Patents
Literature
513 results about "Rule processing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
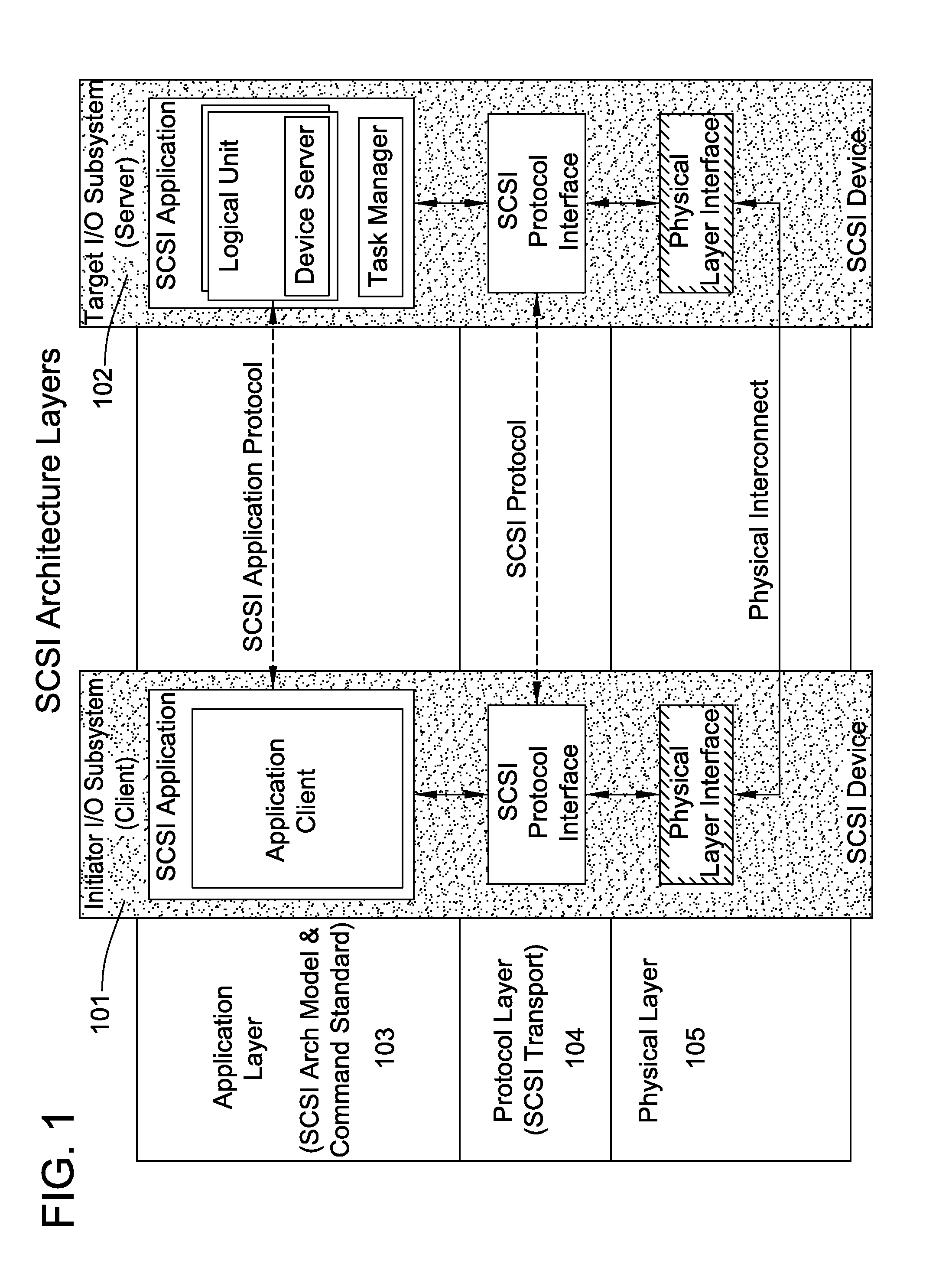
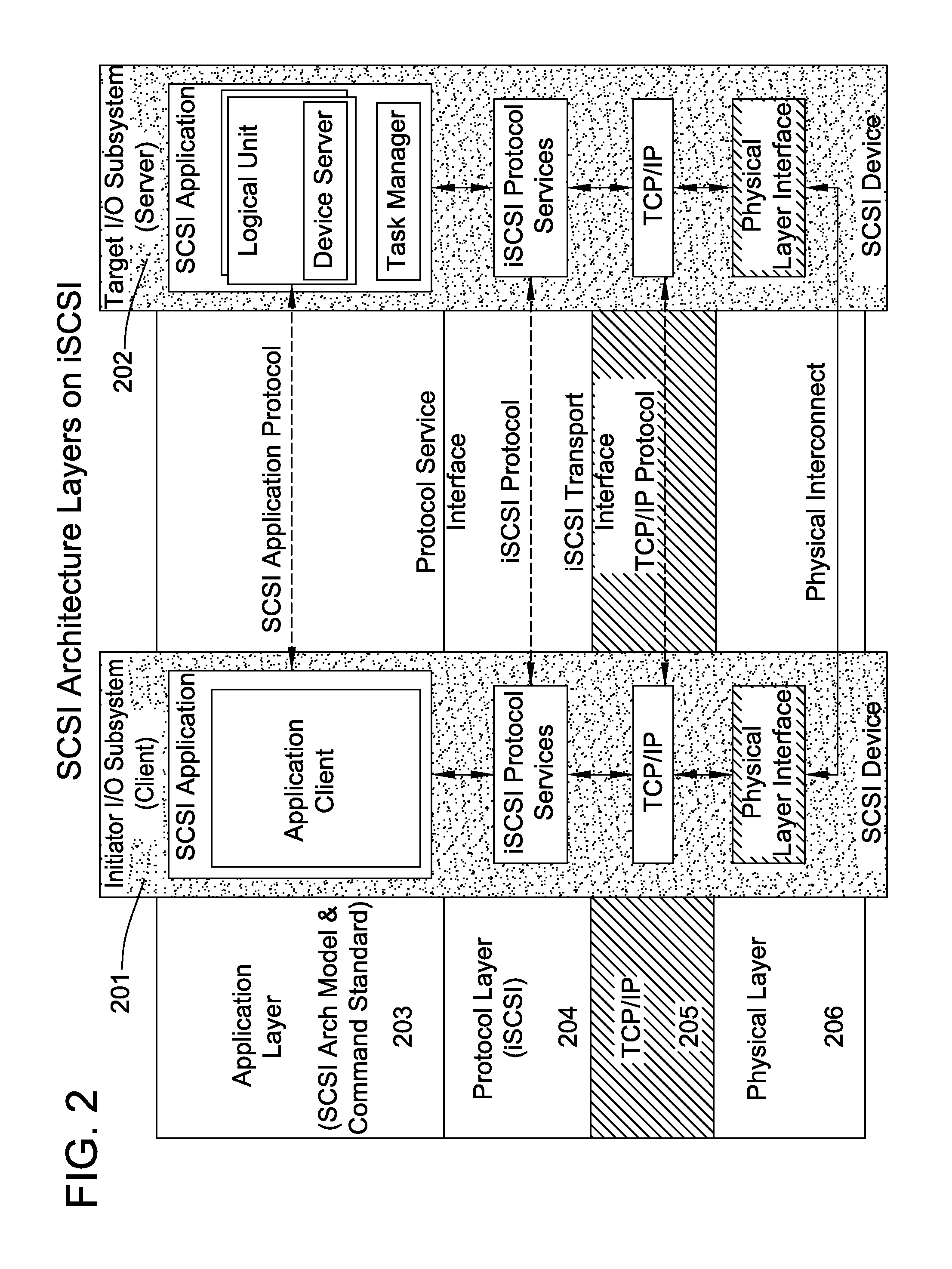
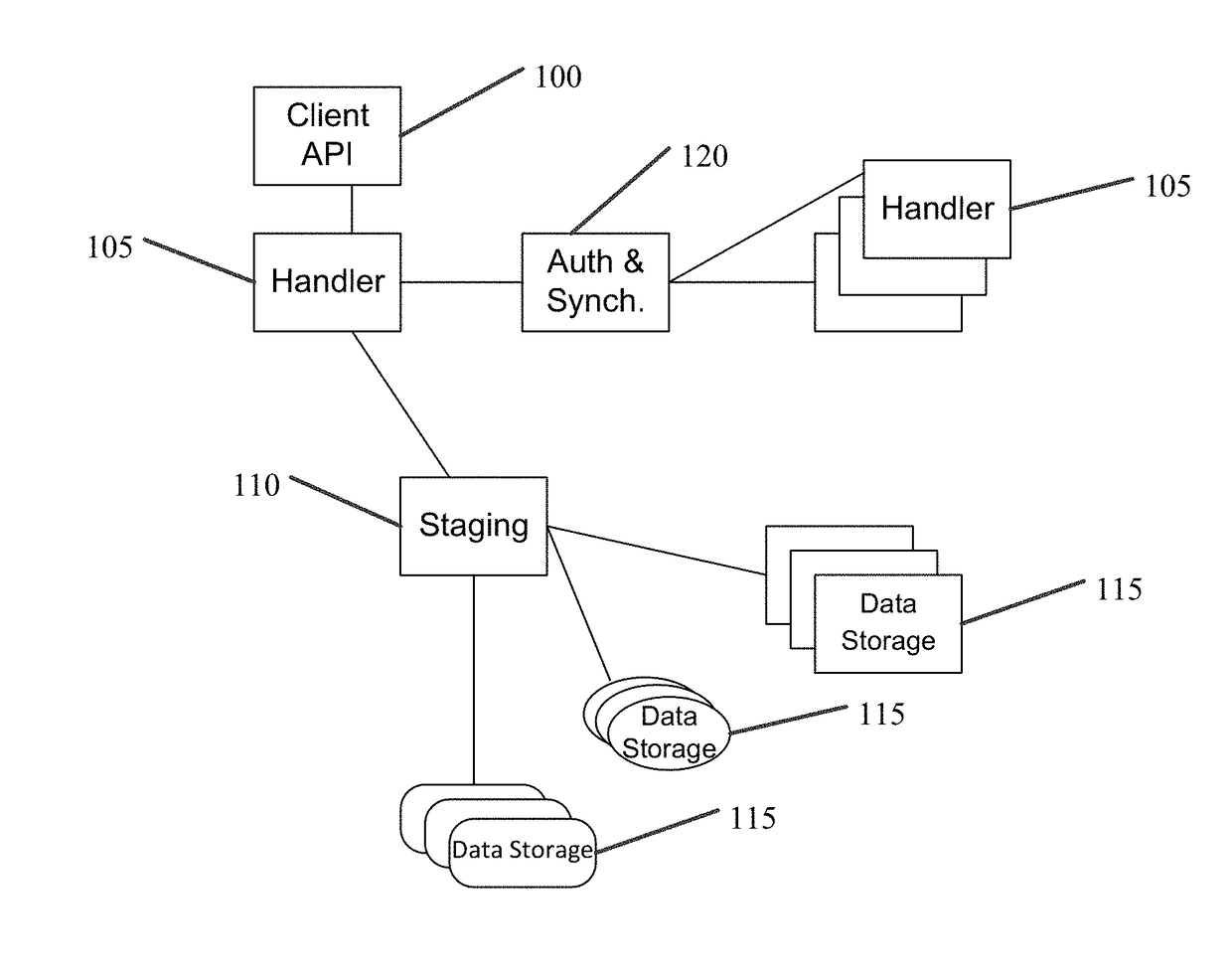
Runtime adaptable search processor
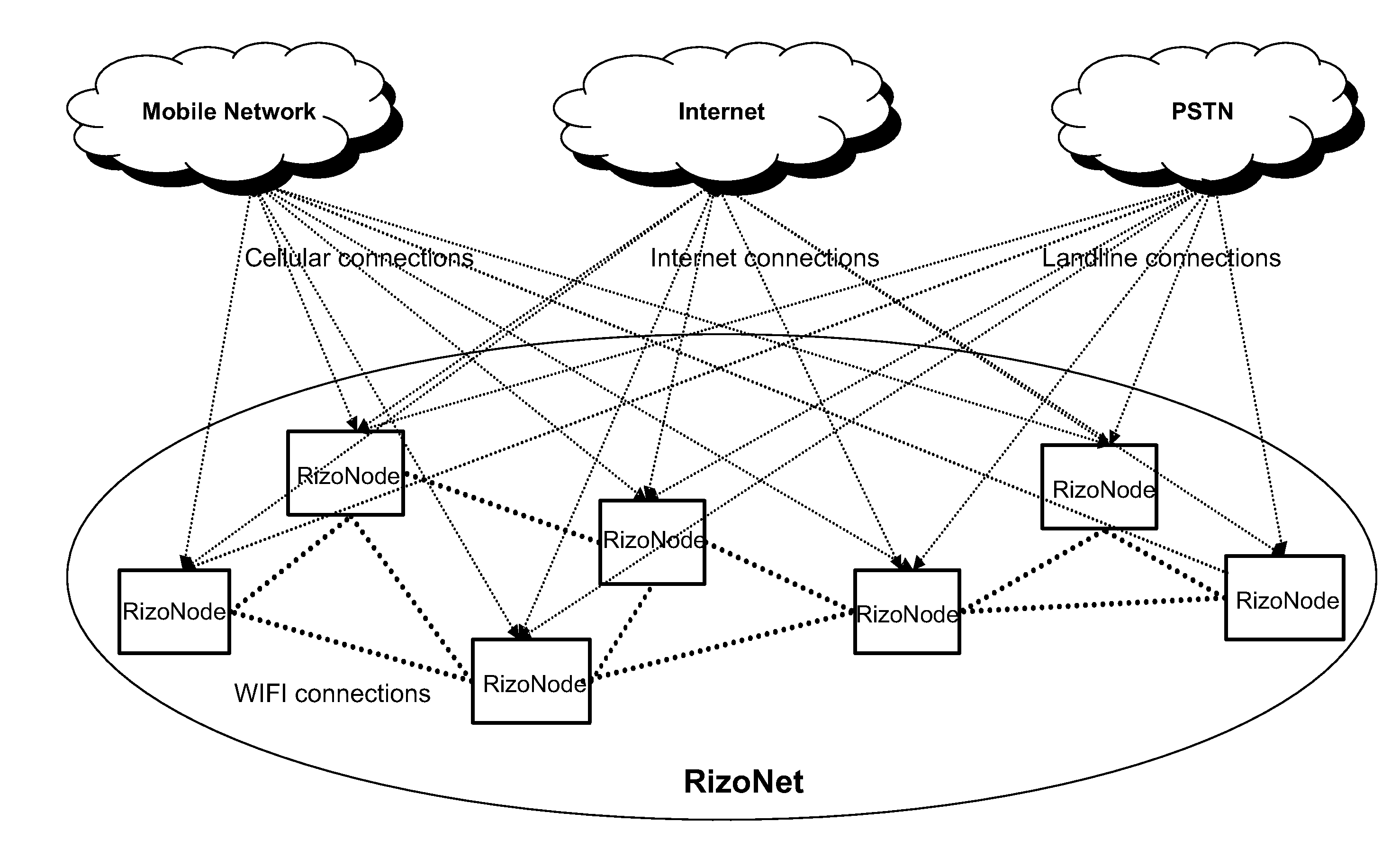
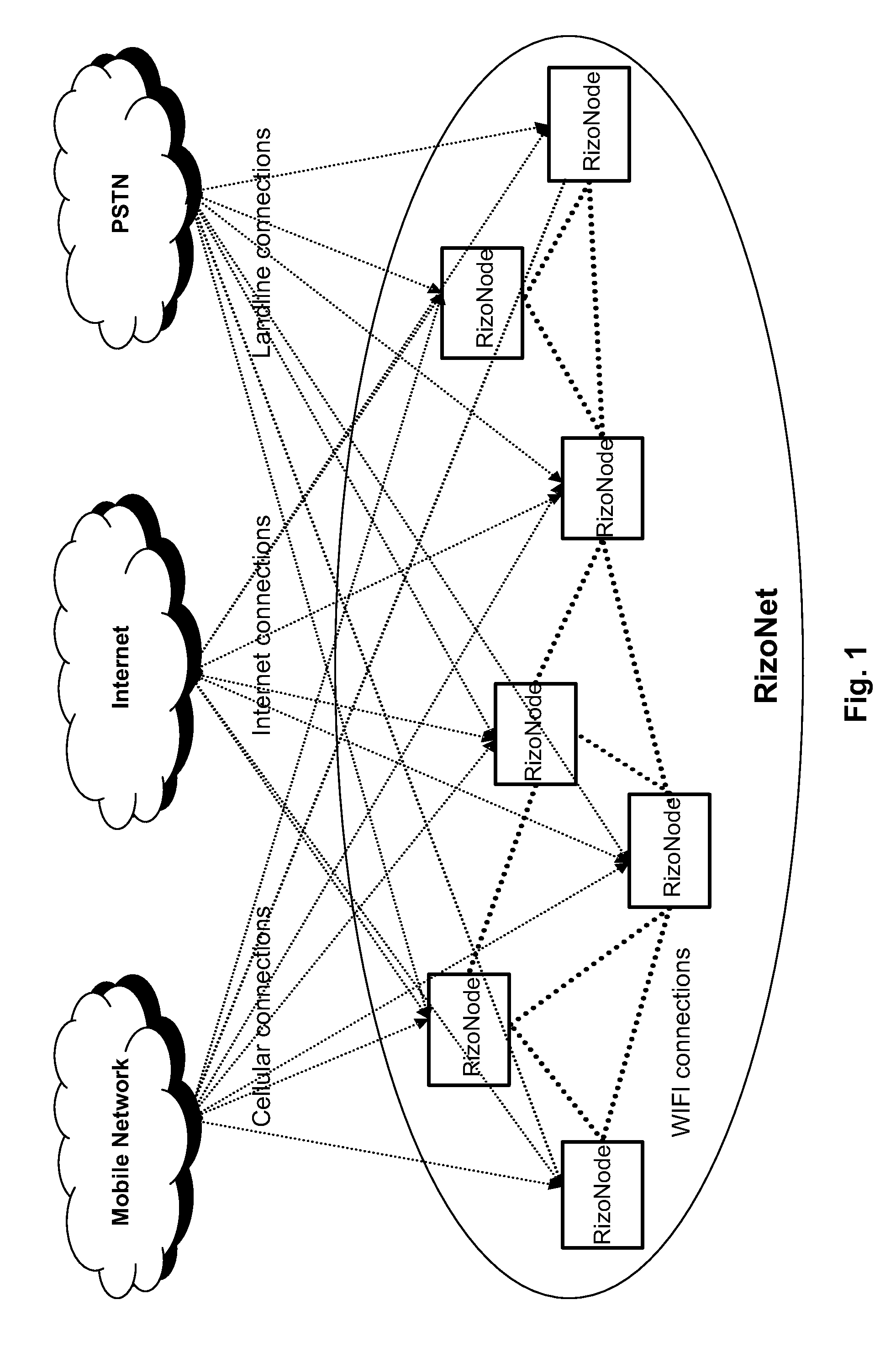
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
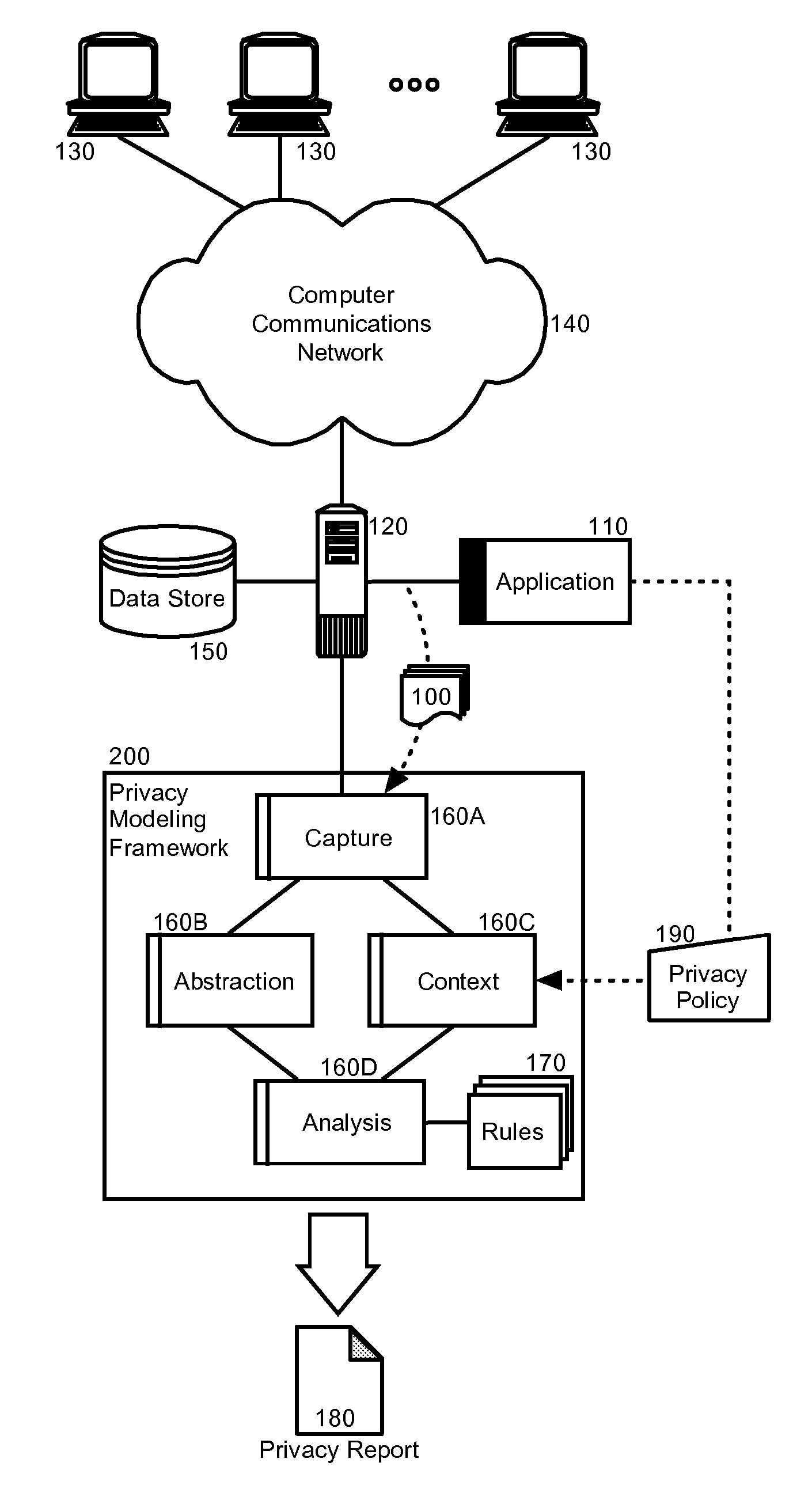
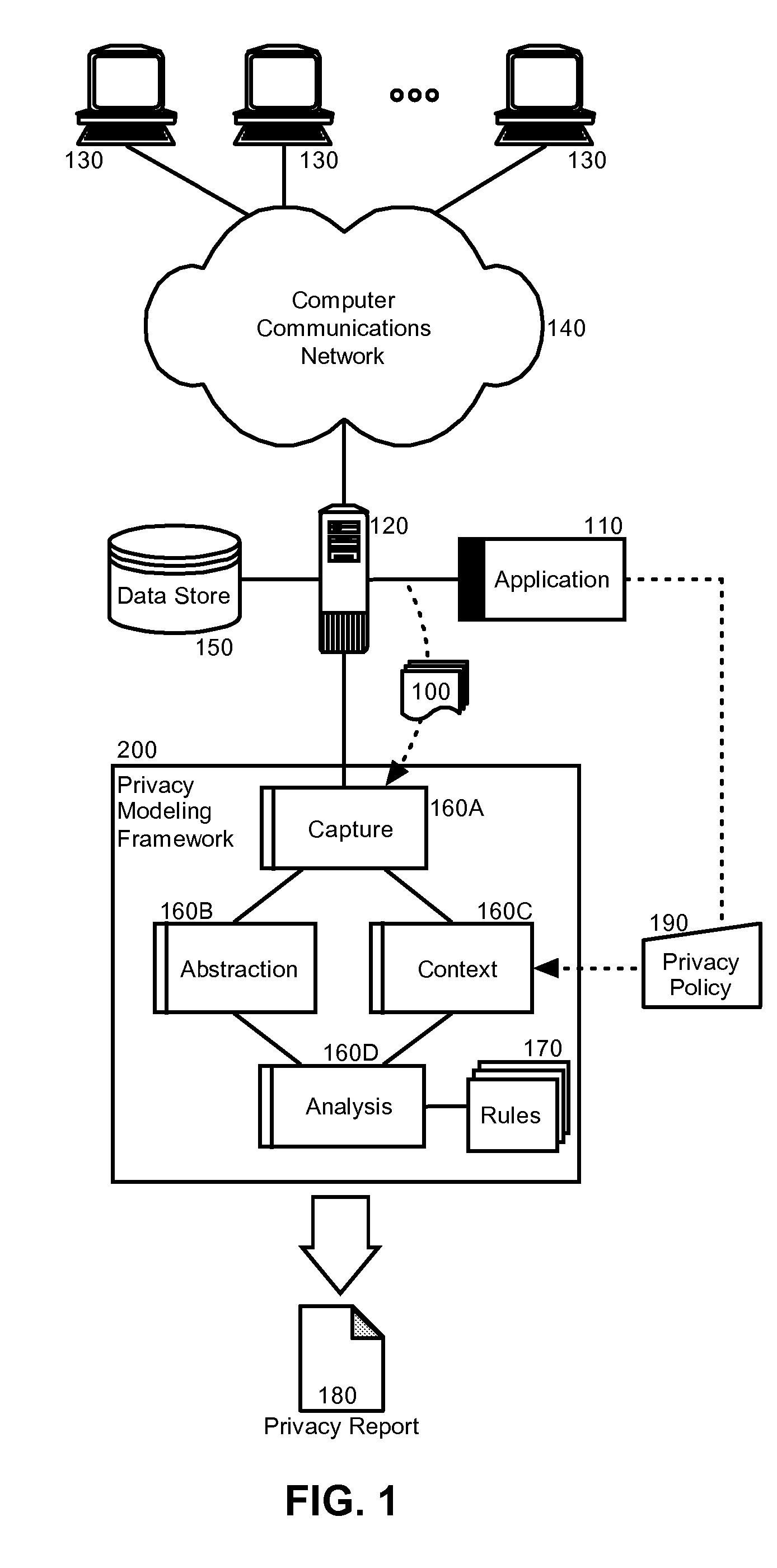
Privacy modeling framework for software applications
InactiveUS20070266420A1Computer security arrangementsOffice automationData processing systemCoupling
Embodiments of the present invention address deficiencies of the art in respect to privacy compliance assessment for computer software and provide a method, system and computer program product for a privacy model framework for software applications. In one embodiment, a privacy modeling data processing system can be provided. The privacy modeling data processing system can include a modeling framework configured for communicative coupling to a software application. The modeling framework can capture information flows from requests to and responses from a coupled software application, and can rules-based process the captured information flows for privacy rules to generate a privacy compliance report for the software application.
Owner:IBM CORP
System and method for testing and deploying rules
Embodiments of the present invention are directed to a method for assessing impact of a rule change in a contact center. The method includes configuring one or more parameters of the rule; receiving a command to assess the rule; retrieving a log of past interactions between end users and the contact center, wherein the log of past interactions reflects interactions prior to deployment of the rule; processing one or more of the past interactions based on the rule; simulating an outcome of the one or more past interactions; and deploying the rule or not to a rules engine based on the simulating.
