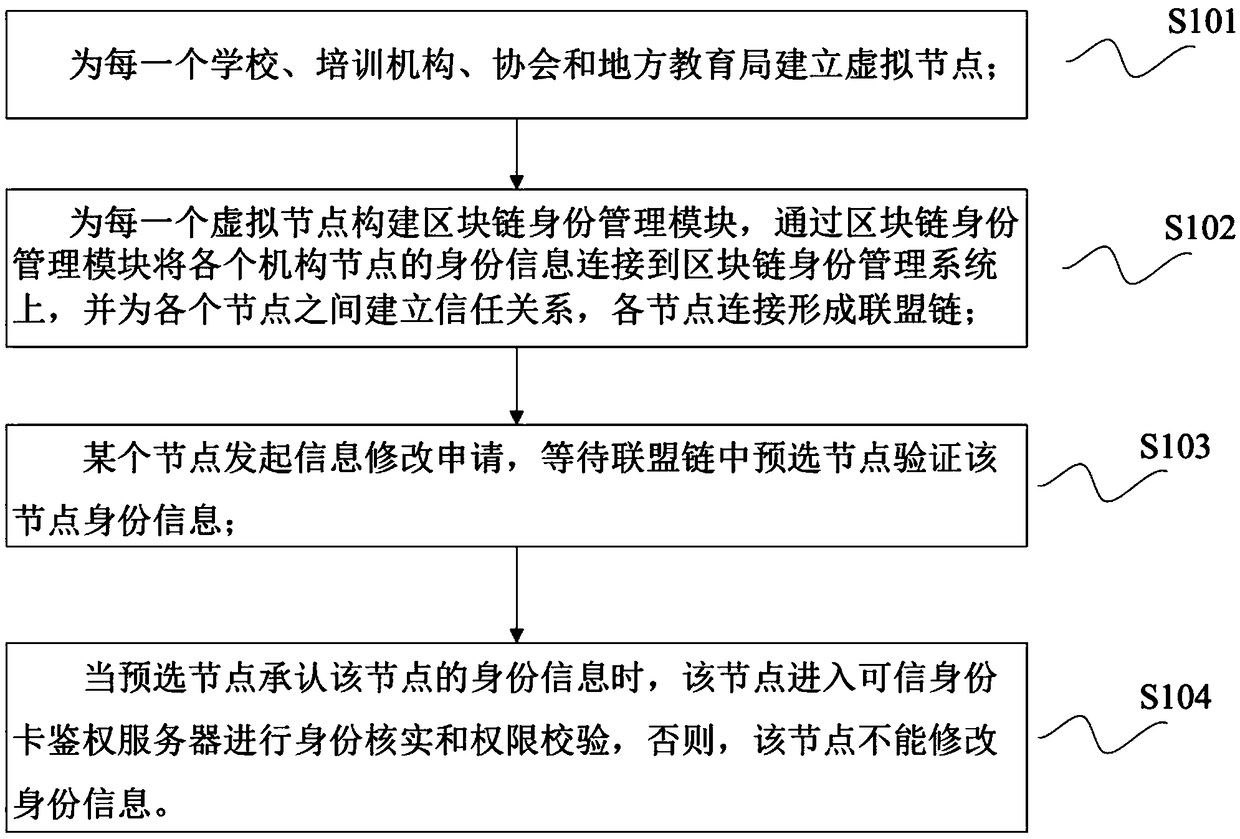
Patents
Literature
87results about How to "Ensure uniqueness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
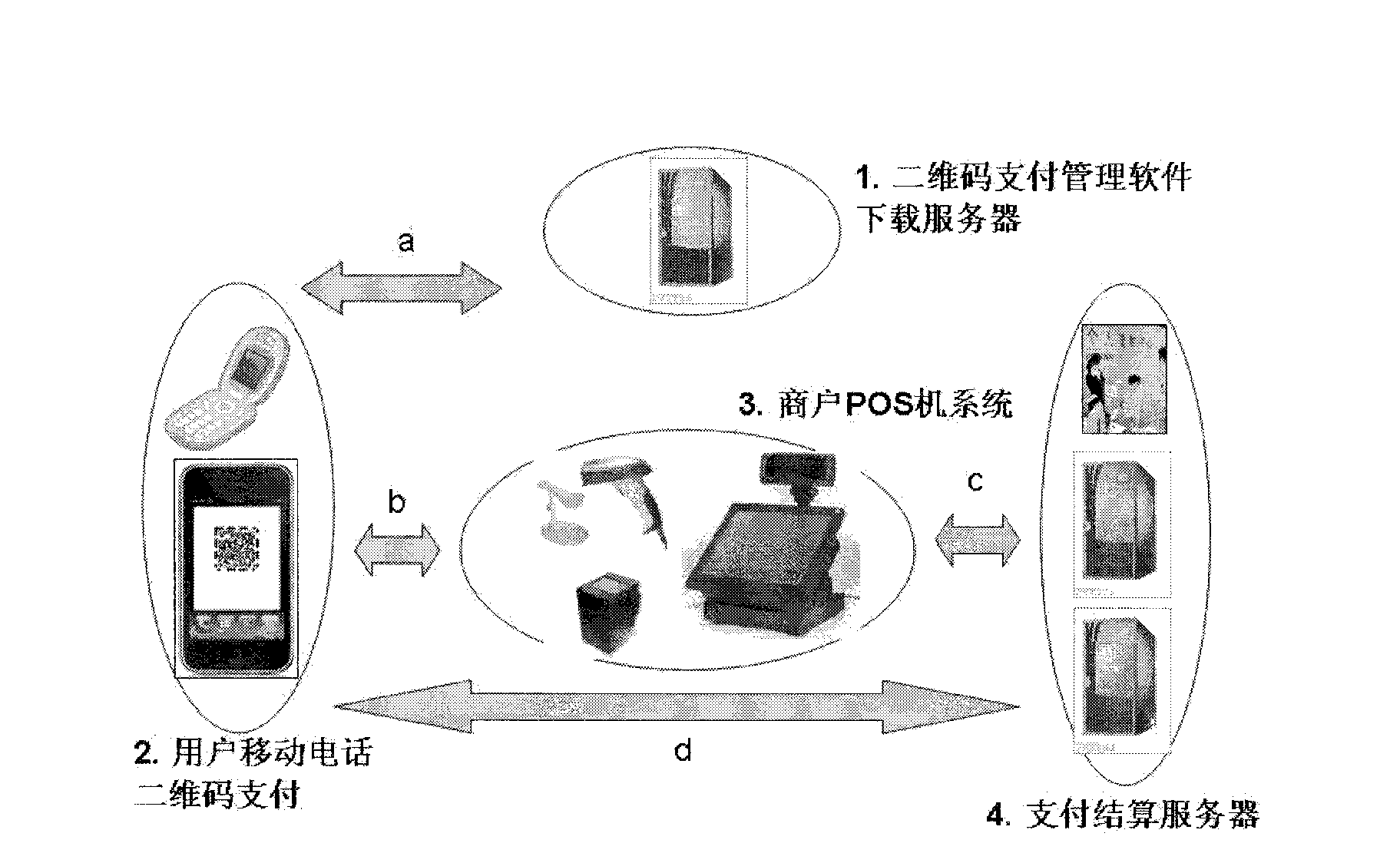
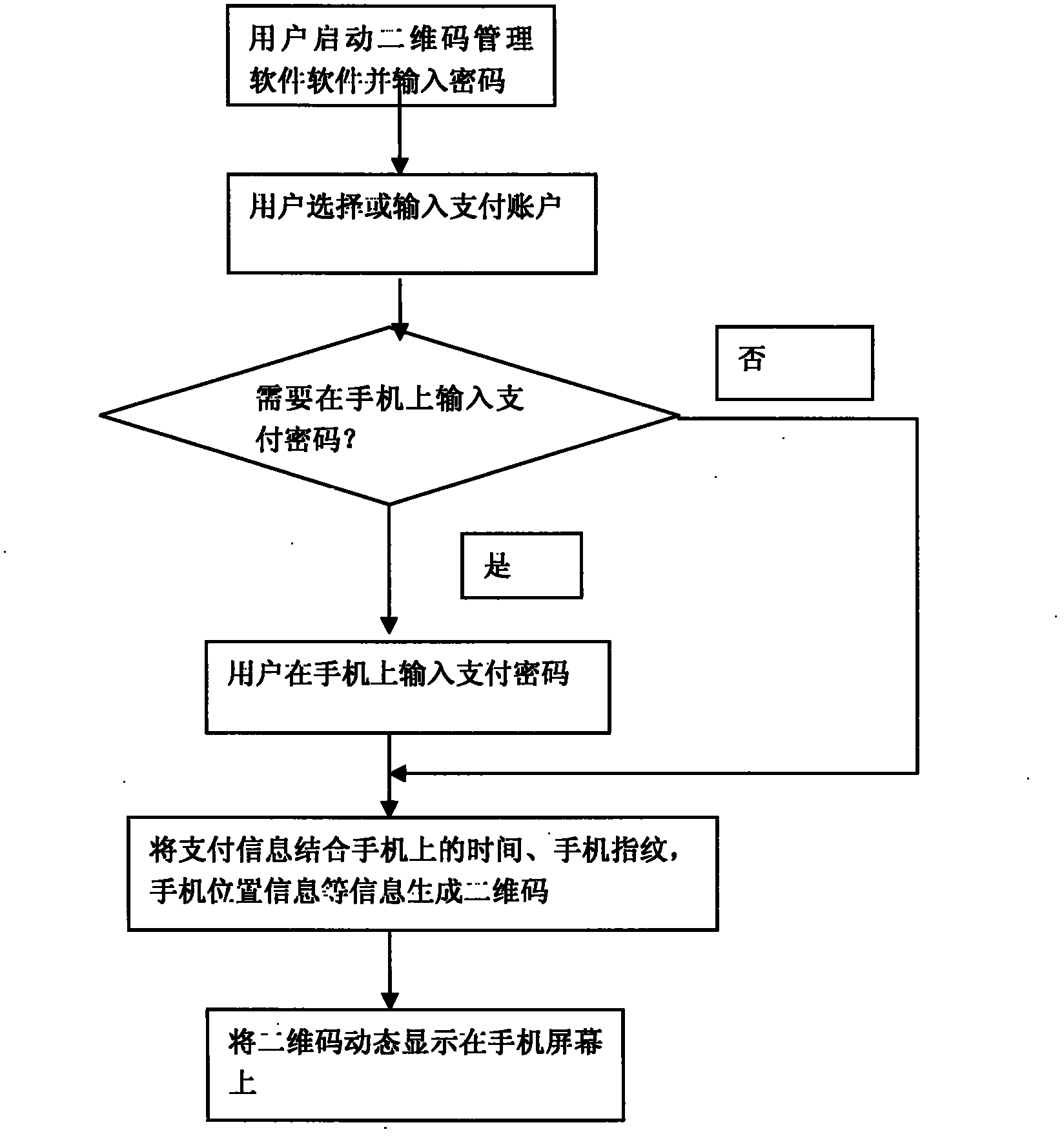
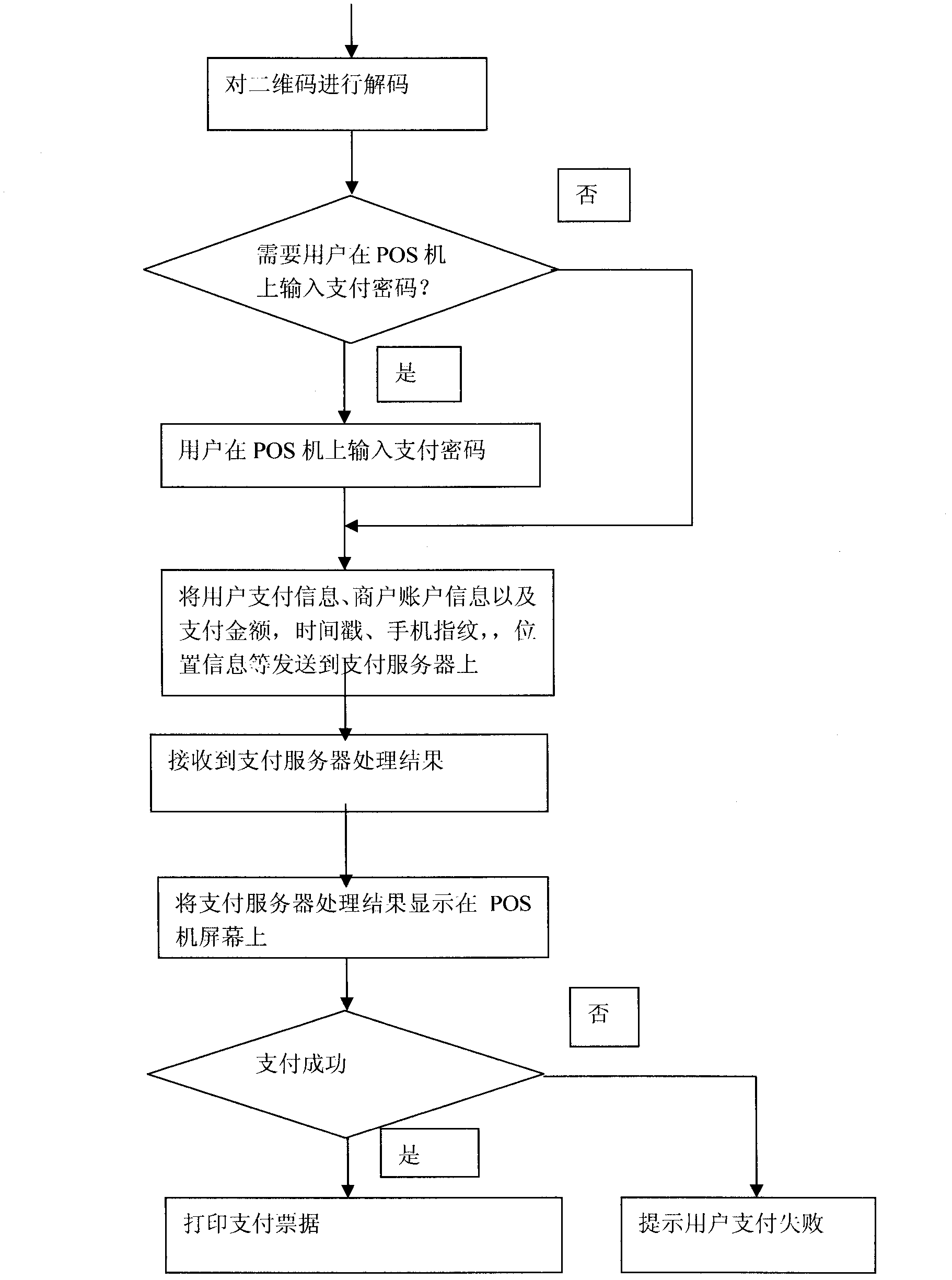
Method for generating two-dimensional code and implementing mobile payment by mobile phone
InactiveCN102842081AEnsure uniquenessEnsure safetyPayment protocolsCoded identity card or credit card actuationComputer hardwareCredit card
The invention relates to a method for generating a two-dimensional code and implementing mobile payment by a mobile phone. A user can input various payment card information (such as bank card account numbers, credit card account numbers, prepaid card account numbers, and third party payment user account numbers) into the mobile phone, the information is enciphered and stored, and then the two-dimensional code is generated and displayed on a screen of the mobile phone. A merchant scans a pattern of the two-dimensional code through a two-dimensional code identifying and reading device, and after user authentication information (such as two-dimensional code generation time, mobile phone fingerprints and mobile phone positions) and the payment card information are decoded, the user authentication information, the payment card information, consumption amount information of the user, merchant account number information and the like are enciphered and sent to a corresponding payment and settlement system. After receiving the information, a payment and settlement server confirms the payment card information to be true or false according to the two-dimensional code authentication information, and carries out payment transaction. The method has the main advantage that the user can save the information of various payment cards, consumption cards and the like in the mobile phone and realize no-card electronic payment transaction instead of the various payment cards.
Owner:上海易悠通信息科技有限公司
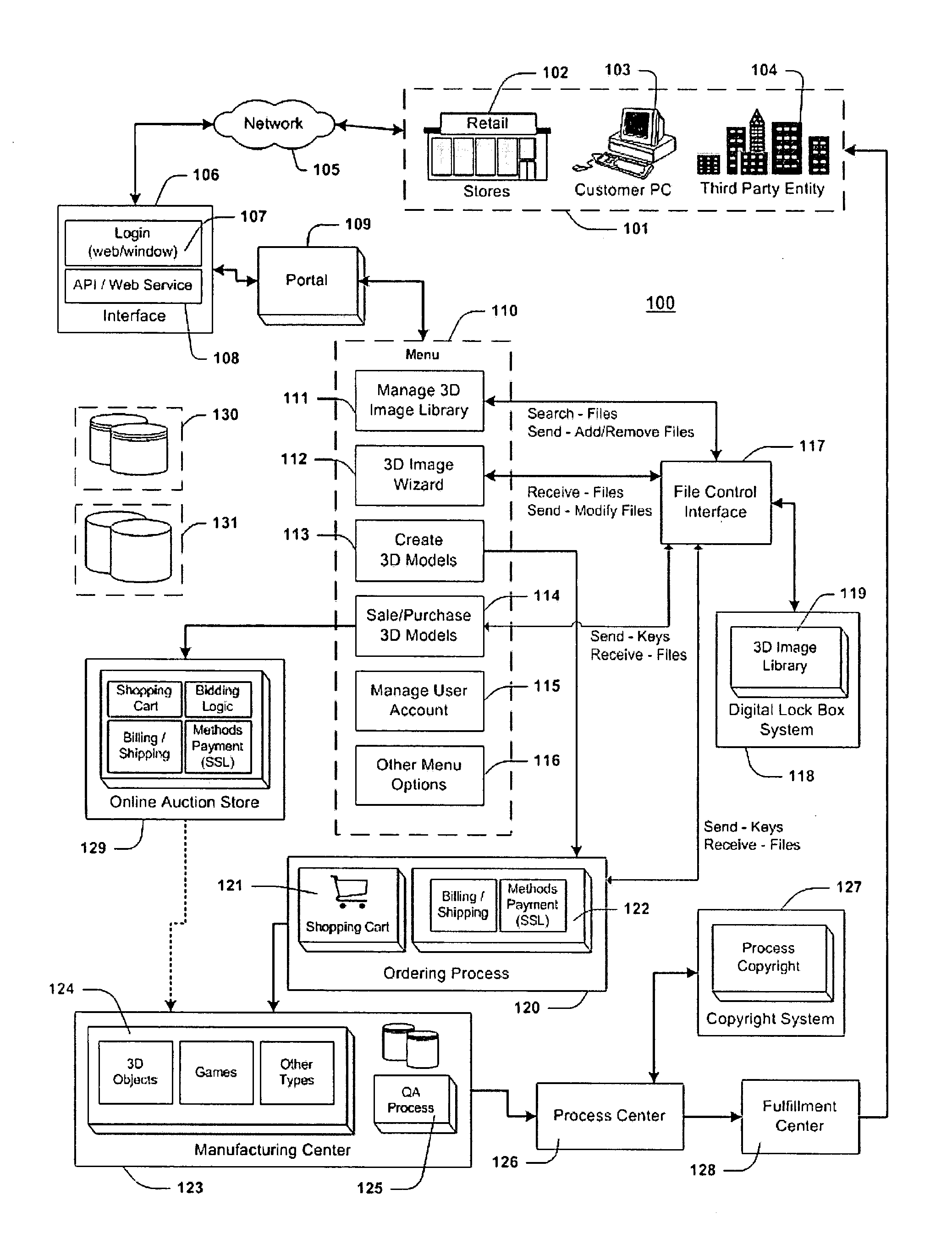
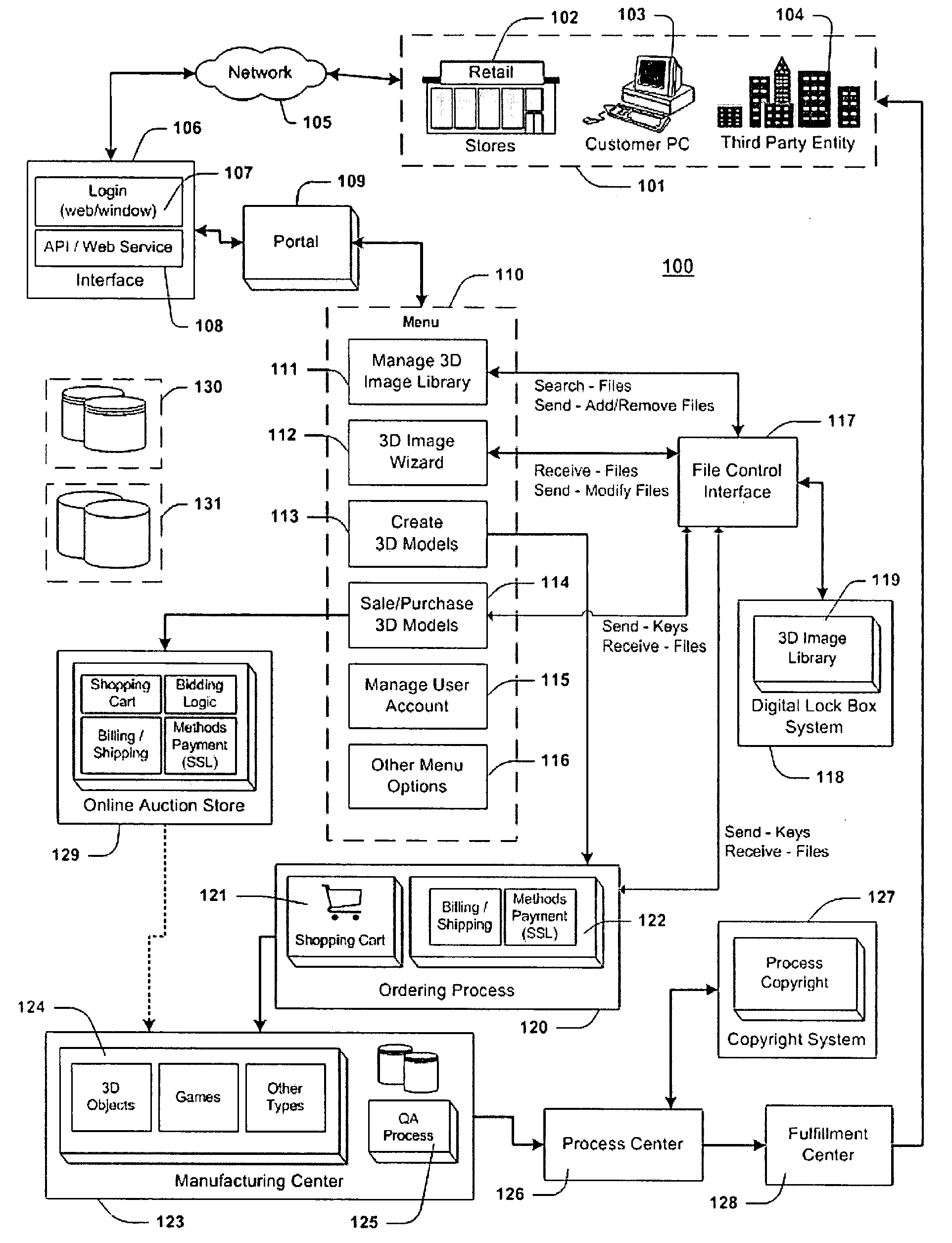
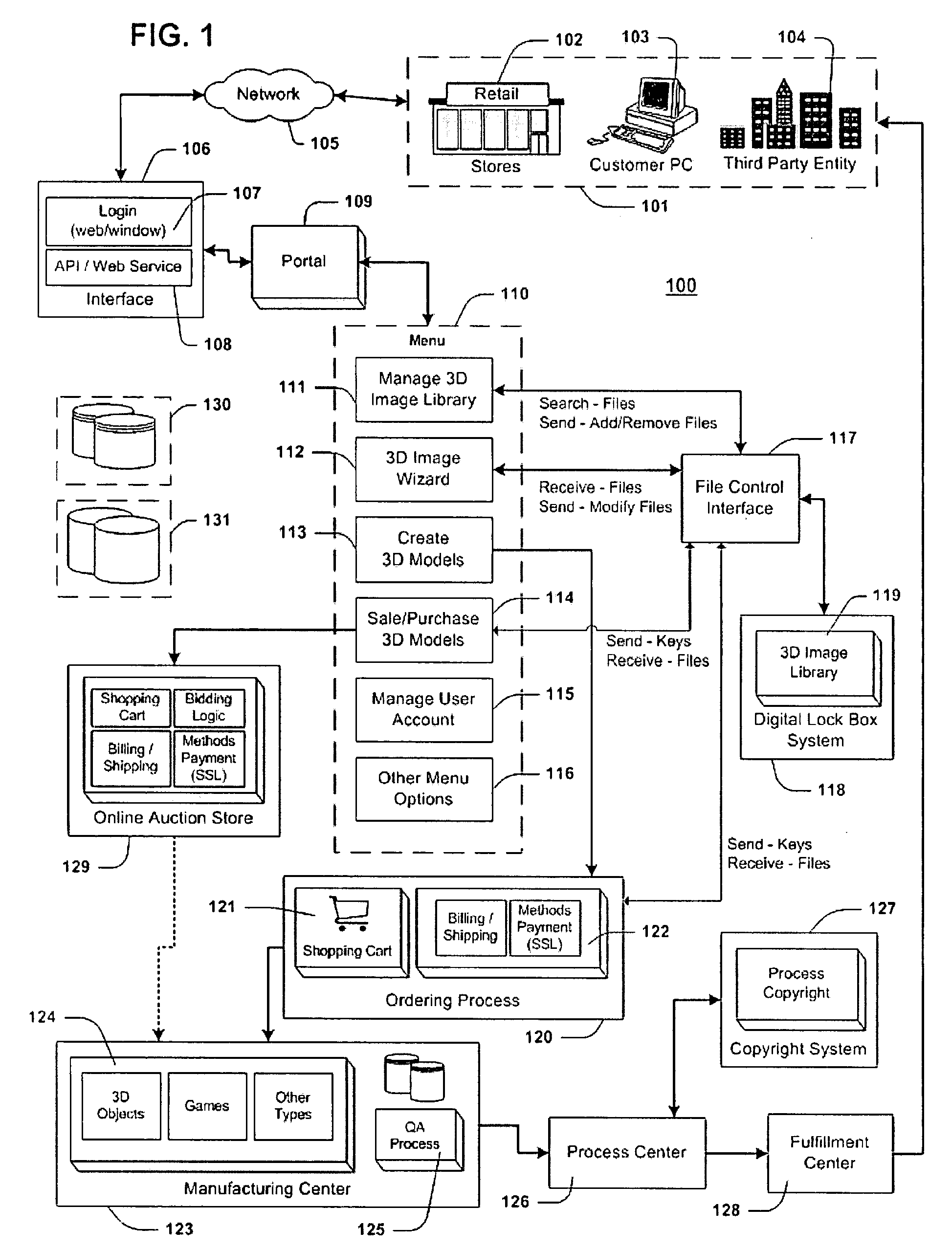
Method for creating, manufacturing, and distributing three-dimensional models
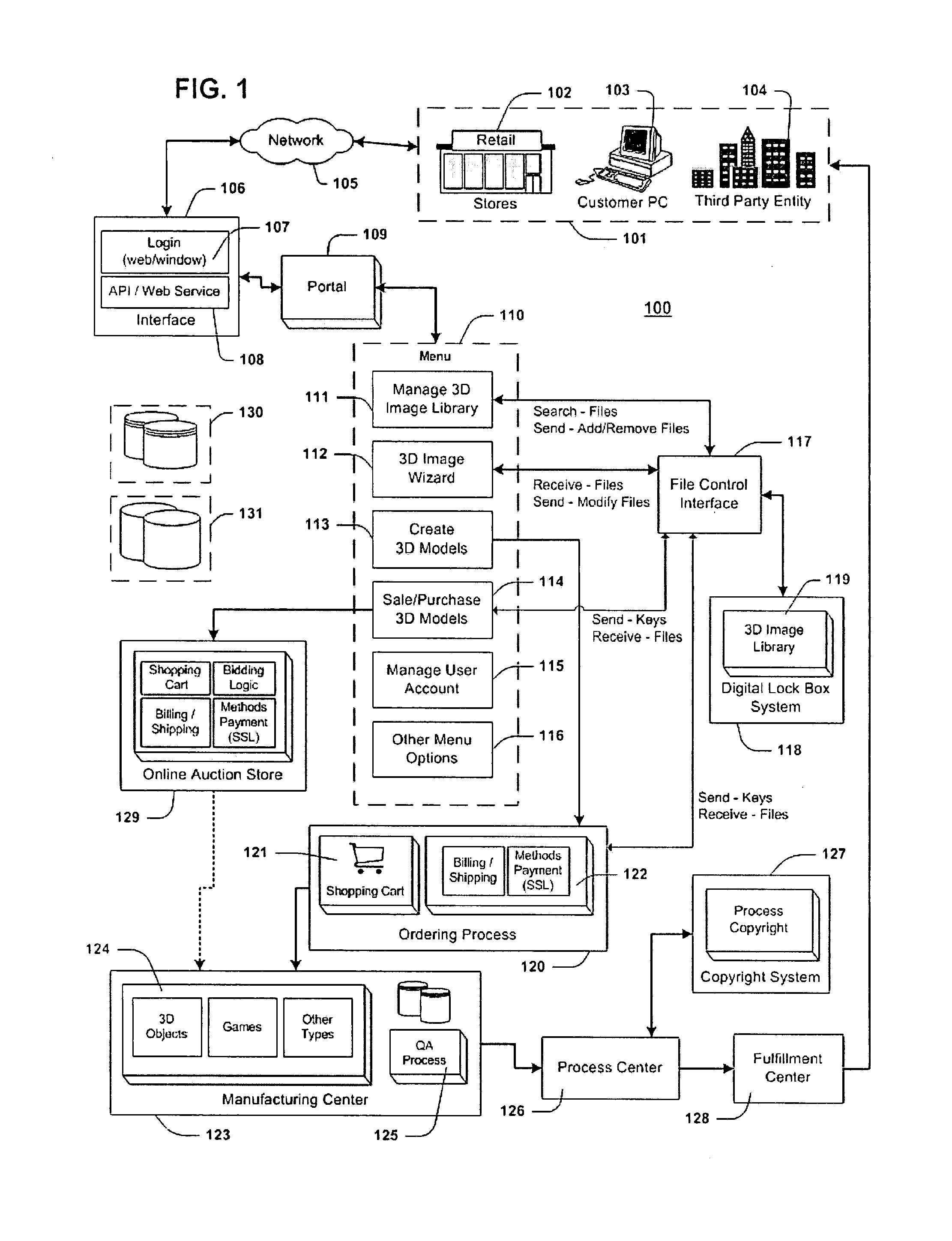
InactiveUS20080111816A1Ensure uniquenessMedical simulationAdditive manufacturing apparatusThird party3d image
A method is provided for producing three-dimensional (3D) models. The invention will take any sculpture, character, or model from artwork, still life models, images of human beings, characters from a computer game, or any other 3D digital image or model that is scanned, and turn the digital image into 3D models. The method is comprised of the following steps: creating a user account in a computer storage area; storing 3D images under the user account; allowing the user to select the 3D image(s) he or she wants to create as 3D models; manufacturing the 3D models; and delivering the models to the user or to a specified third-party. An online storefront and / or auction system may allow each user the opportunity to sell their 3D models or purchase other users' 3D models. The system may also create 3D models for a mobile phone and portable media player while transferring the models to either of these devices.
