Patents
Literature
37 results about "Privacy model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Model Privacy Form. The model privacy form is a two-page disclosure form. It is designed to be succinct and comprehensible and allow consumers to easily compare the privacy practices of different financial institutions. Use of the model privacy form is voluntary.
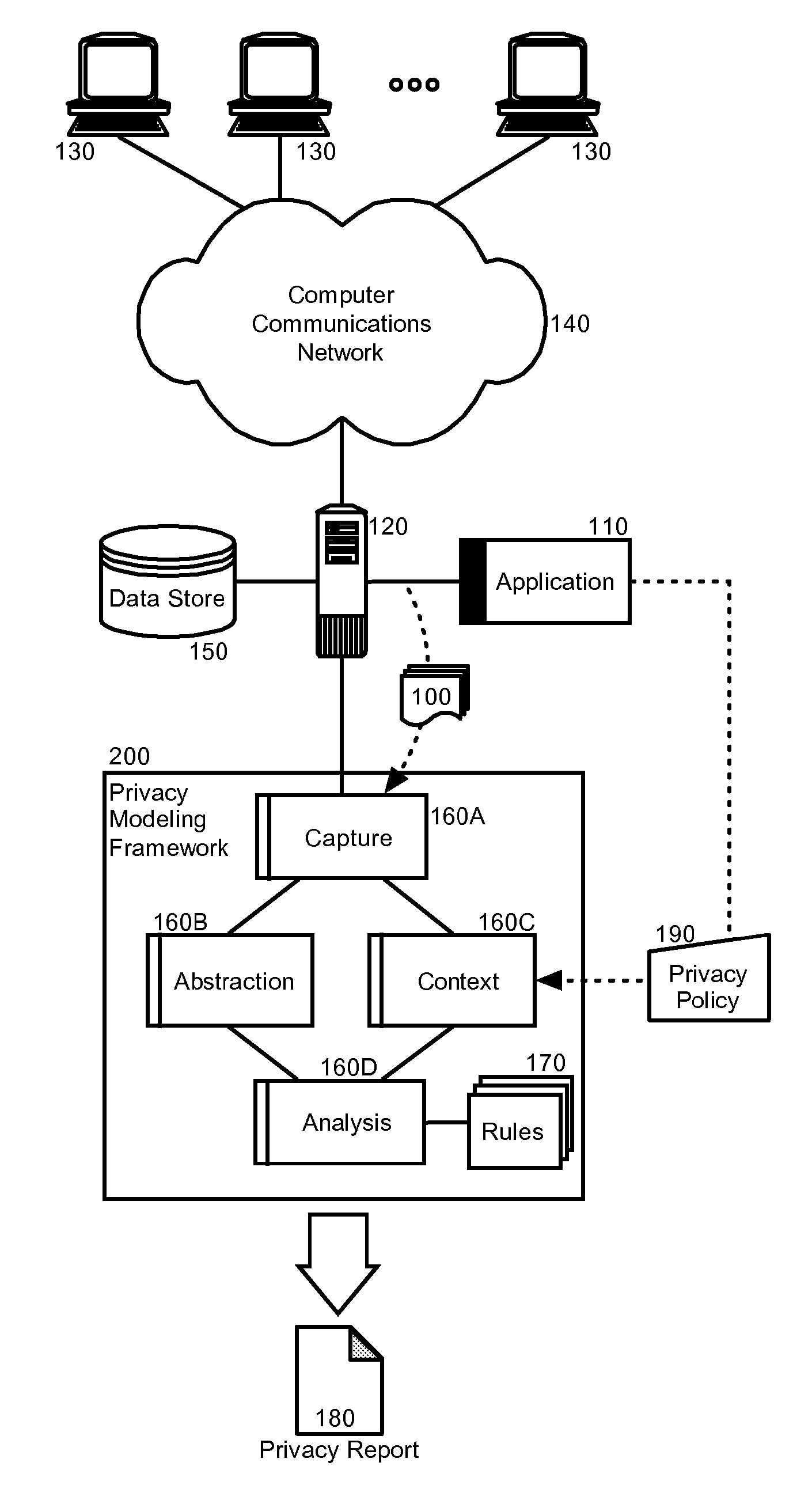
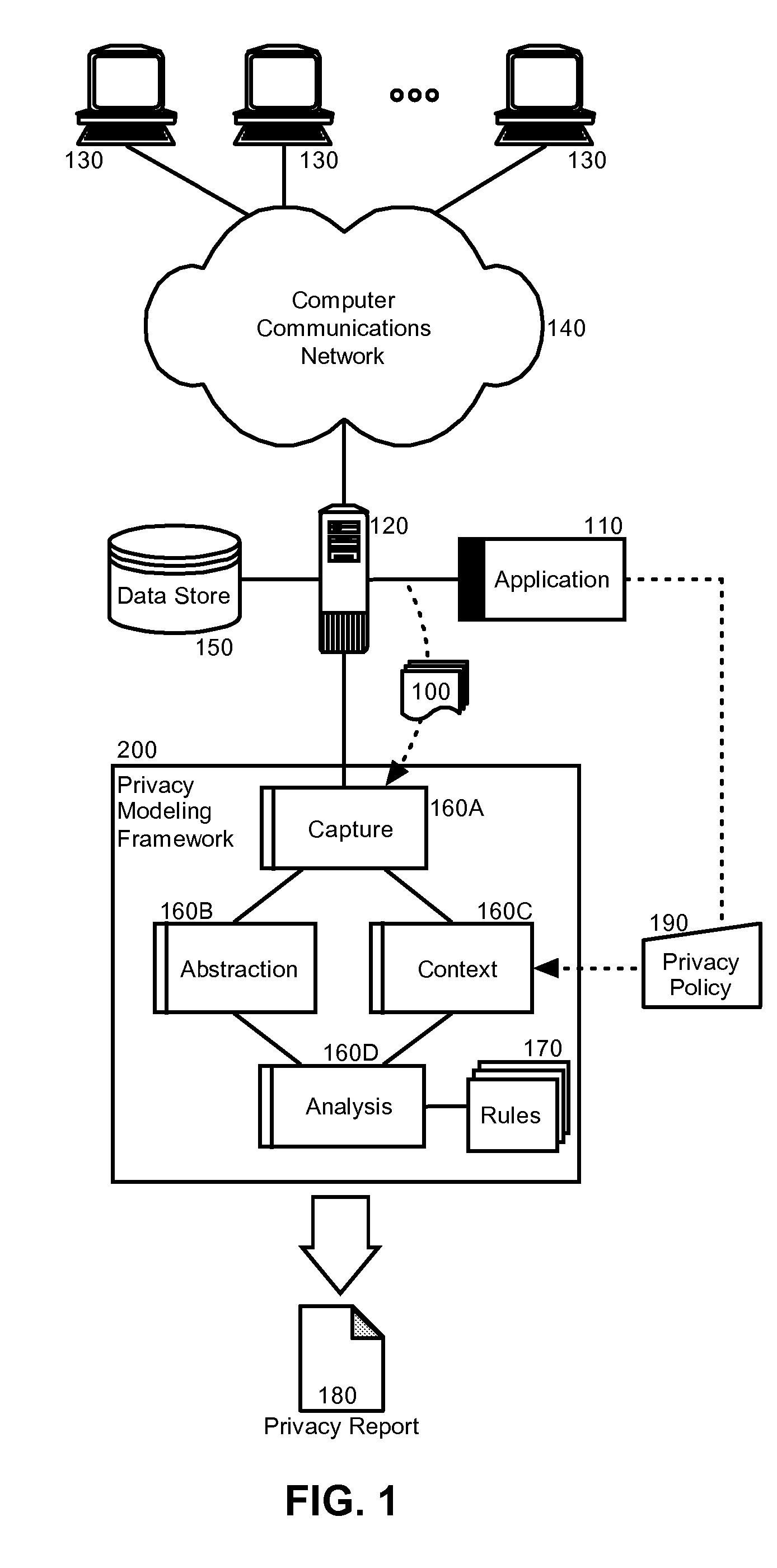
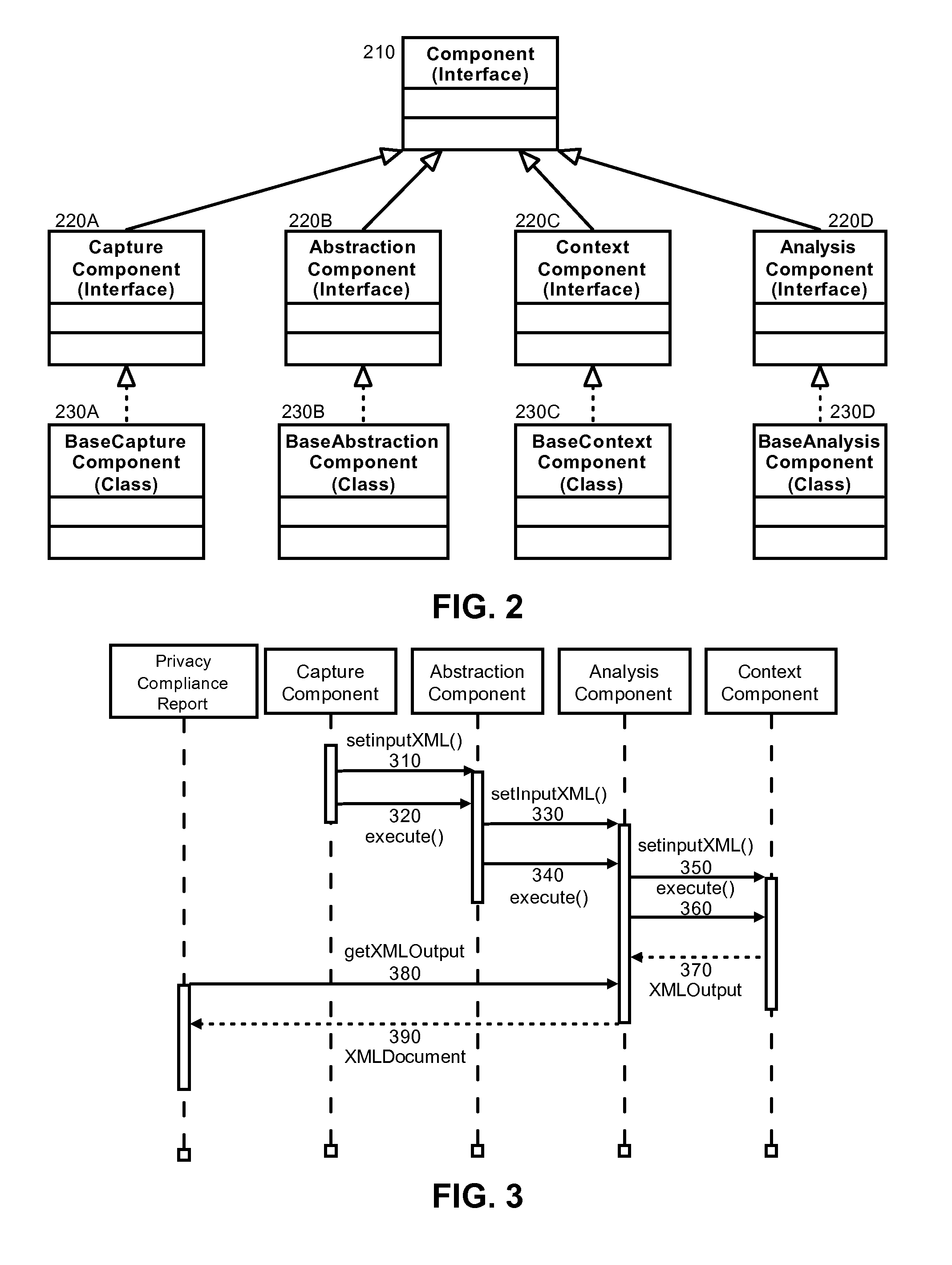
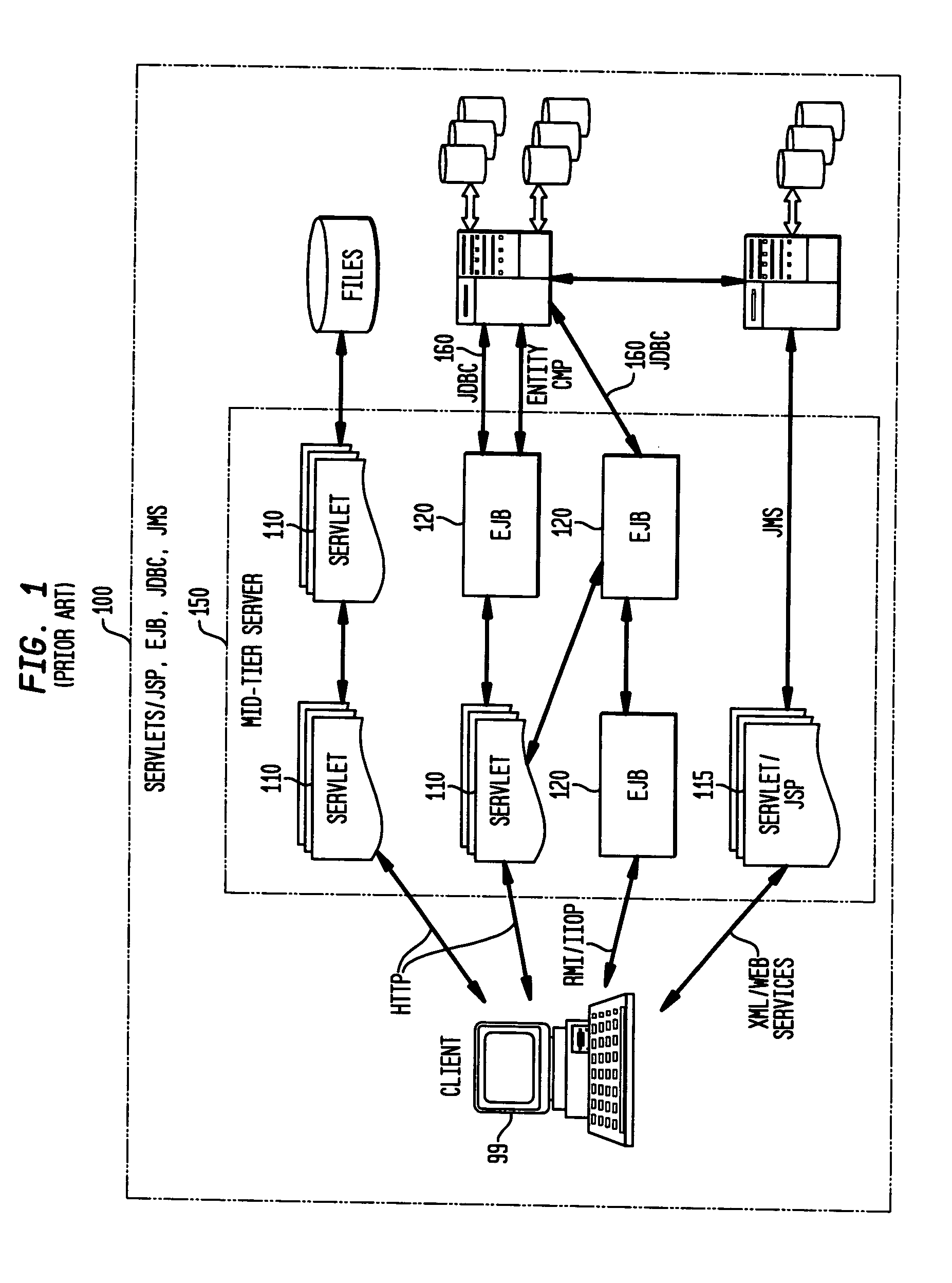
Privacy modeling framework for software applications
InactiveUS20070266420A1Computer security arrangementsOffice automationData processing systemCoupling
Embodiments of the present invention address deficiencies of the art in respect to privacy compliance assessment for computer software and provide a method, system and computer program product for a privacy model framework for software applications. In one embodiment, a privacy modeling data processing system can be provided. The privacy modeling data processing system can include a modeling framework configured for communicative coupling to a software application. The modeling framework can capture information flows from requests to and responses from a coupled software application, and can rules-based process the captured information flows for privacy rules to generate a privacy compliance report for the software application.
Owner:IBM CORP
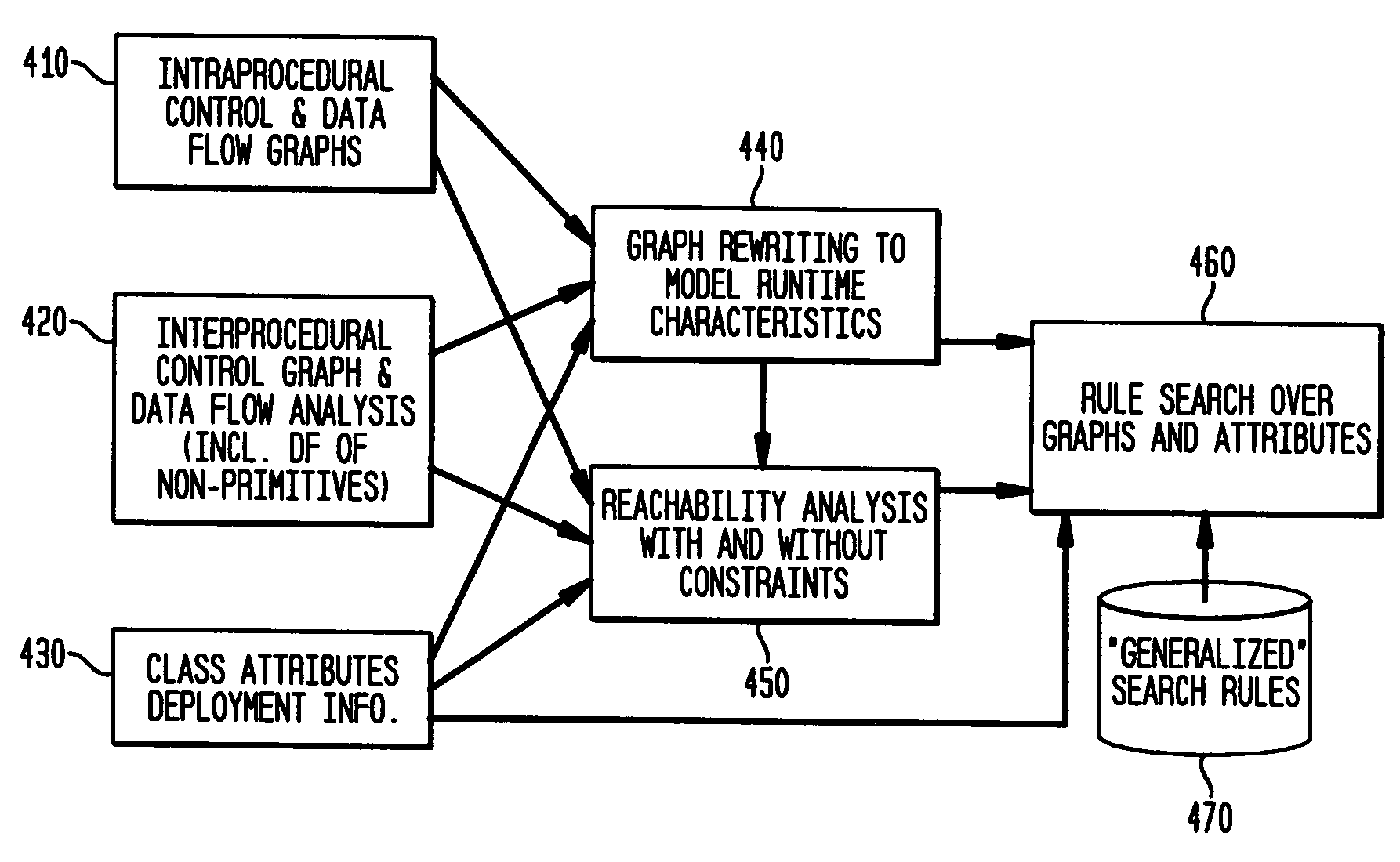
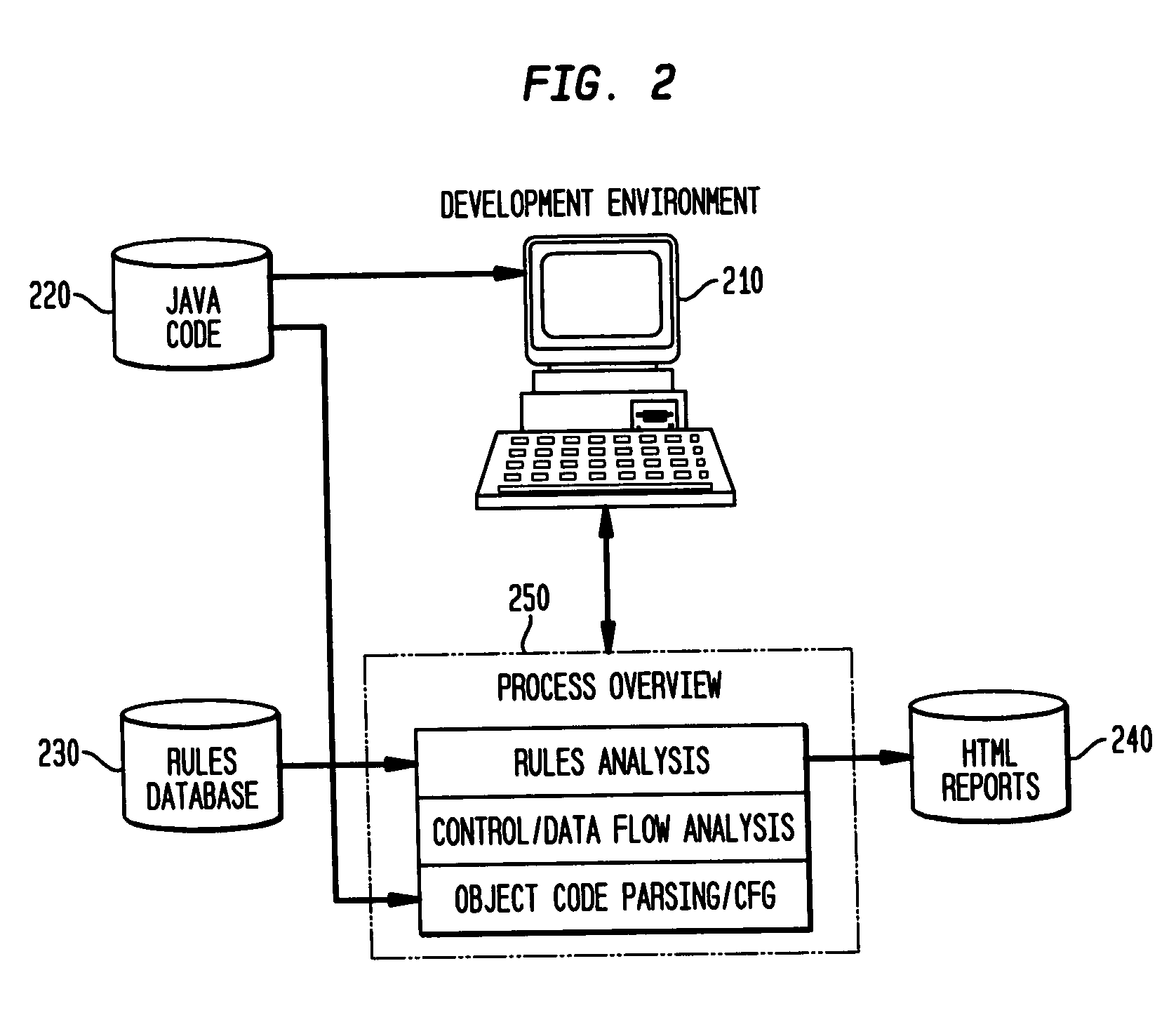
Static analysis based error reduction for software applications
InactiveUS20050015752A1Easy to liftSimple technologyError detection/correctionSpecific program execution arrangementsError reductionMaintainability
A system and method for providing “static analysis” of programs to aid in improving runtime performance, stability, security and privacy characteristics of deployed application code. The method includes performing a set of analyses that sifts through the program code and identifies programming security and / or privacy model coding errors. In particular the invention focuses on identifying coding errors that cause loss of correctness, performance degradation, security, privacy and maintainability vulnerabilities. A deep analysis of the program is performed using detailed control and data flow analyses. These deeper analyses provide a much better perspective of the overall application behavior. This deep analysis is in contrast to shallow analyses in current industry tools, which inspect or model a single or a few classes at a time.
