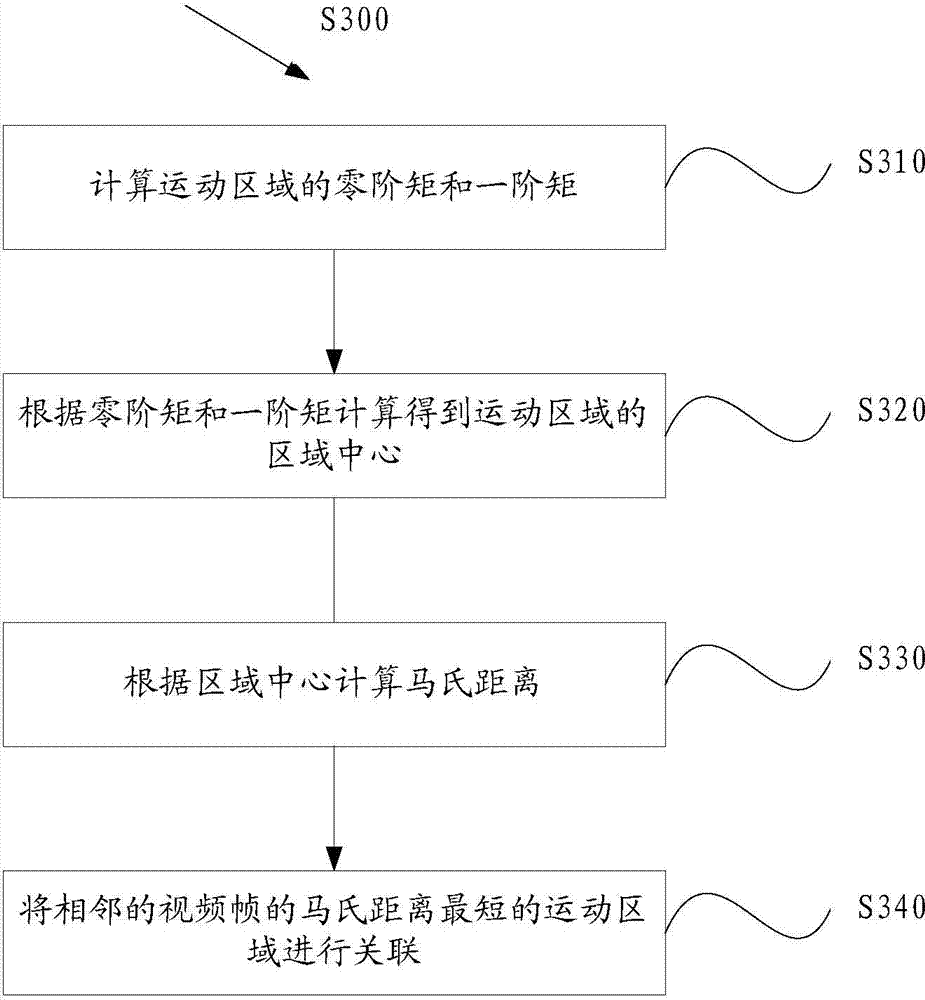
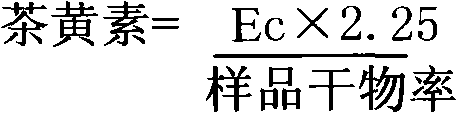Patents
Literature
6884 results about "Safety risk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safety is defined as freedom from risk and risk is the possibility of suffering harm or loss. Both controllable and uncontrollable factors affect risk. Awareness of these factors and a willingness to manage controllable risk by modifying driver behavior is essential to any safety and risk management goals.
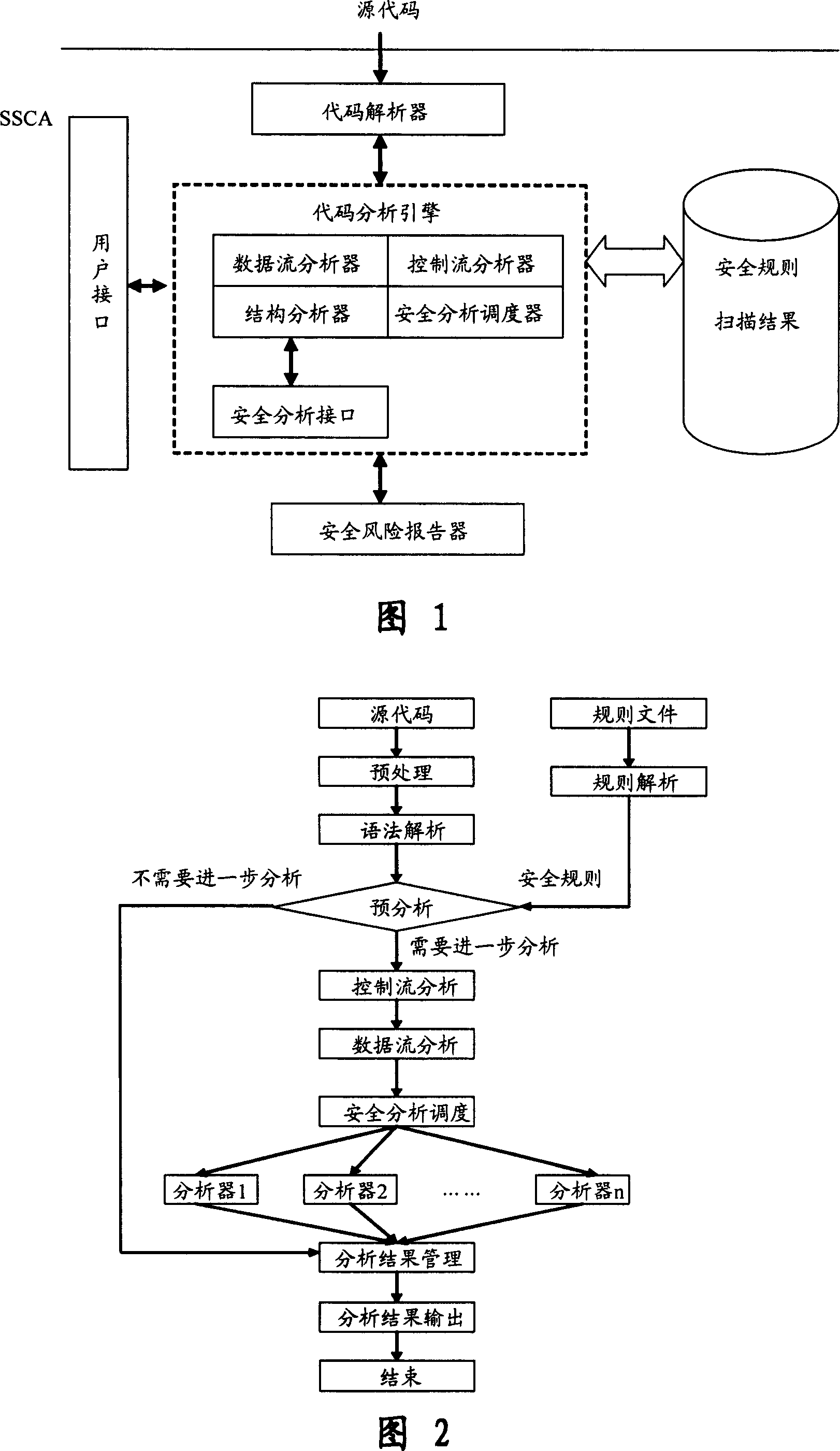
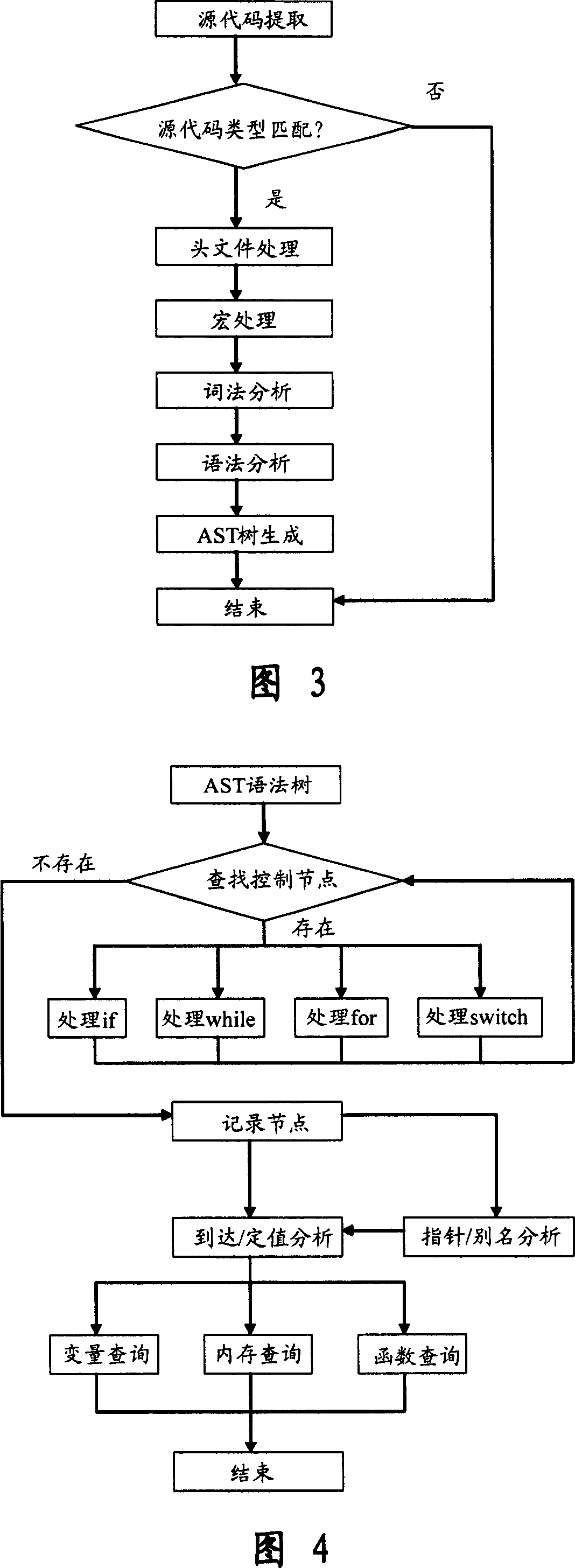
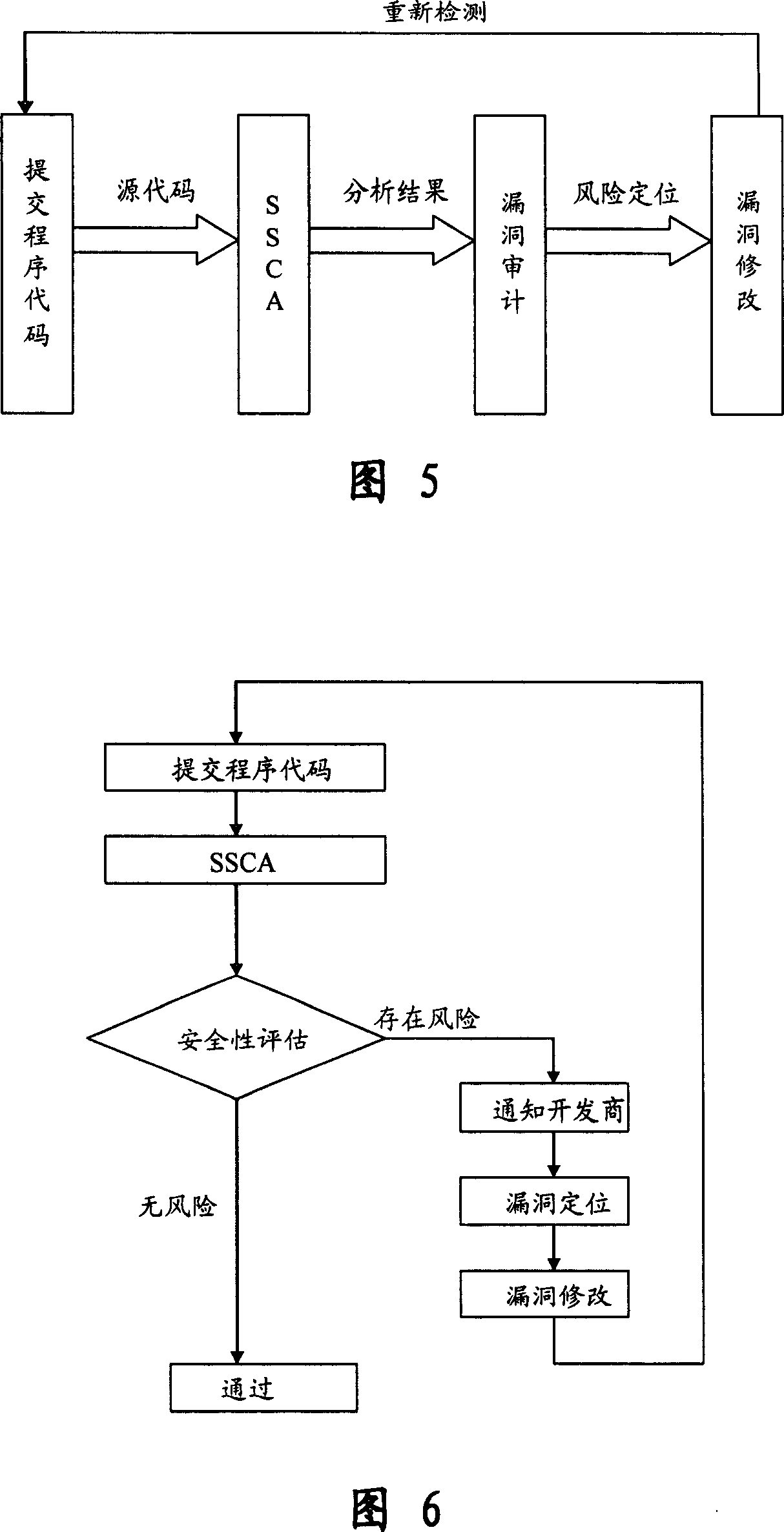
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
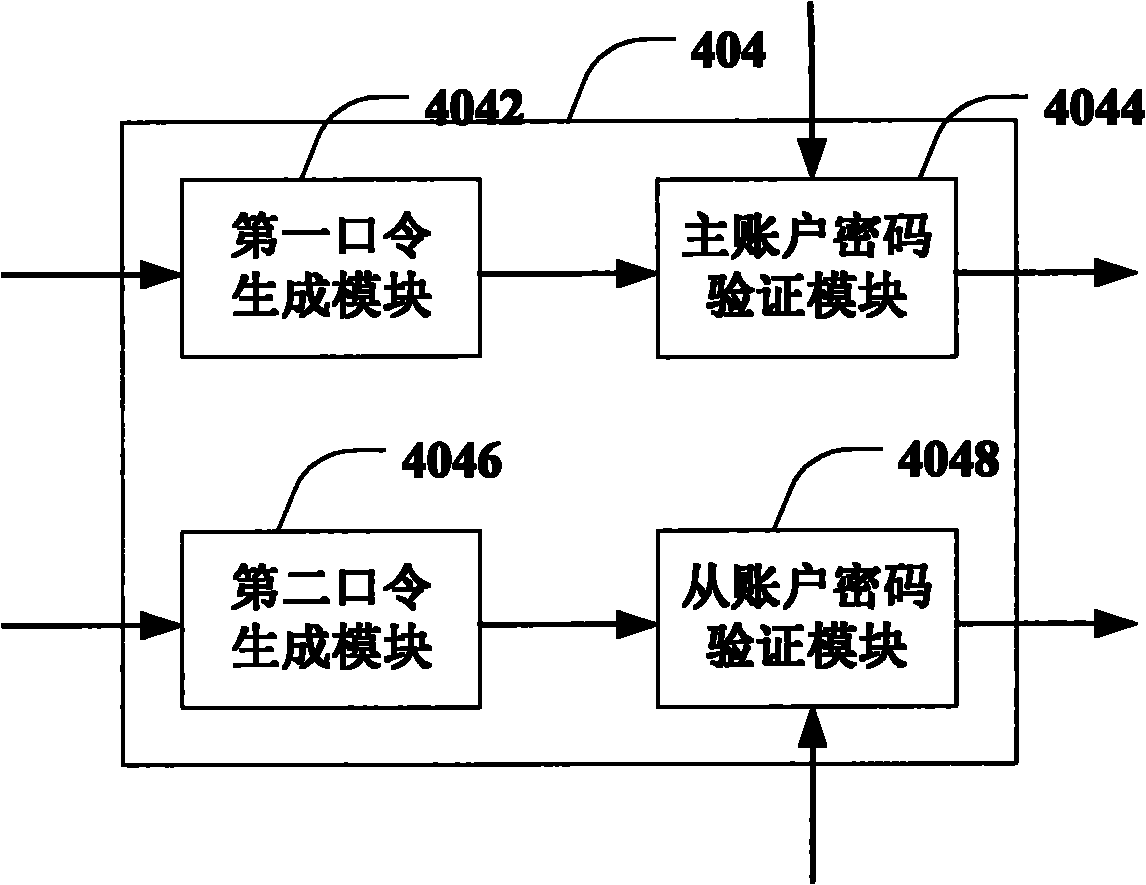
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
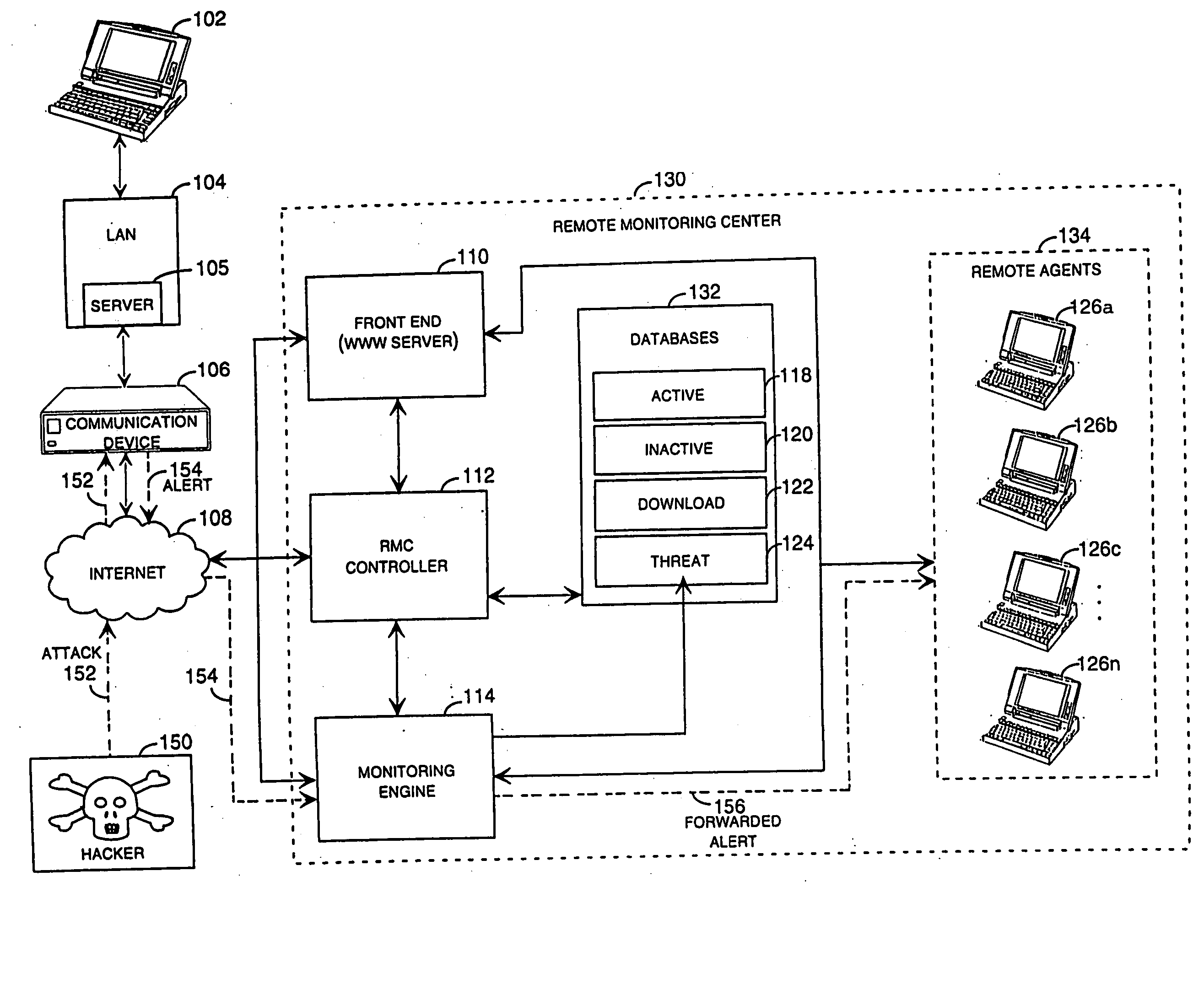
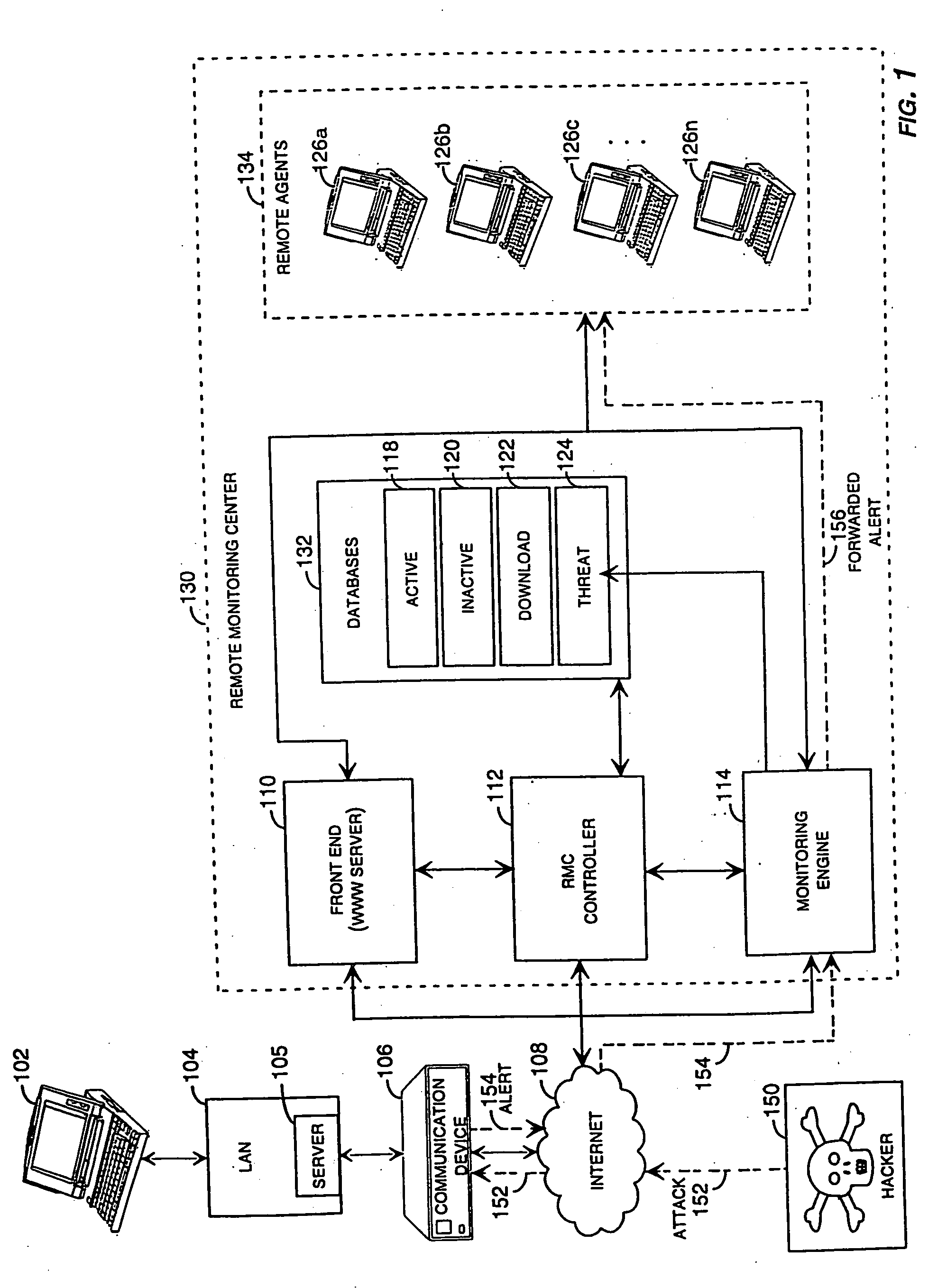
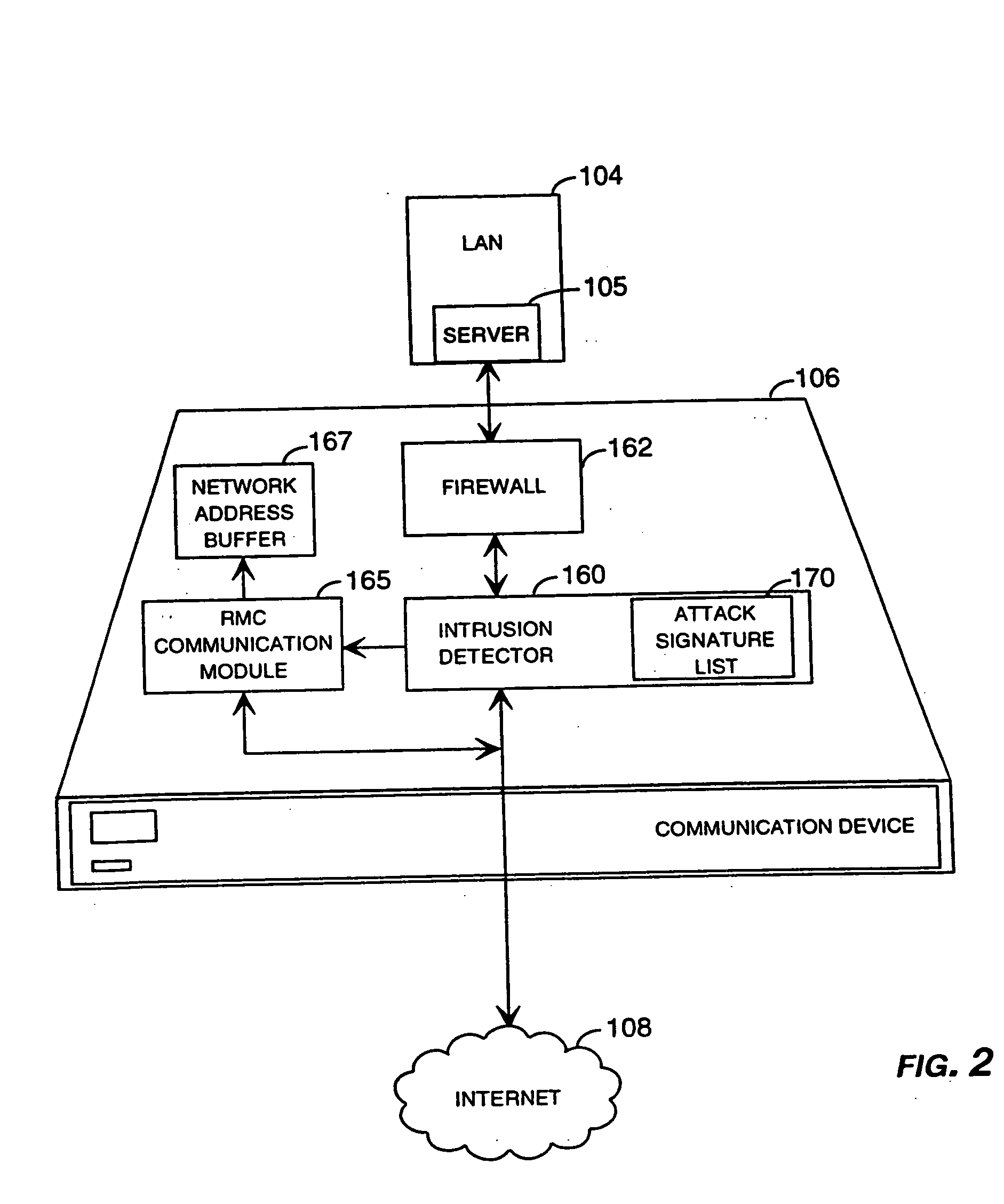
Method and system for remotely configuring and monitoring a communication device
InactiveUS20050235360A1Rapid responseMemory loss protectionUnauthorized memory use protectionImage resolutionThe Internet
Methods and systems for remotely configuring and monitoring a communication device are provided, especially useful in a computer network environment such as the Internet. A communication device or network appliance compares communications entering the communication device to a list of communication types established as known security risks, for example hacker attacks, unauthorized attempted access to network resources, or similar network security threats. If the received communication corresponds to a known security risk, the communication is classified as either a high security risk or low security risk, and an alert signal is transmitted to a remote monitoring center. Upon receiving the alert signal, the remote monitoring center assigns a priority to the alert signal based upon the type of the communication that triggered the transmission of the alert signal. Based on the assigned priority, the prioritized alert signal is then forwarded to a remote monitoring agent for resolution. The remote monitoring agent may then analyze the communication, contact the end user of the communication device with an appropriate resolution, or take other appropriate action in response to the received communication. The communication device may also be remotely configured.