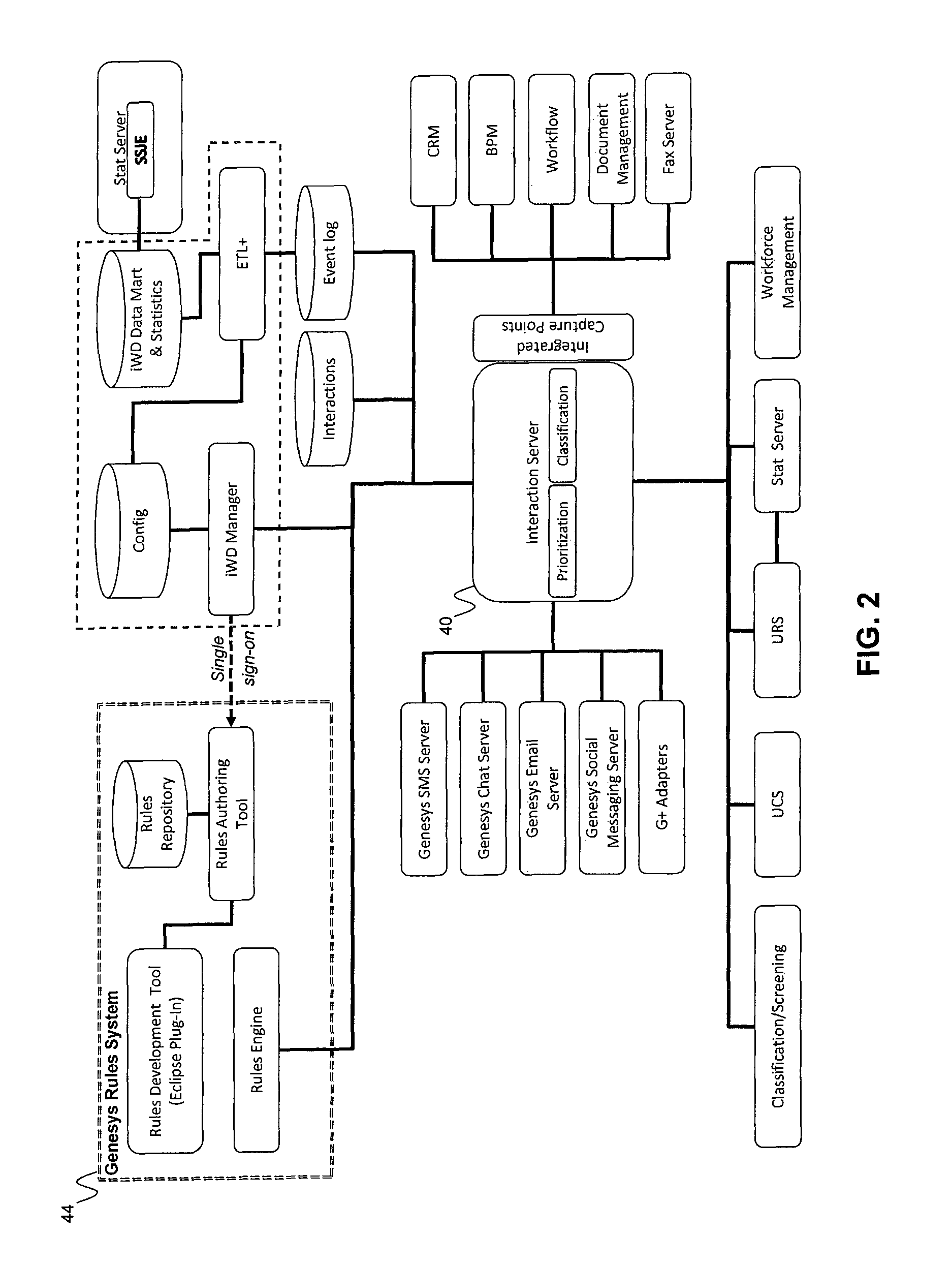
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
System and method for routing media
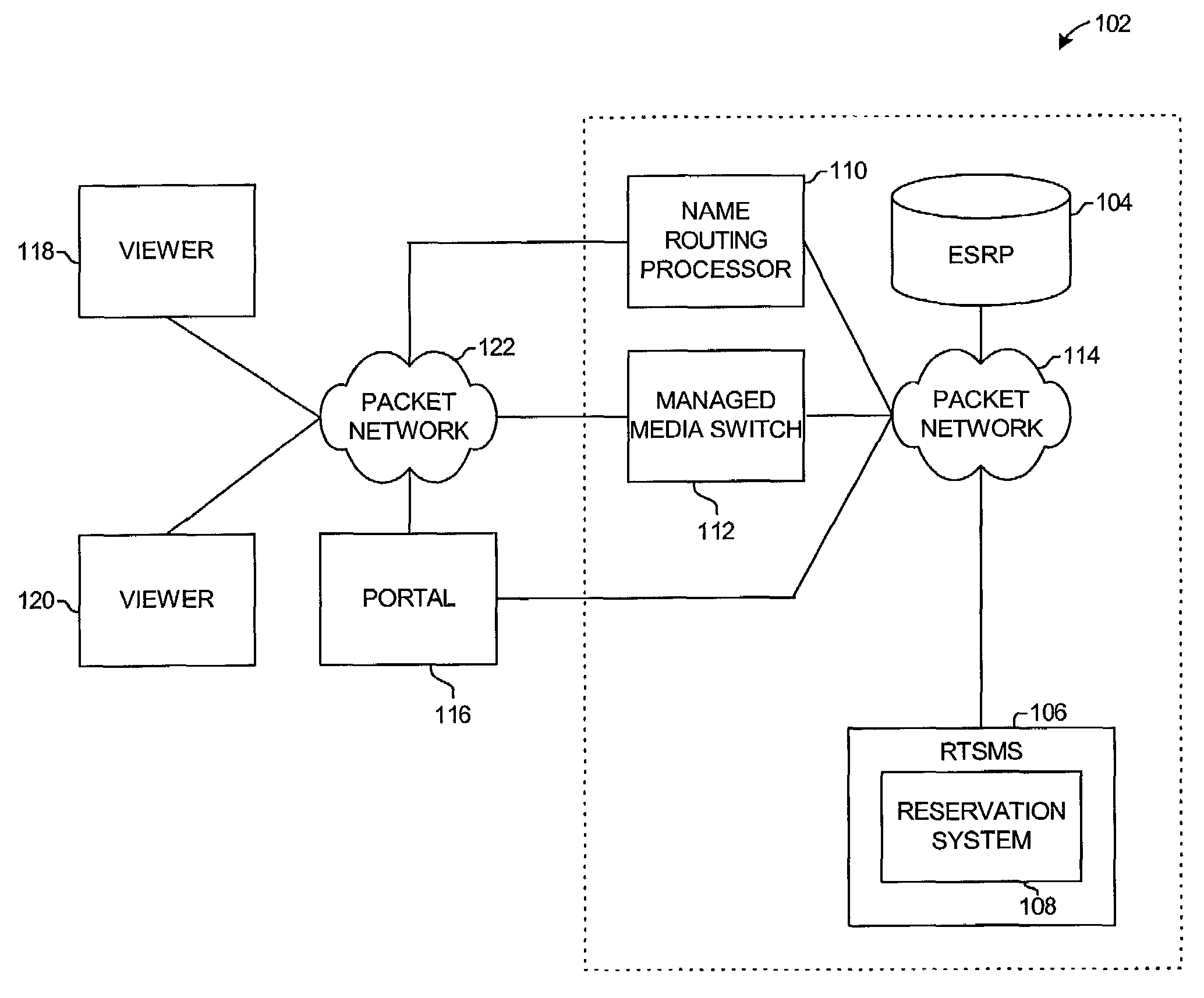
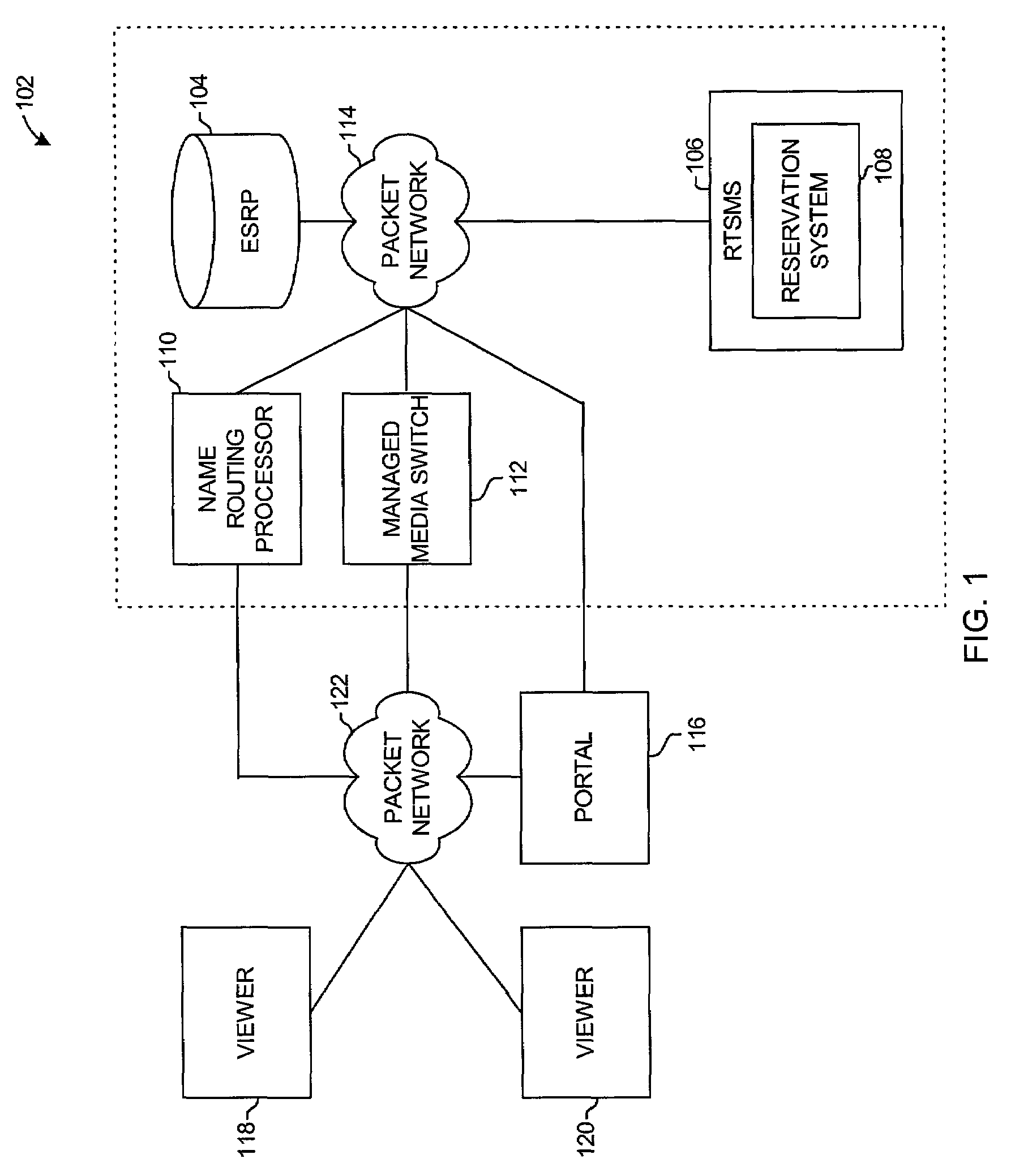
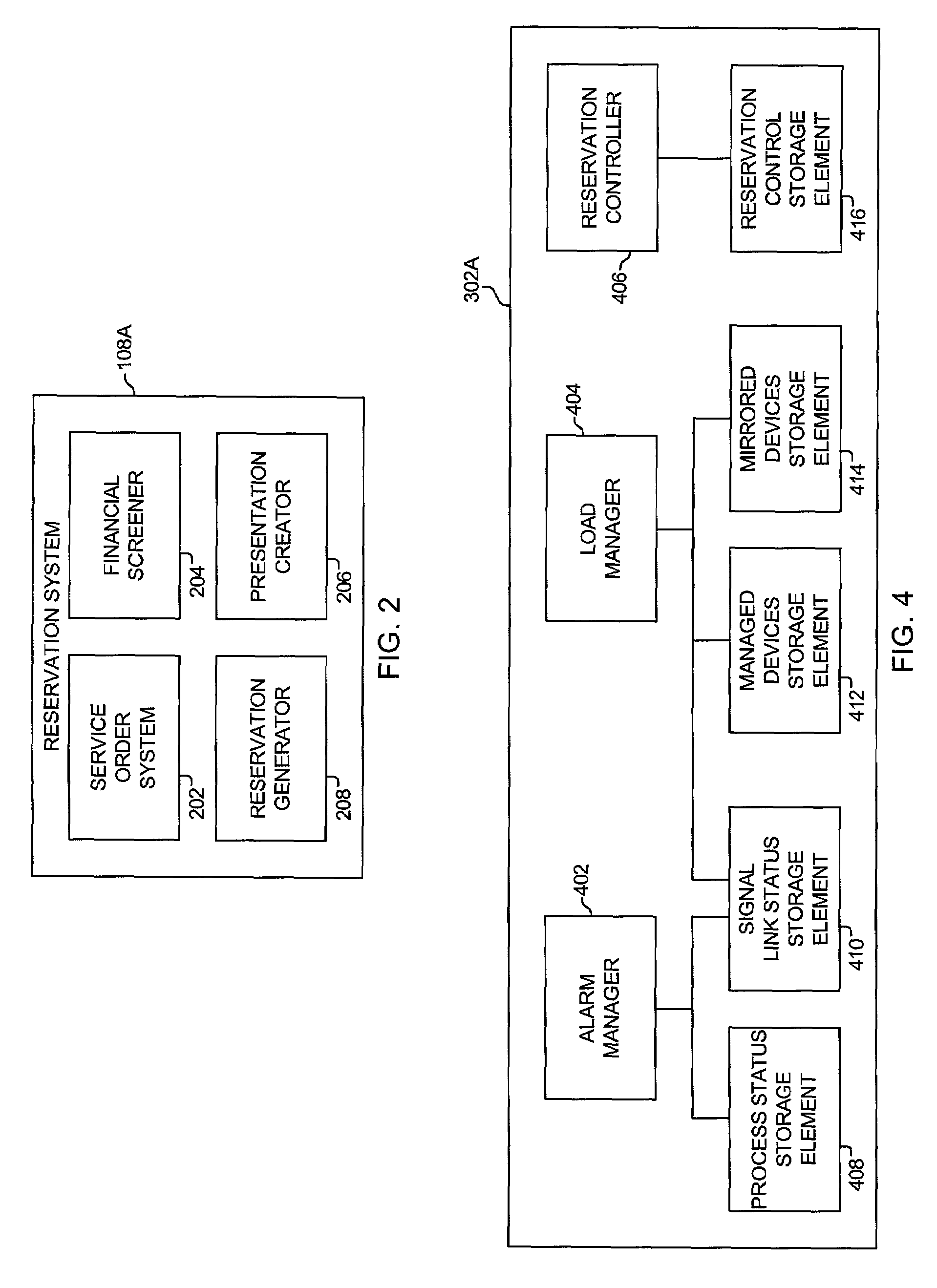
The system and method for streaming media to a viewer and managing the media comprises and an enhanced service routing processor (ESRP), a real time switch management system (RTSMS), a name routing processor (NRP), and a managed media switch (MMS). The RTSMS has a reservation system. The ESRP receives media from an owner, manages the media according to media rules and order rules defined by the owner, and distributes the media to one or more switches, such as the MMS, according to the media rules and the order rules. The RTSMS is configured to receive the media rules and to receive a viewer's media request via the reservation server. The reservation system of the RTSMS processes the media request according to the media rules and builds a reservation for the requested media. The RTSMS generates the reservation to the viewer and to the NRP. The NRP receives the reservation data from the viewer and from the RTSMS. The NRP processes the reservation data and locates an MMS that can stream the media to the viewer. The NRP transmits the IP address of the MMS to the viewer and transmits the reservation data to the MMS. The viewer initiates a session or connection with the MMS using the reservation number. If the reservation data from the viewer matches the reservation data from the NRP, the MMS streams the media to the viewer.
Owner:SITO MOBILE R&D IP
Creating, distributing and enforcing relational and business rules at front-end application
InactiveUS20020147726A1Ensure consistencyLittle or no reuseDigital data processing detailsOffice automationProcessing InstructionOff the shelf
A method and system and computer readable medium for: (1) the creation and representation of business rule definitions, (2) the creation and representation of enforcing rule handlers, (3) the creation and representation of a framework to check the existence of rules then, apply the appropriate handler, (4) and the distribution of the rule definitions and handlers to clients. The present invention defines a rule language and provides a framework that separates the definition of the rules, the enforcing handler, the system at which rules are generated and the system at which rules are enforced. Further, in one embodiment, the present invention uses standard XML notations to define rules and standard XSL and XSLT processing instructions to enforce rules. Using standard XML, XSL and SXLT allows clients to use off-the-shelf XML parser and XSL processors in lieu of developed code or rule based engines.
Owner:PARTNERCOMMUNITY
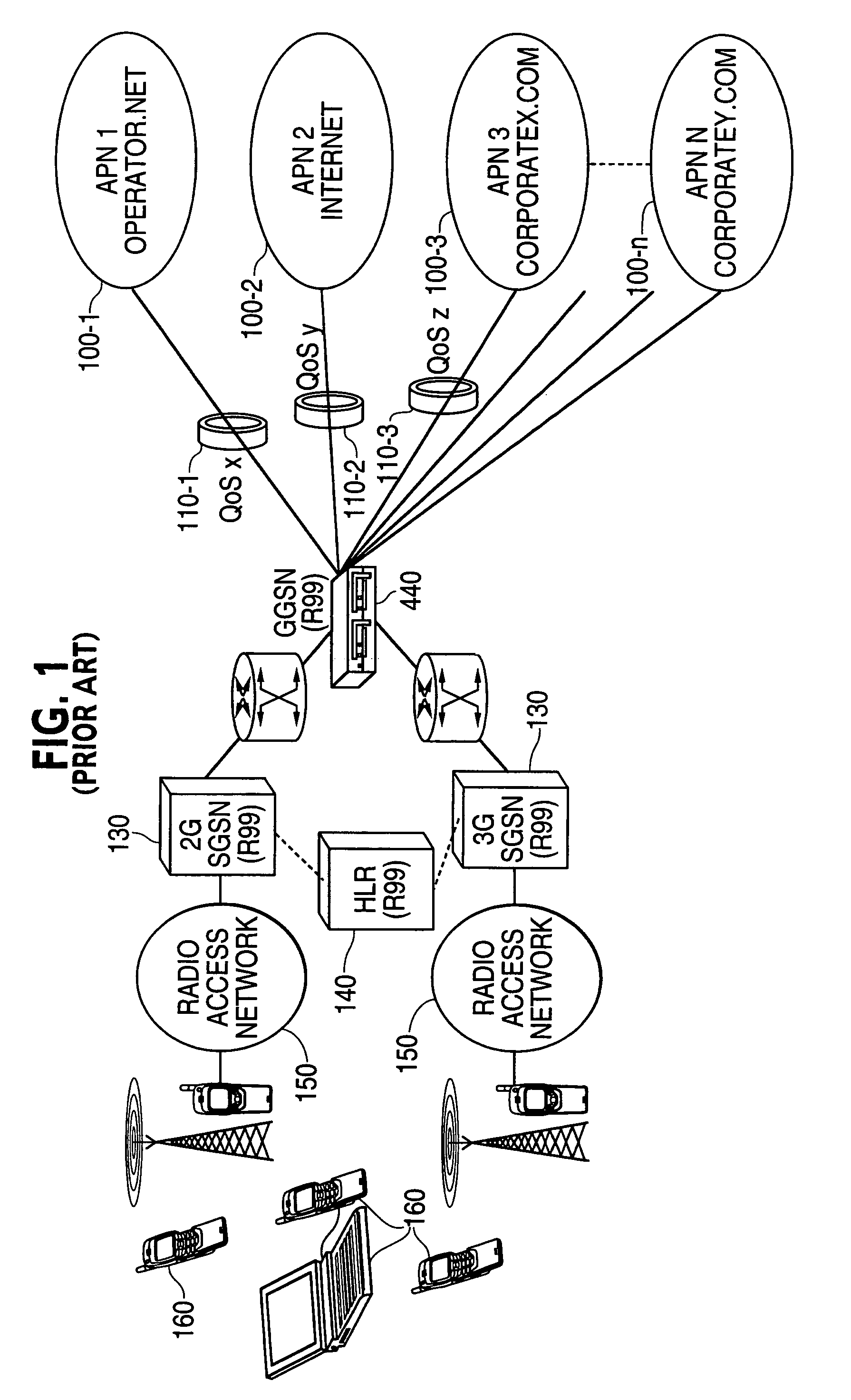
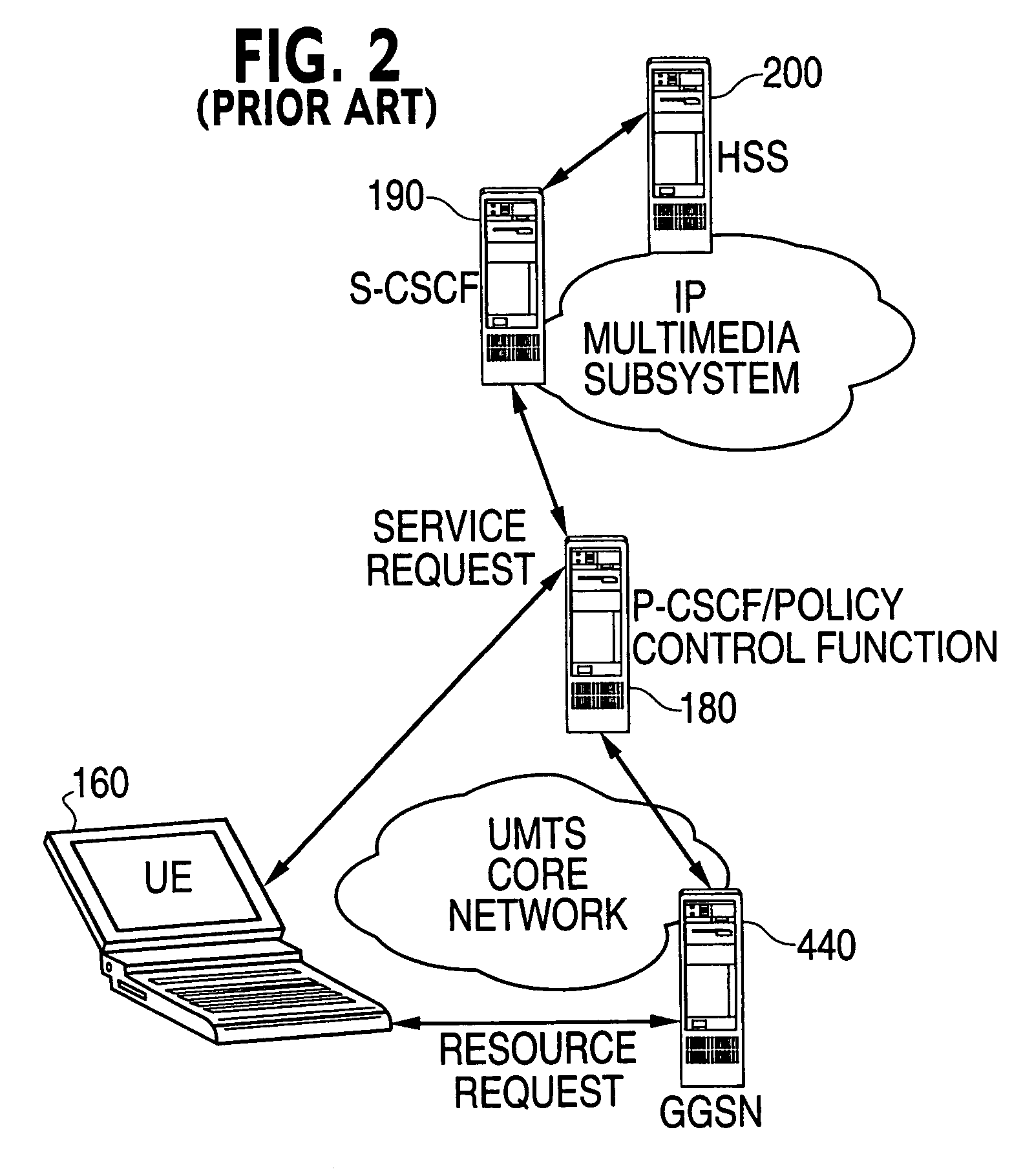
Enhanced QoS control
ActiveUS7209458B2Easy to controlNetwork traffic/resource managementData switching by path configurationPolicy decisionService information
The invention is a method and a system for the providing of service to user equipment (UE). A method of providing services to user equipment in accordance with the invention includes providing from a database (420) to a policy decision entity (405) subscriber information regarding permitted conditions for the users to obtain the services; providing service information from at least one network or server (100), regarding service offered by the at least one network or server to the user equipment, forming policy rules at the policy decision entity based upon the subscriber information and the service information. A requesting user equipment transmits a request for service to the communications network which is processed by the policy decision entity in accordance with the policy rules to determine if the service is to be allowed and if the service is allowed characteristics of the service to be provided to the requesting user equipment and the policy enforcement entity enforces at least one characteristic of an allowed service upon the communication network to insure that the allowed service obtained by the requesting user equipment has the at least one characteristic of the allowed service.
Owner:NOKIA TECHNOLOGLES OY
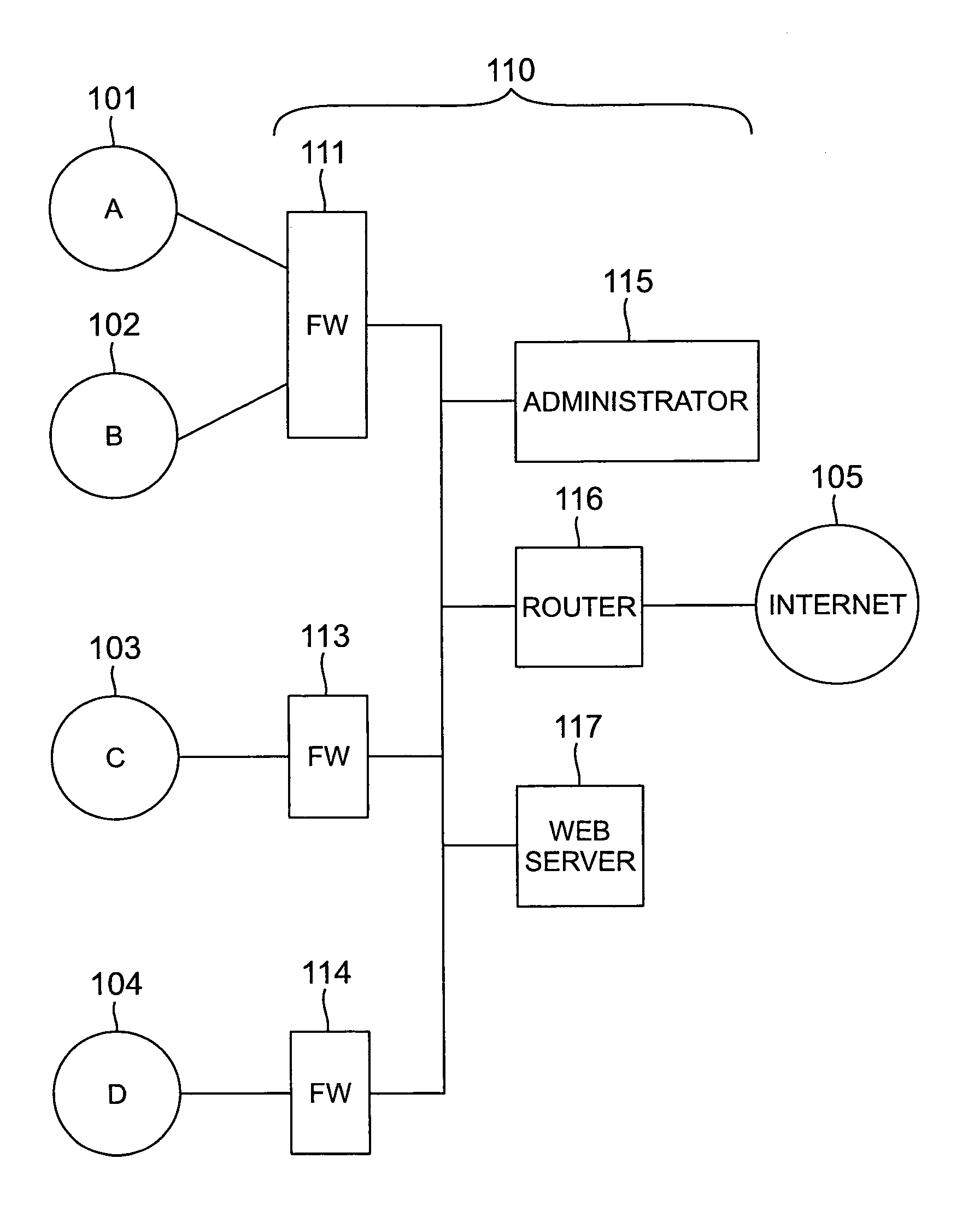
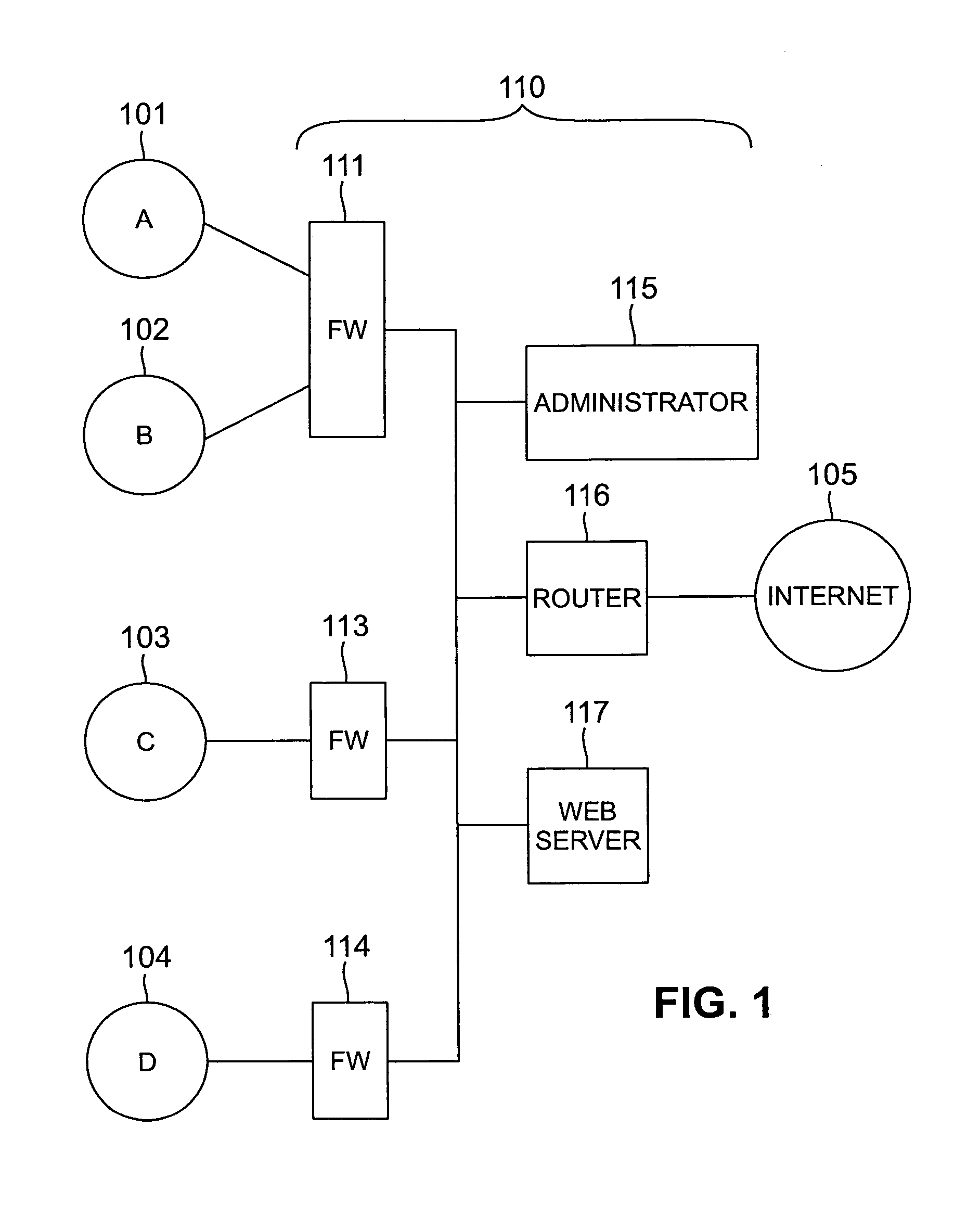
Methods and apparatus for a computer network firewall with multiple domain support
InactiveUS7143438B1Improve processing efficiencyIncrease access rule flexibilityUser identity/authority verificationHardware monitoringData packEngineering
The invention provides improved computer network firewalls which include one or more features for increased processing efficiency. A firewall in accordance with the invention can support multiple security policies, multiple users or both, by applying any one of several distinct sets of access rules. The firewall can also be configured to utilize “stateful” packet filtering which involves caching rule processing results for one or more packets, and then utilizing the cached results to bypass rule processing for subsequent similar packets. To facilitate passage to a user, by a firewall, of a separate later transmission which is properly in response to an original transmission, a dependency mask can be set based on session data items such as source host address, destination host address, and type of service. The mask can be used to query a cache of active sessions being processed by the firewall, such that a rule can be selected based on the number of sessions that satisfy the query. Dynamic rules may be used in addition to pre-loaded access rules in order to simplify rule processing. To unburden the firewall of application proxies, the firewall can be enabled to redirect a network session to a separate server for processing.