Owner:IBM CORP
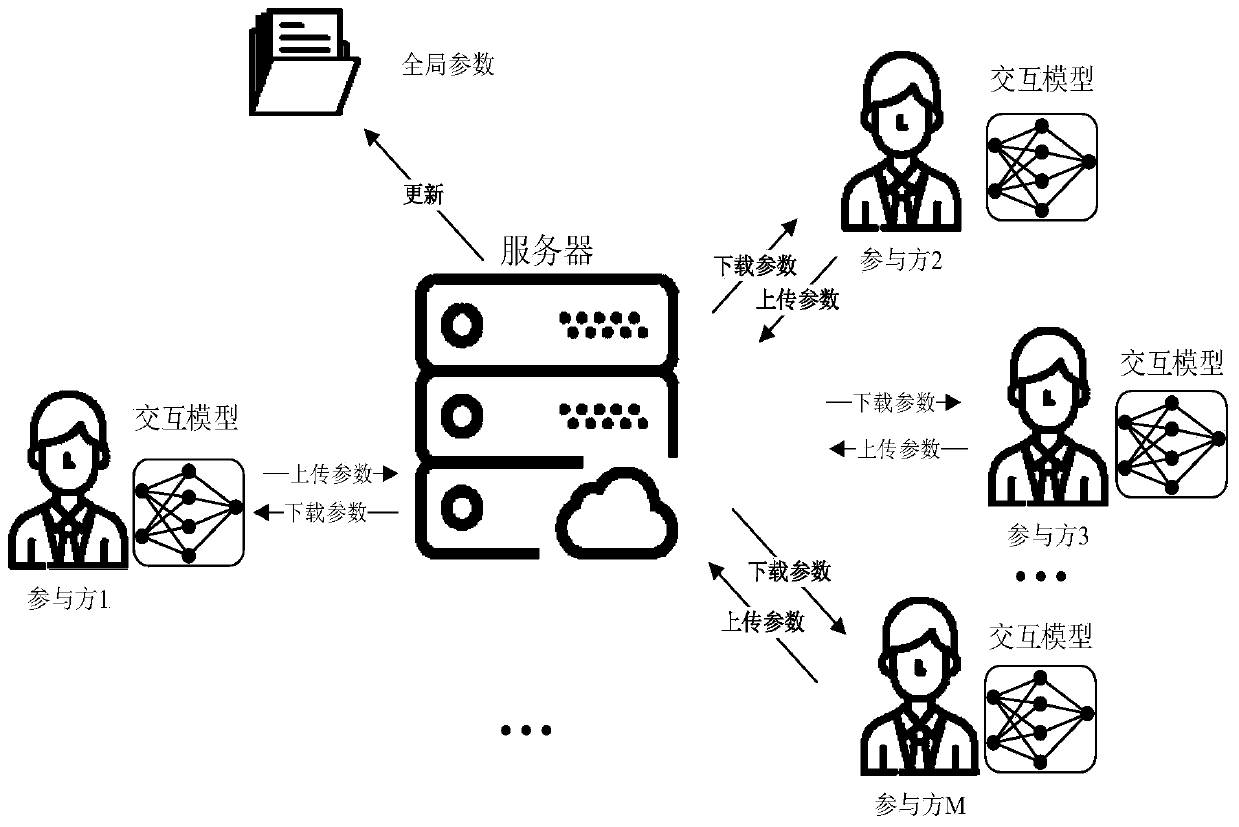
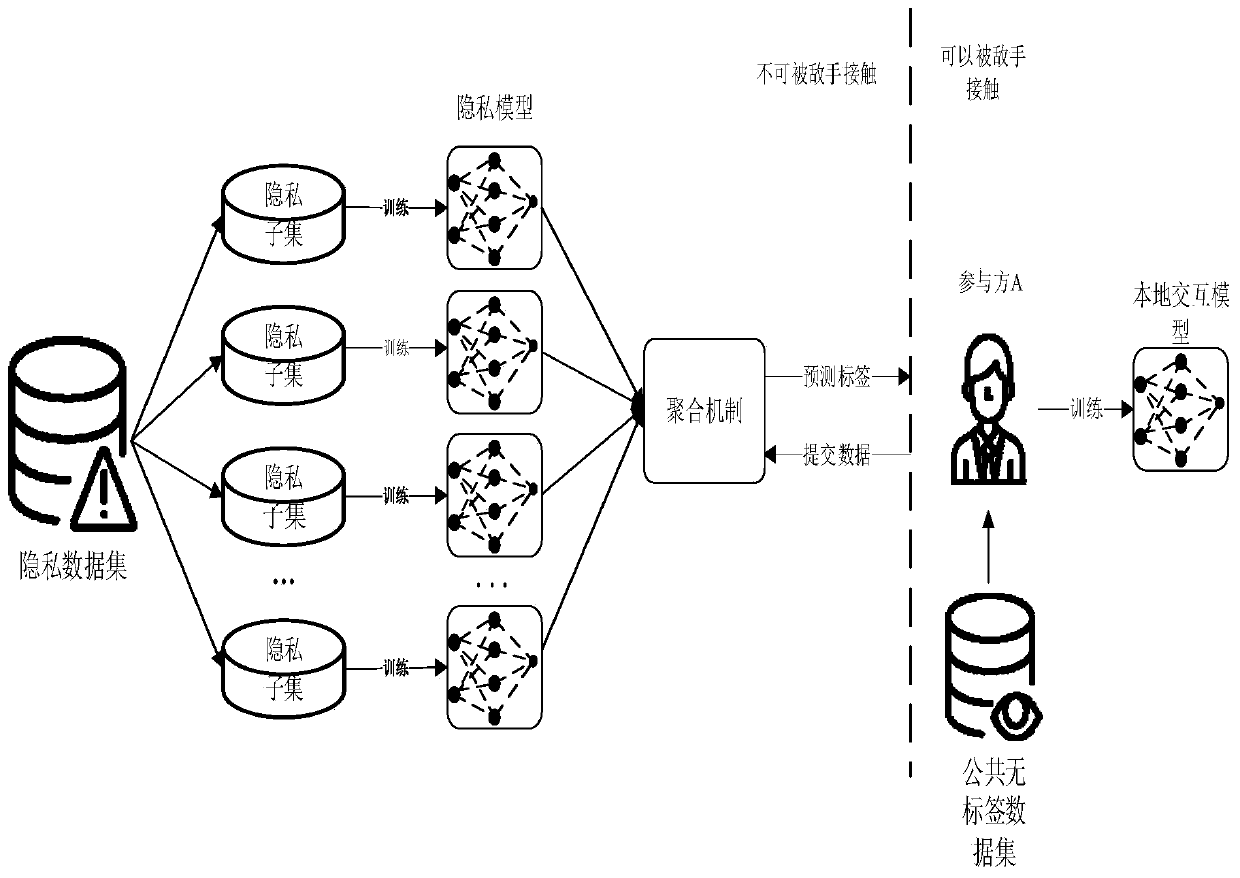
Privacy protection method and system based on knowledge migration under collaborative learning framework
ActiveCN110647765ALess labeled dataImprove accuracyDigital data protectionData setPrivacy protection
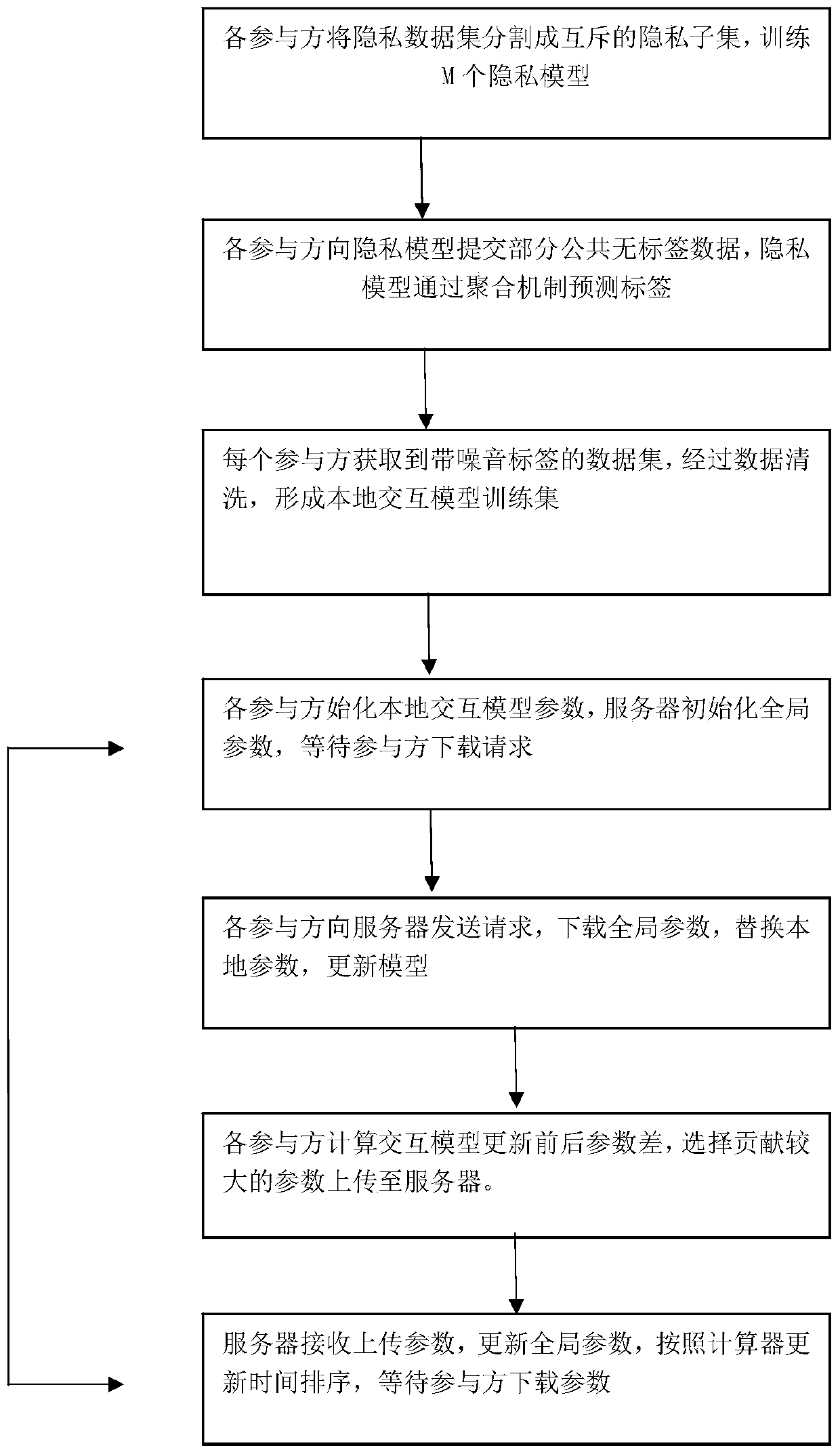
The invention provides a privacy protection method and system based on knowledge migration under a collaborative learning framework. The method comprises the following steps: segmenting a local privacy data set into a plurality of disjoint privacy subsets, and training a corresponding privacy model based on each privacy subset; collaborative learning: submitting the public data to a privacy model,using an aggregation mechanism by the privacy model, and migrating knowledge to a public data set to label a label; after enough labeled data is obtained, a local interaction model is trained, part of parameters are uploaded to a server in each round of training, the server updates and maintains global parameters and provides latest parameters for all parties to download, and participants download the latest parameters to optimize the local interaction model. According to the invention, multiple parameter interactions of collaborative learning can also be ensured, and even if the interactionmodel obtains less annotation data, high accuracy can still be maintained after multiple rounds of training.
Owner:杭州量安科技有限公司
Vehicle position privacy protection method of vehicular ad hoc network
InactiveCN103338444AHigh location privacy and securityLower energy billsParticular environment based servicesNetwork topologiesPrivacy protectionWireless network
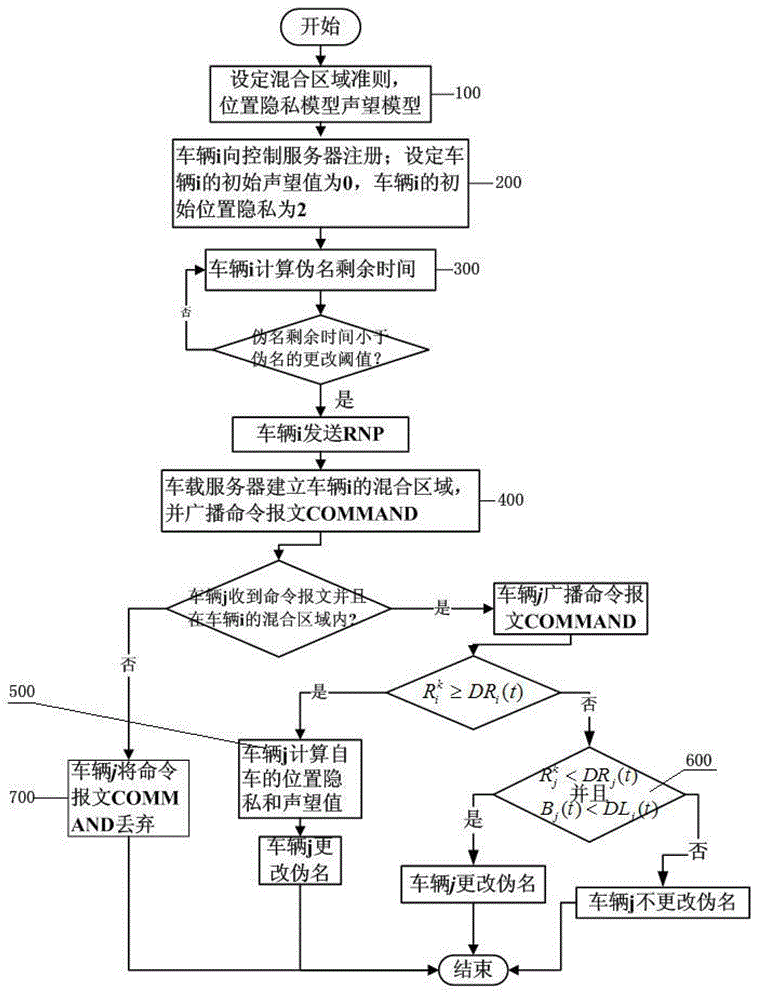
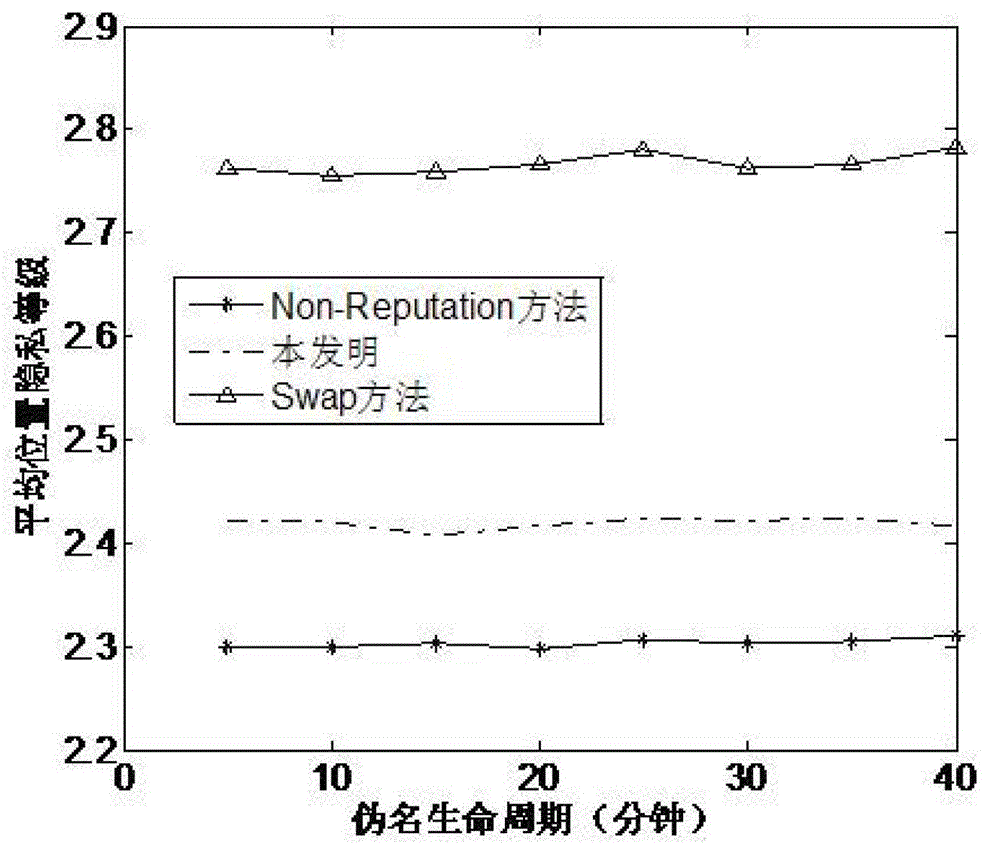
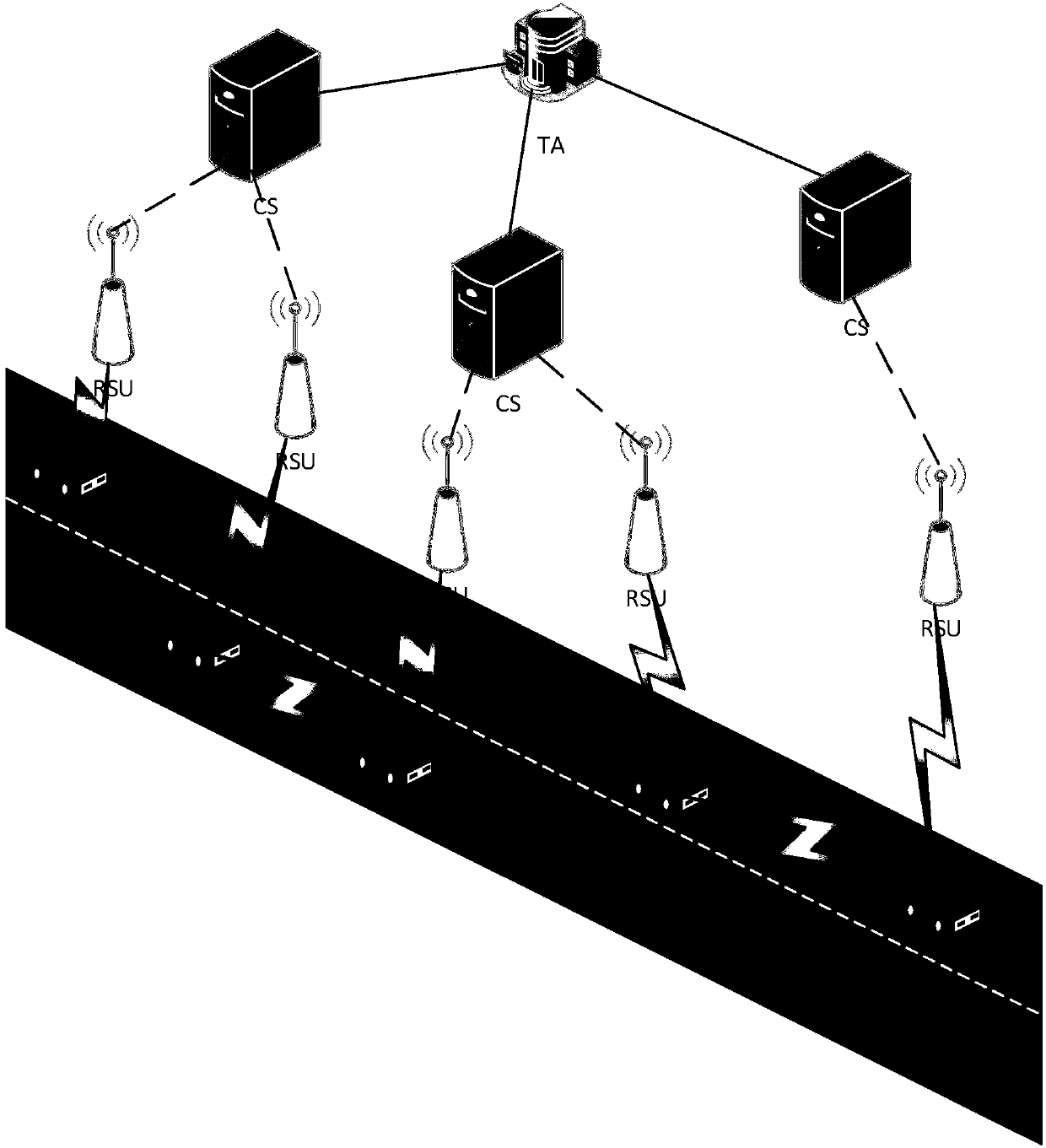
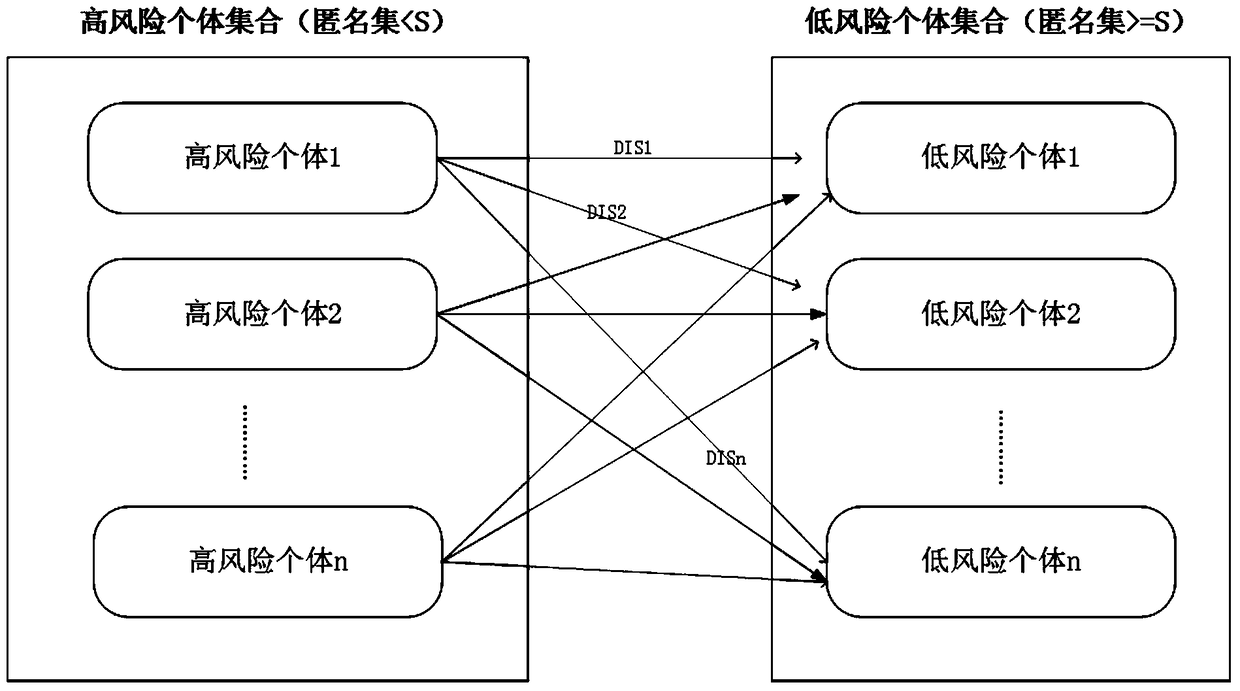
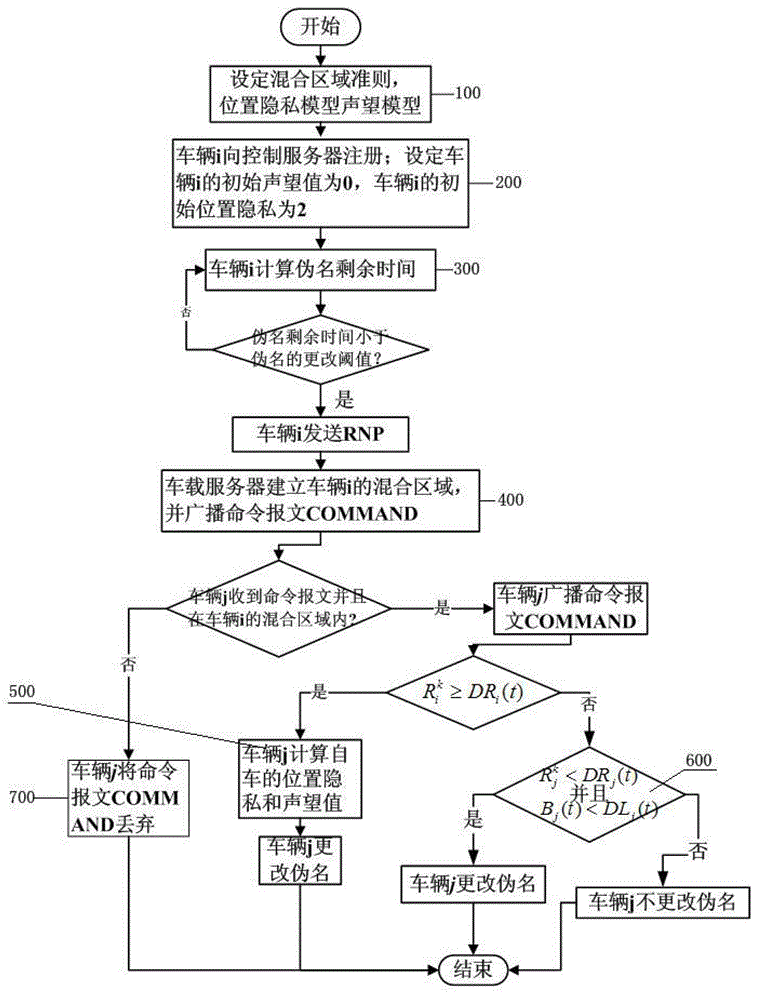
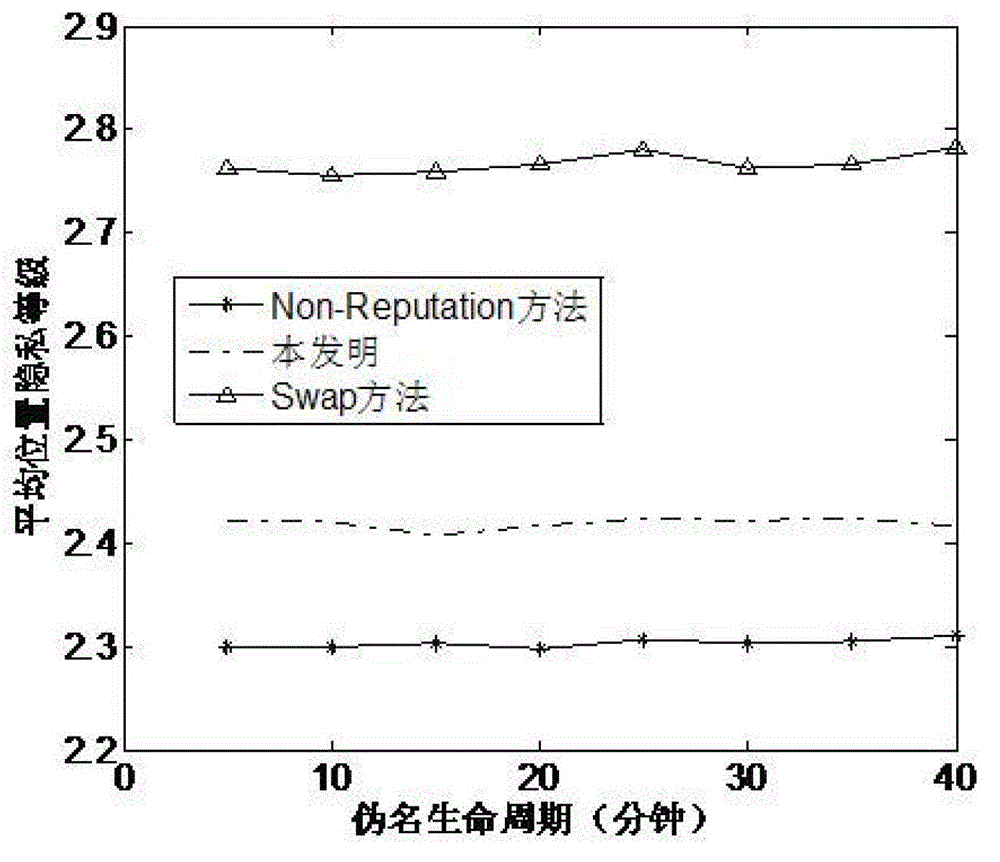
The invention discloses a vehicle position privacy protection method of a vehicular ad hoc network. The method comprises the following steps: a privacy model is first set to assess a current position privacy of different vehicles so as to reflect a reputation module and a mix-zone criterion of a cooperation degree of the current vehicle; any one vehicle in the vehicular ad hoc network determines whether to cooperate and change a pseudo name to protect a vehicle i according to a current reputation value of the vehicle i sending a pseudo name request and based on a judgment whether the one vehicle is within a mix-zone of the vehicle i; and the reputation value of the one vehicle can be dynamically adjusted according to the current position privacy of the one vehicle and pseudo name residual time. The method of the invention can meet the requirement of protecting the current position of the vehicle and can substantially reduce the energy cost; and the method has the advantages that more vehicles are involved in the pseudo name change and the safety of the position privacy of the vehicular wireless network is greater.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Vehicle position privacy protection method based on group signature and reputation
ActiveCN107947942AIncrease confusionReduce threatUser identity/authority verificationPrivacy protectionBroadcasting
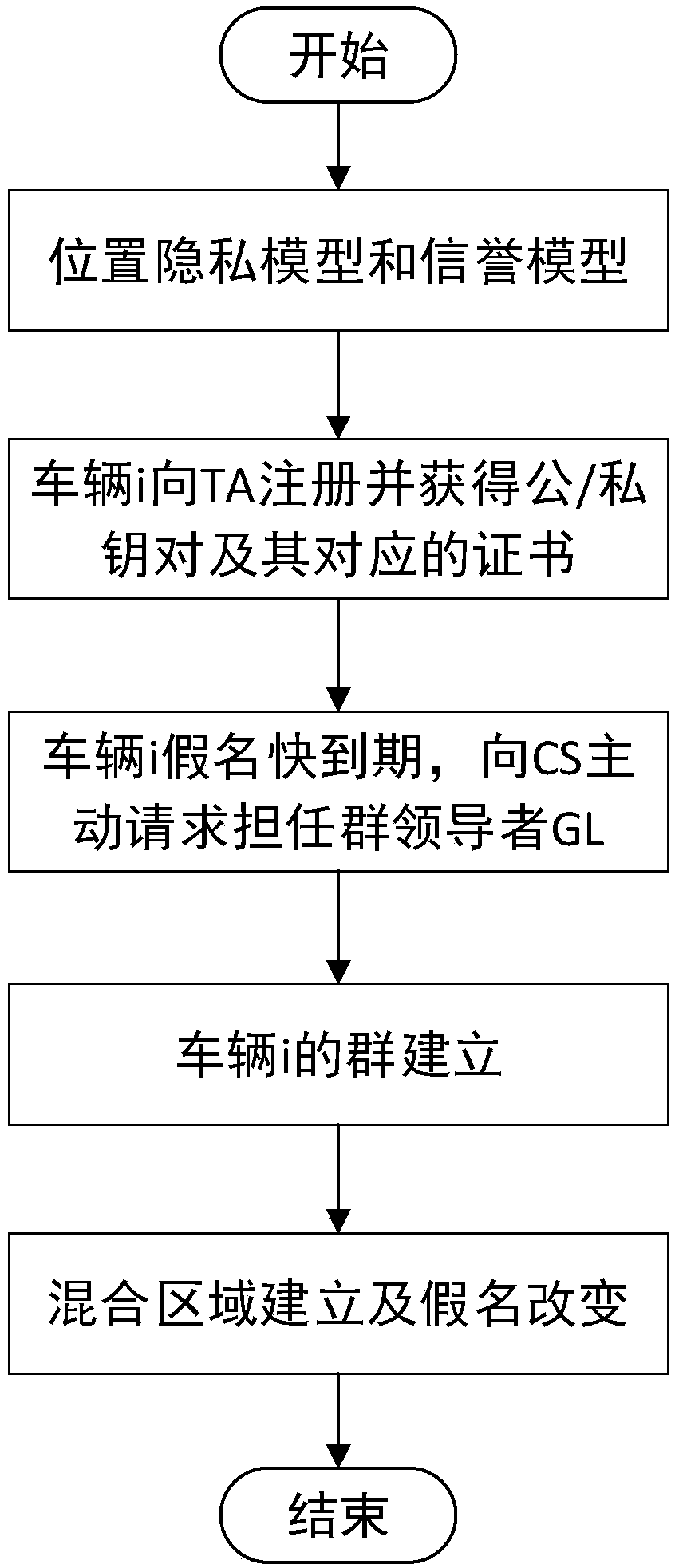
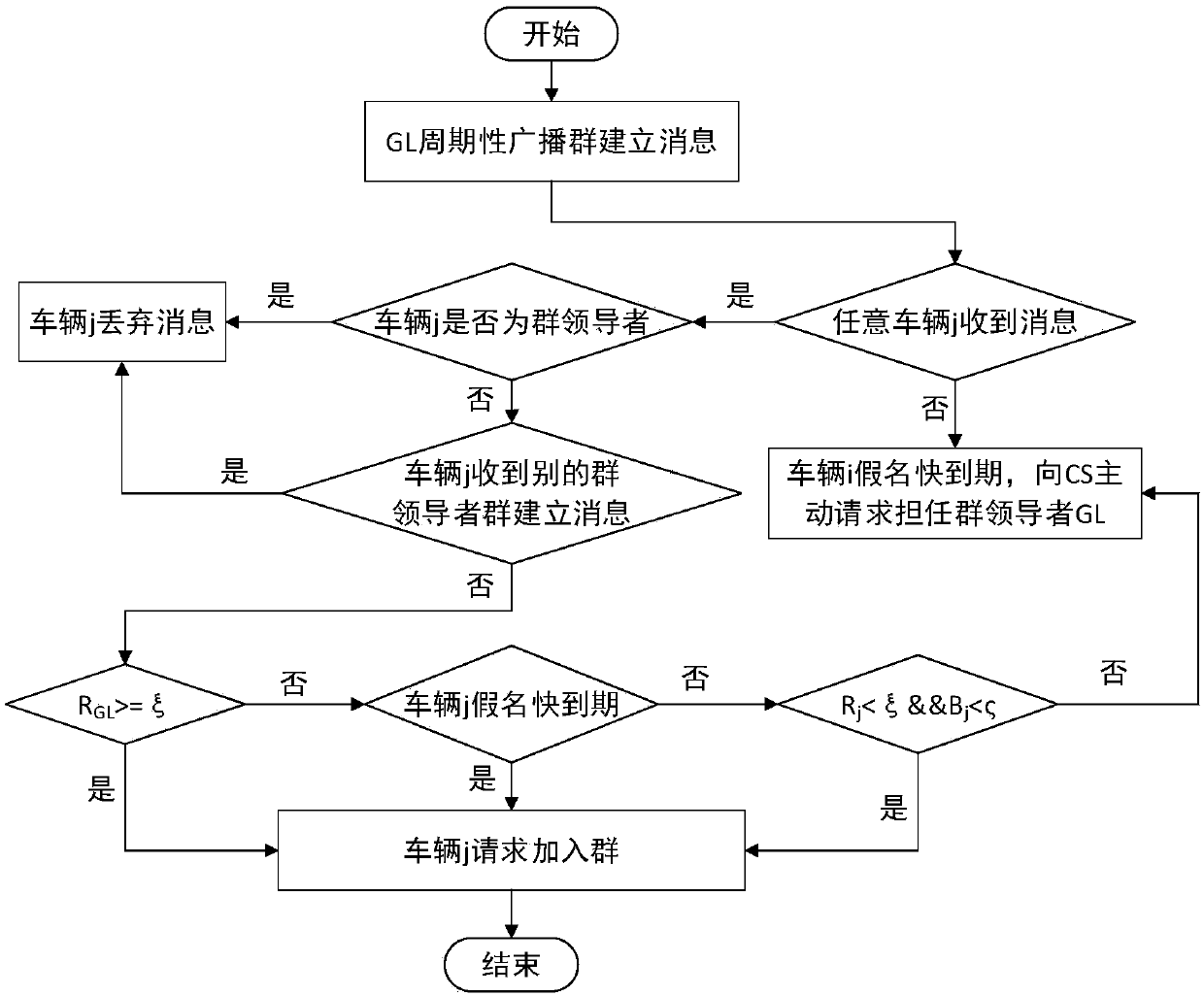
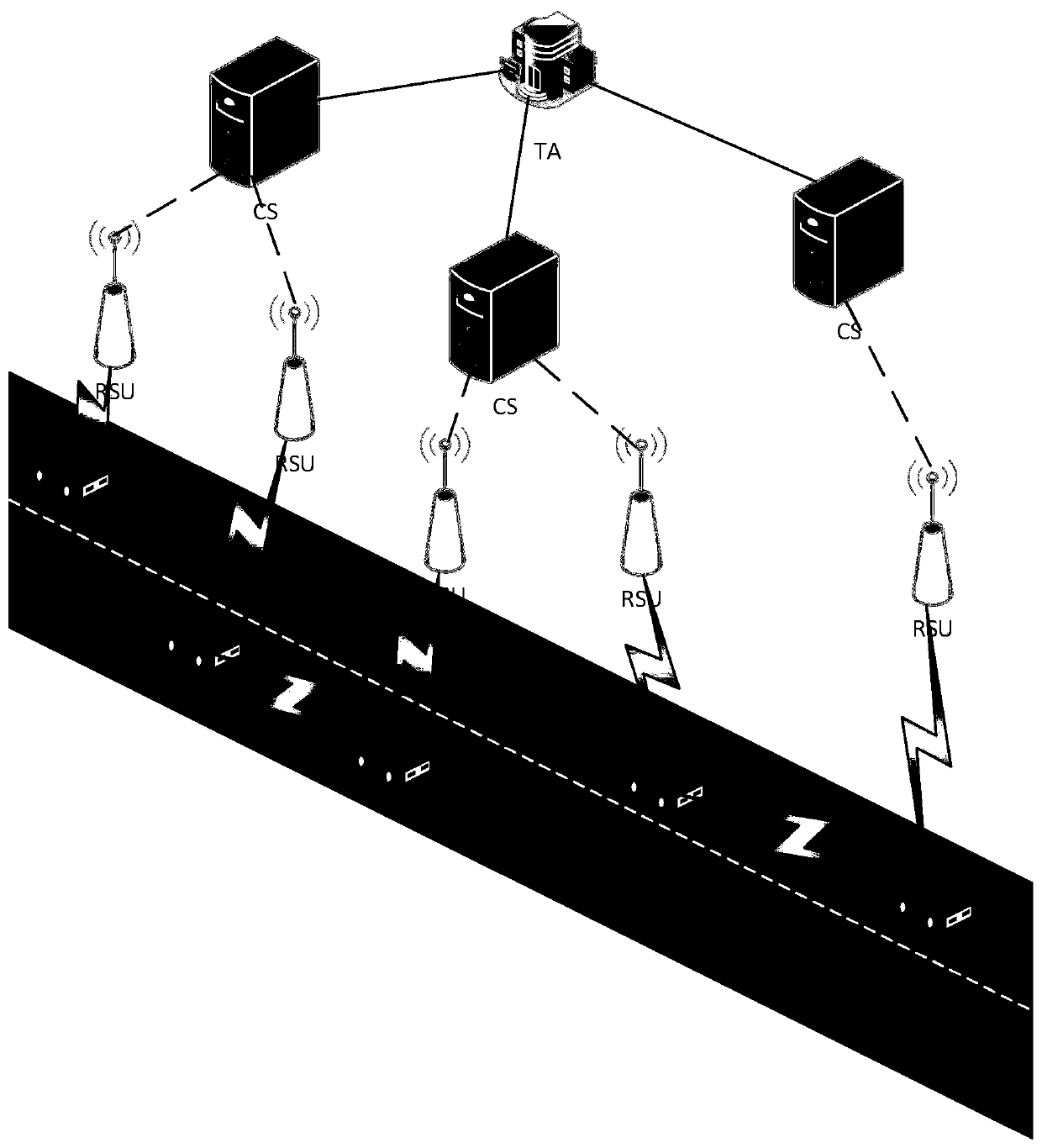
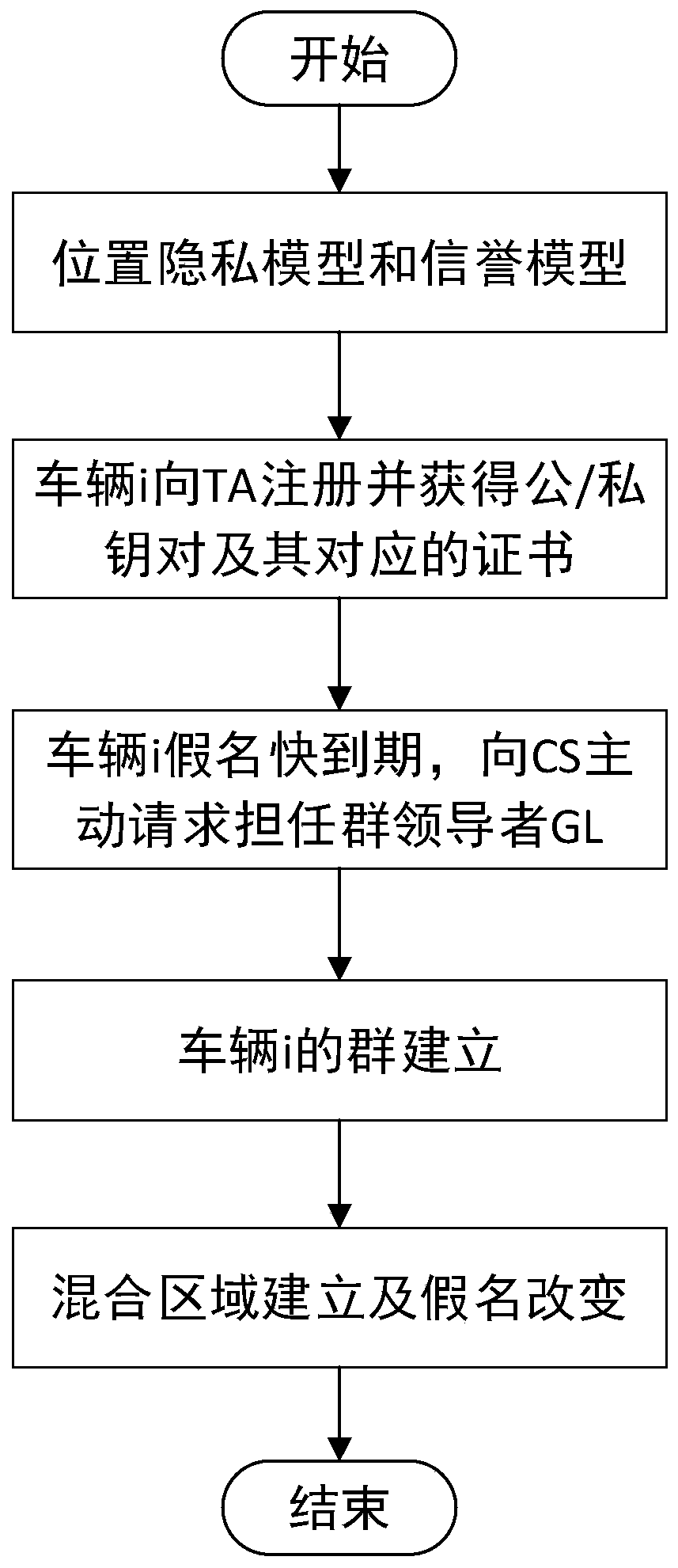
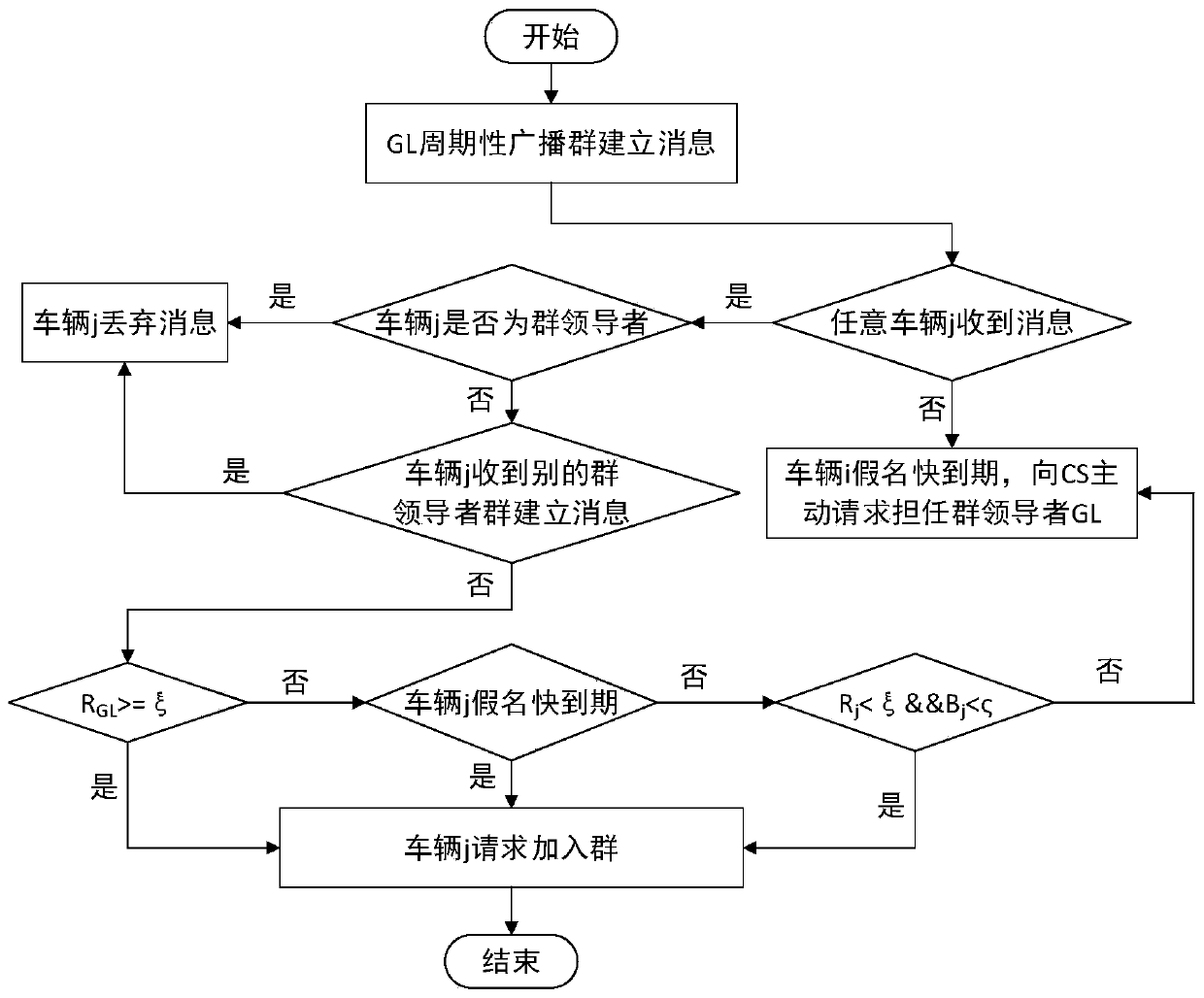
