Patents
Literature
13037 results about "Network element" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
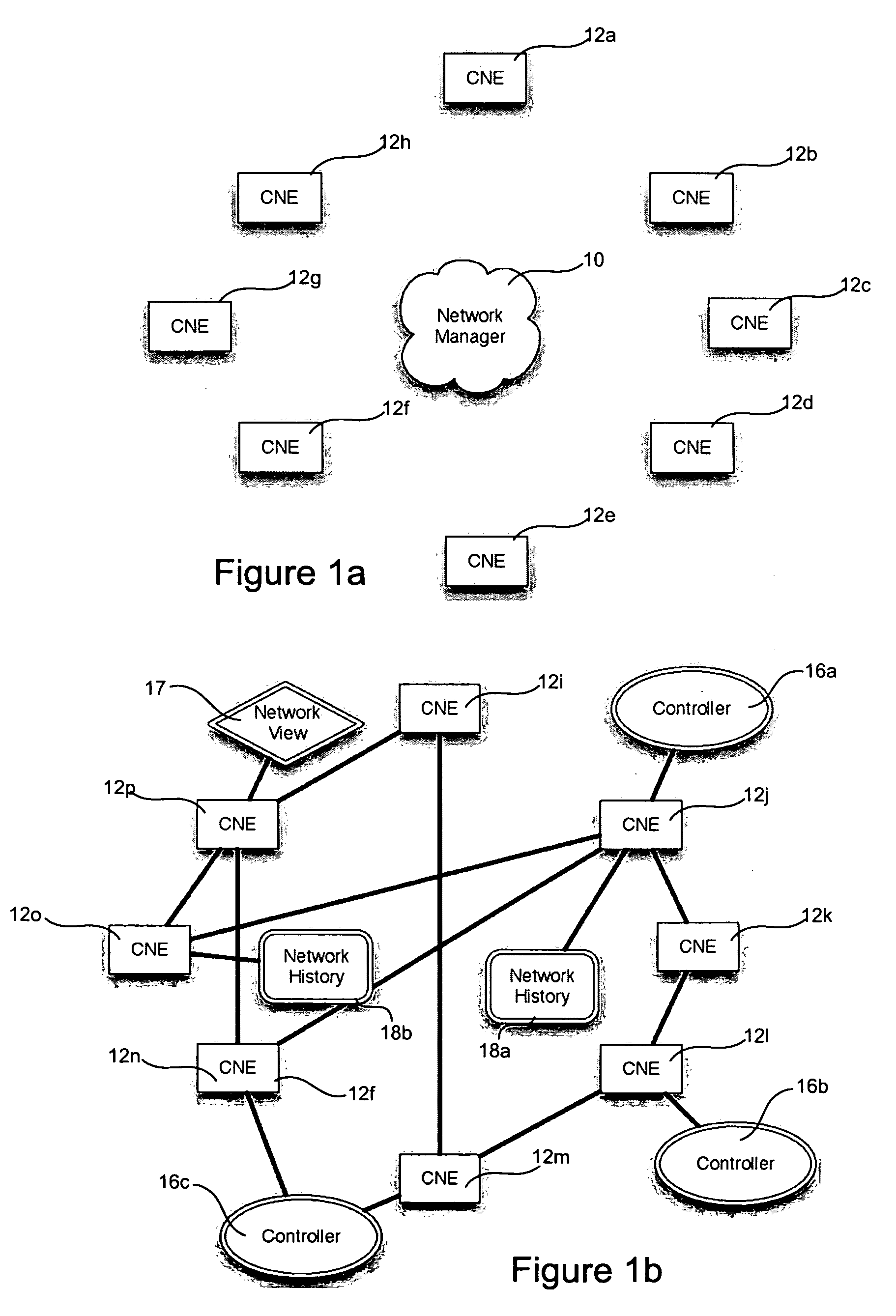
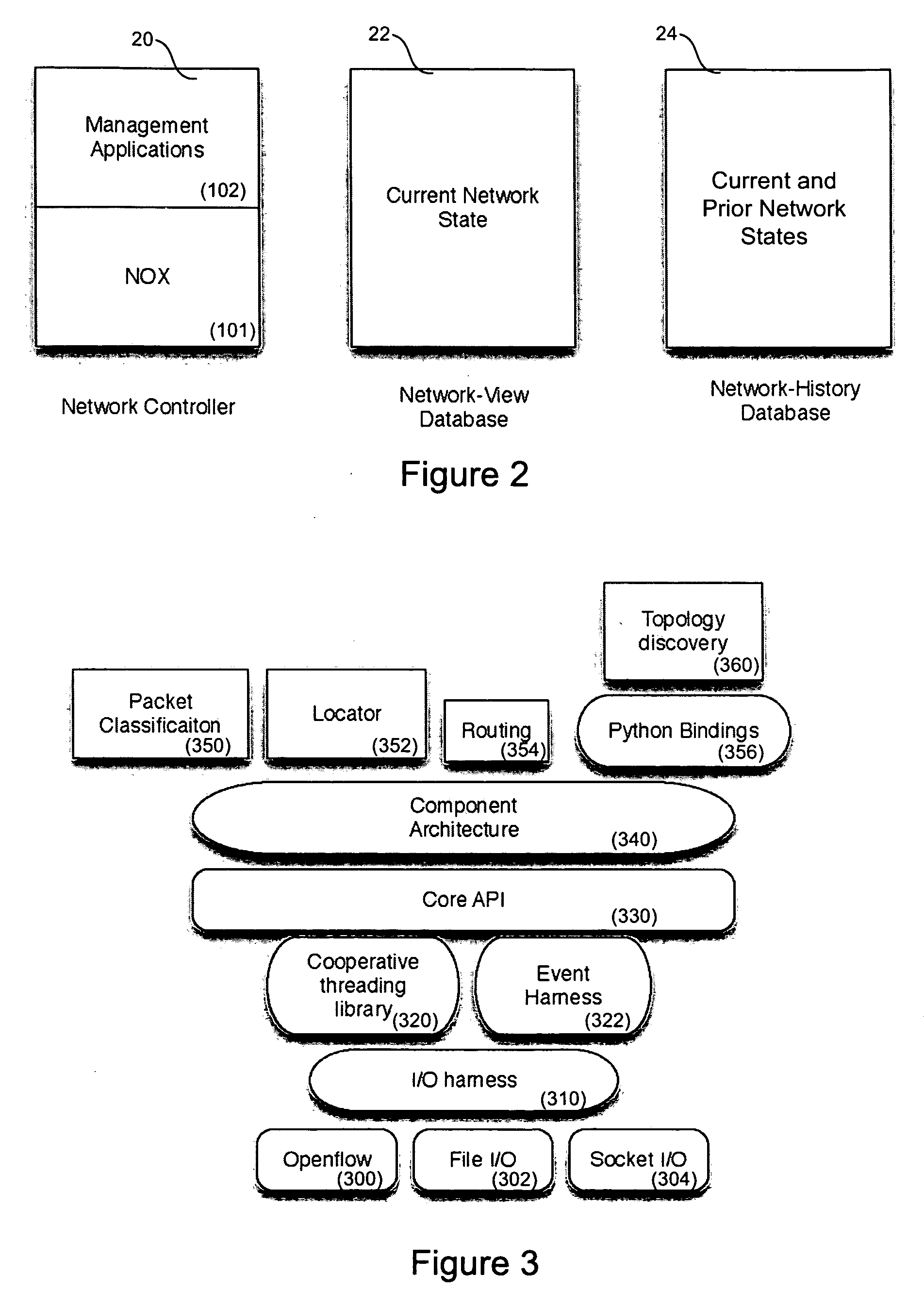
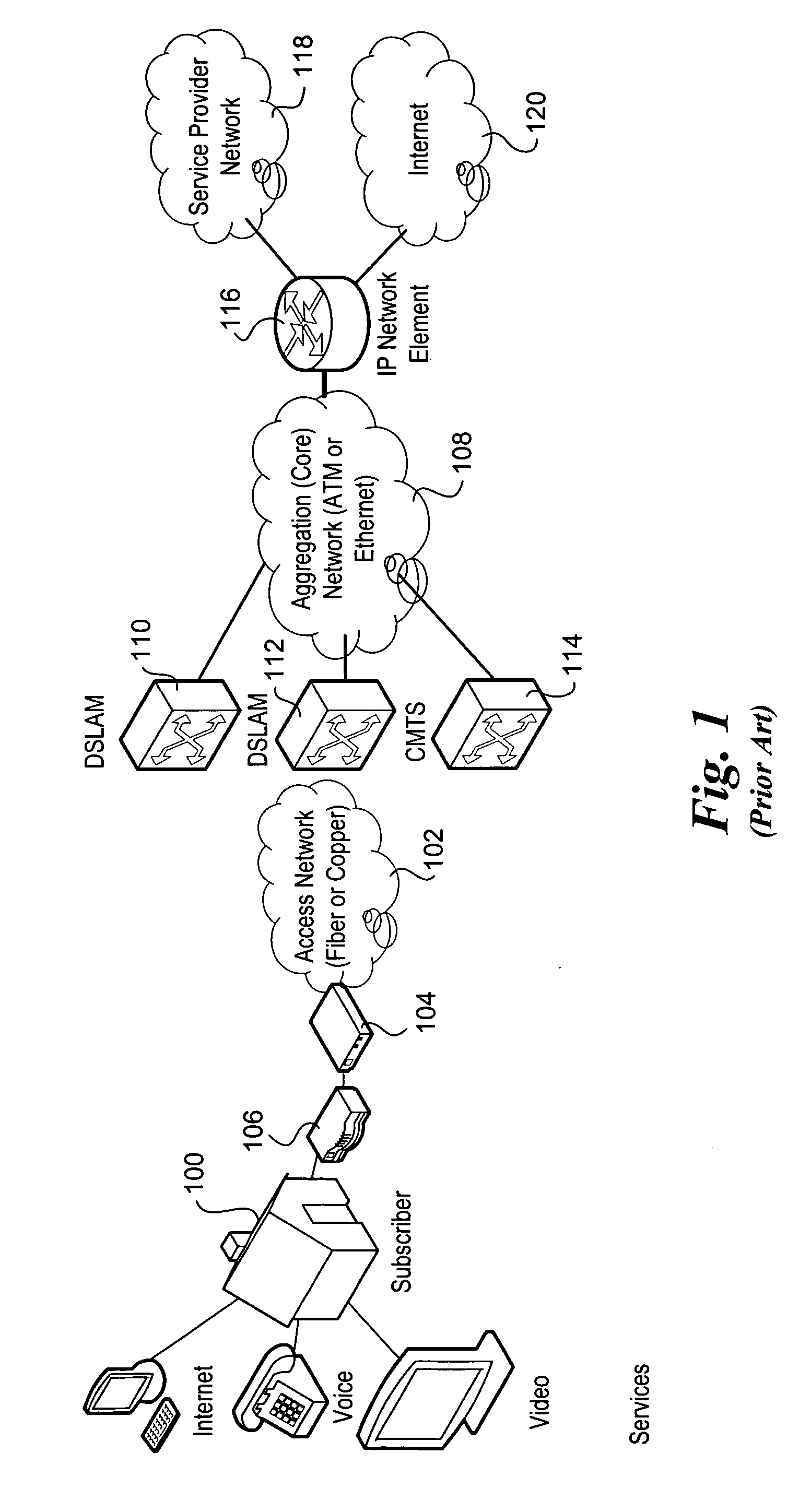
In computer networks, a network element is a manageable logical entity uniting one or more physical devices. This allows distributed devices to be managed in a unified way using one management system. According to the Telecommunications Act of 1996, the term 'network element' means a facility or equipment used in the provision of a telecommunications service. Such term also includes features, functions, and capabilities that are provided by means of such facility or equipment, including subscriber numbers, databases, signaling systems, and information sufficient for billing and collection or used in the transmission, routing, or other provision of a telecommunications service.
Software fault management system
InactiveUS6012152ASupervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsInformation repositoryManagement information systems
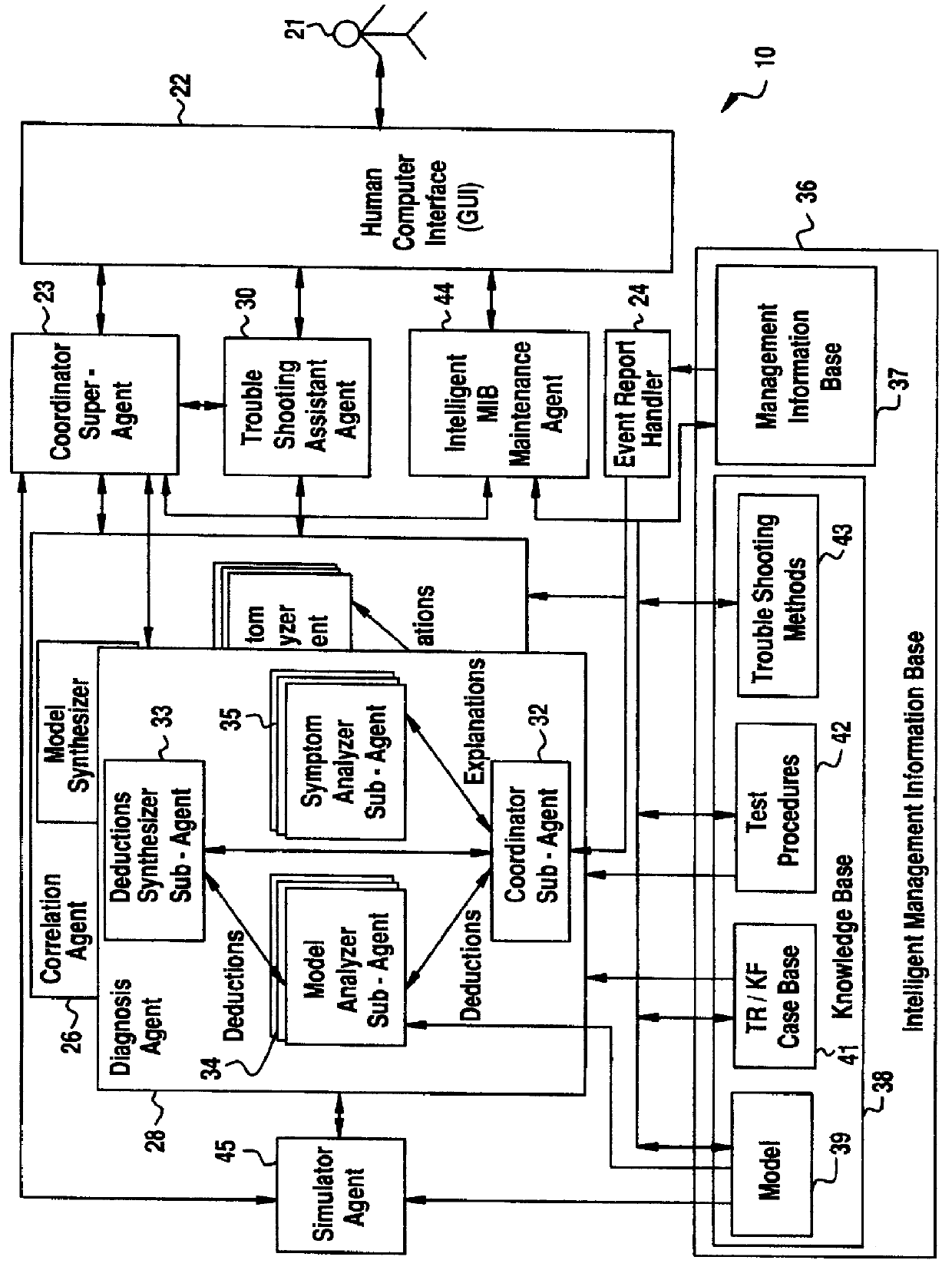
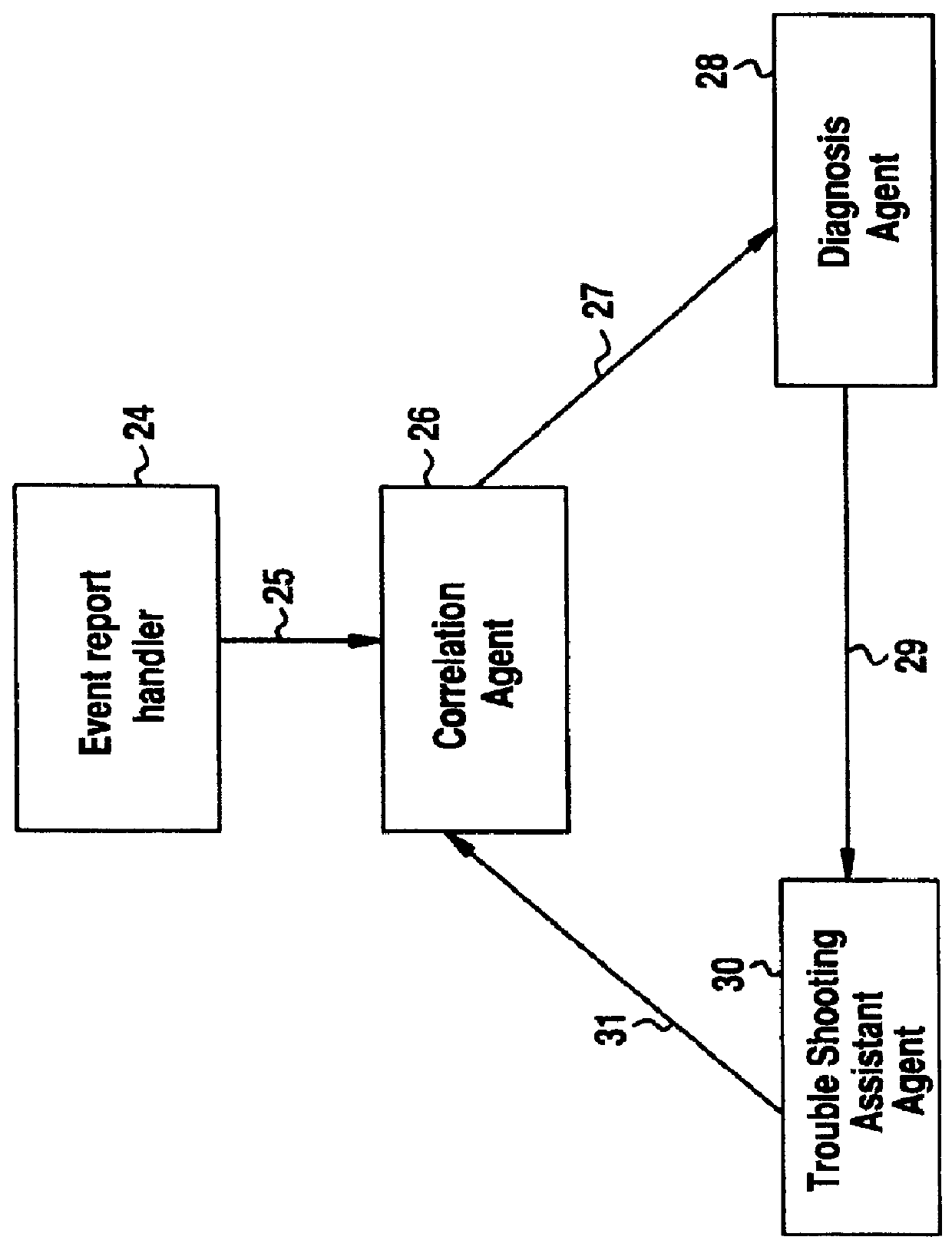
A Software Fault Management (SFM) system for managing software faults in a managed mobile telecommunications network. The SFM system includes an Intelligent Management Information Base (I-MIB) comprising a Management Information Base (MIB) and a Knowledge Base (KB) having a functional model of the managed network and a trouble report / known faults (TR / KF) case base. The SFM system also includes an intelligent multi-agent portion having a plurality of agents which process the software faults utilizing the functional model from the I-MIB, case-based information, and other management information. The I-MIB and the intelligent multi-agent portion are compliant with Telecomunications Management Network (TMN) principles and framework. Fault management is both proactive and reactive. The SFM system is made independent of technology-specific implementations by representing the underlying switch design knowledge in a modular and changeable form which is then interpreted by the intelligent multi-agent portion. A clear separation is maintained between the generic procedural inference mechanisms and agents, and the specific and explicit models of the different network elements of a mobile telecommunications network.
Owner:TELEFON AB LM ERICSSON (PUBL)
Surface wave power line communications system and method
InactiveUS20050111533A1Electric signal transmission systemsInterconnection arrangementsCommunication interfaceCommunications system
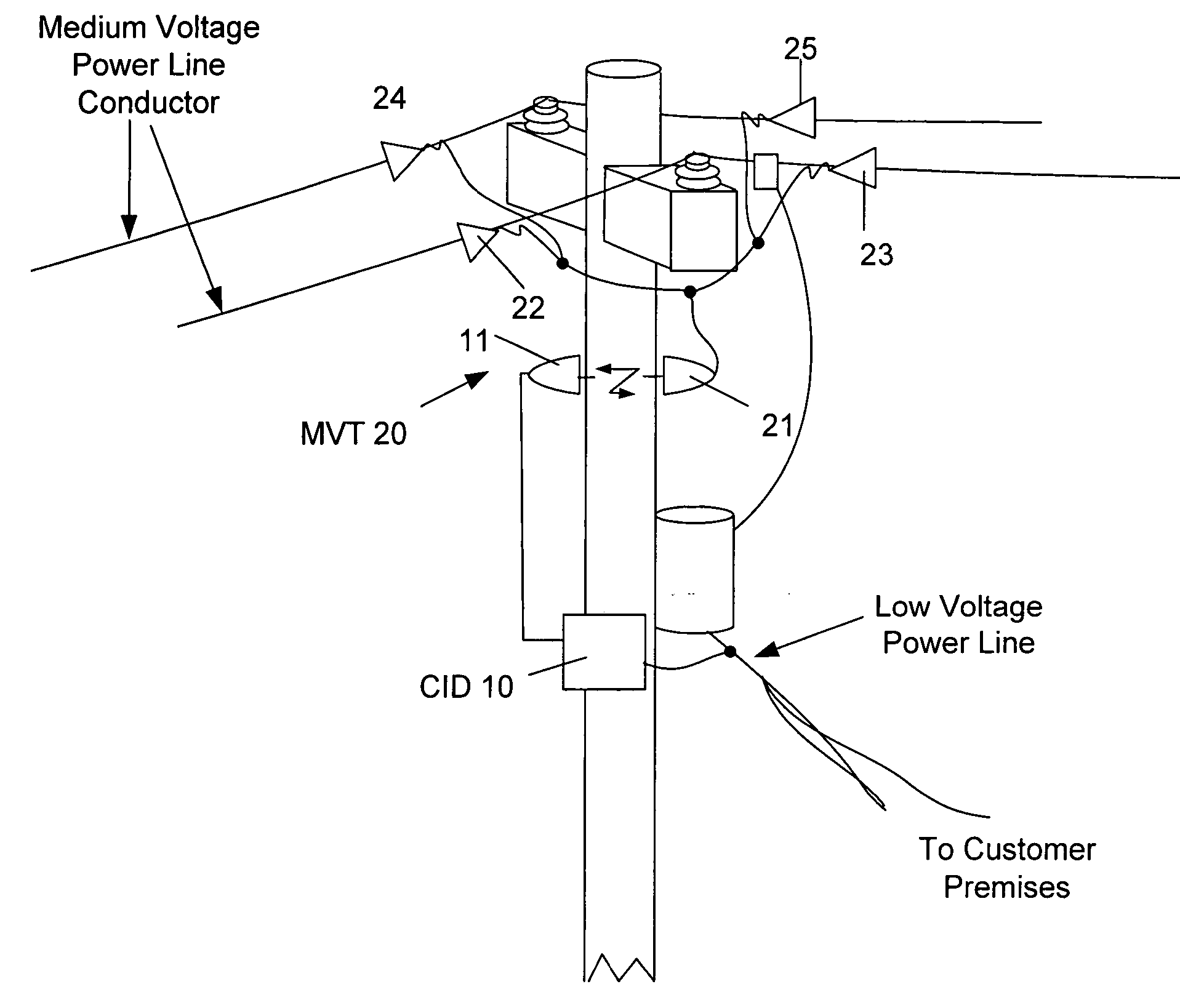
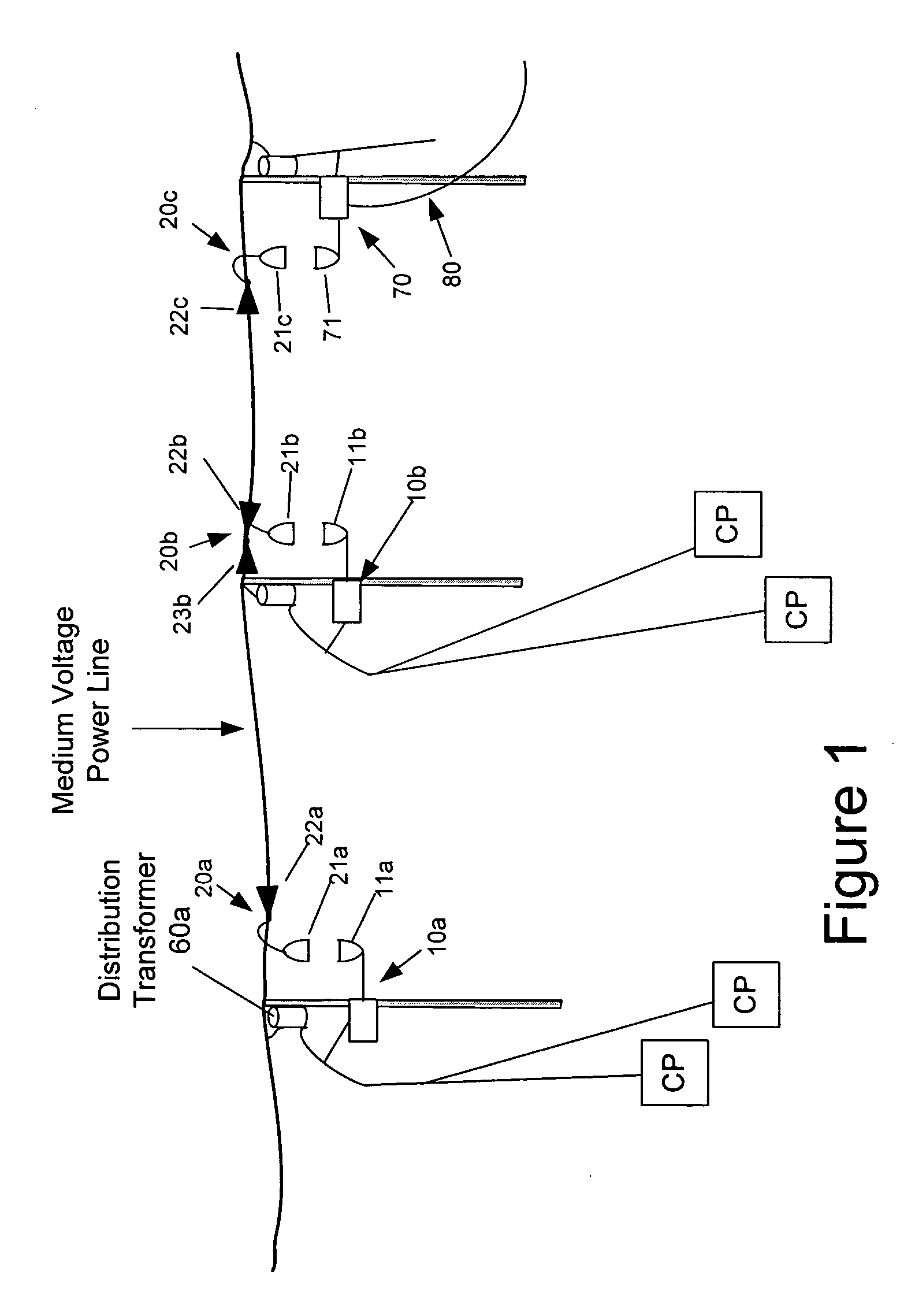
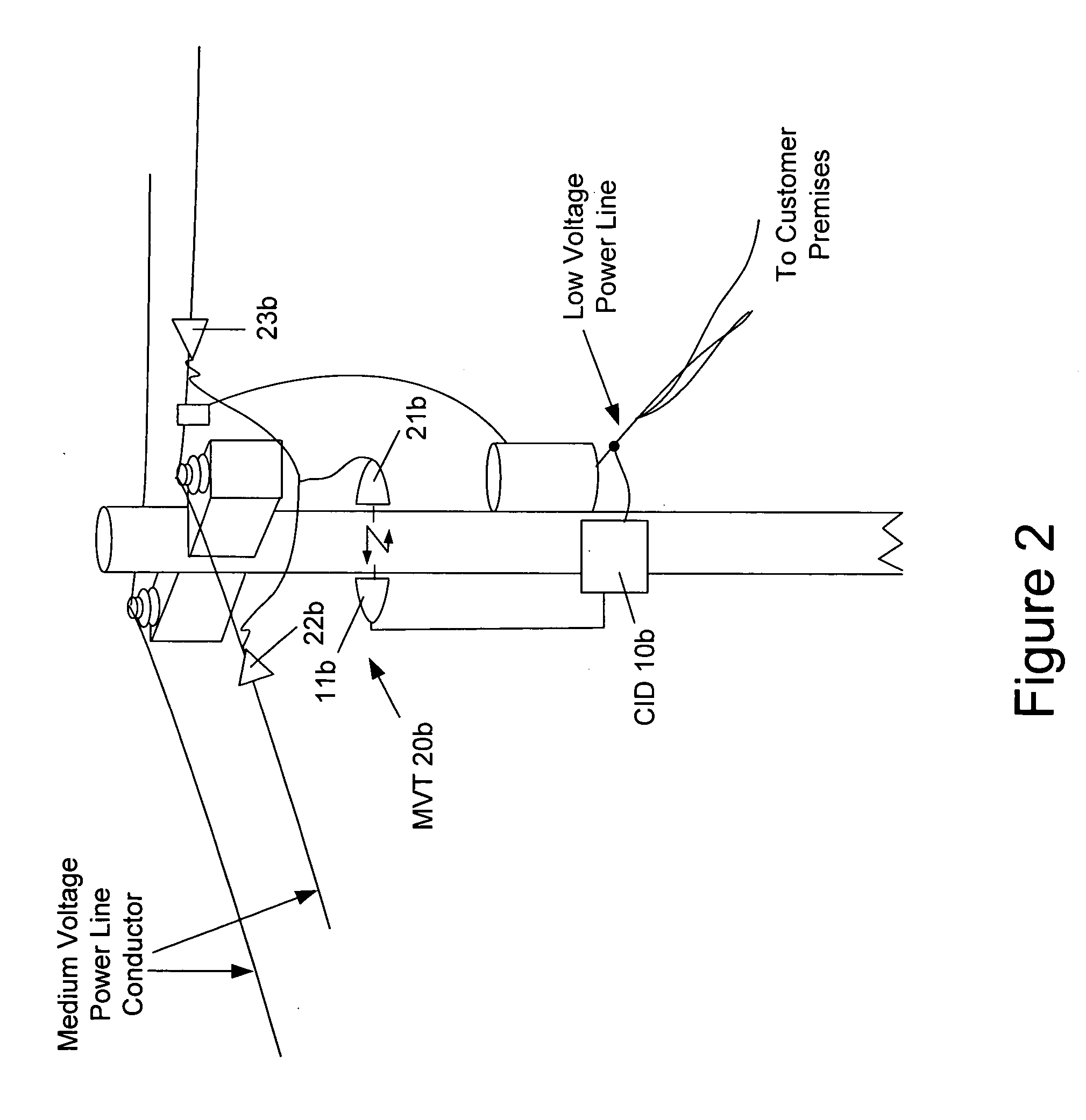
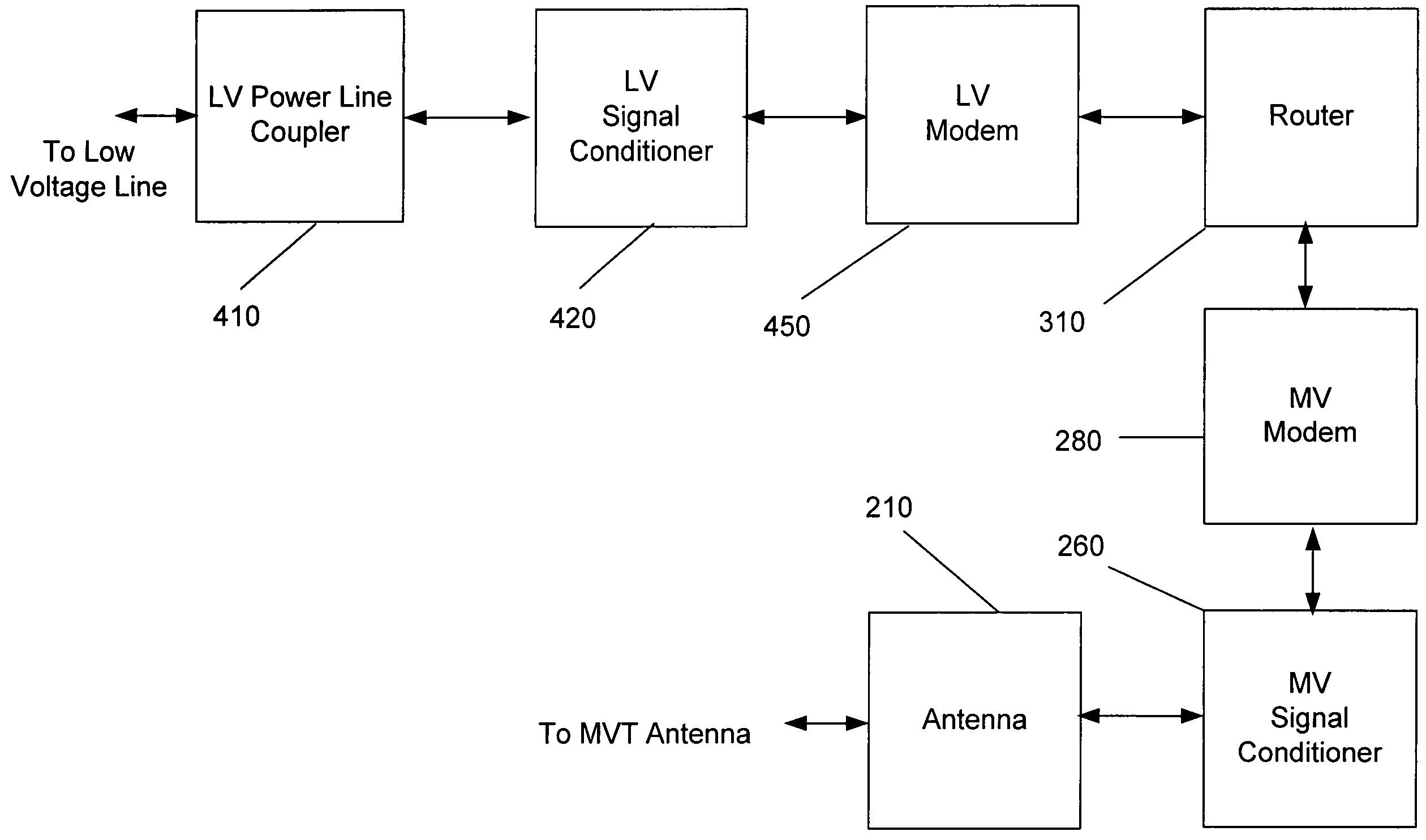
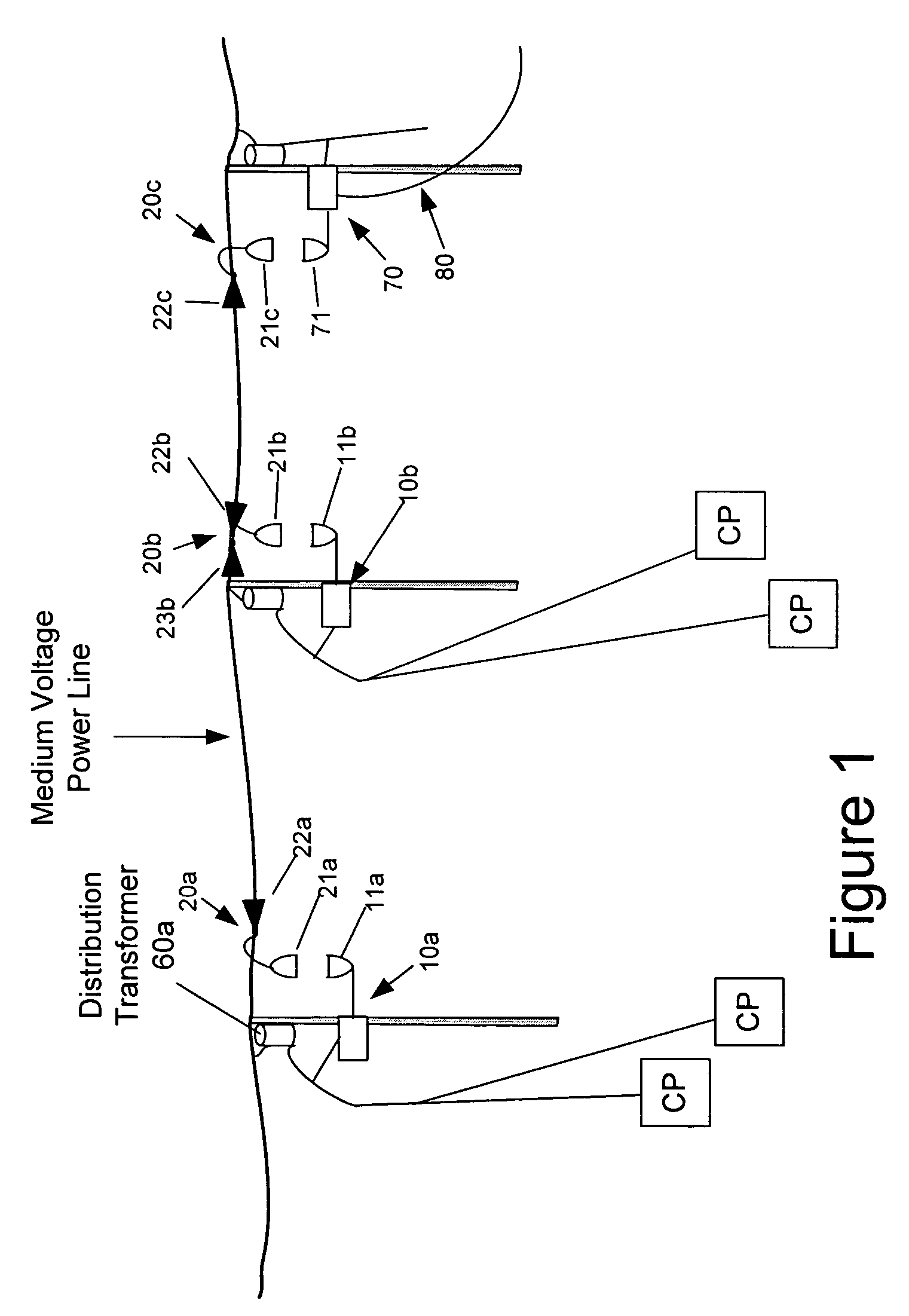
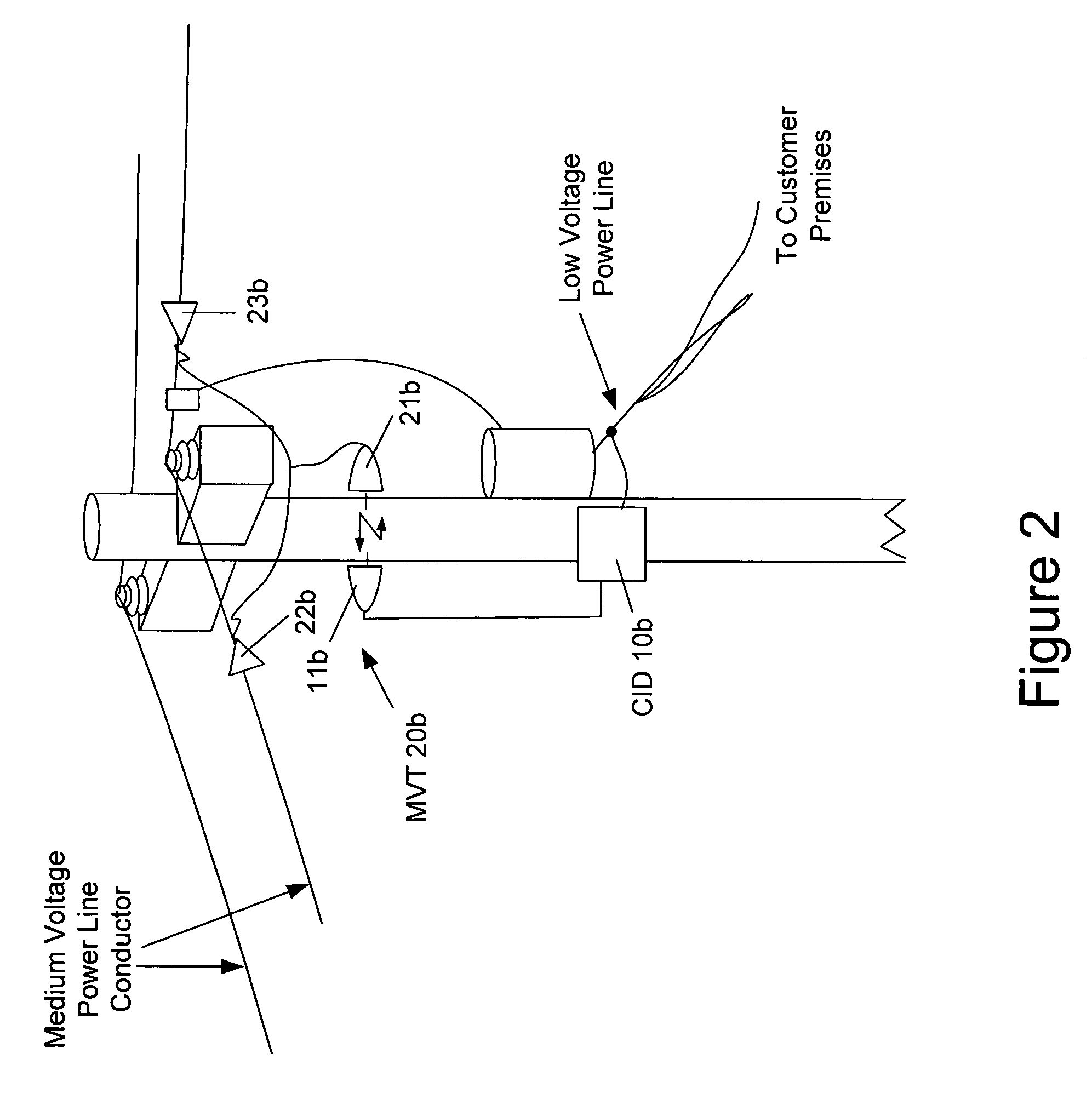
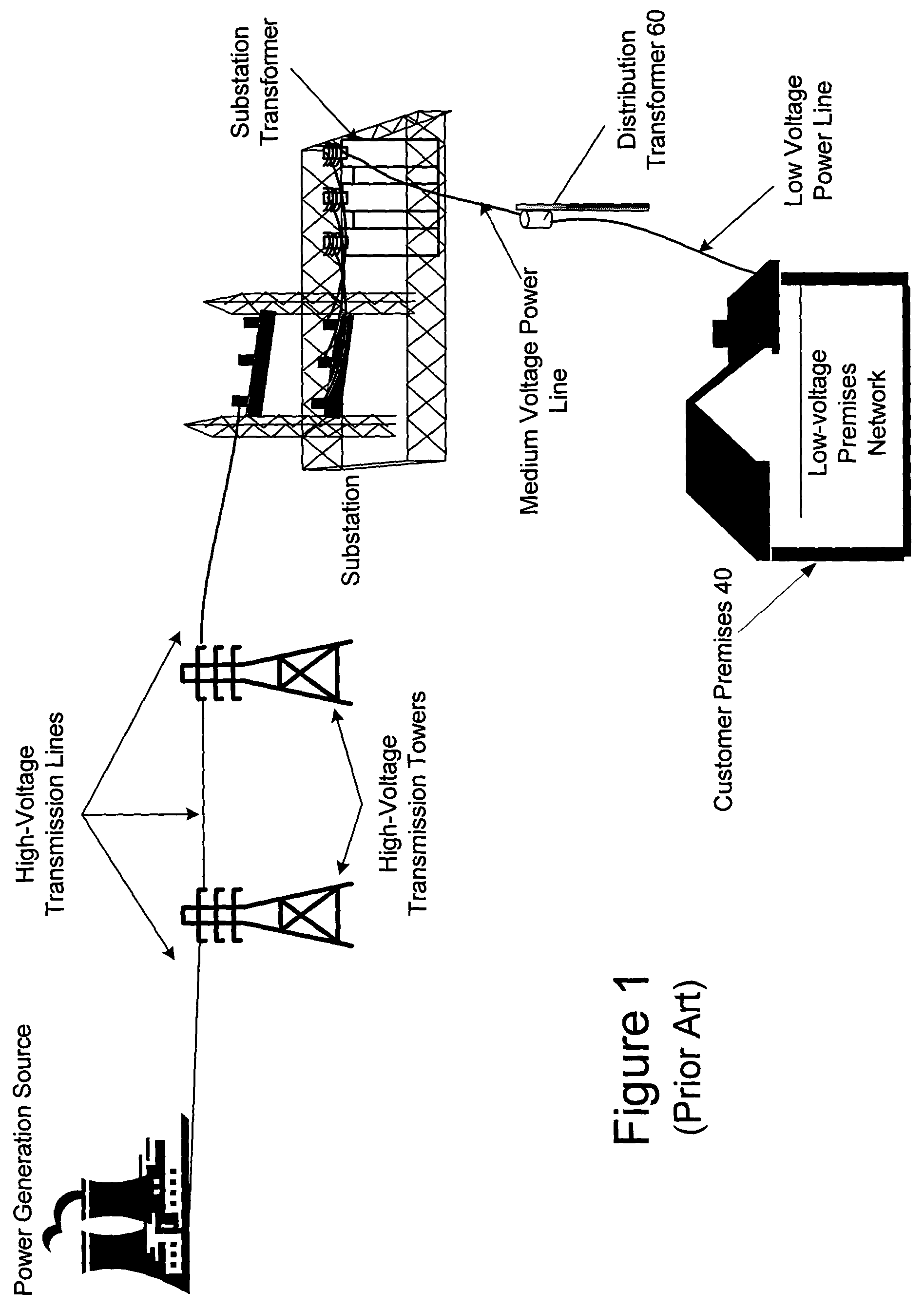
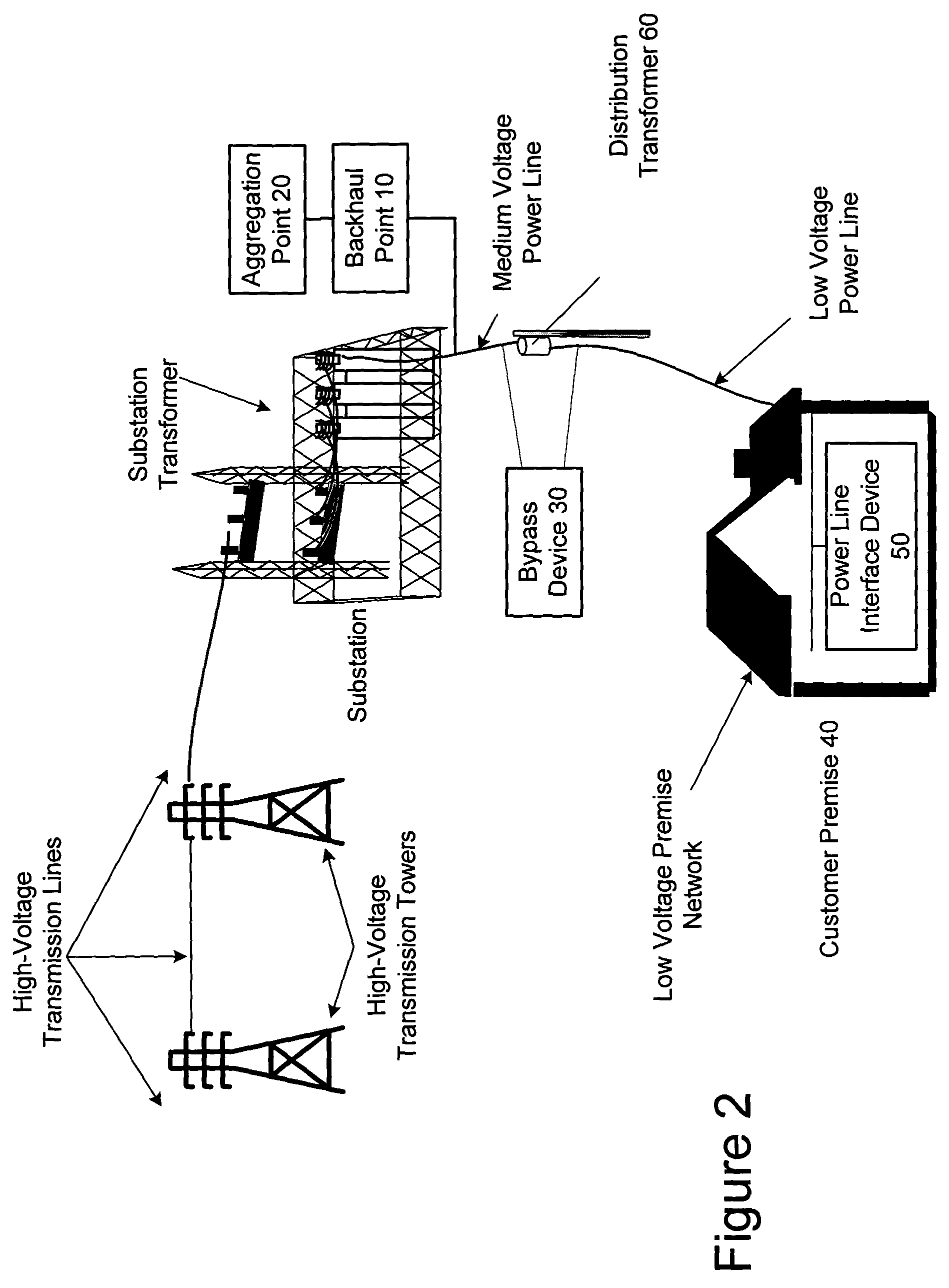
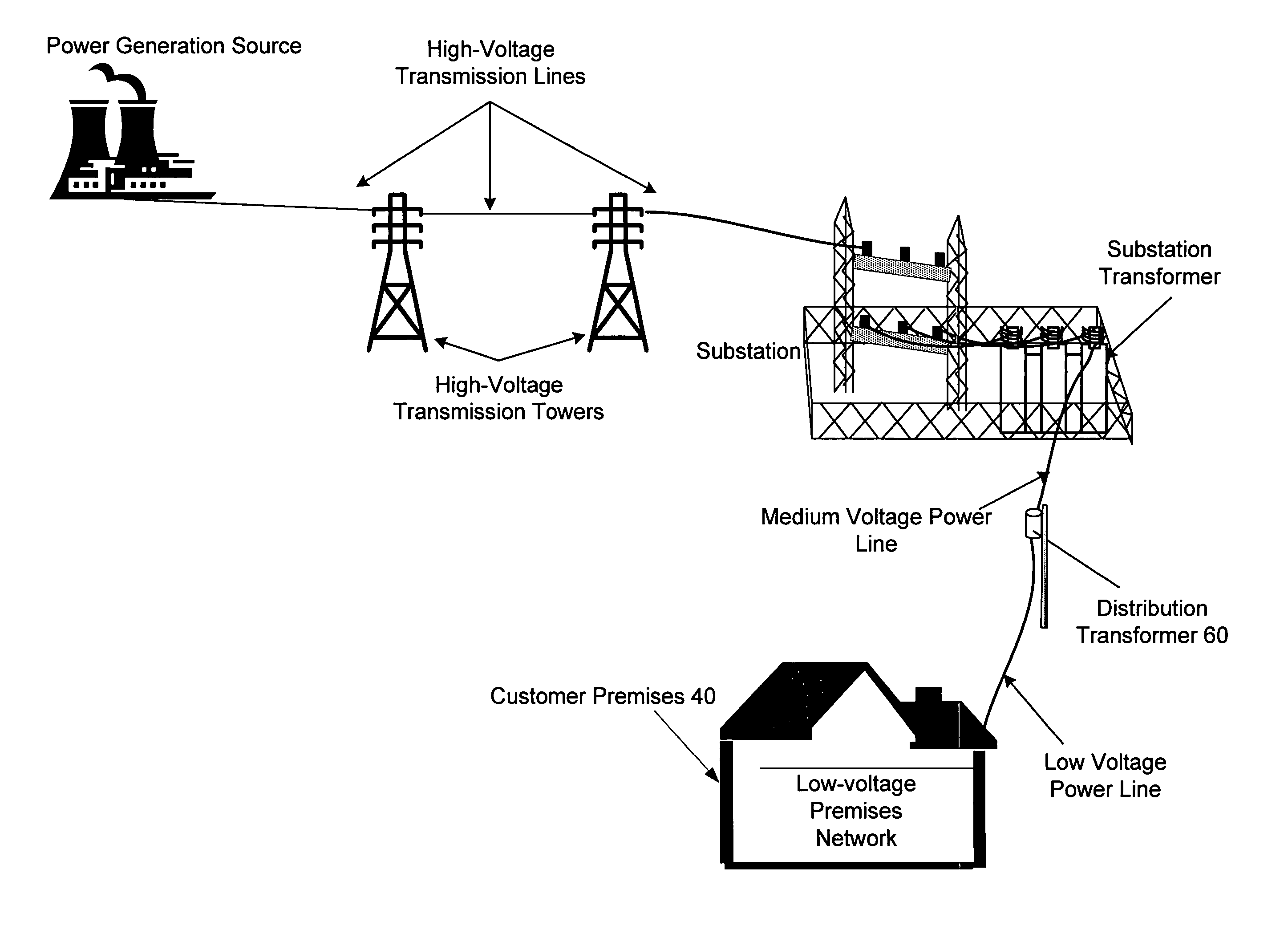
