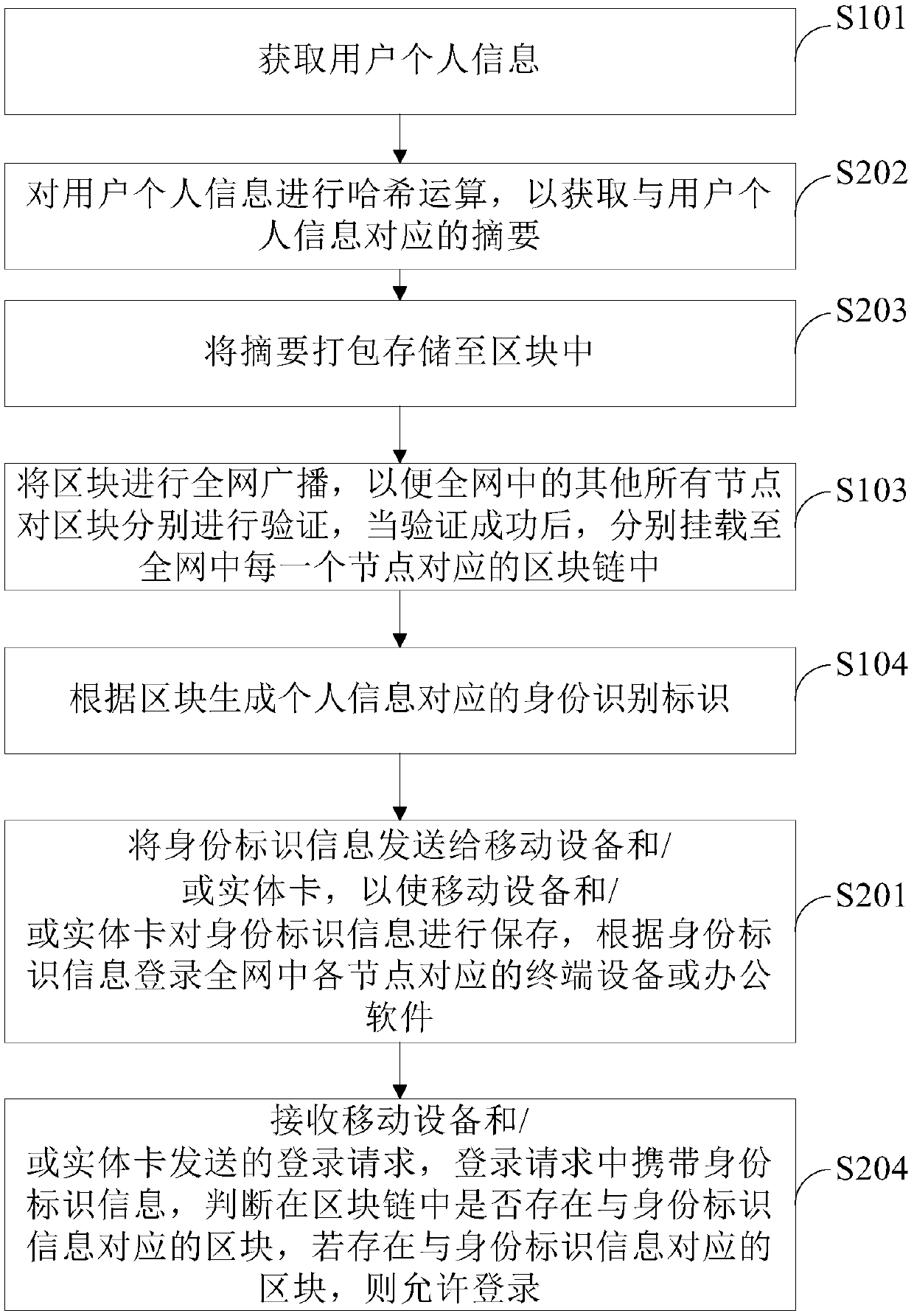
Patents
Literature
99results about How to "Improve credit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
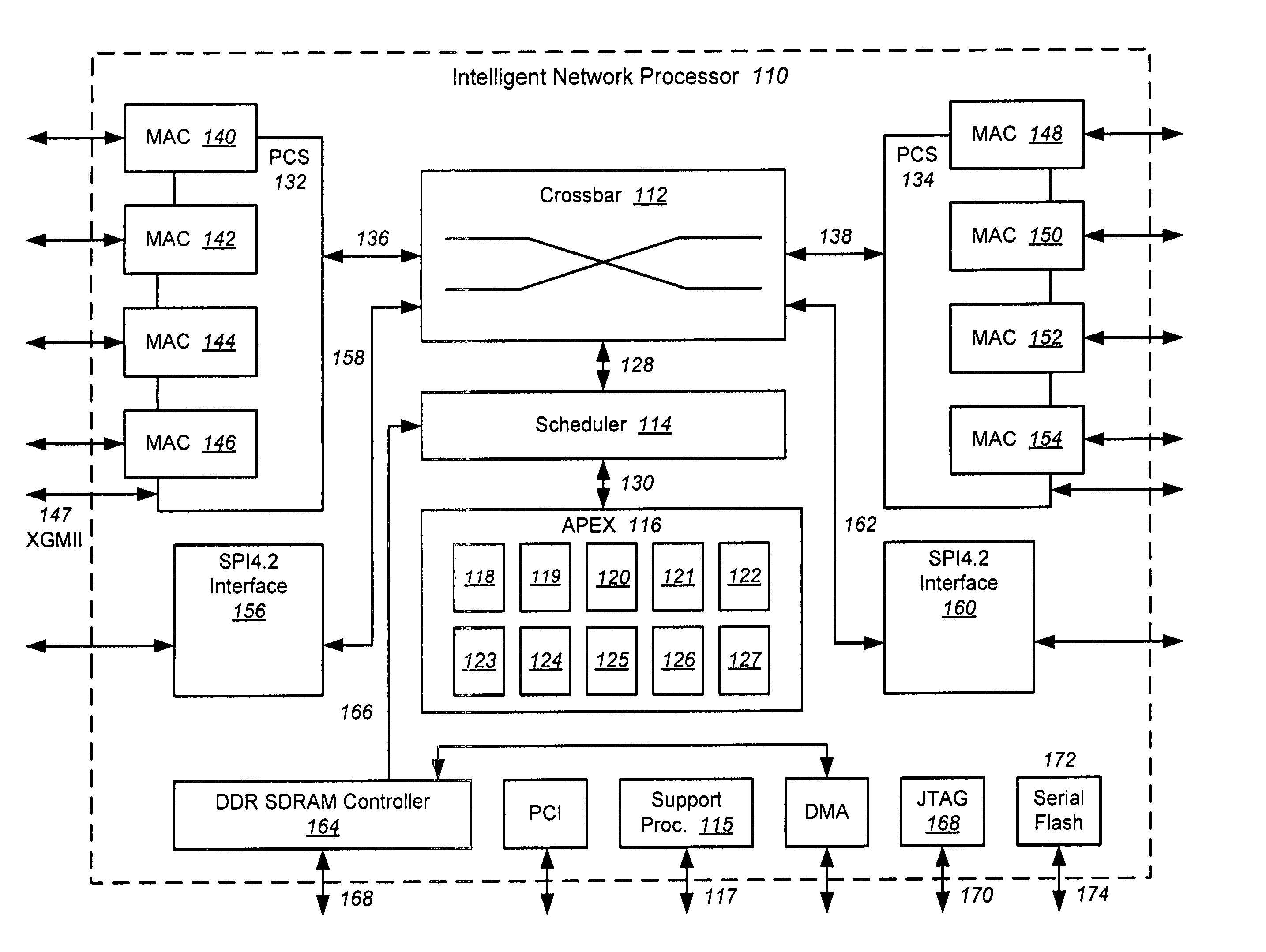
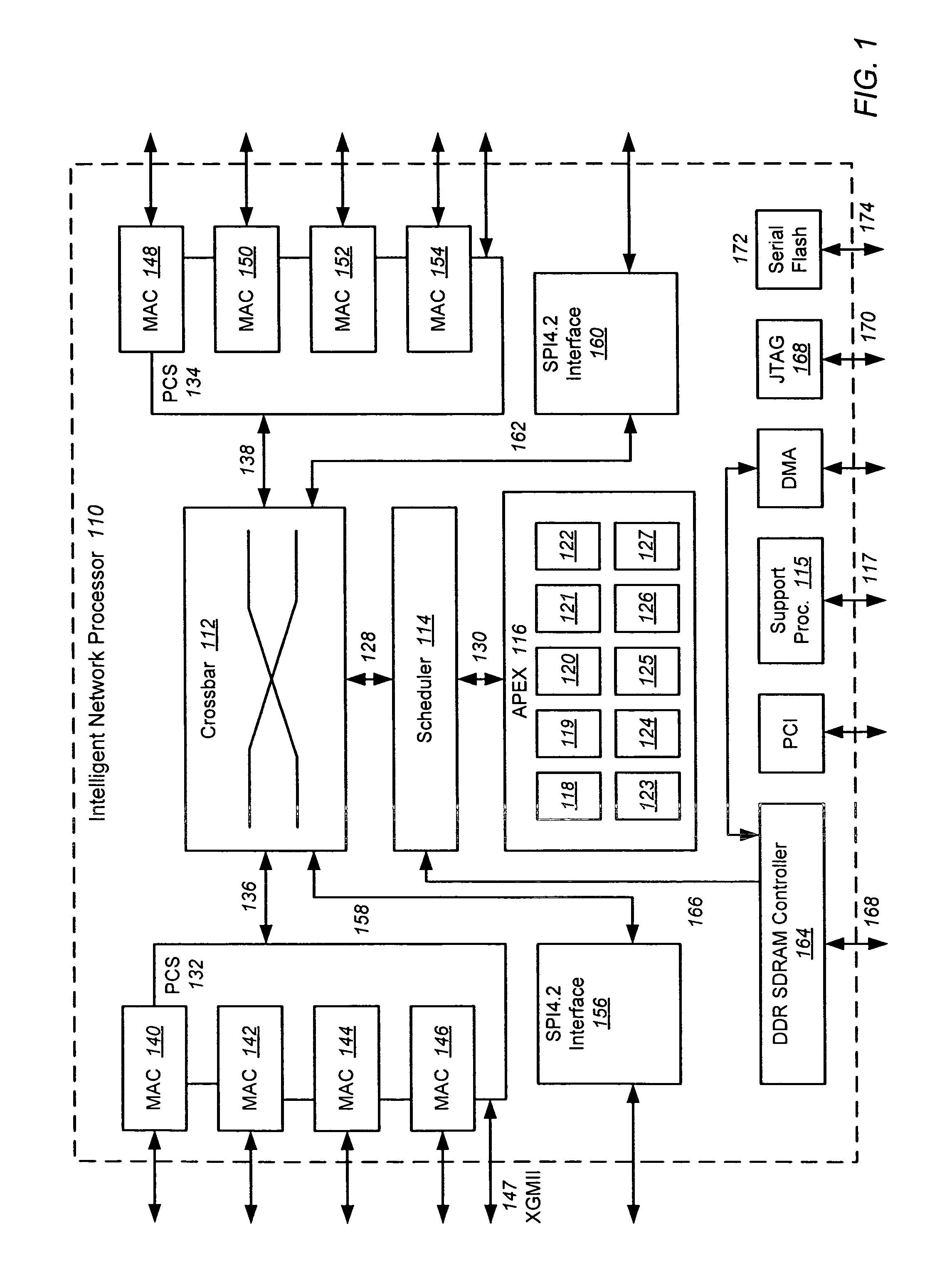
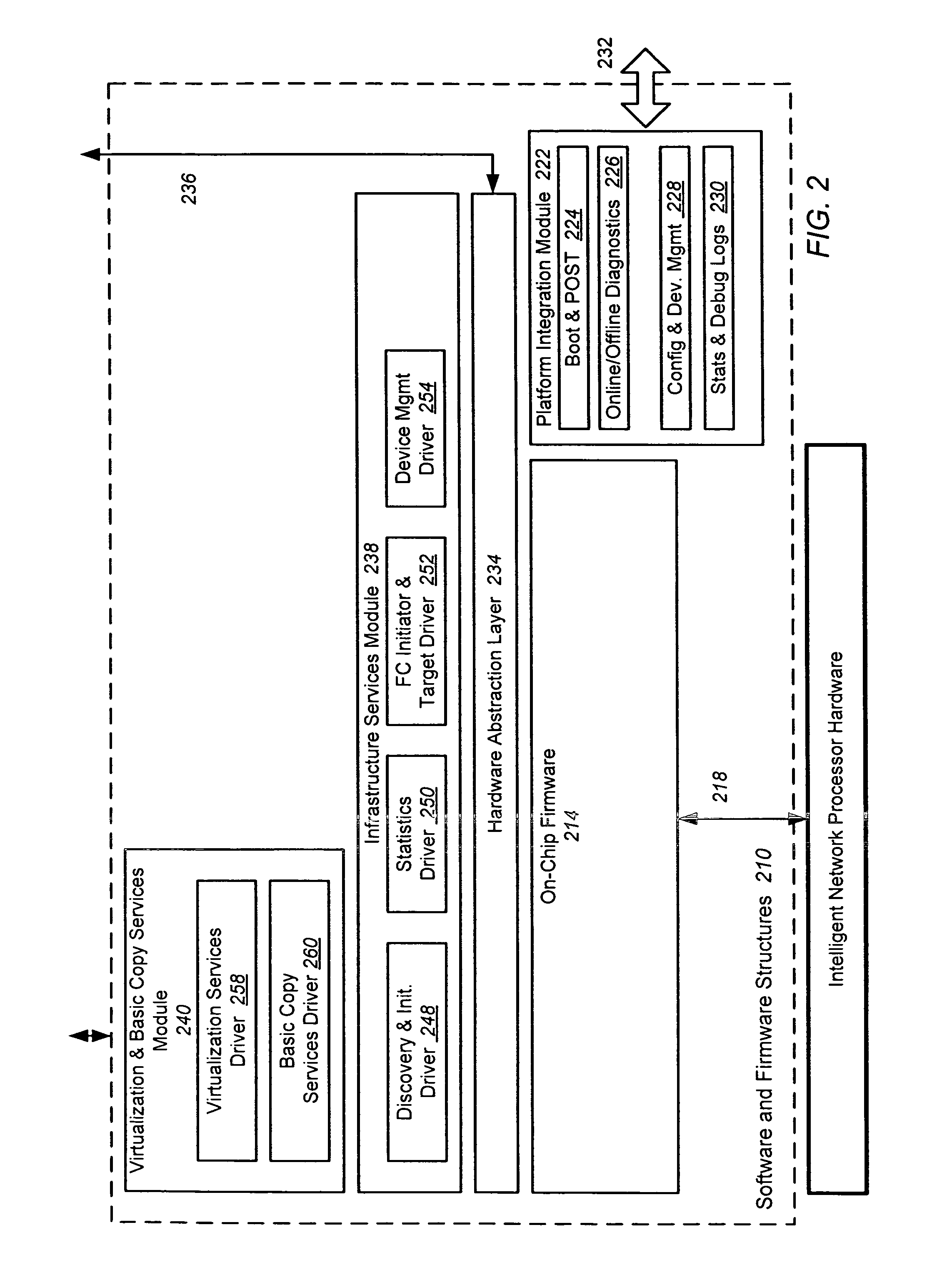
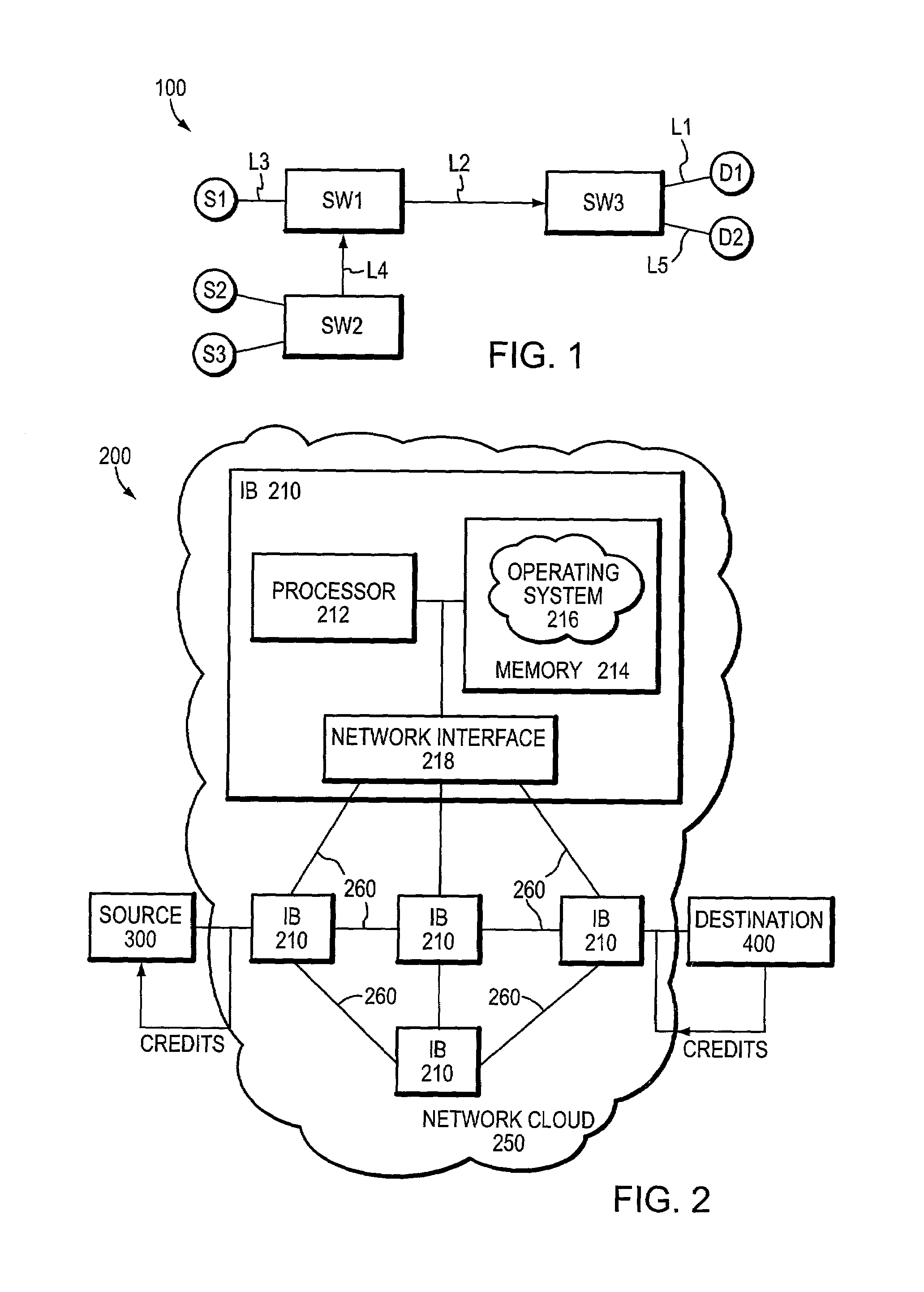
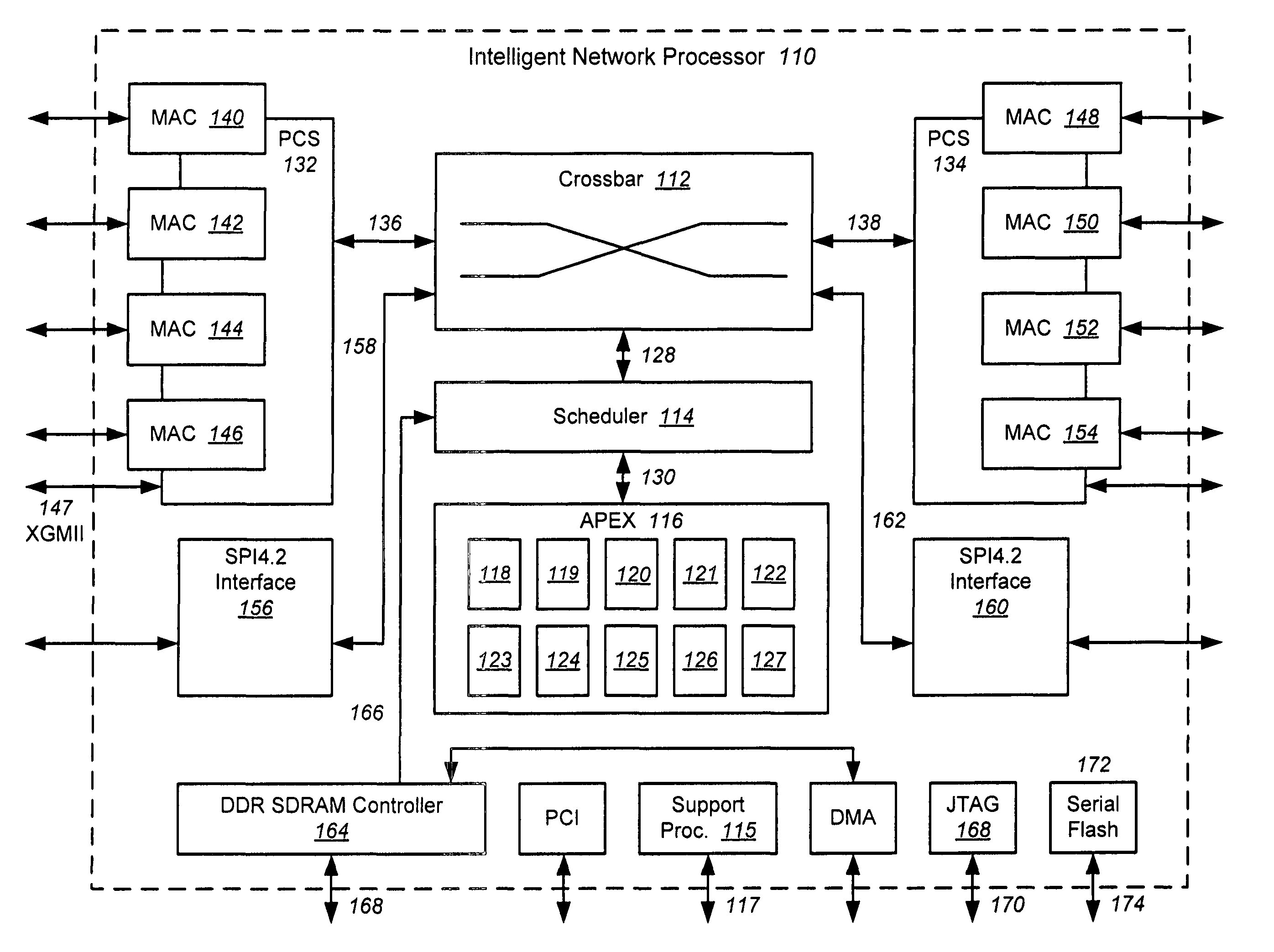
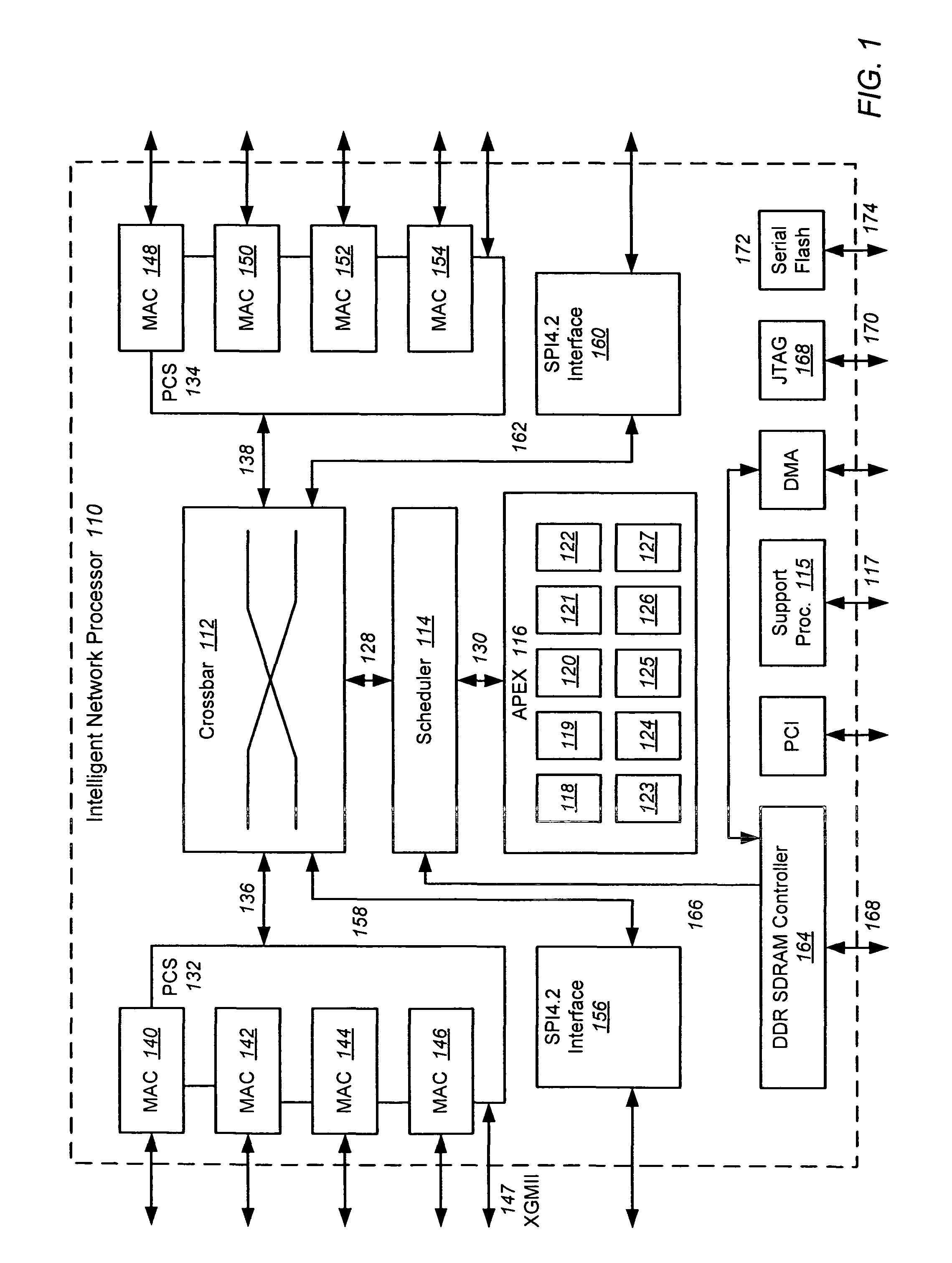
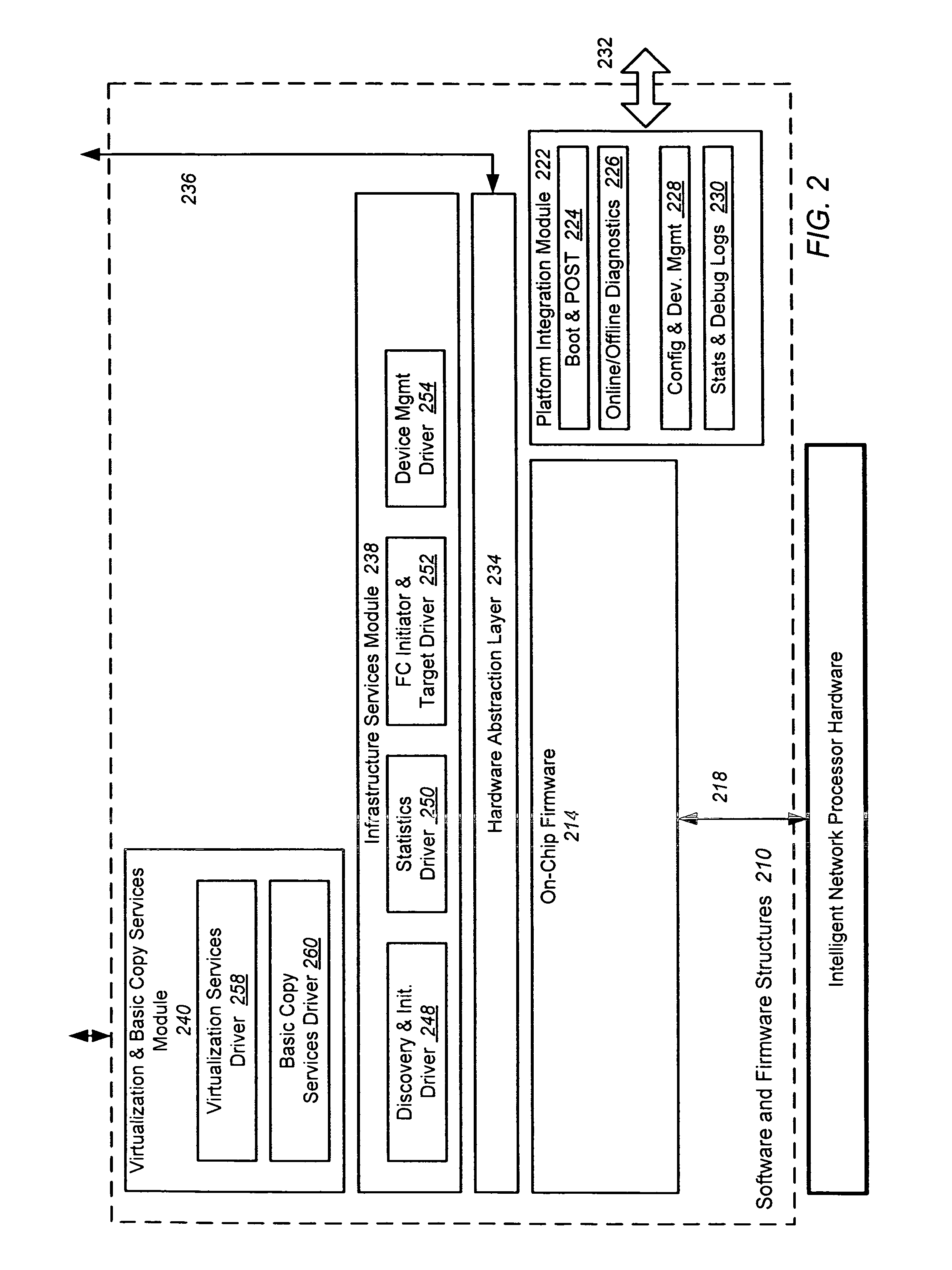
Intelligent network processor and method of using intelligent network processor
ActiveUS20070266179A1Efficient accessImprove creditMultiple digital computer combinationsData switching networksIntelligent NetworkPCI Express
An intelligent network processor is disclosed that provides a PCI express (PCIe) host bus adapter with firmware selectable hardware capabilities and firmware enabled emulation of capabilities not supported by hardware. Support for Fibre Channel (FC) and Gigabit Ethernet (GbE) protocols are provided through the same fabric ports, including multiple port trunking for both protocols. On chip protocol conversion is provided for switching and routing between FC and GbE ports. Switching using the same crossbar module is provided for both FC and GbE protocols. The crossbar module is coupled to directly access external DDR memory so that messages from FC, GbE, and PCIe interfaces may be switched directly to the DDR memory.
