Patents
Literature
203 results about "Intrusion prevention system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
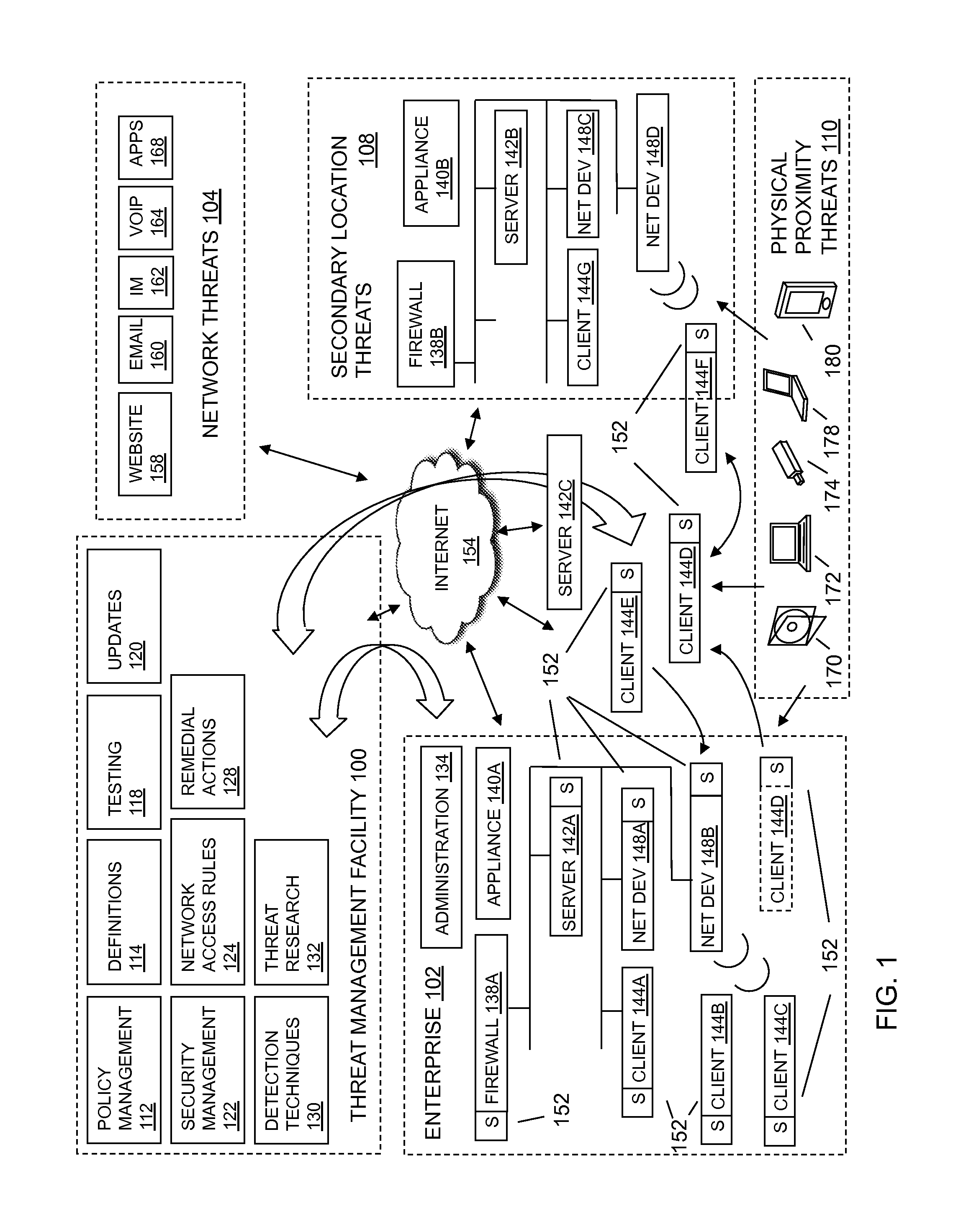
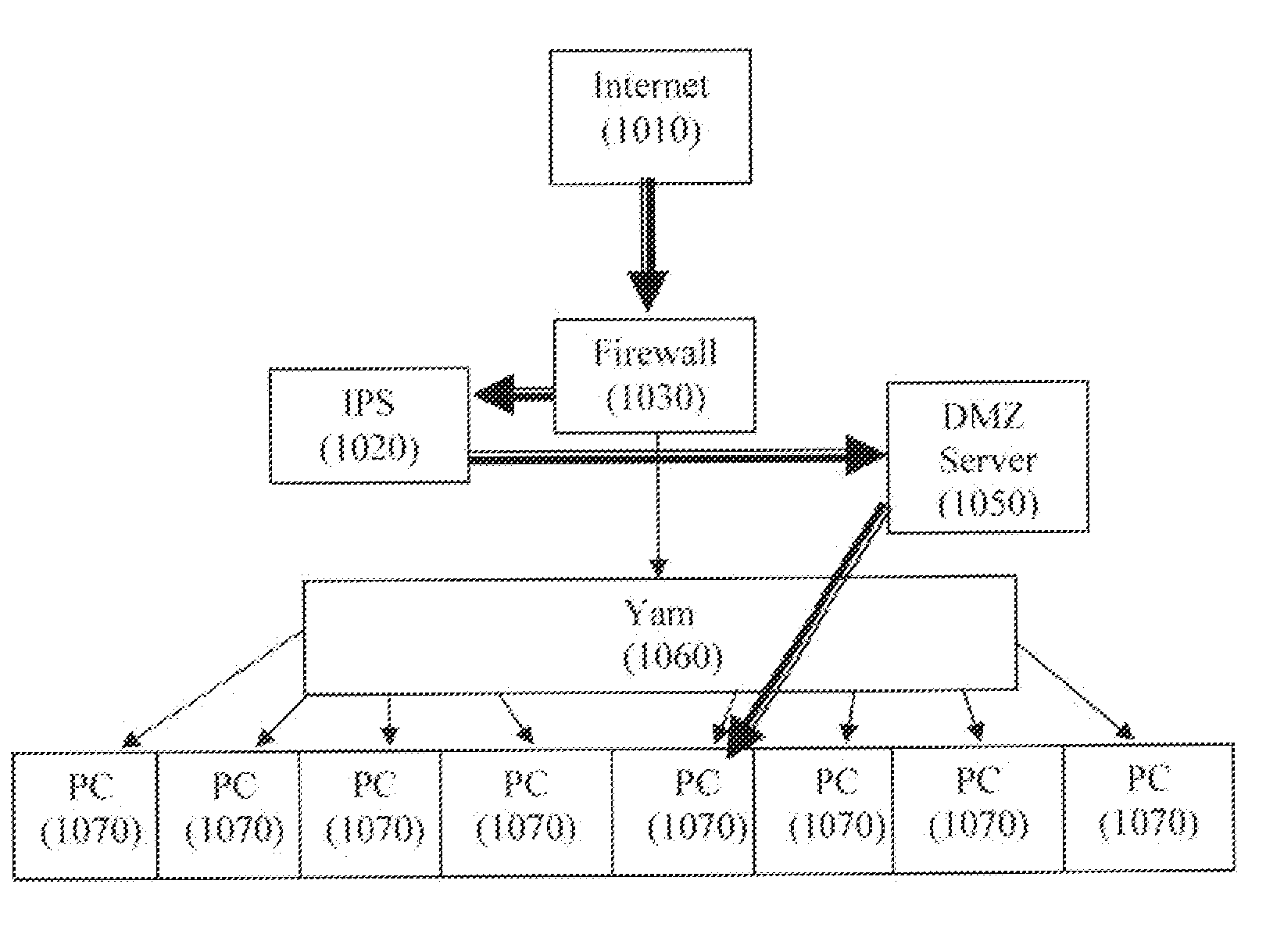
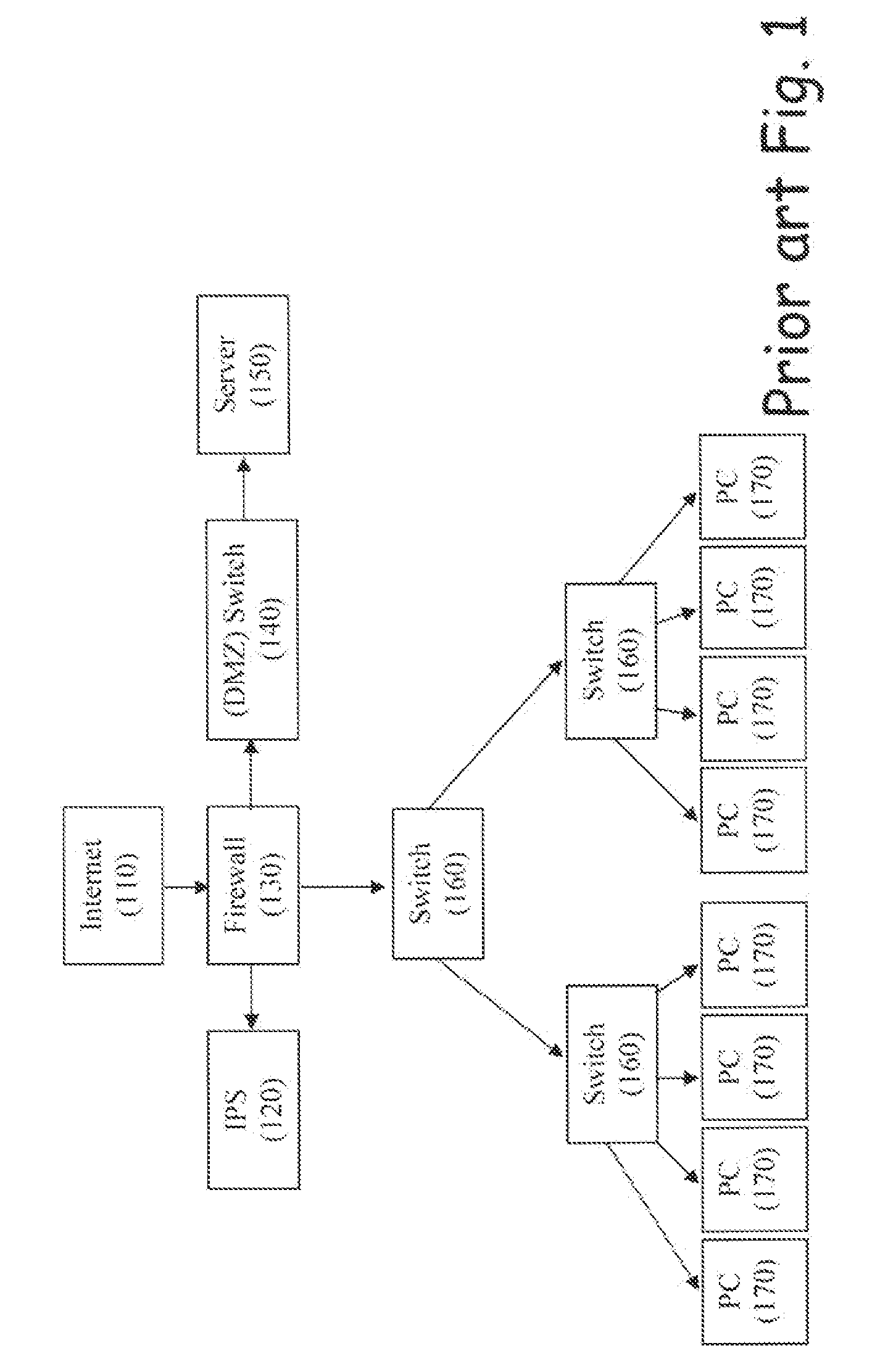
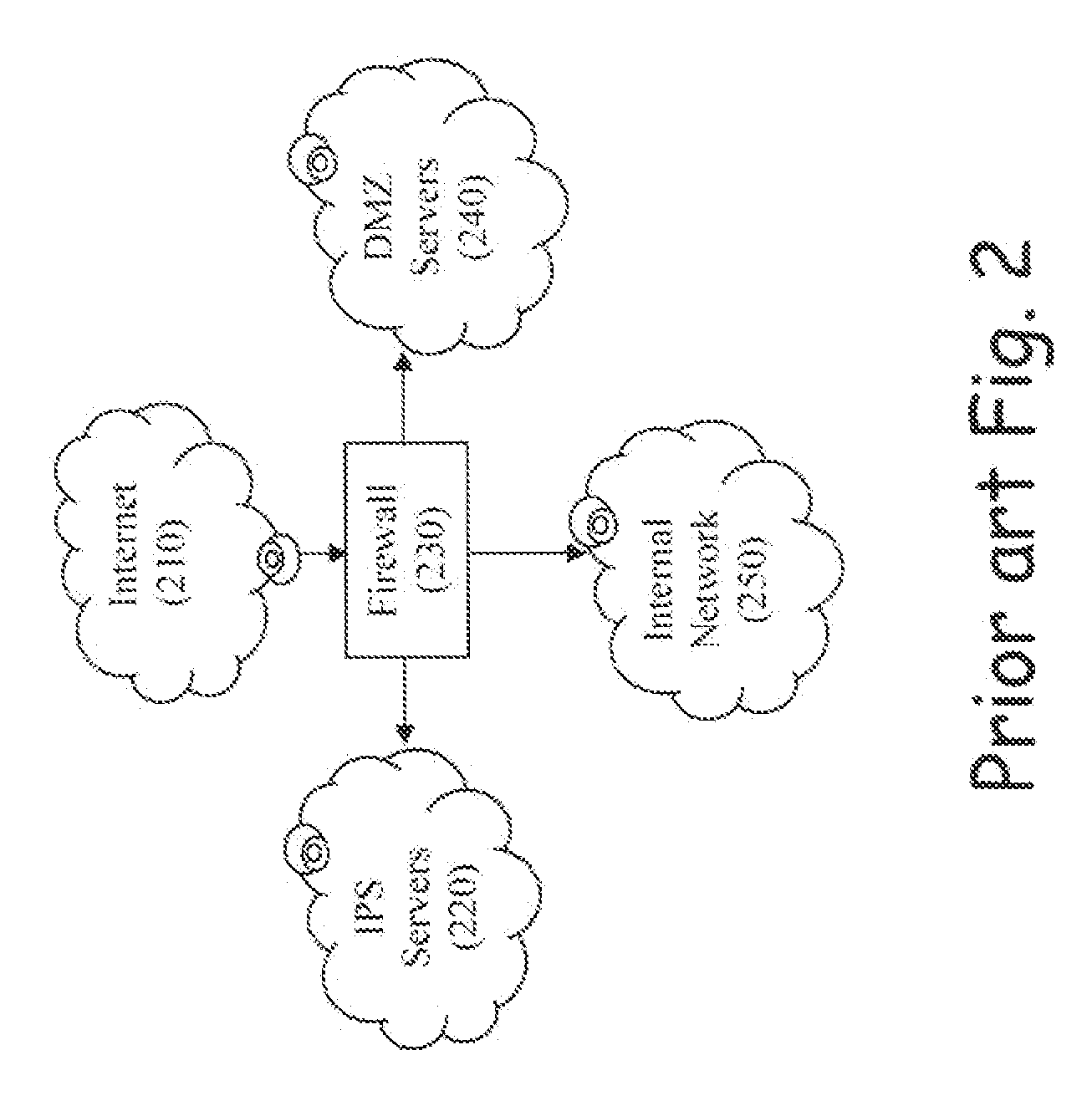
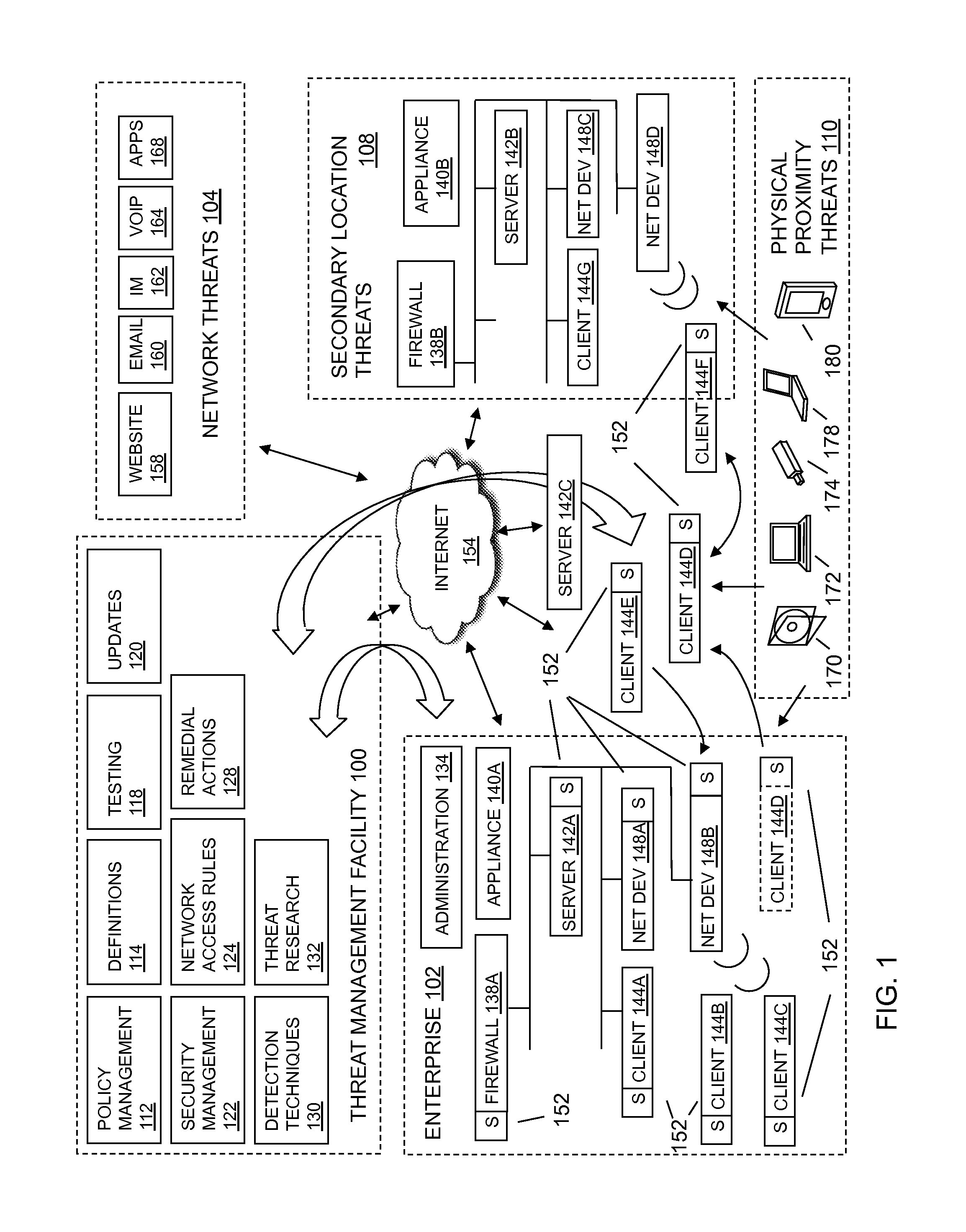
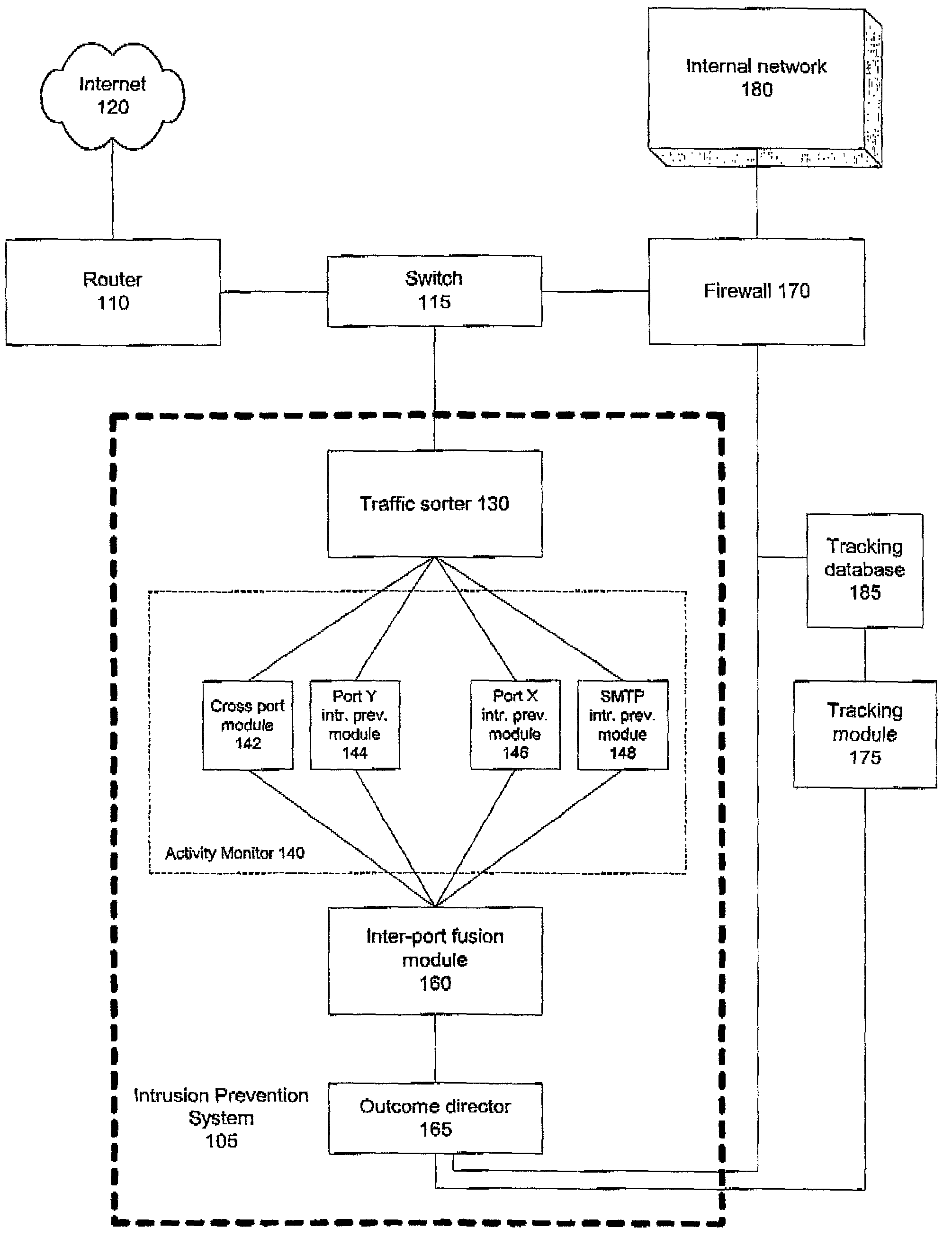
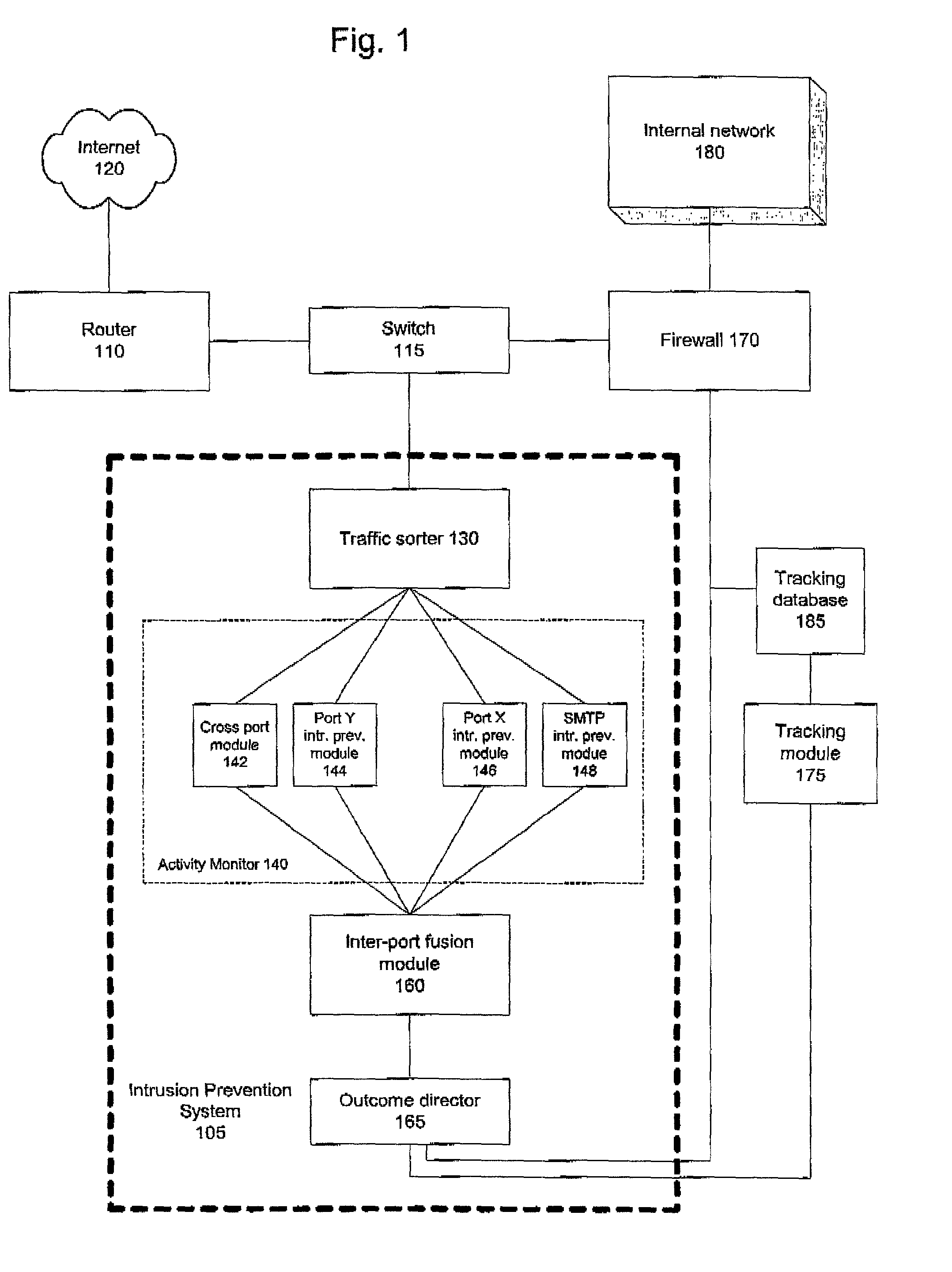
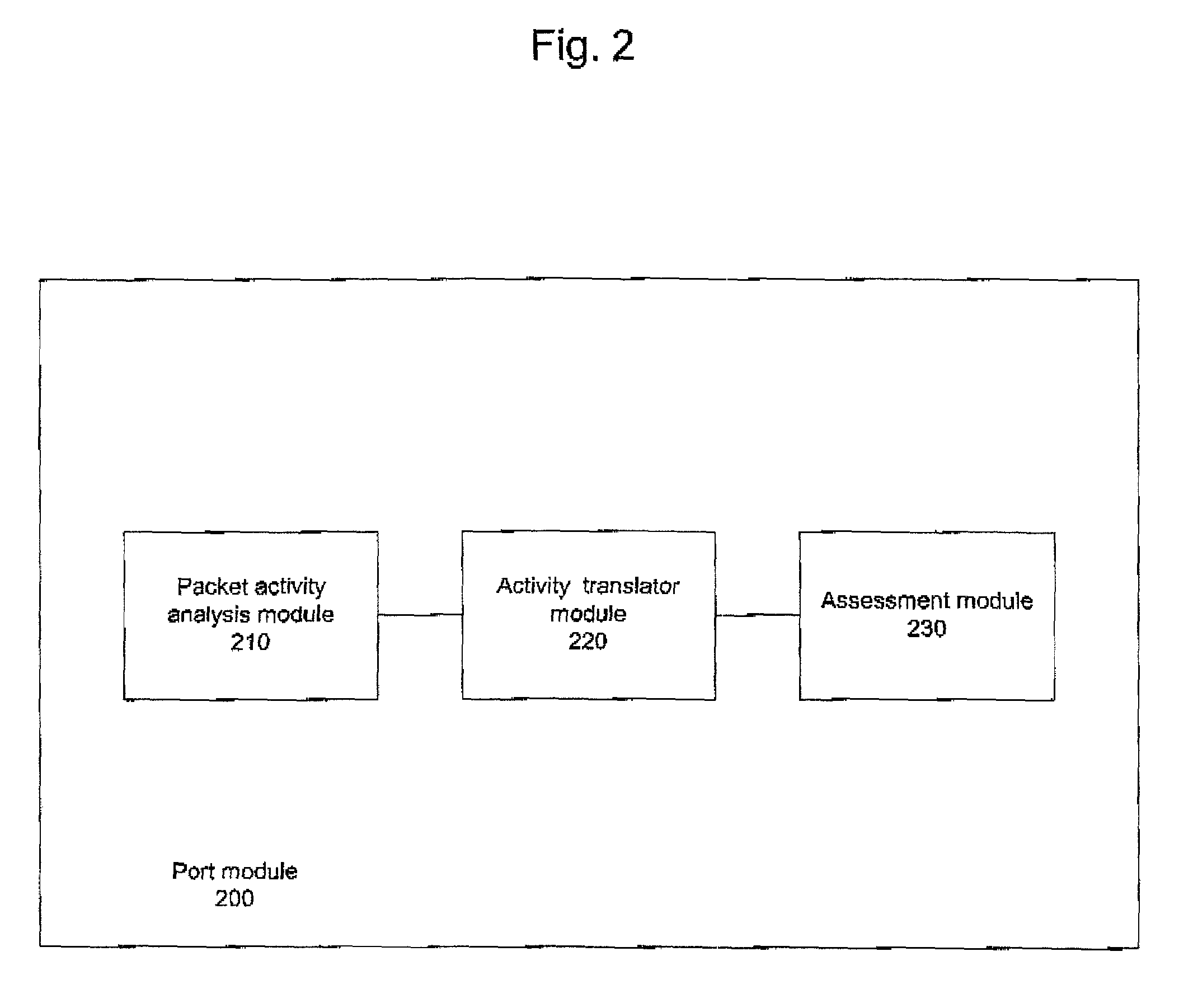
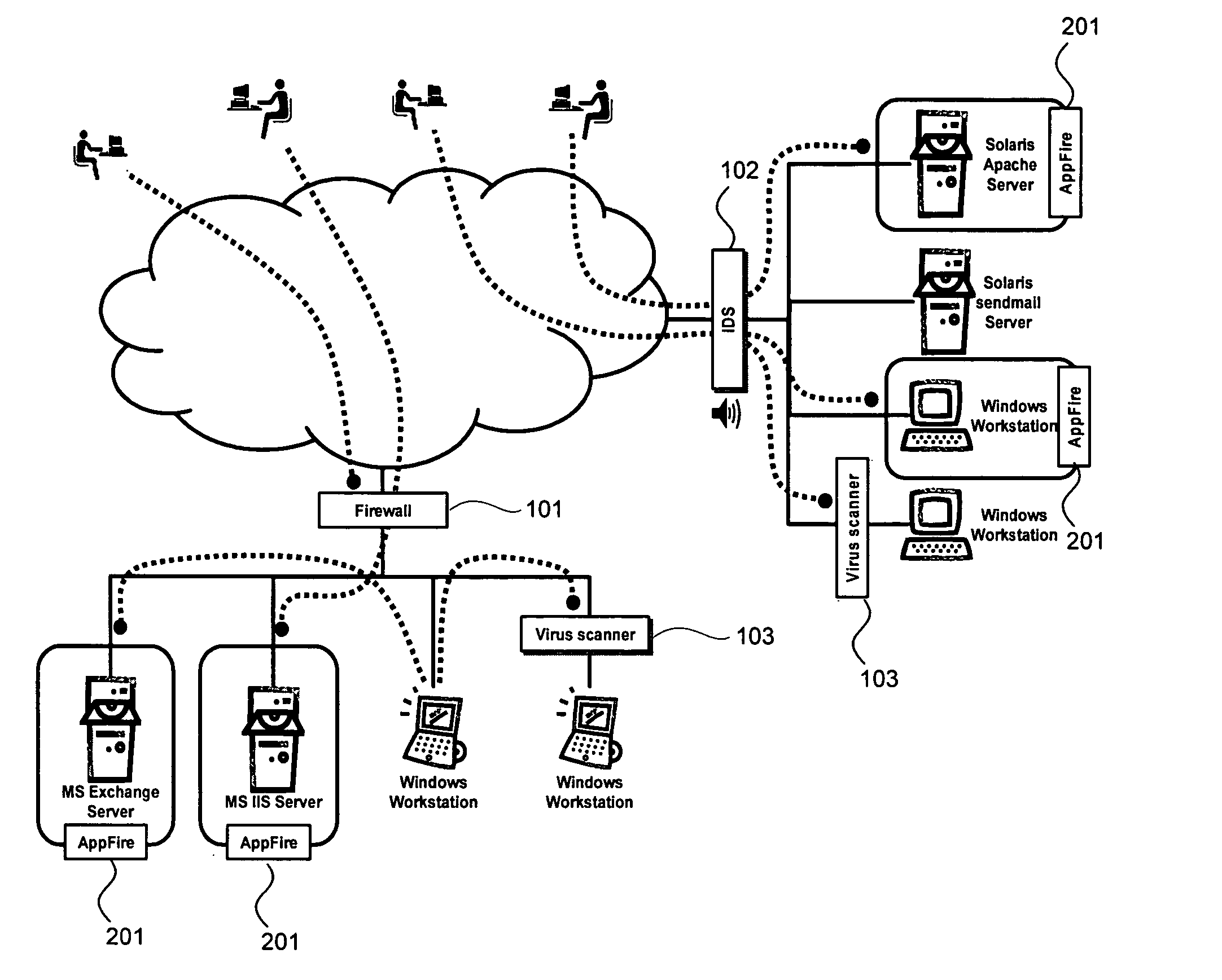
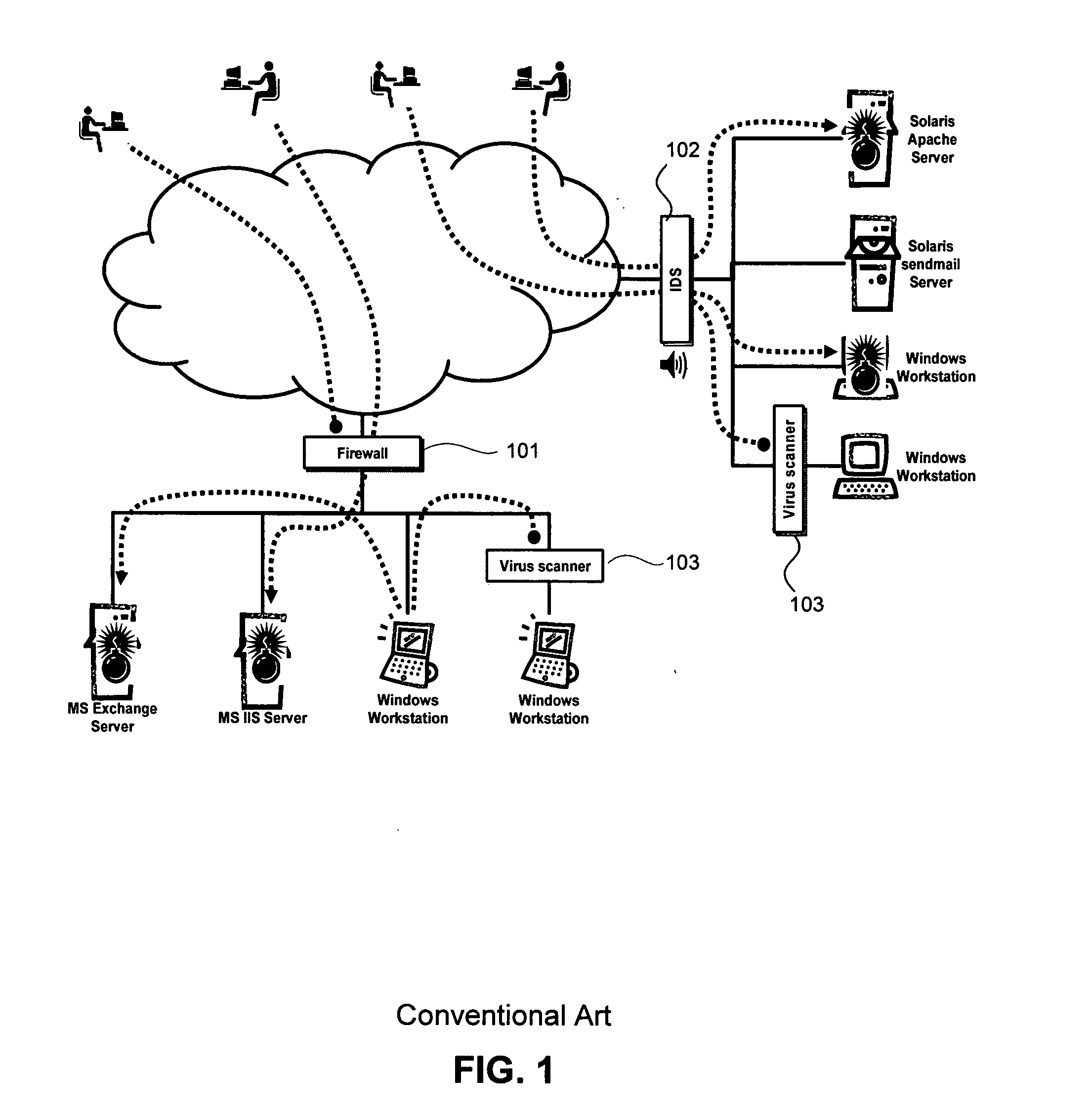
Intrusion prevention systems, also known as intrusion detection and prevention systems, are network security appliances that monitor network and/or system activities for malicious activity. The main functions of intrusion prevention systems are to identify malicious activity, log information about this activity, attempt to block/stop it, and report it. Intrusion prevention systems are considered extensions of intrusion detection systems because they both monitor network traffic and/or system activities for malicious activity. The main differences are, unlike intrusion detection systems, intrusion prevention systems are placed in-line and are able to actively prevent/block intrusions that are detected. More specifically, IPS can take such actions as sending an alarm, dropping the malicious packets, resetting the connection and/or blocking the traffic from the offending IP address. An IPS can also correct Cyclic Redundancy Check errors, unfragment packet streams, prevent TCP sequencing issues, and clean up unwanted transport and network layer options.