Owner:LUCENT TECH INC
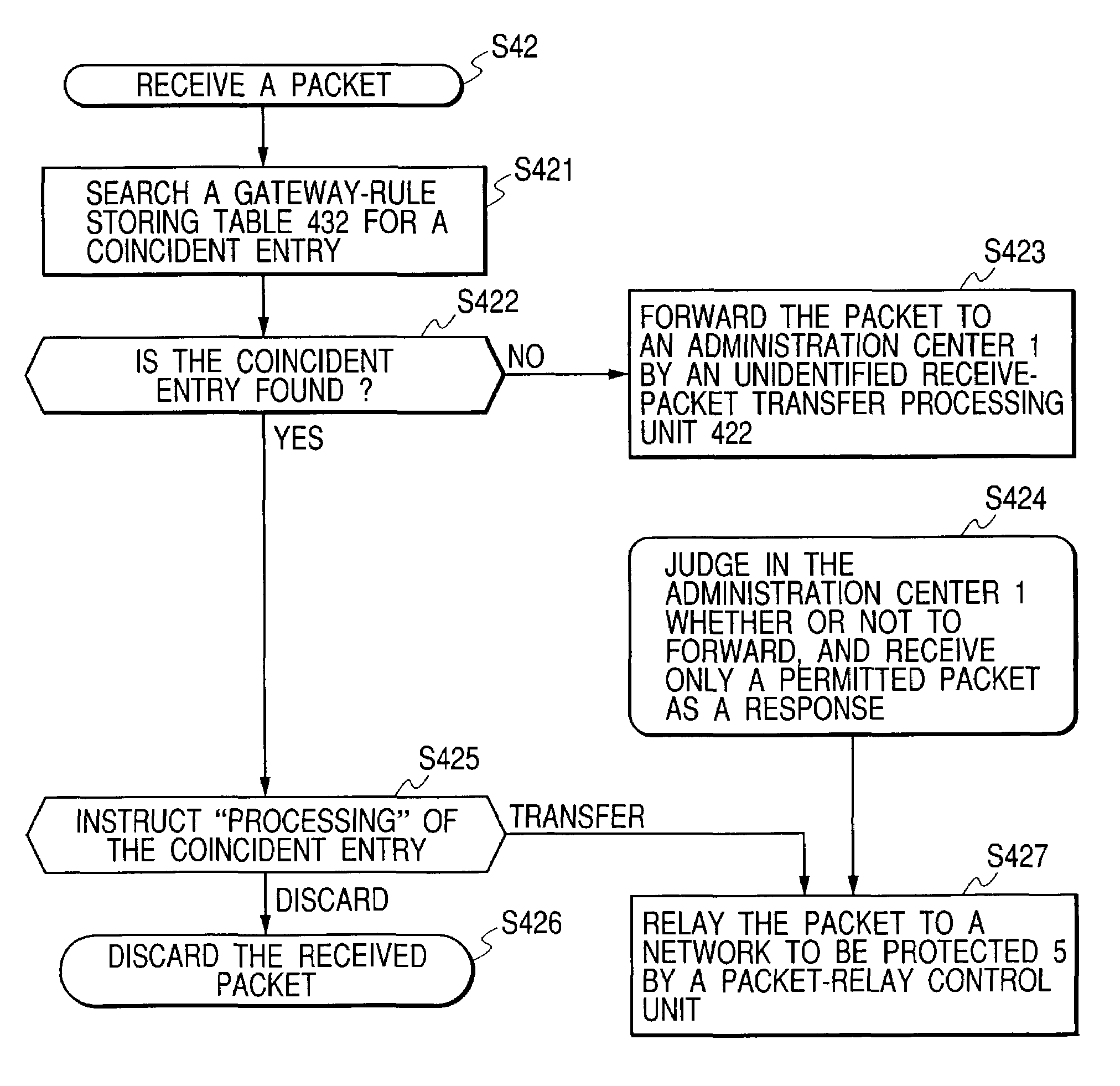
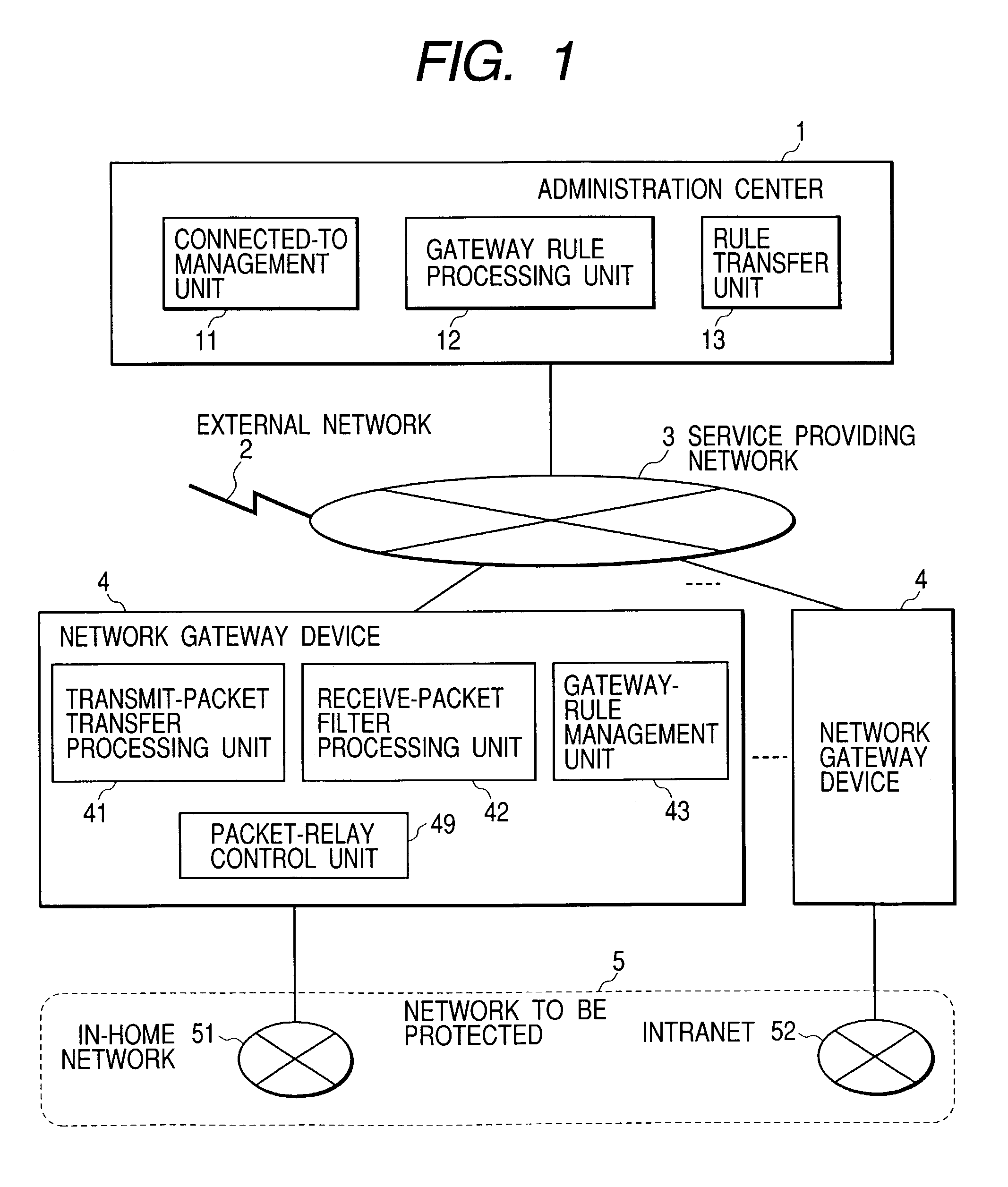
Communication apparatus
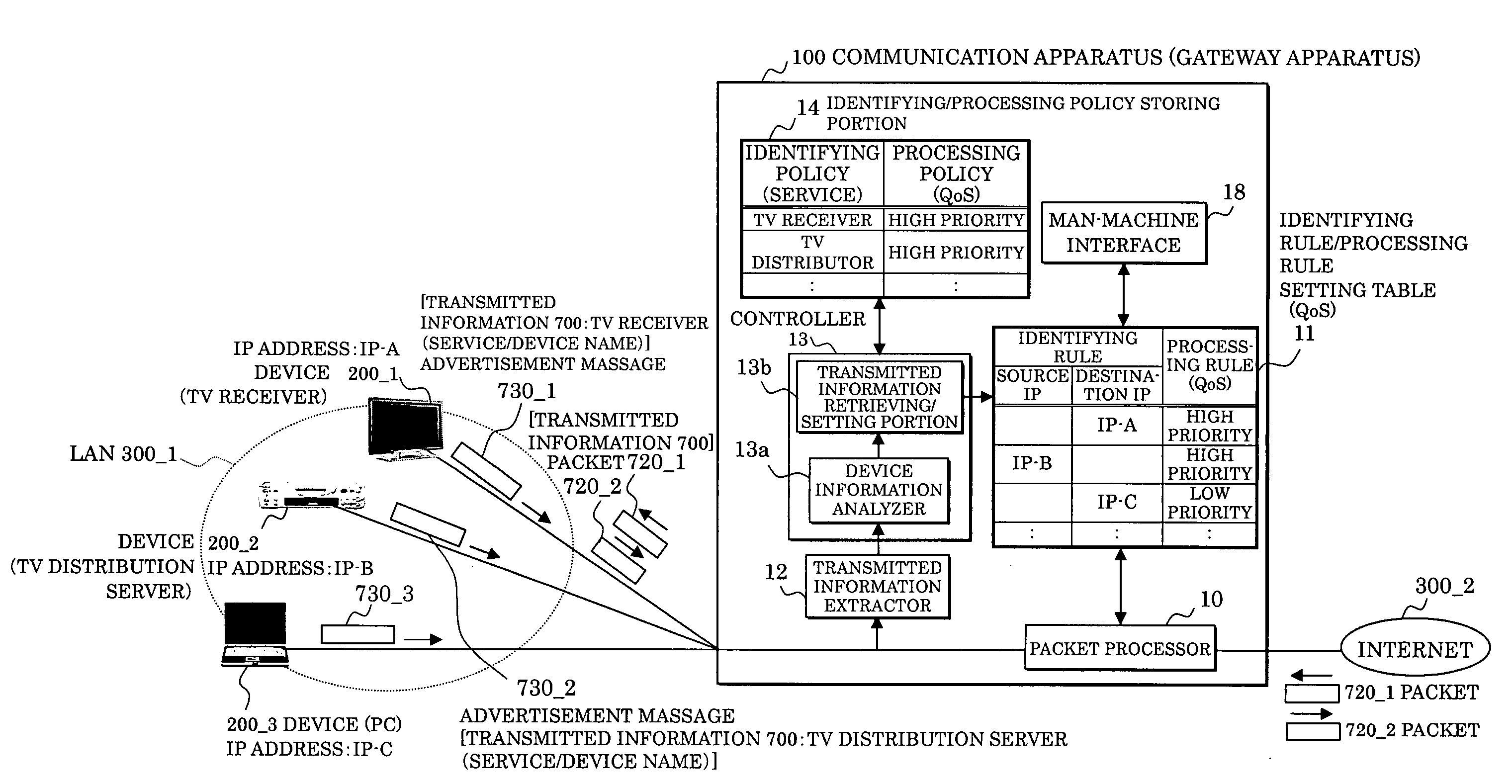
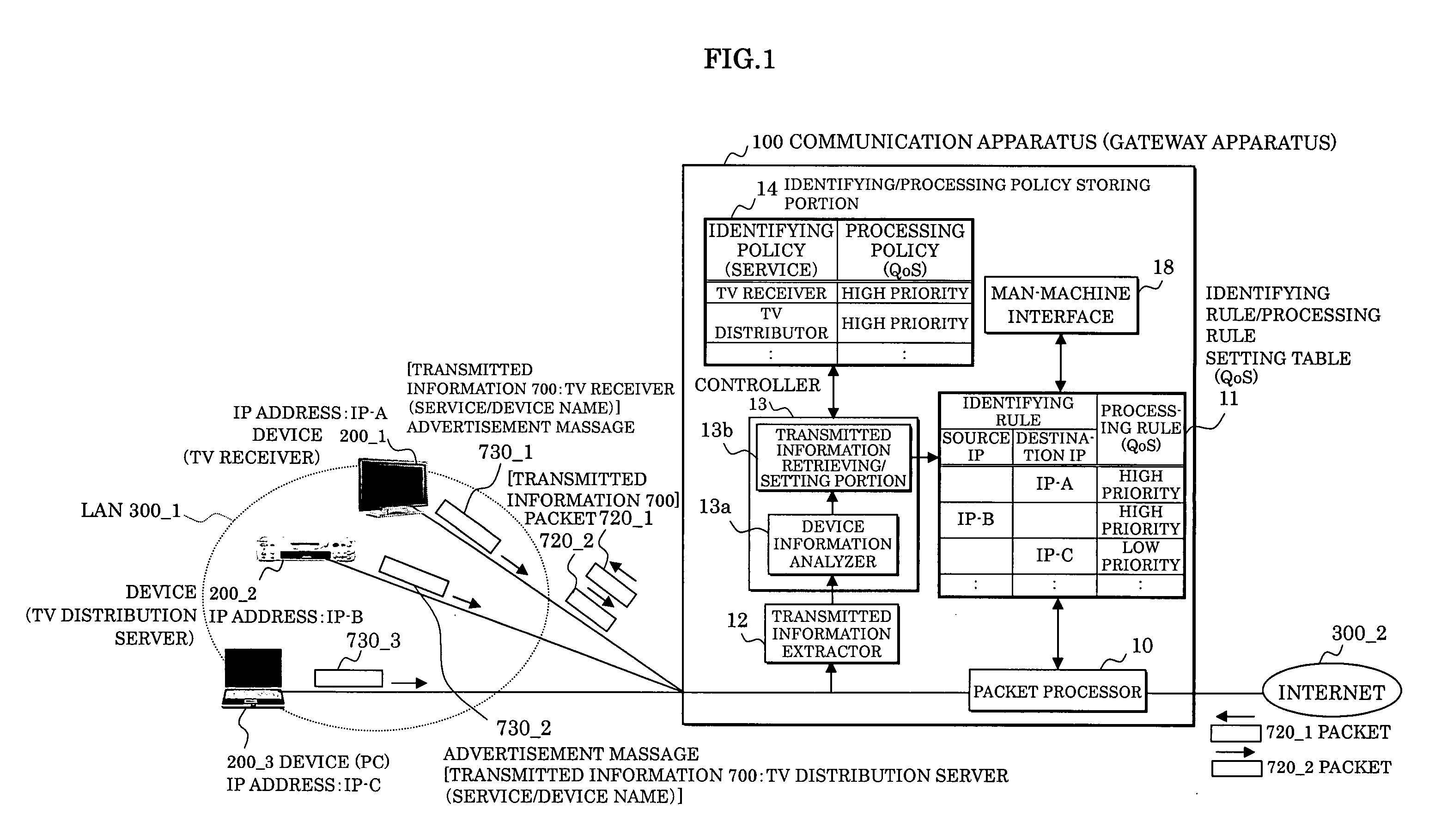
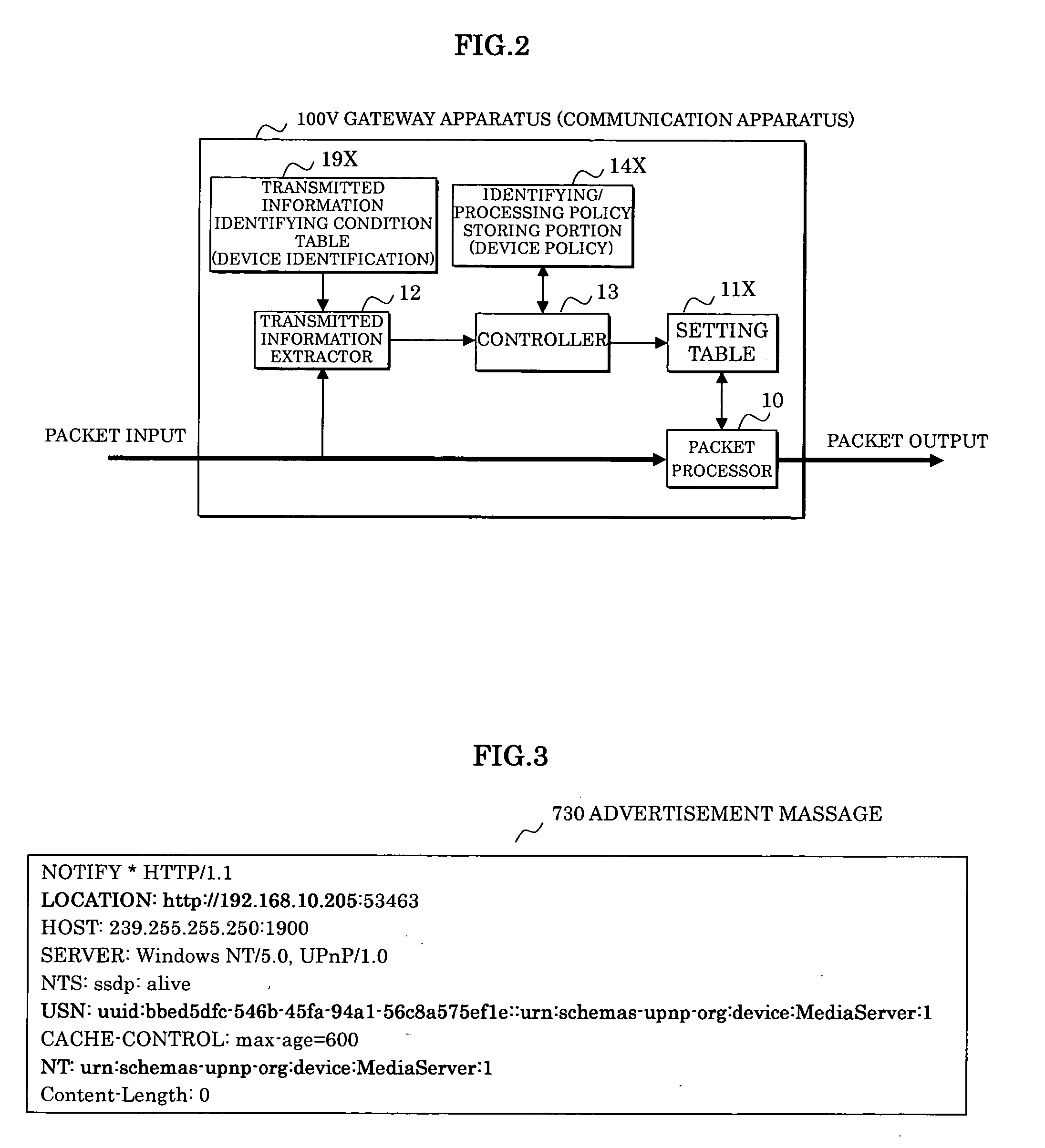
InactiveUS20060136987A1Data switching networksSpecial data processing applicationsComputer scienceCommunication device
In a communication apparatus processing a packet transmitted / received by a device connected to a network, an identifying / processing policy storing portion stores a basic identifying policy and processing policy for determining an identification and processing of a packet corresponding to transmitted information from a device, a transmitted information extractor extracts the transmitted information, and a controller determines a rule for identifying and processing a received packet based on the identifying policy and the processing policy corresponding to the transmitted information extracted and prepares an identifying rule / processing rule setting table which indicates the rule. A packet processing identifies the received packet based on the identifying rule and processes the identified packet based on the processing rule.
Owner:FUJITSU LTD
Apparatuses for Hybrid Wired and Wireless Universal Access Networks
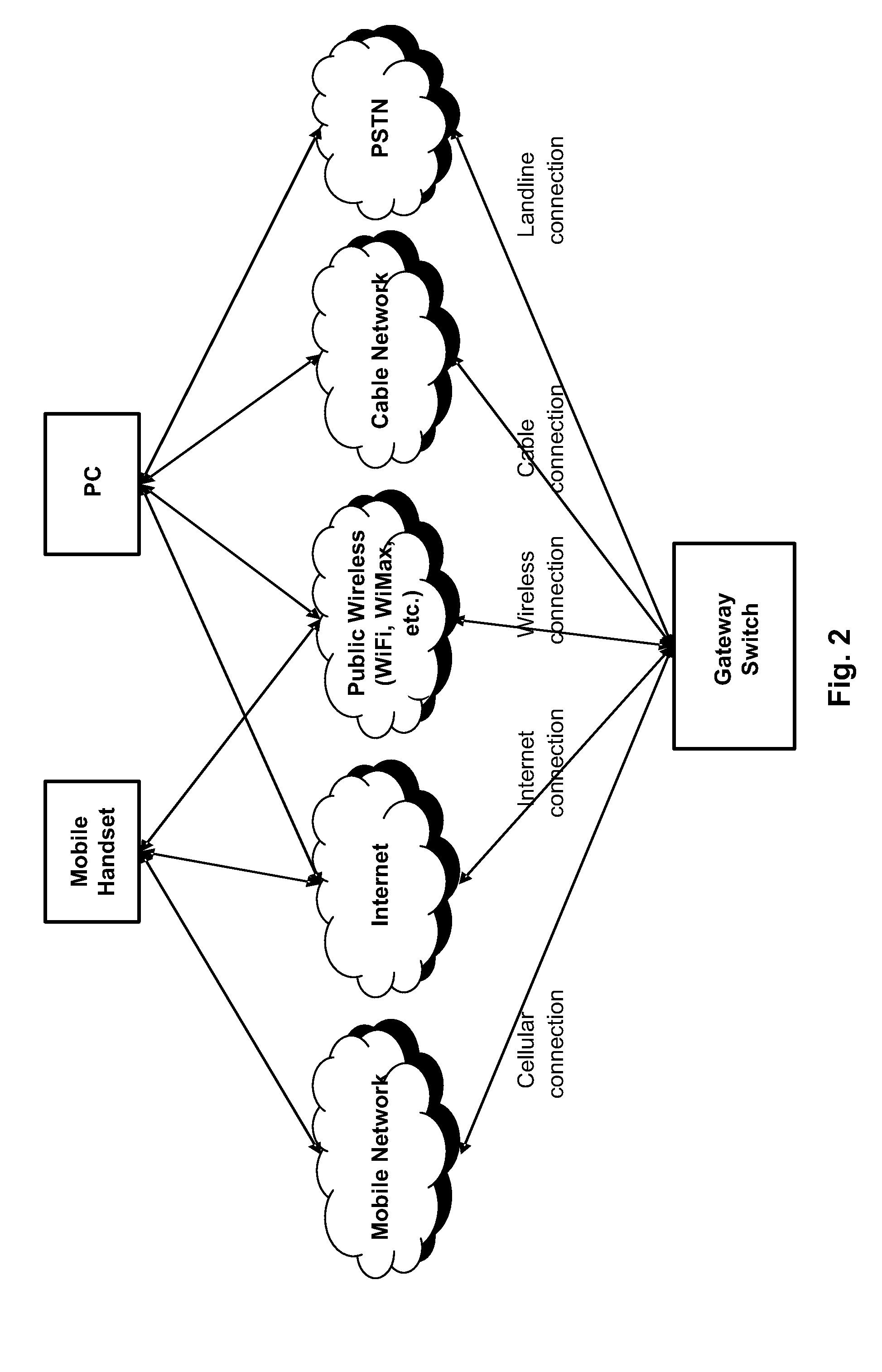
InactiveUS20100085948A1Data switching by path configurationRadio transmissionAccess networkNetwork connection
A gateway switch comprises: two or more transceiving modules, wherein each of the transceiving modules is capable of transmitting and receiving data, wherein the data is an analog signal or a digital signal, and wherein each of the transceiving modules provides a different network connection type; a system module for processing the received data in accordance with one or more rules; and a switching module for symmetrically switching the processed data from any one of the transceiving modules to a selected one of the transceiving modules for transmission of the processed data; wherein the system module selects one of the transceiving modules for the transmission of the processed data as a function of the rules.
Owner:NOOSPHERE COMM
Runtime adaptable security processor
InactiveUS20120117610A1Sharply reduces TCP/IP protocol stack overheadImprove performanceComputer security arrangementsSpecial data processing applicationsInternal memoryApplication software
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer.
Owner:MEMORY ACCESS TECH LLC
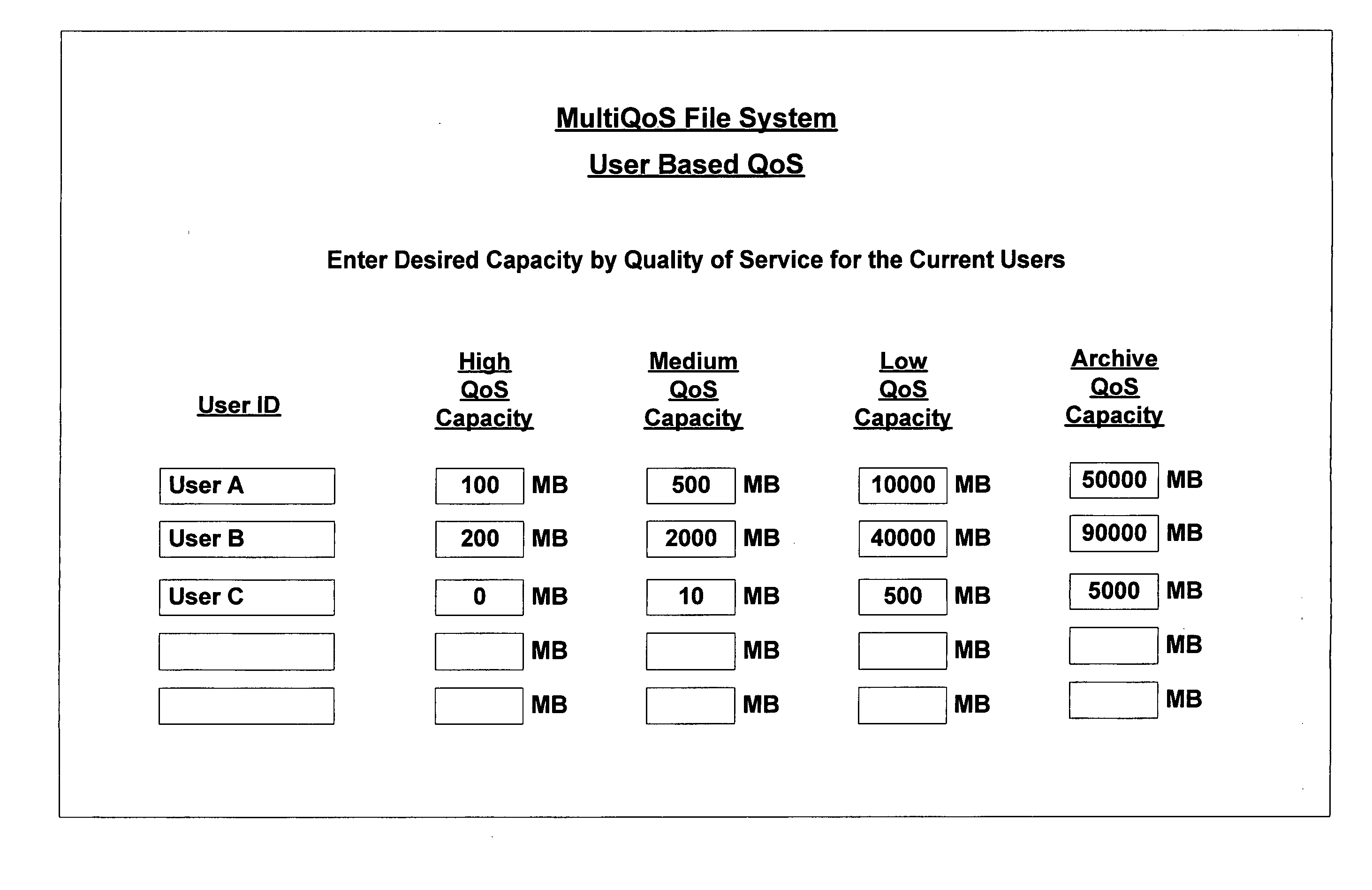
Multiple quality of service file system
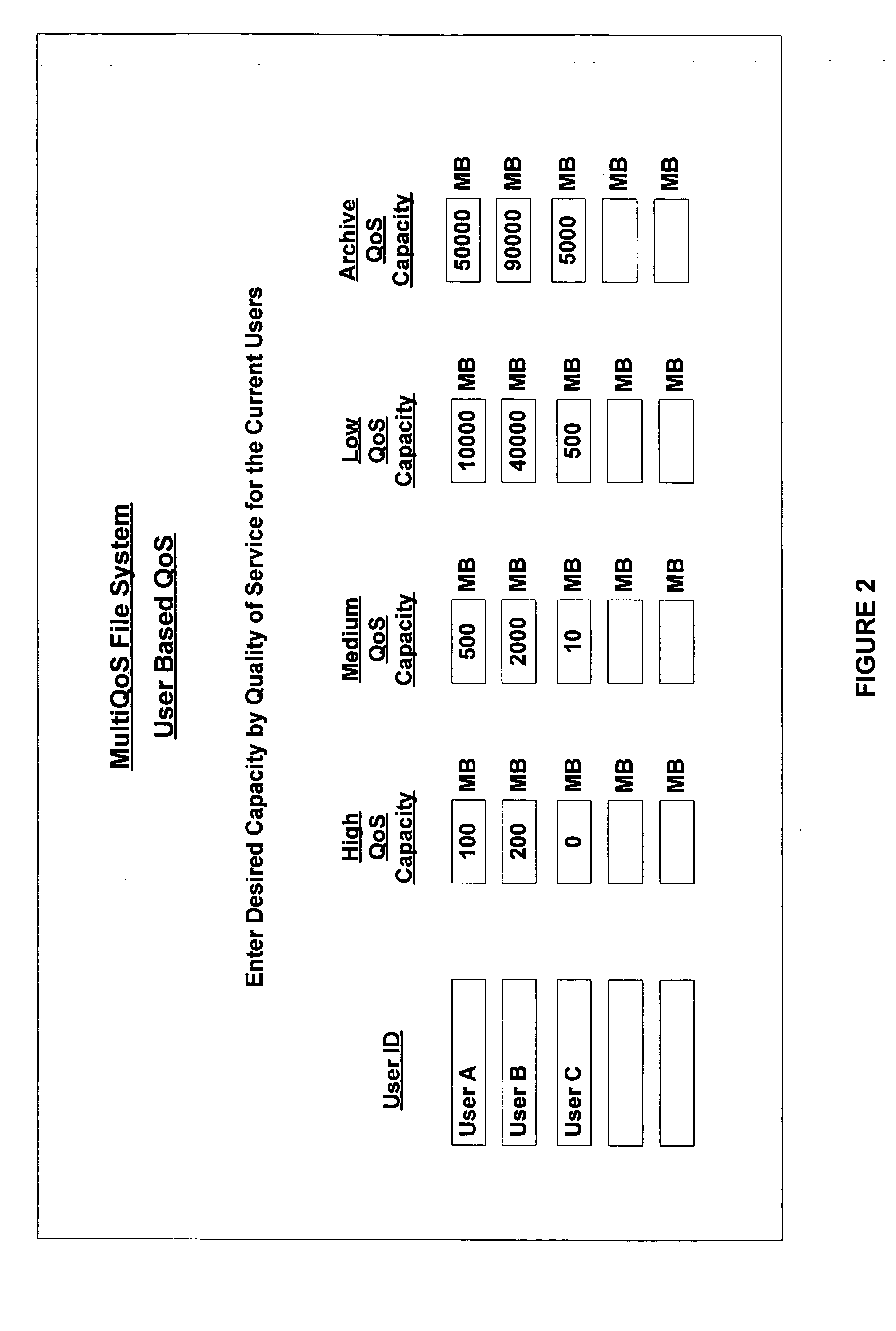
InactiveUS20070083482A1Enhances descriptive informationIncreasing the IT administrator workloadDigital data information retrievalSpecial data processing applicationsQuality of serviceFile system
The invention relates to a multiple QoS file system and methods of processing files at different QoS according to rules. The invention allocates multiple VLUNs at different qualities of service to the multiQoS file system. Using the rules, the file system chooses an initial QoS for a file when created. Thereafter, the file system moves files to different QoS using rules. Users of the file system see a single unified space of files, while administrators place files on storage with the new cost and performance according to attributes of the files. A multiQoS file system enhances the descriptive information for each file to contain the chosen QoS for the file.