Owner:EMULEX COMM CORP
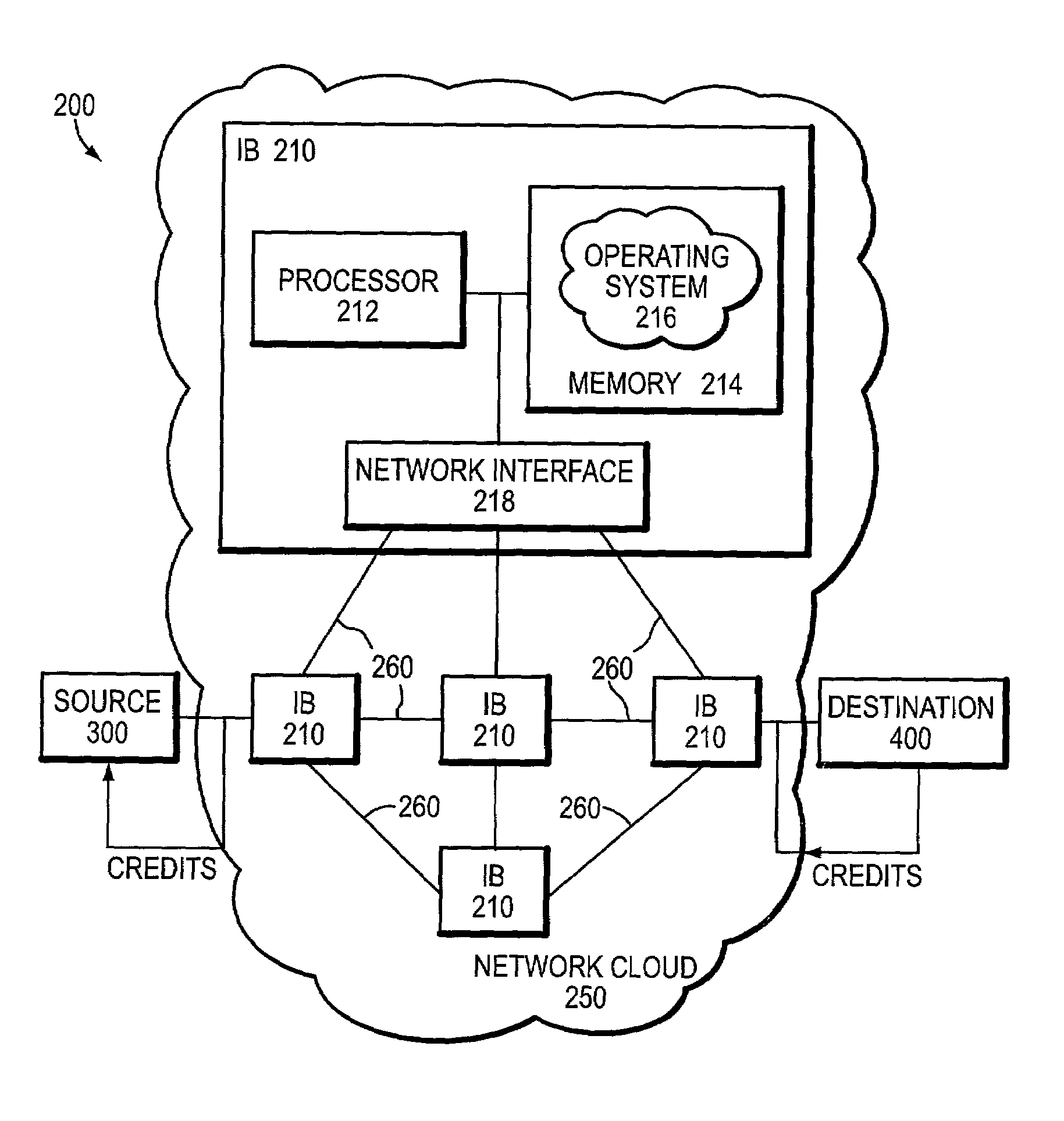
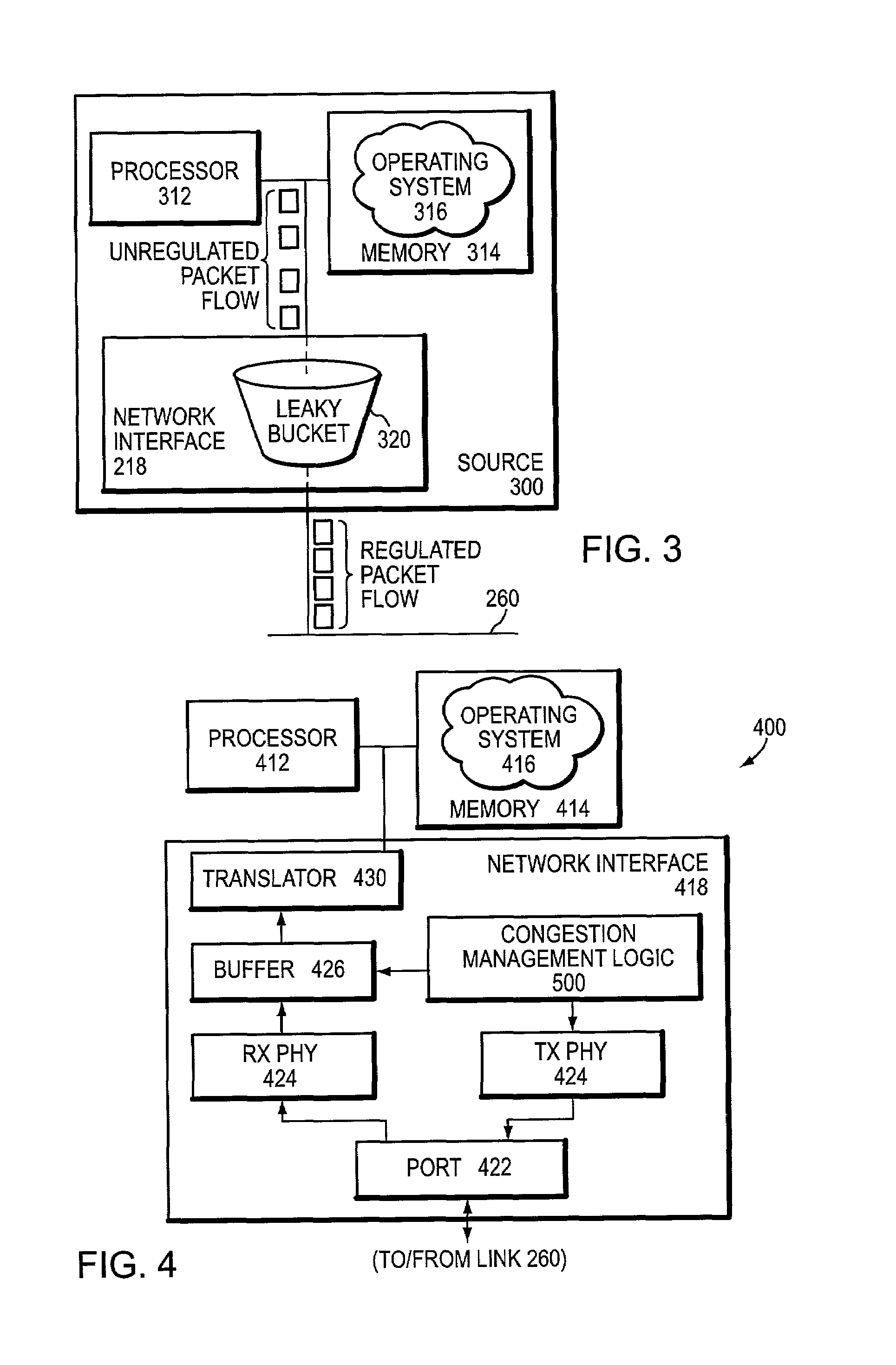
Technique for providing end-to-end congestion control with no feedback from a lossless network
InactiveUS7035220B1Improve creditError preventionTransmission systemsEnd to end congestion controlDistributed computing
A congestion management technique achieves an end-to-end data flow rate that is supported by a lossless communications network. The end-to-end rate extends from a source end node to destination end node of the network and is preferably at or slightly below a bottleneck rate of the network. The destination end node determines, on its own and without any help from network elements, a supportable rate of activity in the network and provides feedback to the source end node. By achieving such a rate, data transmitted by the source end node can flow through the network without loss of packets and without the use of substantial buffering.
Owner:INFINISWITCH CORP +1
System and method for virtualizing PCIe devices
ActiveUS7743197B2Efficient accessImprove creditMultiple digital computer combinationsData switching networksCrossbar switchIntelligent Network
An intelligent network processor is disclosed that provides a PCI express (PCIe) host bus adapter with firmware selectable hardware capabilities and firmware enabled emulation of capabilities not supported by hardware. Support for Fibre Channel (FC) and Gigabit Ethernet (GbE) protocols are provided through the same fabric ports, including multiple port trunking for both protocols. On chip protocol conversion is provided for switching and routing between FC and GbE ports. Switching using the same crossbar module is provided for both FC and GbE protocols. The crossbar module is coupled to directly access external DDR memory so that messages from FC, GbE, and PCIe interfaces may be switched directly to the DDR memory.
Owner:EMULEX COMM CORP
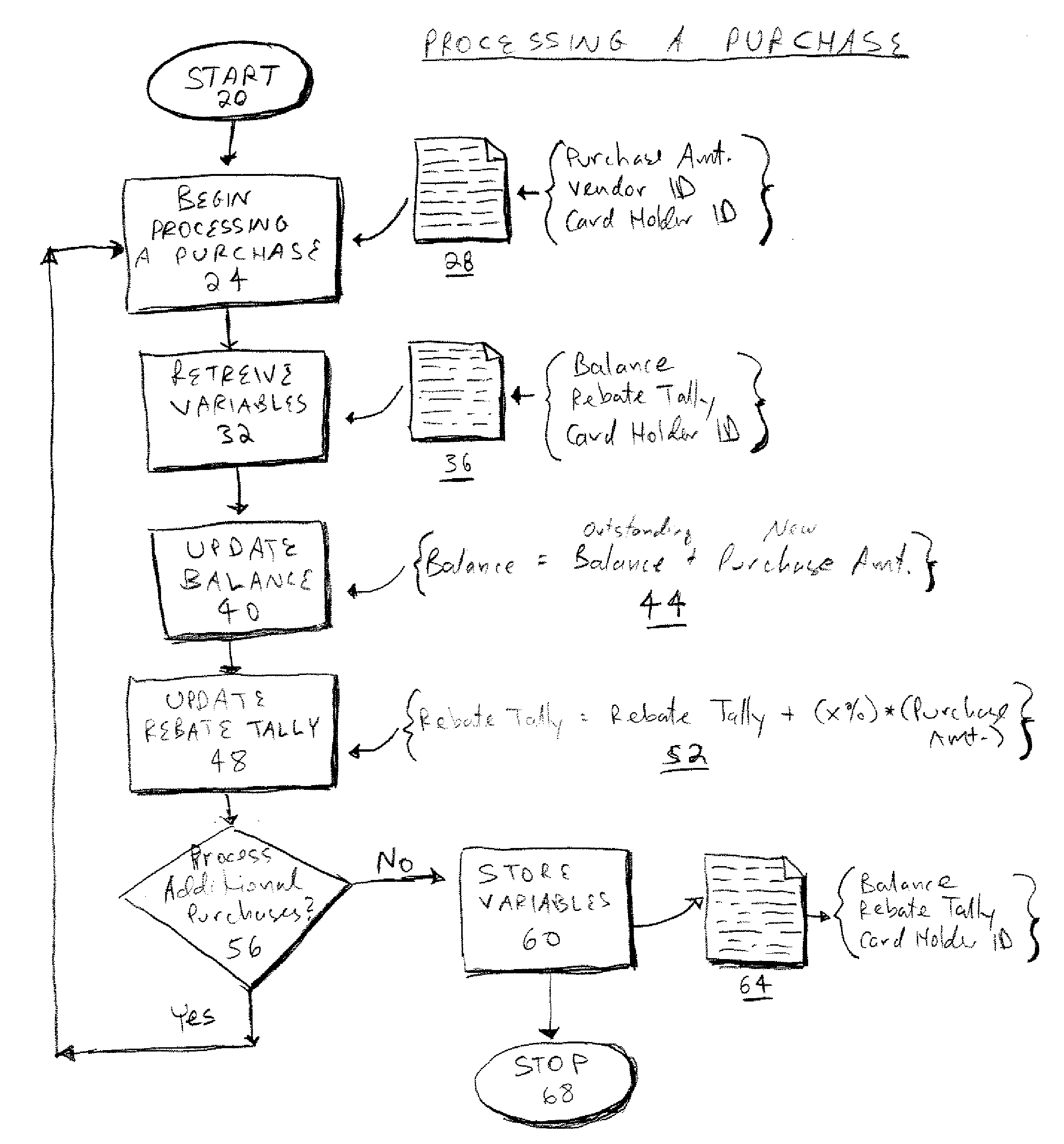
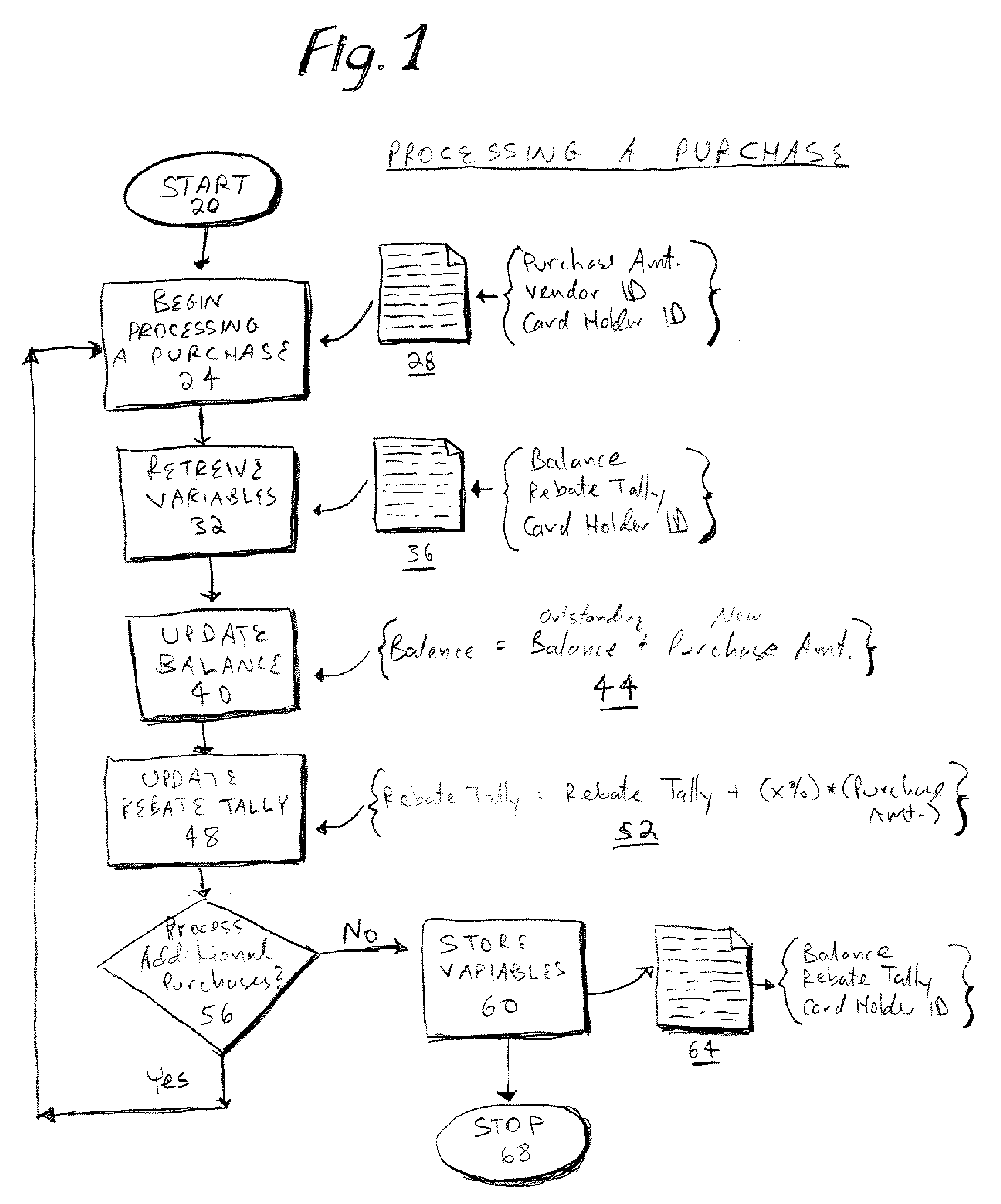
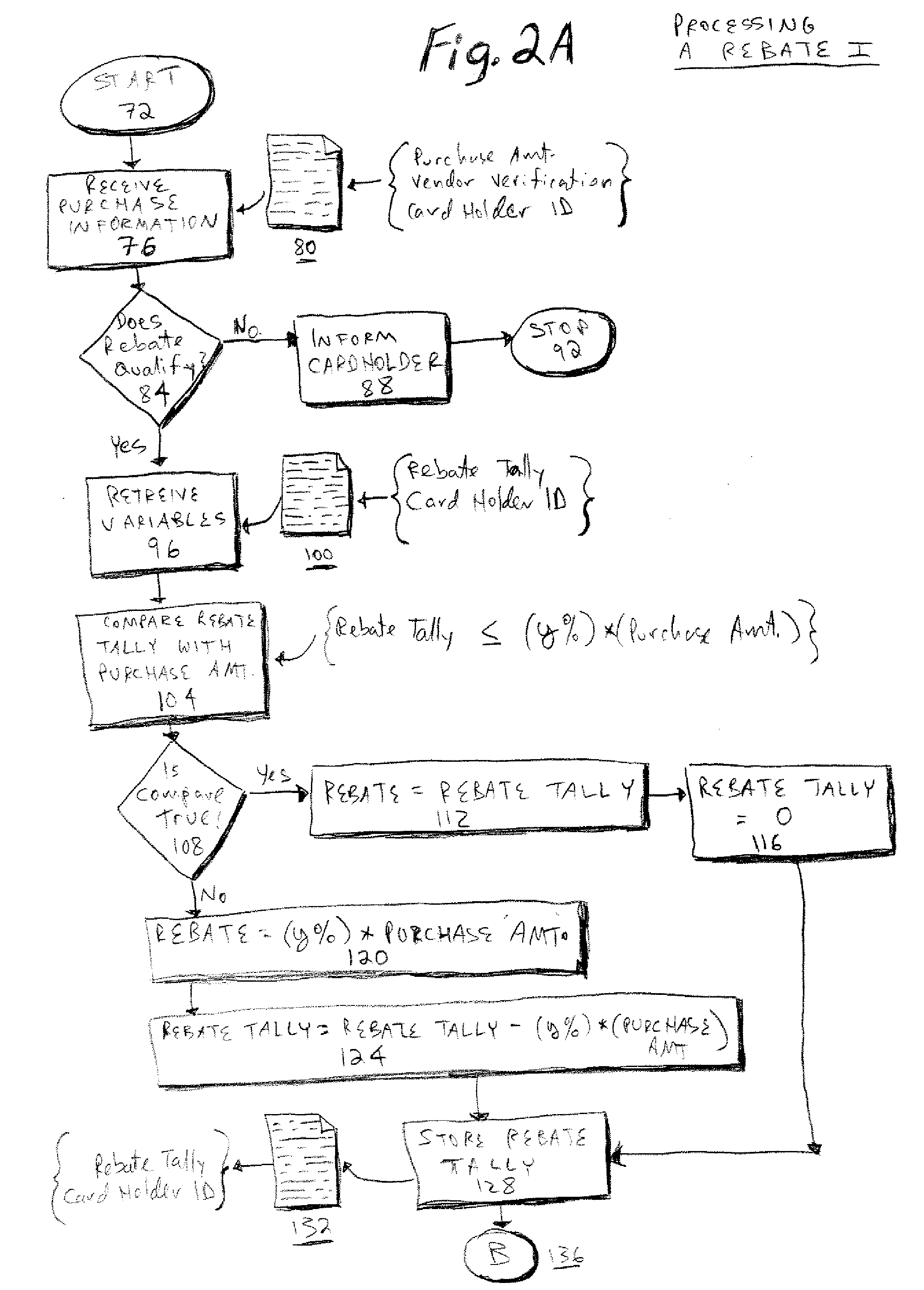
Method and system for awarding rebates based on credit card usage to credit card holders
InactiveUS20070288372A1Improve creditEncouraging increased useFinanceMarketingOperating systemCard holder
A method and system for awarding rebates based on credit card usage to a consumer credit card holder is provided. A rebate tally is accrued based on a percentage of eligible purchases made by the consumer card holder. The rebate is earned when the consumer card holder makes a qualifying purchase, which may be, for example, an automobile sold by any manufacturer. The rebate program disclosed does not associate the rebate earned with any particular manufacturer. The rebate is paid directly by the credit card issuer to the credit card holder.
Owner:CITIBANK
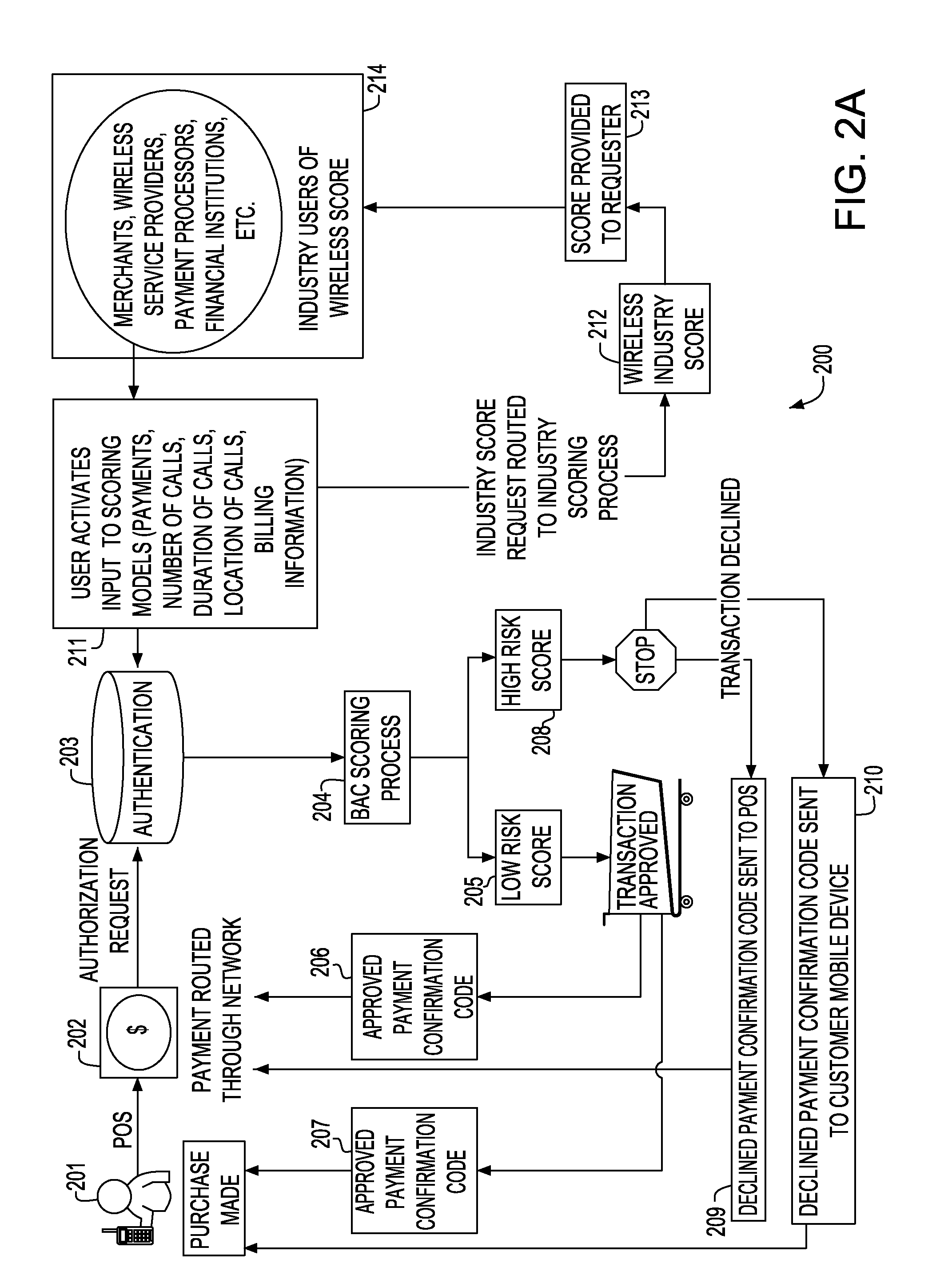
Wireless number risk scores for use with mobile payments
InactiveUS20100070405A1Evaluate credit worthinessImprove creditFinancePoint-of-sale network systemsAuthorizationMobile payment
Apparatus and methods for evaluating risk of nonpayment for mobile payments. Wireless phone numbers with associated customer history and account information may be used as a proxy to determine risk of nonpayment. Risk scores may be continually updated with new purchase and payment information. In some embodiments, authorization for a point of sale transaction may include evaluation of the mobile wireless risk score. A low wireless number risk score may result in authorization of the transaction. A high wireless number risk score may result in denial of the transaction.
