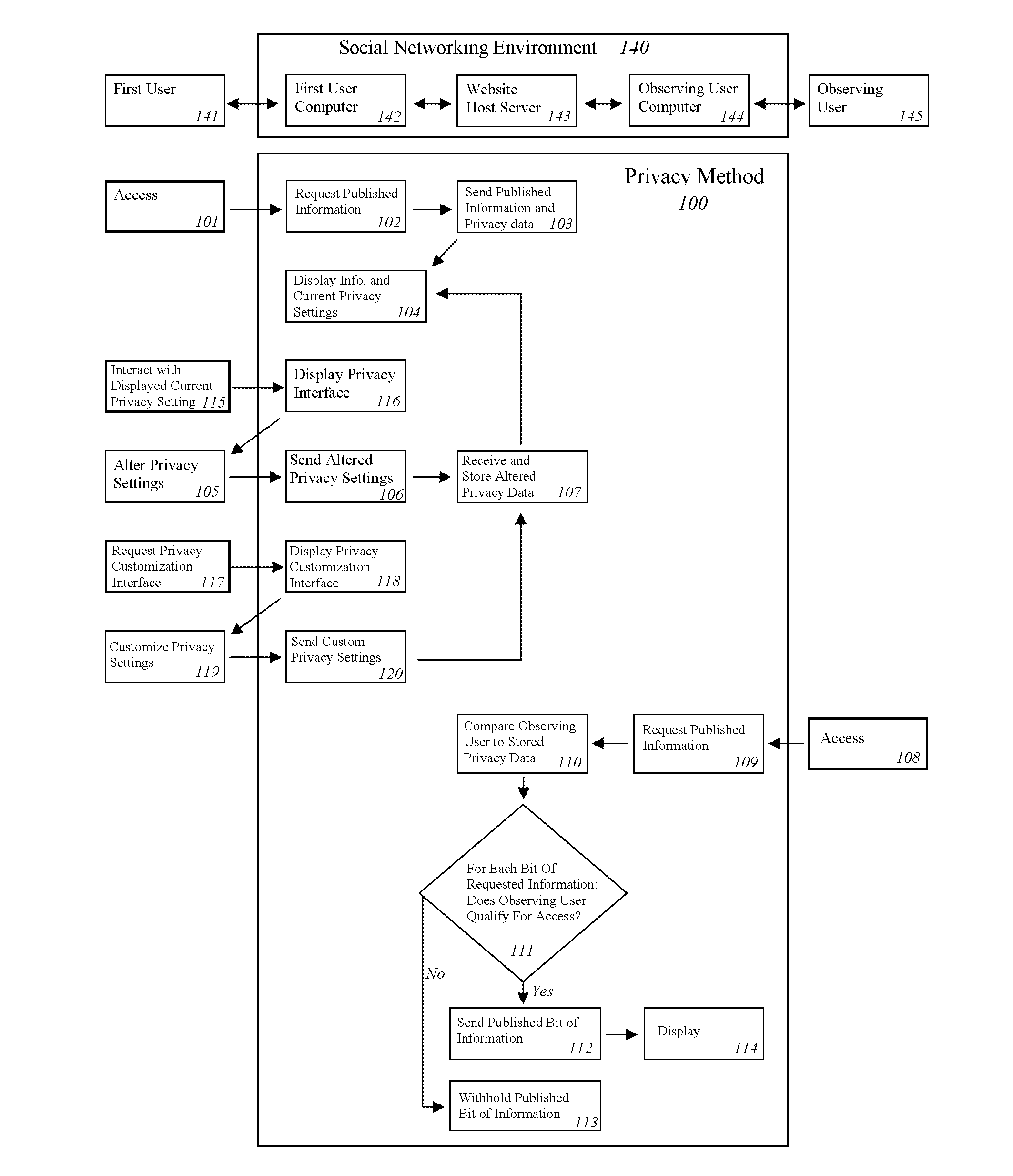
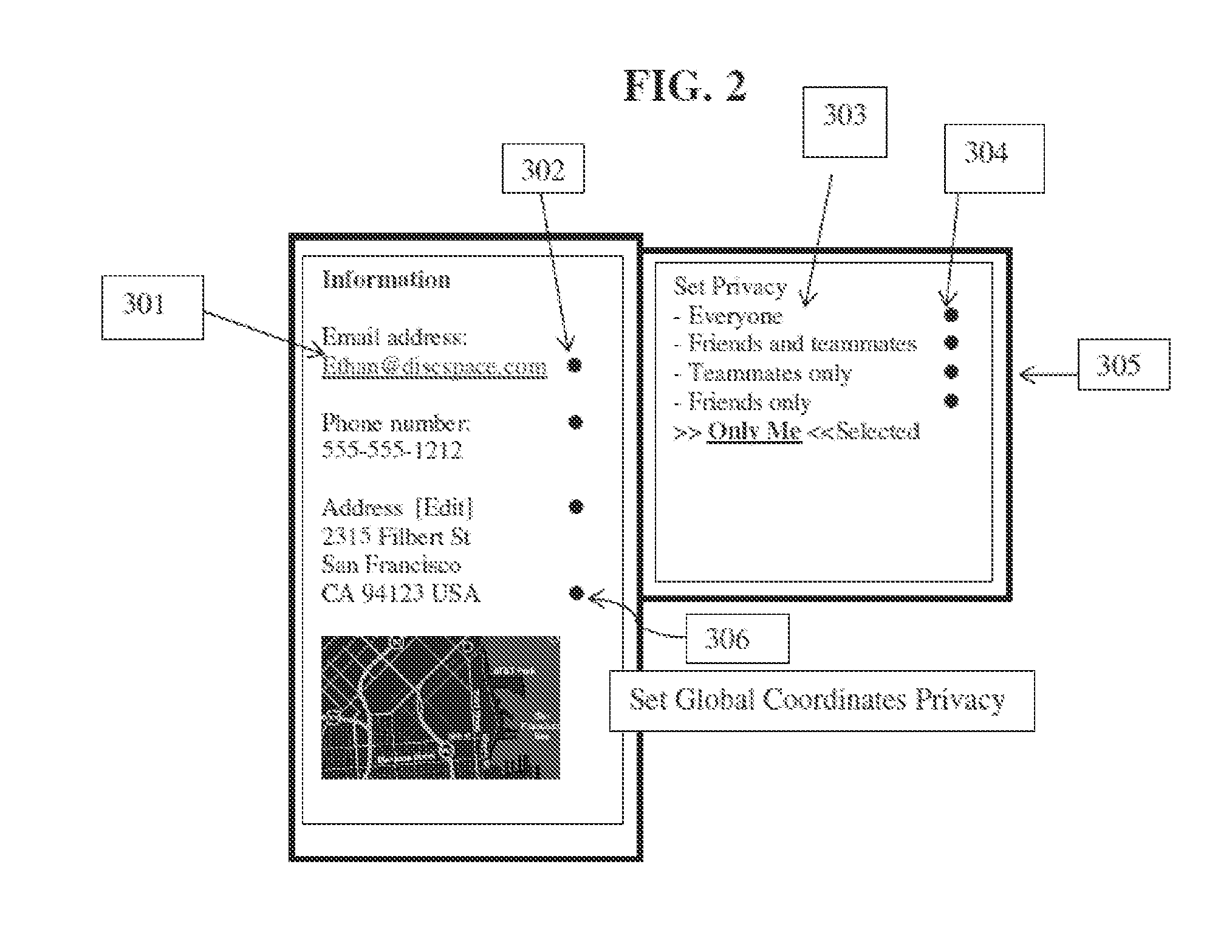
Patents
Literature
175 results about "Privacy Level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
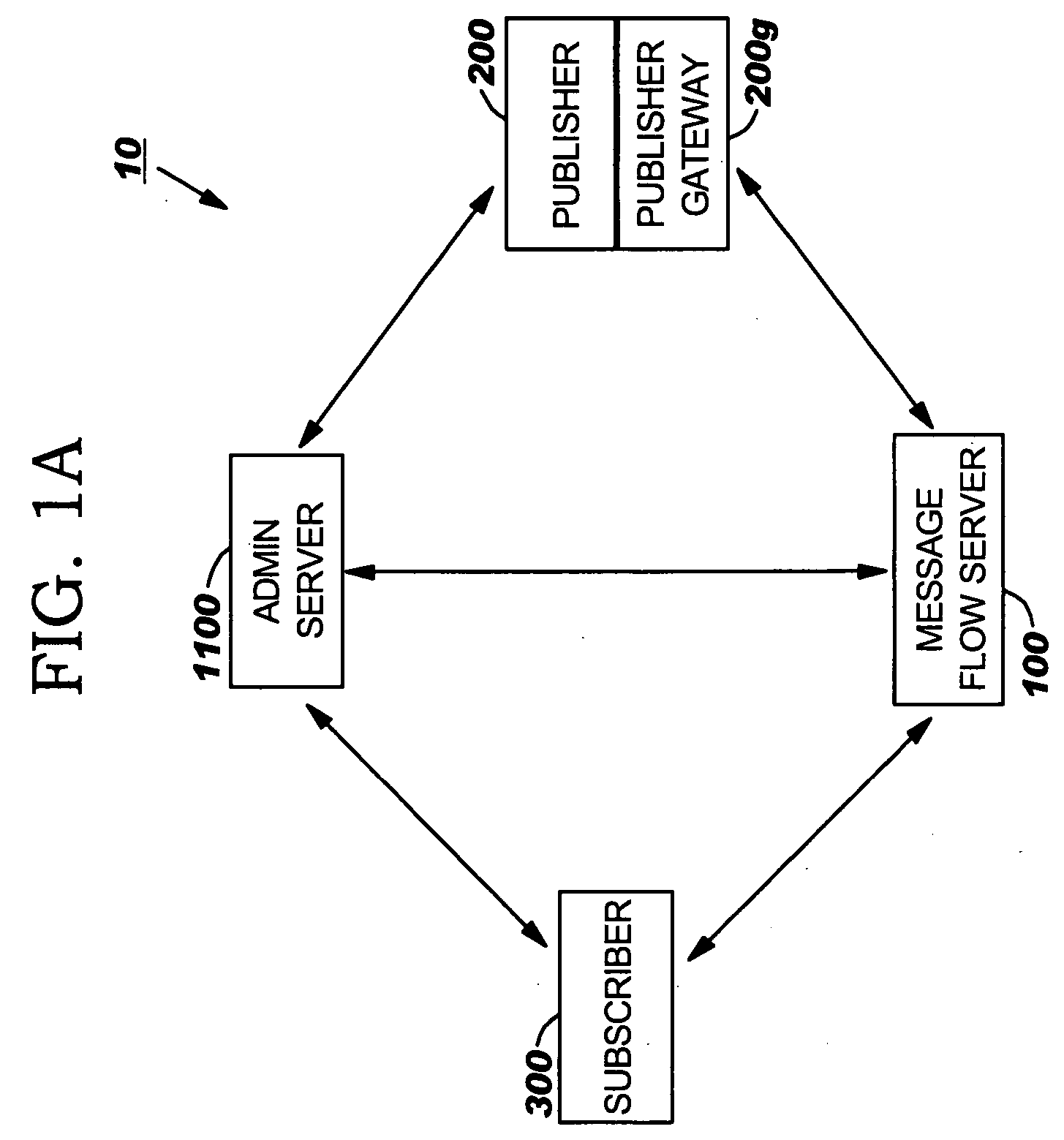
System for Enabling Secure Private Exchange of Data and Communication Between Anonymous Network Participants and Third Parties and a Method Thereof
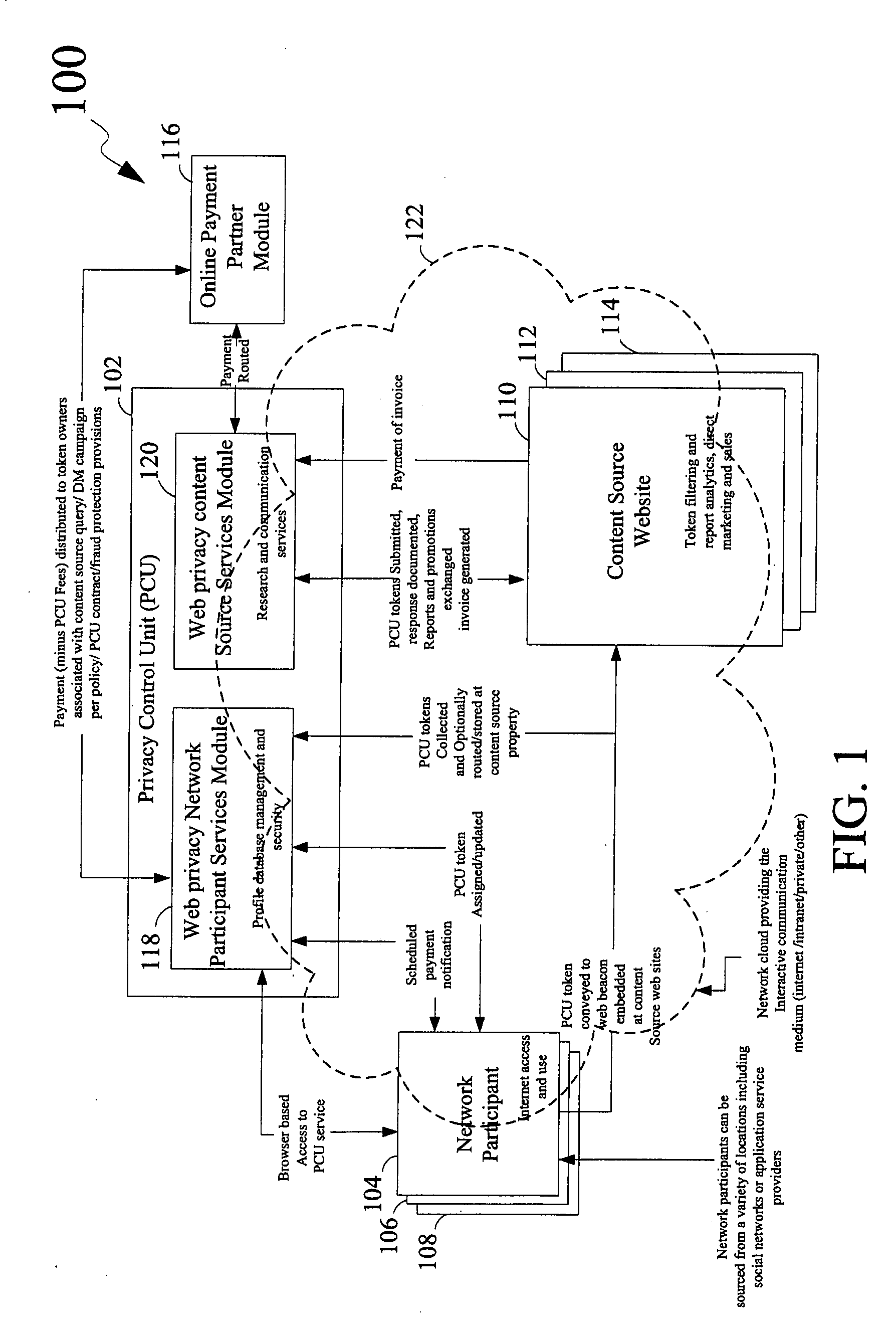
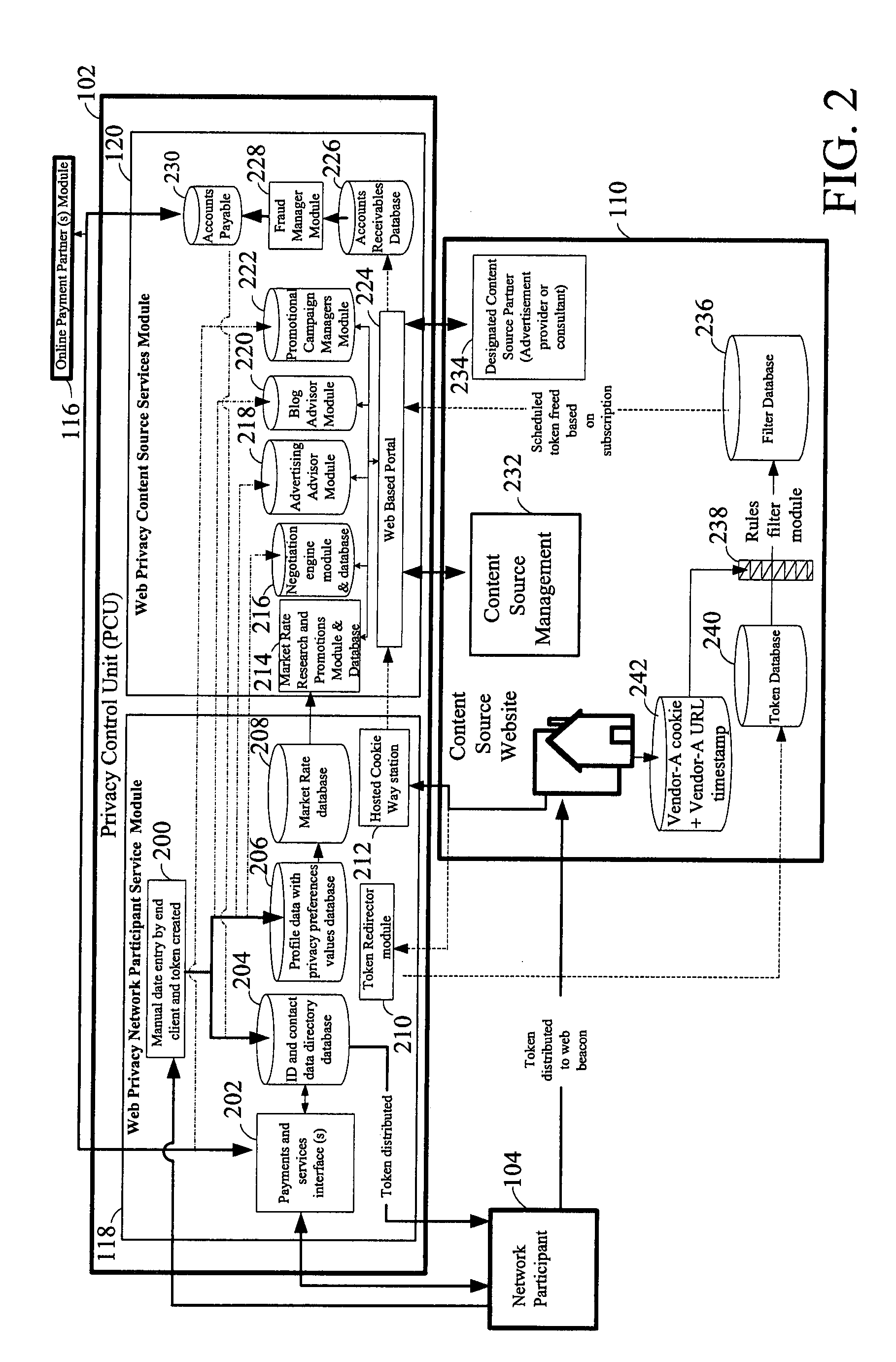
Disclosed is a method for providing secure private exchange of a profile data of a network participant between the participant and a plurality of third parties. The method comprises registering profile data by the network participant with a privacy control unit, assigning privacy levels to each of the plurality of attributes of the profile data, transferring the profile data along with privacy levels assigned to each of a plurality of attributes of the profile data to a privacy control unit generating a report for research and for targeting promotion campaigns to the network participant by using the profile data. The report is accessed by the plurality of third parties for communications with the network participant, wherein the plurality of third parties are registered with and invoiced by the privacy control unit. A portion of the invoice is provided as a fee to the network participant for providing the profile data.
Owner:KINDCAST
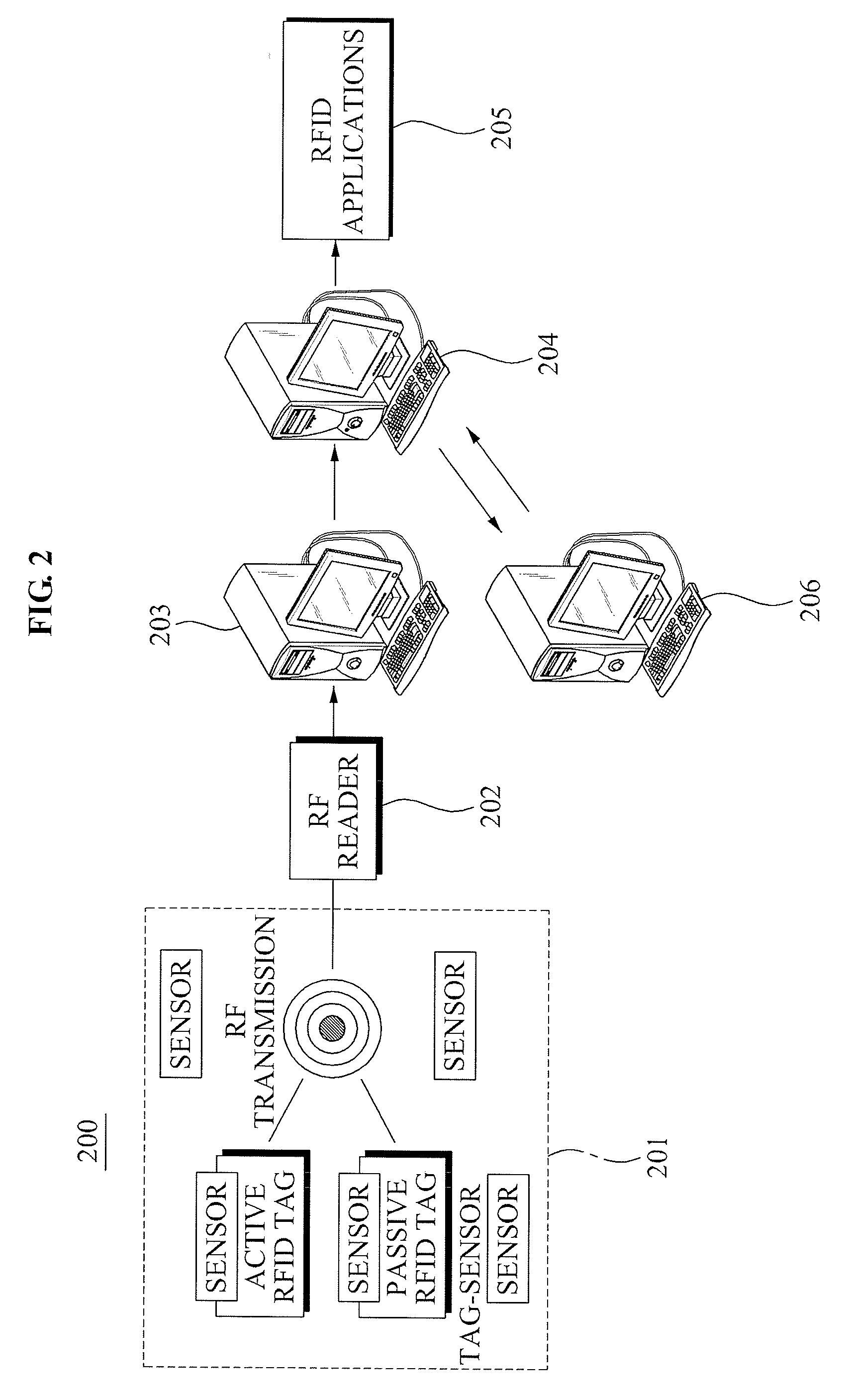
Context-aware based RFID privacy control system and personal privacy protection method using the same
InactiveUS8681984B2Avoid contactImprove securityDigital data processing detailsUnauthorized memory use protectionControl systemPrivacy protection
Owner:ELECTRONICS & TELECOMM RES INST
Managing personal information on a network
ActiveUS8713638B2Regulate privacy levelsEasy to controlDigital data processing detailsComputer security arrangementsInternet privacyMultiple layer
Devices, systems, and methods for managing personal information by providing a centralized source or database for a user's information, and enabling the user to regulate privacy levels for each information item or category of information. Templates are provided as a table of hierarchies, or an onion layers model. Private information may be stored in an inner layer while public information may be stored in an outer layer, with the ability to define and customize multiple layers and categories within the template. A requesting entity requests information via a disseminating server that acts as a gateway for authenticating, authorizing, and providing access to the requesting entity. The user may therefore control and regulate their online presence simply by monitoring who requests their information and adjusting privacy levels accordingly.
