Patents
Literature
1333 results about "Access management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Access management, Access control. When used in traffic and traffic engineering circles, this generally refers to the regulation of interchanges, intersections, driveways and median openings to a roadway. Its objectives are to enable access to land uses while maintaining roadway safety and mobility through controlling access location, design, spacing and operation. This is particularly important for major roadways intended to provide efficient service to through-traffic movements.
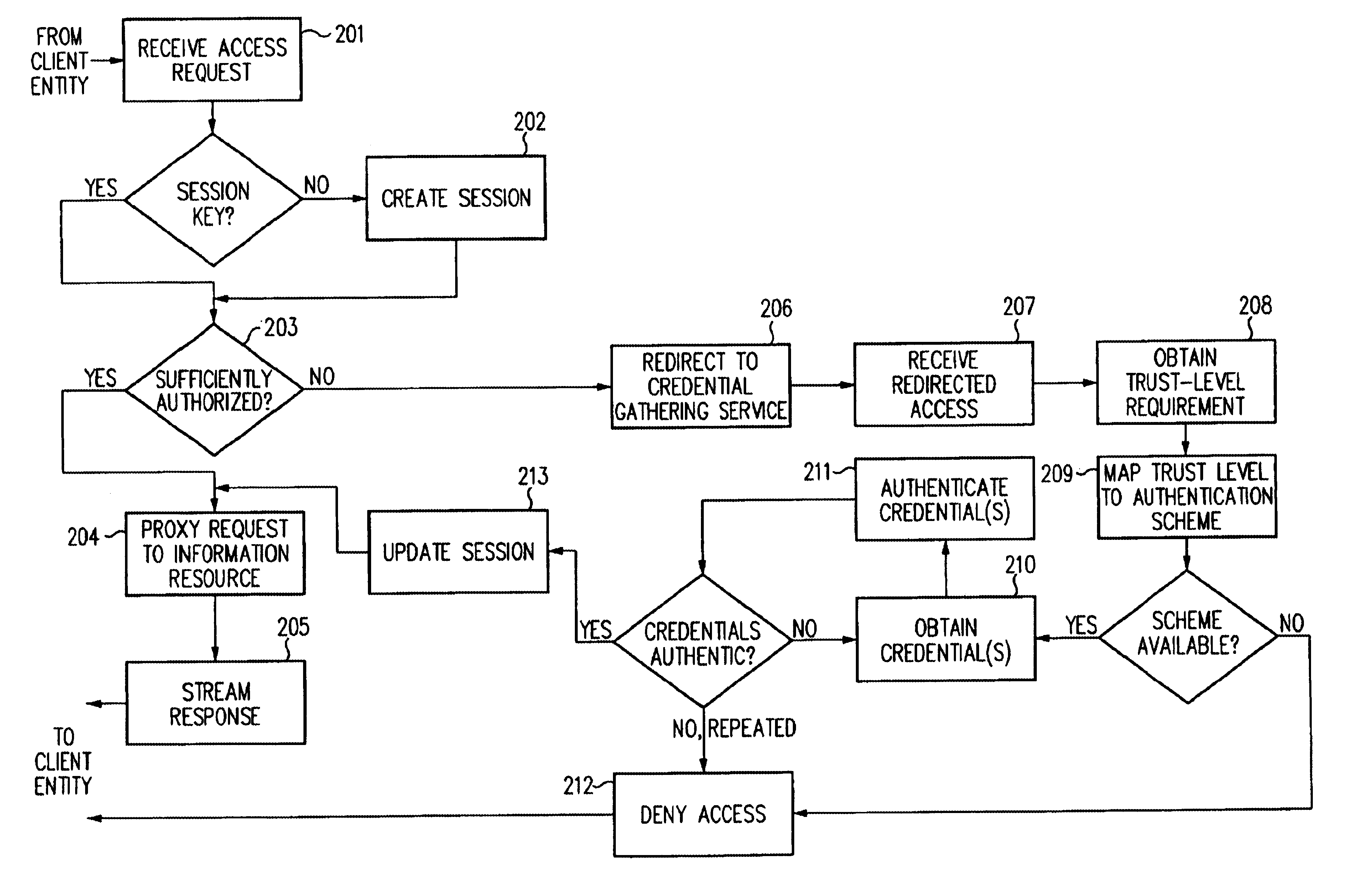
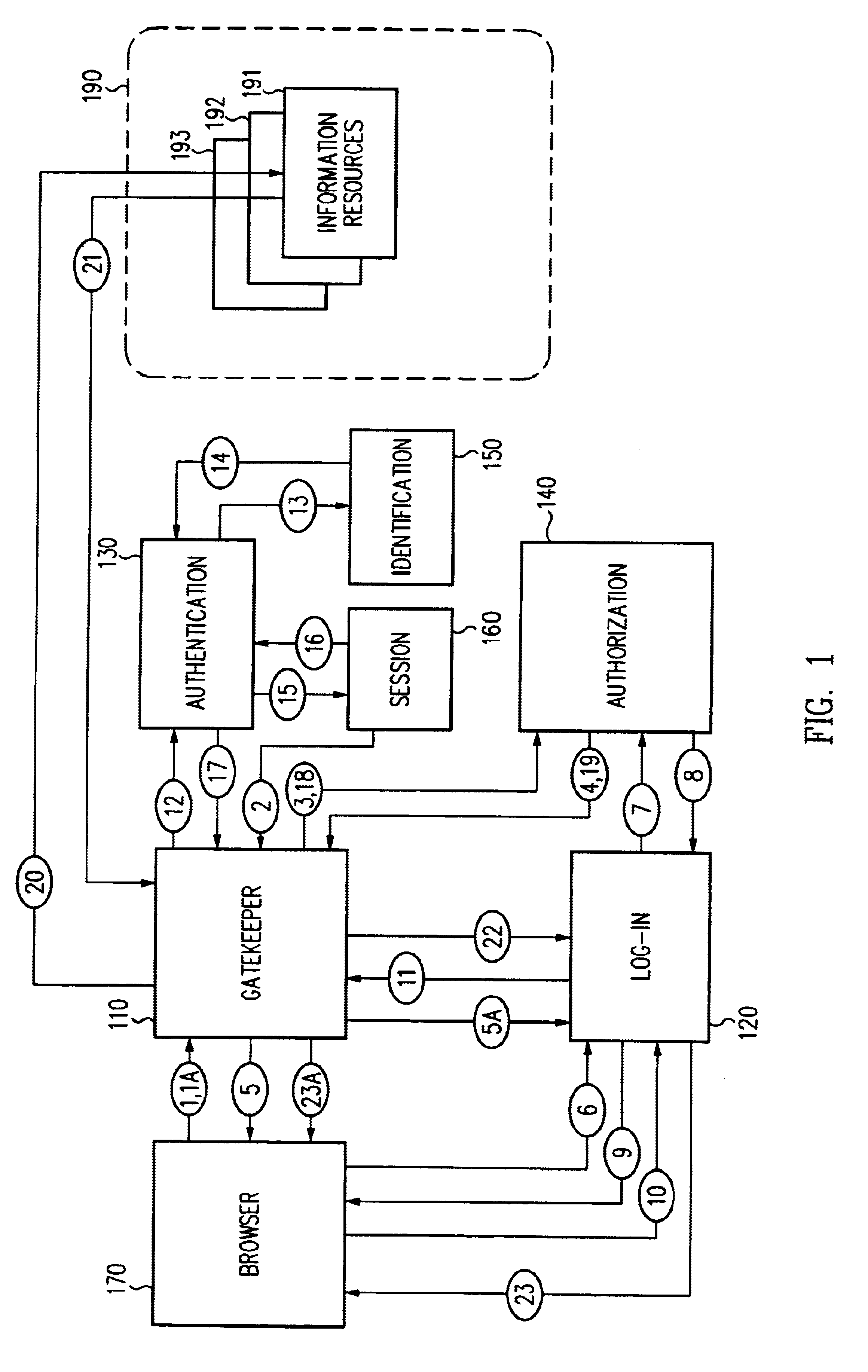
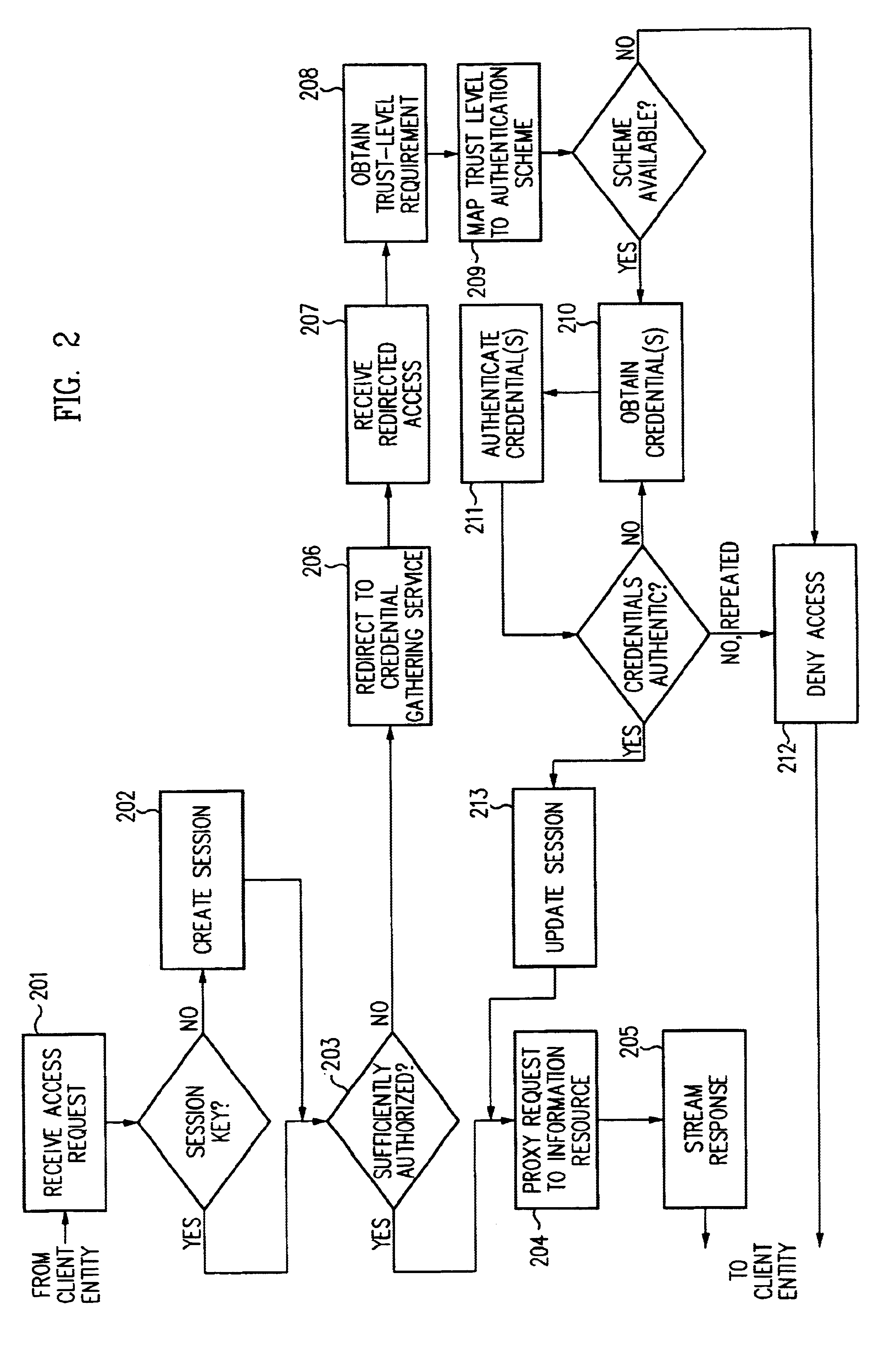
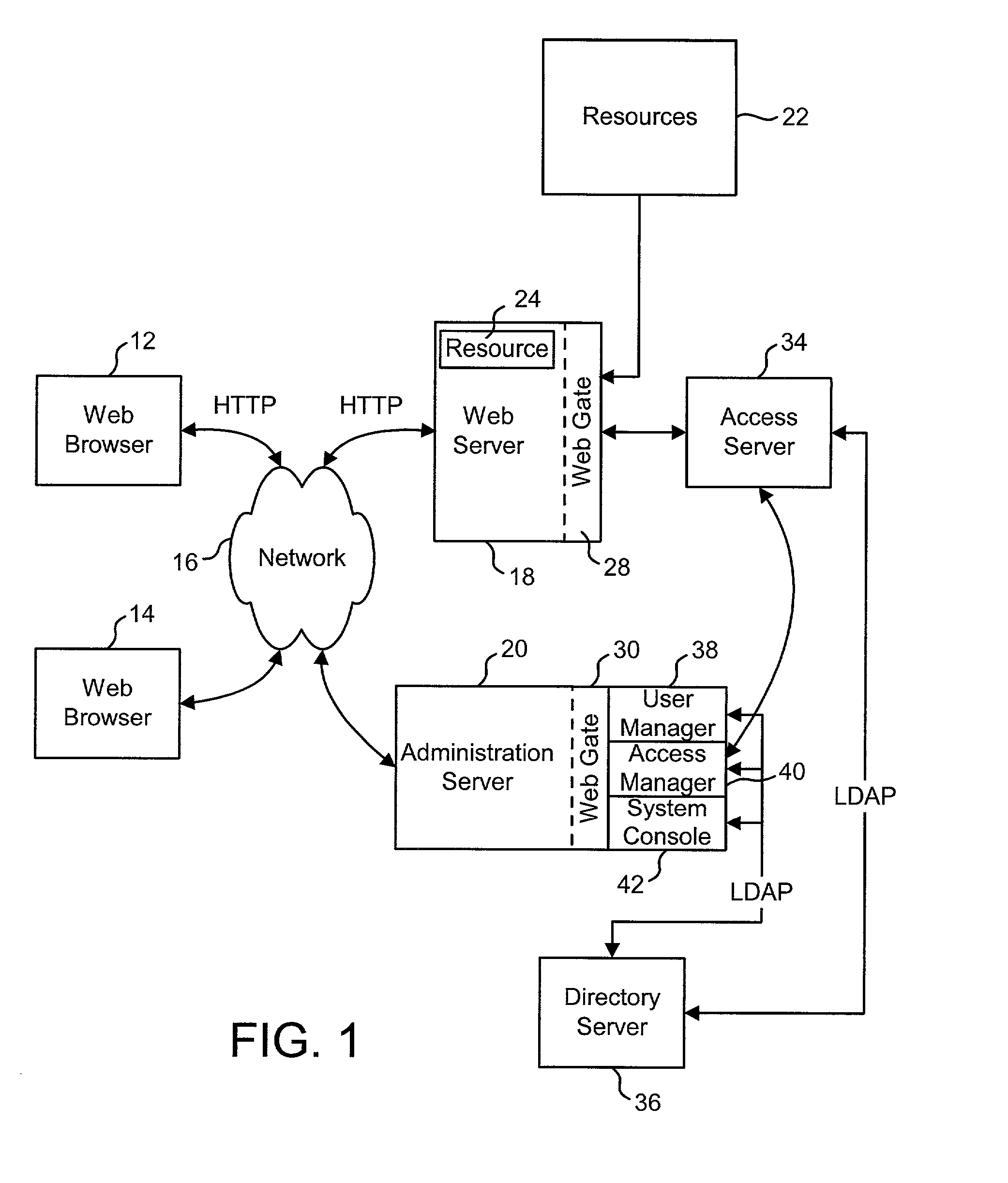
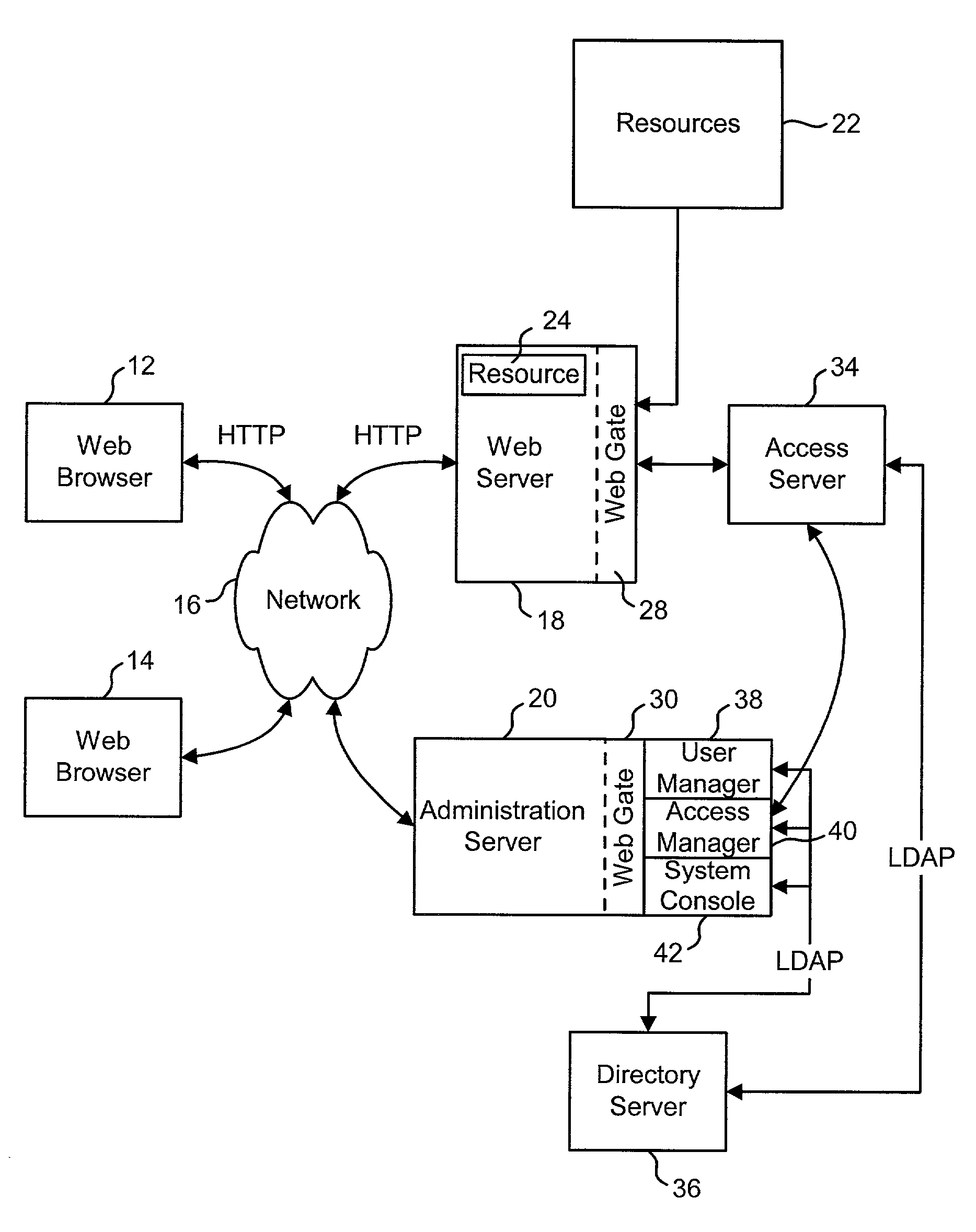
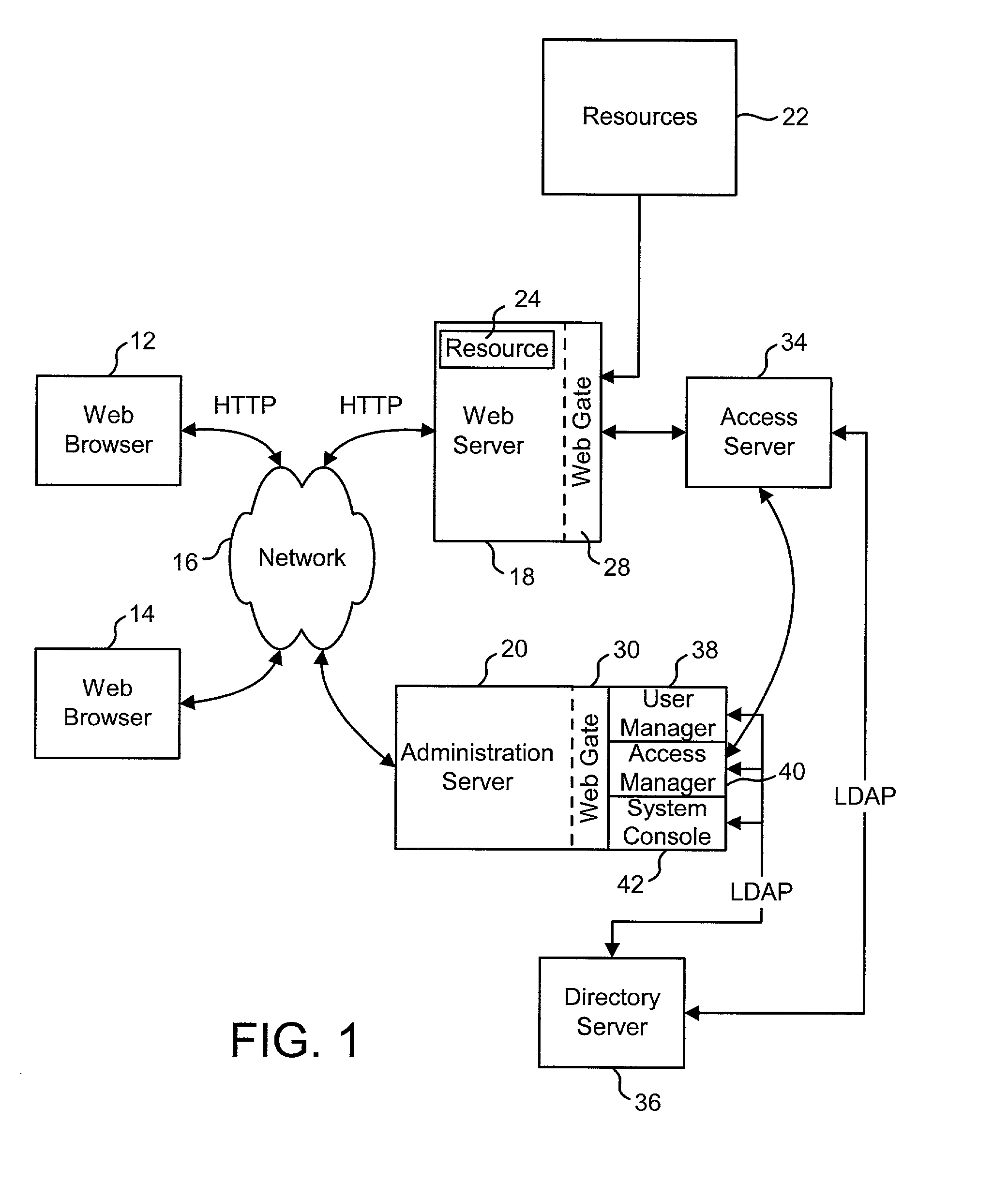
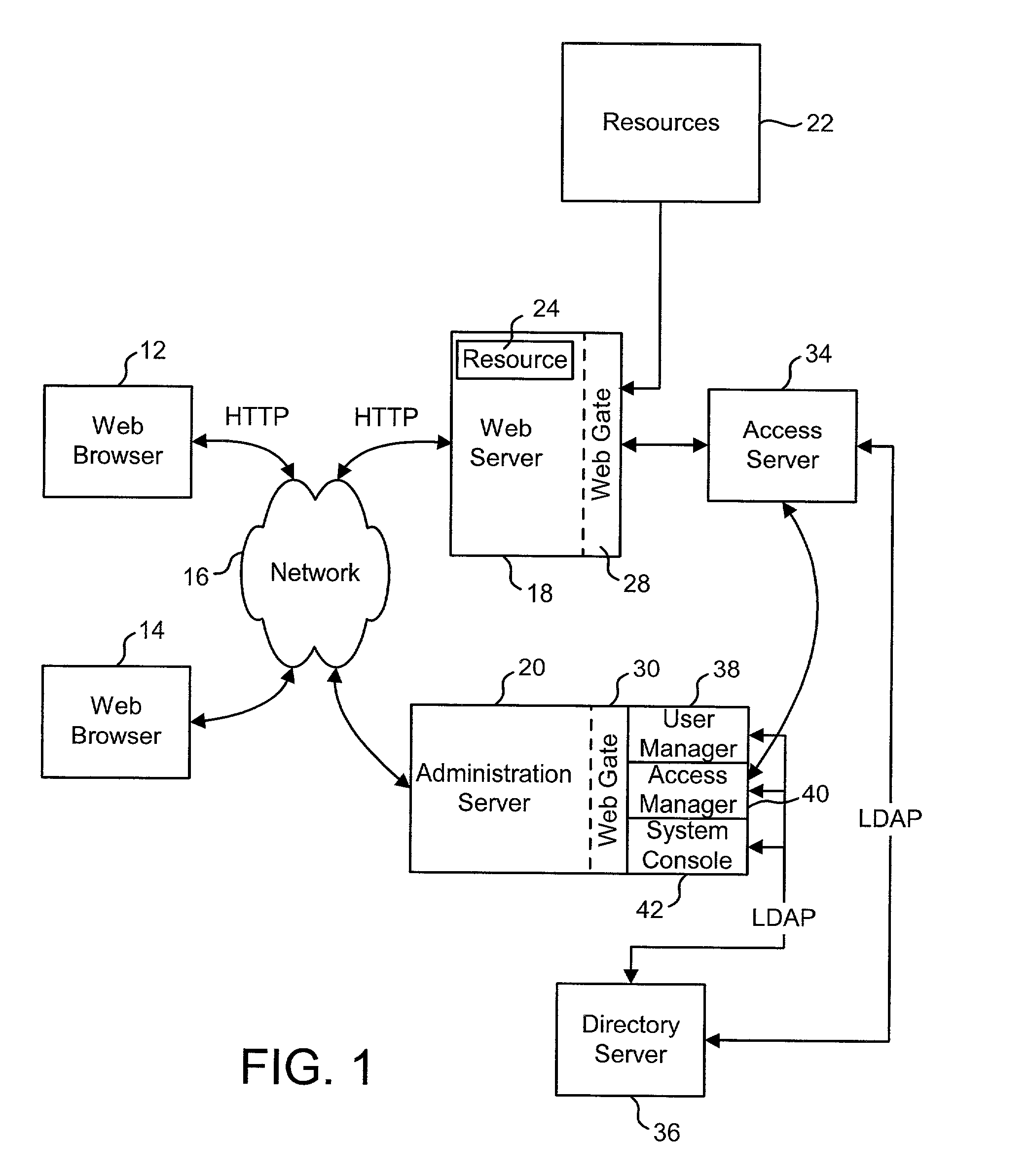
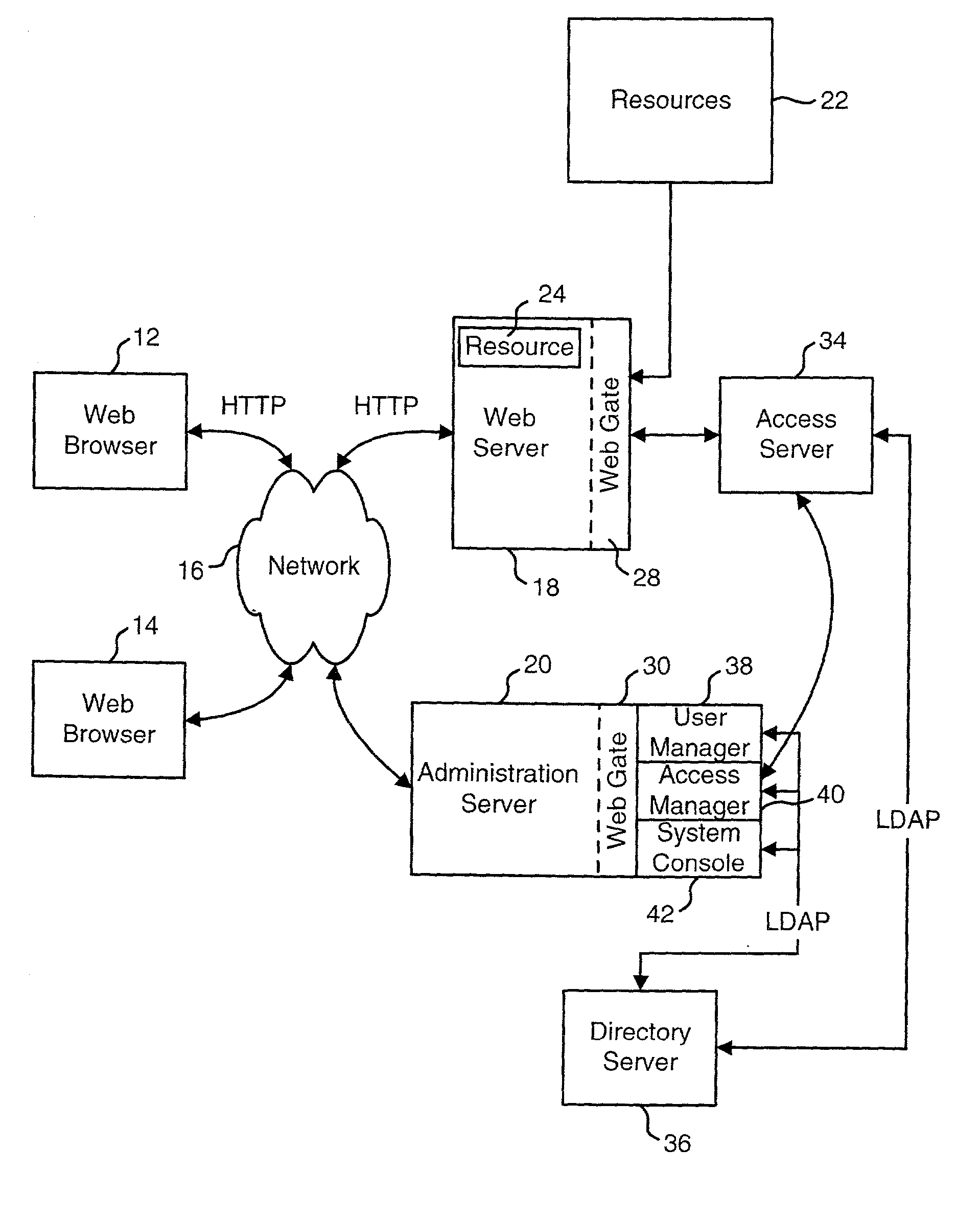
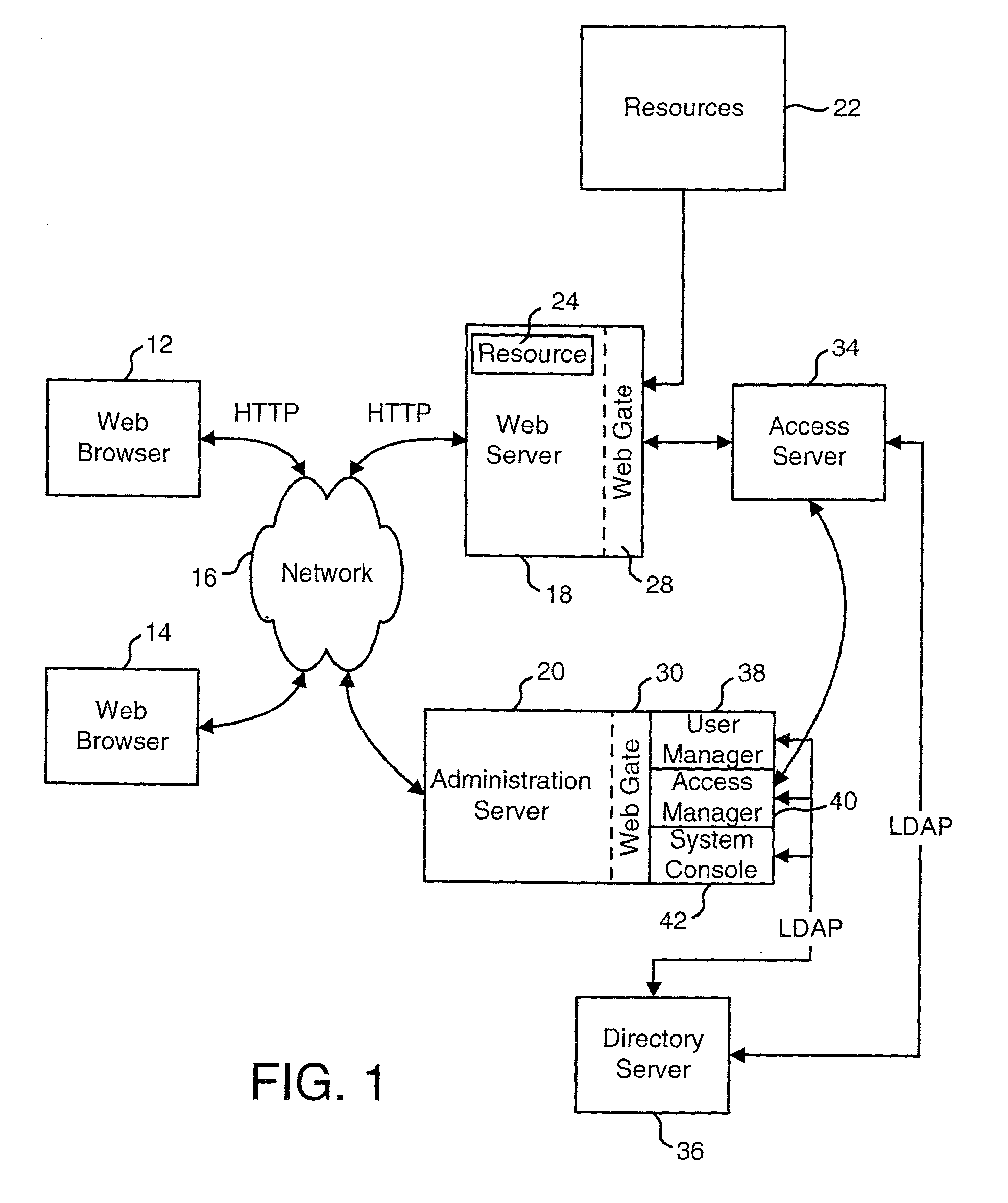
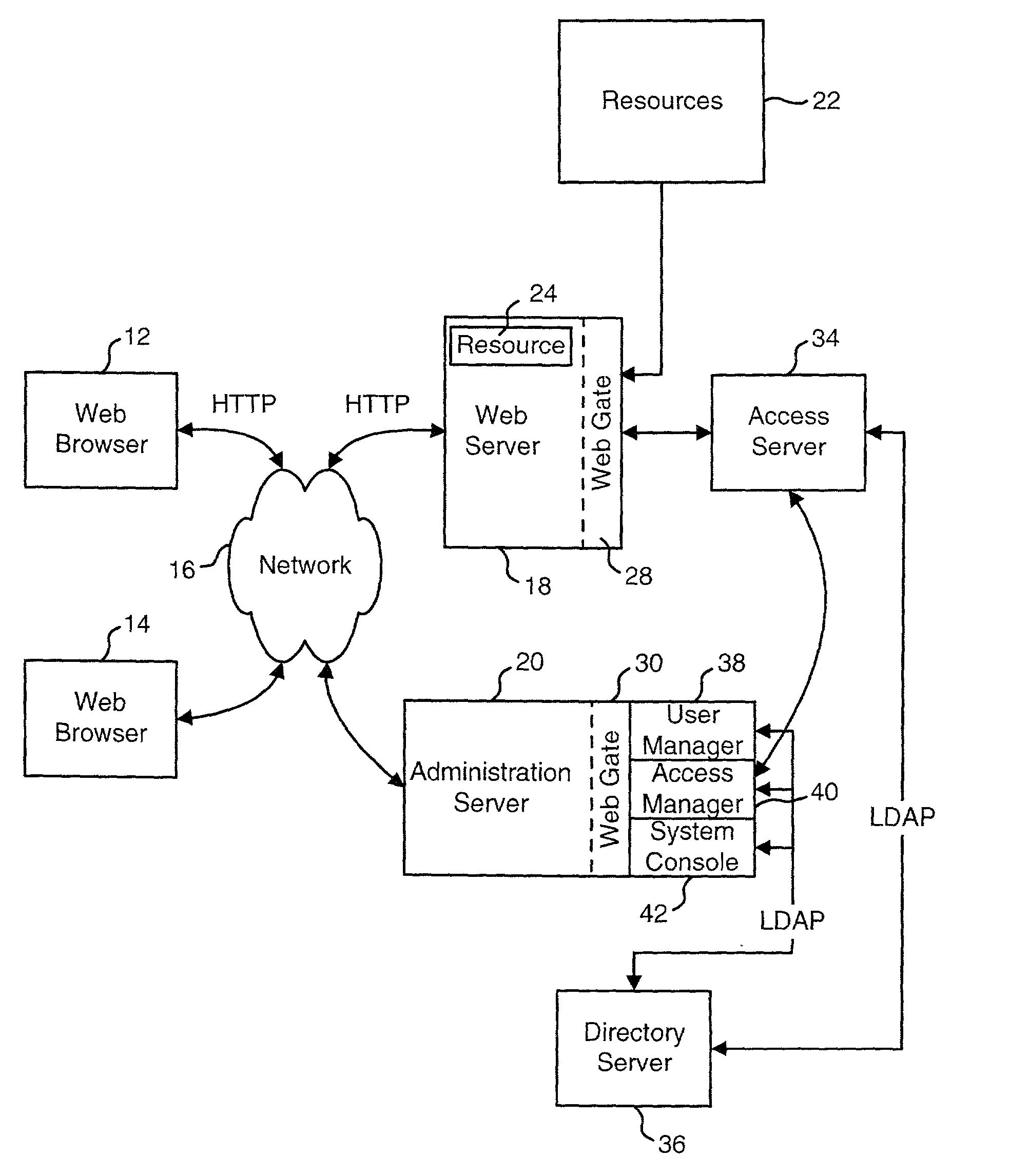
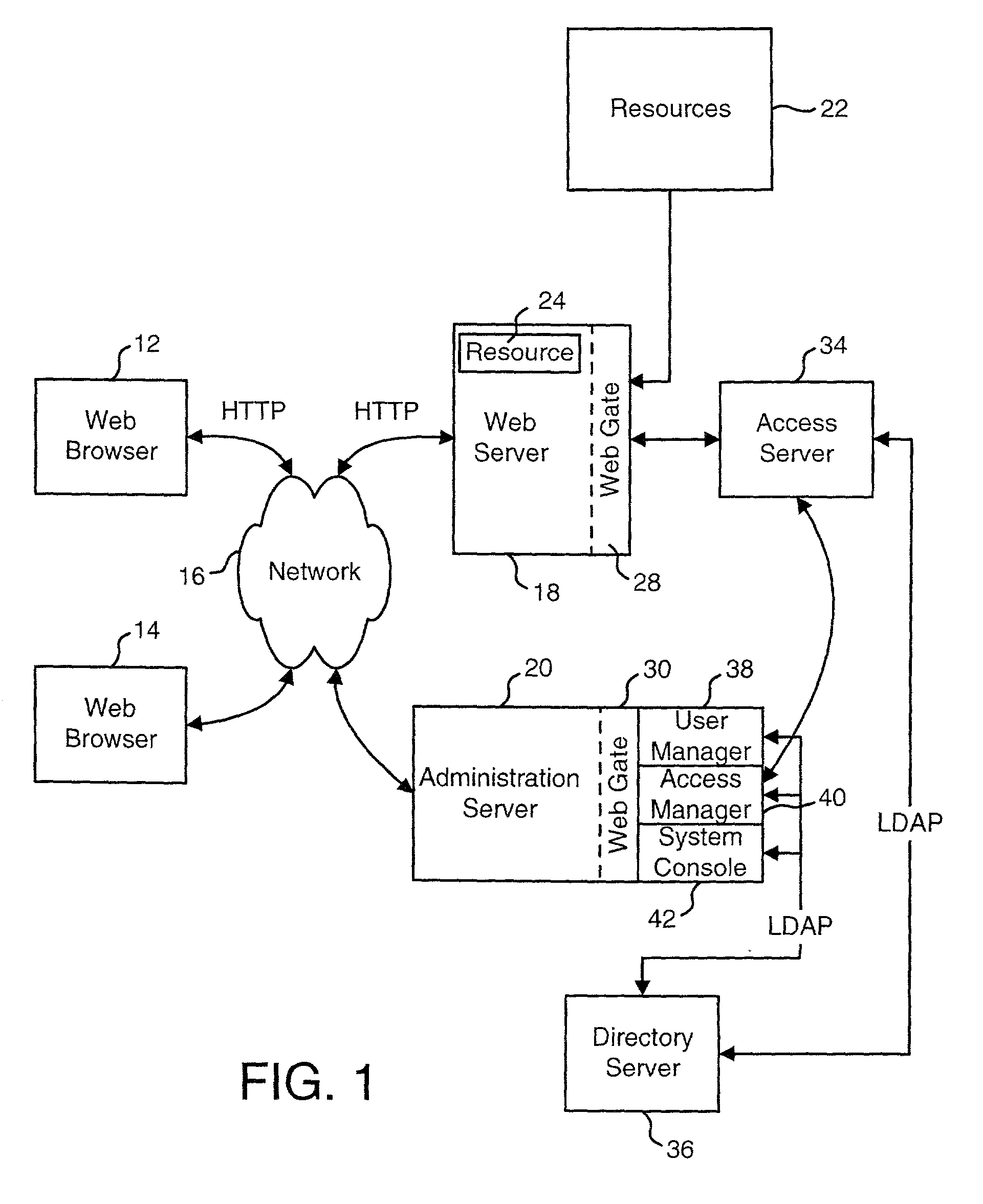
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
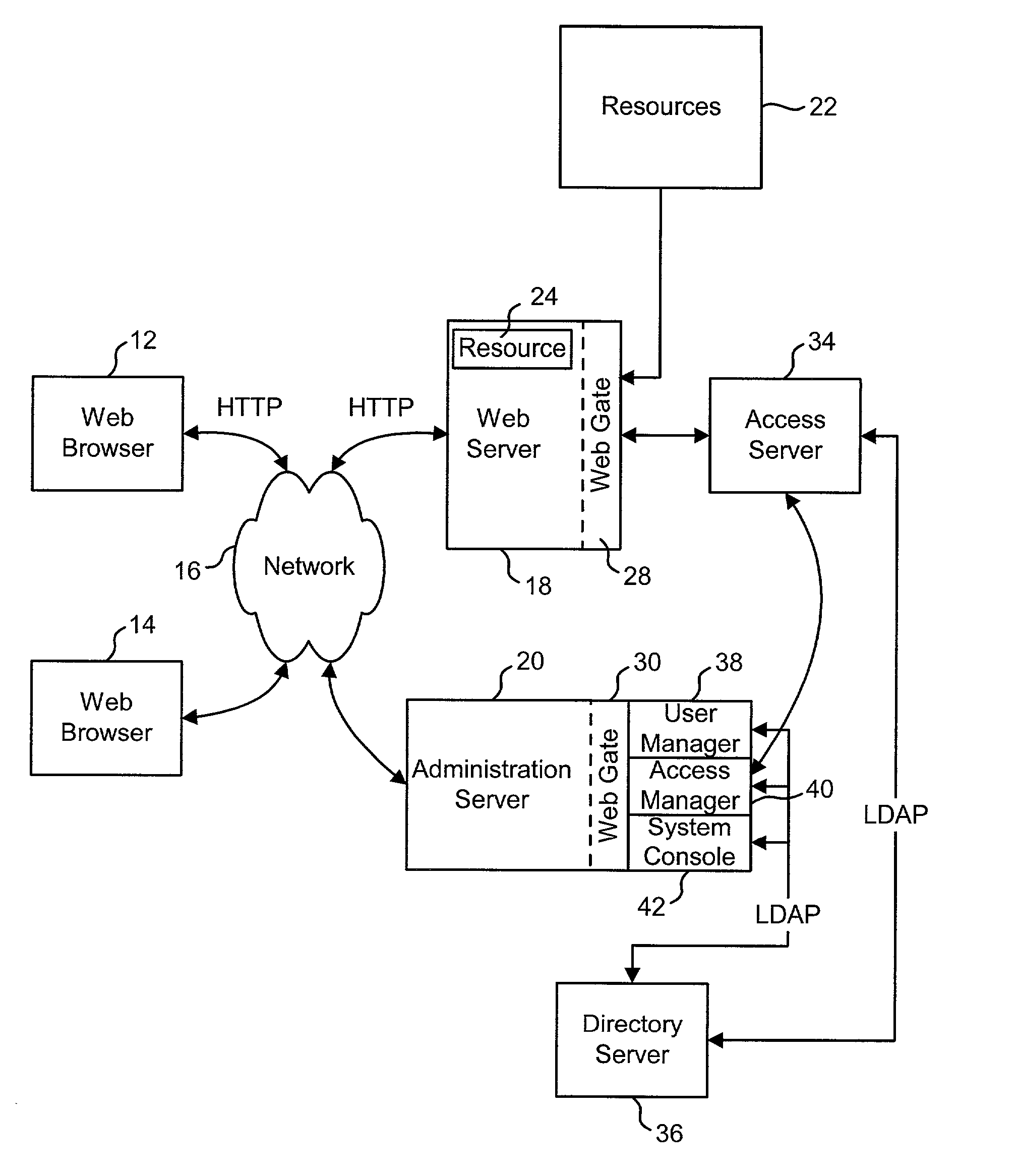
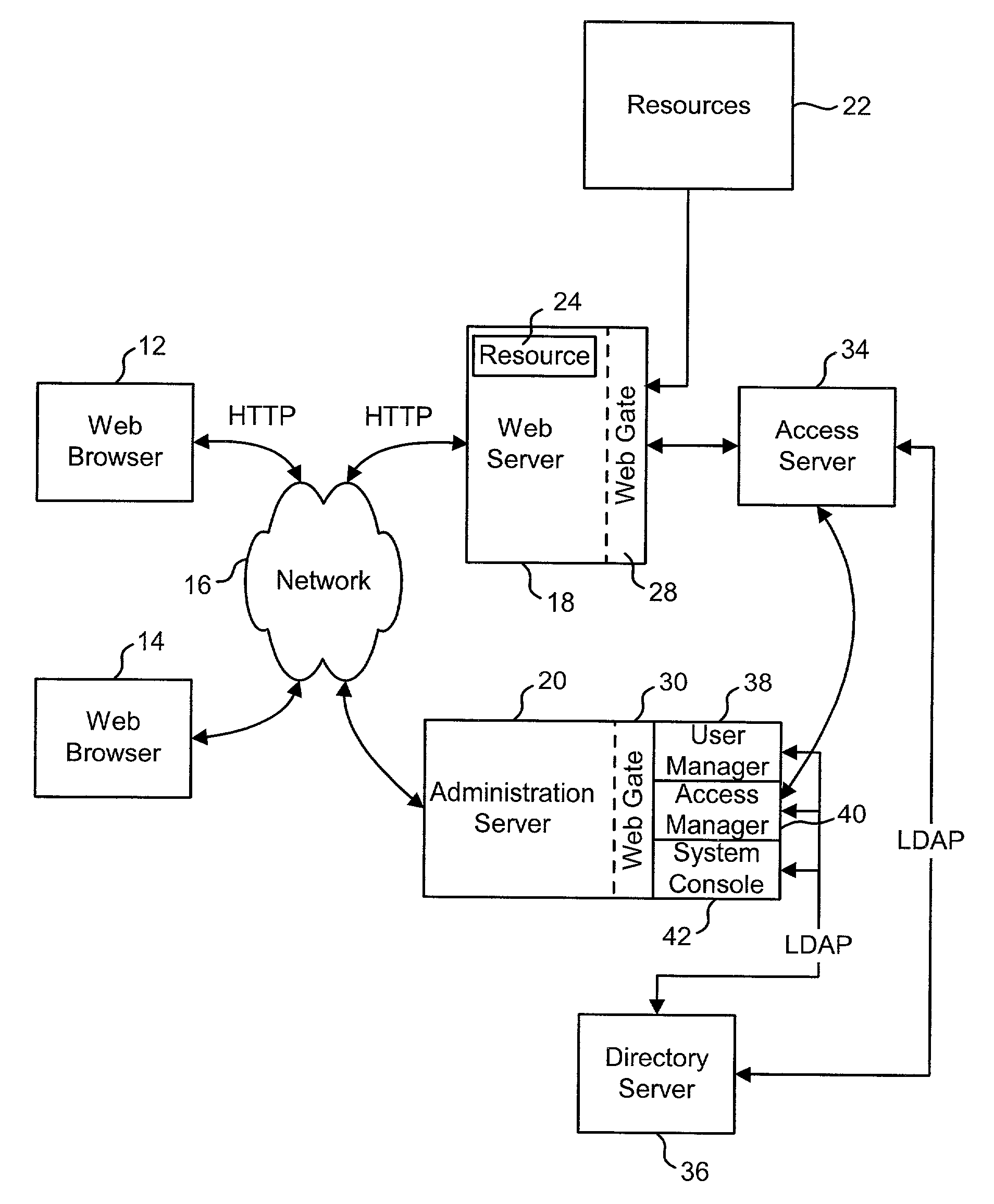
Access system interface
InactiveUS20030074580A1Easy mappingEasy to useDigital data processing detailsUser identity/authority verificationWeb serviceApplication software
An access system provides identity management and / or access management services for a network An application program interface for the access system enables an application without a web agent front end to read and use contents of an existing encrypted cookie to bypass authentication and proceed to authorization. A web agent is a component (usually software, but can be hardware or a combination of hardware and software) that plugs into (or otherwise integrates with) a web server (or equivalent) in order to participate in providing access services.
Owner:ORACLE INT CORP
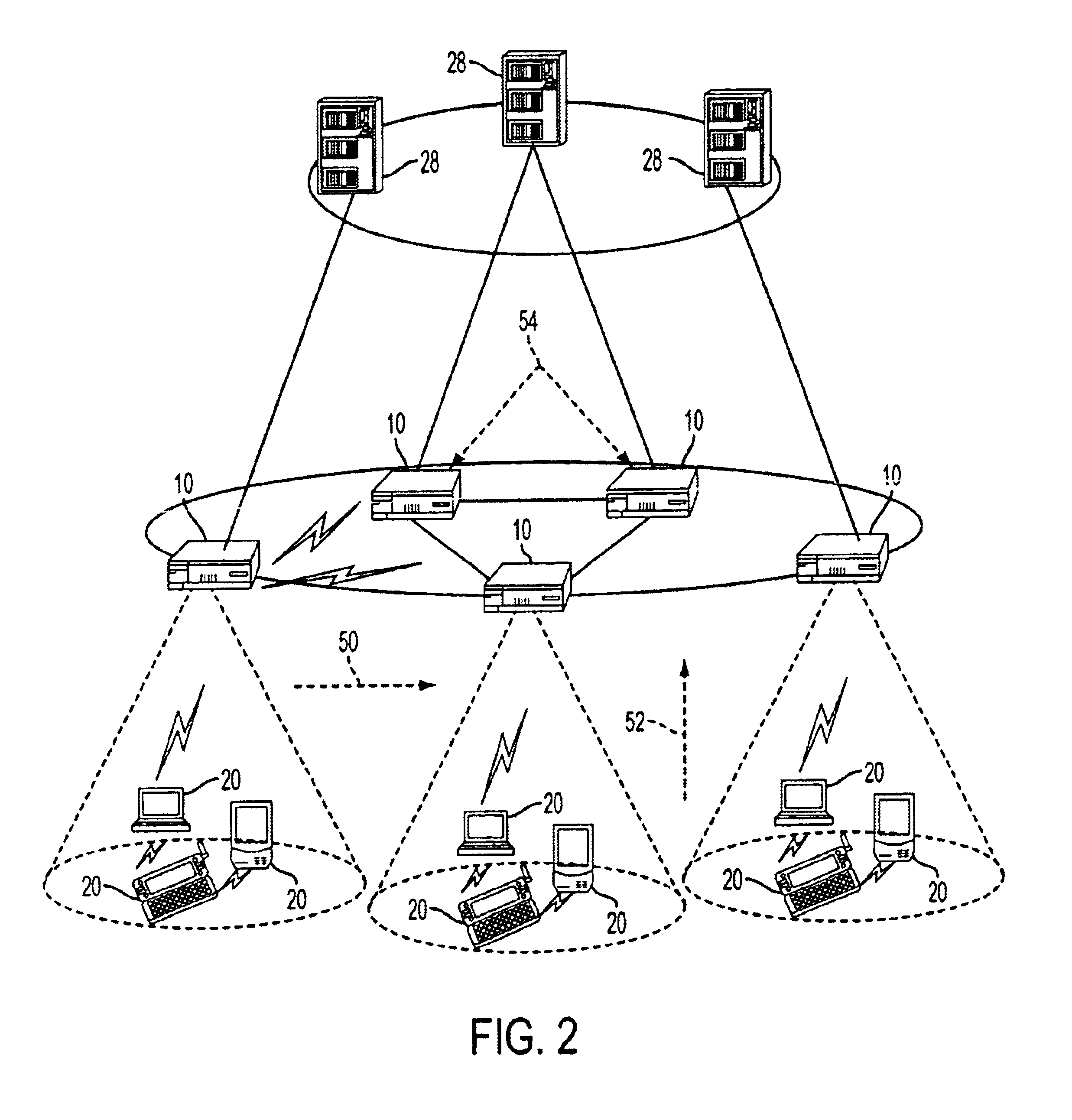
Network-based mobile workgroup system
InactiveUS6954790B2Multiple digital computer combinationsWireless network protocolsClient-sideAccess technology
A network-based mobile workgroup system has considerably wider appeal and application than normal virtual private networks in that it provides seamless mobility across a number of access technologies at the same time as it offers a granular security separation down to workgroup level. The mobile workgroup system is an access management system for mobile users with VPN and firewall functionality inbuilt. The mobile user can access the mobile workgroup system over a set of access technologies and select server resources and correspondent nodes to access pending their workgroup membership approvals. All workgroup policy rules are defined in a mobile