The invention discloses a vehicle position privacy protection method based on group signature and reputation, which comprises a reputation model for encouraging more vehicles to cooperate with each other to form a group, a privacy model for evaluating the position privacy strength of the vehicle, a group forming and dynamic mixed region establishing mechanism, and a pseudonym replacement mechanism. Any vehicle in the vehicle-mounted ad hoc network actively requests establishment of a group from a control server according to the reputation value of the vehicle when the pseudonym of the vehicleis soon to be expired; the control server allocates a group leader role to the requesting vehicle and dynamically forms a mixed region according to the current position of the requesting vehicle; theother vehicles in the mixed region judge whether the cooperation is participated in or not to change the pseudonym according to the reputation value, privacy strength and the remaining time of the pseudonym of the other vehicles; and the reputation value of the vehicles can be dynamically adjusted. According to the method, more vehicles can be encouraged to join the group, thereby changing the pseudonym in cooperation and ensuring the position privacy of the vehicles; meanwhile, the vehicles do not need to keep a silent state in the formed mixed region but broadcast messages as a group identity so that the running safety of the vehicles is guaranteed; furthermore, resource expenditure caused by unnecessary frequent change of the pseudonym can be effectively reduced.
Owner:ANHUI UNIVERSITY
Graded privacy protection method in hierarchical data release
ActiveCN107766745AControl ratioSolving the Proximity Attack ProblemCharacter and pattern recognitionDigital data protectionData privacy protectionData publishing
The invention discloses a graded privacy protection method in hierarchical data release. The graded privacy protection method comprises the following steps: firstly, grading sensitive attributes of original hierarchical data according to actual sensitivity; then, limiting the appearing frequency of the sensitive attributes with different grades in an equivalence class according to a divided gradesetting frequency parameter alphai; then realizing a given privacy model by adopting a clustering method. By adopting the graded privacy protection method disclosed by the invention, the problem of privacy leakage, caused by close-in attack, of the sensitive attributes of an existing hierarchical data release technology is solved very well, the protection intensity on the privacy protection of thehierarchical data is improved and the safety of the data is enhanced; the graded privacy protection method in the hierarchical data release, disclosed by the invention, has certain real meaning and practical value in the protection of the hierarchical data.
Owner:GUANGXI NORMAL UNIV
Spatial aggregation based trajectory data privacy protection method and system
ActiveCN105205408AReduce computational complexityMake up for privacy issuesDigital data protectionComputation complexityPopulation Risk
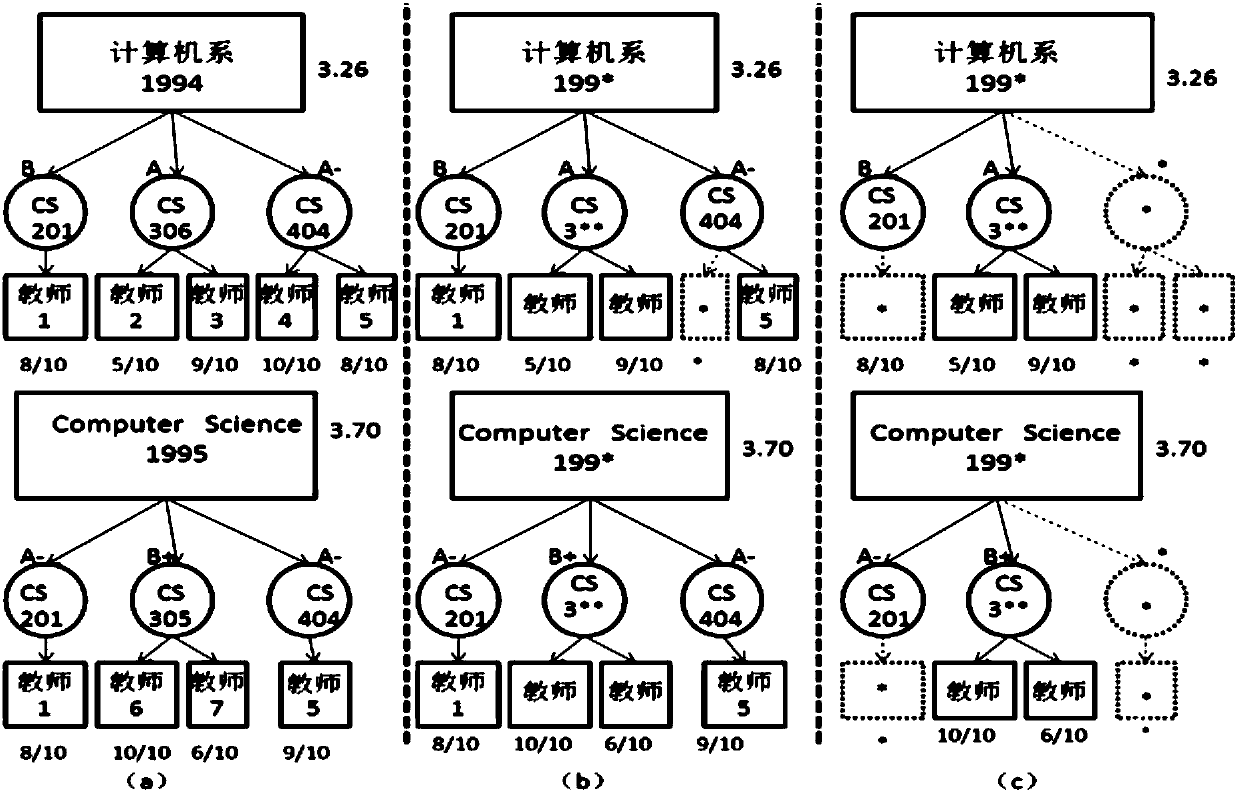
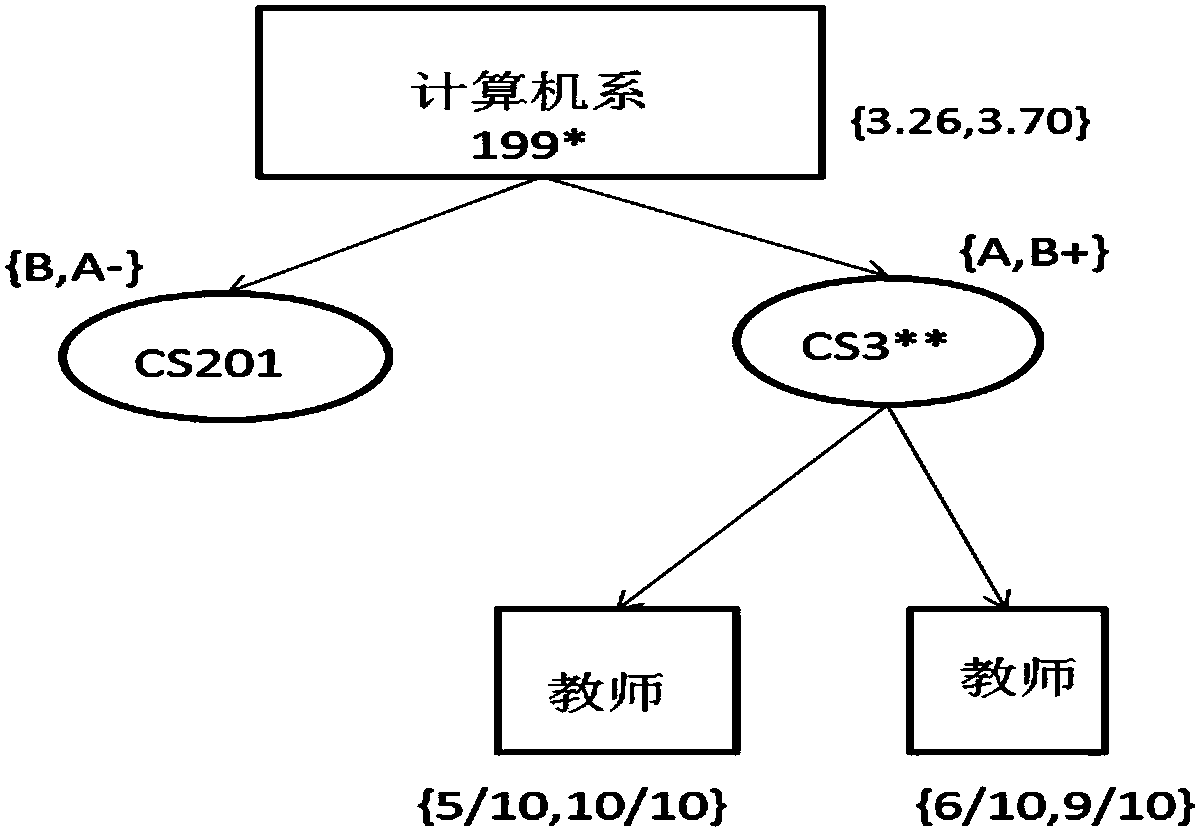
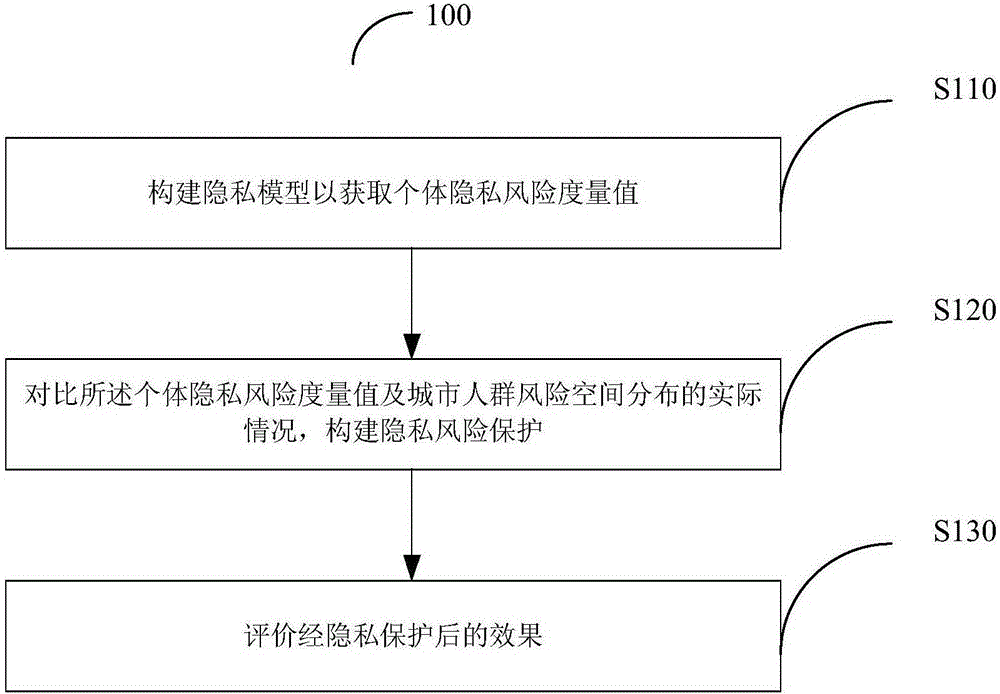
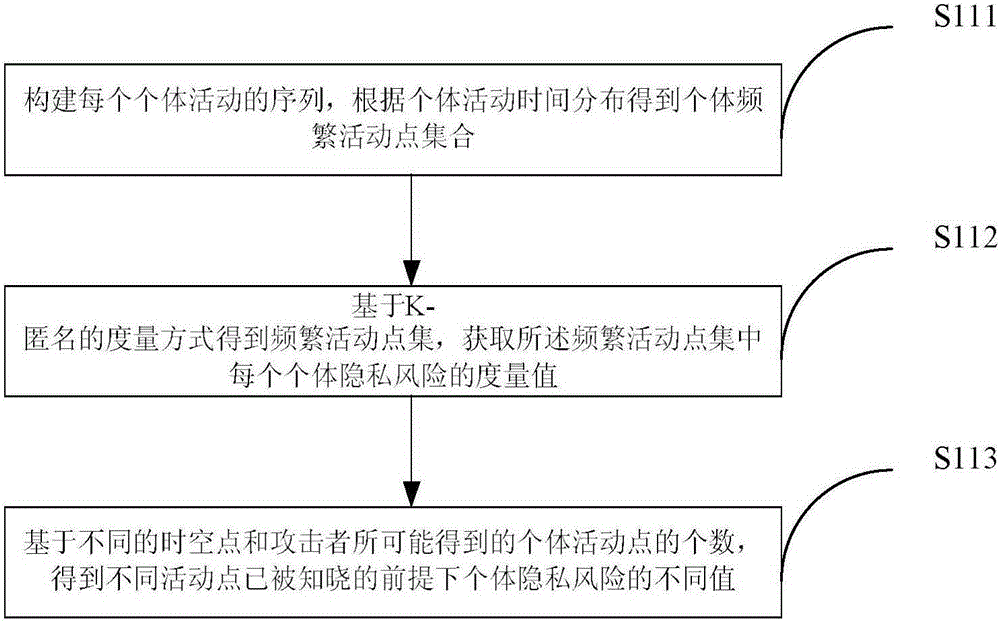
The invention provides a spatial aggregation based trajectory data privacy protection method and system. According to the method, an individual privacy risk metric value is acquired through establishment of a privacy model, the individual privacy risk metric value and the actual condition of urban population risk spatial distribution are compared, privacy risk protection is established, and an effect after privacy protection is evaluated. The method is simple, low in calculation complexity and applicable to spatial data with large data volume.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
A location privacy protection strategy based on differential privacy
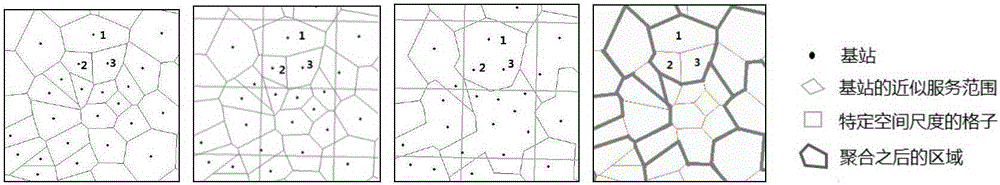
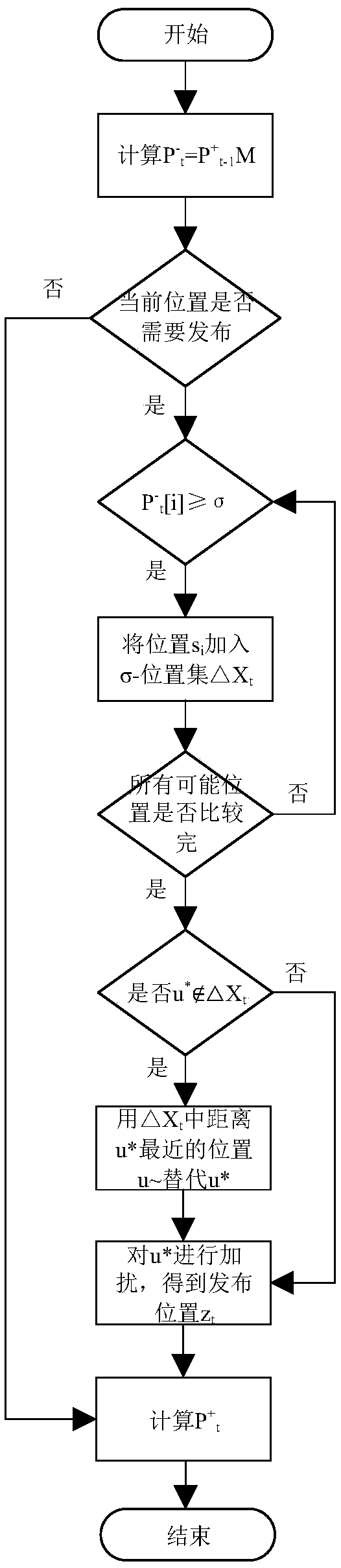
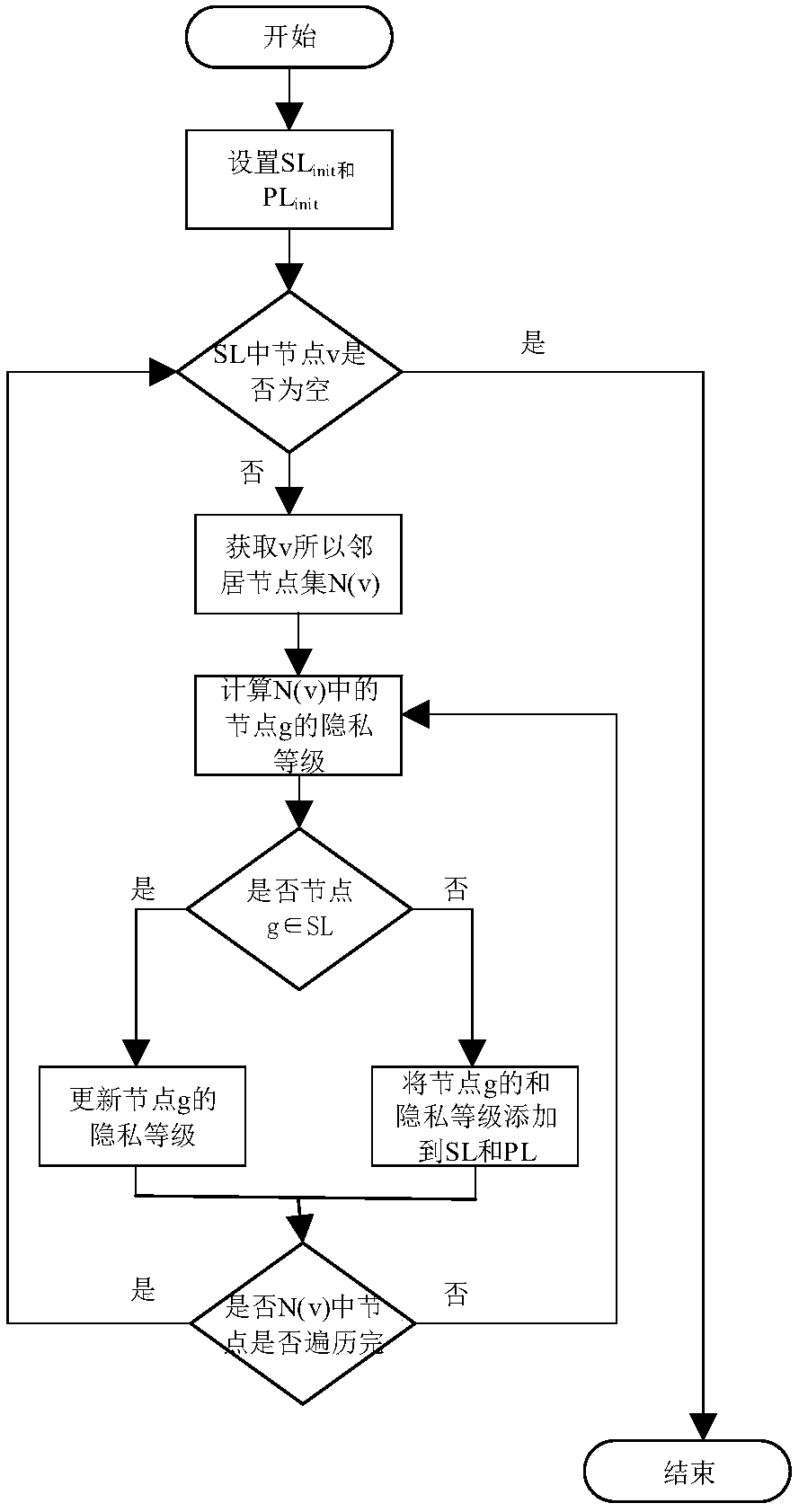
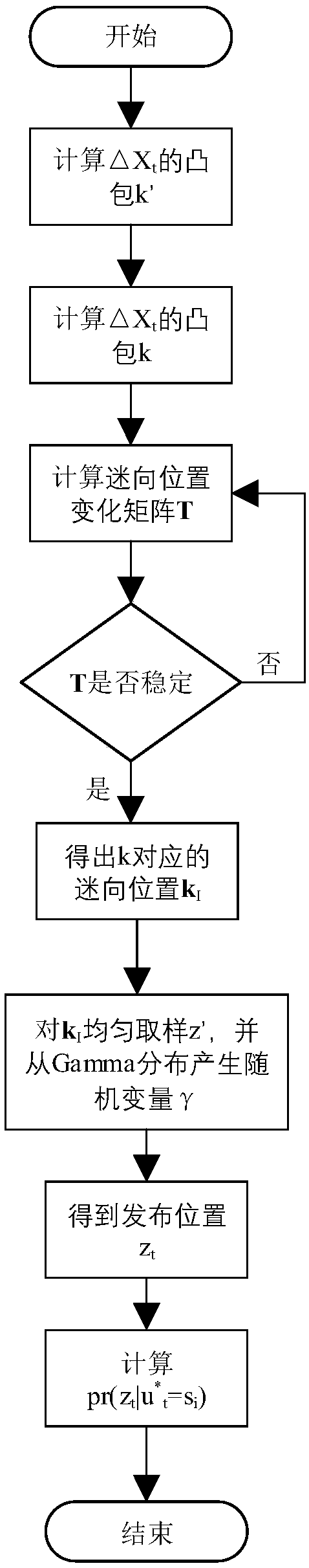
