Patents
Literature
153 results about "System of systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System of systems is a collection of task-oriented or dedicated systems that pool their resources and capabilities together to create a new, more complex system which offers more functionality and performance than simply the sum of the constituent systems. Currently, systems of systems is a critical research discipline for which frames of reference, thought processes, quantitative analysis, tools, and design methods are incomplete. The methodology for defining, abstracting, modeling, and analyzing system of systems problems is typically referred to as system of systems engineering.
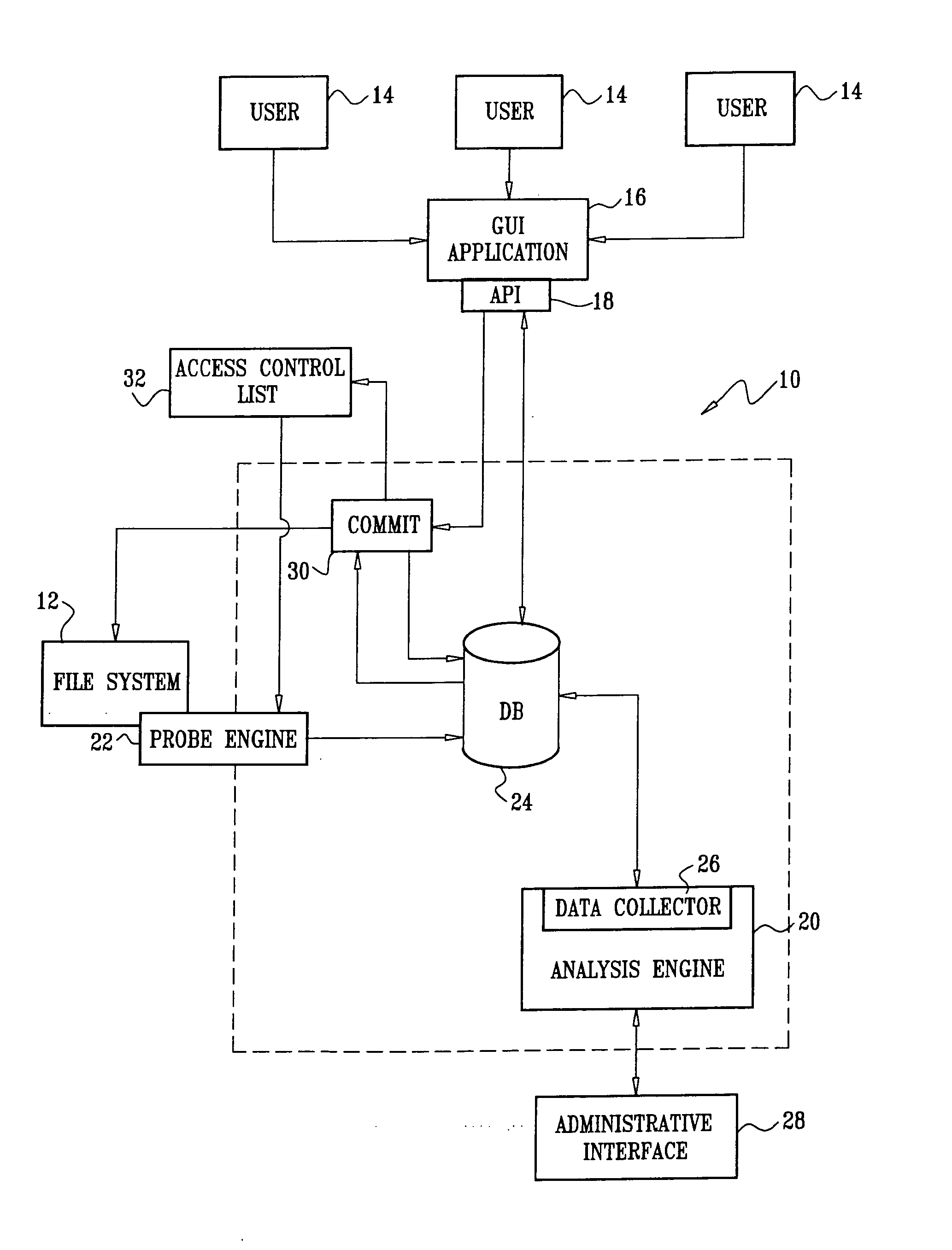
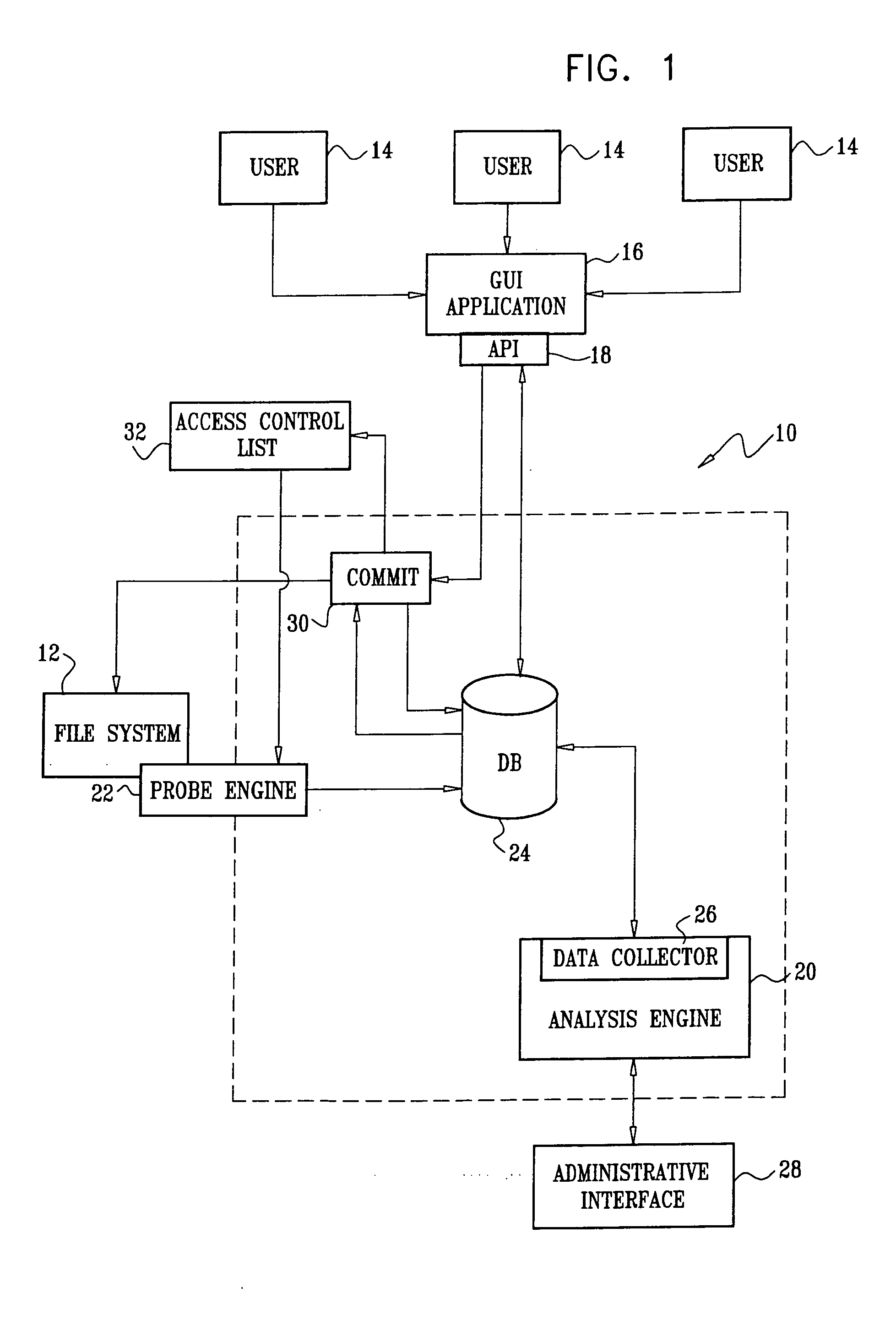
Automatic management of storage access control
ActiveUS20060277184A1Easy to controlDigital data protectionPayment architectureSemi automaticData access
Owner:VARONIS SYSTEMS
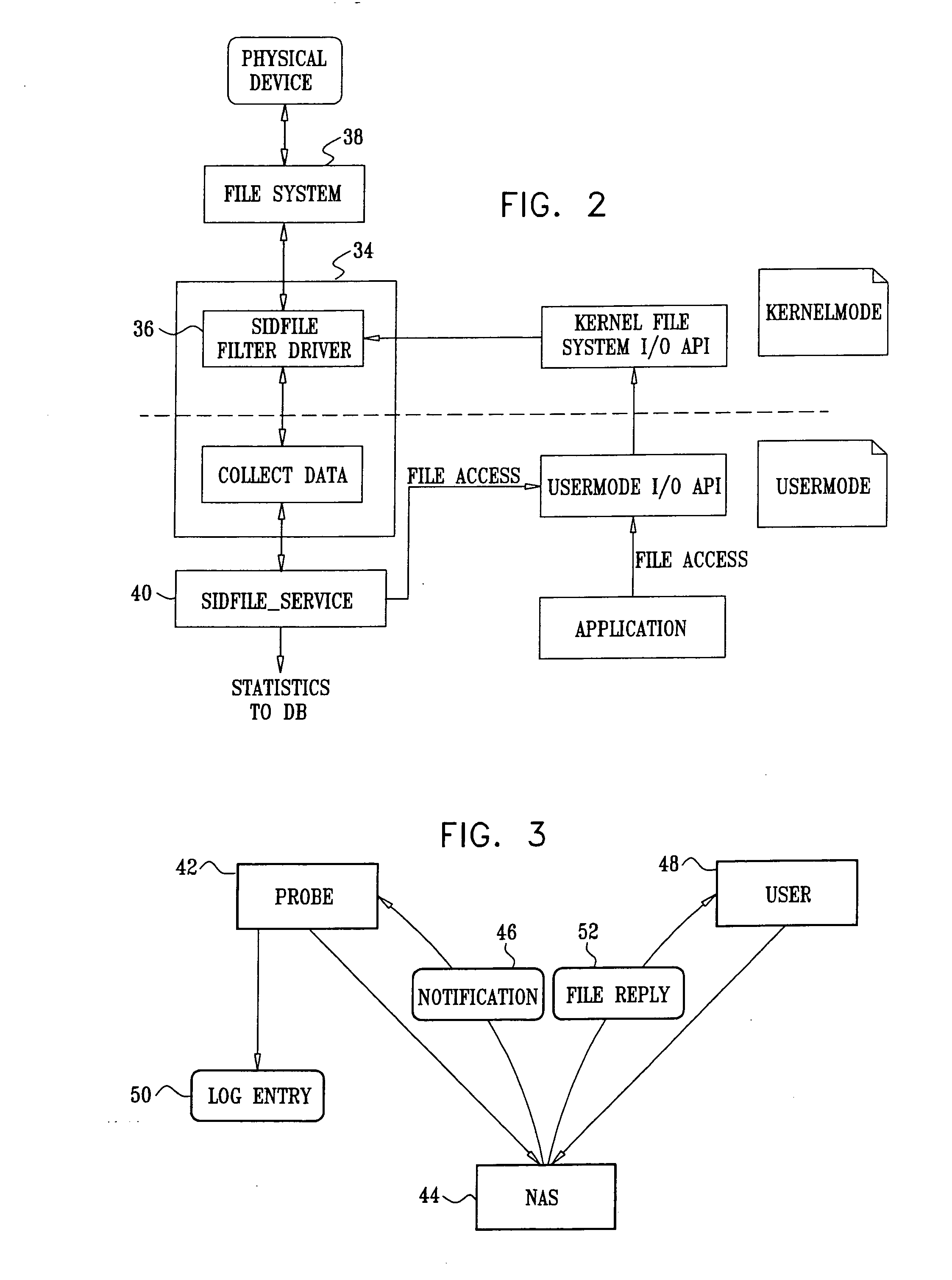
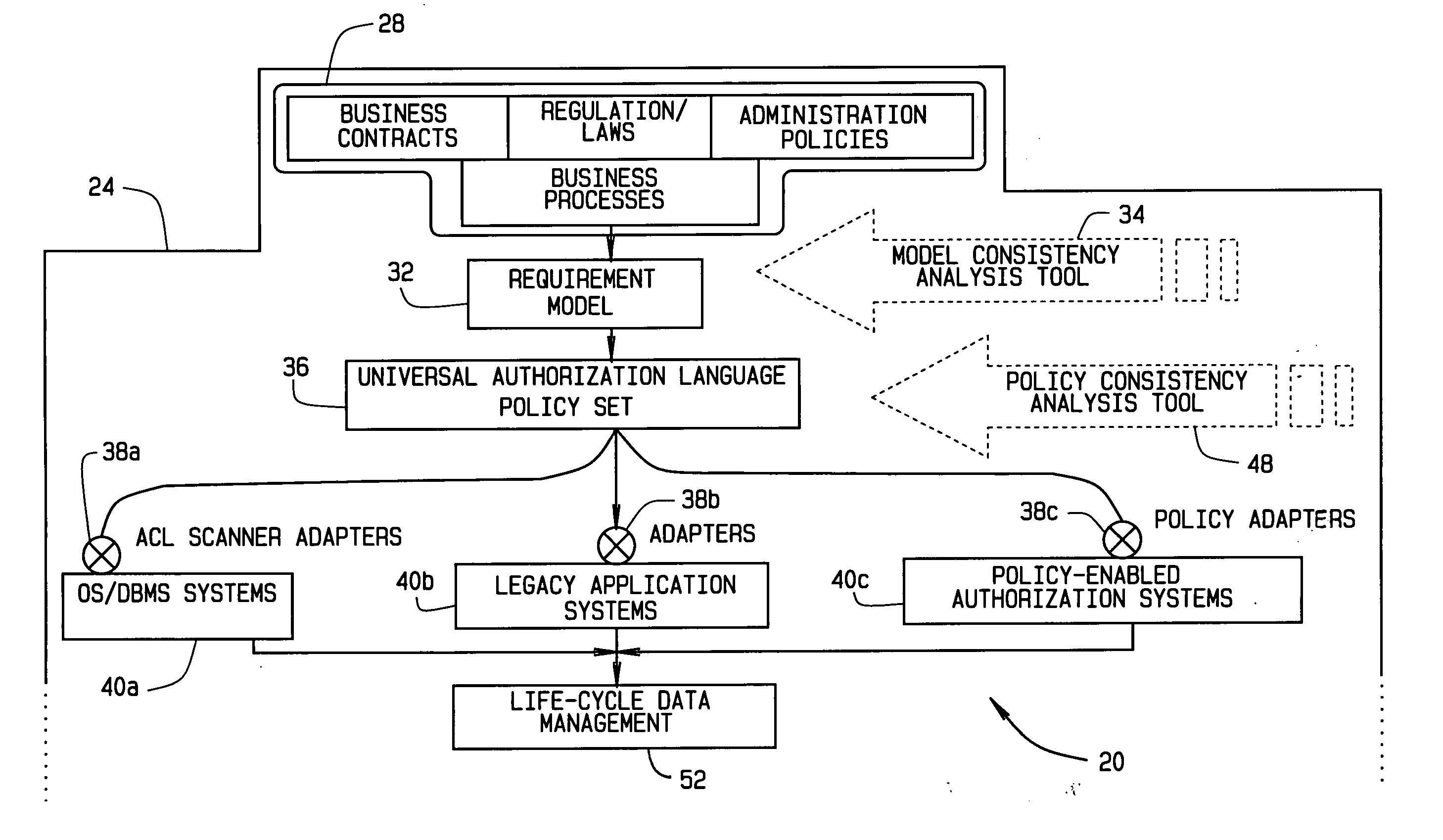
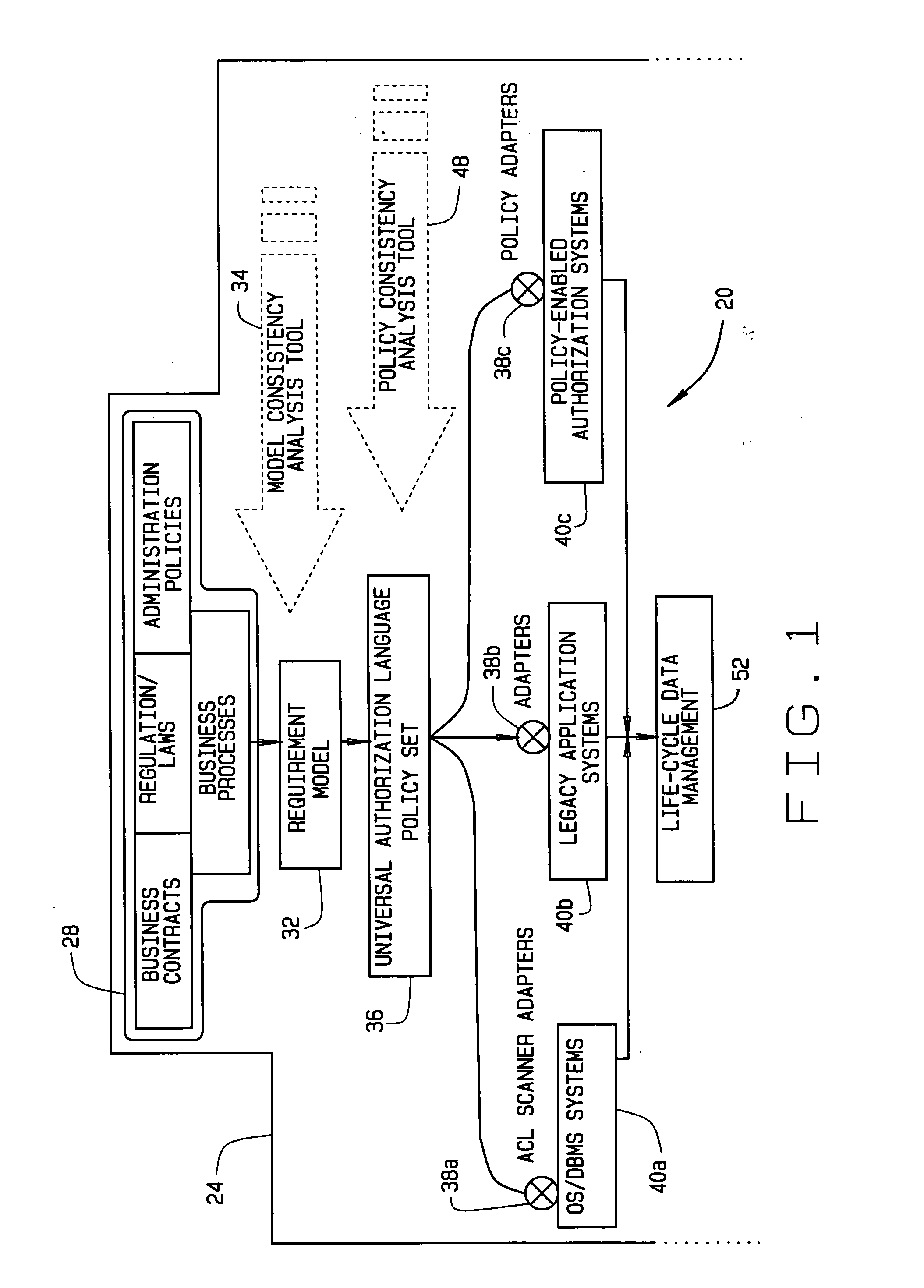
Implementing access control policies across dissimilar access control platforms
ActiveUS20070056019A1Digital data processing detailsAnalogue secracy/subscription systemsSet representationGoal system
A method of implementing access control requirements to control access to a plurality of system resources. The requirements are modeled as contents of security policies. The security policy contents are integrated into a policy set. Representations of the integrated policy set are generated, each representation corresponding to a target system that controls access to the resources. The policy set representation(s) are integrated with the corresponding target system(s) to implement the policy set. This method makes it possible to implement high-level security requirements correctly and consistently across systems of a system-of-systems (SoS) and / or distributed system.
Owner:THE BOEING CO
System for distributed intelligent remote sensing systems
ActiveUS20180054490A1Detection of traffic movementPosition fixationDistributed intelligenceSystem of systems
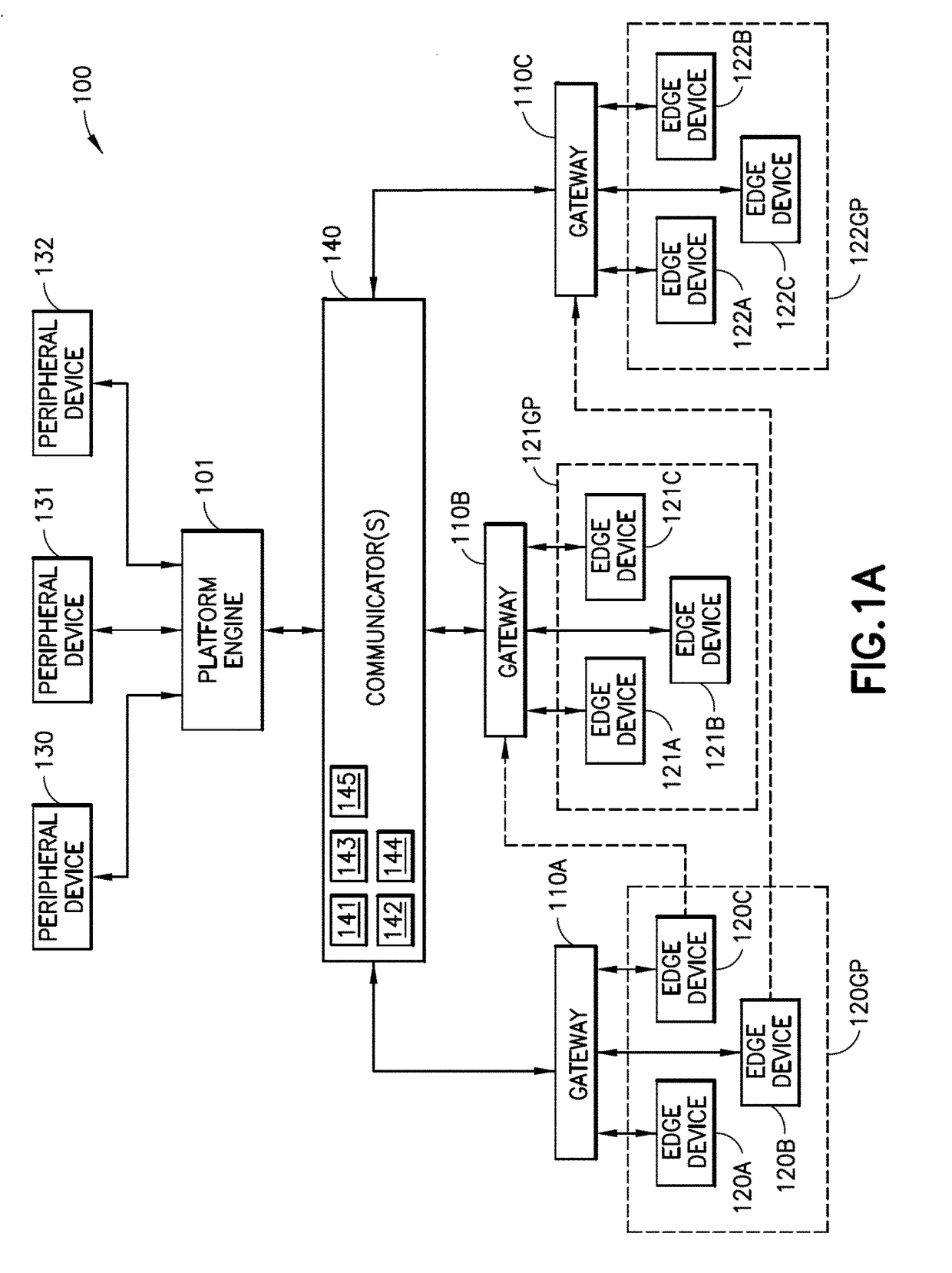
An Internet of things (IoT) system, including a distributed system of virtual machines, includes at least one IoT platform system control engine, that includes a platform system control engine secure system space and a IoT platform system control engine user defined space, at least one network node device that includes a network node device secure system space and an IoT network node device user defined space, and at least one edge device that includes an edge device secure system space and an edge device user defined space, where the secure system space of the control engine, the network node device, and the edge device are each configured to be secured to prevent unauthorized access, and the user defined spaces of the platform system control engine, the network node device and the edge device each define a respective virtual machine.
Owner:FYBR
Systems and methods for display of supplemental content responsive to location
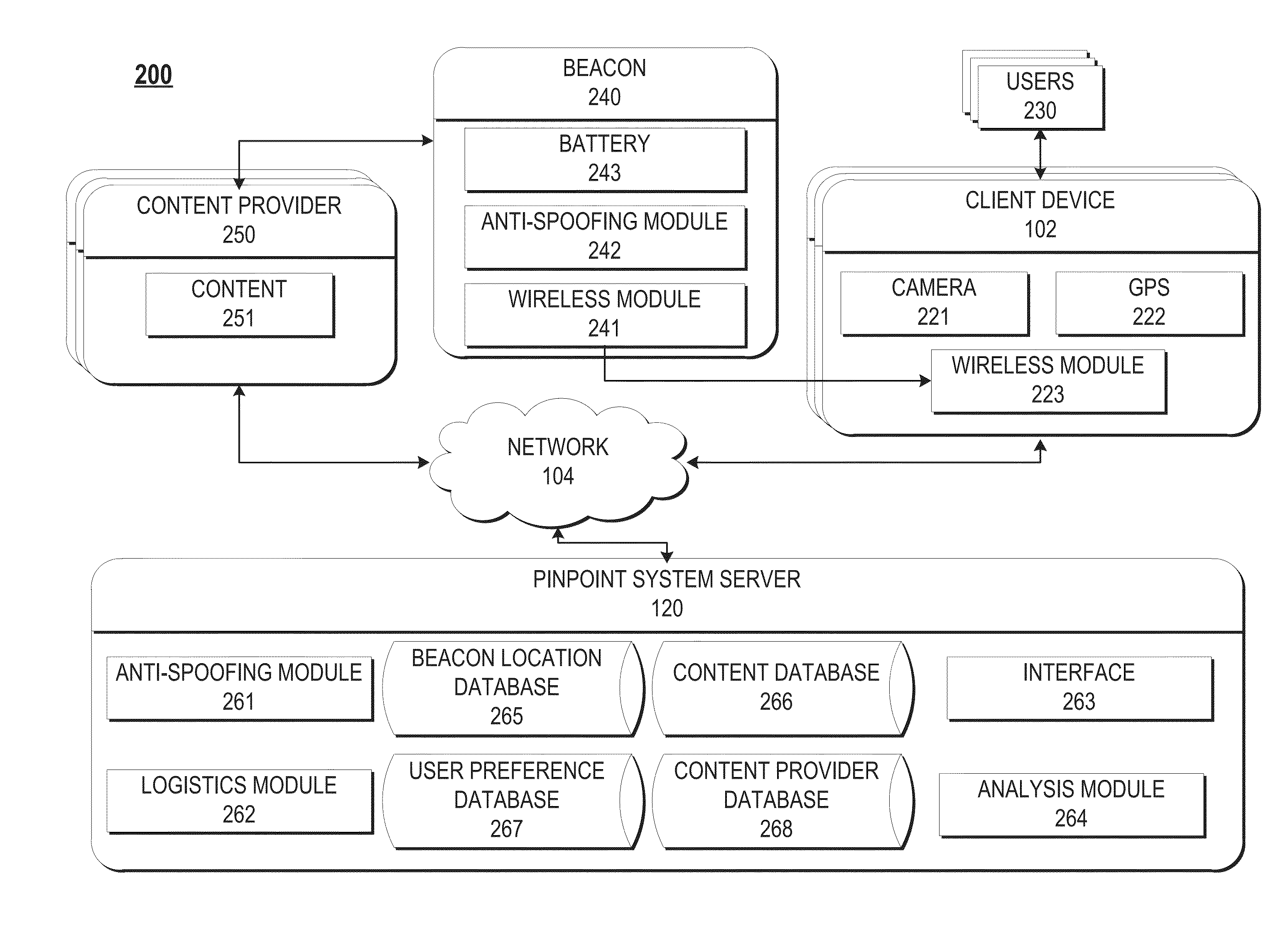
The present disclosure provides a system and method for providing a user with supplemental content based on the user's preferences and location. The disclosure provides a computer program that allows users to discover and organize content from a platform that is accessible from a mobile device or computer. Additionally, the disclosure provides a system for determining a user's location while indoors. The system can associate the user's location with specific content or items in a store and provide the user with supplemental content related to those items.