service manager and pushed down to one or more mobile service routers for policy enforcement. The mobile service router closest to the mobile client, and being part of the mobile virtual private network, performs regular authentication checks of the mobile client during service execution. At the same time it performs traffic filtering based on the mobile user's workgroup memberships. Together, these two components constitute an unprecedented security lock, effectively isolating a distributed workgroup into a mobile virtual private network.
Owner:LONGHORN HD LLC
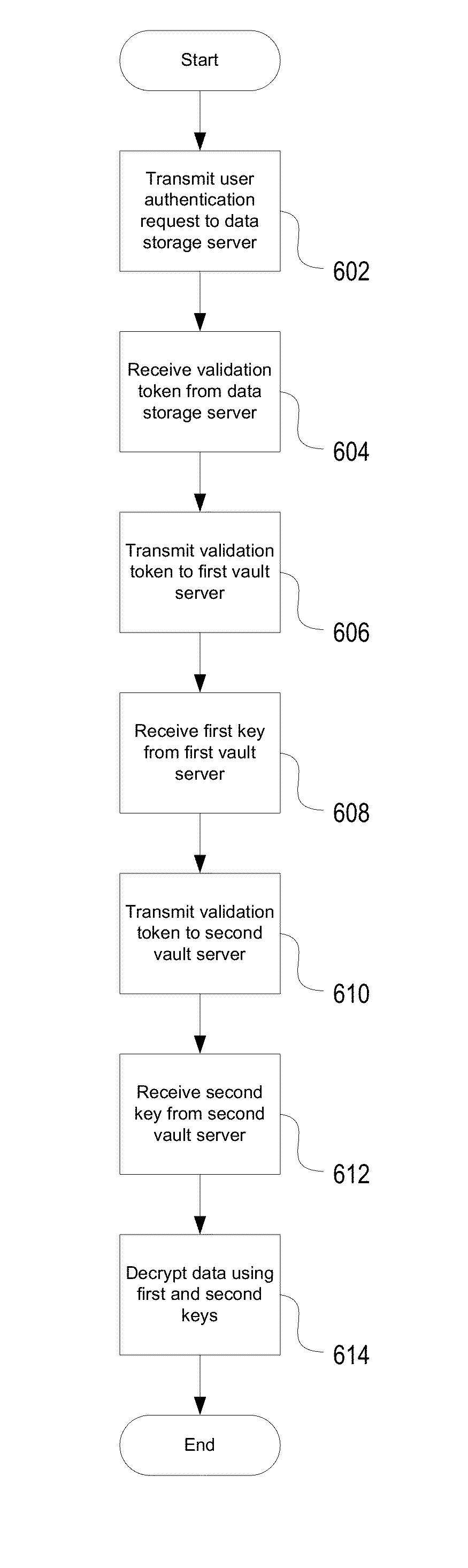
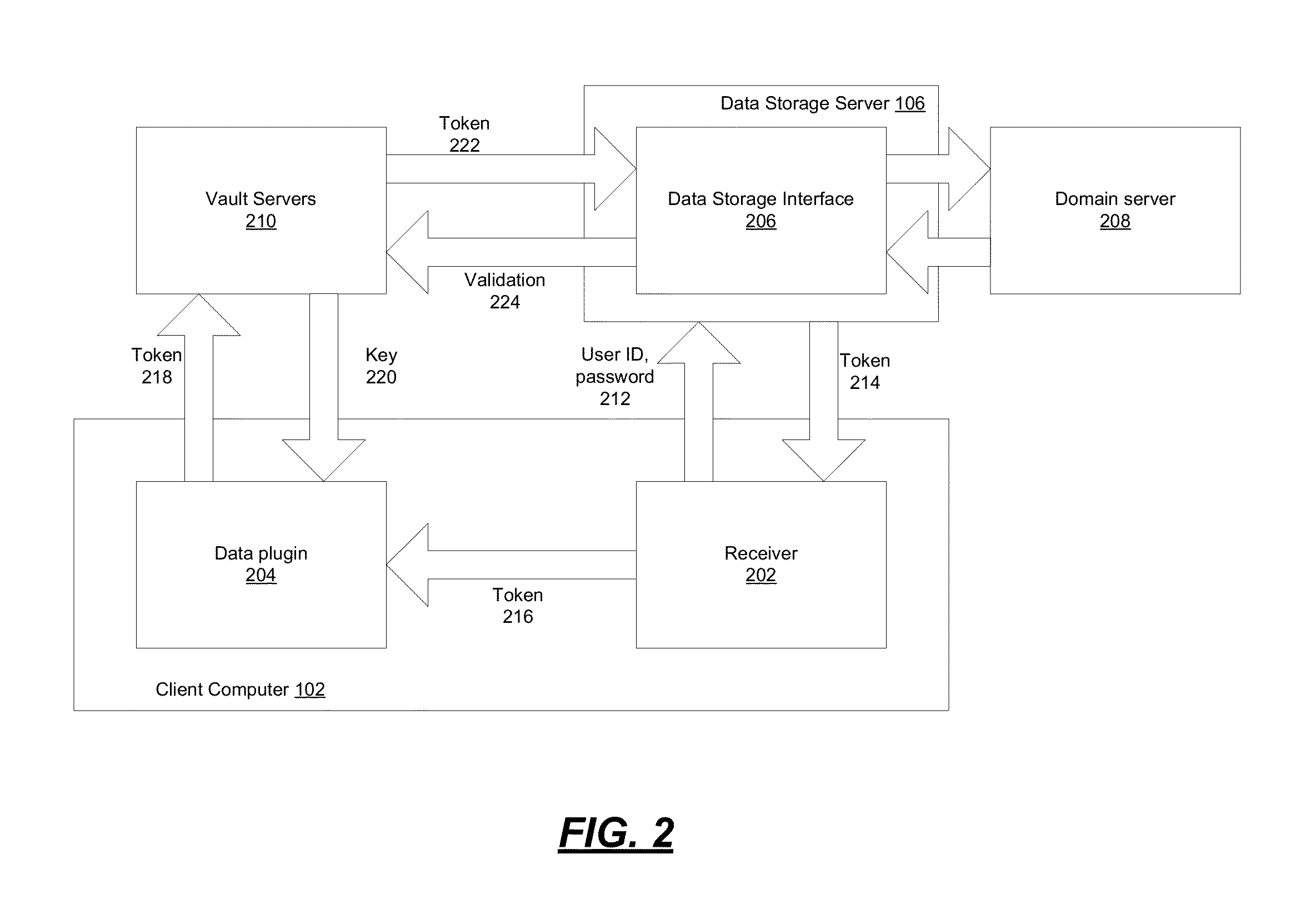
Encryption-Based Data Access Management
ActiveUS20140164774A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesKey serverData access
Encryption-based data access management may include a variety of processes. In one example, a device may transmit a user authentication request for decrypting encrypted data to a data storage server storing the encrypted data. The computing device may then receive a validation token associated with the user's authentication request, the validation token indicating that the user is authenticated to a domain. Subsequently, the computing device may transmit the validation token to a first key server different from the data storage server. Then, in response to transmitting the validation token the computing device may receive, from the first key server, a key required for decrypting the encrypted data. The device may then decrypt at least a portion of the encrypted data using the key.
Owner:CITRIX SYST INC
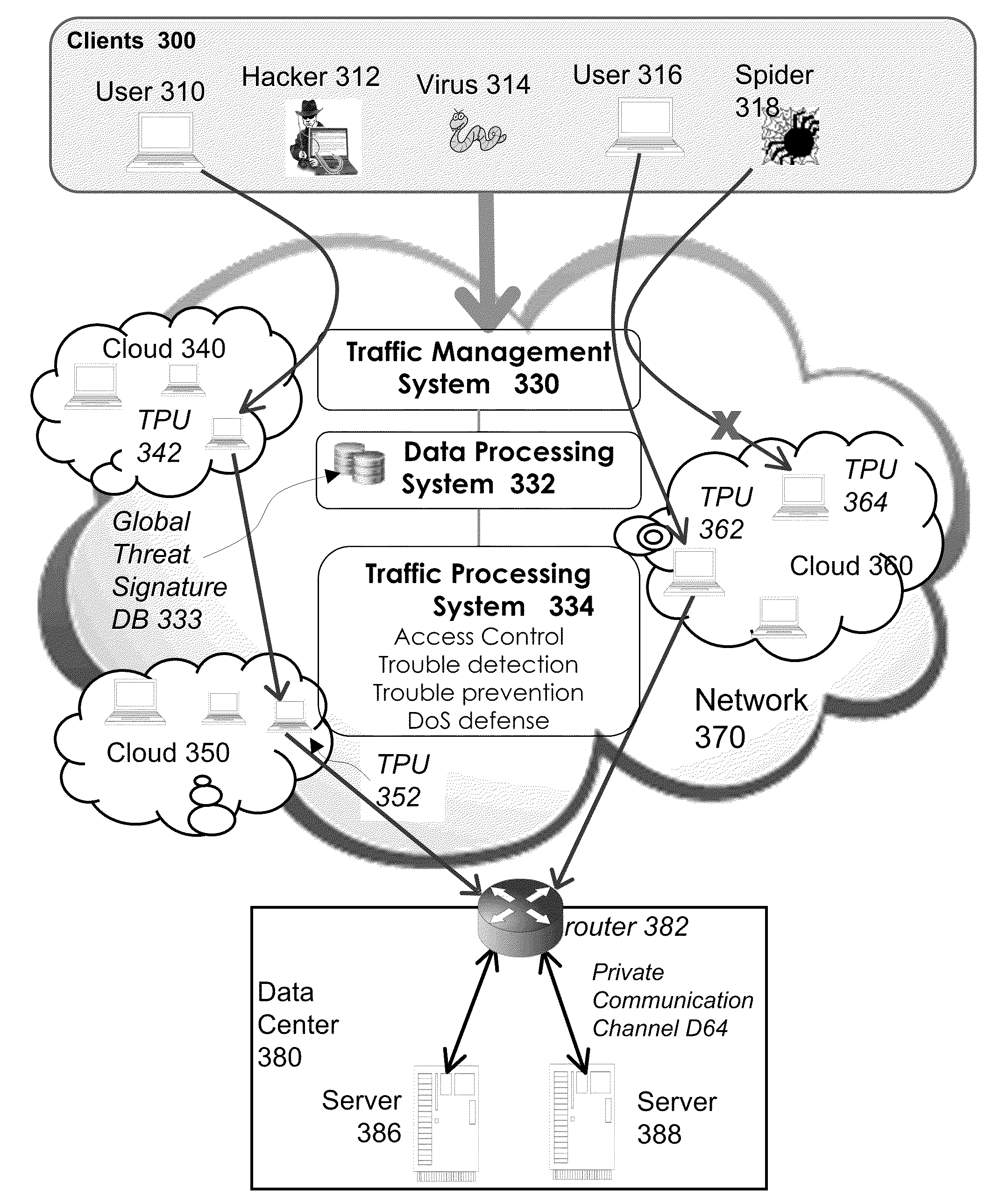
System and method for access management and security protection for network accessible computer services
InactiveUS20100251329A1Detection problemGrows and shrinks capacity and bandwidth capacityMemory loss protectionError detection/correctionTraffic capacityService provision
A method for providing access management and security protection to a computer service includes providing a computer service that is hosted at one or more servers and is accessible to clients via a first network, providing a second network that includes a plurality of traffic processing nodes and providing means for redirecting network traffic from the first network to the second network. Next, redirecting network traffic targeted to access the computer service via the first network to a traffic processing node of the second network via the means for redirecting network traffic. Next, inspecting and processing the redirected network traffic by the traffic processing node and then routing only redirected network traffic that has been inspected, processed and approved by the traffic processing node to access the computer service via the second network.