The invention provides a system solution for protecting position privacy on the premise of strictly ensuring privacy, belonging to the field of data information security. For most spatial transformation techniques, the proposed method relies on semantic privacy model, such as k-anonymous, or ad hoc uncertainty models that do not provide strict privacy. Many of them consider only static scenarios or disturbance locations on a single timestamp, rather than the temporal dependency of the mobile user's location, and are therefore vulnerable to various inferential attacks to propose solutions. Firstly, according to the topological relation of the geographic space, the algorithm is proposed to calculate the privacy level of each region on the map. Secondly, a differential privacy based onsigma-location set is proposed to protect the real position of each time point, and the sensitivity package is used to capture the geometric meaning of two-dimensional sensitivity. Finally, a special position perturbation mechanism is proposed to implement the algorithm based on sigma-Differential privacy of the location set.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Location anonymous method and device for continuous queries and privacy protection system
InactiveCN103596133AGood location privacy protectionPrevent speculationLocation information based serviceSecurity arrangementPrivacy protectionData mining
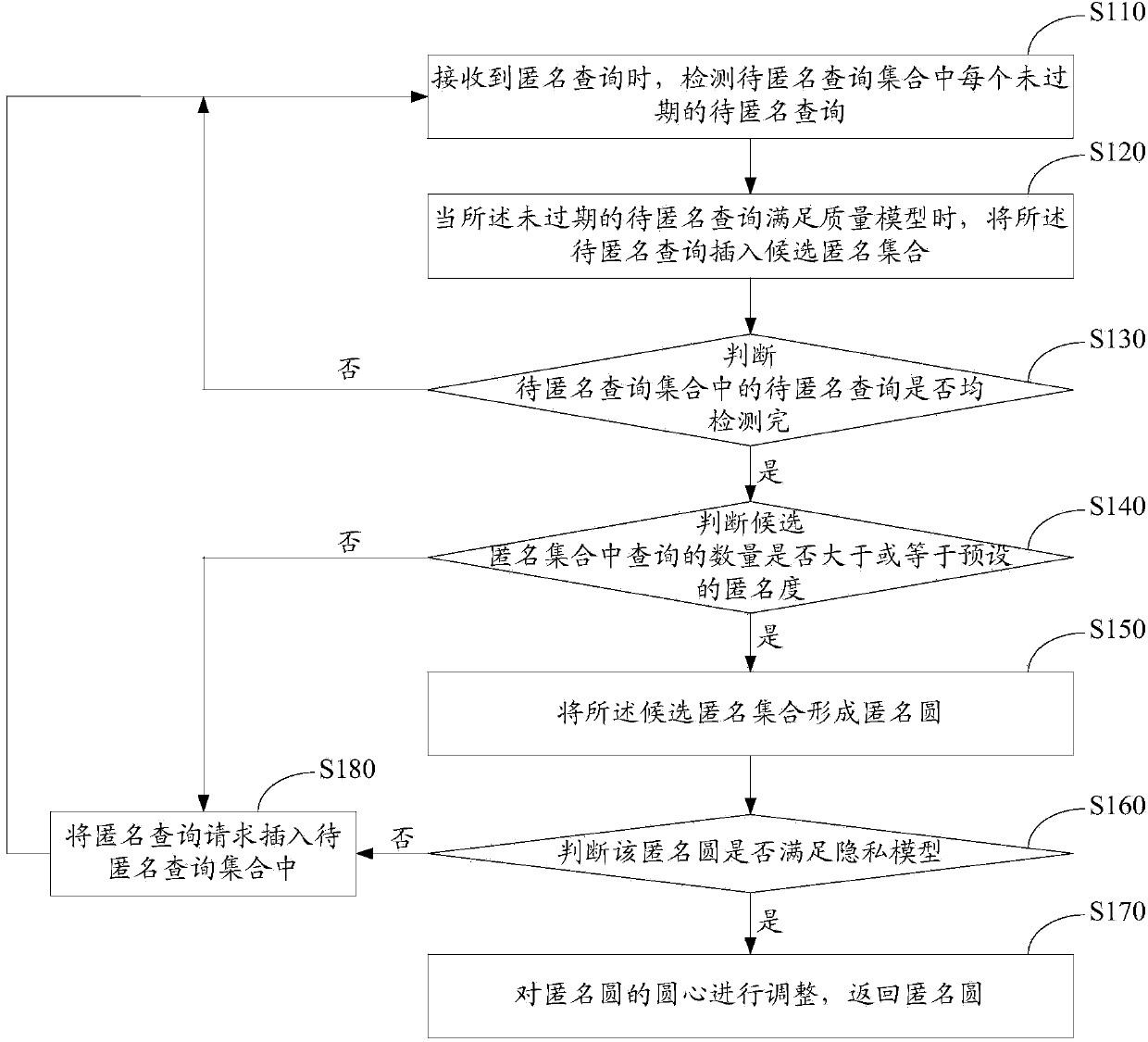
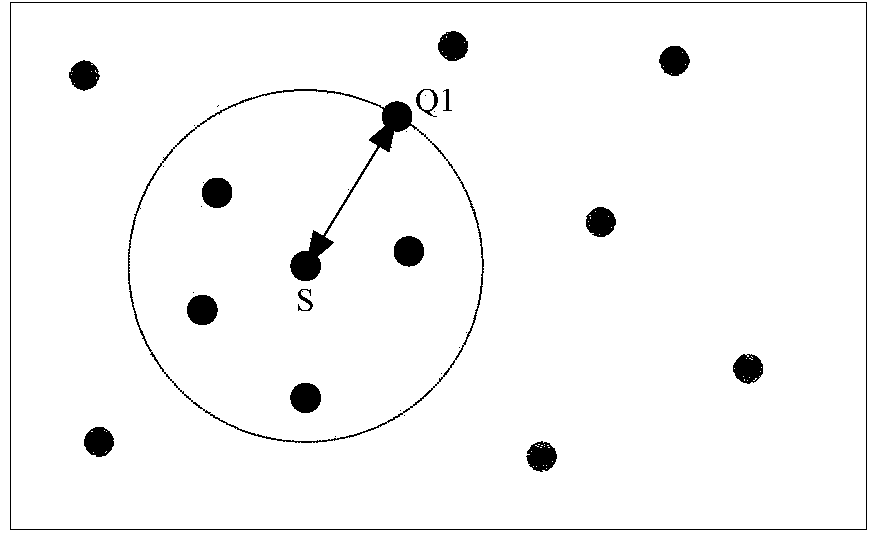
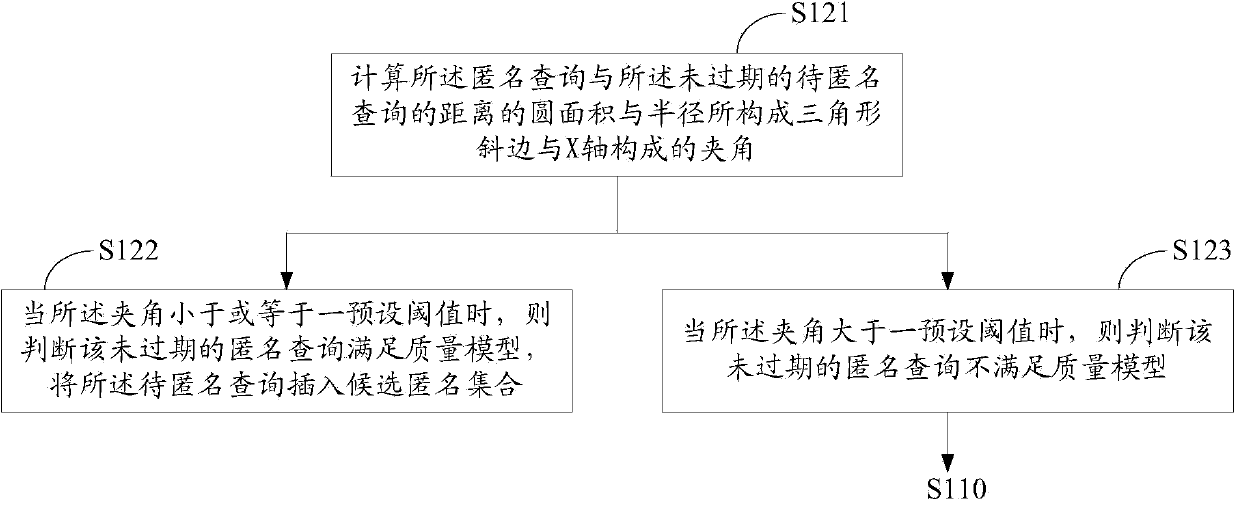
The invention discloses a location anonymous method for continuous queries. The method comprises the steps that when an anonymous query is received, each unexpired query to be anonymous in a query set to be anonymous is detected; when the unexpired queries to be anonymous meet a quality model, the queries to be anonymous are inserted into a candidate anonymous set; when the detection of the queries to be anonymous in the query set to be anonymous is finished, and the number of queries in the candidate anonymous set is larger than or equal to that of a preset anonymity degree, the candidate anonymous set forms an anonymity circle, and whether the anonymity circle meets a privacy model or not is judged; when the anonymity circle meets the privacy model, the center of the anonymity circle is adjusted, and the anonymity circle is returned. The invention further discloses a location anonymous device for the continuous queries and a privacy protection system. The privacy protection on the continuous queries is improved, and location service quality and anonymity efficiency are improved.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
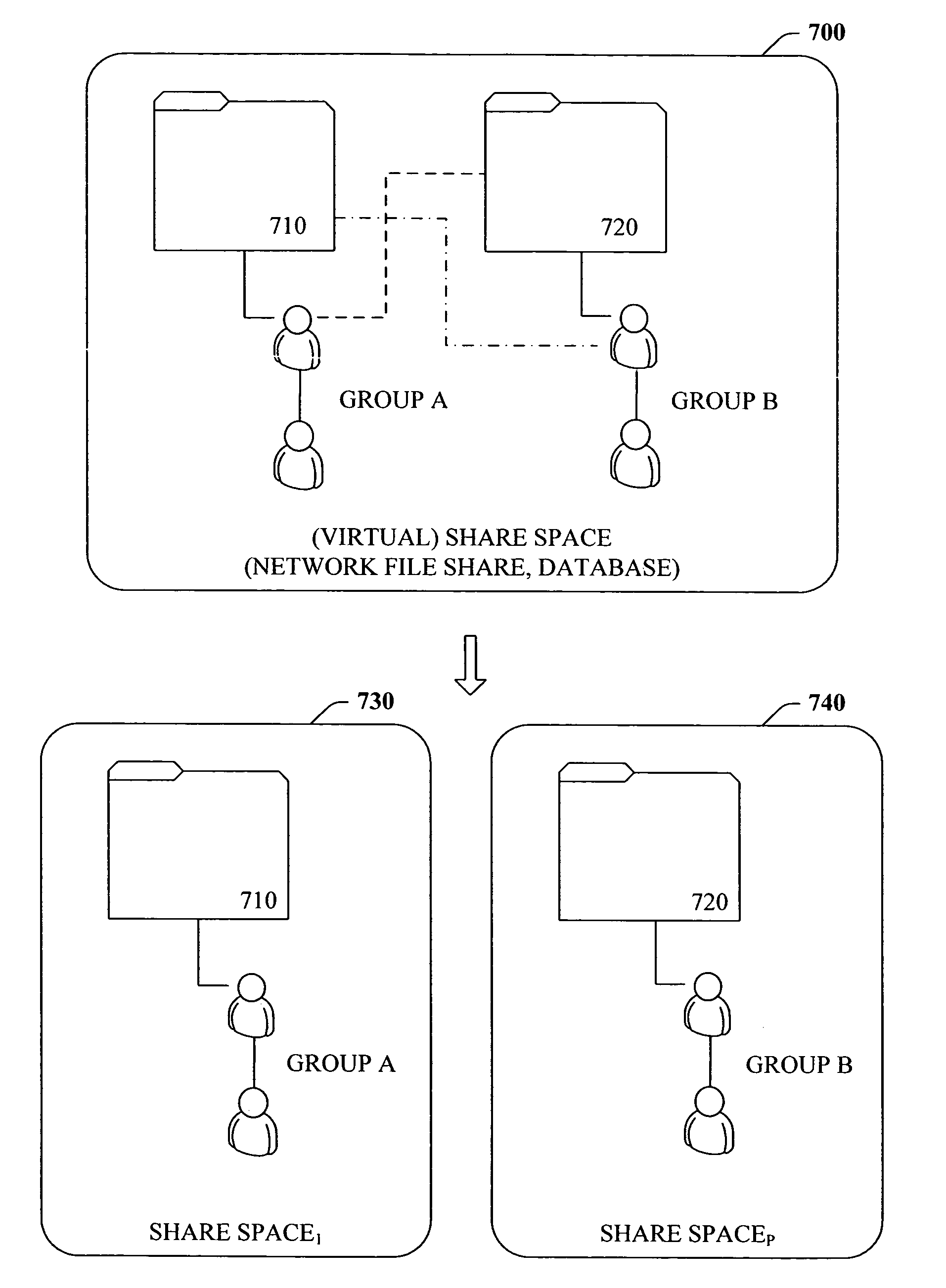
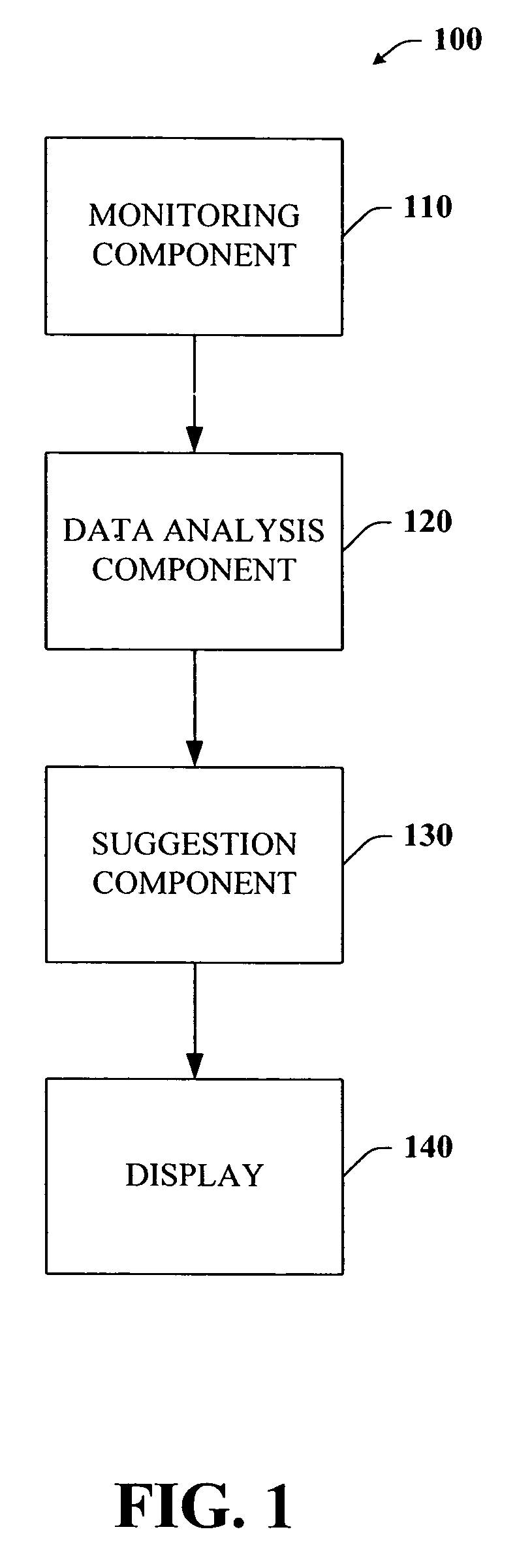
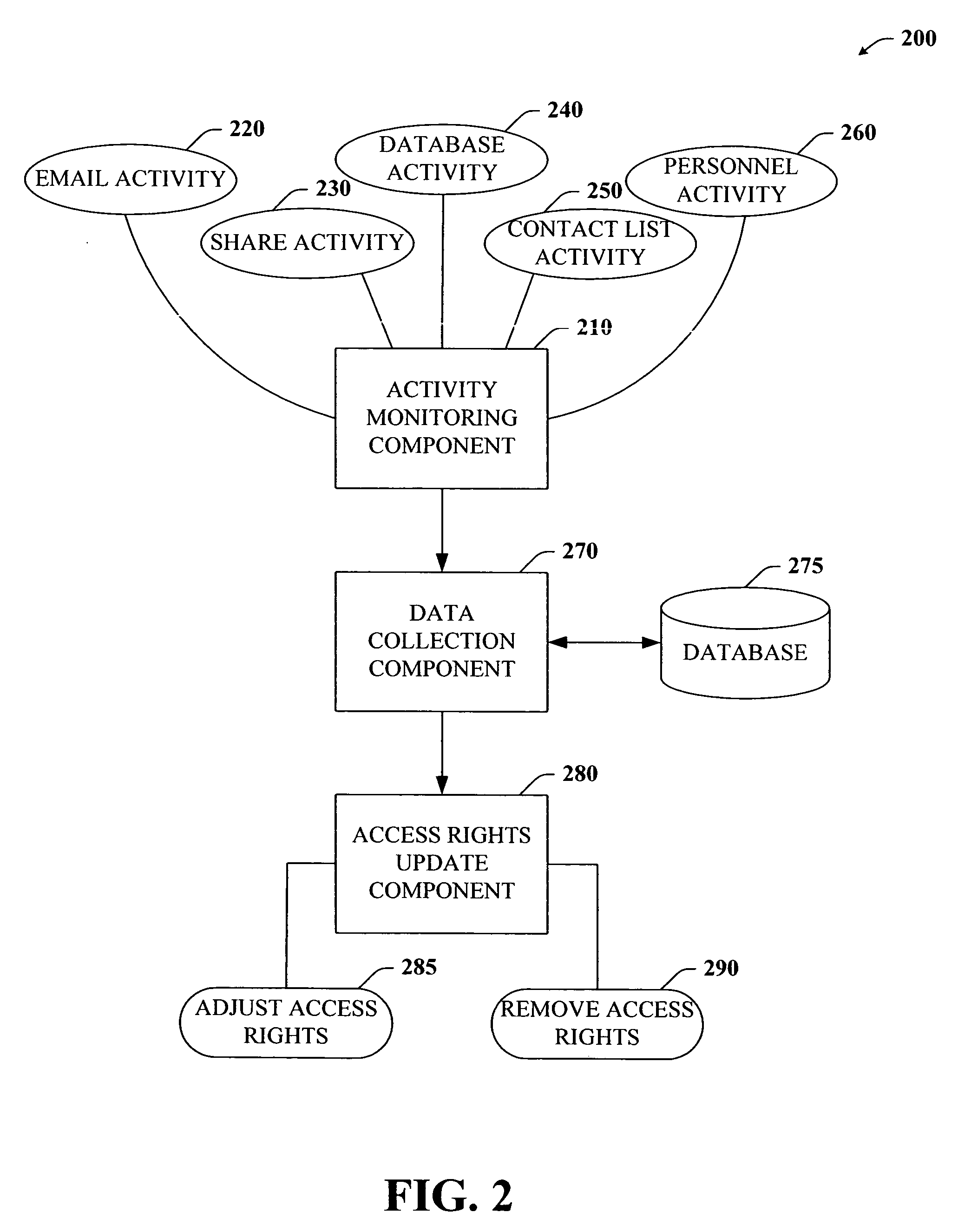
Privacy model that grants access rights and provides security to shared content
ActiveUS8234374B2Reduce contentEasy accessMemory loss protectionHardware monitoringInternet privacyClient-side
Systems and / or methods that mitigate overexposure of shared content and that facilitate improving security of content in a computing environment are provided. In particular, the systems and methods involves monitoring resource activities such as user interactions (between users and / or between users and resources), email activity, share space activity, shared content activity, distribution lists, contact lists, personnel or organization structures, and the like. Data can be collected as one or more resource activities are monitored and then analyzed to determine where, if any, changes have taken place. For example, if a user has been removed from a distribution list or a user has not accessed the shared content within a time period, a recommendation can be formulated to suggest an adjustment to the affected access rights. Furthermore, the systems and / or methods can be integrated with other applications such as an email client, whereby an out-of-office indicator can leave access rights as they are.
