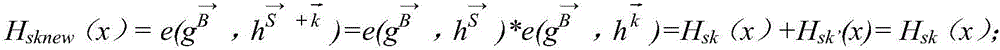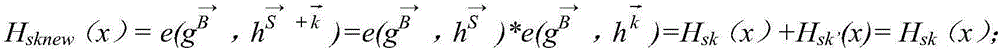Patents
Literature
649results about How to "Reduce the possibility of leaks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
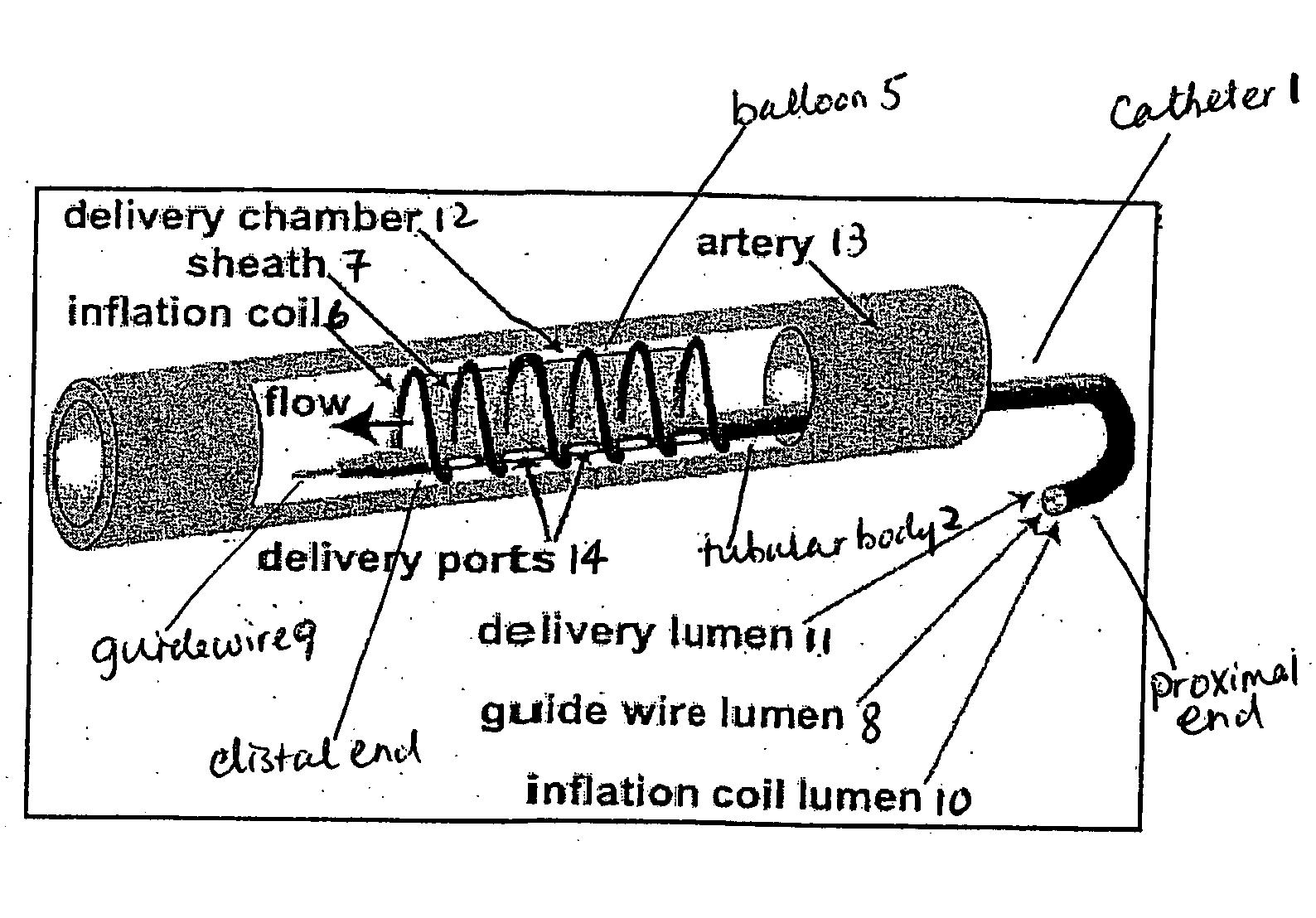
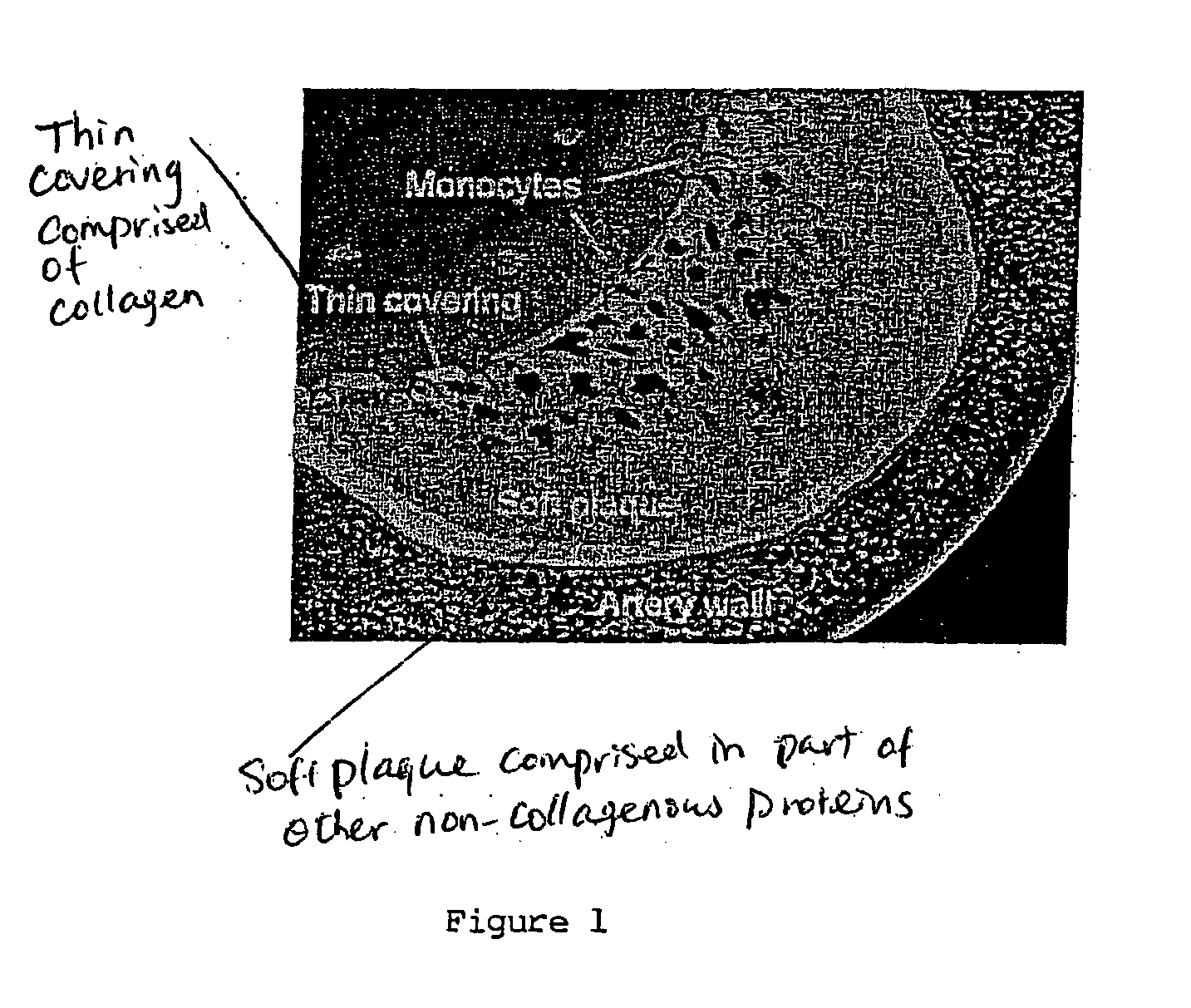
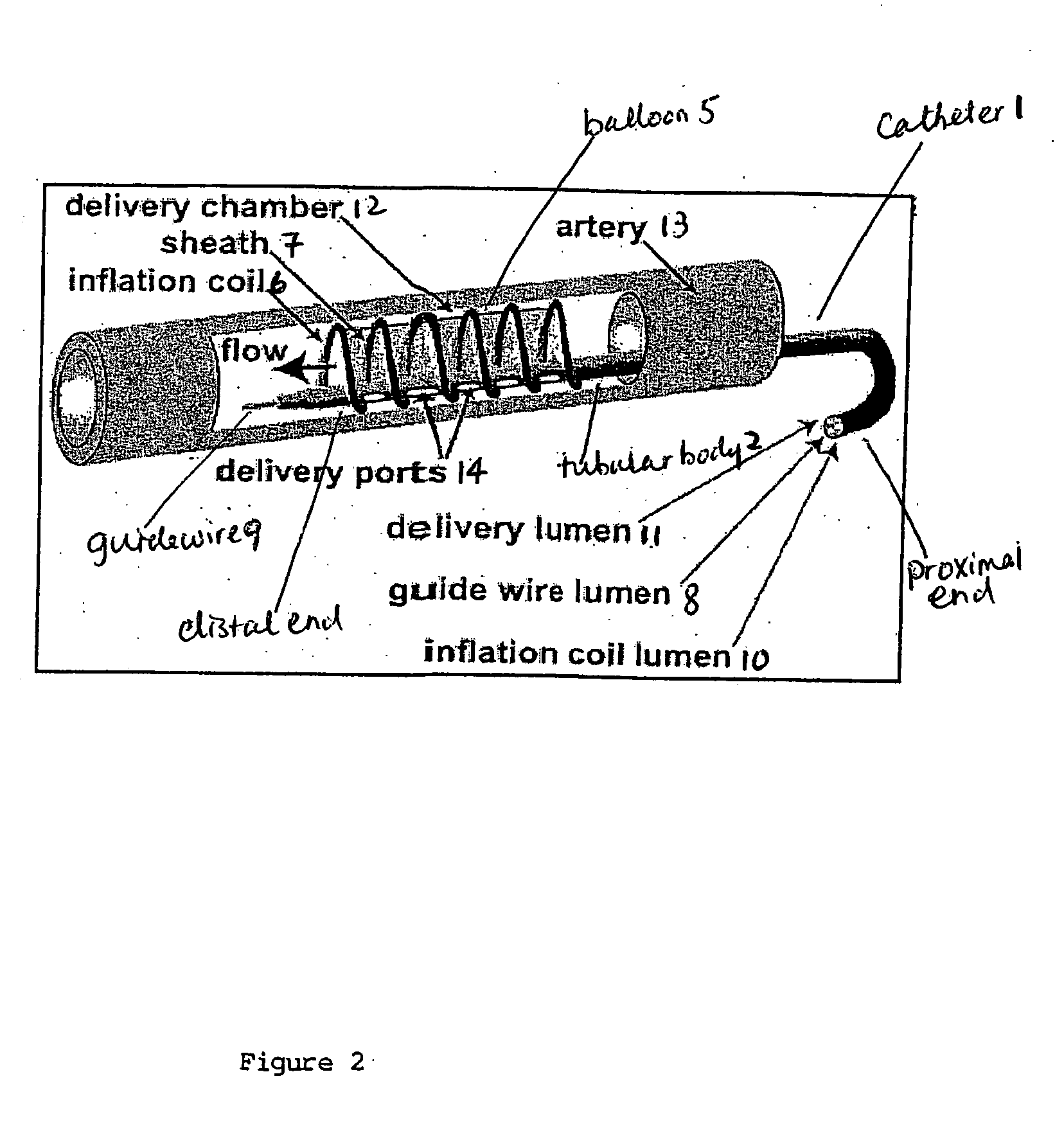
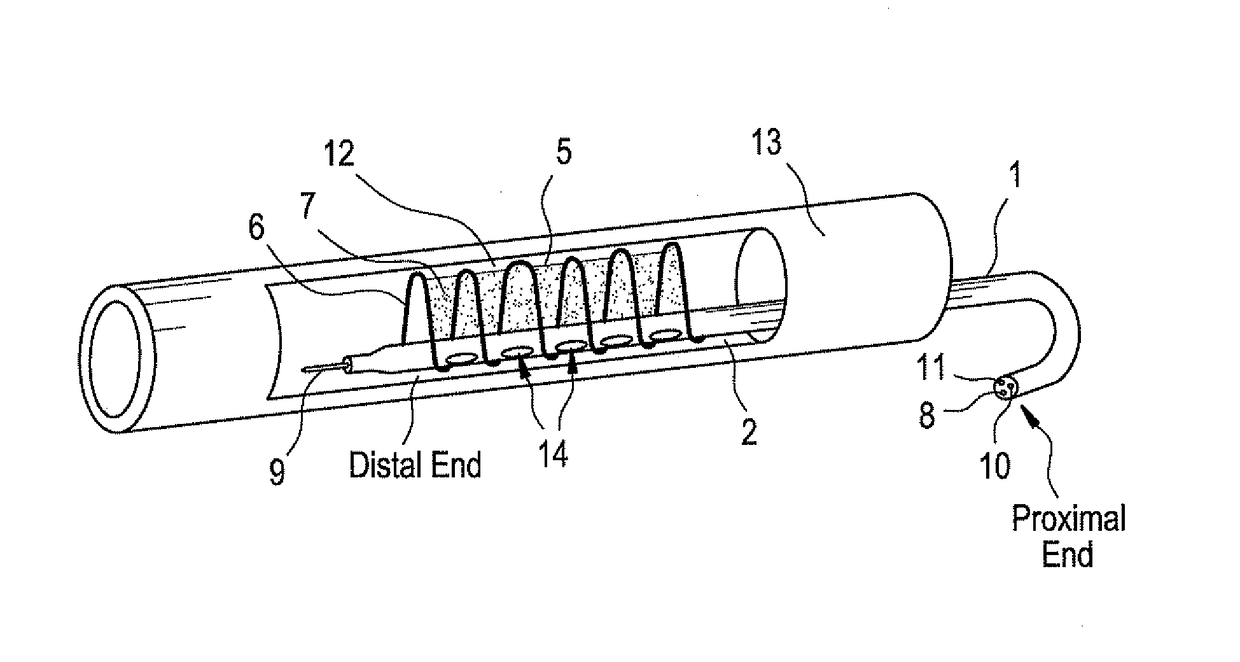
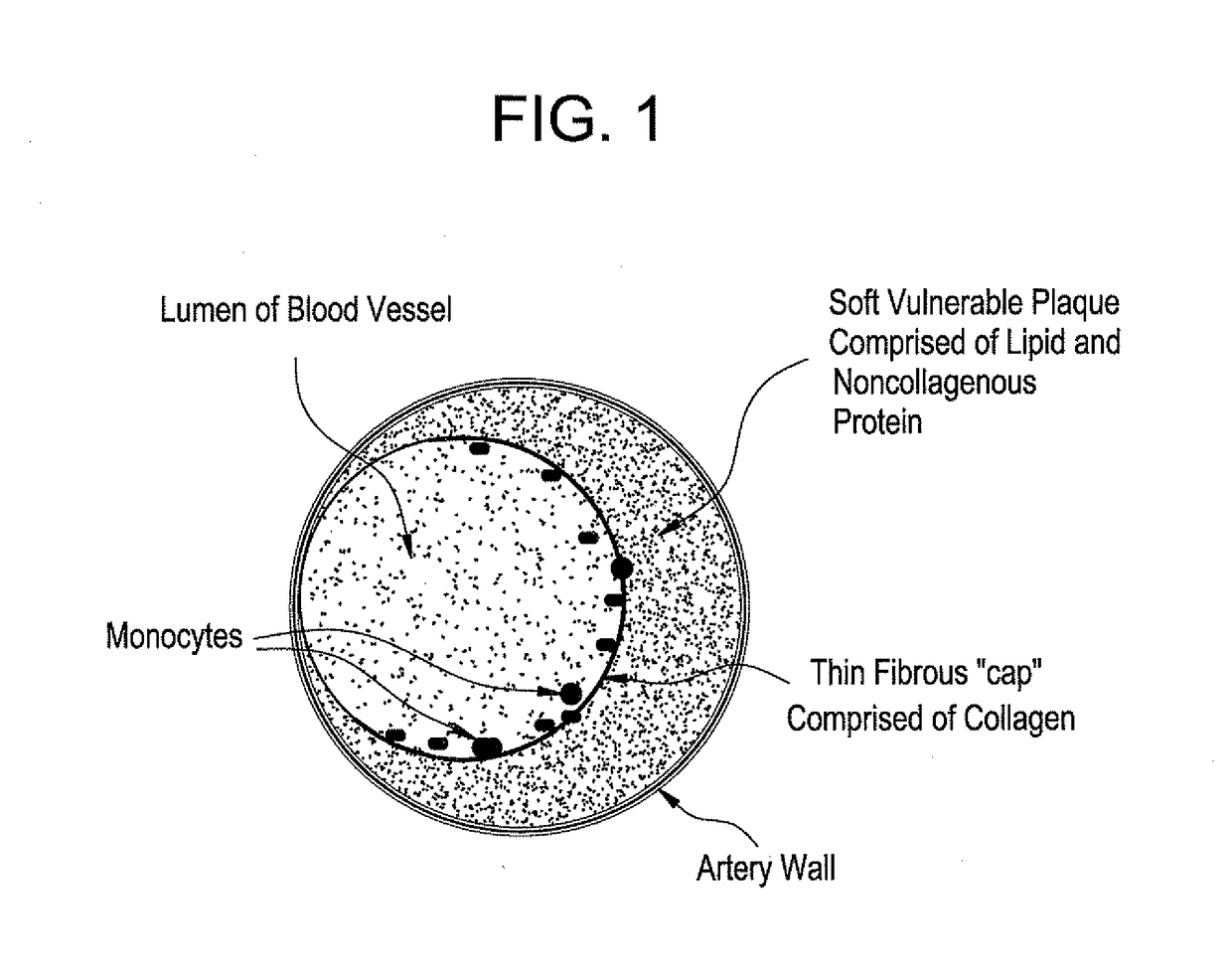
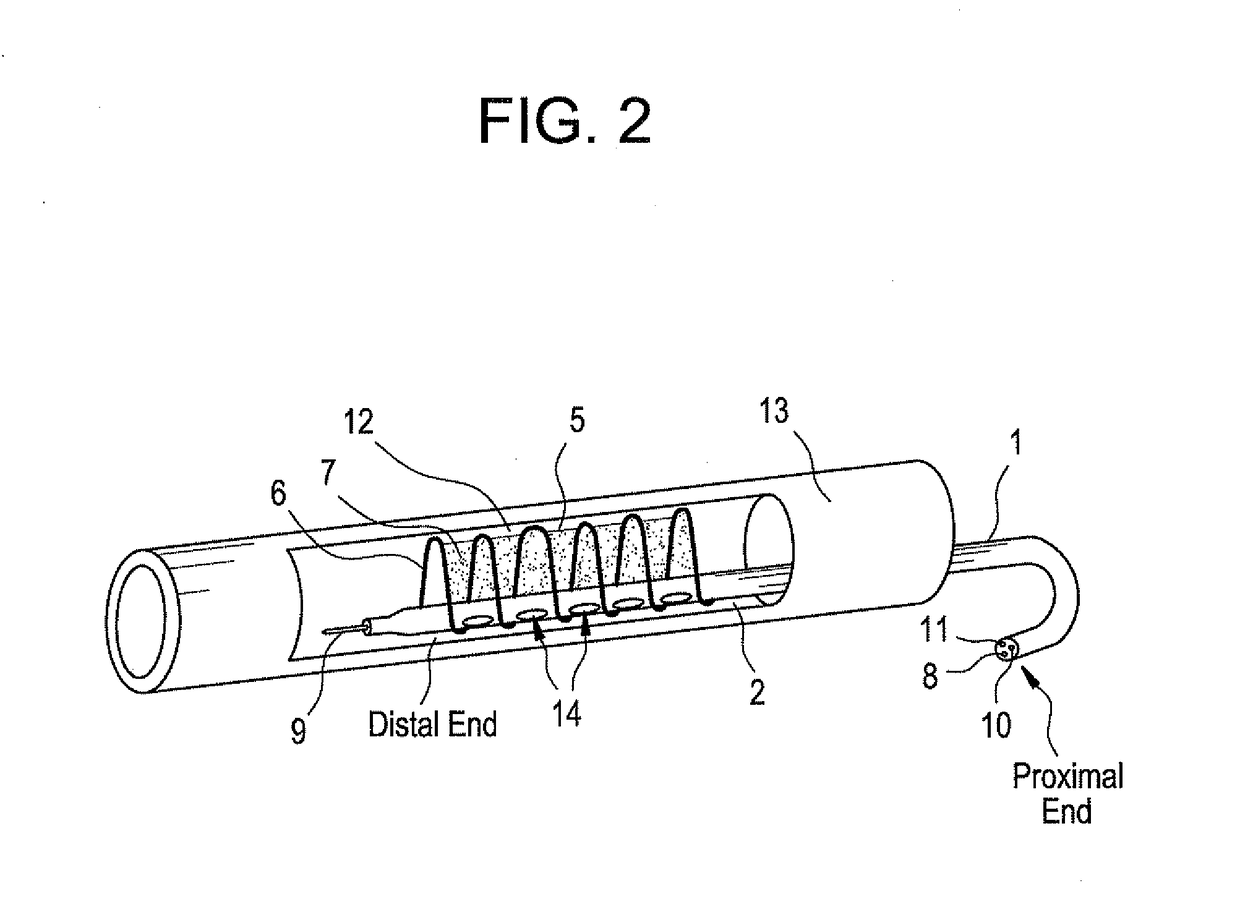
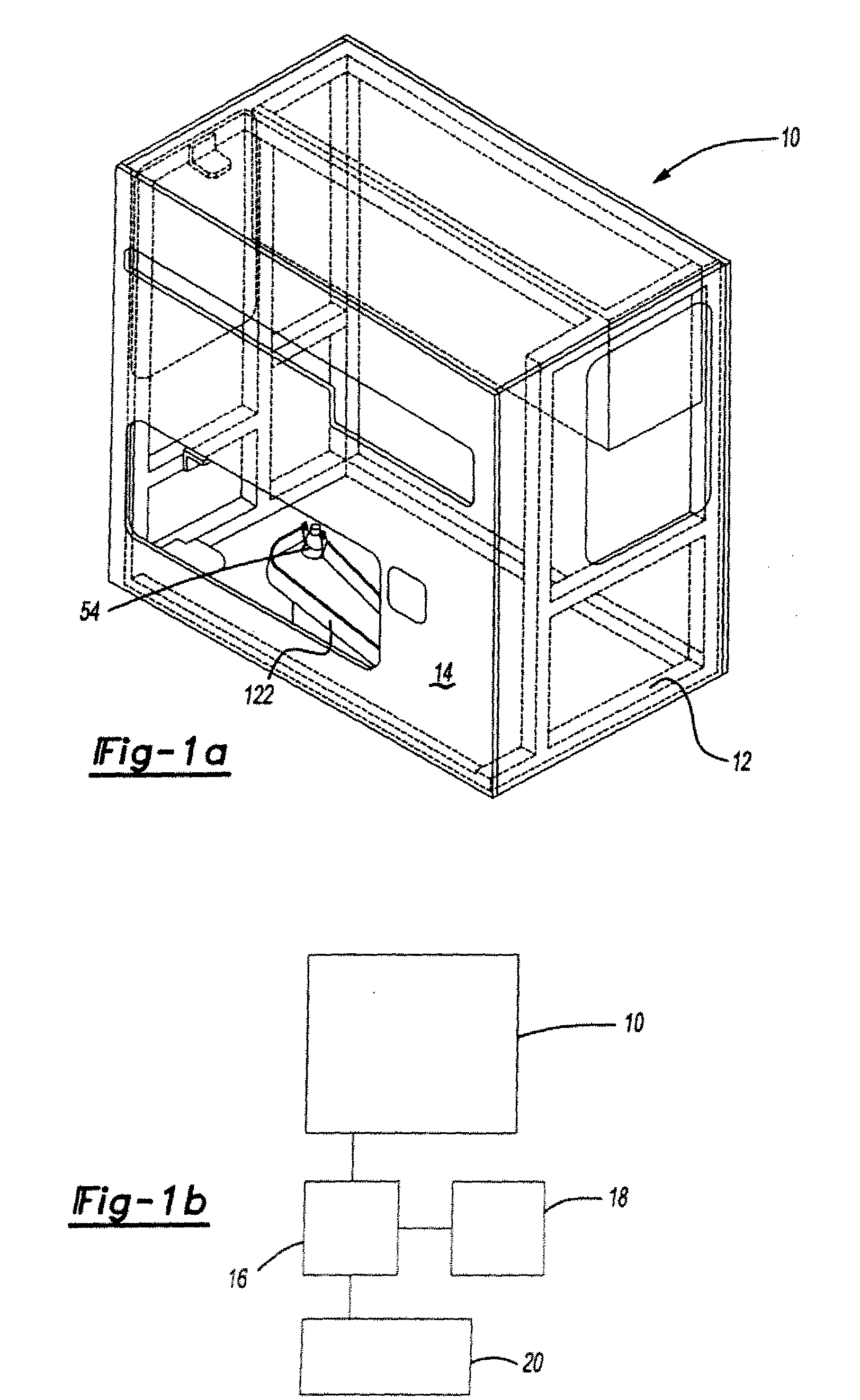
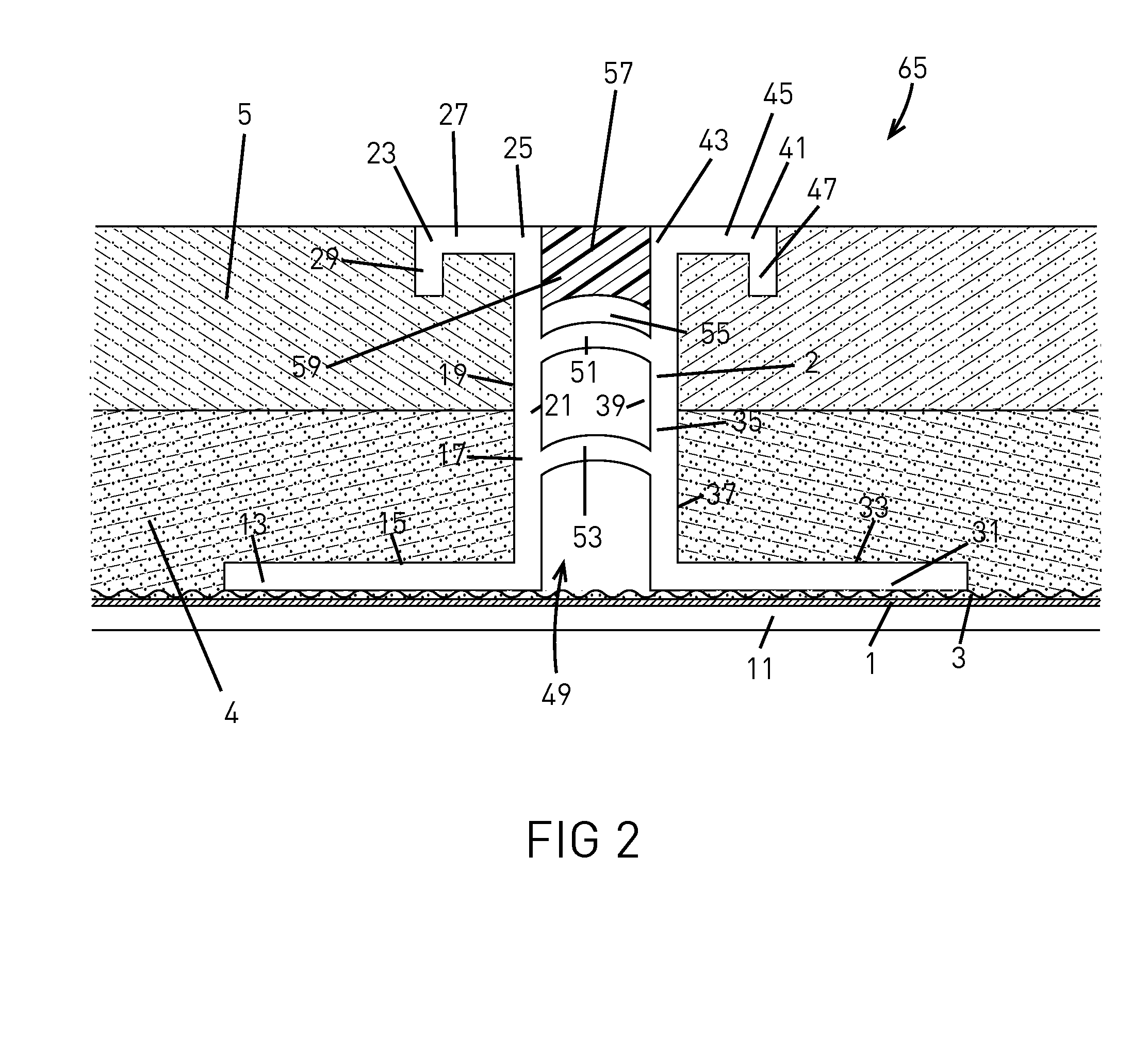
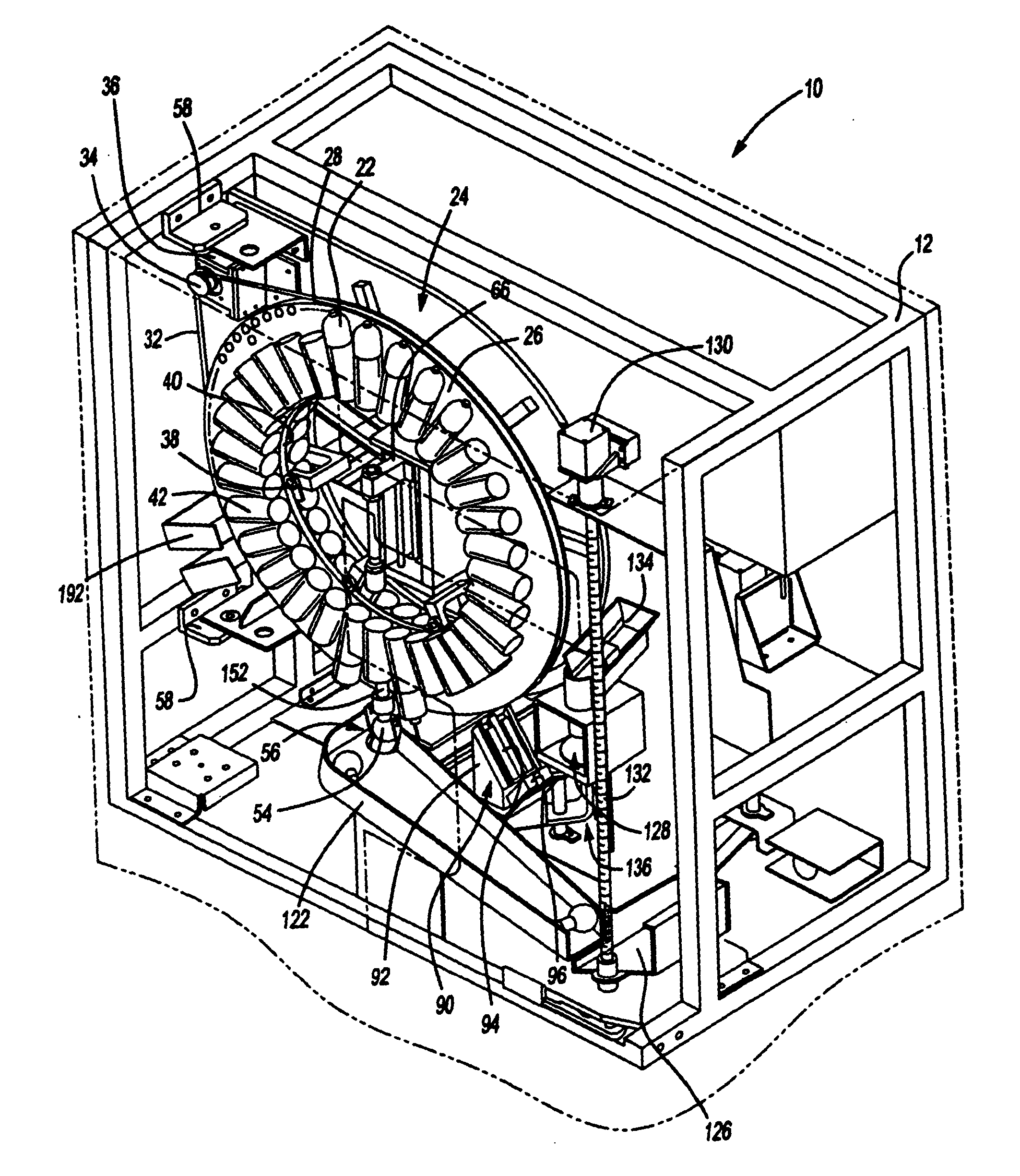
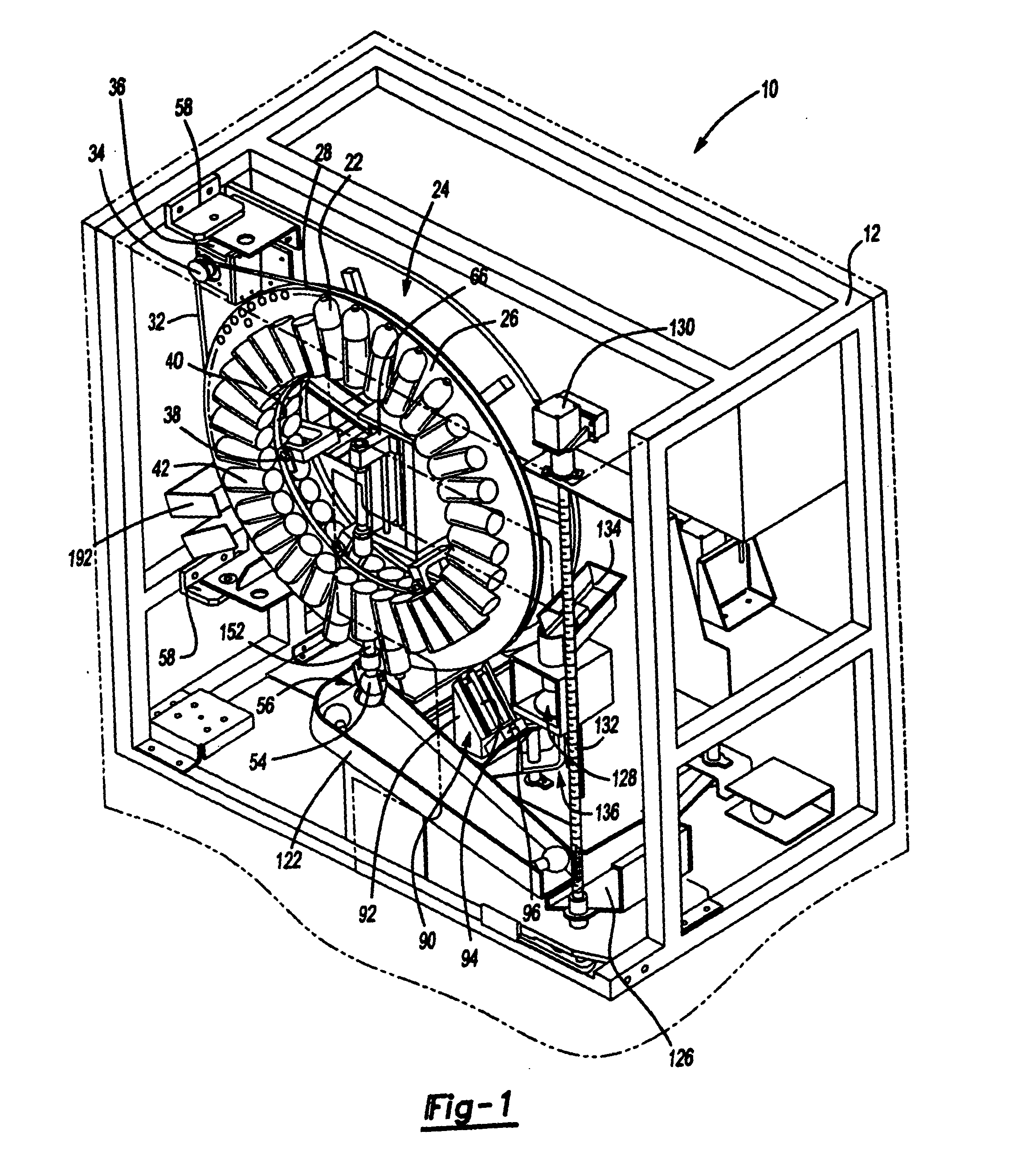
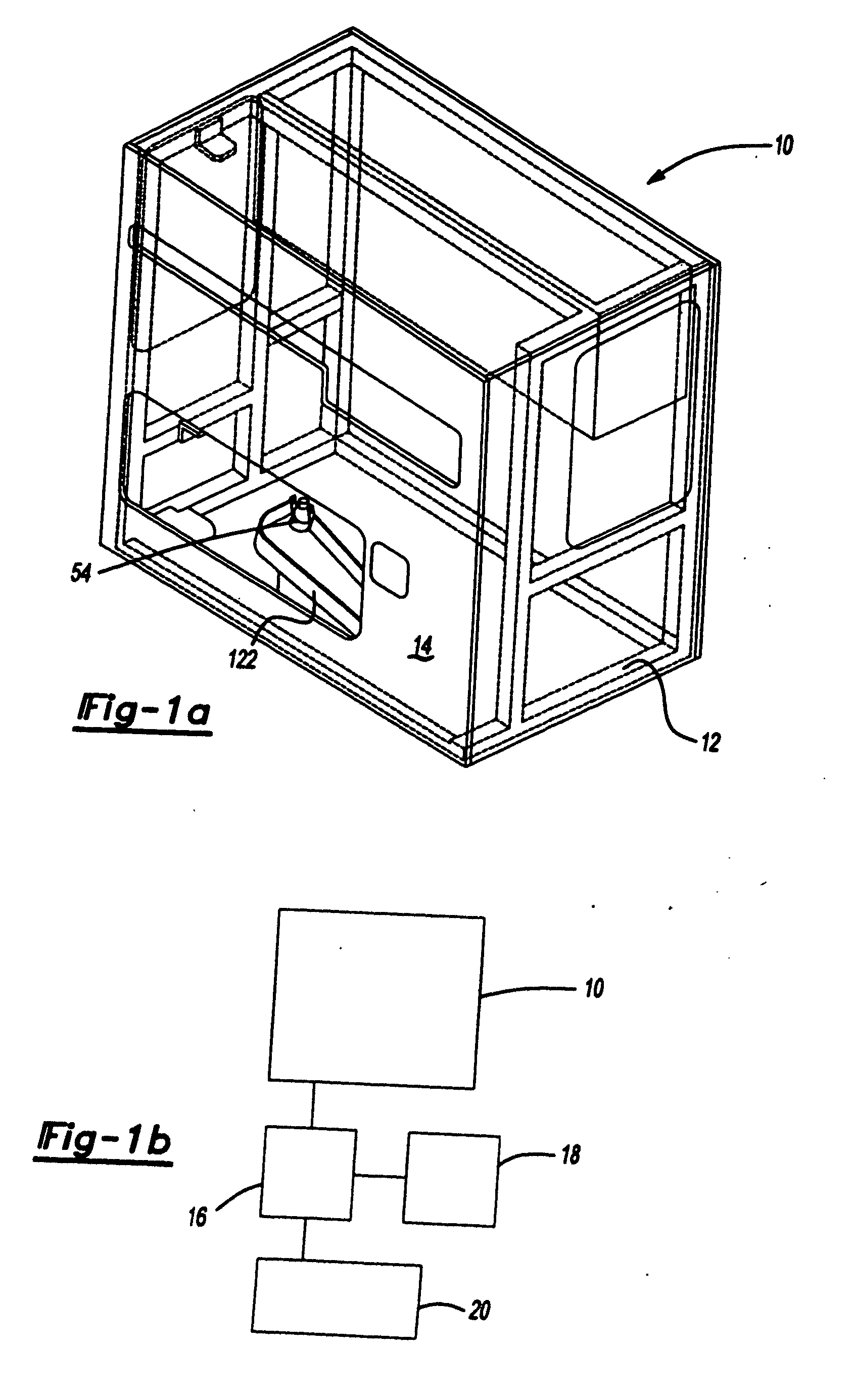
Methods and devices for treating vulnerable plaque
ActiveUS20070123839A1Reduce the possibility of leaksControlled diffusionStentsElectrotherapyCoronary arteriesVulnerable plaque
This invention provides methods, devices and kits for treating coronary artery disease, particularly “soft” or vulnerable plaque. The invention is based on the local delivery of crosslinking means to crosslink the collagen covering the plaque and other proteins that may be present at the site to stabilize the plaque and prevent leakage of thrombogenic material into the lumen of the coronary artery. In certain embodiments, catheters are employed to achieve local delivery of a crosslinking agent or ultraviolet light.
Owner:CARDINAL HEALTH SWITZERLAND 515 GMBH
Apparatus and method for custom cosmetic dispensing
InactiveUS6883561B2Reduce the possibility of leaksDispensing tip blockage is substantially avoidedCosmetic preparationsMake-upAdditive ingredientBiomedical engineering
Improved custom cosmetic formulation dispensing system including ingredients reservoirs for syringe dispensing. The ingredients reservoirs are carried by a translatable carrier to bring the respective reservoirs into dispensing alignment with a package, into which a preselected amount of the ingredient is dispensed.
Owner:COSMETIC TECH L L C
Apparatus and method for custom cosmetic dispensing
InactiveUS20120152406A1Reduce the possibility of leaksDispensing tip blockage is substantially avoidedLiquid fillingLiquid transferring devicesEngineeringBiomedical engineering
Improved custom cosmetic formulation dispensing system including ingredients reservoirs for syringe dispensing. The ingredients reservoirs are carried by a translatable carrier to bring the respective reservoirs into dispensing alignment with a package, into which a preselected amount of the ingredient is dispensed.
