Blockchain-based personalized k-anonymity privacy protection motivation method
A privacy protection and blockchain technology, applied in the field of LBS privacy protection, can solve the problem of easy leakage of user location privacy, and achieve the effect of avoiding security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] Example 1: Same privacy level
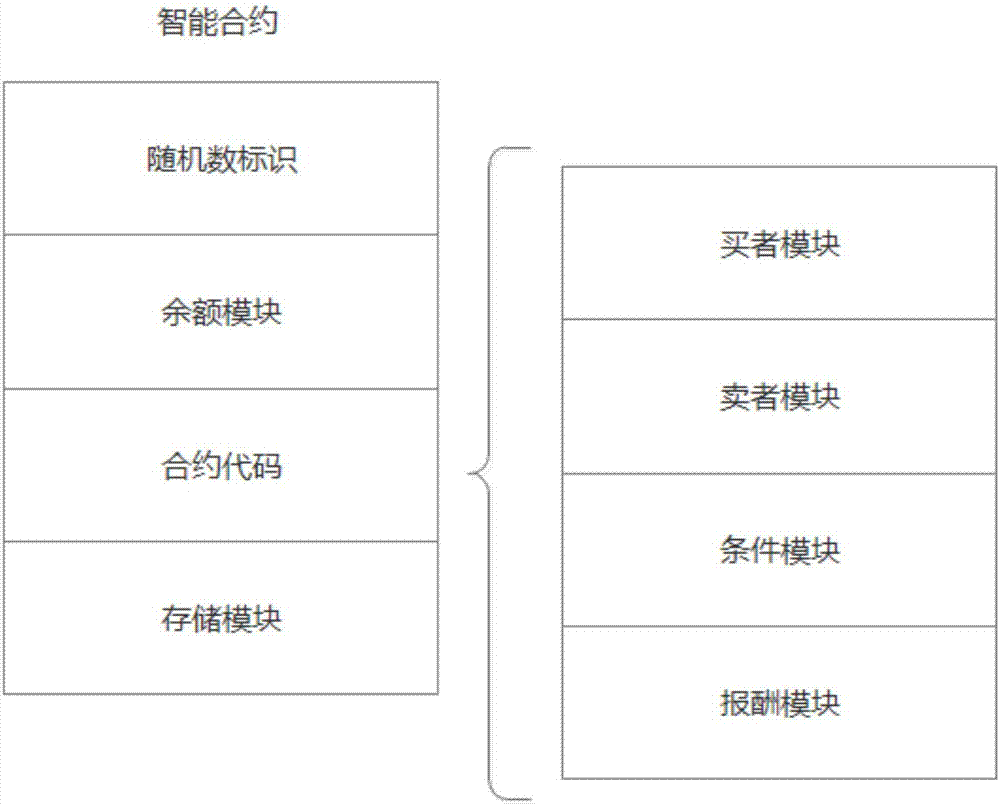
[0045] 1. Construct smart contracts, figure 1 It is a smart contract structure diagram, and the smart contract includes:
[0046] 1) Random number identification: used to uniquely identify smart contracts;
[0047] 2) Balance module: used to record user balance;
[0048] 3) Contract code, including buyer module, buyer module, condition module and remuneration module:
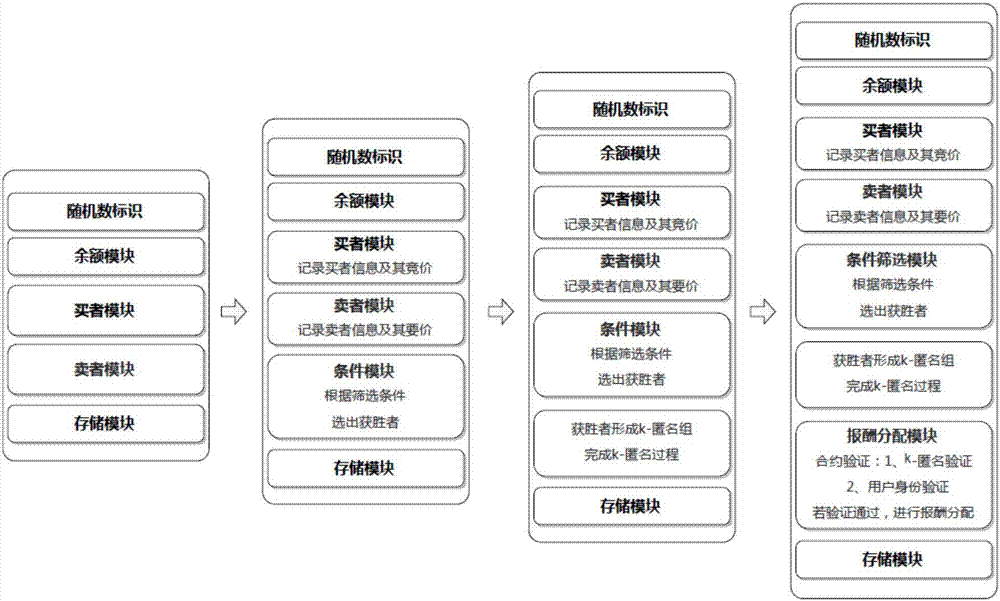
[0049] Buyer module: record buyer information The buyer's k-anonymous demand and its bid b i ={b 1 ,b 2 ,...,b n};
[0050] Seller module: record seller information and its participation in k-anonymous asking price a j ={a 1 ,a 2 ,...,a m};
[0051] Condition module: used for auction game, according to the filter conditions:
[0052]
[0053] The winning buyer W is selected b ={W 1 b ,W 2 b ,...,W n-1 b},Sell by Where k-n+1 is the number of sellers participating in the anonymous set, n is the number of buyers, a k-n+2 Indicates the asking price...
Embodiment 2
[0064] Example 2: Different Privacy Levels
[0065] 1) Users in a certain area form a group, and buyers and sellers are divided in the group, and smart contracts are constructed; the contract structure is roughly the same as the contract structure of the same privacy level, including buyer modules, seller modules, condition modules and rewards module. image 3 Smart contract structure diagram for different privacy levels k-anonymity incentive mechanism.
[0066] 2) The buyer puts forward k-anonymity requirements. According to the privacy protection requirements of different levels of users, the contract divides the buyers into q groups in the order of increasing privacy protection requirements. for any buyer grade k i =λ g . Then, still according to the buyer's bid b i Sort the buyers in descending order, and add the sorted sequence of buyers and their corresponding bids to the smart contract buyer module; sellers see k-anonymous tasks, and each seller gives his own as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com