Owner:MICROSOFT TECH LICENSING LLC
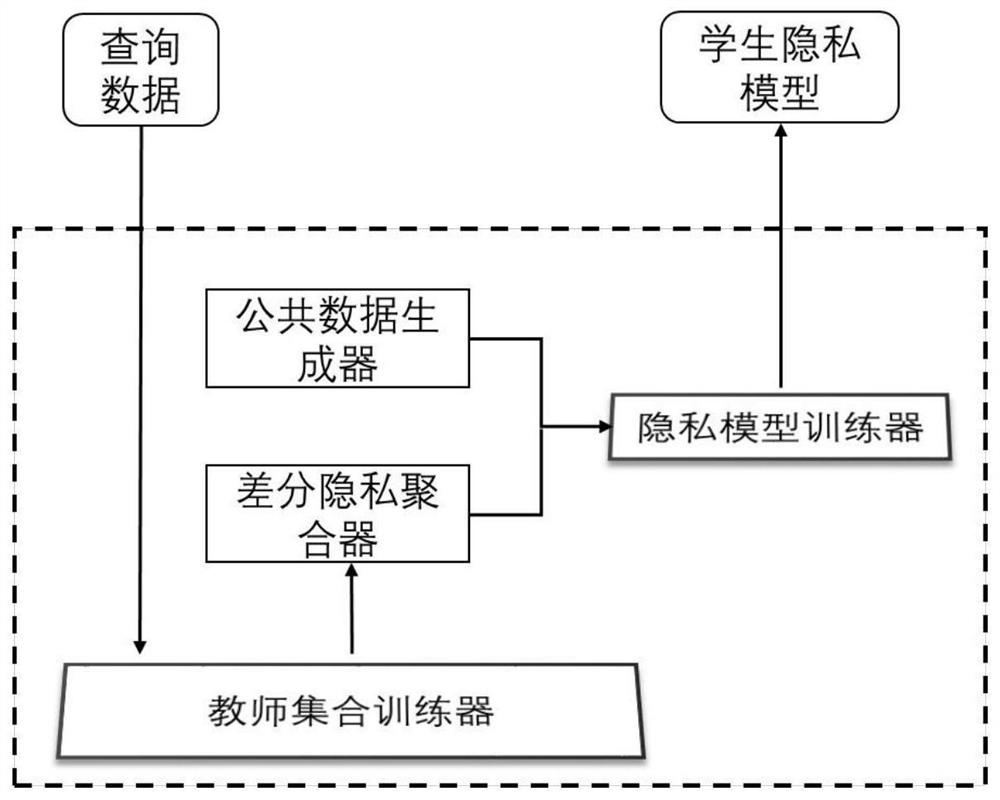
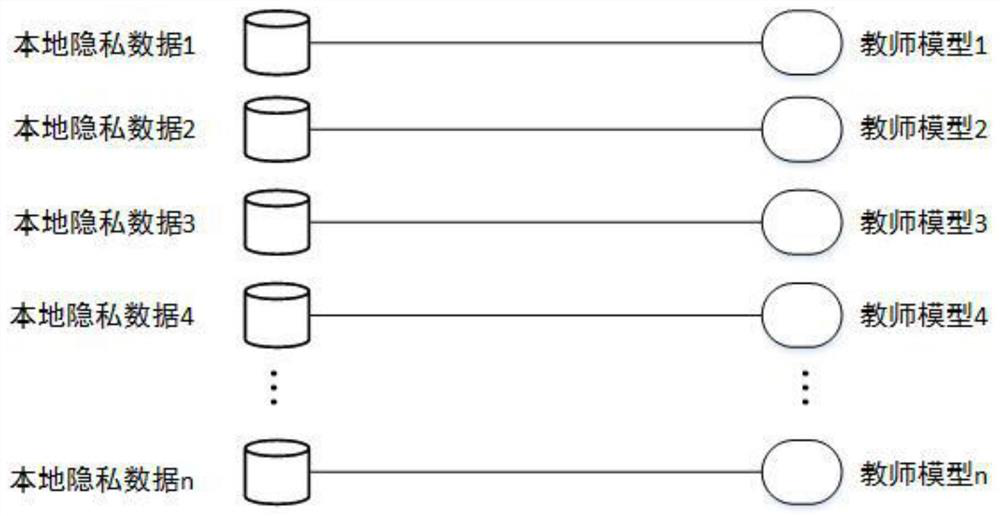
Privacy model training method and device based on small amount of public data
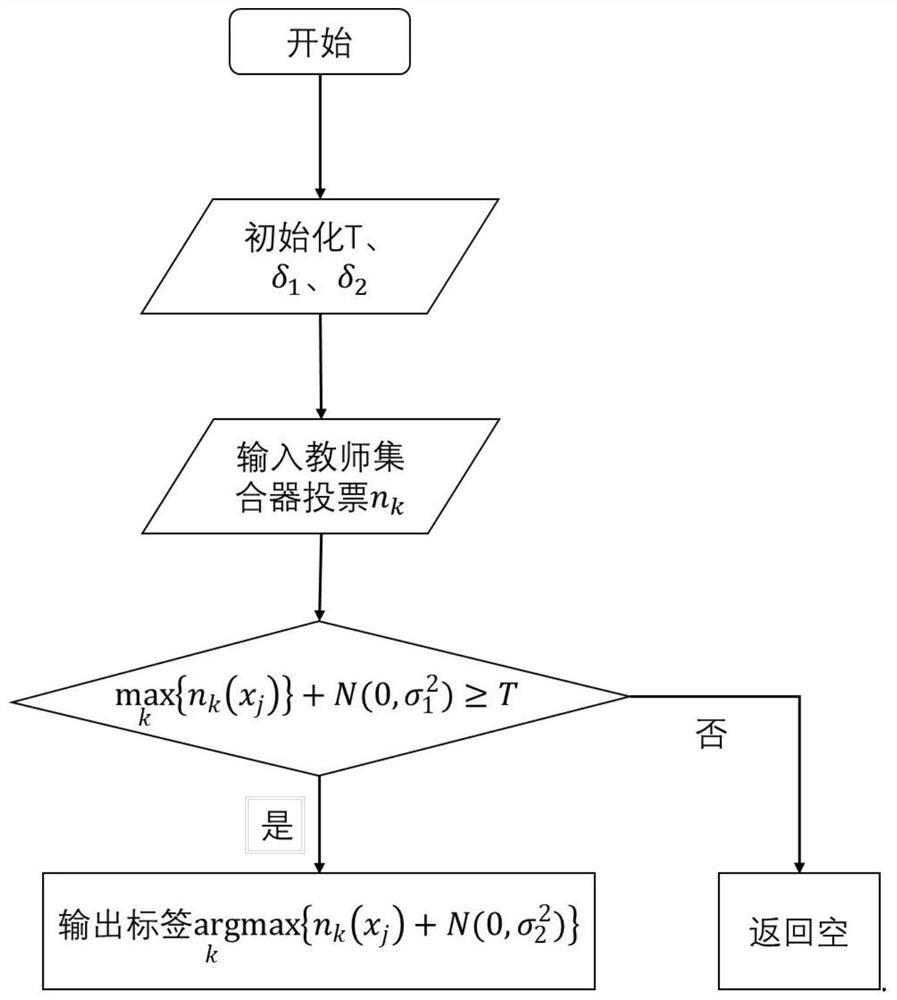
PendingCN112199717AEasy to deployAchieve physical isolationDigital data protectionMachine learningDifferential privacyEngineering
The invention provides a privacy model training method based on a small amount of public data and an electronic device. The privacy model training method comprises steps of obtaining N neural networkteacher models by using a plurality of trainings; respectively inputting a small amount of public data xi into the N neural network teacher models to obtain a statistical voting result of each publicdata xi for each label k; noise being added to all statistical voting results, and public data xi and corresponding labels meeting the differential privacy principle being obtained; optimizing an adversarial generative network through a large number of random noise vectors and a pre-trained discriminant neural network, and generating a large number of label-free data; and jointly training a student model through the public data xi meeting the differential privacy principle, the corresponding label and a large amount of unlabeled data pair pre-trained auto-encoders to obtain a private student model. According to the method, only a small amount of public data is needed to train one private student model, physical isolation and network isolation of sensitive data are realized, and a problem of low accuracy of the private student model is solved.
Owner:INST OF INFORMATION ENG CAS
Blockchain privacy protection method, system and device
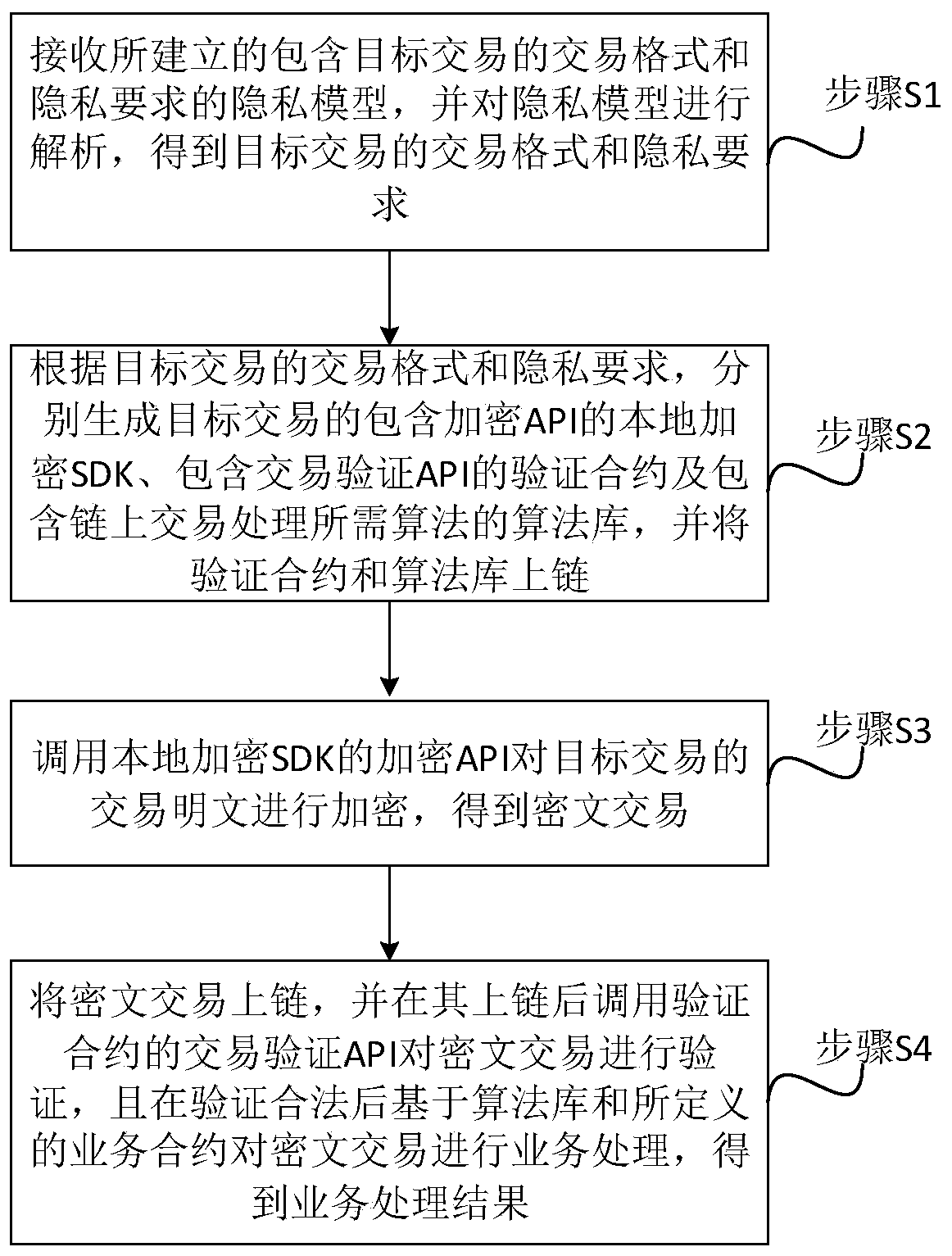
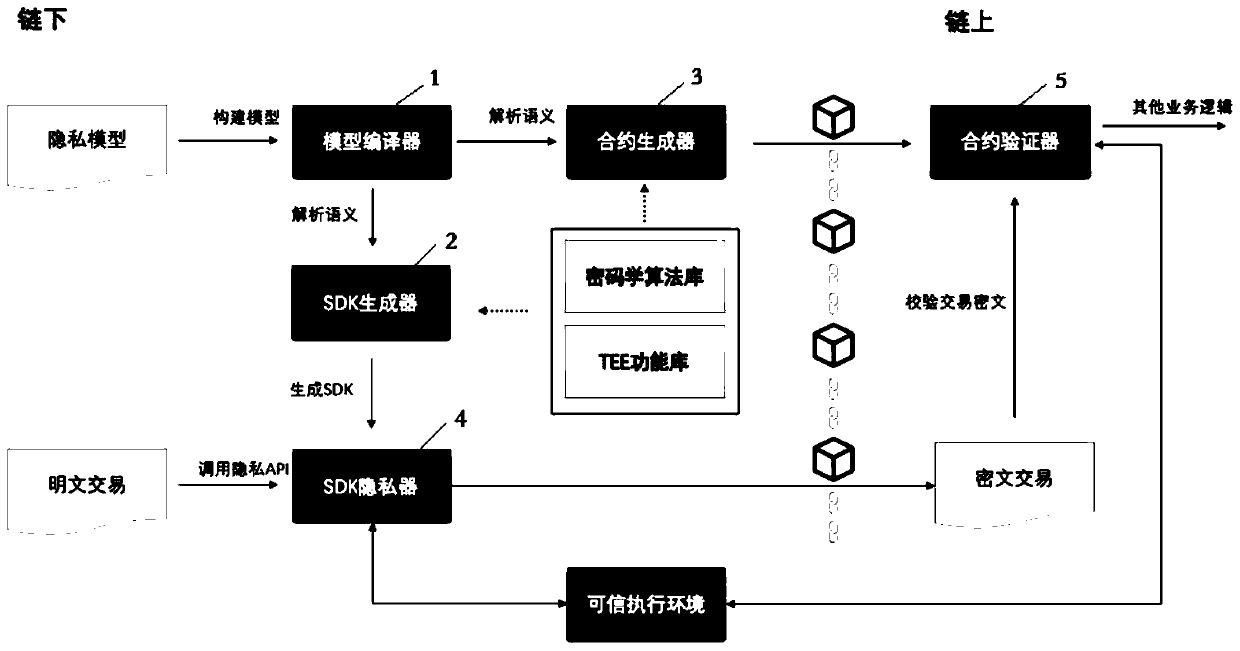
ActiveCN111597586AReduce learning costsDigital data protectionPlatform integrity maintainancePlaintextCiphertext
The invention discloses a blockchain privacy protection method, system and device. The method comprises the steps of receiving an established privacy model containing a transaction format and a privacy requirement of a target transaction; respectively generating a local encryption SDK (Software Development Kit) containing an encryption API (Application Program Interface), a verification contract containing a transaction verification API and an algorithm library containing algorithms required by on-chain transaction processing according to the transaction format and the privacy requirement, andlinking the verification contract and the algorithm library; calling an encryption API to encrypt the transaction plaintext of the target transaction to obtain a ciphertext transaction; and after theciphertext transaction is linked, calling a transaction verification API to verify the ciphertext transaction, and after the verification is legal, performing service processing on the ciphertext transaction based on the algorithm library and the defined service contract to obtain a service processing result. Therefore, a brand-new privacy protection scheme is provided, a user only needs to provide a privacy model, the system can automatically execute model analysis, transaction encryption, transaction verification, transaction processing and other work, and the learning cost is low.
Owner:牛津(海南)区块链研究院有限公司
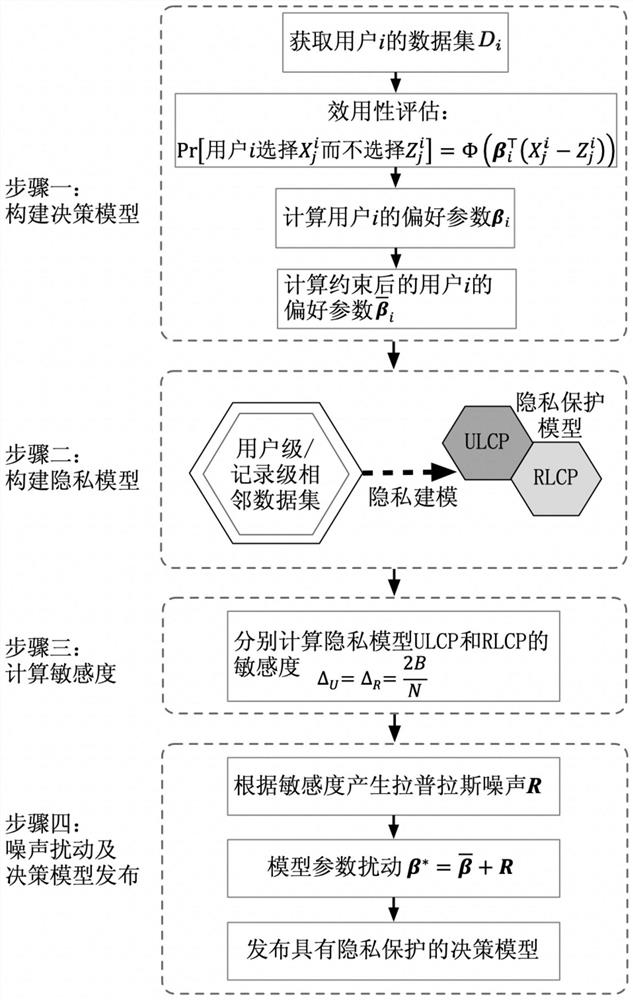
Centralized privacy protection method for decision model release
PendingCN113204782AGuaranteed accuracyRealize privacy protection releaseDigital data protectionPrivacy protectionComputer science
The invention discloses a centralized privacy protection method for decision model release, and aims to overcome the defects of the existing privacy protection technology for issuing the decision model. According to the method, firstly, decision model construction and privacy modeling are carried out respectively according to an intelligent decision scene data model and privacy protection requirements, then, sensitivity is calculated based on a privacy model, finally, Laplace noise is added to model parameters of the decision model to realize privacy protection, and the decision model which can be directly published is obtained. Compared with a common privacy protection method oriented to simple data statistics, the invention has the advantages that privacy modeling is carried out according to the data model in the decision-making scene, the defect of lack of privacy protection normal forms is made up theoretically, privacy protection is achieved based on Laplace noise disturbance, and meanwhile the accuracy of the decision-making model is guaranteed.