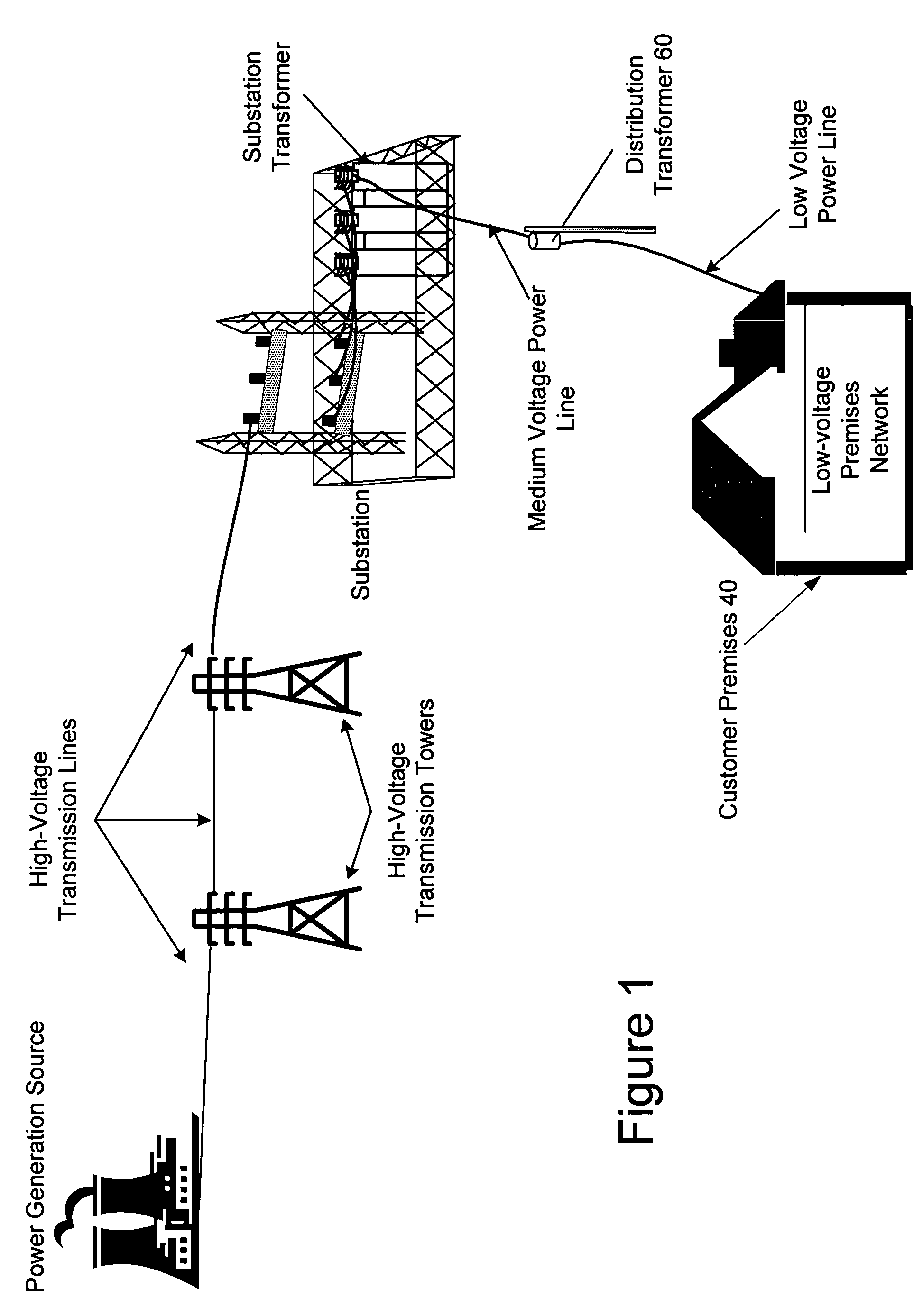
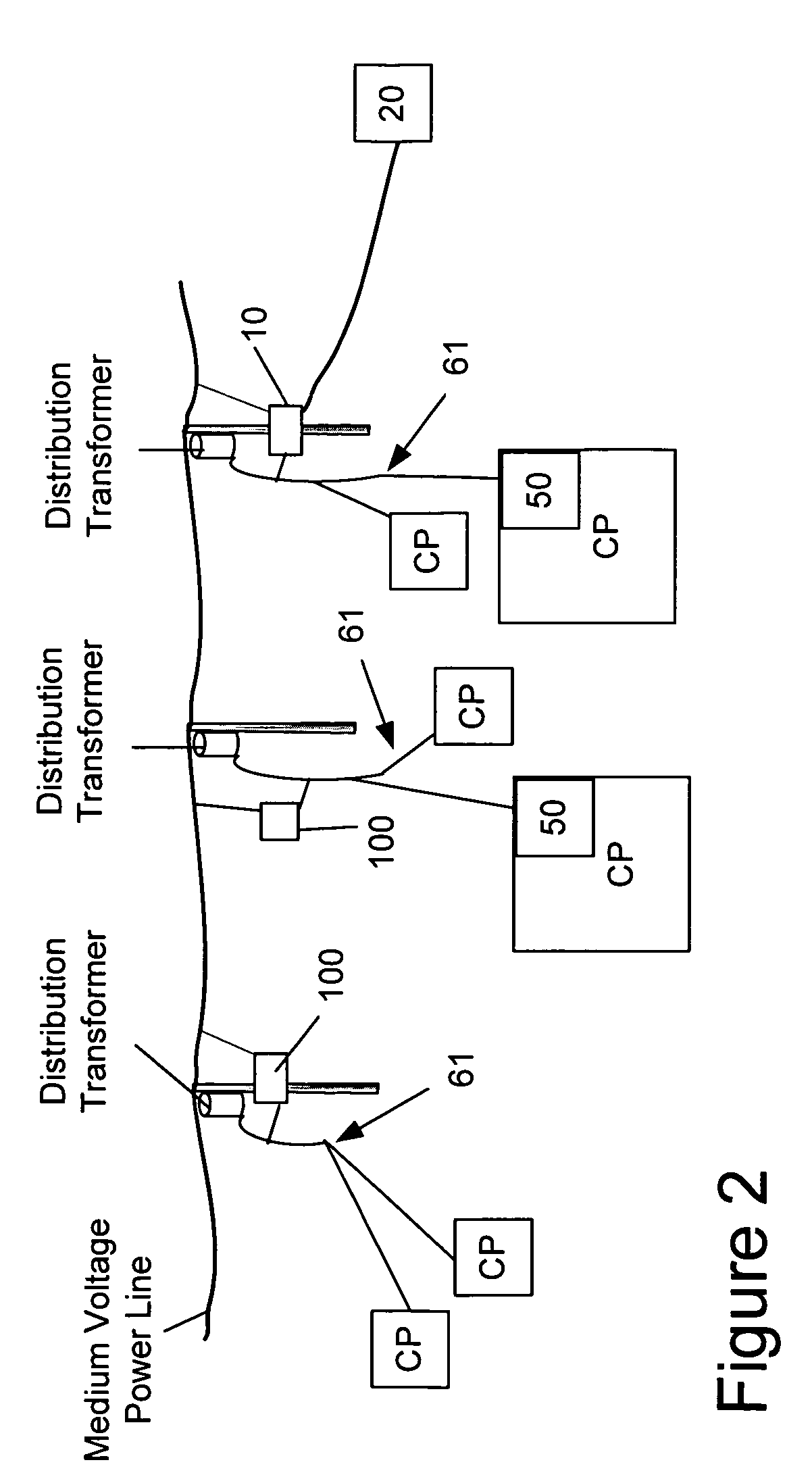
The present invention provides a system for operating a power line communications system that employs surface wave communications and conducted communications. The system is comprised of a plurality of network elements, which may take the form of repeaters, communication interface devices, backhaul devices, medium voltage transducers, distribution points, aggregation points, and others. In one embodiment, surface waves are communicated over the medium voltage power lines and the conducted communications are communicated via the low voltage power lines to and from customer premises.
Owner:CURRENT TECH
Surface wave power line communications system and method
InactiveUS7280033B2Electric signal transmission systemsInterconnection arrangementsCommunication interfaceCommunications system
The present invention provides a system for operating a power line communications system that employs surface wave communications and conducted communications. The system is comprised of a plurality of network elements, which may take the form of repeaters, communication interface devices, backhaul devices, medium voltage transducers, distribution points, aggregation points, and others. In one embodiment, surface waves are communicated over the medium voltage power lines and the conducted communications are communicated via the low voltage power lines to and from customer premises.
Owner:CURRENT TECH
Time-scheduled and time-reservation packet switching
InactiveUS20050058149A1Optimum advantage and efficiencyImprove accuracyMultiplex system selection arrangementsTime-division multiplexData packTime schedule
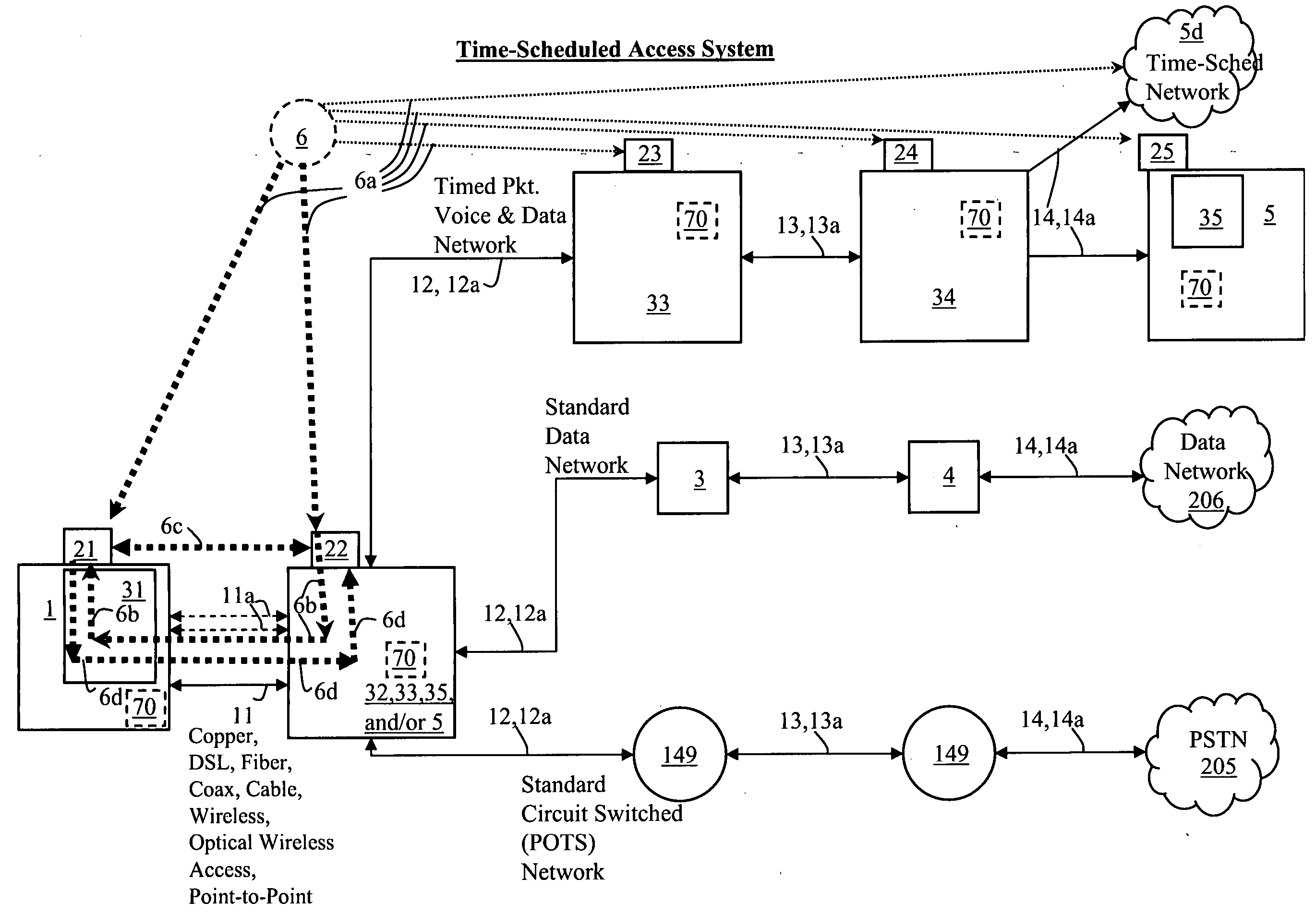
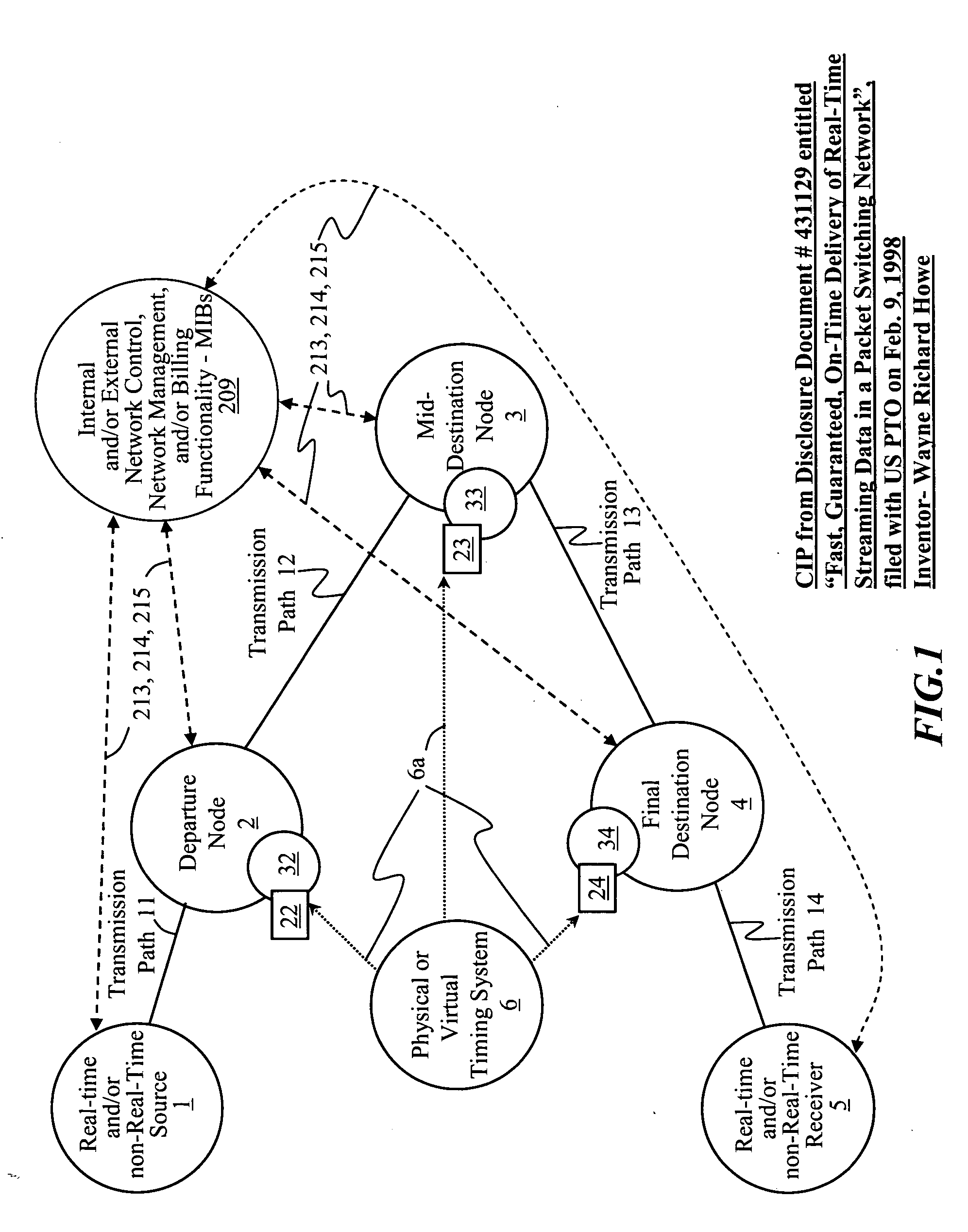
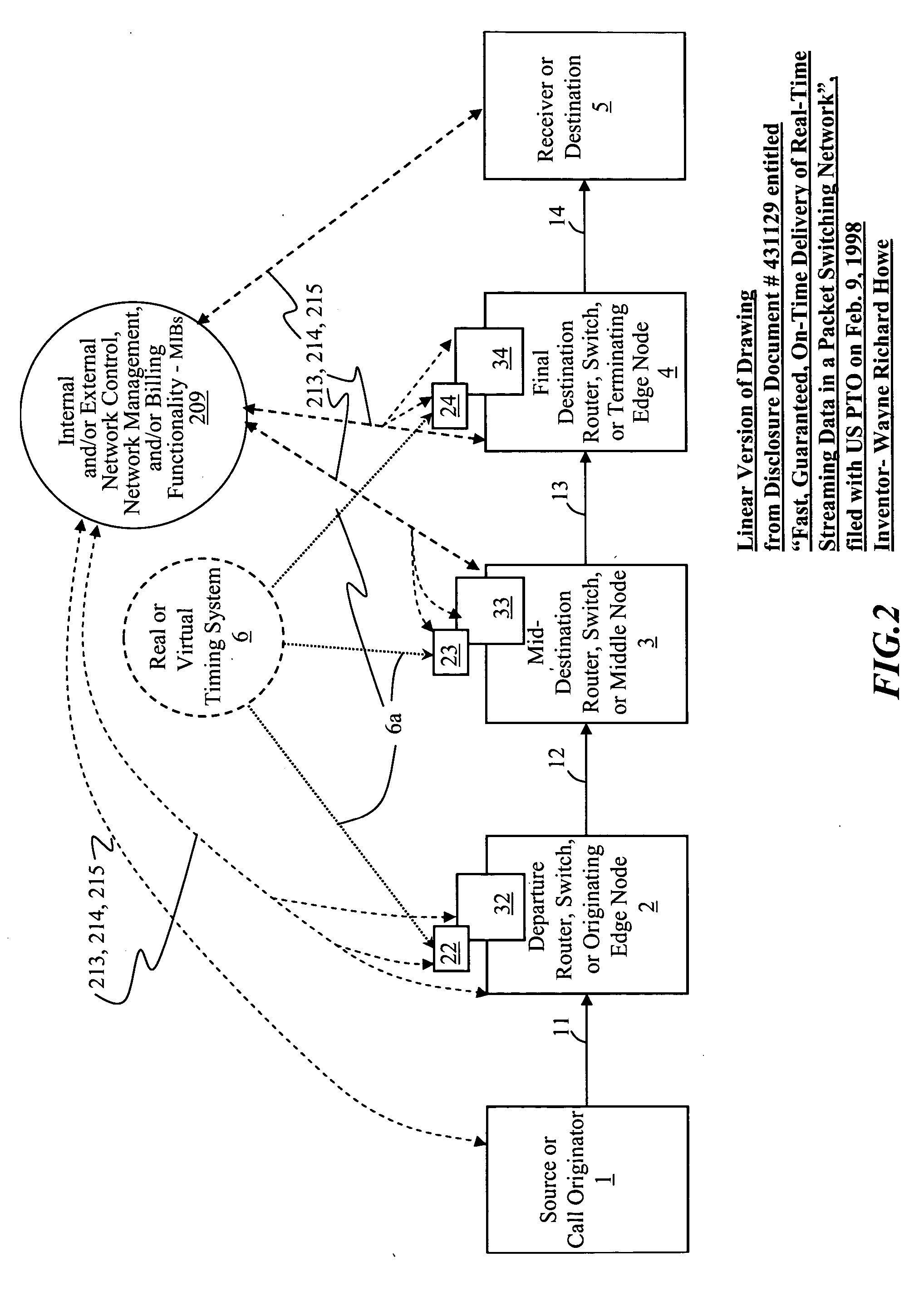
Systems, methods, devices, processes, procedures, algorithms, networks, and network elements are described for time-scheduled and / or time-reserved dat networks. Invention provides capabilities for synchronizing data networks and / or data network links; for establishing time-schedules, time-reservations, time-schedule reservations, and / or reservation time-slots for packets, cells, frames, and / or datagrams; and for transferring, transmitting, switching, routing, and / or receiving time-sensitive, high-reliability, urgent, and / or other time-scheduled, time-reserved, time-allocated, and / or time-scheduled-reservation packets, cells, frames, and / or datagrams, such as real-time and high-priority messages over these networks. The invention(s) enables packet-, cell-, datagram- and / or frame-based networks to thereby efficiently, reliably, and in guaranteed real-time, to switch and / or route data such as voice, video, streaming, and other real-time, high-priority, high-reliability, and / or expedited data with guaranteed delivery and guaranteed quality of service. Networks may be fixed, point-to-point, mobile, ad-hoc, optical, electrical, and / or wireless.