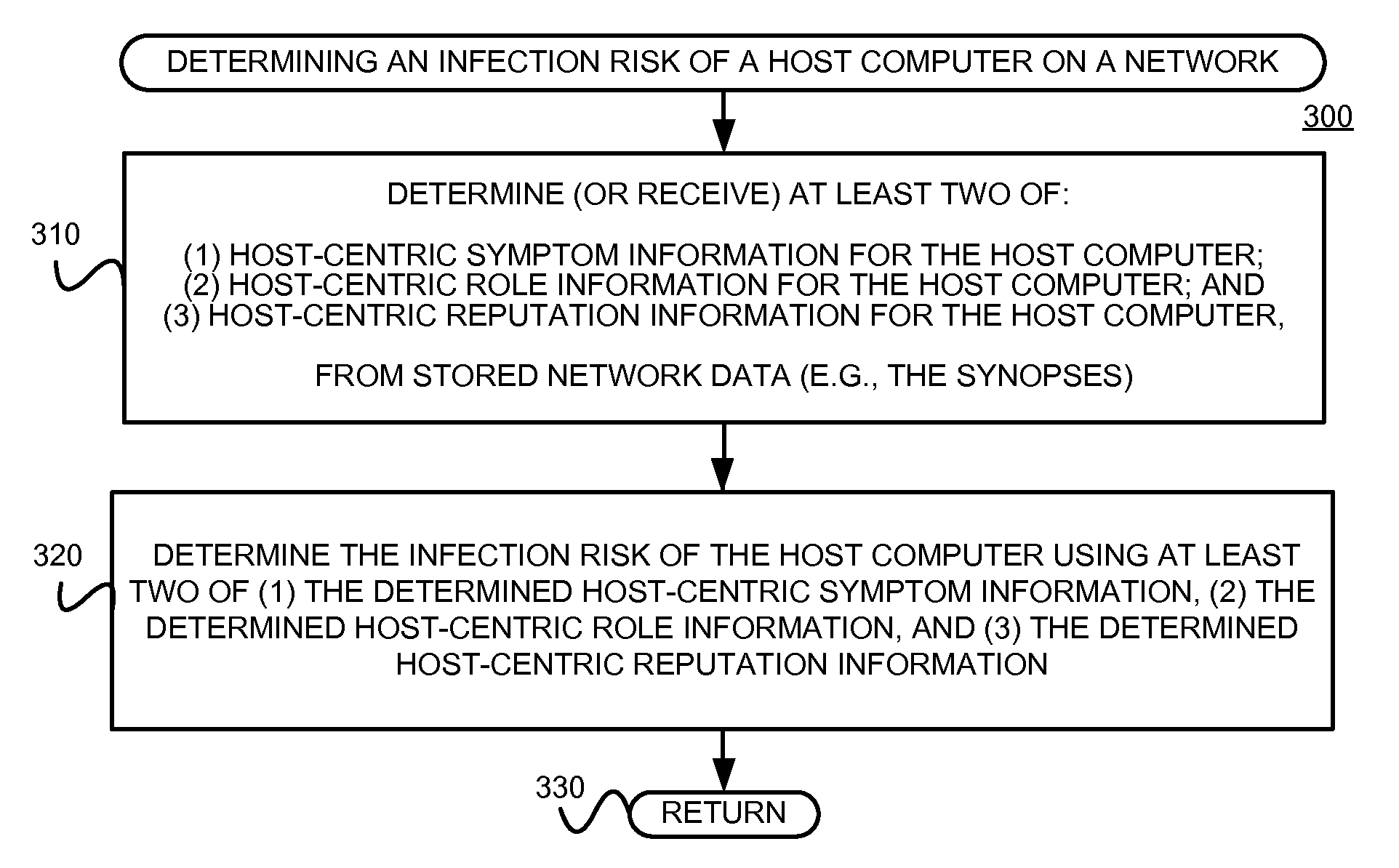
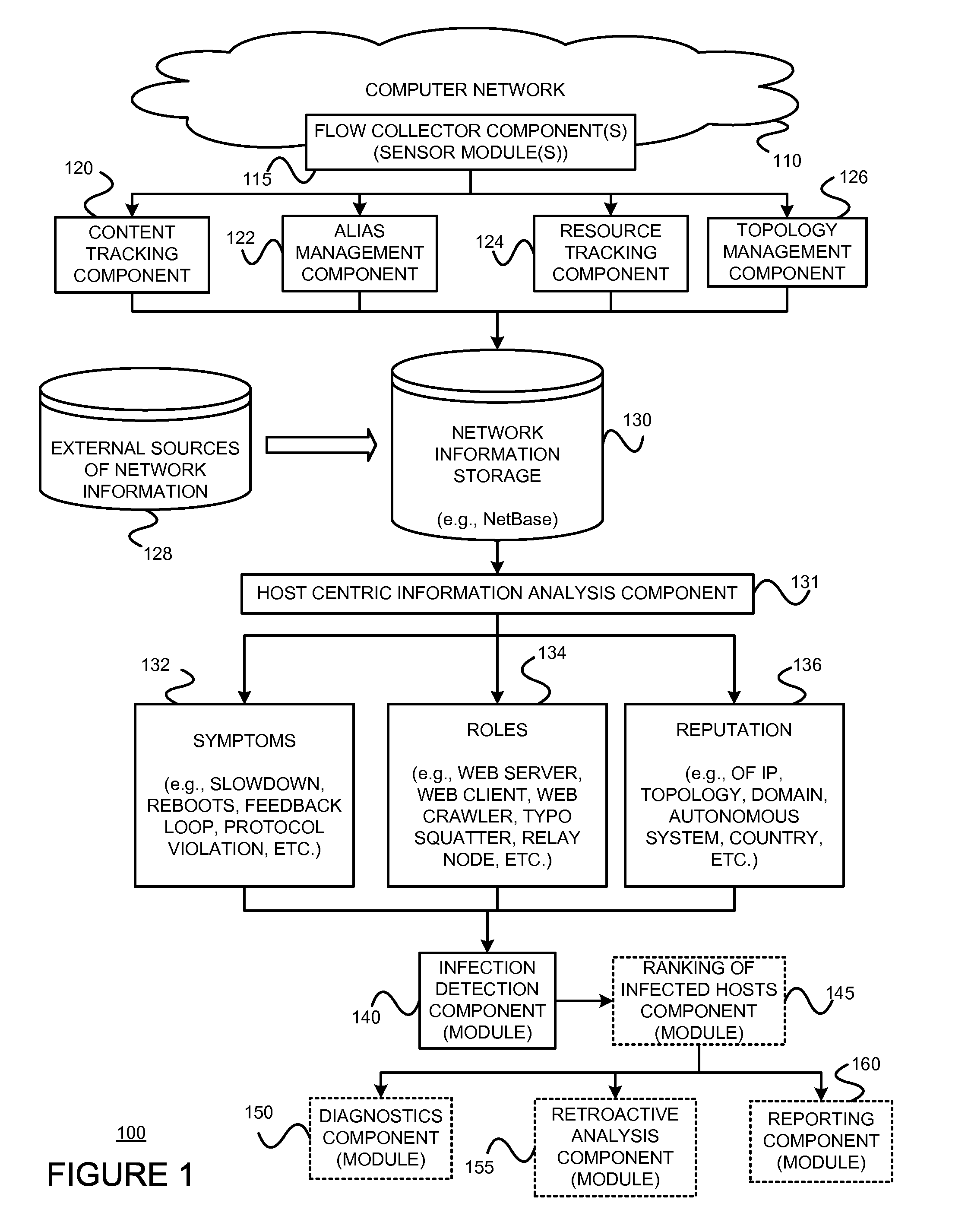
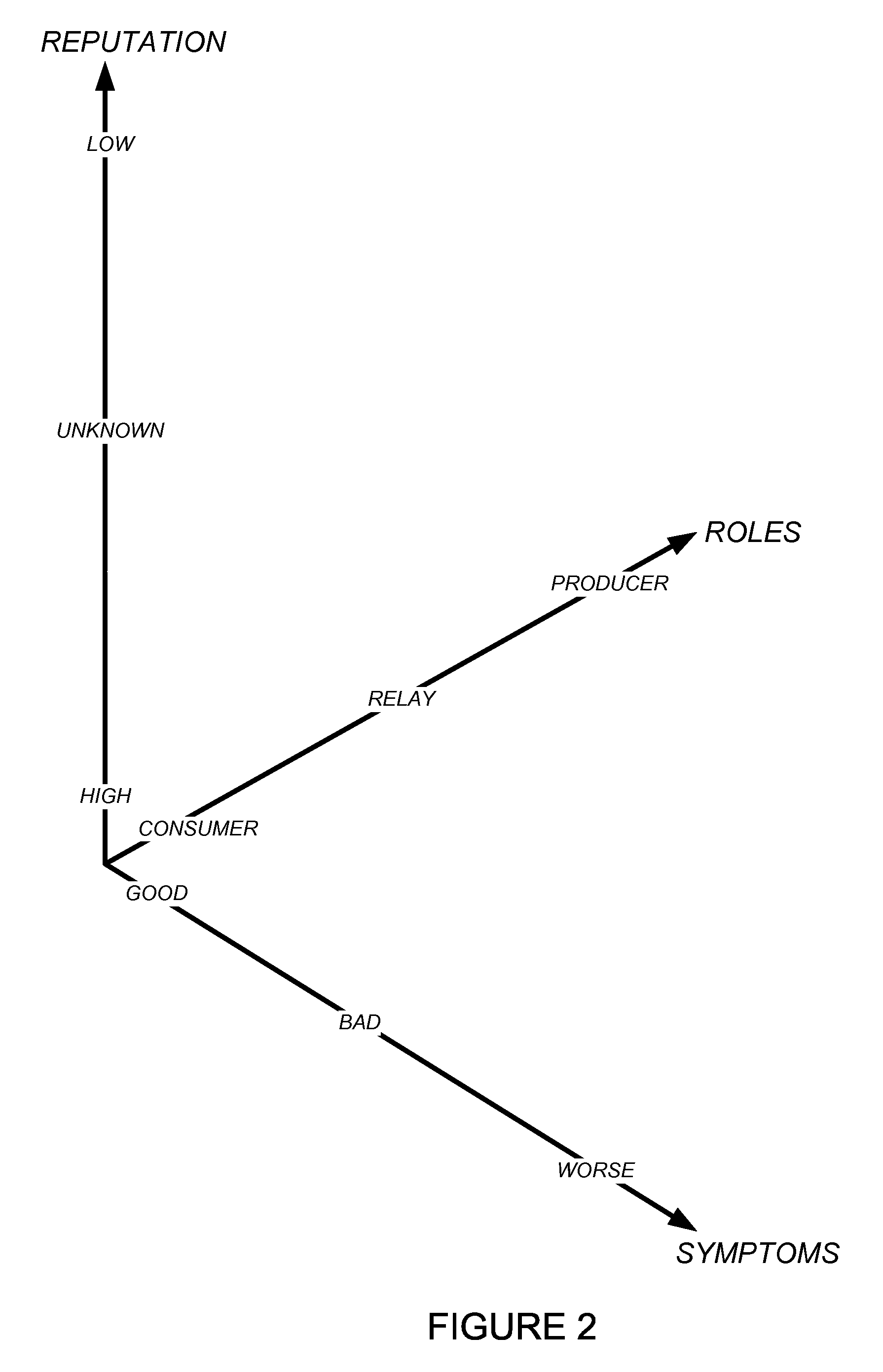
Using host symptoms, host roles, and/or host reputation for detection of host infection
InactiveUS20100235915A1Memory loss protectionError detection/correctionMalwareIntrusion prevention system
Detecting and mitigating threats to a computer network is important to the health of the network. Currently firewalls, intrusion detection systems, and intrusion prevention systems are used to detect and mitigate attacks. As the attackers get smarter and attack sophistication increases, it becomes difficult to detect attacks in real-time at the perimeter. Failure of perimeter defenses leaves networks with infected hosts. At least two of symptoms, roles, and reputations of hosts in (and even outside) a network are used to identify infected hosts. Virus or malware signatures are not required.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Host intrusion prevention system using software and user behavior analysis
ActiveUS20110023115A1Reduce processing stepsNetwork access restrictionMemory loss protectionError detection/correctionGraphicsGraphical user interface
In embodiments of the present invention improved capabilities are described for threat detection using a behavioral-based host-intrusion prevention method and system for monitoring a user interaction with a computer, software application, operating system, graphic user interface, or some other component or client of a computer network, and performing an action to protect the computer network based at least in part on the user interaction and a computer code process executing during or in association with a computer usage session.
Owner:SOPHOS
Behavior-based host-based intrusion prevention system
InactiveUS20040143749A1Memory loss protectionError detection/correctionMonitoring systemIntrusion prevention system
A method of protecting a system from attack that includes monitoring processes running on a system, identifying behavior of the processes and attributes of the processes, grouping the processes into process sets based on commonality of attributes, and generating behavior control descriptions for each process set.
Owner:SYMANTEC CORP
Process control methods and apparatus for intrusion detection, protection and network hardening
ActiveUS20060053491A1Memory loss protectionError detection/correctionEnvironmental control systemIntrusion prevention system
The invention provides an improved network and methods of operation thereof for use in or with process control systems, computer-based manufacturing or production control systems, environmental control systems, industrial control system, and the like (collectively, “control systems”). Those networks utilize a unique combination of firewalls, intrusion detection systems, intrusion protection devices and / or other devices for hardening (e.g., security against hacking, intrusion or other mischievous conduct) and / or intrusion detection. The networks and methods have application, by way of example, in plants, sites and other facilities in which networks that support control systems interface with corporate, business or other networks.
Owner:SCHNEIDER ELECTRIC SYST USA INC
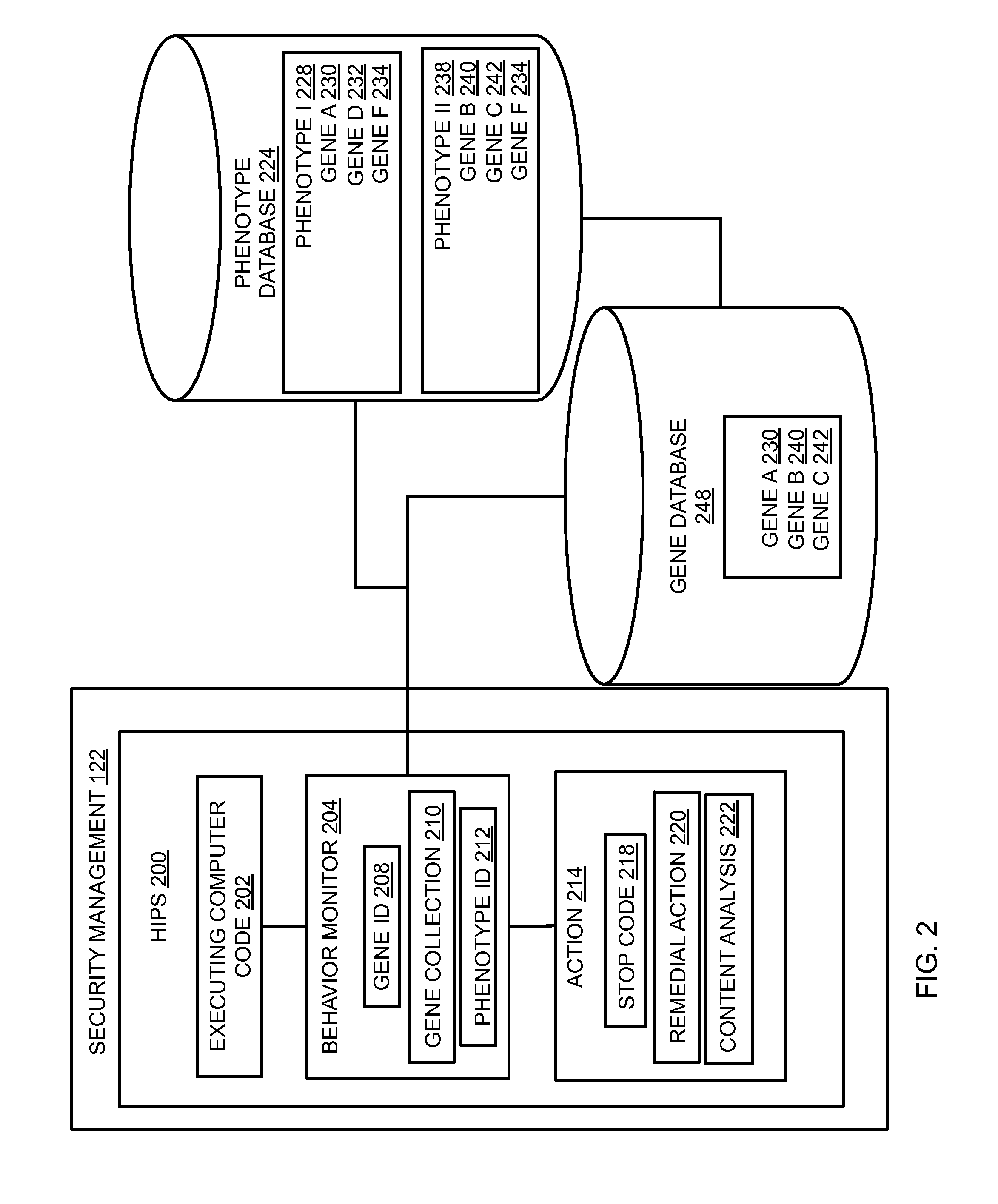
Behavioral-based host intrusion prevention system
ActiveUS20110023118A1Memory loss protectionUnauthorized memory use protectionApplication softwareIntrusion prevention system
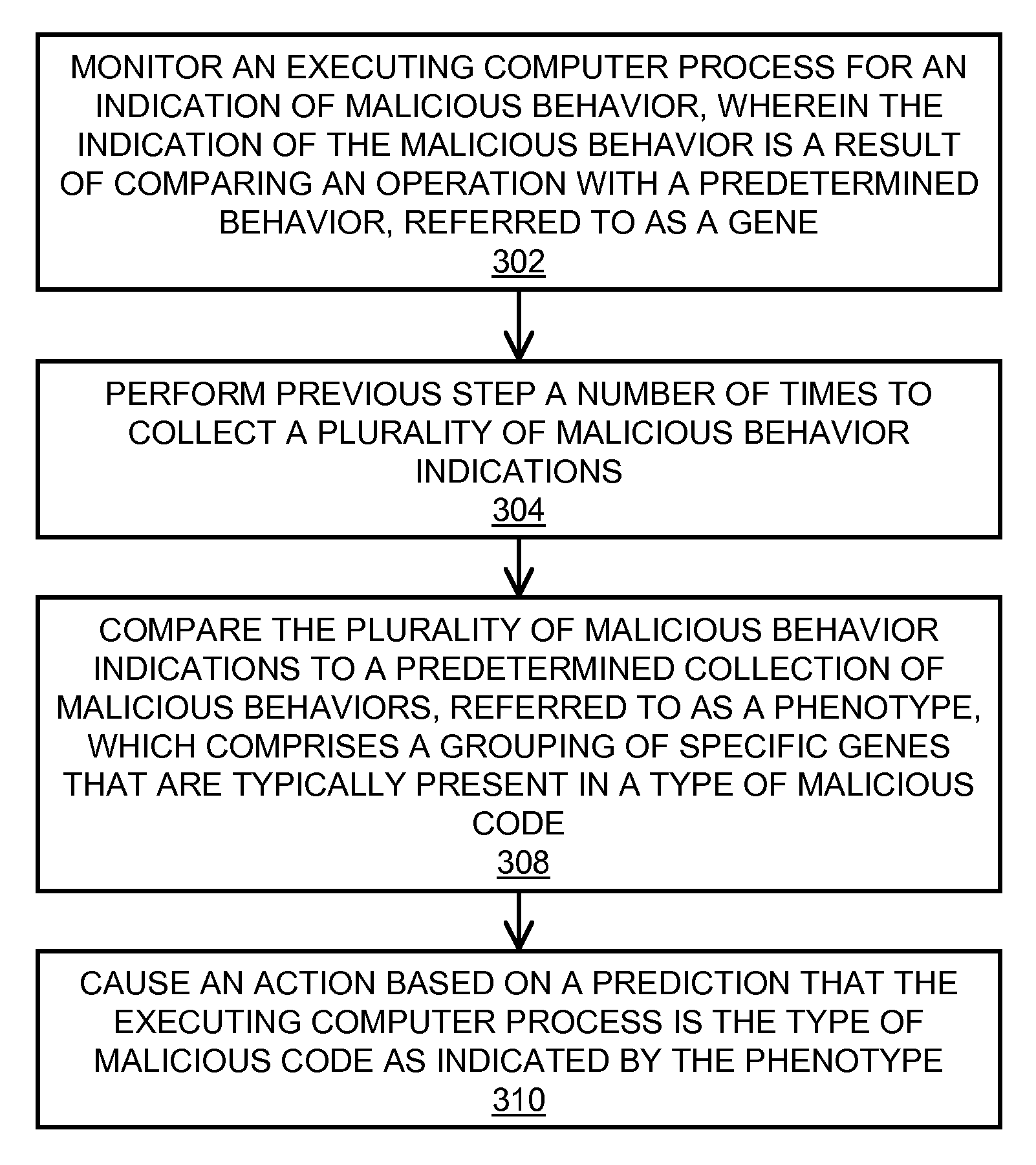
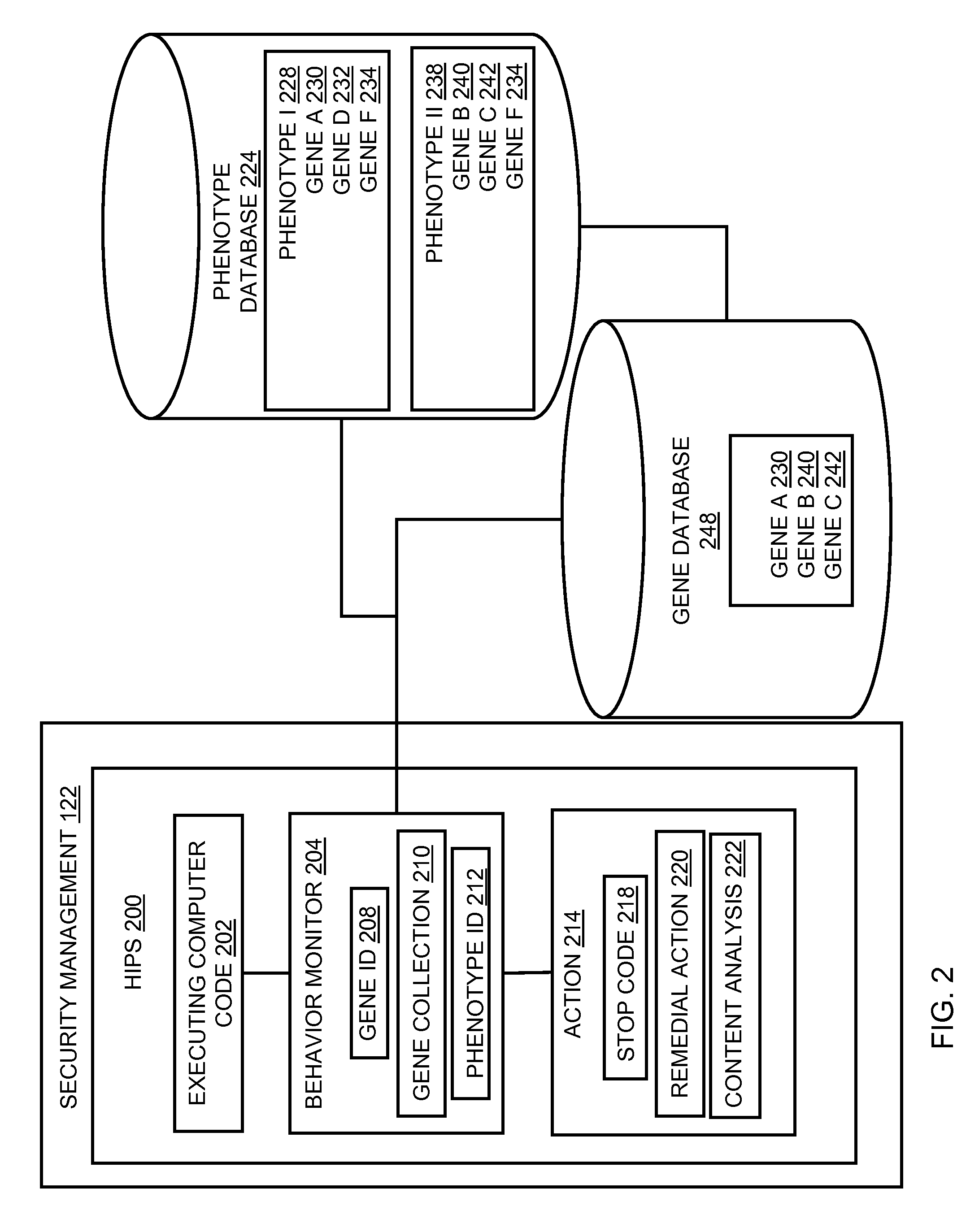
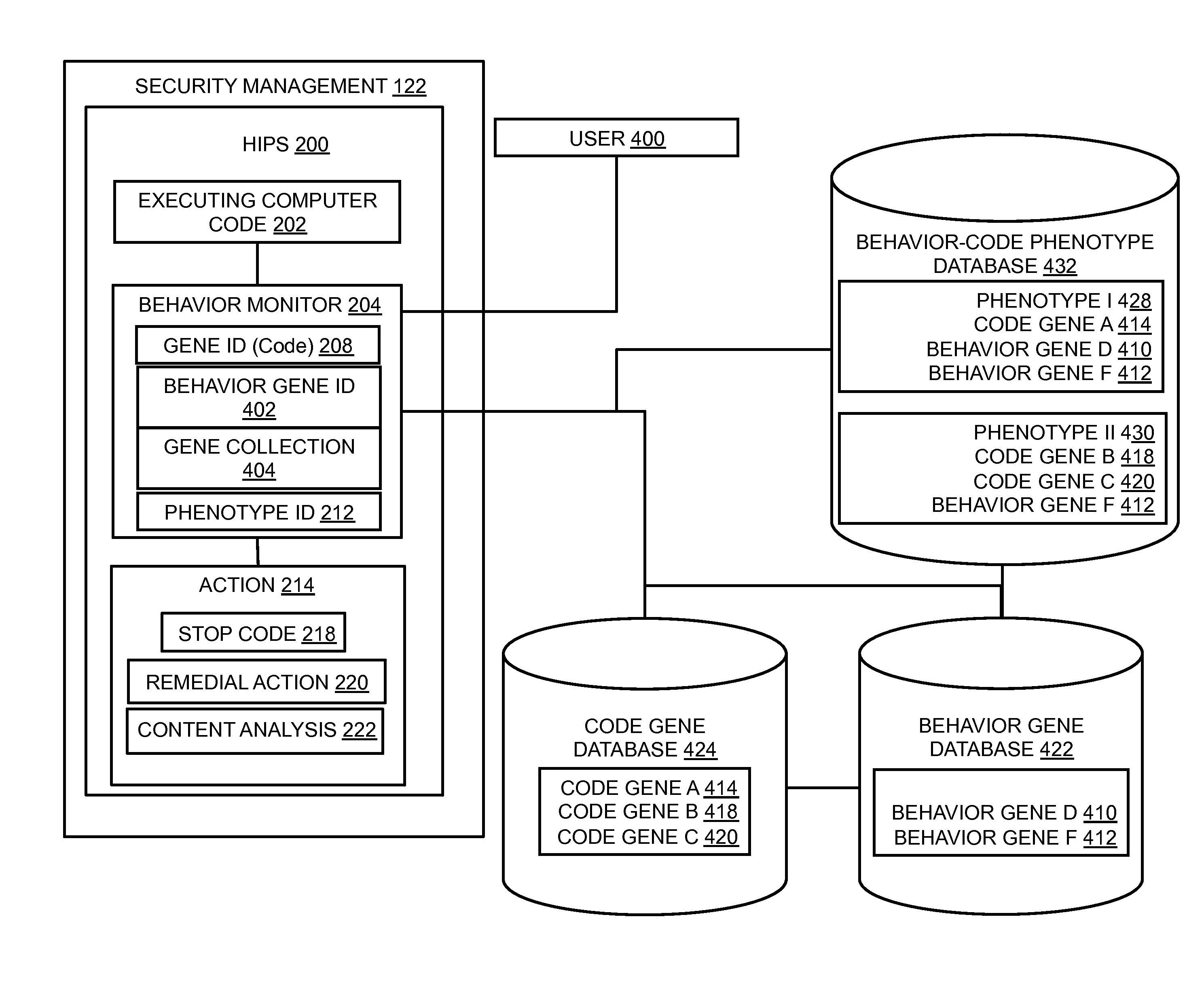
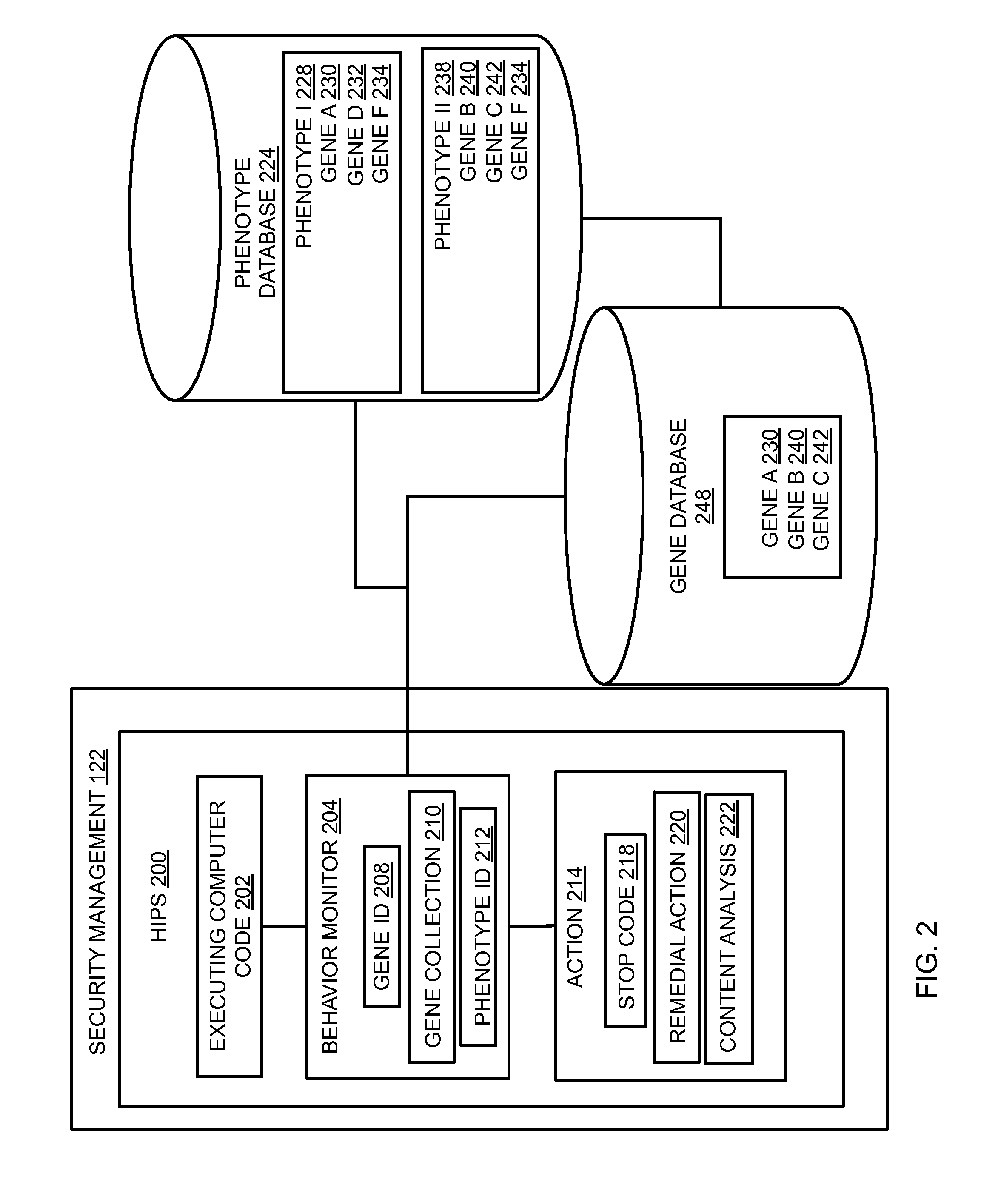
In embodiments of the present invention improved capabilities are described for behavioral-based threat detection. An executing computer process is monitored for an indication of malicious behavior, wherein the indication of the malicious behavior is a result of comparing an operation with a predetermined behavior, referred to as a gene. A plurality of malicious behavior indications observed for the executing process are compared to a predetermined collection of malicious behaviors, referred to as a phenotype, which comprises a grouping of specific genes that are typically present in a type of malicious code. Upon matching the malicious behavior indications with a phenotype, an action may be caused, where the action is based on a prediction that the executing computer process is the type of malicious code as indicated by the phenotype. Related user interfaces, applications, and computer program products are disclosed.
