-party of the consumer's choice. Alternately, the temporary authorization may be transmitted to a designated third-party or device on behalf of the consumer.
Owner:CXT SYST INC
Methods and apparatus providing automatic client authentication
ActiveUS7194761B1Avoid disruptionDigital data processing detailsUser identity/authority verificationClient-sideServer appliance
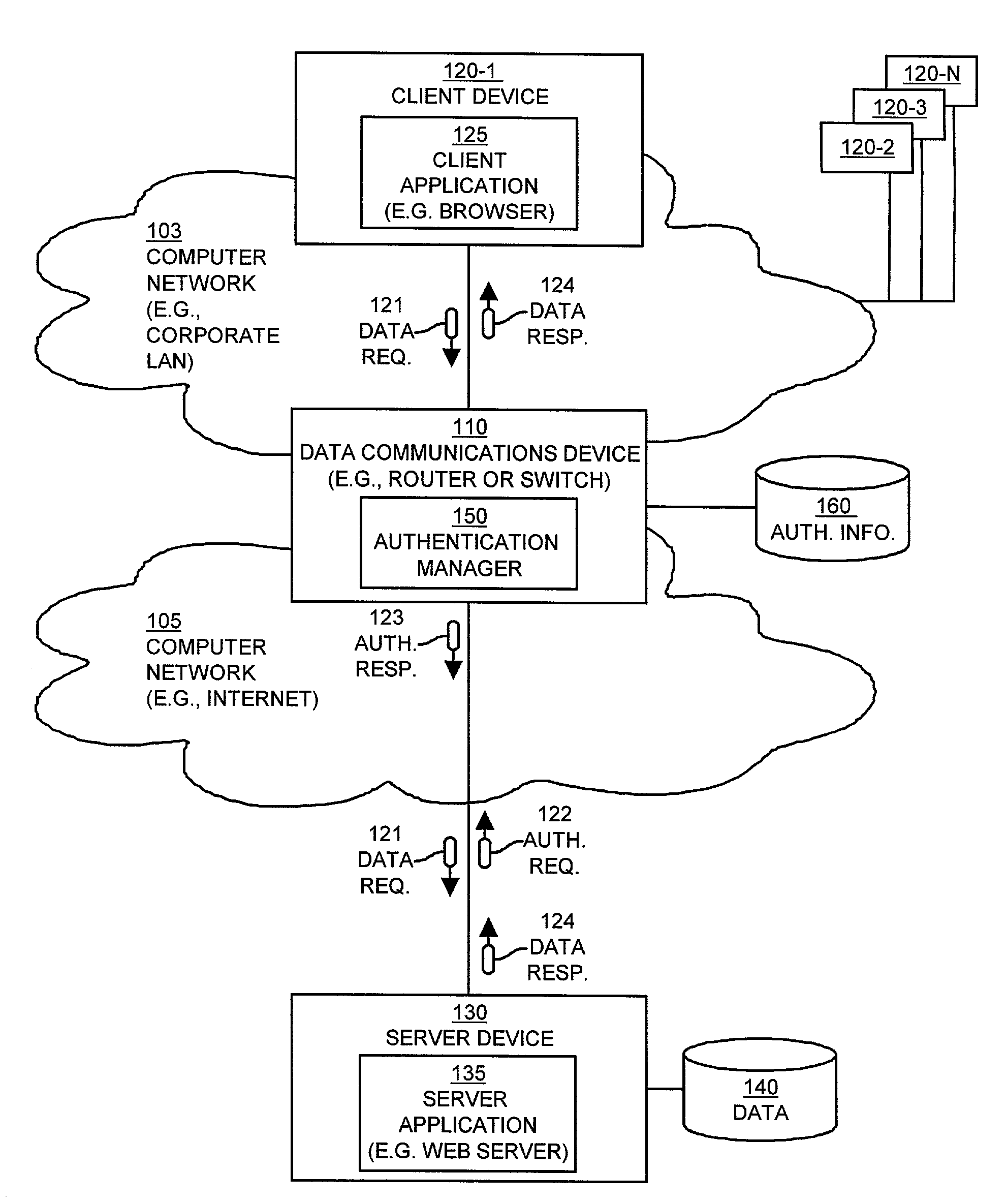
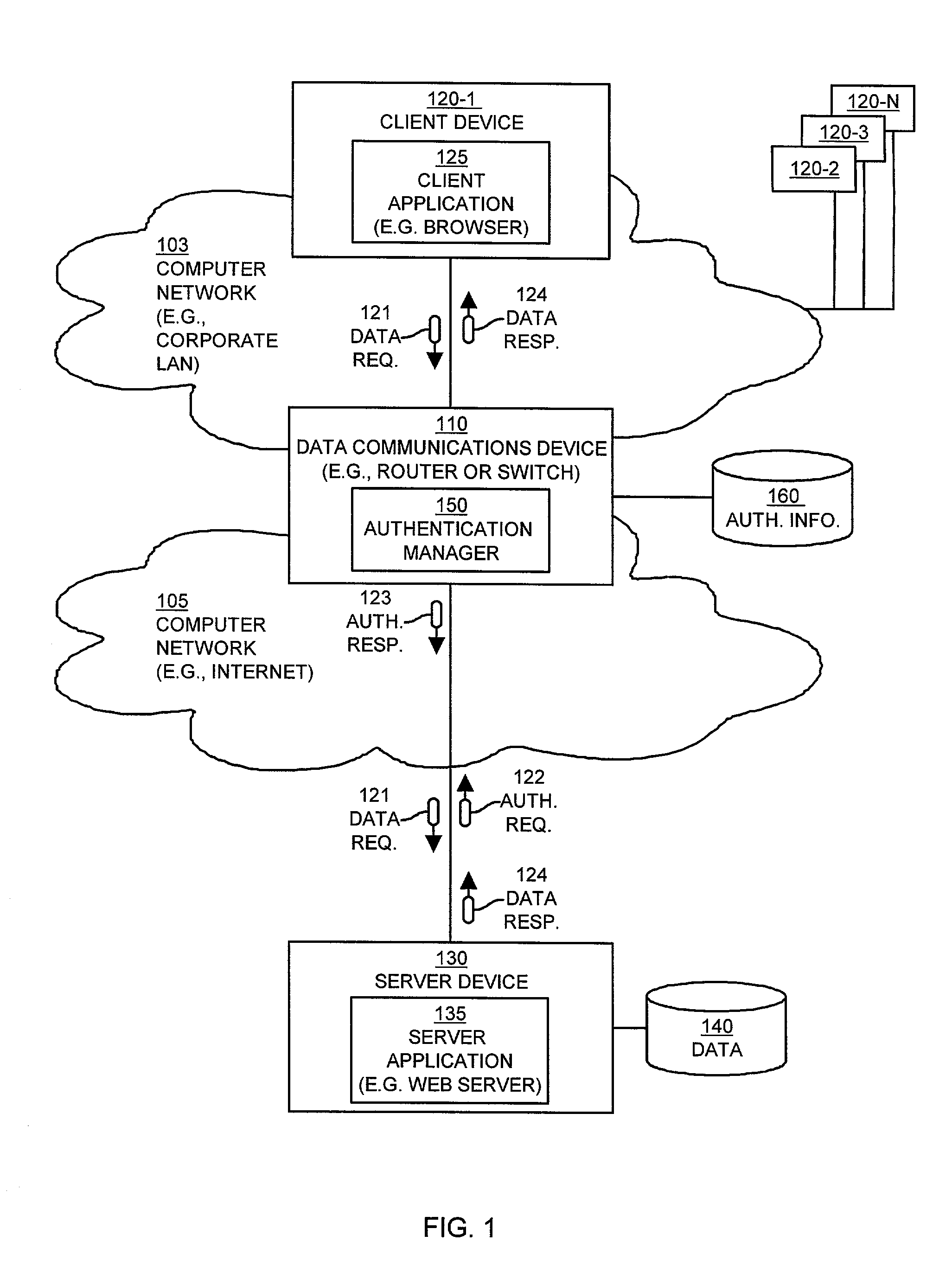
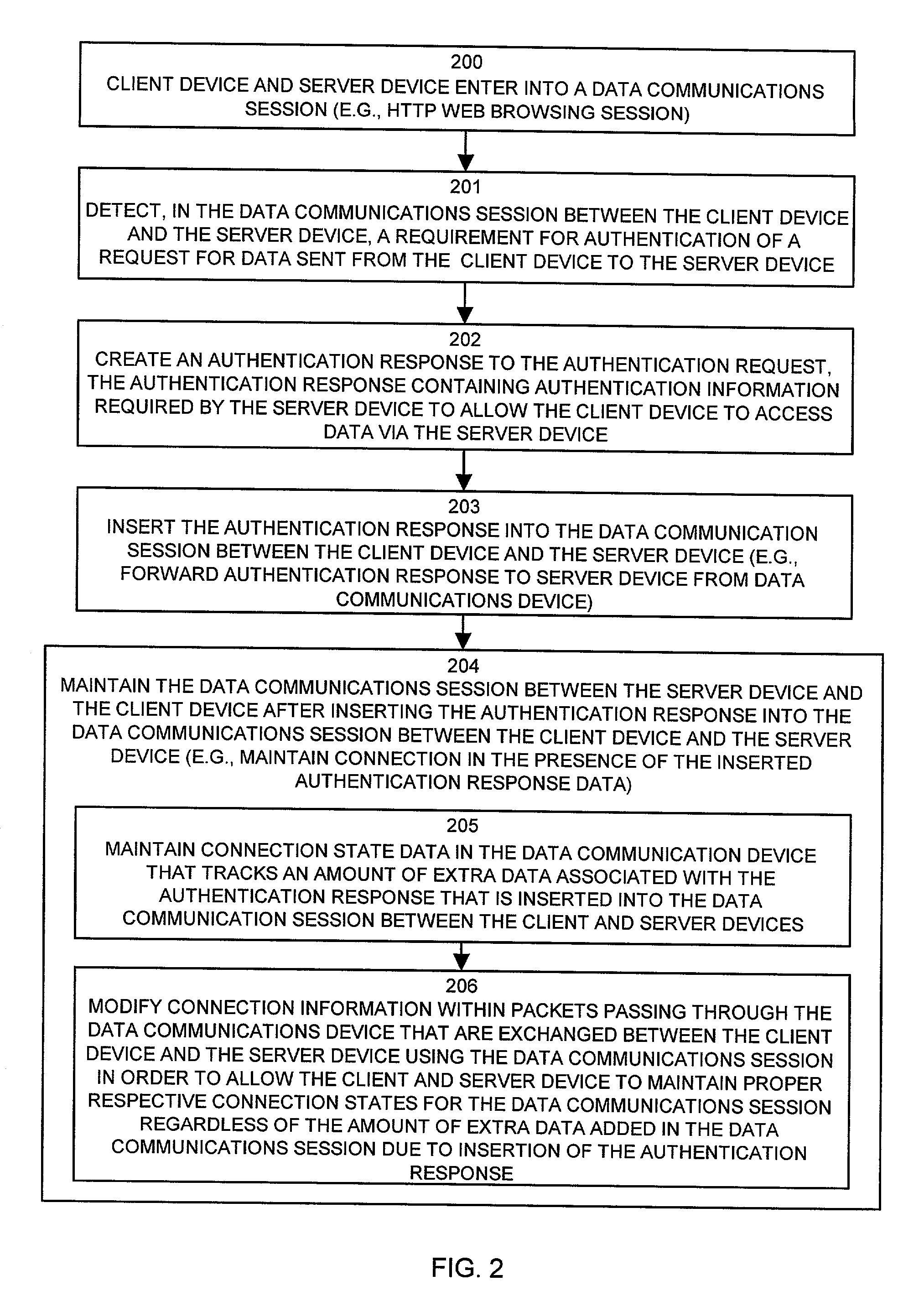
Mechanisms and techniques provide a system that operates in a data communications device to provide automatic authentication of a client device to a server device. The mechanisms and techniques (i.e., the system) operate to detect a requirement for authentication of a request for data sent from a client device to a server device. In response, the system creates an authentication response in response to detecting the requirement for authentication. The authentication response contains authentication information required by the server device to allow the client device to access data via the server device. The system then automatically inserts the authentication response into the data communications session between the client device and the server device. The authentication response authenticates, to the server device, access to the data by the client device. The system also maintains the data communications session between the server device and the client device in the presence of authentication response information inserted into the data communications session between the client device and the server device.