Owner:BBY SOLUTIONS
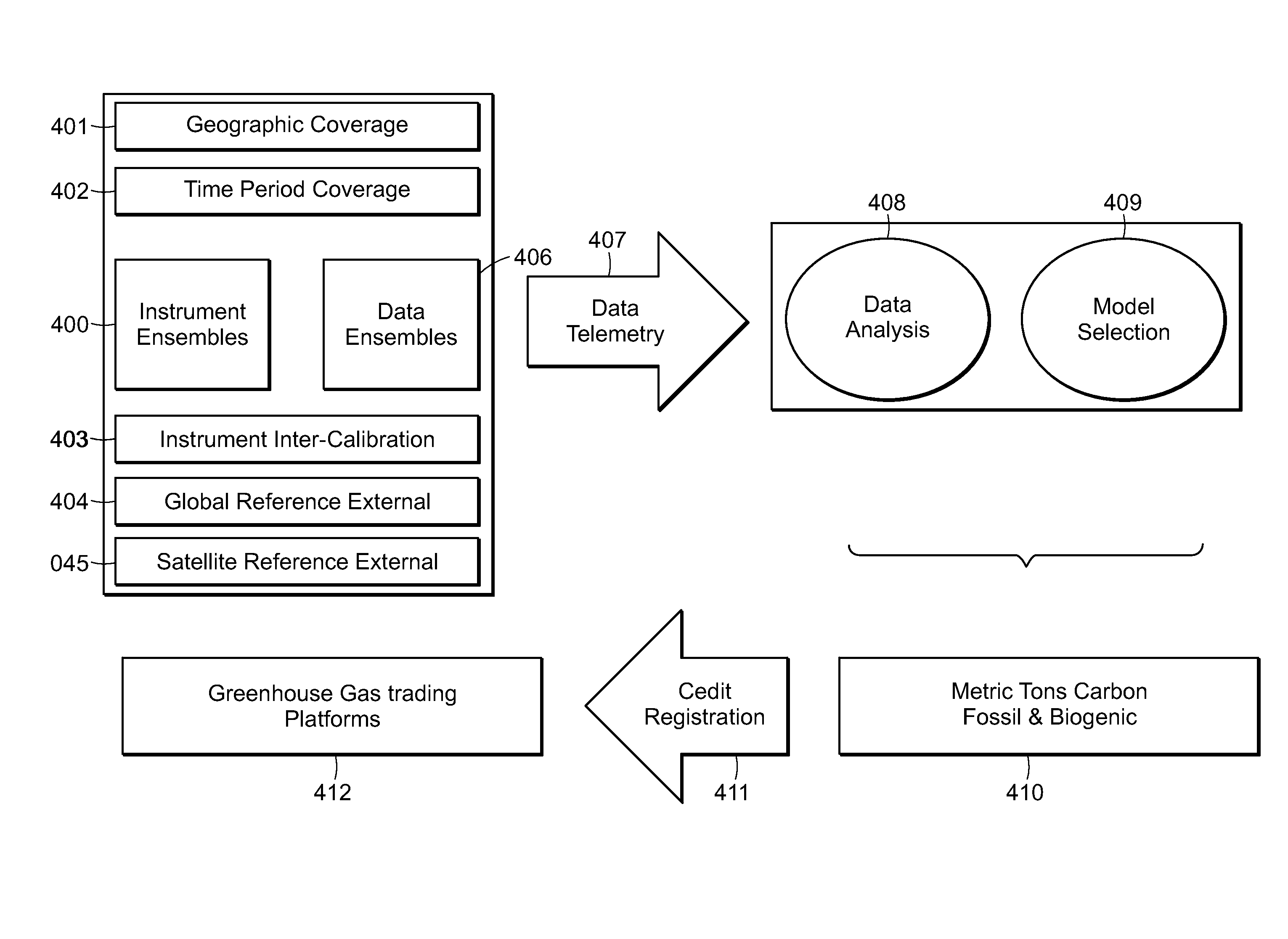
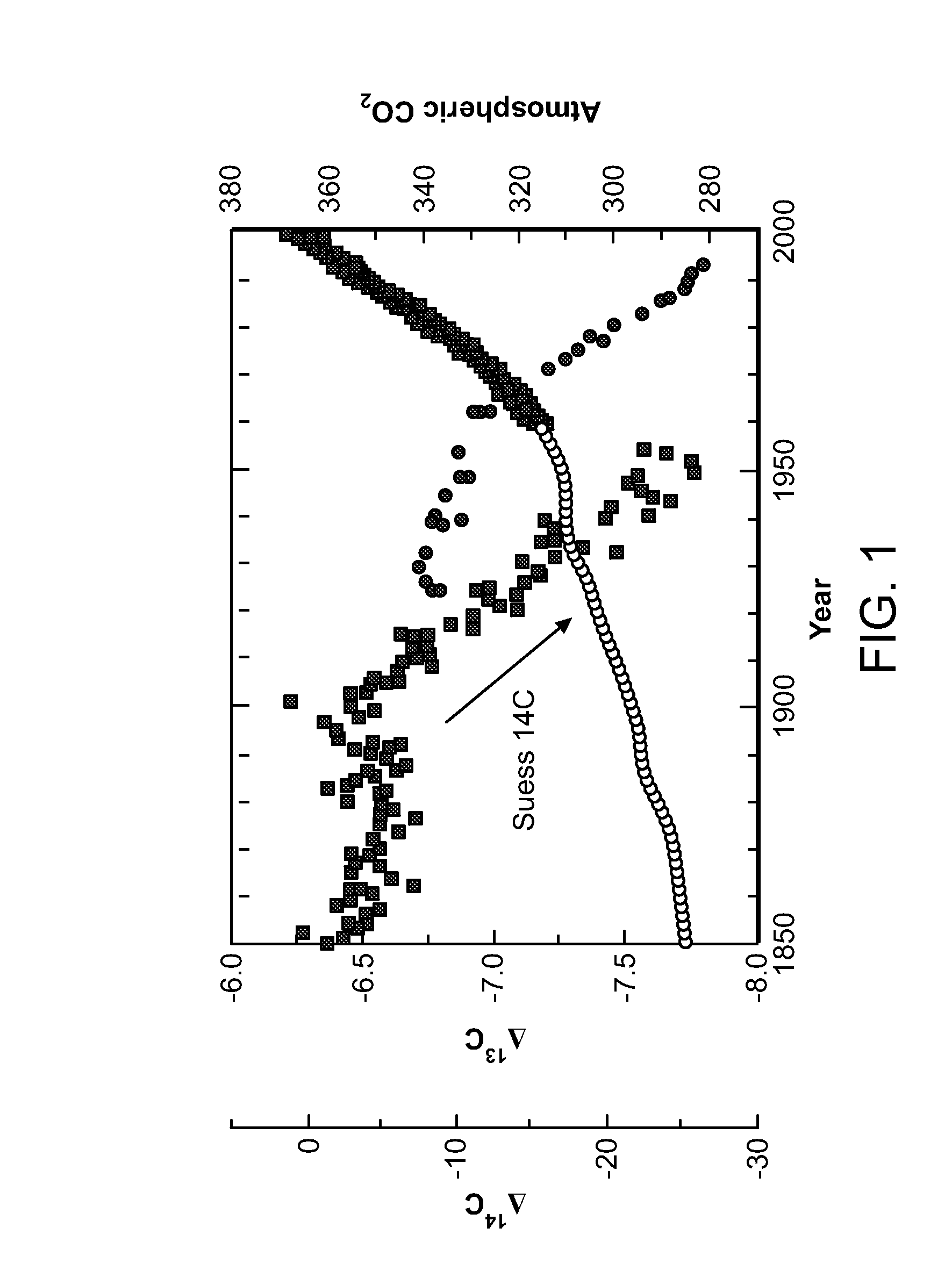
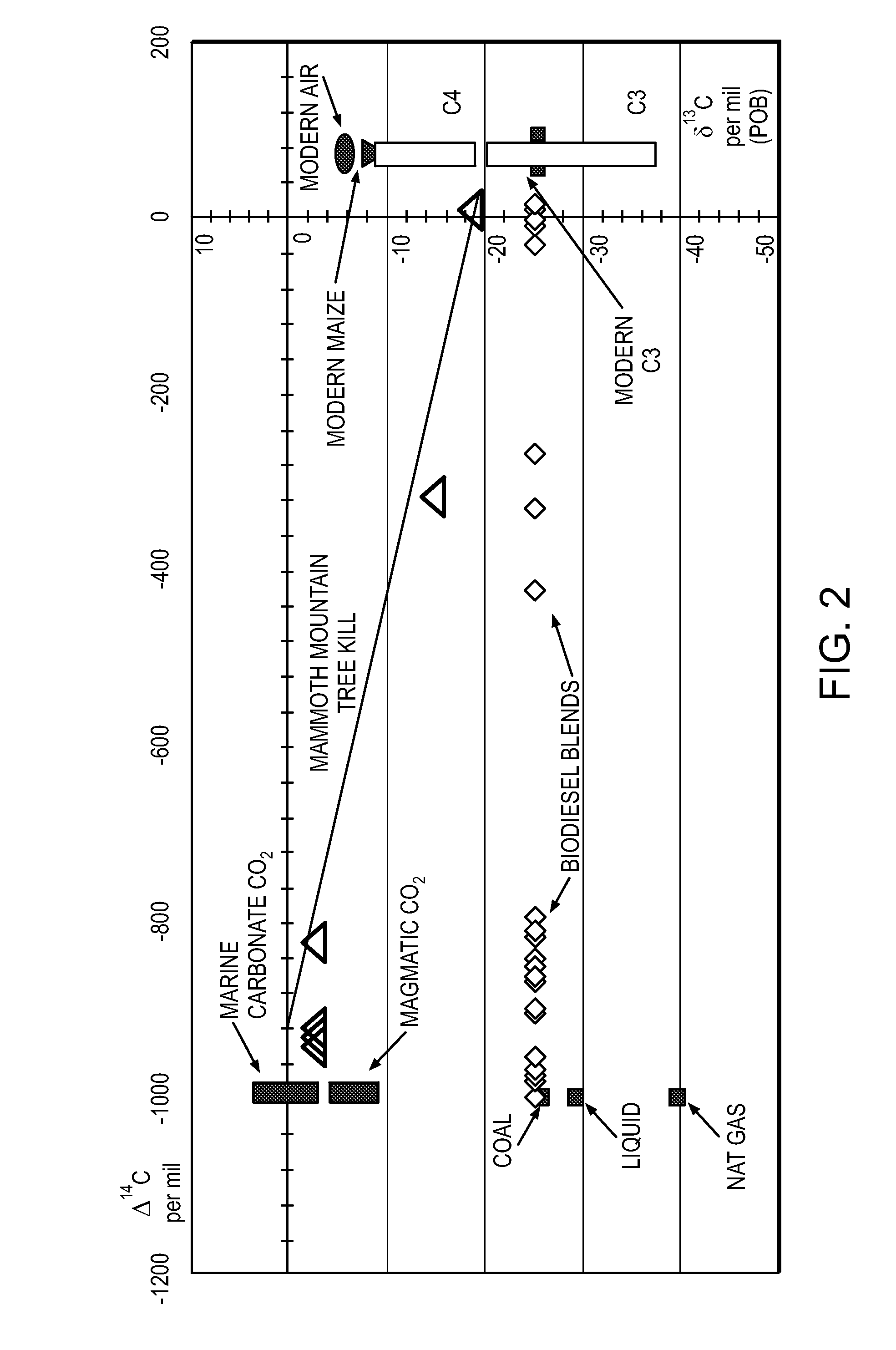
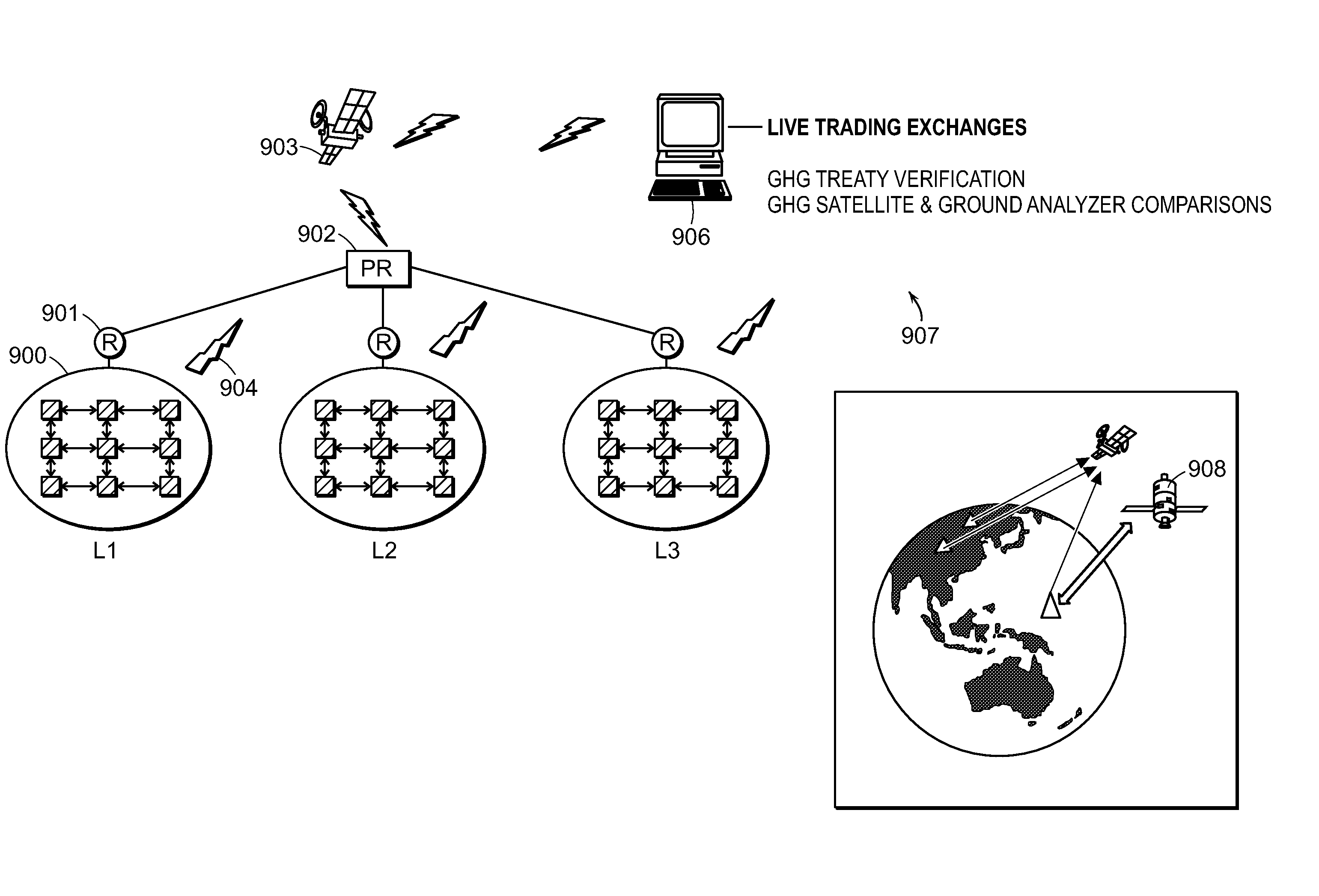
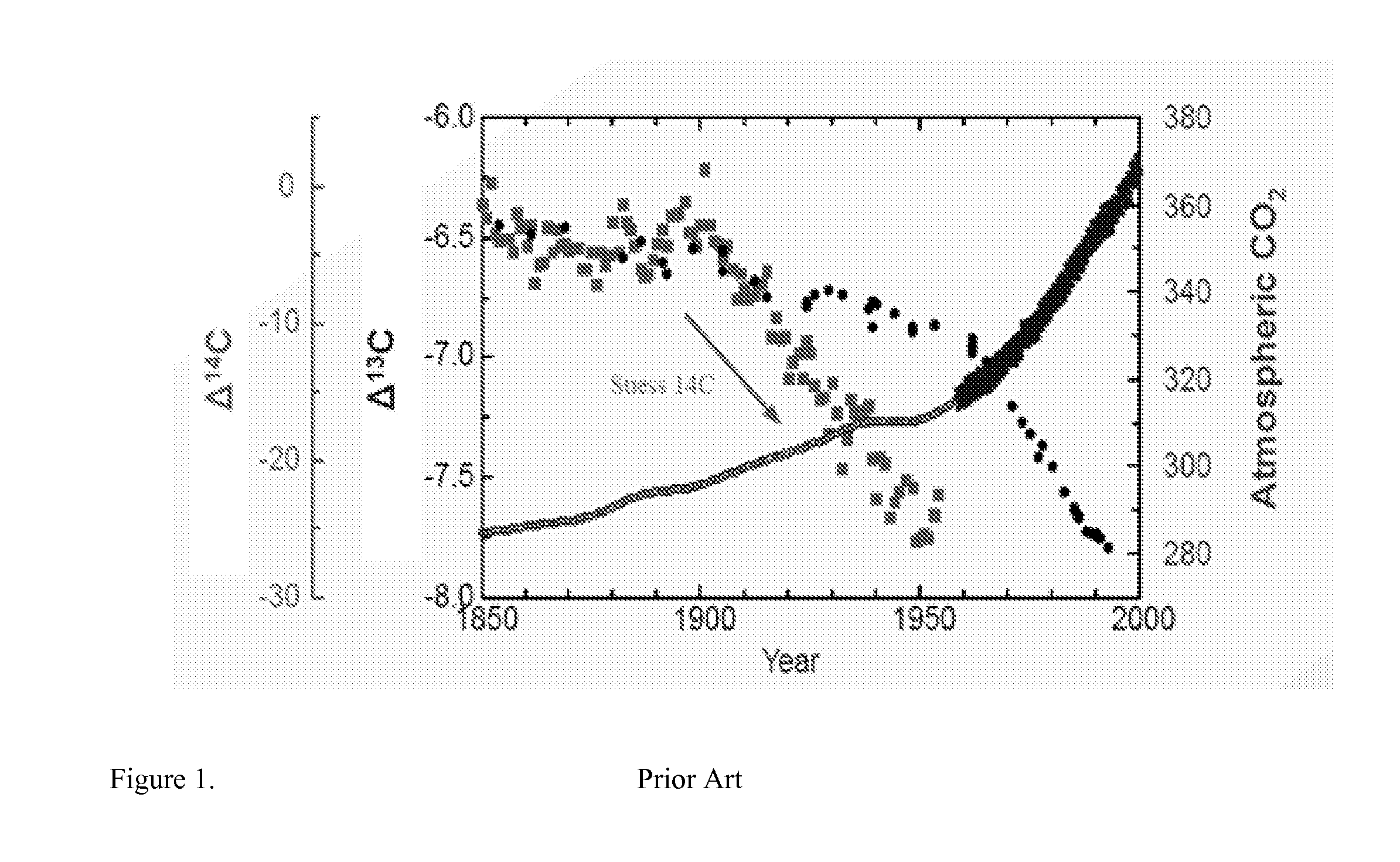
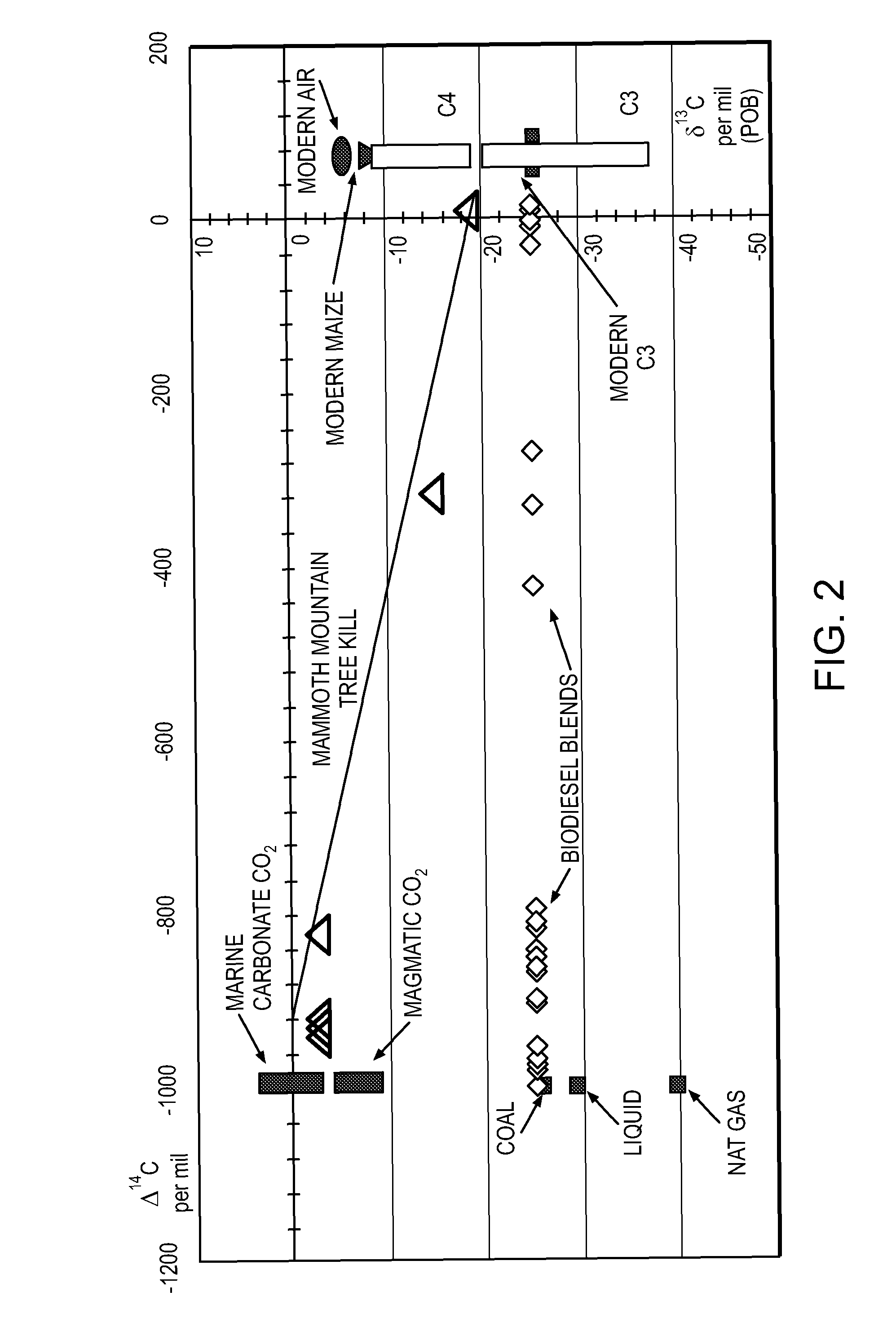
System of systems for monitoring greenhouse gas fluxes
ActiveUS20100198736A1High precisionReduce uncertaintySustainable waste treatmentCarbon compoundsNatural sourceGreenhouse gas flux
A system of systems to monitor data for carbon flux, for example, at scales capable of managing regional net carbon flux and pricing carbon financial instruments is disclosed. The system of systems can monitor carbon flux in forests, soils, agricultural areas, body of waters, flue gases, and the like. The system includes a means to identify and quantify sources of carbon based on simultaneous measurement of isotopologues of carbon dioxide, for example, industrial, agricultural or natural sources, offering integration of same in time and space. Carbon standards are employed at multiple scales to ensure harmonization of data and carbon financial instruments.
Owner:PLANETARY EMISSIONS MANAGEMENT
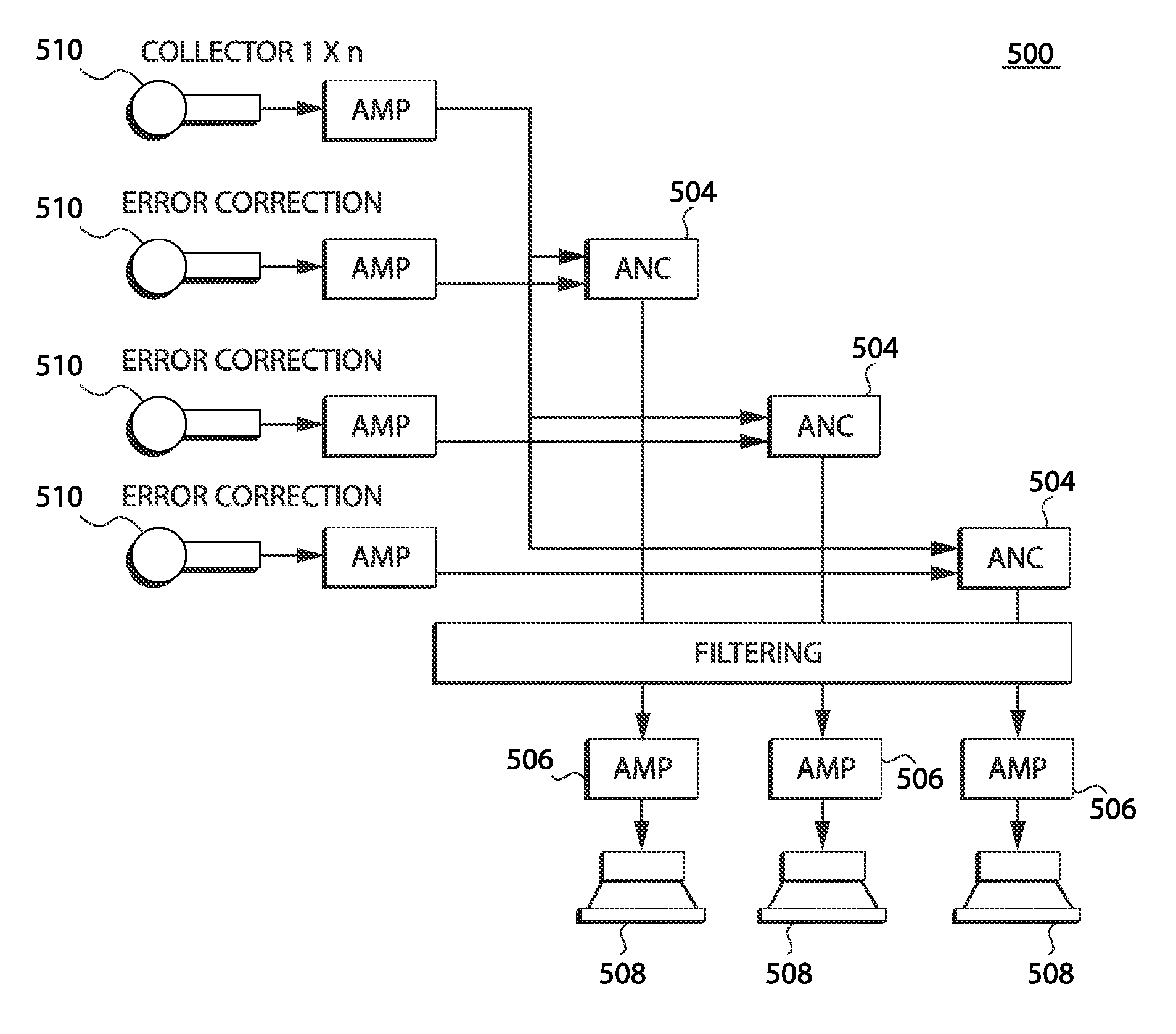
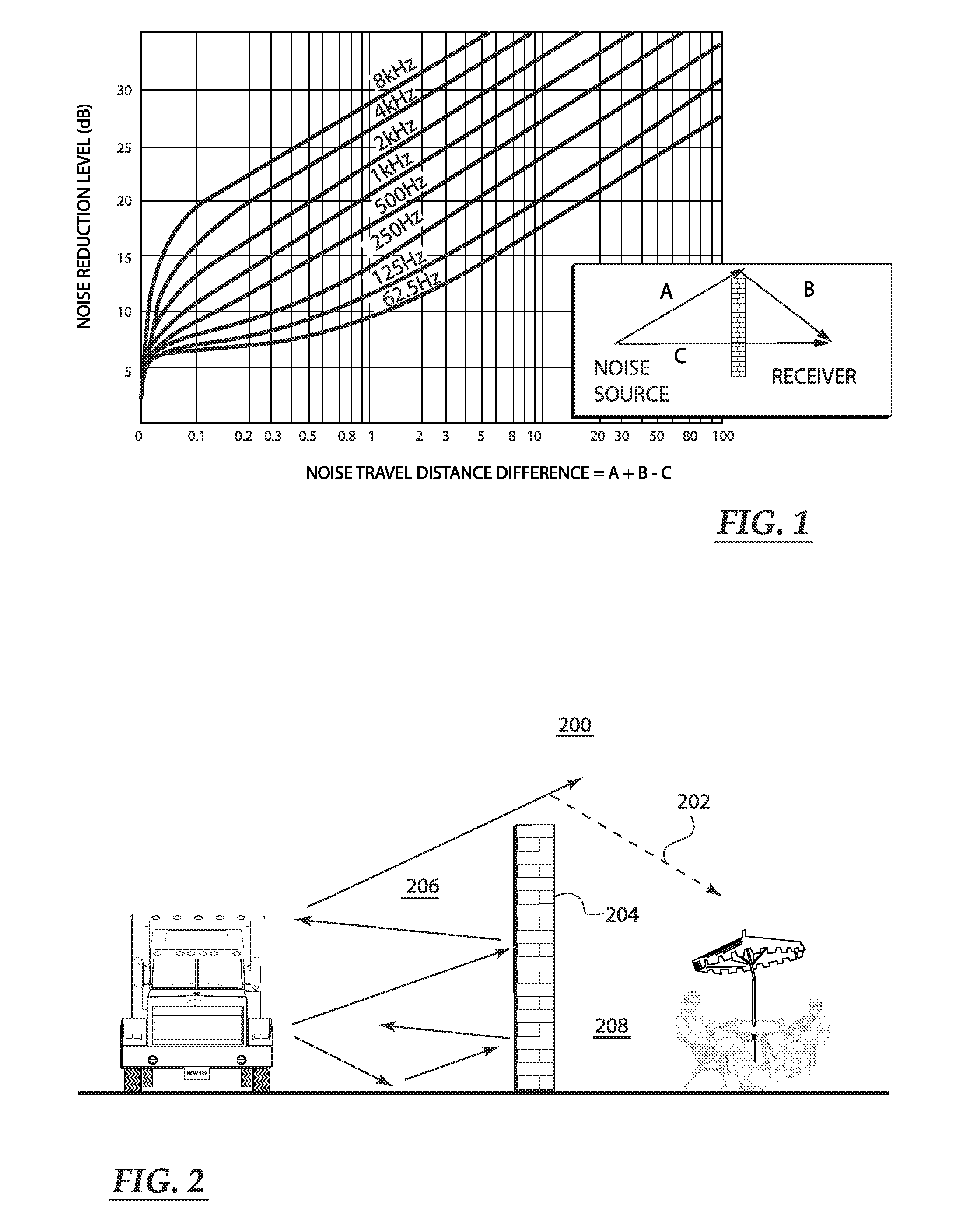
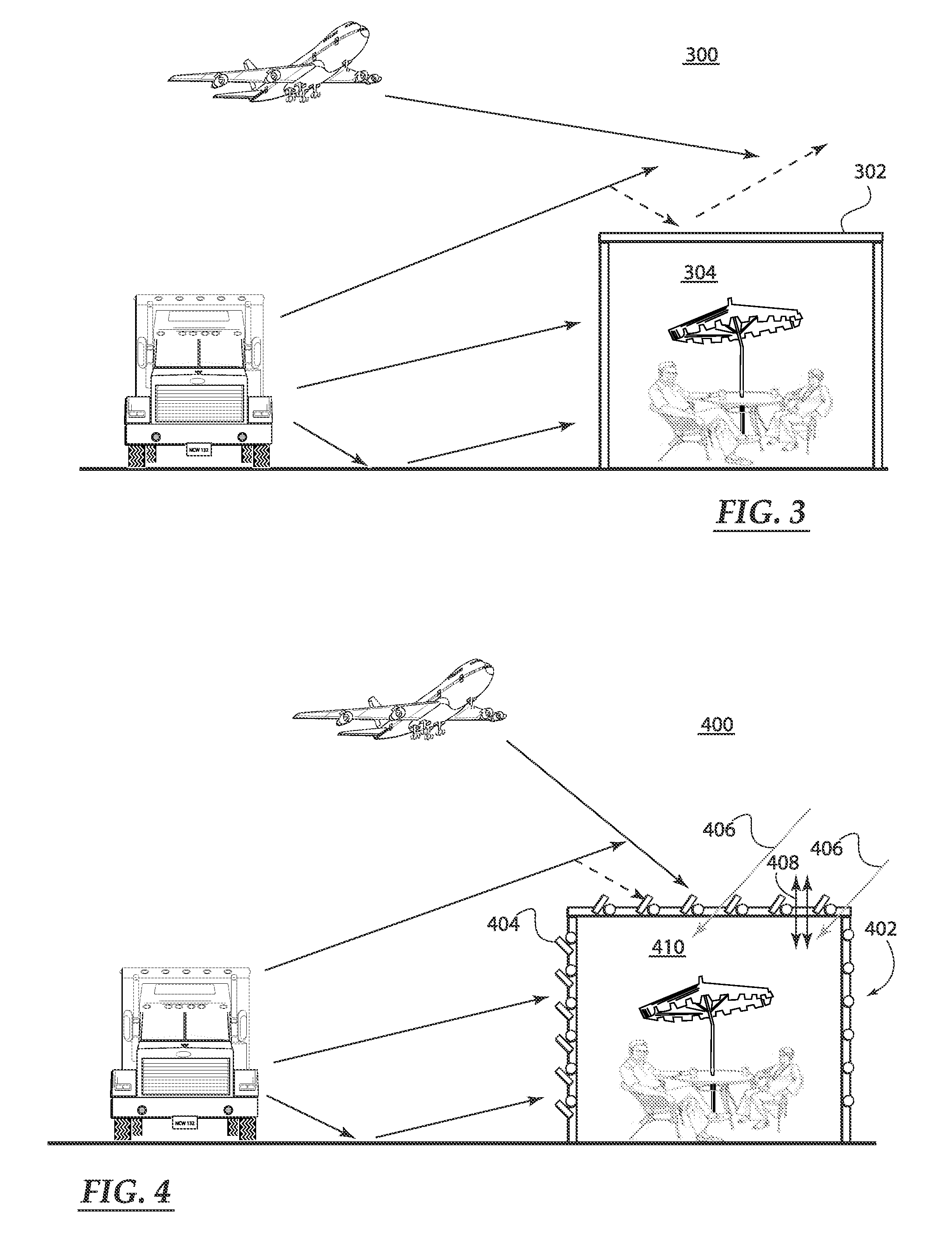
Open-air noise cancellation system for large open area coverage applications
InactiveUS20070223714A1Reduce the impactReduce the amount requiredEar treatmentNoise generationWindow shutterSystem of systems
A variety of open-air noise cancellation systems are disclosed. The systems are configured to suit the needs of the particular application, for example, an open-air sound wall installation, an open-air enclosure for a quiet area, or a window / door treatment application. A particular system may a digital-based processing architecture having a digital power amplifier that shares a common circuit board. The processing architecture receives noise signals, processes out-of-phase noise cancellation signals in response to the noise signals, and generates out-of-phase sound waves that effectively cancel low frequency components of the noise signal. One system variation utilizes passive sound absorbing blades or shutters to reduce high frequency components of the noise signal. The blades can be installed as a door or window shutter mechanism.
