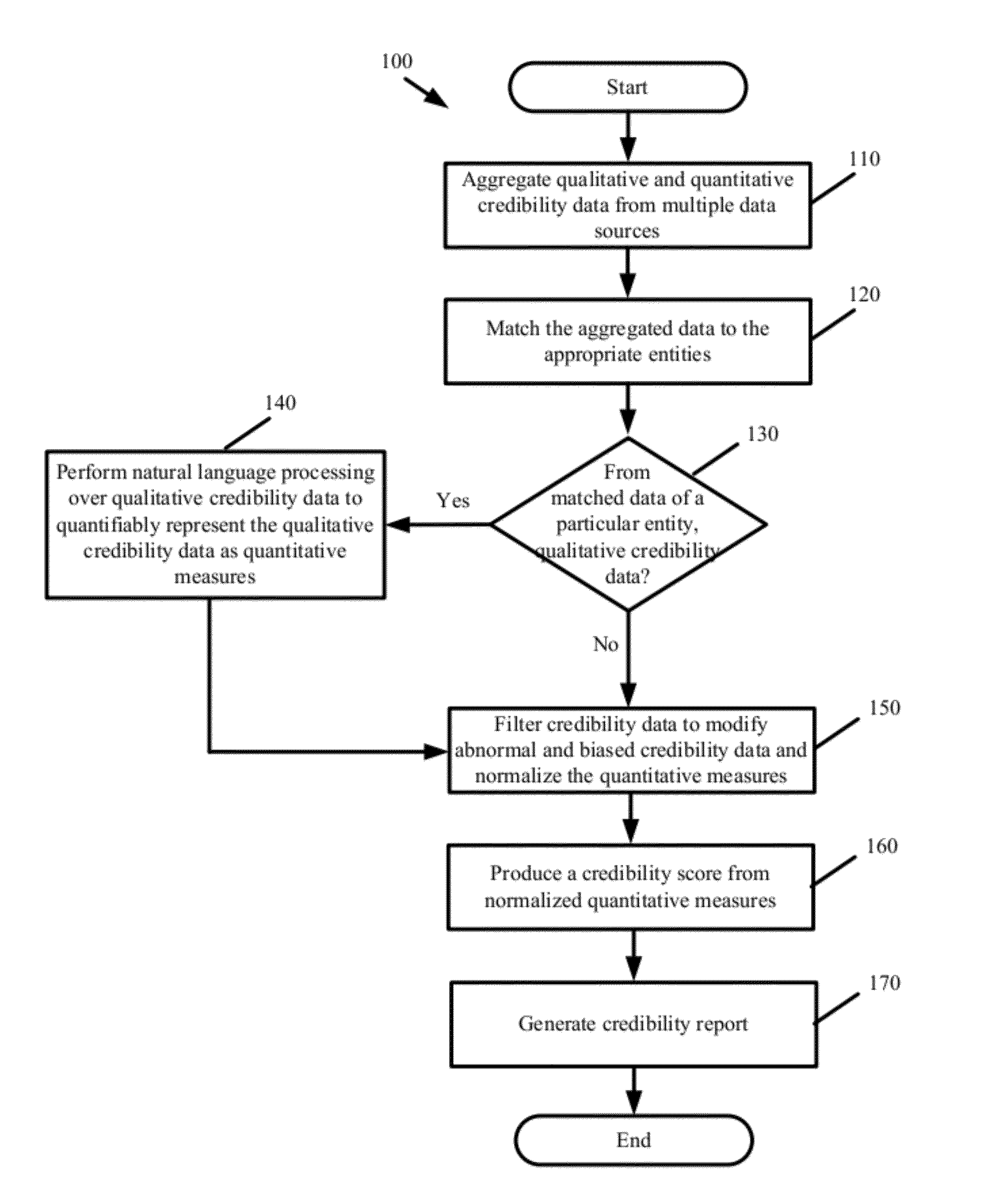
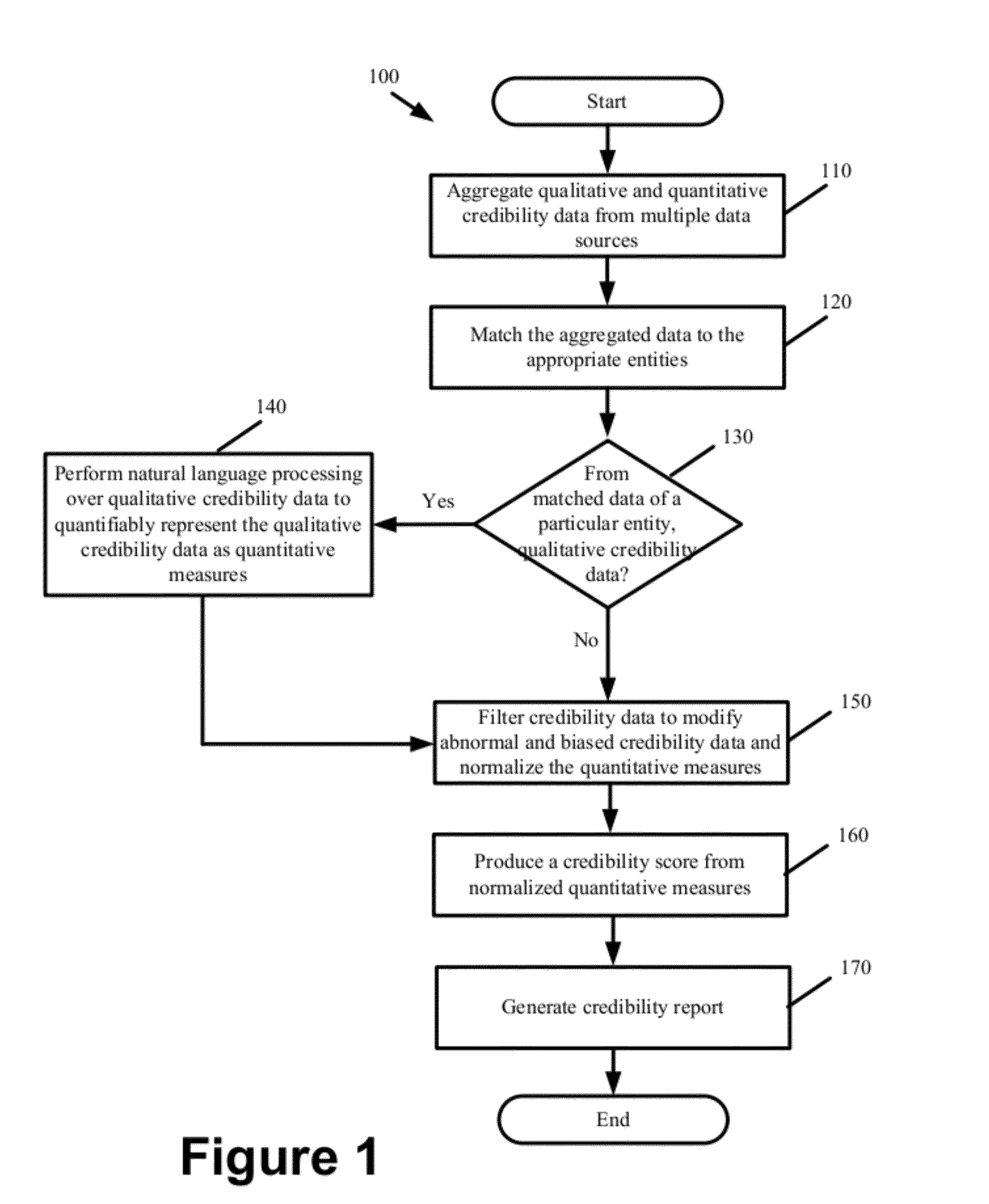
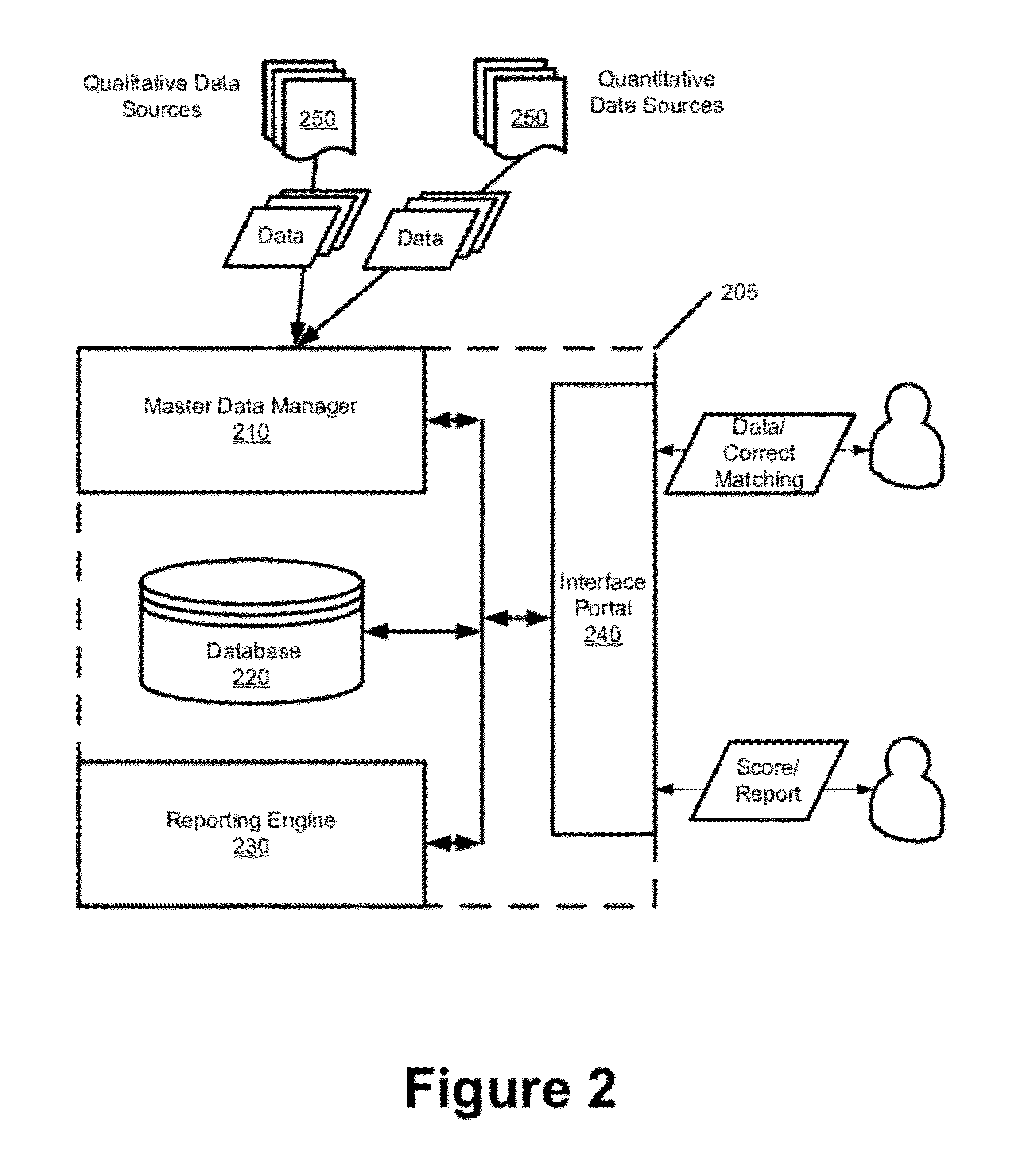
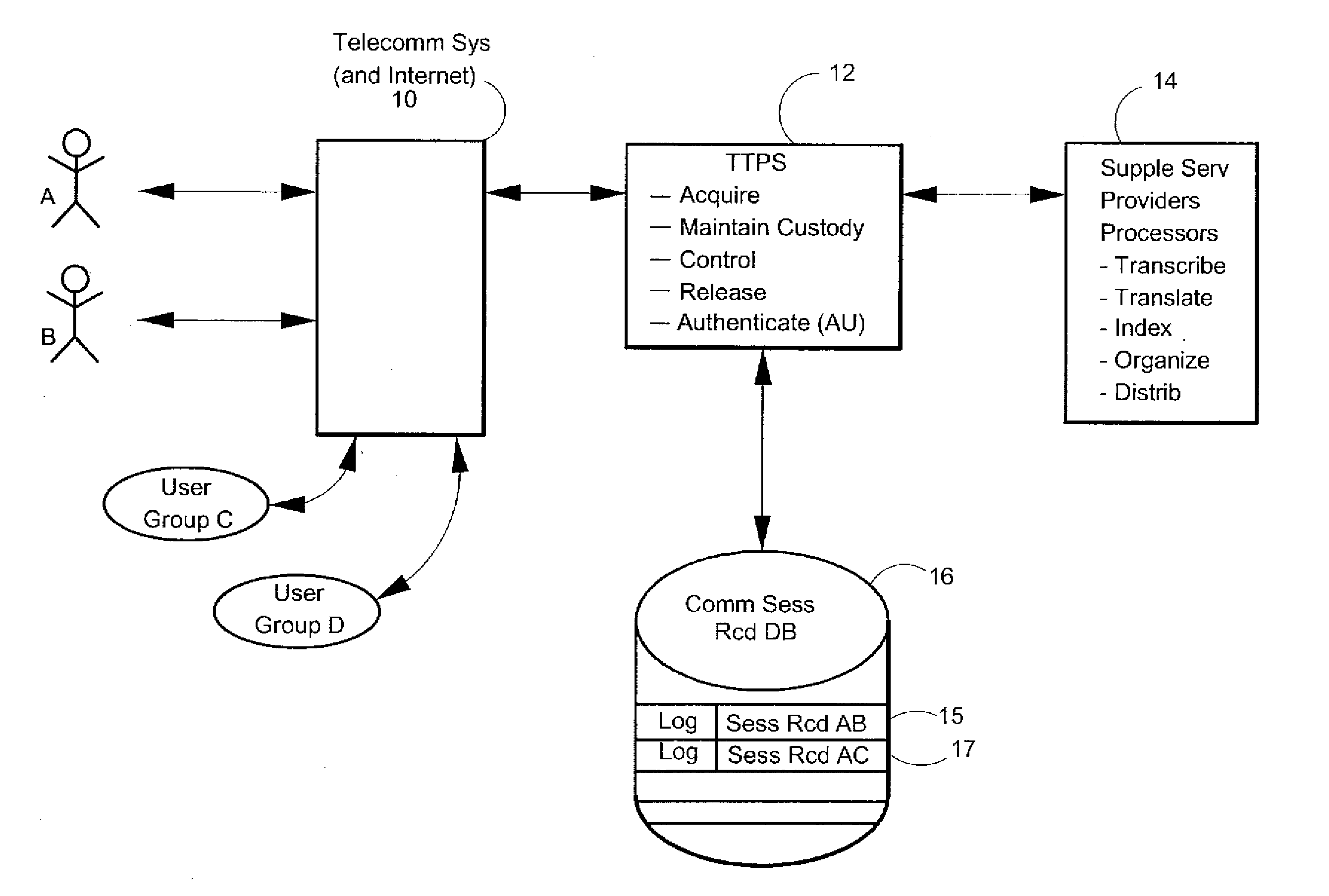
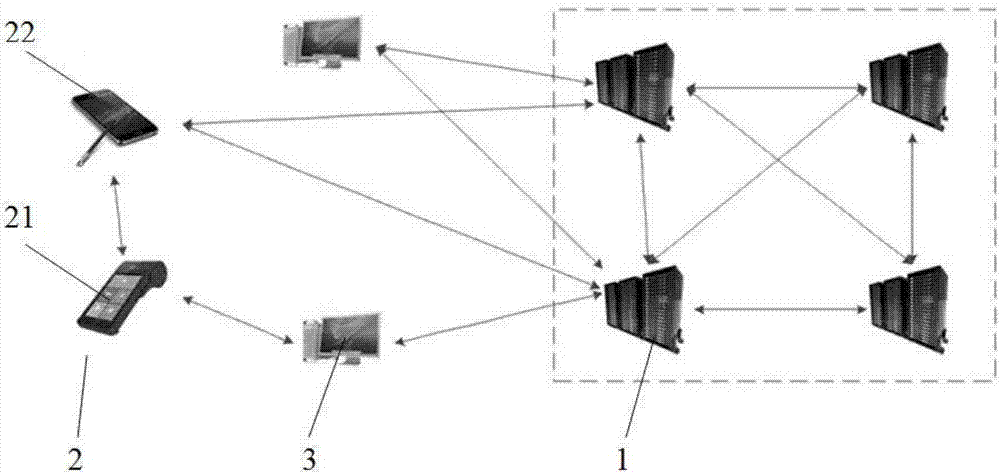
Patents
Literature
7484results about How to "Increase credibility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Social networking website & web-based system for collecting & presenting real-time user generated information on parties & events.
InactiveUS20120124458A1Increase credibilityImprove the level ofData processing applicationsMultiple digital computer combinationsTime informationWeb site
This invention is a social networking website & web-based system that allows users to post ‘party reports’—detailed, real-time information about current ongoing parties and events that they know of; allows users to comment and upload pictures & videos on the posted information in real-time; and presents this information in an organized fashion—by city, school or location, by date & time, or by both. The system also contains algorithms used to determine the top or best party cities, schools or locations based on predetermined formulas & user posted information. The website also allows users to connect with other registered users on the website and define them as their ‘peeps’ as well as create ‘crews’, which are close-knit groups of people that they usually party to go out with.
Owner:CRUZADA NAZARENO BRIER
Indices for Credibility Trending, Monitoring, and Lead Generation
ActiveUS20120278767A1Credibility of may fallIncrease credibilityFinanceInput/output processes for data processingBusiness enterpriseBusiness practice
Some embodiments provide a credibility system that computes credibility scores to quantify the credibility of different businesses and to coalesce the generated credibility scores into various indices. The indices comparatively present the credibility of a particular business relative to other businesses along one or more dimensions. Based on the indices, the system identifies trends in the credibility of a particular business. The system derives preliminary credibility for a new business for which credibility data has not yet been obtained based on credibility that has been previously established for other businesses in an index associated with the new business. The system provides automated services for monitoring credibility of a business and for generating alerts to notify the business that its credibility has reached various thresholds. The system identifies business practices that improve upon or adversely affect the credibility of a particular business.
Owner:DUN & BRADSTREET EMERGING BUSINESSES
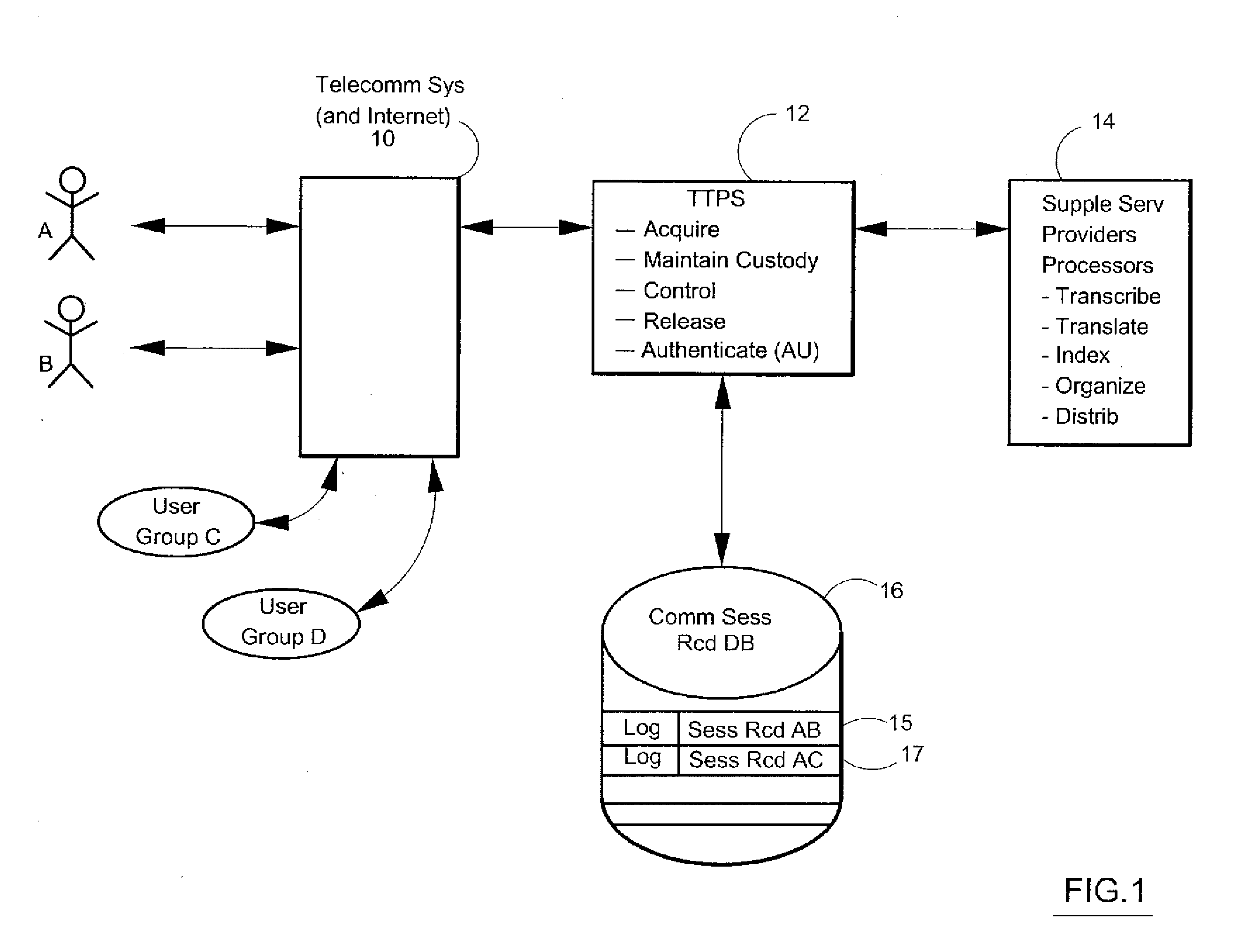
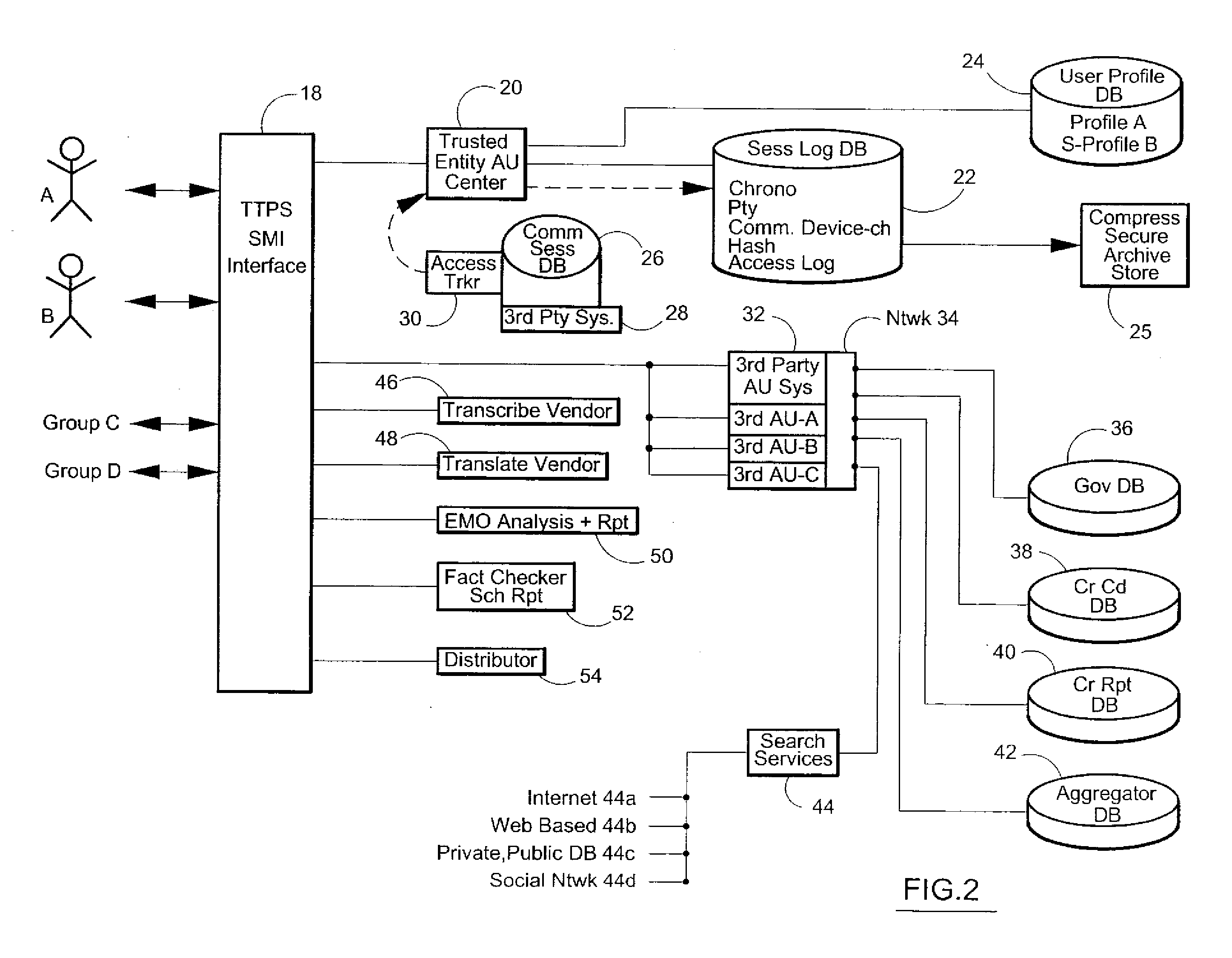
Consent, Signature and Recording Retention in a Certified Communications System
InactiveUS20110287748A1Increase credibilityHigh quality archivalInterconnection arrangementsSpecial service for subscribersComputer hardwareData acquisition
System has consent, signature, recording and retention functions. Near post-sessional data acquisition gathers nominal comm device information from participants. Active online phones are sent a SMS with the recorded event ID, a hyperlink and password for system access. Otherwise, data is acquired for another text message enabled phone or user email. If disconnected, the user is called for additional data. A contractual relationship is established with these functions. With an ACK-consent upon system access, an ACK-consent by the parties, a RECORD ON command, and a recorded intent-to-contract, the system creates an enforceable contract by storing the ACKs and recorded session.
