Patents
Literature
835results about How to "Prevent unauthorized access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Undetectable firewall
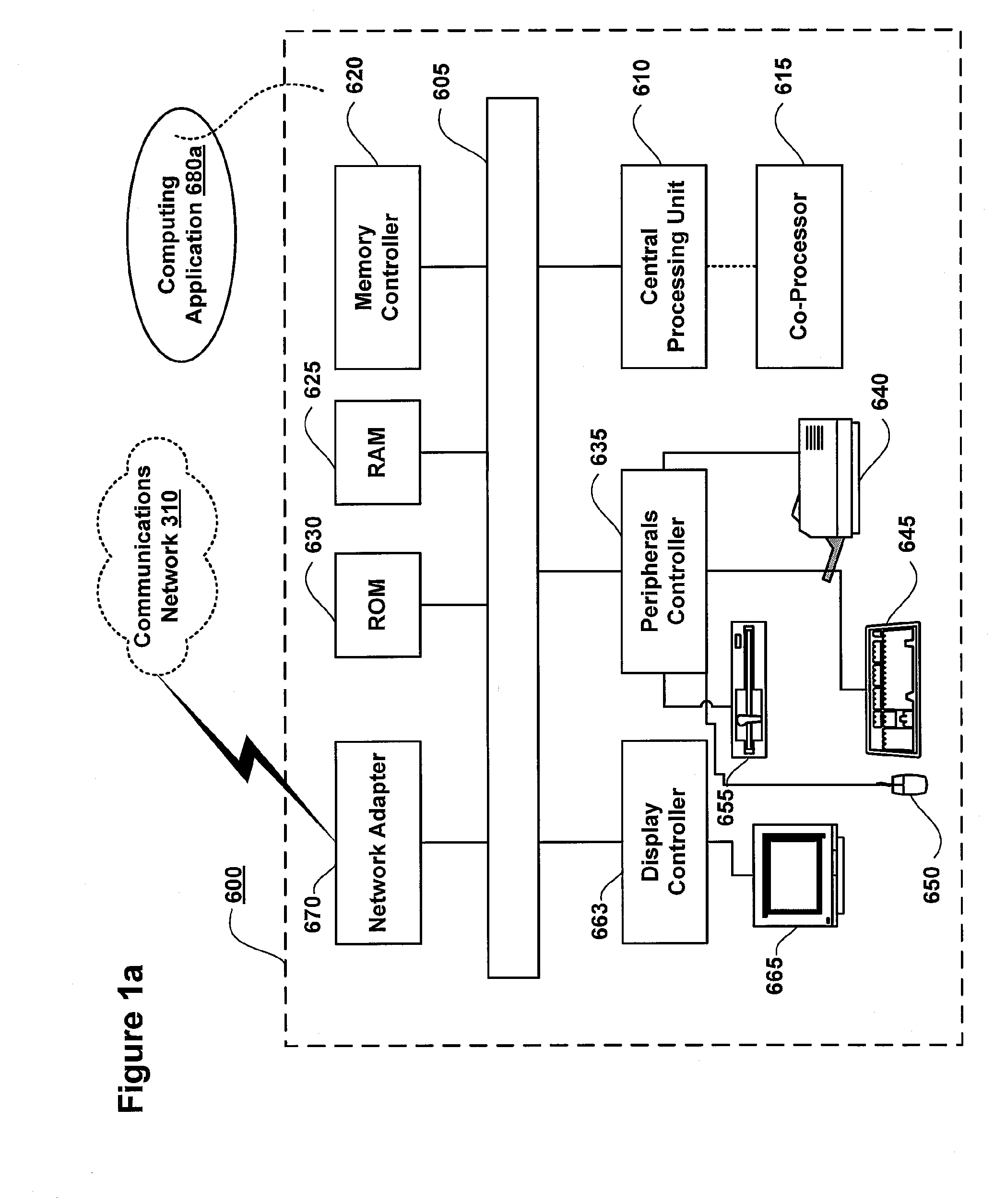
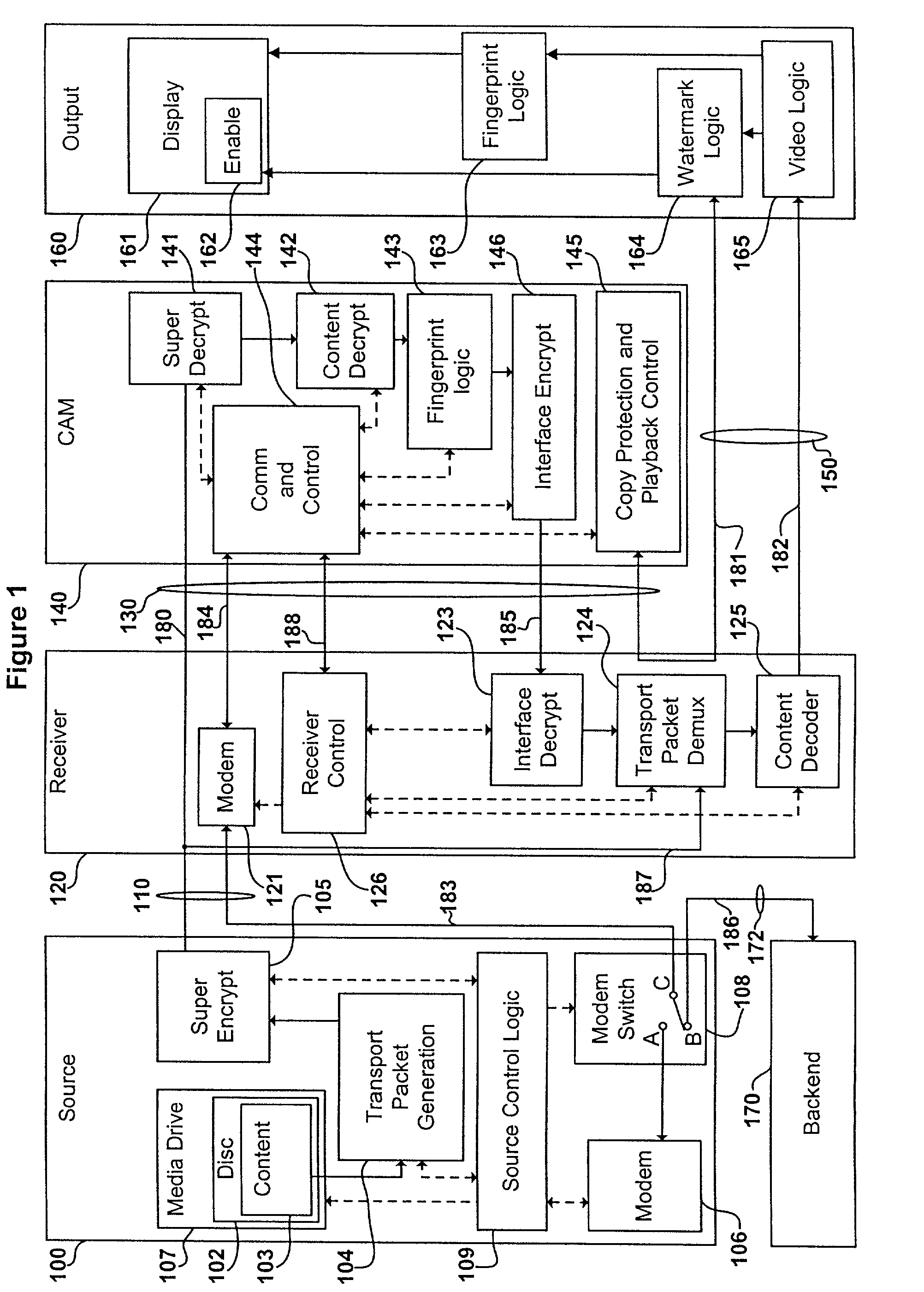
ActiveUS7100201B2Prevent unauthorized accessMemory loss protectionDigital data processing detailsAnalysis dataNetwork packet
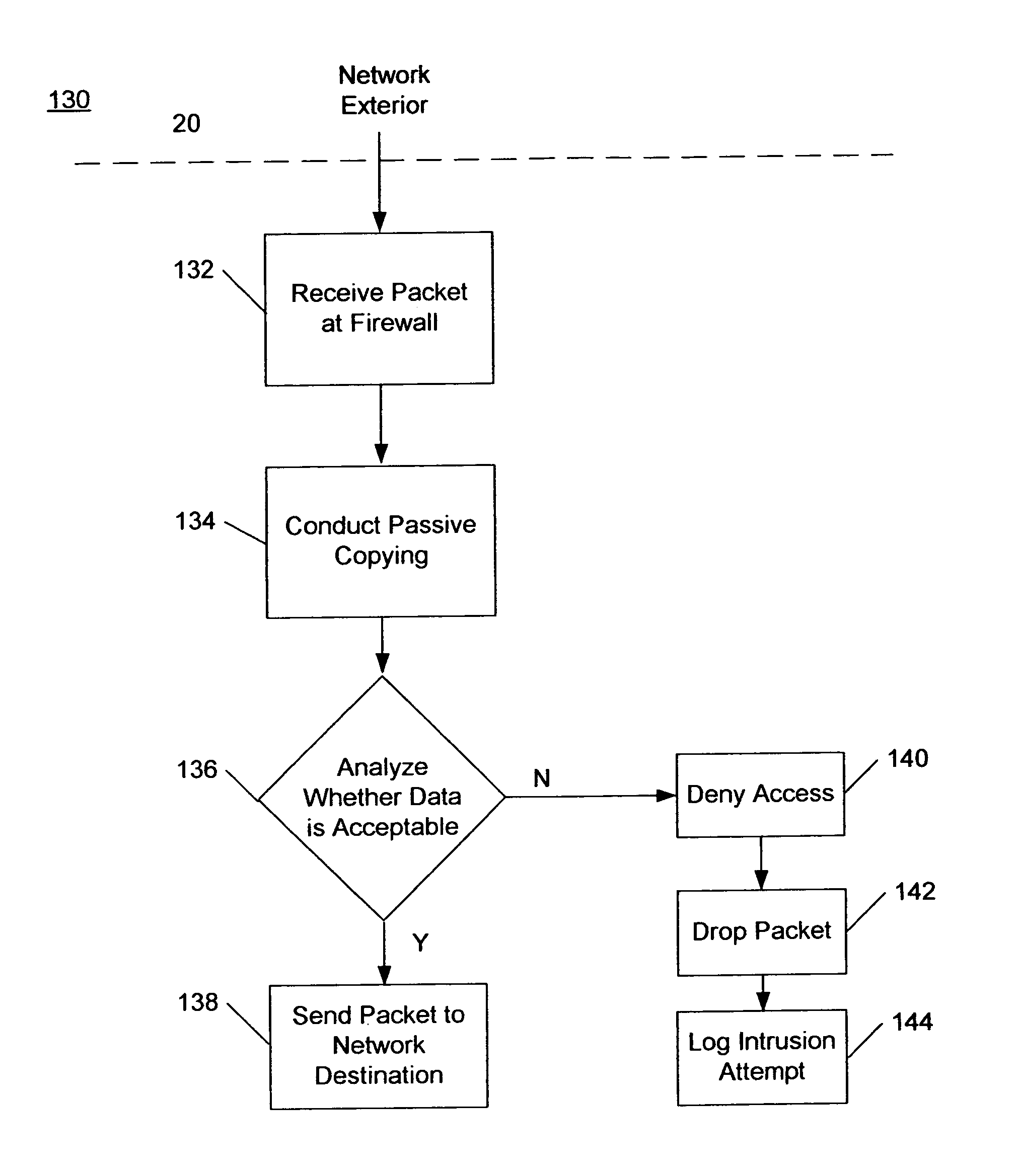
An undetectable firewall for network protection has been developed. The invention includes a method of preventing unauthorized access to a computer system. The firewall receives a data packet and copies its contents exactly. Next, the firewall analyzes the data packet and determines if it is authorized to access the network. If the packet is authorized to access the network, it is sent on to its destination. If the packet is unauthorized to access the network, it is dropped by the firewall.
Owner:ARXCEO CORP
Providing A Generic Gateway For Accessing Protected Resources
InactiveUS20080178278A1Facilitates secure exposurePrevent unauthorized accessComputer security arrangementsMultiple digital computer combinationsWeb applicationWeb service
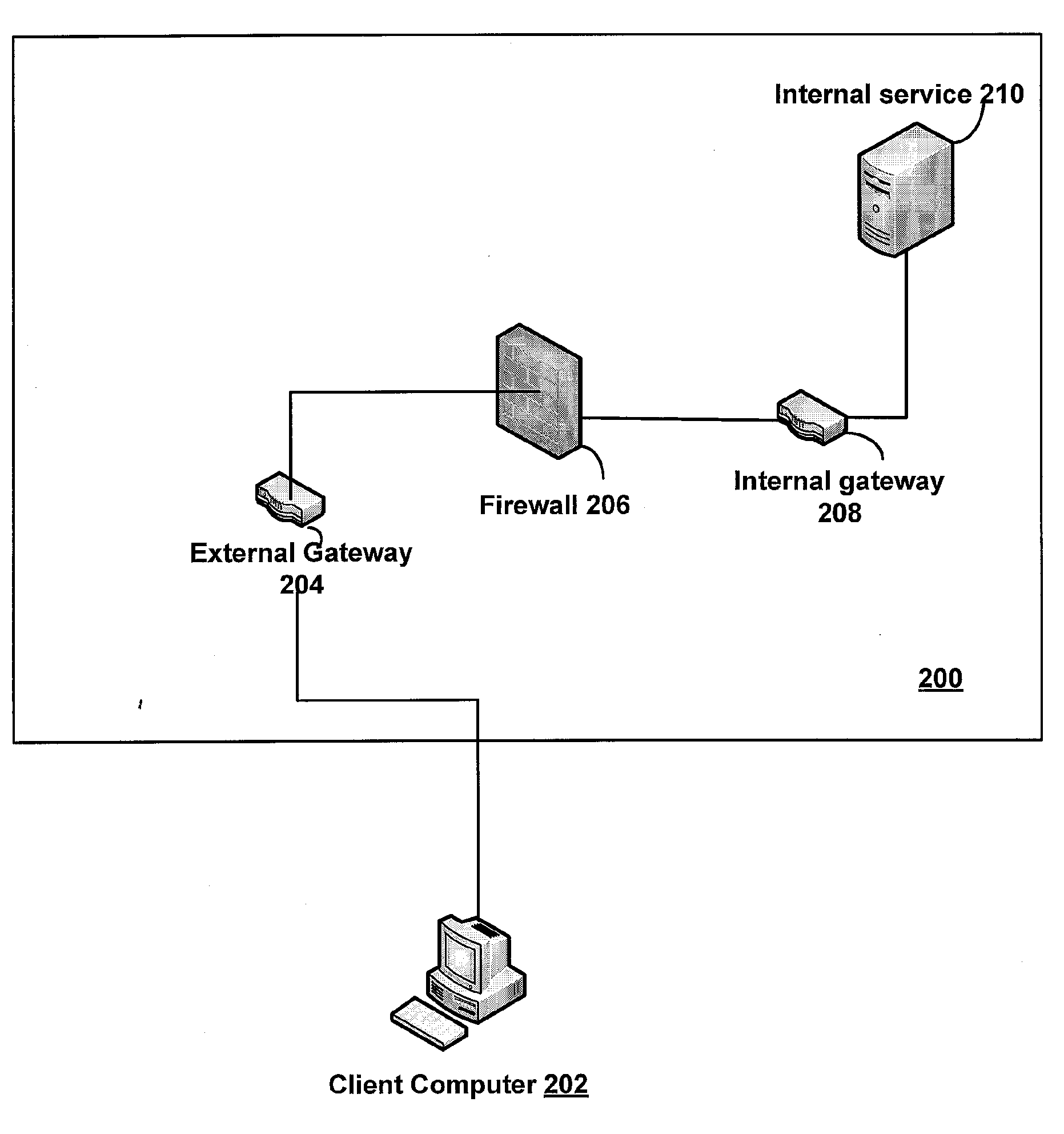
An internal gateway establishes persistent connections to an external gateway through permitted ports and protocols of a firewall. Software on the external gateway and the internal gateway collaborate in order to make available internal, firewall-protected resources to external clients securely and without having to modify network or firewall configurations. Any computing resource such as a web service, web application, or any other network addressable resource residing behind a firewall can be securely exposed in a generic fashion to clients on the external network. No special software is required by clients.
Owner:BITKOO
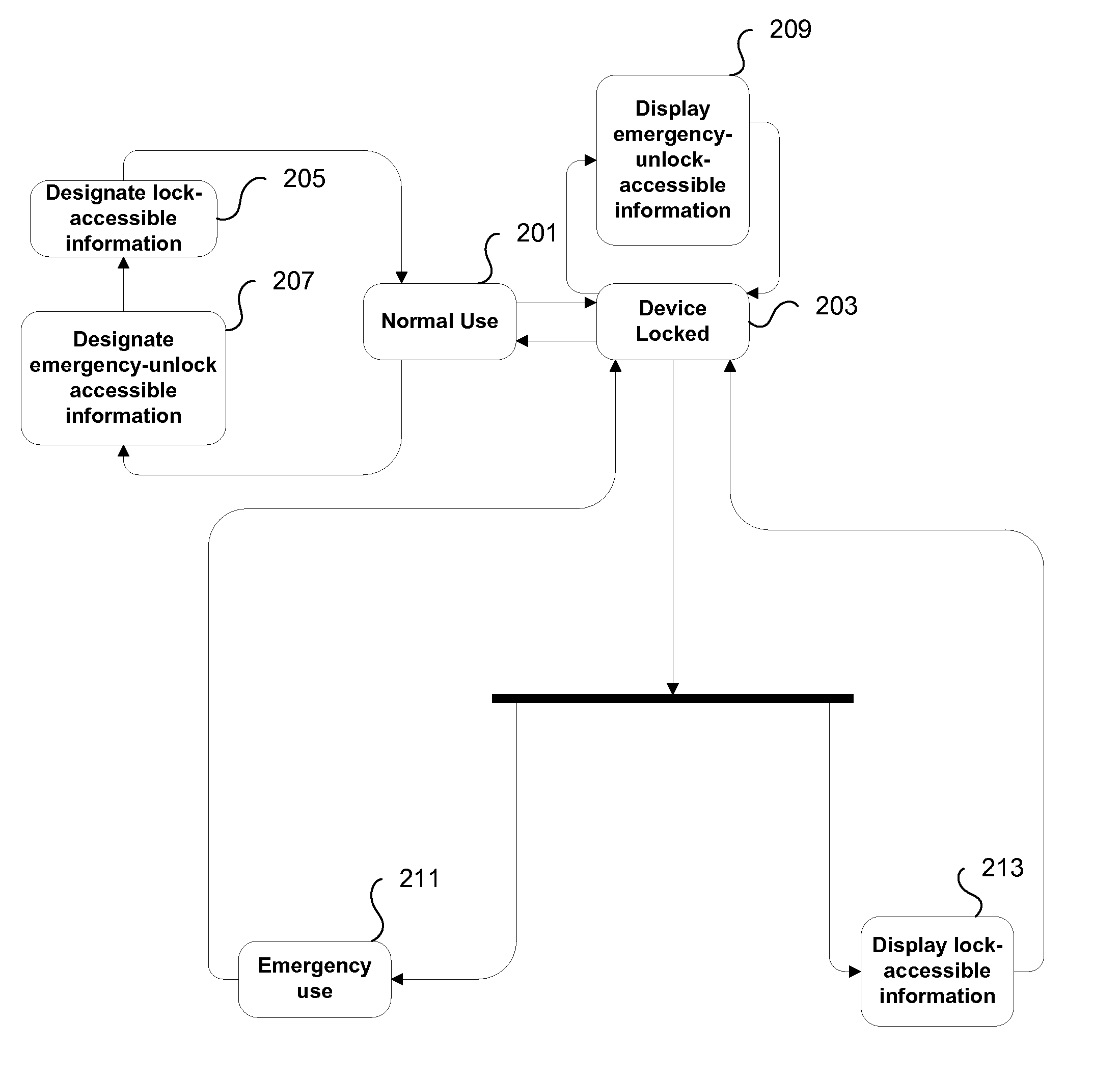
Emergency Information Access on Portable Electronic Devices
ActiveUS20090205041A1Prevent unauthorized accessEmergency connection handlingDigital data processing detailsPasswordInformation access
Improved techniques for facilitating emergency access to one or more contacts stored on a portable electronic device are disclosed. One or more contacts on the portable electronic device are designated as emergency contacts. While the portable electronic device is password-locked, a request to display the one or more emergency contacts on the password-locked portable electronic device is received. Without requiring a password, the one or more emergency contacts are displayed on the portable electronic device.
Owner:APPLE INC
Integrated computer security management system and method
InactiveUS7331061B1Centralized controlIncrease speedMemory loss protectionError detection/correctionSafety management systemsSecurity management
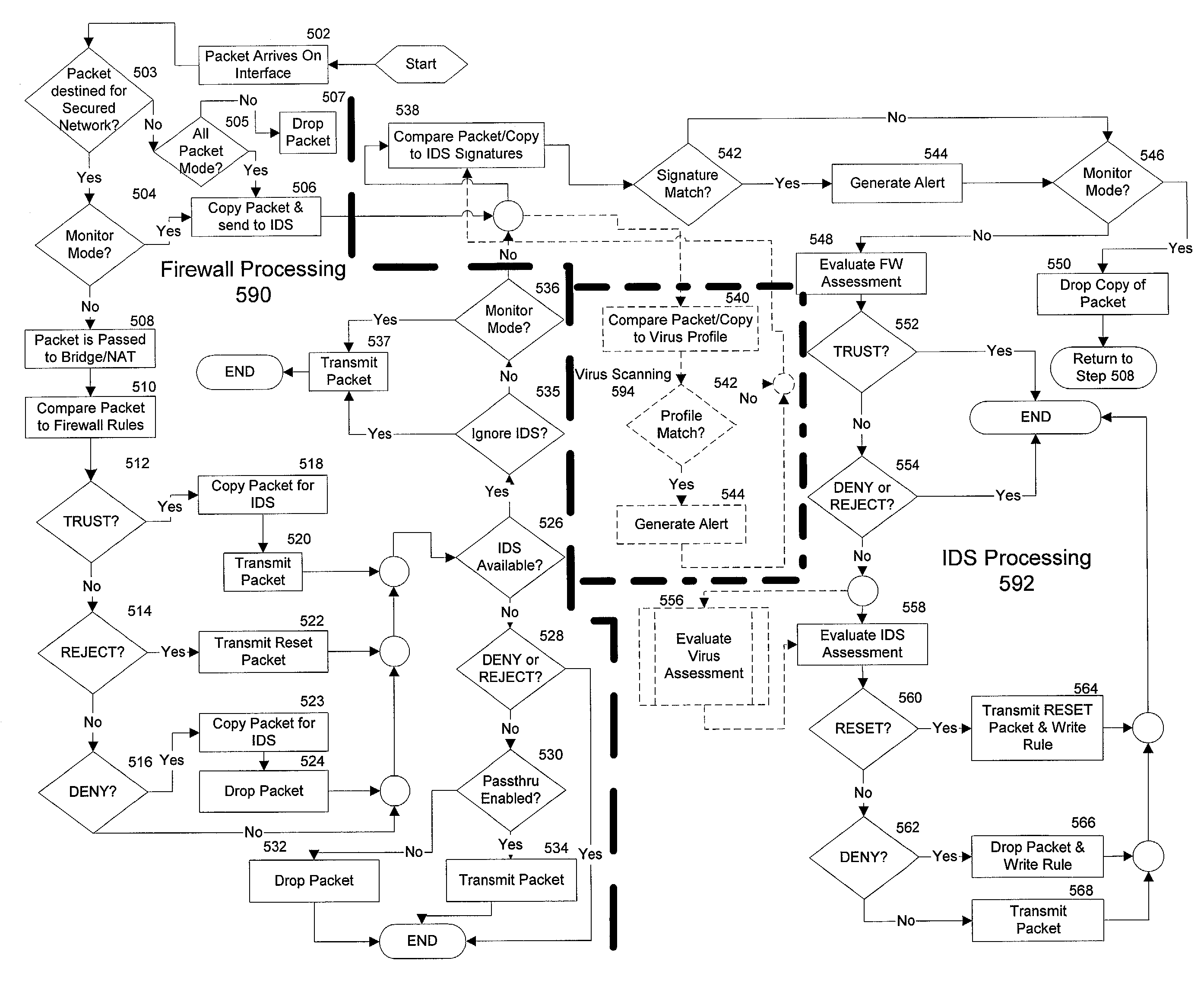
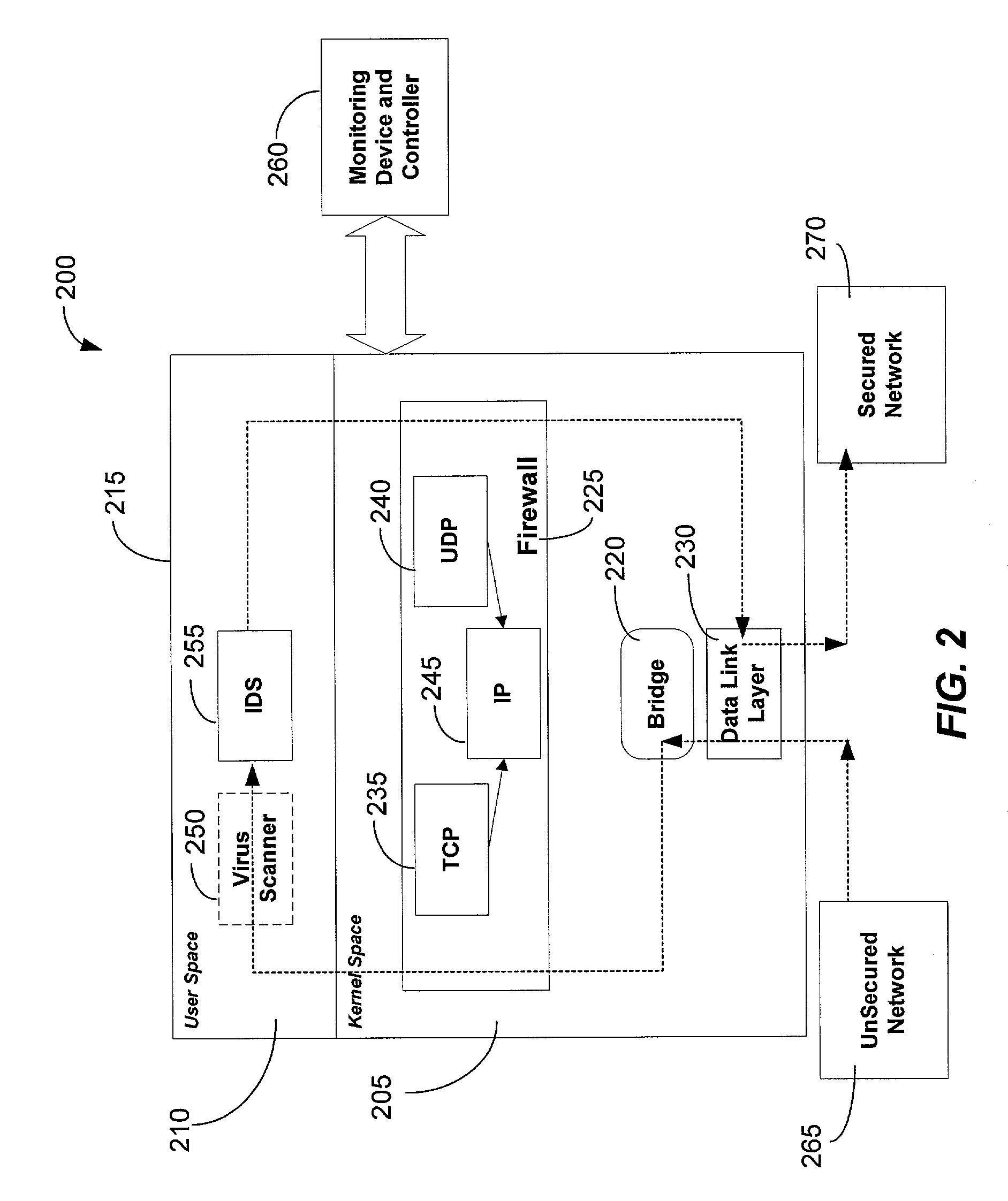
The present invention is generally directed to a computer security management system that integrates a firewall with an intrusion detection system (IDS). In other words, the firewall and IDS of the present invention can be designed to communicate process or status information and packets with one another. The present invention can facilitate centralized control of the firewall and the IDS and can increase the speed at which packets are passed between a secured computer network and an external network. Increased packet processing speed can be achieved in several ways. For example, the firewall and IDS can process packets in series, in parallel, and sometimes singularly when one of the components is not permitted to process a packet. Alternatively, singular processing can also be performed when one component is permitted to pass a packet to the secured computer network without checking with the other component.