Owner:BANK OF AMERICA CORP
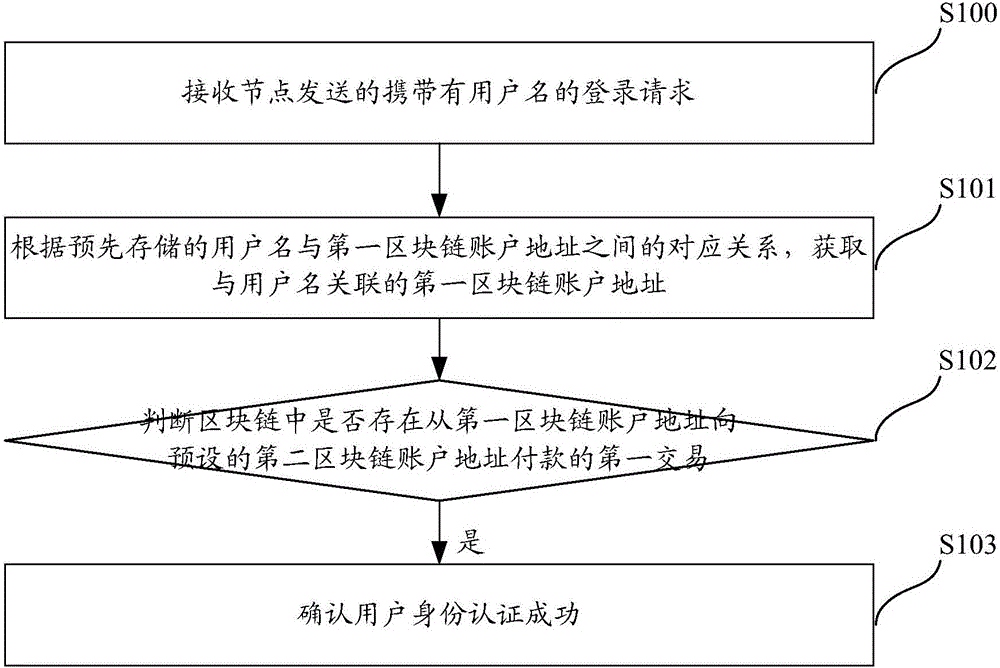
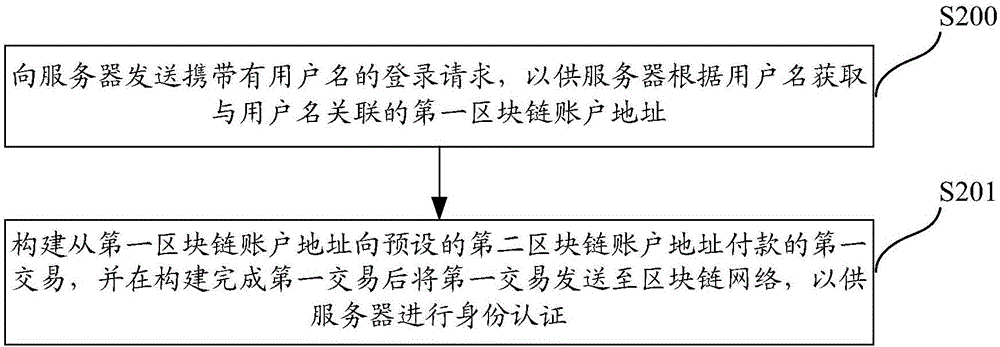
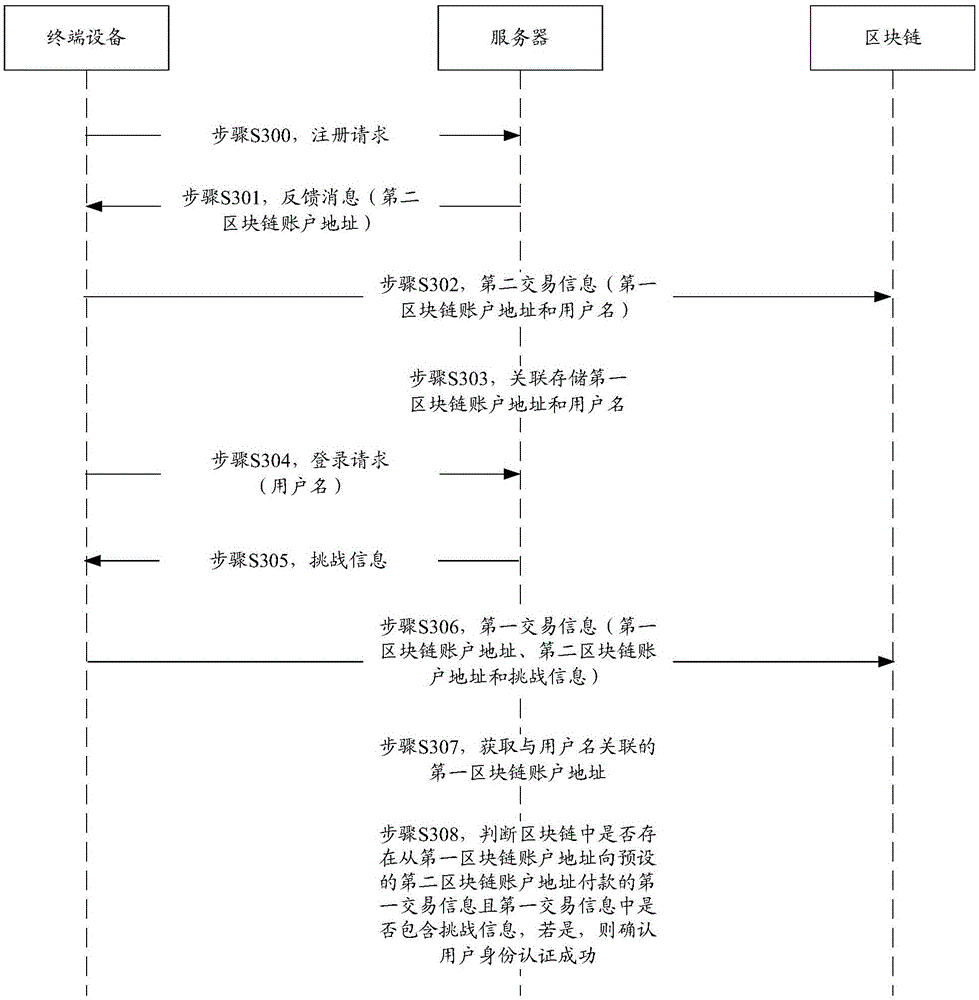
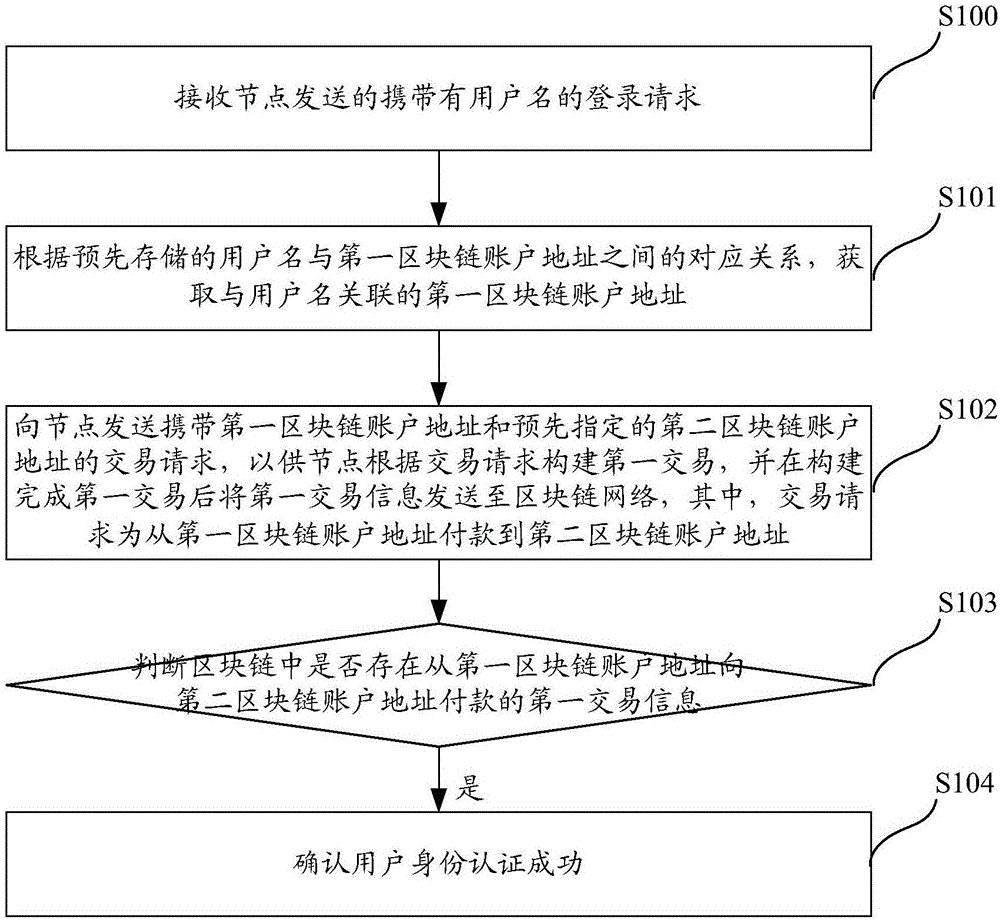
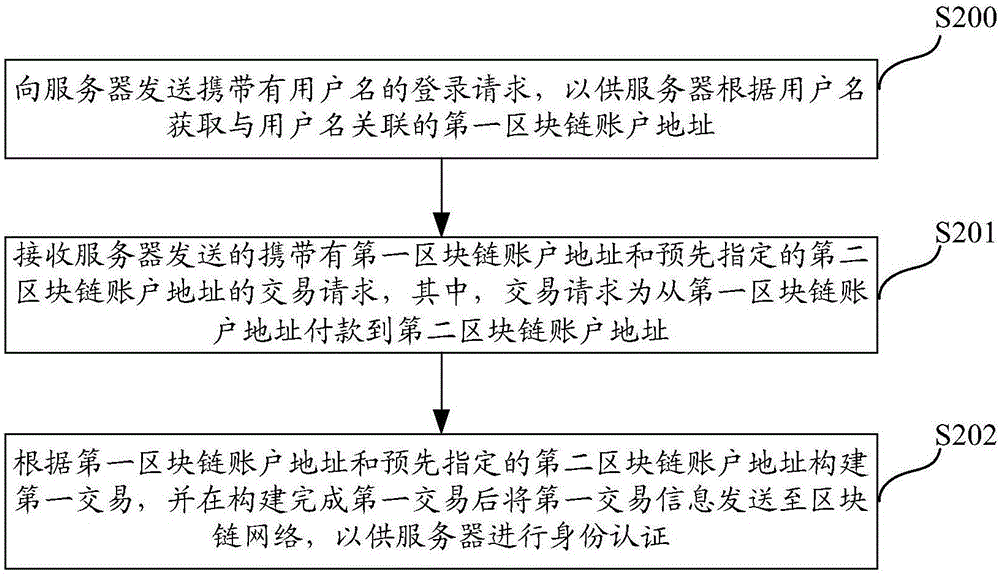
Method, system and server for authenticating identities on basis of block chain networks
The invention discloses a method, a system, a server and terminal equipment for authenticating identities on the basis of block chain networks. The method, the system, the server and the terminal equipment are used for authenticating the identities for nodes in the block chain networks. The method includes receiving login requests with user names; acquiring first block chain account addresses according to preliminarily stored corresponding relations between the user names and the first block chain account addresses; judging whether first transaction of payment from the first block chain account addresses to preset second block chain account addresses is available in block chains or not; determining that the identities of users are successfully authenticated if the first transaction is available in the block chains. The login requests are transmitted by the nodes. The first block chain account addresses are associated with the user names. The method, the system, the server and the terminal equipment have the advantages that transaction information stored in the block chains cannot be tampered and can be traced back and queried, and accordingly the authentication safety and the credibility of authentication procedures can be improved; the users do not need to input passwords during login and do not need to remember the passwords, accordingly, the convenience can be improved, and database collision attack due to the fact that other malicious personnel log in other websites by the aid of stolen user names and passwords can be prevented.
Owner:JIANGSU PAYEGIS TECH CO LTD
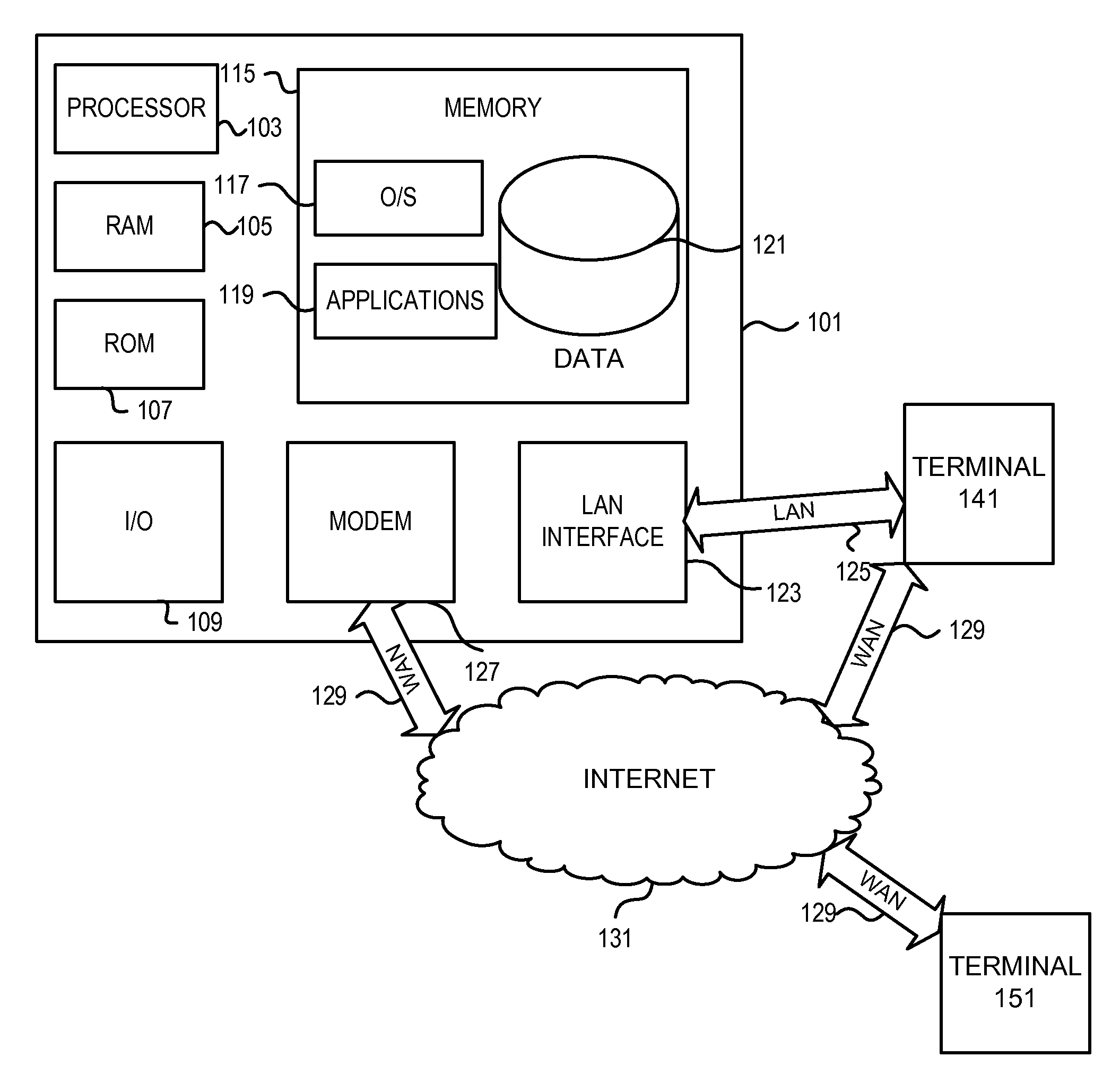
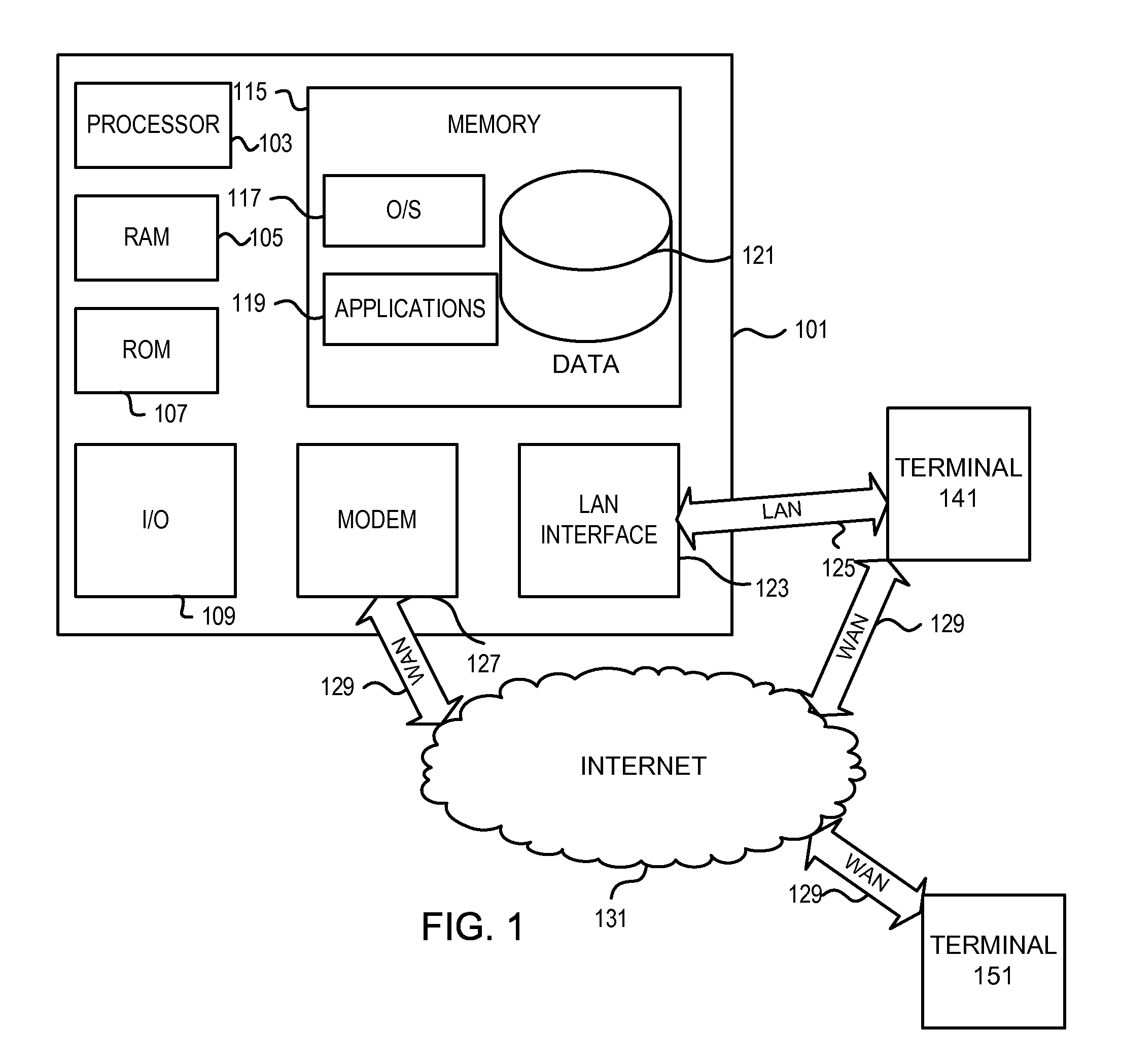
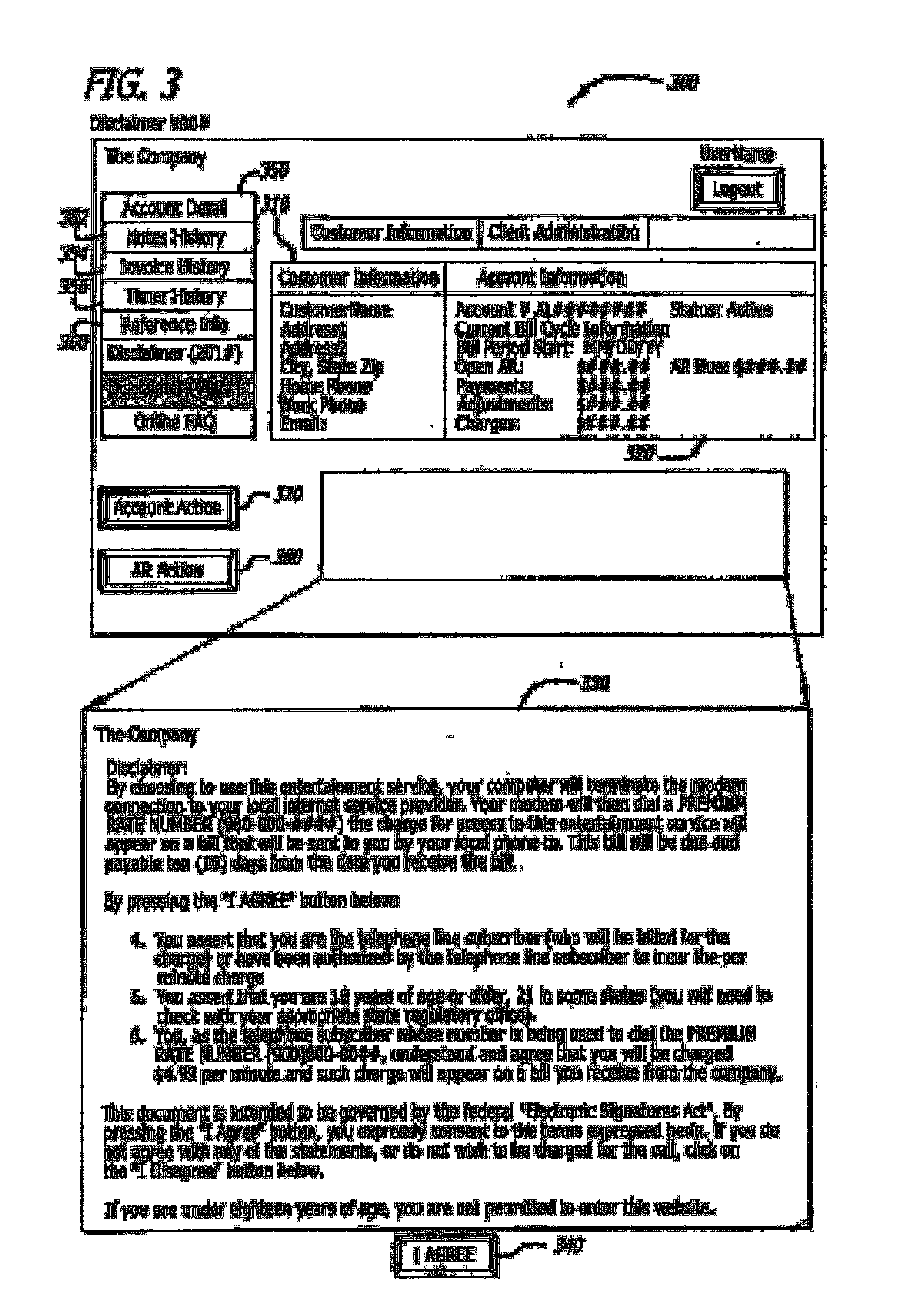
Computer-implemented method and system for managing accounting and billing of transactions over public media such as the internet
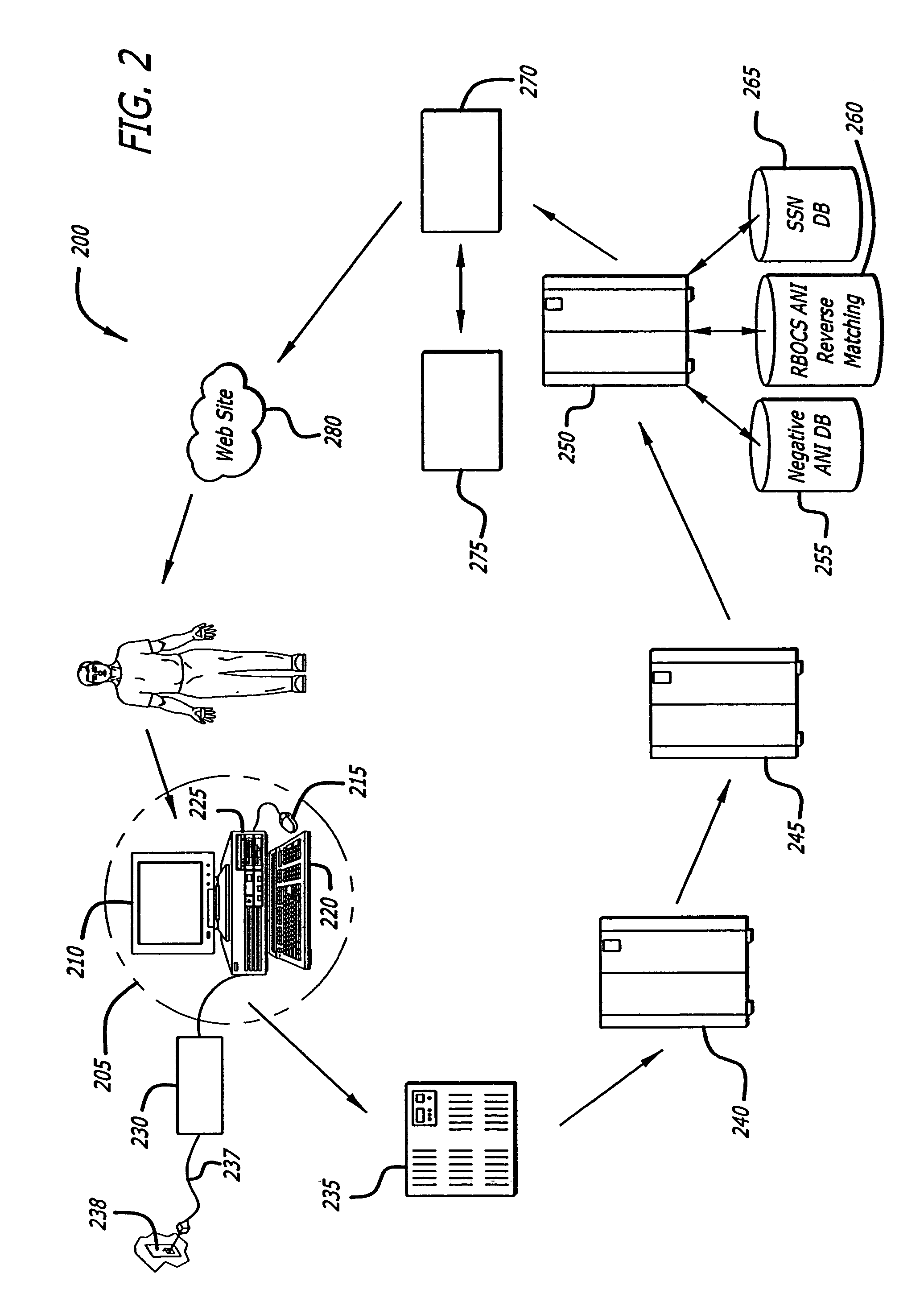
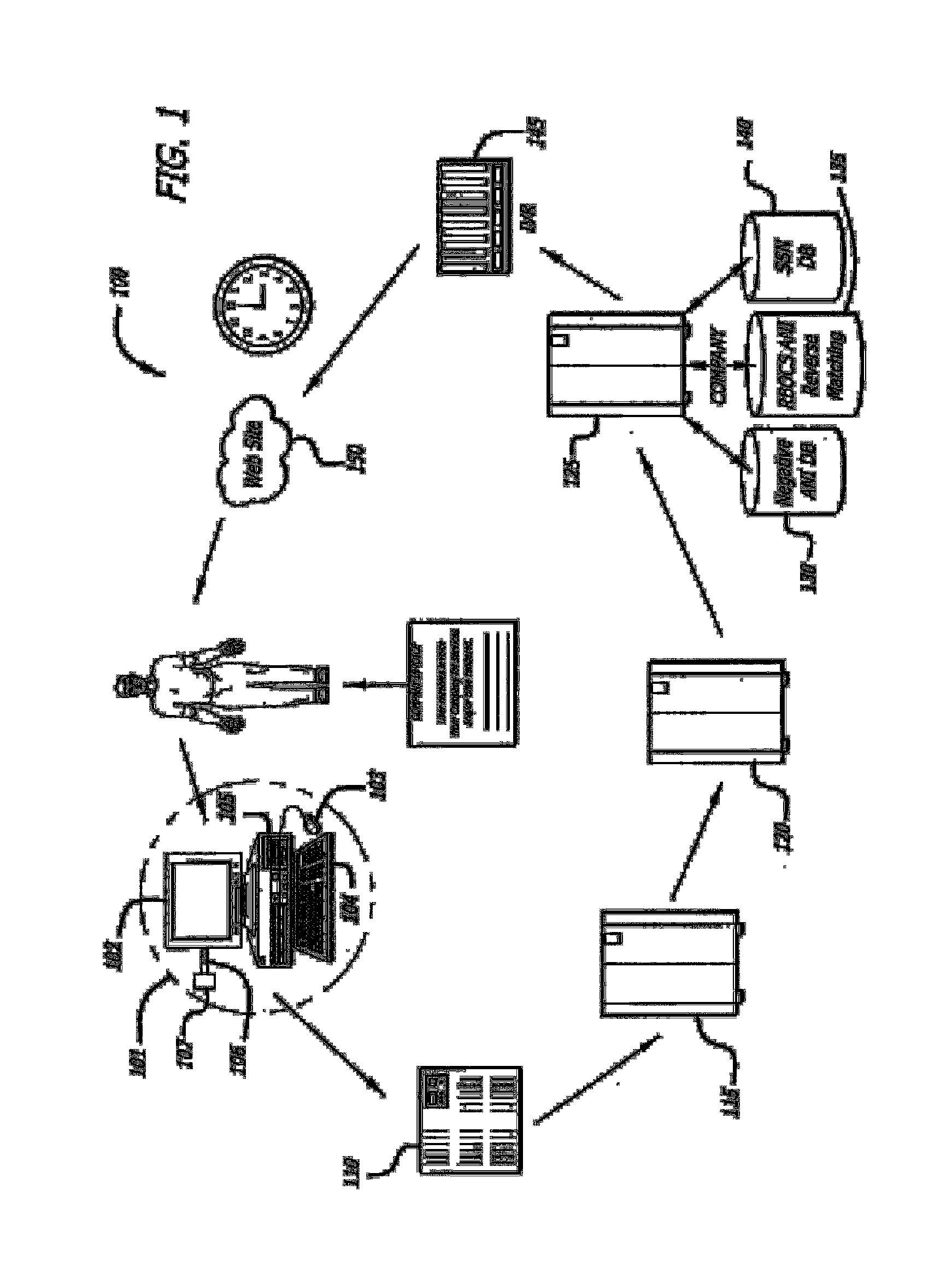
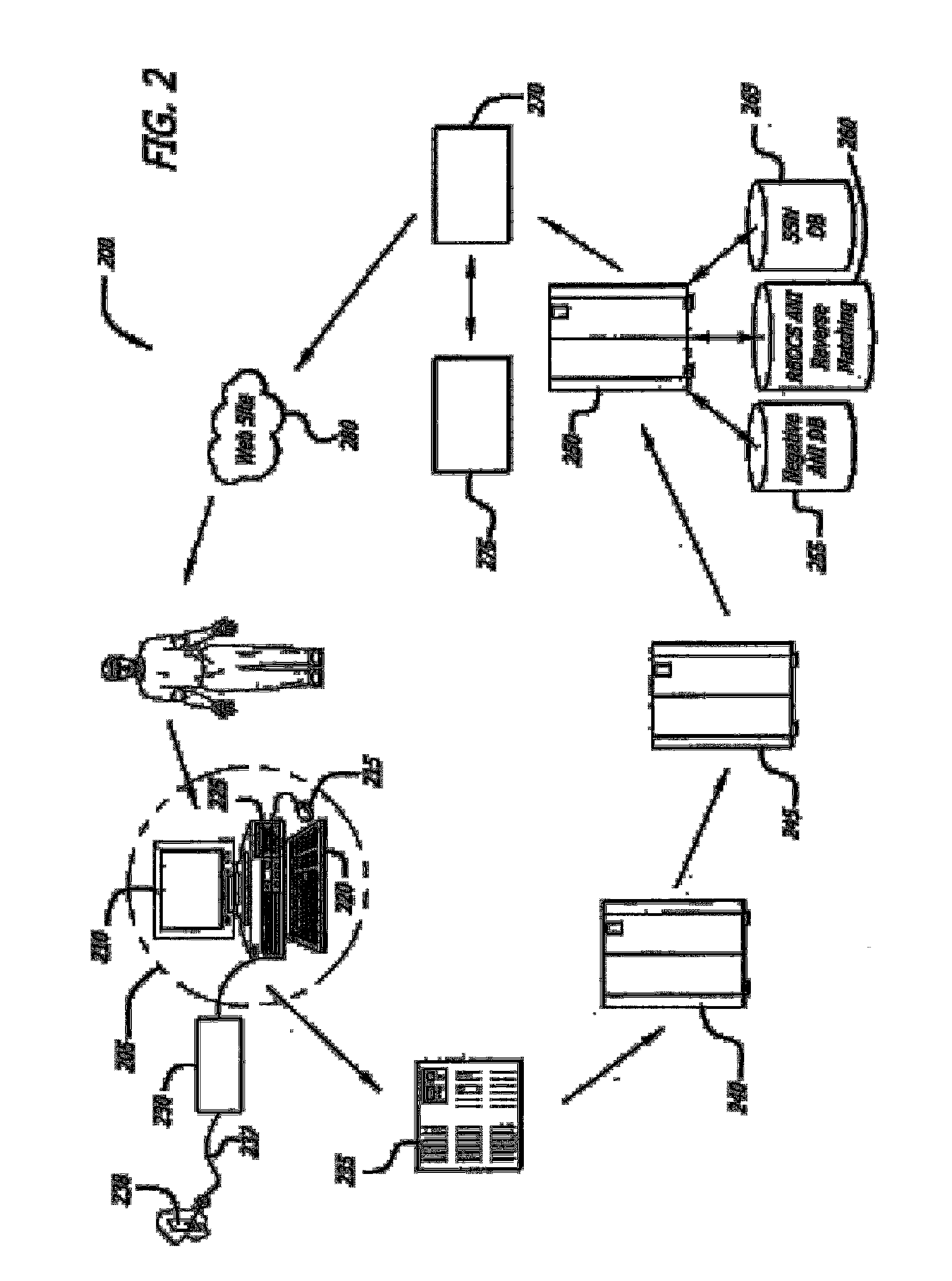
InactiveUS7177837B2Enforcing a debt against a network userImprove creditComplete banking machinesFinancePersonal identification numberThe Internet
A system and method for managing accounting and billing e-commerce (including m-commerce) transactions. The user may connect to the e-commerce network by placing a call from a land line or sending a text message. The user may then purchase goods and / or services after meeting required user qualifications, such as minimum age or credit rating. The user qualifications may be established within the framework of a gateway that assigns a unique identifier or personal identification number (PIN) for e-commerce network access once the qualifications are met. The user qualifications may also be established within the framework of a remote access server (RAS) that is accessed by a user through a downloadable automatic dialer having code containing a unique identifier relating to a merchant, product or service. The user is invoiced for the product or service according to the telephone from which the call originated.