Owner:CERTICALL
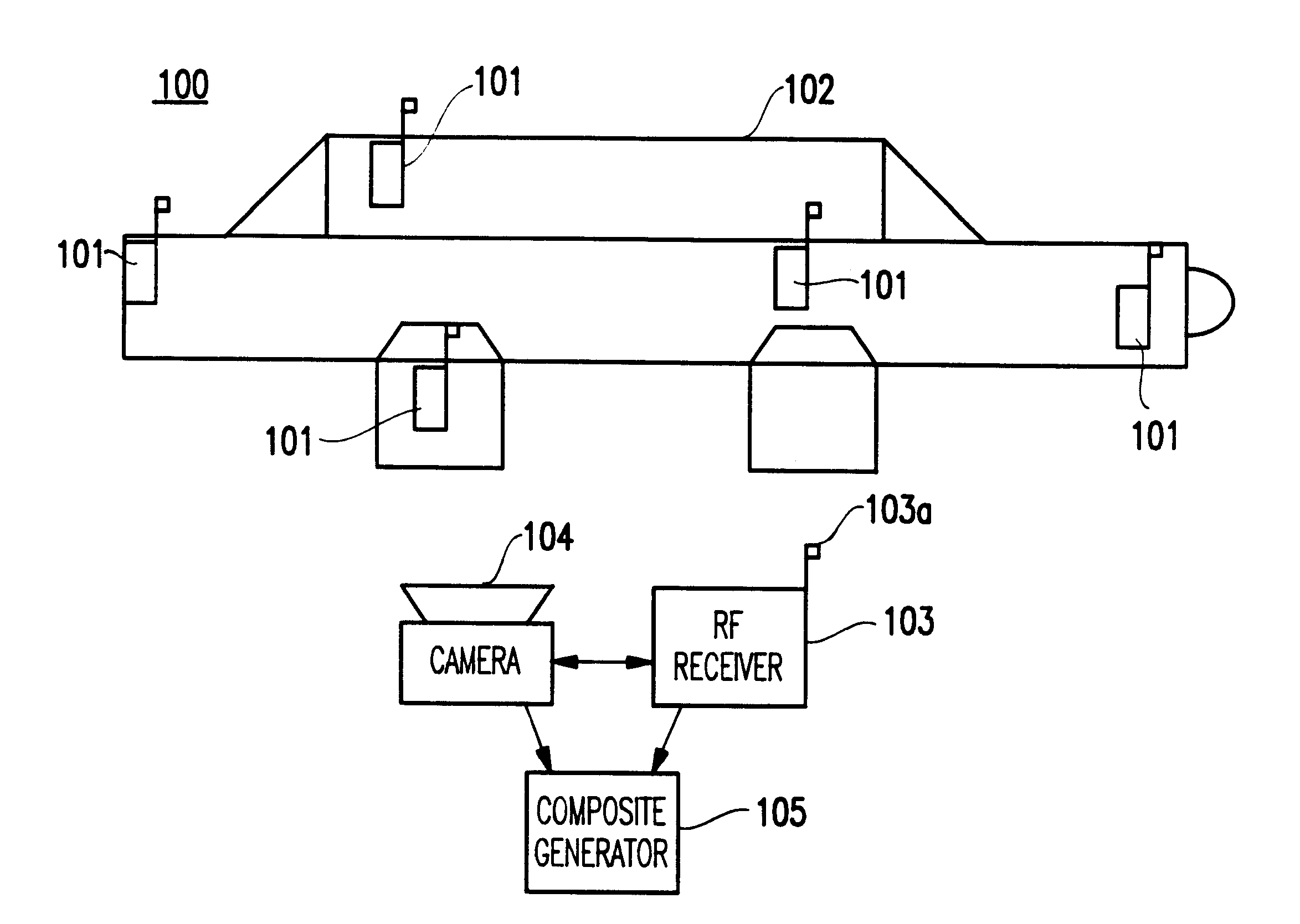
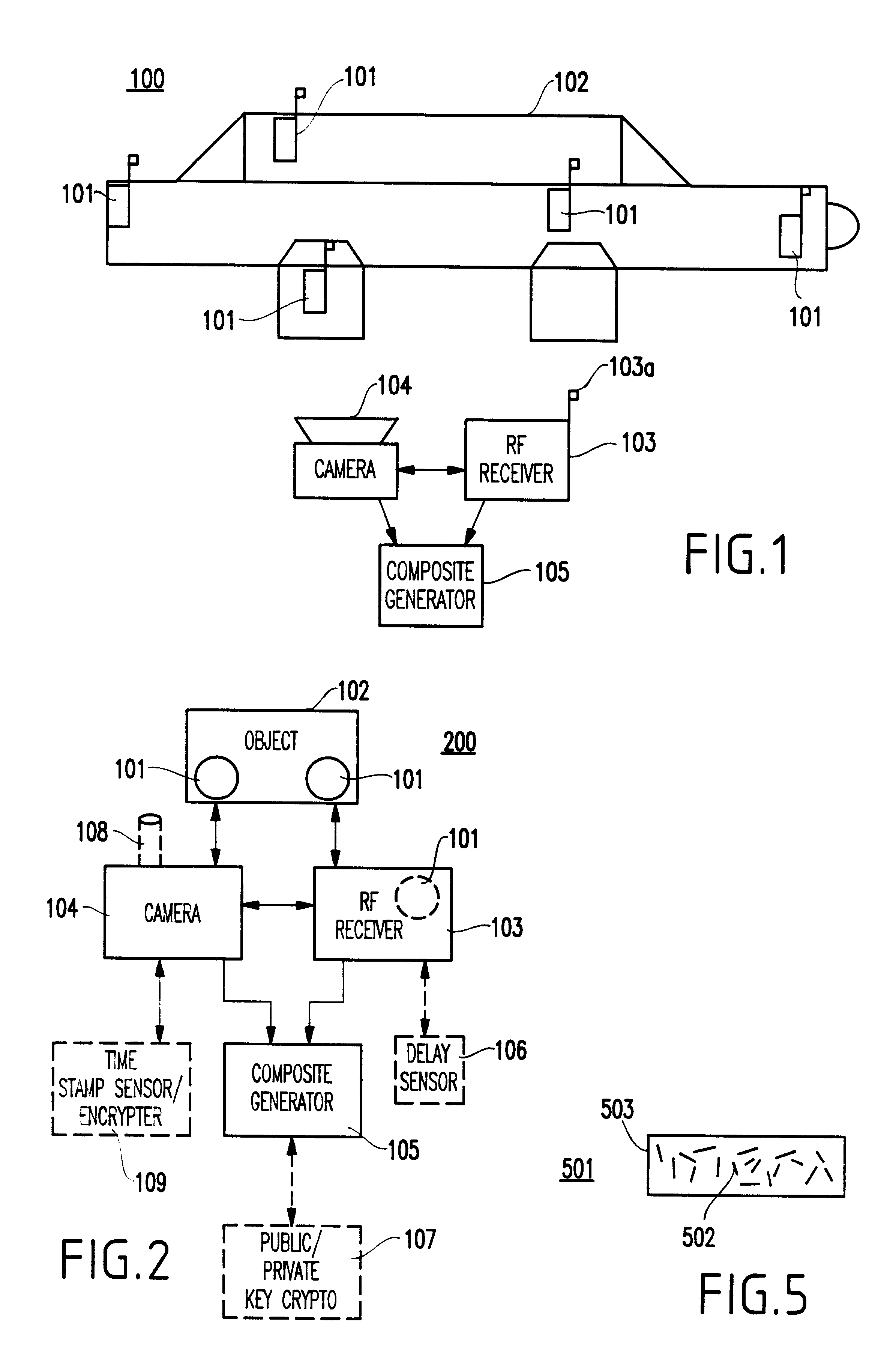
Method and system for authenticating objects and object data
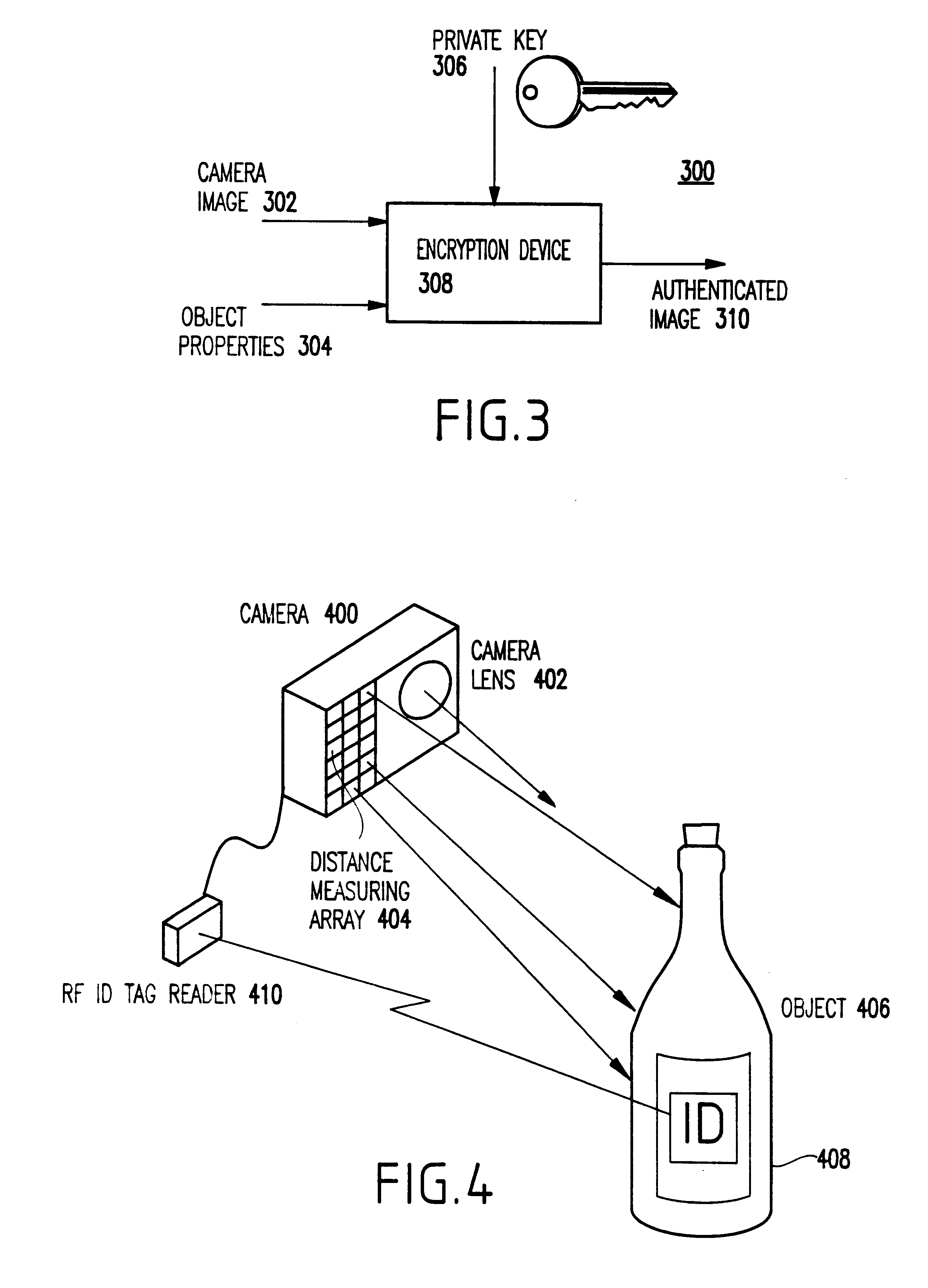
InactiveUS6397334B1Improve reliabilityIncrease credibilityTelevision system detailsFinanceVideo camera
A system and method for authenticating an image of an object, include at least one identifier associated with the object, a receiver for interrogating the at least one identifier to produce identification information, a camera system for recording an image from the object including the at least one identifier, and a composite generator for encoding the identification information from the receiver along with the image acquired by the camera system, to produce composite data.
Owner:IBM CORP
Automated Omnipresent Real-time Credibility Management System and Methods
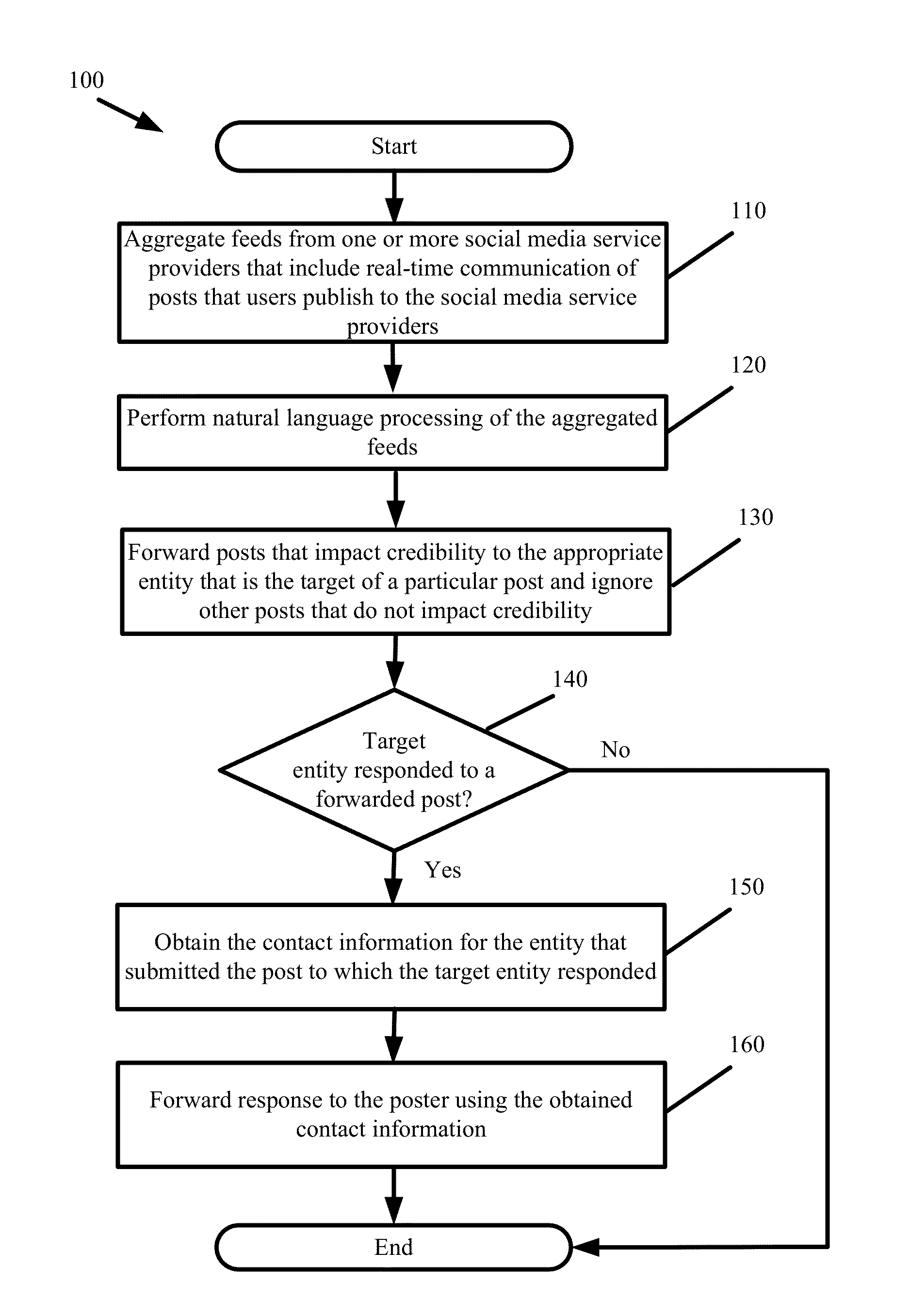
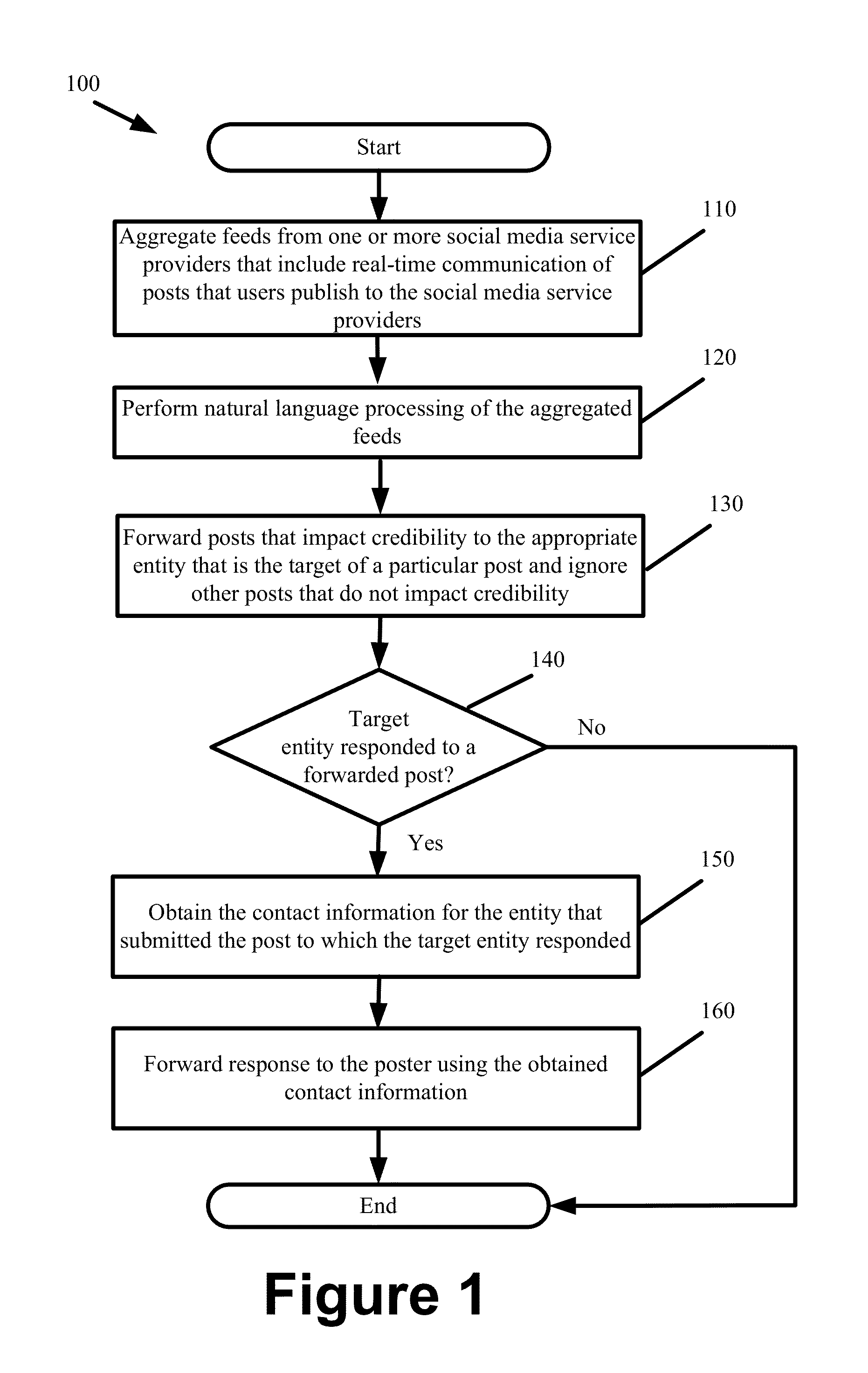
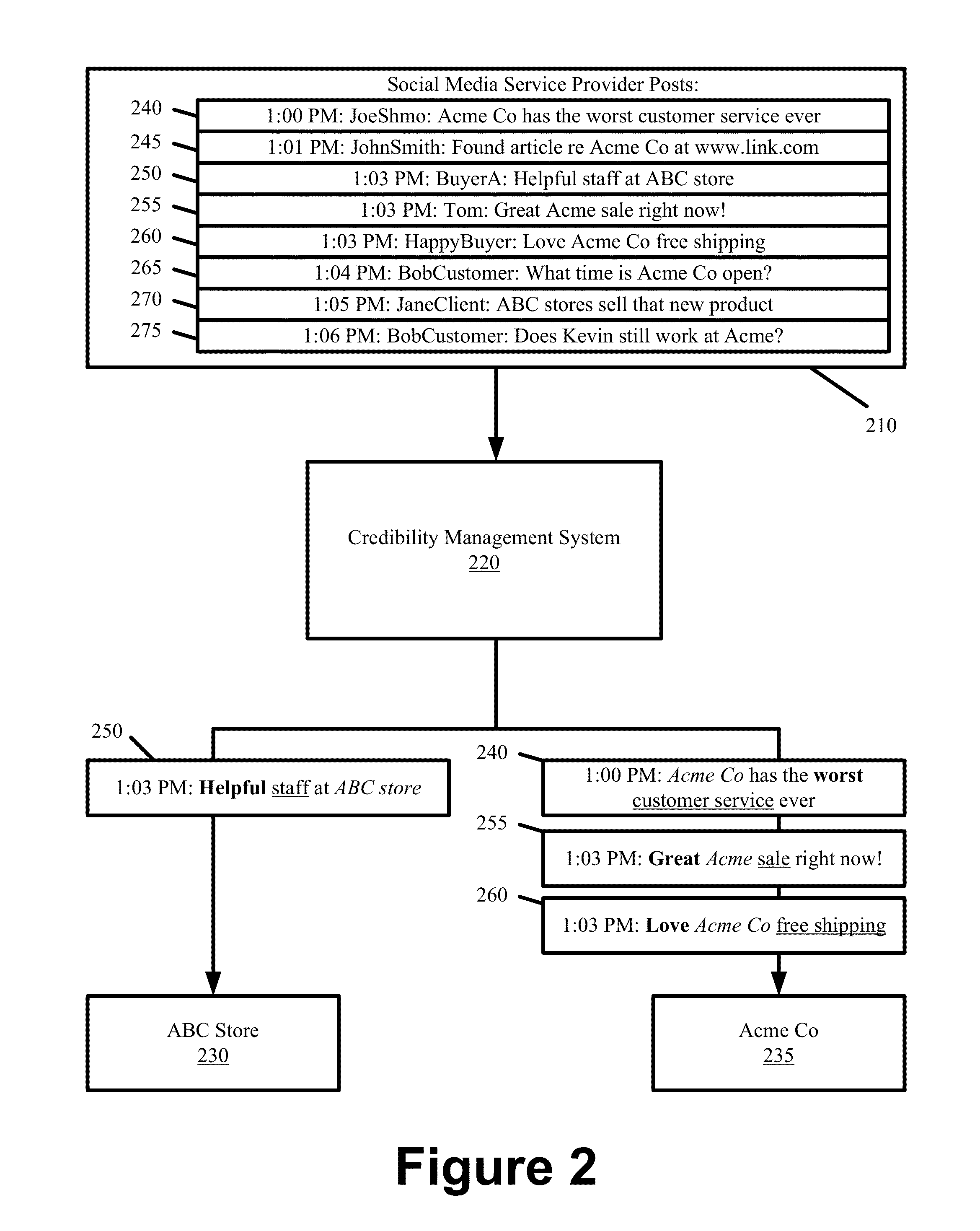
ActiveUS20130132151A1Reduce impactIncrease credibilityFinanceOffice automationSocial mediaManagement system
Some embodiments provide a credibility management system that aggregates user posts from several social media sites contemporaneously with the posts being published to those sites. The system parses each of the aggregated posts to identify an entity that is targeted in each of the posts and presents the posts to the targeted entities in a real-time manner. The credibility management system computes a score to determine the impact that a user post would have on the credibility of a targeted entity. By presenting the computed scores and aggregated posts to the targeted entities, the credibility management system notifies the targeted entities about what is being said about them across social media, identifies the impact of those posts, and provides a platform whereby the targeted entities can reply in order to mitigate or improve the impact that the posts would have on credibility.
Owner:DUN & BRADSTREET EMERGING BUSINESSES
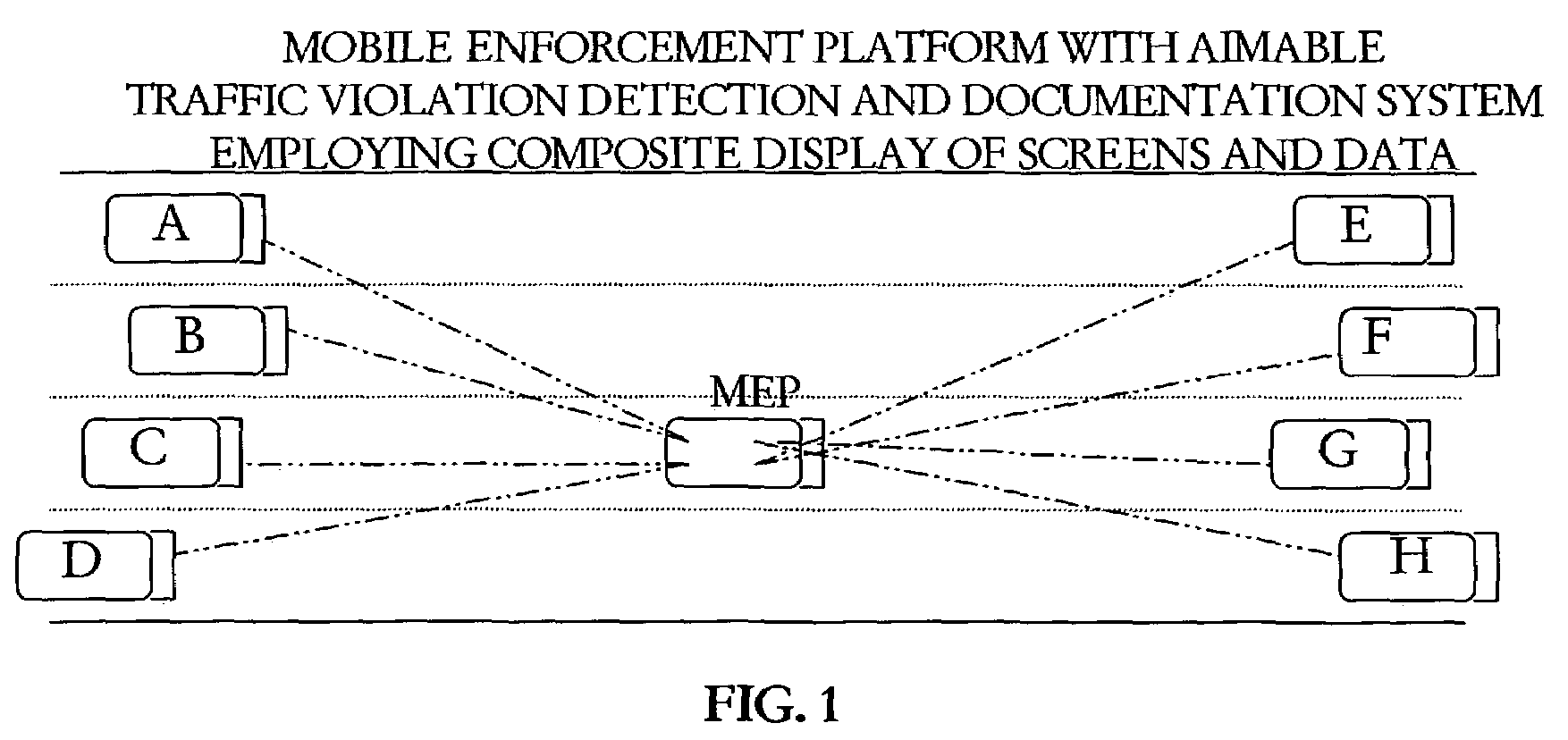
Mobile enforcement platform with aimable violation identification and documentation system for multiple traffic violation types across all lanes in moving traffic, generating composite display images and data to support citation generation, homeland security, and monitoring
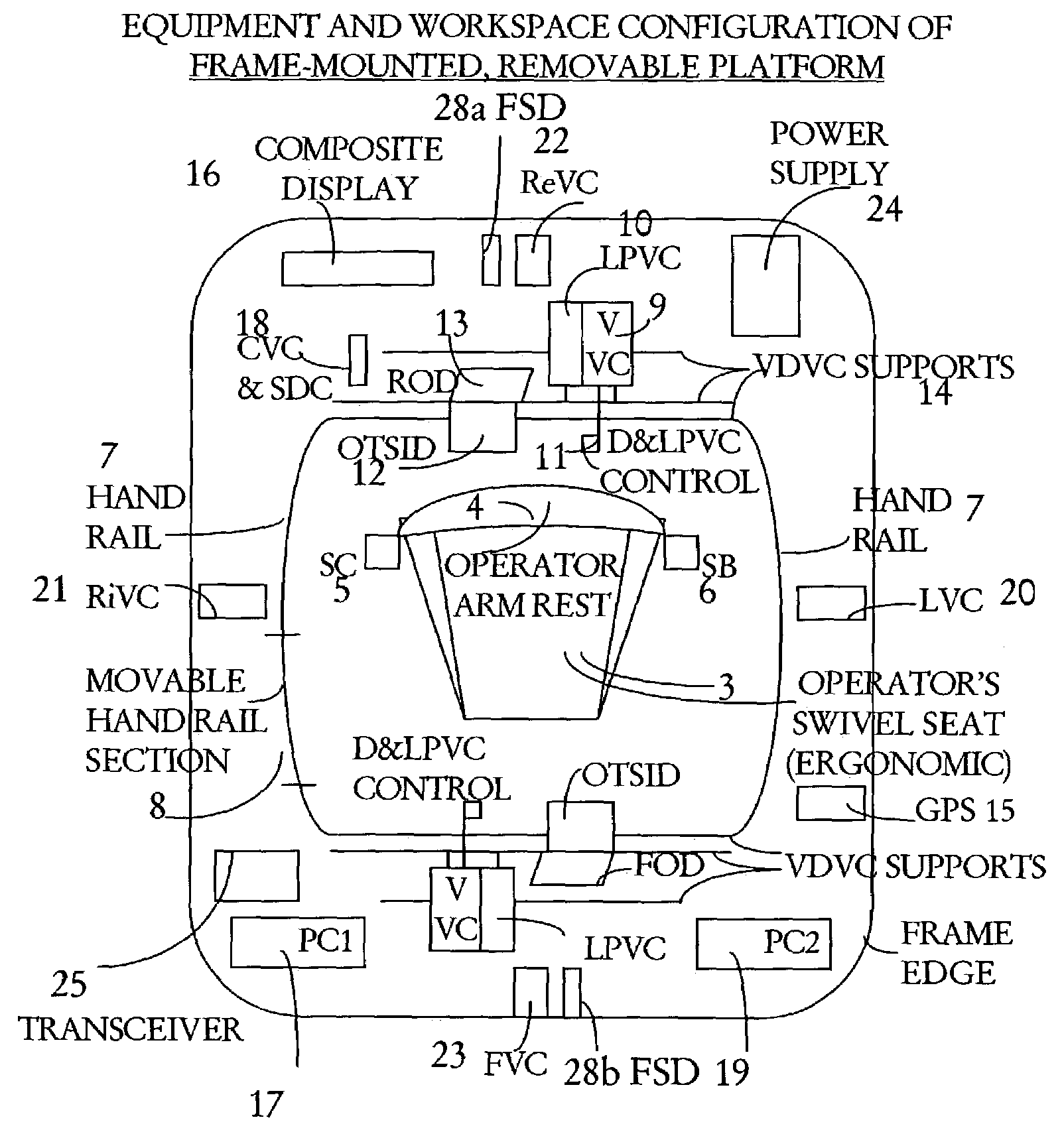
InactiveUS7262790B2Enhance it credibility and constructive impactIncrease credibilityAnalogue computers for vehiclesAnalogue computers for trafficData inputDocumentation system
A manned, mobile traffic enforcement platform with aimable violation detection and documentation devices, employing digital video and still images, incorporating contextual information as well as data input by the system operator and driver, with numerous commercial-off-the-shelf components and a physically integrated composite display. The mobile enforcement platform (MEP) is operated by trained system operators, typically sworn-officers, who apply pre-determined criteria, protocols, procedures and routines to generate conclusive, court-acceptable violation documentation. MEP supports detection, identification, and documentation of violations in any lane behind or in front of the moving MEP vehicle or from the roadside. MEP captures most types of moving violations, including aggressive driving, in readily retrievable documentation formatted for later mail citation and court use. MEP increases police and court productivity, reduces police officer paperwork and court time, increases enforcement credibility, reduces crash costs and fatalities, improves highway safety, and augments homeland security capabilities.
