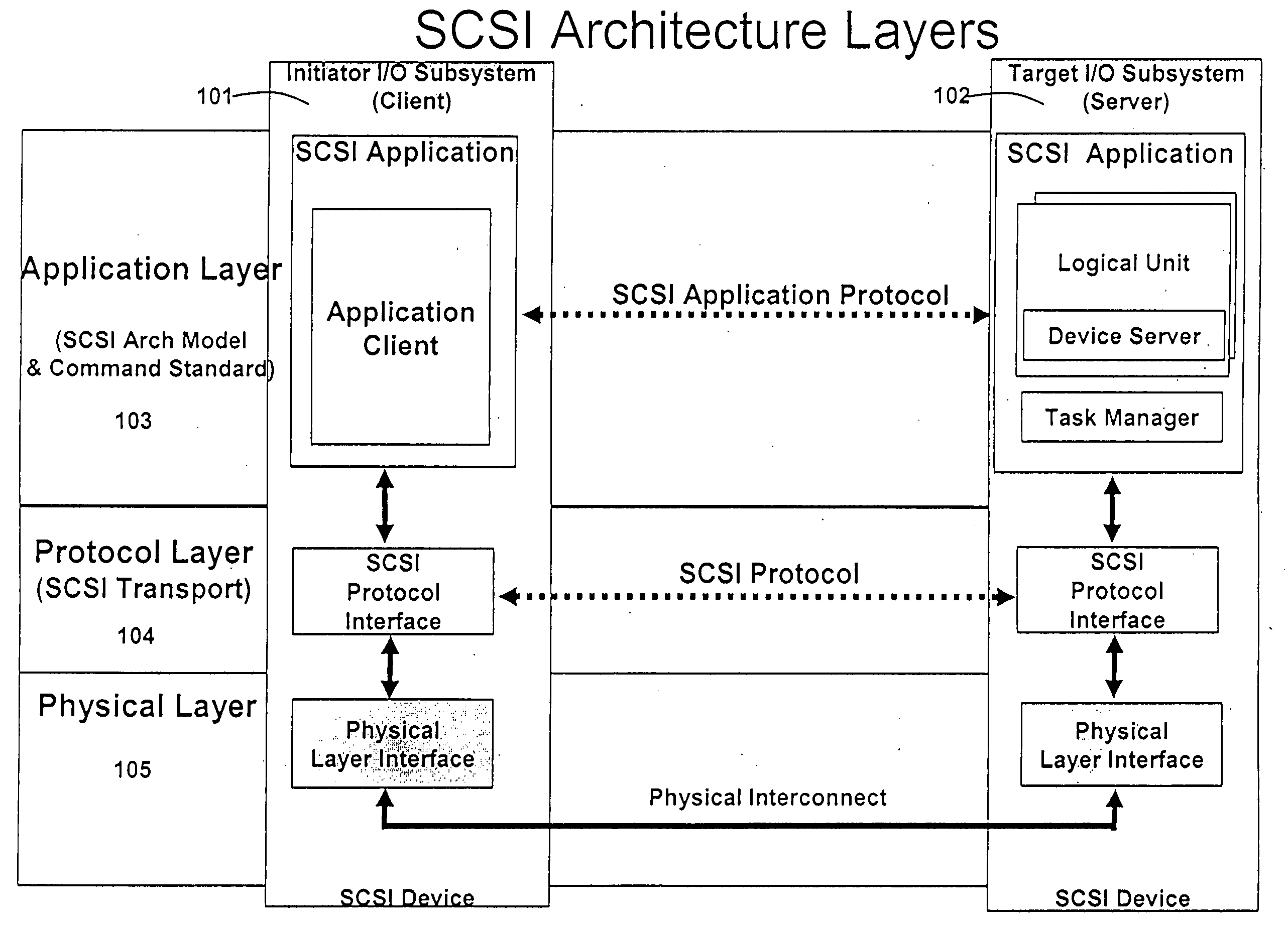
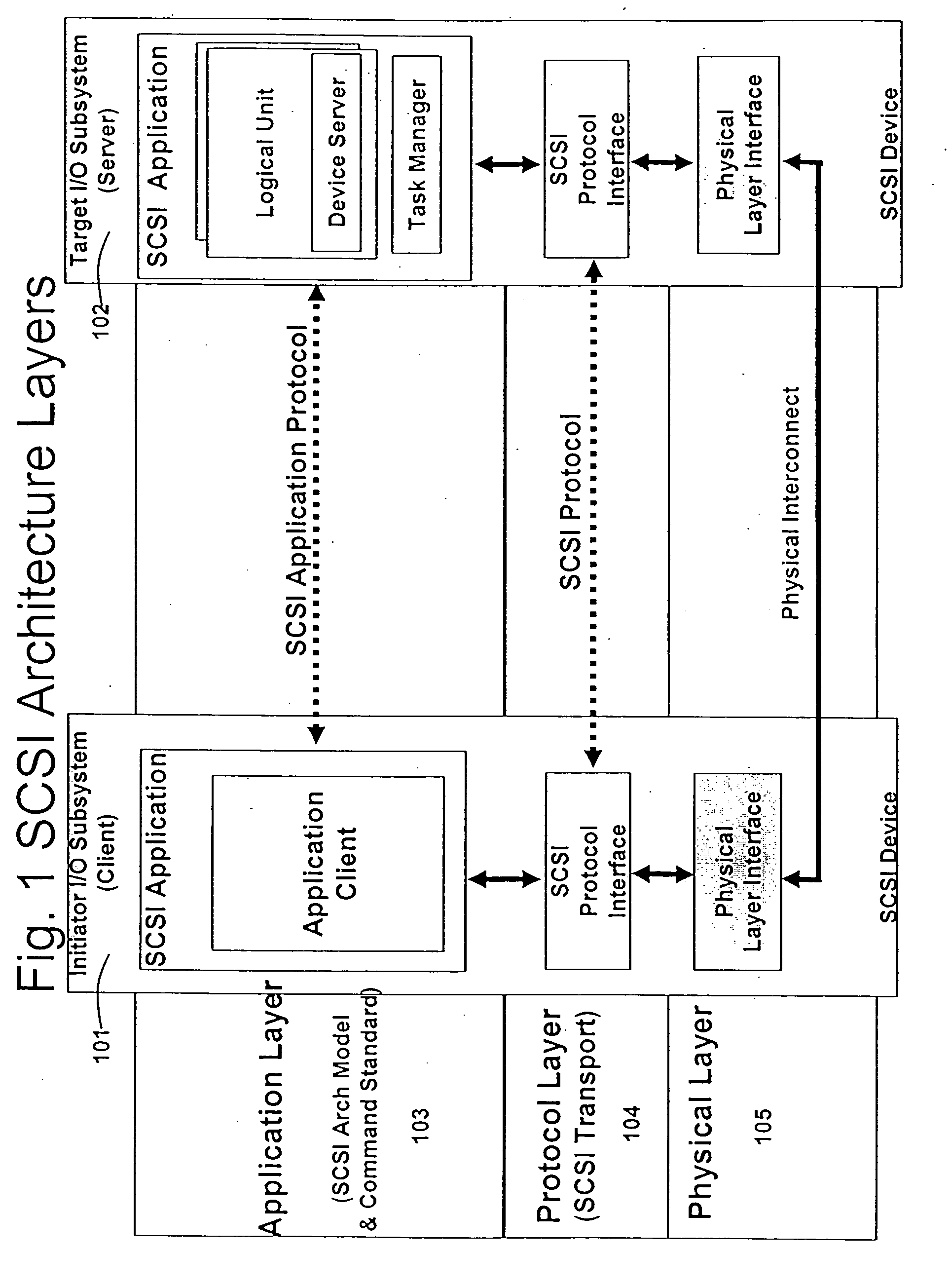
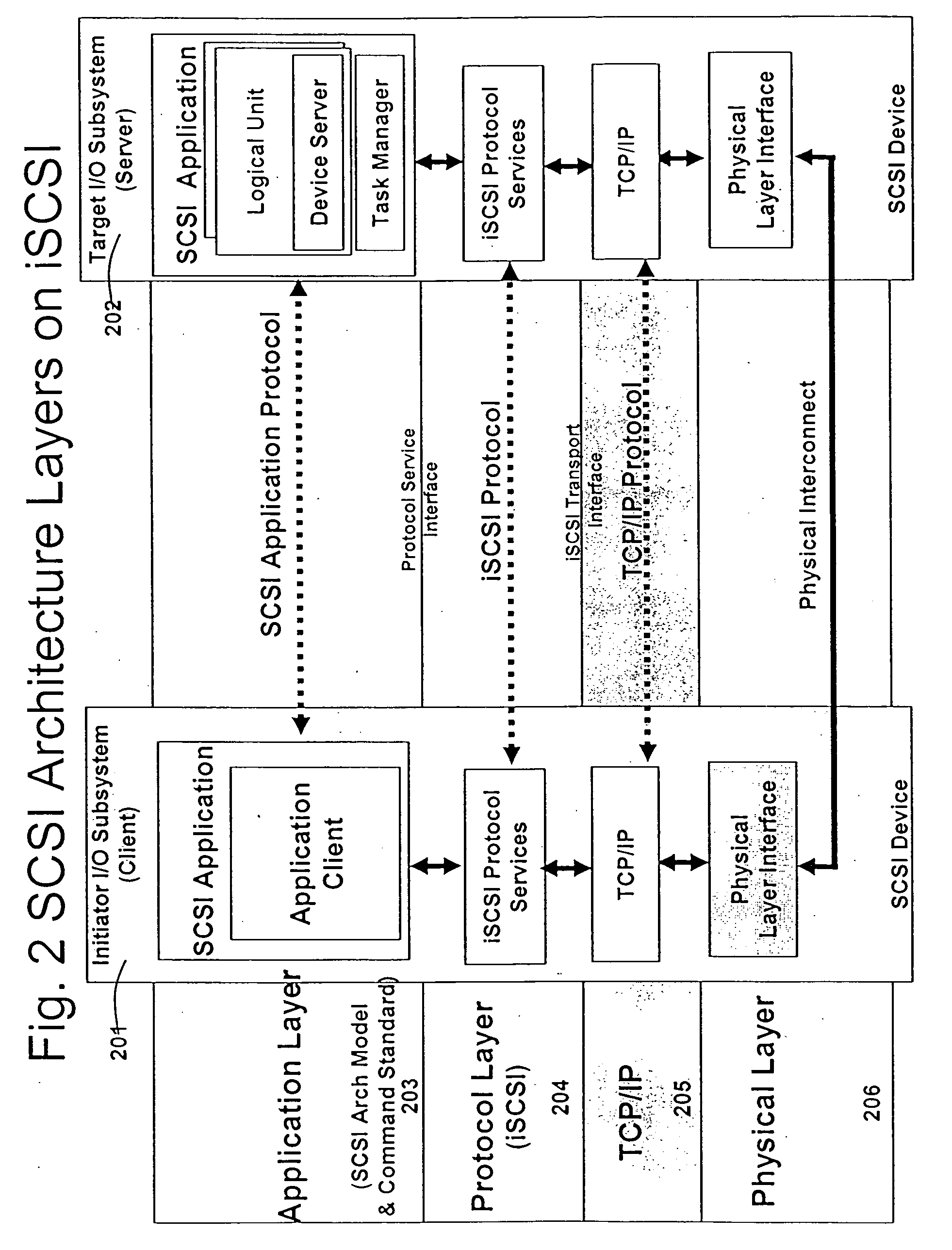
Patents
Literature
12955 results about "Information data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
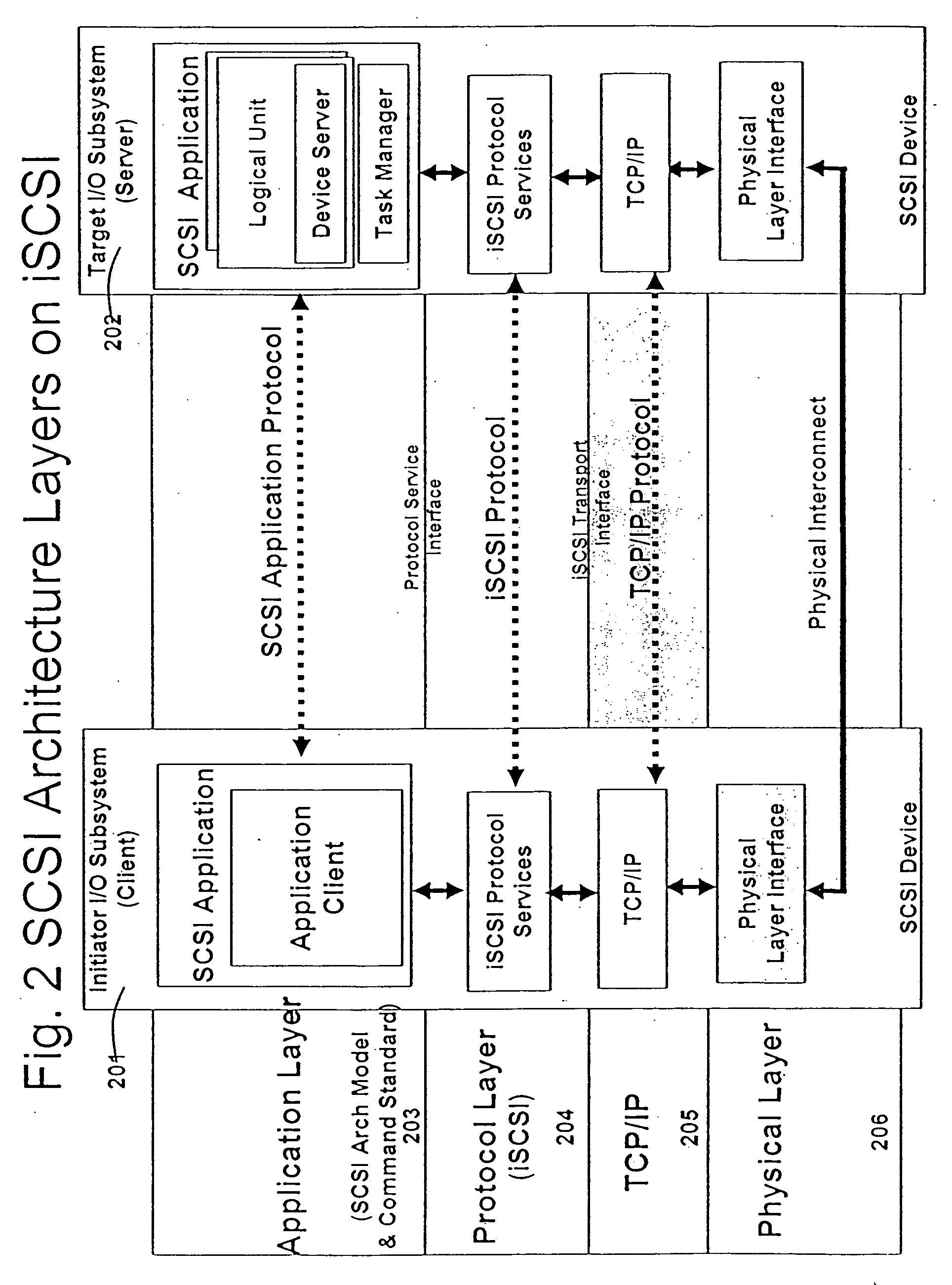
In computing, data is information that has been translated into a form that is efficient for movement or processing. Relative to today's computers and transmission media, data is information converted into binary digital form. It is acceptable for data to be used as a singular subject or a plural subject.