Owner:SECUREWORKS
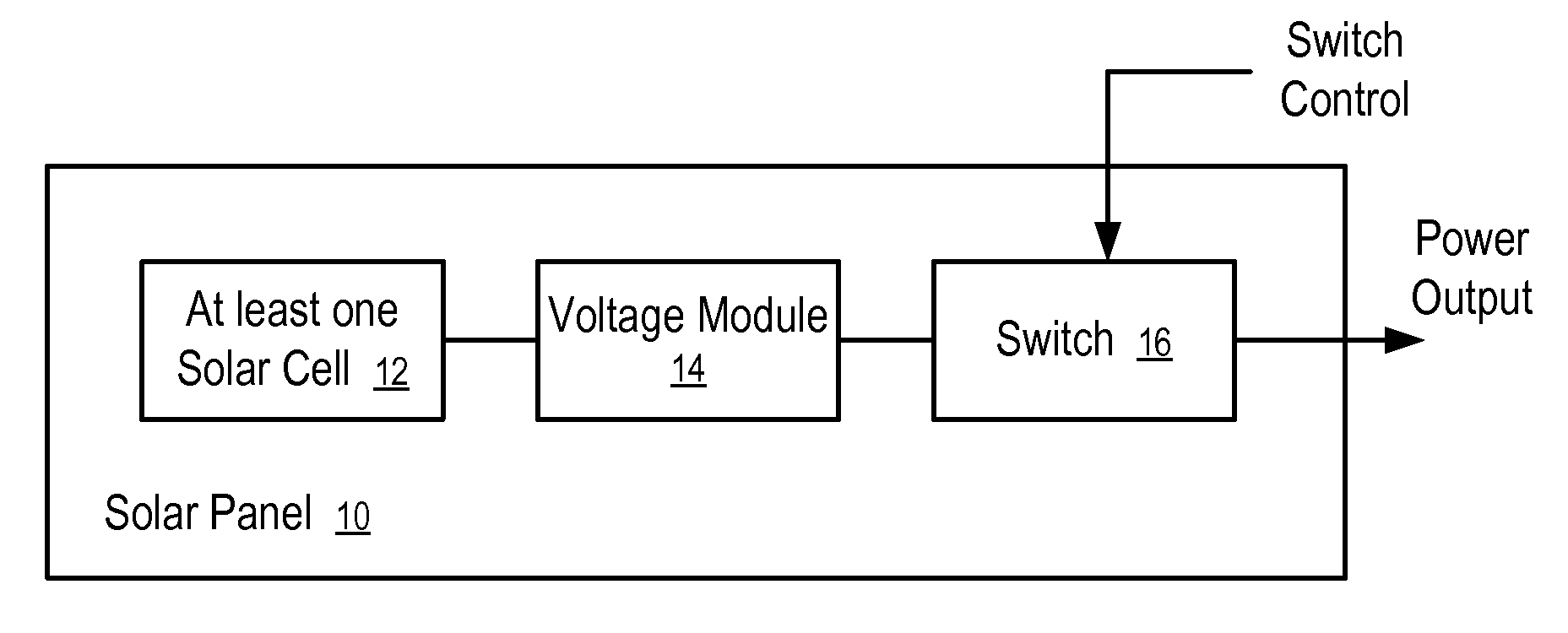
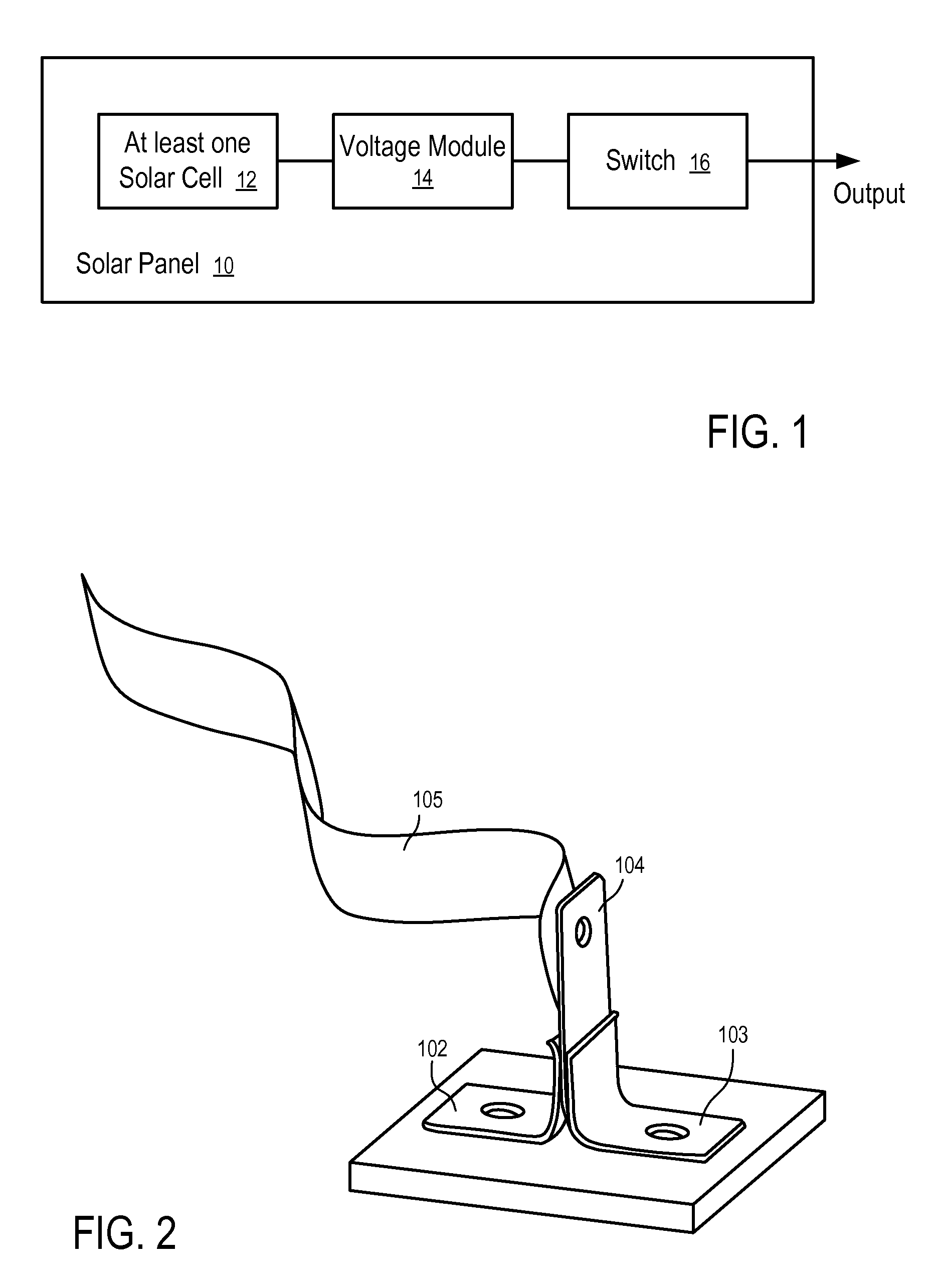
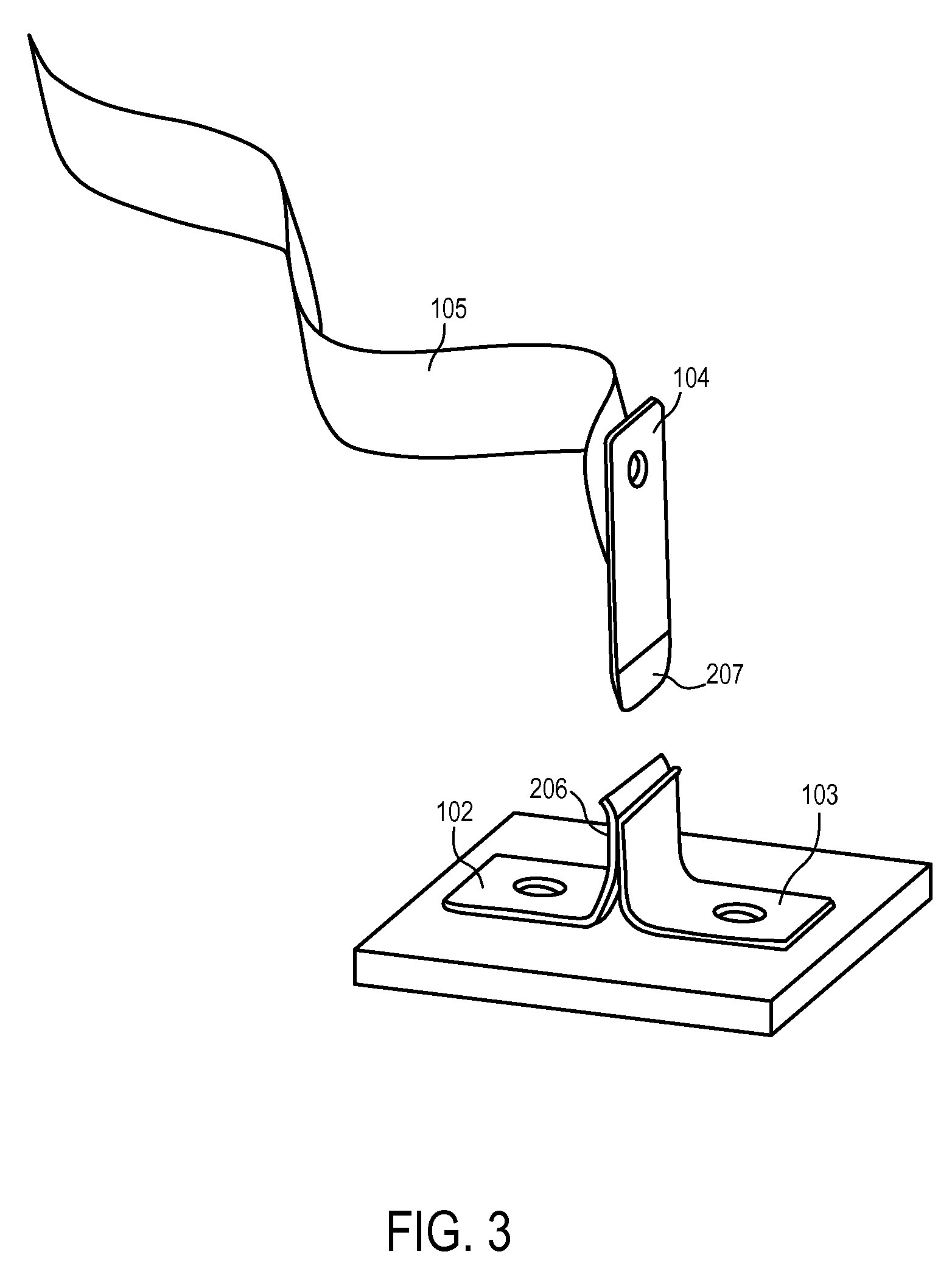
Apparatuses and Methods to Reduce Safety Risks Associated with Photovoltaic Systems
Apparatuses and methods to reduce safety risks associated with photovoltaic systems by providing a safety switch on a photovoltaic panel. In one embodiment, a photovoltaic panel includes: at least one photovoltaic cell; a connector to output energy from the photovoltaic panel; and a switch coupled between the at least one photovoltaic cell and the connector. The switch is configured to disconnect the at least one photovoltaic cell from the connector during installation of the photovoltaic panel, and to connect the at least one photovoltaic cell with the connector after installation of the photovoltaic panel.
Owner:NEWLIGHT CAPITAL LLC
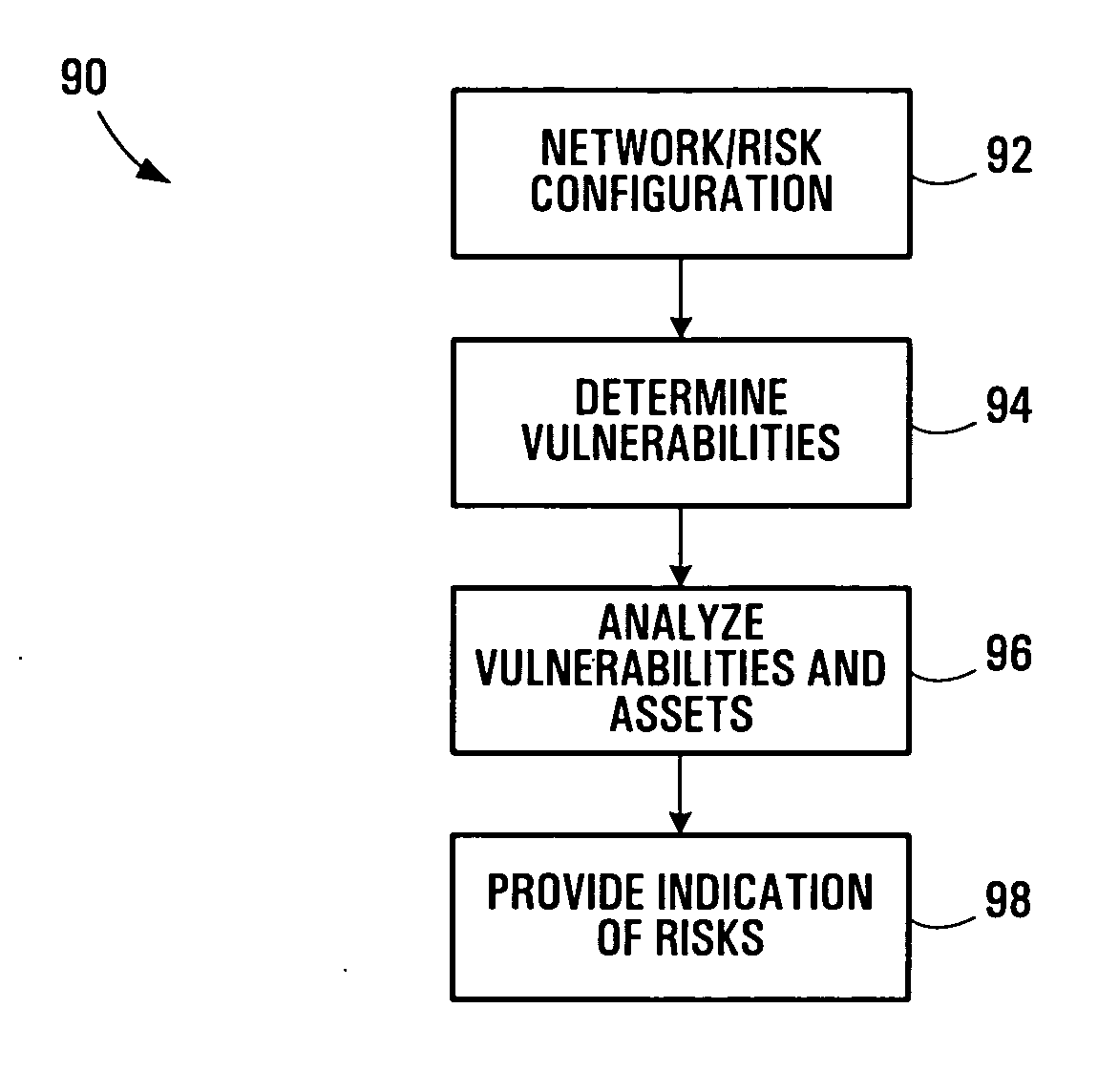
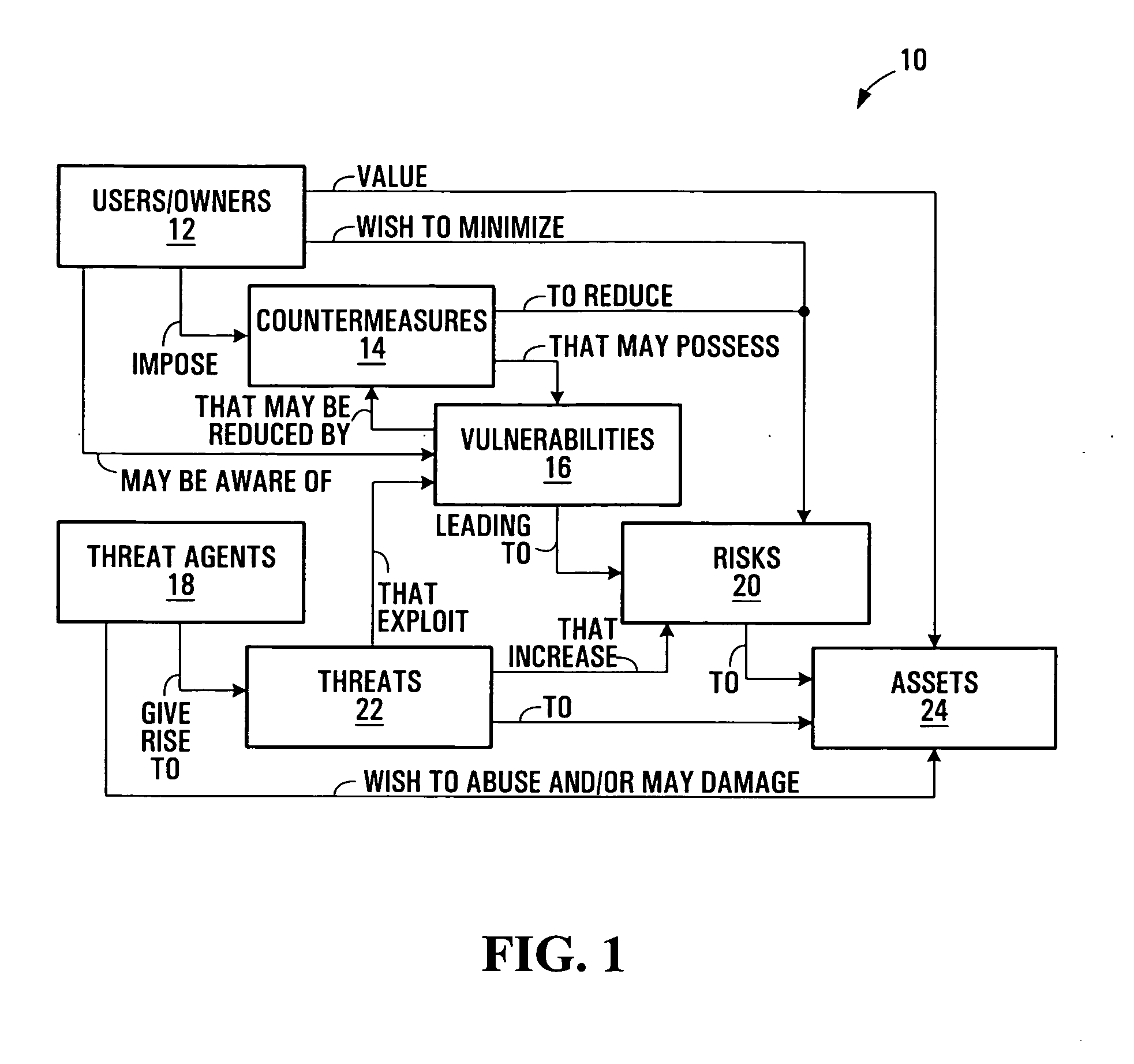
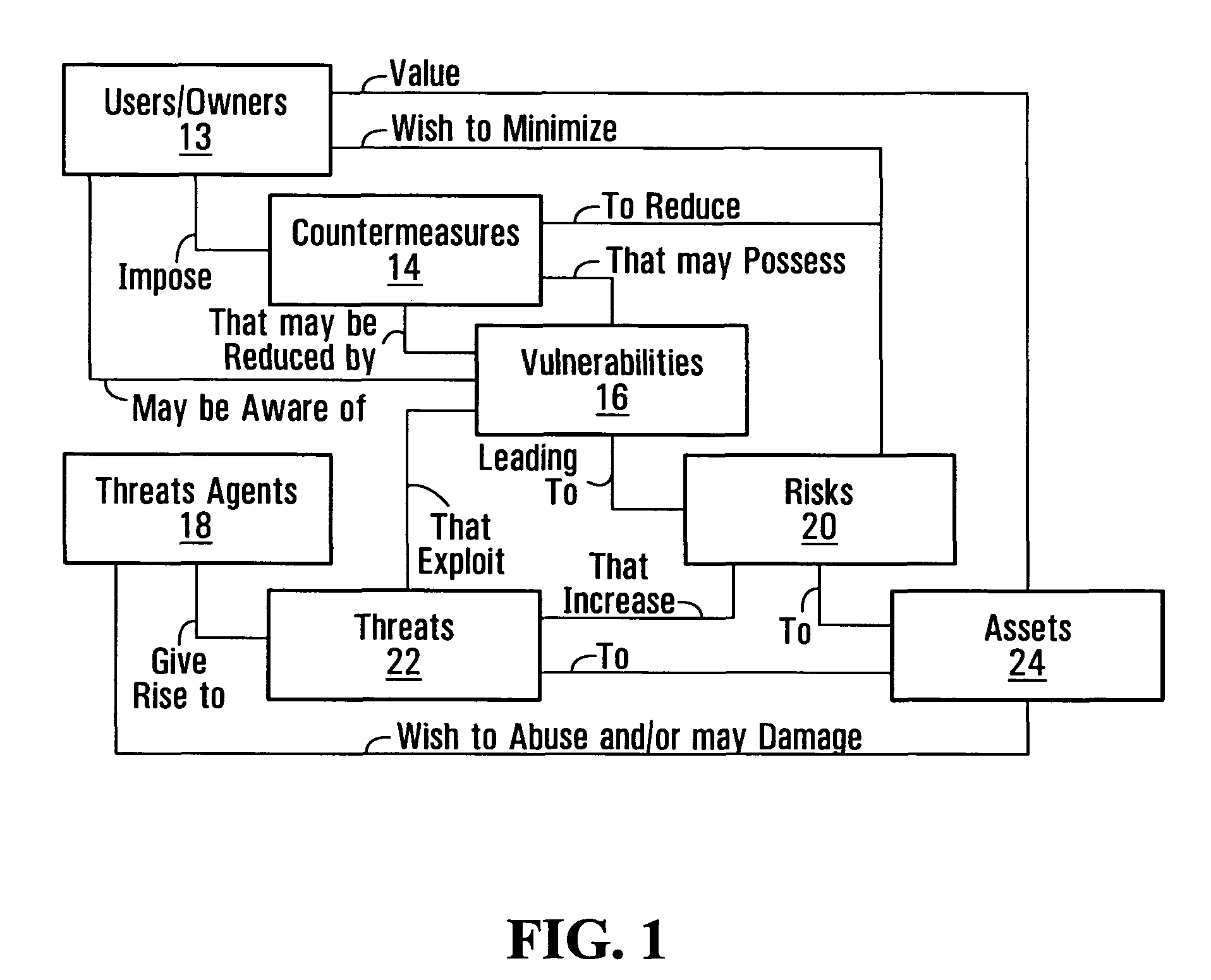
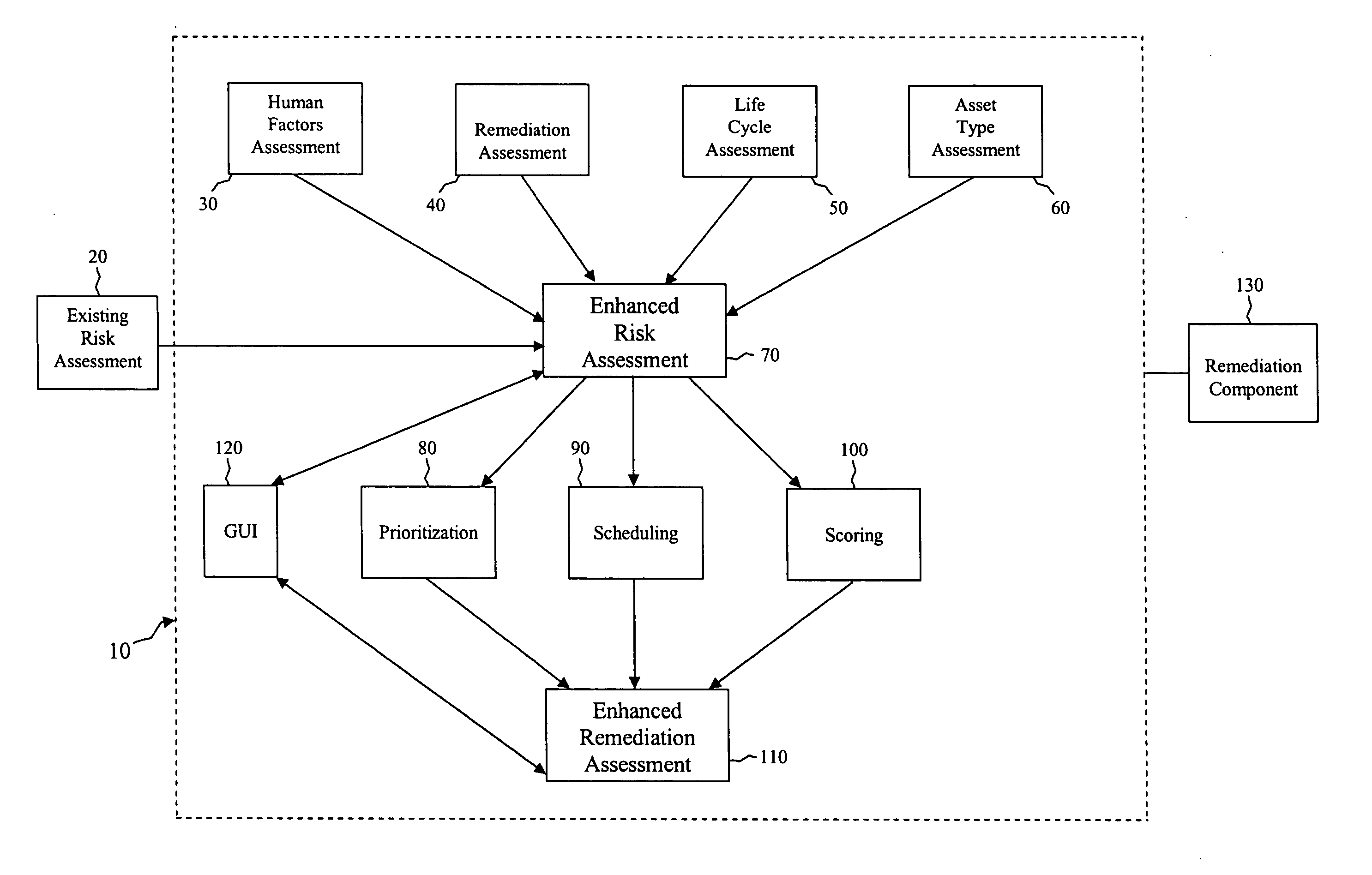
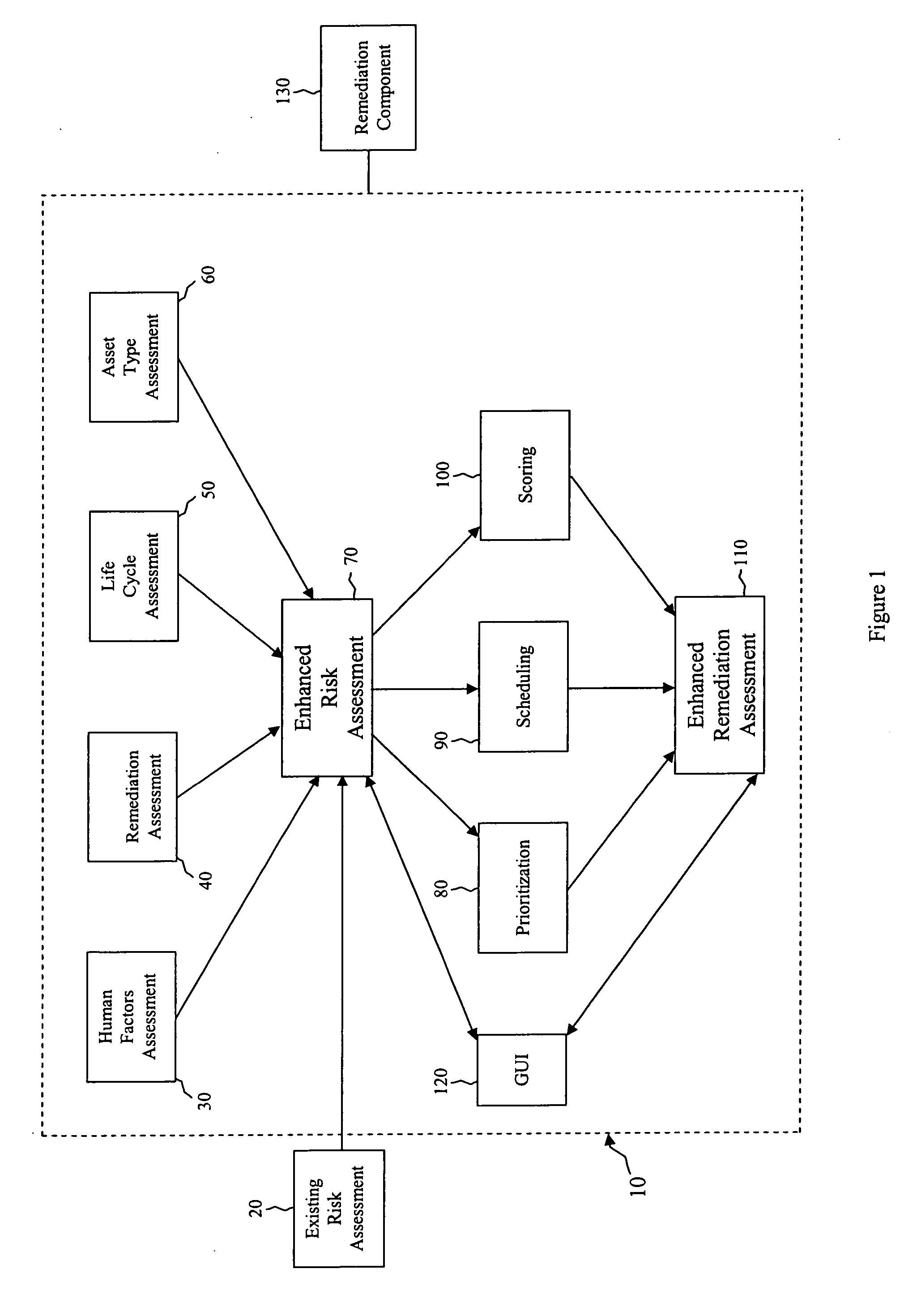
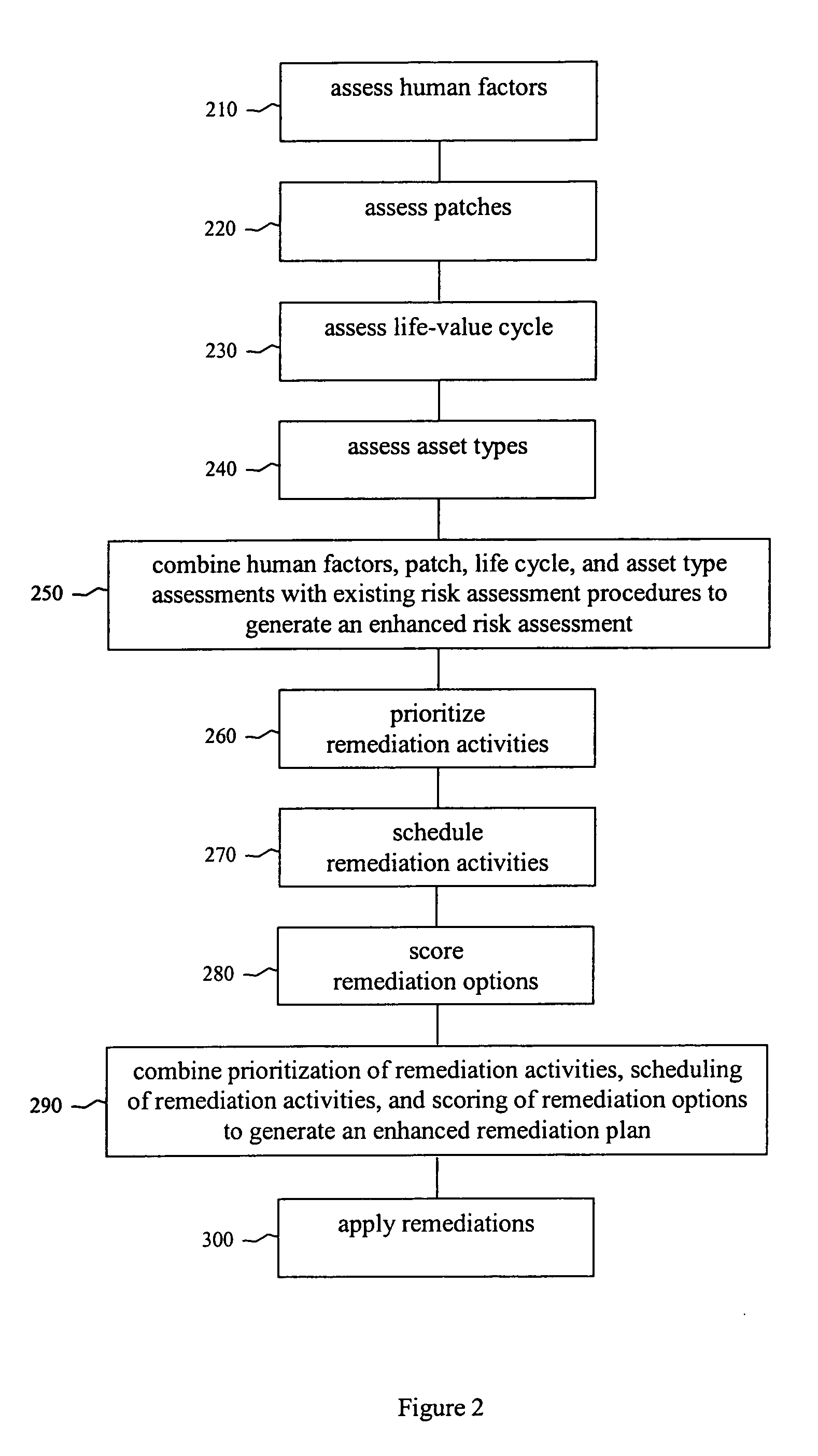
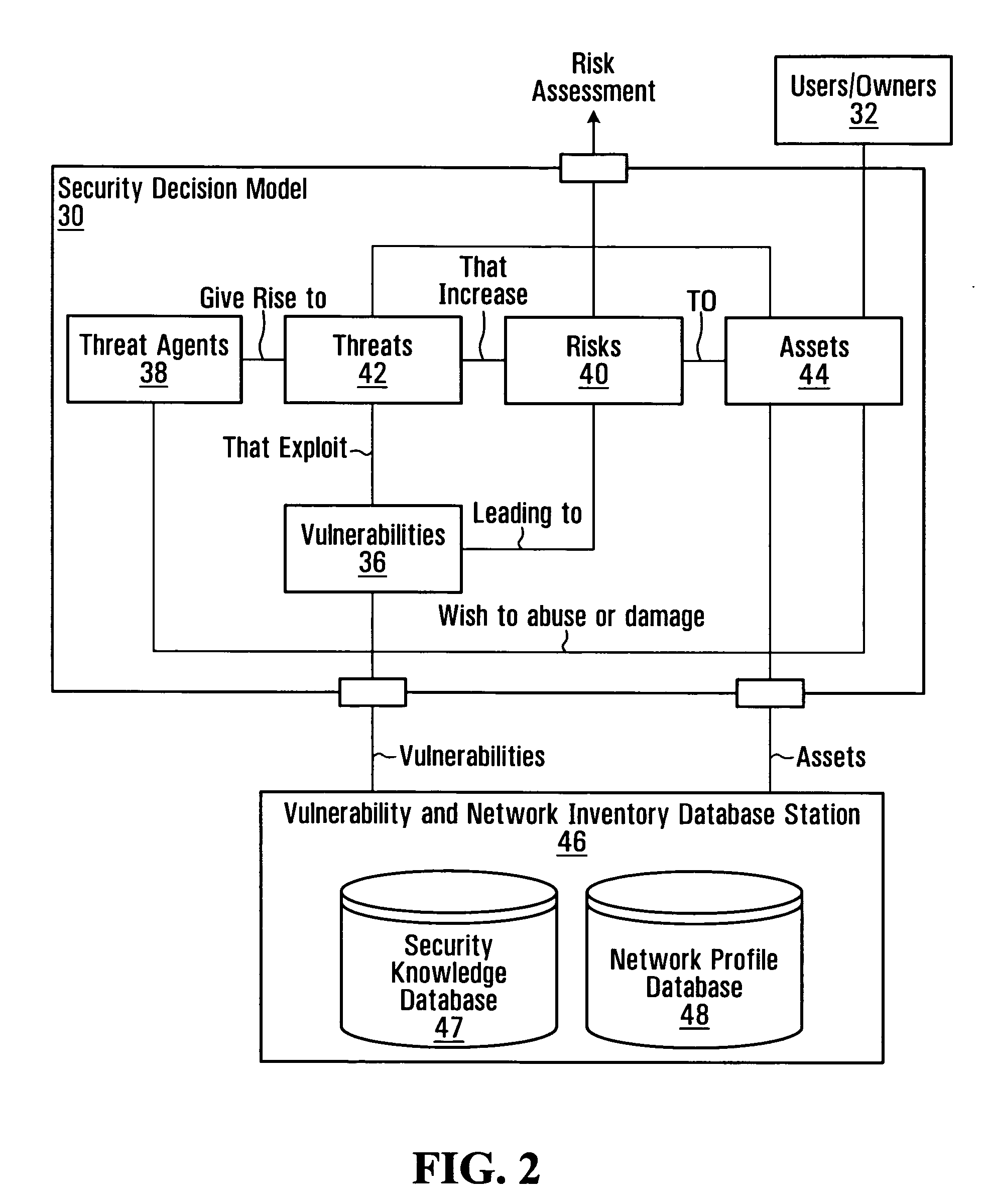
Security risk analysis system and method
A system and method for assessing risks to computer network is provided. The system includes a first module assesses a human factor related to a risk to the computer network. A second module assesses a remediation to the computer network, and a third module is operable to assess a life cycle of an asset on the computer network. A fourth module assesses a type of the asset used by the computer network.