Owner:PILLAR DATA SYSTEMS
Information-embedding apparatus, encoder, tamper-detecting apparatus, information-embedding method, tamper-detecting method, and recording medium having program recorded therein for executing both of the methods
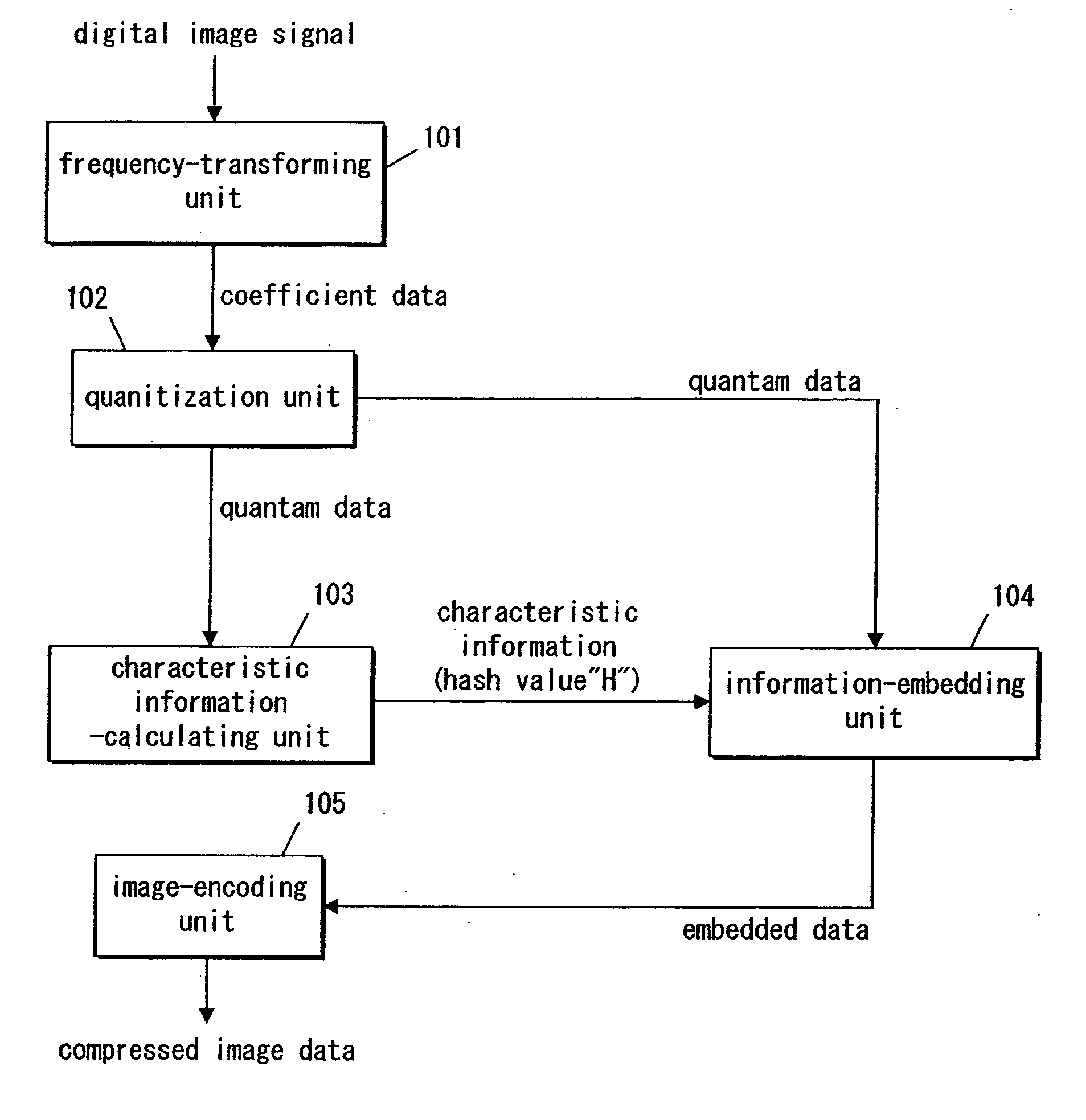
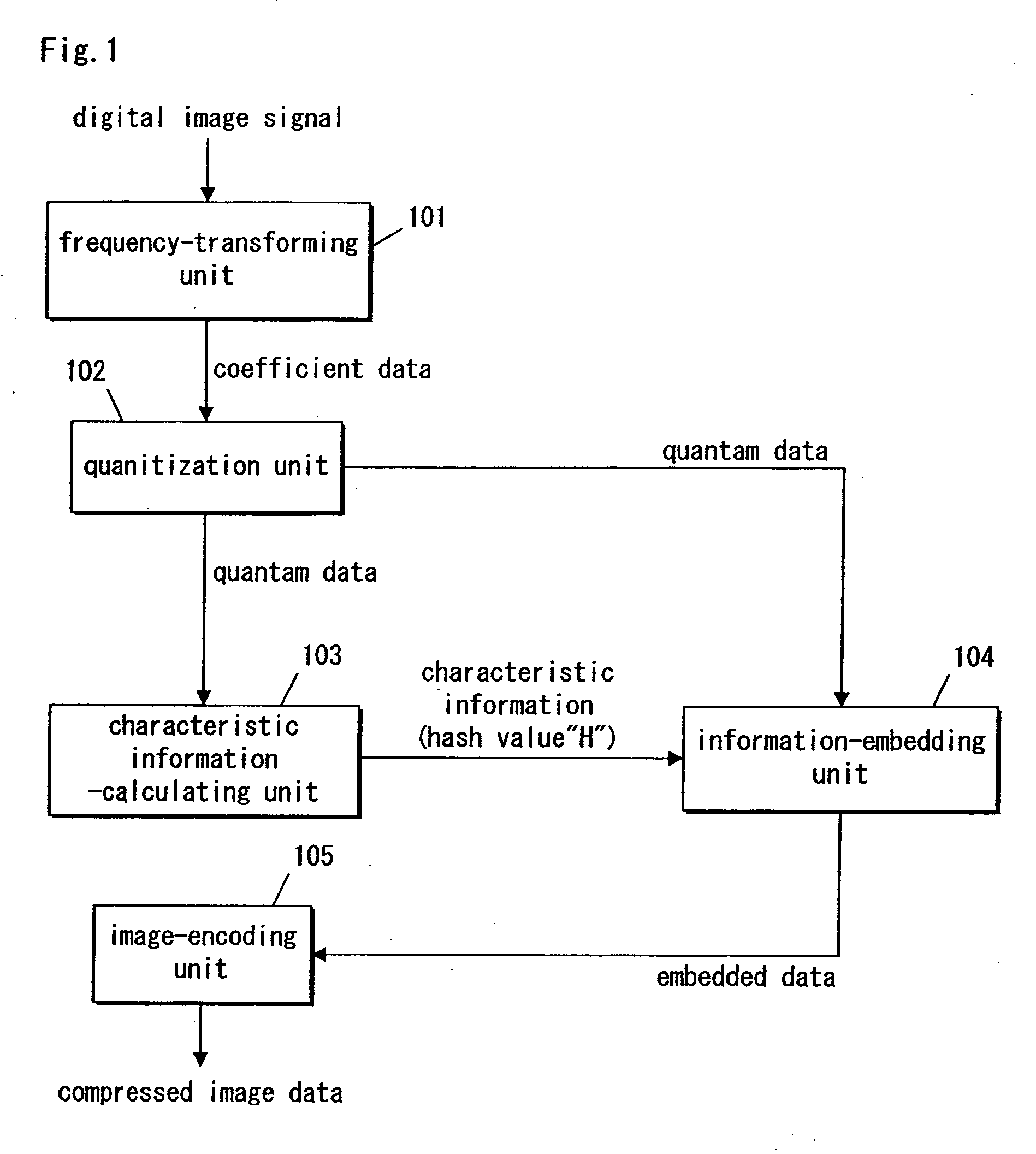
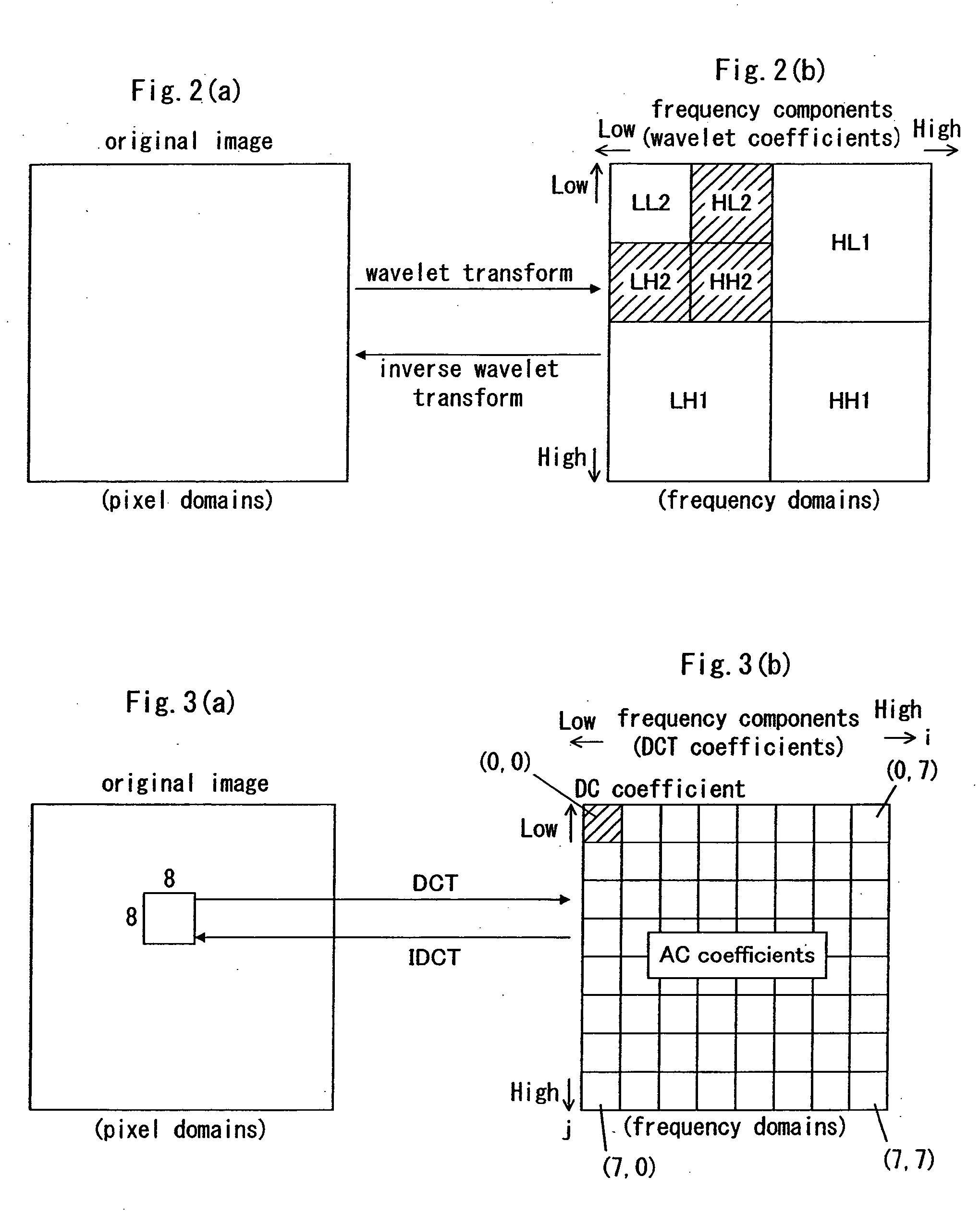
InactiveUS20060013488A1Possible to detectEliminate needCharacter and pattern recognitionImage watermarkingInformation embeddingDigital image
A digital image signal is transformed in frequency, thereby providing partitioned frequency components. Characteristic information is calculated in accordance with a coefficient at a first frequency domain that is selected from among the partitioned frequency components. A coefficient at a second frequency domain is handled in accordance with predetermined rules, thereby embedding the characteristic information into the coefficient at the second frequency domain. The second frequency domain is selected from among areas that differ from the first frequency domain. The frequency coefficients that exhibit several frequency components are encoded in a predetermined manner, thereby producing compressed image data.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Content Access Rights Management
ActiveUS20080215509A1Easy to manageEasy access managementDigital data processing detailsDigital computer detailsDocument handlingRights management
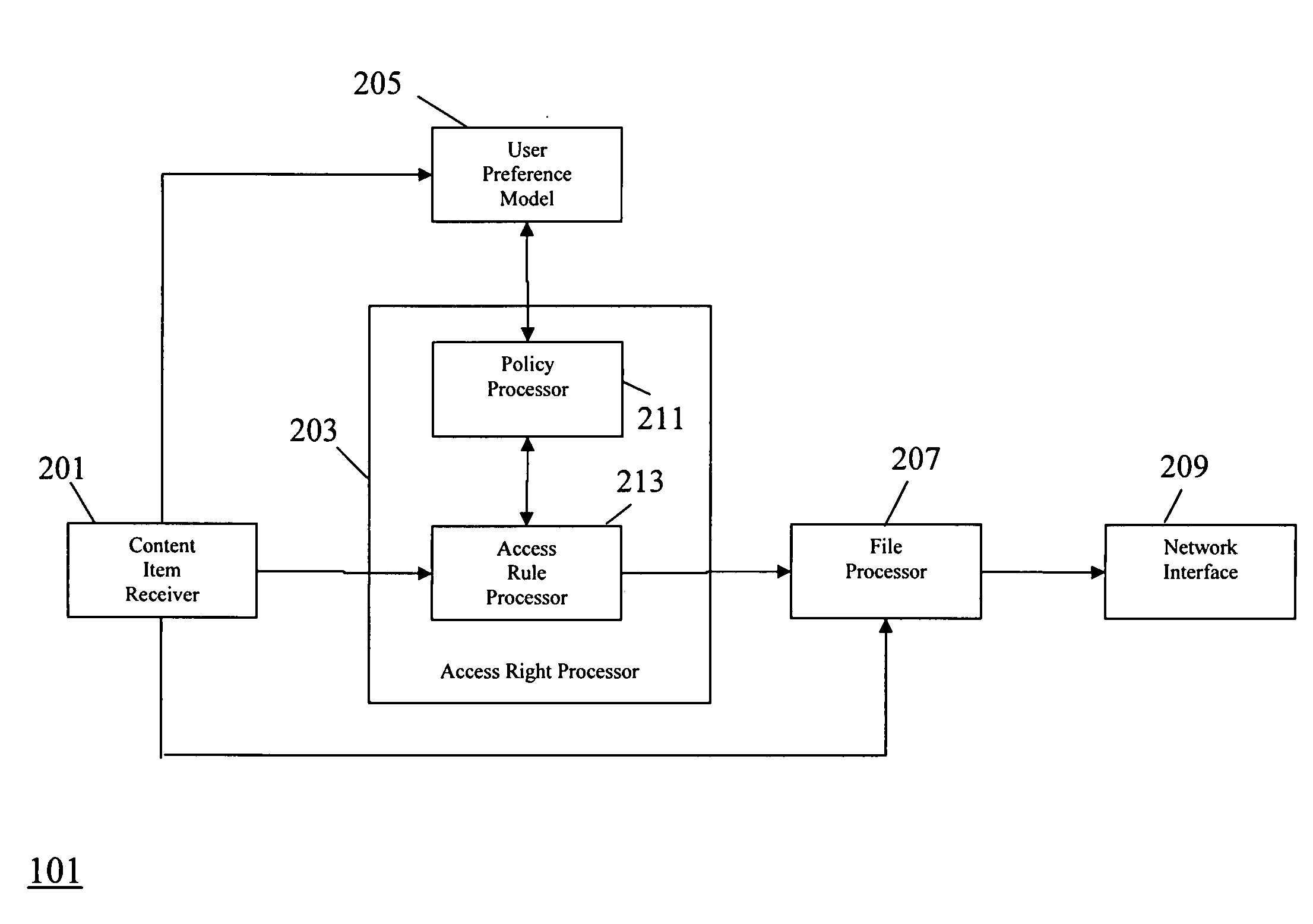
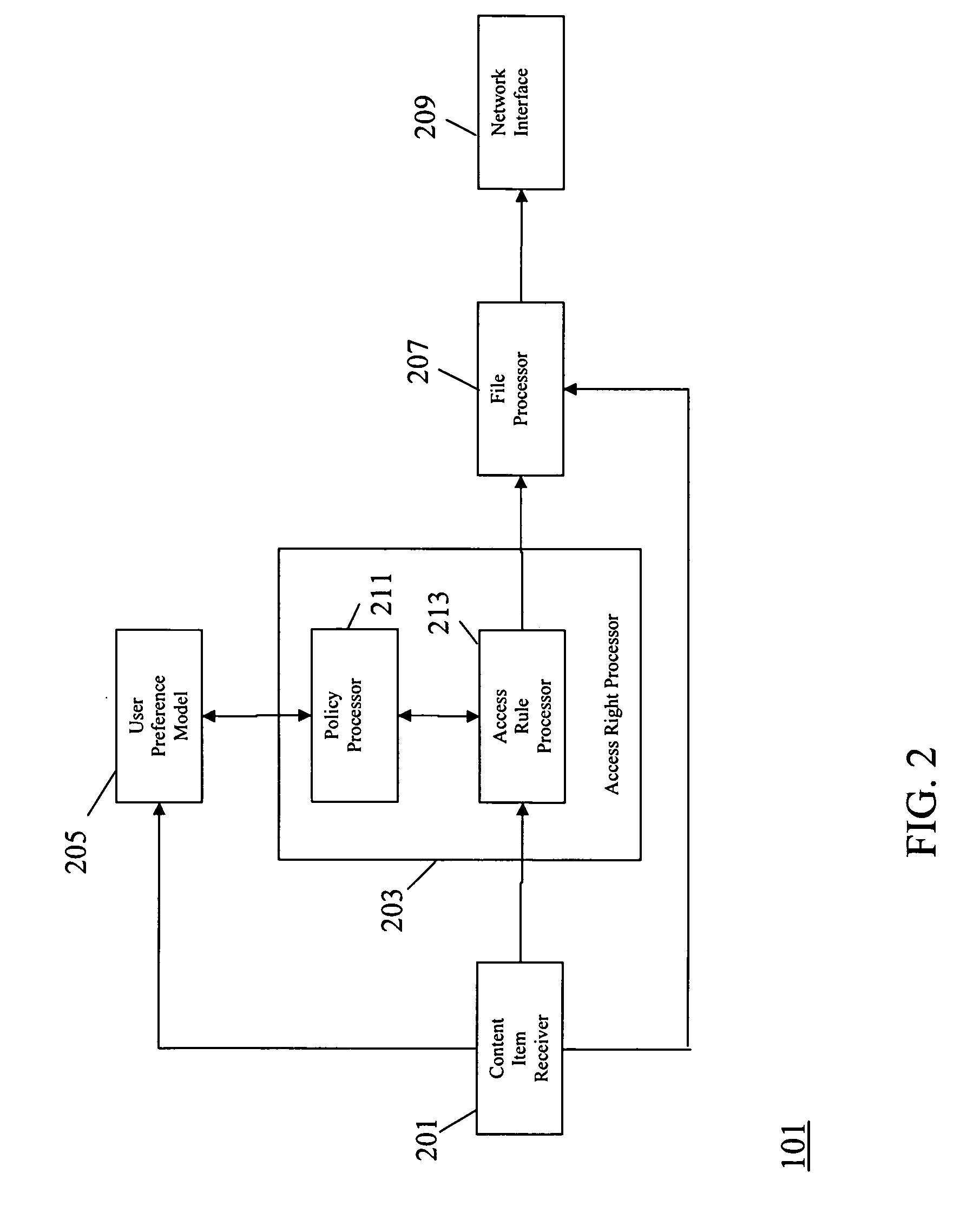
An apparatus (101) comprises a content item receiver (201) which receives a content item such as a digital photo or an audio or video clip. A user preference model (205) generates data indicative of user preferences for content item access. An access rule processor (203) determines a set of self-governance rules for the first content item in response to the user preference model. The self-governance rules are indicative of allowable actions for the first content item in other devices. A file processor (207) includes the set of self-governance rules with the content item and a network interface (209) transmits the content item to a second apparatus (103). The second apparatus (103) comprises functionality for restricting access to the content item in accordance with the set of self-governance rules. The invention may provide improved access rights management and in particular for personal content items.
Owner:MOTOROLA SOLUTIONS INC
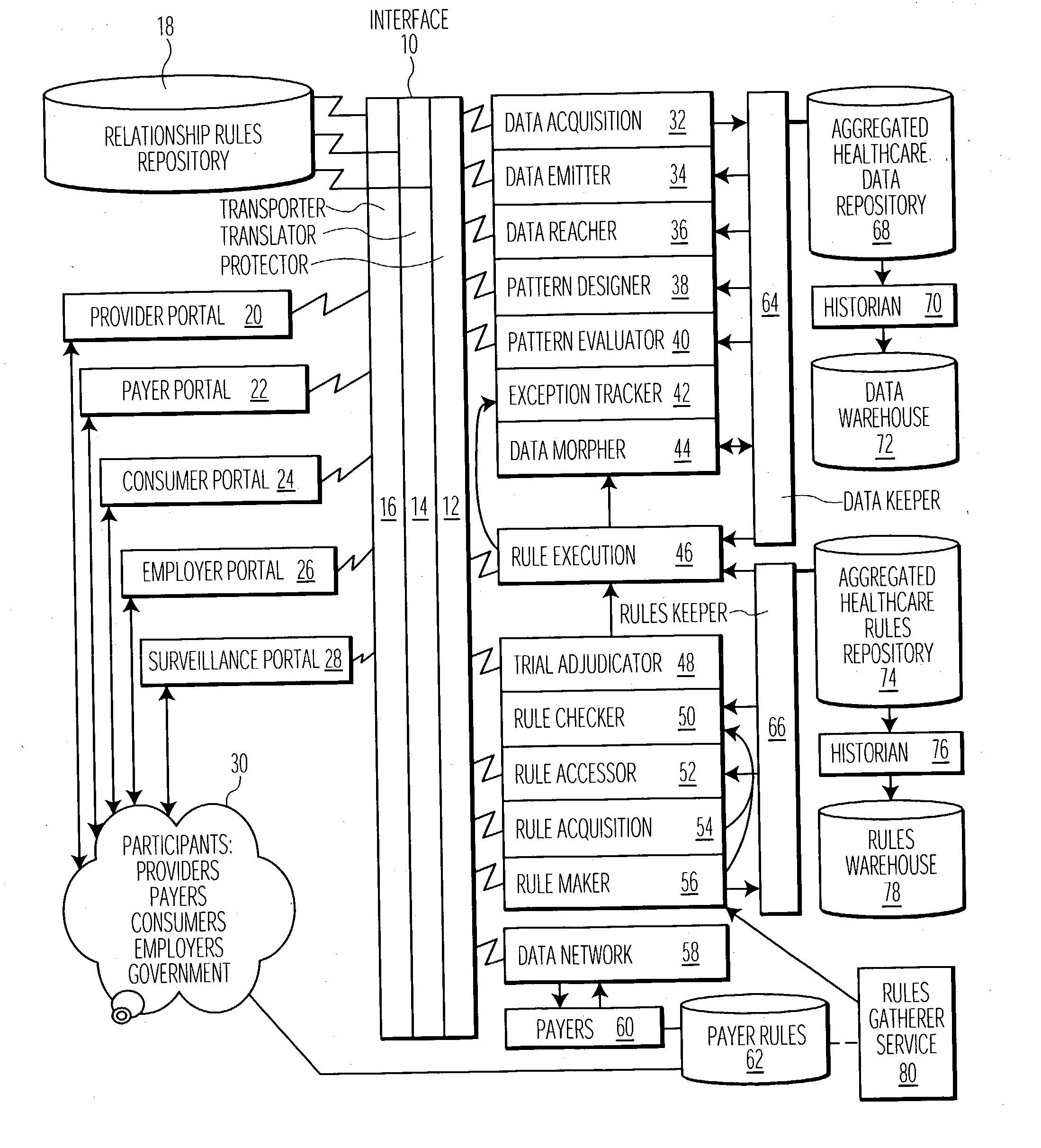
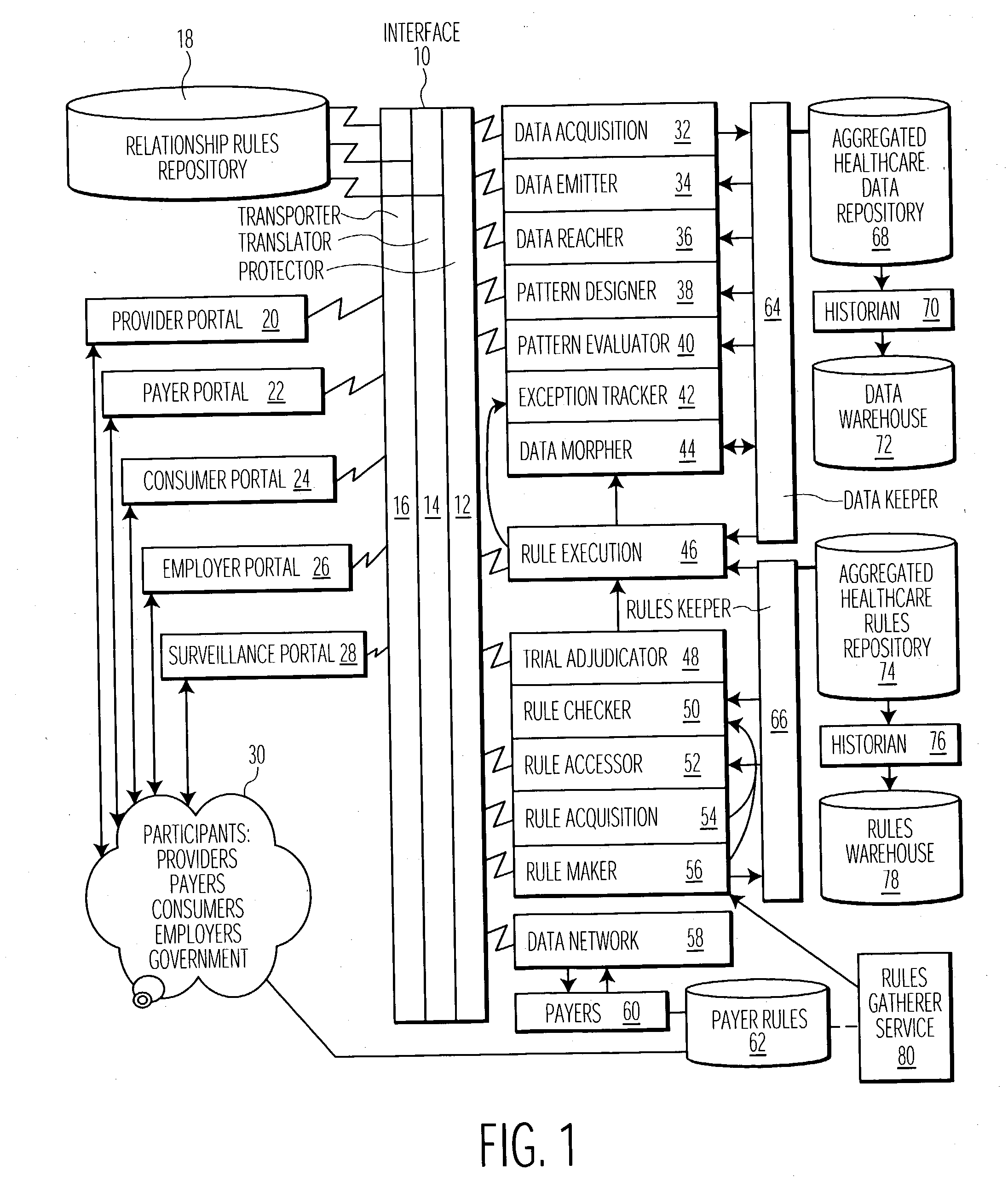
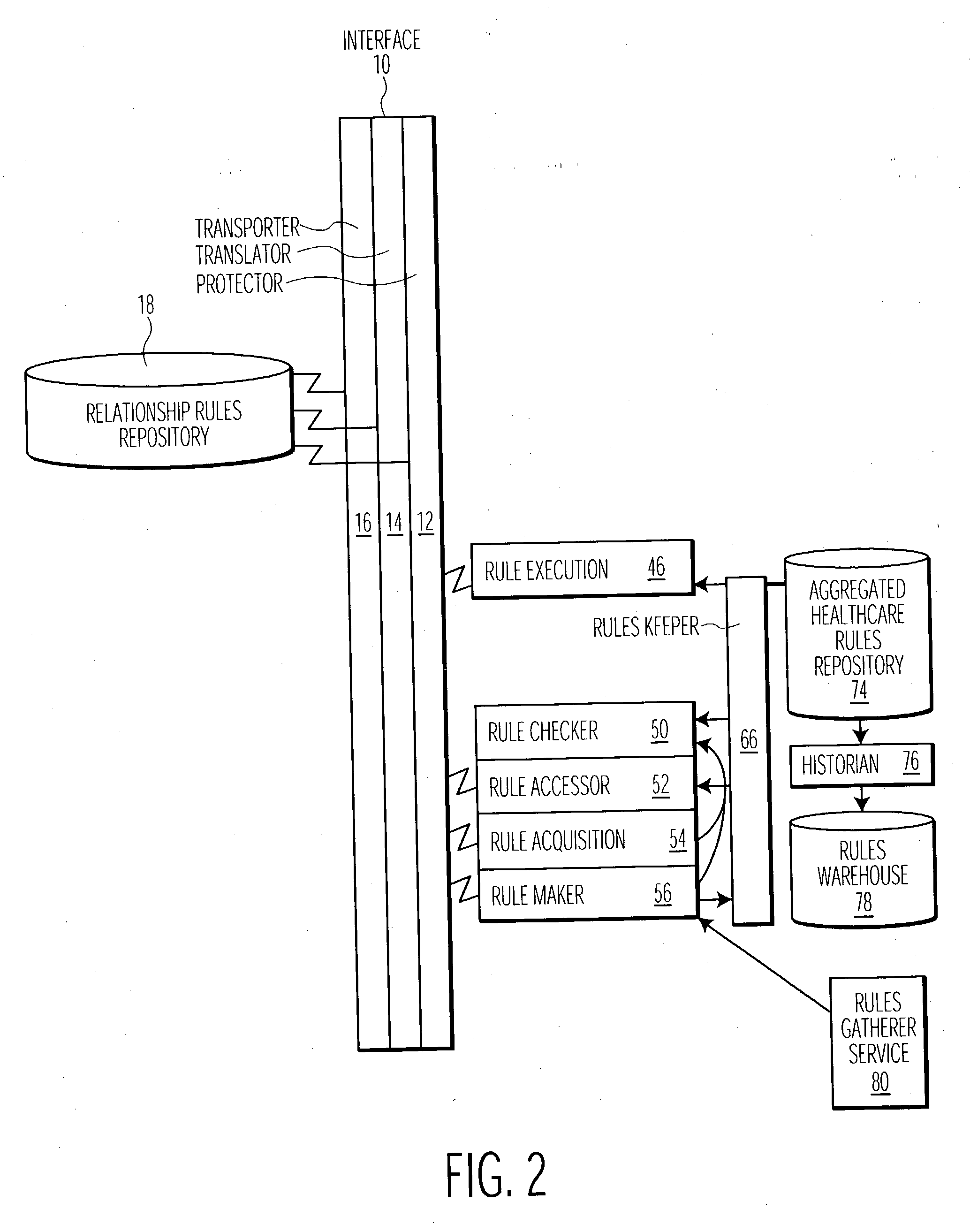
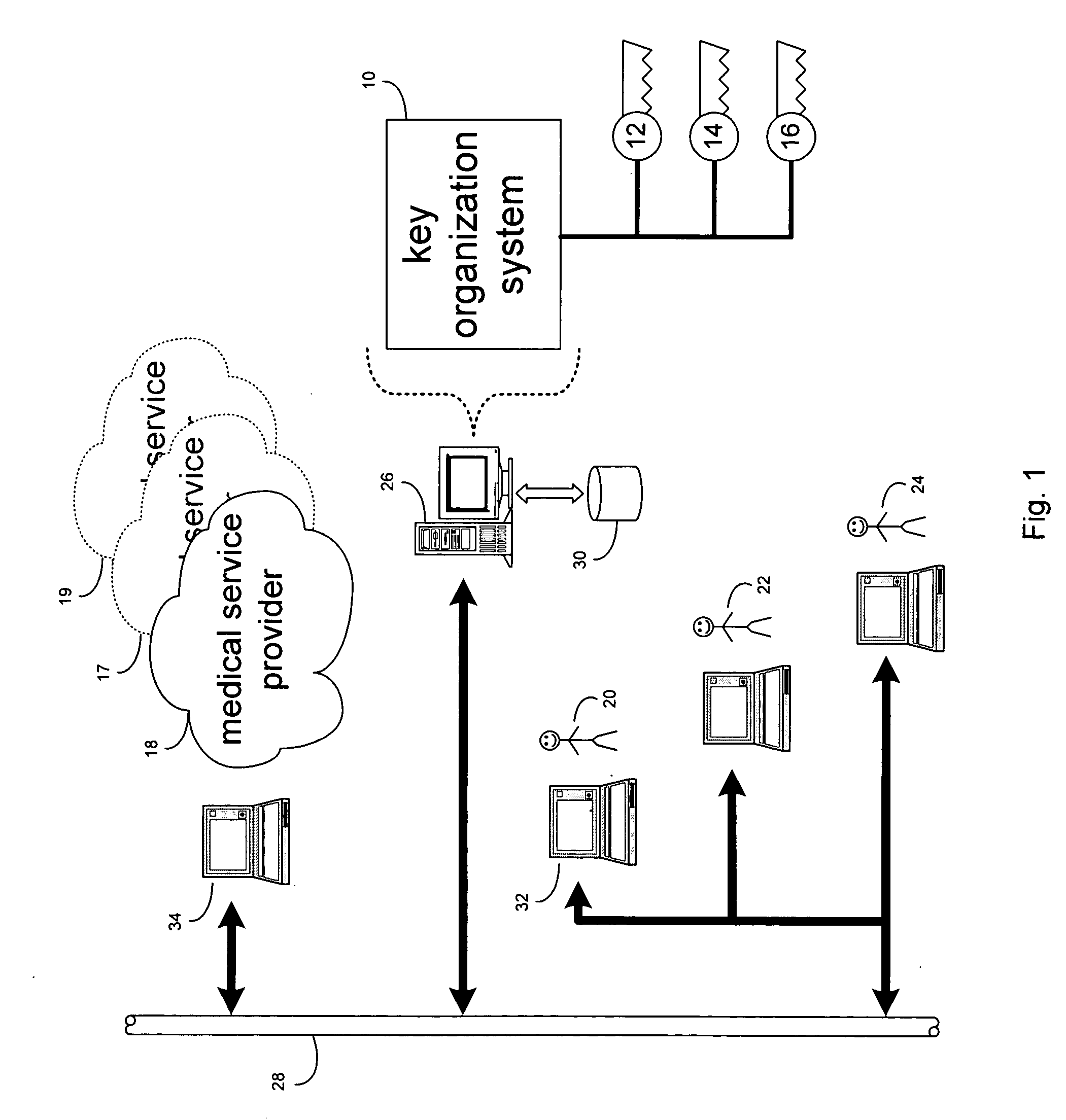
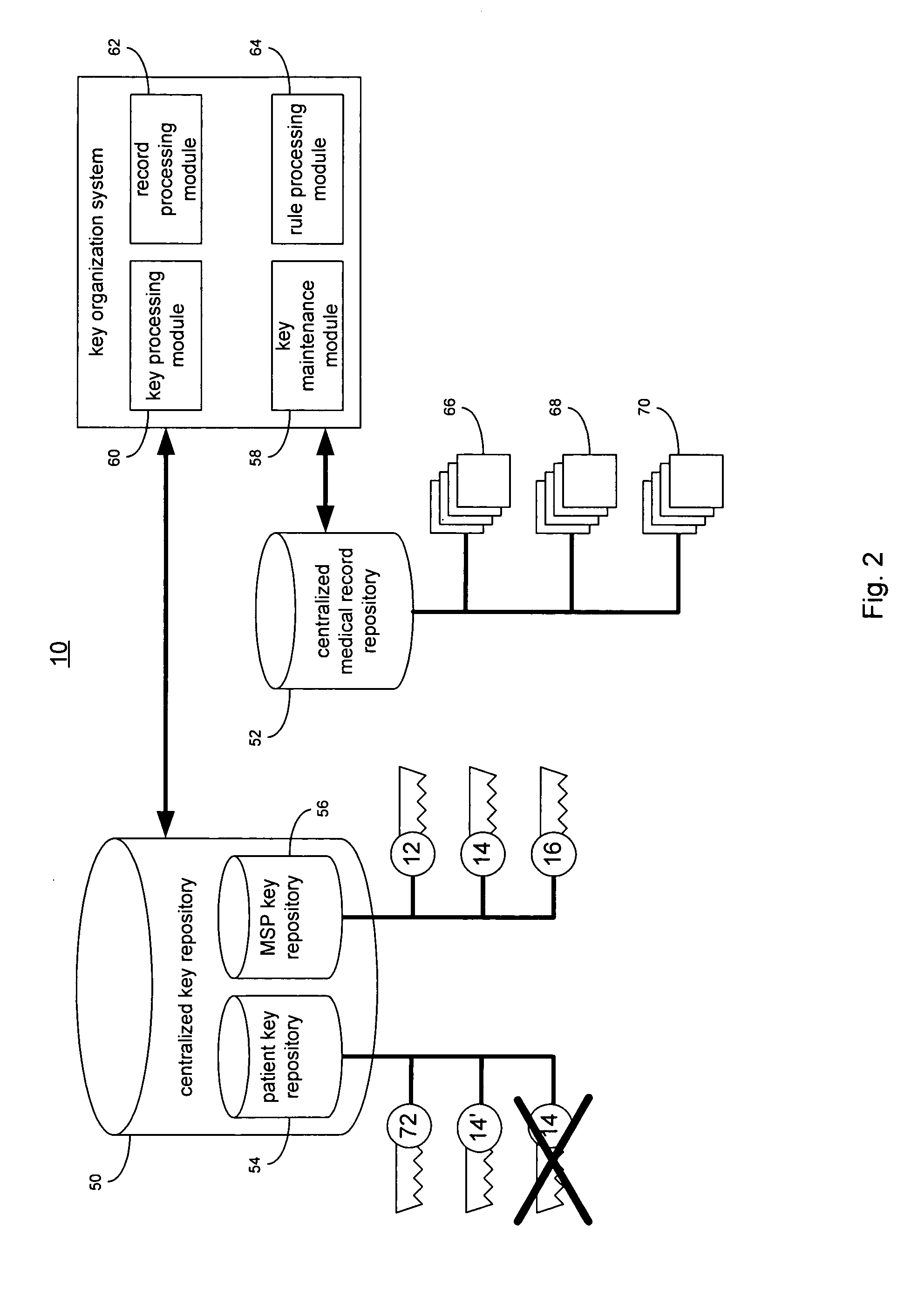
System and user interface supporting use of rules for processing healthcare and other claim data
A centralized rules repository maintains consistently expressed rules used to process patient claim data in supporting medical procedure eligibility verification, patient referrals, treatment authorization, data entry editing, electronic claim submission, claim status determination and electronic remittance processing. A system for managing rules used for processing claim data related to provision of healthcare to a patient includes an interface processor for acquiring data representing rules from a plurality of different sources. The system includes a rules repository for accumulating data representing acquired rules and a rules processor for initiating application of a selected rule derived from the repository to process claim data in response to a received message. A result processor processes a result being derived by the application of the selected rule to the claim data for output. The interface processor also transforms acquired rules to a common syntax suitable for storage in the rules repository.