Owner:TOUBOUL STEPHANE +2
Method and system for processing transaction data and payment system
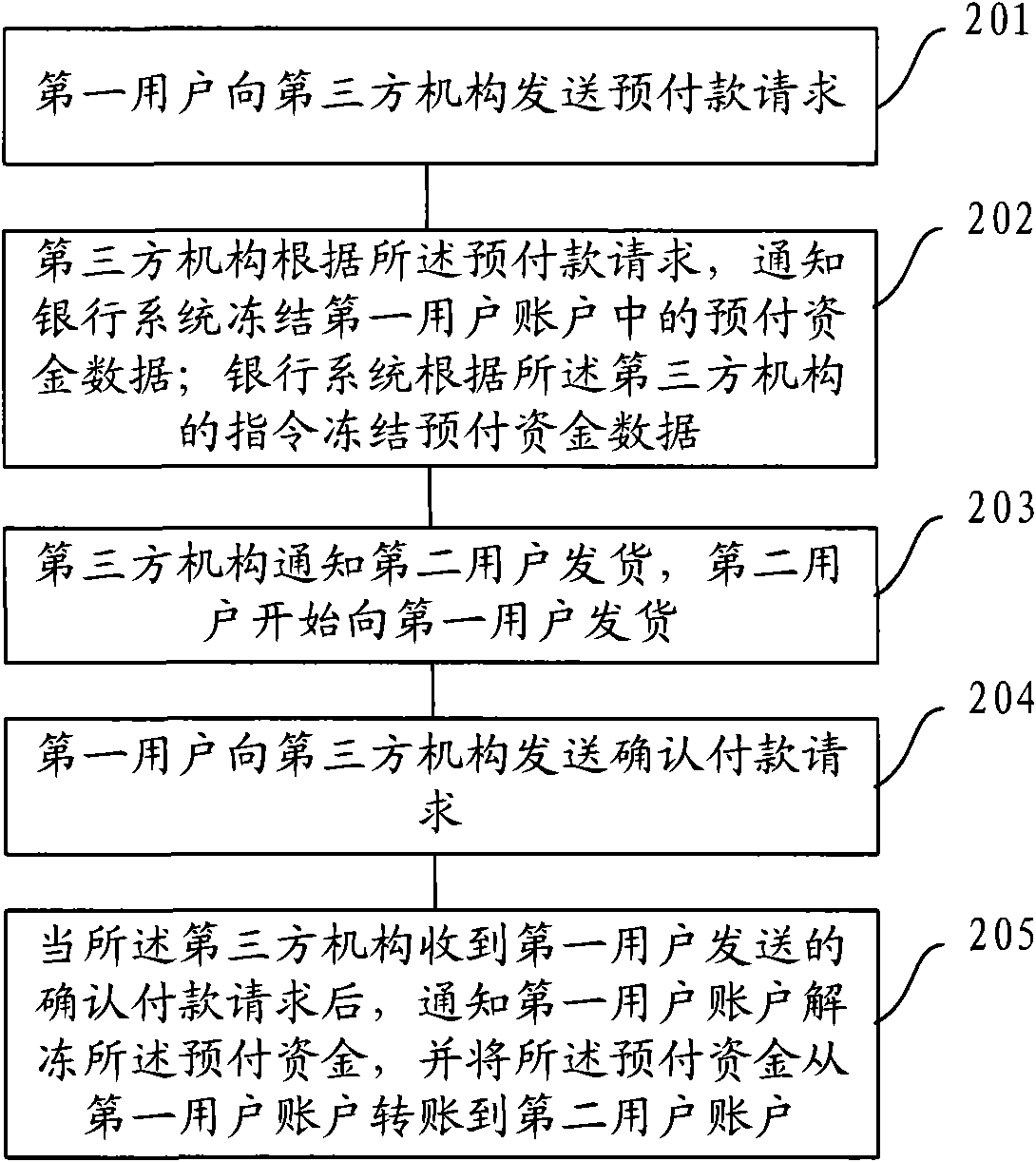
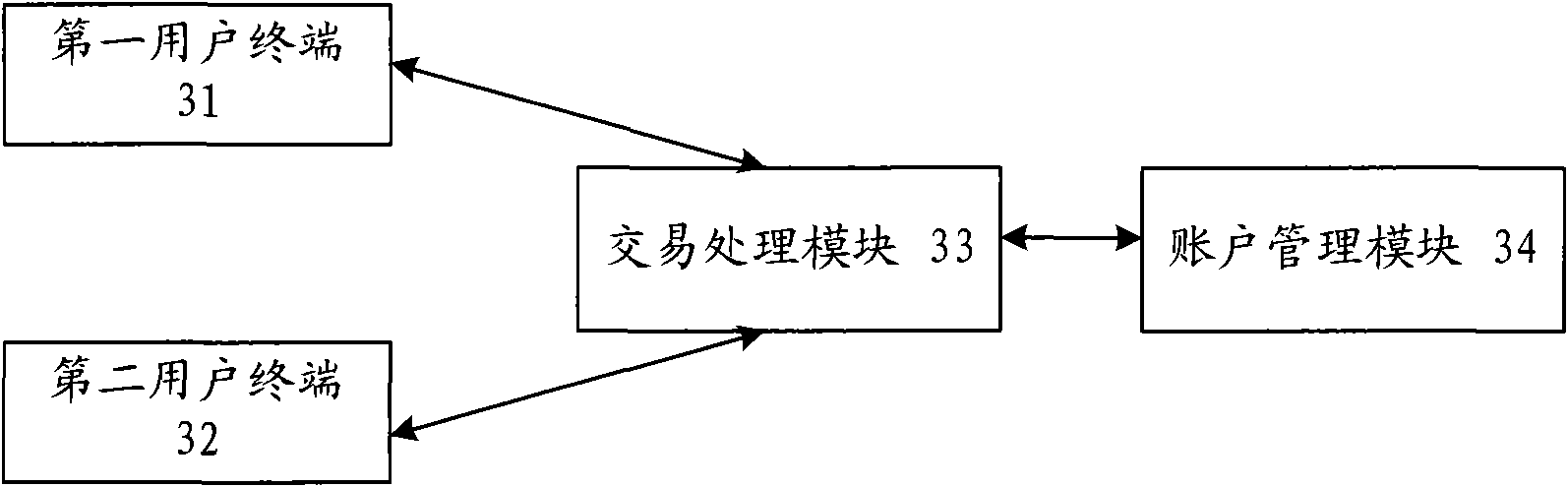
The invention discloses a method and a system for processing transaction data and a payment system, solving the problem of complicated data processing procedures and low security in the prior transaction method. The method comprises the steps: sending an advance payment request to a third party system by a first user terminal; notifying a bank system to freeze the advance fund data in a first user account by the third party system according to the advance payment request; freezing the advance fund data in the first user account by the bank system according to an instruction of the third party system; sending a confirmation payment request to the third party system by the first user terminal; and notifying the bank system to unfreeze the advance fund data by the third party system according to the confirmation payment request and transferring the advance fund data from the first user account to a second user account. The invention is unnecessary to deposit to the third party organization before the transaction is finished and only freeze the part of the fund data, thereby reducing the processing procedures of the transaction data and ensuring the security of the transaction.
Owner:CHINA UNIONPAY
Computer-implemented method and system for managing accounting and billing of transactions over public media such as the internet
InactiveUS20040143523A1Improve creditComplete banking machinesFinancePersonal identification numberThe Internet
Abstract of the Disclosure A system and method for managing accounting and billing e-commerce (including m-commerce) transactions. The user may connect to the e-commerce network by placing a call from a land line or sending a text message. The user may then purchase goods and / or services after meeting required user qualifications, such as minimum age or credit rating. The user qualifications may be established within the framework of a gateway that assigns a unique identifier or personal identification number (PIN) for e-commerce network access once the qualifications are met. The user qualifications may also be established within the framework of a remote access server (RAS) that is accessed by a user through a downloadable automatic dialer having code containing a unique identifier relating to a merchant, product or service. The user is invoiced for the product or service according to the telephone from which the call originated.
Owner:TOUBOUL STEPHANE +2
Block chain-based identity authentication method and device and computer readable storage medium
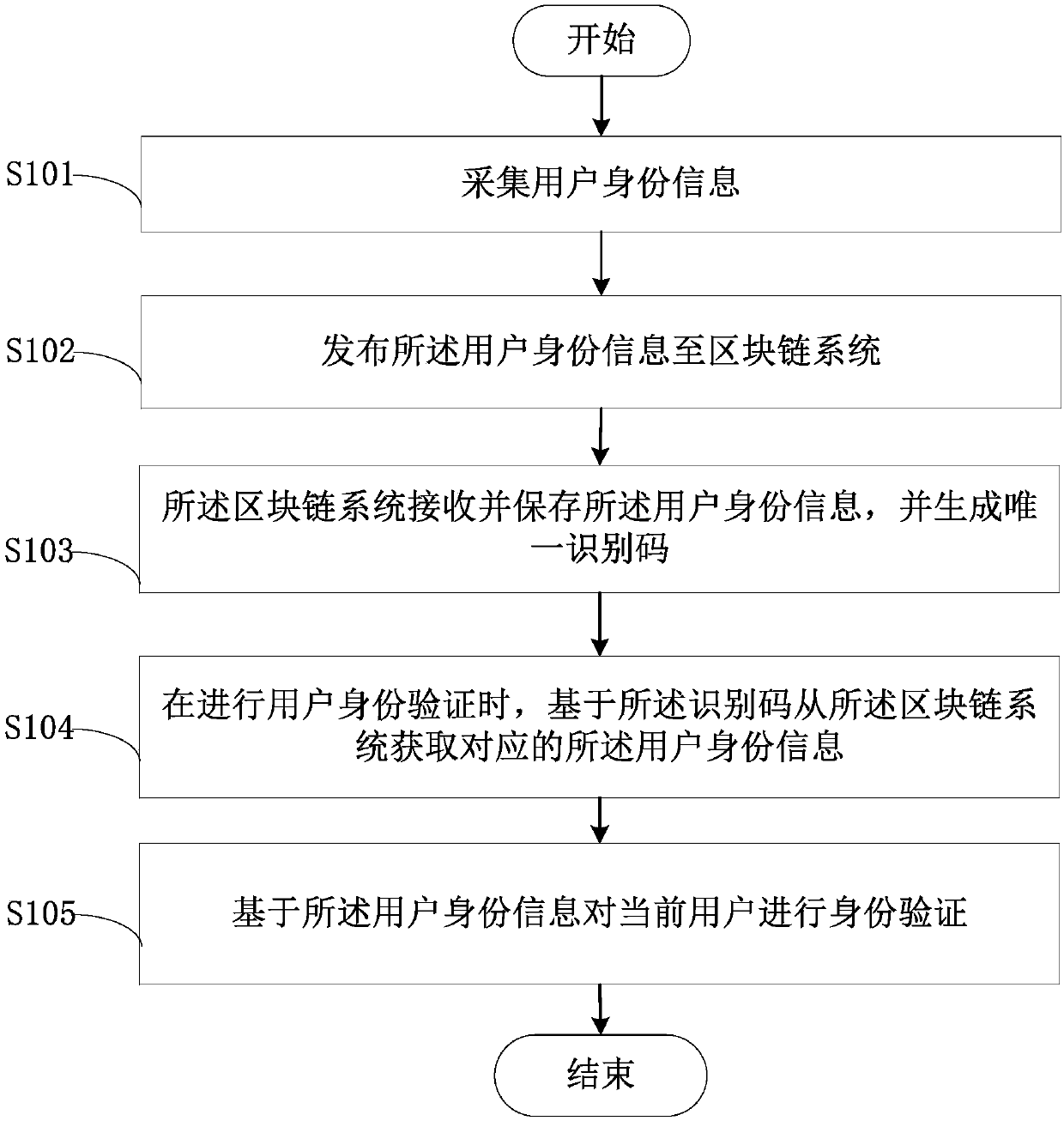
The invention relates to the technical field of computers, and provides a block chain-based identity authentication method. The method comprises the steps that user identity information is acquired; the user identity information is published to a block chain system; the block chain system receives and stores the user identity information and generates unique identification codes; when user identity authentication is conducted, the corresponding user identity information is acquired from the block chain system on the basis of the identification code; and identification authentication is conducted on a current user on the basis of the user identity information. According to the method, the information storage security is improved, the information storage credit degree is increased, and the reliability and accuracy of user identity authentication are improved. The invention further provides a block chain-based identity authentication device and a computer readable storage medium.
Owner:XIAMEN KUAISHANGTONG INFORMATION TECH CO LTD
Method, system and server for authenticating identities on basis of block chain networks
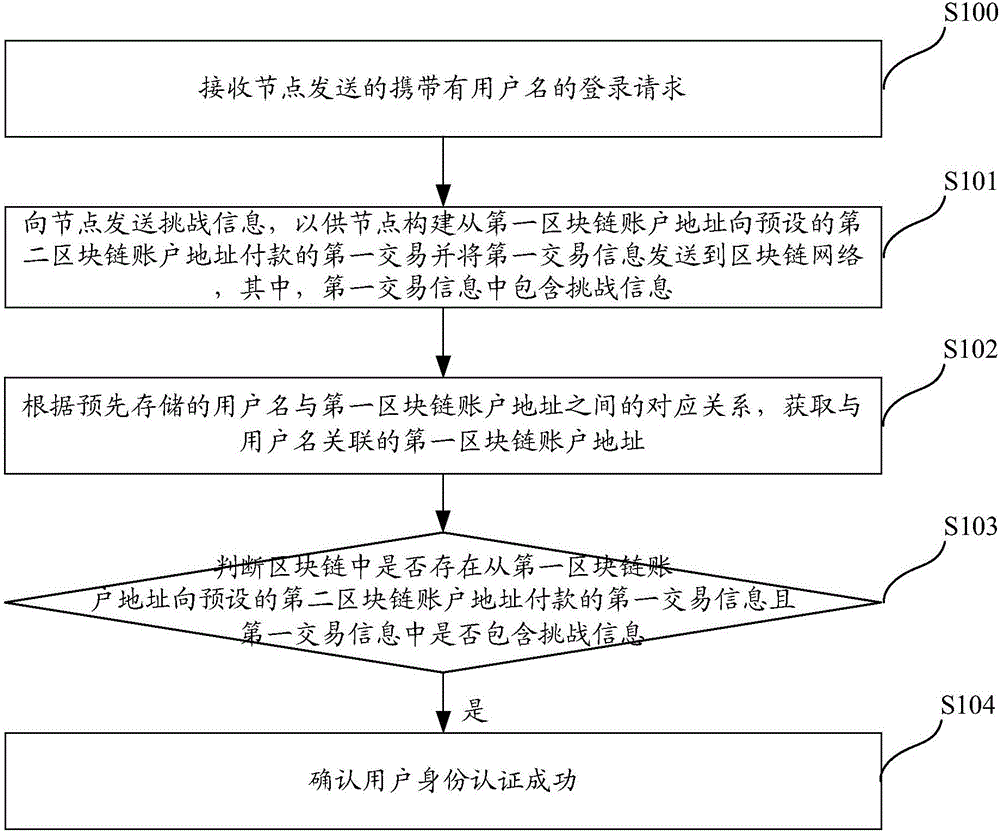
ActiveCN106357644AImprove securityImprove creditTransmissionProtocol authorisationPaymentTerminal equipment
The invention discloses a method, a system, a server and terminal equipment for authenticating identities on the basis of block chain networks. The method, the system, the server and the terminal equipment are used for authenticating the identifies for nodes in the block chain networks. The method includes receiving login requests with user names; transmitting challenge information to the nodes to allow the nodes to establish first transaction of payment from first block chain account addresses to preset second block chain account addresses and transmit first transaction information with the challenge information to the block chain networks; acquiring the first block chain account addresses according to preliminarily stored corresponding relations between the user names and the first block chain account addresses; judging whether the first transaction information of the payment from the first block chain account addresses to the preset second block chain account addresses is available in block chains or not and whether the first transaction information contains the challenge information or not; determining that the identities of users are successfully authenticated if the first transaction information is available in block chains and contains the challenge information. The login requests are transmitted by the nodes. The first block chain account addresses are associated with the user names. The method, the system, the server and the terminal equipment have the advantage that the authentication safety and the credibility of authentication procedures can be improved.