Owner:SECUREWORKS
Security System And Method For Computer Operating Systems
InactiveUS20080104348A1Prevent unauthorized accessDigital data processing detailsUser identity/authority verificationOperational systemData access
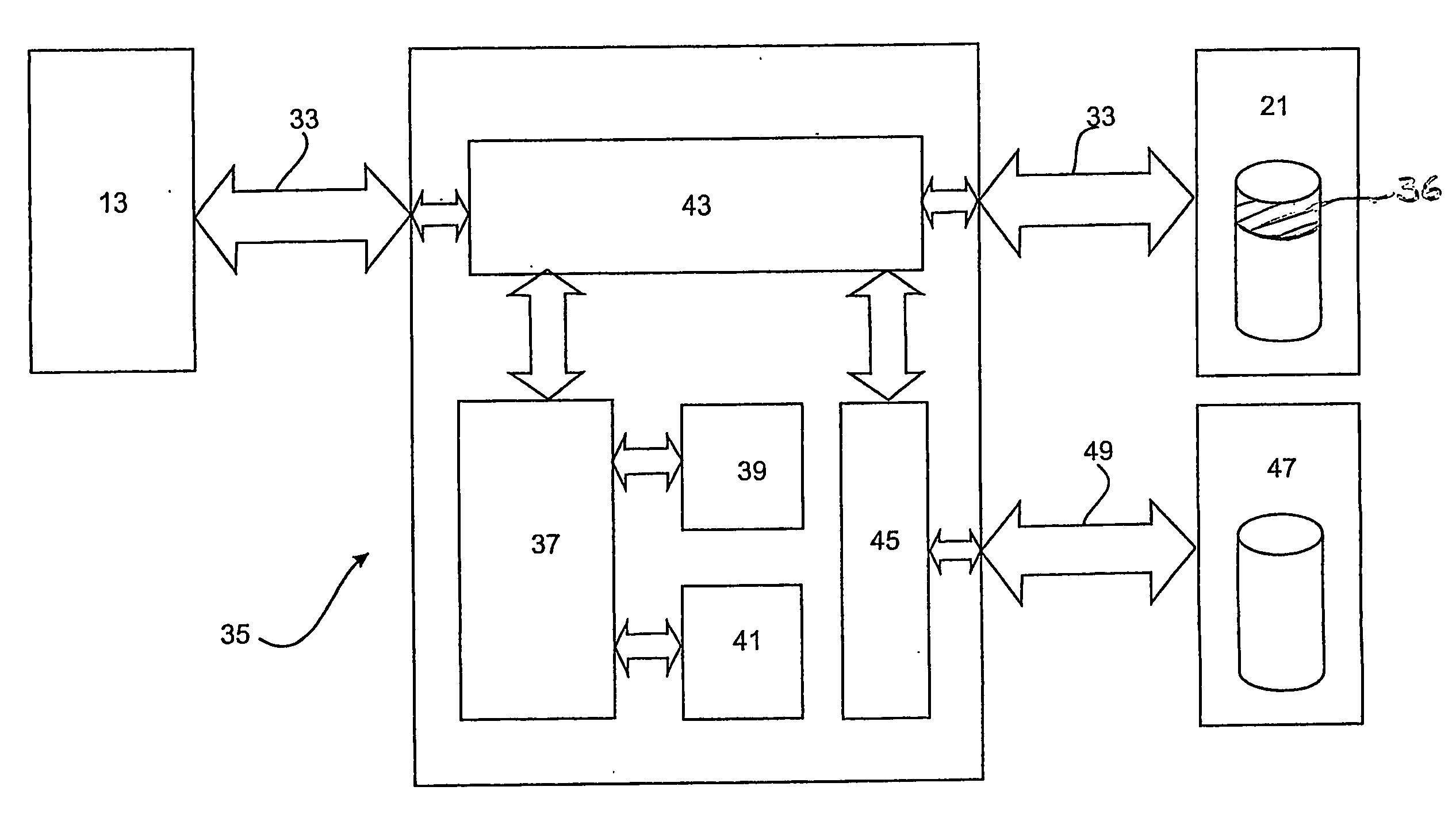
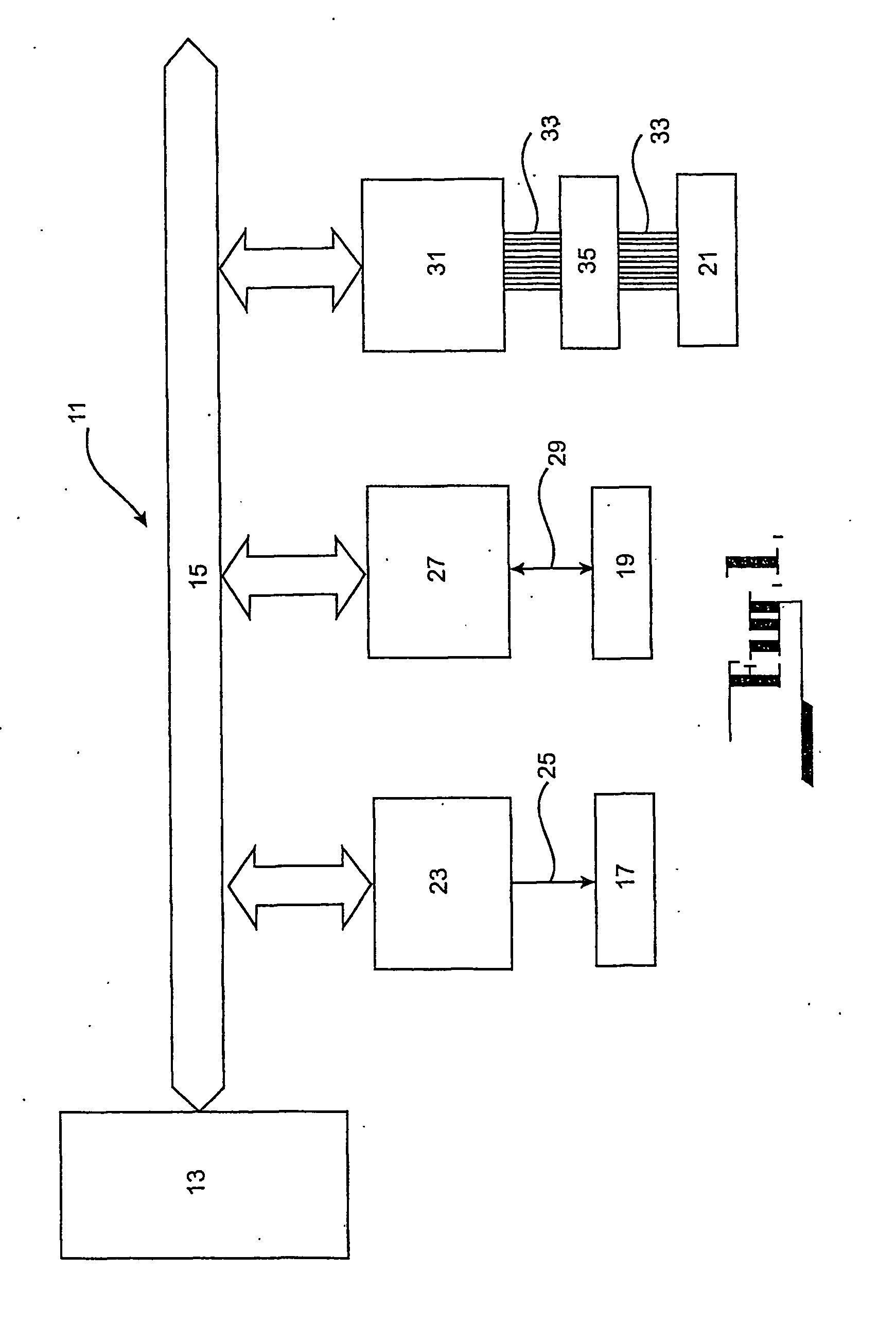
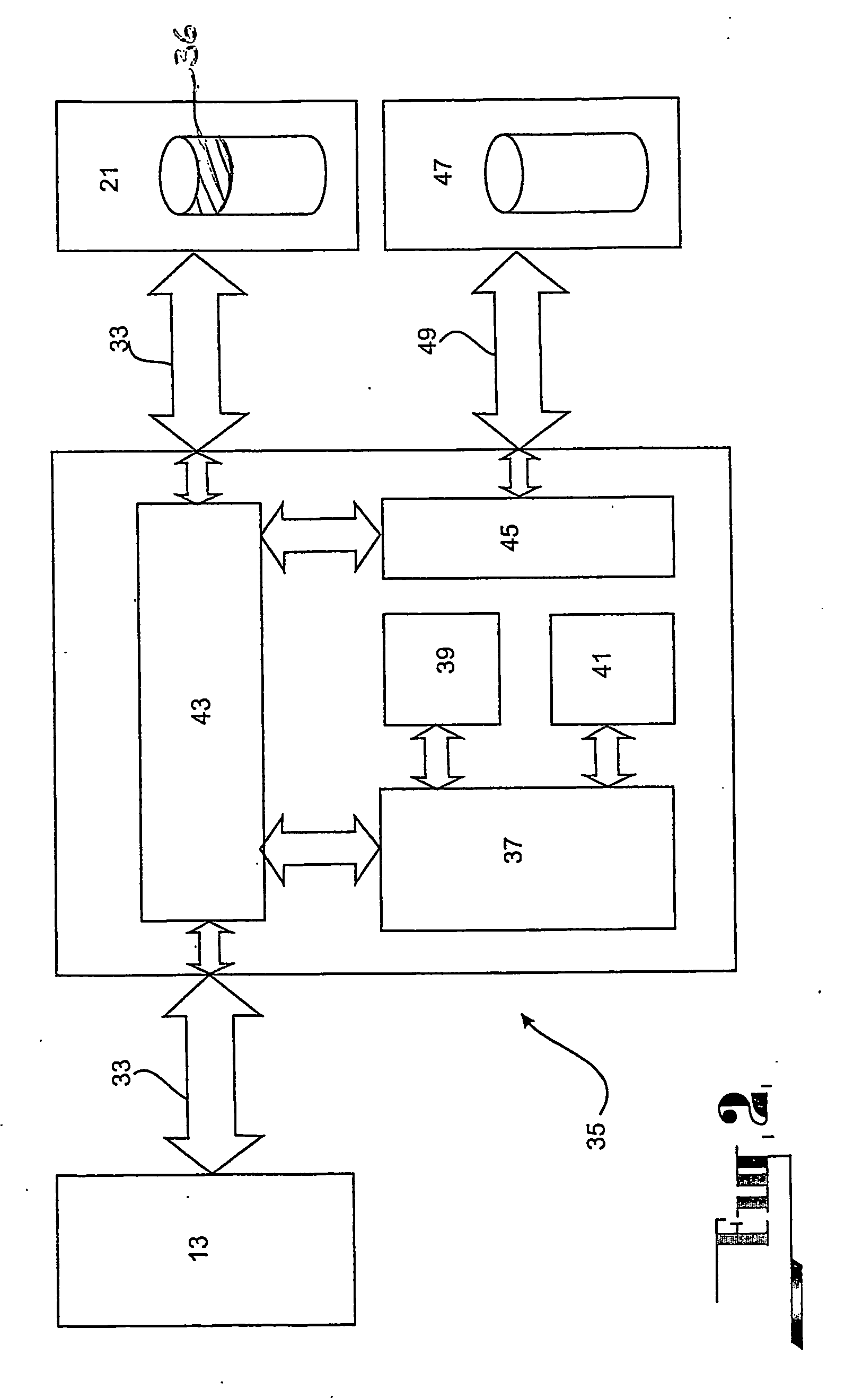
A security system for a computer operating system comprising a processor (37) that is independent of the host CPU (13) for controlling access between the host CPU (13) and a security partition formed in the storage device (21) for storing the operating system. A program memory (41) that is independent of the computer memory and the storage device (21) unalterably stores and provides computer programs for operating the processor (37) in a manner so as to control access to the security partition in the storage device (21). All data access by the host CPU (13) to the data storage device (21) is blocked before initialisation of the security system and is intercepted immediately after the initialisation under the control of the processor (37). The processor (37) effects independent control of the host CPU (13) and configuration of the computer (11) to prevent unauthorised access to the security partition on the storage device (21) during the interception phase. All users of the computer (11) are authenticated with a prescribed profile of access to the operating system files in the security partition on the storage device (21) and data access to the storage device remains blocked until a user of the computer (11) is correctly authenticated.
Owner:SECURE SYST LTD
Digital content distribution system and method
InactiveUS7162642B2Prevent unauthorized accessObtaining unauthorized accessDigital data processing detailsUser identity/authority verificationContent distributionDigital content
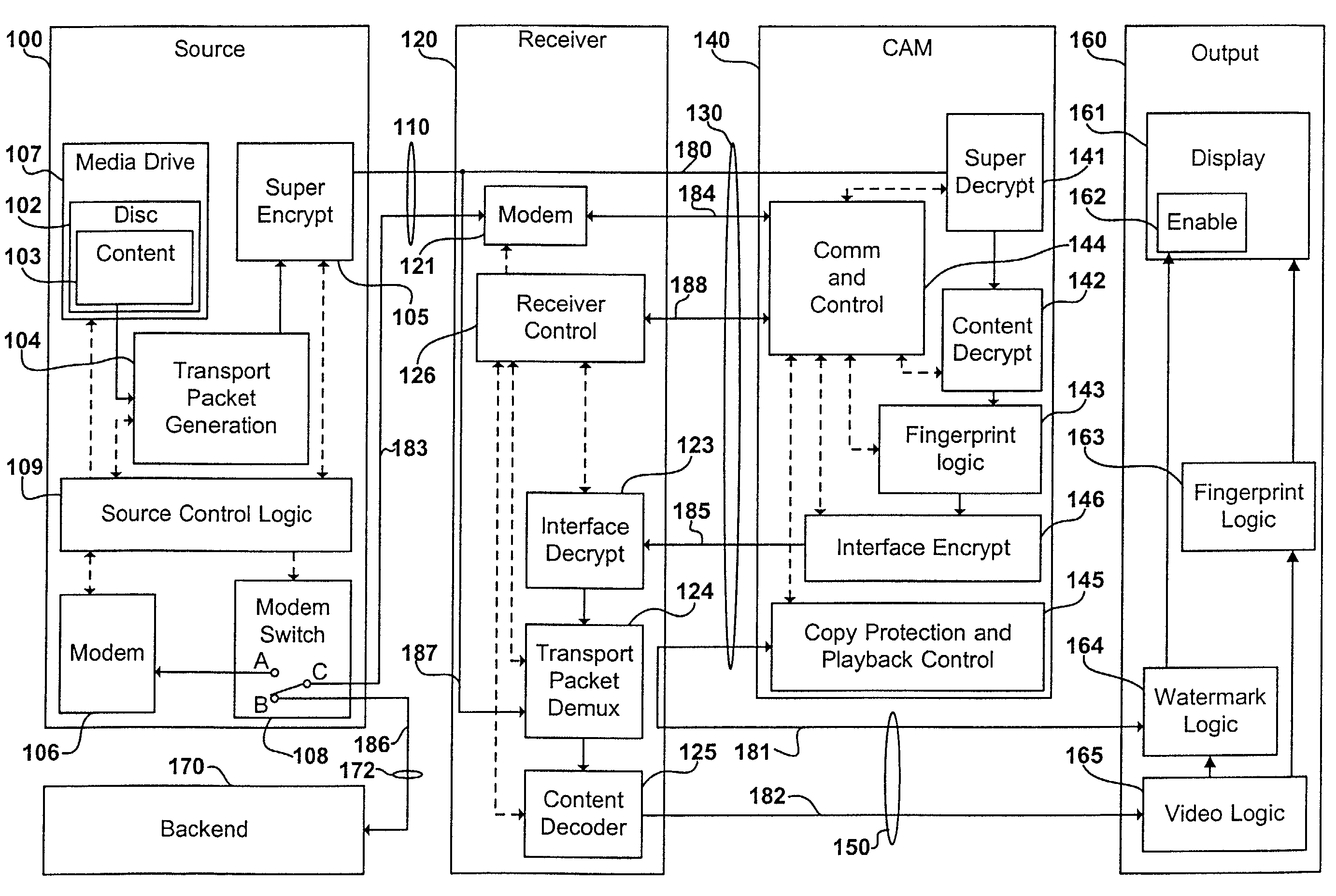
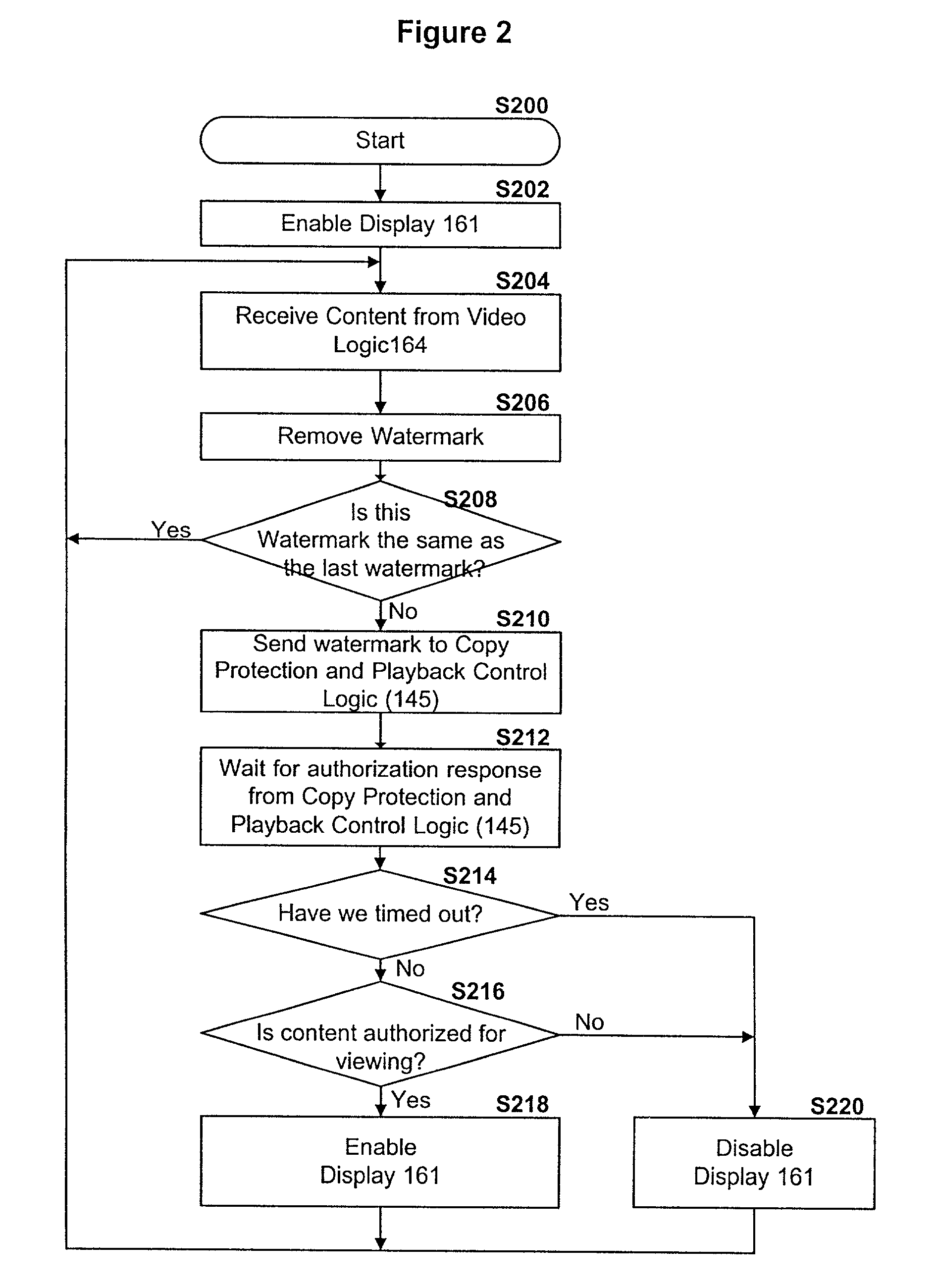
A content distribution system and method which prevents unauthorized access to secured content such as movies and music. The apparatus includes a source, a receiver, an authorized security device such as a conditional access module (CAM) for decrypting authorized content, an output device for outputting content and a backend for managing accounts and system operations. One aspect of this invention provides a mechanism for providing secured content on a medium such as a DVD optical disc. These devices may verify that there is authorization to play the secured content, add watermarks to the secured content, convert the secured content to a displayable form and provide a means for preventing output of the secured content.
Owner:GOOGLE LLC
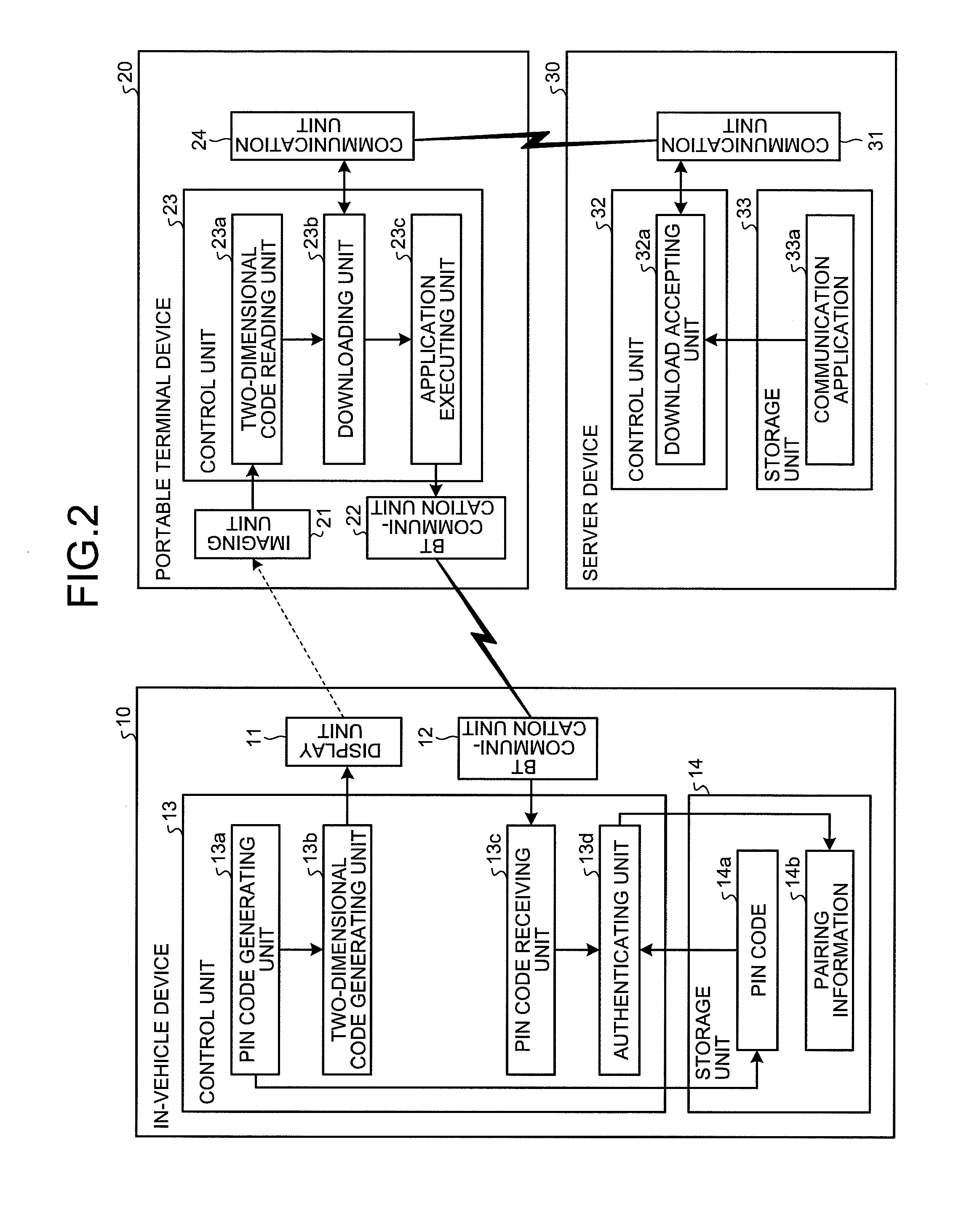
Authentication method, authentication system, in-vehicle device, and authentication apparatus
InactiveUS20100241857A1Prevent unauthorized accessSimple wayKey distribution for secure communicationAnti-theft devicesIn vehicleTerminal equipment
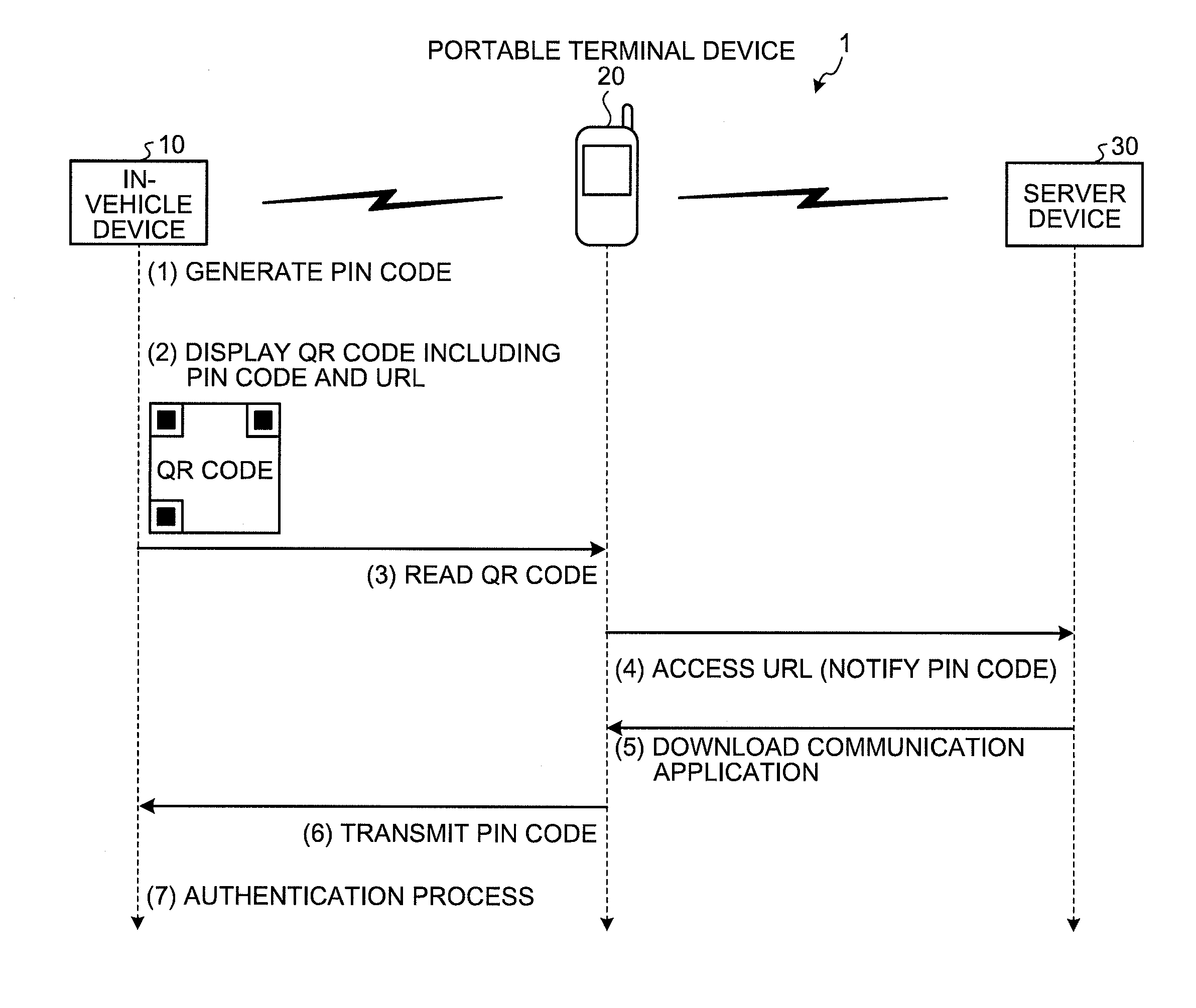
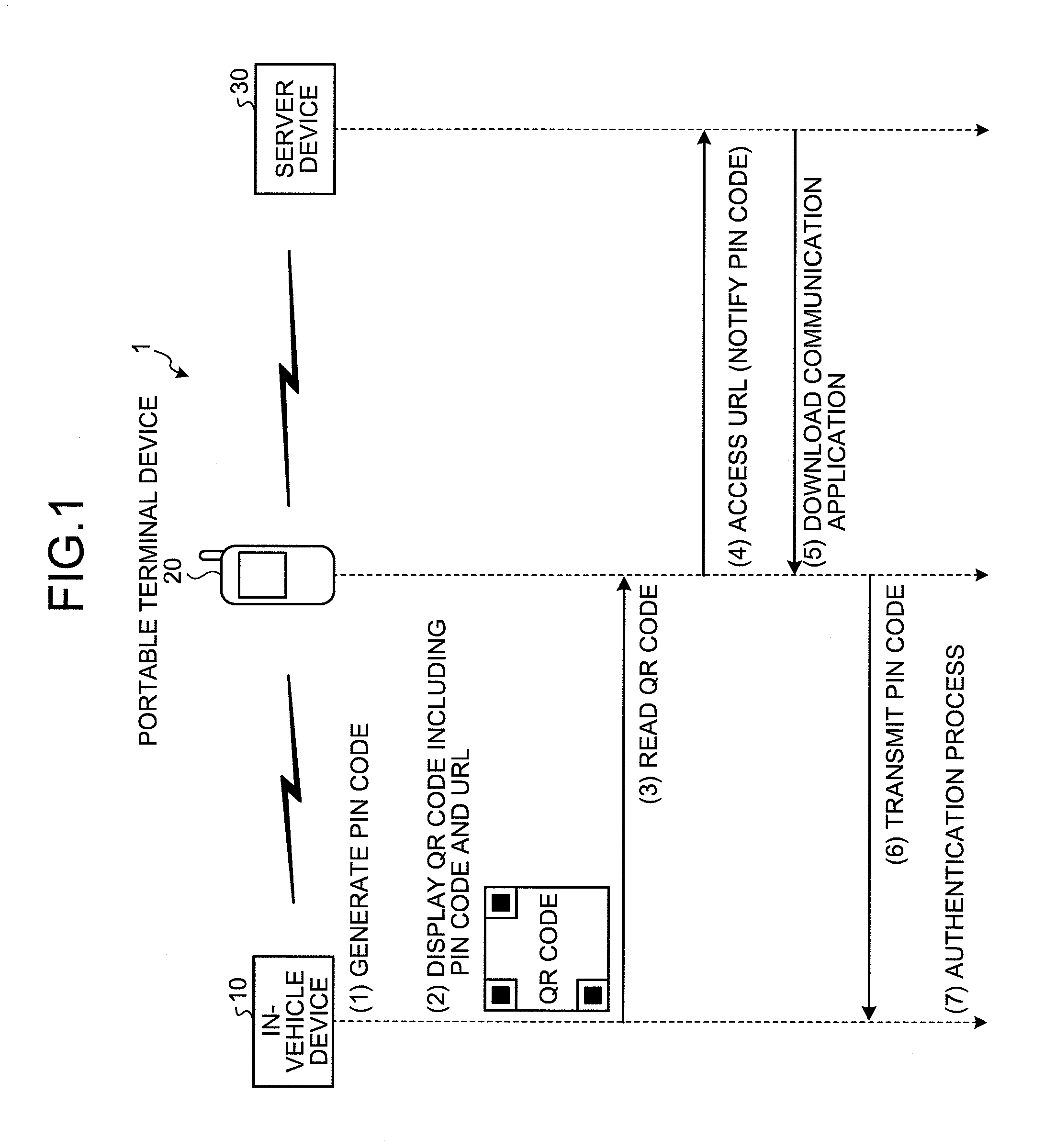
An authentication system is configured such that: an in-vehicle device generates an authentication key, and displays on a display unit, a two-dimensional code including the generated authentication key and a URL indicating a predetermined WEB page on a network; and a portable terminal device acquires the authentication key and the URL from the two-dimensional code by reading the two-dimensional code via an imaging unit, downloads a communication program for communicating with the in-vehicle device from the WEB page indicated by the URL, and transmits the authentication key to the in-vehicle device by causing the downloaded communication program to operate.