Owner:SIEMENS MEDICAL SOLUTIONS HEALTH SERVICES CORPORAT
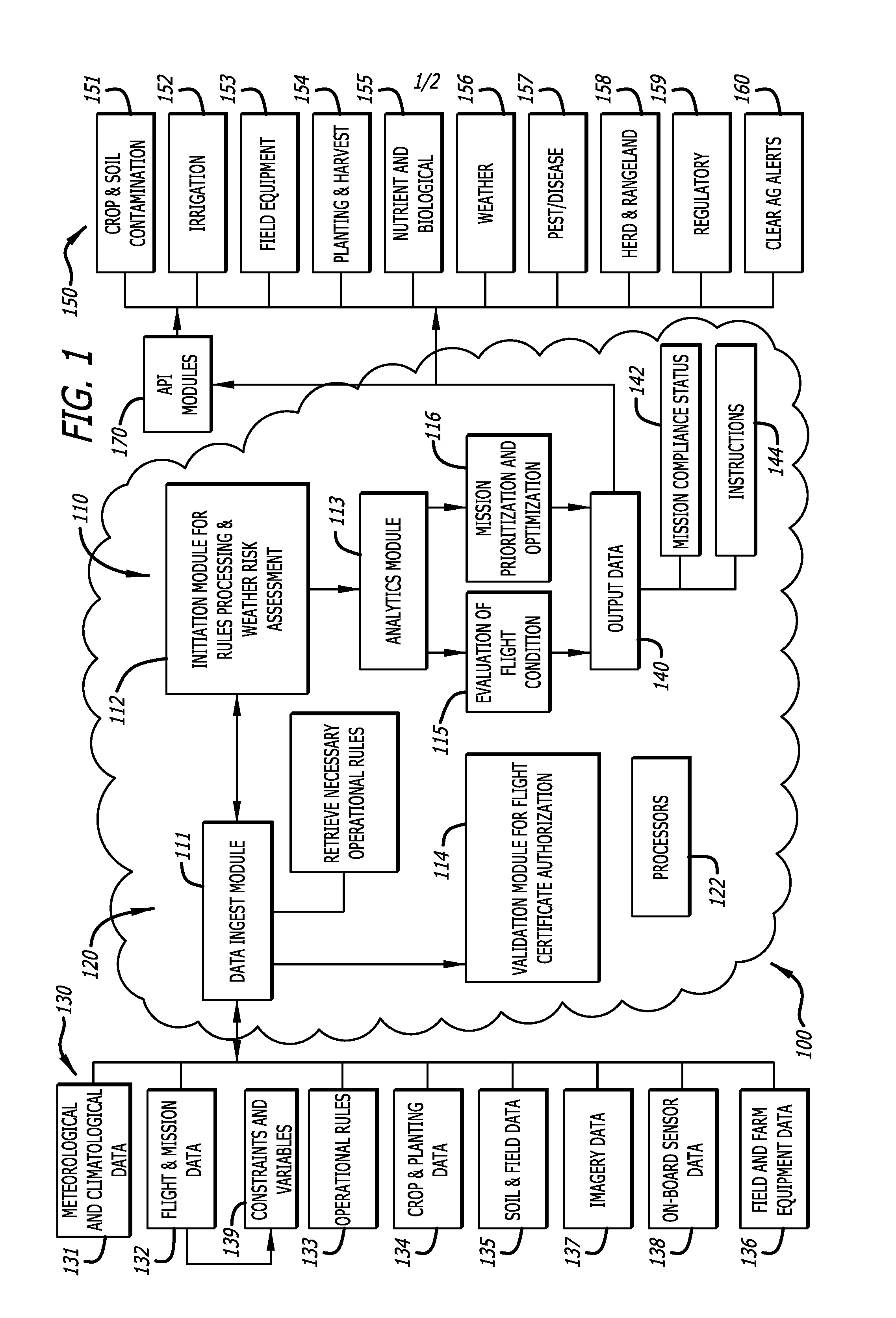
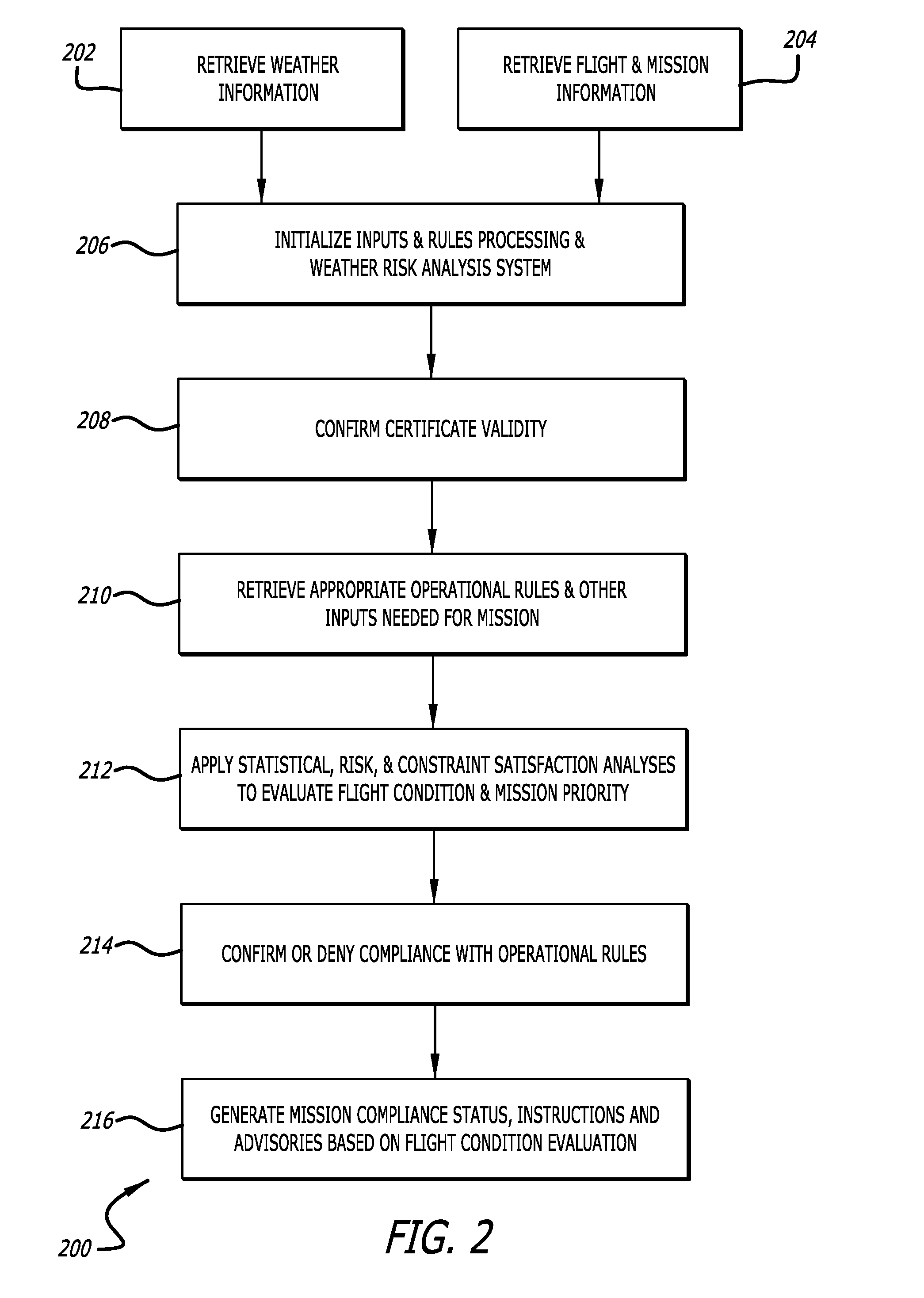
Mission prioritization and work order arrangement for unmanned aerial vehicles and remotely-piloted vehicles
ActiveUS20160225263A1Avoid interferenceUnmanned aerial vehiclesRemote controlled aircraftJet aeroplaneFlight vehicle
A framework for combining a weather risk analysis with appropriate operational rules includes a data initialization component, a rules processing component, and one or more weather risk analysis and assessment tools to evaluate a flight condition. The framework applies current, historical, predicted and forecasted weather data to the one or more operational rules governing a mission, a payload, a flight plan, a craft type, and a location of the mission for aircraft such as an unmanned aerial vehicle or remotely-piloted vehicle, and generates advisories based on the evaluation of flight conditions such as a mission compliance status, instructions for operation of unmanned aircraft, and management advisories. The flight condition advisories include either a “fly” advisory or a “no-fly” advisory, and the framework may also provide a mission prioritization and optimization system.
Owner:DTN LLC
Method and system for capturing streaming data by an actionable information engine
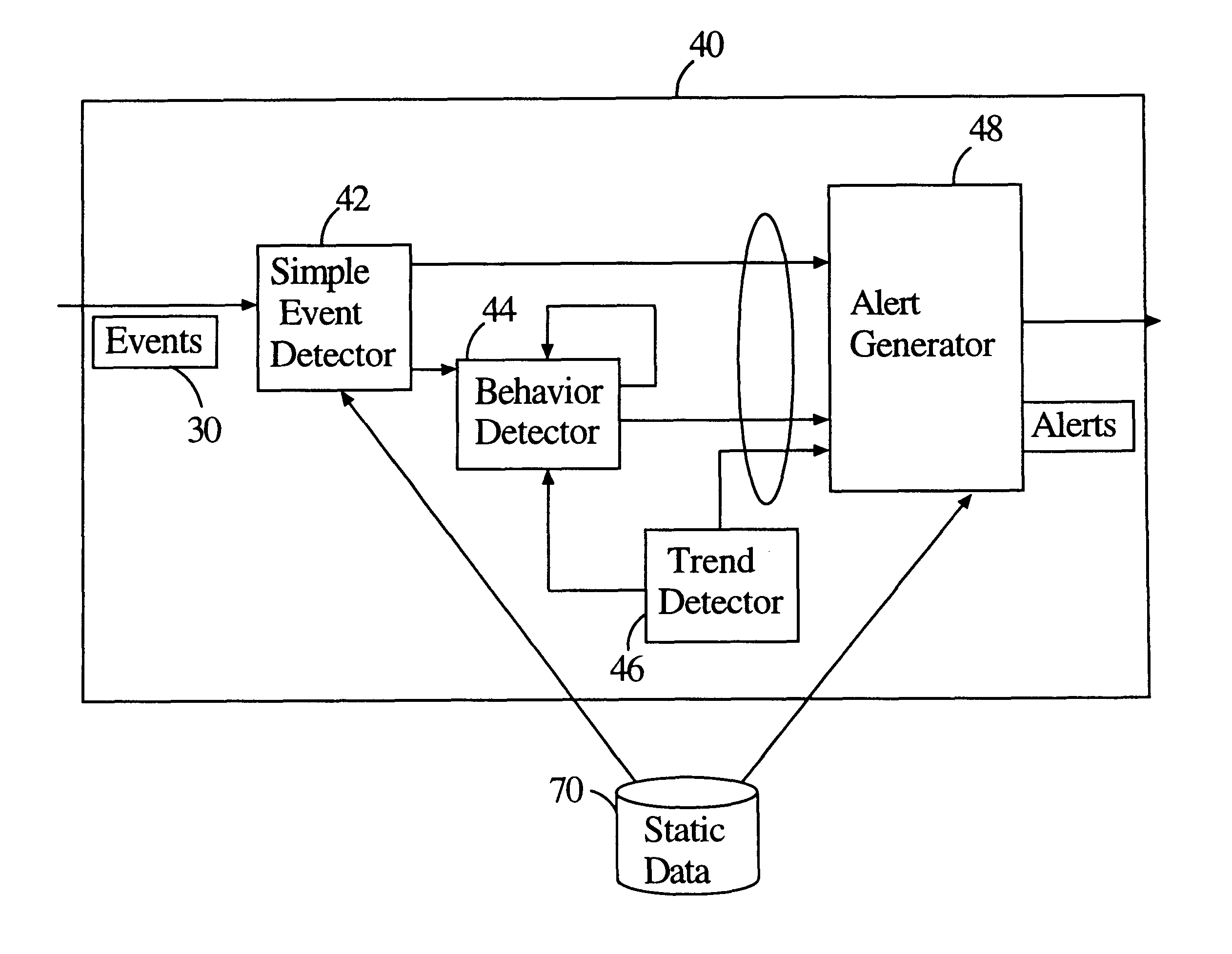
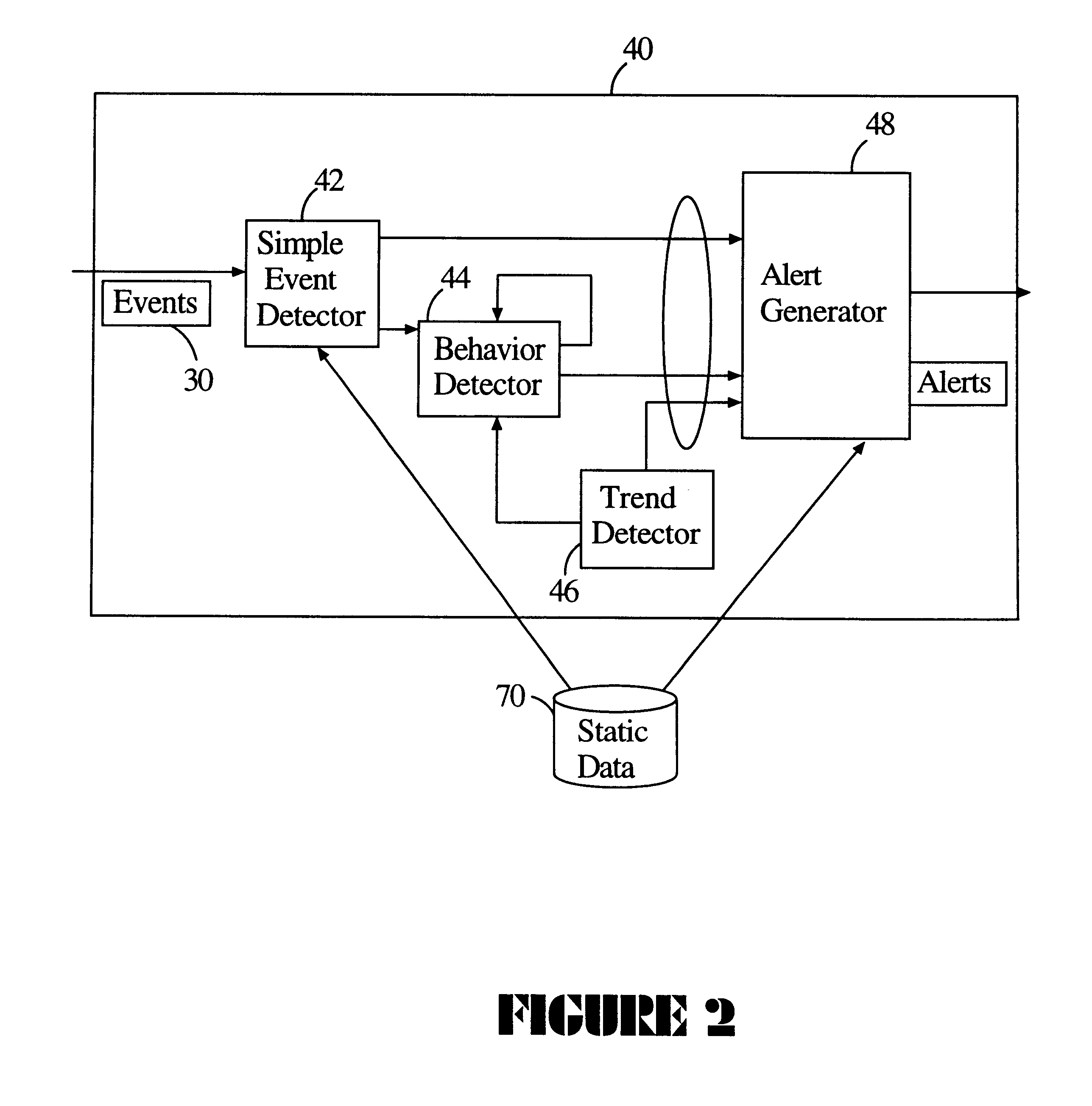
The present invention captures streaming data and avoids continual retrieval. The invention only looks at data once, has a time dependency built into it, and data that is not consumed or relevant is discarded. The invention includes an engine processor that processes data according to stored information; stored rules that define engine operation, an input events module for receiving events which provides a plurality of events. Events are processed according to stored rules for generating a series of valid results when input events match the rules. Rule states that have been matched to an input event but have not produced a valid result are stored in state storage. The state of a rule as stored enables the engine to provide a valid result output upon a future reception of an input event necessary to complete the rule. Transaction log module monitors the operation of the engine for specified time period.
Owner:ELITY SYST
Rule management method and system
A rule processing method includes defining a target group of patients chosen from a group of existing patients. An action to be taken concerning one or more patients within the target group of patients is defined, and an execution time for the action is scheduled.
Owner:COGNIZANT TRIZETTO SOFTWARE GRP INC
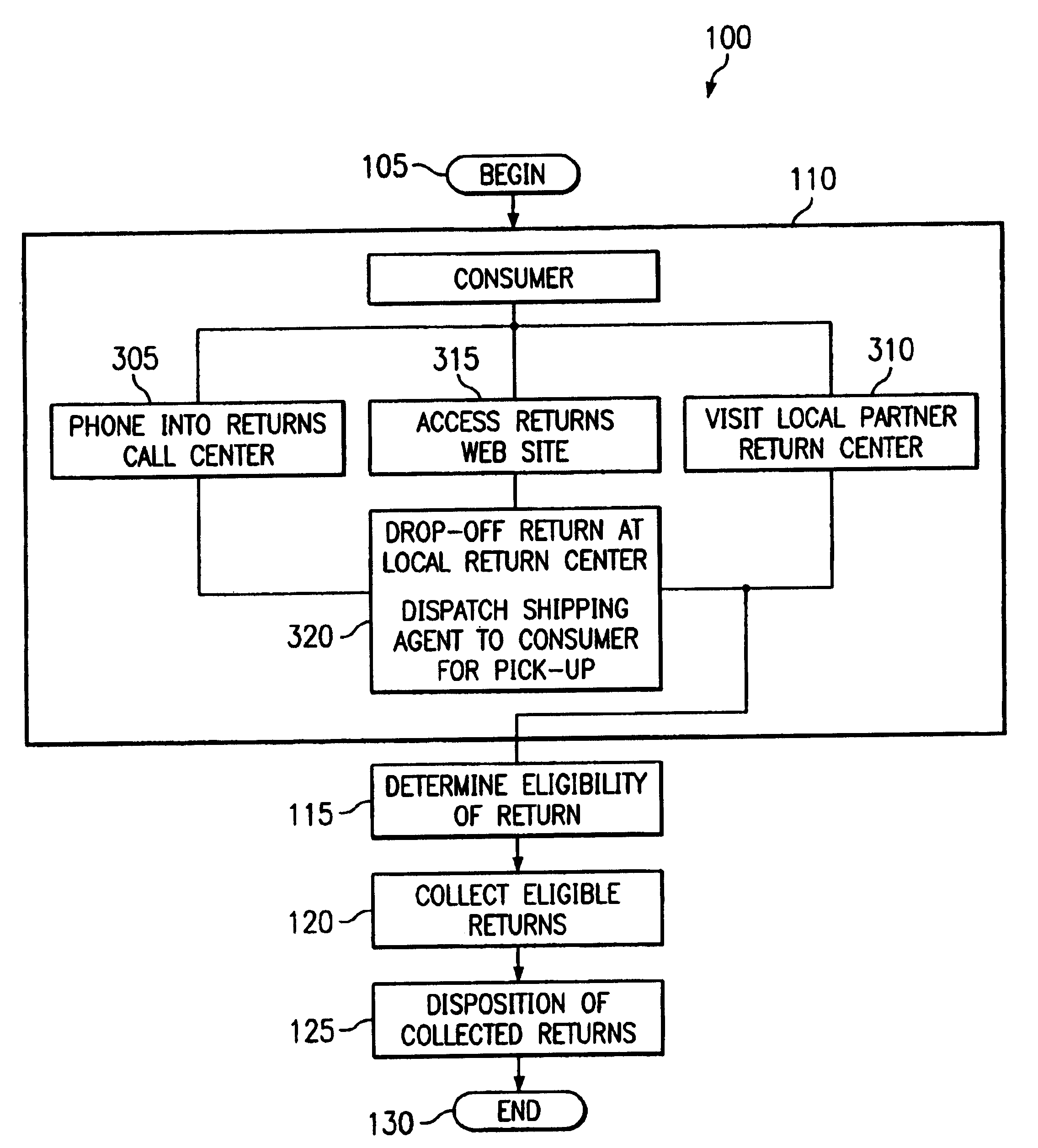
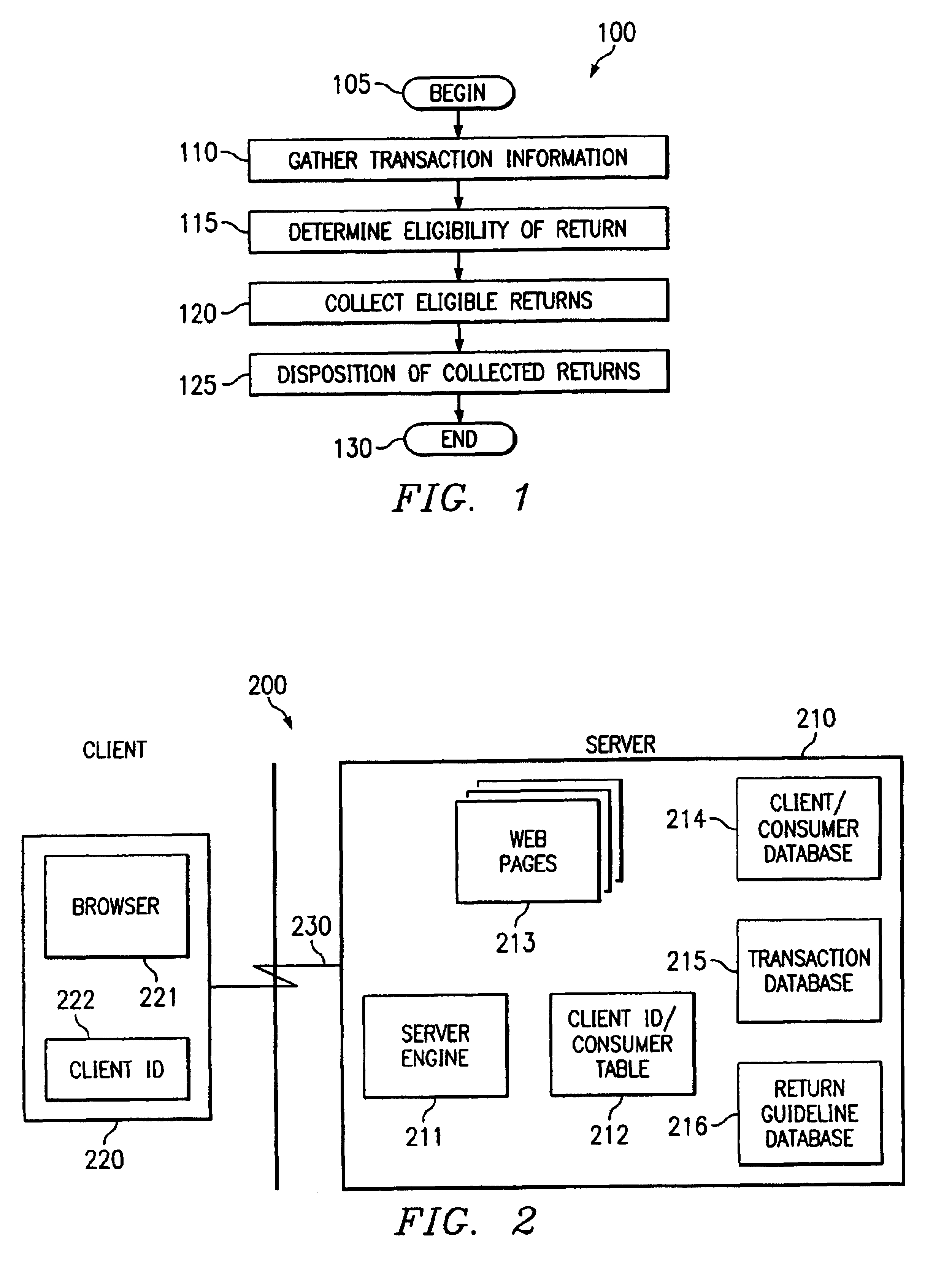
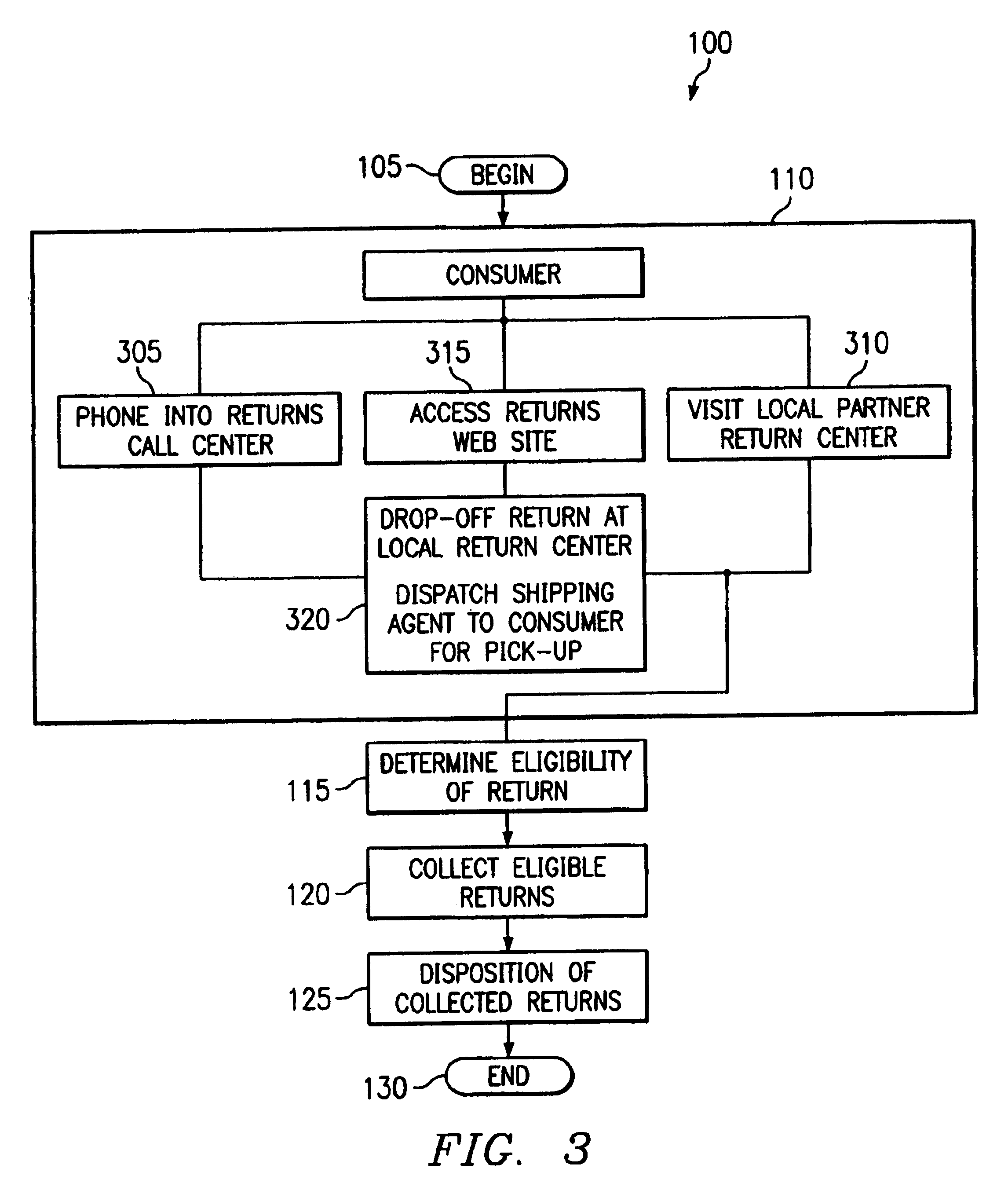
Return centers with rules-based dispositioning of merchandise
InactiveUS7376572B2Eliminates unnecessary shippingLow costFinancePayment architectureDatabaseRule processing
The present invention provides a method and system for processing returns at a return center. The return center accesses return rules of a merchant associated with an item of merchandise that has been returned by a customer. The item is then processed according to one or more of the return rules. The processing may include determining the eligibility of the return, notification to a merchant associated with the return, crediting of an account associated with the customer, and / or subsequent disposition of the return.