Owner:AT&T INTPROP I LP +1
Apparatus and method for privacy protection of data collection in pervasive environments
ActiveUS20060064384A1Improve emergency responseImprove securityElectric signal transmission systemsDigital data processing detailsVideo monitoringPrivacy protection
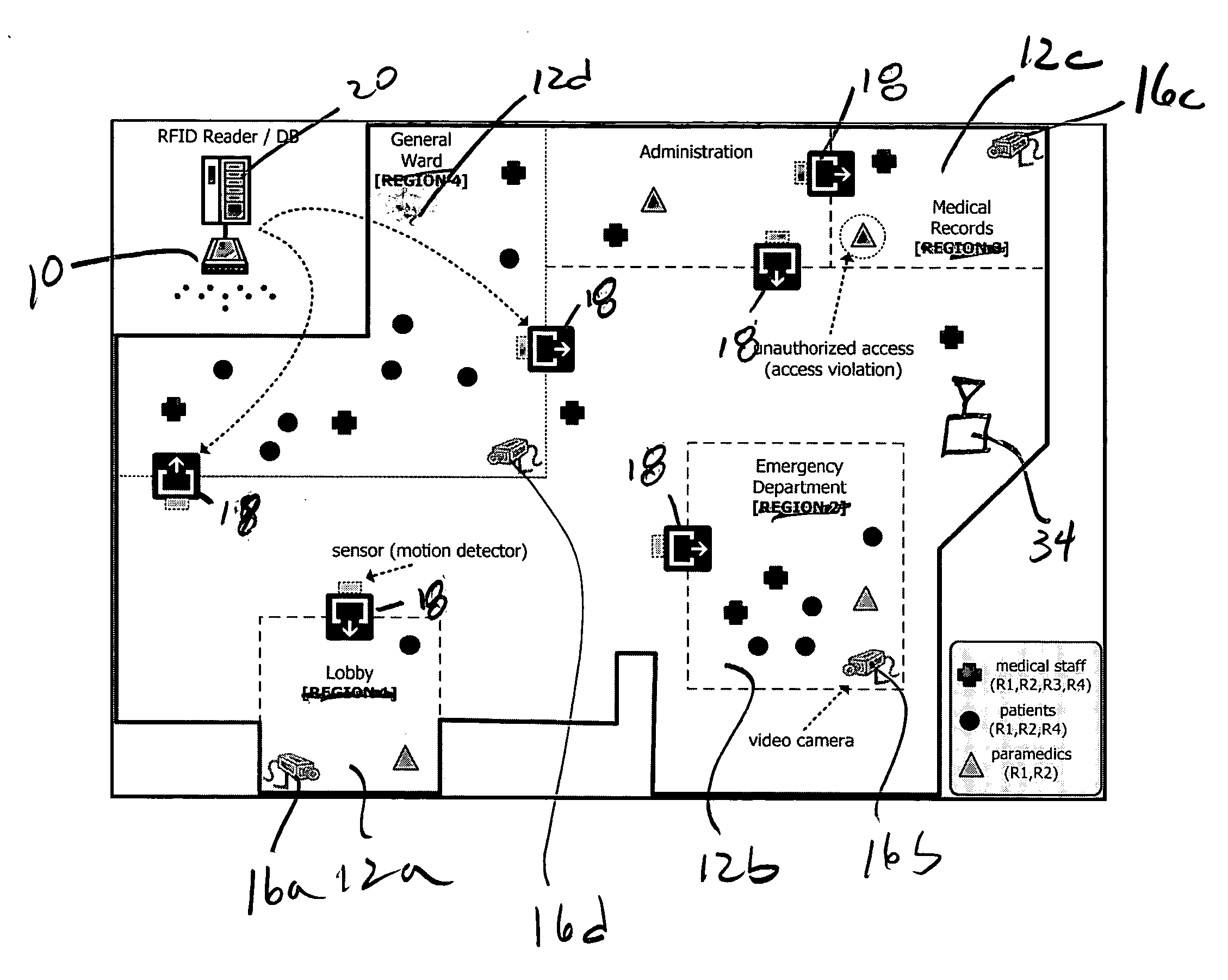
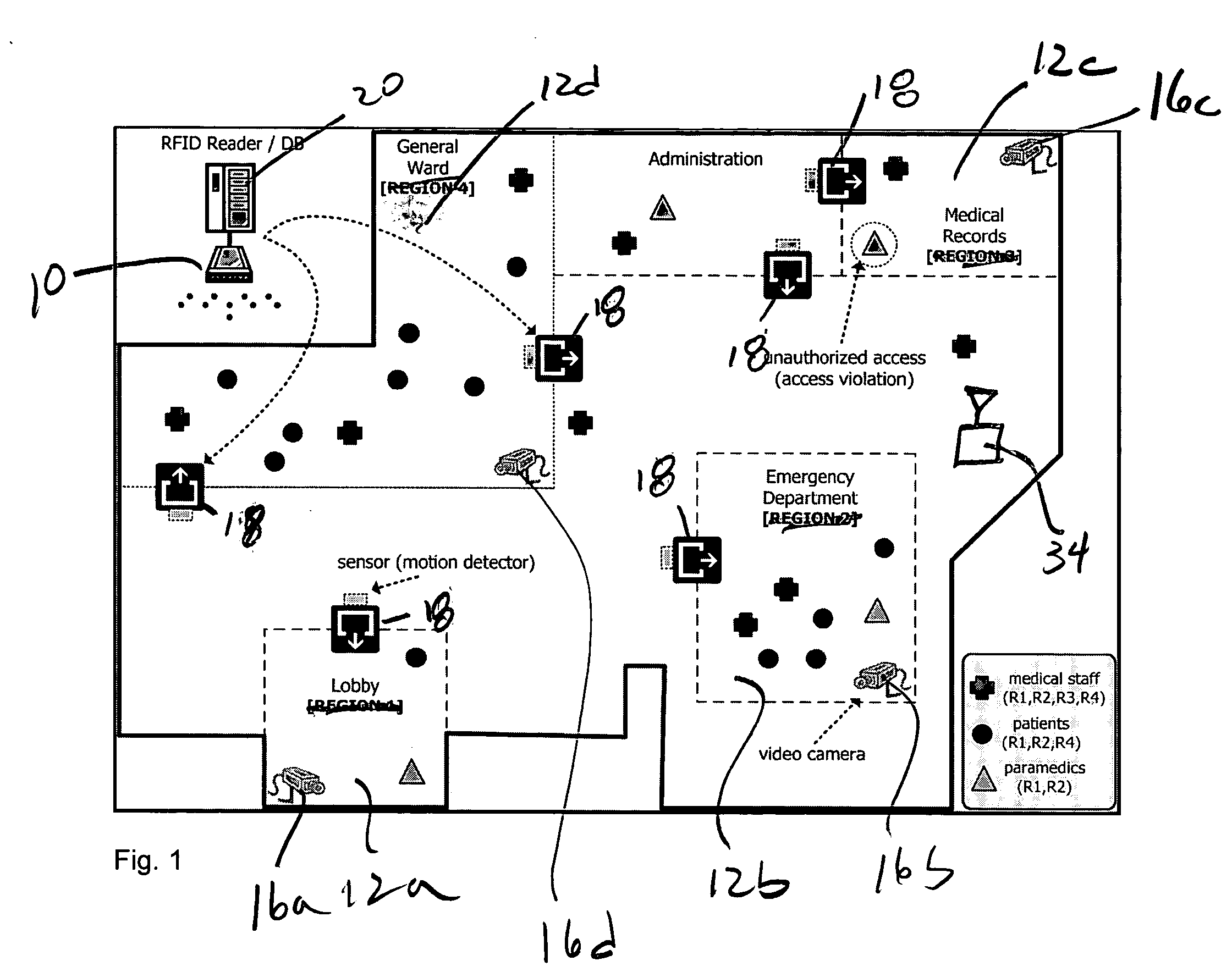
A security system which is nonintrusive of personal privacy of a person in a space comprises at least a first localization sensor subsystem, if any, in the possession of the person; a video surveillance subsystem arranged and configured to collect visual data related to the person in the space; and a computer subsystem coupled to the localization sensor subsystem and video surveillance subsystem to associate a predetermined privacy level with the localization sensor subsystem, and to provide an access control privilege with the localization sensor subsystem, the computer subsystem determining how to present, store and / or retrieve the visual data while meeting predetermined the privacy level associated with the person.
Owner:RGT UNIV OF CALIFORNIA
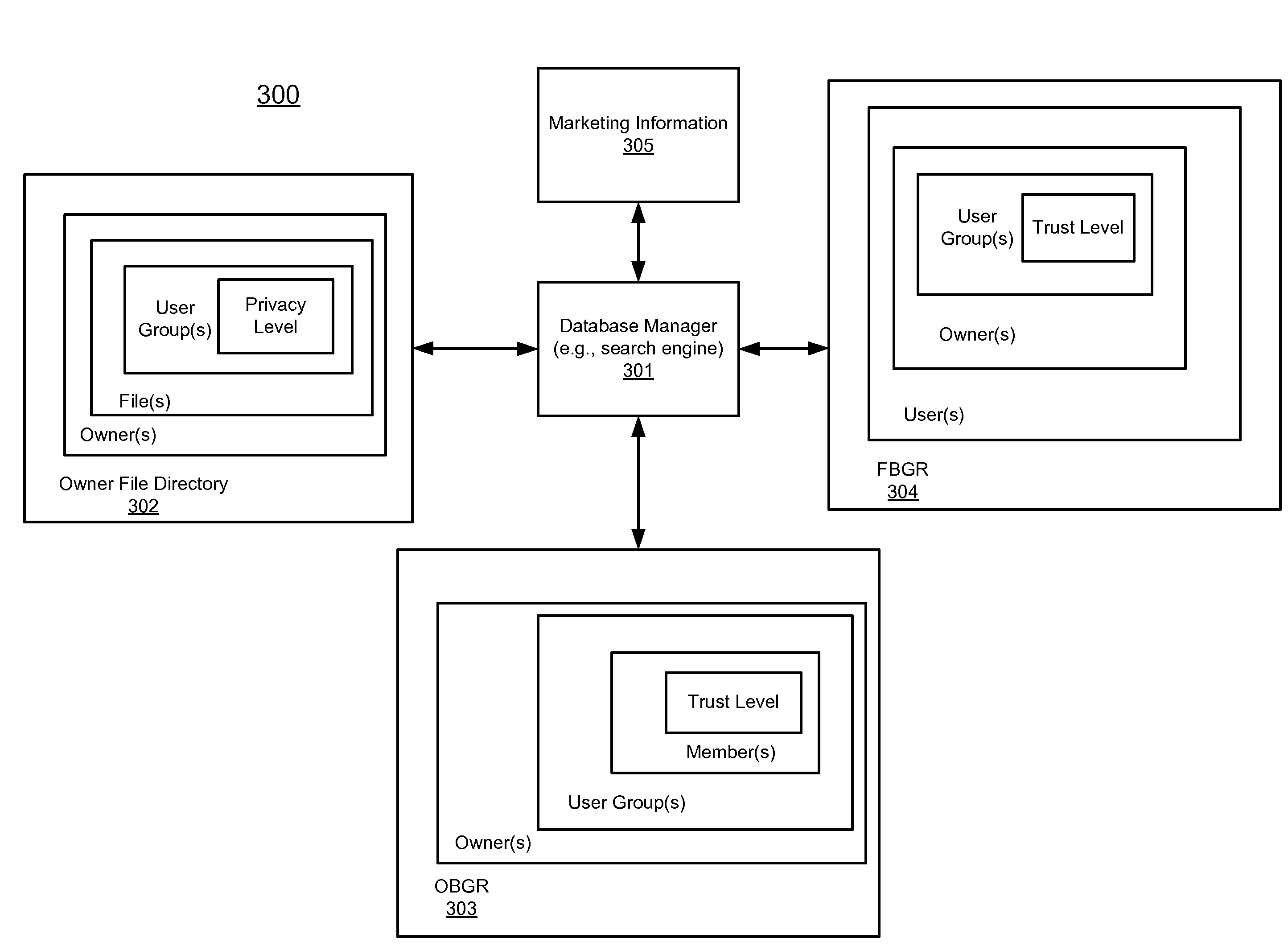
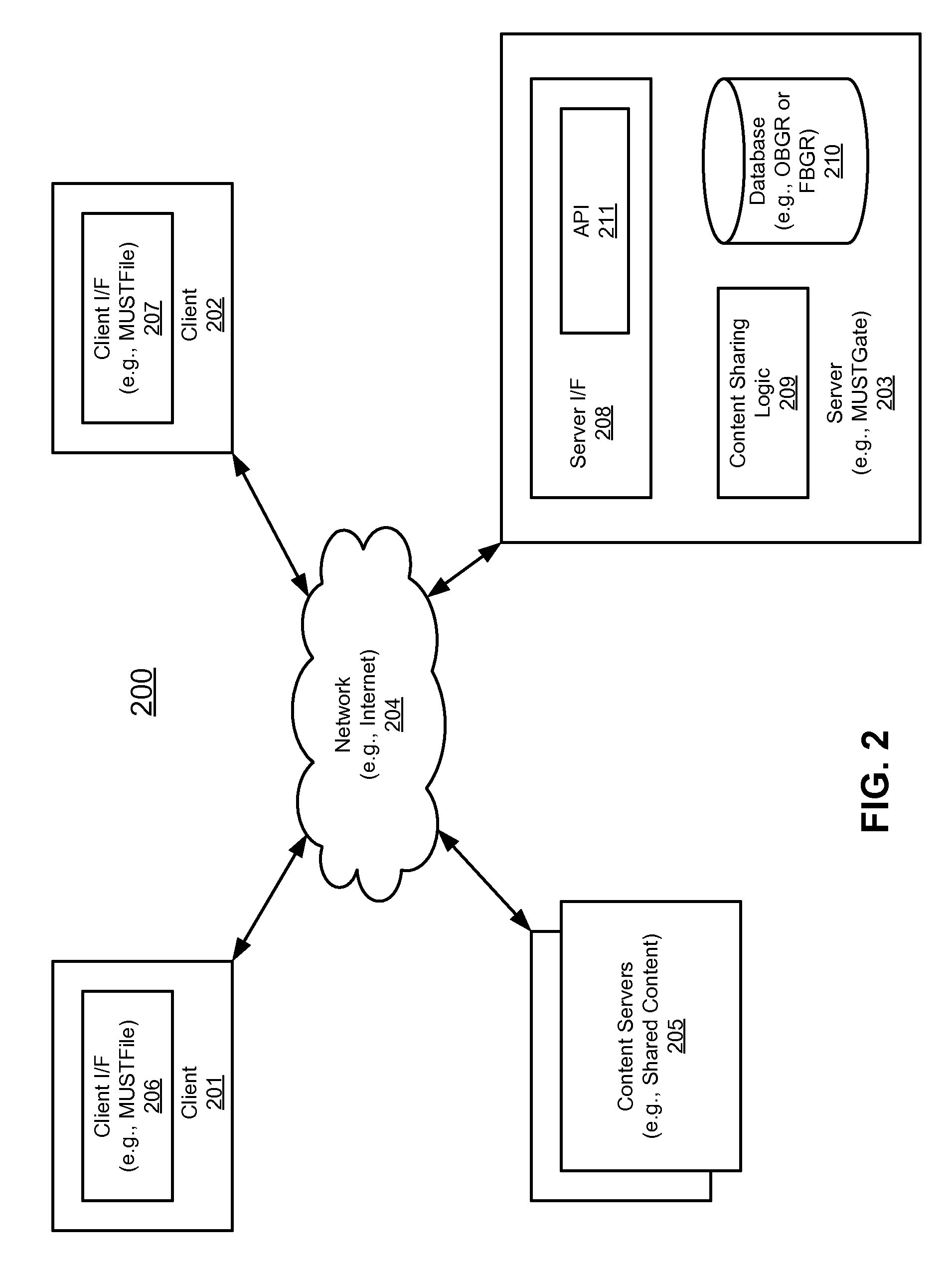
Method and apparatus for sharing content among multiple users
InactiveUS20090216859A1Digital data processing detailsComputer security arrangementsInternet privacyTrust level
Techniques for sharing content among multiple users are described herein. According to one embodiment, content is received from an owner to be shared among multiple members of one or more communities, where the owner defines the one or more communities. In response to the received content, a privacy level associated with the content to be shared is determined, where the privacy level is assigned by the owner. A trust level associated with each member of the one or more communities is determined, where each member is associated with a trust level assigned by the owner previously to represent a relationship between each member and the owner. The content is shared among selected members of the one or more communities if trust levels of the selected members and the privacy level associated with the content satisfy a predetermined relationship. Other methods and apparatuses are also described.
Owner:WILLIAMS SUSAN BARNHARDT
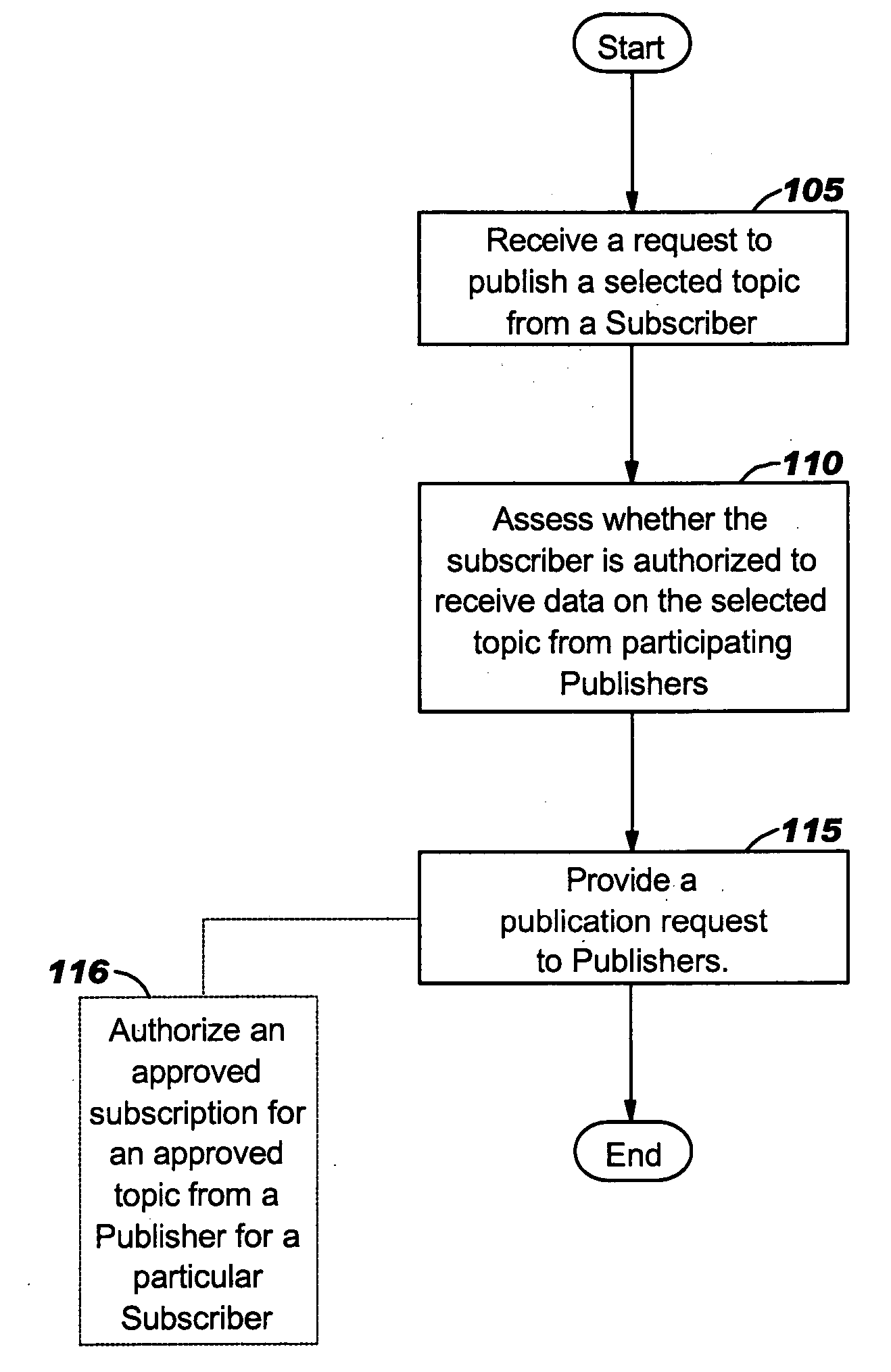
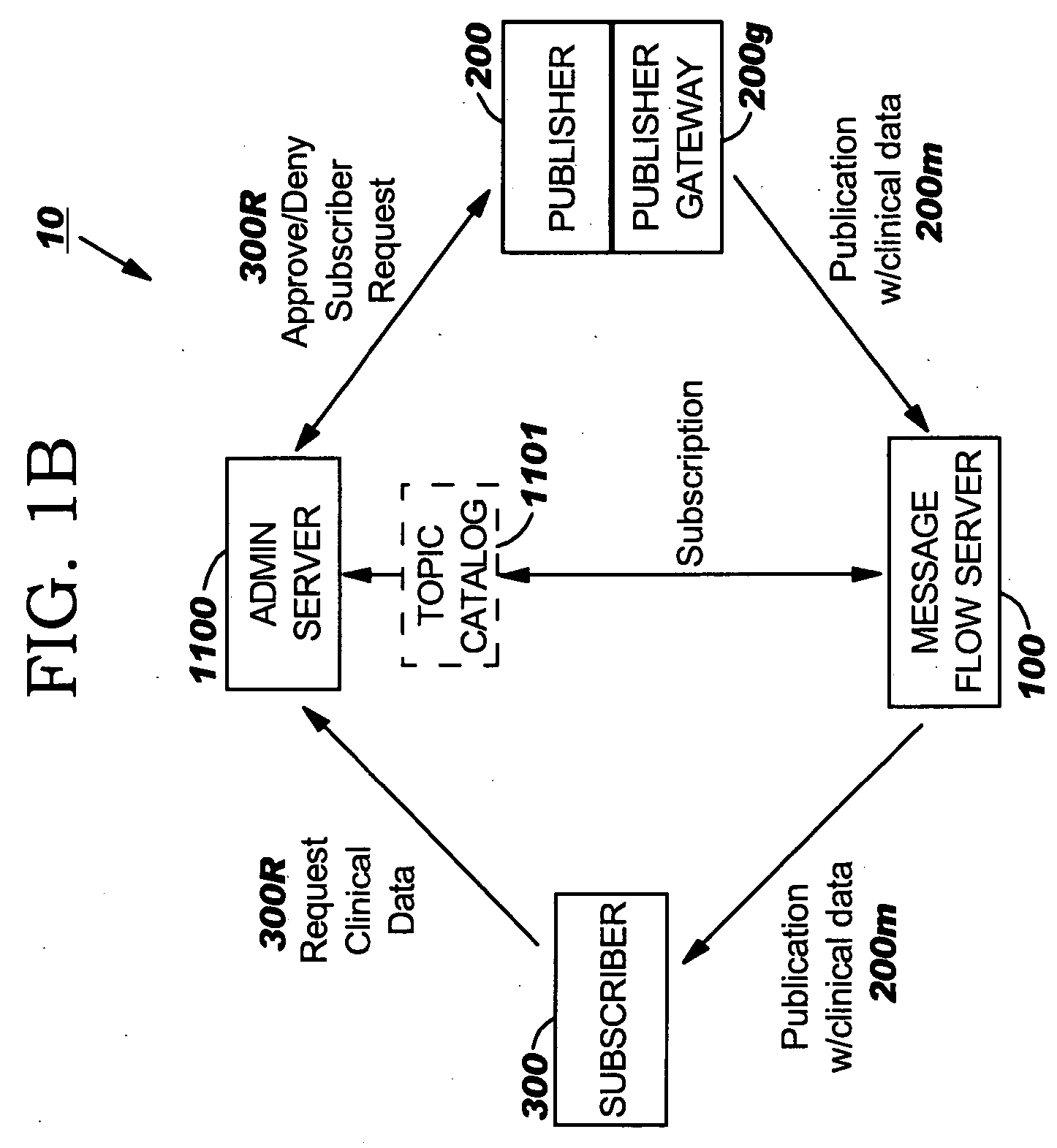
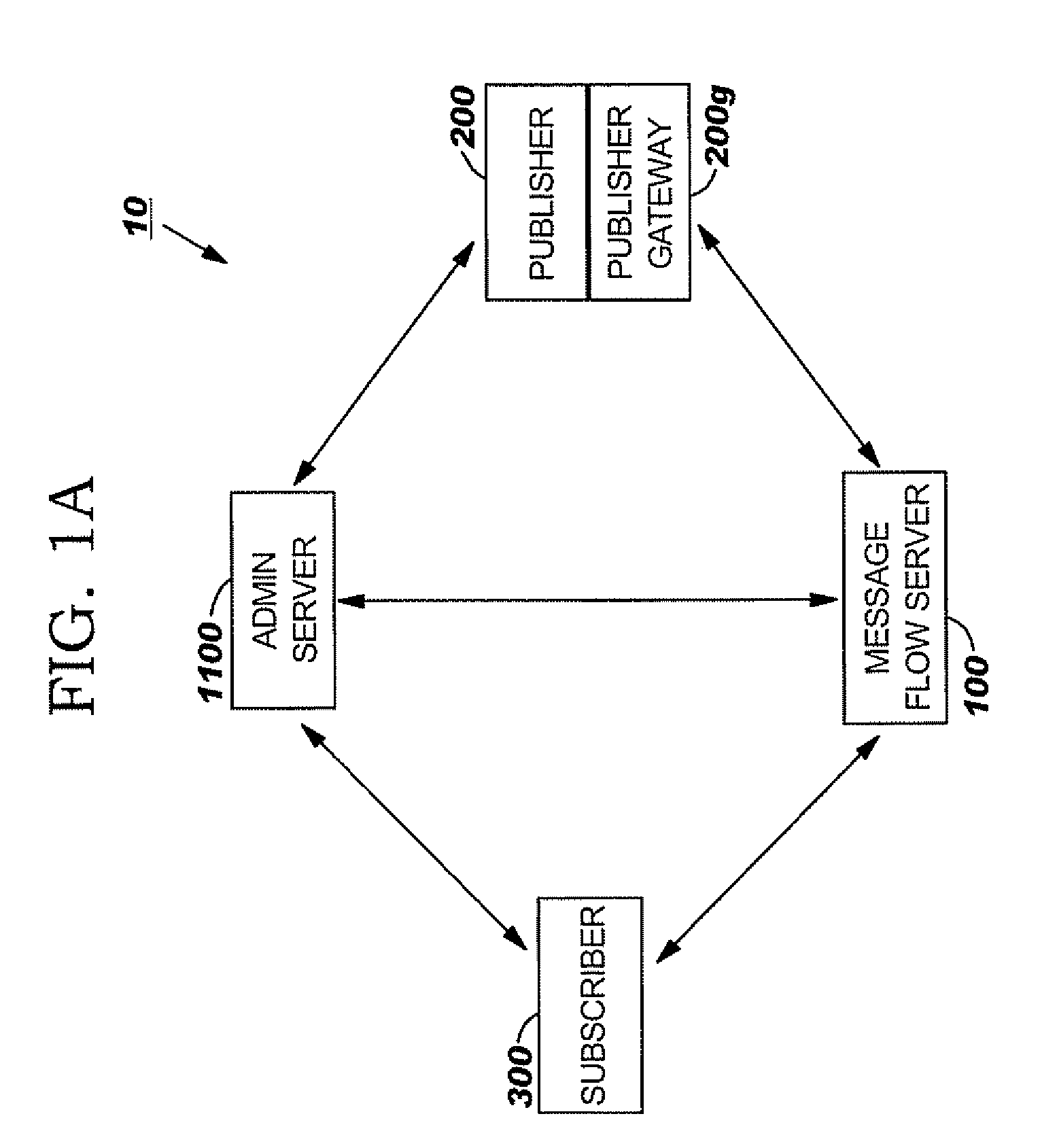
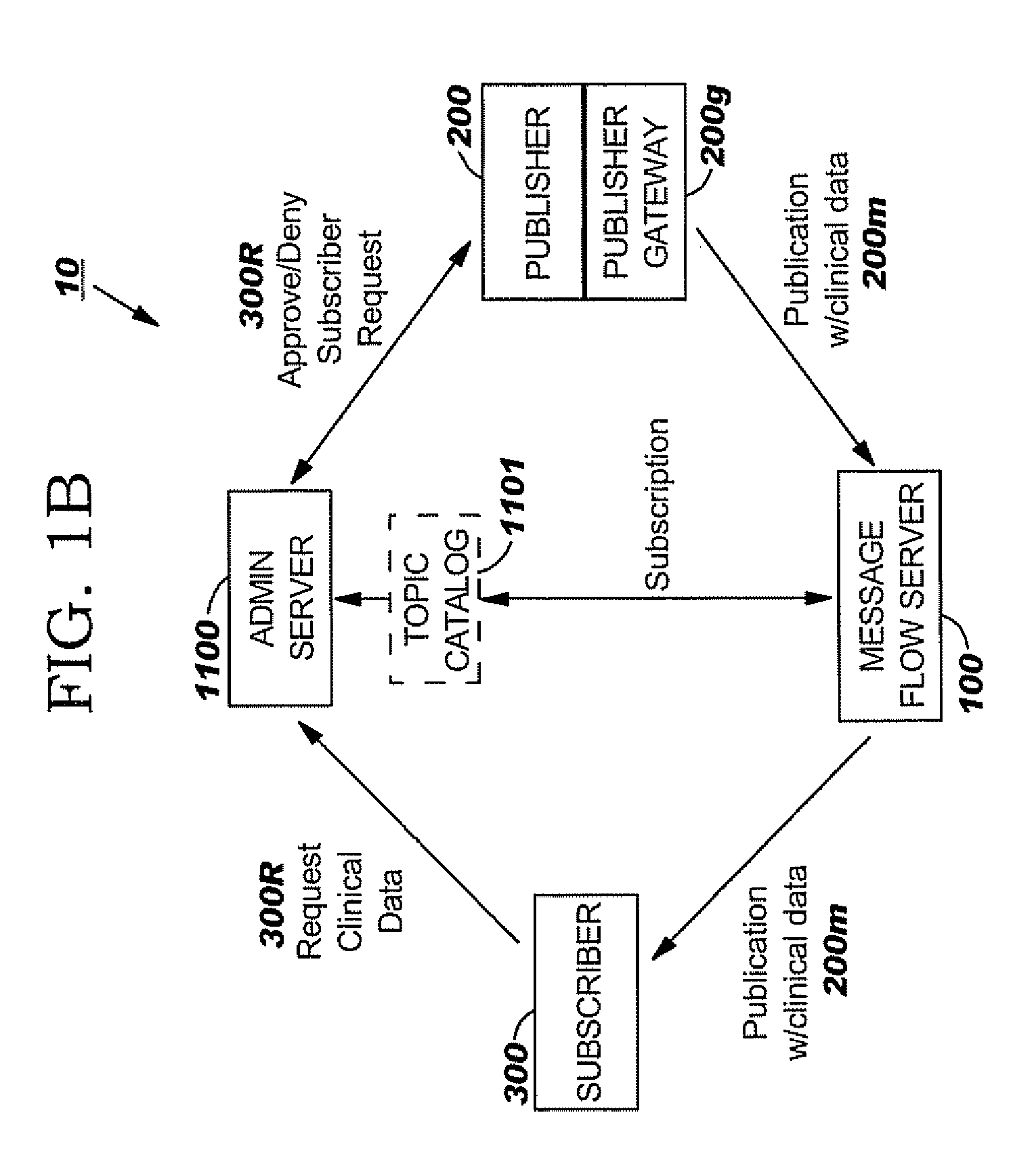
Privacy entitlement protocols for secure data exchange, collection, monitoring and/or alerting
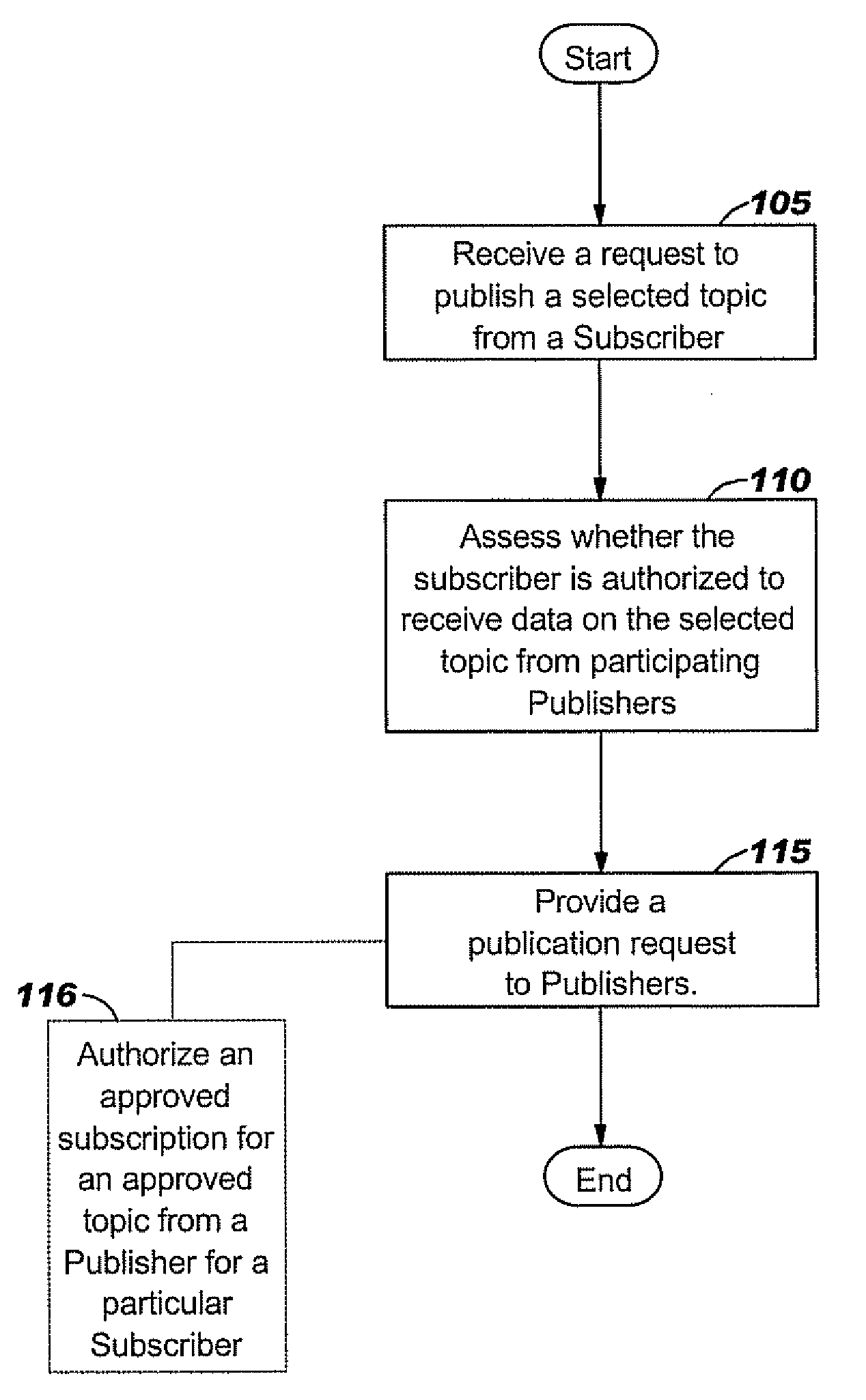
InactiveUS20060155578A1Epidemiological alert systemsDigital data protectionProcessor registerInternet privacy
Methods, systems and related computer products for providing entitlement controlled levels of collaborative exchange of data using a computer network of Subscribers and Publishers, are configured to: (a) define a set of different privacy levels, each privacy level having associated data sharing parameters that control a participating Publisher's ability to send and a participating Subscriber's ability to receive content specific data; and (b) provide an electronic privacy level register that defines the different data sharing parameters for each of the different privacy levels and identifies an associated at least one privacy level for each participating Subscriber and Publisher.