Owner:MCAFEE LLC
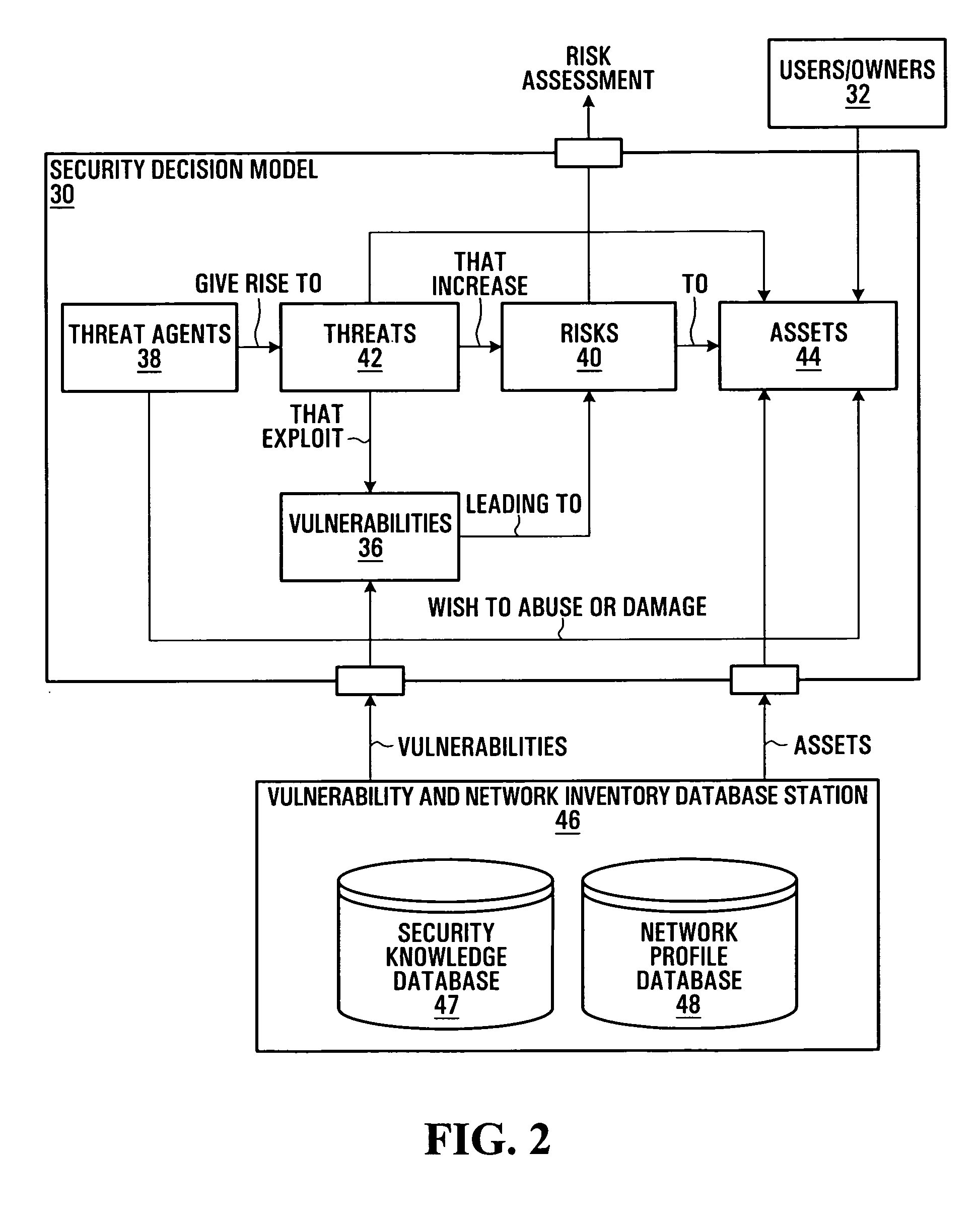
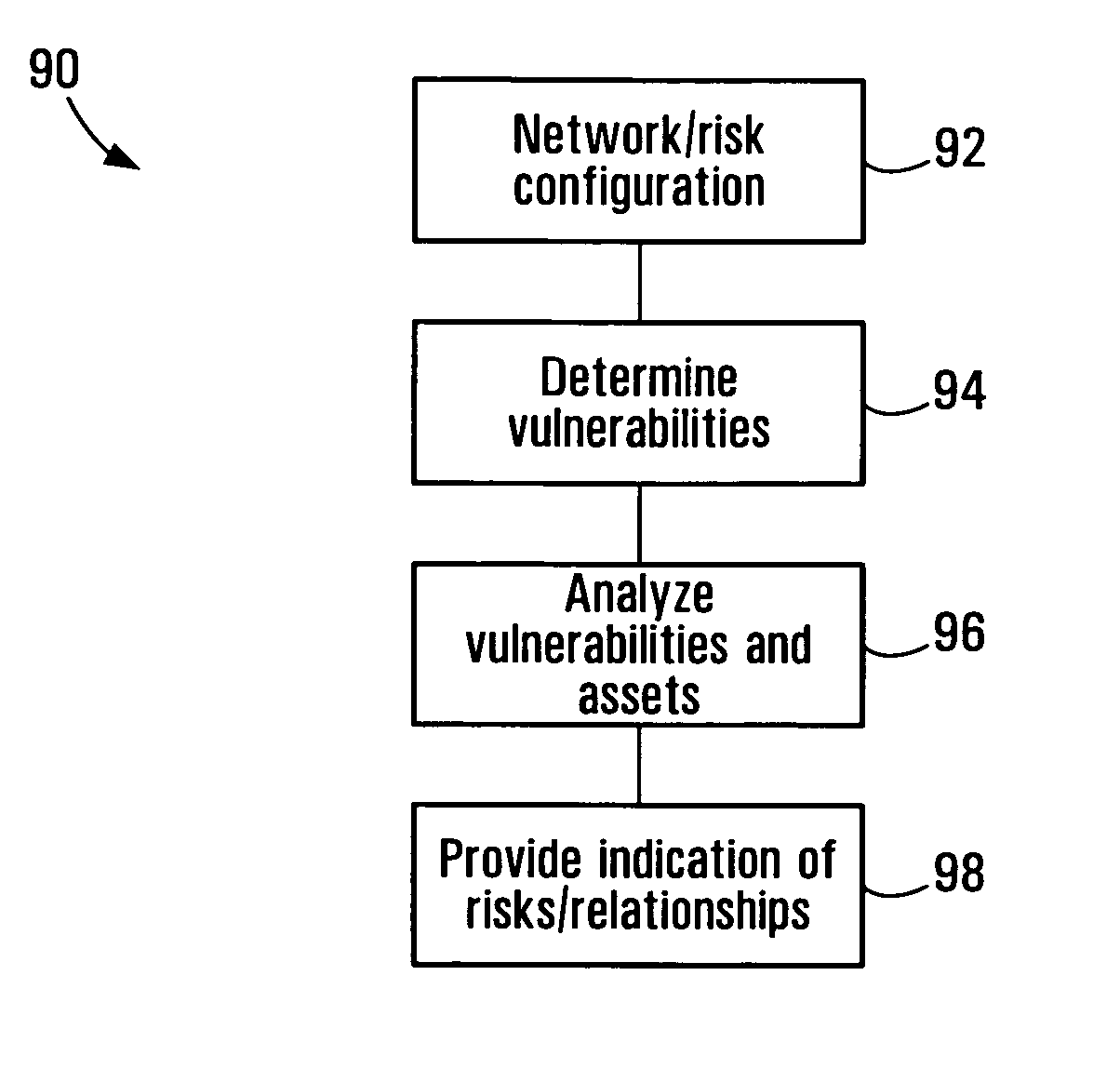
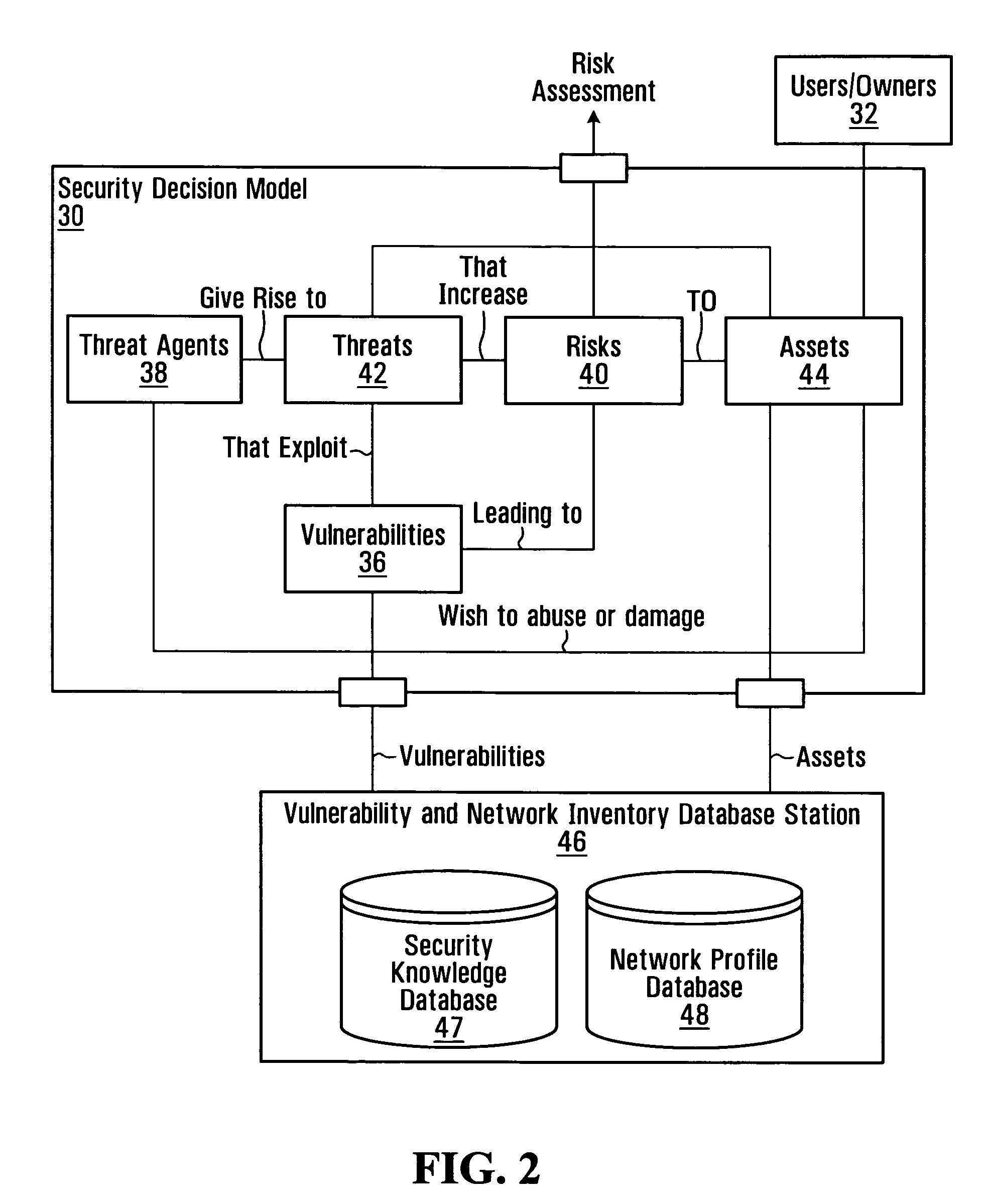
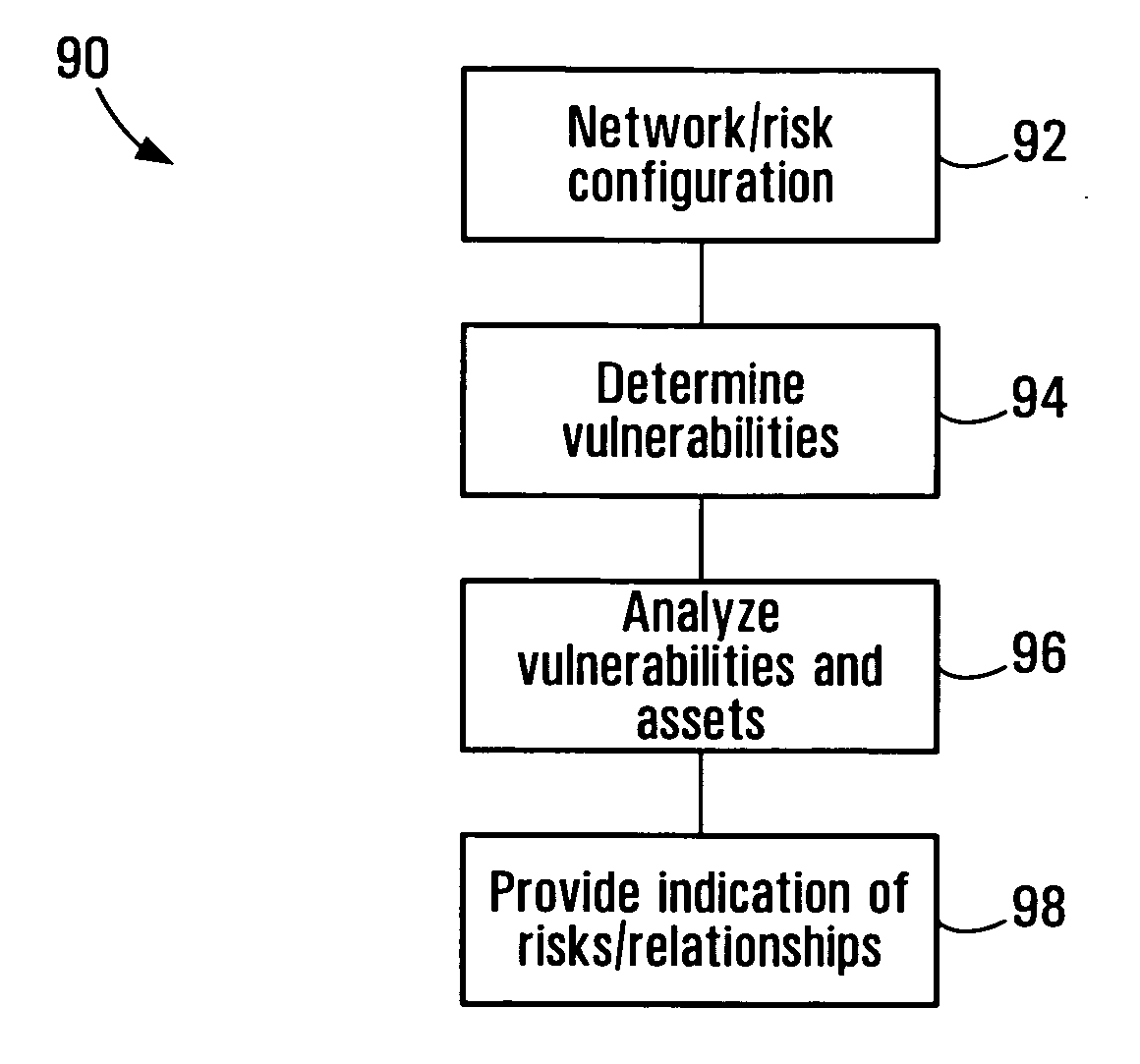
Information system service-level security risk analysis
Information system service-level security risk analysis systems, methods, and Graphical User Interfaces are disclosed. Assets of an information system that have relationships with a service provided by the information system are identified, and at least one security risk to the service is determined by analyzing security vulnerabilities associated with the identified assets. A consolidated representation of the service is provided, and includes an indication of the determined security risk(s) and an indication of a relationship between the service and at least one of the identified assets. The security risk indication may include indications of multiple security parameters. Security risks may be represented differently depending on whether they arise from a security vulnerability of an asset that has a relationship with the service or a security vulnerability of an asset that has a relationship with the service only through a relationship with an asset that has a relationship with the service.