Owner:BAKEWELL CHARLES ADAMS
Methods for encouraging charitable social networking
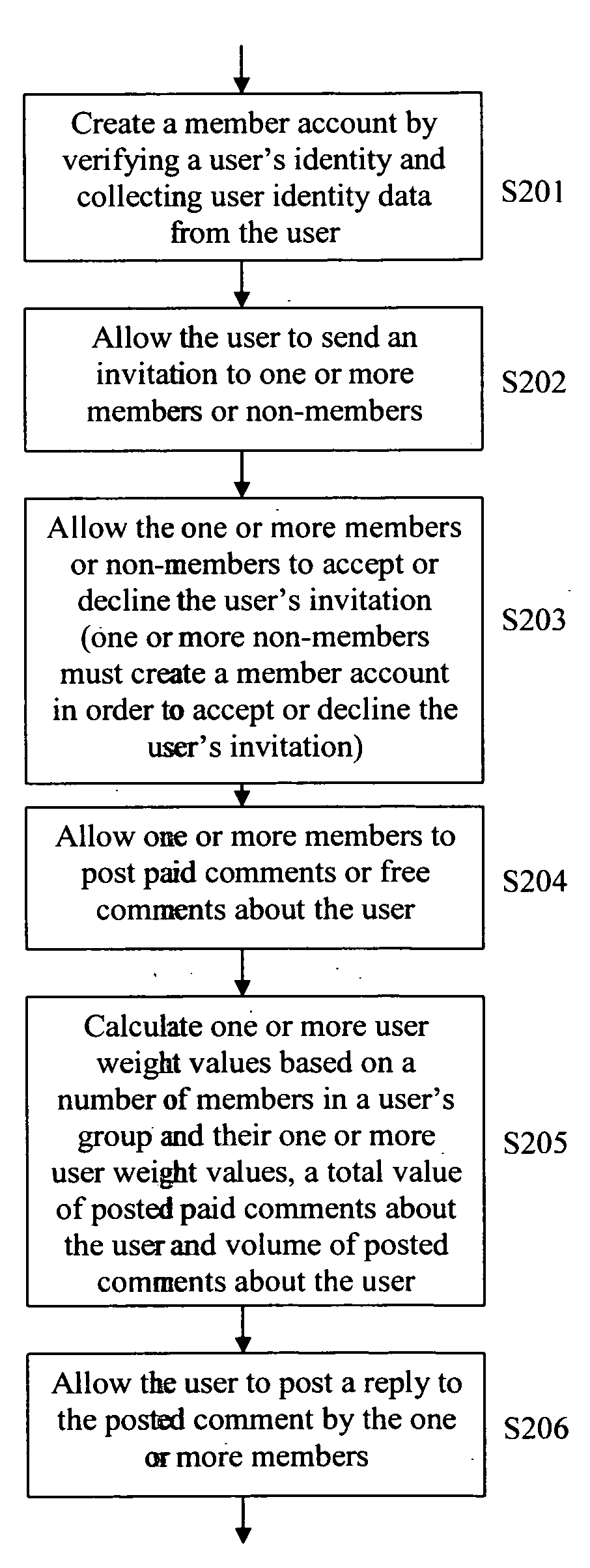
A method of encouraging charitable donations by individuals who are members of a social network is disclosed. A user creates a member account by supplying user identity data from the user and creates a campaign, wherein the created campaign is associated with one or more charities and a financial goal. The user sends invitation to one or more members or non-members and the one or more members or non-members may accept or decline the user's invitation. The one or more members are given the option to donate any amount of money to a charity to post comments about the user, where the monetary value of the donation is associated with the comments posted such that a higher amount donated represents a higher trustworthiness of the comments. The one or more members or non-members may support the campaign by donating money to the one or more charities to help reach the financial goal. One or more user weight values are calculated based at least on a total volume of members or non-members who support the campaign by donating money to the one or more charities and / or a total monetary value of the money donated by the one or more members or non-members, where the one or more user weight values represent reliability of a user's reputation.
Owner:STAY AWAKE INC
Method and system for constructing electronic evidence
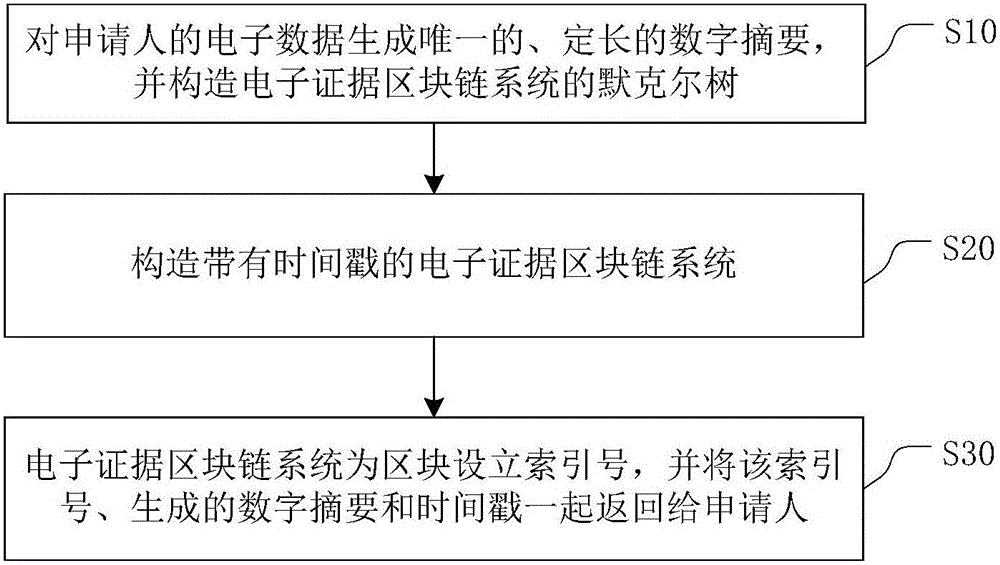
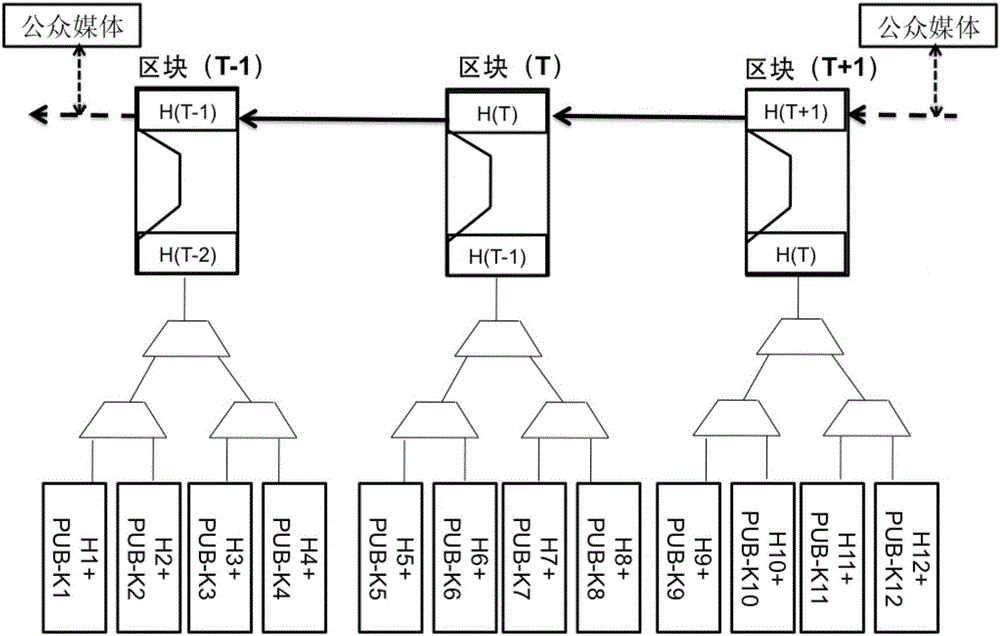
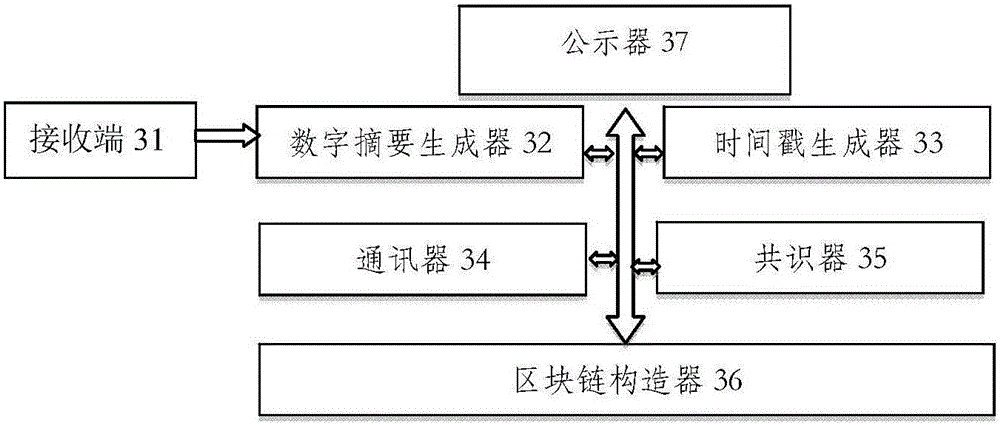
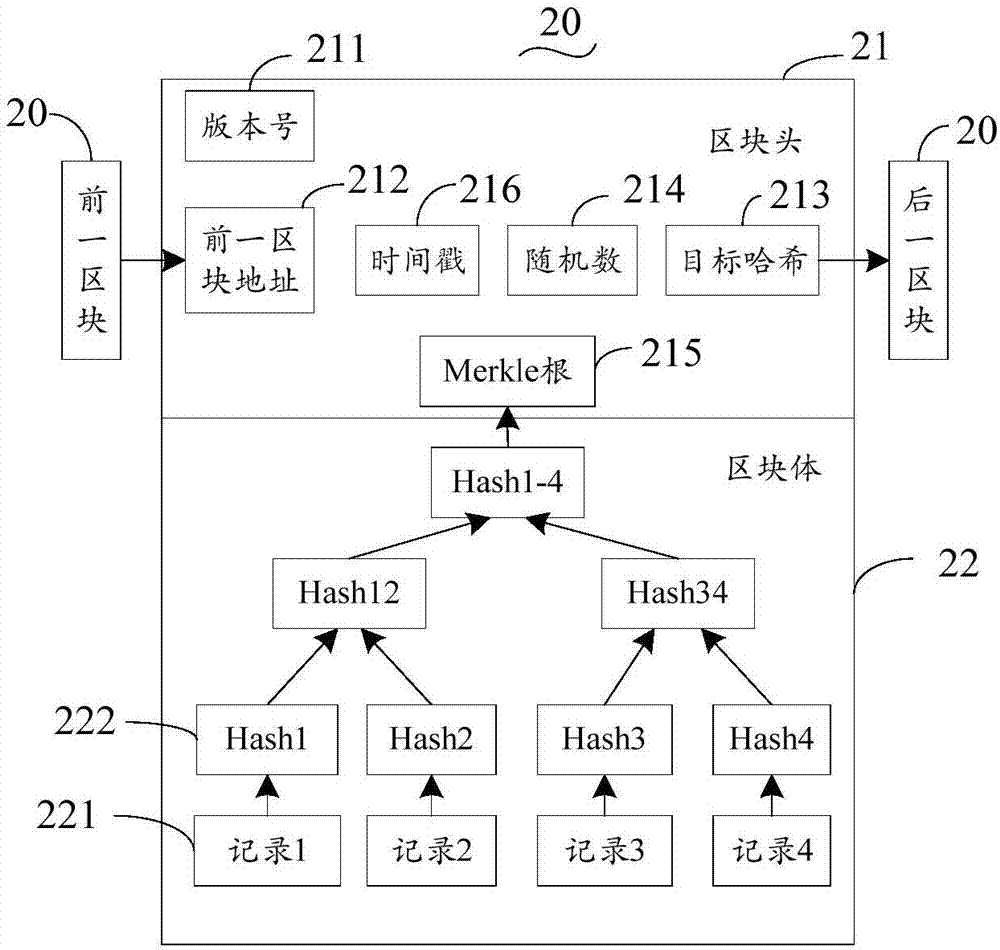
ActiveCN105790954AReduce identification costsImprove objectivityUser identity/authority verificationTimestampChain system
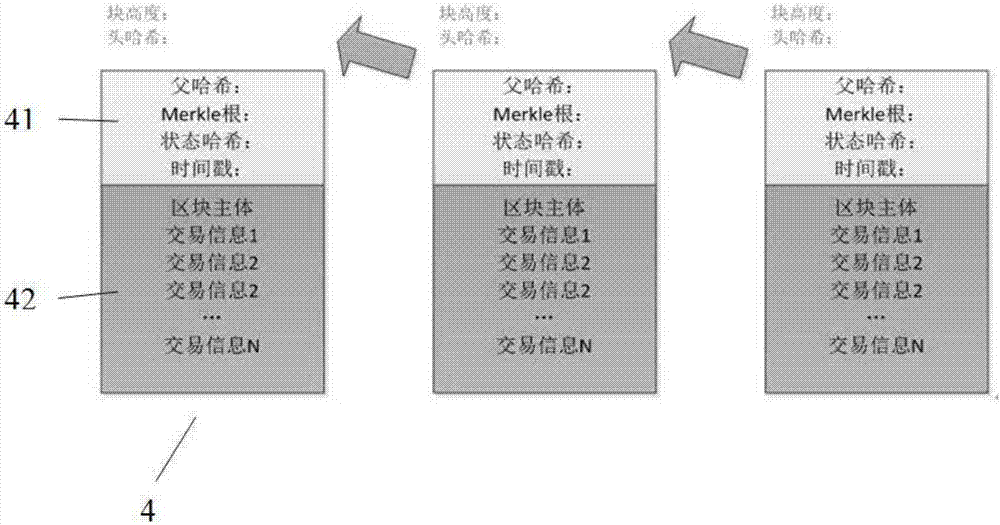
The invention relates to a method for constructing an electronic evidence. The method specifically comprises the following steps: generating a unique length-fixed digital abstract for electronic data of an applicant, and constructing a Merkle tree of an electronic evidence block chain system; constructing the electronic evidence block chain system with a timestamp; and setting an index number for a block by the electronic evidence block chain system, and returning the index number, the generated digital abstract and the timestamp to the applicant together. According to the method and the system disclosed by the invention, all participating parties can construct jointly, maintain jointly and supervise jointly, thereby meeting the right to know and the supervision right of each party; the identification cost of the electronic evidence is reduced, the identification efficiency is improved, and the objectivity and the reliability of the electronic evidence are enhanced.
Owner:BUBI BEIJING NETWORK TECH CO LTD
Electronic device, priority connection method and priority connection program
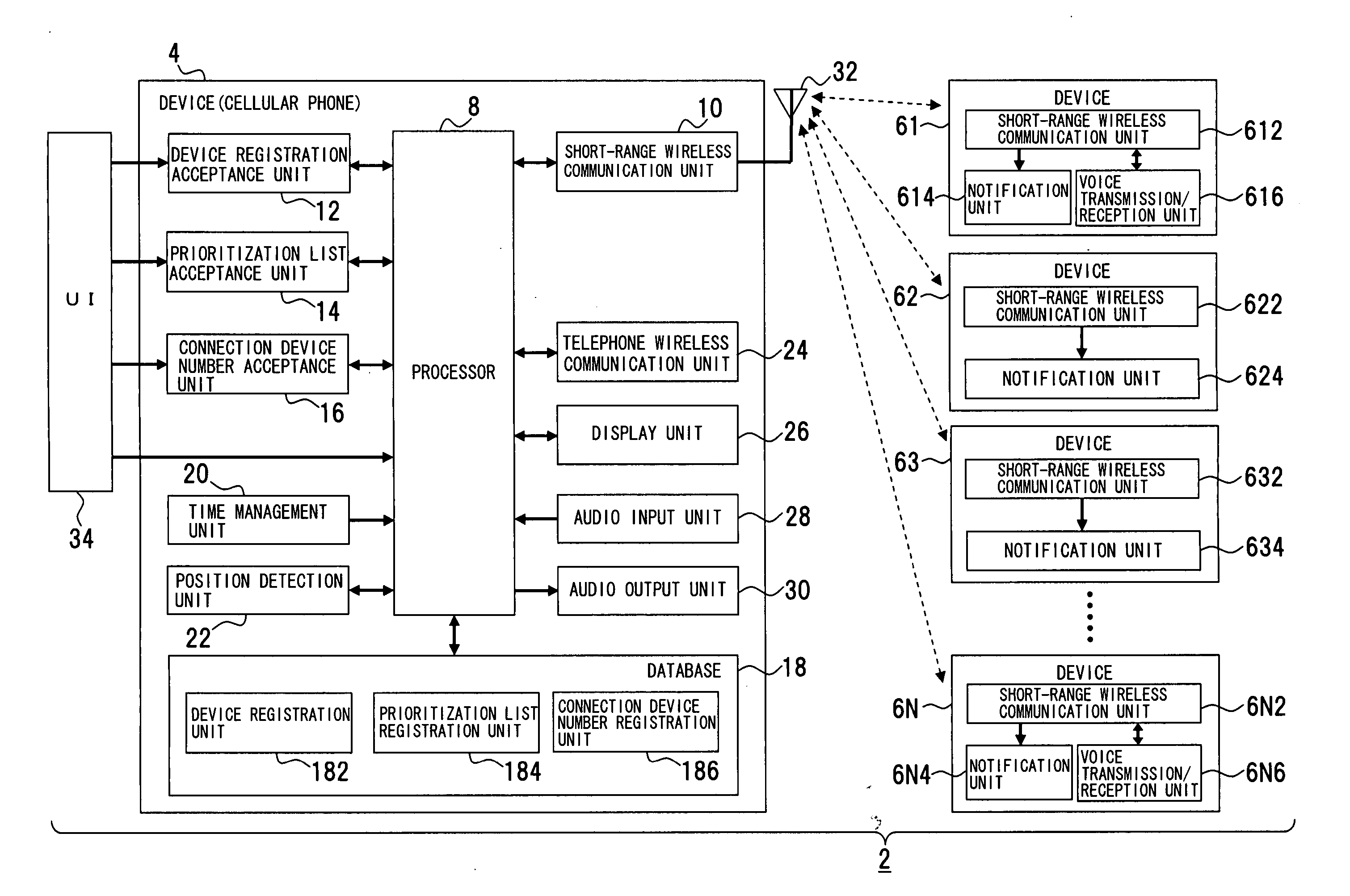
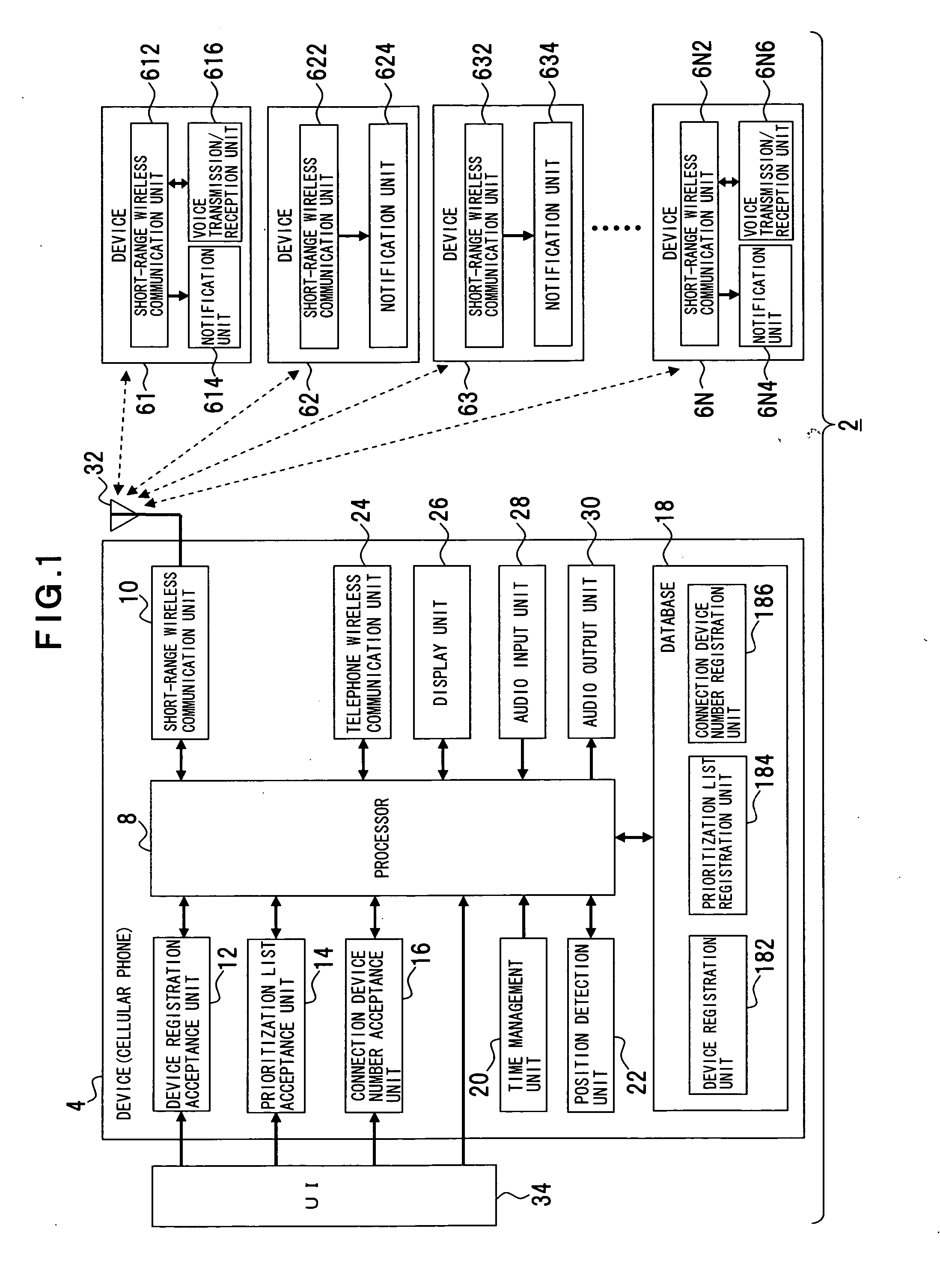
InactiveUS20060229014A1Improve usabilityIncrease credibilityNear-field transmissionAssess restrictionCommunication unitComputer science
The present invention is comprised of a communication unit (short-range wireless communication unit 10) for transmitting / receiving a short-range wireless signal to / from one or more devices (devices 61 to 6N) with a short-range wireless communication function, a registration unit (database 18) for adding priorities to the plurality of the devices and registering a prioritization list representing one or more devices sorted by the priorities, and a control unit (processor 8) for dynamically selecting one or more devices based on the prioritization list and controlling connection through the communication unit with the selected one or more devices.
Owner:FUJITSU CONNECTED TECH LTD
Methods and Apparatus for Analysing and/or Pre-Processing Financial Accounting Data
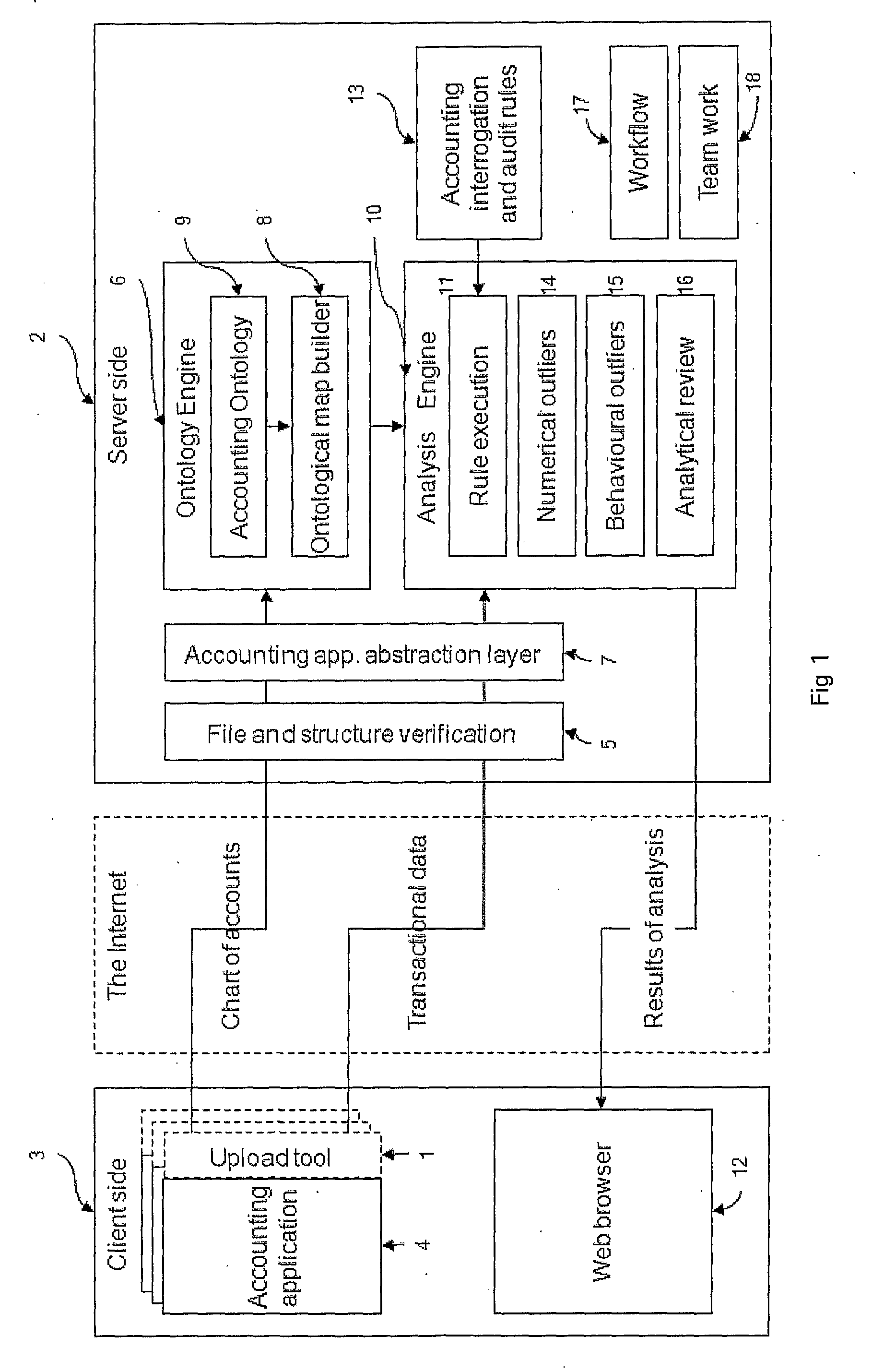
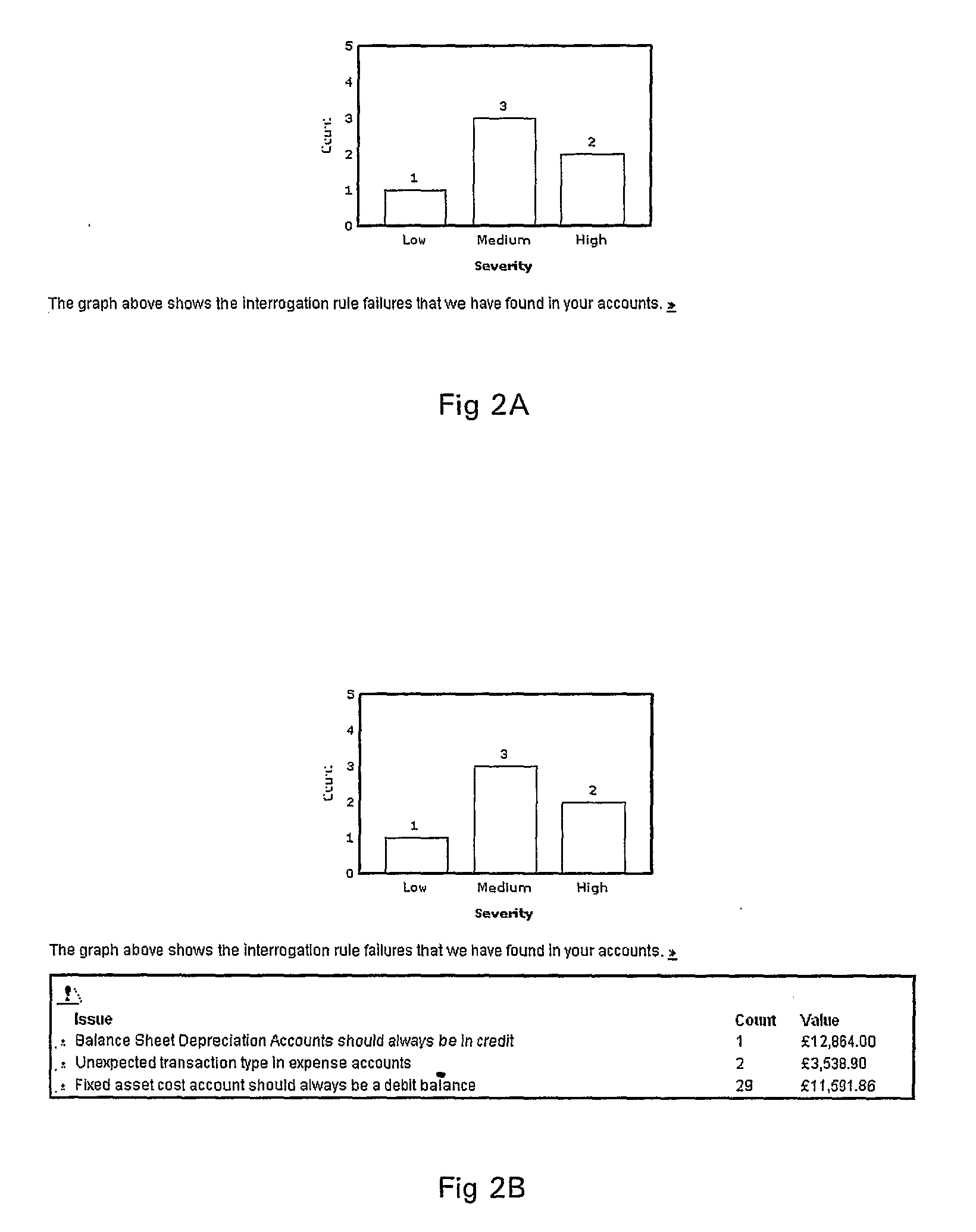
ActiveUS20100205076A1Increasing relevance and occurrence and completeness and sufficiencyLow costComplete banking machinesFinanceAnalysis dataClient-side
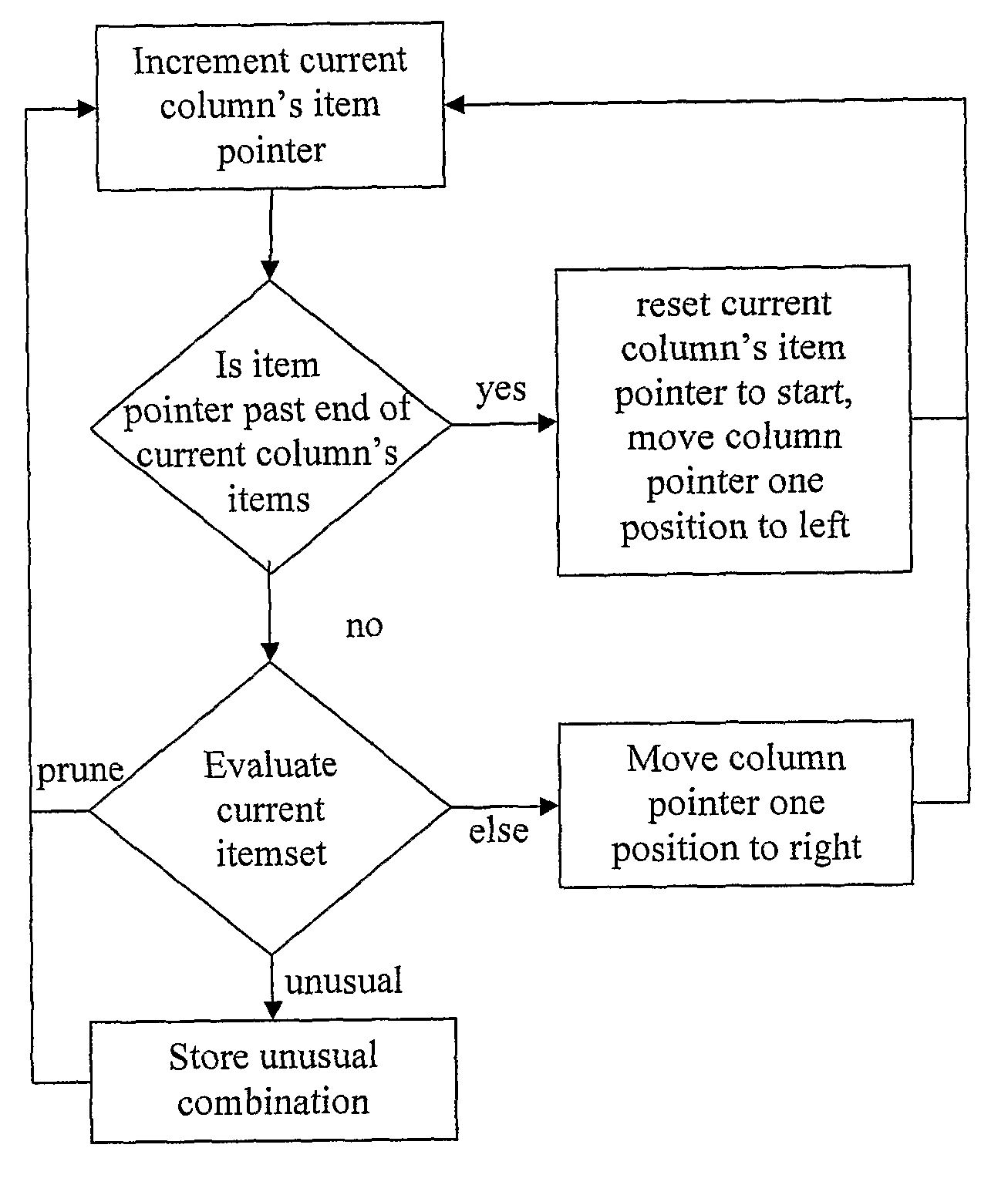
In an on-line method of analysing financial accounting data, uploaded financial accounting data is received at a server (2) from a client computer (3). The data is analysed at the server (2) to identify anomalies in the data. A display is provided at the client computer (3) representing the anomalies that have been identified. Further, in a method of pre-processing financial accounting data prior to analysis of the data, the financial accounting data is abstracted to correspond to a pre-stored accounting ontology. Further, in a method of analysing financial accounting data, the method checks the data for violation of a particular state to identify inconsistent combinations of values in the data.