Owner:HOWE WAYNE RICHARD
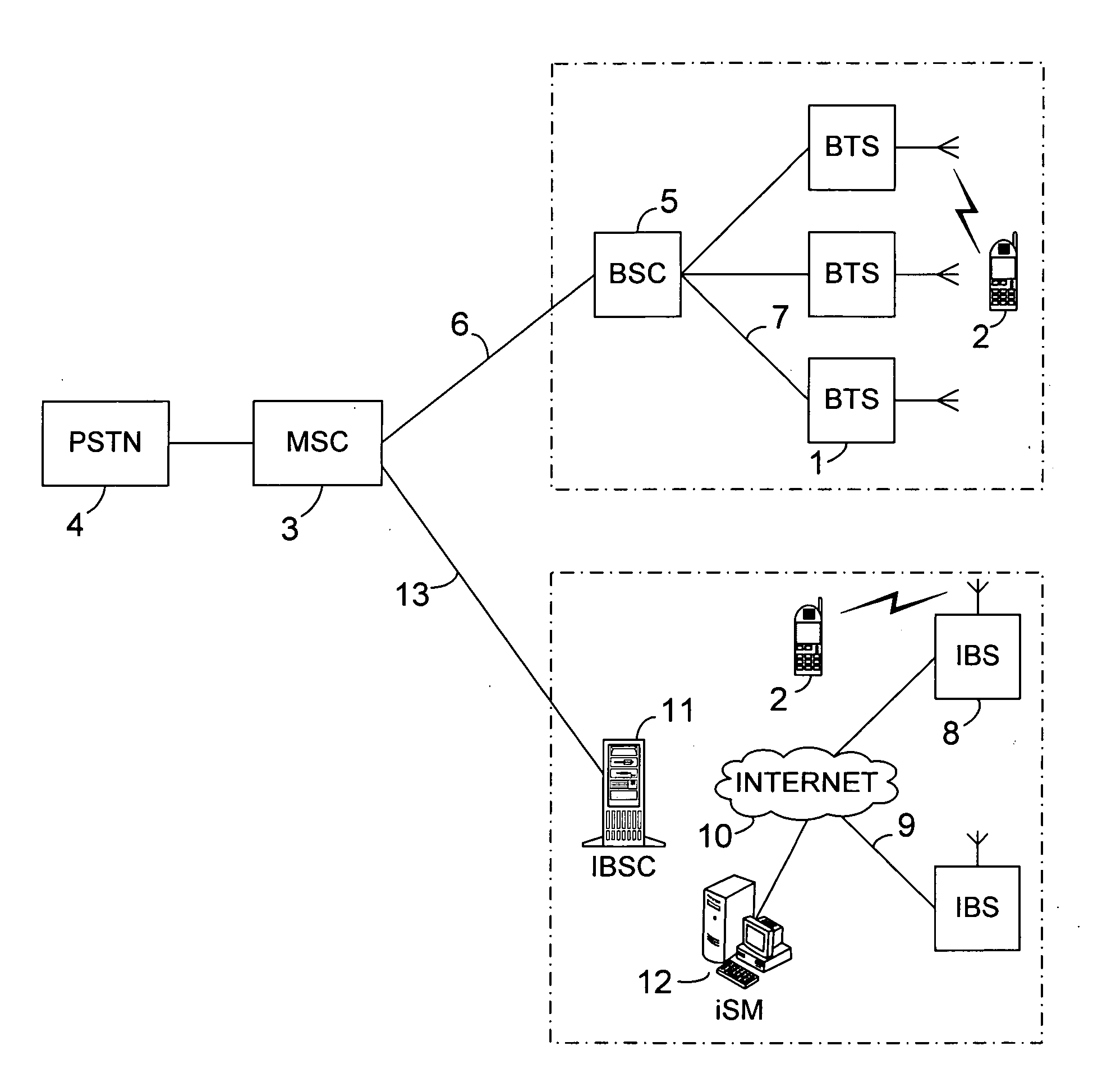
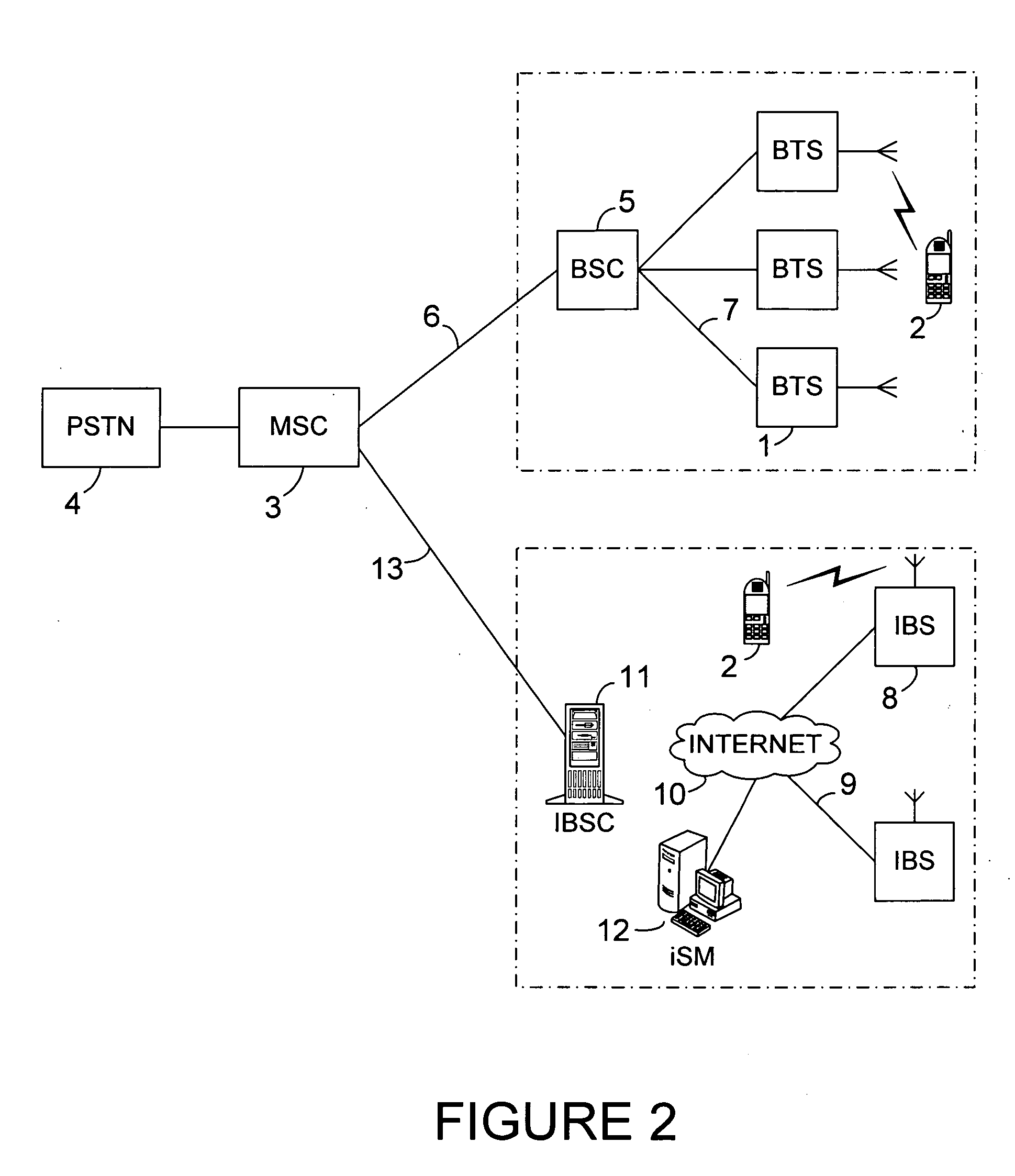
System and method for automatically configuring and integrating a radio base station into an existing wireless cellular communication network with full bi-directional roaming and handover capability
ActiveUS20050148368A1High densityAvoid the needNetwork traffic/resource managementNetwork topologiesAuto-configurationRoaming
A radio base station in a mobile communication network collects information about the network and exchanges data with a configuration device, the Internet System Manager (iSM). The iSM automatically configures and integrates the base station into the network by defining configuration parameter settings that allow fill interoperation of the base station with the network, with regards to roaming and handover in particular, without the need to add or modify parameter settings in other existing network elements. A very large number and high geographical density of such base stations is supported with full interoperation between them, allowing to overcome limitations of conventional mobile communication networks in this regard, by utilizing a certain combination of parameter settings and a new method to address the different base stations in the network.
Owner:APPLE INC
Network operating system for managing and securing networks
ActiveUS20090138577A1Reduced power modeDigital computer detailsTransmissionTraffic capacityAuto-configuration
Systems and methods for managing a network are described. A view of current state of the network is maintained where the current state of the network characterizes network topology and network constituents, including network entities and network elements residing in or on the network. Events are announced that correspond to changes in the state of the network and one or more network elements can be configured accordingly. Methods for managing network traffic are described that ensure forwarding and other actions taken by network elements implement globally declared network policy and refer to high-level names, independently of network topology and the location of network constituents. Methods for discovering network constituents are described, whereby are automatically configured. Routing may be performed using ACL and packets can be intercepted to permit host to continue in sleep mode. The methods are applicable to virtual environments.
Owner:NICIRA
Policy-based network security management
ActiveUS7237267B2Memory loss protectionError detection/correctionNetwork resource managementCourse of action
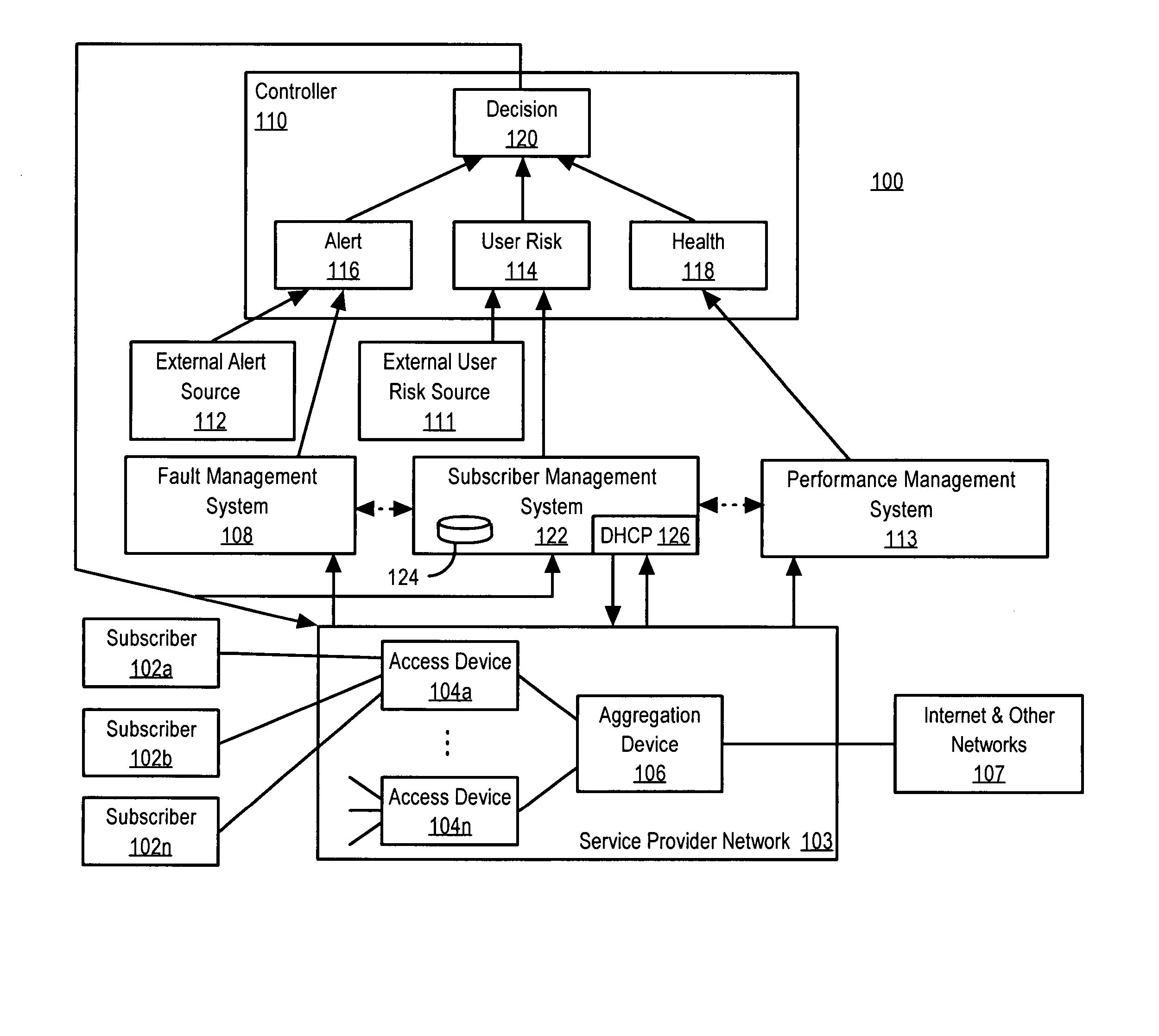
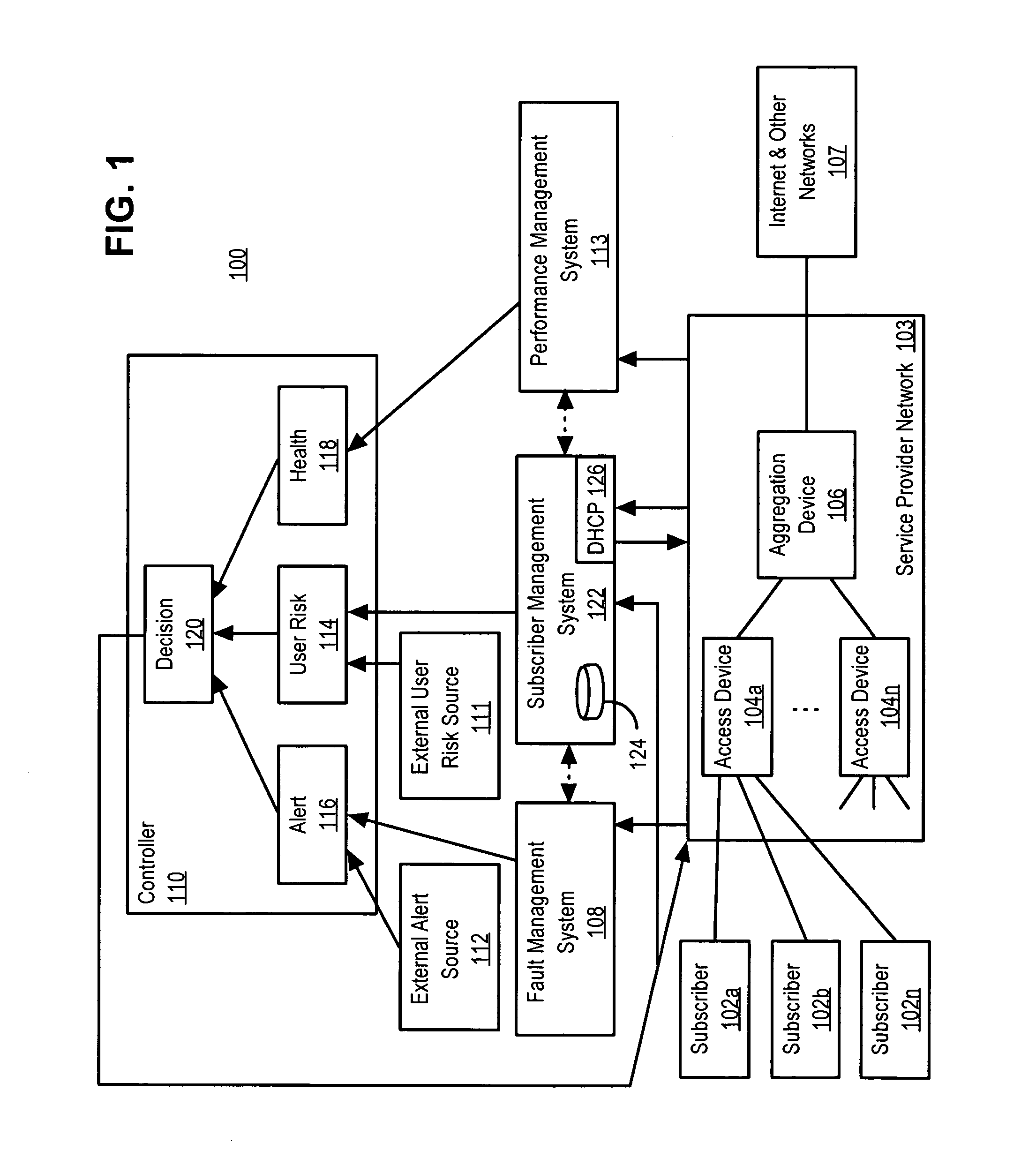
A policy-based network security management system is disclosed. In one embodiment, the system comprises a security management controller comprising one or more processors; a computer-readable medium carrying one or more sequences of instructions for policy-based network security management, wherein execution of the one or more sequences of instructions by the one or more processors causes the one or more processors to perform the steps of receiving a set of data regarding a user of a computer network; automatically deciding on a course of action based on the set of data, wherein the course of action may be adverse to the user although the set of data is insufficient to establish whether the user is performing a malicious action; and sending signals to one or more network elements in the computer network to implement the decision.
Owner:CISCO TECH INC
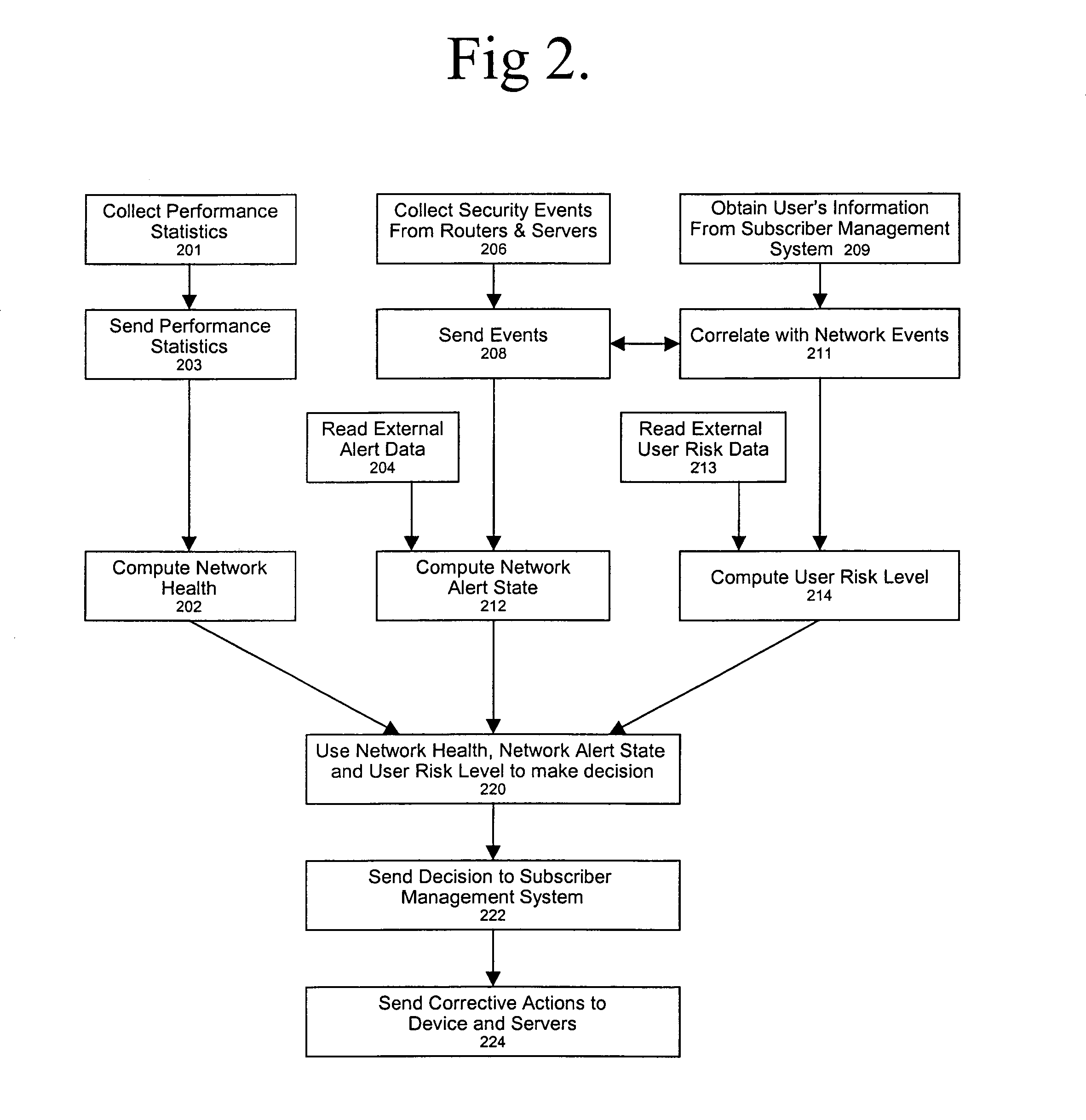
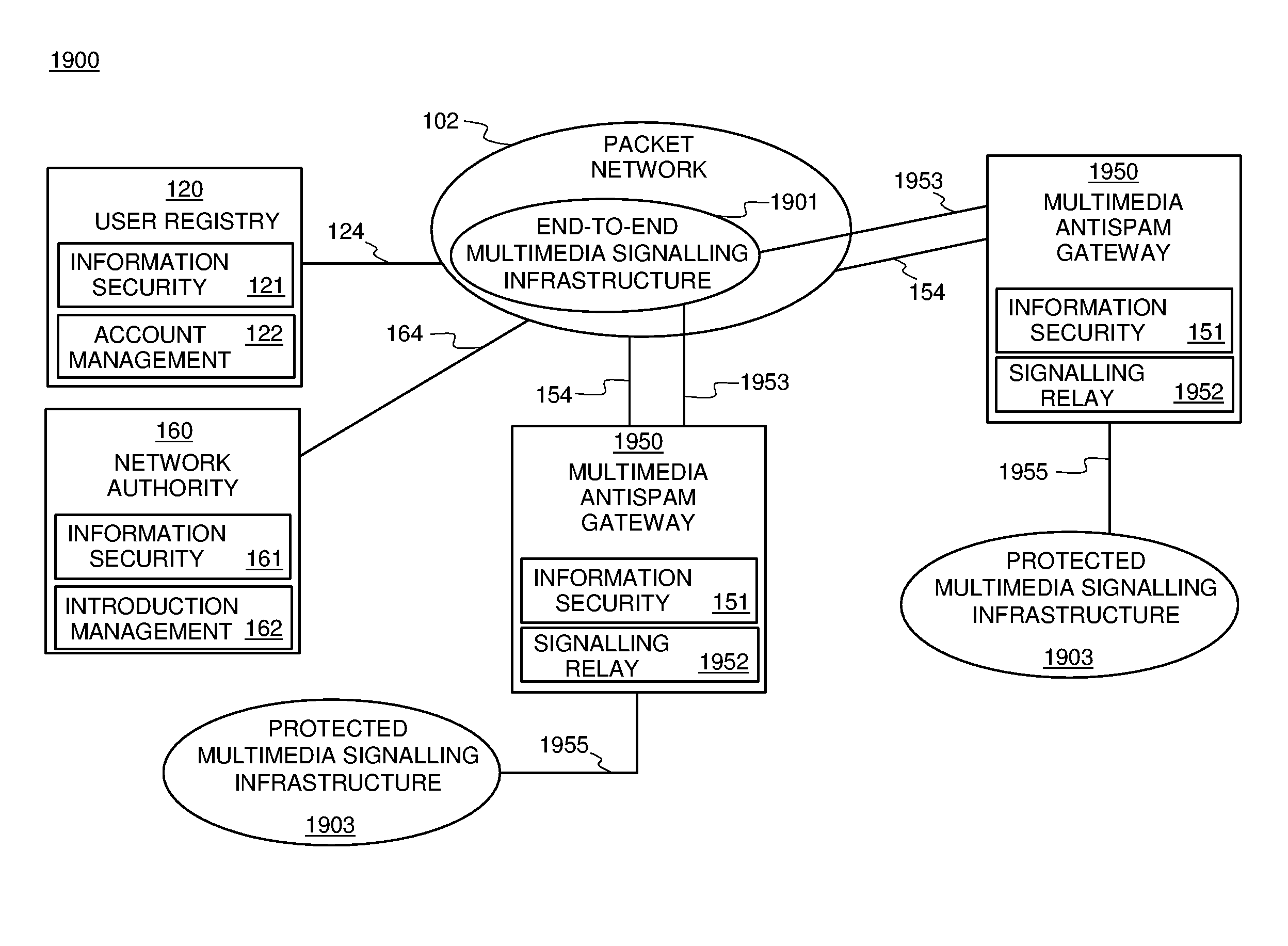
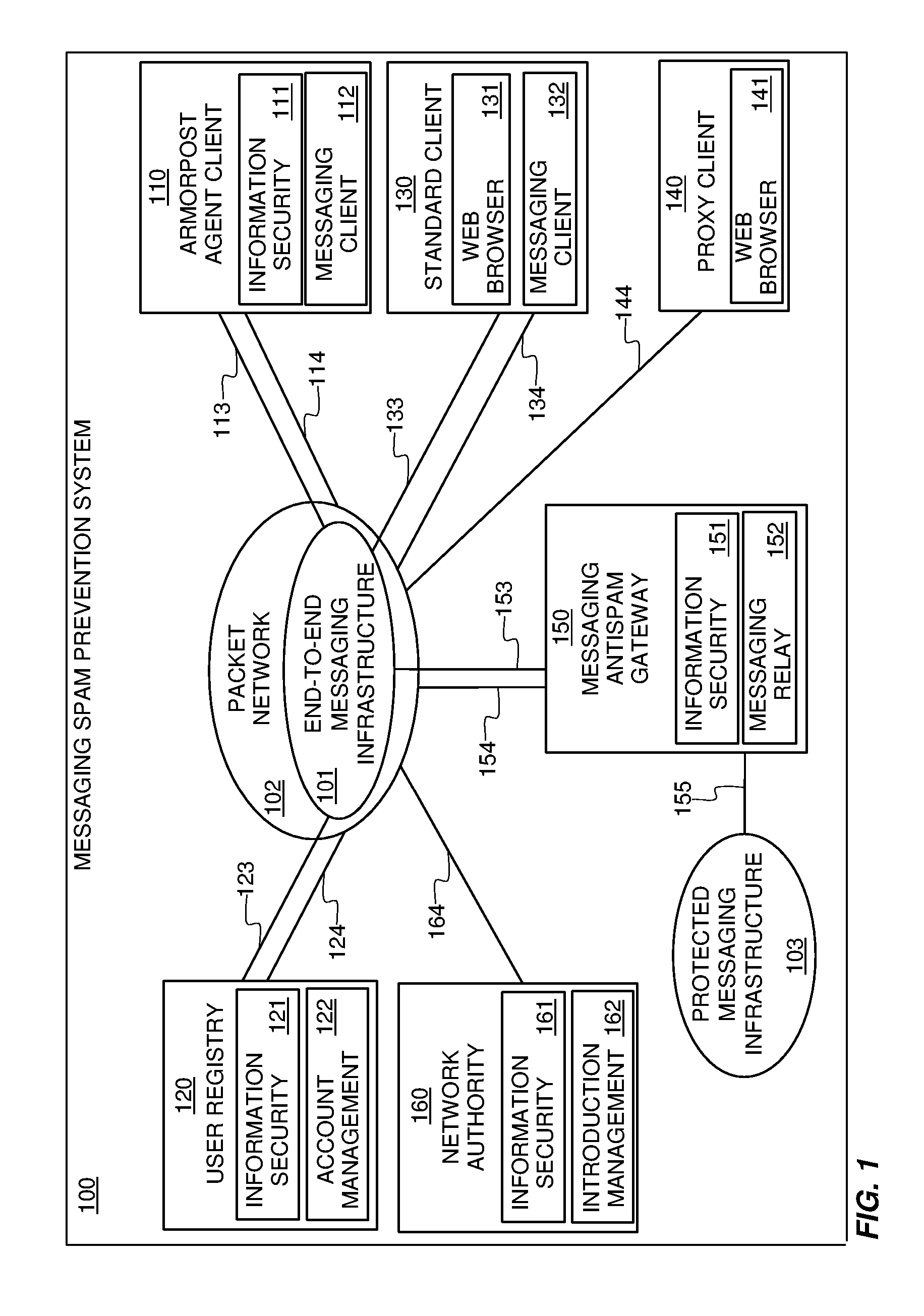
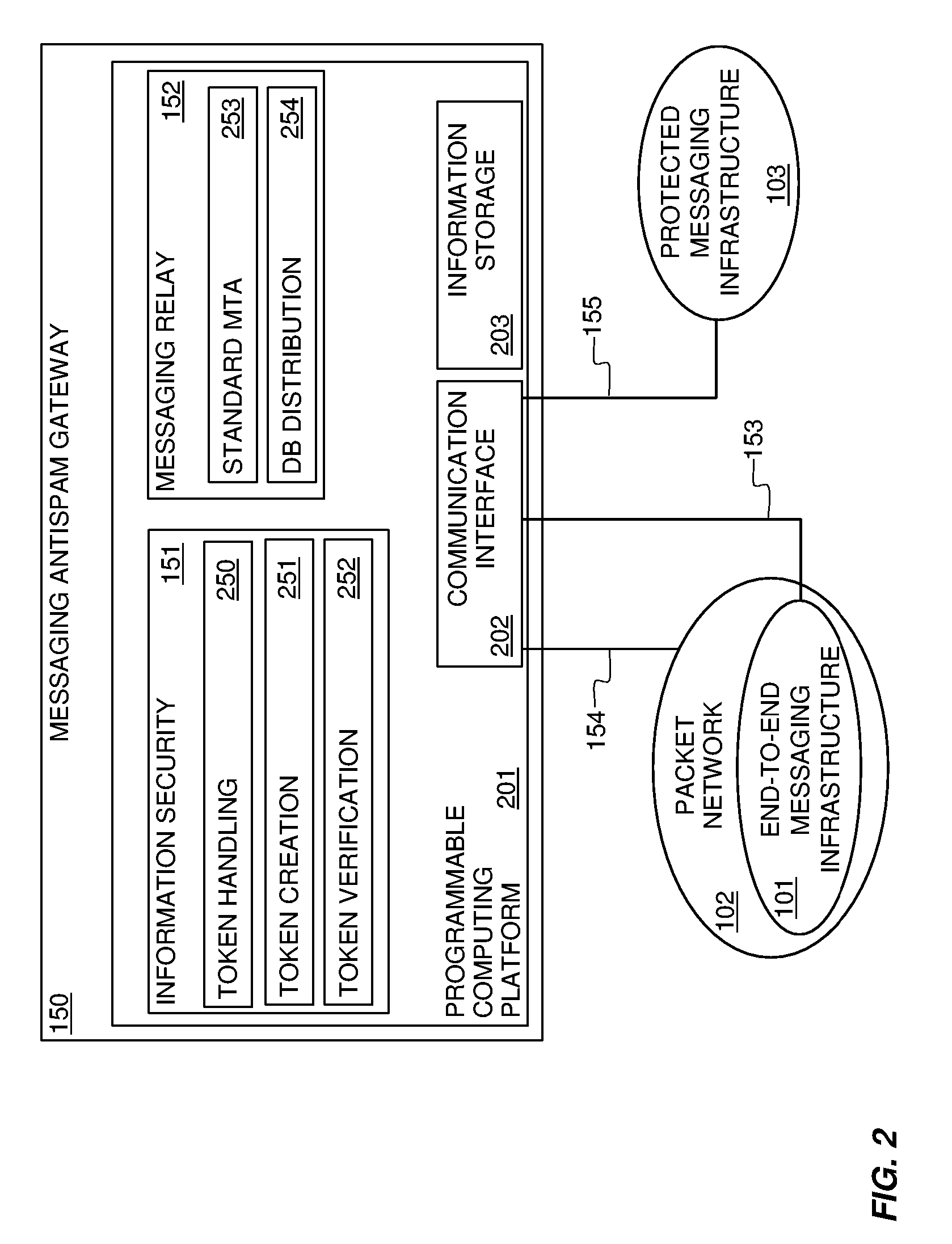
Systems and methods for preventing spam and denial of service attacks in messaging, packet multimedia, and other networks
InactiveUS20050132060A1Low costRaise priorityMultiple digital computer combinationsData switching networksData packSpamming
A system, various methods, and various apparatuses are provided for the purpose of supplying and including in an electronic message or multimedia session signalling unit a valid cryptographic authentication token, verifying said token's validity upon arrival of said message or signalling unit, and thereby providing message recipients or session parties with the assurance that said message or signalling unit is from a valid sender. A system, apparatus, and various methods are further provided for the purpose of protecting legitimate application traffic and the network elements exchanging it from intrusion by wild packets attempting to consume application resources and thereby deny service to legitimate users or network elements. A system, various methods, and various apparatuses are further provided for the purpose of enabling legitimate advertising via electronic messages, relying upon message and sender authentication to assure both advertisers and viewers of advertising messages that all participants are valid, legitimate, and accountable for any abuse that may occur.