Owner:ALCATEL LUCENT SAS
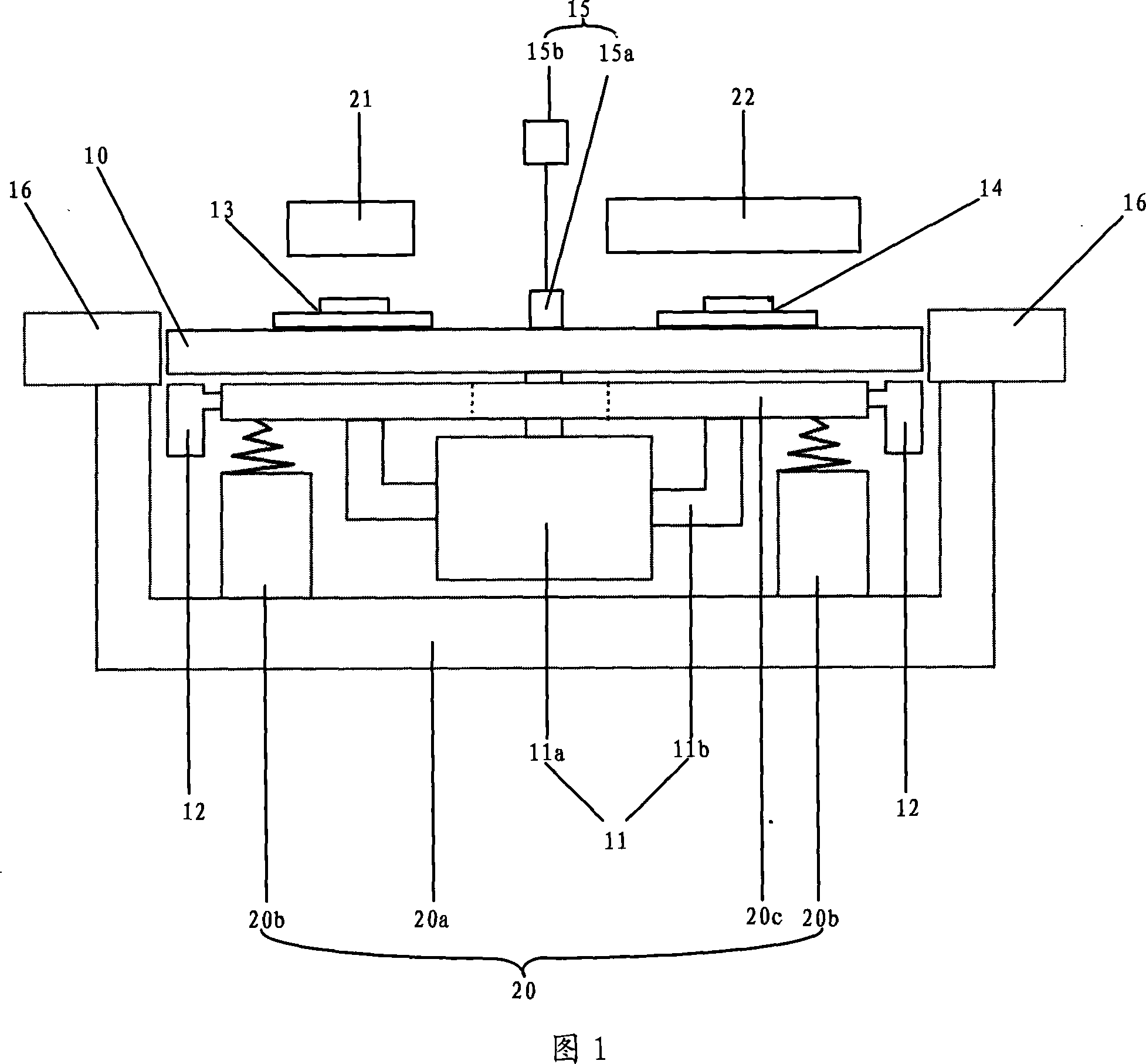
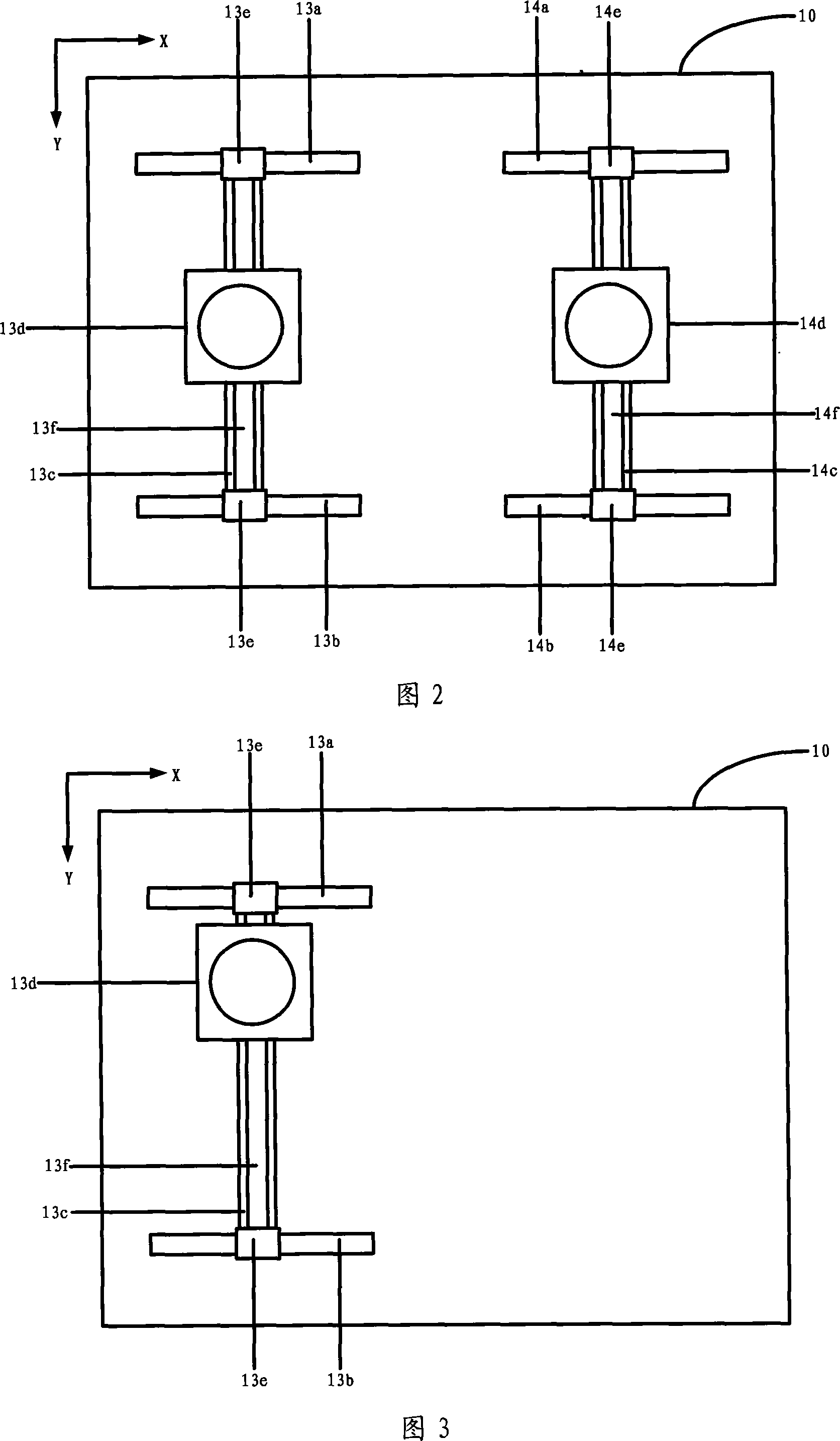
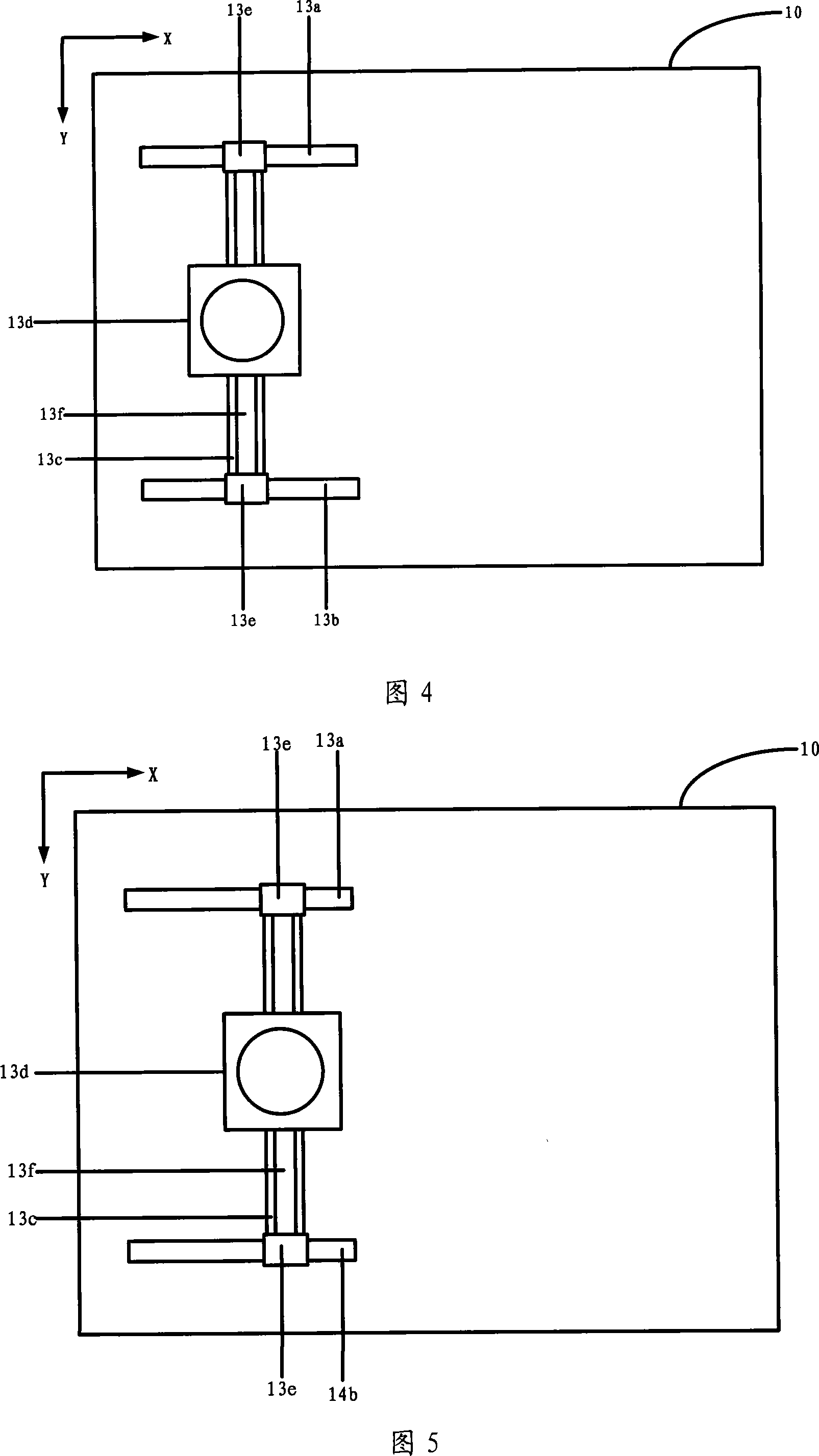
[Automated system and method for providing accurate, non-invasive insurance status verification]
InactiveUS20050209892A1Limiting featureCurrent failureFinanceSpecial data processing applicationsData streamNon invasive
The present invention relates generally to automatic insurance verification, and more specifically, to a non-invasive method and system for automatically determining, by any person with computer, wireless, or telephone access and in real-time, if an insured object of value is or is not insured irrespective of insurer location, jurisdiction, language, type, time, and also the internal operations, software platform and communications protocols used by insurers and / or governmental entities. It is an insurance verification, not an insurance reporting or tracking system and because it maintains no personal data of any kind, and can modify no record, it can deliver only very limited features regarding reporting or tracking. The present invention can however, provide absolute assurance of current insurance status at all times, provides a unique method of access which resolves all current failures and is non-invasive, providing complete privacy for all parties involved, (the absence of all personal information and the access method used ensures that all access and data is inherently non-invasive). This invention further ensures that any check of status, at insurer or governmental registration, (including “e-registration”, inspection, or any other location and time when and where a jurisdiction or insurer requires such a status check, will result in an instant and totally accurate status response. This system is based upon the assignment of a unique identifier, also known in this present art as a “UC” or “Unique Code” which then provides a method of accurate data, (including status checks), without reliance on “VINs”, (vehicle identification numbers), policy number or other identifiers which are often incorrect. The UC is assigned to any combination of two or more elements that are “gleaned”, (file field extraction and related system and methods), one of which is always current status. The extraction of these selected fields from data streams may be done by a number of prior art techniques, and the three most common have been detailed. First demonstrated to government officials in 1999 as a medical version and later the same year as a vehicle version, it has been demonstrated and documented since to a great many Federal and State governmental entities. This present invention has also been demonstrated to several foreign governments but incorporates no technologies that create any possible security risk for any government, insurer, individual, and especially to the national security of the United States.
Owner:MILLER JONATHAN K
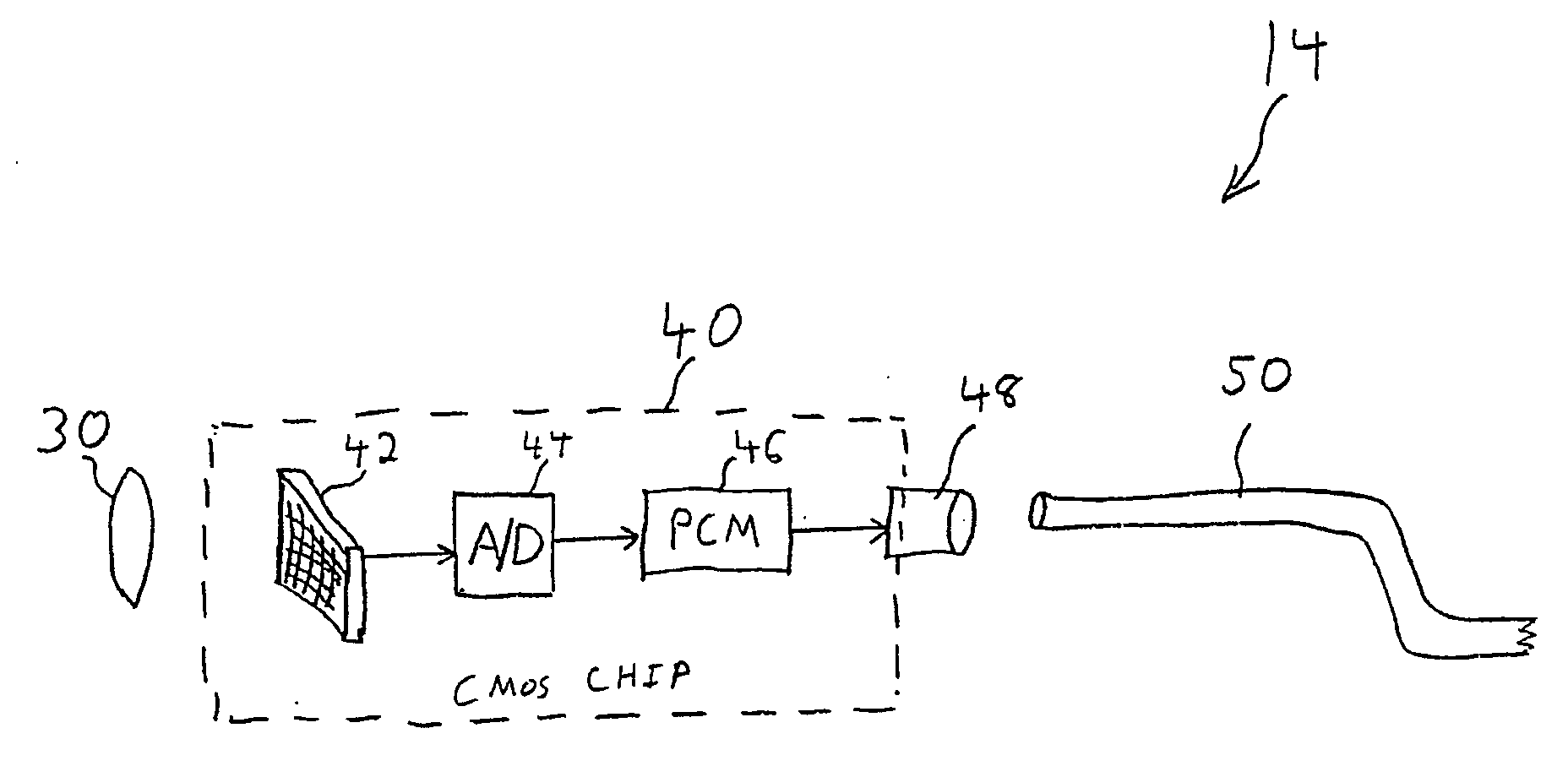
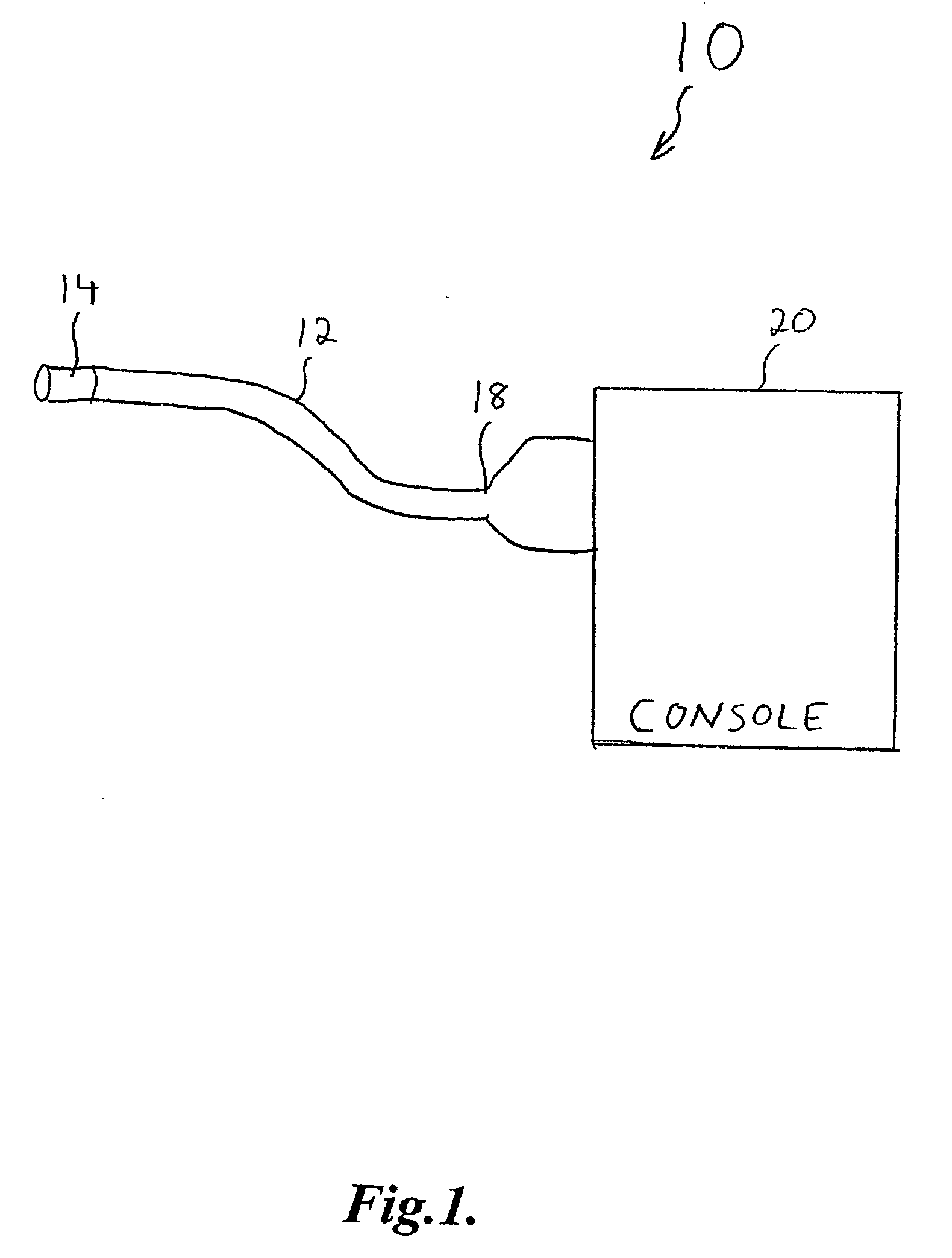
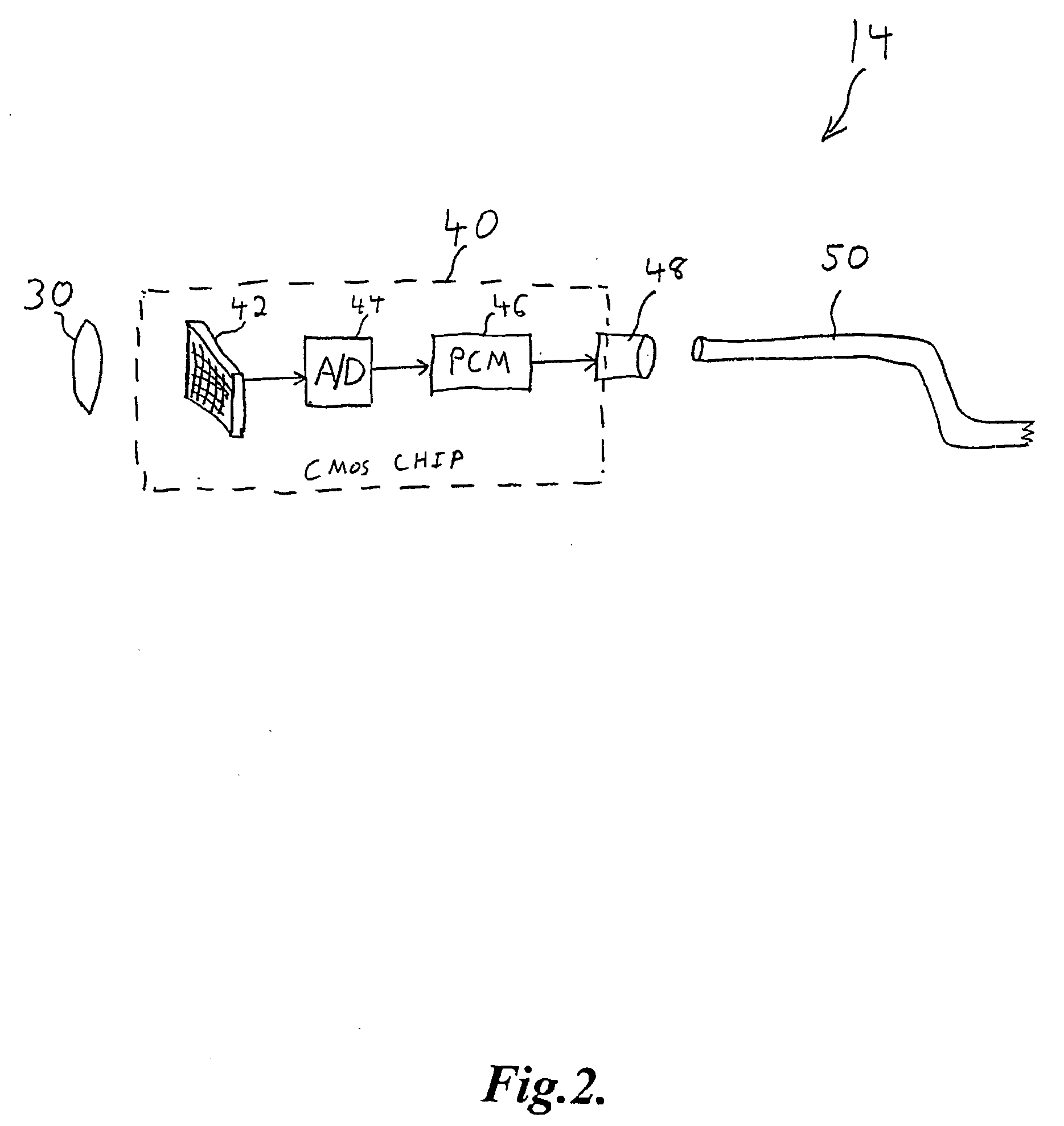
Endoscope with fiber optic transmission of digital video
A video endoscope in which the imaging chip at the distal tip is connected to the proximal connector and operator console by an optical fiber. Video data (preferably digital) is impressed on the optical fiber by a pulse-code modulator (PCM) circuit and light emitter with lensing. A small, inexpensive, flexible optical fiber in the endoscope body conveys the PCM optical data to the receiving circuit, preferably via an optical connector at the proximal end of the endoscope, and to decoding and display circuits in the operator console. The fiber optic transmission overcomes the difficulty of electrical transmission of wide band (digital video) signals via miniature cables, which can be expensive, bulky, inflexible, susceptible to noise and interference, and constitute a potential electrical safety risk by leakage currents. The PCM circuits may be integrated into the camera chip.
Owner:SCI MED LIFE SYST
Collection block with multi-directional flow inlets in oilfield applications
The disclosure provides a collection block that aggregates multiple incoming flow lines and provides a consolidated outgoing flow path. The collection block can be remote from a given well that is being fractured to minimize safety risk in operations around the well. The collection block has dual capabilities of being connected to individual incoming flow lines as well as to manifold systems for distributing the out flowing fluids. The one or more inlets can be formed in the collection block at an offset to a centerline of a longitudinal bore through the collection block. In some to embodiments, frac trucks can connect along an extended connection zone that provides the fluids from the truck to the collection block.
Owner:T 3 PROPERTY HLDG
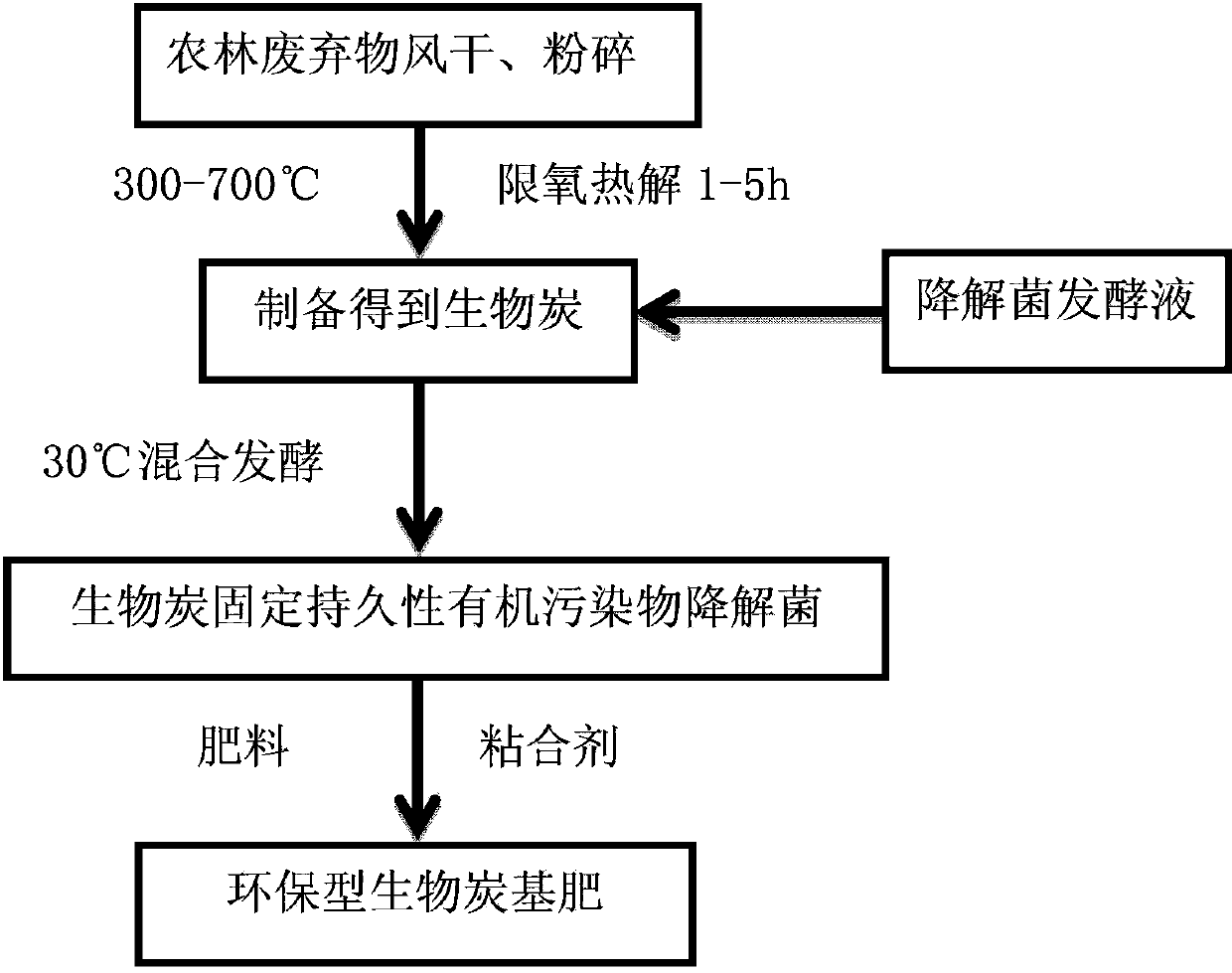
Environmentally friendly biochar-based fertilizer and application method thereof
ActiveCN103396171AGood sustained release effectHigh survival rate of live bacteriaFertilising methodsOrganic fertilisersPolycyclic aromatic hydrocarbonSurface layer
The invention discloses an environmentally friendly biochar-based fertilizer and an application method thereof. The preparation of the biochar-based fertilizer comprises the following steps of: drying and crushing forestry and agricultural residues, then performing oxygen limited pyrolysis on the crushed materials for 1-5 hours at 300 to 700 DEG C, and sieving, thereby obtaining biochar; and after the biochar is fixed with persistent organic pollutant degrading bacteria, mixing the biochar with a fertilizer, stirring the two thoroughly, and adding a binder accounting for 1wt%-4wt% of the total weight, thus obtaining the environmentally friendly biochar-based fertilizer. For application, the prepared environmentally friendly biochar-based fertilizer is applied to soil by 100-1000 kg per hectare; the surface layer of soil, to which the biochar-based fertilizer is applied previously, is turned over by 0-20 cm, so that the biochar-based fertilizer is mixed with the soil thoroughly, and then the soil can be used for planting crops. The environmentally friendly biochar-based fertilizer provided by the invention overcomes the shortcoming that present biochar-based fertilizers contain organic pollutants such as polycyclic aromatic hydrocarbon, the influence of the fertilizer on soil and environment is alleviated, and the safety risk of agricultural products is reduced; moreover, the environmentally friendly biochar-based fertilizer has the advantages of simple and practicable preparation process, low cost and the like.
Owner:上海孚祥生态环保科技股份有限公司
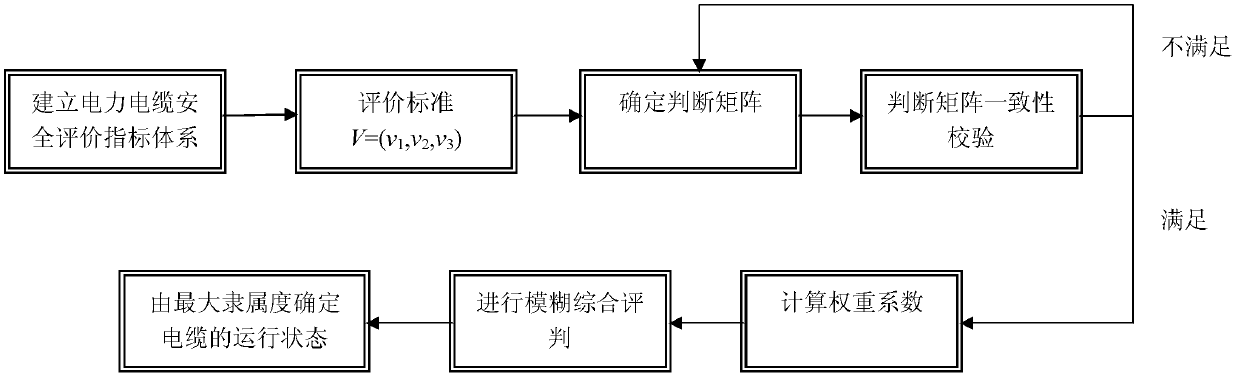
Cable multimode safe operation evaluation method based on fuzzy analytic hierarchy process (FAHP)
ActiveCN102496069ATimely discovery of potential safety hazardsSolve the problem that quantitative analysis cannot be performedData processing applicationsPower cableWeight coefficient
The invention relates to a cable multimode safe operation evaluation method based on a fuzzy analytic hierarchy process (FAHP). The evaluation method comprises the following steps of: establishing a power cable safety evaluation index system, establishing a power cable safety evaluation index comment set, and establishing a judgment matrix; judging matrix consistency check, and if the matrix does not meet consistency, returning the previous step; if the matrix meets the consistency, entering the next step; calculating a weight coefficient; and carrying out fuzzy comprehensive judgment, and determining an operating mode of the cable by maximum degree of membership. Multimode parameters are utilized to do safety evaluation on the operating mode of a power cable, and can relatively comprehensive evaluate system operation, and the evaluation method is simple and safe and reliable; and a cable multimode safe operation evaluation model is established based on the fuzzy analytic hierarchy process (FAHP) and can correctly do safety evaluation on a cable system, thereby being beneficial to finding out potential safety hazard existing in the power cable for staff in time, thus having a certain practical significance and a good development prospect.