Owner:IBM CORP
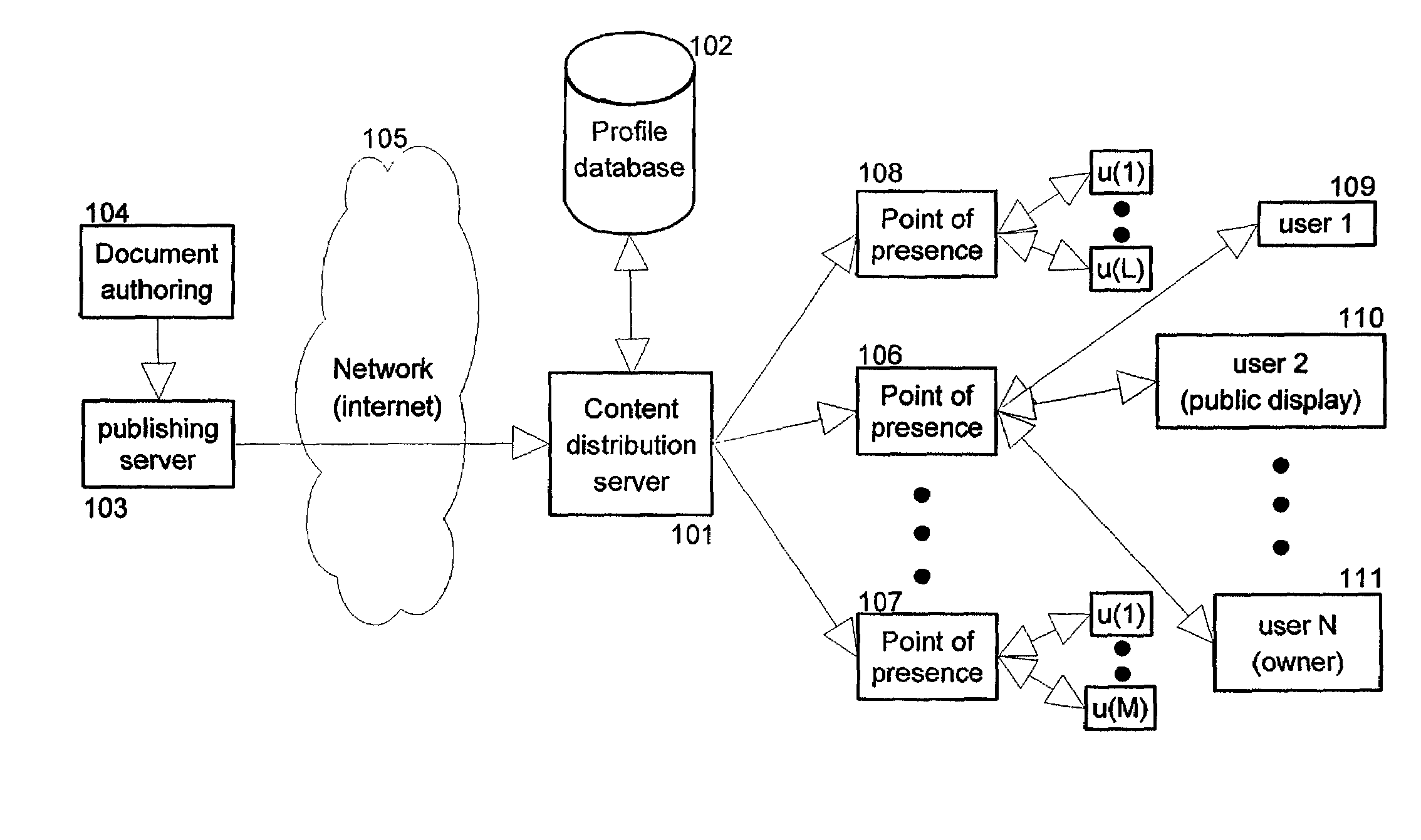
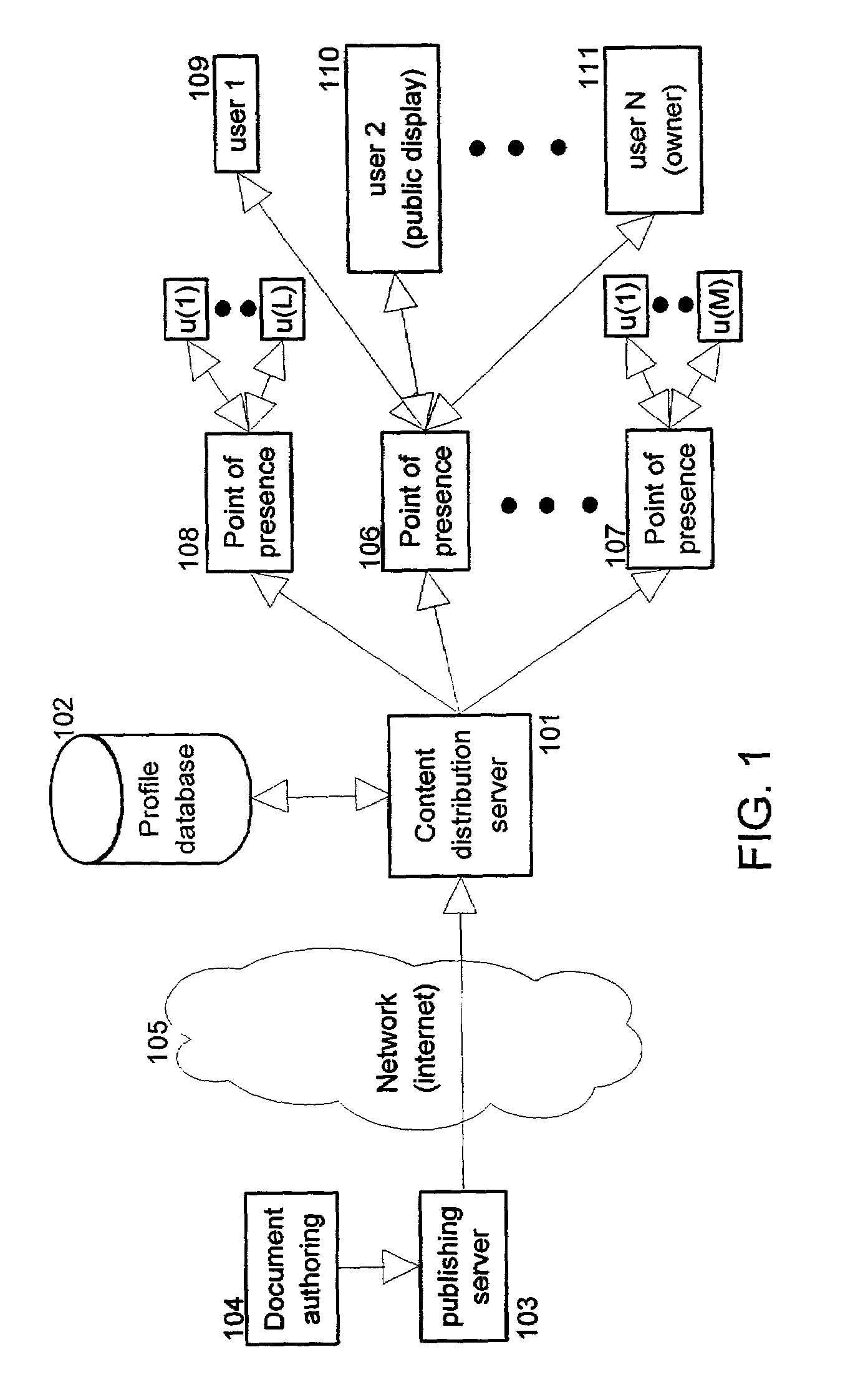
Information content distribution based on privacy and/or personal information
InactiveUS7162451B2Protect user privacyData representation error detection/correctionError preventionContent distributionPublic place
The present invention provides methods and apparatus to protect user privacy while accessing information in public places, using both public and personal devices. This is achieved by employing a mechanism that prevents private information from being displayed on public devices. Instead, this type of information is made available only to a user's personal device(s) that the user carries and / or trusts. An example embodiment of the invention shows relevant parts of the information content, referred to also as information documents or simply documents, to multiple devices based on privacy level and user preferences. Embodiments of the present invention also provide personalized services based on privacy levels defined by users. These users can for example be customers of a retail store. The service provided is sometimes also based on user history of accessing information documents. It permits personalized information to be sent to a customer's personal device.
Owner:IBM CORP
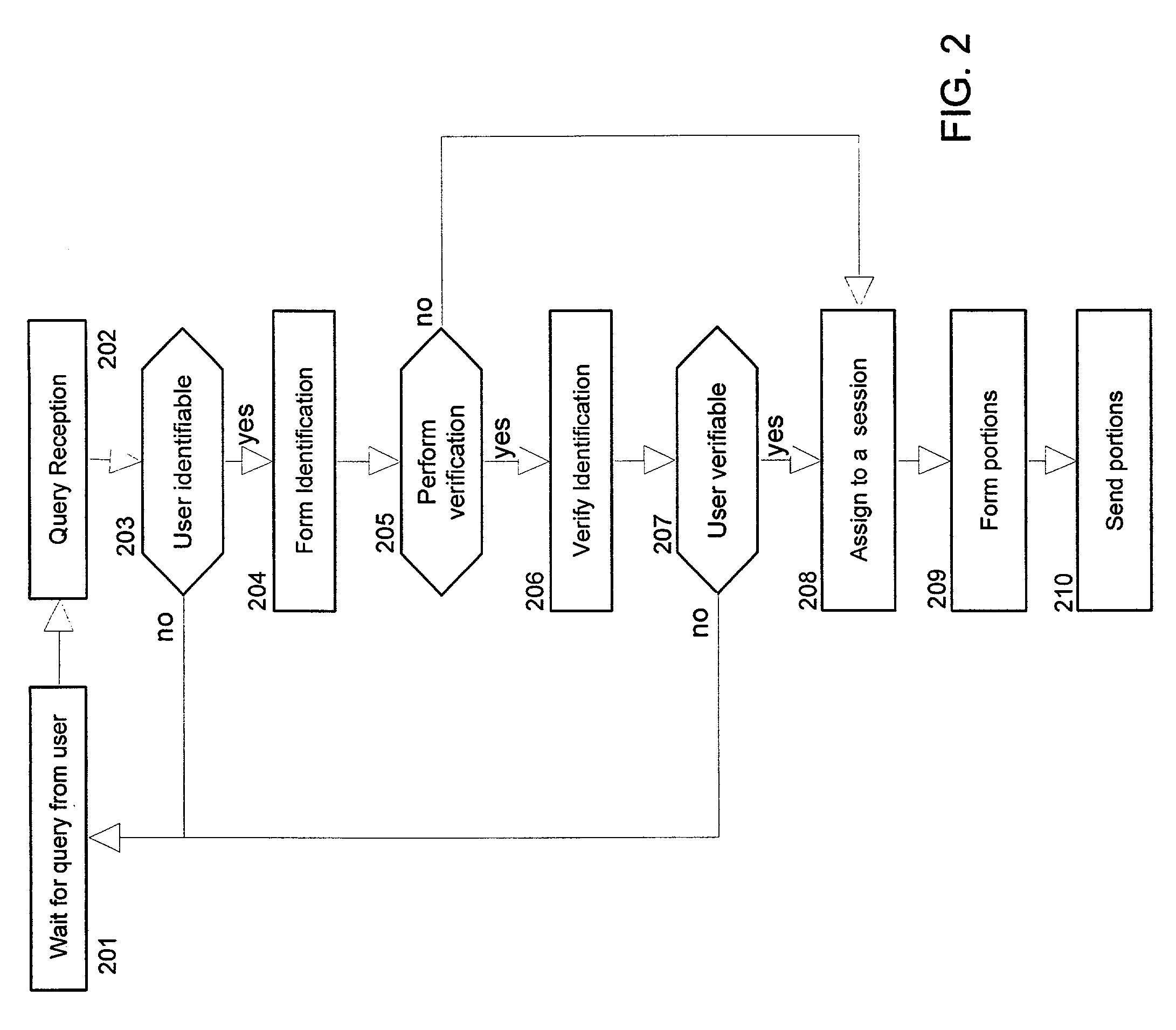
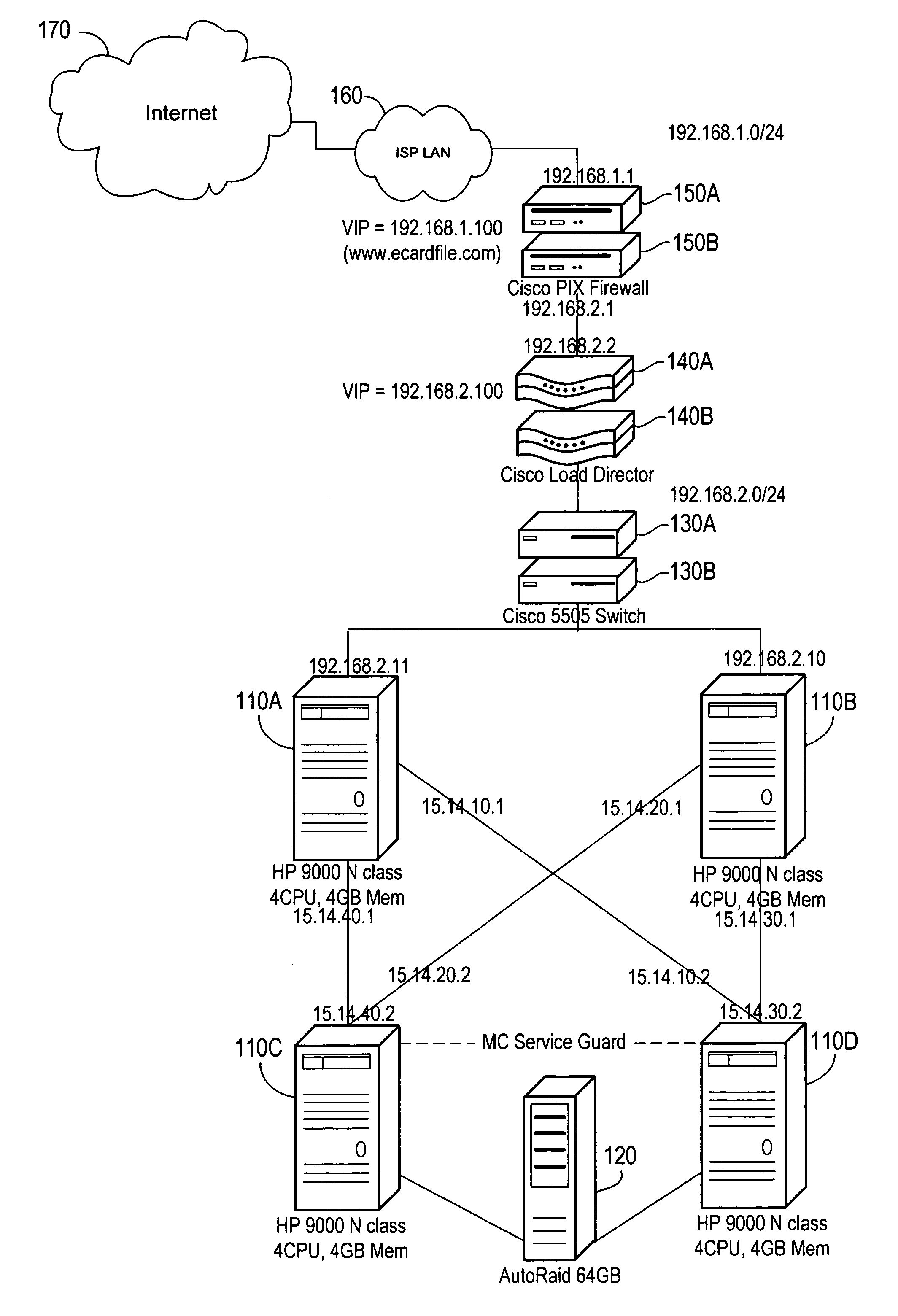
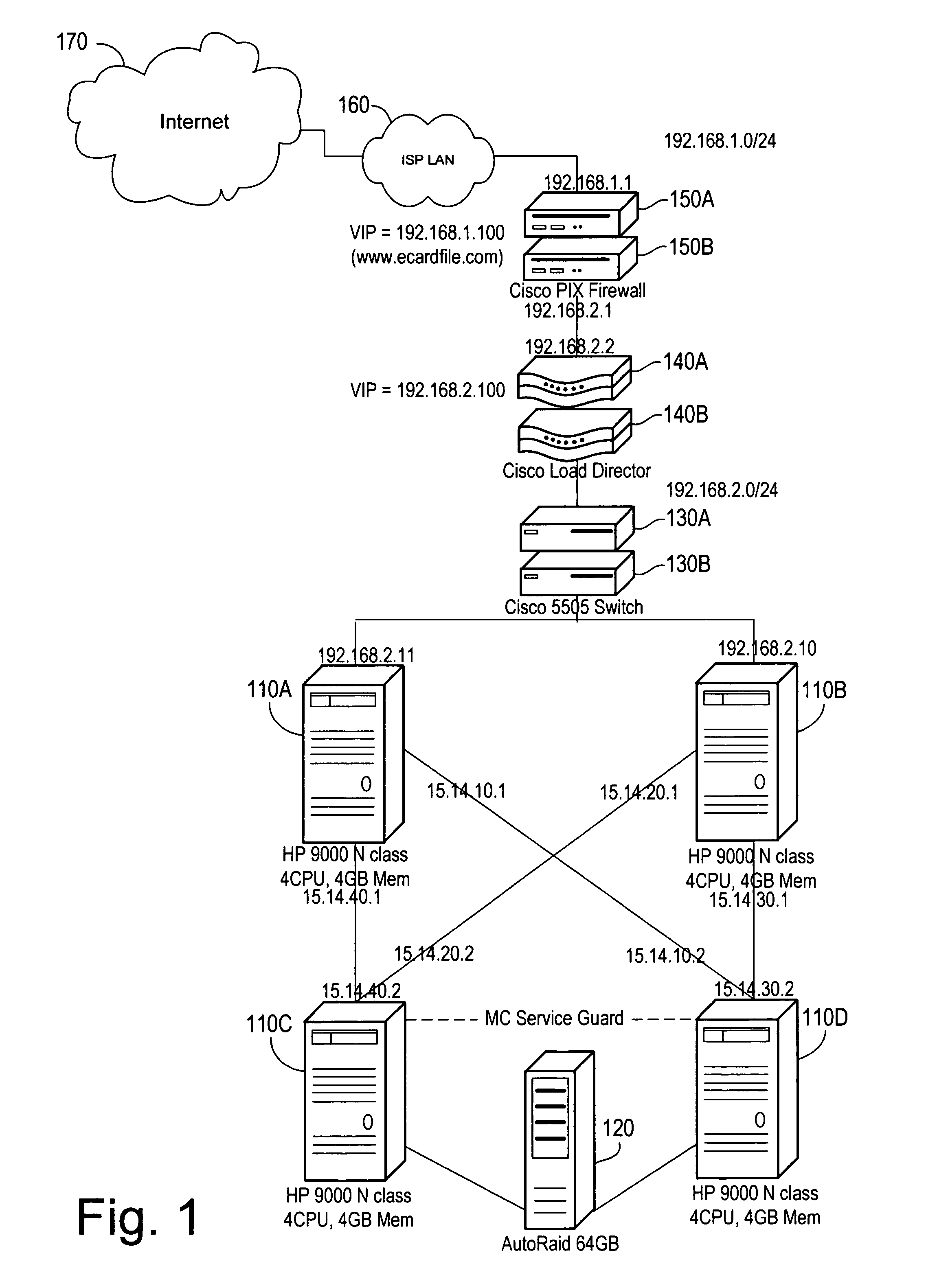
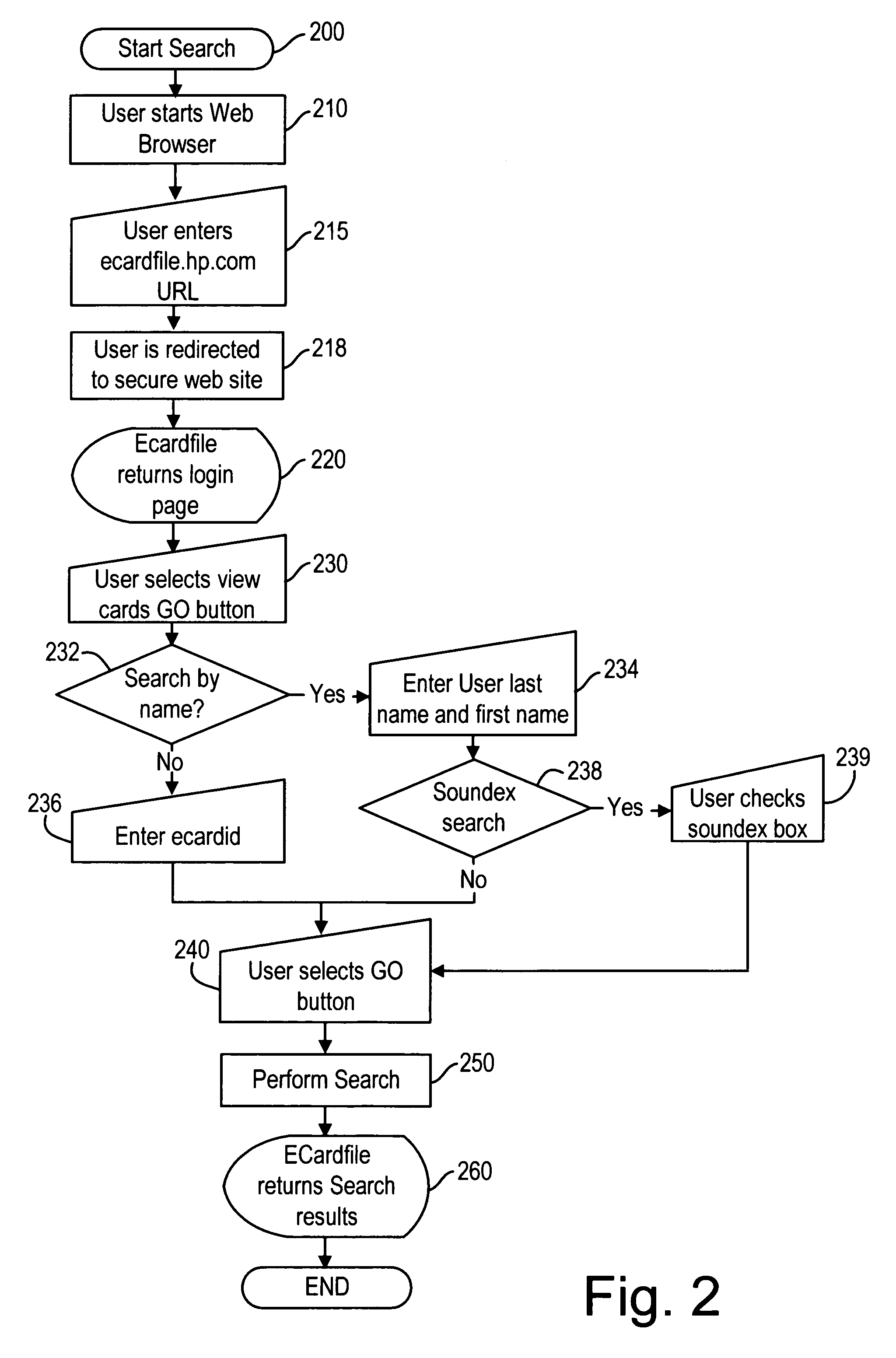
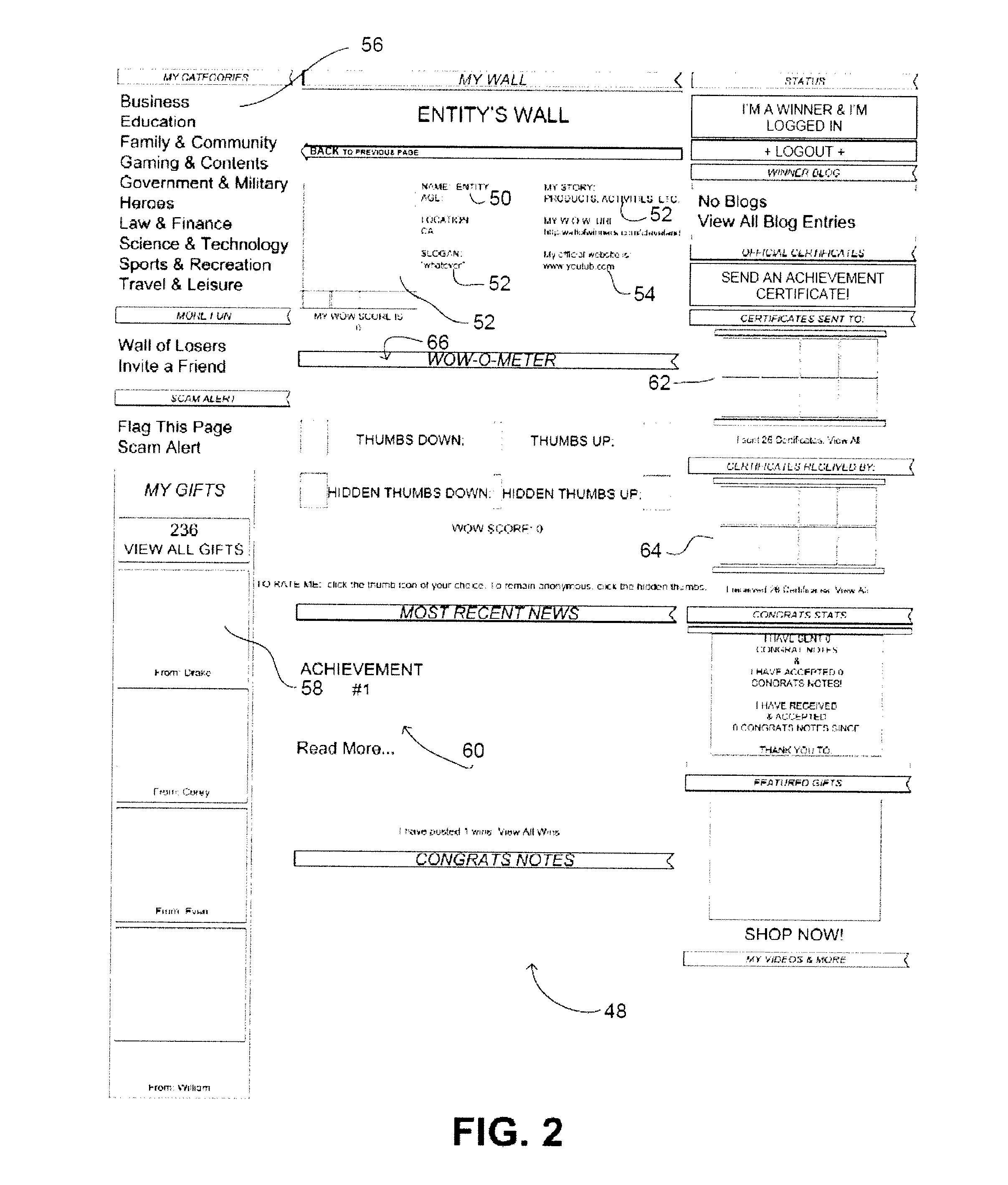
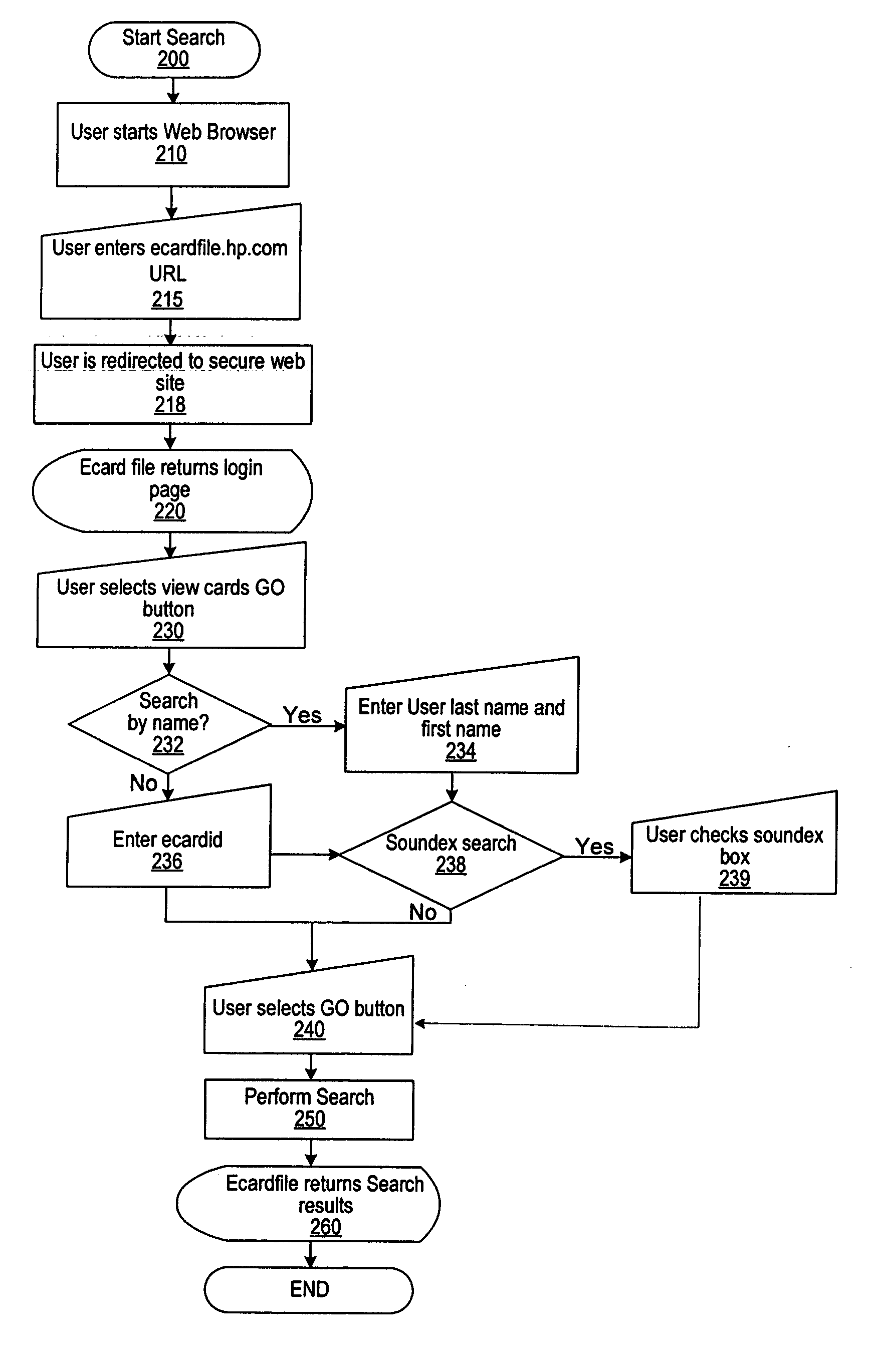
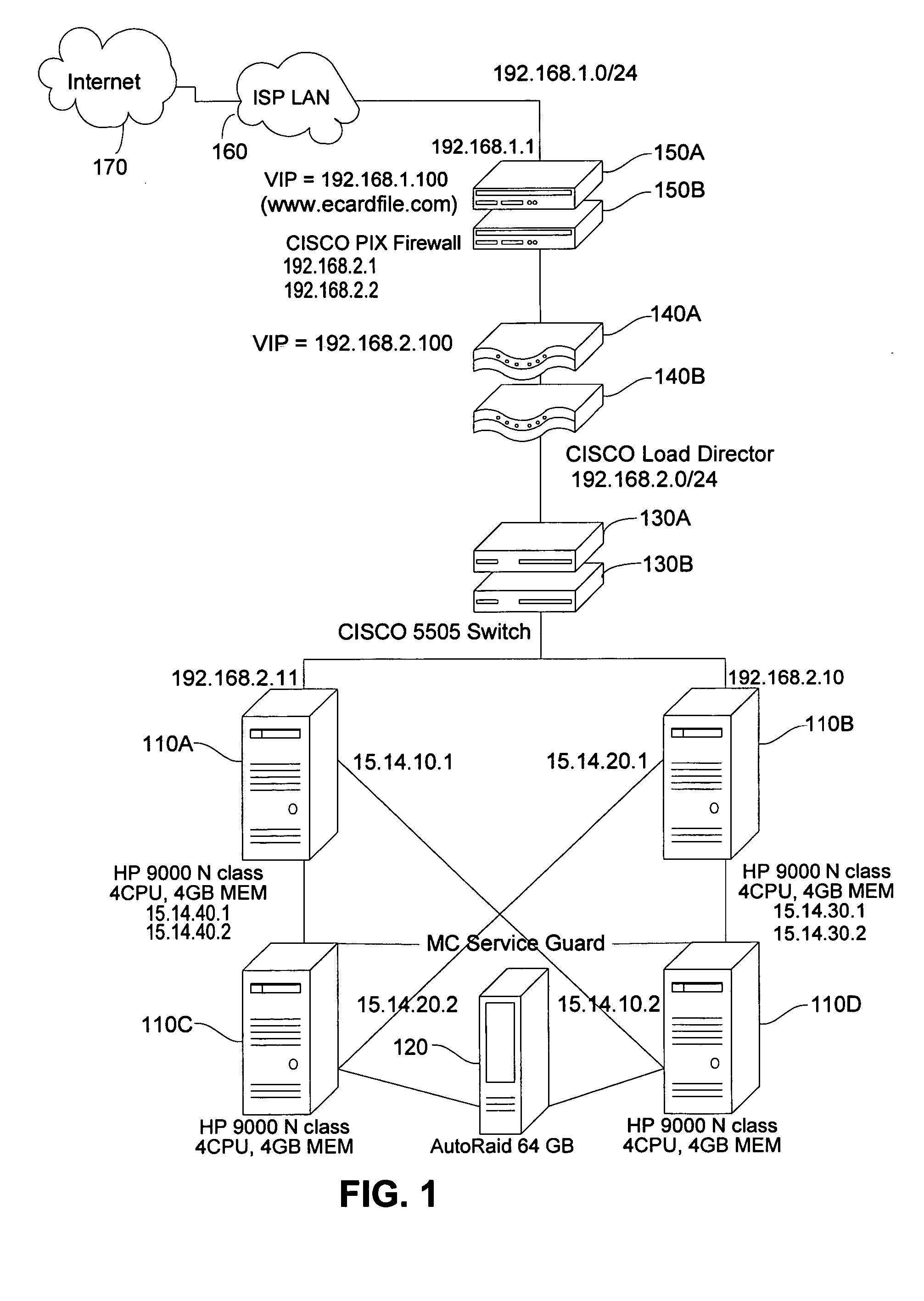
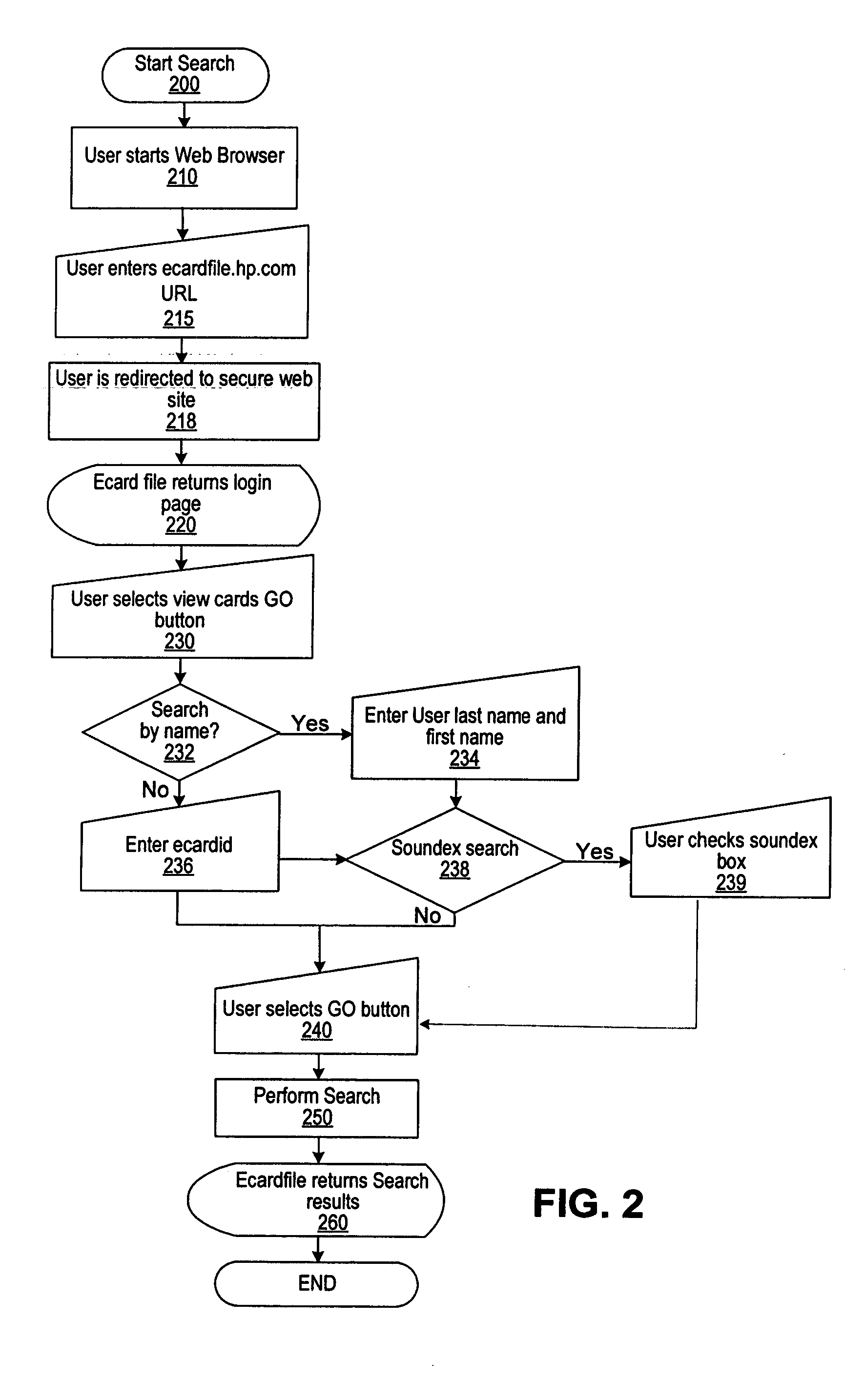
E-service to manage contact information and signature ECards
InactiveUS7017109B1Easy for userEasy accessOffice automationSpecial data processing applicationsElectronic mailData bank
A method of providing an electronic business card (EBC) access and organization service on the Web. The cardholder database is accessible and searchable from any browser connected to the Internet or the EBC service may be installed behind a conventional firewall and thus accessible only to intranet users. The service thus provides easy access to cardholder contact information with privacy assured by use of integrated access restrictions. Access to and delivery of contact information by the service is not limited to a Web browser interface as commonly known today. The service provides multi-mode access and / or data delivery interfaces. The service also provides an export feature that formats search results into a pre-defined file structure readable by a conventional contact management programs. Custom export file formats may also be defined provide even wider connectivity and cross-platform utility. Access to individual records is controlled at both the record level and the field level, with multiple privacy levels for each field, in addition to the well-known “public” and “private” levels. Users having certain permissions are permitted to read a defined group of records, though not necessarily all fields