Owner:AUTOUPTODATE LLC
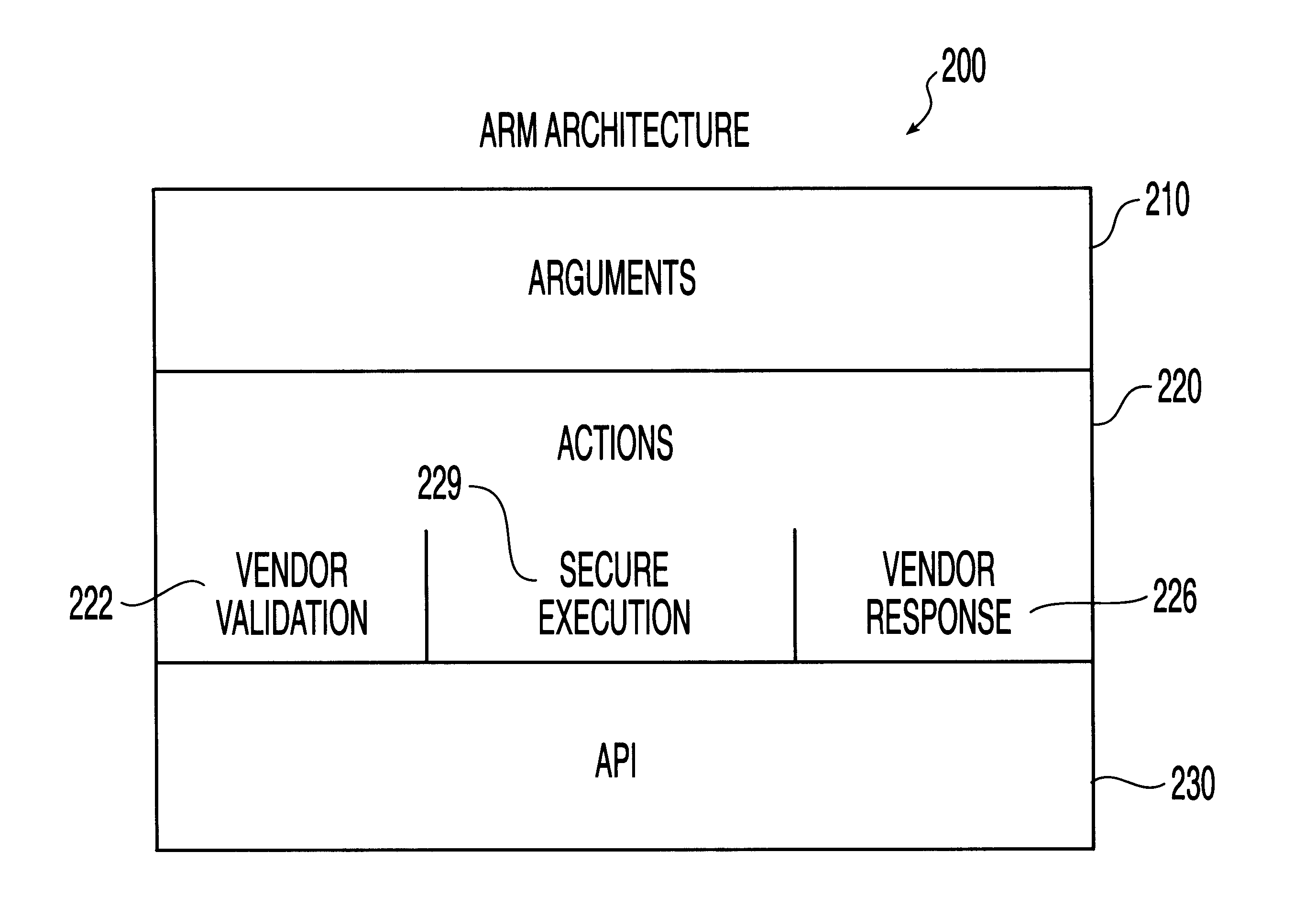
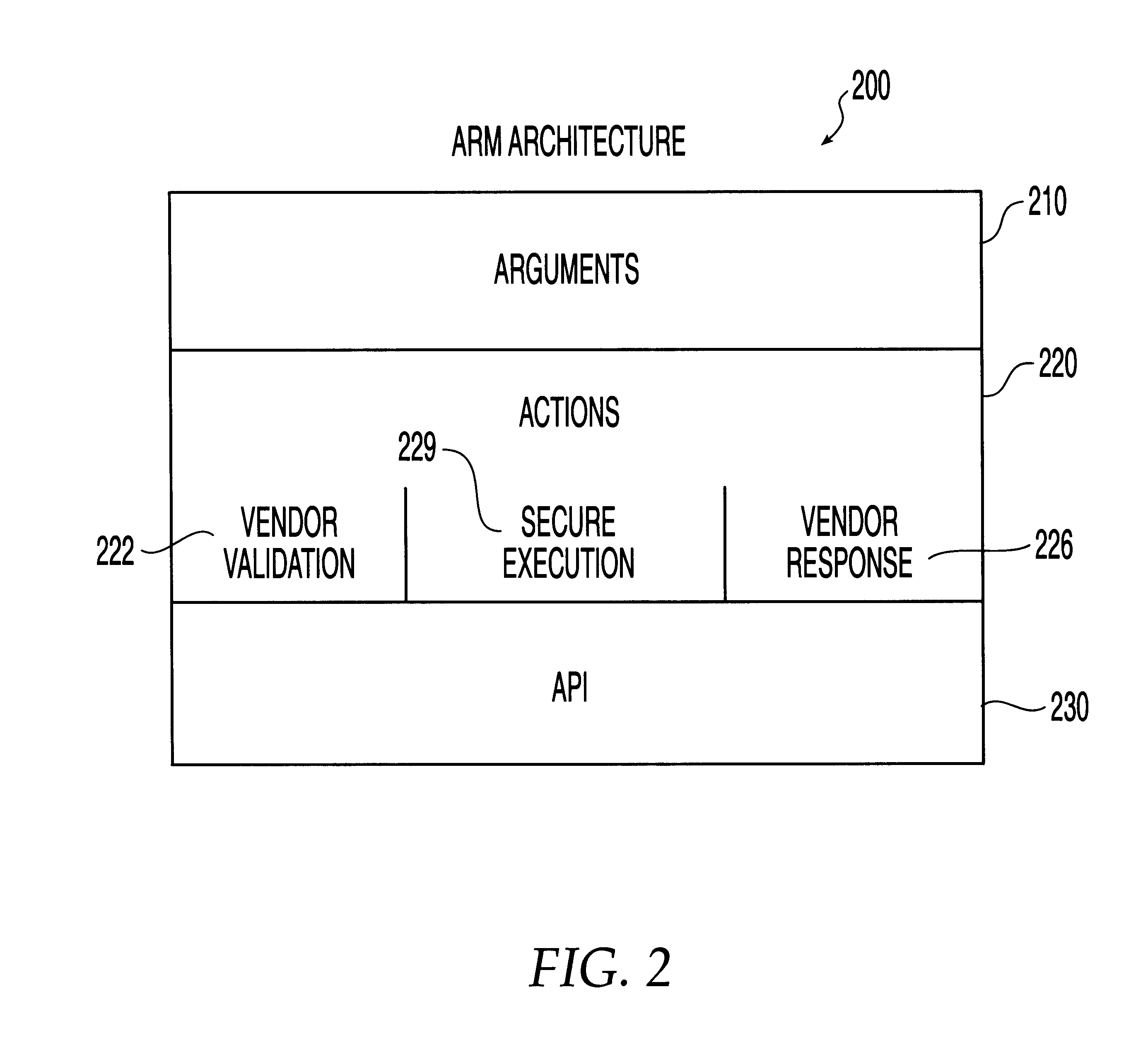
System, method and computer program product for automatic response to computer system misuse using active response modules
InactiveUS6275942B1Rapid responseMemory loss protectionDigital data processing detailsSoftware engineeringSecurity level
A system, method and computer program product for automatic response to computer system misuse using active response modules (ARMs). ARMs are tools that allow static intrusion detection system applications the ability to dynamically increase security levels by allowing real-time responses to detected instances of computer misuse. Several classes of ARMs exist which allow them to interface with several types of network elements found within a computing environment (e.g., firewalls, web servers, Kerberos severs, certificate authorities, etc.). The ARMs, once defined, are deployed in a "plug and play" manner into an existing intrusion detection system within a computing environment. A user (e.g., system administrator) may then configure the ARMs by linking them to specific computer misuses. Upon receipt of an instance of the computer misuse from the intrusion detection system, each ARM linked to the misuse collects pertinent data from the intrusion detection system and invokes a response specified by the ARM class and the collected pertinent data.
Owner:MCAFEE LLC +1
Power line communication system and method of operating the same
The present invention provides a system for operating a power line communications system that is comprised of a plurality of network elements, which may take the form of repeaters, bypass devices, backhaul devices, wireless backhaul devices, enhanced bypass device, communication interface devices and others. In one embodiment, two groups of network elements in the same electrical distribution system are isolated except selected communication link.
Owner:CURRENT TECH
MAC layer reconfiguration in a mobile communication system
ActiveUS20070047452A1Effective controlEfficient triggerError preventionTransmission systemsRadio access networkMobile communication systems
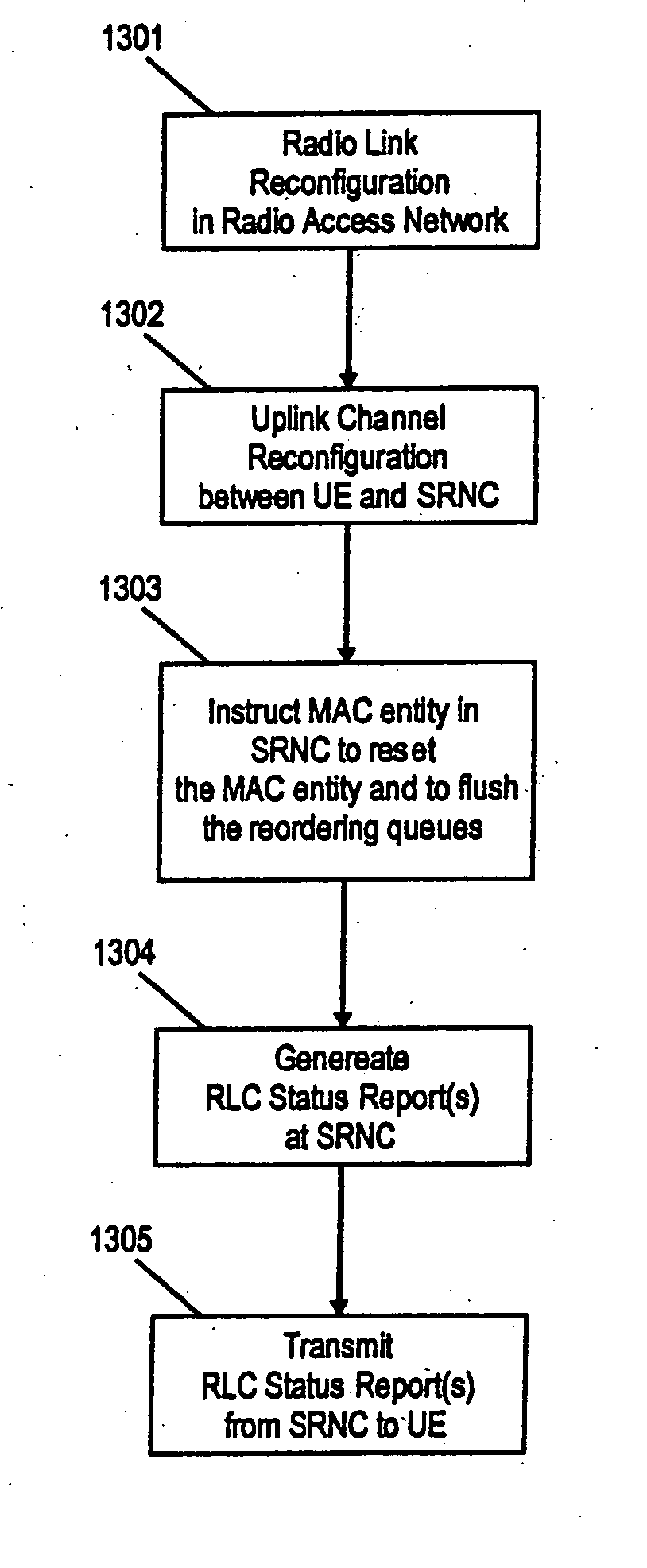
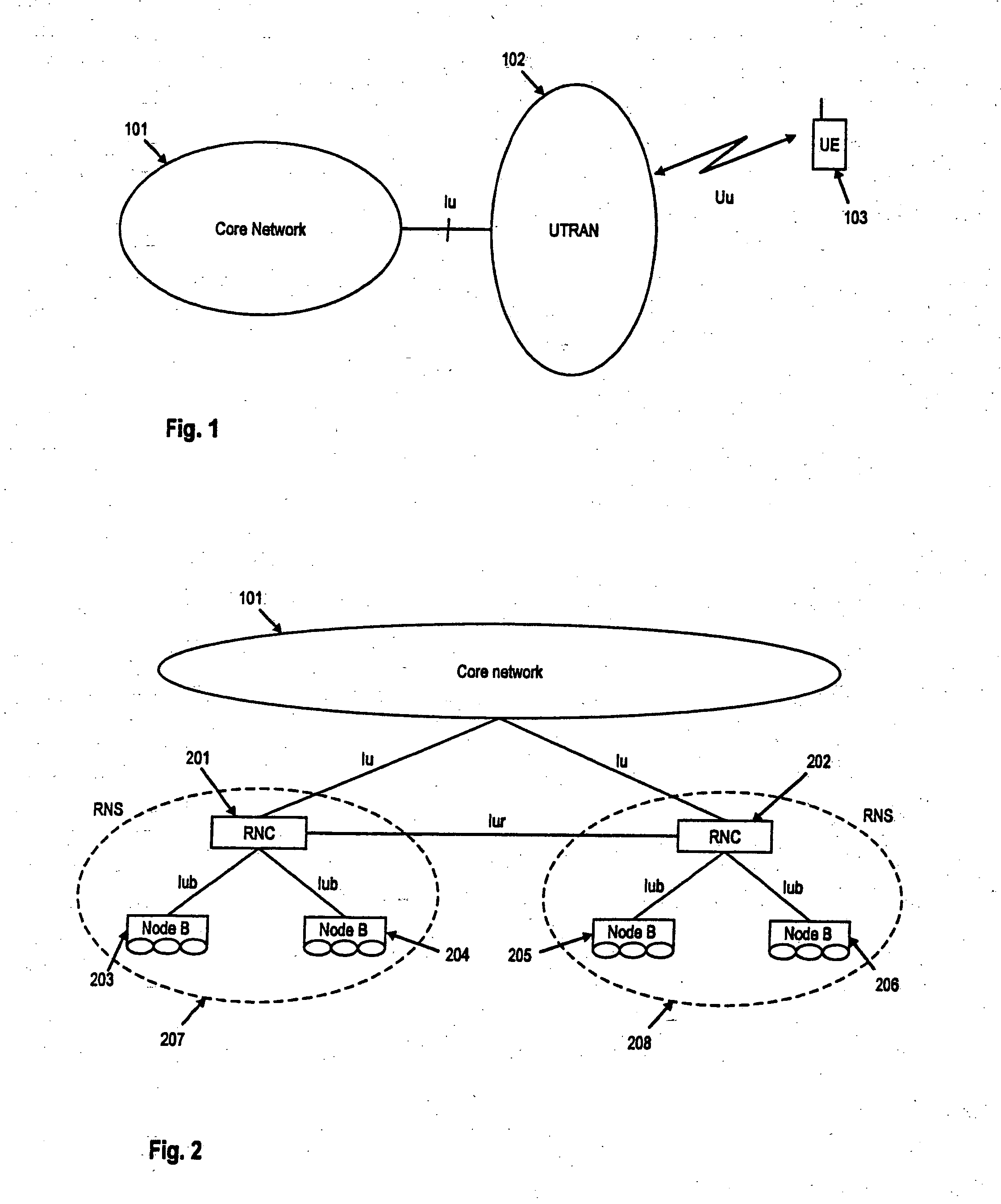
The invention relates to method and apparatus for reconfiguring a MAC entity of a MAC layer of the apparatus receiving protocol data units from a mobile terminal via on uplink upon reconfiguration of the uplink channel. Further, the invention relates to methods and mobile terminals for triggering the transmission of a status report from an RLC entity configured for an uplink channel of a network element in a radio access network, as well as a method and terminal for configuring the MAC layer of the mobile terminal. In order to enable an efficient and fast generation of RLC status reports after an uplink channel reconfiguration the invention suggests new mechanisms to trigger the transmission of status reports upon uplink reconfiguration as well a new operation and configuration of radio access network elements and UEs upon uplink channel reconfiguration, in particular a transmission time interval (TTI) reconfiguration.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Method and apparatus for exchanging routing information and the establishment of connectivity across multiple network areas
InactiveUS8223668B2Easy to operateMultiple digital computer combinationsNetworks interconnectionStructure of Management InformationNetwork structure
Owner:RPX CLEARINGHOUSE
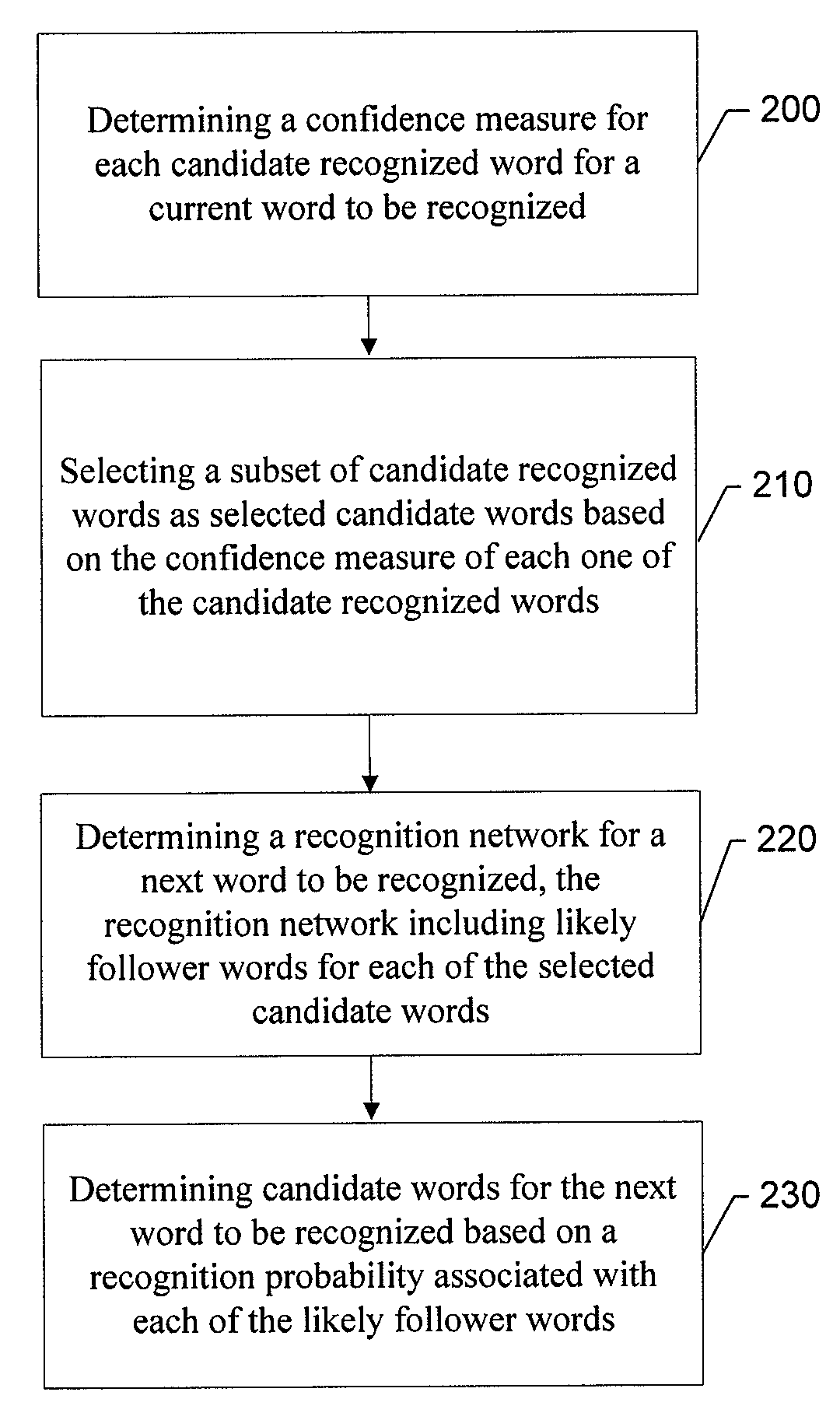
System, Method, Apparatus and Computer Program Product for Providing Dynamic Vocabulary Prediction for Speech Recognition
InactiveUS20080154600A1Improve speech processingAccurate word recognitionSpeech recognitionNatural language processingConfidence measures
An apparatus for providing dynamic vocabulary prediction for setting up a speech recognition network of resource constrained portable devices may include a recognition network element. The recognition network element may be configured to determine a confidence measure for each candidate recognized word for a current word to be recognized. The recognition network element may also be configured to select a subset of candidate recognized words as selected candidate words based on the confidence measure of each one of the candidate recognized words, and determine a recognition network for a next word to be recognized, the recognition network including likely follower words for each of the selected candidate words, e.g. using language model and highly frequently used words.
Owner:NOKIA CORP
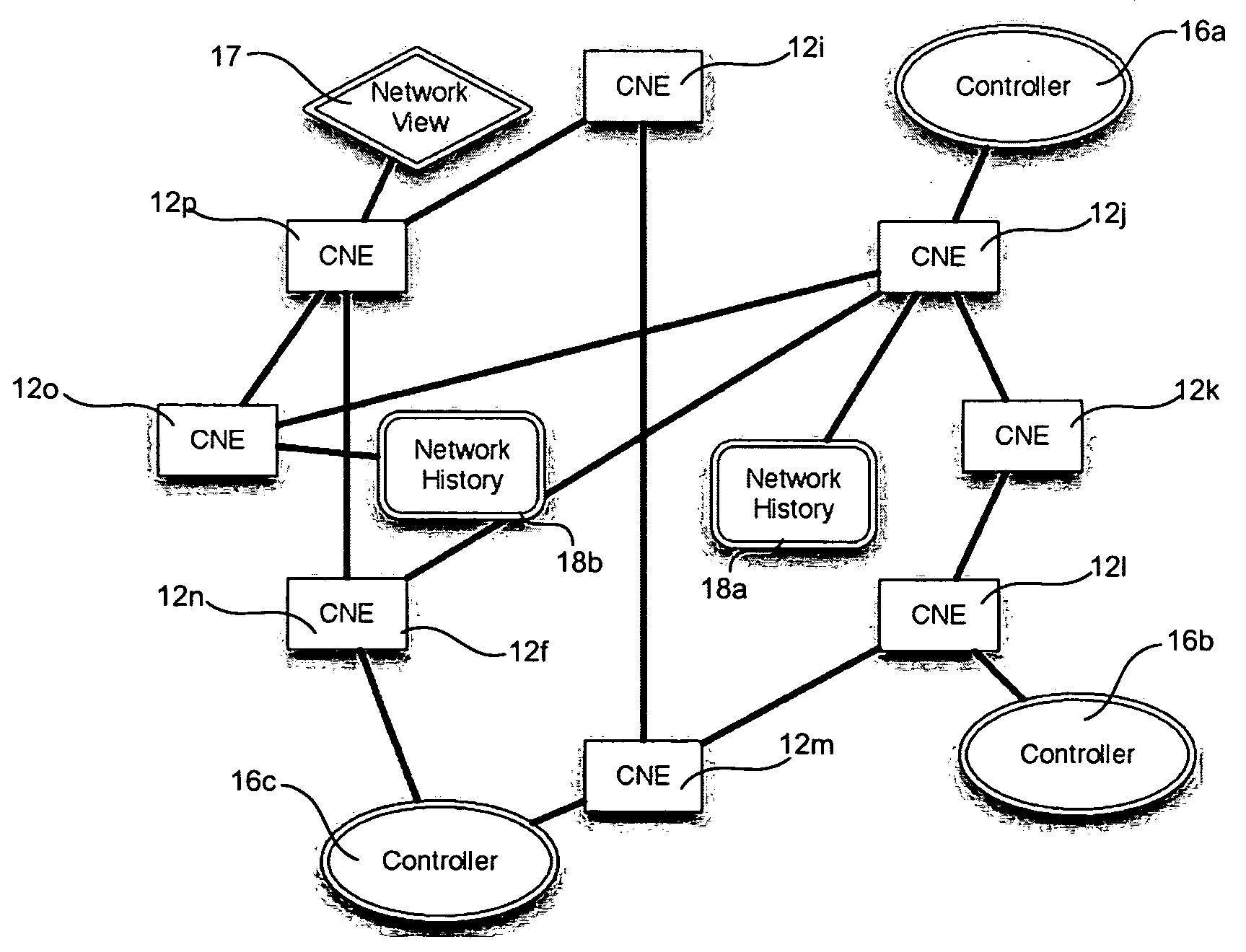
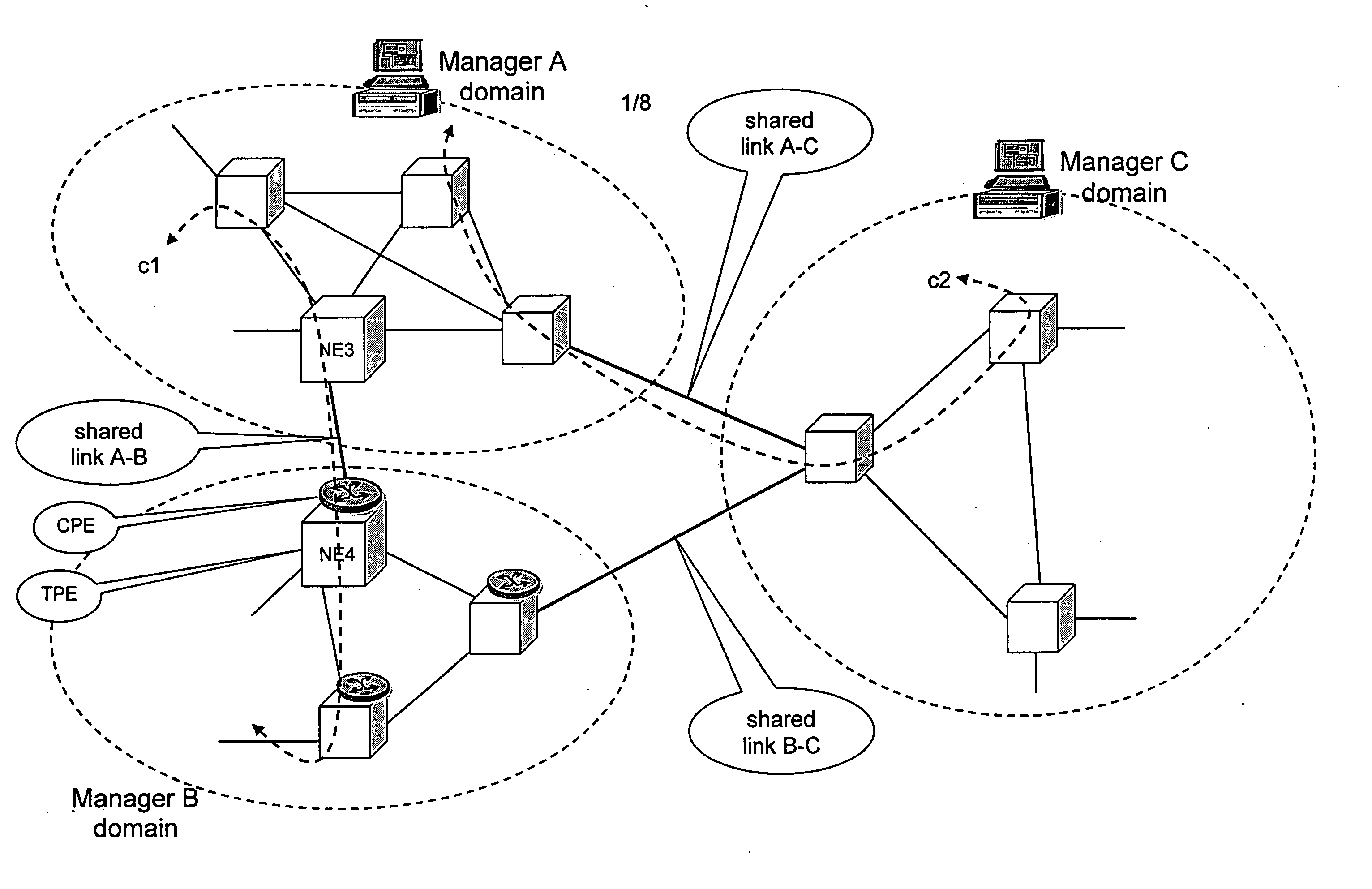
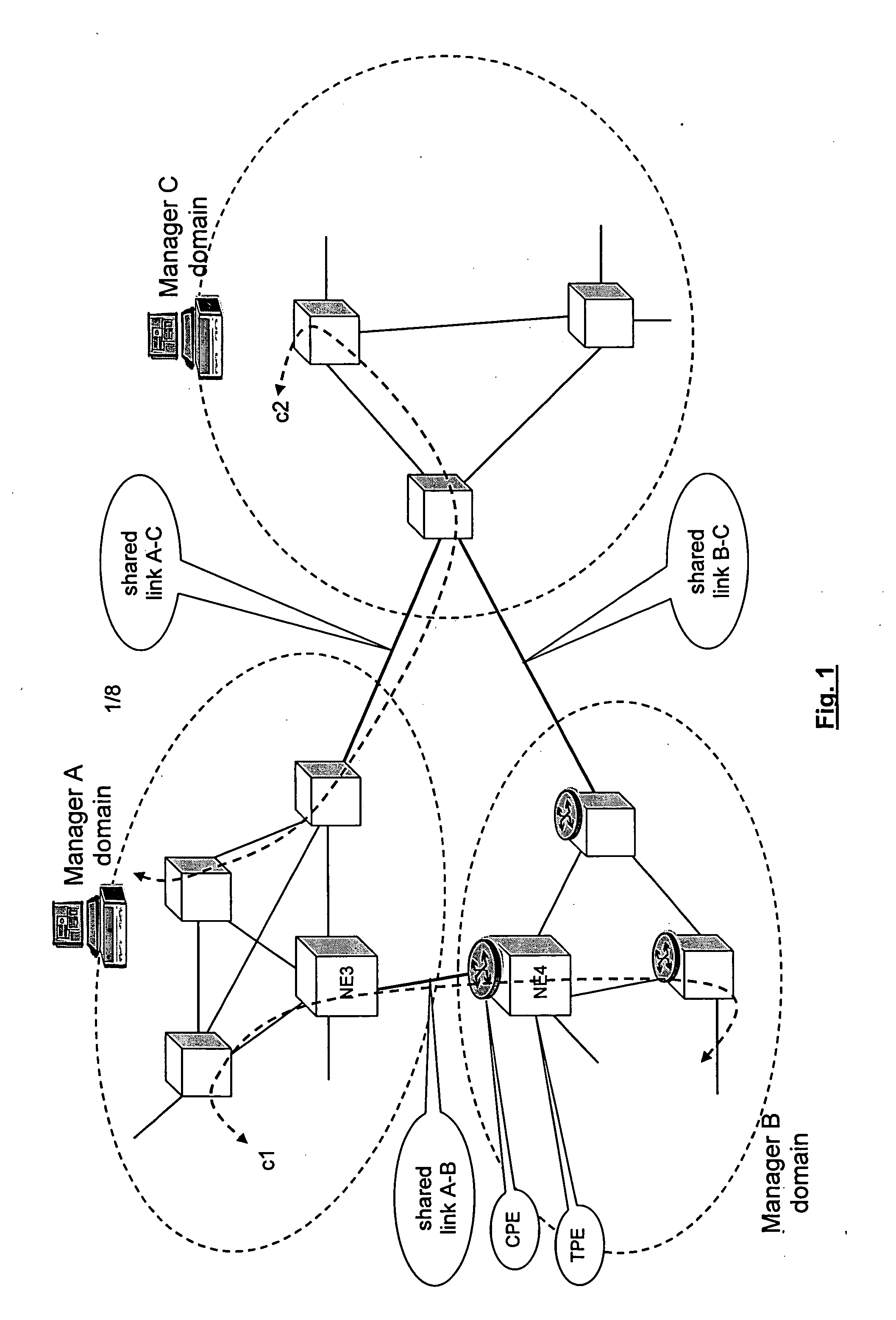
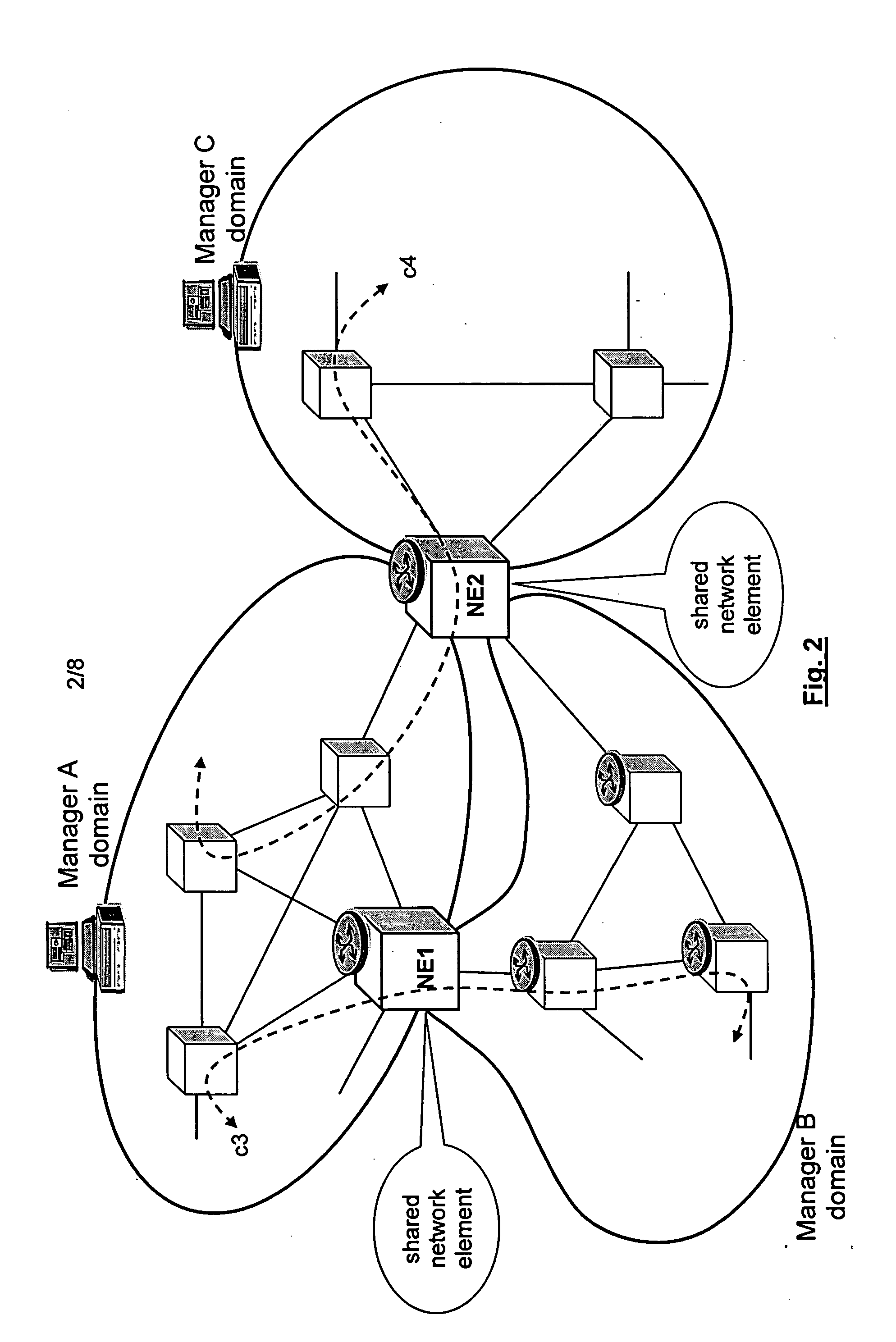
Shared resources in a multi manager environment
ActiveUS20060026225A1Reduce network element performanceMultiple digital computer combinationsTransmissionInformation repositoryManagement information base
A method is described for controlling a shared resource for interconnecting two or more network domains being controlled by different Managers. Multiple Managers control the shared resource for the configuration of a segment of a connection between two different domains and the Managers cooperate in order to control dynamically the shared resource. Different network domains can be connected by a network element or by a link between different network elements belonging to the different network domains. In the first case the shared resource is a connection matrix of the network element, in the second case the shared resource includes the connection matrixes of the different network elements and the link between the network elements. A shared connection matrix includes some connection points for performing the cross-connections within the matrix: some connection points are controlled by one Manager, other connection points are controlled by another Manager and some shared connection points are controlled by both Managers. Multiple Managers control the shared resource by reading and writing information stored into a management information base, according to an explicit or implicit mode, or alternatevely by transmitting messages in the network directly between the Managers, according to a signalling protocol.