Owner:STATE GRID SHANDONG ELECTRIC POWER
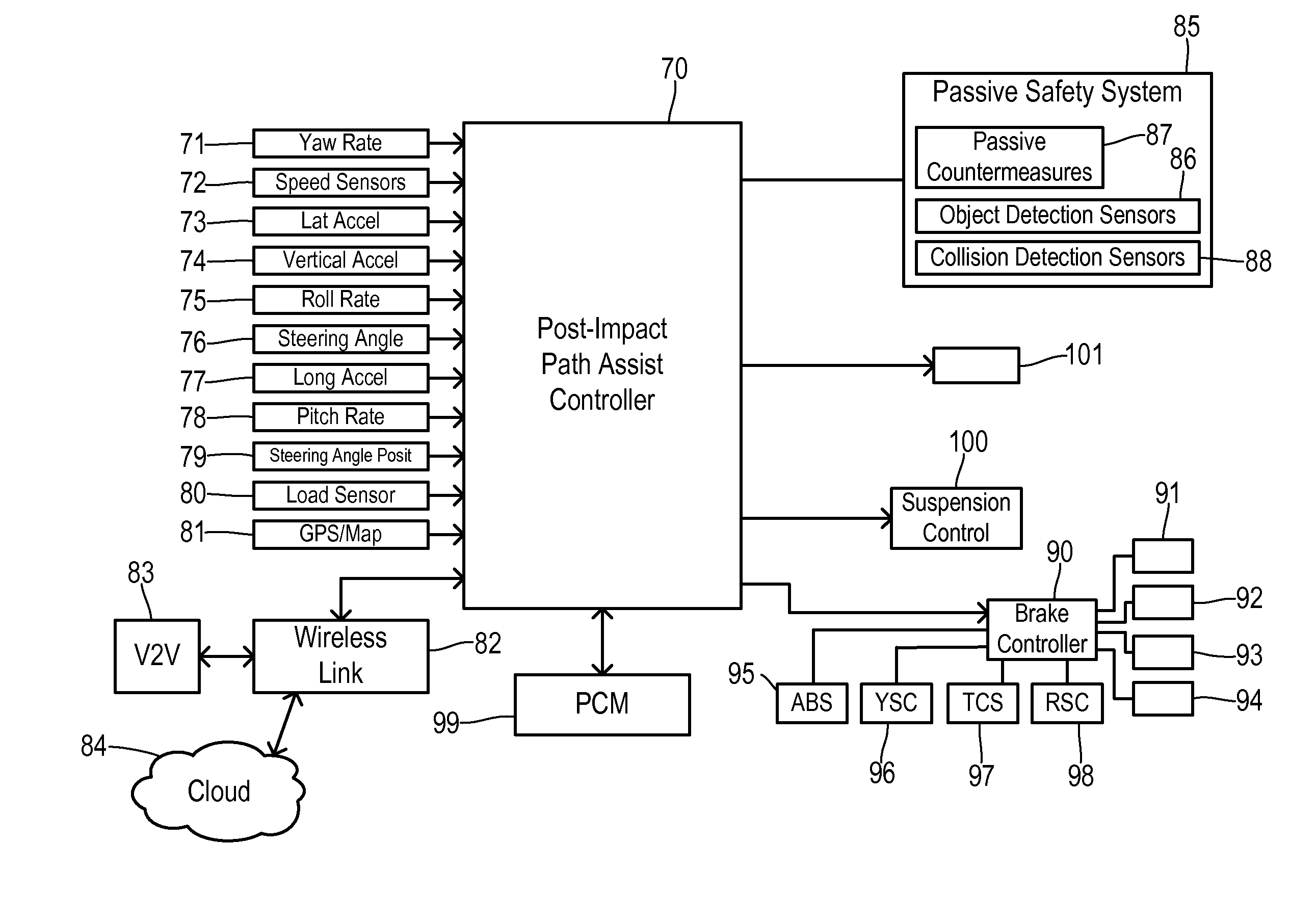
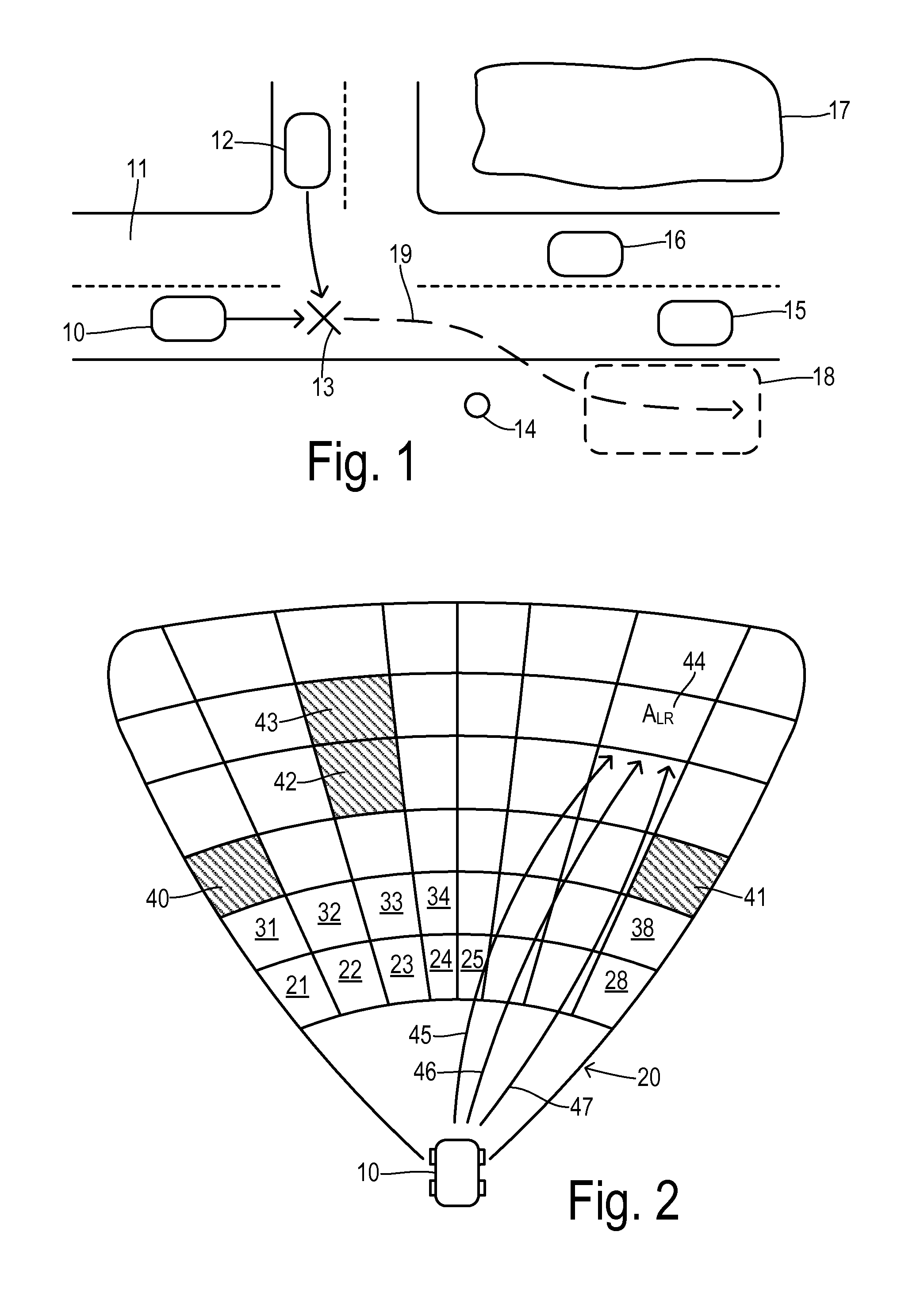
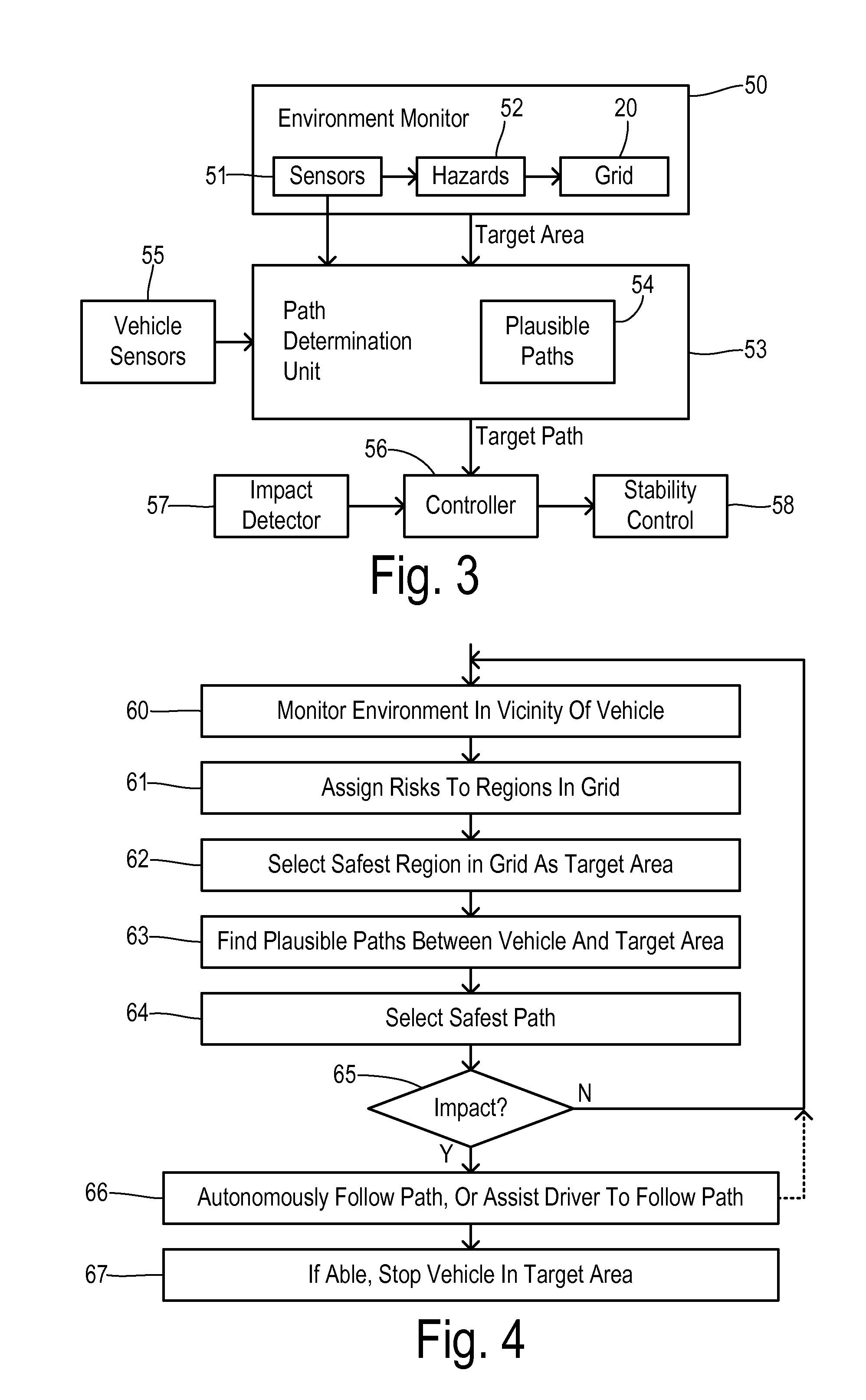
Post-impact path assist for vehicles
ActiveUS20150019063A1Control safety arrangementsExternal condition input parametersEngineeringSafety risk
An environment monitor has a plurality of sensors for detecting predetermined safety risks associated with a plurality of potential destination regions around a vehicle as the vehicle moves over a roadway. The environment monitor selects one of the potential destination regions having a substantially lowest safety risk as a target area. A path determination unit assembles a plurality of plausible paths between the vehicle and the target area, monitors predetermined safety risks associated with the plurality of plausible paths, and selects one of the plausible paths having a substantially lowest safety risk as a target path. An impact detector detects an impact between the vehicle and another object. A stability control is configured to autonomously steer the vehicle onto the target path when the impact is detected.
Owner:FORD GLOBAL TECH LLC
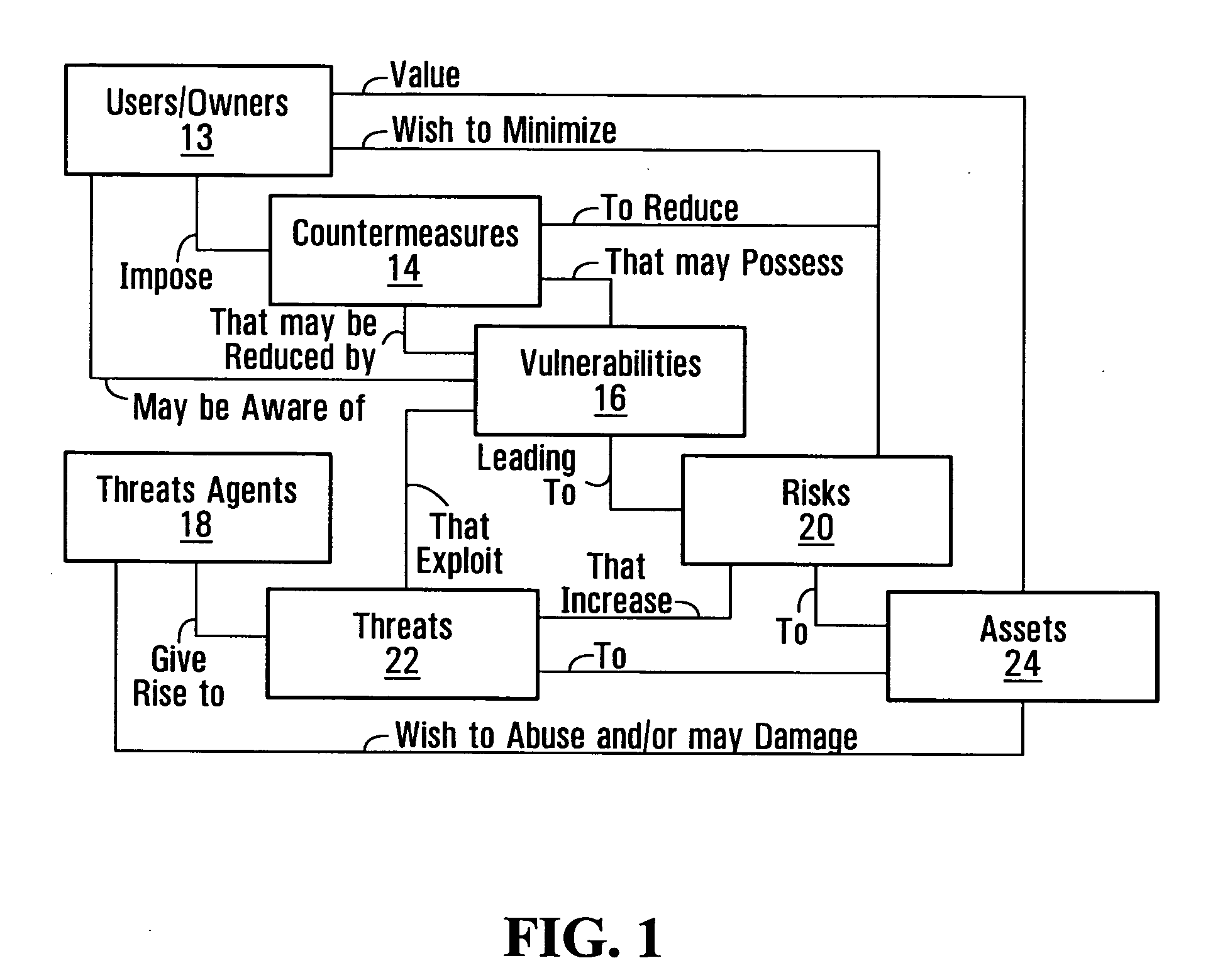
Security risk analysis systems and methods
Security risk analysis systems and methods are disclosed. Vulnerabilities affecting assets of a communication network are associated with other assets of the communication network according to relationships between assets. Security risk may thus be assessed on the basis of both vulnerabilities which directly affect assets and vulnerabilities which indirectly affect assets through their relationships with other assets. Risk exposure calculators which determine respective types of exposure of assets to vulnerabilities, illustratively direct and indirect exposures, are selectable so as to provide for customizable security risk analysis.
Owner:ALCATEL LUCENT SAS
Intelligent hazardous chemical substance warehouse management system
InactiveCN103971220AActive connectionGuaranteed to workSensing record carriersLogisticsManagement unitData collecting
The invention discloses an intelligent hazardous chemical substance warehouse management system. The management system comprises an automatic warehouse checking unit, a real-time warehouse management unit, a warehouse environment monitoring unit, a background control server and a goods management unit based on an electronic tag. According to the automatic warehouse checking unit, a robot automatically checks goods information based on a self-established storage environment map. The real-time warehouse management unit carries out real-time positioning and recording on the positions and in-out warehouse states of goods. A warehouse data collecting unit carries out on-line monitoring on the warehouse environment in real time, and transmits the monitored data to the background control server. The background control server coordinates the cooperation among the units and stores and manages the data uploaded by the units. The whole operation procedures are organically combined through the scheme, workers work more efficiently, the contact probability between the workers and hazardous chemical substances is greatly reduced, potential safety hazards are reduced, and the humanized management mode is shown.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
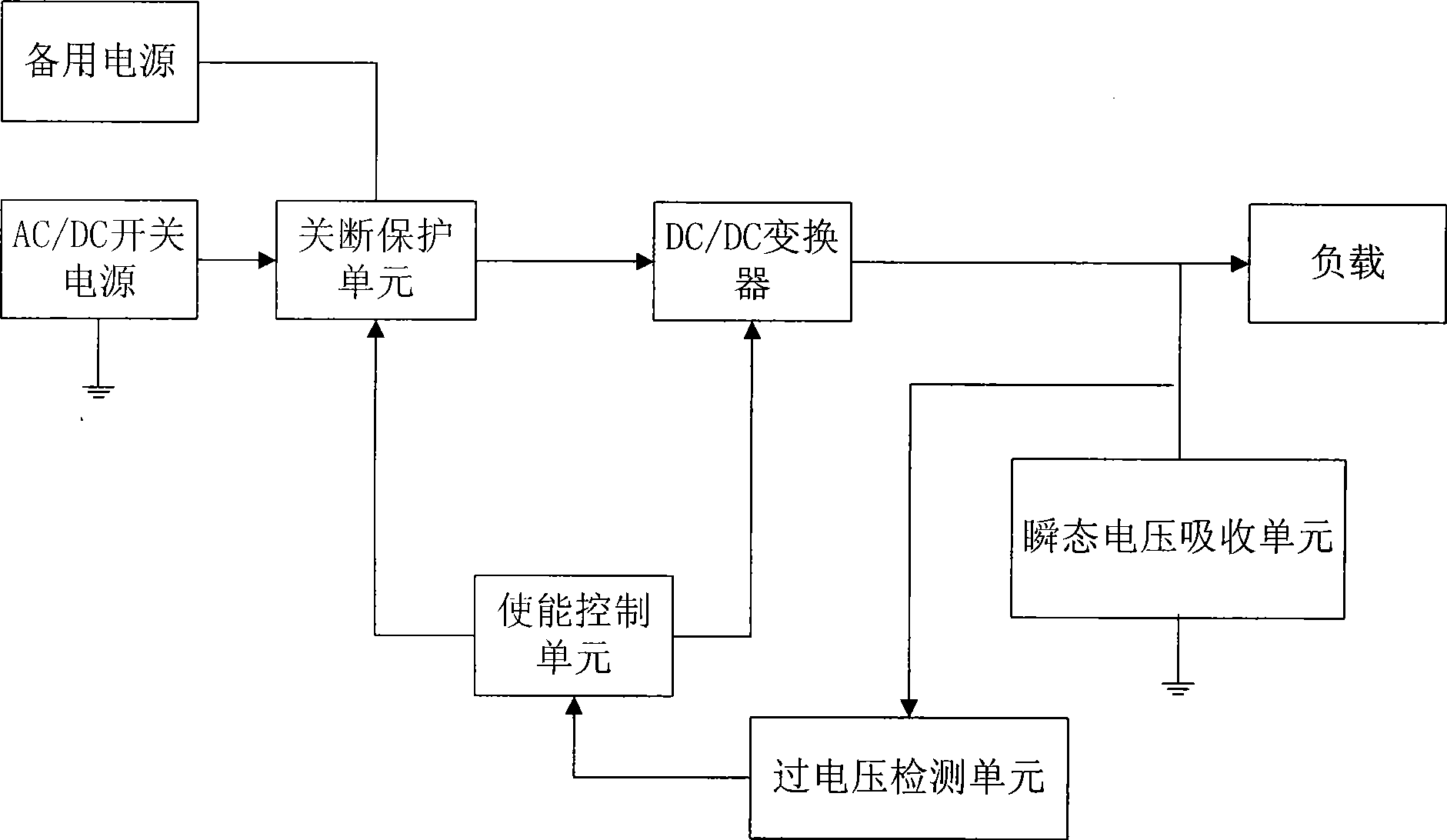
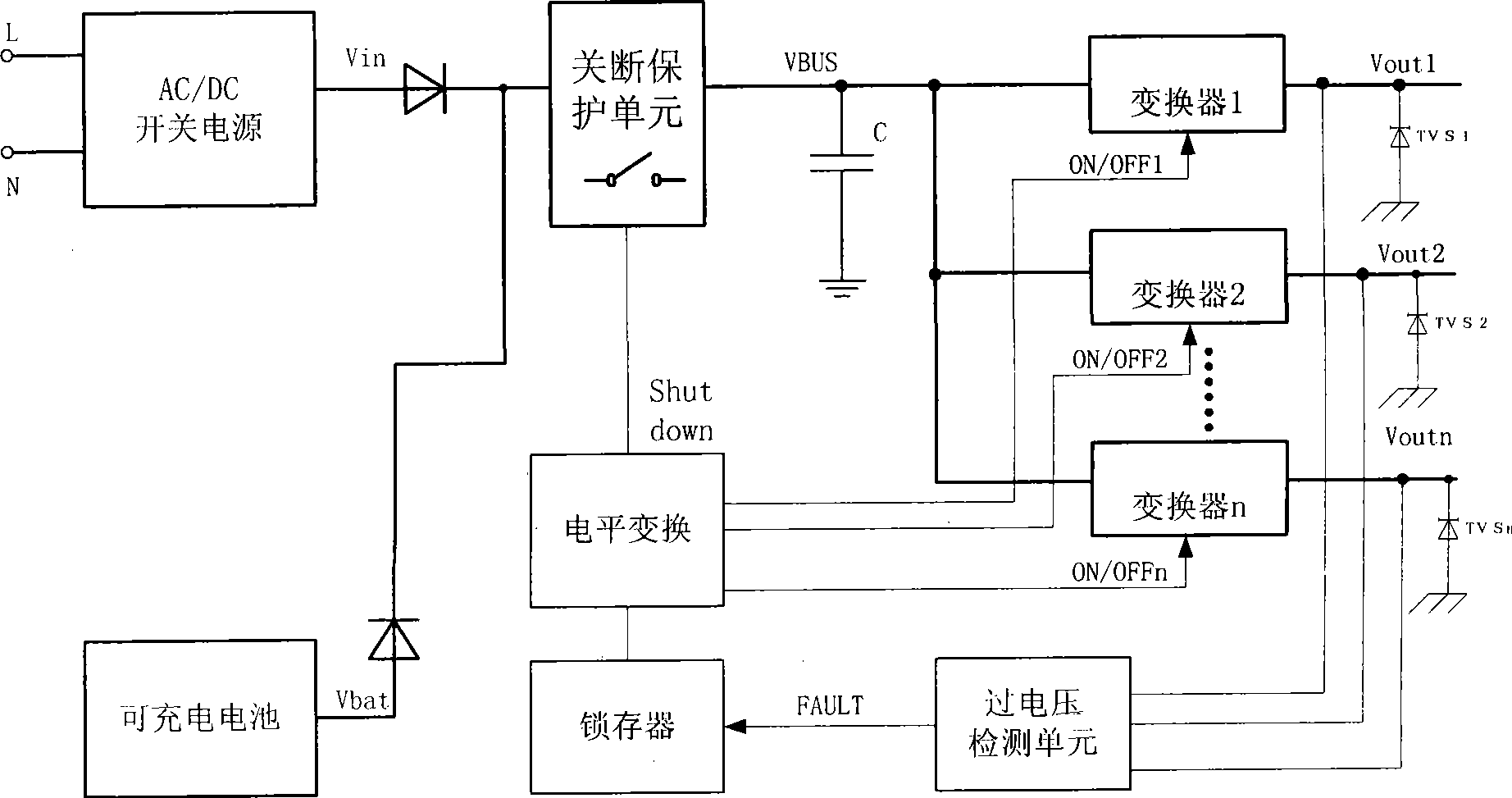
Power supply system and power overvoltage safety protection control method
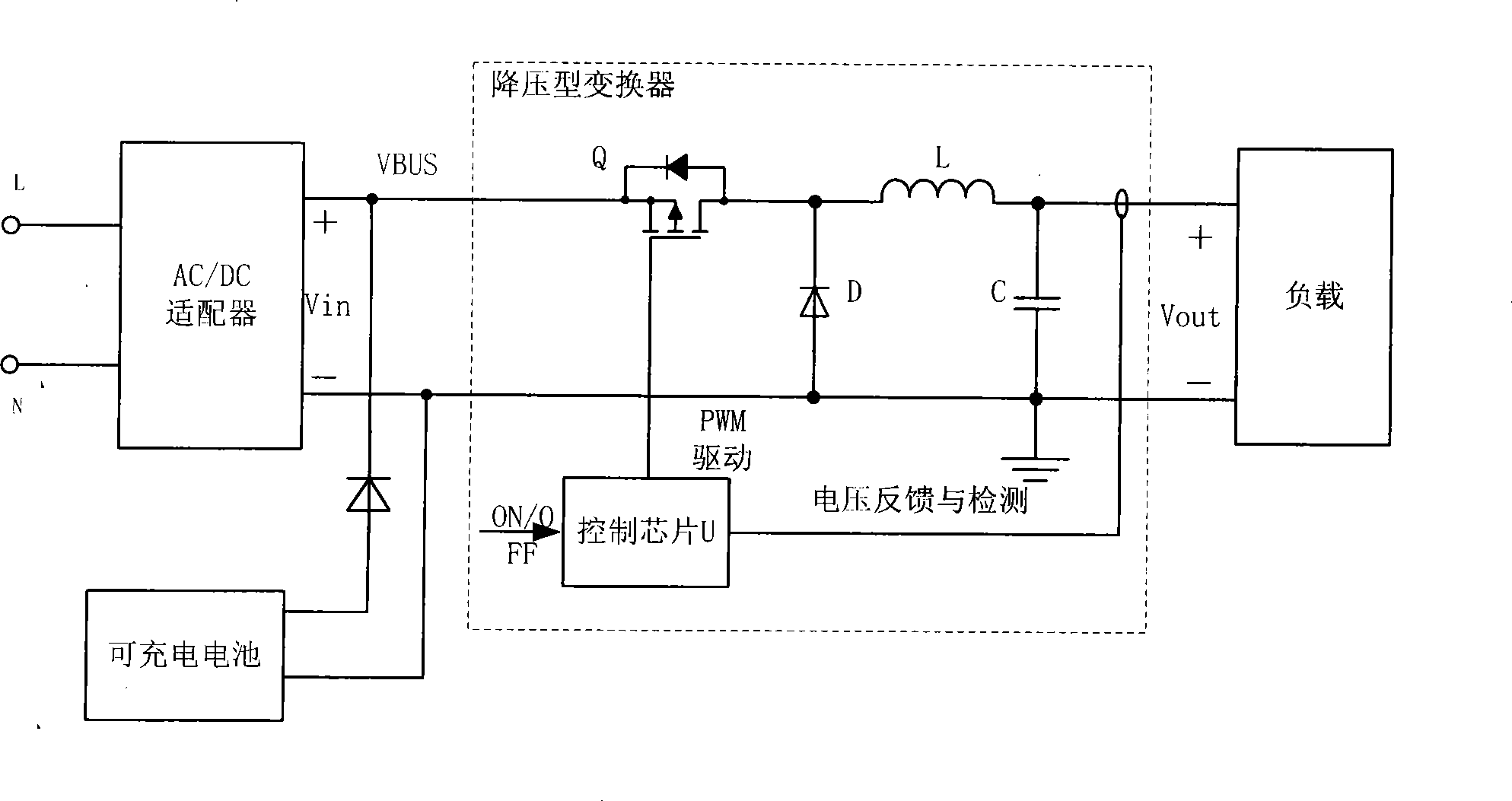
ActiveCN101447666AAvoid security risksRealize three levels of protectionDc-dc conversionArrangements responsive to excess voltageOvervoltageDc transformers
A power supply system and power overvoltage safety protection control method, the power supply system comprises an AC / DC switching power supply, a spare battery and at least one DC / DC transformer, and further comprises an overvoltage detection unit which is used for detecting the output voltage of each DC / DC transformer in real time, comparing the output voltage of the DC / DC transformer with a reference voltage and outputting a fault signal. When detecting a dangerous voltage at a later stage output, the system firstly clamps and absorbs a transient dangerous voltage, uses the overvoltage detection unit to detect an overvoltage fault signal synchronously, cuts off the power supply to each transformer from the AC / DC switching power supply and the spare battery, and directly turns off a control chip after converting the fault signal into a proper voltage, thereby realizing the tertiary protection of the system, avoiding the safety risk possibly resulted from the input and output short circuit of the transformer, and improving the reliability of the system.