Owner:SOPHOS
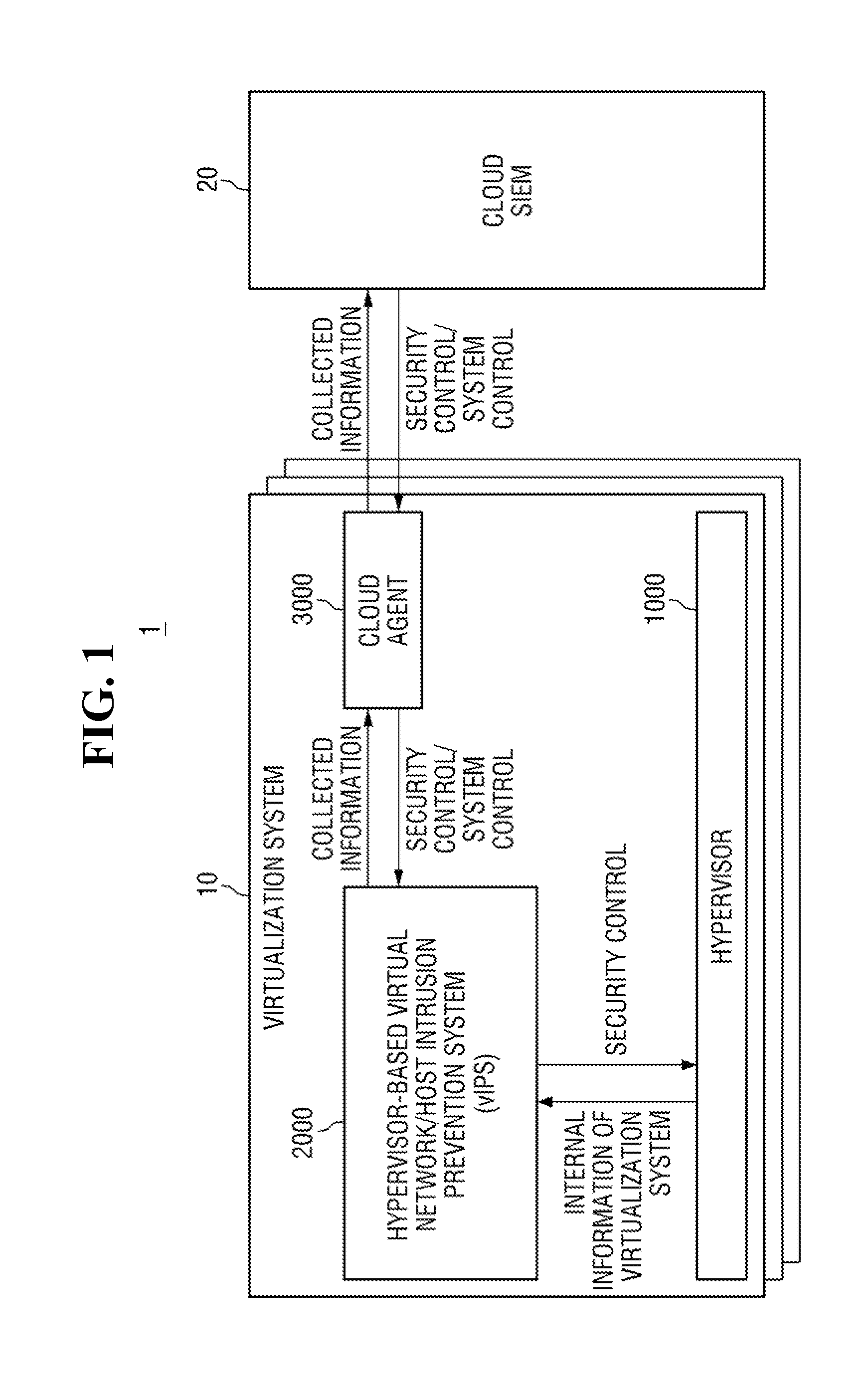
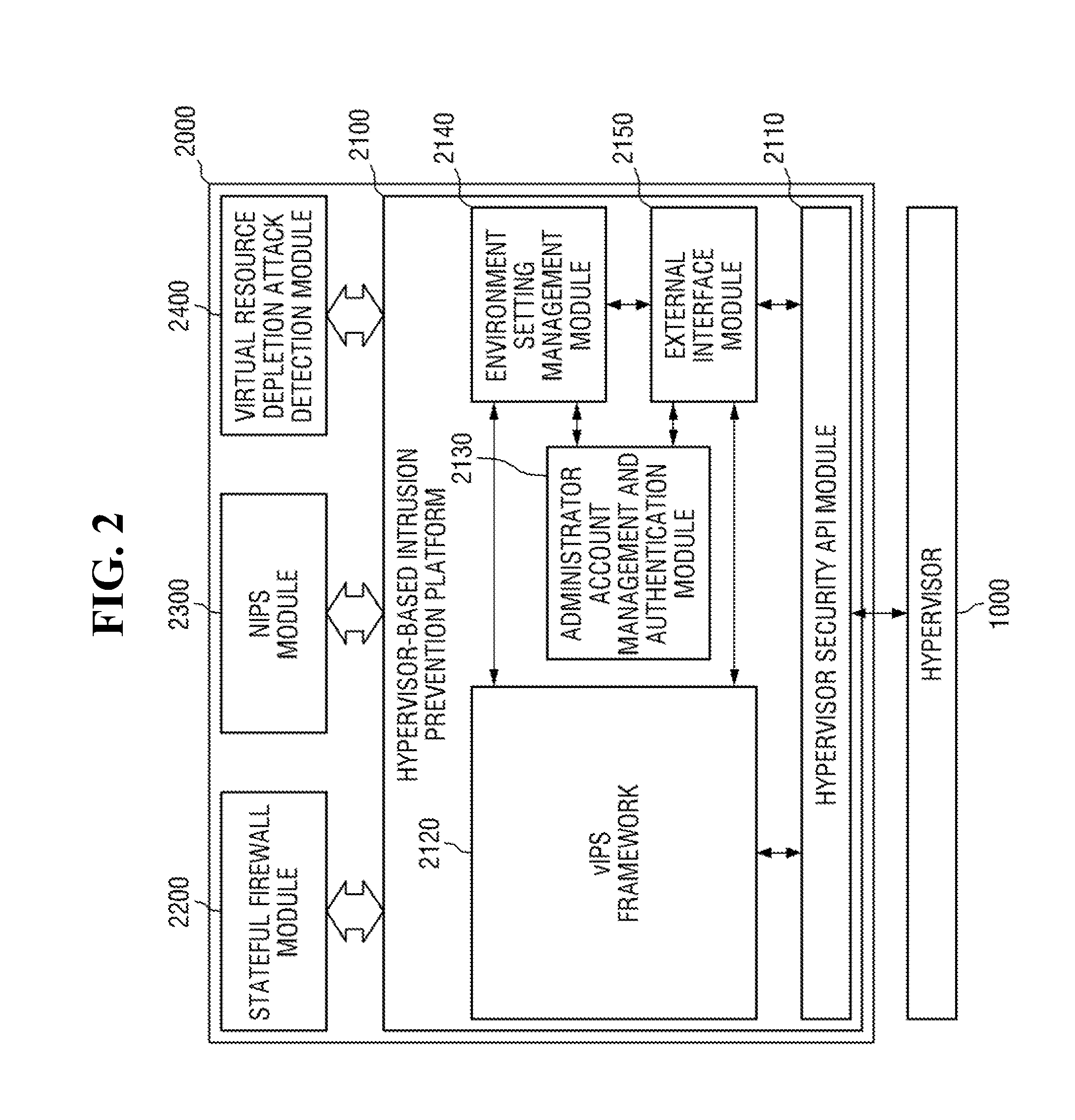
Hypervisor-based intrusion prevention platform and virtual network intrusion prevention system
InactiveUS20140317737A1Memory loss protectionData taking preventionApplication programming interfaceIntrusion prevention system
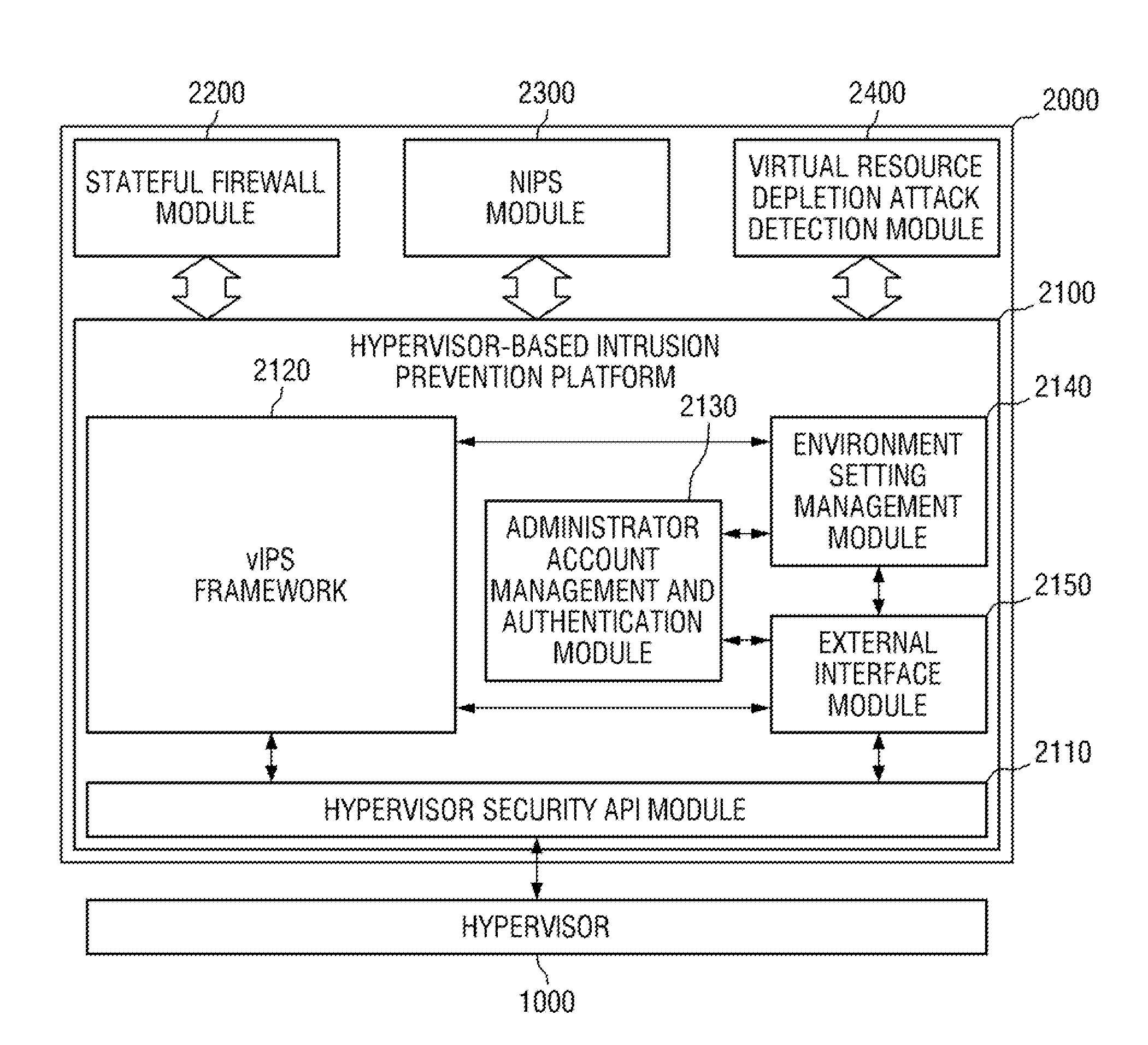
Hypervisor-based intrusion prevention platform is provided. The hypervisor-based intrusion prevention platform comprises a virtual network intrusion prevention system (vIPS) framework which obtains internal information of a virtualization system from a hypervisor and performs security control on the hypervisor in response to the result of intrusion detection carried out by using the internal information of the virtualization system, a hypervisor security application programming interface (API) module which provides an API used by the vIPS framework to access the hypervisor, an administrator account management and authentication module which manages an administrator account of a vIPS and authenticates the administrator account, an environment setting management module which manages environment setting values of modules within the vIPS, and an external interface module which provides an interface for system control and security control.
Owner:KOREA INTERNET & SECURITY AGENCY
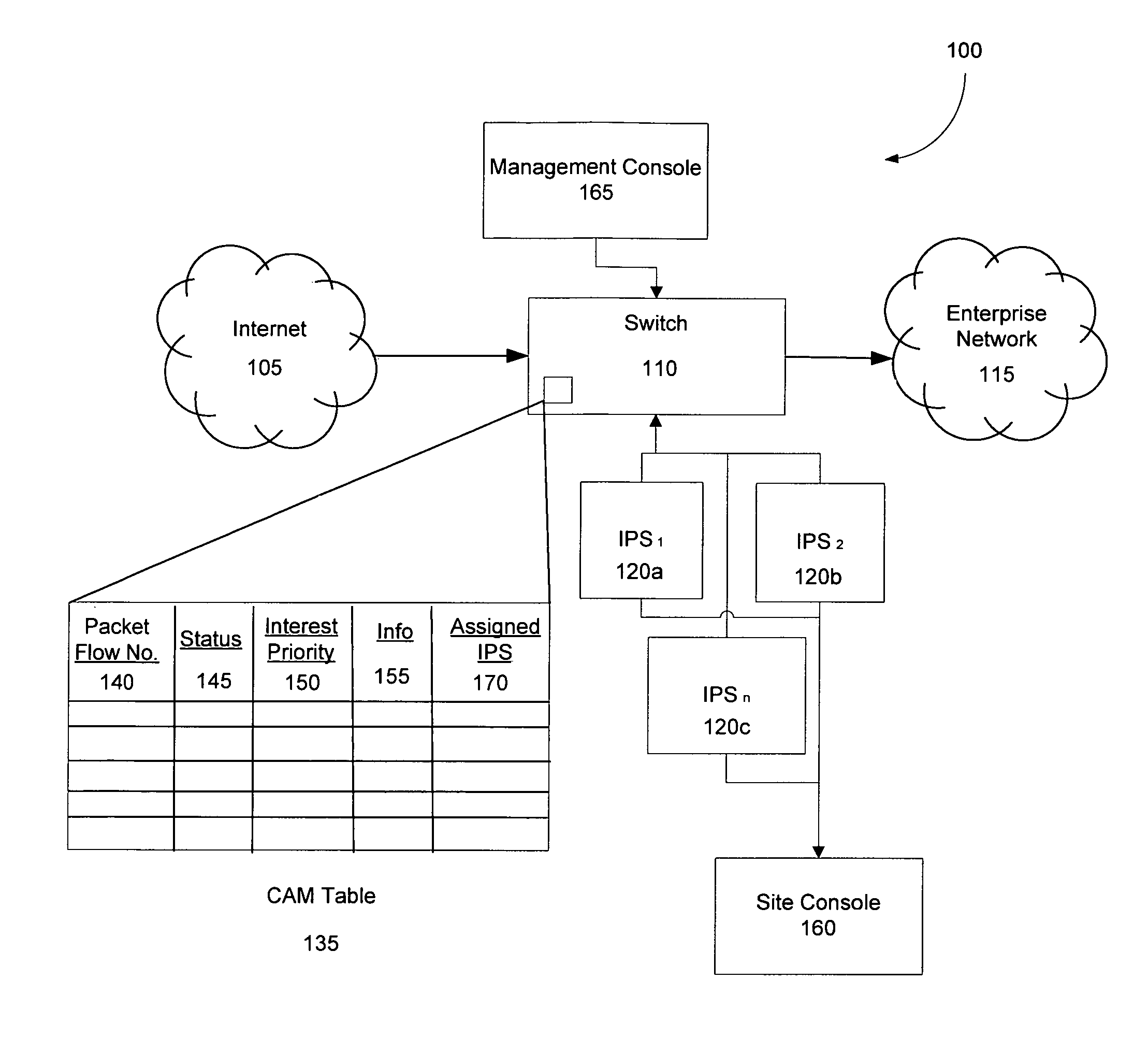
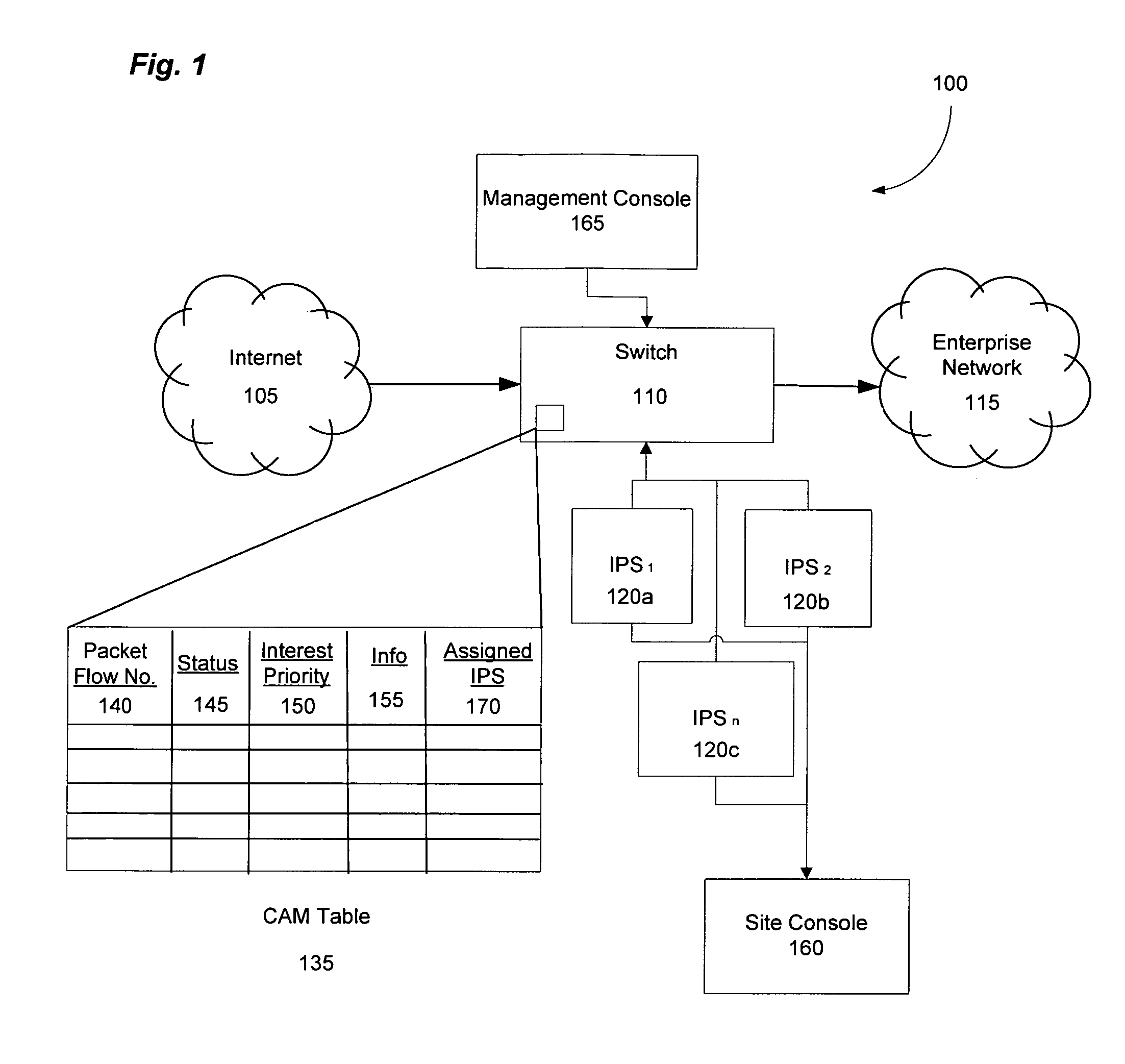
Fast network security utilizing intrusion prevention systems
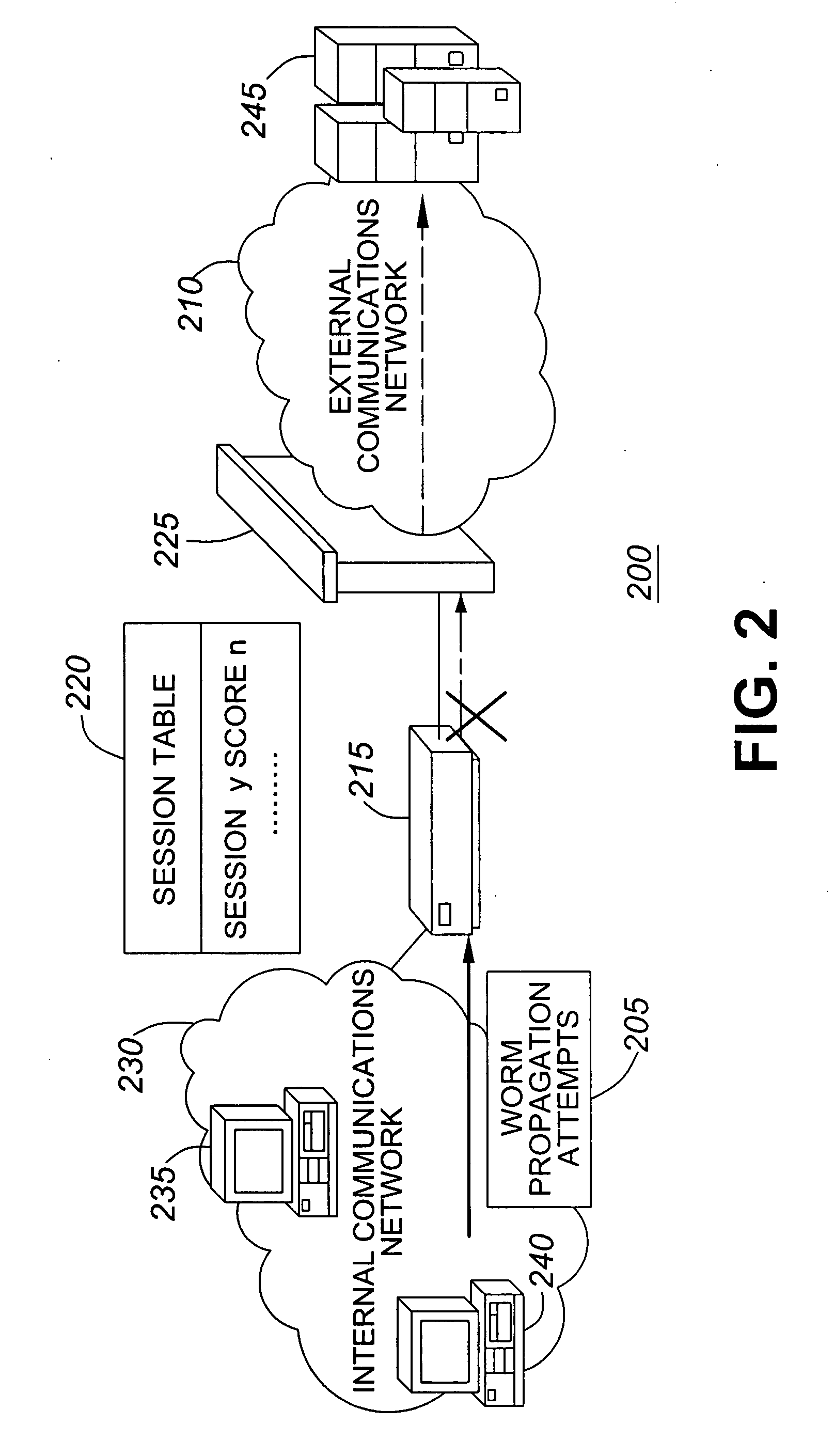
InactiveUS7808897B1Avoid OverloadingIncrease the number ofError preventionFrequency-division multiplex detailsTraffic capacityNetwork data
Intrusion Prevention Systems (“IPSs”) are used to detect and / or prevent intrusion events from infiltrating a computer network. However, in large computer networks the IPSs cannot conduct their analysis on network data traffic quickly enough in the network core to meet the demand placed on them by the computer networks, thereby causing delays in the transmission of network data traffic from a source to a destination. To prevent this delay, the IPSs can be configured to intelligently communicate with a high-capacity network switch. The IPSs conduct the initial inspection of the network data traffic flows to determine if an intrusion event is present. However, after the initial inspection, the IPS can inform the switch of what actions to take for future traffic flows including determining which future traffic flows are inspected by the IPSs and which future traffic flows are allowed to be blocked or transmitted to their destination by the switch.
Owner:LINKEDIN
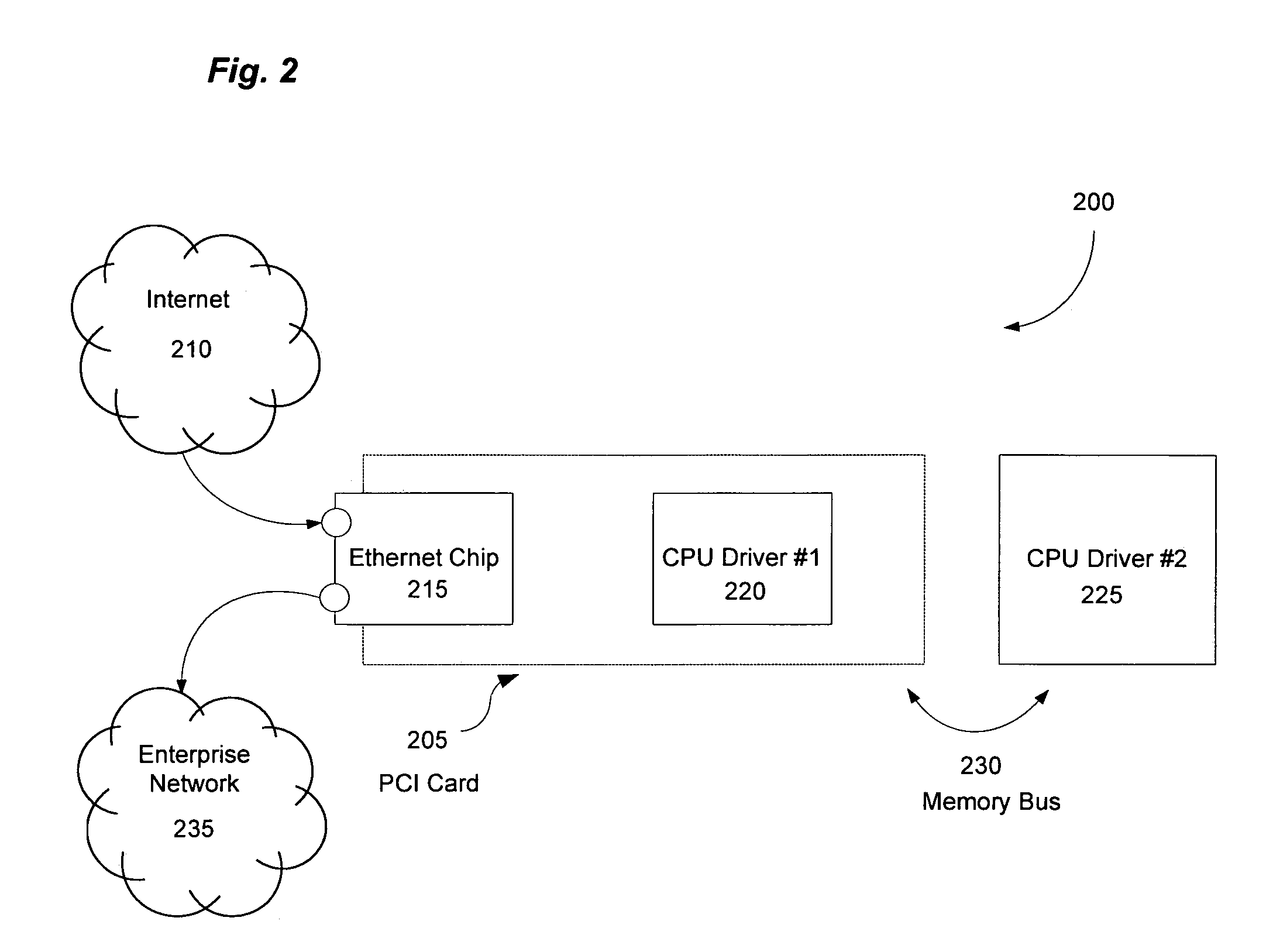
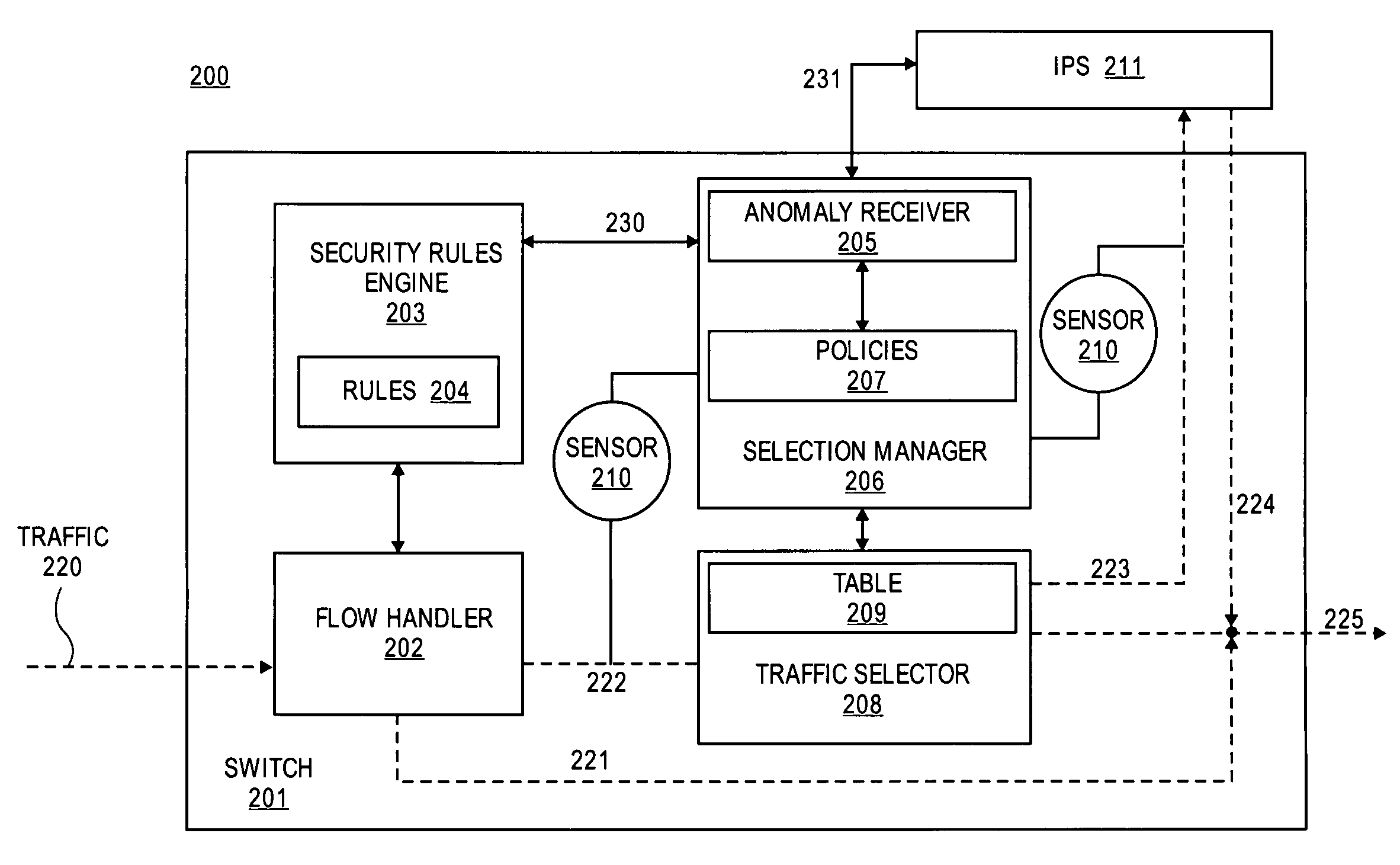
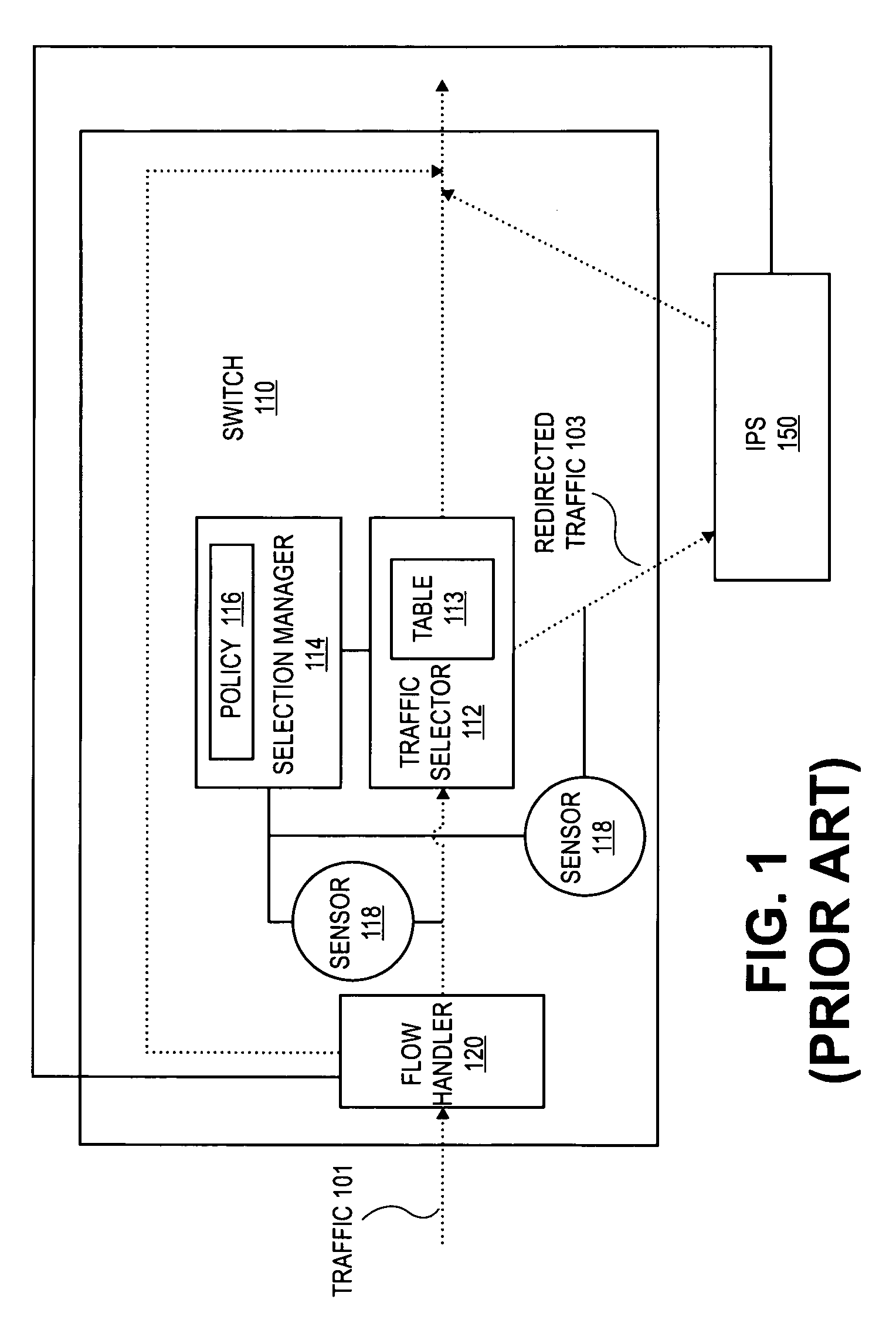
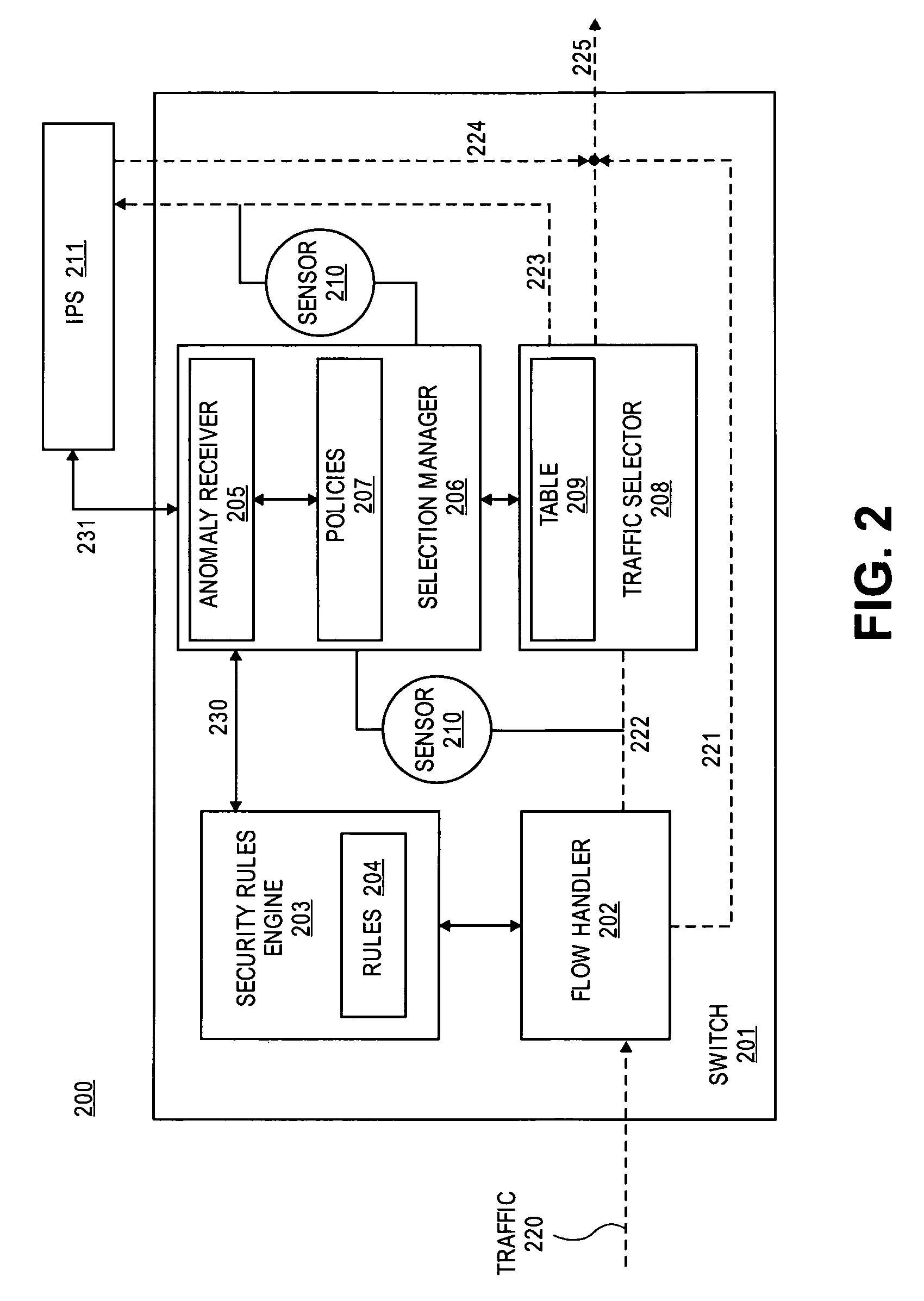
Method and apparatus for dynamic anomaly-based updates to traffic selection policies in a switch
ActiveUS20080163333A1Multiplex system selection arrangementsMemory loss protectionTraffic capacityComputer network
Techniques and architectures to dynamically modify policies used to determine how data in switched network traffic is selected for security inspection. One embodiment of the invention modifies policies used to determine how data in network traffic is redirected from a switch to an intrusion prevention system, without the policy modifications interrupting the handling of network traffic by the switch.