in each record. A location tracking feature is also provided to allow the cardholder to rapidly designate a pre-defined contact location. Alternately, the cardholder may define a temporary contact location not normally stored in the database system. Electronic mail sent by the cardholder is automatically formatted to contain a signature hypertext link directing recipients of the email to the EBC service. This hyperlink enables the recipient of the email to rapidly access the EBC system to locate the cardholder and / or obtain additional information.
Owner:META PLATFORMS INC
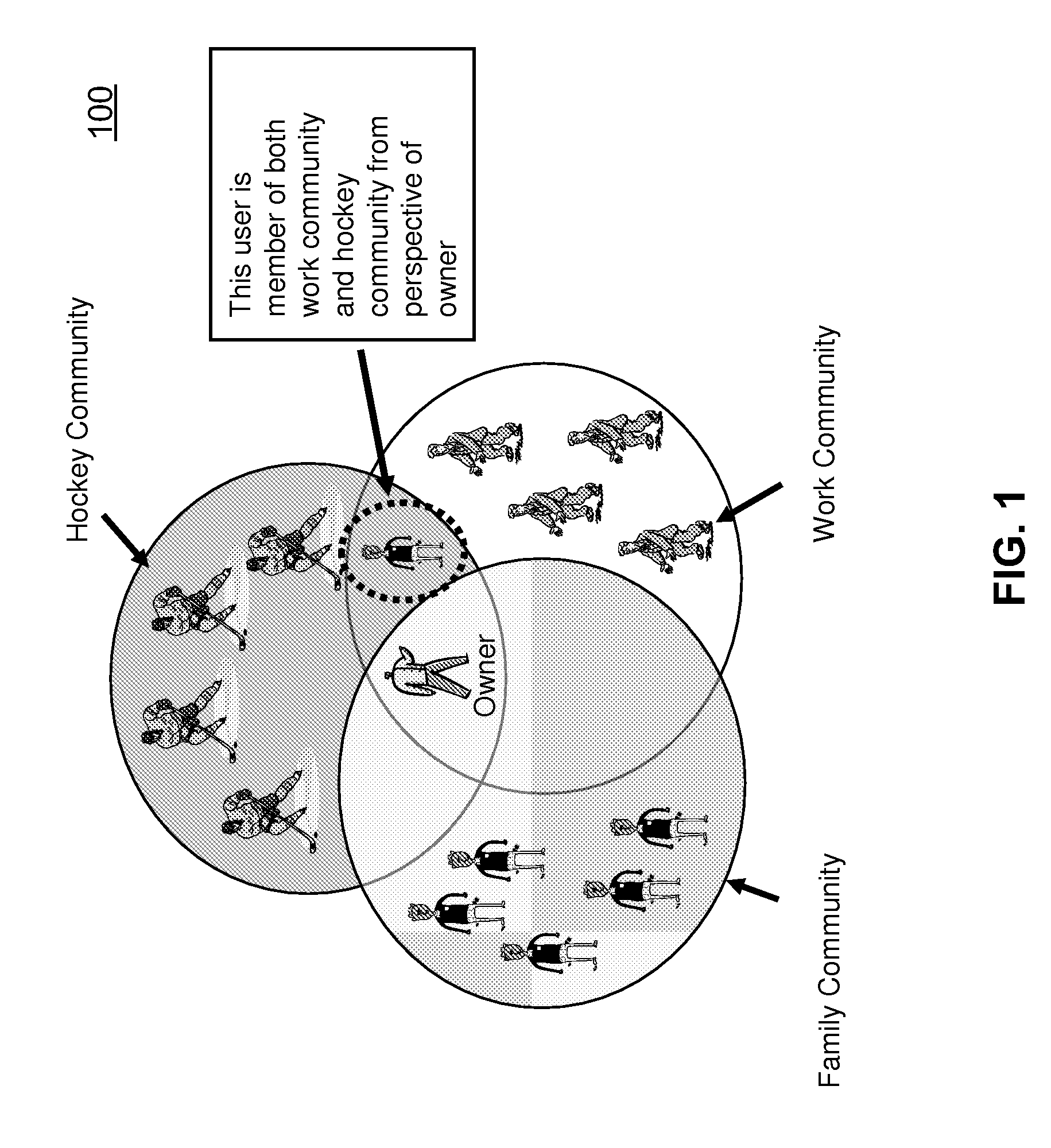
Walled gardens
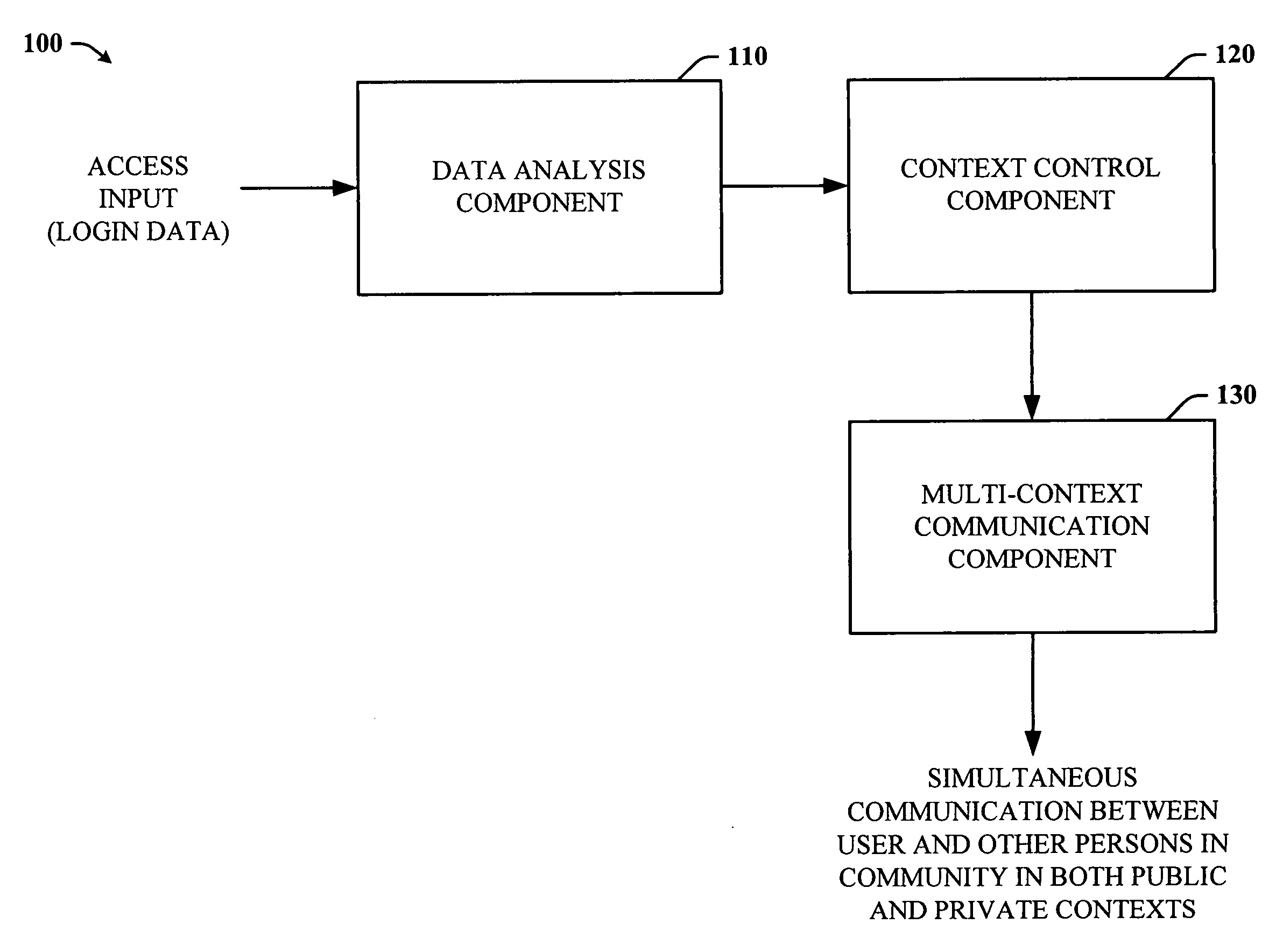
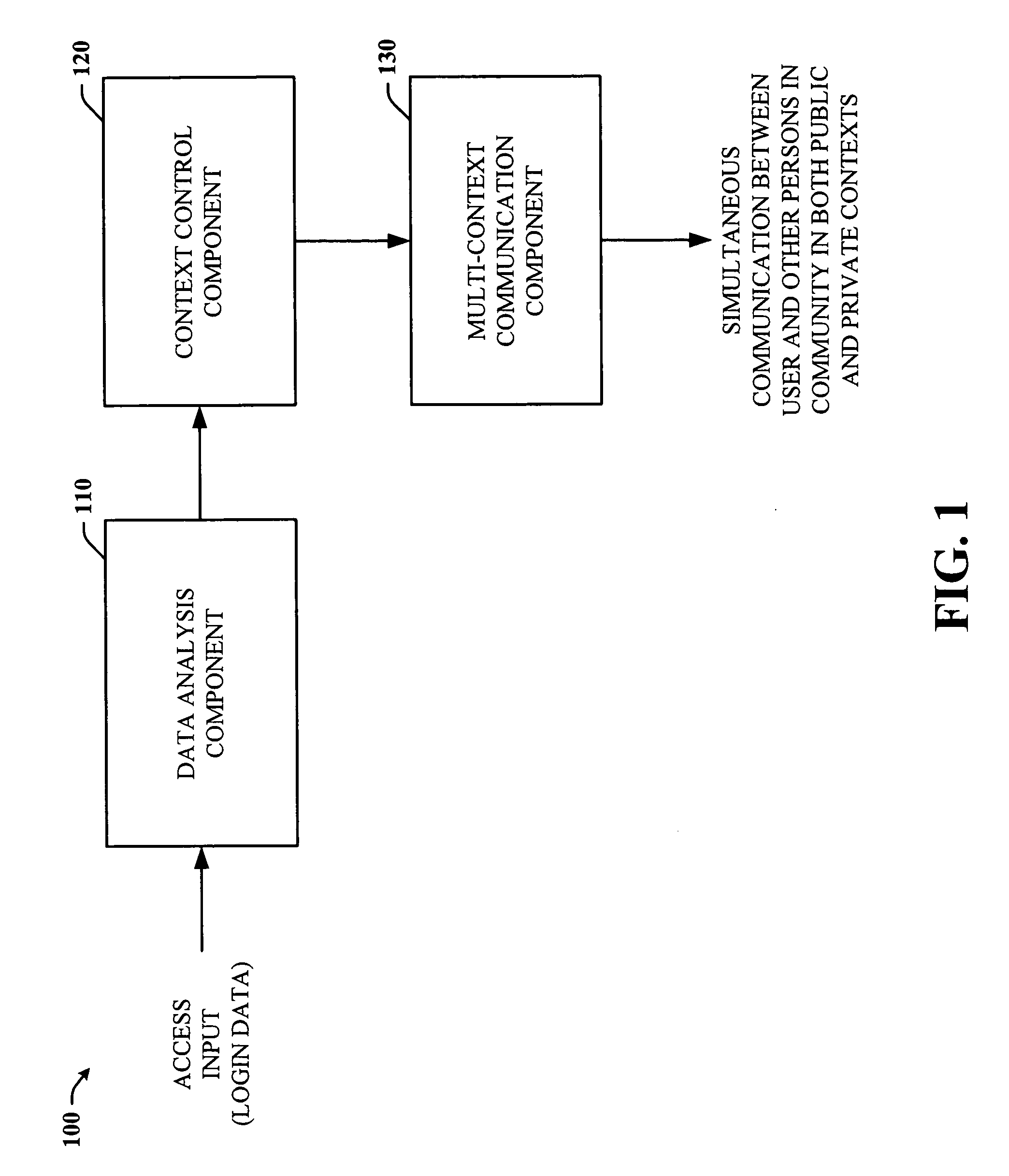
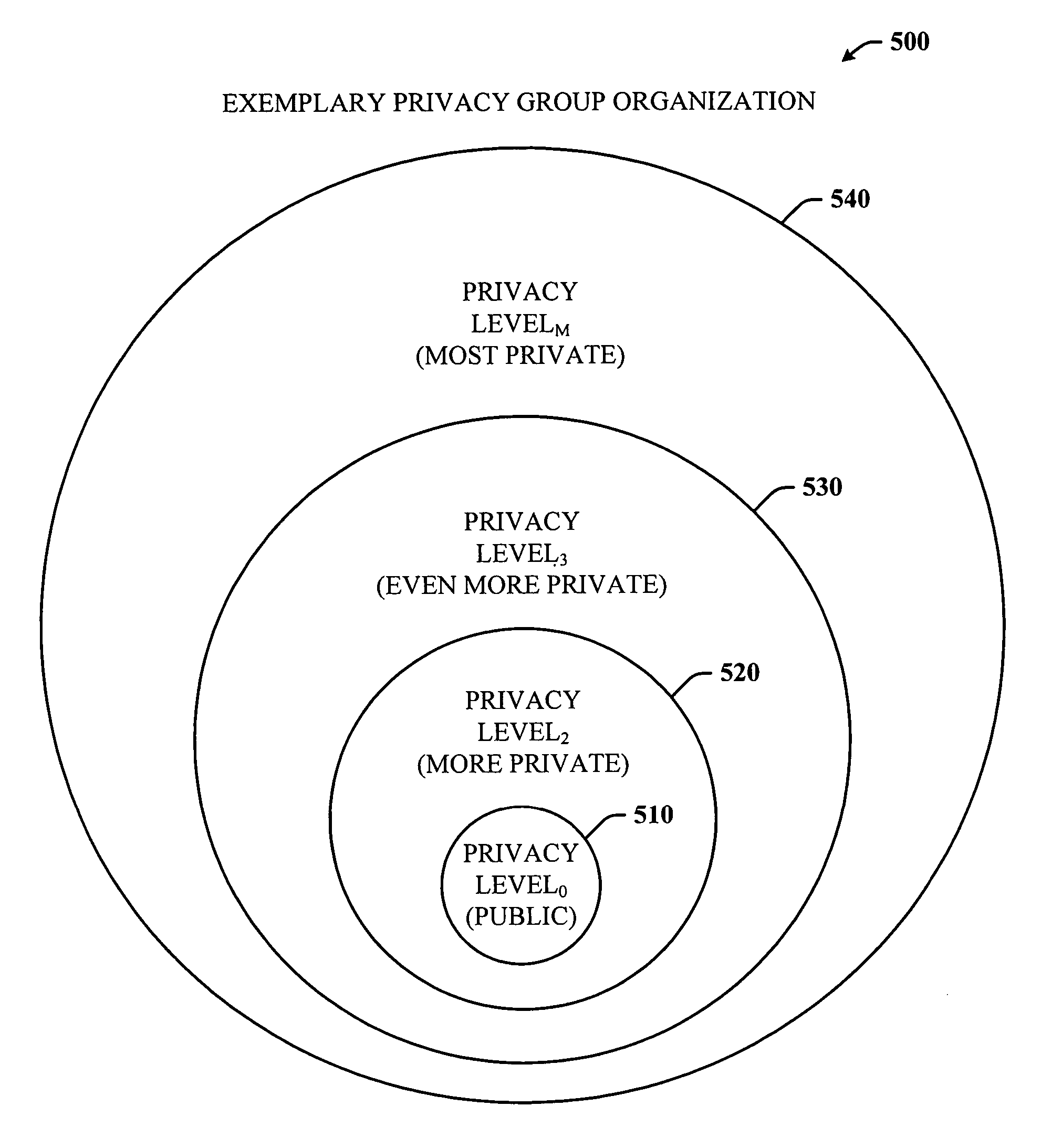
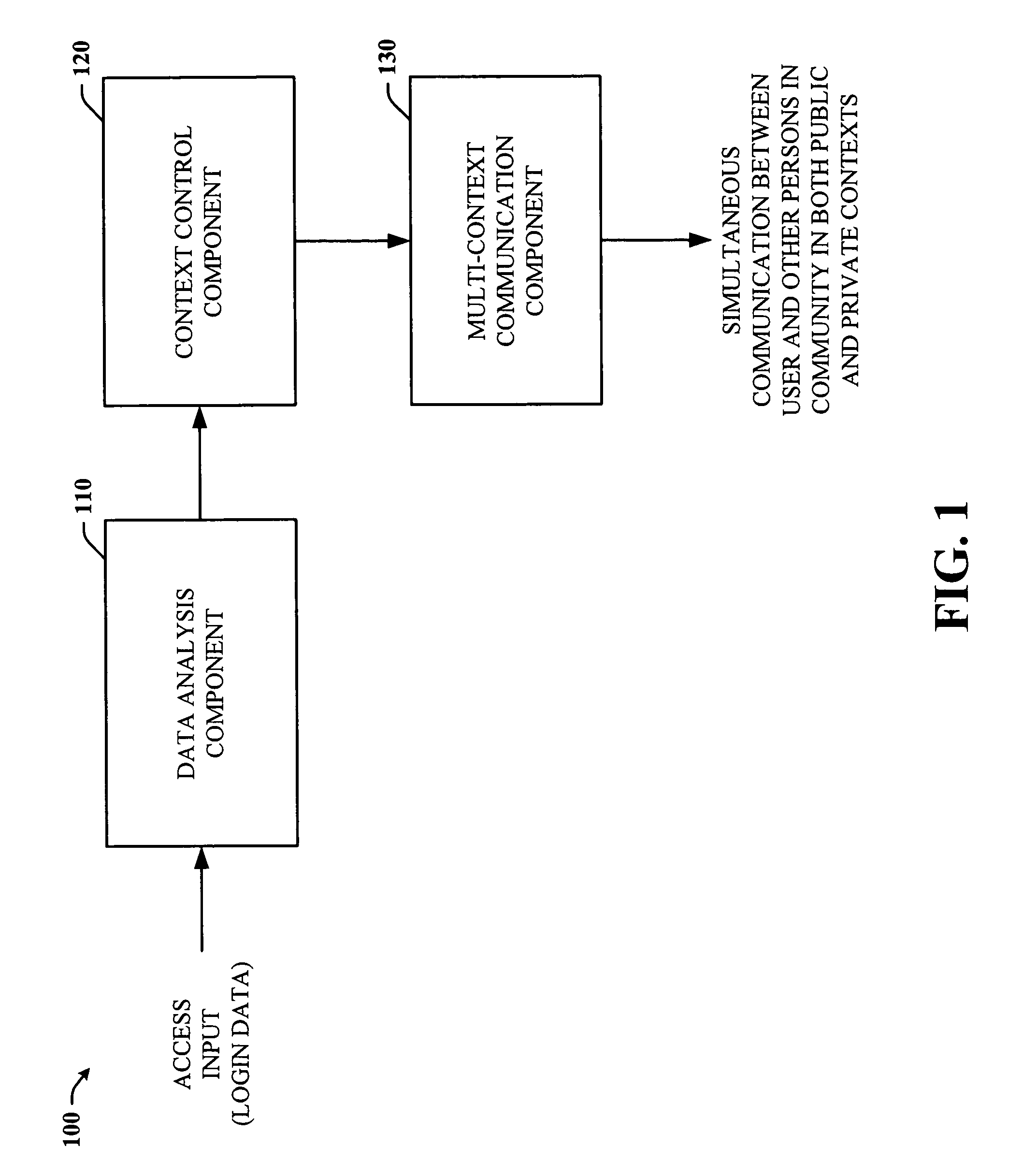
ActiveUS20060248584A1Facilitates simultaneous communicationEffectively transparentDigital data processing detailsUnauthorized memory use protectionVisibilityInternet privacy
The subject invention provides a unique system and method that facilitates a controlled communication environment which allows a user to participate in a plurality of privacy contexts with other people in a simultaneous manner in an online community. A user can assign or define varying levels of privacy to his / her information or content to control the visibility of such information by others. In particular, a first user can maintain one or more “gardens” or stores of content which may be accessible to at least a subset of the online community. Access to the contents of any one garden can be based on the privacy level of the garden and the privacy level (e.g., access parameters) granted to the person. The privacy levels and arrangement of content can be hierarchal and / or non-overlapping. Thus, a user can seamlessly communicate with multiple users at the same time regardless of their context or privacy level while maintaining the privacy boundaries of each garden.
Owner:MICROSOFT TECH LICENSING LLC
Privacy entitlement protocols for secure data exchange, collection, monitoring and/or alerting
InactiveUS20100256994A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyProcessor register
Owner:IBM CORP
Context-aware based RFID privacy control system and personal privacy protection method using the same
InactiveUS20090115600A1Avoid contactImprove securityCo-operative working arrangementsRadio/inductive link selection arrangementsControl systemPrivacy protection
Disclosed are a Radio Frequency Identification (RFID) personal privacy control system and a personal privacy protection method using the same which may dynamically process a privacy level according to peripheral circumstances of an RFID tagged object and an owner of the object, thereby securely protecting personal information associated with the RFID tag. The RFID privacy control server, the RFID privacy control server includes a context-aware information collecting unit to collect at least one context-aware information about a user; a privacy level adjusting unit to adjust a privacy level of the user based on the collected context-aware information; and a privacy control unit to determine, according to the adjusted privacy level, whether access of an RFID reader to RFID tag information is allowed, the RFID tag information corresponding to an RFID tag associated with the user.