Owner:YOTTAA
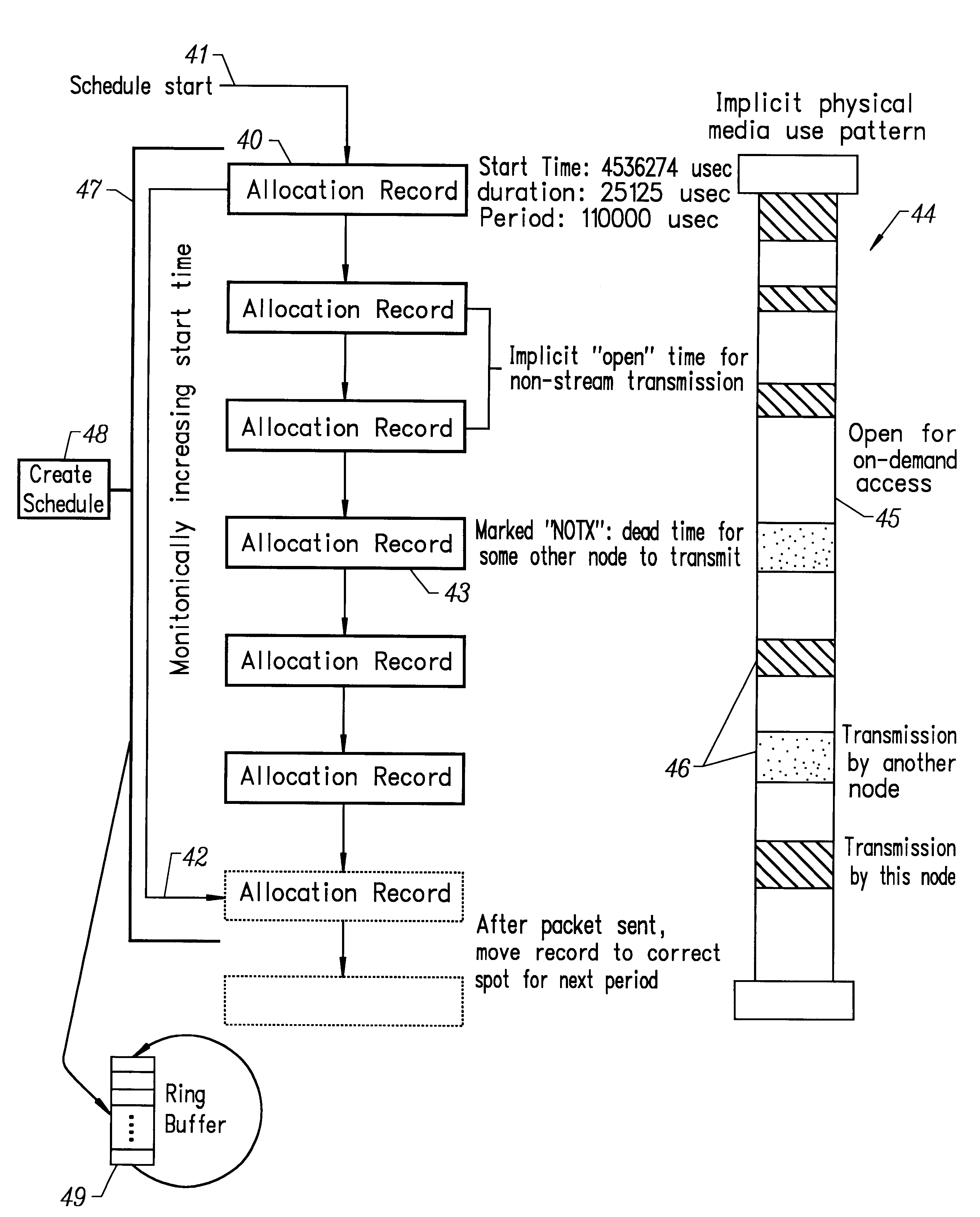
Method and apparatus implementing a multimedia digital network
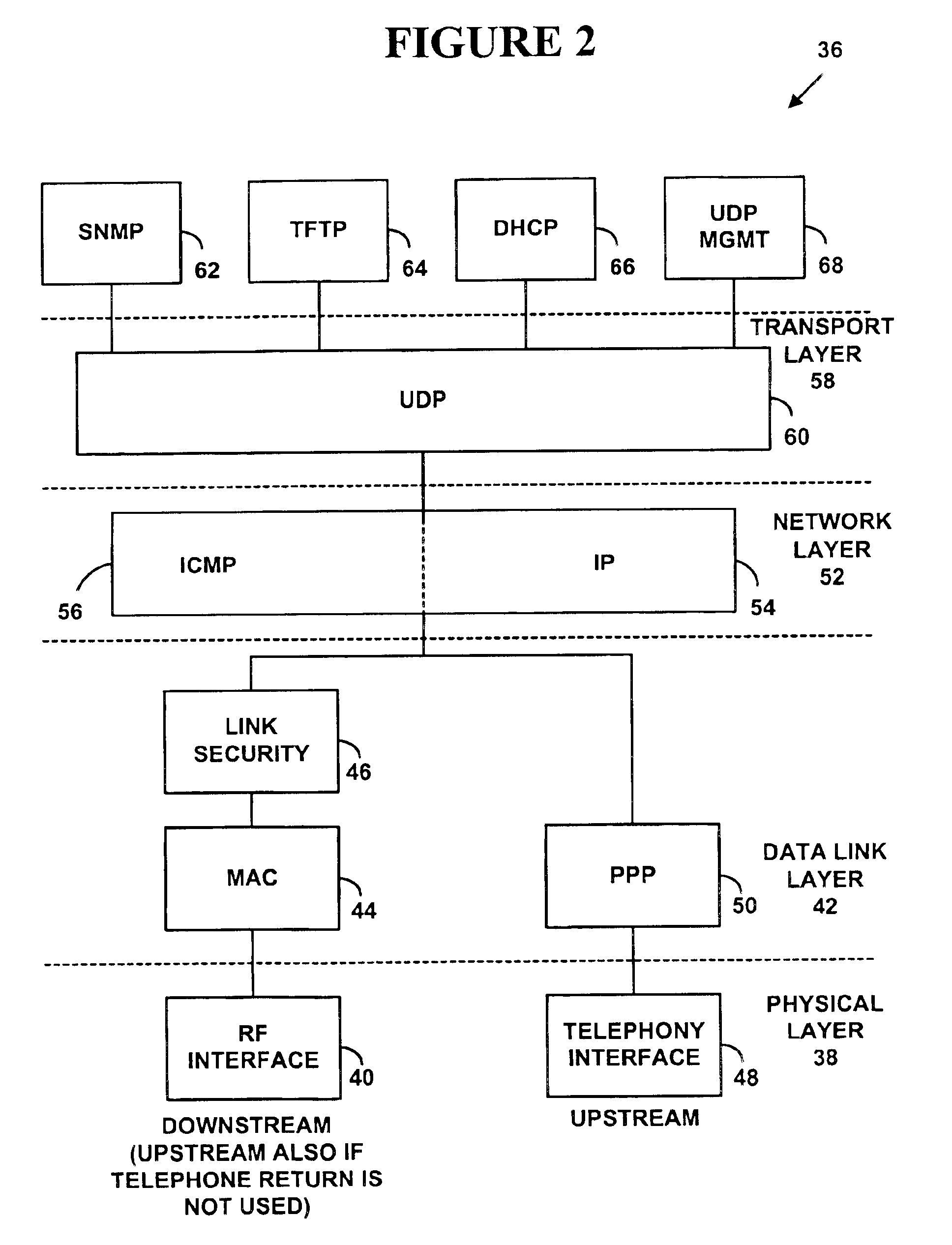
InactiveUS6310886B1Most efficientHybrid switching systemsTime-division multiplexData capacityLong term data
A method and apparatus for efficiently managing the allocation of available data capacity on a physically shared digital network among devices connected to that network is disclosed. Also disclosed is a method and apparatus for managing the ongoing timely movement of data on the shared network such that precise long-term data rates are achieved between attached devices with minimal additional buffering. The invention further comprises a method and apparatus which allows the use of any remaining network capacity for non time-critical data movement without the need for centralized access management.
Owner:TIVO SOLUTIONS INC
Back-end decoupled management model and management system utilizing same
InactiveUS6871346B1Easy to manageDigital data processing detailsMultiprogramming arrangementsWeb-Based Enterprise ManagementWindows management instrumentation
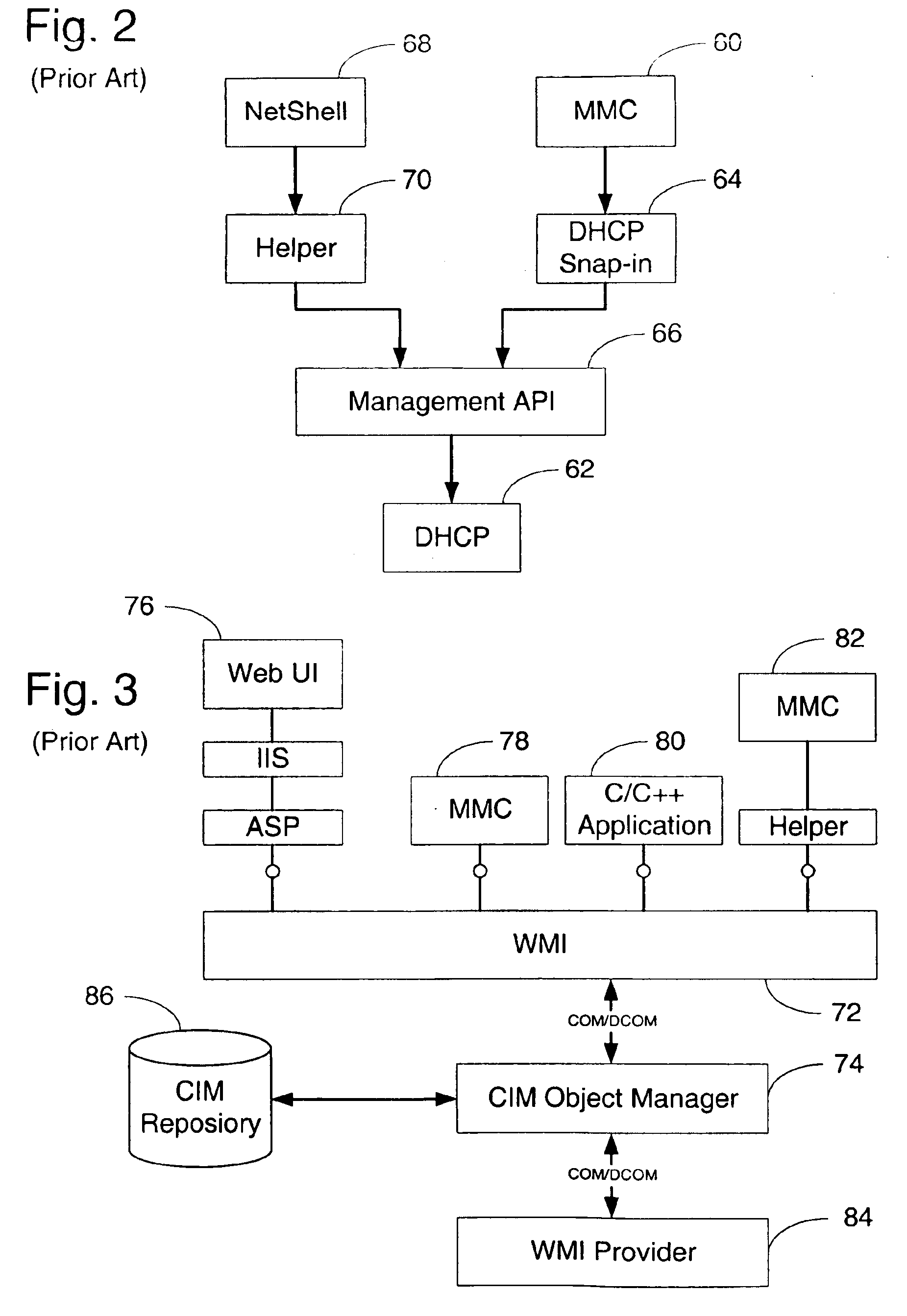
Presented is a web-based enterprise management compliant management framework whose back end components are decoupled from the various user interfaces available for accessing the management system. In the Windows environment, the management system of the instant invention is also compliant with the Windows management instrumentation (WMI) requirements. This management system includes WMI providers which implement standard interfaces which decouple all semantic and syntactic checks from the user interface and which provide common error strings, help, etc. to a user regardless of the user interface being used. The providers of the management system of the instant invention store and access data in the active directory. As such, these providers present a customizable user interface which may be based on a user's expertise level and which may be dynamically localized to the user's preferred language. Transaction support is also provided which prevents multiple users from changing the same attributes at the same time through different user interfaces.
Owner:MICROSOFT TECH LICENSING LLC
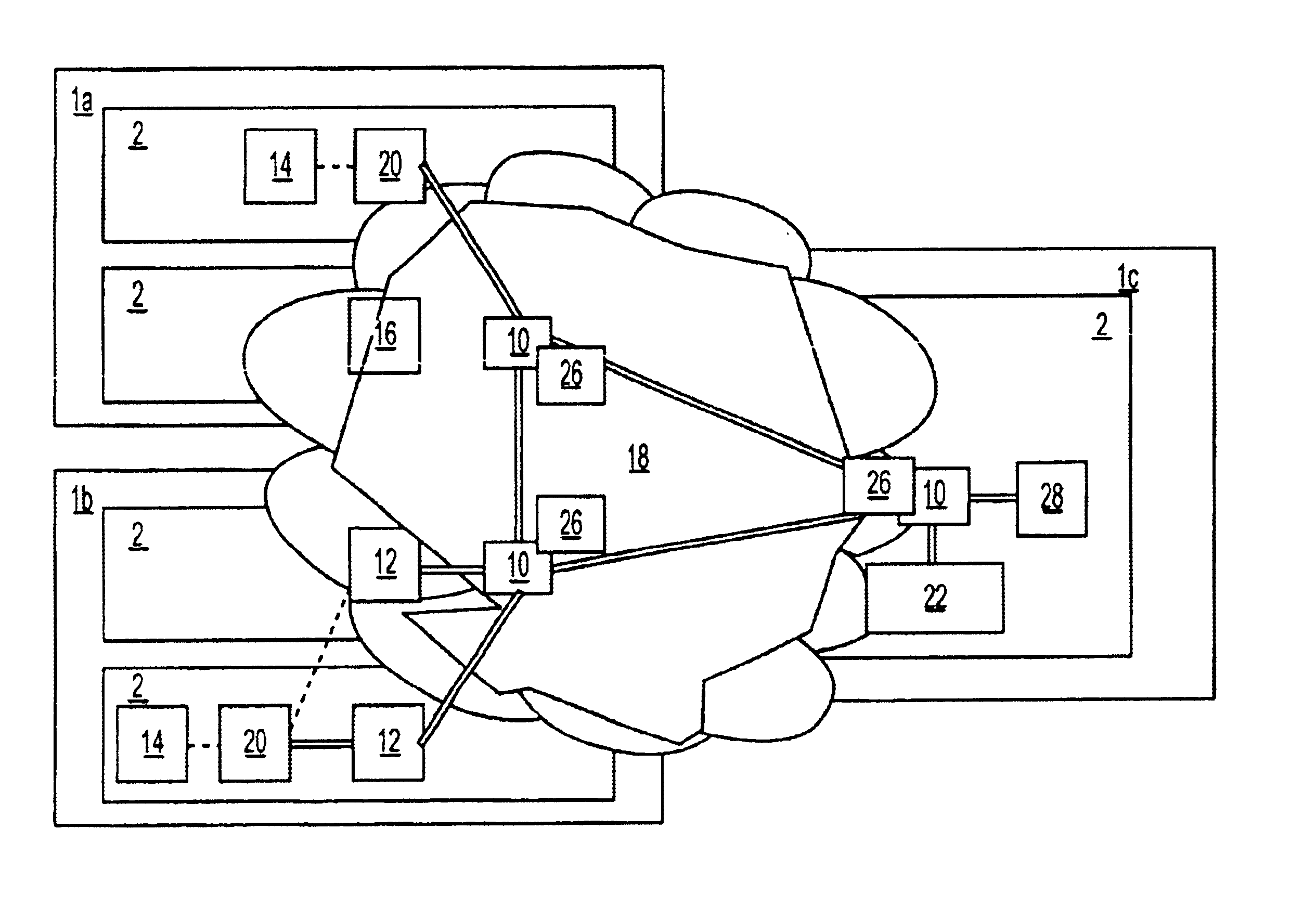
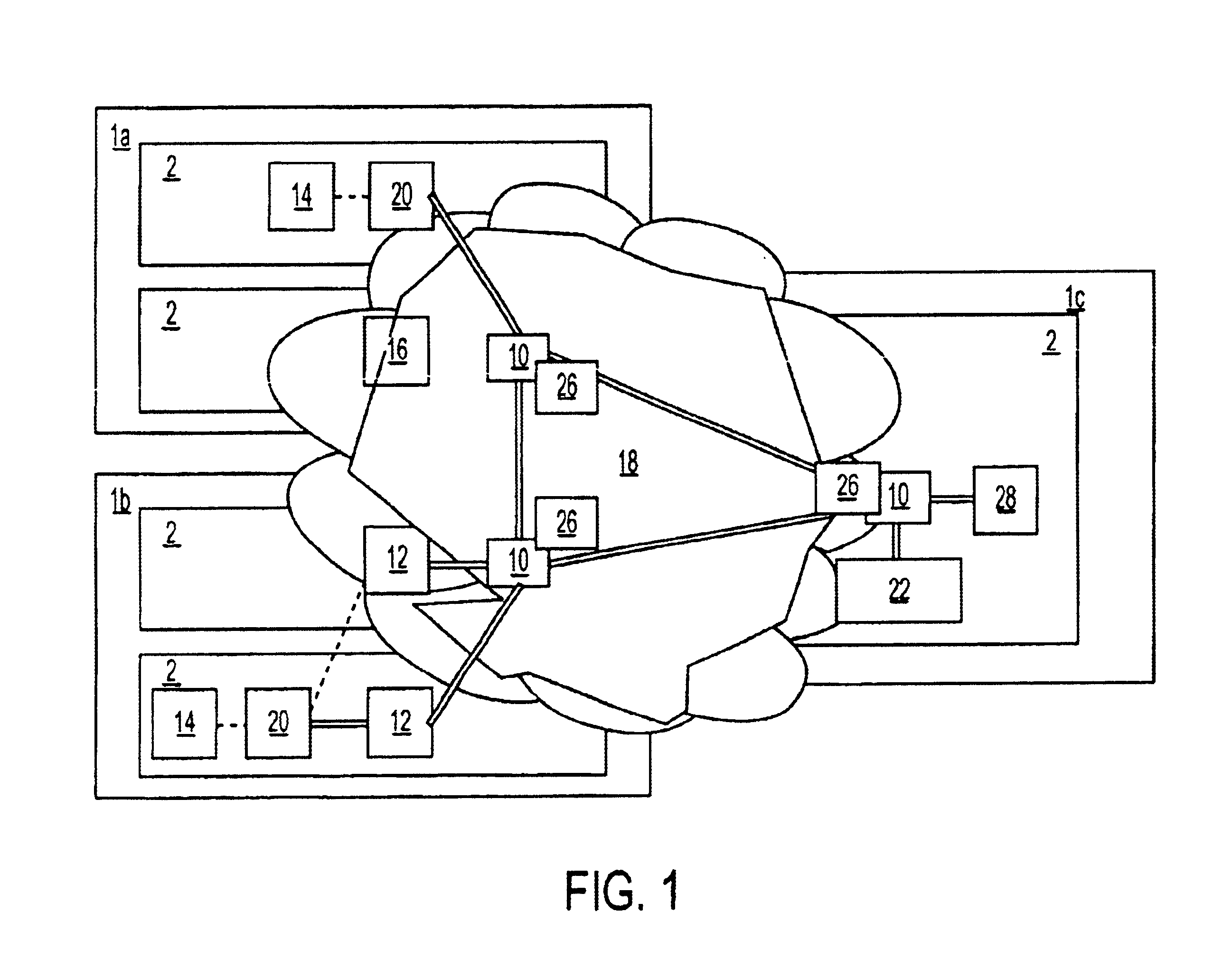
Enterprise management system
InactiveUS6983317B1Improve availabilityImprove robustnessDigital computer detailsTransmissionRoot cause analysisAccess management
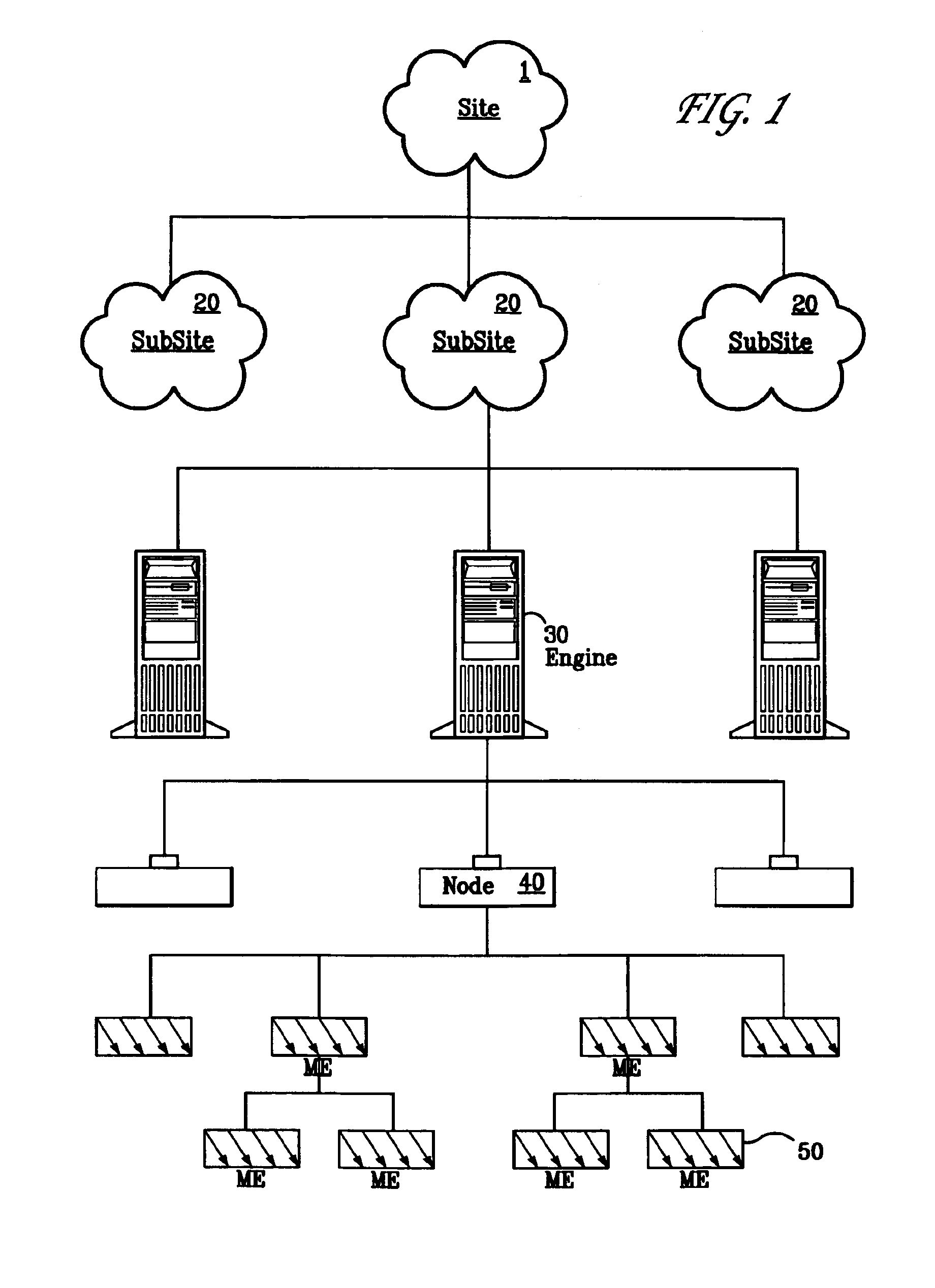
A Managed Site (10), a logical network entity, is composed of a number of Sub Sites (20) in a one to many relationship. A Sub Site (20) is a logical component, which is composed of a number of Engines (30). Nodes (40) similarly relates to their Engine (30) in a many to one relationship. A Node (40) is a collection of Managed Elements (ME's) (50) (while being an ME (50) itself), which represent network state information. The subsite (20) consists of the engine (30) connected to server nodes (40). One or more clients (110) are connected to the management engine (30) and access management engine (30) information relating to managed elements (50) including nodes (40). The connected manager engines may communicate with one another so that, for example, in the event of a failure, one of the manager engines remaining on line commences monitoring of manage elements assigned to the failed manager engine. Upon accessing the manager engine (30), the client interface displays relationships among managed elements (50) using meaningful connectors and tree-like structures. In addition to basic managed element state monitoring functionality, the manager engine (30) provides a variety of automated tasks ensuring the health of the network and optimal failure correction in the event of a problem. For example, the manager engine (30) performs root cause analysis utilizing an algorithm tracing through manged element (50) relationships and indicating the source of the failure.
Owner:MICROSOFT TECH LICENSING LLC
Access system interface
InactiveUS7185364B2Digital data processing detailsUser identity/authority verificationWeb serviceApplication software
An access system provides identity management and / or access management services for a network. An application program interface for the access system enables an application without a web agent front end to read and use contents of an existing encrypted cookie to bypass authentication and proceed to authorization. A web agent is a component (usually software, but can be hardware or a combination of hardware and software) that plugs into (or otherwise integrates with) a web server (or equivalent) in order to participate in providing access services.
Owner:ORACLE INT CORP
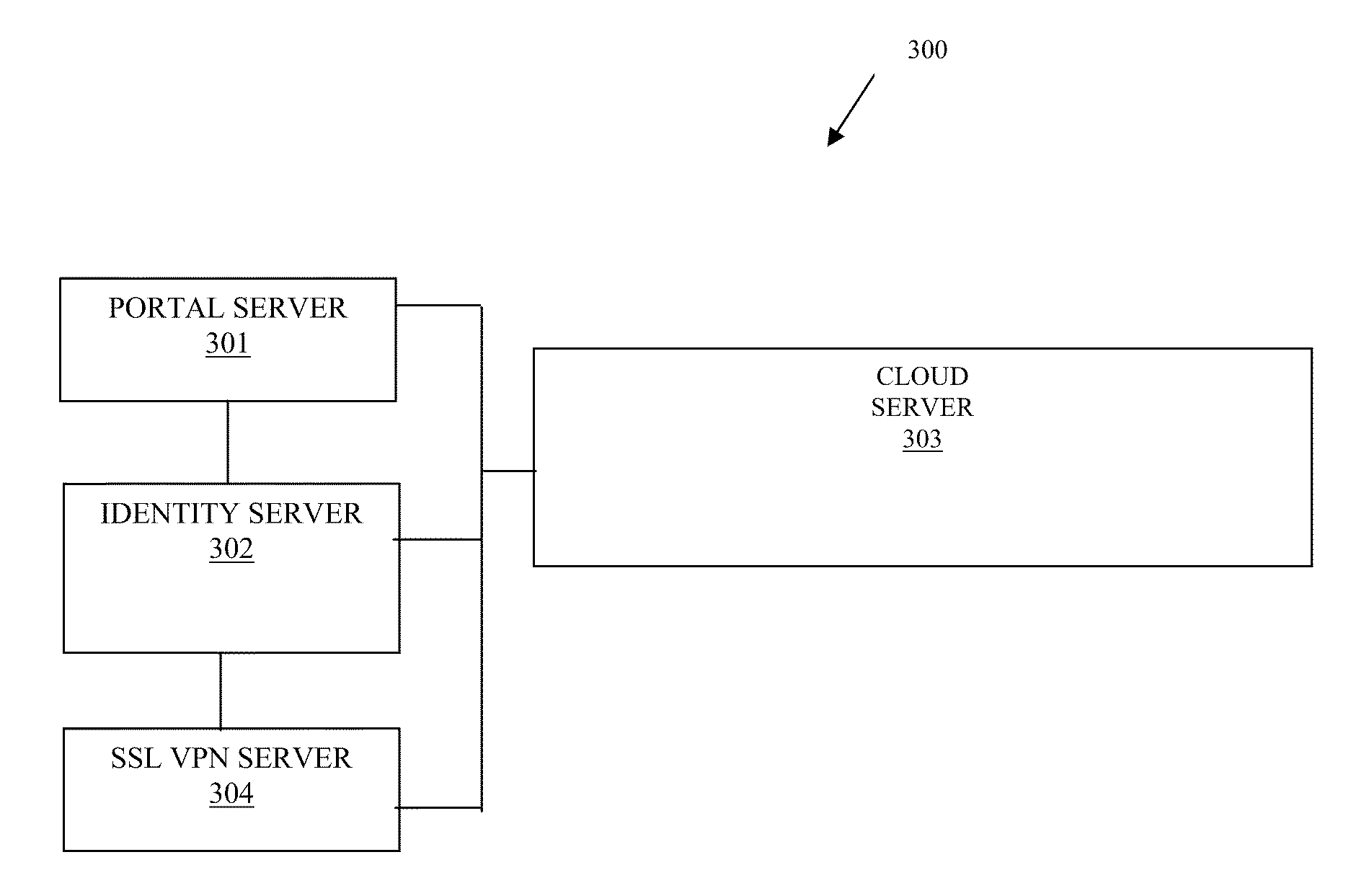
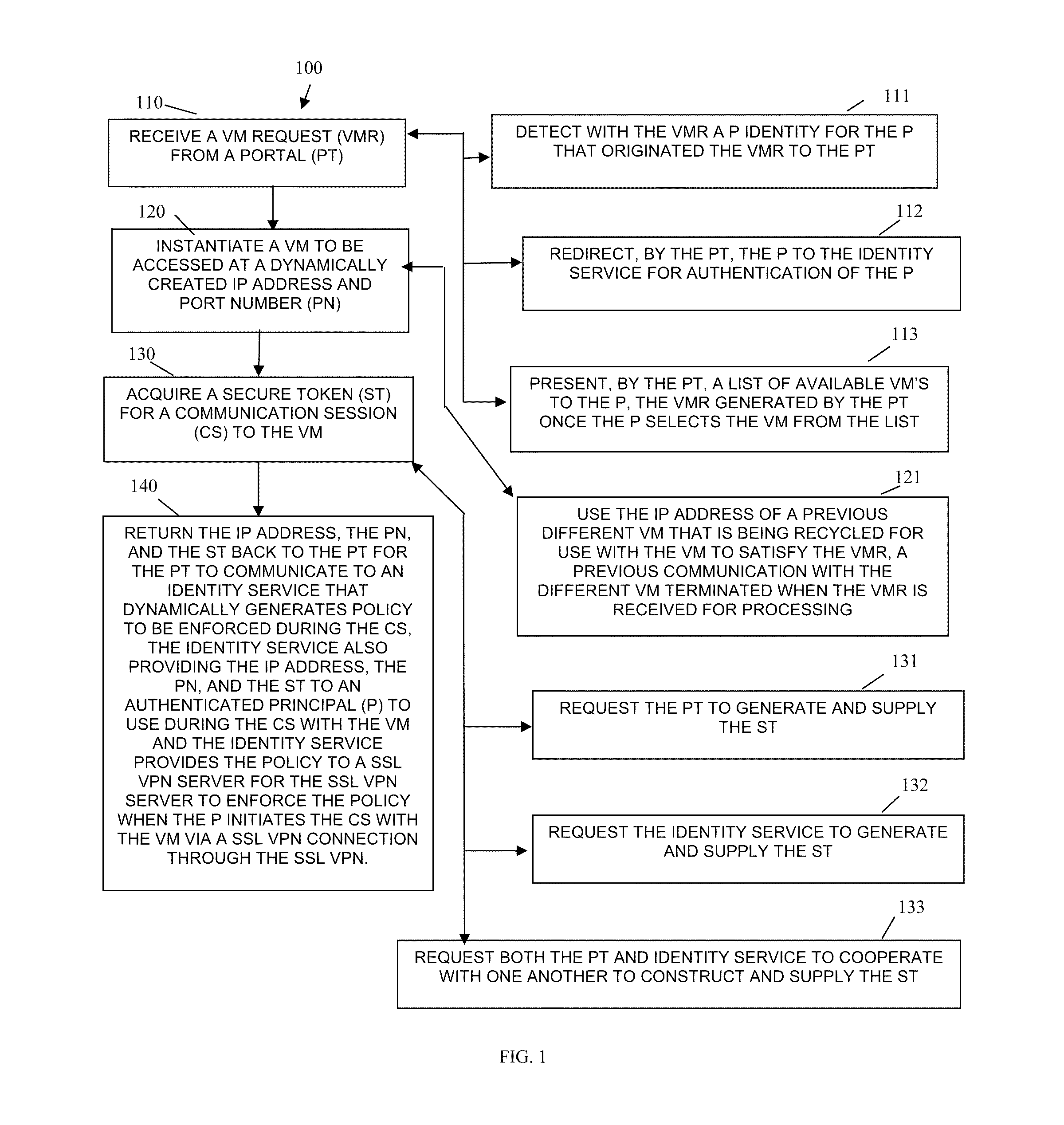
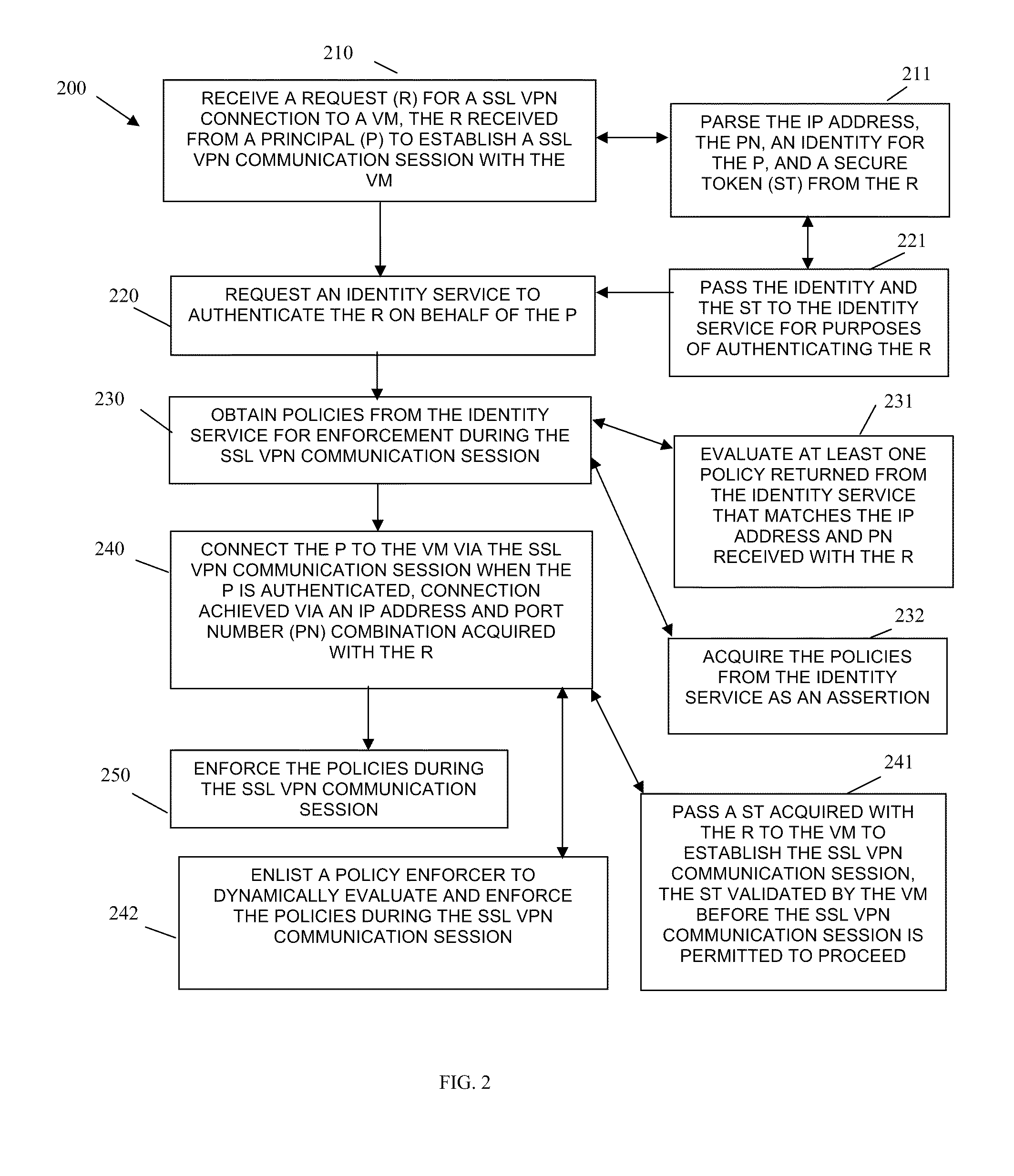
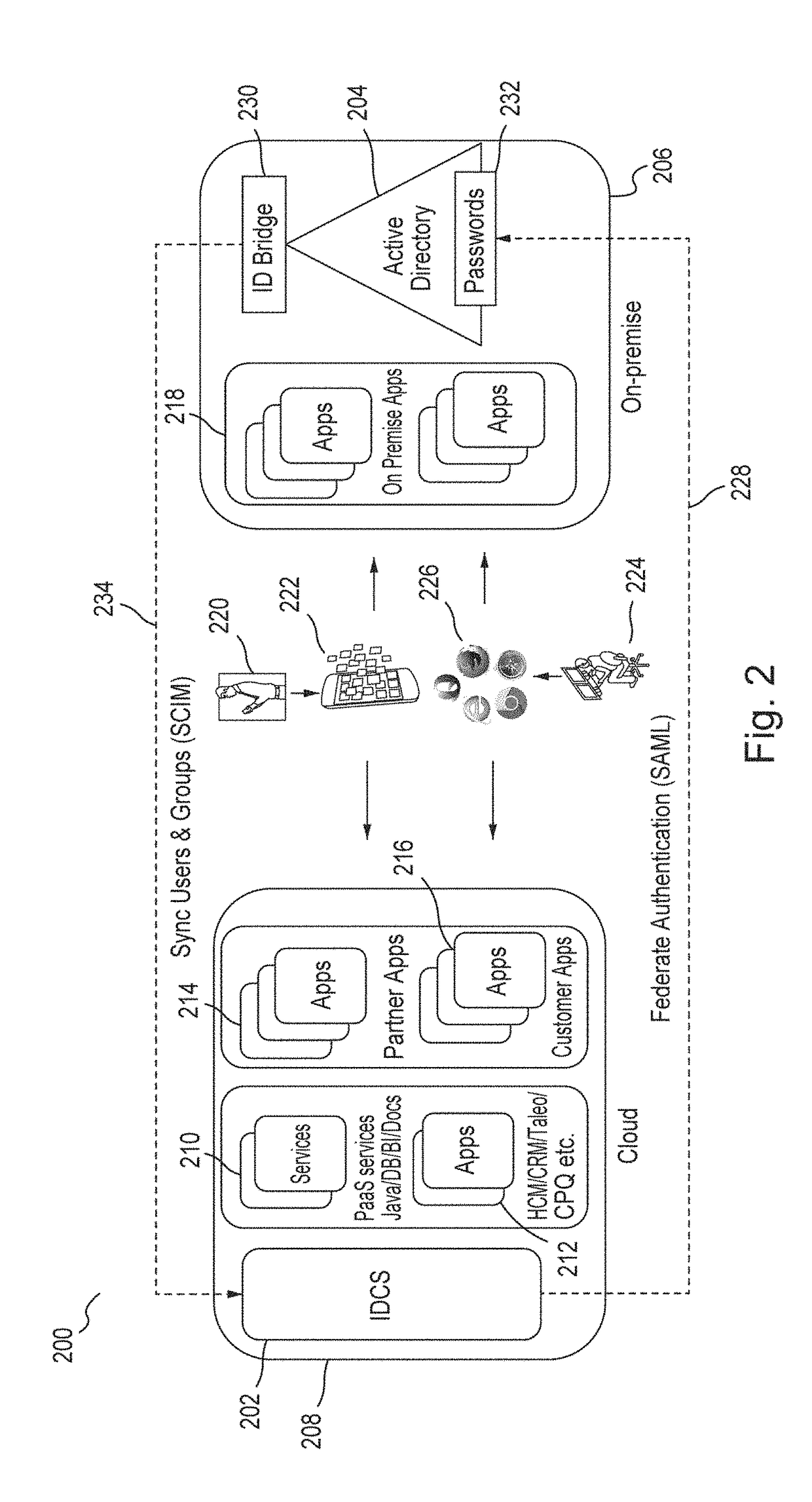
Techniques for secure access management in virtual environments
ActiveUS20110214176A1Multiple digital computer combinationsDigital data authenticationPrivate networkAccess management
Techniques for secure access management to virtual environments are provided. A user authenticates to a portal for purposes of establishing a virtual machine (VM). The portal interacts with a cloud server and an identity server to authenticate the user, to acquire an Internet Protocol (IP) address and port number for the VM, and to obtain a secure token. The user then interacts with a secure socket layer virtual private network (SSL VPN) server to establish a SSL VPN session with the VM. The SSL VPN server also authenticates the token through the identity server and acquires dynamic policies to enforce during the SSL VPN session between the user and the VM (the VM managed by the cloud server).