Owner:ALCATEL LUCENT SAS
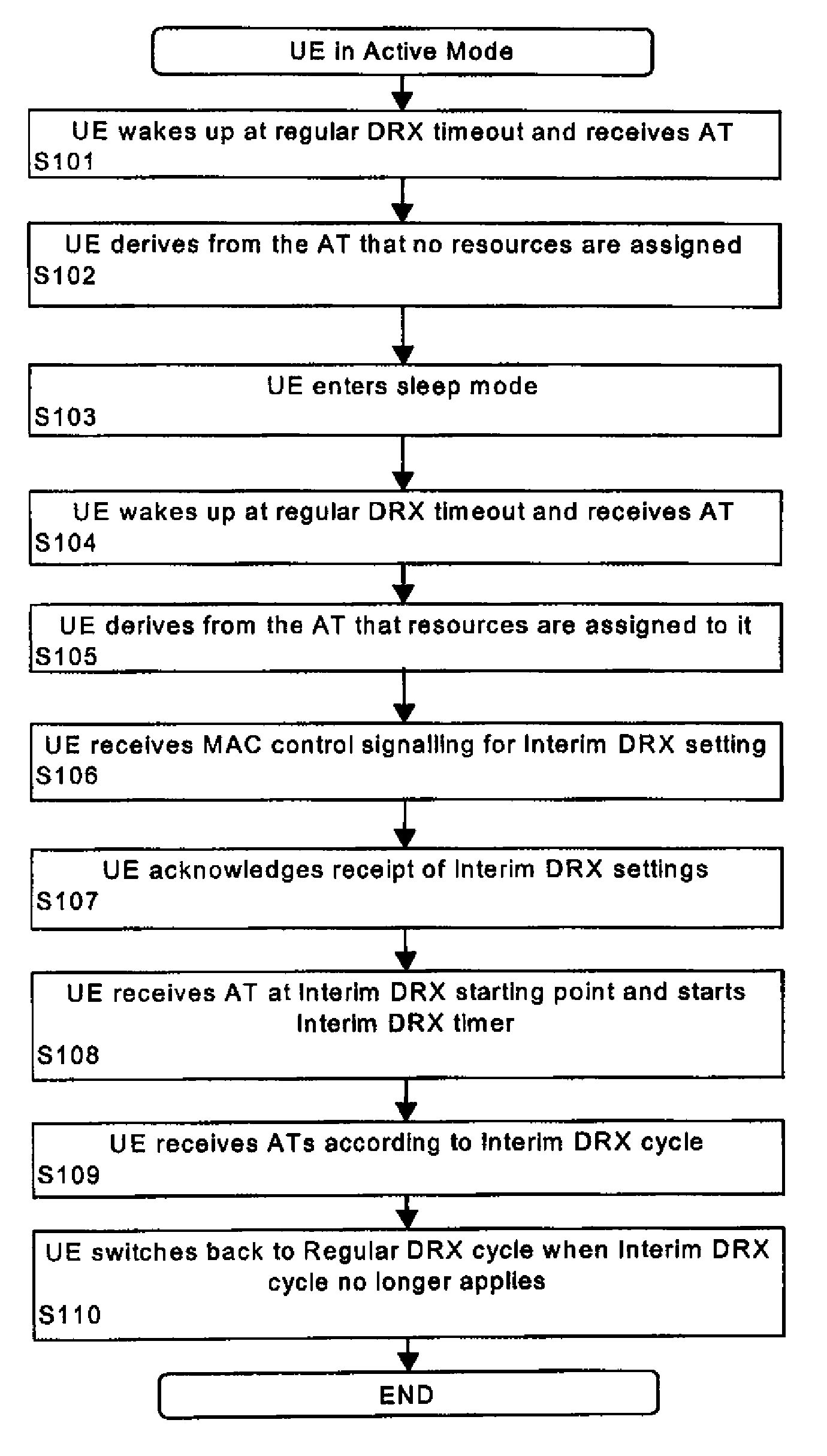
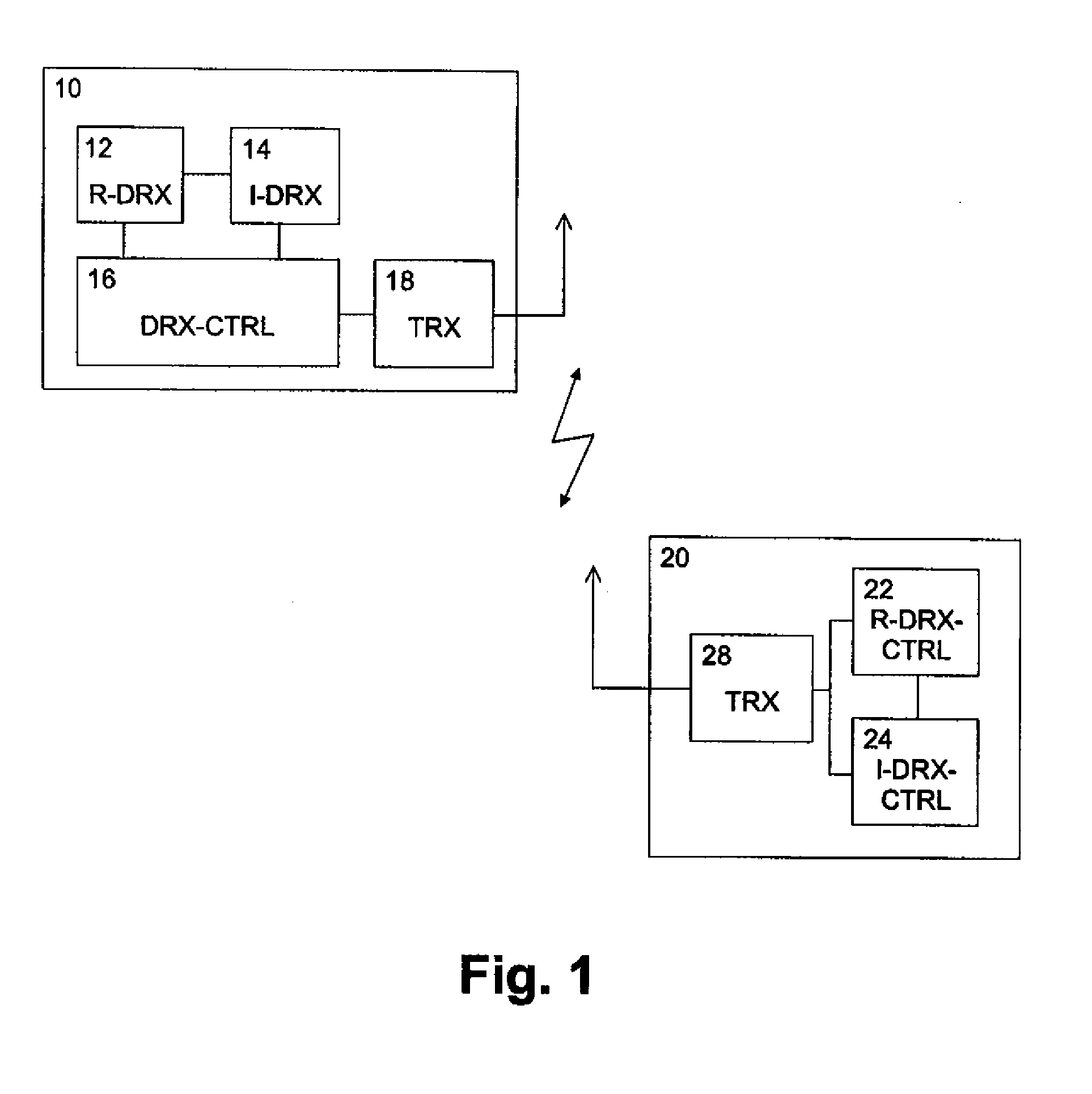
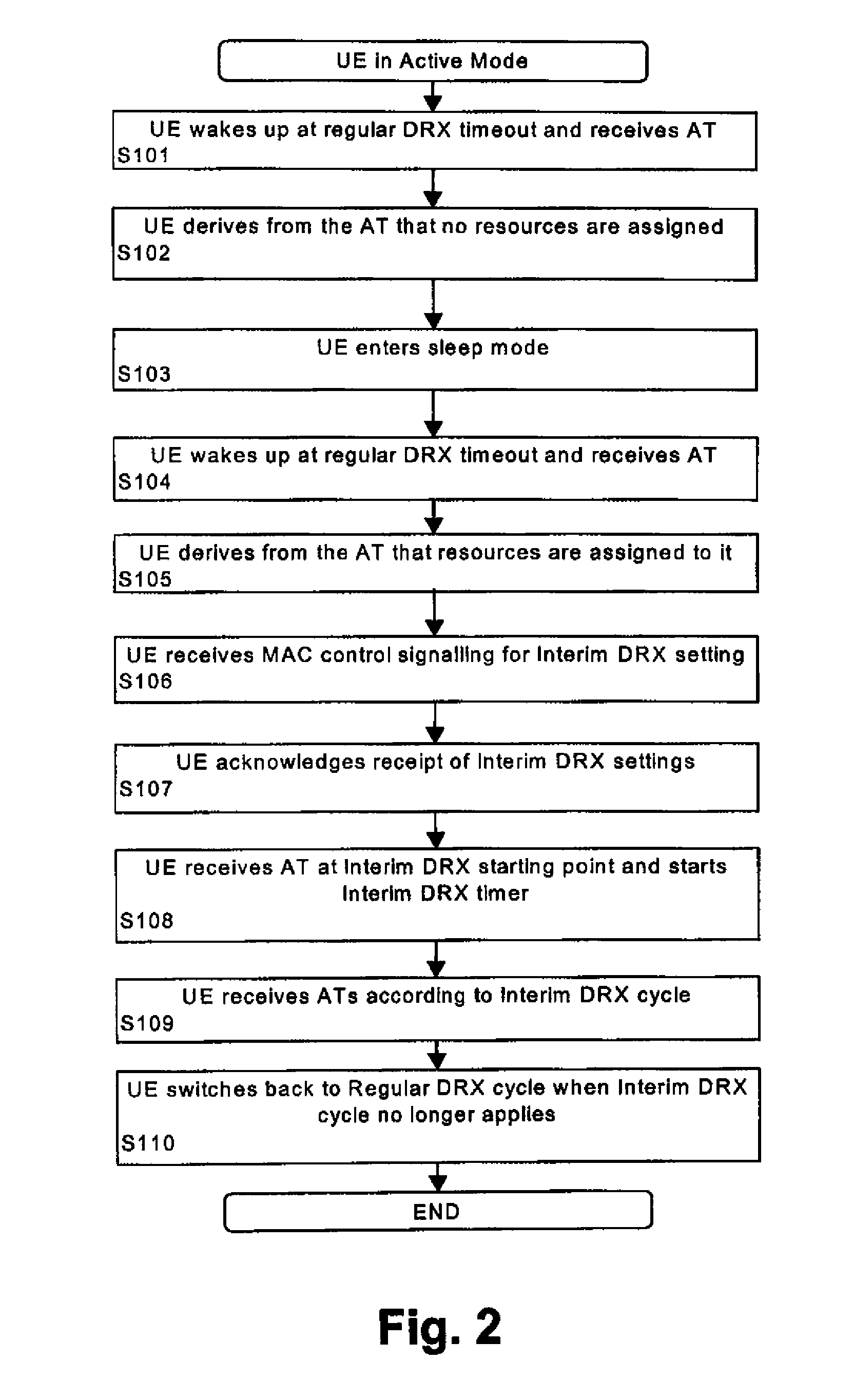
Method and system for providing interim discontinuous reception/transmission
ActiveUS20070291728A1Flexible DRX/DTXEasy to adjustPower managementEnergy efficient ICTComputer hardwareControl layer
A method, terminal device, network element, system and computer program product for controlling discontinuous reception or transmission at a terminal device of a communication network are disclosed. A regular discontinuous reception or transmission cycle of a regular discontinuous reception or transmission scheme is set by using a first control layer, and in addition thereto a shorter temporary discontinuous reception or transmission cycle of an interim discontinuous reception or transmission scheme can be set by using a second control layer. This arrangement provides long discontinuous reception or transmission cycles for power consumption improvements while at the same time ensuring that the network can easily and flexibly shorten these cycles for increased data throughput, if needed.
Owner:NOKIA TECHNOLOGLES OY
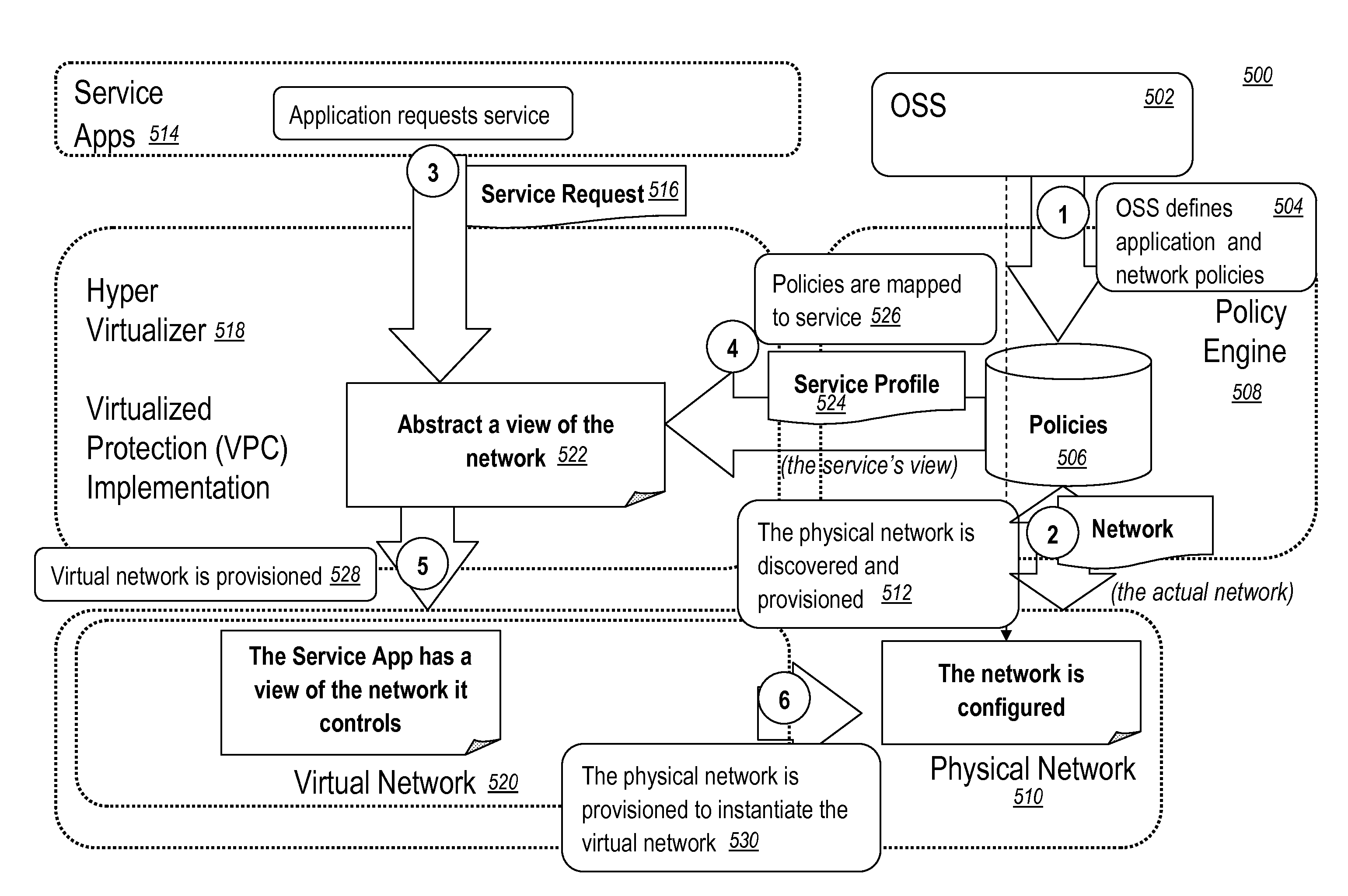
Virtualized shared protection capacity
The present disclosure relates a network, a network element, a system, and a method providing an efficient allocation of protection capacity for network connections and / or services. These may be for services within a given Virtual Private Network (VPN) or Virtual Machine (VM) instance flow. Network ingress / egress ports are designed to be VM instance aware while transit ports may or may not be depending on network element capability or configuration. A centralized policy management and a distributed control plane are used to discover and allocate resources to and among the VPNs or VM instances. Algorithms for efficient allocation and release of protection capacity may be coordinated between the centralized policy management and the distributed control plane. Additional coupling of attributes such as latency may provide more sophisticated path selection algorithms including efficient sharing of protection capacity.
Owner:CIENA
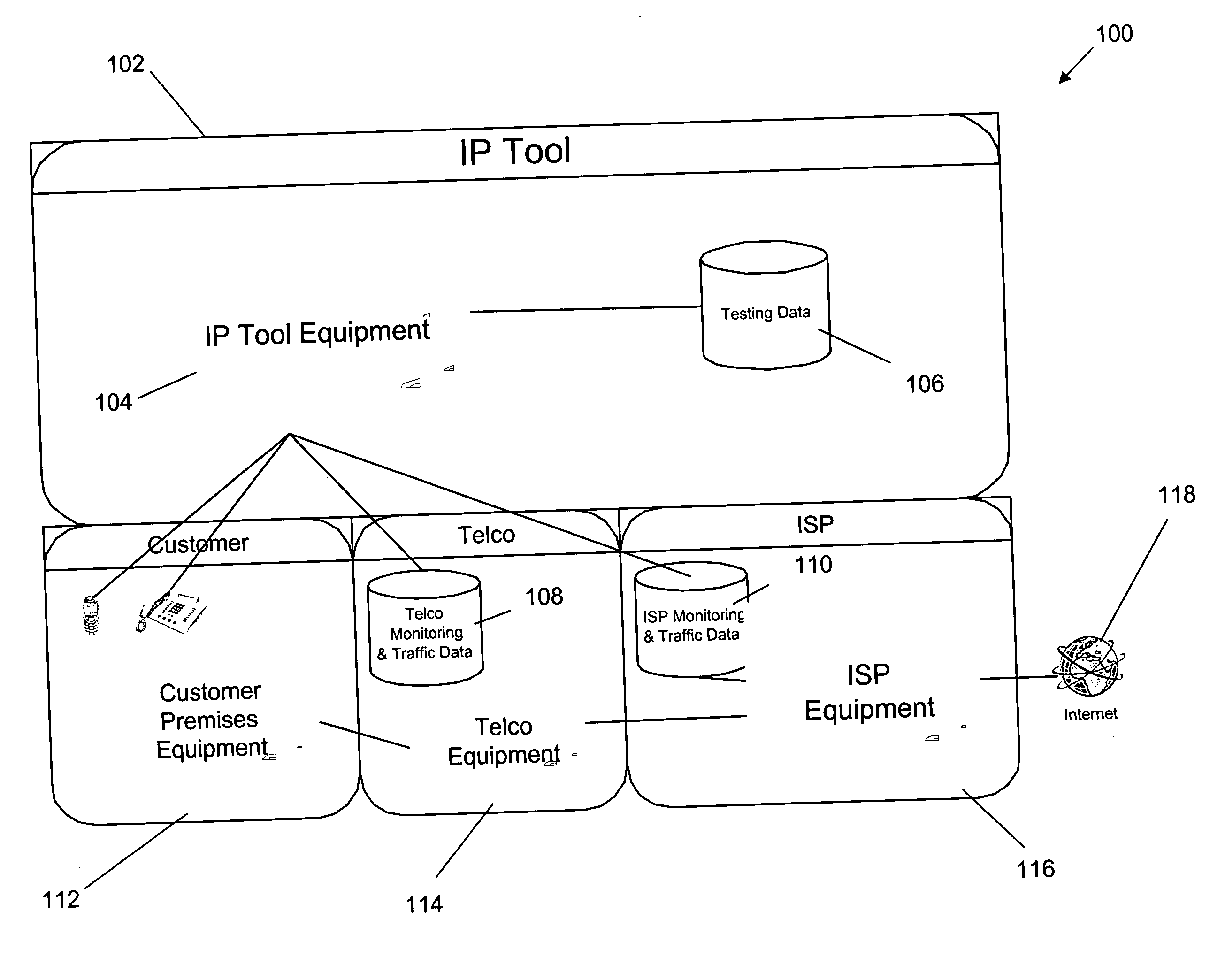
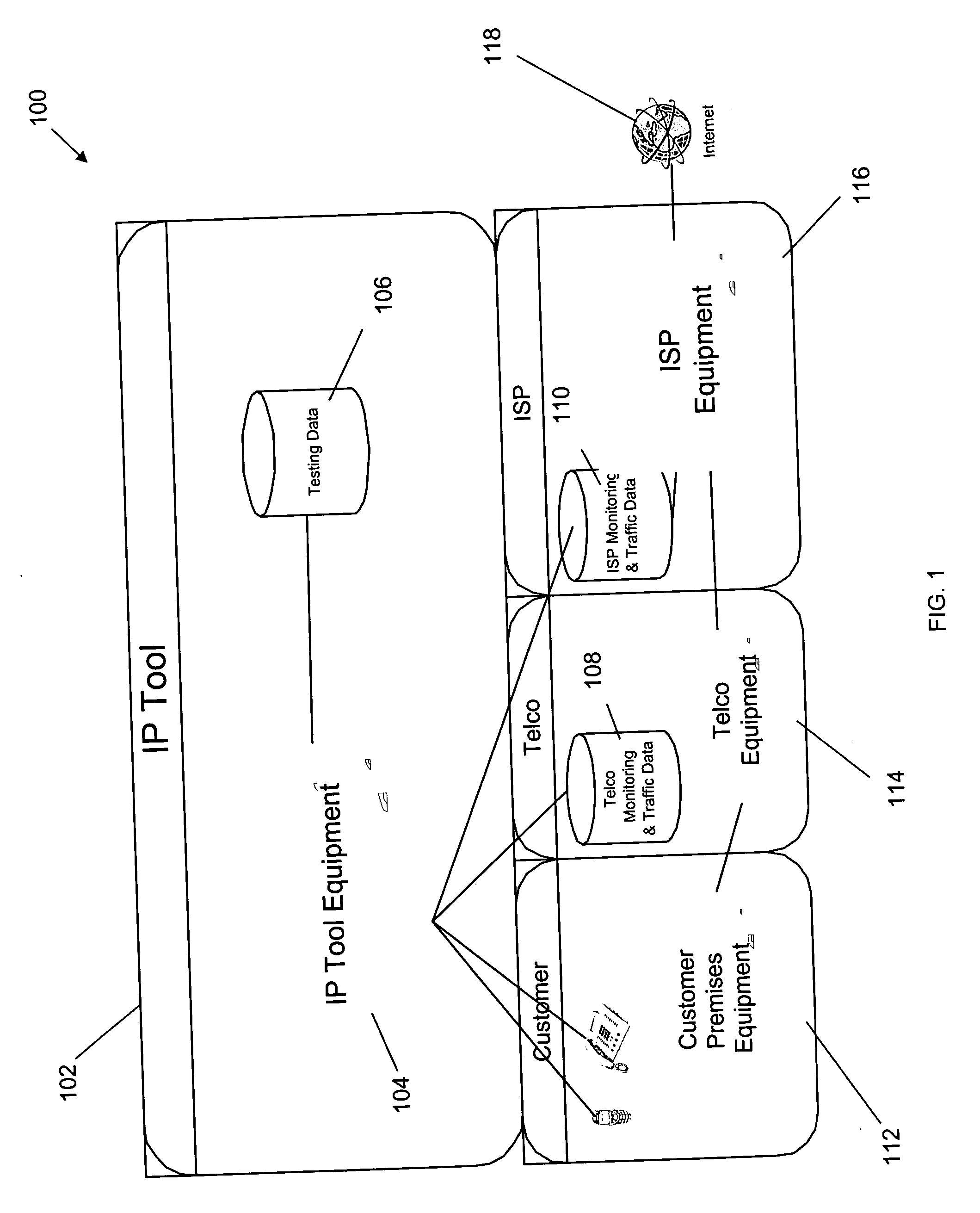
Method and system for comprehensive testing of network connections
InactiveUS20070041554A1Special service for subscribersSupervisory/monitoring/testing arrangementsData setNetwork connection
The present invention is an system and method for comprehensively testing a customer connection to a communications network. A customer is identified from information obtained at a customer interface. A test can be performed on the customer connection. A typical test compares two datasets related to the customer connection to determine a state of the customer connection. The first and second dataset can include historical data. A parameter in the first dataset obtained from a network element can be compared to a parameter in a second dataset obtained from a customer database. The comparison can be made in light of changes recorded in a provisioning database. Relevant network data can be obtained from customer premises equipment (CPE). The customer can be notified of a network issue proactively or upon customer inquiry.