Owner:ELECTRONICS & TELECOMM RES INST
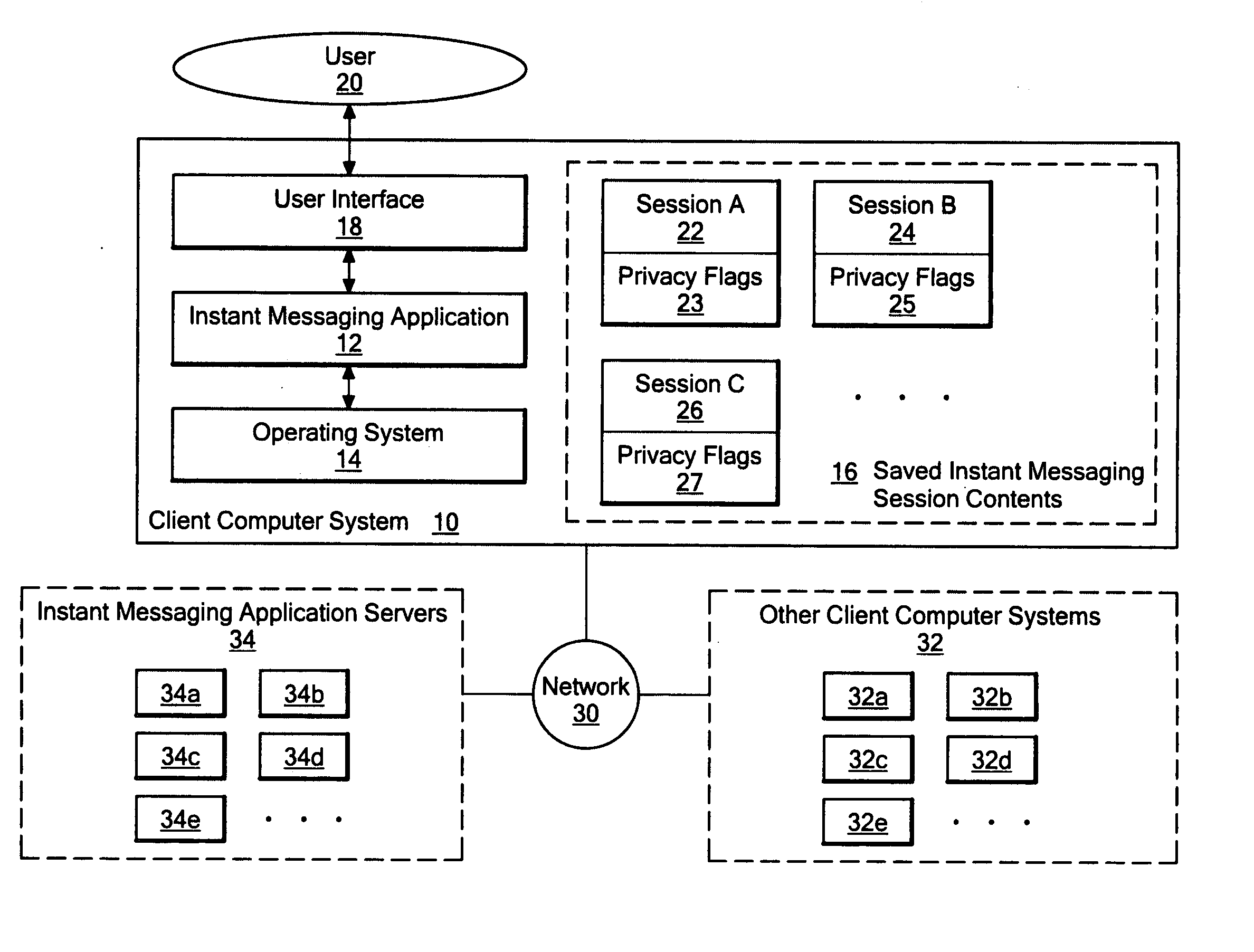
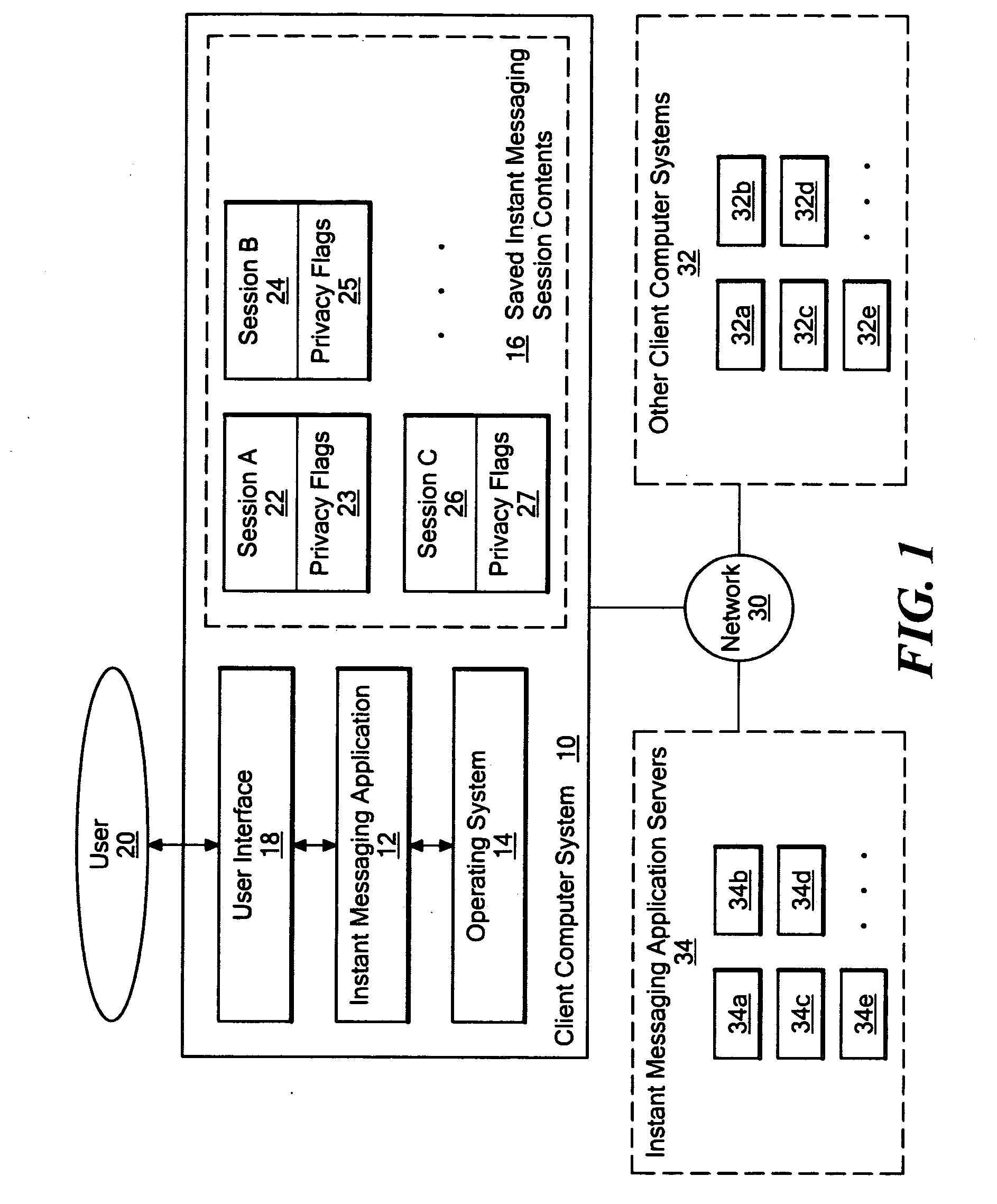
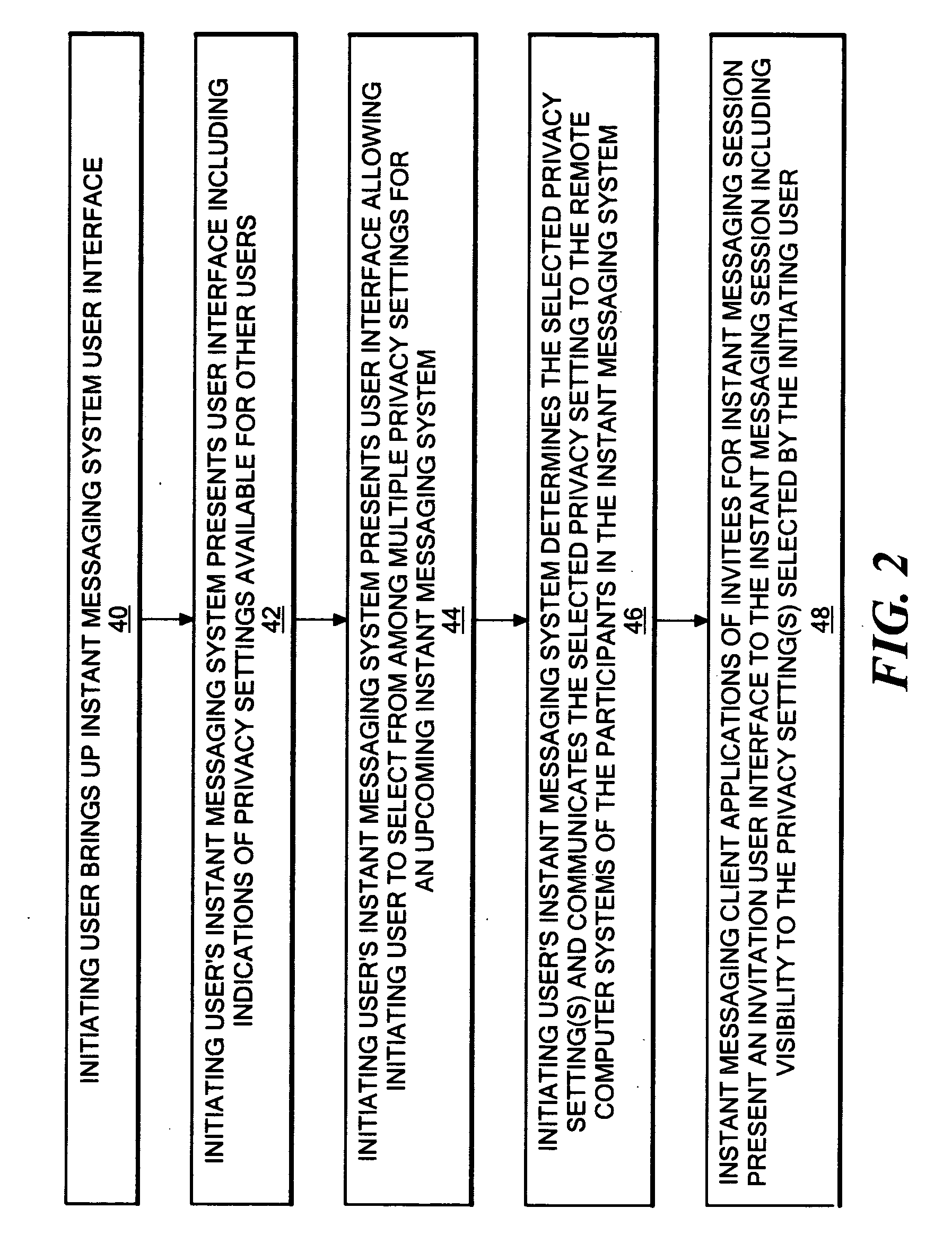
Method and system for allowing a session initiating user to select one or more privacy settings to be applied to an instant messaging session from among multiple possible privacy controls
InactiveUS20070143423A1Computer security arrangementsMultiple digital computer combinationsInternet privacyMessage passing
A system and method allowing a session initiator to select from among multiple privacy levels to be applied to an instant messaging session. When a user initiates an instant messaging session, multiple selectable privacy settings are presented, from which the user can select. The disclosed system may provide a session initiator with a user interface that enables selection from among privacy settings that prevent the session contents from being copied and pasted while the session is in progress, prevent any saving of the session contents by any user, prevent the session contents from being forwarded via electronic mail, prevent display of previously viewed session contents while the session is in progress, and / or prevent screen shots from being made of the session contents while the session is in progress. Flags representing one or more of the multiple privacy settings may be stored in association with an ongoing session, and / or in association with the stored contents of a previous session. In one embodiment, only the session initiator can select from among the multiple privacy settings, and may be provided with indication in the user interface of the privacy settings that are supported by individuals listed in their buddy list.
Owner:IBM CORP
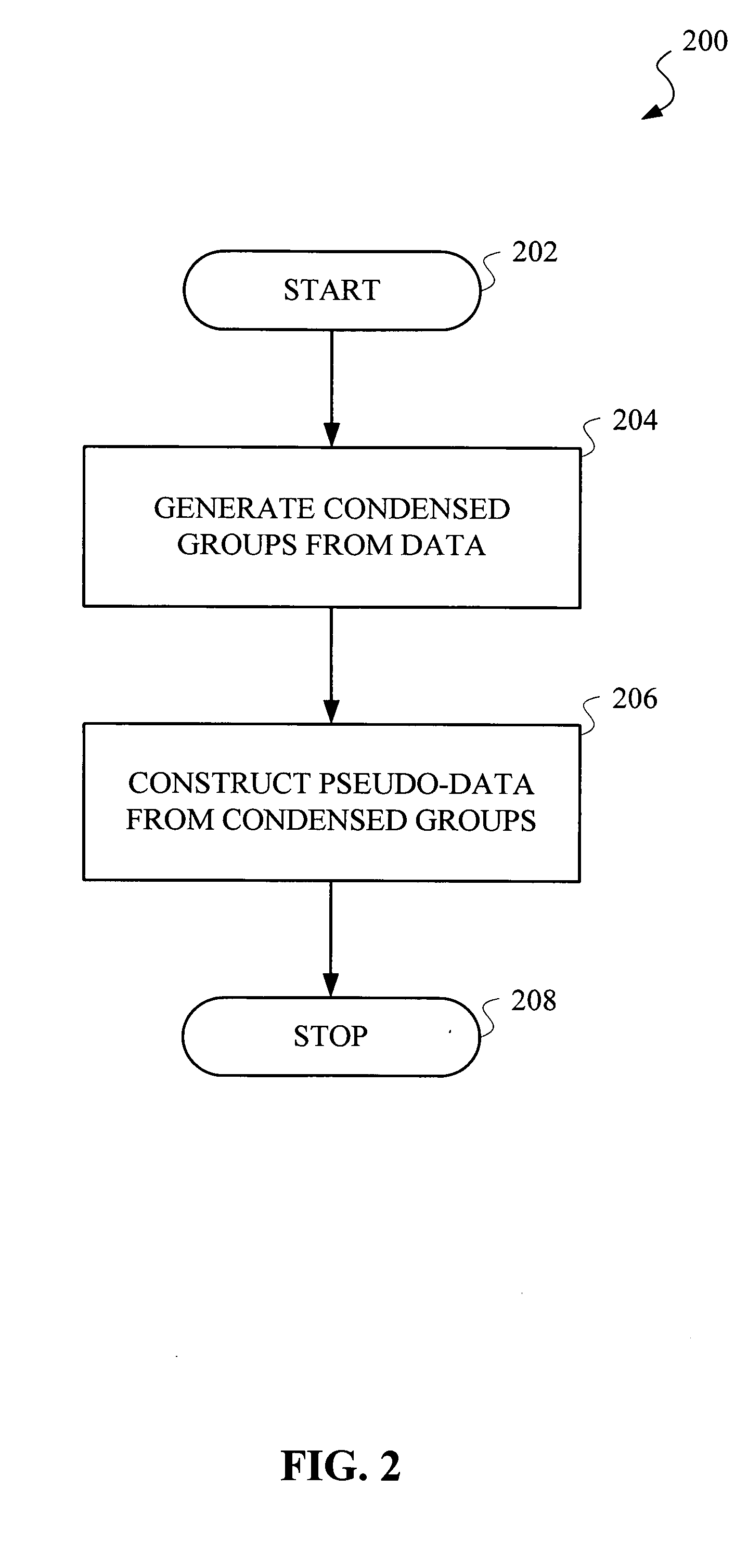
Methods and apparatus for privacy preserving data mining using statistical condensing approach
ActiveUS7302420B2Improve privacyImprove classification accuracyData processing applicationsDigital data processing detailsData setEngineering
Methods and apparatus for generating at least one output data set from at least one input data set for use in association with a data mining process are provided. First, data statistics are constructed from the at least one input data set. Then, an output data set is generated from the data statistics. The output data set differs from the input data set but maintains one or more correlations from within the input data set. The correlations may be the inherent correlations between different dimensions of a multidimensional input data set. A significant amount of information from the input data set may be hidden so that the privacy level of the data mining process may be increased.