Owner:VALIDIS UK LTD
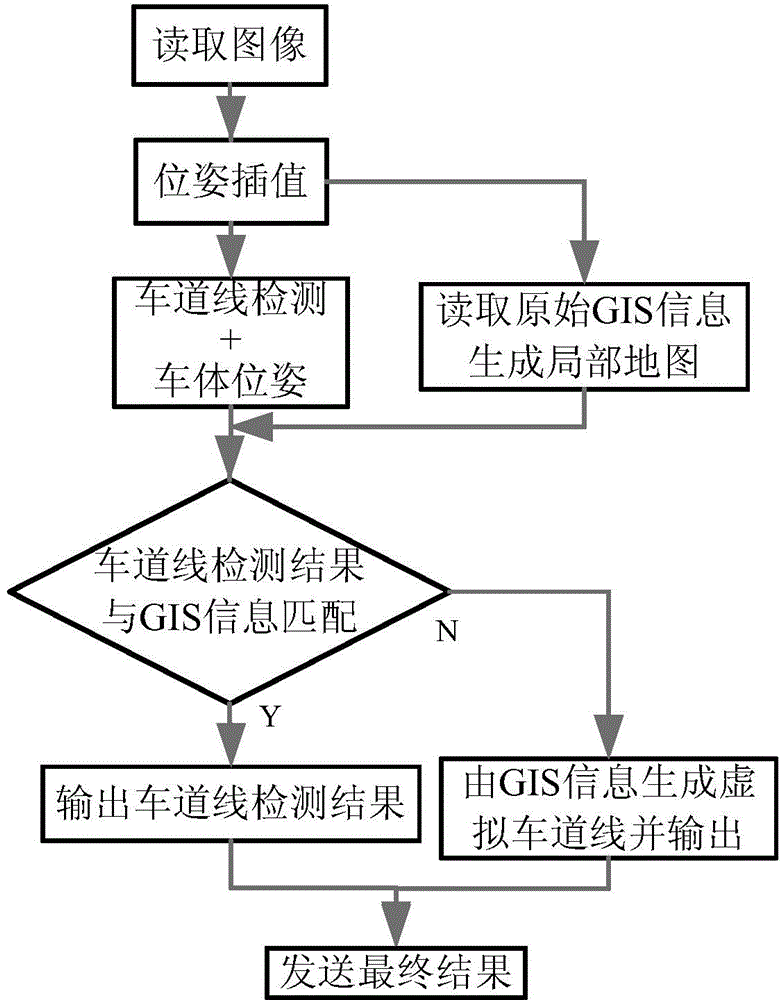
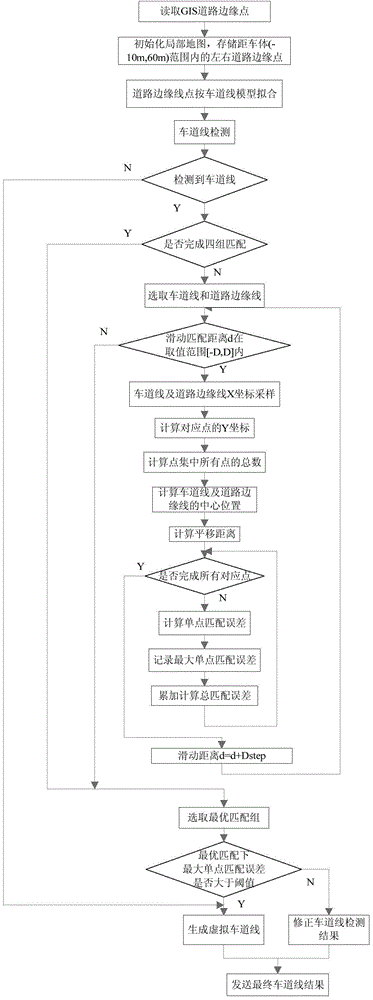
Lane line detection and GIS map information development-based vision navigation method
ActiveCN103954275AFix false positivesAmendmentInstruments for road network navigationCouplingNavigation system
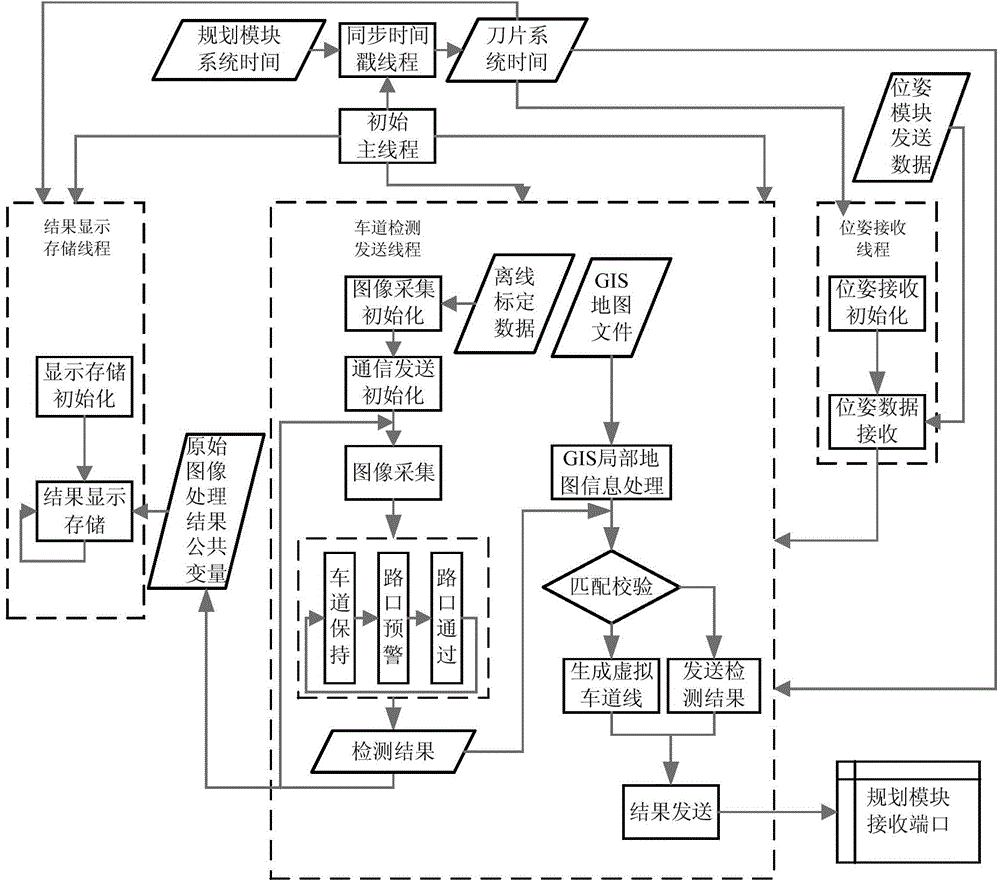
The invention discloses a lane line detection and GIS map information development-based vision navigation method. The method comprises the following steps: acquiring GIS map information, preprocessing, carrying out real-time image acquisition and lane line detection to generate a GIS local map in real-time, carrying out coupling verification on a track line detection result and the GIS local map through an ICP algorithm, and generating a high-credibility track line result according to the coupling result. The method can realize the credibility evaluation of the lane line detection through a geographic information system, corrects when false detection or missing inspection appears, expands the application range of the lane detection algorithm, and also can improve the map positioning precision through visual perception information, so the performances of a vision navigation system in a whole intelligent driving and aided driving system are improved, thereby the system can adapt to more complex environments.
Owner:长沙谱蓝网络科技有限公司
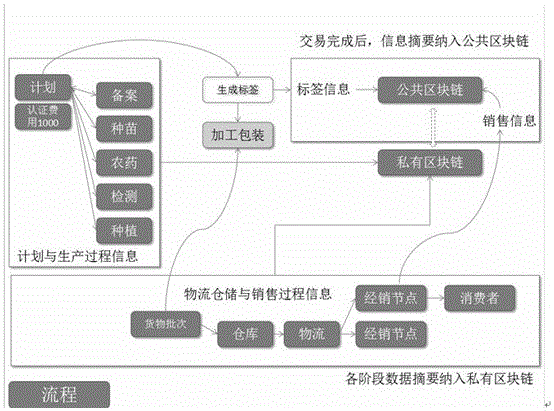
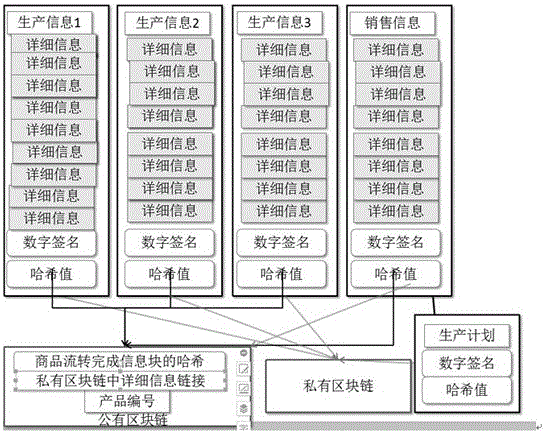
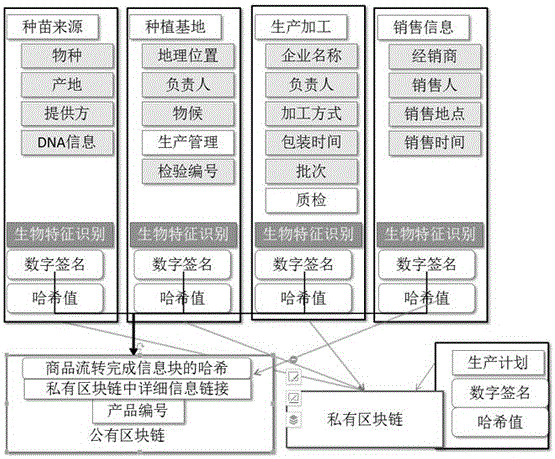
Product traceability verification method based on block chain technique
The invention discloses a product traceability verification method based on a block chain technique, which comprises a traceability step and a verification step. The traceability step comprises the following sub steps: 1) plan and production process information data are used for building blocks, and the blocks are stored in a private block chain; 2) three pieces of basic information are used for building verifiable label information; and 3) a distribution node adds the product consumption information and the label information to a public block chain. The verification step comprises the following sub steps: a, a product label is acquired; b, the product label is queried in the public block chain; and according to related records for the product label and the public block chain, the authenticity and the uniqueness of the product are determined. By adopting the method of the invention, the authenticity and the reliability of the traceability information can be ensured, technical problems that products are copied and over distributed and a responsibility person can not be bound can be solved, and besides, high-efficiency operation and the control cost of the traceability system can be ensured.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Dynamic EMS memory mappings method of virtual machine manager
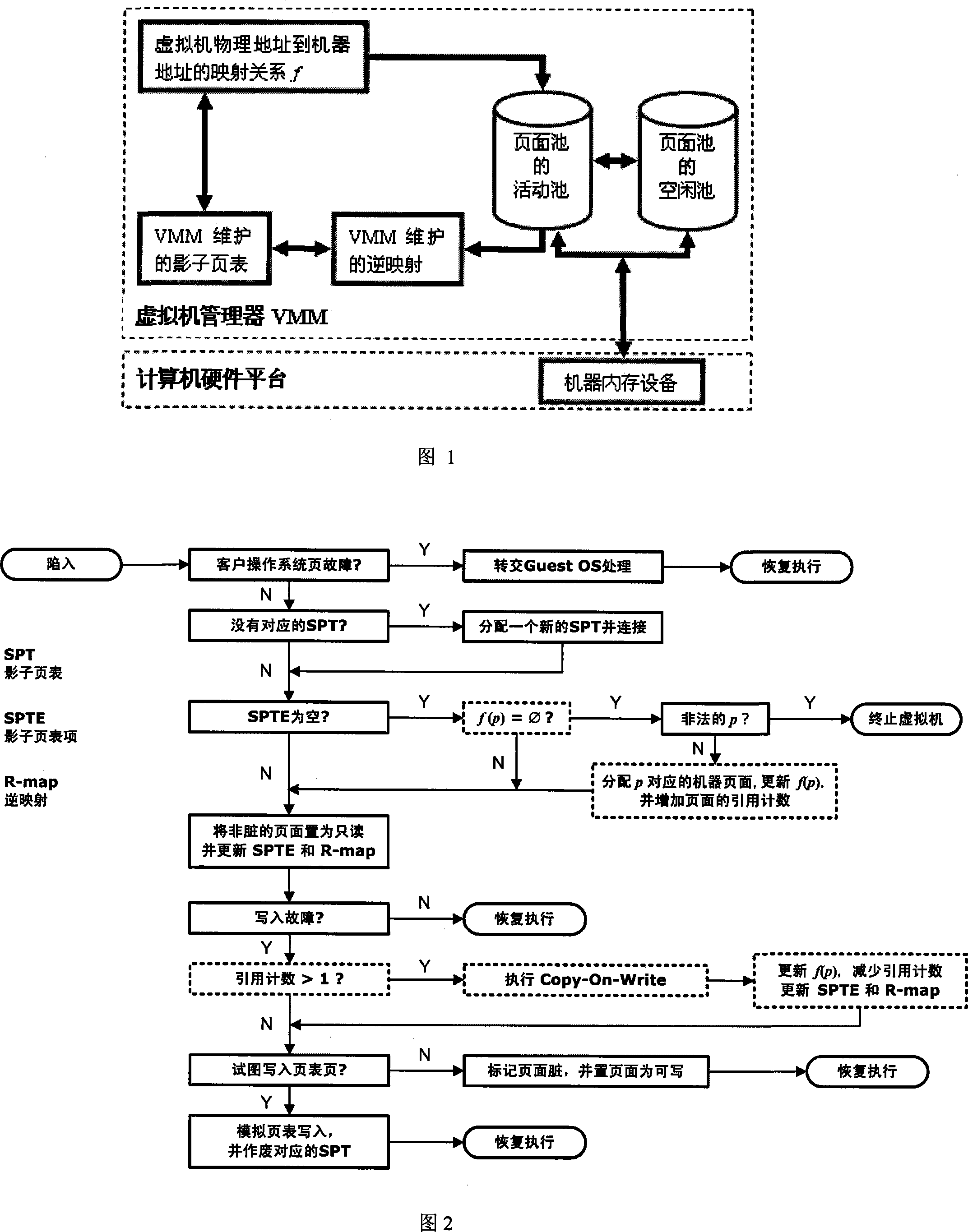
InactiveCN101158924ARealize page fetching on demandImplement memory sharingMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationDynamic managementMemory sharing
The invention discloses a dynamic memory mapping method of a virtual machine manager, the steps are that: separately establish a virtual machine page pool and a virtual machine manager page pool; when the virtual machine access is violated, the virtual machine manager dynamically establishes and updates the mapping relations f(p) form a physical memory collection P to a machine memory collection M in the virtual machine manager page pool; the inventive method can simultaneously support obtaining pages according to the requirements at upper layer, virtual storage, as well as memory shared functions, so as to make the virtual machine manager realize dynamic management and allocation of the virtual machine memory on the premise that the virtual machine manager sufficiently guarantees the virtual machine access memory performance.
Owner:PEKING UNIV
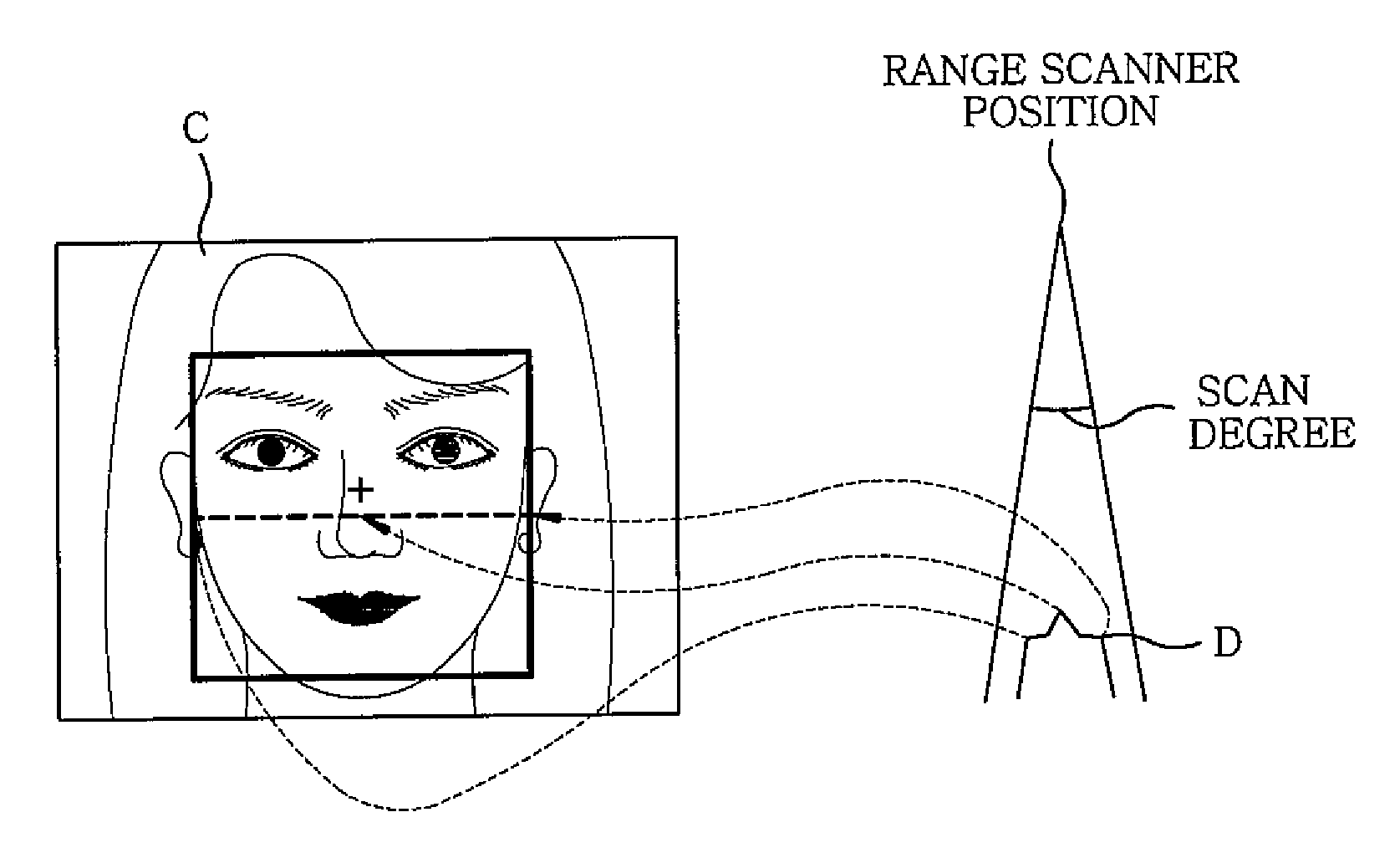
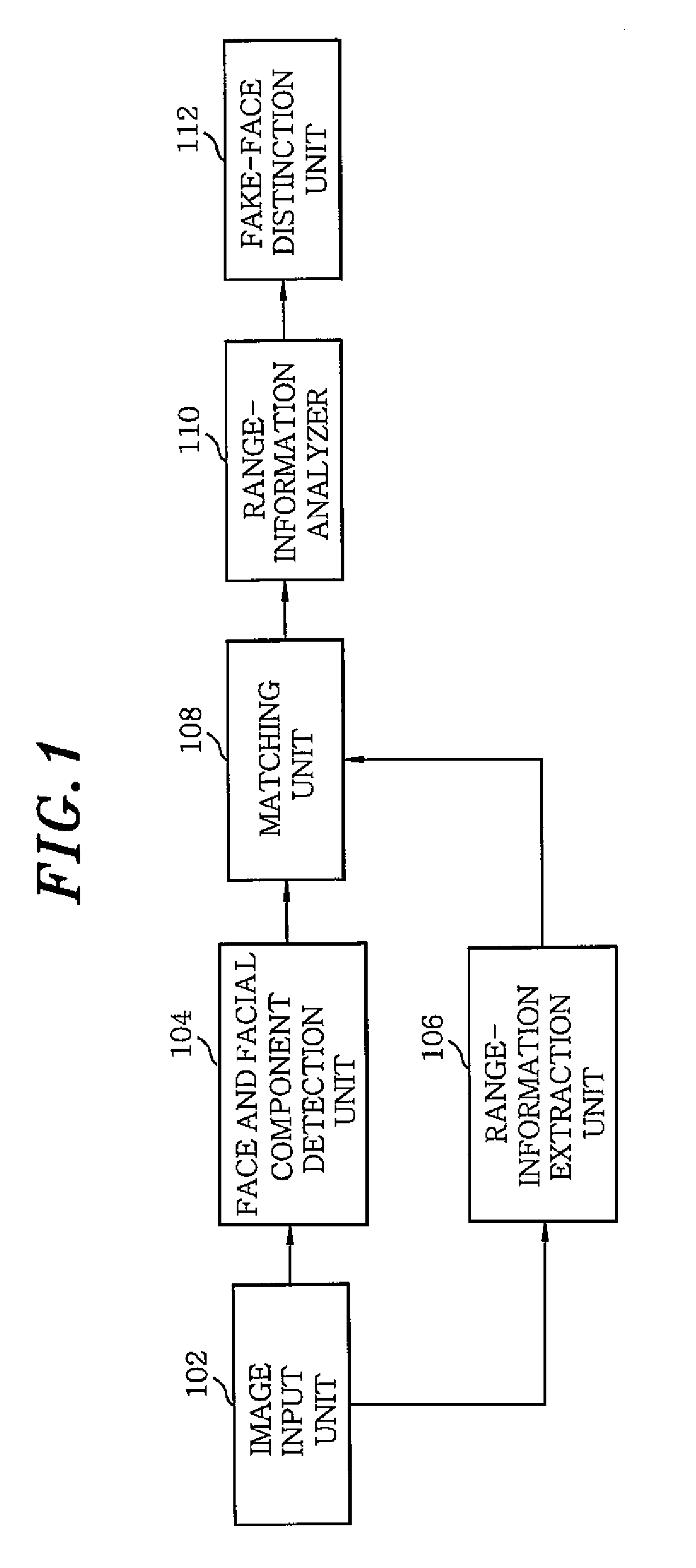
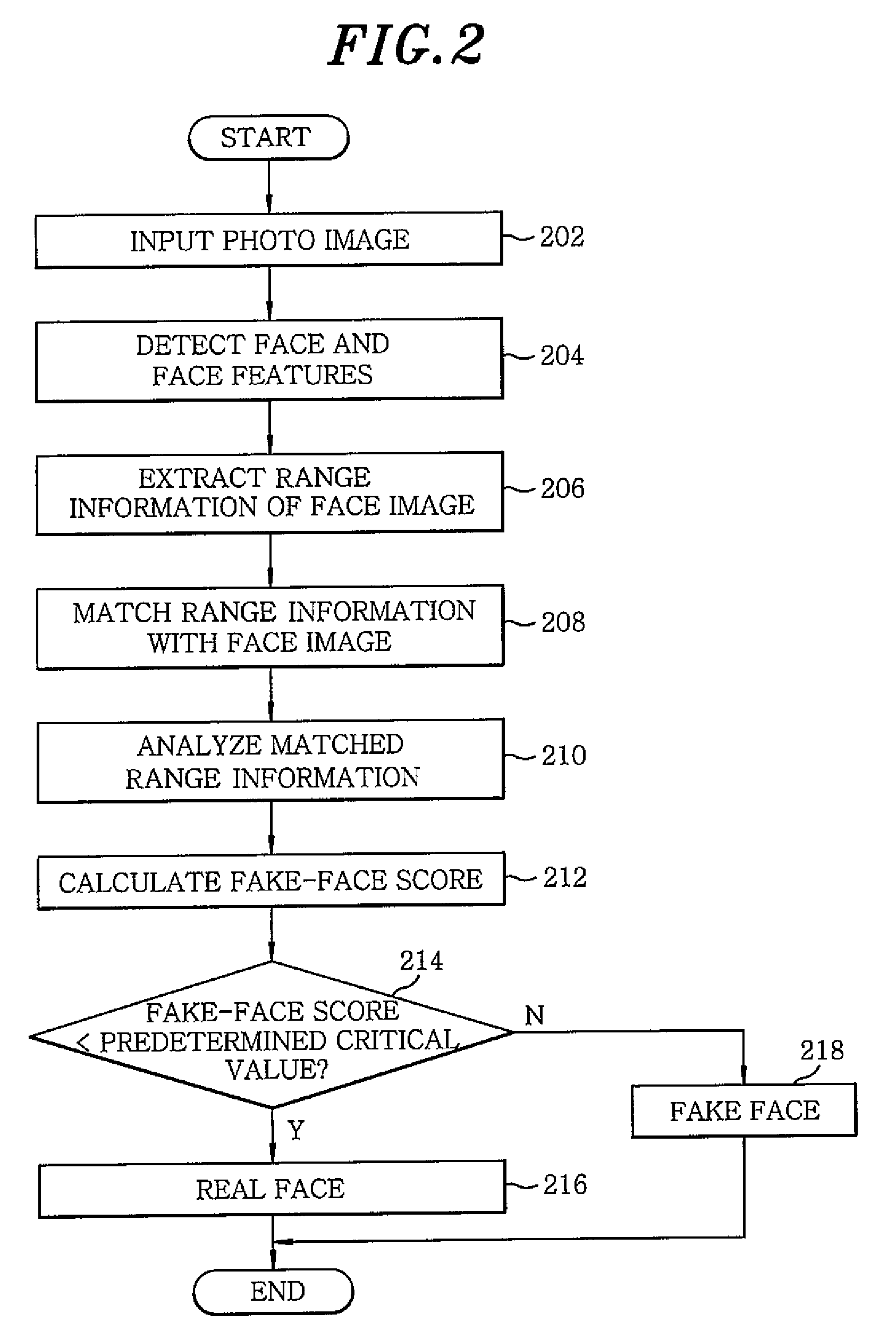
Method and apparatus for fake-face detection using range information
InactiveUS20100158319A1Increase credibilityImprove securityImage analysisSteroscopic systemsFace detectionComputer vision
A fake-face detection method using range information includes: detecting face range information and face features from an input face image; matching the face image with the range information; and distinguishing a fake face by analyzing the matched range information.