Owner:TAG LLC (US)
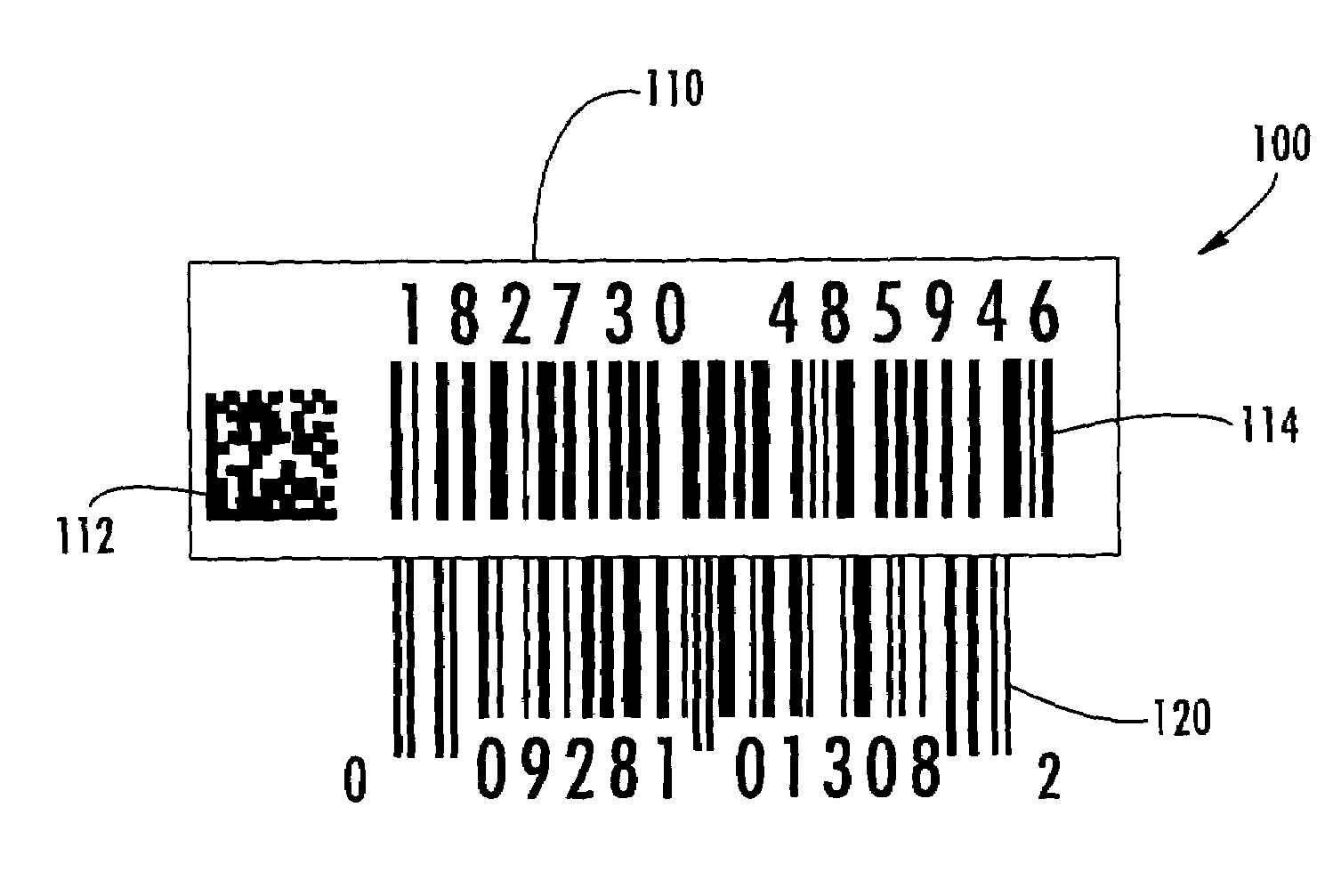
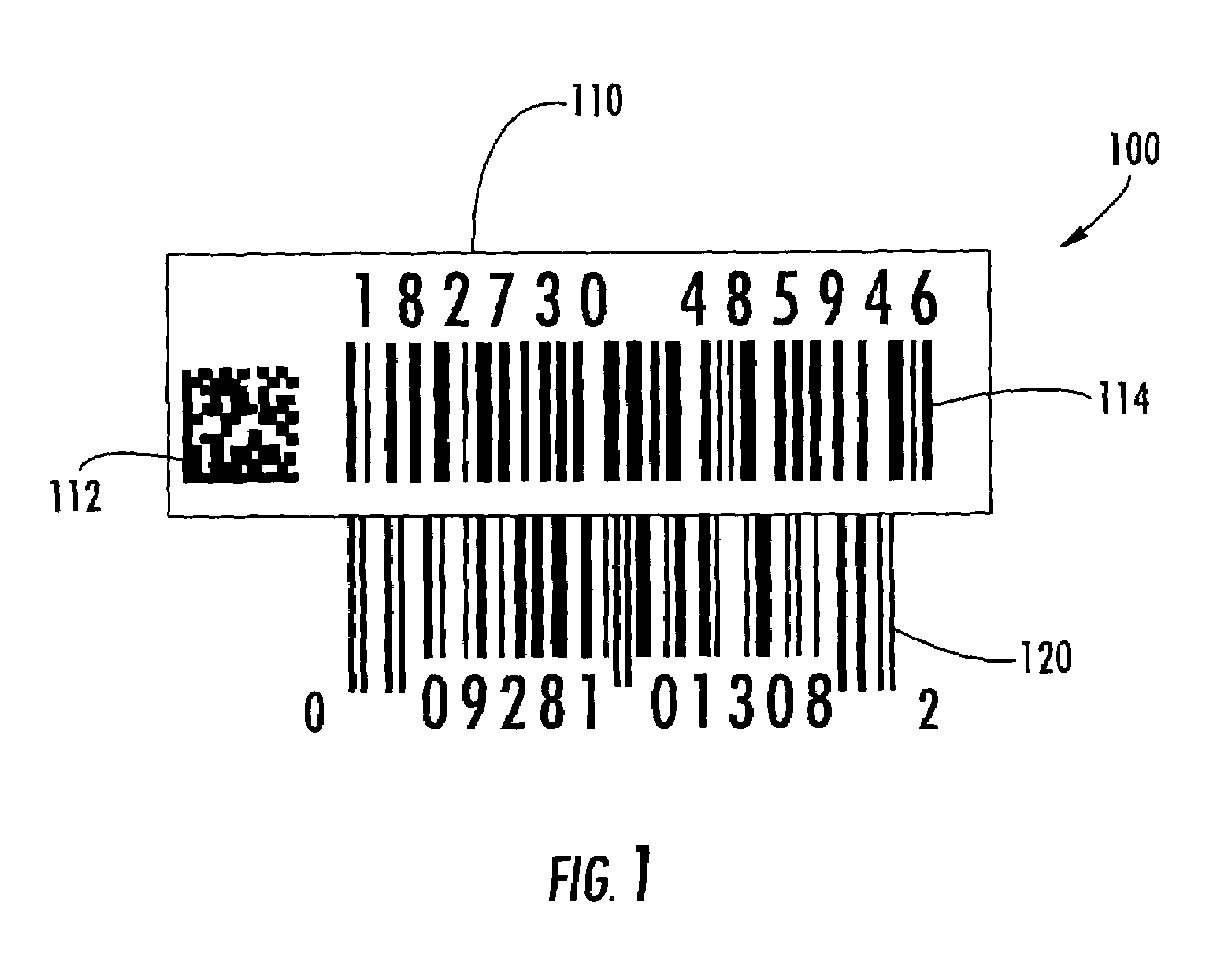
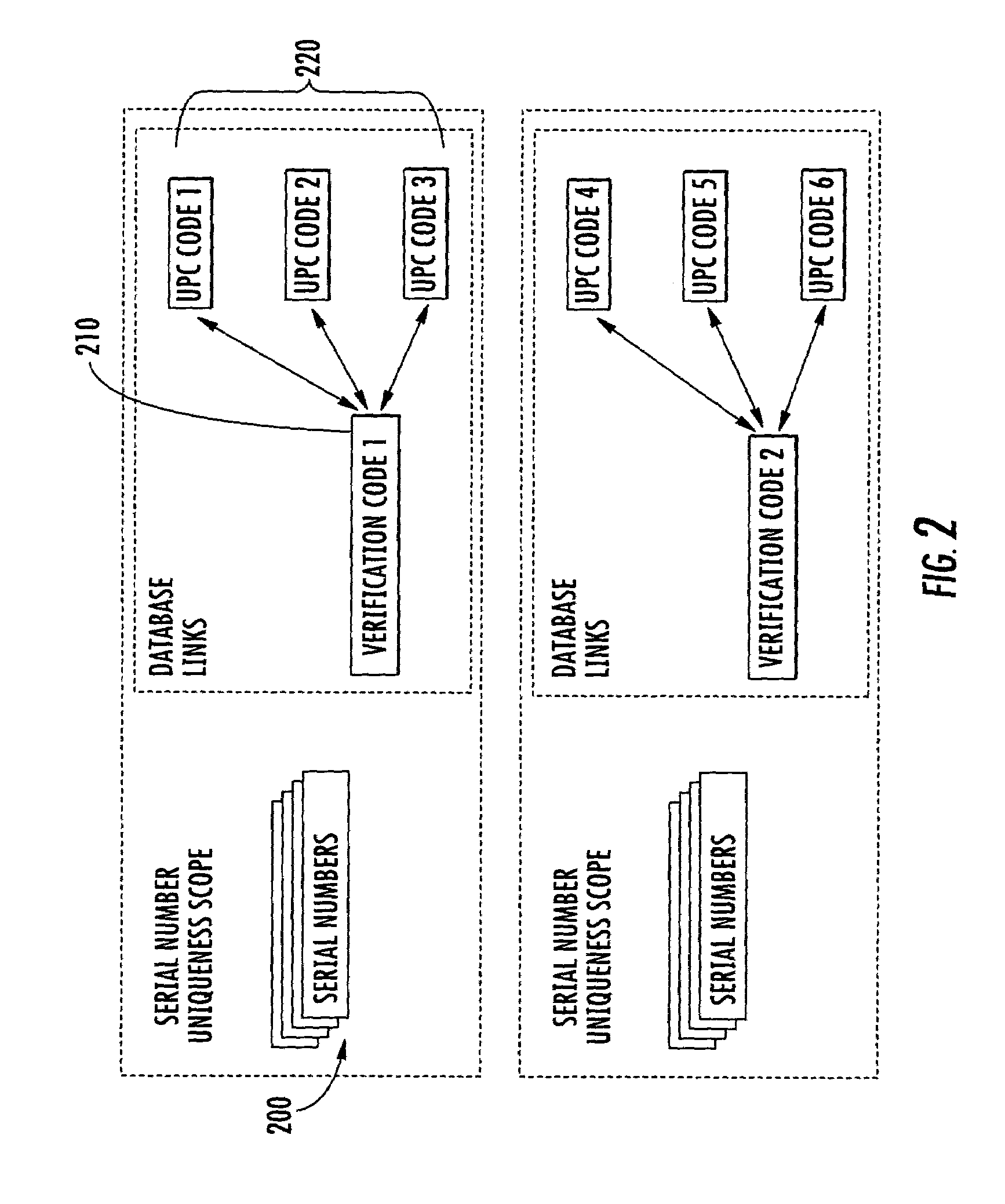
Method of labeling an item for item-level identification
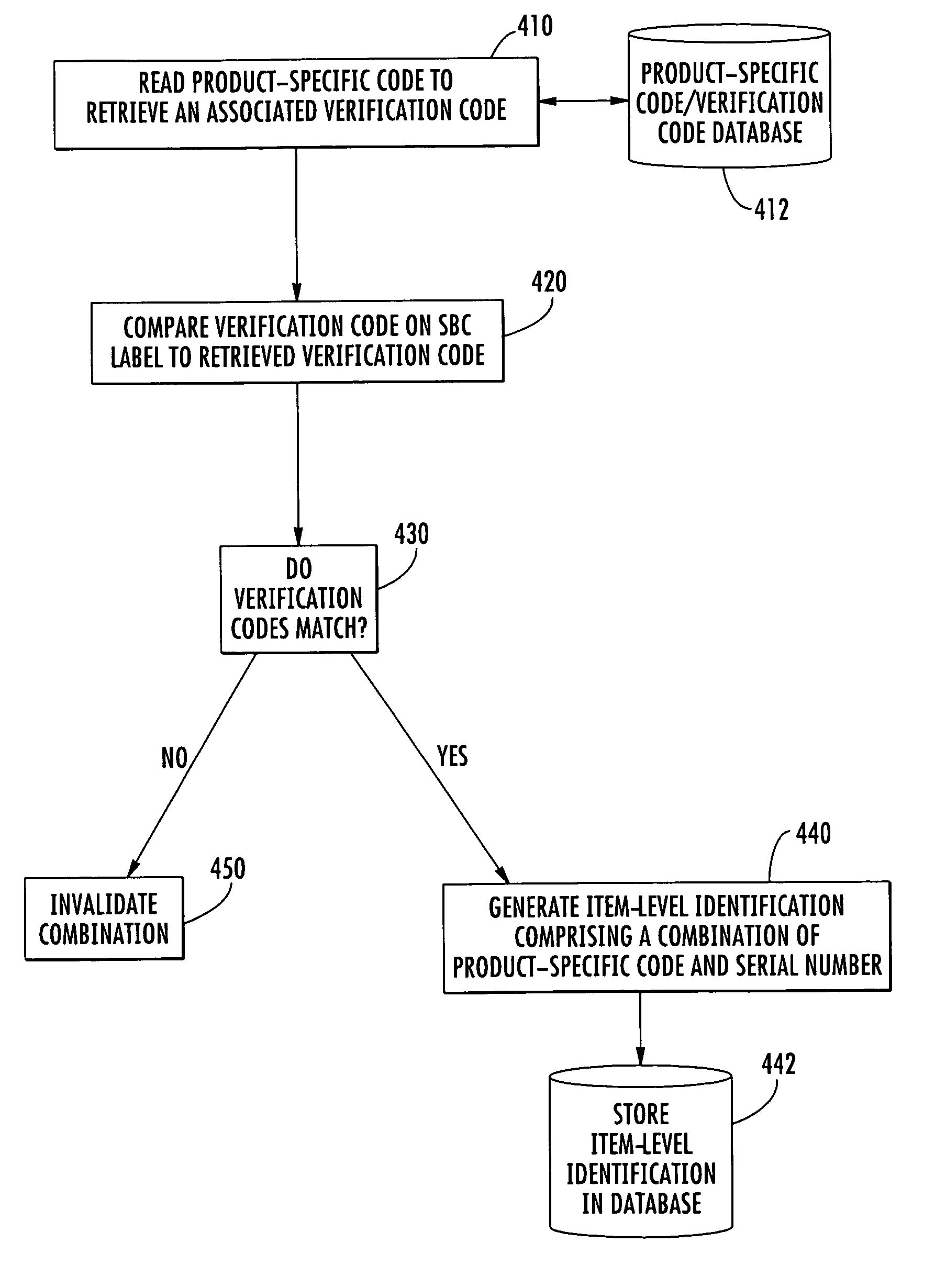
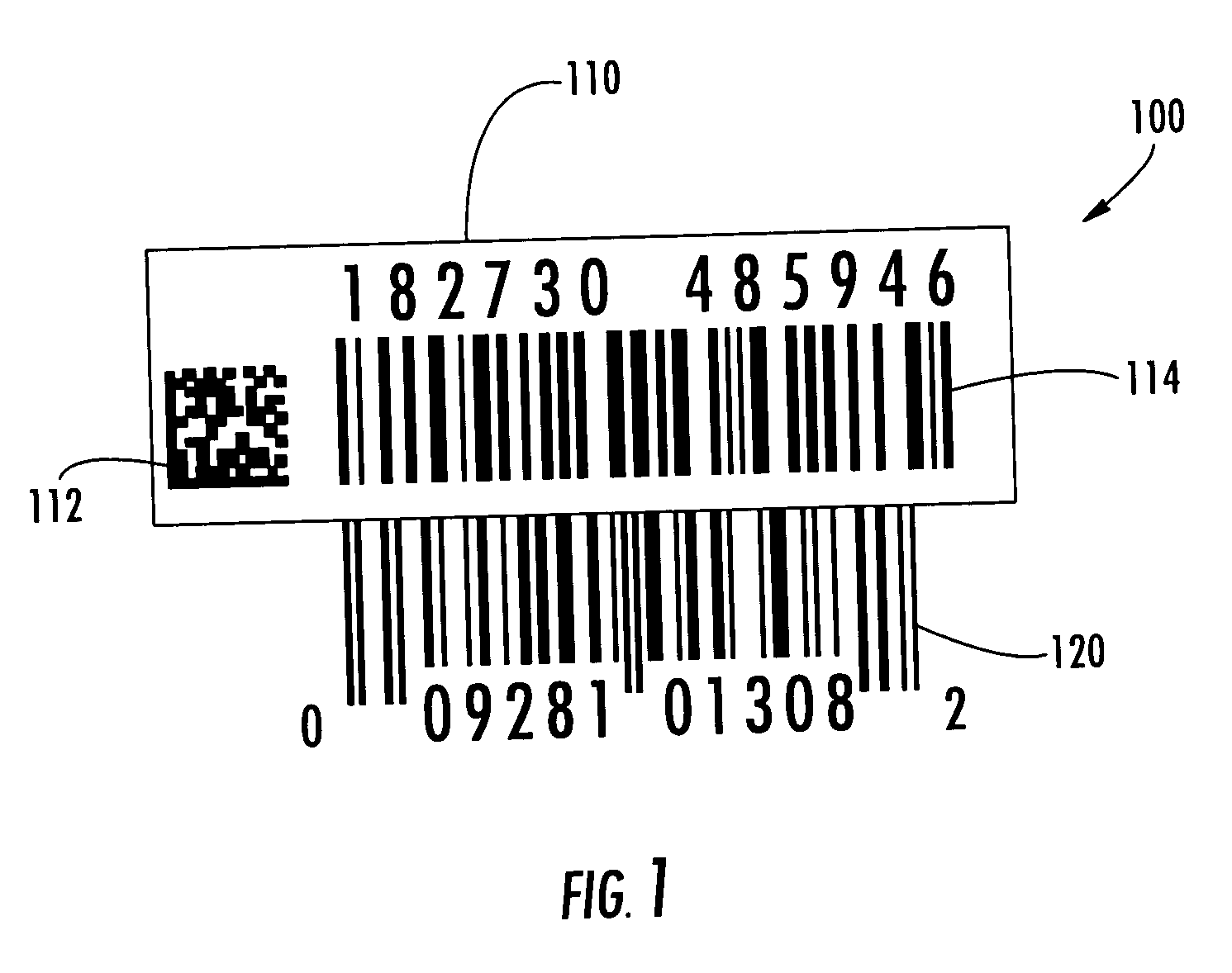
ActiveUS20060175401A1Efficient managementEnsure uniquenessCharacter and pattern recognitionCash registersProgramming languageAlgorithm
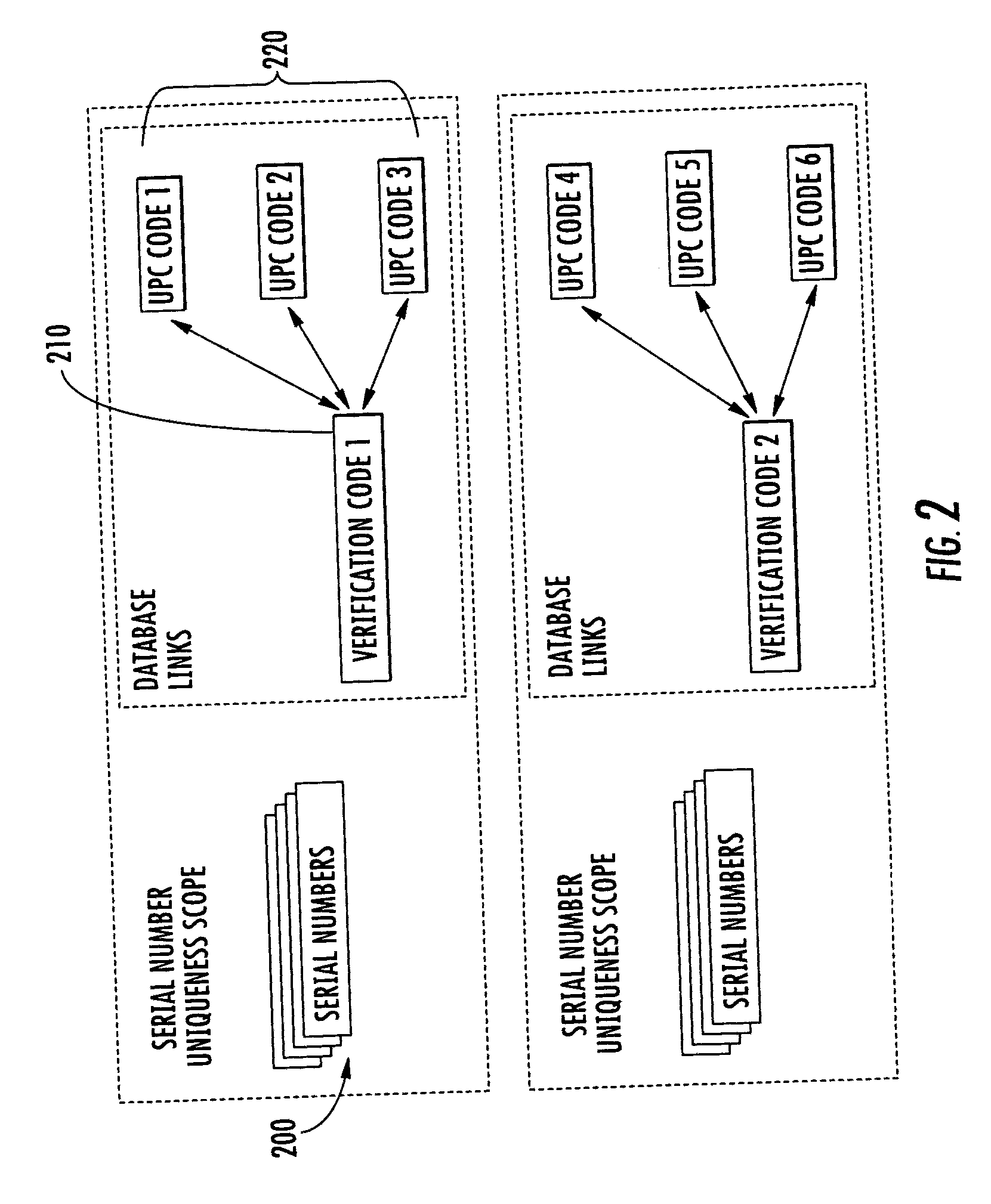
The invention is a method of validating a label that includes the steps of reading a product-specific code disposed on an item; retrieving a stored verification code corresponding to the product-specific code; reading a label verification code disposed on a label having a serial number encoded thereon; and determining whether the stored and label verification code match. If the stored and label verification codes match, the label is considered valid. In one embodiment, once the label is validated, the product-specific code and the serial number may be combined to generate a unique item-level identification code for the particular item. The use of the stored verification code and label verification code may help prevent attaching an incorrect label to the item.