Owner:COMFOZONE
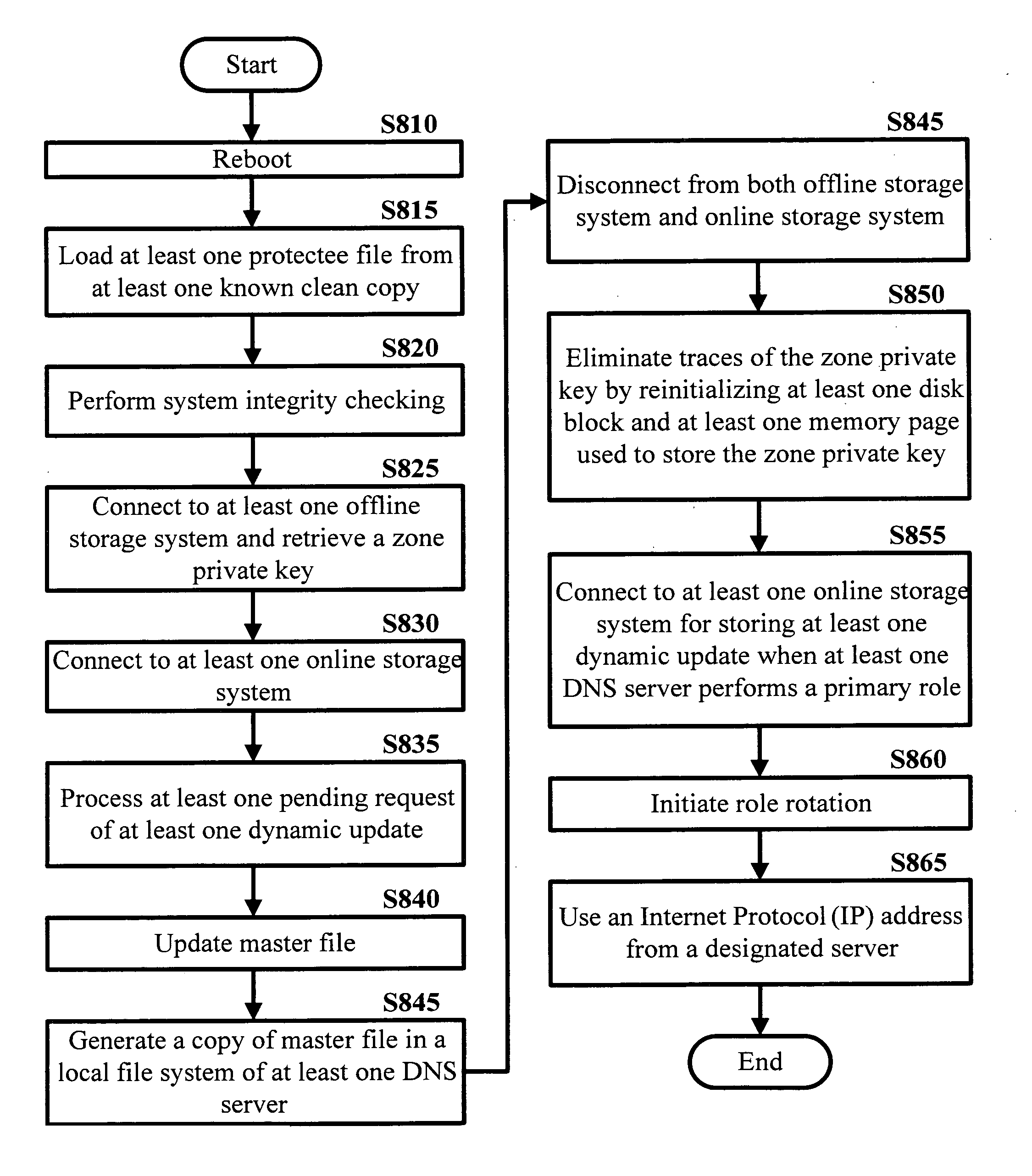
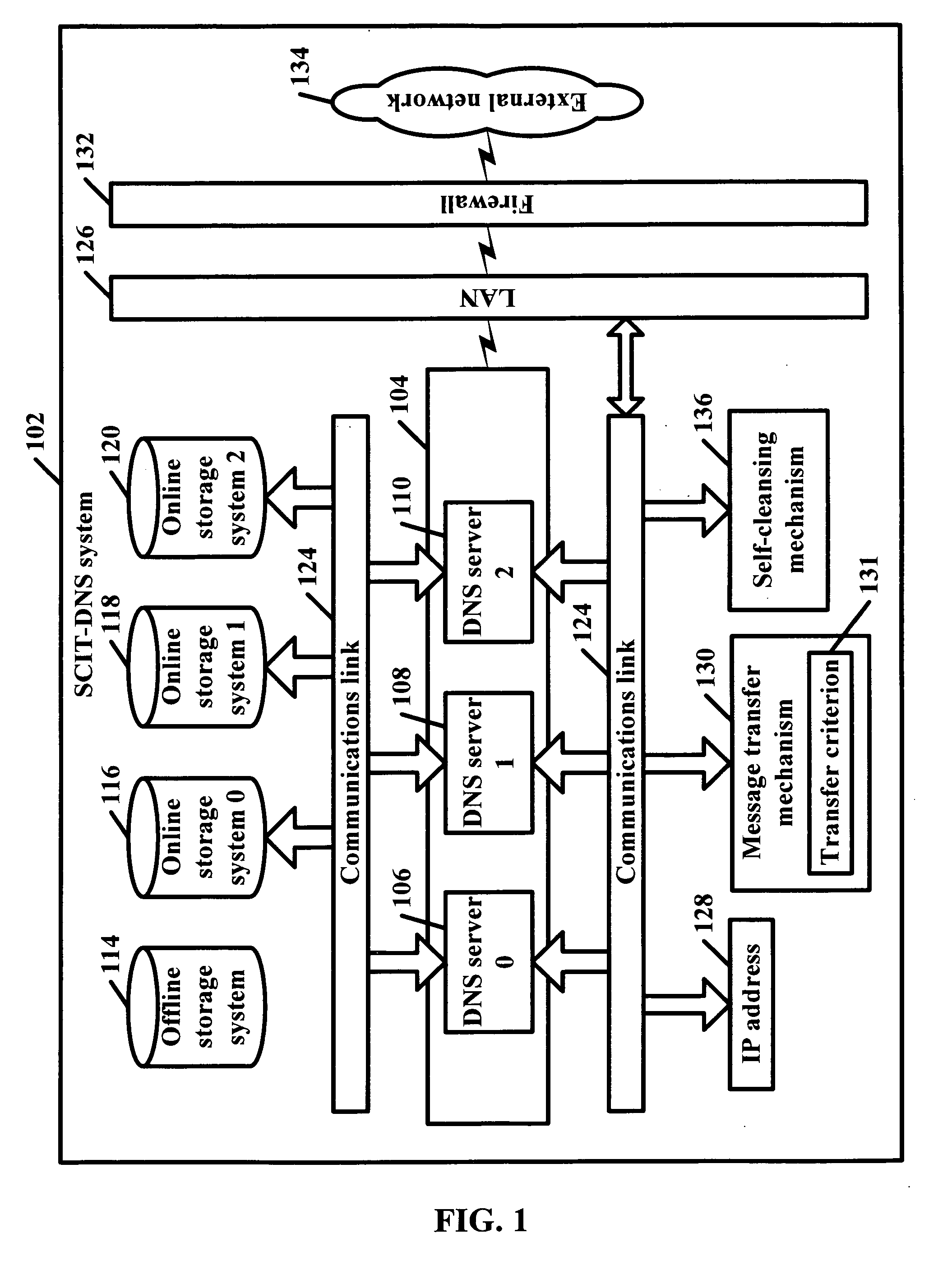
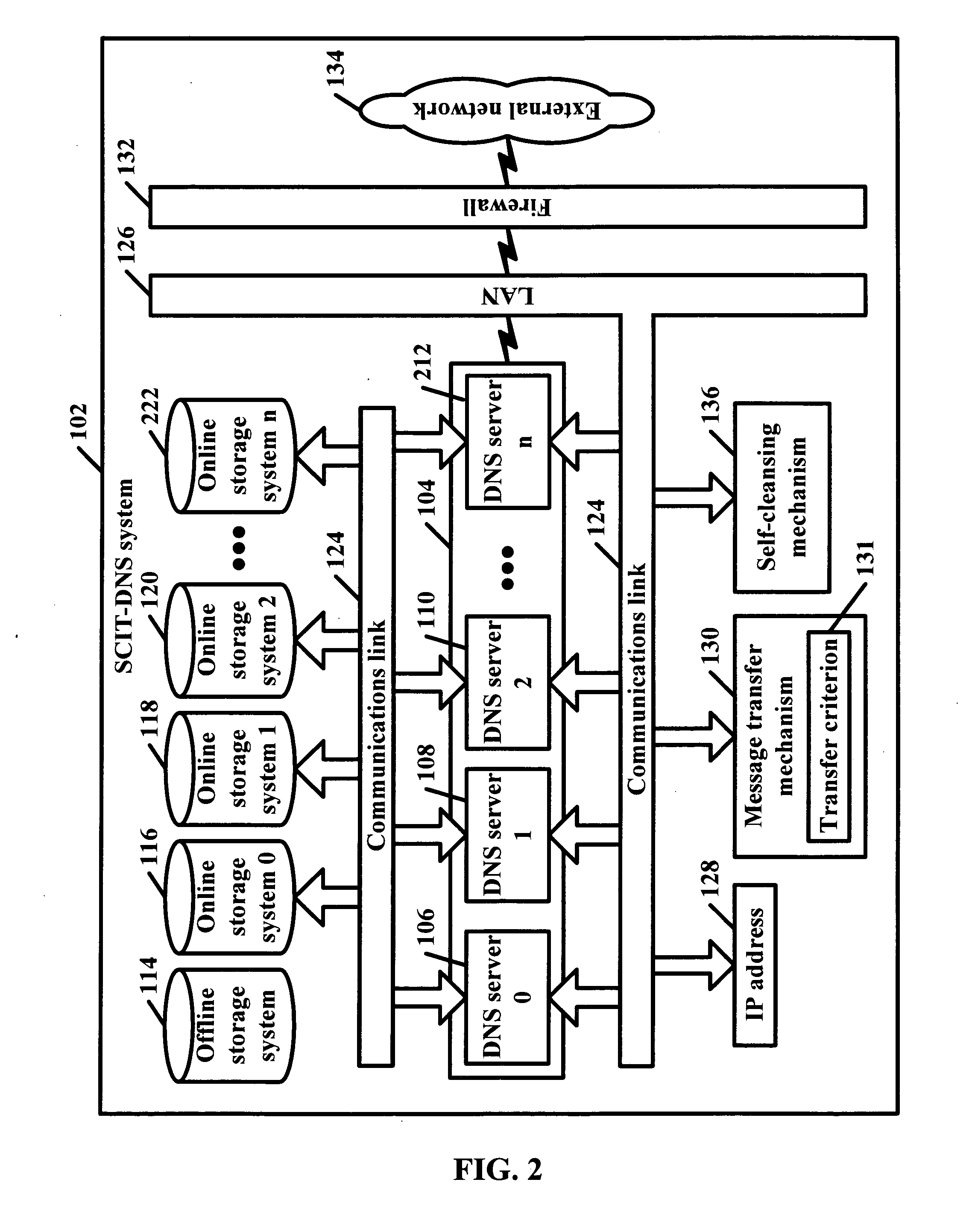
SCIT-DNS: critical infrastructure protection through secure DNS server dynamic updates
ActiveUS20060143711A1Protect resourcesEliminate tracesMemory loss protectionError detection/correctionDomain nameTelecommunications link
Disclosed is a self-cleansing intrusion tolerance-domain name systems system comprising at least three DNS servers, at least four storage systems accessible by the DNS servers, a communications link, a message transfer mechanism, and a self-cleansing mechanism. The storage systems include at least three online storage systems and at least one offline storage system. The communications link can connect the DNS servers with the storage systems, as well as connect the DNS servers with a local area network, which can connect the DNS servers with an external network. The message transfer mechanism can rotate the DNS servers into a plurality of roles, including a primary role, a secondary role, a designated role, and a self-cleansing role. The self-cleansing mechanism can be used to perform the self-cleansing role.
Owner:GEORGE MASON INTPROP INC
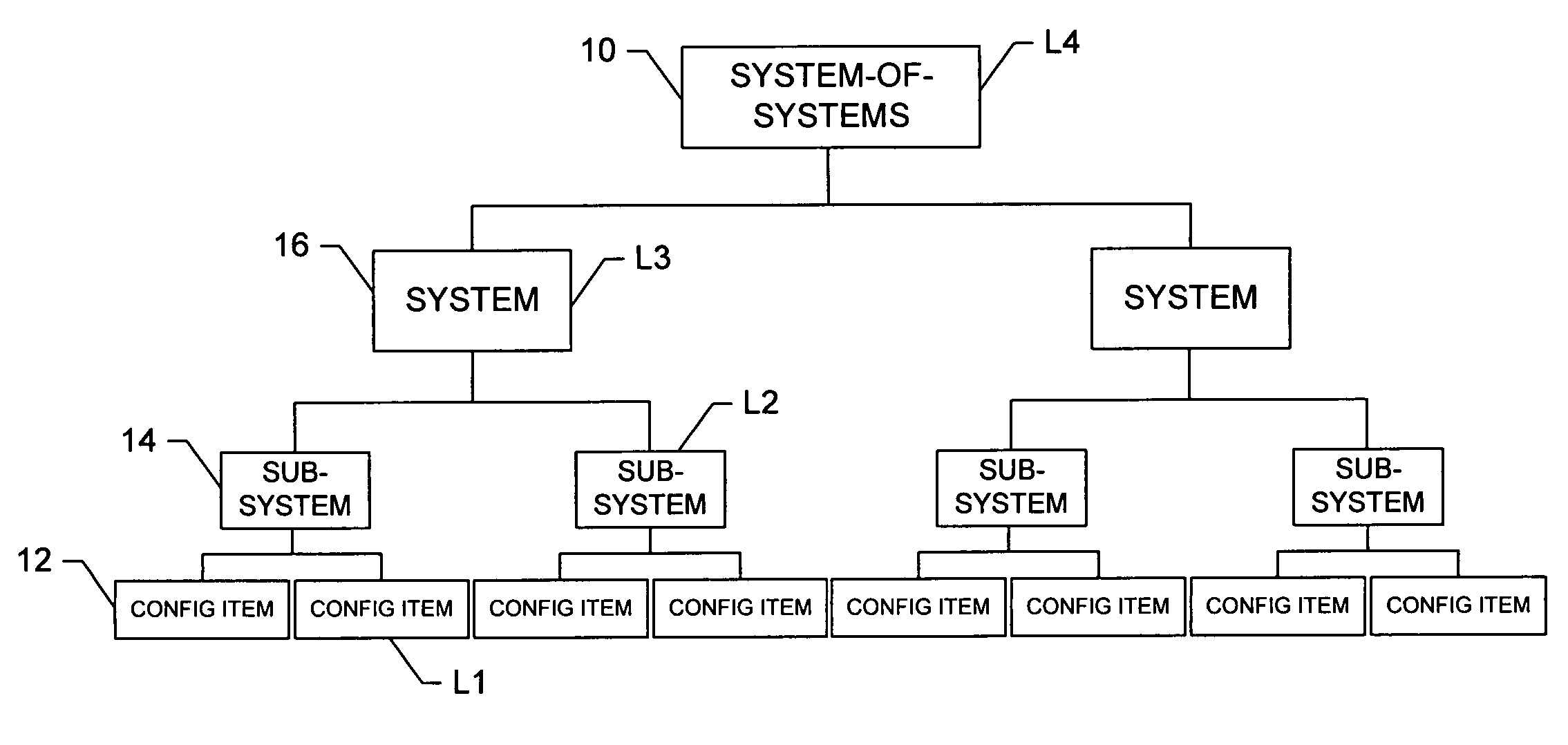
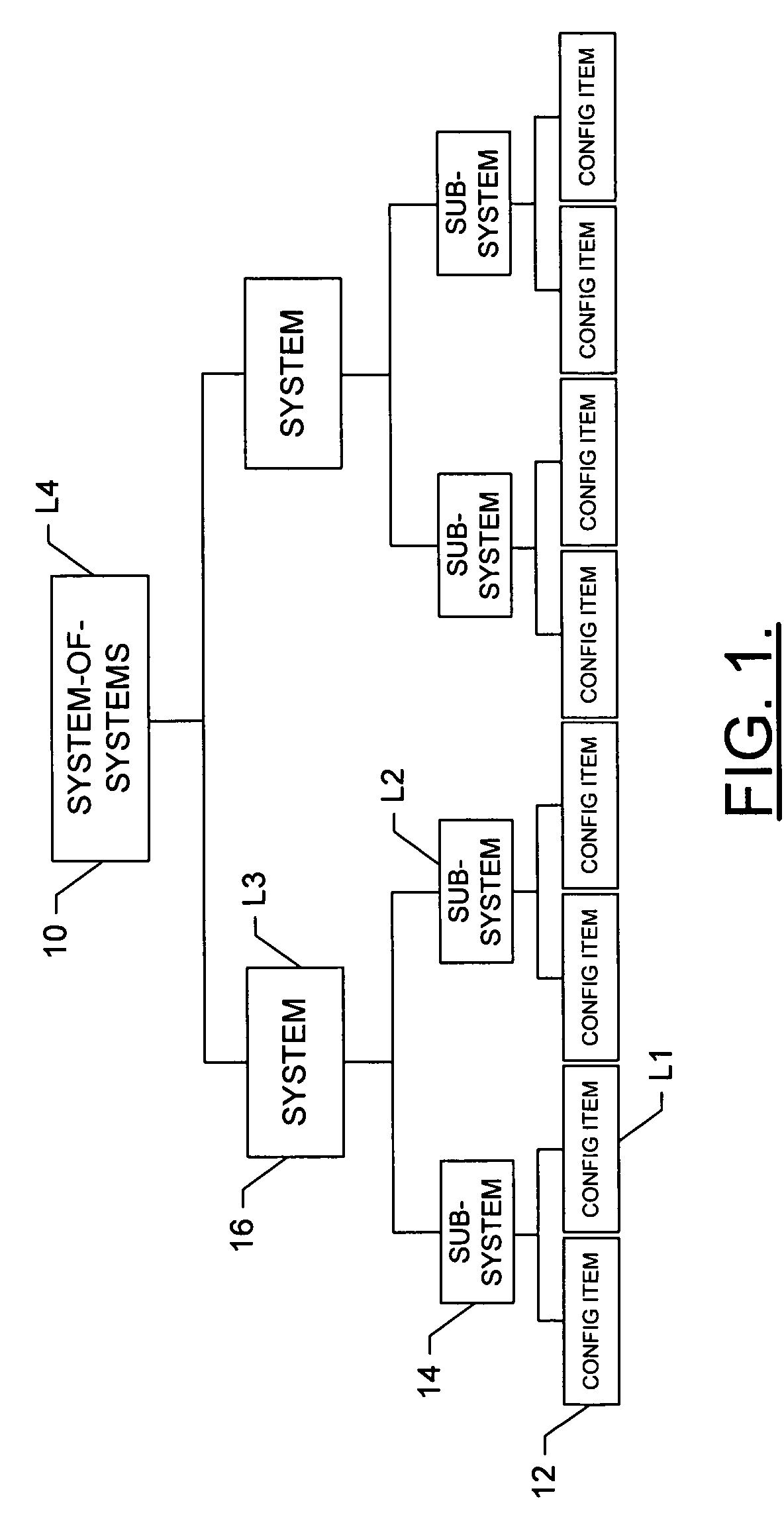
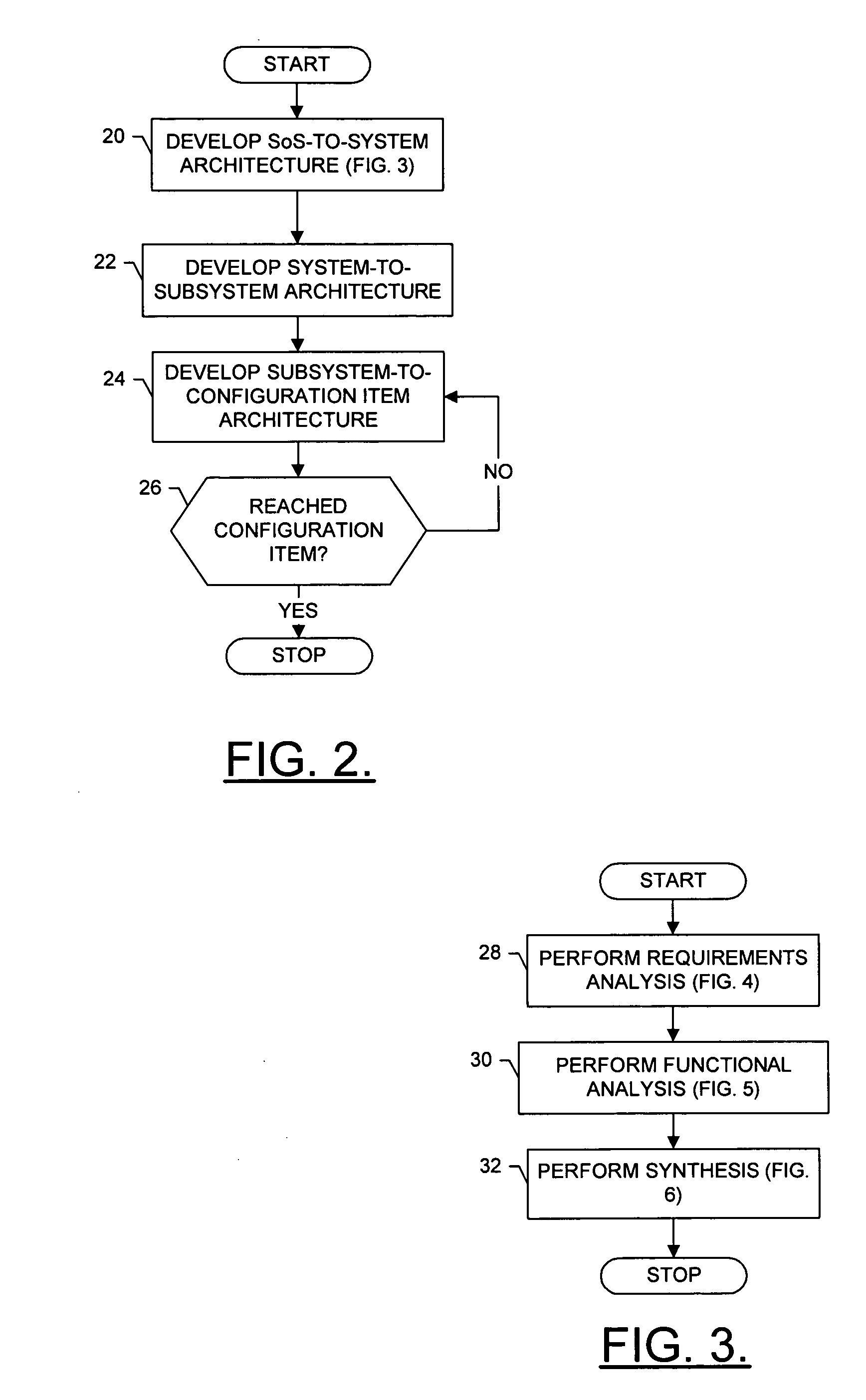
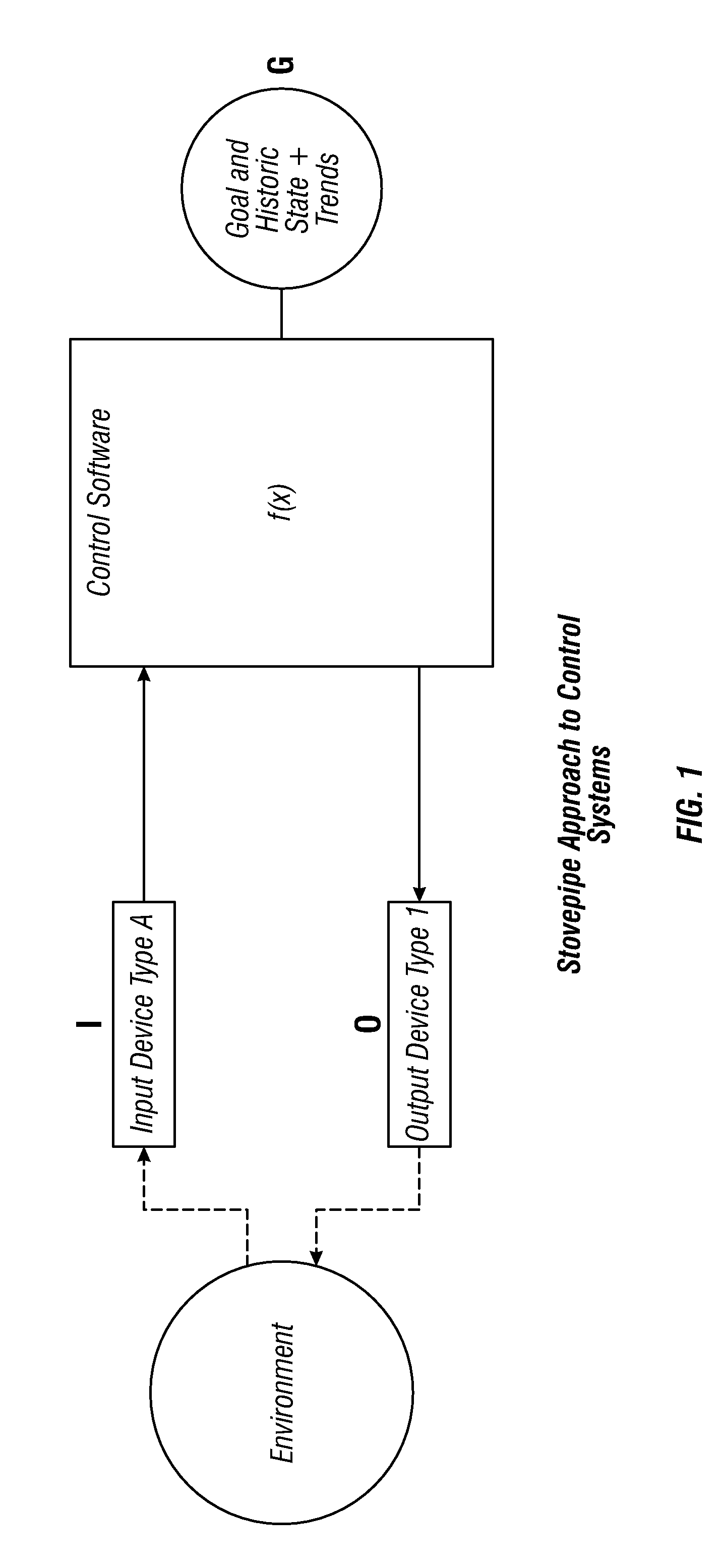
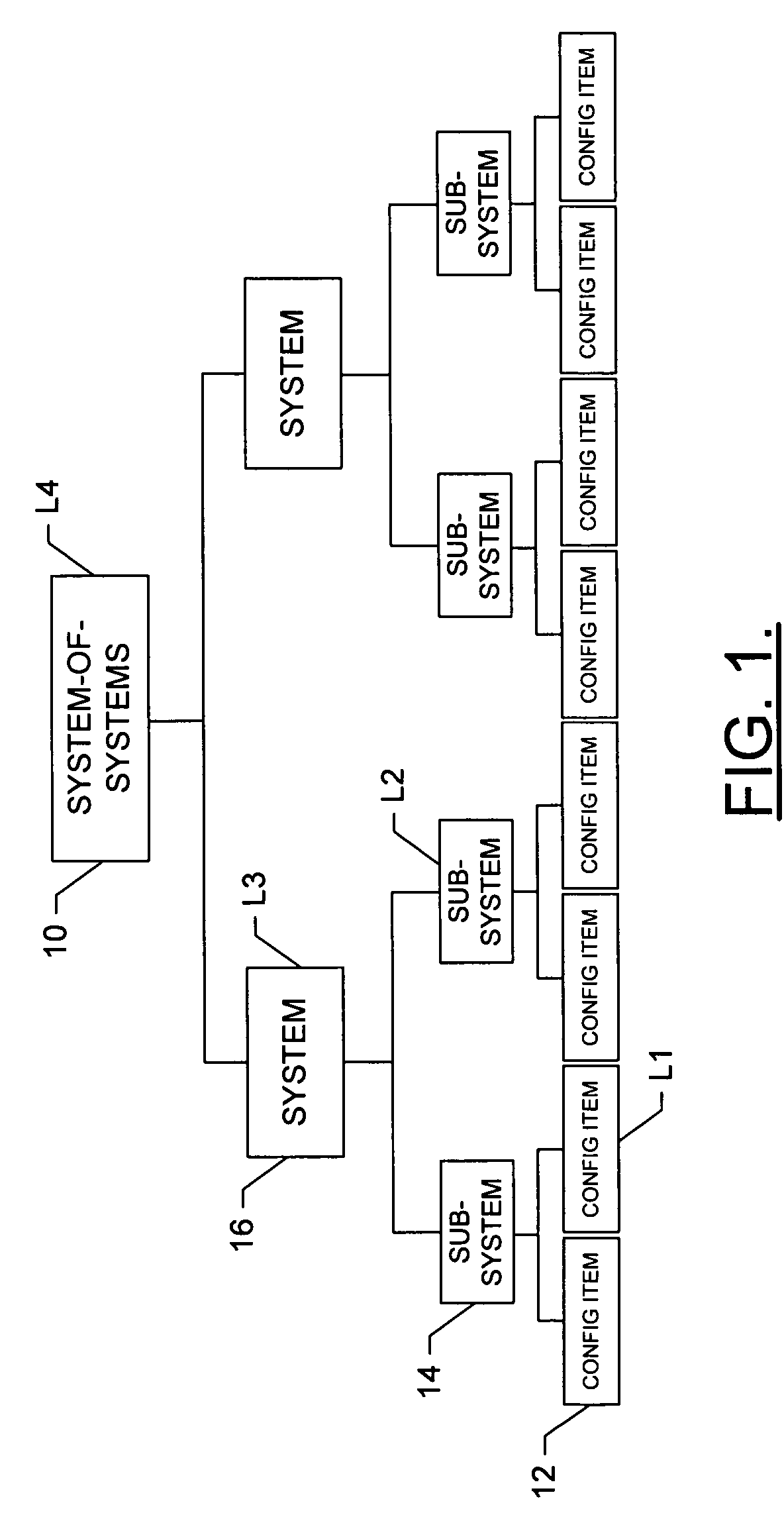
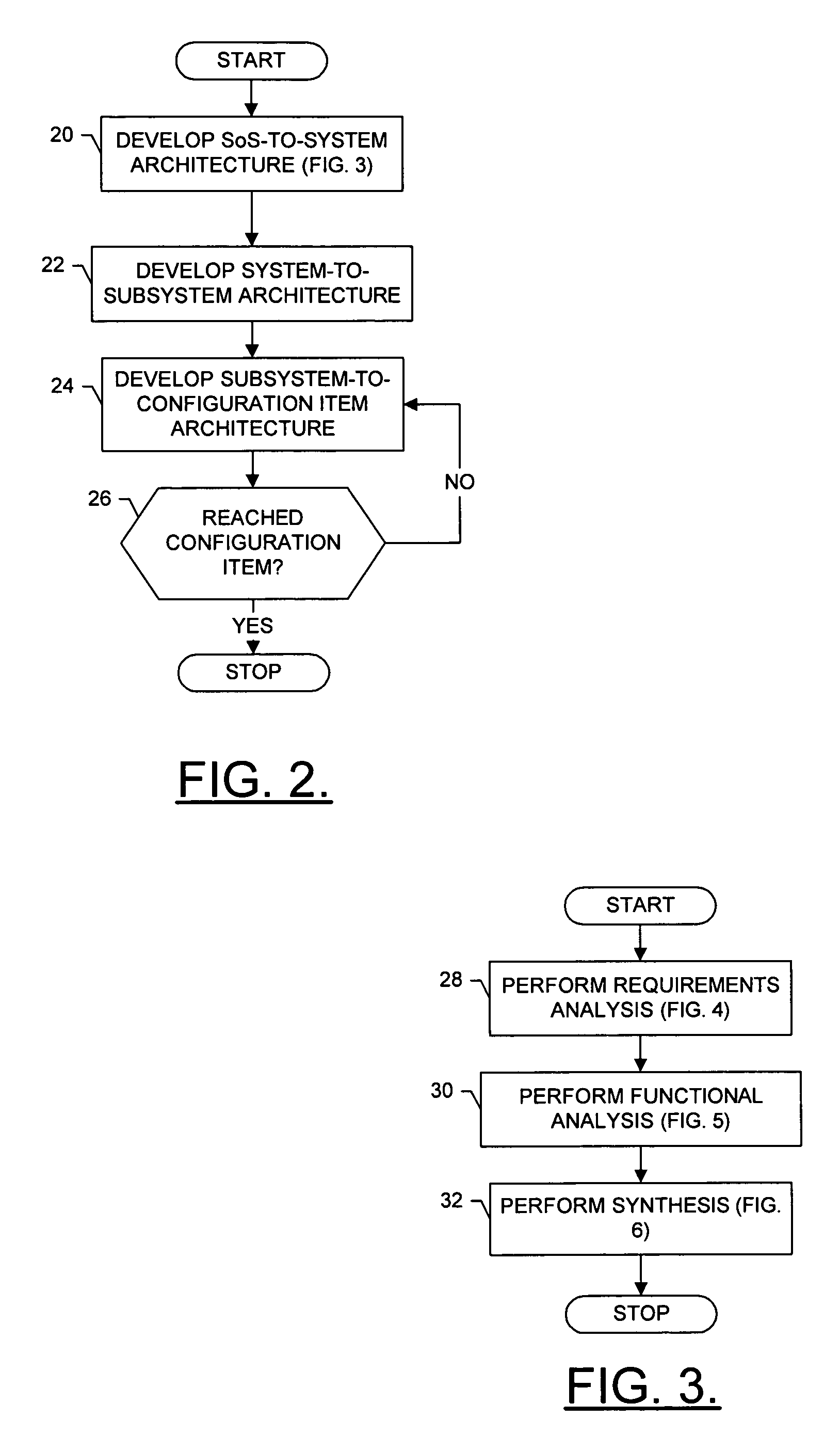
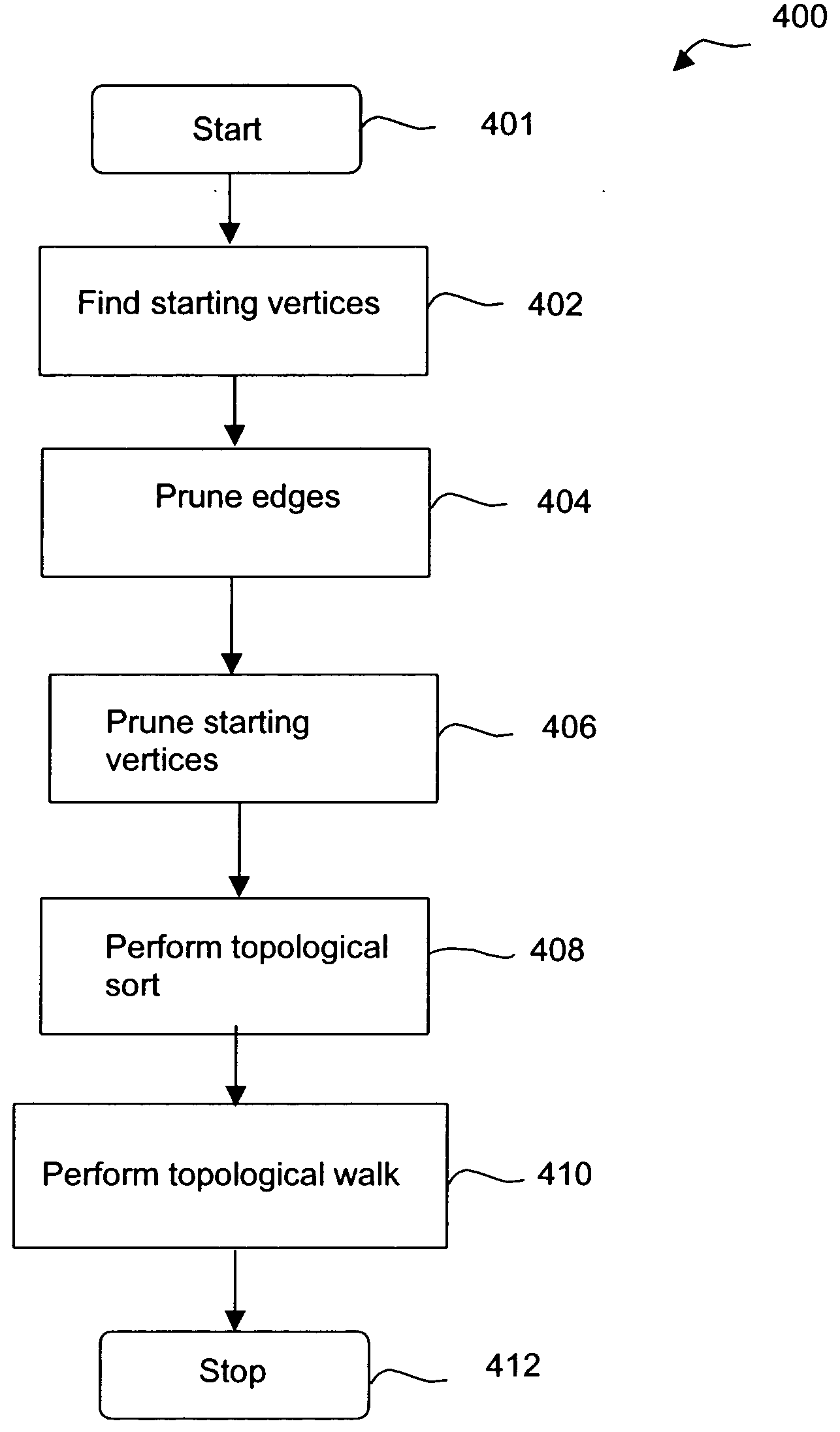
System, method and computer program product for developing a system-of-systems architecture model
ActiveUS20060064178A1Easy to captureEasy to useComputer controlSimulator controlEngineeringSystem of systems
A method is provided for developing an architecture model for a system-of-systems (SoS) that includes n system levels L1 . . . Ln, each of which includes at least one component of the SoS. For at least i>1, each system level Li includes at least one component of level Li-1. The method includes developing an architecture model for at least one level of the SoS. For at least i>1, the level Li-1 architecture model can be developed by developing a functional architecture model for level Li-1, and thereafter transforming the level Li-1 functional architecture model into a physical architecture model for level Li-1. The functional architecture model includes a functional and a logical structure for level Li-1. And as such, the functional architecture model is developed based upon a concurrent functional and logical decomposition of a functional architecture model developed for level Li.