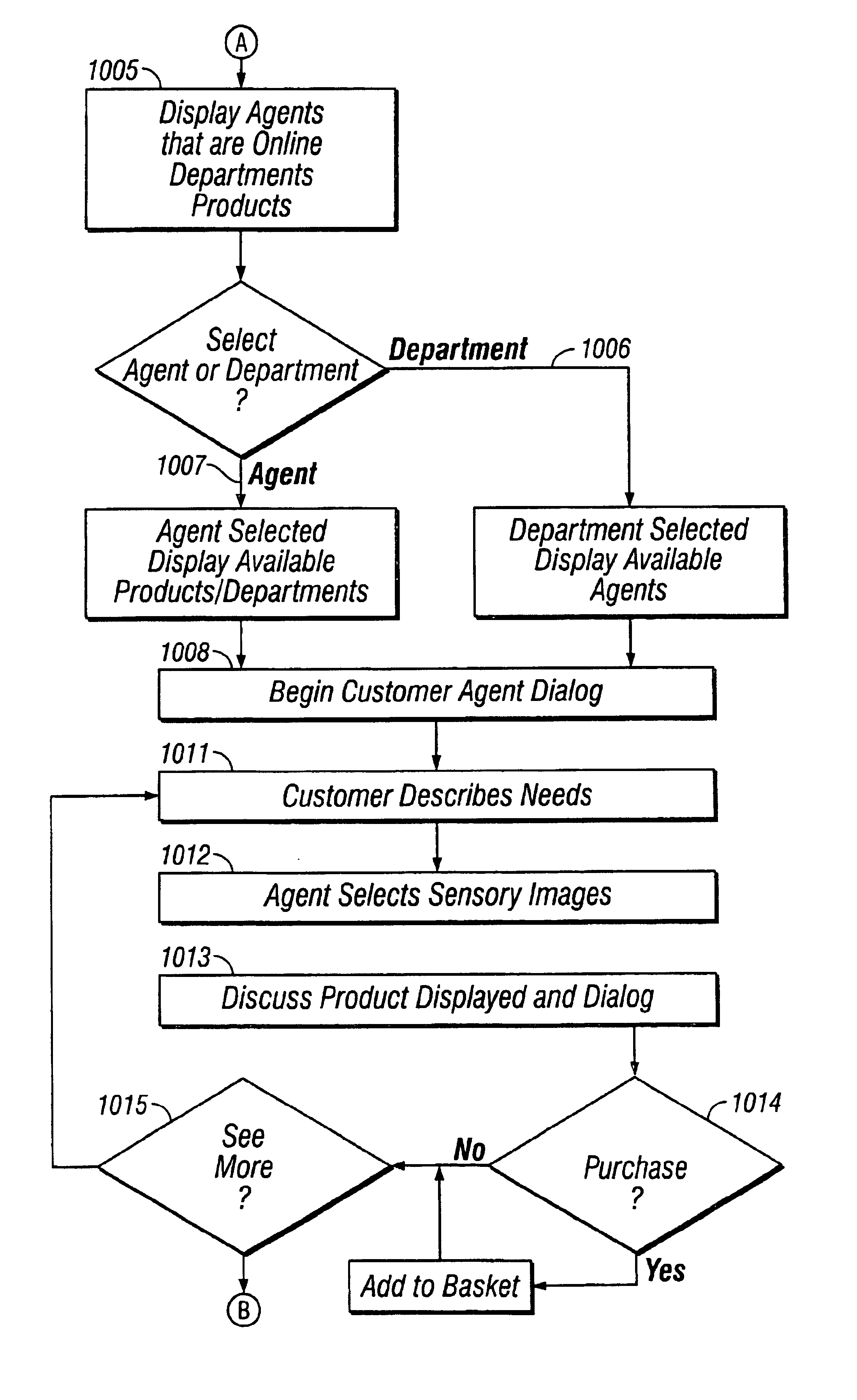
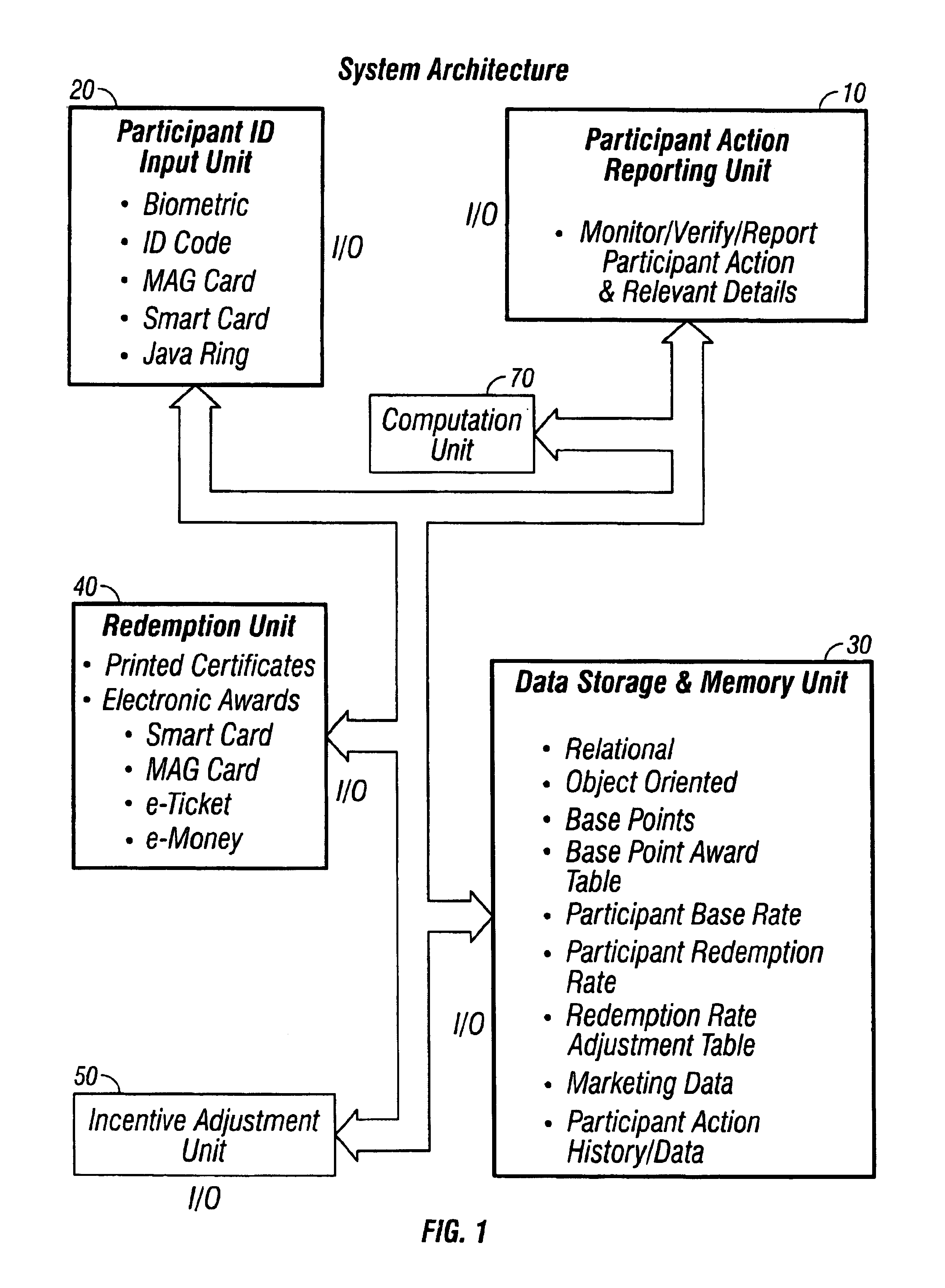
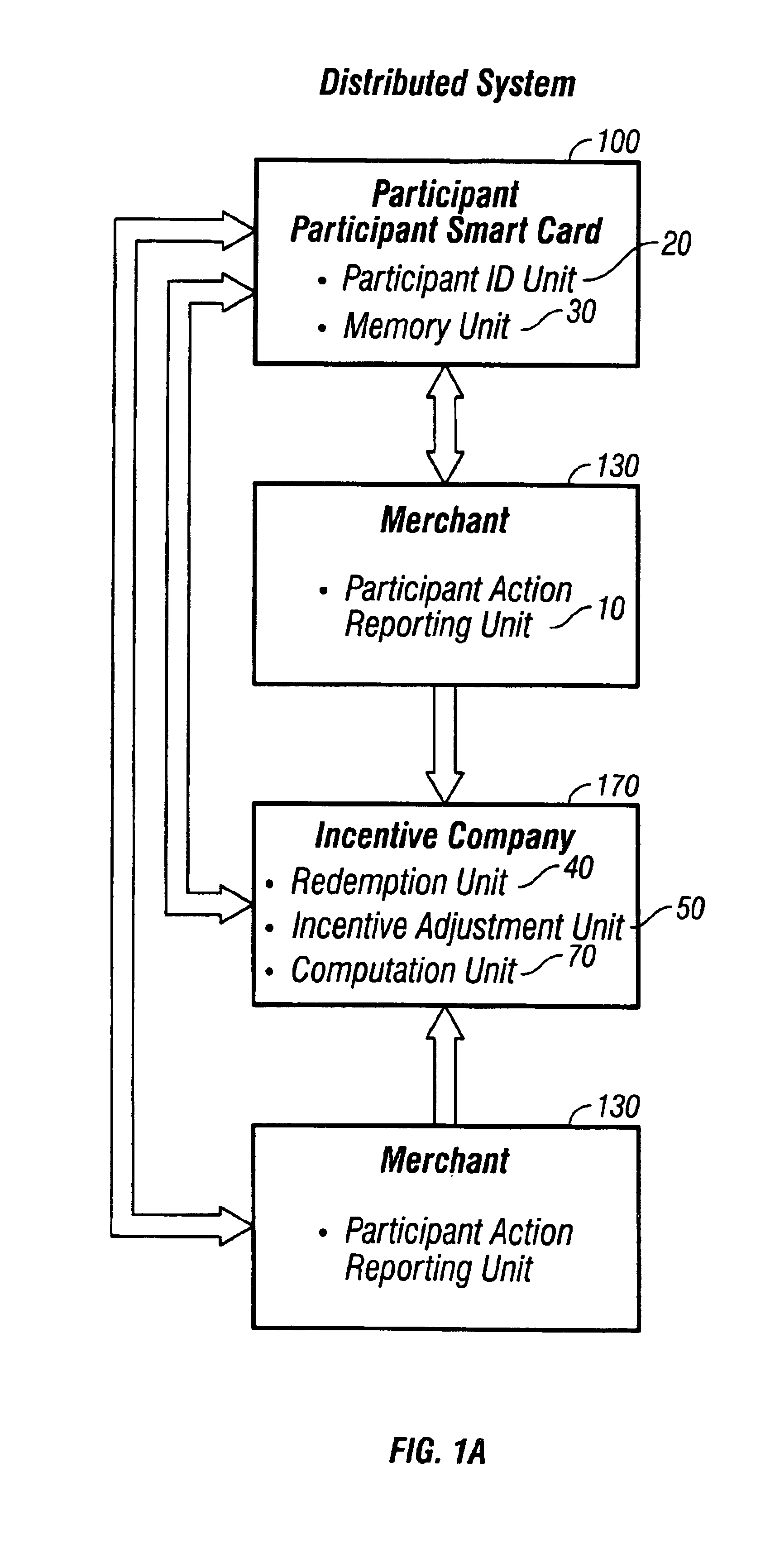
System and method for promoting commerce, including sales agent assisted commerce, in a networked economy
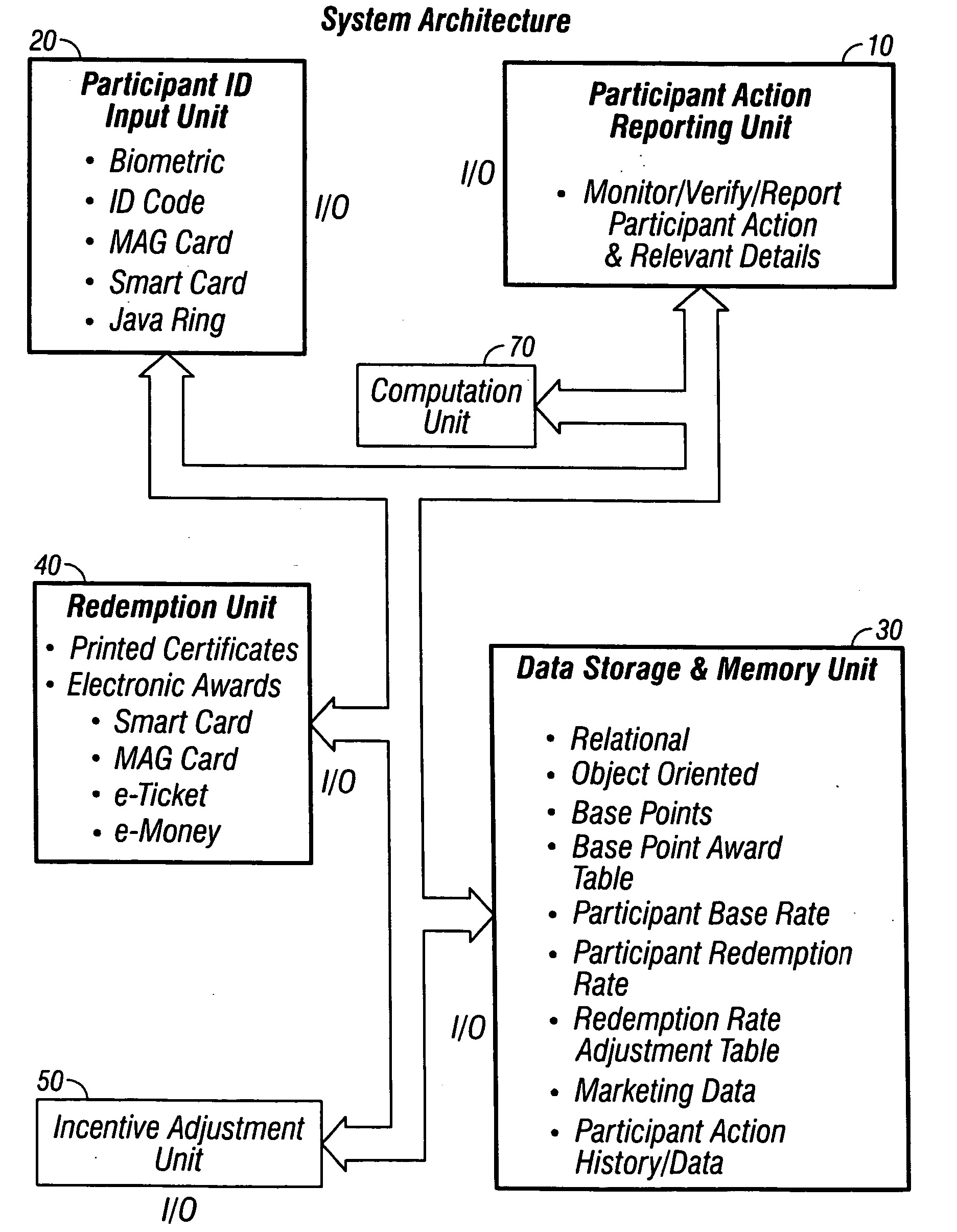
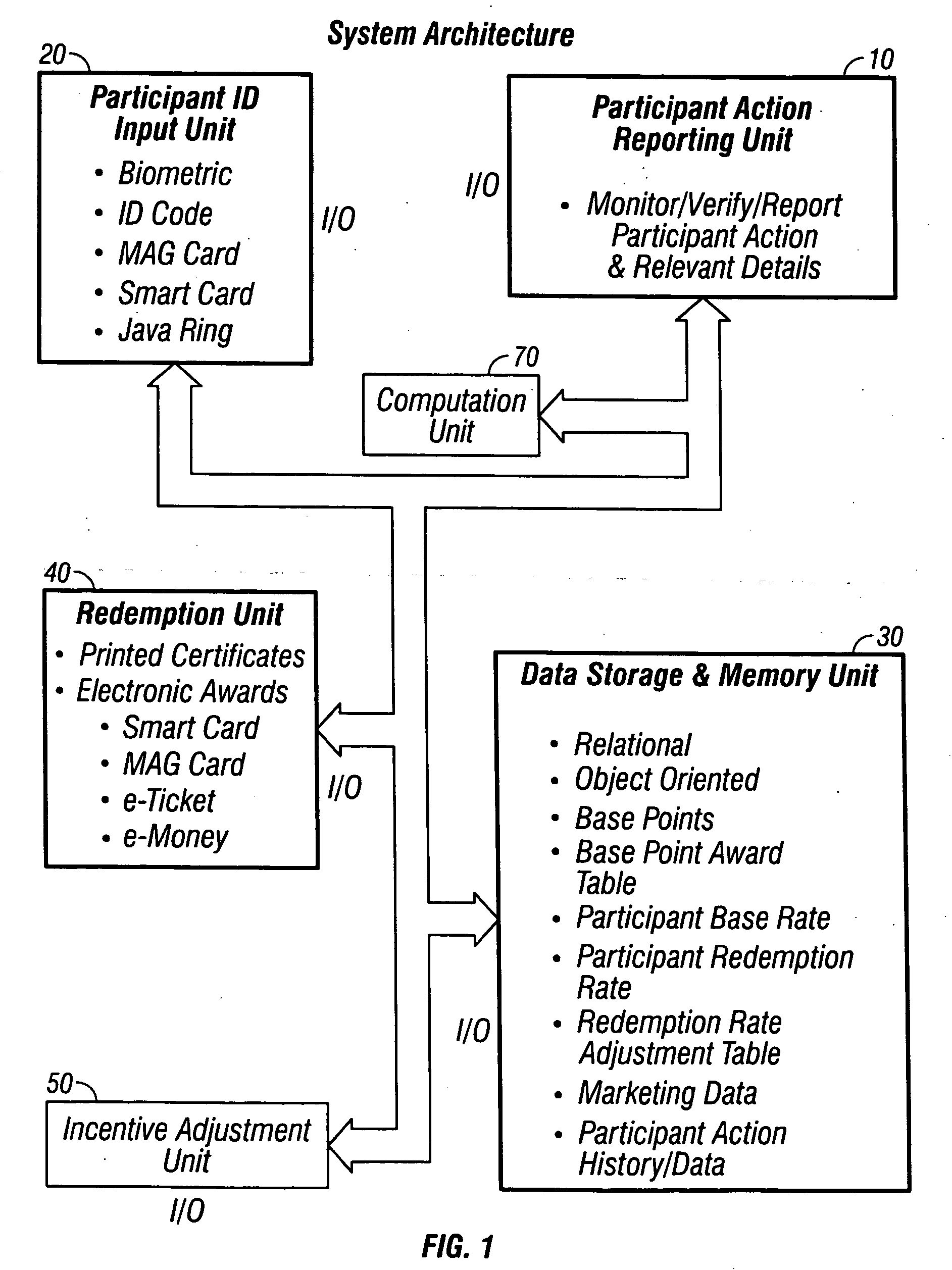
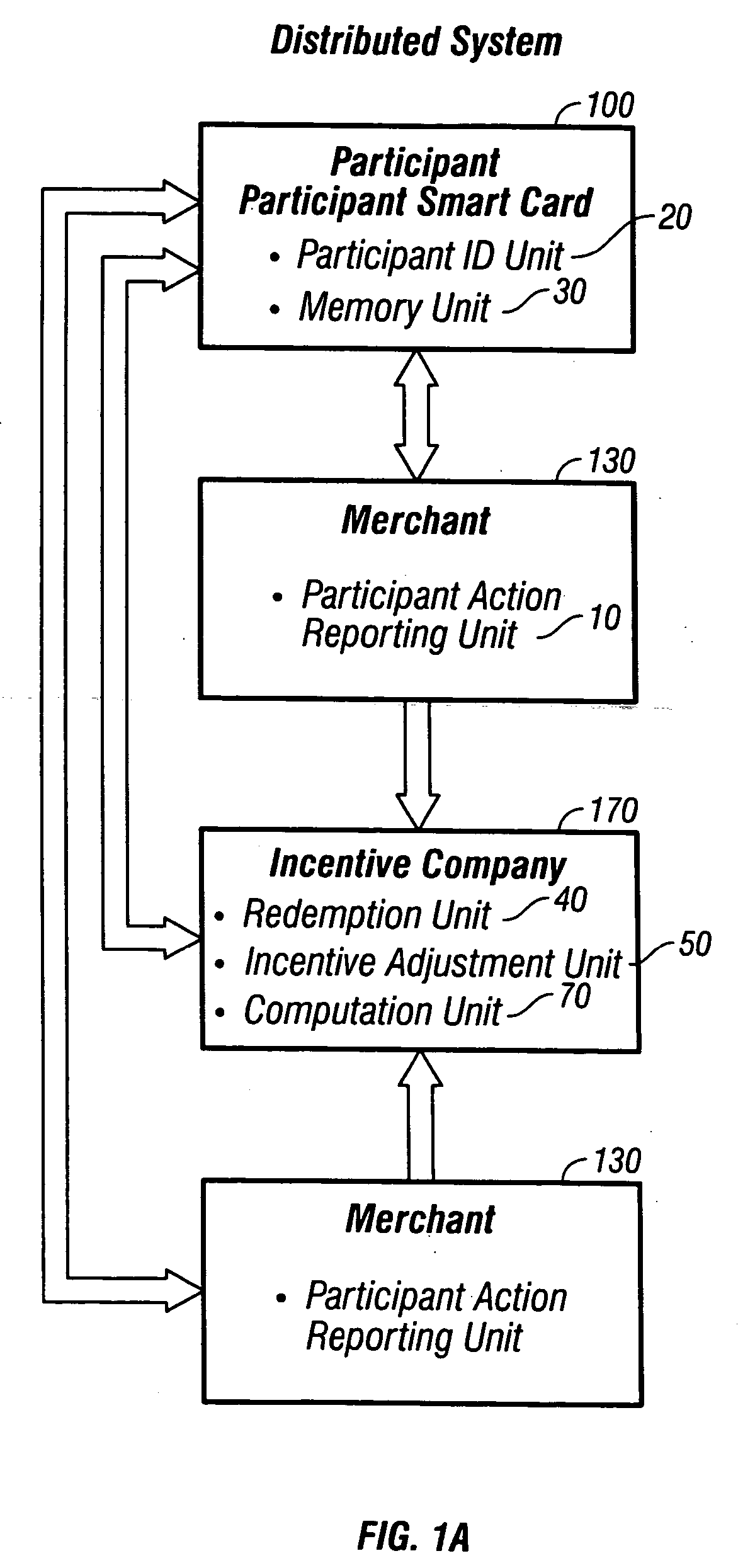
A personal communication and electronic commerce system for use by participating users and participating merchants in connection with incentive programs in the Network Economy. The system includes a cellular communication network that includes geographically spaced base stations that are linked to a fixed communication network. Users may have personal communication devices that can be used to allow a digital message generated on the personal communication devices by placing a call through one of the base stations and memory for storing a digital value corresponding to a monetary value. The personal communication device may also be used as a cellular position locator to determine one's geographic location and, if desired, to access information from a merchant information database containing information pertaining to a plurality of participating merchants located within the geographic territory covered by the cellular communication network. The merchant information may be stored on a database that is accessible by merchants so those merchants can add, delete or alter information contained in their respective listings. An incentive system is also provided for creating incentives for participating users to encourage. This computer implemented incentive program for encouraging certain participant actions includes a first reward program under which participants may earn points for certain actions and a second reward program through which the redemption rate associated with a particular participant is adjusted in response to certain participant action. The incentive program has a wide range of applications, including transportation, financial services and computer gaming.
