Patents
Literature
6172 results about "Analysis data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
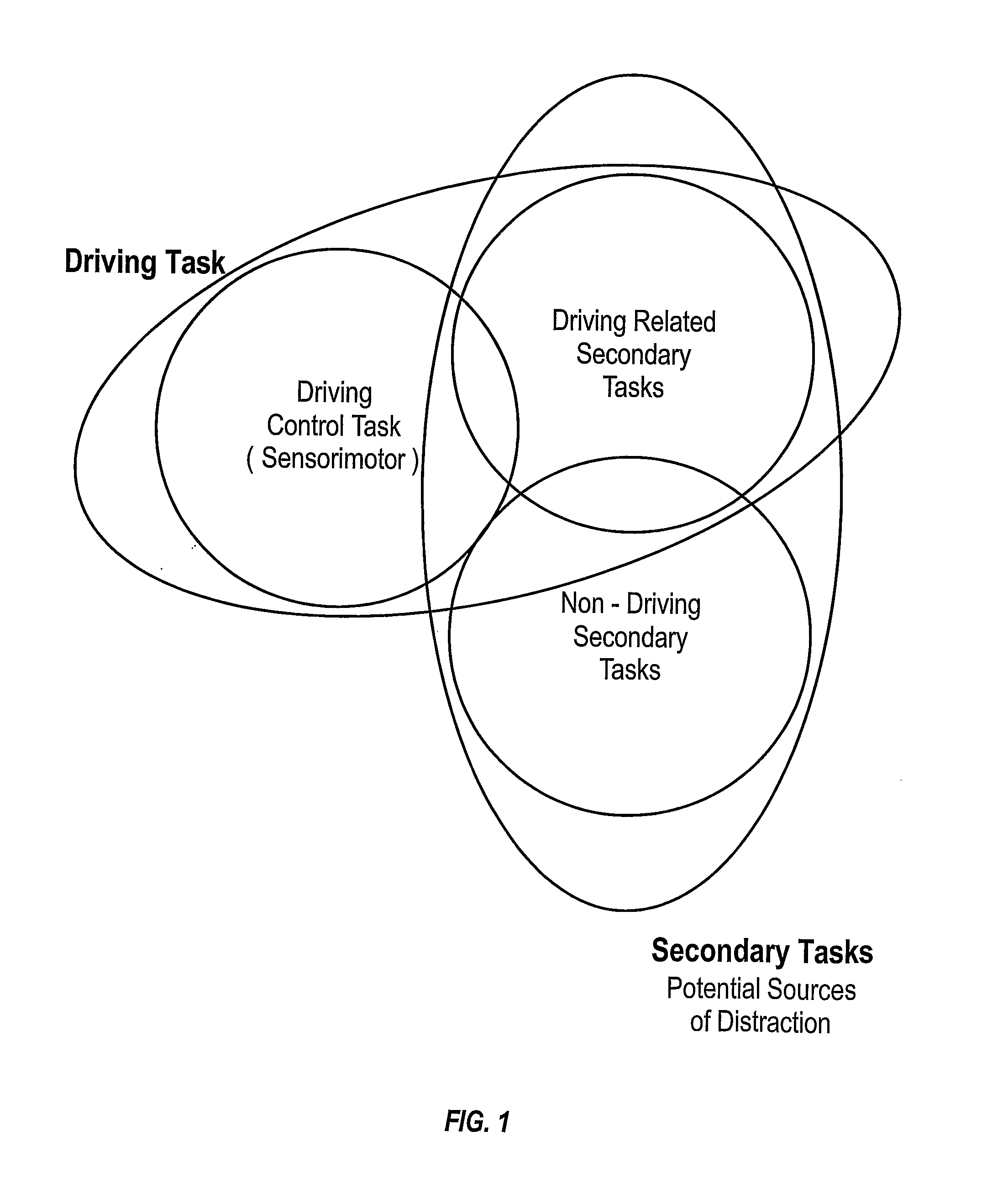
Data Analysis is the process of systematically applying statistical and/or logical techniques to describe and illustrate, condense and recap, and evaluate data.
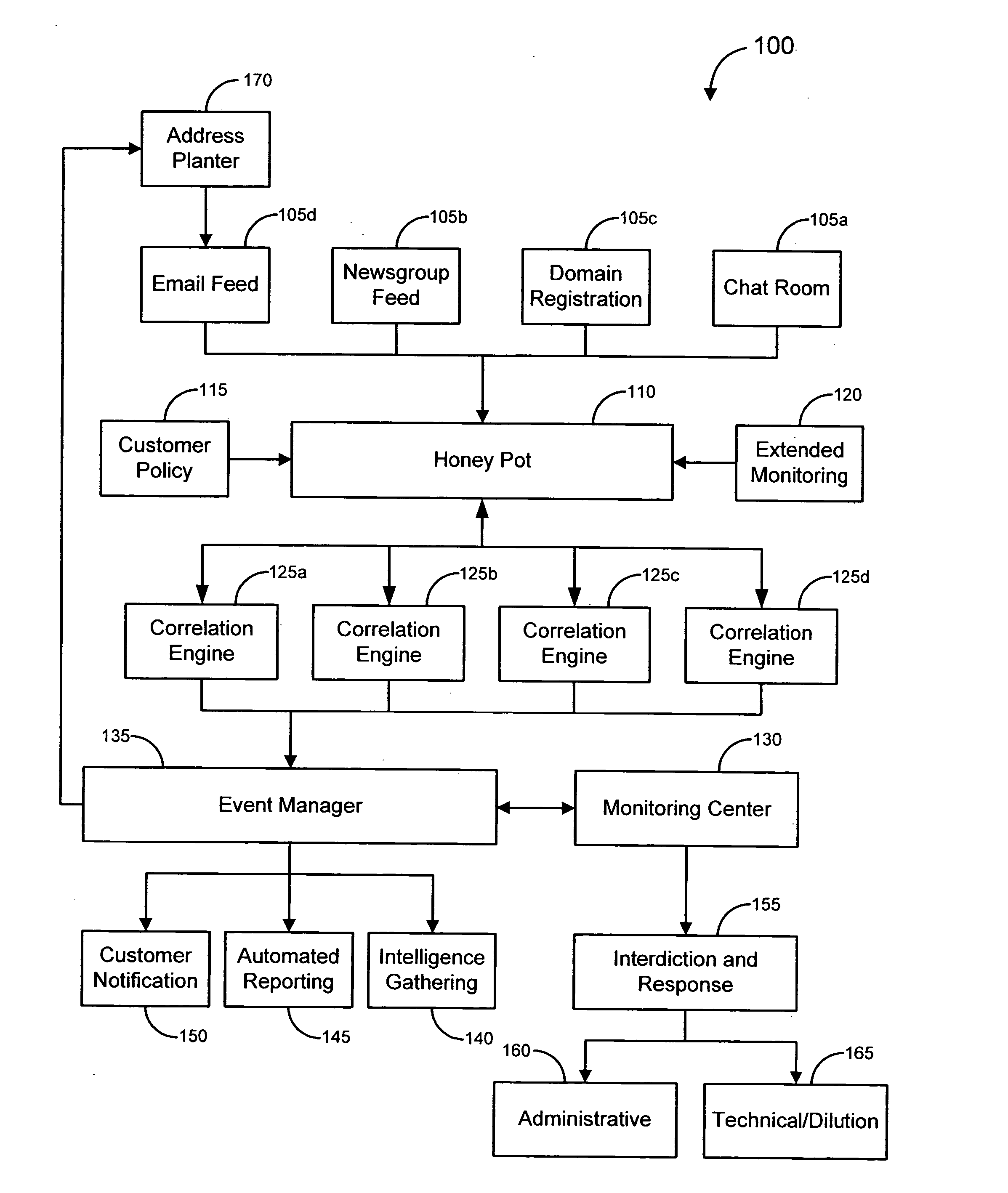
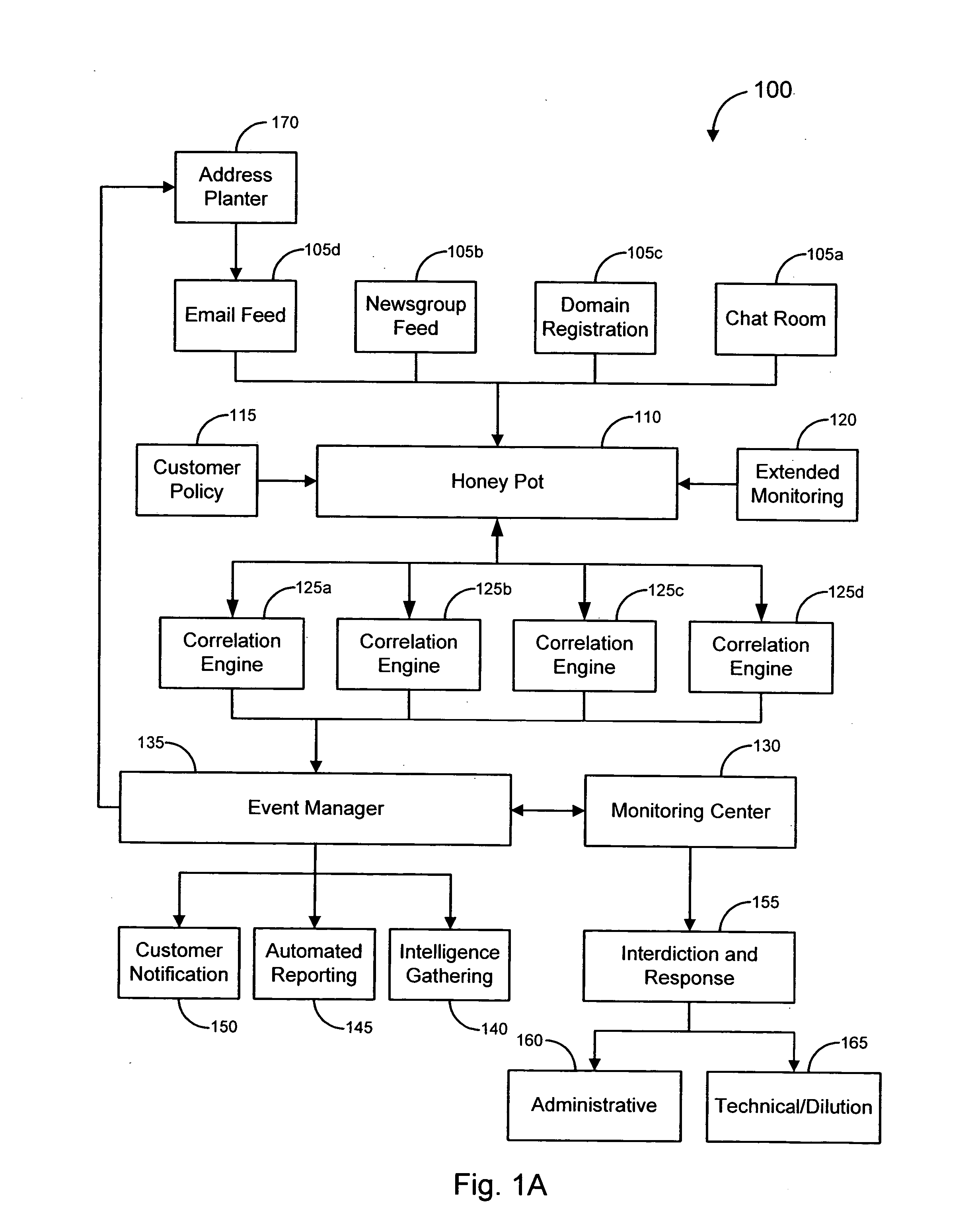
Music Recommendation system and method
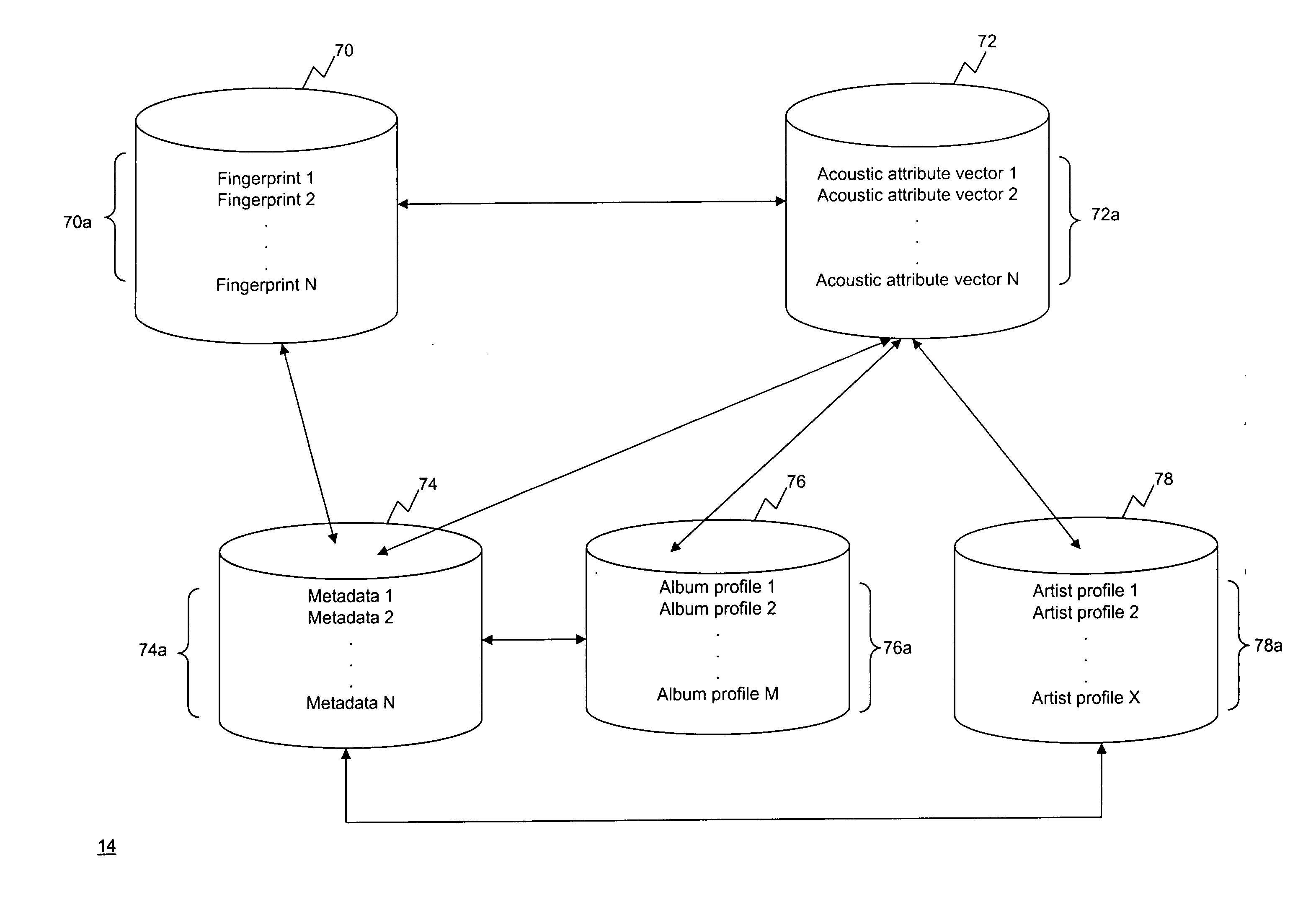
A music recommendation system receives a user selection of desired music, retrieves analysis data associated with the selected music, and generates a playlist of songs based on the analysis data. The analysis data is generated based on a processing of one or more audio signals associated with the selected music. The analysis data may downloaded from a central server. If the analysis data is not available from the central server, it is generated locally at a user end, and uploaded to the central server. A plurality of user-selectable shuffling mechanisms are provided to allow the order of the songs to be shuffled according to the selected shuffling mechanism. The end user device may also receive recommendation of new music from different providers based on the analysis data of music for which the recommendation is to be based.
Owner:MUSICIP CORP
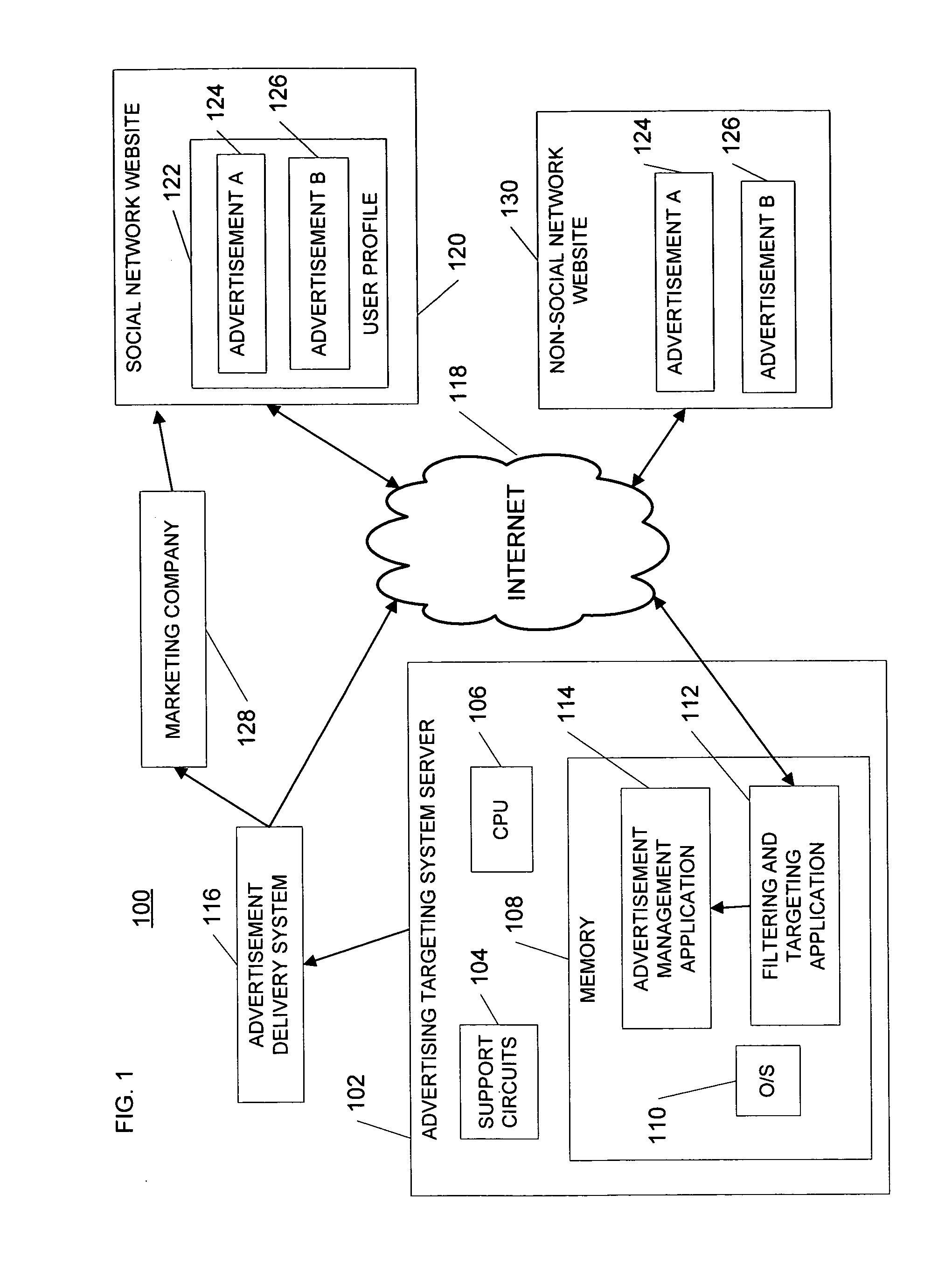
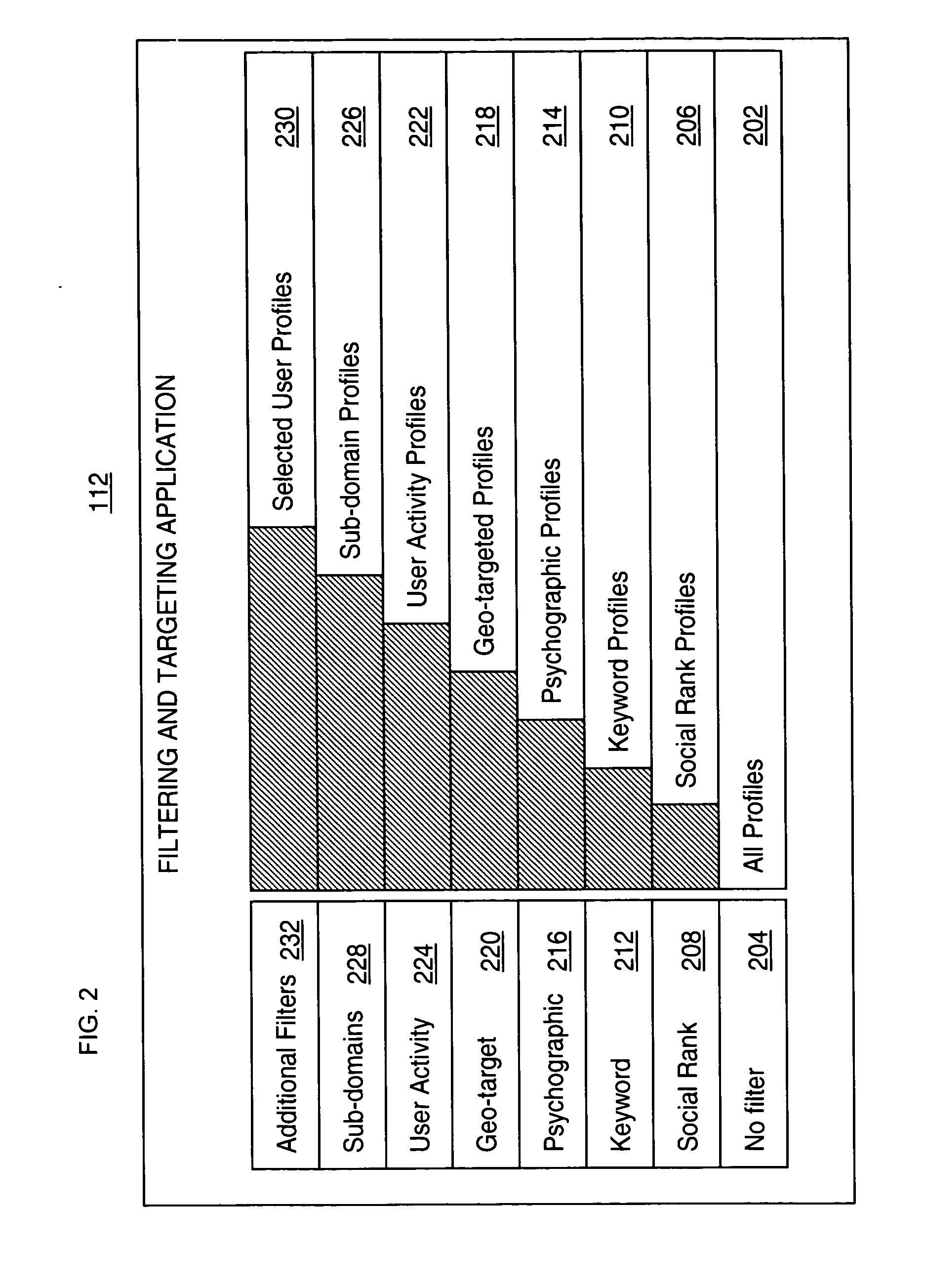
System and method for implementing advertising in an online social network
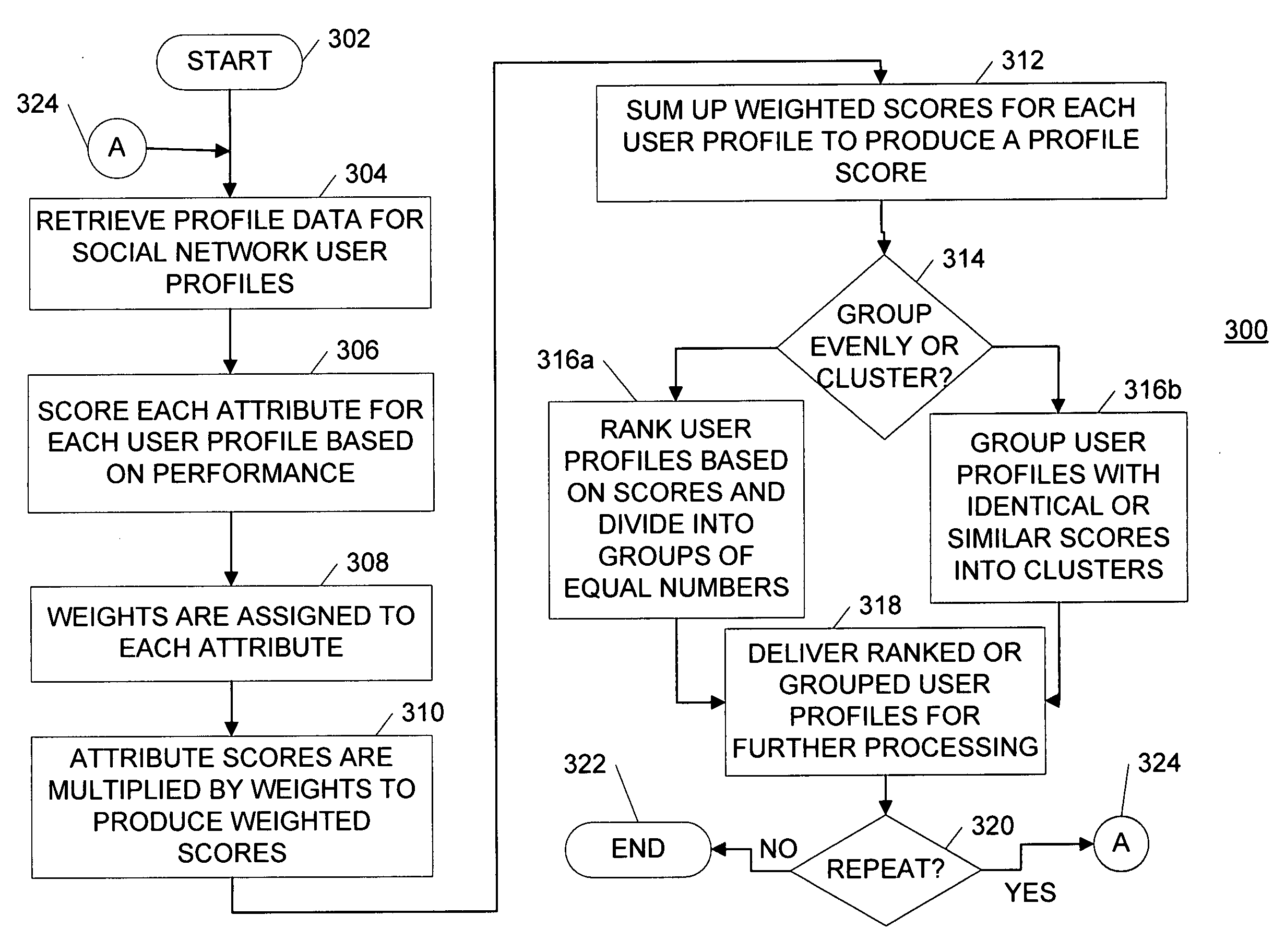
A system and method for integrating analytics data of user profiles within a social network with targeted ad campaigns. The system includes an advertisement targeting system that obtains analytics data of user profiles and utilizes the data to filter through the user profiles to select desired user profiles for delivery of advertisements targeted to the interests and personality of the desired user profiles. Utilization of the analytics data includes generating a social rank of each user profile relevant to other user profiles in the social network. An advertising marketplace is implemented for use by ad marketers to purchase advertisement rights on a user profile webpage, to filter through user profiles in a social network for select user profiles with desired analytics data, and to generate advertisement campaigns targeted to the selected user profiles within a social network.
Owner:SIZMEK TECH +1
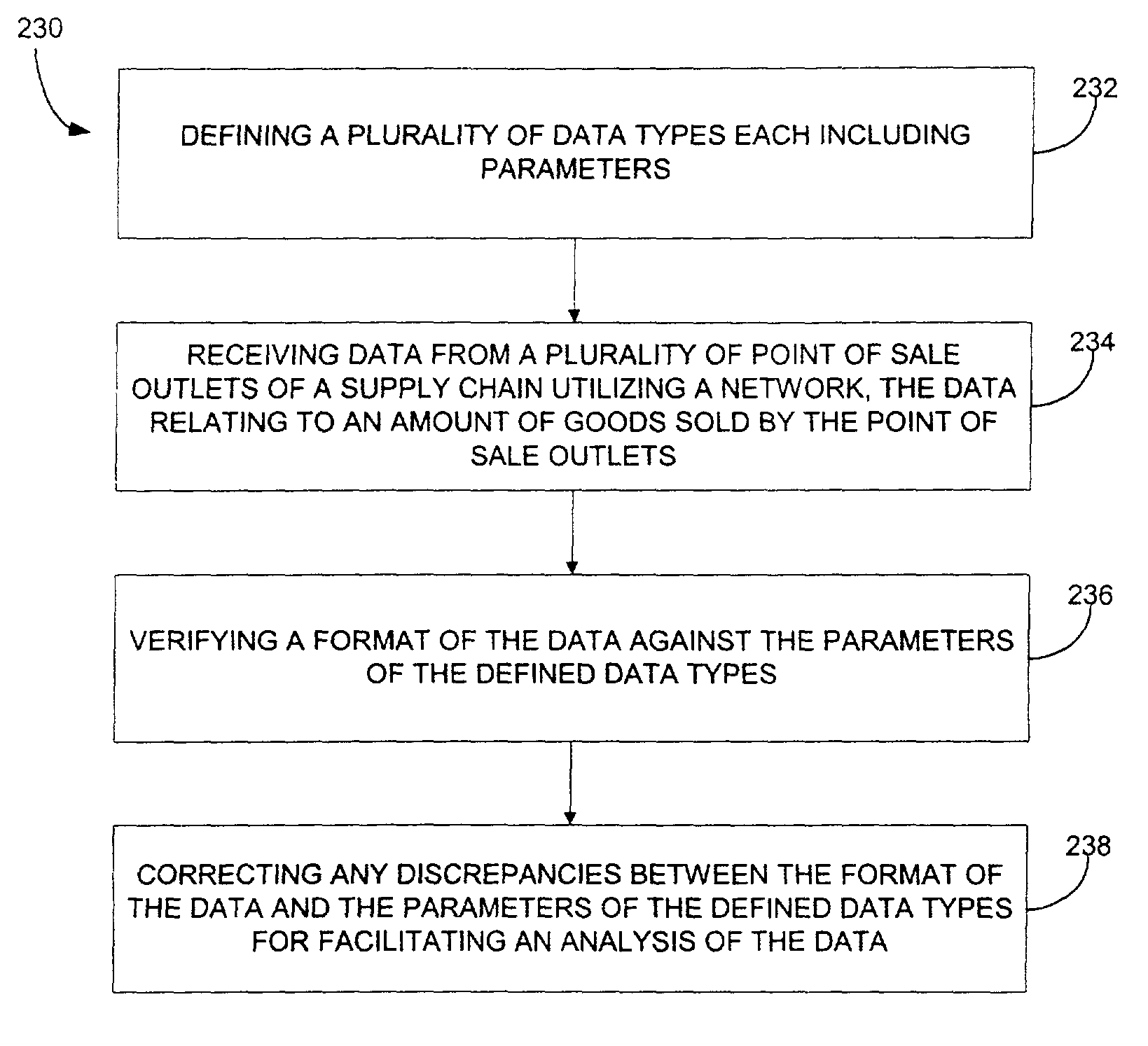
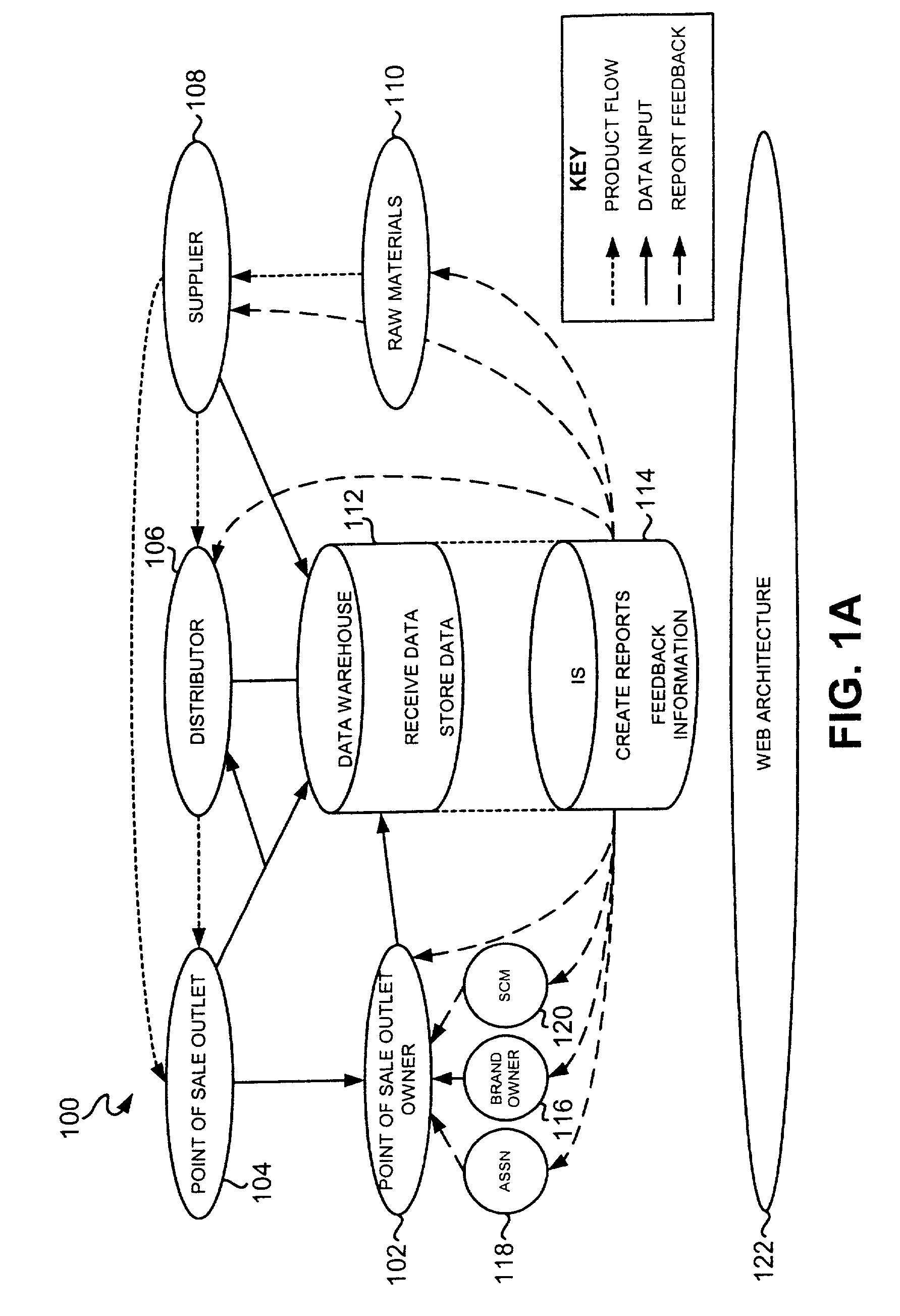
System, method and computer program product for normalizing data in a supply chain management framework
A system, method and computer program product are disclosed for normalizing data in a supply chain management framework. A plurality of data types are defined with each data type including parameters. Data is received utilizing a network from a plurality of point of sale outlets of a supply chain that relates to an amount of goods sold by the point of sale outlets. A format of the data is verified against the parameters of the defined data types and any discrepancies between the format of the data and the parameters of the defined data types are corrected for facilitating an analysis of the data.