Owner:EXTREME NETWORKS INC
Network element and an infrastructure for a network risk management system
InactiveUS20090044270A1Easy to manageImprove securityMemory loss protectionError detection/correctionNetwork managementIntrusion prevention system
A system for a communication infrastructure in a network including at least one connected system (CS) and at least one network risk management network element (SW), wherein the network acts as a virtual network comprising at least one virtual network element, and wherein the at least one virtual network element takes over the roles of existing network elements comprising at least one of a switch, a router, a firewall and an intrusion prevention system (IPS), and wherein the virtual network is comprised of physical elements that work together to form the network's infrastructure.
Owner:SHELLY ASAF +1
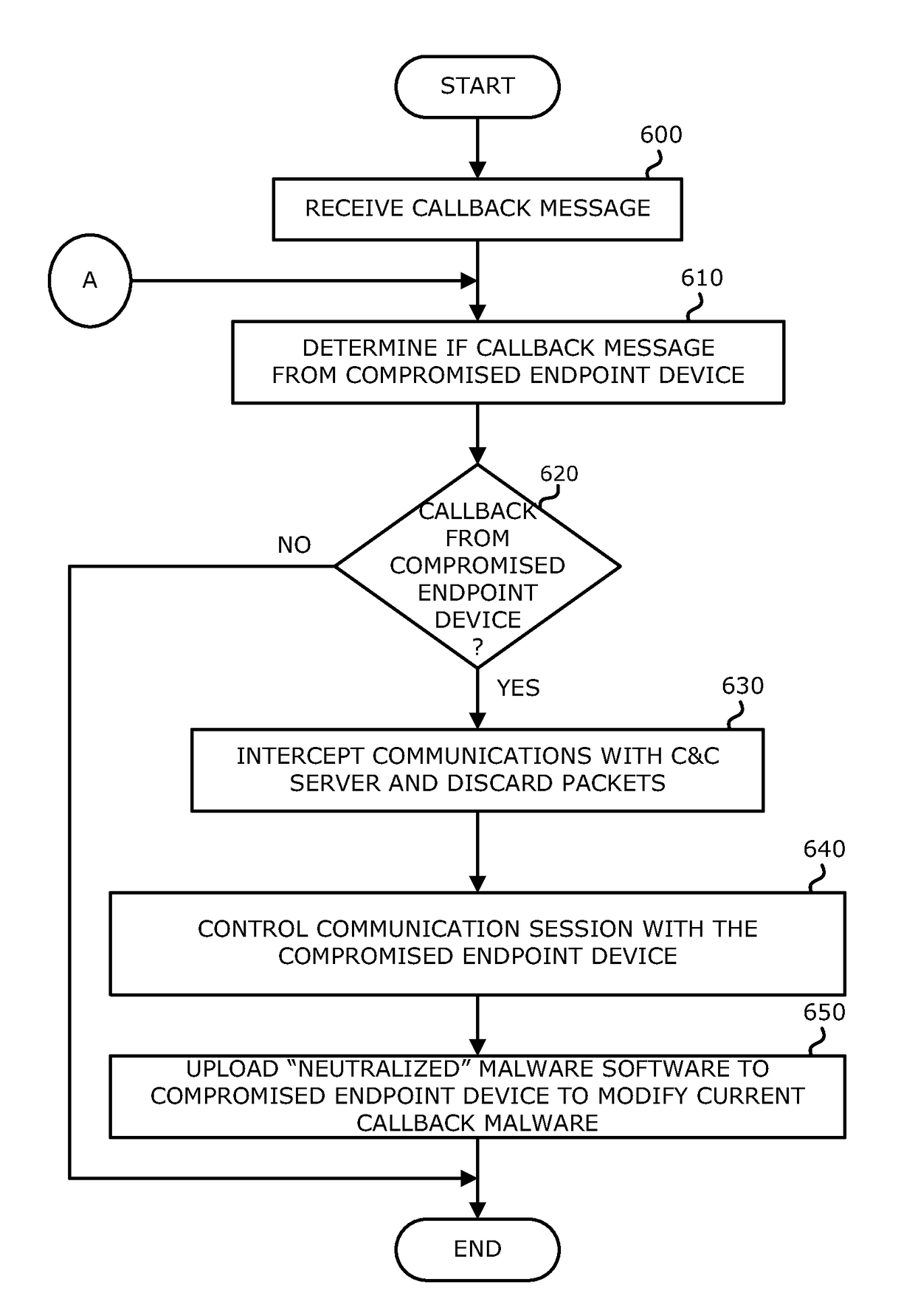
Intrusion prevention and remedy system
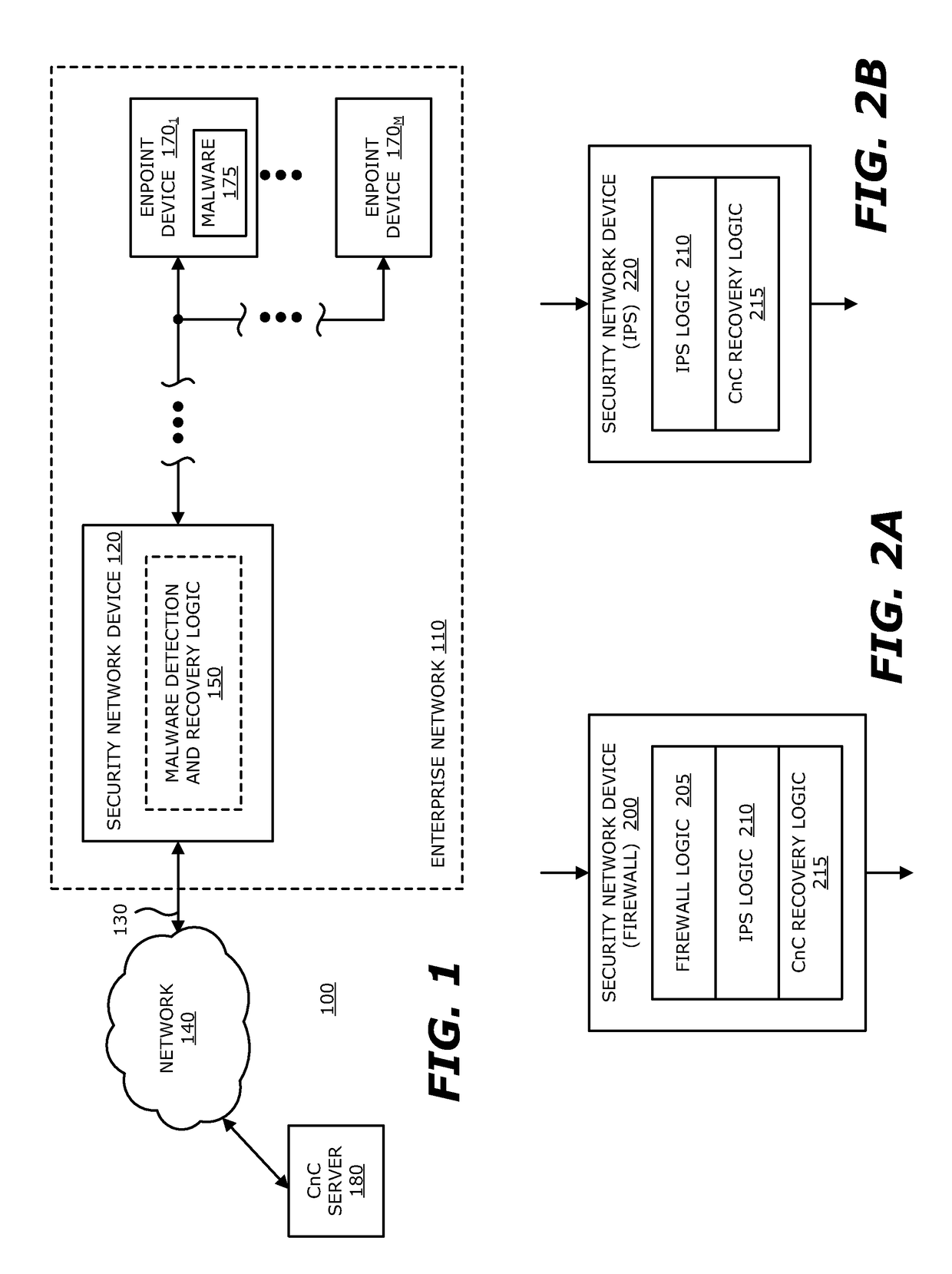
According to one embodiment, a computerized method is directed to neutralizing callback malware. This method involves intercepting an incoming message from a remote source directed to a compromised endpoint device. Next, a first portion of information within the incoming message is substituted with a second portion of information. The second portion of information is designed to mitigate operability of the callback malware. Thereafter, the modified incoming message, which includes the second portion of the information, is returned to the compromised endpoint device.
Owner:FIREEYE SECURITY HLDG US LLC
Score-based intrusion prevention system
InactiveUS20090077663A1High accuracy rateReduce in quantityMemory loss protectionError detection/correctionTraffic volumeIntrusion prevention system
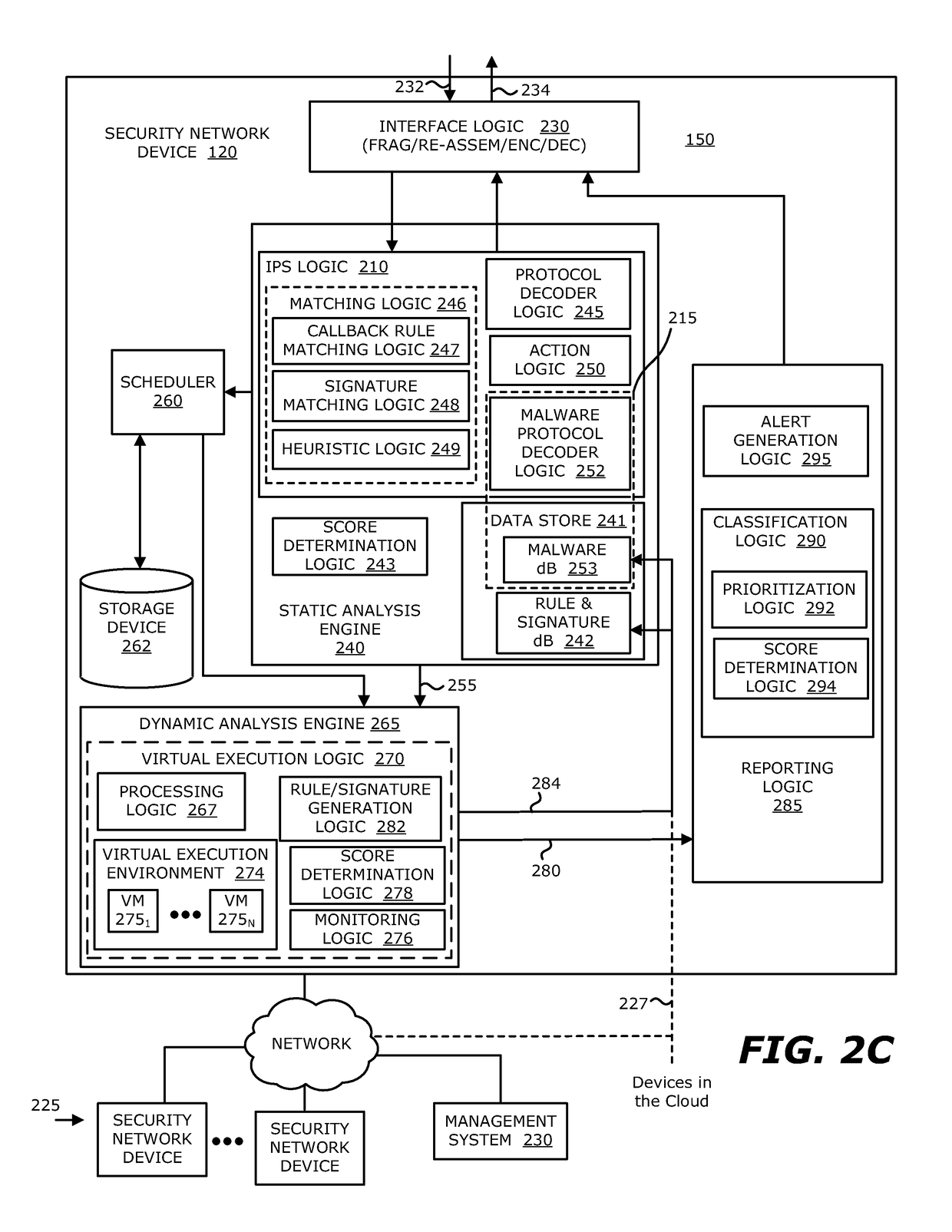
A score-based method of preventing intrusion, and related apparatus and systems, including one or more of the following: receiving traffic including new packets; decoding a protocol for same; determining that no session exists to which the packets are associated; creating a session entry for a session corresponding to the packets; setting a total score for the session to zero; performing an anomaly analysis on the packets identifying an anomaly; adding an anomaly score for the anomaly to the total score for the session; determining that the total score for the session does not exceed a threshold; determining that the anomaly analysis is finished; determining that the signature of the received new packets matches a threat signatures; adding a score assigned to the threat signature to the total score for the session; determining that the total score for the session exceeds the threshold; and triggering a threat response action.
Owner:ALCATEL LUCENT SAS
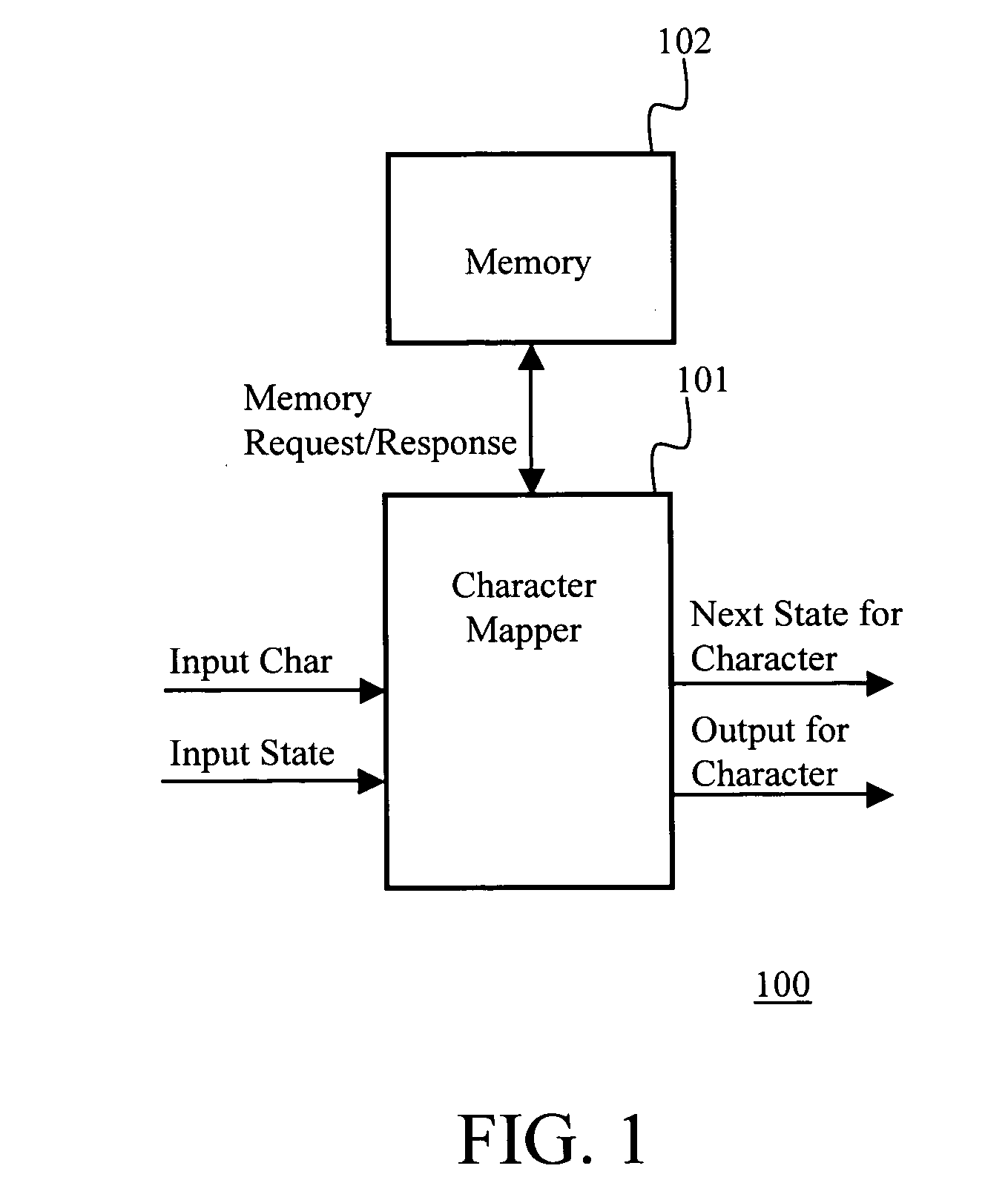
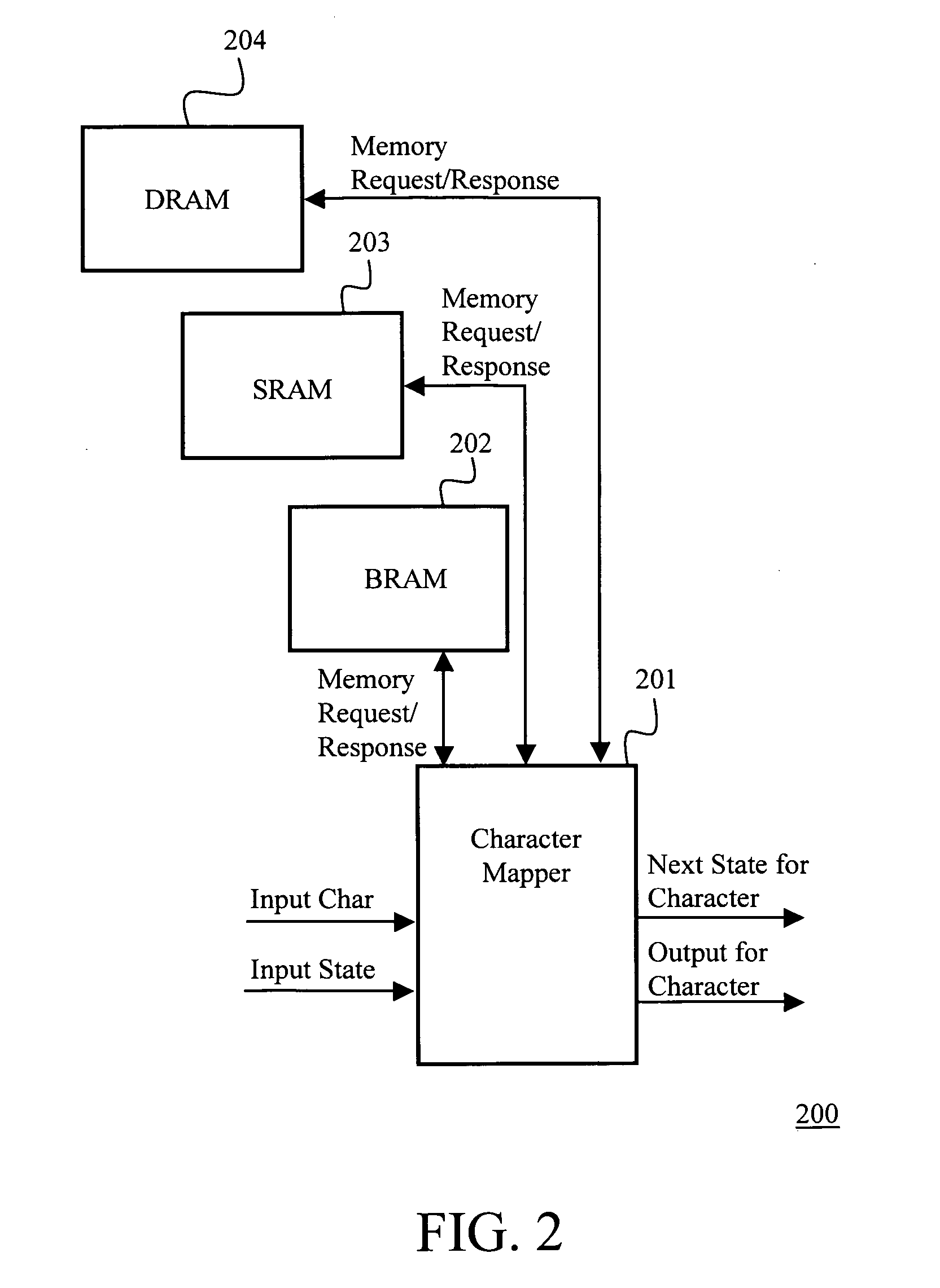
Layered memory architecture for deterministic finite automaton based string matching useful in network intrusion detection and prevention systems and apparatuses
ActiveUS20060101195A1Reduce decreaseTransmissionMemory systemsLine rateDeterministic finite automaton
Owner:FORTINET
System and method for intrusion prevention in a communications network
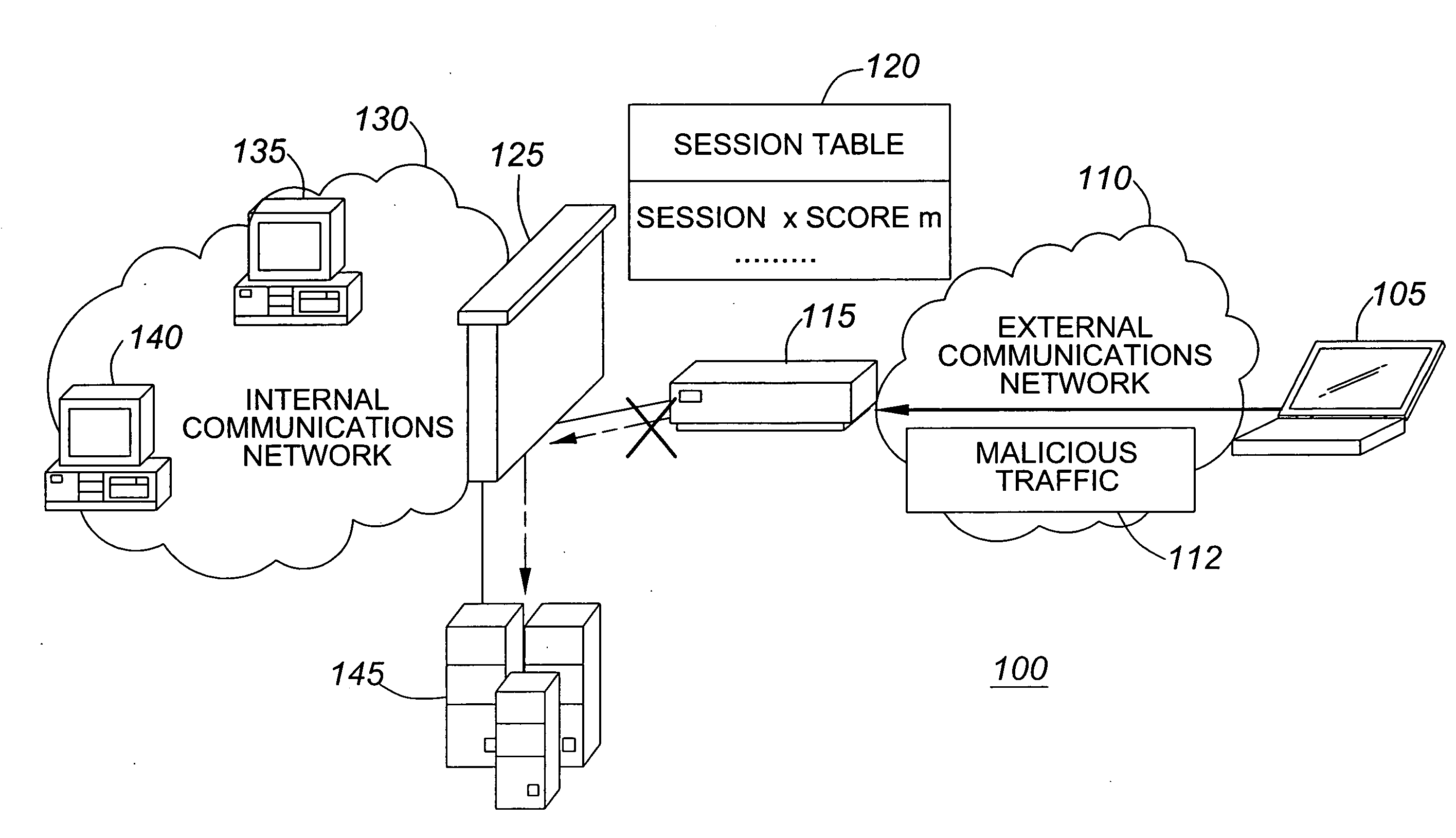
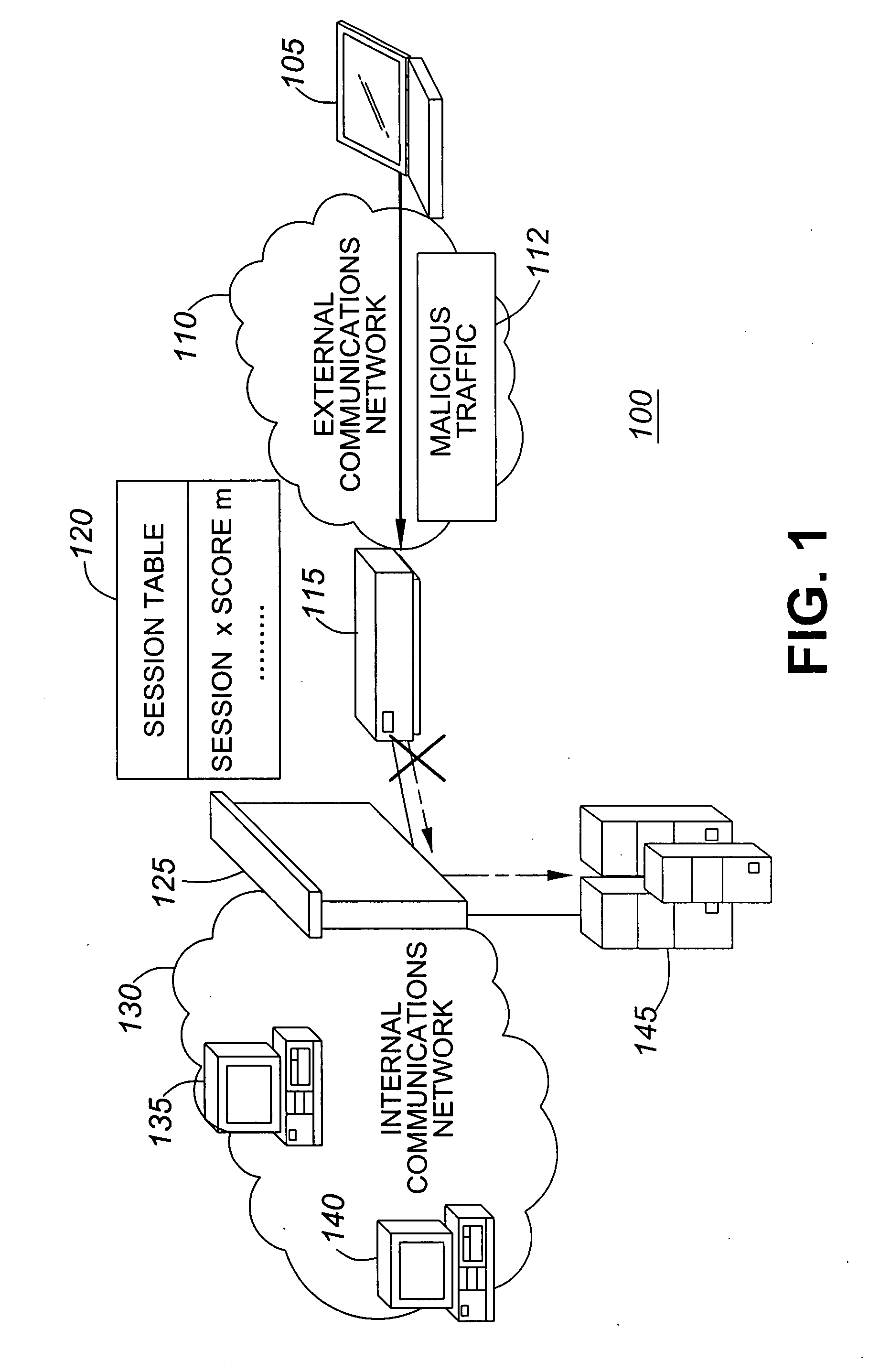
InactiveUS7386889B2Avoid connectionIncrease resourcesDigital data processing detailsAnalogue secracy/subscription systemsIntrusion prevention systemNetwork service
A method, system and program for preventing intrusion in a communications network. A source node initiates a request for network services, such as session establishment, database access, or application access. Known network resources and authorized user information is stored in a database at a network portal along with access policy rules that are device and user dependent. Identification of the source node is required before the source node can construct a transformed packet header that is included with a synchronization packet before transmission to a destination node. An appliance or firewall in the communications network receives and authenticates the synchronization packet before releasing the packet to its, intended destination. The authentication process includes verification of the access policy associated with the source node. Once received at the destination node, the transformed packet header is reformed by extracting a key index value. The extracted key index is subsequently used to transform the packet header in the response transmitted to the source node.