Owner:JIANGSU PAYEGIS TECH CO LTD
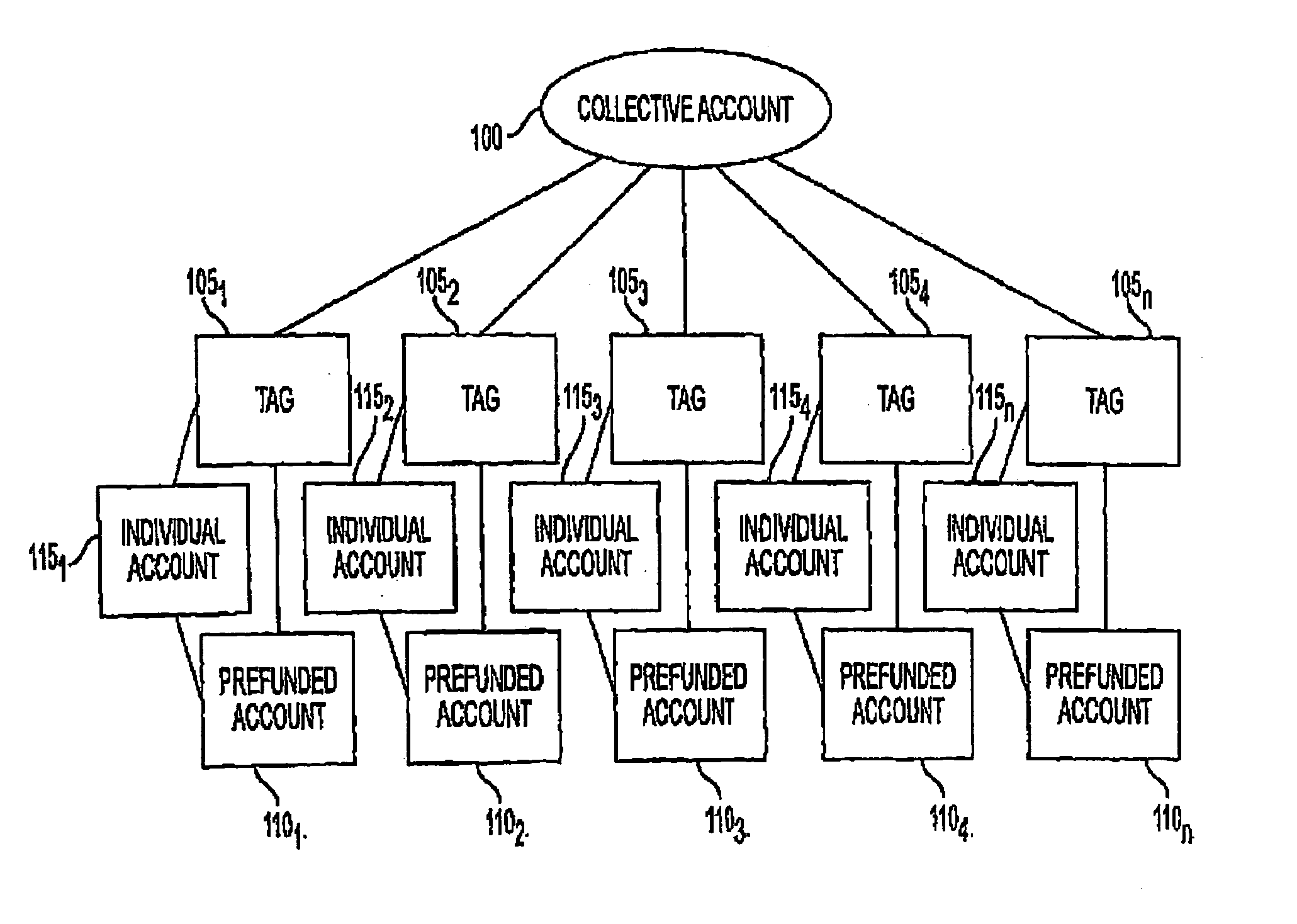
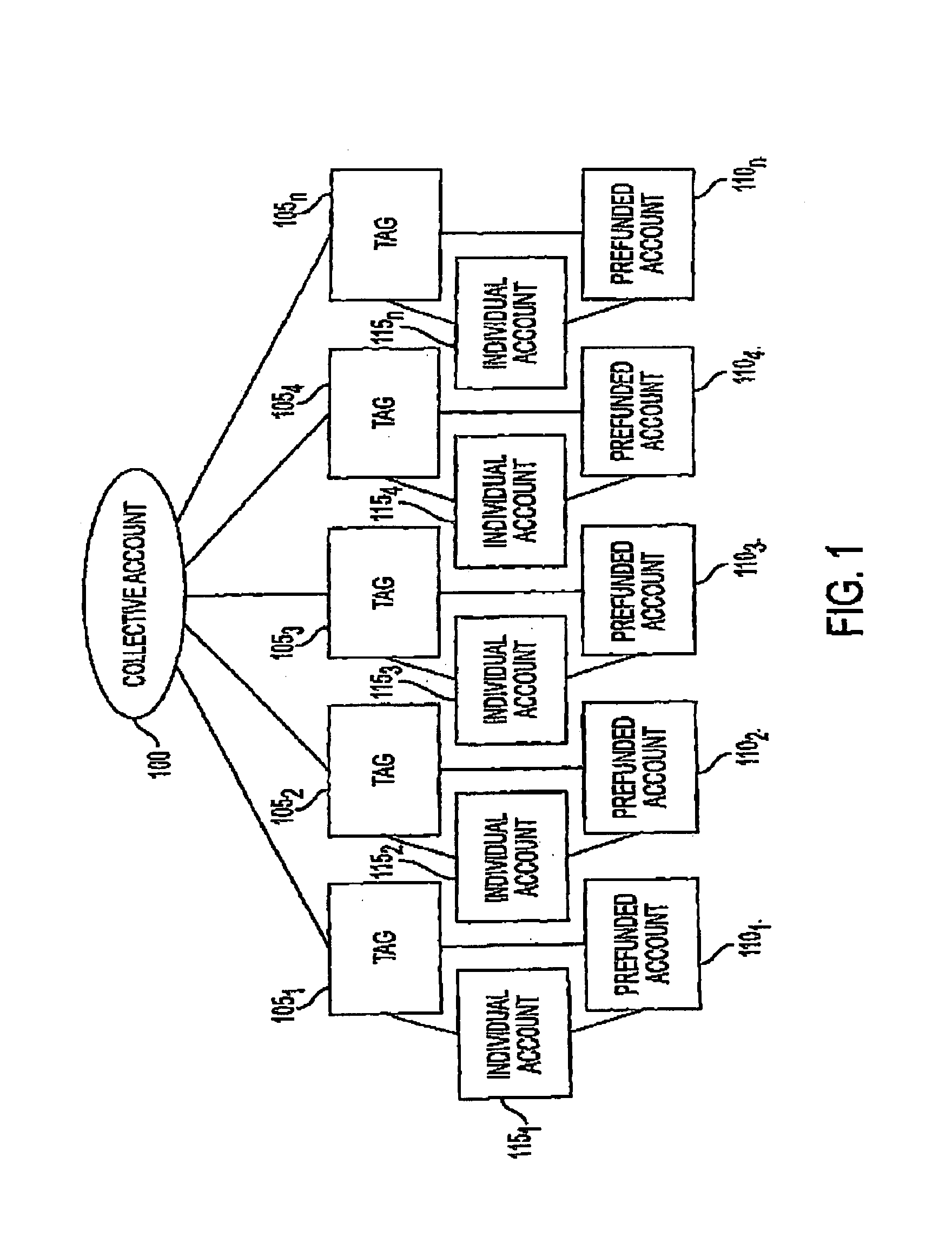
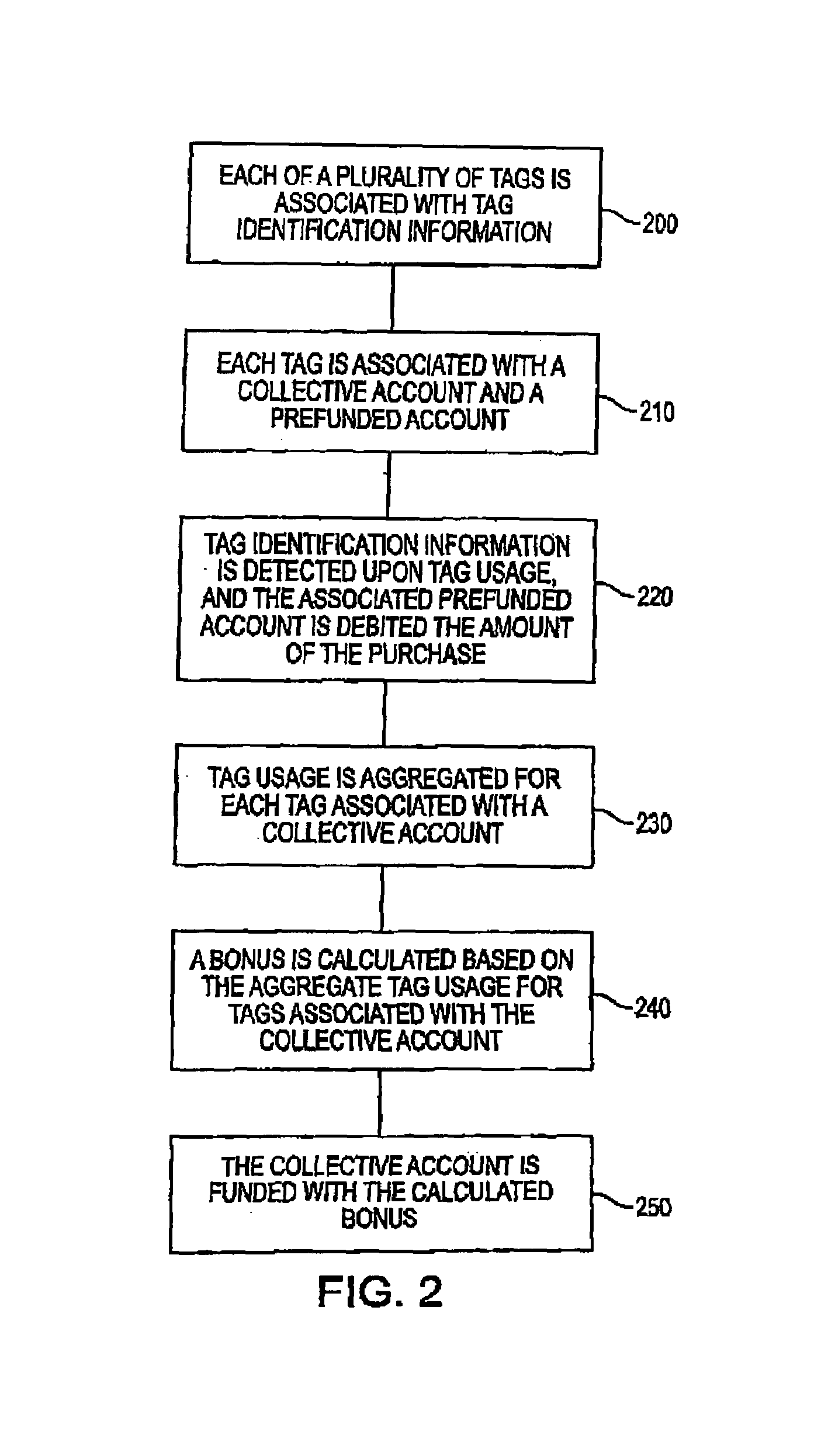
System and method for funding a collective account by use of an electronic tag
InactiveUS7306141B1Raise the possibilityReducing motorist distractionTicket-issuing apparatusFundraising managementComputer scienceData science
A system and method for funding a collective account via aggregating usage of electronic tags is disclosed. The system and method promotes the use of electronic tags, and the funding of collective accounts that may be associated with charitable or other philanthropic causes. Further benefits may be realized by replenishing the prefunded account that serves as the source of funds for the electronic tag to an affinity account that also benefits the charitable or other philanthropic cause.
Owner:JPMORGAN CHASE BANK NA
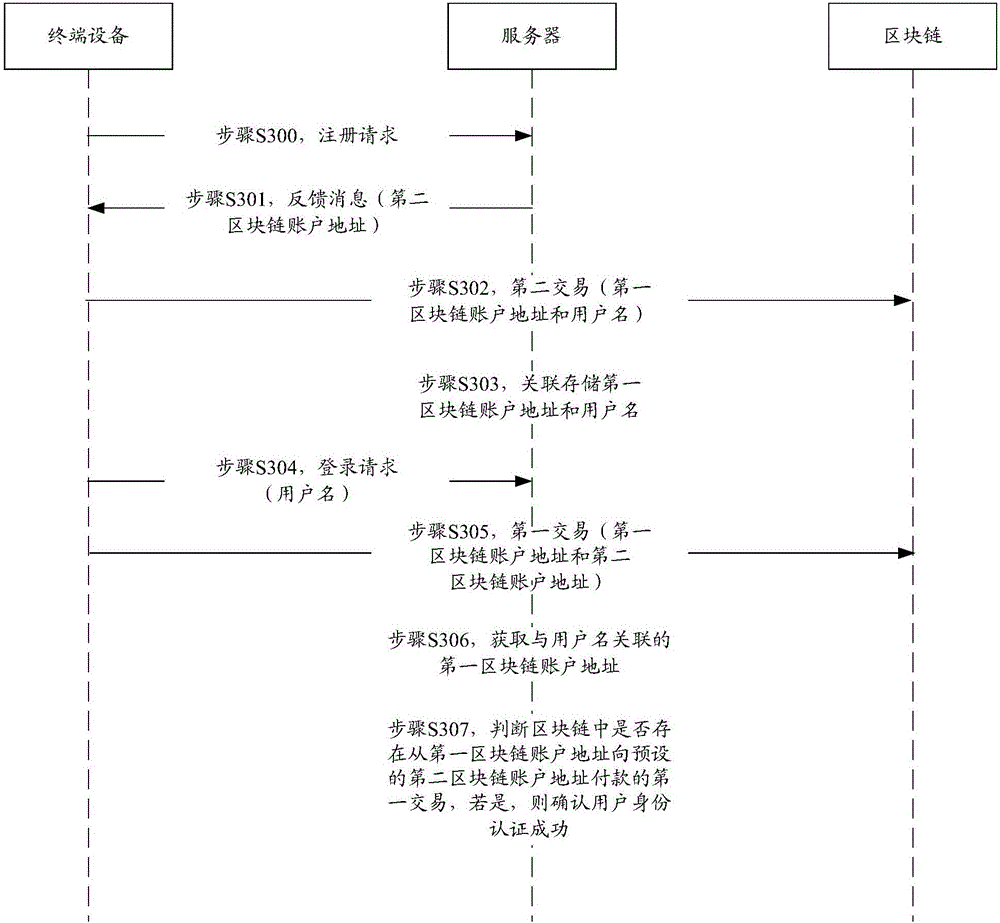
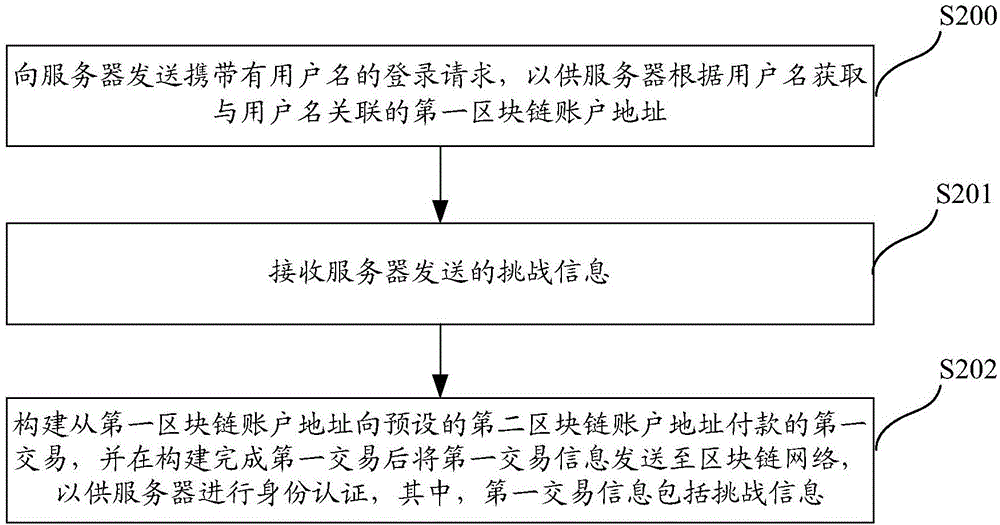
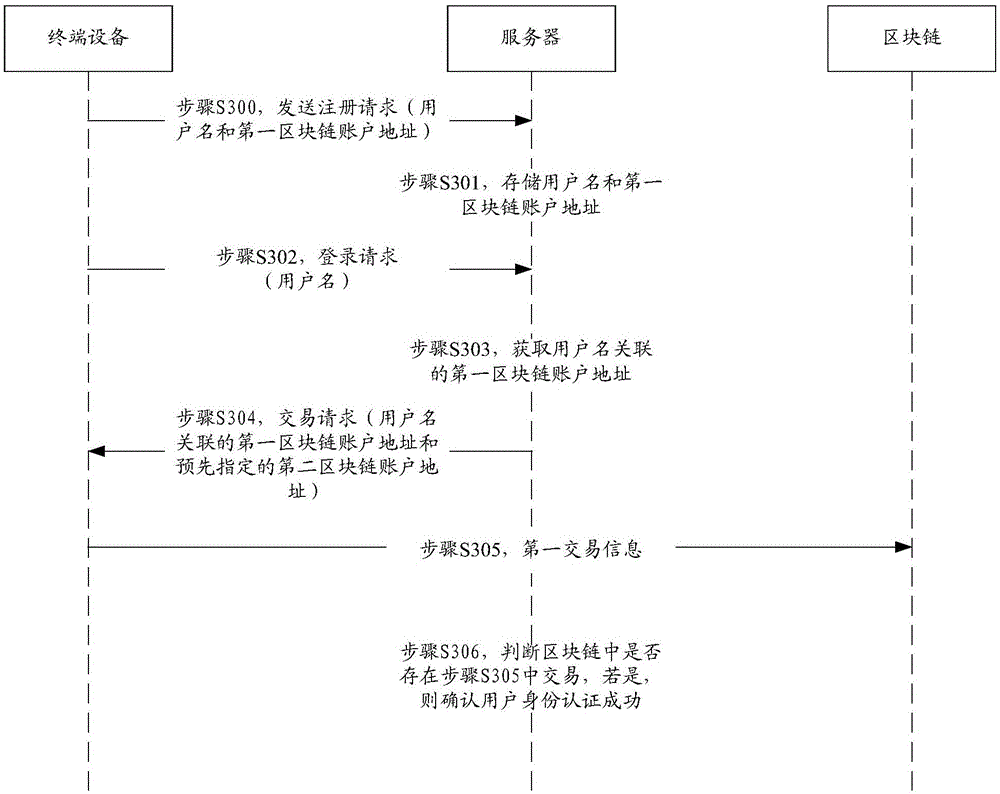
Identity authentication method based on block chain network, server and terminal device
The present invention discloses an identity authentication method based on a block chain network, a server and a terminal device. The objective of the invention is to perform identity authentication of nodes in the block chain network. The method comprises: receiving a registration request carrying user names sent by nodes; obtaining a first block chain account address associated with the user names according to the corresponding relation between the stored user names in advance and the first block chain account address; sending a transaction request carrying the first block chain account address and assigned second block chain account address in advance to the node to allow the nodes to construct a first transaction according to the transaction request and send the first transaction information to the block chain network after the first transaction is constructed, wherein the transaction request shows the operation of performing payment from the first block chain account address to the second block chain account address; determining whether the block chain has the first transaction information of performing payment from the first block chain account address to the second block chain account address or not; and if block chain has the first transaction information of performing payment from the first block chain account address to the second block chain account address, confirming the successful user identity authentication to improve the safety of the authentication.
Owner:JIANGSU PAYEGIS TECH CO LTD
Interactive automated article dispensing system
Disclosed is an interactive automated system for dispensing cloth articles, the principles of which may be readily adapted for use in systems for dispensing a wide variety of articles suitable for distribution by use of a vending style device, such as, but not limited to hospital scrub outfits, clean rooms suits, towels, blankets, sweat suits, t-shirts, socks, underwear, under shirts, ties, scarves, hats, and rain suits. Further, systems of the present invention will be of benefit to a variety of institutions and outlets, such as, but not limited to, hospitals, hotels, motels, resorts, health clubs, country clubs, swimming pools, college and university dormitories, shopping malls, tourist attractions, sport stadiums and arena, fair ground, sport shops, factories, laboratories and the like. The general principles of the present invention include: providing an article dispensing device; receiving a user order; ascertaining if the order may be fulfilled by the dispensing device at which such order was placed; if “yes”, then fulfilling the order; and if “no” providing an alternative ordering solution based on the user's requested order and information from a system wide database. The alternative ordering solutions may include an alternate article from the dispensing device at which the order is received, the location of an alternate dispensing device at which the desired article may be obtained, or a request that the user return a used article to an associated return device. The system may be configured for loaning articles with the intention that the articles be returned. Alternatively, the system may be configured for vending articles.
Owner:POLYTEX TECH
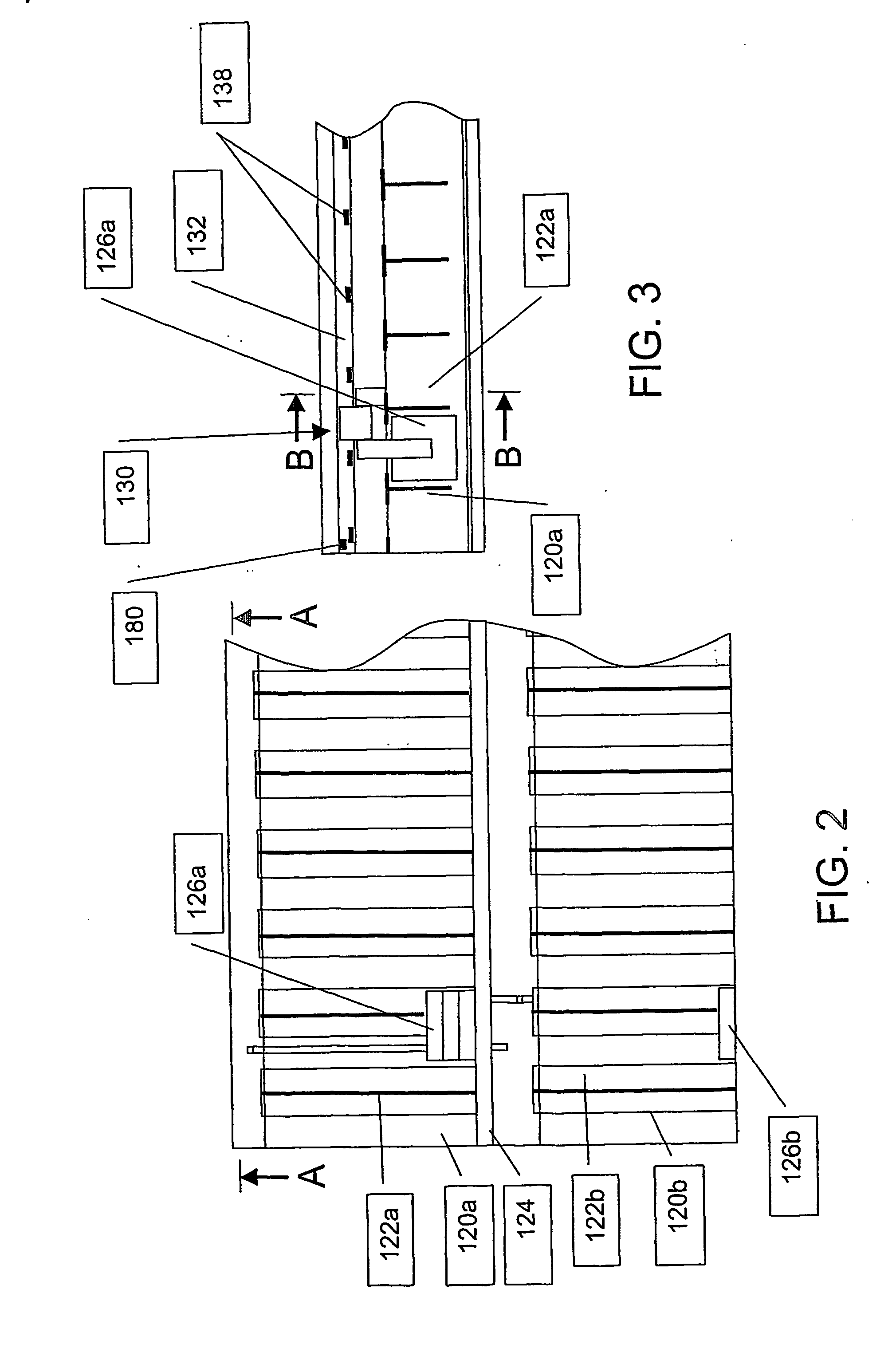
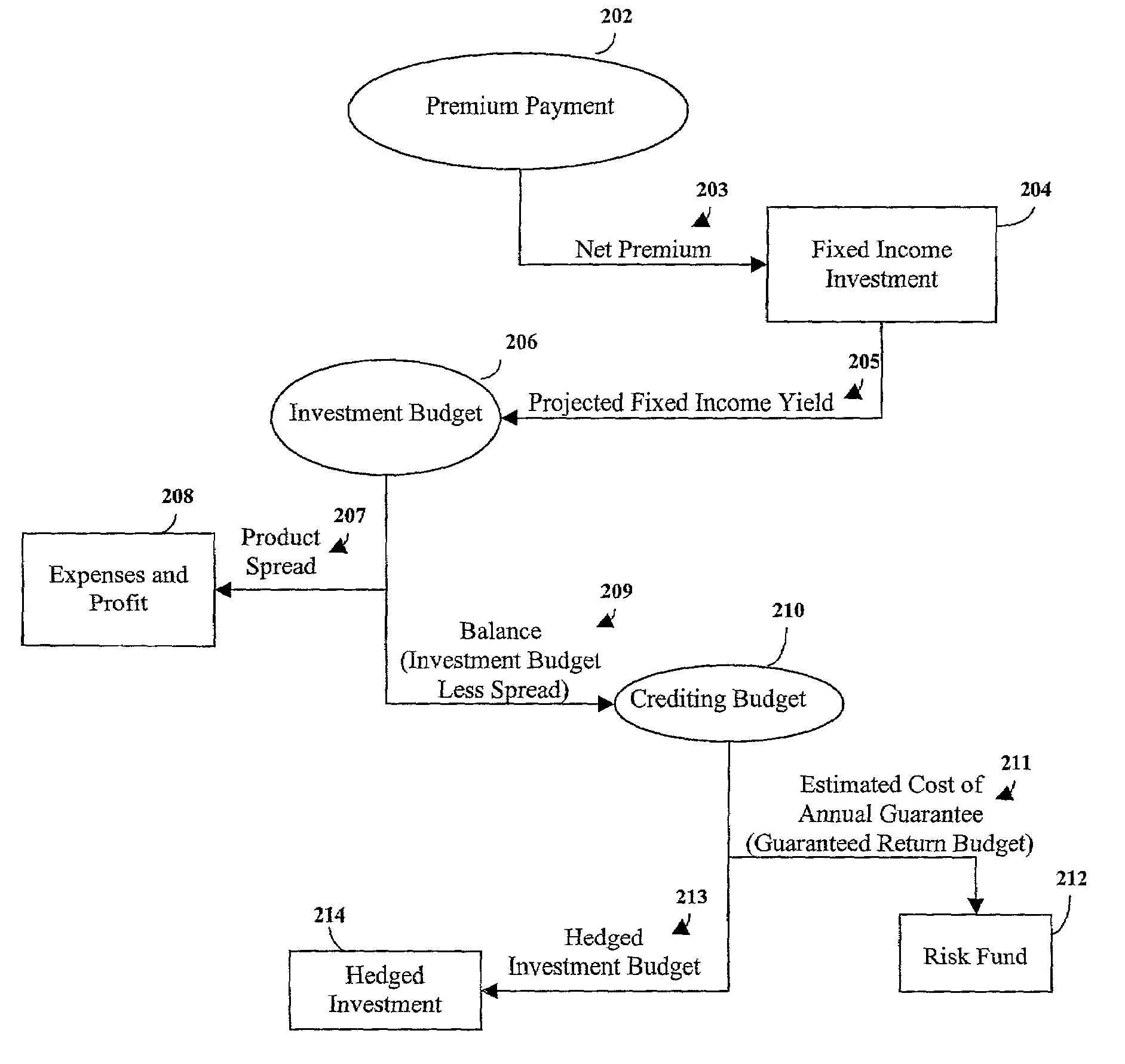
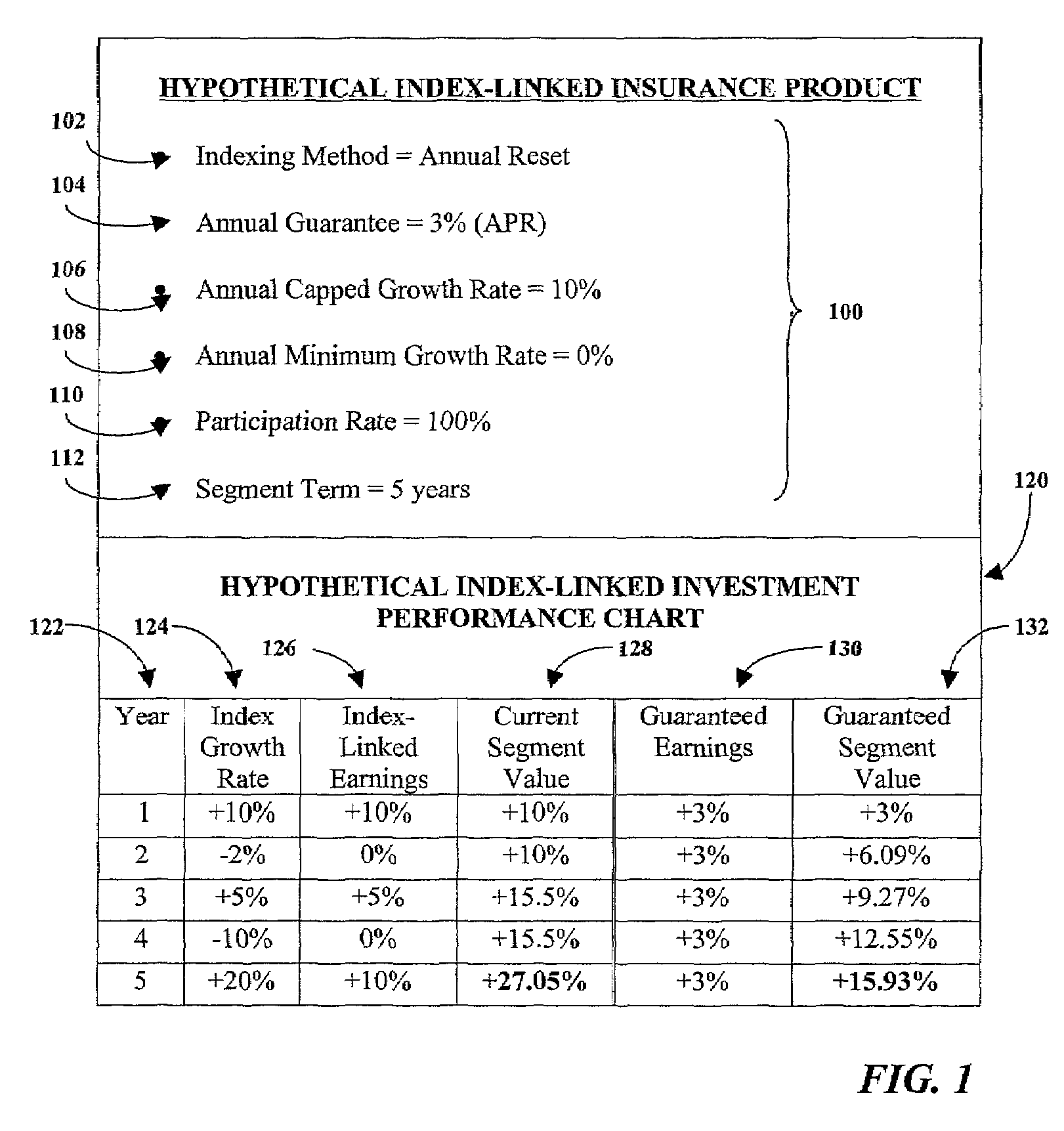
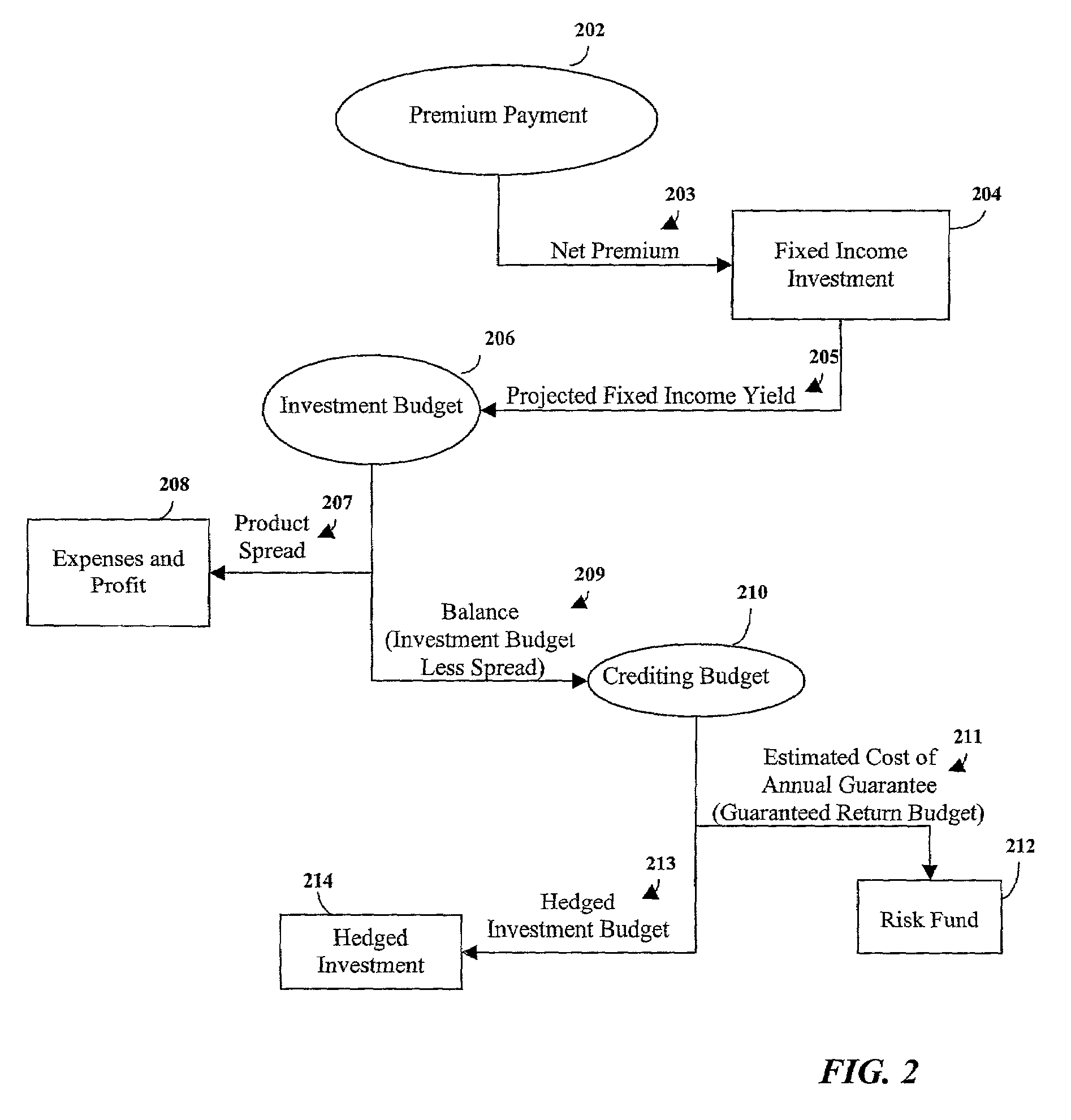
Maximization of a hedged investment budget for an index-linked insurance product
An index-linked insurance product having an annual guarantee is implemented having a maximized hedged investment budget. A net premium payment is allocated to a fixed income investment and an annual fixed income yield is projected. The maximized hedged investment budget is determined by deducting from the projected annual fixed income a product spread and an estimated cost of the annual guarantee. The deducted estimated cost of the annual guarantee is allocated to a risk fund. The maximized hedged investment budget is allocated to a hedged investment designed to generate proceeds for supporting index-linked earnings credited to the index-linked insurance product. Upon expiration of the product term, if the amount credited based on the index-linked earnings does not equal to at least the compounded annual guarantee, the amount credited is increased to be equal to the compounded annual guarantee. The increased credit may be supported using funds from the risk fund and other reserves if necessary.