Owner:XIAN UNIV OF POSTS & TELECOMM
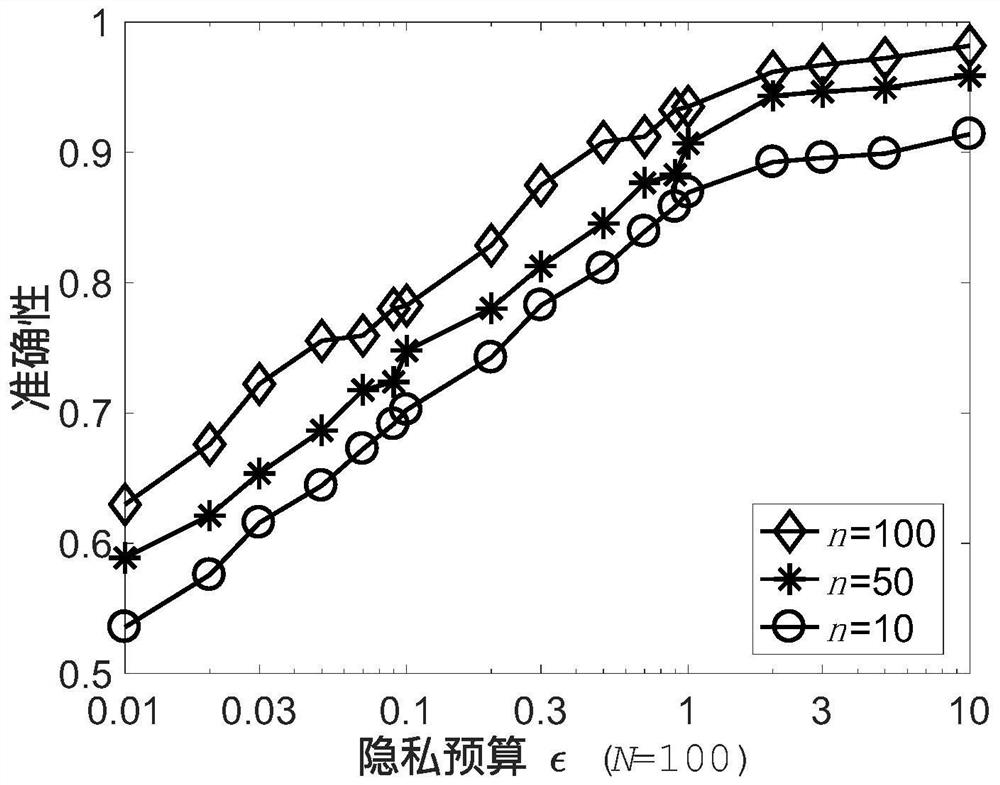
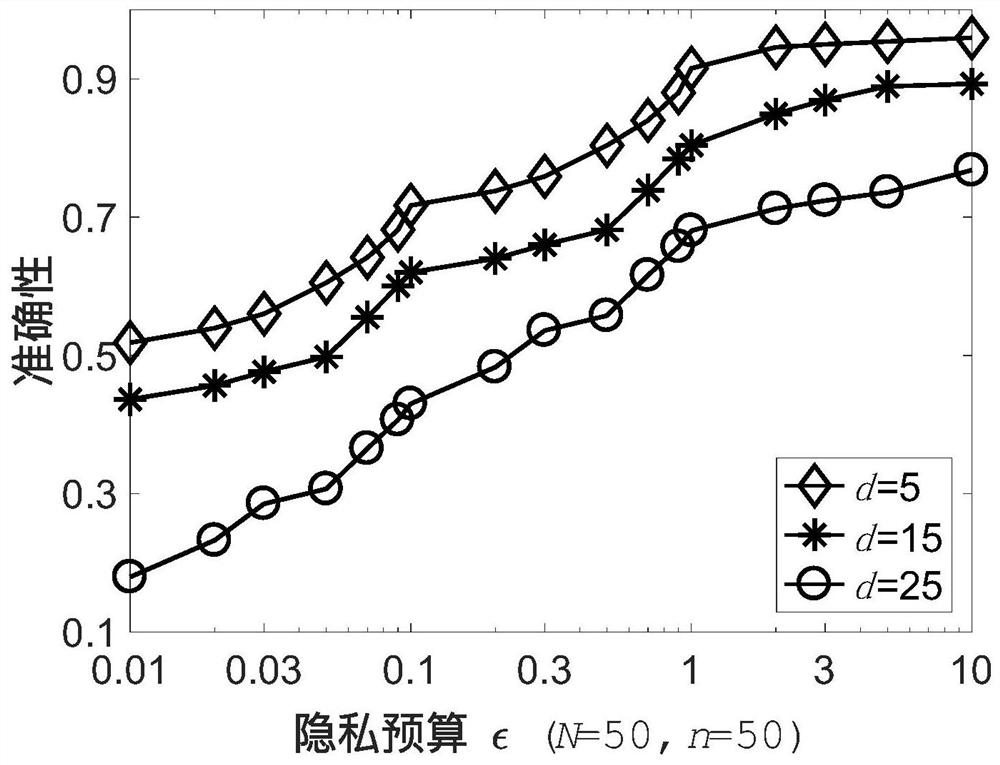
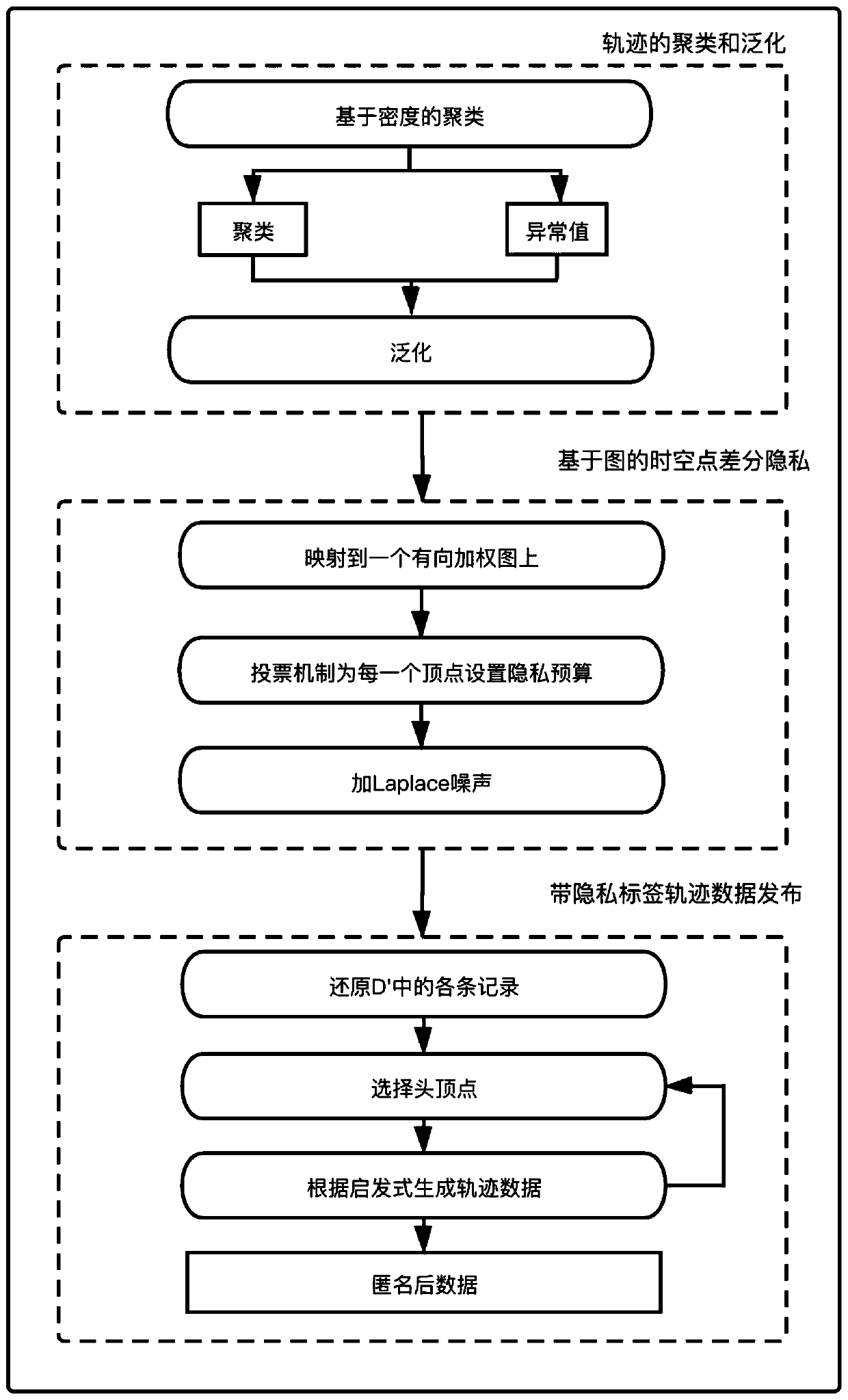
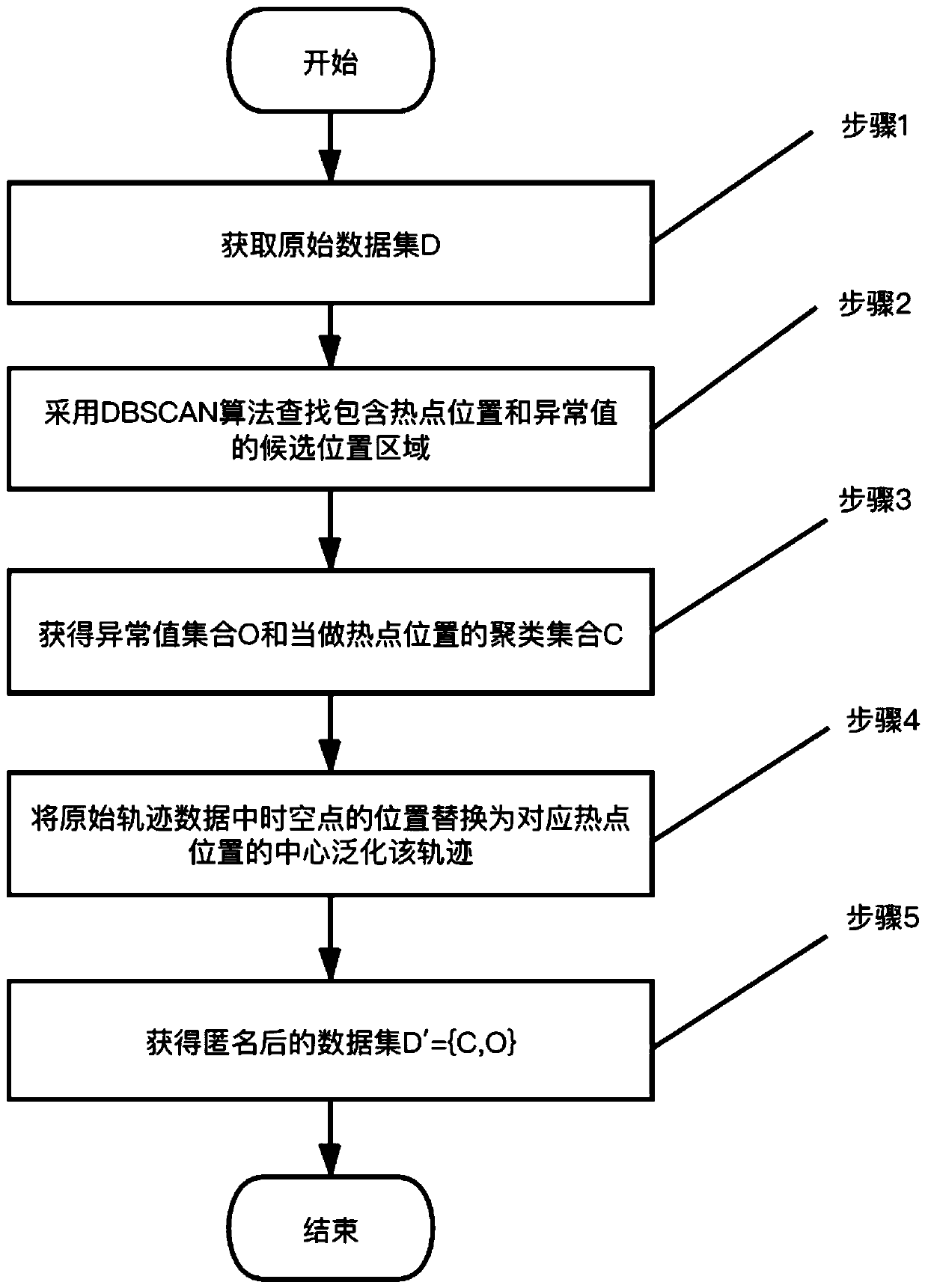
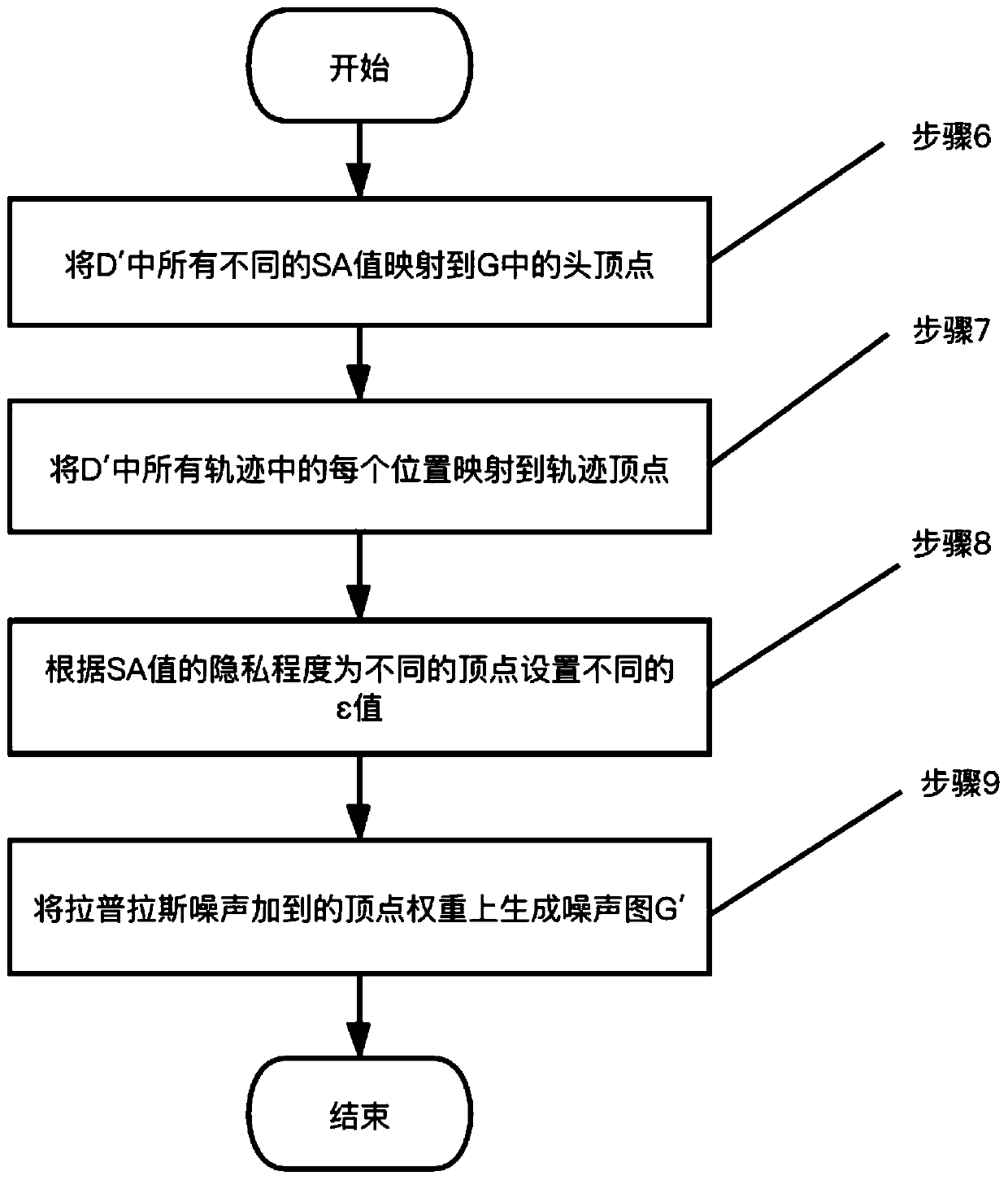
Sensitive label track data publishing method using graph difference privacy model
ActiveCN111353173AGuaranteed availabilityAddress privacy breachesDigital data protectionData setDifferential privacy
The invention belongs to the technical field of information security, and relates to a sensitive label track data publishing method based on a graph differential privacy model. The method comprises the steps: clustering and generalizing tracks, performing graph-based time-space point differential privacy and publishing track data with privacy labels. In the first stage, firstly, all space-time points are divided into hot spot areas and abnormal values, and then the center positions of the hot spot areas are used for generalizing each specific position in the trajectory data; in the second stage, a noise map is established, hot spots, abnormal values and privacy tags are mapped to a directed weighted graph, different privacy budgets are set for different vertexes in order to control the size of the added noise and protect the availability of the data as much as possible, and then Laplace noise is added to achieve differential privacy; in a publishing stage, each record in the generalized trajectory data set is restored, the overhead point is selected, the trajectory data is generated according to the heuristic expression, anonymous data is obtained, and high availability of the datais ensured.
Owner:DALIAN UNIV OF TECH
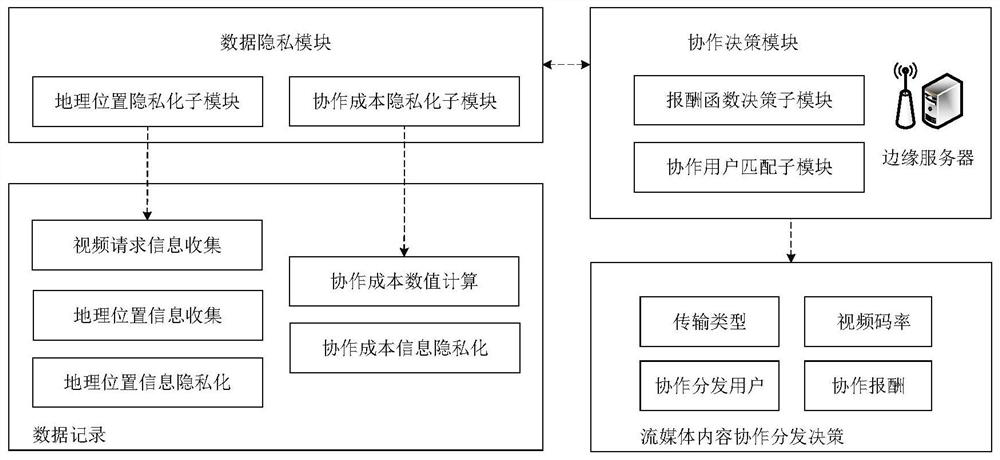
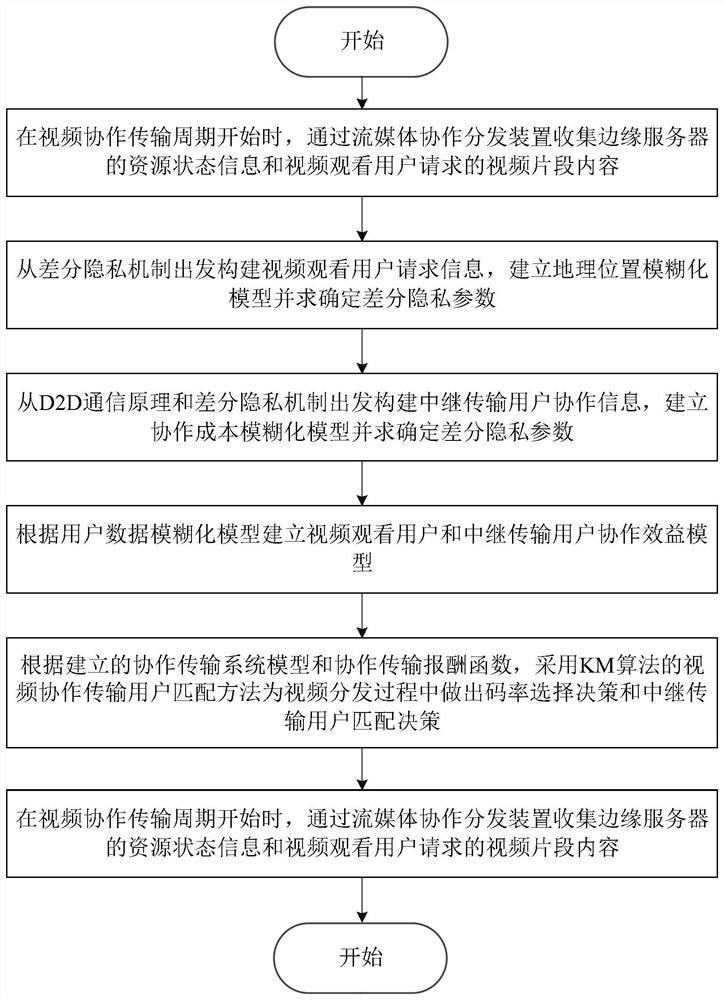
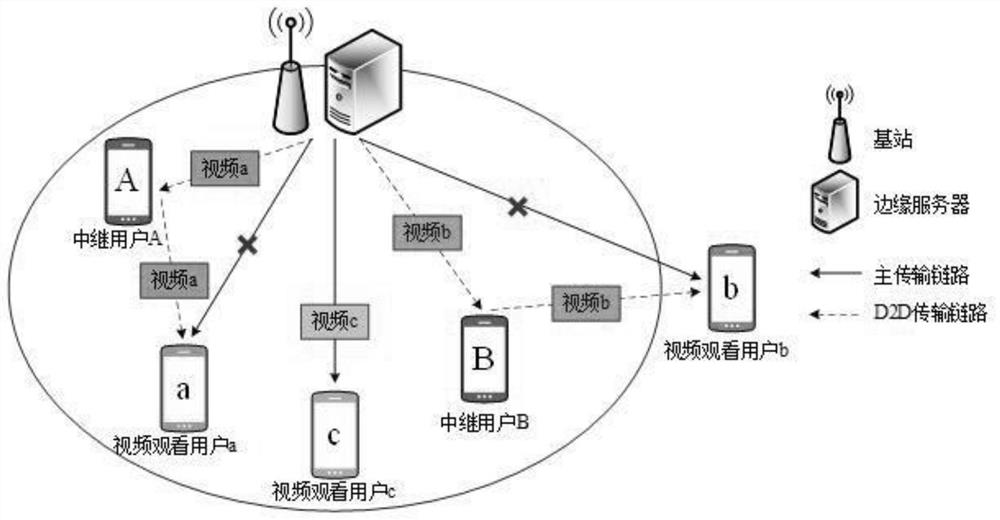
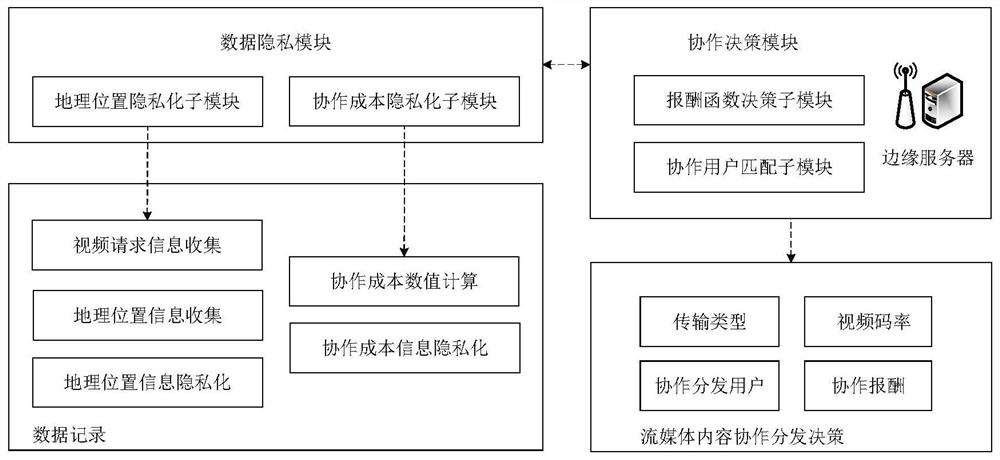
Mobile streaming media edge cooperative distribution device and method based on differential privacy
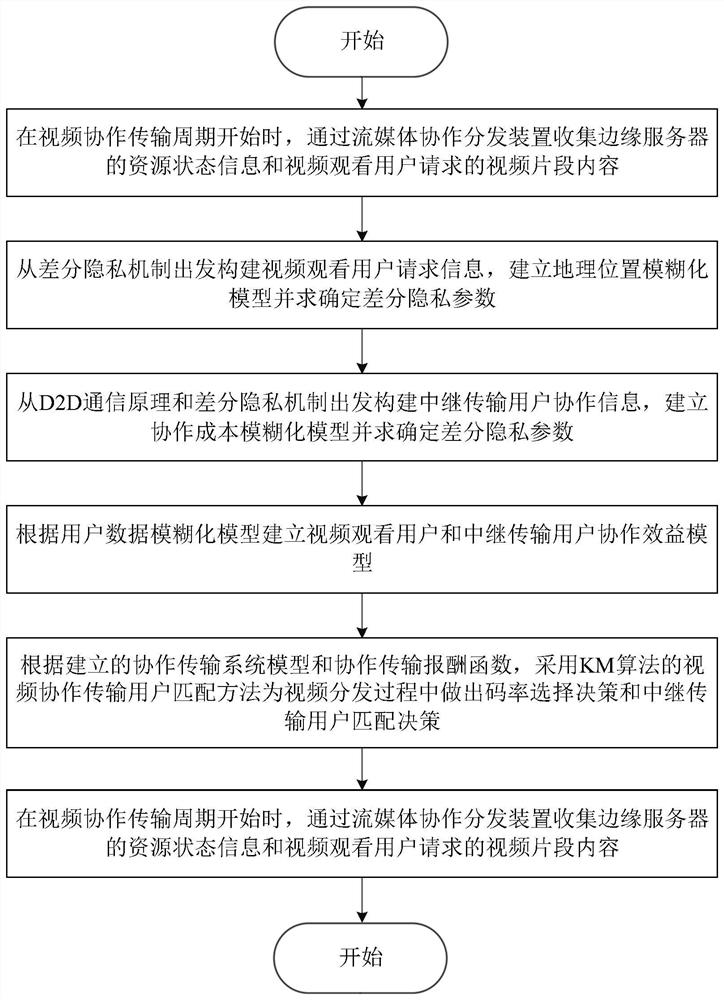
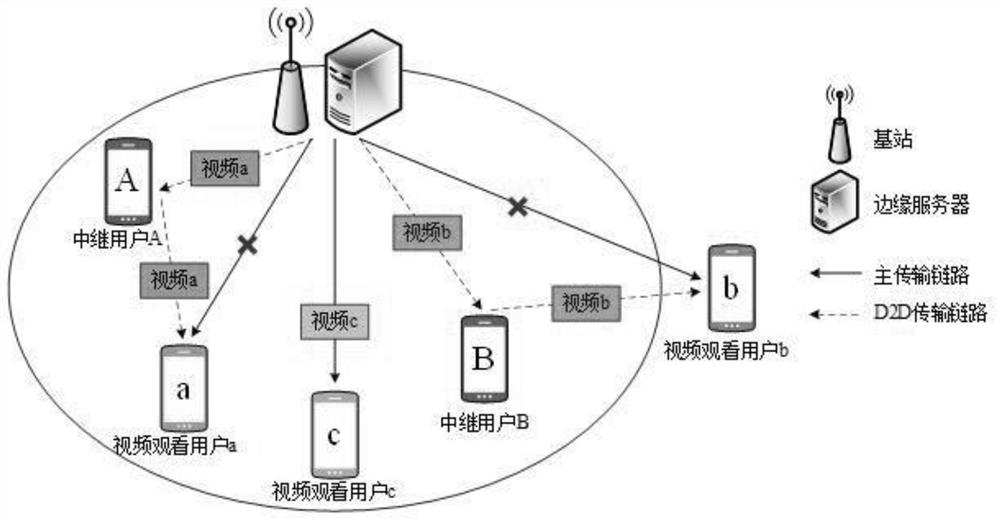
ActiveCN112423027AImprove quality of experienceLow costSelective content distributionContent distributionEdge server
The invention belongs to the technical field of mobile edges, and discloses a mobile streaming media edge cooperative distribution device and method based on differential privacy, and the device comprises a data privacy module and a cooperative decision module. When a streaming media cooperative transmission period starts, resource state information of an edge server and request video clip information of a streaming media watching user is collected. fuzzification request information of a streaming media watching user is acquired. A geographic position privacy model is created. Cooperation information of a relay transmission user is acquired. A cooperation cost privacy model and a reward function decision model are established. A collaborative user matching model is created and a streamingmedia content distribution path is determined according to the reward function decision model. Streaming media content edge cooperative distribution is completed, and related information is updated. The problem that in the prior art, the privacy of sensitive data cannot be guaranteed through streaming media cooperative transmission is solved, leakage of user privacy data can be prevented, and thecost of streaming media cooperative distribution is reduced.
Owner:WUHAN UNIV OF TECH
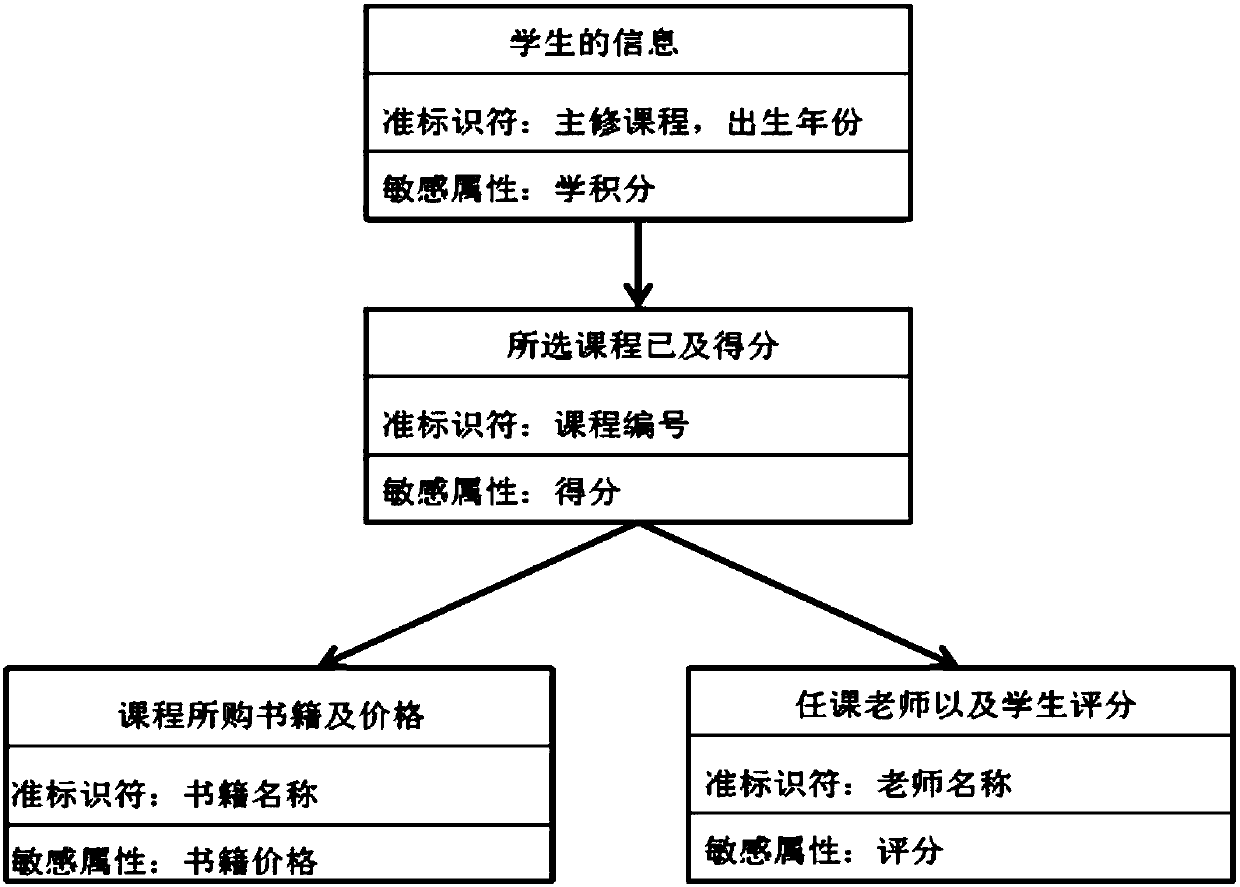
Multi-attribute data privacy removing method taking practicability into consideration
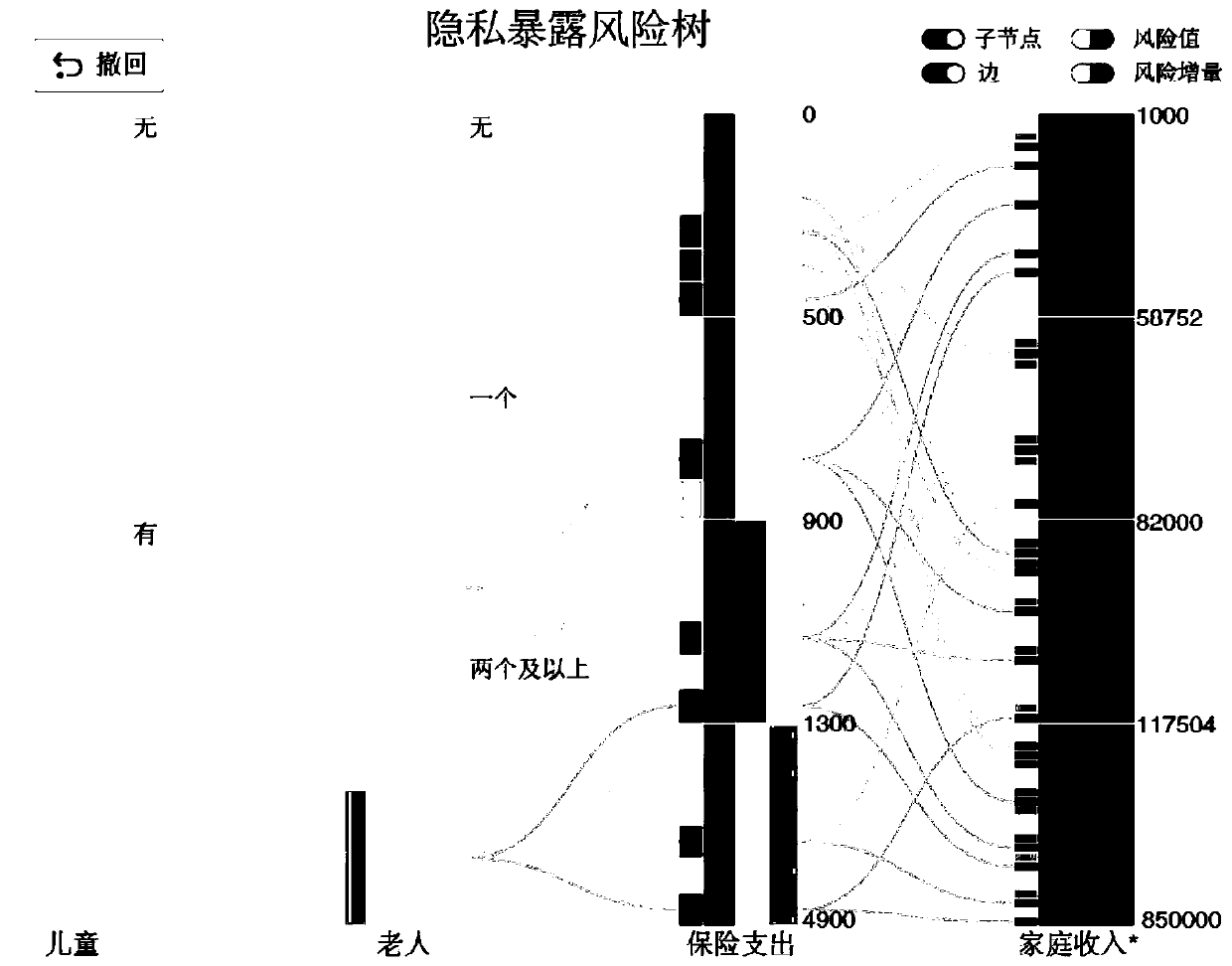
ActiveCN107358115AMeet various privacy needsCompact designDigital data protectionInternet privacyGrammaticality
The invention discloses a multi-attribute data privacy removing method taking practicability into consideration. The method comprises the following steps of S1, importing preprocessed multi-attribute data; S2, defining necessary attributes and sensitive attributes according to attribute descriptions, setting pre-grouping rules of the necessary attributes, and defining the sequences of the necessary attributes according to the attribute characteristics; S3, establishing a privacy exposure risk tree, and taking the attribute sequences and the pre-grouping rules in the step S2 as hierarchical sequences of the privacy exposure risk tree and the basis for generating branches of each hierarchy; and S4, measuring result information according to coding risks of the sensitive attributes on nodes and borders of the privacy exposure risk tree. According to the method, the suitable method can be flexibly selected from a plurality of common grammar anonymization and difference privacy models for solving the privacy problem, thereby satisfying various privacy demands for different data. Through utilization of special advantages of the privacy exposure risk tree, a multi-dimensionally aggregated space is designed compactly.