Owner:SBC KNOWLEDGE VENTURES LP
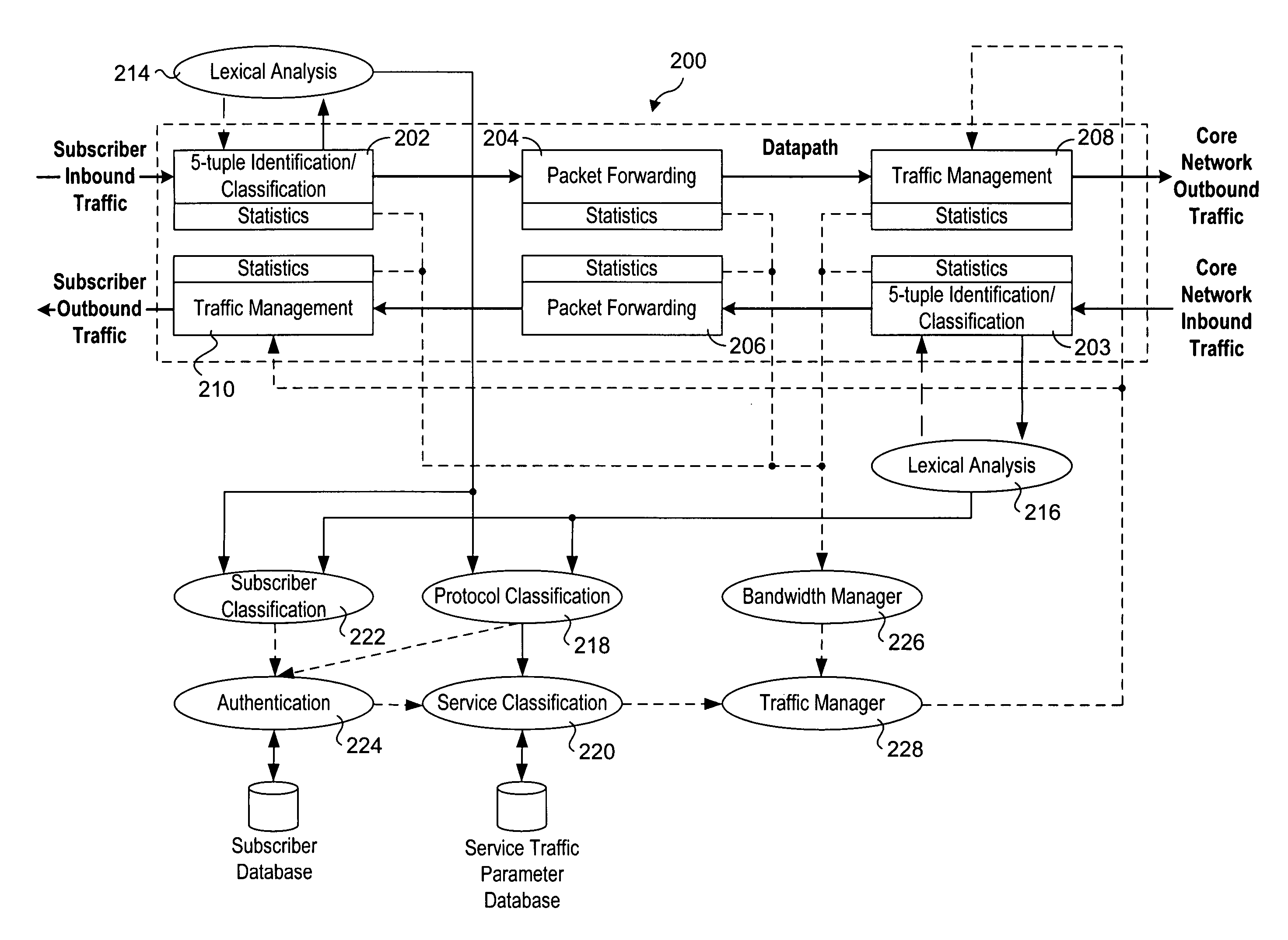
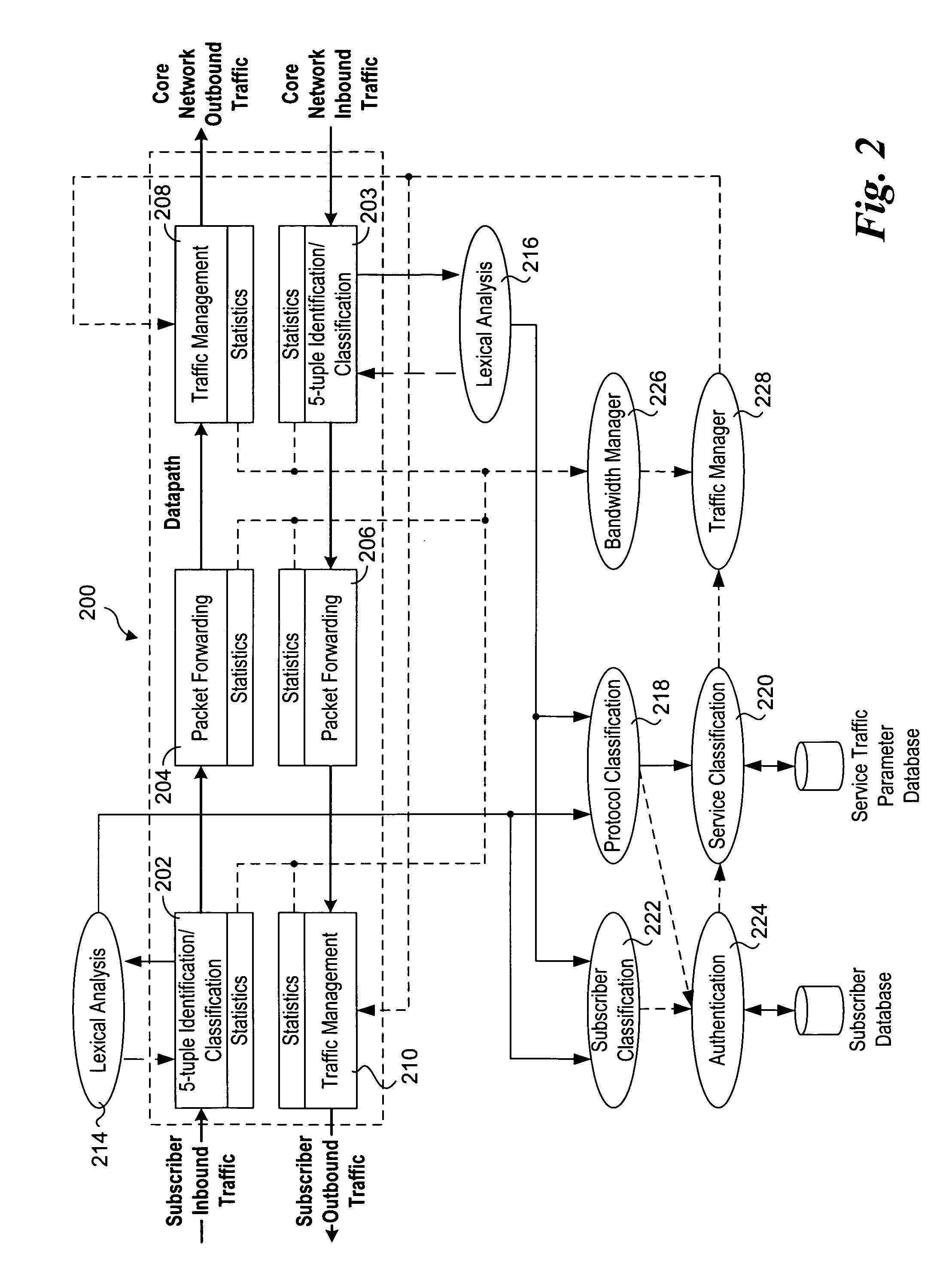
Methods and apparatus to support dynamic allocation of traffic management resources in a network element
Methods and apparatus to support dynamic allocation of traffic management resources in a network element. Shared pools of traffic management resources comprising an aggregation of local line card resources distributed across the line cards or a network element maintained by apparatus software. Incoming packets are classified into subscriber flows using a hierarchical classification scheme. In view of subscriber services and flow application types, traffic management resources are dynamically allocated from the shared pools, and traffic management policies associated with the subscriber services and application types are applied to the subscriber flows via the allocated resources. In response to detecting a subscriber flow has terminated, the allocated resources are release and made available to be dynamically re-allocated to subsequent subscriber flows.
Owner:TELLABS COMM CANADA
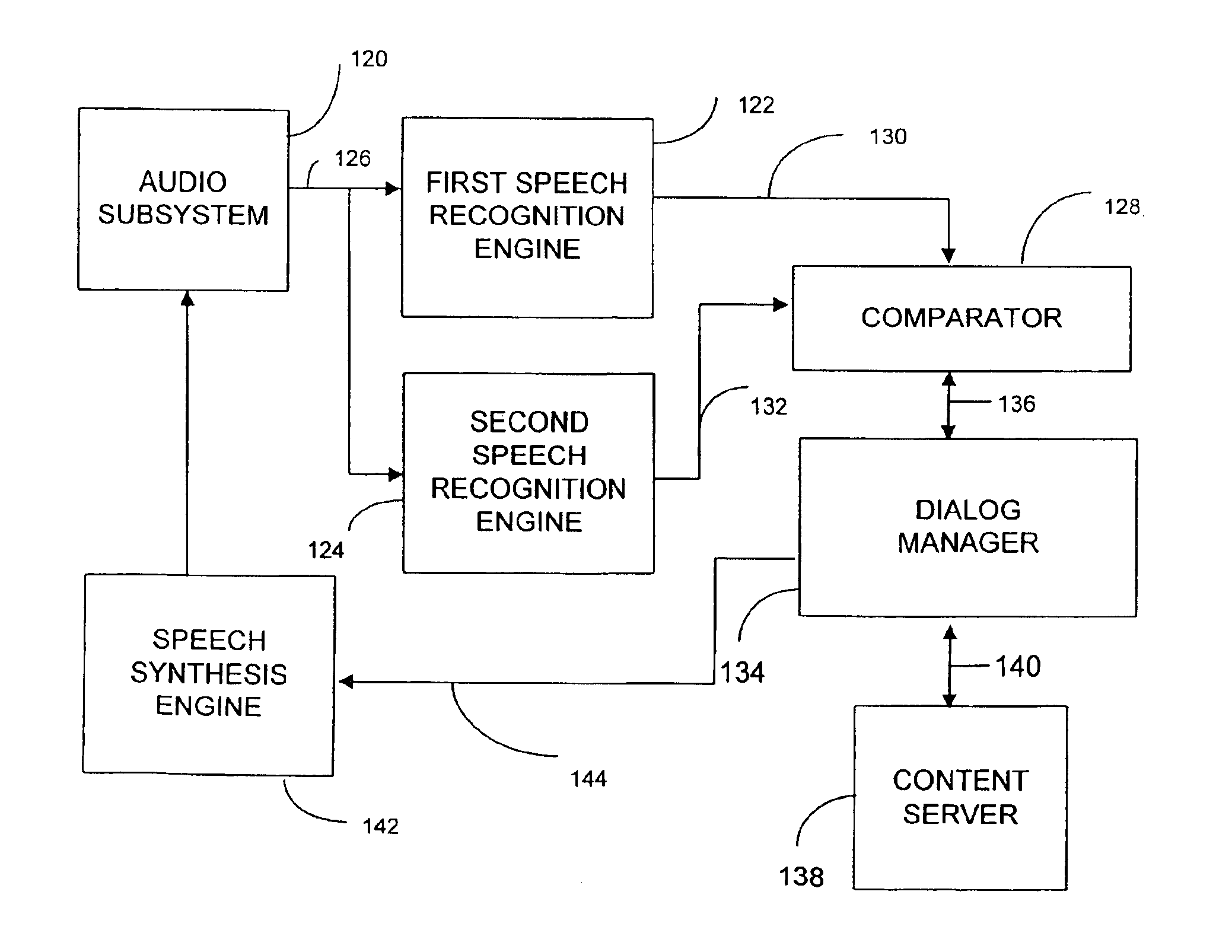
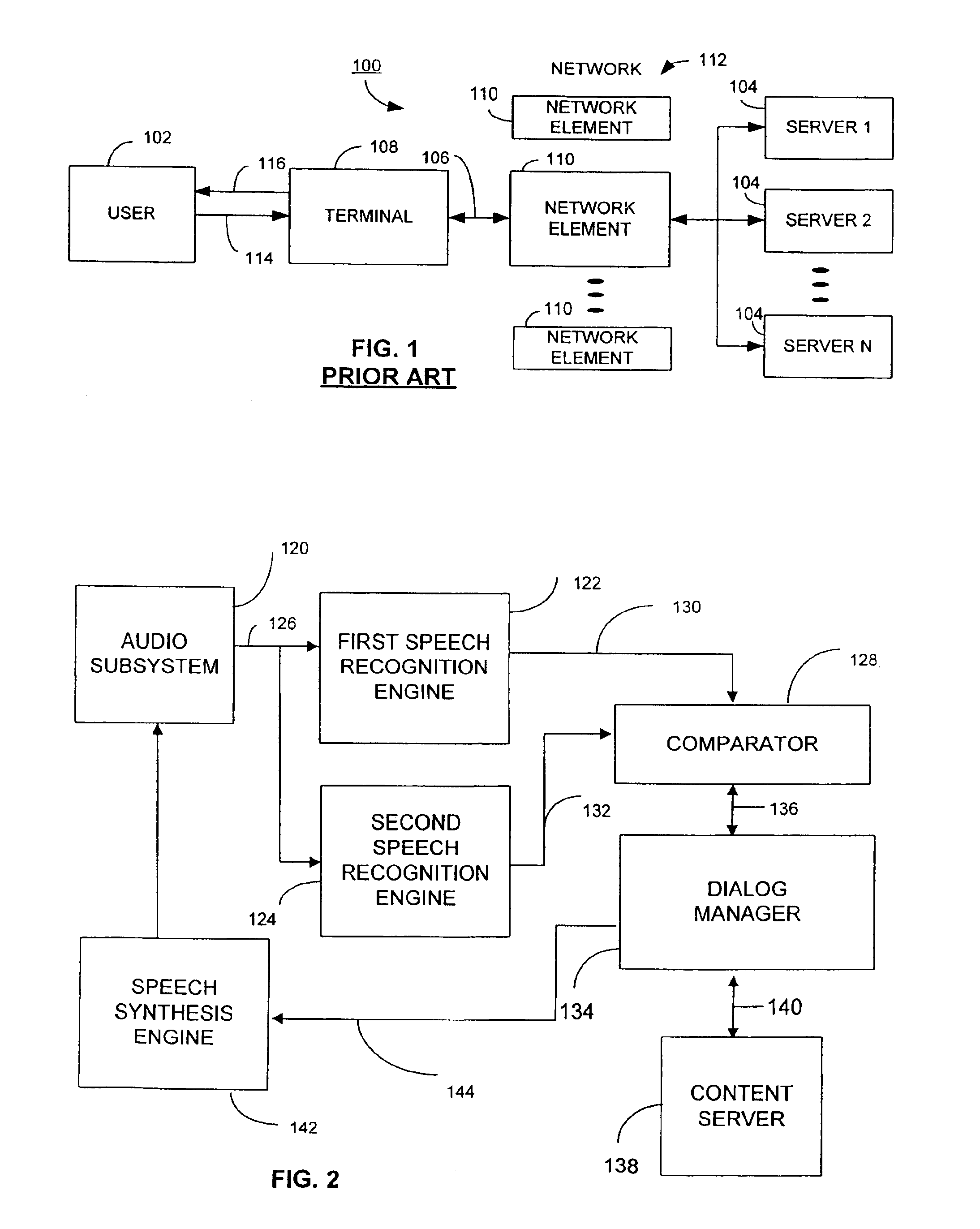
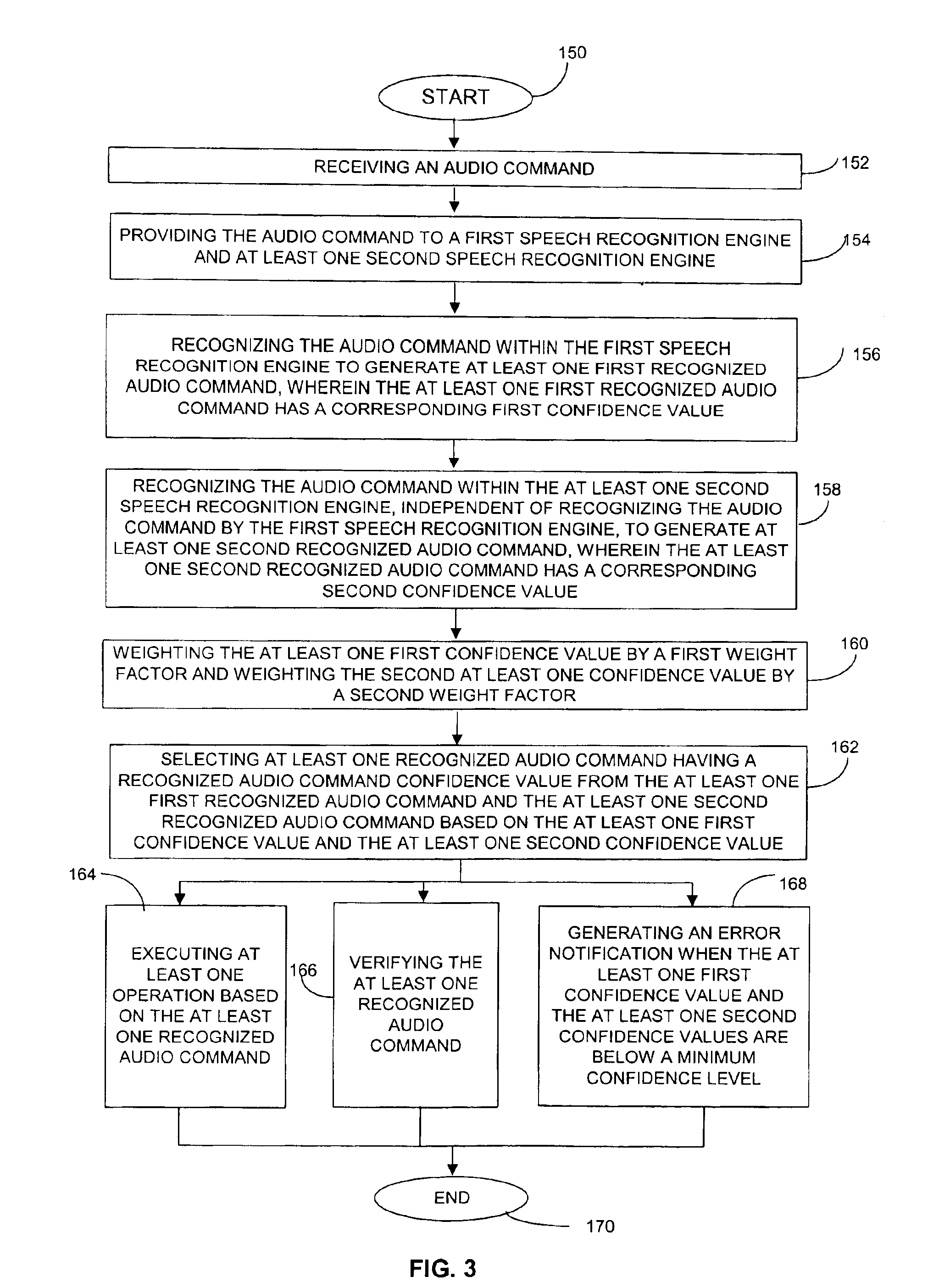
Method and apparatus for multi-level distributed speech recognition
A system and method for multi-level distributed speech recognition includes a terminal (122) having a terminal speech recognizer (136) coupled to a microphone (130). The terminal speech recognizer (136) receives an audio command (37), generating at least one terminal recognized audio command having a terminal confidence value. A network element (124) having at least one network speech recognizer (150) also receives the audio command (149), generating a at least one network recognized audio command having a network confidence value. A comparator (152) receives the recognized audio commands, comparing compares the speech recognition confidence values. The comparator (152) provides an output (162) to a dialog manager (160) of at least one recognized audio command, wherein the dialog manager then executes an operation based on the at least one recognized audio command, such as presenting the at least one recognized audio command to a user for verification or accessing a content server.
Owner:GOOGLE TECH HLDG LLC
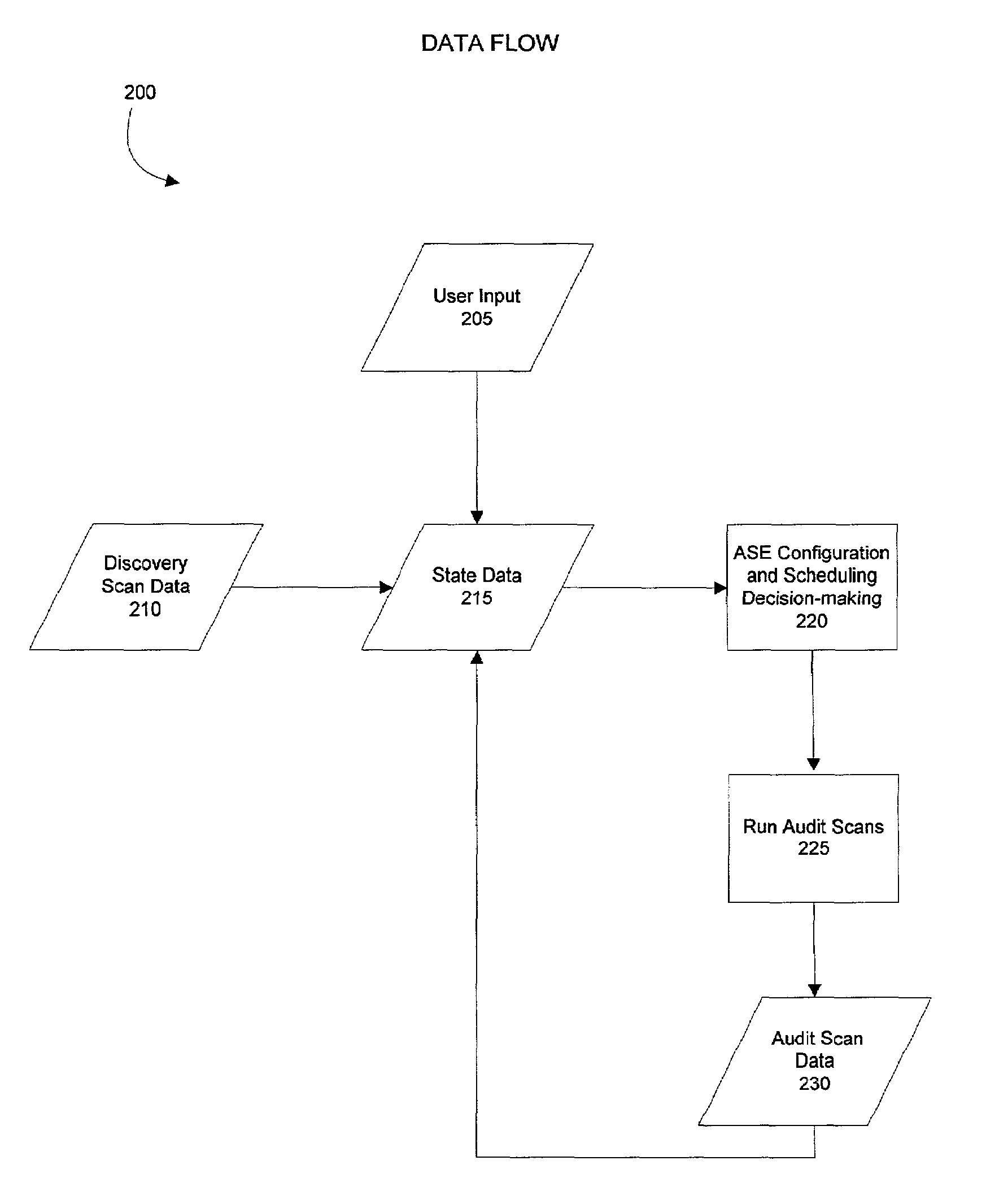
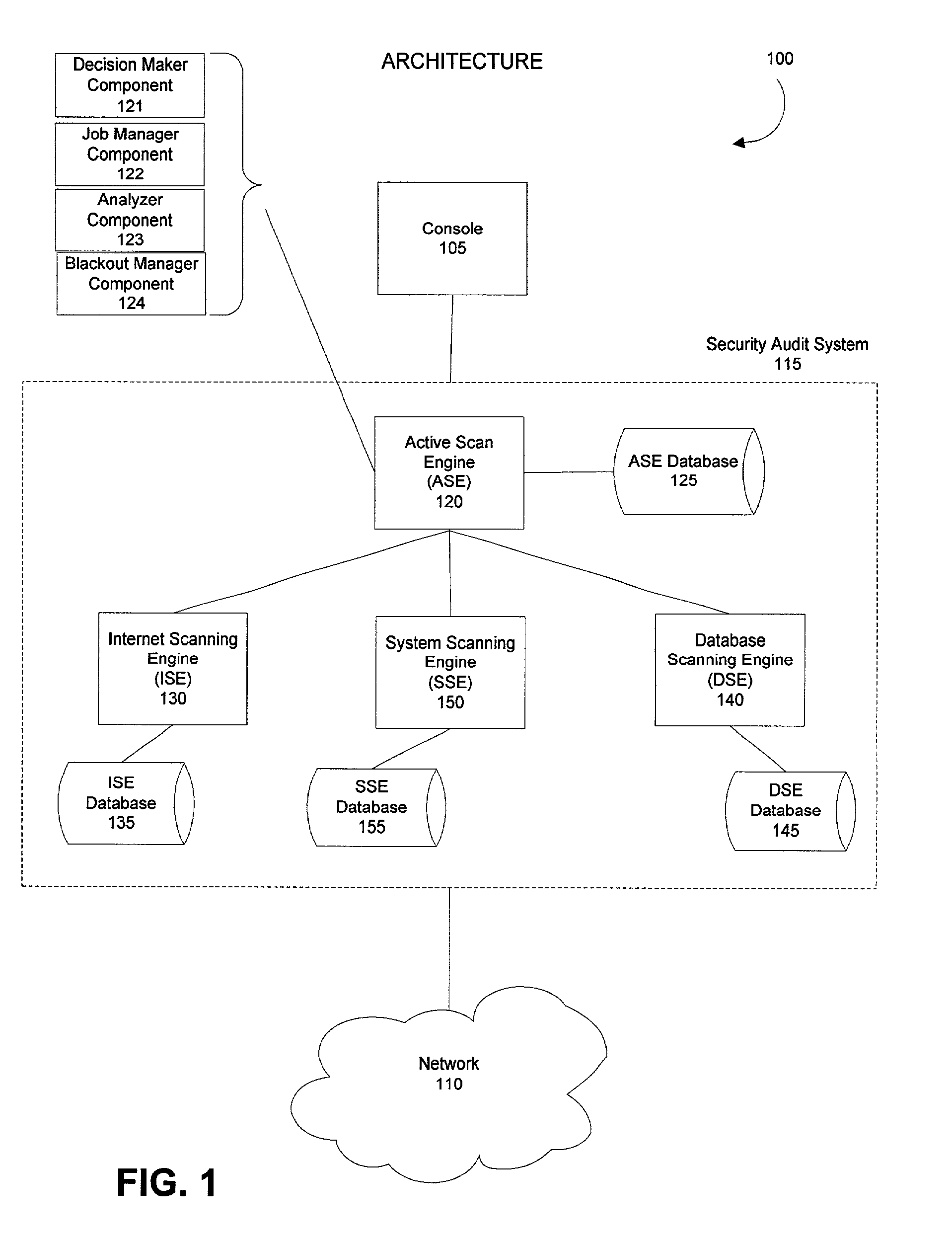
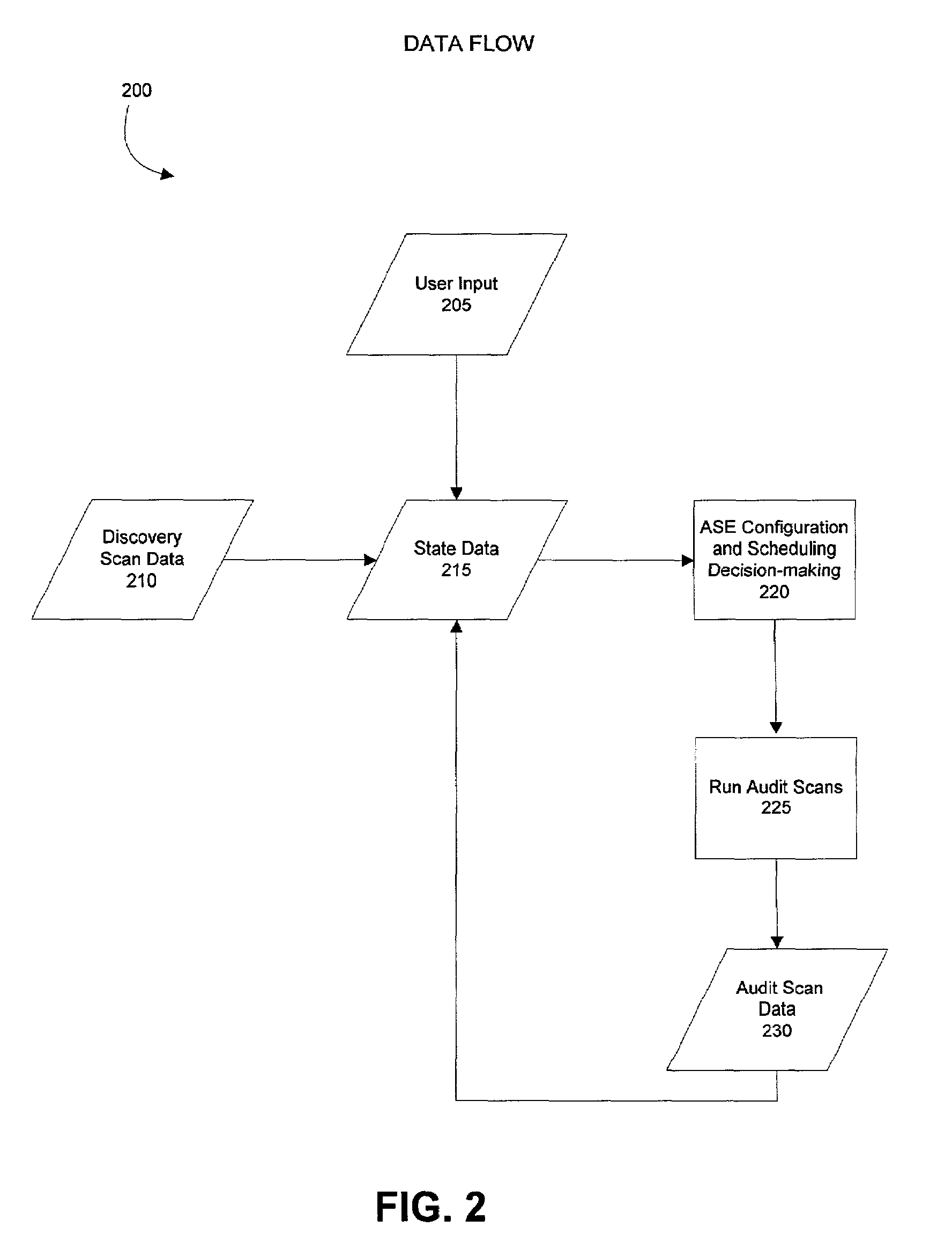
Method and system for configuring and scheduling security audits of a computer network
ActiveUS7340776B2Improves existing network security techniquesNetwork security issueMemory loss protectionDigital data processing detailsOperational systemVulnerability assessment
Managing the selection and scheduling of security audits run on a computing network. The computer network is surveyed by a security audit system to determine the function and relative importance of the elements in the network. Based on function and priority, a more thorough type of security audit is selected to run against each of the network elements by the security audit system. The security audit can also be automatically scheduled based on the information gathered from the survey. Once the system runs the security audit, a vulnerability assessment can be calculated for each element in the network. The vulnerability assessment can be presented in a format that facilitates interpretation and response by someone operating the system. The vulnerability assessment can also be used to configure and schedule future security audits.
Owner:FINJAN BLUE INC
Highly scalable architecture for application network appliances
A highly scalable application network appliance is described herein. According to one embodiment, a network element includes a switch fabric, a first service module coupled to the switch fabric, and a second service module coupled to the first service module over the switch fabric. In response to packets of a network transaction received from a client over a first network to access a server of a data center having multiple servers over a second network, the first service module is configured to perform a first portion of OSI (open system interconnection) compatible layers of network processes on the packets while the second service module is configured to perform a second portion of the OSI compatible layers of network processes on the packets. The first portion includes at least one OSI compatible layer that is not included in the second portion. Other methods and apparatuses are also described.
Owner:CISCO TECH INC
Ethernet OAM domains and ethernet OAM frame format
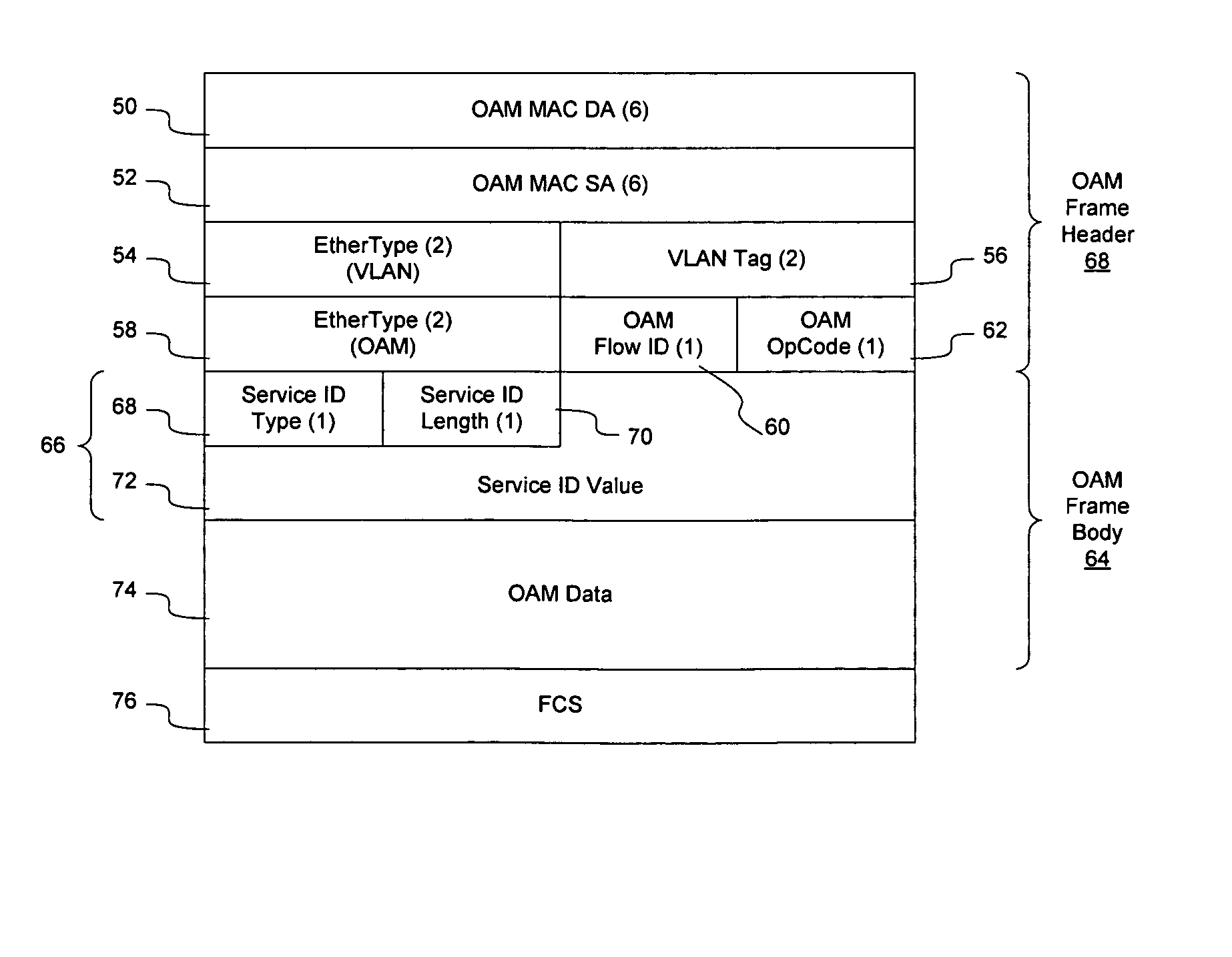
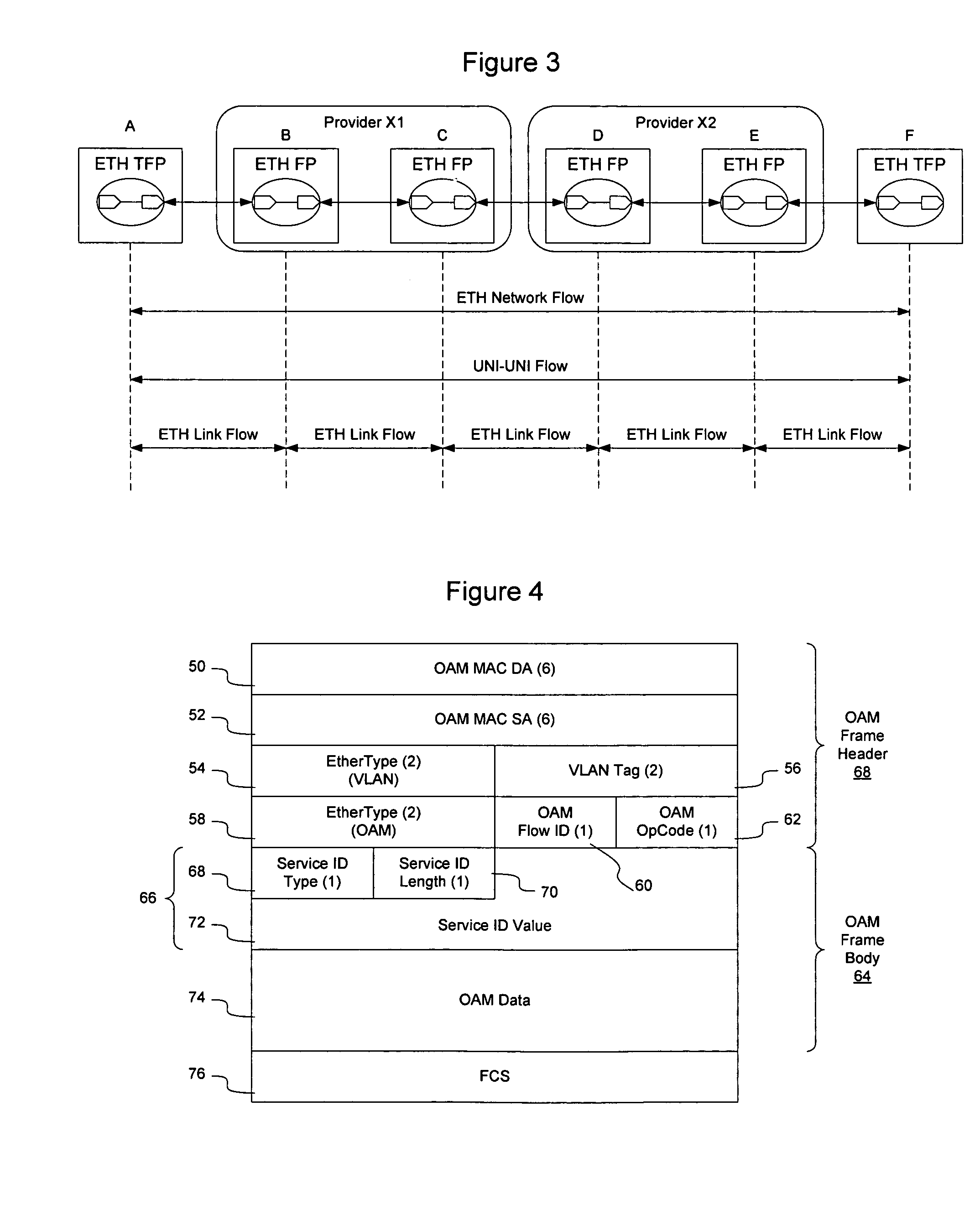
Ethernet OAM domains may be defined by defining reference points on the Ethernet network and using the reference points to insert and extract Ethernet OAM flows. The reference points may be network elements at the edge of a provider's domain, customer elements, or network elements configured to perform OAM flow handoffs between domains. By defining OAM multicast addresses and OAM flow identifiers, and allowing the reference points to be addressed by the multicast address and filtering to be performed by the reference points based on the OAM flow identifiers, OAM flows may be defined on the network. For example, customer-customer OAM flows may be defined, intra-provider and inter-provider OAM flows may be defined, and various segment OAM flows may be defined. An OAM frame format is provided to enable the OAM flows to be carried in a conventional Ethernet network.