Owner:BEDNAREK MICHAEL DAVID
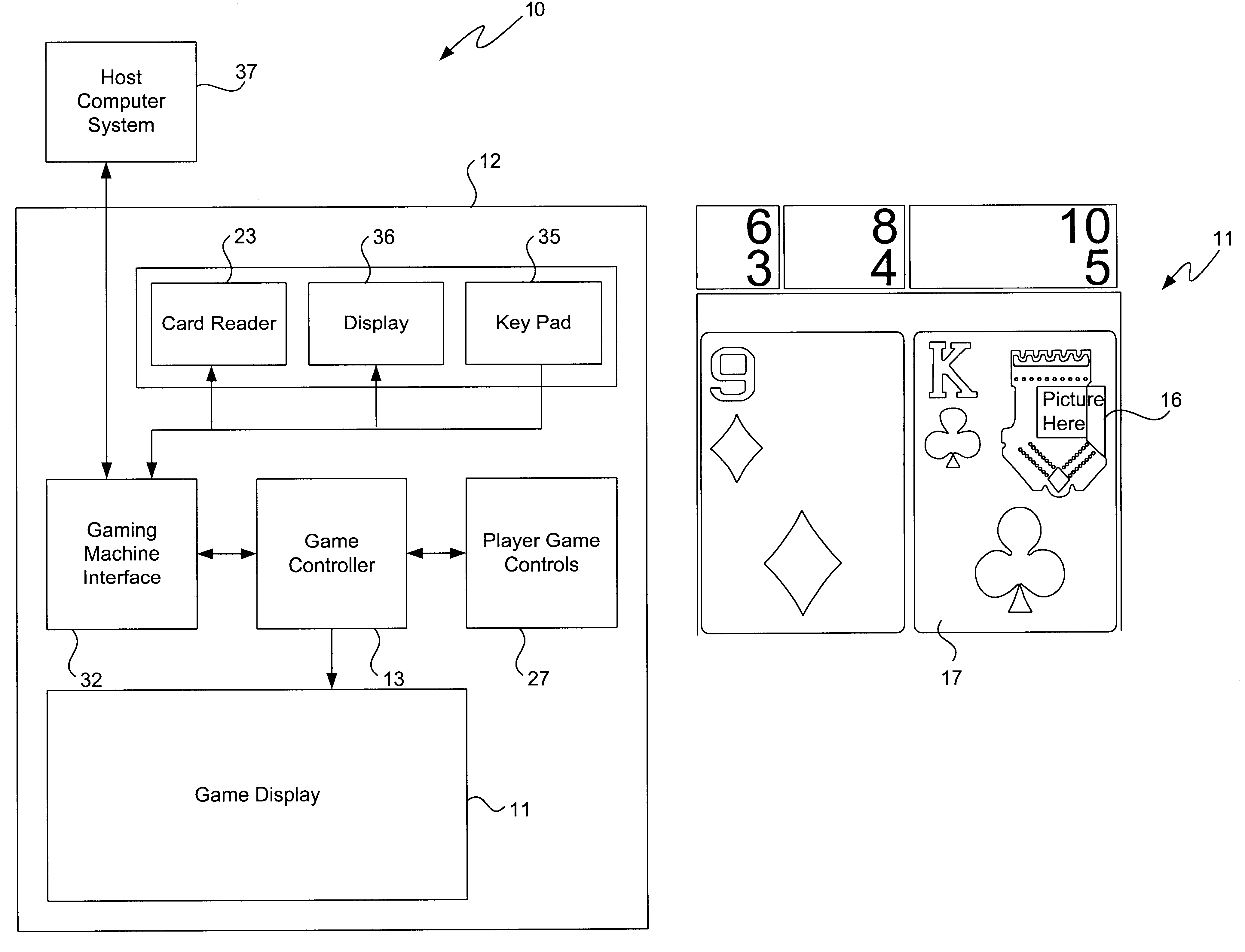
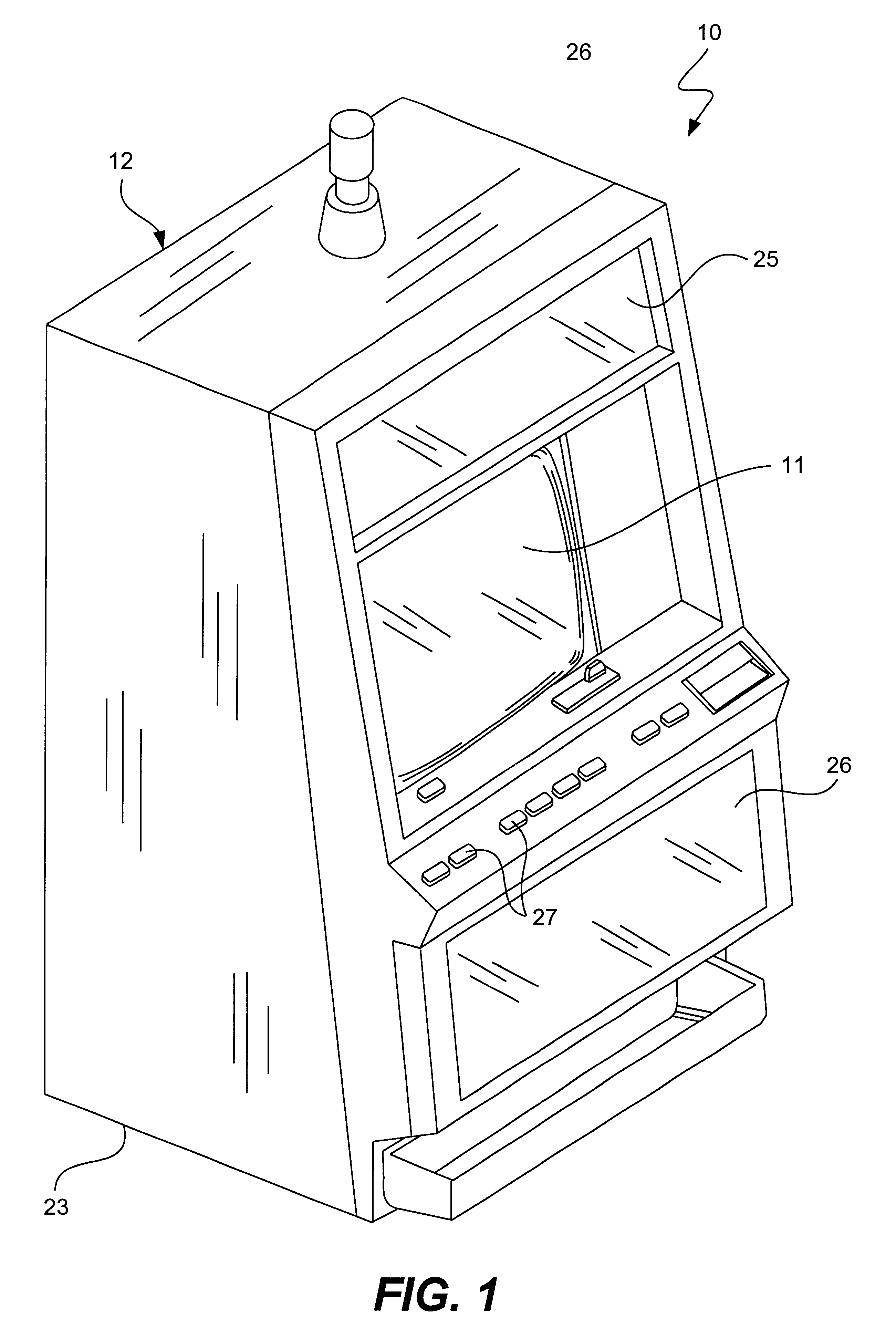
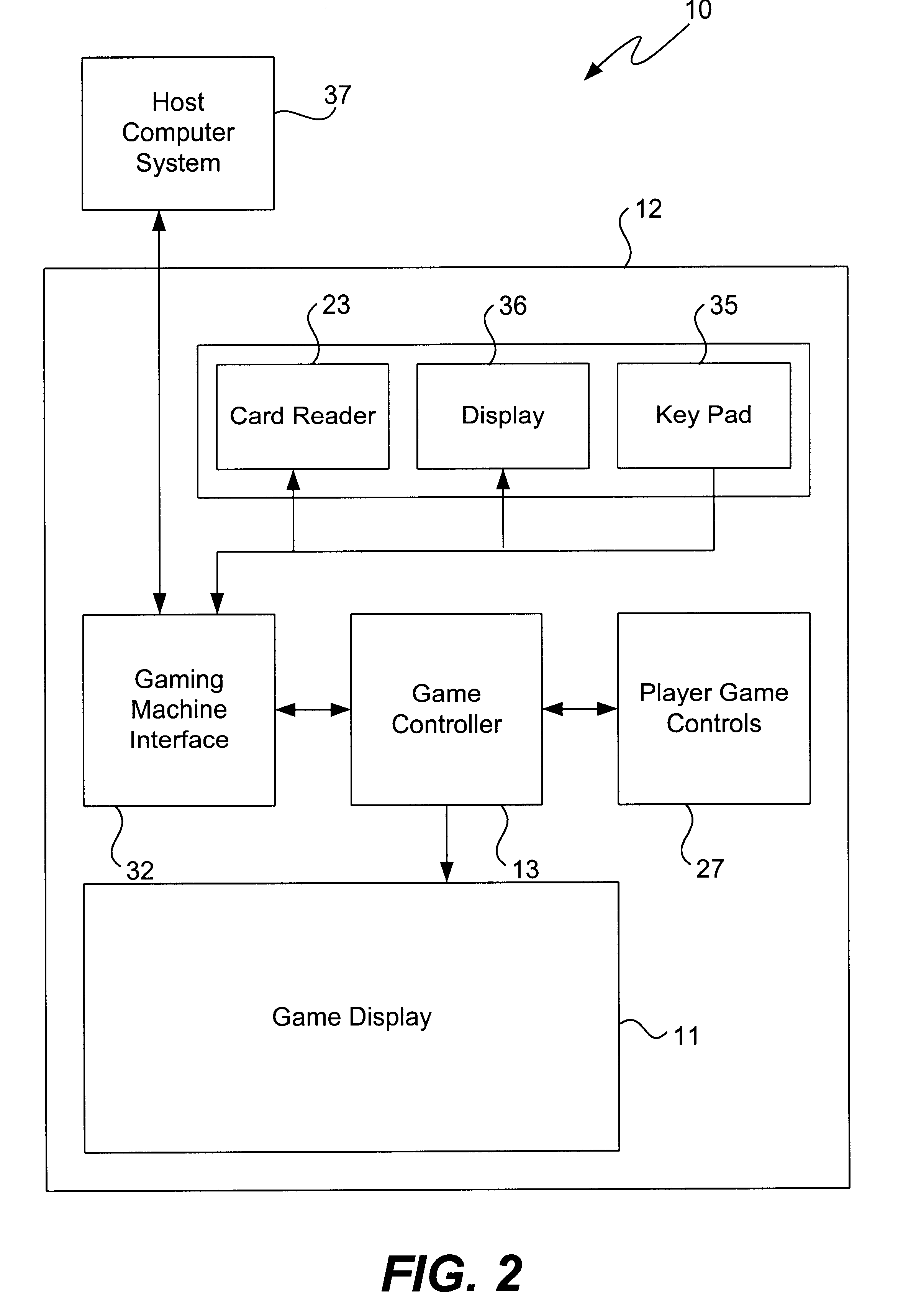
Interactive gaming machine and method with customized game screen presentation
InactiveUS6350199B1Enhanced interactionEnhance interestApparatus for meter-controlled dispensingVideo gamesInteractive videoDisplay device
A method and apparatus for an interactive video game to be displayed on a video display device. The gaming apparatus includes a game controller adapted to control the outcome of a game played on the gaming machine for display on the display device. A player interface is coupled to the gaming apparatus and is configured to input information data personally identifying a player operating the gaming machine. This personal identification data, such as a players name, birthdate, digitized facial pictures of player, etc., is then integrated into the game for integral display in the game outcome on the display device. Thus, player interaction is increased by customizing the game screen presentation to include their personal information.
Owner:IGT
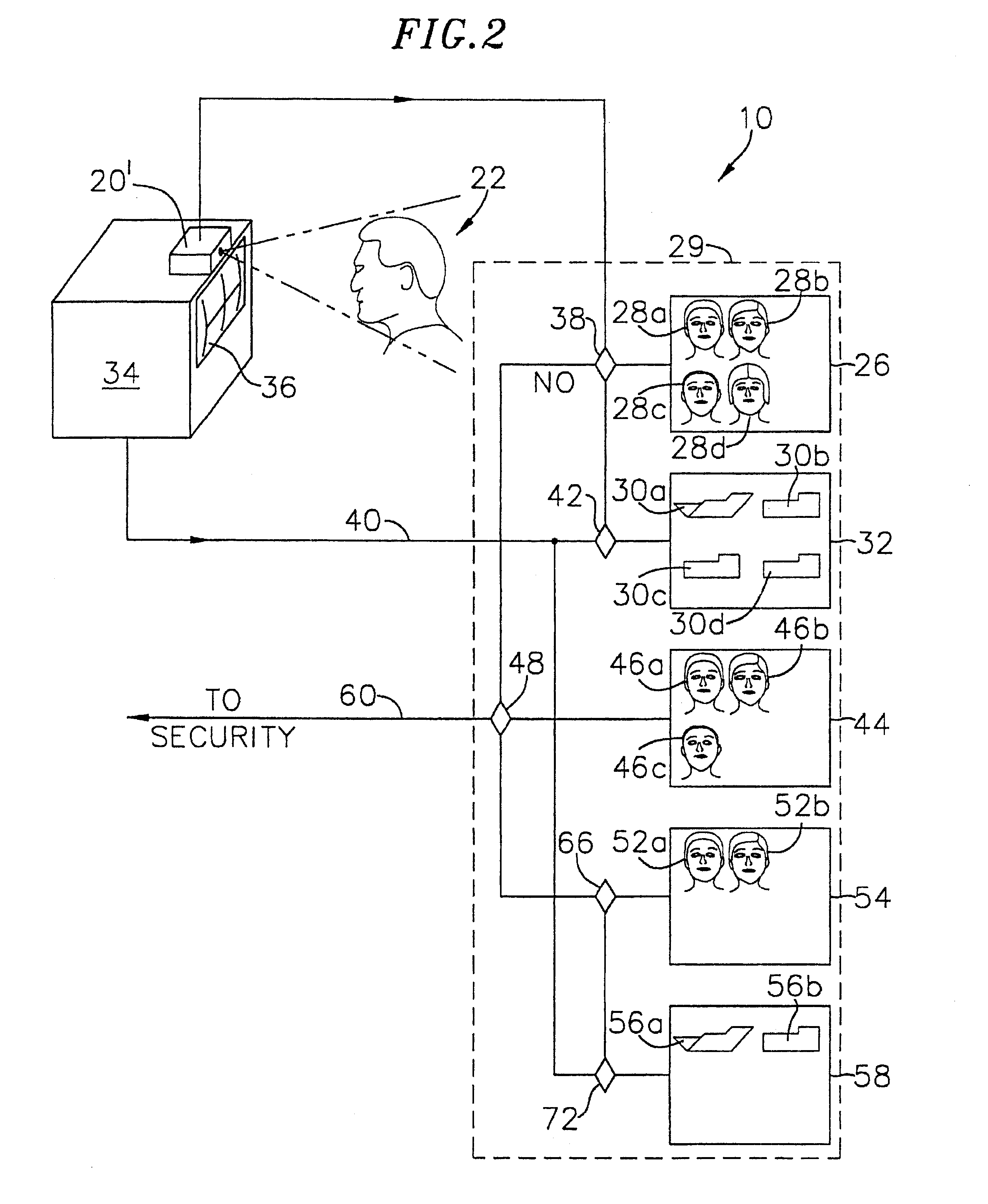
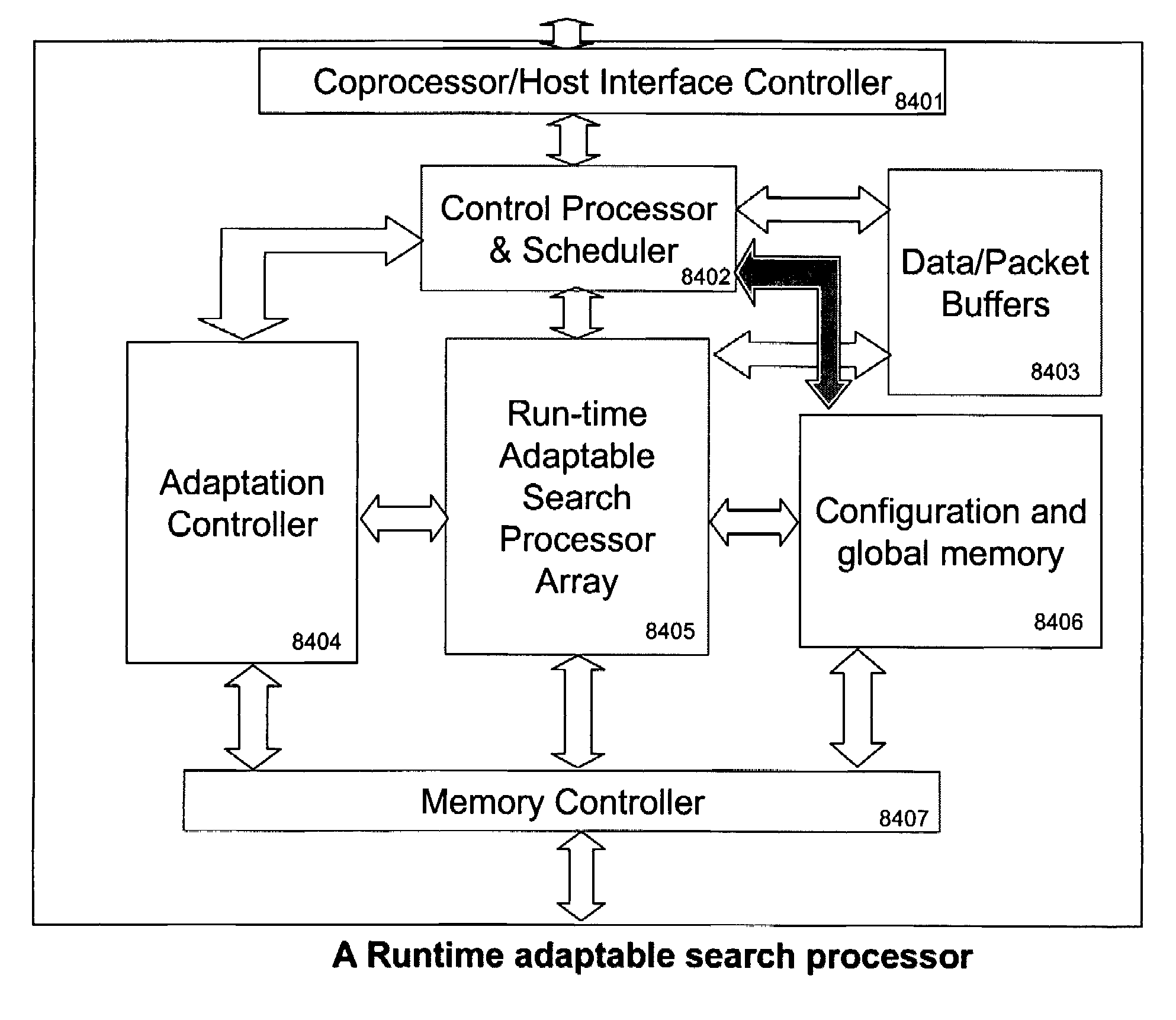
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
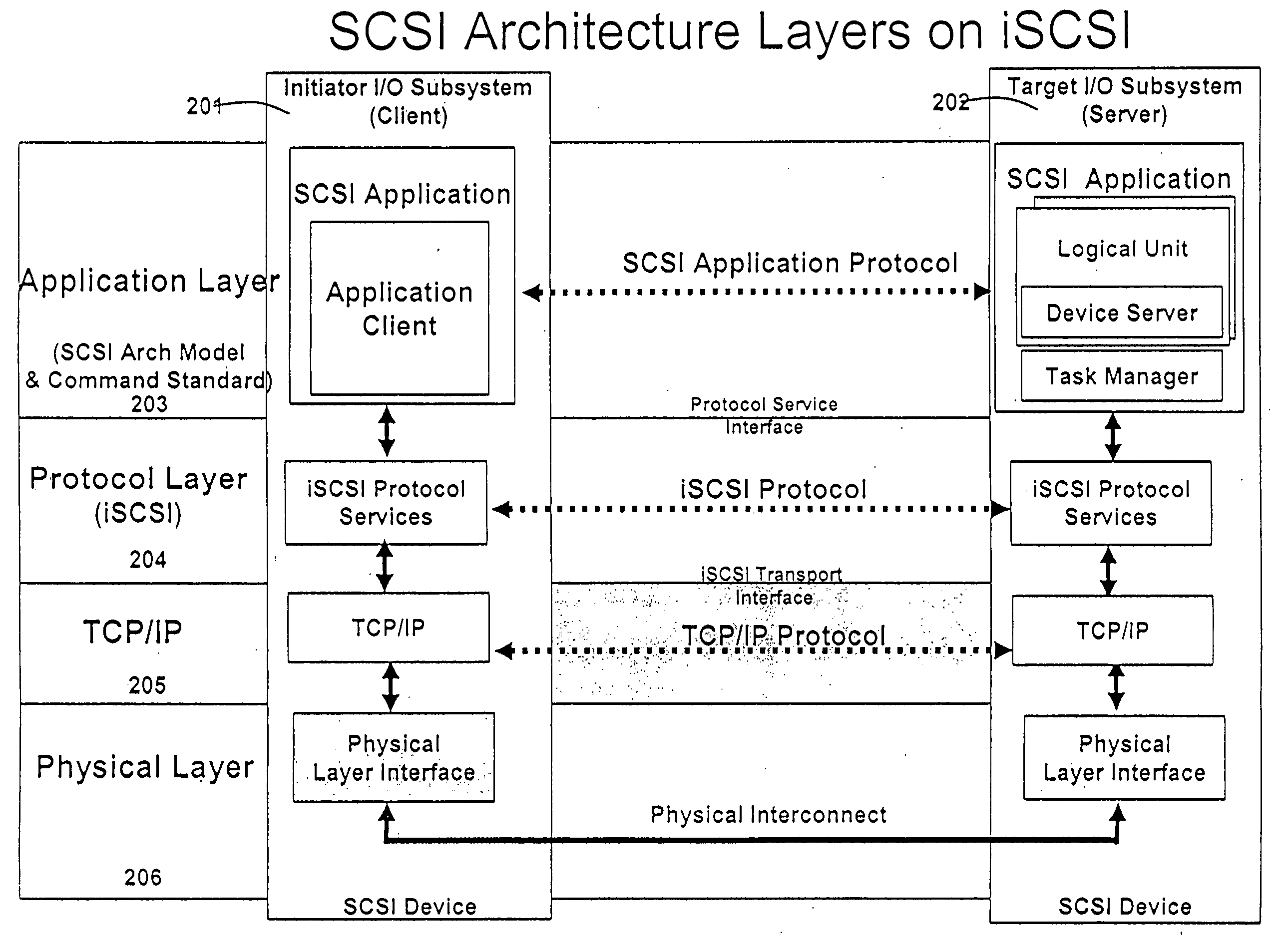
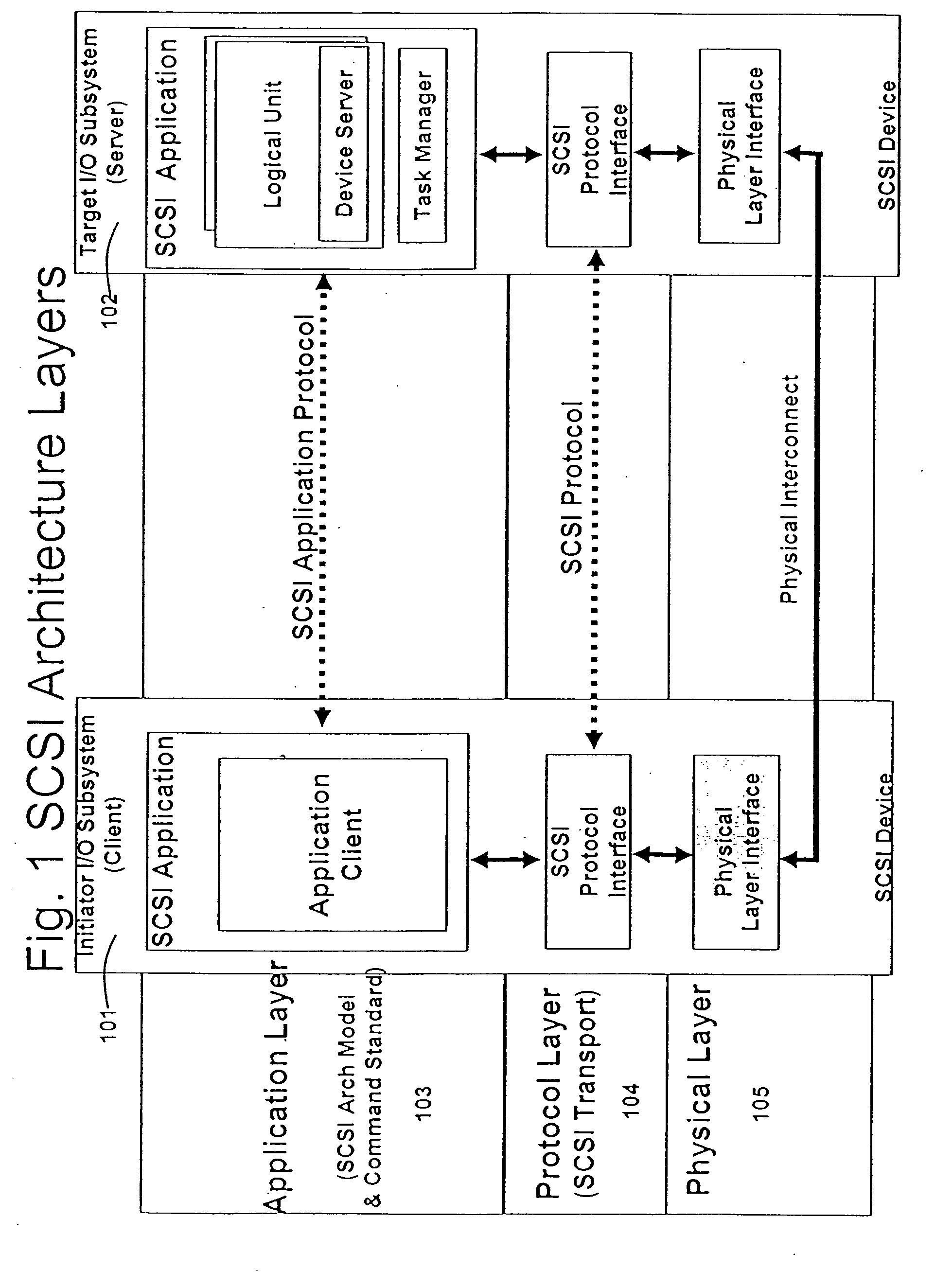