Owner:RESTAURANT SERVICES
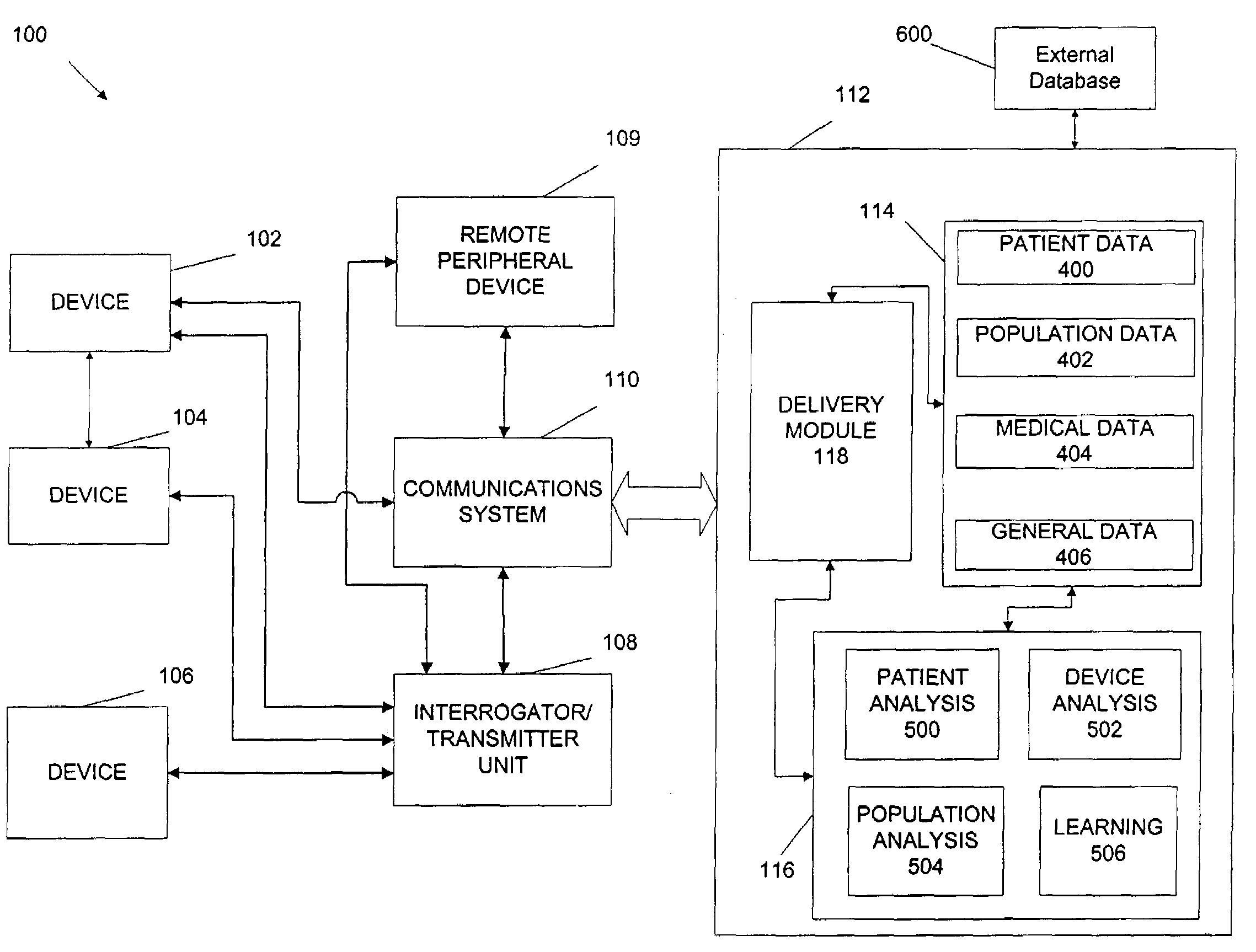
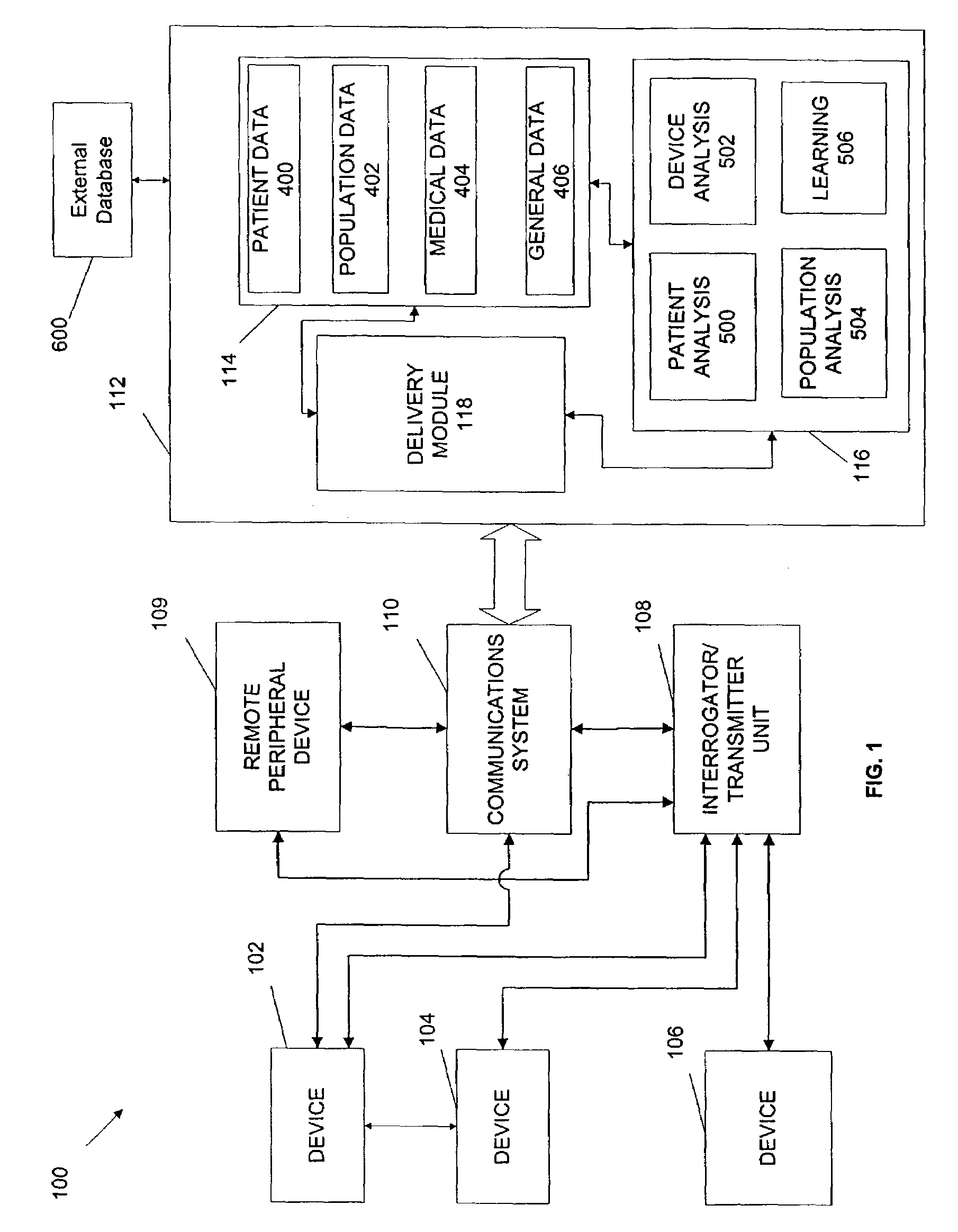
Repeater device for communications with an implantable medical device
A repeater device for an advanced patient management system communicates with a medical device coupled to a patient to obtain data about the medical device and / or patient's condition. The repeater device maintains the data while if considers various factors when coordinating transfer of the data to a repository of the advanced patient management system. The repeater device may be configured to analyze the data to determine a degree of urgency, such as whether an emergency exists, and then determine when to transfer the data based on the degree of urgency. The repeater device may also be configured to test the condition of the communication medium being used to transfer the data to the repository, such as determining whether a telephone line is in use, and then determine when to transfer the data based on the condition of the of the communication medium.
Owner:CARDIAC PACEMAKERS INC
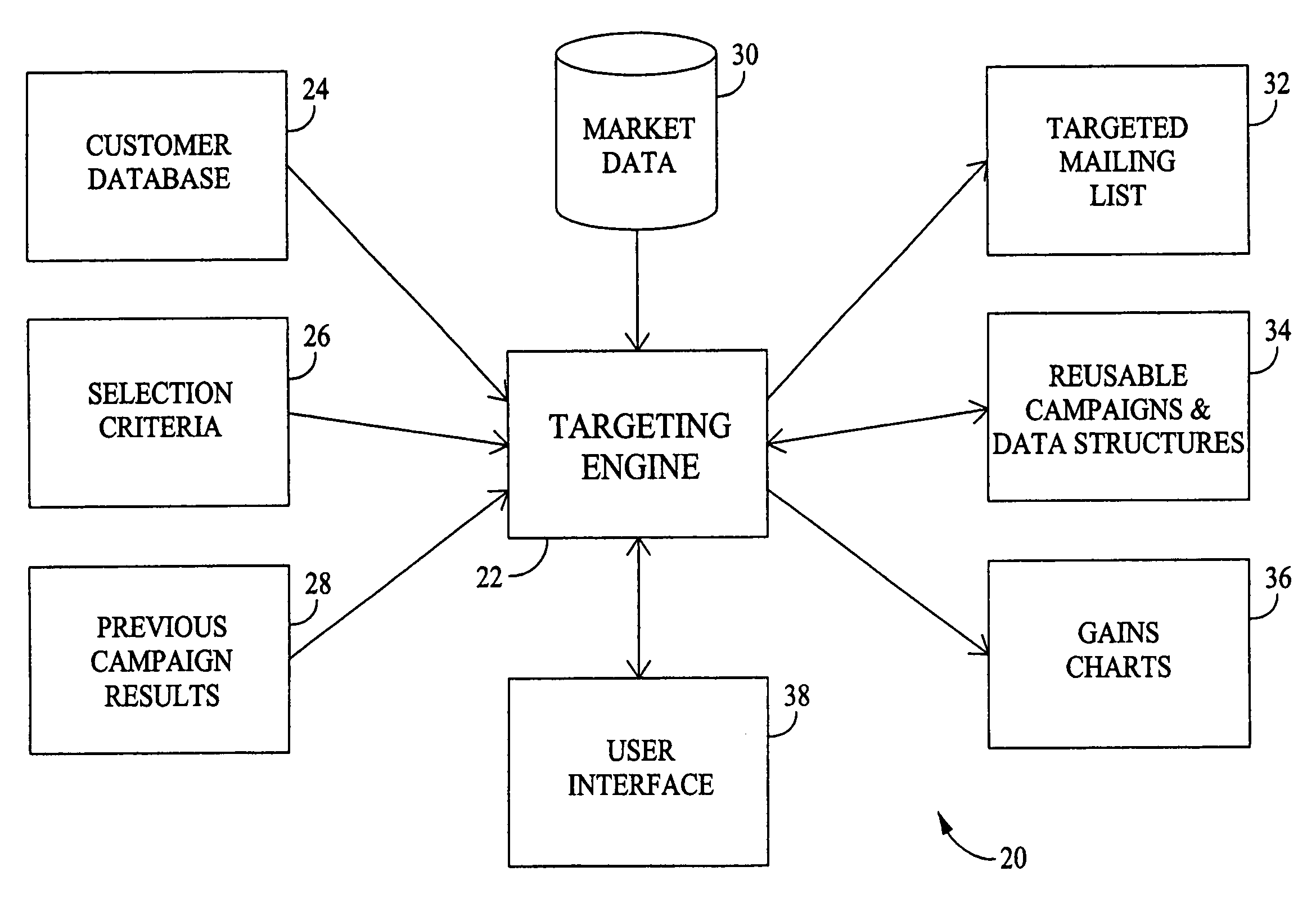
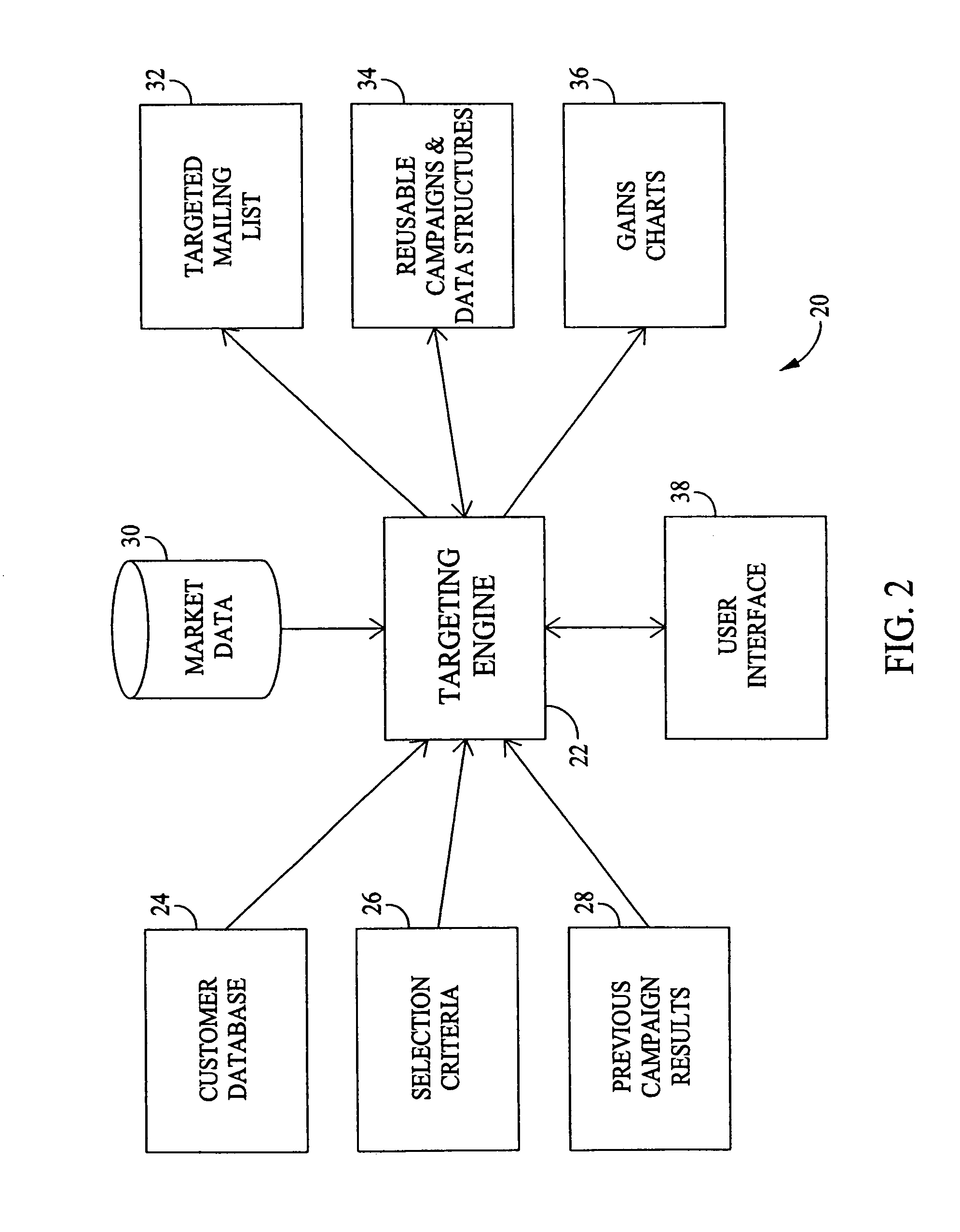
Methods and systems for defining targeted marketing campaigns using embedded models and historical data
Methods and systems for increasing the efficiency of marketing campaigns are disclosed. A targeting engine is used for analyzing data input and generating data output. The method includes the steps of using historical data to determine a target group based upon a plurality of embedded models and directing the marketing campaign towards the target groups flagged by the models.
Owner:GEN ELECTRIC CAPITAL
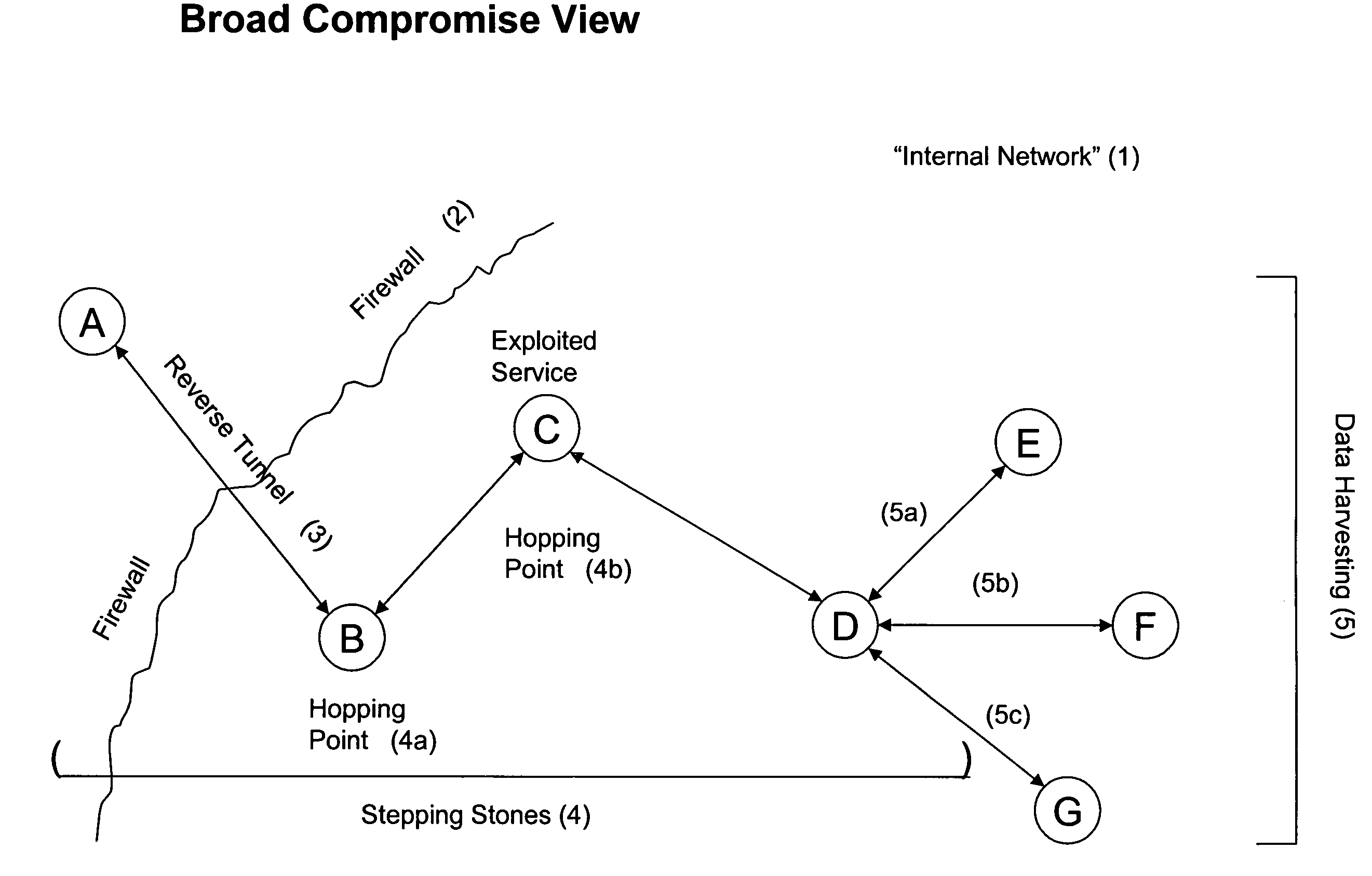
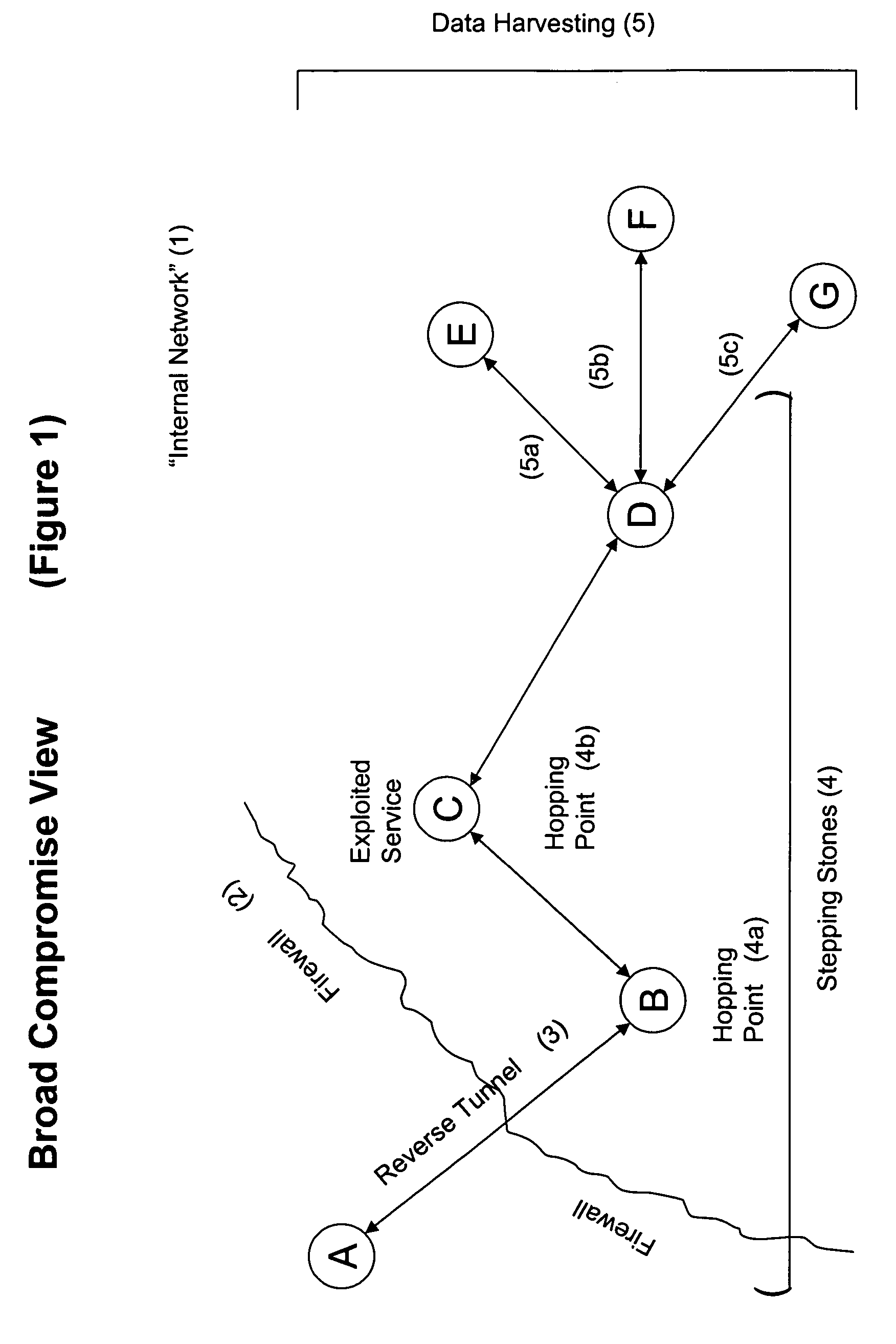
Systems and methods for detecting a compromised network
InactiveUS20050157662A1Reduce false positive resultsDigital data processing detailsComputer security arrangementsAnalysis dataData transmission
Systems and methods are disclosed for monitoring data transmissions on a network and detecting compromised networks. The systems and methods monitor communications involving network hosts and analyze the communications in view of the business function of the hosts. In certain embodiments the analysis is performed by associating a set of rules of operation for the sessions, hosts, and / or environment, and analyzing data packet transmissions to ascertain violations of the rules.
Owner:INTRUSIC
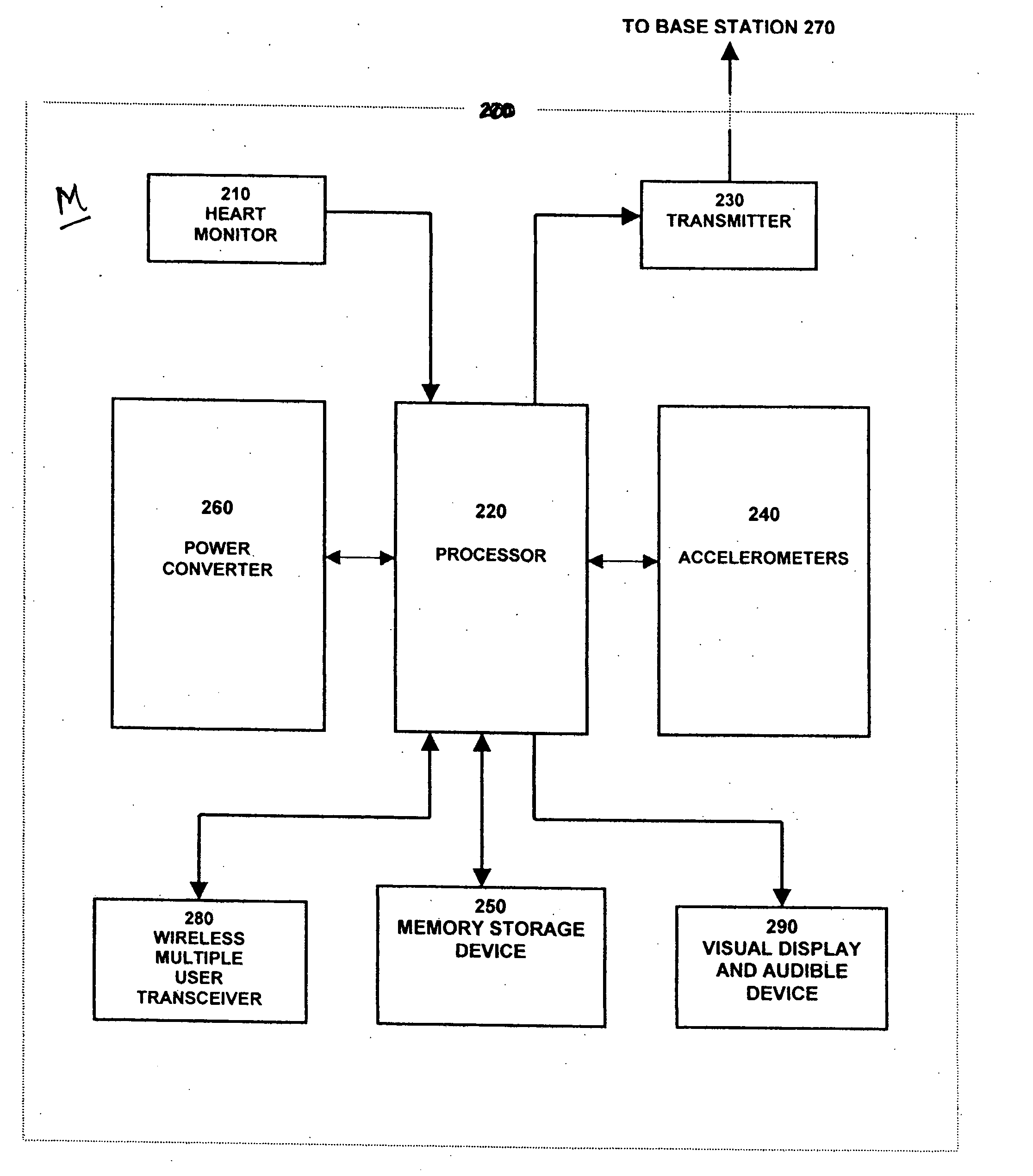
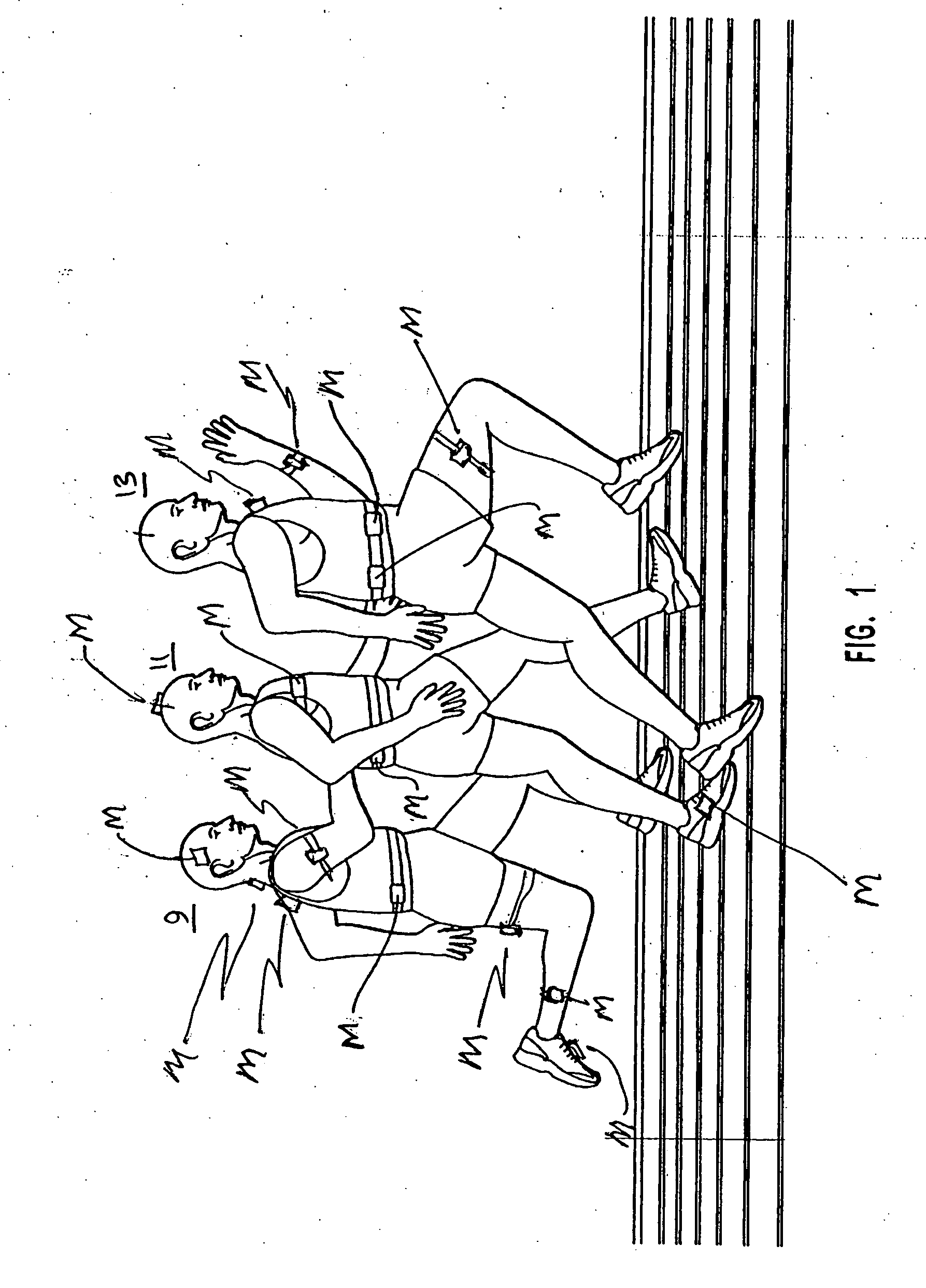
Methods and apparatus for determining work performed by an individual from measured physiological parameters
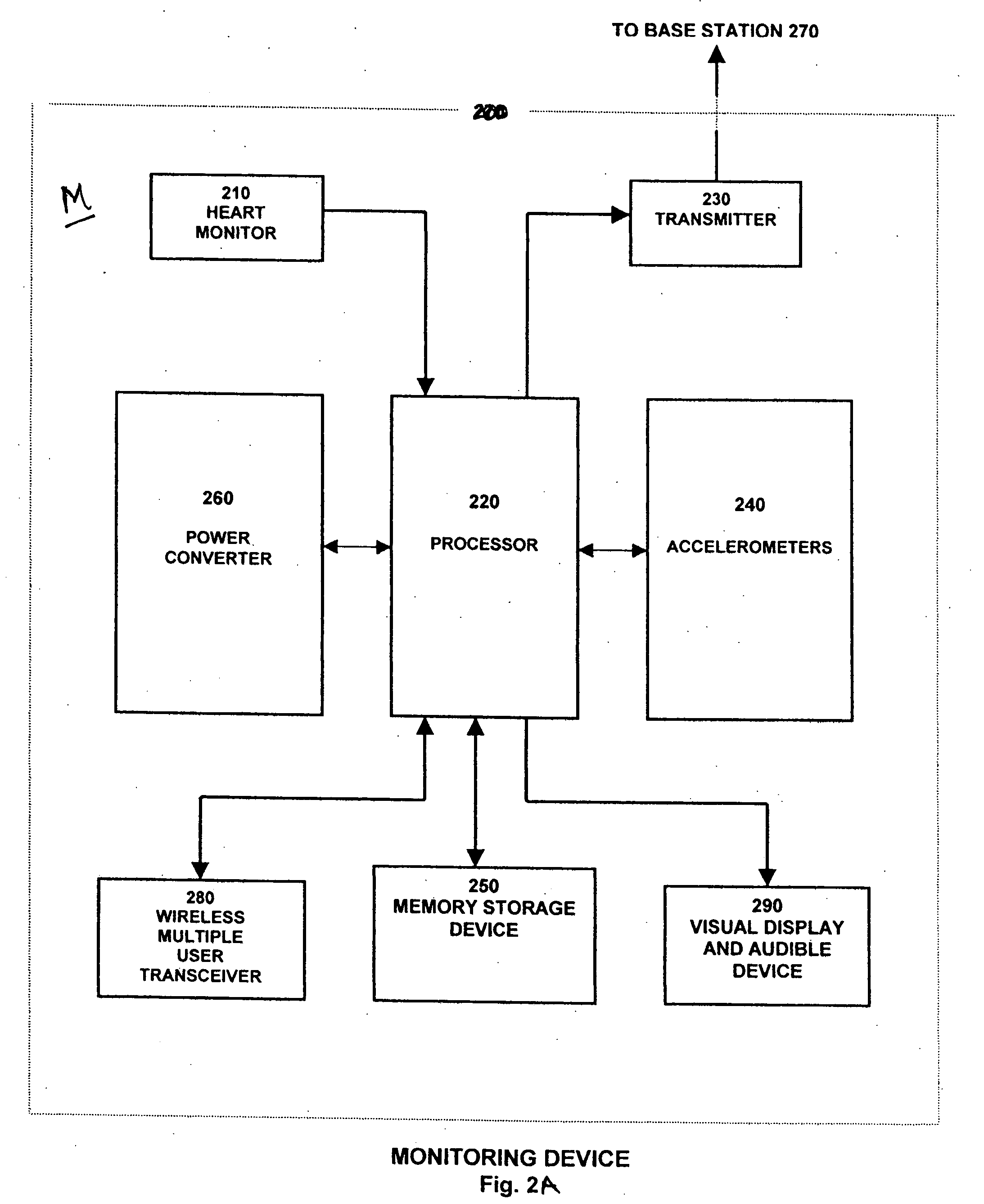
InactiveUS20050107723A1Promote productionPhysical therapies and activitiesPerson identificationAccelerometer dataGas analysis
Methods and apparatus for gathering and processing data sensed on an individual from portable heart monitors and accelerometers aligned along three orthogonal axes determine substantially equivalent oxygen consumption information during an individual's physical activities without requiring gas-flow or gas-analysis equipment. Such information promotes calculations of physiological energy expenditures, and analyses of the accelerometer data associated with a specific sensing location on an individual's body provide indication of the particular physical activity for selecting appropriate scaling factors and filtering requirements in analyzing the data to determine various parameters indicative of the individual's expenditure of physiological energy, and other health-oriented factors.