Owner:ZHEJIANG UNIV
High-dimensional position trajectory data privacy protection publishing system and method based on TP-MFSA suppression publishing
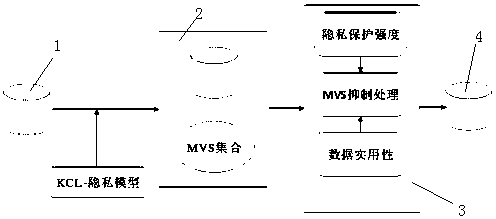
The invention discloses a high-dimensional position trajectory data privacy protection publishing system and method based on TP-MFSA suppression publishing, and belongs to the field of privacy protection algorithms. In order to resist an identity link attack and an attribute link attack caused by a track sequence in a high-dimensional track data release process and consider the data set mining practicability after anonymous processing, the invention provides a high-dimensional position trajectory data privacy protection publishing system and method based on TP-MFSA inhibition publishing. The method comprises: finding a minimum violation sequence set with privacy leakage according to a KCL-privacy model; judging the suppression mode of each time-space point in the MVS, namely, local suppression or global suppression; and designing an inhibition sequence model of each time-space point in the MVS based on the privacy protection intensity and the data practicability, and performing inhibition operation on the data set according to the sequence to obtain a publishable high-dimensional trajectory data set.
Owner:黑龙江省科学院智能制造研究所
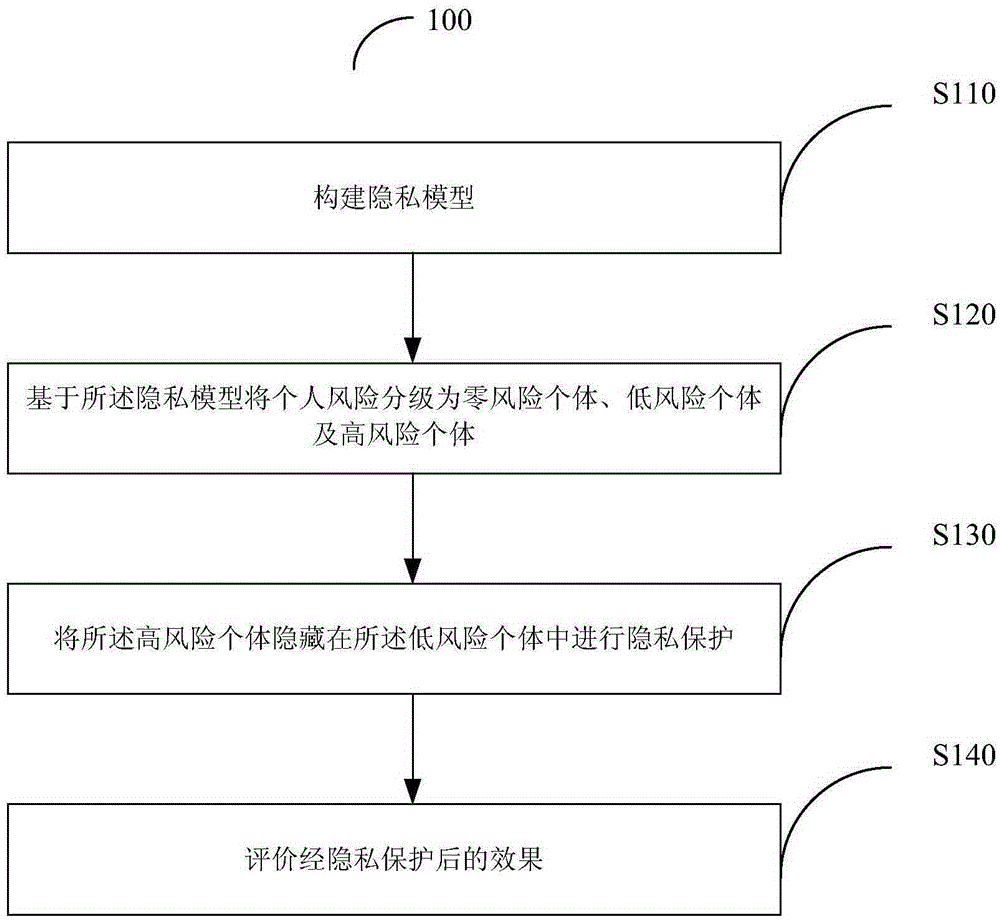
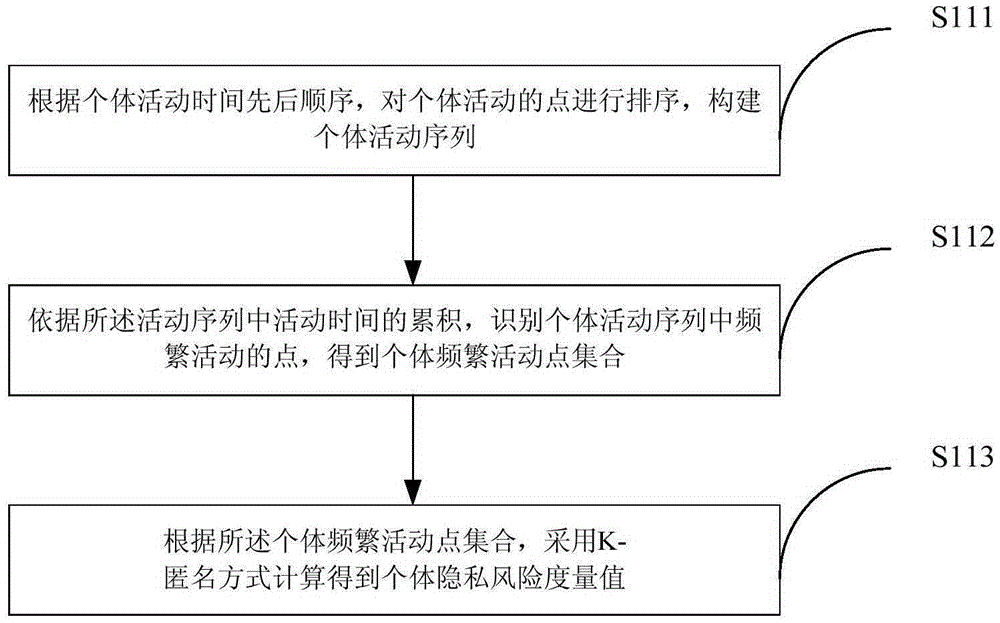
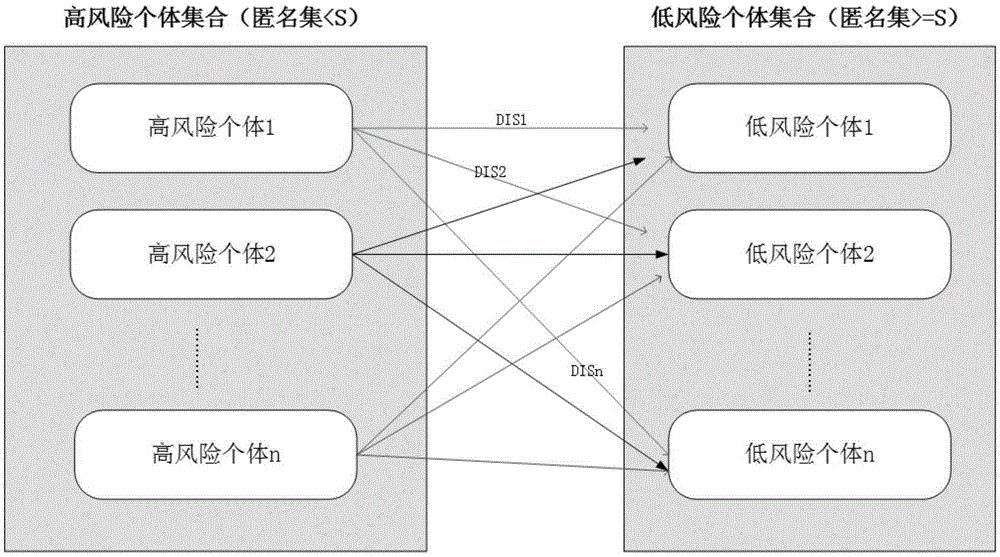
Privacy protection method and system based on high-risk frequent activity point replacement strategy
ActiveCN105260670BReduce computational complexityClarify the level of protectionDigital data protectionComputation complexityLower risk
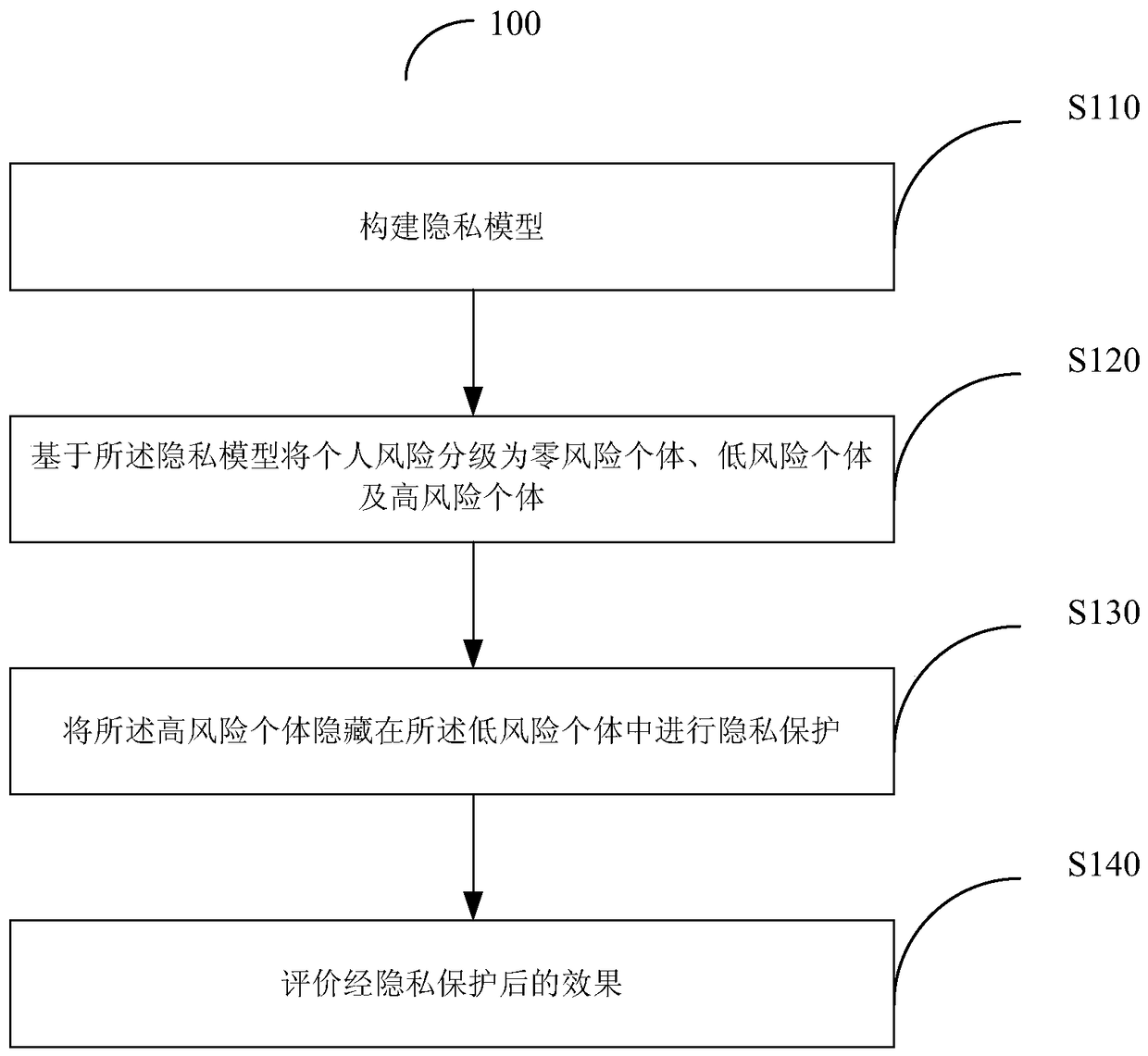
The invention provides a privacy protection method and system based on a high-risk frequent active point replacement policy. The privacy protection method comprises the following steps: establishing a privacy model, grading individual risks into zero-risk individuals, low-risk individuals and high-risk individuals based on the privacy model, hiding the high-risk individuals in the low-risk individuals for privacy protection, and evaluating a privacy protection result. The method is simple, is low in calculation complexity and can be applicable to spatial data with large data sizes.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Vehicle location privacy protection method based on group signature and reputation
ActiveCN107947942BIncrease confusionReduce threatUser identity/authority verificationPrivacy protectionBroadcasting
The invention discloses a vehicle position privacy protection method based on group signature and reputation, which comprises a reputation model for encouraging more vehicles to cooperate with each other to form a group, a privacy model for evaluating the position privacy strength of the vehicle, a group forming and dynamic mixed region establishing mechanism, and a pseudonym replacement mechanism. Any vehicle in the vehicle-mounted ad hoc network actively requests establishment of a group from a control server according to the reputation value of the vehicle when the pseudonym of the vehicleis soon to be expired; the control server allocates a group leader role to the requesting vehicle and dynamically forms a mixed region according to the current position of the requesting vehicle; theother vehicles in the mixed region judge whether the cooperation is participated in or not to change the pseudonym according to the reputation value, privacy strength and the remaining time of the pseudonym of the other vehicles; and the reputation value of the vehicles can be dynamically adjusted. According to the method, more vehicles can be encouraged to join the group, thereby changing the pseudonym in cooperation and ensuring the position privacy of the vehicles; meanwhile, the vehicles do not need to keep a silent state in the formed mixed region but broadcast messages as a group identity so that the running safety of the vehicles is guaranteed; furthermore, resource expenditure caused by unnecessary frequent change of the pseudonym can be effectively reduced.
Owner:ANHUI UNIVERSITY
Privacy protection method and system based on high-risk frequent active point replacement policy
ActiveCN105260670AReduce computational complexityClarify the level of protectionDigital data protectionComputation complexityLower risk
The invention provides a privacy protection method and system based on a high-risk frequent active point replacement policy. The privacy protection method comprises the following steps: establishing a privacy model, grading individual risks into zero-risk individuals, low-risk individuals and high-risk individuals based on the privacy model, hiding the high-risk individuals in the low-risk individuals for privacy protection, and evaluating a privacy protection result. The method is simple, is low in calculation complexity and can be applicable to spatial data with large data sizes.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
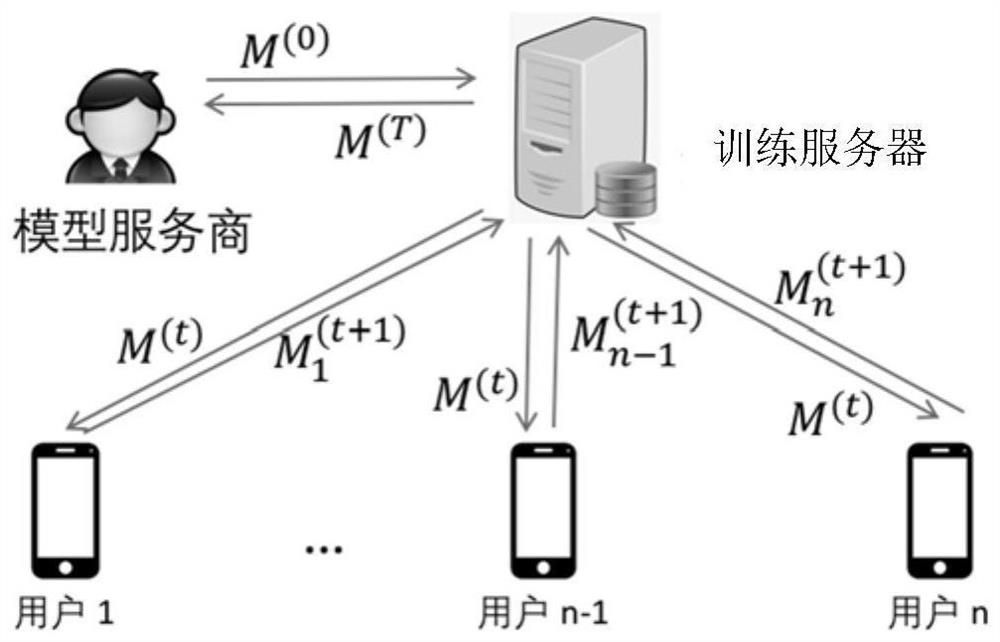
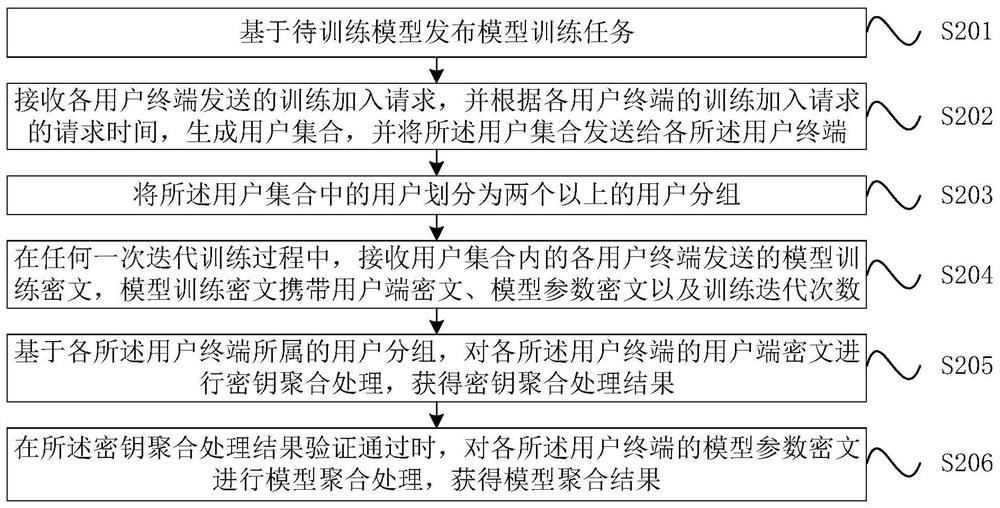
Privacy model training method
The invention relates to a privacy model training method and device, computer equipment and a storage medium. The method of one embodiment comprises the steps of issuing a model training task based on a to-be-trained model; receiving a training joining request sent by each user terminal, generating a user set according to the request time of the training joining request of each user terminal, and sending the user set to each user terminal; dividing the users in the user set into user groups; in any iteration training process, receiving a model training ciphertext which is sent by each user terminal in the user set and carries a user terminal ciphertext, a model parameter ciphertext and training iteration times; based on the user group to which each user terminal belongs, performing key aggregation processing on the user terminal ciphertext of each user terminal to obtain a key aggregation processing result; and when the key aggregation processing result passes verification, performing model aggregation processing on the model parameter ciphertext of each user terminal to obtain a model aggregation result. By adopting the method, the safety and the stability during model training can be improved.
Owner:THE CHINESE UNIV OF HONG KONG SHENZHEN
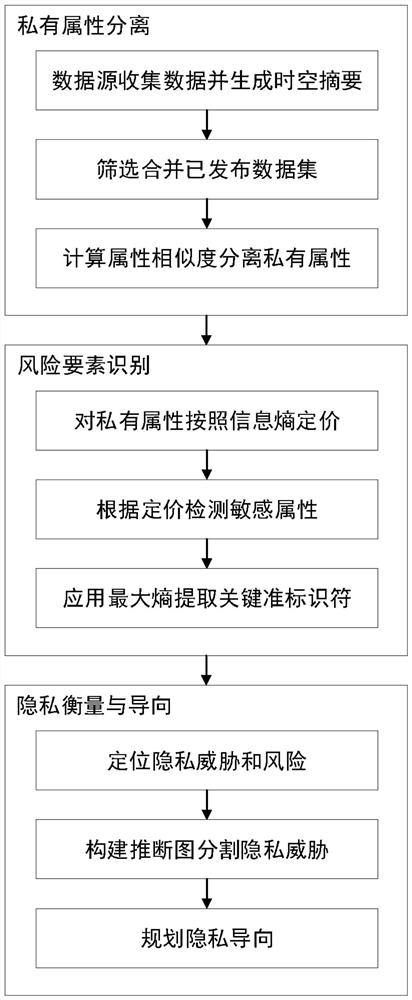
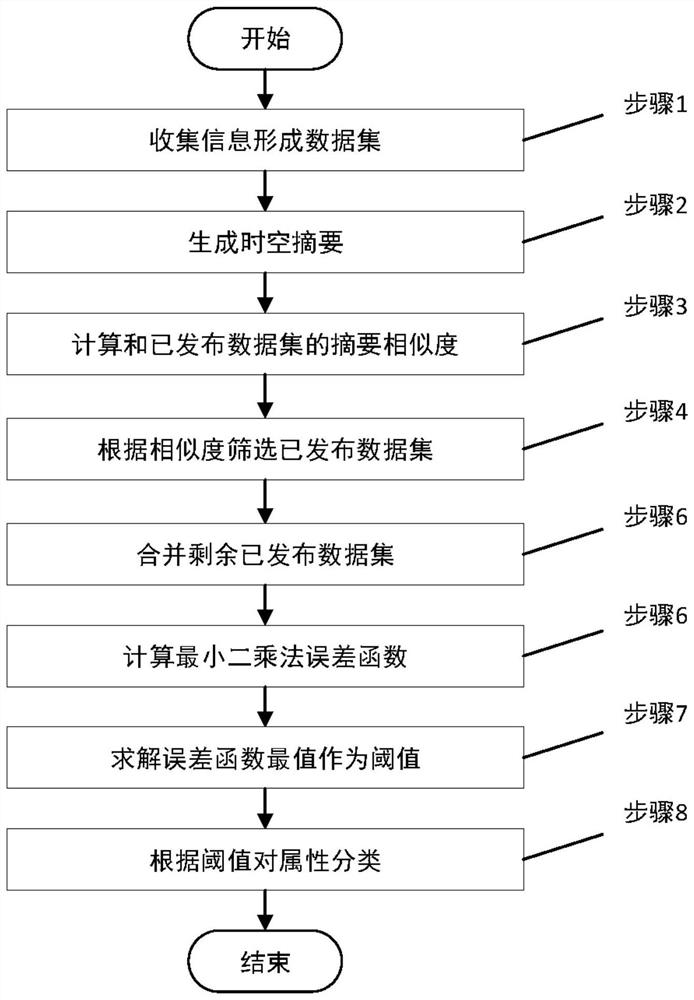
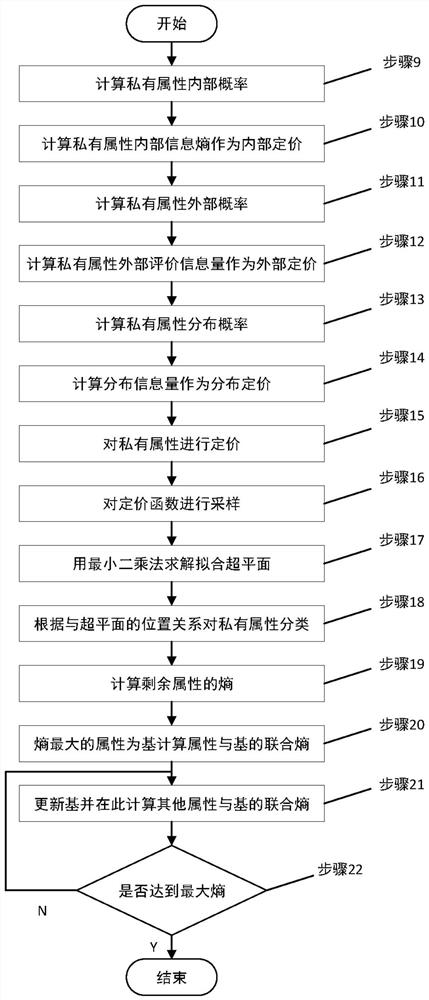
Privacy measurement algorithm for structured data in data release environment
PendingCN113378229AGuaranteed privacy and securityReduce the efficiency of publishingDigital data protectionOther databases clustering/classificationIdenticonInformation security
The invention belongs to the technical field of information security, and provides a privacy measurement algorithm for structured data in a data release environment. Firstly, a data source collects user information and generates a user information abstract, an external data set is screened according to abstract information, and attribute similarity is calculated to distinguish private attributes and non-private attributes. Then, external and internal average information amount and distribution information amount of the private attributes are calculated, sensitive attributes for the private attributes are priced and identified based on demand and time loss, quasi-identifiers are extracted by applying a maximum entropy principle, and risk elements are identified in the data. Finally, the data privacy is measured according to the privacy model, a privacy-oriented anonymous technology is given, and it can be proved that the privacy and availability under the orientation reach the best balance.