Owner:FUJITSU GENERAL LTD
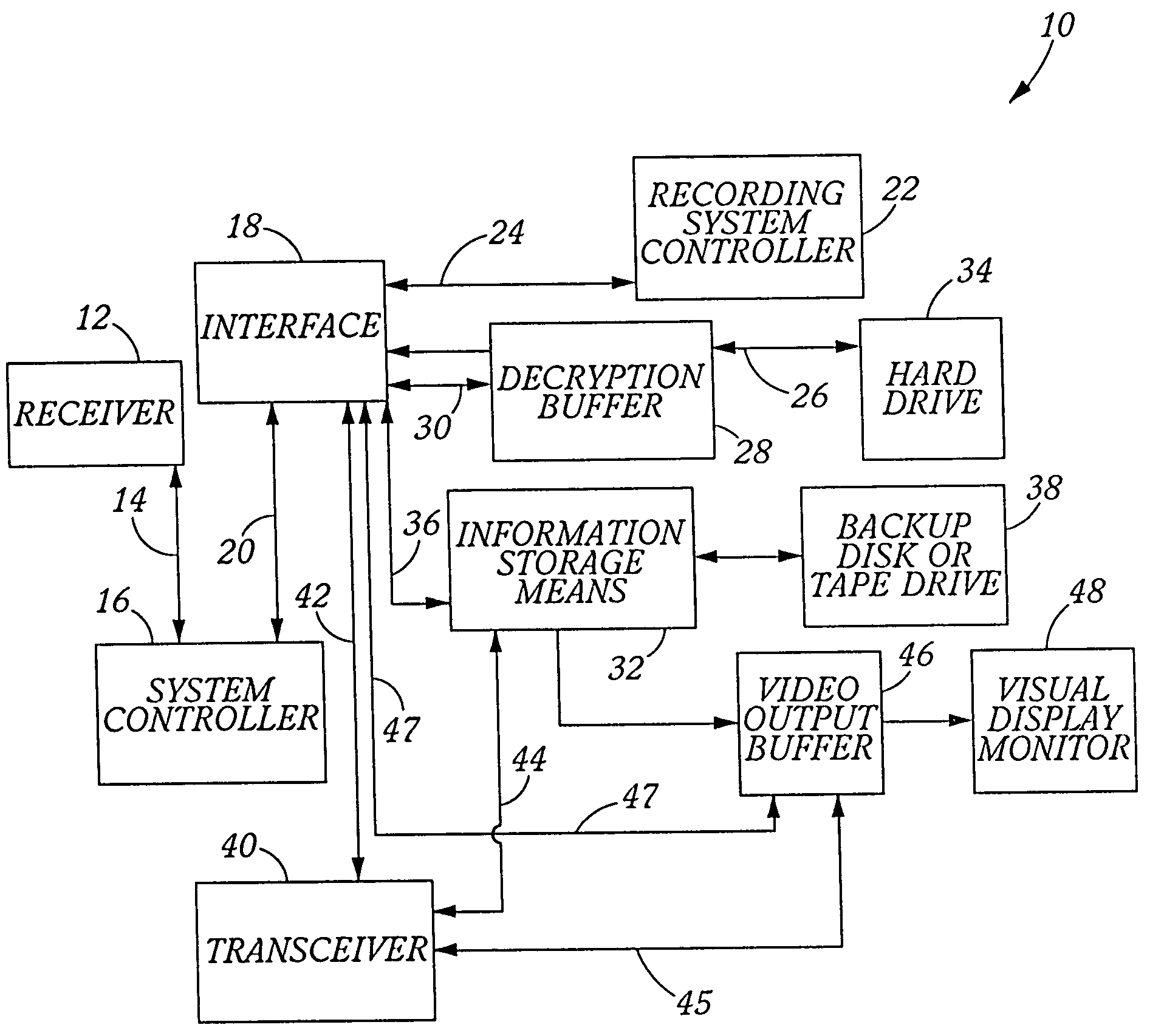
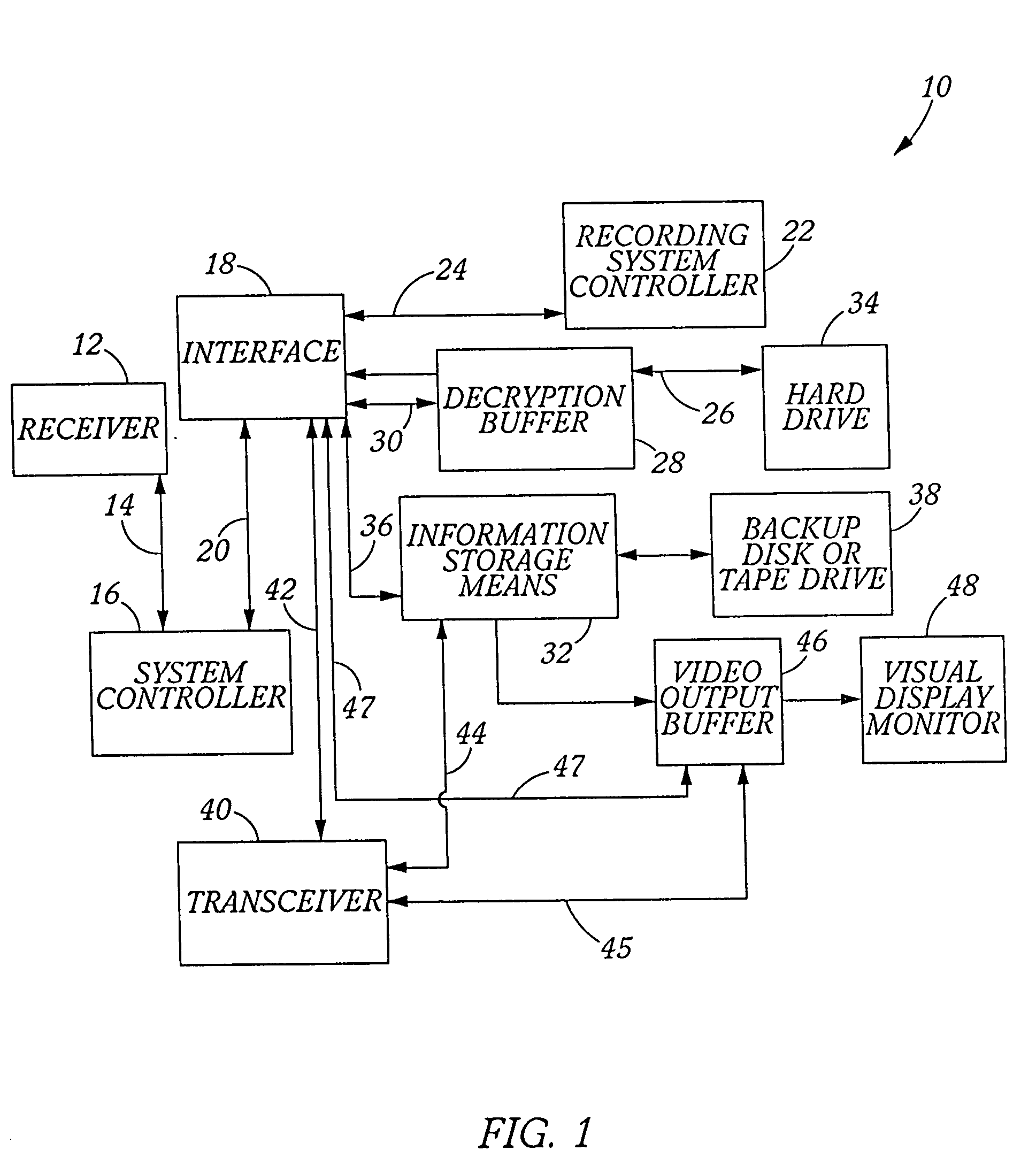
Incident recording information transfer device
InactiveUS20050259151A1Convenient investigationMaintain integrityRegistering/indicating working of vehiclesAnti-theft devicesTransceiverDisplay device
A novel device for remote information download and transfer for downloading a secure, permanent record of criminal activity and / or accident evidence relating to a vehicle for evidentiary purposes which may be directly transferred to an information center and / or the authorities through a transmission link which is preferably a satellite up / link-down / link or saved directly onto the downloading device. The remote downloading device may be activated automatically or upon a trigger signal and comprises an interface, an information capturing storage device, a video monitor display and preferably a transceiver. The interface communicates with an information storage device, downloads the information saved therein and transmits it to the capture storage device, transceiver or both. The information may be displayed on the visual display monitor or transmitted via the transceiver to an off site location.
Owner:HAMILTON JEFFREY A +1
Security method and apparatus for controlling the data exchange on handheld computers
InactiveUS7346778B1Avoid accessTransparent to userDigital data processing detailsUnauthorized memory use protectionData transmissionAuthorization
A method and system for protecting portable computer data from unauthorized transfer or using portable computers to download unauthorized data. The invention is applicable to any computer capable of transferring data, but in one embodiment a portable computer is described. Authorization is enabled by an interface permitting synchronization of the portable computer with a host computer by authentication of the particular portable computer identity. For instance, in one embodiment, when a portable computer is docked with a compatible interface connected to a host desktop computer, it is sensed and identified by the interface. If the particular portable computer identity is authenticated as authorized for that desktop, then synchronization will be enabled by the interface. The computers may then transfer data. However, if the identity is not an authorized one, then authentication will not occur, synchronization is correspondingly disabled, and data transfer is prevented. Various systems can enable the identity authentication.
Owner:ACCESS
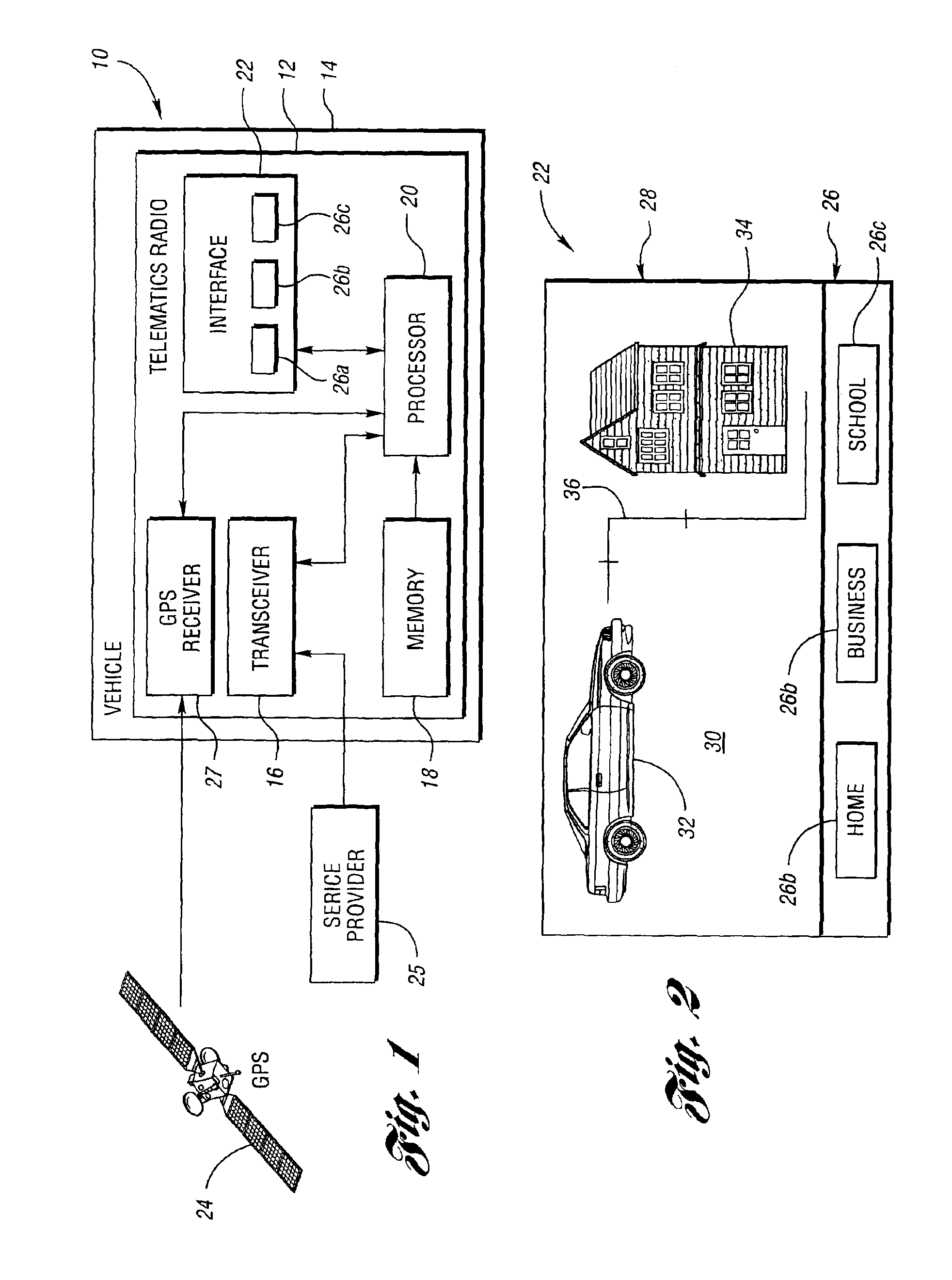
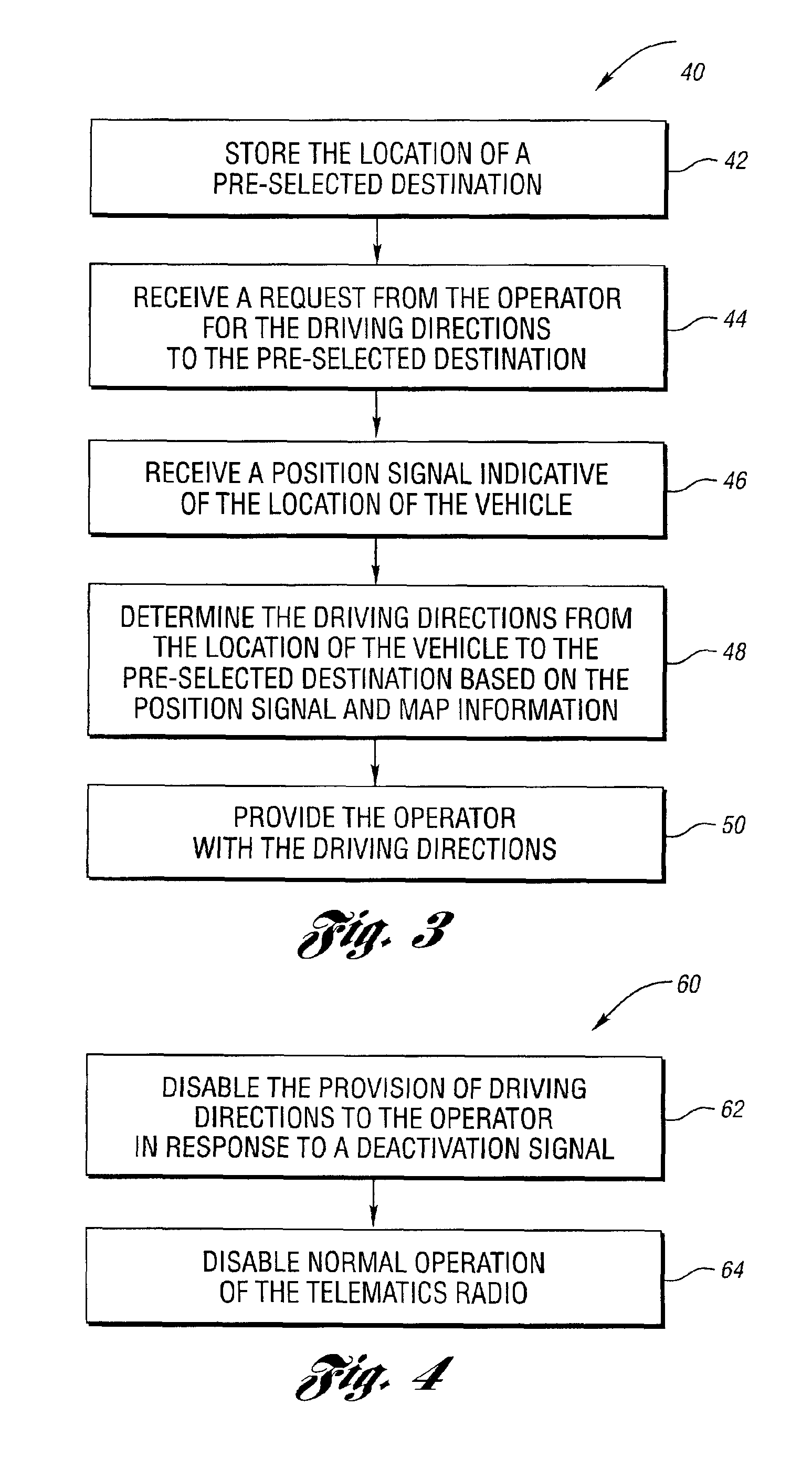
Vehicle telematics radio operable for providing and disabling driving directions to pre-selected destinations
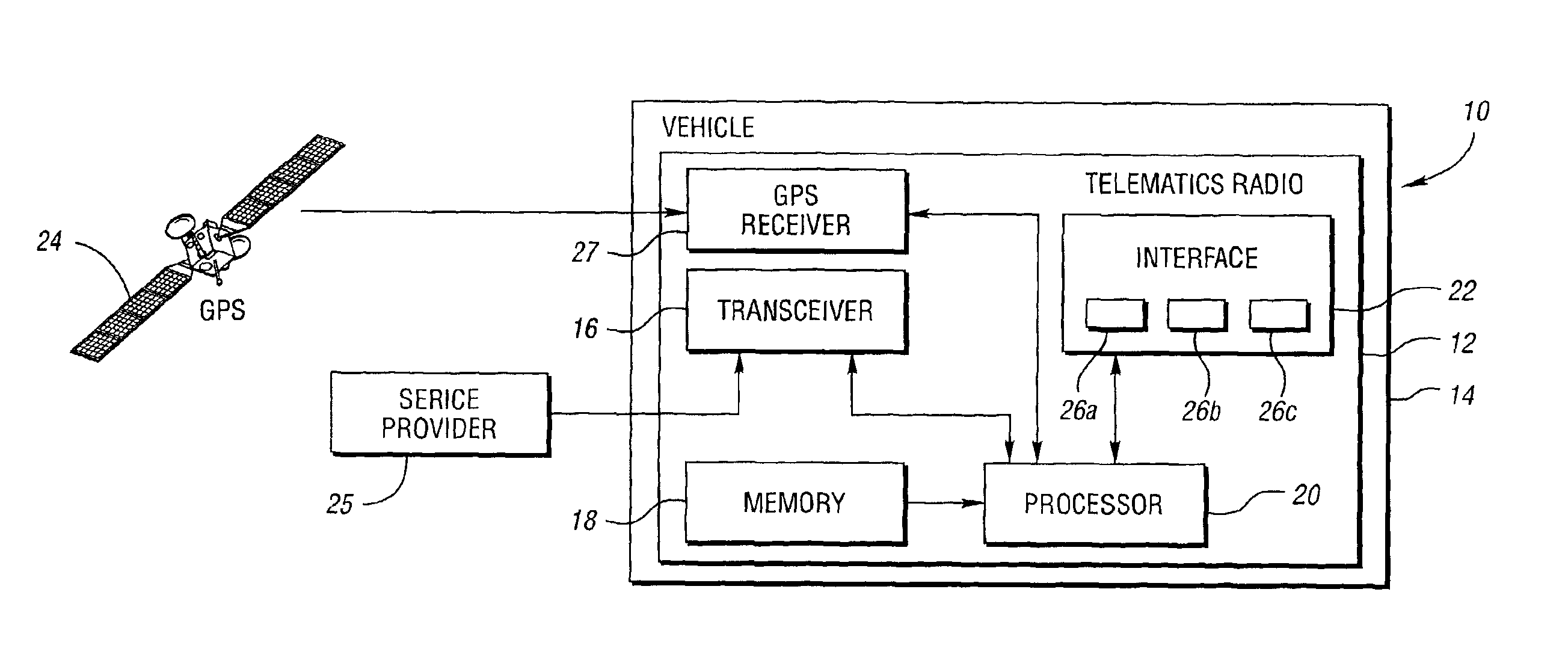
InactiveUS6912396B2Prevent unauthorized accessInstruments for road network navigationRadio/inductive link selection arrangementsEngineeringTelematics
A vehicle telematics radio operable for providing and disabling driving directions to pre-selected destinations includes a receiver, memory, a processor, and an interface. The memory stores the location of at least one pre-selected destination. The interface receives a request from a vehicle operator for the driving directions to a desired pre-selected destination. The receiver receives a position signal indicative of the current location of the vehicle. The processor determines the driving directions from the current location of the vehicle to the pre-selected destination based on the position signal and map information. The interface then provides the operator with the driving directions to the desired pre-selected destination. In special situations such as when either the vehicle or telematics radio is stolen or missing, the telematics radio may be disabled from providing driving directions in response to receiving a deactivation signal.
Owner:VISTEON GLOBAL TECH INC
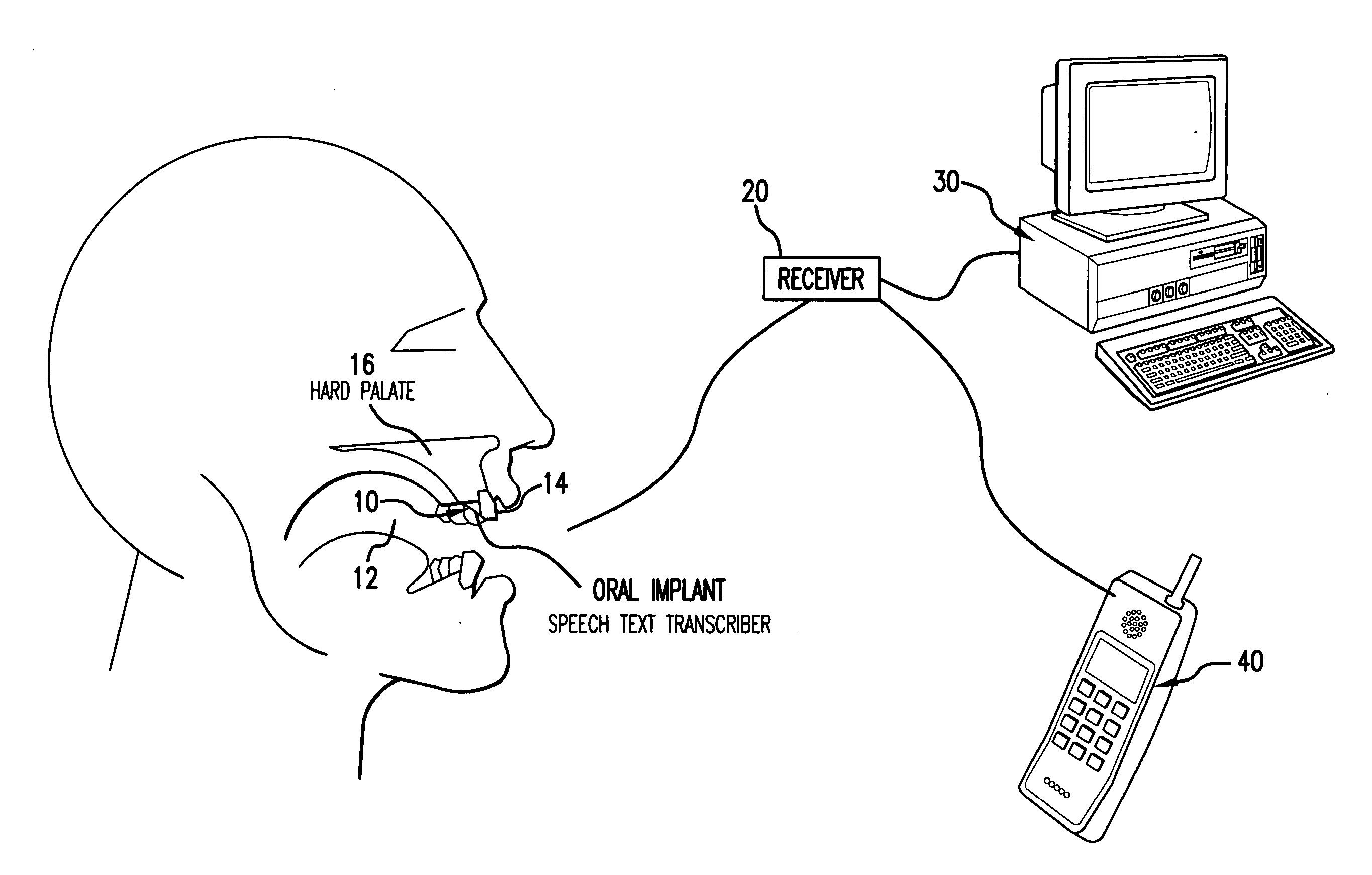
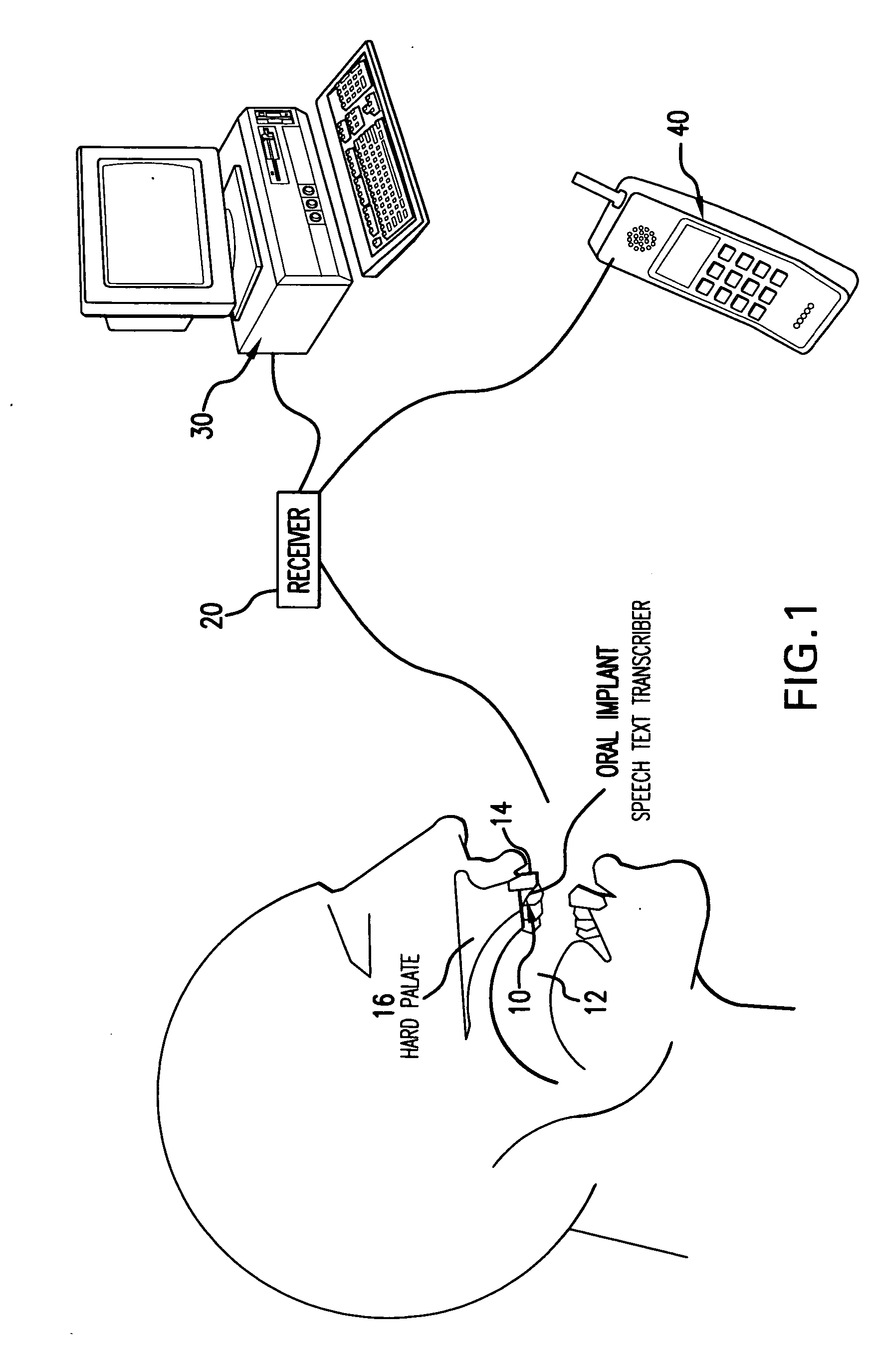
Orally mounted wireless transcriber device
InactiveUS20070105072A1Prevent unauthorized accessTransducer detailsBone conduction transducer hearing devicesDigital dataSpoken language
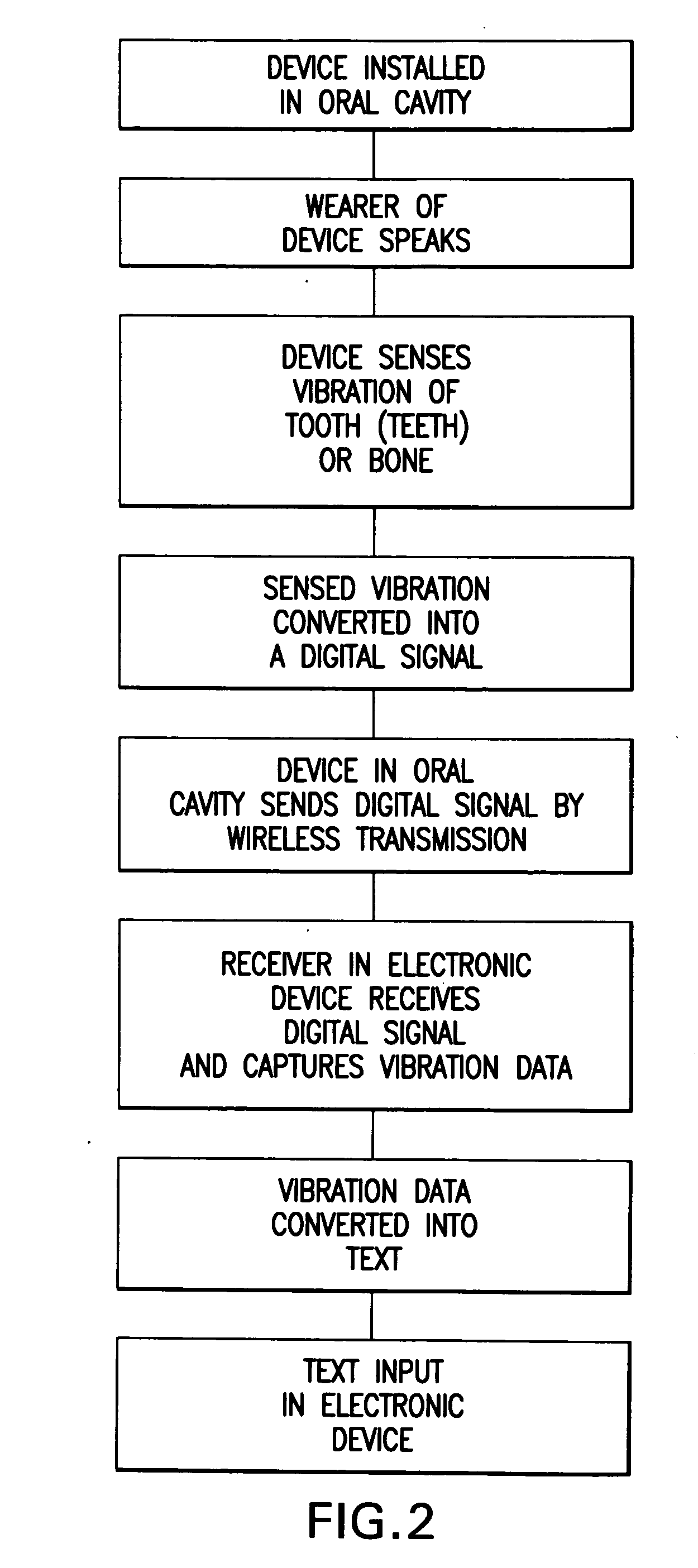
A wireless electronic device transcribes spoken words into text for input on an electronic device such as, but not limited to, a computer, cell phone, handheld computer, Blackberry or vehicle navigation system. The wireless transcriber device mounts within the oral cavity, preferably to the back side of a tooth, and detects vibration of the tooth and / or palate bone structure as the wearer of the device speaks. The sensed vibrations are converted to digital signals for wireless transmission to the electronic device. The electronic device receives the signals and captures the digital data containing the sensed vibrations. A software program in the electronic device reads the vibration data and converts the vibration data to text for input on the electronic device. The input text can be used for various purposes such as to create a document, fill in a form, send a text message or to give an operational command to the electronic device.