Owner:TELECOM MEDICAL
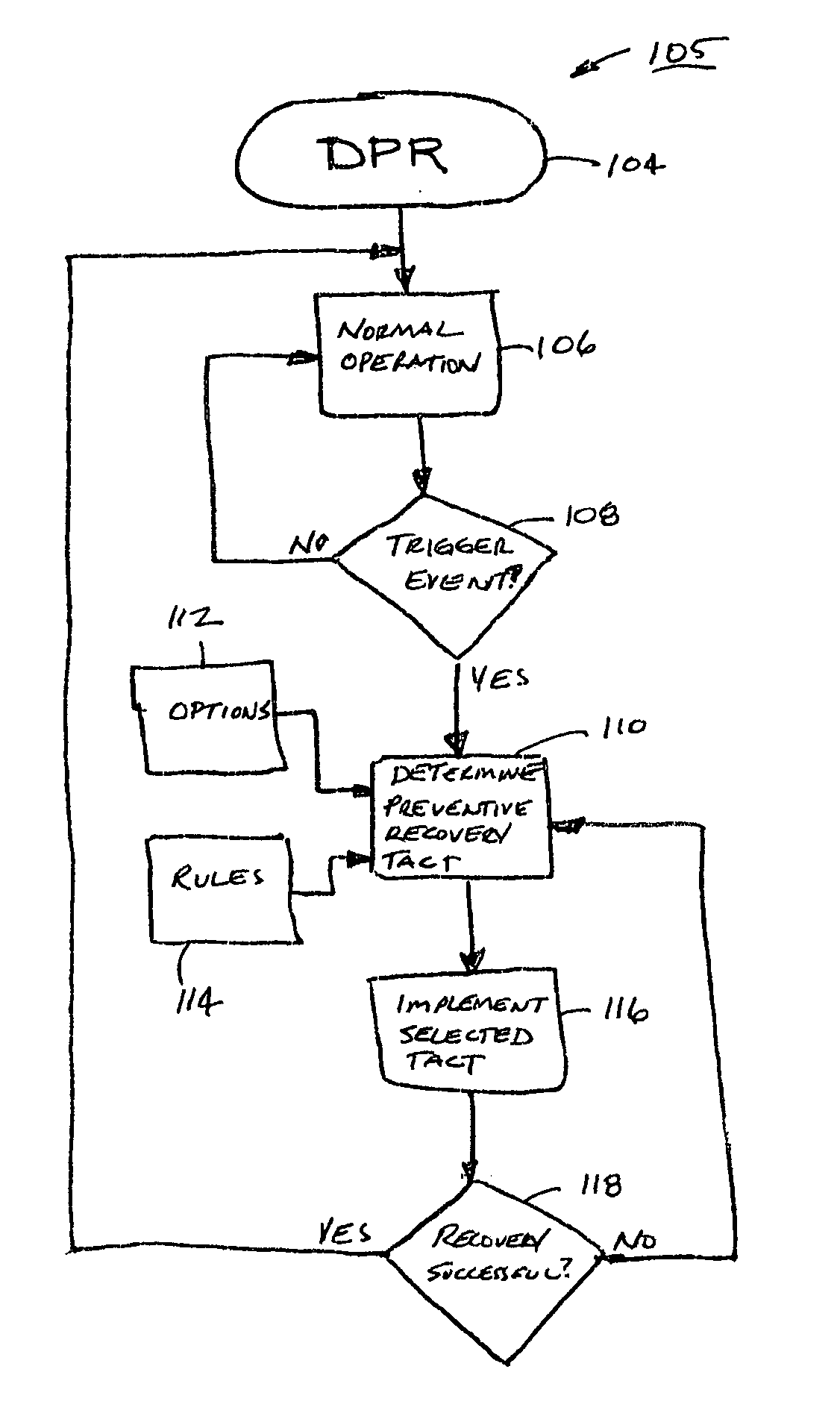
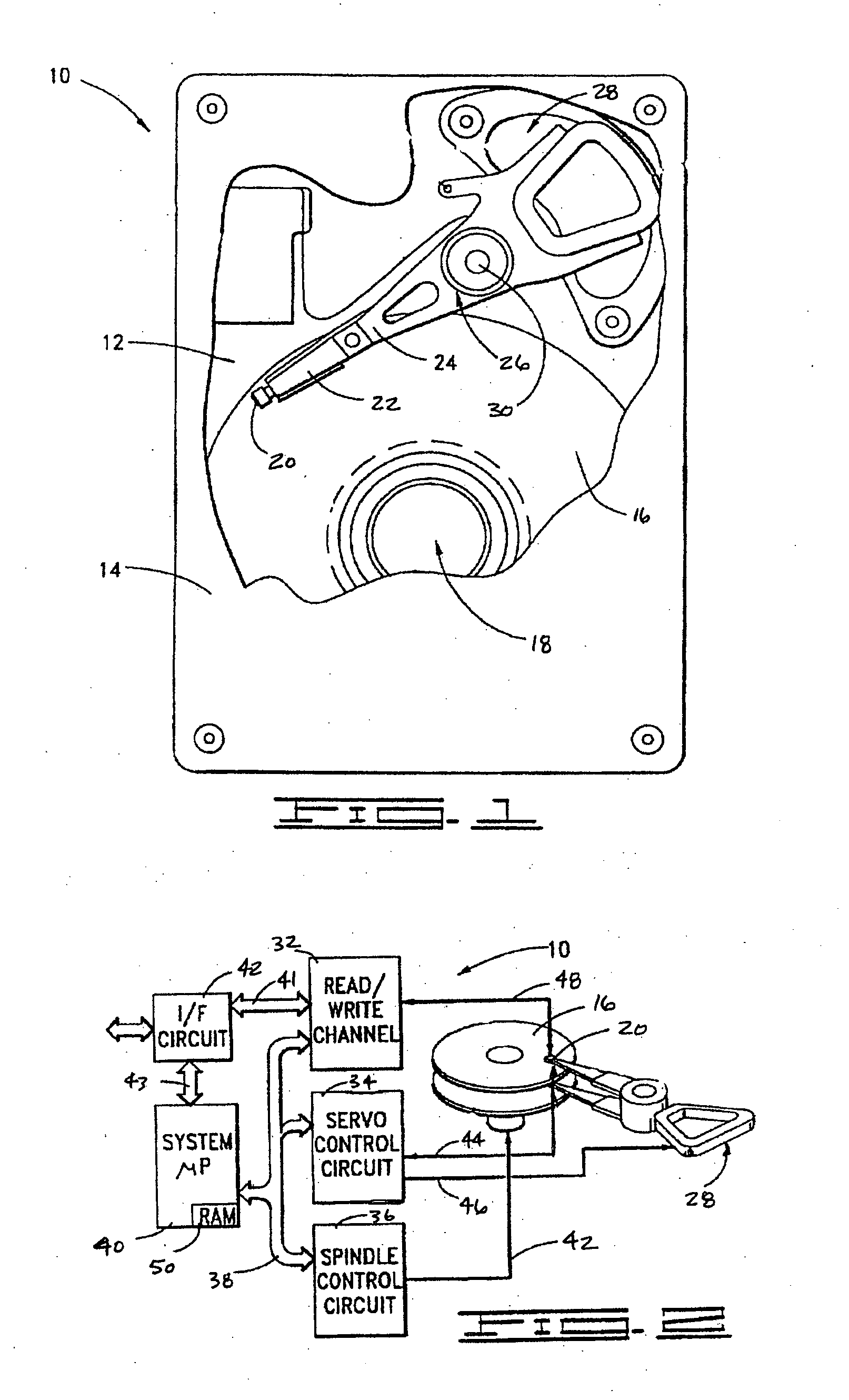
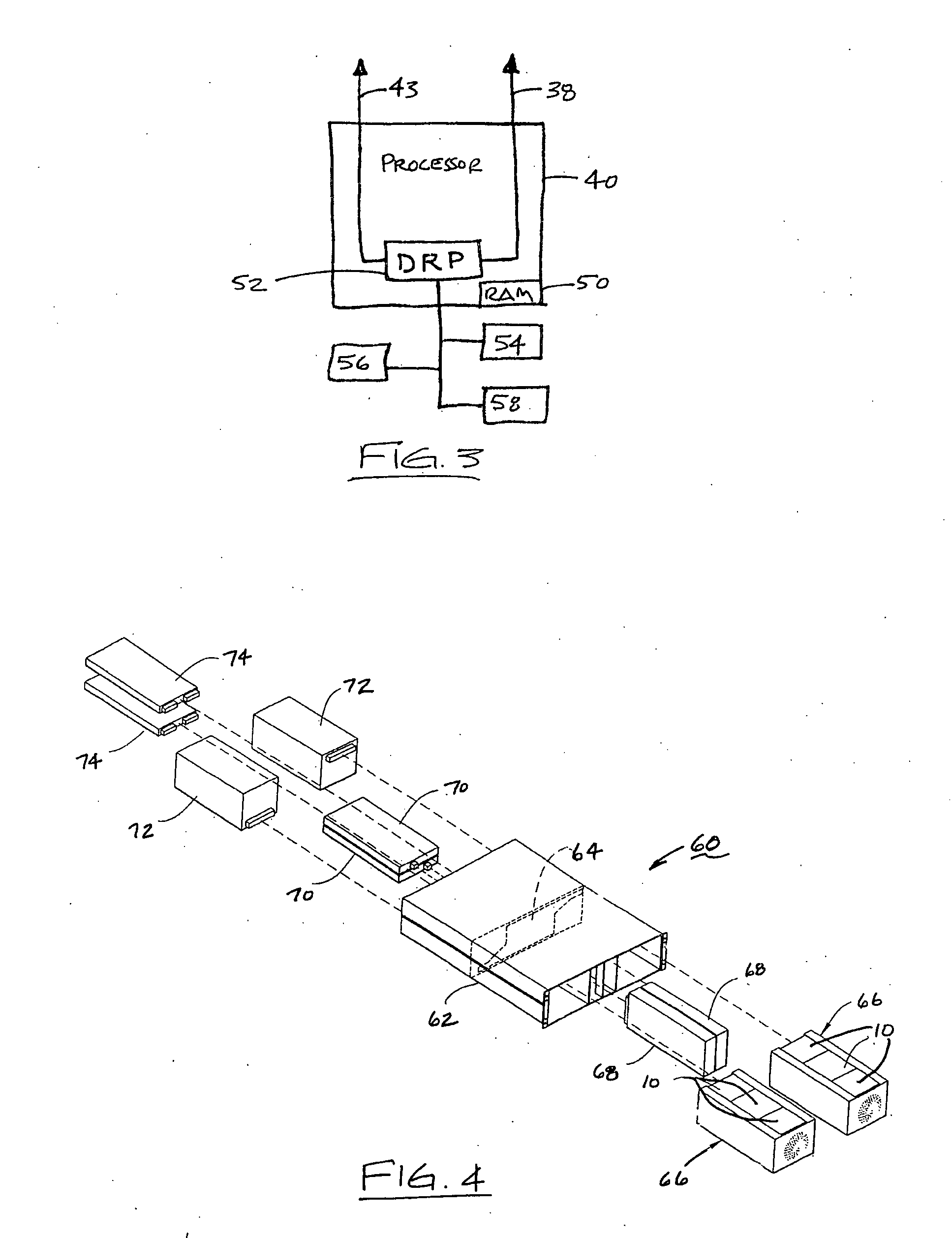
Deterministic preventive recovery from a predicted failure in a distributed storage system
A data storage subsystem in a distributed storage system having a plurality of predictive failure analyzing data storage devices. The subsystem furthermore has a circuit that is responsive to a predicted failure indication by a data storage device in relation to predetermined rules stored in memory for deterministically initiating a preventive recovery either by a data recovery procedure in the data storage device or by a fault tolerance storage arrangement in the subsystem.
Owner:SEAGATE TECH LLC
System and methods for real-time detection, correction, and transformation of time series data
InactiveUS20140032506A1Digital data information retrievalDigital data processing detailsAnalysis dataData set
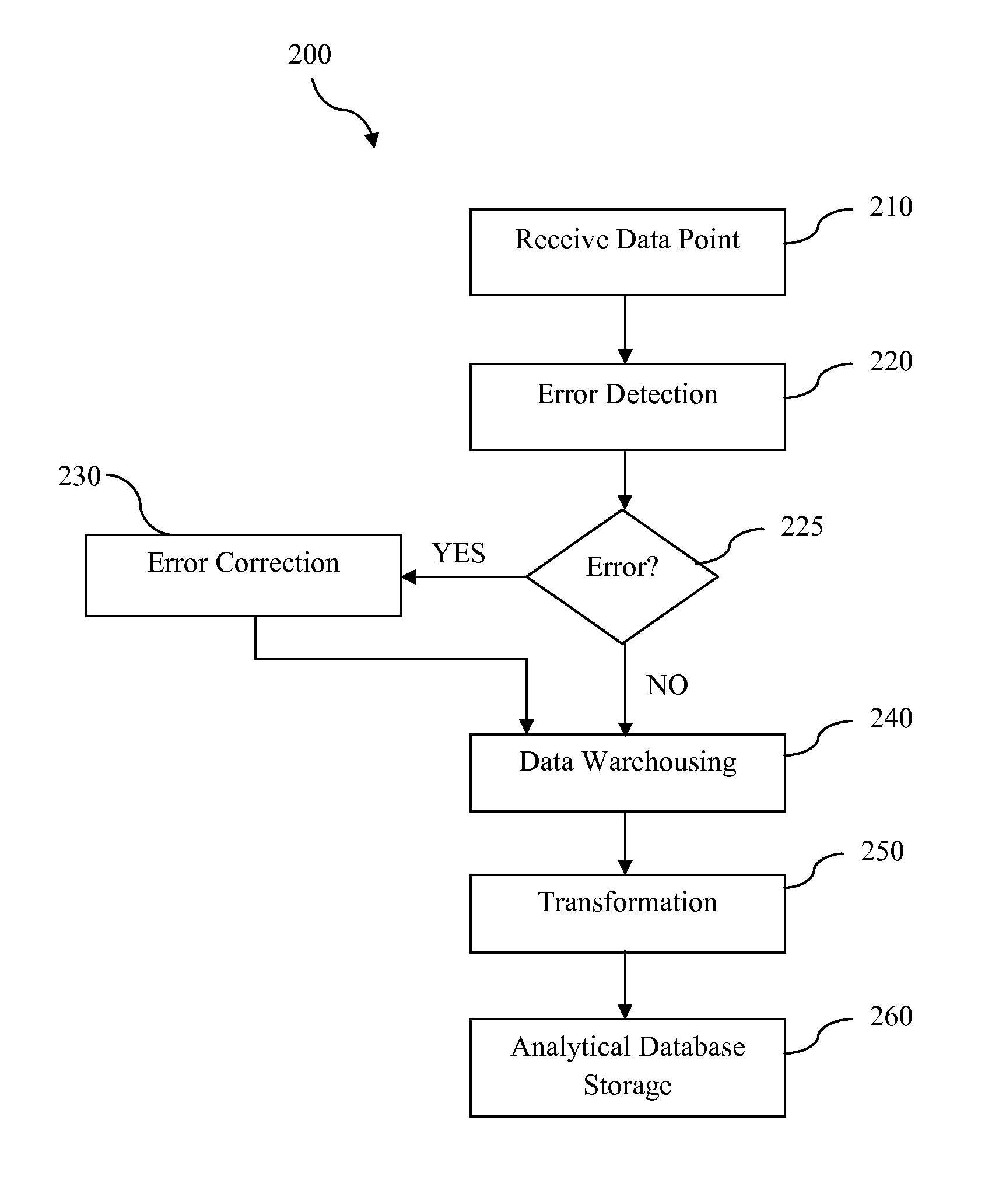
Systems and methods for time series data error detection, correction, and transformation may detect gaps and anomalies in time series data, such as from a meter device, and may correct the gaps and adjust the anomalies prior to long-term record storage. Data forecasting may be used to correct the errors in the time series data. The error corrected data may be regarded as an actual set of time series data and become a base data set against which additional heuristic projections are generated. In addition, the time series data may be transformed into any number of physical and virtual device hierarchies that represent the underlying data source configurations, and may then be stored in an analytical database for further analysis. The hierarchies may be irregular and may change over time.
Owner:SUMITOMO CHEM U K
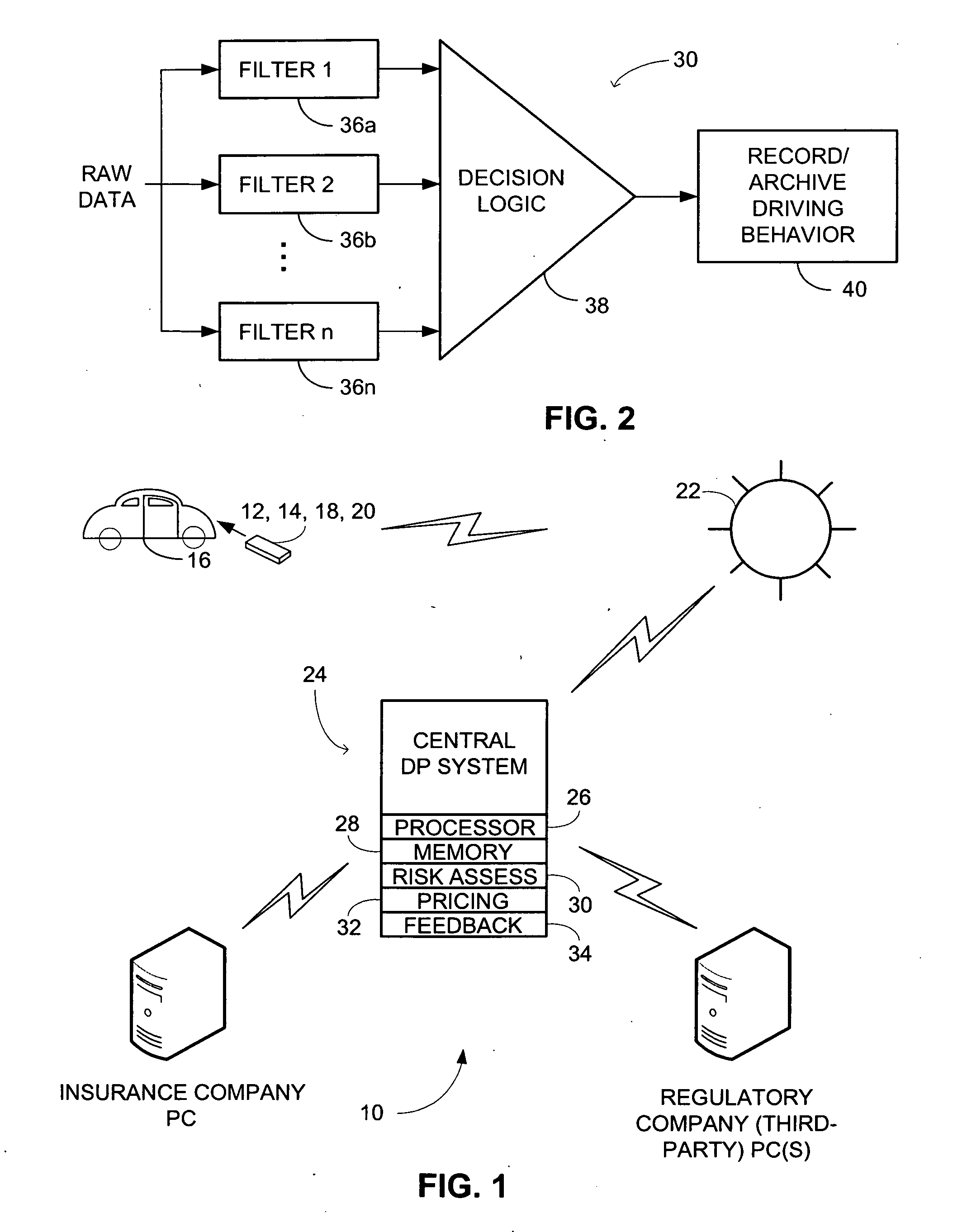
System and method for monitoring driving behavior with feedback
InactiveUS20080243558A1Accelerate emissionsReduce fossil fuel reservesFinanceRegistering/indicating working of vehiclesData processing systemAnalysis data
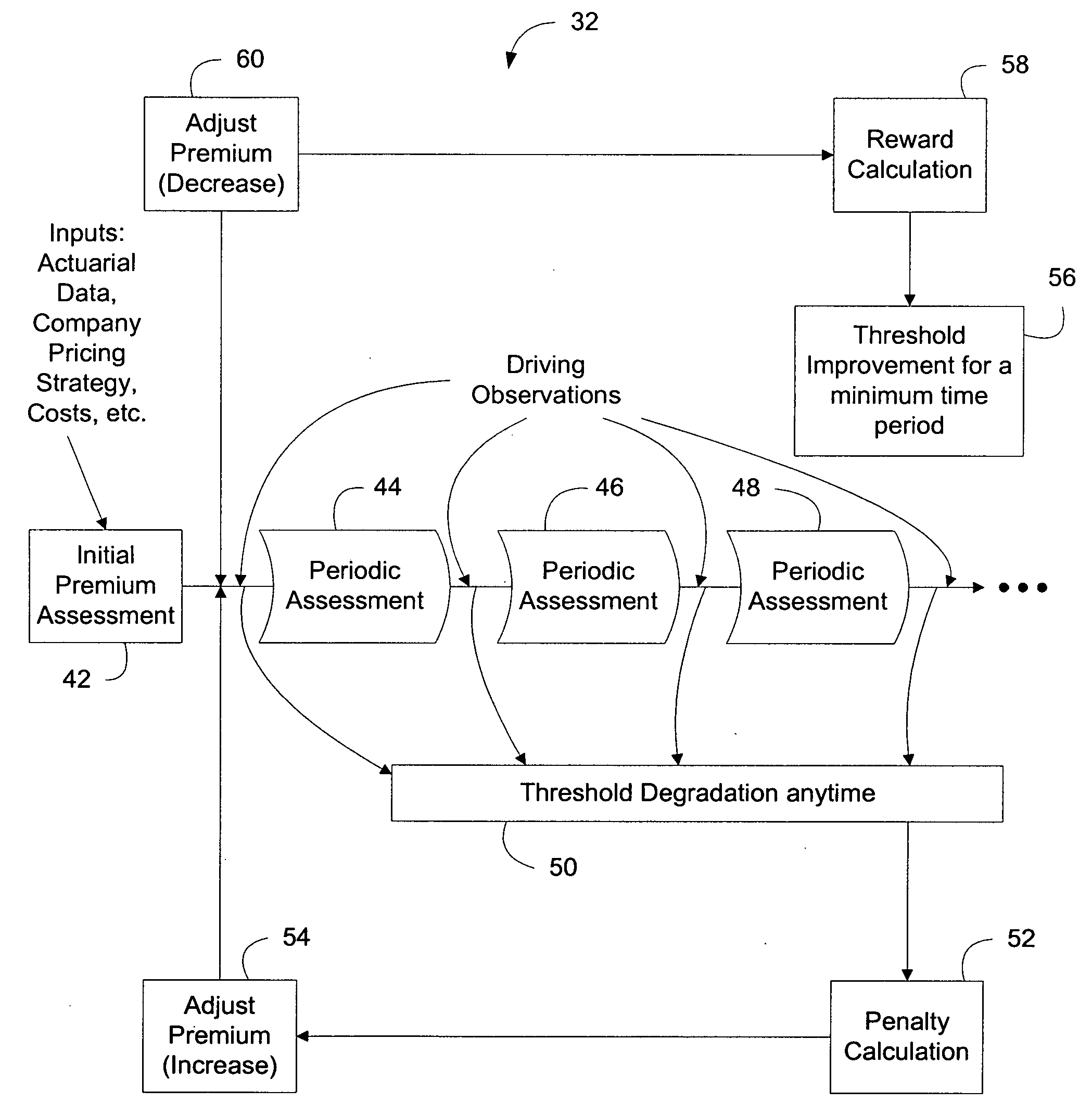
In accordance with an embodiment of the present invention, a network system for monitoring driving behavior comprises one or more vehicle-mountable motion sensing mechanisms that generate a plurality of data relevant to vehicle moving attitude. The data being indicative of manual or mental risks for a vehicle operator is wirelessly transmittable. The network system also comprises a central data processing system that collects the data transmitted from the motion sensing mechanisms. A risk assessment engine operatively coupled to the central data processing system analyzes the collected data to determine the manual or mental risks. The central data processing system further comprises a feedback engine operable to yield indicia based on the analyzed data that is reportable to the vehicle operator or an authorized data recipient. A reward engine operatively coupled to the feedback engine provides incentives to encourage good or improved driving behavior.
Owner:GUPTE ASH
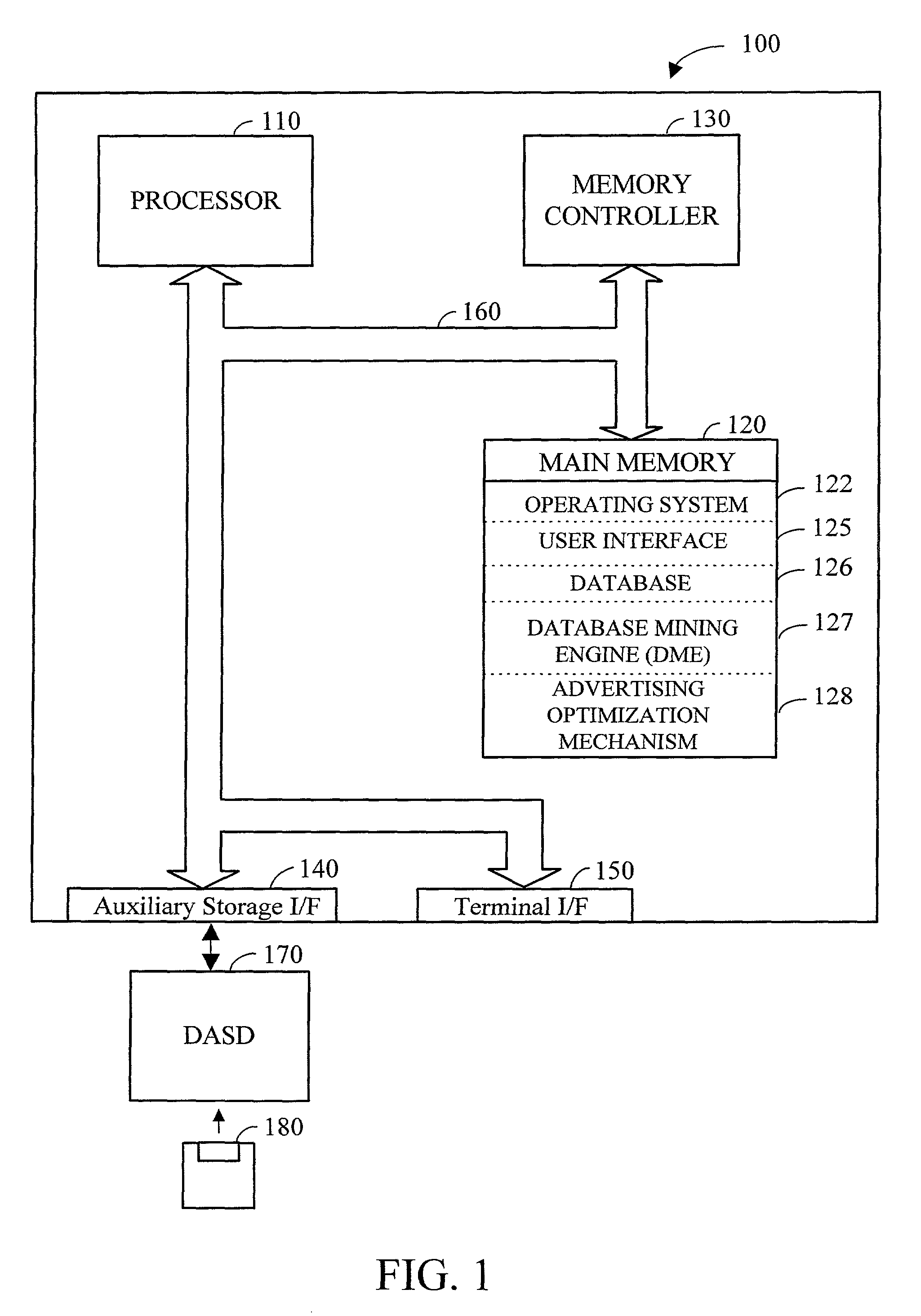
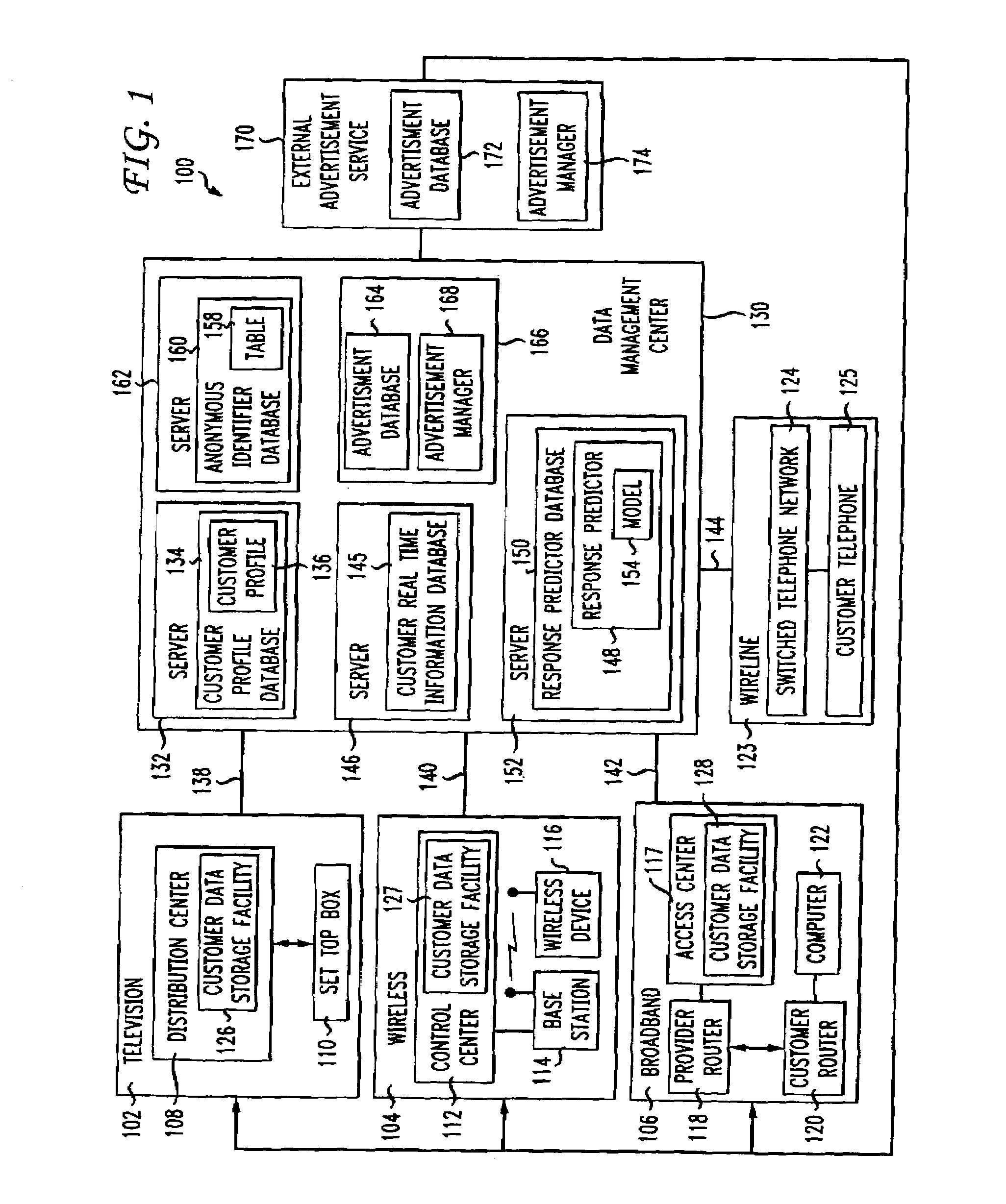
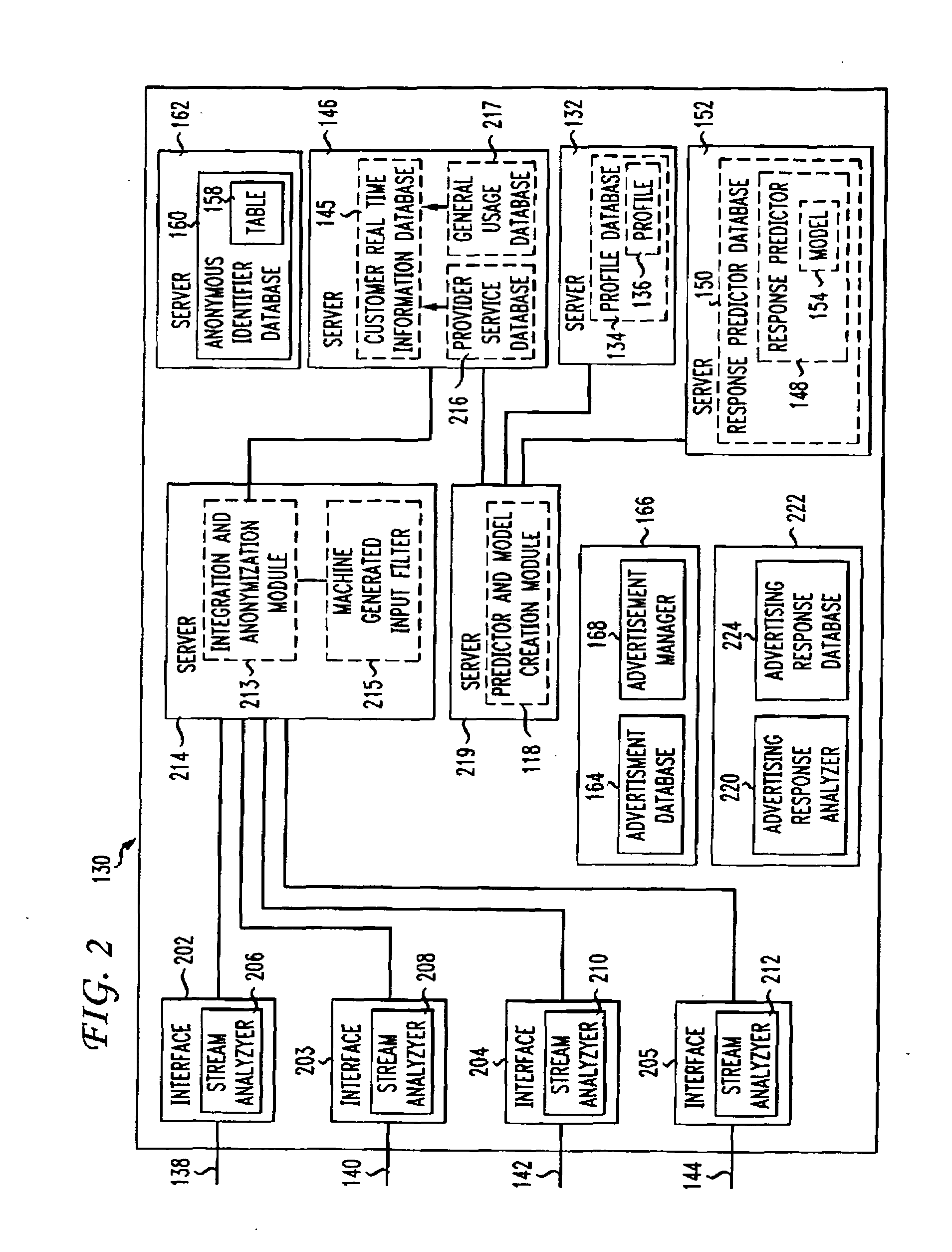
Method and apparatus for analyzing data and advertising optimization
InactiveUS20010020236A1Readily availableGood choiceDigital data processing detailsBroadcast services for monitoring/identification/recognitionAnalysis dataDecision maker
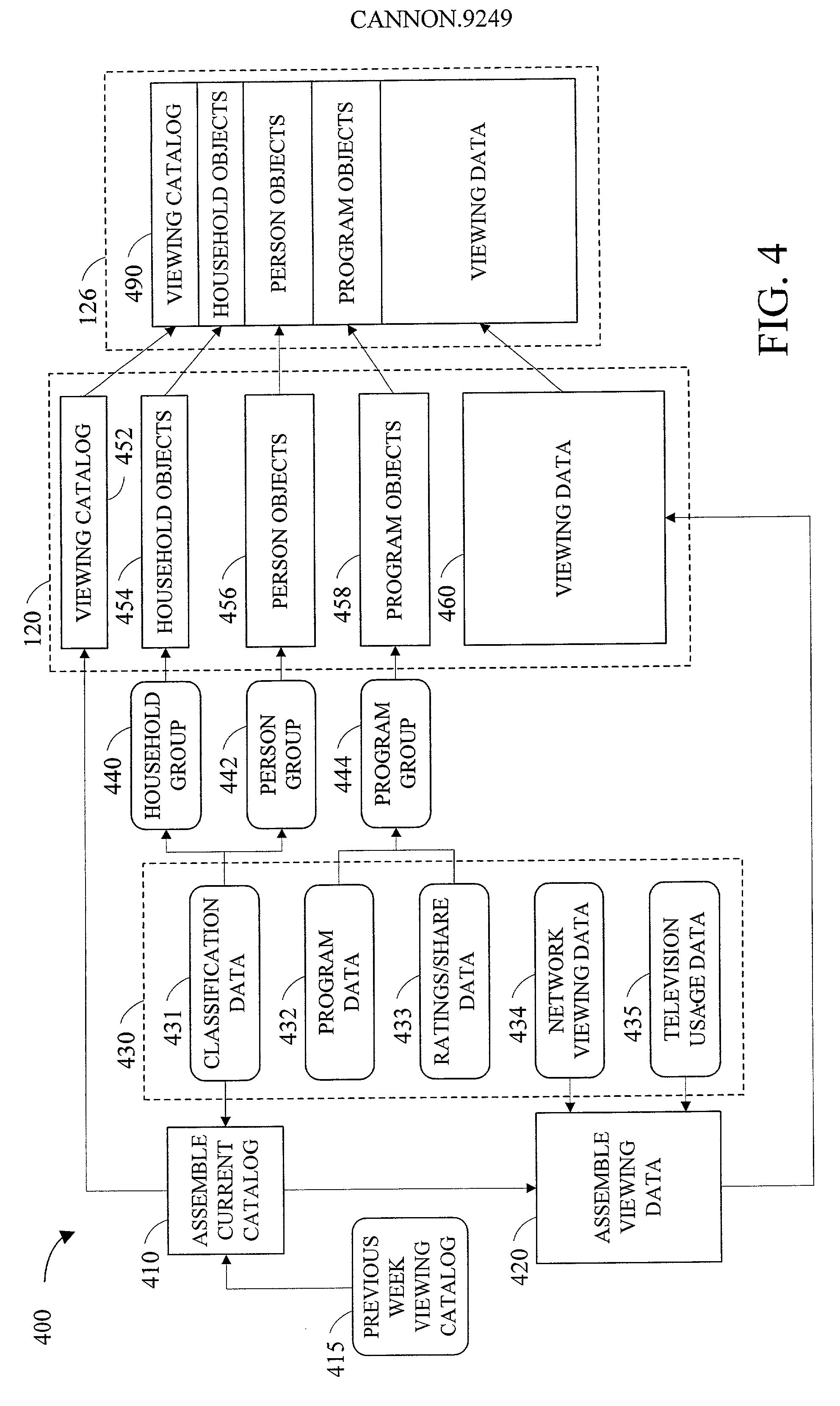
The most preferred embodiment of the present invention is a computer-based decision support system that includes three main components: a database mining engine (DME); an advertising optimization mechanism; and a customized user interface that provides access to the various features of the invention. The user interface, in conjunction with the DME, provides a unique and innovative way to store, retrieve and manipulate data from existing databases containing media-related audience access data, which describe the access habits and preferences of the media audience. By using a database with a simplified storage and retrieval protocol, the data contained therein can be effectively manipulated in real time. This means that previously complex and lengthy information retrieval and analysis activities can be accomplished in very short periods of time (typically seconds instead of minutes or even hours). Further, by utilizing the advertising optimization mechanism of the present invention, businesses, networks, and advertising agencies can interactively create, score, rank and compare various proposed or actual advertising strategies in a simple and efficient manner. This allows the decision-makers to more effectively tailor their marketing efforts and successfully reach the desired target market while conserving scarce advertising capital. Finally, the user interface for the system provides access to both the DME and the optimization mechanism in a simple and straightforward manner, significantly reducing training time.