Owner:COSMETIC TECH L L C
Methods and devices for treating vulnerable plaque
ActiveUS9687262B2Reduce the possibility of leaksControlled diffusionStentsBalloon catheterVulnerable plaqueCoronary artery disease
This invention provides methods, devices and kits for treating coronary artery disease, particularly “soft” or vulnerable plaque. The invention is based on the local delivery of crosslinking means to crosslink the collagen covering the plaque and other proteins that may be present at the site to stabilize the plaque and prevent leakage of thrombogenic material into the lumen of the coronary artery. In certain embodiments, catheters are employed to achieve local delivery of a crosslinking agent or ultraviolet light.
Owner:CARDINAL HEALTH SWITZERLAND 515 GMBH
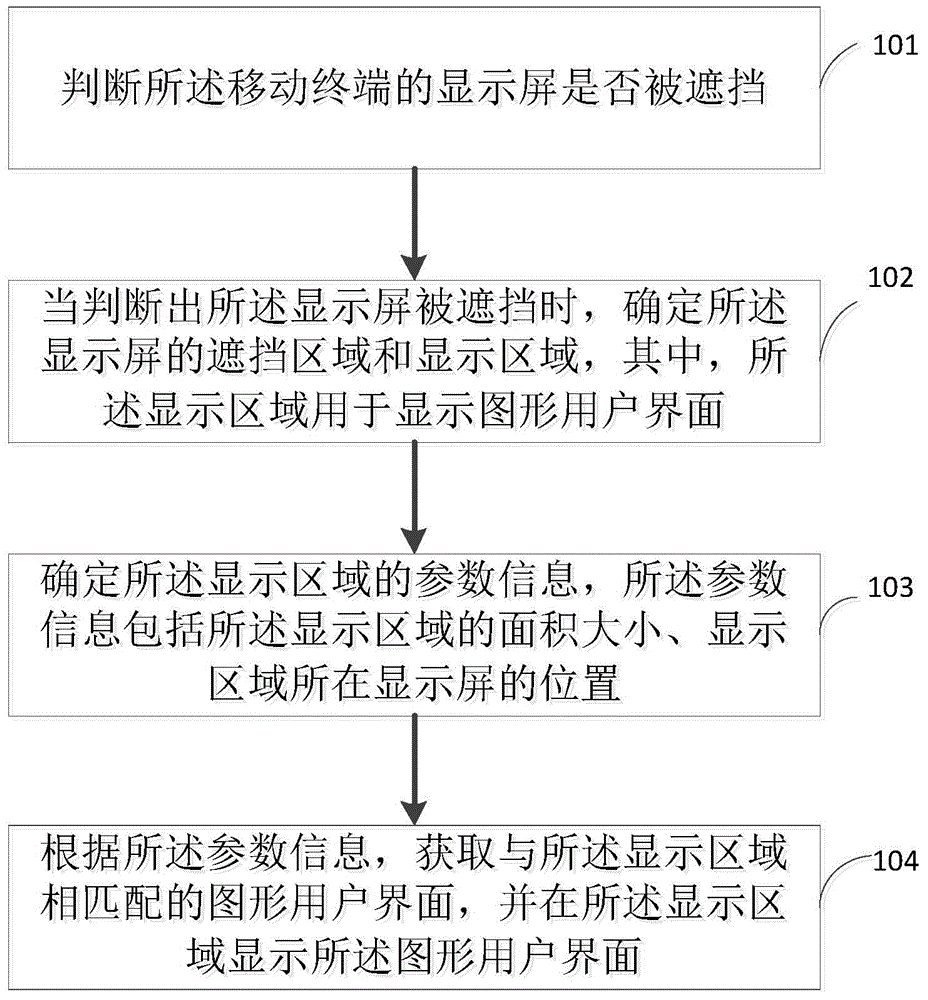
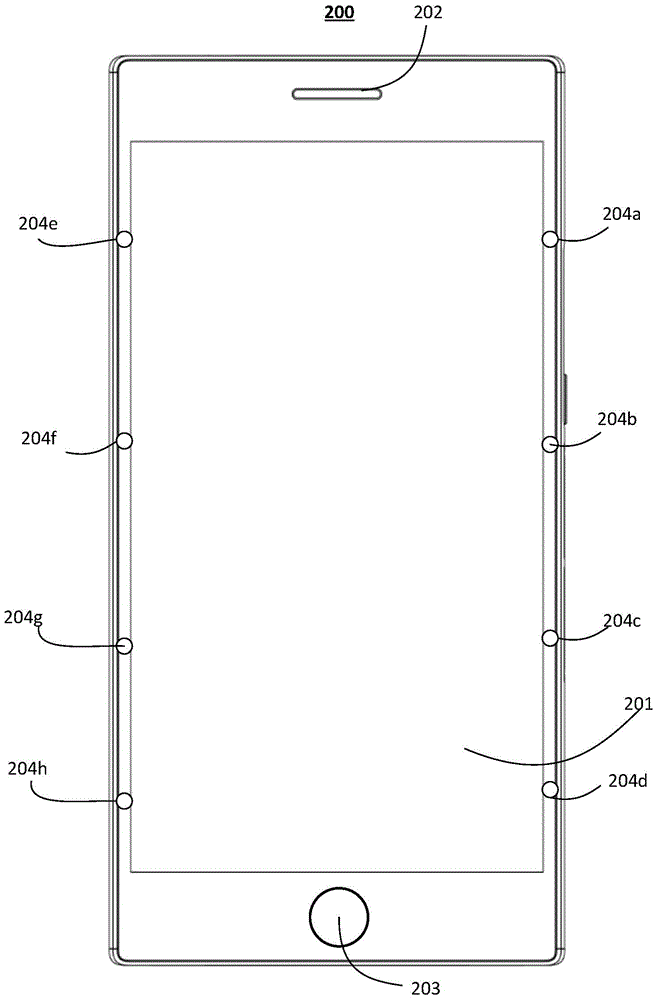
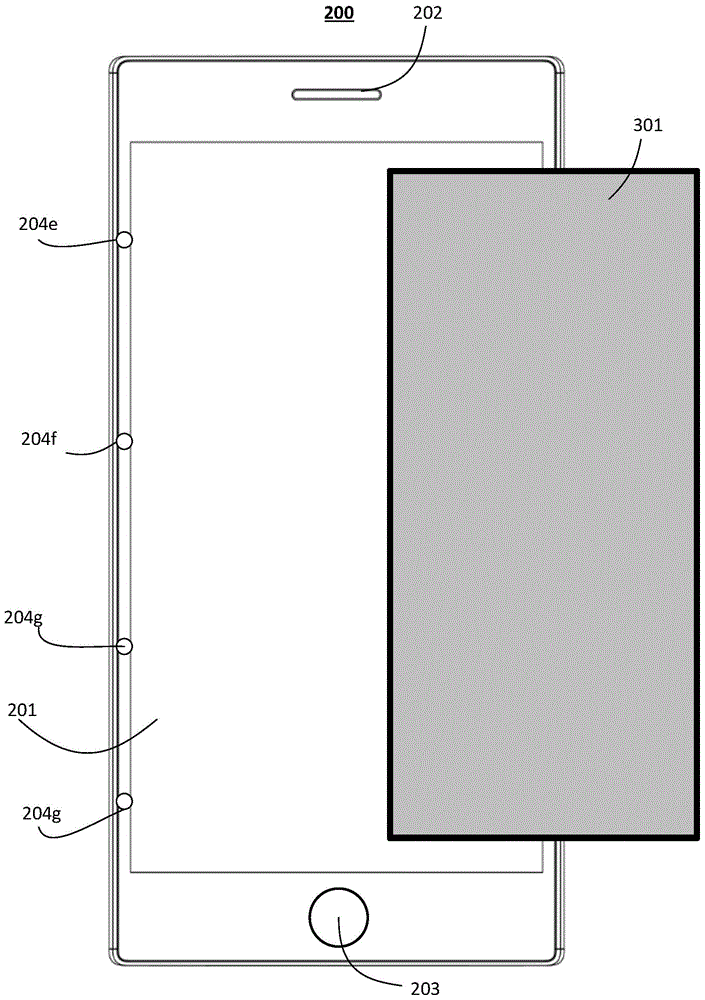
Display method of graphical user interface, and mobile terminal
ActiveCN105808040AReduce the possibility of leaksImprove privacyDigital data processing detailsDevices with sensorGraphicsMobile data terminal
The embodiment of the invention provides a display method of a graphical user interface, and a mobile terminal, and relates to the field of data processing. The method specifically comprises the following steps: judging whether the display screen of the mobile terminal is blocked or not; when a judgment result shows that the display screen is blocked, determining the blocking area and the display area of the display screen, wherein the display area is used for displaying the graphical user interface; determining the parameter information of the display area, wherein the parameter information comprises the area size of the display area and the position of the display screen where the display area is positioned; and according to the parameter information, obtaining the graphical user interface matched with the display area, and displaying the graphical user interface in the display area. The embodiment of the invention judges whether the touch screen of the mobile terminal is blocked or not, when the touch screen is blocked, the graphical user interface is displayed in the display area, the graphical user interface can be only displayed in the display area of the display screen without full-screen display, information leakage possibility is reduced, and privacy is good.