Owner:KOLJONEN REINO
Control of access to a memory by a device
ActiveUS20040177261A1Prevent unauthorized accessAvoid it happening againMemory adressing/allocation/relocationDigital computer detailsComputer hardwareSecurity domain
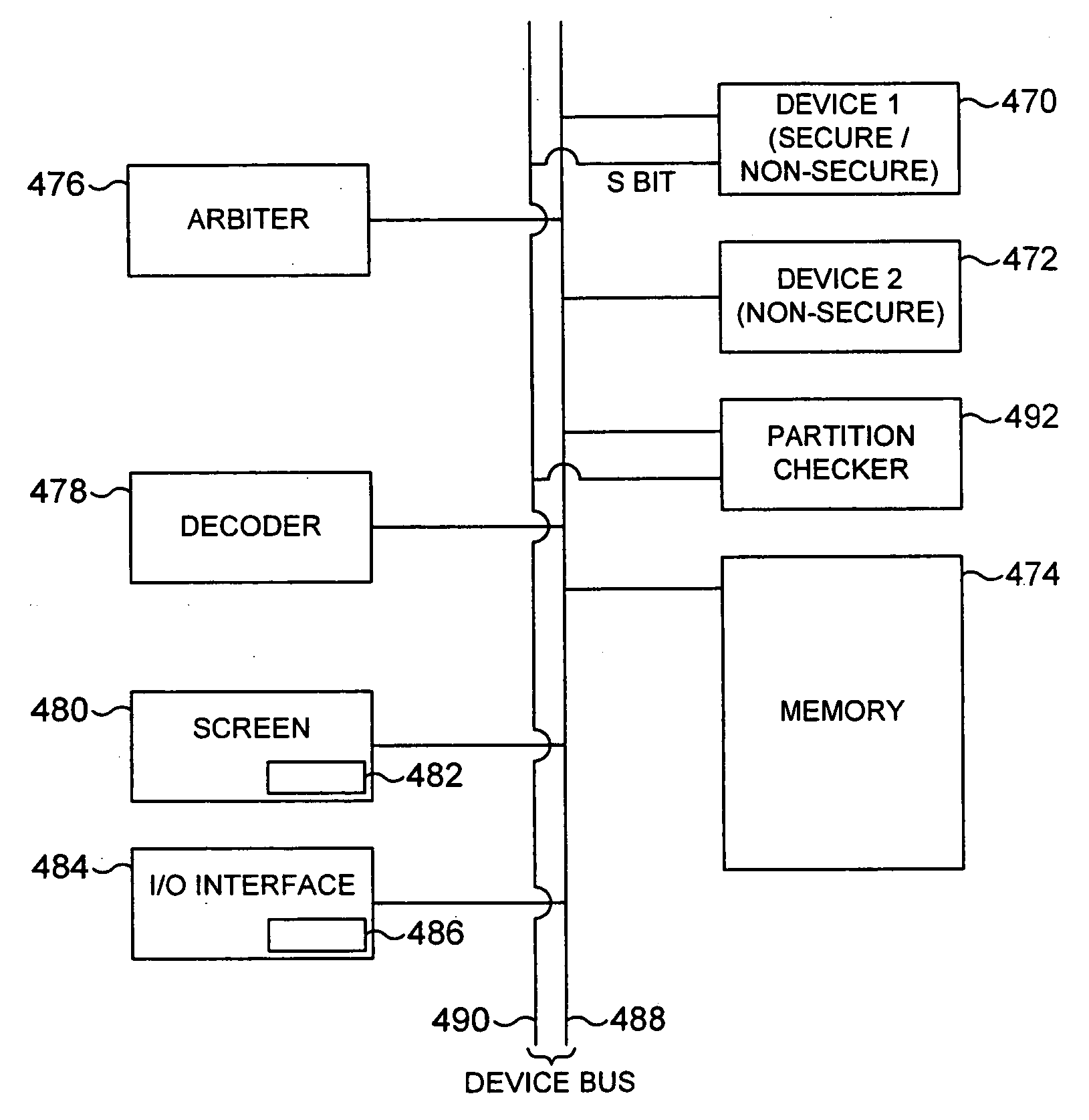
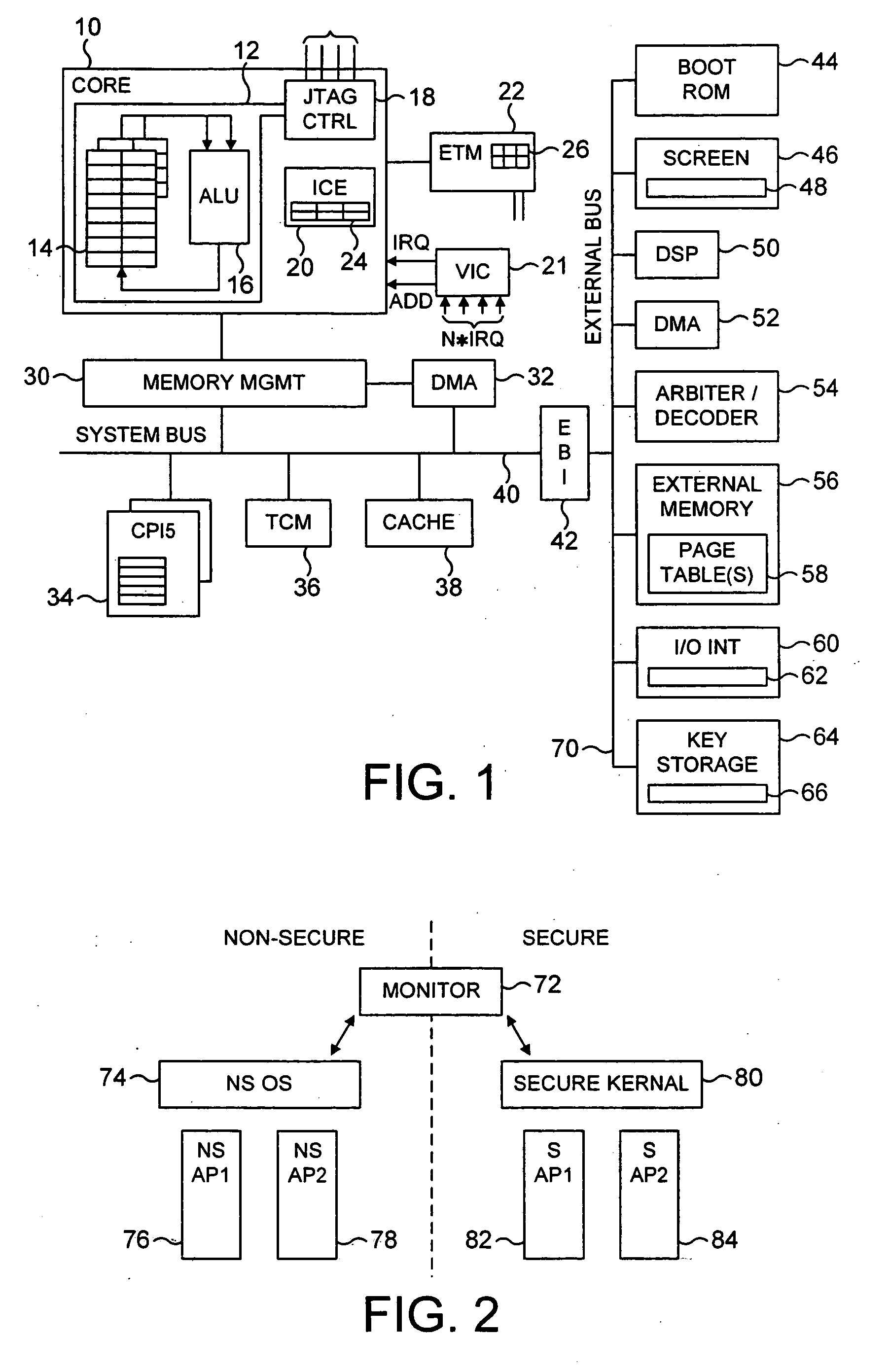
The present invention provides a data processing apparatus and method for controlling access to a memory. The data processing apparatus has a secure domain and a non-secure domain, in the secure domain the data processing apparatus having access to secure data which is not accessible in the non-secure domain. The data processing apparatus comprises a device coupled to a memory via a device bus, and operable, when an item of data in the memory is required by the device, to issue onto the device bus a memory access request pertaining to either the secure domain or the non-secure domain. The memory is operable to store data required by the device, and contains secure memory for storing secure data and non-secure memory for storing non-secure data. In accordance with the present invention, the data processing apparatus further comprises partition checking logic coupled to the device bus and operable whenever the memory access request as issued by the device pertains to the non-secure domain, to detect if the memory access request is seeking to access the secure memory and upon such detection to prevent the access specified by that memory request. This approach significantly improves the security of data contained within a secure portion of memory.
Owner:ARM LTD
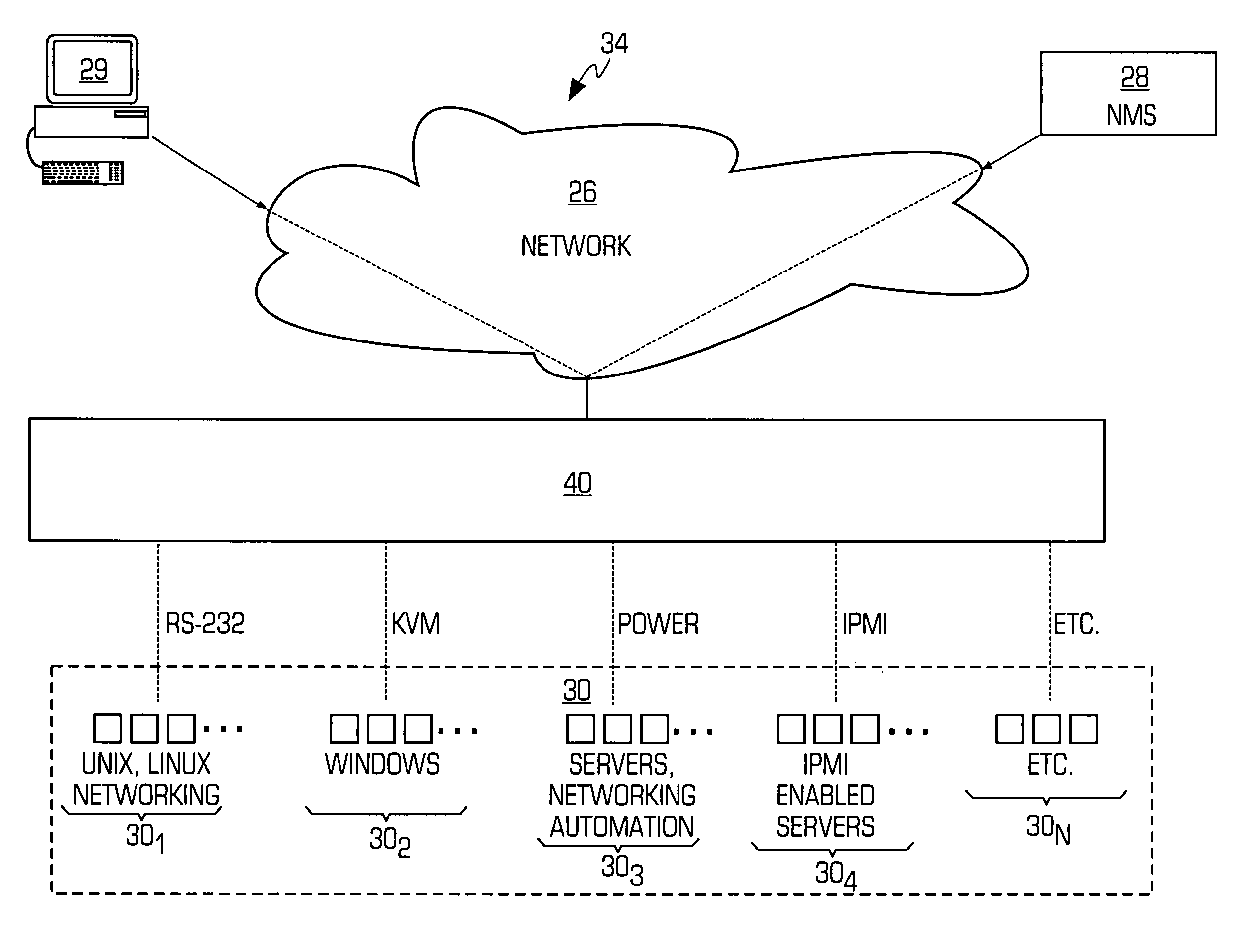
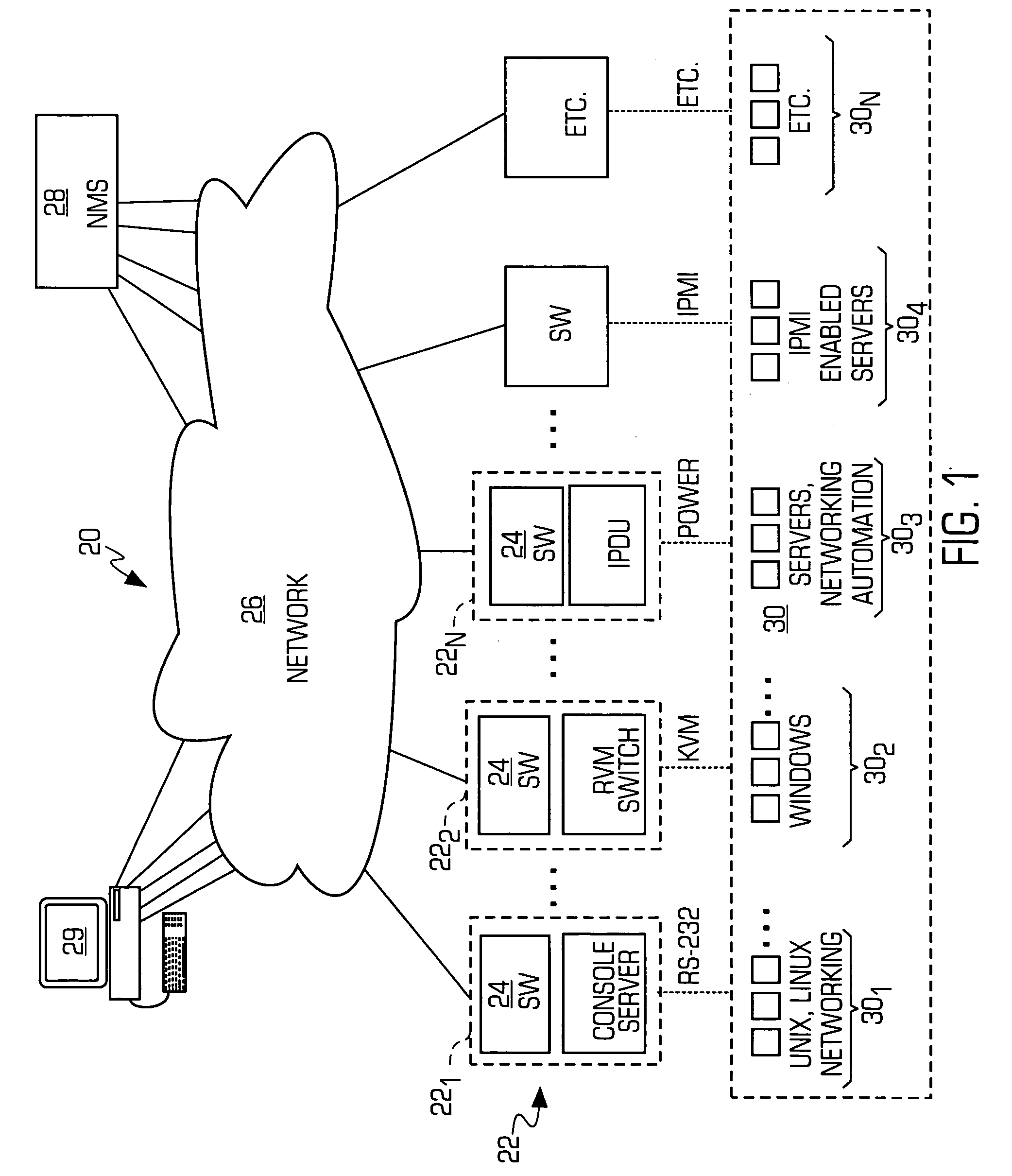
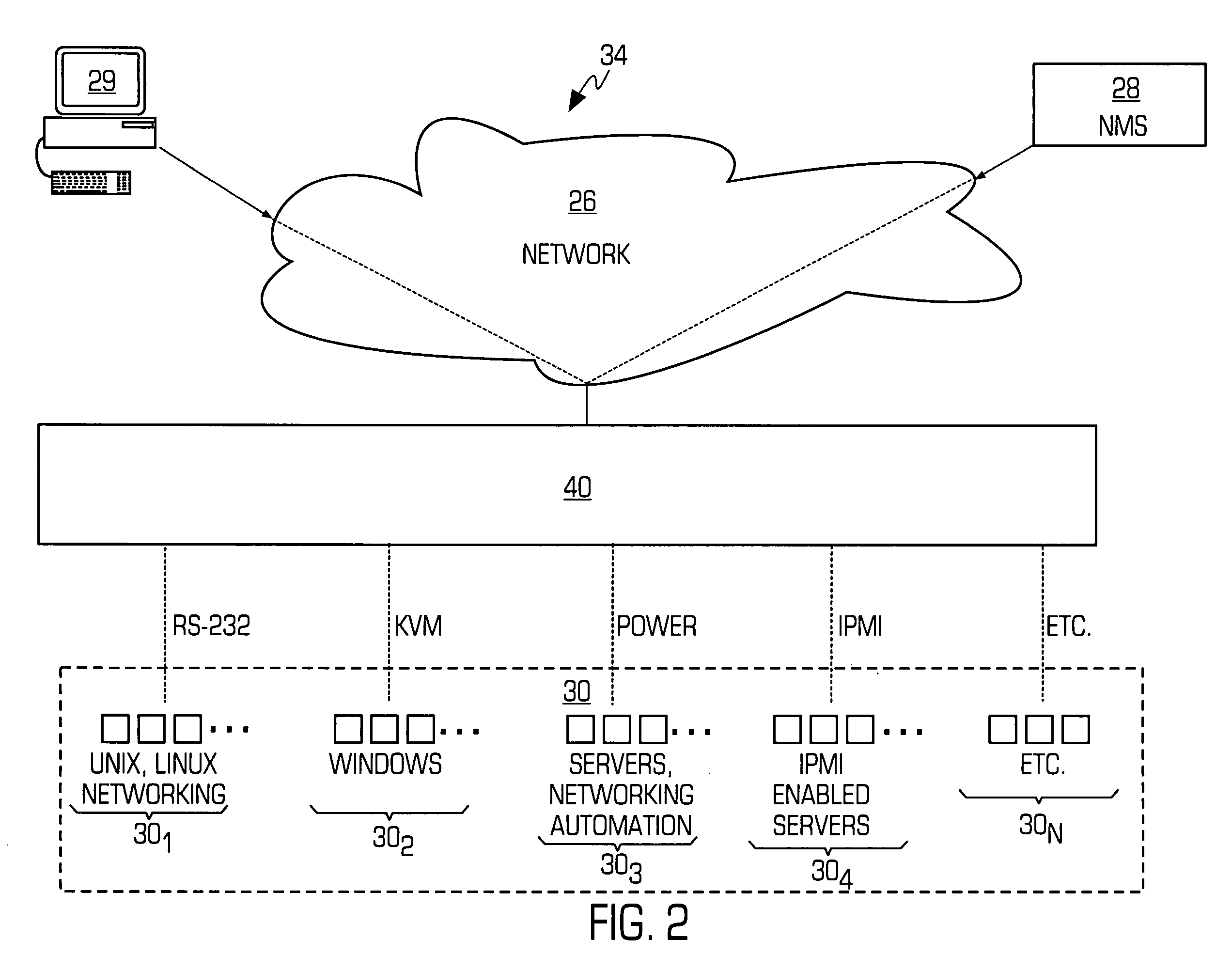
System and method for consolidating, securing and automating out-of-band access to nodes in a data network
ActiveUS20060031447A1Avoid transportPrevent unauthorized accessEnergy efficient ICTDigital computer detailsNetwork managementAccess management
A system and method for out-of-band network management is provided wherein one or more different management interfaces are converted into a common format management data. The system may encrypt the common format management data. The system may also authenticate each user that attempts to access the management interfaces.
Owner:VERTIV IT SYST INC +1
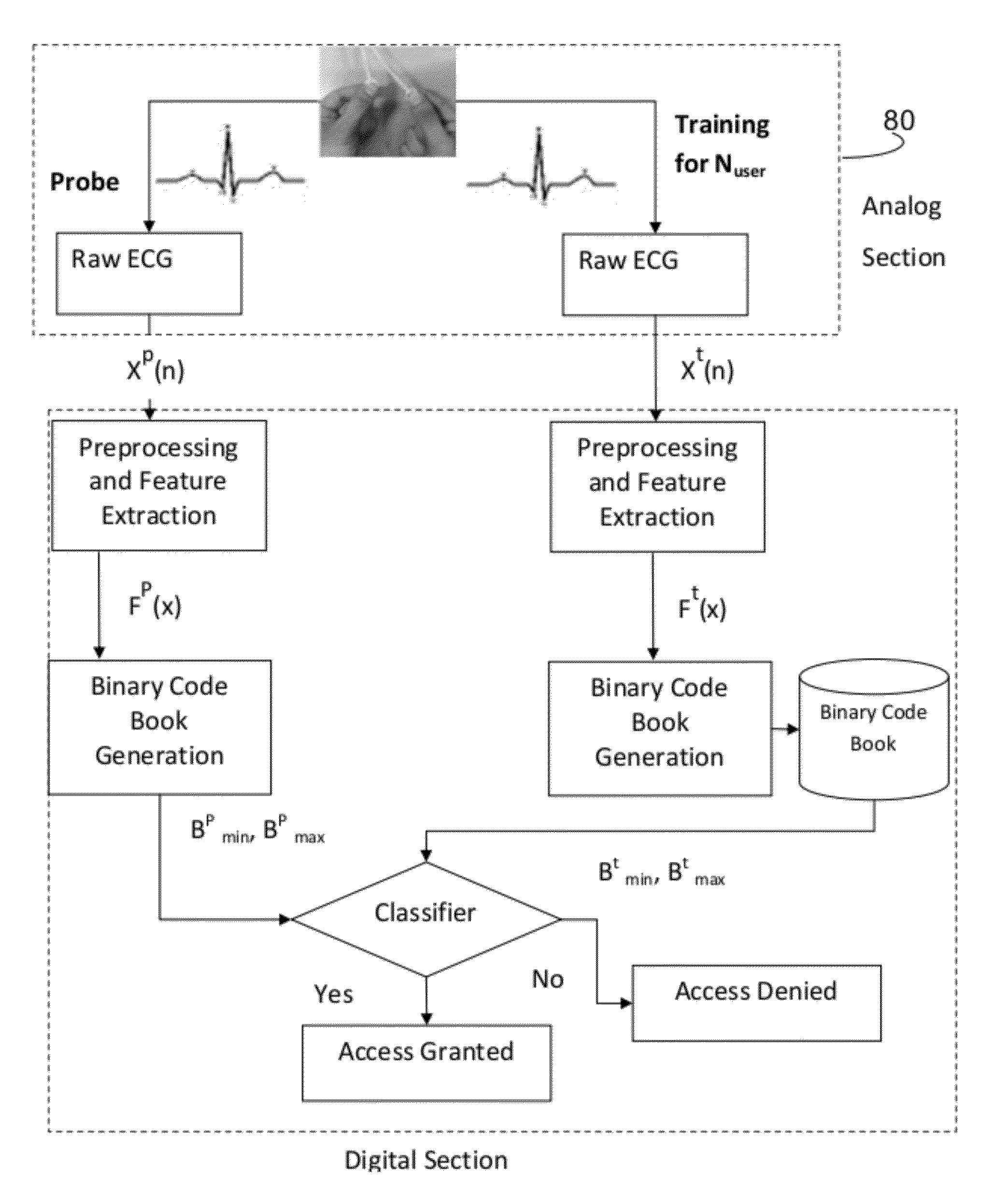
System for vehicle security, personalization and cardiac activity monitoring of a driver
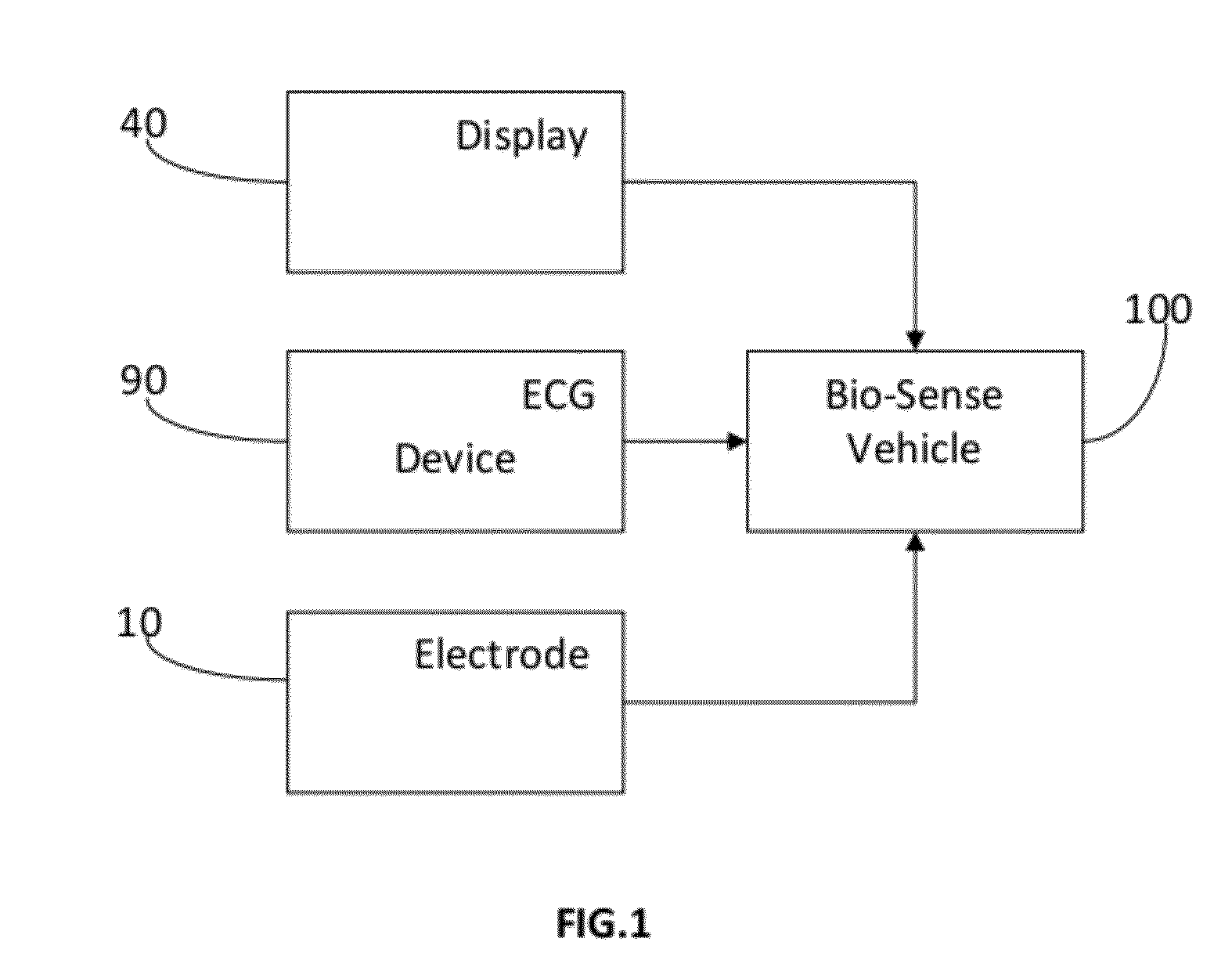
ActiveUS9144389B2Prevent unauthorized accessElectrocardiographyDigital data processing detailsPersonalizationDriver/operator
The present invention provides a system for vehicle security, personalization, and cardiac activity monitoring of a driver wherein electrocardiography of a driver is monitored and registered which is used for identification of a person entering in the vehicle and personalization of vehicle based on user preferences thereby act as intruder detection towards vehicle security. In addition to registration the present invention also monitors cardiac activity of driver in a continuous and real time fashion without any intrusion to driver with the facility of generation of alert and making emergency call.
Owner:TATA CONSULTANCY SERVICES LTD
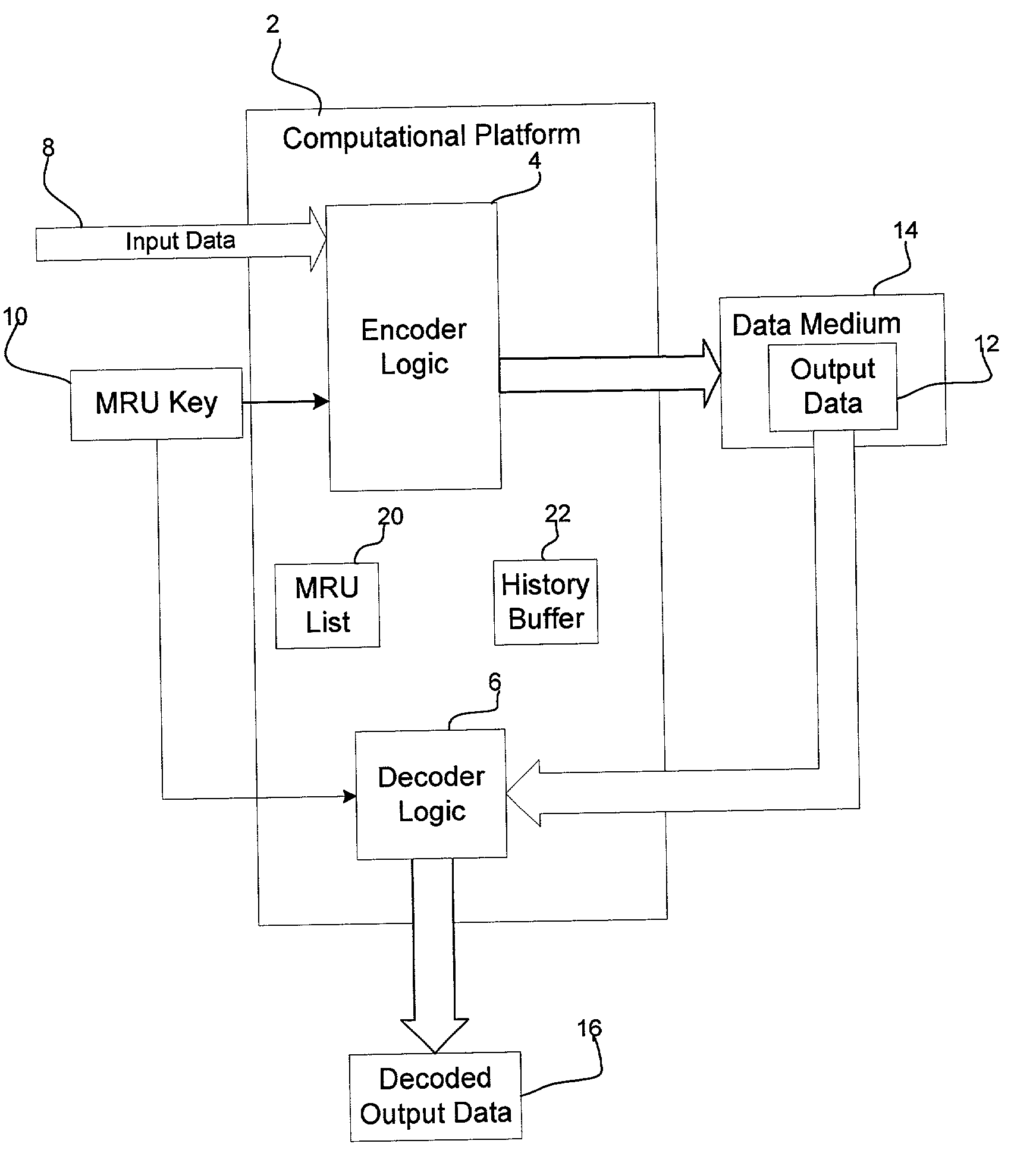
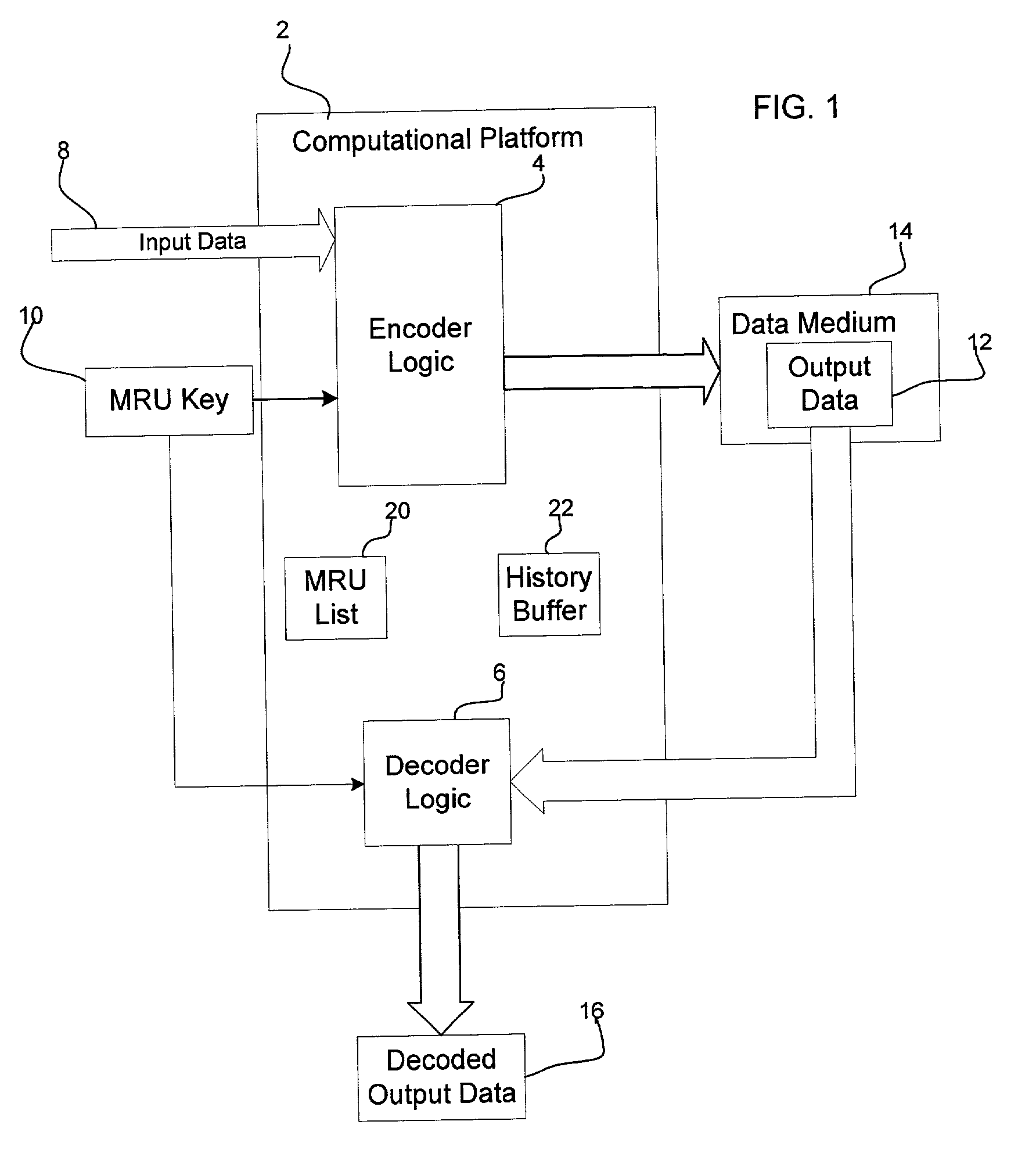
Method, system, and program for securely providing keys to encode and decode data in a storage cartridge
InactiveUS20030074319A1Prevent unauthorized accessExtension of timeDigital data processing detailsAnalogue secracy/subscription systemsData storingData store
Provided is a method, system, and program for enabling access to data in a storage medium within one of a plurality of storage cartridges capable of being mounted into a interface device. An association is provided of at least one coding key to a plurality of storage cartridges. A determination is made of one coding key associated with one target storage cartridge, wherein the coding key is capable of being used to access data in the storage medium within the target storage cartridge. The determined coding key is encrypted. The coding key is subsequently decrypted to use to decode and code data stored in the storage medium.