Owner:SHENZHEN MINDRAY BIO MEDICAL ELECTRONICS CO LTD
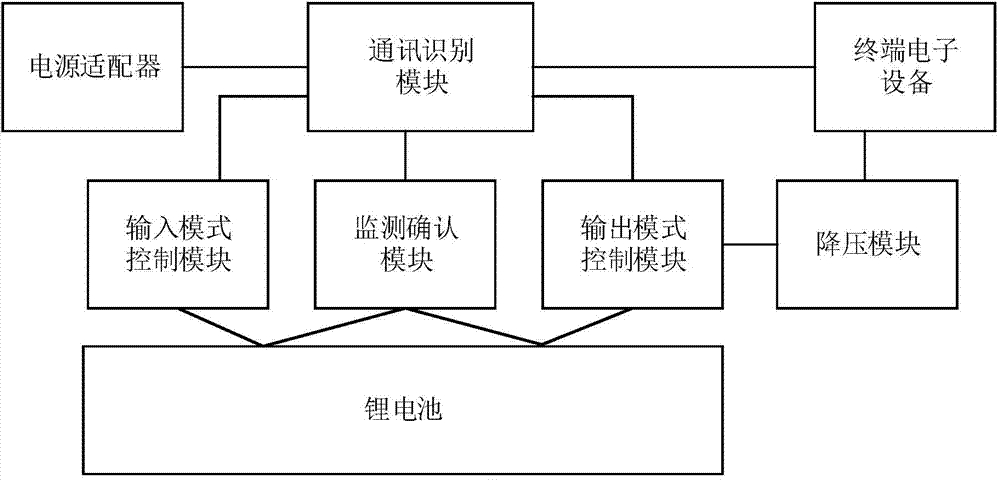
Rapid charging method and system for portable power source
ActiveCN104124483AFast chargingShorten charging timeCircuit monitoring/indicationDifferent batteries chargingMode controlFast charging
The invention discloses a rapid charging method and system for a portable power source. A communication recognition module is connected to a power adaptor or terminal electronic equipment for recognizing whether to support a large-current charging mode, an input mode control module and an output mode control module are connected with the communication recognition module simultaneously, and a charging input mode or a charging output mode is selected according to a recognition result of the communication recognition module, so that the portable power source is charged or the portable power source is used for charging the terminal electronic equipment. According to the method and the system, the input and output current can be intelligently selected and controlled, and 2-5A large current can be supplied to increase the charging speed and shorten the charging time; when the electronic equipment is charged, the voltage-reduction scheme is adopted to improve the charging efficiency; a monitoring confirmation module is additionally arranged, thus well ensuring the charging safety and preventing safety risk.
Owner:DONGGUAN LARGE ELECTRONICS CO LTD
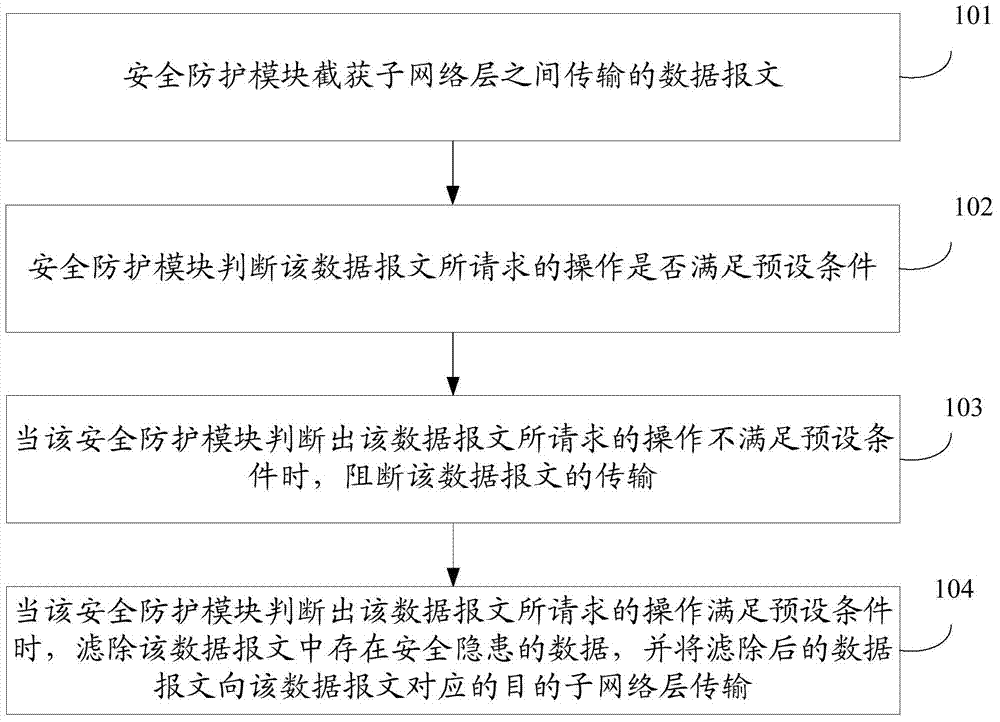
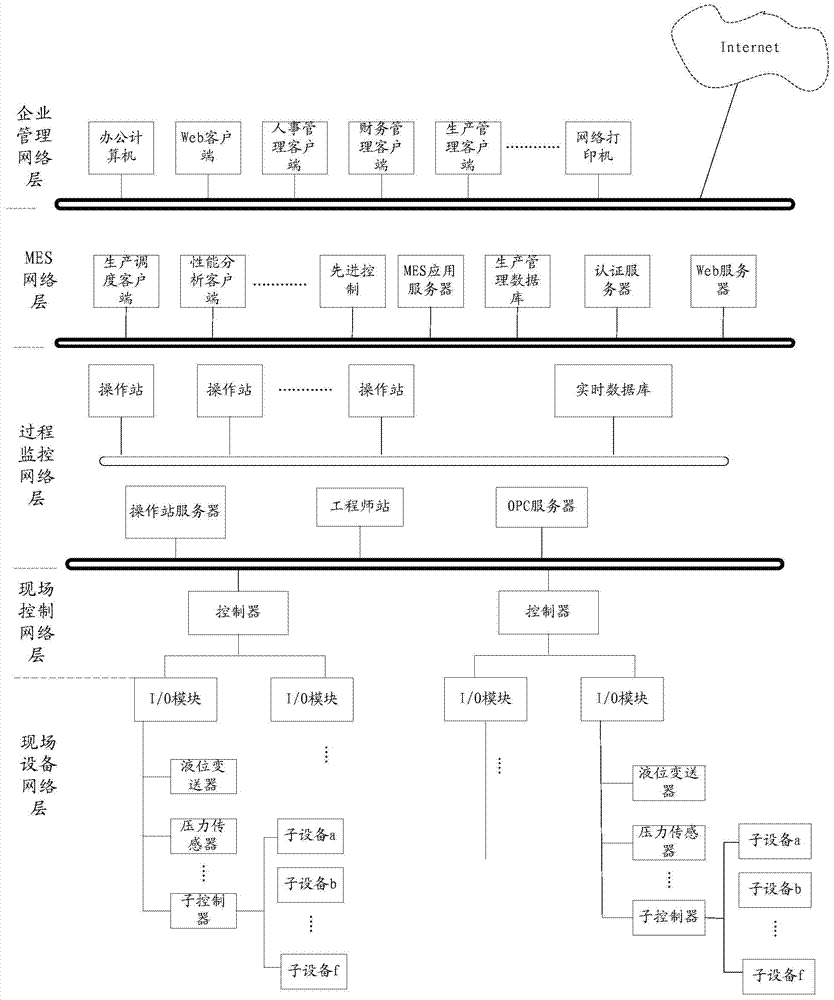
Method and system for security protection of industrial control network
ActiveCN103491108AAvoid paralyzing situationsImprove securityTransmissionData transmissionComputer science
The invention discloses a method and system for the security protection of an industrial control network. According to the method, the industrial control network is divided into at least two sub-network layers, wherein a firewall is arranged between the industrial control network and external networks, and a security protection module which controls data transmission among the sub-network layers is arranged in the industrial control network. The method comprises the following steps that the security protection module intercepts data messages transmitted among the sub-network layers; the security protection module judges whether operations requested by the data messages meet preset conditions or not; when judging that the operations do not meet the preset conditions, the security protection module interrupts the transmission of the data messages; when judging that the operations meet the preset conditions, the security protection module removes data with potential security risks from the data messages, and then transmits the data messages, from which the data with potential security risks are removed, to destination sub-network layers corresponding to the data messages. Through the method, the security and reliability of the industrial control network can be improved.
Owner:ZHEJIANG SUPCON RES
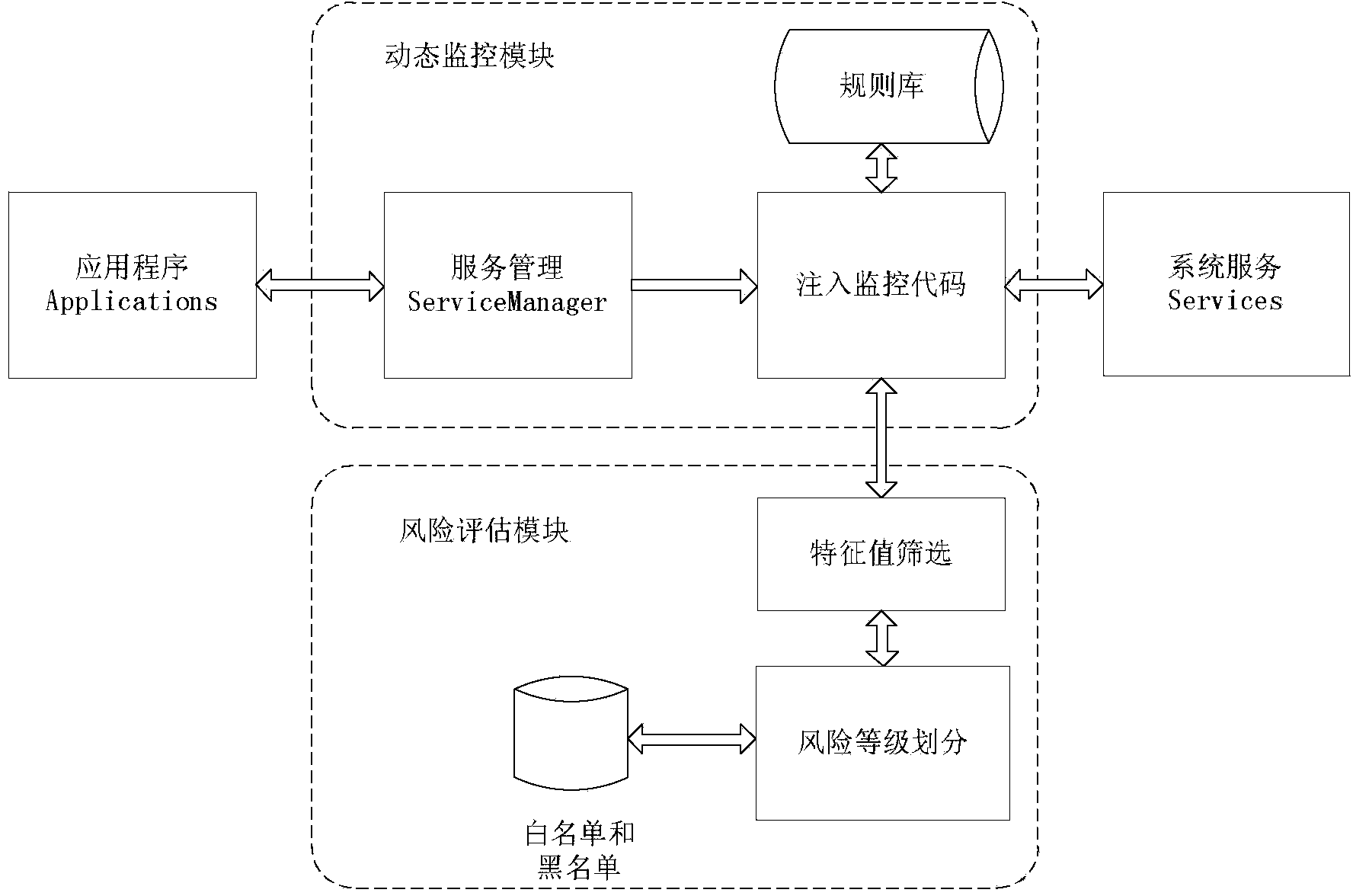
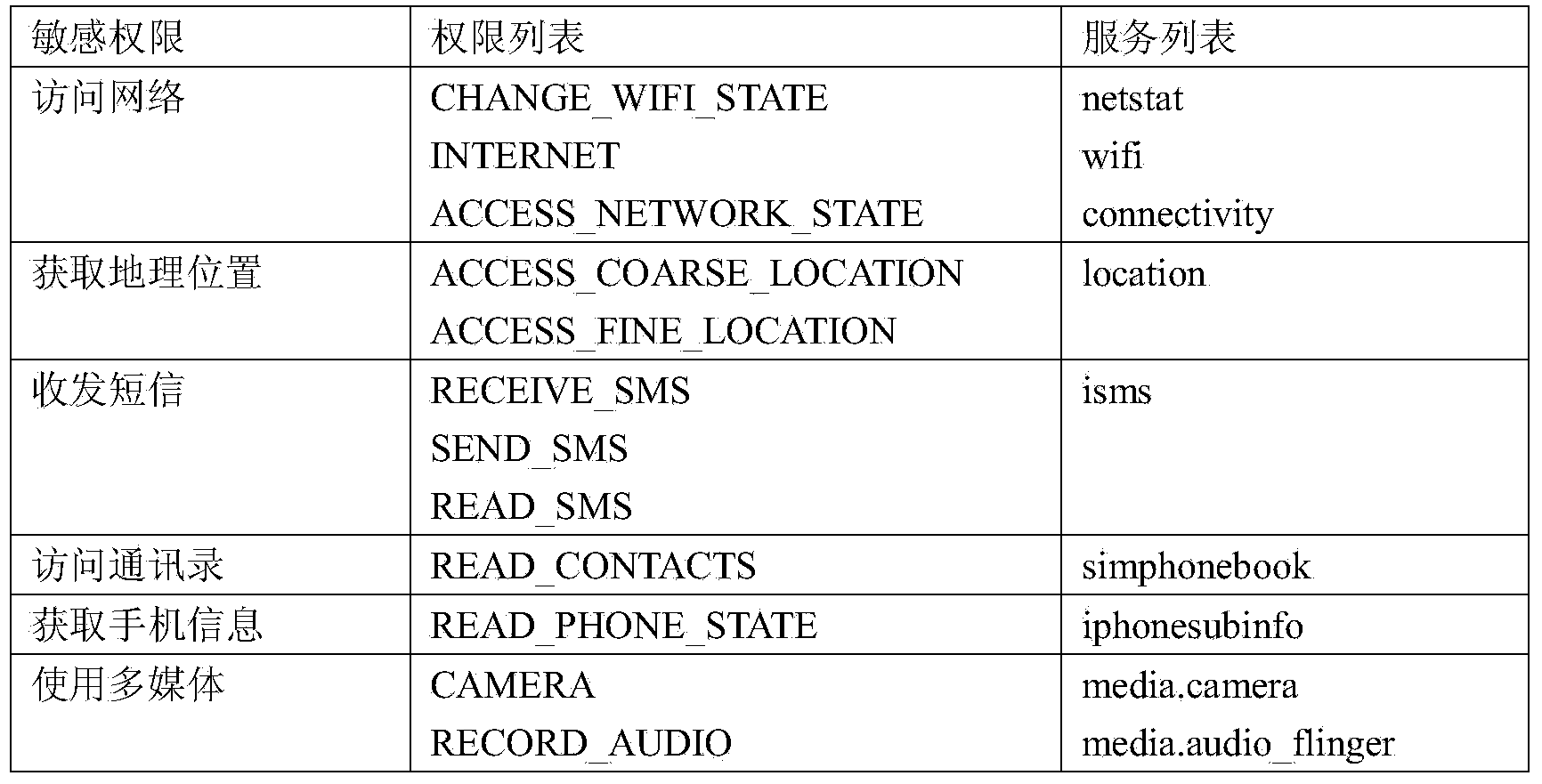
Android application program risk assessment method based on dynamic monitoring
InactiveCN103927485ADetect security risksPredict maliciousnessPlatform integrity maintainanceDynamic monitoringInformation security
The invention discloses an Android application program risk assessment method based on dynamic monitoring, and belongs to the technical field of information safety. The method comprises the steps that firstly, monitoring codes are dynamically injected to a ServiceManager system process, and the aim of monitoring behaviors is achieved by monitoring an application service of an application program; then the risk grade of the application program is determined according to the behavior features of the application program, wherein the behavior features comprise whether a sensitivity operation is executed or not, whether operating is carried out in a background or not, whether operation frequency exceeds a certain threshold value or not and the like. The risk is divided into five grades, and meanwhile a white list and black list mechanism is set up to improve efficiency and accuracy. According to the method, maliciousness of unknown (malicious) software can be predicated, and potential safety hazards of an Android platform can be detected.
Owner:SOUTHEAST UNIV
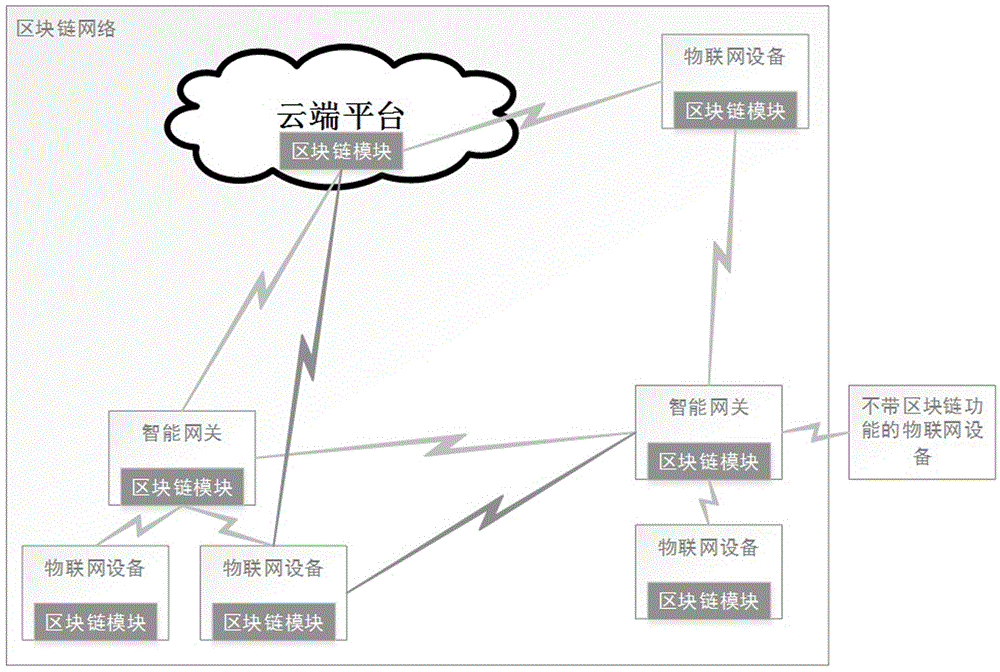
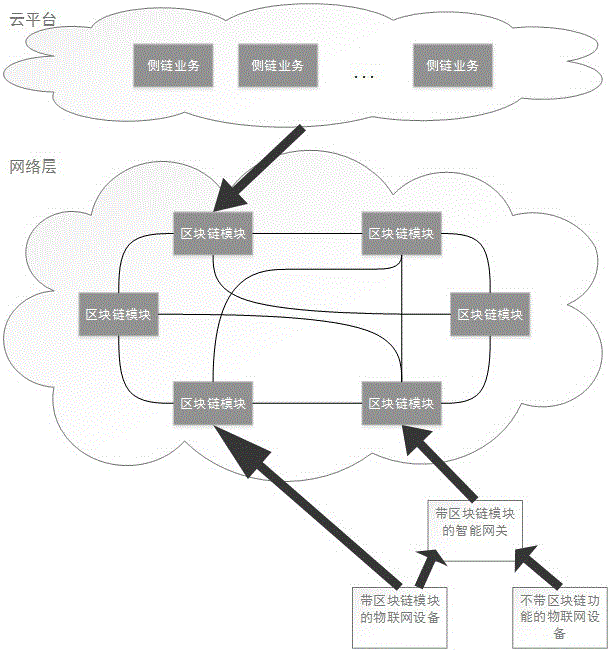
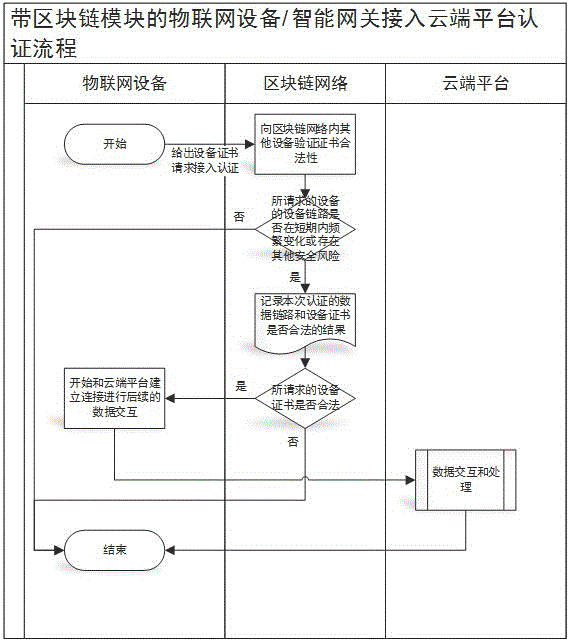
Access authentication method of internet-of-things fog device at cloud platform based on blockchain
The present invention relates to an access authentication method of an internet-of-things fog device at a cloud platform based on a blockchain. An internet-of-things device initiates an agent request of accessing a cloud platform to an intelligent gateway with a blockchain module through the means of device authentication; the blockchain module of the intelligent gateway accesses a blockchain network and gives out device certificate of the internet-of-things device and the device certificate of the intelligent gateway to the blockchain network for requiring authentication, wherein the blockchain network determines whether the request link of the intelligent gateway is frequently changed in a short period or has safety risk or not, and then verifies the legality of the intelligent gateway certificate; the same mode is employed to verify the legality of the device certificate of the internet-of-things device; and if the internet-of-things device with the blockchain module also can initiate the agent request of accessing the cloud platform, the authentication access mode is the same as the authentication mode of the intelligent gateway. The dependence on the cloud platform and the usage frequency are reduced, and the risks of the cloud platform being sniffered and injected at the aspect of the device access are reduced.
Owner:FUJIAN SHIDA COMP EQUIP
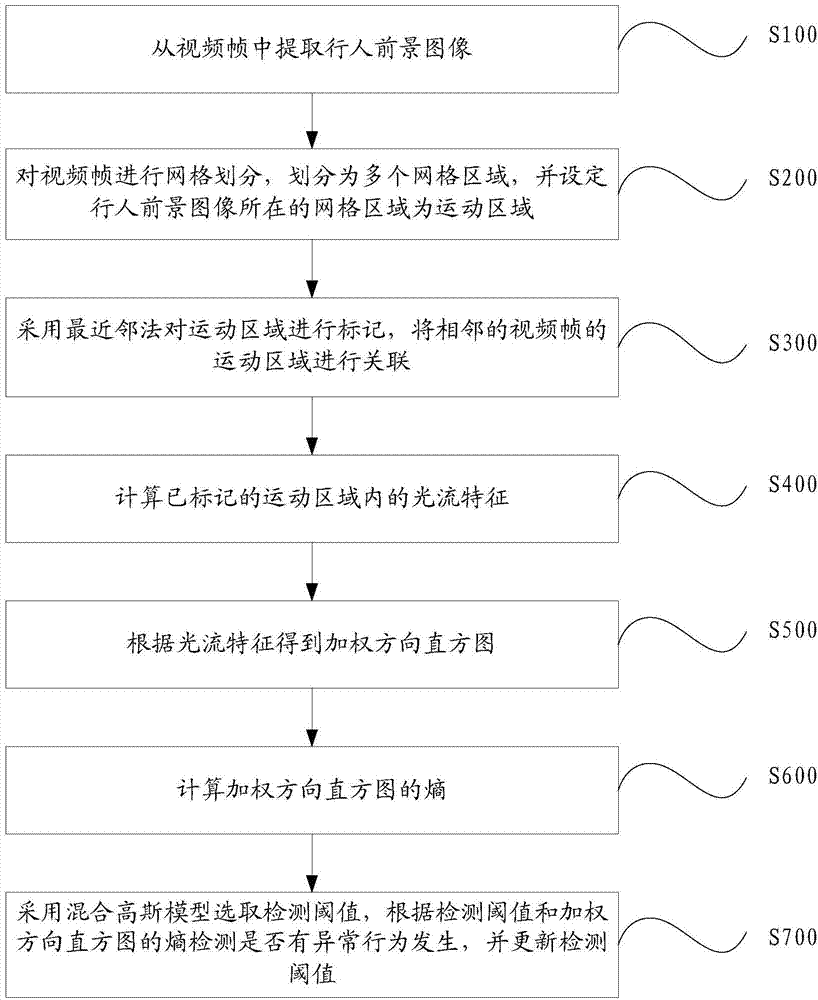
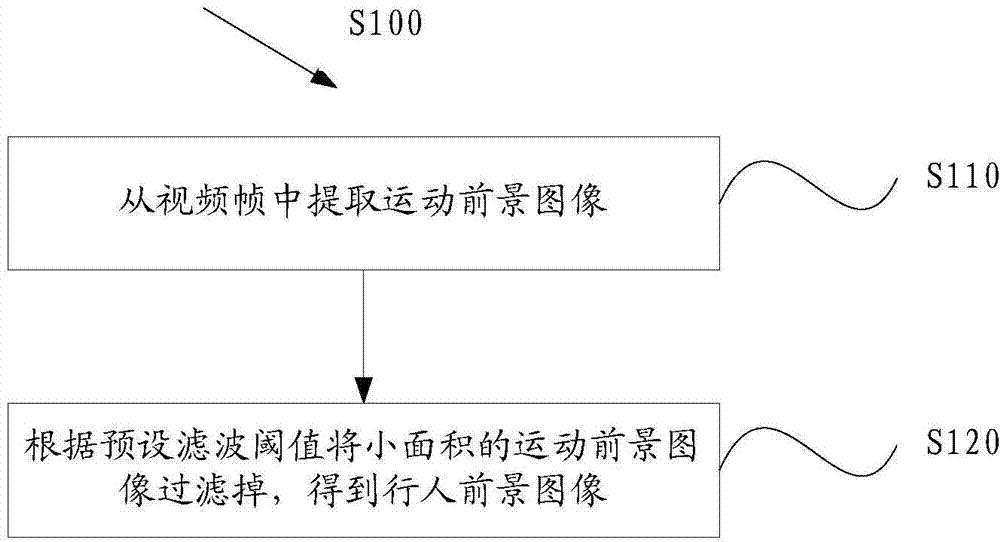
Video analysis based abnormal behavior detection method and system
ActiveCN104123544AReduce workloadEndanger public safetyCharacter and pattern recognitionAnomalous behaviorNear neighbor
The invention provides a video analysis based abnormal behavior detection method and system. The video analysis based abnormal behavior detection method comprises the following steps of extracting pedestrian foreground images from video frames; performing mesh generation on the video frames to divide the video frames into a plurality of mesh areas and setting the mesh areas in which the pedestrian foreground images are arranged to be movement areas; marking the movement areas through a nearest neighbor method and correlating the movement areas of the adjacent video frames; calculating light stream characteristics of the marked movement areas; obtaining a weighting direction histogram according to the light stream characteristics; calculating entropy of the weighting direction histogram; selecting a detection threshold value through a Gaussian mixture model, detecting whether an abnormal behavior is generated or not according to the detection threshold value and the entropy of the weighting direction histogram and updating the detection threshold value. The nested state machine based deduction process control method can automatically detect the abnormal behavior in a video scene, avoid the abnormal behavior disturbing the public plate order and endangering the public security and personal safety, reduce personnel workload and avoid potential risks caused by leak detection and error detection.