Owner:ACCORDIA LIFE & ANNUITY
Blockchain-based identity authentication method
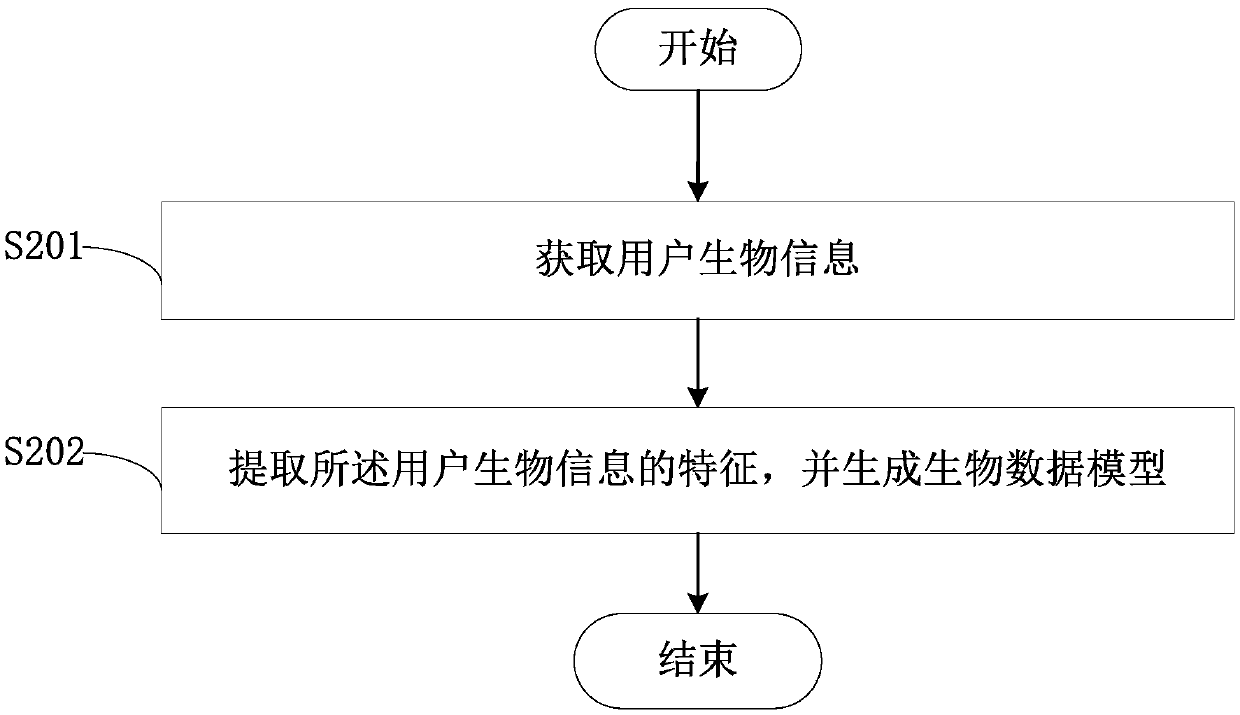
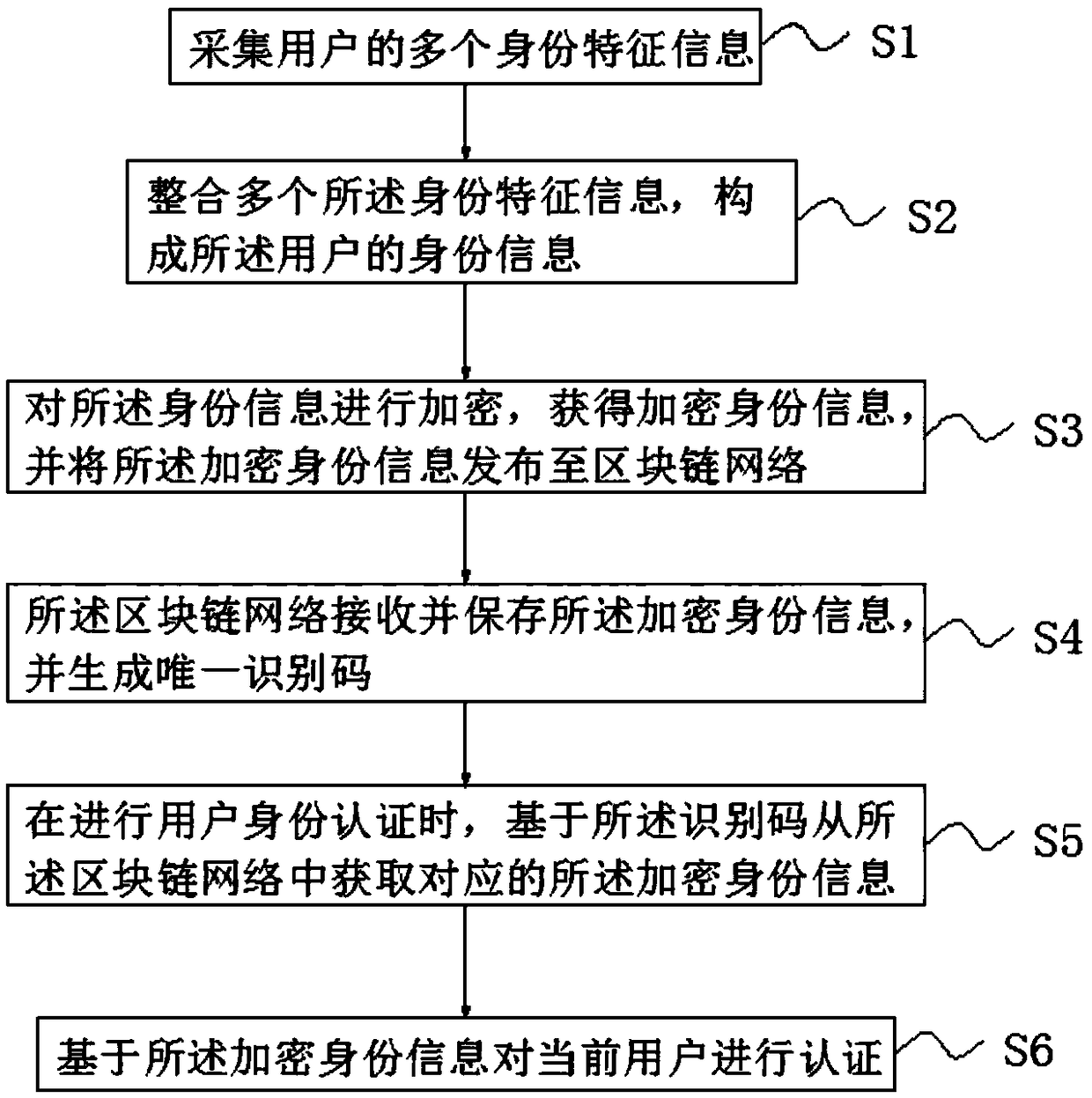
InactiveCN108881301AImprove securityImprove creditPublic key for secure communicationUser identity/authority verificationInternet privacyThe Internet
The invention, which belongs to the technical field of internet, discloses a blockchain-based identity authentication method. The method comprises: a plurality of pieces of identity feature information of a user is collected; the identity feature information is integrated to form identity information of the user; the identity information is encrypted to obtain encrypted identity information and the encrypted identity information is issued to a blockchain network; the blockchain network receives and stores the encrypted identity information and generates a unique identification code; when identity authentication of the user is carried out, the corresponding identity information is obtained from the blockchain network based on the identification code; and the curent user is authenticated based on the encrypted identity information. According to the blockchain-based identity authentication method provided by the invention, the identity information of the user is stored based on the characteristics of decentralization, openness, autonomy, information non-tamper property, and anonymity of the blockchain system, so that the information storage safety and credit level are improved.
Owner:宏桥高科技集团有限公司
Evaluated spam community interactive platform system and method and purpose
InactiveCN105913285AQuick response to demandSatisfy multi-level consumptionBuying/selling/leasing transactionsMarket data gatheringData acquisitionCustomer information
The invention discloses an evaluated spam community interactive platform system and method and purpose, relating to a community mobile shopping platform, especially a system which relates to customer information legal dealing, goods O2O sale from on-line to off-line, spam prevention and filtering, advertisement accurate delivery, product market prospect and consumption capability investigation, and customer and merchant credit rating. The system is characterized in that a merchant first purchases customer information, and then the customer purchases products from the merchant, and comprises a data acquisition distribution center and an information transmit-receive system; the system helps community merchants to lock nearby customers in a certain range, and realizes O2O sale with the customers on line.
Owner:王勇
Data storage and query method and device, computer system and readable storage medium
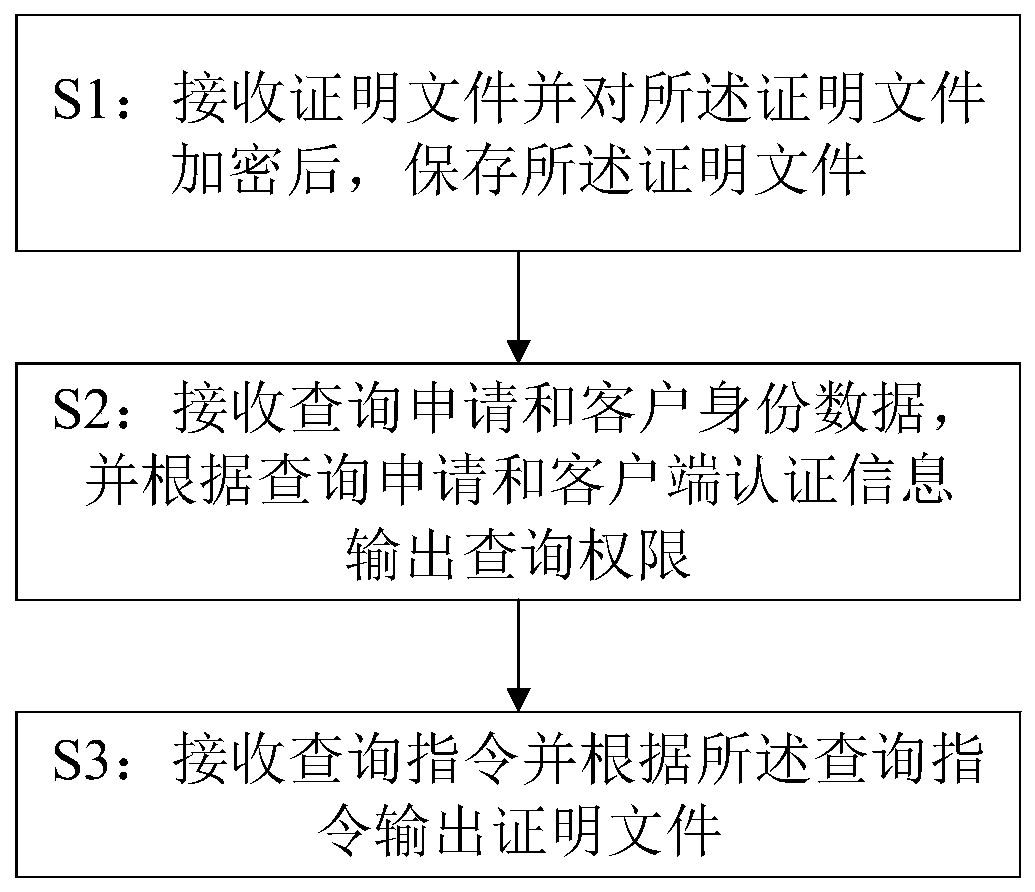
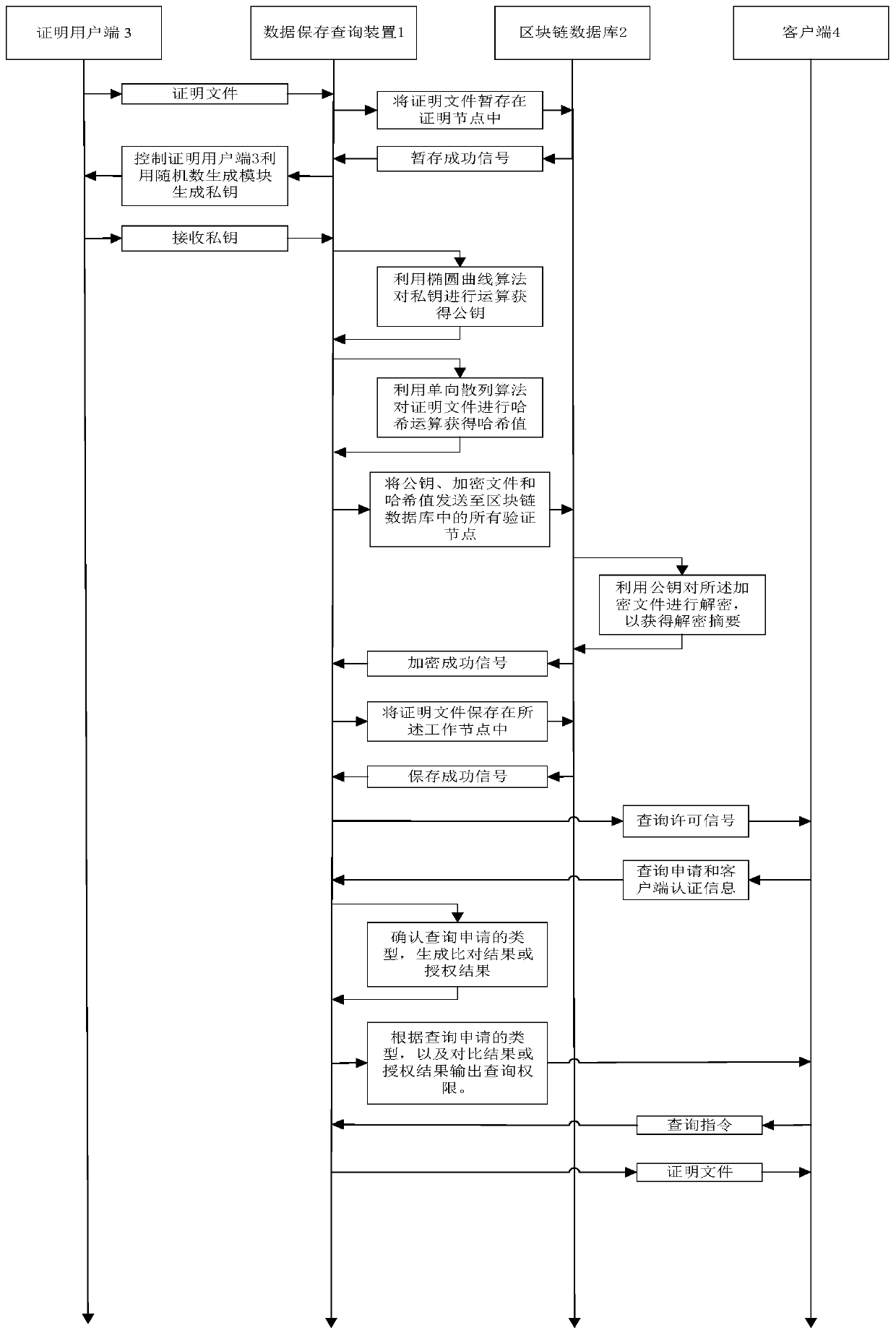
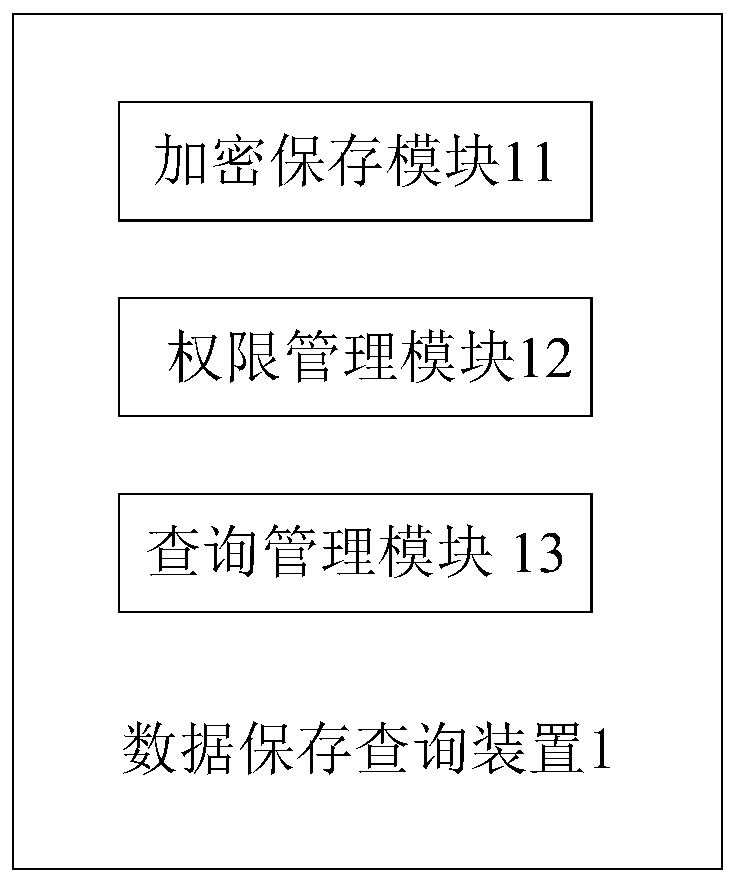
PendingCN109886026ACircumstances Affecting Comprehensive Assessment ResultsImprove creditDigital data protectionTamper resistanceComputerized system
The invention discloses a data storage and query method and device, a computer system and a readable storage medium. By utilizing a block chain database, the block chain database is provided with a plurality of proof nodes, and the method comprises the following steps of receiving a proof file, encrypting the proof file, and storing the proof file; receiving the query application and the client authentication information, and outputting a query authority according to the query application and the client authentication information; and receiving a query instruction and outputting the proof fileaccording to the query instruction. According to the invention, nodes except the block chain database are prevented from tampering the proof file; the comprehensive evaluation result of the company is influenced by counterfeiting and counterfeiting, and meanwhile, the situation that a certain proof node in the block chain database tampers proof files responsible for other proof nodes is also avoided, so that the credit of the comprehensive evaluation result of the company is improved. The method adapts to the requirement of the related party for the proof file of the client, protects the private data, and eliminates the risk of commercial secret leakage.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method and system for network reservation application
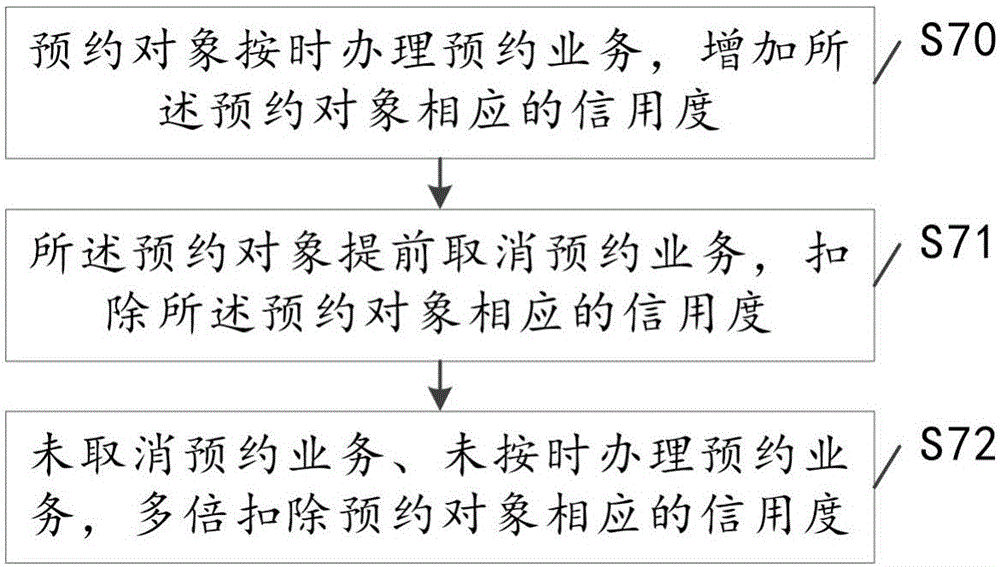
InactiveCN106485336AEasy to find an appointmentAppointment to avoidReservationsComputer terminalCentralized management
The invention discloses a network reservation application method. The method comprises the following steps: S20, service reservation information related to various types of service is displayed on a terminal screen, wherein the service reservation information comprises reservation service and reservation reference information; S30, a service type selected by a reservation object on the terminal screen, the reservation service corresponding to the type of service and the reservation reference information for the reservation service are acquired, wherein the reservation object comprises an individual user and an enterprise user; S40, the credit accumulated by the reservation object after network reservation application of each time is completed is queried; and S50, according to the reservation service for the reservation object, the reservation reference information for the reservation service and the credit of the reservation object, network reservation application processing is carried out. Network reservation for various types of service is managed in a centralized mode, reservation query by the user and reservation of service corresponding to each type of service are facilitated, and the reservation process and the reservation time of the user are saved.