Owner:THE BOEING CO
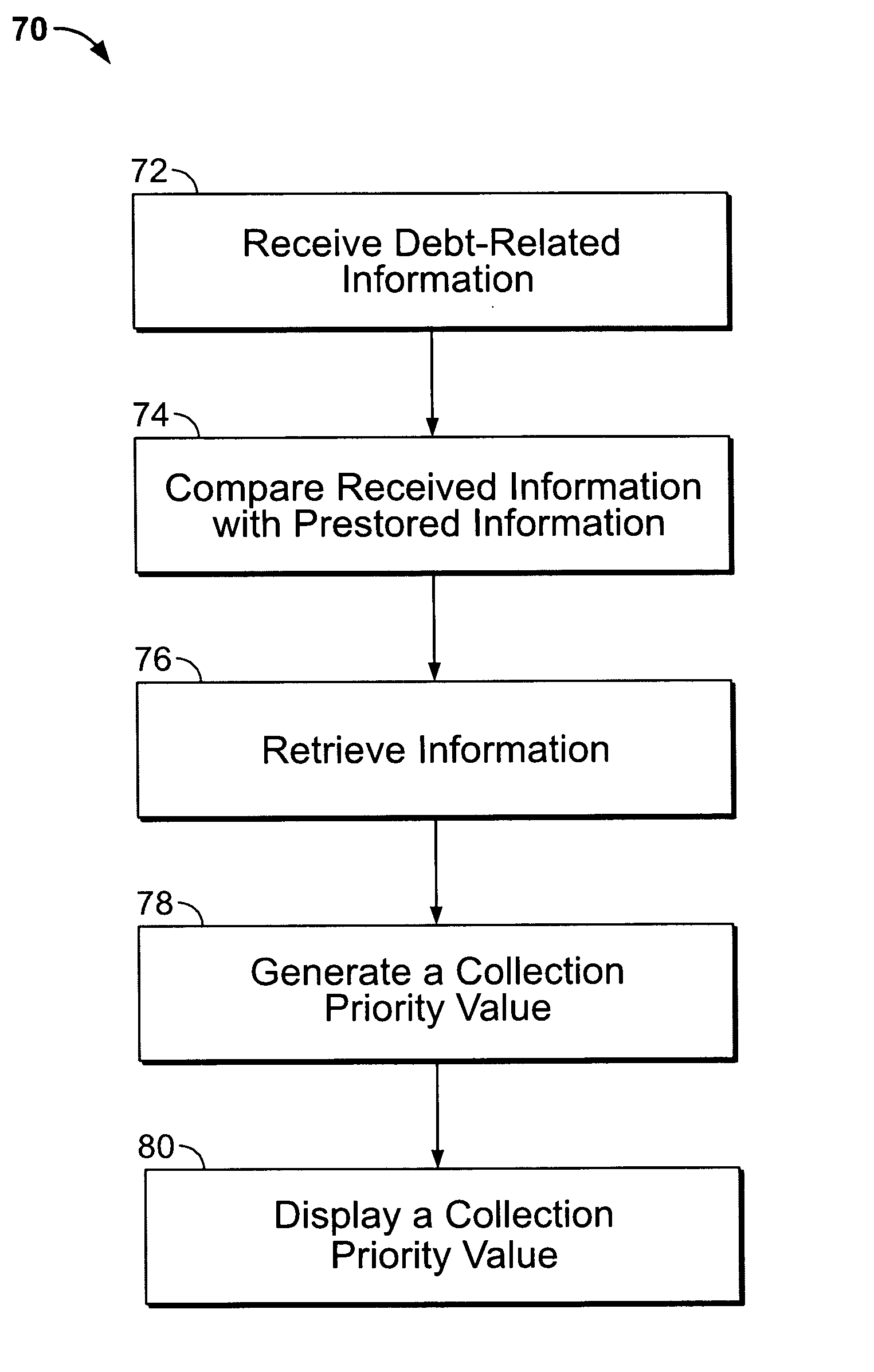
Method and system for prioritizing debt collections
A collections prioritization method and system for use in a financial services business is disclosed. The system is configured to generate a collection priority value from information stored on the system and queue the accounts for collection action based on the priority value and user entered filtering criteria. In one embodiment, the system is further configured to generate a report on the efficiency of collection by a collector.
Owner:GENERAL ELECTRIC CO
Application-independent and component-isolated system and system of systems framework
InactiveUS8078357B1Easy to understandEasy to operateComputer controlDigital data processing detailsIsolated systemInformation object
Embodiments of an application-independent and component-isolated system and system of systems framework are provided. In some embodiments, a Distributed Integration Operating Schema (“DIOS”) framework allows integration of disparate software and hardware components and permits addition, removal, modification, failure of, and information exchange among such components. In some embodiments, DIOS uses an information model that comprises a user-defined hierarchy of information objects to facilitate communication of information among agents of a control system.
Owner:DISTRIX NETWORKS
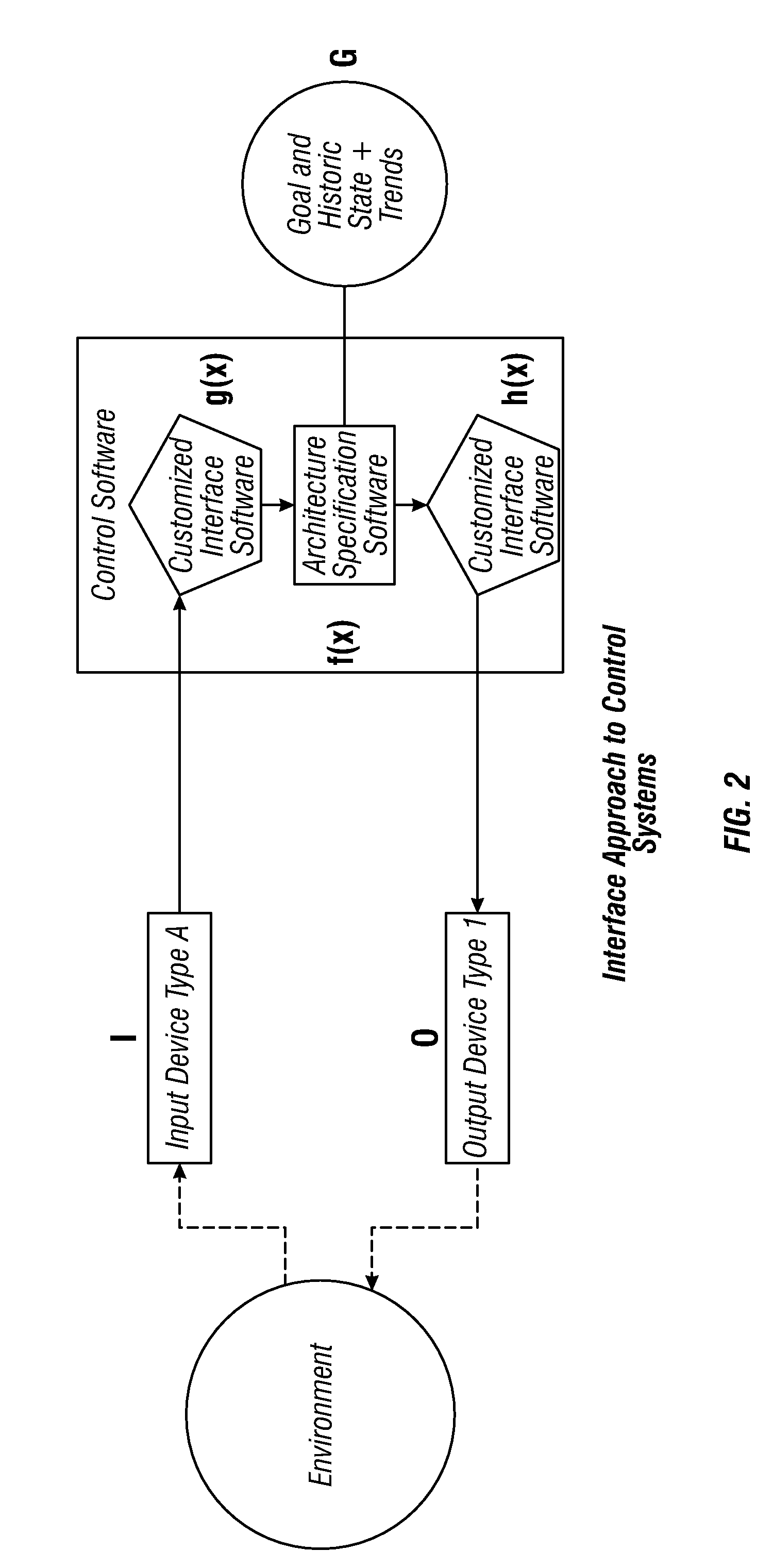
System, method and computer program product for developing a system-of-systems architecture model
ActiveUS7430498B2Easy to captureEasy to useMultiple digital computer combinationsComputation using non-denominational number representationEngineeringSystem of systems
A method is provided for developing an architecture model for a system-of-systems (SoS) that includes n system levels L1 . . . Ln, each of which includes at least one component of the SoS. For at least i>1, each system level Li includes at least one component of level Li-1. The method includes developing an architecture model for at least one level of the SoS. For at least i>1, the level Li-1 architecture model can be developed by developing a functional architecture model for level Li-1, and thereafter transforming the level Li-1 functional architecture model into a physical architecture model for level Li-1. The functional architecture model includes a functional and a logical structure for level Li-1. And as such, the functional architecture model is developed based upon a concurrent functional and logical decomposition of a functional architecture model developed for level Li.
Owner:THE BOEING CO
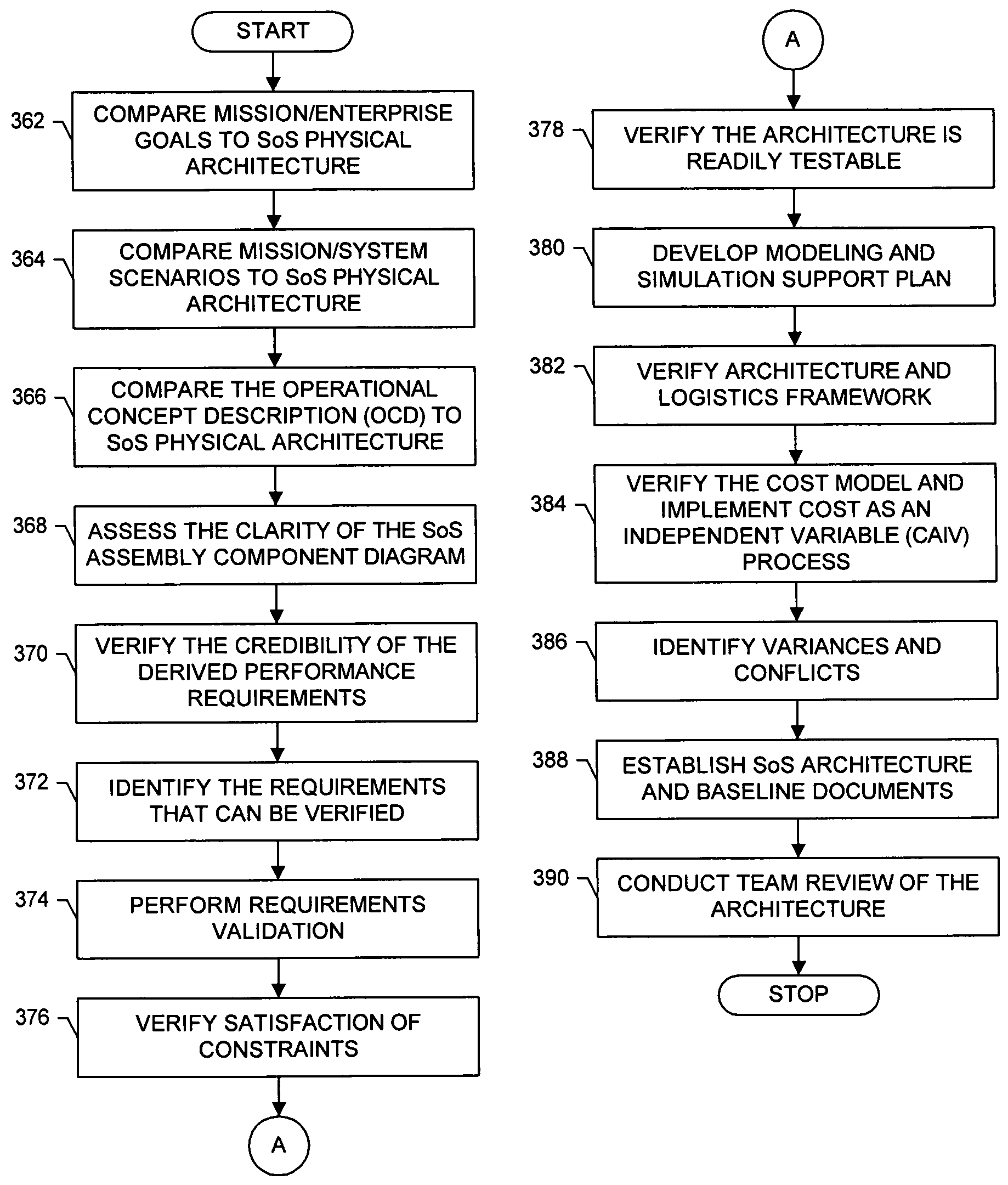
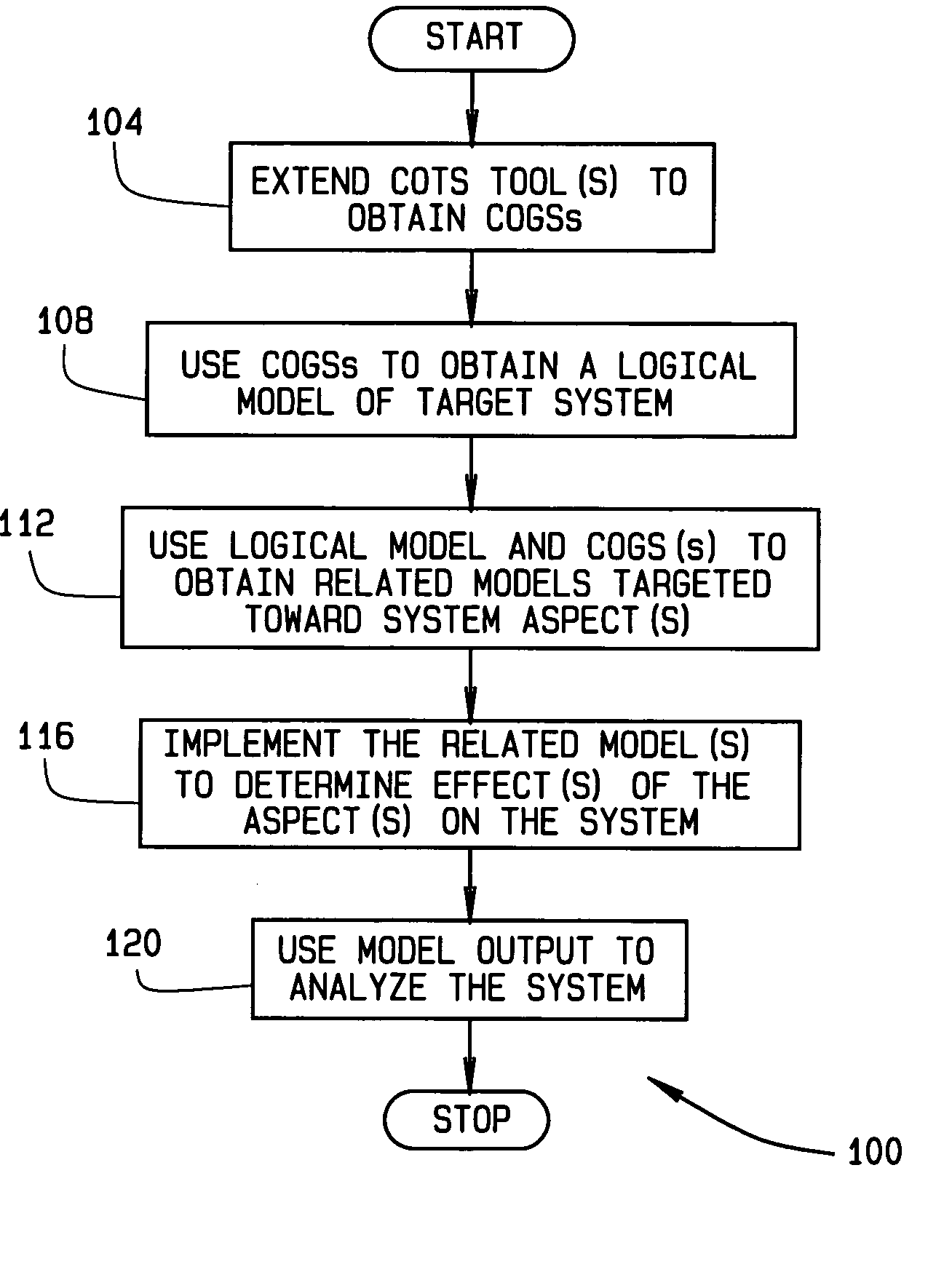
Integrated system-of-systems modeling environment and related methods
A method of modeling operational and / or logical aspects of a system in a system-of-systems environment. Modeling components of generic structure are used to obtain a logical model of the system. The logical model and the modeling components of generic structure are used to obtain related models targeted toward the aspects. The related models are implemented to determine effects of the aspects on the system and / or system-of-systems.
Owner:THE BOEING CO
Method and system for fault isolation within a network element in an optical network
A method and system for fault isolation within a network element in an optical network is described. A single fault in the system can give rise to multiple alarms detected at multiple points. Finding the root cause alarm corresponding to the fault that has triggered these alarms is important for fault isolation and is the focus of attention for this invention. The network element is modeled by a directed acyclic graph that captures the interactions among various components in the network element. Using a graph-based technique the invention analyzes the various topological faults raised and their locations for identifying root cause alarms and masking all correlated alarms.
Owner:ALCATEL LUCENT CANADA
System of systems for monitoring greenhouse gas fluxes
ActiveUS8595020B2Provide real-timeEasy to understandPigmenting treatmentSustainable waste treatmentNatural sourceGreenhouse gas flux
A system of systems to monitor data for carbon flux, for example, at scales capable of managing regional net carbon flux and pricing carbon financial instruments is disclosed. The system of systems can monitor carbon flux in forests, soils, agricultural areas, body of waters, flue gases, and the like. The system includes a means to identify and quantify sources of carbon based on simultaneous measurement of isotopologues of carbon dioxide, for example, industrial, agricultural or natural sources, offering integration of same in time and space. Carbon standards are employed at multiple scales to ensure harmonization of data and carbon financial instruments.
Owner:PLANETARY EMISSIONS MANAGEMENT
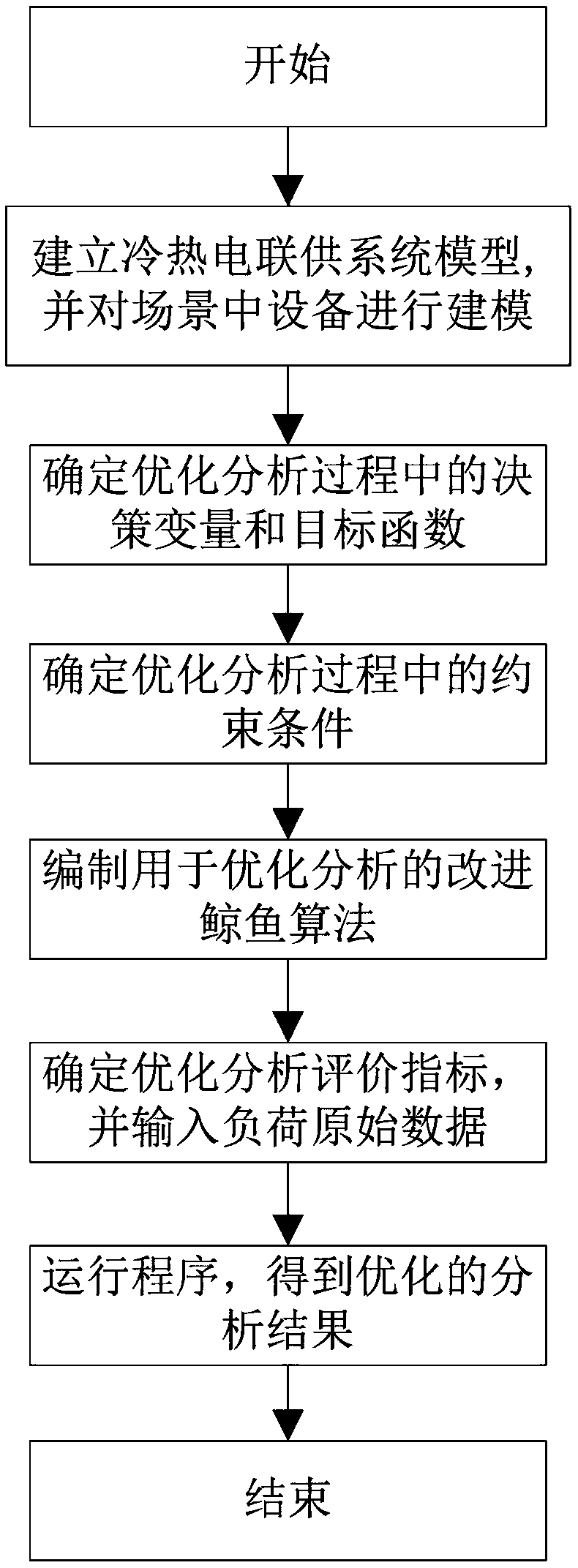
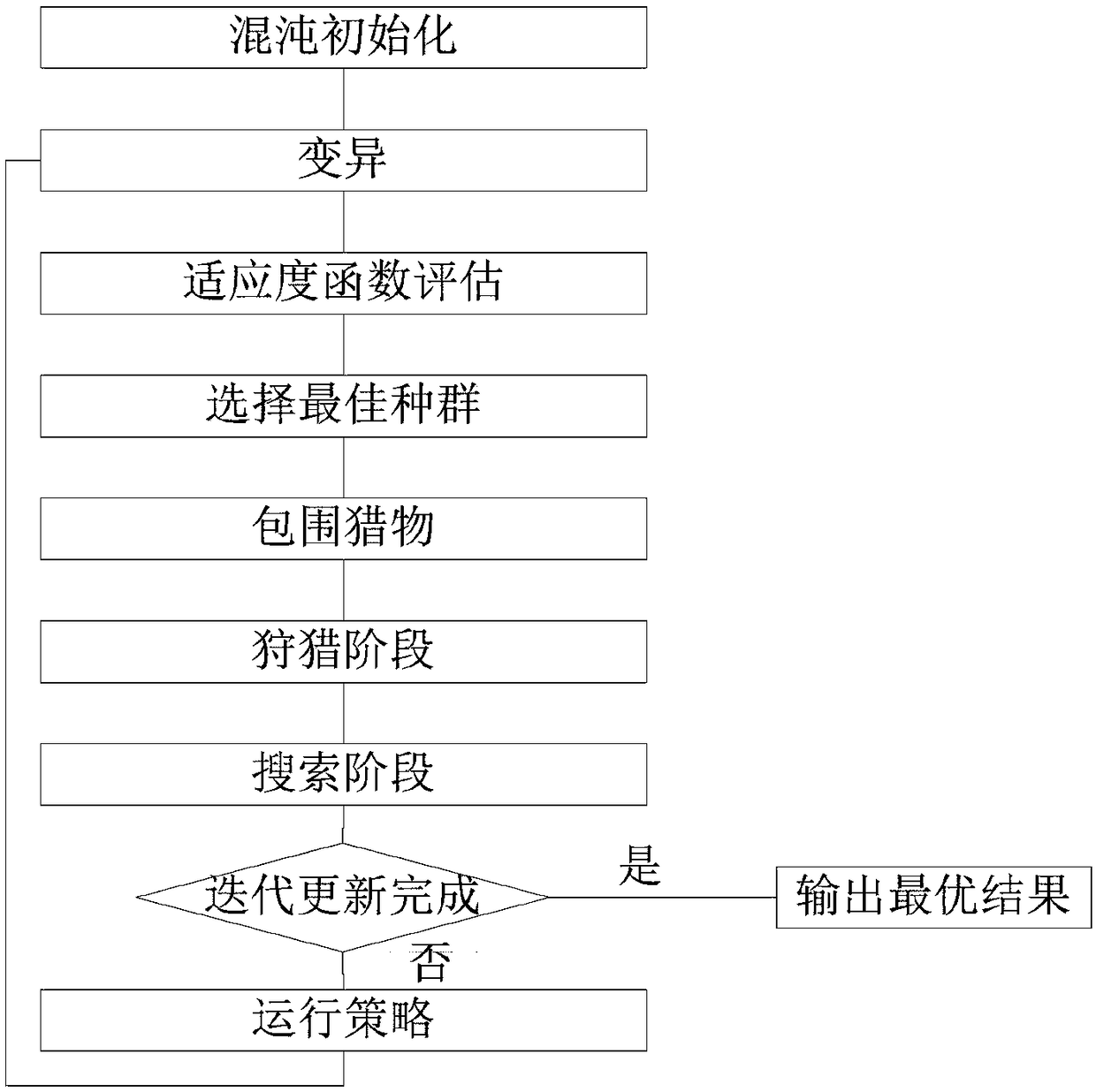
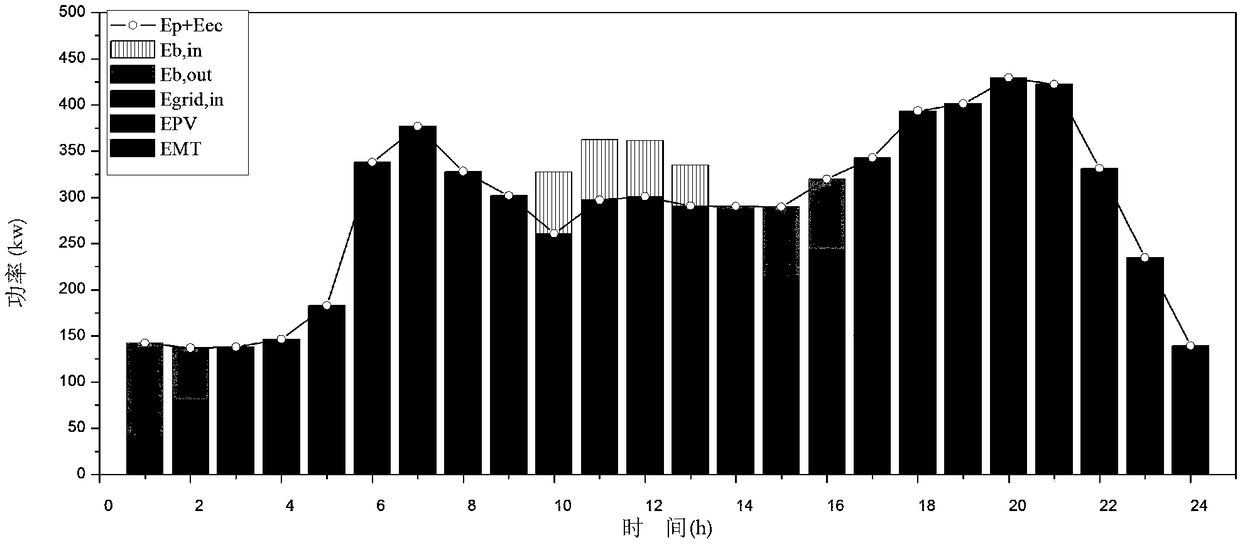
An optimization method of a combined cooling, heating and power system
ActiveCN109165788ASmooth load fluctuation phenomenonIncrease flexibilityForecastingResourcesElectricitySystem of systems
The invention relates to an optimization method of a combined cooling, heating and power supply system, the method comprising the following steps: establishing a model of the combined cooling, heatingand power supply system, selecting a combined cooling, heating and power supply type micro-network as an optimization object to carry out mathematical modeling on the equipment in the scene; determining the decision variables and objective functions of the optimization analysis of the combined cooling, heating and power system; determining the constraint conditions of the optimal operation of thecombined cooling, heating and power system; choosing a whale optimization algorithm and introducing chaotic cube mapping and mutation rules to optimize initial population and behavior rules; adoptinga hybrid heating and power supply strategy as the operation strategy of the combined cooling, heating and power supply system; determining and evaluating the optimized evaluation index. The method adopts the strategy of mixing heat and electricity and applies the improved whale algorithm to solve the combined cooling, heating and power micro-grid model. In the initial stage, the chaotic initialization operation improves the searching ability, and the mutation operation introduced in the trapping stage can find the global optimal value more quickly, thus realizing the purpose of quickly finding the optimal solution for the optimal operation of the combined cooling, heating and power system.
Owner:HEBEI UNIV OF TECH
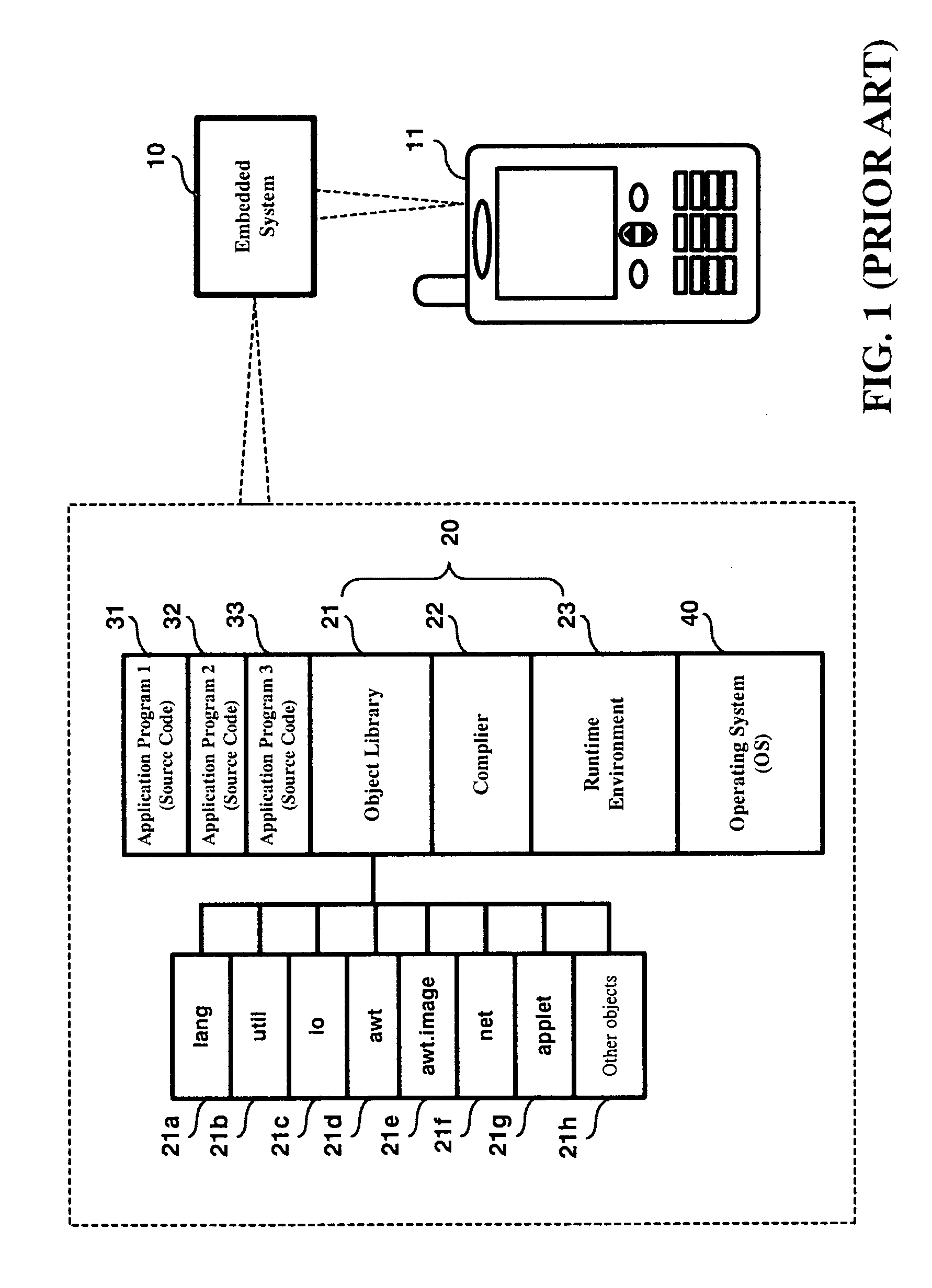
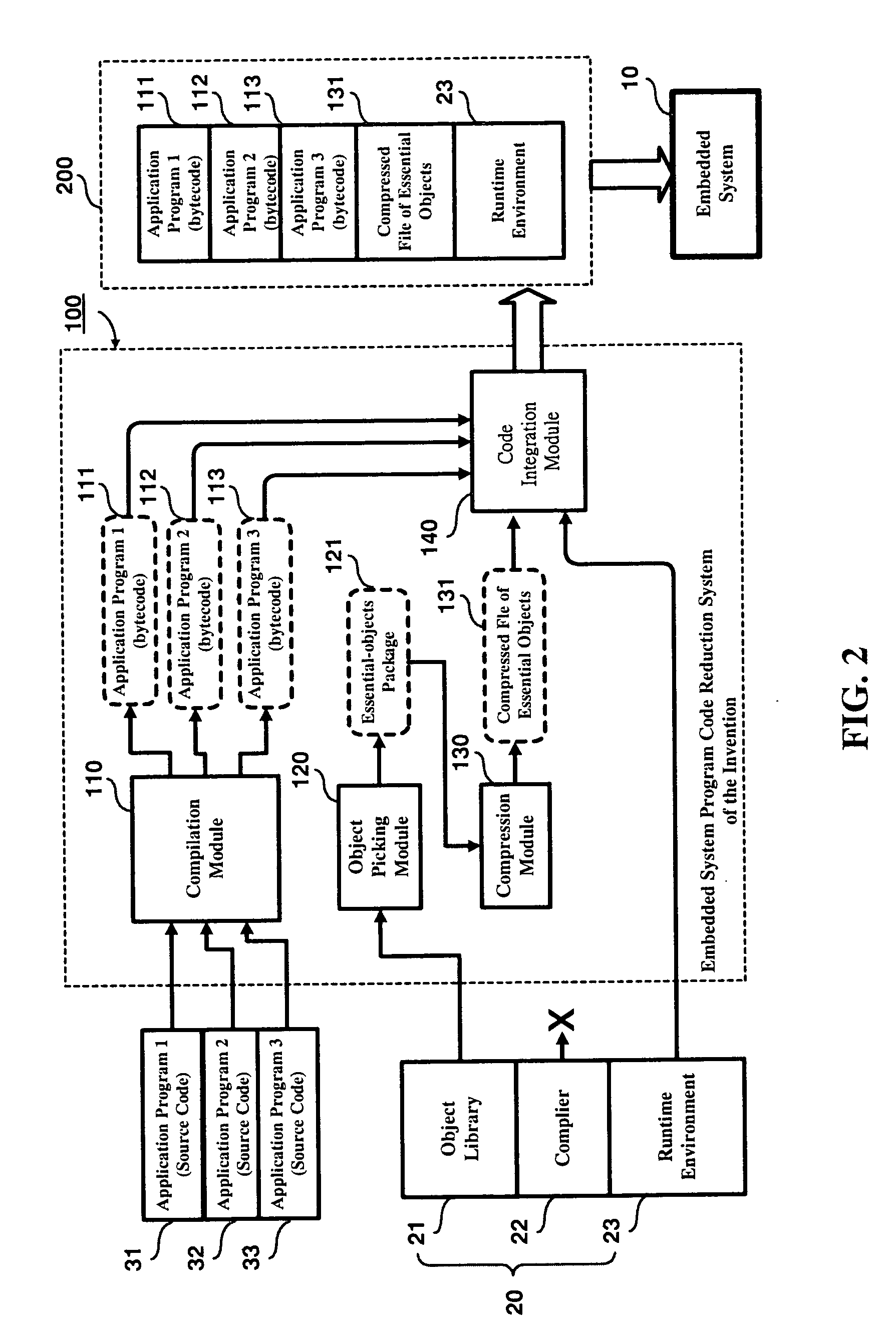
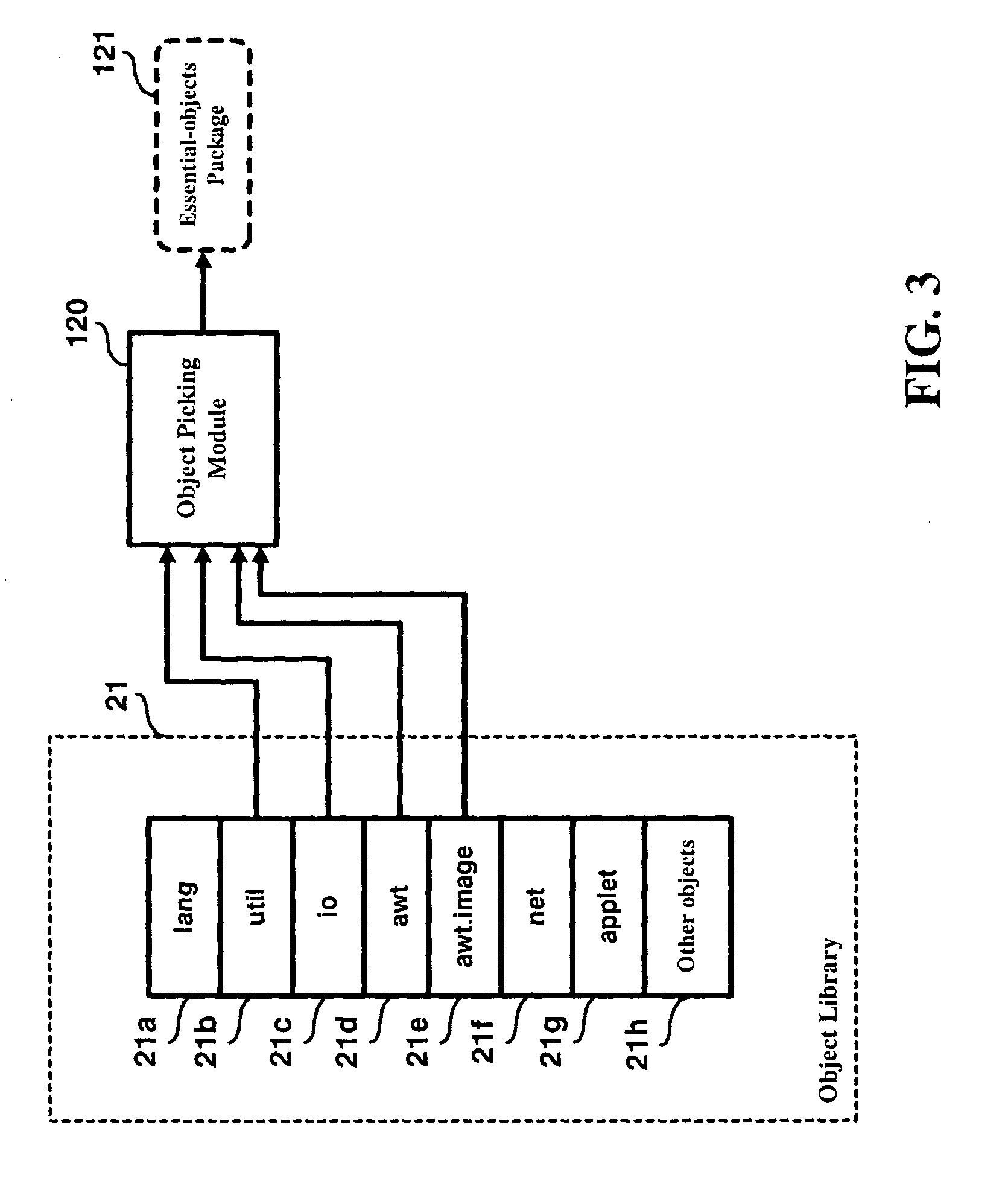
Embedded system program code reduction method and system
InactiveUS20050060272A1Reduce memory requirementsImprove performanceSoftware engineeringDigital computer detailsSystem of systemsApplication software
An embedded system program code reduction method and system is proposed, which is designed for use to scale down the total amount of program code that is to be burned into an embedded system for the purpose of reducing the embedded system's memory requirement and thereby increasing the embedded system's performance. The proposed method and system is characterized by that the program code loaded into the embedded system only includes bytecode-based application programs (rather than source code based application programs), those essential objects that are required by these application programs during runtime, and the runtime environment from the virtual machine, while excluding the complier of the virtual machine. This feature allows the embedded system to have a reduced memory requirement and a higher system performance.