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
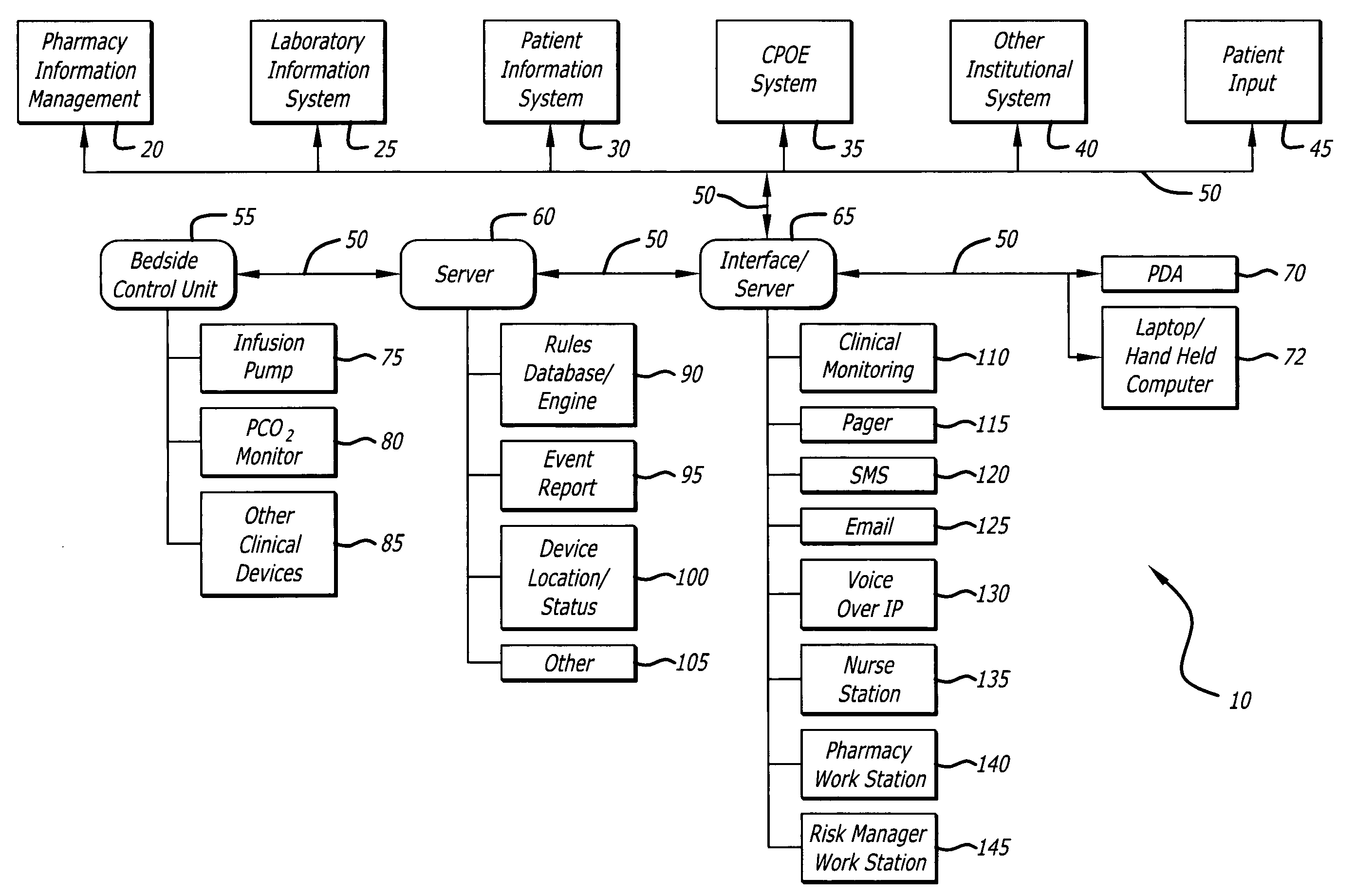
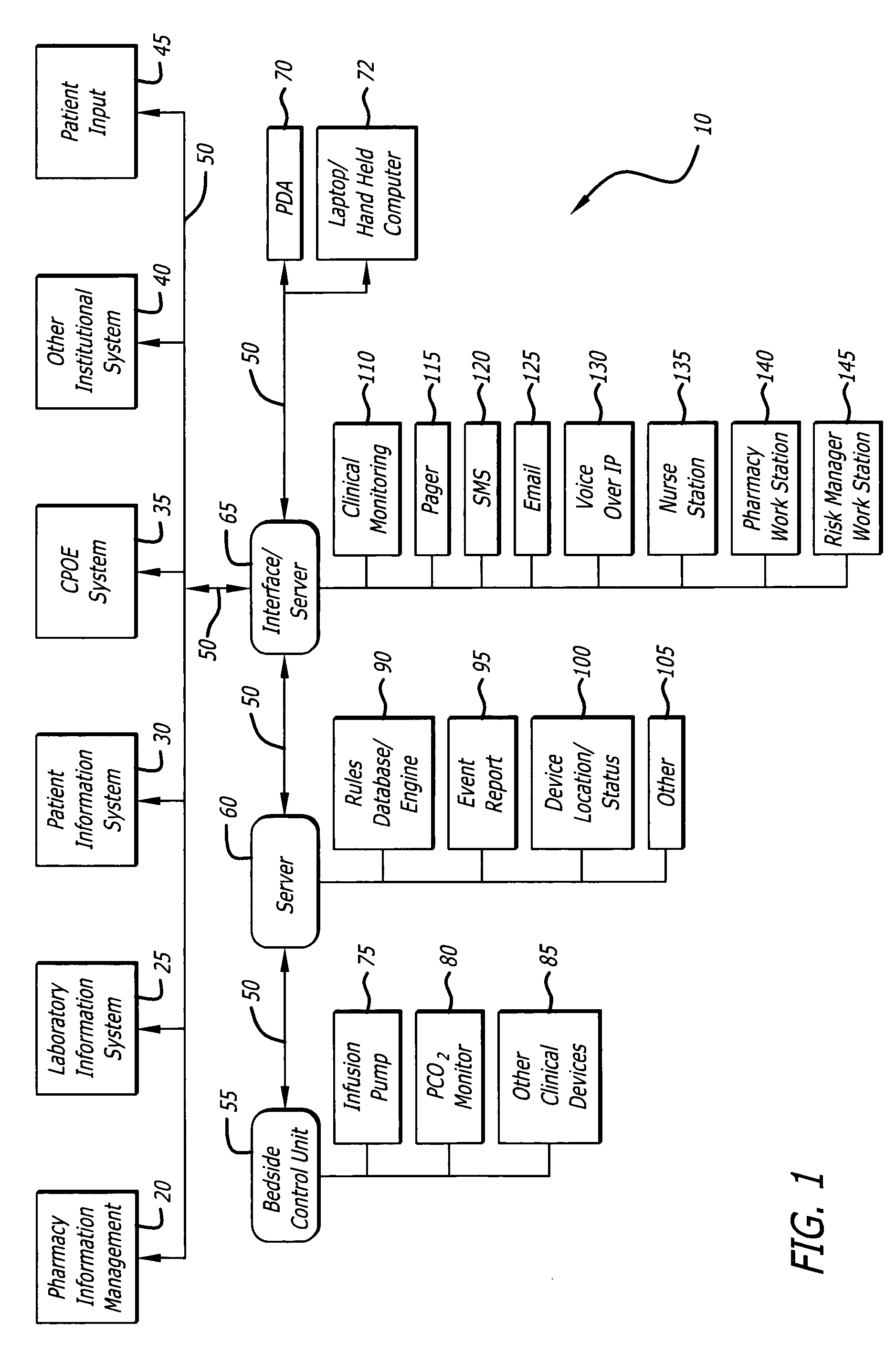
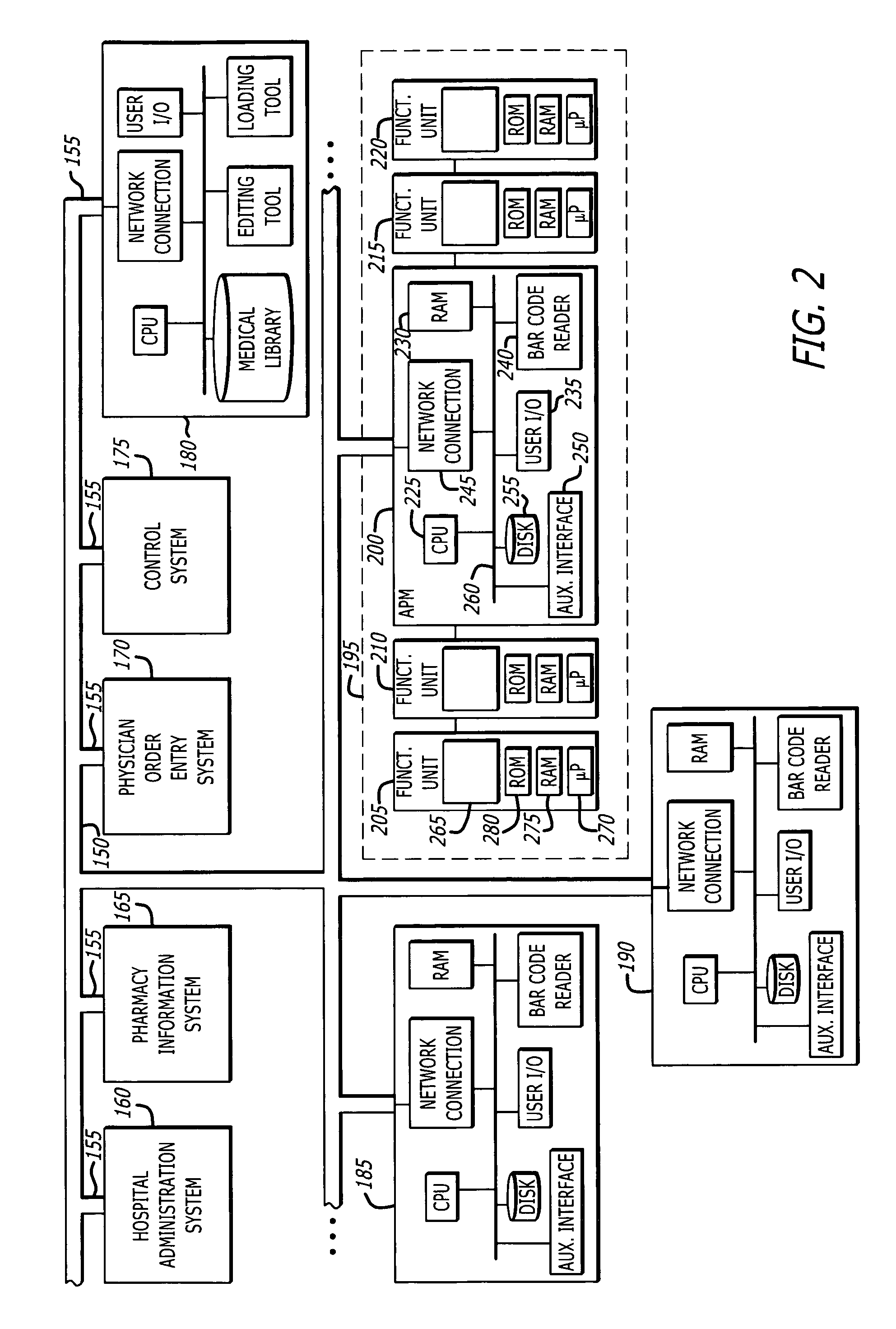
System and method for dynamically adjusting patient therapy
ActiveUS20060047538A1Computer-assisted treatment prescription/deliveryComputer-assisted medicine prescription/deliveryGuidelinePatient factors
A system and method of managing therapy provided to patients in an institution. The system monitors all aspects of the medication delivery to a patient, as well as other information related to the patient, such as values of vital signs, laboratory results and patient factors such as history, diagnosis, allergies and the like. The system includes one or more databases of information, including institutionally developed rules, guidelines and protocol representing the best medical practices of the institution. The system provides alerts and / or recommendations based on the application of the rules to the information being monitored, and alerts care givers accordingly, providing for dynamic adjustment of the patient's therapy. The system also monitors the status of the alerts, and if no action is taken in a selected period of time, may escalate the priority of the alert and / or halt the delivery of medication to the patient until the alert is resolved.