Owner:PHICOMM (SHANGHAI) CO LTD
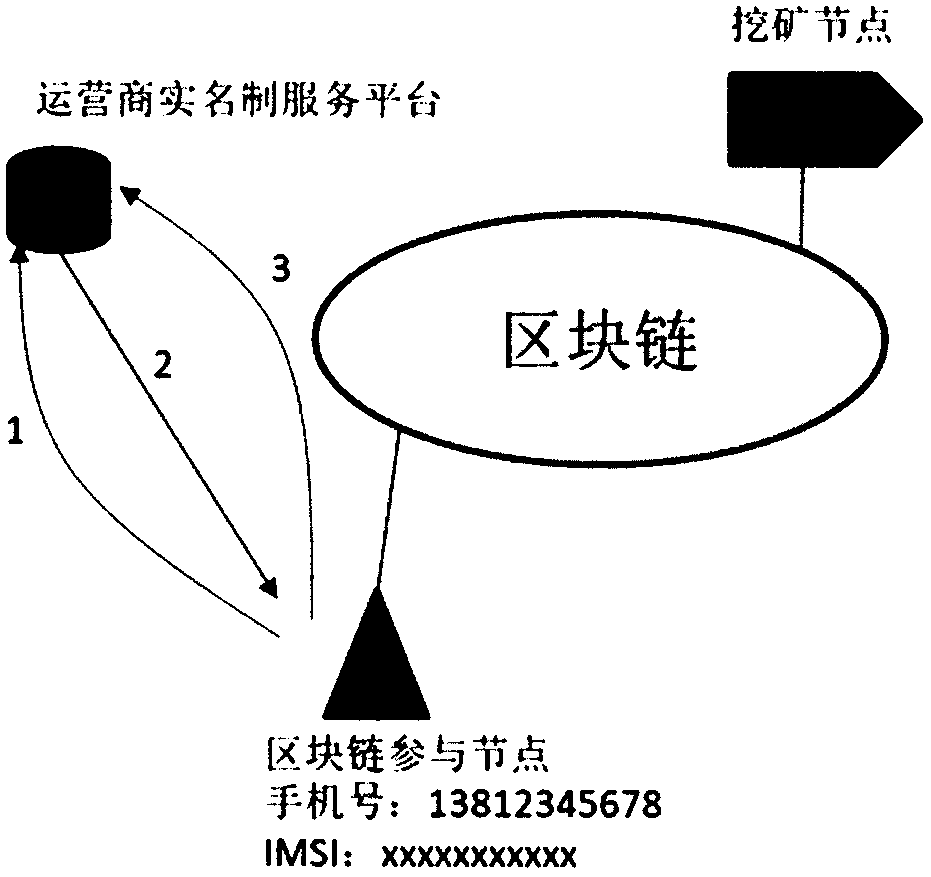
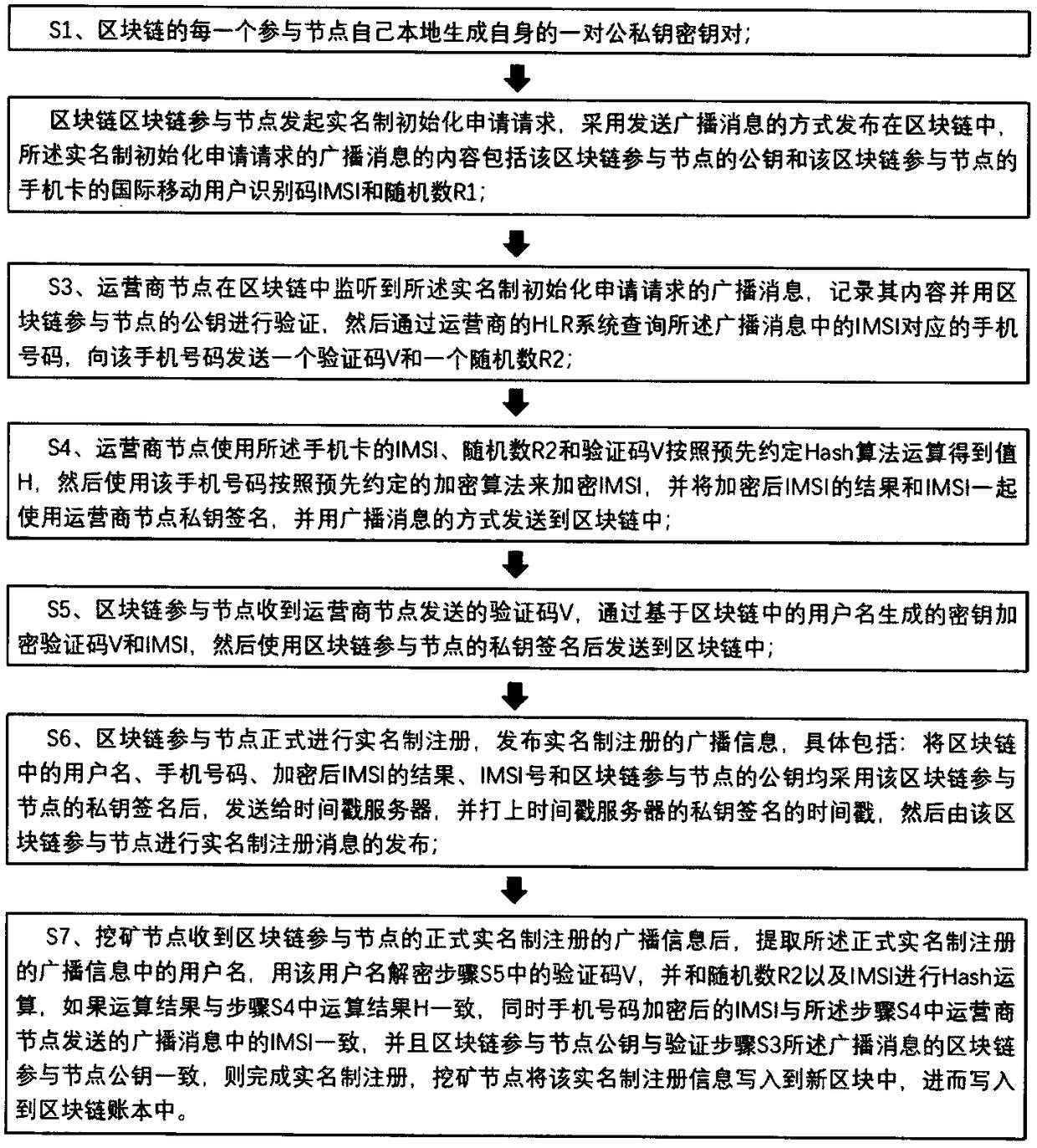
Method for achieving real name registration of block chain based on mobile phone number
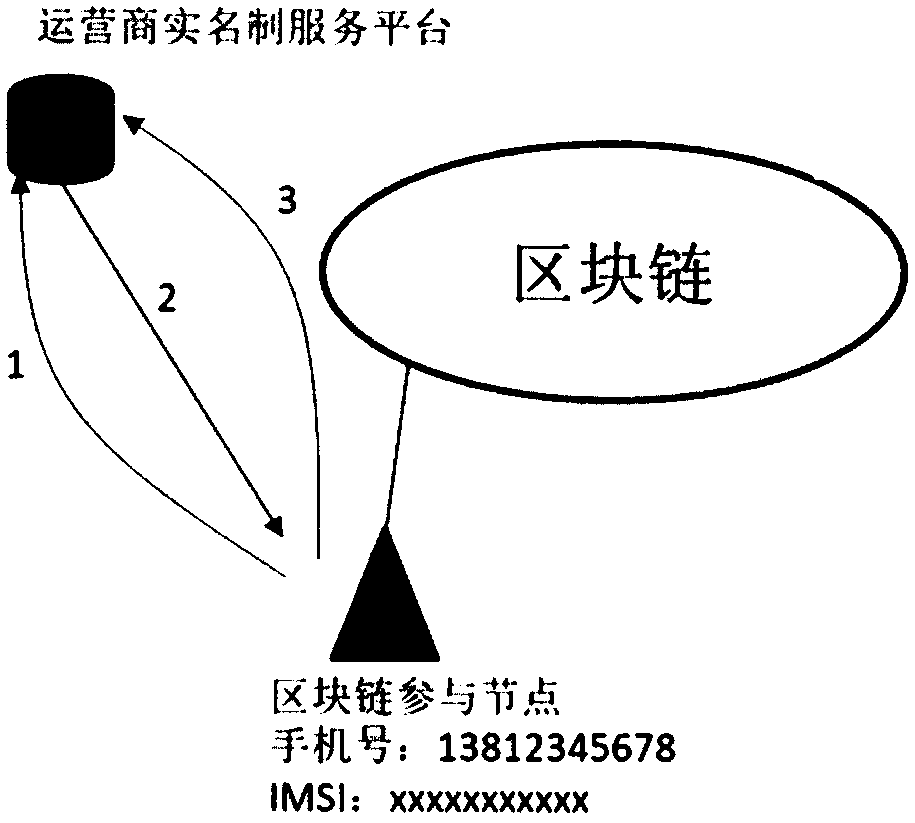
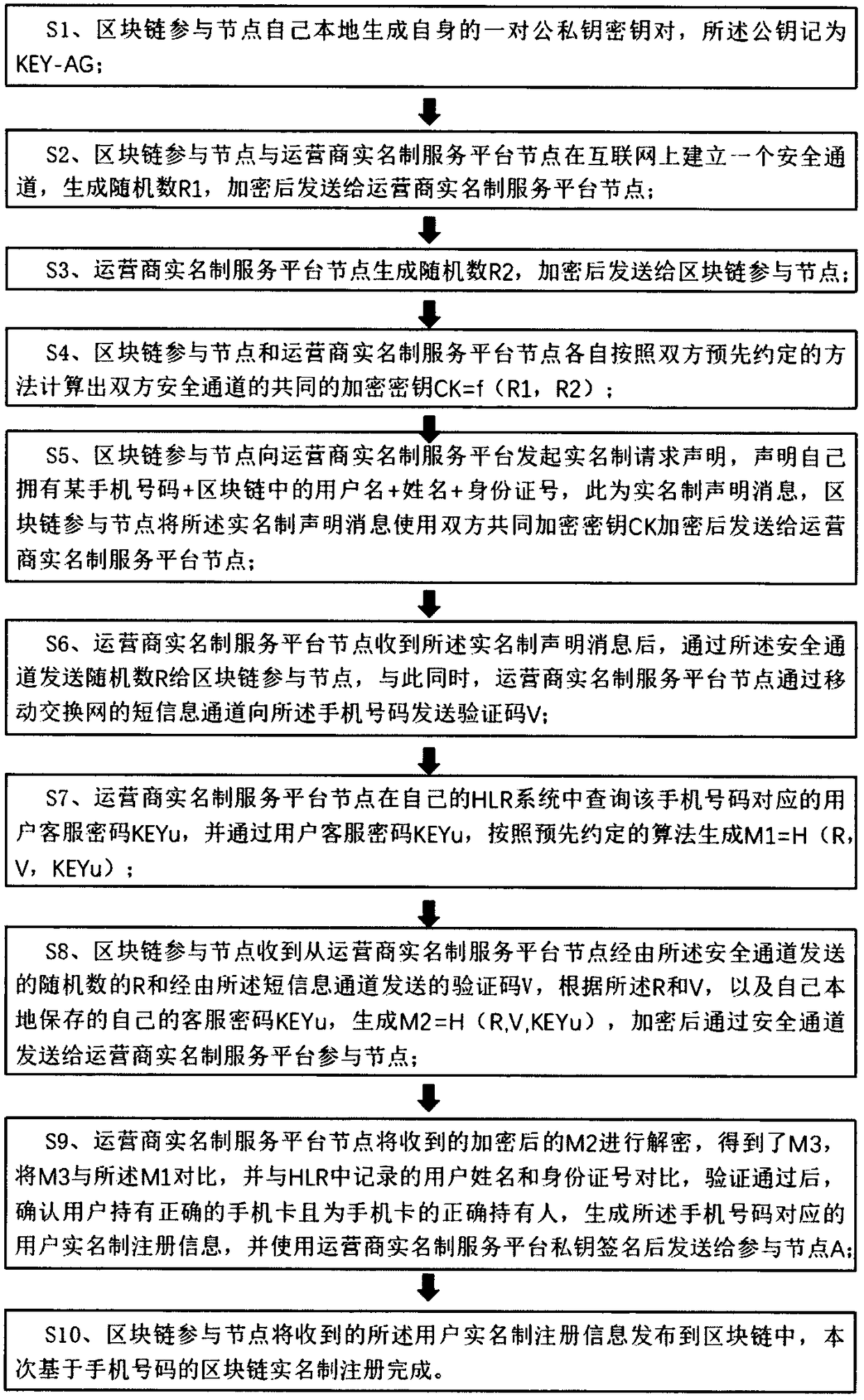
InactiveCN109150546ARealize real-name registrationImprove creditKey distribution for secure communicationUser identity/authority verificationThe InternetMobile phone
The invention relates to the field of Internet real name systems, and concretely relates to a method for achieving real name registration of a block chain based on a mobile phone number. According tothe method, an operator is incorporated into the block chain as an initiator of the block chain or a service node of the real name registration; each of block chain participators provides the mobile phone number corresponding to a real life, and a real identity of each of the participators is confirmed by declaring their own mobile phone number in the block chain; an operator node in the block chain offline challenges the participators, and the participators and the operator node issue response messages corresponding to the challenge through the block chain, verification is performed by miningnodes, if the verification passes, real name declaration of the node passes, and the real name registration is completed. The method is simple, fast and reliable; a cumbersome process of on-site identity authentication is omitted; an operator real-name service verification platform is not required; centralized attacks are avoided; the credit of the block chain is improved, impersonation fraud behaviors in the block chain are effectively prevented; and popularization and application of the block chain are promoted.
Owner:全链通有限公司
Shopping sharing rebate promotion method and device and computer readable storage medium
InactiveCN108713214AIncrease transaction volumeIncrease profitMarketingGeneration timeComputer engineering
The invention discloses a shopping sharing rebate promotion method and device and a computer readable storage medium, the method comprising the steps of: acquiring the order information of the same product in real time, and storing an order amount in a cash back fund pool based on a preset proportion; generating a cash back order queue and presetting a cash back proportion according to the generation time of the order information; adjusting the priority of the order in the cash back order queue according to the order amount generated by the customer sharing link of the order information; whenthe cash back fund pool reaches a cash back amount corresponding to the preset cash back proportion, returning the cash back amount to the customer account of the order information. By pushing and forwarding the share link information to the customer, according to the generated new order situation, the priority of the corresponding order in the cash back order queue is adjusted, and the cash backproportion of the corresponding order can be adjusted to encourage the customer to share the link.
Owner:SHENZHEN HAPPY SHARE INTERNET TECH CO LTD
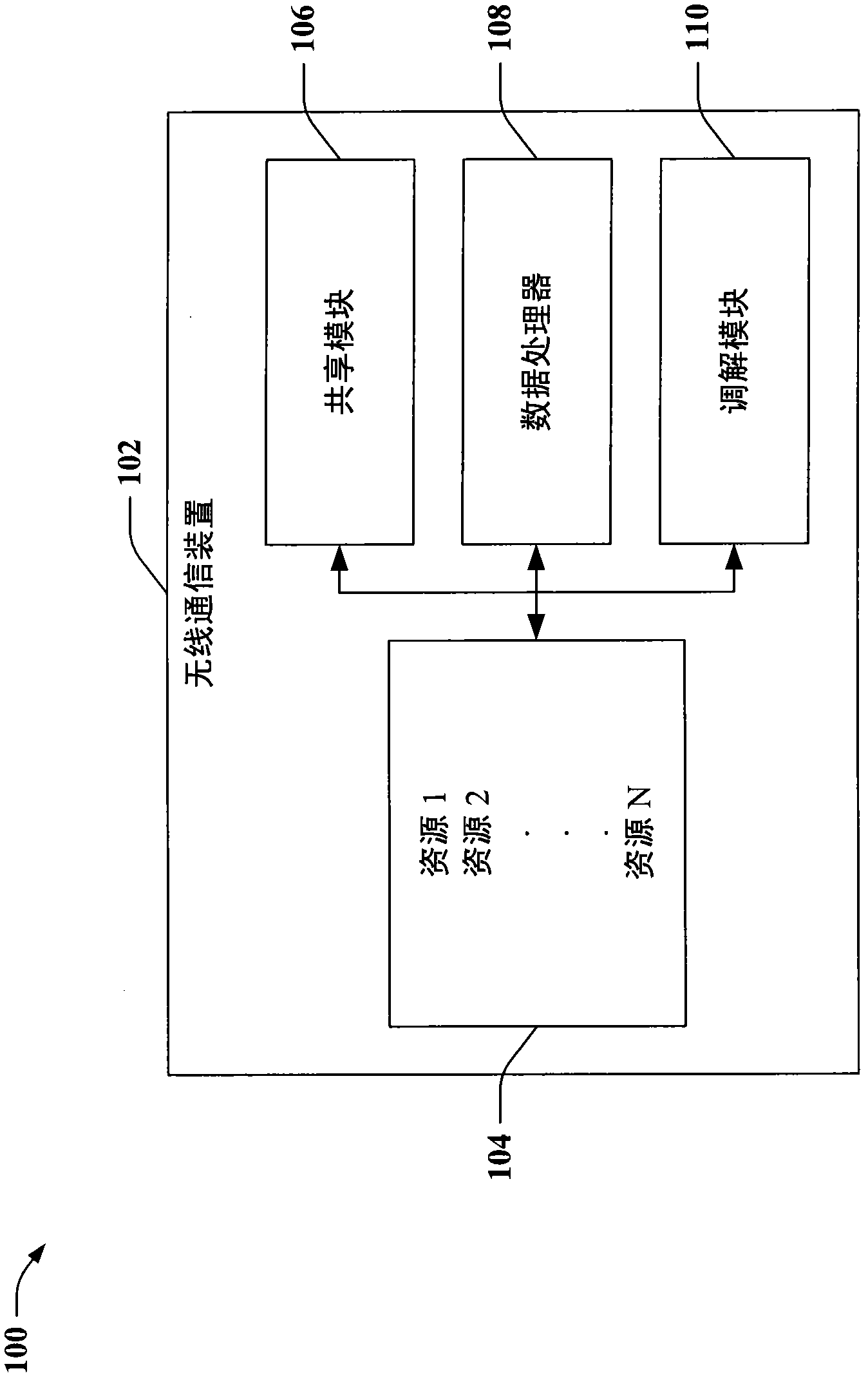
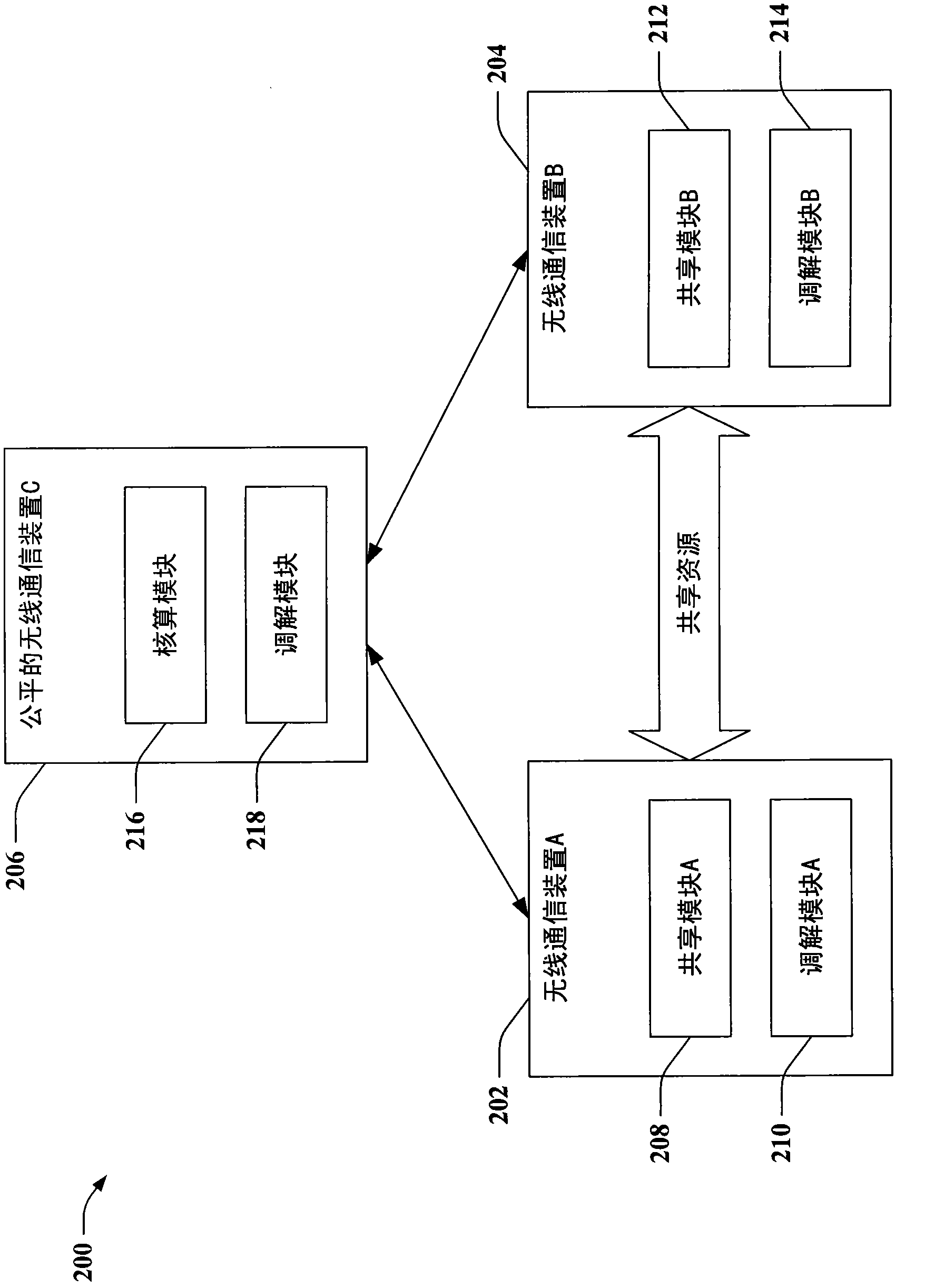
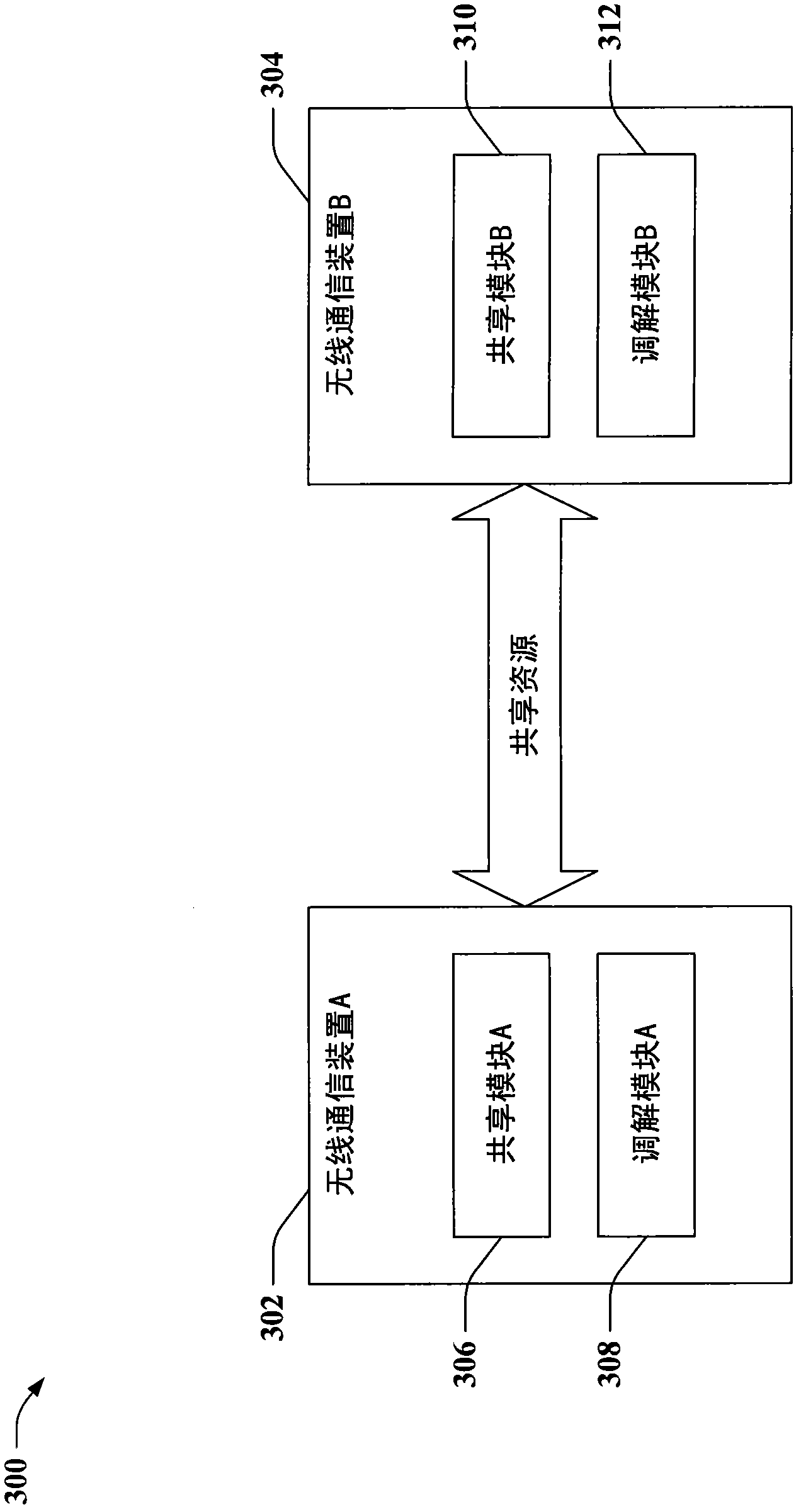
Fair resource sharing in wireless communications
InactiveCN102067696ACredit reductionImprove creditCriteria allocationNetwork topologiesResource consumptionShared resource
Providing for fair resource sharing among wireless nodes in a wireless communication environment is described herein. By way of example, fairness can comprise establishing a set of resource sharing credits for wireless nodes. By expending credits, a node can borrow a resource of another node, to enable or enhance operation of the borrowing node. Credits for the borrowing node are decreased based on consumption of a shared resource, or credits for the lending node are increased based on such consumption, or both. Once an amount of credits expires, a node can be restricted from borrowing further resources until enough resources are lent to build up a suitable amount of credits. Accordingly, fairness can comprise correlating shared resource consumption with shared resource provisioning, to encourage participation in cooperative wireless communications.
Owner:QUALCOMM INC
Method for automatically sorting demand response users
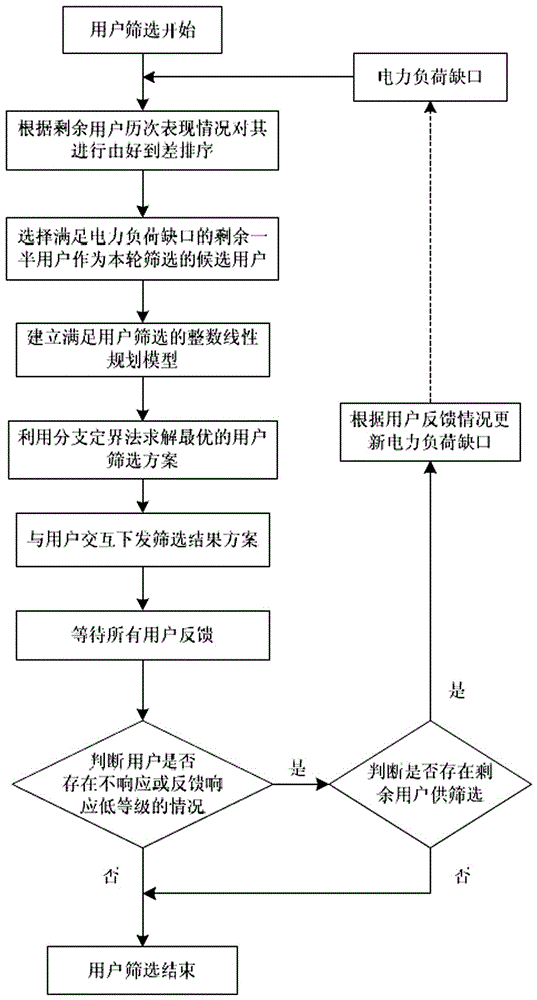
InactiveCN105096040AImprove performanceImprove creditResourcesPower userInteger linear programming model
The invention discloses a method for automatically sorting demand response users. Some users are selected from remaining response users as candidate sorting users of the round, and an integer linear planning model is established according to power load gap and load reduction capability of the candidate users. The solution is obtained through the branch and bound method to interact with users. Whether a next round of sorting is necessarily is determined according to feedback, and process is repeated until the power load gap defined by an upper-level system is met. The method adheres to the sorting principles of fairness, higher priority with higher creditability and maximally approaching the power load gap, and flexible interaction with power users and multiple rounds of dynamic sorting ensure matching level with the power load gap. Users are fairly selected to participate in demand response, the power user participation is improved, and the risk that real response capacity can not satisfy the expected power load gap capacity is reduced.