Owner:NORTEL NETWORKS LTD
Authentication and authorization in heterogeneous networks
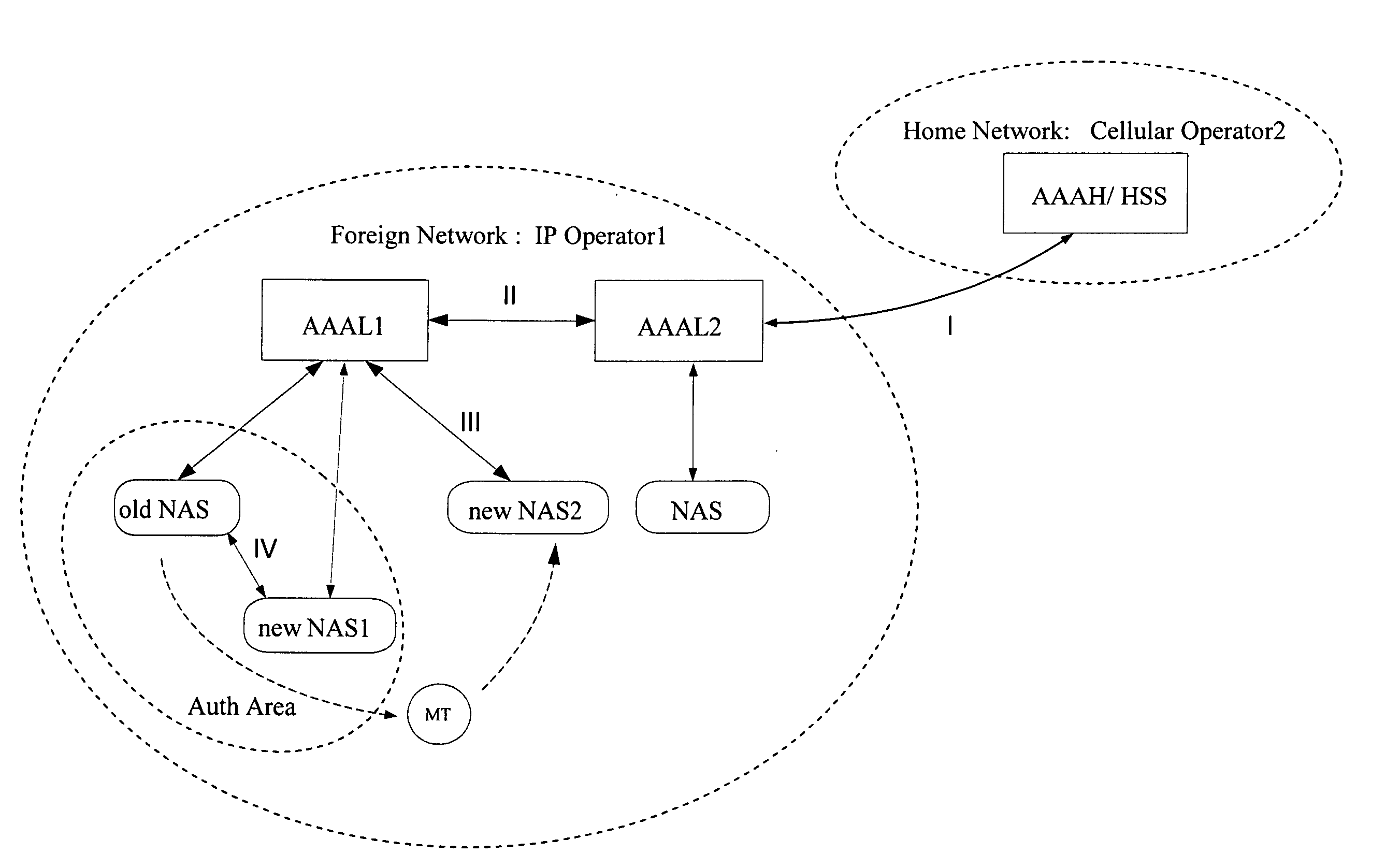
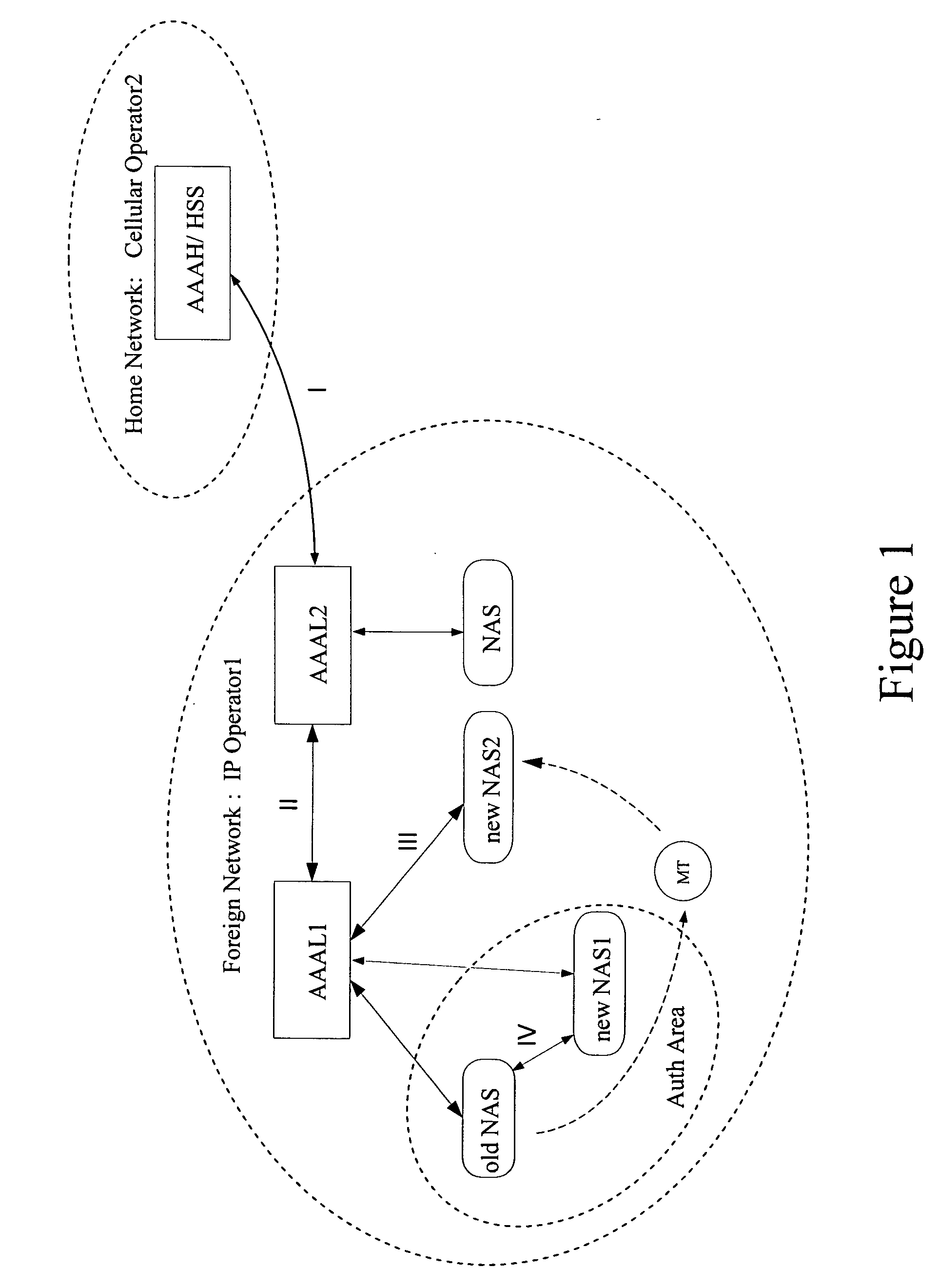
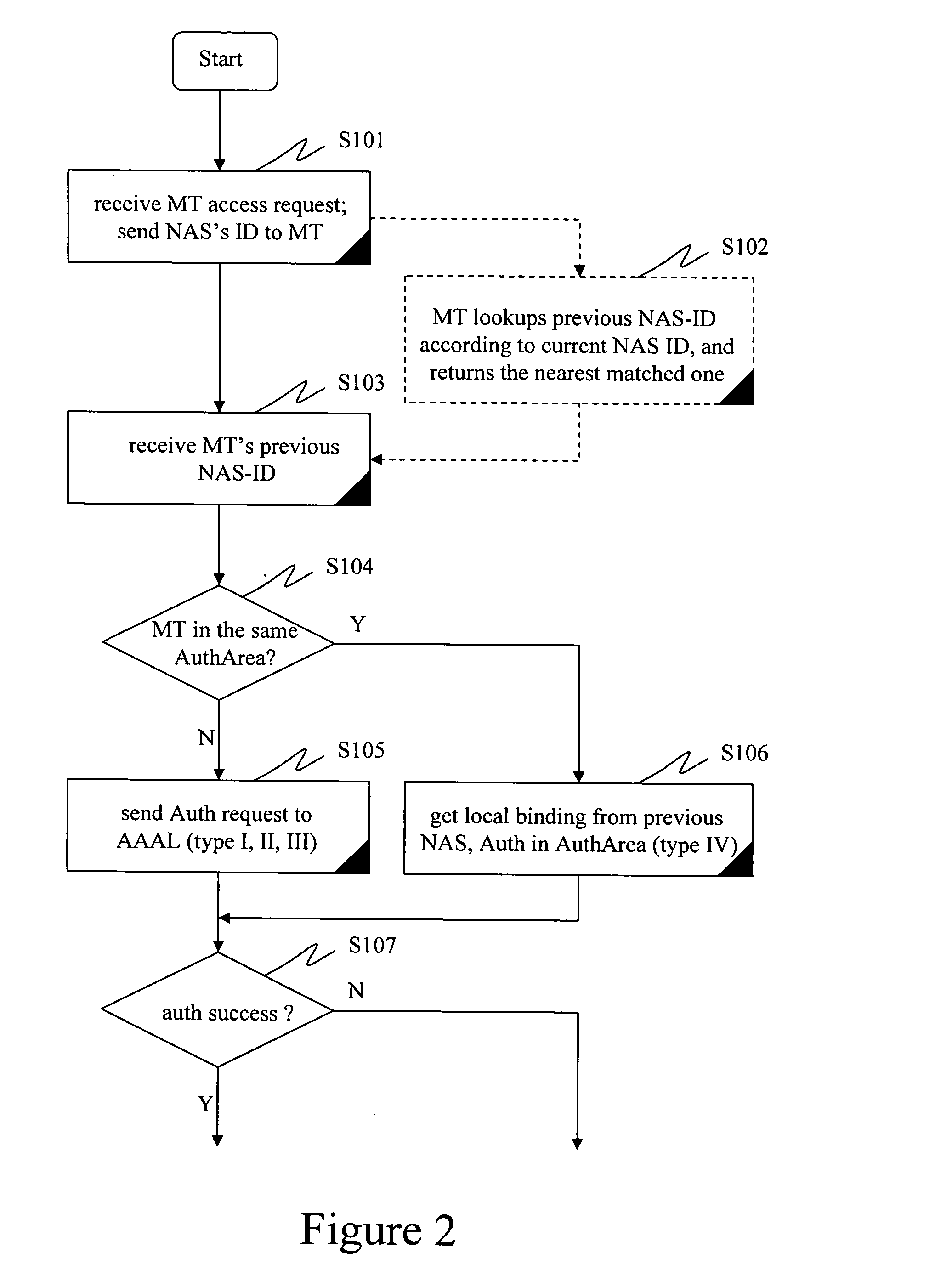
ActiveUS20050166043A1Optimized network access performanceImproved AAA performanceMultiplex system selection arrangementsData switching networksNetwork access serverHeterogeneous network
A method, system, and network elements for authentication and authorization of a mobile terminal (MT) roaming to or in a foreign network different from its home network is provided, the home network having an authentication and authorization home server (AAAH), and the foreign network having a plurality of domains each of which comprises at least one local server (AAAL1, AAAL2) for authentication, authorization and accounting, each of which local servers being connected to at least one network access server (NAS) for handling access for mobile terminals roaming to or in the foreign network, wherein an authentication and authorization of the mobile terminal is performed whenever the mobile terminal performs a roaming, wherein the authentication and authorization is performed according to a procedure pursuant to one of a plurality of hierarchy levels, whereby a combination of network elements involved in the roaming determines the hierarchy level to be used.
Owner:NOKIA TECHNOLOGLES OY
High-throughput, low-latency next generation internet networks using optical tag switching
InactiveUS6111673AEfficient comprehensive utilizationSignificant overheadMultiplex system selection arrangementsLaser detailsSignal routingInternet network
An optical signaling header technique applicable to optical networks wherein packet routing information is embedded in the same channel or wavelength as the data payload so that both the header and data payload propagate through network elements with the same path and the associated delays. The header routing information has sufficiently different characteristics from the data payload so that the signaling header can be detected without being affected by the data payload, and that the signaling header can also be removed without affecting the data payload. The signal routing technique can be overlaid onto the conventional network elements in a modular manner using two types of applique modules. The first type effects header encoding and decoding at the entry and exit points of the data payload into and out of the network; the second type effects header detection at each of the network elements.
Owner:RGT UNIV OF CALIFORNIA +1
IMS diameter router with load balancing
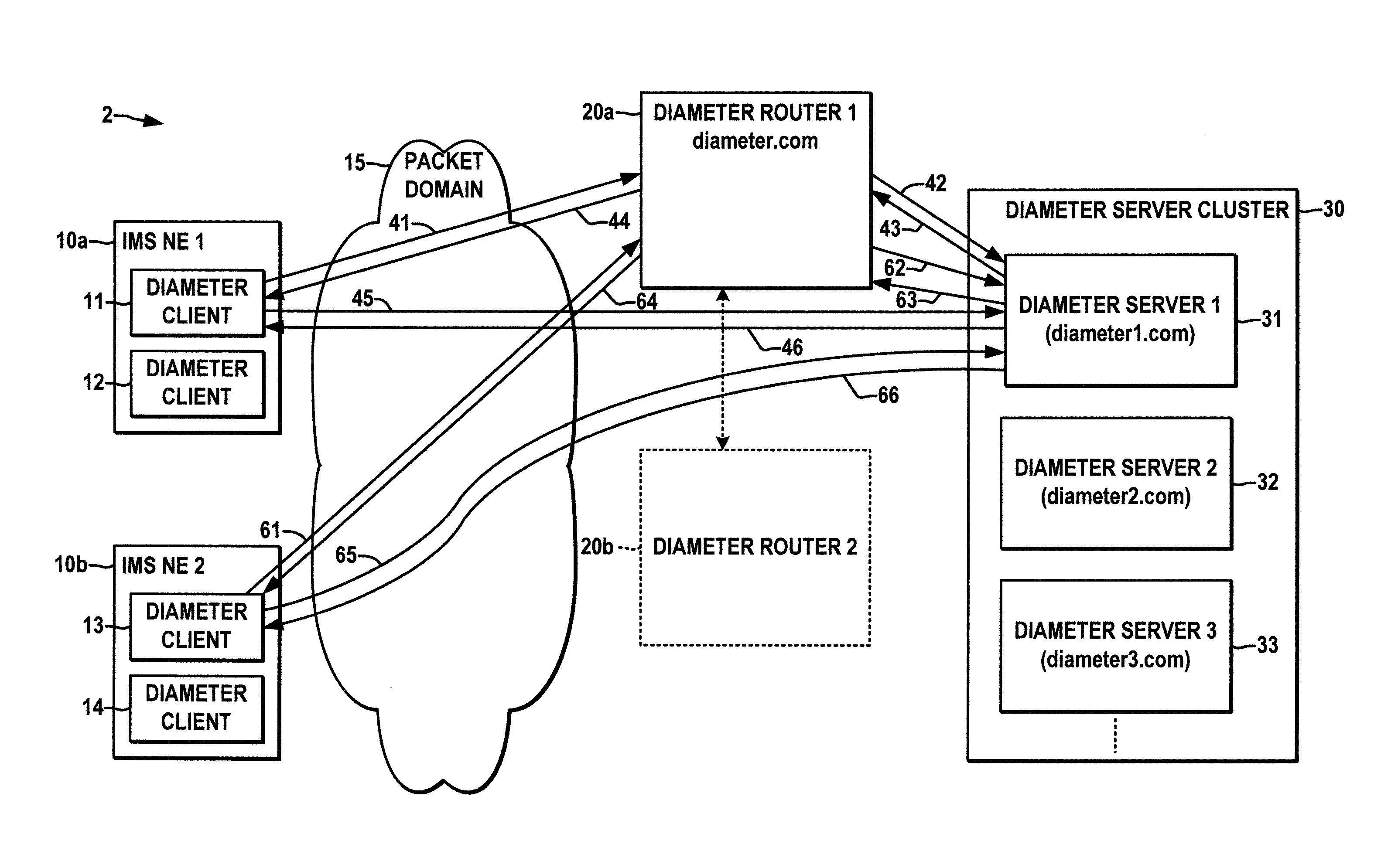
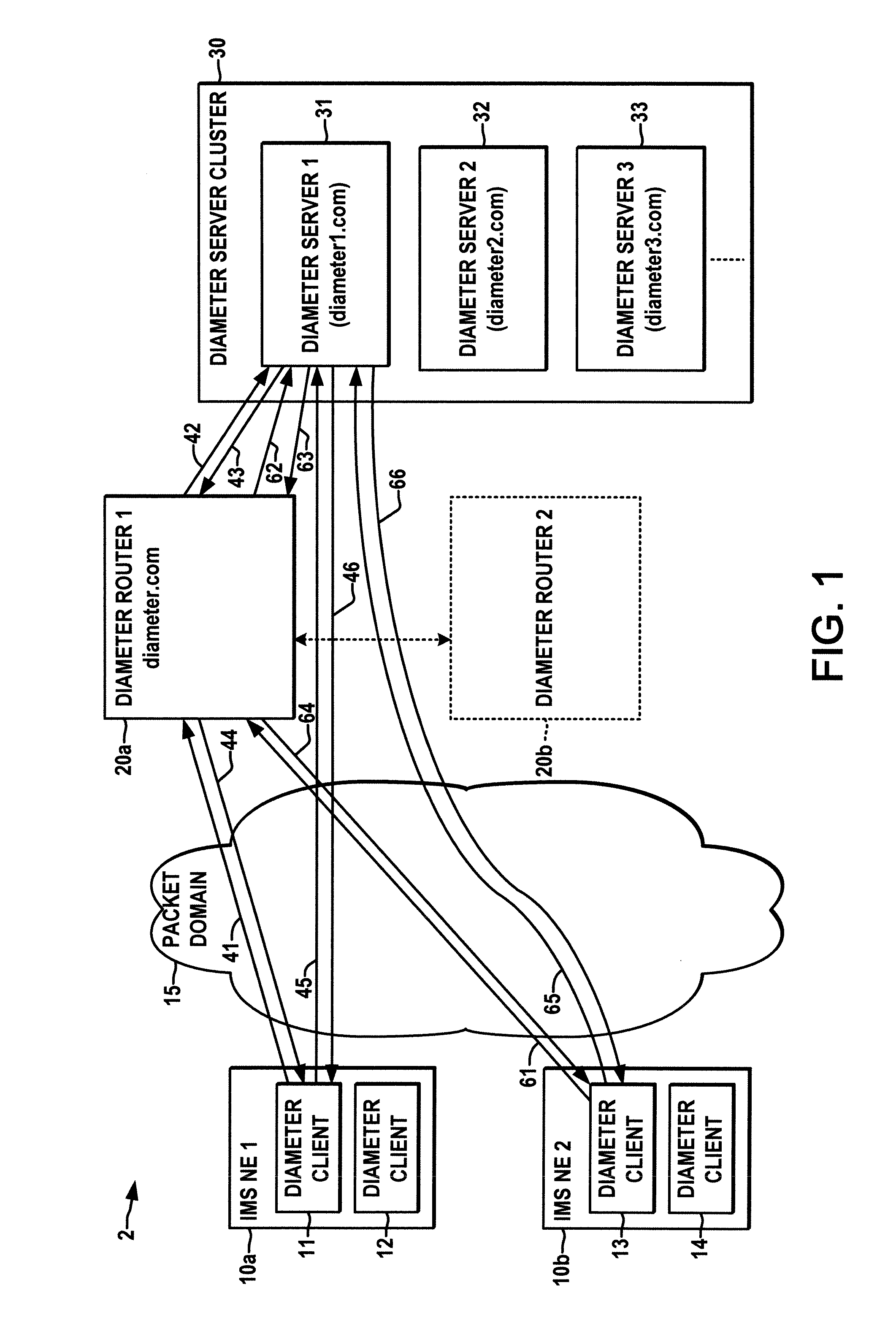
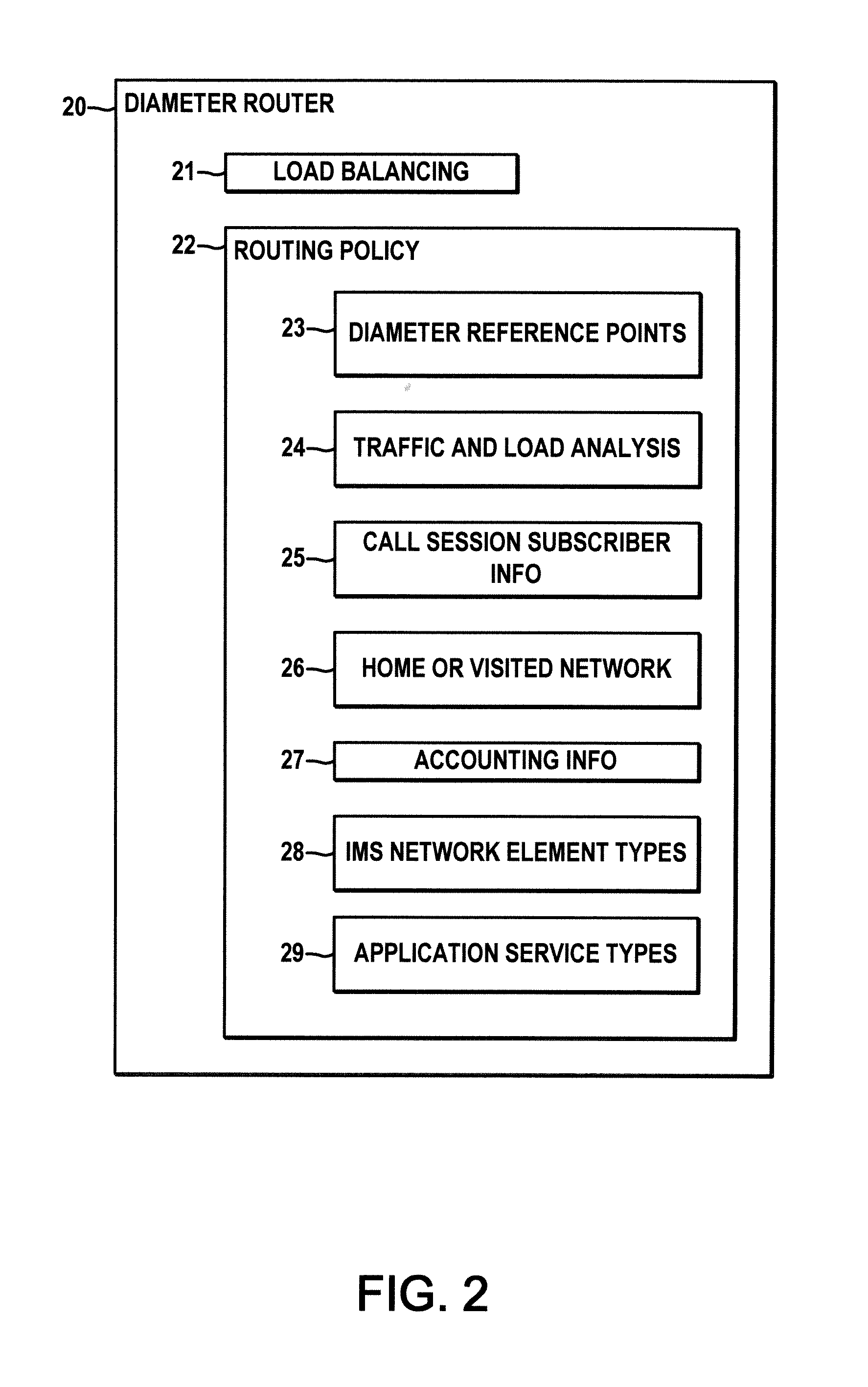
ActiveUS20100299451A1Easy to understandWell formedMultiple digital computer combinationsTransmissionMessage routingClient-side
A Diameter router (20) is presented for performing load balancing and initial Diameter message routing in an IMS network, where clients in network elements (10) are provisioned with the address of the router and send an initial Diameter request message (41) for a given session to the router. The router selects a server (31) based at least partially on a type of IMS message session, application services, subscriber information, or billing information, and sends a relayed initial Diameter request message (42) to the selected server. The selected server sends an initial Diameter response (43) to the router which then forwards a relayed initial response (44) to the client. Thereafter, the client and the selected server send messages directly to each other for the remainder of the session.
Owner:ALCATEL LUCENT SAS
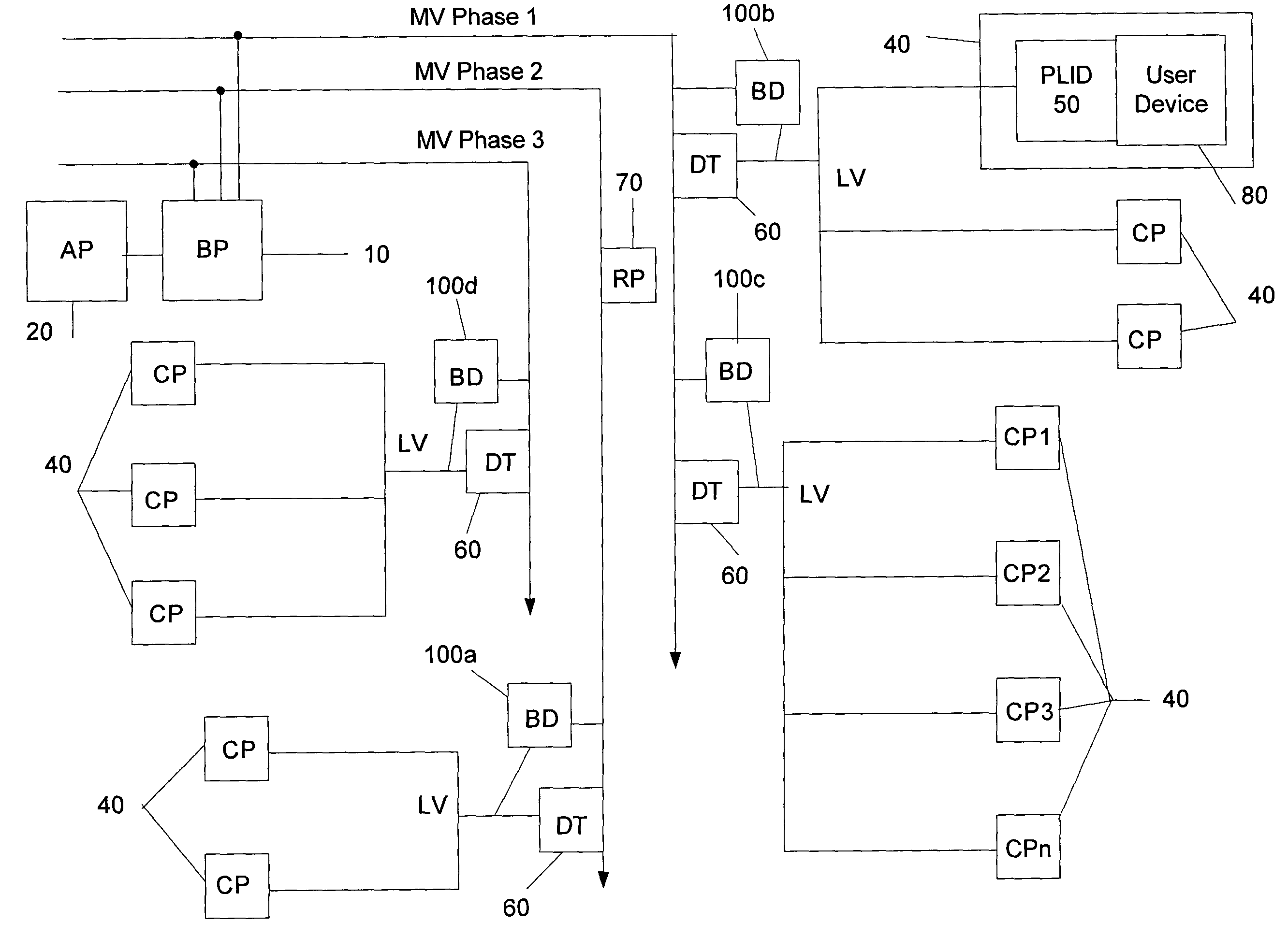
Power line repeater system and method
InactiveUS7224272B2Electric signal transmission systemsFrequency-division multiplex detailsUser deviceComputerized system
A PLCS network element that provides communications to one or more user devices and may also repeat data for other network elements is provided. In one embodiment, the device includes software for discovering its upstream gateway, for acting as a gateway for other devices, and for relaying DHCP transmissions. In addition, the device includes software for receiving and processing commands from a remote computer system that may include commands enabling and disabling the repeater functionality. Finally, the device may also include software for receiving and processing configuration information that may include, for example, information of the other network devices for which it will repeat.
Owner:CURRENT TECH
Integrated forensics platform for analyzing it resources consumed to derive operational and architectural recommendations
ActiveUS20110145657A1Easy to analyzeHardware monitoringResourcesStructure of Management InformationPhysical system
A method for facilitating forensic analysis of operational data for an IT infrastructure includes deriving performance data from a plurality of physical systems, network elements and storage devices in an IT infrastructure via a toolset comprising a plurality of IT monitoring and metrics tools, importing the performance data into an integrated forensics platform, aggregating the imported data, and analyzing the aggregated data to determine resources consumed. Each tool is communicatively interfaced with one or more of the physical systems, network elements and storage devices.