Owner:CANNON MARK E
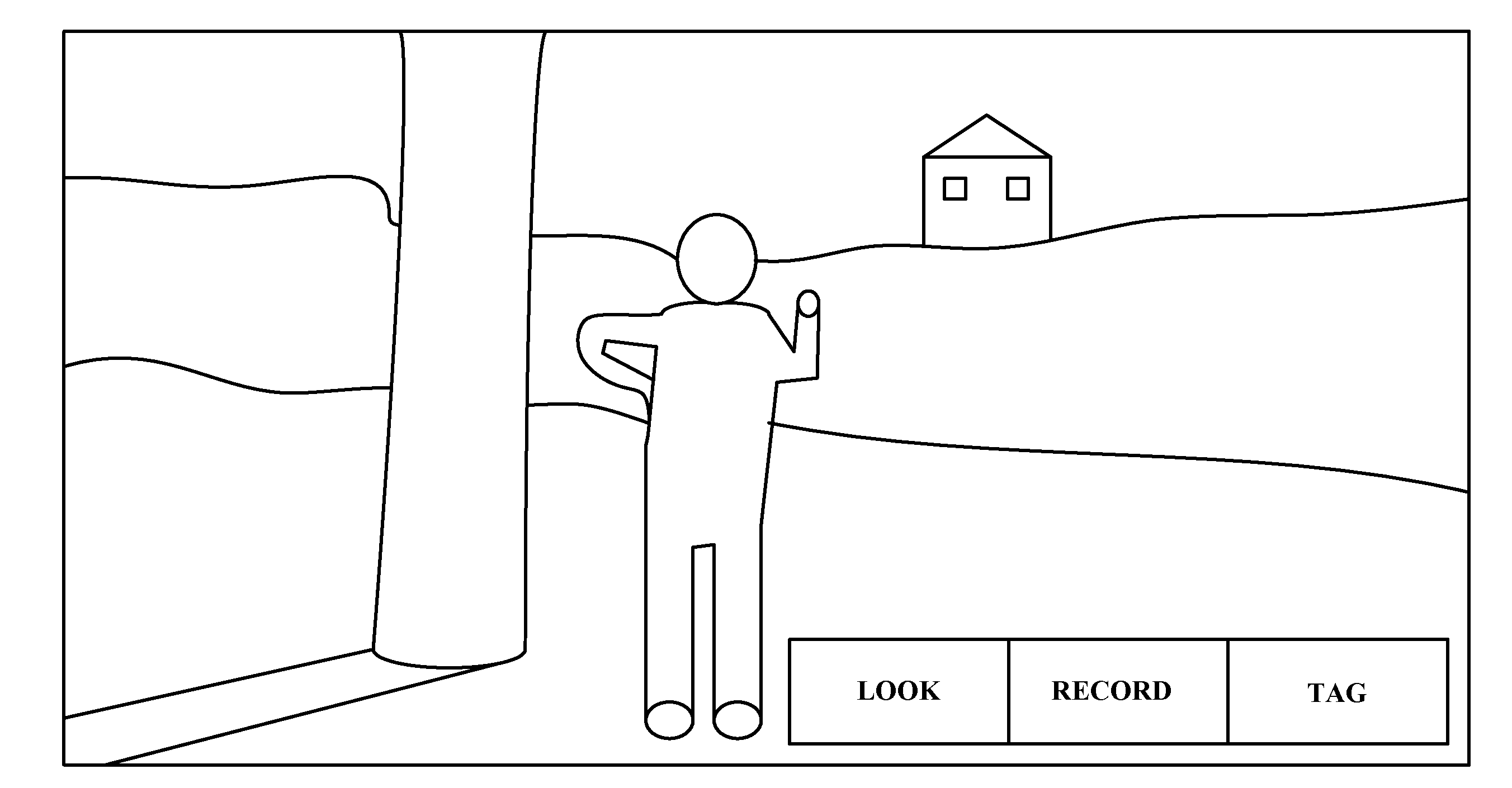
Augmented reality system for position identification
A system, method, and computer program product for automatically combining computer-generated imagery with real-world imagery in a portable electronic device by retrieving, manipulating, and sharing relevant stored videos, preferably in real time. A video is captured with a hand-held device and stored. Metadata including the camera's physical location and orientation is appended to a data stream, along with user input. The server analyzes the data stream and further annotates the metadata, producing a searchable library of videos and metadata. Later, when a camera user generates a new data stream, the linked server analyzes it, identifies relevant material from the library, retrieves the material and tagged information, adjusts it for proper orientation, then renders and superimposes it onto the current camera view so the user views an augmented reality.
Owner:SONY CORP
Undetectable firewall
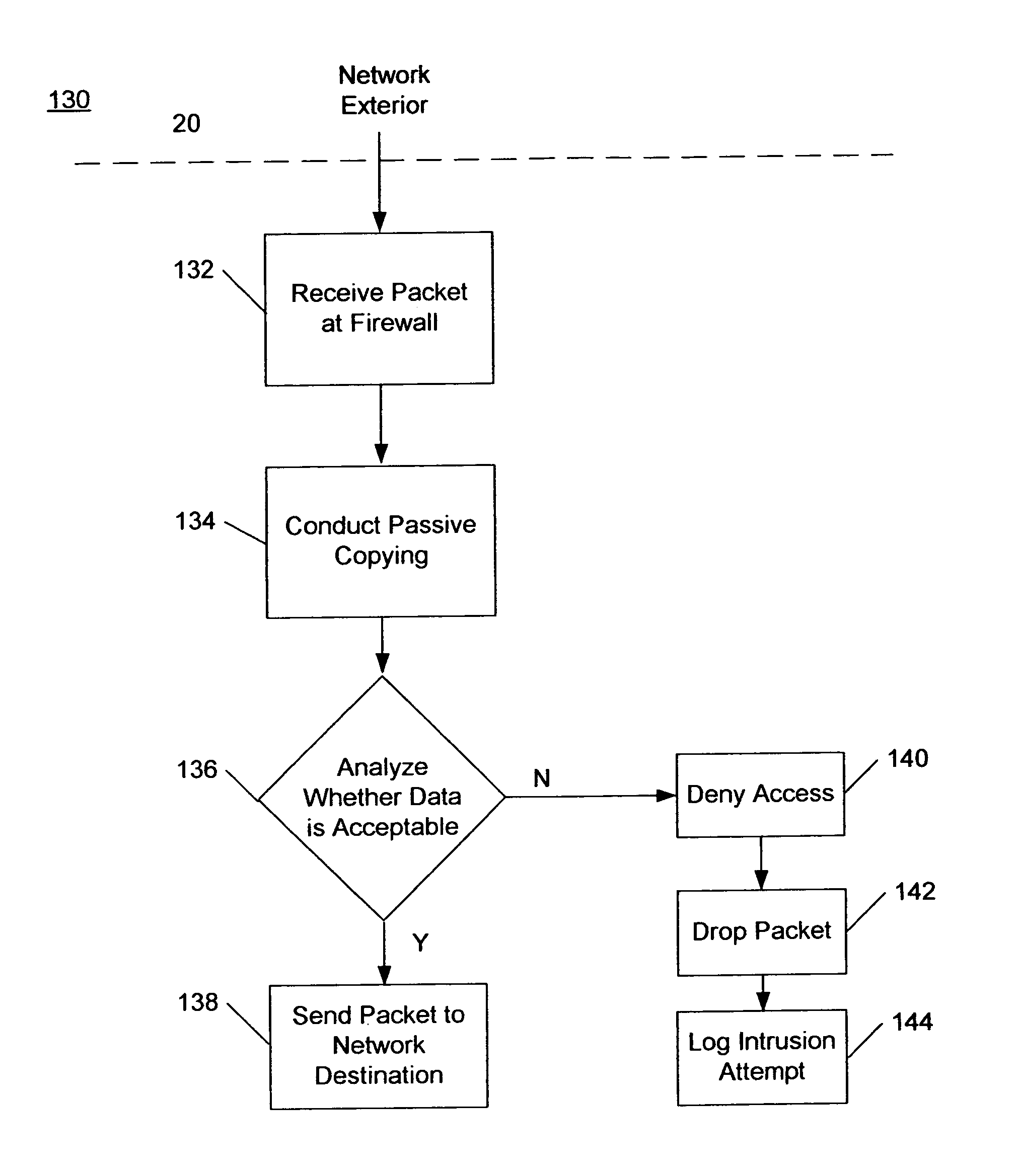
ActiveUS7100201B2Prevent unauthorized accessMemory loss protectionDigital data processing detailsAnalysis dataNetwork packet
An undetectable firewall for network protection has been developed. The invention includes a method of preventing unauthorized access to a computer system. The firewall receives a data packet and copies its contents exactly. Next, the firewall analyzes the data packet and determines if it is authorized to access the network. If the packet is authorized to access the network, it is sent on to its destination. If the packet is unauthorized to access the network, it is dropped by the firewall.
Owner:ARXCEO CORP
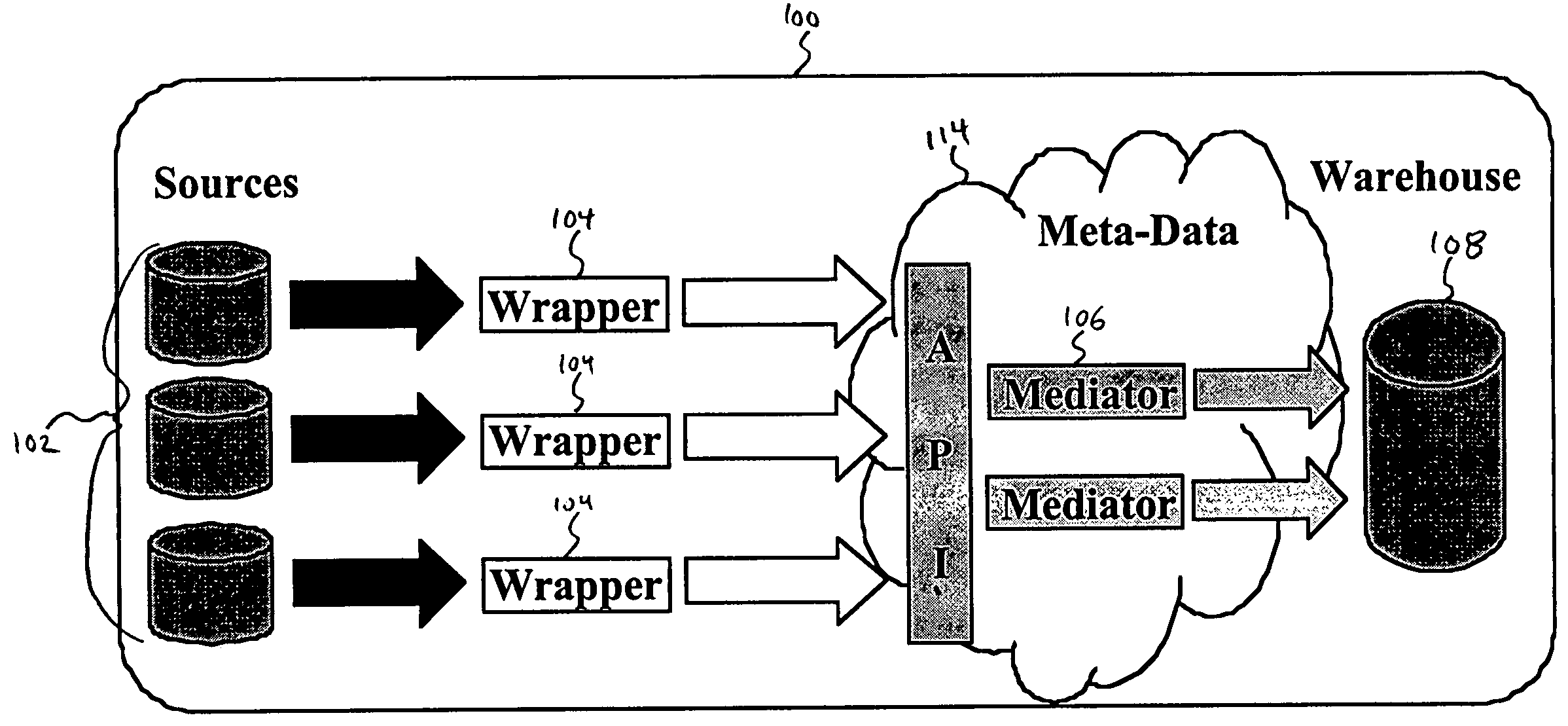
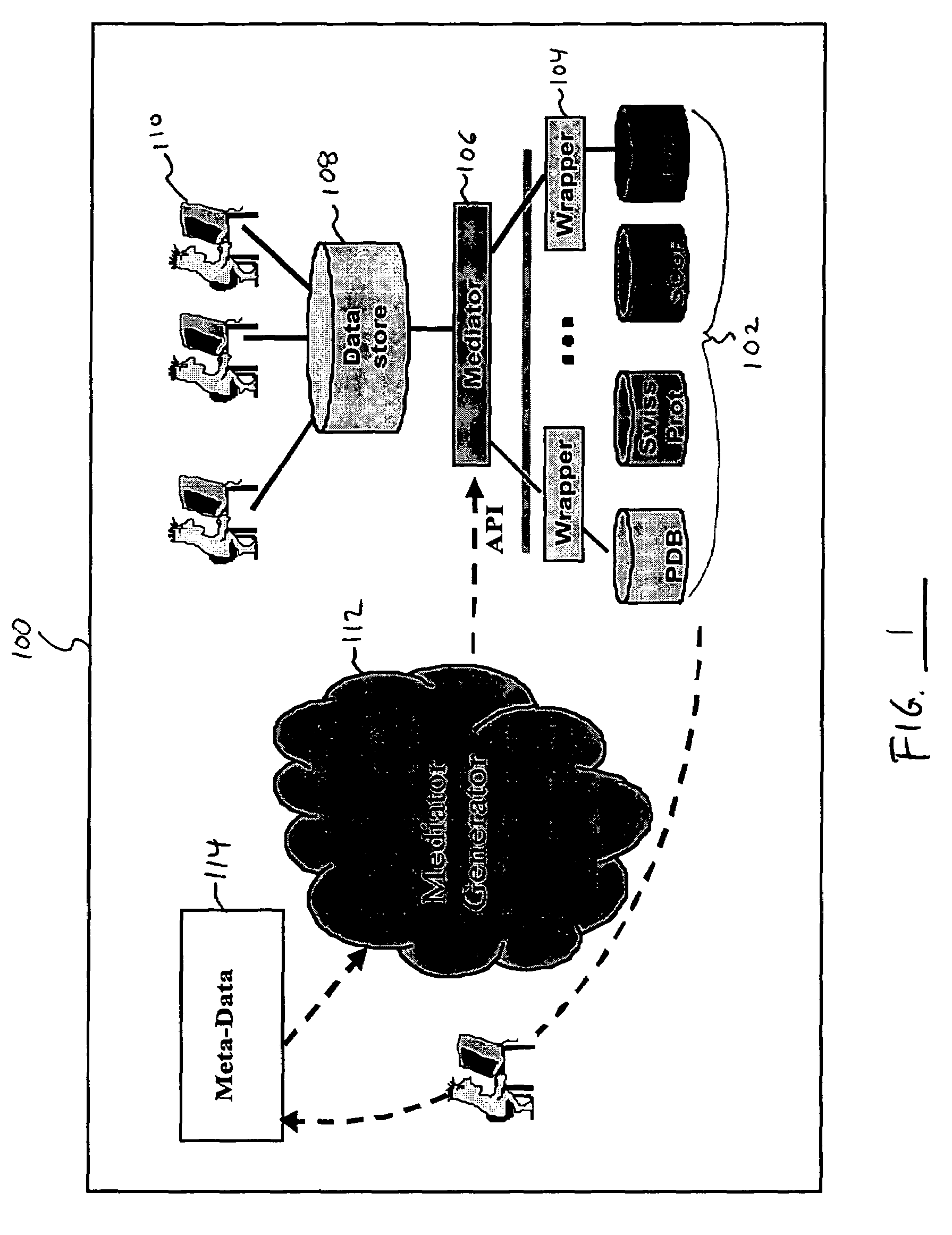
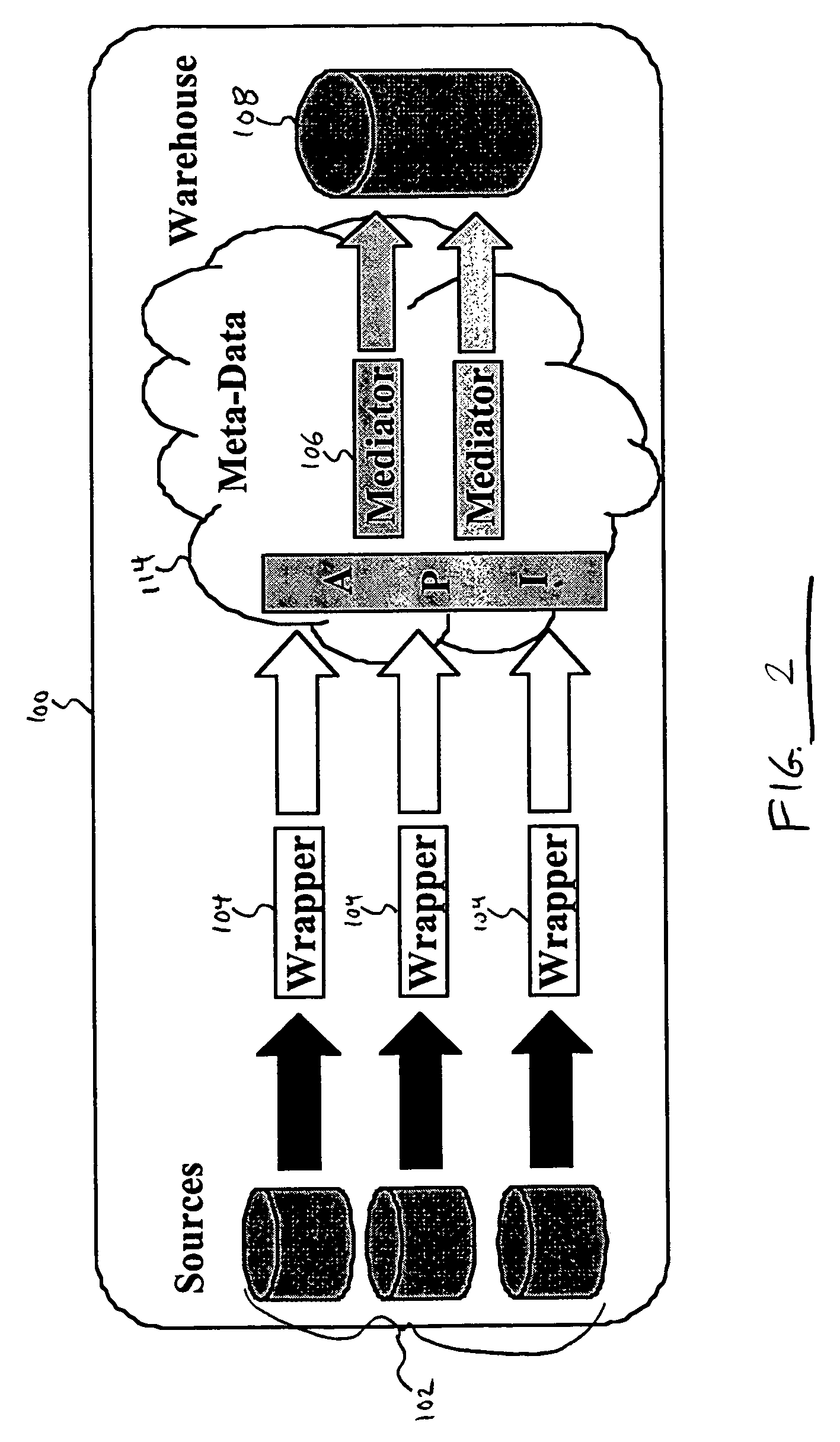
System and method for integrating and accessing multiple data sources within a data warehouse architecture
InactiveUS7152070B1Data processing applicationsDigital data information retrievalPresent methodAnalysis data
A system and method is disclosed for integrating and accessing multiple data sources within a data warehouse architecture. The metadata formed by the present method provide a way to declaratively present domain specific knowledge, obtained by analyzing data sources, in a consistent and useable way. Four types of information are represented by the metadata: abstract concepts, databases, transformations and mappings. A mediator generator automatically generates data management computer code based on the metadata. The resulting code defines a translation library and a mediator class. The translation library provides a data representation for domain specific knowledge represented in a data warehouse, including “get” and “set” methods for attributes that call transformation methods and derive a value of an attribute if it is missing. The mediator class defines methods that take “distinguished” high-level objects as input and traverse their data structures and enter information into the data warehouse.
Owner:LAWRENCE LIVERMORE NAT SECURITY LLC
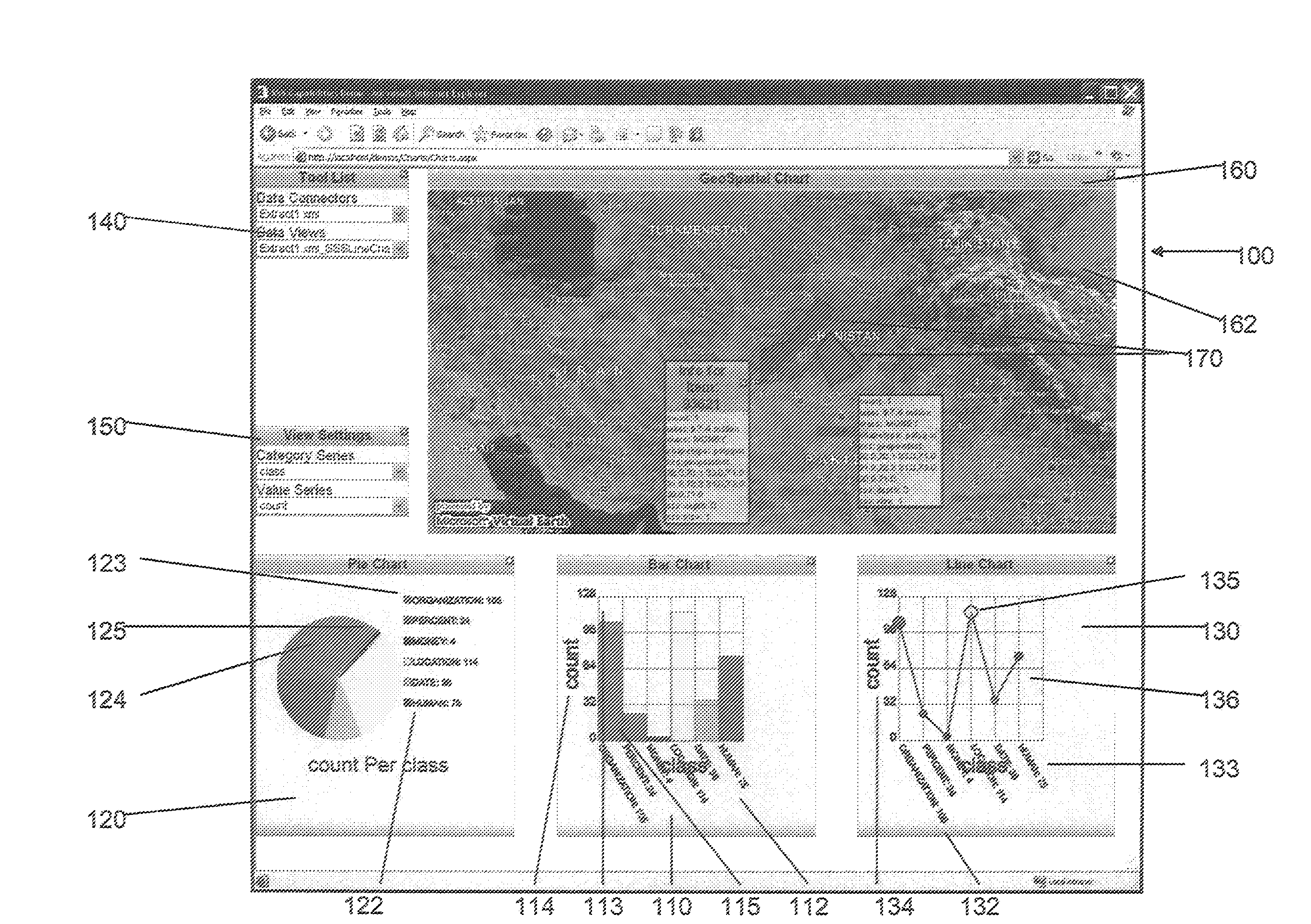
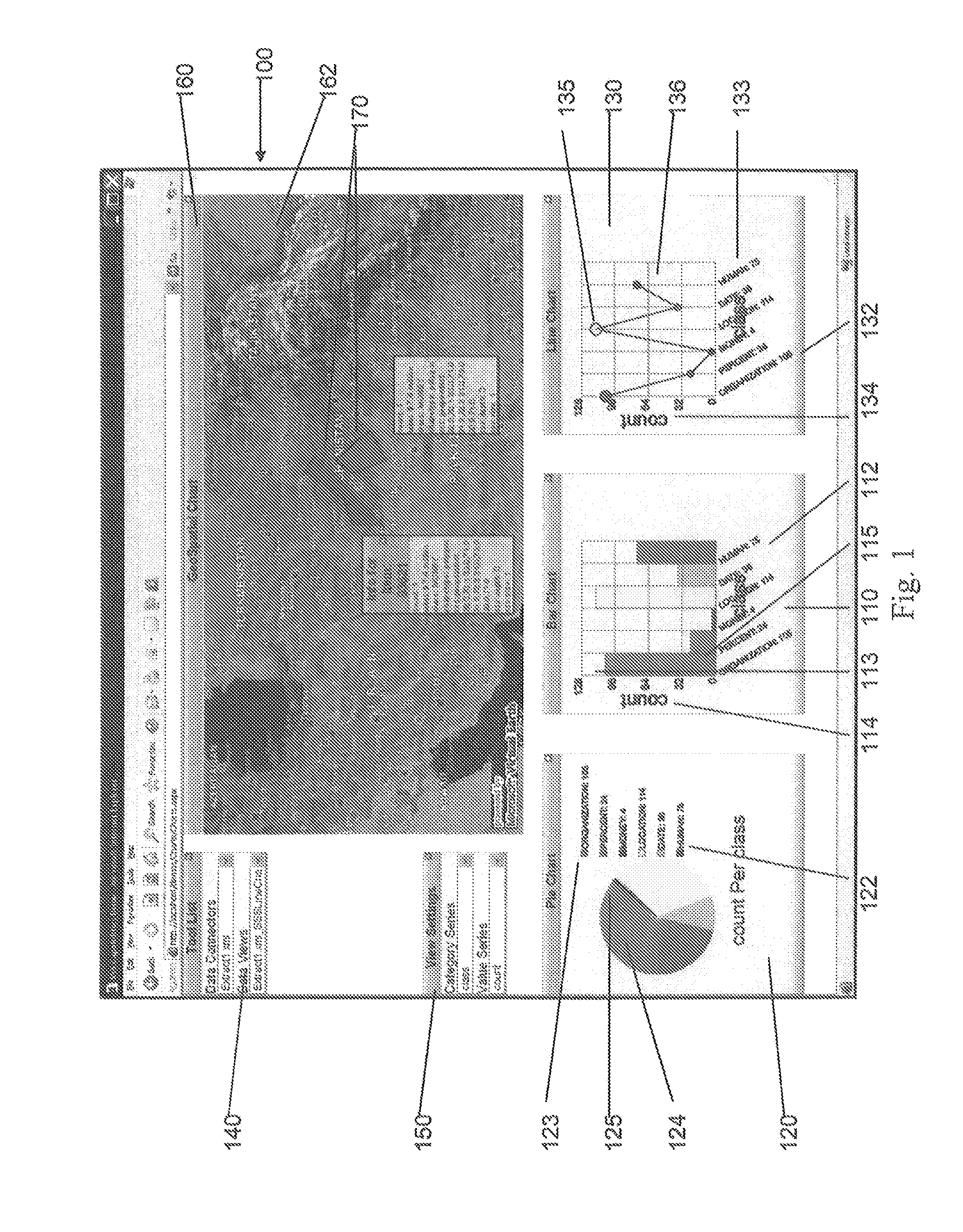
Server-based systems and methods for enabling interactive, collabortive thin- and no-client image-based applications
InactiveUS20070226314A1Eliminates start-stop-start-stop natureDirect operation2D-image generationMultiple digital computer combinationsGraphicsAnalysis data
A server receives image, graphic and / or analytic data and processes and asynchronously outputs that data to a thin / no client. The server inputs image data in a variety of different formats and renders a normalized format that can be streamed to the thin / no client using light-weight protocol(s). The server updates the image, feature and / or analytic data in real time. The server inputs feature, analytic, business logic and other data and process it into various format(s) that can be streamed to the thin / no client and overlaid on the image data. The server provides application services, which can include collaboration, tracking, alerting, business, workflow and / or other desired services. The server can receive collaboration data from one thin / no client and stream that collaboration data to other thin / no clients to enable shared situational awareness between the thin / no clients. The server includes a programming environment for programming thin / no clients contained within server-based web pages.