Owner:LIQUIDWARE LABS
Network Intrusion Protection
ActiveUS20100125900A1Data taking preventionData switching by path configurationNetwork packetIntrusion prevention system
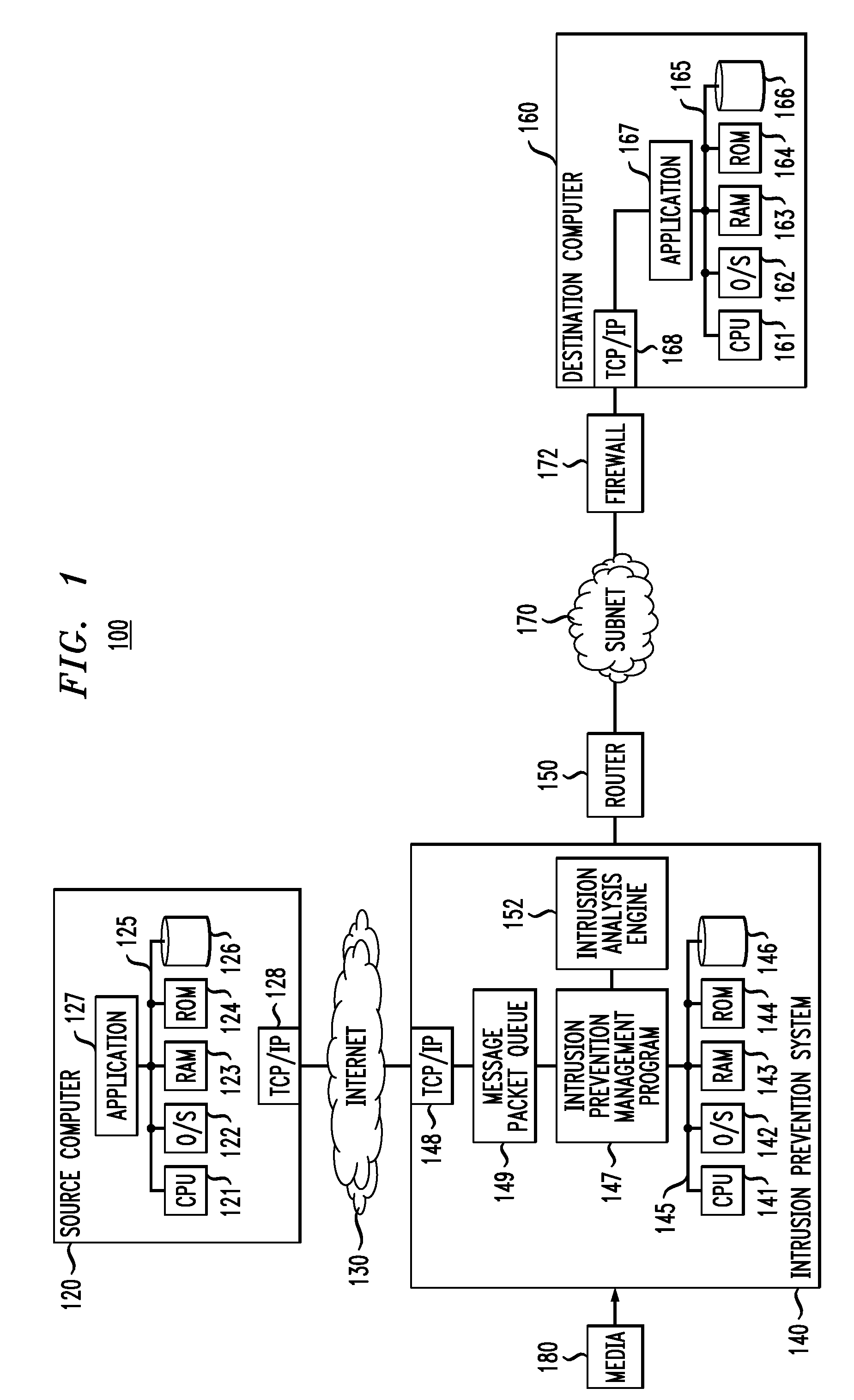
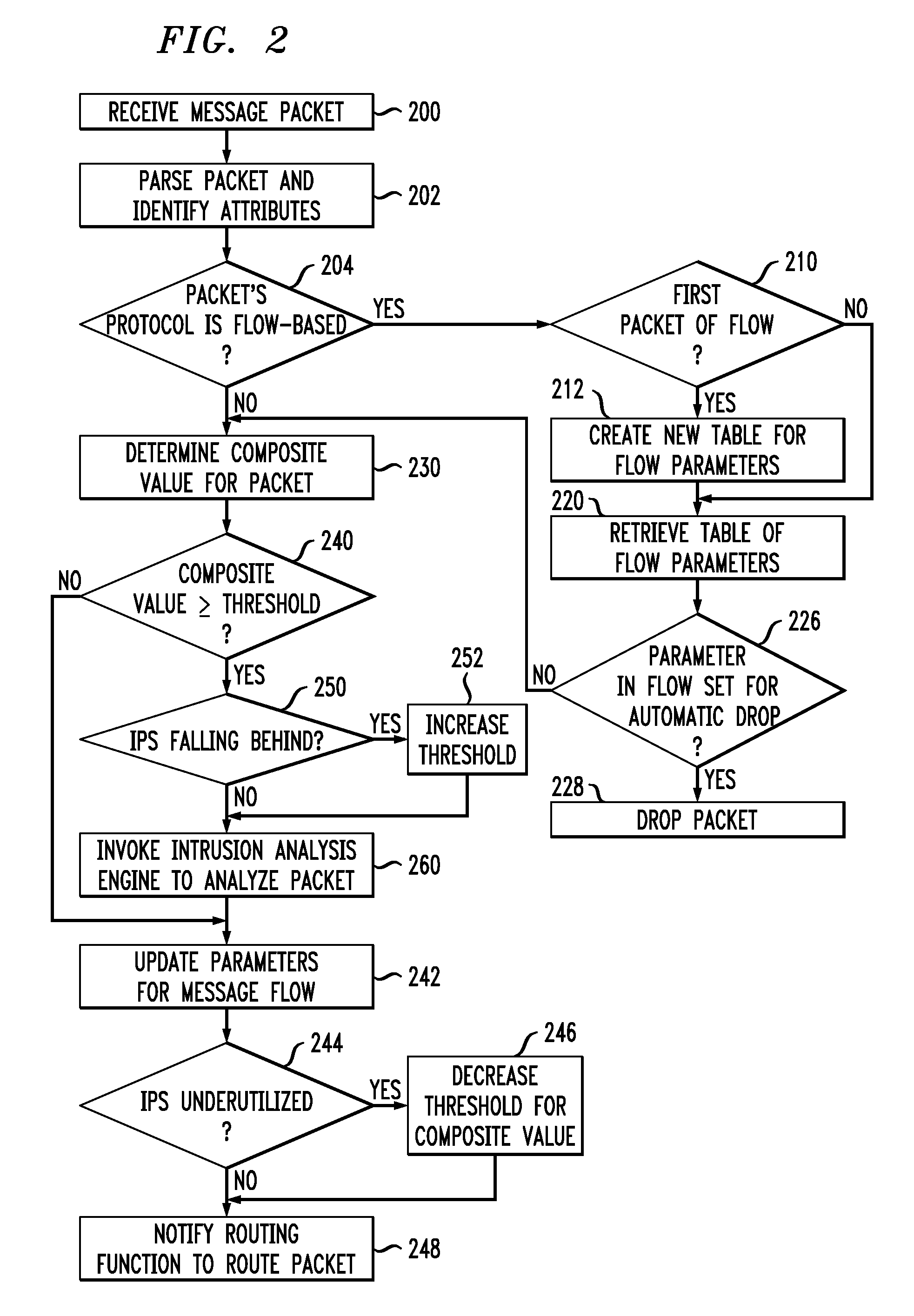
Improved techniques are disclosed for use in an intrusion prevention system or the like. For example, a method comprises the following steps performed by a computing element of a network. A packet of a flow is received, the flow comprising a plurality of packets, wherein the plurality of packets represents data in the network. A network intrusion analysis cost-benefit value is determined representing a benefit for analyzing the received packet for intrusions in relation to a cost for analyzing the received packet for intrusions. The method compares the network intrusion analysis cost-benefit value to a network intrusion analysis cost-benefit threshold to determine whether analyzing the received packet for intrusions before forwarding the received packet is warranted. Responsive to a determination that analyzing the received packet for intrusions before forwarding the received packet is not warranted, the received packet is forwarded, an indication is made that subsequent packets of the flow should be forwarded, and a determination is made whether the received packet indicates an intrusion after forwarding the received packet.
Owner:IBM CORP
Sip intrusion detection and response architecture for protecting sip-based services
InactiveUS20100154057A1Without degrading qualityAvoid callingMemory loss protectionError detection/correctionTraffic capacitySession Initiation Protocol
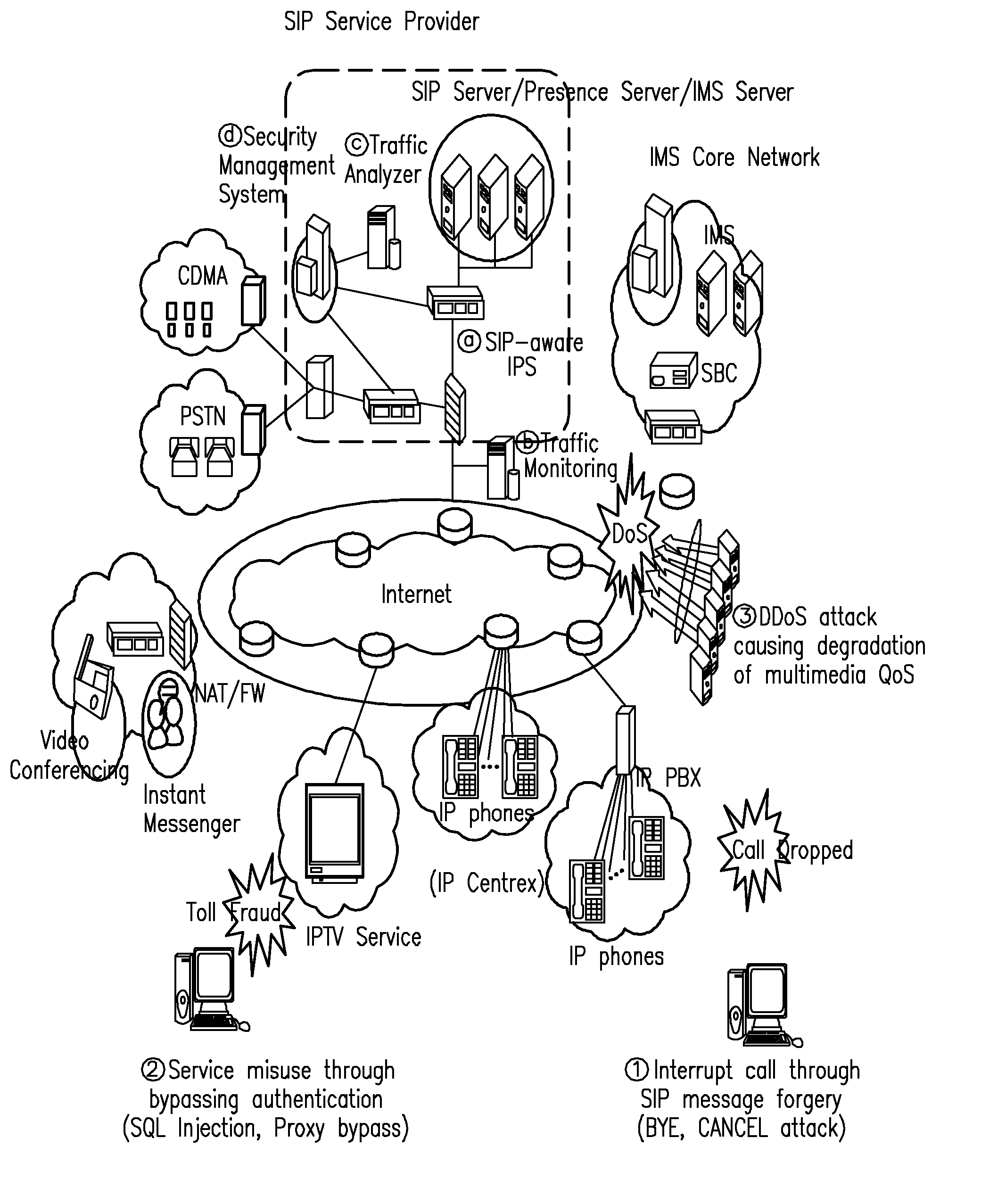
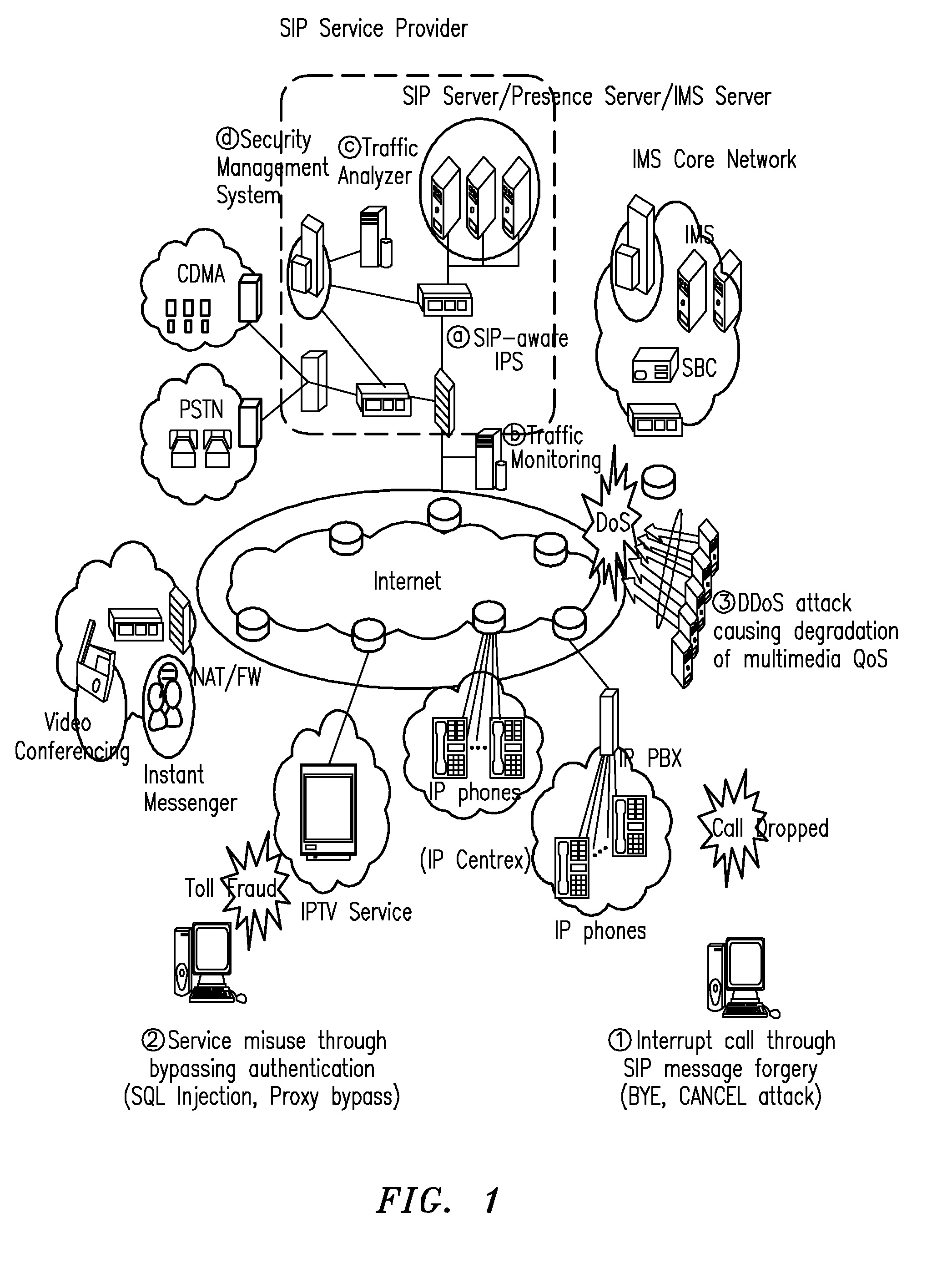
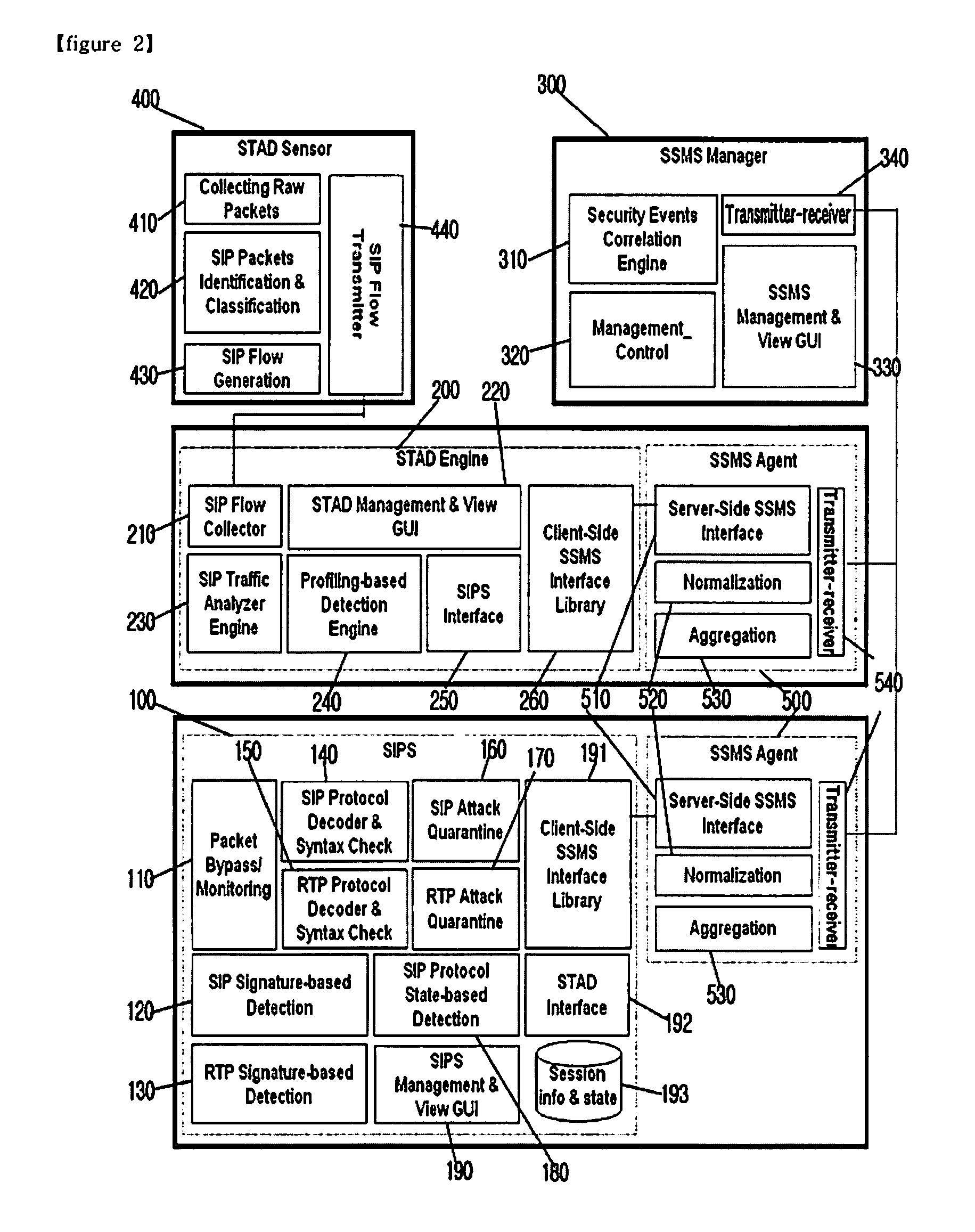
The present invention relates to a Session Initiation Protocol (SIP) intrusion detection and response architecture for protecting SIP-based services, and more specifically, to an SIP intrusion detection and response architecture for protecting SIP-based services, in which SIP-based attacks of a new type can be coped with by detecting the SIP-based attacks and SIP traffic anomalies and managing an SIP-aware security device without degrading quality of multimedia, and signal and media channels can be examined through an SIP-aware intrusion prevention system (IPS) for the purpose of preventing an attacker from hindering a call through manipulation of an SIP message and session-hijacking among legitimate users and attempting a toll fraud by detouring authentication.
Owner:KOREA INTERNET & SECURITY AGENCY
Host intrusion prevention system using software and user behavior analysis
In embodiments of the present invention improved capabilities are described for threat detection using a behavioral-based host-intrusion prevention method and system for monitoring a user interaction with a computer, software application, operating system, graphic user interface, or some other component or client of a computer network, and performing an action to protect the computer network based at least in part on the user interaction and a computer code process executing during or in association with a computer usage session.
Owner:SOPHOS
Intrusion prevention system
InactiveUS7458094B2Effective protectionAvoid damageMemory loss protectionDigital data processing detailsIntrusion prevention systemComputer security
The invention provides a method and system for monitoring a computer network and determining whether the network faces a threat from users. In the event that the existence of a threat is determined, the system in accordance with the invention provides a real-time assessment of the threat to the network and responds to prevent damage to the network.
Owner:LEIDOS
Behavior-based host-based intrusion prevention system
ActiveUS20050108578A1Digital data processing detailsUser identity/authority verificationMonitoring systemIntrusion prevention system
A method of protecting a system from attack that includes monitoring processes running on a system, identifying behavior of the processes and attributes of the processes, grouping the processes into process sets based on commonality of attributes, and generating behavior control descriptions for each process set.
Owner:CA TECH INC
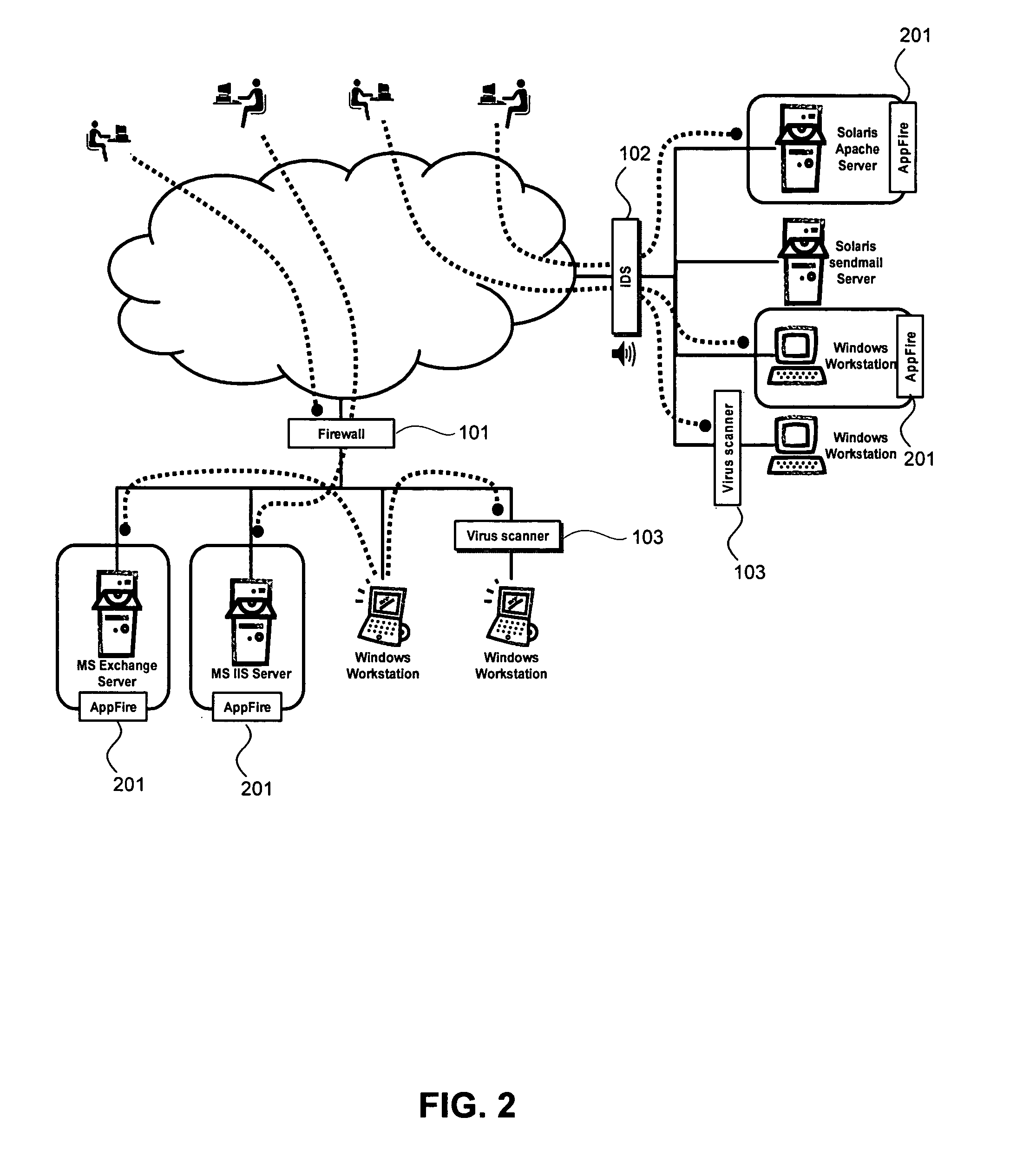
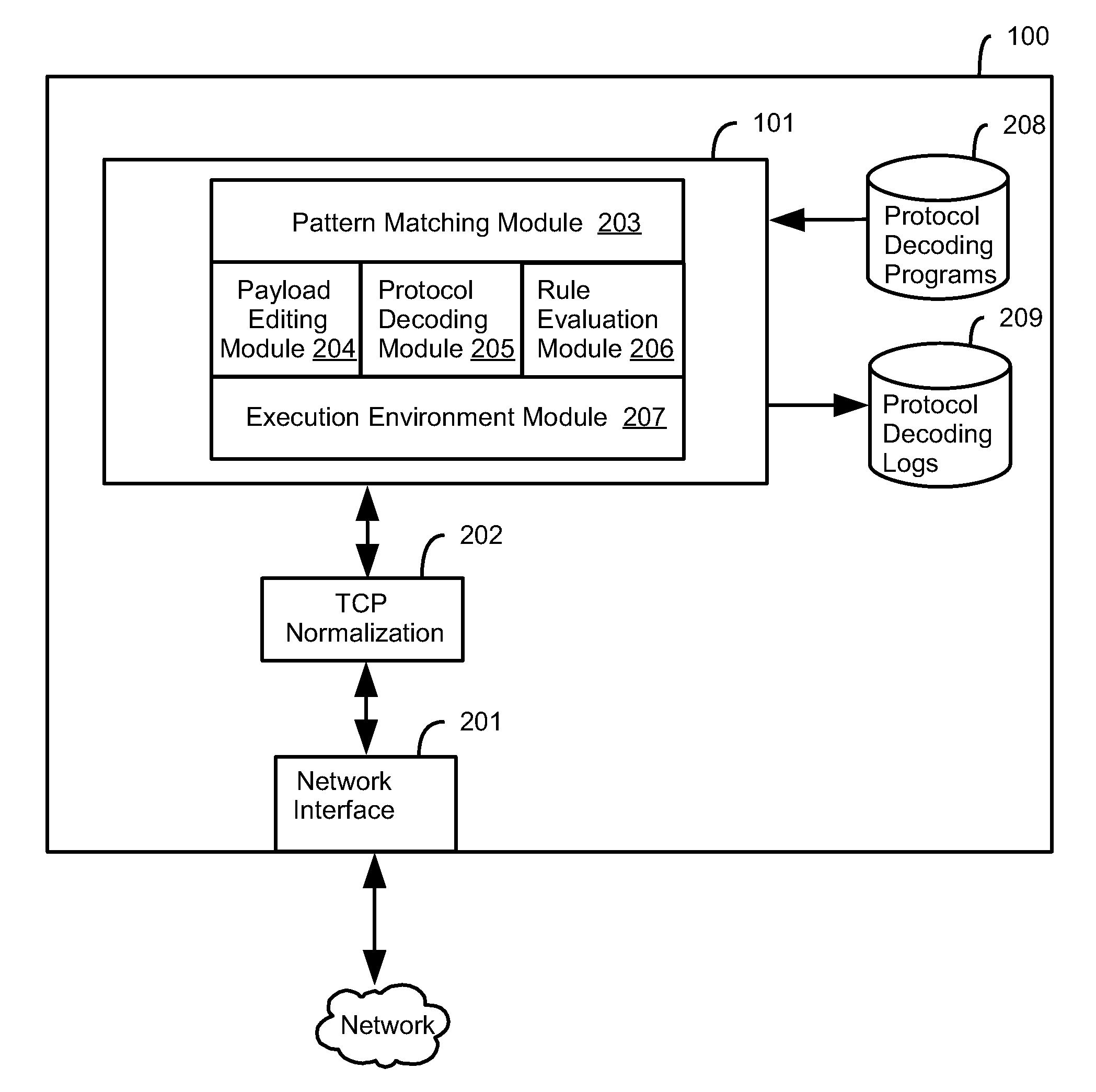
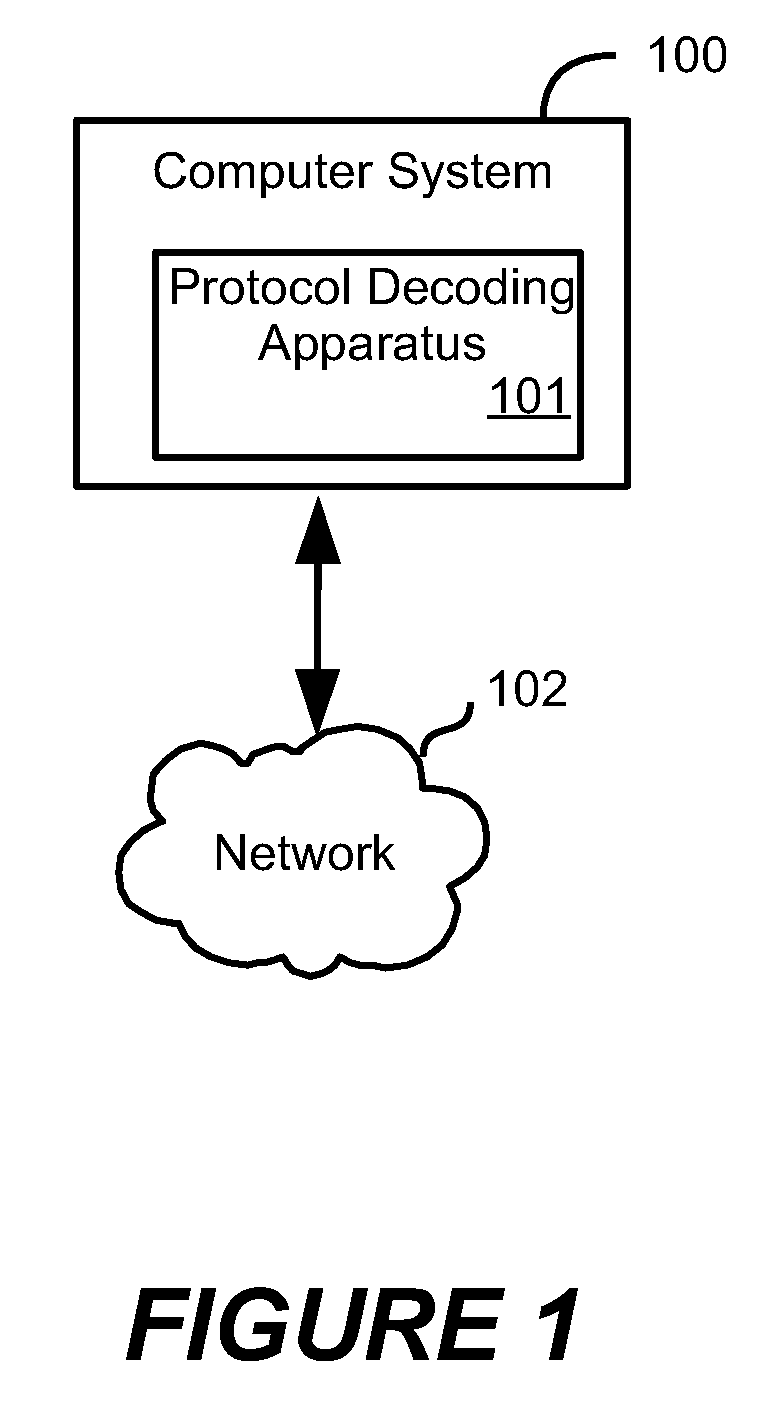
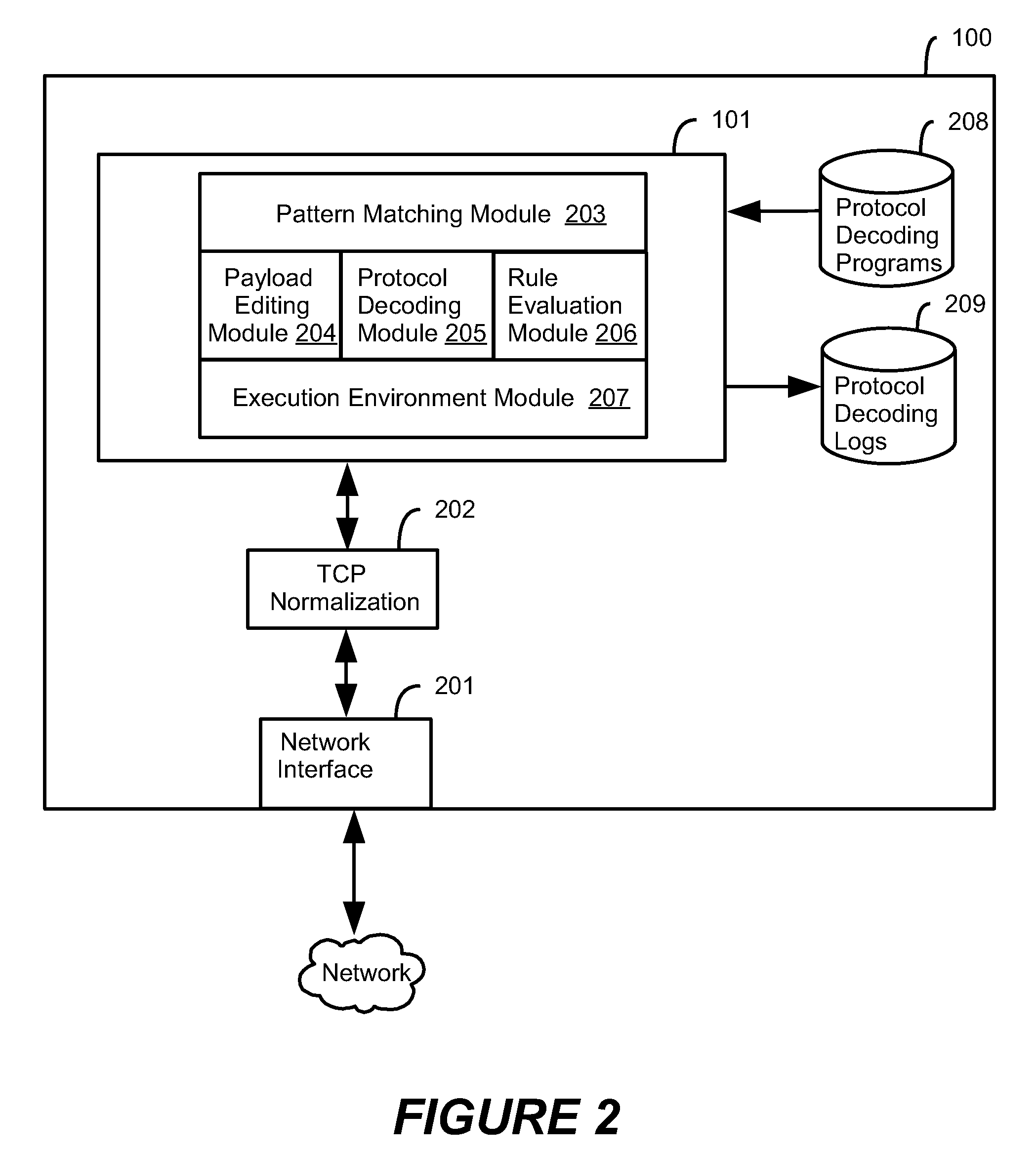
Method and system for dynamic protocol decoding and analysis
ActiveUS20090077619A1Memory loss protectionError detection/correctionComputerized systemApplication software
A method for dynamically decoding protocol data on a computer system is provided using a protocol decoder, which inspects and analyzes protocol data received by the computer system. A protocol decoding program controls the decoding and analysis process. The method may be used by an intrusion prevention system to identify anomalous protocol data that may cause harm to applications receiving the data.