Owner:CAREFUSION 303 INC
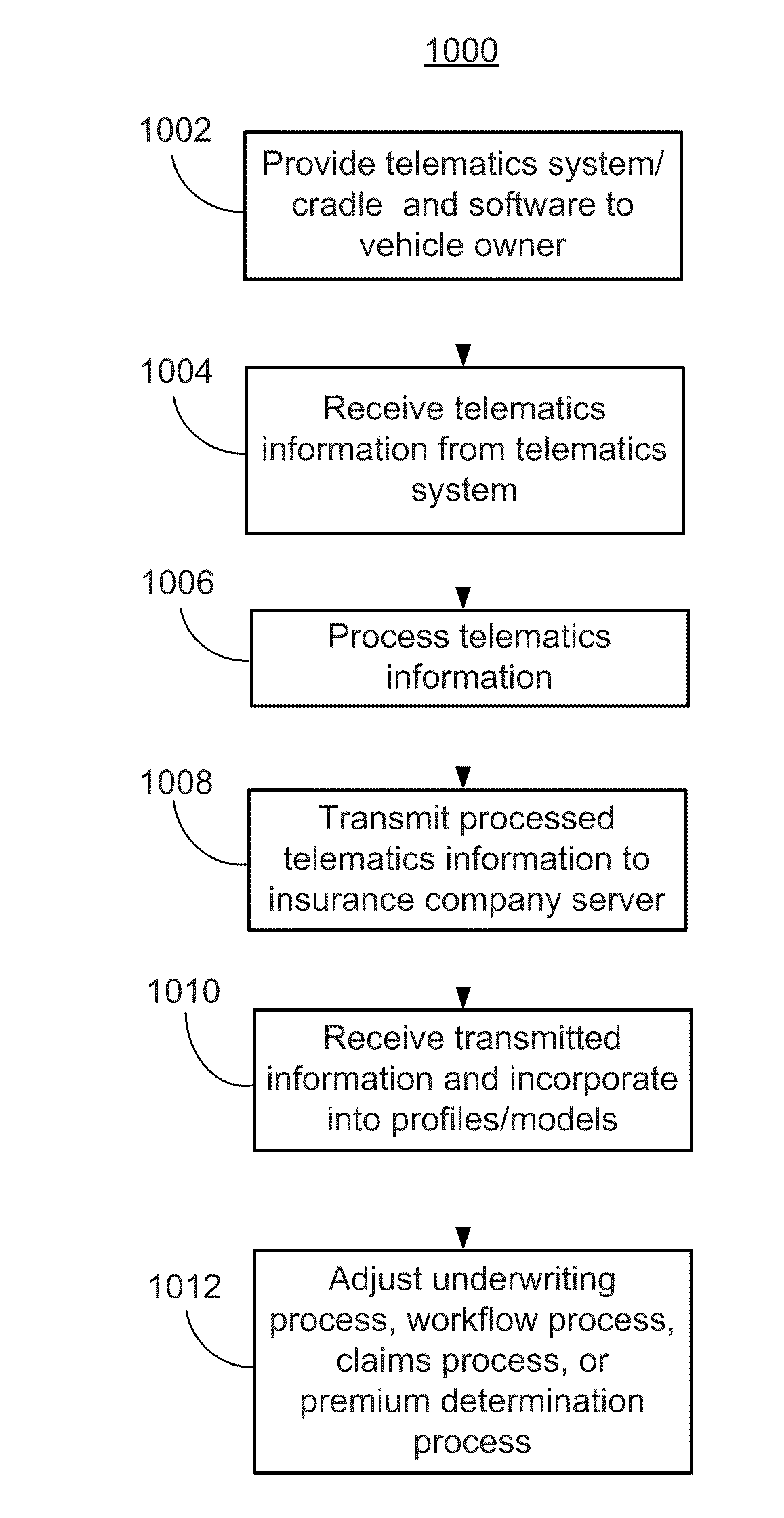
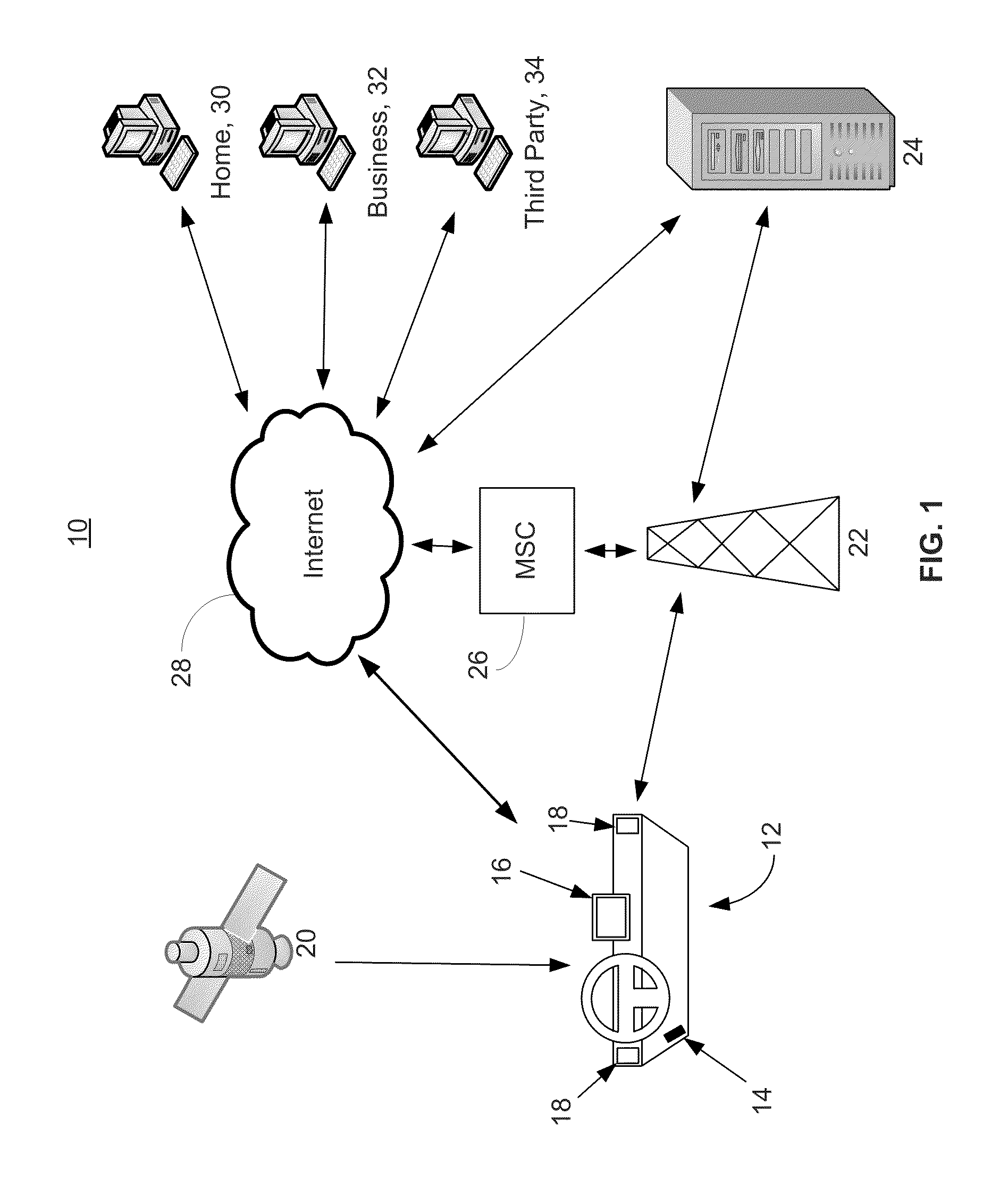
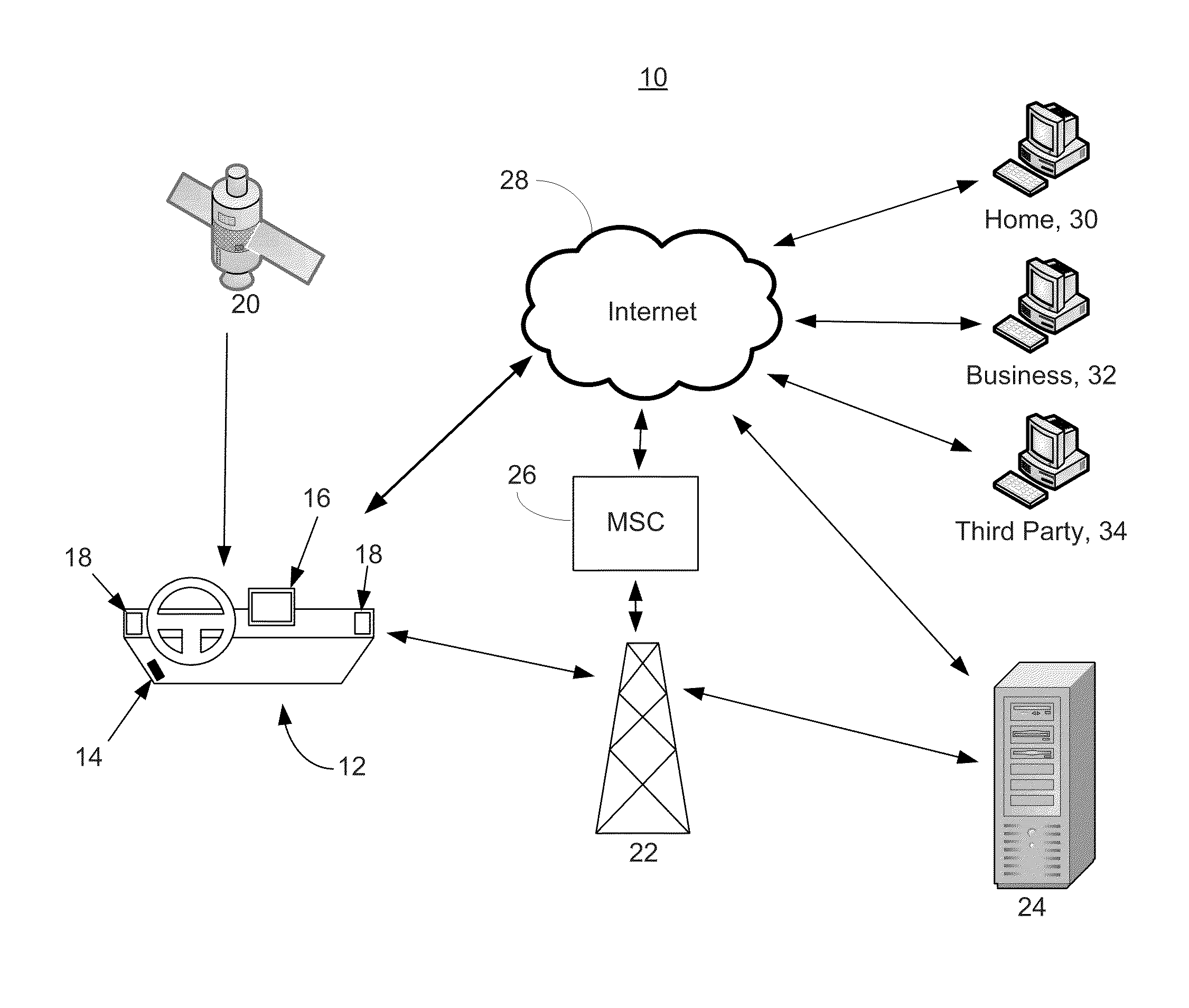
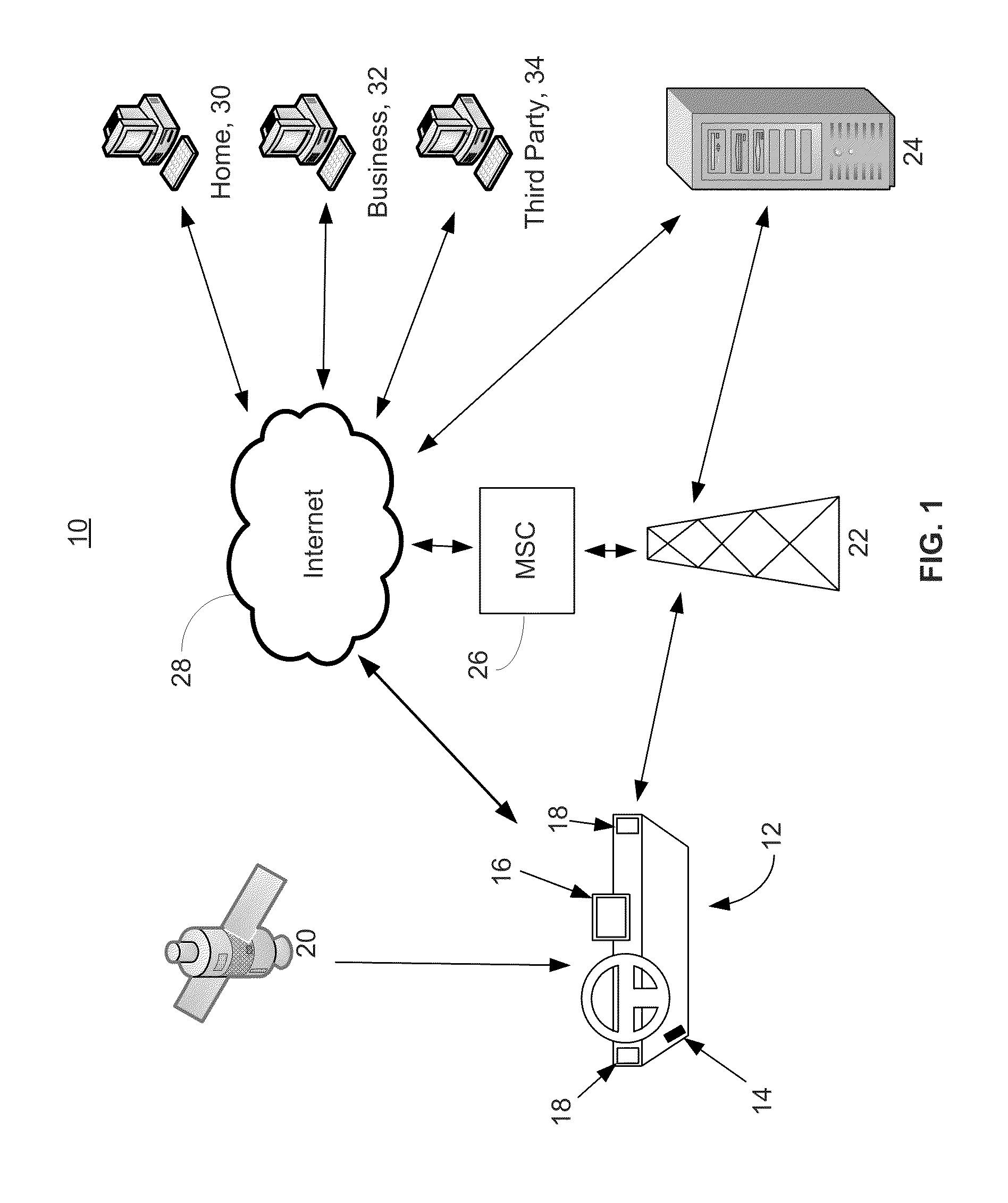
Systems and methods for linking vehicles to telematics-enabled portable devices
InactiveUS20110153367A1Prevent removalVehicle speed is limitedVehicle testingFinanceAccelerometer dataData port
Systems and methods are disclosed herein for transmitting telematics data from a vehicle. The systems include a smartphone holder that provides a communications link between a smartphone and a vehicle computer, through the smartphone dataport and the vehicle onboard diagnostics (OBD) port. The smartphone holder is configured to keep the smartphone in a stable, known position and orientation with respect to the vehicle, such that data from an accelerometer in the smartphone can be calibrated. The smartphone accelerometer data and telematics data from vehicle telematics sensors is then transmitted via the smartphone or stored locally.
Owner:HARTFORD FIRE INSURANCE
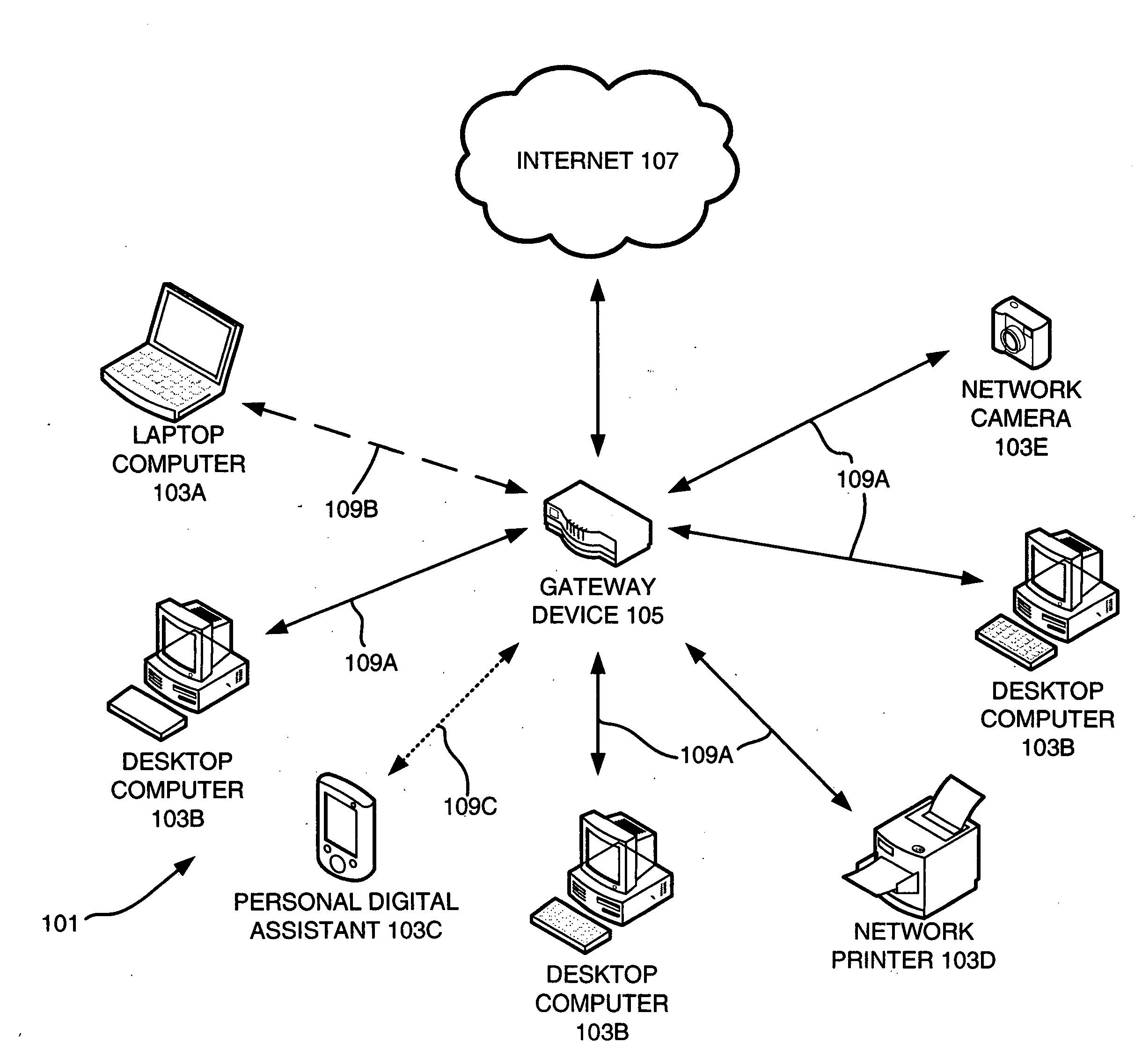
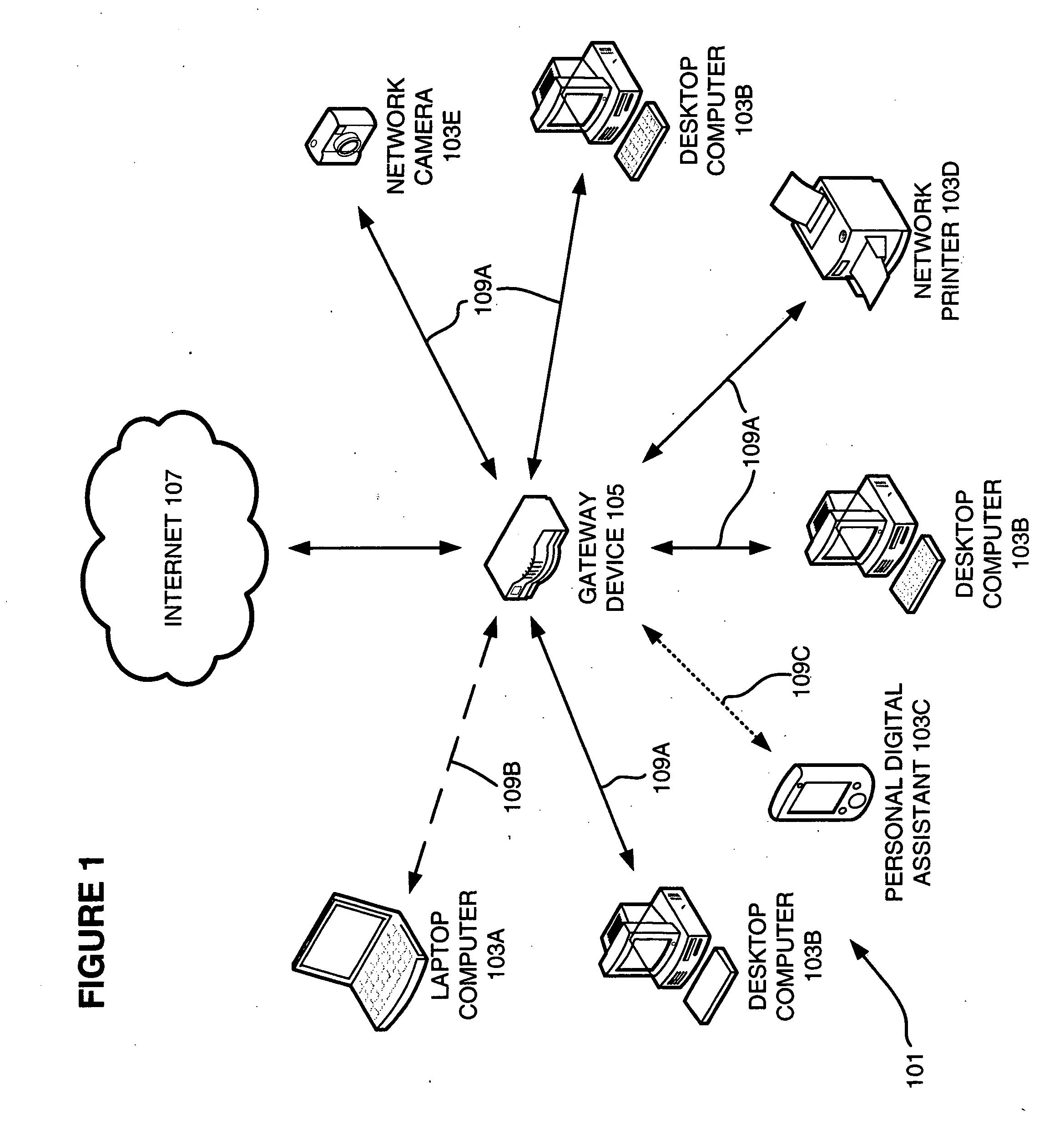
Network management
ActiveUS20090019141A1Digital computer detailsHome automation networksDevice PropertiesNetwork management
A tool for managing a computer network includes a gateway service module that identifies a gateway for a network and a network information service module. The network information service module identifies devices in the network, determines at least one property for each of the identified devices, and creates a network information data structure for storing device properties. A communication agent service module transmits at least one determined device property to other agent service modules associated with the network, receives at least one device property from another agent service module associated with the network, and provides the received at least one property device to the network information service module. A method of monitoring a computer network is also provided. The method includes identifying devices in a network, determining at least one property for each of the identified devices, receiving at least one determined device property from another device the network, and creating a network information data structure for storing the determined device properties.
Owner:CISCO TECH INC
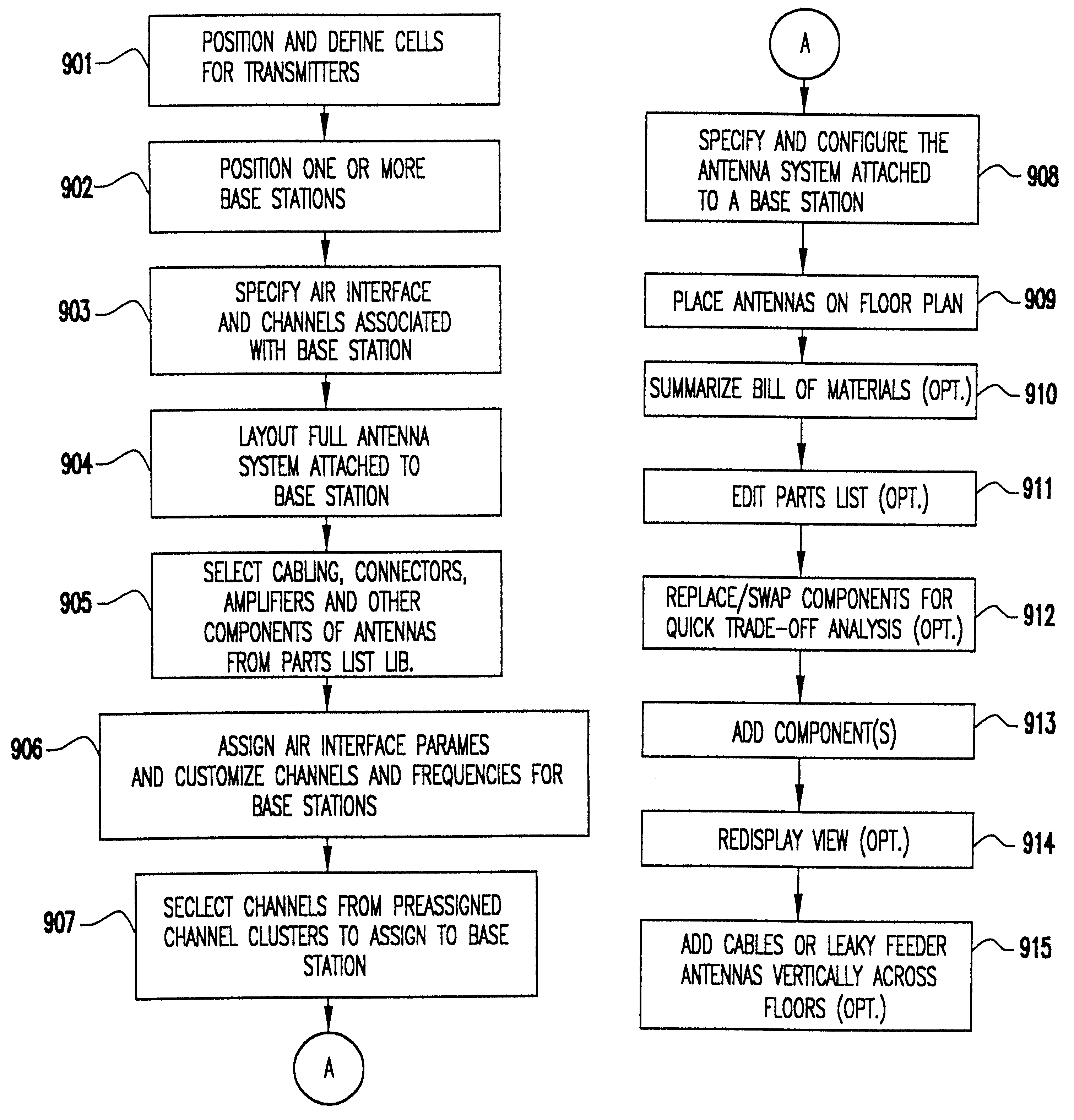
Method and system for automated optimization of antenna positioning in 3-D
InactiveUS6317599B1Quick fixSignificant valueMachines/enginesComputation using non-denominational number representationEngineeringRadio frequency
A method for engineering management and planning for the design of a wireless communications network in three-dimensions (3-D) combines computerized organization, database fusion, and radio frequency (RF) site-specific planning models. The method enables a designer to keep track of wireless system performance throughout the process of pre-bid design, installation and maintenance of a wireless system. Using a database of information that defines the desired environment, predictions of antenna coverage, system coverage and interference, and other wireless system performance criteria, such as frame error rate and network throughput, can be made. Watch points are created to ensure, in real time, that any modifications to the design of the wireless system do not degrade the performance of the system with respect to the watch point locations.