Owner:CISCO TECH INC
Method and apparatus for facilitating communication in a content centric network
ActiveUS8386622B2Easy flow controlMultiple digital computer combinationsTransmissionContent centricWorld Wide Web
One embodiment of the present invention provides a system for facilitating communication in a content centric network (CCN). During operation, the system receives at a first node from an interest owner an interest in a piece of content. The interest indicates a structured name for the content. Furthermore, the name is unique and persistent with respect to the content, and where the name includes authentication information for the content. Next, the system determines whether content available at the first node satisfies the interest. If so, the system sends the content to the interest owner. Otherwise, the system marks the interest as pending, and forwards the interest to a second node in the network based on the interest. After receiving content from the second node in response to the forwarded interest, the system un-marks the interest as pending and sends the content to the interest owner.
Owner:CISCO TECH INC
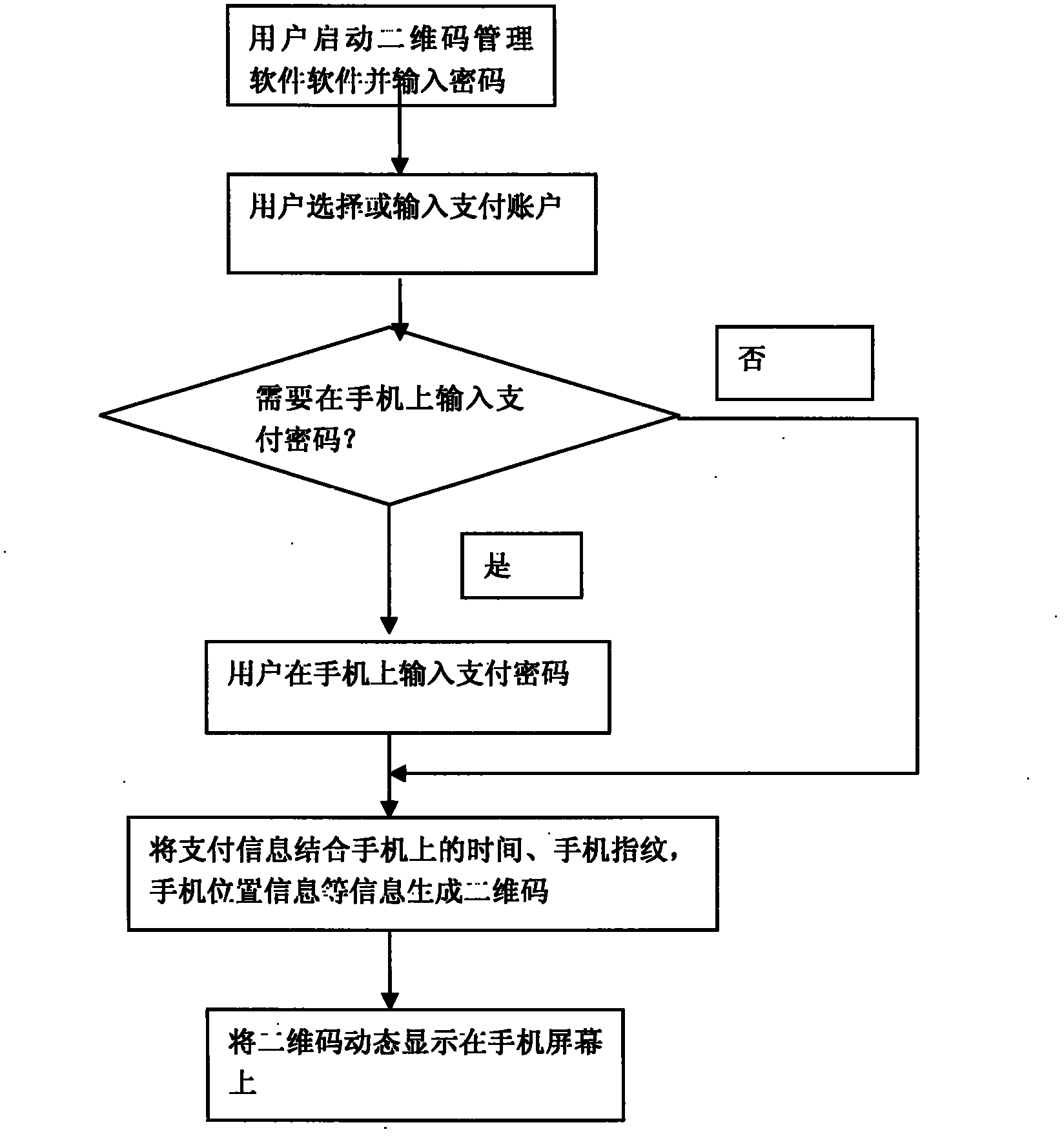
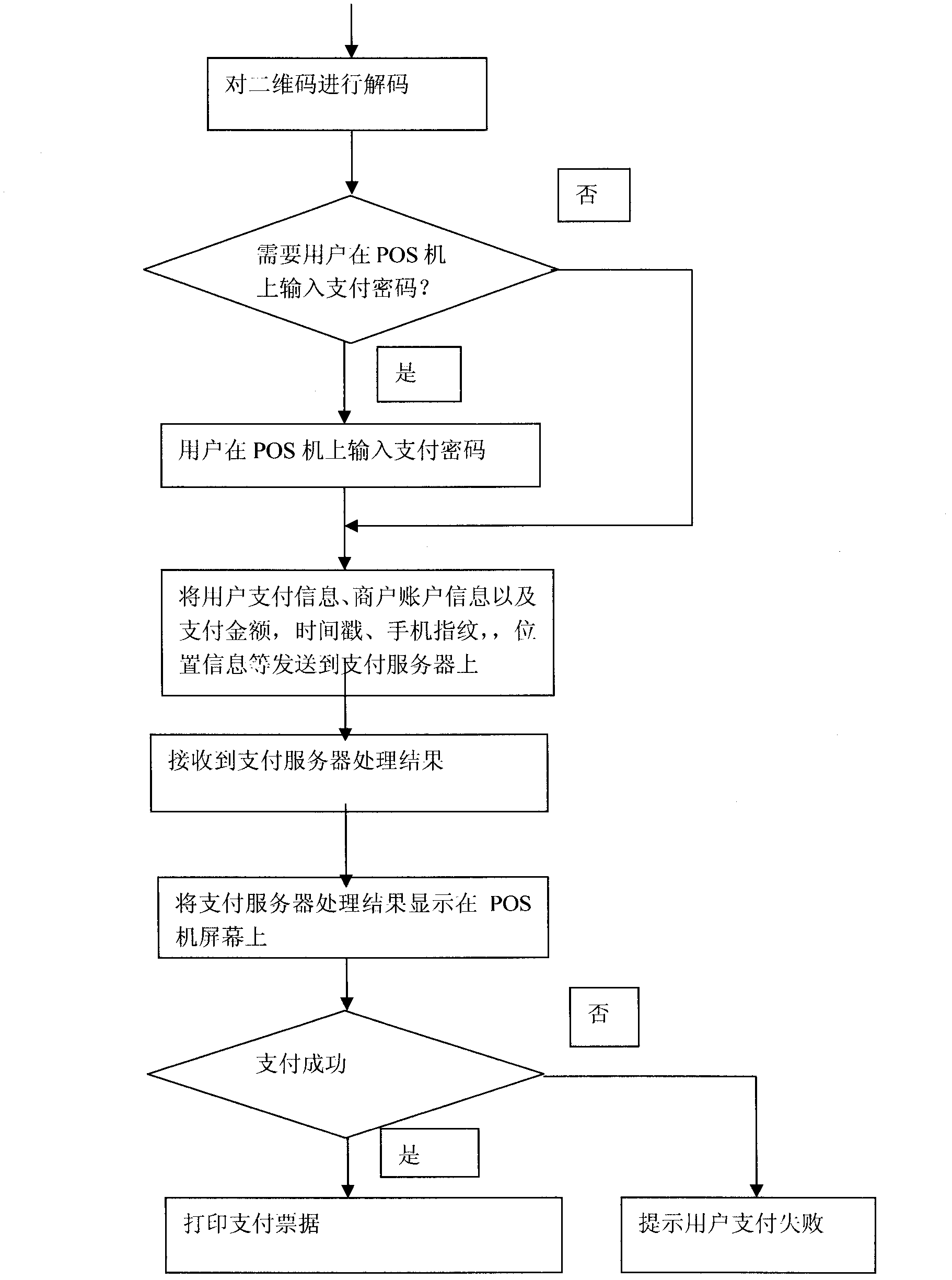