Owner:VISTRACKS
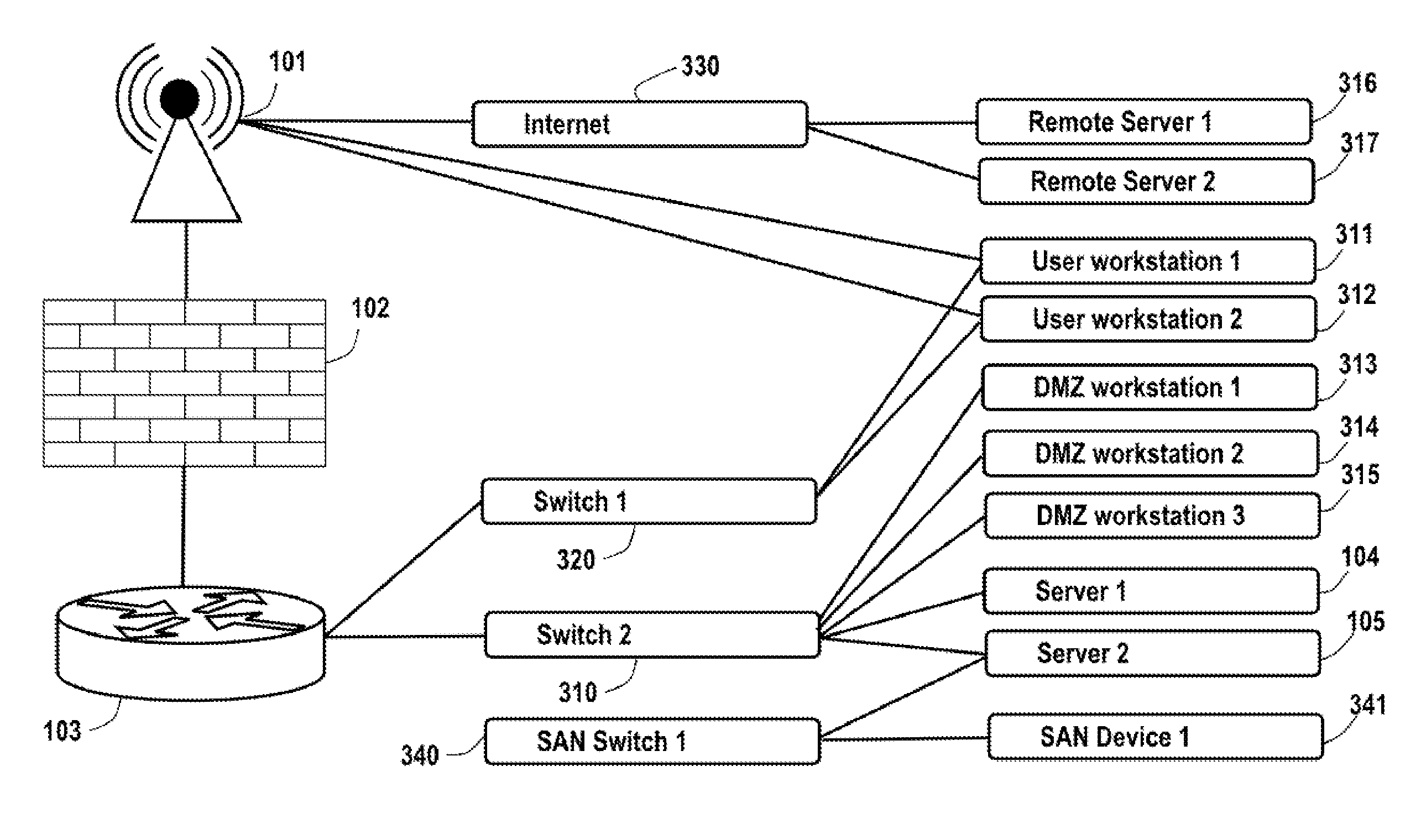
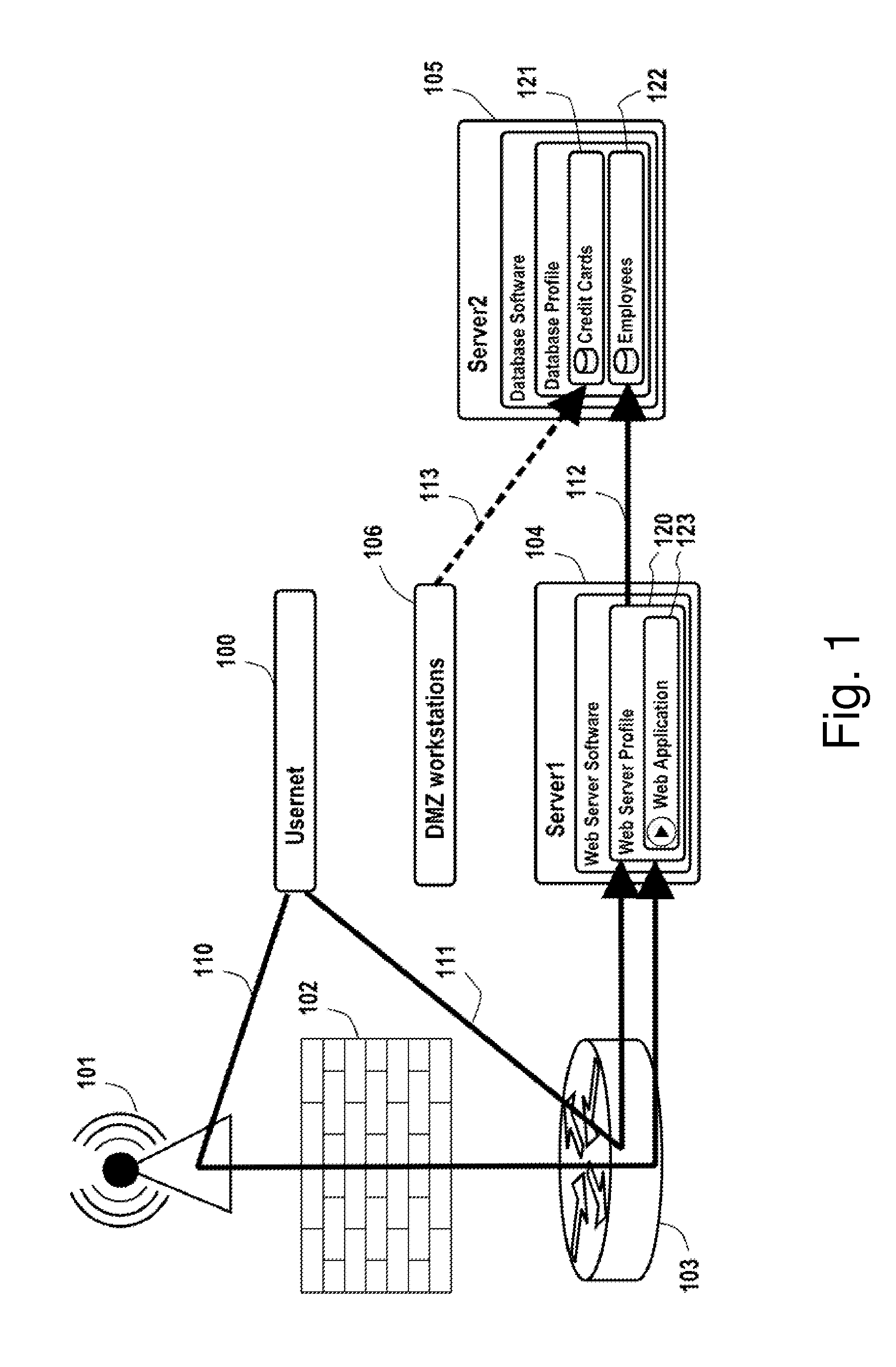
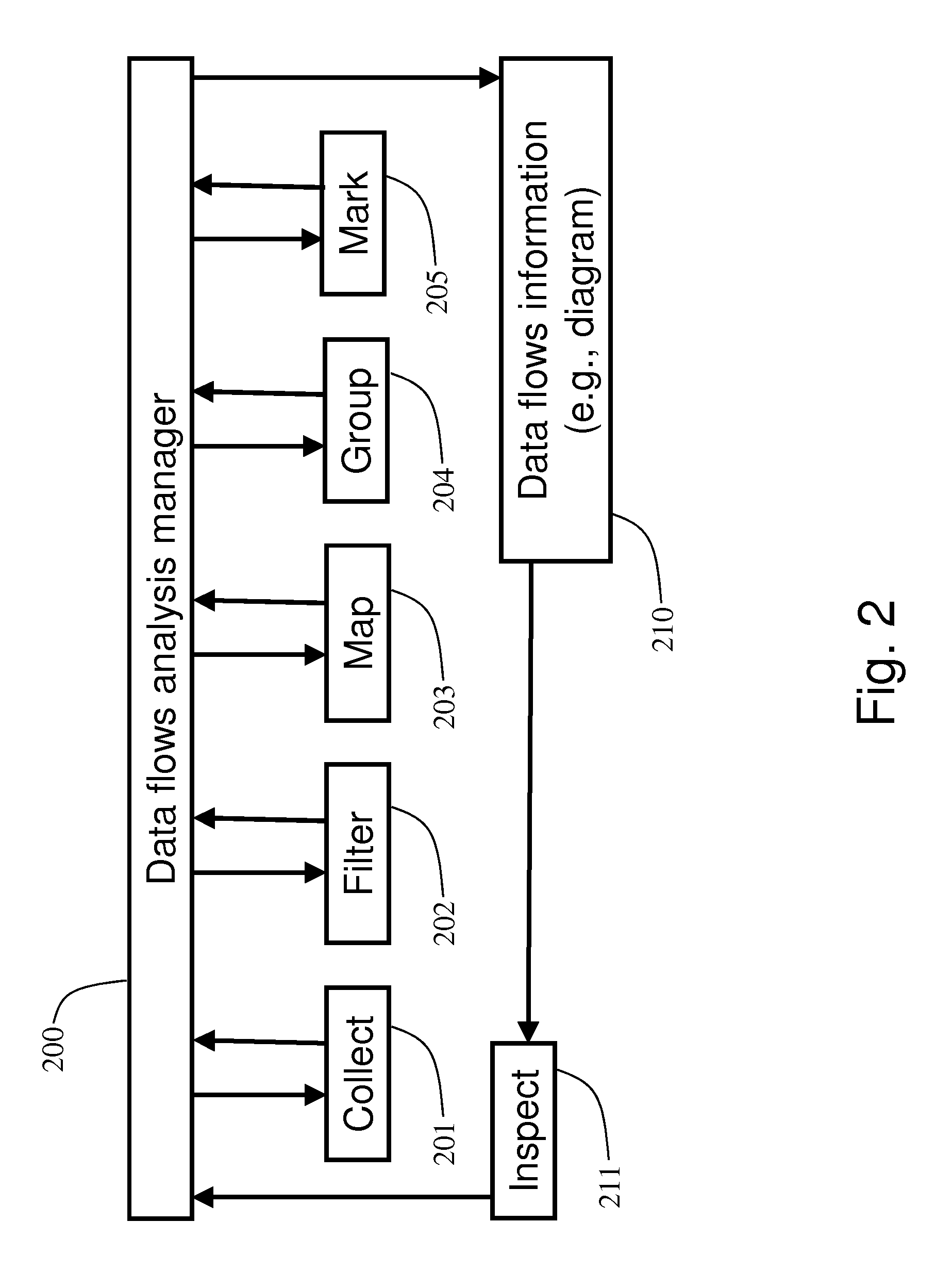
Analysis of data flows in complex enterprise it environments
The present technology enables identification, visualization, and analysis of data flows via network components in complex enterprise IT environments including but not limited to servers, workstations, switches, routers, wireless access points, traffic shapers, firewalls, storage systems and SAN systems. The technology is based on a combination of information collection, information filtering, mapping, grouping, marking, report generation, and verification.
Owner:MODELIZEIT INC
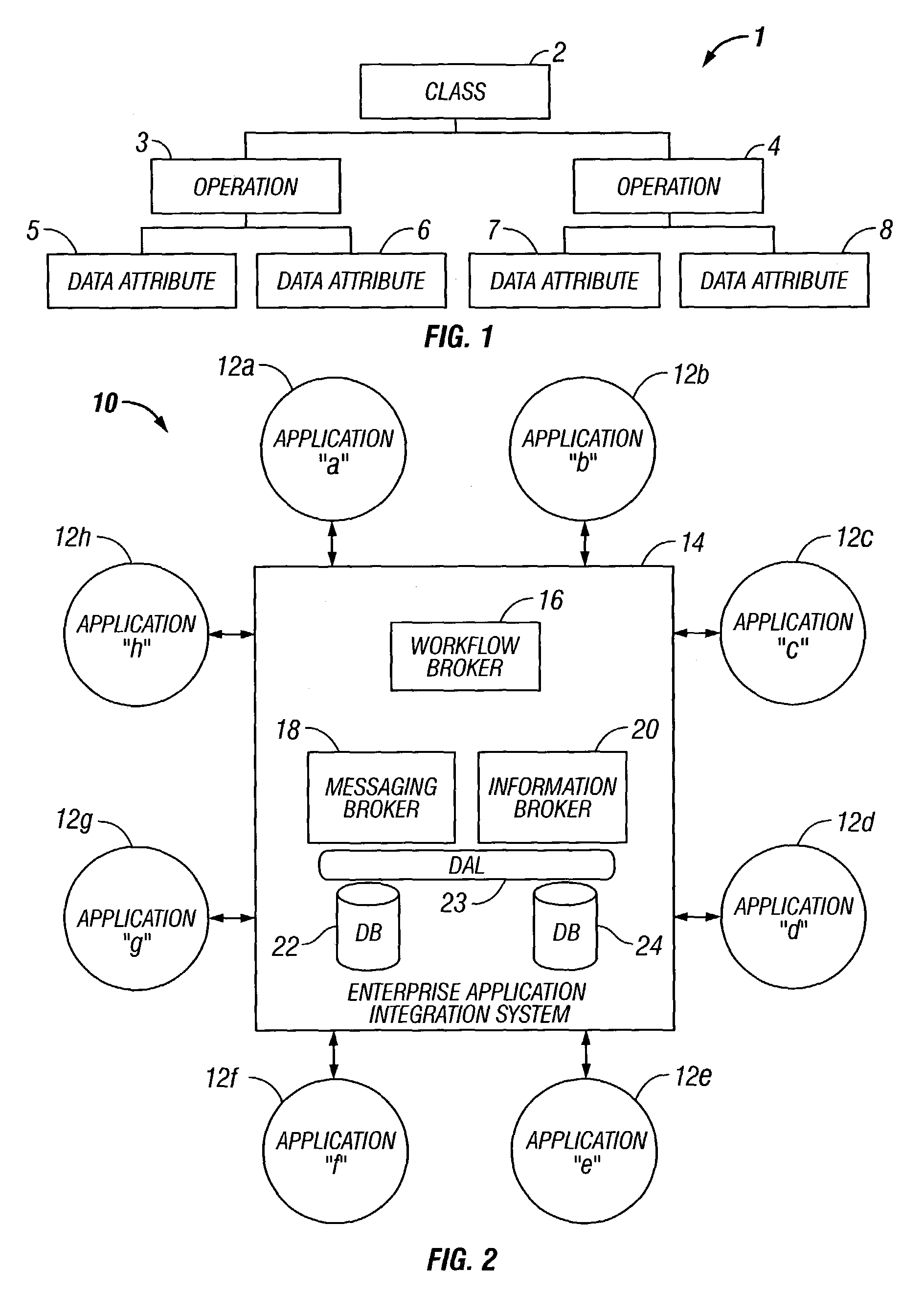
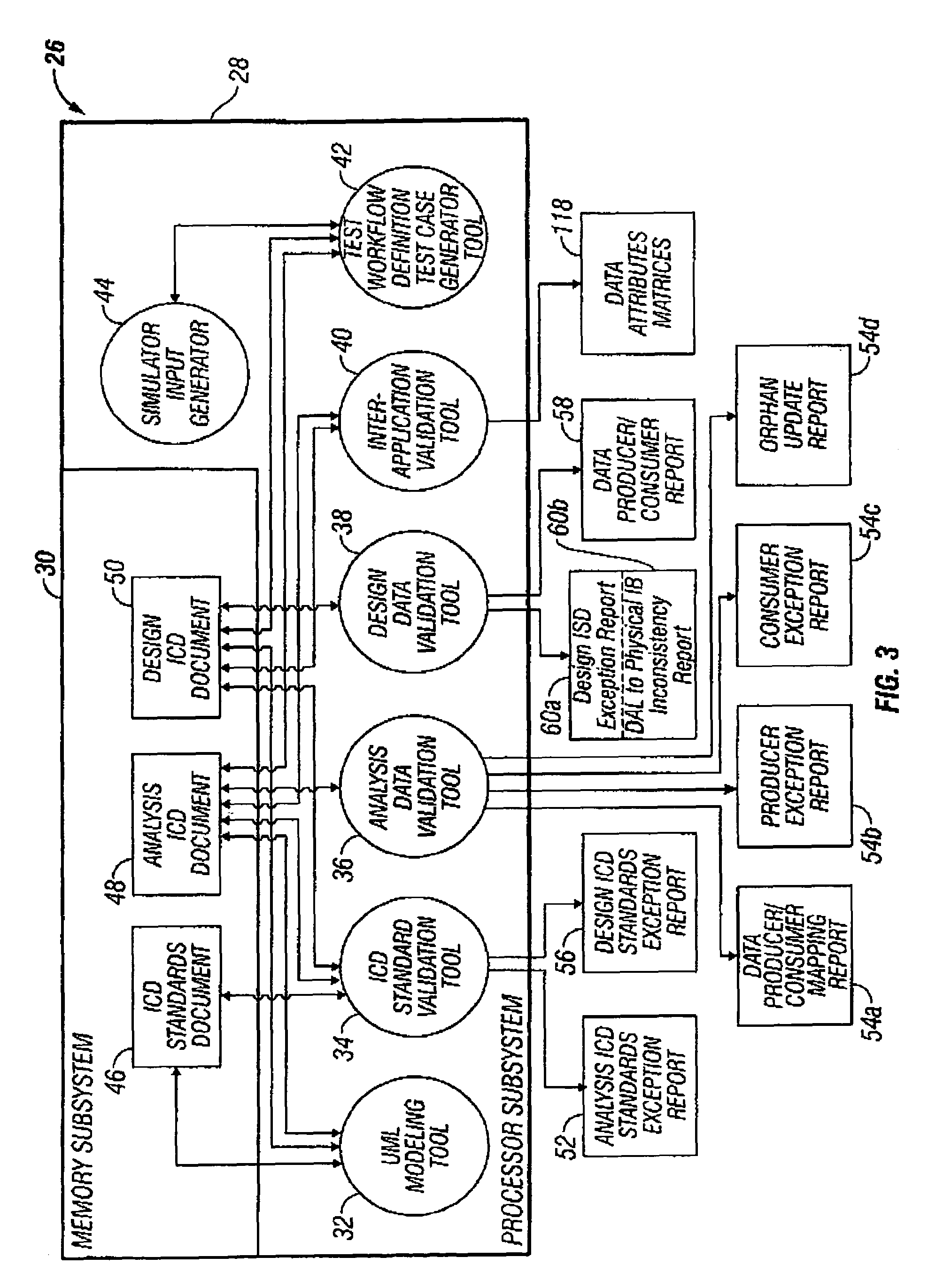
Analysis data validation tool for use in enterprise architecture modeling with result based model updating
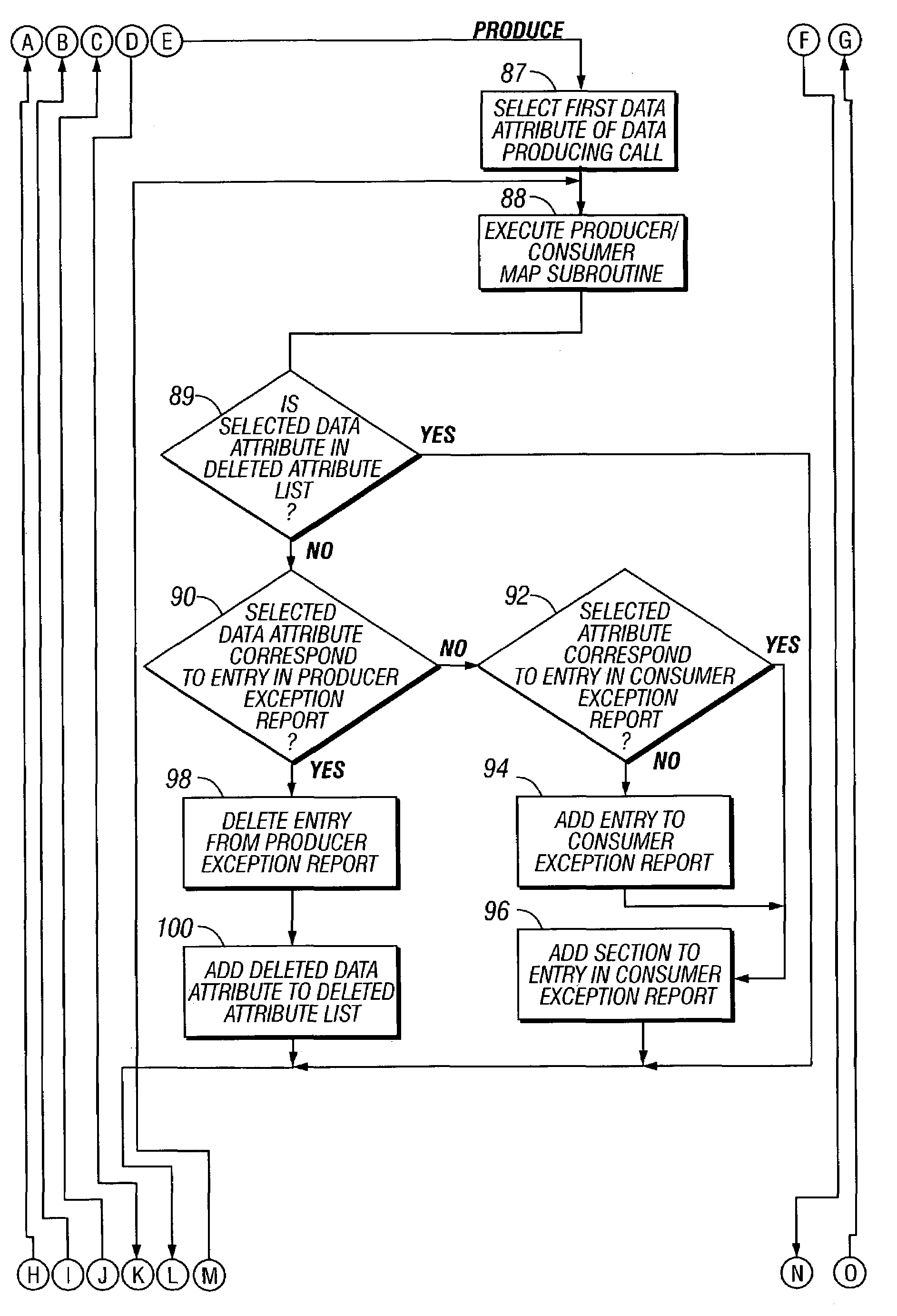
InactiveUS7216340B1Digital data information retrievalSpecial data processing applicationsAnalysis dataEnterprise architecture
A device for modeling an integrated enterprise includes a first tool for constructing a model of the integrated enterprise and a second tool for analyzing calls, contained in the constructed model, between applications of the integrated enterprise and a database shared thereby. The call analysis tool identifies data attribute imbalances in calls between the applications of the integrated enterprise and the shared database. Data attribute imbalances result if the calls attempt to consume data which was never produced or if the calls produce data which is never consumed. The call analysis tool also generates producer / consumer maps of the data attributes used in the model, producer exception reports which identify data attributes which are consumed but never produced and consumer exception reports which identify data attributes which are produced but never consumed.
Owner:SPRINT CORPORATION
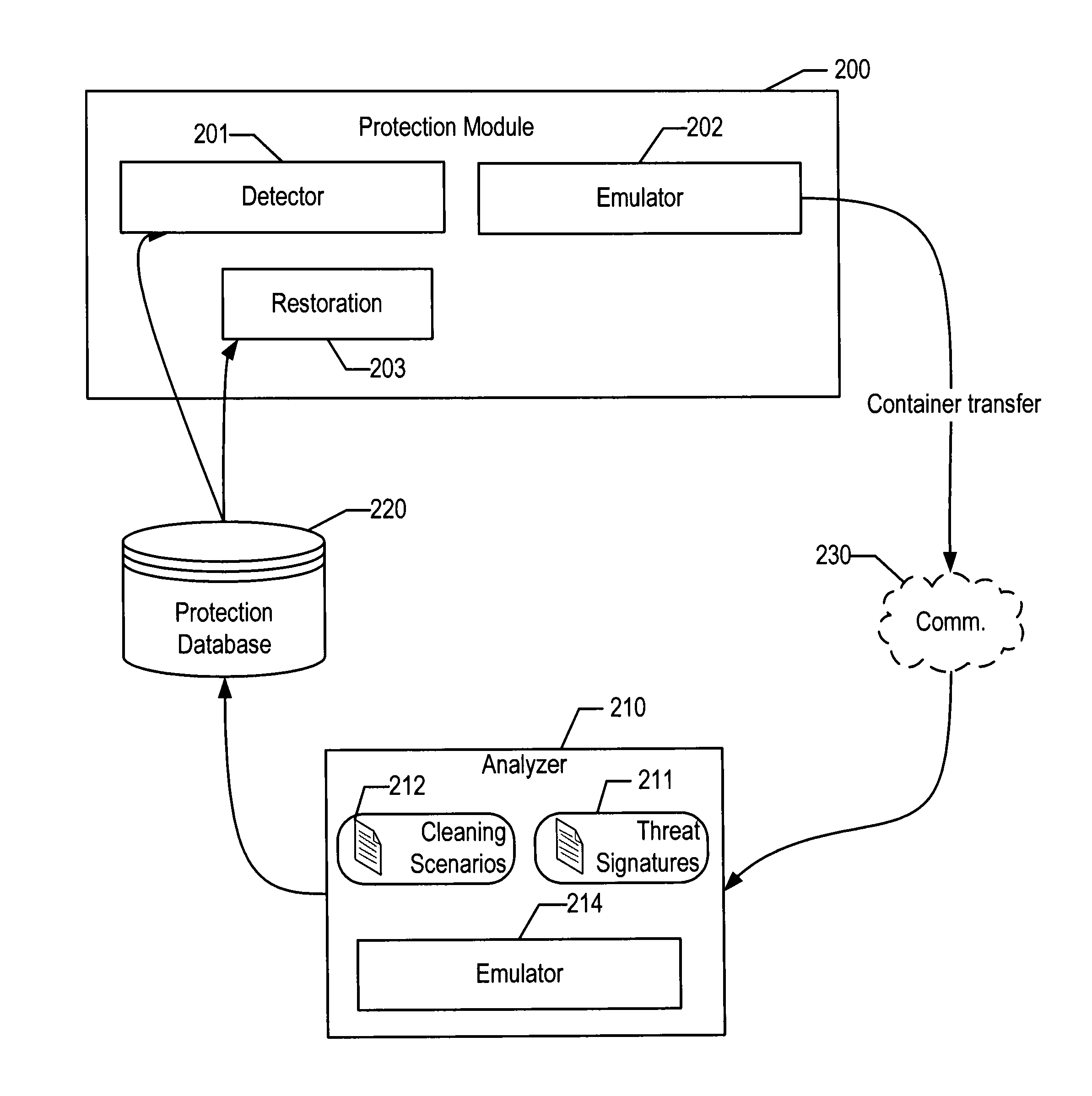
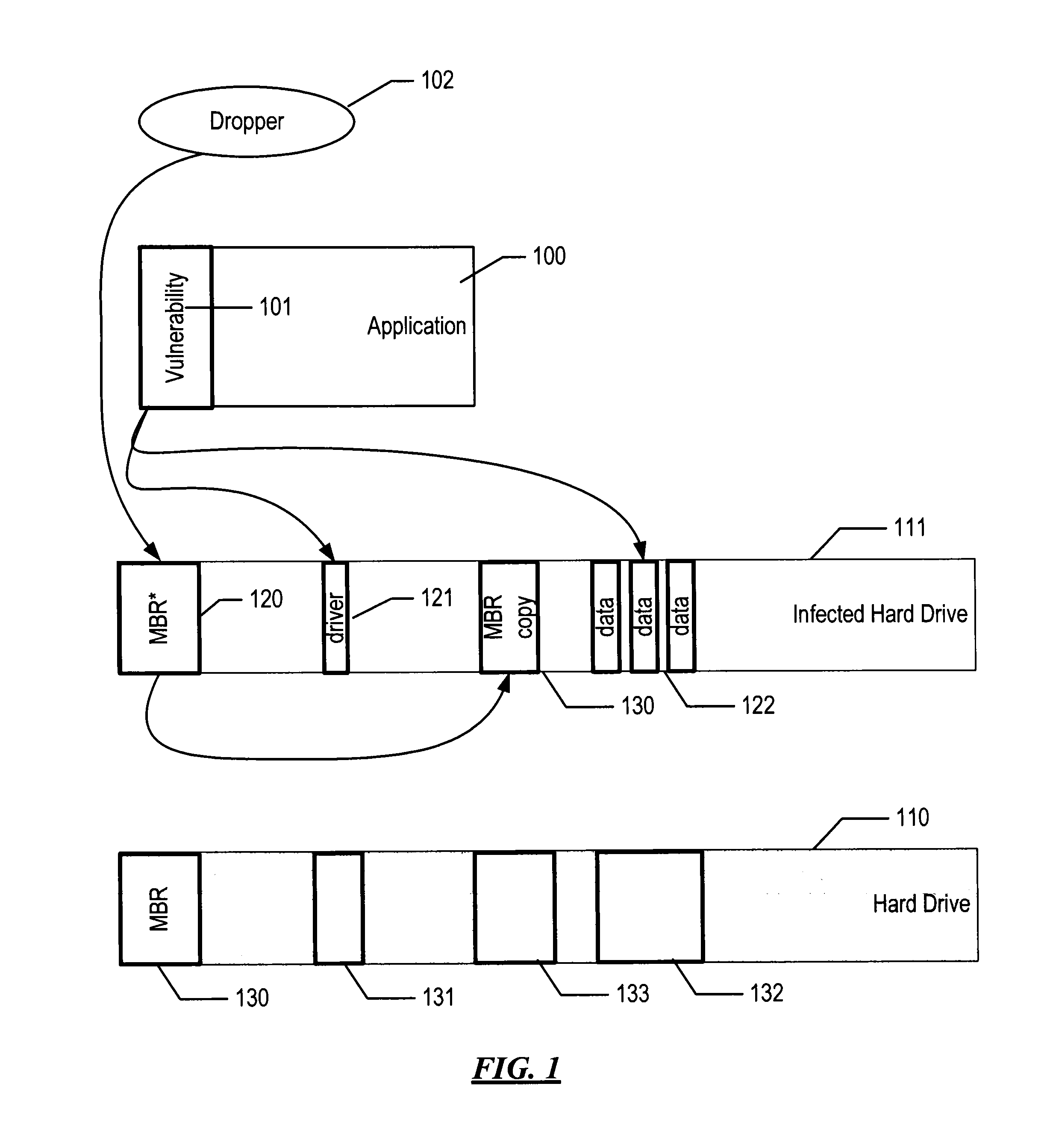
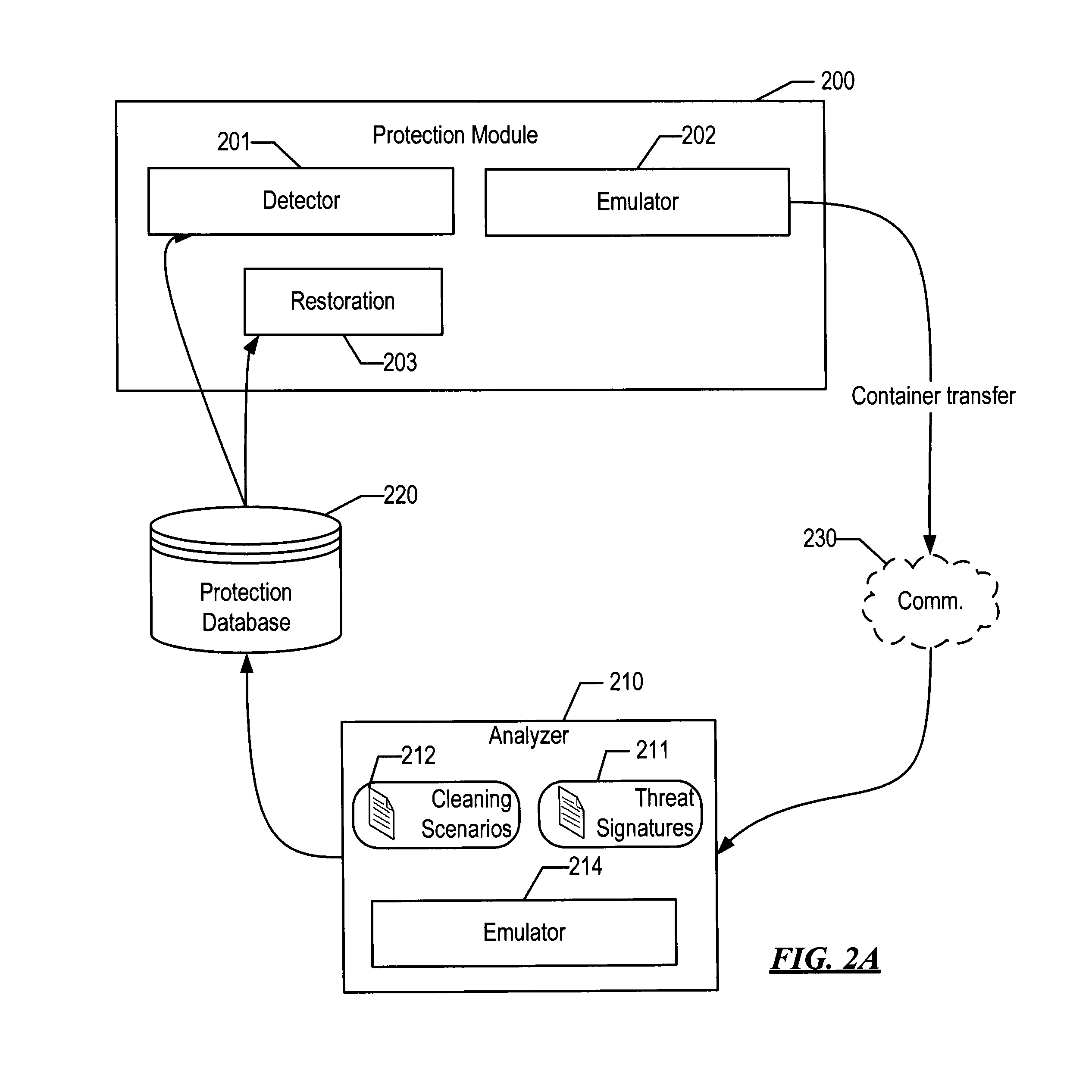
System and method for detecting malware targeting the boot process of a computer using boot process emulation
ActiveUS8365297B1Shorten the timeDigital data processing detailsDigital computer detailsComputer hardwareAnalysis data
System and method for detecting malware on a target computer system having a bootable device. Boot process information stored on the bootable device that at least partially defines a boot process of the target computer system is obtained, along with physical parameter data defining a storage arrangement structure of the bootable device. The boot process of the target computer system is emulated based on the boot process information and on the physical parameter data. The emulation includes executing instructions of the boot process information and tracking data accessed from the bootable device. A data structure representing the data accessed from the bootable device is stored during the emulation of the boot process. The data structure can be analyzed for any presence of boot process malware.