Owner:CRYOVAC ILLC
Stocking system and method for managing stocking
InactiveUS20070069867A1Improve bindingIncrease flexibilitySignalling system detailsStorage devicesSensor arrayElectrical and Electronics engineering
A stocking system including at least one support for goods to be stocked, a communications network, and a computing unit for deriving inventory data. The stocking system has a gravimetric sensor element that, for detecting the goods, is in the form of a sensor array or sensor matrix. This sensor element can also be supplemented with an optical sensor element. By recording a multitude of measured values of the goods, the entire stocking system can be in the form of a sensor network and, with regard to the model, is configured for deriving inventory data whereby enabling both an identification of the type of the stocked goods as well as the determination of the quantity thereof.
Owner:UNIV ST GALLEN HOCHSCHULE FUR WIRTSCHAFTS RECHTS UND SOZIALWISSENSCHAFTEN +1
Method for creating, manufacturing, and distributing three-dimensional models
InactiveUS7656402B2Ensure uniquenessMedical simulationAdditive manufacturing apparatusThird party3d image
A method is provided for producing three-dimensional (3D) models. The invention will take any sculpture, character, or model from artwork, still life models, images of human beings, characters from a computer game, or any other 3D digital image or model that is scanned, and turn the digital image into 3D models. The method is comprised of the following steps: creating a user account in a computer storage area; storing 3D images under the user account; allowing the user to select the 3D image(s) he or she wants to create as 3D models; manufacturing the 3D models; and delivering the models to the user or to a specified third-party. An online storefront and / or auction system may allow each user the opportunity to sell their 3D models or purchase other users' 3D models. The system may also create 3D models for a mobile phone and portable media player while transferring the models to either of these devices.
Owner:TAG LLC (US)
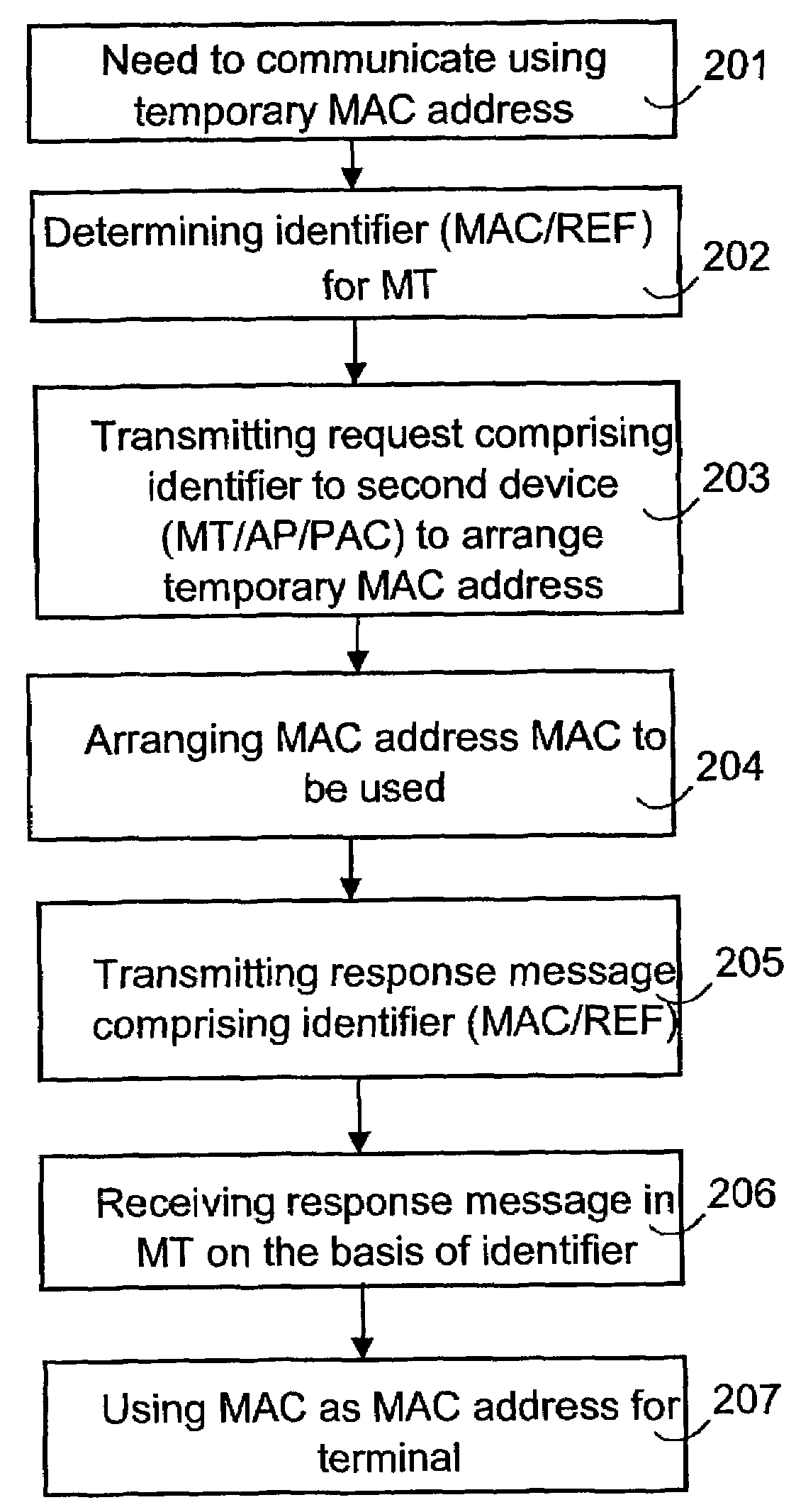
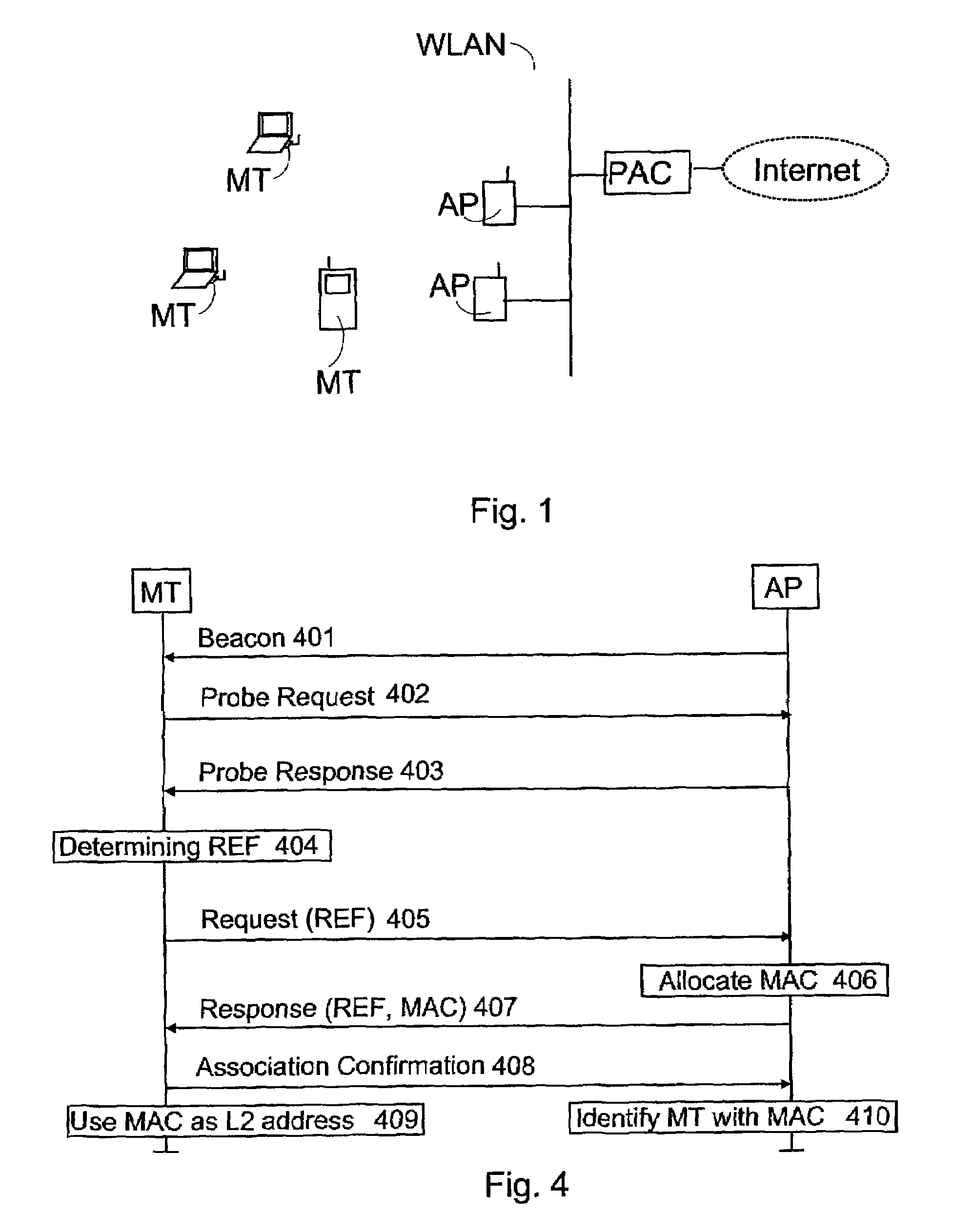
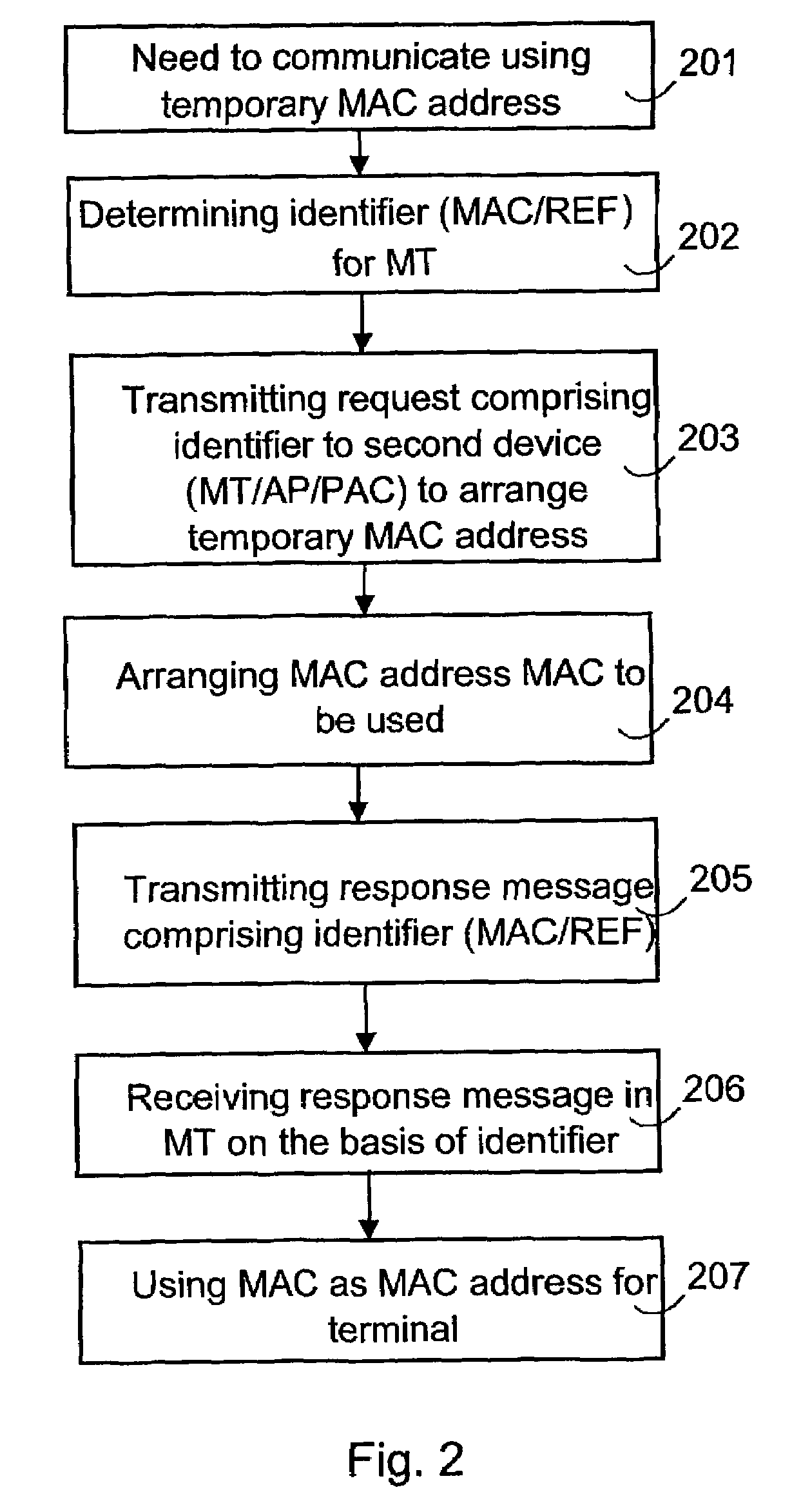
Addressing in wireless local area networks
InactiveUS7359989B2Small probabilityReduced risk of collisionError prevention/detection by using return channelNetwork topologiesMAC addressReal-time computing
The invention relates to a method of transferring required messages for acquiring a temporary MAC address in a wireless local area network. In a first device in the local area network, a first identifier is determined to identify the first device. A message comprising the first identifier is transmitted from the first device to a second device to arrange a temporary MAC address. A response message relating to the acquisition of the MAC address and comprising the first identifier is transmitted from the second device to the first device. The first device identifies on the basis of the first identifier that the response message is intended for it.
Owner:NOKIA CORP
Credible data transmission method
ActiveCN109361668AIncrease credibilityIntegrity guaranteedKey distribution for secure communicationUser identity/authority verificationTransfer procedureClient-side
The invention discloses a credible data transmission method, which comprises the following steps: authenticating, by the SGX (Singapore Exchange Limited), a client and a server which are in data transmission; verifying, by a client authentication module, legalities of a platform where the client is positioned and a user to the corresponding server; after the client is authenticated, establishing asession between the client and the server to enable the client and the server to perform a one-off supply protocol, and sealing confidential data of a client application onto a platform where the application is positioned, wherein an independent secure channel for communication connection is established between the server and the client, and each channel corresponds to a unique client, and the server encrypts data sent by the client in a transmission process; and after a protected file is encrypted in an enclave, sending a specific file to the client according to a file request of the client,and then distributing the file to an authenticated and authorized application user to check or perform other operations. Based on credible hardware, the method effectively solves a security bug.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
Identifying and tracing system with unique identity and method
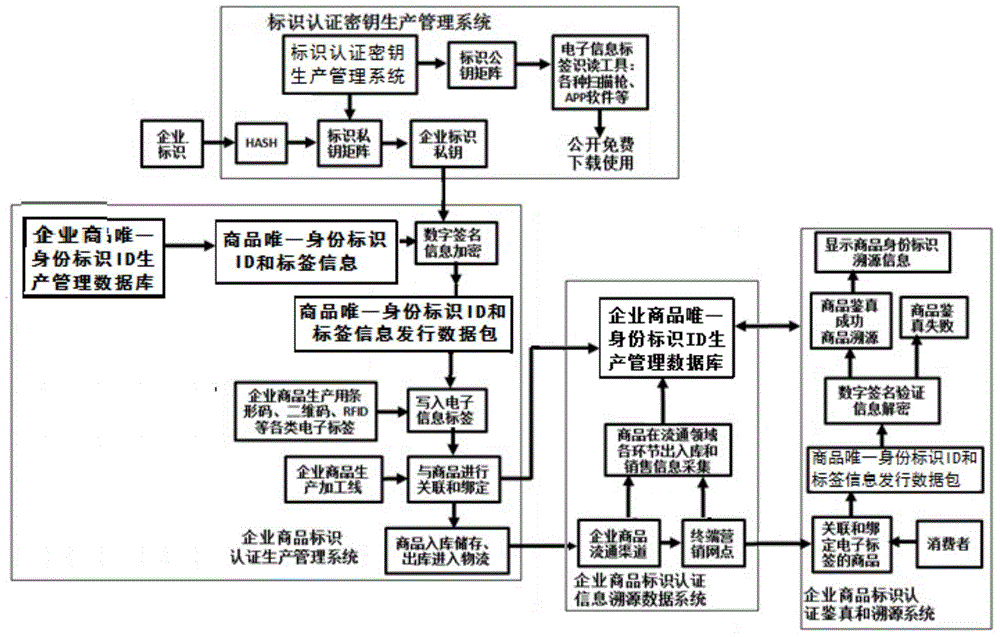
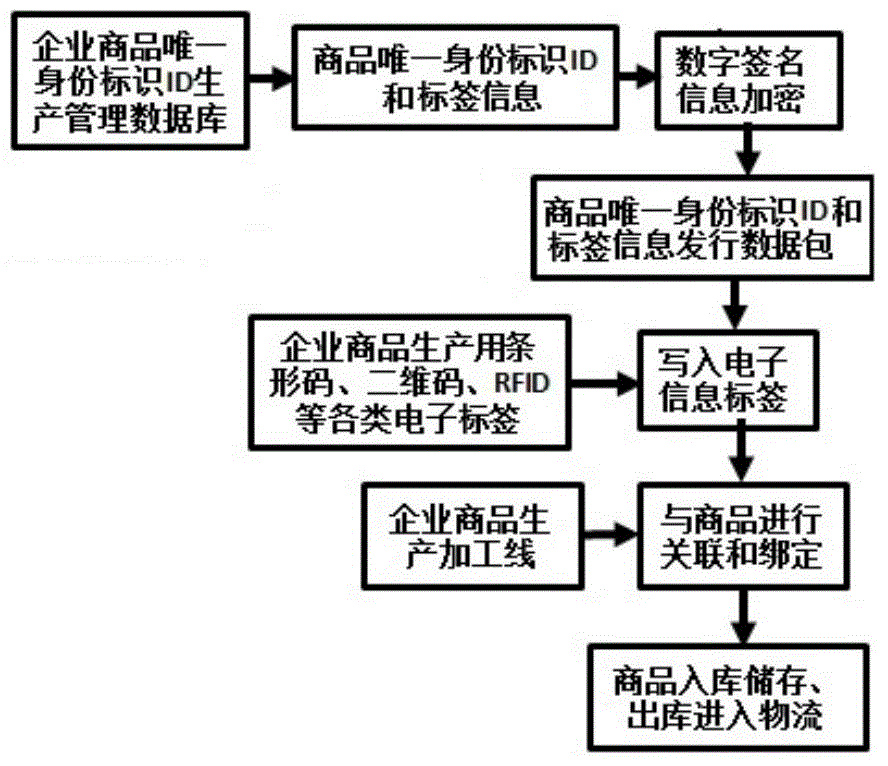
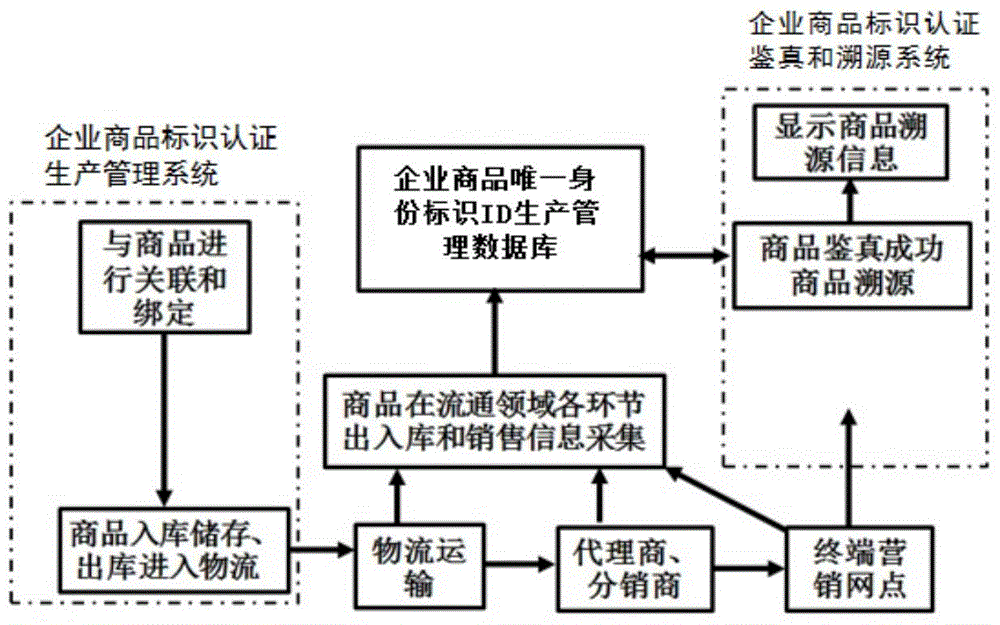
InactiveCN104091272AEnsure uniquenessSimple and reliable security managementCommerceUnique identifierClosed loop
The invention discloses an identifying and tracing system with unique identity and a method. Through combination of combined public key cryptography system and an identity authentication technology, the closed-loop commodity identifying and tracing system based on unique identity IDs and label information of commodities is built; as a unique identity ID issuing system of the enterprise commodities is designed, uniqueness of the identity of the enterprise commodities in the circulation domain is ensured, and then electronic information label carriers and the enterprise commodities are correlated and bound to set up an enterprise commodity tracing information database system. According to the system and the method, as a terminal verification procedure module is disclosed, different enterprises and the different types of commodities can be incorporated into the identifying and tracing system, a common consumer can identify and trace the enterprise commodities conveniently, fast and efficiently through a handheld terminal, and the enterprises can effectively manage and efficiently circulate the commodities produced by the enterprises.