Owner:IBM CORP
Virtual private network (VPN)-as-a-service with load-balanced tunnel endpoints
ActiveUS20150188823A1Facilitate (VPN)-as-a-serviceEfficient use ofError preventionFrequency-division multiplex detailsPlaintextData stream
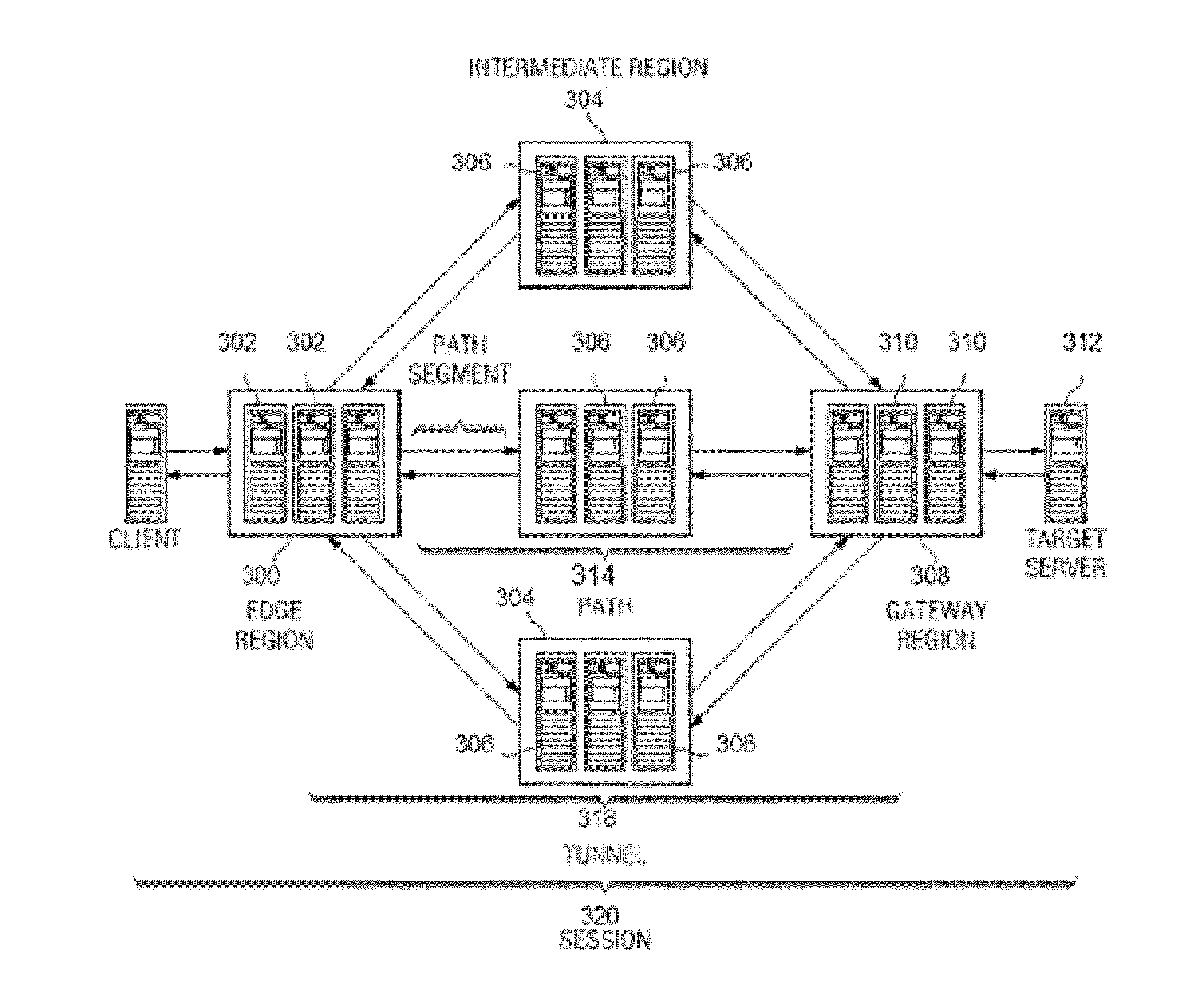
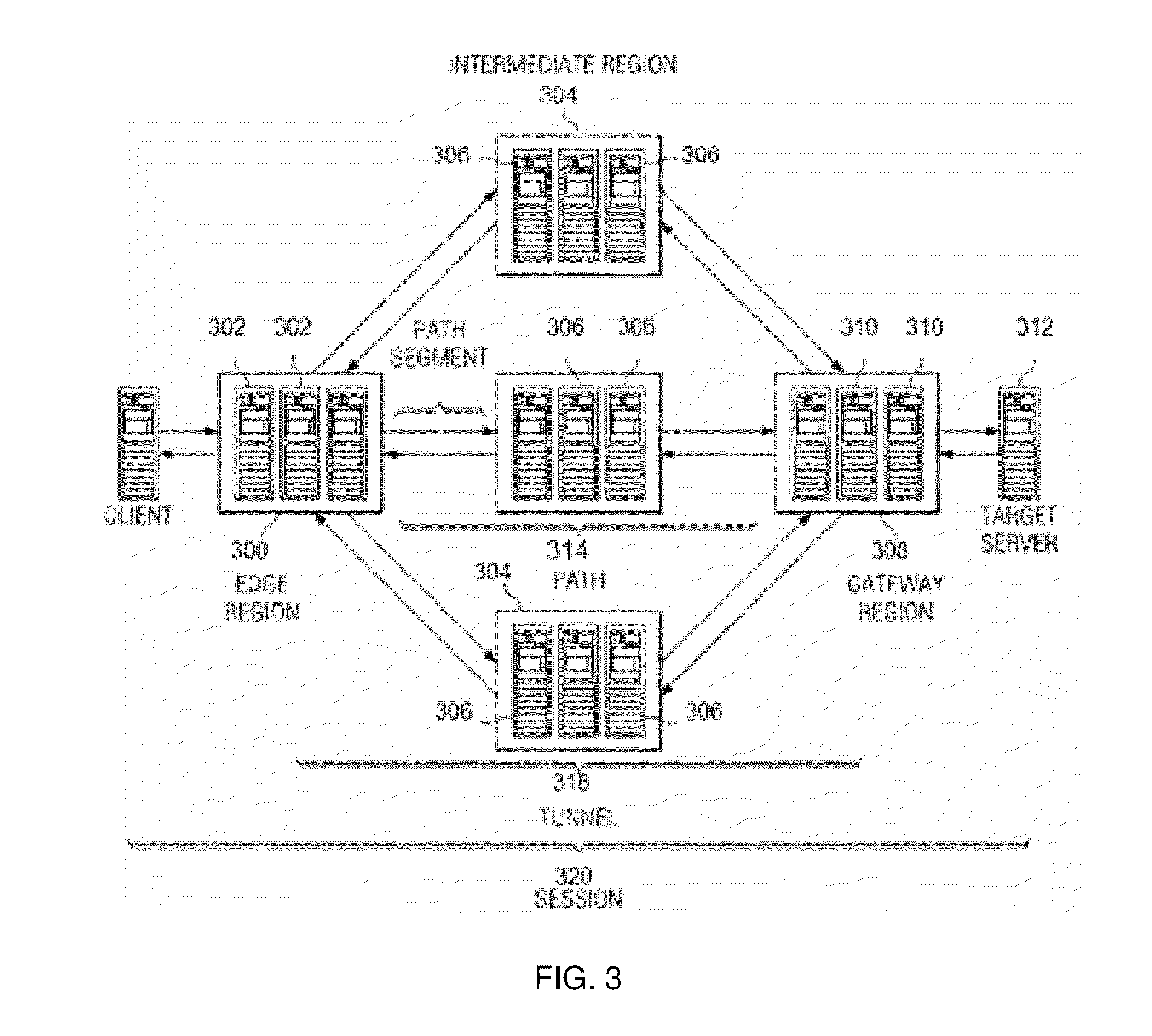
A mechanism to facilitate a private network (VPN)-as-a-service, preferably within the context of an overlay IP routing mechanism implemented within an overlay network. The overlay provides delivery of packets end-to-end between overlay network appliances positioned at the endpoints. During such delivery, the appliances are configured such that the data portion of each packet has a distinct encryption context from the encryption context of the TCP / IP portion of the packet. By establishing and maintaining these distinct encryption contexts, the overlay network can decrypt and access the TCP / IP flow. This enables the overlay network provider to apply one or more TCP optimizations. At the same time, the separate encryption contexts ensure the data portion of each packet is never available in the clear at any point during transport. According to another feature, data flows within the overlay directed to a particular edge region may be load-balanced while still preserving IPsec replay protection.
Owner:AKAMAI TECH INC
User-friendly multifactor mobile authentication
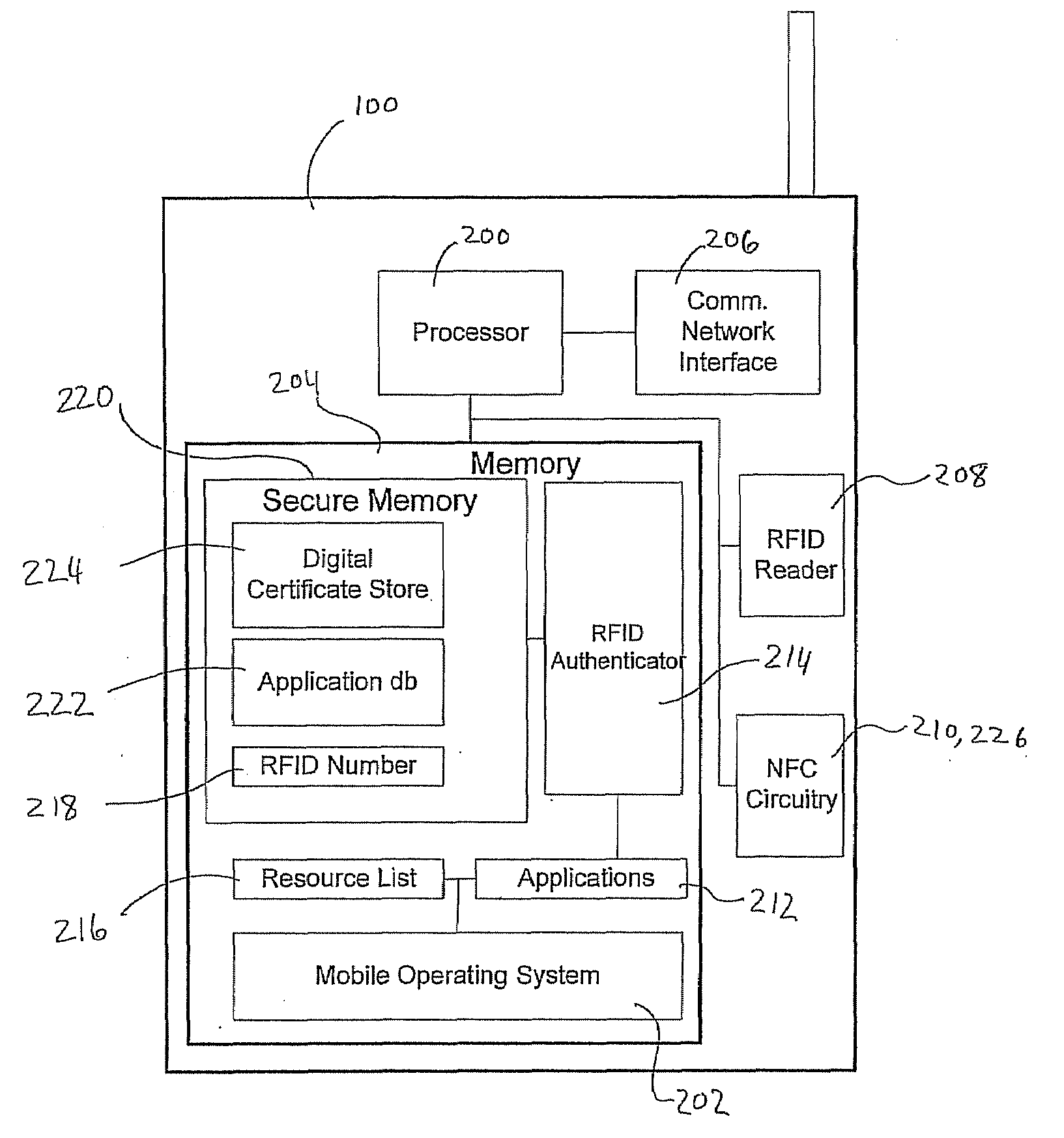
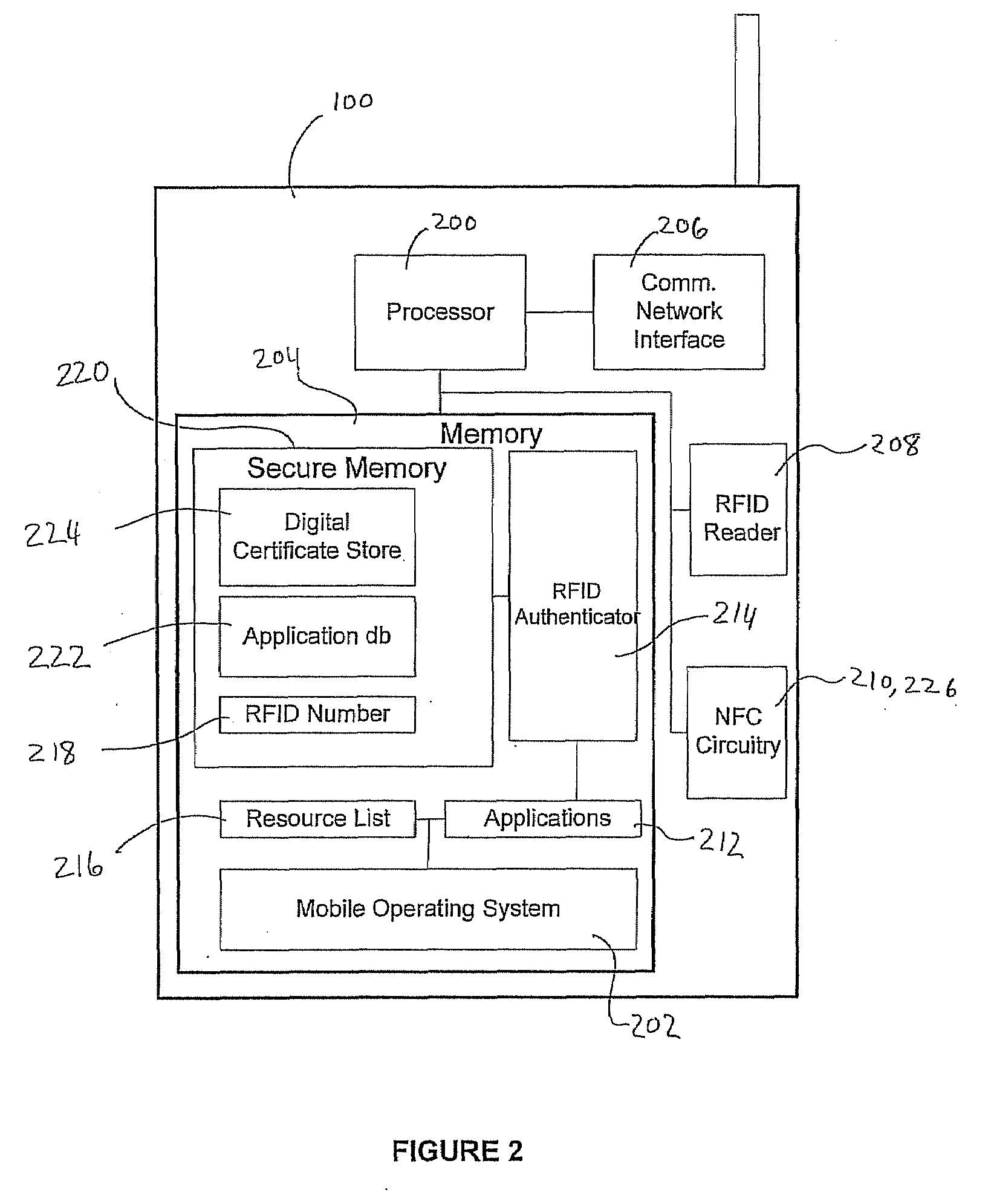
ActiveUS20080289030A1Prevent unauthorized accessEliminate needDigital data processing detailsMultiple digital computer combinationsComputer hardwareRfid authentication
A system and method for performing multifactor mobile authentication are described whereby a mobile communications device includes a contactless reader for receiving and validating a unique identifier stored in an external authenticating module prior to granting access to locally stored electronic authenticating material required to access an external resource. In one embodiment, the mobile communications device is a mobile telephone having an RFID reader for receiving the unique identifier from an RFID tag incorporated into the external authenticating module. Preferably, the external authenticating module is associated with a user, such as by being part of the user's jewelry or clothing. The mobile authentication device includes an RFID authenticator module that detects external resource access requests and checks whether the requested resource is on a list of resources that require additional user authentication prior to granting access to locally stored authenticating material.
Owner:U S CELLULAR
Systems and methods for detecting and preventing unauthorized access to networked devices
InactiveUS20050108557A1Prevent unauthorized accessReduce impactUser identity/authority verificationUnauthorized memory use protectionNetwork outputInput device
Devices, systems, and methods for detecting and preventing unauthorized access to computer networks. Devices include a server enabled with an application that interacts with a counter-part PC application to determine whether input devices of the PC have been active within a predetermined time. Methods include providing a subscription-based service for PC users to determine whether unauthorized network output activity has occurred from a respective user's PC.
Owner:KAYO DAVID GEORGE +2
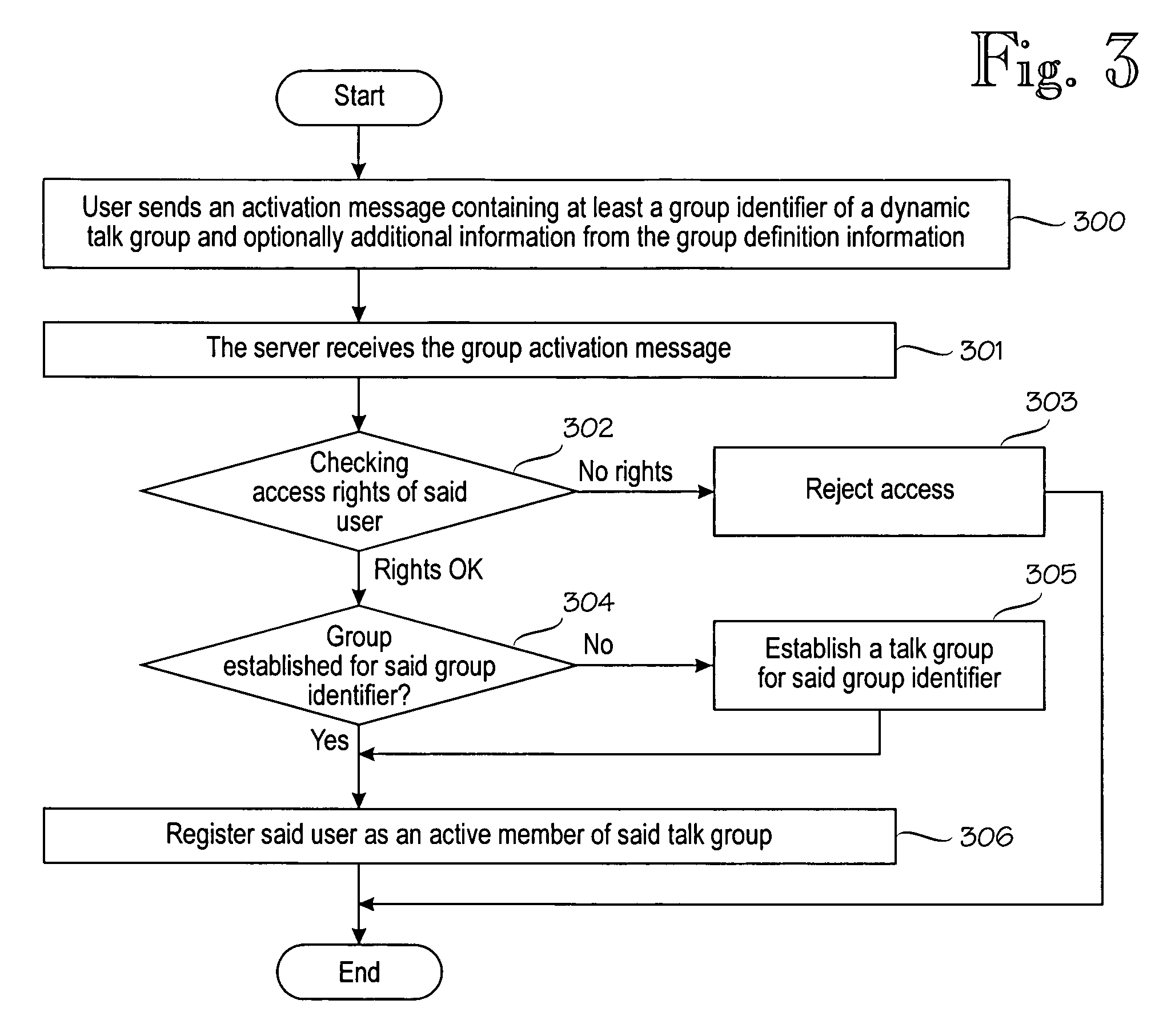
Method for creating a dynamic talk group
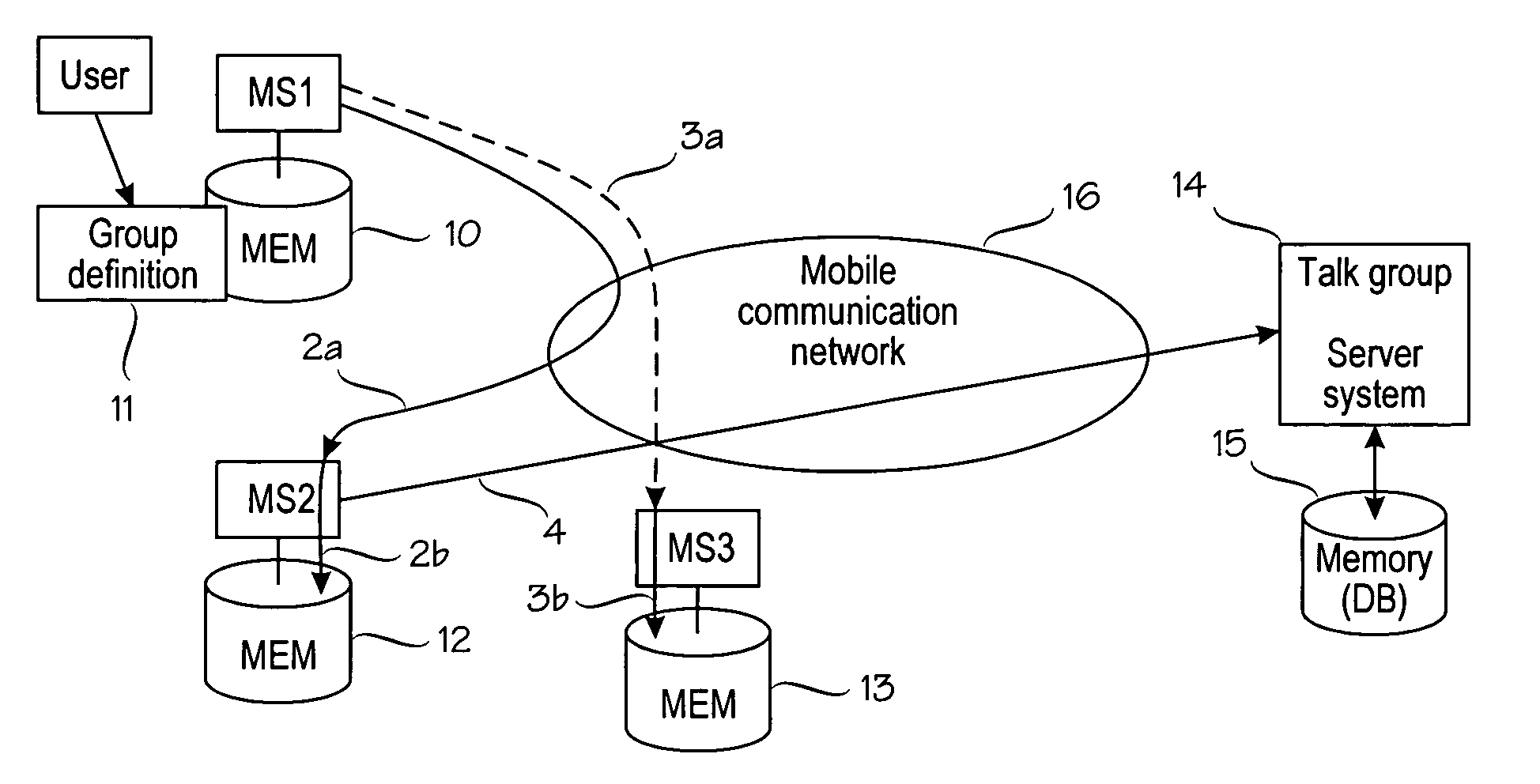
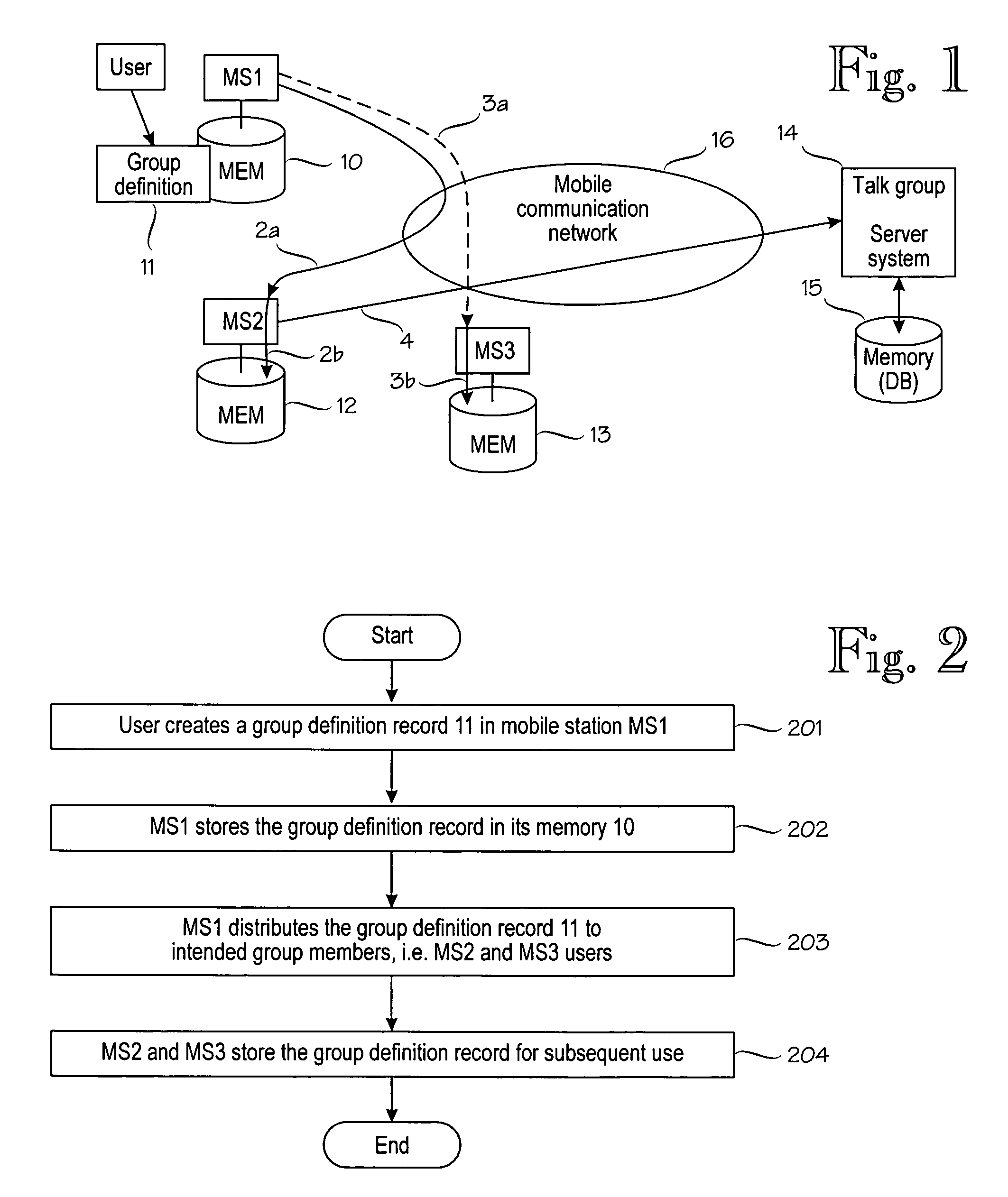
InactiveUS6999783B2Technically simplePrevent unauthorized accessBroadcast service distributionRadio/inductive link selection arrangementsCommunications systemMessage passing
The invention relates to dynamically creating talk groups in a communications system. A new dynamic group is created by a user who defines a group definition message in his subscriber station. This group definition message uniquely identifies the new group in the system, and can be distributed to the intended group members using the usual messaging facilities available in the specific communications system. The recipients of the group definition message can store the message in their subscriber stations for subsequent use. Thus, group creation and membership management are handled at user level without interacting with the system. The role of the system is restricted to establishing a means for communication in the group whenever there are users who have activated the group for communication.