Owner:CRSC COMM & INFORMATION GRP CO LTD
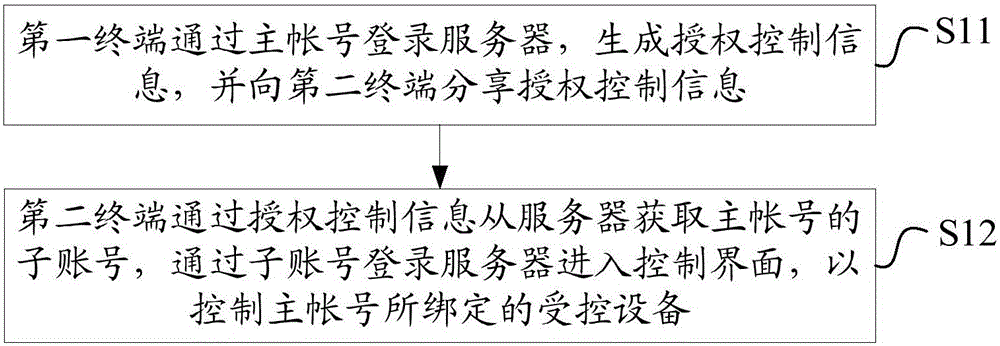
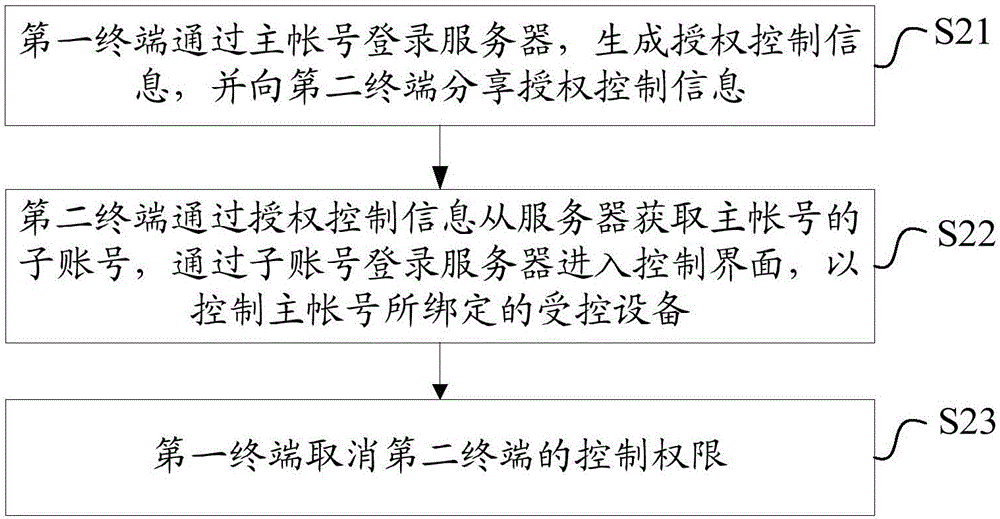
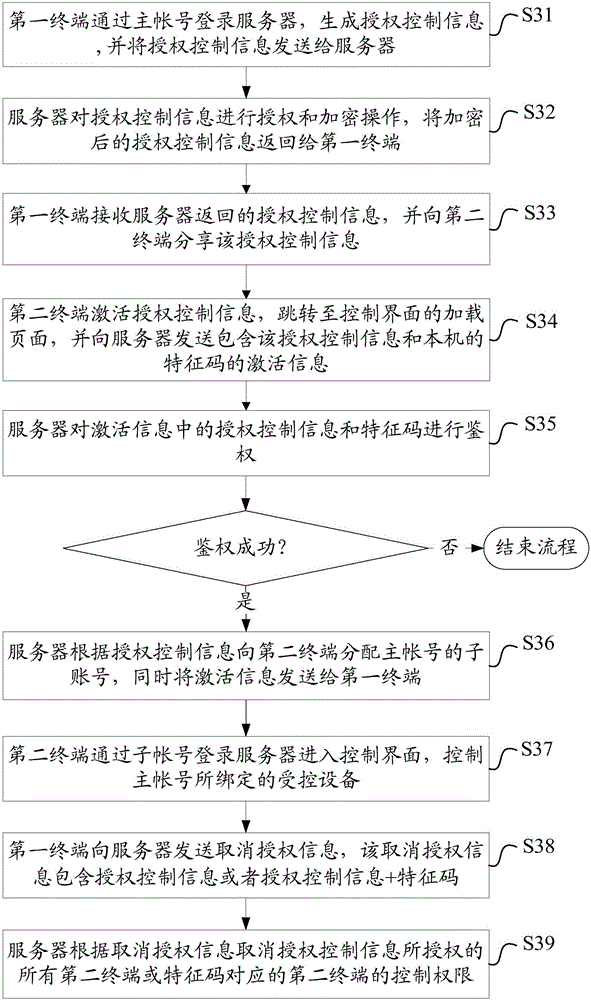
Control authority sharing method and system
The invention discloses a control authority sharing method and system. The method comprises the following steps that: a first terminal logs in to a server through a master account number to generate authorization control information, and shares the authorization control information with a second terminal; the second terminal obtains a sub account number of the master account number from the server through the authorization control information, logs in to the server through the sub account number to enter a control interface so as to control a controlled device bound by the master account number. Thus, the rapid sharing of control authority of an intelligent household appliance is realized, so that temporary users do not need to download and install applications, register and log in and carry out device binding and other complicated operations, the intelligent household appliance can be controlled only by activating the authorization control information, the operation is simple and convenient, and the flexibility of the intelligent household appliance in control is improved. At the same time, the sub account number is controlled by the master account number, security risks caused by authority conflict do not exist, and the reliability of control on the intelligent household appliance is improved.
Owner:SHENZHEN OURUIBO ELECTRONICS
Double platform system for rotary exchange
ActiveCN101071275ASimple structureAvoid safety hazardsSemiconductor/solid-state device manufacturingPhotomechanical exposure apparatusEngineeringElectronic equipment
The invention provides a rotating dual-exchange system. The technology in the two-station system has complex structures, and the high costs and dual-exchange potential safety problems when there are problems. The invention of the rotary dual-exchange system for one of the main frame and has operations in the two electronic devices, including set up its main base on the framework of the operations of the two should be installed in the symmetry and the stage - The first and second operations desk, base stations used to drive along the base of the center-rotating drives used to control devices and base stations driven deviser base rotation in order to achieve the first - and second operation Taiwan transposition operation control module. By the invention of the rotary dual-exchange system can improve the efficiency and reduce costs.
Owner:SHANGHAI MICRO ELECTRONICS EQUIP (GRP) CO LTD
Information system service-level security risk analysis
Information system service-level security risk analysis systems, methods, and Graphical User Interfaces are disclosed. Assets of an information system that have relationships with a service provided by the information system are identified, and at least one security risk to the service is determined by analyzing security vulnerabilities associated with the identified assets. A consolidated representation of the service is provided, and includes an indication of the determined security risk(s) and an indication of a relationship between the service and at least one of the identified assets. The security risk indication may include indications of multiple security parameters. Security risks may be represented differently depending on whether they arise from a security vulnerability of an asset that has a relationship with the service or a security vulnerability of an asset that has a relationship with the service only through a relationship with an asset that has a relationship with the service.
Owner:ALCATEL LUCENT SAS
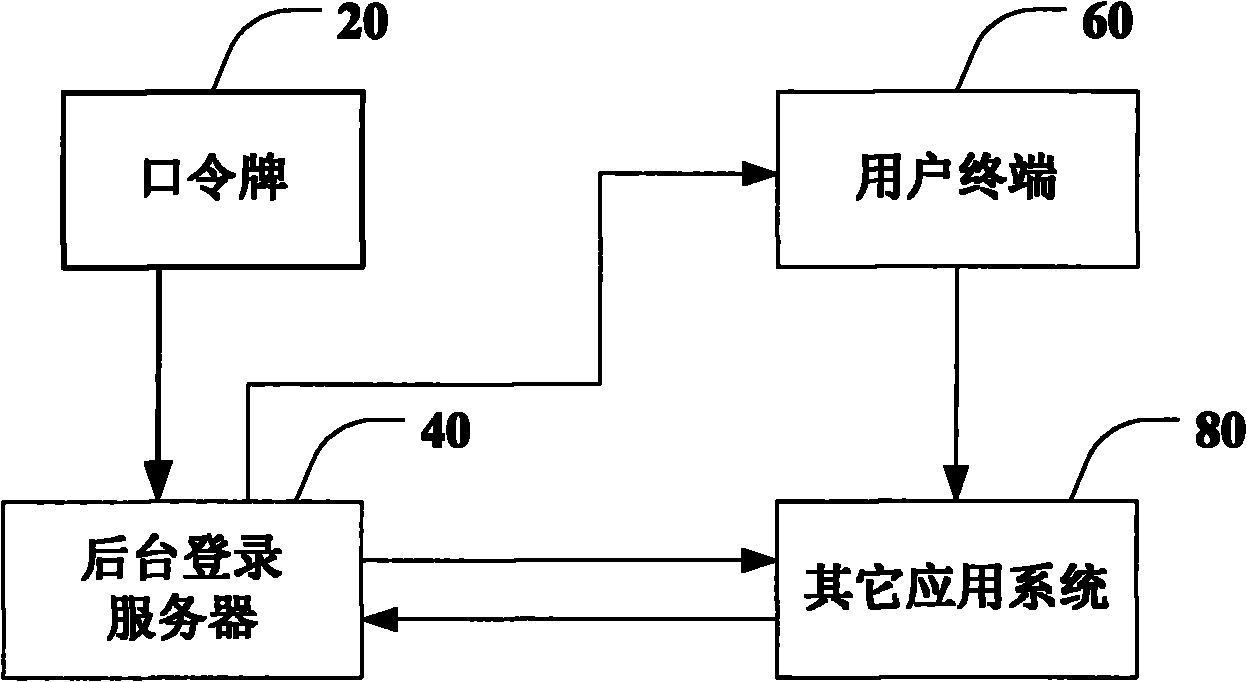
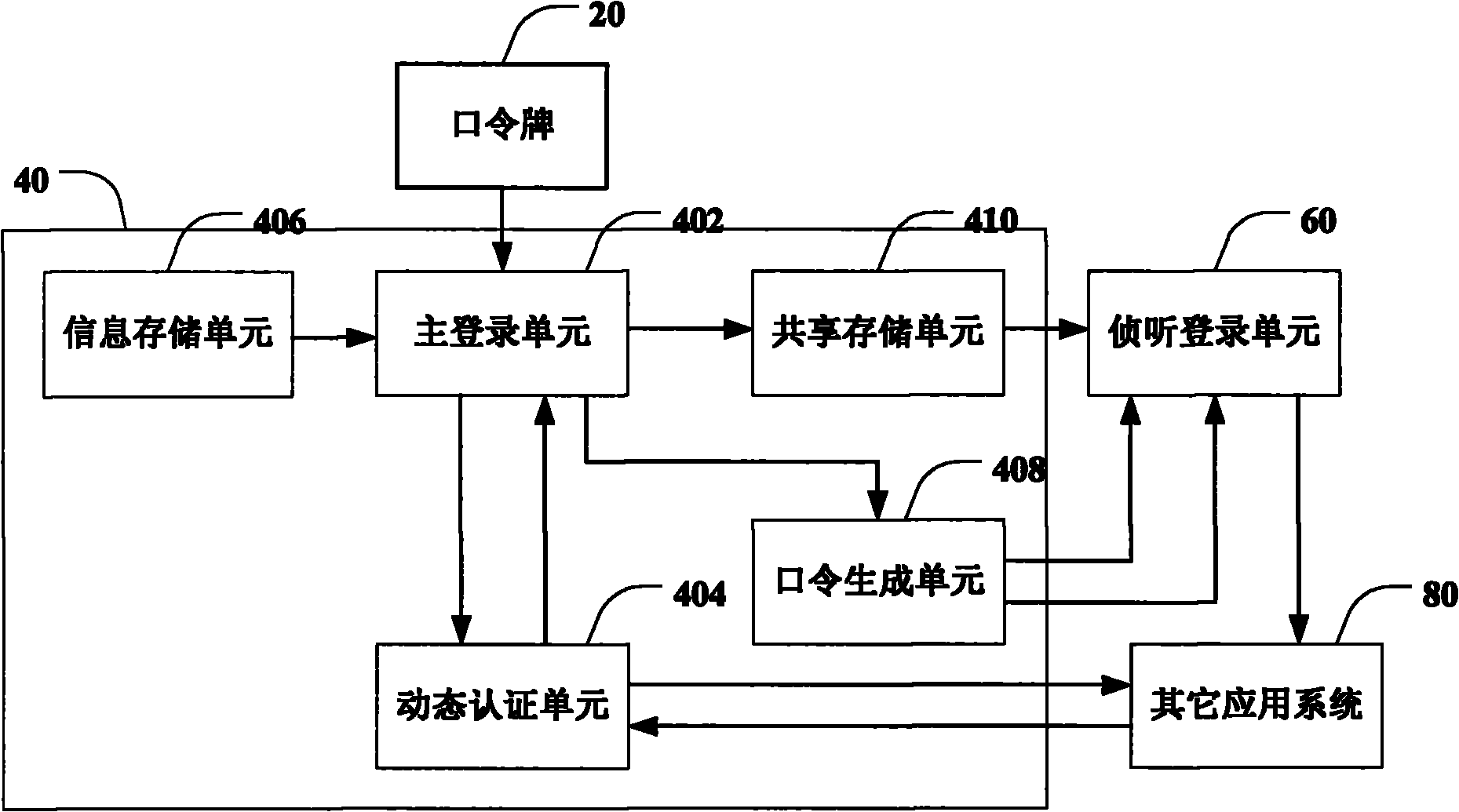
Single sign-on method and single sign-on system
InactiveCN101877637AReduce security risksReduce complexityUser identity/authority verificationPasswordSafety risk
The invention discloses a single sign-on method and a single sign-on system. The single sign-on method comprises the steps of: receiving and authenticating a primary account name and a primary account password of a user; acquiring sub account names for all applications of the user after the user passes primary account authentication; generating a corresponding sub account password according to the sub account name selected by the user, and sending the sub account name and the sub account password to an application system corresponding to the sub account; receiving the sub account name and the sub account password which are forwarded by the application system, and generating a sub account authentication password according to the sub account name to authenticate the sub account password; and when the authentication is successful, completing the signing on to the application system. In the single sign-on method and the single sign-on system of the embodiment of the invention, secondary sign on authentication is realized by automatically generating the sub account passwords of all the application systems and filling out to all the application systems in a substitute way, thereby reducing the safety risks of application systems, caused by the disclose of all the application system passwords stored in a single sign-on platform, and also reducing the operation complexity.
Owner:中国移动通信集团江西有限公司 +1
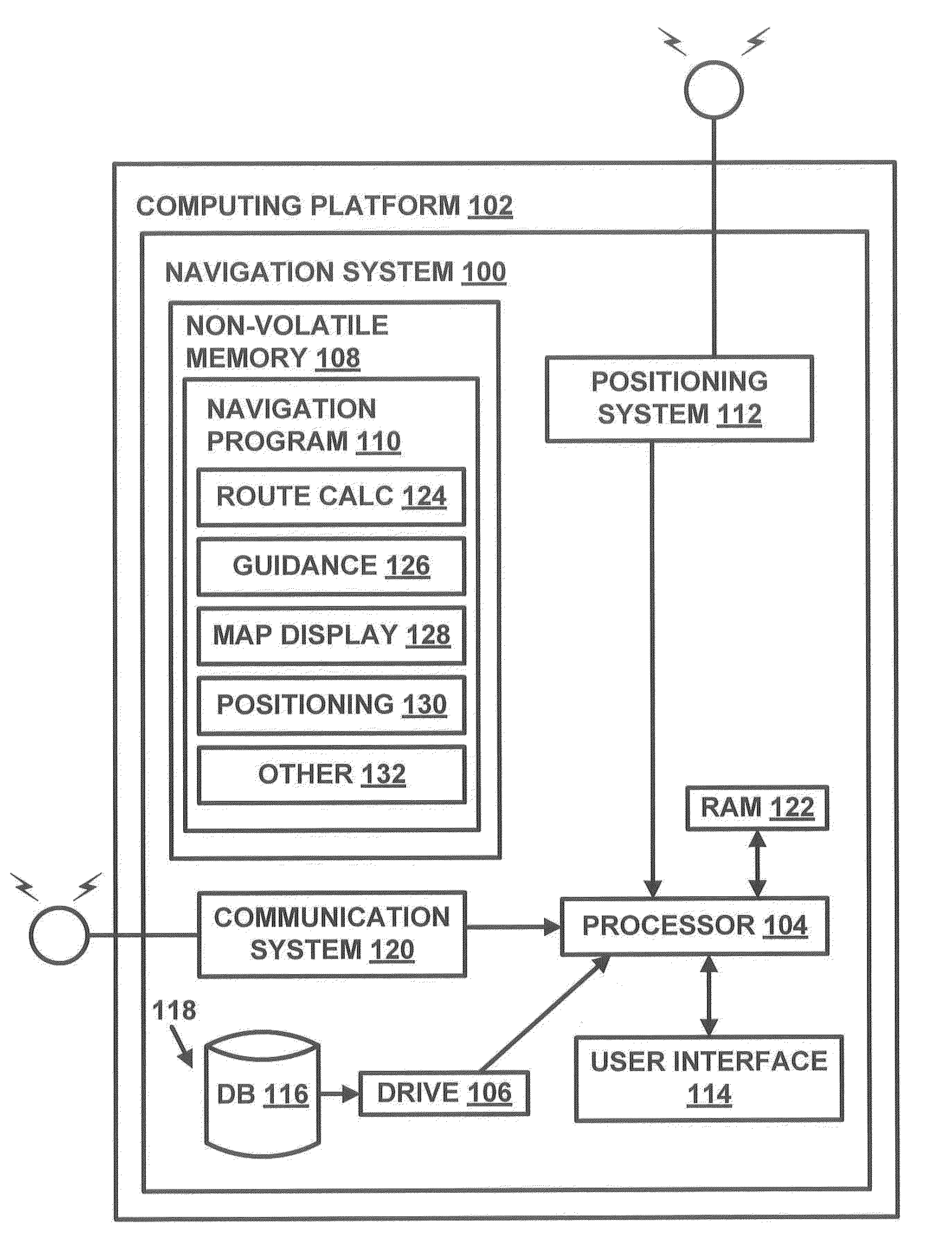
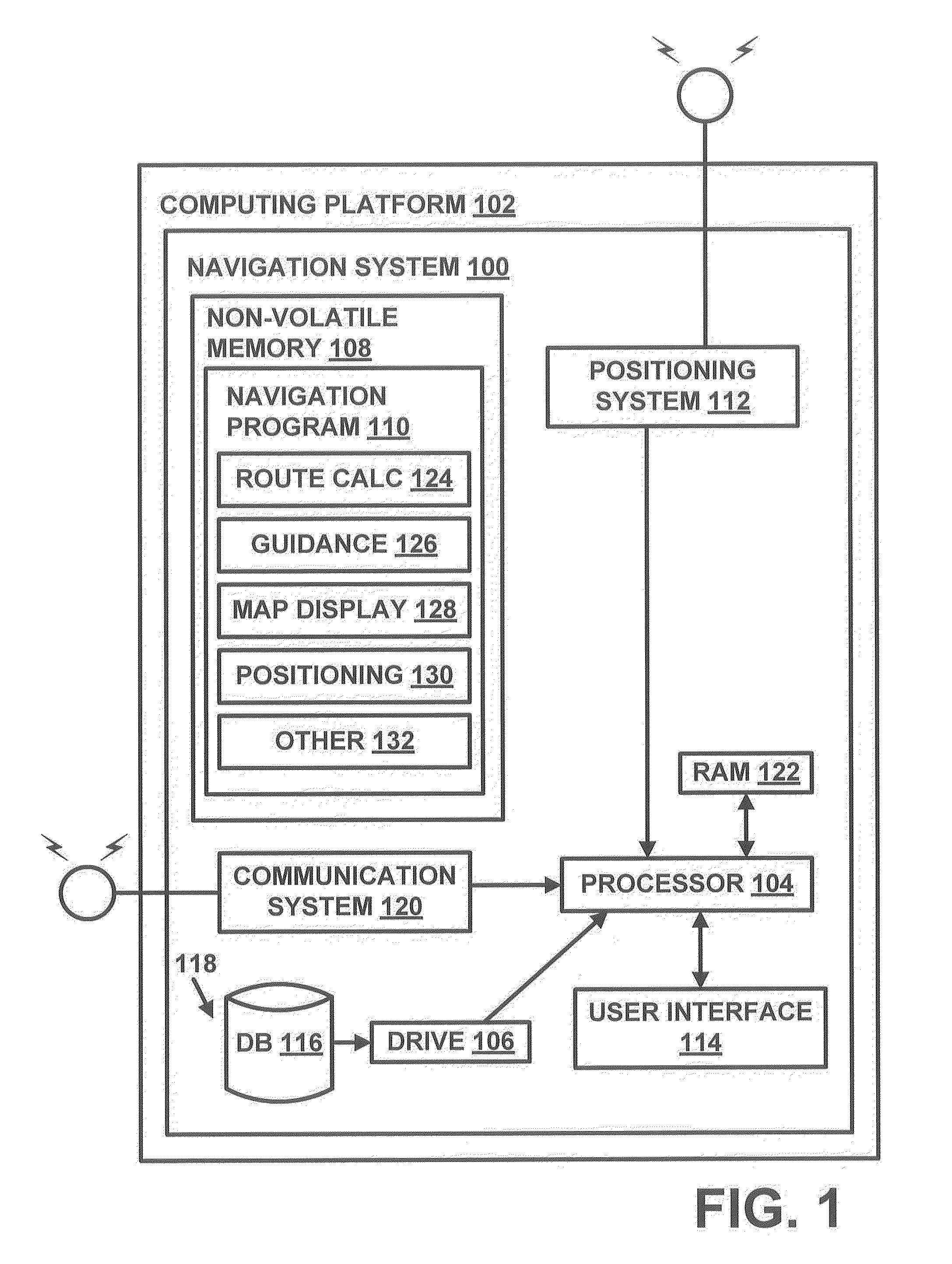
Method of operating a navigation system to provide a pedestrian route
ActiveUS20110246055A1Minimize safety costMinimizes safety costInstruments for road network navigationRoad vehicles traffic controlNavigation systemPedestrian
A computer implemented method of operating a navigation system to provide a pedestrian route is provided. The method comprises receiving a request for a route from an origin to a destination. The method evaluates a plurality of pedestrian paths by accessing data representing the pedestrian paths to determine a safety cost associated with including the pedestrian path in the route. The safety cost indicates a safety risk for the pedestrian. The method provides the route comprising the pedestrian paths that form a continuous navigable route between the origin and the destination that minimize the safety cost.
Owner:HERE GLOBAL BV
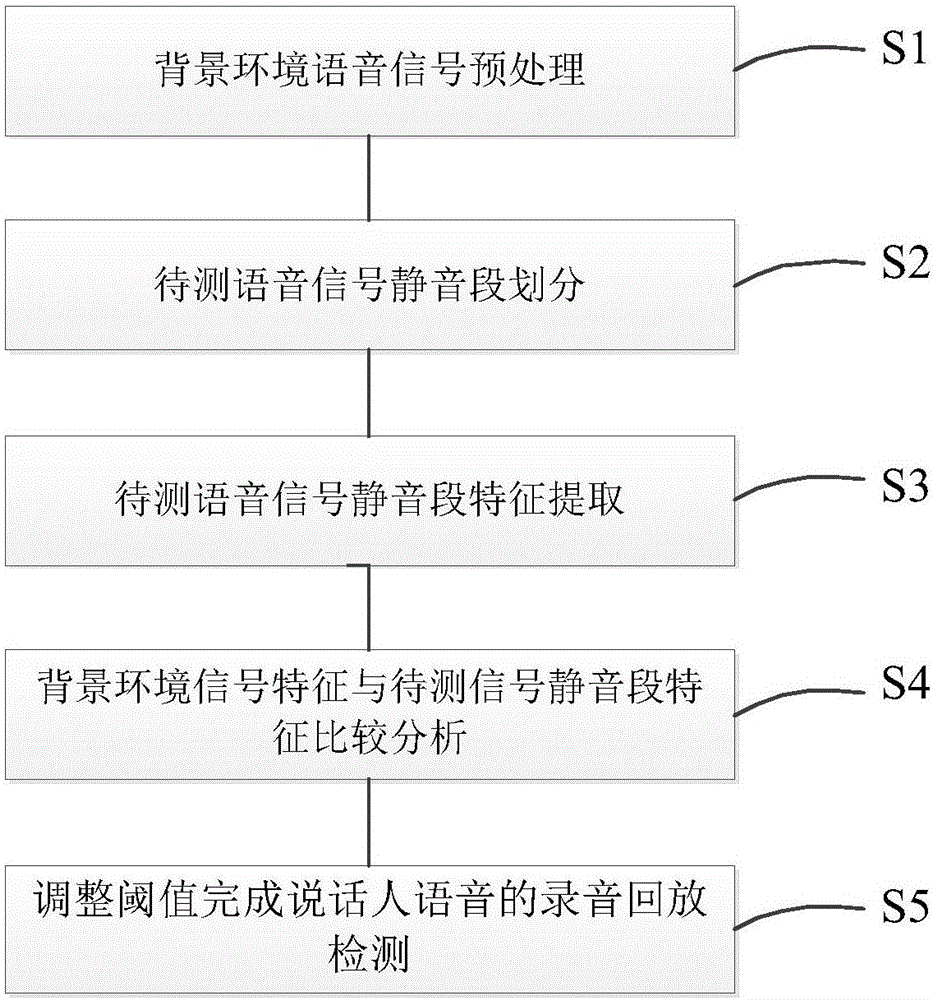
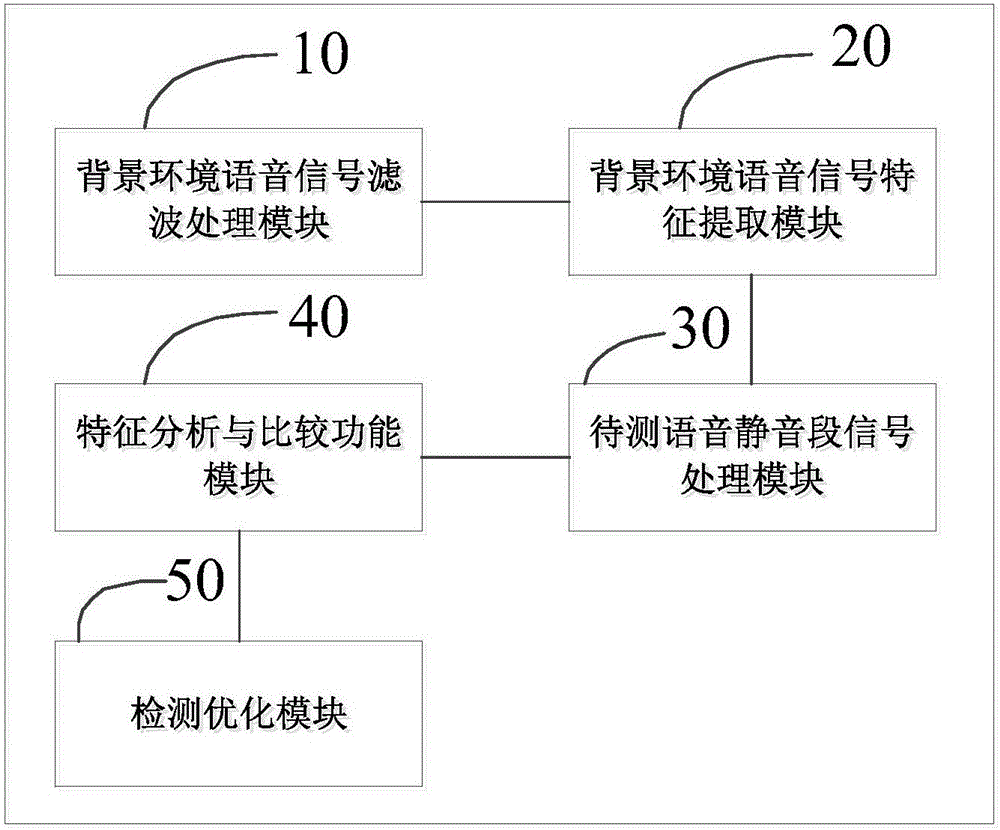
Speaker voice playback identification method and system based on environmental noise change detection
ActiveCN106531172ARealize recording playback attack detectionAvoid safety hazardsSpeech analysisEnvironmental noiseAutomatic speech
The invention relates to a speaker voice playback identification method and an identification system, in particular to a speaker voice playback identification method and an identification system based on environmental noise change detection. According to the identification method and the identification system provided by the invention, on the basis of environmental noise change before and after to-be-detected voice, it detects whether new noise (including noise introduced due to play equipment channel characteristics) is introduced with the playing of voice recording equipment or not so as to judge whether it is playback or not, so that playback attack detection of an ASV (automatic speech verification) system is implemented in voice detection independent of a specific text, potential safety risks of the ASV system due to playback attack are avoided and the safety guarantee of voice print recognition is completed; and meanwhile, by detecting the play equipment, an assisting effect is also achieved on the detection of speech synthesis invasion and speech switching invasion.