Method for generating two-dimensional code and implementing mobile payment by mobile phone
InactiveCN102842081AEnsure uniquenessEnsure safetyPayment protocolsCoded identity card or credit card actuationComputer hardwareCredit card
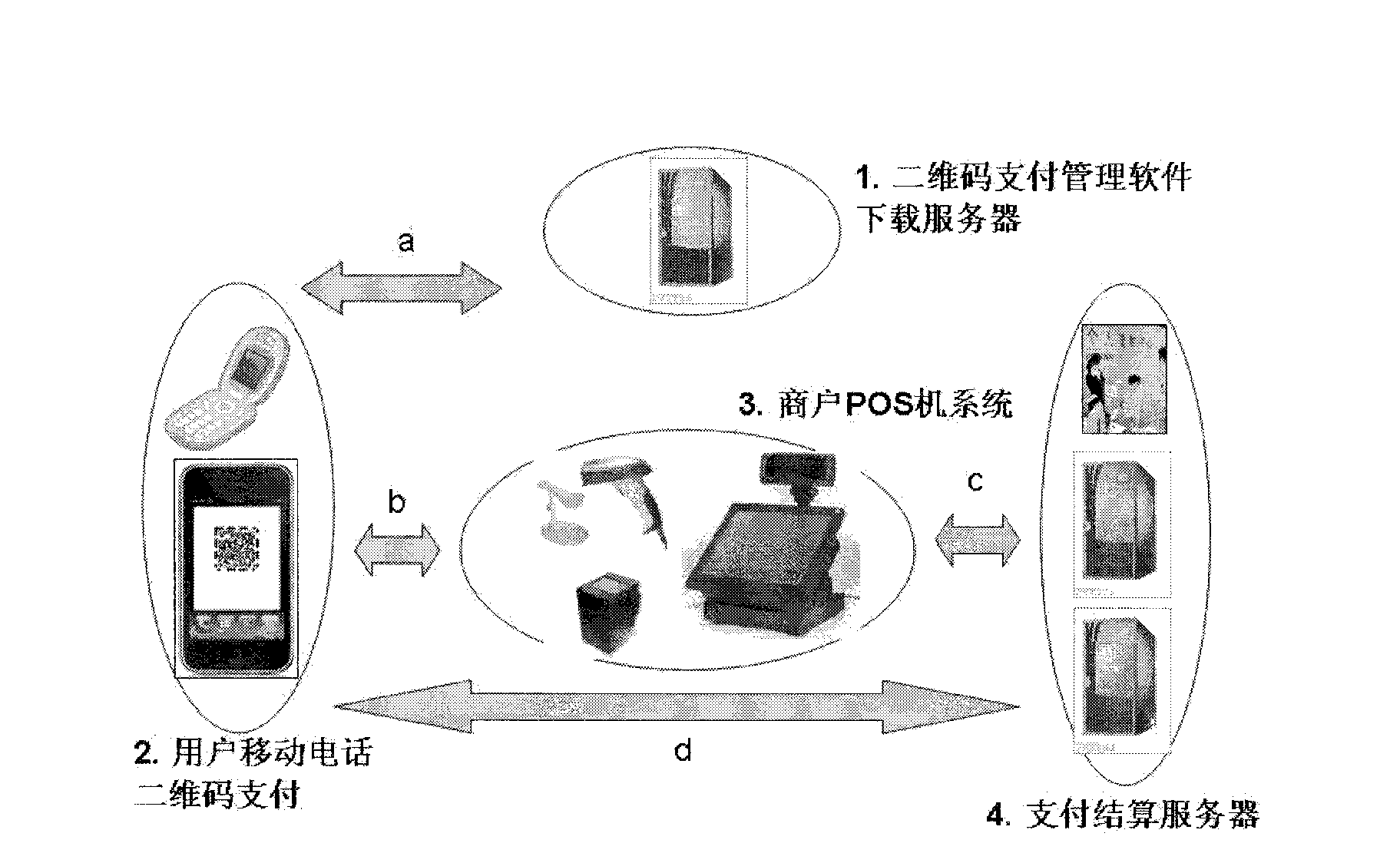
The invention relates to a method for generating a two-dimensional code and implementing mobile payment by a mobile phone. A user can input various payment card information (such as bank card account numbers, credit card account numbers, prepaid card account numbers, and third party payment user account numbers) into the mobile phone, the information is enciphered and stored, and then the two-dimensional code is generated and displayed on a screen of the mobile phone. A merchant scans a pattern of the two-dimensional code through a two-dimensional code identifying and reading device, and after user authentication information (such as two-dimensional code generation time, mobile phone fingerprints and mobile phone positions) and the payment card information are decoded, the user authentication information, the payment card information, consumption amount information of the user, merchant account number information