Owner:AO KASPERSKY LAB
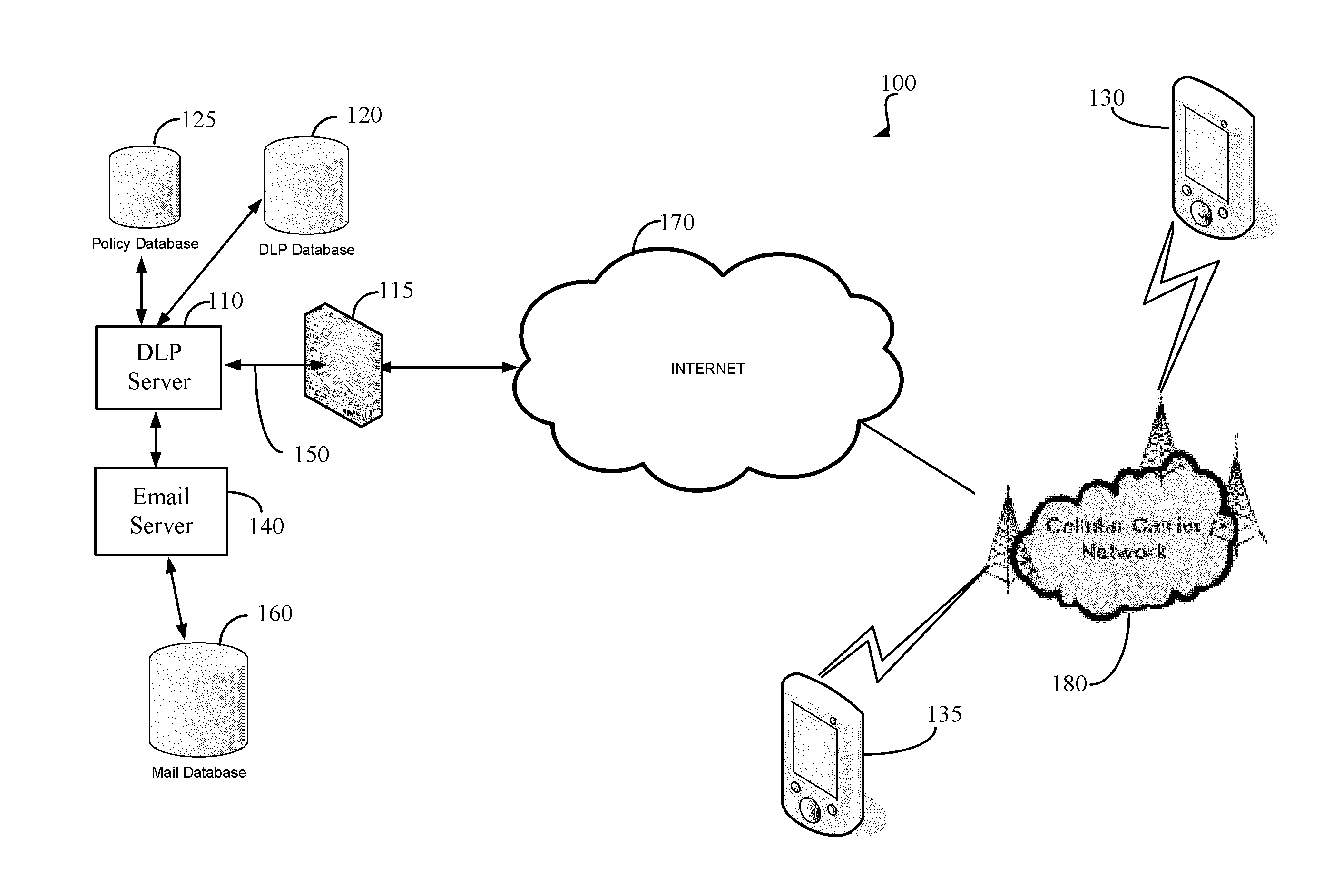
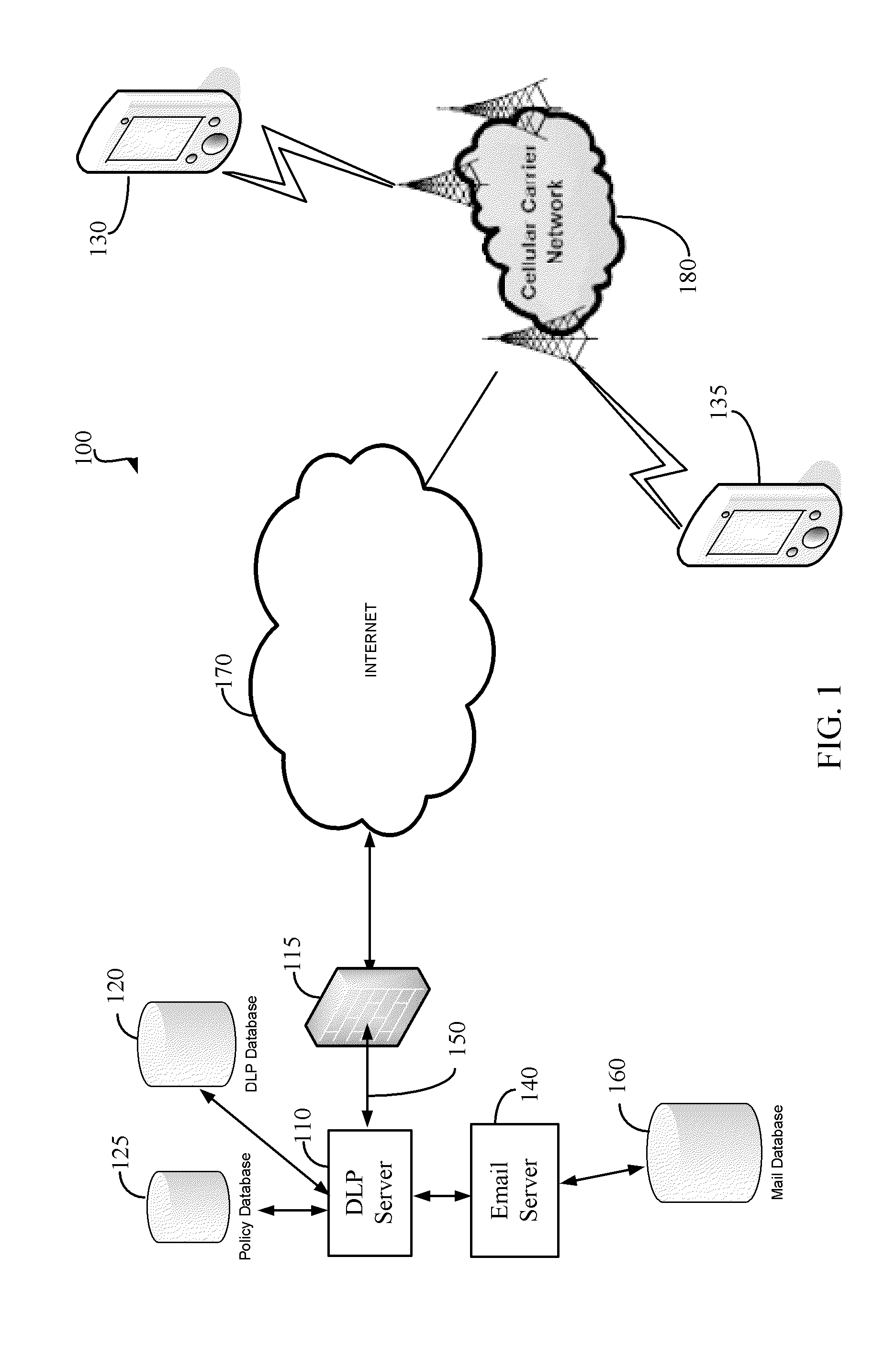
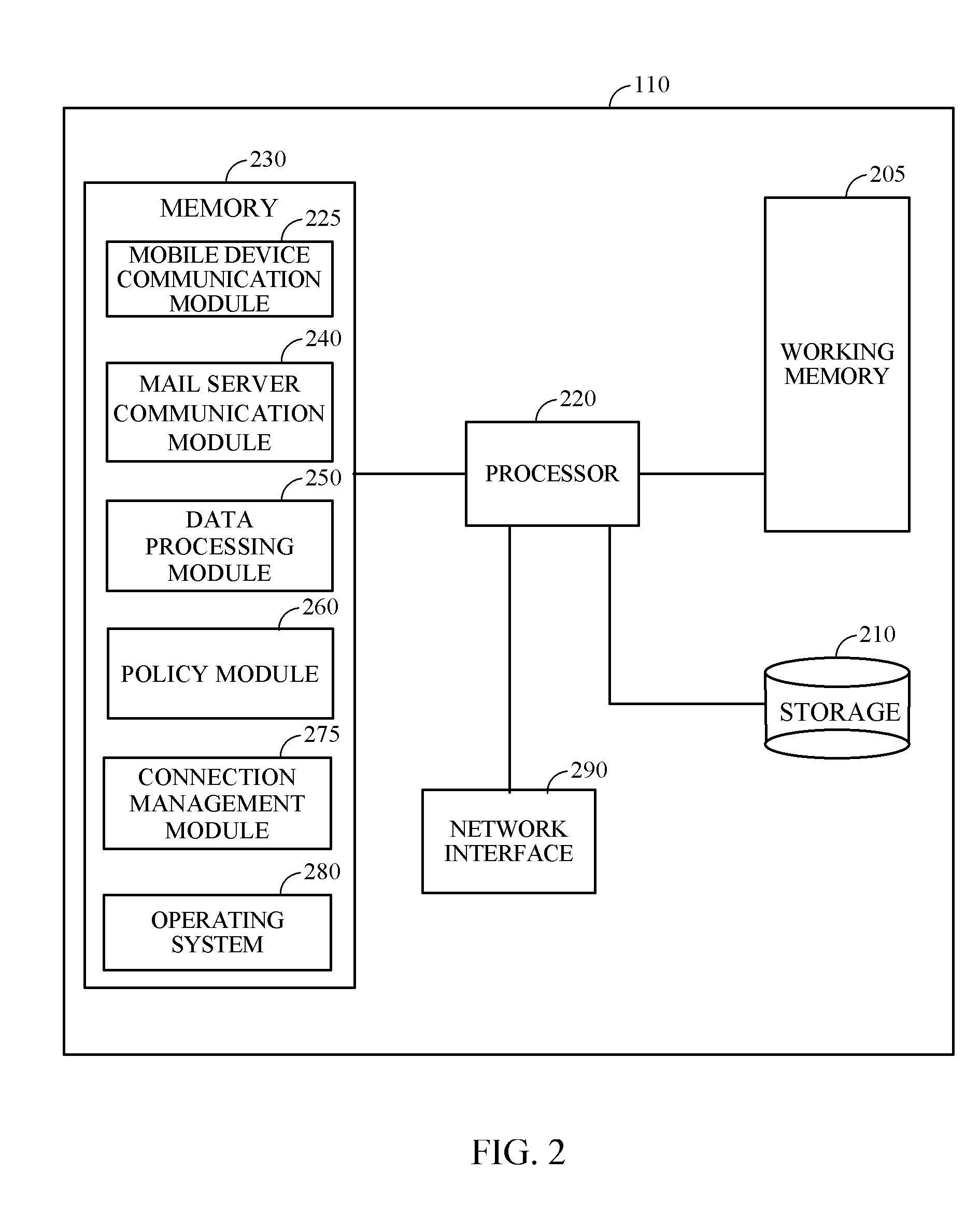
Method and apparatus for managing the transfer of sensitive information to mobile devices
ActiveUS9241259B2Avoid lostUnauthorised/fraudulent call preventionData switching networksAnalysis dataMobile device
Methods and apparatus provide data loss protection for mobile devices. In one aspect, data is analyzed by a data loss protection server to determine if it is authorized by data loss protection policies to be transferred to a mobile device. The time necessary to analyze the data may exceed a mobile device timeout value. To prevent the mobile device from timing out, the DLP server may send one or more portions of a response to the mobile device at a time interval less than the mobile device timeout value. Some portions of the response may be sent before the analyzing of the data is completed.
Owner:FORCEPOINT LLC
Intelligent motion capture element
ActiveUS20130128022A1Accurate and power efficientIncrease capacityGymnastic exercisingDevices with sensorPower applicationAnalysis data
Intelligent motion capture element that includes sensor personalities that optimize the sensor for specific movements and / or pieces of equipment and / or clothing and may be retrofitted onto existing equipment or interchanged therebetween and automatically detected for example to switch personalities. May be used for low power applications and accurate data capture for use in healthcare compliance, sporting, gaming, military, virtual reality, industrial, retail loss tracking, security, baby and elderly monitoring and other applications for example obtained from a motion capture element and relayed to a database via a mobile phone. System obtains data from motion capture elements, analyzes data and stores data in database for use in these applications and / or data mining. Enables unique displays associated with the user, such as 3D overlays onto images of the user to visually depict the captured motion data. Enables performance related equipment fitting and purchase. Includes active and passive identifier capabilities.
Owner:NEWLIGHT CAPITAL LLC
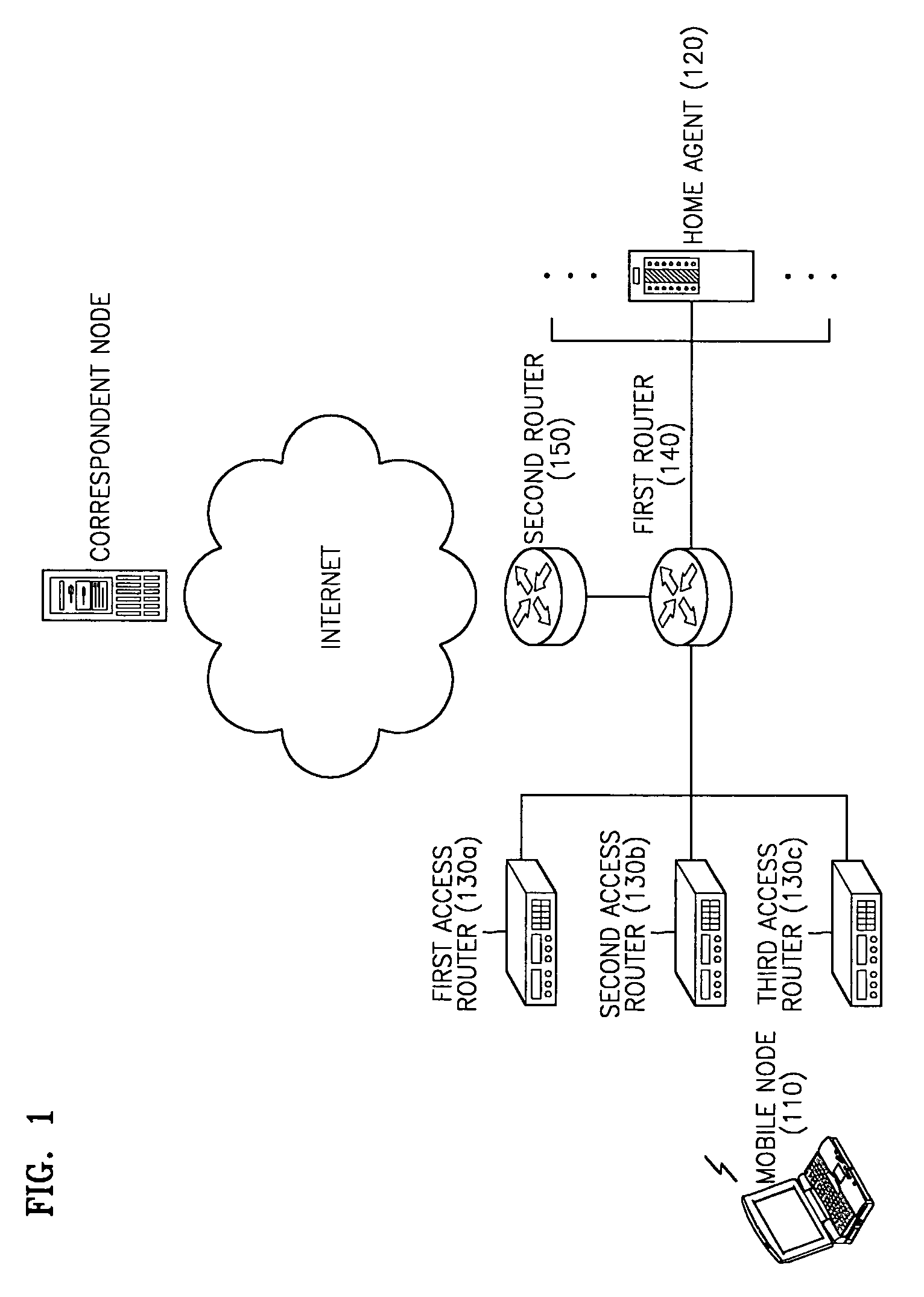
Home agent management apparatus and method
InactiveUS7626957B2Raise countTime-division multiplexData switching by path configurationComputer networkAnalysis data
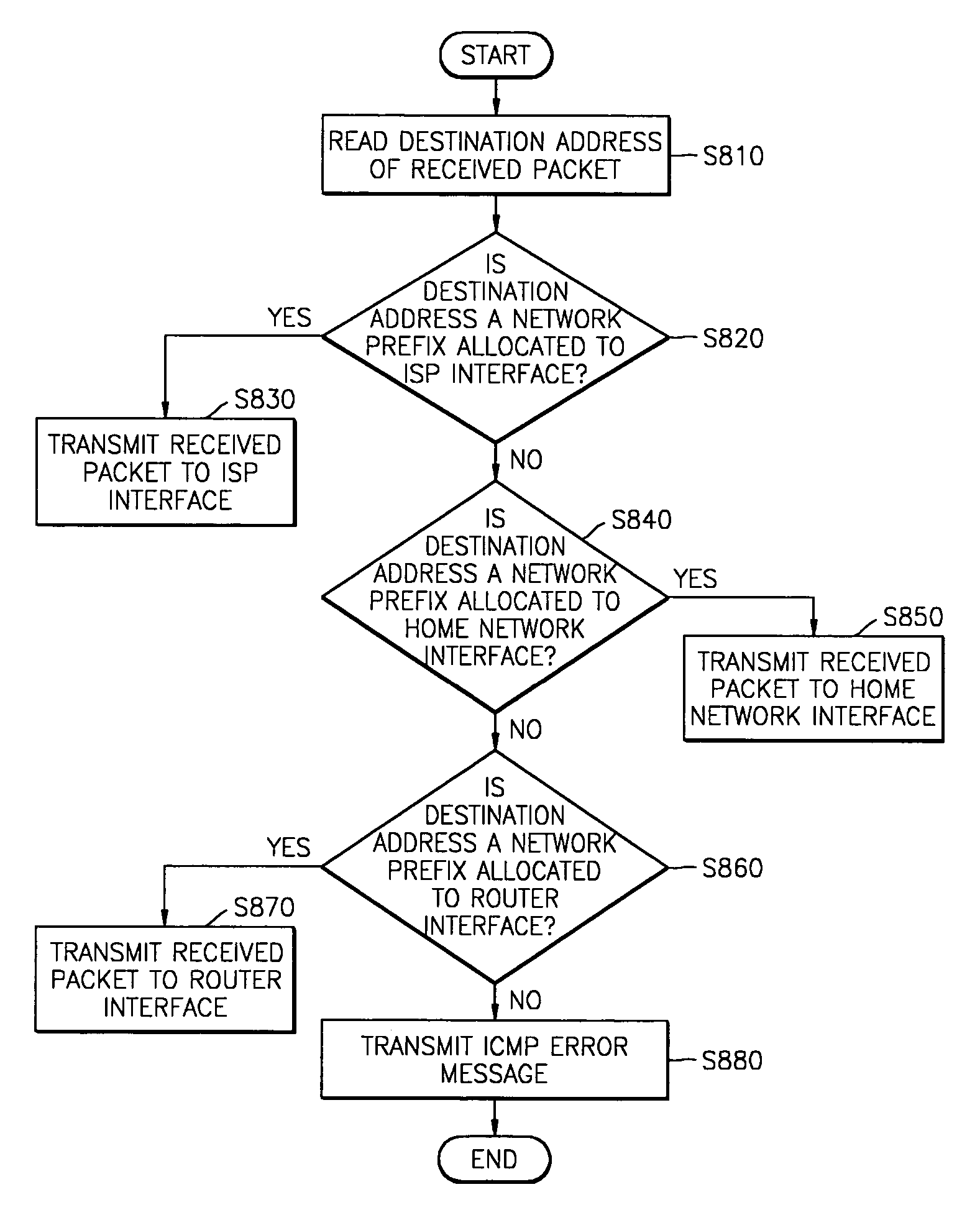
A home agent management apparatus and method for routing a packet using a home network equipment as a home agent in a mobile Inter Protocol version 6 (IPv6) are provided. The home agent management apparatus includes a packet analyzer, which receives a packet and analyzes the packet; a database, which stores information indicating whether a home agent of a home network operates normally according to the result of the analysis; and a home agent function executor, which performs a home agent function in place of the home agent when the home agent does not operate normally. Accordingly, a load concentrated on a home agent of an Internet Service Provider (ISP) can be split.
Owner:SAMSUNG ELECTRONICS CO LTD
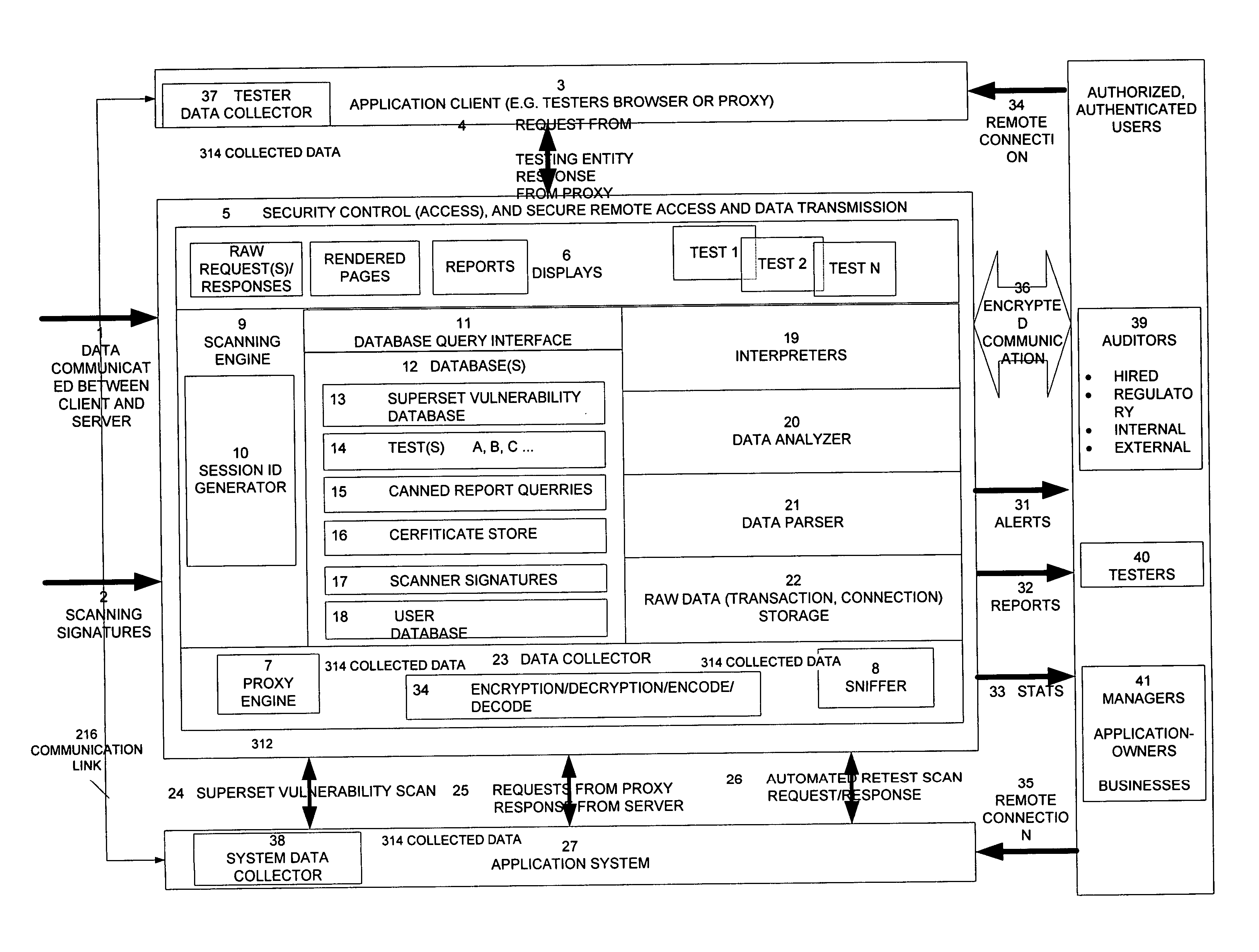
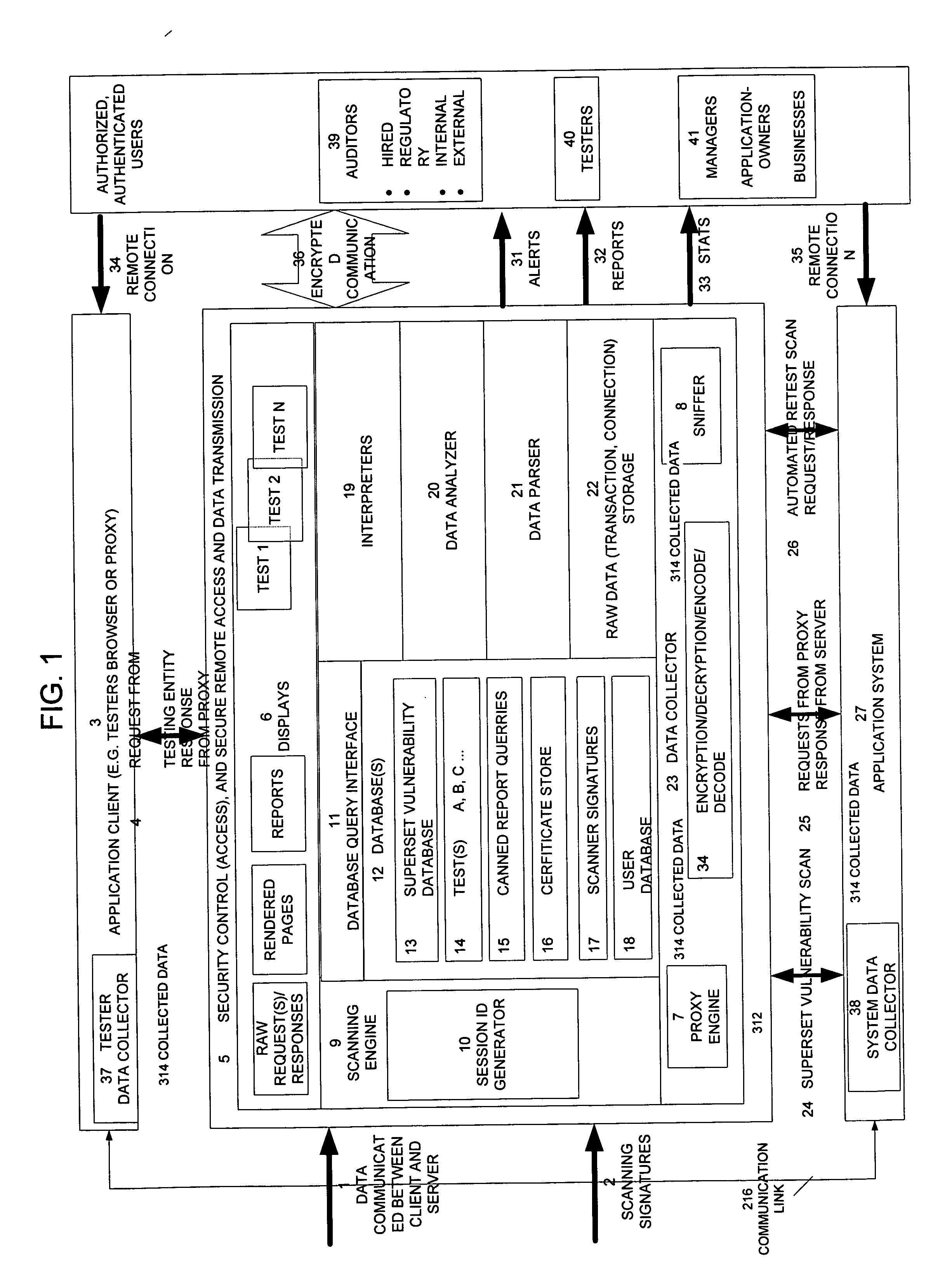
Method, system, and apparatus for managing, monitoring, auditing, cataloging, scoring, and improving vulnerability assessment tests, as well as automating retesting efforts and elements of tests
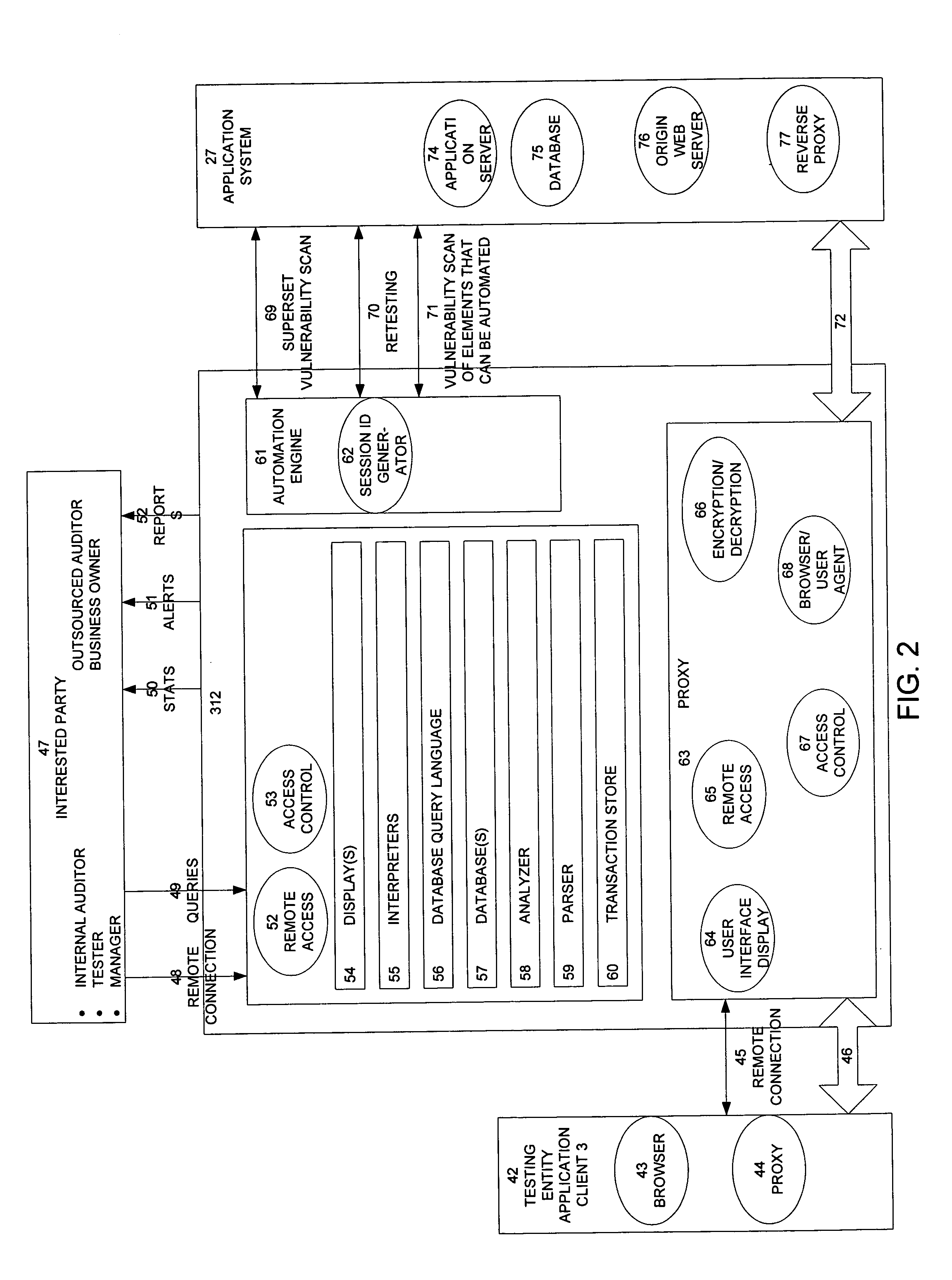
InactiveUS20050138426A1Streamline and improve test effortImprove consistencyDigital data processing detailsHardware monitoringAnalysis dataWeb application
A scalable method, system, and apparatus for non-intrusively auditing and improving security assessments includes capturing, storing, presenting, displaying, inspecting, monitoring, and analyzing data flow in client-server security assessments and / or network / infrastructure security assessments. The invention provides interested parties with a mechanism to non-intrusively audit in real-time the vulnerability test effort, as well as review, replay, and analyze all aspects of the security assessment during and after the test. For web application assessments, the data capture includes one of the following or some combination: an intermediary with all data passing through the intermediary; a sniffer that can passively extract all data being communicated between the application and tester; and a plurality of computing modules (e.g., software, appliances, etc.) installed in the tester environment or within the application system environment (e.g., software installed on the tester's computer, or on the computer where the intermediary is running, or software installed on the application systems proxy or web server, or an appliance in either environment) for storing, processing, analyzing, reporting, and displaying the data.