Owner:INVENTEC CORP
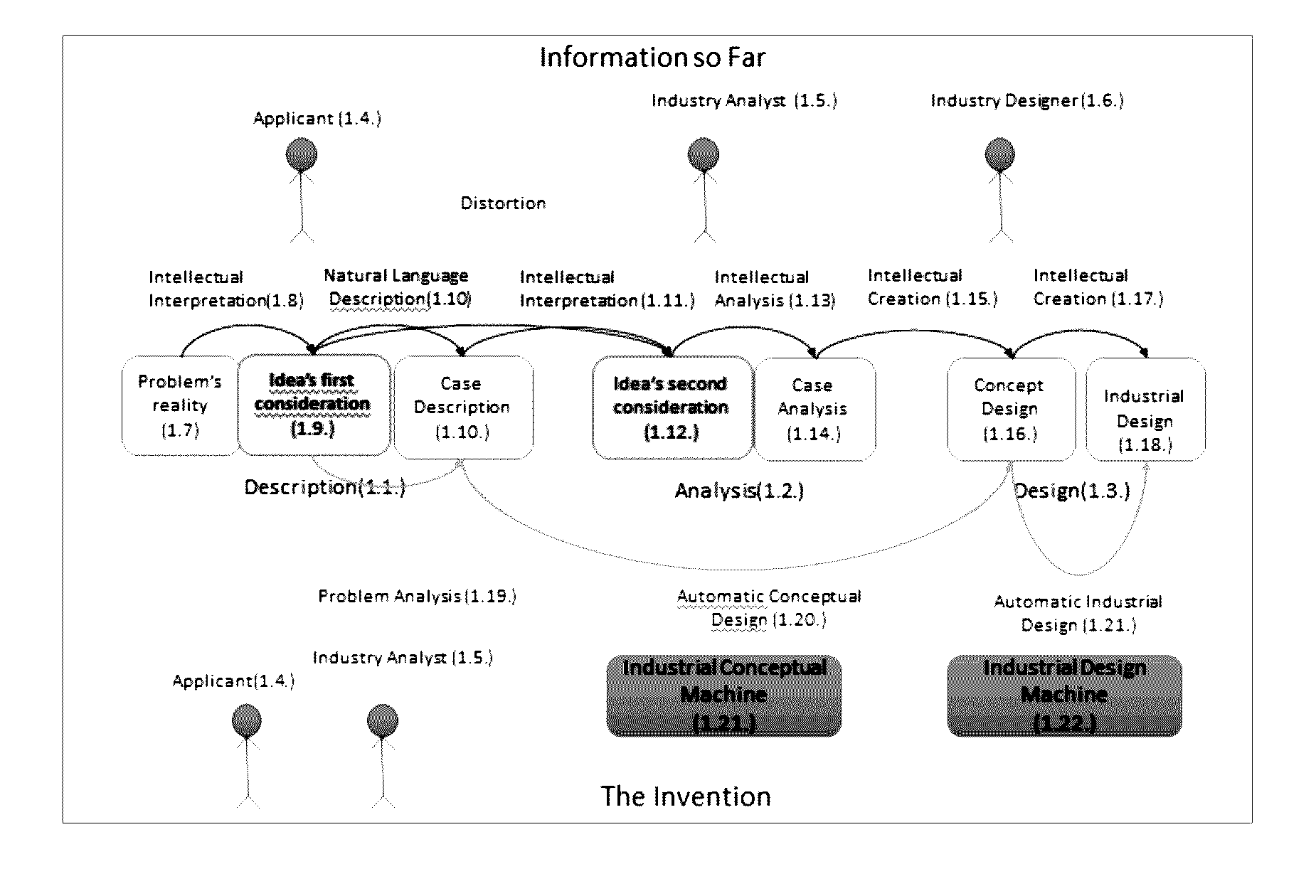
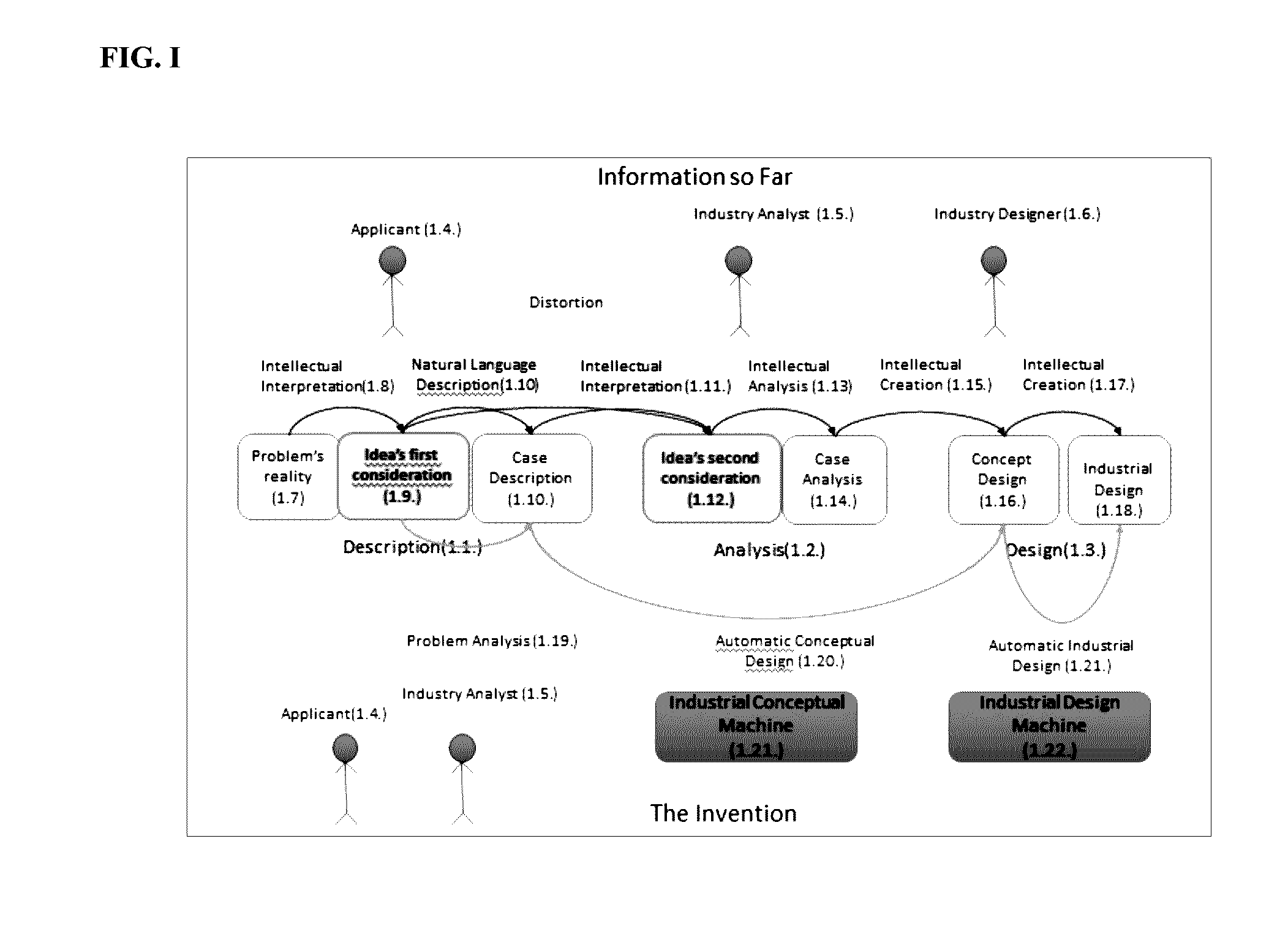
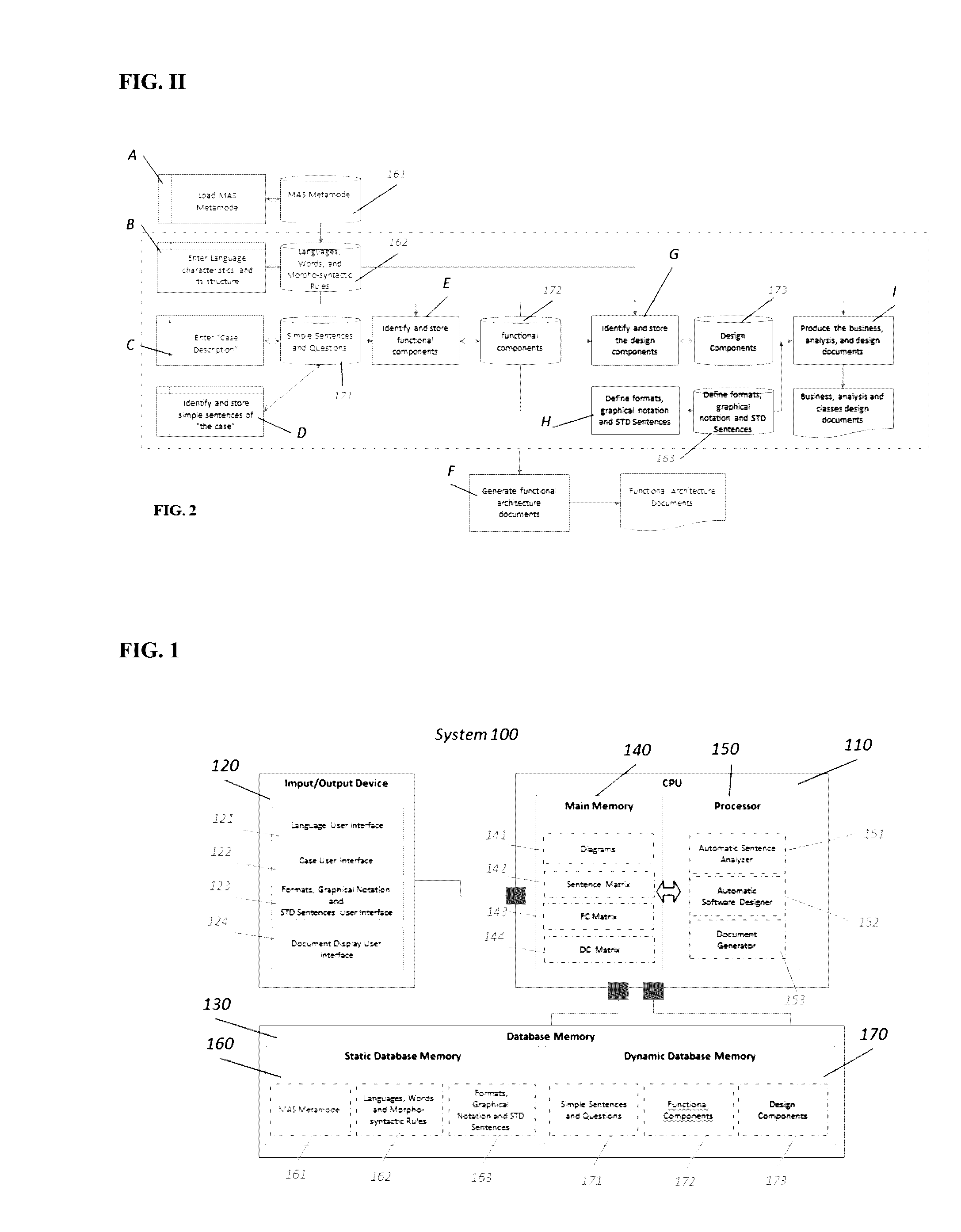
Process and system for automatic generation of functional architecture documents and software design and analysis specification documents from natural language
ActiveUS20170003937A1Accurate understandingReduce designProgram documentationNatural language data processingDocumentation procedureSpecification document
The present invention is a computer-implemented system and method for automatic generation of Functional Architecture, business, analysis and software design documents based on phrases expressed in natural language.Eligible languages and their syntactic and grammatical features can be entered into the system. The system receives the description of the case in natural language, in one of the eligible languages, through an input / output device. The processor automatically analyses the description, automatically extracts the functional components from its morphosyntactic structure and automatically generates functional architecture documents for use in industry. Based on the functional components of the text, the processor automatically generates design components in order to produce business, analysis, and software design specification documents.
Owner:HUEBRA NADIA ANALIA
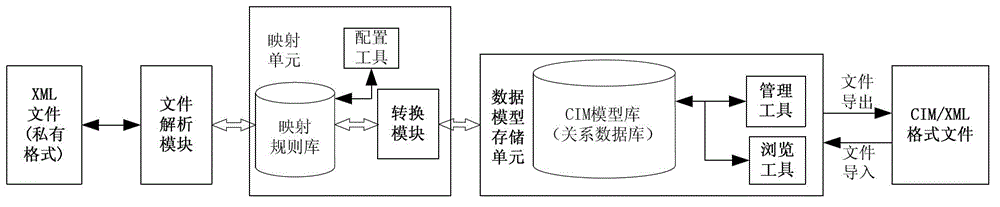
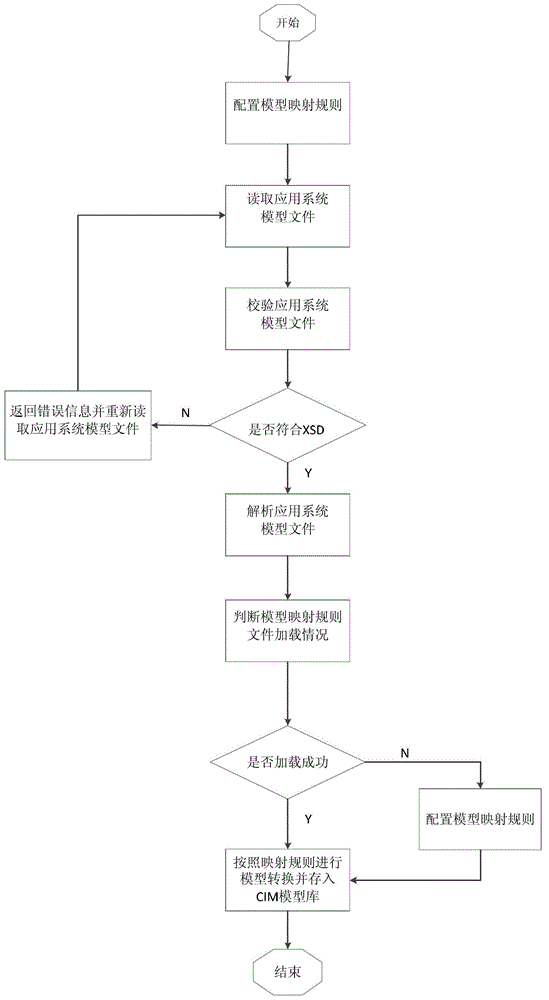
Mapping method and system of system data model to common information model (CIM)
ActiveCN102750358AAvoid conversionStrong scalabilitySpecial data processing applicationsSystem of systemsRDF
The invention relates to a mapping method and a system of a system data model to a CIM. The method includes configuring model mapping rules, receiving model files from corresponding application systems, and verifying and analyzing the model files to obtain information data of the application systems; judging whether model mapping rule files are loaded by the mapping system, if the files are not loaded, building a mapping rule between a private data model and the CIM through a configuration tool for model mapping rules; according to the mapping rule, private information data of the application systems are converted into CIM data and are stored in a CIM library through a mapping unit; and finally, obtaining all information data by browsing the list structure of a whole CIM data library, organizing information data according to resource description framework (RDF) specifications, exporting standard CIM / extensible markup language (XML) files for being called by other application services and components.
Owner:STATE GRID CORP OF CHINA +2
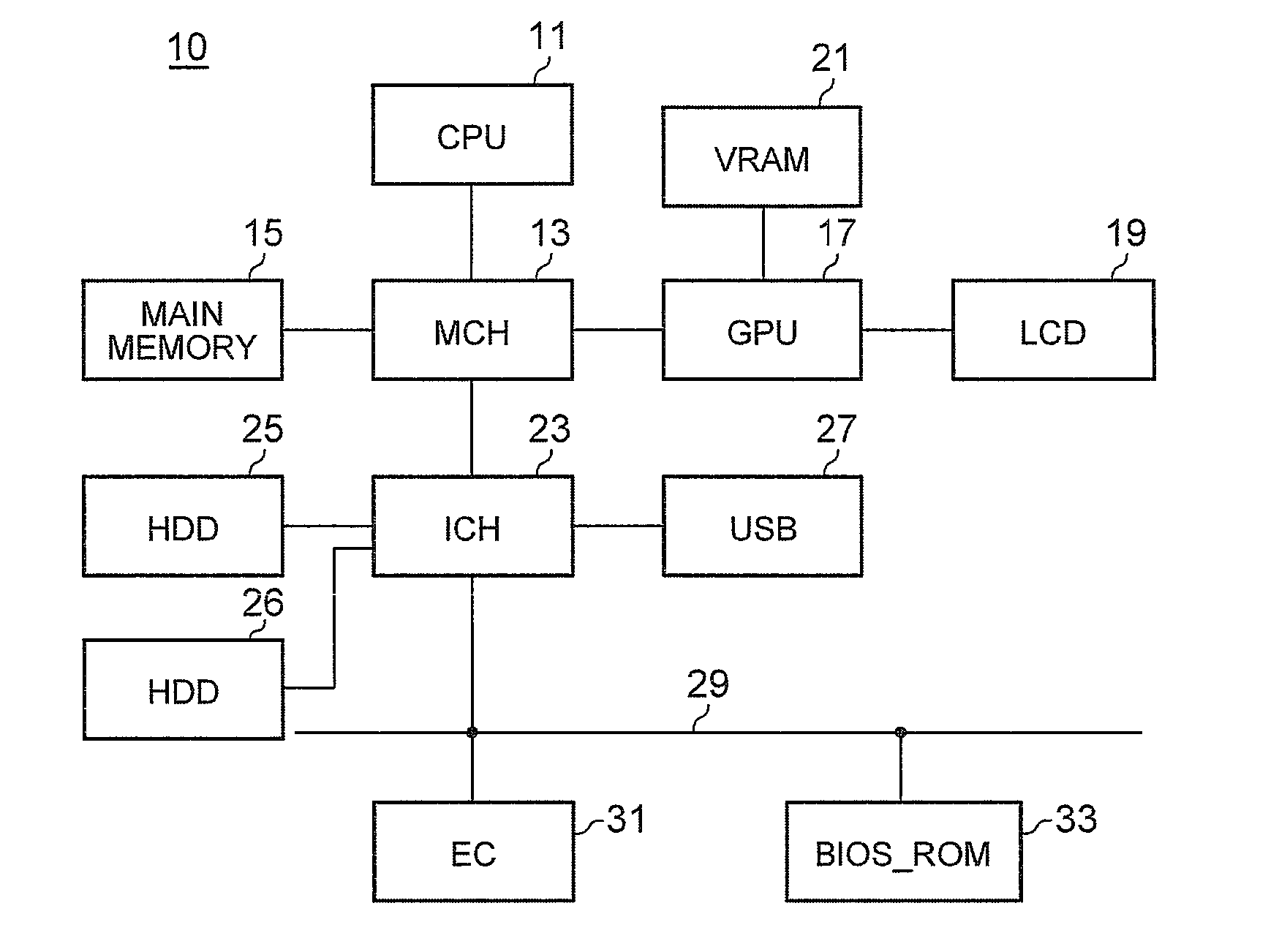
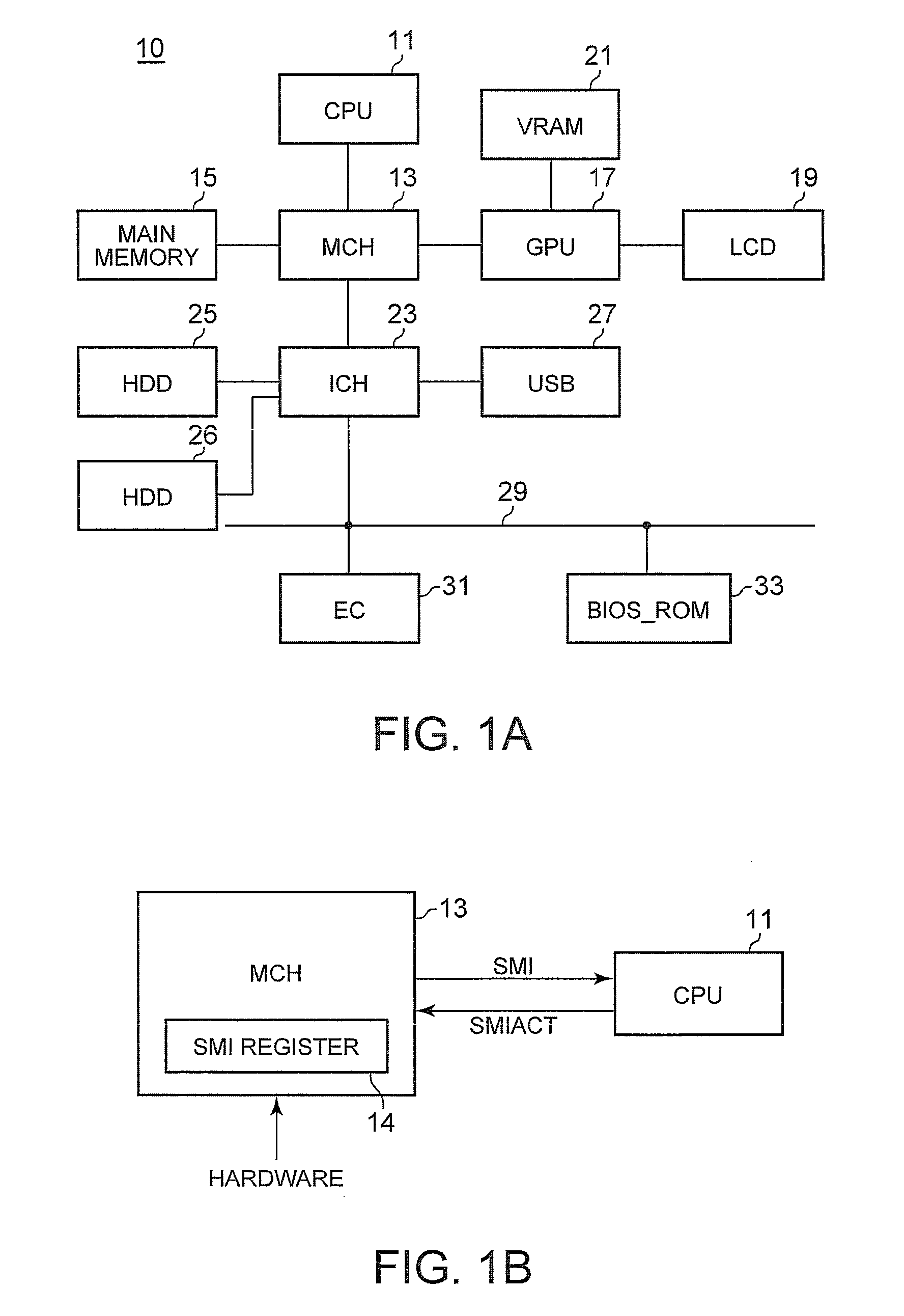
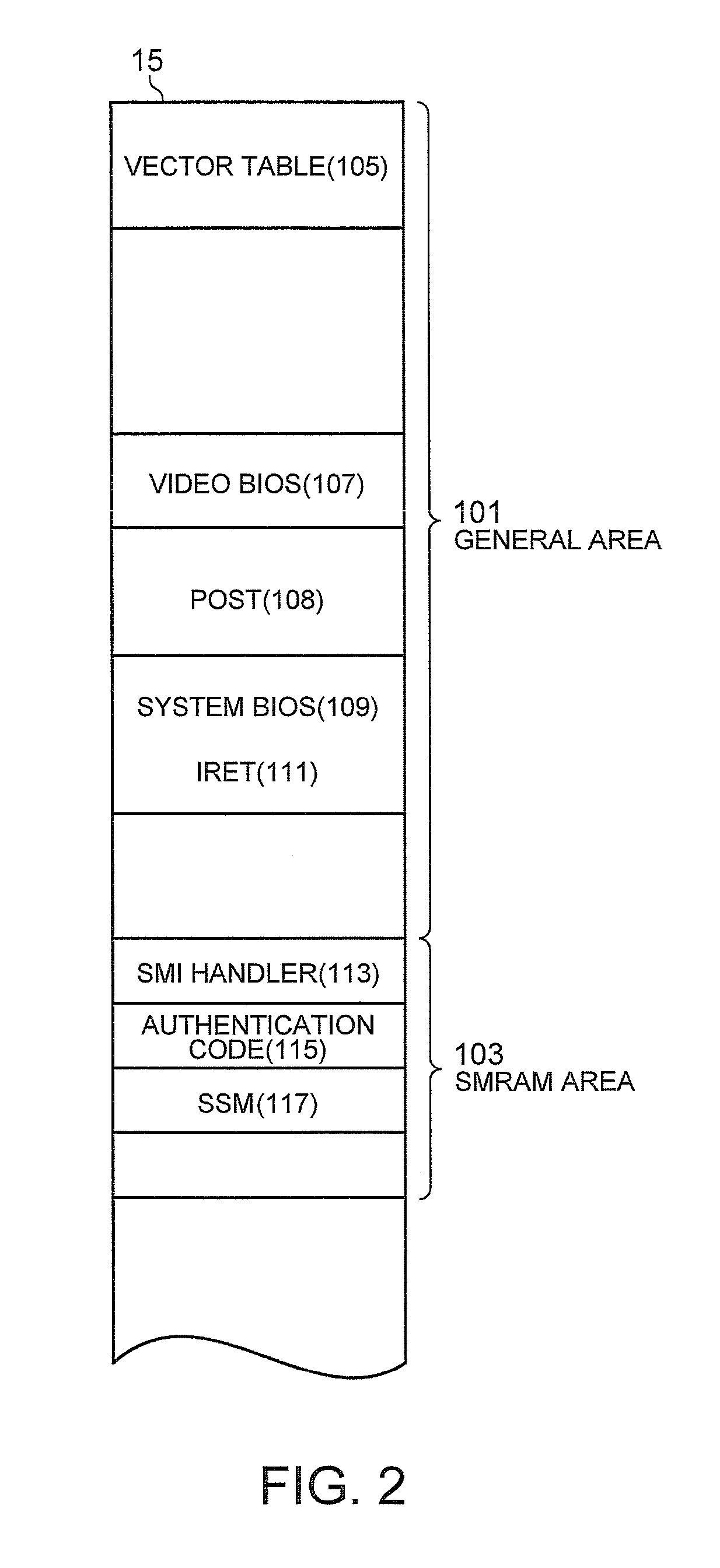
Method for Protecting a Privilege Level of System Management Mode of a Computer System
ActiveUS20110078408A1Memory adressing/allocation/relocationDigital computer detailsOperational systemSystem of systems
A method for protecting a privilege level of a system management mode (SMM) of a computer system is disclosed. A SMM program is loaded into a special memory (SMRAM) area within a system memory of a computer. A first program, a second program, and a vector table are loaded into a general area of the system memory. Before the booting process of the computer has been completed, a reference hash value of the first program is determined by the SMM program, and the reference hash value is stored in the SMRAM area. A hash value of the first program is the computed by the SMM program. After the computer has been operating under an operating environment of an operating system, the computed hash value is compared to the reference hash value. When the computed hash value matches the reference hash value, the first program is called by the SMM program.