Owner:TREND MICRO INC
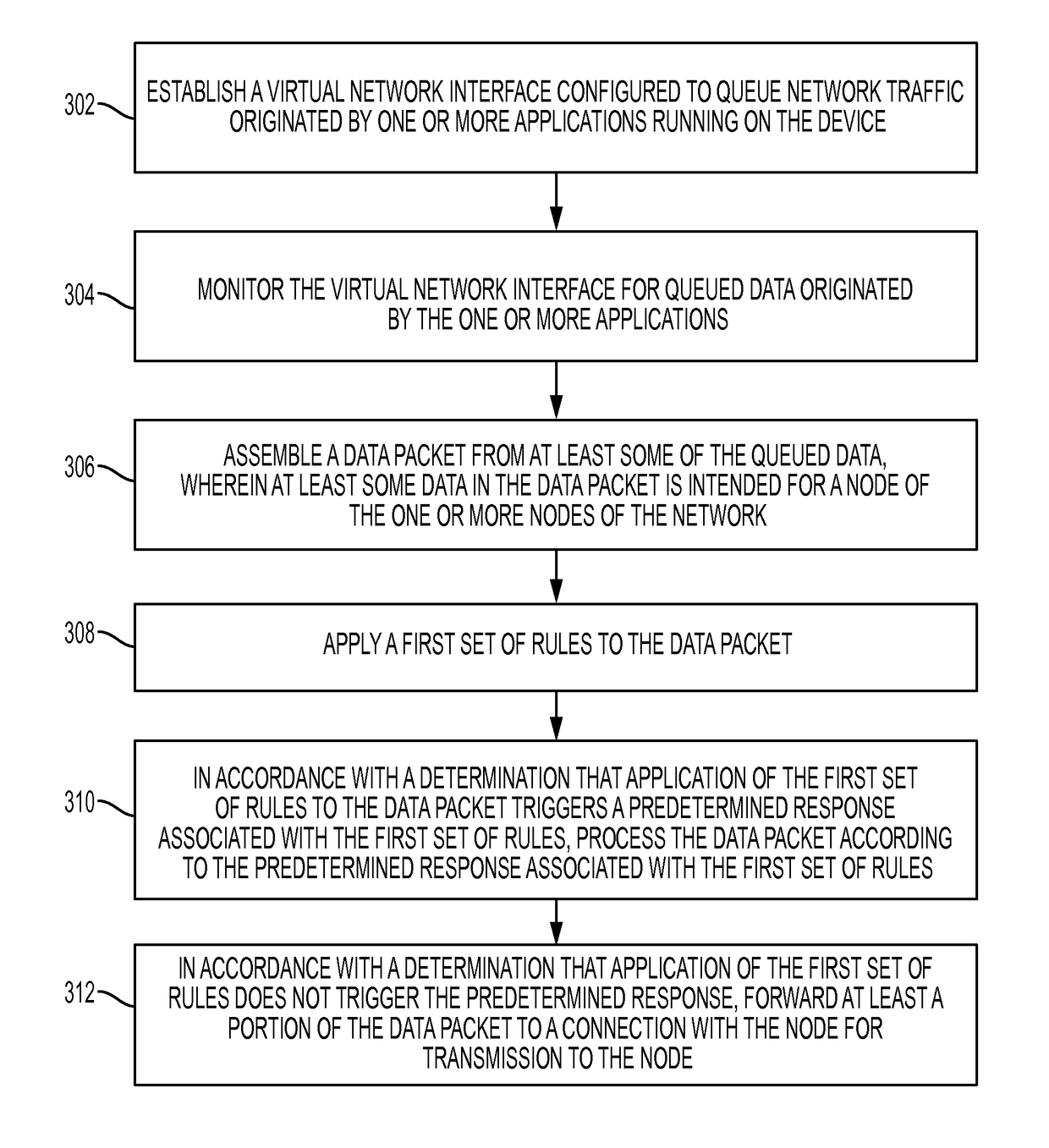
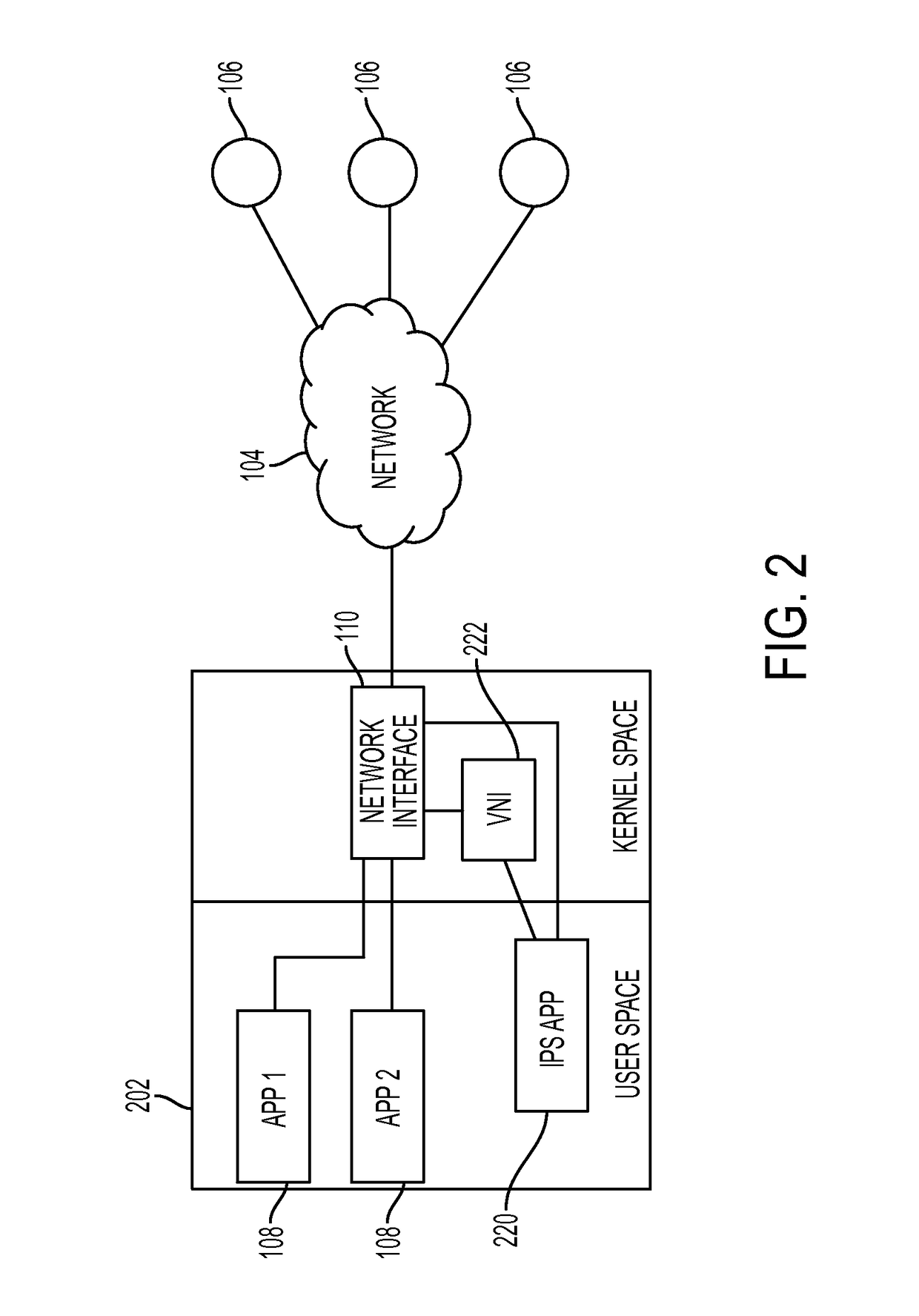
Mobile device-based intrusion prevention system
ActiveUS20170093891A1Data switching networksWireless communicationTraffic capacityApplication software
A method for managing network traffic at a portable electronic device connected to a network that includes establishing a virtual network interface to queue network traffic originated by applications running on the device, monitoring the virtual network interface for queued data, assembling a data packet from the queued data, wherein at least some data in the data packet is intended for a node of the network, applying a first set of rules to the data packet, in accordance with a determination that application of the first set of rules triggers a predetermined response associated with the first set of rules, processing the data packet according to the predetermined response, and in accordance with a determination that application of the first set of rules does not trigger the predetermined response, forwarding at least a portion of the data packet to a connection with the node for transmission to the node.
Owner:MITRE SPORTS INT LTD
Preventive intrusion device and method for mobile devices
ActiveUS20140181972A1Improve securityPrevent hackingMemory loss protectionUnauthorized memory use protectionTraffic capacityNetwork packet
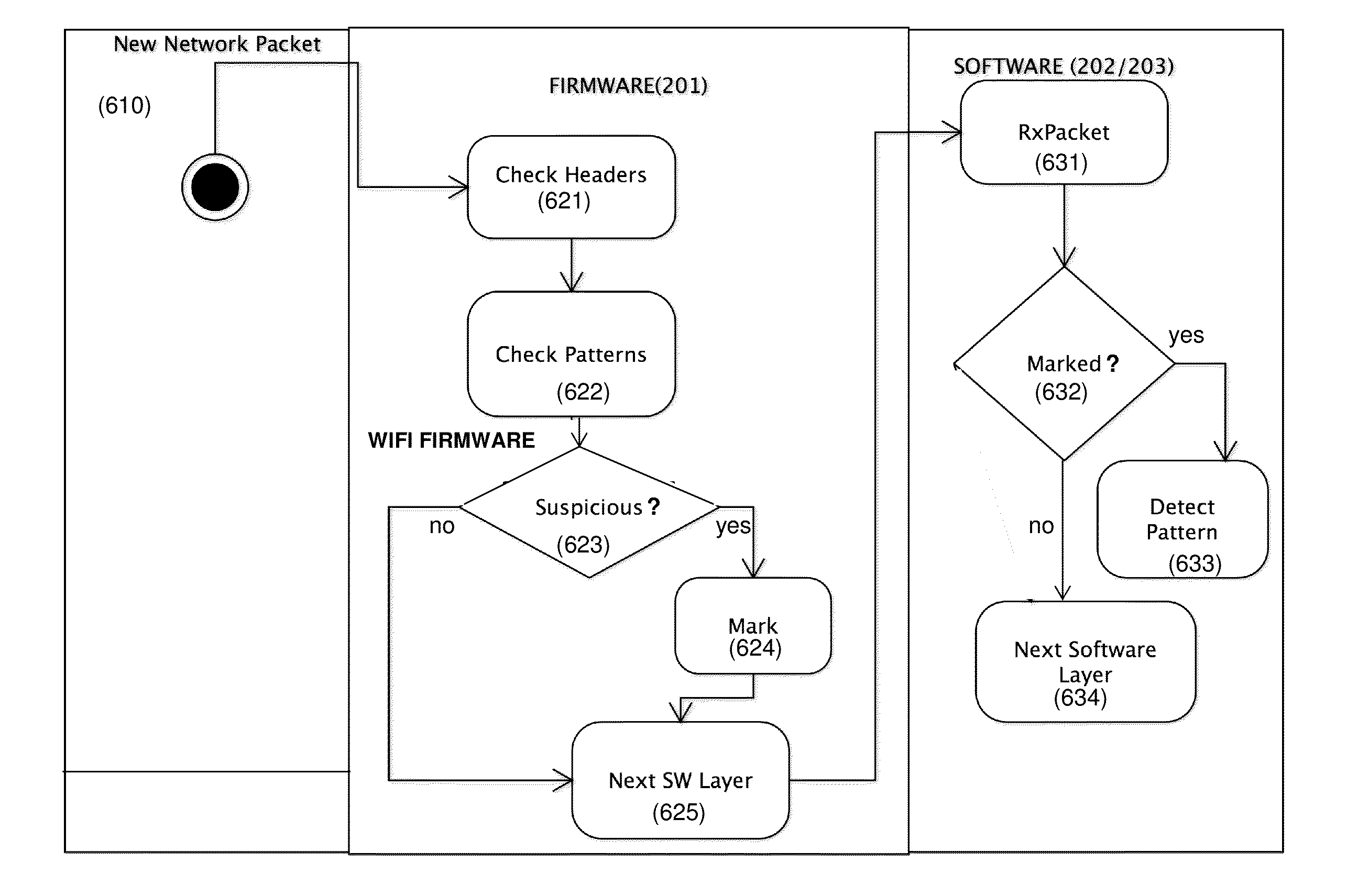
A method for providing an intrusion prevention system to prevent hacking into files located on enterprise users' endpoint devices functioning as mobile computing platforms. The method includes filtering low-level network packets for each of a plurality of received network packets, offloading the received packets to an inspecting processing module and marking suspicious packets based on at least one of a header and pattern of each of said received packets. The method also includes taking preventive measures by the system to ensure protection of the device and network, taking active steps by the system to block suspicious traffic and disconnecting the current connection by the system, when it detects suspicious traffic.
Owner:ZIMPERIUM INC
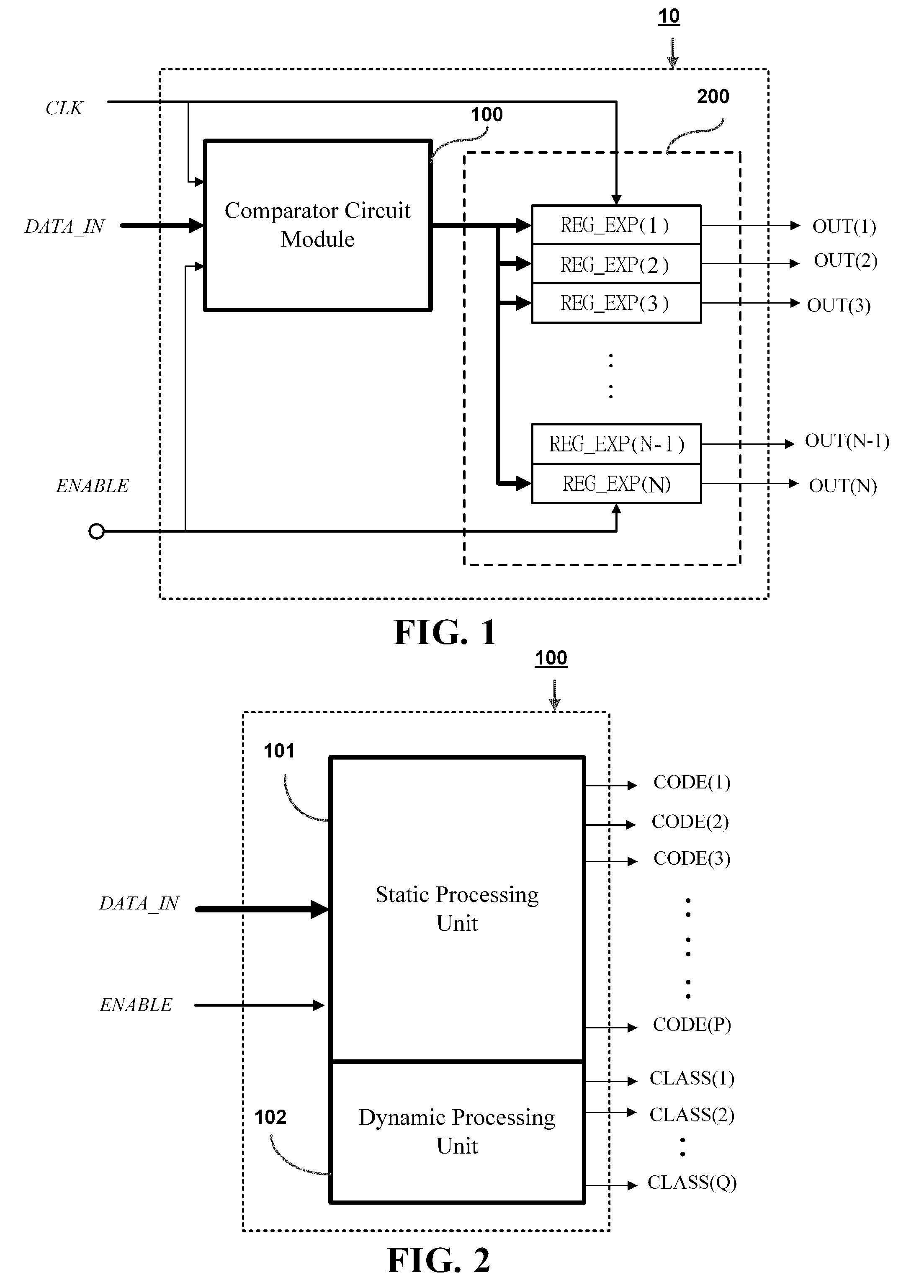
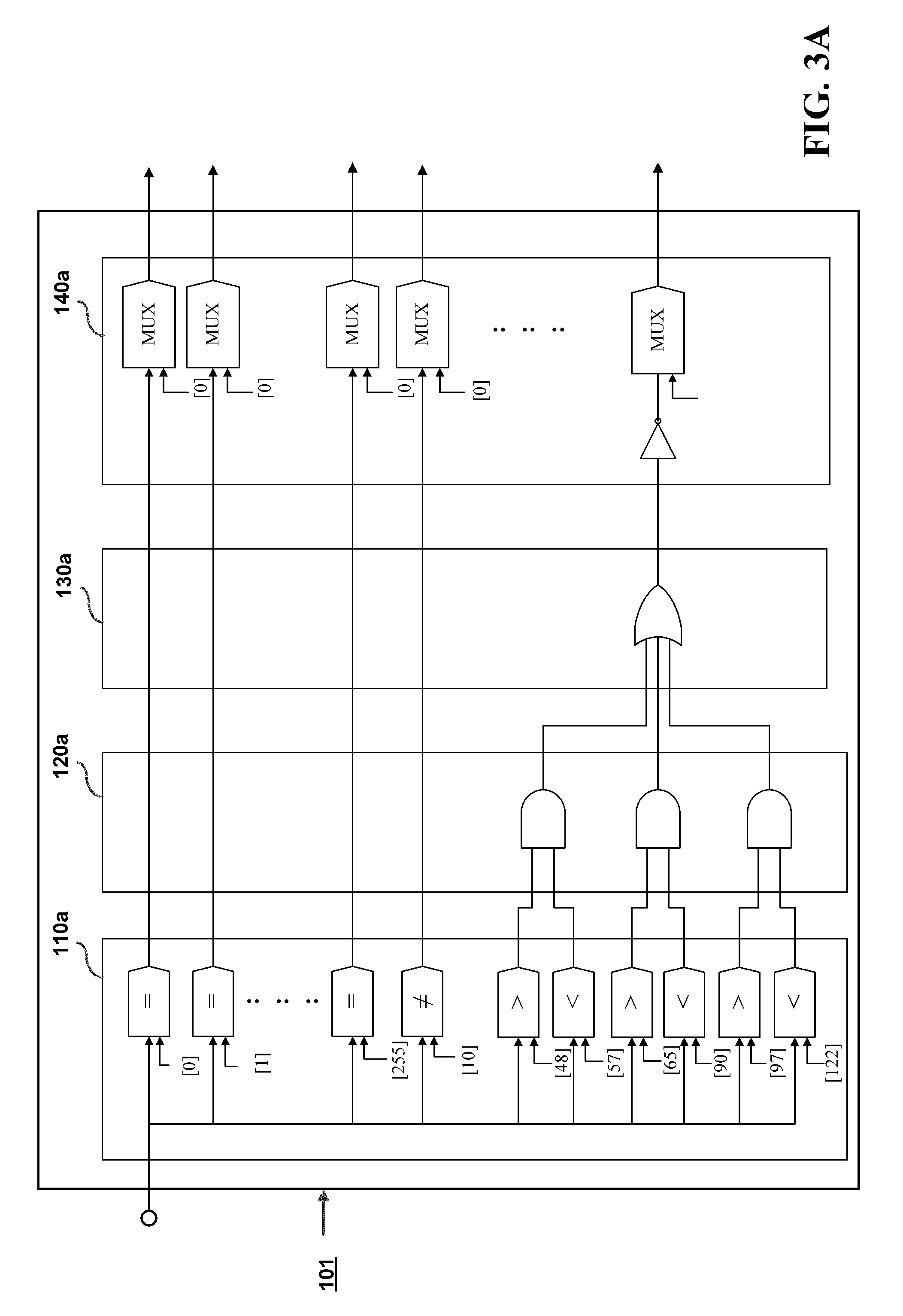
Regular expession pattern matching circuit based on a pipeline architecture
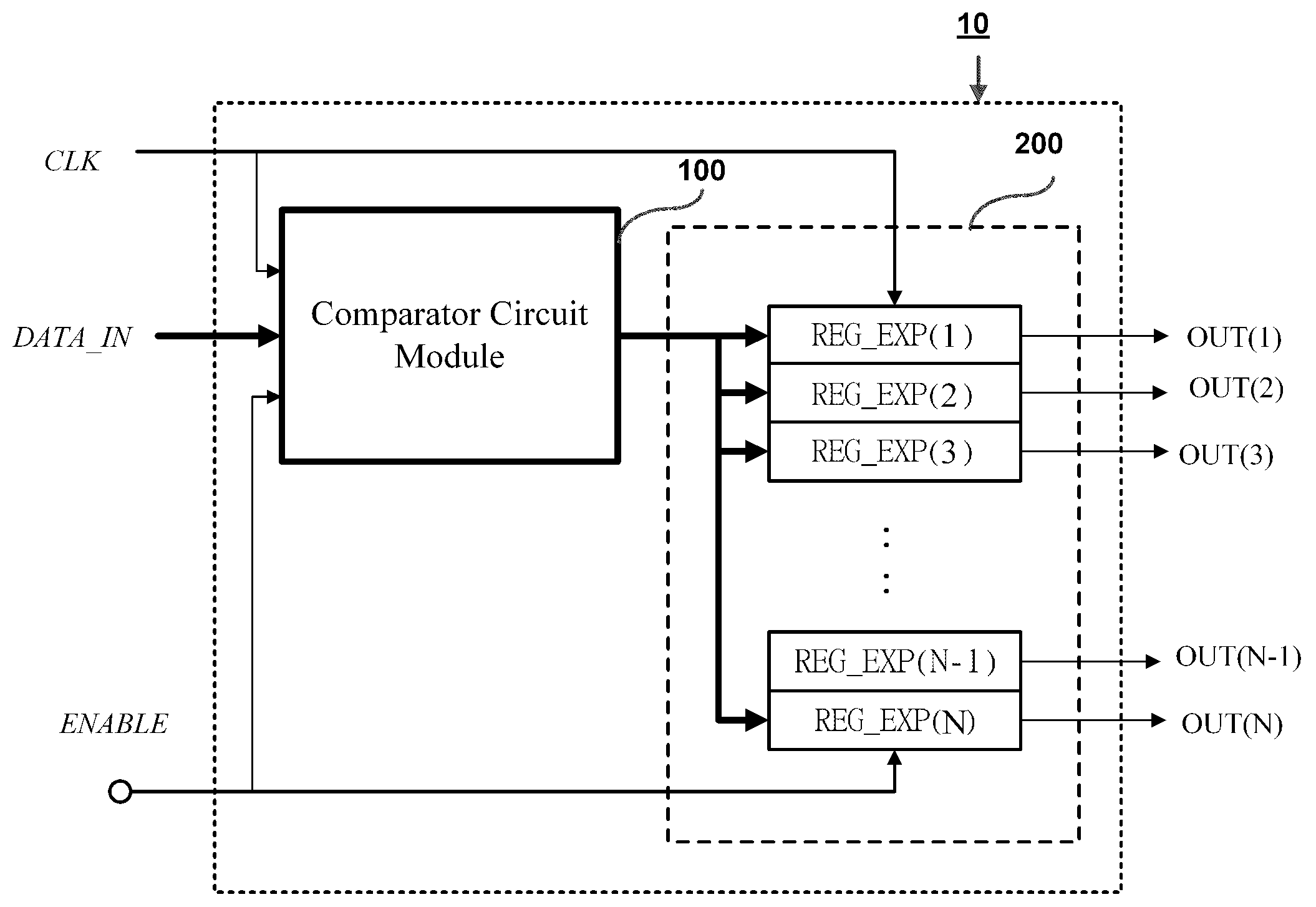
InactiveUS20100158394A1Improve processing speedIncrease speedDigital data information retrievalCharacter and pattern recognitionData packComputer architecture
A regular expression pattern matching circuit based on a pipeline architecture is proposed, which is designed for integration to a data processing system, such as a computer platform, a firewall, or a network intrusion detention system (NIDS), for checking whether an input code sequence (such as a network data packet) is matched to specific patterns predefined by regular expressions. The proposed circuit architecture includes an incremental improvement on an old combination of a comparator circuit module and an NDFA (non-deterministic finite-state automata) circuit module, where the incremental improvement comprises a data signal delay circuit module installed to the comparator circuit module and an enable signal delay circuit module installed to the NDFA circuit module to thereby constitute a multi-sage pipeline architecture that allows a faster processing speed than the prior art.
Owner:NAT TAIWAN UNIV
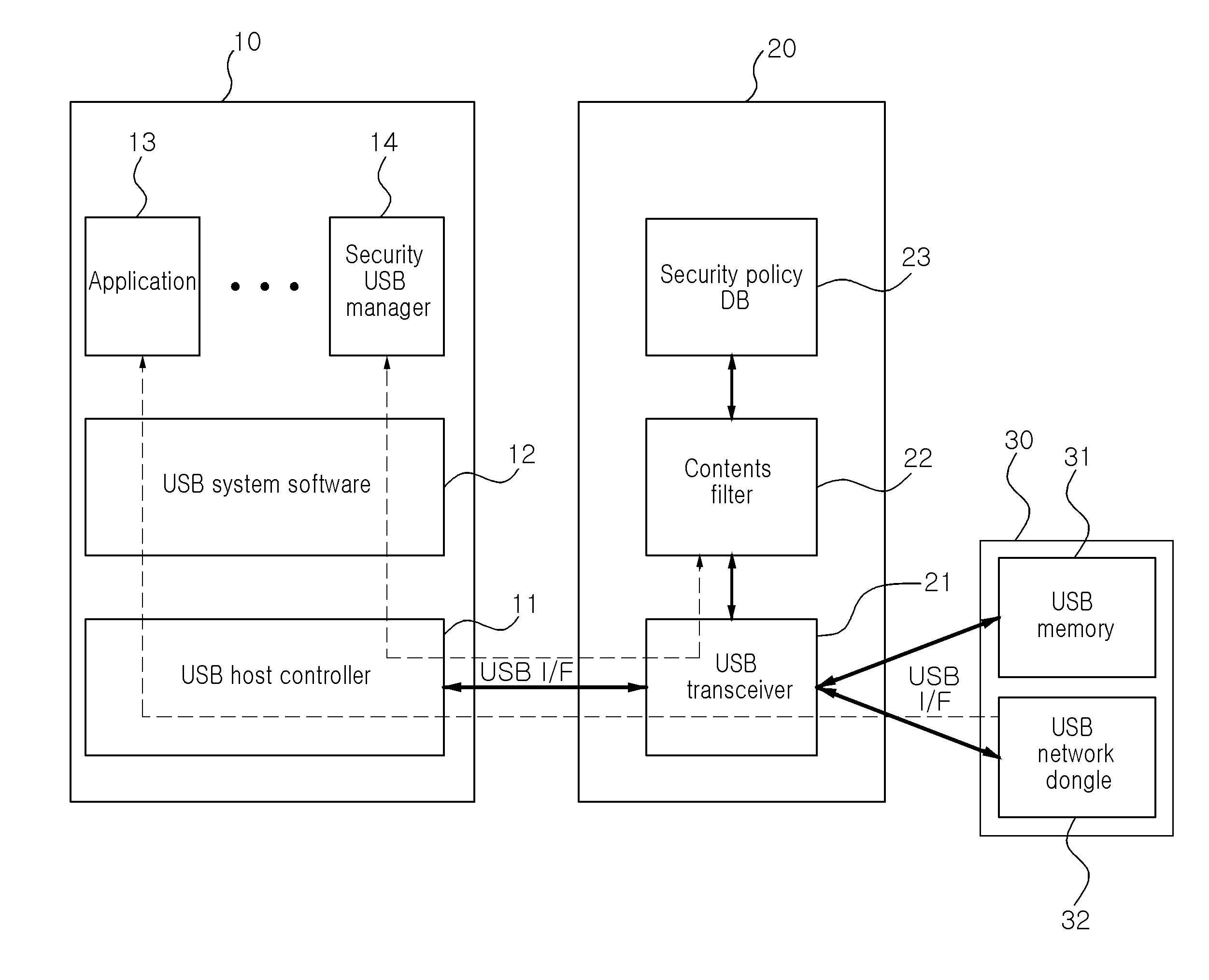
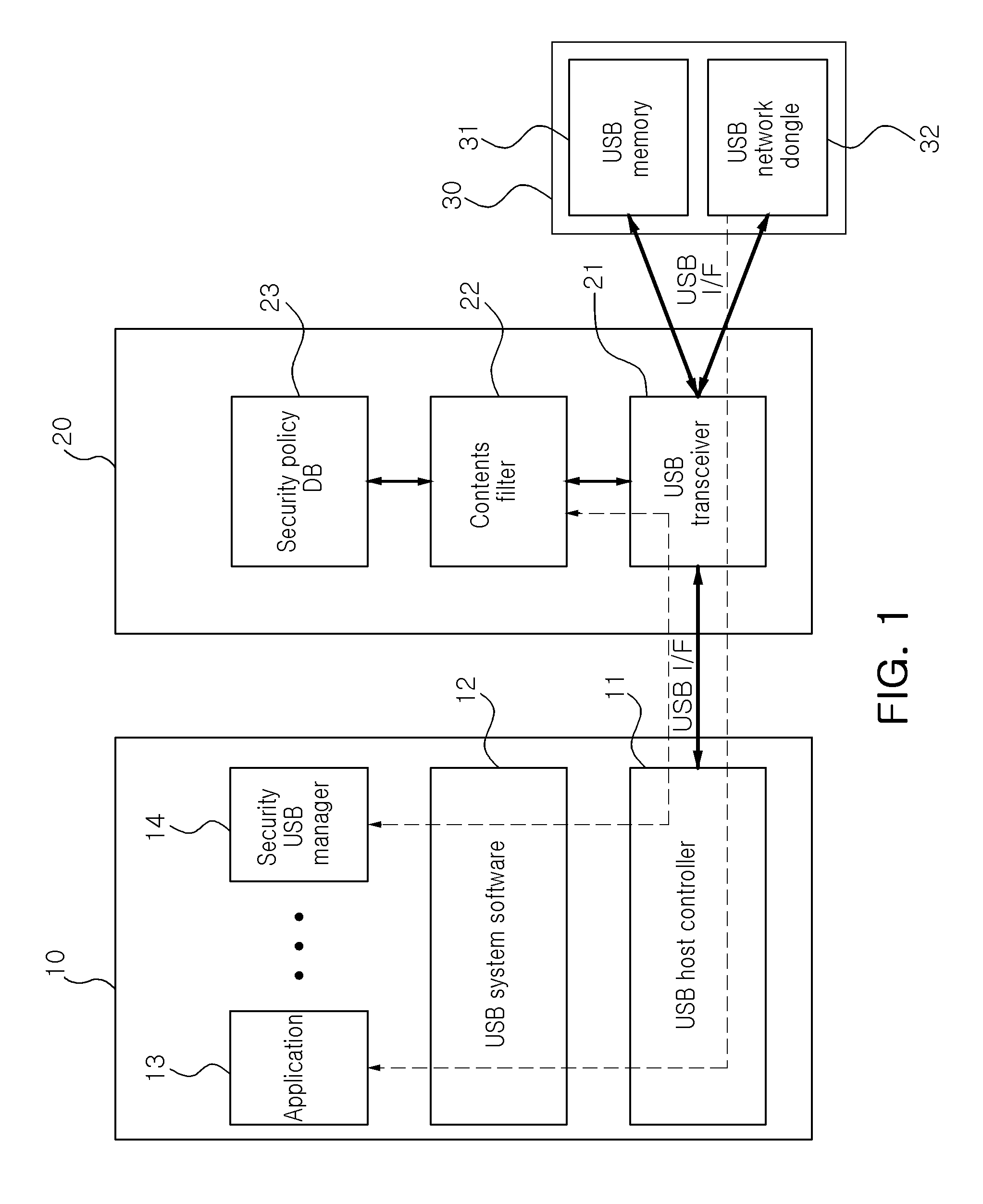
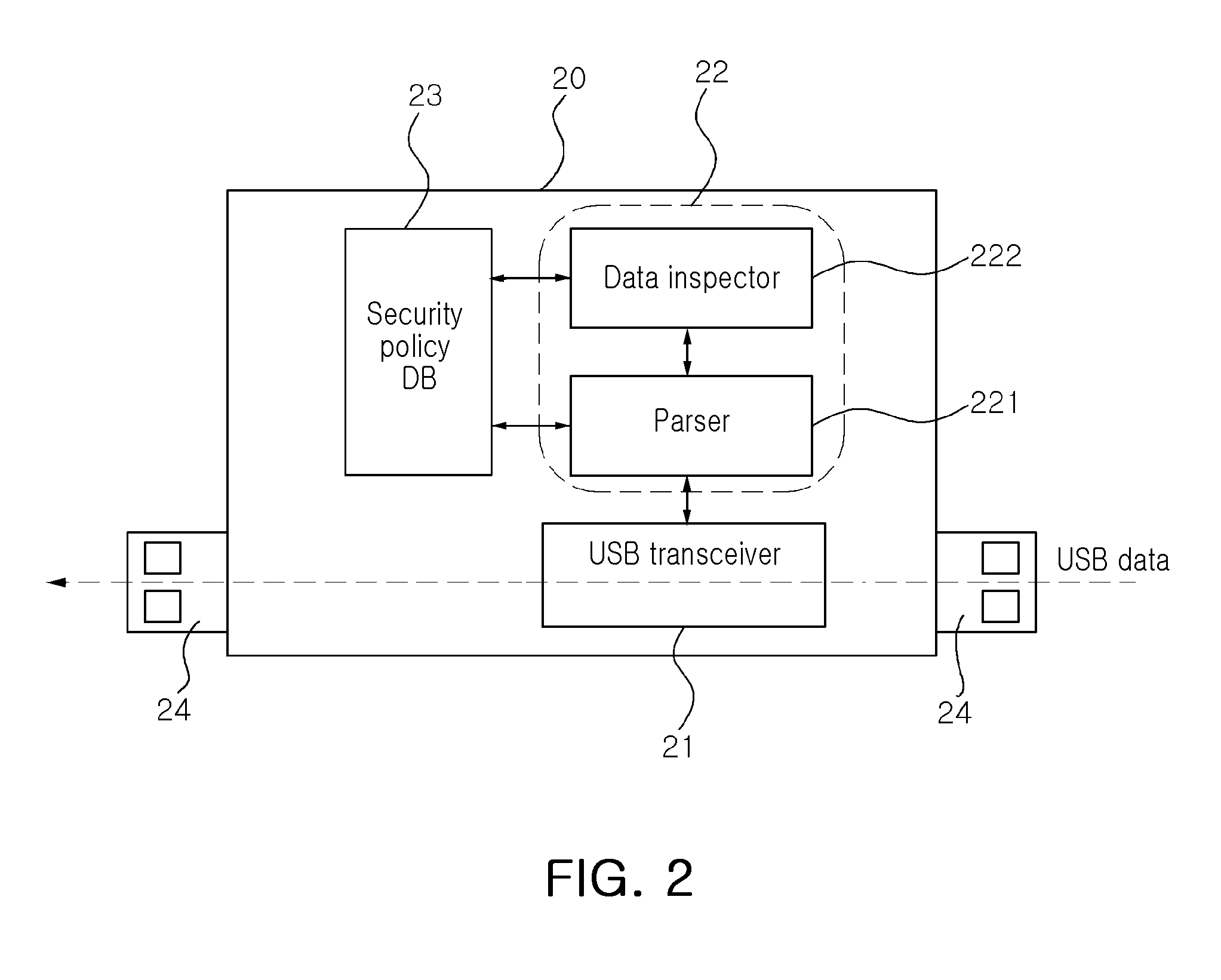
USB connector and intrusion prevention system using the same
InactiveUS20110088093A1Minimizing host terminal resource consumptionHinders its propagationMemory loss protectionError detection/correctionResource consumptionEngineering
A security USB connector implements an intrusion prevention function preventing the propagation of malicious codes to a host terminal from a USB device while minimizing host terminal resource consumption, and an intrusion prevention system using the same are disclosed. A security USB connector is positioned between the host terminal supporting a USB host and a USB device, and a security inspection is performed on data transferred from the USB device to the host terminal through the security USB connector. Also, a host terminal without an intrusion prevention function can prevent an intrusion by using the portable security USB connector.