and the like are enciphered and sent to a corresponding payment and settlement system. After receiving the information, a payment and settlement server confirms the payment card information to be true or false according to the two-dimensional code authentication information, and carries out payment transaction. The method has the main advantage that the user can save the information of various payment cards, consumption cards and the like in the mobile phone and realize no-card electronic payment transaction instead of the various payment cards.
Owner:上海易悠通信息科技有限公司
Tokenless financial access system
The present invention shows a method and a device system for tokenless authorization of commercial transactions between a user and a seller. The user registers at least one registration biometric sample, and at least one user financial account. The seller registers with the computer system at least one seller financial account. The seller offers a proposed commercial transaction to the user, which includes price information. The user accepts the seller's proposed commercial transaction by adding to the proposed commercial transaction the user's personal authentication information. The bid biometric sample is forwarded to the computer system. The computer system compares the bid biometric sample with registration biometric samples. Upon successful match, a financial account of the user is debited and a financial account of the seller is credited, wherein a commercial transaction is conducted without the user having to use any portable man-made memory devices such as smartcards or swipe cards.
Owner:EXCEL INNOVATIONS +1
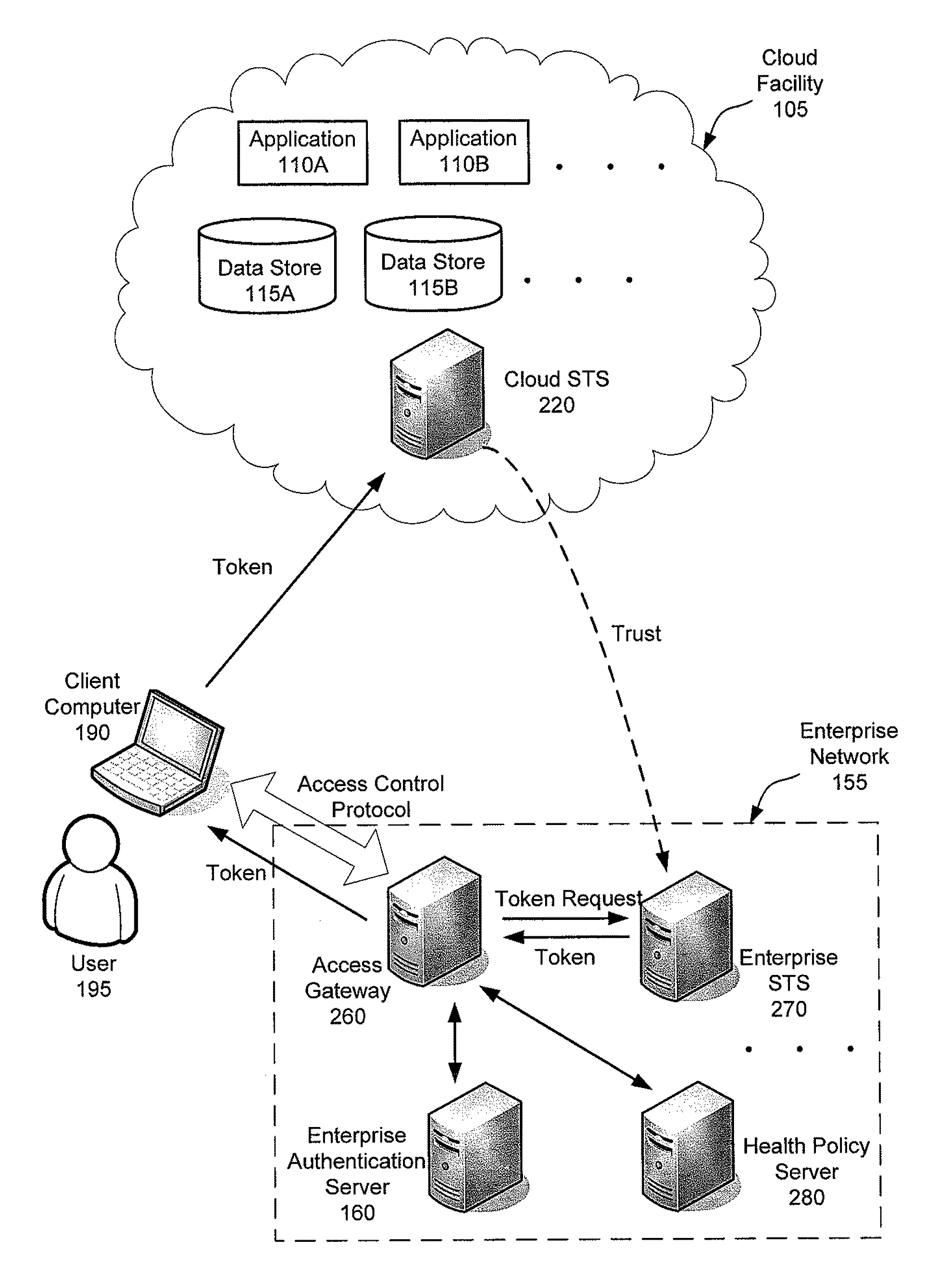
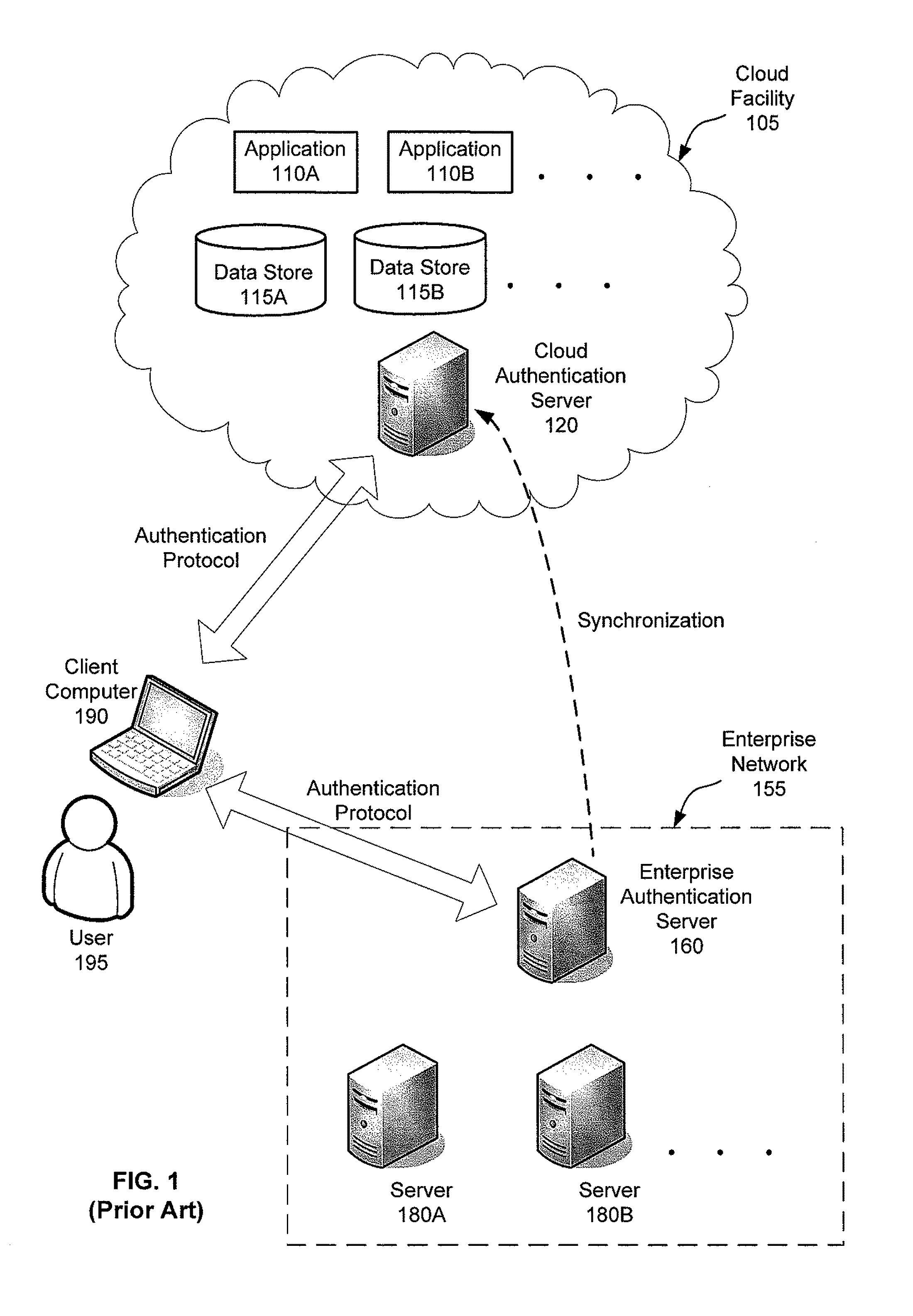
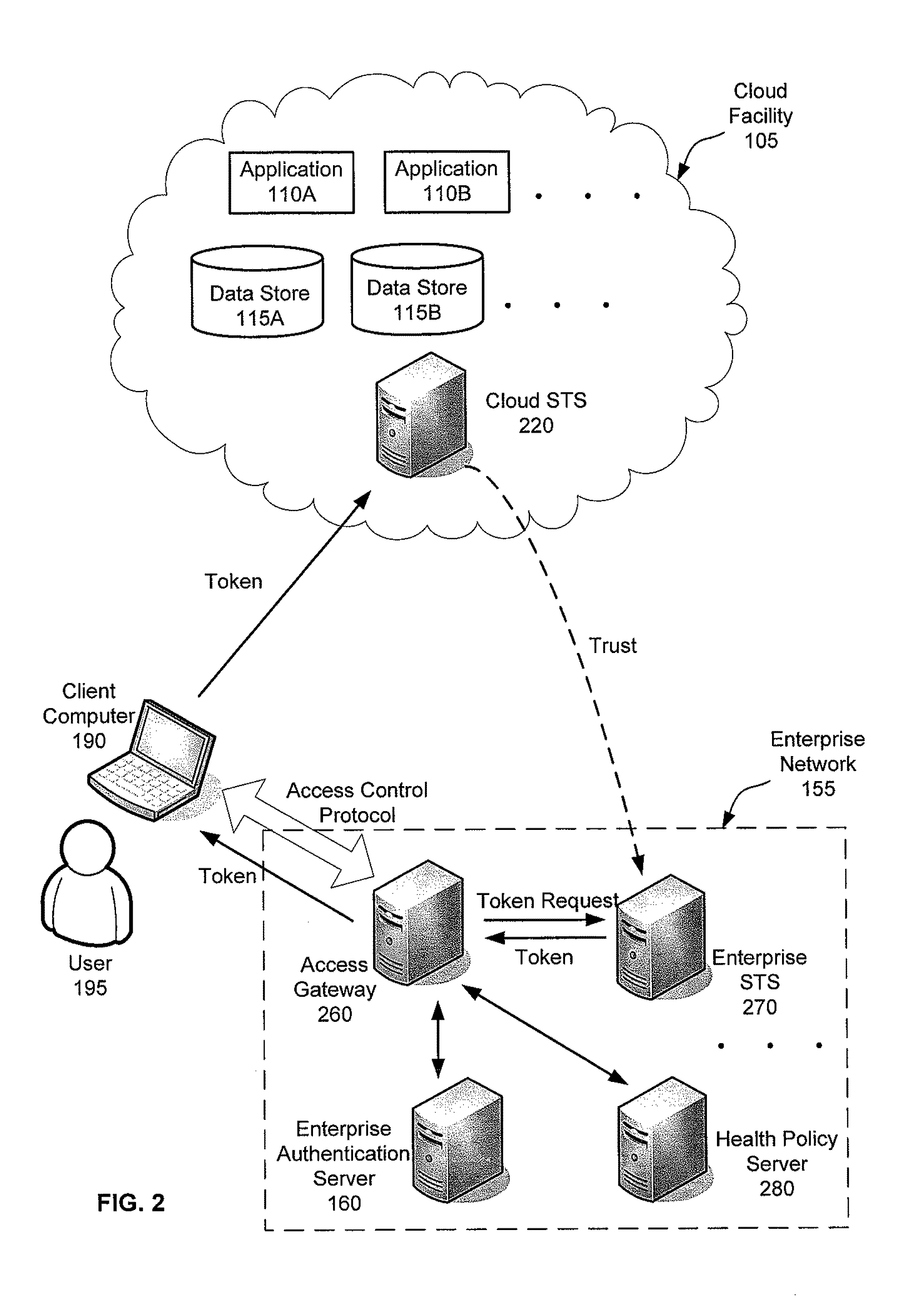
Flexible end-point compliance and strong authentication for distributed hybrid enterprises
ActiveUS20110307947A1Digital data processing detailsMultiple digital computer combinationsUser authenticationClient-side
Systems, methods and apparatus for accessing at least one resource hosted by at least one server of a cloud service provider. In some embodiments, a client computer sends authentication information associated with a user of the client computer and a statement of health regarding the client computer to an access control gateway deployed in an enterprise's managed network. The access control gateway authenticates the user and determines