Owner:北京信长城技术研究院
Matching authentication method, device and system for wireless communication
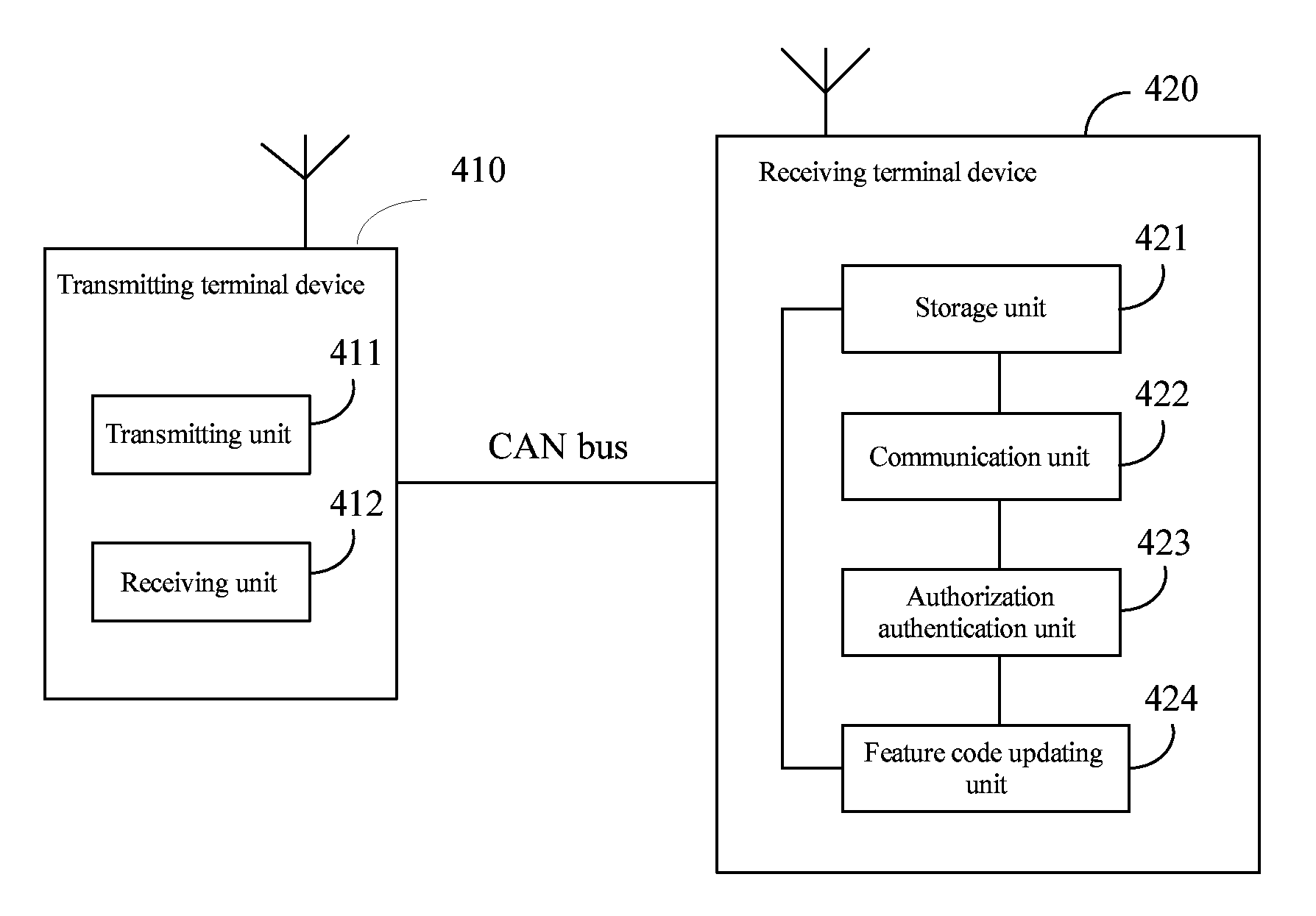
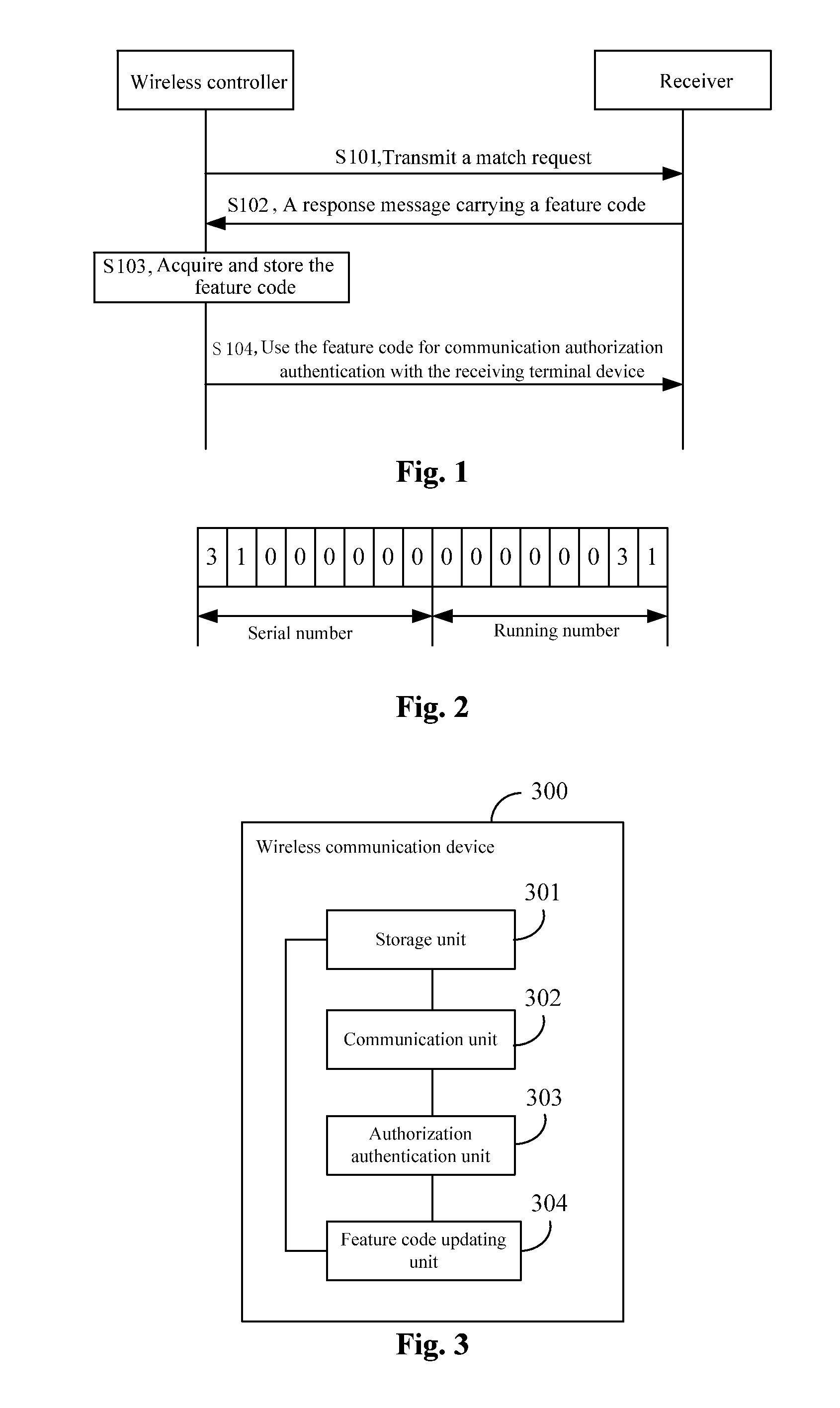
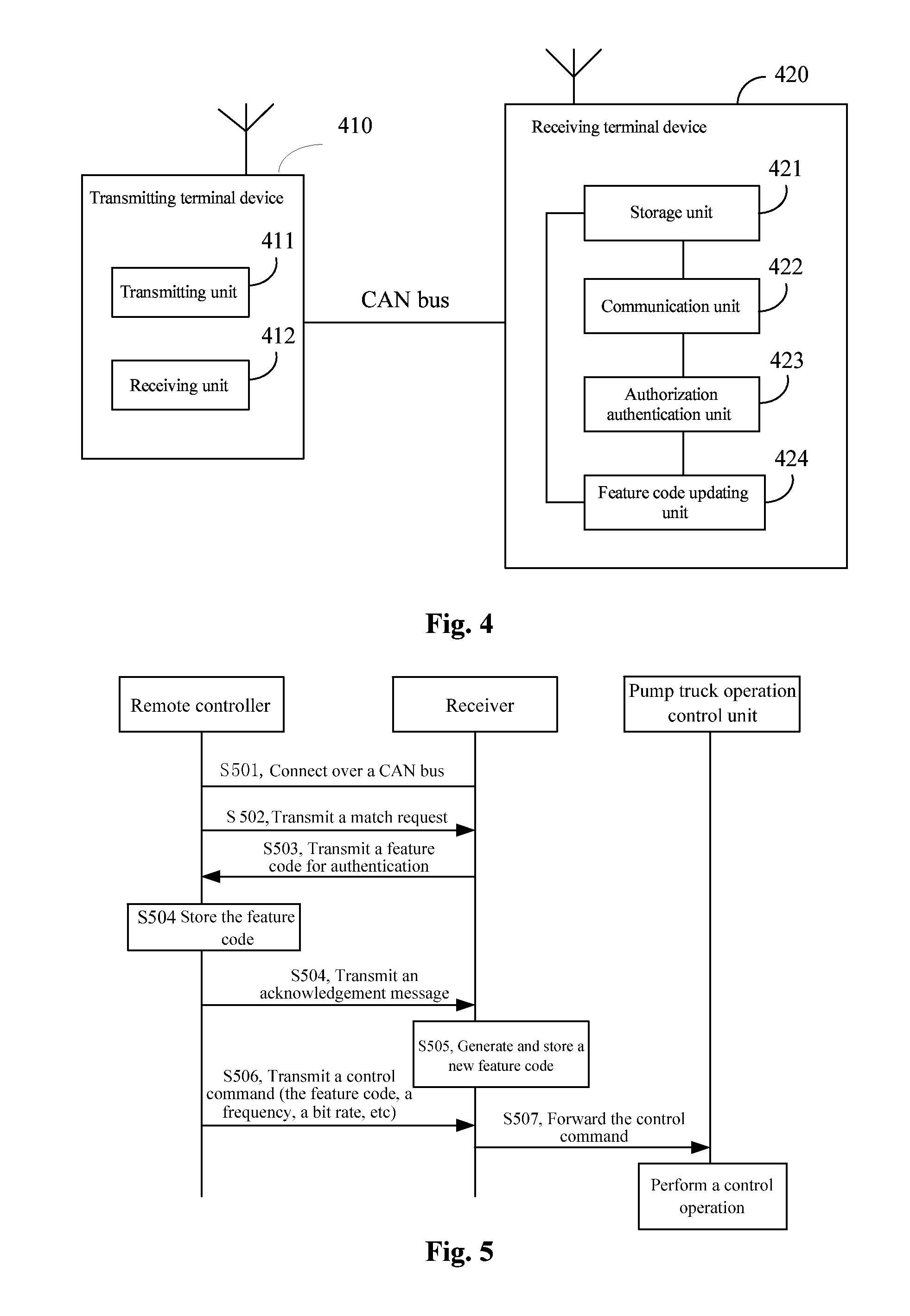
InactiveUS20110191833A1Simplification of featureHigh interchangeabilityDigital data processing detailsUser identity/authority verificationFeature codeAuthorization
A matching authentication method for wireless communication equipment comprises that: a device at the transmitting end sends a matching request (S101) to a device at the receiving end; the device at the transmitting end receives the response messages feedback from the device at the receiving end, and the response message carry with feature codes (S102); the device at the transmitting end obtains the feature codes and takes the feature codes as the authentication and authorization codes communicating with the receiving end. The invention also provides a wireless communication device with the function of matching authentication correspondingly. The wireless communication device comprises a memory unit, a communication unit, and an authentication and authorization unit and a feature code updating unit. The invention also provides a wireless communication system with the function of matching authentication correspondingly.
Owner:HUNAN SANY INTELLIGENT CONTROL EQUIP +1
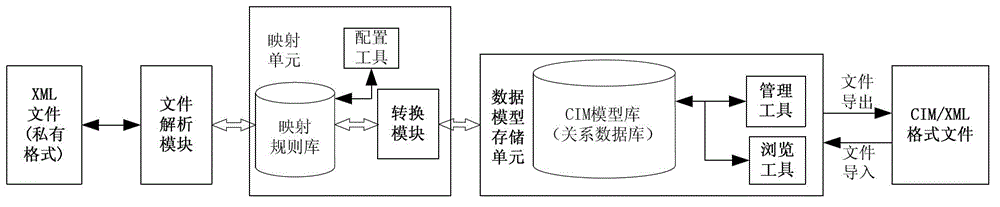
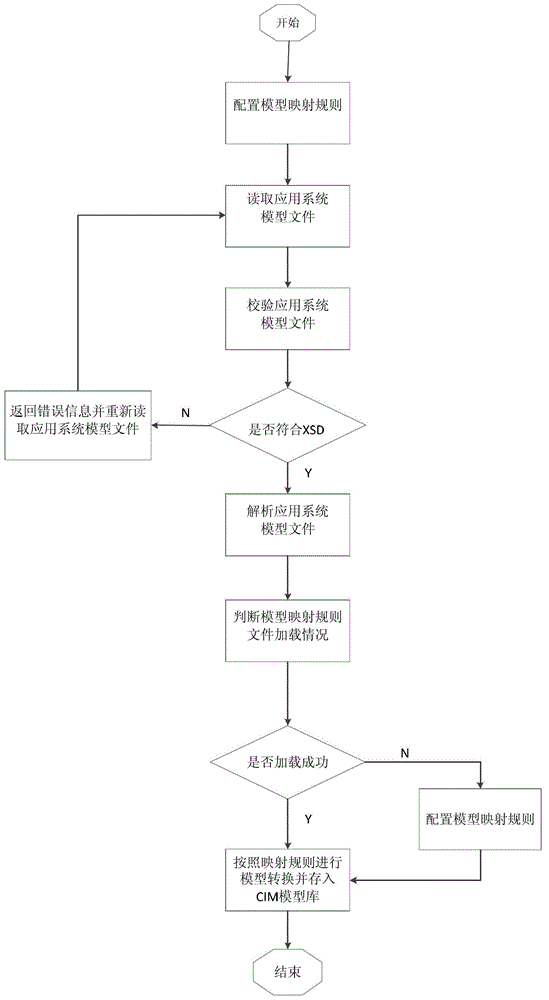
Mapping method and system of system data model to common information model (CIM)
ActiveCN102750358AAvoid conversionStrong scalabilitySpecial data processing applicationsSystem of systemsRDF
The invention relates to a mapping method and a system of a system data model to a CIM. The method includes configuring model mapping rules, receiving model files from corresponding application systems, and verifying and analyzing the model files to obtain information data of the application systems; judging whether model mapping rule files are loaded by the mapping system, if the files are not loaded, building a mapping rule between a private data model and the CIM through a configuration tool for model mapping rules; according to the mapping rule, private information data of the application systems are converted into CIM data and are stored in a CIM library through a mapping unit; and finally, obtaining all information data by browsing the list structure of a whole CIM data library, organizing information data according to resource description framework (RDF) specifications, exporting standard CIM / extensible markup language (XML) files for being called by other application services and components.
Owner:STATE GRID CORP OF CHINA +2
Method of labeling an item for item-level identification
ActiveUS7303123B2Efficient managementEnsure uniquenessCharacter and pattern recognitionCash registersTheoretical computer scienceSerial code
The invention is a method of validating a label that includes the steps of reading a product-specific code disposed on an item; retrieving a stored verification code corresponding to the product-specific code; reading a label verification code disposed on a label having a serial number encoded thereon; and determining whether the stored and label verification code match. If the stored and label verification codes match, the label is considered valid. In one embodiment, once the label is validated, the product-specific code and the serial number may be combined to generate a unique item-level identification code for the particular item. The use of the stored verification code and label verification code may help prevent attaching an incorrect label to the item.
Owner:CRYOVAC ILLC
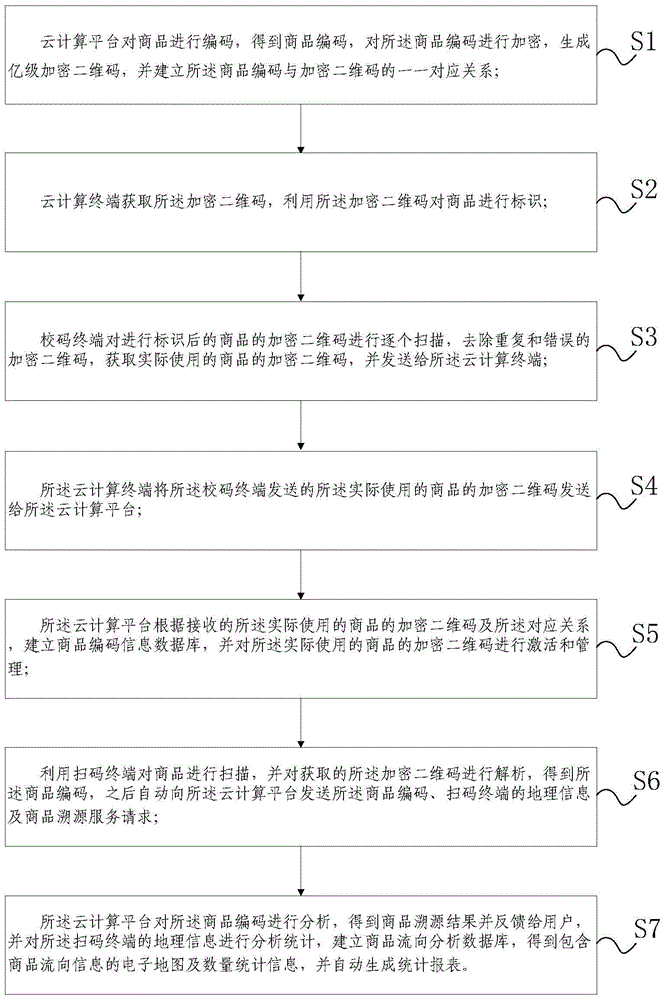
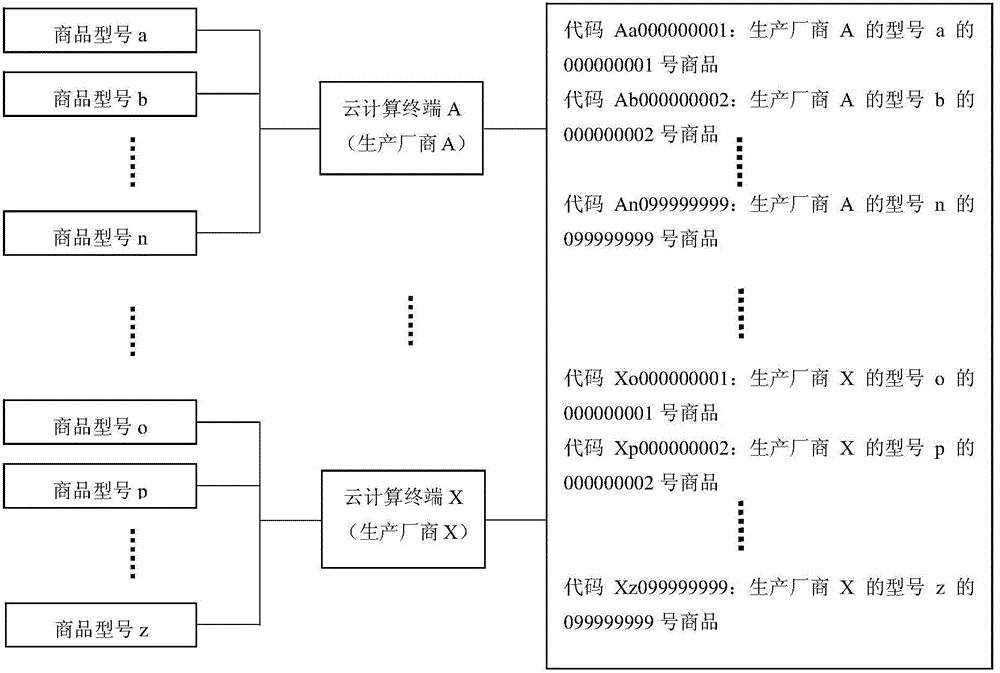
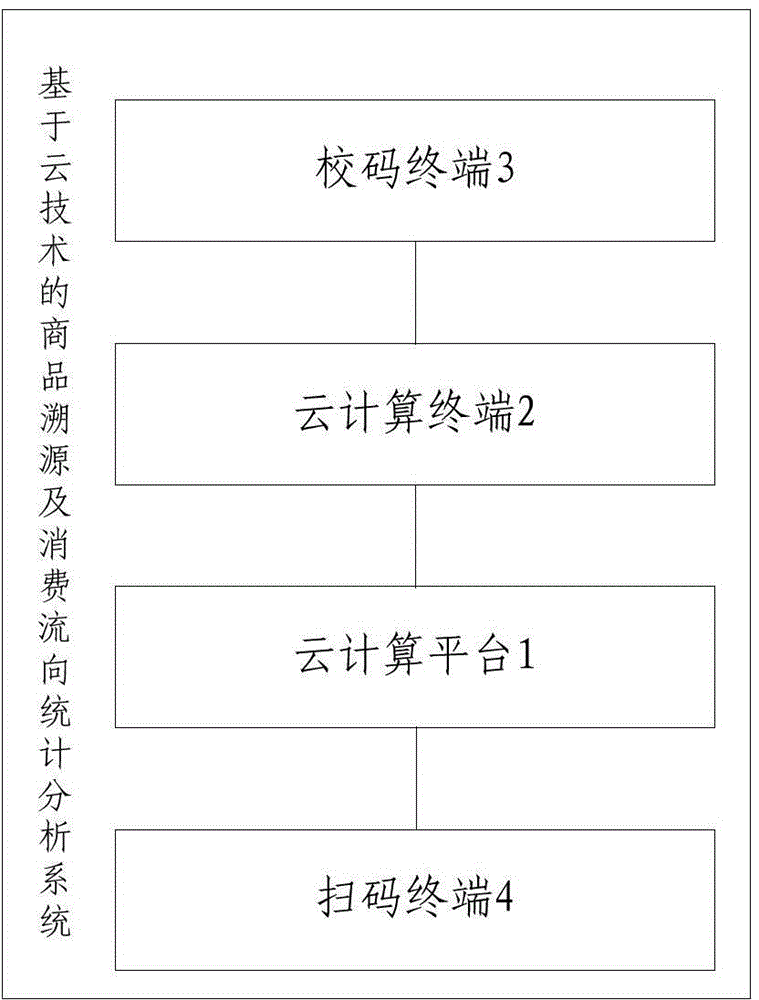
Cloud technology-based commodity traceability and consumption flow statistical analysis method and system
ActiveCN104834999AStrong computing powerImprove performanceResourcesCommerceStatistical analysisBiological activation
The invention discloses a cloud technology-based commodity traceability and consumption flow statistical analysis method and system. According to the cloud technology-based commodity traceability and consumption flow statistical analysis method and system, a cloud technology architecture in which a cloud computing platform and a cloud computing terminal coordinate with each other is adopted, wherein the cloud computing platform is responsible for coding, compression, encryption, generation and activation, assignment and management of hundred-million-level encrypted two-dimension codes and providing traceability services for consumers and providing consumption flow statistical analysis services for enterprises, and the cloud computing terminal is responsible for assigning identifiers for the encrypted two-dimension codes of commodities; since the powerful computing ability and performance of cloud technologies are utilized, and a convenient automated centralized management mode is adopted, the operational efficiency, reliability, flexibility and robustness of the system can be ensured.