Owner:MICRO FOCUS SOFTWARE INC
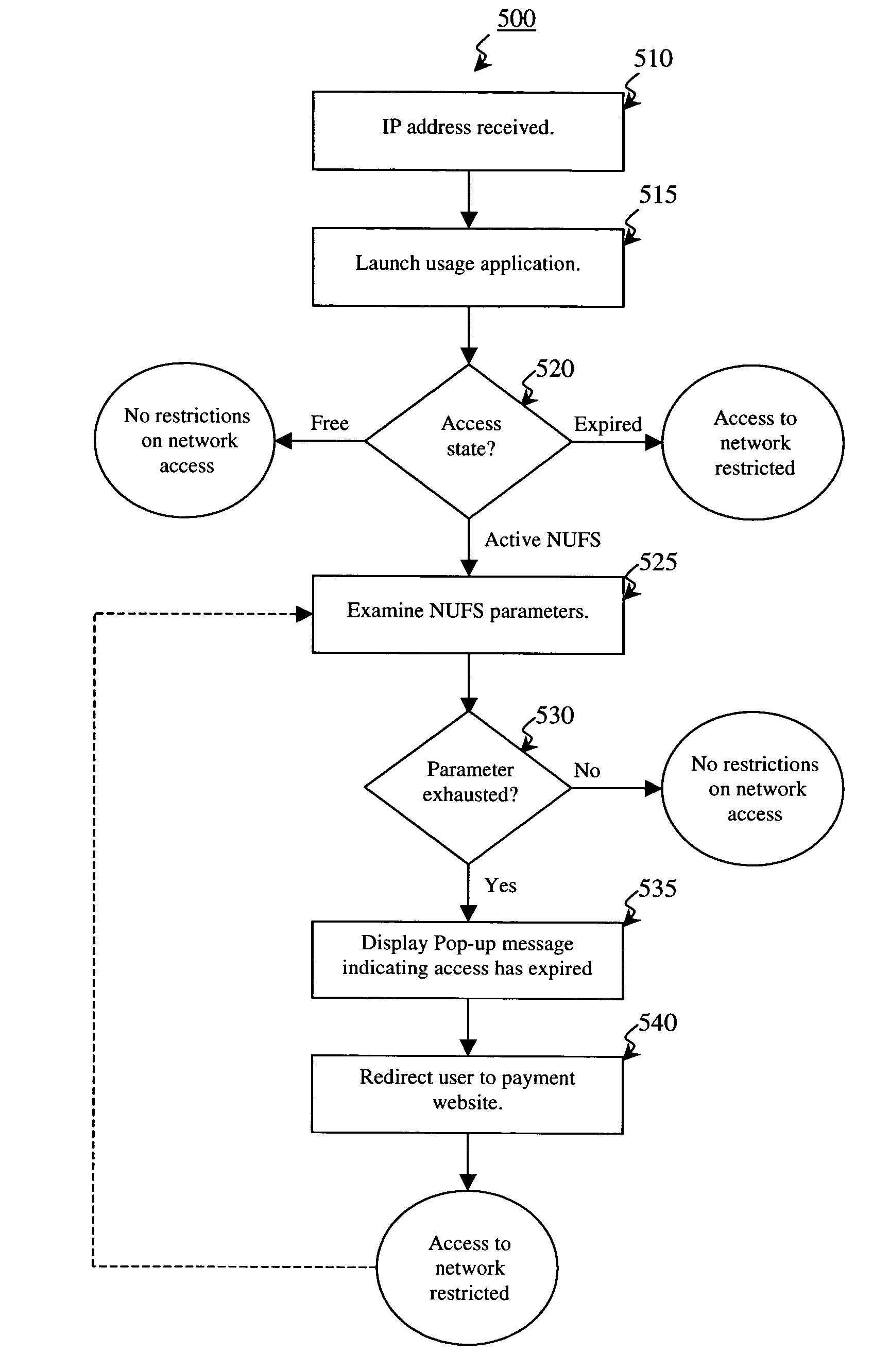
Self-managed network access using localized access management
ActiveUS7574731B2Provide usageAvoid modificationRandom number generatorsUser identity/authority verificationProgram planningBack end server
The invention provides a method and system for locally tracking network usage and enforcing usage plans at a client device. In an embodiment of the invention, a unique physical key, or token, is installed at a client device of one or more networks. The key comprises a usage application and one or more access parameters designated the conditions and / or limits of a particular network usage plan. Upon initial connection to the network, the usage application grants or denies access to the network based on an analysis of the current values of the access parameters. Therefore, network usage tracking and enforcement is made simple and automatic without requiring any back-end servers on the network while still providing ultimate flexibility in changing billing plans for any number of users at any time.
Owner:KOOLSPAN
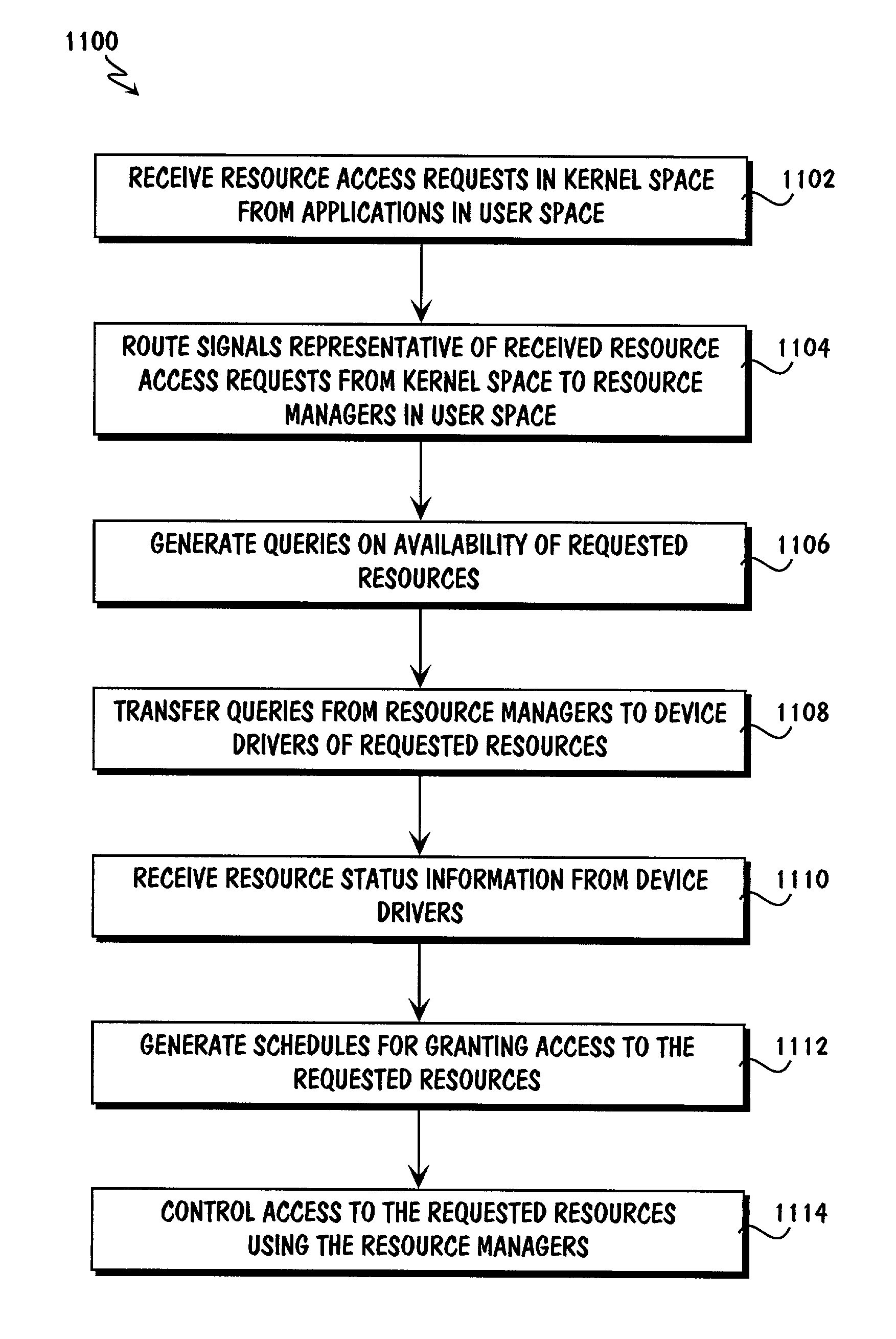
Open platform architecture for shared resource access management
An open platform architecture and methods for shared resource access management are provided. A redirection module in kernel space receives requests for access to resources from applications in user space. The redirection module routes signals representative of the received requests to a device driver interface in user space. Components of the device driver interface include resource management modules and device drivers that correspond to available resources. The resource management modules generate queries to the device drivers regarding availability of the requested resources. Upon receipt of resource status information from the device drivers, components of the device driver interface generate schedules for granting access to the requested resources. Further, the device driver interface components control access to the resources in accordance with the generated schedules including issuing responses to the requesting applications and the device drivers of the requested resources.
Owner:WI LAN INC
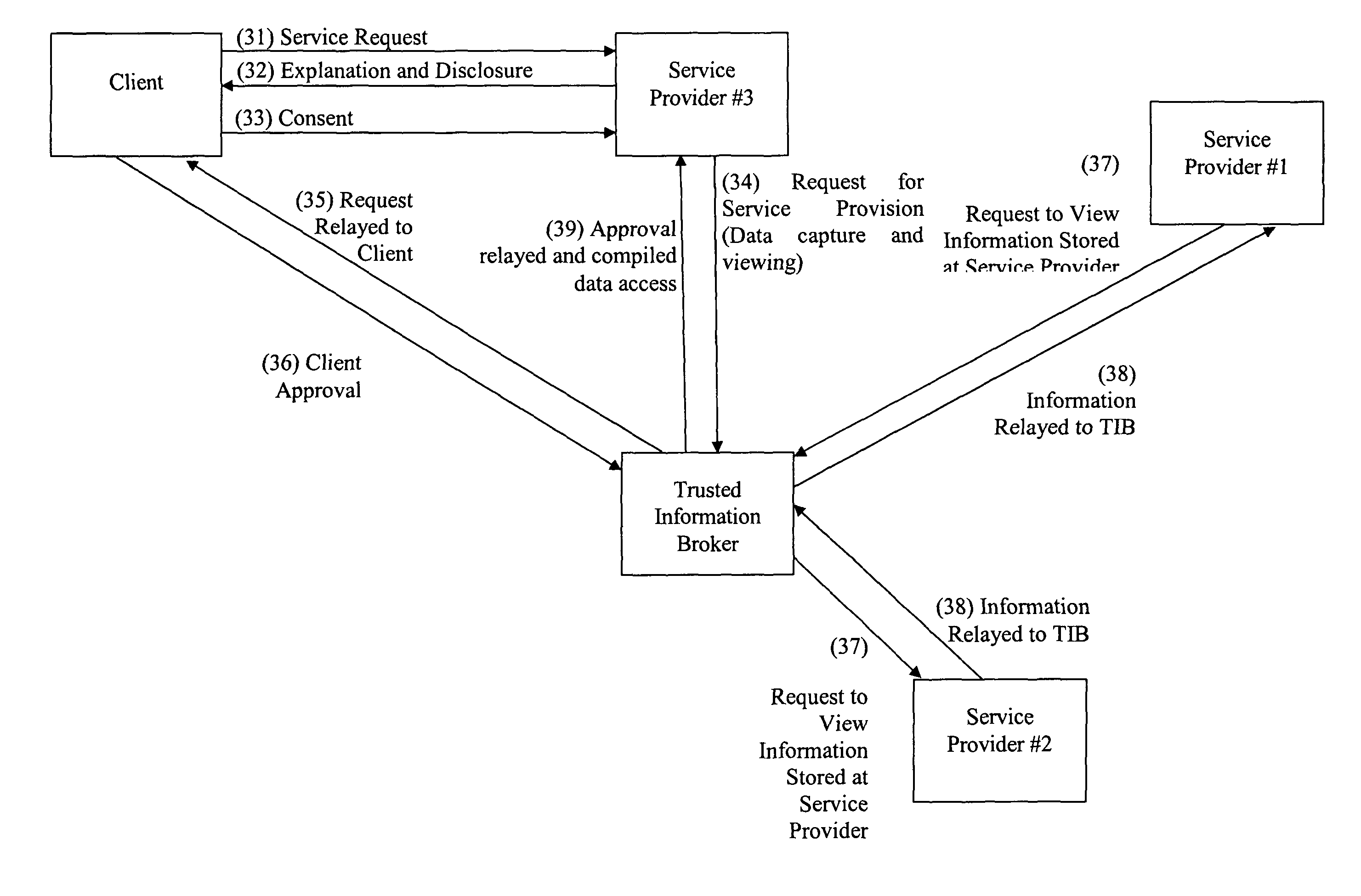
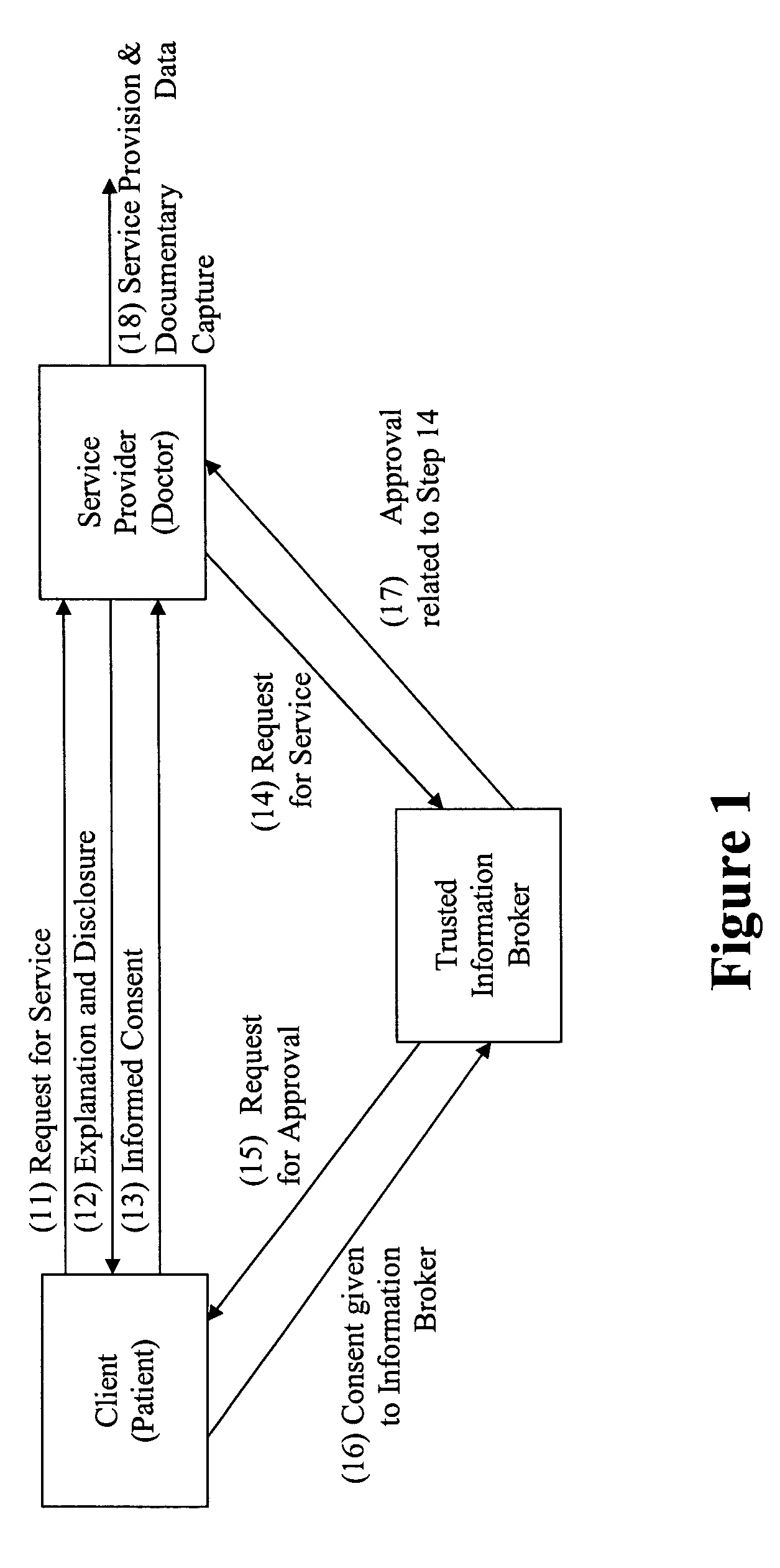
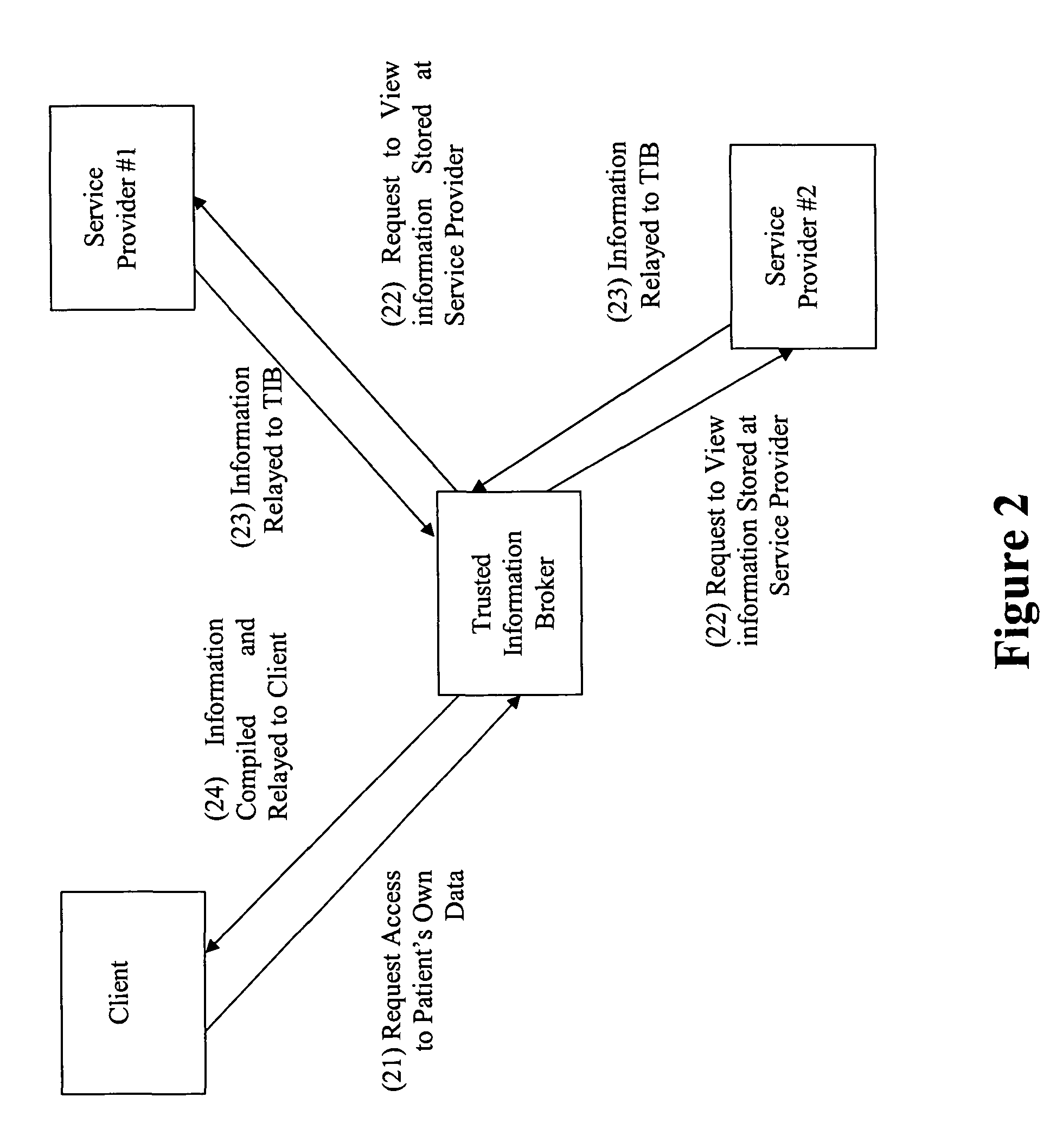
Privacy compliant consent and data access management system and methods
ActiveUS8275632B2Many choicesEasy accessFinanceMultiple keys/algorithms usageInternet privacyData access
An information management system for restricting access to personal data in compliance with law or regulation includes a database having restricted records stored therein, at least one of the records including an identification of a client or group of clients about whom said record concerns. A computer system under the control of a trusted information broker is configured to receive via a communication medium a request initiated by a requester for access to at least one of the restricted records in the database, the request including an identification of the requester. The computer system is further configured to transmit a request for consent to the client and receive an indication from the client that the client consents or does not consent to access to the restricted record by the requestor. The computer system grants or denies access to the restricted records based upon the indication from the client.
Owner:PRIVIT
Authorization services with external authentication
InactiveUS7231661B1Digital data processing detailsUser identity/authority verificationInternet Authentication ServiceIdentity management
An Access System can provide identity management and / or access management services. Examples of access management services include authentication and authorization services. In some implementations, users of an Access System want to use the authorization services of the Access System but do not want to use the authentication services of the Access System. The present invention allows some or all of the resources protected by the Access System to use the authentication services of the Access System and some or all of the resources protected by the Access System to use external authentication services.
Owner:ORACLE INT CORP
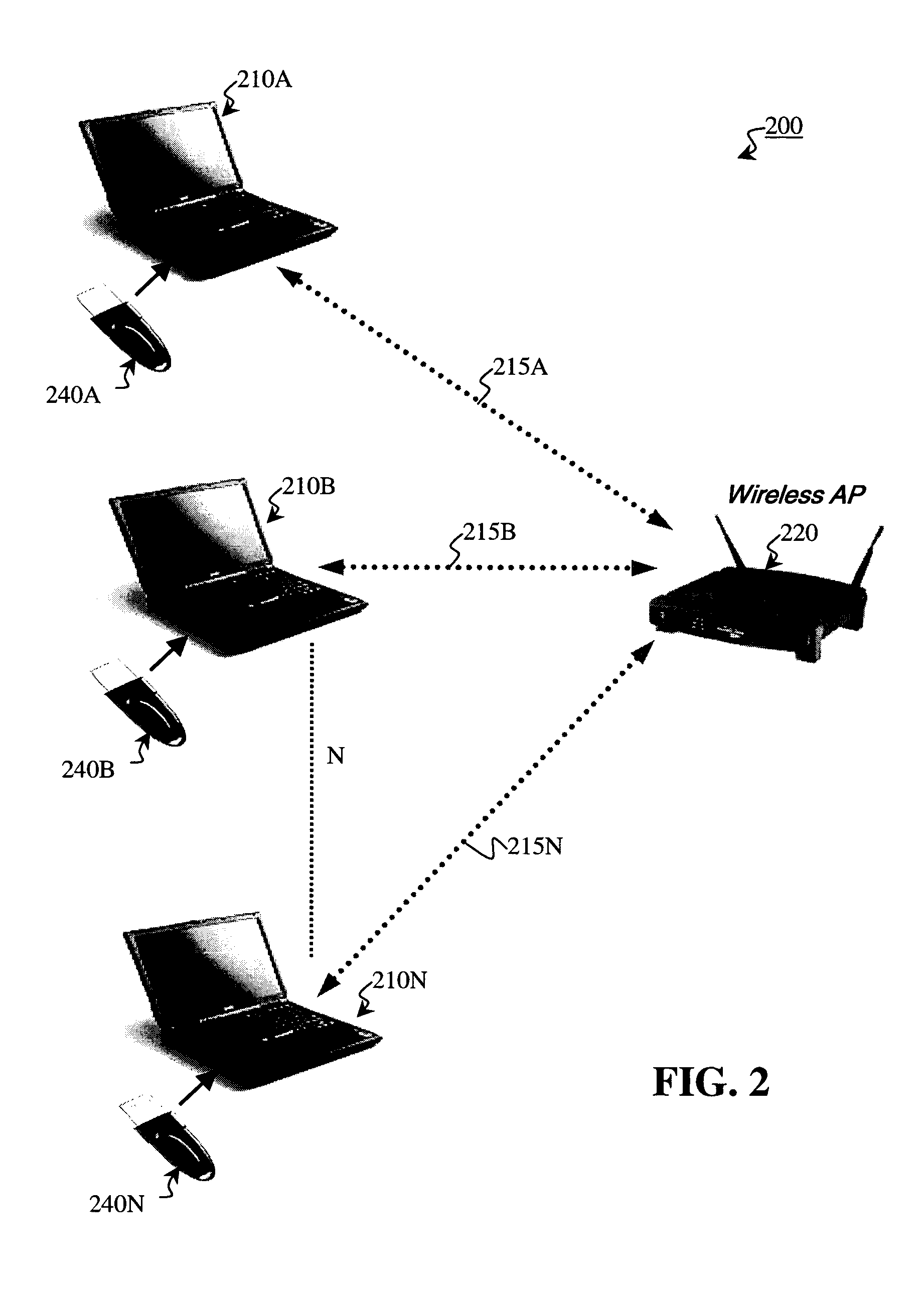
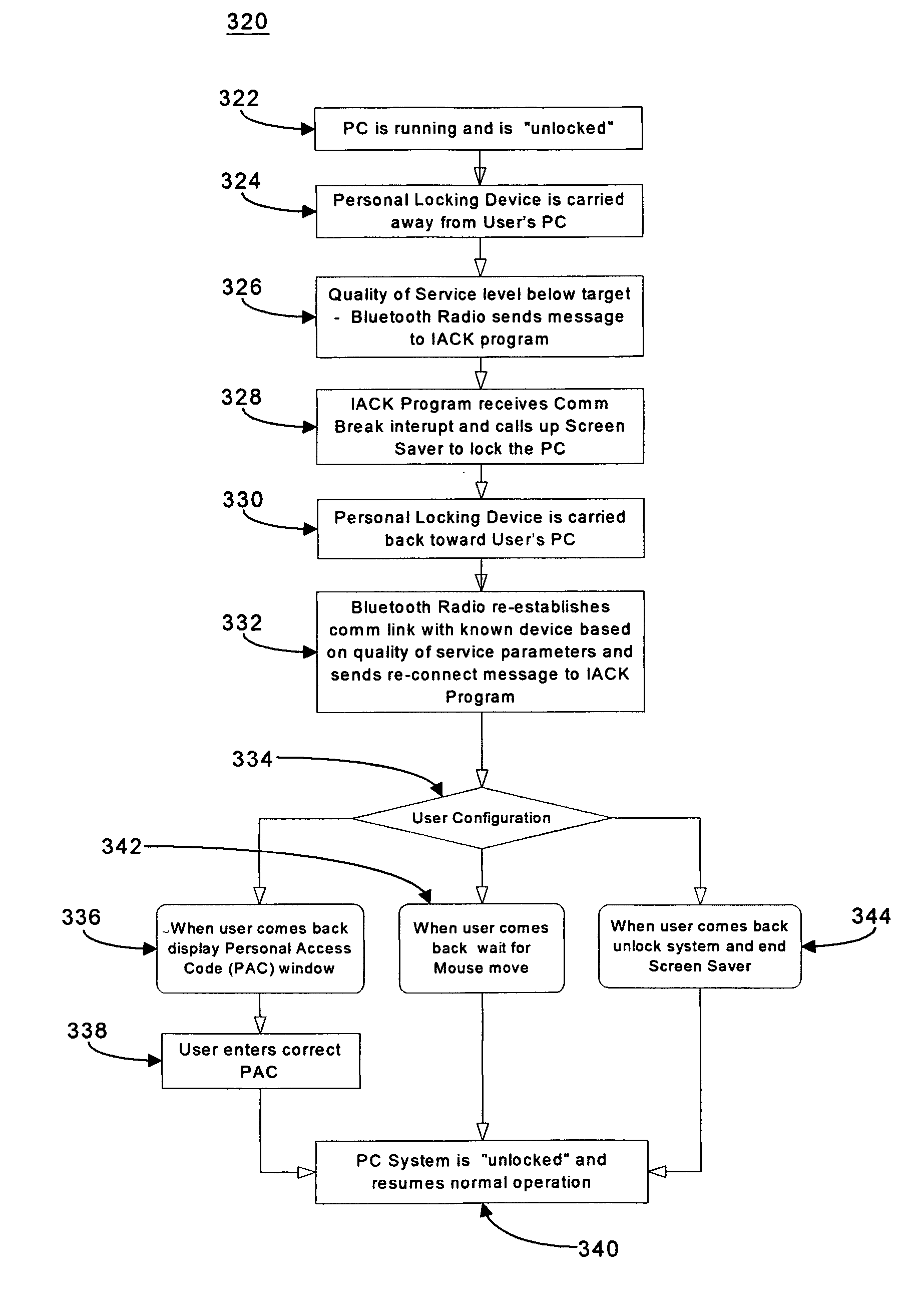
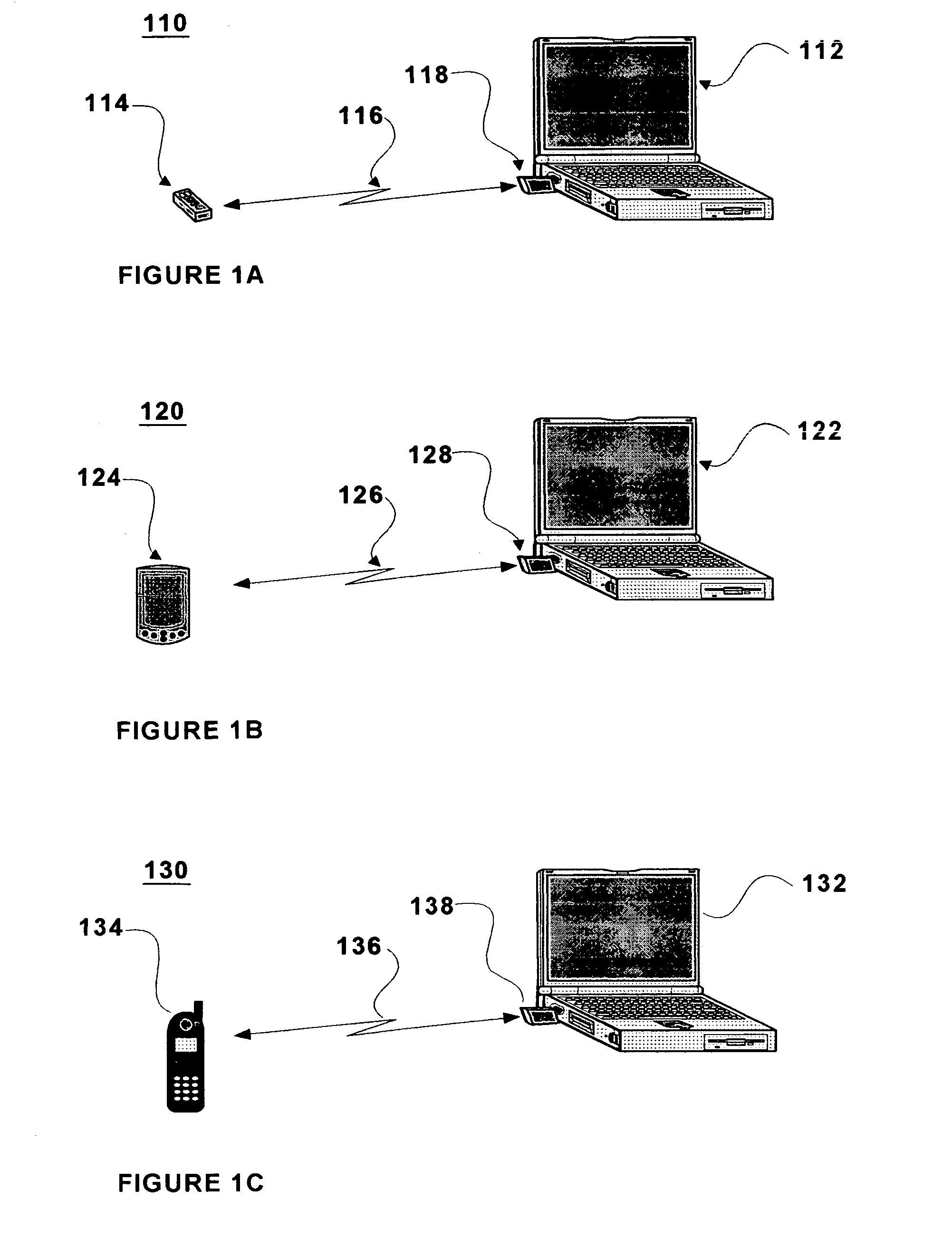
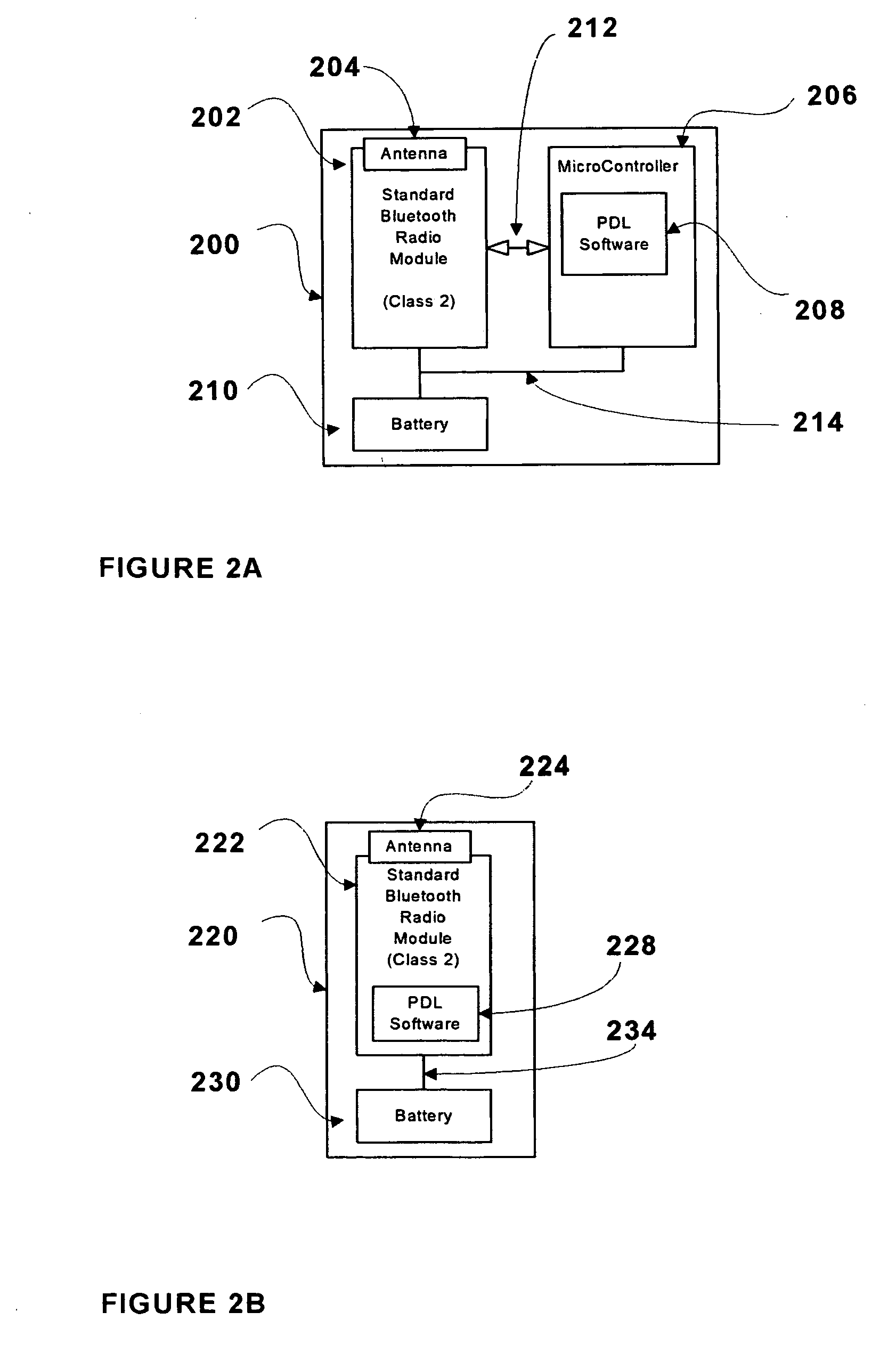
Wireless access management and control for personal computing devices
InactiveUS20050076242A1Monitoring quality of serviceDigital data processing detailsNetwork topologiesQuality of serviceControl system
A wireless access control system for an electronic device comprises a personal locking device and an access control software module. The electronic device and personal locking device are Bluetooth-enabled and use Bluetooth to communicate with each other. The access control software is used to establish a Bluetooth link between these devices, based on the unique Bluetooth identifiers of the personal locking device and the electronic device. The personal locking device is preferably portable and is carried by the user at all times. Examples of preferred personal locking devices are cellular telephones, personal digital assistants, and pocket PCs. The Bluetooth radio chip and the Bluetooth communications protocol monitor the quality of service of the Bluetooth link between the devices. When the quality of service falls below a predetermined threshold, the access control software may switch the electronic device from an unlocked state to a locked state. When the quality of service rises above a predetermined threshold from below the threshold, the software may switch the electronic device from a locked state to an unlocked state.