Owner:LENOVO PC INT
Methods and apparatus to control transition of backup data
InactiveUS20090210462A1Eliminate the problemError detection/correctionSpecial data processing applicationsMagnetic tapeSystem of systems
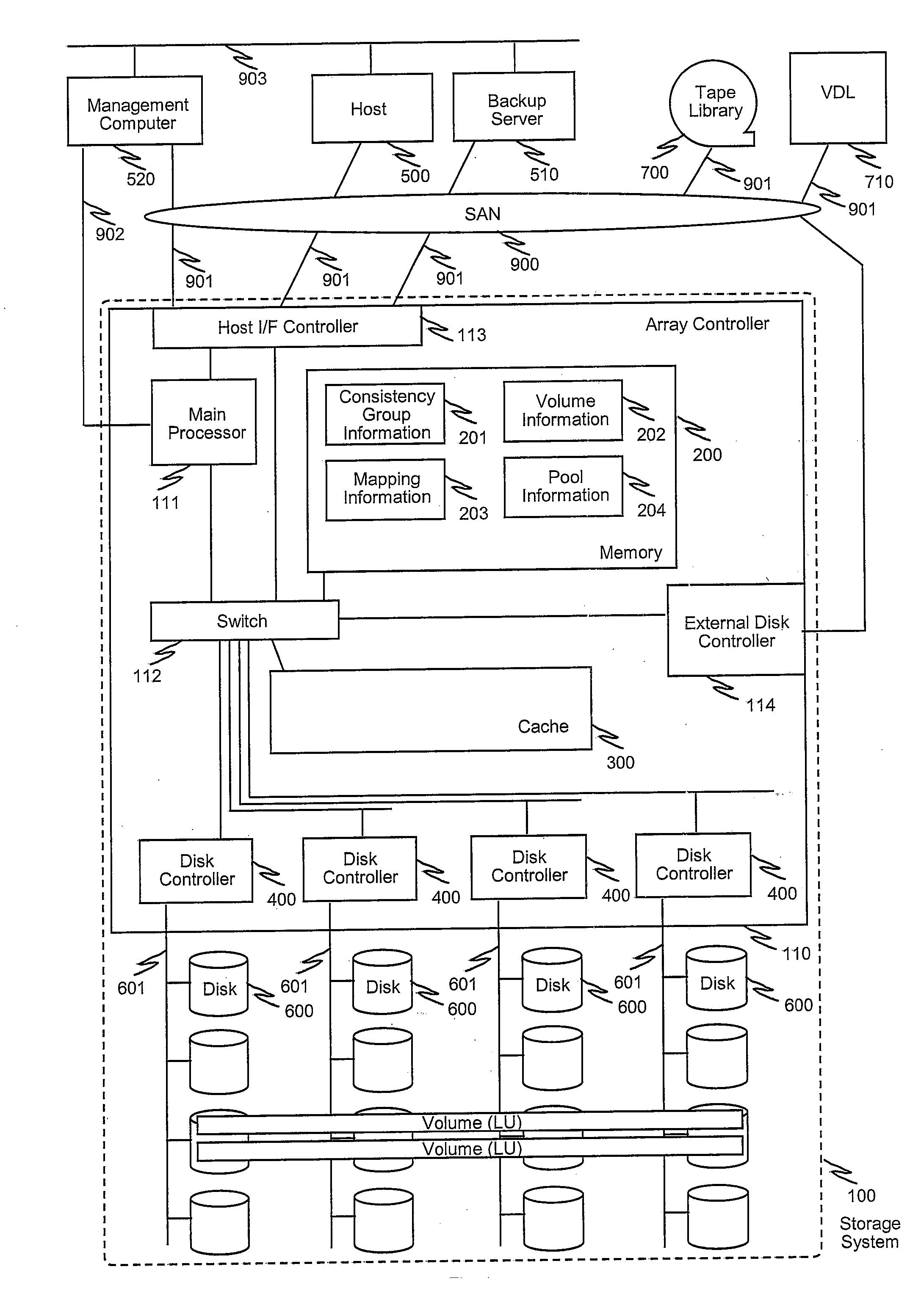
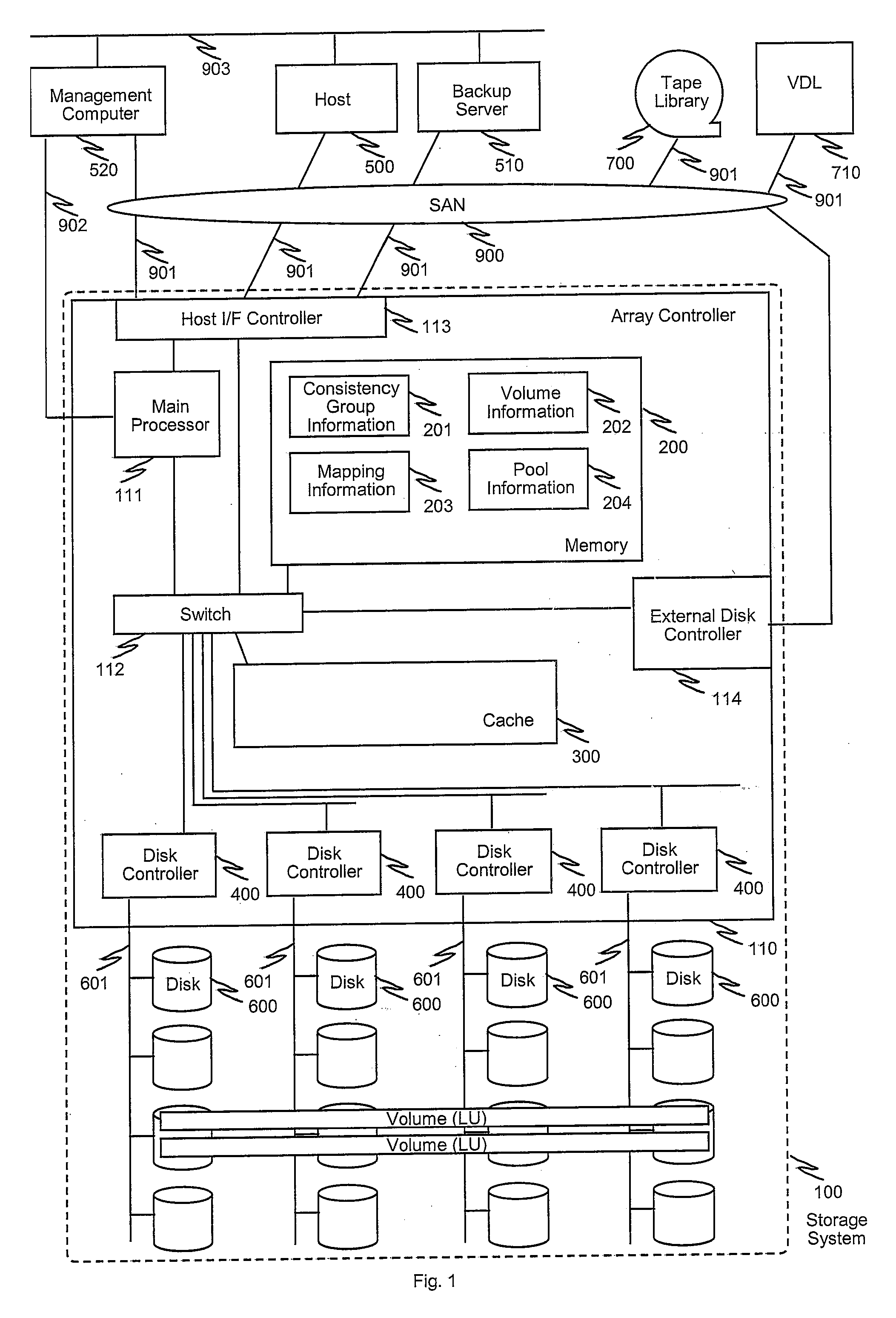
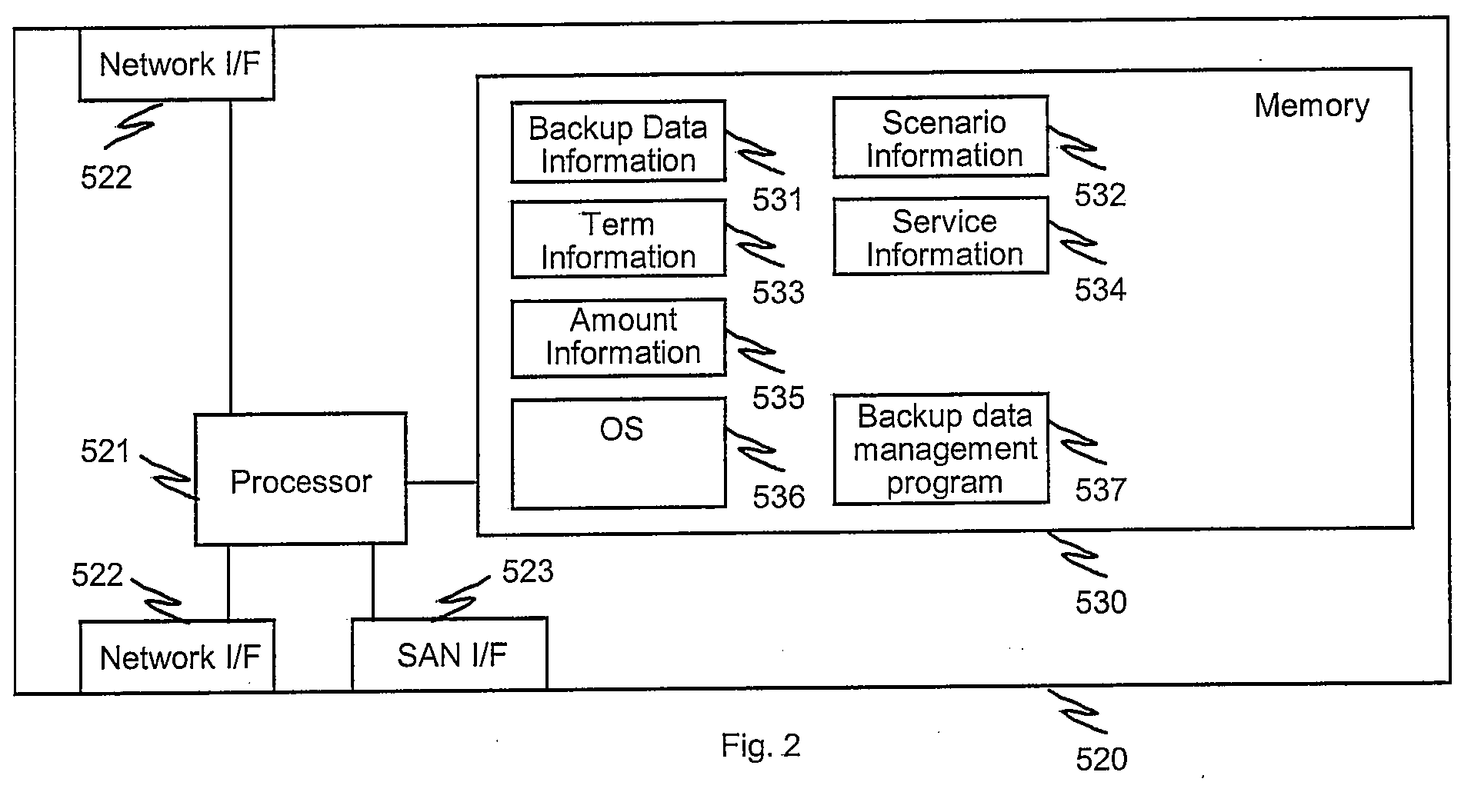
Disclosed is a system incorporating a management computer, host computers, a backup server and at least one storage system. Backup data generated in the system are stored in various storage system such as disk array, tape library and VTL (virtual tape library) with various methods such as continuous data protection and snapshot, and management information of the backup data is maintained by the management computer. The management computer conducts transition of mode of the backup data by detecting that a condition to perform the transition is satisfied, determining a plan of transition according to predetermined scenario, performing (instructing) the transition based on the plan and updating the management information of the backup data. By keeping the management information up to date, the management computer can provide a unified means to restore necessary data from the backup data even if the transition (moving and / or change) of the backup data has been performed.
Owner:HITACHI LTD
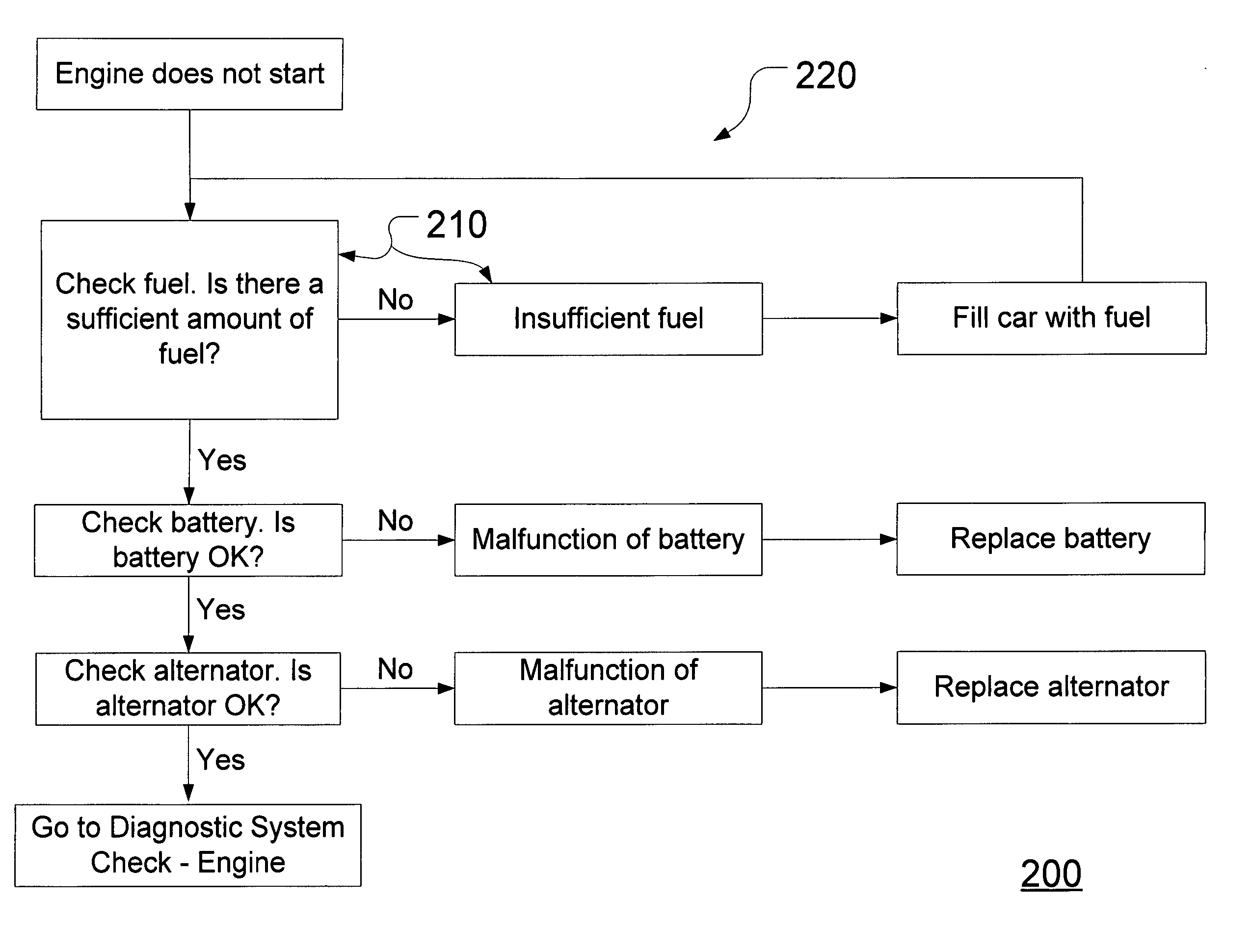
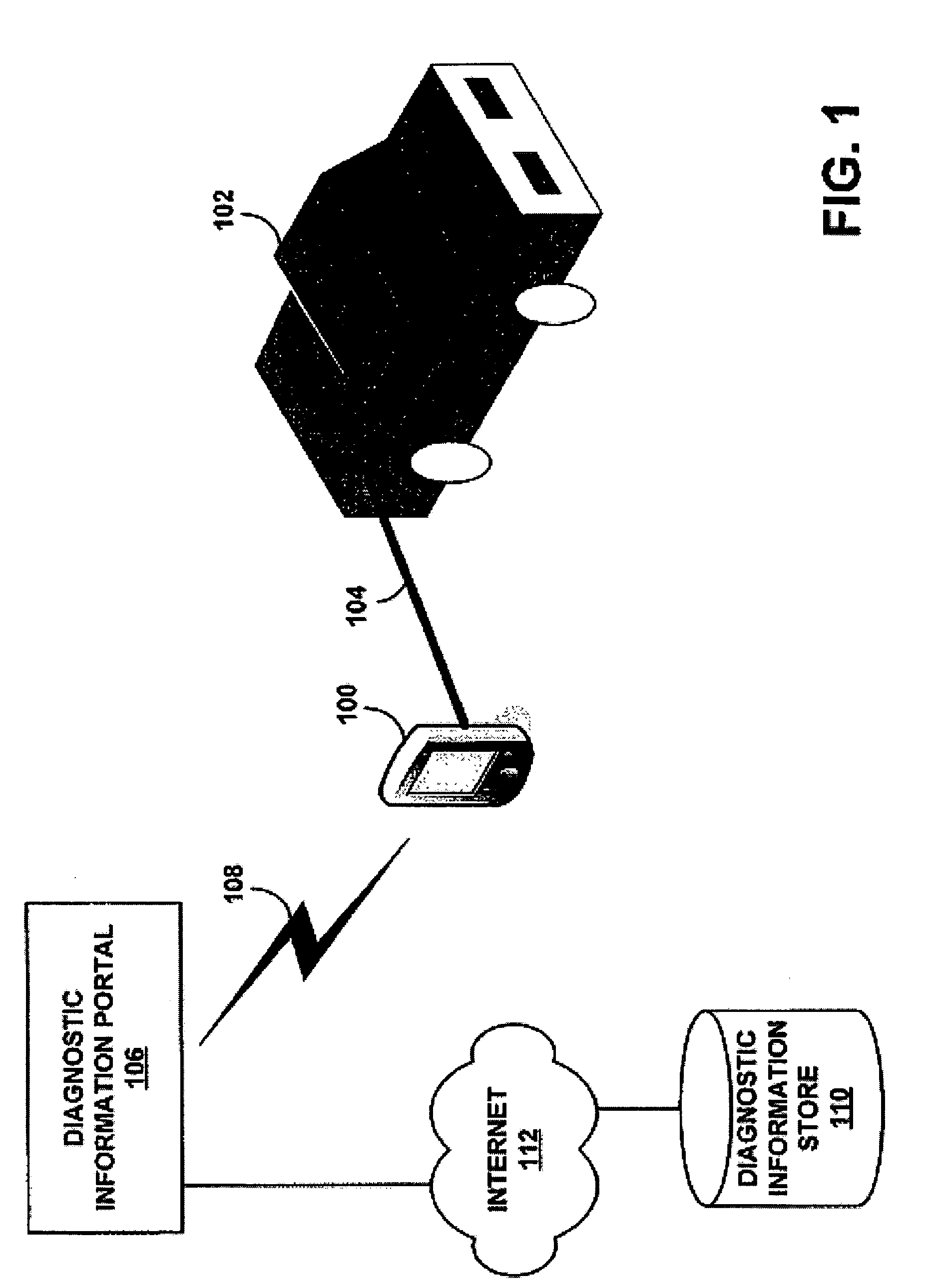
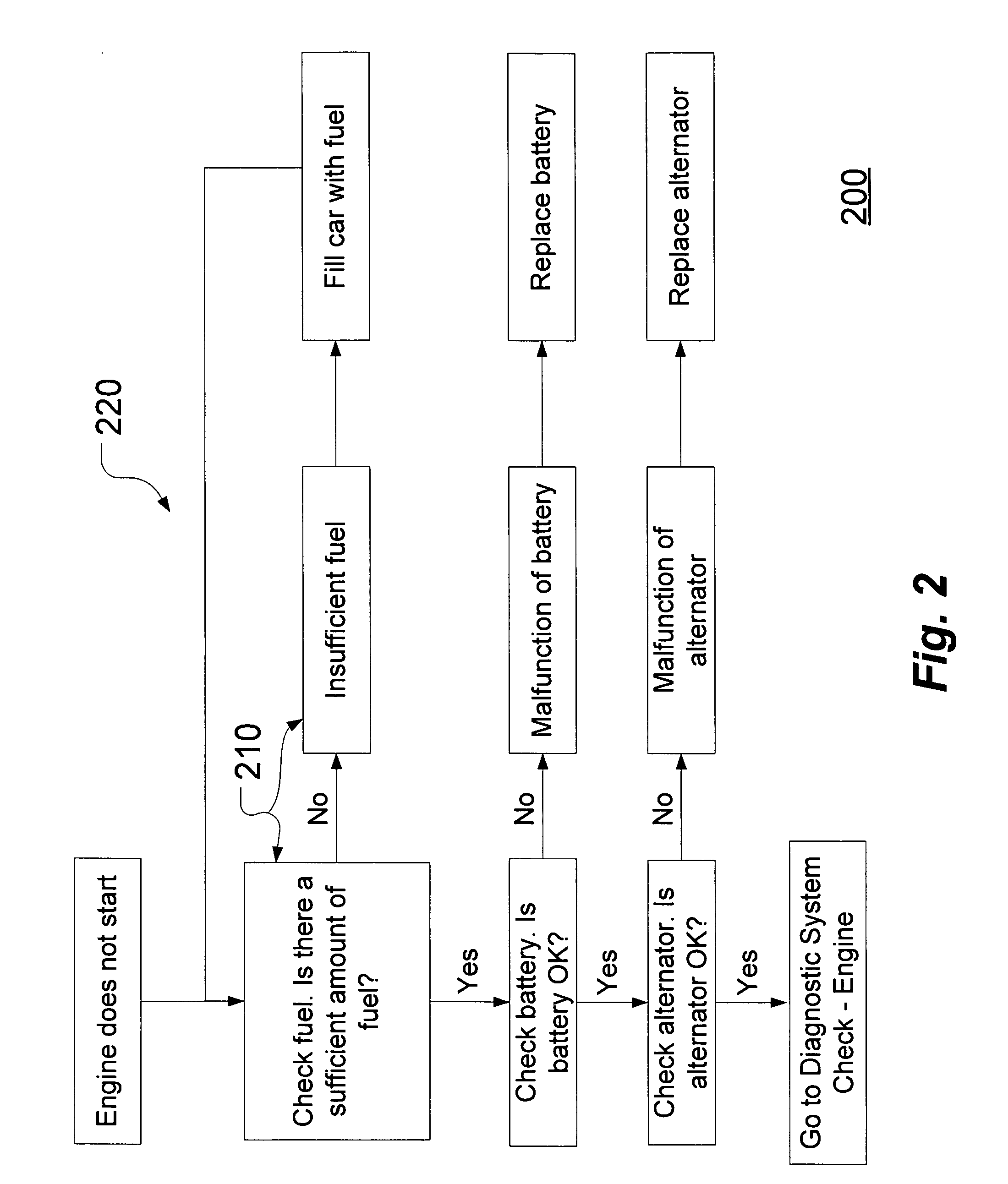
Method and system for adaptively modifying diagnostic vehicle information
InactiveUS20070055420A1Vehicle testingRegistering/indicating working of vehiclesSystem of systemsArtificial intelligence
A method and system for adaptively modifying diagnostic vehicle information is provided. A system can automatically optimize default OEM diagnostic vehicle information by recognizing when to make text and non-text modifications within the information. Manual changes that are made once can be learned and used over and over again. Modifications may be made based on a desired use of the diagnostic vehicle information.
Owner:SNAP ON INC
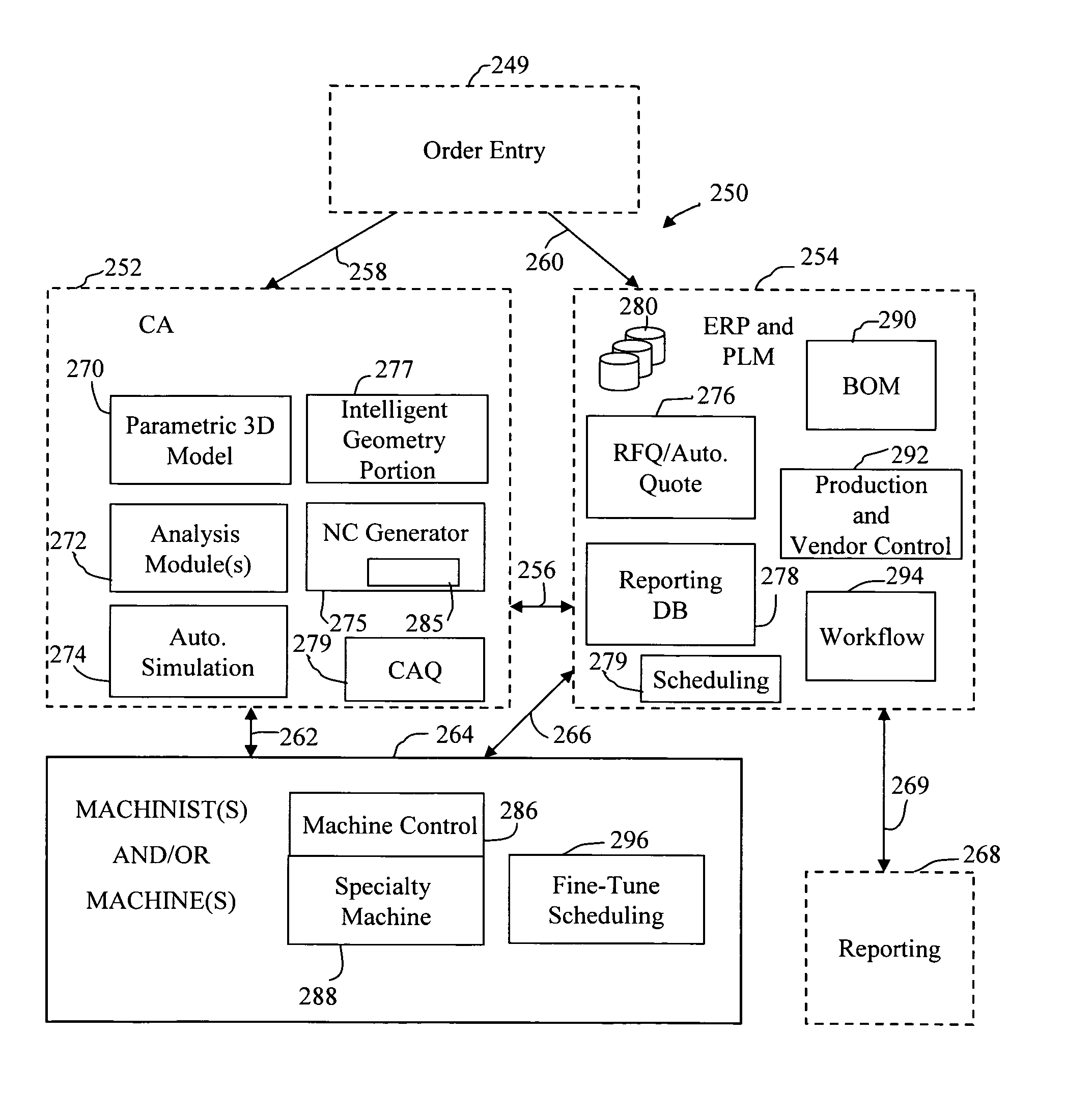
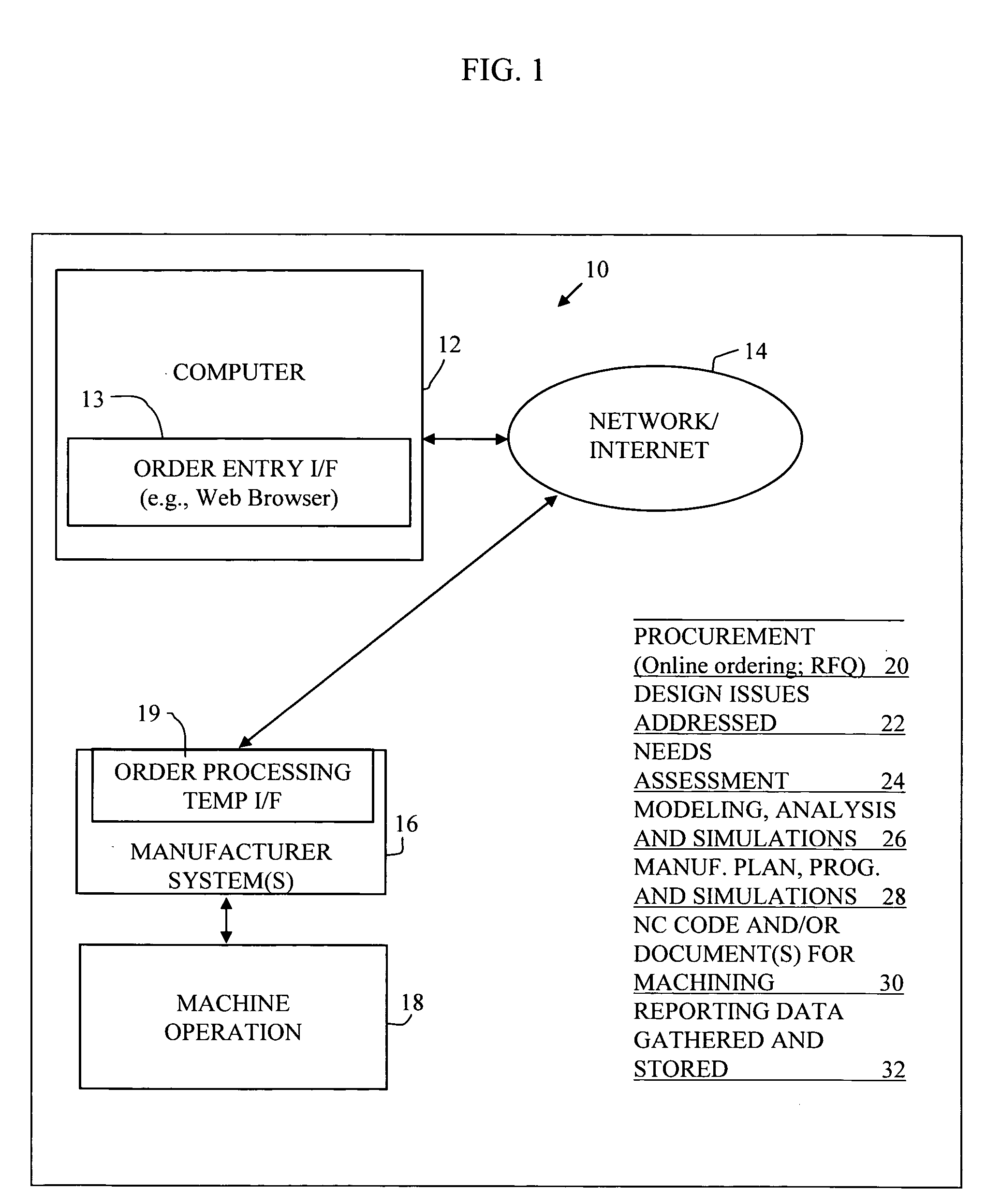
Processes and systems for creation of machine control for specialty machines requiring manual input
InactiveUS20060129270A1Increased riskImprove product qualityComputer controlSimulator controlComputer architectureMachine control
A system is provided for creating specialty machine control programs for manufacturing a part. A CA (computer aided) computer system is provided. The CA system may comprise a computer aided design and computer aided manufacture (CAD / CAM) computer system. The CA computer system may further comprise a computer aided engineering (CAE) computer system. The CA computer system may further comprise a computer aided quality (CAQ) computer system. The CA computer system comprises a parametric design mechanism to specify geometries of the part with parameters. In addition, an intelligent geometry portion is provided to determine machining cycles to manufacture the part. A 3D solid modeling function is provided, and one or more simulation components are provided. A human-readable control program generator is provided to generate from the CA computer system a human-readable control program including instructions for a human to carry out.