Owner:ELECTRONICS & TELECOMM RES INST
Block chain technology-based service transaction method and system, and transaction server
InactiveCN106897902AIncrease credibilityBuying/selling/leasing transactionsMarketingPayment service providerOperating system
The invention discloses a block chain technology-based service transaction method and system, and a transaction server. The method comprises the steps of obtaining service demand information and service quoted price information through the transaction server; performing matching based on a predetermined rule; pushing the matched service quoted price information to a client, thereby enabling the client to finally determine whether to make a deal or not and to make a deal with which of service providers; and finally, recording transaction information through a block chain technology. On one hand, the service provider is recommended to a user through reverse matching and pushing, and on the other hand, the transaction information is recorded based on the block chain technology, so that a transaction record cannot be counterfeited and the service transaction reliability is improved.
Owner:苏州朗润创新知识产权运营有限公司
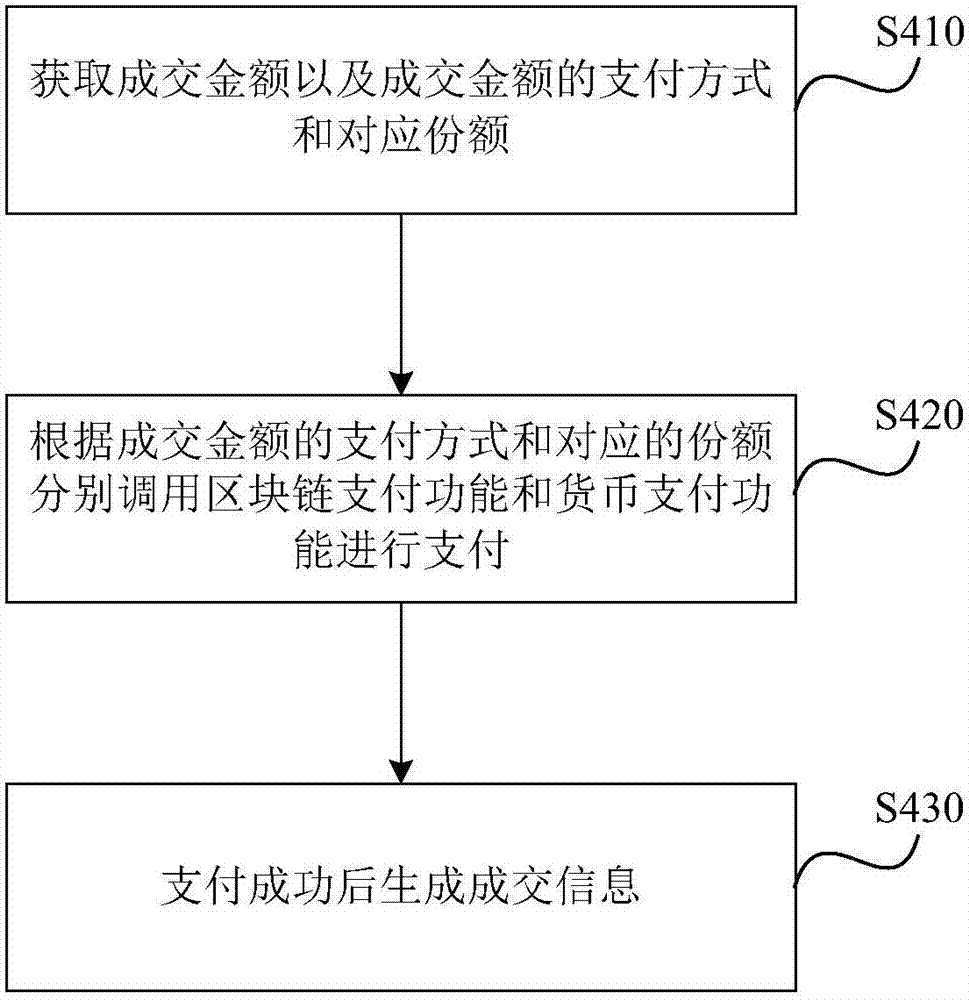
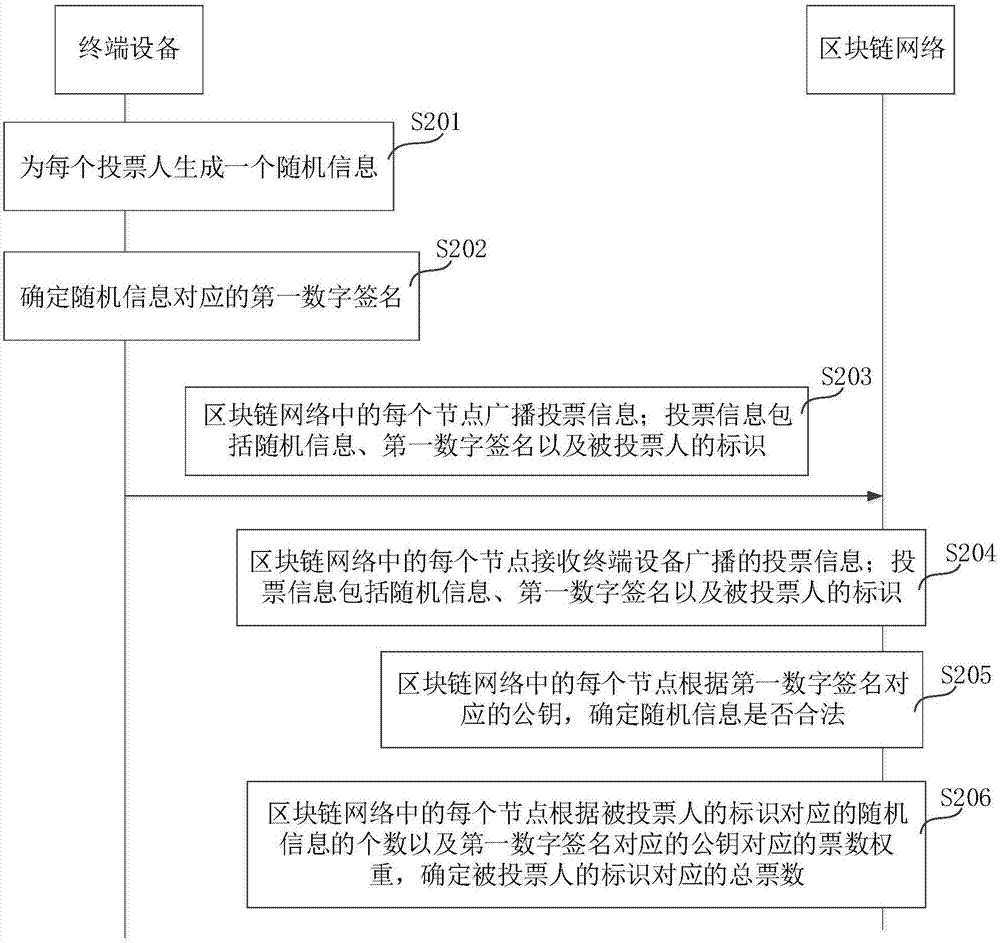
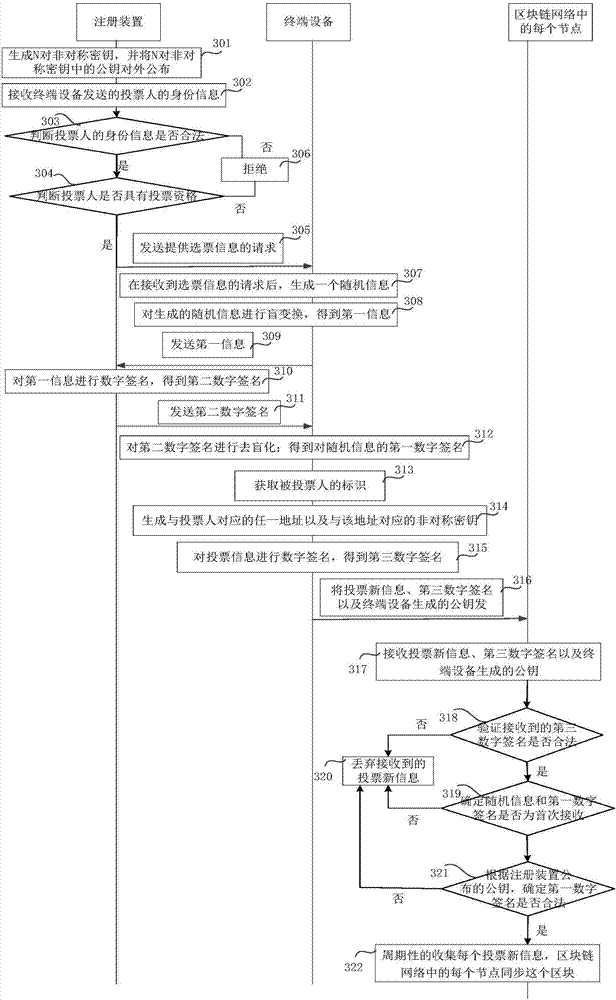
Electronic voting method, terminal device and block chain network
ActiveCN107294727AIncrease credibilityVoting apparatusKey distribution for secure communicationDigital signatureTerminal equipment
The invention belongs to the communications technical field and relates to an electronic voting method, a terminal device and a block chain network which are used for improving the credibility of a voting result. According to the embodiments of the present invention, the terminal device generates a piece of random information for each voter; the terminal device determines first digital signatures corresponding to the random information; the terminal device broadcasts voting information to each node in the block chain network, wherein the voting information includes the random information, the first digital signatures and the identifiers of candidates; since blocks in a block chain in each node in the block chain network are generated according to a time sequence, and the sequence of the blocks in the block chain network is equivalent to the effect of time stamps; and each block stores the index of a previous block, so that the voting information in the block chains cannot be tampered, and therefore, the credibility of the voting result is enhanced.
Owner:UNION MOBILE PAY
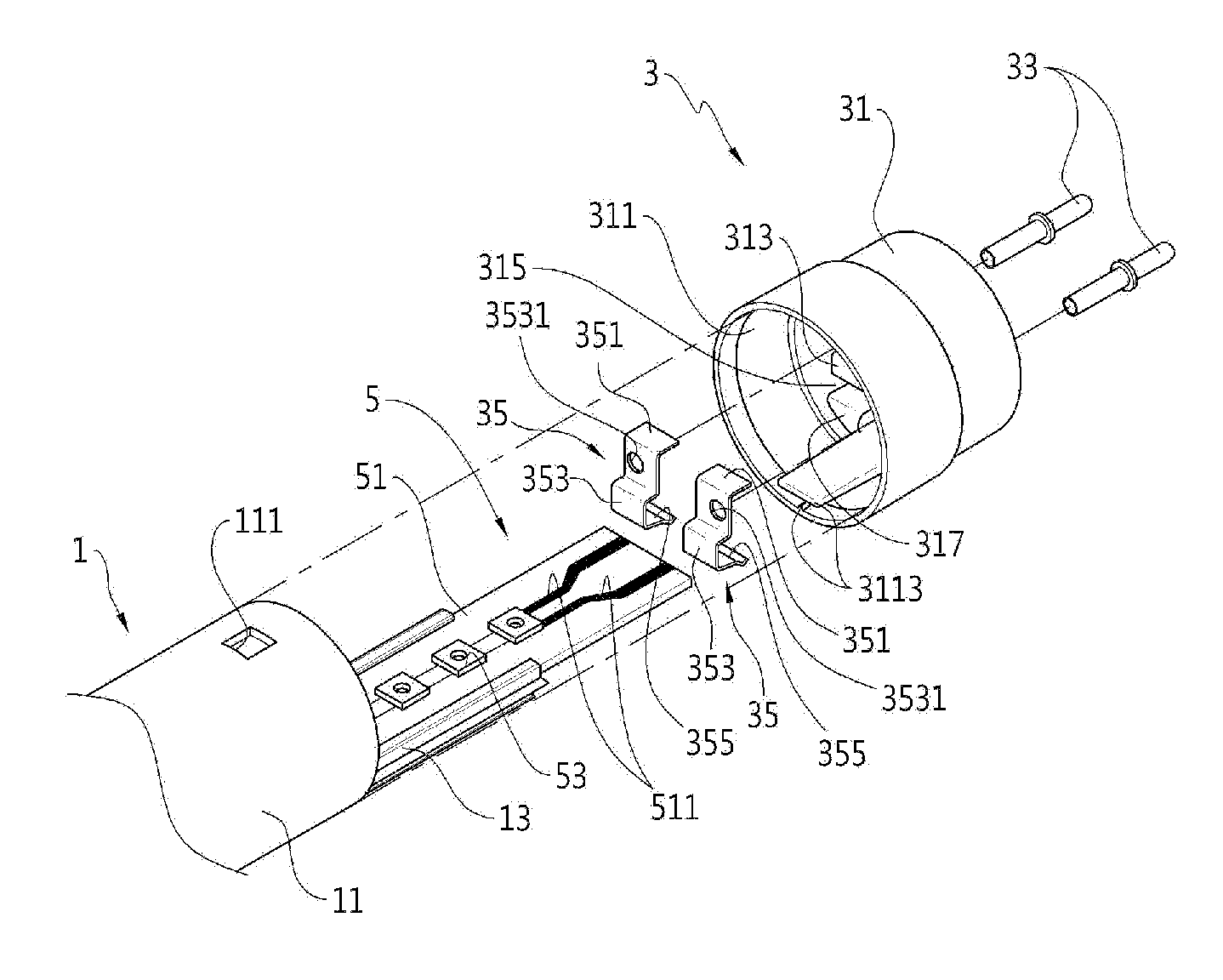
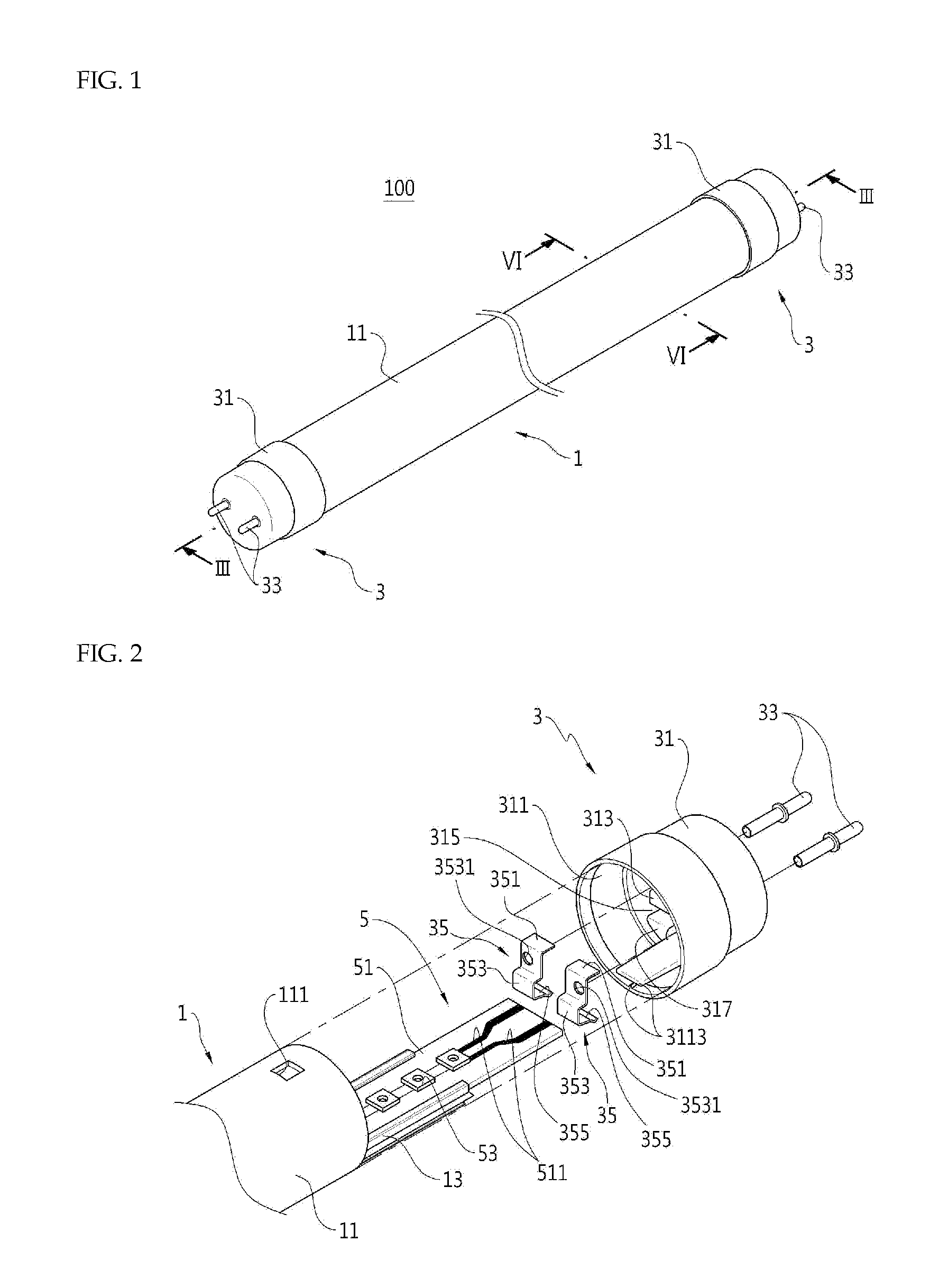
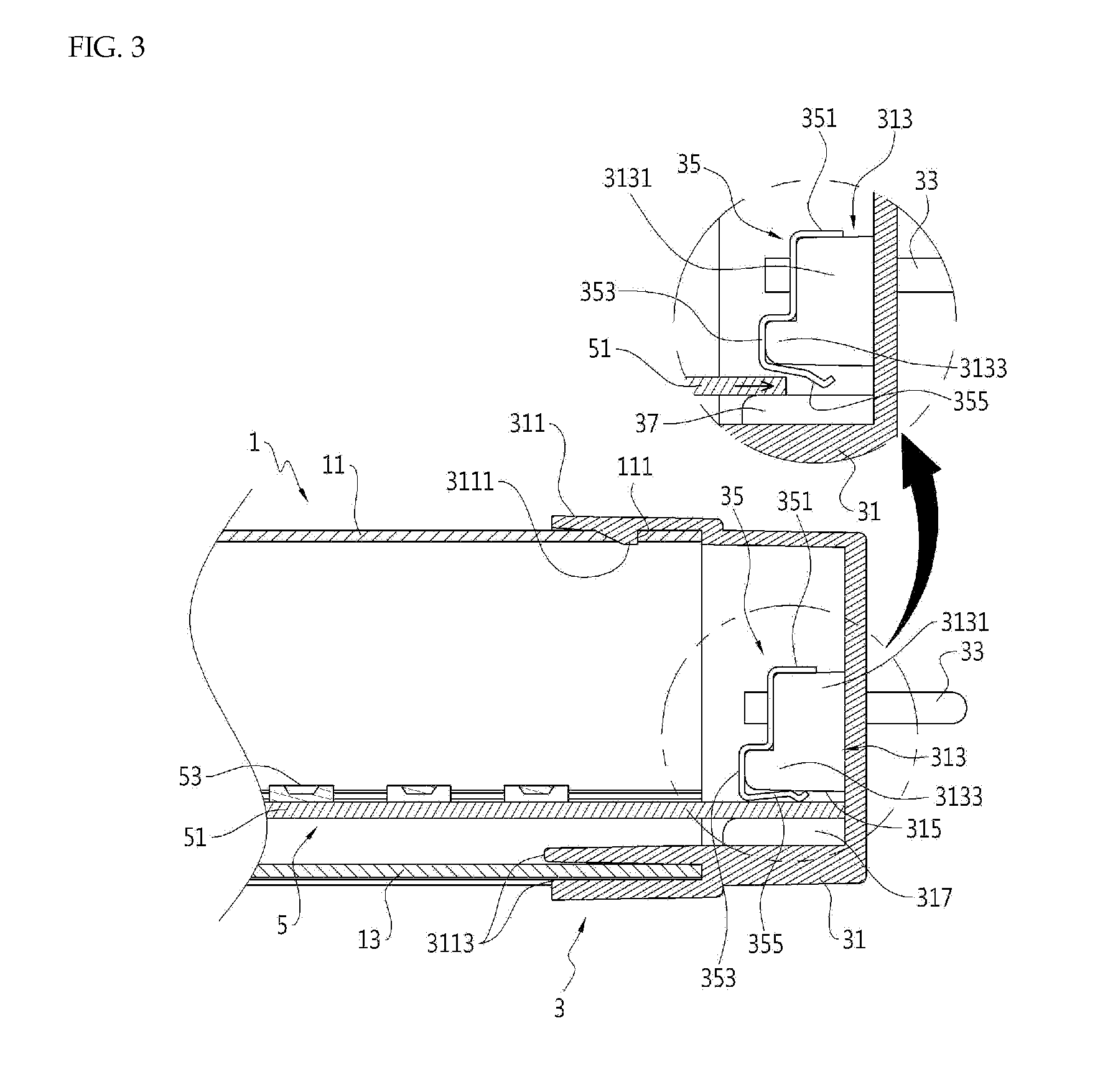
LED lighting apparatus
ActiveUS20130301255A1Improve workabilityEasy to separateLighting support devicesElongate light sourcesCouplingEngineering
The light emitting diode lighting apparatus includes: a tubular cover; a cap portion which is coupled to an end of a longitudinal direction of the cover; and a light emitting diode module which is coupled to the cap portion and is disposed within the cover. The cap portion includes: a cap which is coupled with the cover and is provided with a coupling portion therein; and a contact terminal which is coupled to the coupling portion to directly contact the light emitting diode module and elastically supports the light emitting diode module.
Owner:CELLEGAIN CO LTD
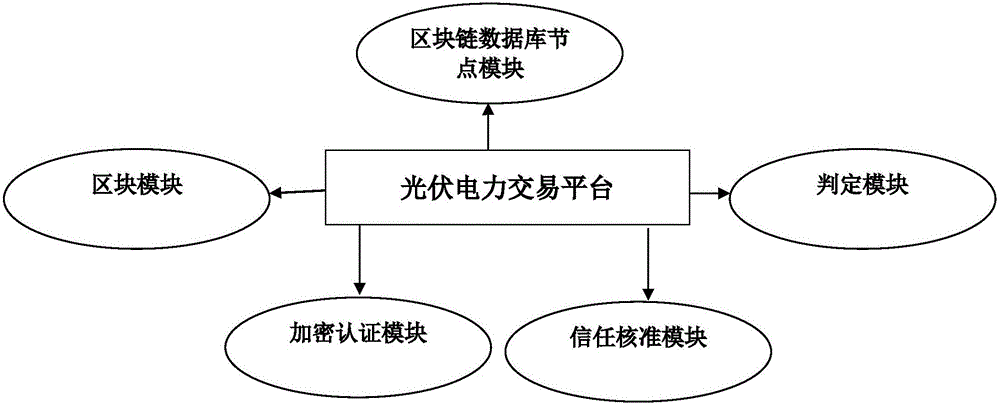
Trusted power grid transaction platform based on block chain technology
InactiveCN106296359AThe transaction is validConduct complianceBuying/selling/leasing transactionsSystems intergating technologiesElectric power transmissionPower grid
The invention provides a trusted power grid transaction platform based on block chain technology. The trusted power grid transaction platform comprises the components of (1), a power chain database node module which stores electric power transaction database copies at a plurality of nodes; (2), a block module, wherein the block chain database is divided into a plurality of blocks which are related with electric power transaction, wherein each block comprises detailed information of transaction; (3) an encryption authentication module which acquires whole-network authentication through combining and encrypting transaction details and signatures of two parties or signature of one party; (4), a trust approval module which is connected with the encryption authentication module and is used for establishing a trusted power grid transaction system of the block chain; and (5), a determining module which determines a fact that the transaction is effect on the condition that encryption records that correspond with all nodes are consistent, and adds the transaction into a historical transaction chain; and if the block is ineffective, the information of a role breaking node is modified through consistent option of the nodes. The trusted power grid transaction platform safely and reliably perform various kinds of power grid transactions and furthermore improves credibility of the block chain technology.
Owner:SHENZHEN FANXI ELECTRONICS CO LTD
Electronic certificate management method and related equipment
ActiveCN107231351ARealize distributed managementImprove storage reliabilityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesChain networkInformation security
The invention discloses an electronic certificate management method and related equipment. The method comprises the steps as follows: the electronic equipment processes an electronic certificate in response to a received processing command; an encrypted processing record is broadcasted into a block chain network, thus allowing a node of the block chain network to store the encrypted processing record into a block chain of the block chain network. According to the scheme of the method provided by the invention, distributed management of the electronic certificate is achieved, storage reliability of the electronic certificate is improved, the risk of tampering or leaking certificate information is reduced, and information security and credibility of the electronic certificate are effectively ensured.