Owner:IBM CORP
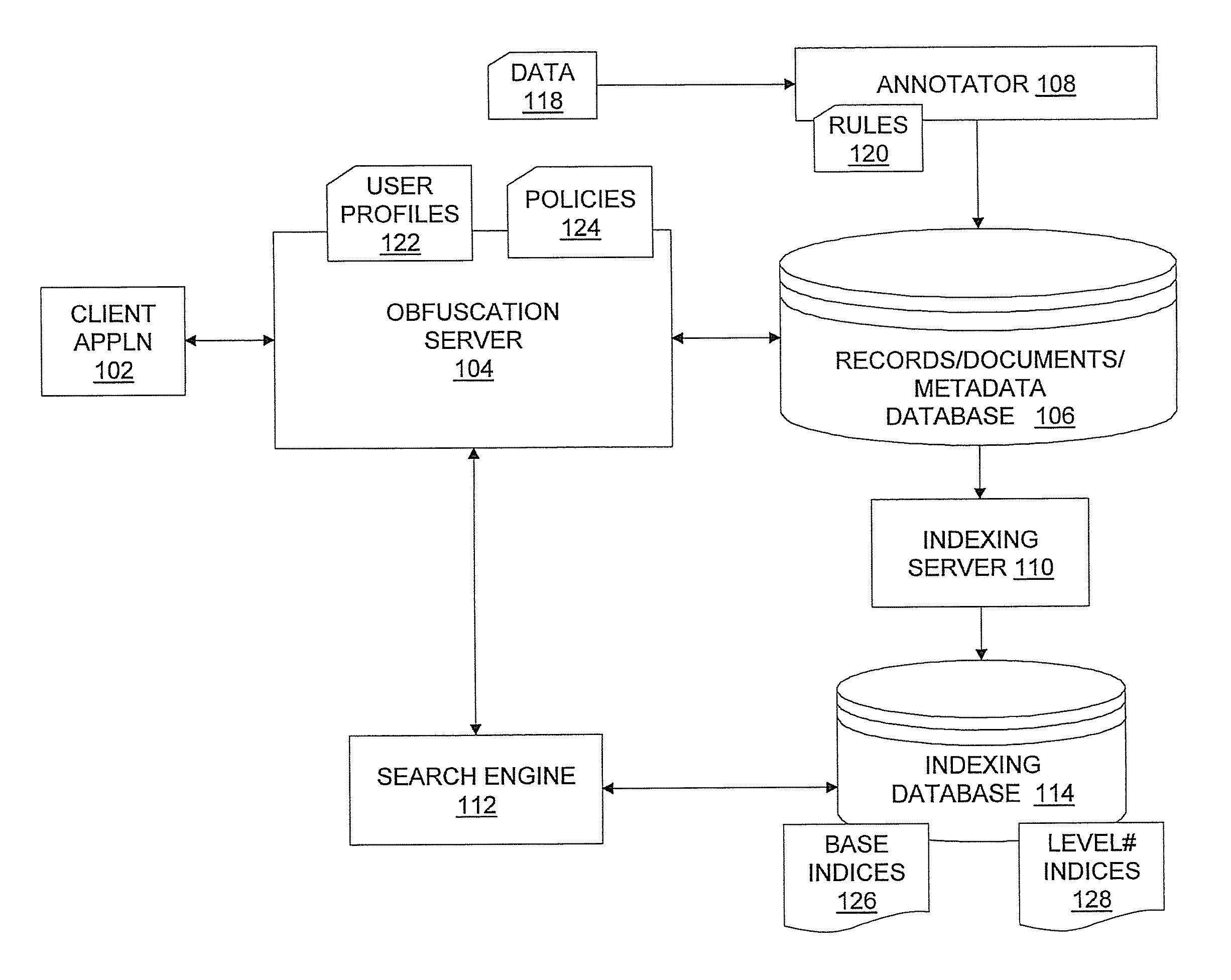
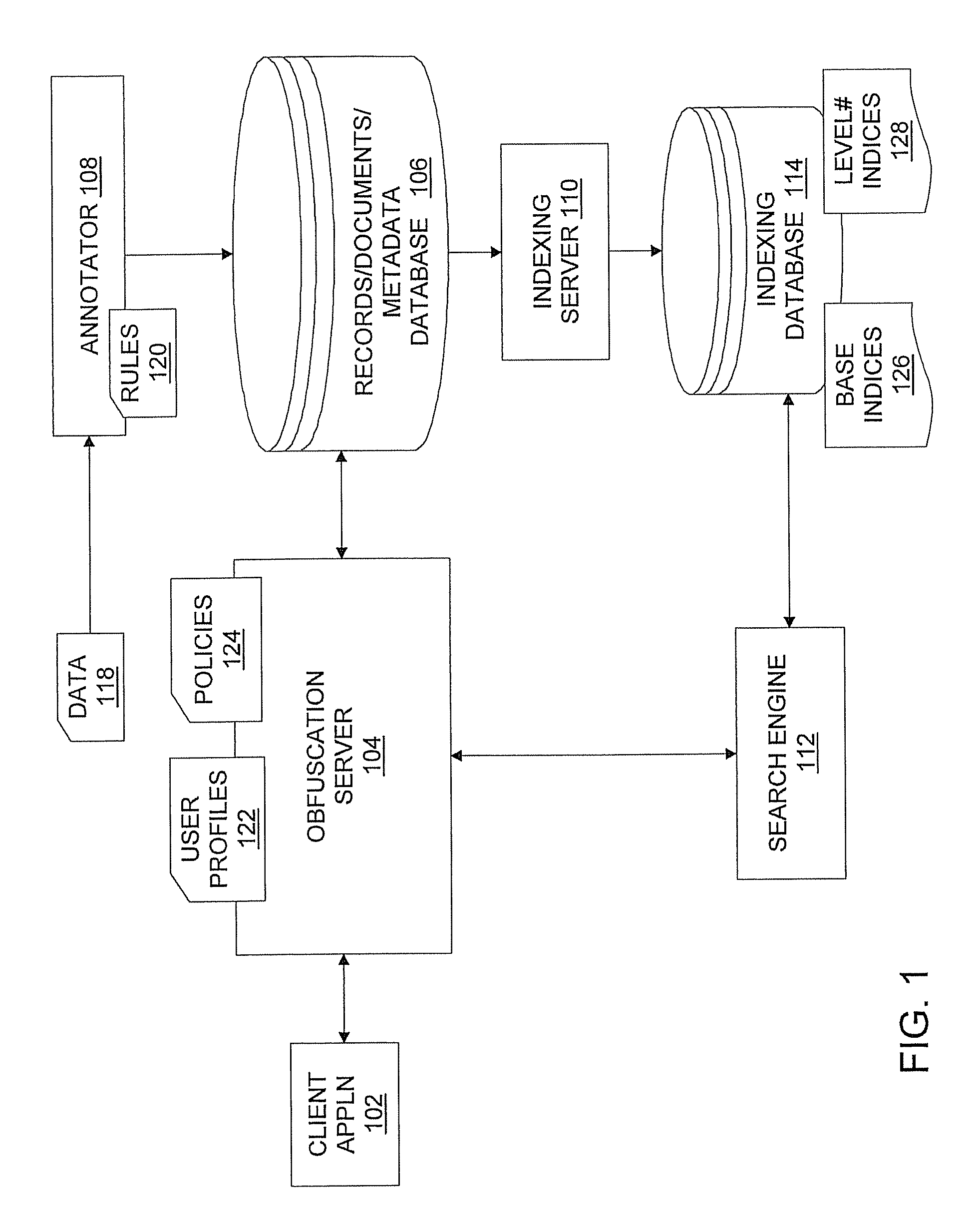
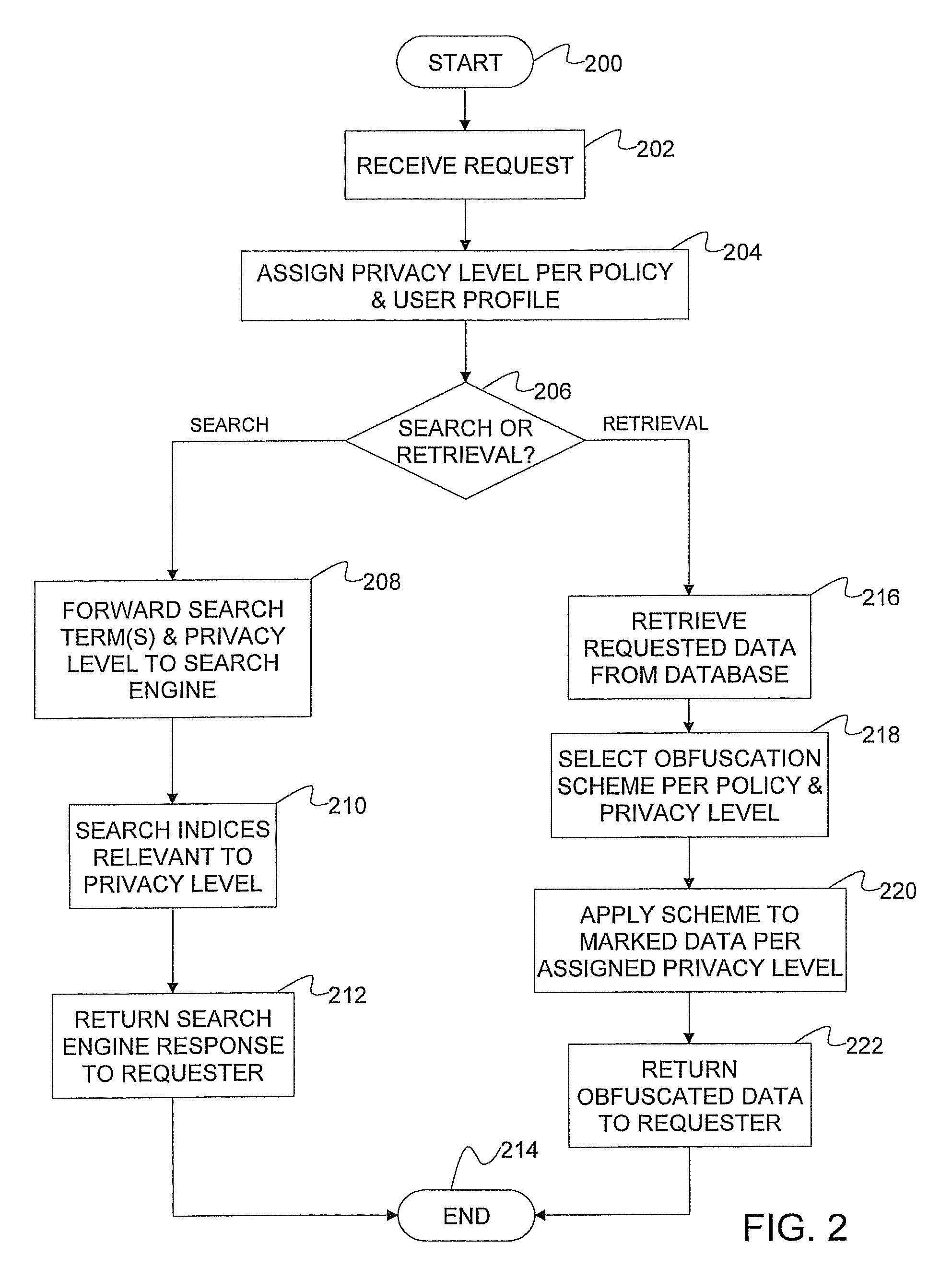
System, method, and computer program product for implementing search-and retrieval-compatible data obfuscation
InactiveUS7512985B1Data processing applicationsDigital data processing detailsObfuscationIndexing Service
A system for implementing search- and retrieval-compatible data obfuscation includes an annotator that annotates data, metadata, and relationships thereof that are privacy sensitive according to privacy policies. The system also includes an indexing server that indexes the annotated data according to the policies that specify rules for controlling access to the data. The system also includes an obfuscation server for serving user requests for data search and retrieval, and specifies data entitlement and access rights for the users by applying the privacy policies to user profiles. In response to receiving a search request from a user, the obfuscation server forwards the search terms in the request, along with a privacy level determined from a corresponding user profile and the policies, to a search engine that searches indices of a database having the privacy level in the request, and returning to the user only the results which match the search terms and the privacy level. In response to receiving a data retrieval request, the obfuscation server retrieves the requested data with annotations from the database, applies the obfuscation scheme to the annotated data according to the privacy policies and the user profile, and returns to the user the obfuscated data in compliance with the privacy policies.
Owner:IBM CORP
System And Method For Hosting A Social Network That Enables Granular Management Of The Privacy Of Posted Information
ActiveUS20110271328A1Improve distributionFacilitate of informationDigital data processing detailsComputer security arrangementsInternet privacySocial web
A system and method for hosting a social network that enables entities to particularly manage the privacy level of content posted on the social network. This may enable an entity to distribute news, congratulations, accolades, invitations, and / or other internal information within the social network to members, employees, students, investors, and / or other parties.
Owner:BIMODAL
E-service to manage contact information with privacy levels
Owner:DOUVIKAS JAMES G +2
Wireless location privacy
InactiveUS20060165100A1Position can be determinedAccurate locationData switching by path configurationWireless commuication servicesTransceiverComputer science
A method for combating the tracking of a mobile transceiver, the mobile transceiver forming a node in a wireless communication network which has at least one other node, the method comprising the steps for enabling, until a first time, the transmission of a radio packet that depends upon a first anonymous address; calculating, dependent on a privacy level for the mobile transceiver, a second time; enabling, from the second time, the transmission of a radio packet that depends upon a second anonymous address; and disabling, between the first time and the second time, the transmission of a radio packet that depends upon either the first anonymous address or the second anonymous address.
Owner:NOKIA CORP
Method and apparatus for nearly optimal private convolution
InactiveUS20150286827A1Ensuring level of privacyPrivacy protectionDigital data processing detailsAnalogue secracy/subscription systemsNoisy dataData mining
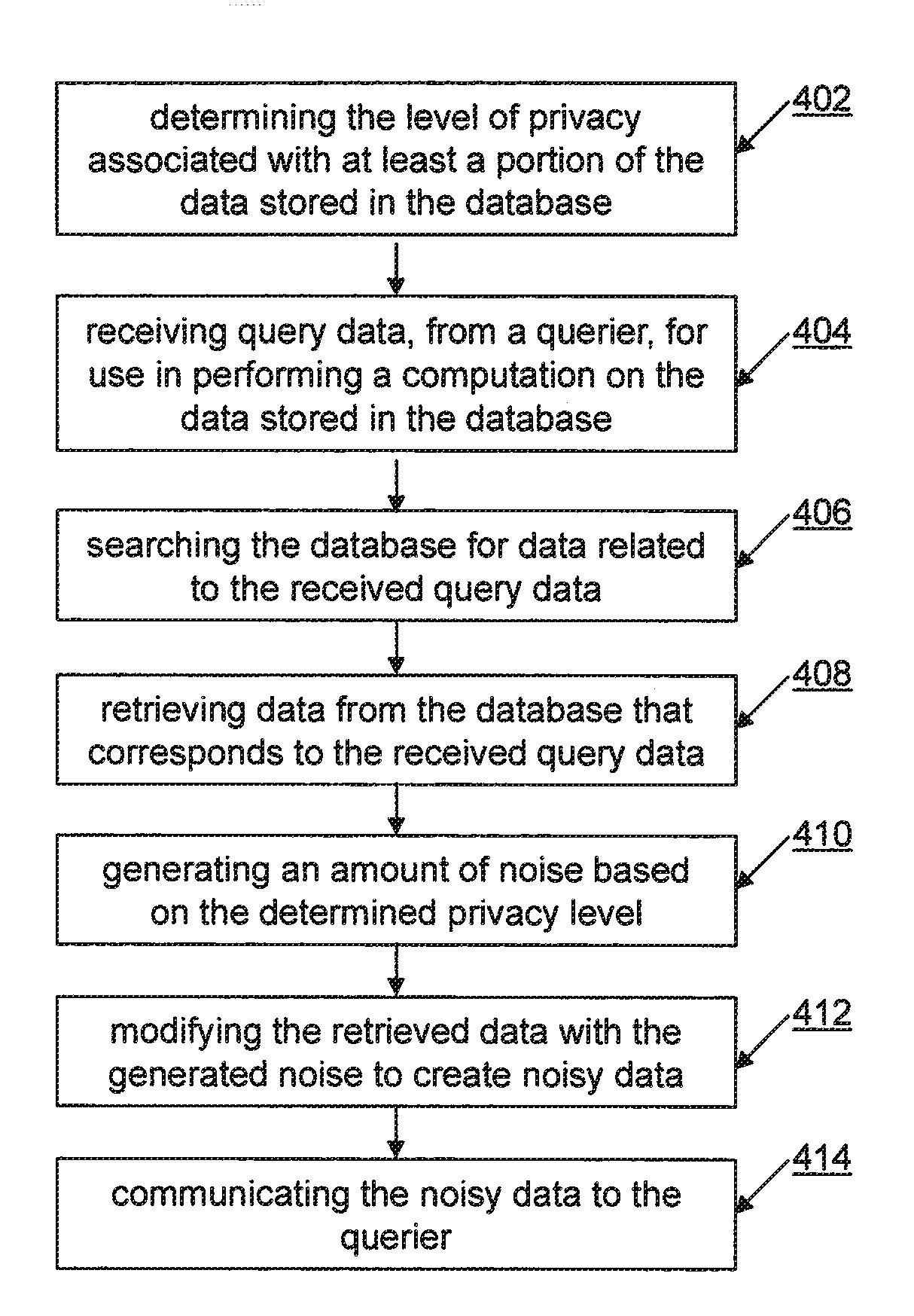
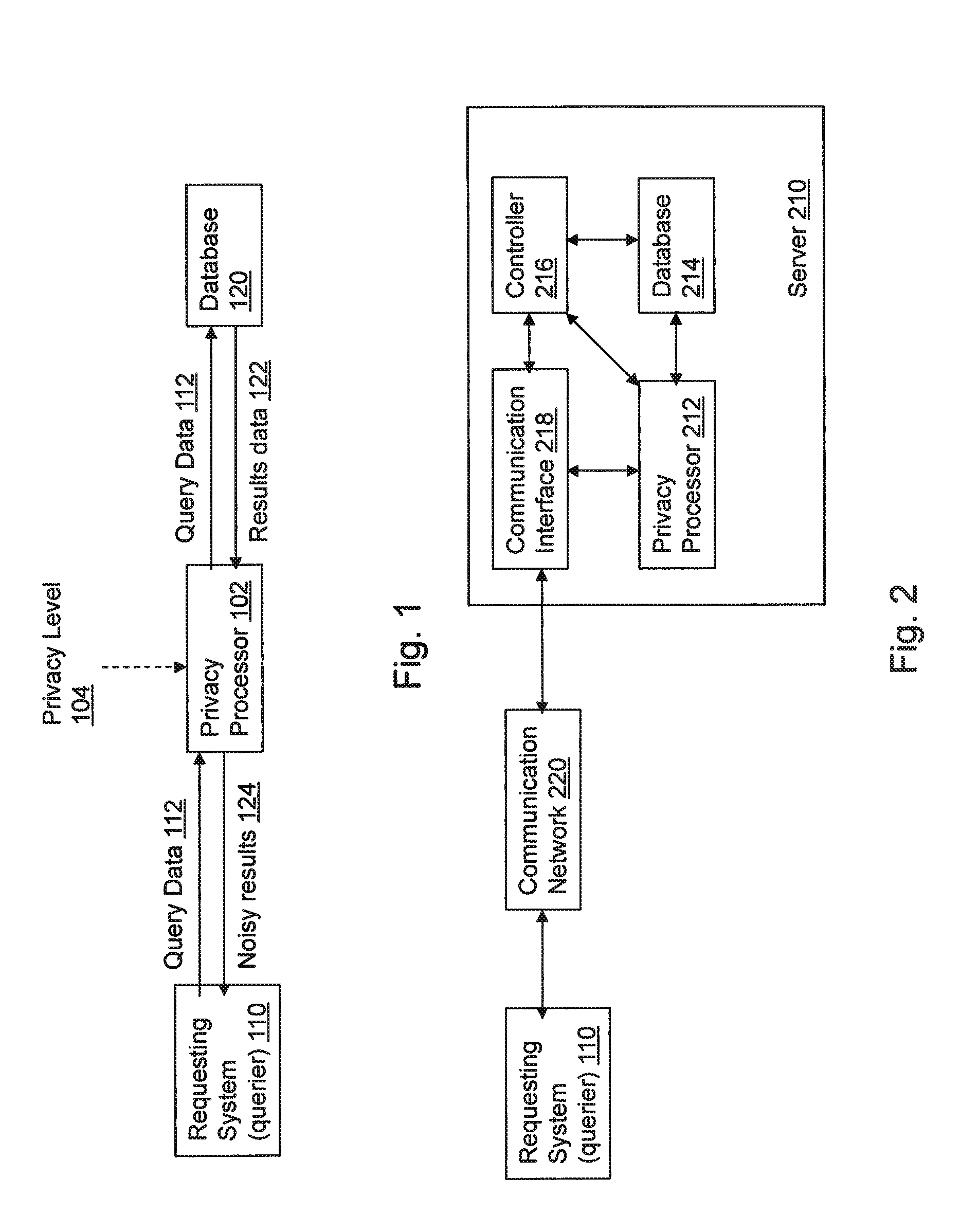
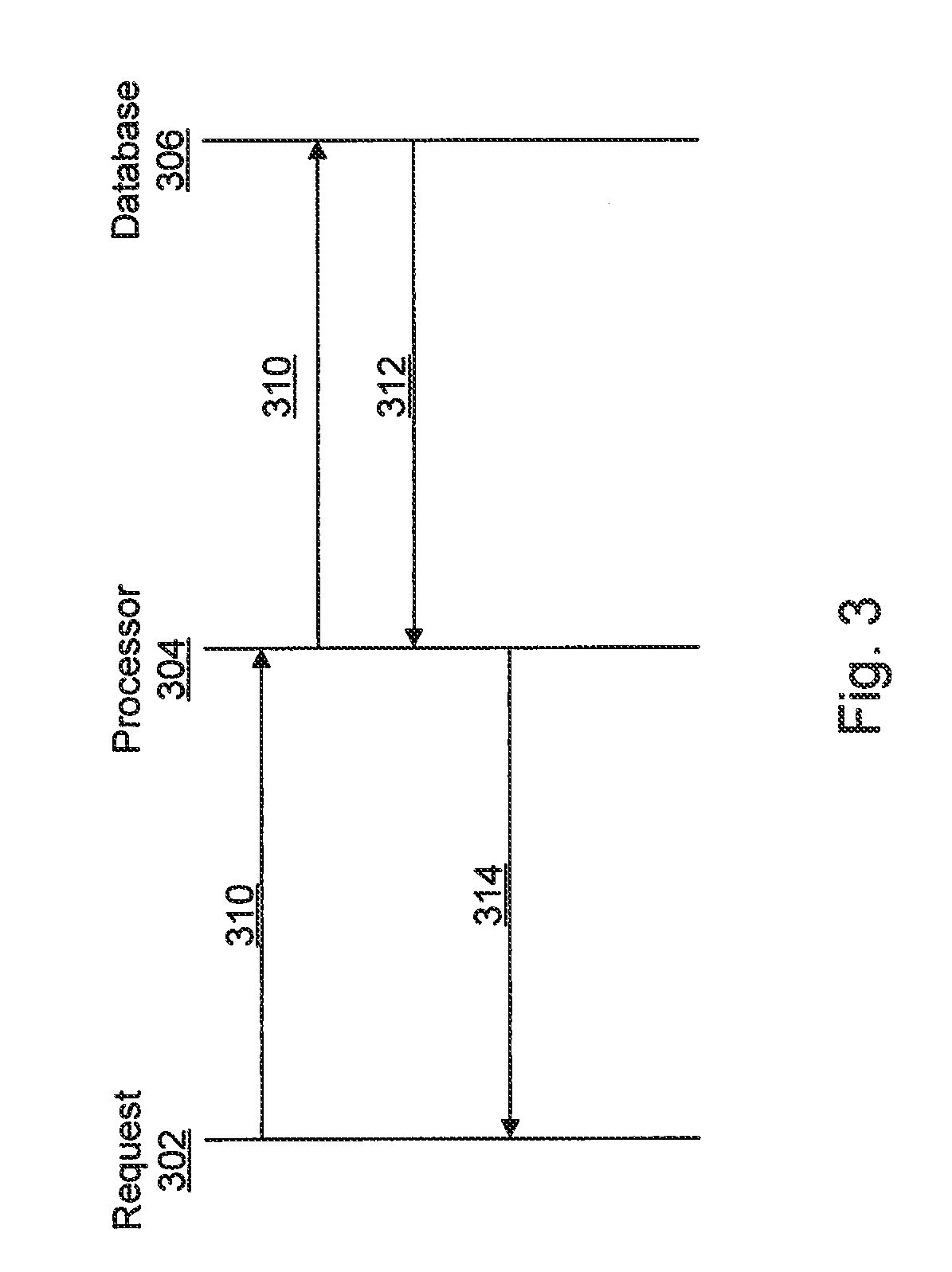
A method and apparatus for ensuring a level of privacy for answering a convolution query on data stored in a database is provided. The method and apparatus includes the activities of determining (402) the level of privacy associated with at least a portion of the data stored in the database and receiving (404) query data, from a querier, for use in performing a convolution over the data stored in the database. The database is searched (406) for data related to the received query data and the data that corresponds to the received query data is retrieved (408) from the database. An amount of noise based on the determined privacy level is generated (410) and added (412) to the retrieved data to create noisy data which is then communicated (414) to the querier.