Owner:EXTREME NETWORKS INC
Method and system for rating patents and other intangible assets
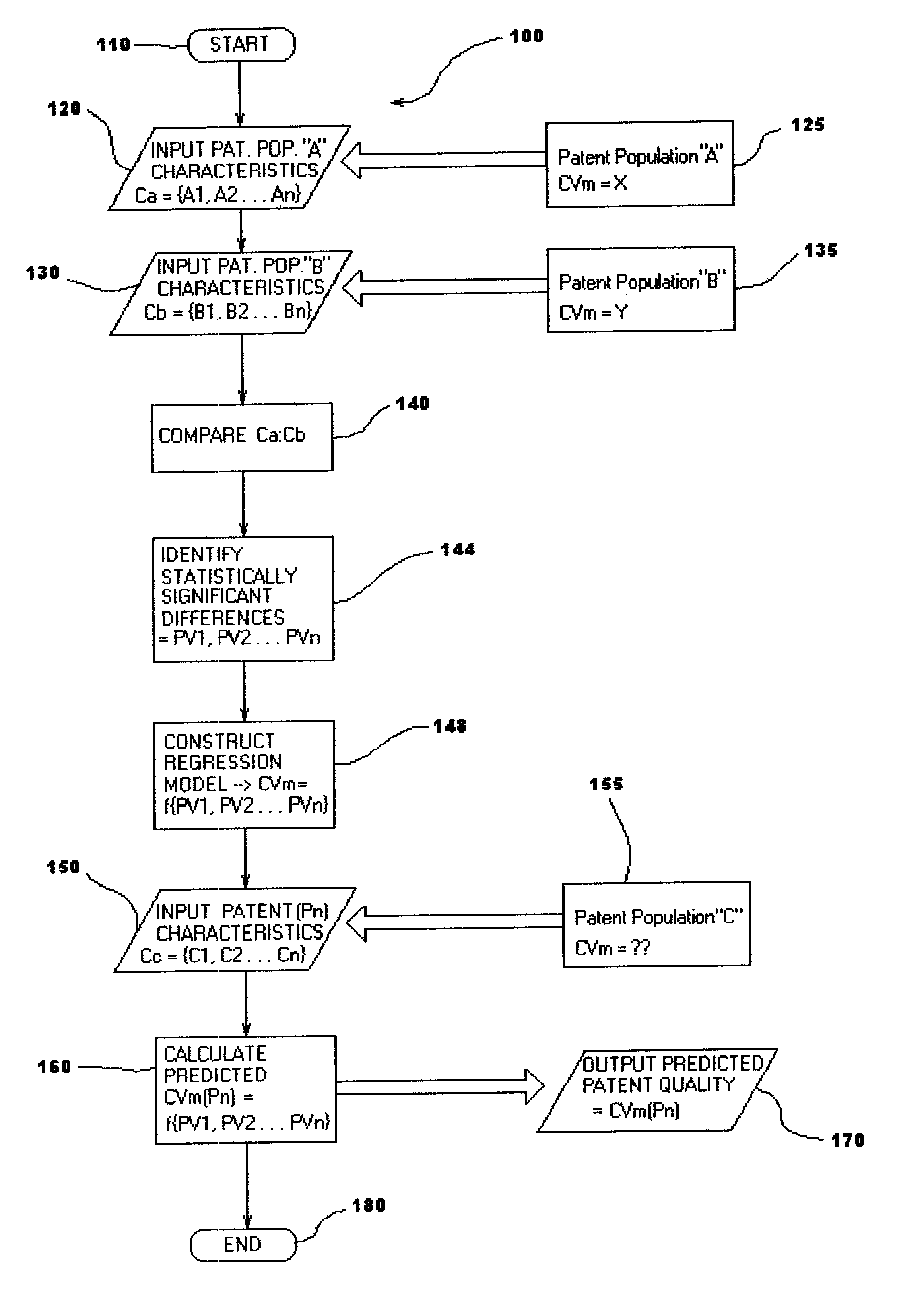
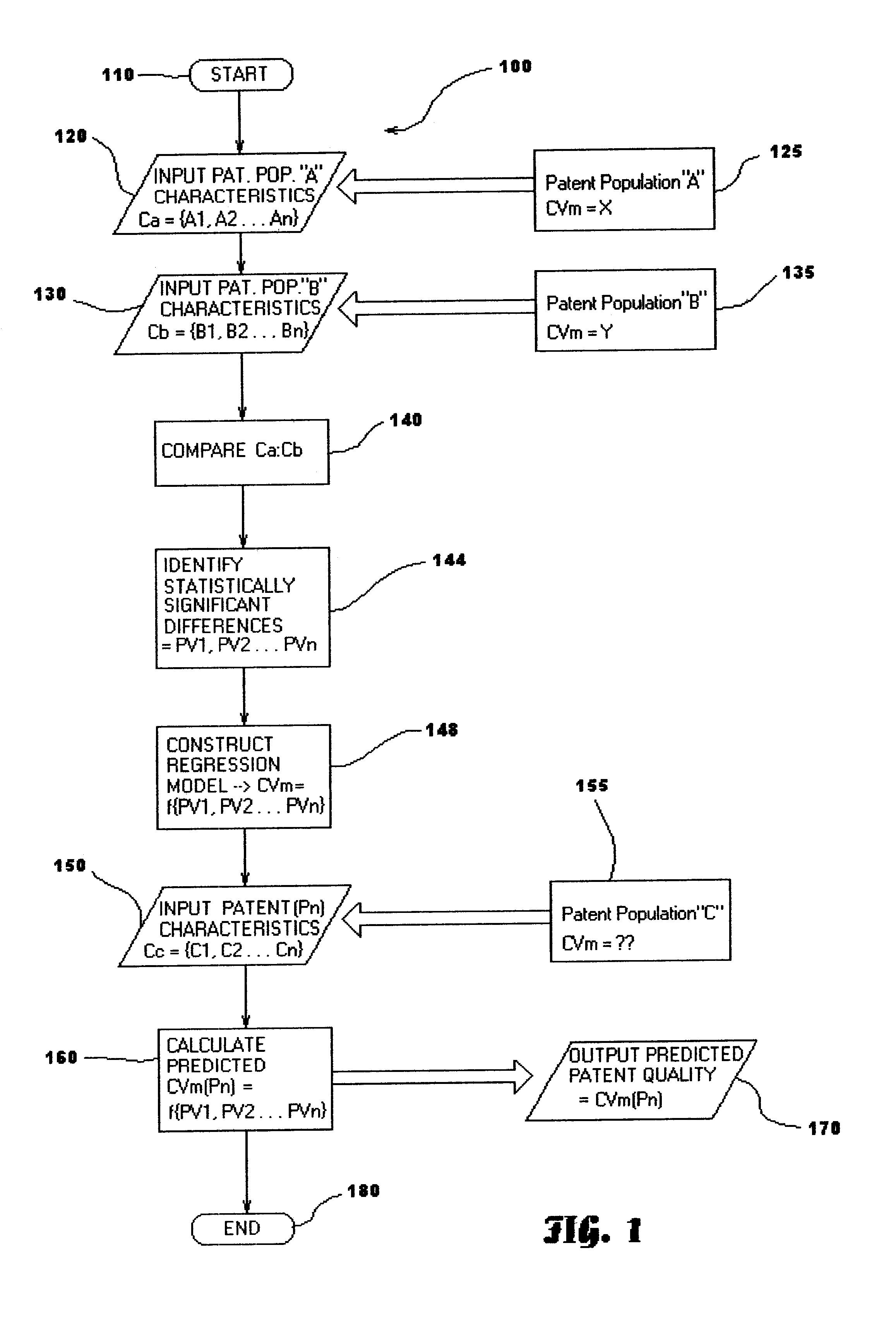
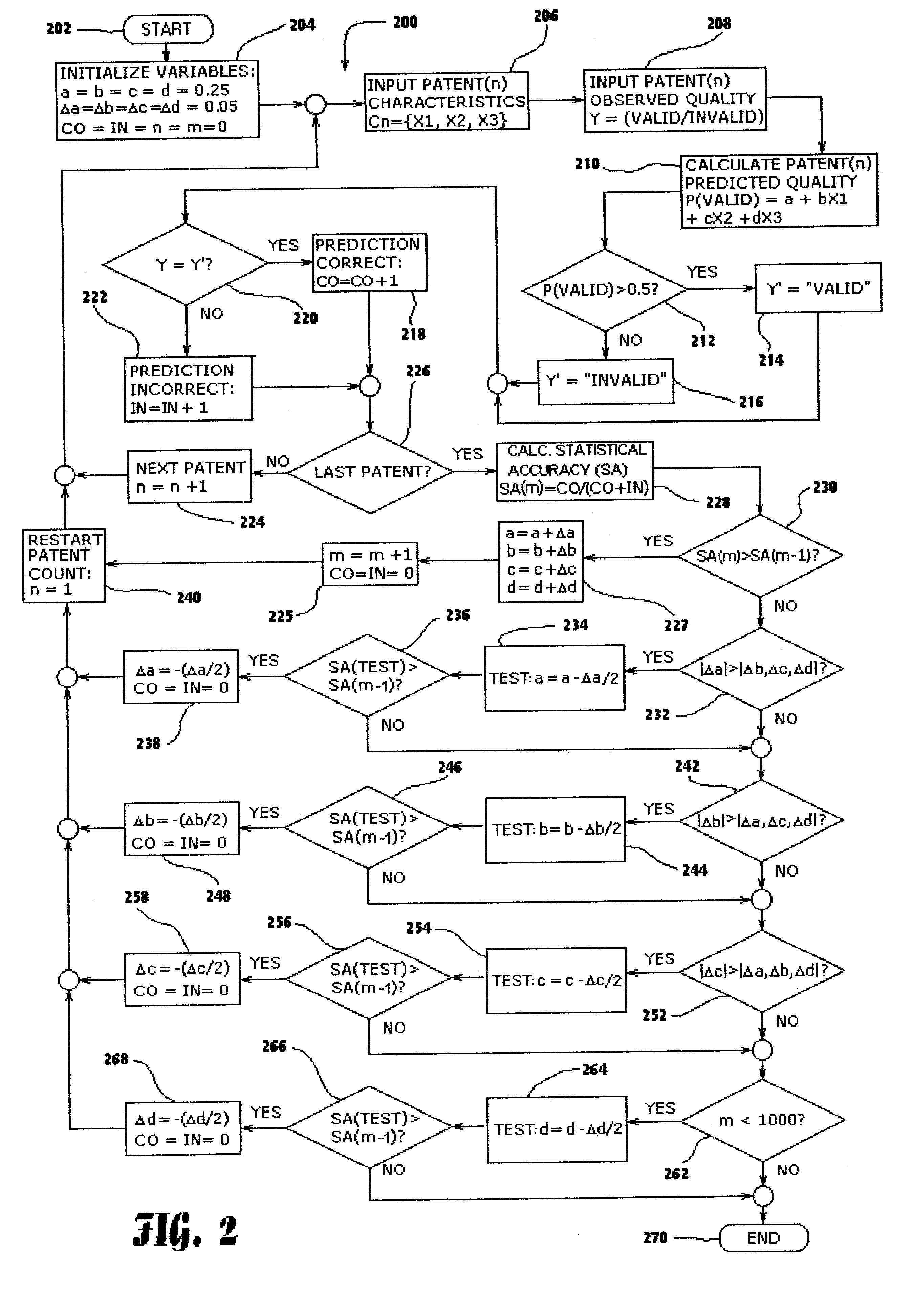
A statistical patent rating method and system is provided for independently assessing the relative breadth ("B"), defensibility ("D") and commercial relevance ("R") of individual patent assets and other intangible intellectual property assets. The invention provides new and valuable information that can be used by patent valuation experts, investment advisors, economists and others to help guide future patent investment decisions, licensing programs, patent appraisals, tax valuations, transfer pricing, economic forecasting and planning, and even mediation and / or settlement of patent litigation lawsuits. In one embodiment the invention provides a statistically-based patent rating method and system whereby relative ratings or rankings are generated using a database of patent information by identifying and comparing various characteristics of each individual patent to a statistically determined distribution of the same characteristics within a given patent population. For example, a first population of patents having a known relatively high intrinsic value or quality (e.g. successfully litigated patents) is compared to a second population of patents having a known relatively low intrinsic value or quality (e.g. unsuccessfully litigated patents). Based on a statistical comparison of the two populations, certain characteristics are identified as being more prevalent or more pronounced in one population group or the other to a statistically significant degree. Multiple such statistical comparisons are used to construct and optimize a computer model or computer algorithm that can then be used to predict and / or provide statistically-accurate probabilities of a desired value or quality being present or a future event occurring, given the identified characteristics of an individual patent or group of patents.
Owner:PATENTRATINGS
System and method for building and manipulating a centralized measurement value database
InactiveUS20020186818A1Low penetrationEasy to aimImage enhancementImage analysisMarket penetrationEfficacy
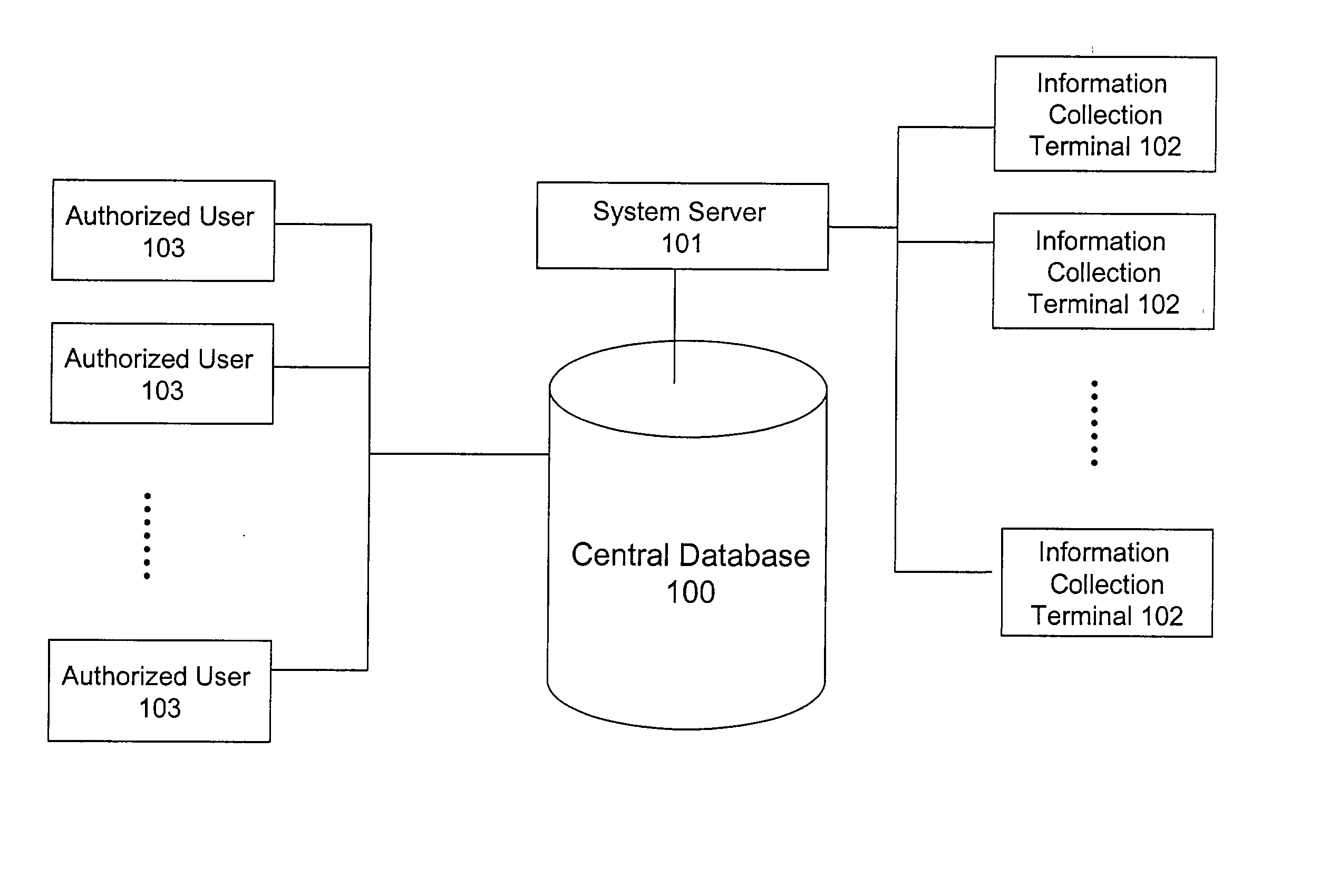
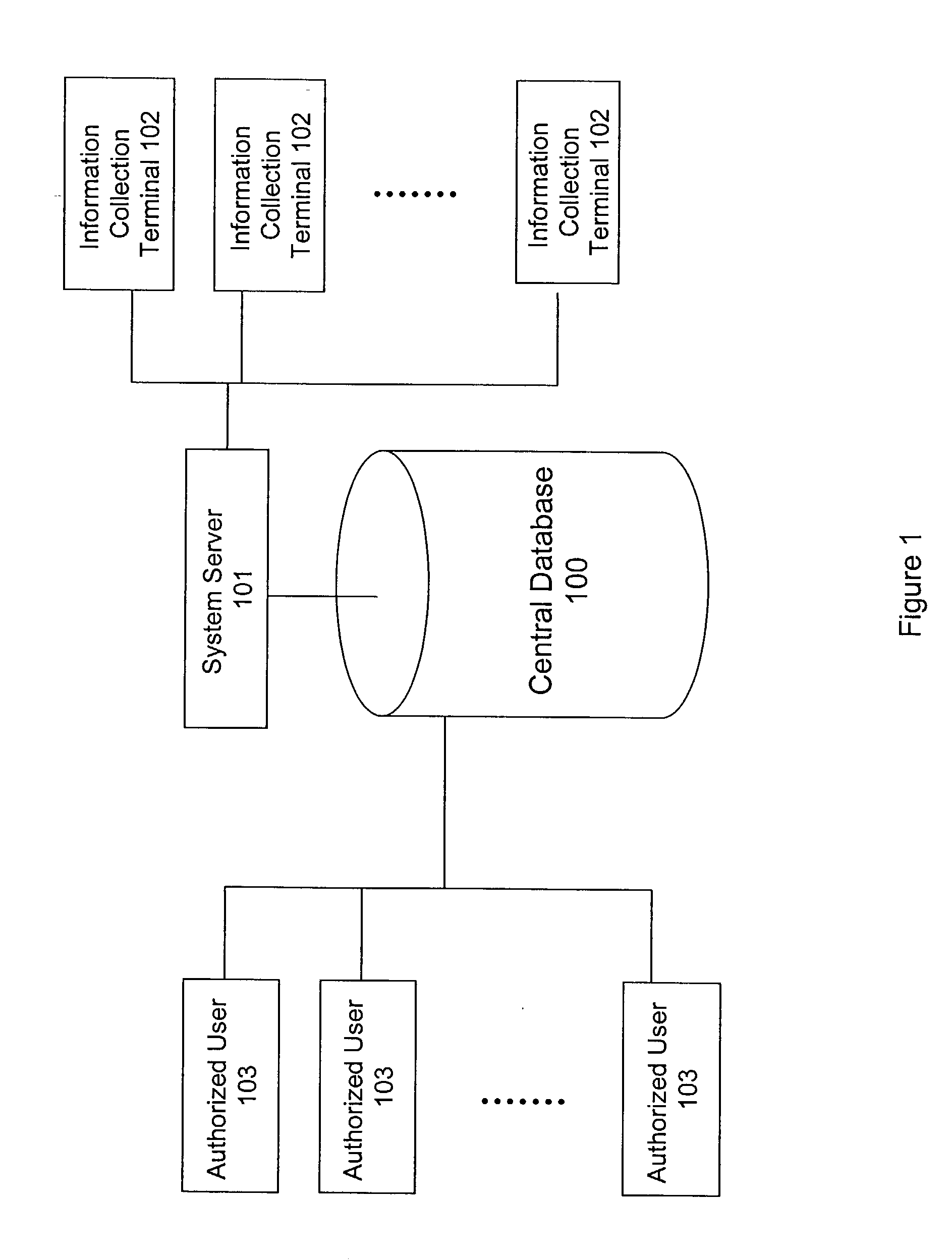
A system and method for building and / or manipulating a centralized medical image quantitative information database aid in diagnosing diseases, identifying prevalence of diseases, and analyzing market penetration data and efficacy of different drugs. In one embodiment, the diseases are bone-related, such as osteoporosis and osteoarthritis. Subjects' medical images, personal and treatment information are obtained at information collection terminals, for example, at medical and / or dental facilities, and are transferred to a central database, either directly or through a system server. Quantitative information is derived from the medical images, and stored in a central database, associated with subjects' personal and treatment information. Authorized users, such as medical officials and / or pharmaceutical companies, can access the database, either directly or through the central server, to diagnose diseases and perform statistical analysis on the stored data. Decisions can be made regarding marketing of drugs for treating the diseases in question, based on analysis of efficacy, market penetration, and performance of competitive drugs.