Owner:HUAWEI DEVICE CO LTD
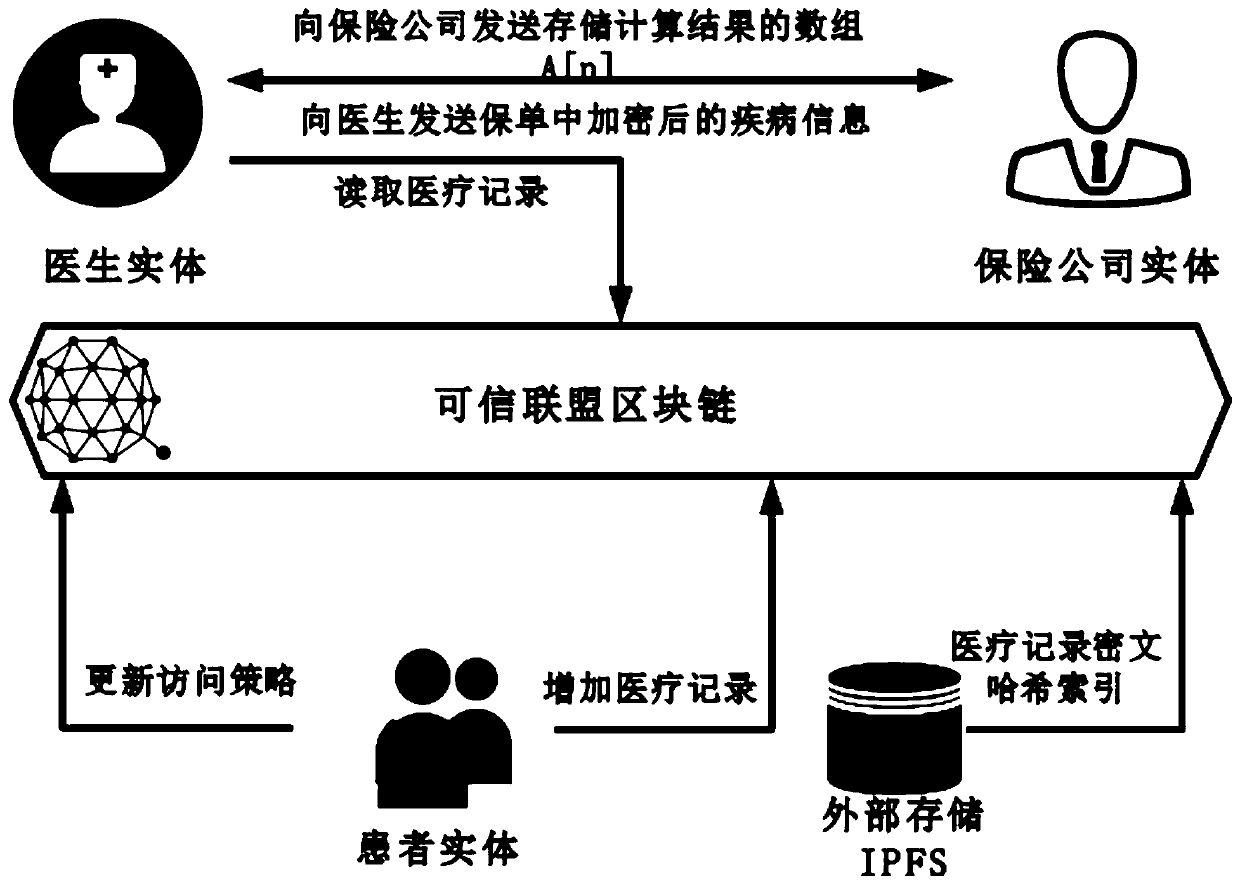
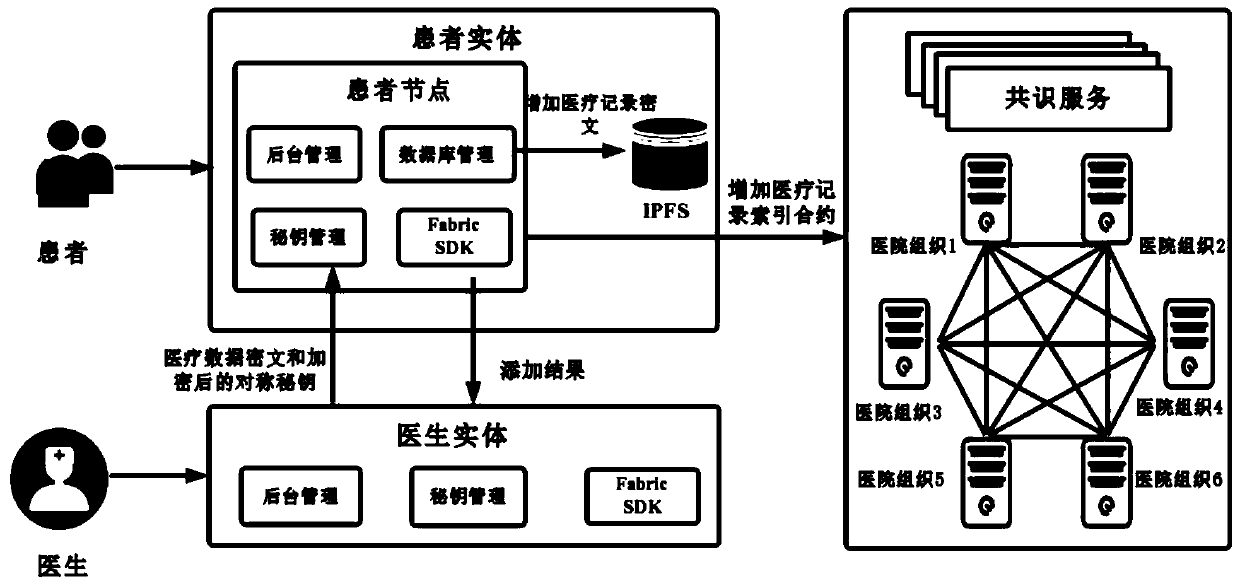
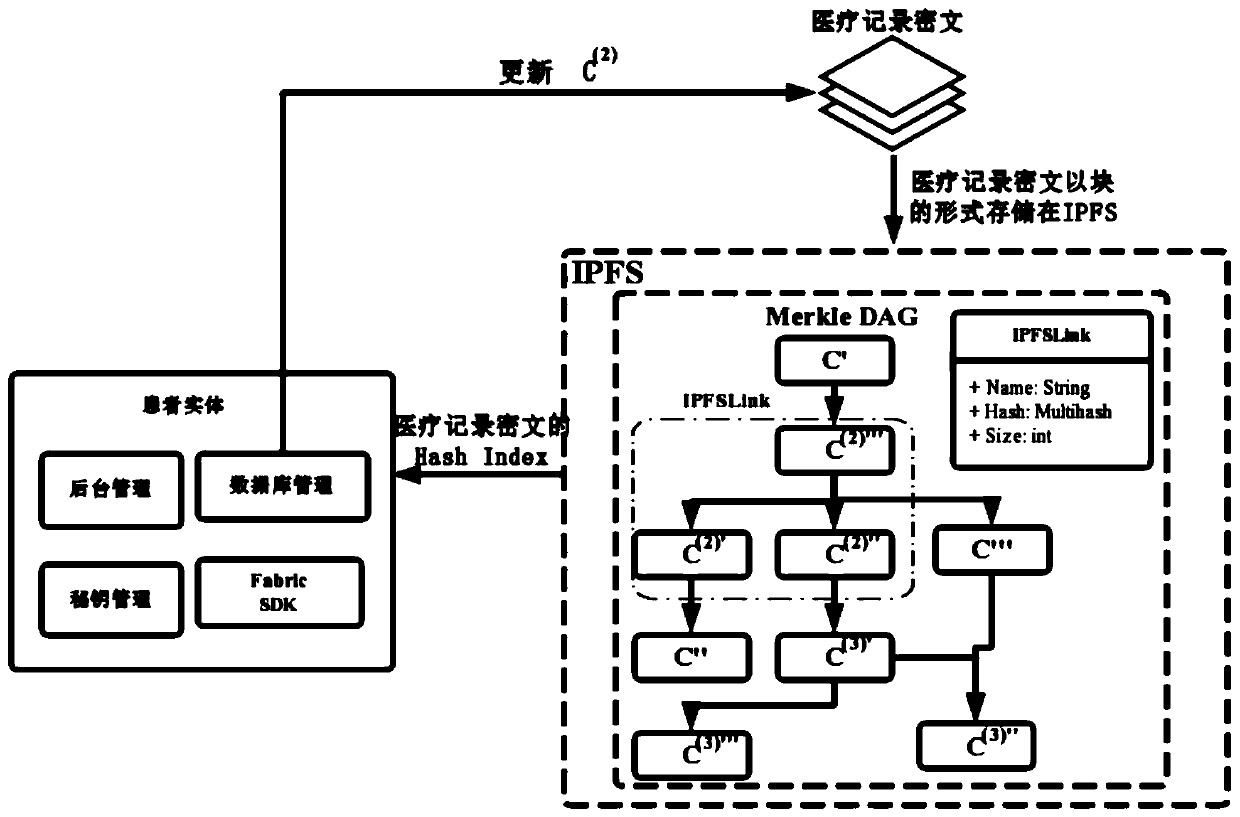
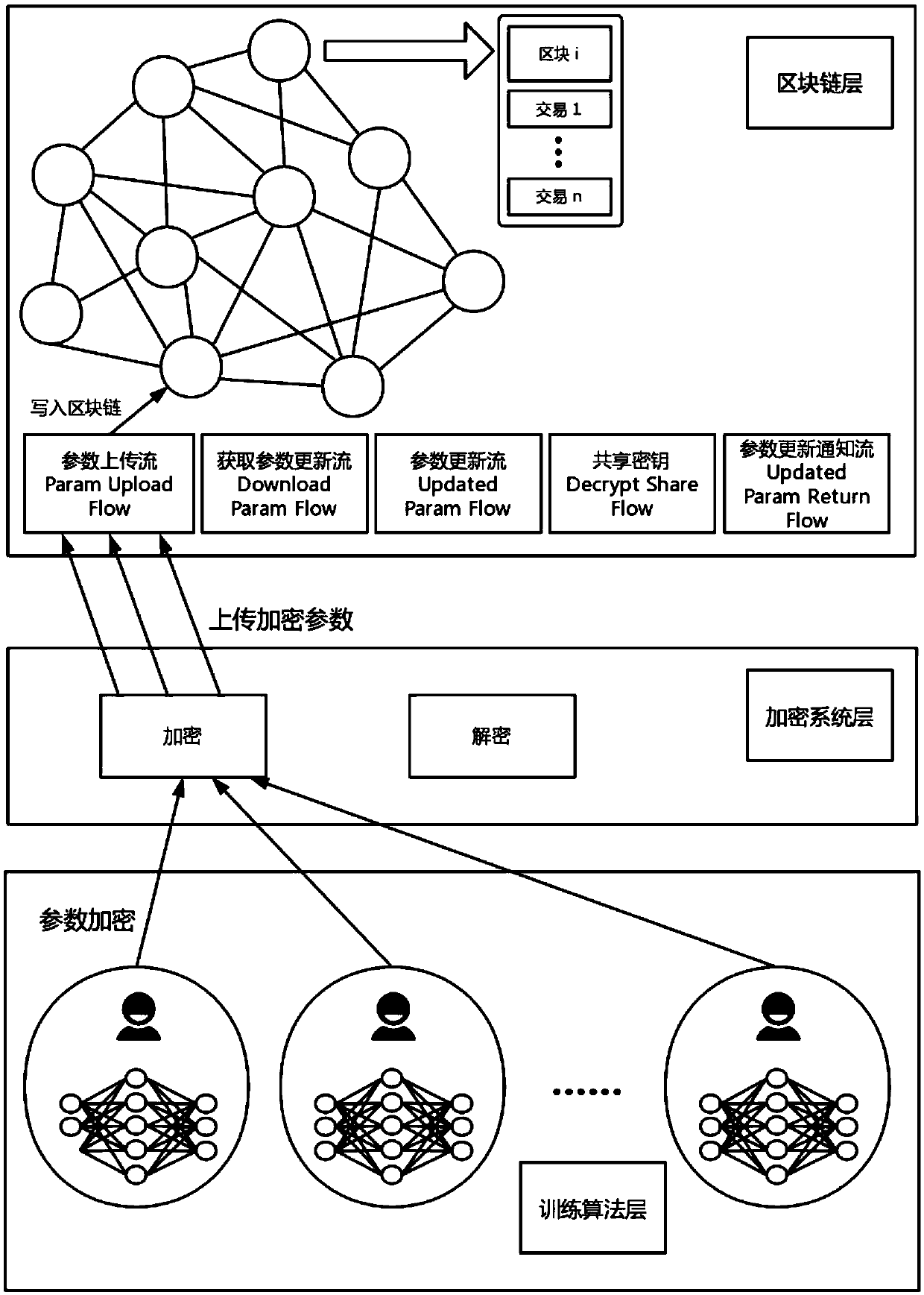
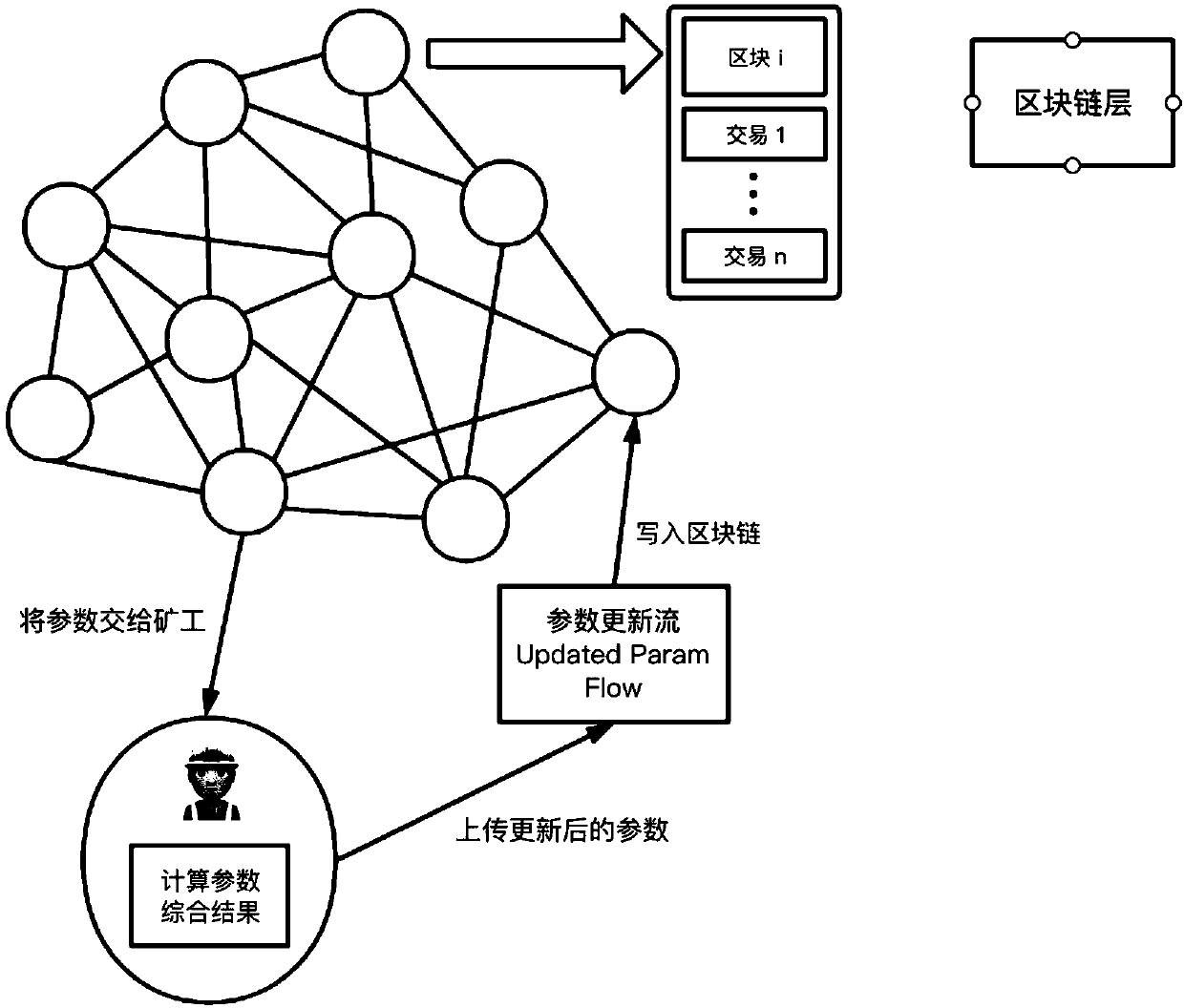
Medical record storage, sharing and security claim settlement model and method based on a block chain
ActiveCN110008746AGuaranteed privacyIncrease resistanceDigital data protectionPatient healthcareMedical recordThird party
The invention belongs to the technical field of medical data management, and relates to a medical record storage, sharing and security claim settlement model and method based on a block chain. Firstly, credible sharing of medical data of patients among medical institutions is achieved through the blockchain technology, and a lifelong medical record is established for the patients; based on a Hashchain type storage structure, the medical data cannot be tampered; secondly, an improved CP-ABE-based cryptographic primitive SHDPCPC-CP-ABE is proposed, security encryption and fine-grained access control on the medical data are realized, and a patient can conveniently and efficiently access and authorize a medical institution to read the medical data; and finally, a Paillier homomorphic encryption technology is utilized to realize safe medical insurance claim settlement, and the privacy of the patient is protected when the patient interacts with a third-party non-medical institution. According to the invention, security, confidentiality, reliability and integrity of medical data can be realized, and confidential sharing of private data is supported.
Owner:DALIAN UNIV OF TECH
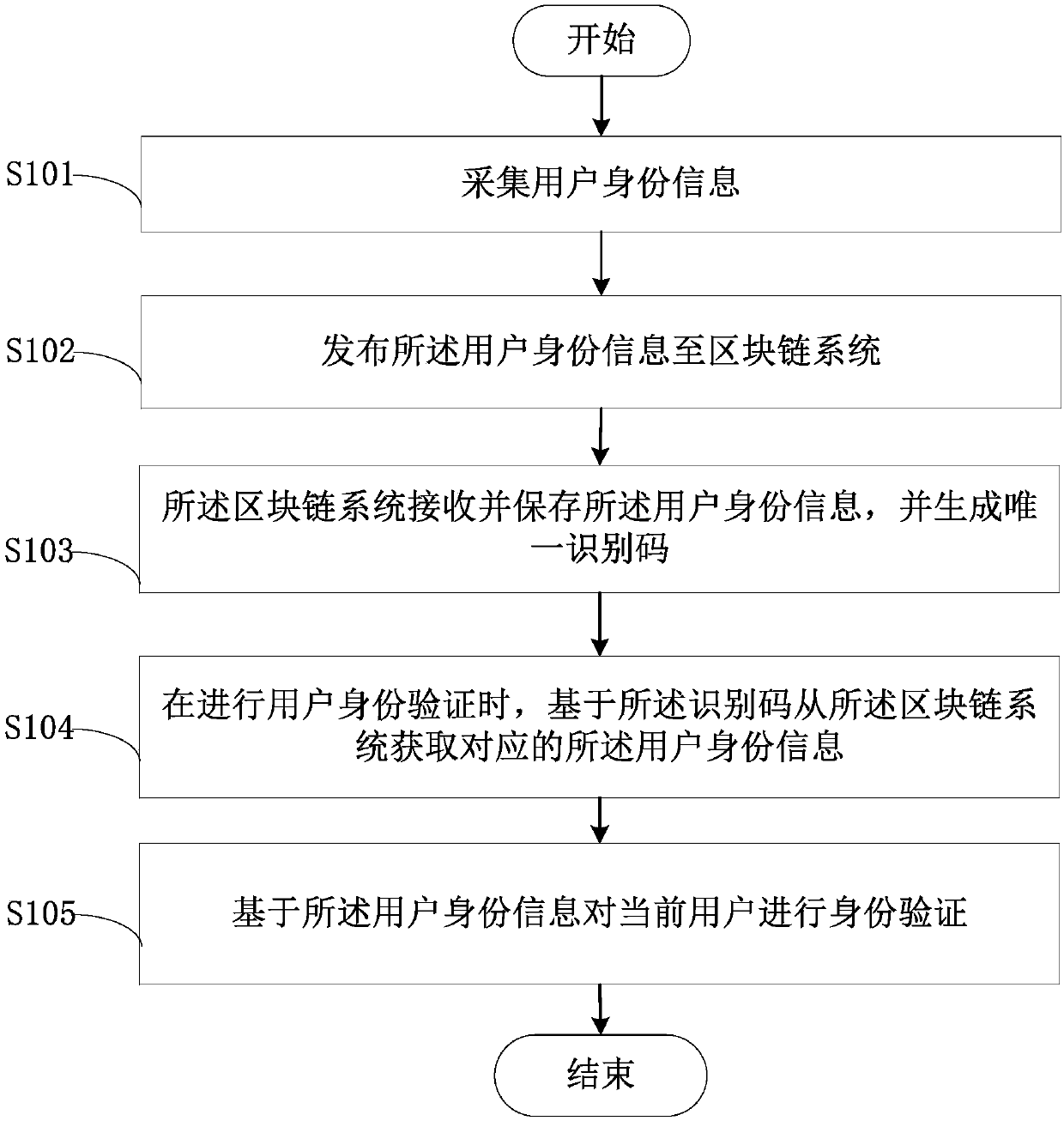
Block chain-based identity authentication method and device and computer readable storage medium
The invention relates to the technical field of computers, and provides a block chain-based identity authentication method. The method comprises the steps that user identity information is acquired; the user identity information is published to a block chain system; the block chain system receives and stores the user identity information and generates unique identification codes; when user identity authentication is conducted, the corresponding user identity information is acquired from the block chain system on the basis of the identification code; and identification authentication is conducted on a current user on the basis of the user identity information. According to the method, the information storage security is improved, the information storage credit degree is increased, and the reliability and accuracy of user identity authentication are improved. The invention further provides a block chain-based identity authentication device and a computer readable storage medium.