Owner:YGSOFT INC
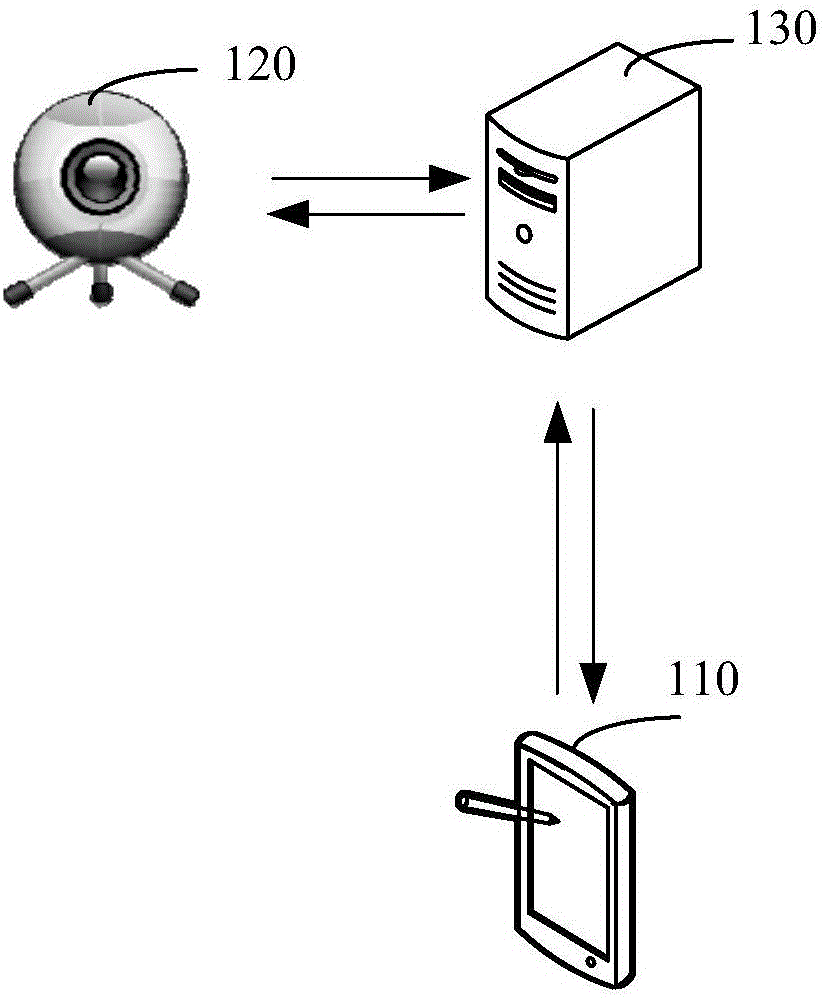
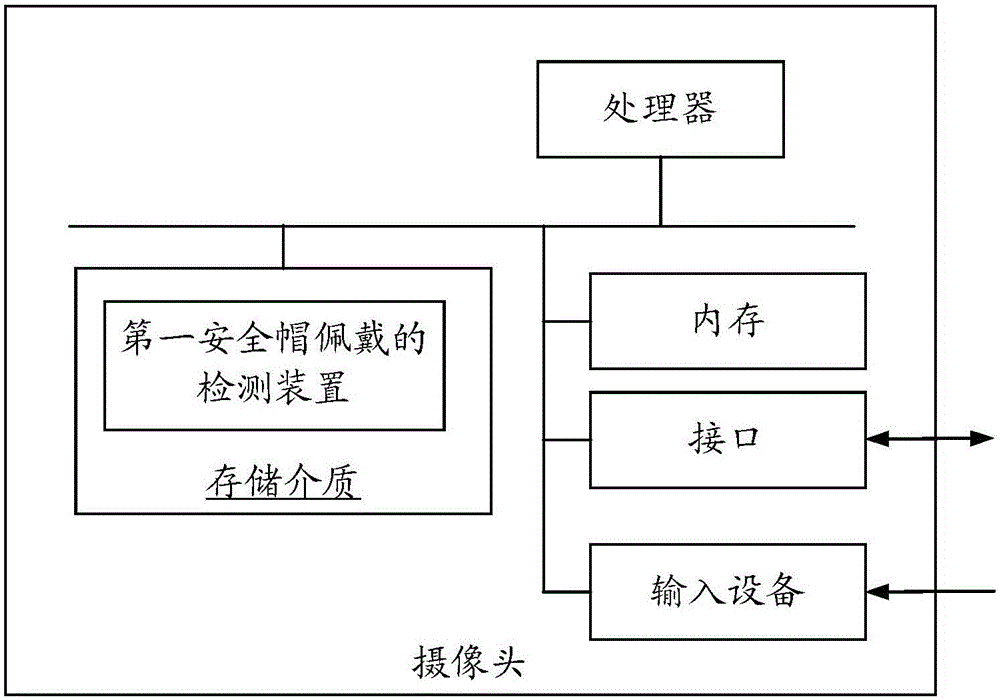
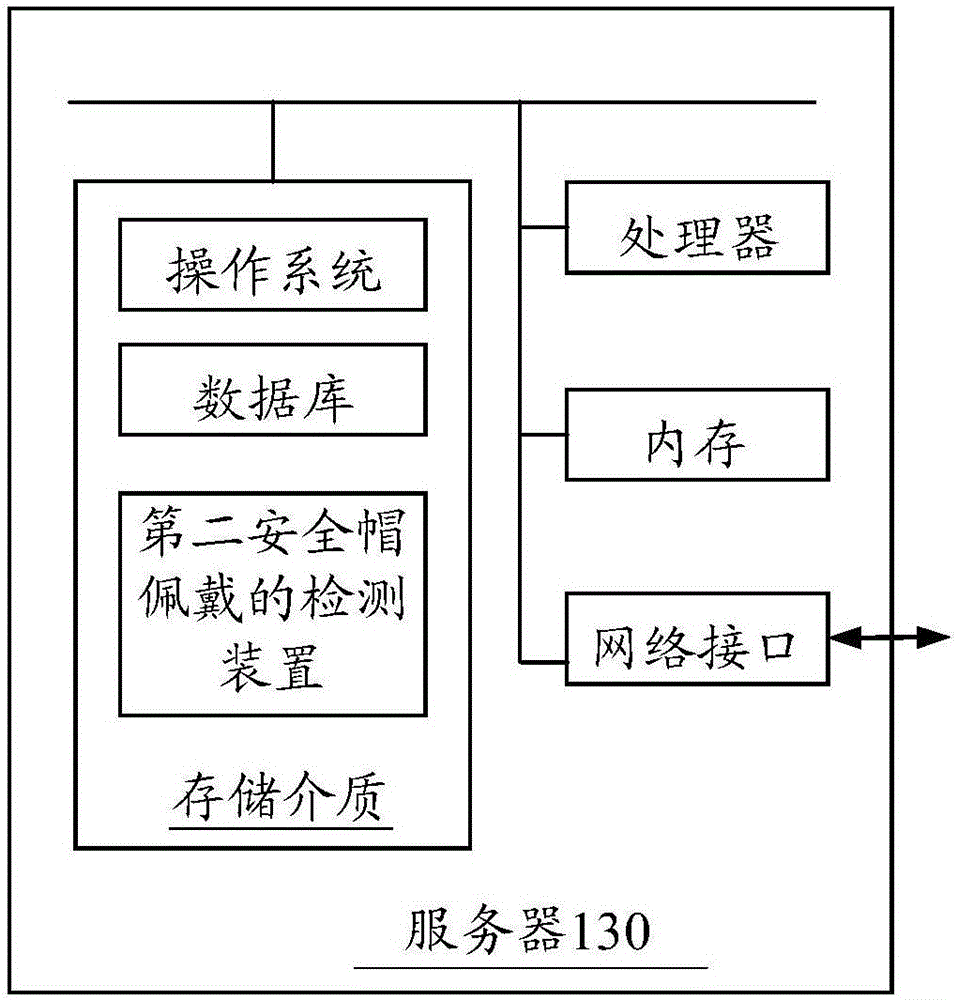
Helmet wearing detection method and device, camera, and server
ActiveCN106372662AImprove accuracyIncrease credibilityCharacter and pattern recognitionPattern recognitionVideo image
The present invention relates to a helmet wearing detection method and device, a camera, and a server. The method comprises: obtaining a scene video image, detecting the scene video image to obtain human position through a human position detection model built by training learning, and determining whether the human position is located in a helmet wearing area or not; if the human position is located in the helmet wearing area, detecting the scene video image to obtain the human head helmet combination state through a human helmet combination detection model built by training learning, and determining whether the helmet is worn or not according to the human helmet combination state, if the helmet is not worn, not passing through the wearing verification of the helmet and if the helmet is worn, detecting the scene video image to obtain the type of the helmet through the helmet type detection model built by training learning, determining if the type of the helmet accords with the rule or not, if the type of the helmet accords with the rule, passing through the wearing verification of the helmet, or else, not passing through the wearing verification of the helmet, and therefore, the accuracy of the detection result of the helmet wearing is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
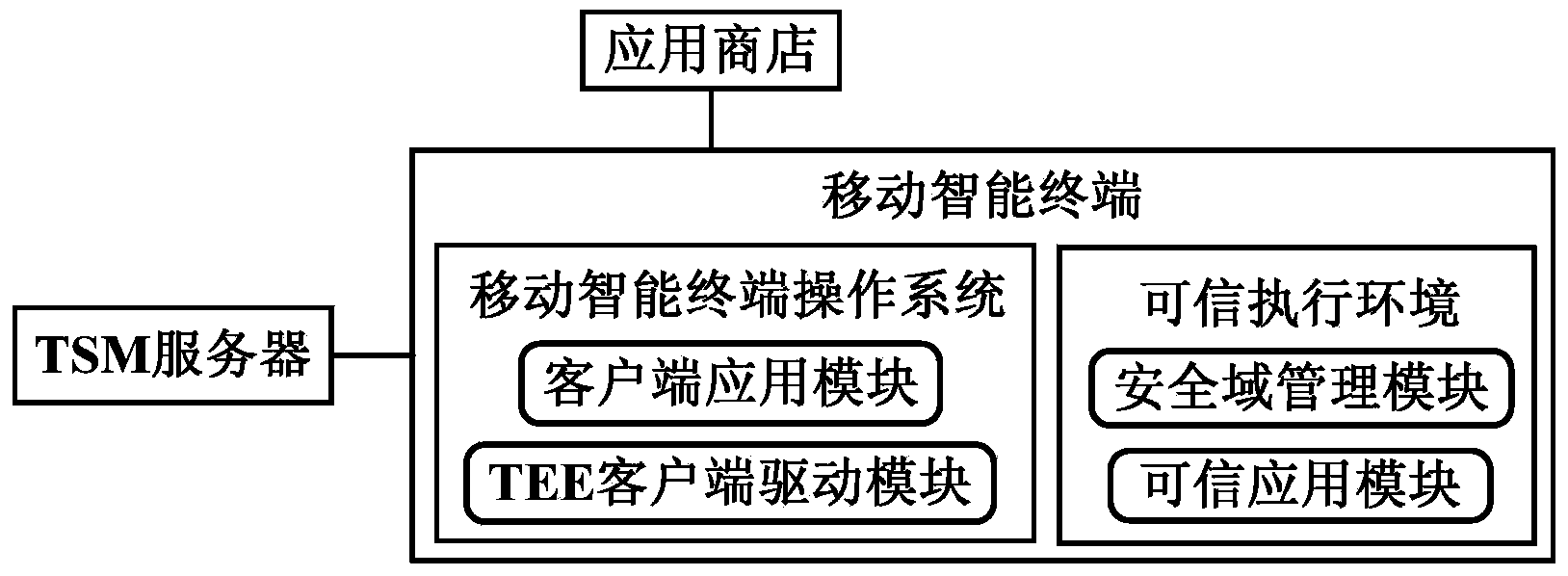
System and method for initializing safety indicator of credible user interface
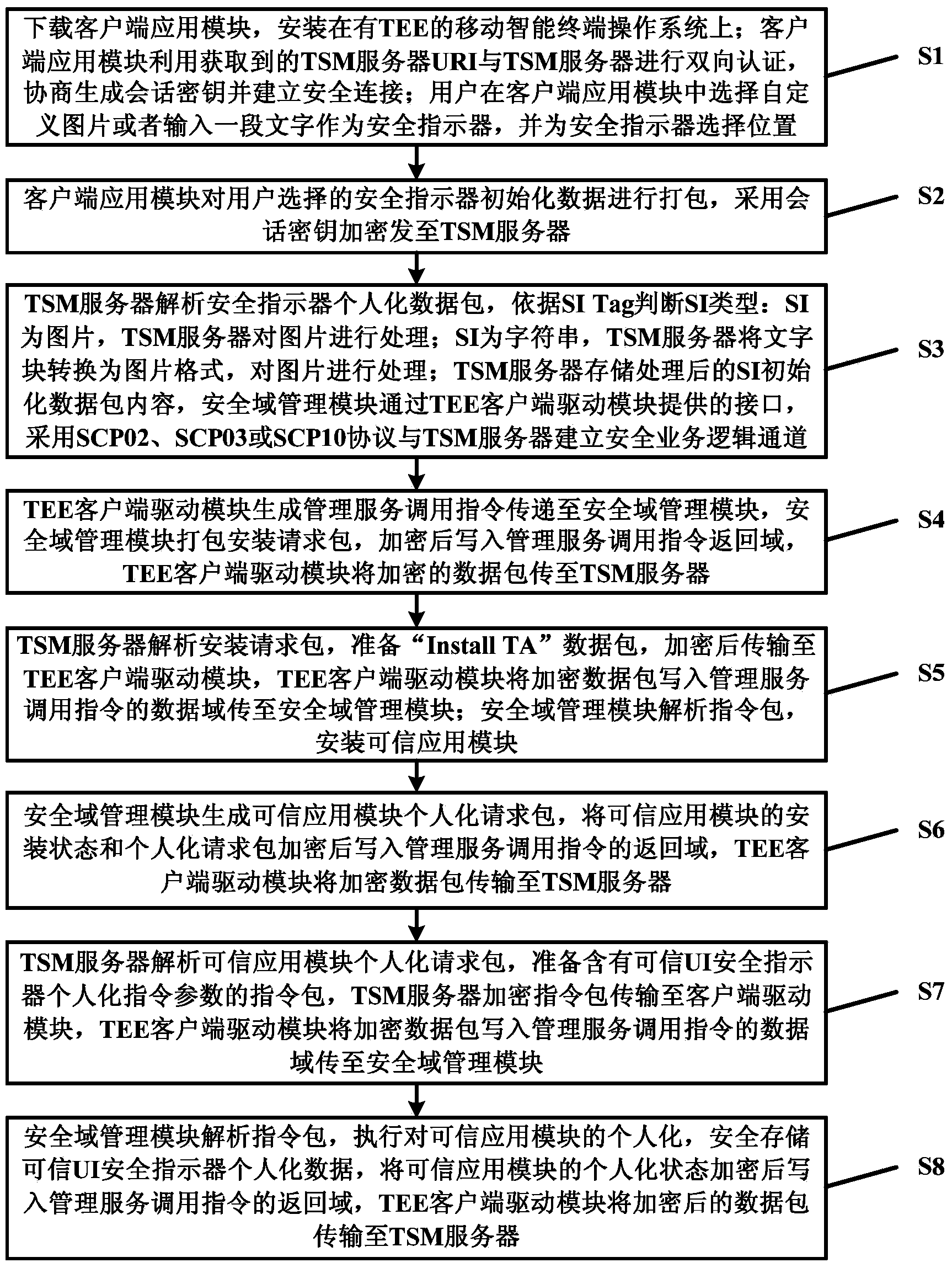
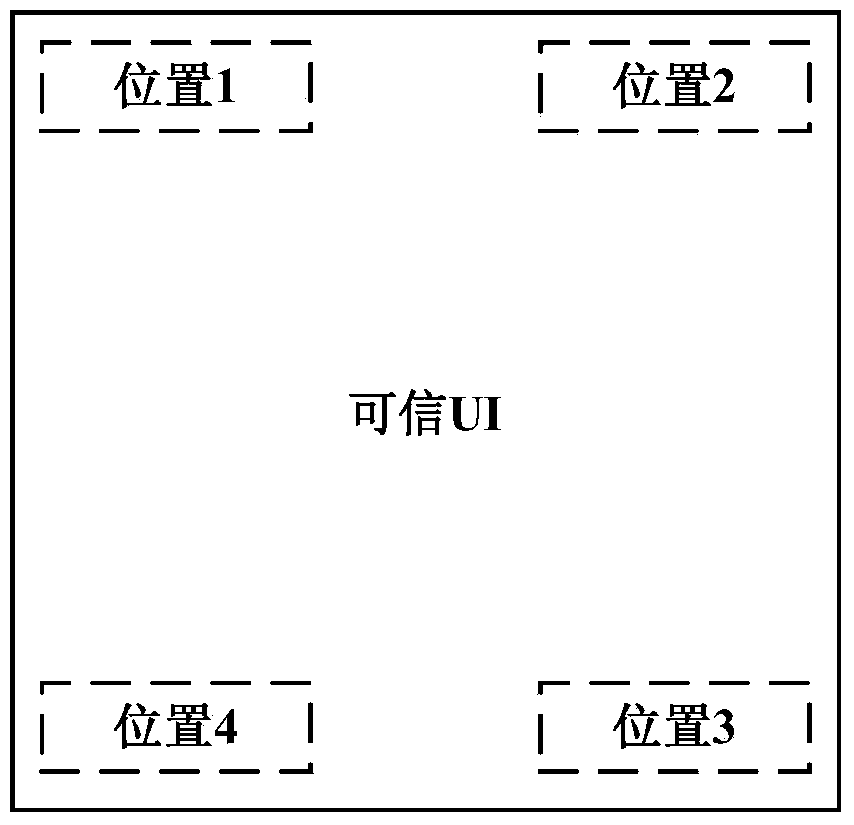
ActiveCN103856485AAchieve securityEnsure safetyTransmissionProgram/content distribution protectionOperational systemSafety indicators
The invention discloses a system and method for initializing a safety indicator of a credible user interface, and relates to the field of mobile intelligent terminals. The system comprises a TSM server, an application store and a mobile intelligent terminal. The mobile intelligent terminal comprises a mobile intelligent terminal operating system and a TEE. The mobile intelligent terminal operating system comprises a client side application module and a TEE client side drive module. The TEE provides a safe operation environment isolated from the mobile intelligent terminal operating system, the interior of the TEE is logically divided into a plurality of safety domains, and mutual isolation and independence of credible applications are guaranteed. Each safety domain is provided with a safety domain management module and a credible application module, and the TEE provides the safe operation environment for the safety domain management modules and the credible application modules. According to the system and method, individualization of the safety indicator in the credible UI provided for the credible application modules can be safely achieved, display credibility of the safety indicator is effectively improved, and the risk that the safety indicator is attacked and intercepted by malicious software is reduced.
Owner:WUHAN TIANYU INFORMATION IND
Methods and systems for capturing biometric data
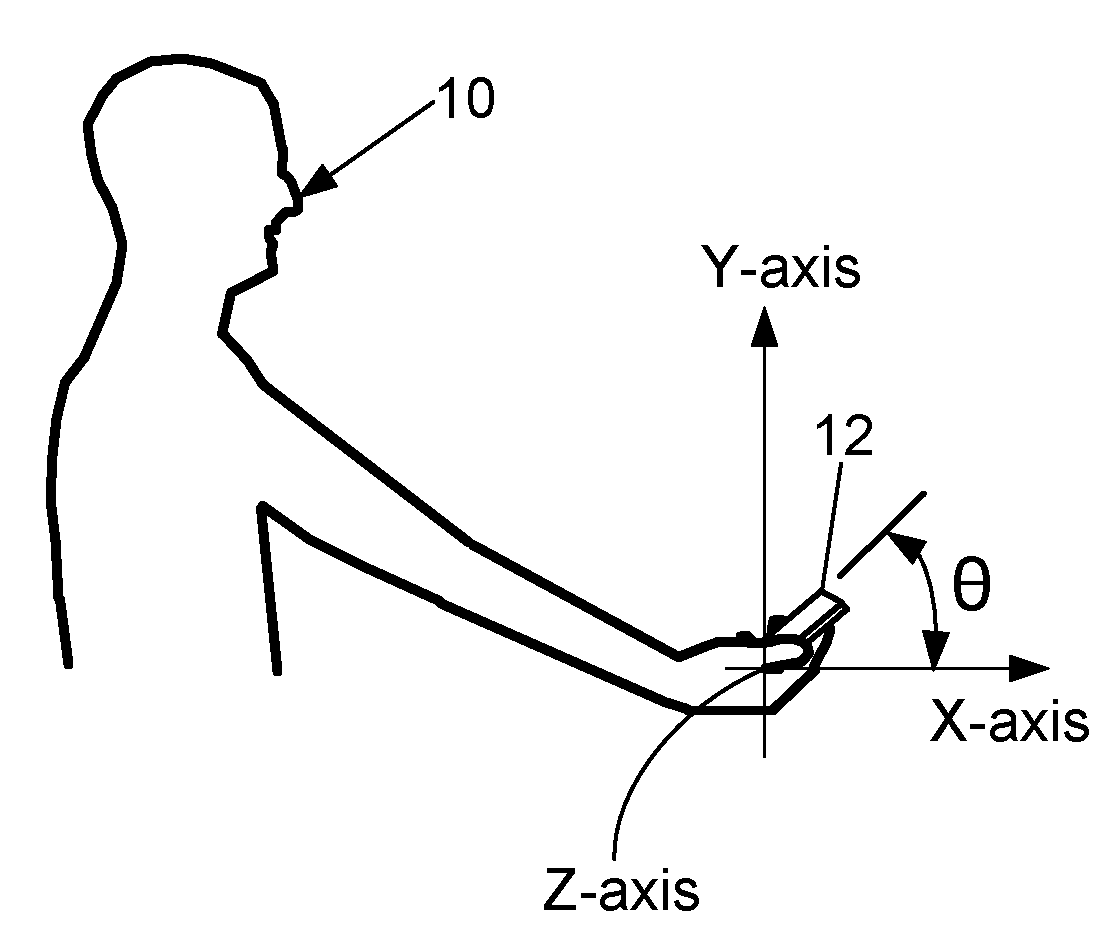
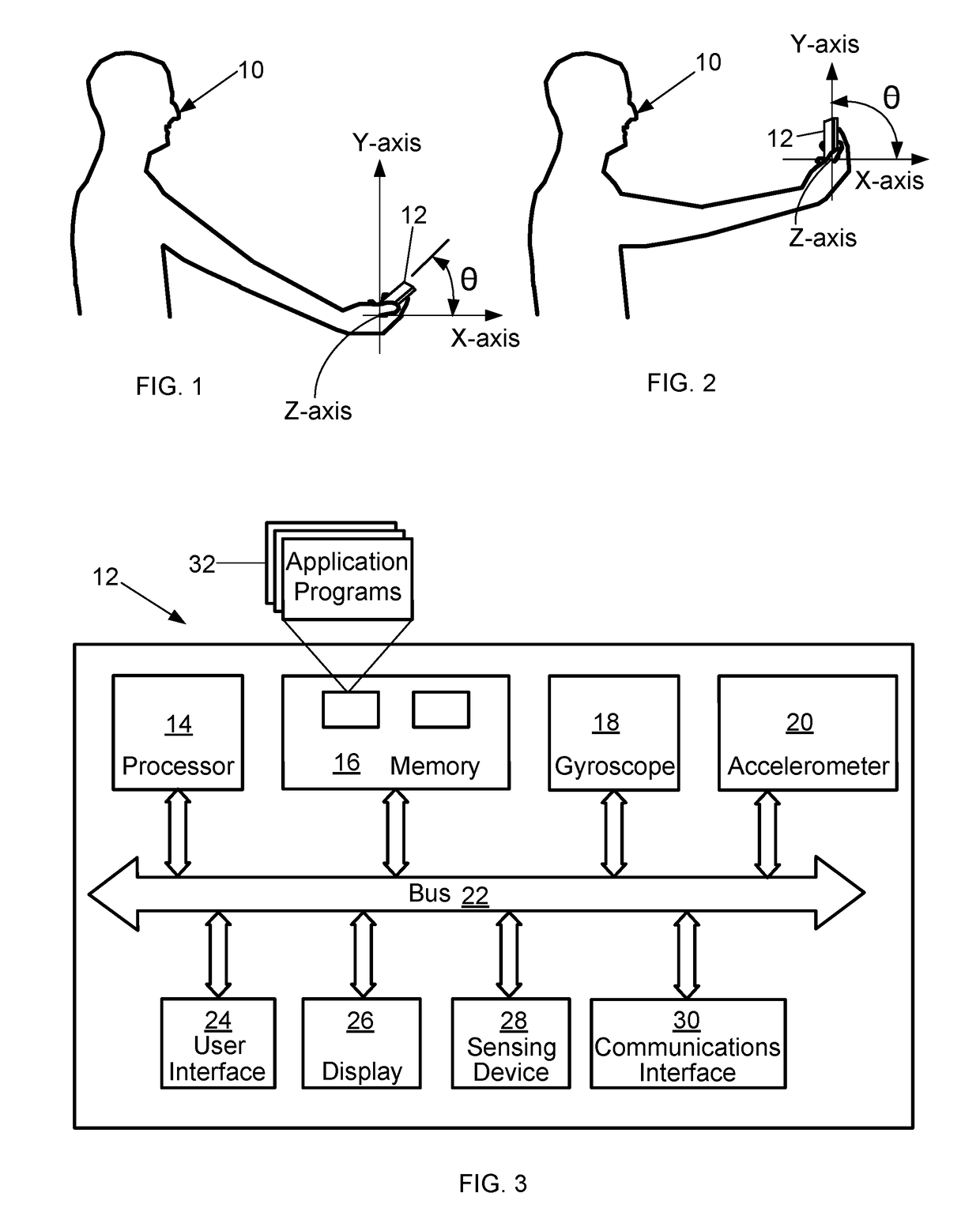
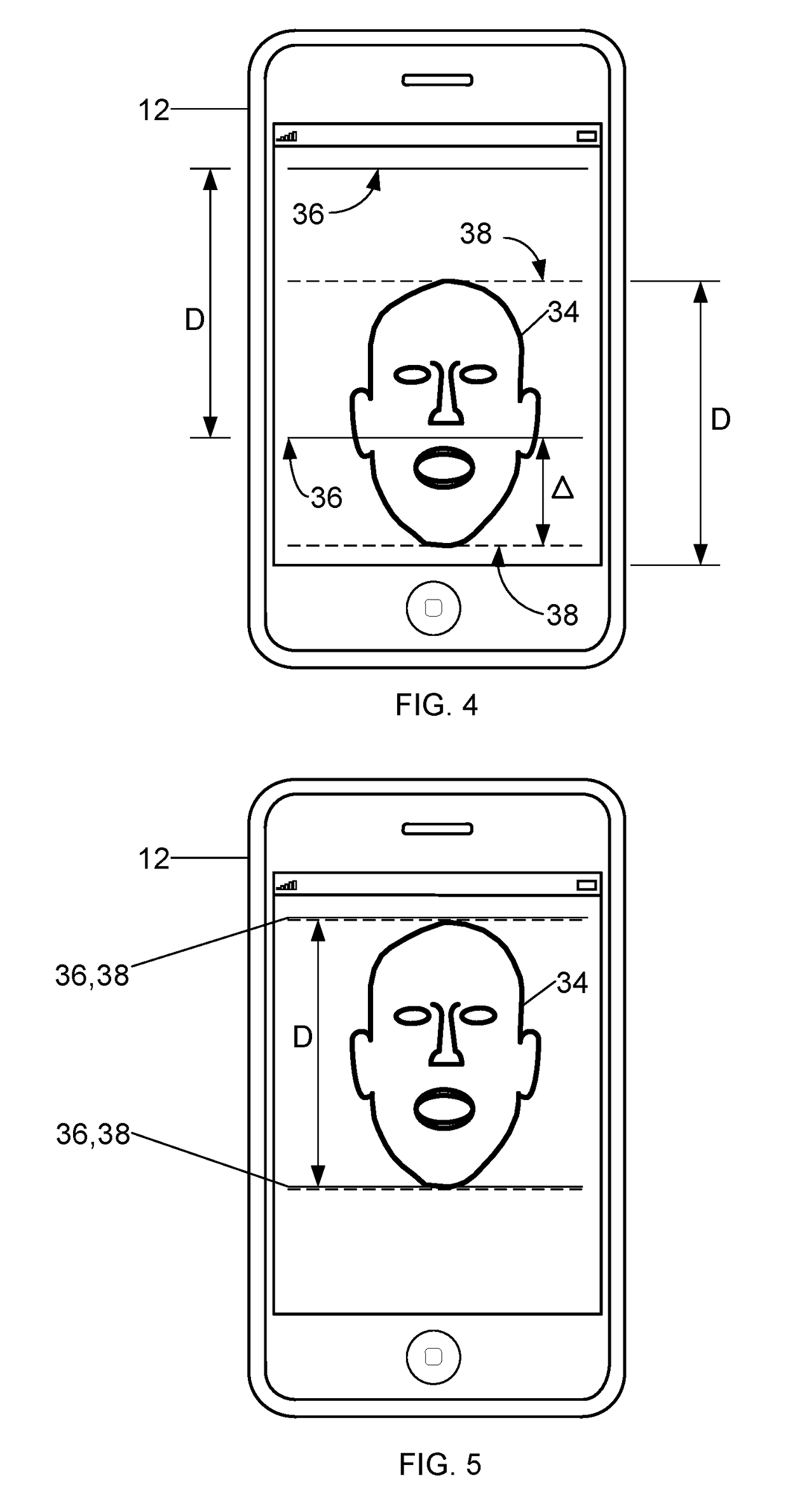
ActiveUS20170169202A1Precise positioningIncrease credibilityCharacter and pattern recognitionDigital data authenticationComputer hardwareBiometric data
A method of capturing biometric data is provided that includes calculating, by a terminal device, an angle between a surface of the terminal device and an X-axis of the terminal device. When the angle is other than ninety degrees, a prompt is displayed on the terminal device that is designed to cause a terminal device user to adjust the position of the terminal device into an optimal position. After adjusting the position of the terminal device, the terminal device calculates the angle and when the angle is ninety degrees the terminal device captures biometric data from the user.
Owner:DAON TECH
Frequency modulation characteristic control policy for doubly-fed wind turbine generator-energy storage system by simulating synchronous machine
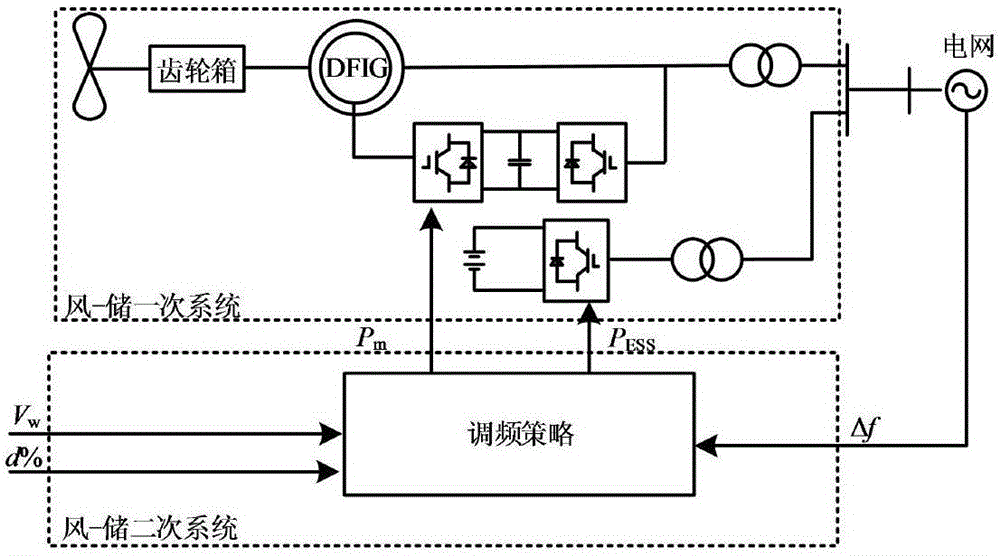
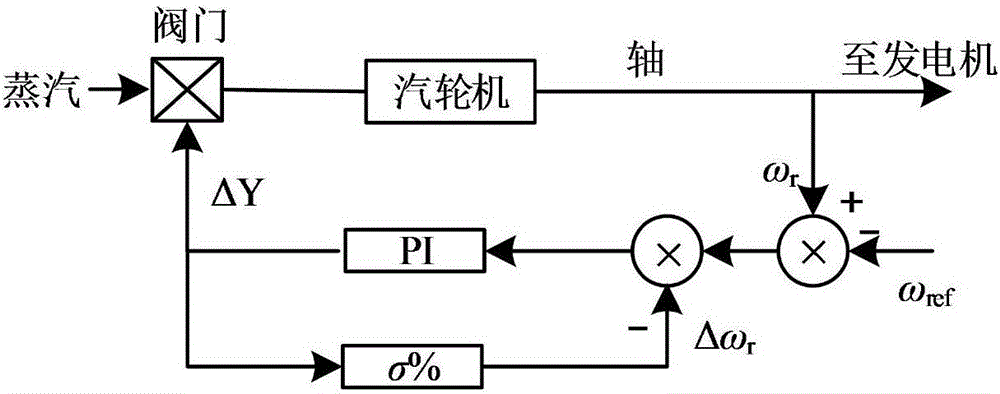
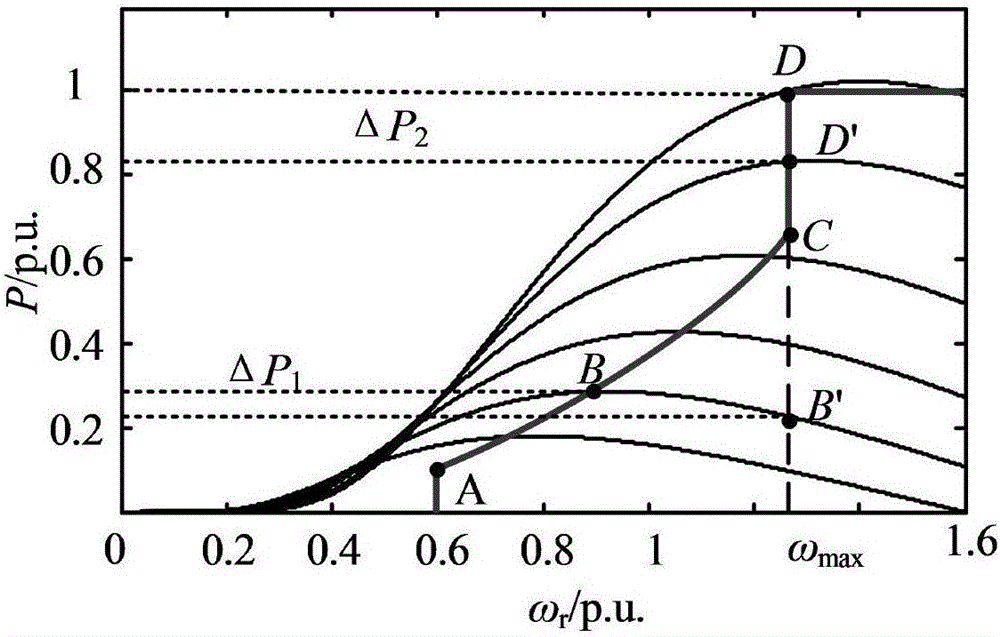
ActiveCN106374496ARealize two-way adjustmentReduce the cost of energy storage configurationSingle network parallel feeding arrangementsEnergy storageElectricityPower modulation
The invention discloses a frequency modulation characteristic control policy for a doubly-fed wind turbine generator-energy storage system by simulating a synchronous machine. The control policy is characterized by comprising the steps of establishing the doubly-fed wind turbine generator-energy storage system considering self wind power frequency modulation capacity; enabling the doubly-fed wind turbine generator-energy storage system to simulate capacity configuration of the frequency modulation characteristic of the synchronous machine, and enabling the doubly-fed wind turbine generator-energy storage system to perform frequency modulation control policy analysis and the like; establishing the doubly-fed wind turbine generator-energy storage system by analysis of the frequency modulation requirement of the system, combination of the self frequency modulation capacity of the doubly-fed wind turbine generator, and reasonable configuration of the energy storage capacity; reasonably allocating the power modulation capacity according to different frequency response time of the wind turbine generator and the energy storage system to endow the doubly-fed wind turbine generator-energy storage system with frequency response capability which is similar to that of a conventional synchronous generator so as to realize bidirectional frequency modulation; and by fully utilizing the complementary advantages of the wind turbine generator and the energy storage system under different air speeds in the aspects of frequency response speed, available frequency modulation energy and the like, lowering the energy storage configuration cost. The control policy has the advantages of scientific and reasonable property, high applicability, excellent effect and the like.