Owner:FAWAZ NADIA +2
Apparatus and method for privacy protection of data collection in pervasive environments
ActiveUS7940302B2Improve responseImprove securityElectric signal transmission systemsDigital data processing detailsPrivacy protectionData harvesting
A security system which is nonintrusive of personal privacy of a person in a space comprises at least a first localization sensor subsystem, if any, in the possession of the person; a video surveillance subsystem arranged and configured to collect visual data related to the person in the space; and a computer subsystem coupled to the localization sensor subsystem and video surveillance subsystem to associate a predetermined privacy level with the localization sensor subsystem, and to provide an access control privilege with the localization sensor subsystem, the computer subsystem determining how to present, store and / or retrieve the visual data while meeting predetermined the privacy level associated with the person.
Owner:RGT UNIV OF CALIFORNIA
Walled gardens
ActiveUS7832003B2Keep full controlControlled communication environmentDigital data processing detailsUnauthorized memory use protectionVisibilityInternet privacy
The subject invention provides a unique system and method that facilitates a controlled communication environment which allows a user to participate in a plurality of privacy contexts with other people in a simultaneous manner in an online community. A user can assign or define varying levels of privacy to his / her information or content to control the visibility of such information by others. In particular, a first user can maintain one or more “gardens” or stores of content which may be accessible to at least a subset of the online community. Access to the contents of any one garden can be based on the privacy level of the garden and the privacy level (e.g., access parameters) granted to the person. The privacy levels and arrangement of content can be hierarchal and / or non-overlapping. Thus, a user can seamlessly communicate with multiple users at the same time regardless of their context or privacy level while maintaining the privacy boundaries of each garden.
Owner:MICROSOFT TECH LICENSING LLC
Information content distribution based on privacy and/or personal information
InactiveCN1596521AData representation error detection/correctionError preventionContent distributionPersonalization
Owner:INT BUSINESS MASCH CORP
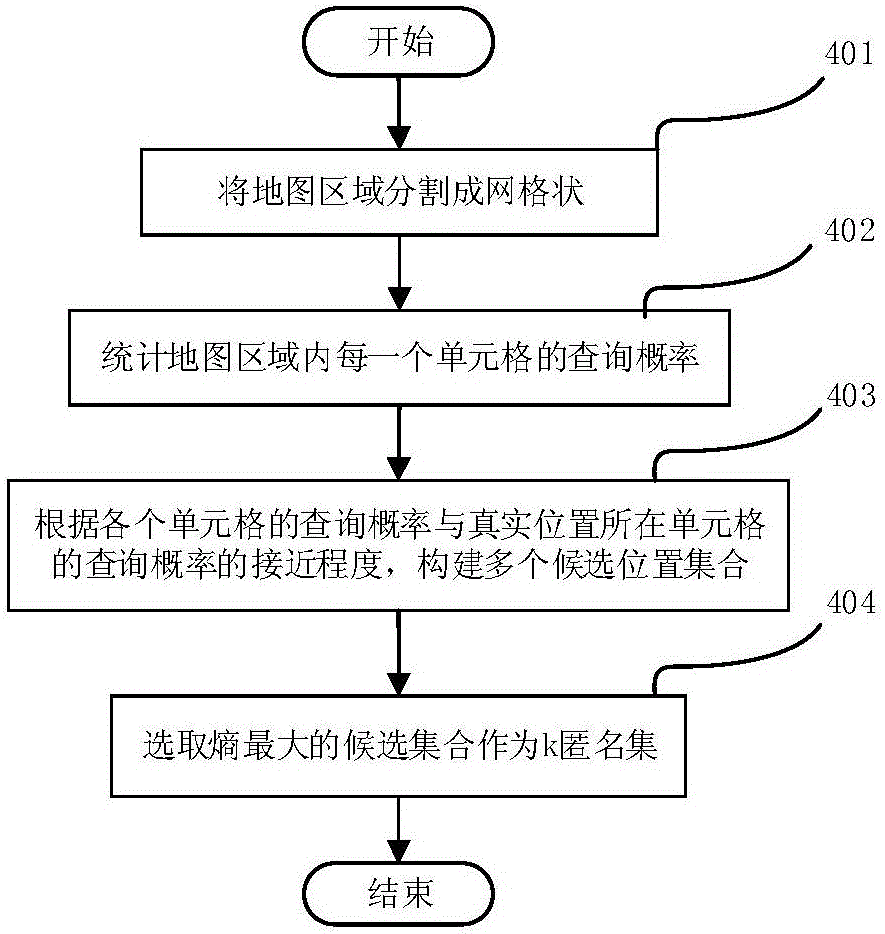
Location anonymization-based privacy protection method and apparatus
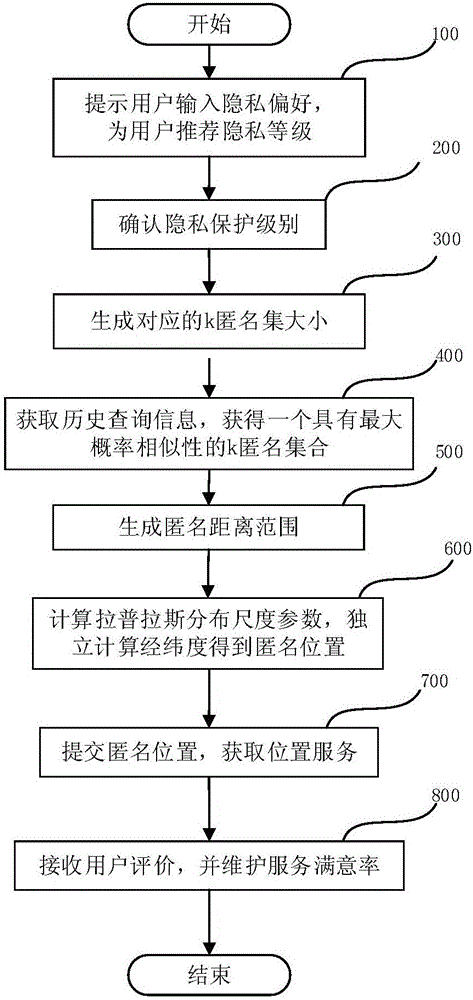
ActiveCN106209813AImprove service qualityImplement location privacy protectionTransmissionPrivacy protectionAnonymity
The invention provides a location anonymization-based privacy protection method. The method comprises the steps of 1) determining an anonymity degree k according to a currently queried privacy level, wherein the higher the privacy level is and the higher the anonymity degree k is; 2) creating a plurality of candidate anonymity sets with k elements by taking the anonymity degree k as the size of a currently queried anonymity set; 3) searching for one candidate anonymity set with a maximum query probability set entropy from the created candidate anonymity sets to serve as the anonymity set; 4) generating an upper bound and a lower bound of an anonymity distance according to the privacy level, wherein the higher the privacy level is, the larger the upper bound of the anonymity distance is, and the larger the lower bound of the anonymity distance is; and 5) generating an anonymous location used for replacing a currently queried real location according to the generated upper bound and lower bound of the anonymity distance in the range of the anonymity set. The invention furthermore provides a corresponding privacy protection apparatus. According to the method and the apparatus, the LBS (Location Based Service) quality is improved while the location privacy protection is realized, and different demands of different users on privacy protection can be guaranteed.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
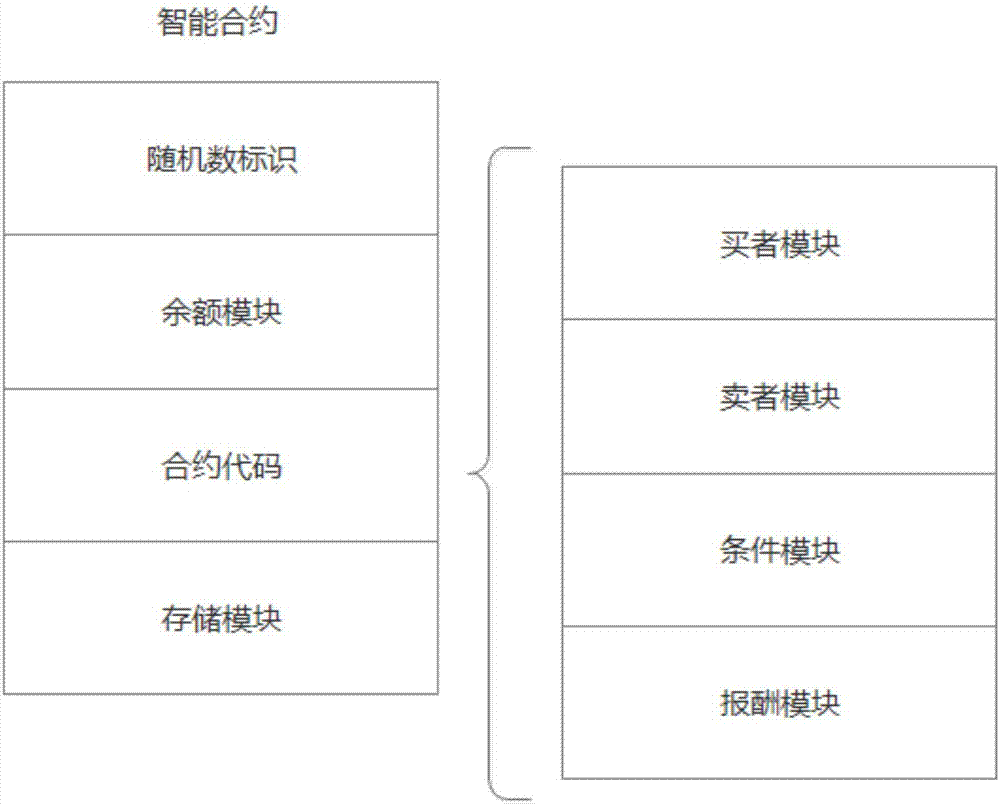
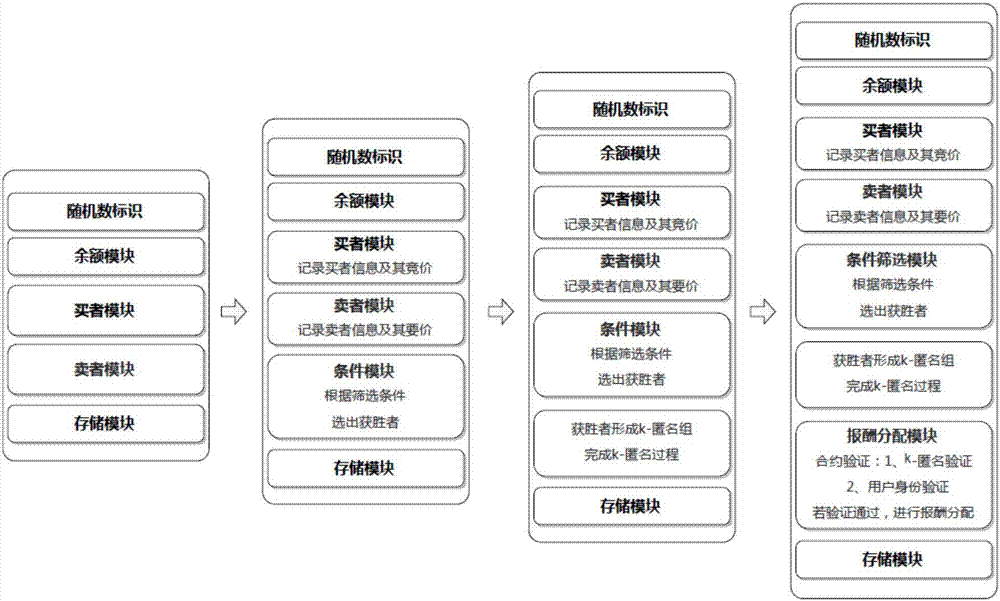
Blockchain-based personalized k-anonymity privacy protection motivation method
ActiveCN107483211AAvoid safety hazardsMeet privacy level requirementsUser identity/authority verificationCommercePersonalizationThird party
The invention relates to a blockchain-based personalized k-anonymity privacy protection motivation method. When the privacy levels of clients are same, buyer clients and seller clients conduct an auction game according to the screening conditions in a smart contract, the winning buyer clients and seller clients are selected out to form an anonymity group, and the clients in the anonymous groups upload the positions of the clients and query requests to a server side together to achieve the k-anonymity process. When the privacy levels of the clients are different, the buyer clients are divided into multiple groups according to the sequence that the privacy levels needed by the buyer clients are increased, an anonymity group is formed by the buyer clients screened out from the buyer client groups of which the numbers n of the buyer clients are larger than k+1, and a k-anonymity group is formed by the seller clients and buyer clients in the other groups. According to the method, the privacy level requirements of different users can be met to complete different privacy levels of k-anonymity privacy protection, and by applying the decentralized smart contract, the security hazards of a trusted third party are avoided.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
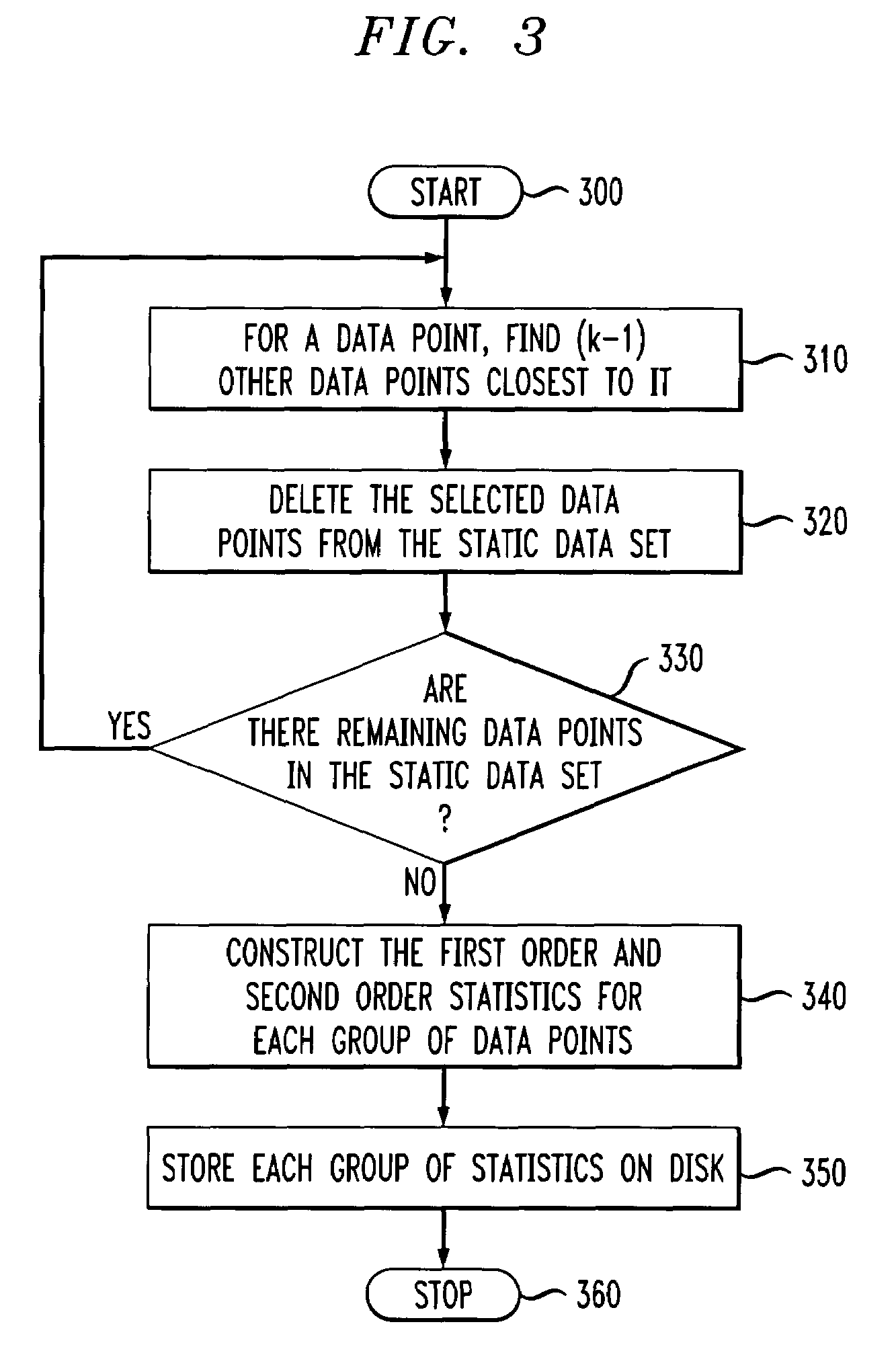
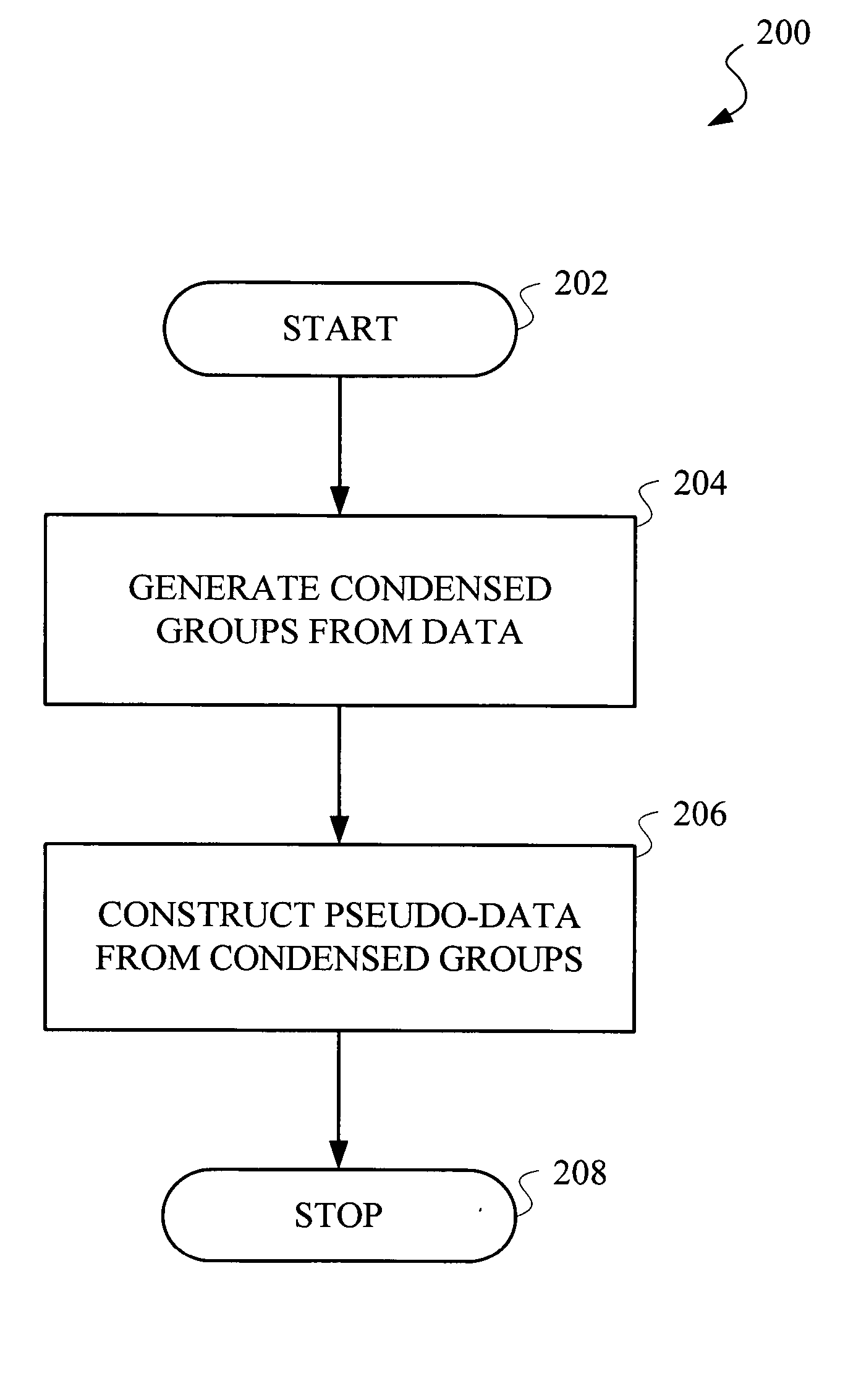
Method and apparatus for variable privacy preservation in data mining
InactiveUS20070239982A1Simple technologyDigital data processing detailsUser identity/authority verificationData setInternet privacy
Improved privacy preservation techniques are disclosed for use in accordance with data mining. By way of example, a technique for preserving privacy of data records for use in a data mining application comprises the following steps / operations. Different privacy levels are assigned to the data records. Condensed groups are constructed from the data records based on the privacy levels, wherein summary statistics are maintained for each condensed group. Pseudo-data is generated from the summary statistics, wherein the pseudo-data is available for use in the data mining application. Principles of the invention are capable of handling both static and dynamic data sets
Owner:IBM CORP
Virtual credentials and licenses
ActiveUS20160380774A1Prevent replay attacksData processing applicationsMultiple keys/algorithms usageGeographic siteVirtualization
Providing virtualized credentials of a holder includes authorizing a subset of credential data to be sent to a device of a relying party that is different from the holder, where the subset of credential data depends on a role of the relying party, selection by the holder, and / or contextual data of the relying party and includes displaying the subset of credential data on a screen of the device of the relying party. The contextual data may be a privacy level setting, distance between the relying party and the holder, and / or geolocation of the relying party. The role of the relying party may be provided by the relying party. Role information provided by the relying party may be provided in a verifiable format. The role information may be digitally signed or securely derived and determined by a mutual authentication algorithm between the relying party and the holder.
Owner:ASSA ABLOY AB
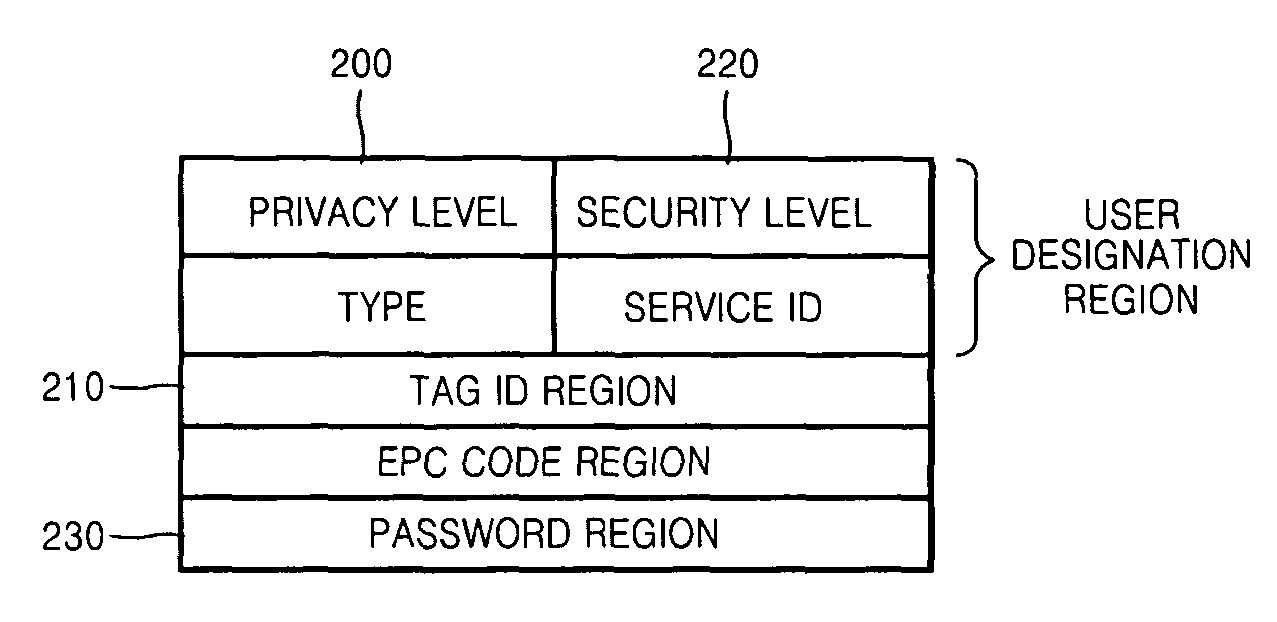
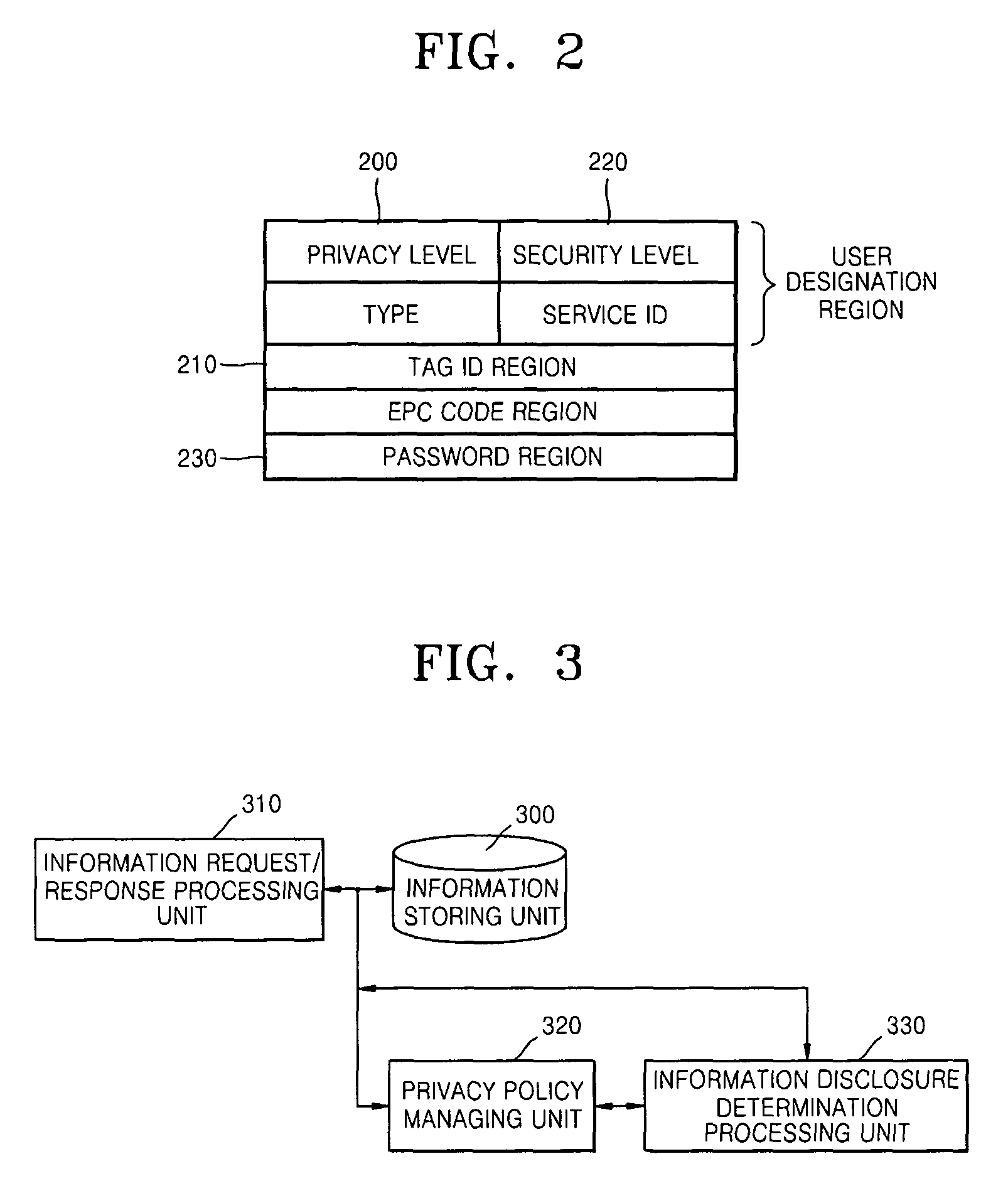
Electronic tag including privacy level information and privacy protection apparatus and method using RFID tag
InactiveUS7847694B2Individual entry/exit registersSubscribers indirect connectionManagement unitPrivacy protection
An electronic tag including privacy level information, and a privacy protection apparatus and method using the electronic tag are provided. The privacy protection apparatus using an electronic tag includes: an information storing unit storing recognition information of an electronic tag and privacy information on the electronic tags; an information request / response processing unit receiving the recognition information of electronic tags and information on a user that requests information on the electronic tags through a predetermined communication network; a privacy policy managing unit determining whether the privacy information on the electronic tags corresponding to the recognition information of electronic tags is stored in the information storing unit; and an information disclosure determination processing unit, if it is determined that the privacy information on the electronic tags is stored in the information storing unit, comparing the information on the user and a predetermined standard for publishing the privacy information, determining how much of the privacy information on the electronic tags is provided to the user, and providing the determined privacy information to the user.