Owner:XIAMEN KUAISHANGTONG INFORMATION TECH CO LTD
Mobile payment device and method thereof based on NFC technology
ActiveCN103501191AImprove securityImprove reliabilityNear-field transmissionUser identity/authority verificationLiquid-crystal displayPassword
The invention discloses a mobile payment device and a method thereof based on an NFC technology, and the NFC technology and hardware encryption are combined. According to the mobile payment device and the method thereof, the NFC technology and the hardware encryption are combined and applied to the field of mobile terminal payment for the first time, and compared with traditional software encryption like dynamic passwords, the hardware encryption is higher in safety and reliability. The mobile payment device is designed in a folding type, a display screen can be folded and put into an outer shell of the mobile payment device when not used, therefore, the occupied space is small, the display screen is protected effectively, and damage to the display screen in the process of mobile carrying can be prevented. The payment device is small in size, easy to carry, and capable of being integrated into a card with a liquid crystal display. According to the mobile payment device and the method thereof, a hardware encryption mode is adopted, a secret key is stored in hardware, safety of the secret key can be guaranteed on the hardware, the secret key in the payment device can not be obtained by the outside through a mobile terminal, possibilities of exposure of the secret key are reduced, and therefore payment can be safer.
Owner:王越 +3
Visible light communication-based limited area authority authentication device and file security method
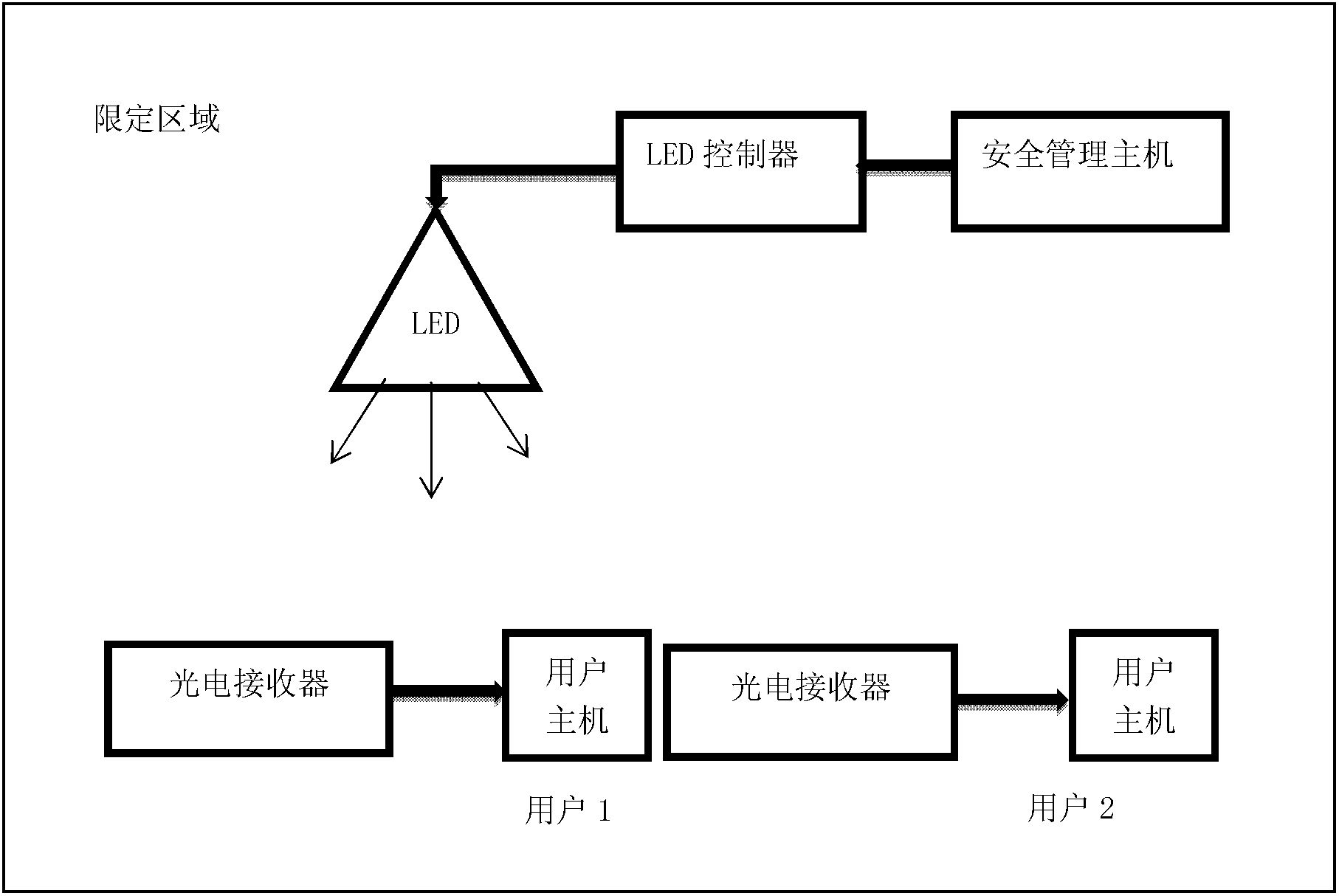
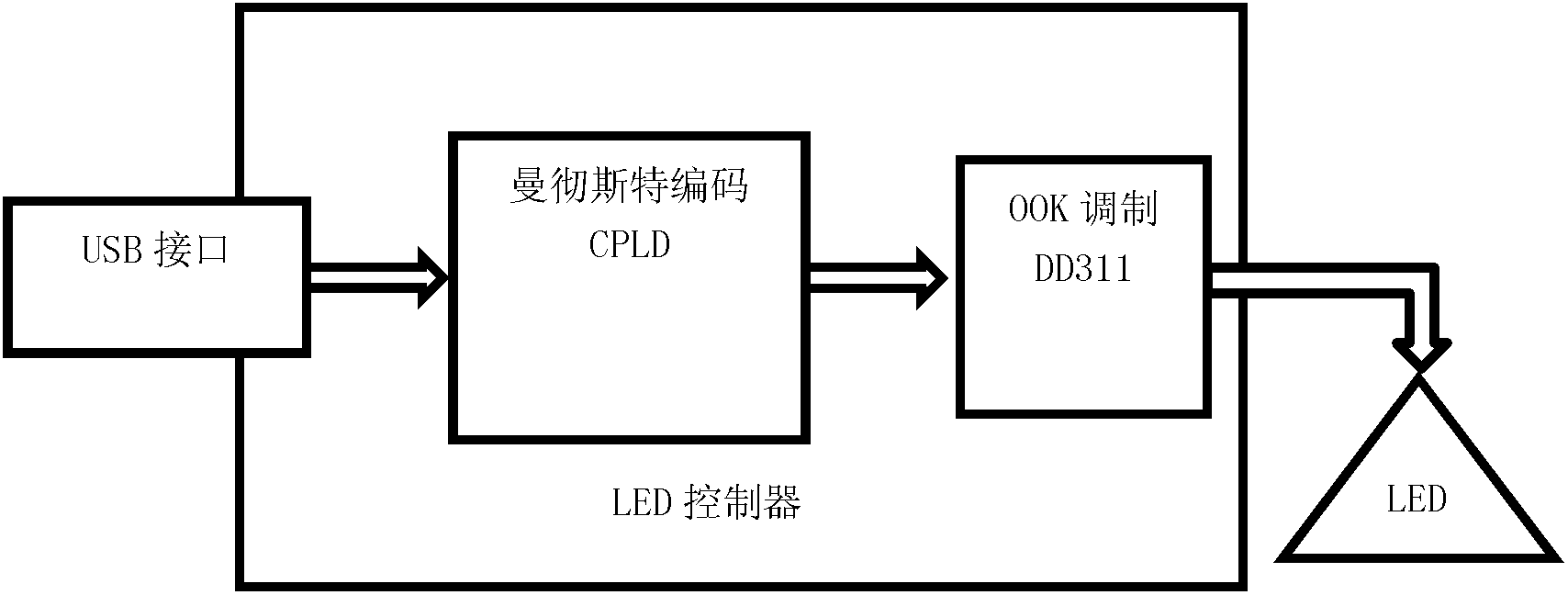
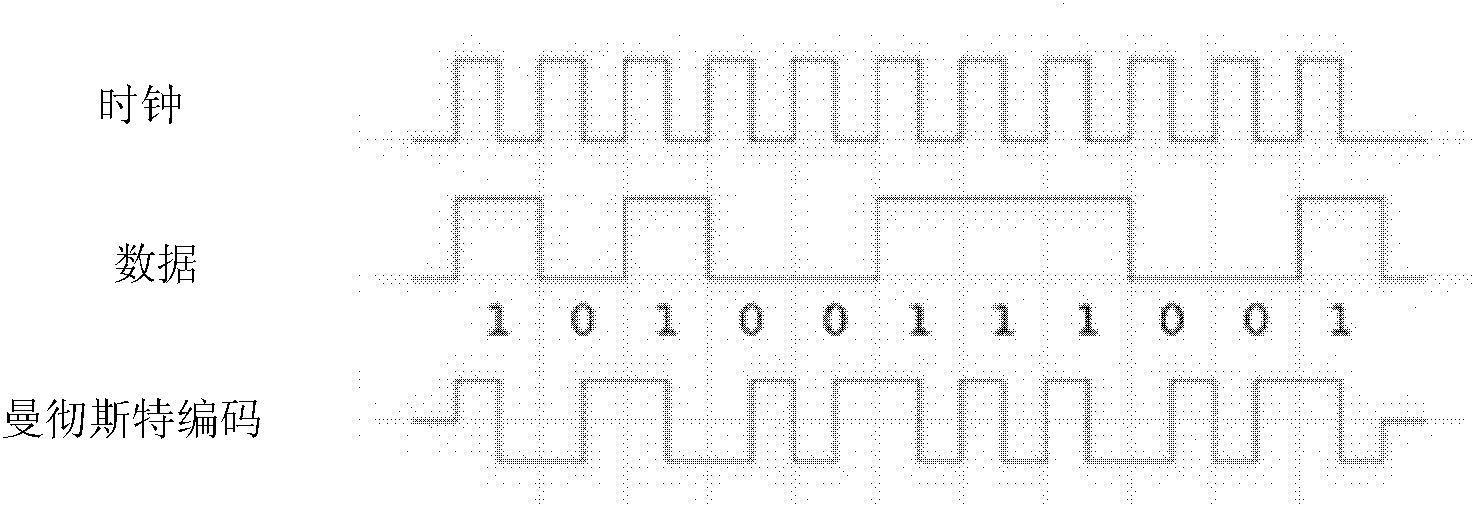
ActiveCN102289634AImprove securityReduce the possibility of leaksDigital data protectionCoding/ciphering apparatusStopped workCiphertext
The invention relates to a restrictive region permission authentication device based on visible optical communication. The device comprises an LED (Light Emitting Diode) controller, a photoelectric receiver, a safety management host and a user host. The LED controller is connected with the safety management host. The photoelectric receiver is connected with the user host. A file encryption methodcomprises the following steps of: 1, numbering files in a unified manner through a file permission management program, hiding in ciphertexts of the files, and distributing to users; 2, numbering fileusers in a unified manner through the file permission management program, and correspondingly establishing a permission database according to user permissions and numbers of the encrypted files; 3, encrypting information and secret keys in the permission database through the file permission management program, and broadcasting the information in a restrictive region through interface equipment; 4, decrypting the permission information and the secrete keys through a file permission service program, and inquiring the user permissions with input user numbers; and 5, regularly executing the step 3 according to application environment requirements, and updating the permission information and the secrete keys till the system stops working.
Owner:中港大公科技(北京)有限公司
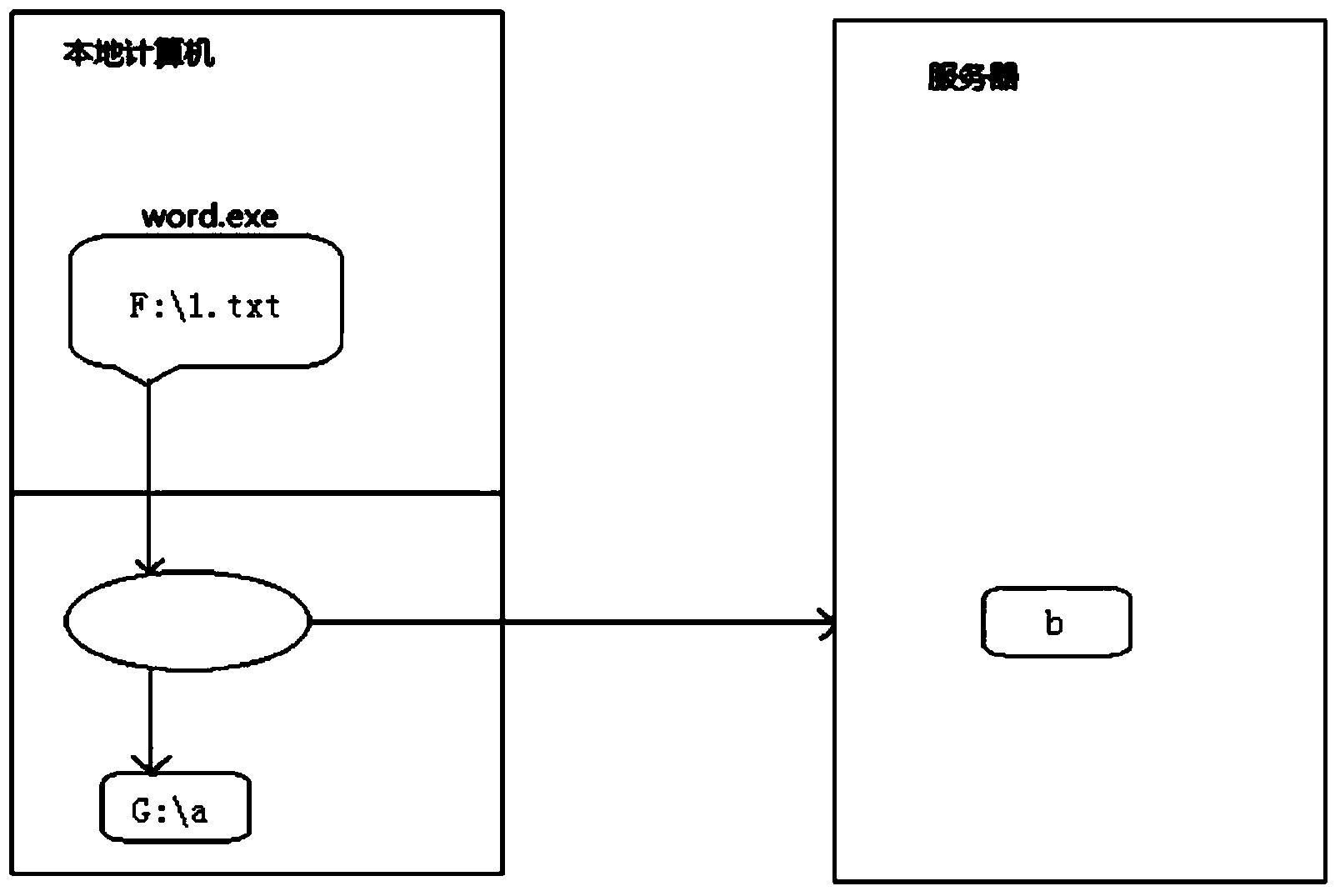
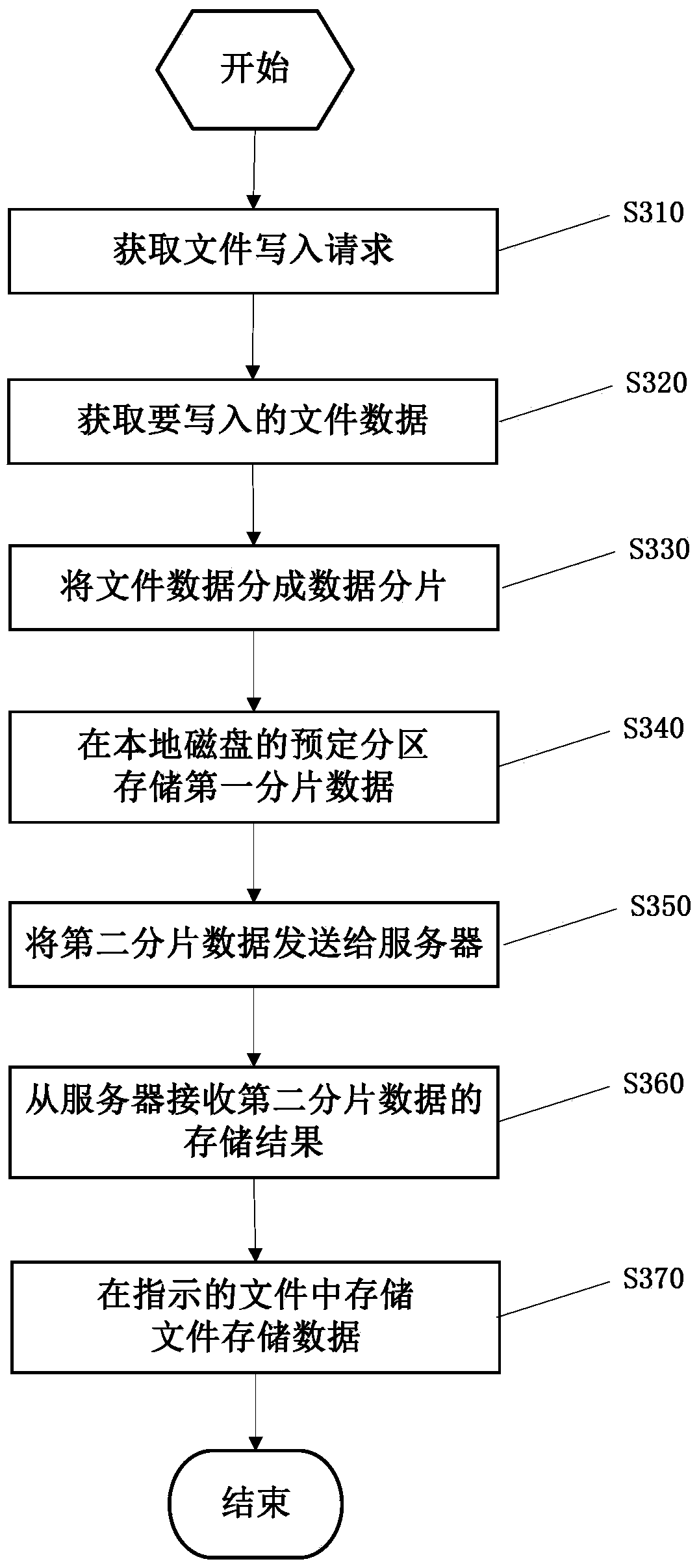
File data writing method, and file data reading method and device
InactiveCN103955528AReduce the possibilityImprove securityDigital data protectionSpecial data processing applicationsFile storageData fragment
The invention provides a file data writing method, and a file data reading method and device. The file data writing method comprises steps of obtaining a file writing request including a file identification and a memory buffer address, obtaining file data to be written according to the memory buffer address, segmenting the file data into two or more data fragments, writing data of the first fragment comprising part of the two or more segmented data fragments in a preset partition in a local disk, sending data of the second fragment comprising the other part of the two or more segmented data fragments to a server, receiving the storage result of the data of the second fragment from the server, and writing data offset values and data size of all data fragments and file store data of the store address in a file indicated by the file identification, wherein storage positions of all the data fragments in the data of the second fragment are preset positions on the server.
Owner:BEIJING HUAXINBOYAN TECH
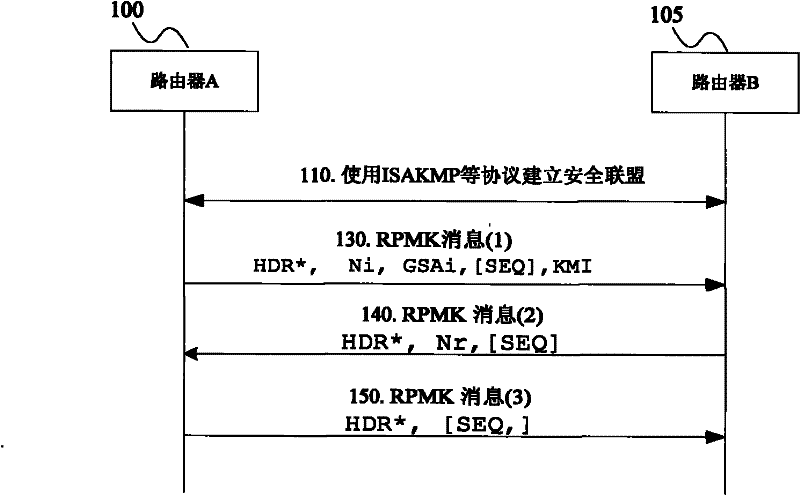
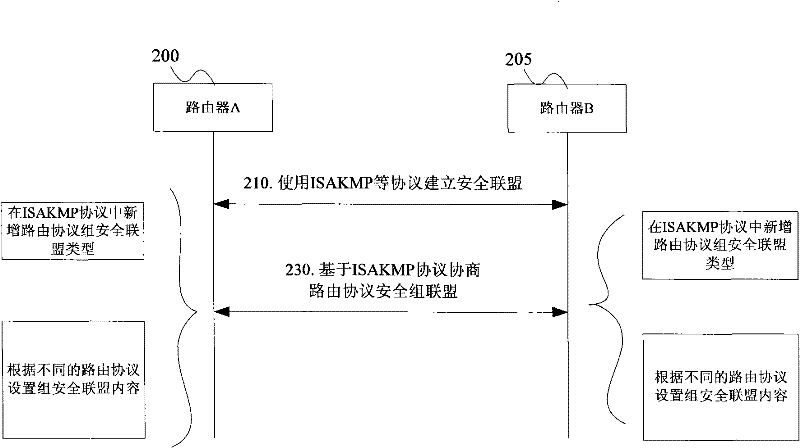
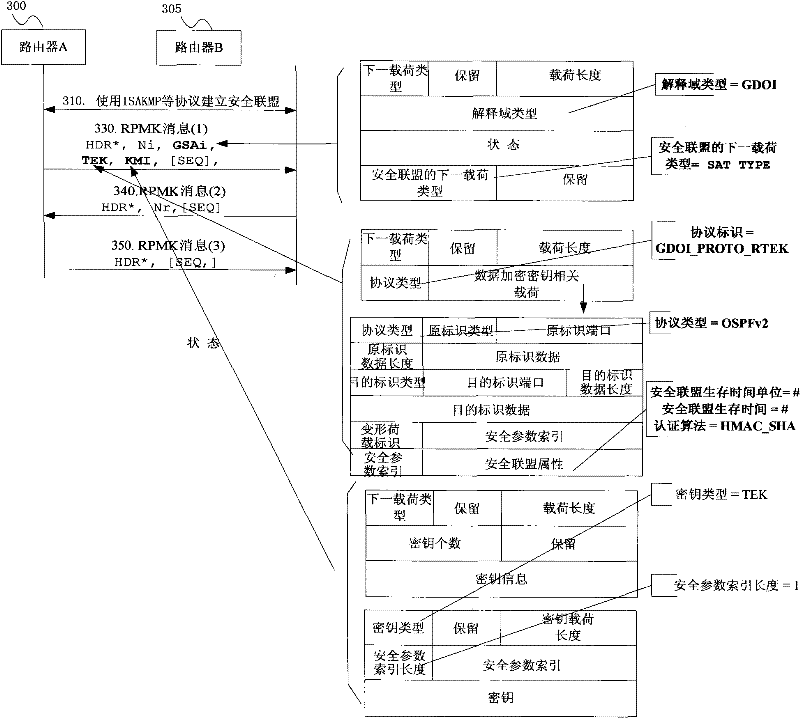
Key management method and network equipment
InactiveCN102447690AMeeting security needs for automated key material managementImprove securityUser identity/authority verificationComputer moduleProtocol for Carrying Authentication for Network Access
The invention discloses a key management method. The method comprises the following steps: security alliances (SAs) are set up among network equipment; the network equipment as a group key sender and the network equipment as a group key receiver carry out negotiation on the group SAs; and the group key sender and the group key receiver use the group SAs after negotiation to protect the routing protocol messages. The invention also discloses the network equipment. The network equipment comprises an SA setup module, a group SA negotiation module and a message protection module, wherein the SA setup module is used for setting up SAs among the network equipment; the group SA negotiation module is used for carrying out negotiation on the group SAs; and the message protection module is used for using the group SAs after negotiation to protect the routing protocol messages. The method and the equipment have the effect of meeting the security demands of the routing protocol automatic management key materials.