Owner:PITNEY BOWES GLOBAL LOGISTICS LLC
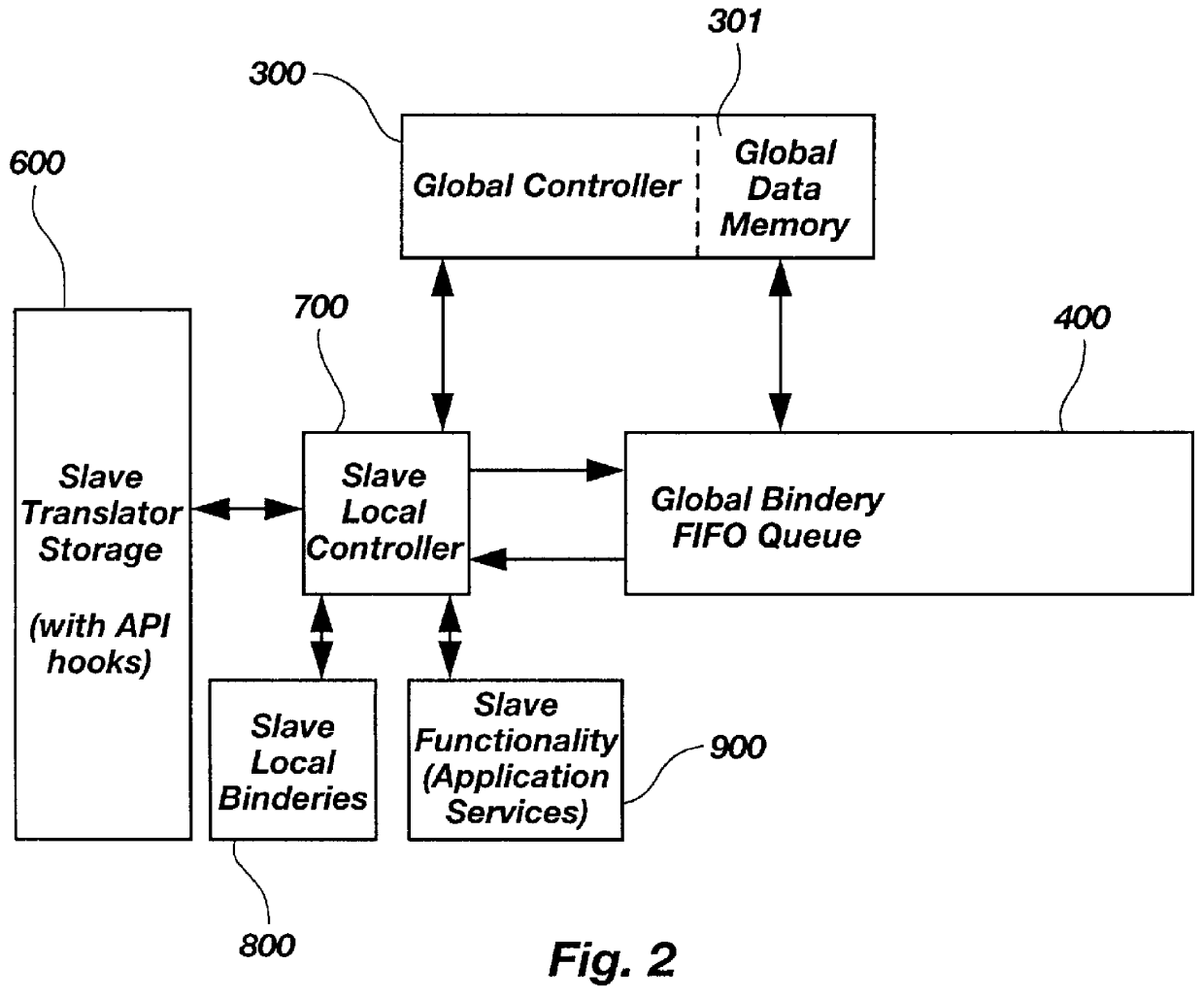
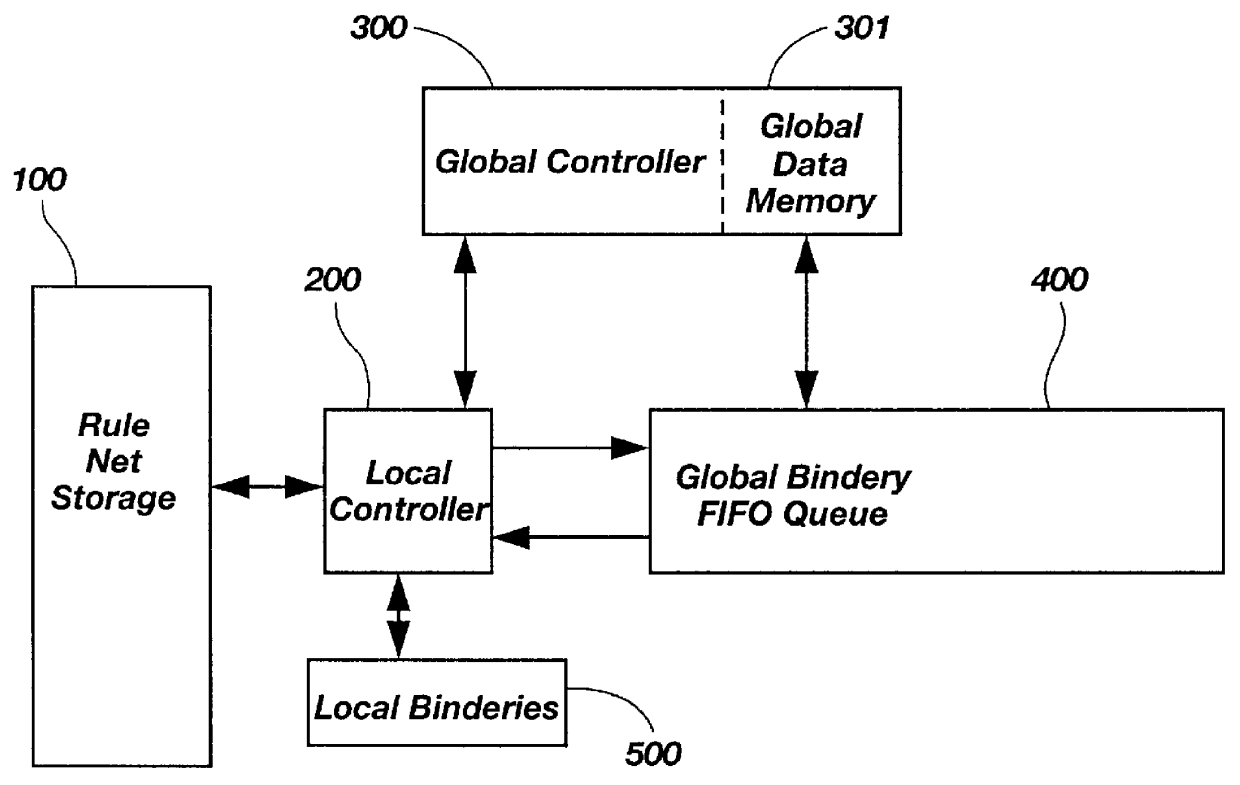
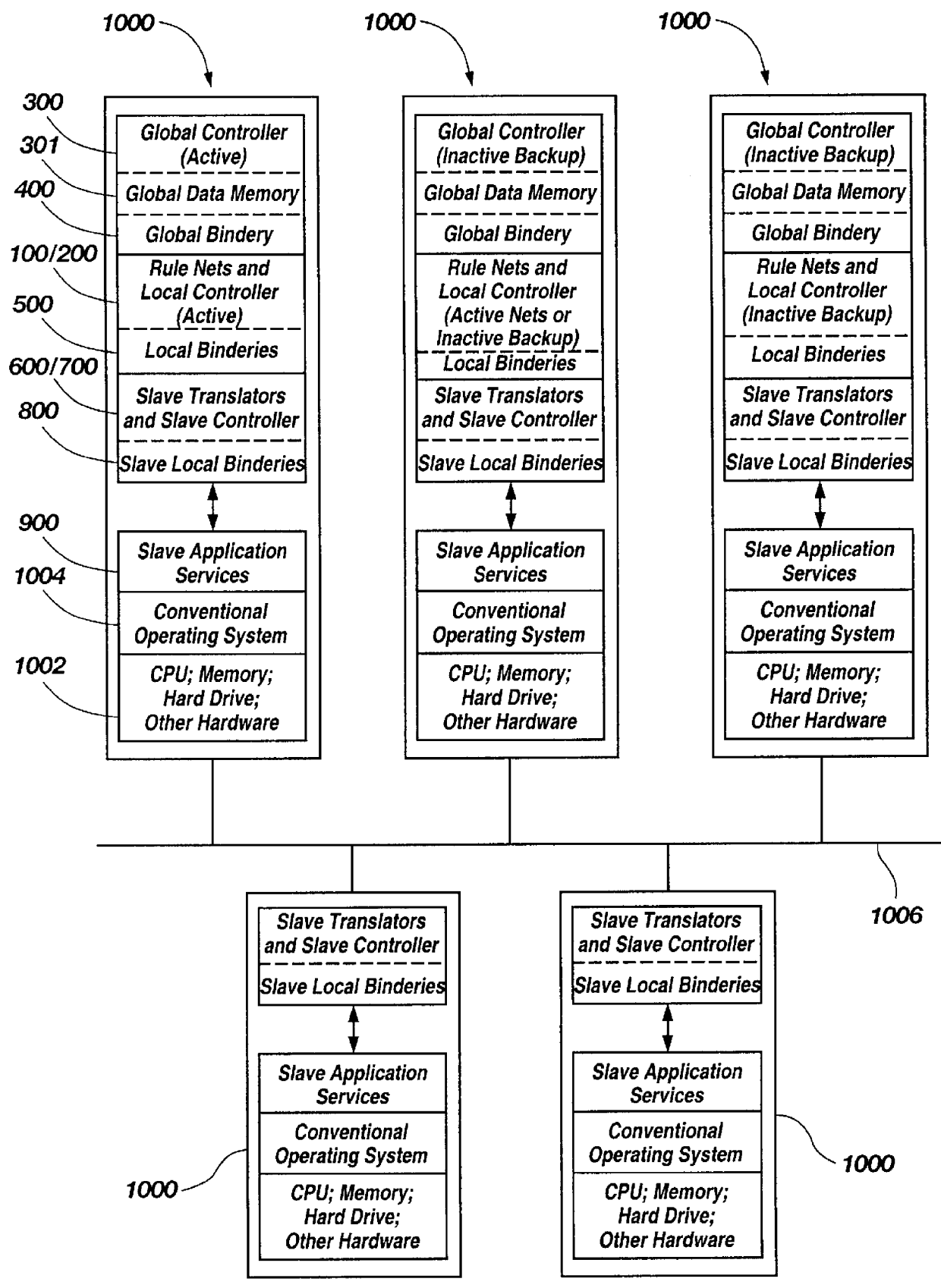
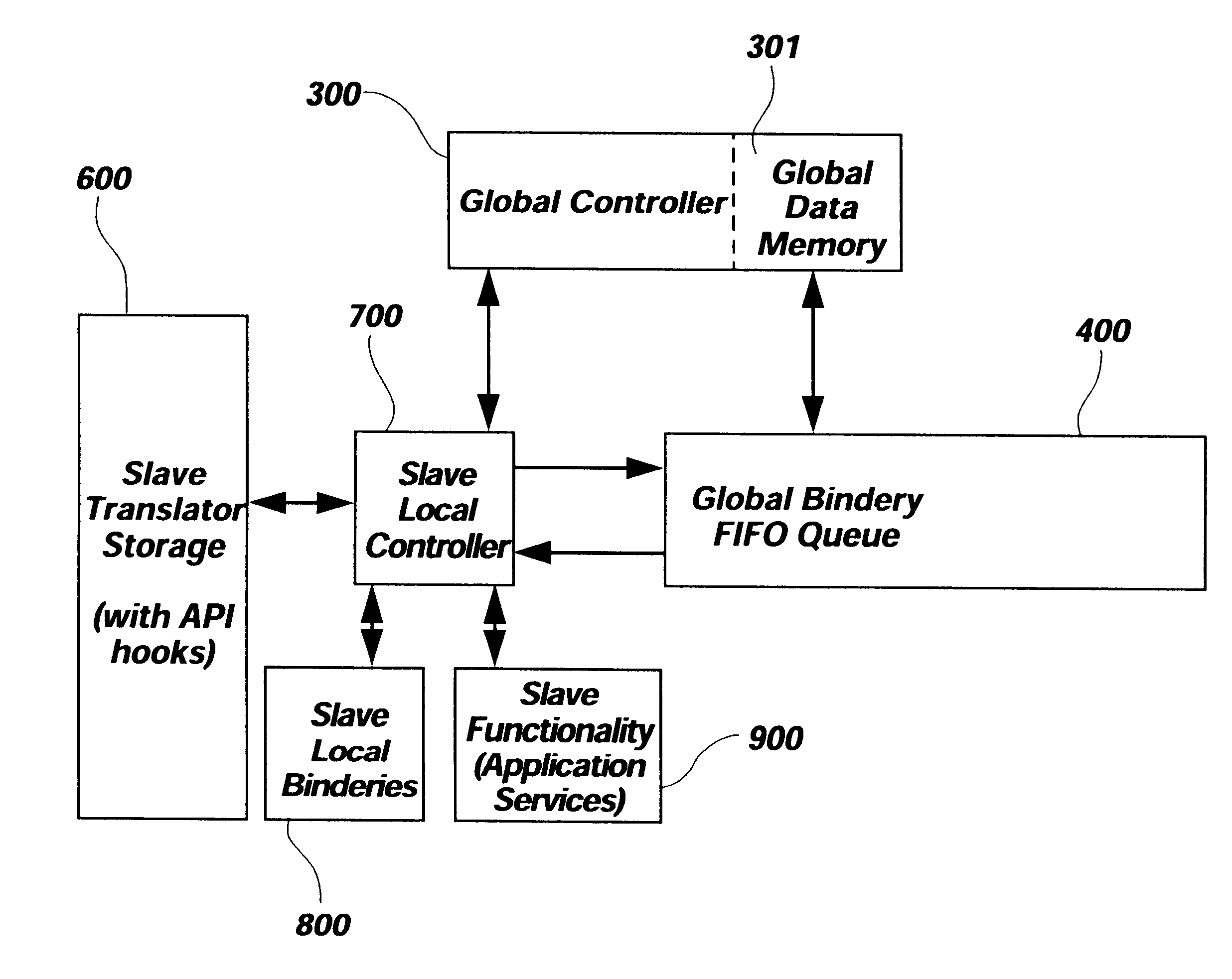
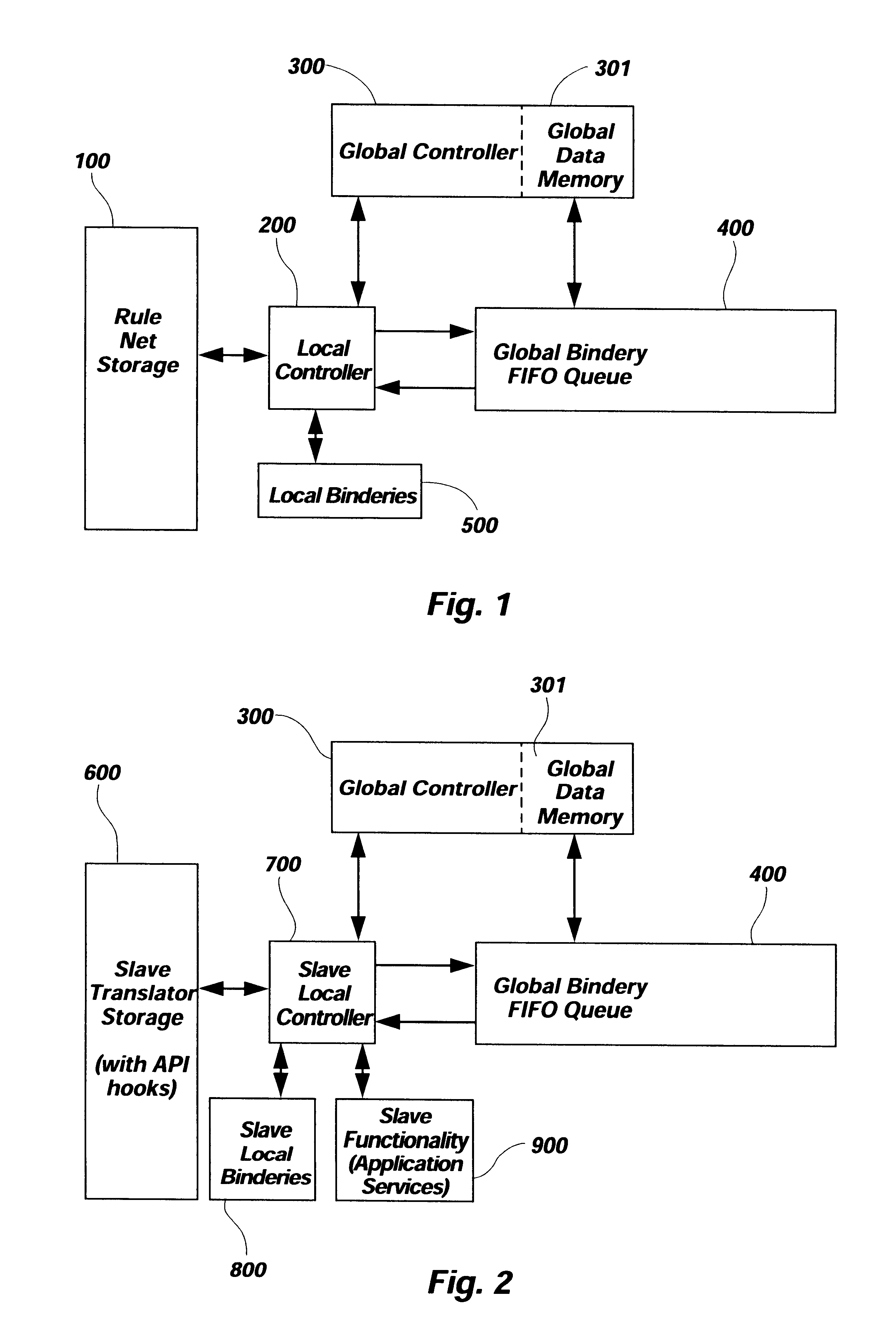
Distributed digital rule processor for single system image on a clustered network and method
InactiveUS6154765AImprove usabilityInterprogram communicationGeneral purpose stored program computerApplication softwareSystem area network
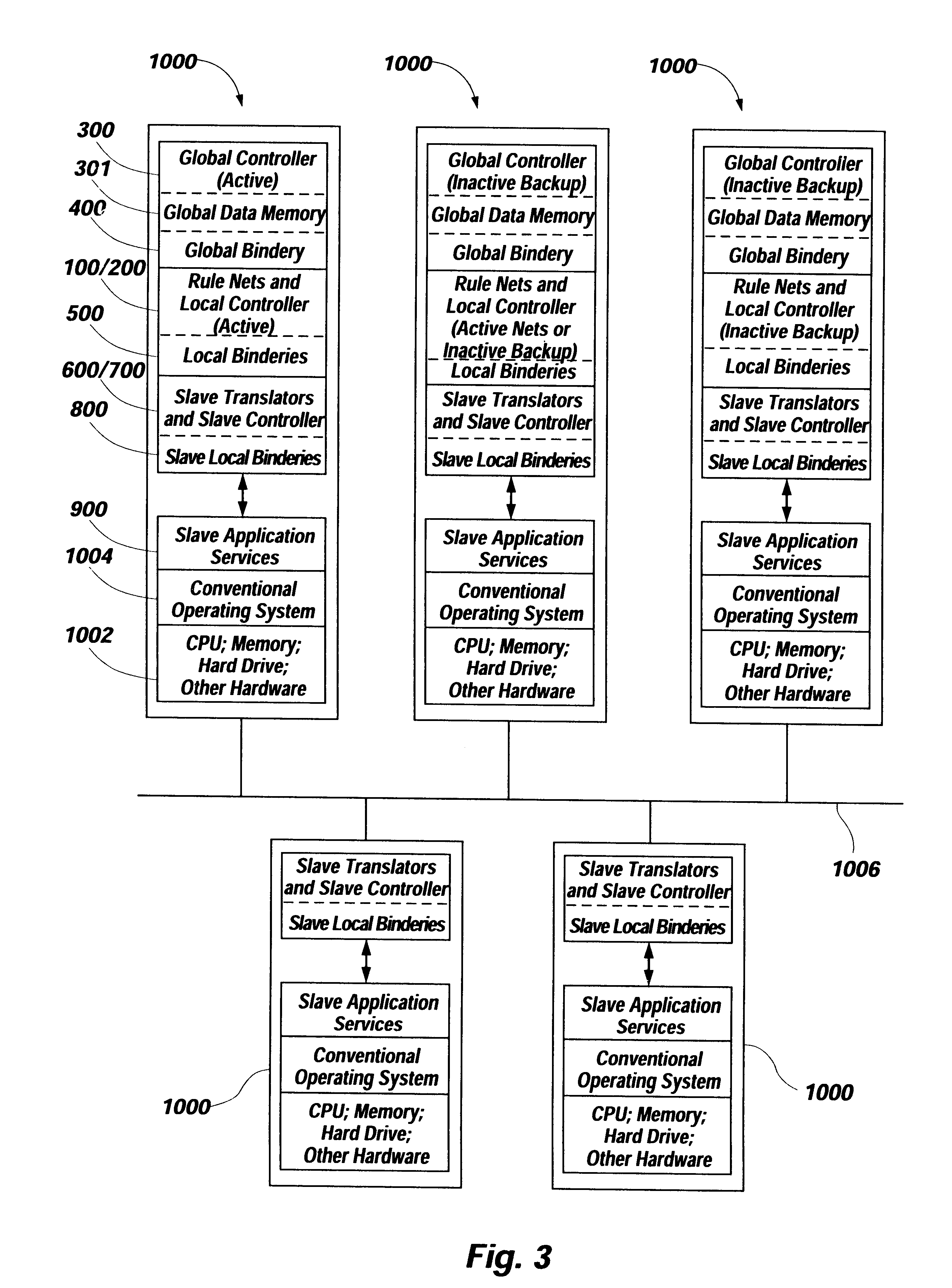
A distributed digital rule processor to create a single system image (SSI) on a cluster of von Neumann processors. The rule processing engine has a group of digital rule nets each having their own local bindery and local controllers which are interconnected by a global bindery. Slave translators are interfaced to the global bindery to receive rule calls from the rule nets and return statuses. A compiler maps the typical source code instructions into groups of rules which are stored in the rule nets' storage area. The rules contain groups of input variables and output variables. The output variables of a calling rule become the input and data for the called rule. Slave application processes on the von Neumann processors perform slave activities for the slave translators, as the rule nets are unable to manipulate data. Rules received from the rule nets by slave translators are processed and processed data or return statuses are sent back to the nets for further instructions. The rule nets contain the code compiled by the programmer and the application data is stored in the global buffers. This separates the code from data. The digital rules include node, processor, and thread addressing variables to permit extending the model to handle multiple nodes in a Wide Area Network, Local Area Network, System Area Network, or cluster.
Owner:JACOB CHARLES
Systems and methods for using a distributed ledger for data handling
ActiveUS20180082296A1Digital data information retrievalCryptography processingClient-sideDistributed ledger
In some embodiments, a method may include establishing a set of distributed ledgers. Each distributed ledger (or blockchain) may include a unique root key that is specific to the client. A series of rules for data handling and / or manipulation may be produced, and the data is handled according to such rules. An entry may be added to the ledger for each transaction, and the ledger is distributed to those end point associated with the client. In the event of an invalid (or unauthorized) transaction, a “side branch” (or “fault branch”) may be added to the ledger, thus easily identifying the transaction as being invalid to the client.
Owner:SEAGATE TECH LLC
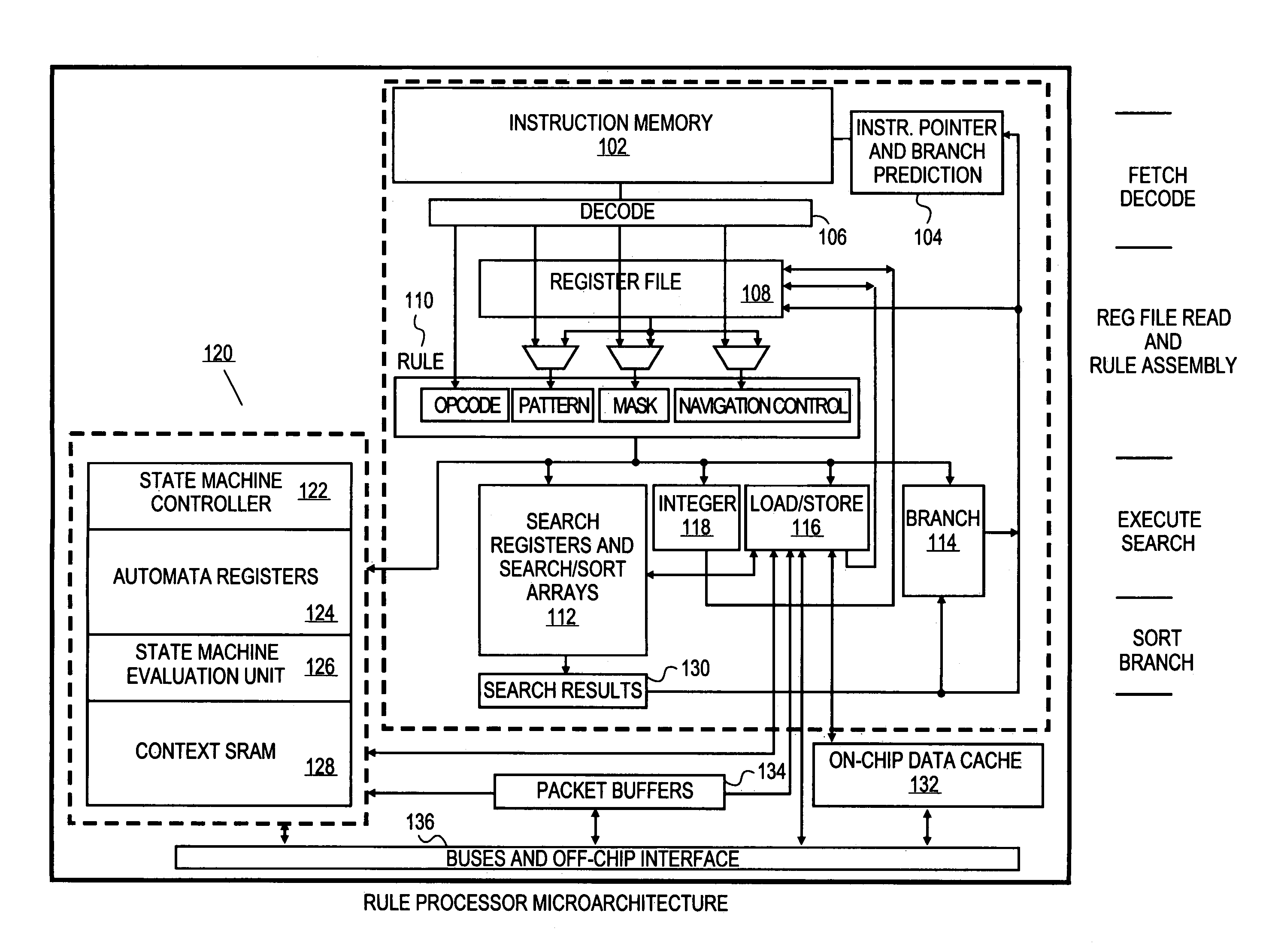
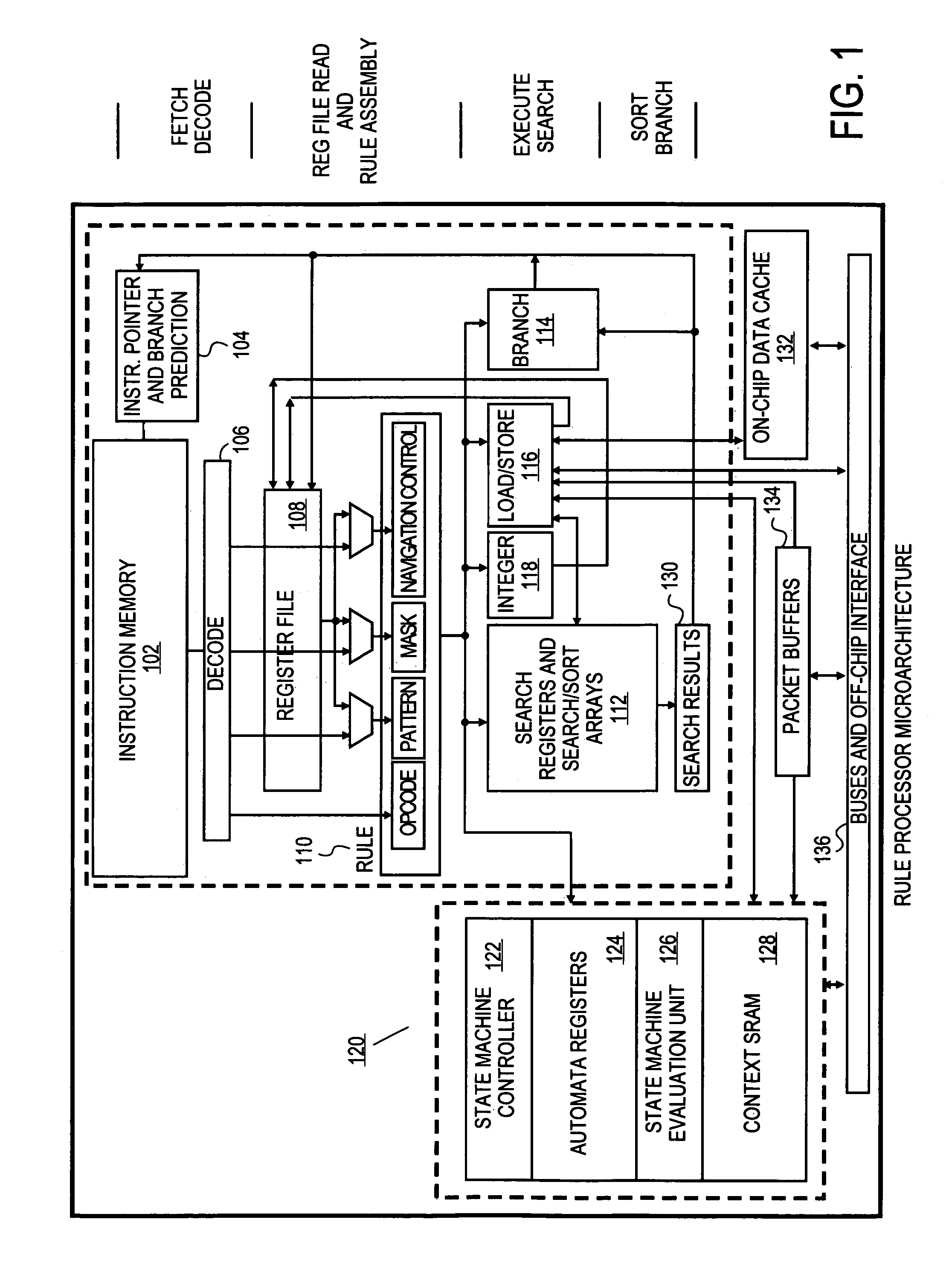
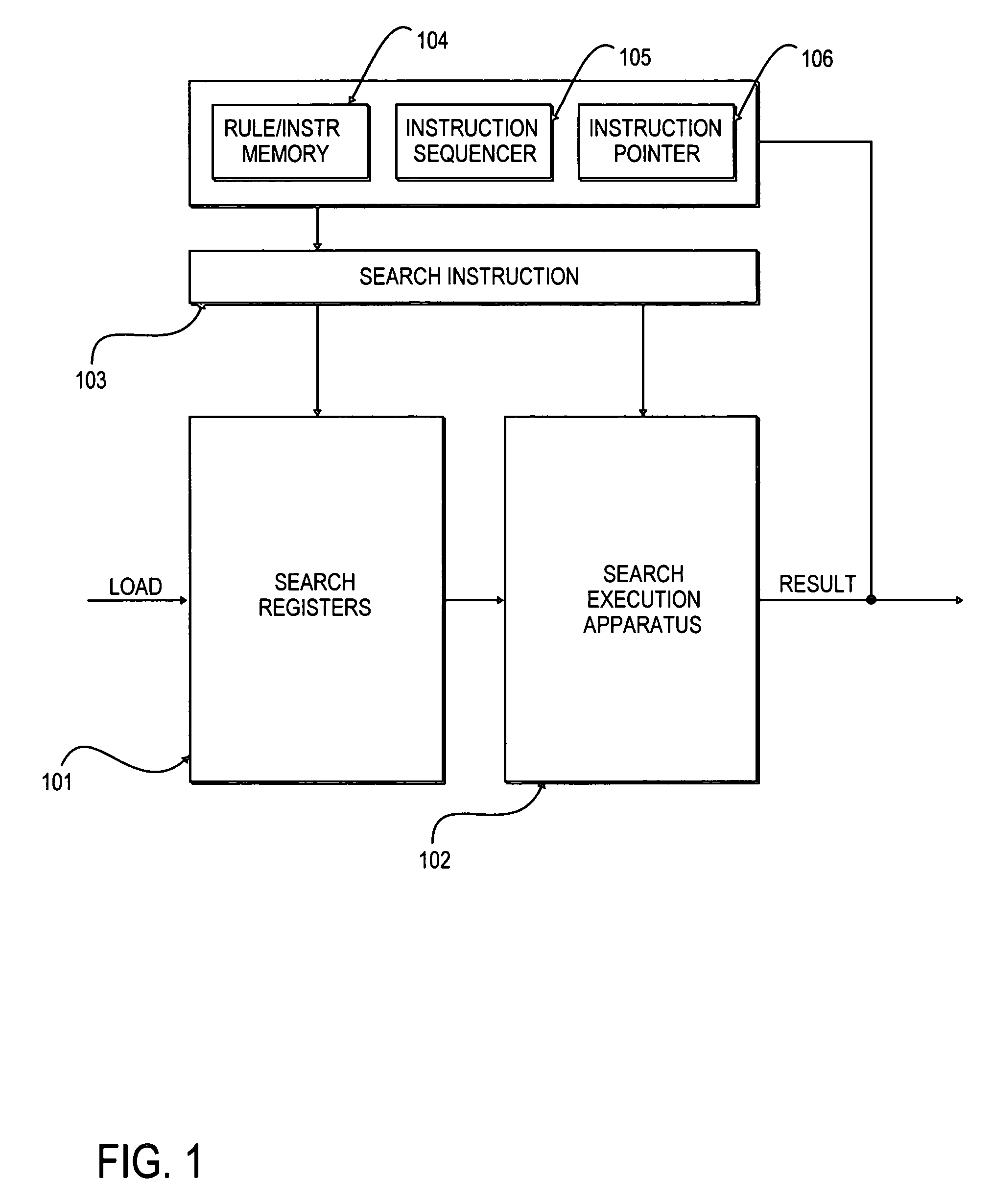
Programmable processor apparatus integrating dedicated search registers and dedicated state machine registers with associated execution hardware to support rapid application of rulesets to data
InactiveUS7464254B2Programme controlDigital data information retrievalGeneral purposeProcessor register
A rule processor and method for using the same are disclosed. In one embodiment, the rule processor comprises a general purpose register file, an instruction sequencer to provide instructions, a decoder coupled to the general purpose register file to decode a set of instructions specified by the instruction sequencer, and a state machine unit coupled to the decoder and having state machine registers to store one or more state machines and state machine execution hardware coupled to the state machine registers to evaluate the one or more state machines in response to executing one or more of the set of instructions and based on information from one or both of the decoder and the general purpose register file.
Owner:CISCO TECH INC
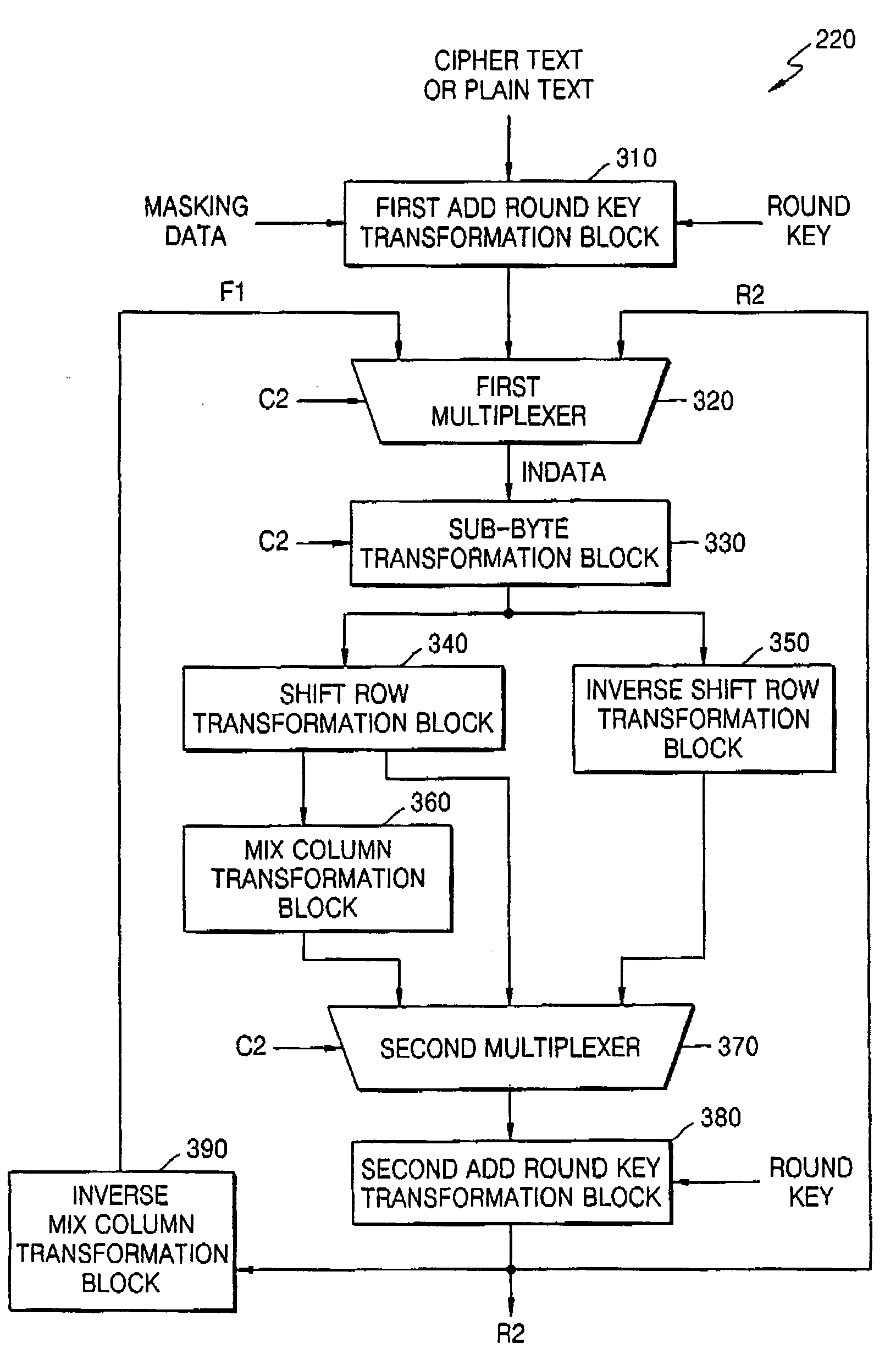
Data cipher processors, AES cipher systems, and AES cipher methods using a masking method
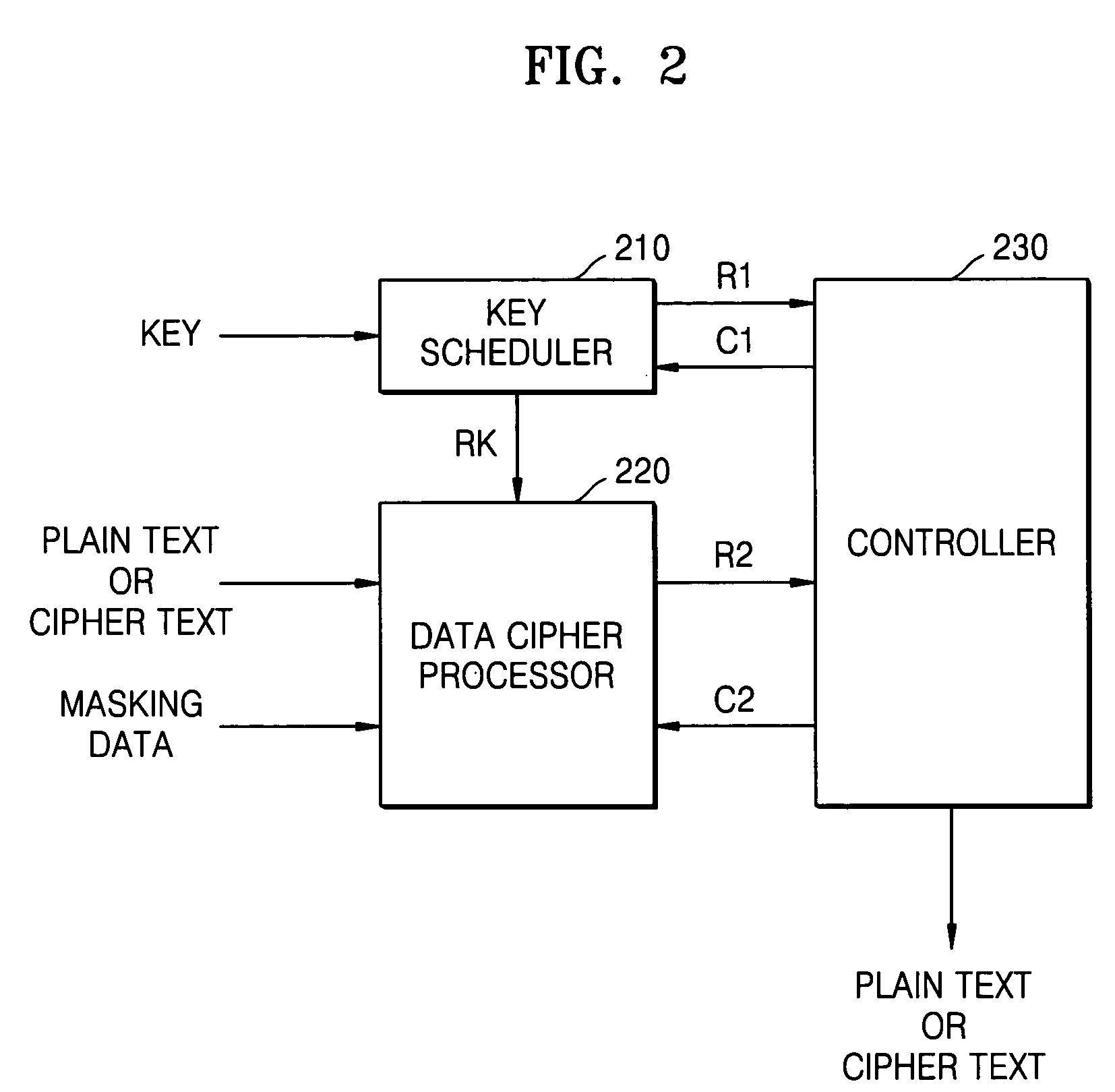
ActiveUS20050207571A1Small sizeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesOriginal dataAdvanced Encryption Standard
Data cipher processors, advanced encryption standard (AES) cipher system, and AES cipher methods using a masking method perform round operations using a round key, a plain text, a cipher text, and masking data. Some of the round operations are implemented over a composite Galois Field GF(•). Original data and predetermined masking data are processed according to a predetermined rule. Sub-byte transformation operations used in the cipher method and system may include an affine transformation, an inverse affine transformation, an isomorphic transformation, and an inverse isomorphic transformation which are linear transformations, and an inverse transformation that is a non-linear transformation.