Owner:PANKL GEROLD +1
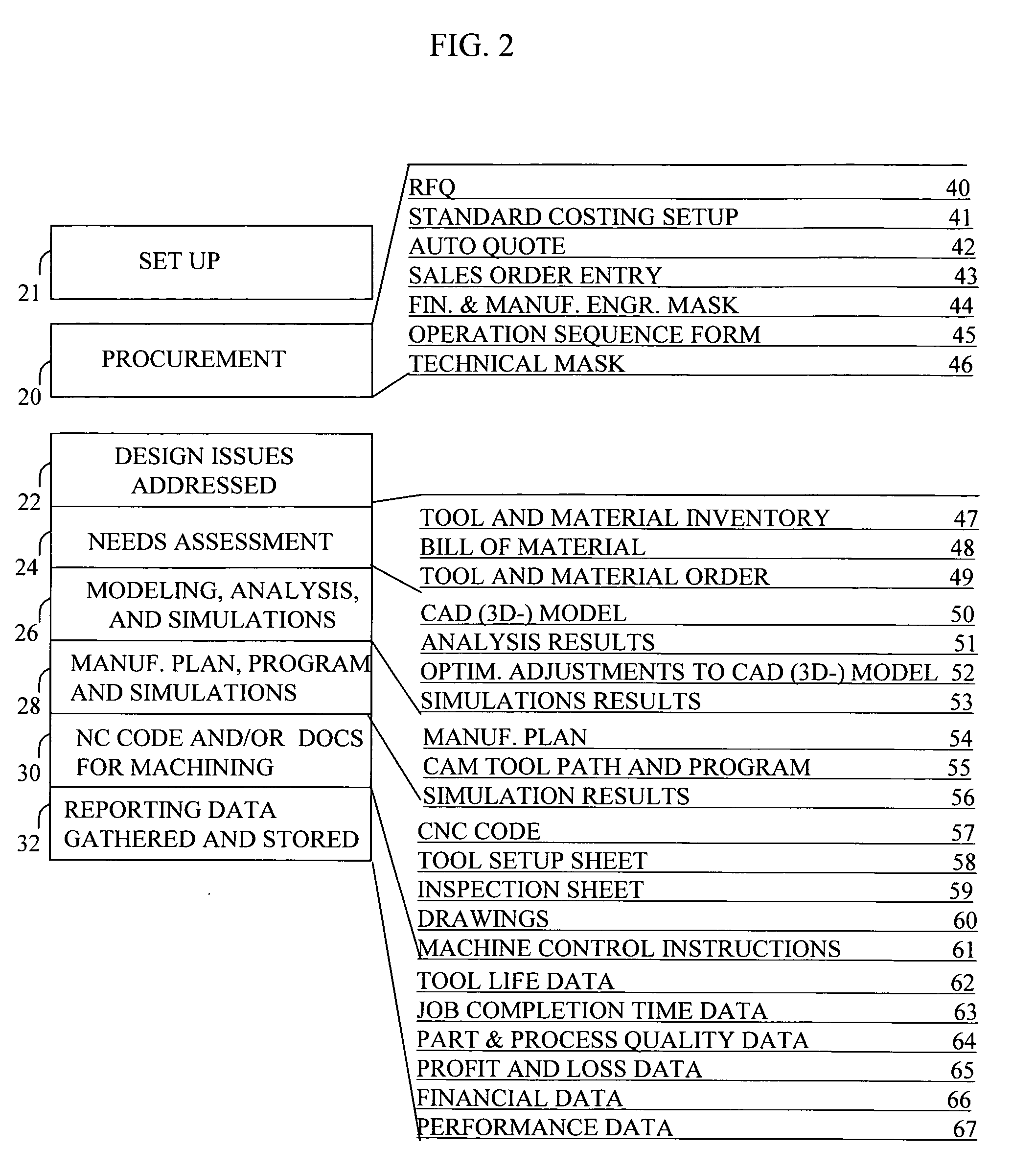
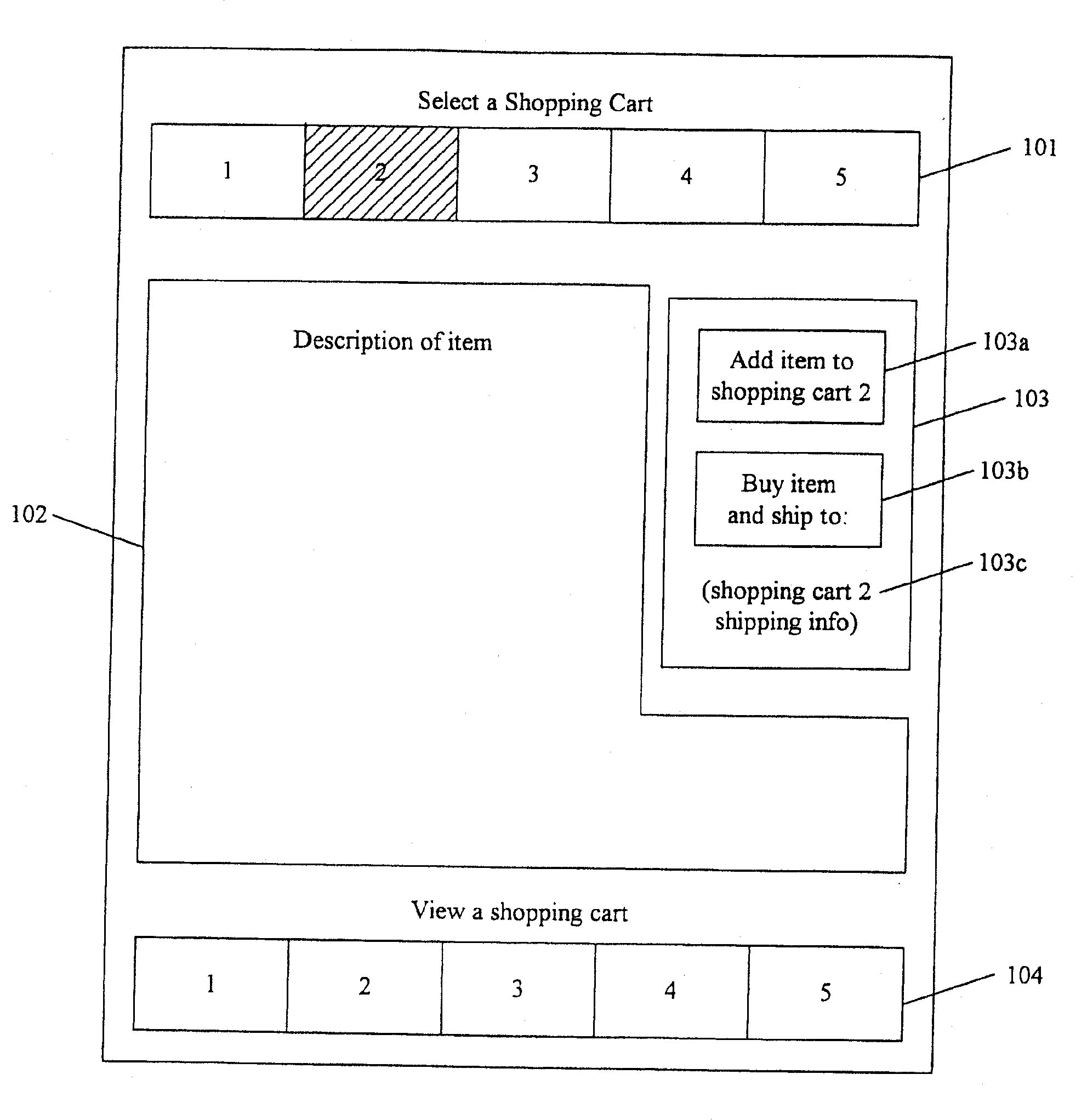
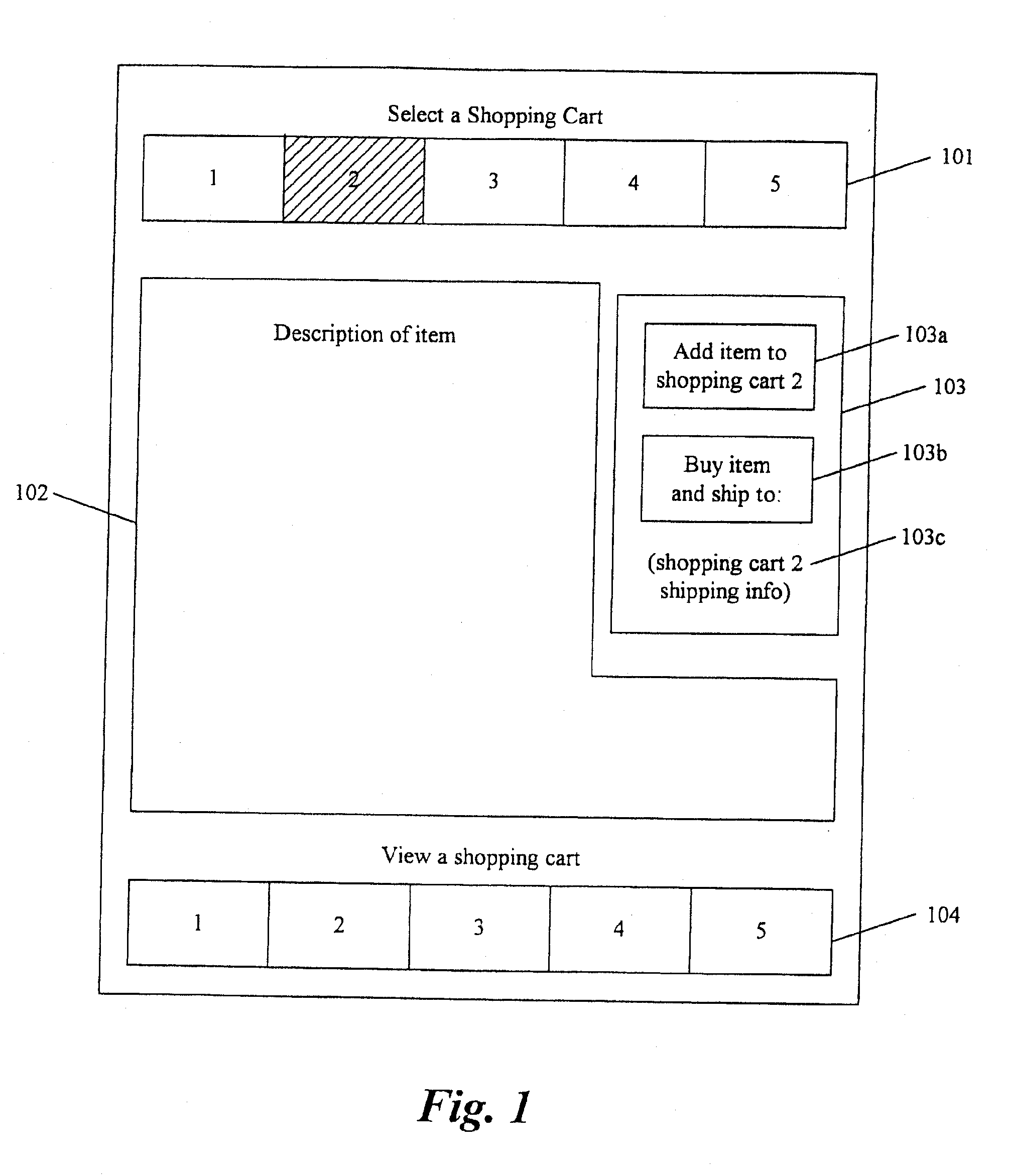
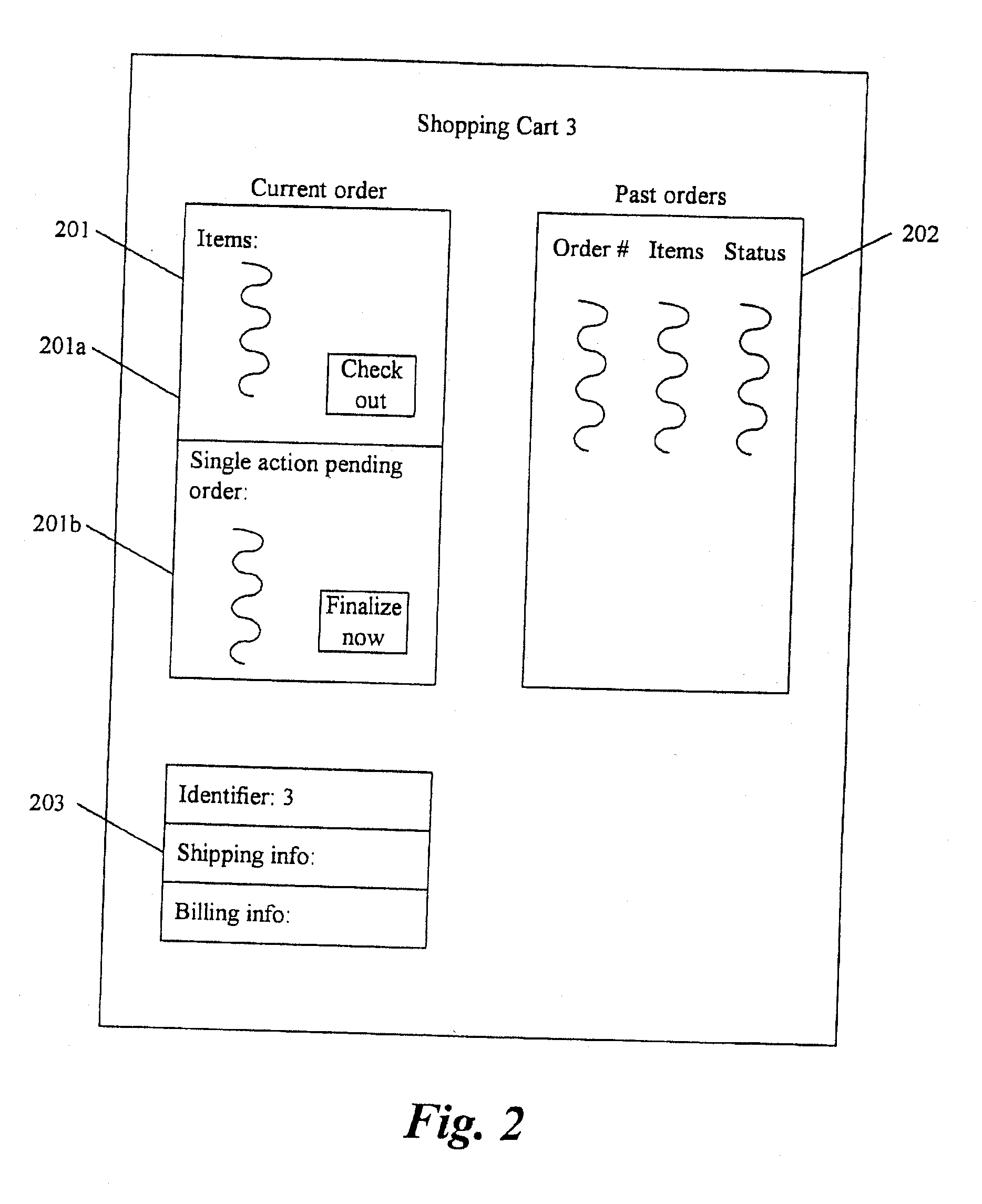
Method and system for electronic commerce using multiple roles
A computer system for conducting electronic commerce. The system provides multiple electronic shopping carts for each user. Each electronic shopping cart has an indication of items currently within the electronic shopping cart and billing and shipment information. The system generates a display that identifies each of the electronic shopping carts and sends the generated display to a user computer system. The system then receives a selection of one of the identified electronic shopping carts from the user computer system and receives a selection of an item from the user computer system. In response to receiving the selection of the item, the system adds the item to the selected electronic shopping cart. The system then receives an indication to checkout the items in the selected electronic shopping cart from the user computer system. In response to receiving the indication to checkout, the system ships the items in the selected electronic shopping cart in accordance with the shipment information of the selected electronic shopping cart and bills for the items in the selected electronic shopping cart in accordance with the billing information for the selected electronic shopping cart. The system thus allows a user to select each of the electronic shopping carts for adding items to each electronic shopping cart.
Owner:AMAZON COM
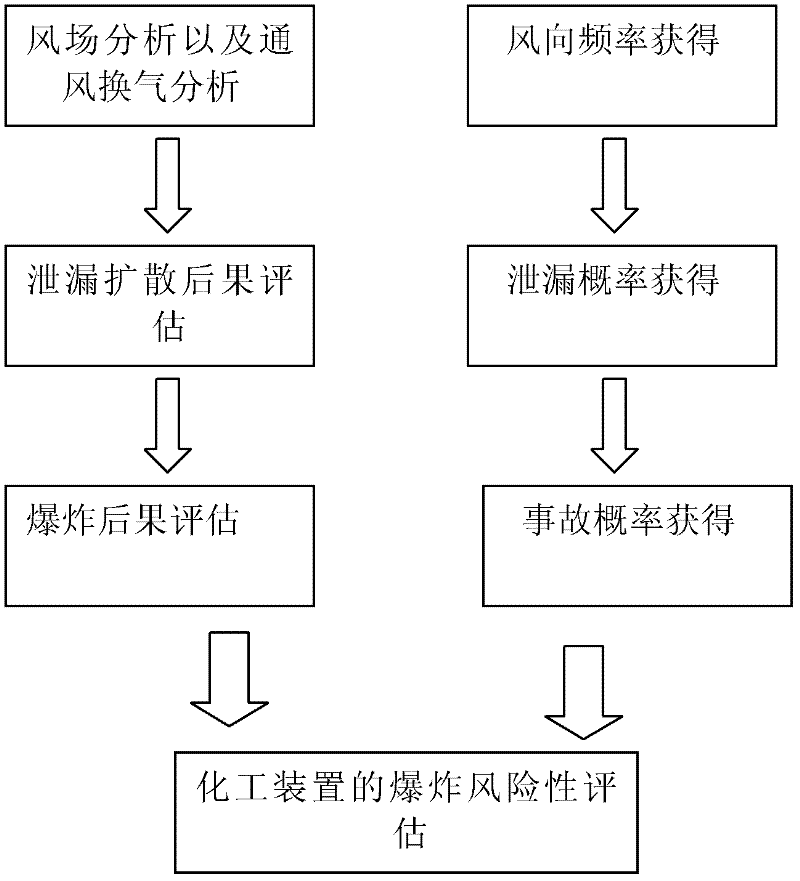
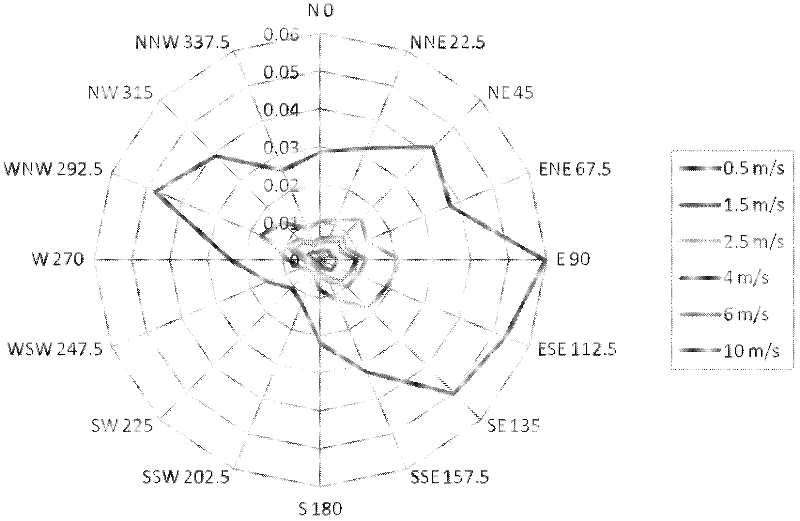
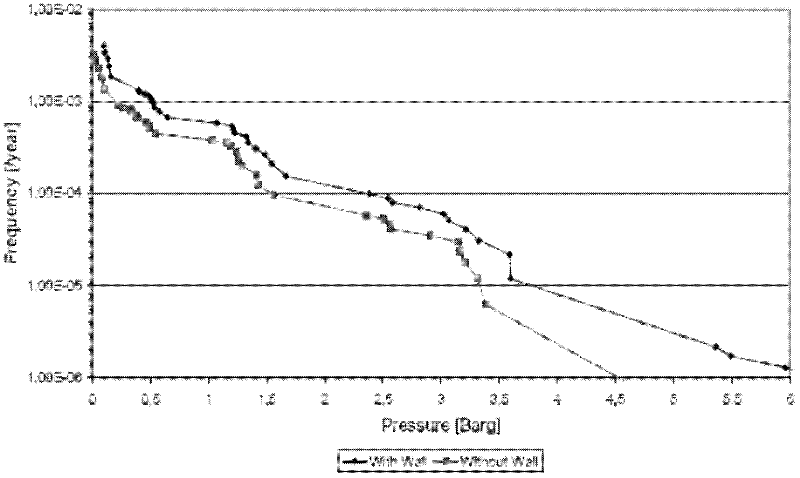
Method and system for evaluating explosion risk of chemical device by utilizing computer
InactiveCN102509003AComprehensive consideration of explosion riskThe results are reasonably accurateSpecial data processing applicationsSystem of systemsRisk evaluation
The invention relates to a method for evaluating explosion risk of a chemical device by utilizing a computer, comprising the following steps of: firstly, calculating limiting pressure when the chemical device explodes under different scenes by utilizing field meteorological data and data obtained by ambient environment of the chemical device; secondly, calculating by utilizing the actual data in production to obtain the explosion probability that the chemical device has an explosion accident; and thirdly, forming an accumulated probability-explosion effect evaluation curve by utilizing the limiting pressure when the chemical device explodes in the first step and the explosion probability that the chemical device has the explosion accident, and finally evaluating the explosion risk of the chemical device. The method and system for evaluating the explosion risk of the chemical device provided by the invention systematacially consider an accident occurrence and development process, and the explosion risk of the chemical device can be comprehensively considered by combining with influence of factors such as an accident probability and the like, thus a result is more reasonable and accurate.
Owner:CHINA PETROLEUM & CHEM CORP +1
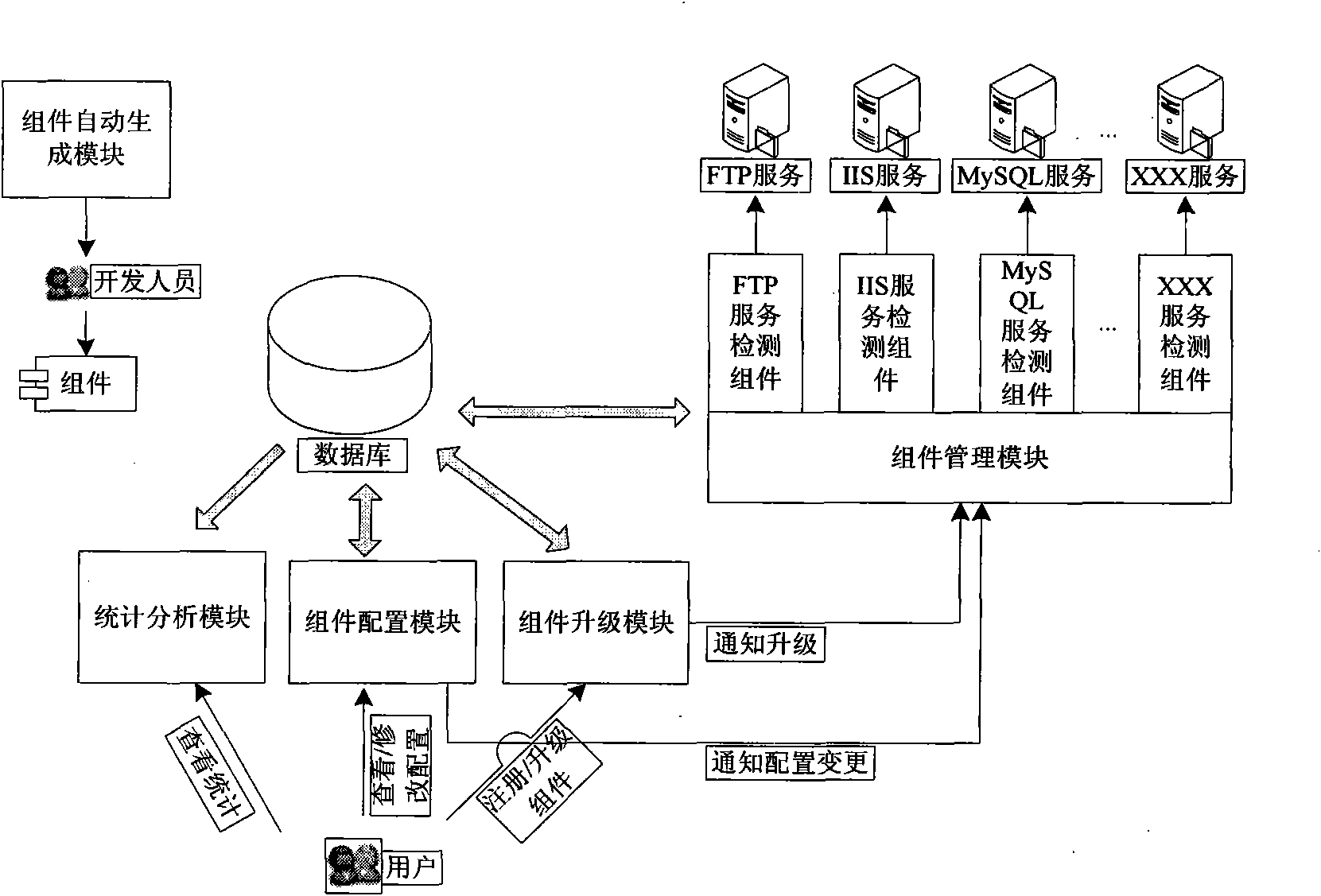
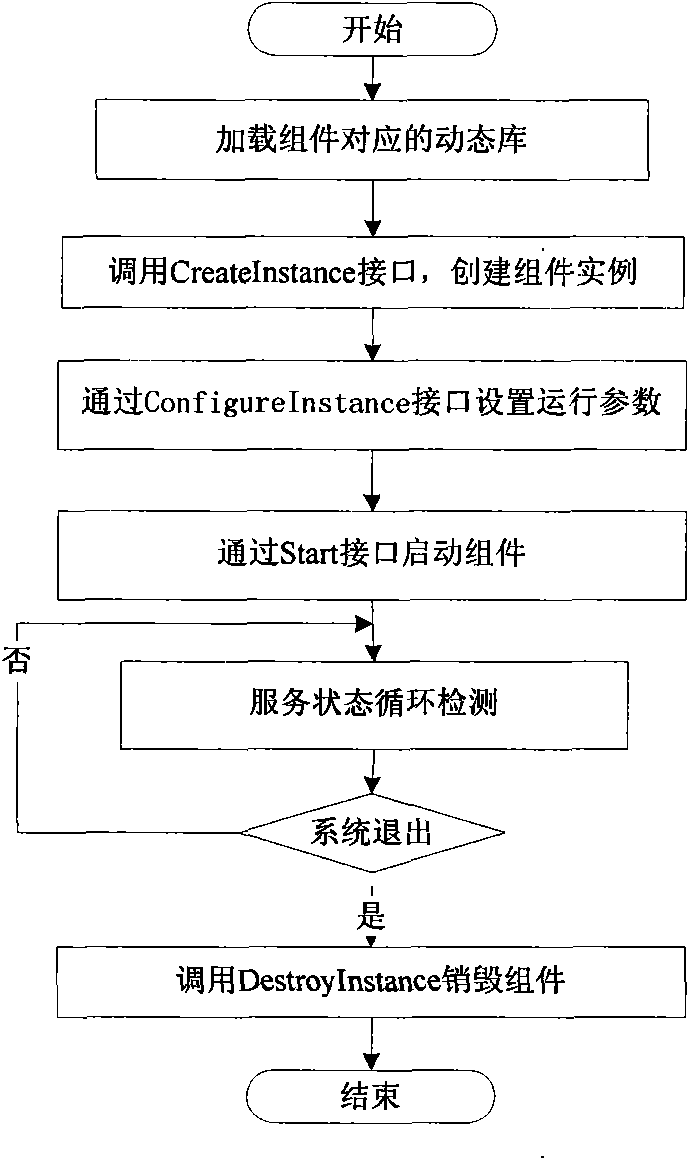
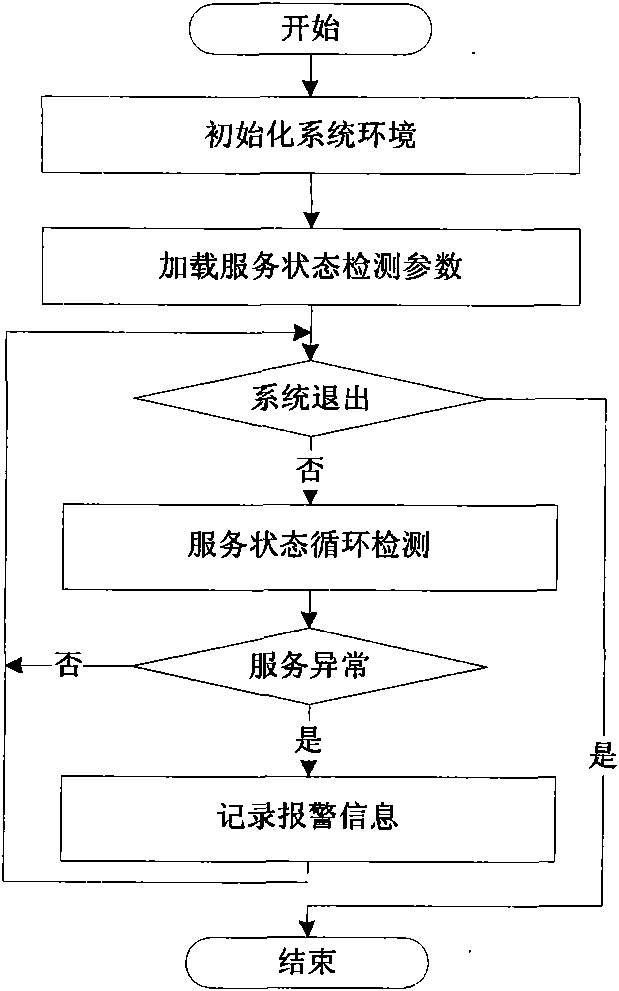
Service state online detection method and system based on components
InactiveCN101840370AImprove efficiencyGood real-time performanceHardware monitoringDynamic ExtensionSoftware engineering
The invention relates to a service state online detection method and system based on components, belonging to the computer field. The system comprises a component automatic generation module, a component management module, a component updating module, a component configuration module, a service state detection module, a statistics and analysis service module and a component output interface. The detection method comprises the following steps: initializing the system, starting the components, component executing, changing the configurations of the components, updating the components and logging out the system. The system of the invention adopts component architecture to provide the service state detection function automatically, efficiently and instantly; the system supports dynamic extension, and can update the components one by one without influencing the system; and the system can form a component gallery supporting various service state detections and effectively realize the reuse and accumulation of the technology.
Owner:DATCENT TECH
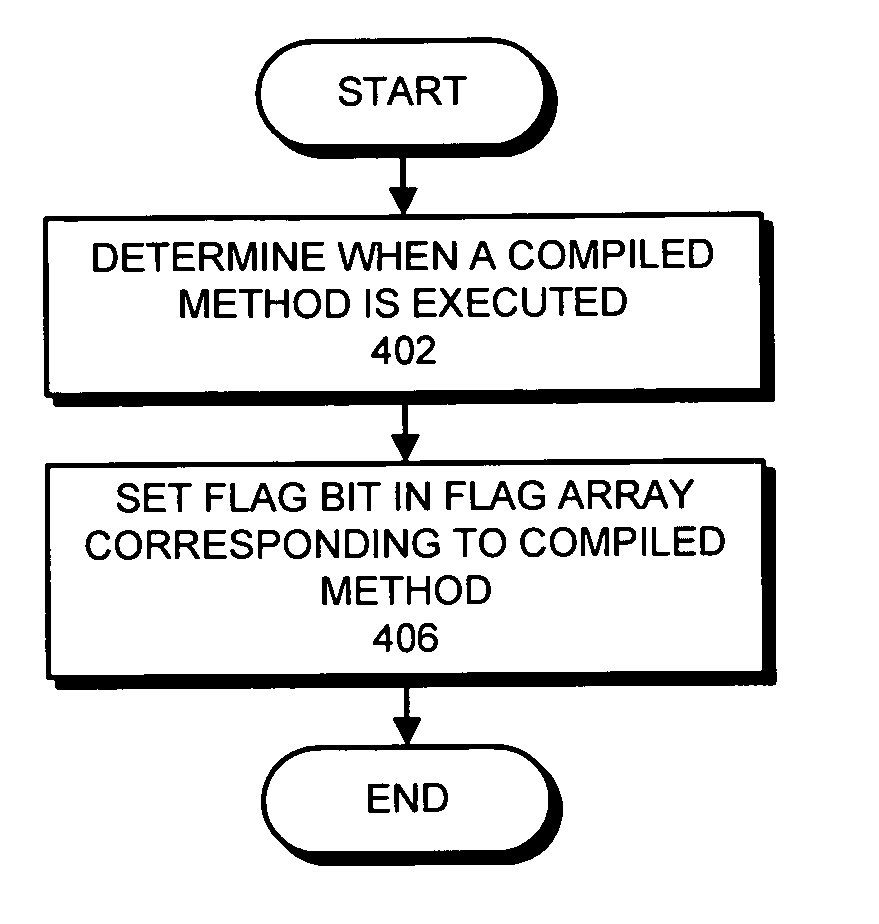
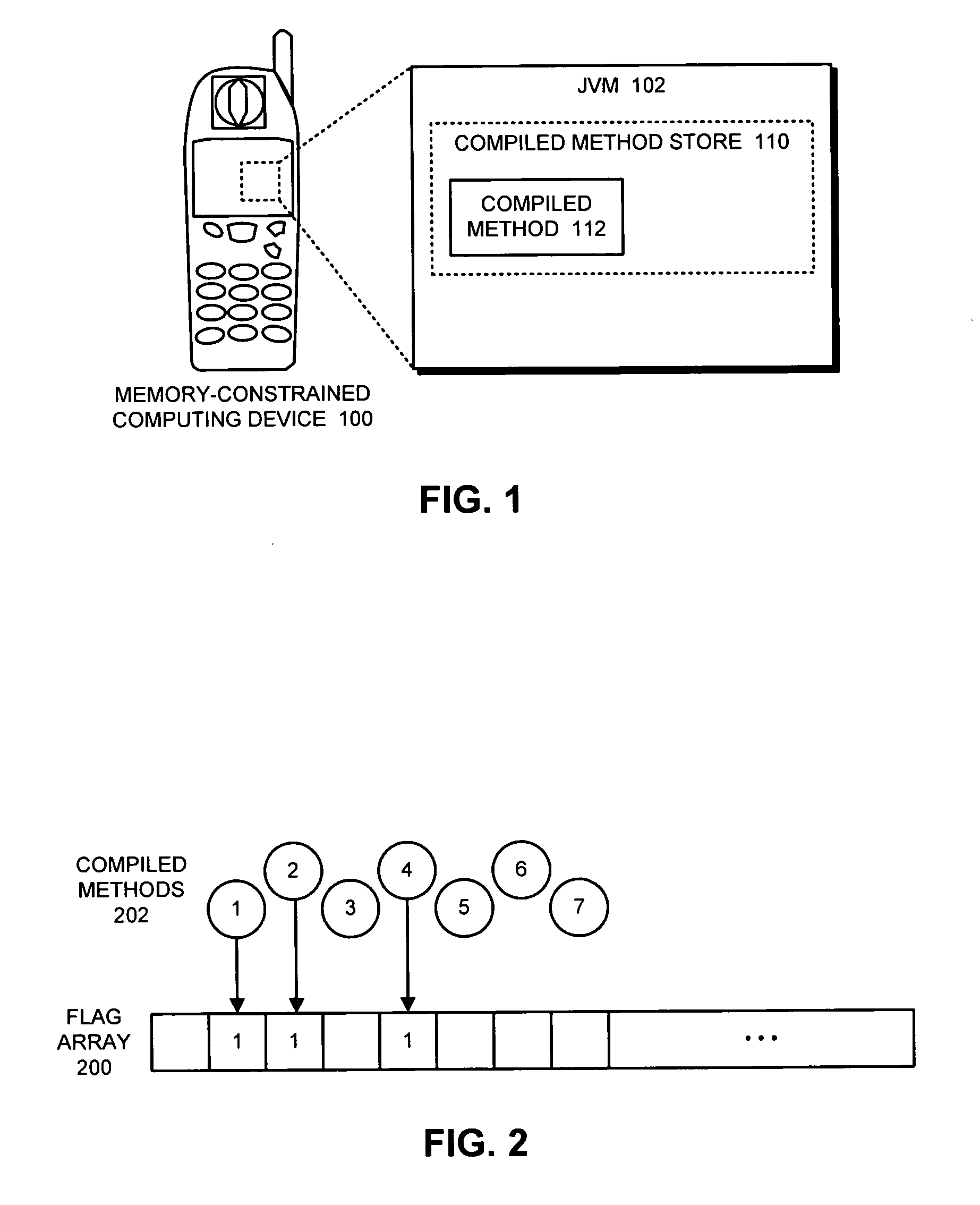
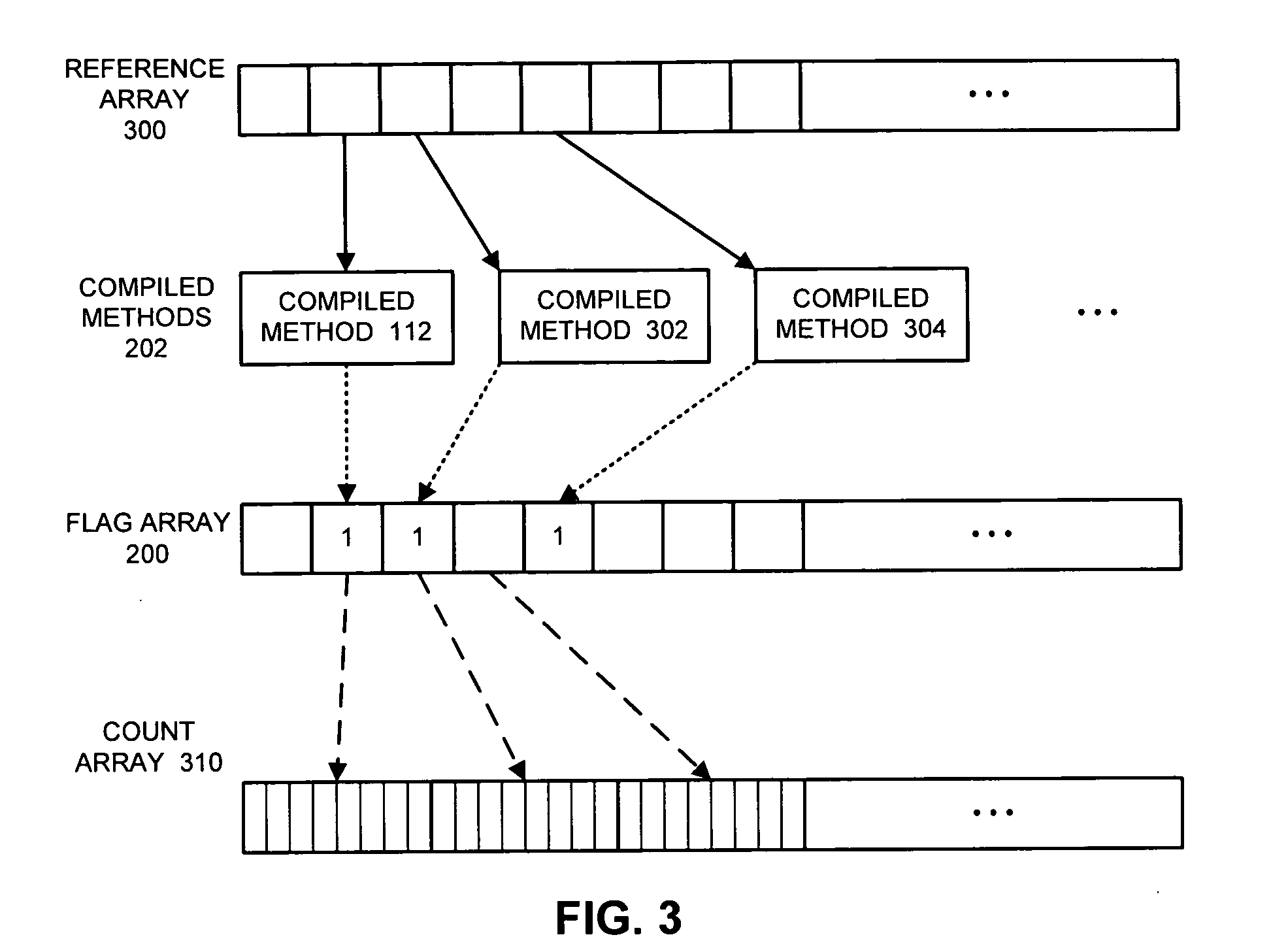
Method and apparatus for determining frequency of execution for compiled methods within a virtual machine
ActiveUS20050198620A1Easy to determineResource allocationHardware monitoringVirtual machineSystem of systems
One embodiment of the present invention provides a system that facilitates determining a frequency of execution of compiled methods within a virtual machine. The system starts by determining if a compiled method is executing. If so, the system sets a flag corresponding to the compiled method to indicate that the compiled method is executing. Periodically, the system scans the flag and increments the value of a corresponding counter if the flag is set, and then resets the flag. Finally, the system analyzes the value of the counter to determine a frequency of execution of the compiled method.