whether the user is authorized to access the at least one resource hosted in the cloud. If the user authentication and authorization succeeds, the access control gateway requests a security token from a security token service trusted by an access control component in the cloud and forwards the security token to the client computer. The client computer sends the security token to the access component in the cloud to access the at least one resource from the at least one server.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for authenticating communications in a network medium
InactiveUS20030149874A1Key distribution for secure communicationUser identity/authority verificationKey exchangeExchange protocol
Pre-authentication information of devices is used to securely authenticate arbitrary peer-to-peer ad-hoc interactions. In one embodiment, public key cryptography is used in the main wireless link with location-limited channels being initially used to pre-authenticate devices. Use of public keys in the pre-authenticate data allows for the broadening of types of media suitable for use as location-limited channels to include, for example, audio and infrared. Also, it allows a range of key exchange protocols which can be authenticated in this manner to include most public-key-protocols. As a result, a large range of devices, protocols can be used in various applications. Further, an eavesdropper is forced to mount an active attack on the location-limited channel itself in order to access an ad-hoc exchange. However, this results in the discovery of the eavesdropper.
Owner:CISCO TECH INC
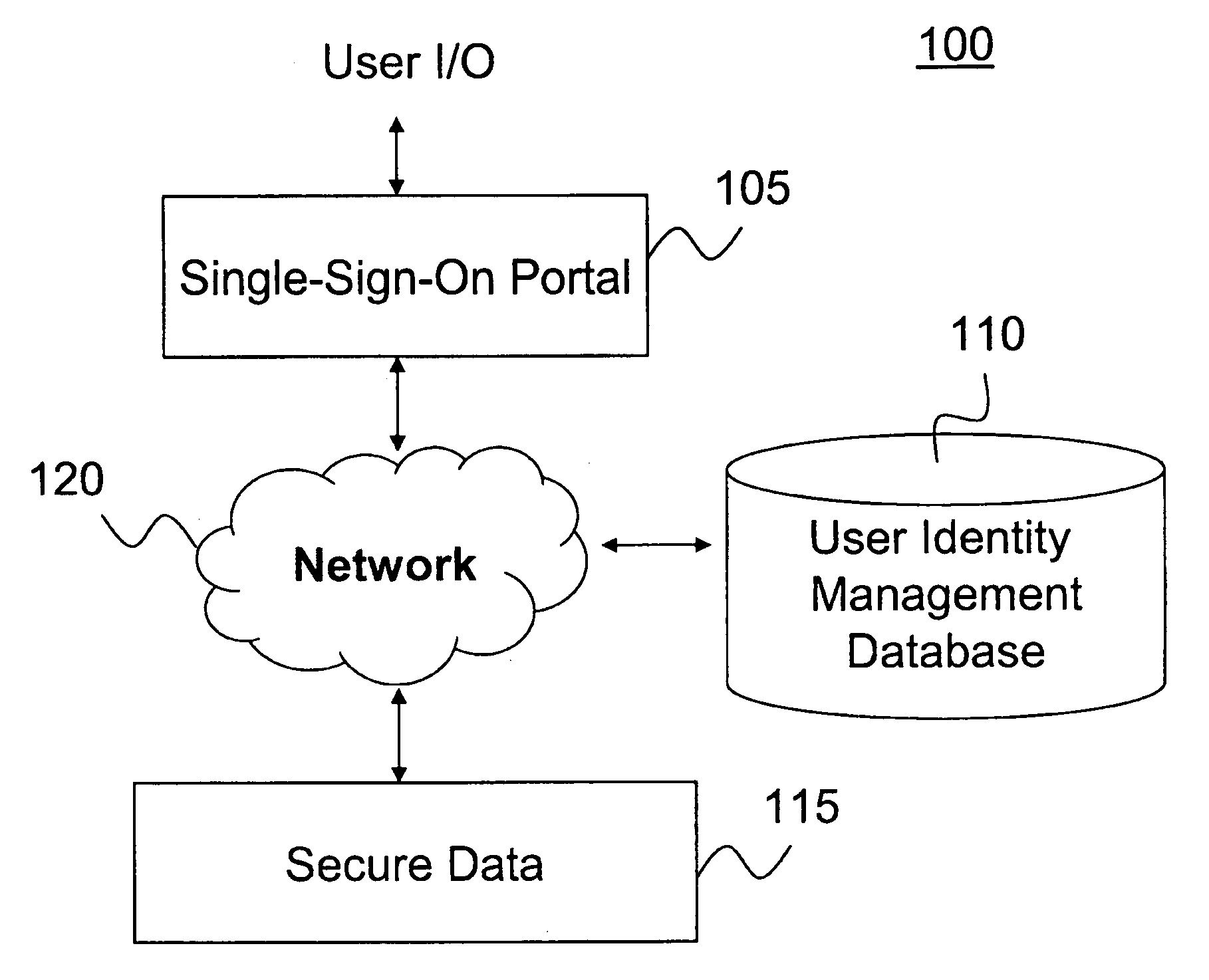
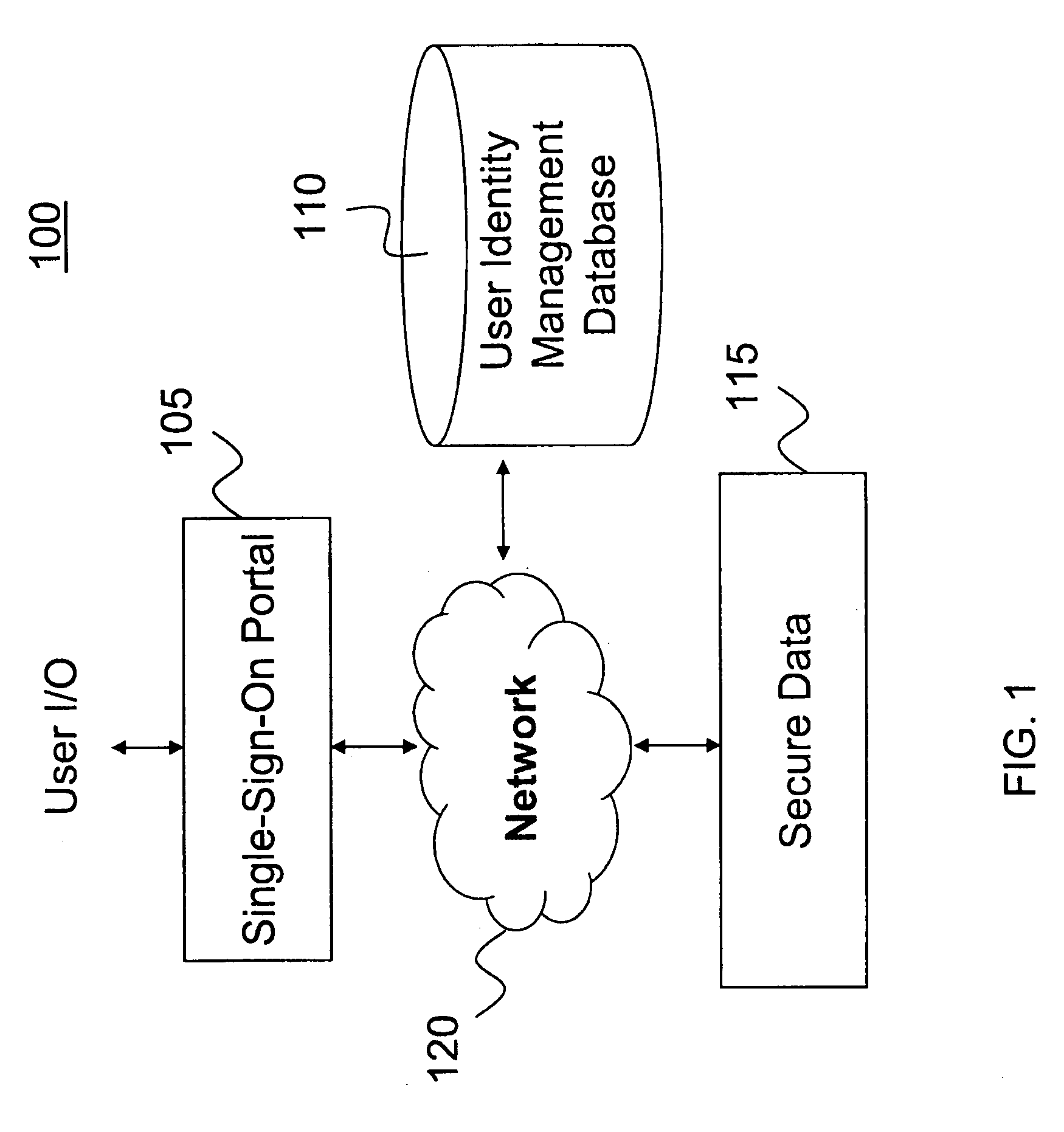
Secure single-sign-on portal system
ActiveUS20090172795A1Reduce decreaseDigital data processing detailsUser identity/authority verificationPasswordThe Internet
A computer-implemented portal system facilitates access to secure data and multiple secure-access internet sites. The system authenticates a user based on a single-sign-on identifier (ID) and password. The system stores user authentication information for the secure-access internet sites so that once the user is authenticated, the system can automatically authenticate the user to the sites, thus allowing the user to access multiple secure sites after a single manual authentication.
Owner:DELUXE CORPORATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com