Owner:SAMSUNG ELECTRONICS CO LTD
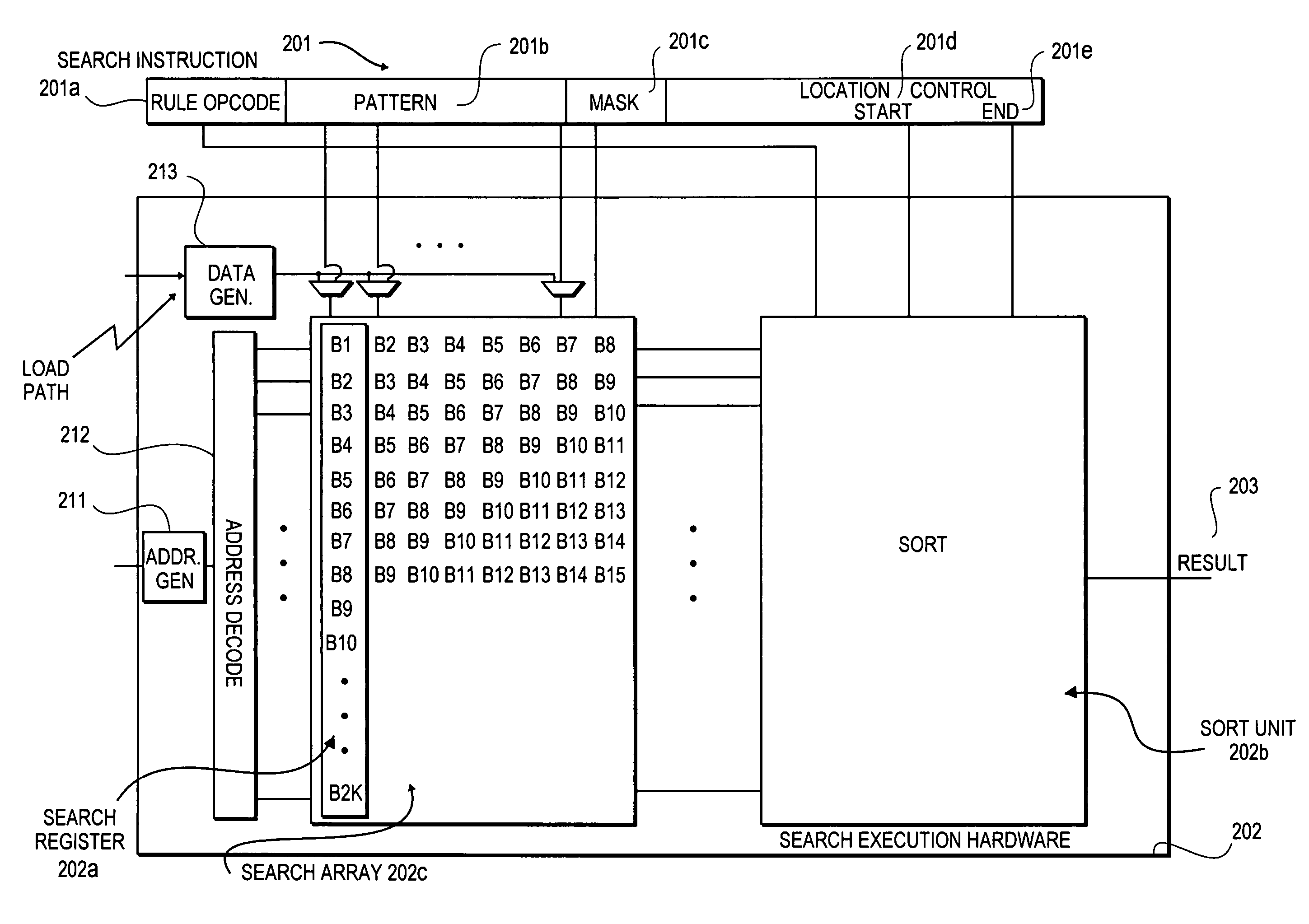
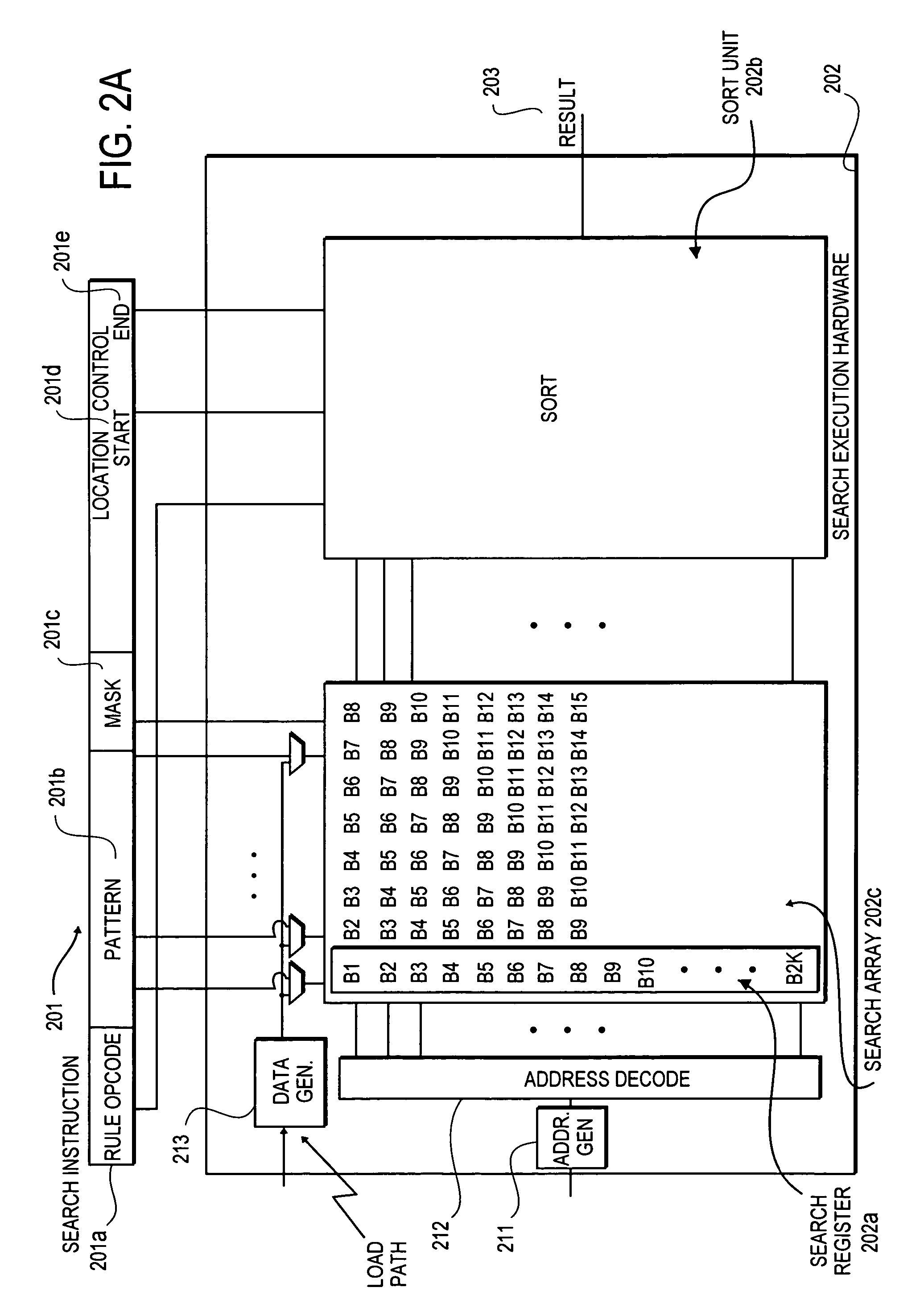
Programmable rule processing apparatus for conducting high speed contextual searches and characterizations of patterns in data
InactiveUS7451143B2Digital data information retrievalProgram controlMultiple contextProcessor register
A method and apparatus is disclosed herein for a rule processor for conducting contextual searches, the processor comprising a plurality of input payload search registers, search execution engine coupled to the plurality of search registers to perform one or more contextual searches on content in the search registers by via parallel pattern matching in response to executing rules specifying the one or more searches, and presenting one or more patterns to the content in the search registers.
Owner:CISCO TECH INC
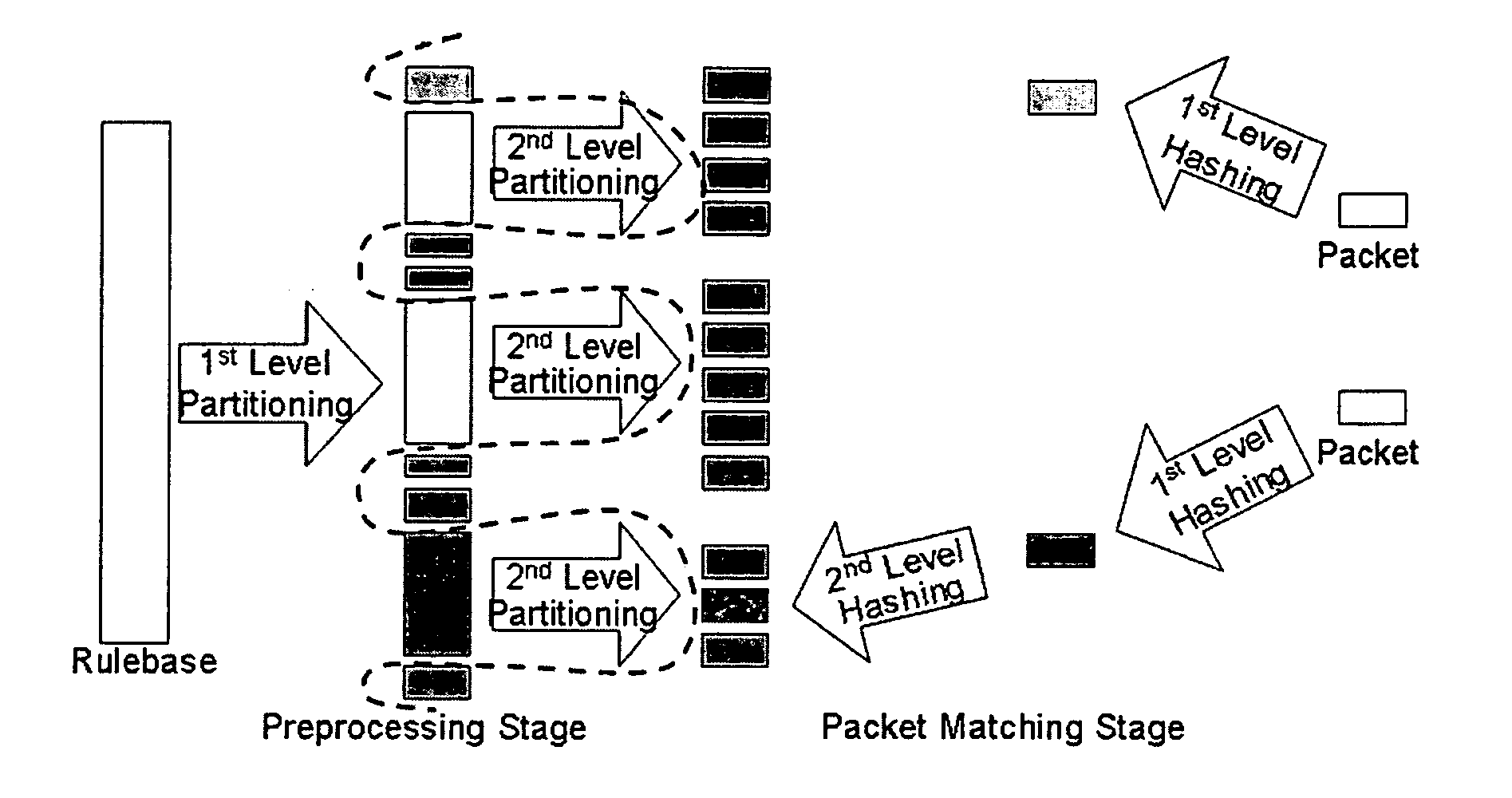
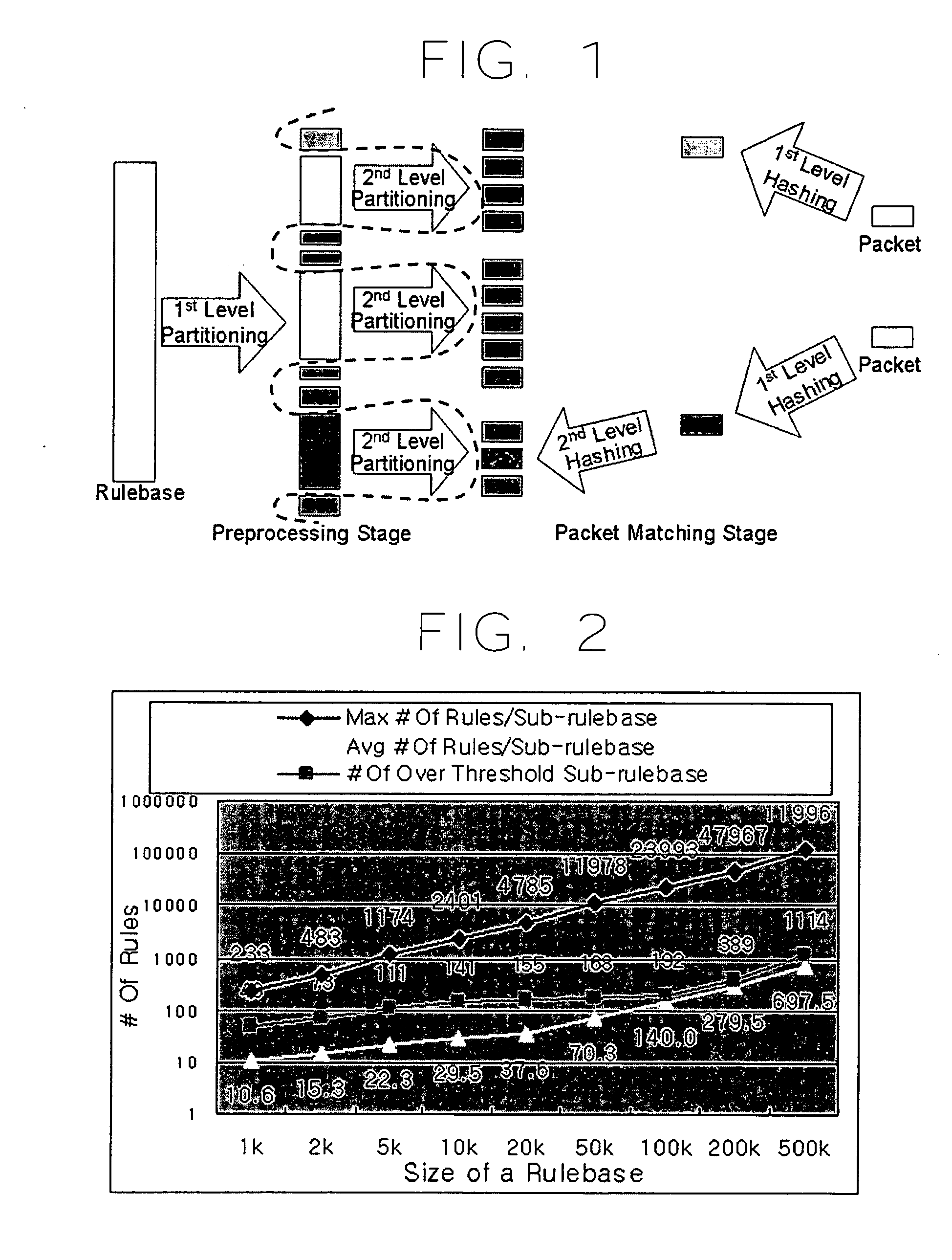
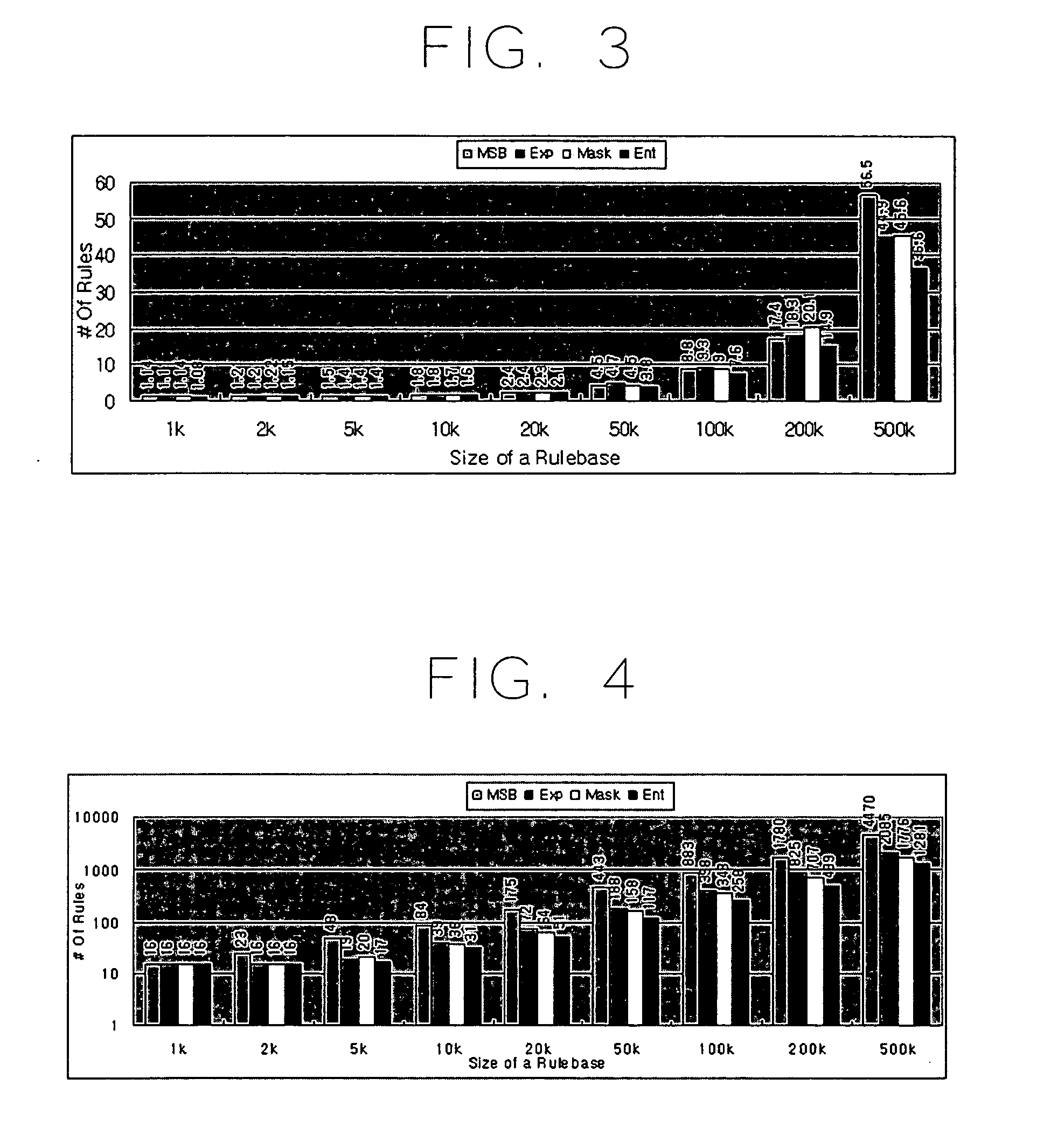
Packet classification method through hierarchical rulebase partitioning
ActiveUS20050254502A1Improve search efficiencyMaximizes the hash key algorithmData switching by path configurationStore-and-forward switching systemsClassification methodsHash table
A packet classification method through hierarchical rulebase partitioning. The packet classification method for searching for a rule having a highest priority and matching among a plurality of rules included in a specified rulebase with respect to a packet input from an external network and processing the packet according to the searched rule. The method includes: a preprocessing step of partitioning the rulebase into a plurality of independent sub-rulebases based on a specified condition and producing a hash table on the basis of the sub-rulebases; and a classification step of classifying the packet by searching the hash table using a hash key extracted from a packet header of the inputted packet and mapping the packet on the sub-rulebase corresponding to the packet.
Owner:SAMSUNG ELECTRONICS CO LTD
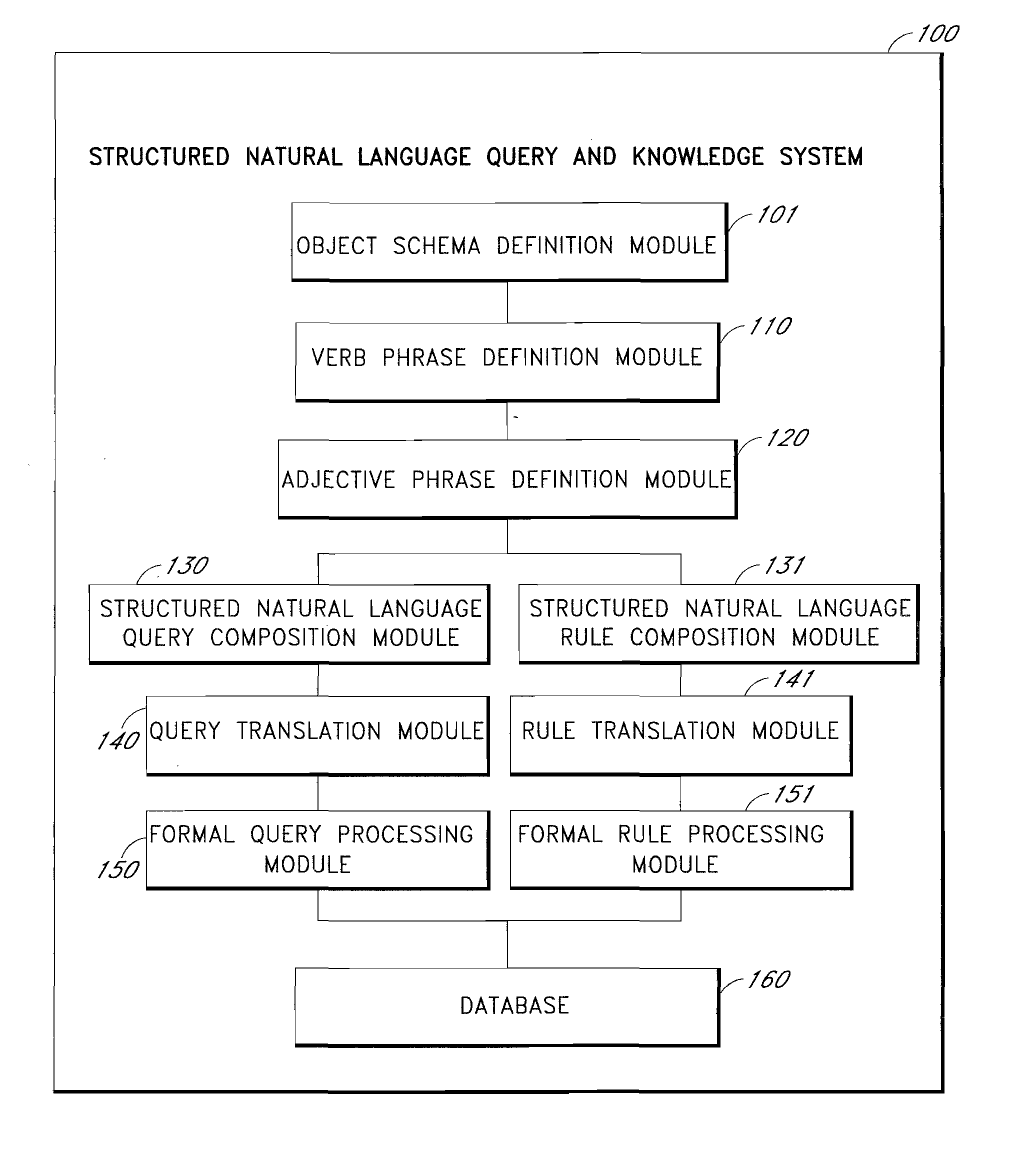
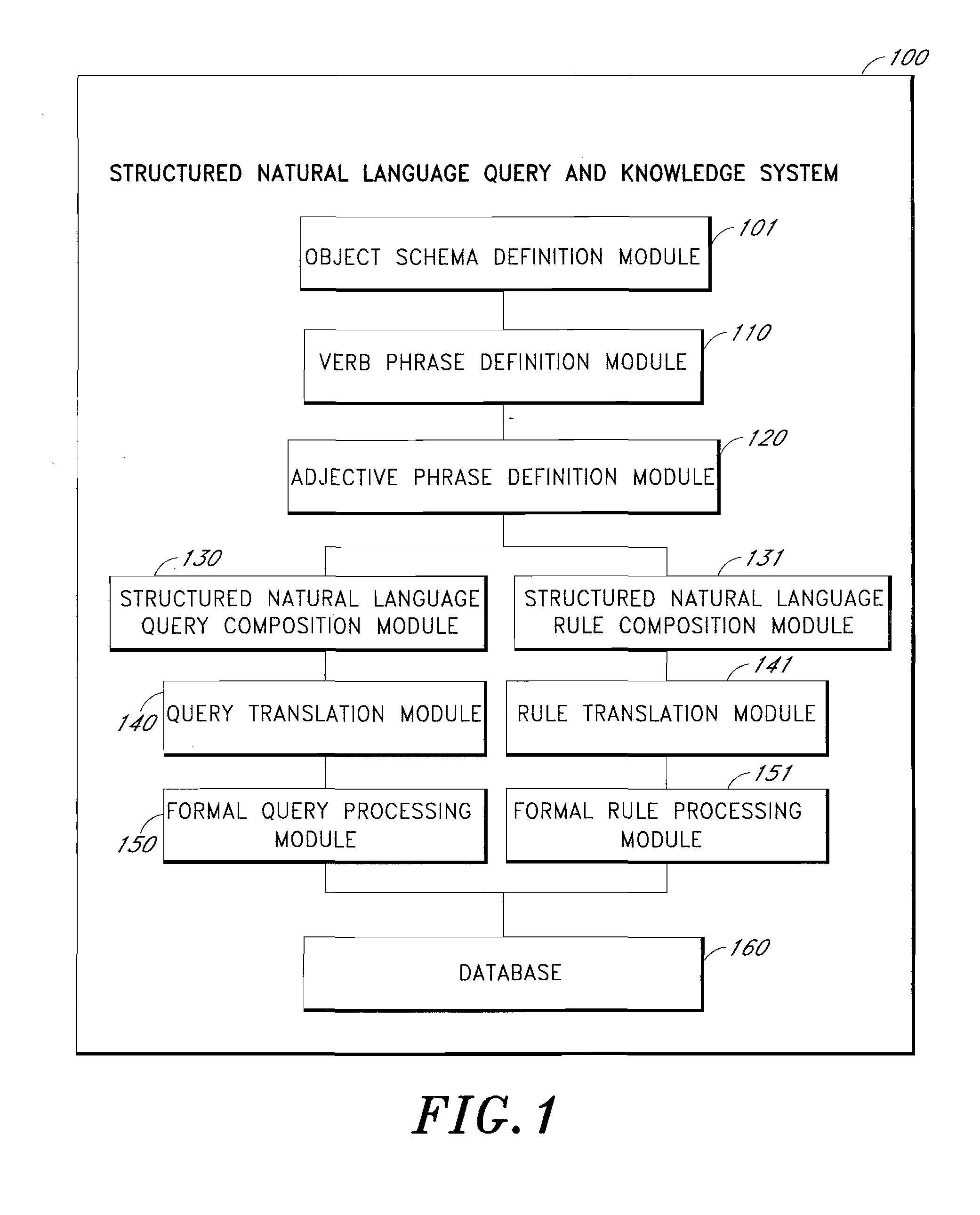
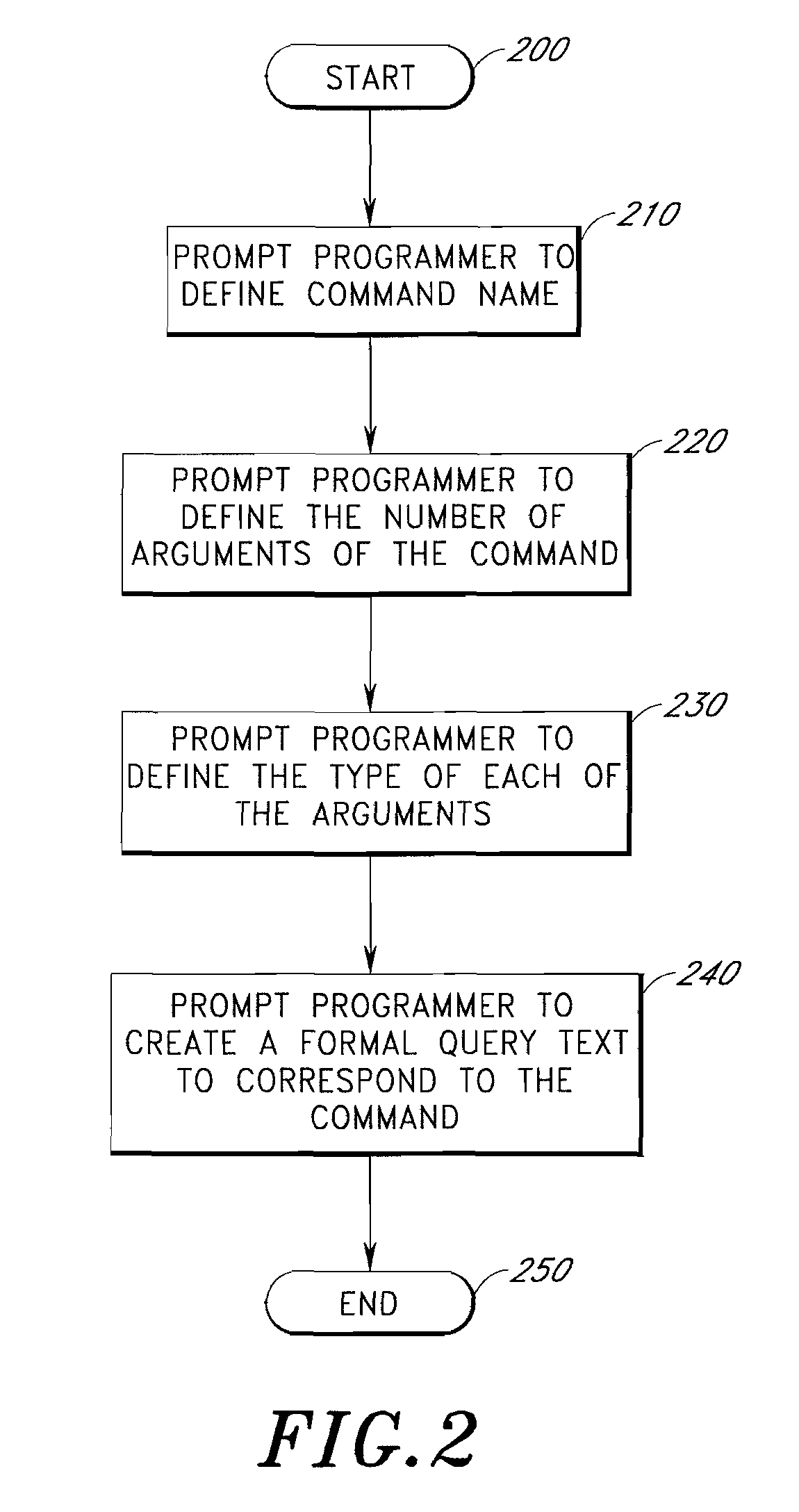
Structured natural language query and knowledge system
InactiveUS20070294233A1Digital data information retrievalData processing applicationsRelational algebraAdjective phrase
A structured natural language query and knowledge system is provided to allow a user who lacks programming skills to enter a database query or a rule in the form of a structured natural language sentence. The scope of the sentence is preferably defined by an improved object relational query language, an object relational algebra, or both. Command and conditions that appear in natural language form are defined with corresponding formal query texts. A user is prompted to compose a structured natural language sentence using the defined commands and conditions. The user-selected command and its arguments appear as the verb phrase of a structured natural language sentence. The user-selected conditions and their parameters appear as the adjective phrases of the sentence. The sentence is parsed and changed into a translated formal query text for formal database query and rule processing.