Owner:BREUER ROLF
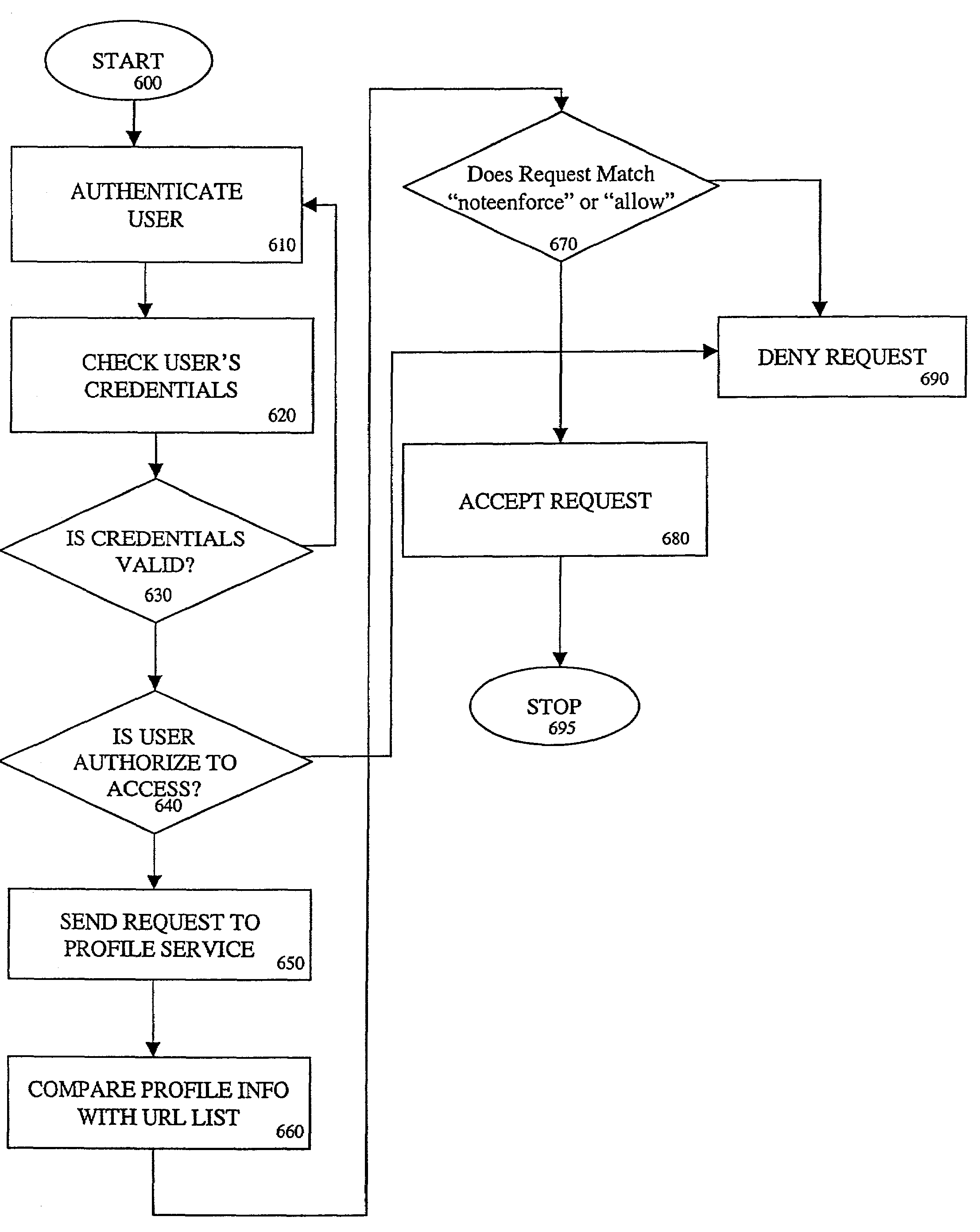
Uniform resource locator access management and control system and method
ActiveUS7243369B2Less costlyImprove efficiencyDigital data processing detailsComputer security arrangementsControl systemUser authentication
In an enterprise server environment having a uniform resource locator (URL) access management and control system. The server includes a user authentication logic to authenticate users attempting to connect to the server to access URL file and directories residing in the server. In one embodiment of the present invention, the user is provided with an identification token and a user URL access policy which allows the user's credentials to be validated and permitted access to a list of URLs in the directory server. In one embodiment of the present invention, a URL access enforcement logic uses the user's URL access policy to determine which URLs in the directory server a user may or may not access. The user's URL access policy may include an access deny or an access allow value which respectively denies or allows the user access to particular URL.
Owner:ORACLE INT CORP
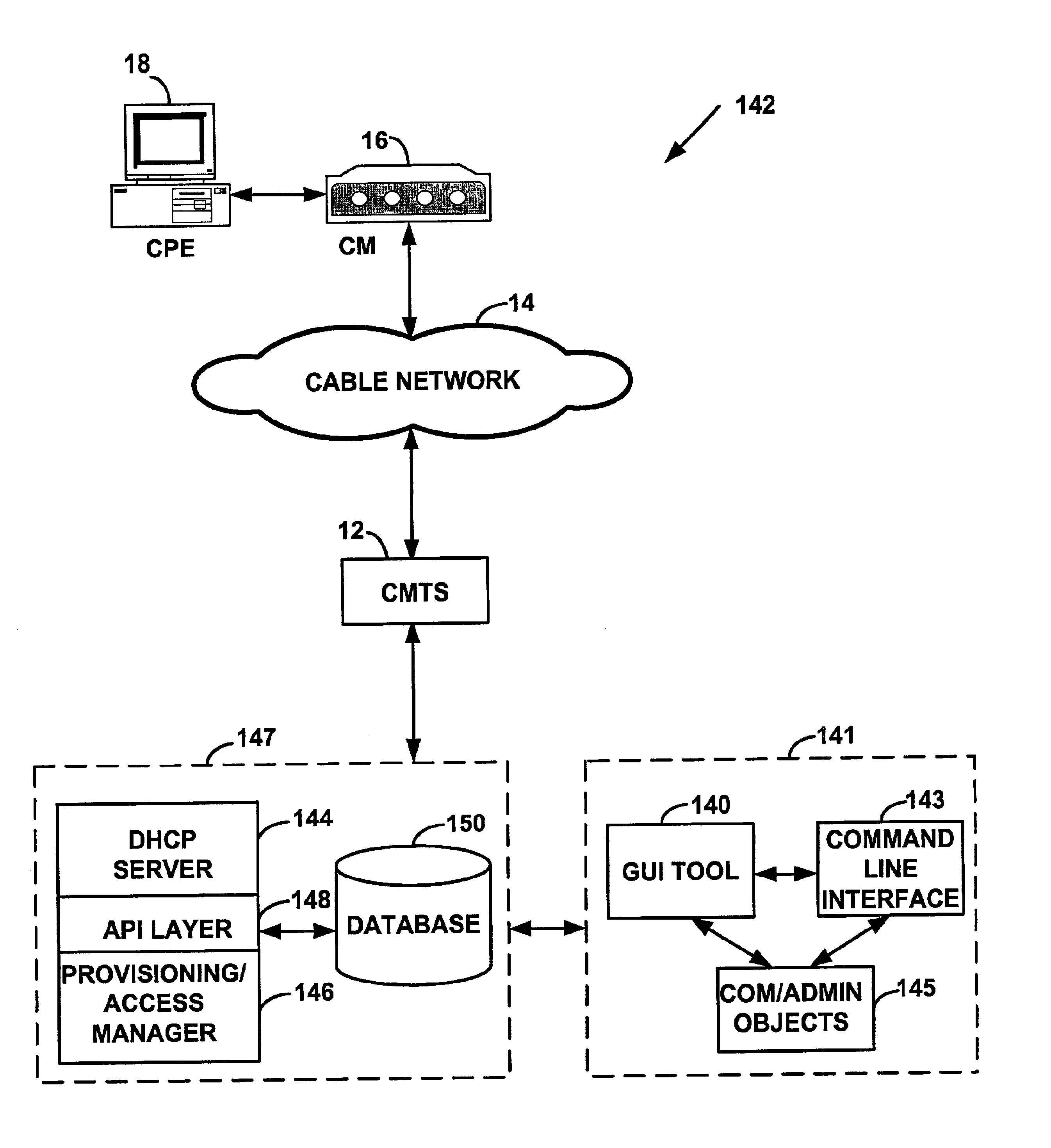
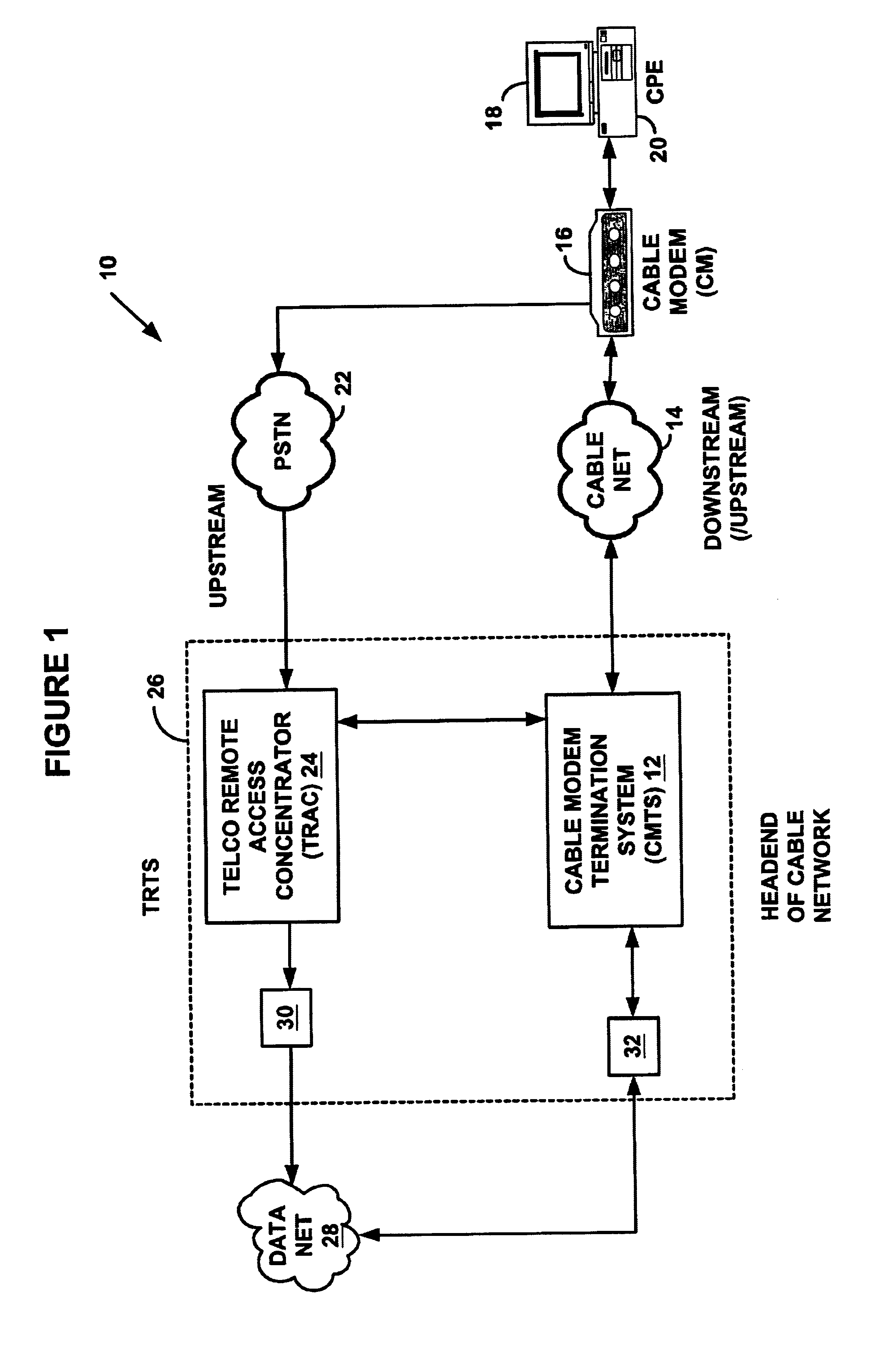
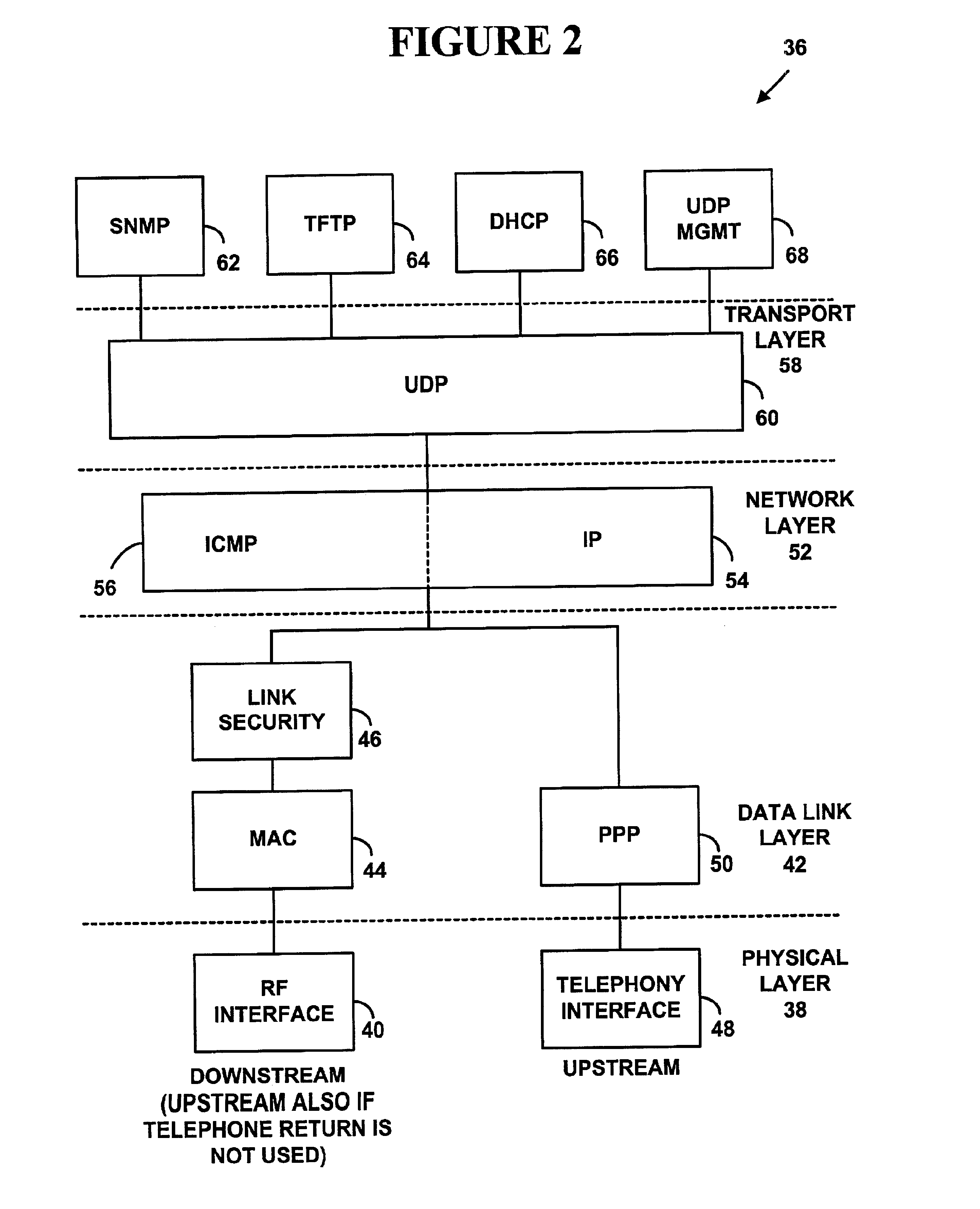
System and method for automatic load balancing in a data-over-cable network
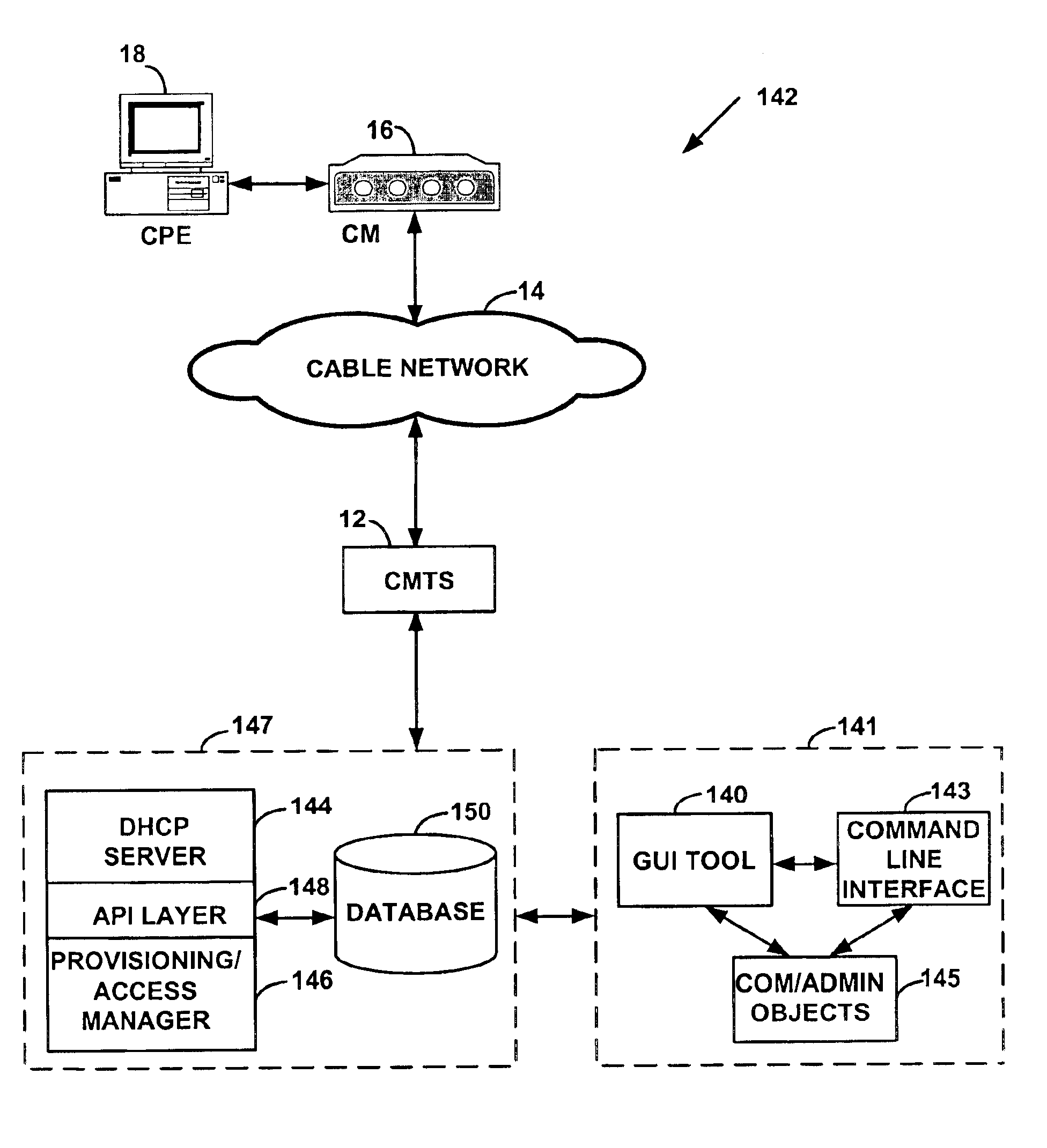
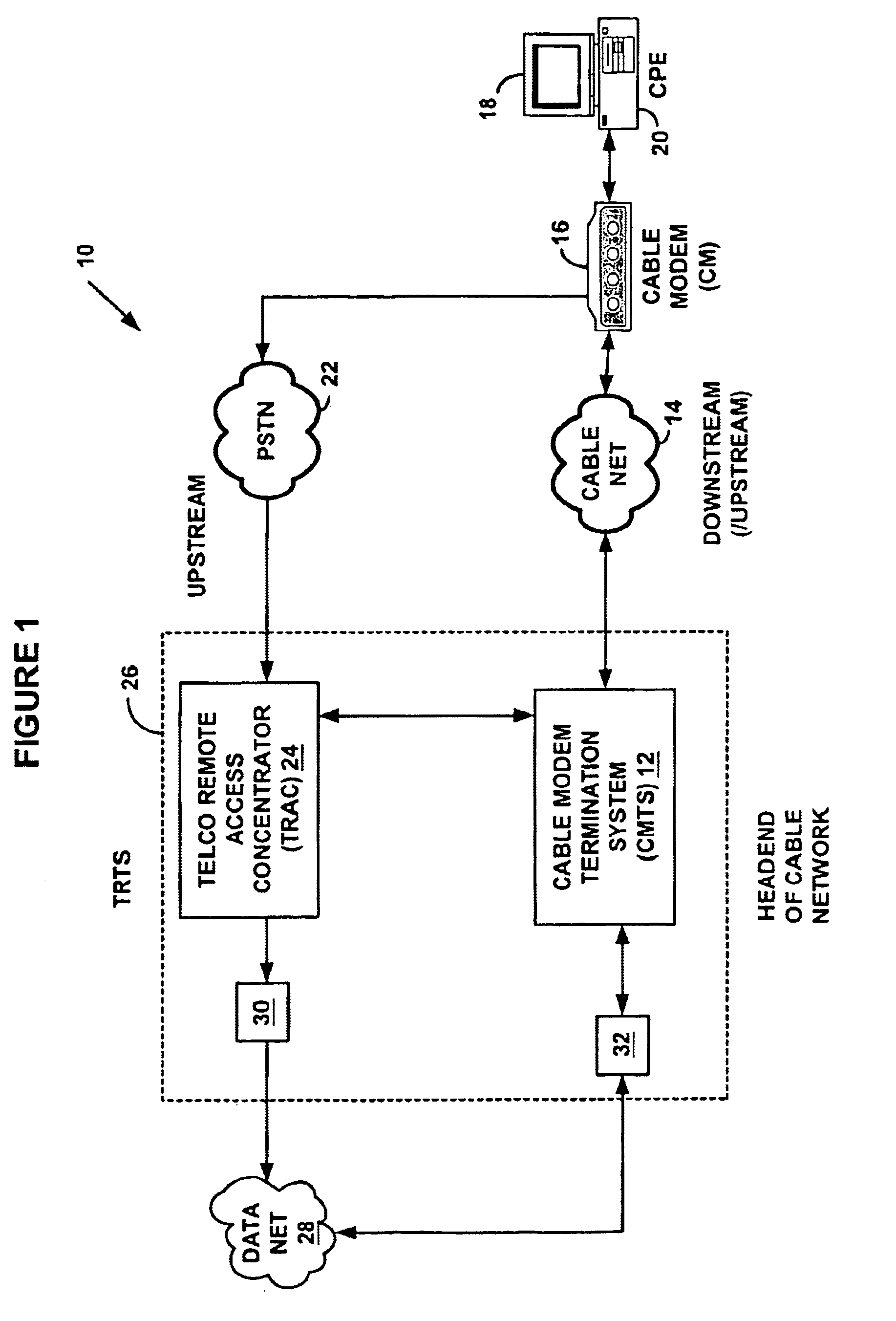
A method and system for load balancing in a network system such as a data-over-cable system. One method includes receiving a first message on a first network device such as a cable modem termination system (“CMTS”) from a second network device and marking the first message with an identifier of a network access device. The method further includes intercepting the first message on a third network device such as a provisioning / access manager prior to any first protocol server such a Dynamic Host Configuration Protocol server receives the first message. When the third network device intercepts the first message, the third network device determines capabilities of the second network device and applies a set of rules to load balance any requests between a plurality of channel pairs. Each charmel pair is associated with at least one capability of a network device and also has a load factor parameter and a threshold value defining a capacity of a channel pair. The third network device assigns the second network device to a predetermined channel pair based on the capabilities of the second network device, a load factor of the channel pair and a capacity of the channel pair.