Owner:STYSLINGER BRIAN
System and method for detecting and managing fraud
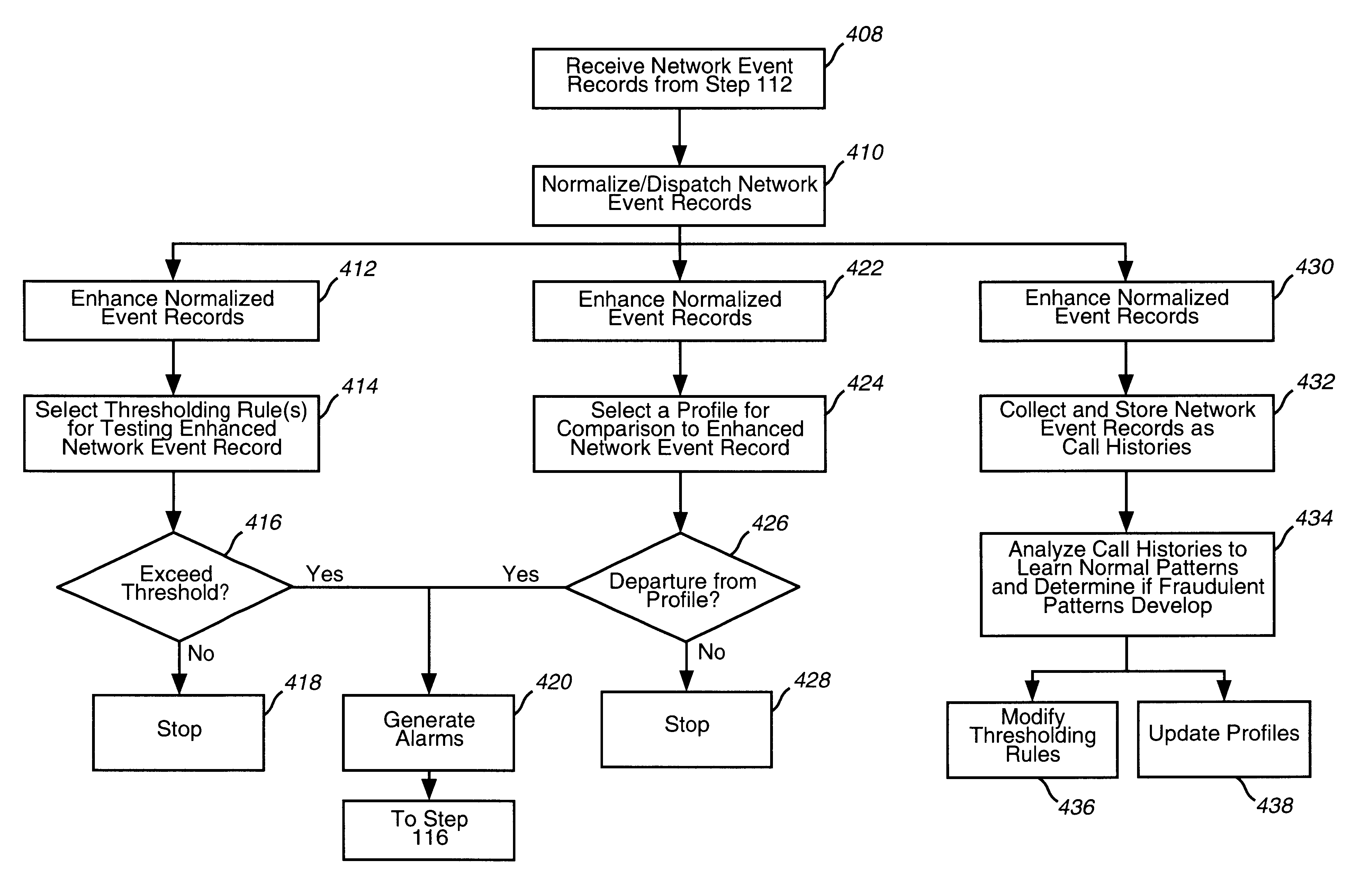
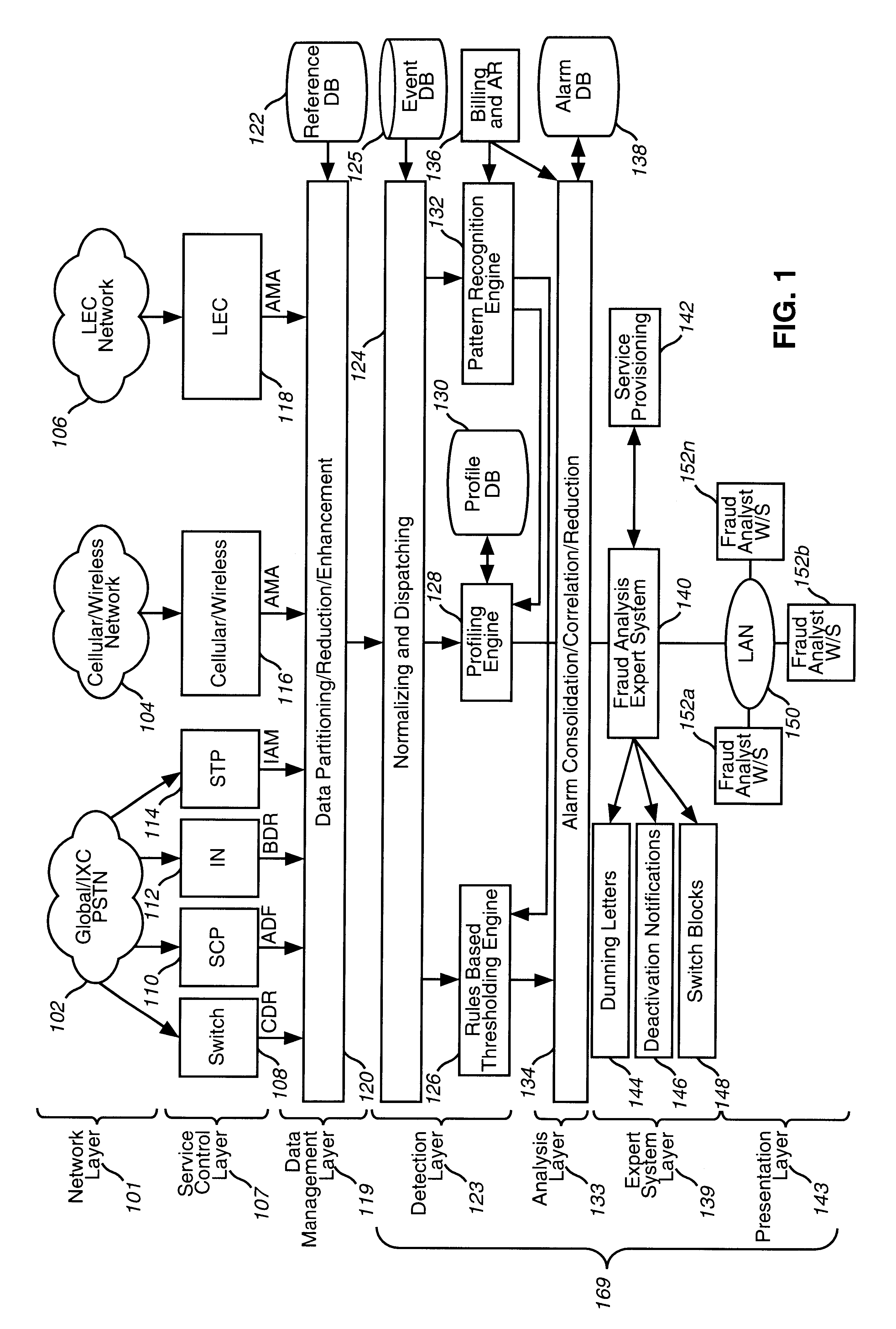
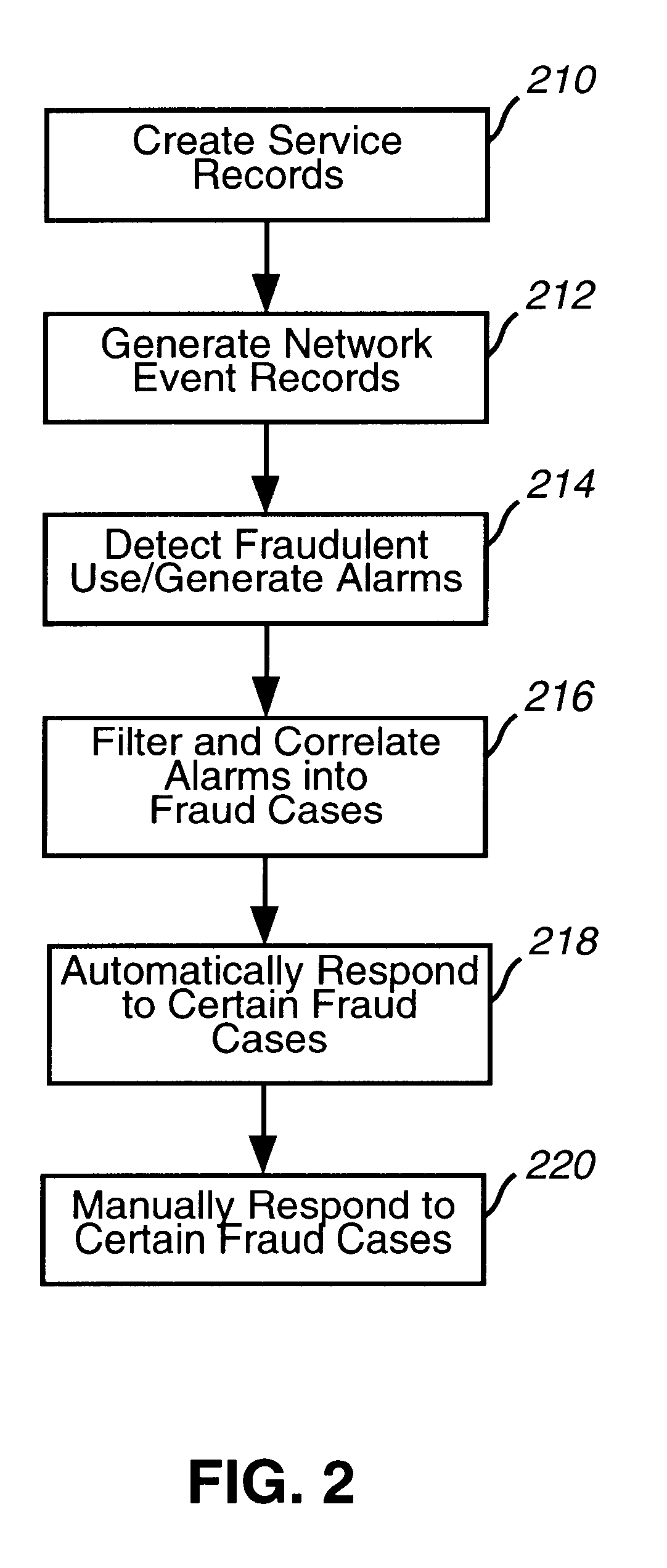
A system, method and computer program product for processing event records. The present invention includes a detection layer, an analysis layer, an expert systems layer and a presentation layer. The layered system includes a core infrastructure and a configurable, domain-specific implementation. The detection layer employs one or more detection engines, such as, for example, a rules-based thresholding engine and a profiling engine. The detection layer can include an AI-based pattern recognition engine for analyzing data records, for detecting new and interesting patterns and for updating the detection engines to insure that the detection engines can detect the new patterns. In one embodiment, the present invention is implemented as a telecommunications fraud detection system. When fraud is detected, the detection layer generates alarms which are sent to the analysis layer. The analysis layer filters and consolidates the alarms to generate fraud cases. The analysis layer preferably generates a probability of fraud for each fraud case. The expert systems layer receives fraud cases and automatically initiates actions for certain fraud cases. The presentation layer also receives fraud cases for presentation to human analysts. The presentation layer permits the human analysts to initiate additional actions.
Owner:VERIZON PATENT & LICENSING INC
Methods and systems for analyzing data related to possible online fraud
ActiveUS20060069697A1Data processing applicationsDigital data processing detailsWeb siteAnalysis data
Various embodiments of the invention provide methods, systems and software for analyzing data. In particular embodiments, for example, a set of data about a web site may be analyzed to determine whether the web site is likely to be illegitimate (e.g., to be involved in a fraudulent scheme, such as a phishing scheme, the sale of gray market goods, etc.). In an exemplary embodiment, a set of data may be divided into a plurality of components (each of which, in some cases, may be considered a separate data set). Merely by way of example, a set of data may comprise data gathered from a plurality of data sources, and / or each component may comprise data gathered from one of the plurality of data sources. As another example, a set of data may comprise a document with a plurality of sections, and each component may comprise one of the plurality of sections. Those skilled in the art will appreciate that the analysis of a particular component may comprise certain tests and / or evaluations, and that the analysis of another component may comprise different tests and / or evaluations. In other cases, the analysis of each component may comprise similar tests and / or evaluations. The variety of tests and / or evaluations generally will be implementation specific.
Owner:OPSEC ONLINE LTD
Method and apparatus for determining and analyzing a location of visual interest
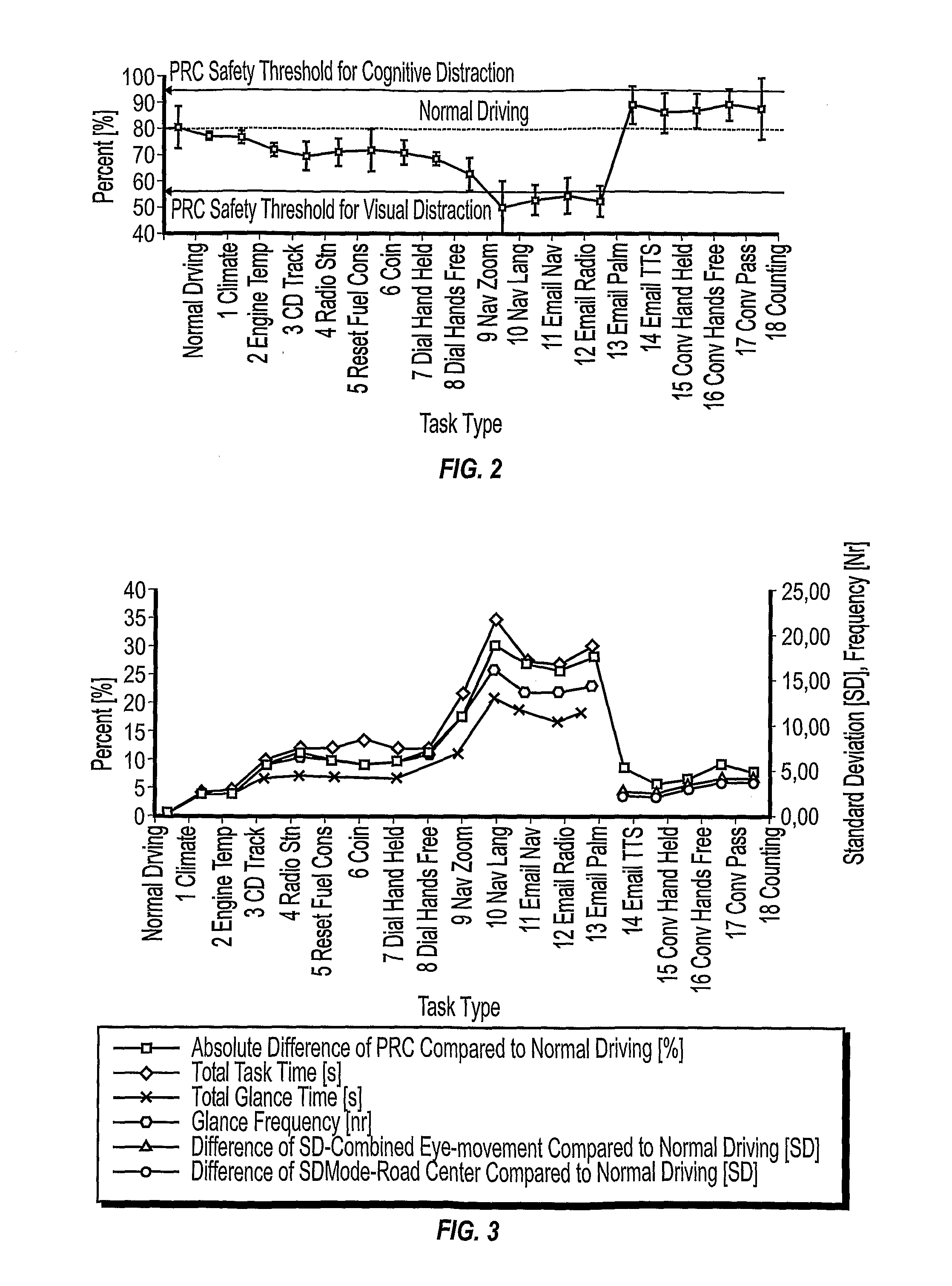
InactiveUS20100033333A1Effect of occurrence is minimizedMinimize impactElectric devicesAcquiring/recognising eyesPattern recognitionDriver/operator
A method of analyzing data based on the physiological orientation of a driver is provided. Data is descriptive of a driver's gaze-direction is processing and criteria defining a location of driver interest is determined. Based on the determined criteria, gaze-direction instances are classified as either on-location or off-location. The classified instances can then be used for further analysis, generally relating to times of elevated driver workload and not driver drowsiness. The classified instances are transformed into one of two binary values (e.g., 1 and 0) representative of whether the respective classified instance is on or off location. The uses of a binary value makes processing and analysis of the data faster and more efficient. Furthermore, classification of at least some of the off-location gaze direction instances can be inferred from the failure to meet the determined criteria for being classified as an on-location driver gaze direction instance.
Owner:VOLVO LASTVAGNAR AB
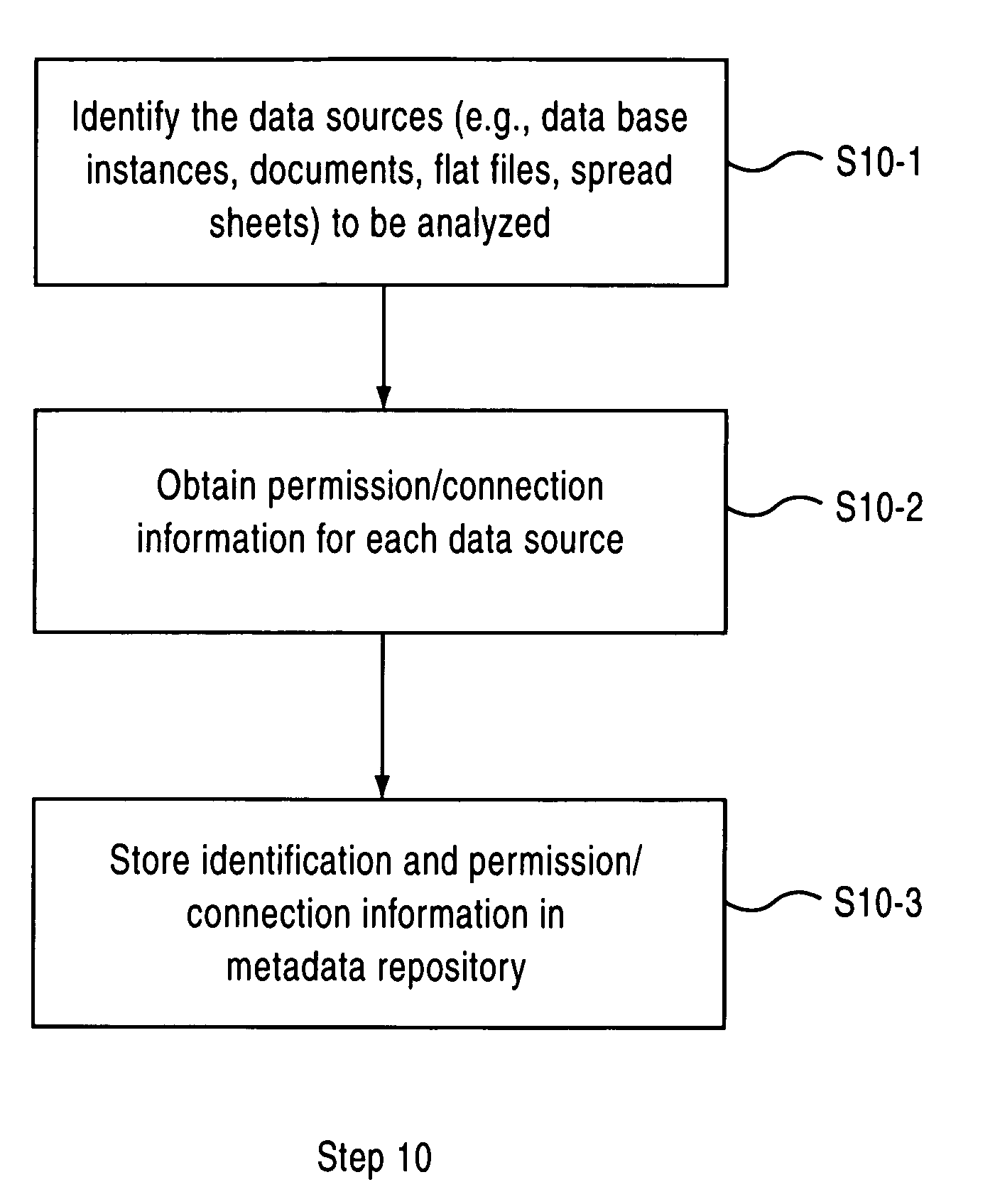
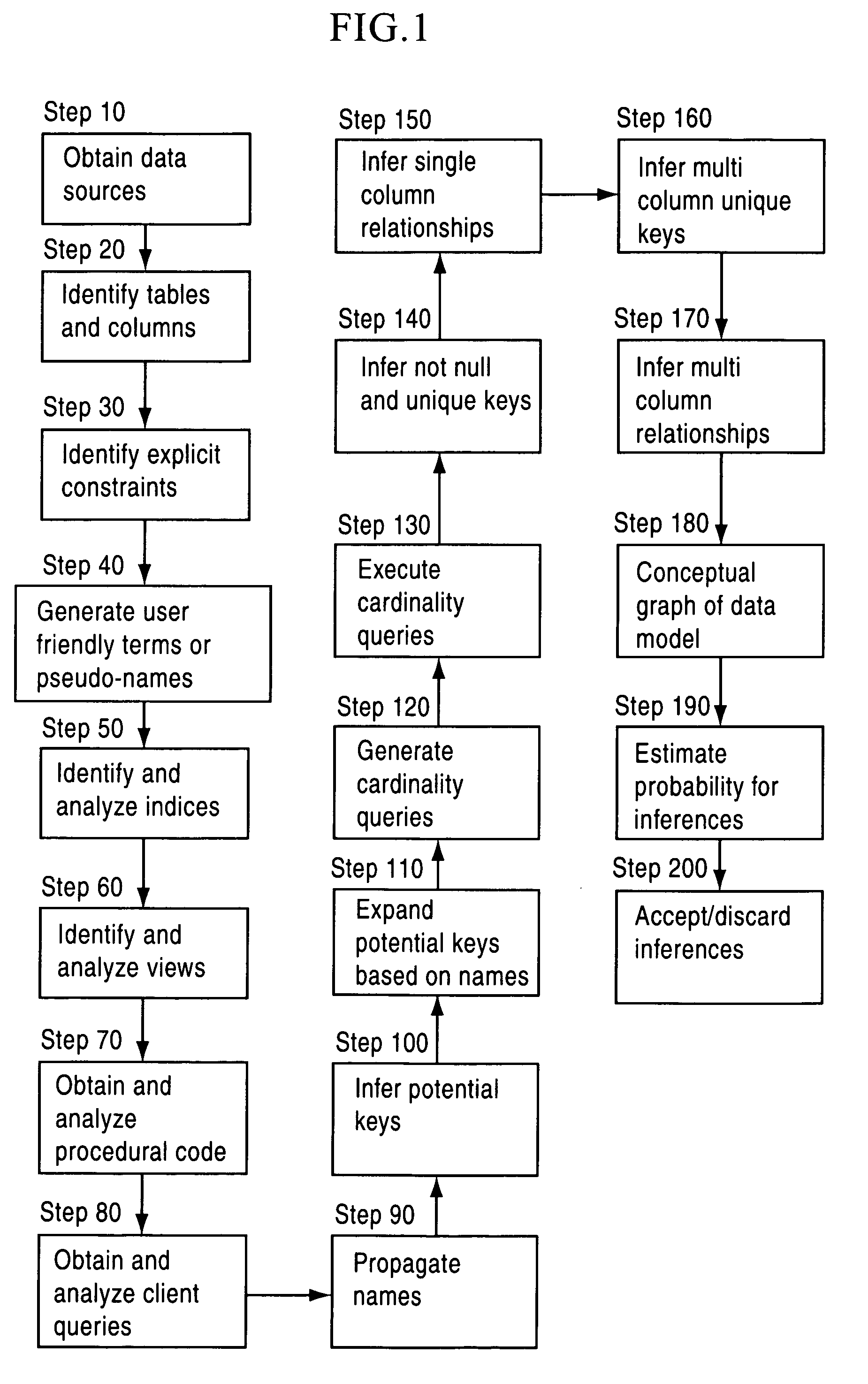
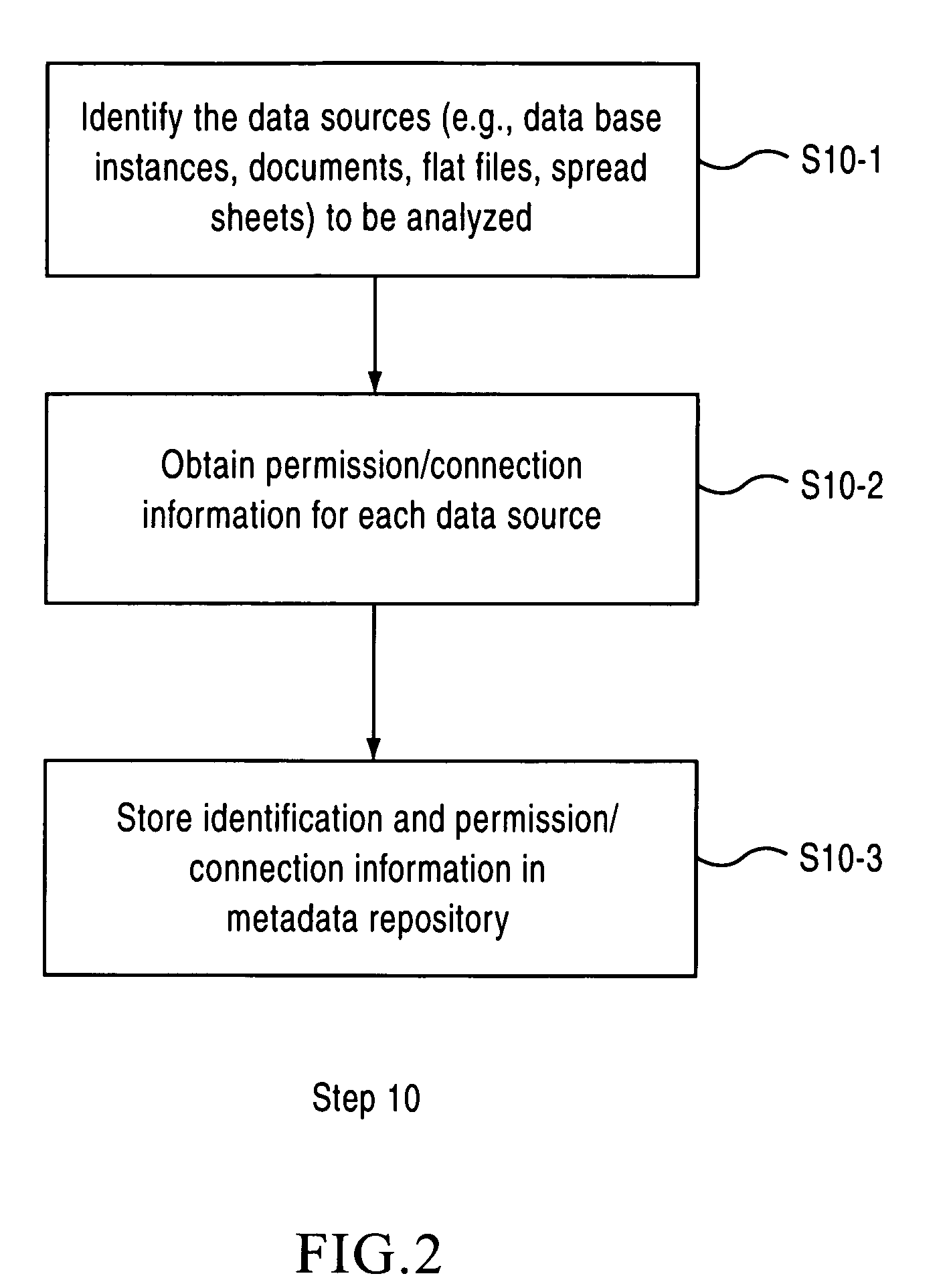
System and method for analyzing data sources to generate metadata
InactiveUS20080140696A1Digital data information retrievalSpecial data processing applicationsAnalysis dataData source
A system and method are provided for generating metadata relating to an enterprise management system including at least one data source having one or more of tables and columns. Constraints existing on at least one of the tables and columns in the data source are inferred based on data in the tables and columns. Metadata that includes information on the inferred constraints is generated.