Owner:NANJING DASHU INTELLIGENT SCI & TECH CO LTD
Device and method for realizing remote signature
PendingCN106383602AAddressing the possibility of forged signaturesUniqueness guaranteedOffice automationInput/output processes for data processingHandwritingComputer security
The invention discloses a device and a method for realizing remote signature. The remote signature device is characterized by comprising a signature pen which obtains handwriting information, and a copy pen apparatus which copies the signature handwriting. Further, the method comprises the steps that the signature pen obtains the signature handwriting information of a signatory and sends the handwriting information to the remote copy apparatus; and the remote copy apparatus receives the handwriting information sent by the signature pen, controls a copy pen to copy the handwriting information of the signatory according to the handwriting information, checks the correctness of the copied signature handwriting and finishes the signature. The abovementioned technical scheme has the following beneficial effects: the signature can be finished in time when the signatory and a to-be-signed file are not in the same place; and the signature handwriting information can be obtained and encoded, so that the technical effect of remotely regenerating the unique effective signature handwriting is achieved through a technical means of remote transmission, a secure and reliable solution is provided for two parties who need to perform signature and are not in the same place, the time and troubles are saved, the efficiency is improved, and the work is facilitated.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
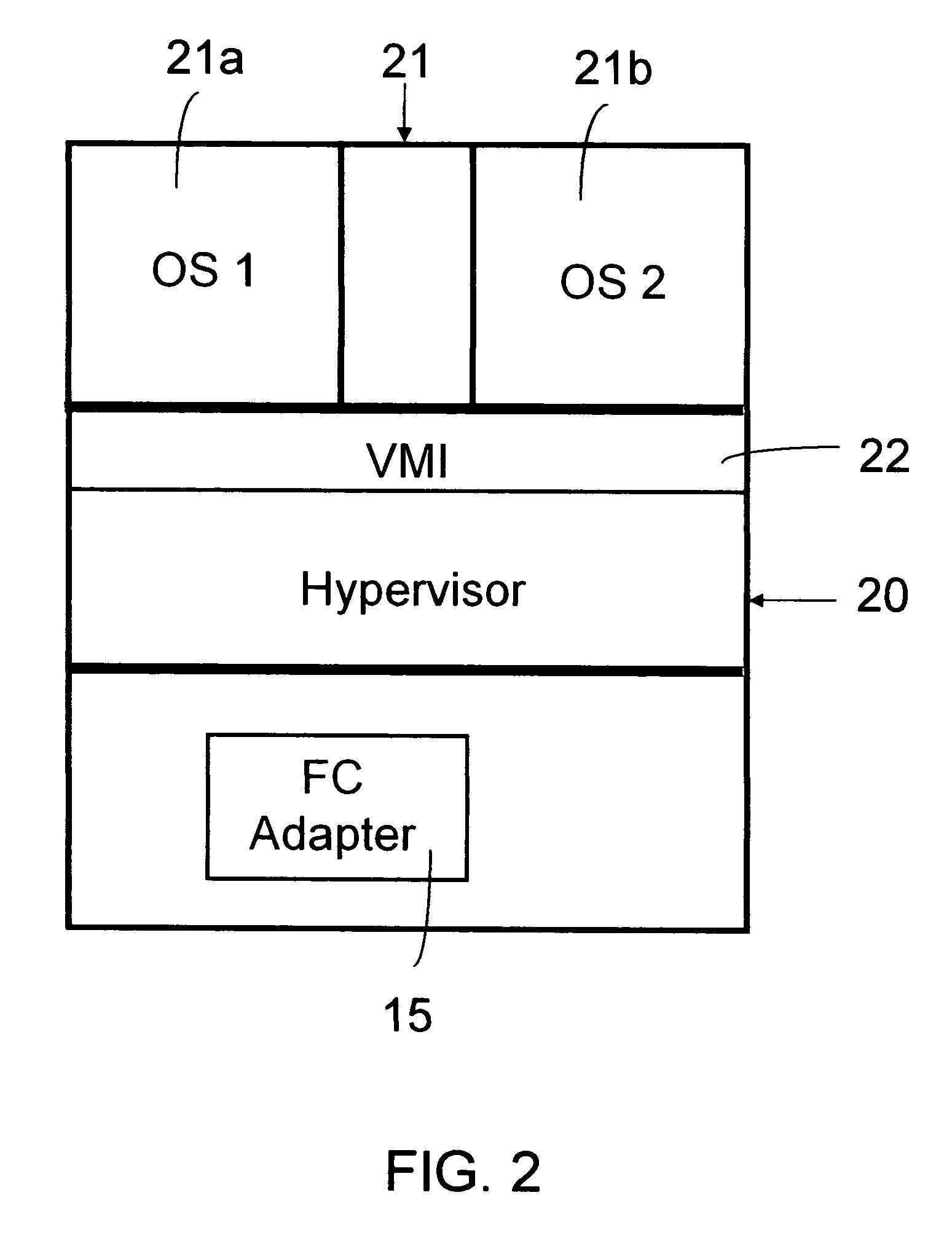
System, detecting method and program
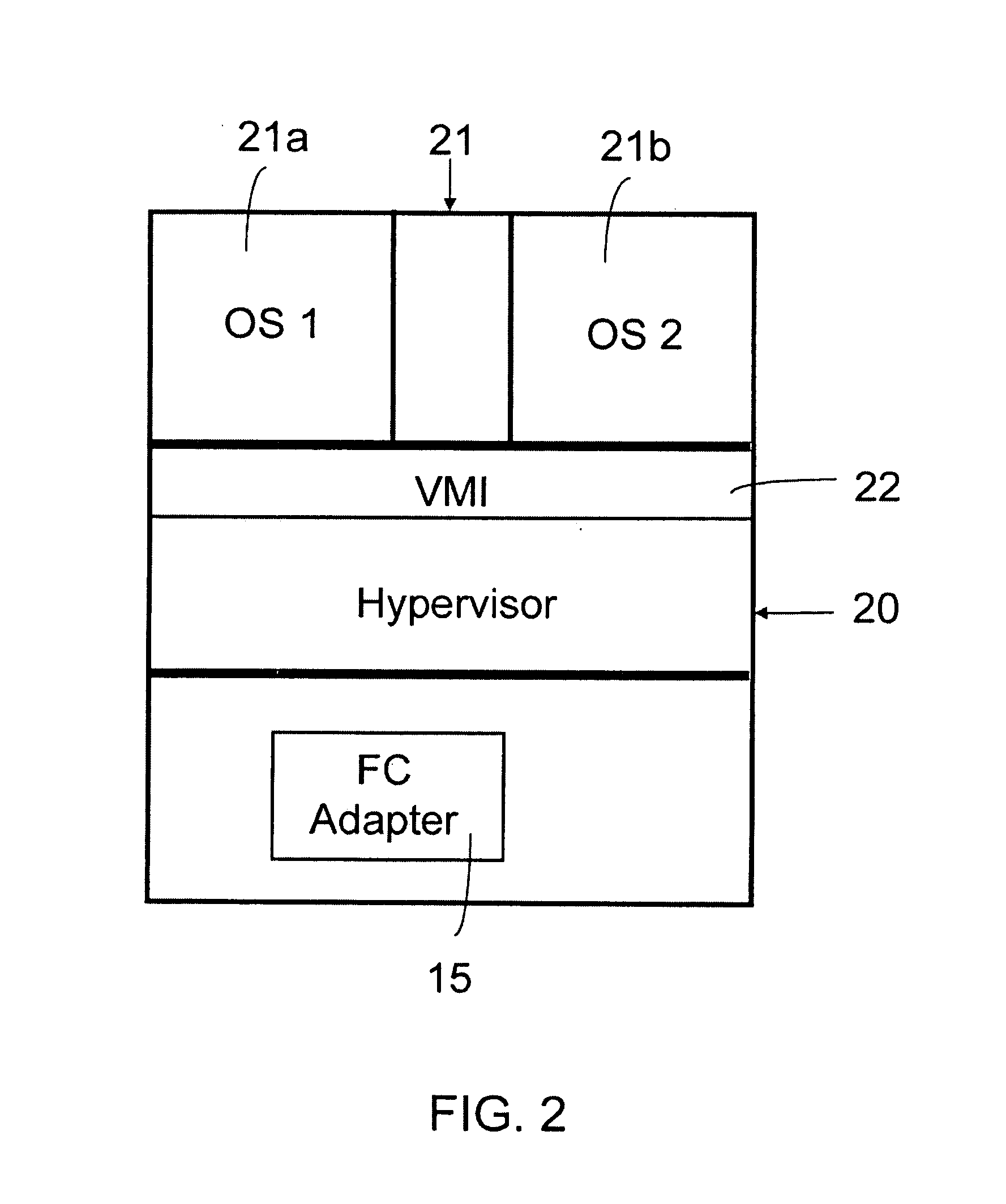
InactiveUS20070005820A1Easy to manageEnsure uniquenessData switching by path configurationMultiple digital computer combinationsVirtualizationOperational system
The present invention relates to a method, a computer program product and a system for managing virtual instances of a physical port attached to a network. The method is based on the Fibre Channel N_Port virtualisation for a physical Fibre Channel N_Port. Multiple virtual Fibre Channel adapters share a single physical N_Port among multiple operating system instances. The invention discloses means for the automatic and persistent generation and administration of unique Worldwide Port Names needed for the N_Port virtualisation.
Owner:IBM CORP
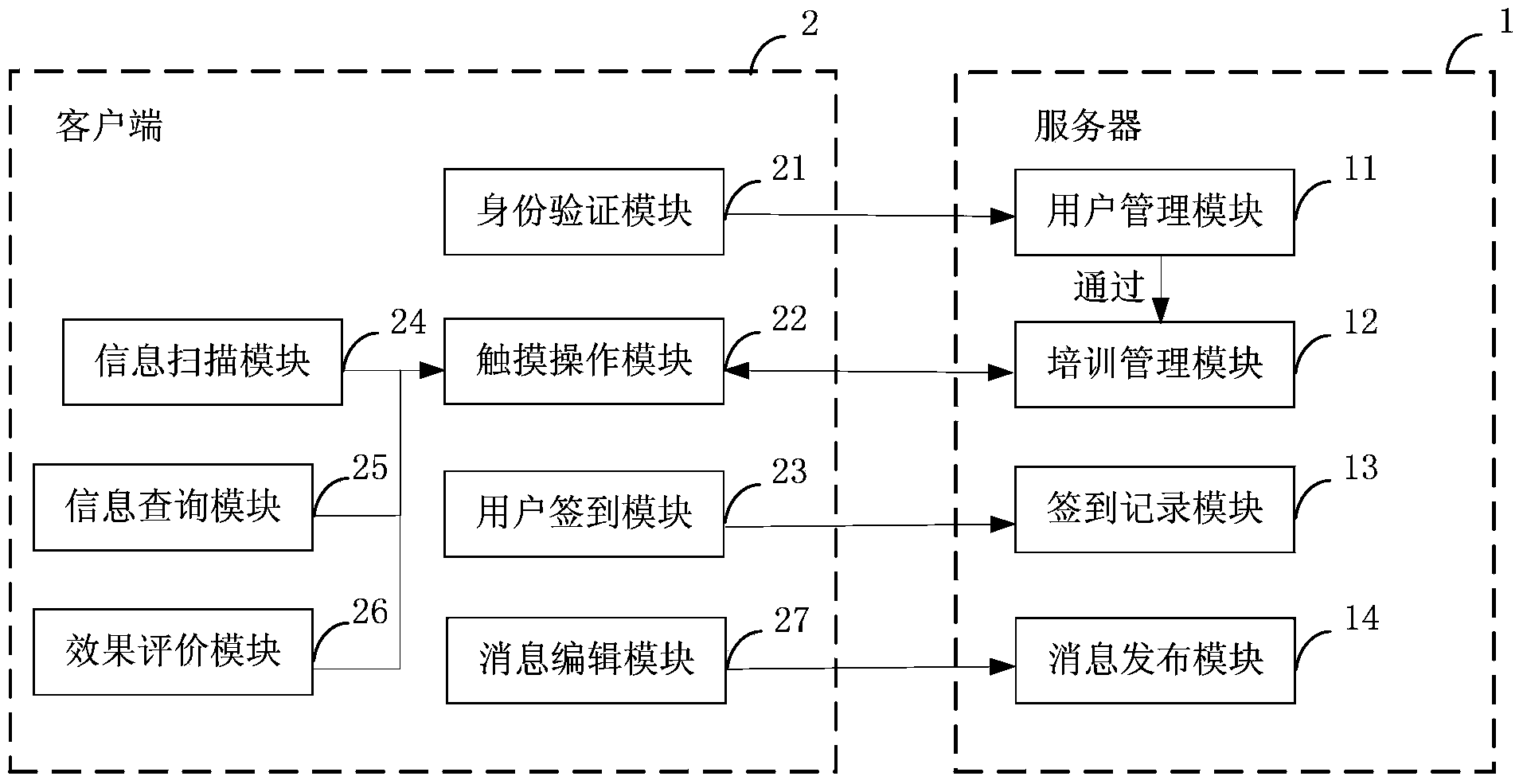
Educational training and evaluating system
InactiveCN104346693AEnsure safetyEnsure uniquenessResourcesTransmissionFingerprintFingerprint detection
The invention is applied to the technical fields of internet and remote education and provides an educational training and evaluating system. The educational training and evaluating system comprises a server and a client connected with the server through a network, wherein the server comprises a user management module and a training management module; the client comprises an identity authentication module and a touch operation module; identity information of an operator is authenticated by using human face recognition or fingerprint detection, so that the security and the uniqueness of user accounts are guaranteed; the operation by the users is simplified and facilitated by the touch operation of the client. According to the educational training and evaluating system disclosed by the invention, the training management work of trainers and the learning and the evaluation of trainees for curriculums are greatly facilitated, the working efficiency and the learning efficiency are improved, and educational training and evaluation are better served and supported.
Owner:GUANGZHOU POWER SUPPLY CO LTD
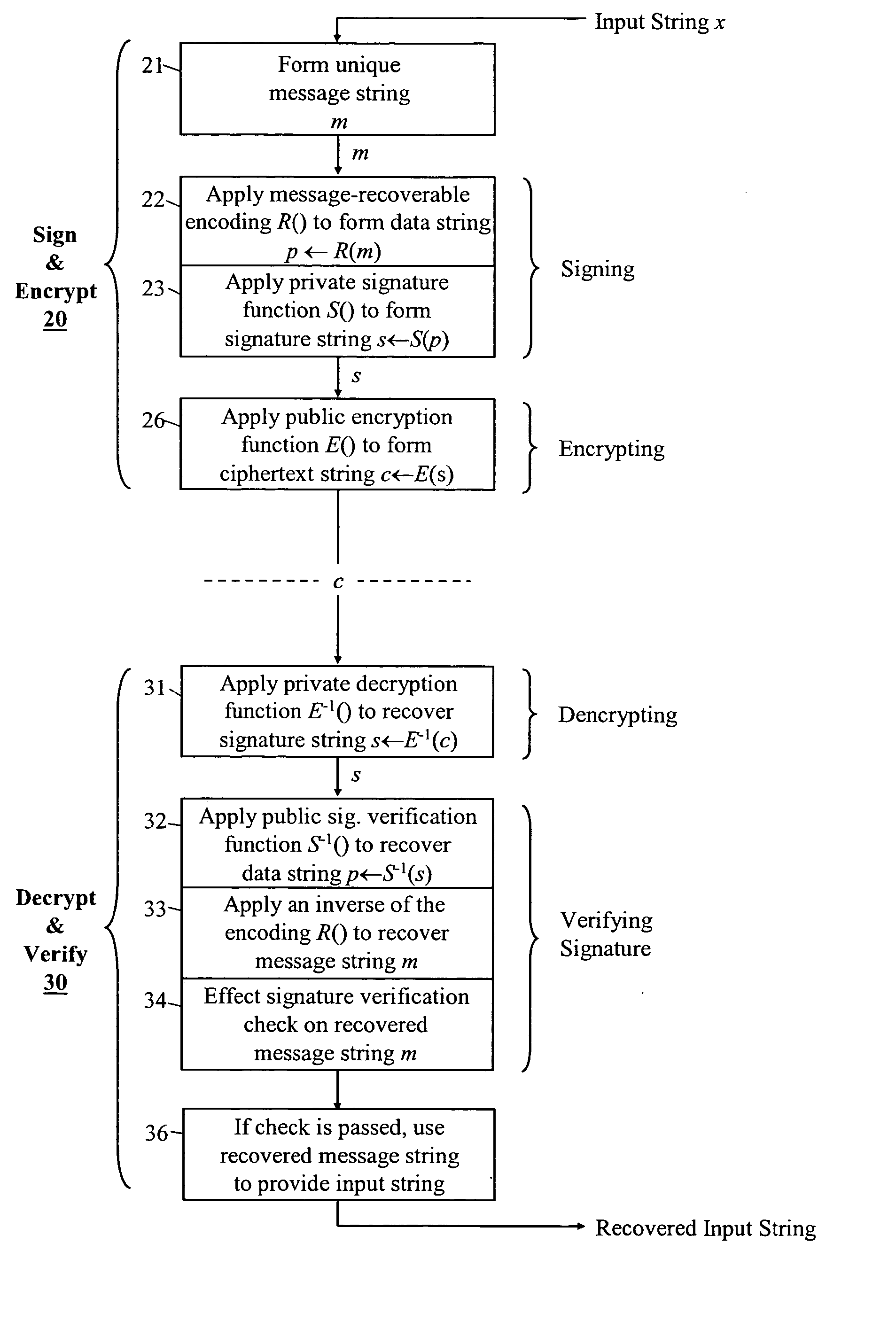
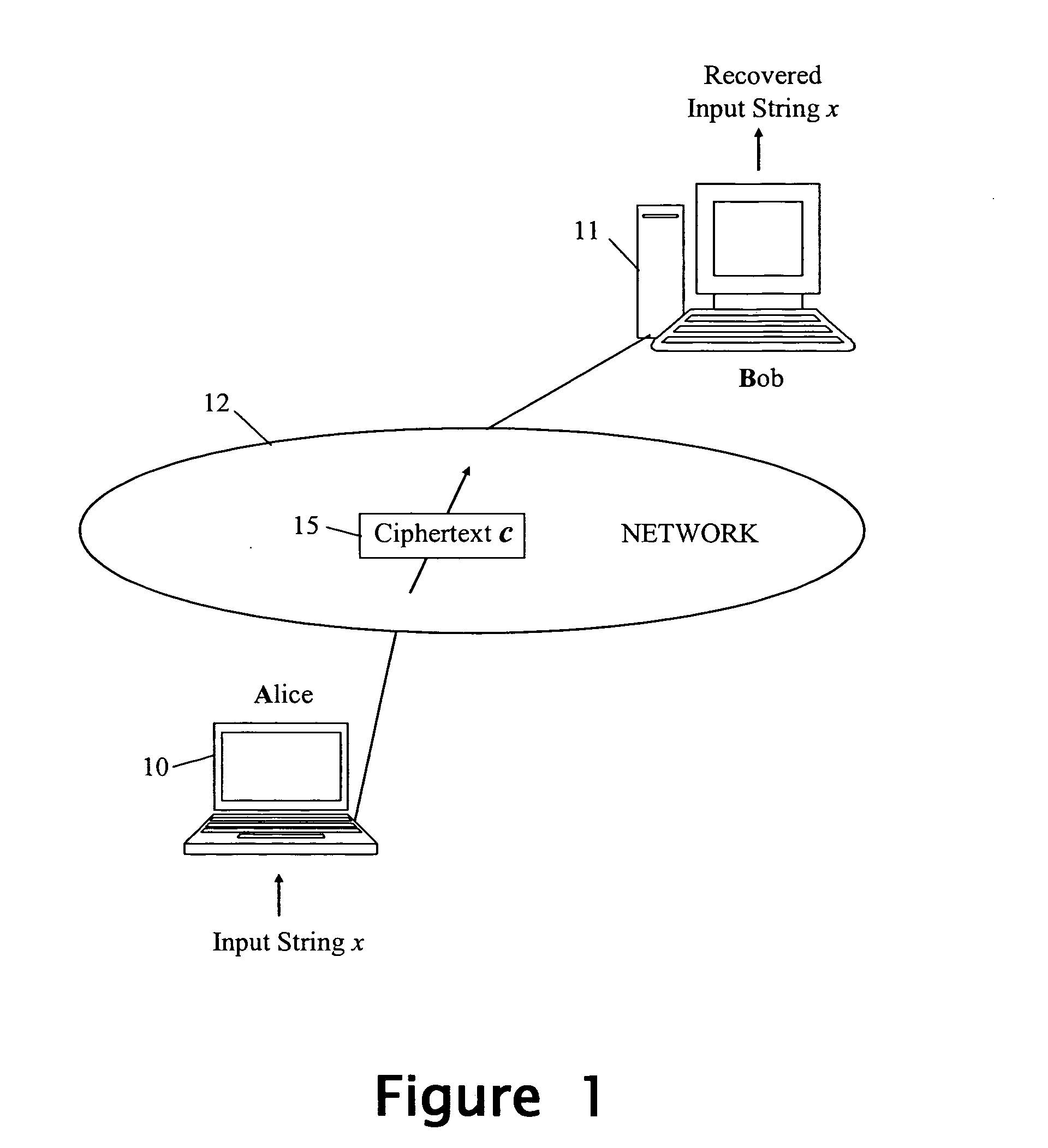
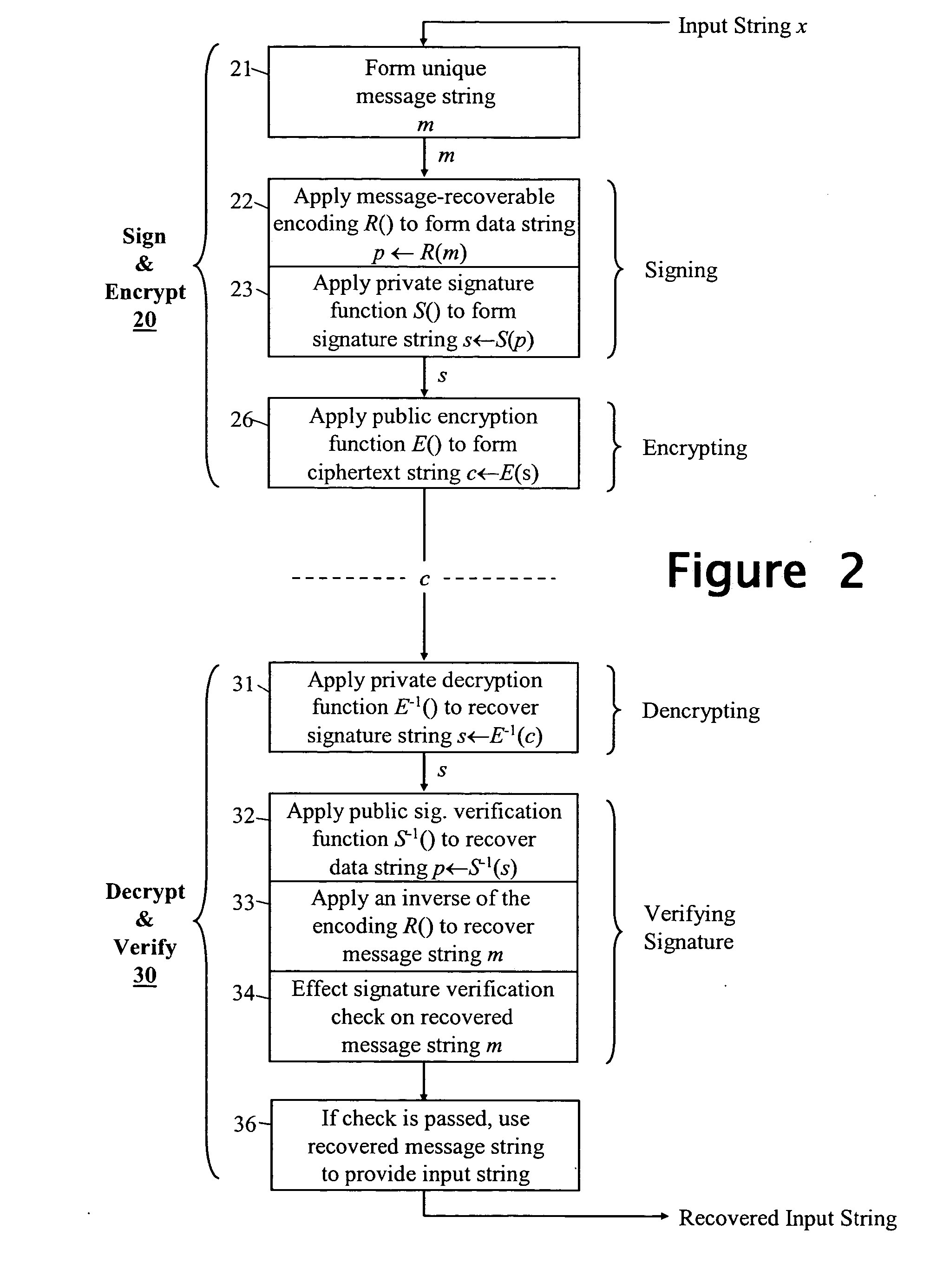
Cryptographic method and apparatus
InactiveUS20050240762A1Ensure uniquenessPublic key for secure communicationUser identity/authority verificationEncrypted functionOne-way function
A method, apparatus and program are provided by which an entity signs and encrypts an input string using particular instances of a private signature-generation function of a signature trapdoor one-way function pair, and a public encryption function of an encryption trapdoor one-way function pair. As an initial step, the input string is used to form a message string that the entity knows is unique in the context of use by the entity of the particular instances of the signature-generation and encryption functions. Thereafter, a message-recoverable encoding scheme is applied to the message string to form a unique data string that is then subject to the private signature-generation function to produce a signature string. The signature string is in turn subject to the public encryption function to obtain a ciphertext string. Semantic security is achieved without the need to generate a quality random number.