Owner:VALTRUS INNOVATIONS LTD
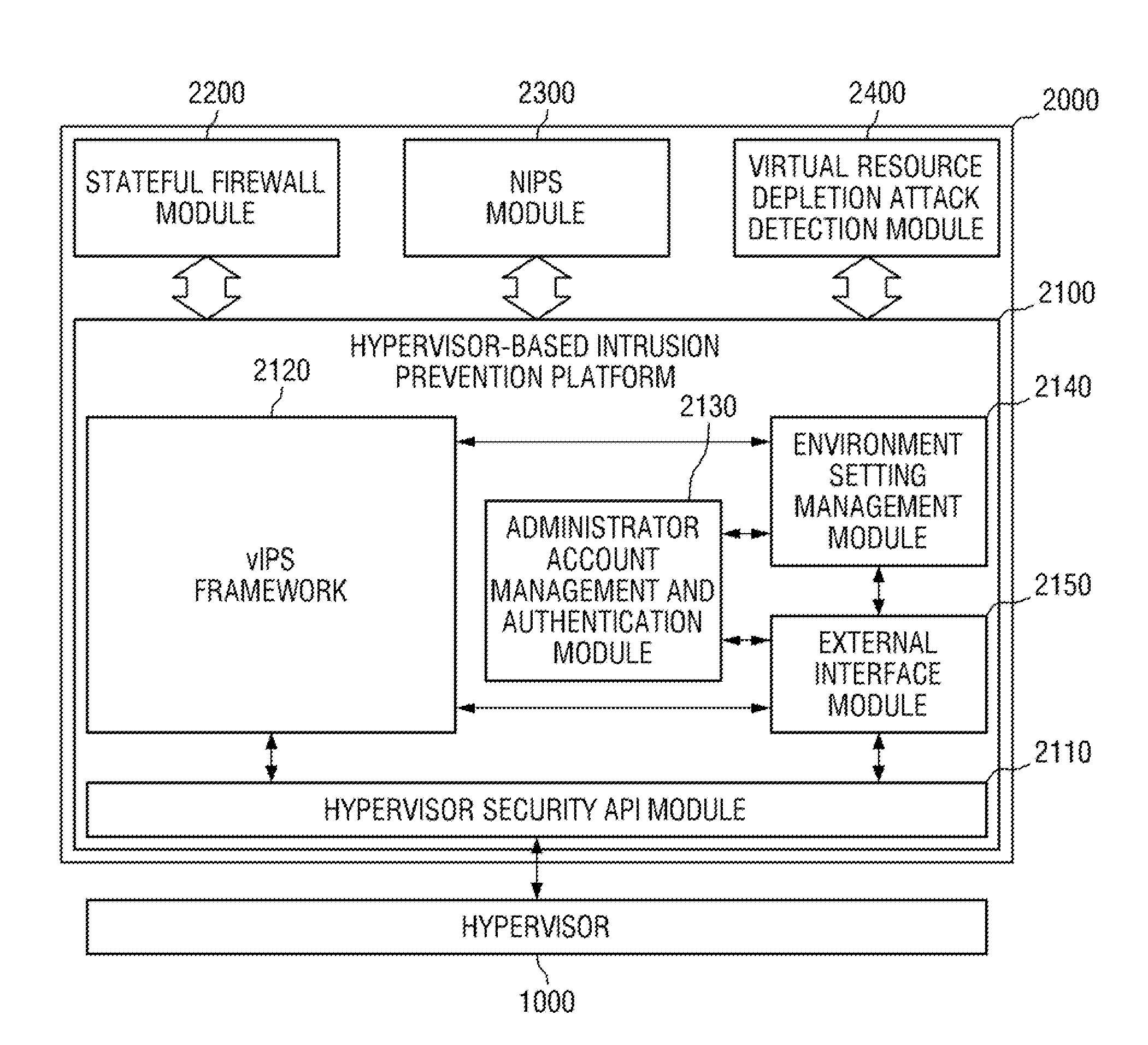
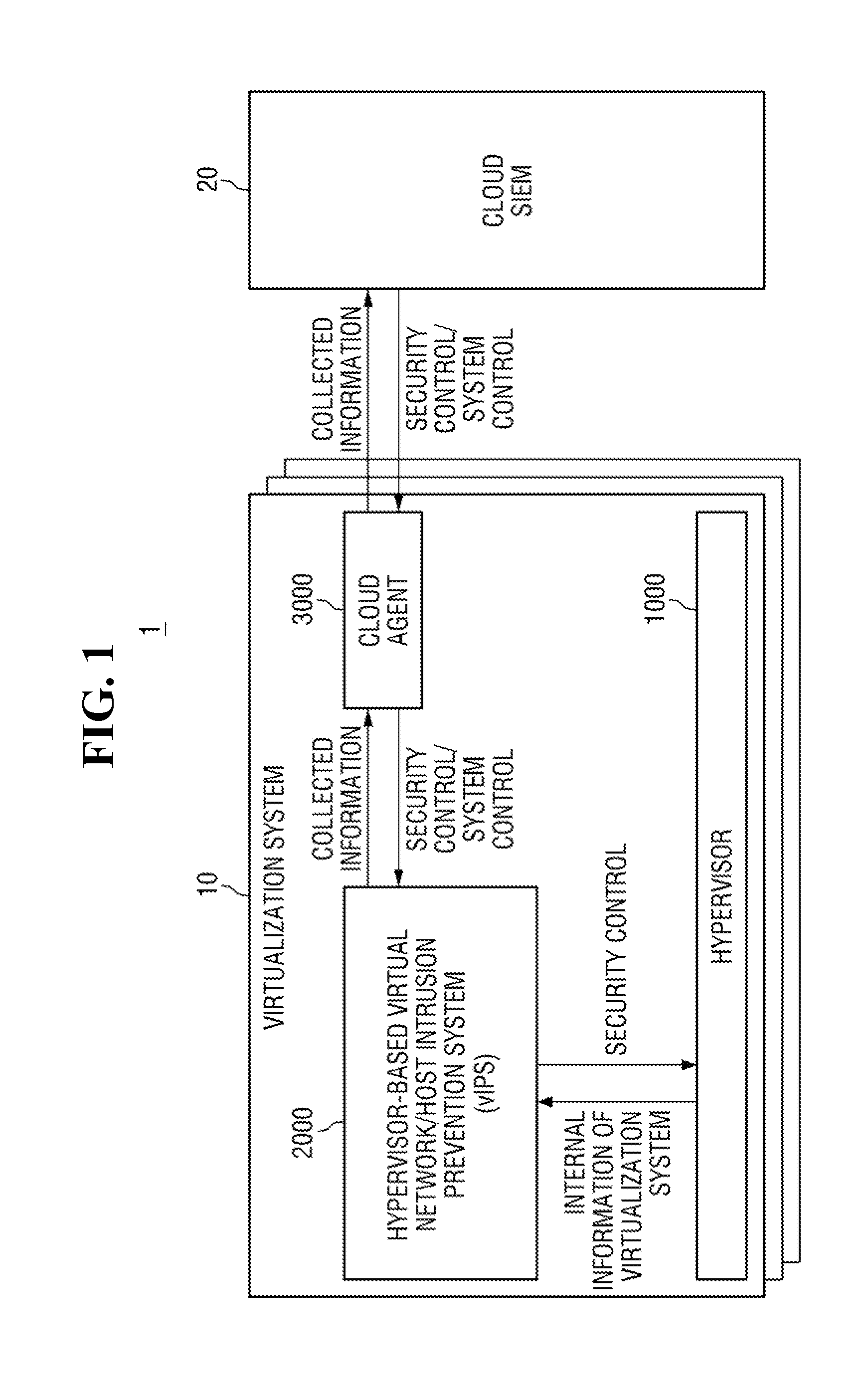
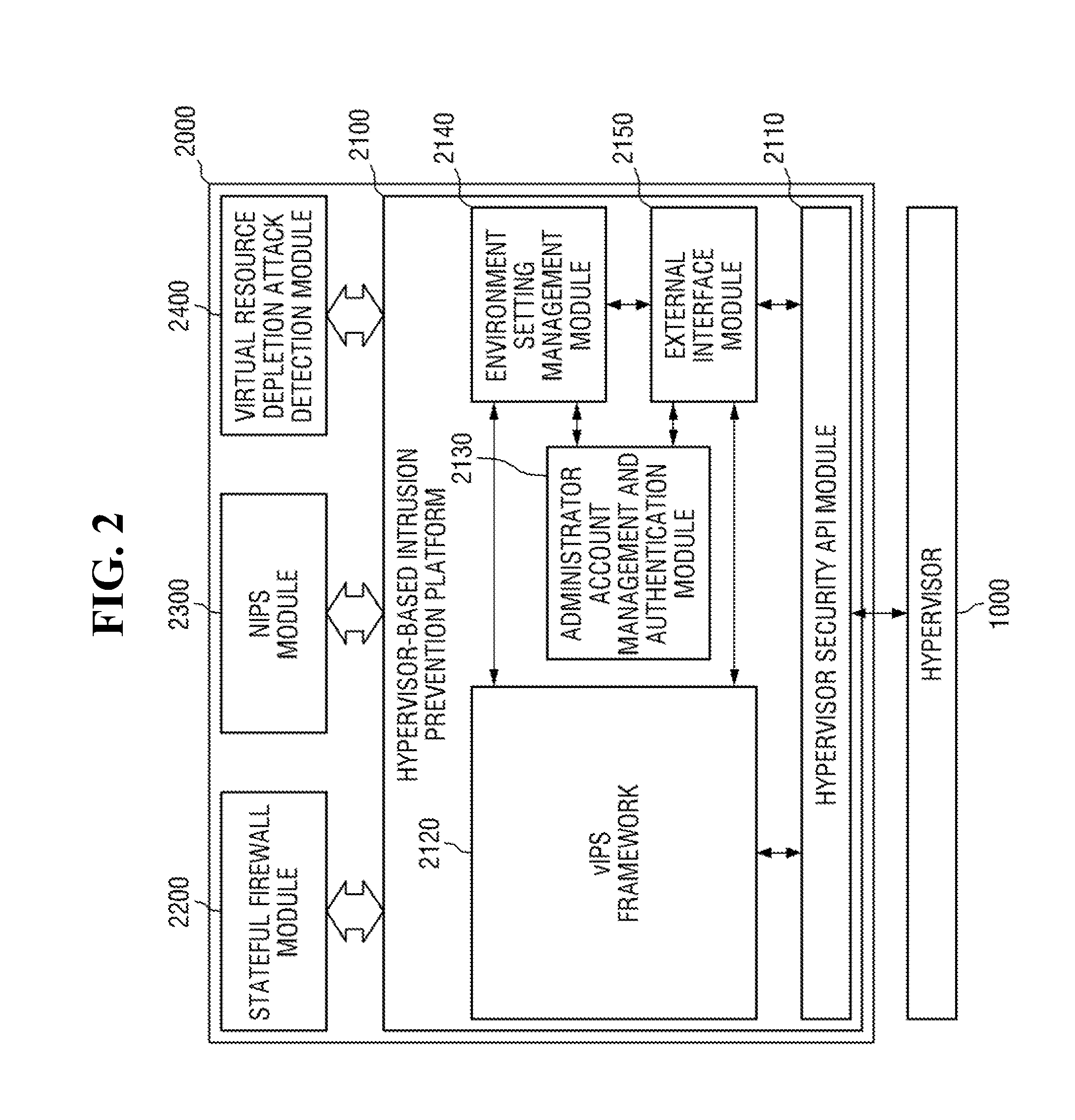
Hypervisor-based intrusion prevention platform and virtual network intrusion prevention system
InactiveUS20140317737A1Memory loss protectionData taking preventionApplication programming interfaceIntrusion prevention system
Hypervisor-based intrusion prevention platform is provided. The hypervisor-based intrusion prevention platform comprises a virtual network intrusion prevention system (vIPS) framework which obtains internal information of a virtualization system from a hypervisor and performs security control on the hypervisor in response to the result of intrusion detection carried out by using the internal information of the virtualization system, a hypervisor security application programming interface (API) module which provides an API used by the vIPS framework to access the hypervisor, an administrator account management and authentication module which manages an administrator account of a vIPS and authenticates the administrator account, an environment setting management module which manages environment setting values of modules within the vIPS, and an external interface module which provides an interface for system control and security control.
Owner:KOREA INTERNET & SECURITY AGENCY
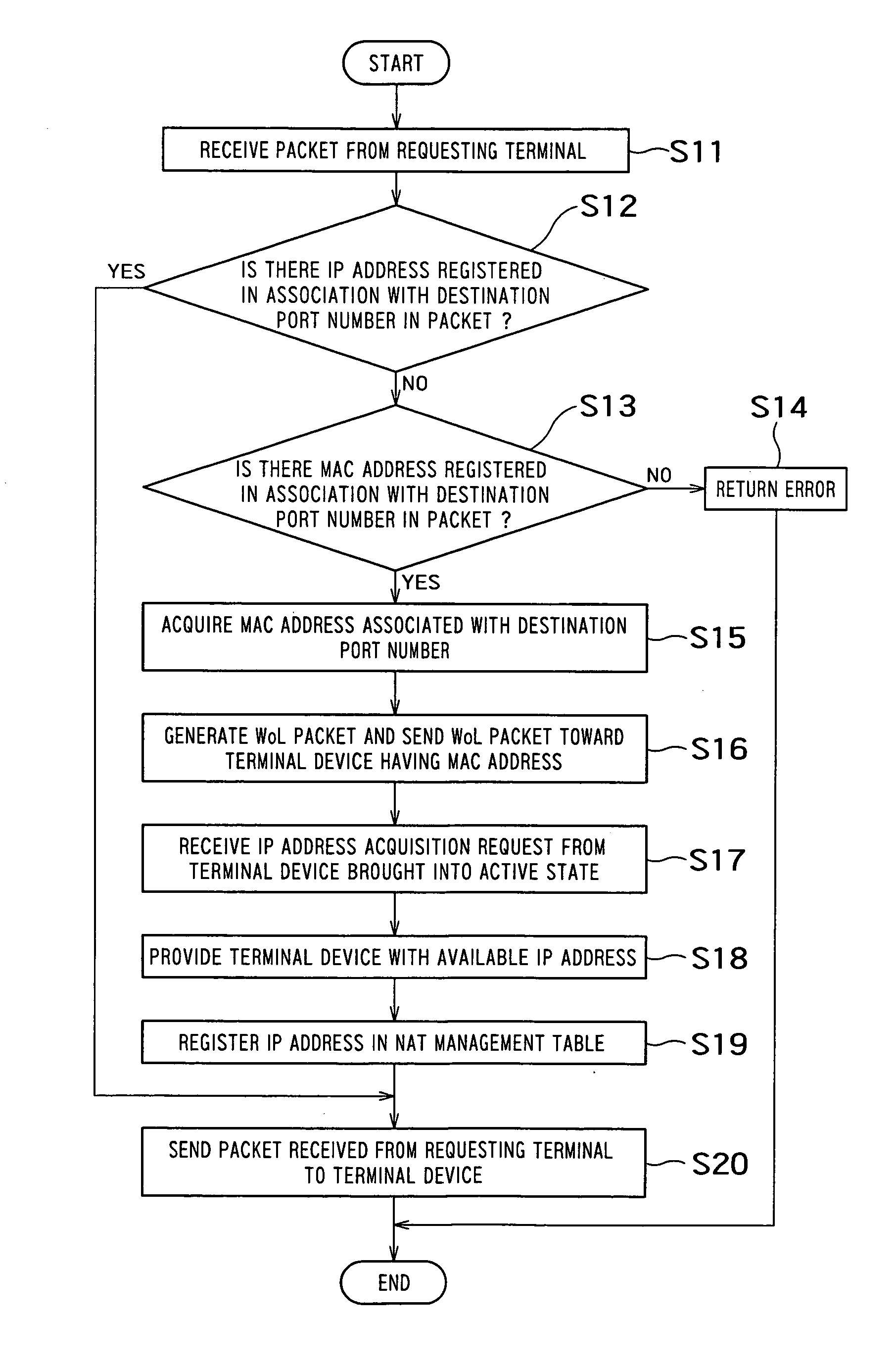
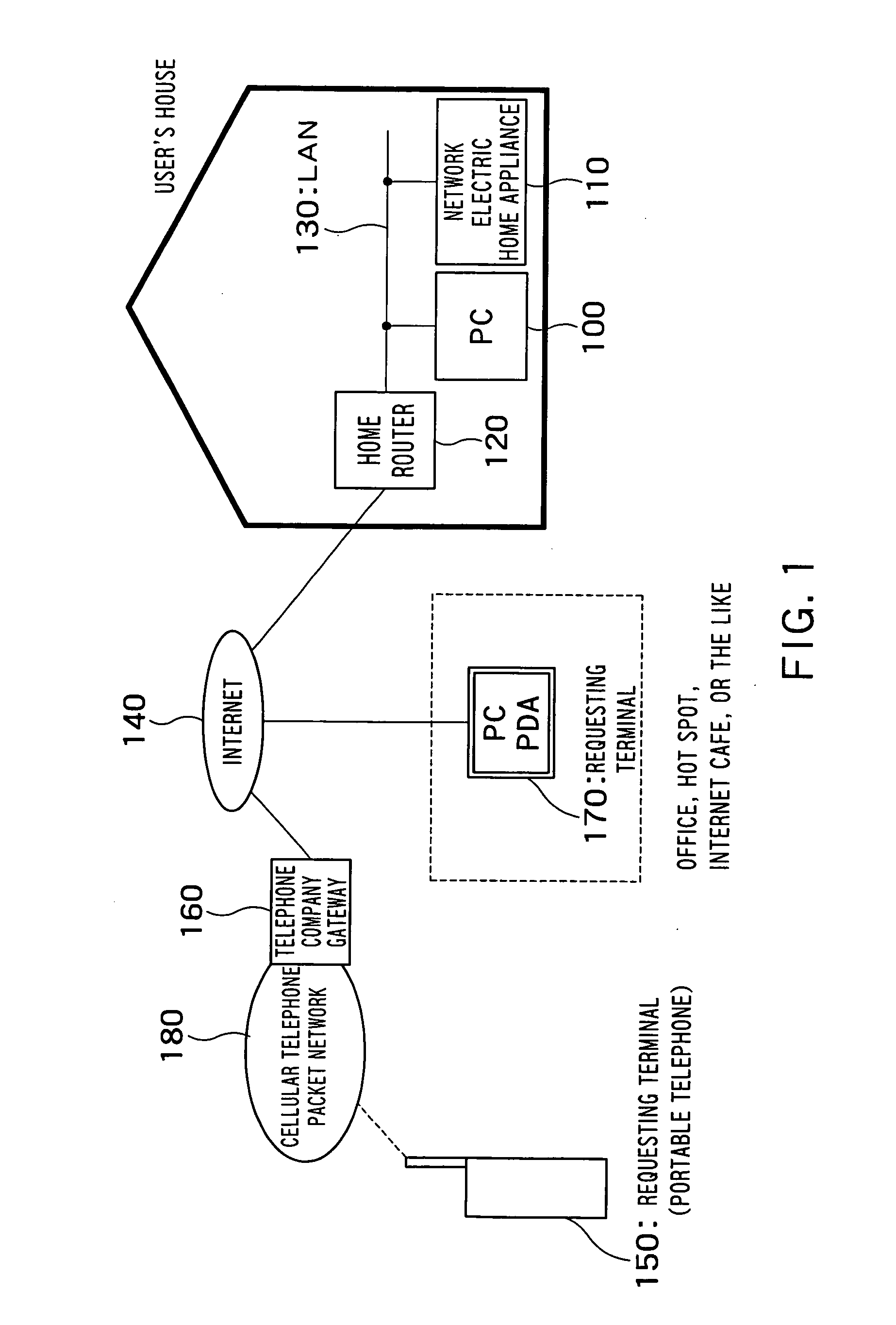
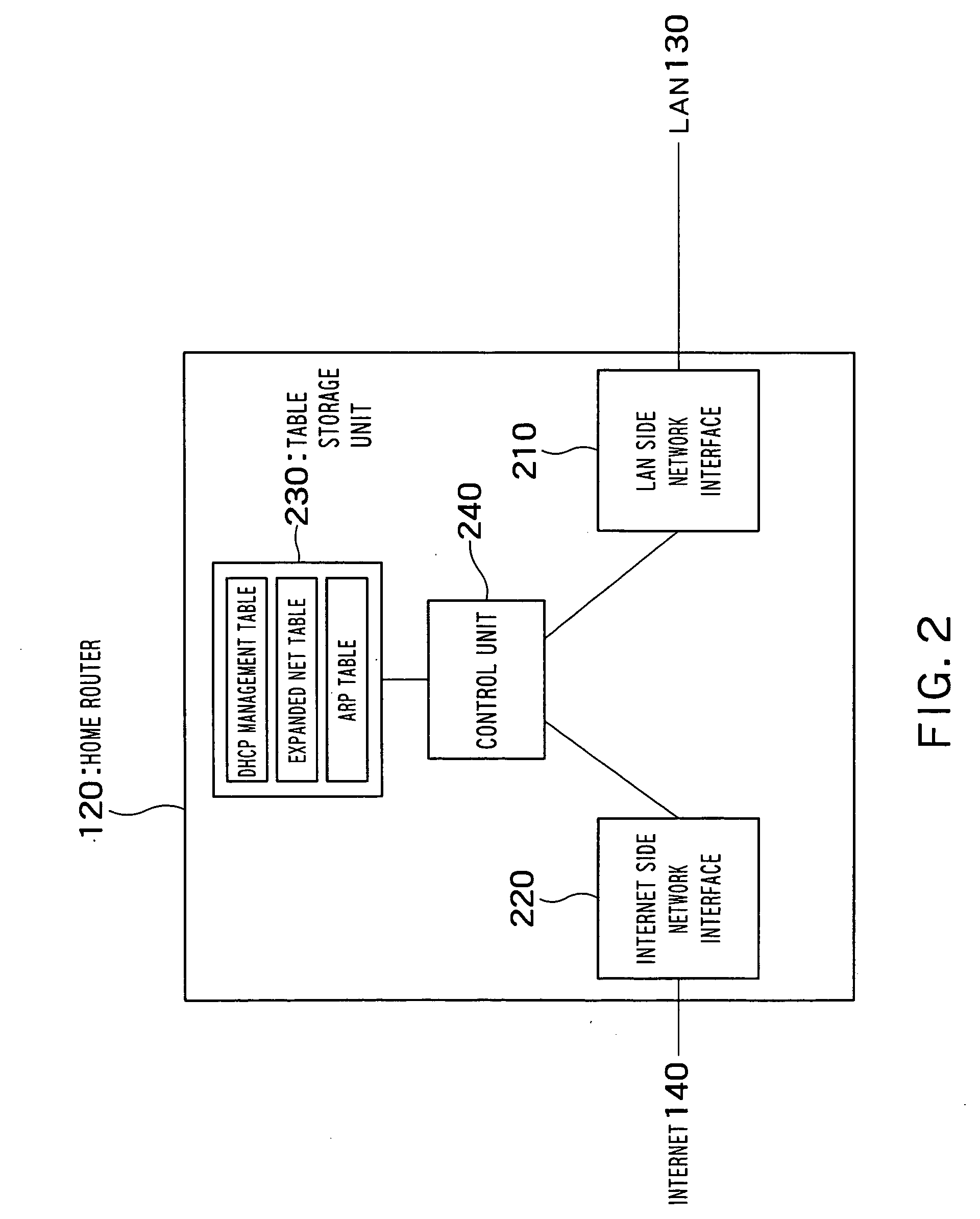
Access management apparatus, program and remote start-up method of terminal device
InactiveUS20060056397A1Data switching by path configurationWireless network protocolsPacket generatorNetwork connection
There is provided with an access management apparatus which connects a communication network to a local area network and which manages access from the communication network to the local area network, the access management apparatus including: a packet receiver which receives a packet according to TCP or UDP from the communication network; a database storage unit which stores a database having a port number of the TCP or UDP in association with a MAC address; a MAC address detector which detects a MAC address associated with a destination port number in the packet received by the packet receiver, from the database; a start-up request packet generator which generates a start-up request packet to start up a terminal device having the detected MAC address on the local area network; and an output unit which outputs the generated start-up request packet to the local area network.
Owner:KK TOSHIBA
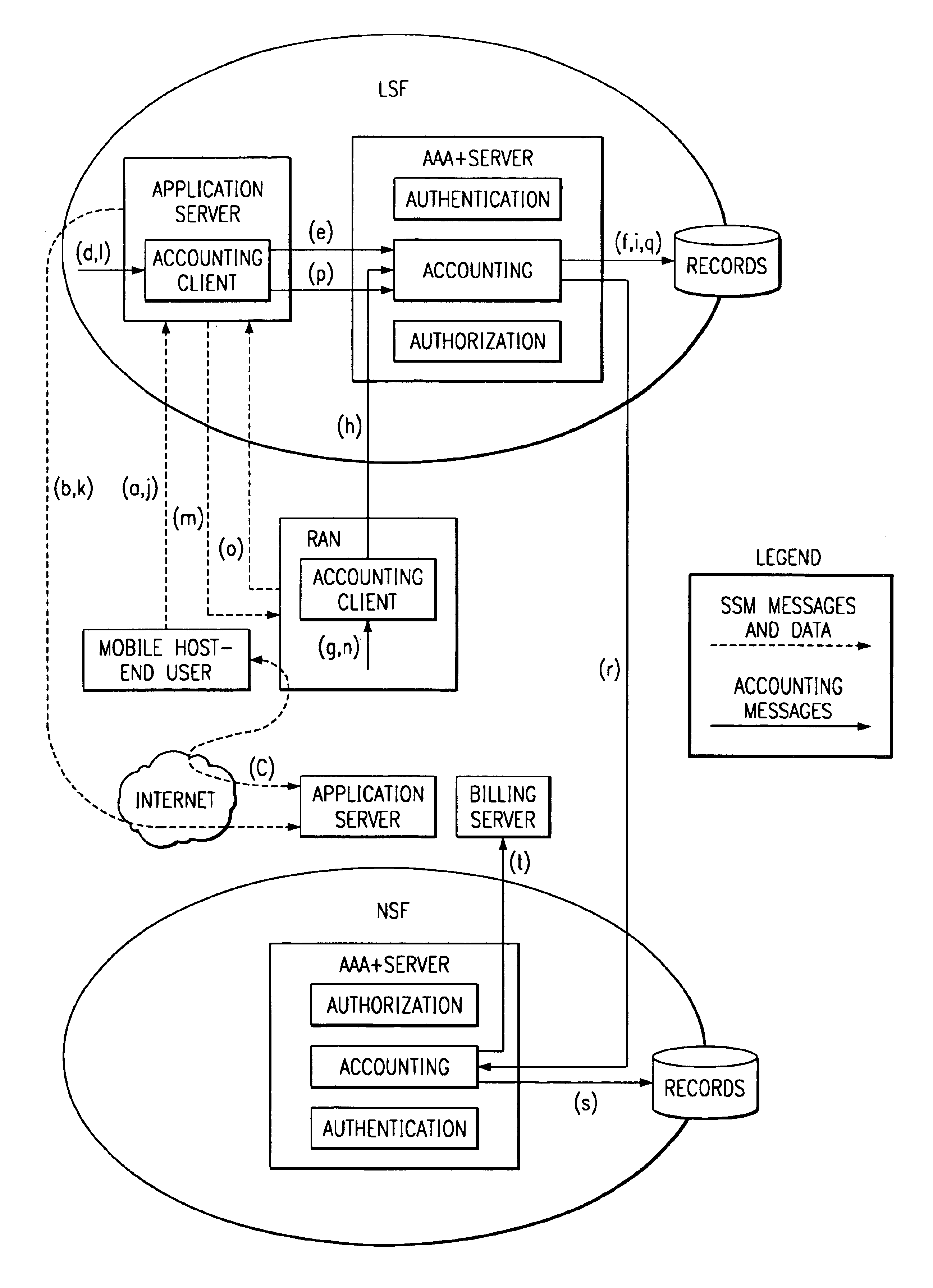
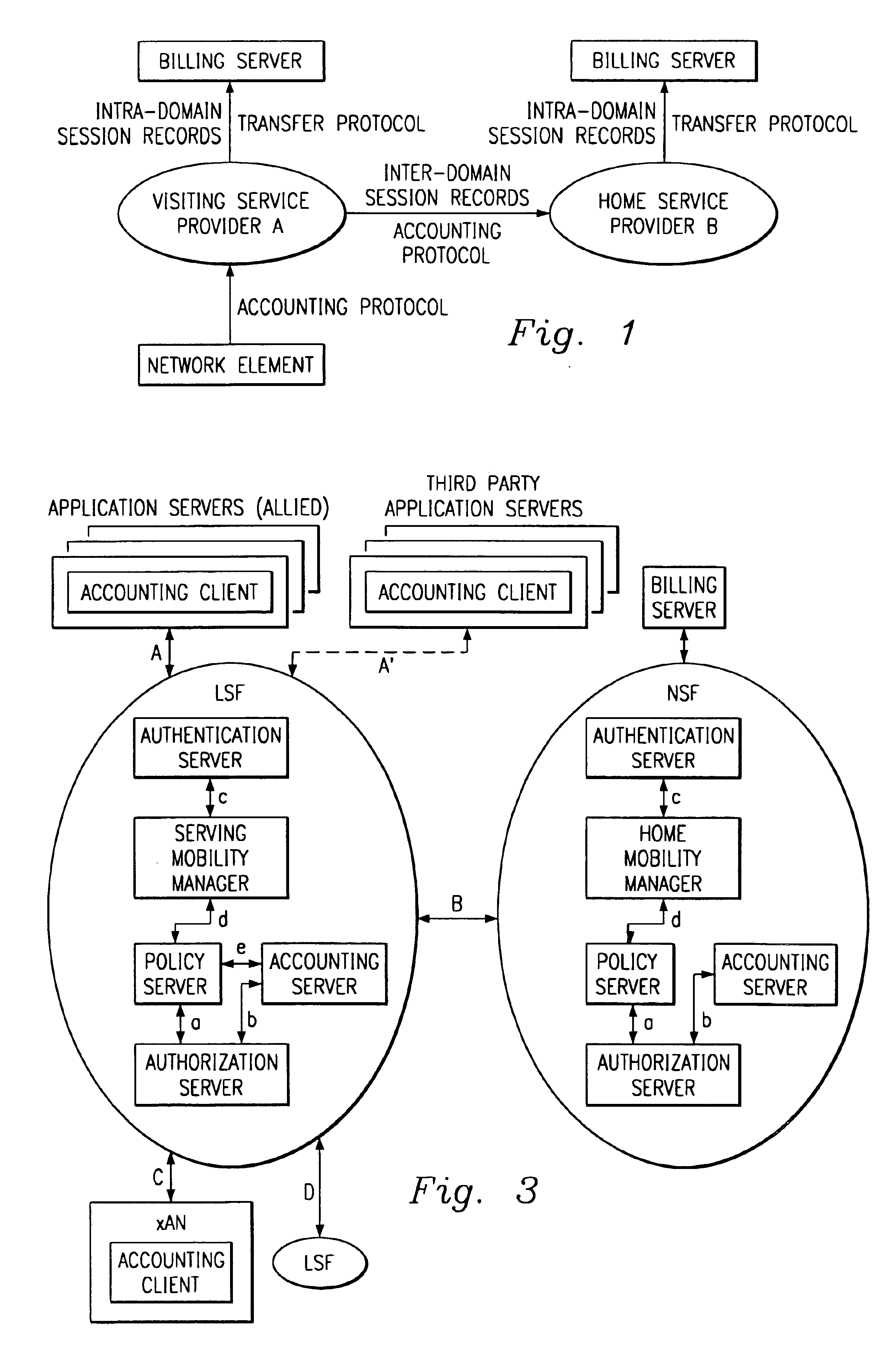
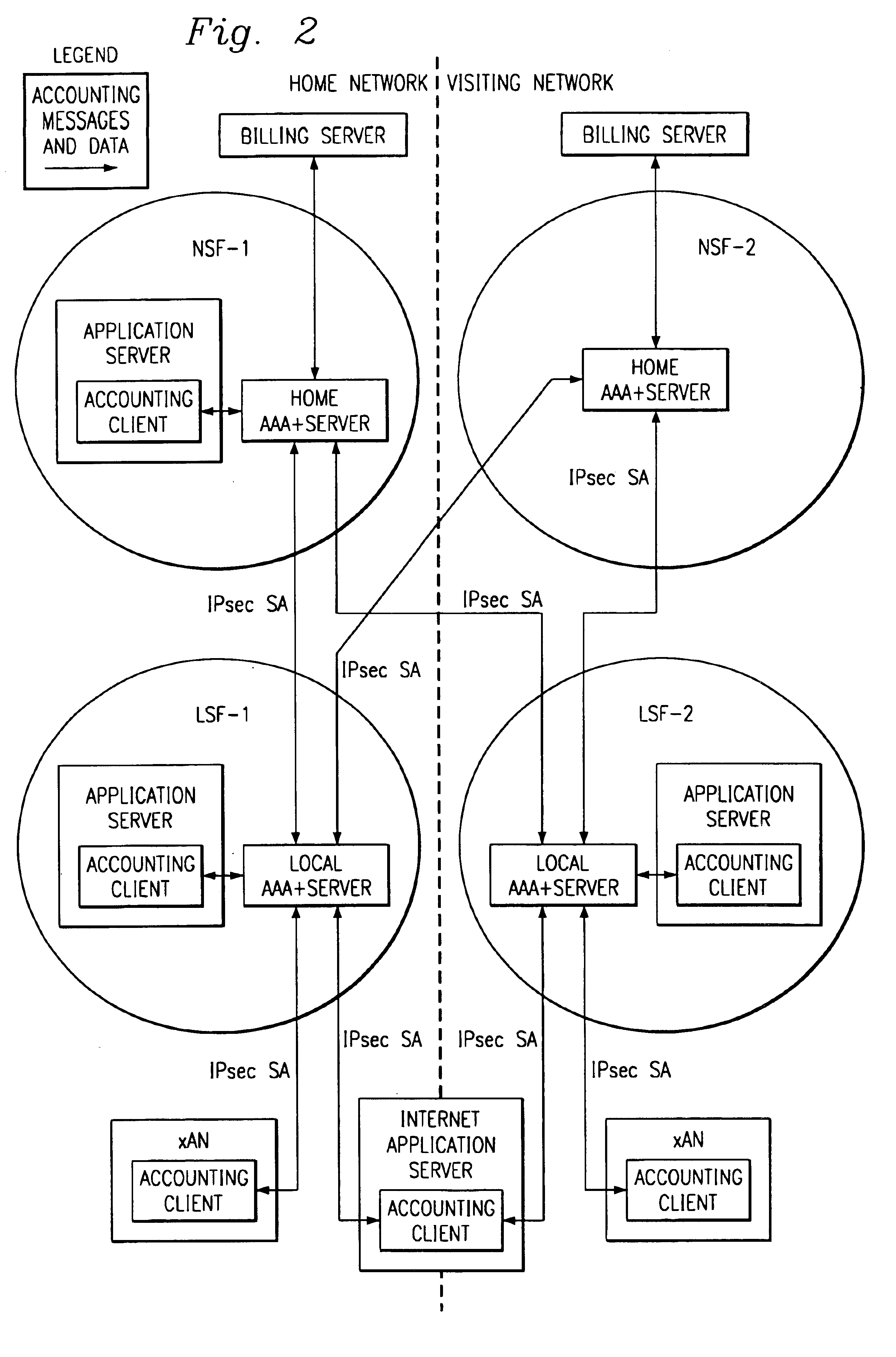
System and method for accounting management in an IP centric distributed network
InactiveUS6854014B1Flexible capacityFacilitate accounting activityMetering/charging/biilling arrangementsMultiple digital computer combinationsApplication serverPoint of presence
A system and method for a first user to communicate in an Internet Protocol (IP) centric distributed network is described. The method can include a plurality of service layers including a network service function layer, a local service function layer, and an access service function layer providing a plurality of functions associated with each of the service layers. The method can also include accessing the network to establish a point of presence at an access management layer and a core portion of the network and to designate a default amount of bandwidth and plurality of default setup parameters; invocating service through an application server on the network to establish an amount of network resources requested by the first user; establishing a transport session to create and manage a connection from the first user to a destination address; and accounting for a service session within the IP centric distributed network.
Owner:APPLE INC
Query string processing
ActiveUS20020099671A1Easy mappingData processing applicationsDigital data processing detailsData matchingQuery string
A system is disclosed that is used to provide access management for resources on a network. The system makes use of query data from a URL (or another identification or request) to identify the appropriate access rule. Examples of an access rule include an authentication rule, an authorization rule, or an audit rule. The system can be configured to require the query data to match order dependent variables or order independent variables. In one option, the system can include two levels of rules and the query data can be used to identify first level rules, second level rules or both.