Owner:ORACLE INT CORP
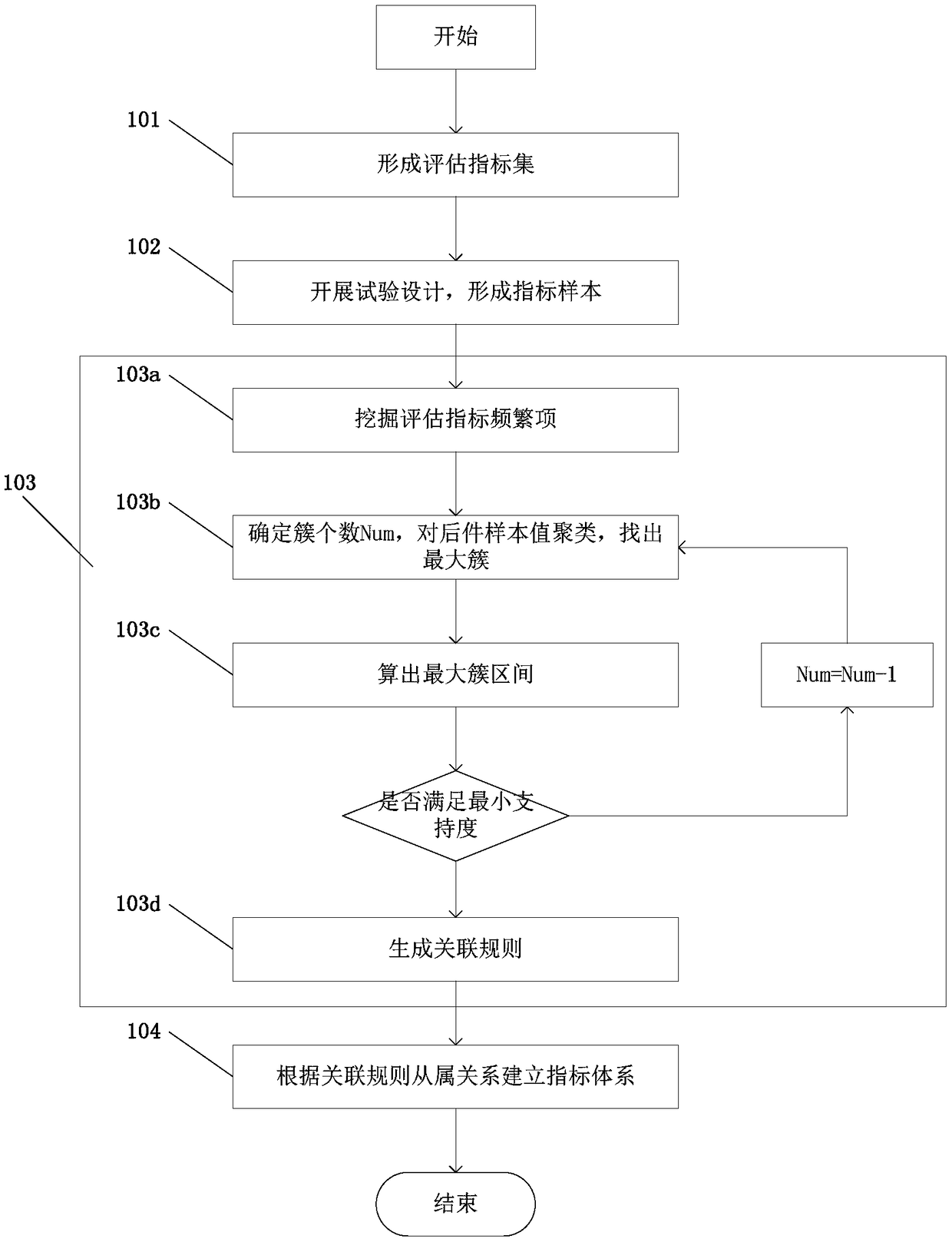
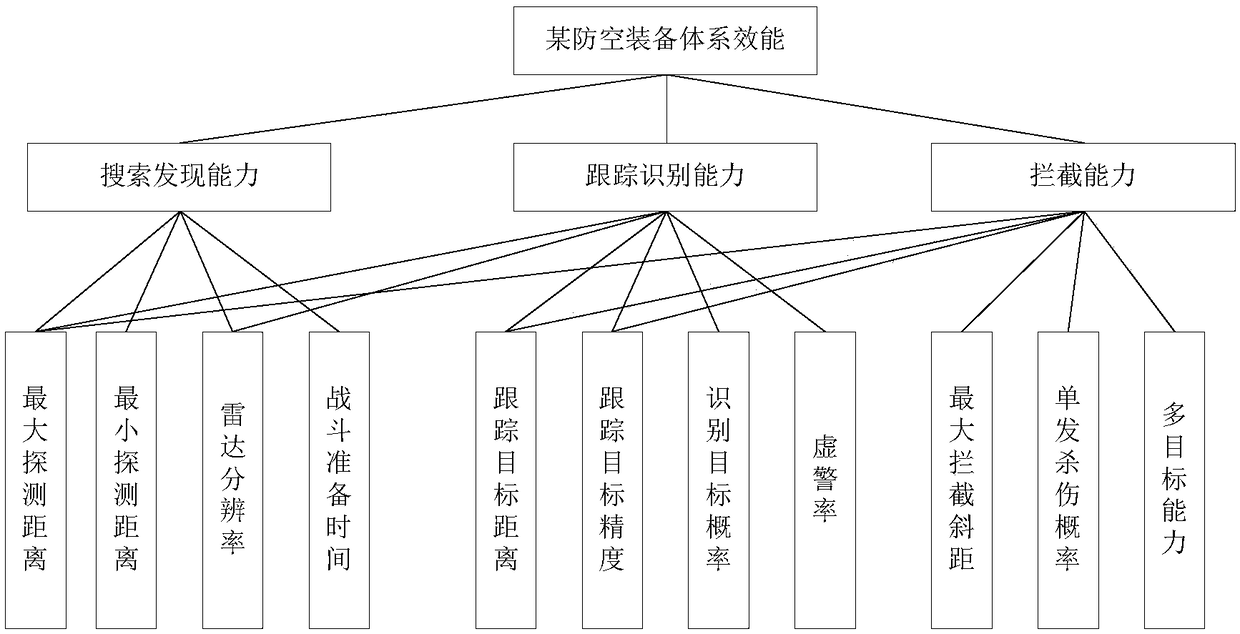
Construction method and system of system effectiveness evaluation index system based on correlation analysis
ActiveCN109409695AThe relationship is accurateCharacter and pattern recognitionDesign optimisation/simulationCorrelation analysisSystem of systems
The invention provides a system effectiveness evaluation index system construction method and system based on association analysis, comprising the steps of primary selection of evaluation index, acquisition of evaluation index sample, extraction of association evaluation index and establishment of evaluation index system. The invention can mine the correlation relationship between the equipment-level performance / efficiency index and the system-level efficiency index. The dynamic discrete method based on clustering analysis is used to realize the discretization of the consequent parts of association analysis, and the result can reflect the relationship between the system-level efficiency index and the minimum support degree, which is more accurate than the static discrete method based on equal depth, equal width and so on. It solves the problem that it is difficult to establish a scientific hierarchical index system by traditional methods because of the deep hinge and serious index coupling among the equipment systems, and provides a new idea and method for the index system construction of other complex problems.
Owner:SHANGHAI INST OF ELECTROMECHANICAL ENG
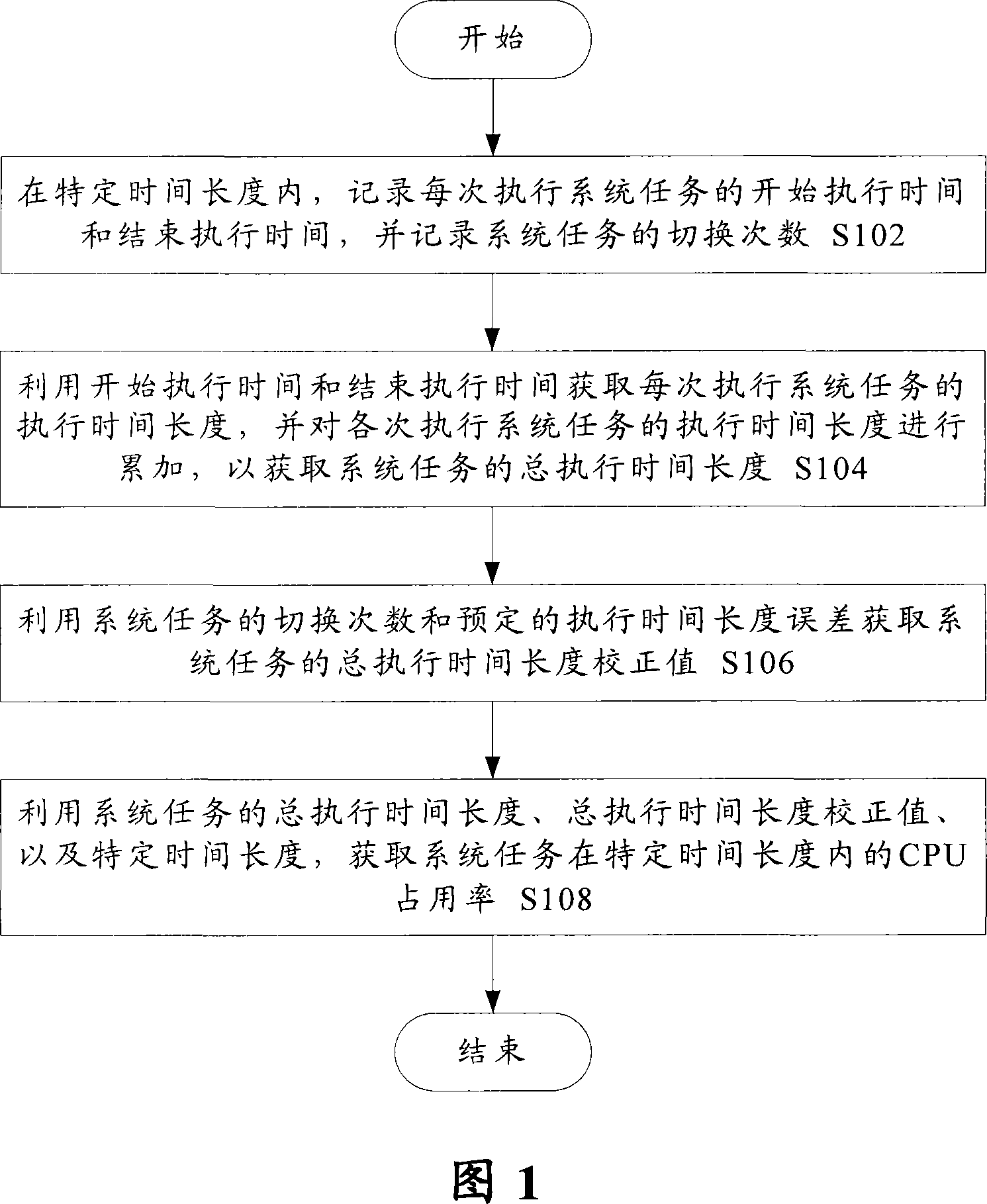
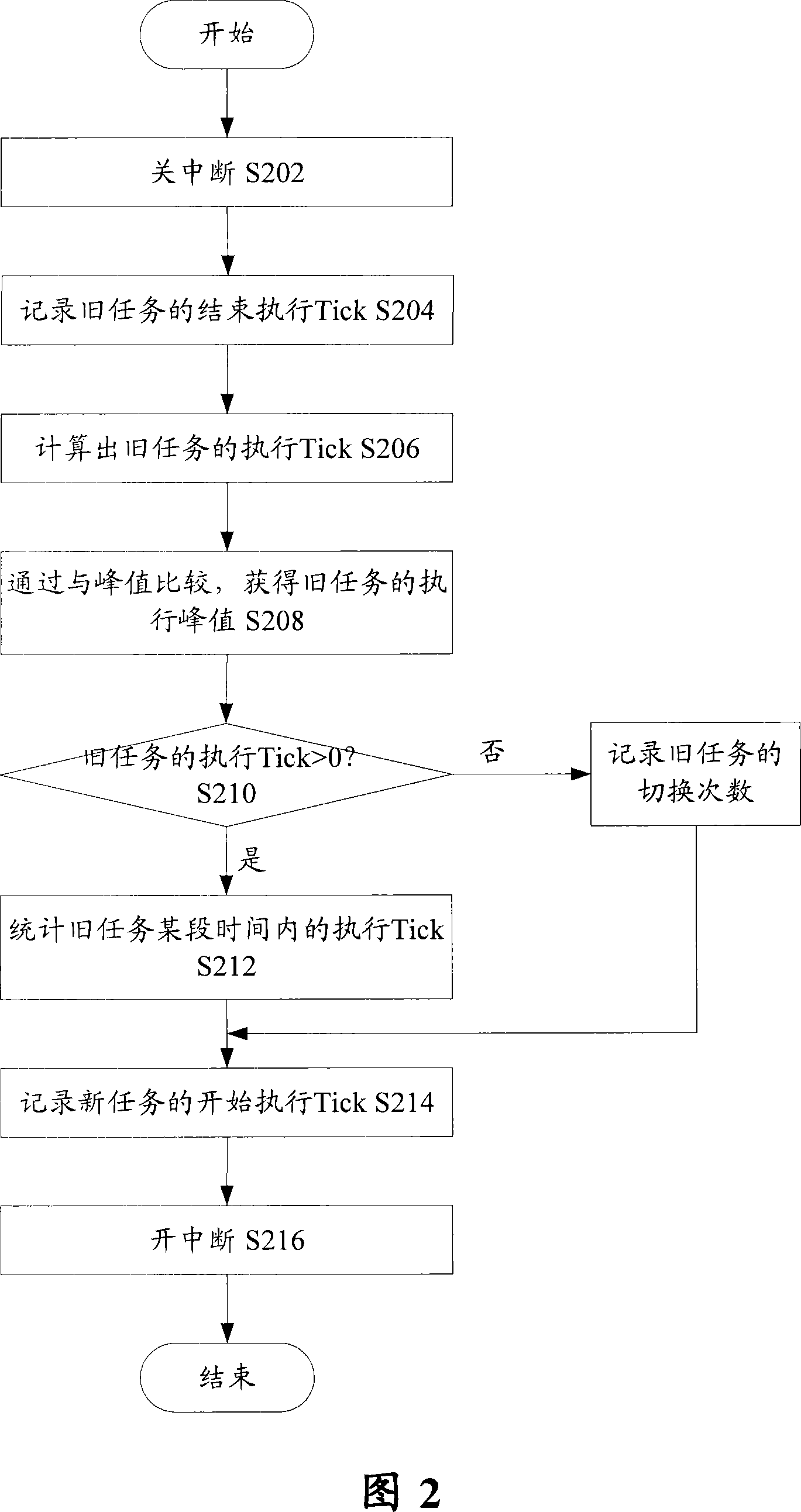
CPU occupancy rate detection method and system of system task
InactiveCN101178688AAccurate detectionHardware monitoringSoftware testing/debuggingOccupancy rateStart time
The invention discloses a central processing unit occupying rate testing method and a system of a system task; wherein, the method comprises the following steps; the invention records the execution starting time and execution finishing time of each executing system task and records the switching times of the system task; the execution starting time and execution finishing time are utilized to obtain the execution time length of each execution system task and accumulate the execution time length of each execution system task, so as to obtain the total execution time length of the system task; the switching times of the system task and the preset execution time length error are utilized to obtain the total execution time length revising value of the system task; and the total execution time length, total execution time length revising value and particular time length of the system task are utilized to obtain the central processing unit occupying rate in the particular time length of the system task.
Owner:ZTE CORP
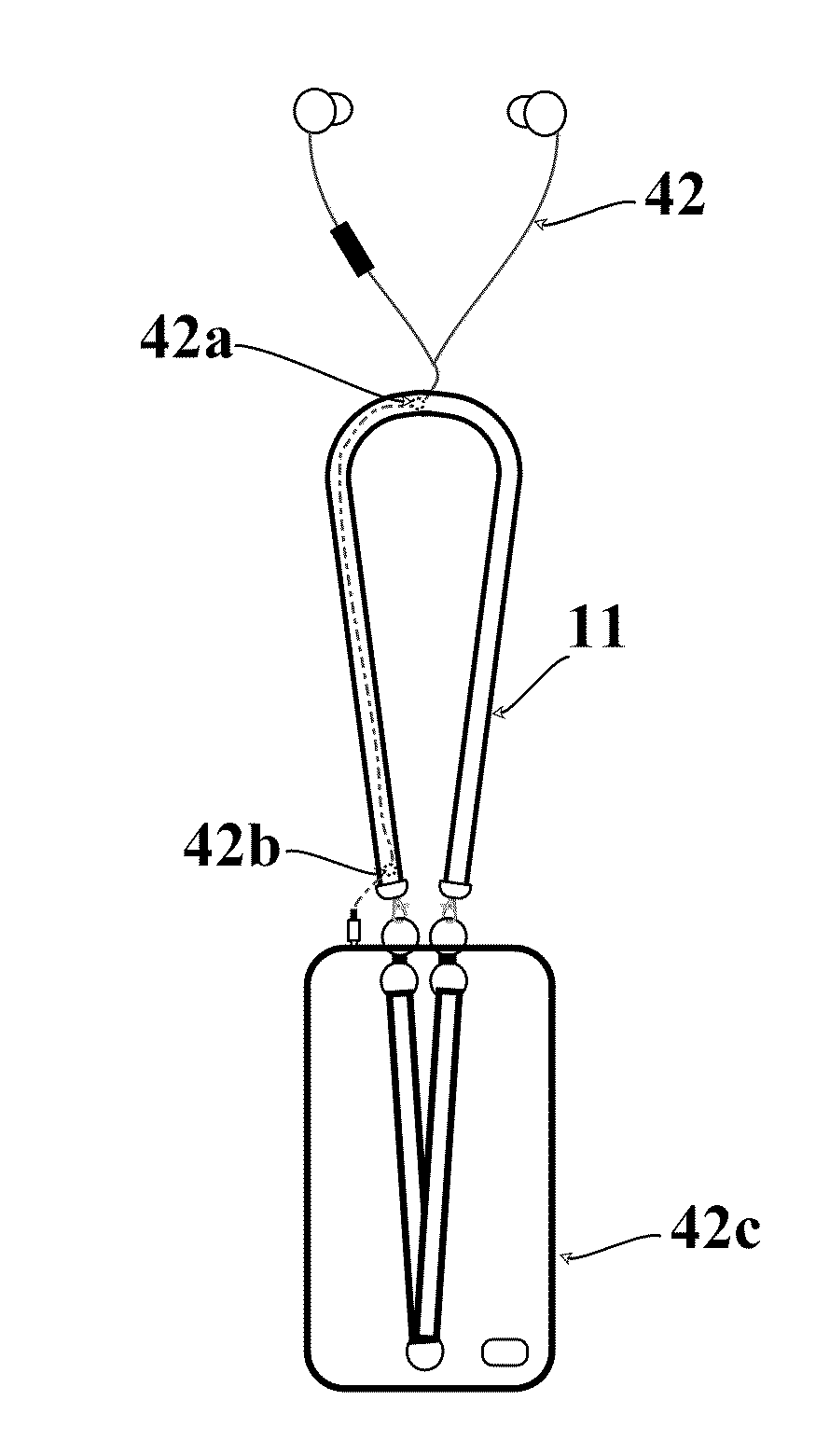
Restraining system for handheld electronic devices
InactiveUS20160007723A1Less-expensive to manufacturePromote resultsTravelling sacksTravelling carriersHand heldSystem of systems
A case-strap system for Handheld Electronic Devices having a case with direct or indirect attachments to receive a handheld electronic device, a strap directly or indirectly mounted on the back of said case with said attachments to receive a user's hand; a handheld electronic device is enclosed inside said case-strap unit, and said strap mounted on the back of said case stretched to receive and catch user's hand; unit is flipped to rest on top of user's hand or wrist; a case-strap is hooked with a lanyard, coupled with an earphone's audio cord attached on the surface or inserted between layers of said lanyard; one end of earphone's audio cord is connected to the device's audio jack and to a user's ear(s); a case-strap unit is enclosed into a magnetized wrist strap system to carry, hold, or manage the handheld electronic device inside said case-strap unit.
Owner:GEOR JEAN EDRICE
System and method for heuristically optimizing a large set of automated test sets
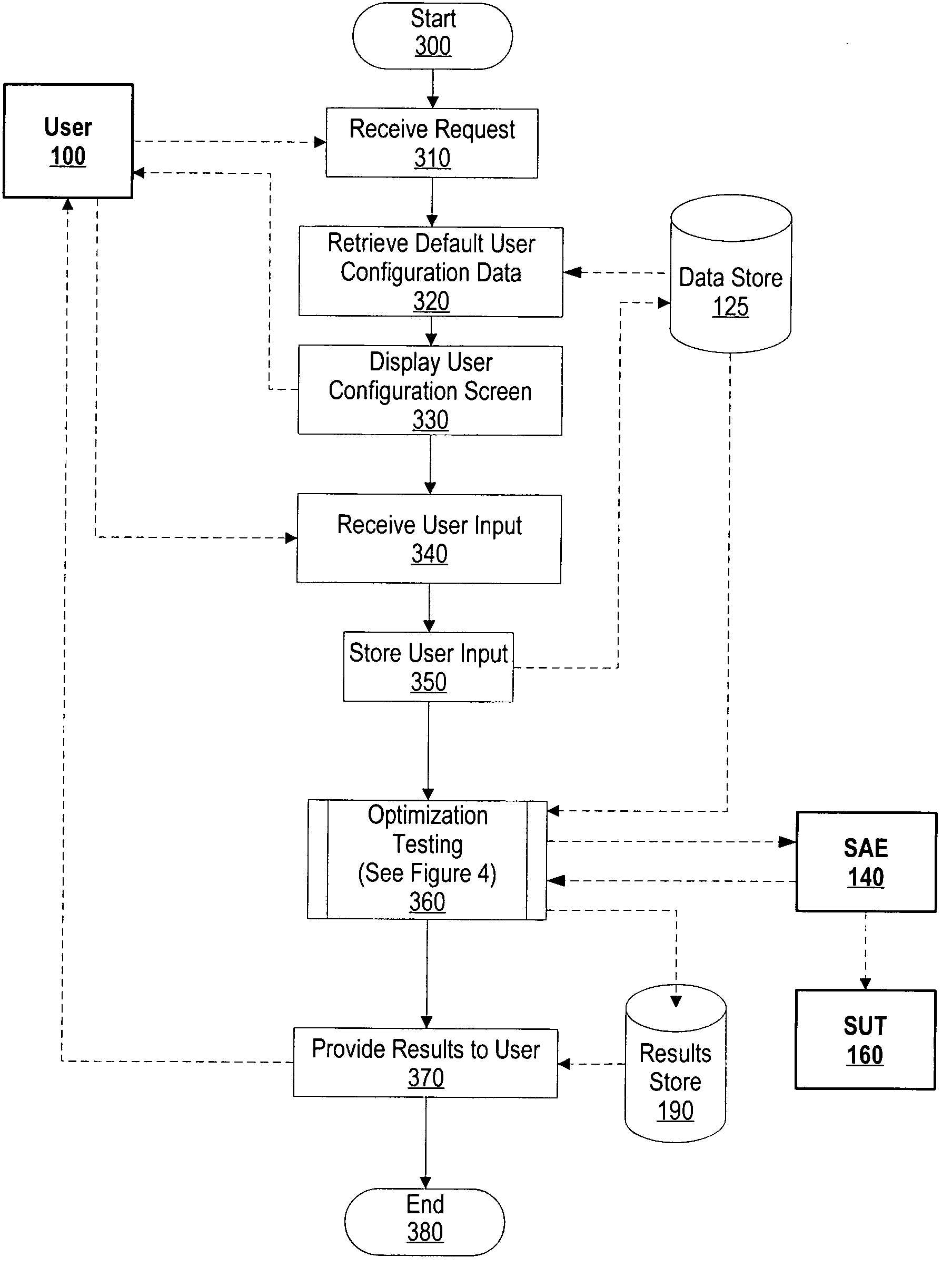
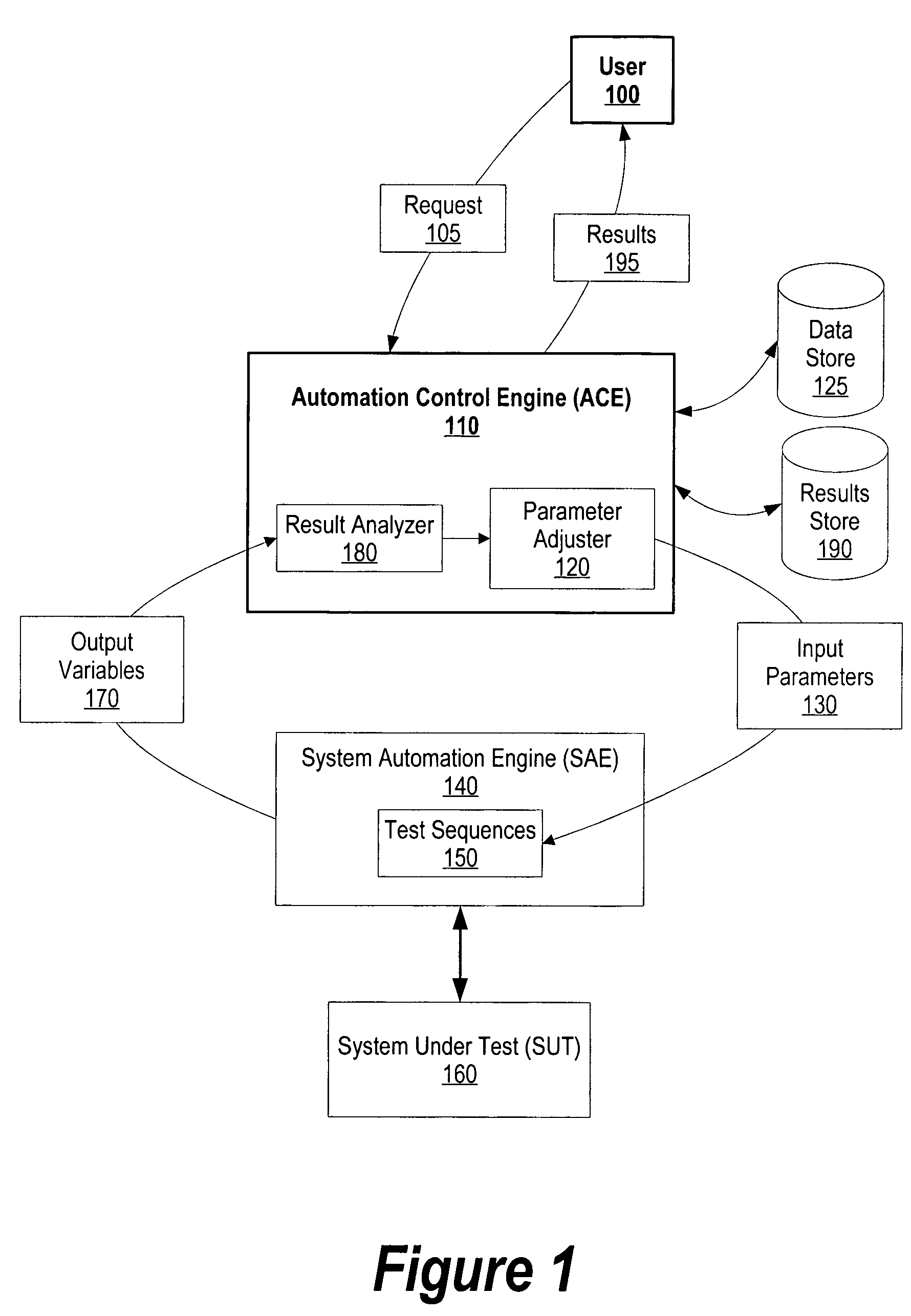
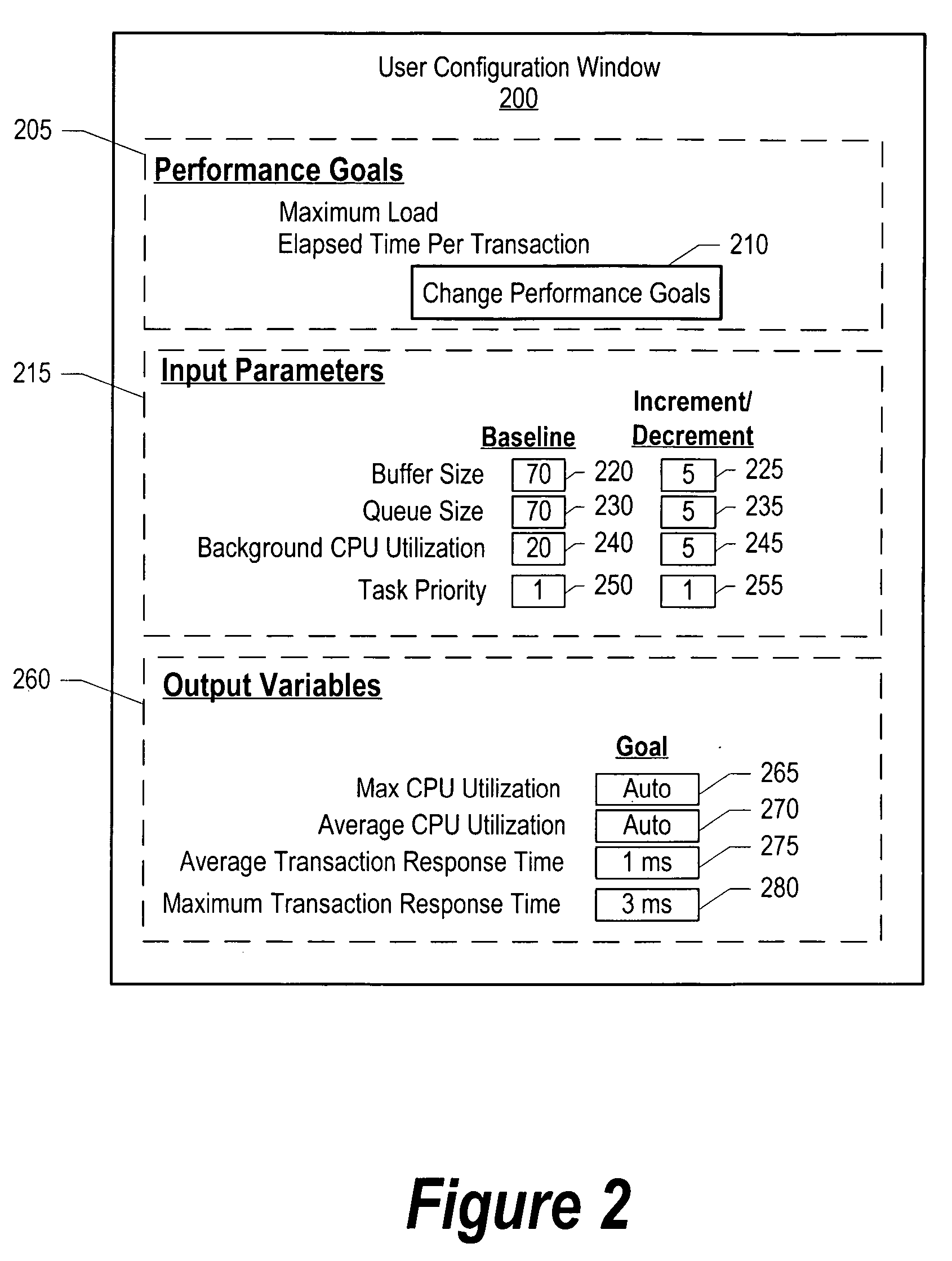
InactiveUS20050154559A1Amount of timeDigital computer detailsNuclear monitoringSystem under testSystem of systems
A system and method for heuristically optimizing a large set of automated test sets is presented. An automation control engine is used as a front end to a system automation engine. The automation control engine provides a set of input parameters, such as a buffer size and queue size, to the system automation engine. The system automation engine uses the input parameters along with a set of test sequences, to test a system under test. The system automation engine receives output variables from the system under test based upon the test, and sends the output variables to automation control engine. The automation control engine adjusts the input parameter values until the output variables meet one or more performance goals.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com