Owner:HEWLETT PACKARD DEV CO LP
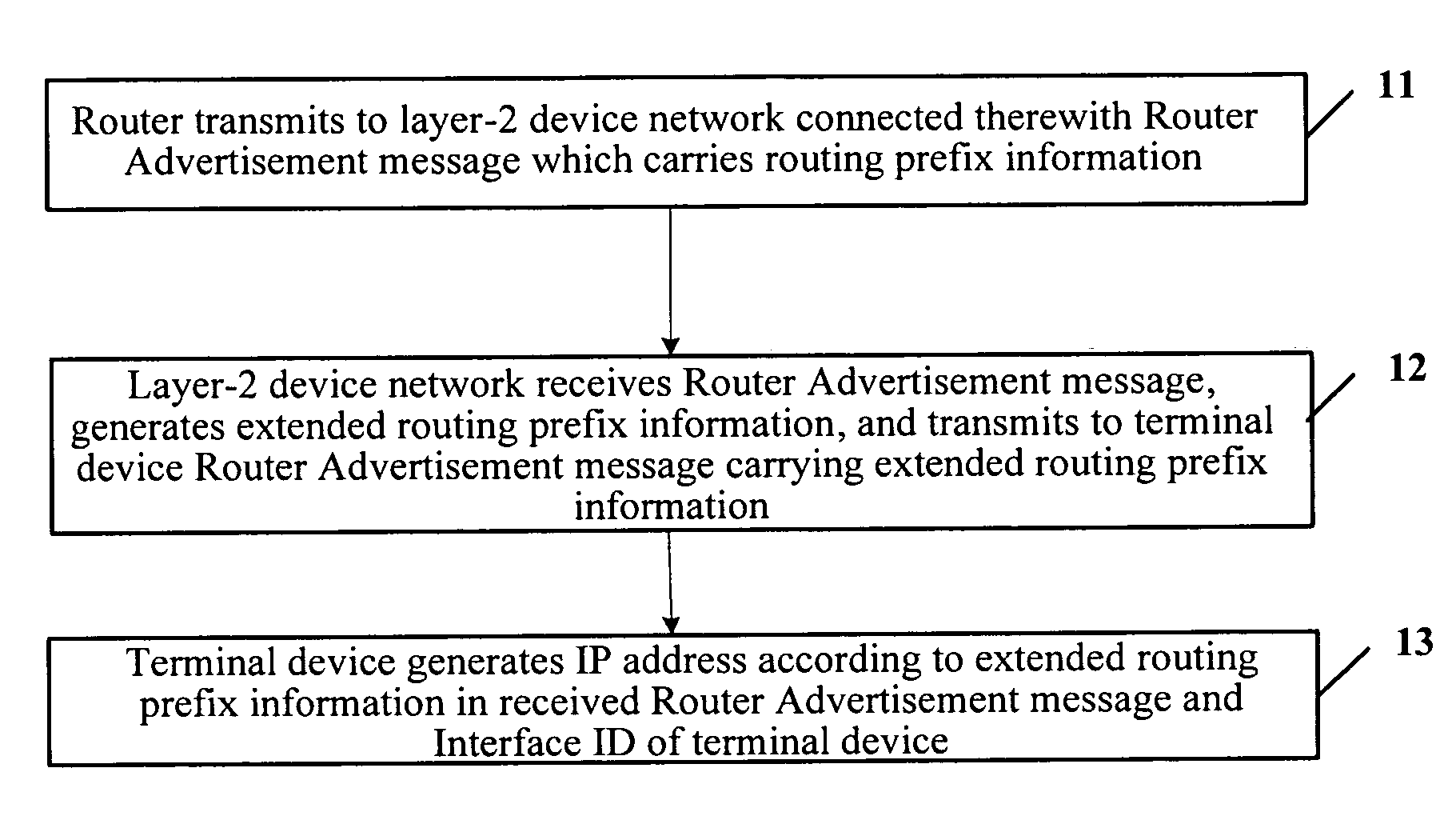
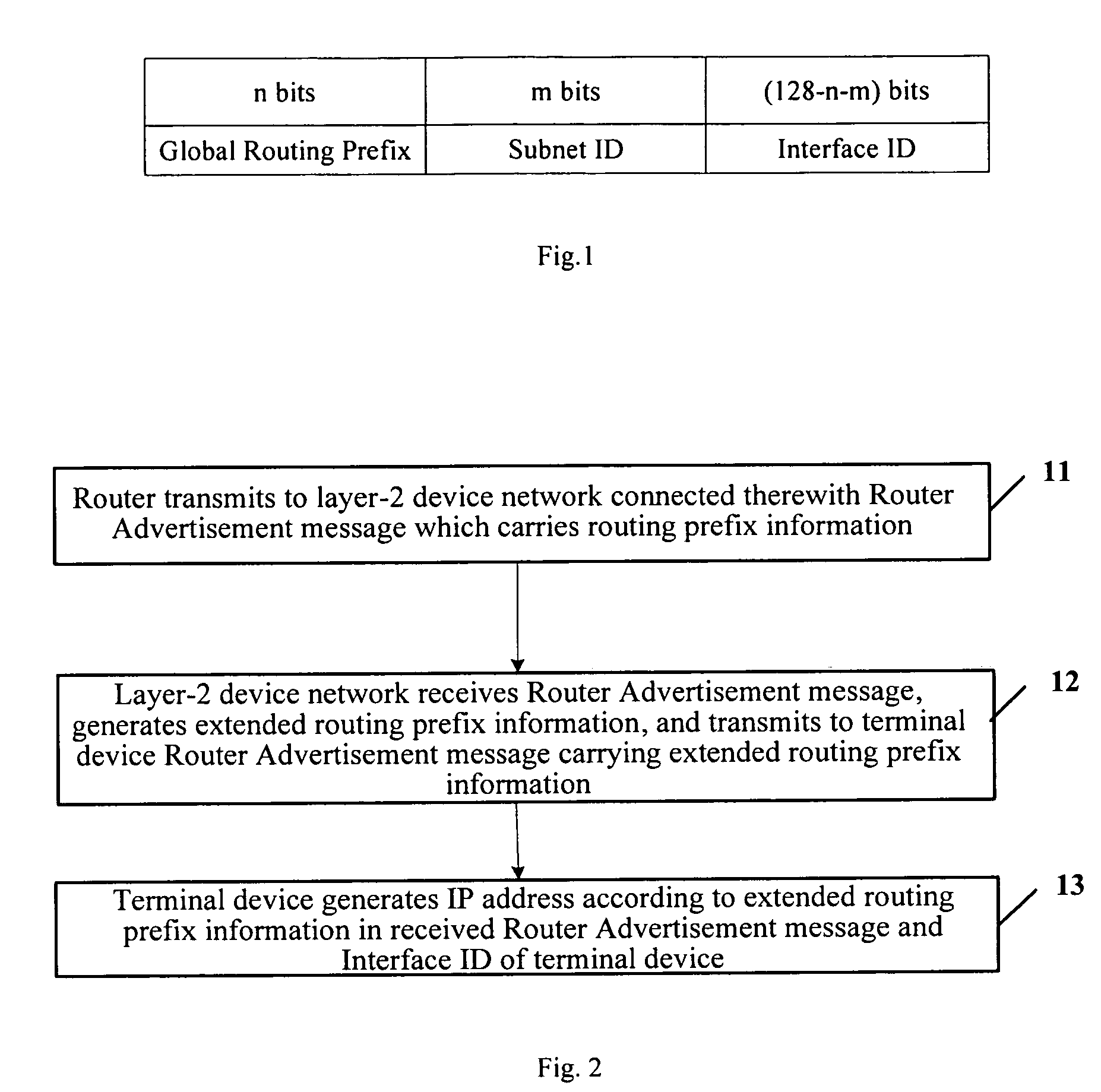
Method for assigning IP address to terminal device and communication system
ActiveUS7706374B2Improve network performanceReduce traffic problemsData switching by path configurationCommunications systemBroadcast domain
Owner:HUAWEI TECH CO LTD
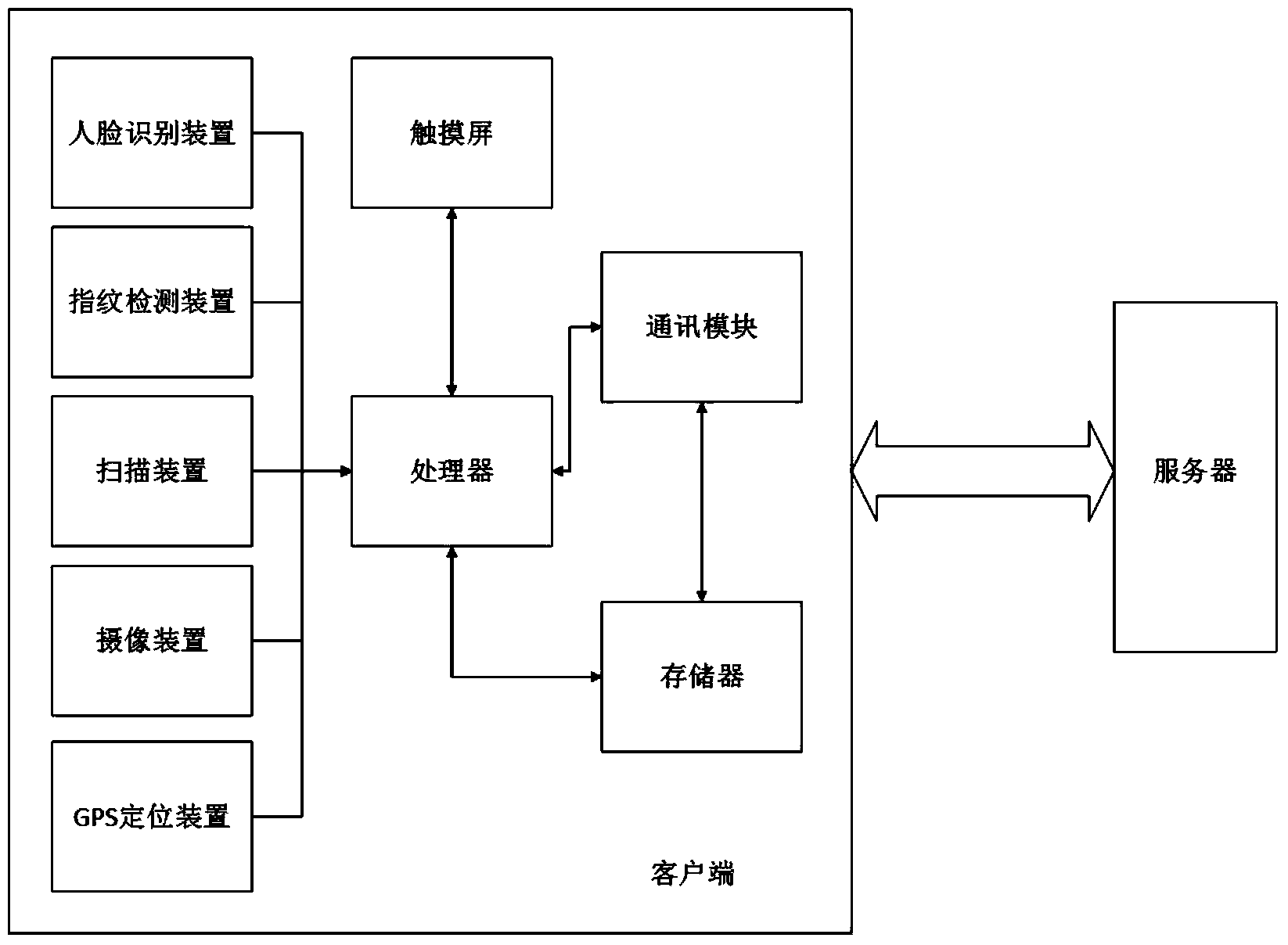
Method and system for recording and recognizing signature of electronic passport
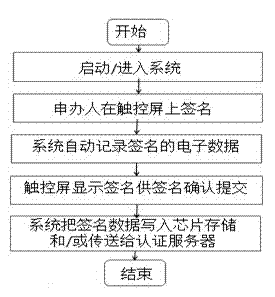
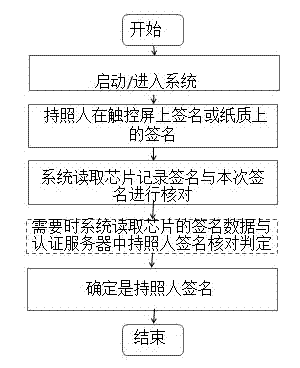
ActiveCN102831391AEnsure uniquenessSecurity identificationCharacter and pattern recognitionInput/output processes for data processingInternet privacyRecognition algorithm
The invention discloses a method and a system for recording and recognizing the signature of an electronic passport. The method comprises the following steps: original electronic data of the signature of an applier are obtained while the electronic passport is handled; a signer signs and affirms on a touch screen; the complete original recording information of the signature writing is recoded by a system automatically; and the data obtained from the recording are stored and filed and written into an electronic passport chip and / or transmitted to an authentication server. The recognizing method comprises steps that a passport owner resigns on the touch screen, and the electronic data of the signature of this time are obtained and are checked with the original signature electronic data stored in the electronic passport chip and / or the authentication server, so as to confirm whether the passport owner is just the signer. By recoding the information of the signature completely, the uniqueness and non-tampering property of the signature are ensured; during the resigning recognition, the accuracy in recognizing the signature is ensured through a safe, reliable and accurate recognition algorithm, so that the method has incontrovertible values and effectiveness.
Owner:CHONGQING AOXIONG INFORMATION TECH
Joint blind key escrow
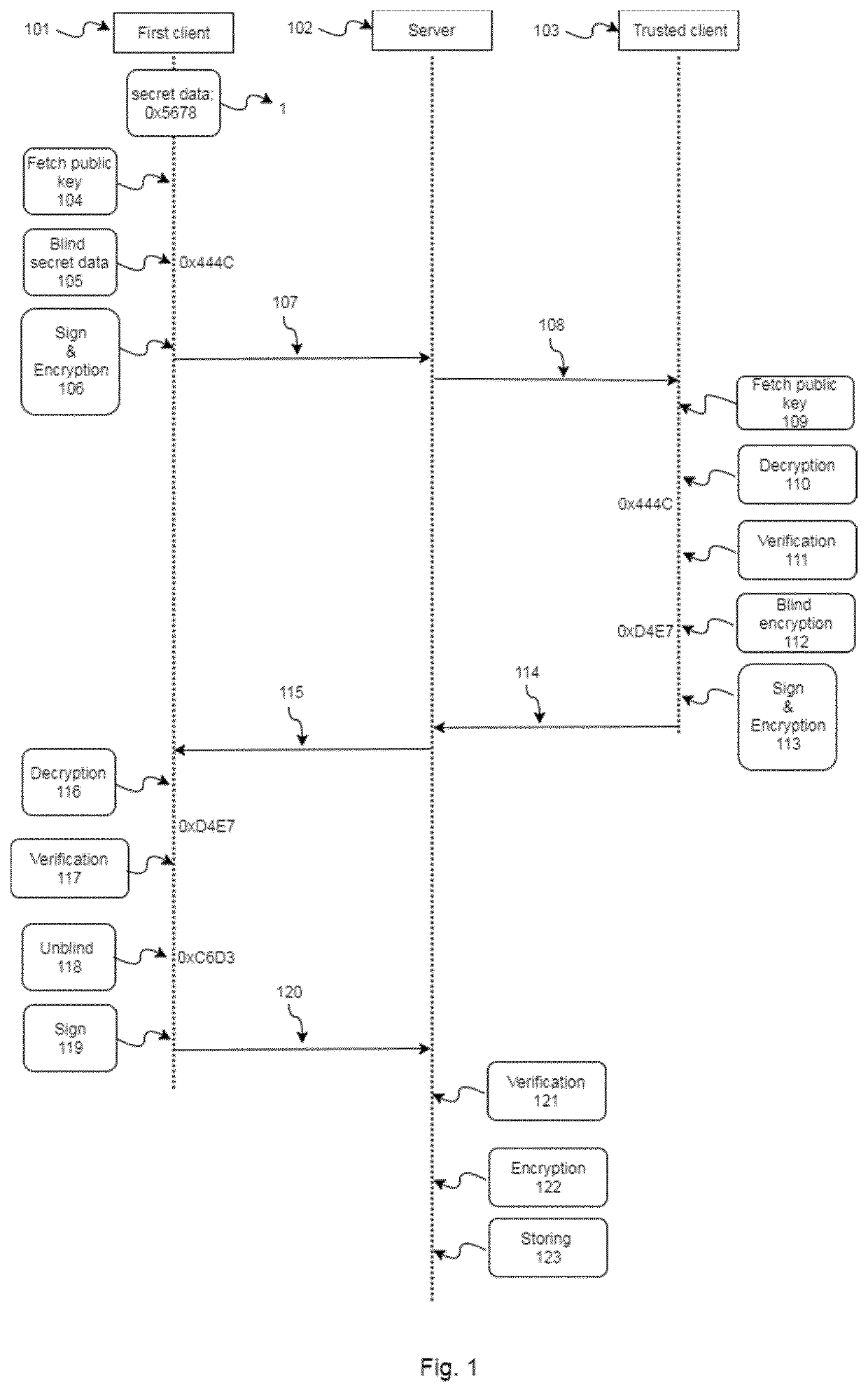
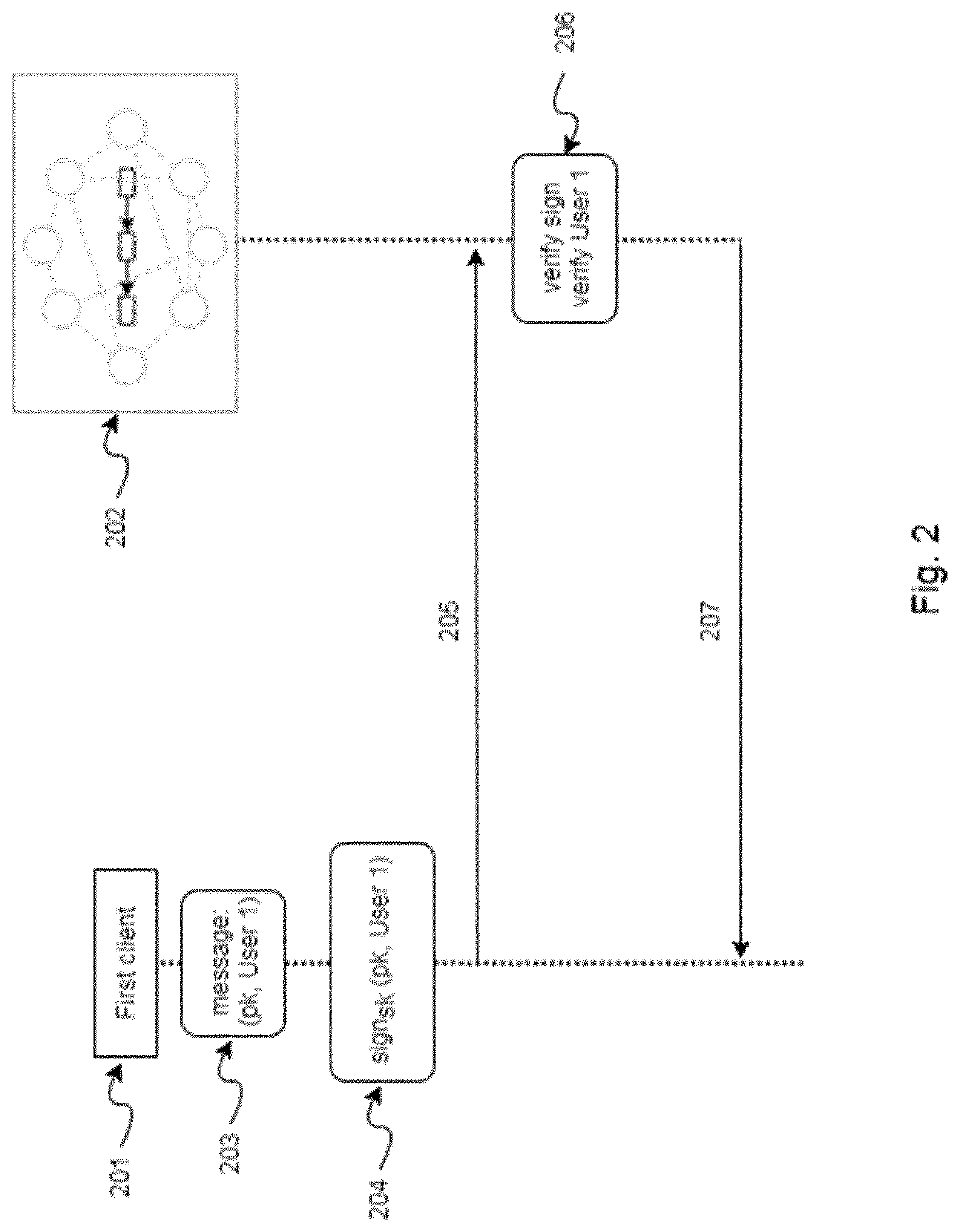
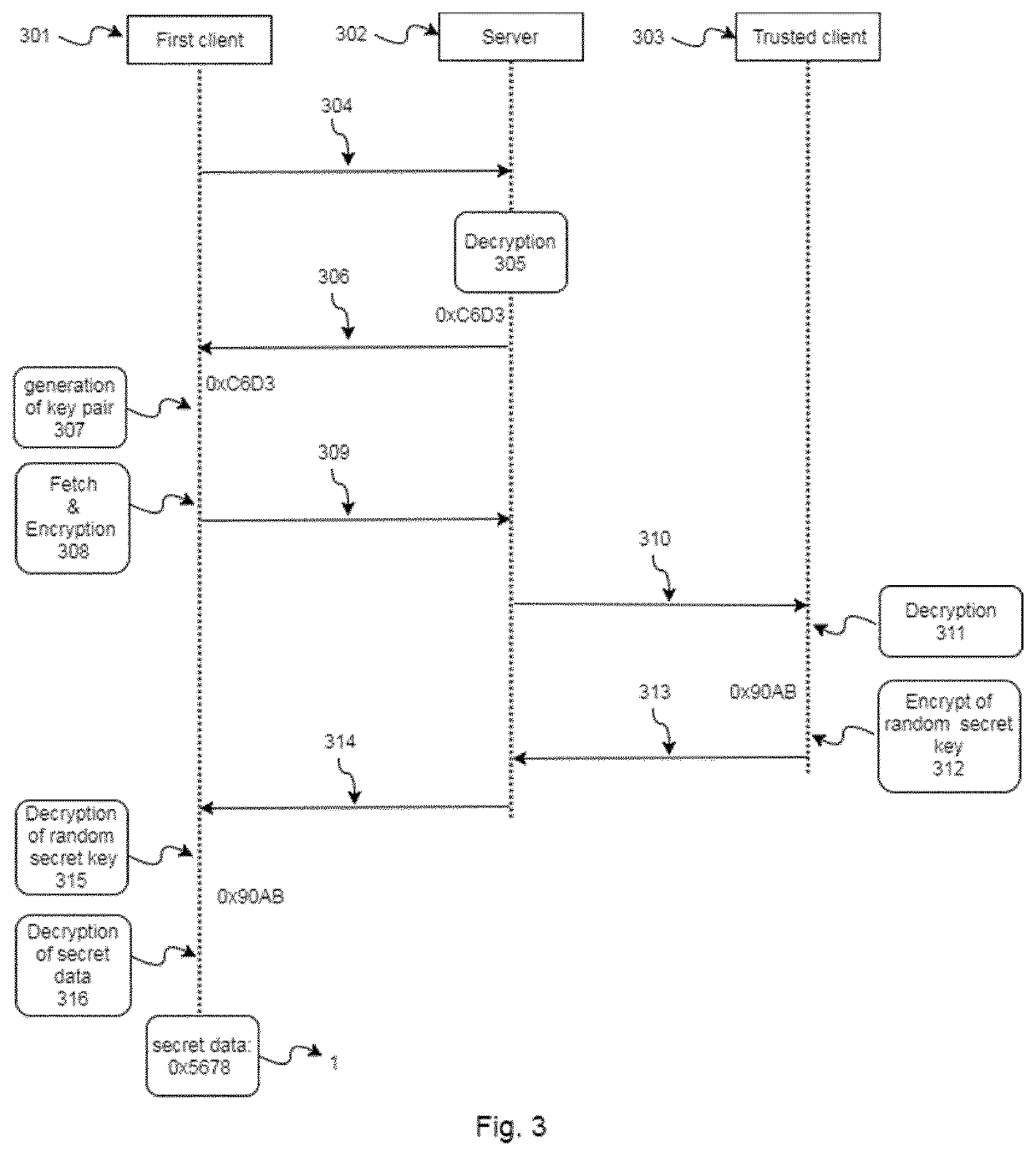
ActiveUS20200295934A1Improve securityImprove integrityKey distribution for secure communicationMultiple keys/algorithms usageInternet privacyTrusted client
A computer-implemented method for escrowing secret data in a server of a client-server network, the client-server network comprising: a first client having at least one public and private client key pairs, at least one trusted client having at least one public and private trusted client key pairs, a server having a public and private server key pairs, a blockchain system comprising a plurality of nodes which are configured to store the public keys of the elements of the client-server network. It is also described a computer-implemented method for obtaining secret data of a server wherein the secret data is escrowed with the above computer-implemented method for escrowing secret data in a server. System, computer-readable mediums and computer programs, which are configured to implement or perform said computer-implemented methods, are also described.