Owner:NORTHEAST DIANLI UNIVERSITY
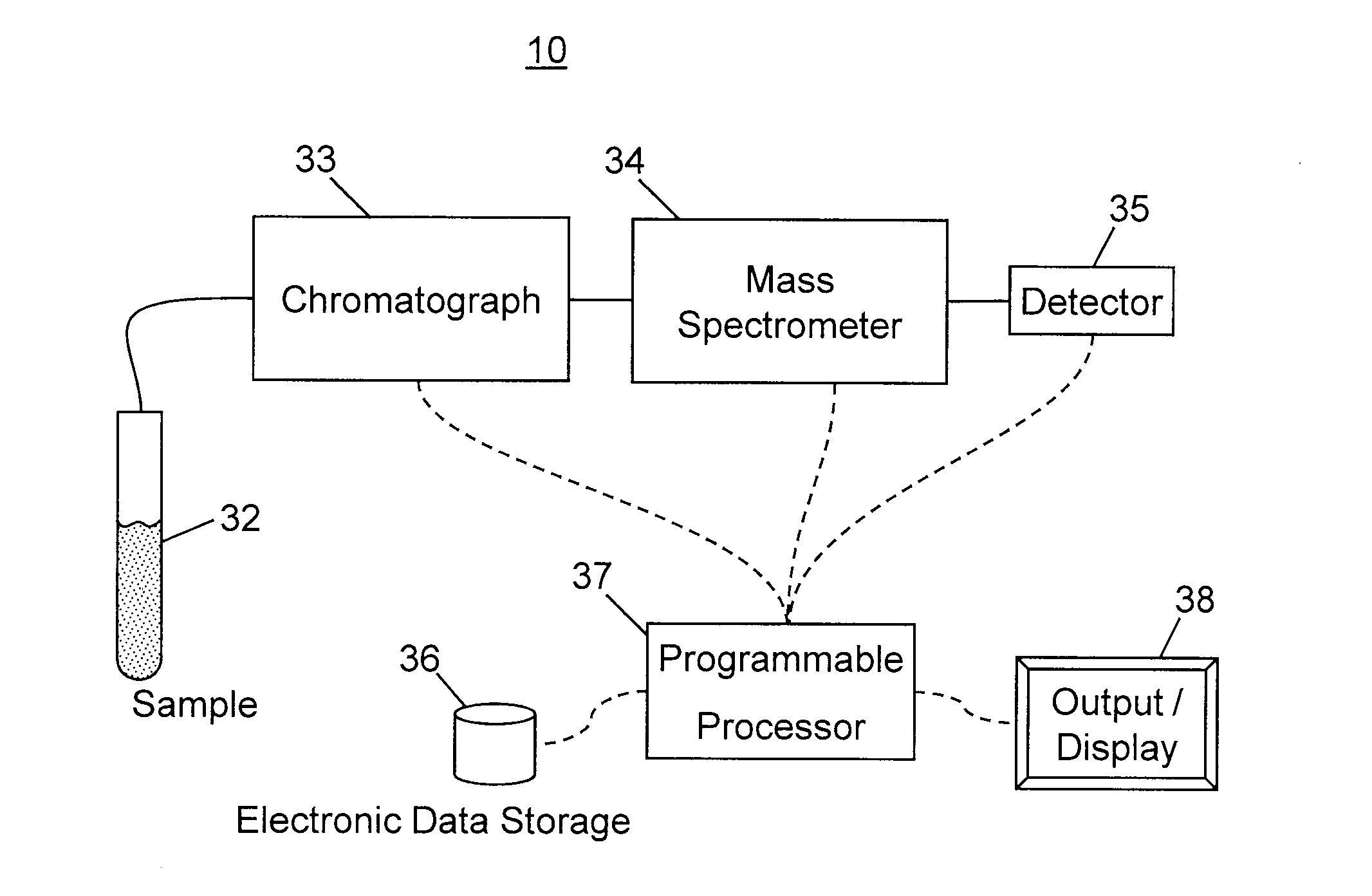
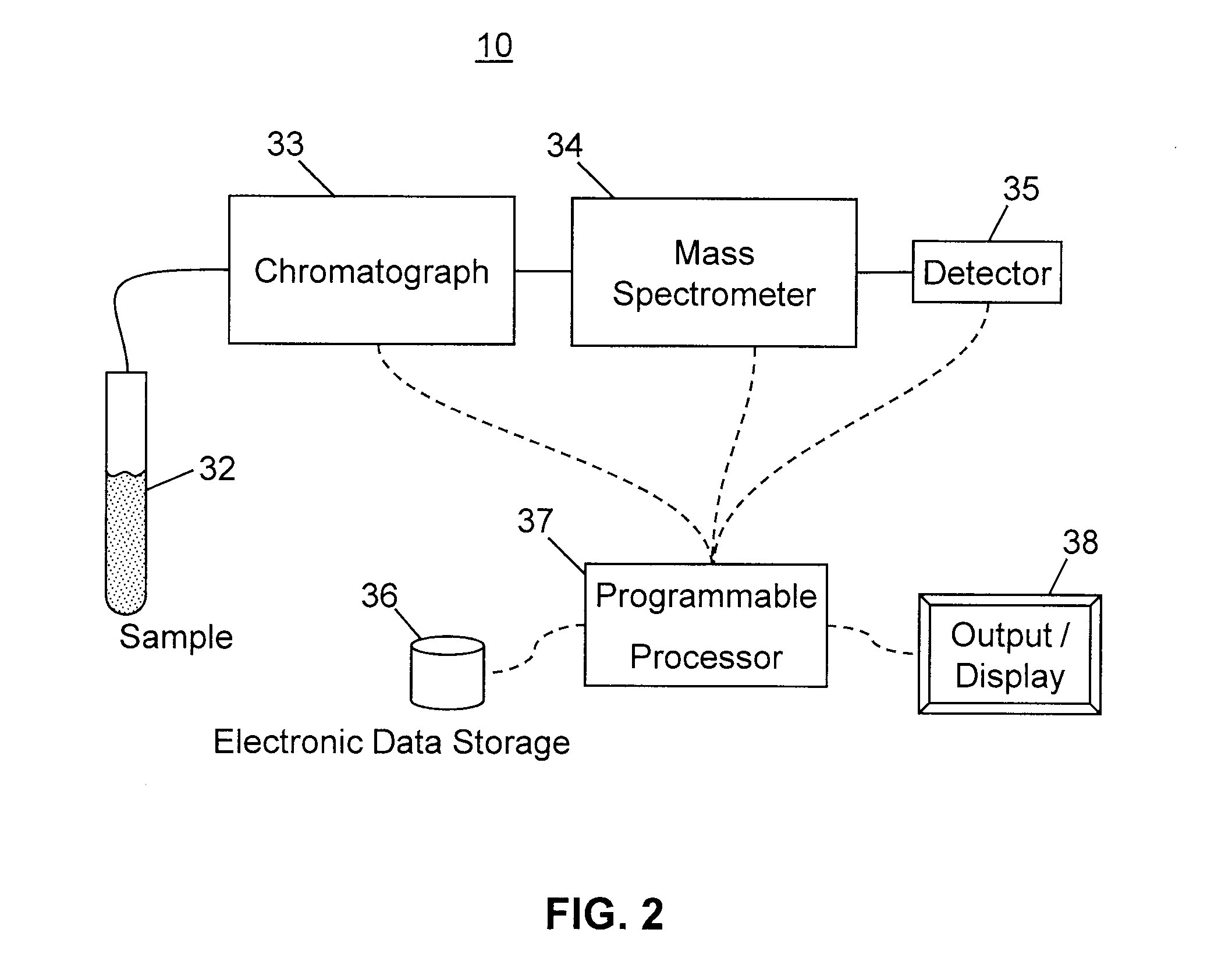
Method and Apparatus for Correlating Precursor and Product Ions in All-Ions Fragmentation Experiments
ActiveUS20120158318A1Good jobReduce noiseMolecular entity identificationComponent separationMass Spectrometry-Mass SpectrometryPeak value
A method for matching precursor ions to product ions generated in a chromatography—mass spectrometry experiment comprises: choosing a time window defining a region of interest for precursor ion data and product ion data generated by the experiment; constructing a plurality of extracted ion chromatograms (XICs) for the precursor ion data and the product ion data within the region of interest; automatically detecting and characterizing chromatogram peaks within each XIC and automatically generating synthetic analytical fit peaks thereof; discarding a subset of the synthetic analytical peaks which do not satisfy noise reduction rules; performing a respective cross-correlation score calculation between each pair of synthetic analytical fit peaks; and recognizing matches between precursor ions and product ions based on the cross correlation scores.
Owner:THERMO FINNIGAN
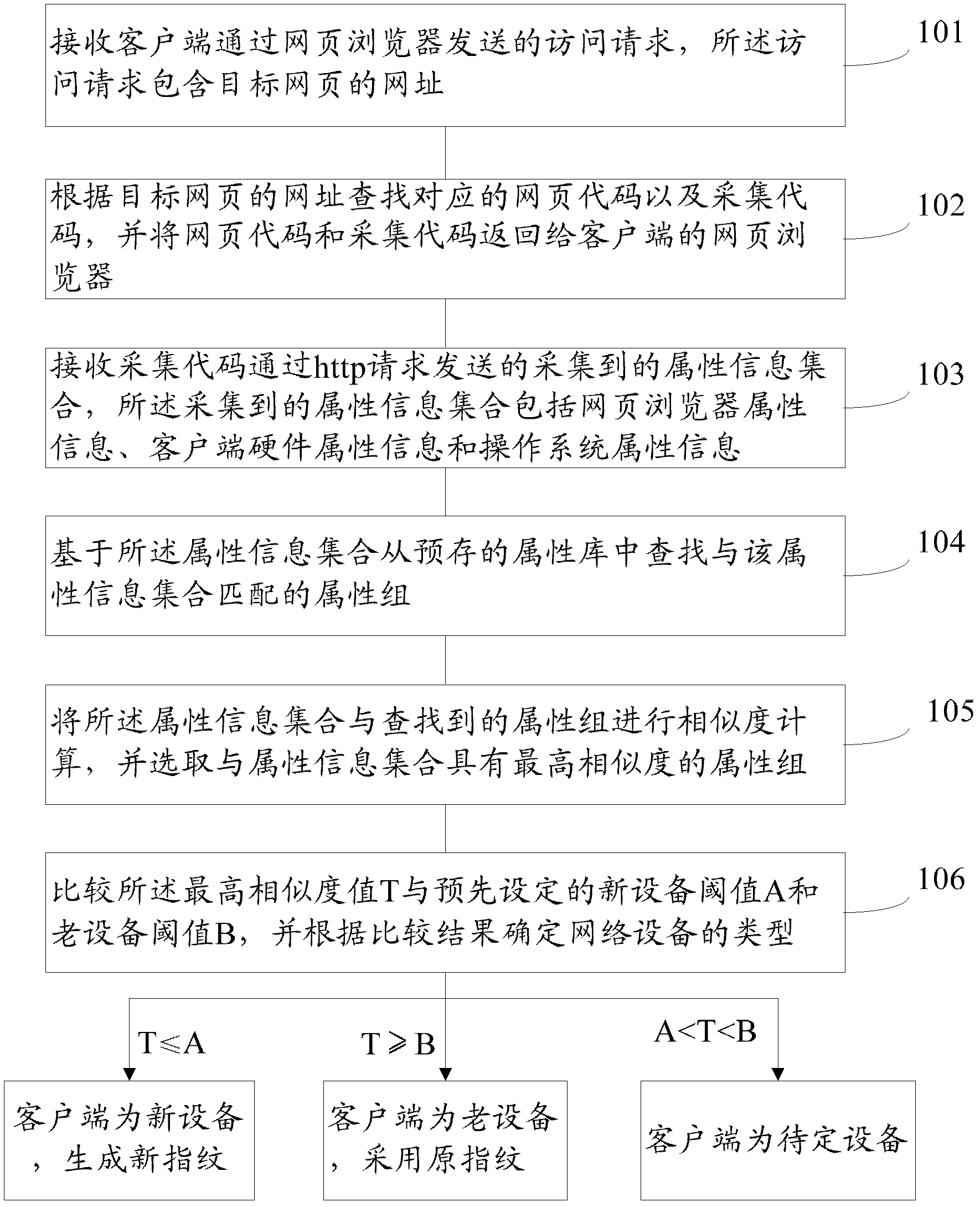
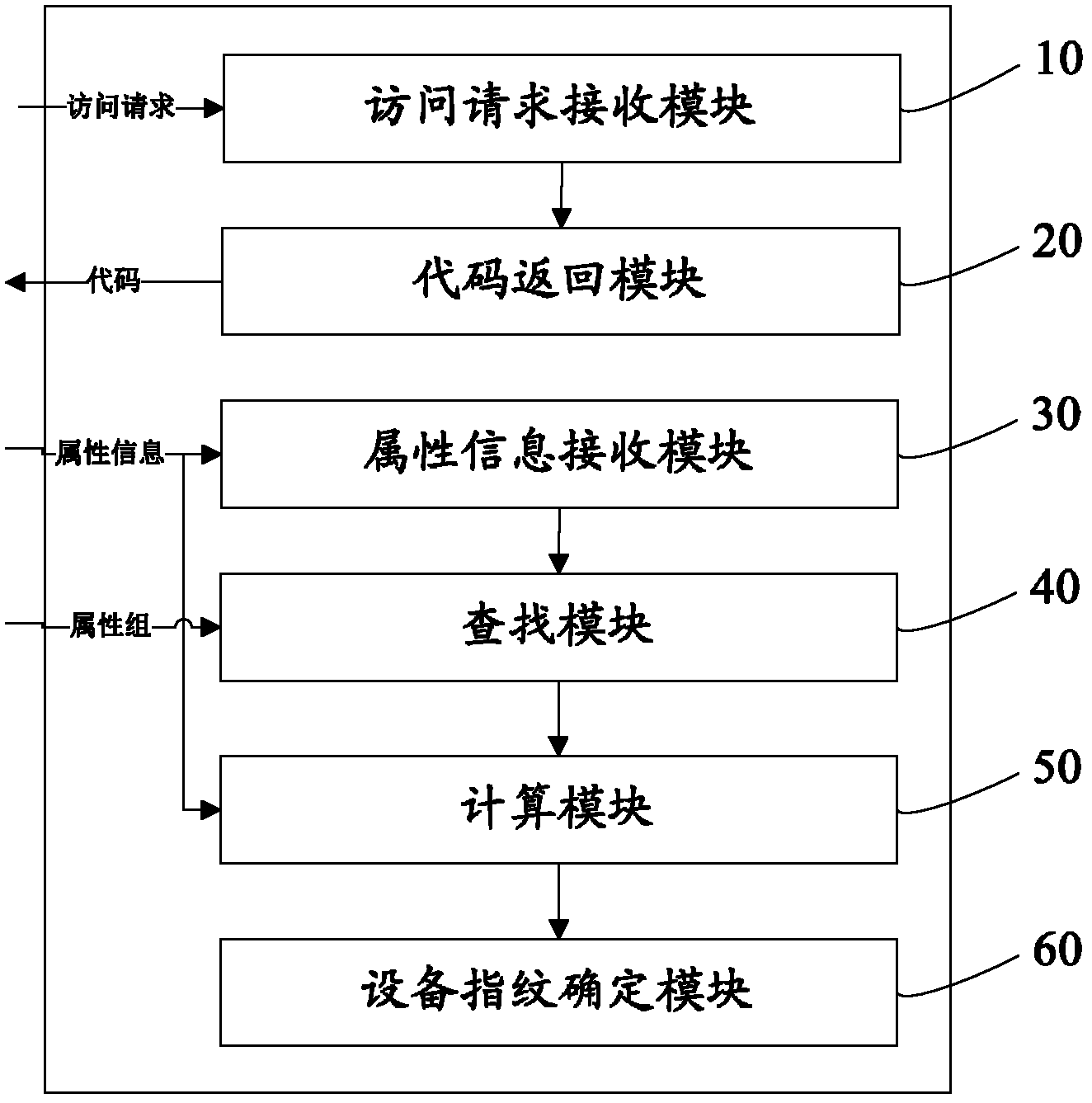
Method and system for network equipment identity recognition
The invention provides a method for network equipment identity recognition. The method for the network equipment identity recognition includes the following steps: receiving visit requests sent by network equipment through a webpage browser; searching corresponding webpage codes and collection codes according to an address of a target webpage and returning the codes to the webpage browser; receiving an attribute vector set collected from the network equipment and sent by the collection codes through the request of hyper text transport protocol (HTTP); searching attribute groups matched with the attribute vector set from a preset attribute bank based on the attribute vector set; carrying out similarity computation on the attribute vector set and the searched attribute groups and selecting the attribute group which has high similarity with the attribute vector set; and comparing the highest similarity value with a preset new equipment threshold value and an old equipment threshold value and determining the type of the network equipment according to comparison results. The invention further provides a network equipment identity recognition system for realizing the method. The method and the system for network equipment identity recognition can reduce occupation on network equipment resources, and improve visit speed and recognition accuracy.
Owner:ALIBABA GRP HLDG LTD
Personalized recommendation method and system based on probability model and user behavior analysis
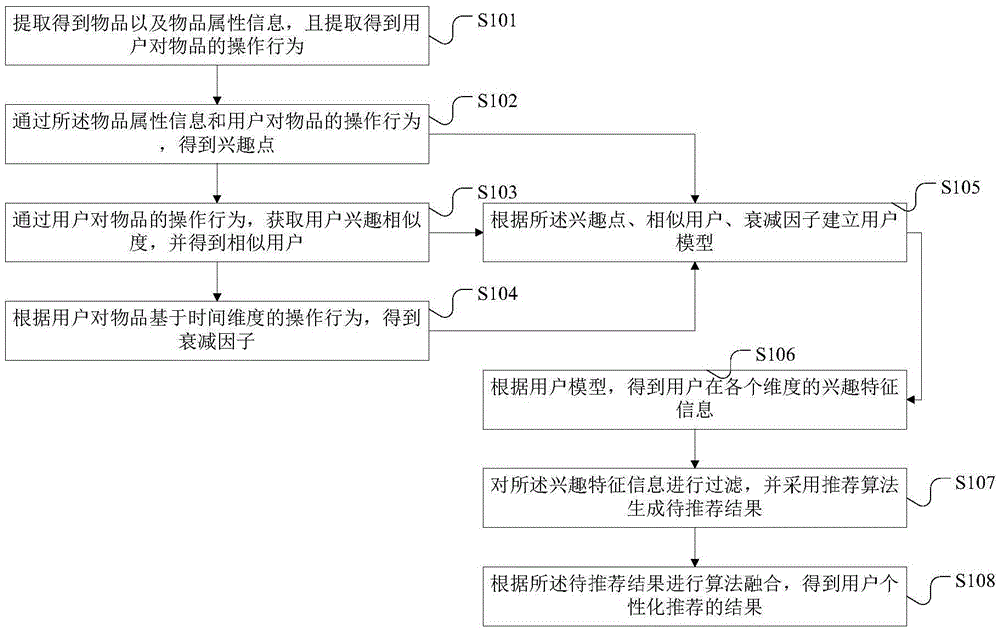
InactiveCN105574216AAccurately characterize acquisition needsSolve overloadSpecial data processing applicationsPersonalizationOriginal data
The invention discloses a personalized recommendation method and system based on a probability model and user behavior analysis. The method includes the steps that article information and article attribute information are extracted, and operation behaviors of users on articles are extracted; interest points are obtained according to the article attribute information and the operation behaviors of the users on the articles; user interest similarity is obtained according to the operation behaviors of the users on the articles, and similar users are obtained; a decay factor is obtained according to the operation behaviors of the users on the articles based on the time dimension, and a user model is set up; interest characteristic information, at all dimensions, of the users is obtained according to the user model; after filtering, a recommendation algorithm is adopted to generate results to be recommended, and algorithm fusion is conducted to obtain personalized recommendation results of the users. After original data is preprocessed, the user model is set up, the interest points of the users and essential information acquisition requirements are depicted accurately to provide accurate personalized recommendation, and therefore the problems of information overload and long-tail articles in the network are solved.
Owner:DATAGRAND TECH INC
Lightweight terminal block chain system
InactiveCN107317672AIncrease credibilityImprove immutabilityFinanceEncryption apparatus with shift registers/memoriesTransaction dataTerminal equipment
The invention provides a lightweight terminal block chain system. The system comprises a plurality of nodes, wherein the nodes comprise a core node and lightweight nodes; the core node is used for participating in block chain consensus, keeping accounts and generating a new block, and the block comprises a block head and a block main body; the lightweight node stores the block head and participates in node discovery, transaction broadcast and transaction validity verification. By adoption of the lightweight terminal block chain system, when a lightweight terminal device accesses the network, the lightweight terminal device participates in the transaction verification, transaction broadcast, block check and other functions of the block chain system, so that the transaction data in the block chain network back up more transaction information that cannot be tampered on more devices, thereby fully utilizing the idle resources of a part of terminal devices, and enhancing the reliability and the non-tampering property of the block chain system. Meanwhile, the system fully considers the limited storage, calculation and network resources of the terminal devices, so that the terminal devices join in the block chain system by the lightweight nodes, that is, maintain the normal operation of the block chain system by very small resource costs.
Owner:GUANGDONG YOUMAI INFORMATION COMM TECH
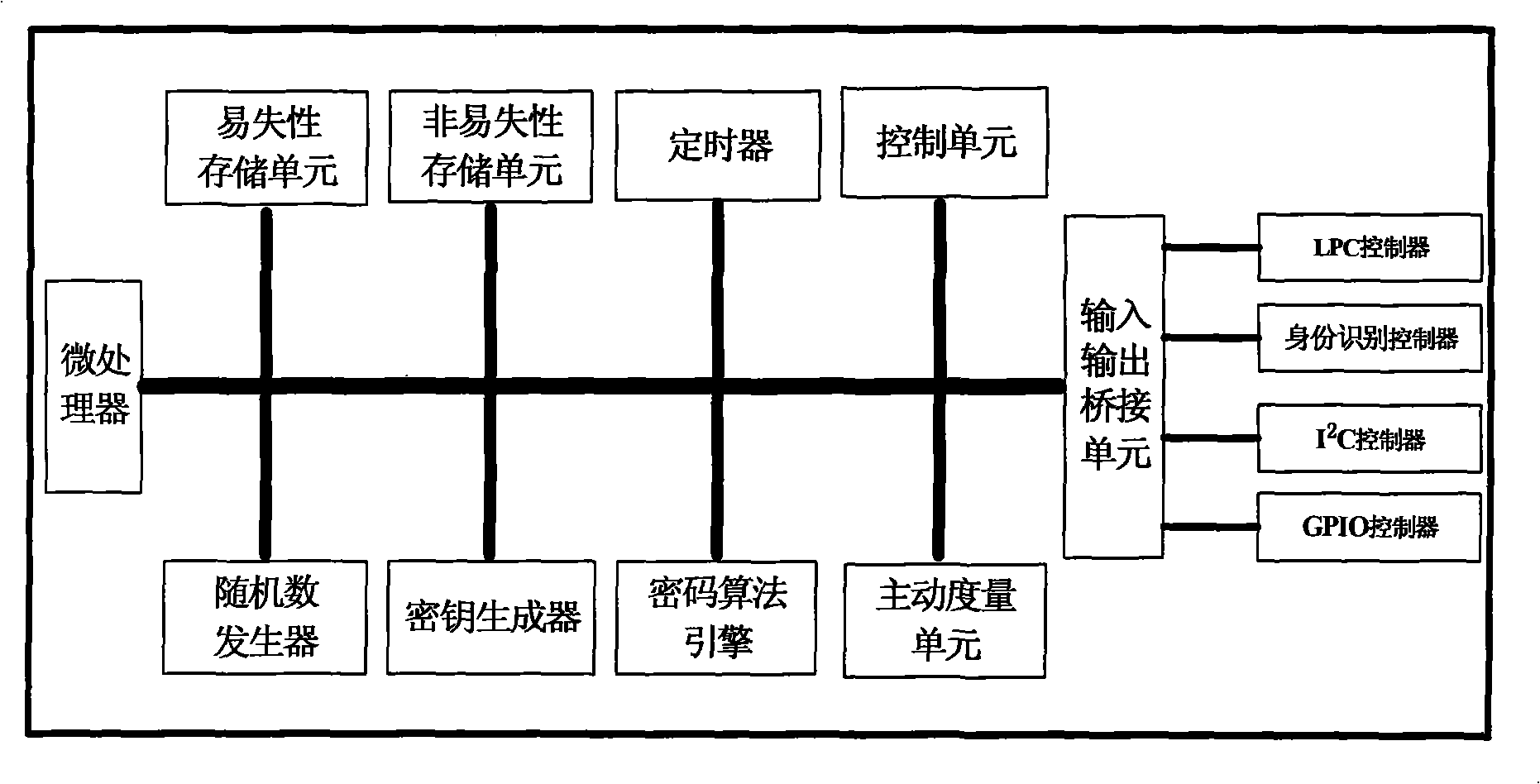
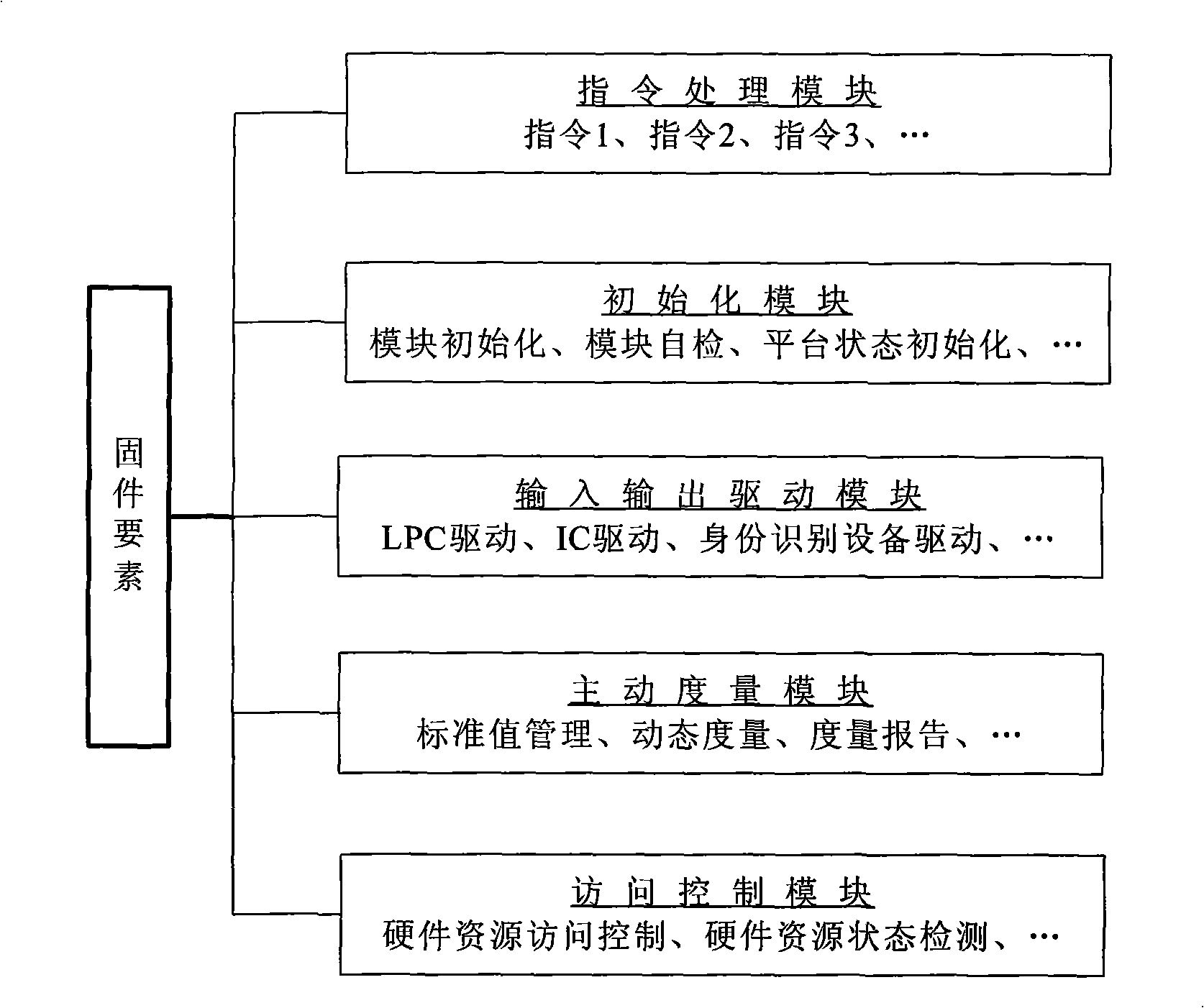
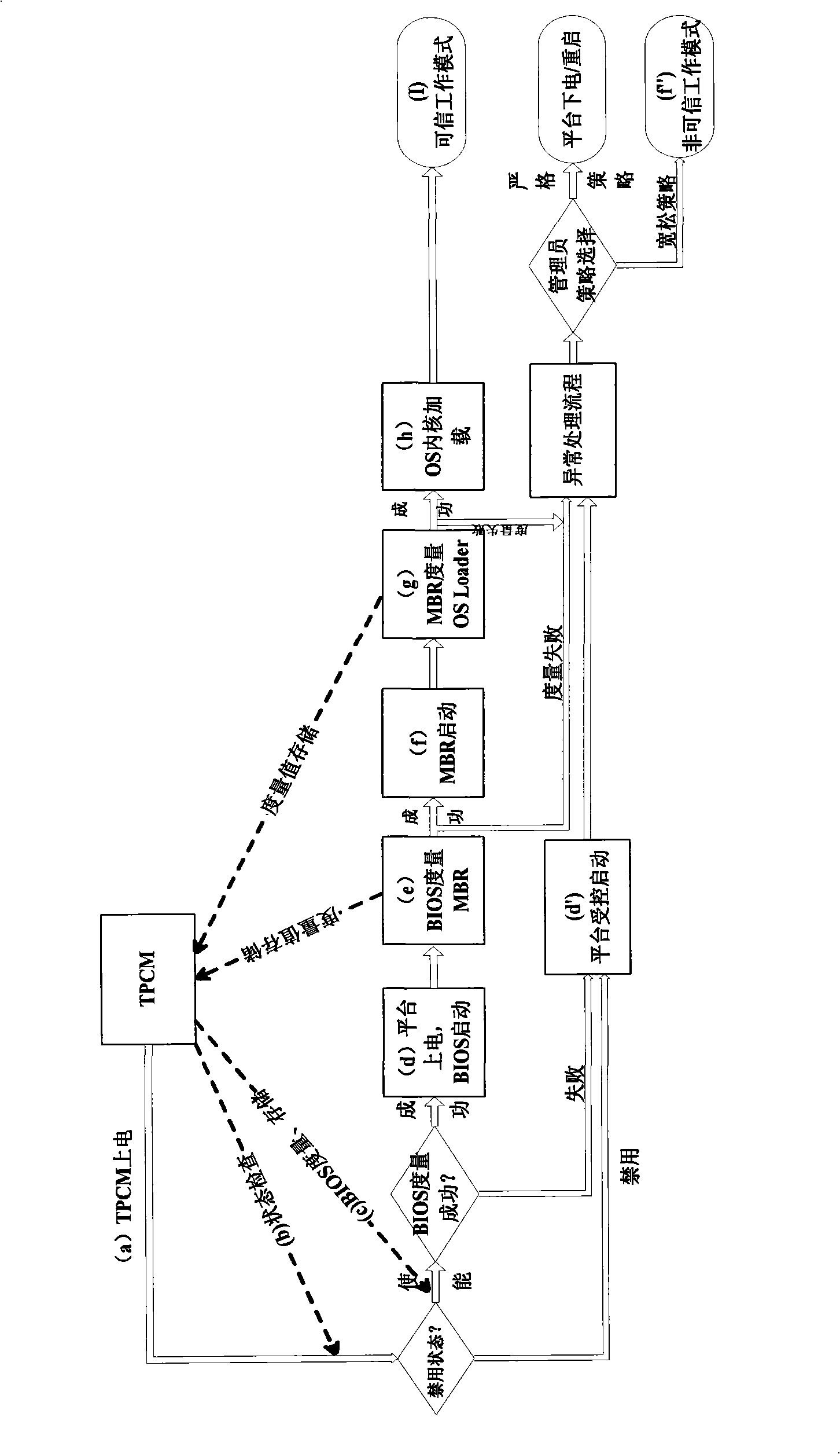
Credible platform module and active measurement method thereof
InactiveCN101295340ARealize functionPrevent tamperingInternal/peripheral component protectionTrusted Platform ModuleTrusted Computing
The invention discloses a trusted platform module and an active measurement method thereof, which relate to the field of information safety. The trusted platform module TPM is a root of trust of a trusted computing platform and a core module of trusted computing; the invention points out CRTM constitution of a root core of measurement in a TPM chip and a problem of establishing an information chain, proposes a new design proposal of the trusted platform module and the measurement method with an active mode based on the trusted platform module, designs the root of trust for measurement of the platform in the trusted platform module, solves the safety threat on the root of trust caused by tampering the BIOS and utilizes the module as the root of trust to establish a trust chain with the active mode. The invention names the module as a Trusted Platform Control Module TPCM and reflects the control function of the root of trust in the whole platform.