Owner:ZTE CORP
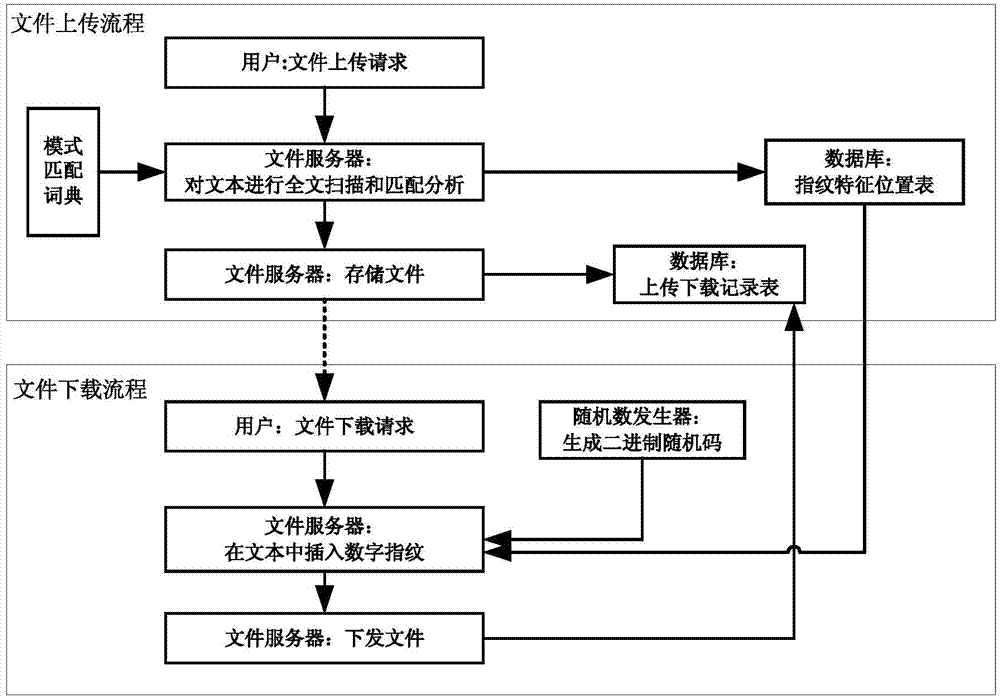
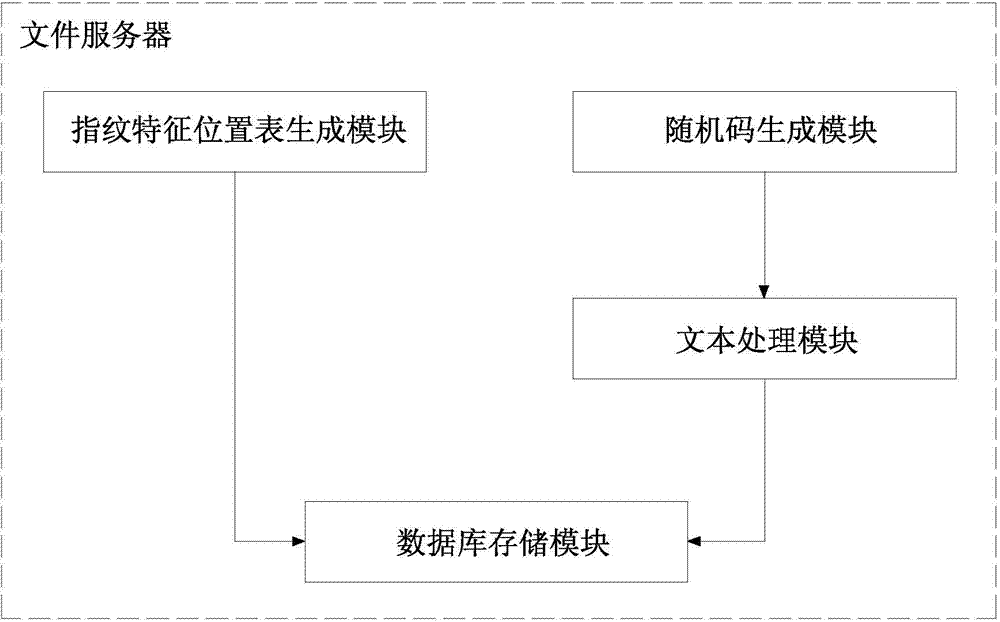
File security control and trace method and system based on digital fingerprints
InactiveCN104715168AImprove robustnessAvoid Malicious ModificationsProgram/content distribution protectionNatural language analysisFile server
The invention discloses a file security control and trace method and system based on digital fingerprints. The method includes the file uploading procedure and the file downloading procedure. In the file uploading procedure, when a user uploads files to a file server, the file server starts a natural language analysis program and conducts full-context scanning and matched analysis on file contexts, a position where the digital fingerprints can be inserted is found, a fingerprint feature position list is generated, the fingerprint feature position list and original files are stored in the file server together, the uploading and downloading record list is generated, and information uploaded this time is recorded. In the file downloading procedure, when the user sends a file downloading request to the file server, the file server generates binary random codes with the same length according to the length of the fingerprint feature position list, when the random code corresponding position is 1, the digital fingerprints are inserted in the contexts at the corresponding position, a new file is generated and sent to the user, and meanwhile the downloaded information is recorded in the uploading and downloading record list. By means of the method and system, the context files can be traced back, and the security of the context files is managed.
Owner:陈佳阳 +1
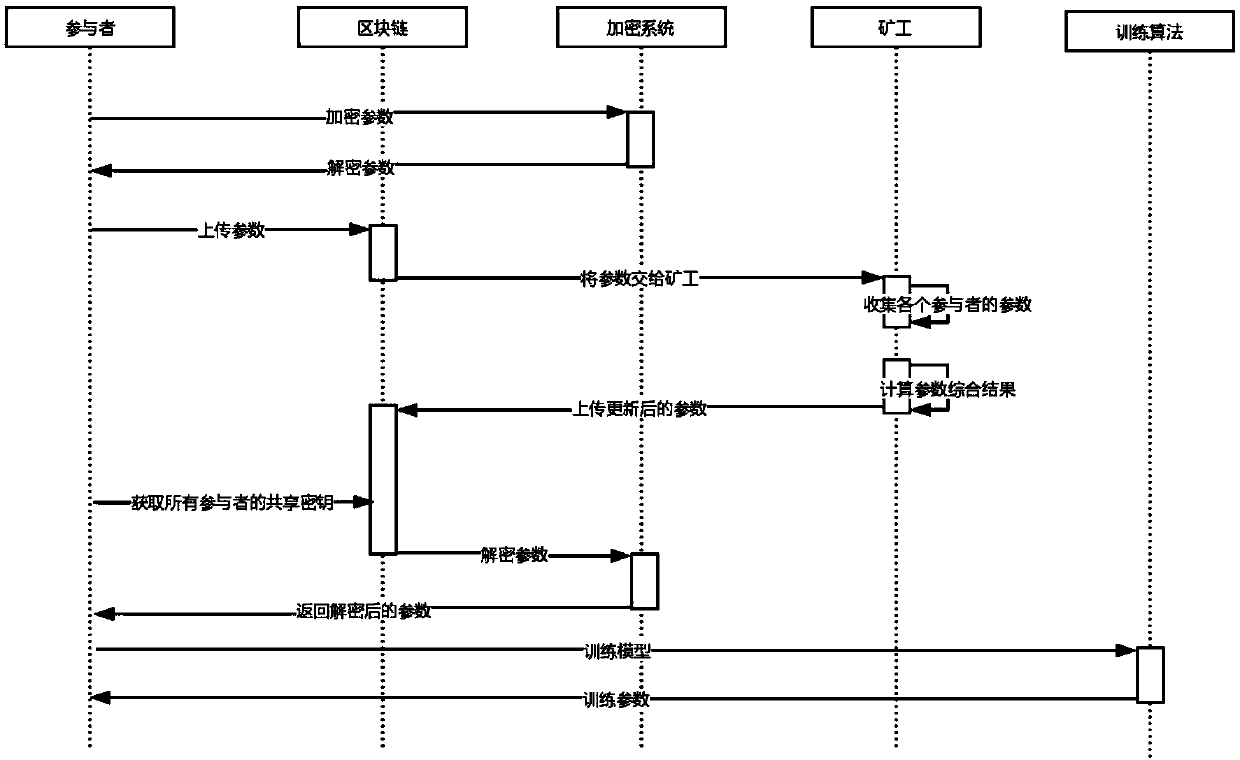
An auditable privacy protection deep learning platform construction method based on a block chain incentive mechanism
ActiveCN109685501AGuaranteed privacyReduce the possibility of leaksFinanceCryptography processingPrivacy protectionState form
Owner:JINAN UNIVERSITY
Apparatus and method for custom cosmetic dispensing
InactiveUS8573263B2Reduce the possibility of leaksDispensing tip blockage is substantially avoidedLiquid fillingLiquid transferring devicesAdditive ingredientEngineering
Improved custom cosmetic formulation dispensing system including ingredients reservoirs for syringe dispensing. The ingredients reservoirs are carried by a translatable carrier to bring the respective reservoirs into dispensing alignment with a package, into which a preselected amount of the ingredient is dispensed.
Owner:COSMETIC TECH L L C
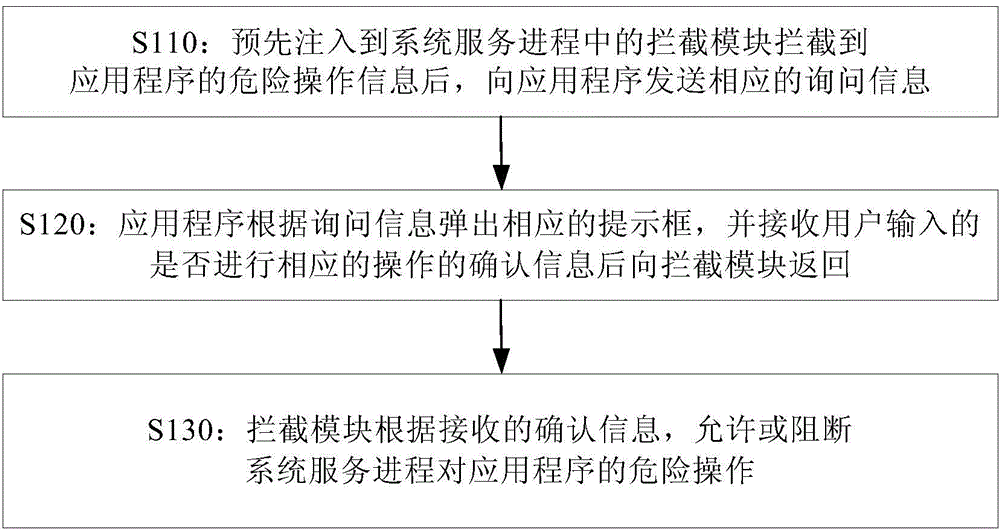
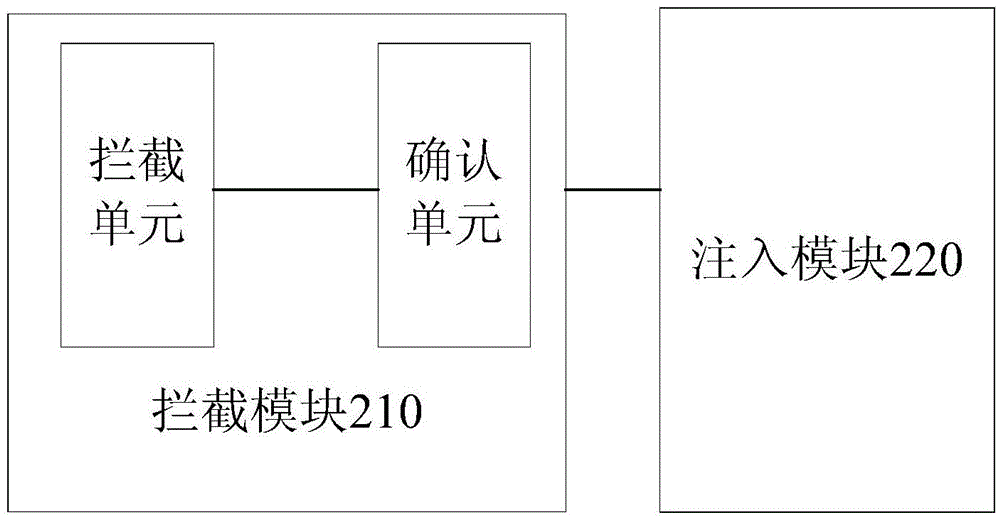
Application behavior intercepting method and application behavior intercepting device
ActiveCN104376263AEffective interceptionImprove experiencePlatform integrity maintainanceTemporary StoppingData information
An embodiment of the invention provides an application behavior intercepting method and an application behavior intercepting device. The method comprises the following steps of transmitting corresponding inquiry information to an application after dangerous operation information of the application is intercepted by an intercepting module which is injected into a system service process in advance; popping a corresponding prompt box by using the application according to the inquiry information; receiving confirmation information of a corresponding operation inputted by a user; returning the confirmation information to the intercepting module; and allowing or stopping a dangerous operation of the system service process on the application by using the intercepting module according to the received confirmation information. By the method and the device, behaviors of the application can be intercepted effectively; after the behaviors of the application are intercepted, the corresponding operation is stopped temporarily, the temporary stopping operation is notified to the user, the corresponding operation only can be carried out after the confirmation information of the user is obtained, so that the leakage possibility of data information and individual privacy information which are stored in the application is reduced, the safety of personal data is improved, and the user experience is also improved.
Owner:BEIJING QIHOO TECH CO LTD
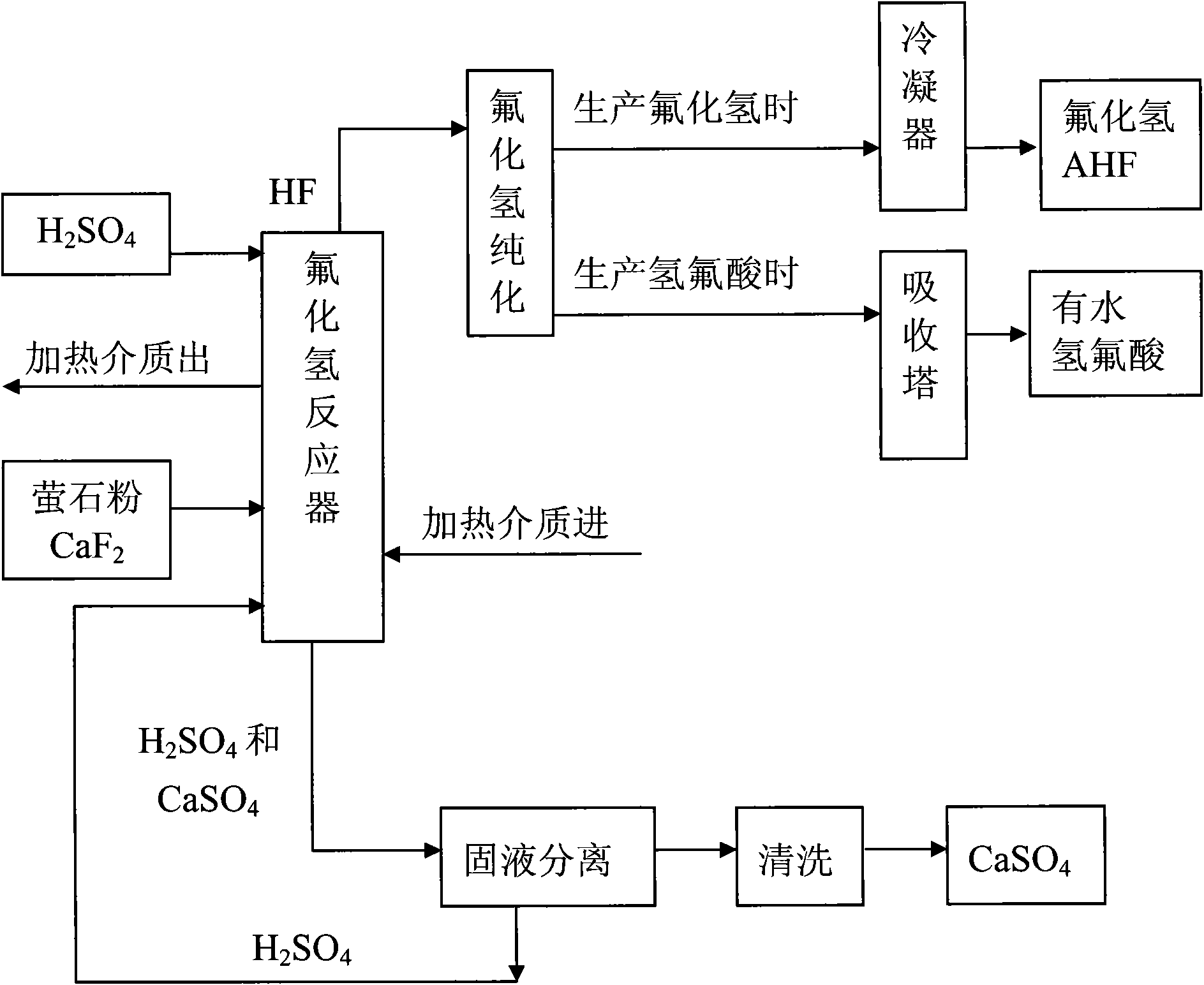
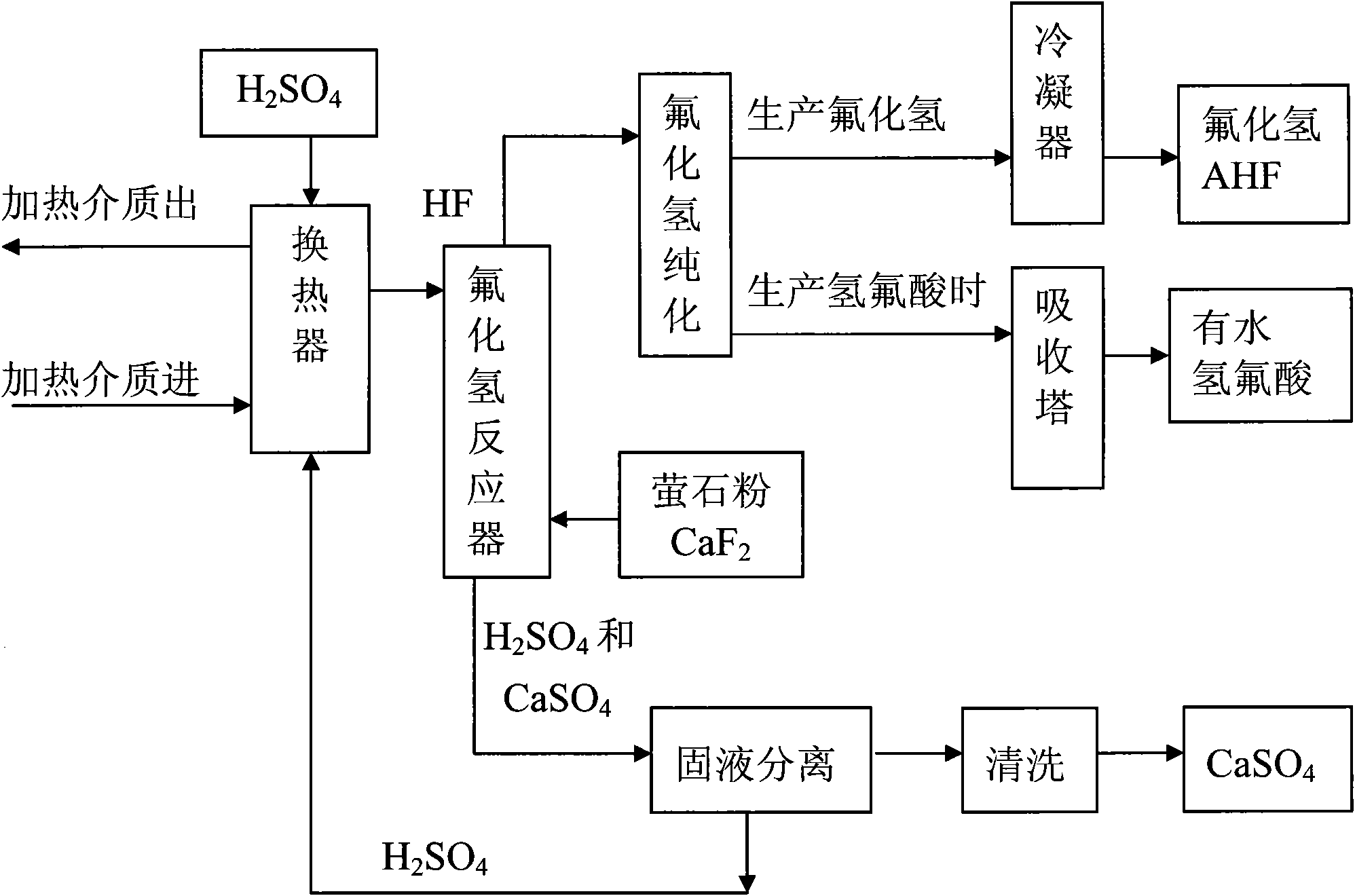
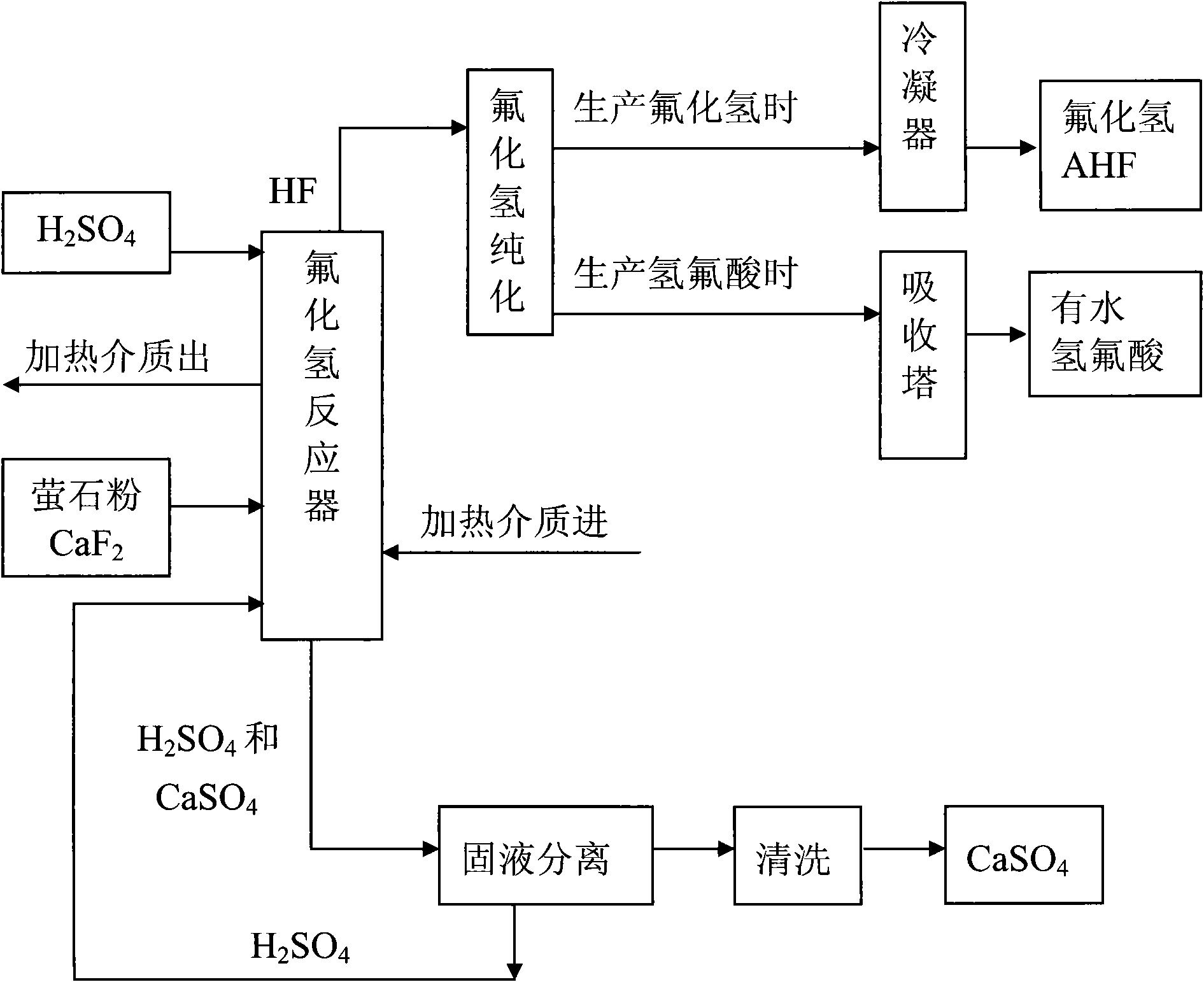
Method for preparing hydrogen fluoride from flousper powder and sulfuric acid
ActiveCN101913565ANovel process routeEasy to operateCalcium/strontium/barium sulfatesFluorine/hydrogen-fluorideHydrofluoric acidHydrogen fluoride
The invention discloses a method for preparing hydrogen fluoride from flousper powder and sulfuric acid. The method comprises the following specific steps of: adding solution of sulfuric acid and the flousper powder into a reactor with a stirrer respectively, wherein the molar ratio of calcium fluoride to the sulfuric acid is 1:3-1:30, the granularity of the flousper powder is 280 to 1,220 meshes, and the reaction temperature is controlled to between 90 and 300 DEG C; generating hydrogen fluoride gas and calcium sulfate solid after the reaction; purifying, condensing and rectifying the hydrogen fluoride gas to obtain anhydrous hydrogen fluoride, or purifying and absorbing the hydrogen fluoride gas to obtain hydrofluoric acid; transferring the calcium sulfate solid and the sulfuric acid toa filtering system from the reactor to perform solid-liquid separation; returning the separated solution of sulfuric acid to the reactor; and washing and drying the calcium sulfate solid separated from the sulfuric acid to form a by-product. The method has the advantages of simple equipment, high reaction efficiency, low cost and easy industrialized production.