Owner:ELECTRONICS & TELECOMM RES INST
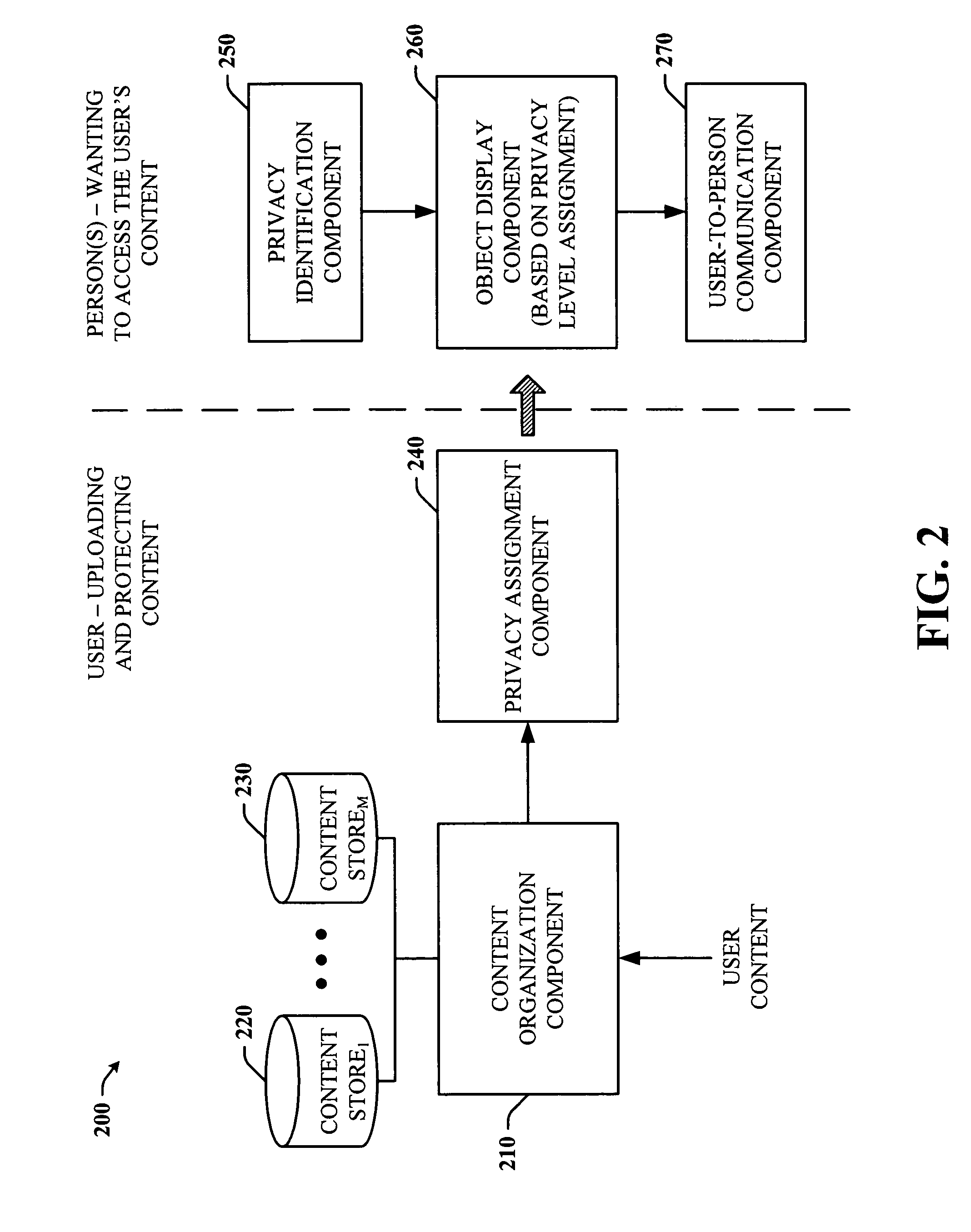
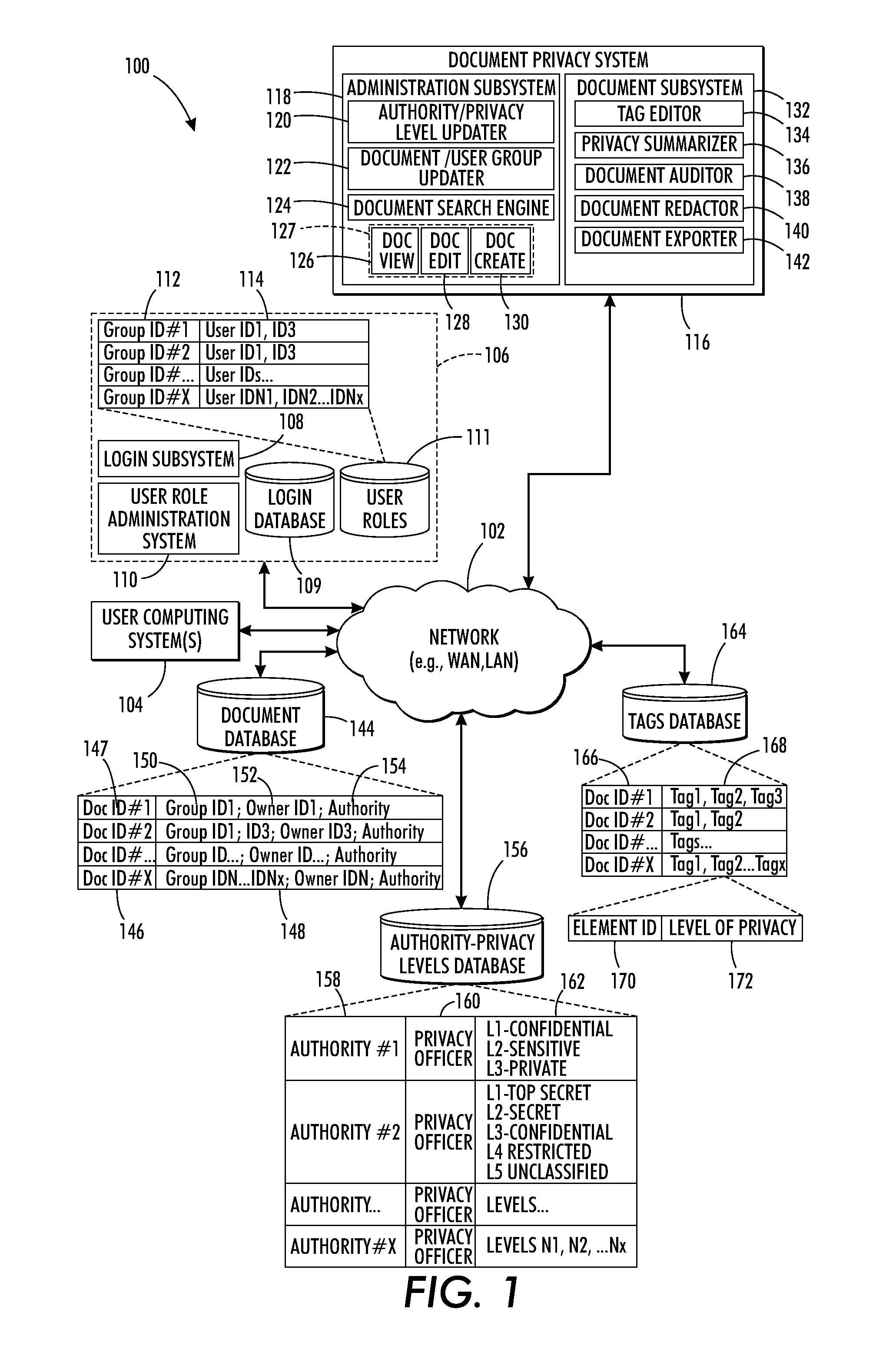
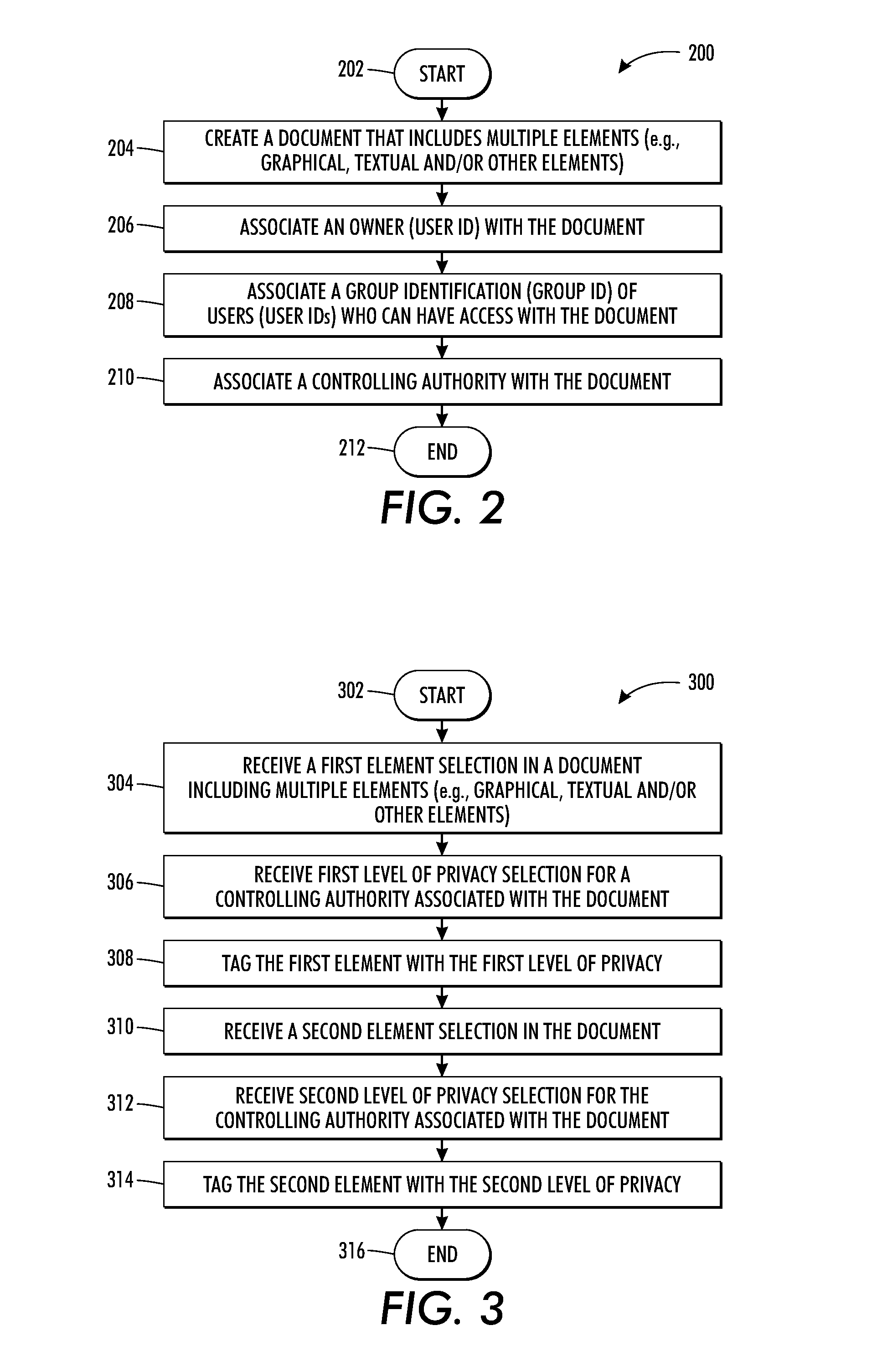
System and method of managing multiple levels of privacy in documents
ActiveUS20120331571A1Promote aggregationDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyDocumentation
There is provided a method and system to manage multiple levels of privacy in a document having a plurality of elements. In accordance with the method, a selection of a first element in the document is received. The first element is tagged with a selected first privacy level of a hierarchical privacy level list. The list includes a plurality of hierarchical levels of privacy associated with a controlling authority. A selection of a second element in the document is received. The selected second element is tagged with a selected second privacy level of the hierarchical privacy level list.
Owner:XEROX CORP
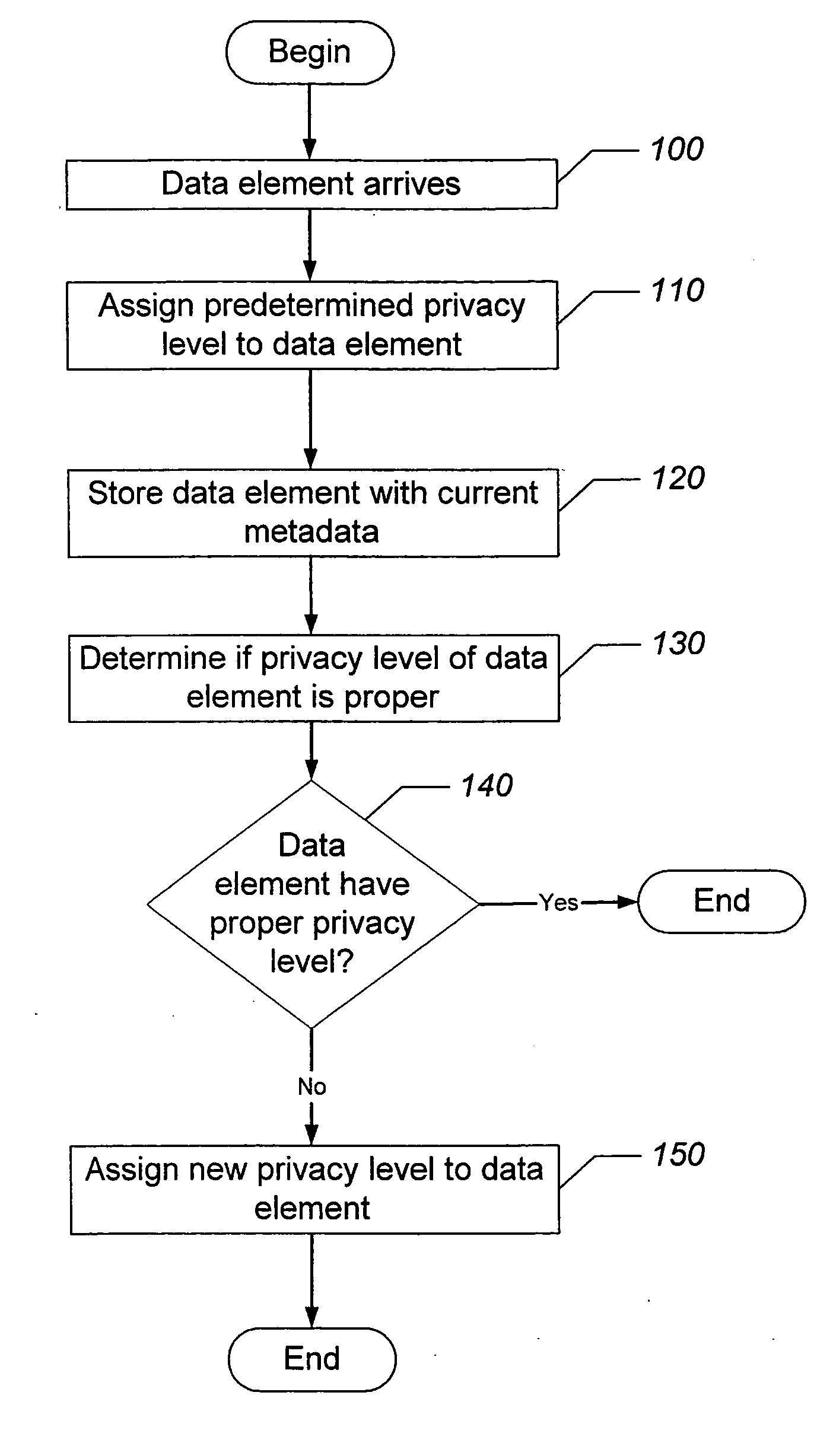
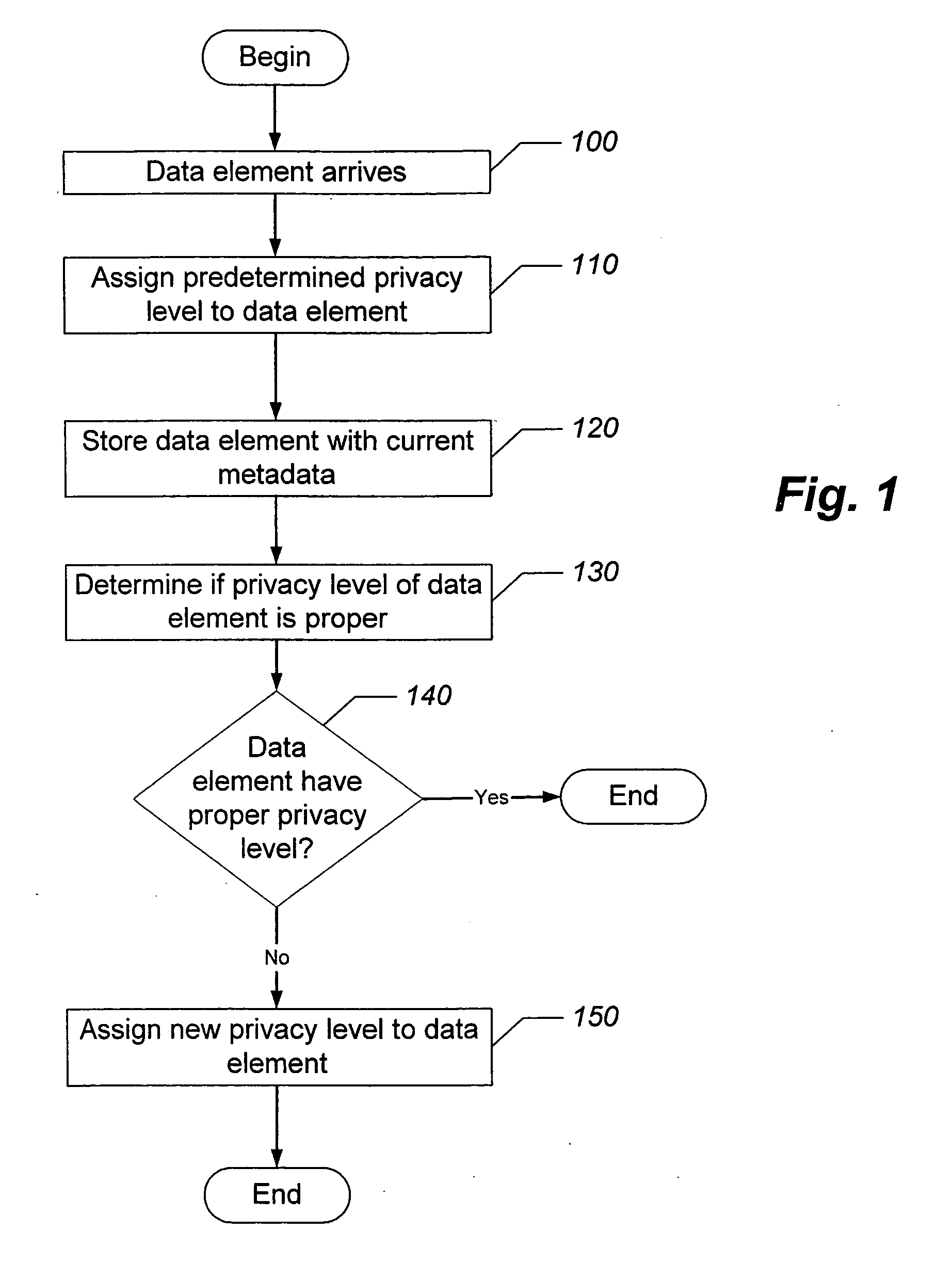
Methods, data processing systems, and computer program products for assigning privacy levels to data elements
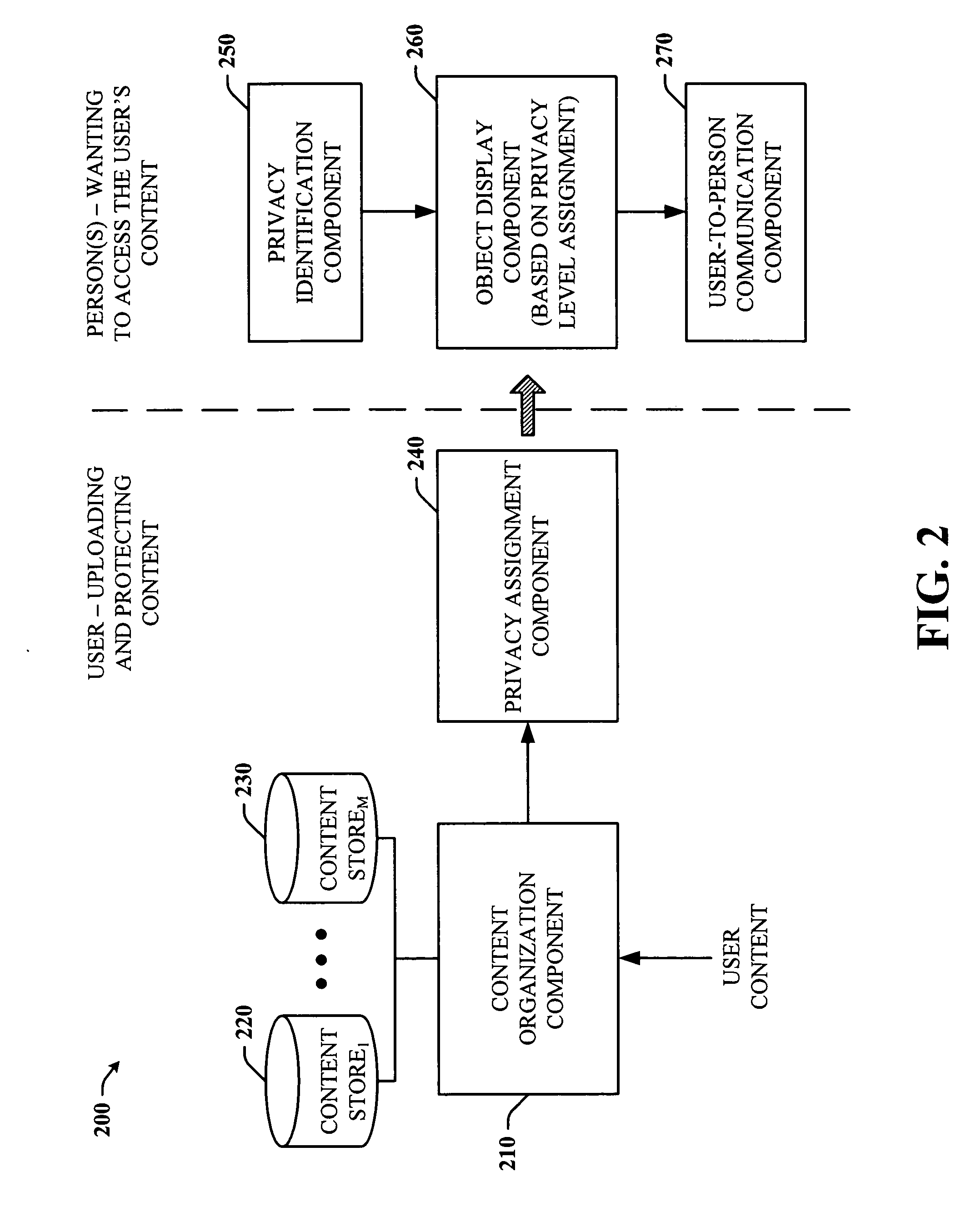
ActiveUS20080127298A1Improve assessmentFacilitate assigning privacy levelDigital data processing detailsAnalogue secracy/subscription systemsData processing systemInternet privacy
Methods, data processing systems and computer program products for assessing and assigning privacy levels to data elements are provided. A method of assigning privacy levels to data elements (e.g., text files, web page files, image files, audio files, video files, and portions thereof) includes assigning a predetermined privacy level to a data element; storing the data element with the assigned privacy level; determining if the assigned privacy level for data element is proper; and assigning a different privacy level to the data element in response to determining that a currently assigned privacy level for the data element is not proper. A predetermined privacy level may be assigned to a data element under various conditions, such as when the data element arrives at a device, when the data element is created by a device, and / or when the data element is modified by a device.
Owner:BELLSOUTH INTPROP COR
Managing Personal Information on a Network
ActiveUS20140007191A1Regulate privacy levelsEasy to controlDigital data processing detailsComputer security arrangementsInternet privacyStructure of Management Information
Devices, systems, and methods for managing personal information by providing a centralized source or database for a user's information, and enabling the user to regulate privacy levels for each information item or category of information. Templates are provided as a table of hierarchies, or an onion layers model. Private information may be stored in an inner layer while public information may be stored in an outer layer, with the ability to define and customize multiple layers and categories within the template. A requesting entity requests information via a disseminating server that acts as a gateway for authenticating, authorizing, and providing access to the requesting entity. The user may therefore control and regulate their online presence simply by monitoring who requests their information and adjusting privacy levels accordingly.
Owner:AT&T INTPROP I L P +1
System for providing privacy of user information in an online social network with inline editing of privacy levels and customized privacy groups
InactiveUS20130014279A1Quick fixMore granular control over privacyDigital data processing detailsAnalogue secracy/subscription systemsInternet privacySocial web
A method of displaying, editing, and enforcing privacy settings for individual pieces of information published on a website. Privacy selections are displayed next to the information they protect. A user interface is presented in response to user-interaction with the displayed privacy selections that allows further privacy selections. The privacy selections indicate which other users may view the associated information. These options may be in the form of tiers of users with granted access or privacy groups. The publishing user may customize the privacy options by creating new tiers or groups for inclusion in the selection interface. Privacy icons may be associated with the privacy options, and may be displayed to the publishing user next to protected information, allowing easy identification of currently selected privacy settings. The publishing user may also upload additional privacy icons. Other users who access the published information are shown only those pieces of information that they have the right to view, based on the selected privacy settings.
Owner:LELAND ETHAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com