Owner:ELECTRONICS & TELECOMM RES INST
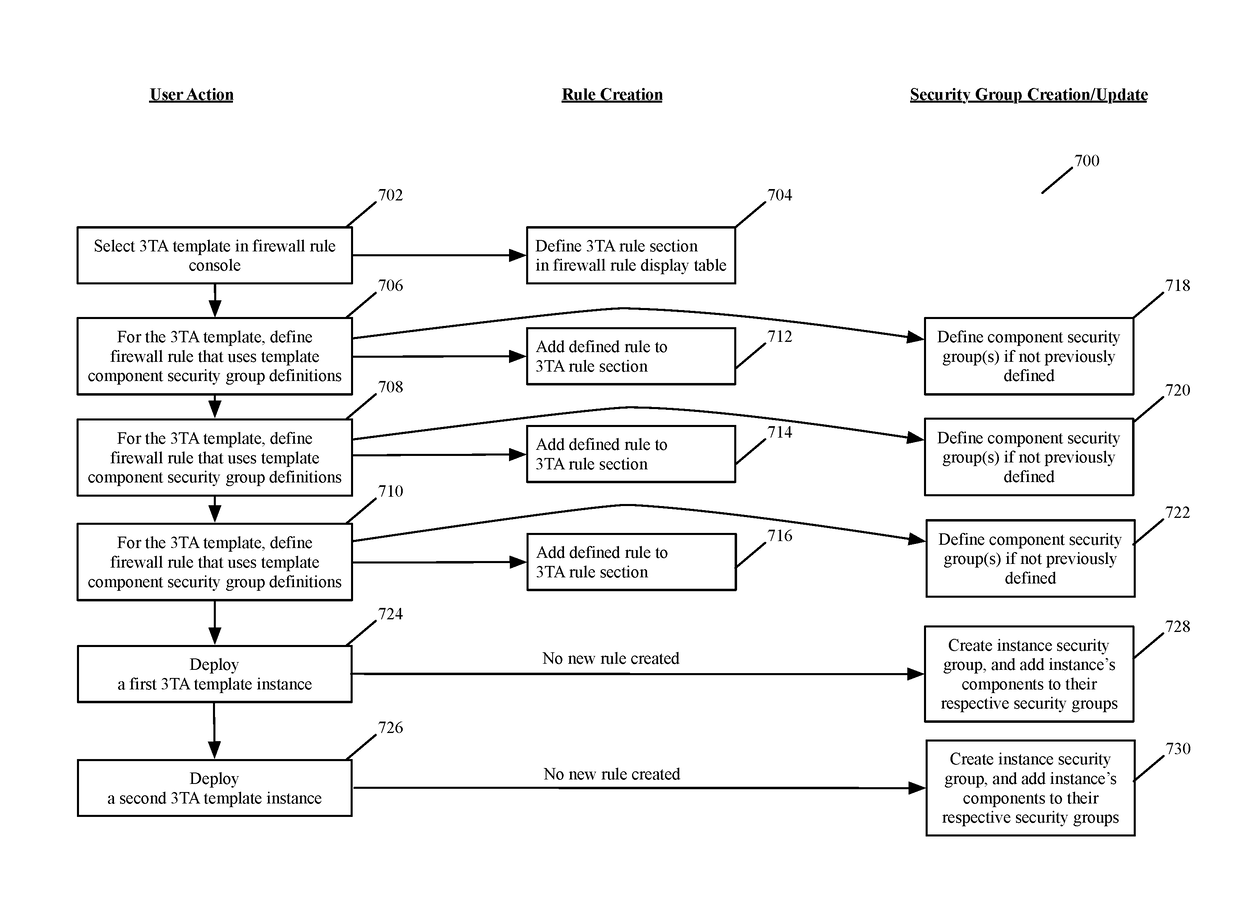
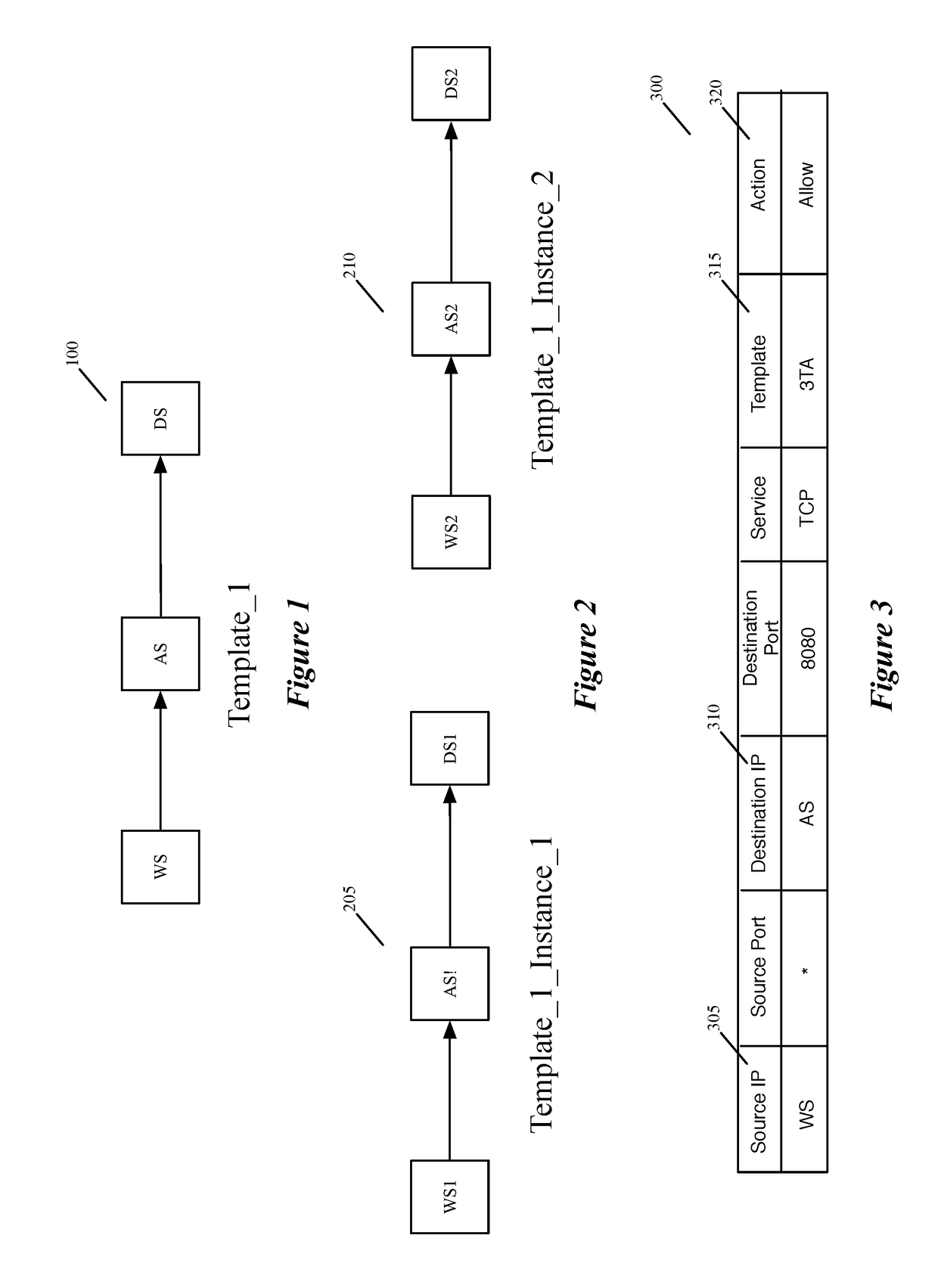
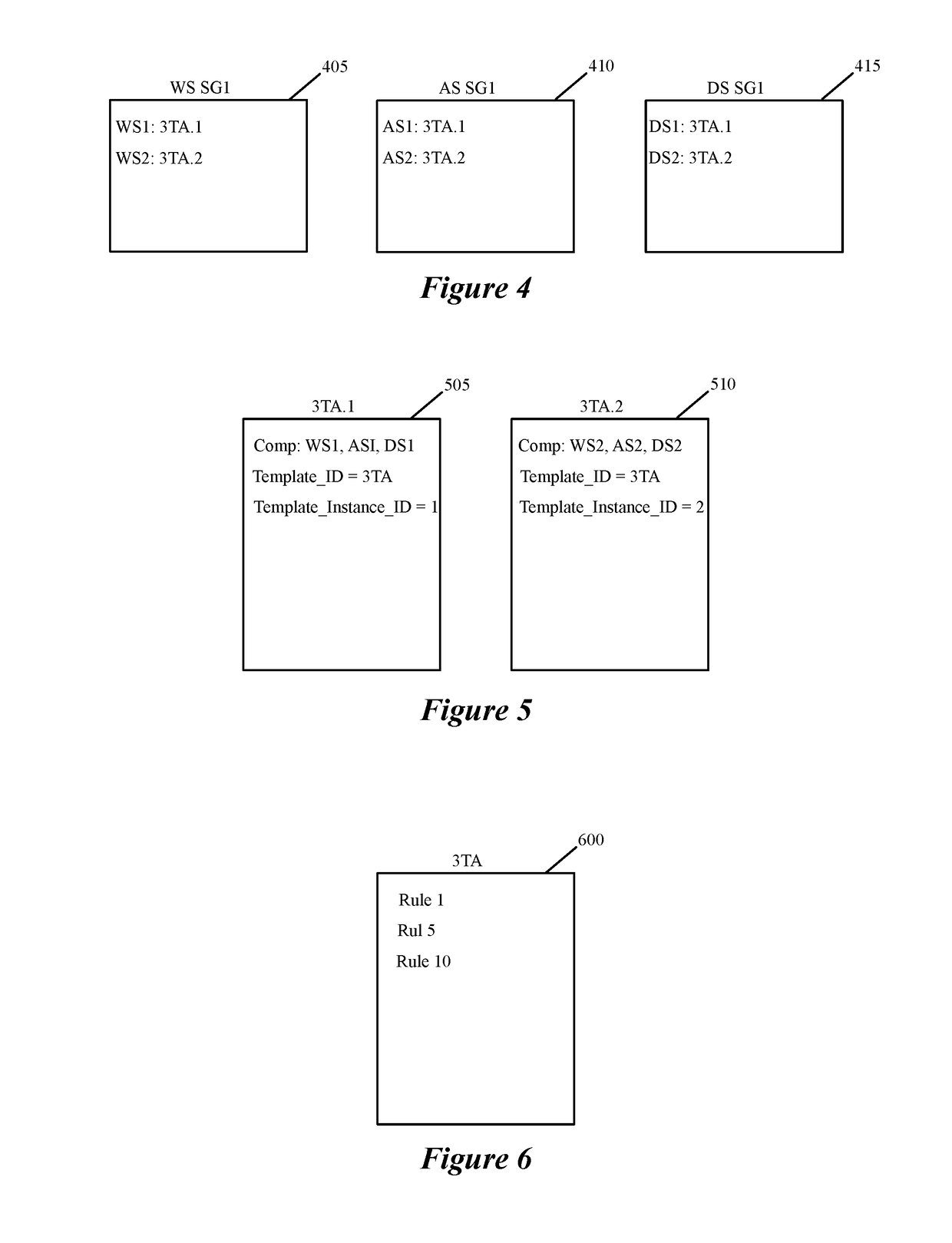
Service rule console for creating, viewing and updating template based service rules
Some embodiments of the invention introduce cloud template awareness in the service policy framework. Some embodiments provide one or more service rule processing engines that natively support (1) template-specific dynamic groups and template-specific rules, and (2) dynamic security tag concepts. A service rule processing engine of some embodiments natively supports template-specific dynamic groups and rules as it can directly process service rules that are defined in terms of dynamic component groups, template identifiers, template instance identifiers, and / or template match criteria. Examples of such services can include any kind of middlebox services, such as firewalls, load balancers, network address translators, intrusion detection systems, intrusion prevention systems, etc.
Owner:NICIRA
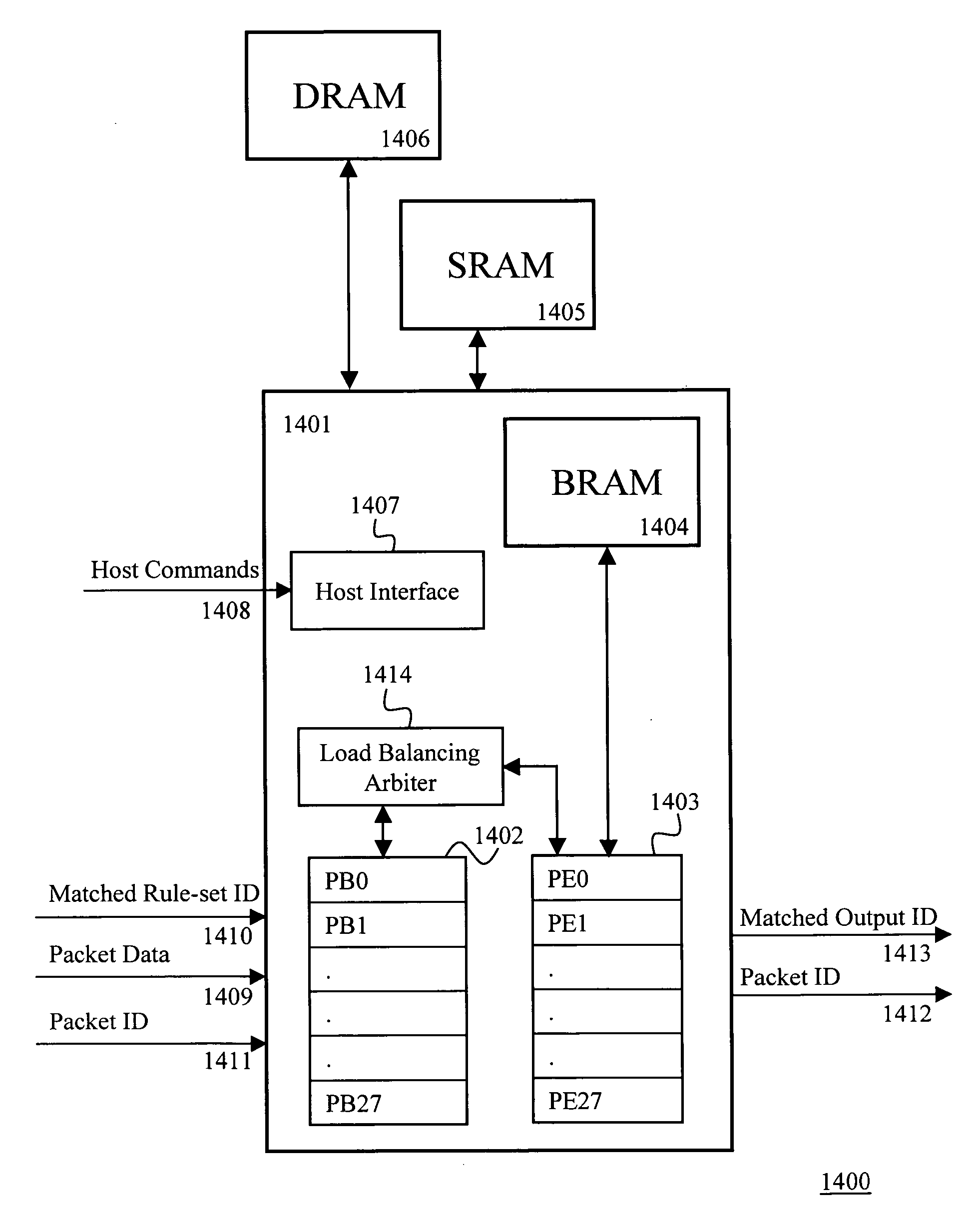
Methods and system for determining performance of filters in a computer intrusion prevention detection system
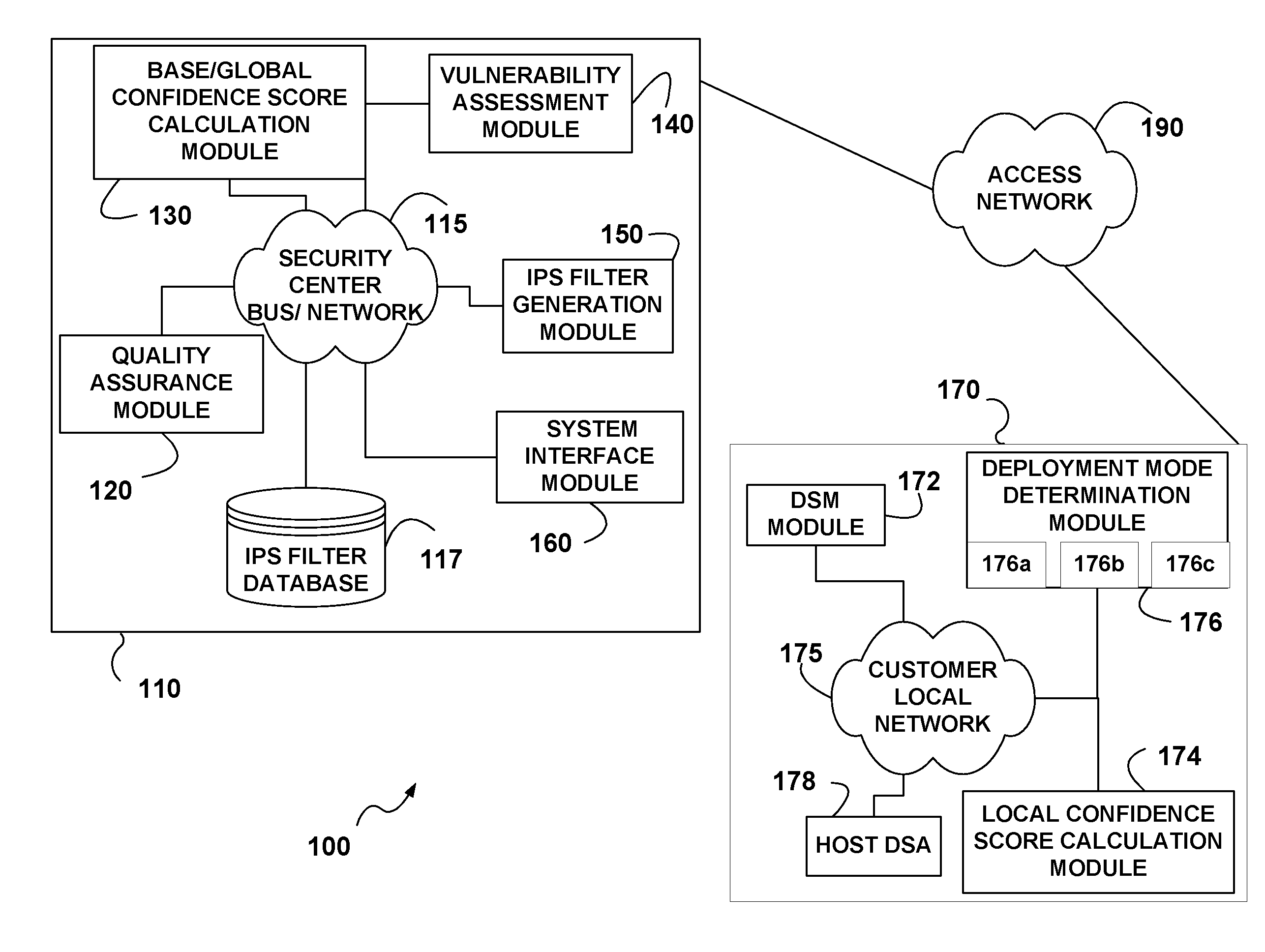
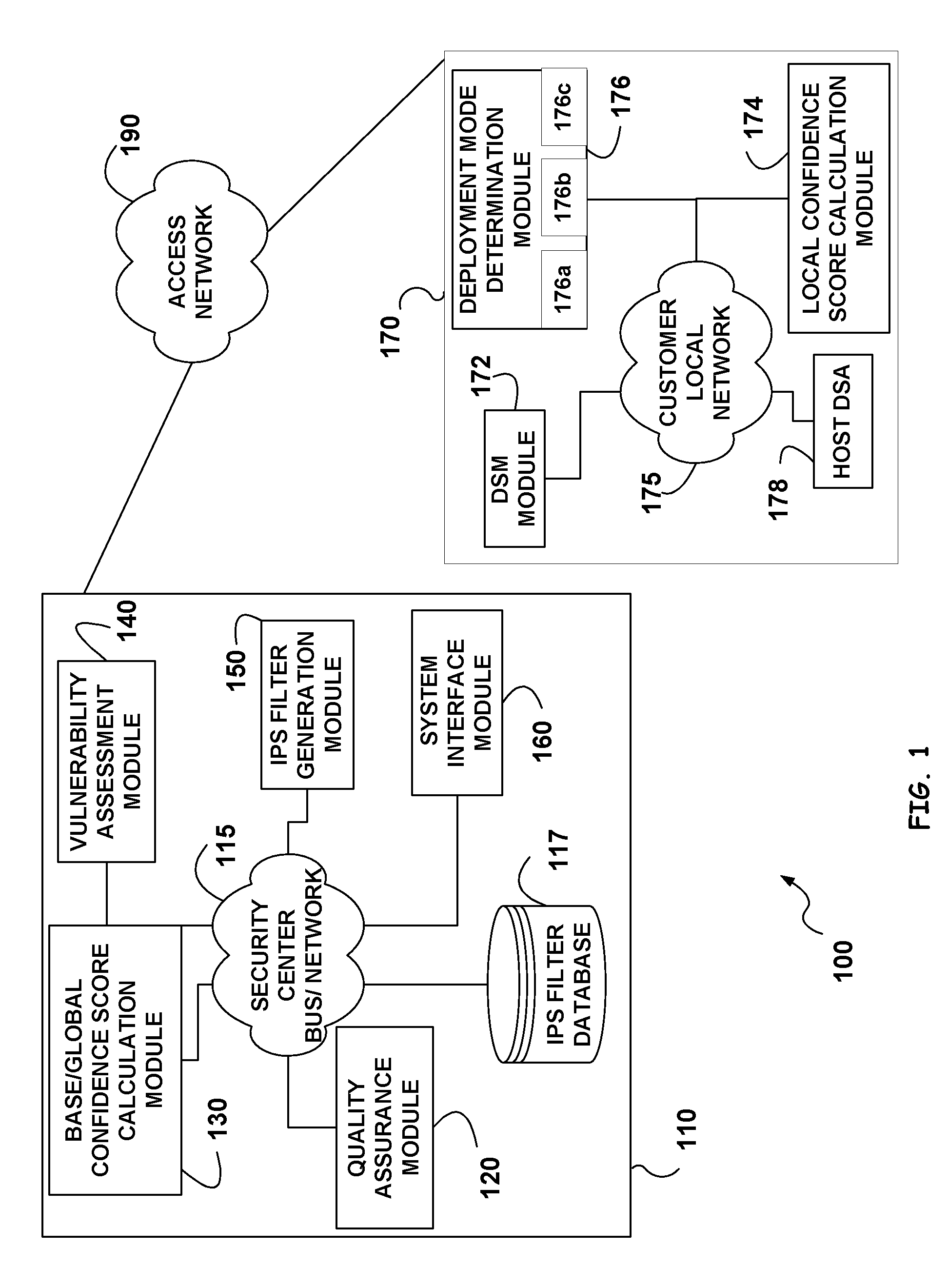
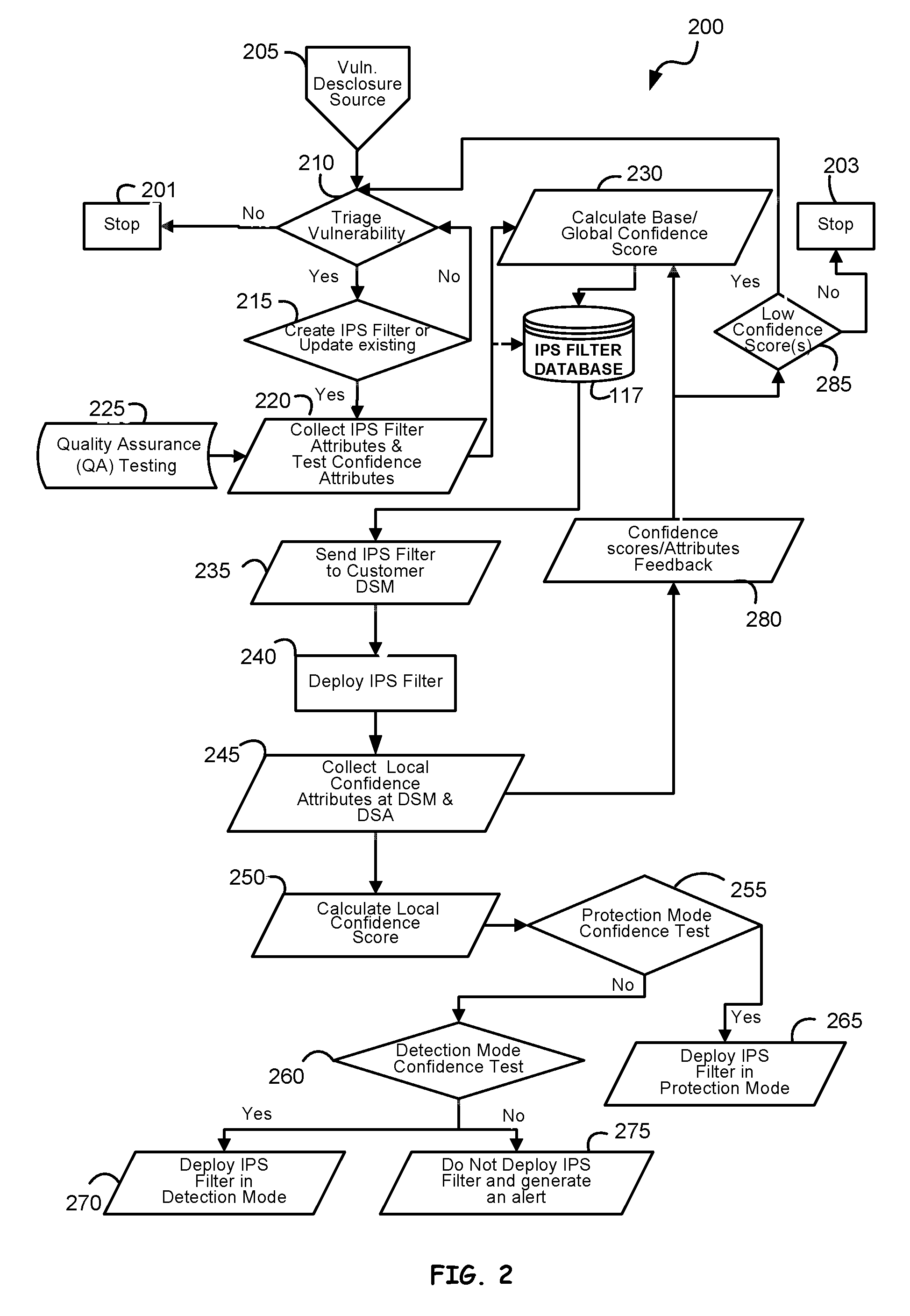
ActiveUS20090172818A1Memory loss protectionError detection/correctionConfidence factorIntrusion prevention system
An intrusion prevention / detection system filter (IPS filter) performance evaluation is provided. The performance evaluation is performed at both the security center and at the customer sites to derive a base confidence score and local confidence scores. Existence of new vulnerability is disclosed and its attributes are used in the generation of new IPS filter or updates. The generated IPS filter is first tested to determine its base confidence score from test confidence attributes prior to deploying it to a customer site. A deep security manager and deep security agent, at the customer site, collect local confidence attributes that are used for determining the local confidence score. The local confidence score and the base confidence score are aggregated to form a global confidence score. The local and global confidence scores are then compared to deployment thresholds to determine whether the IPS filter should be deployed in prevention or detection mode or sent back to the security center for improvement.
Owner:TREND MICRO INC
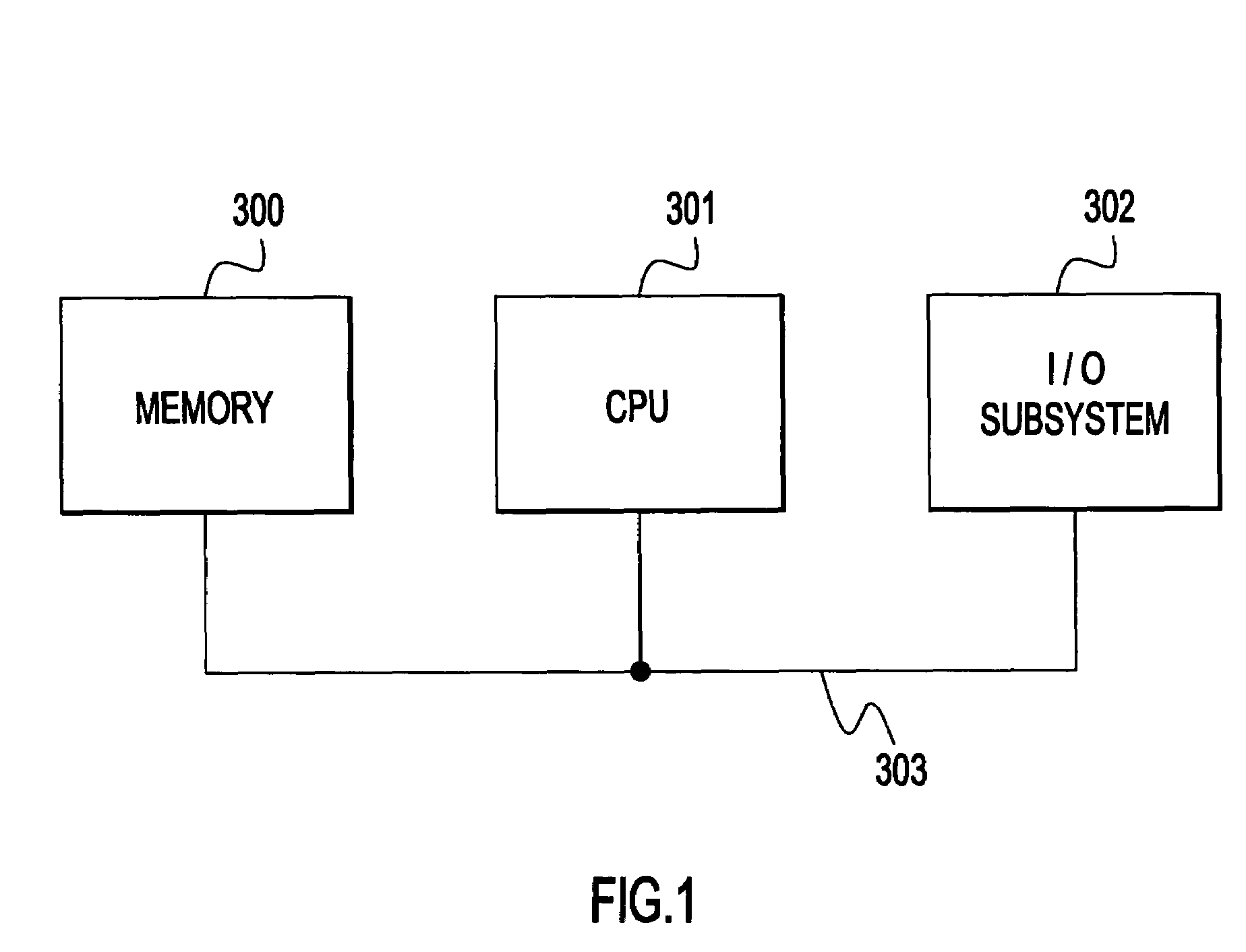
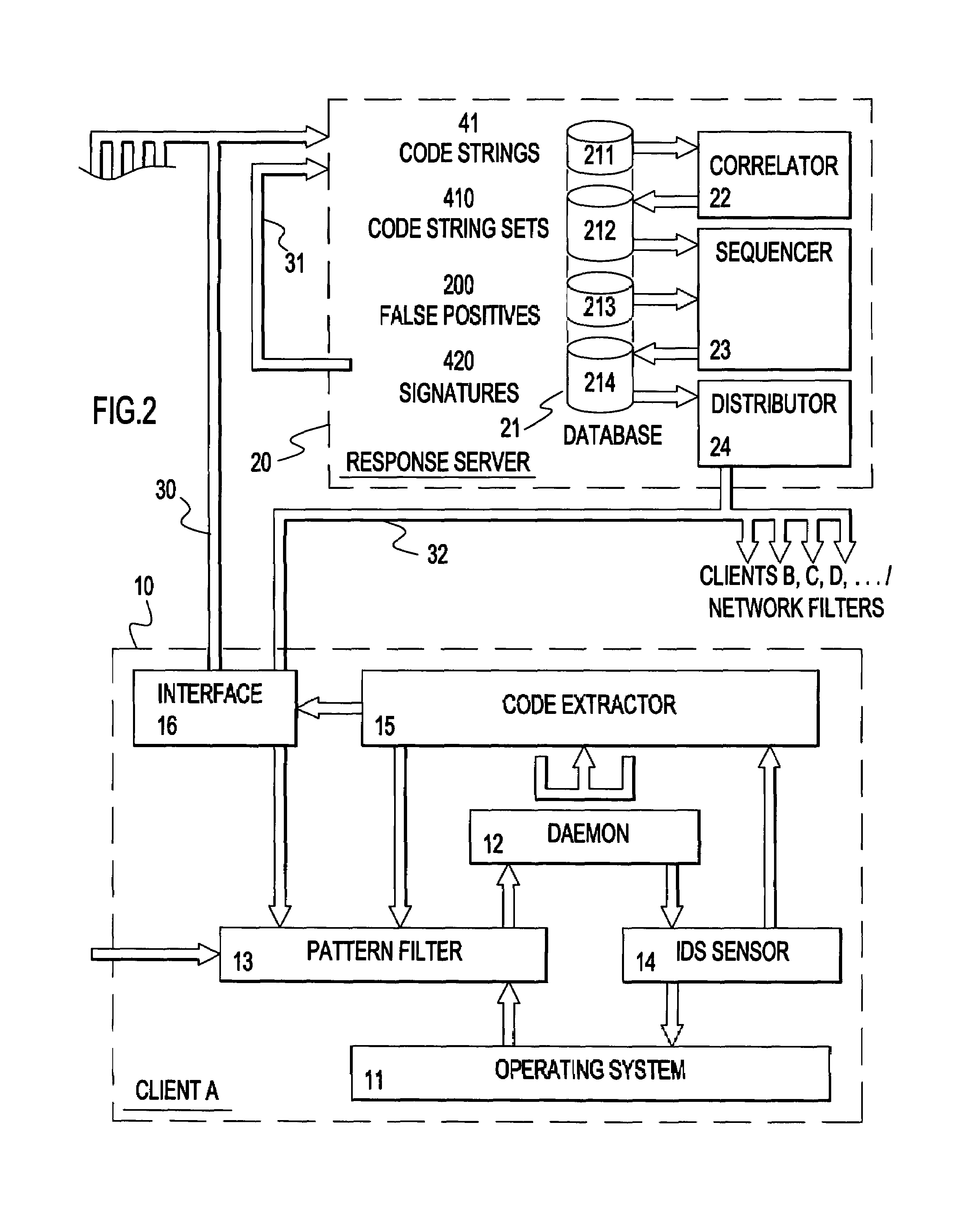
Preventing attacks in a data processing system
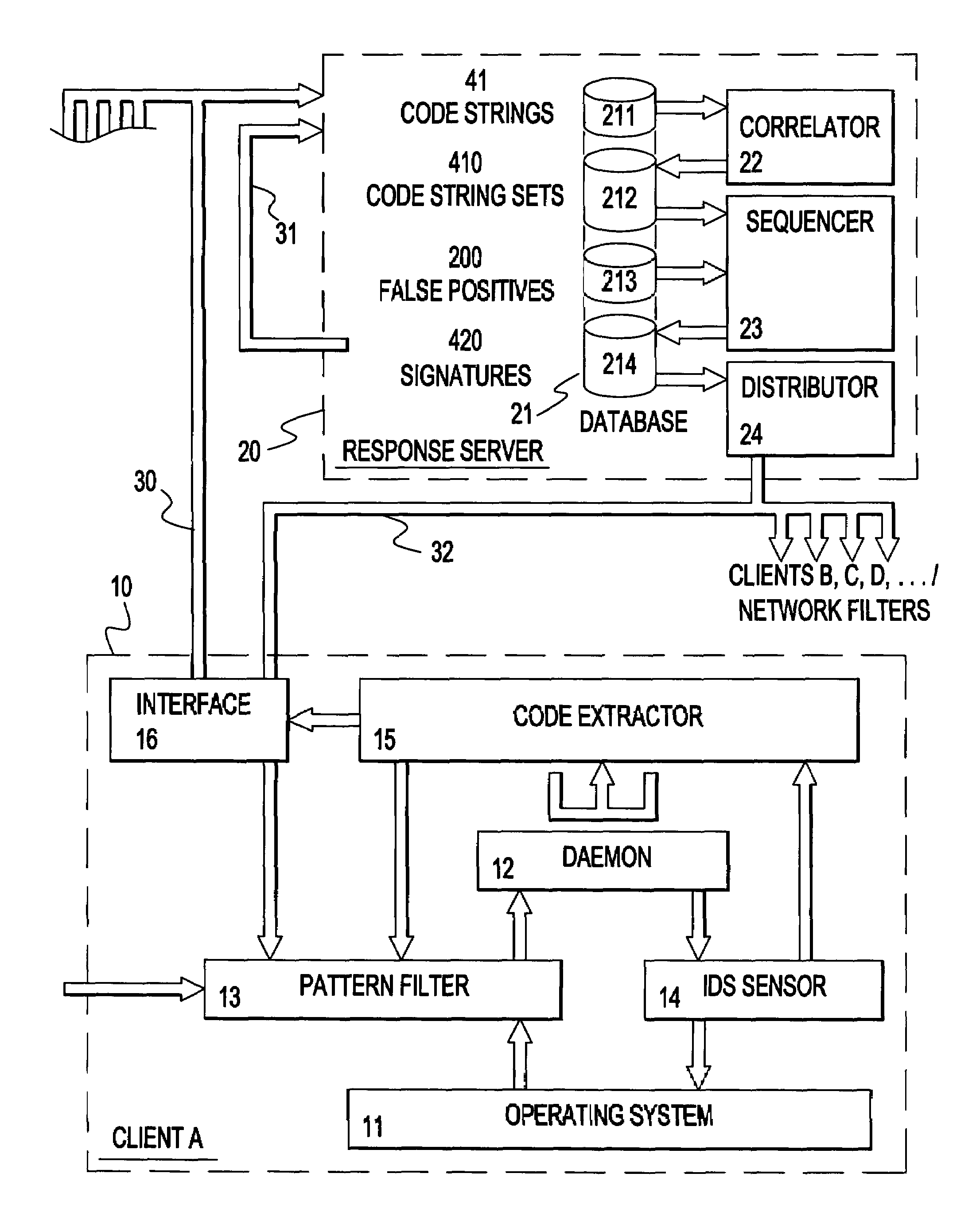
InactiveUS7555777B2Improve protectionLower Level RequirementsMemory loss protectionUnauthorized memory use protectionData processing systemMonitoring system
A method and apparatus for facilitating reduction in successful attacks on a monitored data processing system, such as a host computer. An intrusion detection system comprises a host or application based sensor for detecting code based intrusions with a relatively low false-positive rate. Malicious code strings related to a detected intrusion are identified, extracted and forwarded to a pattern filter located in the monitored data processing system to prevent further intrusions using said malicious code strings. The malicious code strings may be forwarded to a response server for assembling sets of similar malicious code strings for which signatures are generated to permit identification of all malicious code strings contained in a set. The generated signatures are then distributed to monitored and / or monitoring systems of a protected network to prevent further intrusions using the malicious code strings and variations thereof.