Owner:衢州市鼎盛化工科技有限公司
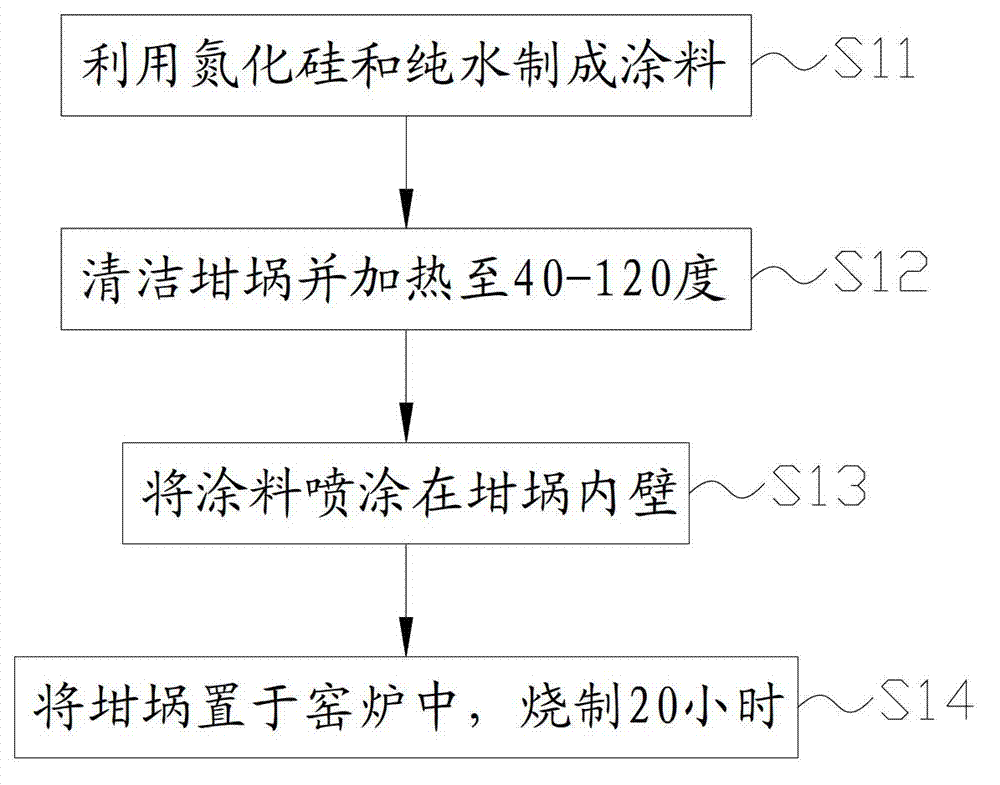
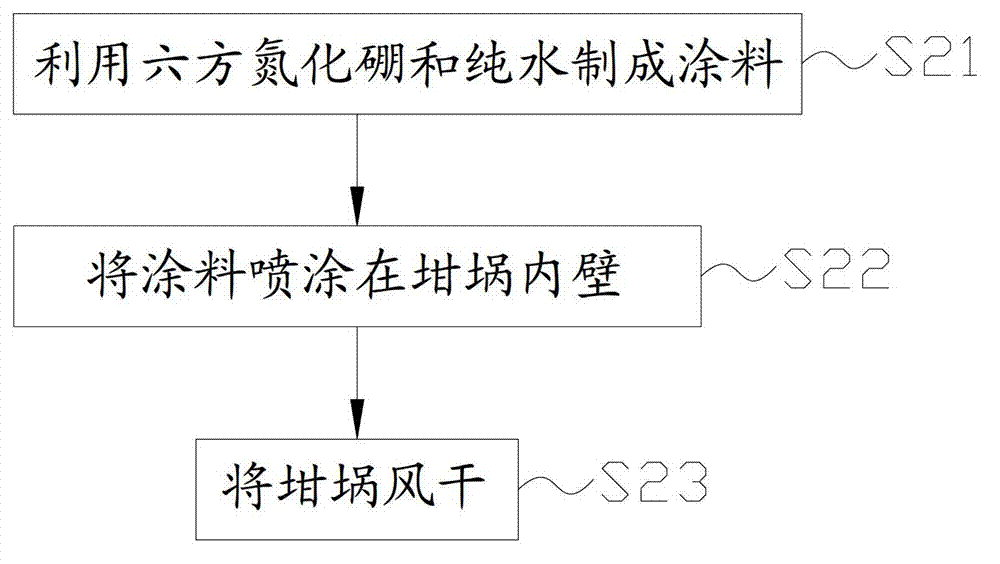
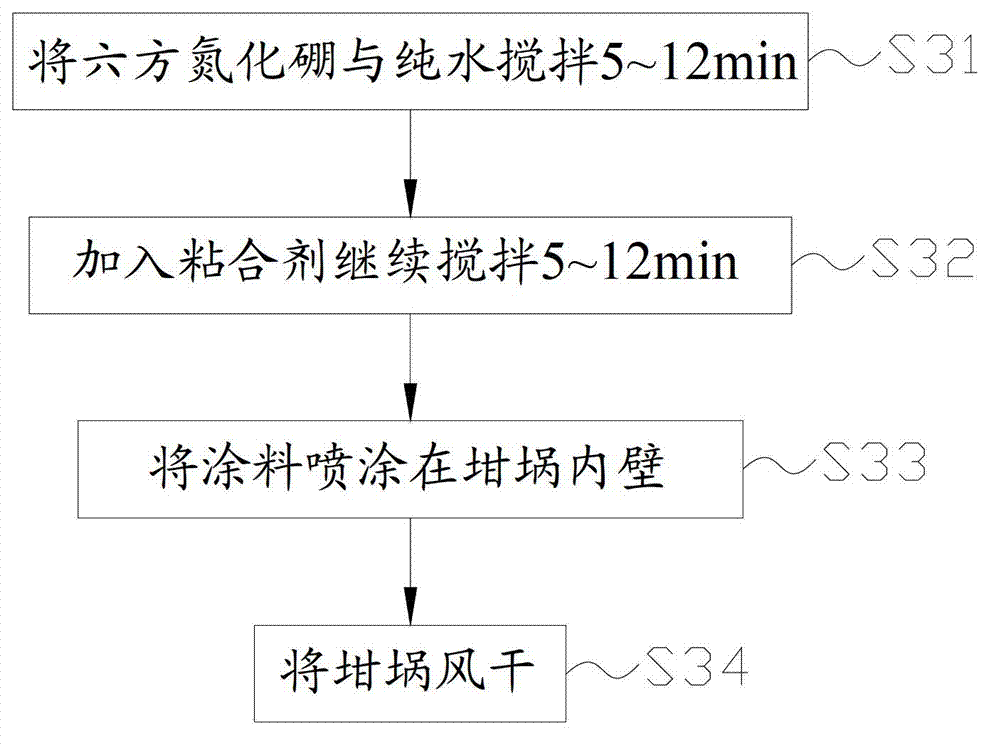
Crucible and coating method thereof
InactiveCN103084325AImprove coating efficiencyIncrease productivityAfter-treatment apparatusPretreated surfacesHexagonal boron nitrideCrucible
The invention discloses a crucible and a coating method of the crucible. The disclosed coating method of the crucible comprises the following steps: coating paint is manufactured, and the coating paint comprises hexagonal boron nitride and pure water; the coating paint is coated on the inner wall of the crucible in a spraying mode; and the crucible is aired to be dry. The possibility of the reaction between the crucible and the hexagonal boron nitride is small, silicone material is not prone to stick to the crucible, the possibility of occurrence of leakage is obviously lowered, and therefore the safety and reliability in the process of production of the silicone material are improved. Meanwhile, a coating is poor in wettability with liquid silicone and is not prone to stick to the silicone materials under the condition of carrying the liquid silicone. In addition, due to the fact that the hexagonal boron nitride has good wettability, demolding of a silicone ingot is good. The coating enables the heat conduction to be more uniform in the growth process of the silicone ingot, so that the interior quality of the silicone ingot is improved. Therefore, the coating method of the crucible is capable of reducing the sticking and permeation between the crucible and the liquid silicone material, plays a role in a protective layer, has the functions of lubrication and demolding, and improves the production quality of the silicone material and production efficiency.
Owner:TIANJIN YINGLI NEW ENERGY RESOURCES
Expansion/control joint for stucco surfaces
ActiveUS9062453B1Limit controlRelieve stress limitCovering/liningsBuilding insulationsEngineeringGypsum
An expansion / control joint, used to separate stucco or plaster material into sub-portions during application of the stucco or plaster material to a wall, and to relieve stress and limit or control cracking in a stucco or plaster wall or surface caused by stucco or plaster shrinkage and thermal movement in the stucco or plaster wall or surface, includes an expansion / contraction member comprising two flexible panels extending between second sides of first and second stucco stop walls, the two panels comprising an upper panel and a lower panel, the panels forming in conjunction with the second sides of the first and second stucco stop walls a flexible hollow tube which extends along and between the second sides of the first and second stucco stop walls and which flexes to accommodate expansion and contraction of the stucco or plaster material responsive to weather induced movement of the stucco or plaster material.
Owner:E Z BEAD
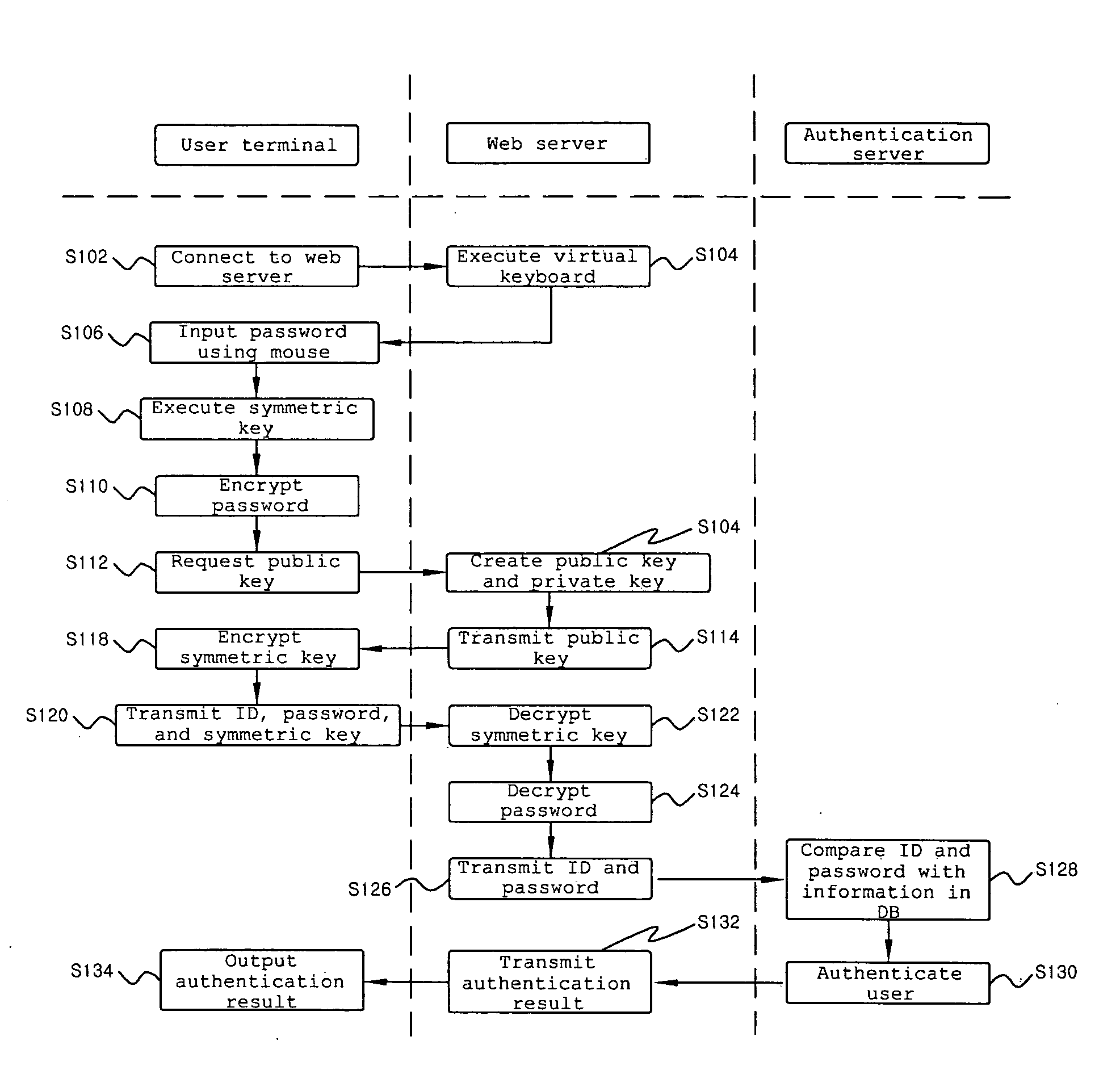
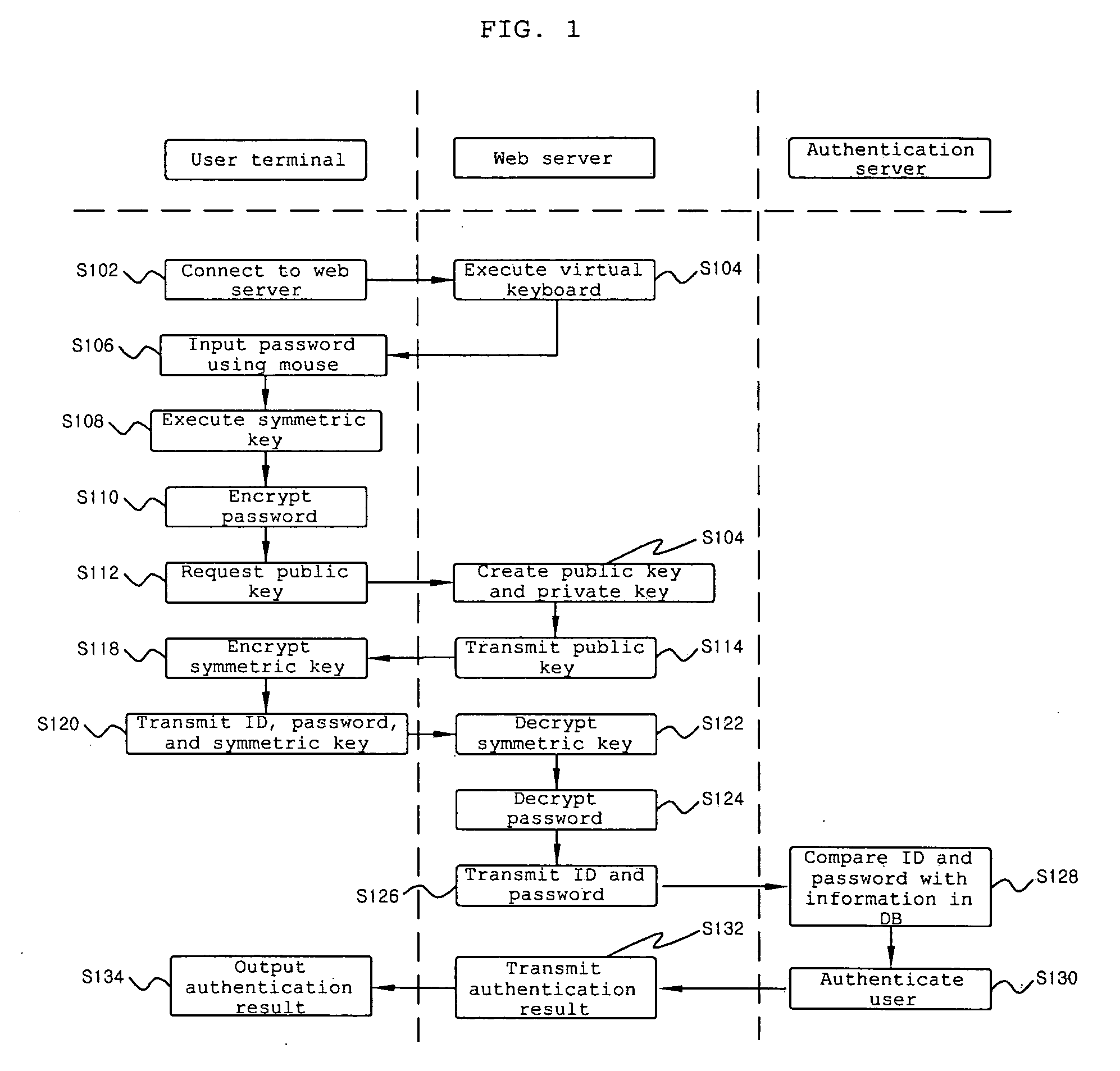
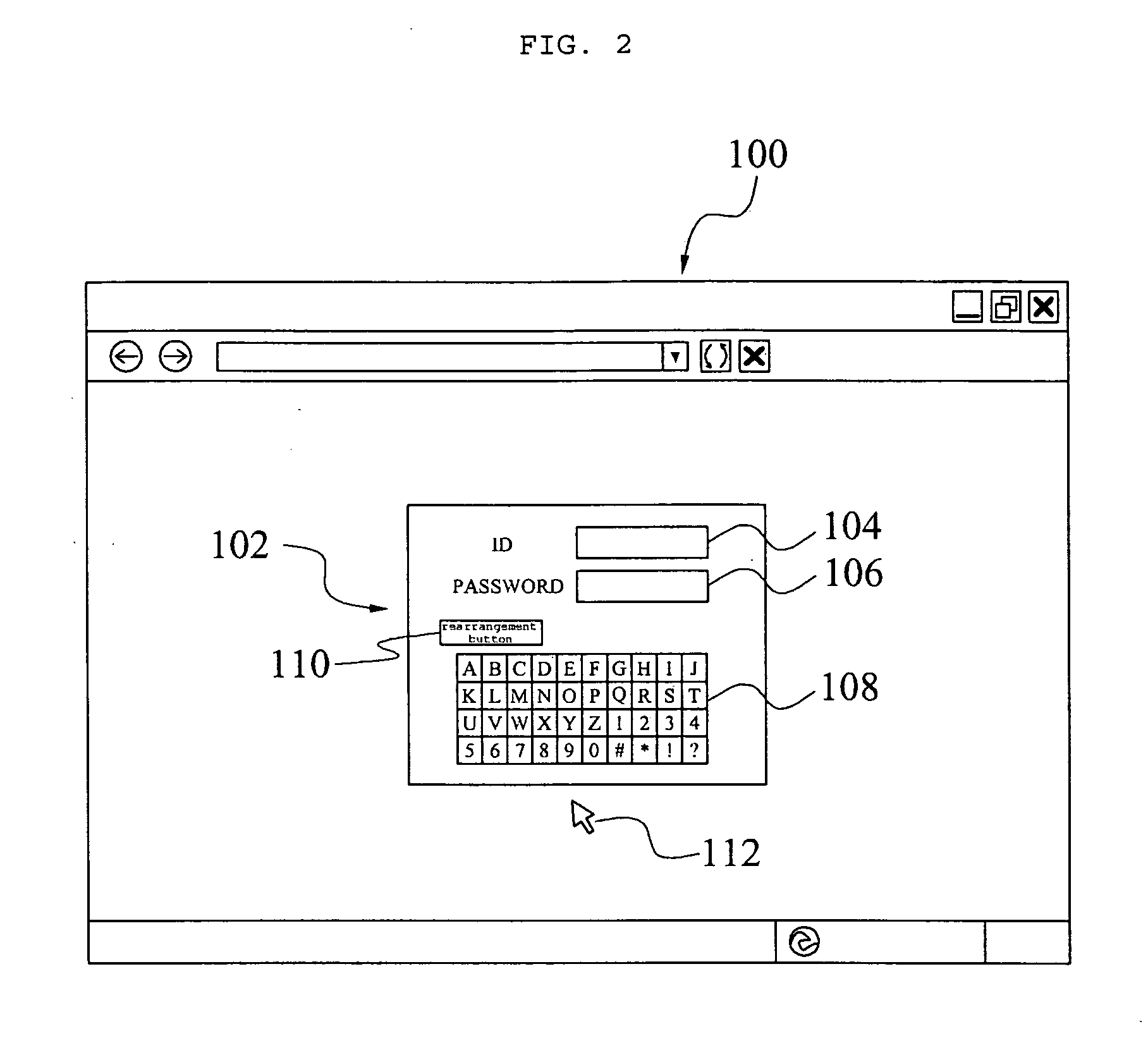
Security method using virtual keyboard
InactiveUS20080288776A1Reduce riskReduce the possibility of leaksPublic key for secure communicationUser identity/authority verificationWeb servicePassword
The present invention relates to a security method using a virtual keyboard, and more specifically, to a security method using a virtual keyboard, in which a user may input information through the virtual keyboard using a mouse when the user logs into a web server by inputting an identification (ID) and a password, and the inputted password is transmitted to the web server after being encrypted, so that personal information is prevented from being leaked by a hacking program and a safe connection is established. According to the present invention, risk of personal information leakage that can be occurred when an ID and a password are inputted through a keyboard may be greatly reduced, and it is effective in that even when a symmetric key is leaked, which is least expected, decipher of data is prevented by maintaining security of a private key.