Owner:IMAGING THERAPEUTICS +1
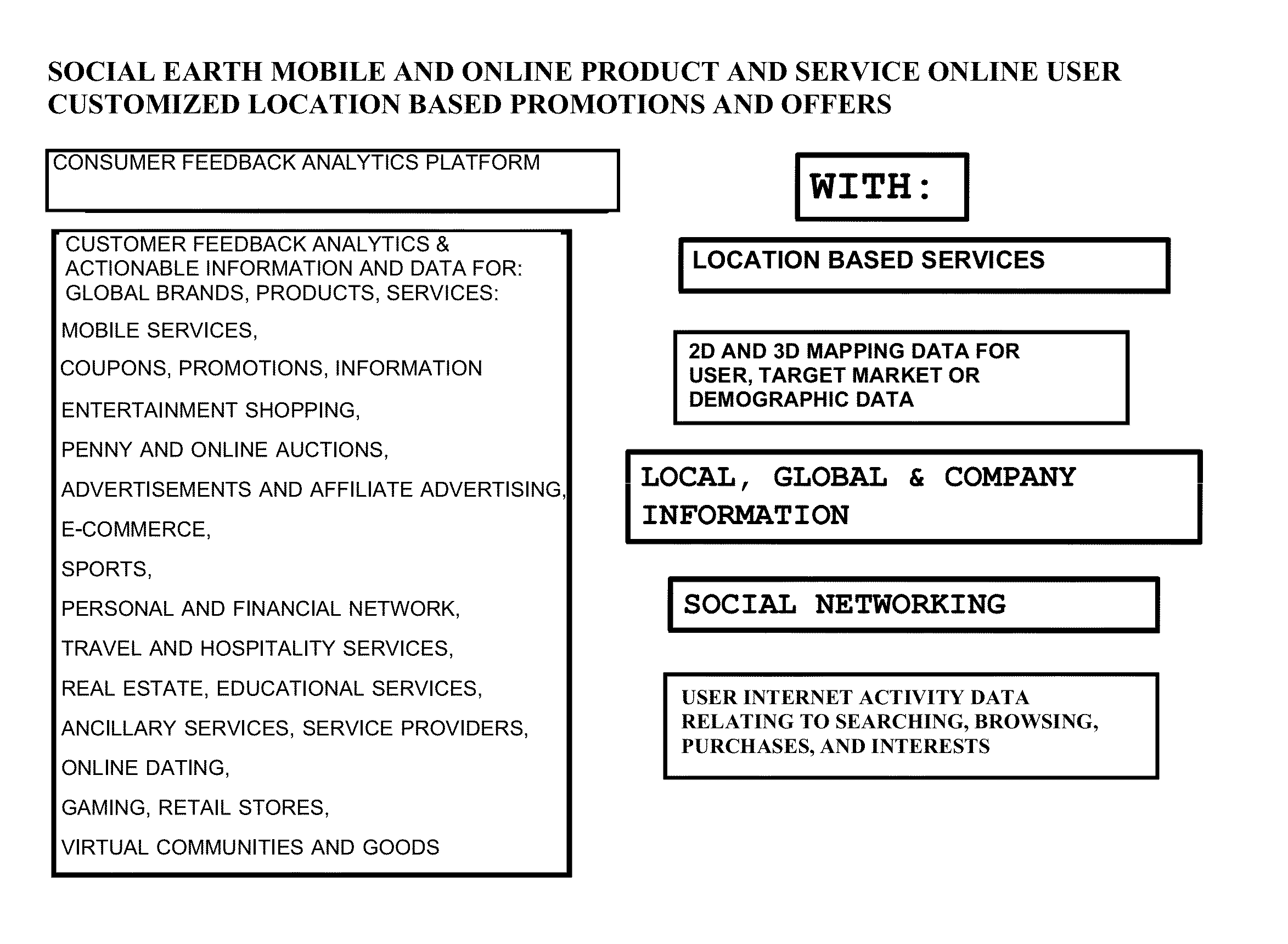
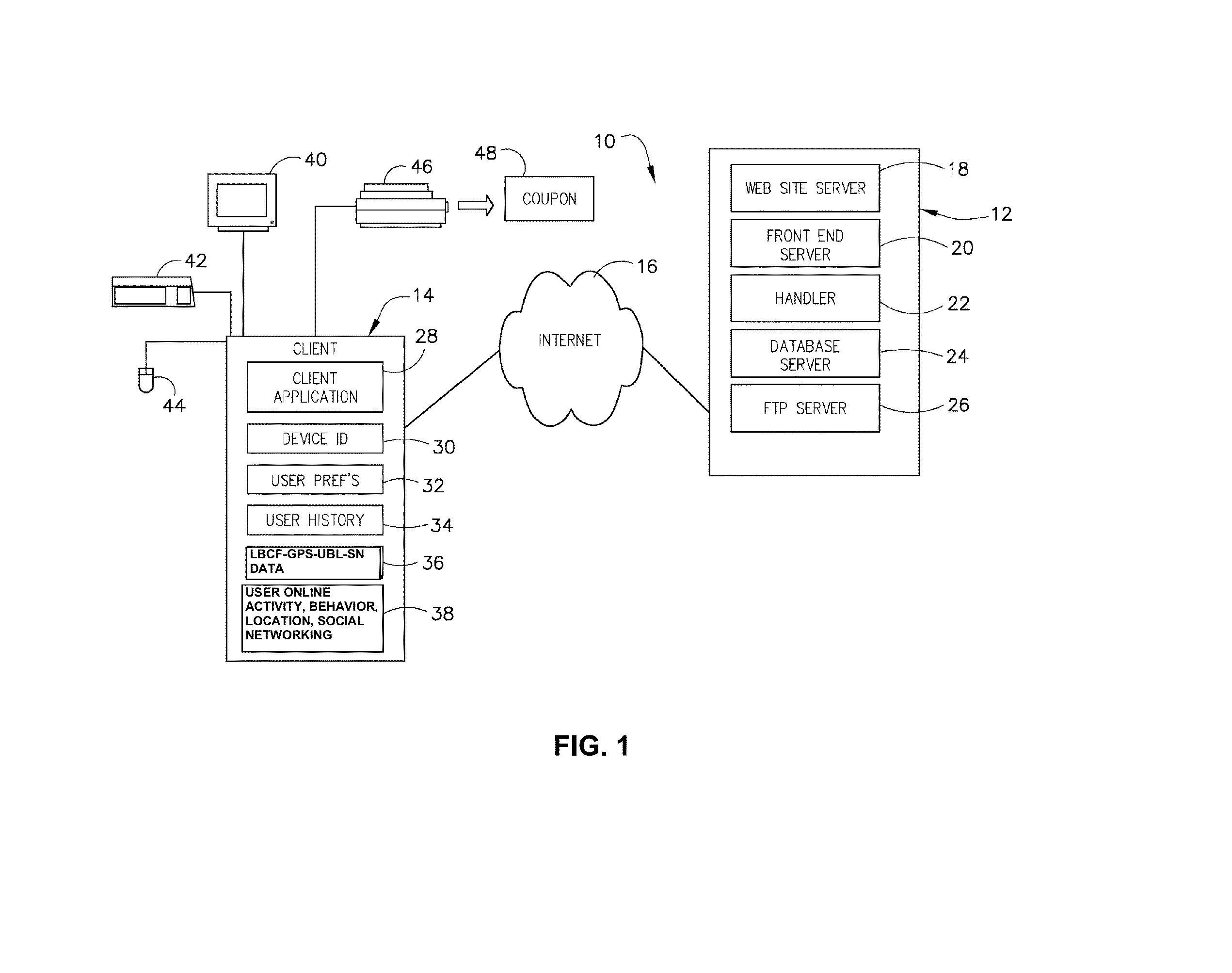
System and method for using global location information, 2d and 3D mapping, social media, and user behavior and information for a consumer feedback social media analytics platform for providing analytic measfurements data of online consumer feedback for global brand products or services of past, present, or future customers, users or target markets
InactiveUS20130073336A1Improved and desired customer perceptionImproved and desired and sentimentMarketingComputerized systemSocial media analytics
A method, apparatus, non-transitory computer readable storage medium, computer system, network, or system, is provided for using location information, 2D and 3D mapping, social media, and user behavior and information to provide alternative a consumer feedback social media analytics platforms for providing analytic measurements data of online consumer feedback for global brand products or services of past, present or future customers, users, and / or target markets, for companies, organizations, government agencies, and the like, by electronically collecting and analyzing, on a networked computer system using a processor, qualitative or quantitative online social media online communications, activity, and online communications and activity relevant to consumer products or services, or promotions thereof, of interest, in order to provide targeted, location based, 2D or 3D mapped, or impressions to generate online location information data or promotions to provide improved or desired customer perception or sentiment regarding a company's products, services or promotions thereof
Owner:HEATH STEPHAN
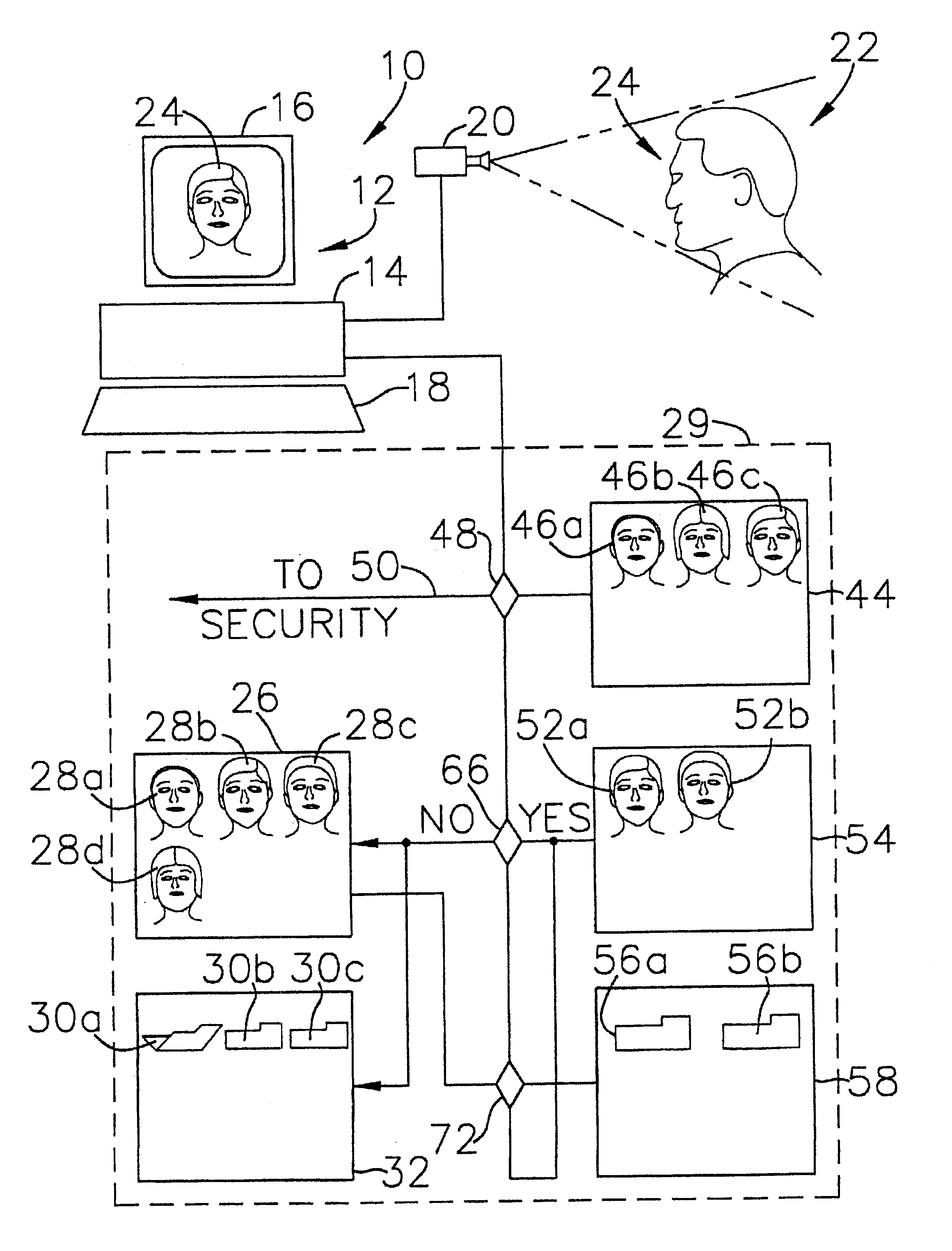
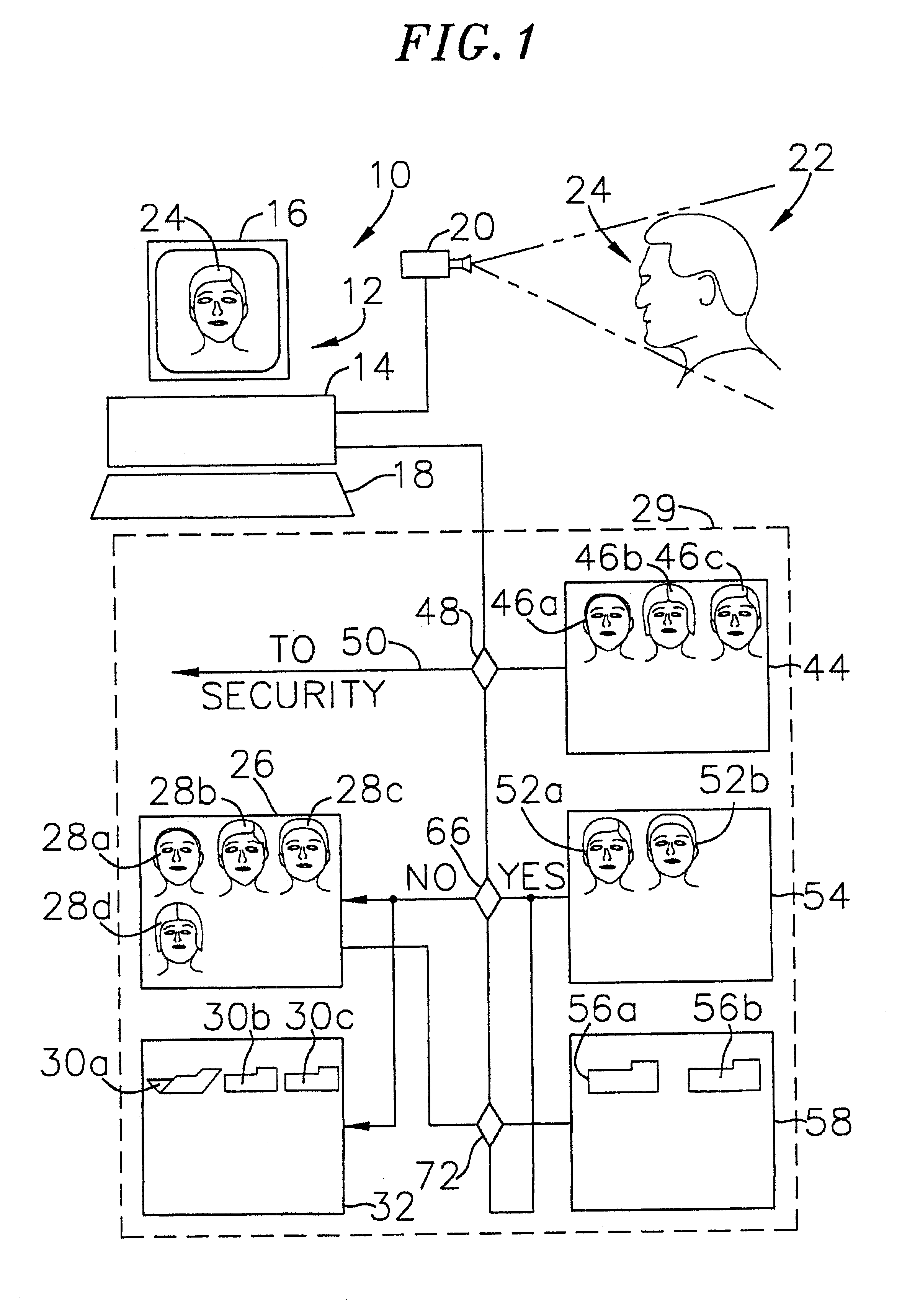
Passive biometric customer identification and tracking system
InactiveUS6554705B1Simplifies search techniqueMinimal useCharacter and pattern recognitionApparatus for meter-controlled dispensingBiometric dataFile allocation
A computer-based customer tracking system uses a passive biometric identification for identifying customers. Neither the customer, nor any establishment personnel, are required to enter any informational data with respect to the customer; identification is done completely biometrically. Biometric identification information is sent to a central computer processor, which searches files in a library for matching biometric data. If no match is found, the processor opens a new file in the library, assigning a code or identification number to the file. Information with respect to the customer's biometric data, along with any transactional information, are stored in the file. If prior activity information stored in the file exceeds a predetermined level, information with respect to the customer's prior activity is retrieved from the file and sent to a terminal, preferably at the location of the transaction. Any new information from the transaction is then sent to the processor and stored for future access. The processor scans the files periodically, and deletes files for which the activity level in the file is below a certain predetermined level over a preselected time period. Deletion of inactive files precludes the processor memory from being overloaded with information which is not useful to the establishment, and also reduces the amount of time necessary for the processor to search library files for biometric matches.
Owner:BIOMETRIC RECOGNITION
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Runtime adaptable security processor
InactiveUS20050108518A1Improve performanceReduce overheadSecuring communicationInternal memoryPacket scheduling
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
System and method for promoting commerce, including sales agent assisted commerce, in a networked economy
InactiveUS20050251440A1Not capableImprove performanceMarket predictionsDiscounts/incentivesE-commerceMonetary value
A personal communication and electronic commerce system for use by participating users and participating merchants in connection with incentive programs in the Network Economy. The system includes a cellular communication network that includes geographically spaced base stations that are linked to a fixed communication network. Users may have personal communication devices that can be used to allow a digital message generated on the personal communication devices by placing a call through one of the base stations and memory for storing a digital value corresponding to a monetary value. The personal communication device may also be used as a cellular position locator to determine one's geographic location and, if desired, to access information from a merchant information database containing information pertaining to a plurality of participating merchants located within the geographic territory covered by the cellular communication network. The merchant information may be stored on a database that is accessible by merchants so those merchants can add, delete or alter information contained in their respective listings. An incentive system is also provided for creating incentives for participating users to encourage. This computer implemented incentive program for encouraging certain participant actions includes a first reward program under which participants may earn points for certain actions and a second reward program through which the redemption rate associated with a particular participant is adjusted in response to certain participant action. The incentive program has a wide range of applications, including transportation, financial services and computer gaming.