Owner:IBM CORP
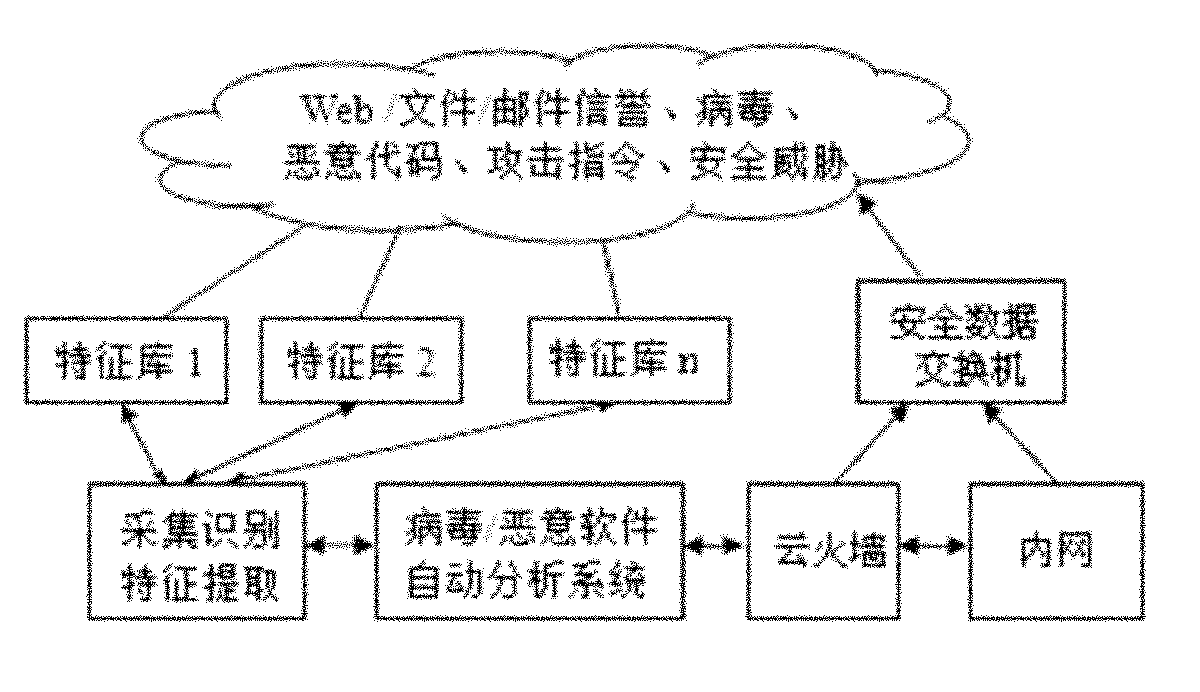
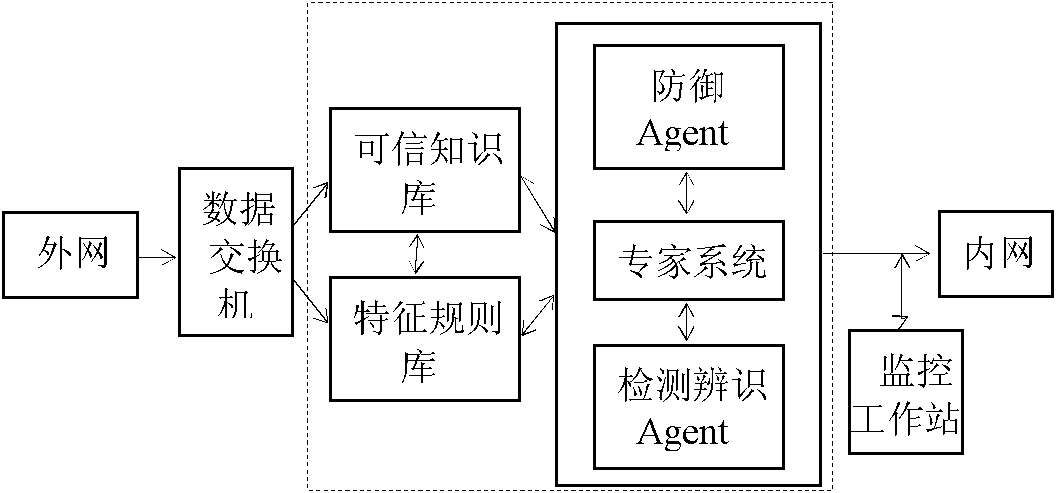
Intelligent NIPS framework based on dynamic cloud/fire wall linkage
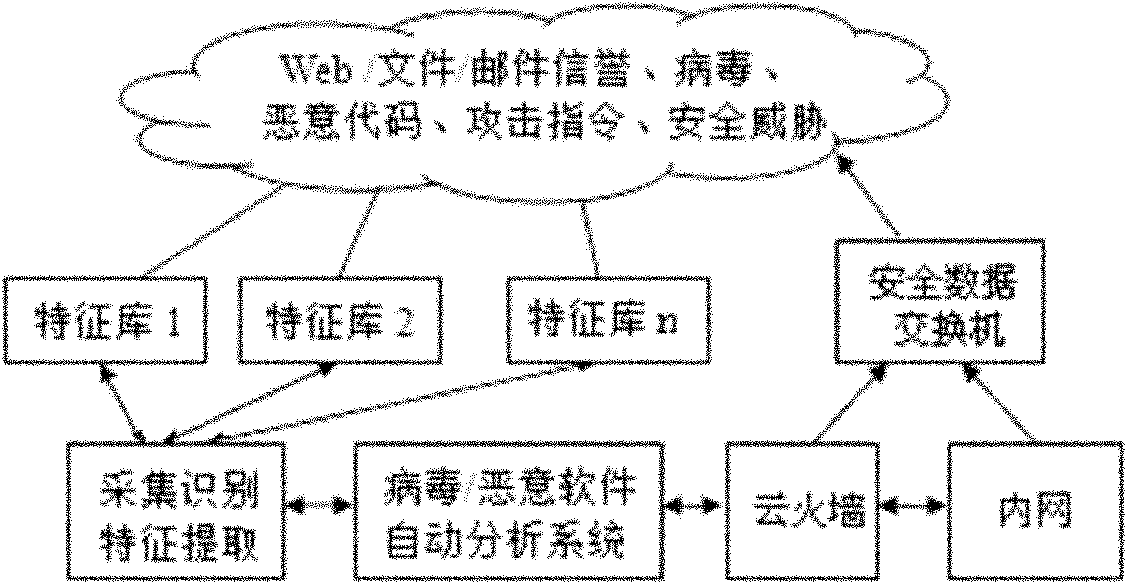
InactiveCN102111420AImprove safety and reliability performanceImprove overall dynamic linkage defense capabilitiesTransmissionLoss rateSmart technology
An NIPS (Network Intrusion Prevention System) adopts the structure that an NIPS framework in linkage with a cloud / fire wall is connected to a cloud security. The cloud security technology, the artificial intelligence technology and the network invasion prevention technology are combined together by adopting a novel design concept and manner. The novel technical characteristics of the cloud security are utilized to combine with the advantages of real-time extraction, interactive coordination and linkage and abnormal information identification of the dynamic cloud / fire wall technology, so that the detection and identification accuracies, the dynamic interactive coordination and linkage performance and the intelligent blocking decision-making performance are improved, false alarm and high alarm loss rate are avoided, and both the key technology and the core problems in integral dynamic defense and detection of the computer network security are well solved, accordingly, the safe reliability and integral dynamic linkage defense capability of the computer network are improved.
Owner:SHANGHAI DIANJI UNIV
Liquid crystal medium and application
InactiveCN104263383AEasy to combineThe absolute value of the negative dielectric anisotropy is largeLiquid crystal compositionsNon-linear opticsDielectric anisotropyActive matrix
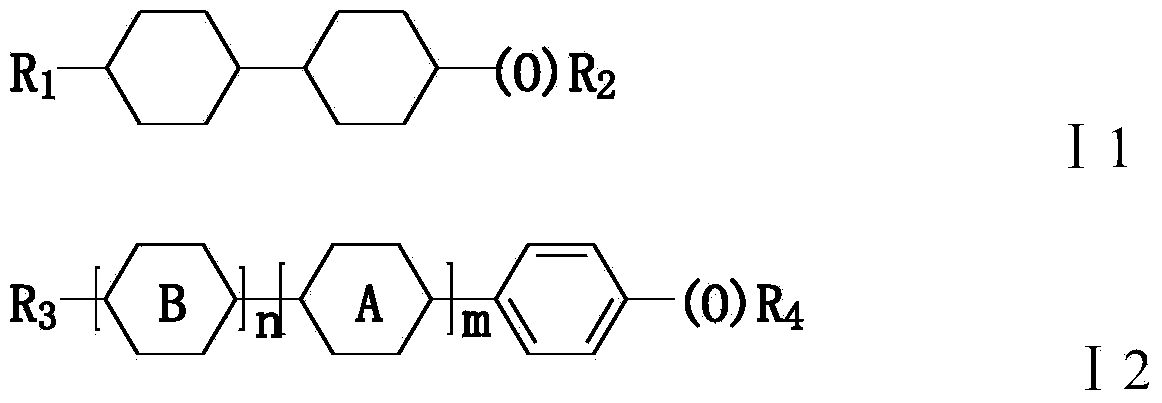
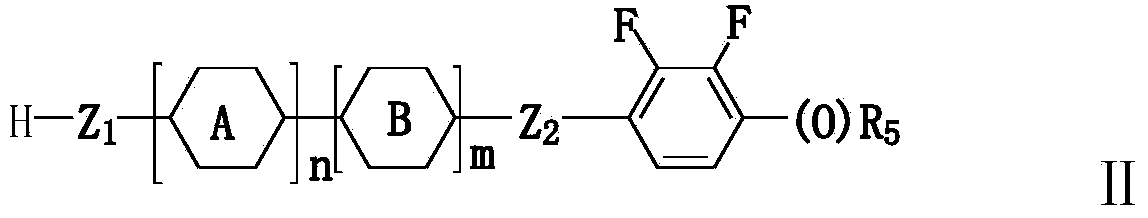
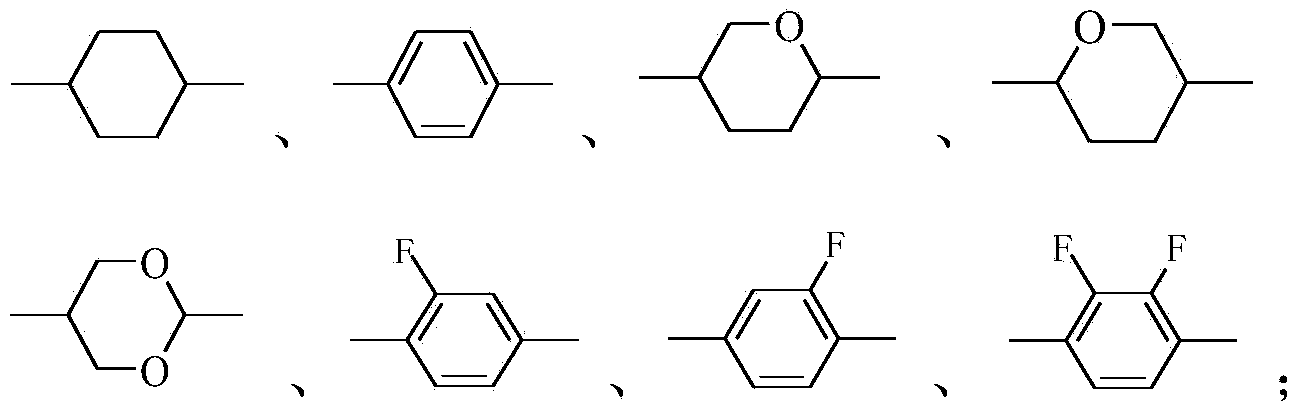
The invention discloses a negative-dielectric anisotropic liquid crystal medium. The liquid crystal medium comprises one or several 1-50wt% of dielectric neutral compounds shown as a general formula I1 or / and a general formula I2, one or several 1-60wt% of dielectric negative compounds shown as a general formula II and one or several 1-80wt% of dielectric negative compounds shown as a general formula III. The optical anisotropy of the liquid crystal medium is in a range of 0.080-0.150. The liquid crystal medium also has relatively lower rotating viscosity, proper negative-dielectric anisotropy and larger K value and can be used for active matrix display elements comprising the liquid crystal medium, such as active matrix displays with ECB (Event Control Block), FFS (Fringe Field Switching) or IPS (Intrusion Prevention System), MVA (Multi-domain Vertical Alignment), PVA (Patterned Vertical Alignment) or HVA effects.
Owner:SHIJIAZHUANG CHENGZHI YONGHUA DISPLAY MATERIALS CO LTD
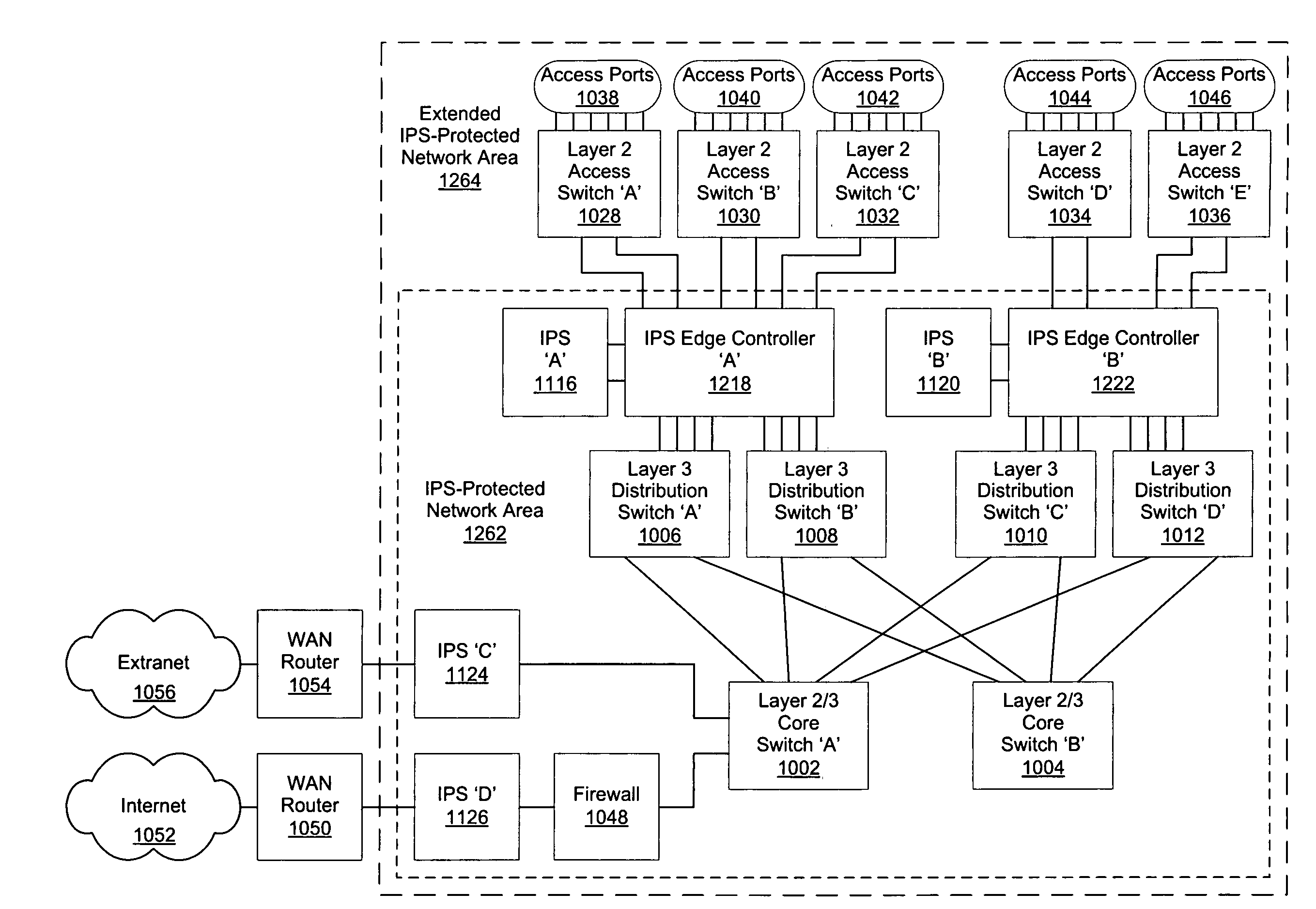
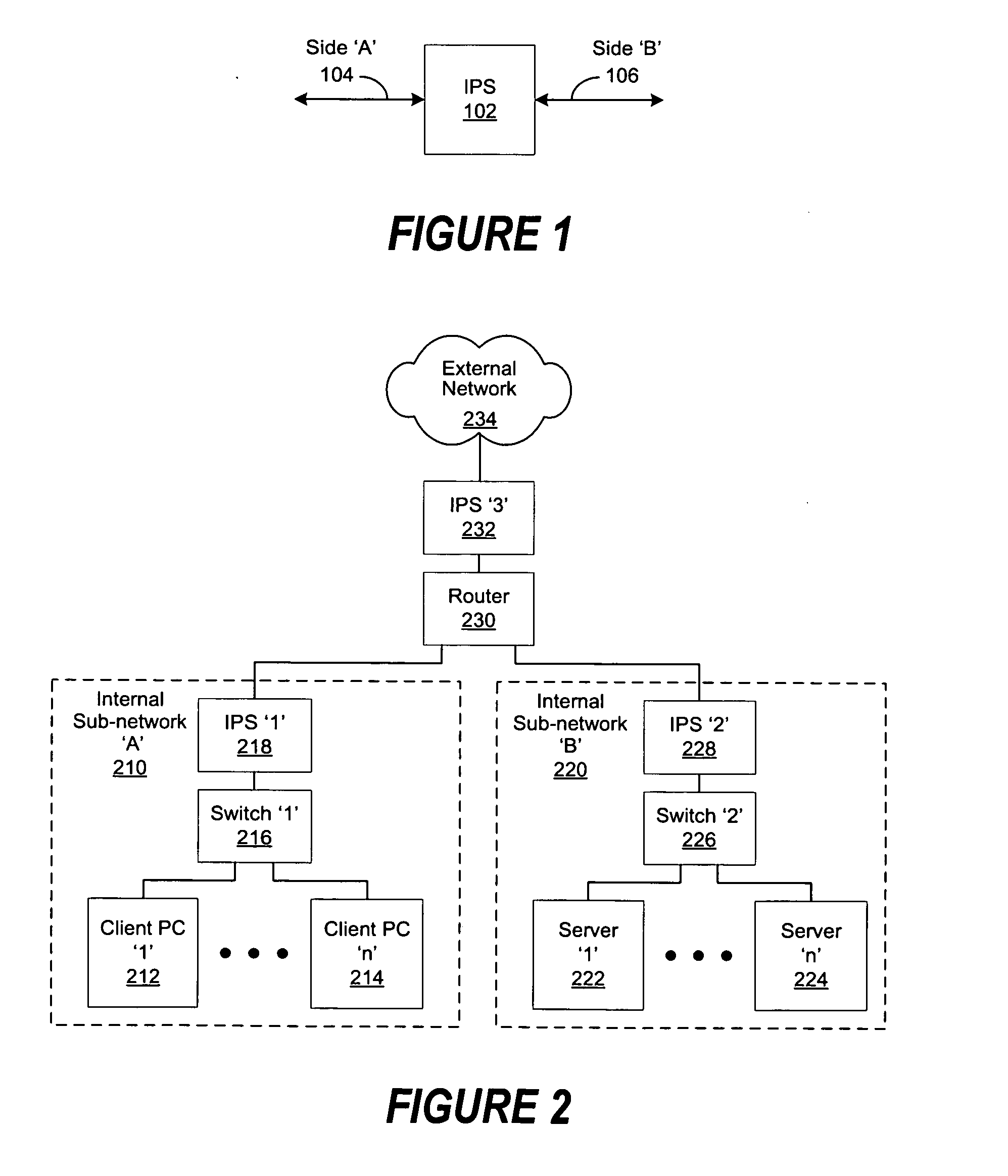
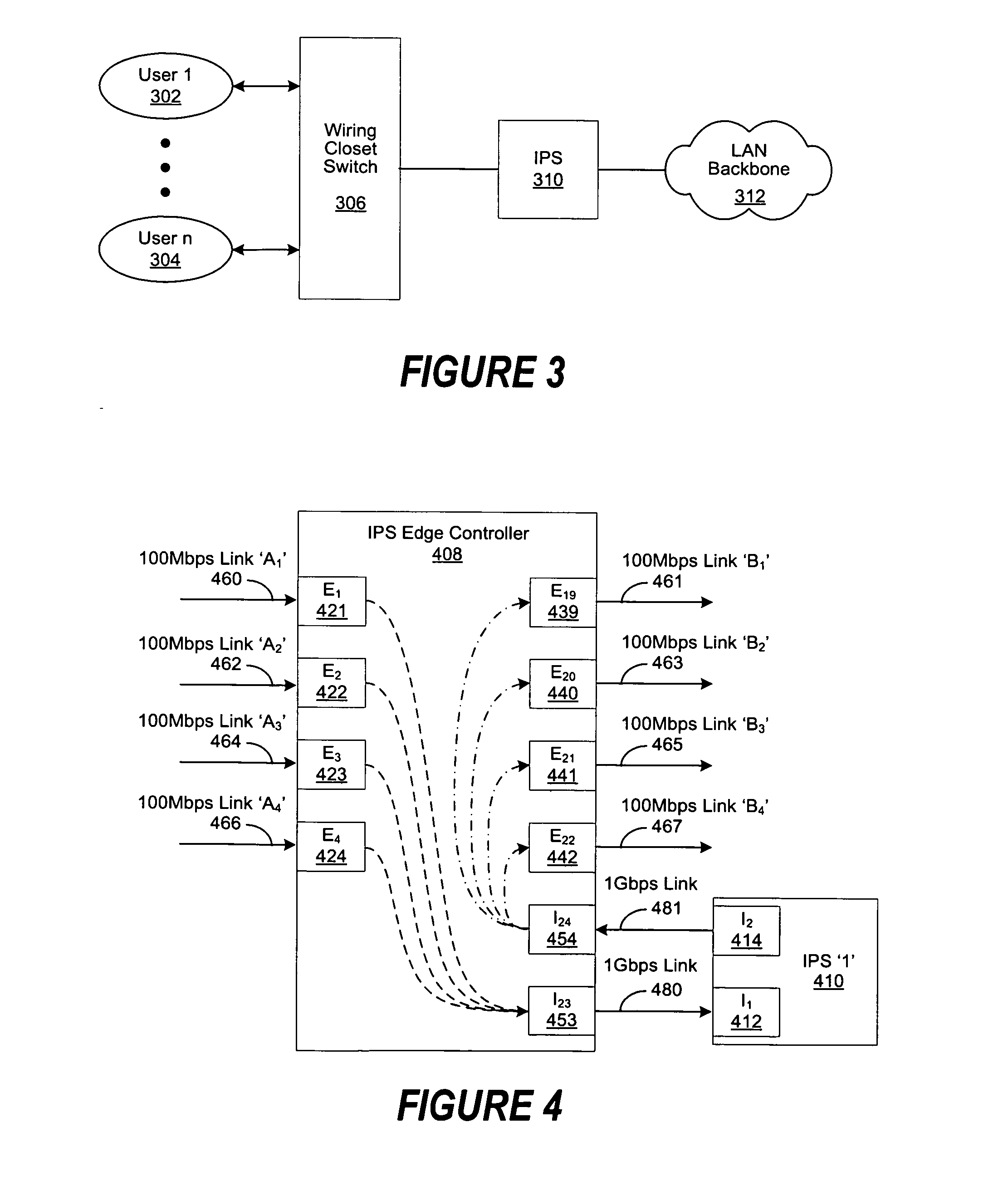
Intrusion prevention system edge controller
ActiveUS20070280222A1High network connection speedImprove usabilityMultiplex system selection arrangementsCircuit switching systemsNetwork connectionPrivate network
A system and method for extending the implementation of one or more Intrusion Prevention Systems (IPSs) such that each user can be placed in the IPS traffic path to create secure containment areas at a granular level, port types and port counts are increased, and higher network connection speeds are supported. In different embodiments of the invention, traffic load is balanced across two or more IPSs, enabling enhanced availability during system failures, replacements or updates. IPS performance is improved by enhancing traffic management of “trusted” (e.g., pass-through) and “known bad” (e.g., discarded) traffic flows and decreasing configuration task workloads. Other embodiments of the invention include, but are not limited to, extending the implementation of proxy devices, virtual private networks (VPNs), session border controllers (SBCs), firewalls, protocol gateways and other bump-in-the-wire systems.
Owner:TREND MICRO INC
Chinese variation text matching recognition method
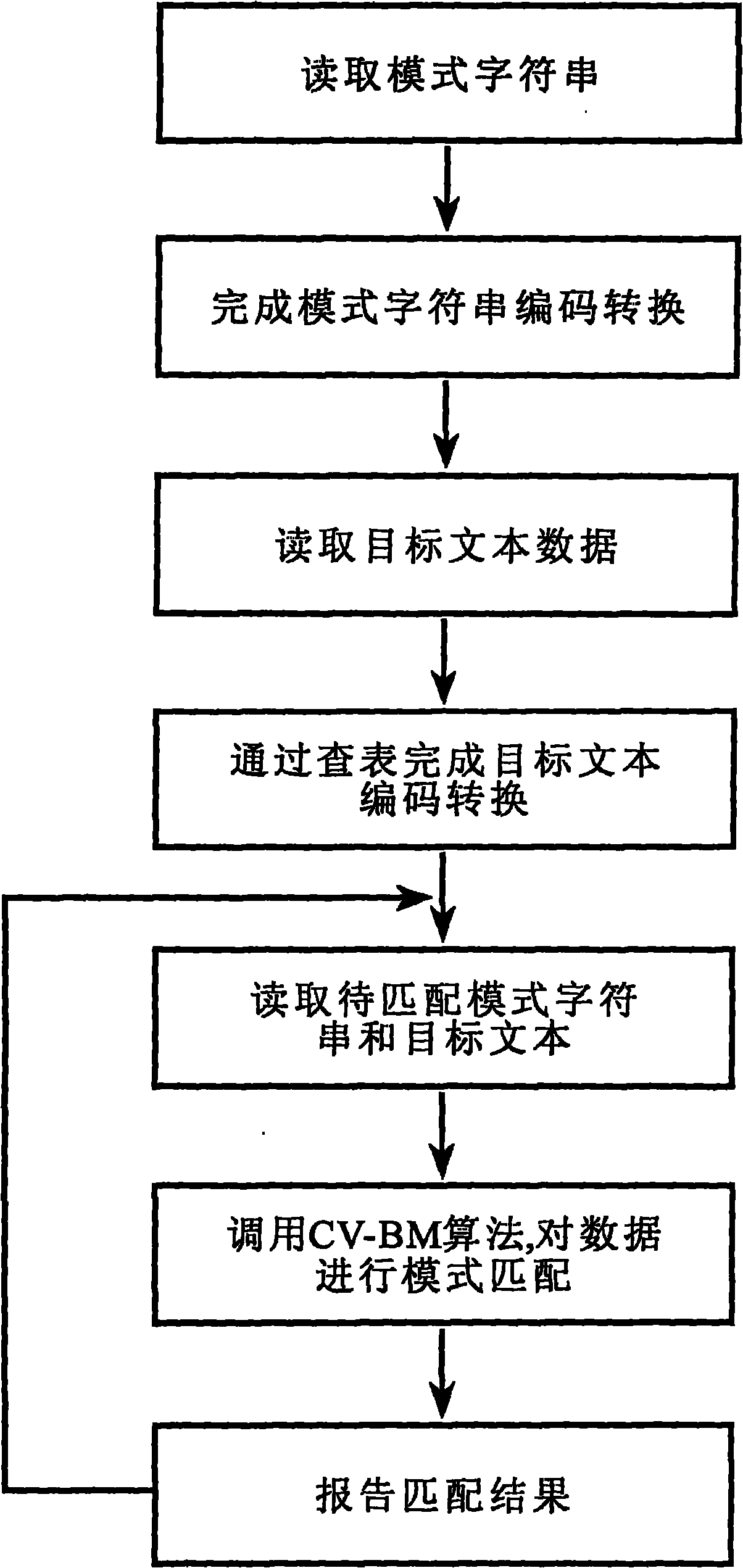
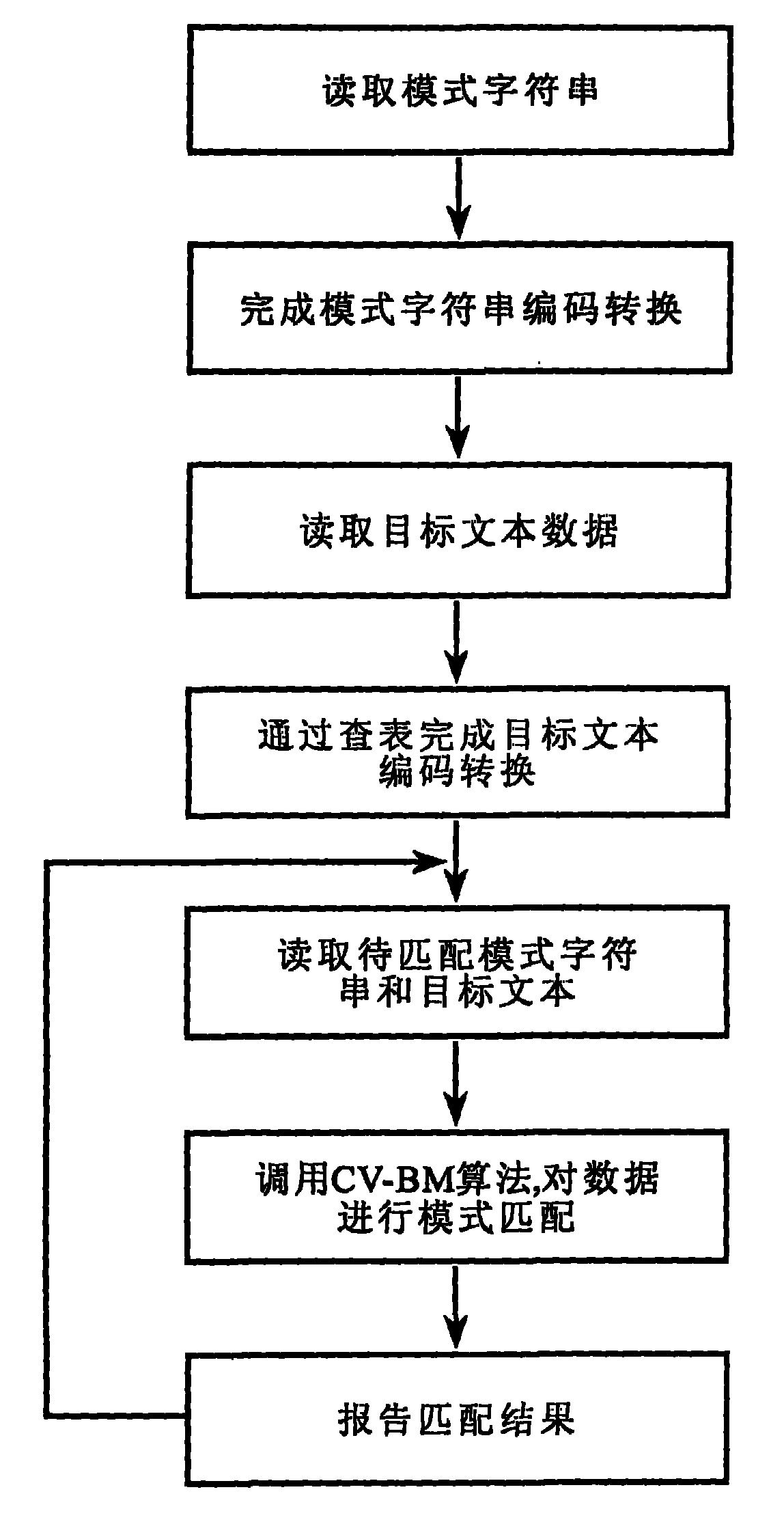
ActiveCN101976253AResolve hard-to-match situationsQuick matchSpecial data processing applicationsChinese charactersTheoretical computer science
The invention relates to a Chinese variation text matching recognition method. The method comprises the following steps of: performing special encoding conversion on a target text and a mode character string to improve the similarity of texts; adding proper wildcard characters into the converted mode character string according to the structural characteristics of Chinese characters in the mode character string; and matching by using a precise character string matching algorithm (namely a CV-BM algorithm). The method solves the problems of the replacement of characters with similar shapes in the variation text and the matching difficulty based on the replacement of wrongly written characters with similar shapes. The problems of the replacement of the characters with the similar shapes in the variation text and the matching difficulty based on the replacement of wrongly written characters with the similar shapes can be solved. Compared with an image partitioning recognition method, the method has smaller time and space complexities, is more suitable for the quick matching of Chinese character information in a high-speed network data transmission environment, and can be widely applied to systems needing to match the Chinese character information, such as an intrusion prevention system, an information retrieval system and the like.
Owner:重庆智载科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com