Owner:ESTSOFT CORP
Apparatus and method for custom cosmetic dispensing
InactiveUS20050067425A1Reduce the possibility of leaksDispensing tip blockage is substantially avoidedCosmetic preparationsMake-upAdditive ingredientBiomedical engineering
Improved custom cosmetic formulation dispensing system including ingredients reservoirs for syringe dispensing. The ingredients reservoirs are carried by a translatable carrier to bring the respective reservoirs into dispensing alignment with a package, into which a preselected amount of the ingredient is dispensed.
Owner:COSMETIC TECH L L C
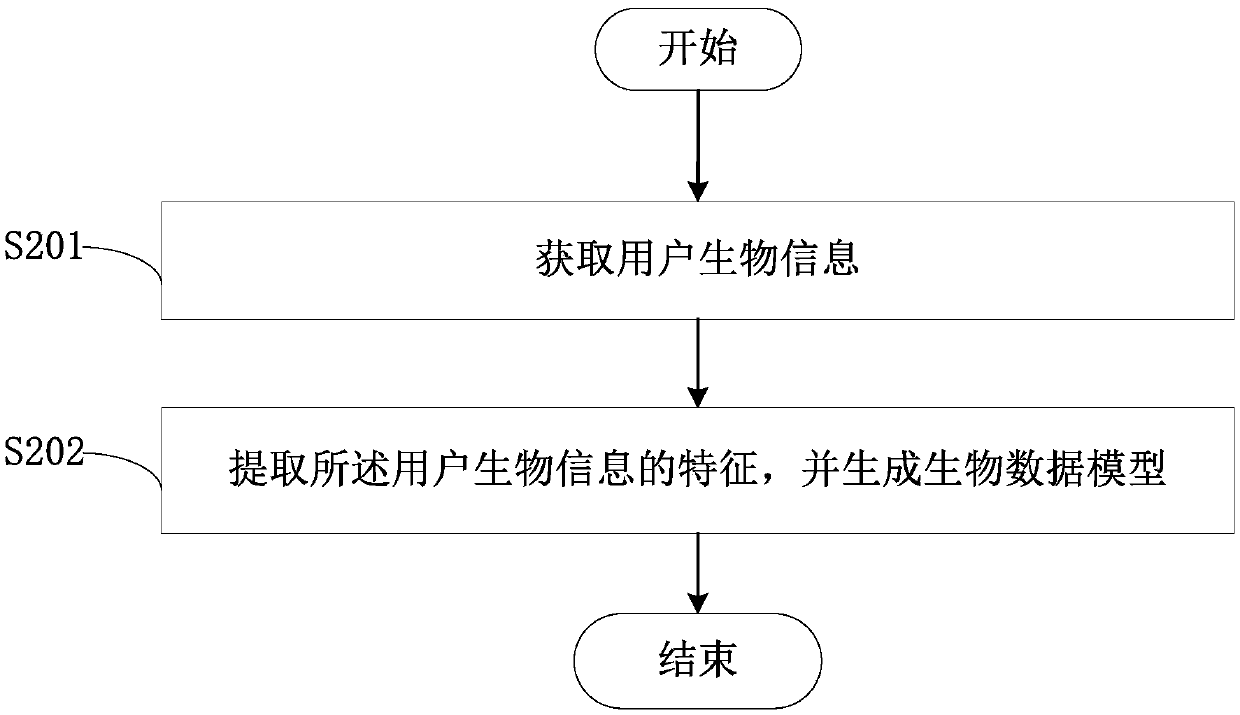
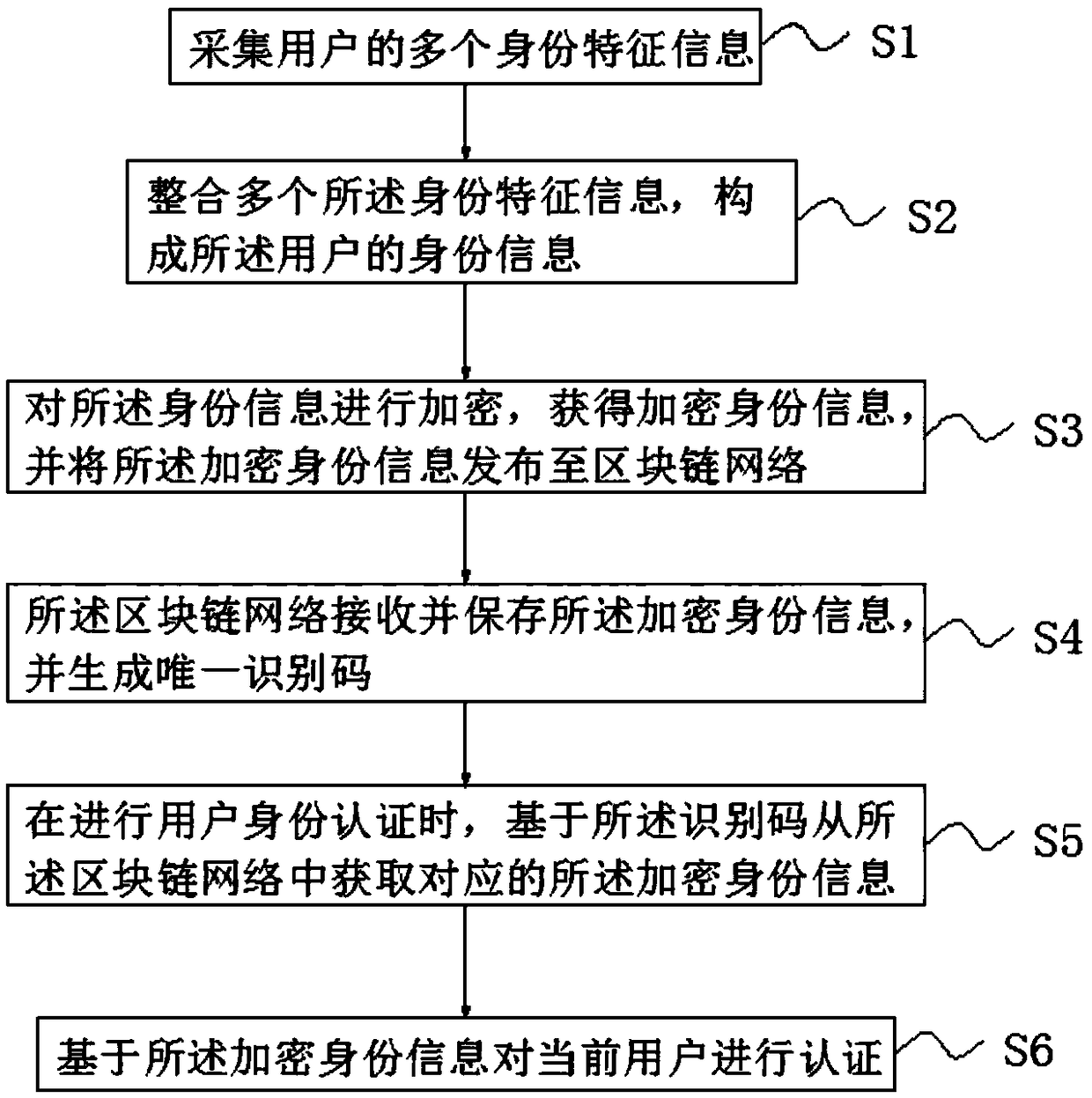
Blockchain-based identity authentication method
InactiveCN108881301AImprove securityImprove creditPublic key for secure communicationUser identity/authority verificationInternet privacyThe Internet
The invention, which belongs to the technical field of internet, discloses a blockchain-based identity authentication method. The method comprises: a plurality of pieces of identity feature information of a user is collected; the identity feature information is integrated to form identity information of the user; the identity information is encrypted to obtain encrypted identity information and the encrypted identity information is issued to a blockchain network; the blockchain network receives and stores the encrypted identity information and generates a unique identification code; when identity authentication of the user is carried out, the corresponding identity information is obtained from the blockchain network based on the identification code; and the curent user is authenticated based on the encrypted identity information. According to the blockchain-based identity authentication method provided by the invention, the identity information of the user is stored based on the characteristics of decentralization, openness, autonomy, information non-tamper property, and anonymity of the blockchain system, so that the information storage safety and credit level are improved.
Owner:宏桥高科技集团有限公司
Method for improving safety of Web service
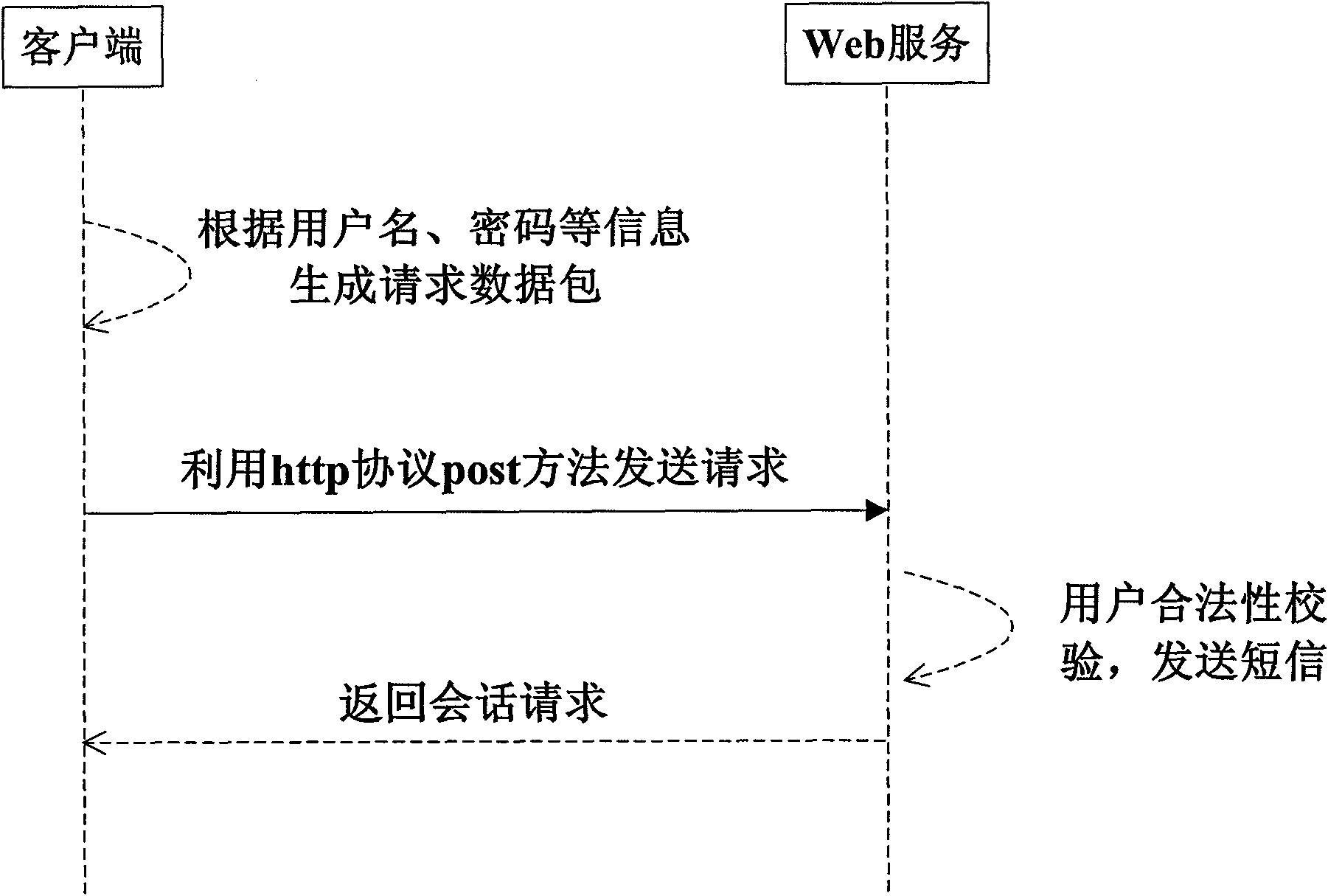
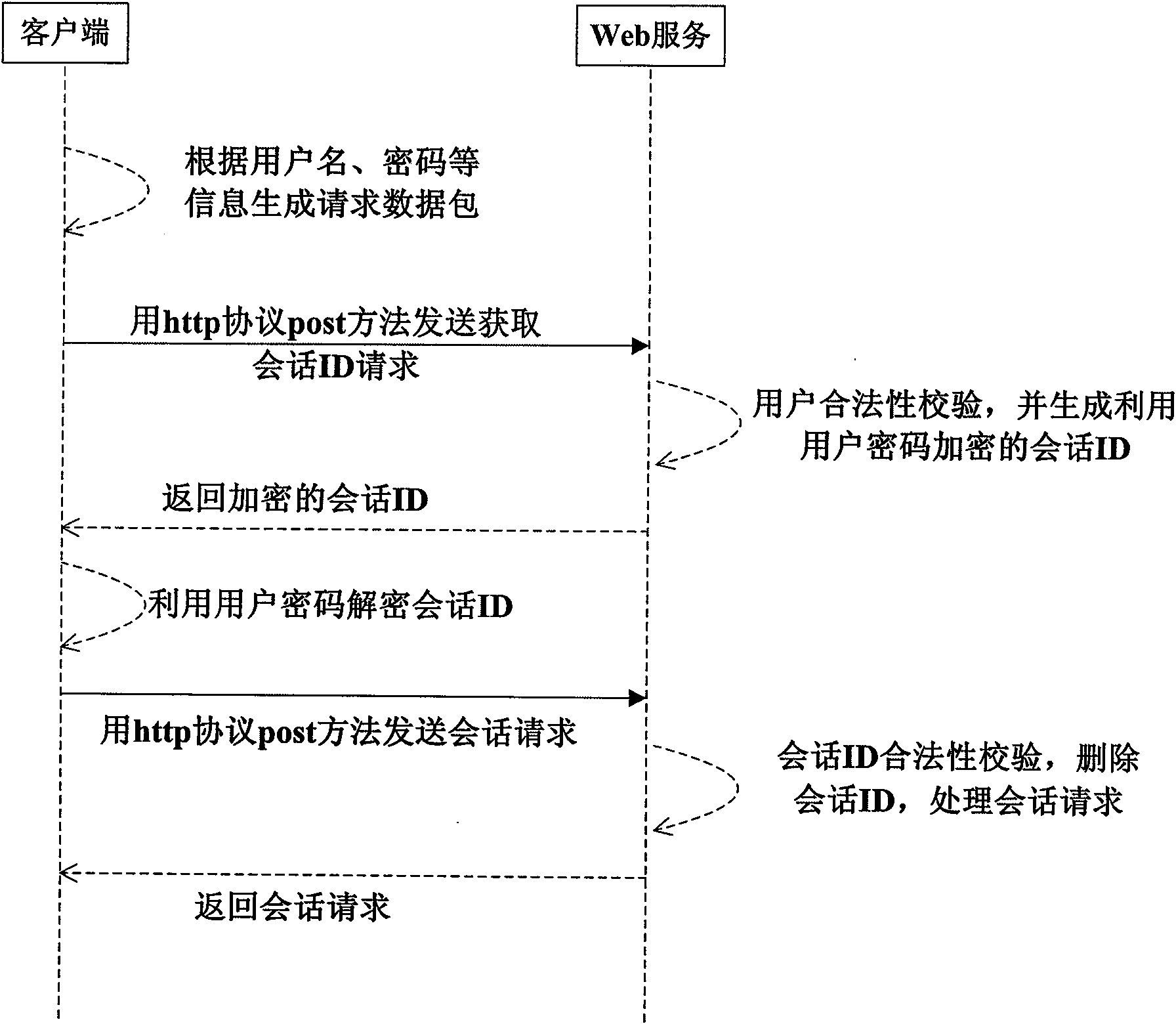
InactiveCN101640682AImprove securityReduce the possibility of leaksPublic key for secure communicationPlaintextWeb service
The invention discloses a method for improving the safety of Web service, which comprises the following steps: generating a request data packet comprising a first message digest generated by encrypting a user password by using a hash algorithm at a client side, and sending the data packet into a server side; using the hash algorithm to encrypt the stored user password by the service side, and generating a second message digest; comparing the first message digest with the second message digest by the server side, generating and storing a session identifier if the first message digest and the second message digest are same, using a symmetric encryption algorithm to encrypt the session identifier by taking the stored user password as a secret key, and sending the session identifier to the client side; using the symmetric encryption algorithm to decrypt the session identifier by taking the user password as the secret key by the client side to obtain a plaintext of the session identifier, and using the plaintext of the session identifier to send a session request to the server side; firstly judging whether the session identifier which is same as the session identifier in the session request exists or not in a memory by the service side, processing the session request and eliminating the session identifier if so, and returning a processing result.
Owner:深圳市励拓软件有限公司
Encryption-domain reversible information hiding method based on classified scrambling and hiding information classification
InactiveCN107103631AAdd classification scrambling encryptionAchieve protectionImage codingPictoral communicationPattern recognitionXML Encryption
Provided is an encryption-domain reversible information hiding method based on classified scrambling and hiding information classification. Variable pixels and fixed pixels are classified into blocks and scrambled in a classified way to reserve a hidden space of an encryption image; during image encryption, the image is divided into variable pixels and fixed pixels, bitwise XOR and scrambling encryption are carried out by taking the pixel as unit, and pixel values and positions are protected by encryption; at the same time, a block classification matrix serves as a part of an image encryption key, and further the possibility of leakage of content of the encryption image is further reduced; and during information hiding, the information to be hidden is divided into disclosed, authorized and private types according to functions, and protection of different levels is realized by using different encryption methods. During information extraction, the information can be extracted correctly by obtaining corresponding authorization, and the private information is very hard to obtain without a hidden secret key; and during image decryption, the encryption image the same with an original image can be obtained via an encryption key only. An algorithm is easy to realize, and the steganographic capacity is large.
Owner:SOUTHWEST JIAOTONG UNIV
Group key management method supporting user identity authentication
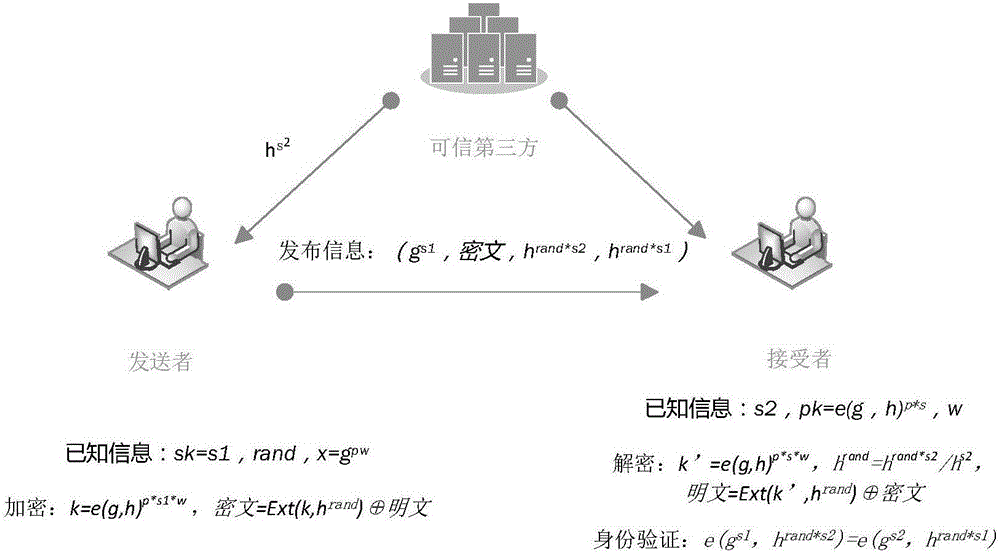
ActiveCN106301788ARelieve pressureReduce the possibility of leaksKey distribution for secure communicationPublic key for secure communicationPaired DataUser authentication
The invention discloses a group key management method supporting user identity authentication. The method comprises steps that comprises steps that an information sender, an information receiver and a trusted third party participating in identity verification and key management are included; the trusted third party is responsible for establishing an integral key system and managing the identity information of users; the information sender is used for acquiring an identity voucher disclosed by the data receiver from the trusted third party, carrying out encryption in combination with the private key pair data, utilizing the private information to realize data signature and then sending the data after signature to a whole multicast system, and the information receiver is used for carrying out decryption and source verification through utilizing a public key and the private key data. Compared with a traditional key scheme, key management pressure and key leakage possibility are greatly reduced.