Owner:HUBEI UNIV
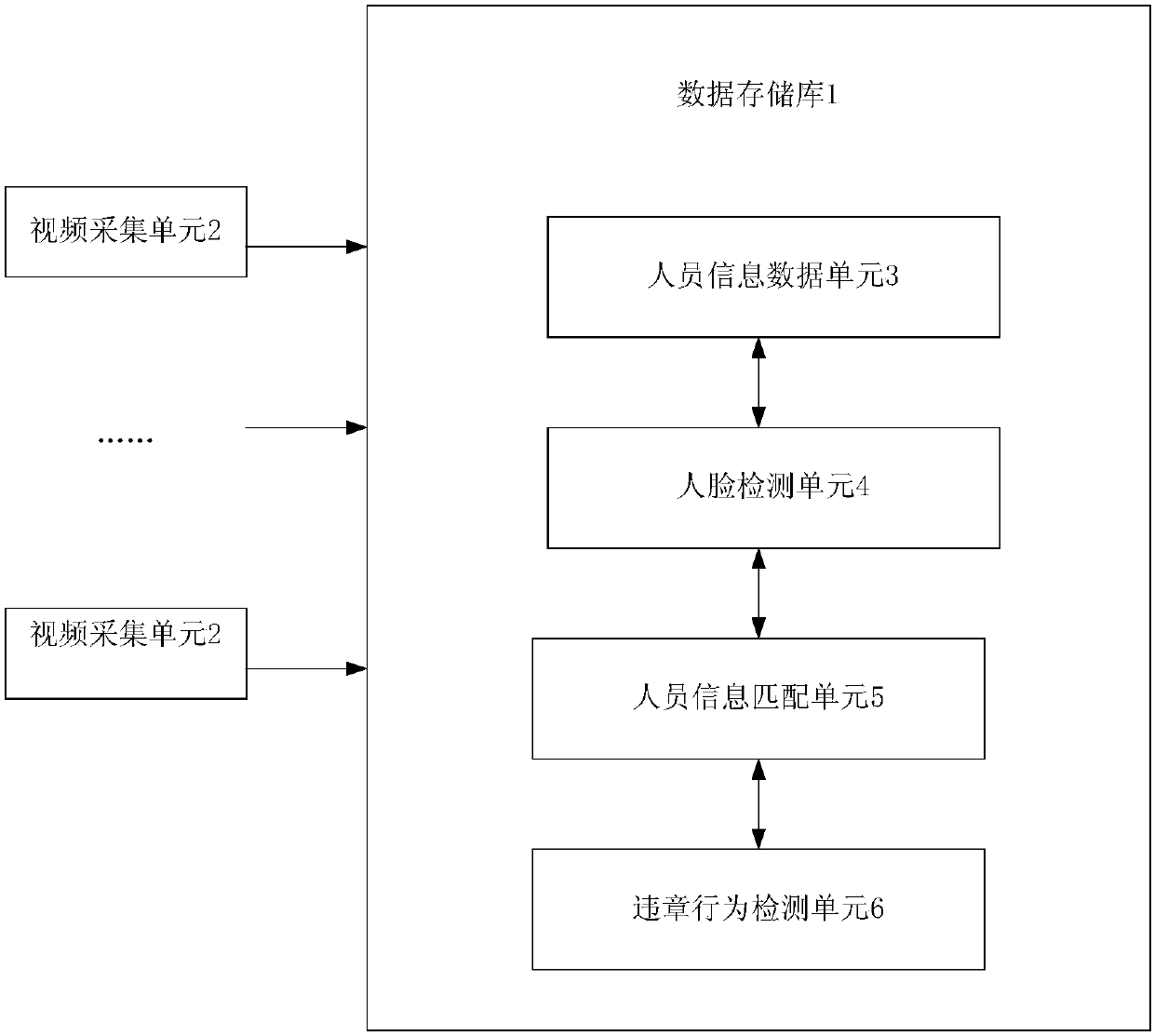
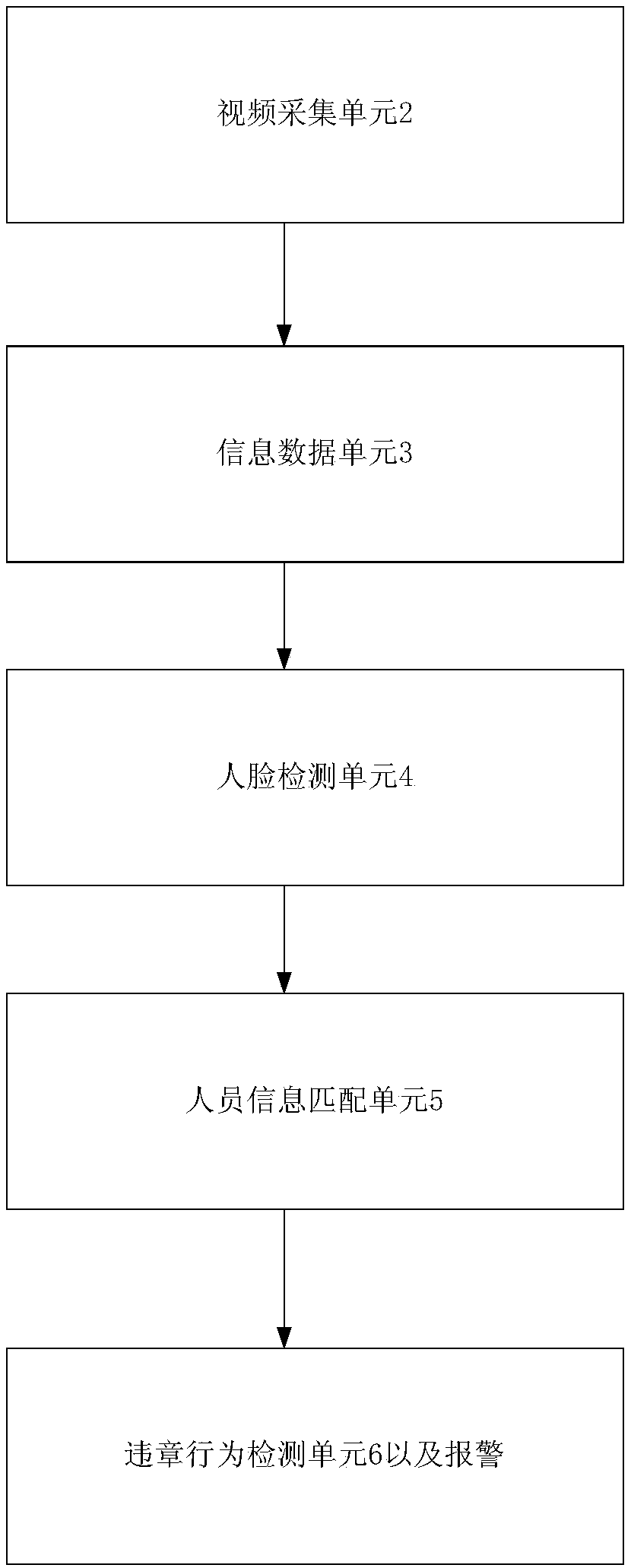
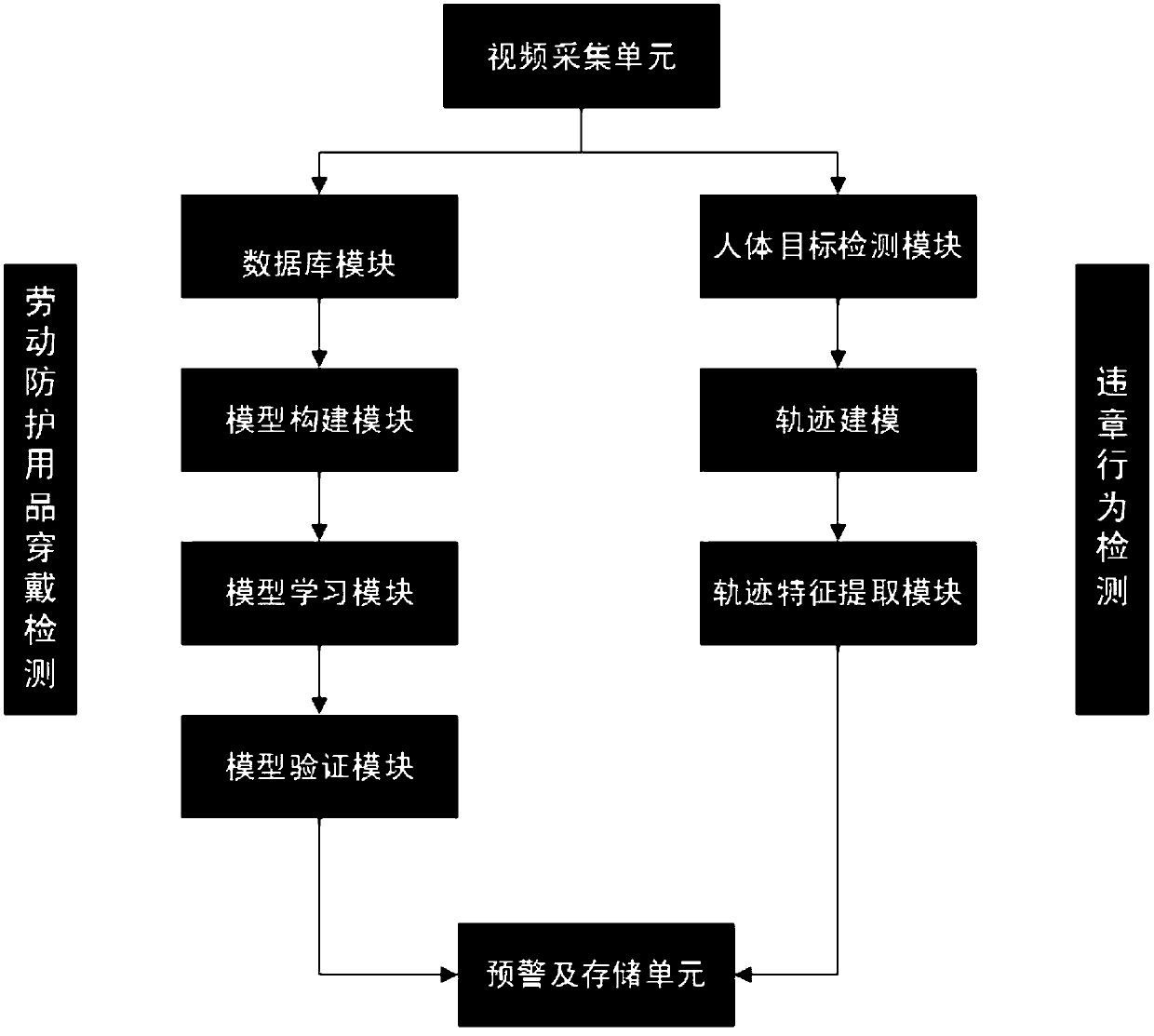
Intelligent monitoring system and on-site violation monitoring method for personnel breaking rules and regulations on working site
PendingCN110119656AEarly warningEffective early warningImage analysisBiometric pattern recognitionFace detectionVideo monitoring
The invention discloses an intelligent monitoring system and an on-site violation monitoring method for personnel violating rules and regulations on a working site. The system comprises a data storagelibrary and a plurality of video acquisition units arranged on a working site. The video acquisition units are in communication connection with the data storage library. The data storage library comprises a personnel information data unit, a face detection unit, a personnel information matching unit and a violation behavior detection unit, the personnel information data unit is in communication connection with the face detection unit, the face detection unit is in communication connection with the personnel information matching unit, and the personnel information matching unit is in communication connection with the violation behavior detection unit. Also provided is an onsite violation monitoring method. Through the machine vision learning network, different violation behaviors of the operating personnel can be early warned rapidly and effectively, factors such as weak personnel safety awareness, behavior habits and difficulty in traditional video monitoring and recognition can be effectively avoided, potential safety hazards caused by the violation behaviors are effectively prevented, and the safety of site construction is improved.
Owner:CHINA PETROLEUM & CHEM CORP +1
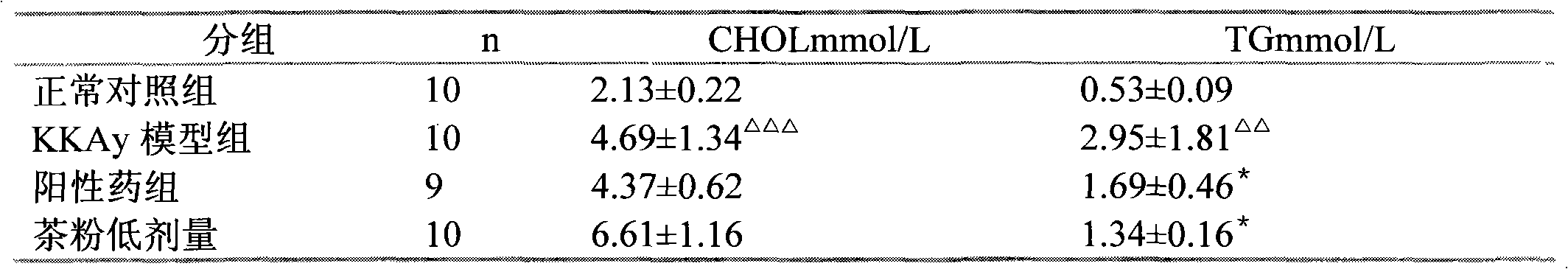
Pu-erh tea extract, preparation method and application
ActiveCN101961061APromote conversionPromote dissolutionMetabolism disorderTea extractionOperabilityBULK ACTIVE INGREDIENT
The invention relates to a Pu-erh tea extract, a preparation method and application. The Pu-erh tea extract has high active ingredient content and low caffeine content, and can reduce blood sugar obviously and lower safety risks. Through the preparation method, active ingredients can be converted and dissolved out effectively. The process has the advantages of meeting the requirements of environmental protection along with simpleness, strong operability, low cost and industrialization; and the quality of the Pu-erh tea extracts is table and controllable.
Owner:TIANJIN TASLY GROUP
Methods of producing antibody conjugates
InactiveUS20050175619A1Easy to useMinimal aggregationHybrid immunoglobulinsAntibody ingredientsAlcoholAntibody conjugate
Owner:SEATTLE GENETICS INC
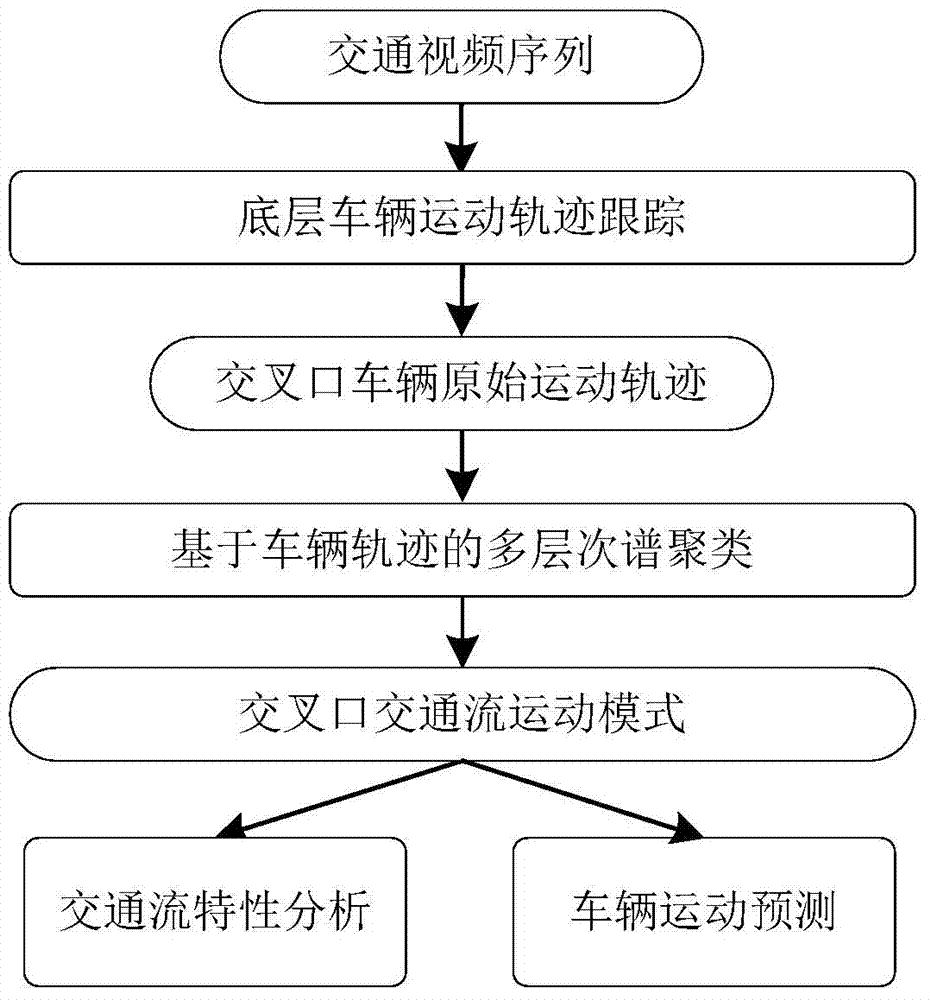
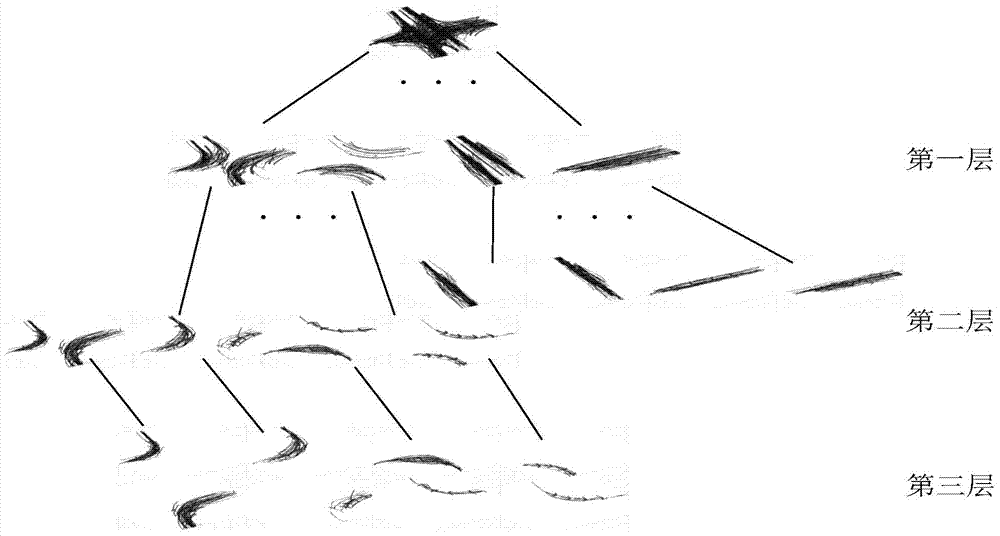
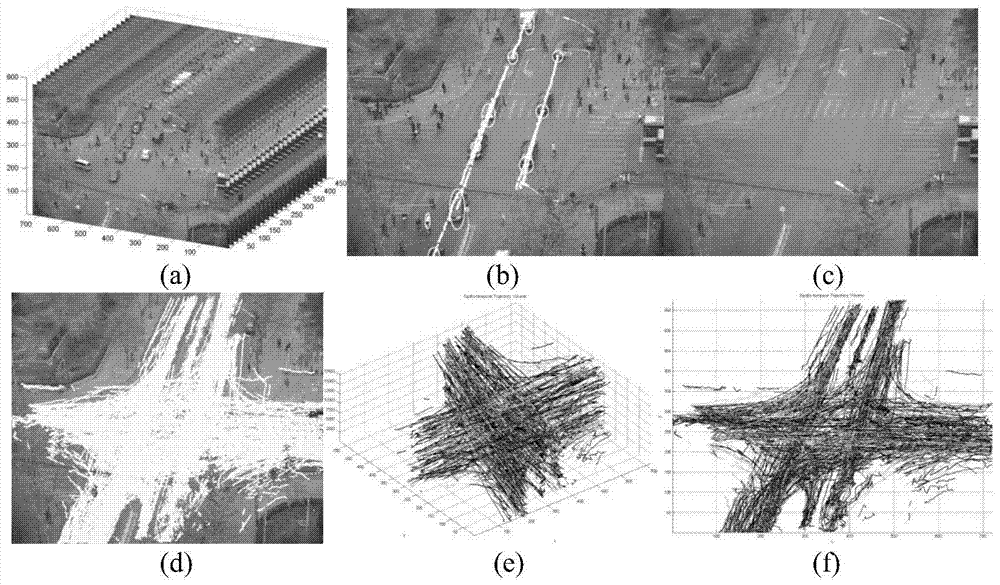
Intersection traffic flow characteristic analysis and vehicle moving prediction method based on trajectory data
ActiveCN104504897AAvoid interferenceReal-time early warning of security risksImage analysisDetection of traffic movementTraffic characteristicMobile vehicle
The invention discloses an intersection traffic flow characteristic analysis and vehicle moving prediction method based on trajectory data, and belongs to the technical field of intelligent traffic system and traffic flow parameter acquisition. The method starts with space transient analysis of a vehicle original trajectory, and describes and analyzes trajectory local geometrical characteristics at different angles, forms a multilevel spectral clustering processing framework based on a vehicle original rough movement track, and automatically extracts and analyzes a plurality of traffic direction modes of an intersection included in the trajectory data. With the basis, the method can acquire intersection sub-phase (signal control intersection) traffic flow and travel time of vehicles in all directions passing through the intersection, and other detailed traffic characteristic parameters, as important complement of conventional traffic data. Through tracking travelling tracks of all moving vehicles at present moment, a traffic direction trajectory mode matching method is used to predict the next behavior of the vehicles, thereby being beneficial for warning safety risks which may exist on an intersection in real time.
Owner:中天思创信息技术(广东)有限公司
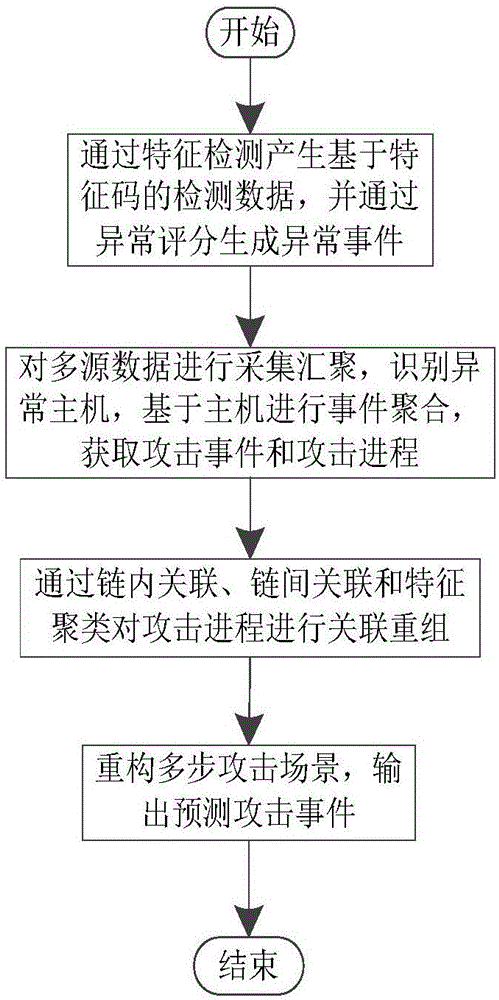
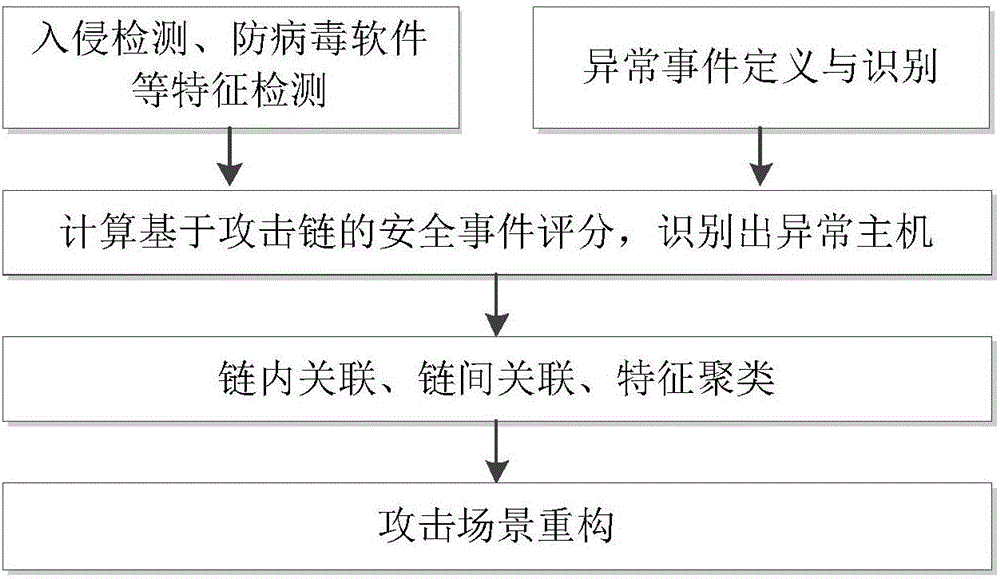
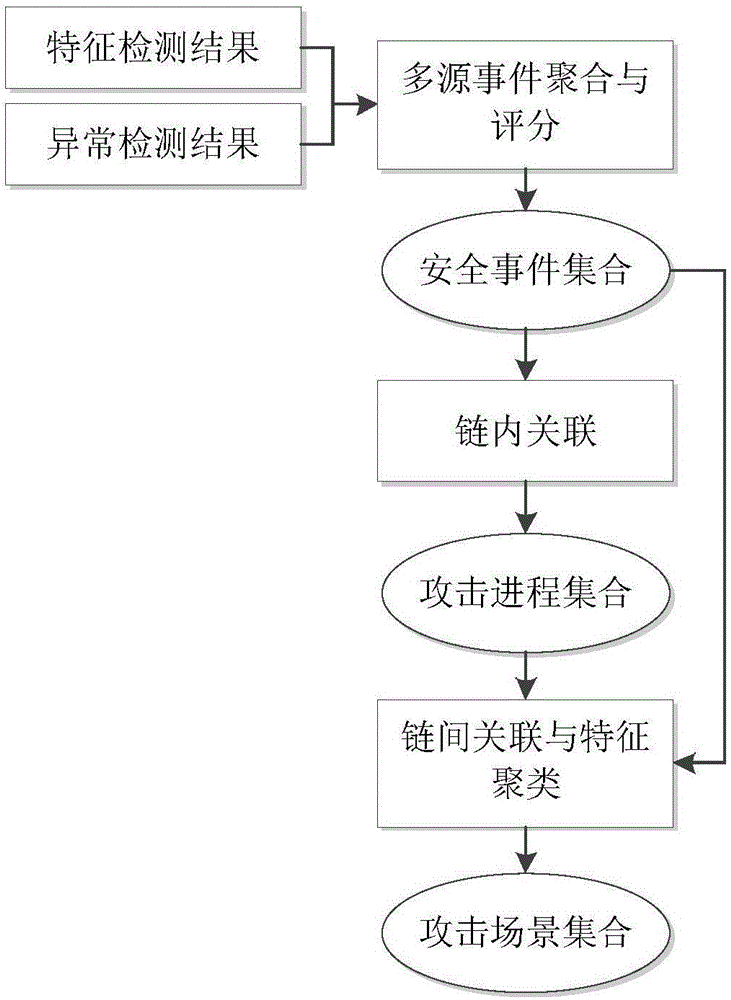
Multi-step attack detection method based on multi-source abnormal event correlation analysis
ActiveCN106790186AImprove Security Analysis CapabilitiesReduce time to discoveryTransmissionFeature extractionCorrelation analysis
The invention relates to a multi-step attack detection method based on multi-source abnormal event correlation analysis. The multi-step attack detection method comprises the following steps: firstly, calculating a safety event score based on an attach chain through feature extraction and abnormal event definition and identification, identifying an abnormal host and clustering various types of events by taking an attacked host as a clue; secondly, carrying out correlated recombination on a suspected attack progress by utilizing means including intra-chain correlation, inter-chain correlation, feature clustering and the like; finally, reconstructing a multi-source attack scene and outputting a predicated attack event. According to the multi-step attack detection method provided by the invention, dispersed and isolated safety events are subjected to the correlation analysis to generate the relative complete multi-step attack scene; a safety analysis capability of safety managers can be improved and a safety view angle is expanded; distributed and scattered multi-step attack threats are effectively coped and the finding time of attack behaviors is shortened; an effective predication and defending solution is provided for high-grade attack means including APT (Advanced Persistent Threat) and the like; the safety risks of a system are reduced and the network information safety is effectively protected.
Owner:THE PLA INFORMATION ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com
![[Automated system and method for providing accurate, non-invasive insurance status verification] [Automated system and method for providing accurate, non-invasive insurance status verification]](https://images-eureka.patsnap.com/patent_img/26c757fa-46fa-4d13-b759-21c21773e943/US20050209892A1-20050922-D00000.png)
![[Automated system and method for providing accurate, non-invasive insurance status verification] [Automated system and method for providing accurate, non-invasive insurance status verification]](https://images-eureka.patsnap.com/patent_img/26c757fa-46fa-4d13-b759-21c21773e943/US20050209892A1-20050922-D00001.png)
![[Automated system and method for providing accurate, non-invasive insurance status verification] [Automated system and method for providing accurate, non-invasive insurance status verification]](https://images-eureka.patsnap.com/patent_img/26c757fa-46fa-4d13-b759-21c21773e943/US20050209892A1-20050922-D00002.png)