Owner:STATE GRID CORP OF CHINA +3
Financial business transaction system and method
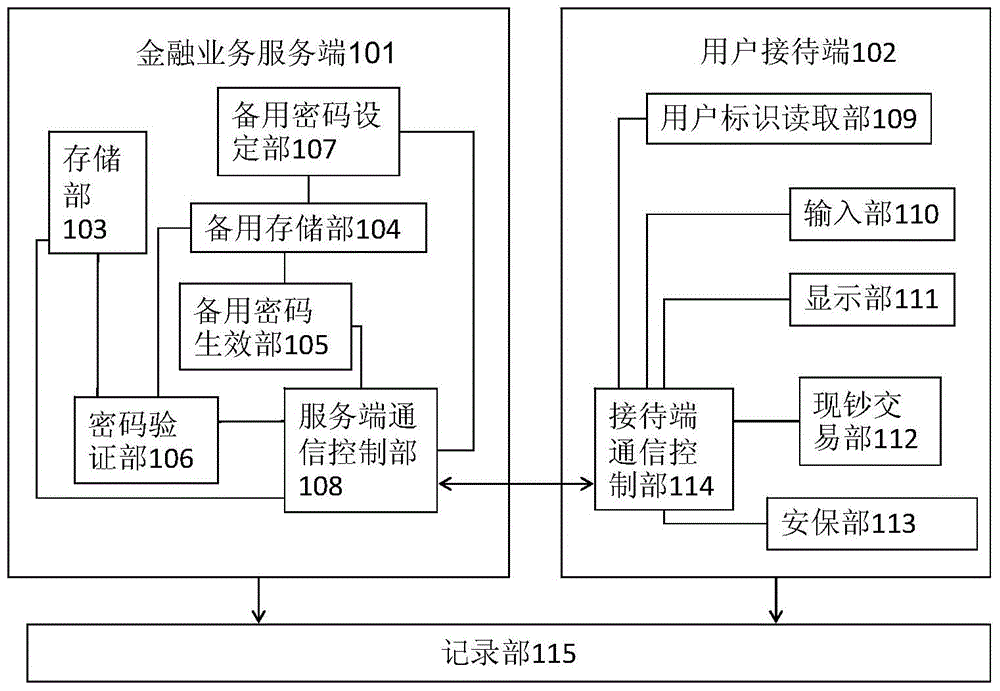
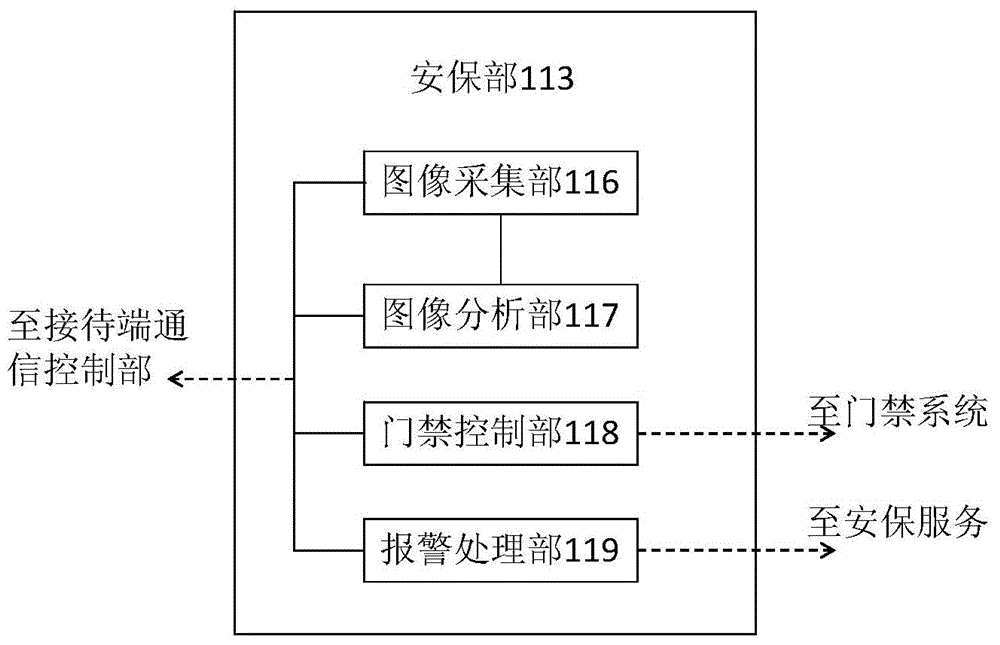
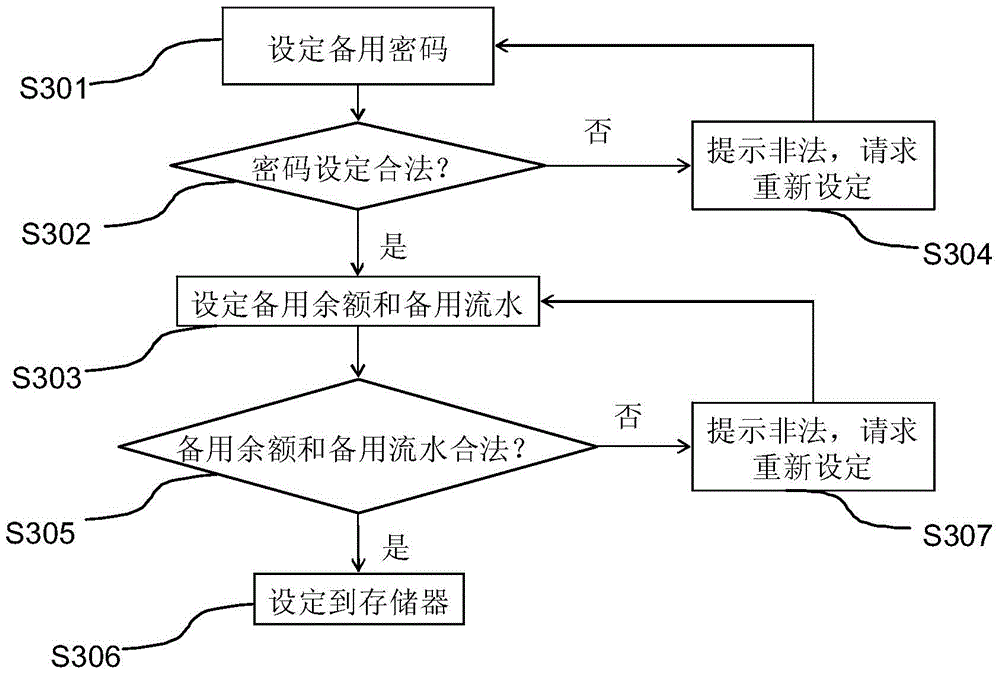
InactiveCN104680669AImprove creditReduce property damageComplete banking machinesIndividual entry/exit registersUser inputPassword
The invention provides a financial business transaction system. The financial business transaction system receives user identification and password input so as to verify a user, and provides financial business to the user. The financial business transaction system comprises a user identification reading portion, an input portion, a storage portion which stores an account password, balance information, a preset backup password and backup balance information corresponding to the preset backup password for the user, a display portion and a control portion, wherein the controller compares a password input by the user with the account password and the backup password after the user inputs the password, and allows the user to log in the financial business transaction system under the circumstance that the input password is consistent with the account password or the backup password, and when the user performs operation through the input potion and processing of the operation needs to use a balance of a user account under the circumstance that the input password is judged to be the account password, the balance information is used as the balance of the user account for the processing of the operation, and under the circumstance that the input password is judged to be the backup password, the backup balance information is used as the balance of the user account for the processing of the operation.
Owner:HITACHI LTD
Data processing method and device based on block chain and computer readable memory medium
InactiveCN108959310ARealize value transferImprove creditTransmissionSpecial data processing applicationsTerra firmaData provider
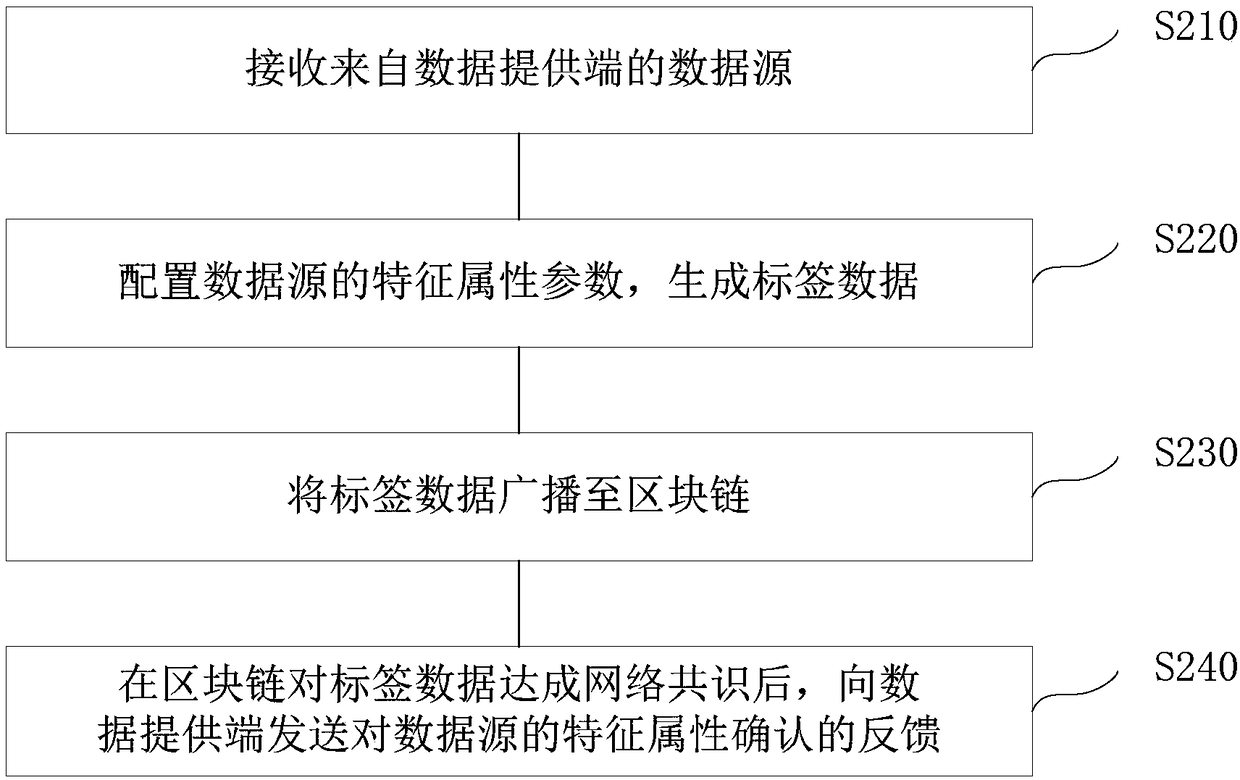
The invention discloses a data processing method and device based on a block chain and a computer readable memory medium. According to the data processing method based on the block chain, the block chain is connected with a client through utilization of a platform. The client comprises a data provider. The method is applied to the platform. The method comprises the following steps of receiving a data source from the data provider; configuring feature attribute parameters of the data source and generating label data; broadcasting the label data to the block chain; and sending feedback of feature attribute acknowledgement for the data source to the data provider after network consensus is carried out on the label data at the block chain. According to the embodiment of the invention, on the basis of features that the data in the block chain is true and reliable and is tamper-resistant, through configuration of the feature attribute parameters, the network consensus is carried out on the label data through utilization of the block chain, so feature attributes such as authenticity and value of the data can be accurately and conveniently identified, credibility of network data is improved, and firm foundation is laid for the realization of an internet industry.
Owner:易链科技(深圳)有限公司
A method for registering a block chain real name system based on a mobile phone number
ActiveCN109005033AImprove creditPrevent impersonation fraudKey distribution for secure communicationSecurity arrangementBlockchainThe Internet
The invention relates to the field of Internet real name system, in particular to a method for realizing block chain real name system registration based on mobile phone number. The invention realizesthe real name system registration of a user by introducing a mobile phone number into a block chain through cooperation with an operator, comprising the following steps: a block chain participating node initiates a real name system request statement; the real-name service platform node of the operator verifies that the user holds the correct mobile phone card and is the correct holder of the mobile phone card; real-name registration information is generated and published to complete registration. The method of the invention converts the real name system confirmation of the ID card of the userinto the real name system confirmation of the mobile phone number of the user. As long as the mobile phone number is guaranteed to be held by the correct person, the real name system registration ofthe block chain can be realized. The method of the invention is simple, quick, reliable and cleverly utilizess the mobile phone number of the real name system, realizes the registration of the real name system of the block chain, saves the tedious process of the on-site identity authentication, improves the credit degree of the block chain, can effectively prevent the impostor fraud on the block chain, and promotes the popularization and application of the block chain.
Owner:全链通有限公司
Commodity anti-counterfeiting method
InactiveCN106529975AImprove accuracyHigh speedCommerceSensing by electromagnetic radiationDimensional modelingComputer terminal
The invention discloses a commodity anti-counterfeiting method. The method comprises the following steps: 1) before commodities are delivered out of a warehouse, an anti-counterfeiting system background compiles two-dimensional codes according to a certain rule; 2) each two-dimensional code in the database of the anti-counterfeiting system background is associated with the information of a corresponding commodity; 3) each two-dimensional code in the database of the anti-counterfeiting system background is associated with a query counter and the counting of the query counter corresponding to the two-dimensional code is accumulated by one each time after a terminal user scans the above two-dimensional code; 4) during the anti-counterfeiting query of the terminal user, the two-dimensional code on the commodity is scanned and the information of the commodity corresponding to the scanned two-dimensional code is sent from the anti-counterfeiting system background to the terminal user. If the counting accumulated number of the query counter corresponding to the scanned two-dimensional code is larger than a preset alarm threshold value of the anti-counterfeiting system background, the anti-counterfeiting system background prompts the terminal user to beware of imitations. The commodity anti-counterfeiting system is high in accuracy rate, fast in speed and high in credit degree. Meanwhile, a smart phone or a scanning terminal is adopted, so that the method is simple and easy to implement, and low in cost.
Owner:北京挖玖电子商务有限公司
Virtual service transition method
InactiveCN103825963AAvoid the problem of dynamic adjustmentAdd custom input parametersData switching networksUser needsComputer network
The invention relates to a virtual service transition method which comprises the following steps: selecting transition evaluation parameters according to service types and user requirements; monitoring virtual nodes in a network by a monitor; obtaining state information of the virtual nodes in regard to the evaluation parameters when a new request is reached or a user request is changed; calculating the service transition cost of each virtual node according to the state information; acquiring the virtual node with the lowest virtual service transition cost as a service node from the virtual nodes through the transition cost calculation method; selecting the service node to transit the virtual service. The virtual service transition method provided by the invention can be used for judging and executing the transition by effectively combining the influences of each factor on the transition, and realizing the management of network resources and improving the user service experience quality by utilizing the service transition.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Block chain autonomous method and system based on credit mechanism
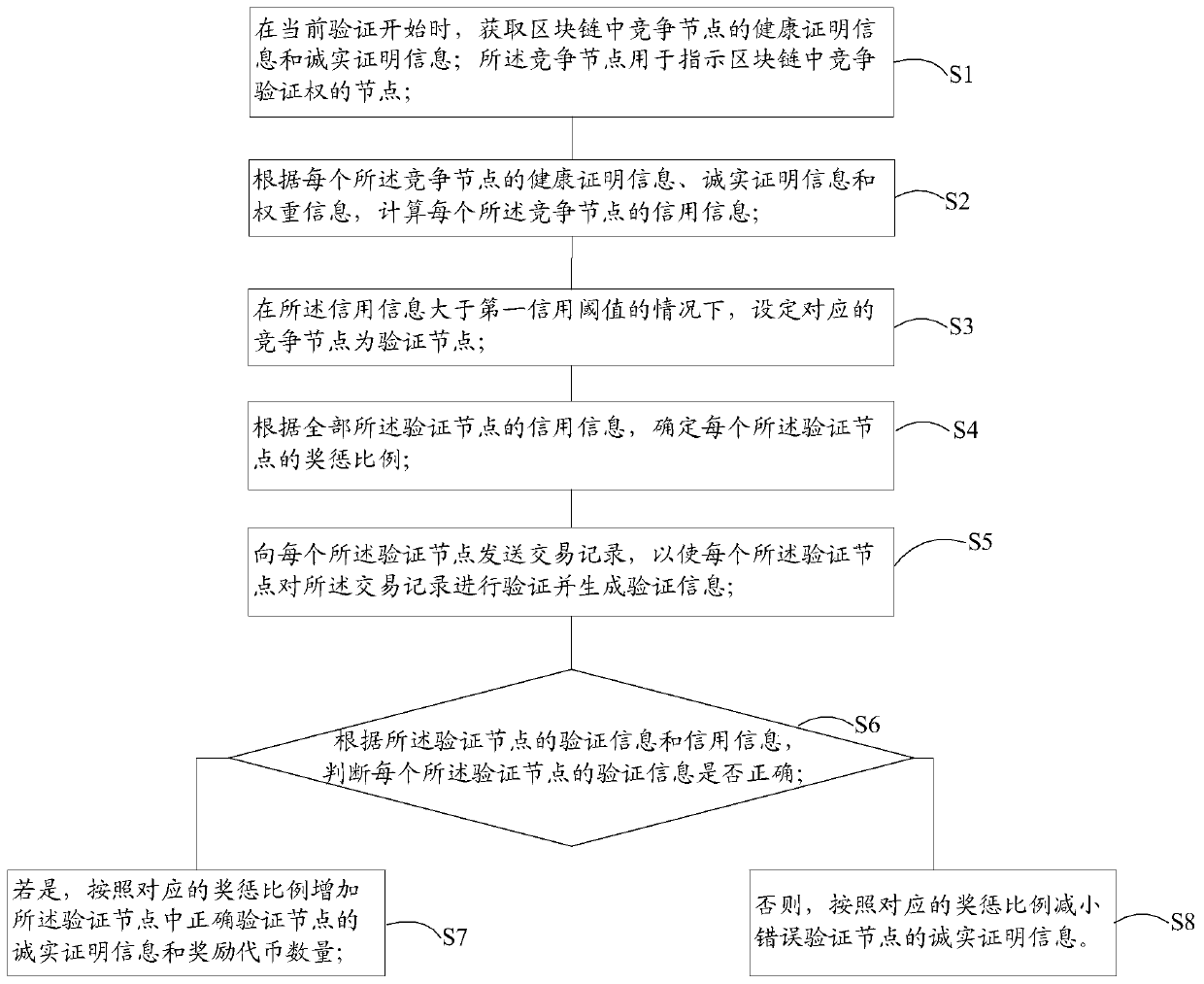
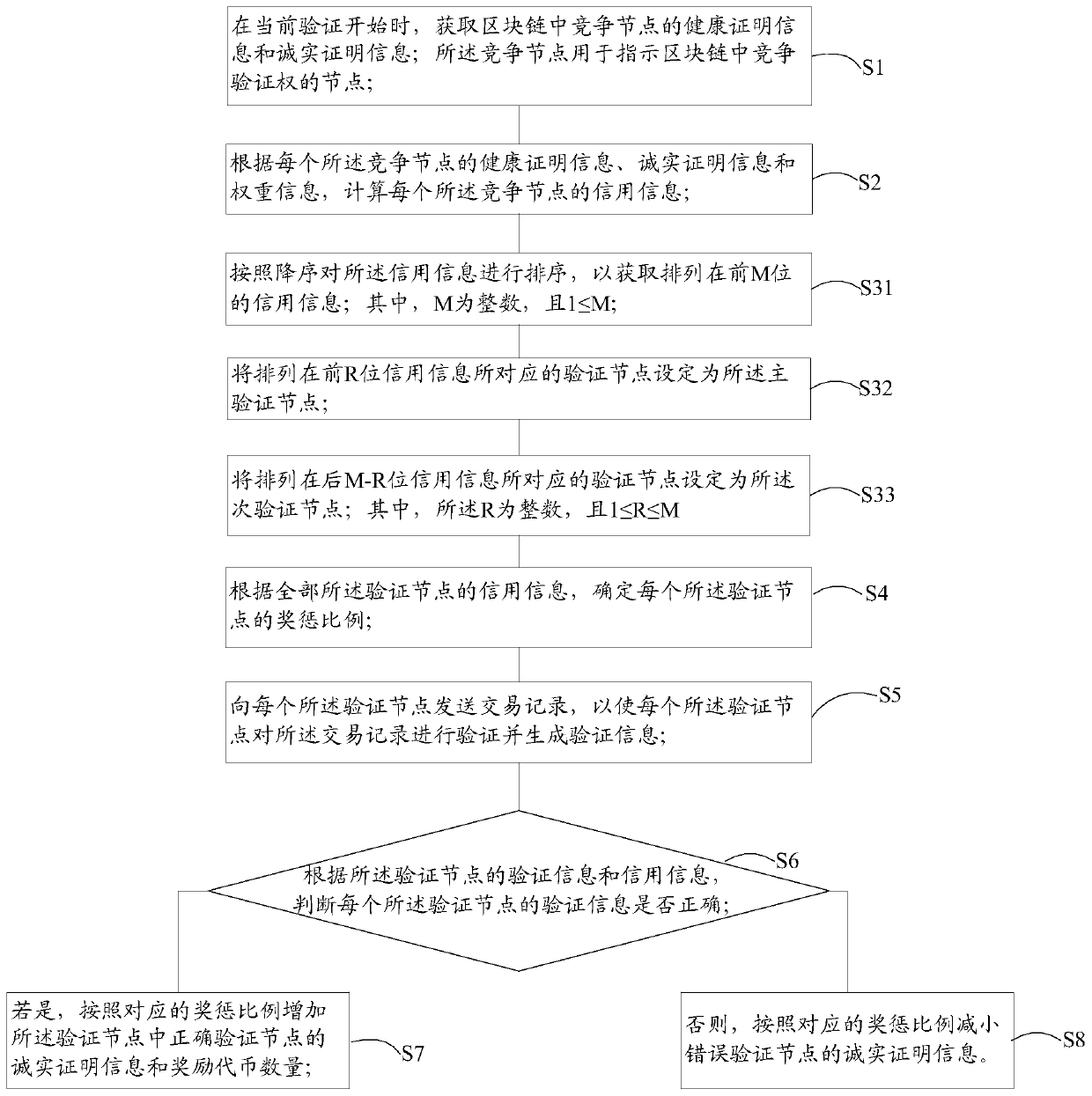
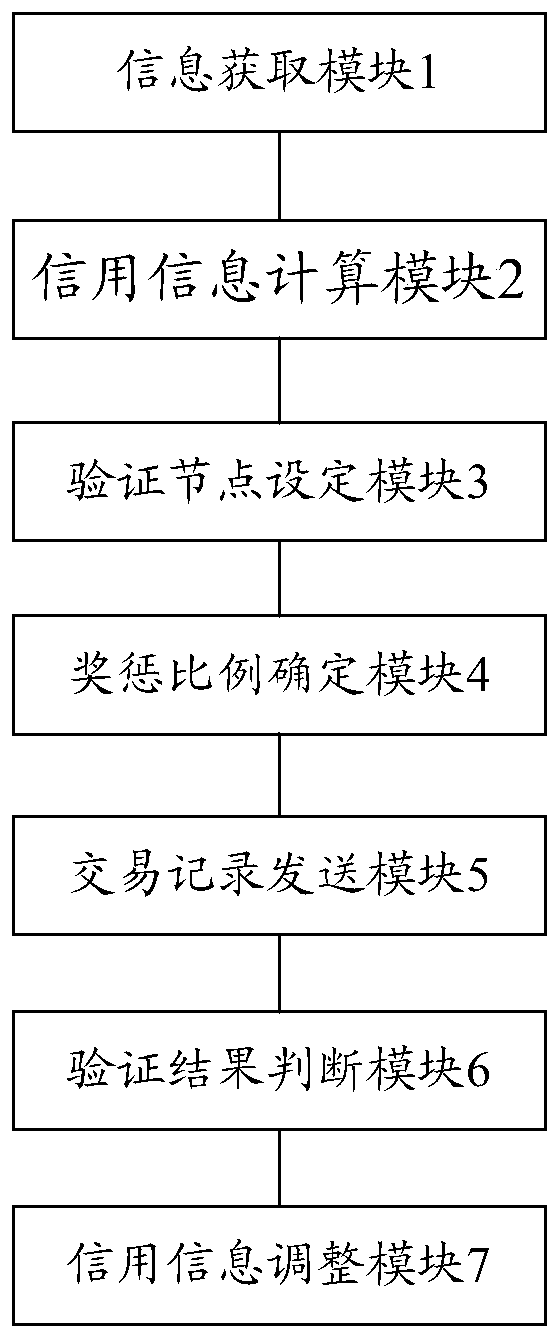
ActiveCN109993004ASave computing resourcesImprove consensus efficiencyFinanceDigital data protectionOperating systemBlockchain
The invention discloses a block chain autonomous method and system based on a credit mechanism, and the method comprises the steps: obtaining the health proof information and integrity proof information of a competition node in a block chain, and calculating the credit information of the competition node; when the credit information is greater than a first credit threshold, setting a correspondingcompetition node as a verification node; determining a reward and punishment proportion of each verification node according to the credit information of all the verification nodes; sending the transaction record to each verification node to verify the transaction record and generate verification information; judging whether the verification information of each verification node is correct or notaccording to the verification information and the credit information of the verification nodes; ifso, adding integrity proof information of the correct verification node and the number of reward tokens according to the corresponding reward and punishment proportion; otherwise, reducing integrity proof information of the error verification node according to the corresponding reward and punishment proportion so as to complete self-governance. According to the method and system, computing resources can be effectively saved, decentralization is achieved, and the phenomenon of node joint dissociation is avoided.
Owner:广州蚁比特区块链科技有限公司
User information processing method, device and equipment and readable storage medium
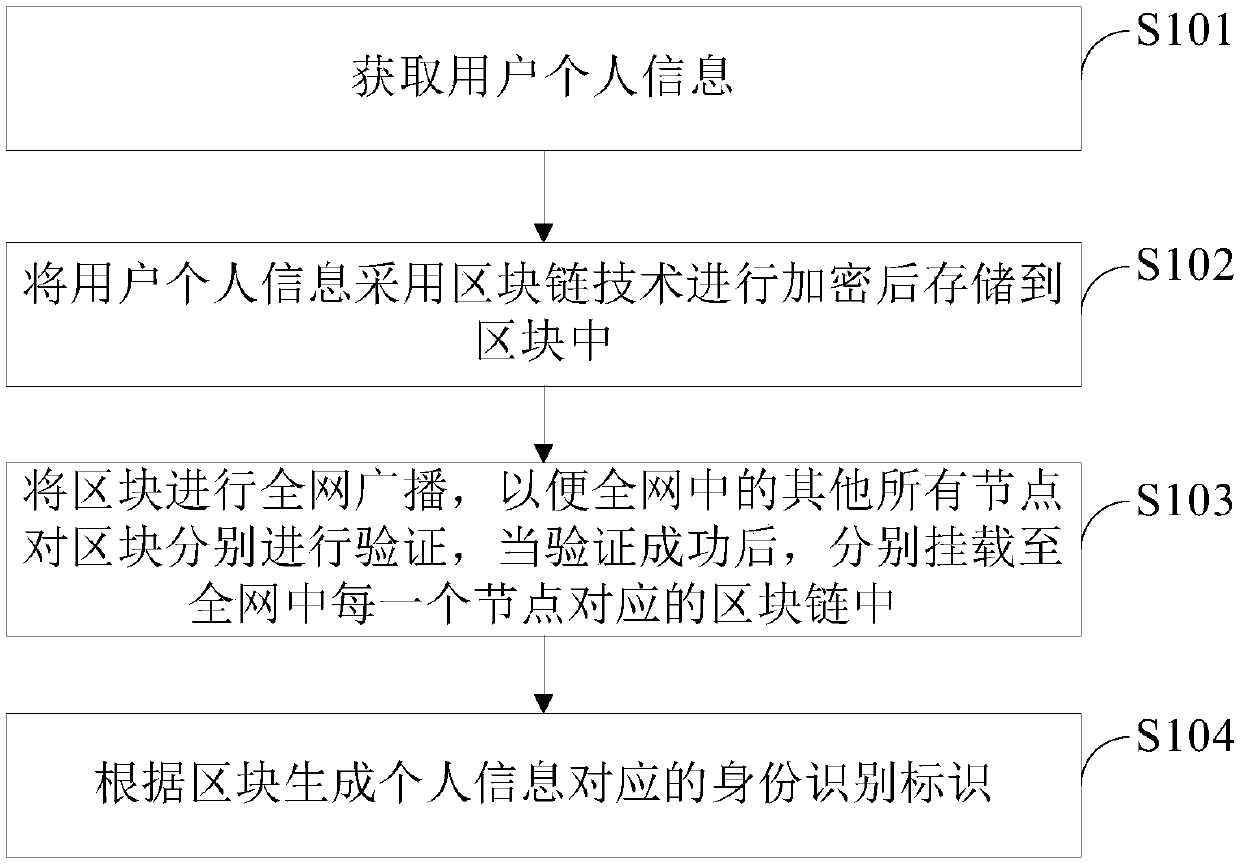
ActiveCN110932859AImprove securityImprove creditFinanceUser identity/authority verificationTamper resistanceIdentity recognition
The invention discloses a user information processing method and device, user information processing equipment and a readable storage medium. The method comprises: encrypting the acquired personal information of the user by adopting a block chain technology, storing the encrypted personal information into a block, mounting the block into a block chain corresponding to each node in the whole network, and generating an identity recognition identifier corresponding to the personal information according to the block. According to the scheme, the characteristics of decentration, unforgeability, verifiability, information tamper resistance, anonymity and the like of a block chain system are used, the personal information of the user is saved, the safety and the credit degree of information saving are improved, verification is carried out based on the unique identity recognition identifier generated by the block chain during user identity verification, the accuracy and the reliability of useridentity information verification are further improved, and the possibility of user identity information leakage is reduced.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com