Owner:NOKIA CORP
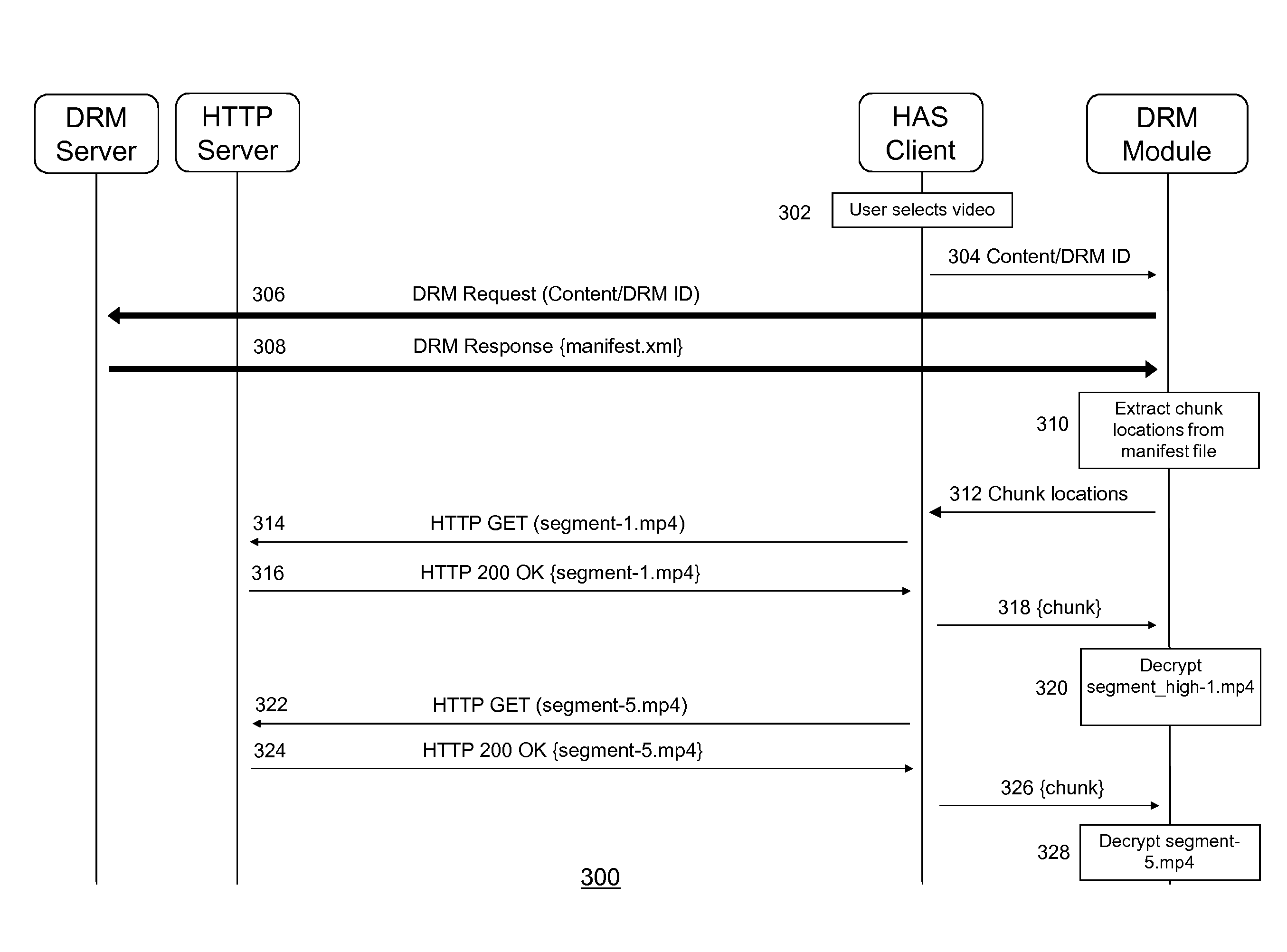
Digital Rights Management for Segmented Content
InactiveUS20160198202A1Prevent unauthorized accessReduce deliveryCarrier indexing/addressing/timing/synchronisingTelevision systemsManifest fileComputer module
A method and a system for enabling delivery of at least part of a digital rights management (DRM) protected segmented content item to a content processing device is described wherein segmented content item is associated with a manifest file, comprising at least a first segment identifier associated with a first segment being encrypted on the basis a first key; and, a second segment identifier associated with a different, second, segment being encrypted on the basis of a second key; said manifest file further comprising key information for enabling decryption of at least one of said first and second encrypted segments. Said method may comprise: a secure module, preferably a DRM module, in said content processing device requesting a DRM server access to at least part of said segmented content item; and, providing said secure module access to at least part of said key information, if said content access request is granted by said DRM server.
Owner:KONINK KPN NV
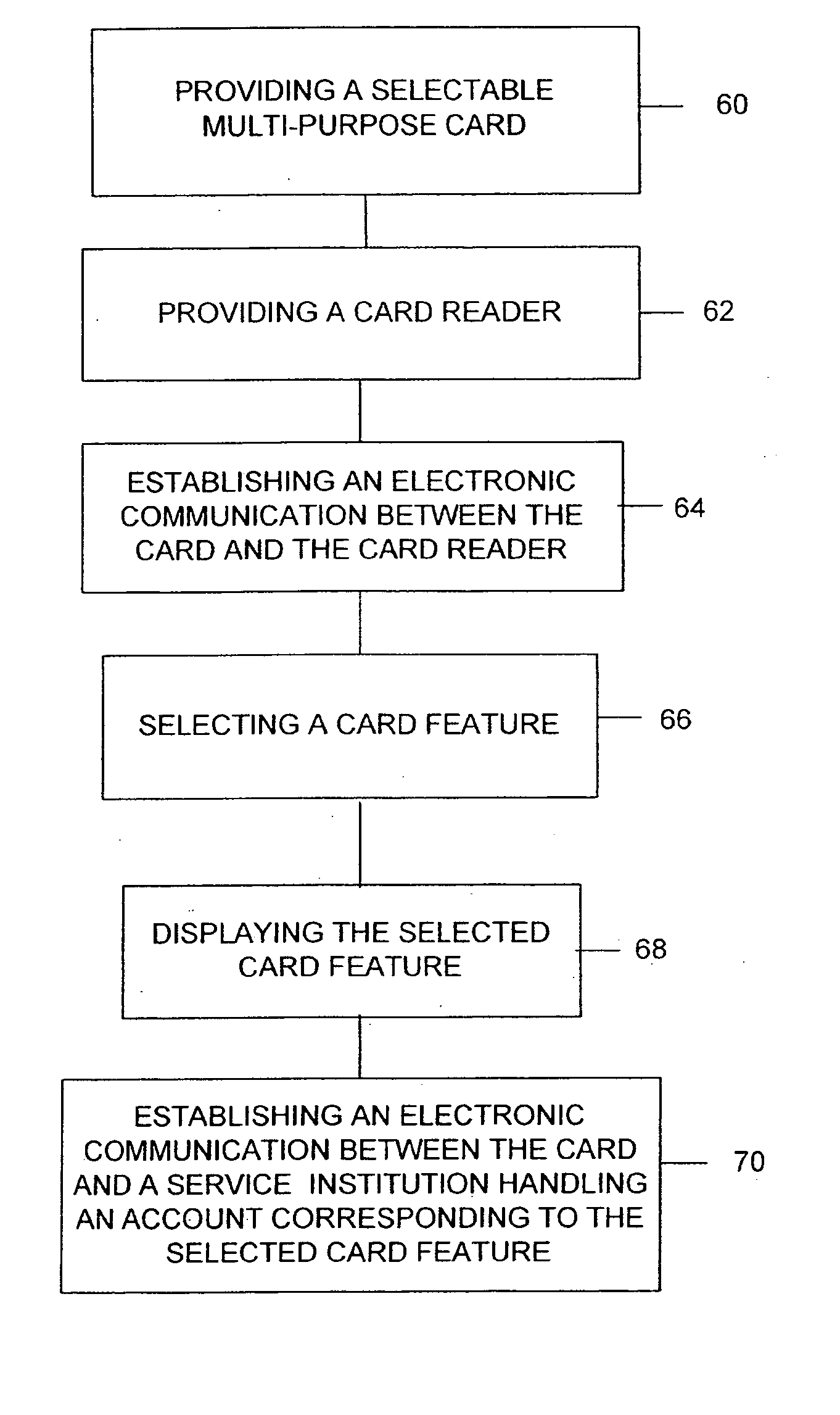
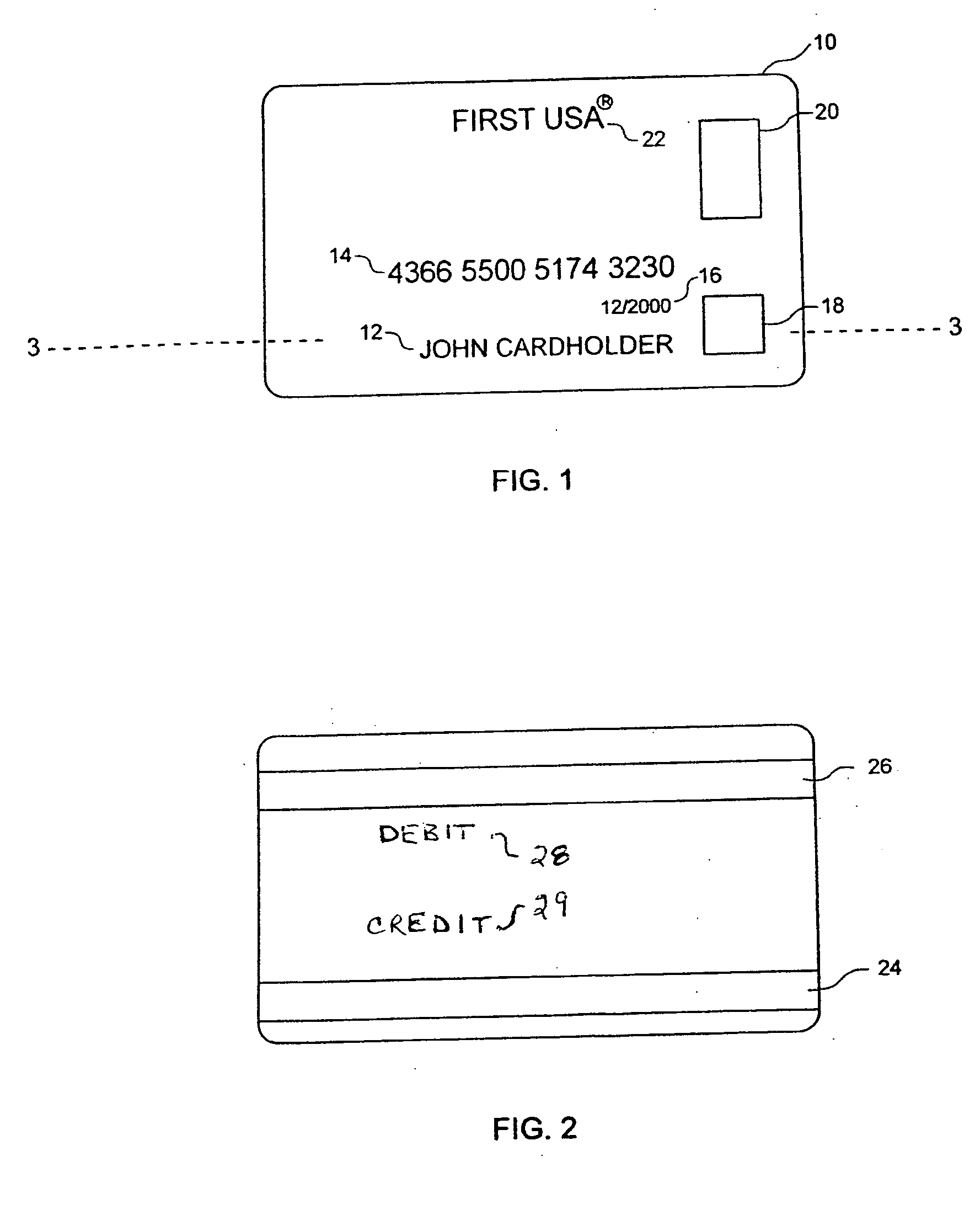
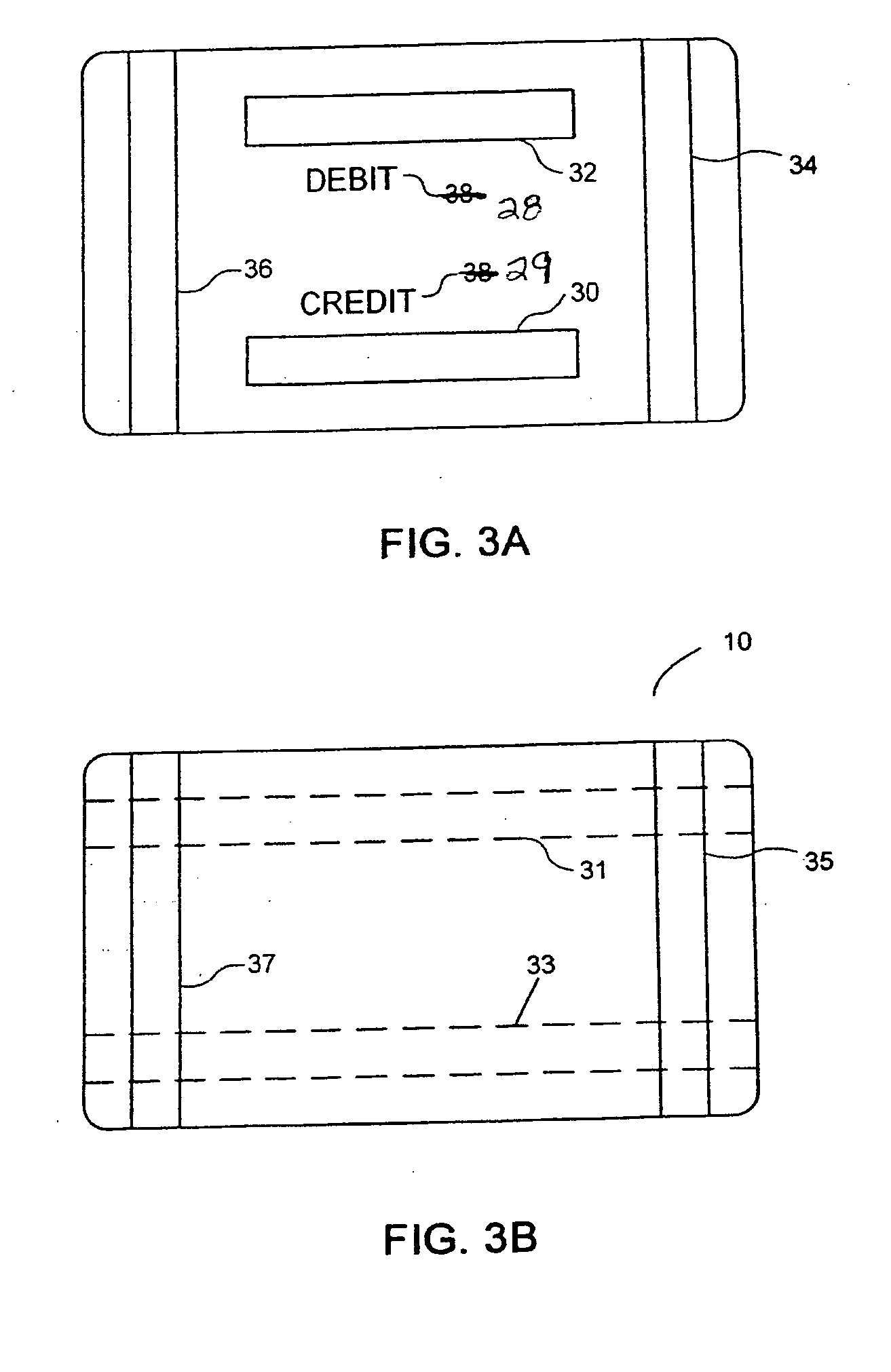
Selectable multi-purpose card
InactiveUS20050092830A1Prevent unauthorized accessPayment architectureRecord carriers used with machinesComputer hardwareFlexible display
A selectable, multi-purpose card comprising a plurality of features stored in memory means operatively mounted on the card and selection means for allowing a user to select a feature in a few simple steps, preferably in a single step. In one embodiment the card includes a plurality of magnetic strips positioned on the card in a manner to allow swiping each magnetic strip separately using conventional reading devices. Each magnetic strip activates a different feature of the card. In another embodiment the card includes a programmable magnetic strip, a plurality of features stored in memory means mounted on the card, a plurality of buttons or contacts, and means for programming the magnetic strip with a different card feature. The card may also include a thin, flexible display.
Owner:JPMORGAN CHASE BANK NA
System and method for providing access to mobile devices based on positional data
InactiveUS6778837B2Prevent unauthorized accessDirection finders using radio wavesSecret communicationInternet networkAutomatic control
The present invention includes as one embodiment a method for automatically controlling access to a mobile computing device with pertinent data. The method includes predefining access parameters of the mobile computing device, determining an actual location of the mobile computing device and using the actual location of the mobile computing device to automatically control access to the mobile computing device based on the predefined access parameters. Also, the method includes storing the predefined access parameters in a private Internet networked location, accessing and updating the predefined access parameters and sending the updated access parameters to the mobile computing device.
Owner:SLINGSHOT IOT LLC
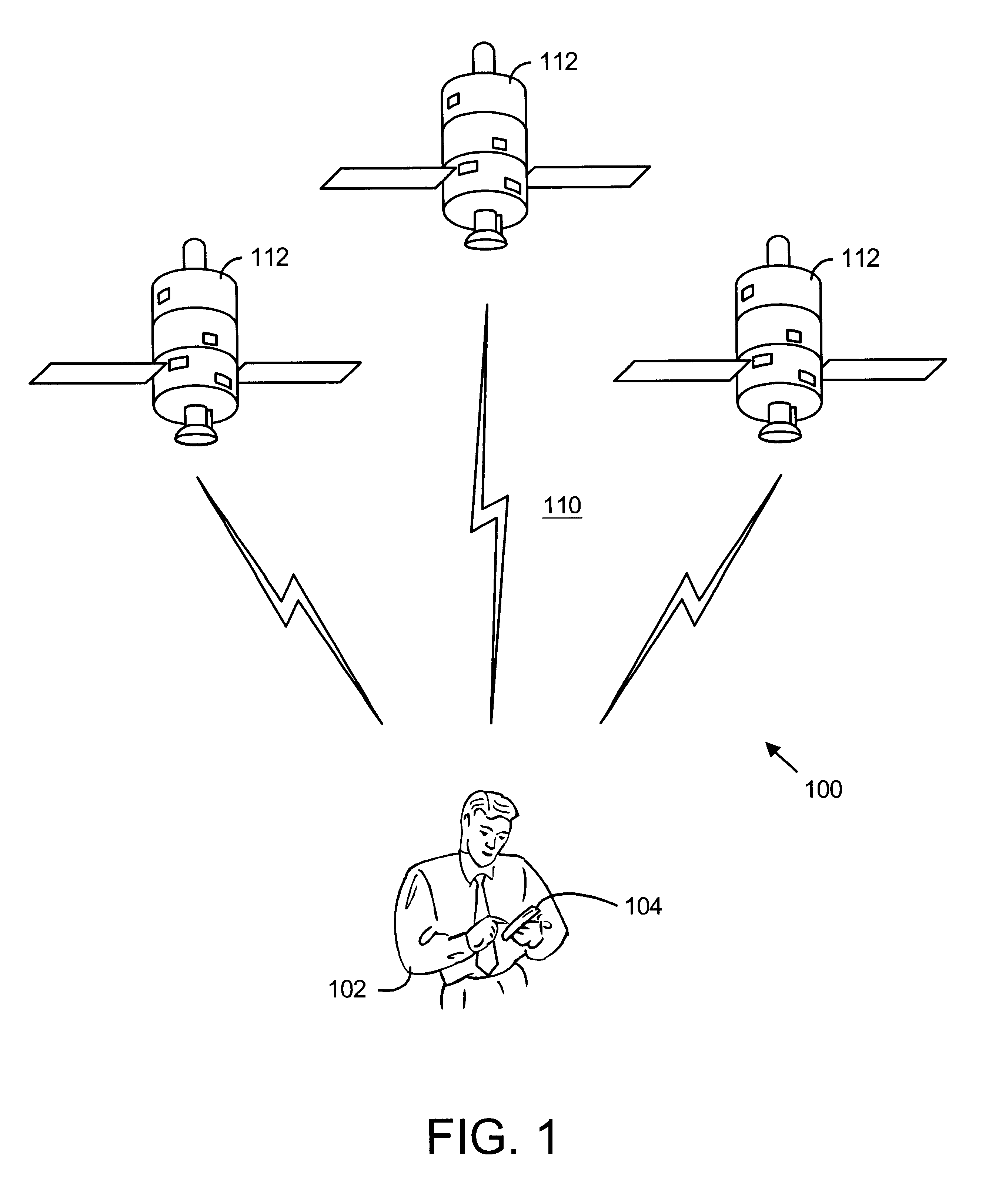
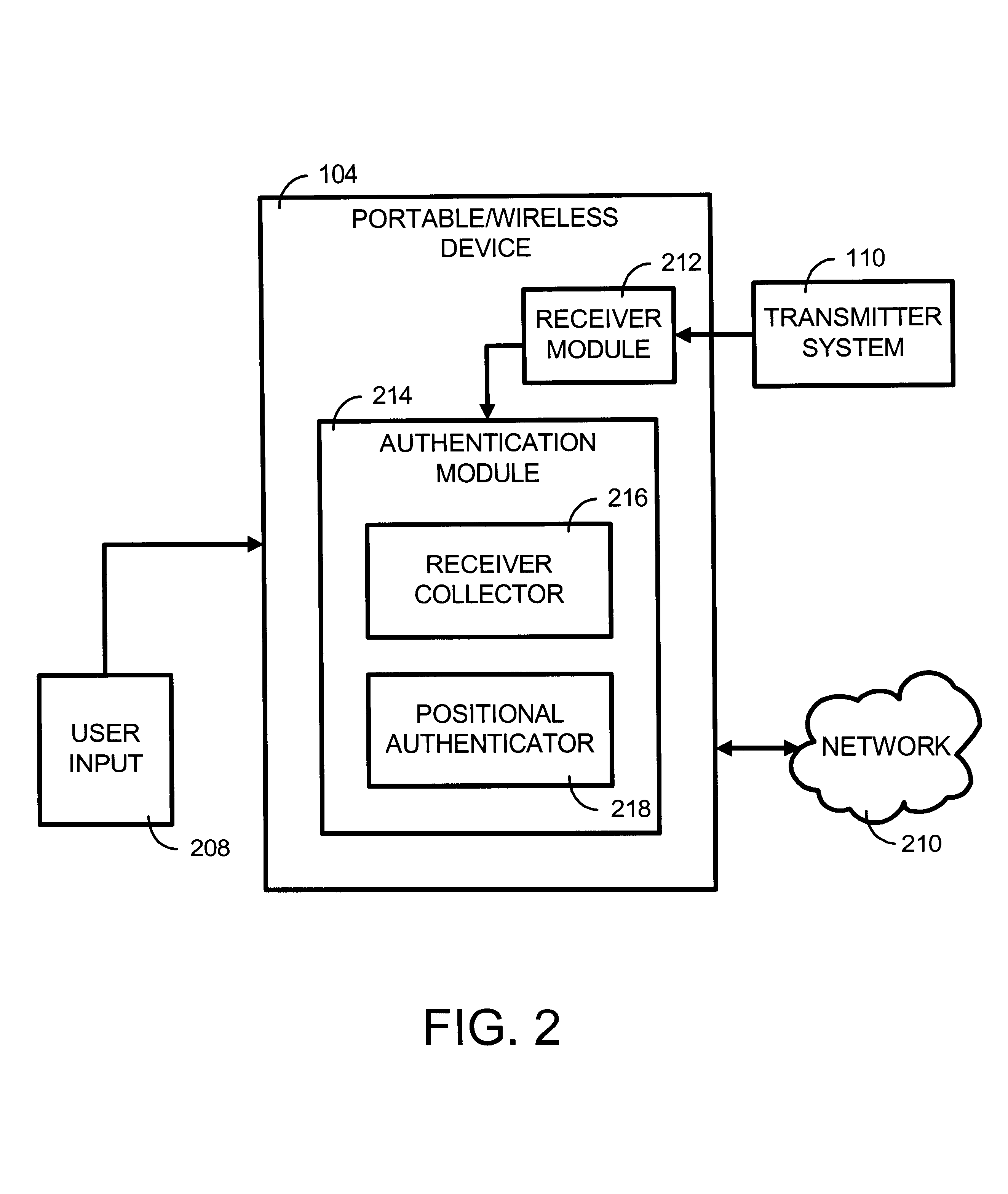
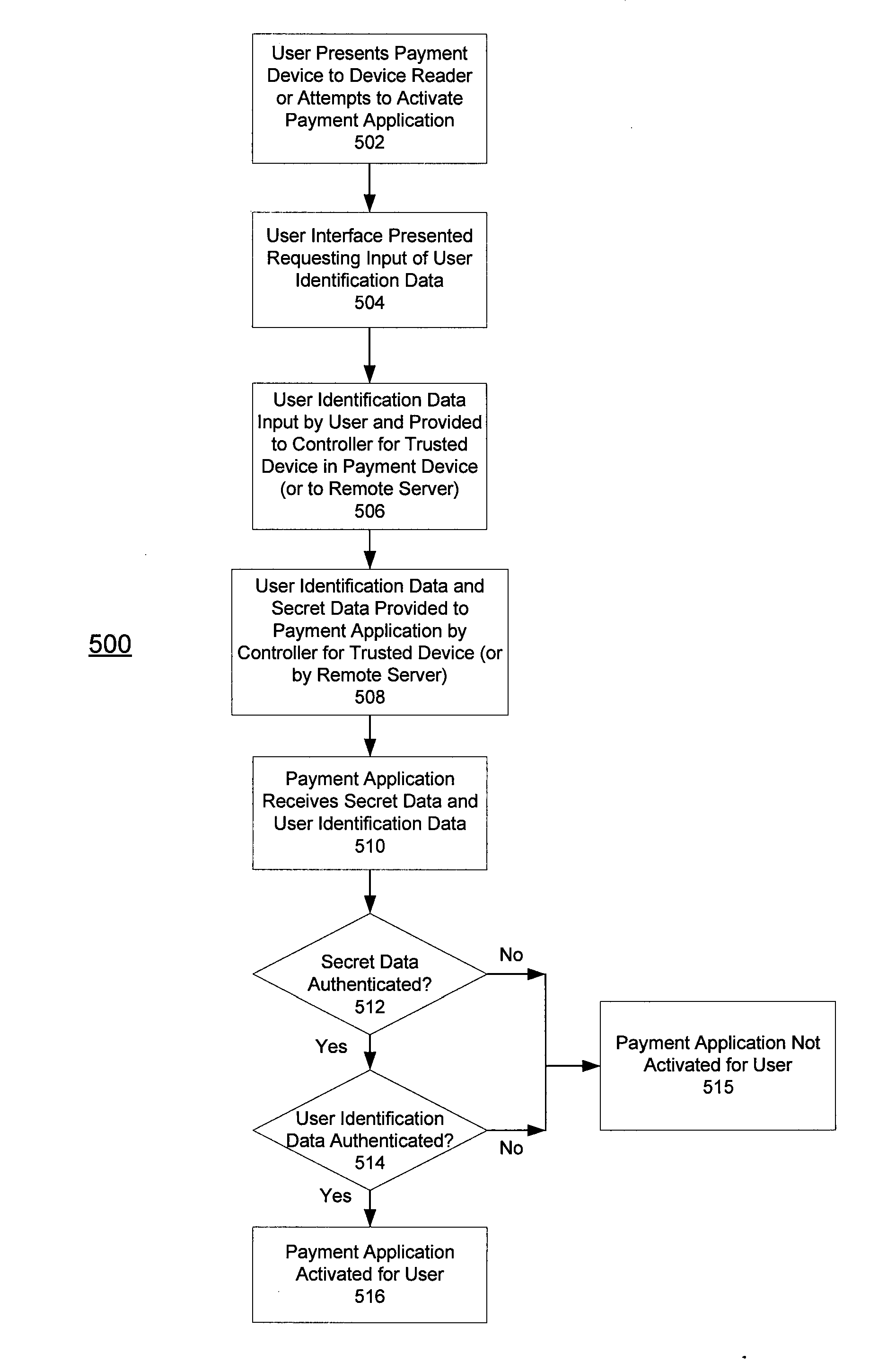
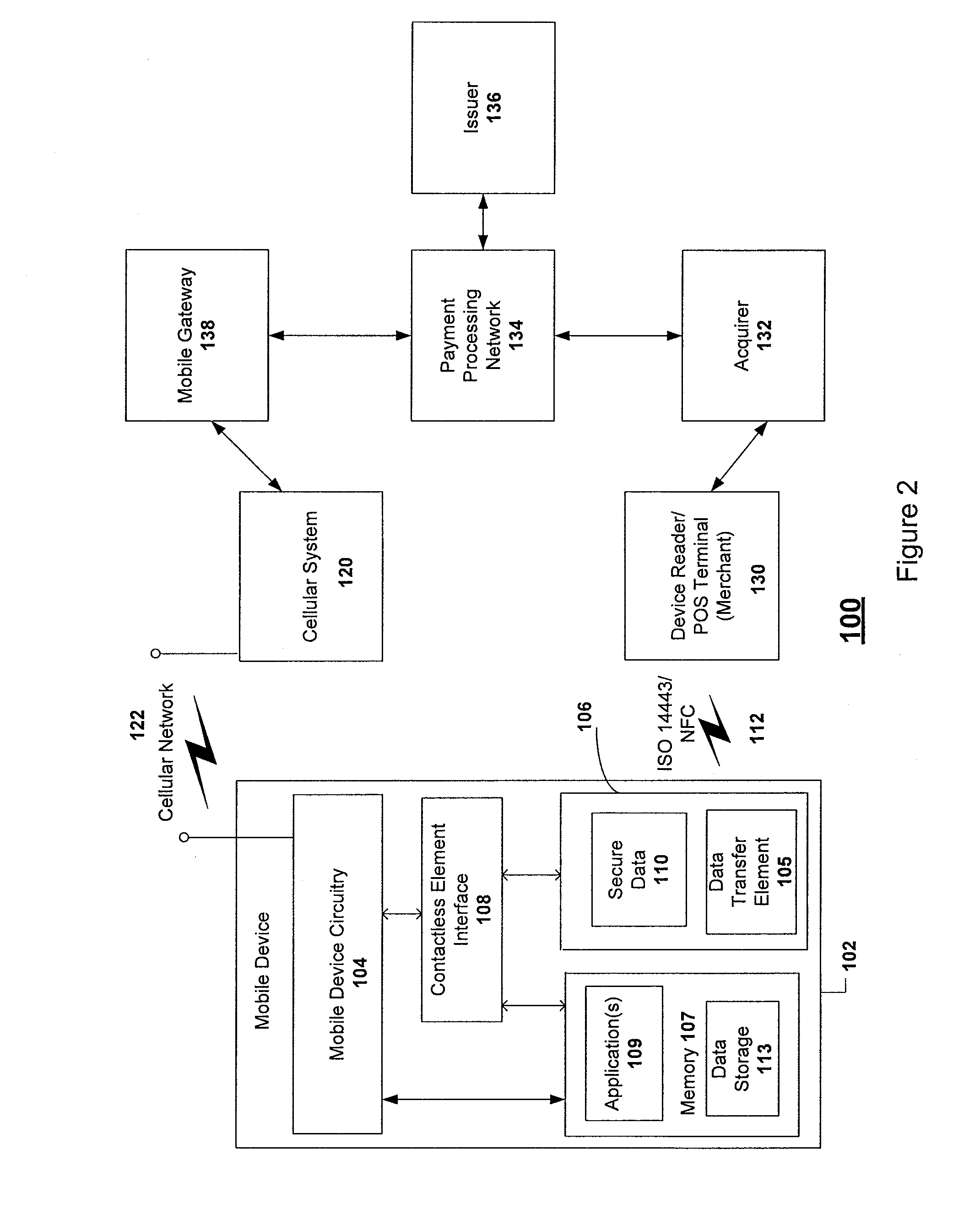
Apparatus and method for preventing unauthorized access to payment application installed in contactless payment device
InactiveUS20100217709A1Prevent unauthorized accessEffective attackFinancePoint-of-sale network systemsTransaction dataApplication software
A system, apparatus, and method for preventing the unauthorized access to a payment application installed on a mobile payment device, or to transaction data stored in the device. The mobile payment device may be a mobile phone that includes a contactless element (such as a contactless smart chip) and that is capable of communication and data transfer using a wireless communications network and a near field communications capability. Unauthorized access to the payment application is prevented by requiring that access control data be received from a trusted source, such as a controller or application in charge of managing inputs from a phone keypad, in order to activate the payment application or to access stored data.