Owner:BEIJING UNIV OF TECH
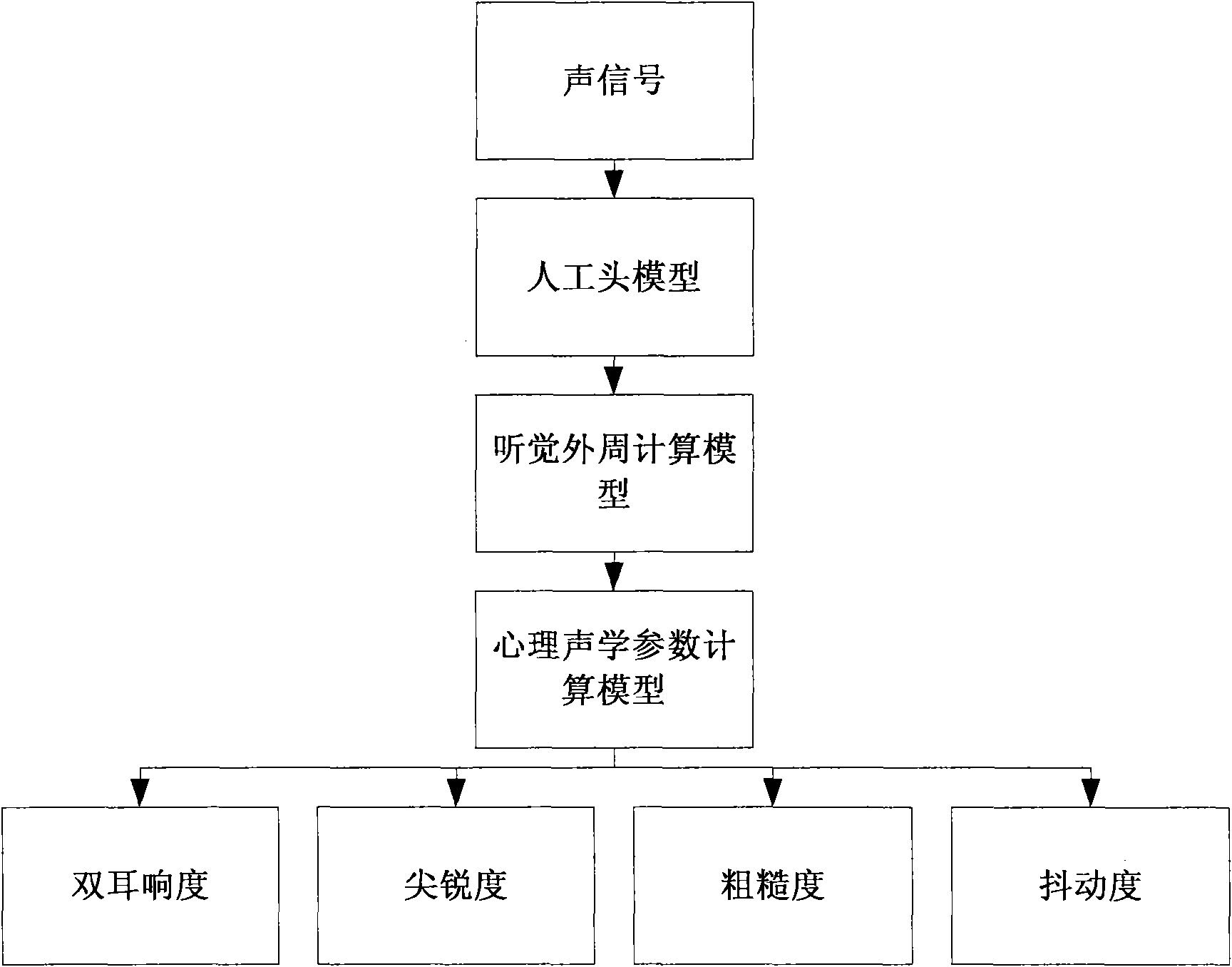
Method for objectively and quantifiably evaluating noise fret degree in vehicle based on auditory model
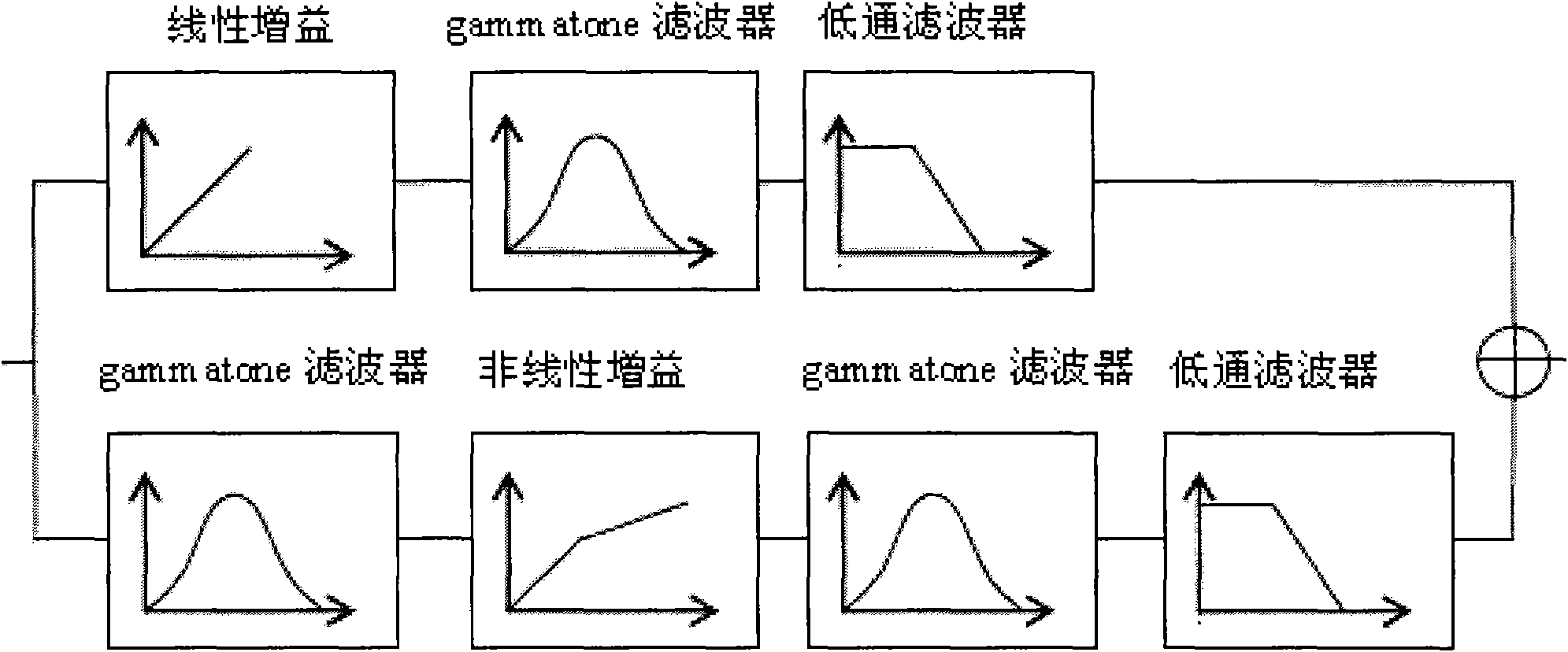
InactiveCN101672690AImprove performanceOvercoming complexityVibration measurement in fluidPsychotechnic devicesHuman bodyProcess mechanism
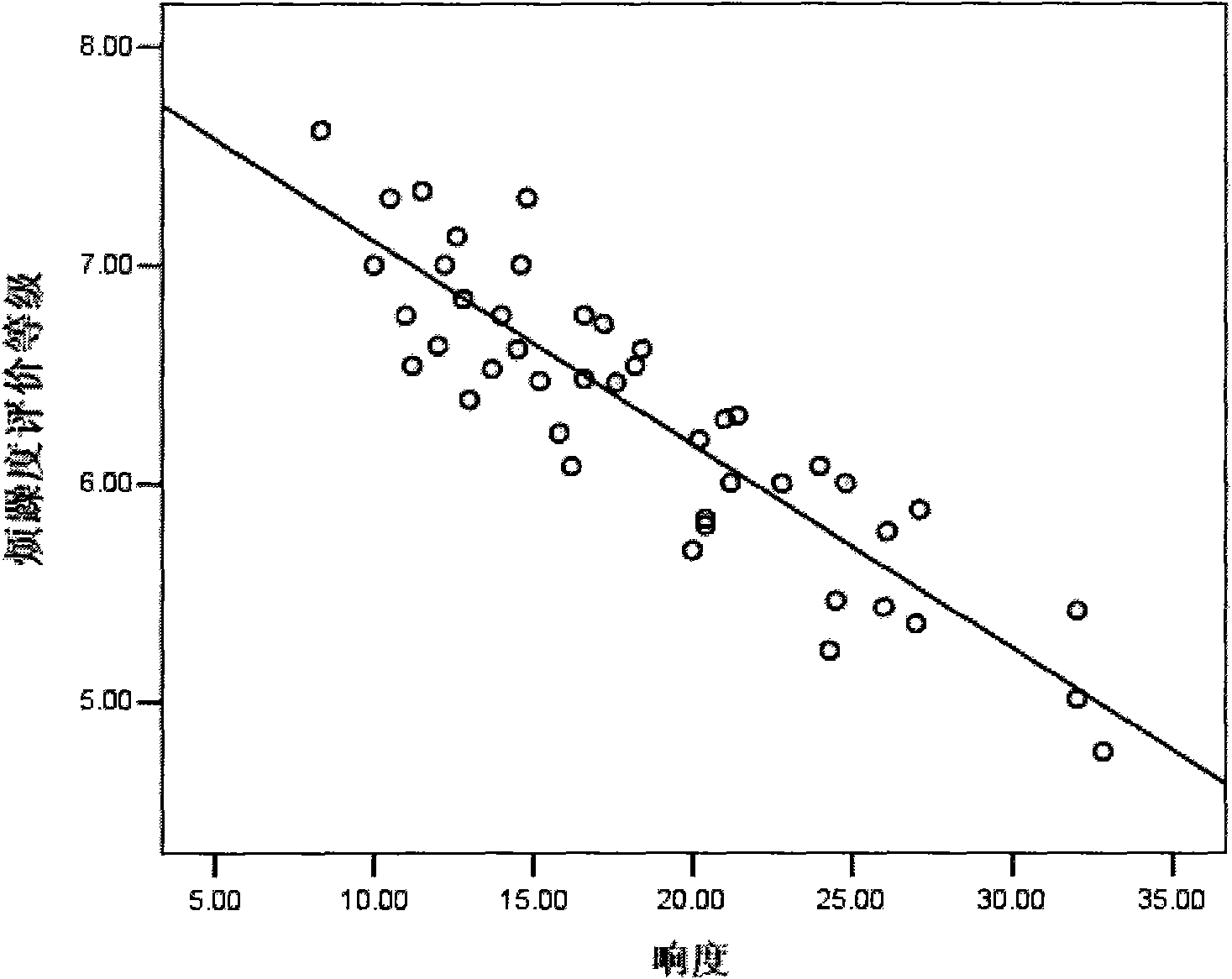
The invention relates to a method for objectively and quantifiably evaluating noise fret degree in a vehicle based on an auditory model, in particular to an evaluation method of psychoacoustics and vehicle sound quality. The method comprises the following steps: designing a dummy head model; imitating a processing mechanism of the middle ear and the inner ear of a human body to the sound by usingan auditory peripheral calculation model; collecting vehicle noise signals under the working conditions of uniform, accelerated and idle speed; pre-treating the noise sample and processing the loudness in specification; obtaining a psychoacoustics parameter by using a sound quality calculation model; obtaining subjective evaluation result test data by using a grouped and paired comparison method;calculating and painting a correlated scatter plot chart between each parameter and the ranking value of the subjective evaluation result; and analyzing and calculating to obtain the objectively quantifiable model of the subjective fret degree under each working condition. The invention can realize the psychoacoustic parameter calculation of objectively evaluating the sound quality with differentvehicle types, gears and speeds, wherein the calculated value has good pertinence and consistency with the evaluated result of the subjective evaluation method. The invention has stable evaluated result and high reliability, and can improve the sound quality and competitiveness of vehicles combined with the design of new CAE cars.
Owner:JILIN UNIV
Path planning method for avoiding of traffic hotspots
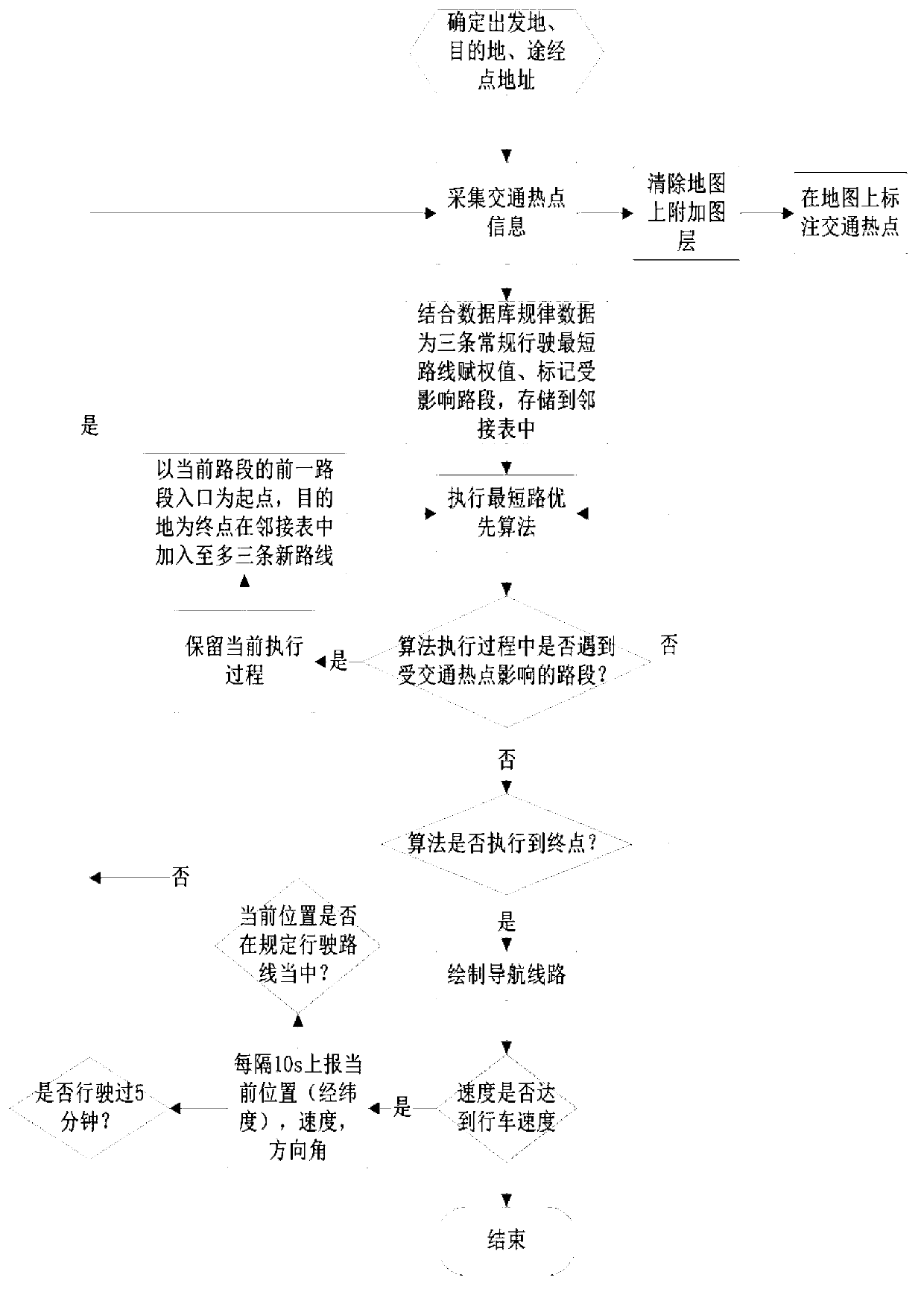
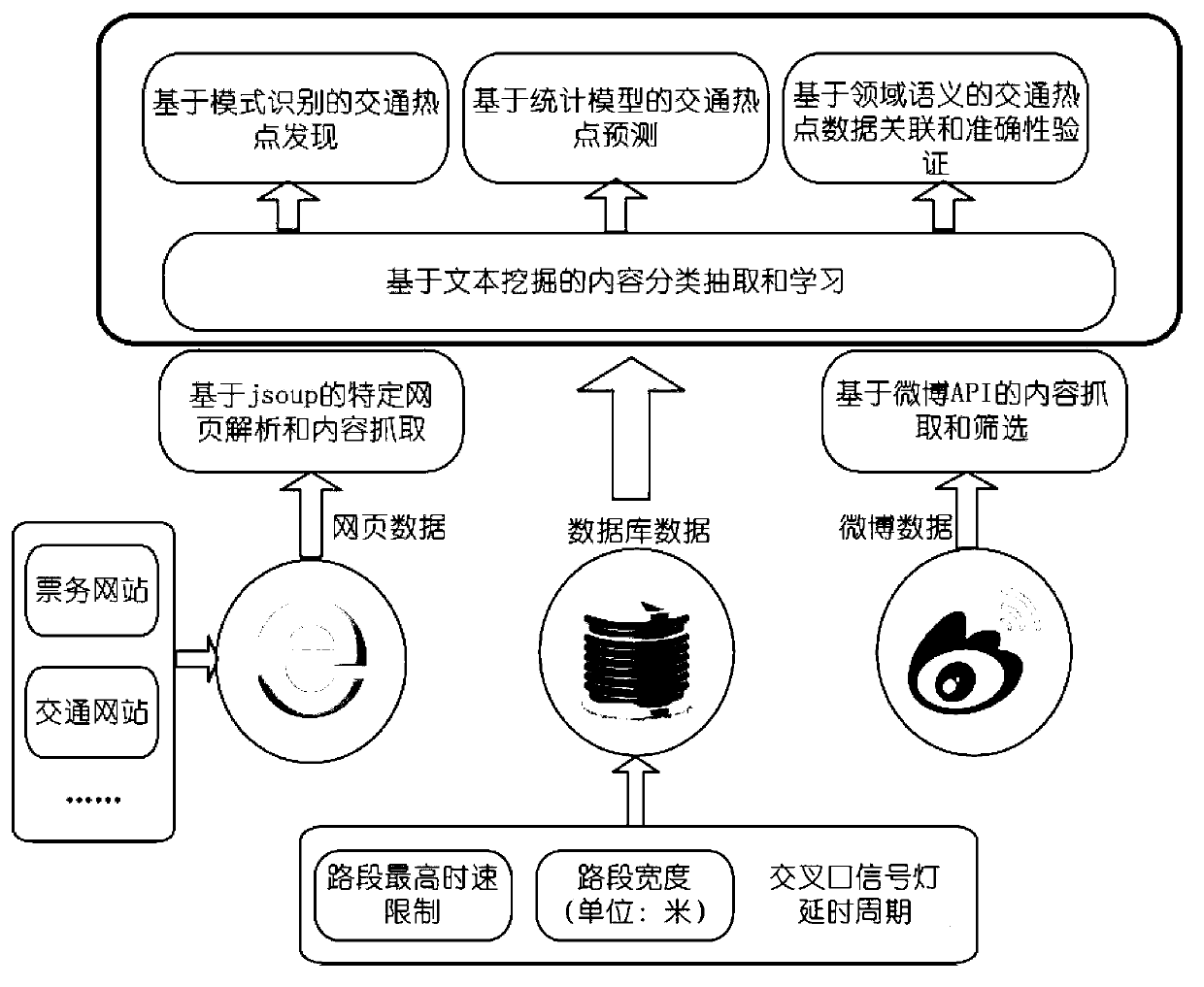
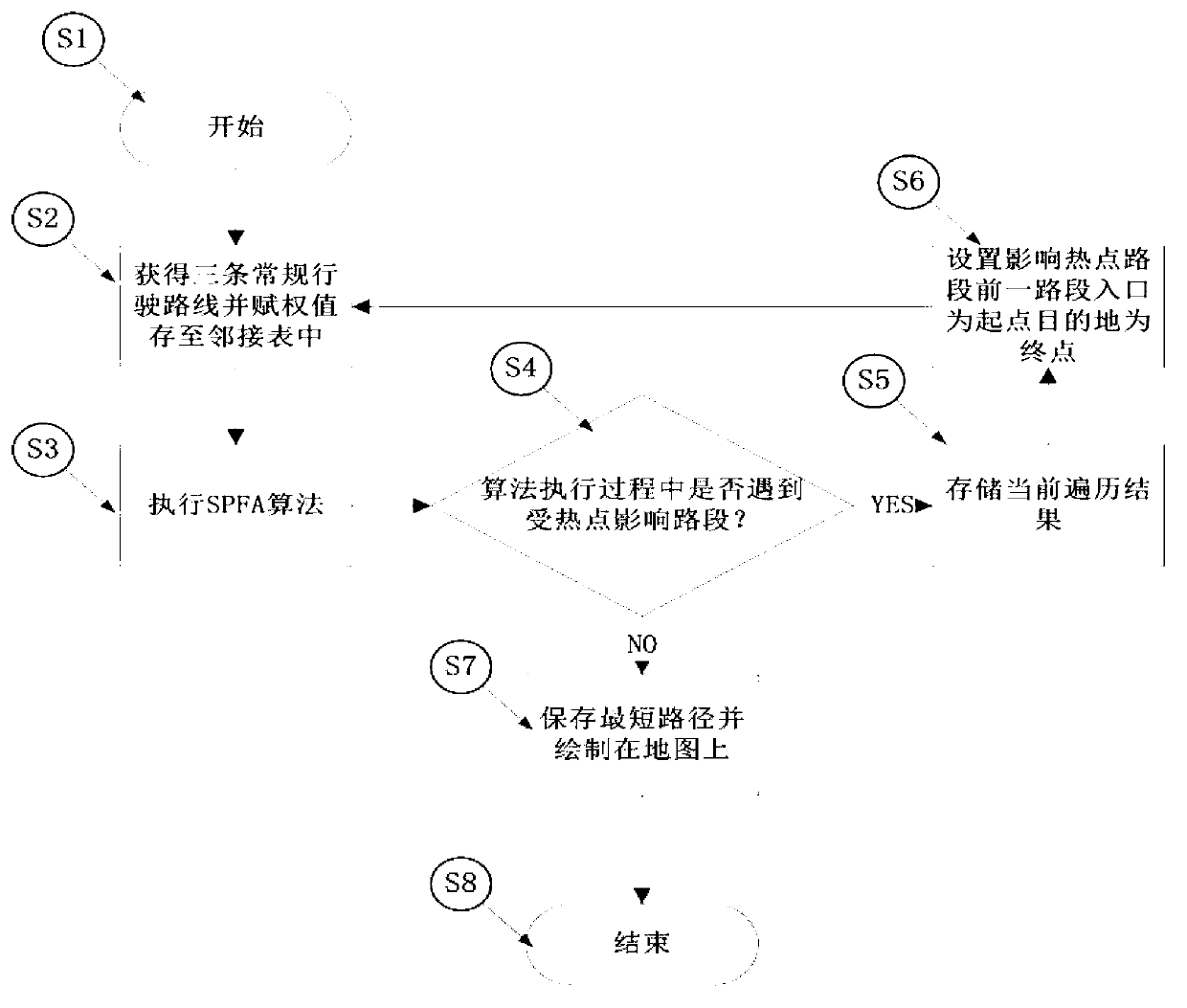
InactiveCN103278168AExtensive sources of dataIncrease credibilityInstruments for road network navigationFast pathMinimum time
A path planning method for avoiding of traffic hotspots helps to realize an intelligent path planning method with a purpose of the shortest journey time, by dynamical planning of paths with an avoiding property, based on a destination where a driving user goes. The traffic hotspot information, such as large-scale activities, traffic accidents, traffic-peak block roads, school time or commuter time of large-scale units, weather information and the like, are mined continually from a plurality of data sources comprising webpages, microblogs, real-time reported traffic information, historical regularity information and the like. By acquisition of the traffic hotspot information in real time, and combination with influences of a road maximum speed limit, road width and traffic light delay at intersections to driving as well as whether a main road containing a non-motor vehicle zone, a rapid navigation route with an avoiding function is planed, and also a dynamic path planning can be carried out in real time base on a current position. The method helps to provide a fastest path to the destination for drivers and alleviate city traffic jam in certain degree.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com