Owner:PANTHEON SYST
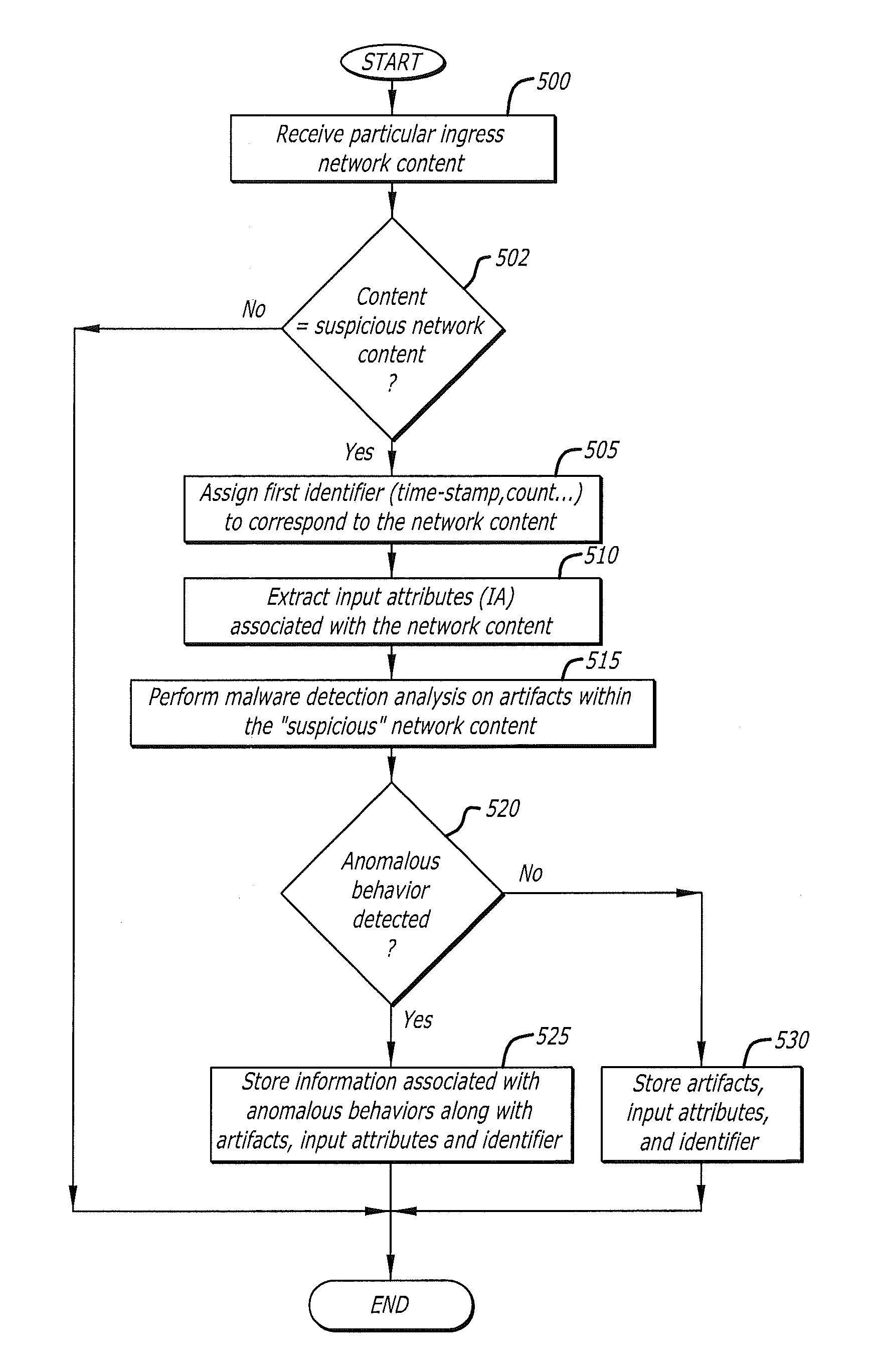
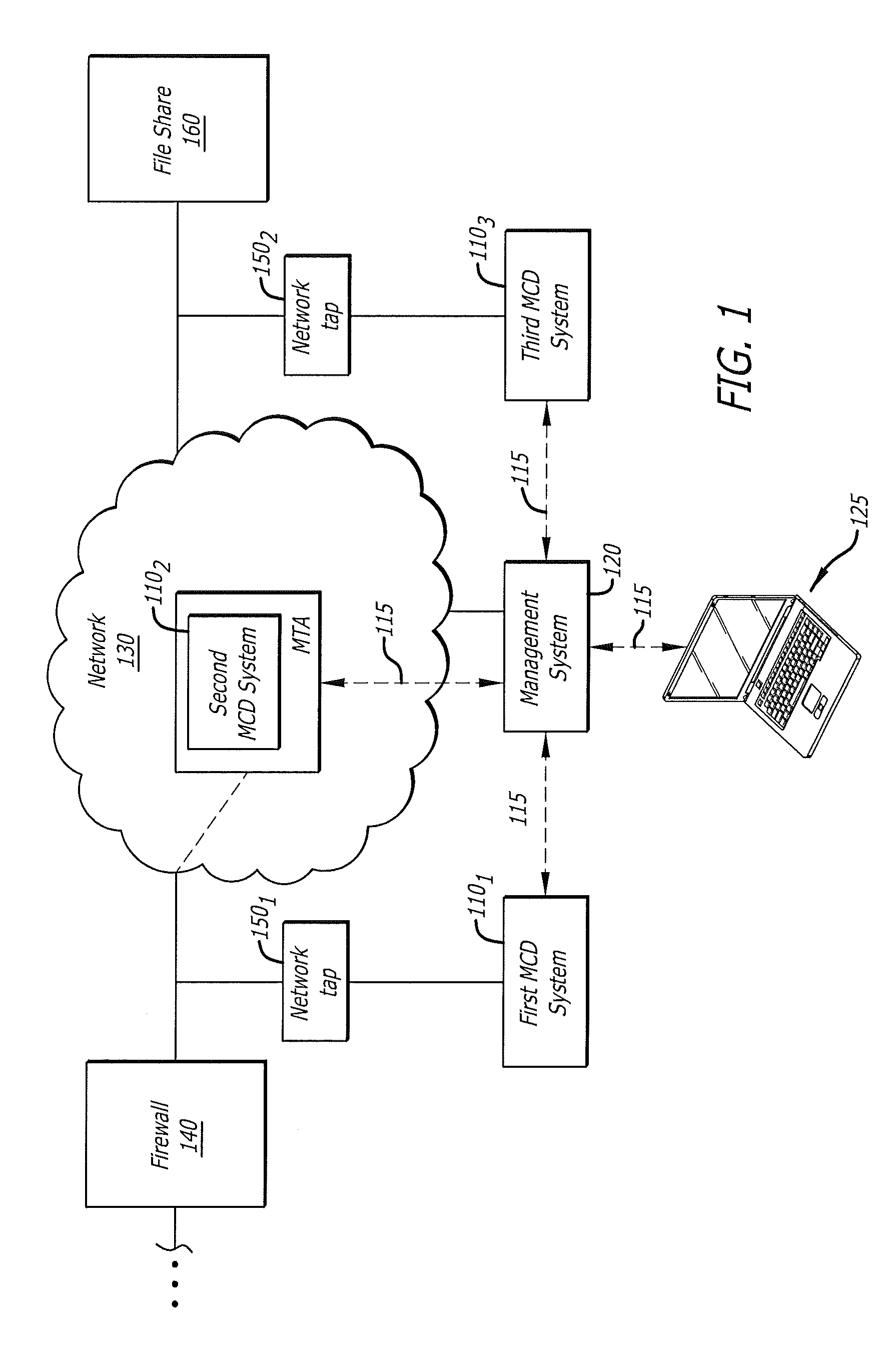
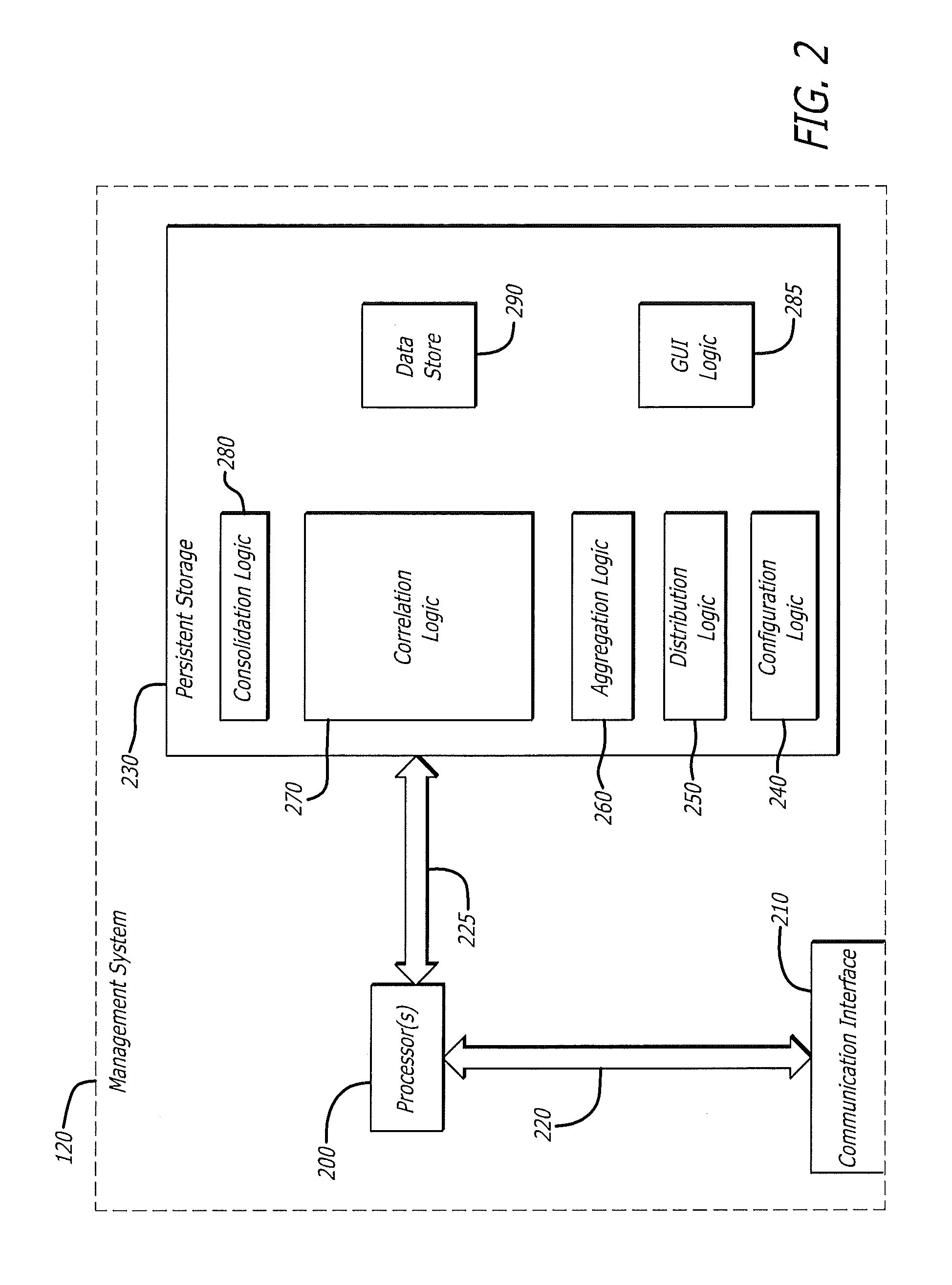
Correlation and consolidation of analytic data for holistic view of a malware attack
According to one embodiment, a method for correlating and consolidating analytic data to provide a holistic view of a malware attack. The method comprises receiving analytic data from a plurality of electronic devices. The analytic data from each electronic device of the plurality of electronic devices comprises input attributes and analysis attributes. Thereafter, the analytic data is correlated by determining whether a first analysis attribute provided by a first electronic device of the plurality of electronic devices matches a second analysis attribute provided by a second electronic device of the plurality of electronic devices. In response determining that the first analysis attribute provided by the first electronic device matches the second analysis attribute provided by the second electronic device, the input attributes associated with the first analysis attribute and the second analysis attribute are consolidated for subsequent display.
Owner:FIREEYE SECURITY HLDG US LLC
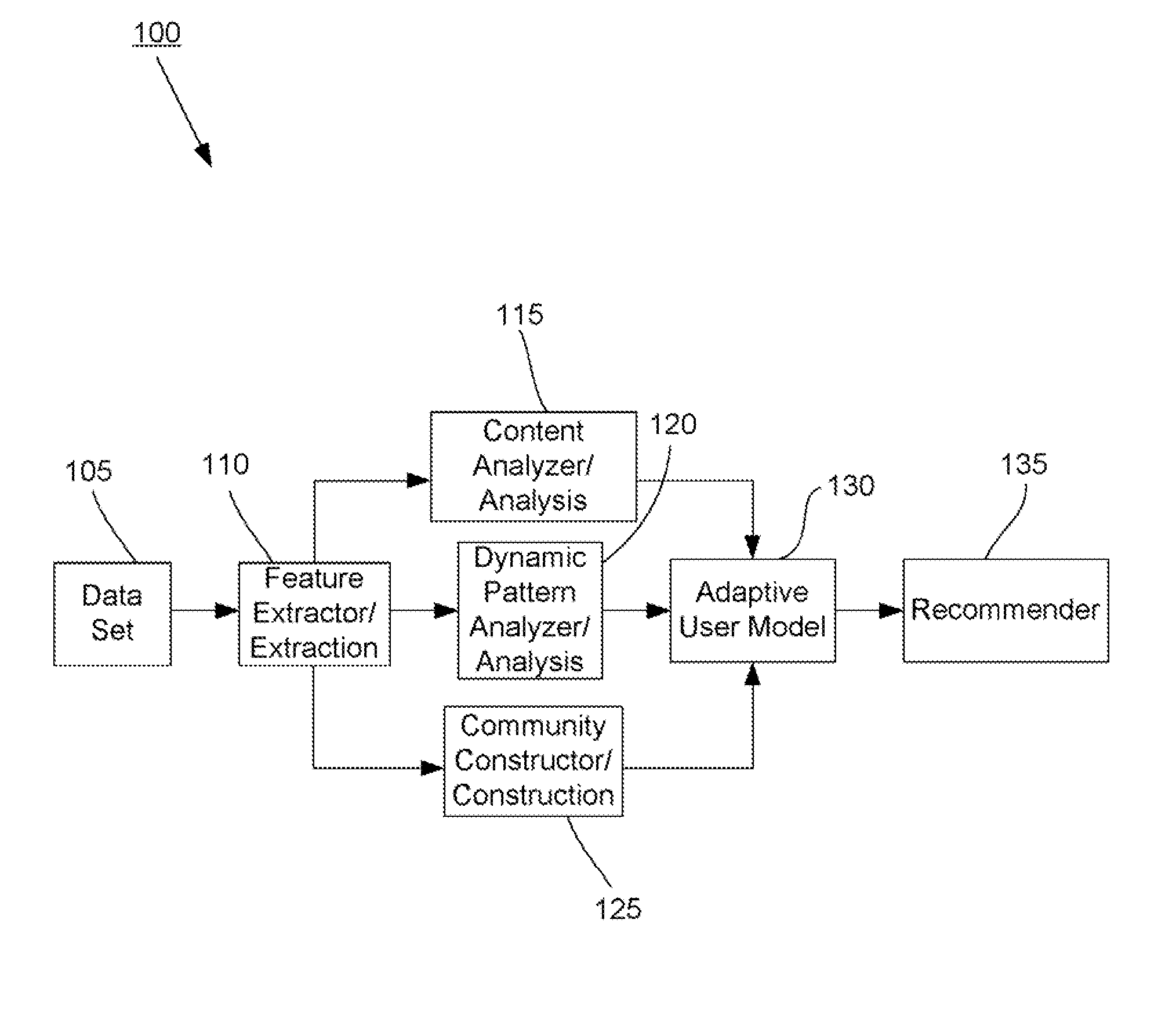
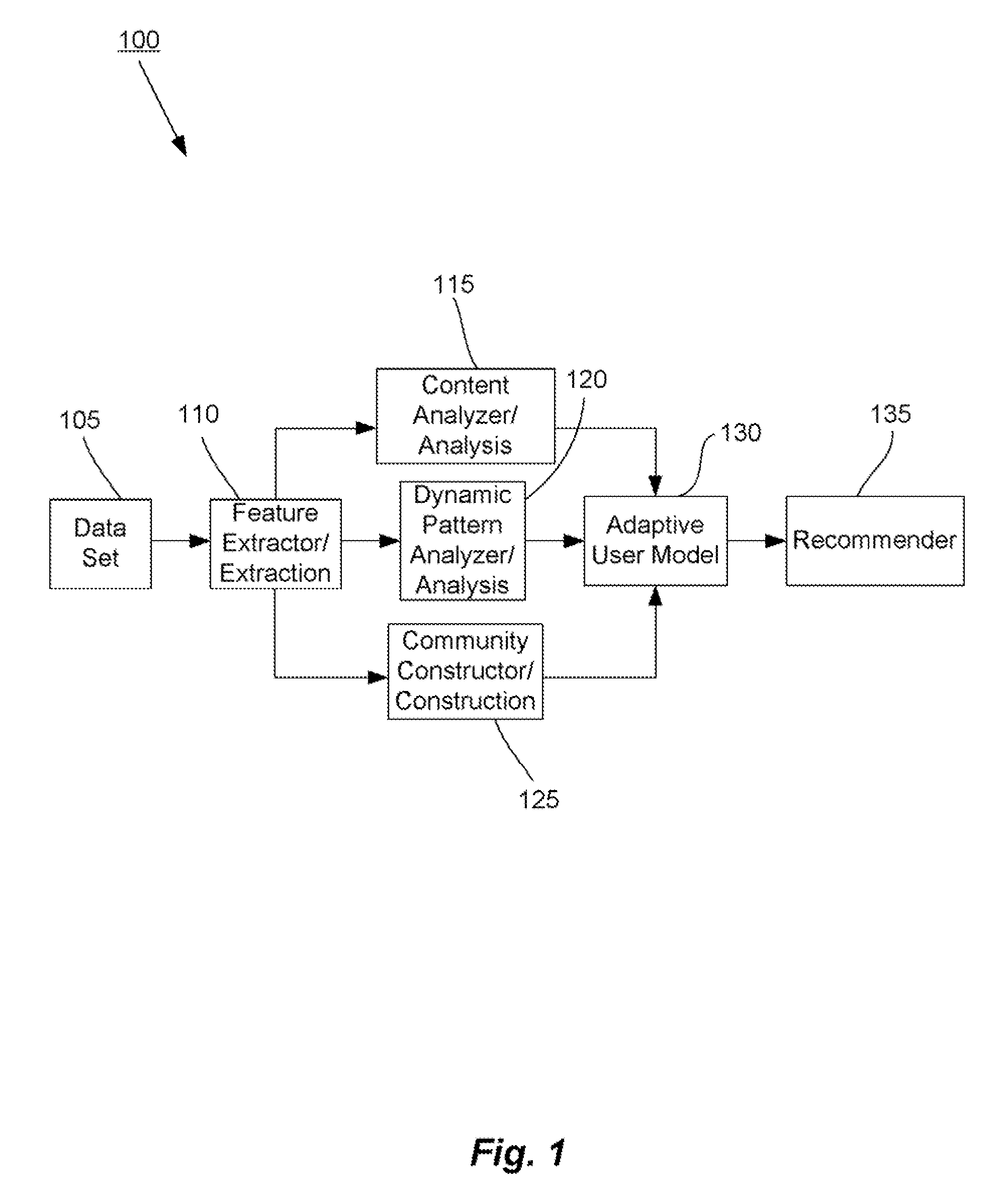
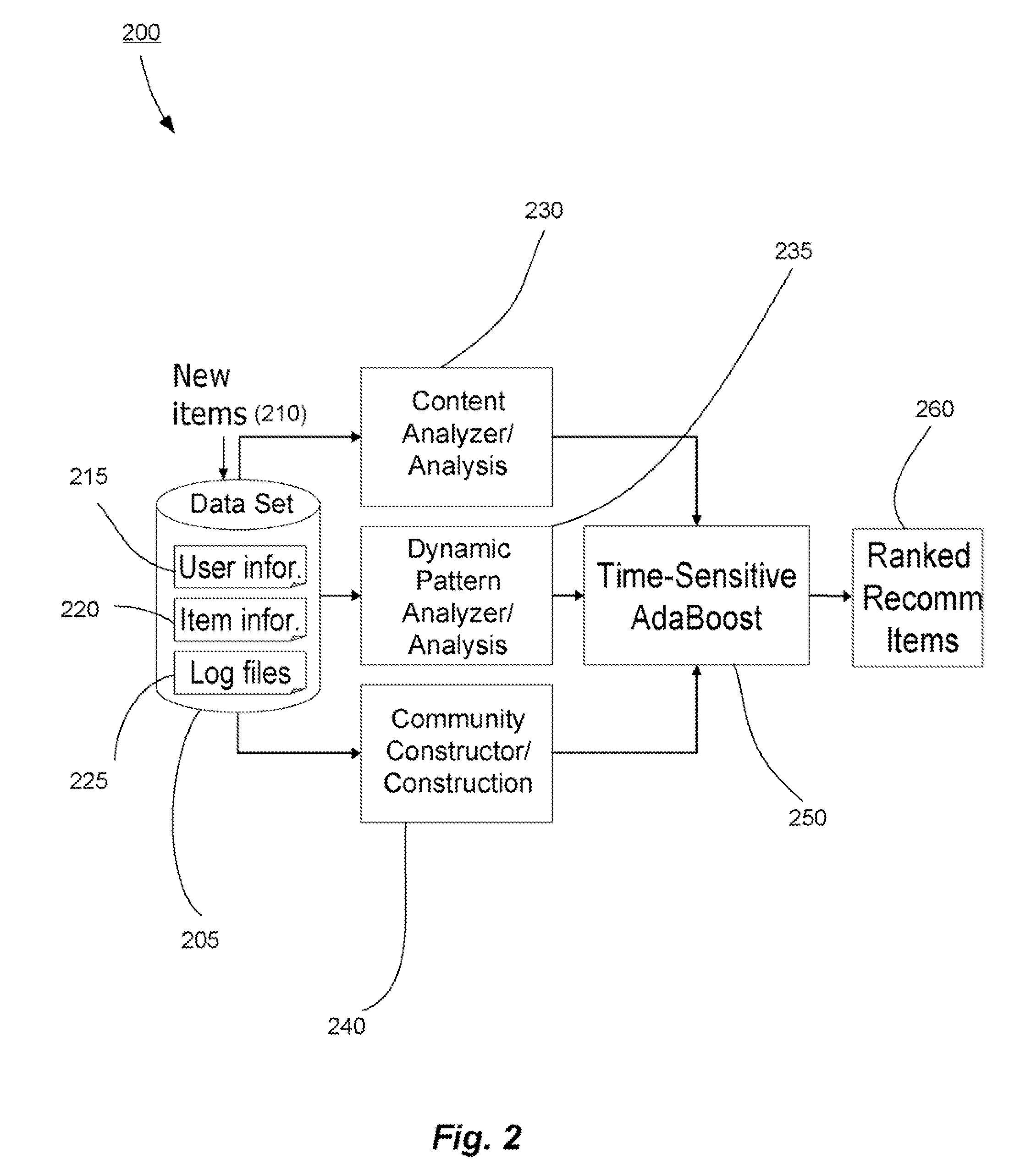
Methods and systems for utilizing content, dynamic patterns, and/or relational information for data analysis
InactiveUS20070118498A1Avoid problemsCommerceSpecial data processing applicationsTemporal changeAnalysis data
The present invention is directed generally to providing systems and methods for data analysis. More specifically, embodiments may provide system(s) and method(s) including dynamic user modeling techniques to capture the relational and dynamic patterns of information content and / or users' or entities' interests. Various embodiments may include system(s) and method(s) that are based on, for example, the past history of content semantics, temporal changes, and / or user community relationship. Various embodiments may include modeling and / or analysis of the dynamic nature of an item of interest's value to a user(s) / entity(ies) over time. The dynamic factors may be consider in any manner, such as, individually or combined, sequentially or simultaneously, etc. Further, some embodiments may include, for example, system(s) and method(s) relating to analyzing data to capture user / entity interests and / or characteristics, consider content semantics and evolutionary information, and / or using community relationships of users / entities to thereby analyze information and provide dynamic conclusion(s) (e.g., recommendation(s)).
Owner:NEC CORP
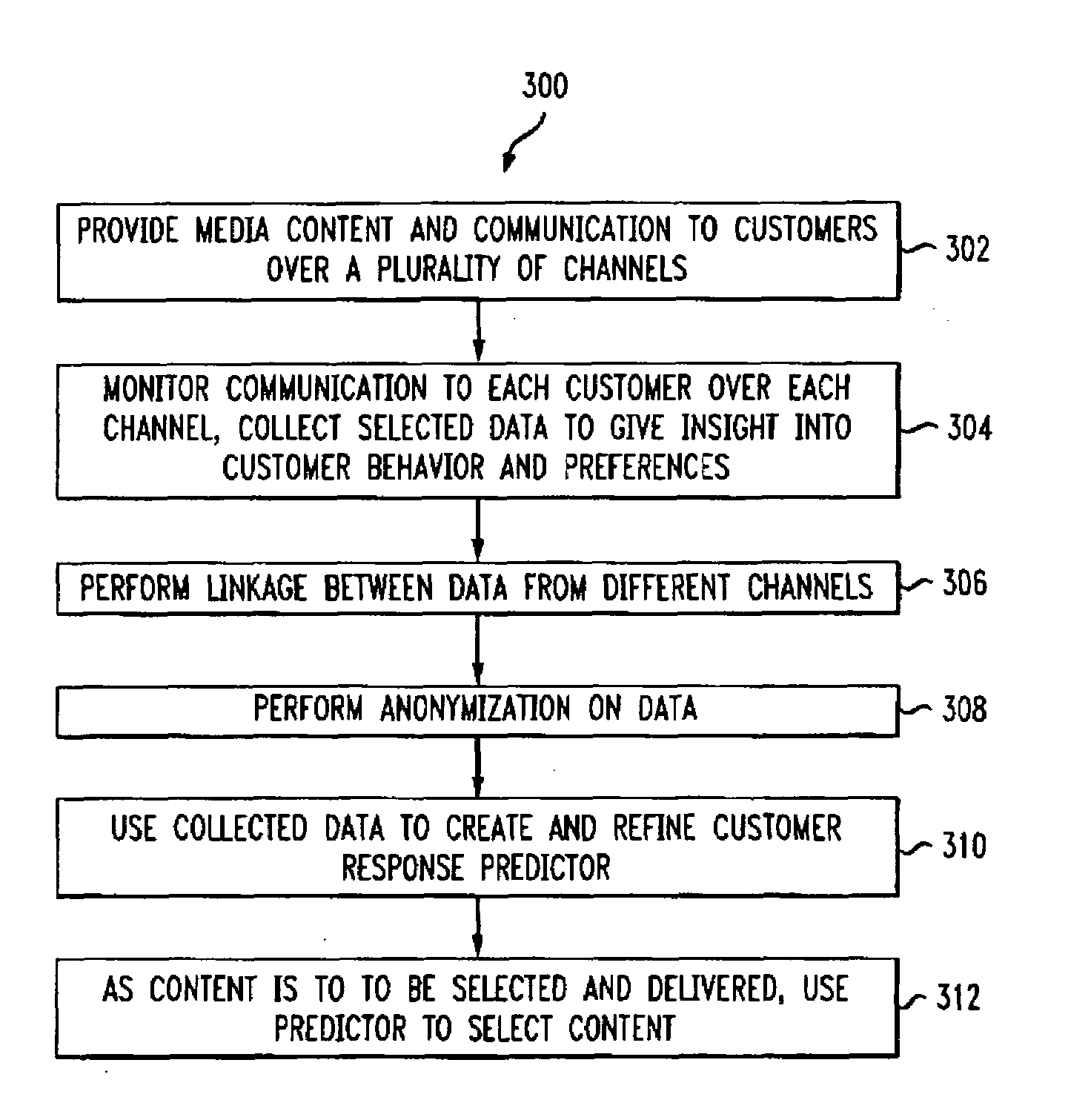
Methods and Apparatus for Individualized Content Delivery
InactiveUS20100057560A1Great and less permanencySelective content distributionMarketingPersonalizationAnalysis data
Owner:AT&T INTPROP I L P
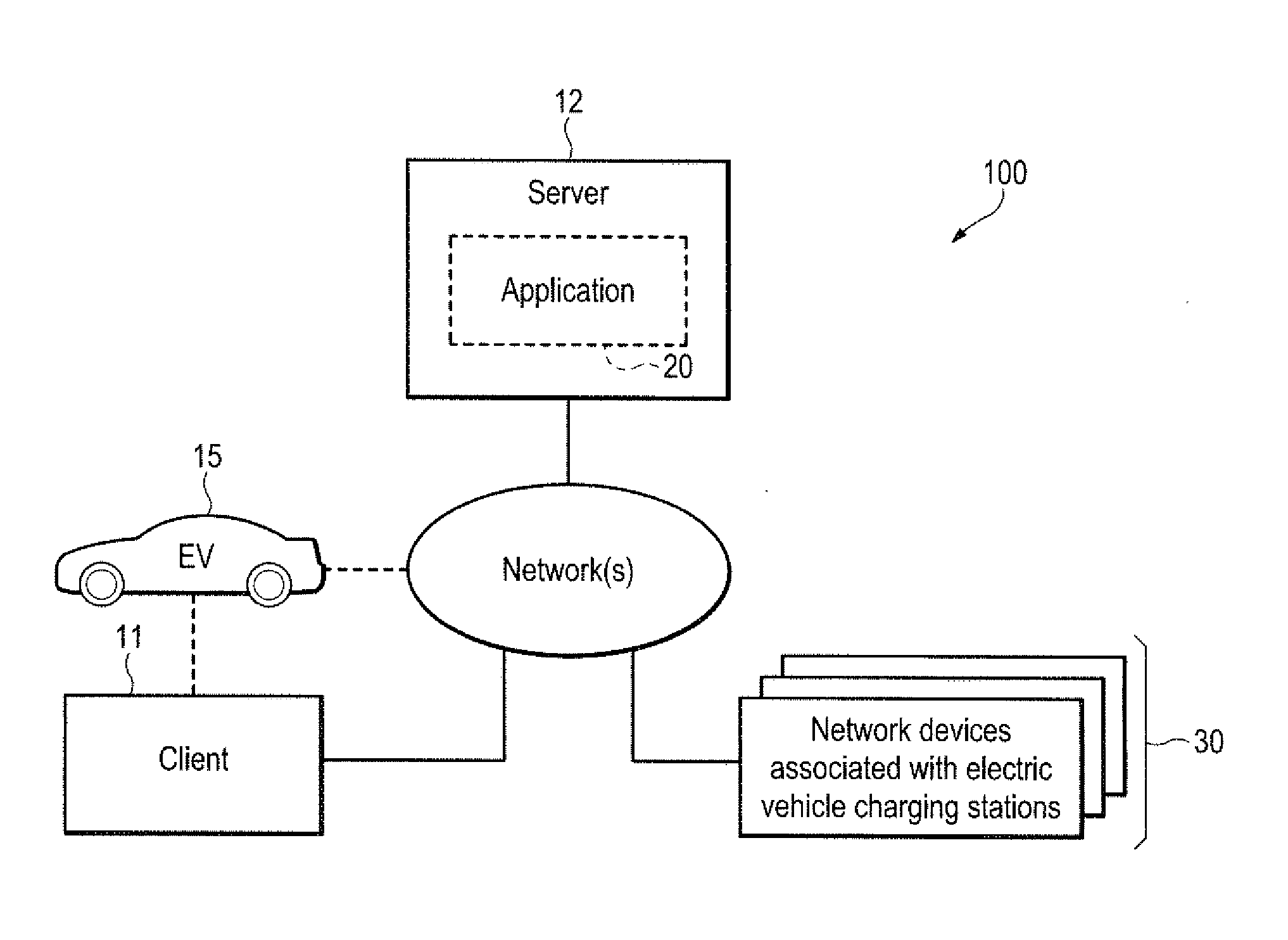
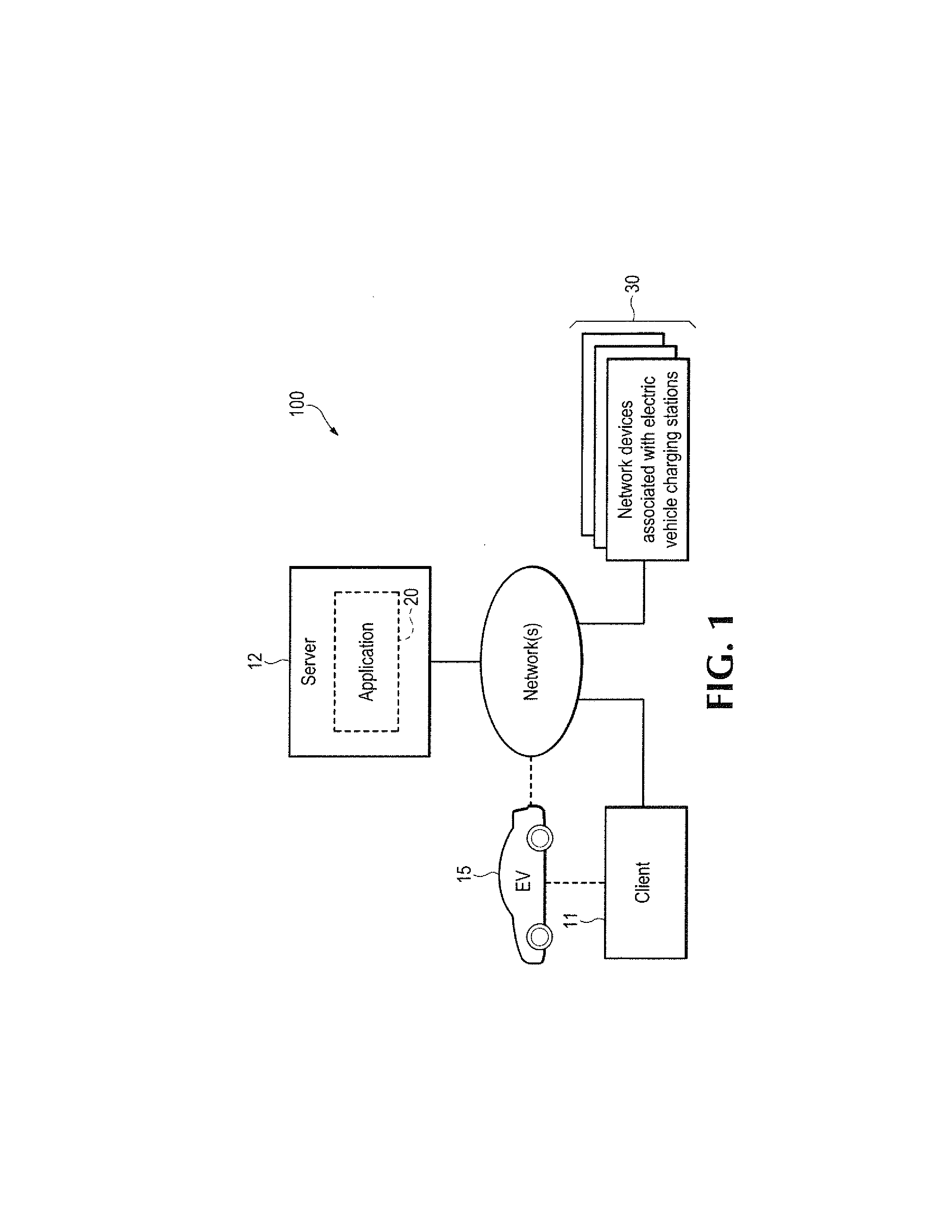
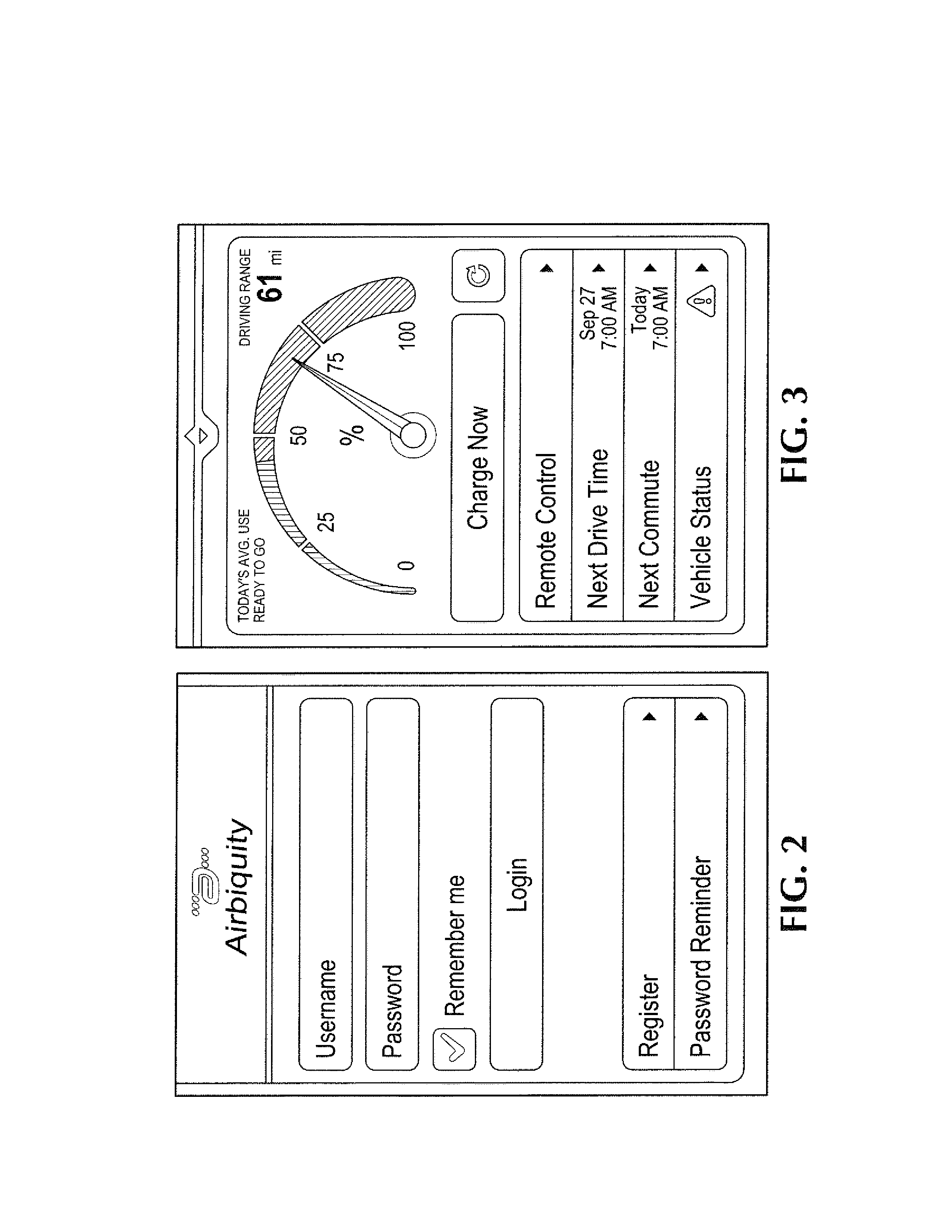
Electric vehicle charging network services
ActiveUS20130179057A1Reduce anxietySufficient rangeAnalogue computers for vehiclesAnalogue computers for trafficAnalysis dataElectronic communication
To provide remote services, including dynamic, interactive assistance to electric vehicle (EV) users, a central server is arranged for electronic communications with EVs (15) and with client devices (11). The server also communicates with at least one EV charging station network, which in turn communicate with individual charging stations (30). Remote services may include trip planning, locating charging stations, checking availability and suitability of charging stations, making reservations at charging stations, and updating plans en route. The server collects data from the EV and analyzes the data to determine various statistics. The system advises a user on readiness of the EV to complete a proposed trip before recharging the EV batteries. Client devices may include smart phones, computers, or a head unit in the EV. Application software programs are executable on the client devices to provide user interfaces for accessing the remote services and for communicating with the central server.
Owner:AIRBIQUITY INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com