Owner:ORACLE INT CORP
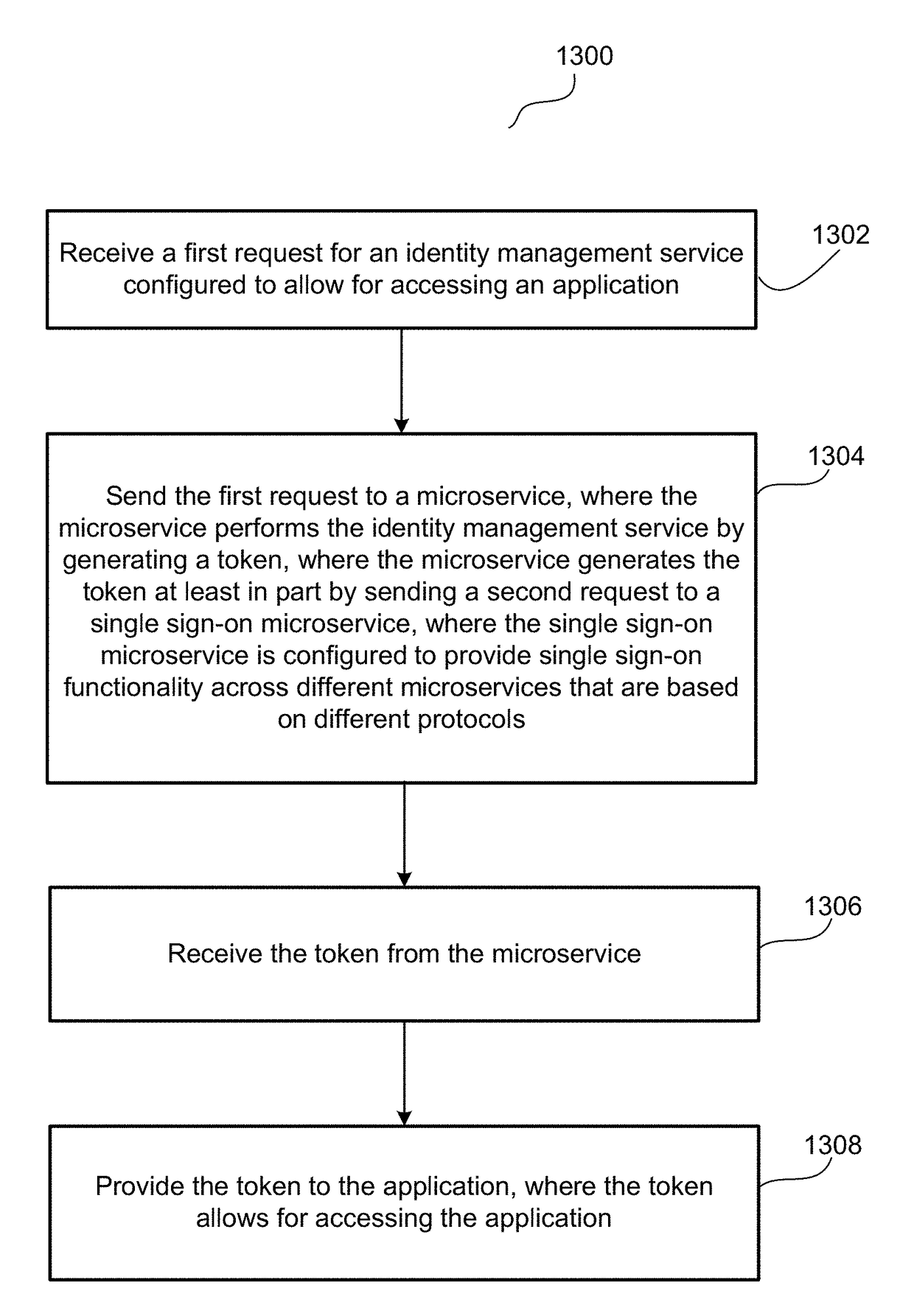
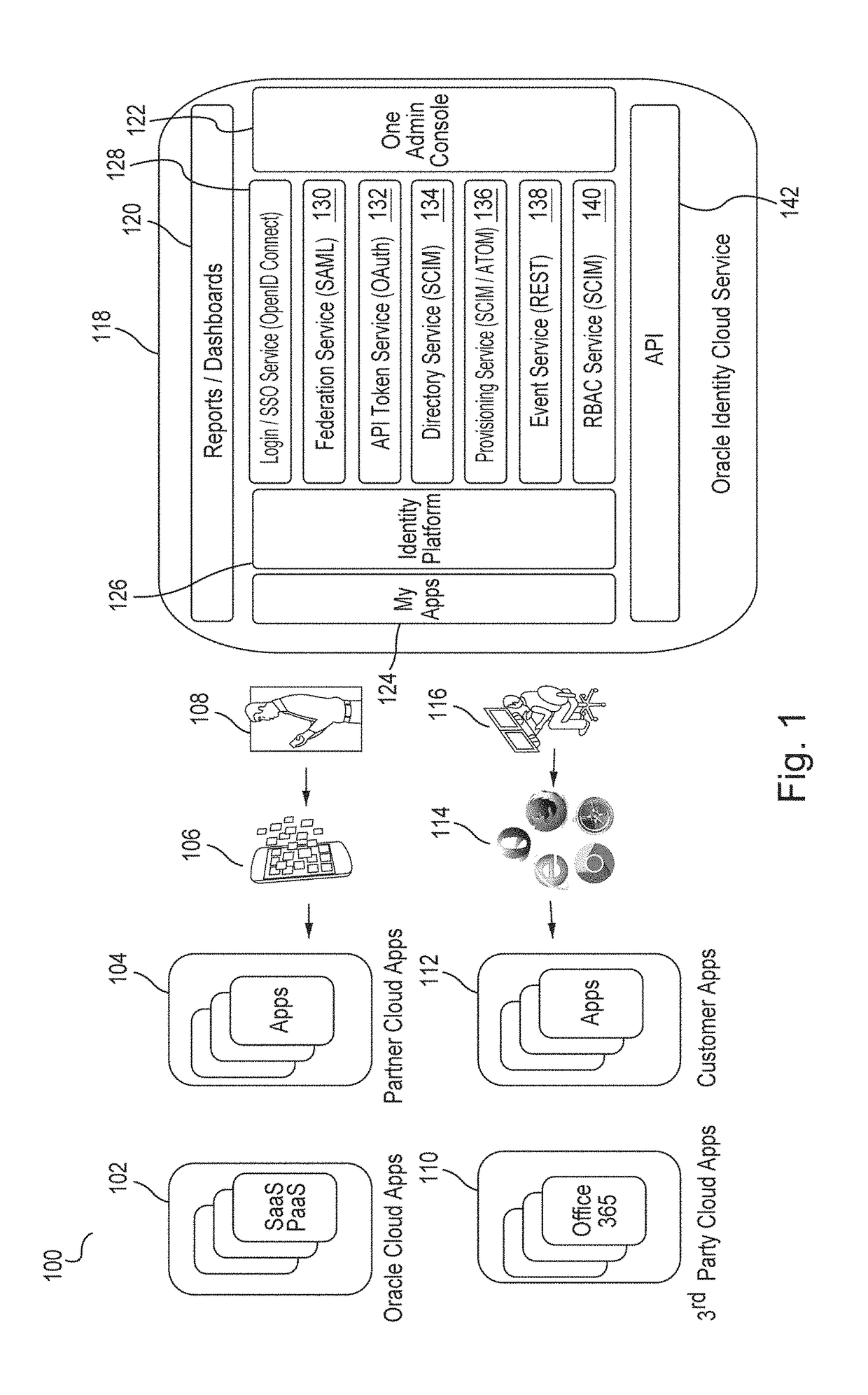
Single sign-on functionality for a multi-tenant identity and data security management cloud service
ActiveUS20180075231A1Digital data information retrievalDigital data authenticationInternet privacyCloud base
A cloud-based identity and access management system that implements single sign-on (“SSO”) receives a first request for an identity management service configured to allow for accessing an application. Embodiments send the first request to a first microservice which performs the identity management service by generating a token. The first microservice generates the token at least in part by sending a second request to a SSO microservice that is configured to provide SSO functionality across different microservices that are based on different protocols. Embodiments then receive the token from the first microservice and provide the token to the application, where the token allows for accessing the application.
Owner:ORACLE INT CORP
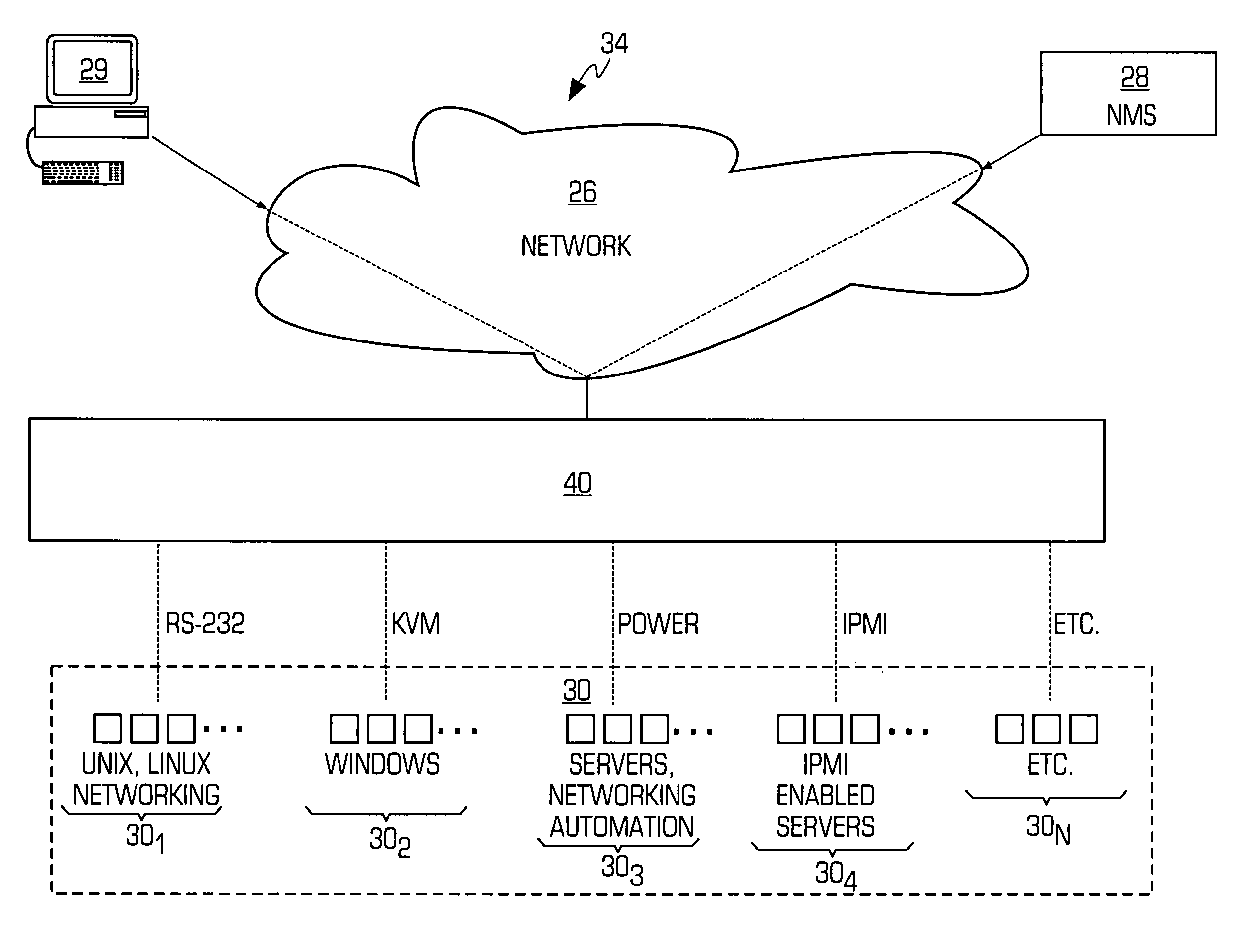
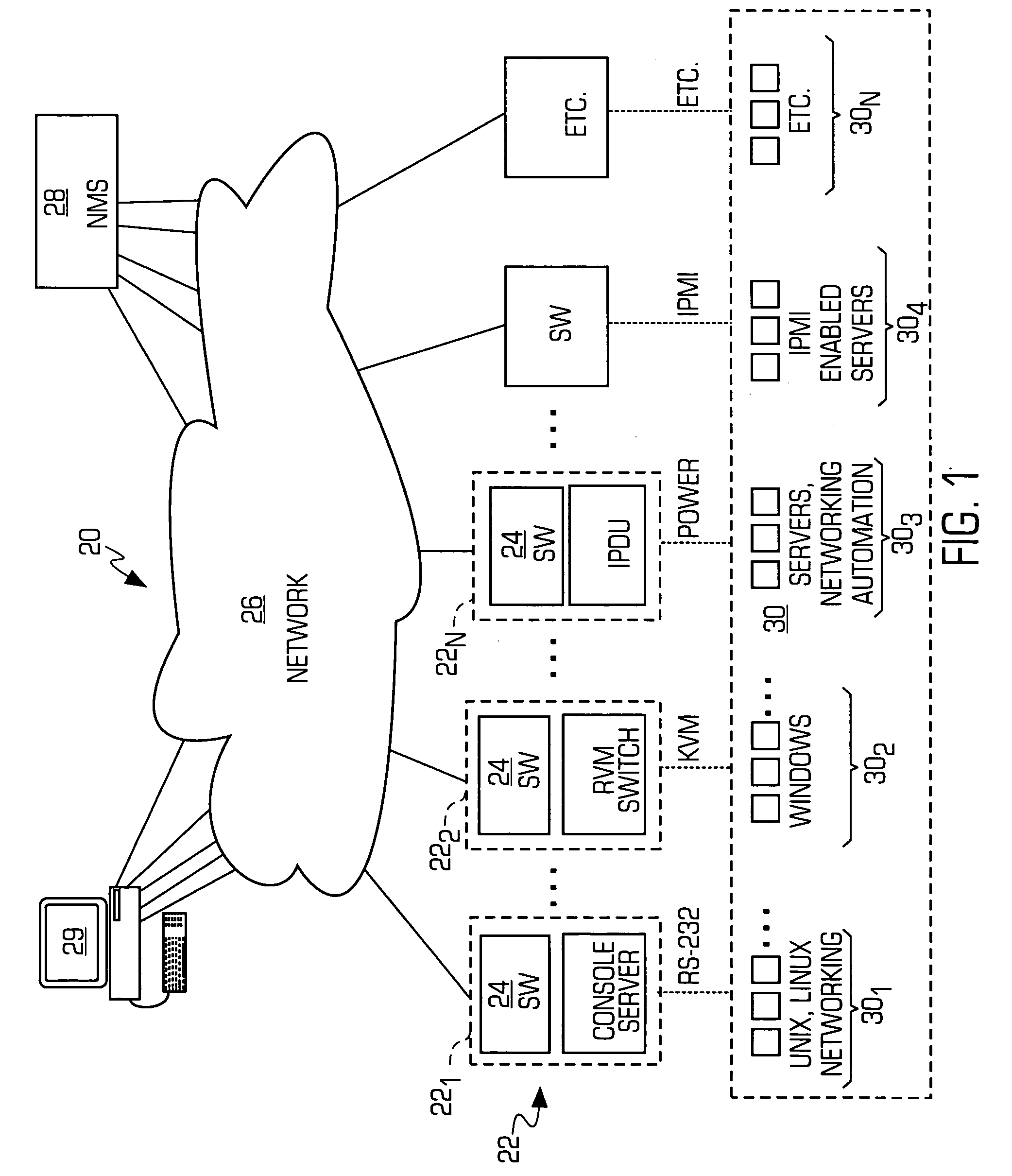
System and method for consolidating, securing and automating out-of-band access to nodes in a data network
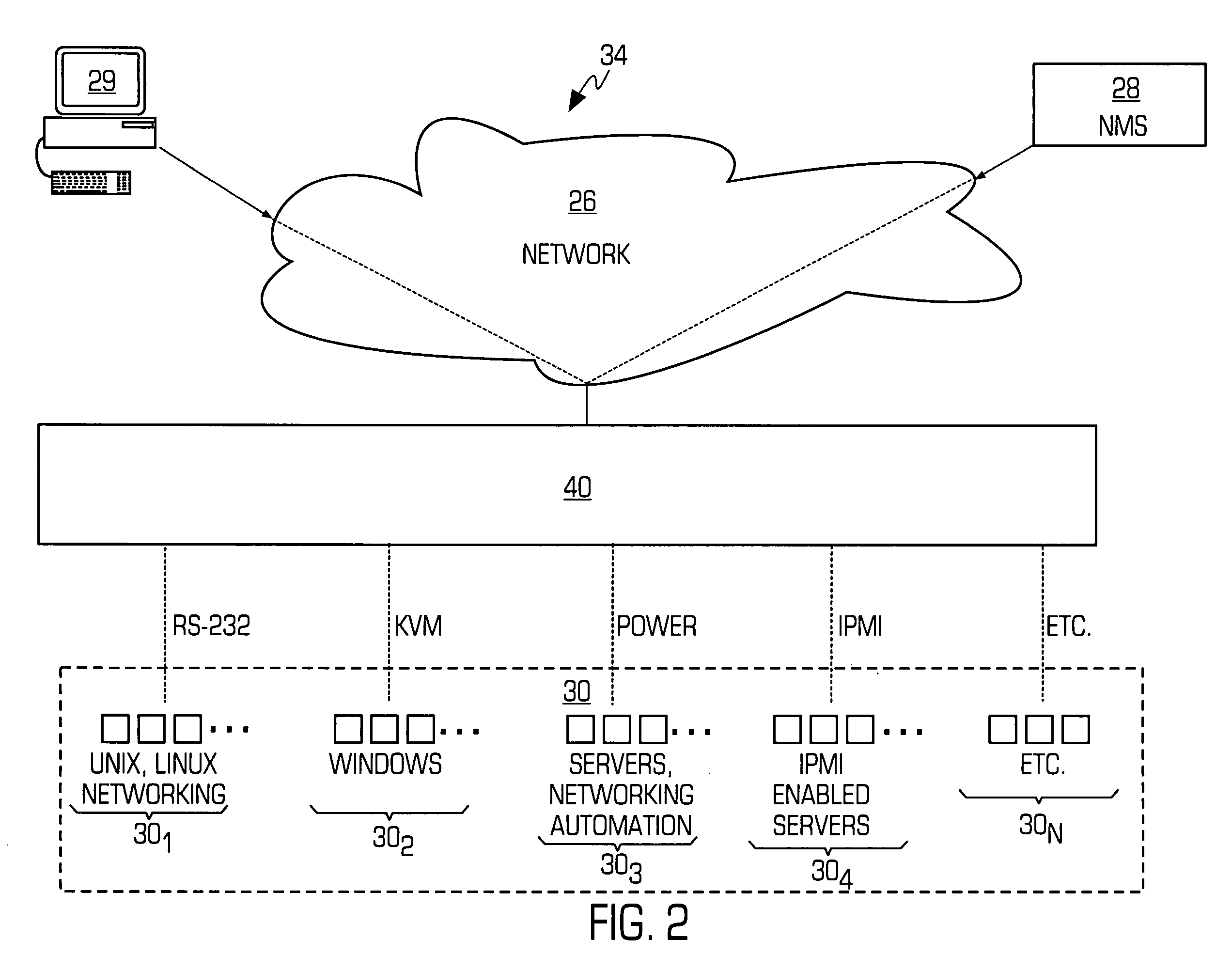
ActiveUS20060031447A1Avoid transportPrevent unauthorized accessEnergy efficient ICTDigital computer detailsNetwork managementAccess management
A system and method for out-of-band network management is provided wherein one or more different management interfaces are converted into a common format management data. The system may encrypt the common format management data. The system may also authenticate each user that attempts to access the management interfaces.
Owner:VERTIV IT SYST INC +1
Automatic folder access management
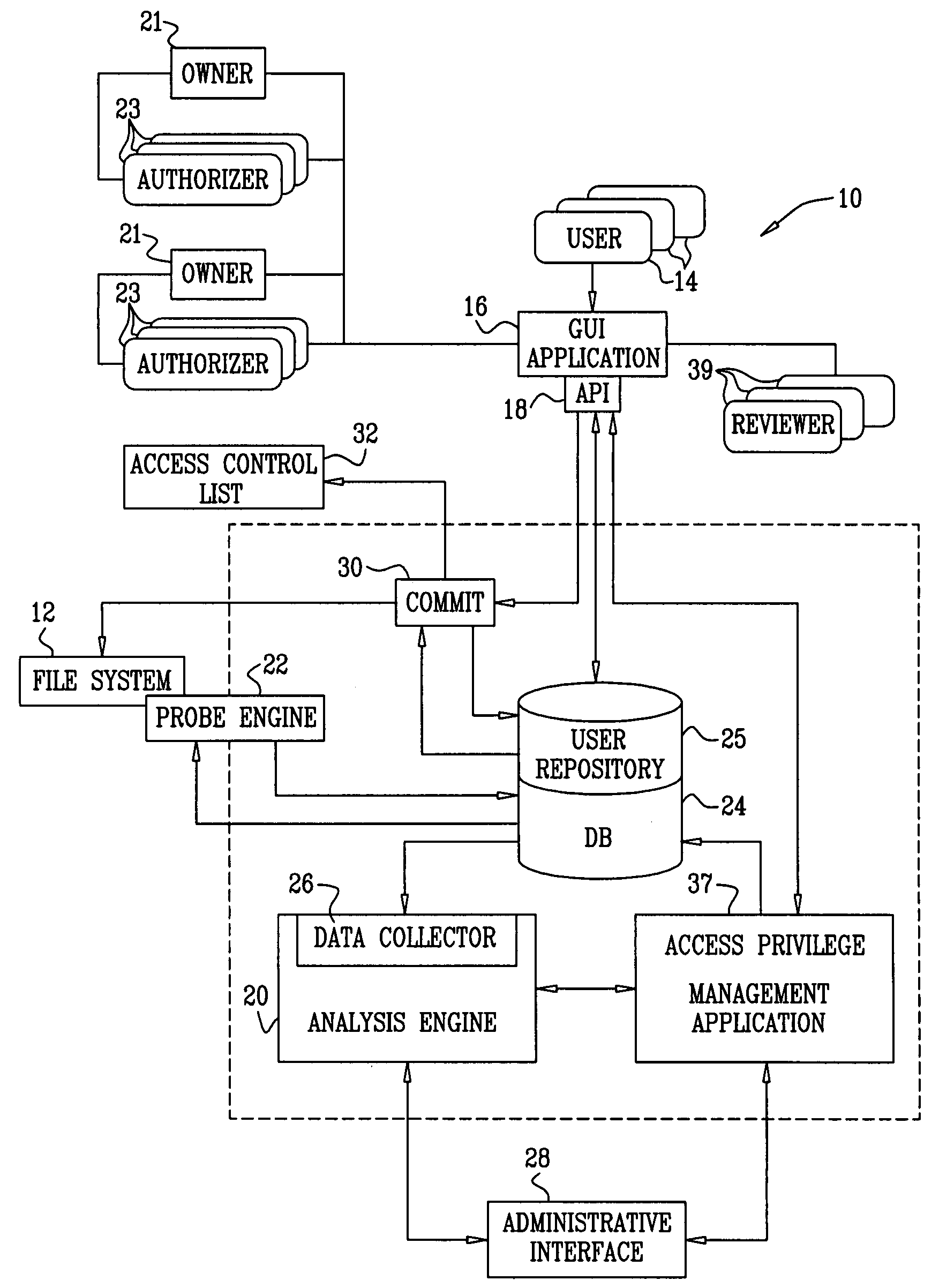
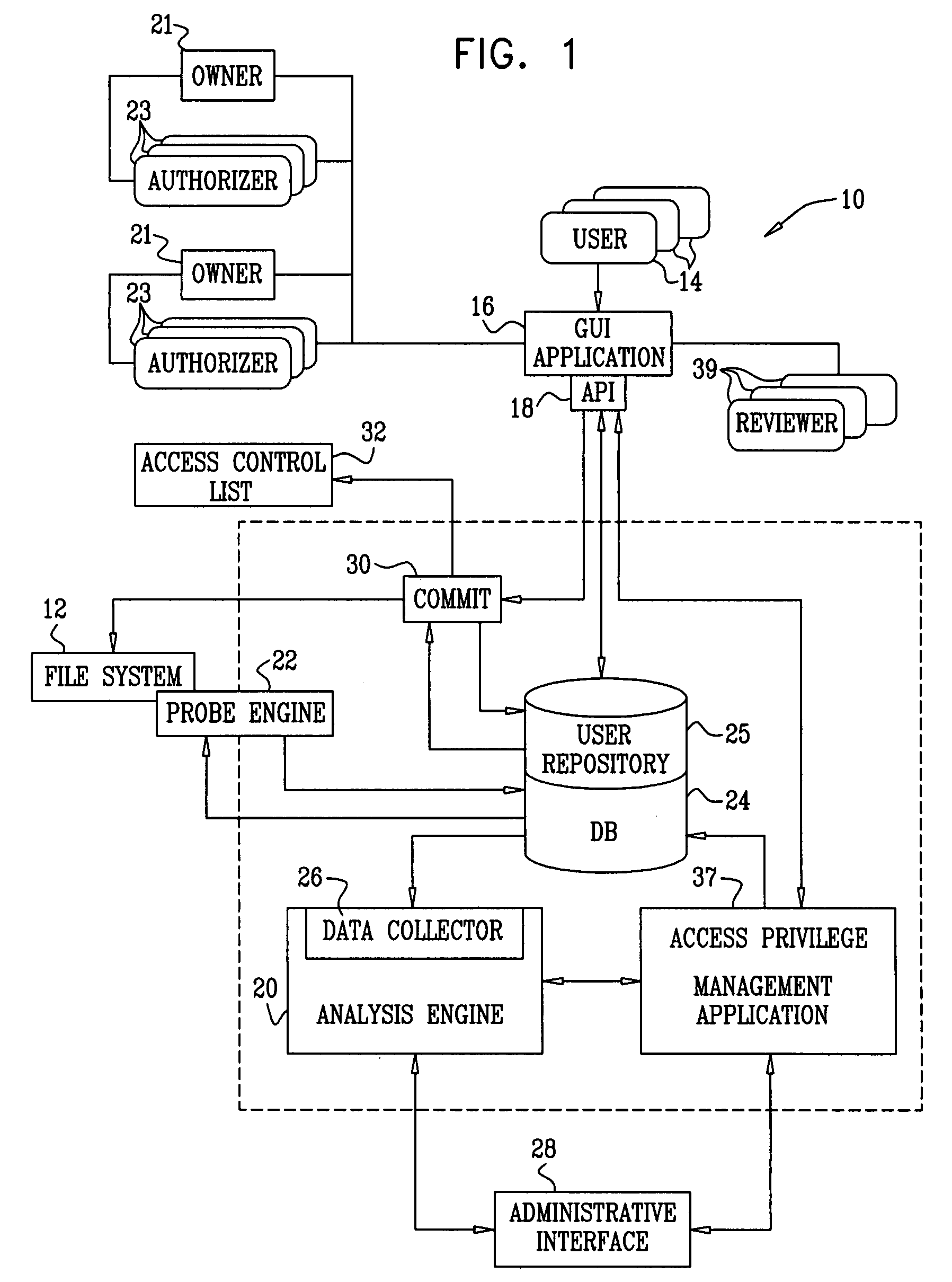
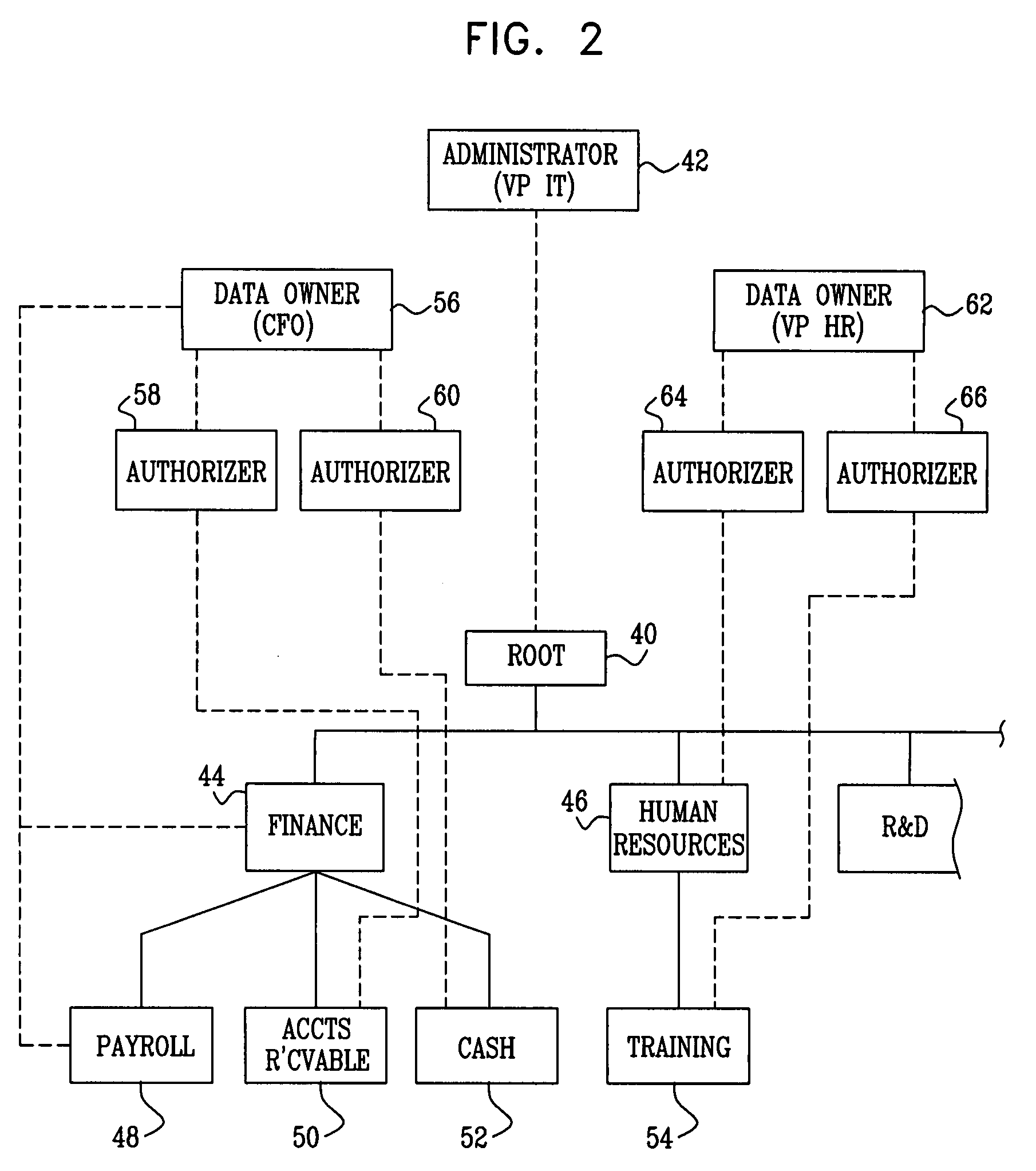
ActiveUS20070244899A1Digital data processing detailsUnauthorized memory use protectionFile systemData access
Methods and systems are provided for decentralizing user data access rights control activities in networked organizations having diverse access control models and file server protocols. A folder management application enables end users of the file system to make requests for access to storage elements, either individually, or by becoming members of a user group having group access privileges. Responsibility for dealing with such requests is distributed to respective group owners and data owners, who may delegate responsibility to authorizers. The application may also consider automatically generated proposals for changes to access privileges. An automatic system continually monitors and analyzes access behavior by users who have been pre-classified into groups having common data access privileges. As the organizational structure changes, these groups are adaptively changed both in composition and in data access rights.
Owner:VARONIS SYSTEMS
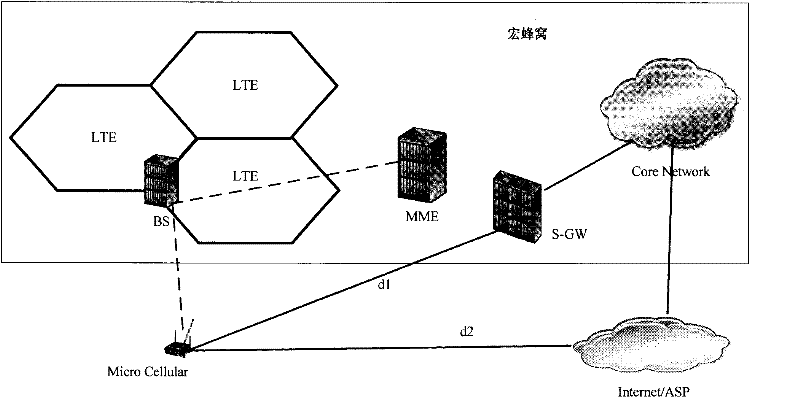
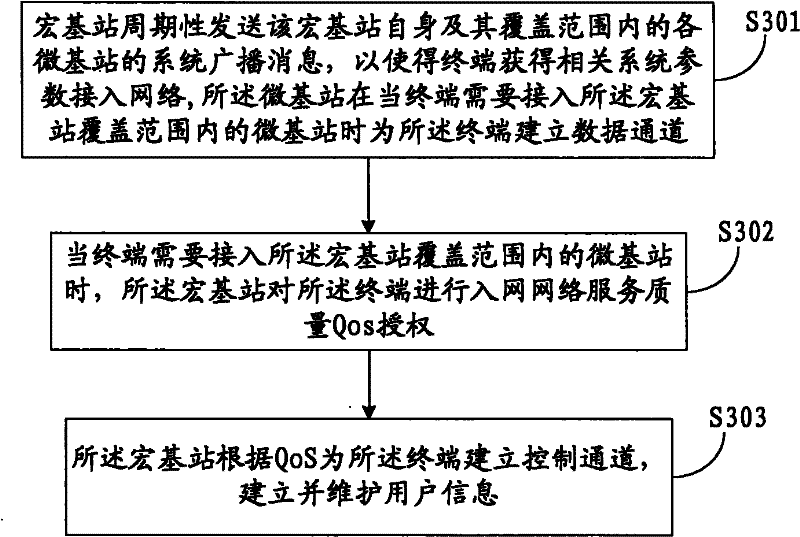
Cellular communication system, method for inter-cell handover of terminal and macro base station
InactiveCN102348244AReduce negative impactAssess restrictionNetwork topologiesMacro base stationsMicro cell
The invention discloses a cellular communication system, a method for the inter-cell handover of a terminal and a macro base station. The cellular communication system comprises the macro base station and at least one micro base station within the coverage of the macro base station. The macro base station is used for establishing a control channel for the terminal of the micro base station, performing accessing management operations on the micro base stations within the coverage, receiving a handover request of the terminal and realizing the handover of the terminal to another micro base station within the coverage. The micro base station is used for establishing a data channel for an accessing terminal to perform data transmission with the terminal. By the system, the method and the macro base station, a user control plane and a data plane under a micro cell can be separated, so that the resources of the micro base station can be better used for data communication. Therefore, negative impact on the system can be reduced in a macro cell-micro cell coexisting networking way.