Owner:NEC SOLUTION INNOVATORS LTD
Distributed digital rule processor for single system image on a clustered network and method
InactiveUS6389451B1Improve usabilityInterprogram communicationGeneral purpose stored program computerApplication softwareSystem area network
Owner:JACOB CHARLES
Rule processing system
InactiveUS20070150429A1Exceeding computational capacity of computingDigital data processing detailsDigital computer detailsPresent dayUser input
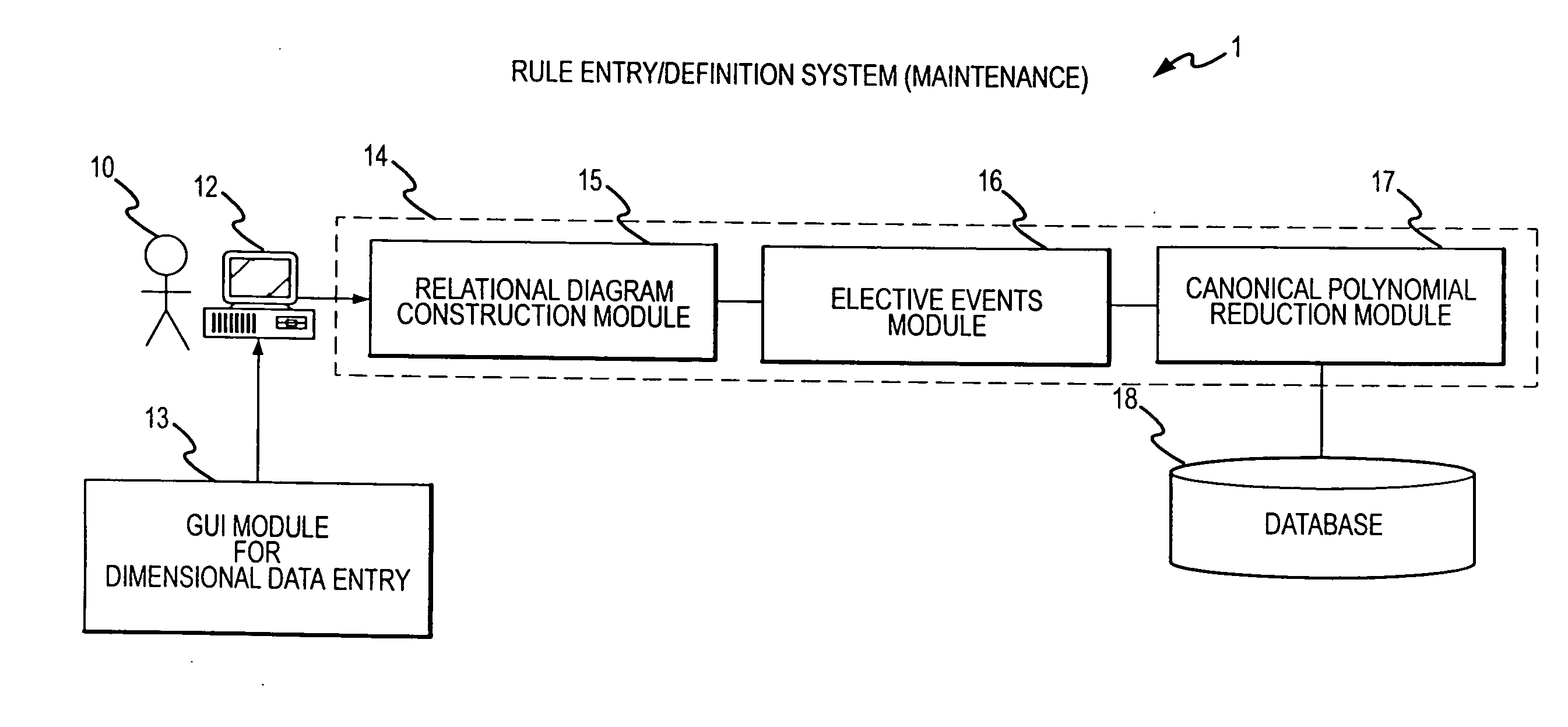
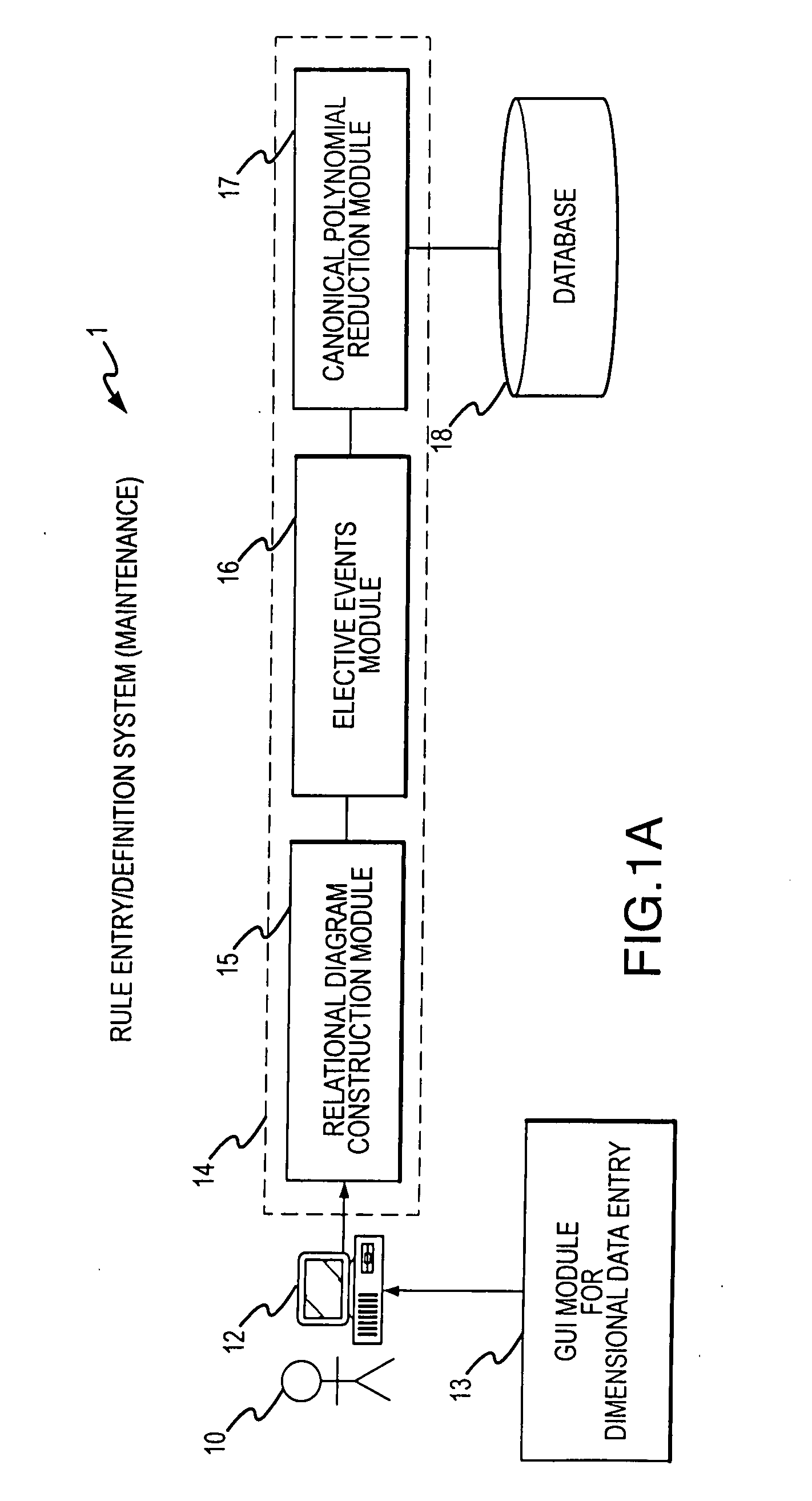
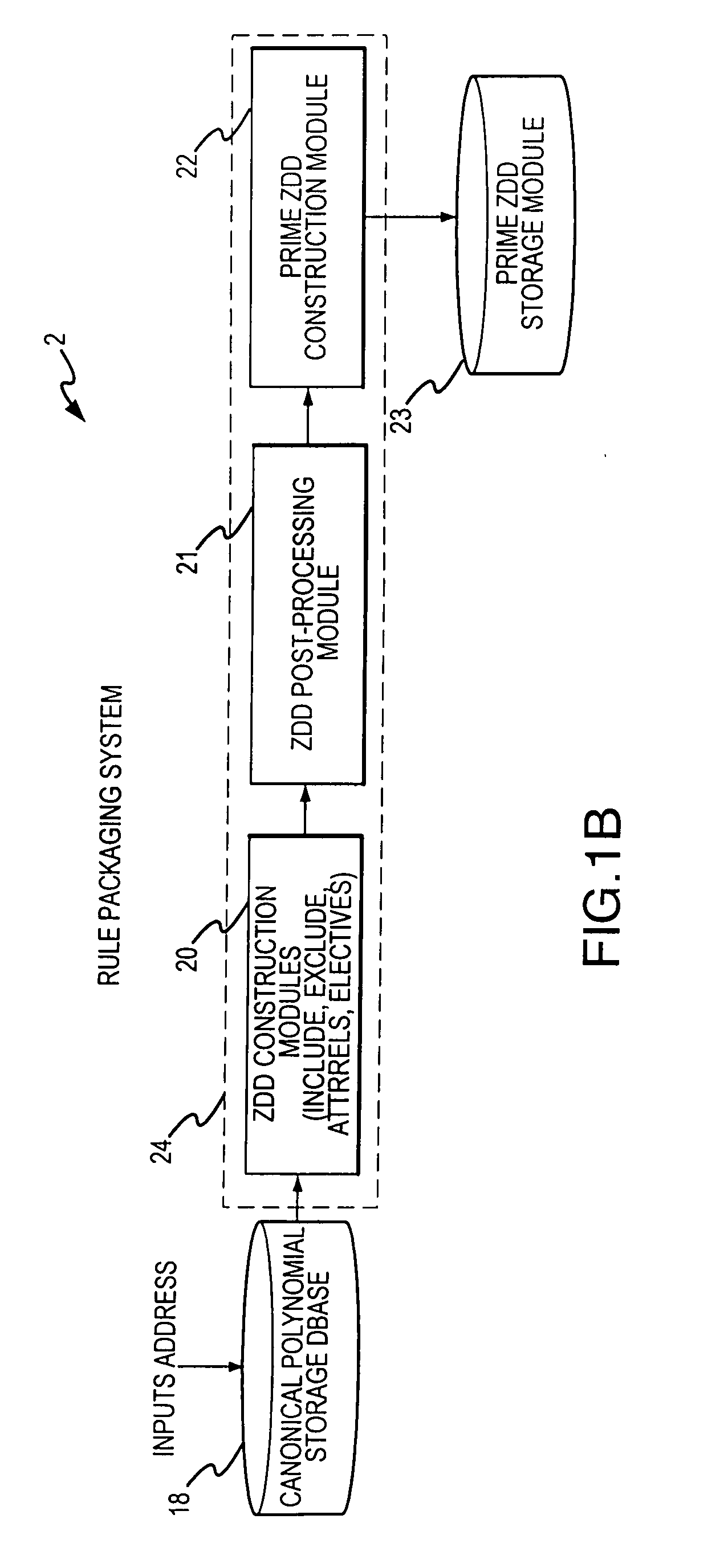
A rule processing apparatus includes modules for defining / entering attributes, enumerations, and / or relationships; packaging the definitions in a reduced canonical form suitable for propositional logic manipulation using zero-suppressed binary decision diagrams (Zdd) to produce a prime Zdd; and / or (iii) executing the rule by applying a series of user inputs to the prime Zdd to determine a result that preferably includes conflict and selection advice to guide the user to satisfaction. Elective events, such as but not limited to the display of messages or the performance of calculations, may optionally be packaged along with the prime rule or components thereof, and presented during execution to help guide the end user to satisfaction or compliancy when choosing among possible selections. The apparatus automates determination of a complex rule having a combinatorial exploded number of rule components, or a combinatorial number of possible outcomes, exceeding computational capacity of present day computing systems.
Owner:MINERAL LASSEN
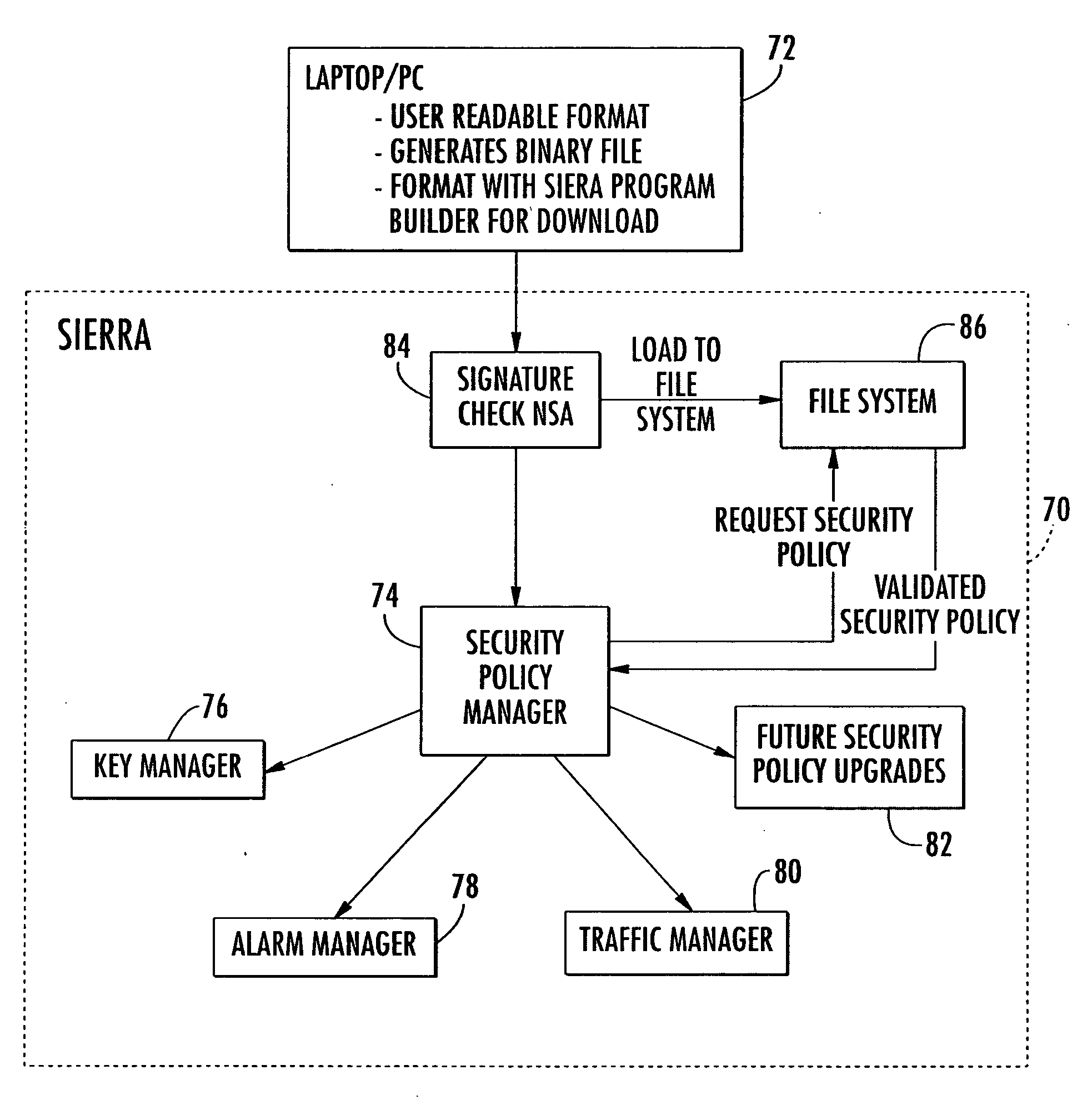
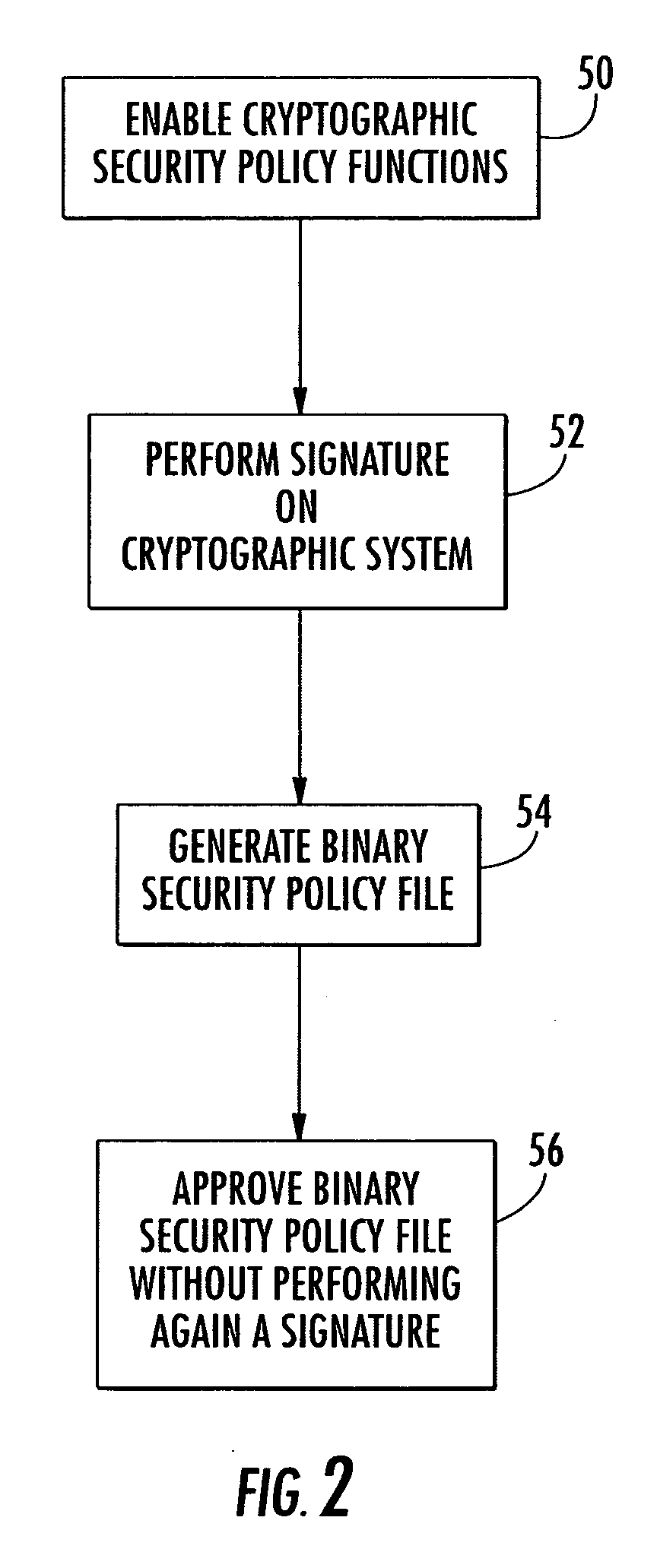
System and method for creating a security application for programmable cryptography module
ActiveUS20060059537A1Digital data processing detailsMultiple digital computer combinationsBinary-safeSecret code
A system and method of the present invention creates a security application for a programmable cryptography module, which includes a security policy software module and mirror security policy data structures. A processor determines a security policy for an implementation specific application as a set of rules governing cryptographic security policy functions of the security policy software module. The processor is operative for generating a binary security policy file representative of the security policy and comparing the binary security policy file with the mirror security policy data structures to determine a violation of the security policy or a successful comparison.
Owner:HARRIS GLOBAL COMM INC
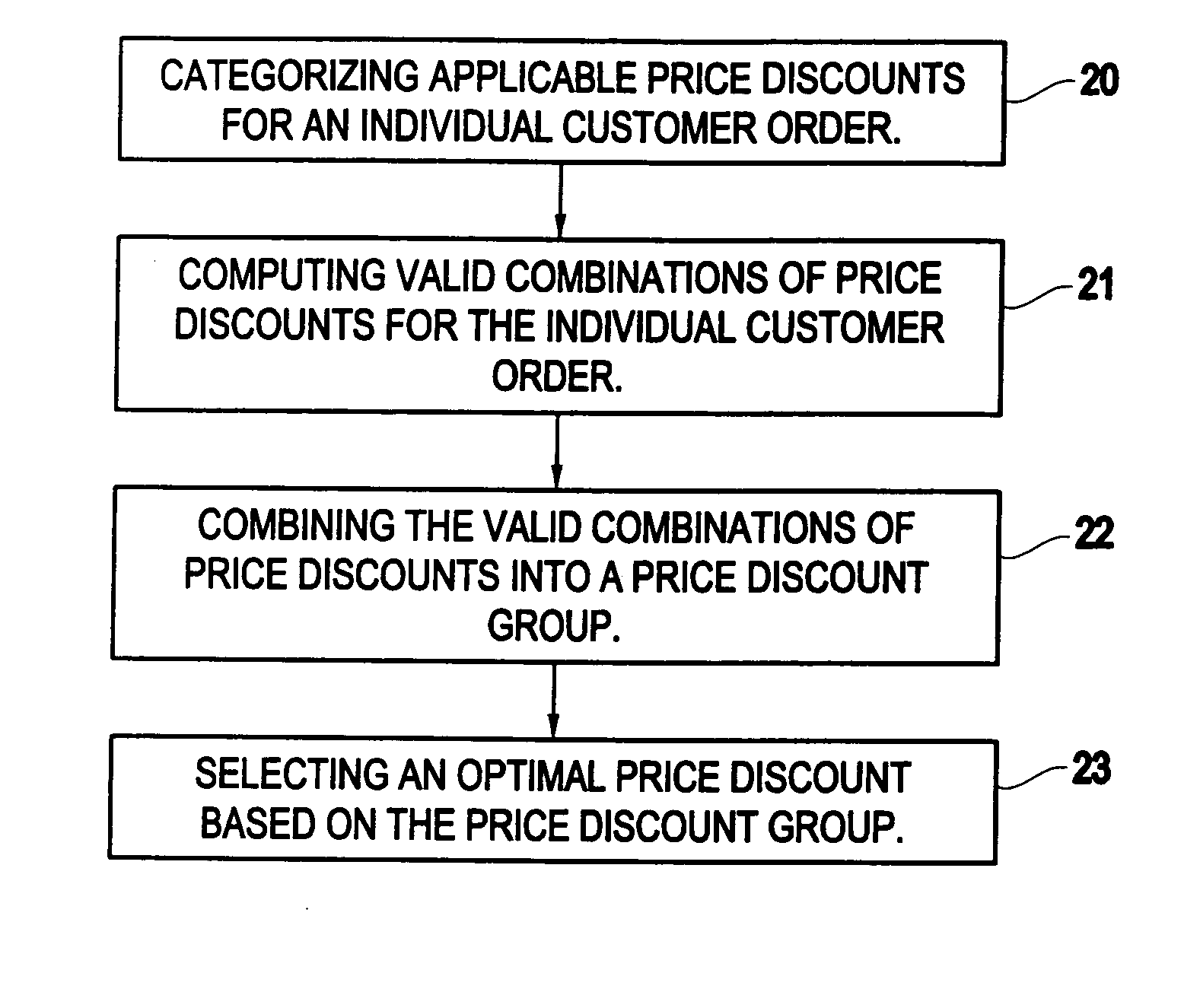
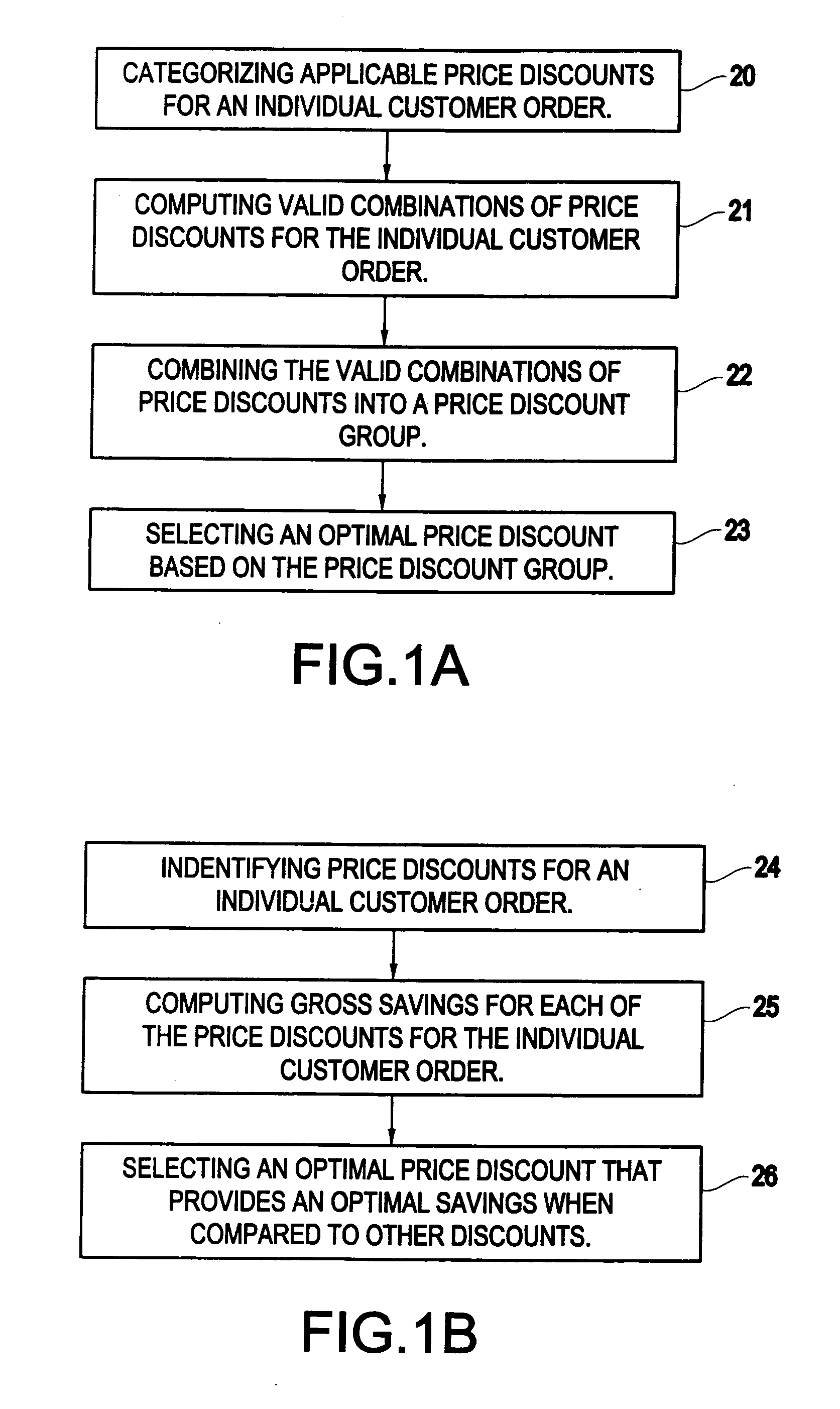
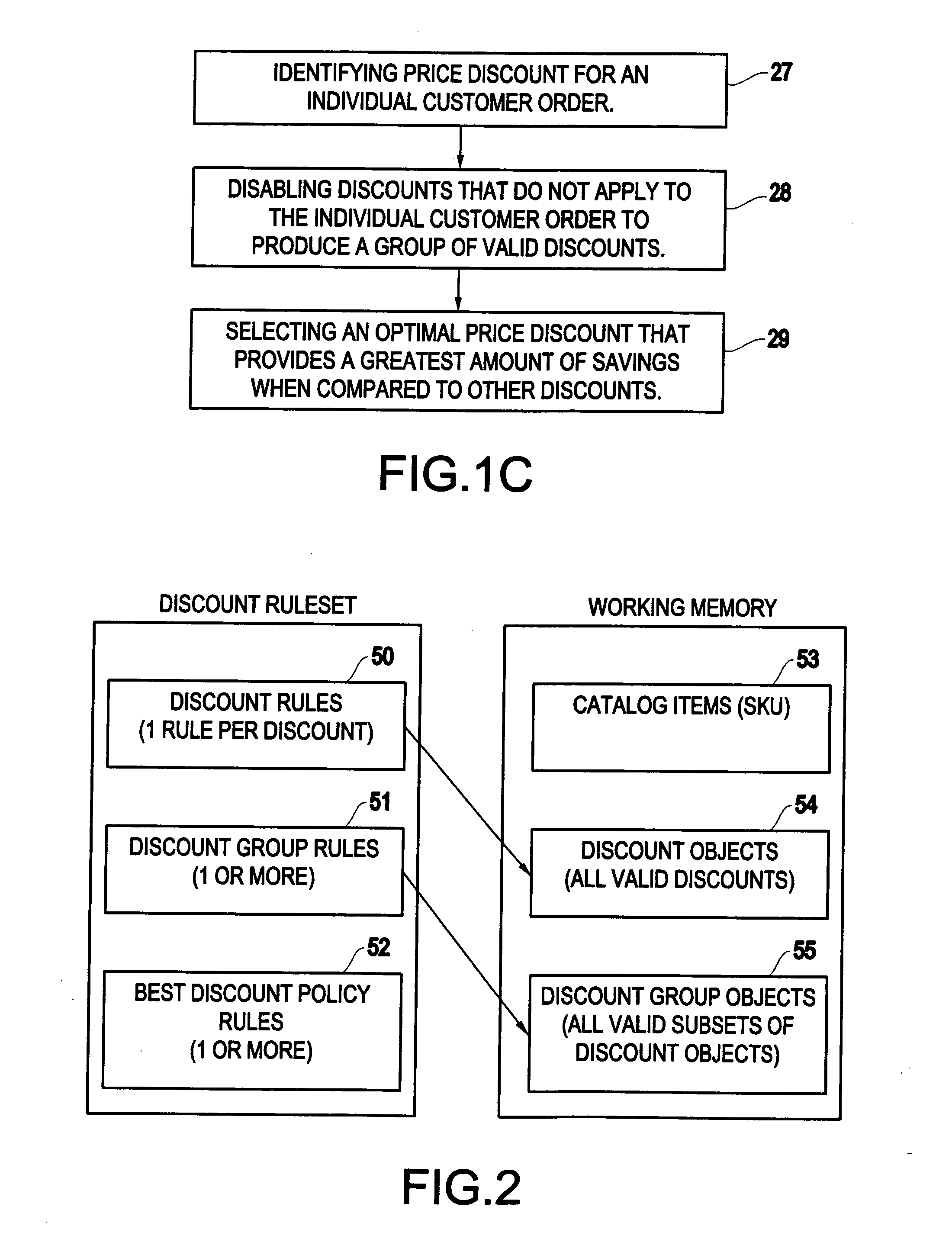
Method for computing price discounts in an e-commerce environment
InactiveUS20050071222A1Improve performanceResolves the allowable discountsMarketingSpecial data processing applicationsPattern matchingE-commerce
A method and structure for a set of rules processed by combining a procedural rule engine and a pattern matching inference engine to compute and apply discounts to customer orders in an electronic commerce system. The rule processing occurs in multiple phases. First all applicable discounts are computed. Then all allowable subsets of discounts are computed. Finally, a set of discounts is selected, based on business policies, and the discounts are applied to the order line items.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com