Owner:DALIAN UNIV OF TECH
Vehicle location privacy protection method in vehicle ad hoc network
InactiveCN103338444BHigh location privacy and securityLower energy billsEnergy efficient ICTParticular environment based servicesIn vehiclePrivacy protection
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Hierarchical Privacy Preservation Method in Hierarchical Data Publishing
ActiveCN107766745BControl ratioSolving the Proximity Attack ProblemCharacter and pattern recognitionDigital data protectionData privacy protectionAttack
The invention discloses a hierarchical privacy protection method in the release of hierarchical data. First, the sensitive attributes of the original hierarchical data are classified according to the actual sensitivity, and then the frequency parameter α is set according to the divided grades. i To limit the frequency of different levels of sensitive attributes in the equivalence class, and then use the clustering method to achieve a given privacy model. The present invention well solves the problem of privacy leakage caused by the proximity attack on the sensitive attributes of the existing hierarchical data publishing technology, improves the protection of hierarchical data privacy, and enhances the security of data; the present invention is for The protection of hierarchical data has certain practical significance and practical value.
Owner:GUANGXI NORMAL UNIV
A mobile streaming media edge cooperative distribution device and method based on differential privacy
ActiveCN112423027BImprove quality of experienceLow costSelective content distributionDecision modelEdge server
The invention belongs to the field of mobile edge technology, and discloses a mobile streaming media edge cooperative distribution device and method based on differential privacy, including a data privacy module and a cooperative decision-making module; when the streaming media collaborative transmission cycle starts, the resource status of the edge server is collected Information, request video clip information of streaming media viewing users; Obtain blurred request information of streaming media viewing users; Establish geographic location privacy model; Obtain cooperation information of relay transmission users; Establish collaboration cost privacy model, reward function decision model ; Build a collaborative user matching model, and determine the streaming media content distribution path according to the reward function decision model; complete the edge collaborative distribution of streaming media content, and update relevant information. The invention solves the problem that the streaming media collaborative transmission cannot guarantee the privacy of sensitive data in the prior art, can prevent user privacy data from leaking, and reduces the cost of streaming media collaborative distribution.
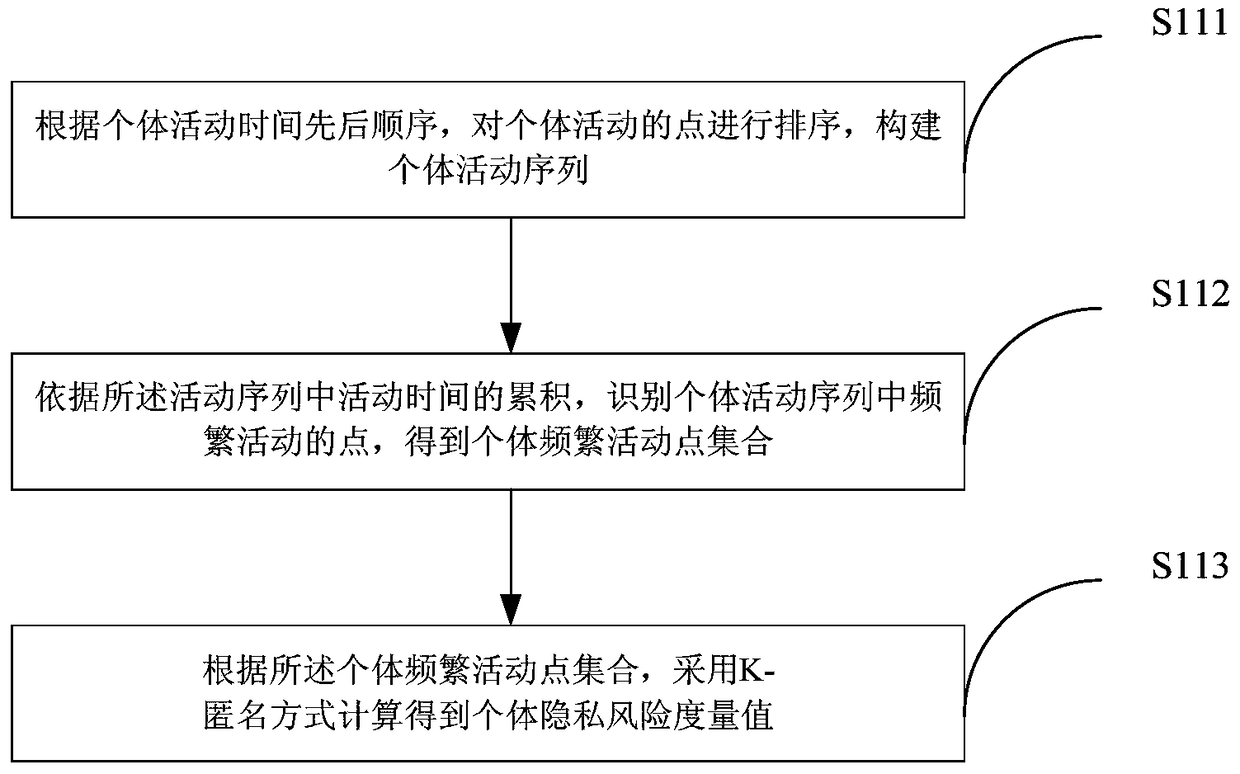
Owner:WUHAN UNIV OF TECH
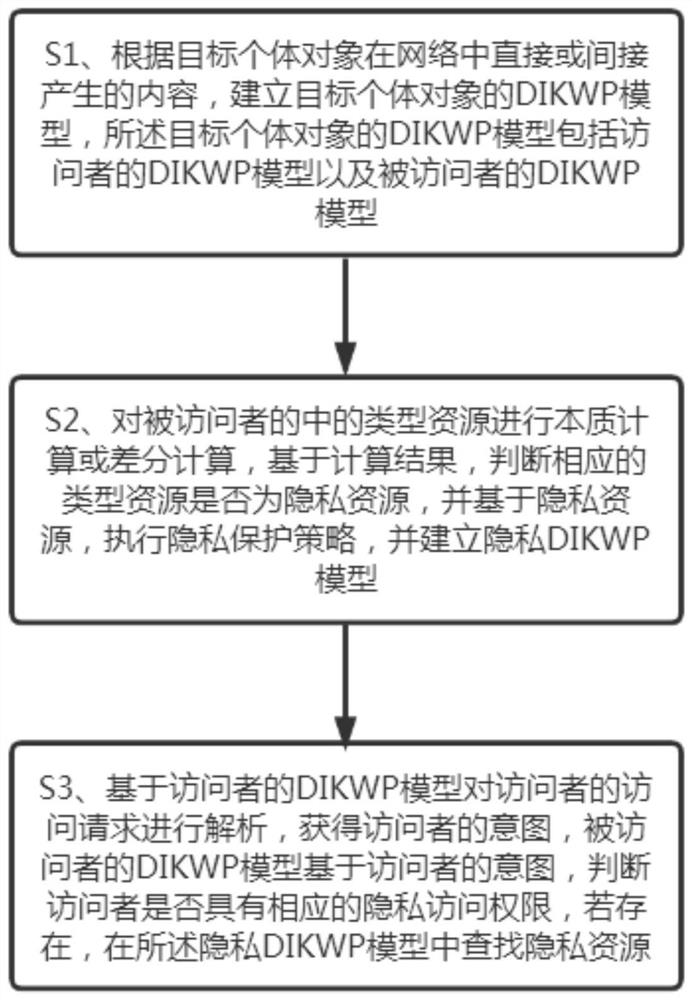
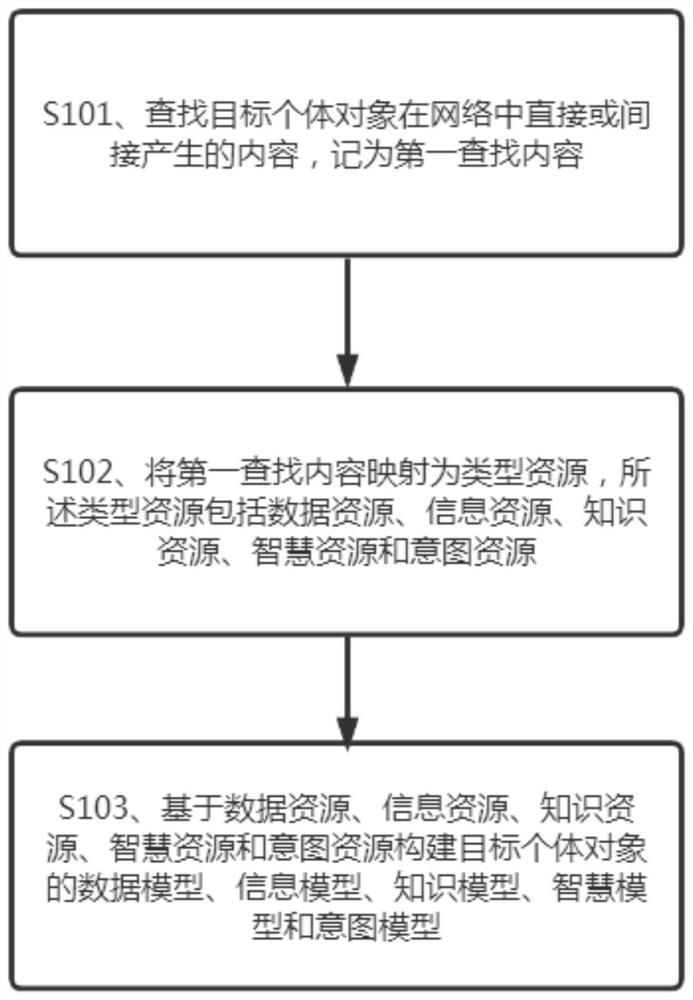
Information privacy protection method oriented to DIKW model driving
The invention provides an information privacy protection method for DIKW model driving, which comprises the following steps: S1, according to contents directly or indirectly generated by a target individual object in a network, establishing a DIKWP model of the target individual object, the DIKWP model of the target individual object comprising a DIKWP model of a visitor and a DIKWP model of a visited person; s2, performing essential calculation or differential calculation on the type resources in the visited person, judging whether the corresponding type resources are privacy resources or not based on a calculation result, executing a privacy protection strategy based on the privacy resources, and establishing a privacy DIKWP model; s3, the access request of the visitor is analyzed based on the DIKWP model of the visitor, the intention of the visitor is obtained, the DIKWP model of the interviewee judges whether the visitor has the corresponding privacy access permission or not based on the intention of the visitor, and if yes, privacy resources are searched for in the privacy DIKWP model.
Owner:HAINAN UNIVERSITY
Multi-user database system and method
PendingCN114096958ADatabase updatingDatabase distribution/replicationEngineeringFinancial transaction
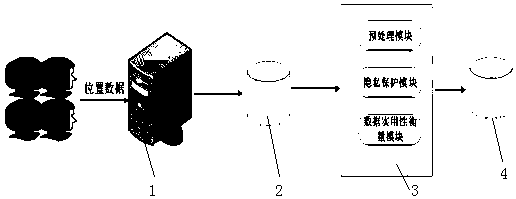
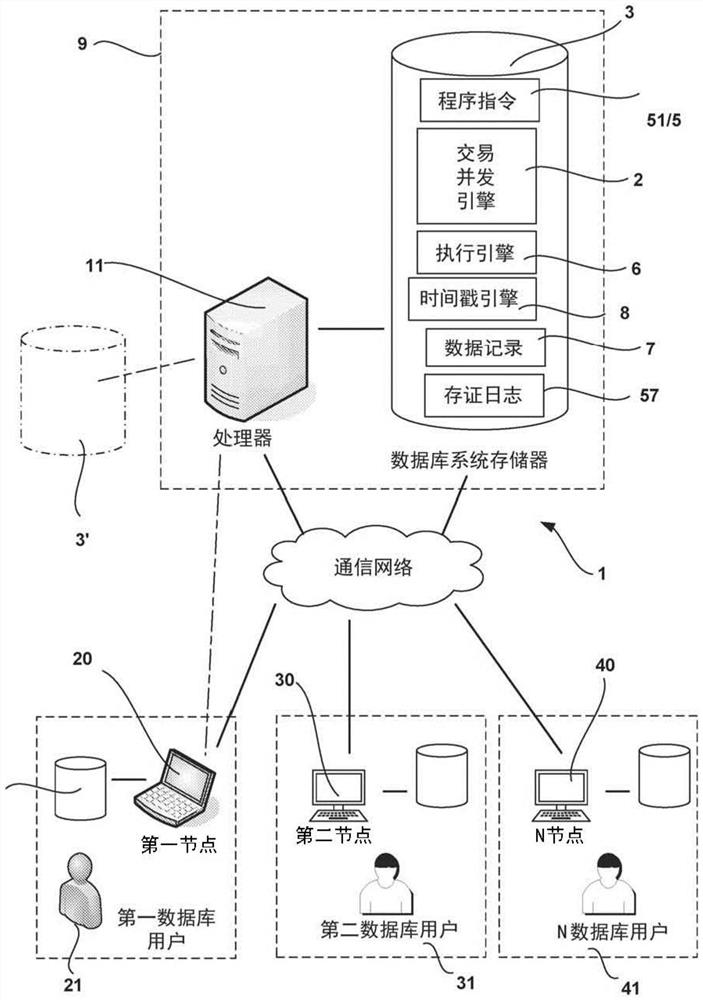
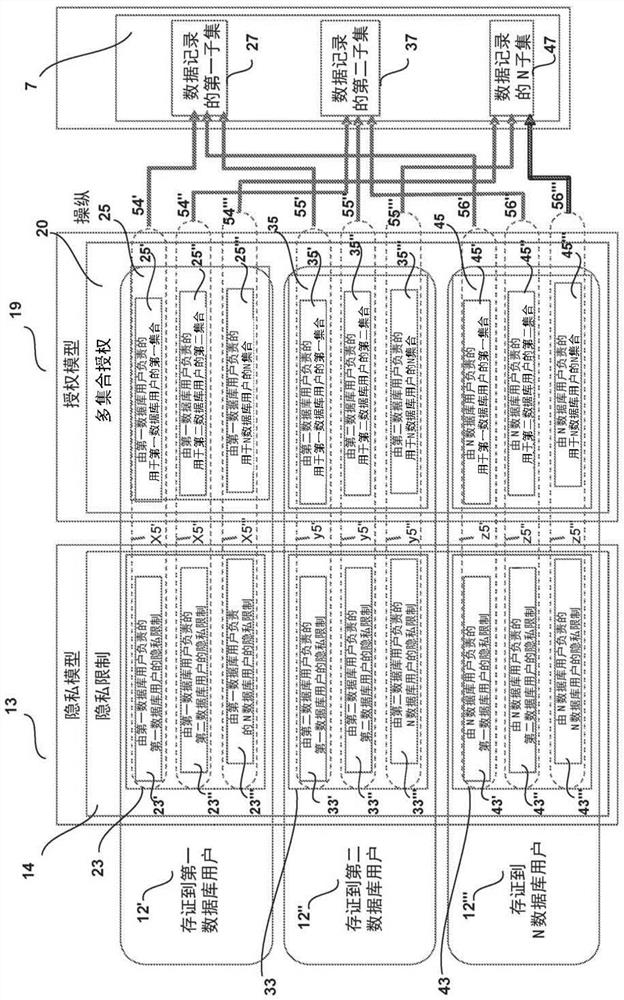
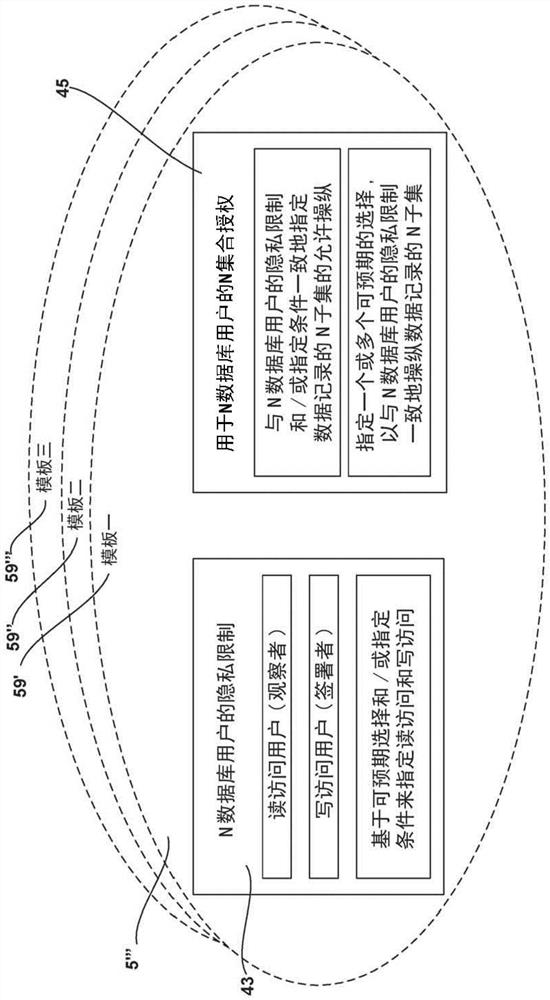
A database system (1) and a method (100), comprising a database system memory (3) and at least a first database server (9). The database system memory (3) stores a database of data records (7) and shared program instructions (51) between first and second database users (21, 31). The shared program instructions (51) define a privacy model (13) comprising privacy restrictions (14, 23, 33) for the first and second database users (21, 31), respectively, and specify an authorization model (19) comprising a first set of authorizations (25', 35') that permit the first database user (21) to manipulate a first subset (27) of the data records consistent with the first user's privacy restrictions (23', 33') and a second set of authorizations (25'', 35'') that permit the second user (31) to manipulate a second subset (37) of the data records consistent with the second user's privacy restrictions (23'', 33''). The database server (9) includes a processor (11) configured to execute the shared program instructions (51), wherein the shared program instructions (51), when executed by the processor (11): (1) process (110) a transaction (53) submitted by the first or second database user (21, 31); (2) determine (120) whether the transaction (53) conforms to the privacy and authorization models (13, 19); and (3) if the transaction passes step 2, commit (130) the transaction (53) and manipulate (55) the first or second subset of data records (27, 37) consistent with privacy and authorization models (13, 19).
Owner:DIGITAL ASSET SWITZERLAND GMBH
A multi-attribute data deprivation method considering practicability
ActiveCN107358115BMeet various privacy needsCompact designDigital data protectionInternet privacyGrammaticality
The invention discloses a multi-attribute data privacy removing method taking practicability into consideration. The method comprises the following steps of S1, importing preprocessed multi-attribute data; S2, defining necessary attributes and sensitive attributes according to attribute descriptions, setting pre-grouping rules of the necessary attributes, and defining the sequences of the necessary attributes according to the attribute characteristics; S3, establishing a privacy exposure risk tree, and taking the attribute sequences and the pre-grouping rules in the step S2 as hierarchical sequences of the privacy exposure risk tree and the basis for generating branches of each hierarchy; and S4, measuring result information according to coding risks of the sensitive attributes on nodes and borders of the privacy exposure risk tree. According to the method, the suitable method can be flexibly selected from a plurality of common grammar anonymization and difference privacy models for solving the privacy problem, thereby satisfying various privacy demands for different data. Through utilization of special advantages of the privacy exposure risk tree, a multi-dimensionally aggregated space is designed compactly.
Owner:ZHEJIANG UNIV
A model training method based on federated learning
ActiveCN110955907BAvoid crackingExamples cannot be limitedDigital data protectionMachine learningAlgorithmTheoretical computer science
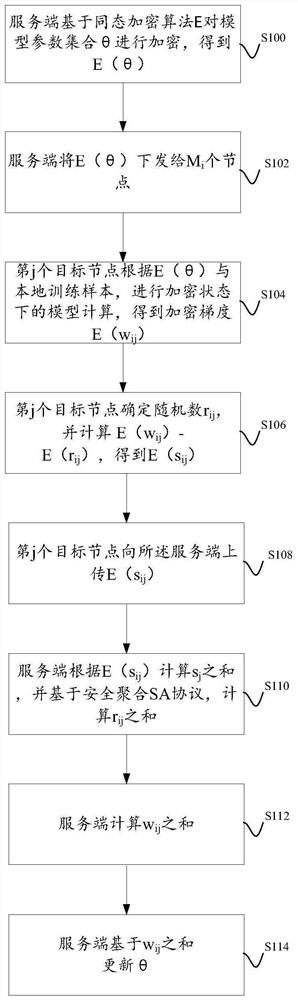
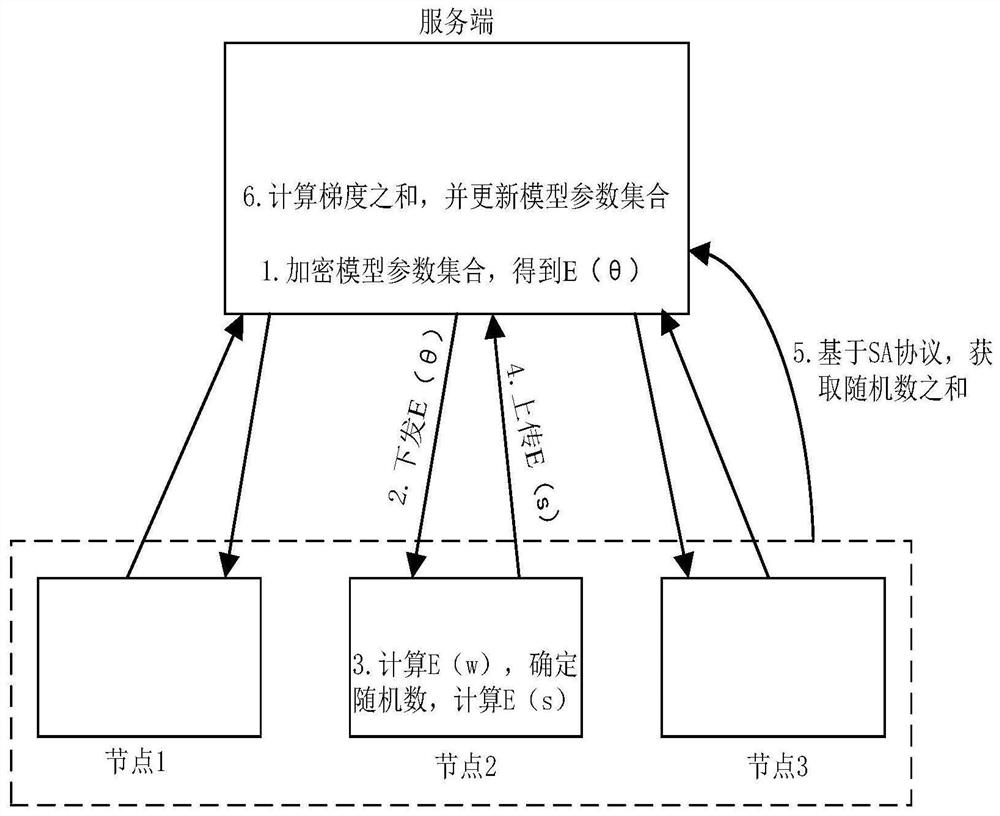
A model training method based on federated learning is disclosed. In order to protect the privacy of the server (model parameters) from being leaked, the server uses a homomorphic encryption algorithm to encrypt the model parameter set and sends it to the node. Based on the principle of homomorphic encryption, the node uses the encrypted model parameters and local training samples to encrypt The model calculation in the state obtains the encrypted gradient. Then, based on the principle of homomorphic encryption, the node calculates the difference between the encrypted gradient and the encrypted random number, which is essentially a meaningless encrypted value. Then, the node uploads the encrypted value to the server. In addition, the server can use the SA protocol to obtain the sum of random numbers on each node without knowing the random number on each node. In this way, the server can restore the sum of the gradients generated by each node based on the encrypted value uploaded by each node and the sum of each random number, so that the model parameters can be updated.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Trusted traceability method and system, and storage medium
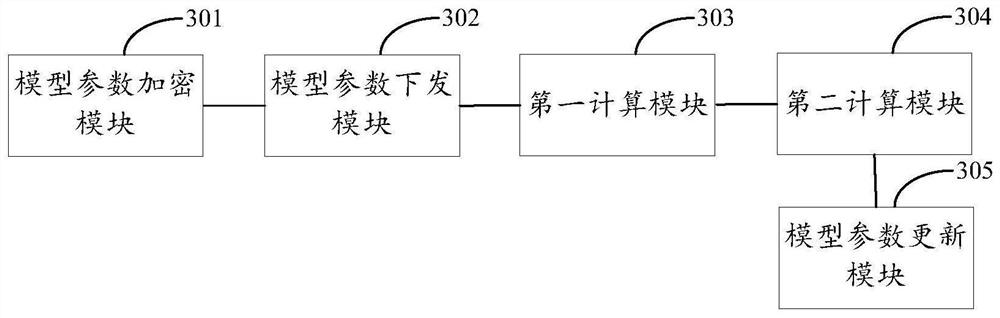
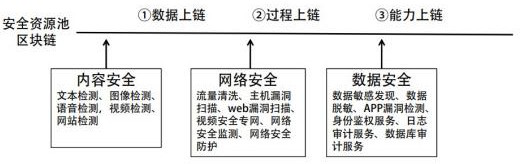
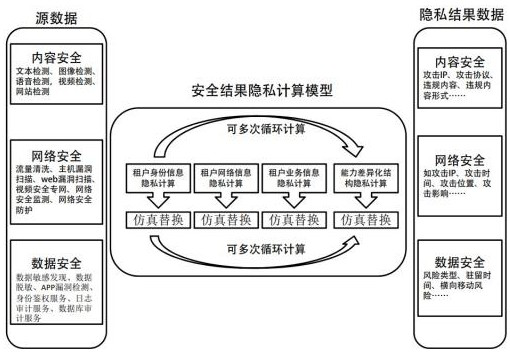
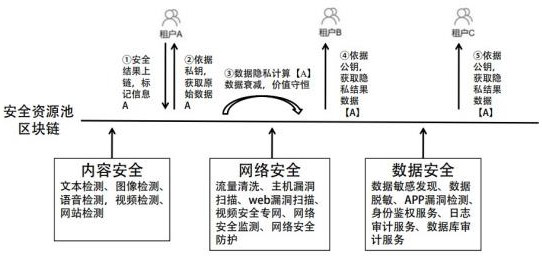
ActiveCN113901523ATroubleshoot secure sharing issuesQuality improvementDatabase distribution/replicationDigital data protectionResource poolEngineering
The invention discloses a trusted traceability method and system based on blockchain, and a storage medium, and belongs to the field of open use of security data and security results. The method comprises the steps: establishing an initial database, wherein the initial database is open, and the security capability type and the security capability of the initial database can be dynamically expanded; constructing a security information chain in a local area network, carrying out data uplink, process uplink and capability uplink on source data stored in the initial database, constructing a privacy model, and carrying out privacy calculation on the uplink data; credibly opening the security data after privacy calculation, expanding the security data, and upgrading the security data into a security capability resource pool. The method further enriches the security data, process and capability of the uplink, constructs an open tenant defense alliance in the extensive local area network, realizes sharing of security resource pool customer security protection results in the local area network, and is suitable for the field of multi-target customer group security of governments, enterprises and the like.
Owner:江苏移动信息系统集成有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com