Owner:VISA INT SERVICE ASSOC
Swivel recoiler
InactiveUS20080035778A1Efficiently pulledUnbalanced blockTravelling carriersHoldersFree rotationEngineering
A recoiler has a retractable cable with an attachment pad on the distal end of the cable for attachment to an item of merchandise. The cable is stored on a spring biased spool located within a recoiler housing. The housing is freely rotatably mounted on a post extending upwardly from a base plate secured to the spool housing by a fastener and adapted to be secured to a support structure.
Owner:INVUE SECURITY PROD INC
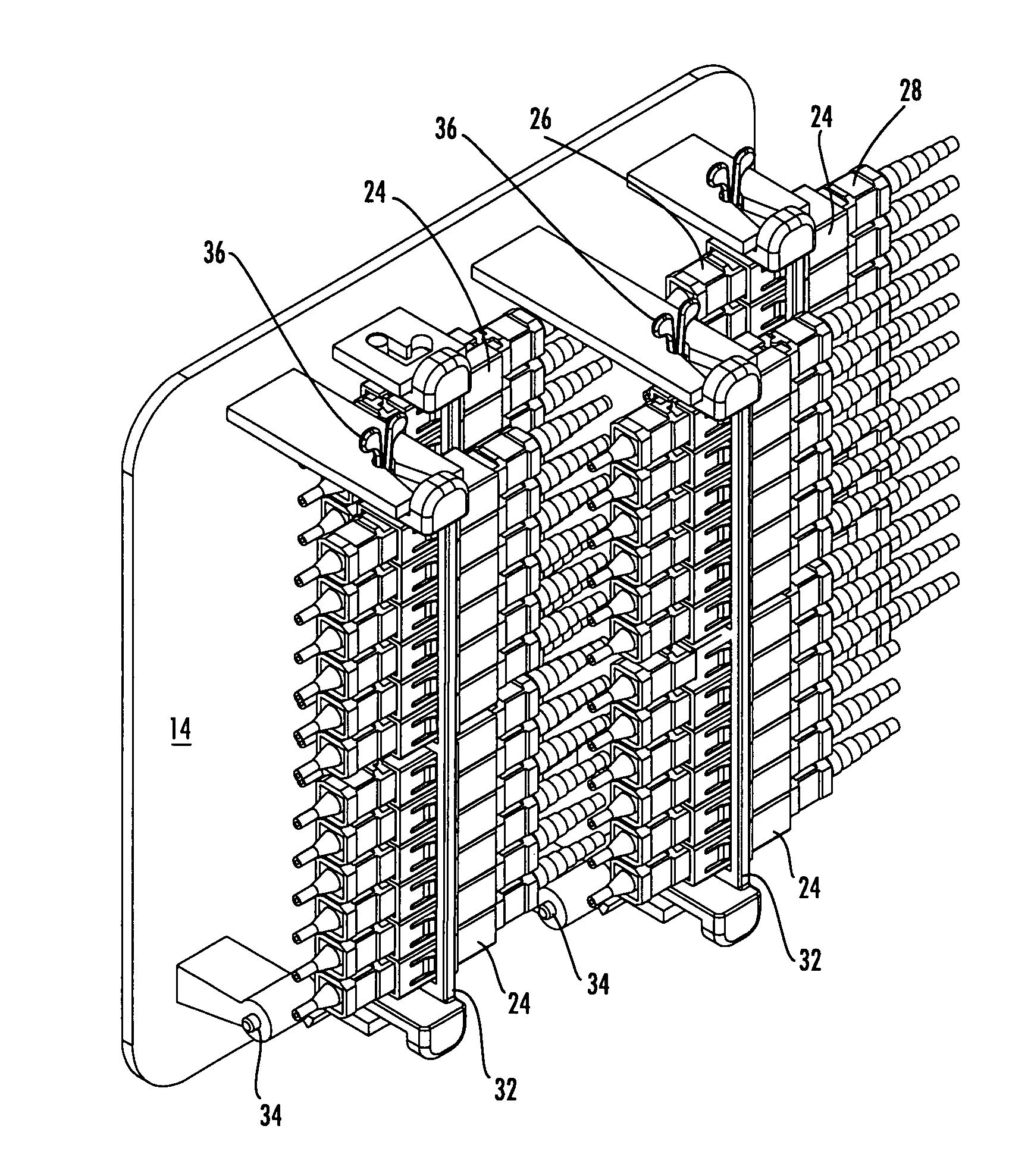
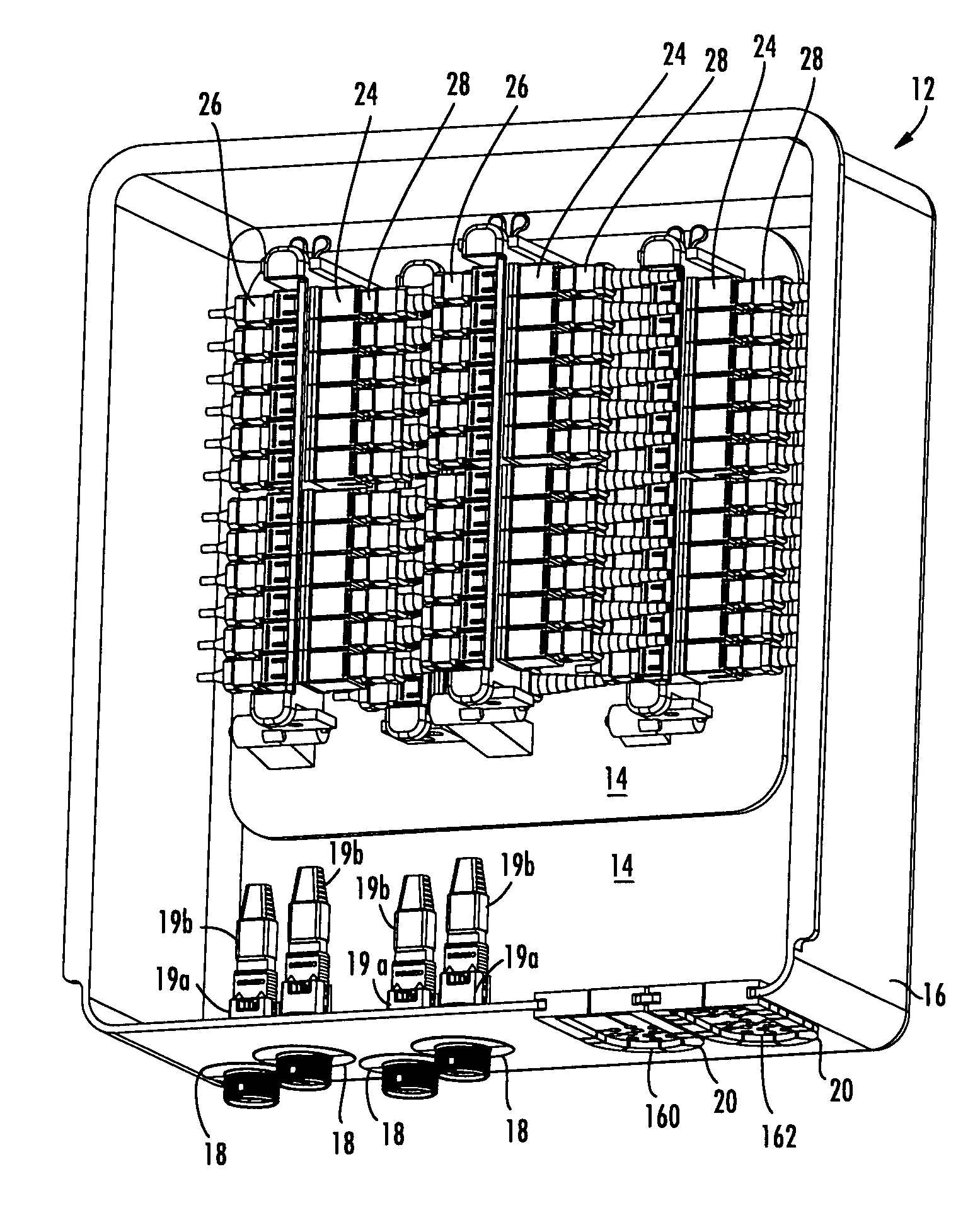
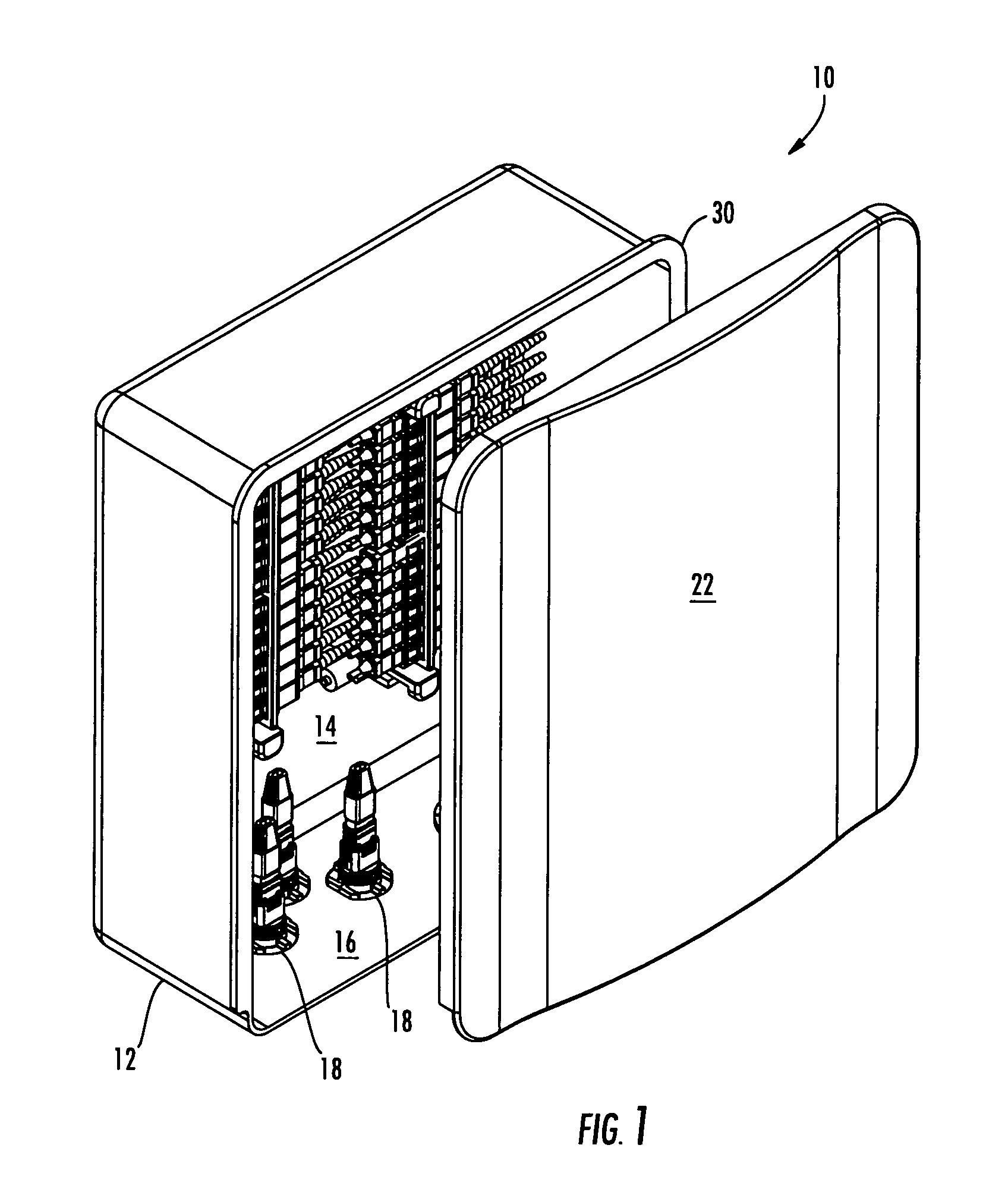
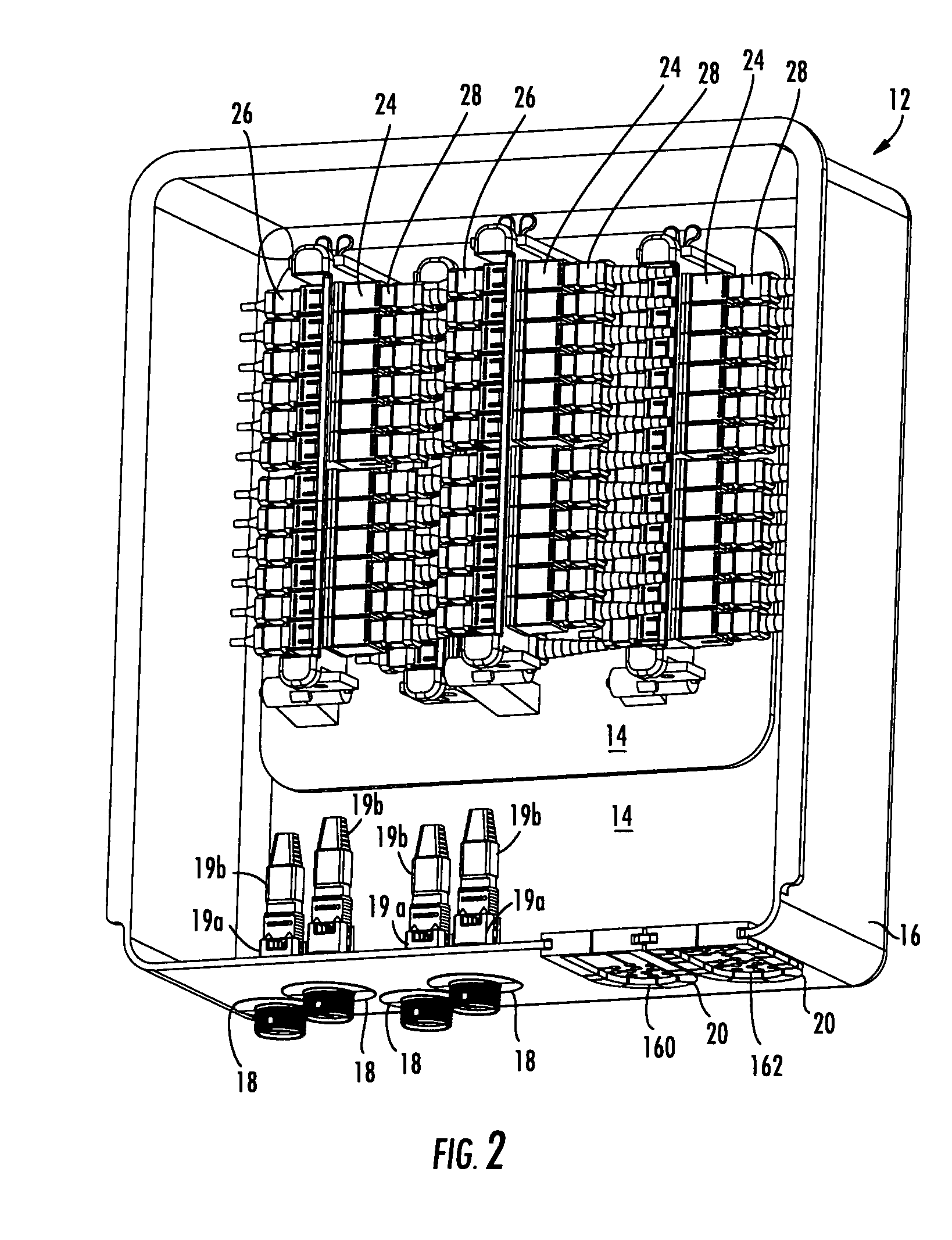
Fiber optic drop terminals for multiple dwelling units
InactiveUS20080205843A1Small “ footprint ”Convenient and secure accessCoupling light guidesSelection arrangementsFiberEngineering
There is provided fiber drop terminals (“FDTs”) and related equipment for providing selective connections between optical fibers of distribution cables and optical fibers of drop cables, such as in multiple dwelling units. The FDTs require relatively little area and / or volume while providing convenient connectivity for a relatively large number of optical connections. The FDTs include adapters for optically connecting the connectors, and the adapters of some FDTs are adapted to rotate, move, or otherwise be removed to provide convenient access for technicians. Some FDTs and the related equipment are adapted for use with microstructured optical fiber having preferred bend characteristics.
Owner:CORNING OPTICAL COMM LLC
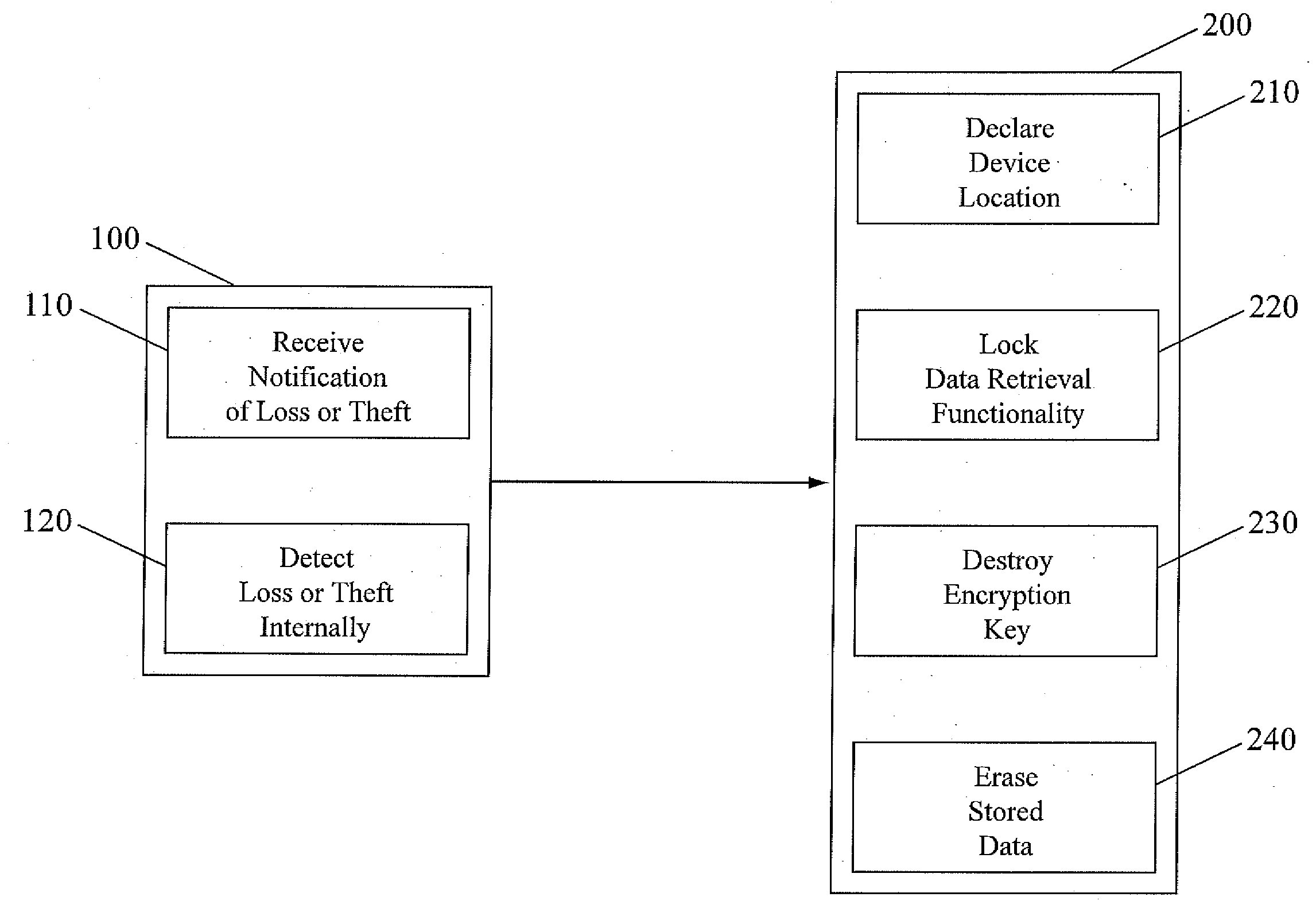
Method and apparatus for protecting data in a portable electronic device
ActiveUS20080034224A1Prevent unauthorized accessKey distribution for secure communicationVolume/mass flow measurementSpecific functionService provision
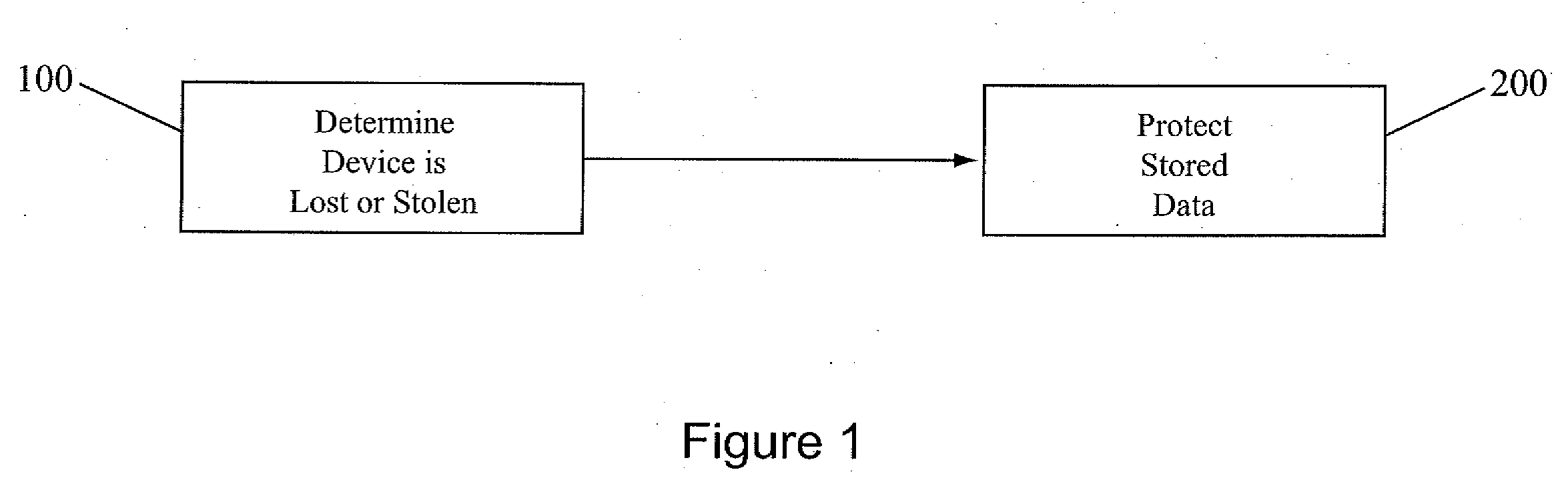
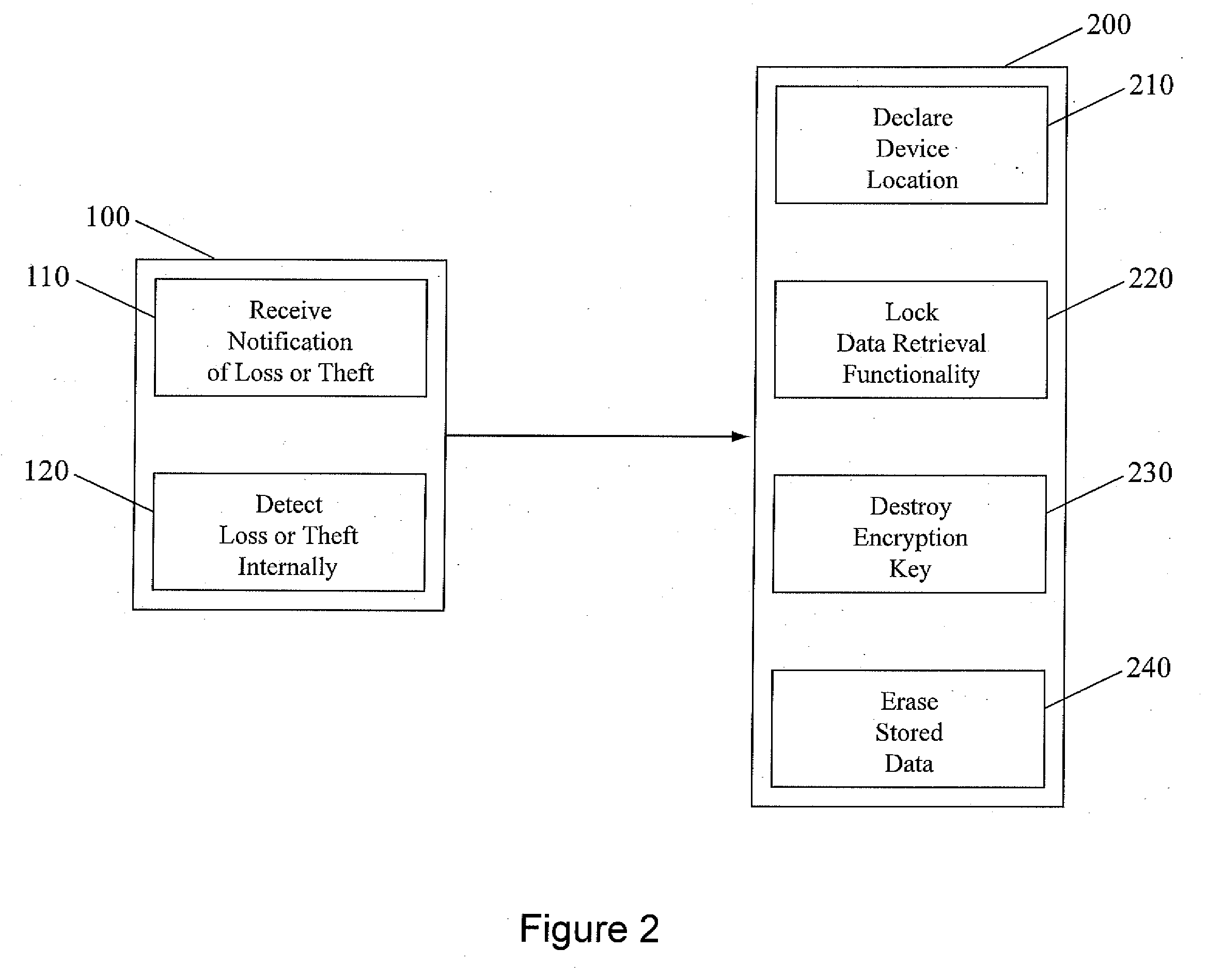
Data in a portable electronic device is protected by using external and internal status detection means to determine if the device is misplaced, lost, or stolen. The device then takes, singly or in combination, one of several actions to protect the data on the device, including declaring its location to an owner or service provider, locking the device or specific functions of the device to disable all data retrieval functionality, erasing or overwriting all the stored data in the device or, where the data has been stored in the device in an encrypted format, destroying an internally-stored encryption key, thereby preventing unauthorized access to the encrypted data in the device.