Owner:BANCO BILBAO VIZCAYA ARGENTARIA
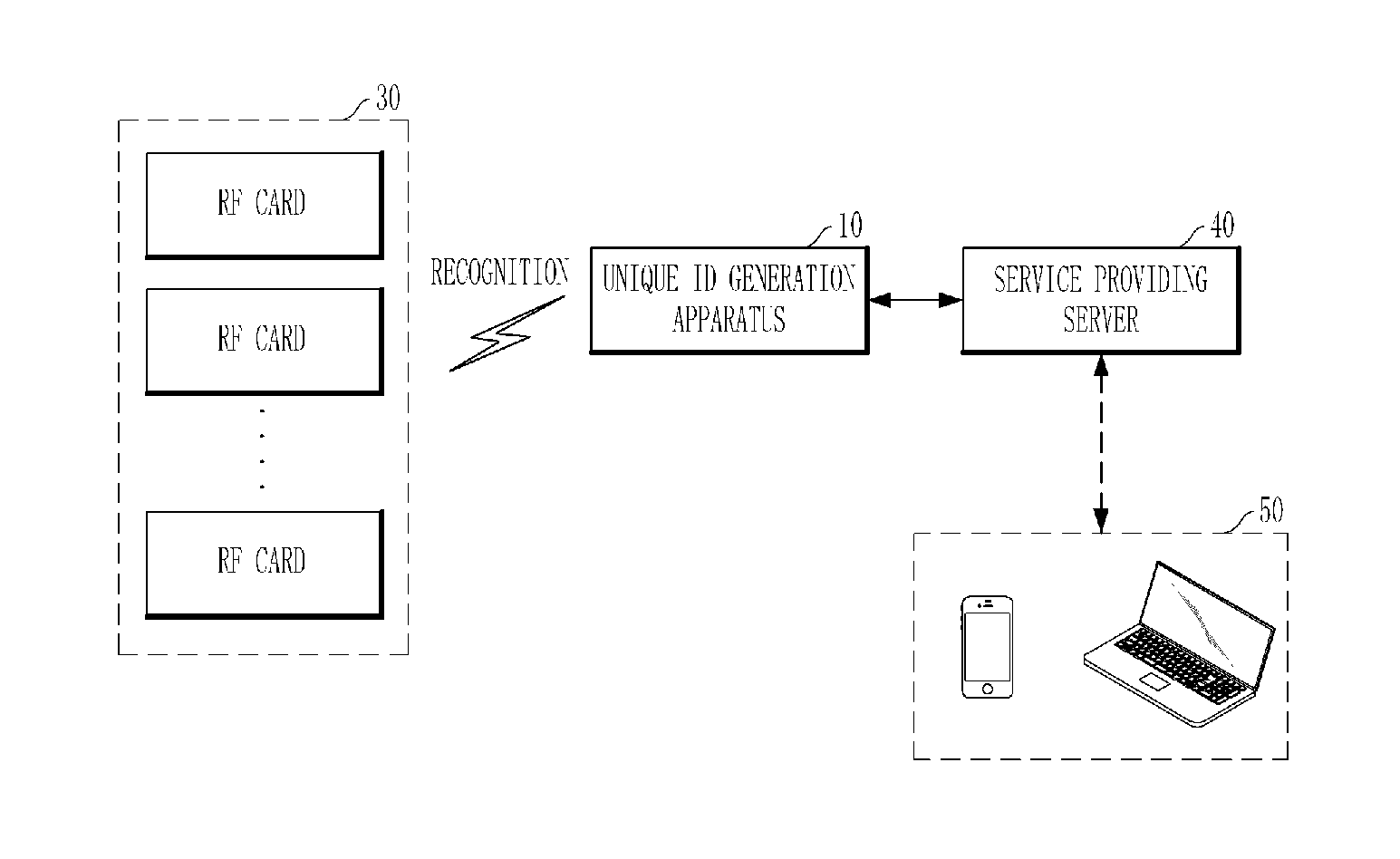
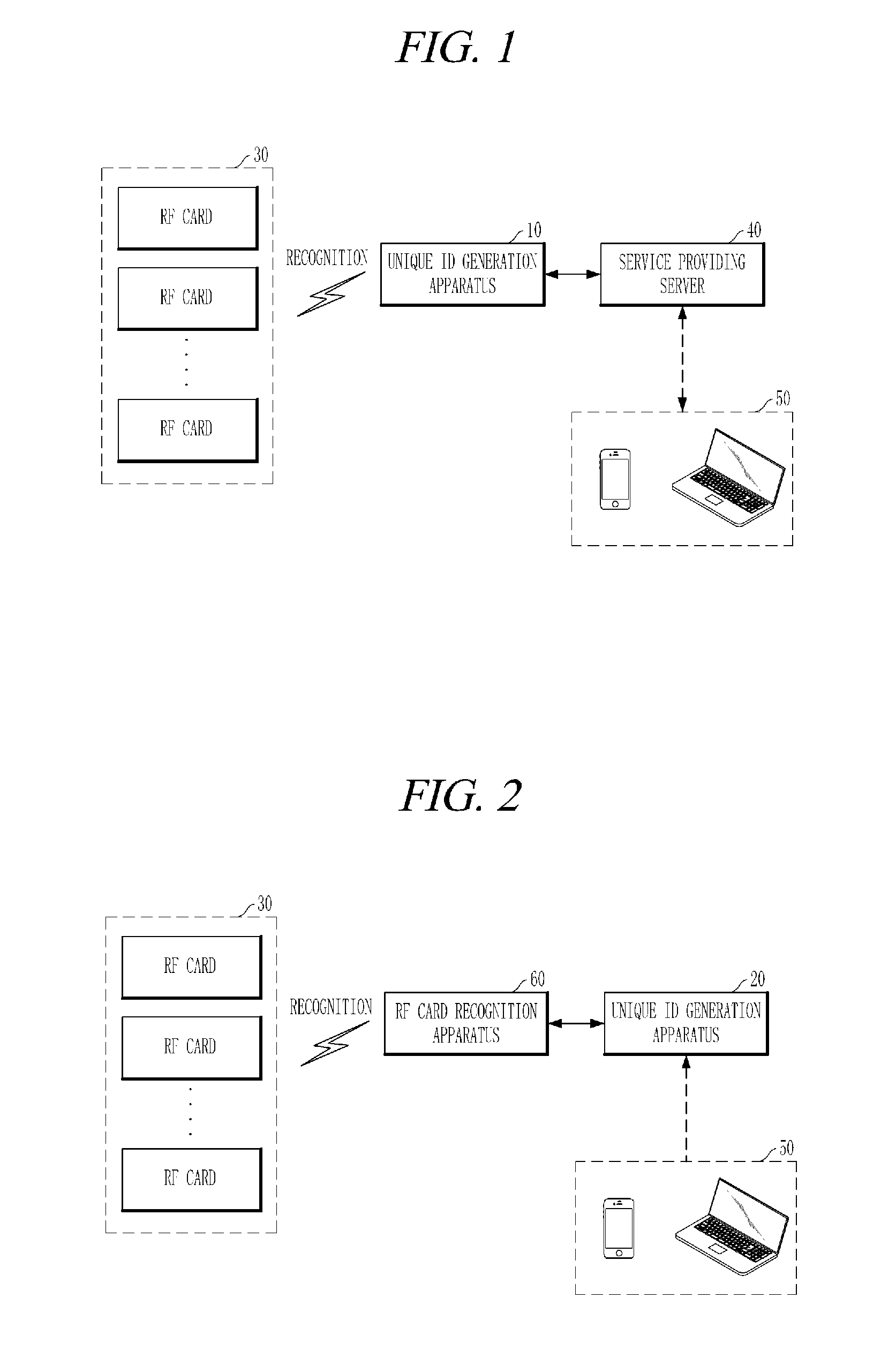
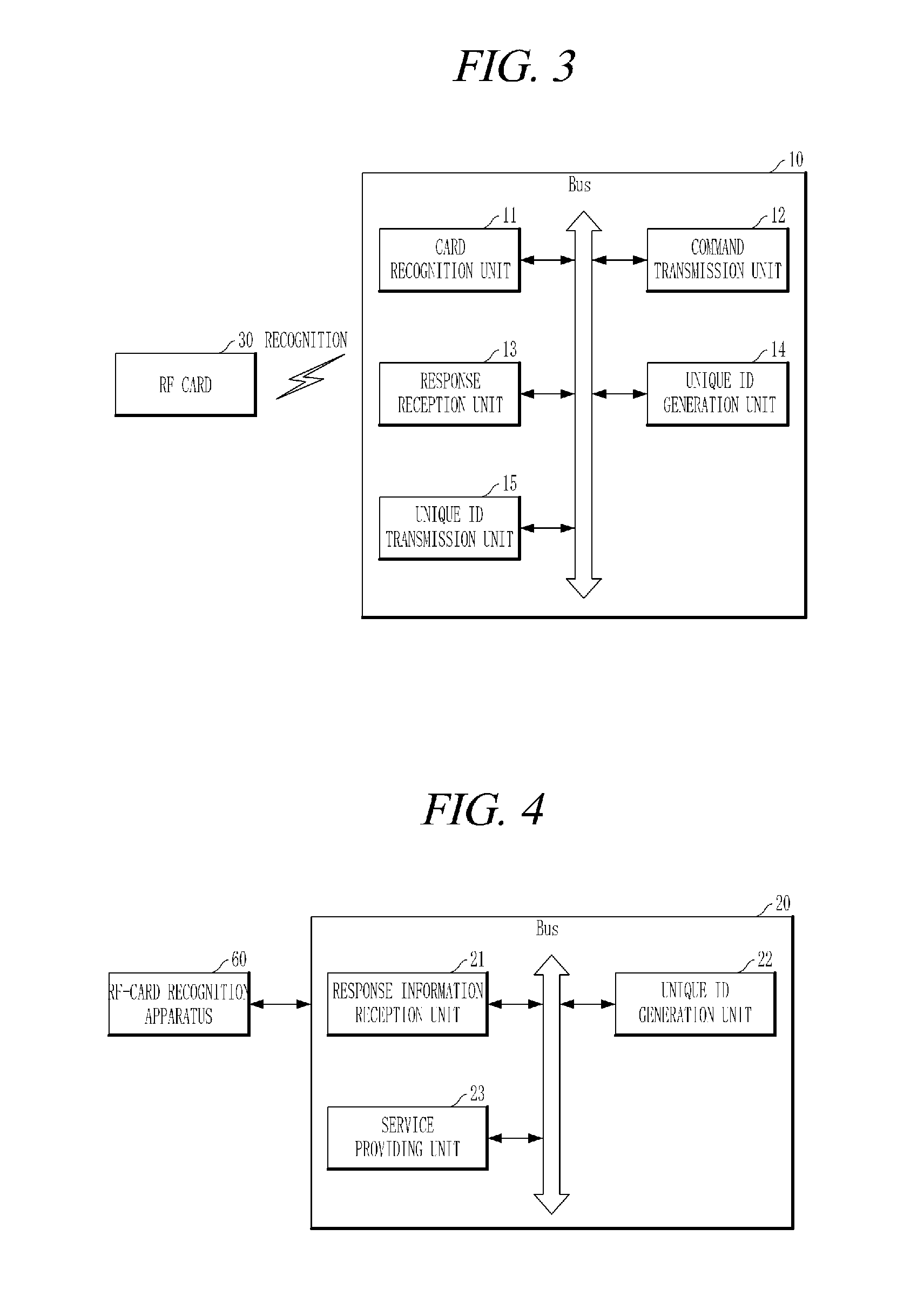
Apparatus and method for generating unique id of RF card
ActiveUS20150324475A1Ensure uniquenessEasy to useCo-operative working arrangementsShort range communication serviceComputer hardwareRadio frequency
A unique ID generation apparatus that may generate a unique ID of a radio frequency (RE) card includes a card recognition unit that recognizes an RF card; a command transmission unit that transmits, to the recognized RF card, a plurality of commands which respectively correspond to a plurality of RF protocols; a response reception unit that receives, from the RF card, responses to one or more of the plurality of commands; and a unique ID generation unit that generates a unique ID of the RF card based on the received responses.
Owner:OKPOS CO LTD
Computer program product and system for managing virtual instances of a physical port attached to a network
InactiveUS20080181232A1Ensure uniquenessData switching by path configurationFibre transmissionVirtualizationFibre Channel
The present invention relates to a method, a computer program product and a system for managing virtual instances of a physical port attached to a network. The method is based on the Fibre Channel N_Port virtualisation for a physical Fibre Channel N_Port. Multiple virtual Fibre Channel adapters share a single physical N_Port among multiple operating system instances. The invention discloses means for the automatic and persistent generation and administration of unique Worldwide Port Names needed for the N_Port virtualisation.
Owner:IBM CORP
X-ray diffraction measurement method and apparatus
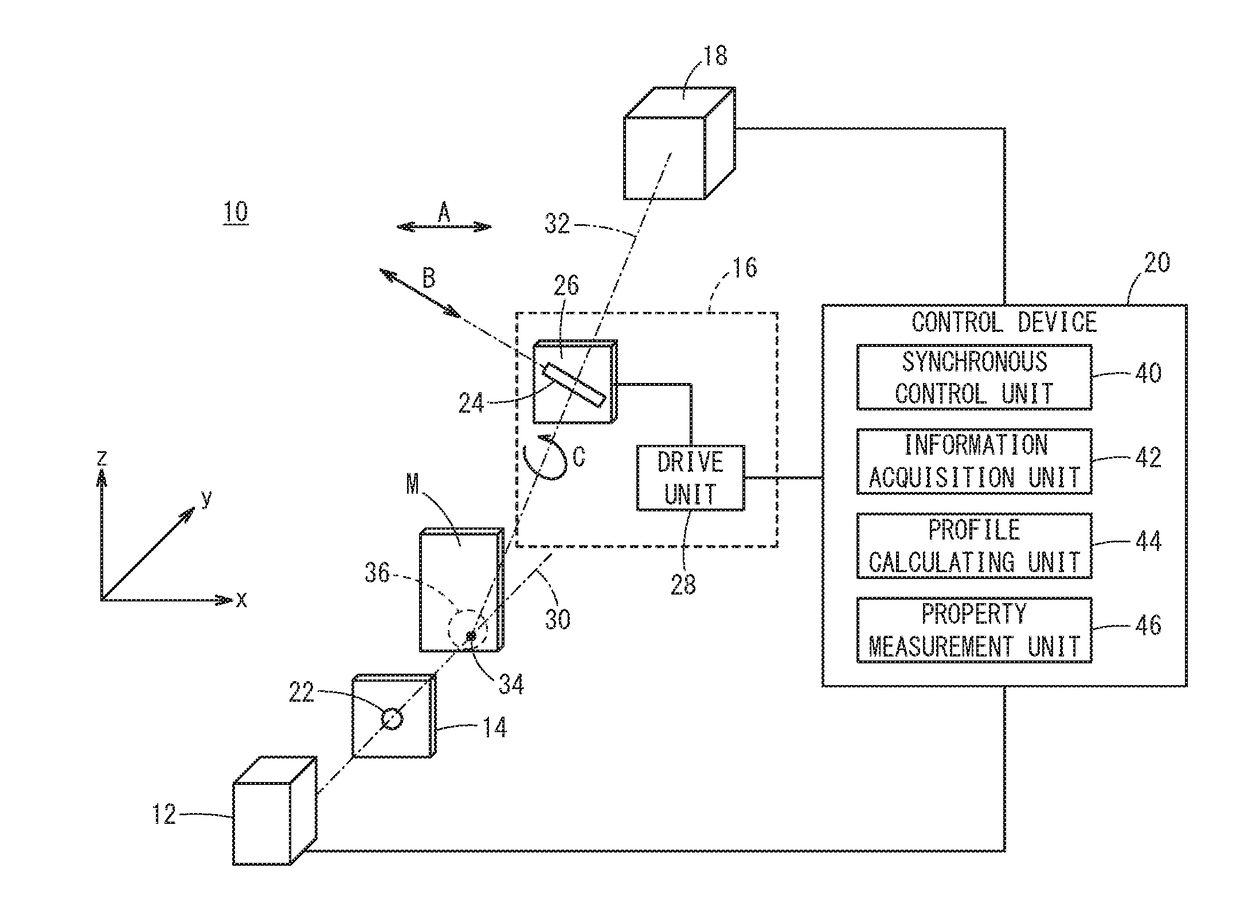
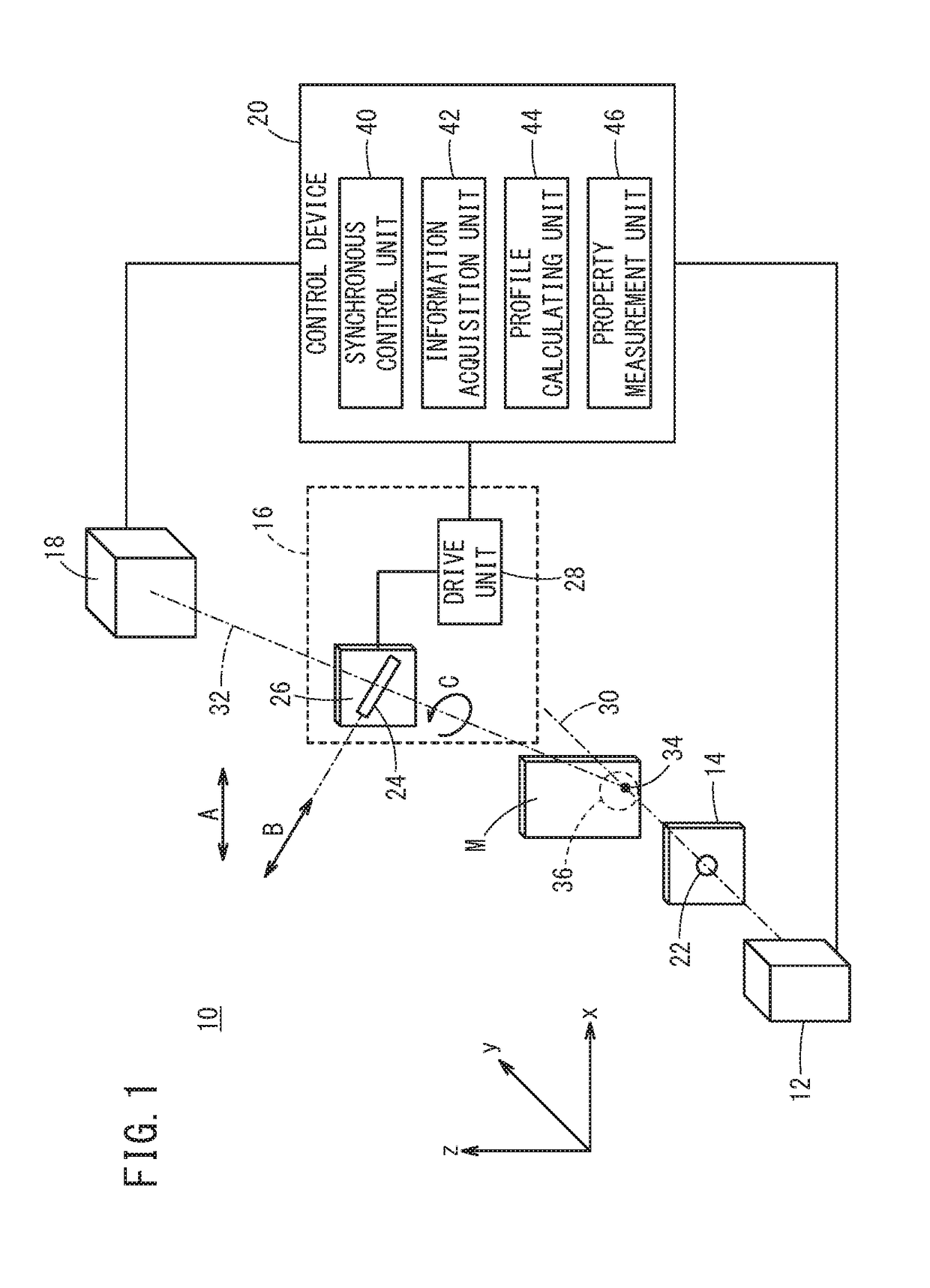
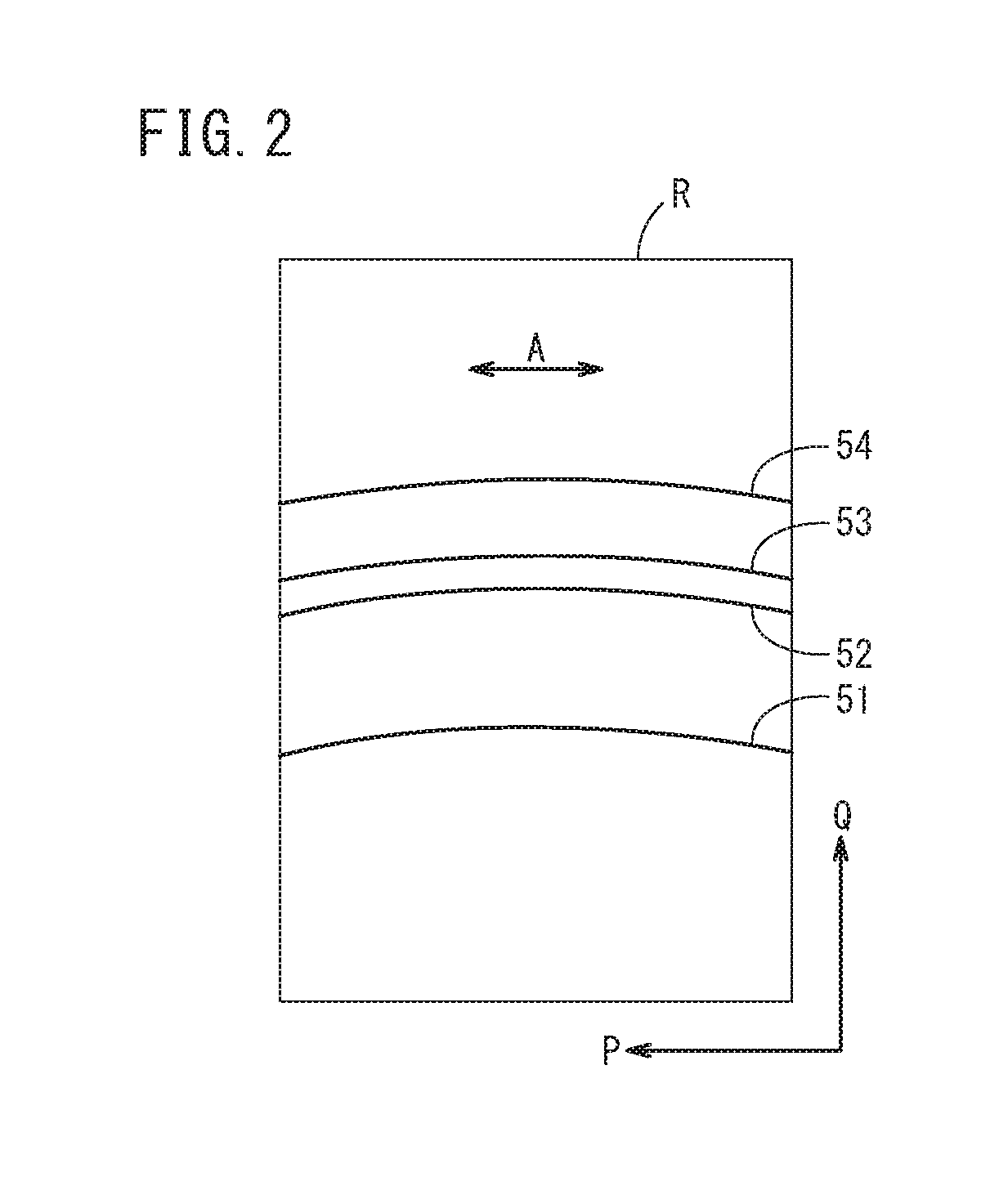
ActiveUS20180202948A1Efficient measurementEnsure uniquenessMaterial analysis using wave/particle radiationTwo dimensional detectorOptical axis
An X-ray diffraction measurement method includes an arranging step of arranging a shielding plate and a two-dimensional detector on an outgoing optical axis, and a calculating step of calculating a diffraction profile indicating an X-ray intensity with respect to a diffraction angle of the object to be measured, on the basis of a two-dimensional X-ray image detected by the two-dimensional detector. In the arranging step, the shielding plate is arranged in a manner so that the slit is inclined at least in a direction about the outgoing optical axis with respect to an orthogonal direction which is orthogonal to both the incident optical axis and the outgoing optical axis.