Owner:WUHAN UNIV
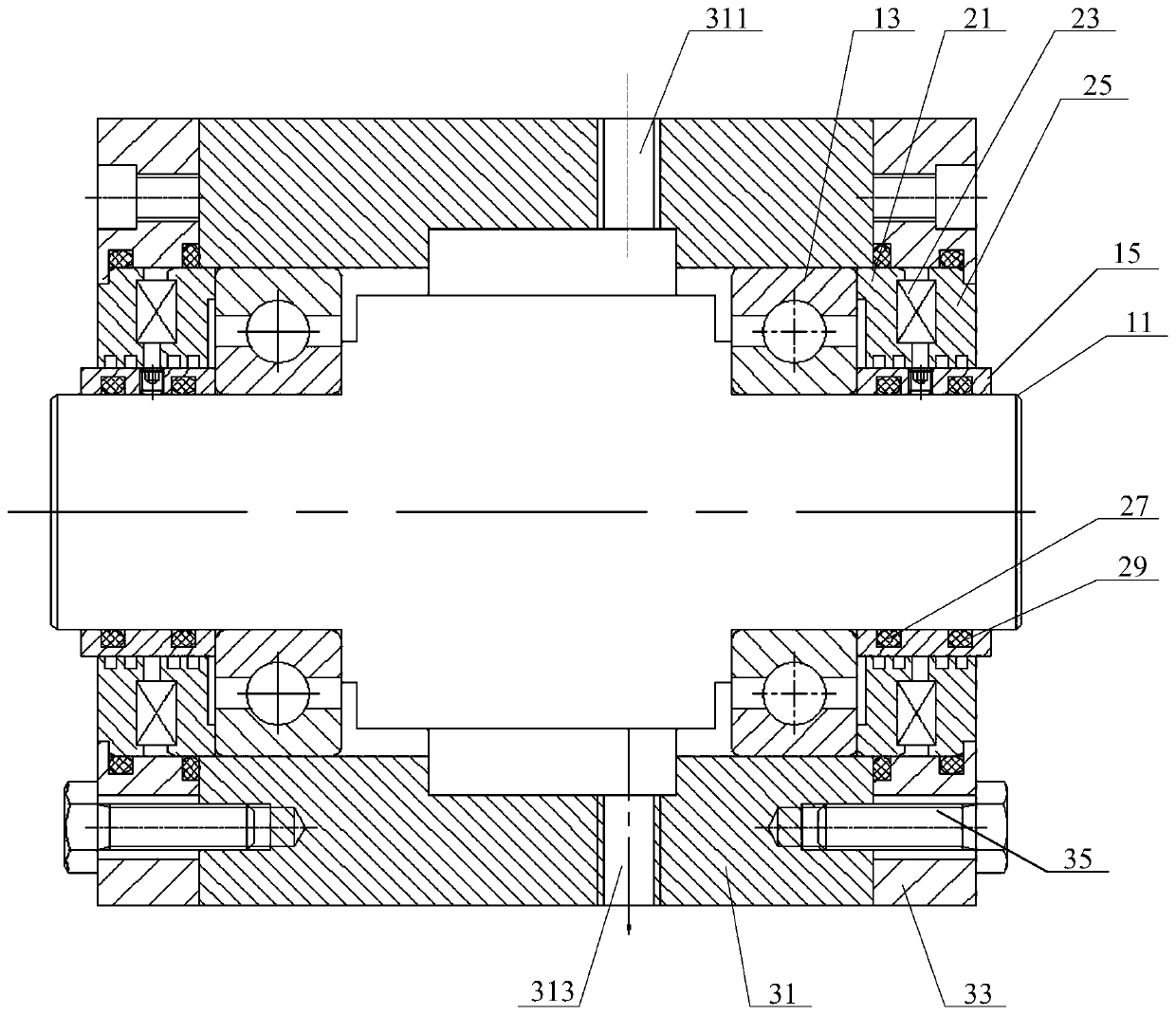
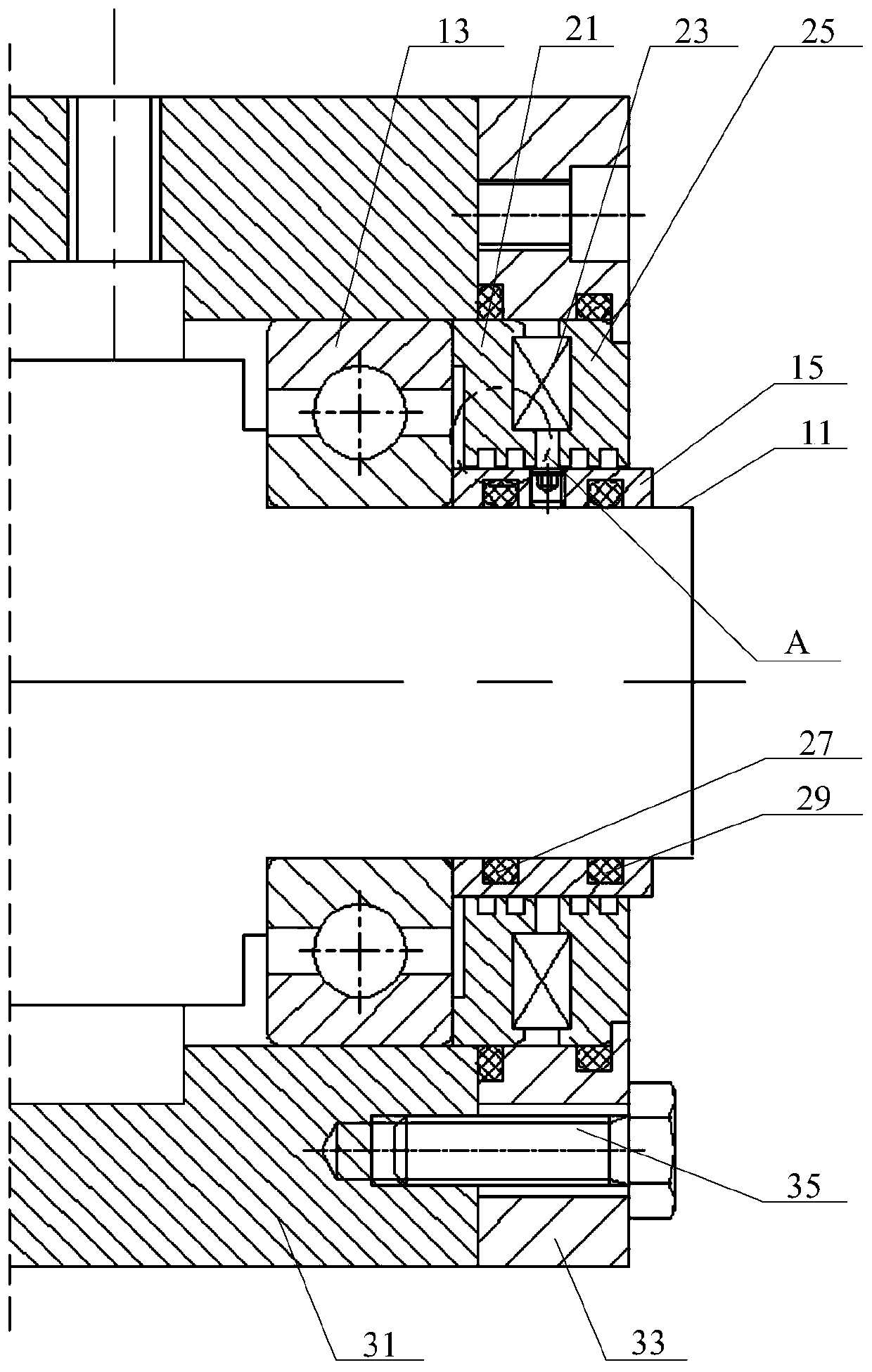
Sealing device and bearing box system
PendingCN110081177AImprove reliabilityGuaranteed service lifeEngine sealsBearing unit rigid supportHuman healthMagnetic line
The invention provides a sealing device and a bearing box system. The device is installed in a bearing cavity which is provided with a shaft, a bearing and a shaft sleeve, wherein the bearing and theshaft sleeve are arranged outside the shaft in a sleeving mode, the shaft sleeve abuts against the end surface of the bearing, and the shaft sleeve is made of a magnetic material; the sealing device comprises a first magnetic conductor, a permanent magnet and a second magnetic conductor; the first magnetic conductor, the permanent magnet and the second magnetic conductor are arranged outside the shaft sleeve in a sleeving mode, the first magnetic conductor abuts against the end surface, the permanent magnet is clamped between the first magnetic conductor and the second magnetic conductor, andthe permanent magnet, the first magnetic conductor, the shaft sleeve and the second magnetic conductor are matched to form a closed magnetic line; and gaps are formed between the outer wall of the shaft sleeve and the inner wall of the first magnetic conductor and between the outer wall of the shaft sleeve and the inner wall of the second magnetic conductor, and pole teeth are arranged on the inner wall of the first magnetic conductor and the inner wall of the second magnetic conductor, and the gaps and the pole teeth are all filled with magnetic fluid. The embodiment of the sealing device caneffectively ensure the sealing effect on the bearing cavity, thereby avoiding environmental pollution and harm to human health.
Owner:BEIJING UNIV OF CHEM TECH
Password safety system and password safety method
InactiveCN102970307AImprove retrieval convenienceEasy to rememberUser identity/authority verificationDigital data protectionUser inputPassword
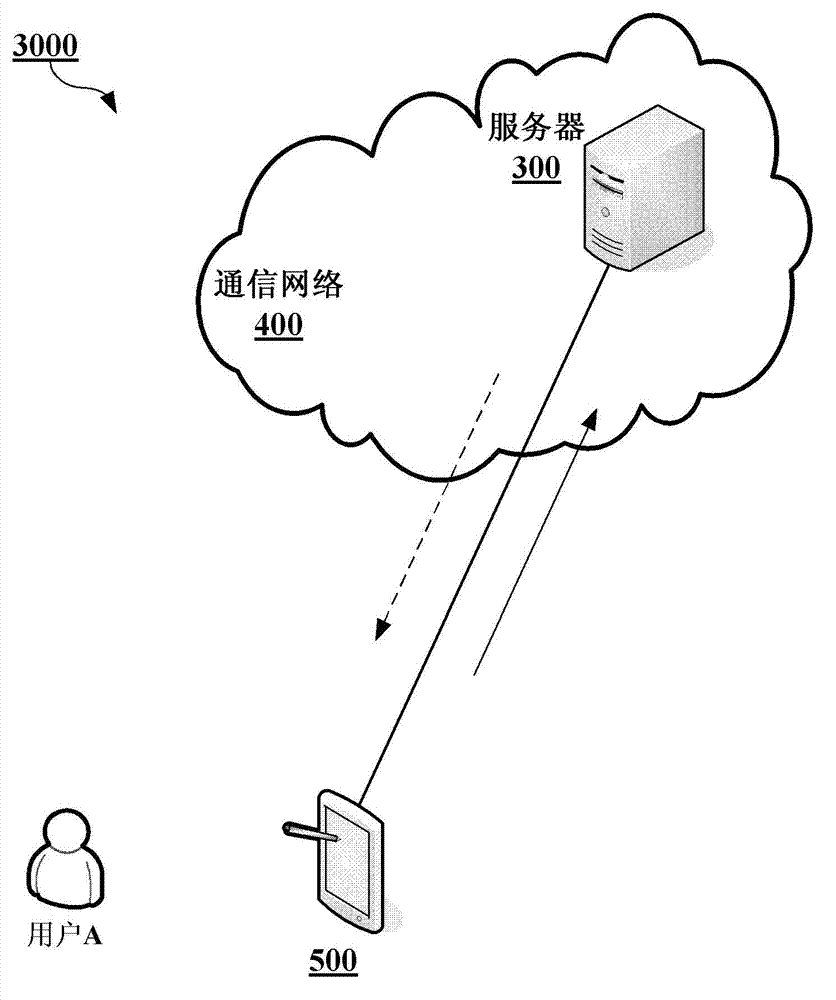
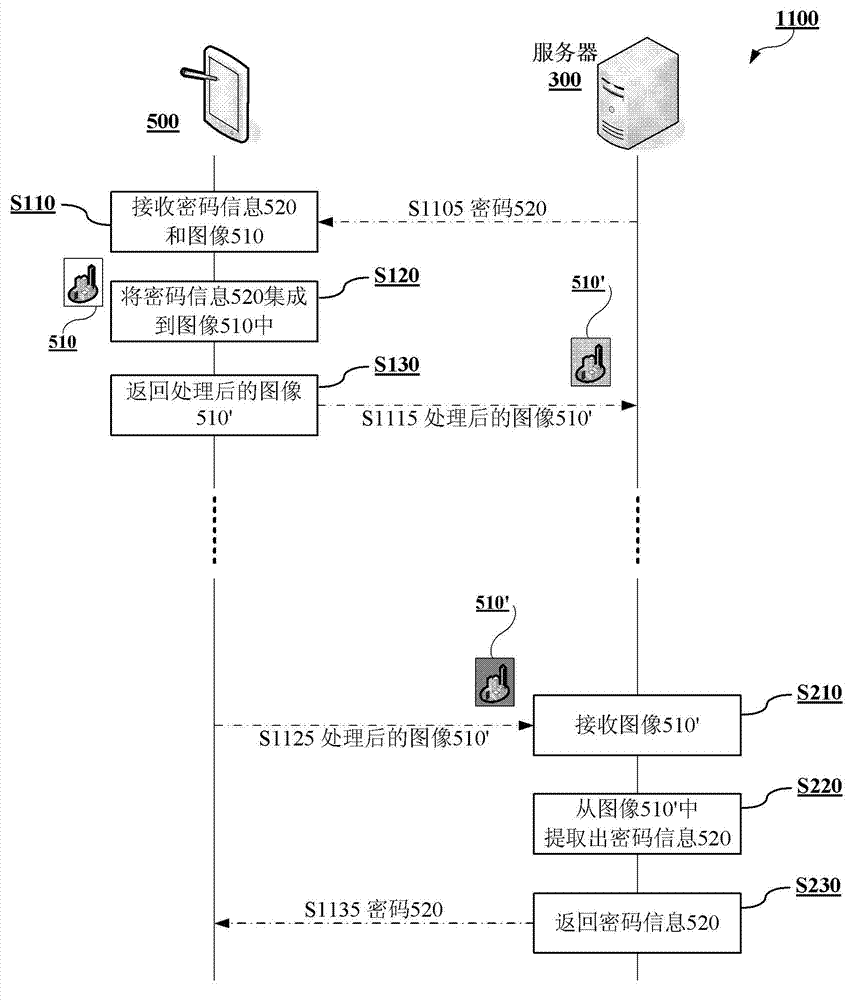
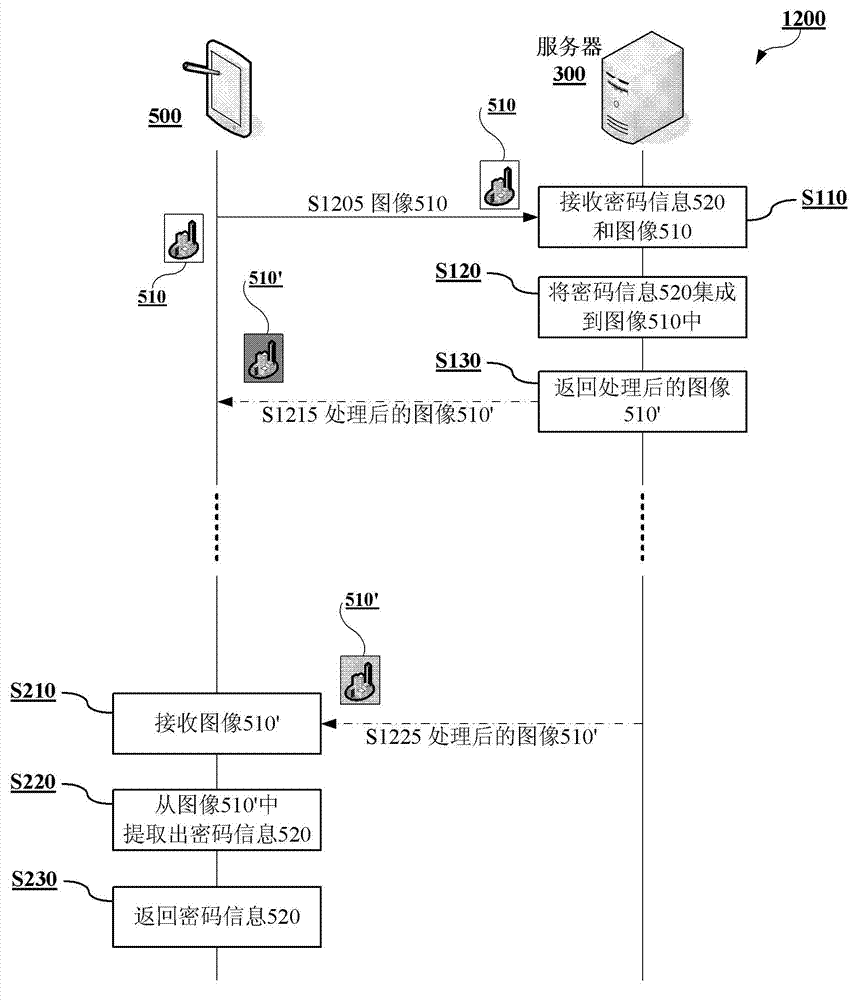
The invention provides a password safety system (3000). The password safety system comprises a server (300) and a terminal (500), wherein the terminal (500) is used for receiving password information and images input by a user, processing the images, integrating the password information into the data of the images in a mode that the use of the images is not influenced, and returning the processed images; and the server (300) is used for receiving the processed images input by the user, processing the processed images input by the user, extracting the password information which is integrated into the processed images input by the user in the mode that the use of the images is not influenced, and returning the extracted password information. The invention also provides a password safety method.
Owner:网秦无限(北京)科技有限公司
Insulated container based on integral cold storage plate and cold filling and cold supply method of insulated container
PendingCN110030781ASimplify manufacturing difficultyReduce the possibility of leaksDomestic cooling apparatusLarge containersEngineeringMechanical engineering
The invention discloses an insulated container based on an integral cold storage plate and a cold filling and cold supply method of the insulated container. The insulated container comprises a container body provided with a heat insulation container wall, and a cold storage plate device and a cold filling pipeline system are arranged in the container body. The cold storage plate device comprises at least one cold storage plate. Each cold storage plate comprises a cold storage plate shell and a longitudinal partition plate connected with the cold storage plate shell into a whole. One part is isolated out of the space in each cold storage plate shell by the corresponding longitudinal partition plate to serve as a cold filling channel, and the rest of parts of the space of each cold storage plate shell serve as a cold storage liquid cavity. The cold filling pipeline system comprises a secondary refrigerant inlet pipe, a secondary refrigerant return pipe and a cold filling connector. The cold filling channels of all the cold storage plates are connected between the secondary refrigerant inlet pipe and the secondary refrigerant return pipe. By means of the cold filling and cold supply method, a ground movable or fixed cold filling station is utilized for filling the cold storage plates with cold, cold storage liquid in the cold storage plates stores cold of the maximum quantity, andsource-free refrigerating in the transporting process is achieved.
Owner:CHINA RAILWAYS CORPORATION +2
Encryption and decryption process method, apparatus and device
ActiveCN103946856AReduce the possibility of leaksIncrease credibilityUser identity/authority verificationDigital data protectionComputer hardwareDigital signature
An embodiment of the invention provides an encryption and decryption process method, an apparatus and a device. The method includes following steps that the device
Owner:HUAWEI TECH CO LTD
Water cooling plate structure applied to electric automobile
InactiveCN105990621AImprove heat transfer efficiencyImproved temperature distribution consistencySecondary cellsEngineeringWater cool
The invention provides a water cooling plate structure applied to an electric automobile. The water cooling plate structure comprises a plurality of cooling plates arranged in sequence, wherein gaps for accommodating batteries are reserved among the adjacent cooling plates. Each cooling plate comprises tube bundle plates respectively located at two ends, a plurality of finned flat tubes are sequentially arranged between the tube bundle plates at two ends, water chambers are arranged on the tube bundle plates, and the finned flat tubes are communicated with the water chambers. The water chambers, on the same side, of the adjacent two cooling plates are communicated. At least one of the water chambers on the same side is provided with a module water inlet-outlet. The water cooling plate structure can improve the heat exchange efficiency and the consistency of temperature distribution, is low in cost and easy to process and can be produced in a large-scale mode. The reliability is improved, and the leakage possibility is reduced. The weight is reduced by 60%-80%, the number of weld joints is decreased by 70%-90%, and therefore the problems existing in existing cooling plate design are effectively solved.
Owner:BEIJING BOSTON POWER BATTERY
Password input method and mobile terminal using same
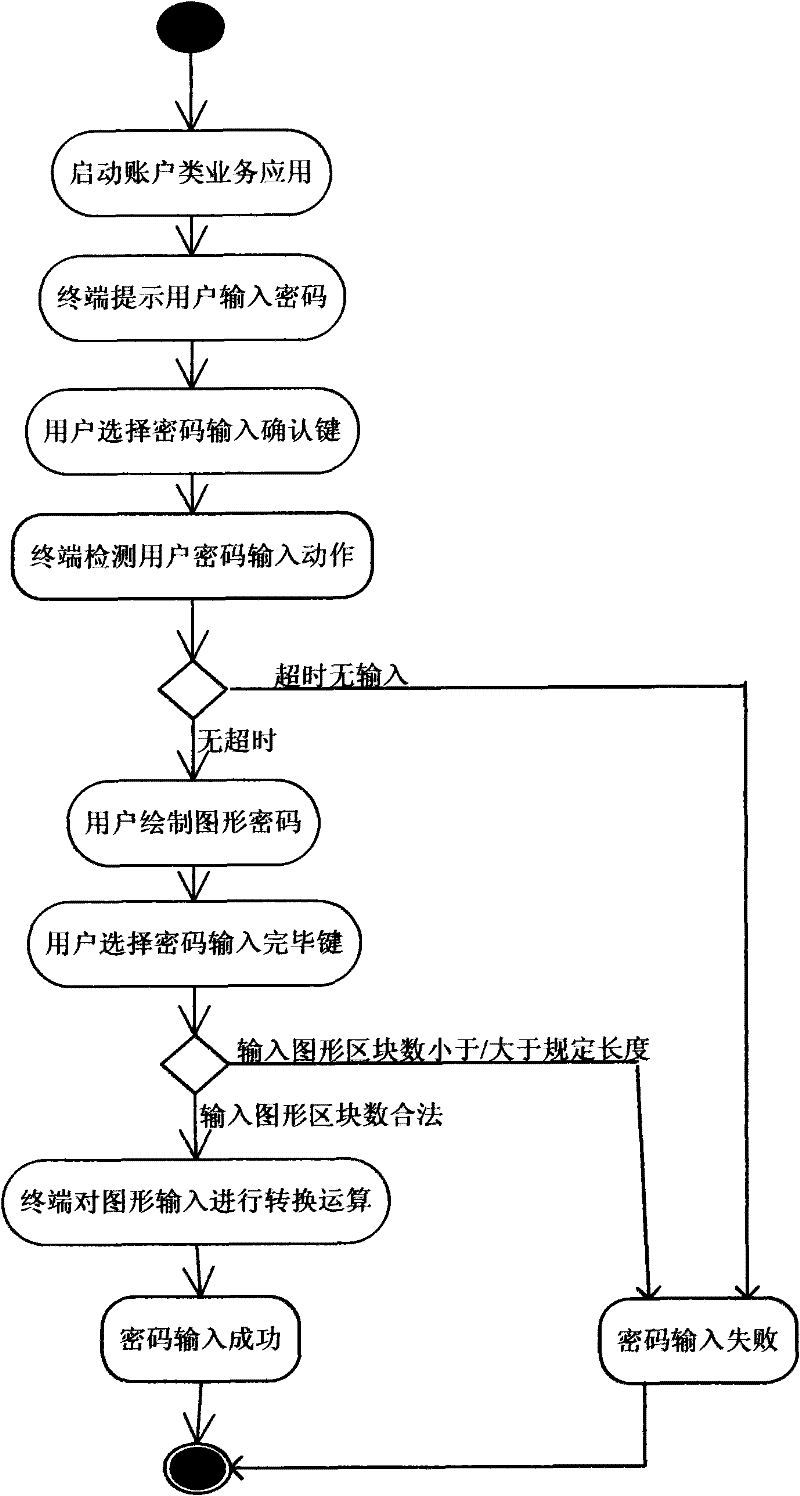
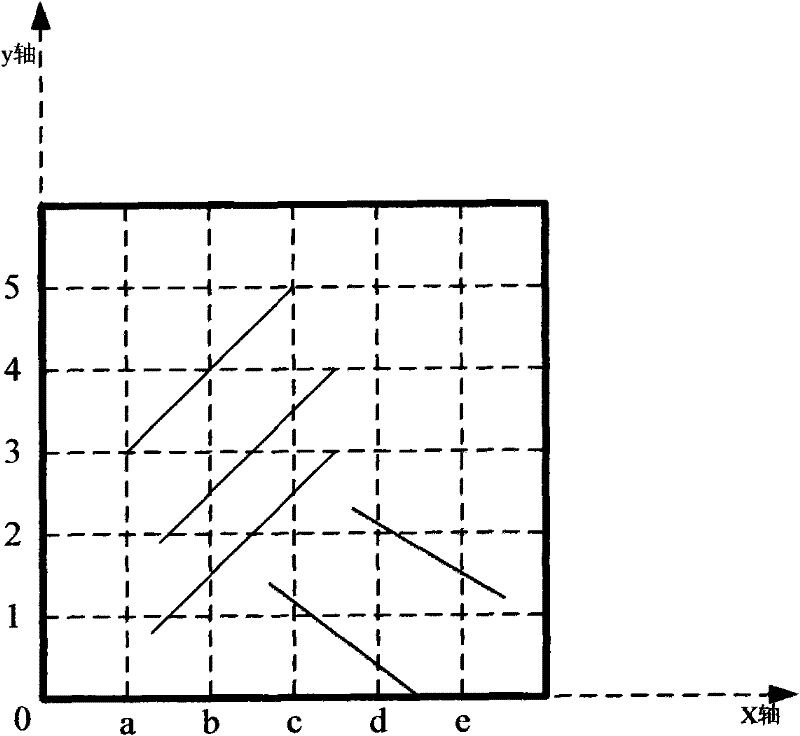
ActiveCN102236440AAvoid disadvantages that are not conducive to entering passwordsReduce the possibility of leaksDigital data authenticationTelephone sets with user guidance/featuresGraphicsForm analysis
The invention relates to a password input method, which mainly comprises the following steps that: a mobile terminal is provided, wherein the mobile terminal has built-in service application, a graphics detection module, a graphics conversion module and a graphics input conversion table, and has a touch display screen; the service application is started, and the mobile terminal prompts a user to input a password; the user confirms the input of the password; the user draws graphics on the touch display screen, and the graphics detection module detects the graphics drawn by the user to form analysis elements; and the graphics detection module submits the analysis elements to the graphics conversion module, and the graphics conversion module maps the analysis elements to the preset graphics input conversion table to obtain a converted character sequence. In addition, the invention provides the mobile terminal using the method. By the password input method provided by the invention, an input way is simple, convenient, fast and favorable for user experiences, and the password setting security is improved.
Owner:SHANGHAI LINKCHIP SEMICON TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com