Owner:EMC IP HLDG CO LLC
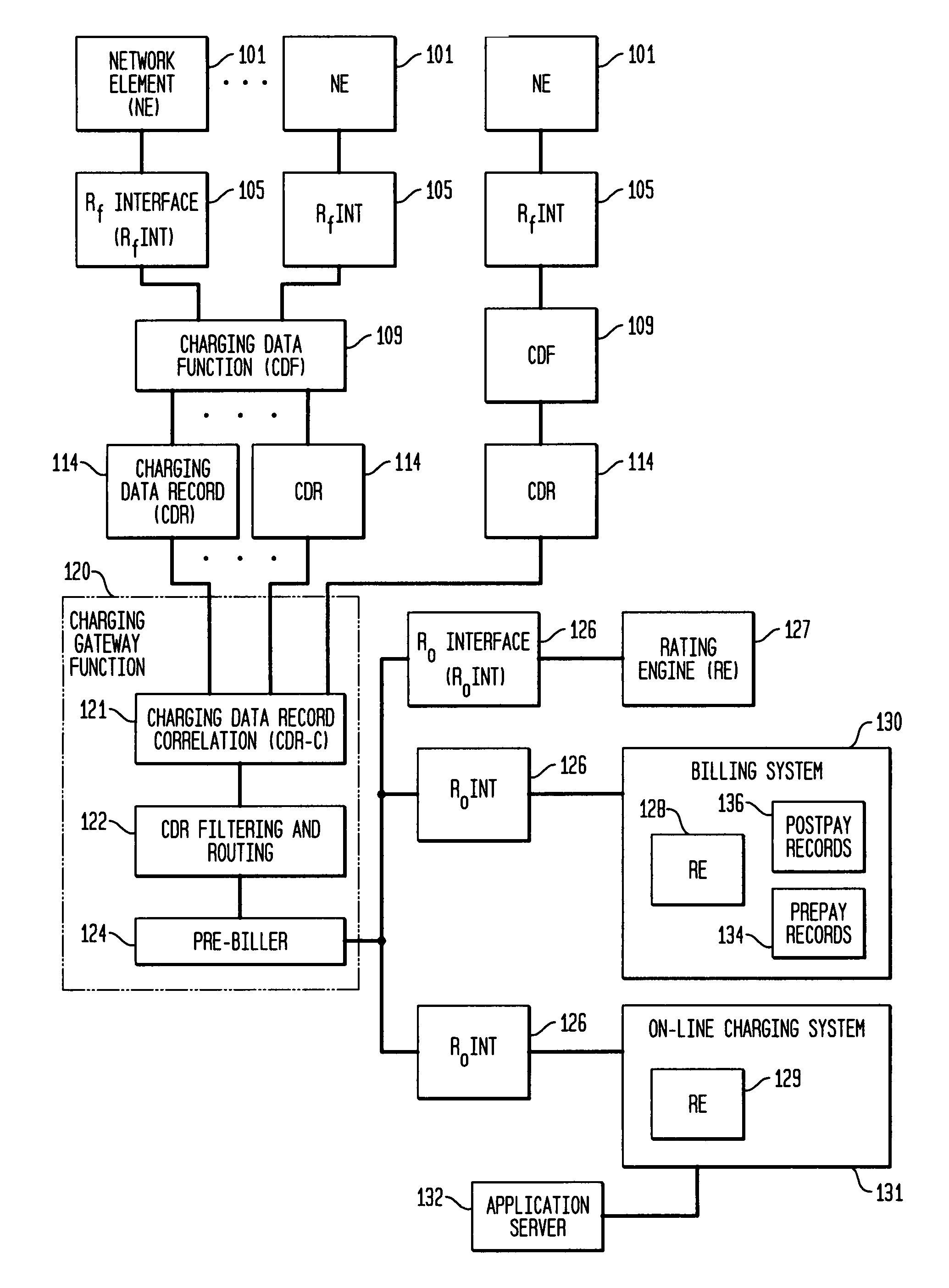
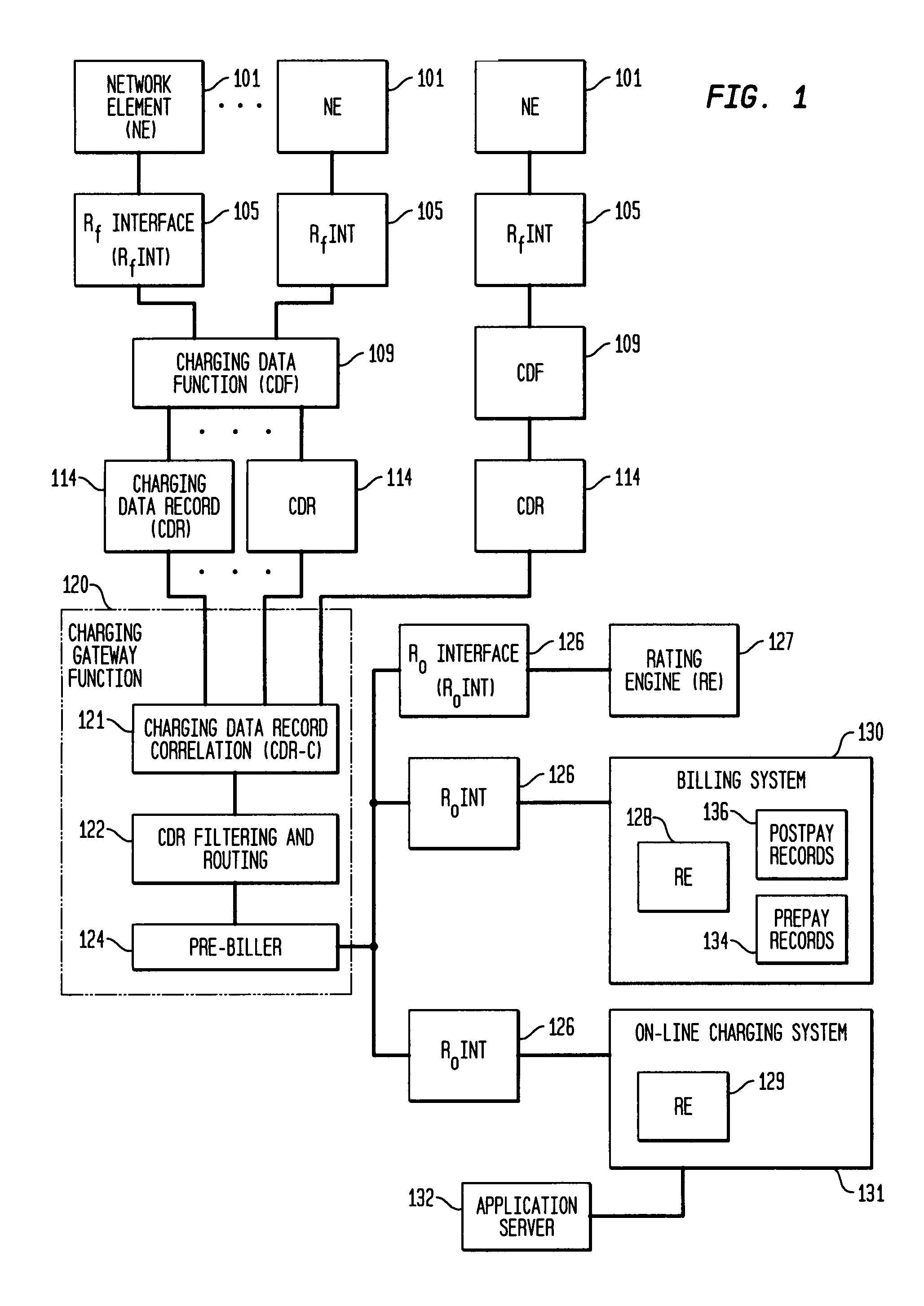
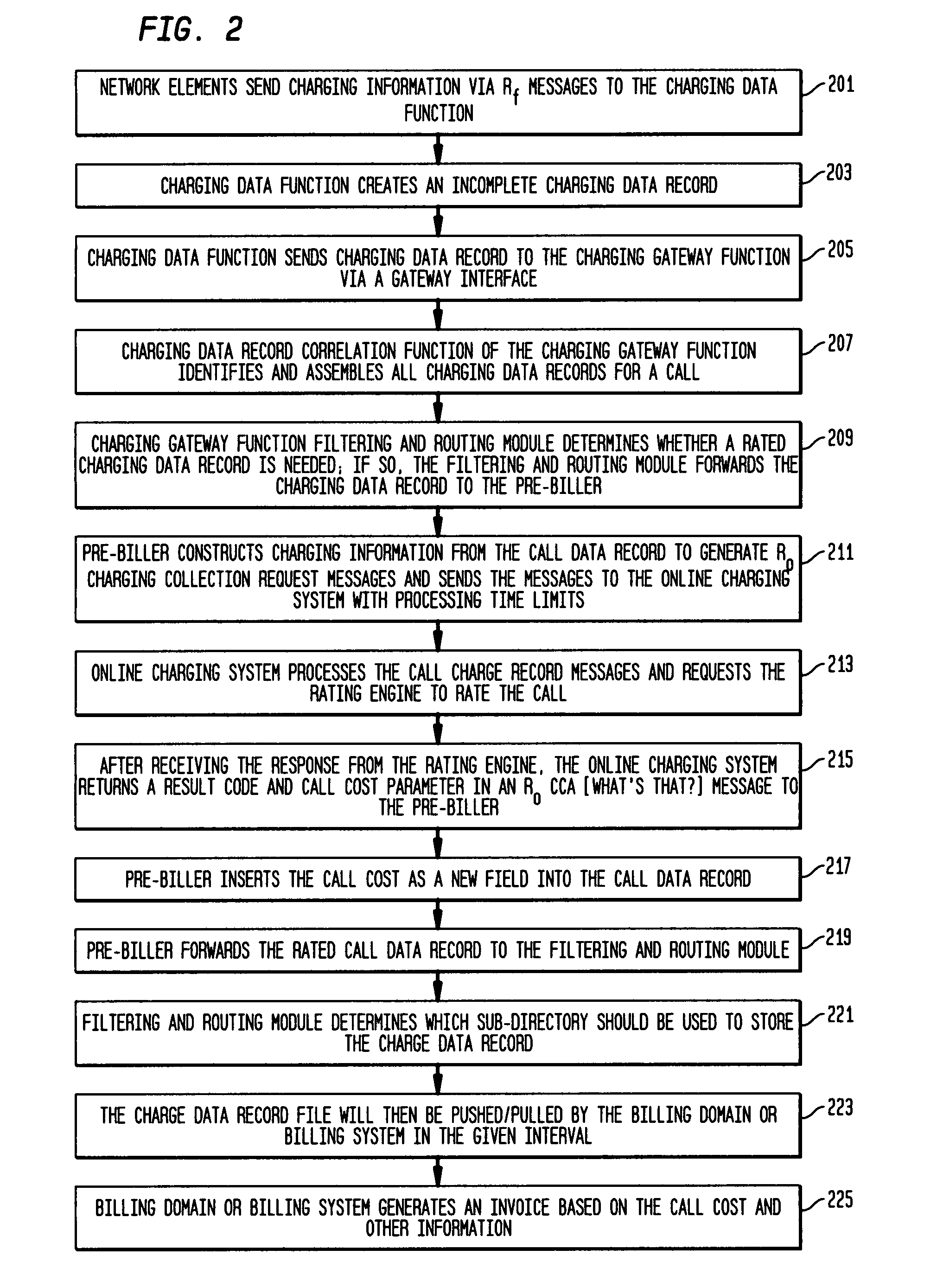
Pre-biller in internet protocol multimedia subsystem (IMS) charging gateway function (CGF)
InactiveUS8126123B2Metering/charging/biilling arrangementsAccounting/billing servicesNetworking protocolCAC protocol
This invention relates to apparatus and a method for assembling and coordinating call data records from a plurality of network elements of an Internet Protocol Multimedia System call to generate charging information. A pre-biller stores an integrated charging record and accesses a rating engine to obtain the charging information to complete a charging data record. Advantageously, the information from a plurality of network elements is integrated into a combined charging data record.
Owner:WSOU INVESTMENTS LLC
Technique for providing end-to-end congestion control with no feedback from a lossless network
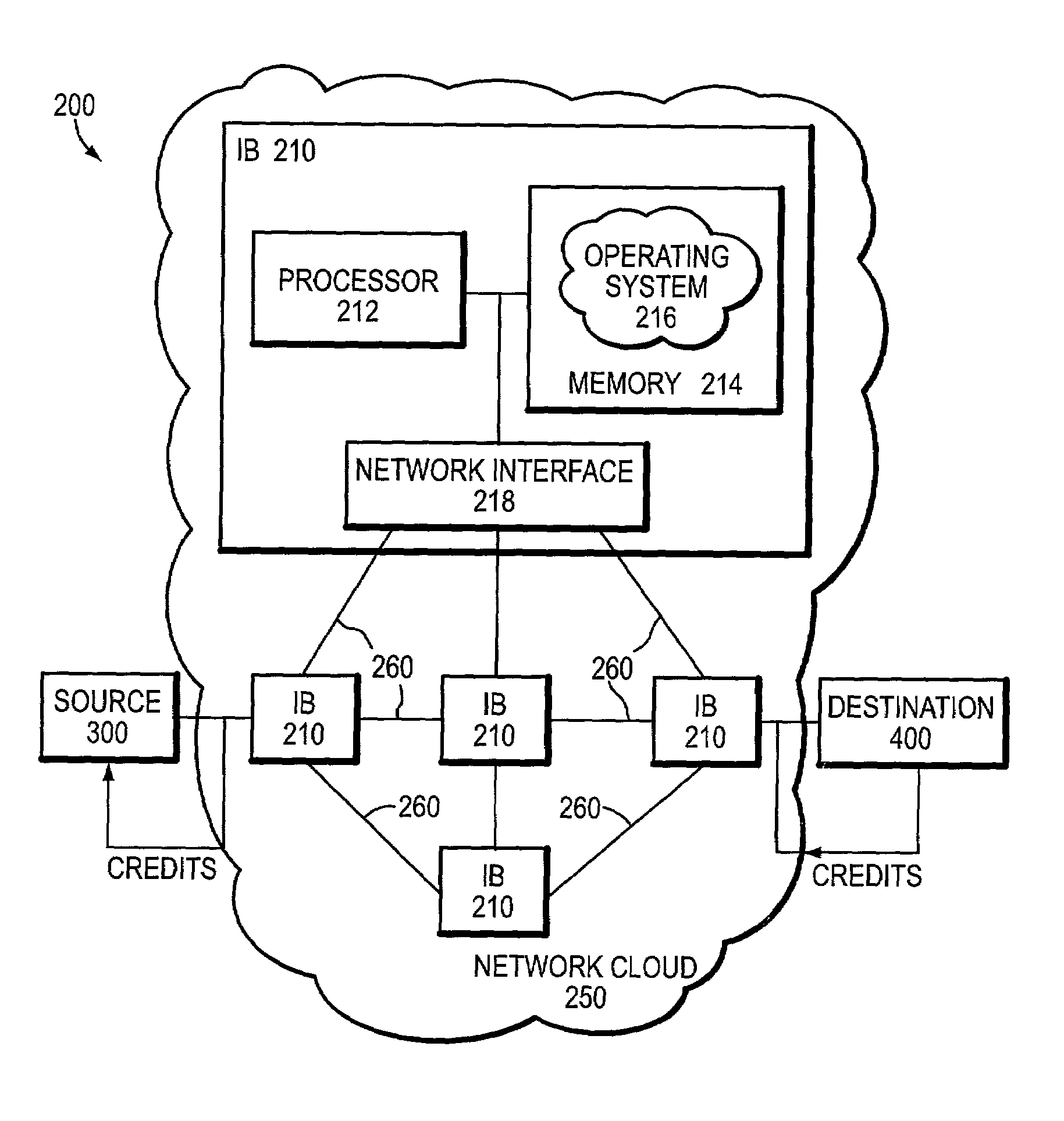
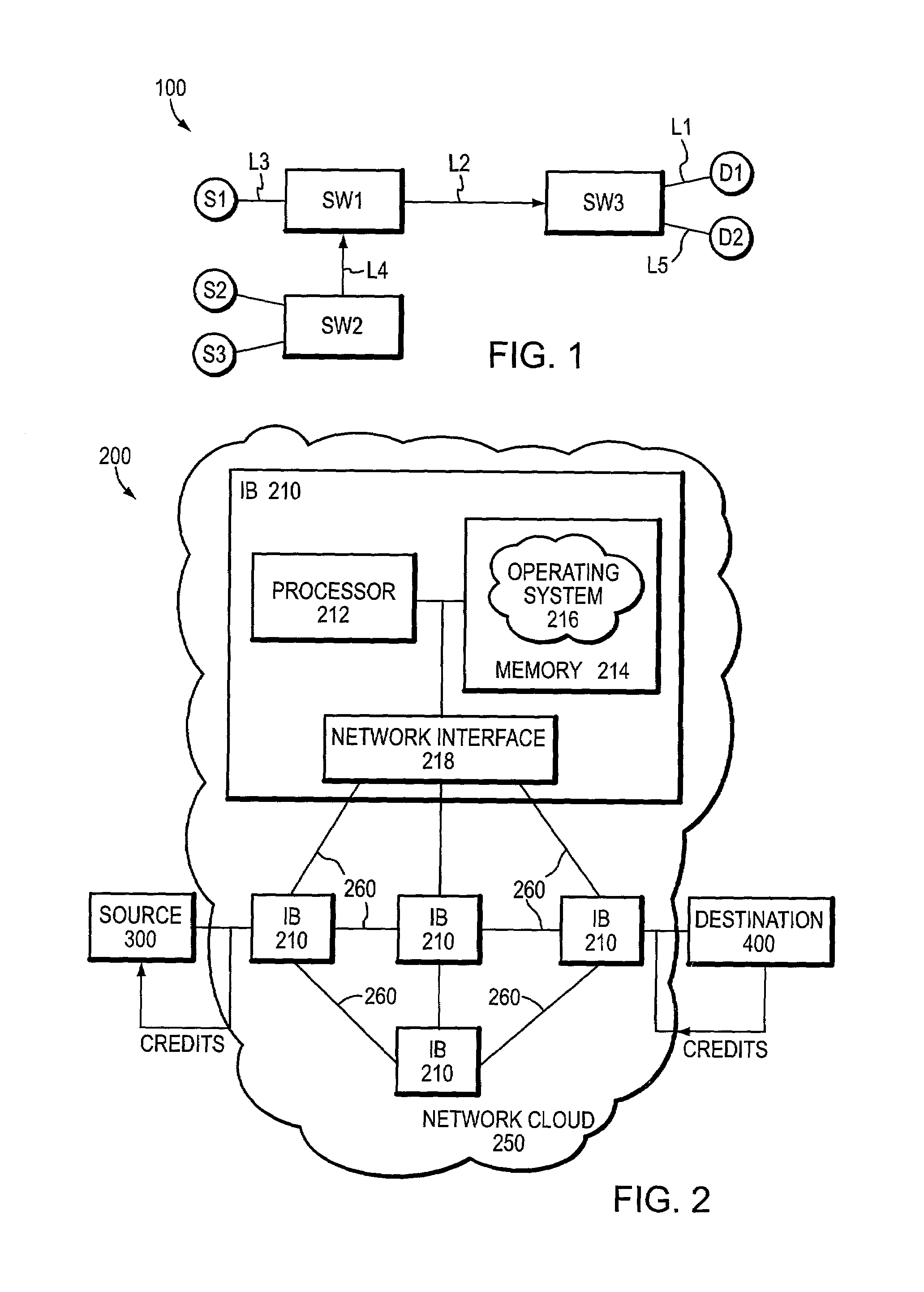
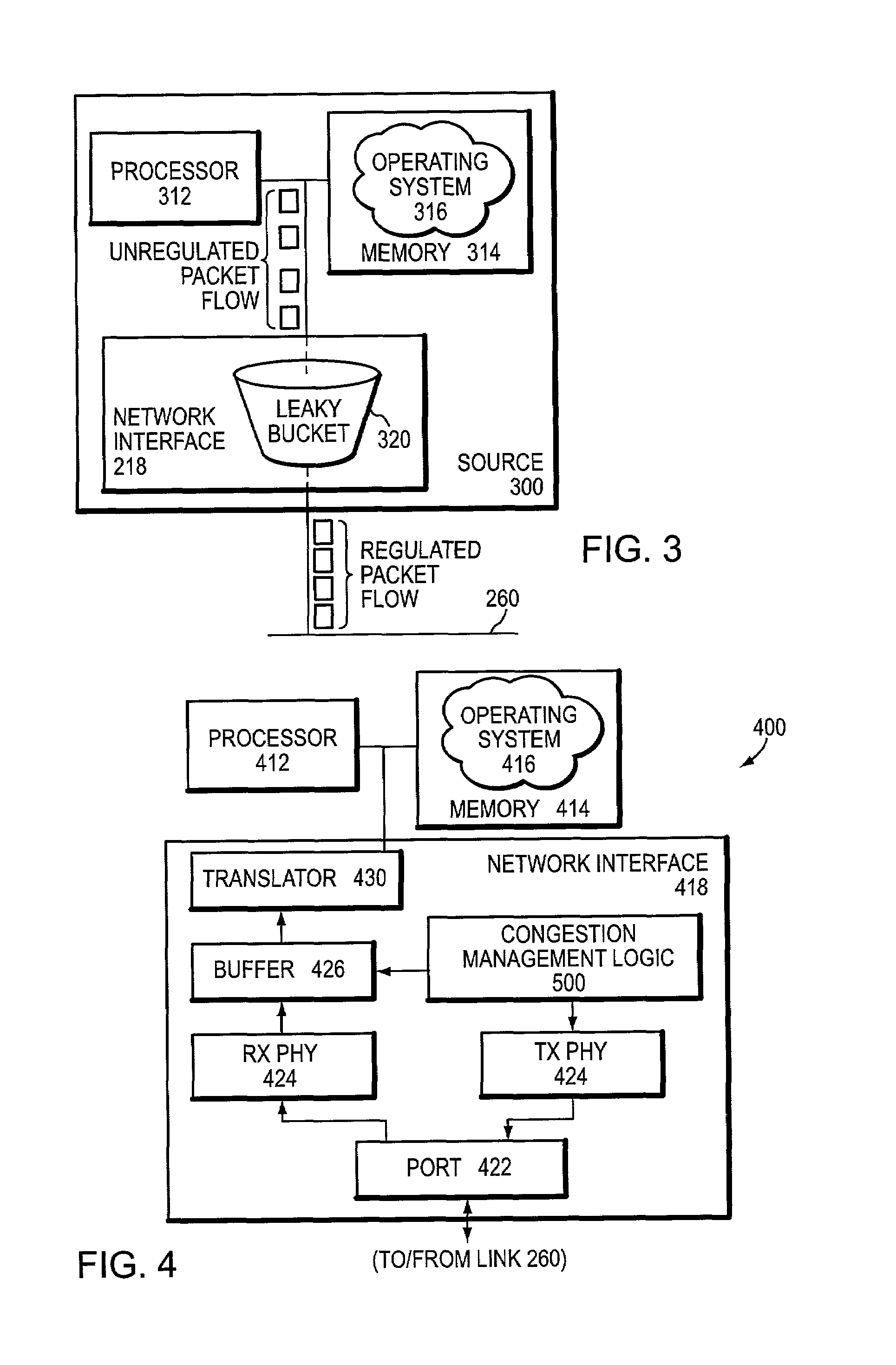
InactiveUS7035220B1Improve creditError preventionTransmission systemsEnd to end congestion controlDistributed computing
A congestion management technique achieves an end-to-end data flow rate that is supported by a lossless communications network. The end-to-end rate extends from a source end node to destination end node of the network and is preferably at or slightly below a bottleneck rate of the network. The destination end node determines, on its own and without any help from network elements, a supportable rate of activity in the network and provides feedback to the source end node. By achieving such a rate, data transmitted by the source end node can flow through the network without loss of packets and without the use of substantial buffering.
Owner:INFINISWITCH CORP +1
Voice-over-IP enabled chat
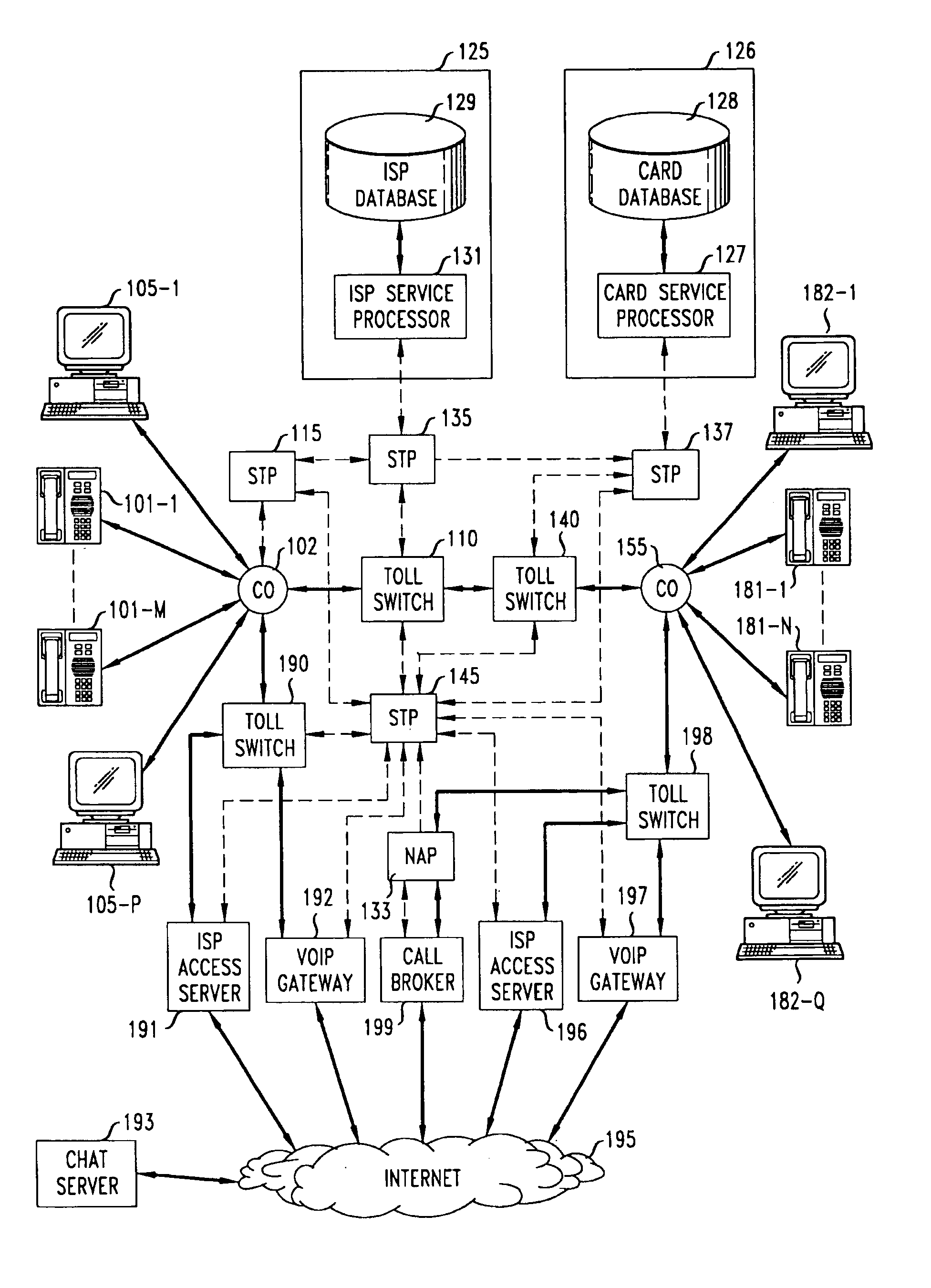
InactiveUS7039040B1Avoid the needSpecial service provision for substationMultiplex system selection arrangementsCredit cardData connection
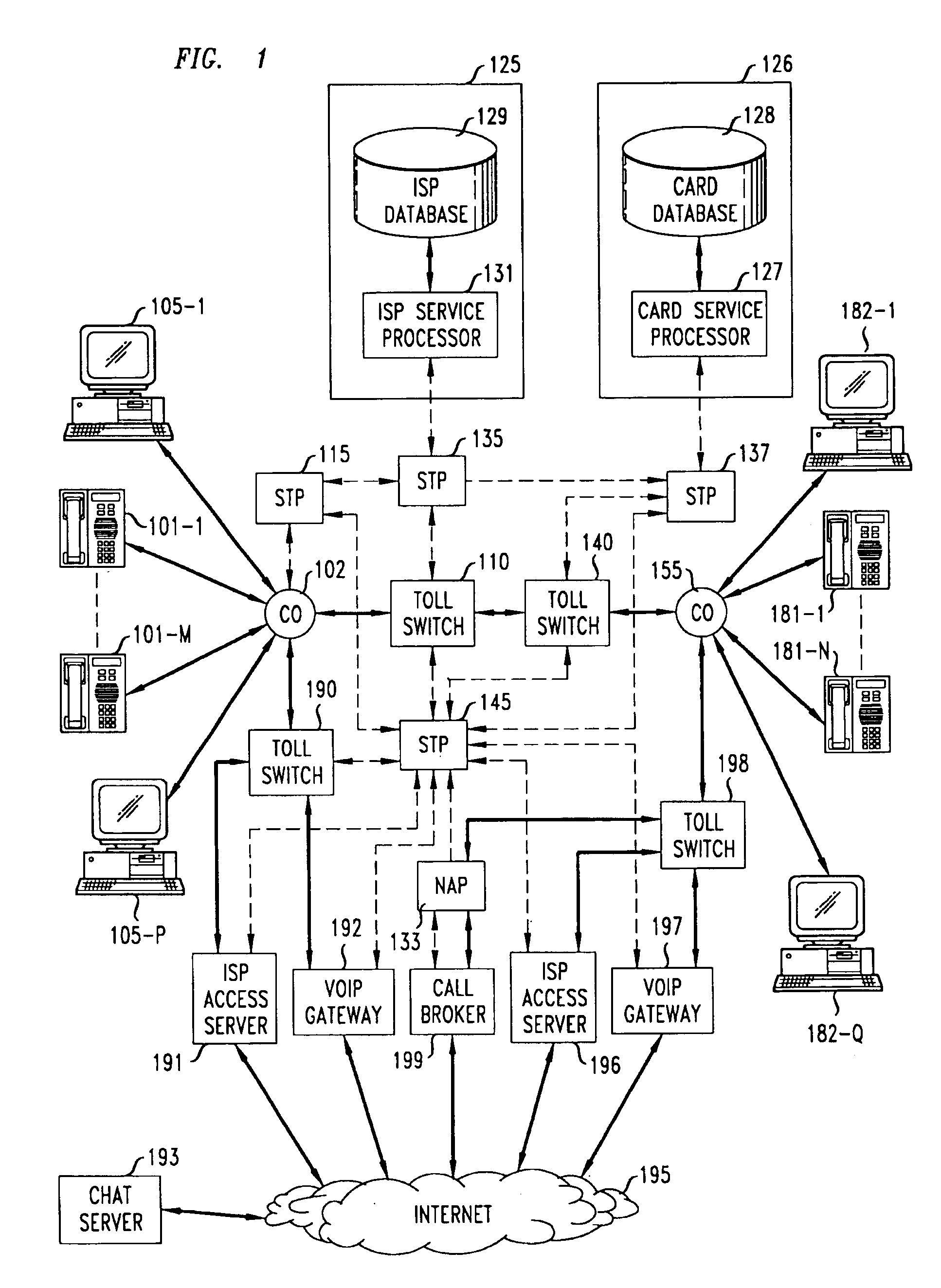
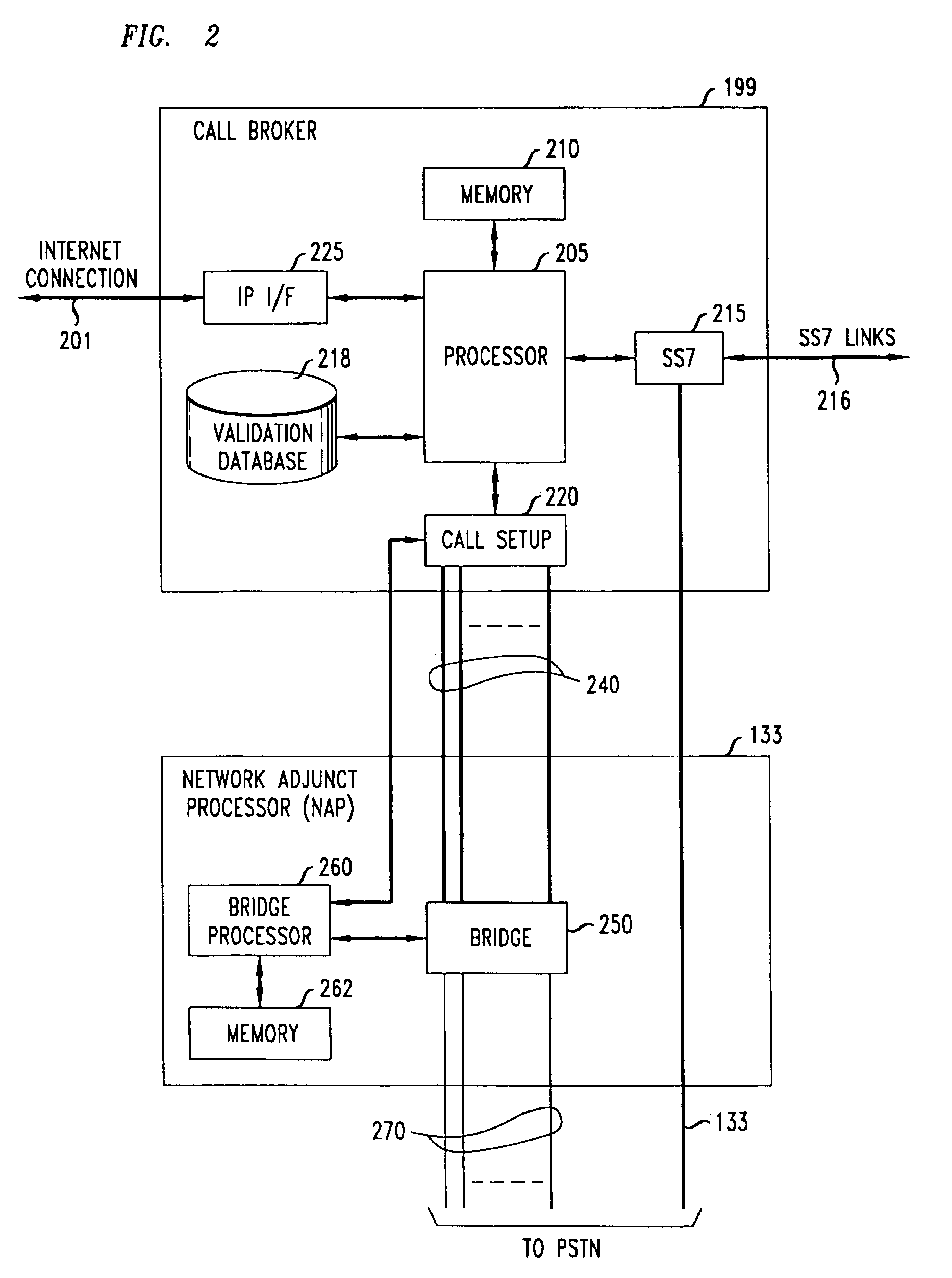
A network-based system and method for providing anonymous voice communications using the telephone network and data communications links under the direction of a Call Broker and associated network elements. A user (the call initiator) present in a text chat room session establishes a data connection to Call Broker and, after qualifying for access (e.g., using credit card information) and providing a callback number, receives voice session information and participant access codes for each desired participant in a voice call. The initiator causes session information and participant codes to be passed to one or more selected chat participants in the current text chat room. When a selected participant uses the received session information, and enters the received participant code and a callback number, the Call Broker in cooperation with a Network Adjunct Processor (NAP) completes voice links to the initiator and the selected participant(s). The need for each party to have a second subscriber line is advantageously avoided by having the Call Broker arrange to have one or more voice links completed through a VoIP link, and further reduces the need for second lines for participants by forwarding a Call Broker—placed call to a busy participant line to the participant's Internet Service Provider (ISP), which then sends a message to the participant announcing one or more options for receiving the incoming call, including receiving the incoming call through a VoIP link.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com