Owner:HONDA MOTOR CO LTD
Method for Making Correspondence Between a Maintenance Point Identifier and a Media Access Control Address
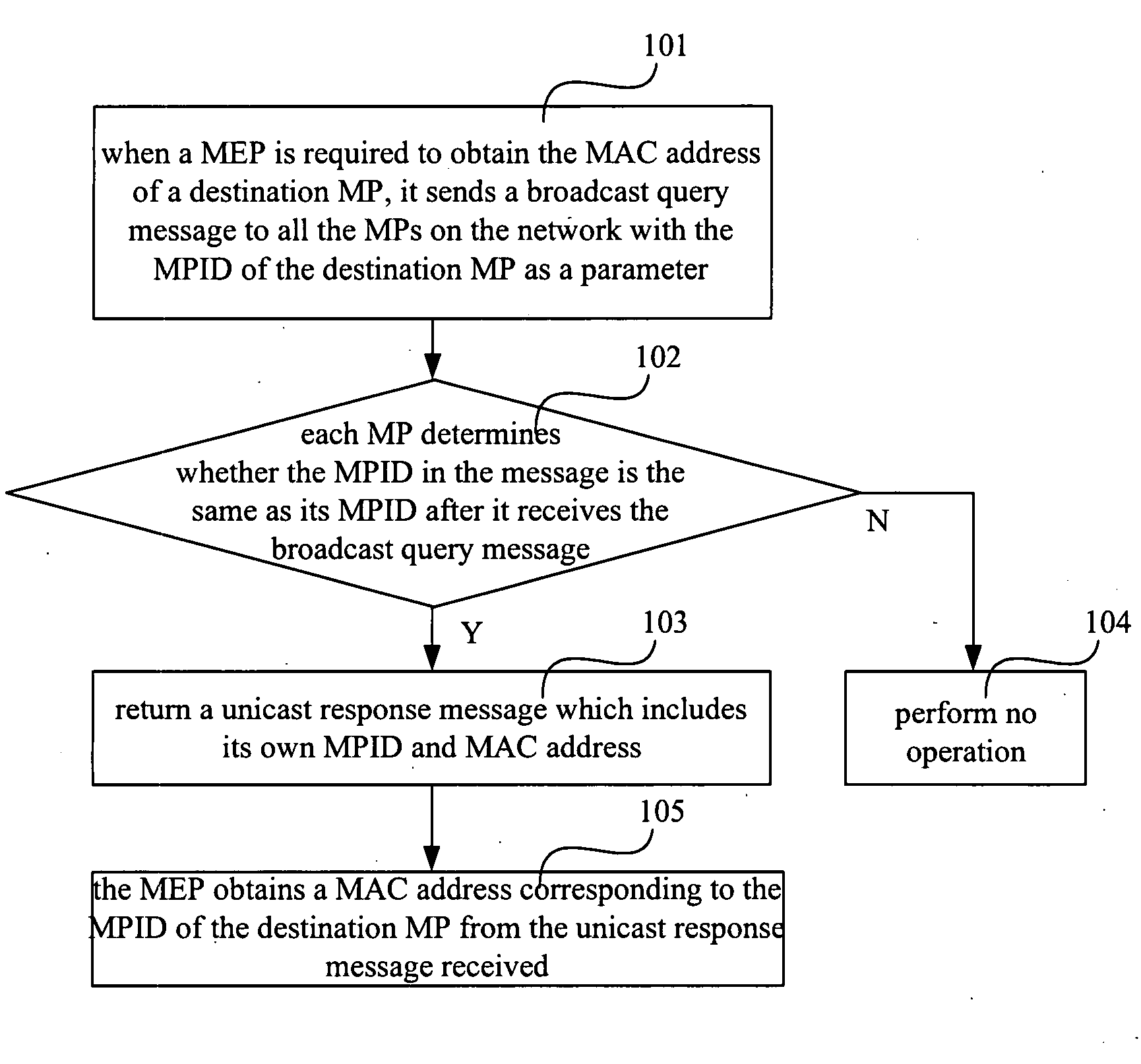
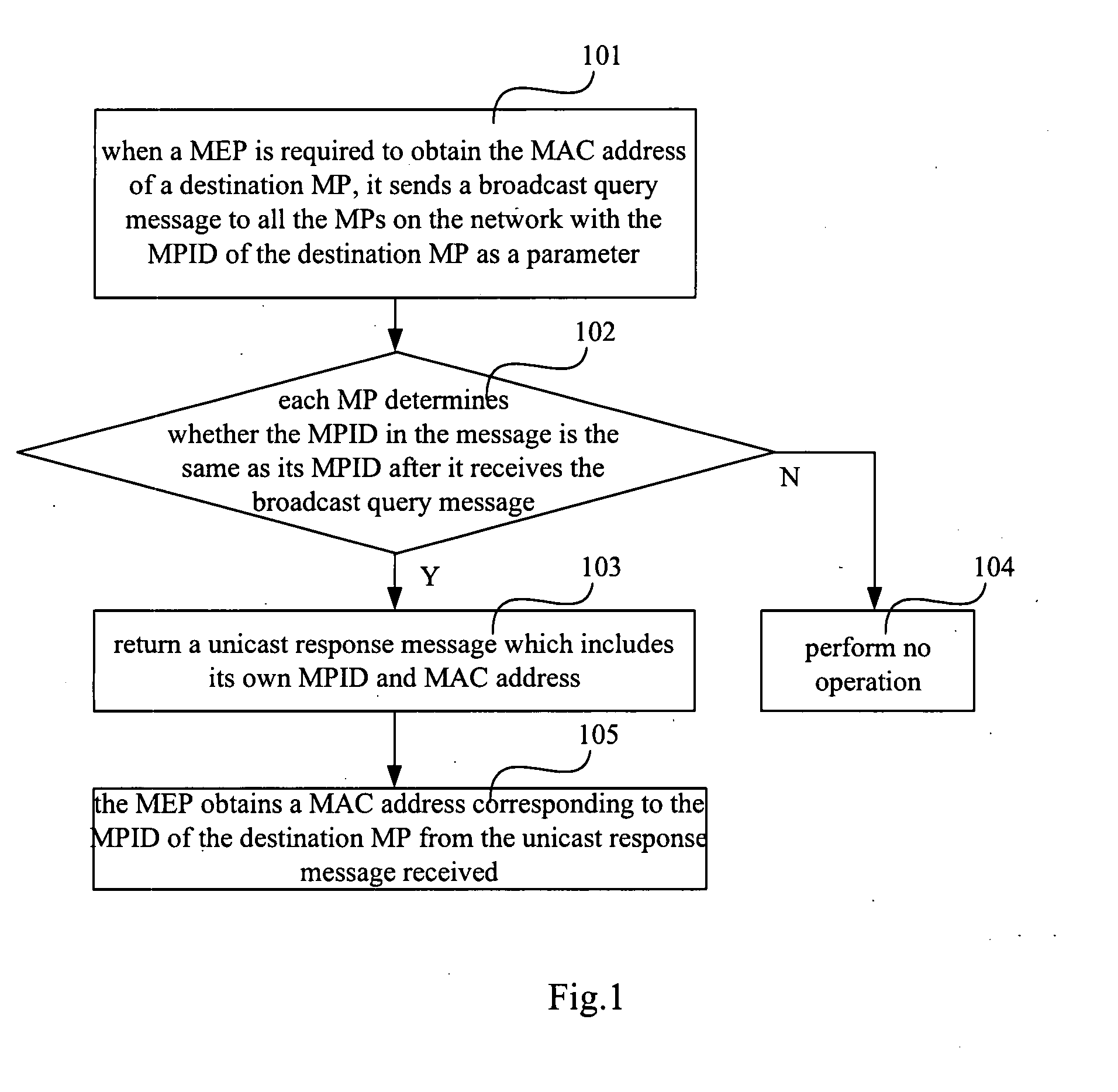
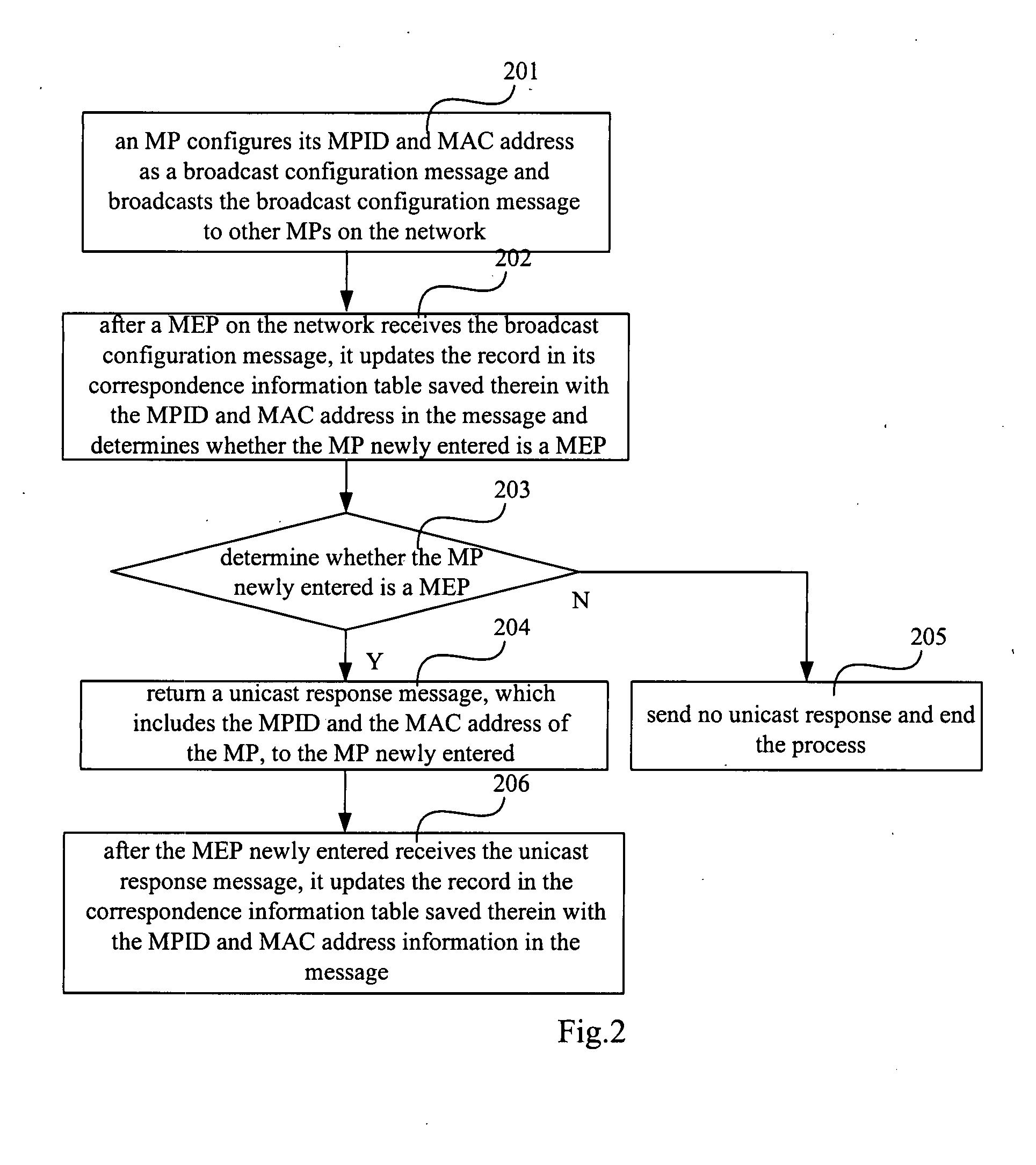
ActiveUS20080144514A1Ensure uniquenessError preventionFrequency-division multiplex detailsMedia access controlMAC address
A method for making correspondence between an MPID and a MAC address, including: each MP on the network is allocated a unique MPID at first; to obtain the MAC address of a destination MP, a MEP sends a broadcast query message to all the MPs on the network with the MPID of the destination MP; after receiving the broadcast query message, each MP determines whether the MPID in the message is the same as its MPID; if they are same, returns a unicast response message which includes the MPID and the MAC address; otherwise, no operation is performed; the MEP obtains the MAC address of the destination MP from the received unicast response message. The invention overcomes the problem of the prior art that an MEP cannot know the MAC address of a destination MP. By the present invention, various functions of the OAM can be accomplished and the uniqueness of the MPID and the MAC address of an MP on the network may also be ensured.
Owner:HUAWEI TECH CO LTD
Online operation management method and system based on ship three-dimensional model and terminal
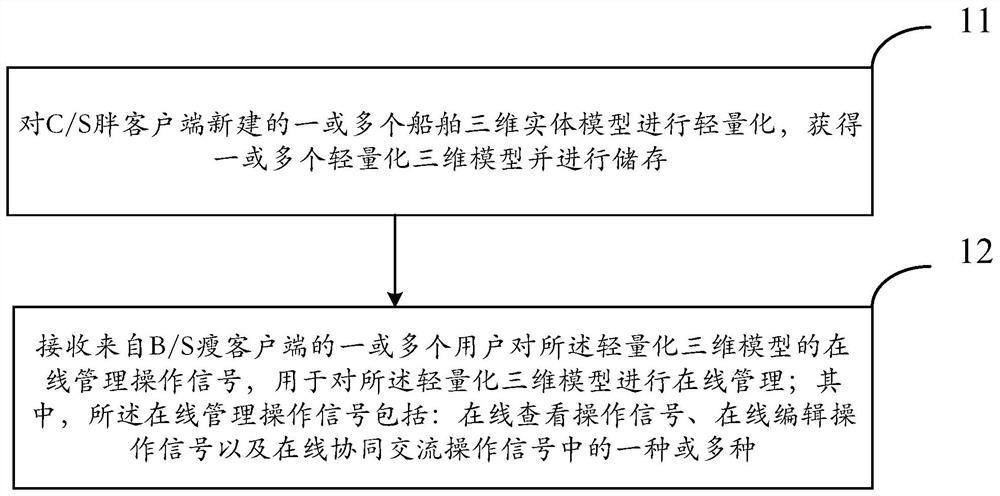
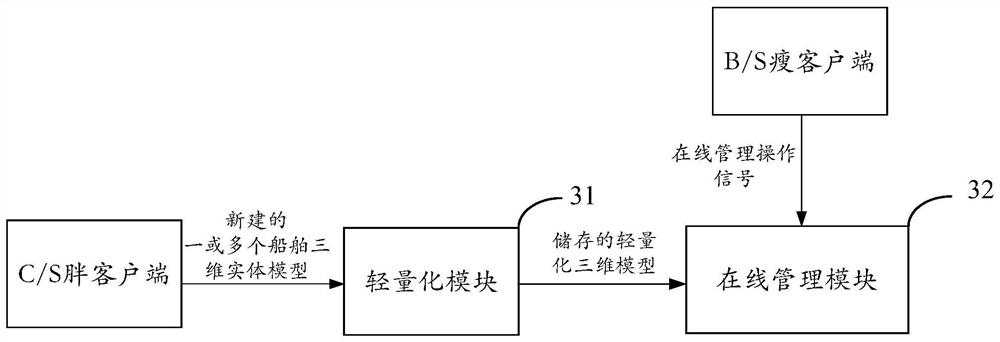
PendingCN111915276AAchieve fast and lightweightLower requirementGeometric CADOffice automationReworkIndustrial engineering
The invention provides an online operation management method and system based on a ship three-dimensional model and a terminal. The method comprises the steps: lightening a ship three-dimensional entity model newly built at a C / S fat client to acquire a light-weight three-dimensional model, and storing the light-weight three-dimensional model; receiving online management operation signals of one or more users from a B / S thin client, wherein the online management operation signals are used for carrying out online management on the lightweight three-dimensional model; wherein the online management operation signal comprises one or more of an online viewing operation signal, an online editing operation signal and an online cooperative communication operation signal. The problems that in the prior art, the requirement for field terminal application equipment is high, the application cost is high, and online cooperation between design and manufacturing cannot be achieved for a three-dimensional model are solved. Online cooperation between ship design and manufacturing is achieved, online communication between field manufacturing personnel and designers is supported, the design problem existing in the manufacturing field is rapidly solved, design change and manufacturing rework are reduced, and the production and construction cost is saved.
Owner:JIANGNAN SHIPYARD GRP CO LTD
Electric vehicle speed tampering prevention method
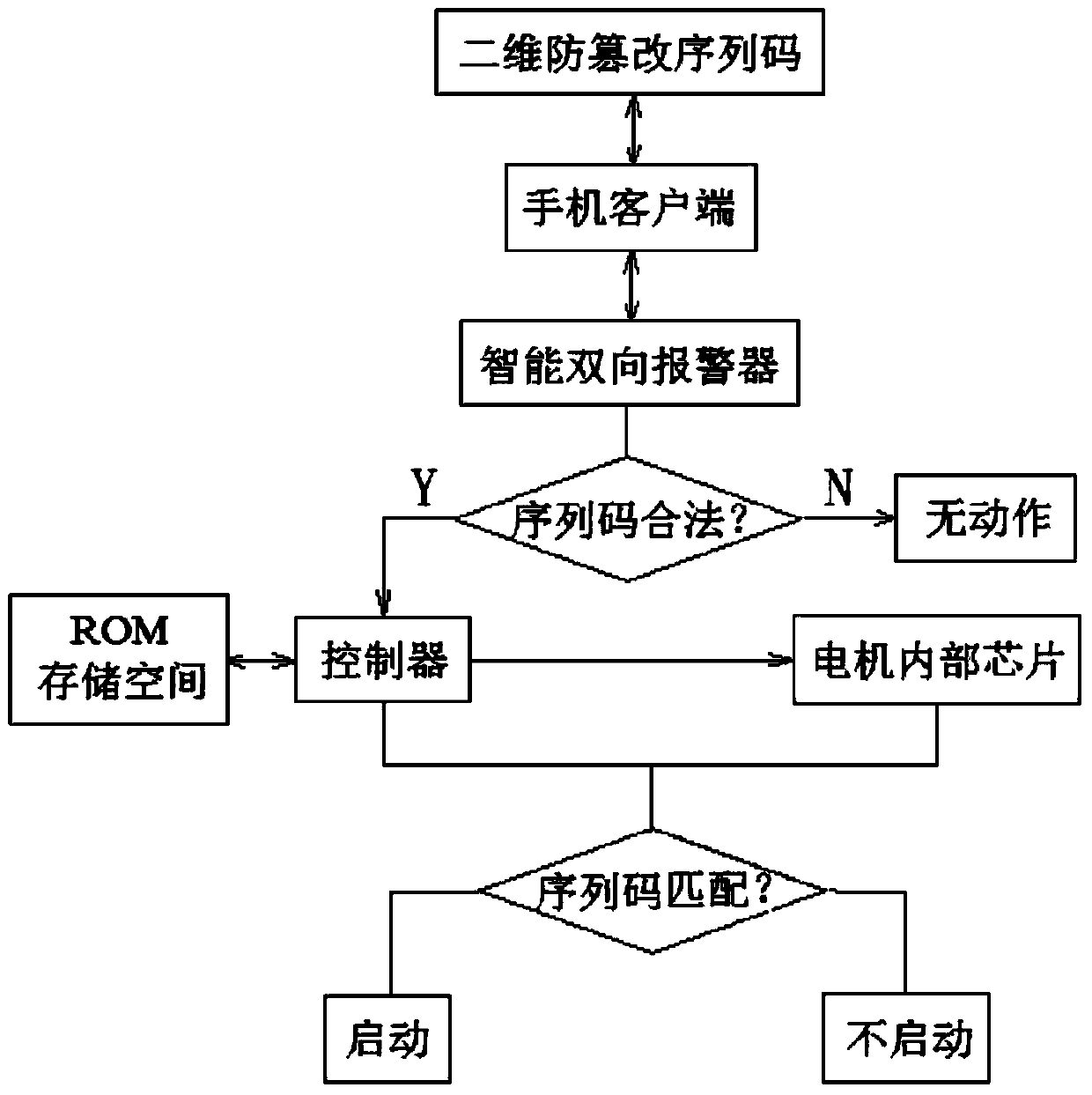
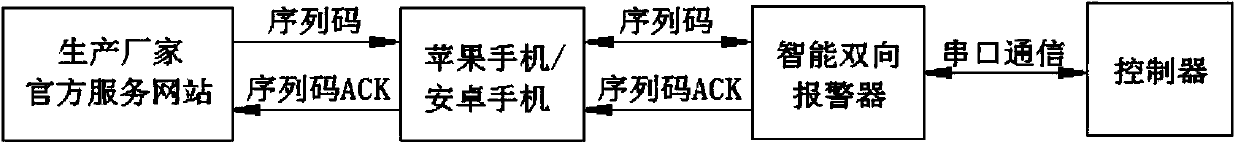
InactiveCN104002762AAchieve a unique matchPut an end to the problem of raising the speed of the vehicle without authorizationAnti-theft devicesElectric machineryClient-side
The invention discloses an electric vehicle speed tampering prevention method, and belongs to the technical field of communications. The electric vehicle speed tampering prevention method includes the following steps that (1) sequence codes are downloaded and obtained through a mobile phone client-side; (2) the sequence codes are sent to an intelligent bi-directional alarm through mobile phone Bluetooth; (3) the intelligent bi-directional alarm judges whether the sequence codes are legal or not, and if the sequence codes are legal, and the sequence codes are sent to a controller; (4) the controller enables the received sequence codes to be stored in an ROM storage space and meanwhile sends the sequence codes to an internal chip of a motor; (5) when a vehicle is started, communication is conducted between the controller and the internal chip of the motor, if the sequence codes of the controller and the sequence codes of the internal chip of the motor are matched, the motor is started, and otherwise the motor is not started. According to the method, unique matching of the motor and the controller is achieved, the problem that an owner increases the speed of the vehicle arbitrarily is avoided, the probability that accidents happen due to the fact that the speed of the vehicle is too fast is lowered, the self-security of the owner is guaranteed, and meanwhile the fame of vehicle manufacturers is maintained.
Owner:CHANGZHOU SUPAQ BICYCLE
Independent self-service bank
InactiveCN102926559AEnsure uniquenessEnsure safetyAdvertisingDisplay meansTelecommunicationsBanking industry
The invention discloses an independent self-service bank, which comprises an integral bank framework, wherein a light box is arranged on the outer side of the integral bank; a light-emitting diode (LED) display screen is arranged on the upper part of the front end oft the integral bank; and a signboard light box special for banking is arranged at the periphery of the integral bank on the top of the bank. The independent self-service bank has the advantages that the self-service bank can operate in all weather, and the operational transactions in the conventional bank counter can be finished within 24 hours, such as cash deposit and withdrawal, account transfer, bankbook making-up, public service payment, financial information query, property storage and other self-service services. Air-conditioners or heating equipment can be arranged in the self-service bank according to regional climate characteristics, the outer wall is made of steel or high-strength glass or bullet-proof glass, the self-service bank is provided with an alarm system, and only a client is allowed to enter the self-service bank for handling the services by swiping cards each time, so that the uniqueness and safety of client transaction services are ensured, and humanized characteristics of the banking services are reflected. The independent self-service bank is low in cost and is not limited by a field environment, and townspeople can conveniently handle the banking services.
Owner:NANJING YINHAO SYST ENG
Electric power material management system based on PBFT alliance chain
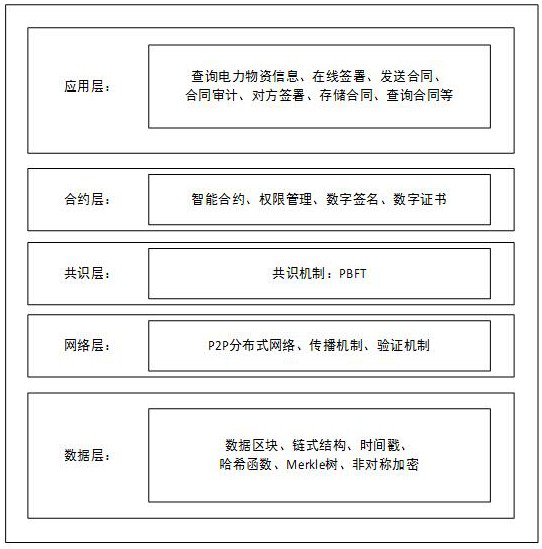
The invention relates to an electric power material management system based on a PBFT alliance chain. The system is composed of a data layer, a network layer, a consensus layer, a contract layer and an application layer. The data layer is responsible for storing electric power material data and electric power material contracts, generating a fixed-length output string through a hash algorithm, generating a corresponding Merkle tree, and packaging the Merkle tree into a data block with a timestamp. The network layer is responsible for enabling all nodes in the alliance chain to participate in the check and accounting process of the data block. The consensus layer solves the consistency problem of the data layer participating in node maintenance data blocks through a PBFT consensus mechanism. The contract layer mainly completes signing of an electric power material contract through an intelligent contract, and an authority management module built by an RBAC model is added to further guarantee the safety of data. The application layer encapsulates various application scenarios of the alliance chain. According to the electric power material management system based on the PBFT alliancechain, electric power material data is subjected to refined management, and meanwhile safety and effectiveness of electric power material contract signing are guaranteed.
Owner:HANGZHOU DIANZI UNIV
A trusted authentication system and method based on block chain
InactiveCN109145647AEnsure authenticityEnsure uniquenessData processing applicationsDigital data protectionValidation methodsAuthentication server
The invention provides a trusted authentication system and a trusted authentication method based on a block chain, the method comprising steps: by using block chain technology instead of traditional data storage and verification methods, decentralization is realized, that is, a centralized agent is not needed, a high efficiency and large-scale interaction mode is directly realized, and users can not easily tamper with the correct information, once the information of a node changes, the entire 'block chain' of each node will perceive the behavior to ensure the authenticity and uniqueness of therelevant data; by using authentication server, different users can be assigned different application privileges to achieve effective management and information protection; the whole system can prevent user information from being tampered with, ensure the authenticity and uniqueness of the relevant data, assign different application rights to different users, and ensure the security and reliability of the system.
Owner:武汉笑脸科技有限公司
Method, kit and primers for detecting of species of Salmo
InactiveCN103966347AGuaranteed specificityImprove accuracyMicrobiological testing/measurementDNA/RNA fragmentationGel electrophoresisBiology
The invention discloses a method, kit and primers for detecting of species of Salmo. The method comprises the following steps: (1) by using genome DNA (deoxyribonucleic acid) of a sample to be detected as a template, amplifying the genome DNA of the sample to be detected by using specific amplification primers, wherein the sequences of the specific amplification primers are respectively disclosed as SEQ ID NO:1-SEQ ID NO:10 in the sequence table; and (2) carrying out gel electrophoresis analysis on the PCR (polymerase chain reaction) amplification product, wherein the sample to be detected with specific strips belongs to Salmo salar or Oncorhynchus keta. Compared with the traditional method, the method disclosed by the invention is accurate and unique. The operating personnel does not need much working experience, and only needs to do the experiment according to the operation steps. The kit has the advantages of short required detection time, low cost, high specificity of detection results and simple detection result judgment method.
Owner:SPH NO 1 BIOCHEM & PHARMA CO LTD
Bluetooth communication-based identity identification method
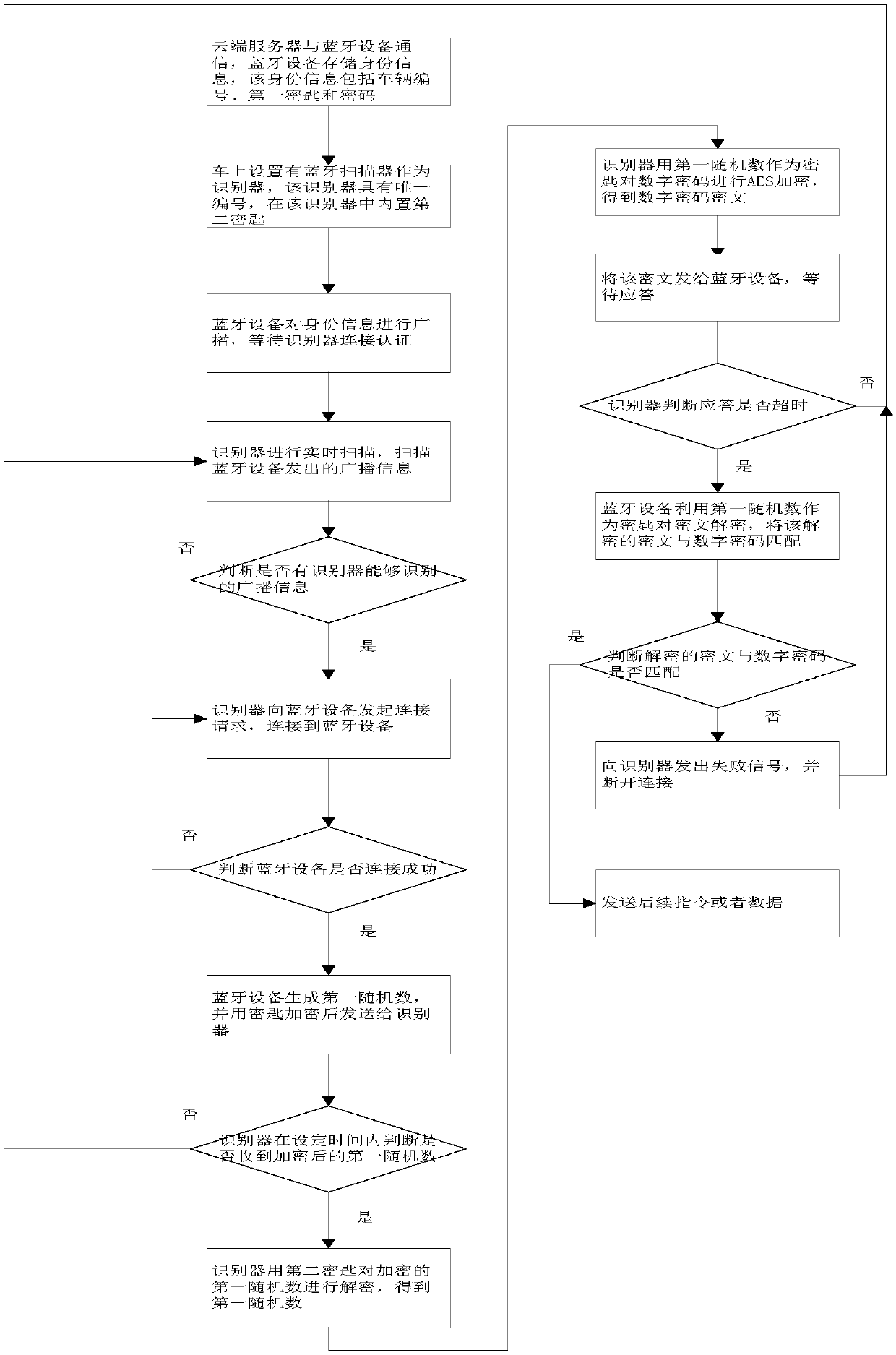
InactiveCN107708098AEnsure uniquenessEnsure safetyBroadcast service distributionTransmissionBroadcast domainPassword
The invention relates to a Bluetooth communication-based identity identification method. The method mainly comprises the following steps that first, a cloud server communicates with a Bluetooth devicethrough a lora network or an NBiot netowrk, the cloud server sends identity information to the Bluetooth device through the network, and the Bluetooth device stores the identity information, whereinthe identity information comprises a vehicle number, a first key and a password; second, a Bluetooth scanner is arranged on a vehicle and is used as an identifier, wherein the identifier has a uniquenumber, a second key is built in the identifier, and the second key is corresponding to the first key; third, the Bluetooth device broadcasts the identity information, and waits for connection and authentication by the identifier; and fourth, the identifier scans the broadcast information sent by the Bluetooth device in real time. In the prior art, a parking lock is unlocked only through operatinga remote controller or a cellphone APP, causing inconvenience to users; to meet the demand of sharing the parking space, one identifier can identify multiple parking locks dynamically, so that a vehicle can automatically identify and unlock when the vehicle is three meters away from the parking space.
Owner:CHONGQING YUNTING ZHILIAN TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com