Owner:APPLIED MINDS
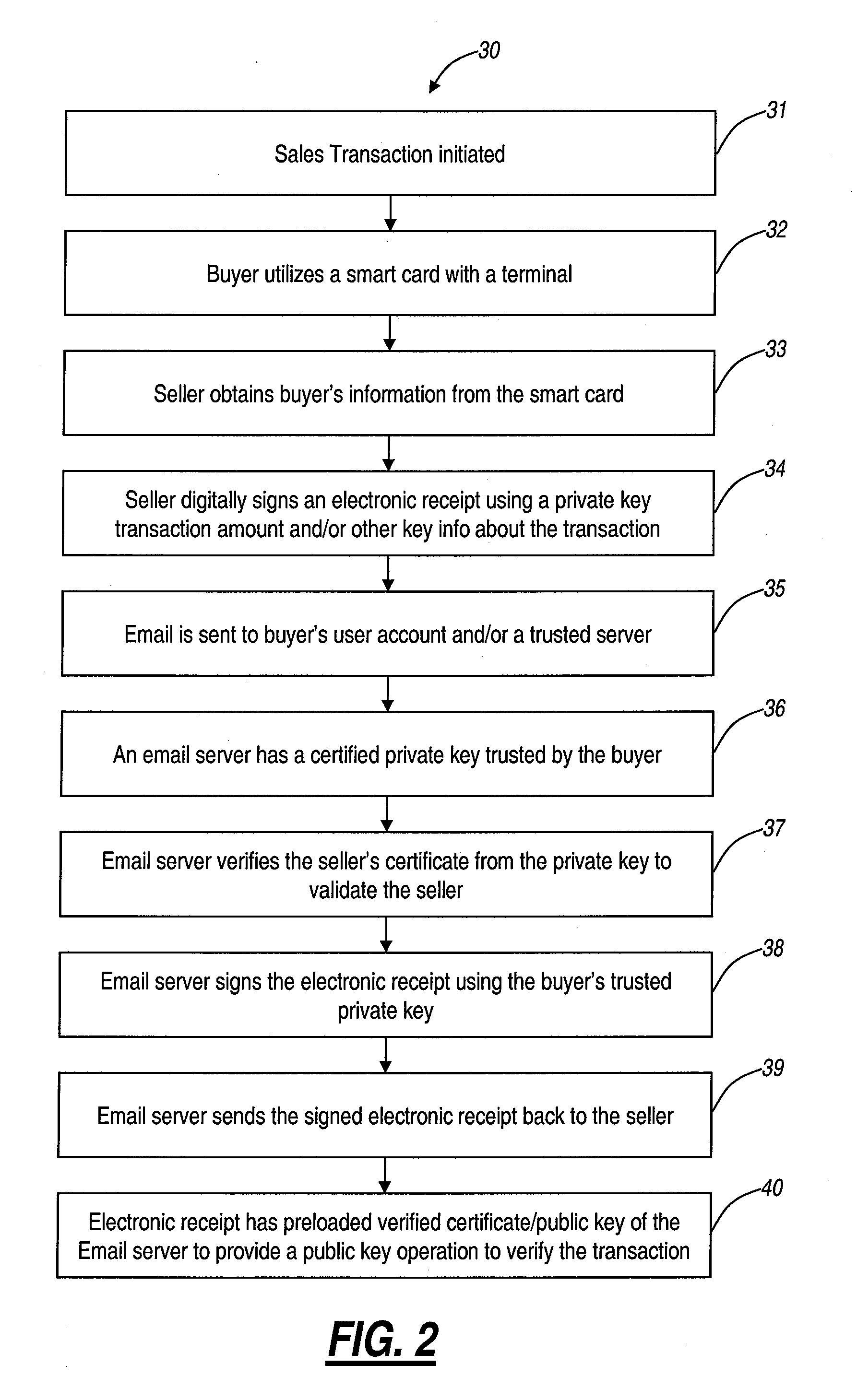
Secure electronic receipt systems and methods
InactiveUS20110137803A1Prevent unauthorized accessHand manipulated computer devicesFinanceDigital signaturePaper based
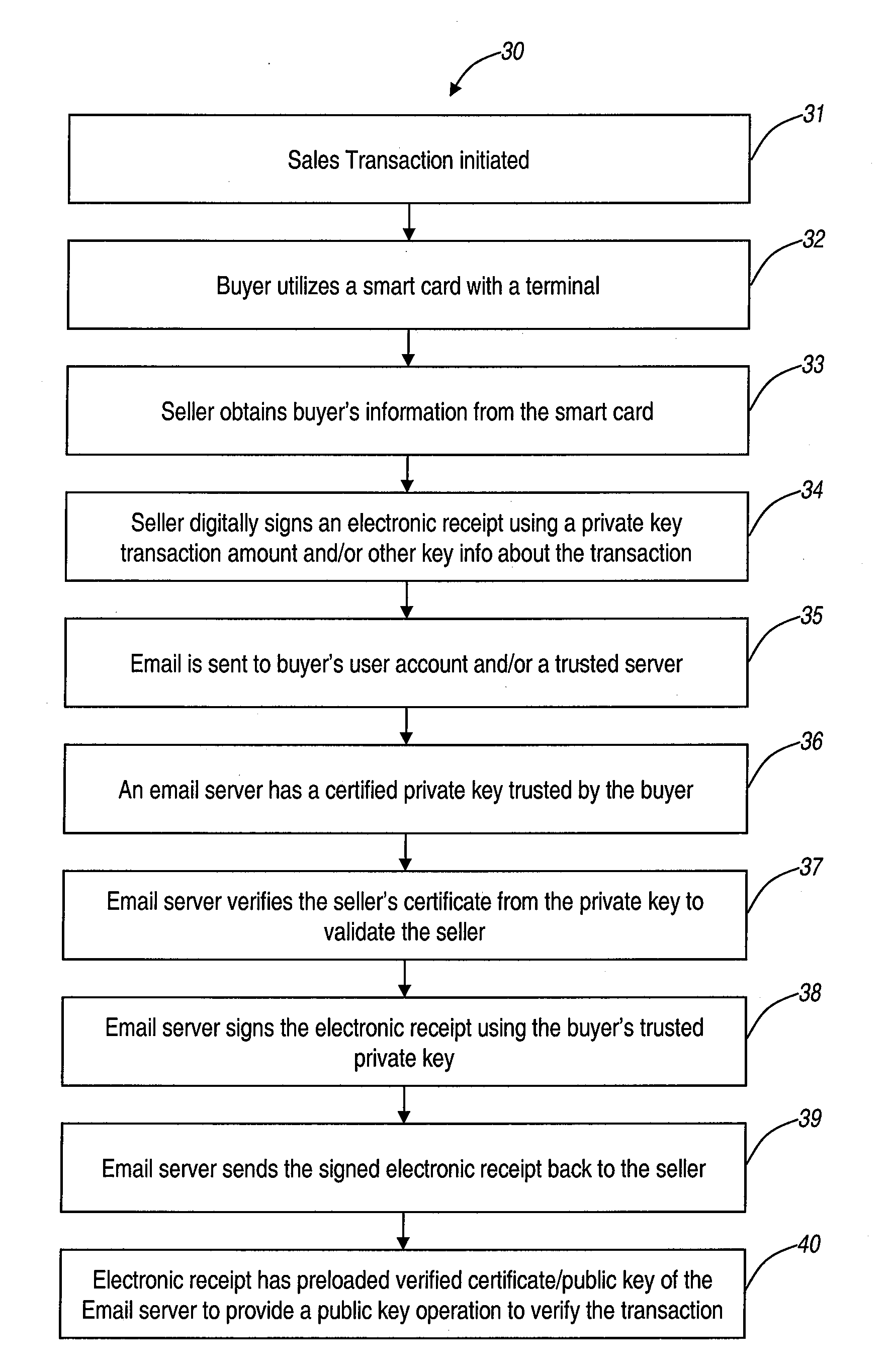
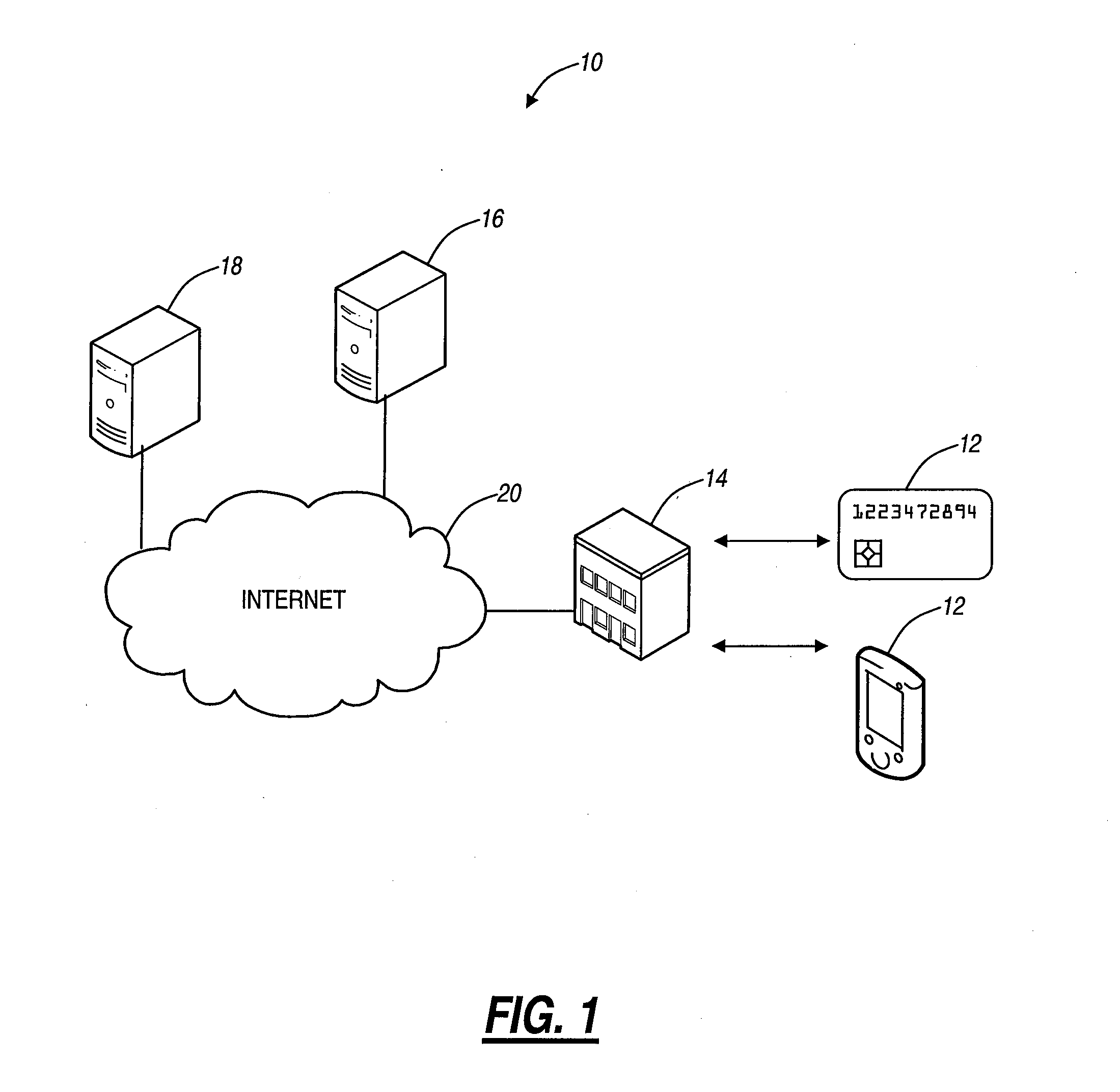
The present disclosure relates to secure electronic receipt systems and methods. The present invention removes the need for paper-based receipts while preserving security through use of a digital signature on each electronic receipt verifying the transaction and other data related to the transaction. In an exemplary embodiment, the present invention includes a trusted email server, an authentication server, a point-of-sale (POS) terminal or the like, and a smart card or the like. A buyer can utilize the smart card to instruct the terminal to provide an electronic receipt. The terminal can utilize the trusted email server and the authentication server to digitally sign the electronic receipt with credentials trusted by the buyer, and these credentials can later be utilized to verify the electronic receipt.
Owner:SYMBOL TECH LLC
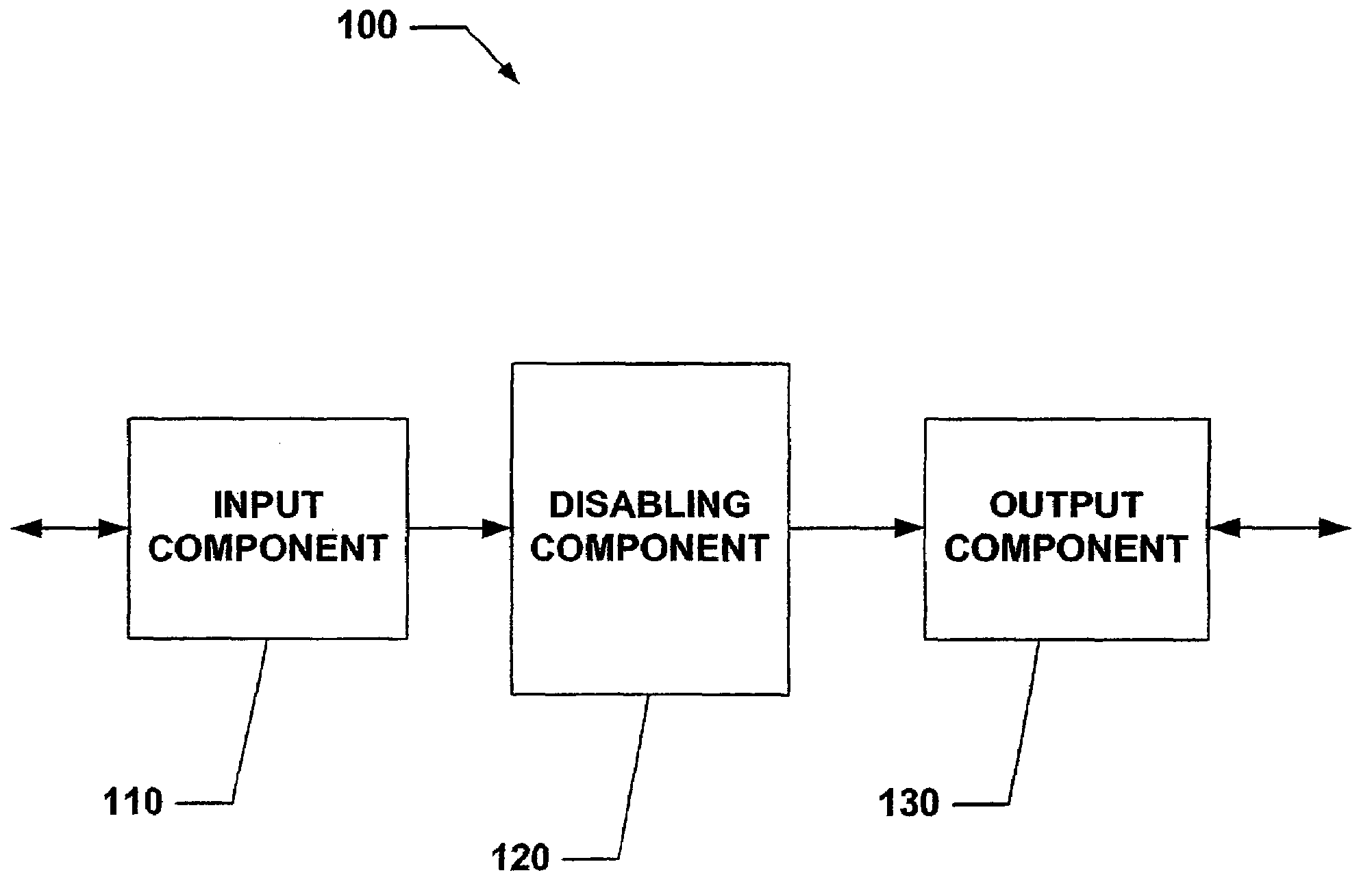
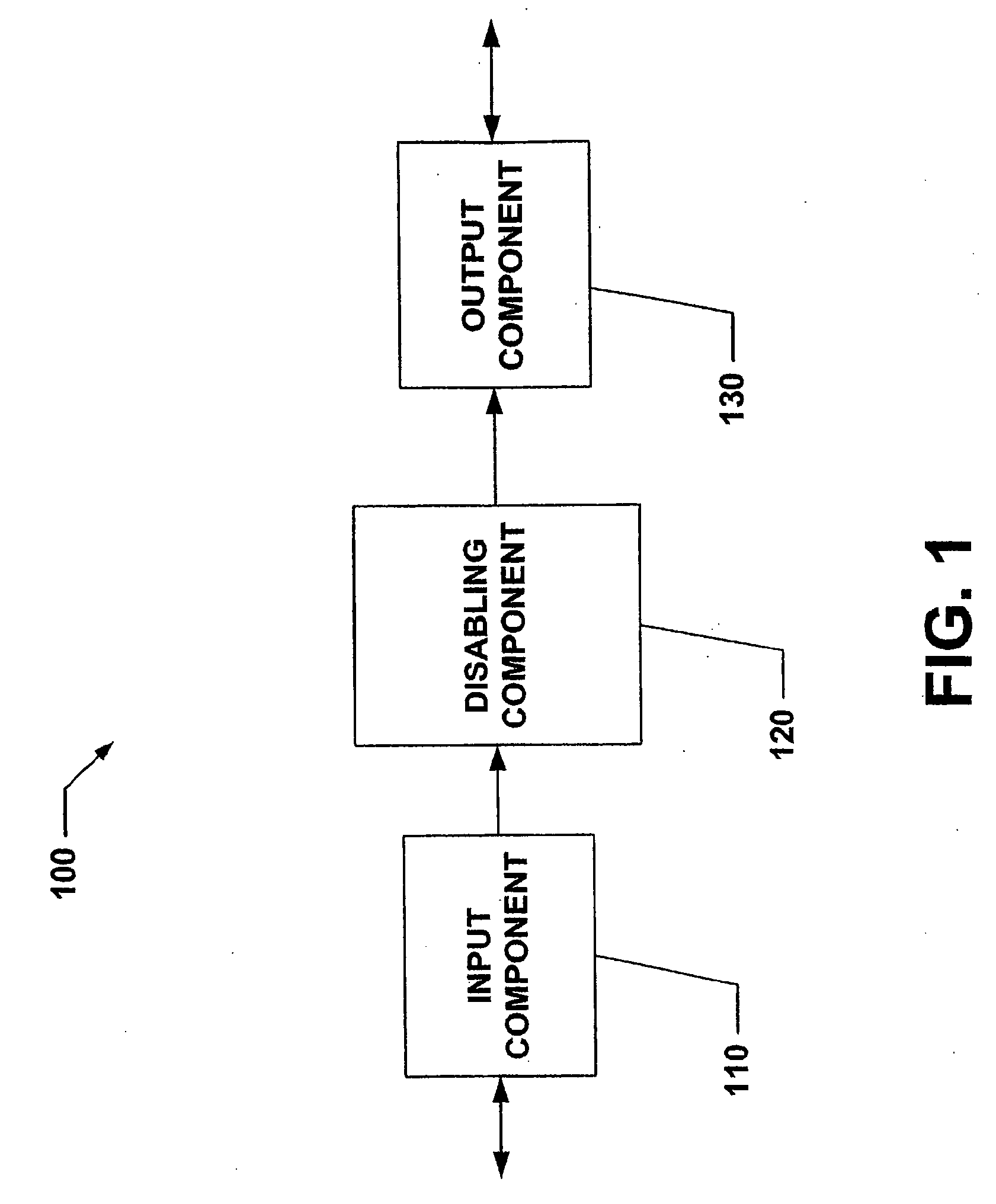
System and Method for Limiting Mobile Device Functionality.
ActiveUS20080233919A1Reduce harmPrevent unauthorized accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCredit cardInternet privacy
The present invention relates to systems and methods that employ various mechanisms to selectively disable mobile device functionality. In general, mobile devices can be utilized to store personal and / or highly sensitive information such as bank account numbers, social security numbers, credit card numbers and the like. If the mobile device is lost or stolen, data stored within the device can be accessed by an unauthorized user; and, thus, any personal and / or highly sensitive information can be obtained. In order to mitigate unauthorized access, the subject invention provides a disabling component that communicates with the lost or stolen device to render data stored thereon inaccessible. Further, the data can be stored in local or remote locations to backup stored information, thereby creating a more robust and reliable method of storing information important to the device owner. These features provide enhancements over conventional mobile device security techniques.
Owner:NOKIA TECH OY
Information delivery system, information delivery method, information delivery server, content delivery server and client terminal
InactiveUS7269601B2Automatically generating a digest of dynamic contentStable deliveryTelevision system detailsVideo data indexingWorld Wide WebData bank
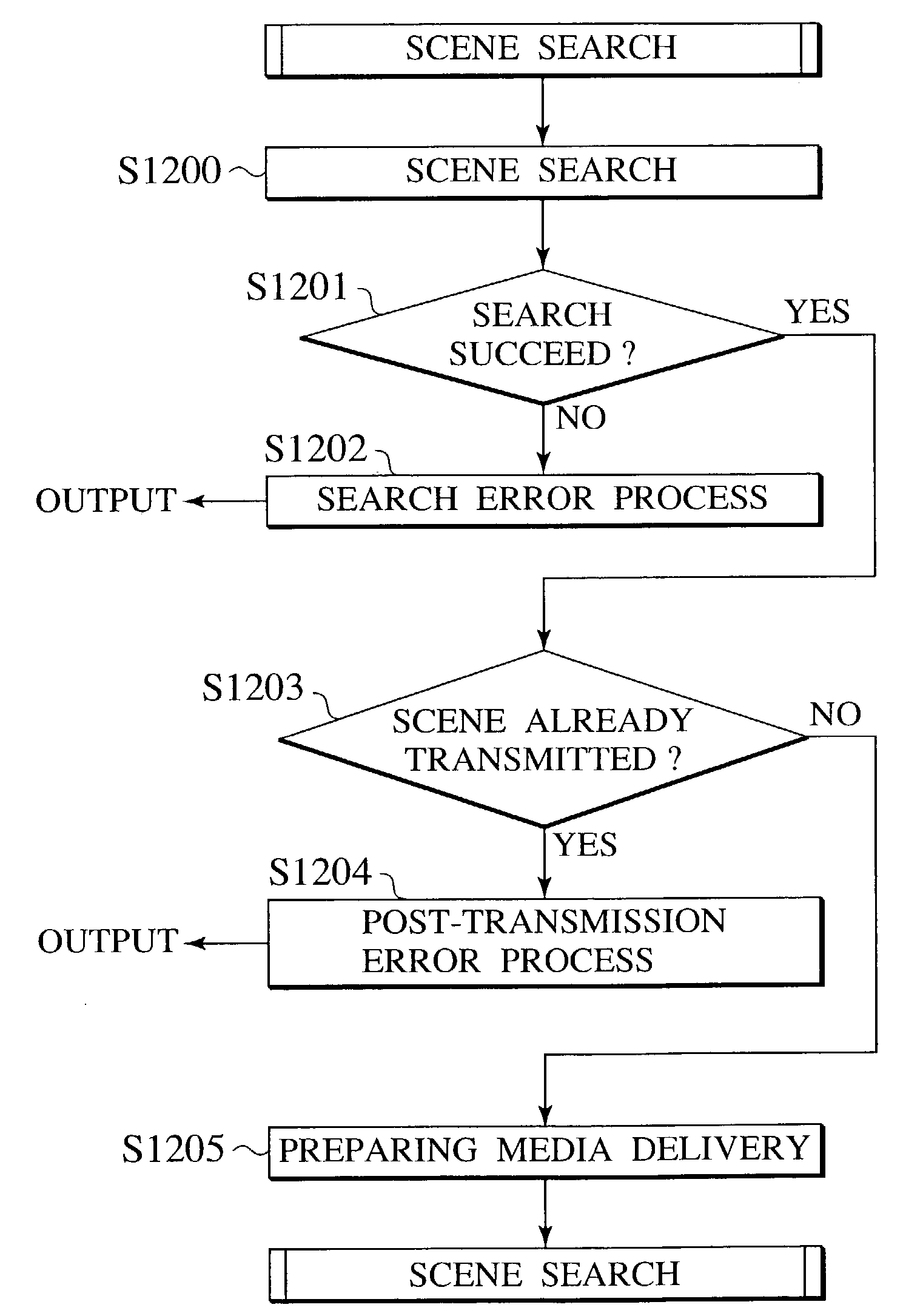
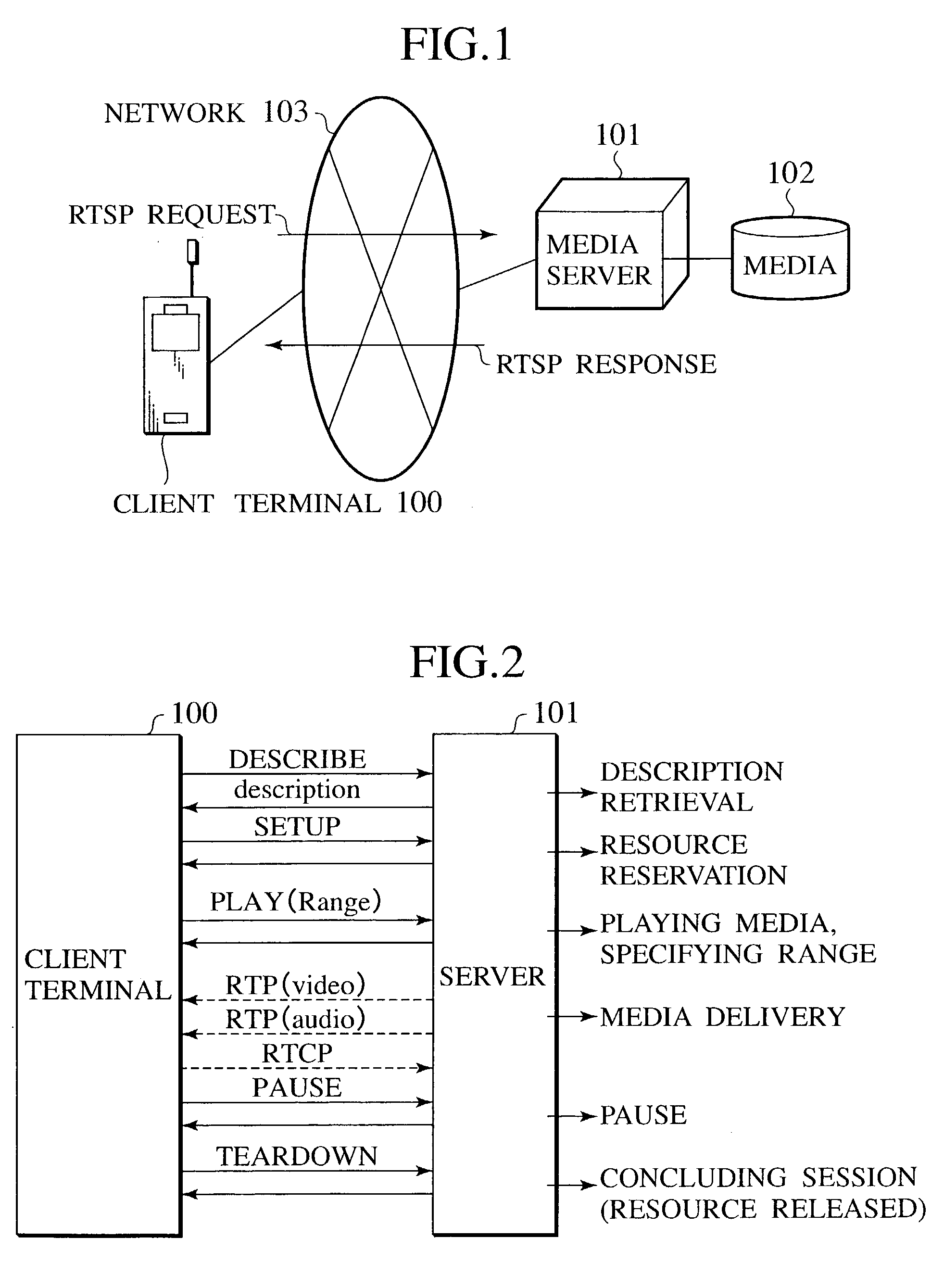
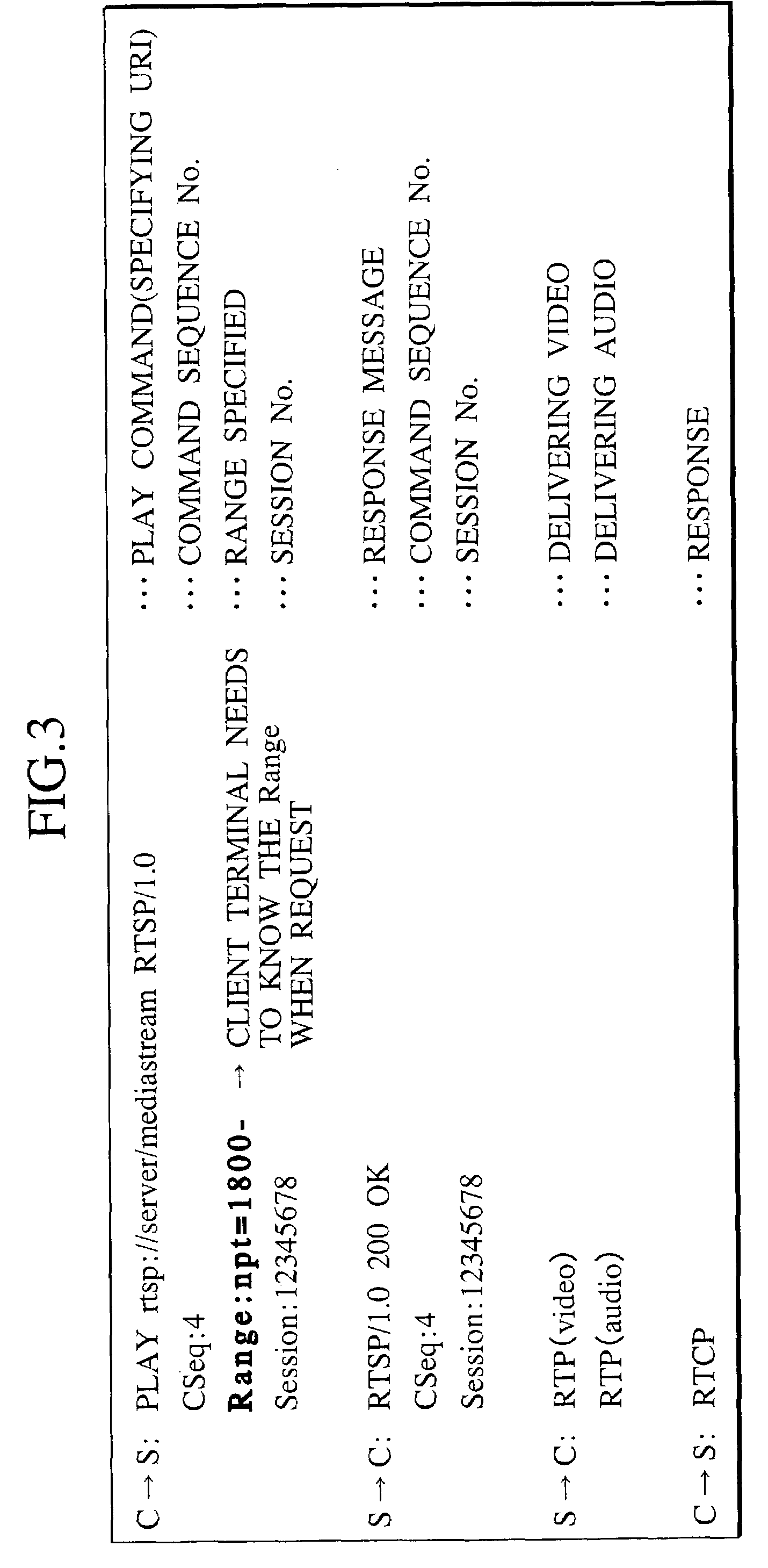
The information delivery system is configured with a media database 1009 which stores media data, a sequence information database 1008 which stores sequence information for specifying the address of media data to deliver, a scene searcher 1005 which verifies the sequence information according to a request of the controlling media received from client terminal 1000 and retrieves appropriate media data from the media database 1009 starting from a prescribed point based on a result of the verification, and an output unit 1006 which delivers the retrieved media data to the client terminal 1000.
Owner:NTT DOCOMO INC
Fiber optic drop terminals for multiple dwelling units
InactiveUS7499622B2Small “ footprint ”Convenient and secure accessOptical light guidesSelection arrangementsFiberEngineering
There is provided fiber drop terminals (“FDTs”) and related equipment for providing selective connections between optical fibers of distribution cables and optical fibers of drop cables, such as in multiple dwelling units. The FDTs require relatively little area and / or volume while providing convenient connectivity for a relatively large number of optical connections. The FDTs include adapters for optically connecting the connectors, and the adapters of some FDTs are adapted to rotate, move, or otherwise be removed to provide convenient access for technicians. Some FDTs and the related equipment are adapted for use with microstructured optical fiber having preferred bend characteristics.
Owner:CORNING OPTICAL COMM LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com