Owner:HUAWEI TECH CO LTD
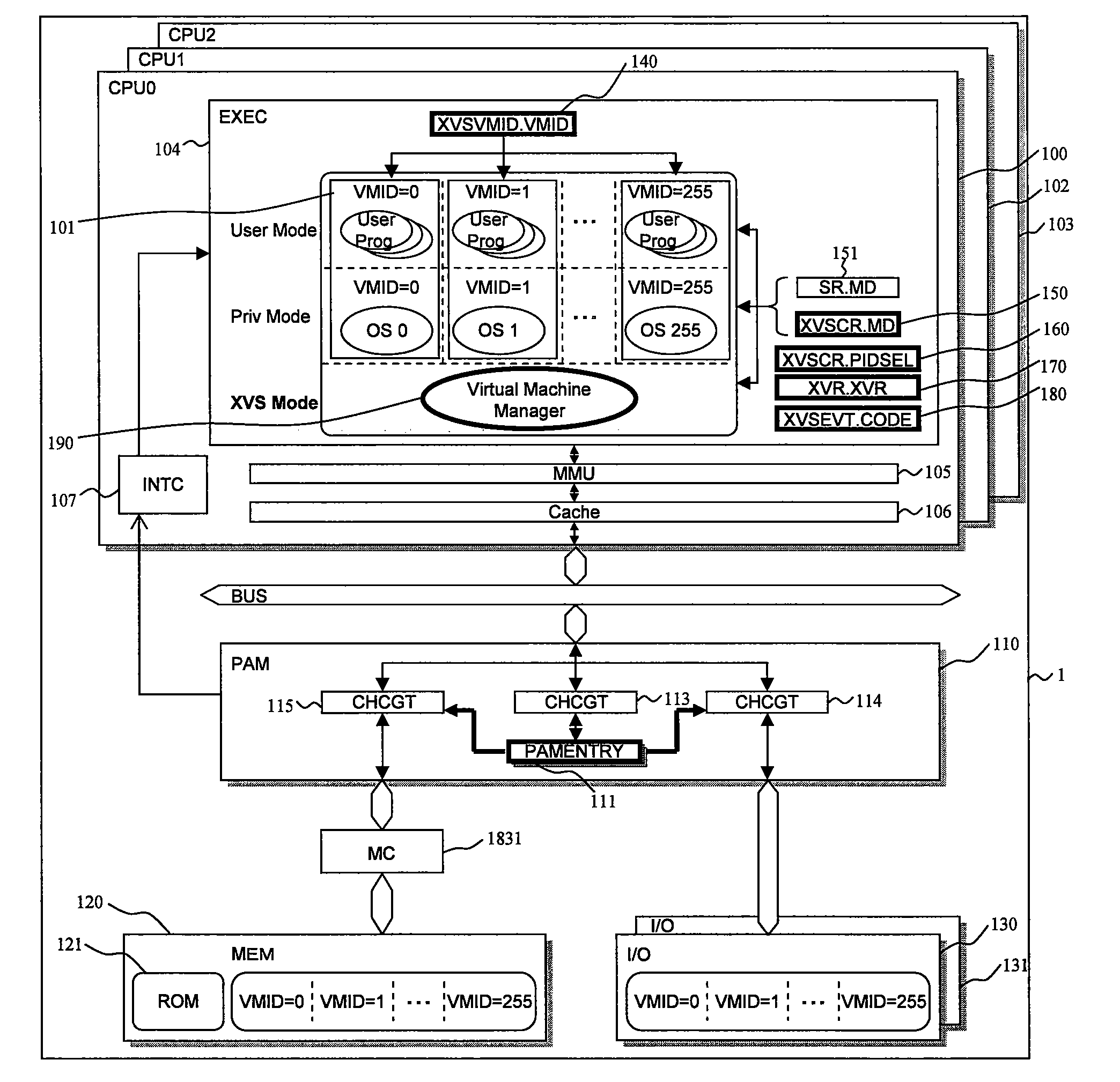
Data processor
ActiveUS20080086729A1Reduce needImprove system reliabilityResource allocationSoftware simulation/interpretation/emulationOperational systemControl register
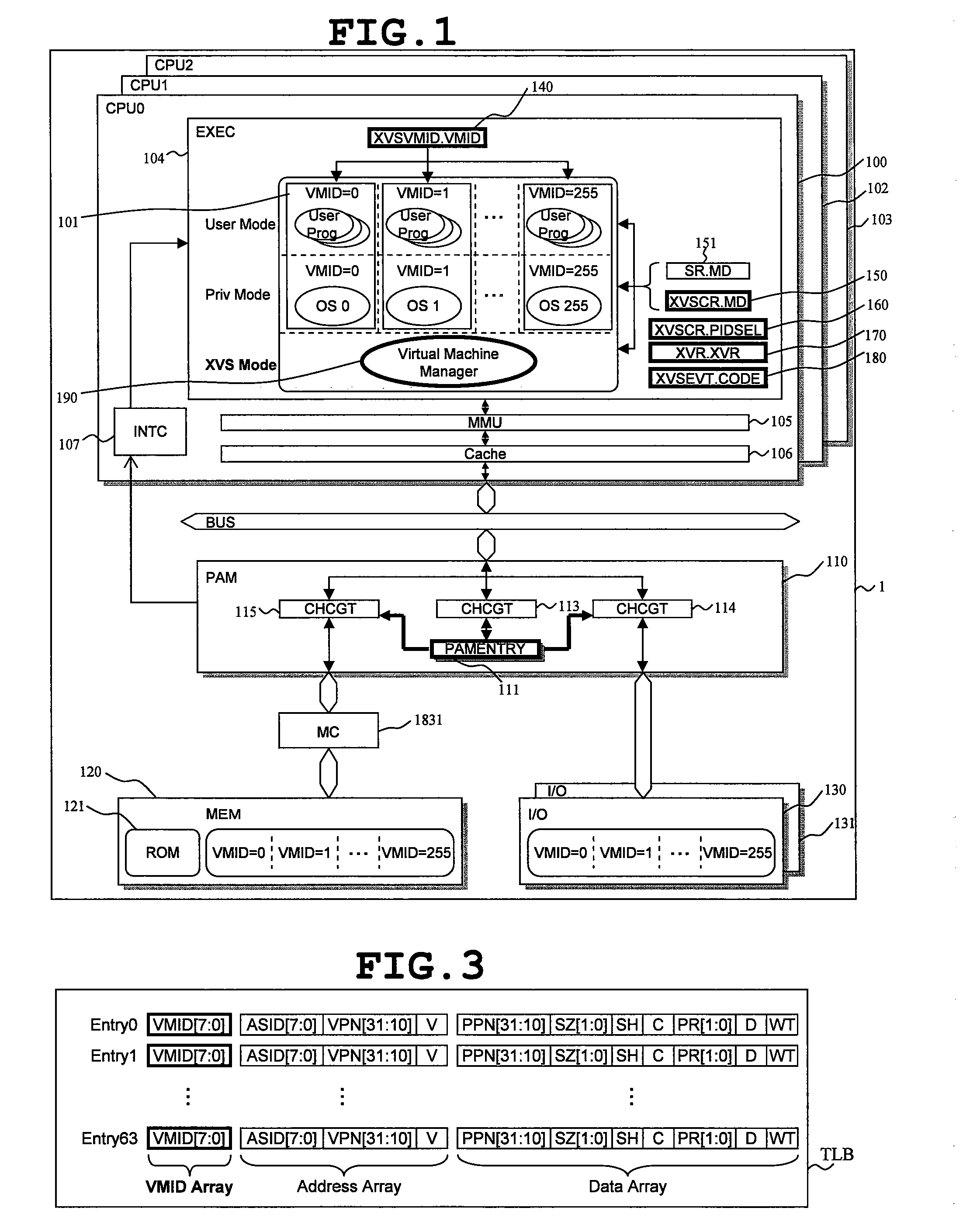
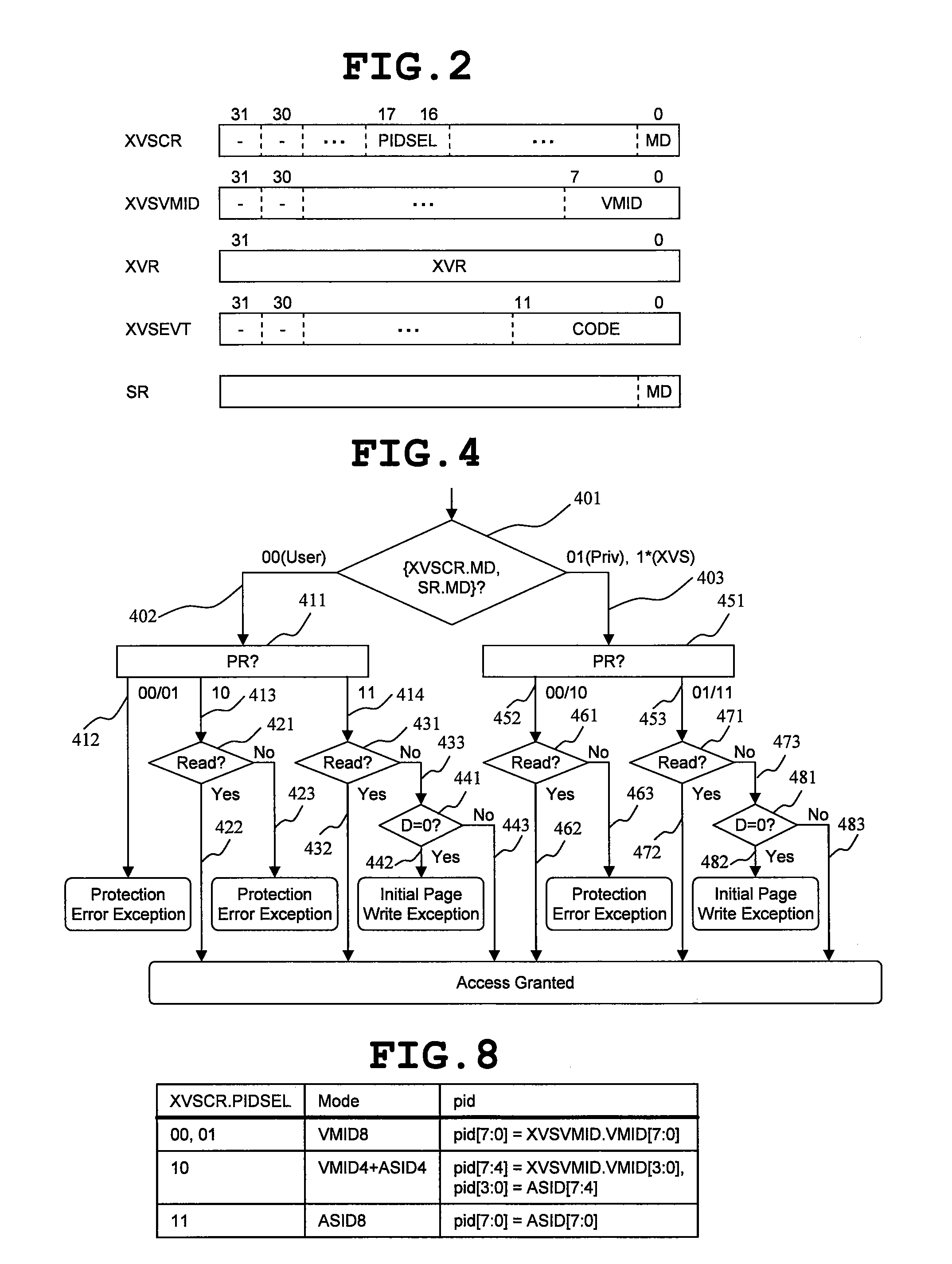
A data processor includes: a central processing unit (CPU), in which a plurality of virtual machines (101), each running an application program under controls of different operating systems, and a virtual machine manager (190) for controlling the plurality of virtual machines are selectively arranged according to information set in mode registers (140, 150, 151); and a resource access management module (110) for managing access to hardware resource available for the plurality of virtual machines. The resource access management module accepts, as inputs, the information set in the mode registers and access control information of the central processing unit to the hardware resource, compares the information thus input with information set in a control register, and controls whether or not to permit access to the hardware resource in response to the access control information. As a result, redesign involved in changes in system specifications can be reduced, and a malfunction owing to resource contention can be prevented. The invention contributes to increase of security.
Owner:RENESAS ELECTRONICS CORP
Method and system for integrating IP address reservations with policy provisioning
A method and system for policy provisioning and access managing on a data-over-cable system. One method includes receiving a first message on a first network device such as a CMTS from a second network device and marking the first message with an identifier of a network access device. The method further includes intercepting the first message on a third network device prior to a first protocol network server such as a Dynamic Host Configuration Protocol (“DHCP”) server receives the first message. When the third network device intercepts the first message, the third network device determines the identity of the second network device. Based on the identity of the second network device and using the identifier of the network access device, the third network device manages an assignment of configuration parameters for the second network device.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Apparatus, system, and method for data access management
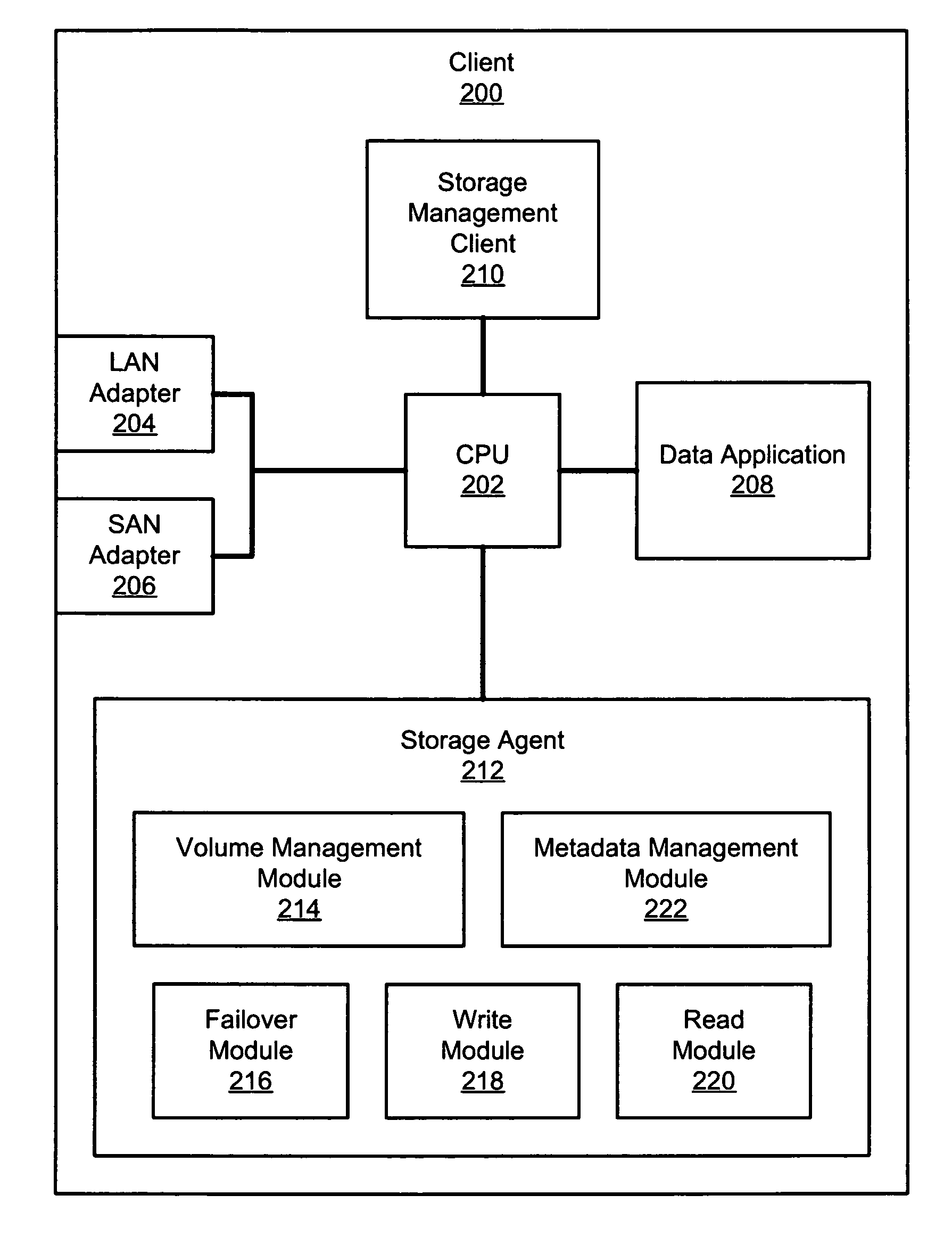
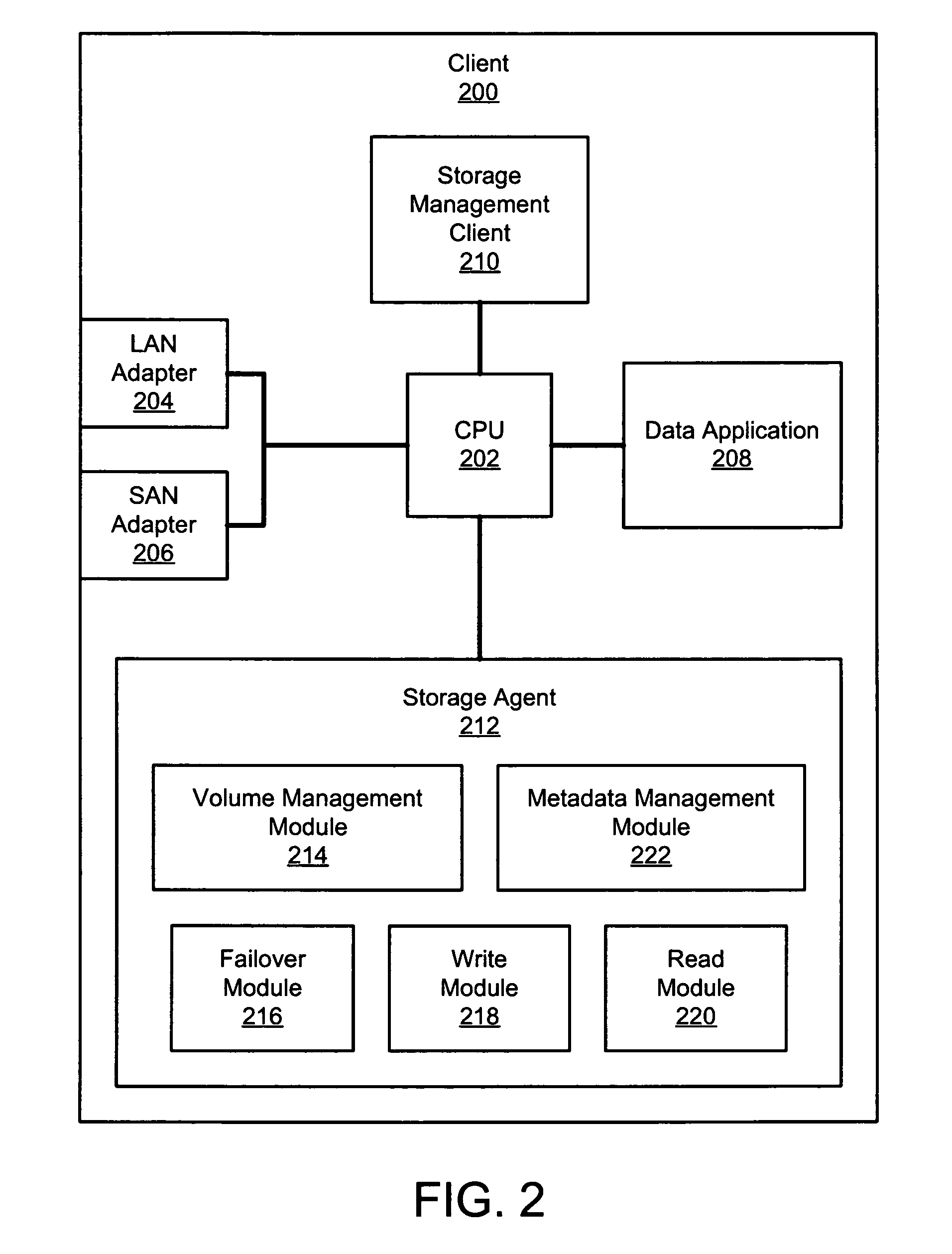
InactiveUS7533181B2Occur more quicklyProduce quicklyInput/output to record carriersMultiple digital computer combinationsNetwork connectionStorage area network
An apparatus, system, and method are disclosed for data access management on a storage device connected to a storage area network. A client includes network connections to a first and second network, where the second network comprises a storage area network (SAN). The client also includes a storage management client and a storage agent. The storage agent is configured to minimize the amount of metadata processing that occurs on the client by sending the metadata or a copy thereof to a storage server to be stored in a centralized metadata database. The storage server also includes a storage manager that is configured to manage data access by the storage agent to the requested storage device.
Owner:IBM CORP
Logging access system events
ActiveUS20020116642A1Easy mappingDigital data protectionSpecial data processing applicationsLibrary scienceAccess management
A system is disclosed that logs access system events. When an access system event occurs, a log entry is created for the access system event. Information from an identity profile is stored in the log entry. The identity profile pertains to a first user. The first user is the entity who caused or was involved with the access system event. In one embodiment, the access system includes identity management and access management functionality.
Owner:ORACLE INT CORP
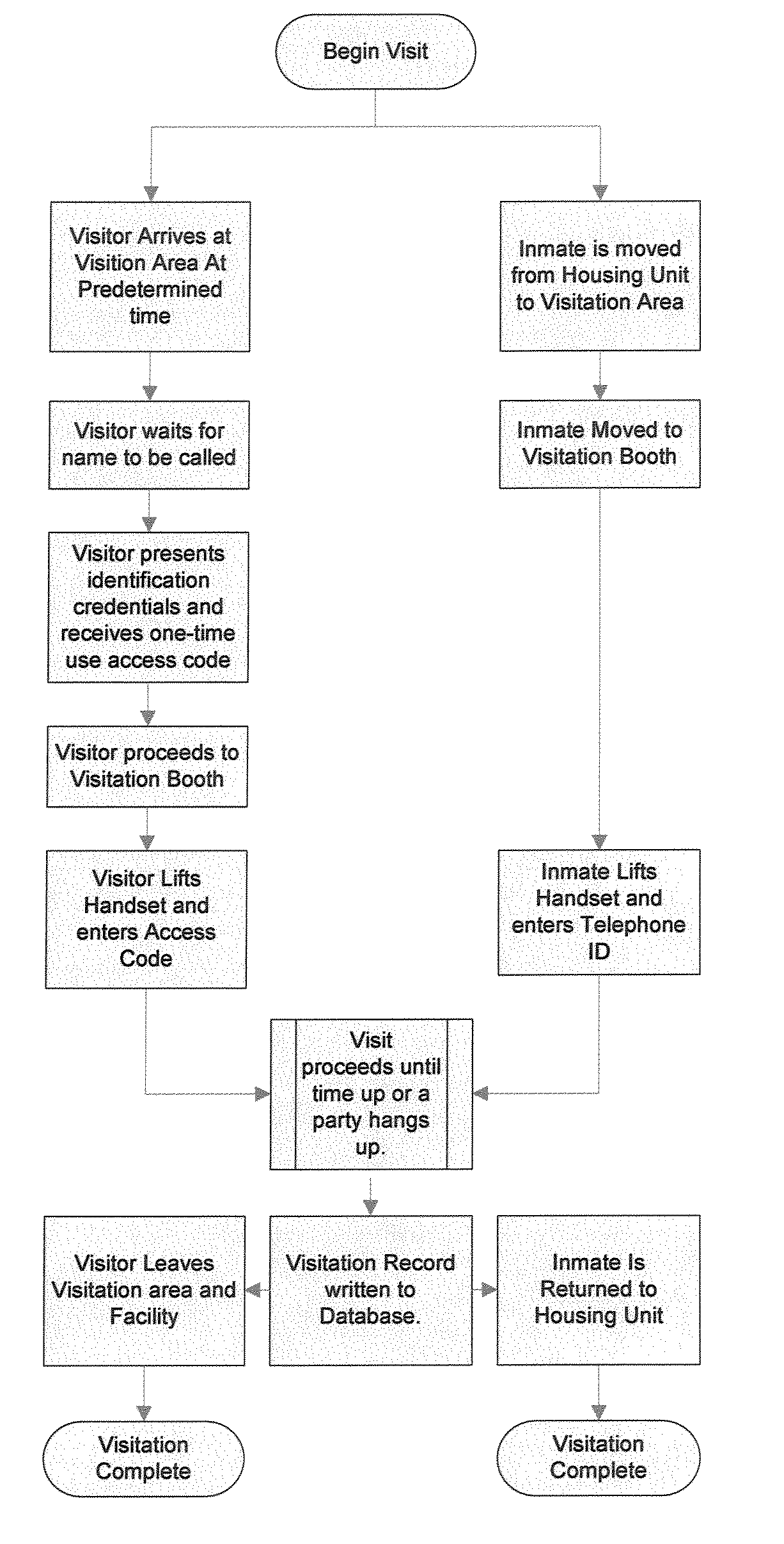
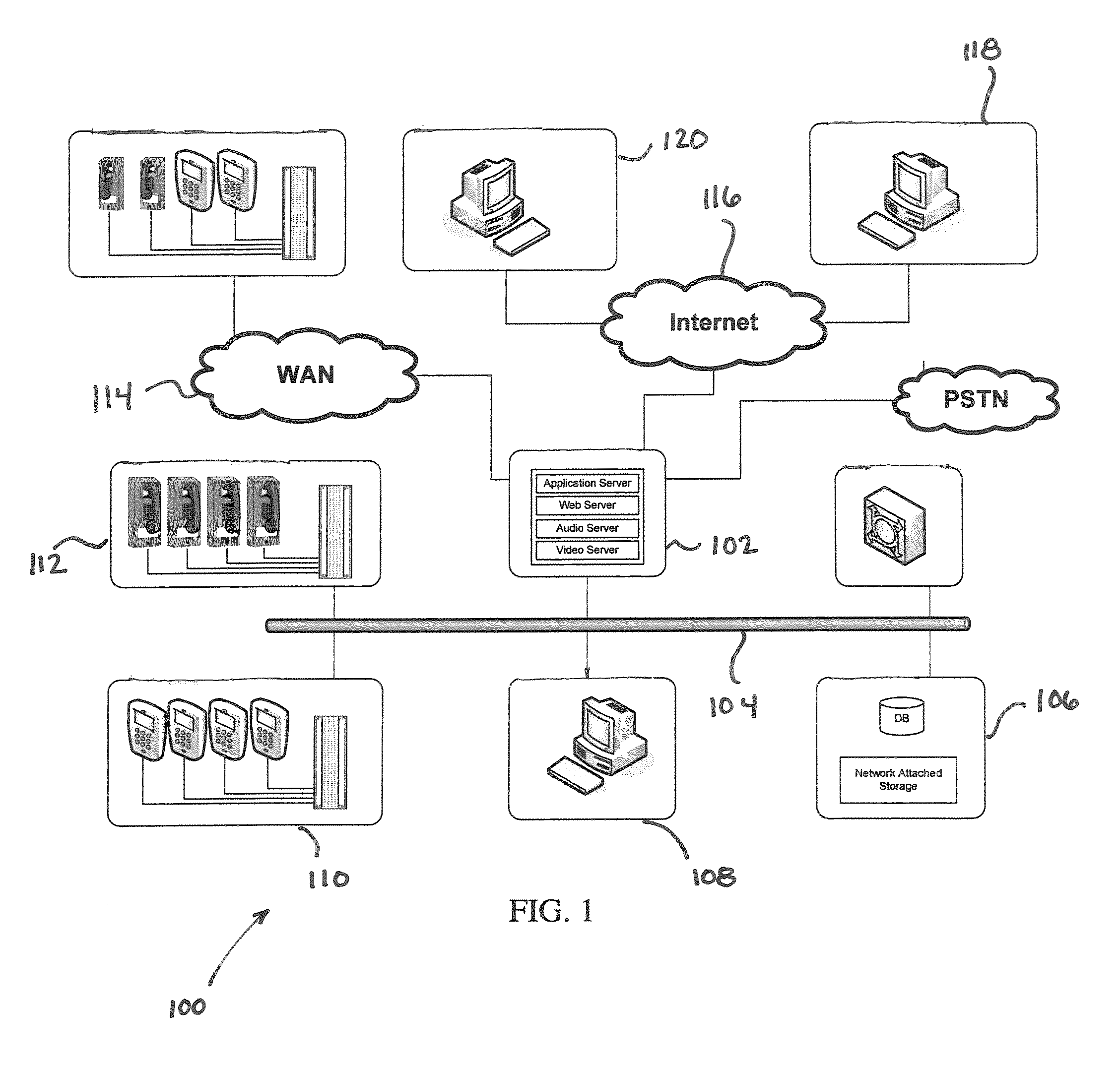
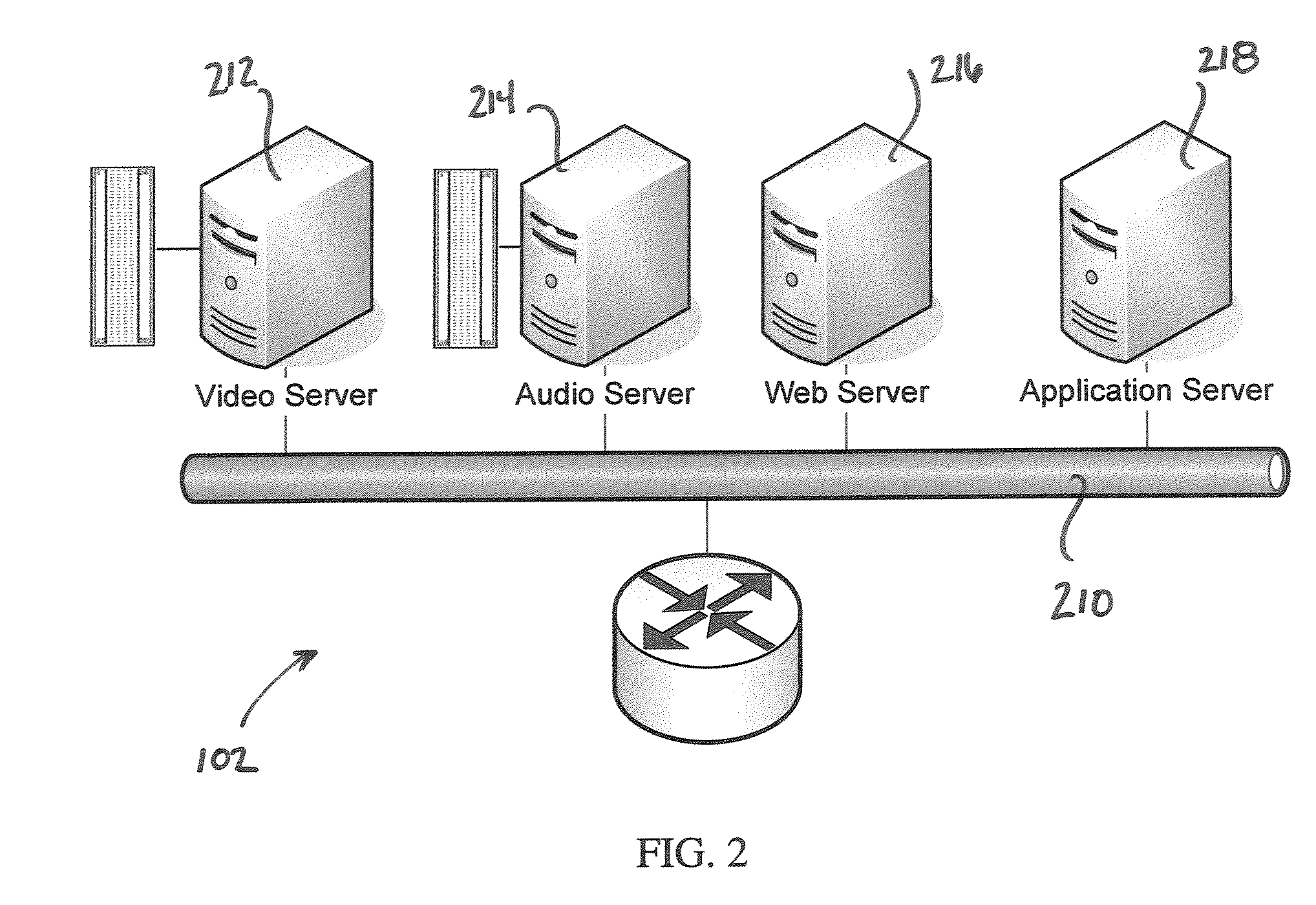
System and method for visitation management in a controlled-access environment
InactiveUS20080201158A1Improve complianceAutomatic exchangesSpeech recognitionControl systemAccess management
A method of managing visitation includes accessing a visitation control system including a visitation session scheduling interface, communications devices, a switching interface, and at least one authentication interface, defining rules governing visitation, requesting a visitation session using the scheduling interface, assessing whether the visitation session complies with the rules governing visitation, scheduling the visitation session if the visitation session complies with the rules, using the at least one authentication interface to authenticate a first party and a second party, establishing communication between the first party and the second party after authenticating both parties, and storing a record of the visitation session in a database. The record preferably includes at least information regarding identities of the first party and the second party. The visitation session may also be monitored (e.g., in real time, near real time, or by recording).
Owner:DSI ITI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com