Owner:BEDNAREK MICHAEL D
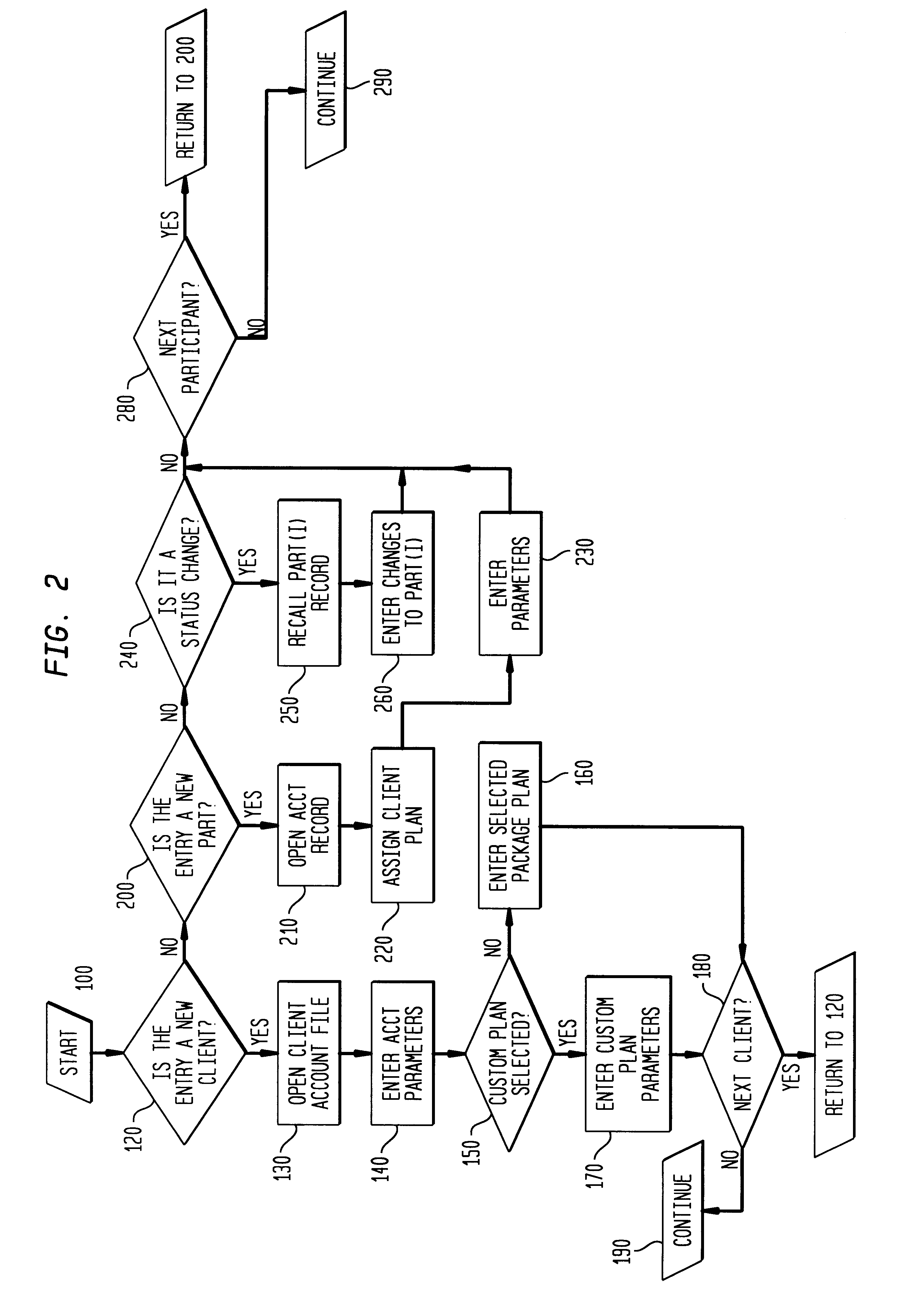
Stock option control and exercise system
A system and method for managing a plurality of stock option accounts each for a plurality of participants. The system invokes a particular option plan defined in the system that governs the transaction choices available to each participants The governing option plans are defined by the sponsoring company in terms of grant, vest and expiration date for the option contracts, and are defined in the system via a database of option holding information for each participant and an axiomatic rule system defining the criteria under which a given participant can exercise given options under the particular plan. The system implements the plans for multiple client companies providing several distinct modes for option exercise by the participant. The system preferably also allows for disbursement of proceeds in a currency different than that in which the underlying security for the option is traded, real time execution of the option transaction, and / or simulating the outcomes of different manners in which the participant may exercise vested options and the resulting economic outcome (disbursement, taxes, transaction fees).
Owner:BANK OF AMERICA CORP
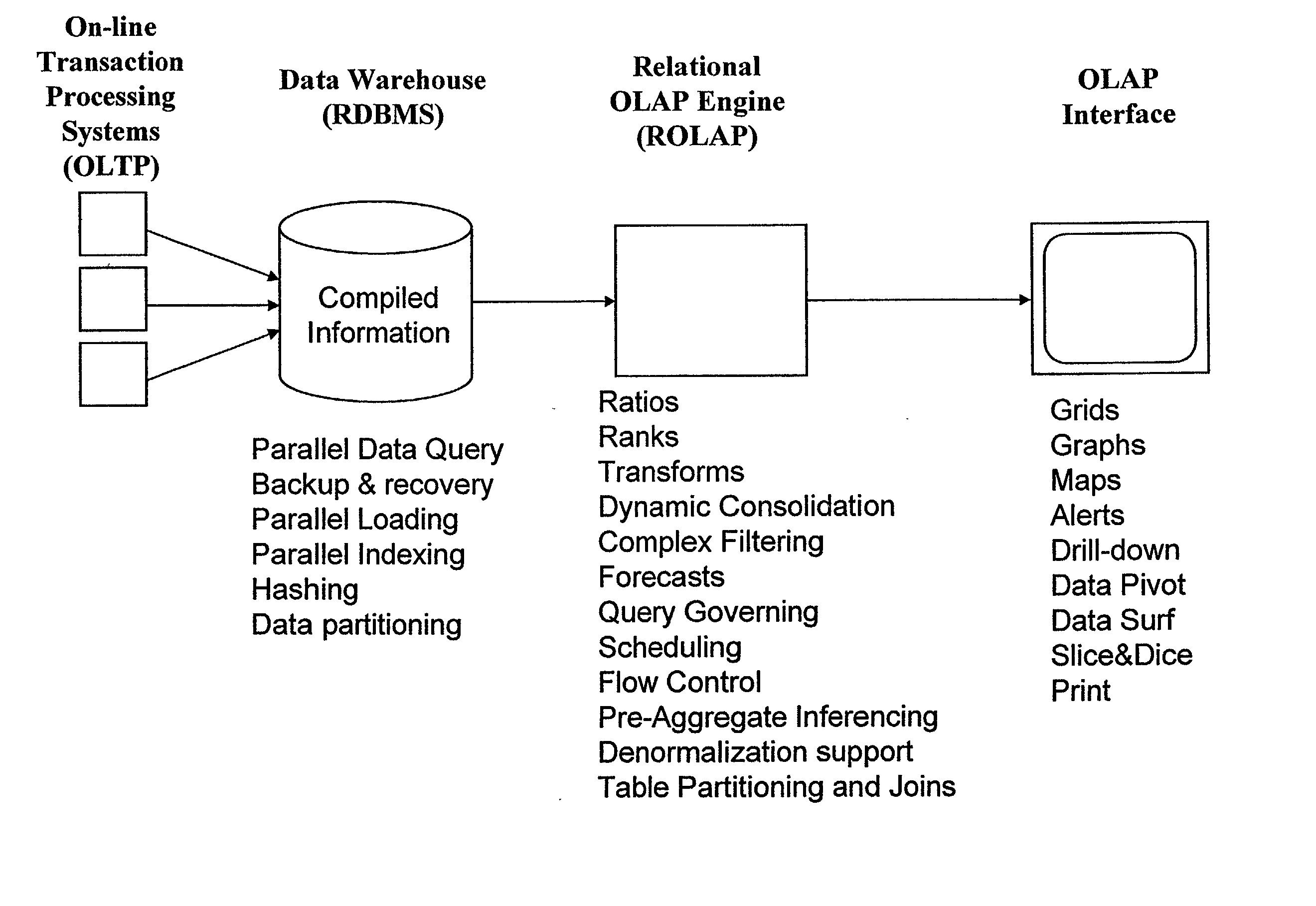
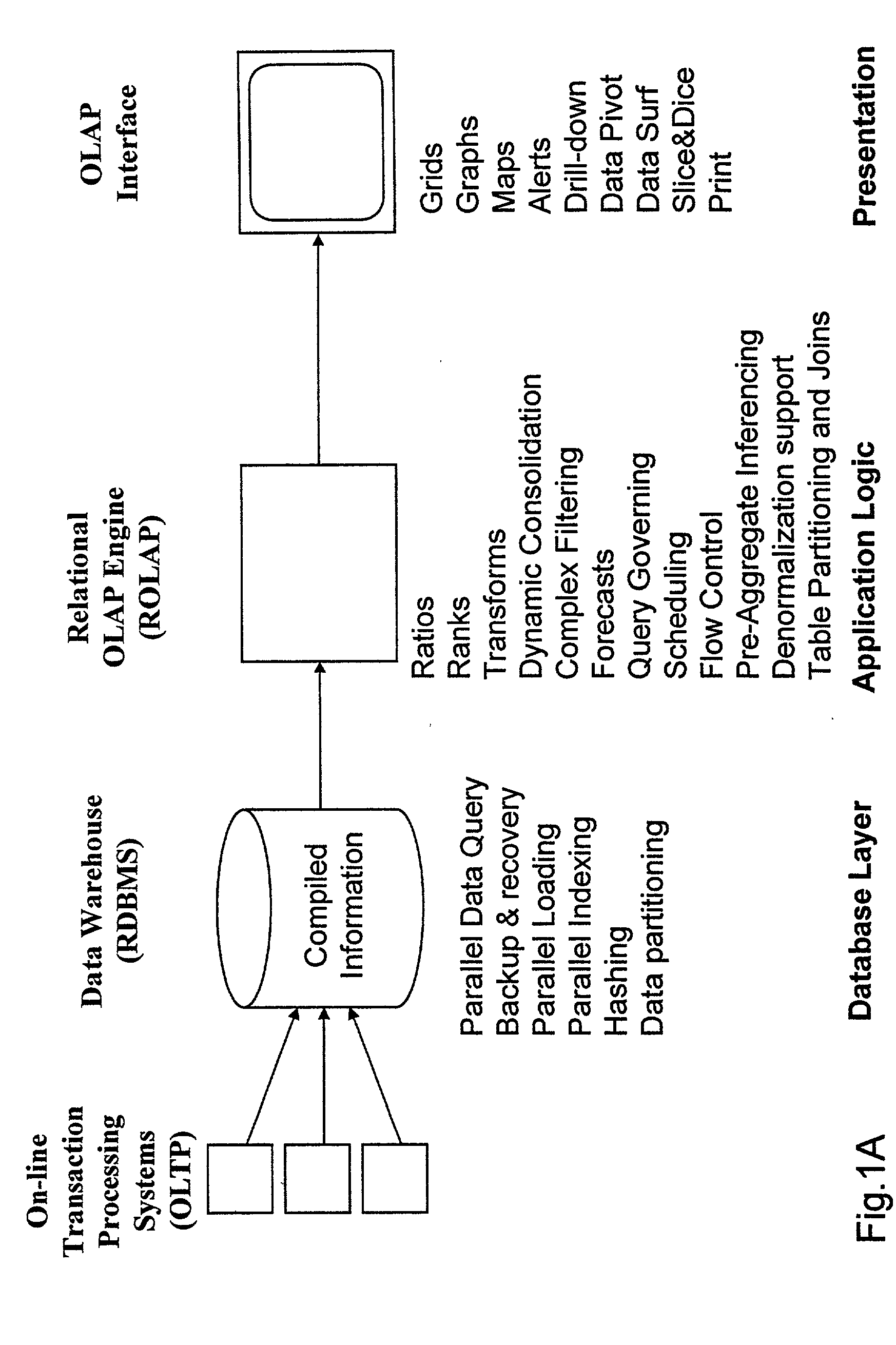
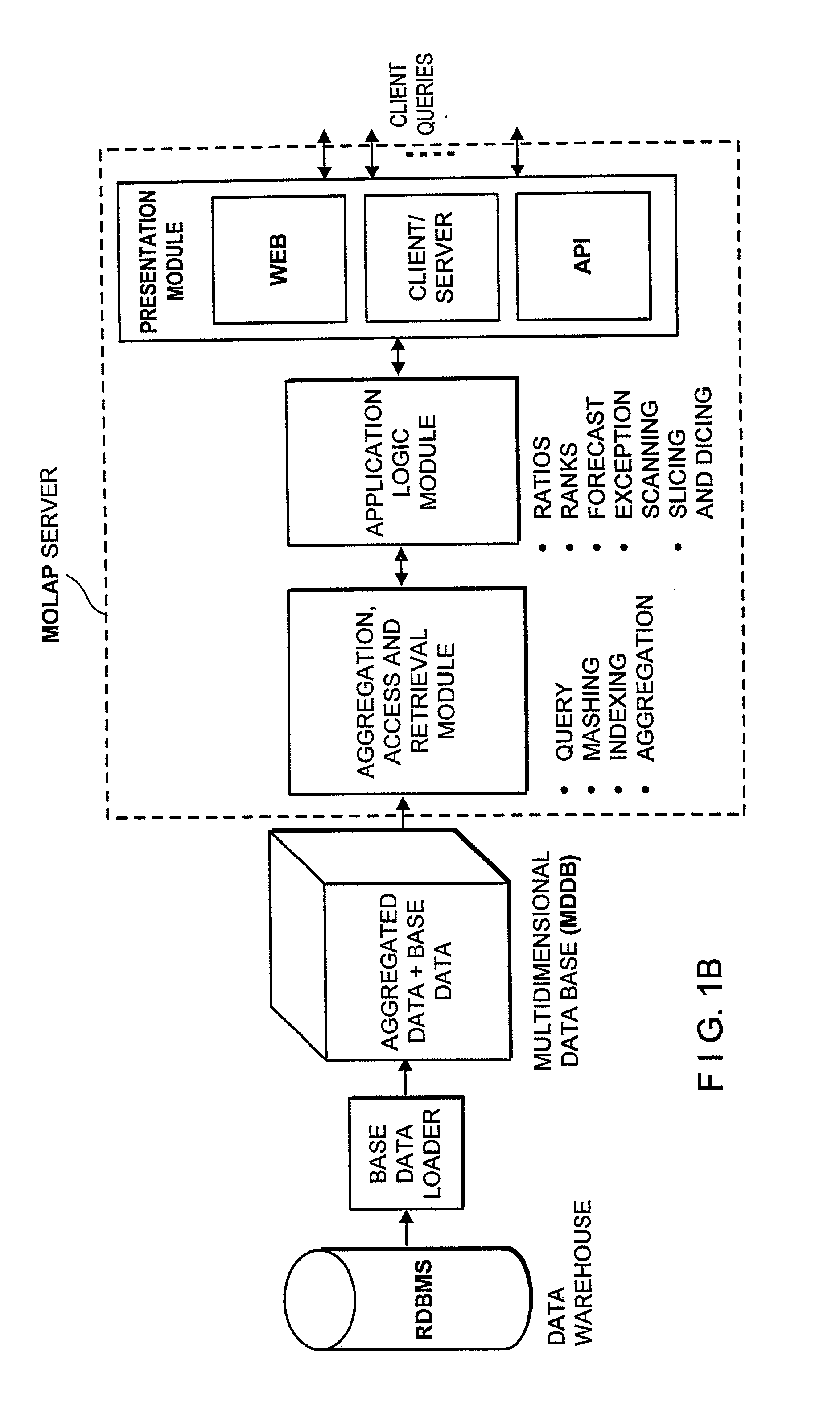
Data aggregation server for managing a multi-dimensional database and database management system having data aggregation server integrated therein
InactiveUS20020029207A1Reduce the burden onImprove system performanceData processing applicationsDigital data processing detailsData aggregatorThe Internet
Improved method of and apparatus for aggregating data elements in multidimensional databases (MDDB). In one aspect of the present invention, the apparatus is realized in the form of a high-performance stand-alone (i.e. external) aggregation server which can be plugged-into conventional OLAP systems to achieve significant improments in system performance. In accordance with the principles of the present invention, the stand-alone aggregation server contains a scalable MDDB and a high-performance aggregation engine that are integrated into the modular architecture of the aggregation server. The stand-alone aggregation server of the present invention can uniformly distribute data elements among a plurality of processors, for balanced loading and processing, and therefore is highly scalable. The stand-alone aggregation server of the present invention can be used to realize (i) an improved MDDB for supporting on-line analytical processing (OLAP) operations, (ii) an improved Internet URL Directory for supporting on-line information searching operations by Web-enabled client machines, as well as (iii) diverse types of MDDB-based systems for supporting real-time control of processes in response to complex states of information reflected in the MDDB. In another aspect of the present invention, the apparatus is integrated within a database management system (DBMS). The improved DBMS can be used to realize achieving a significant increase in system performance (e.g. deceased access / search time), user flexibility and ease of use. The improved DBMS system of the present invention can be used to realize an improved Data Warehouse for supporting on-line analytical processing (OLAP) operations or to realize an improved informational database system, operational database system, or the like.
Owner:YANICKLO TECH LIABILITY +1
Providing multiple perspectives for a venue activity through an electronic hand held device
Methods and systems for receiving and displaying venue-based data at hand held devices are disclosed herein. Data transmitted from one or more venue-based data sources may be received by at least one hand held device present within a venue, such as a sports stadium or concert arena. Such data can be processed for display on a display screen associated with the hand held device. The processed data may be then displayed on the display screen, thereby enabling a user of the hand held device to view venue-based data through the hand held device. Such venue-based data viewable through the hand held device within the venue may include real-time and instant replay video images and clips, advertising and promotional information, scheduling, statistical, historical and other informational data, or a combination thereof.
Owner:FRONT ROW TECH
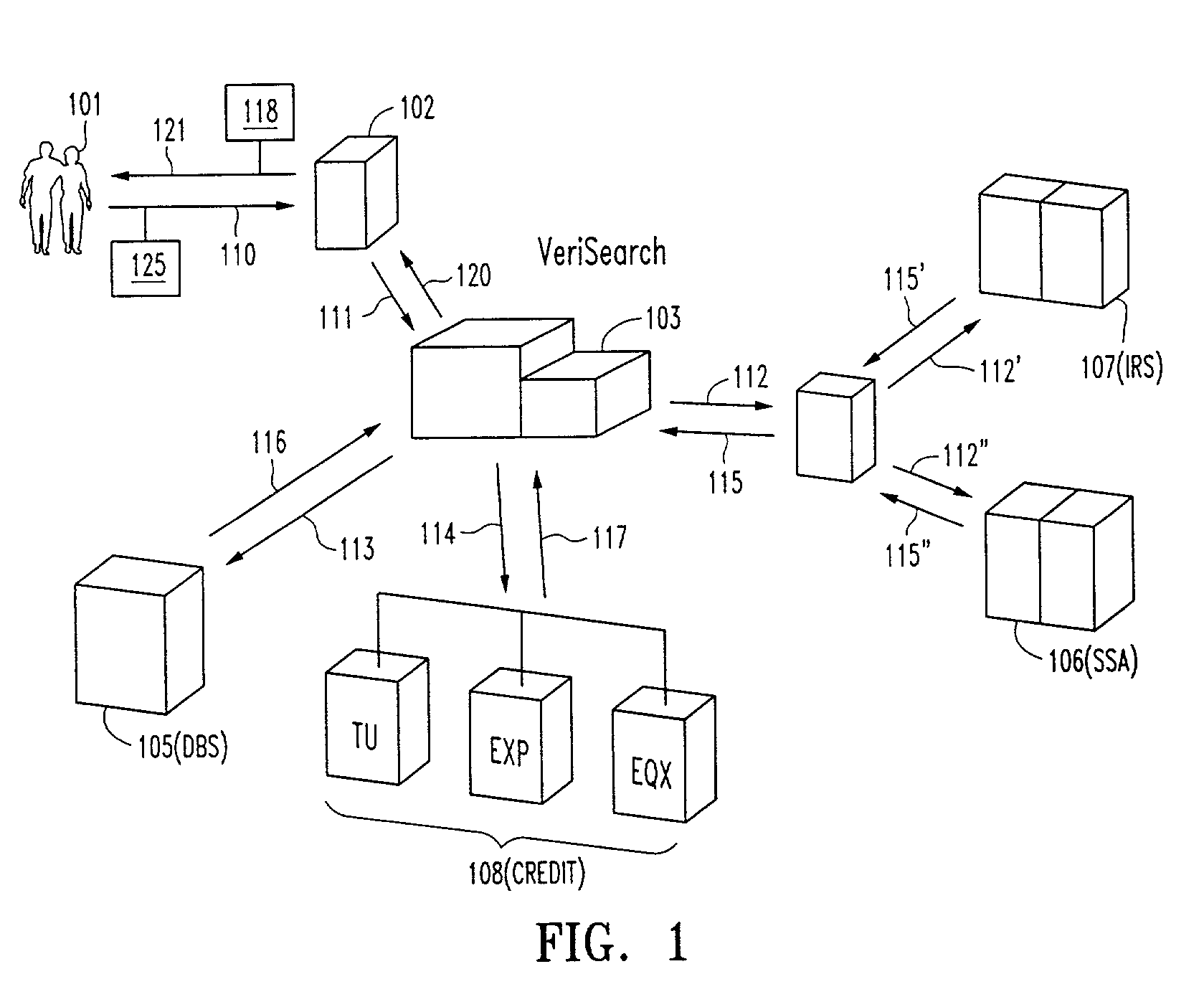
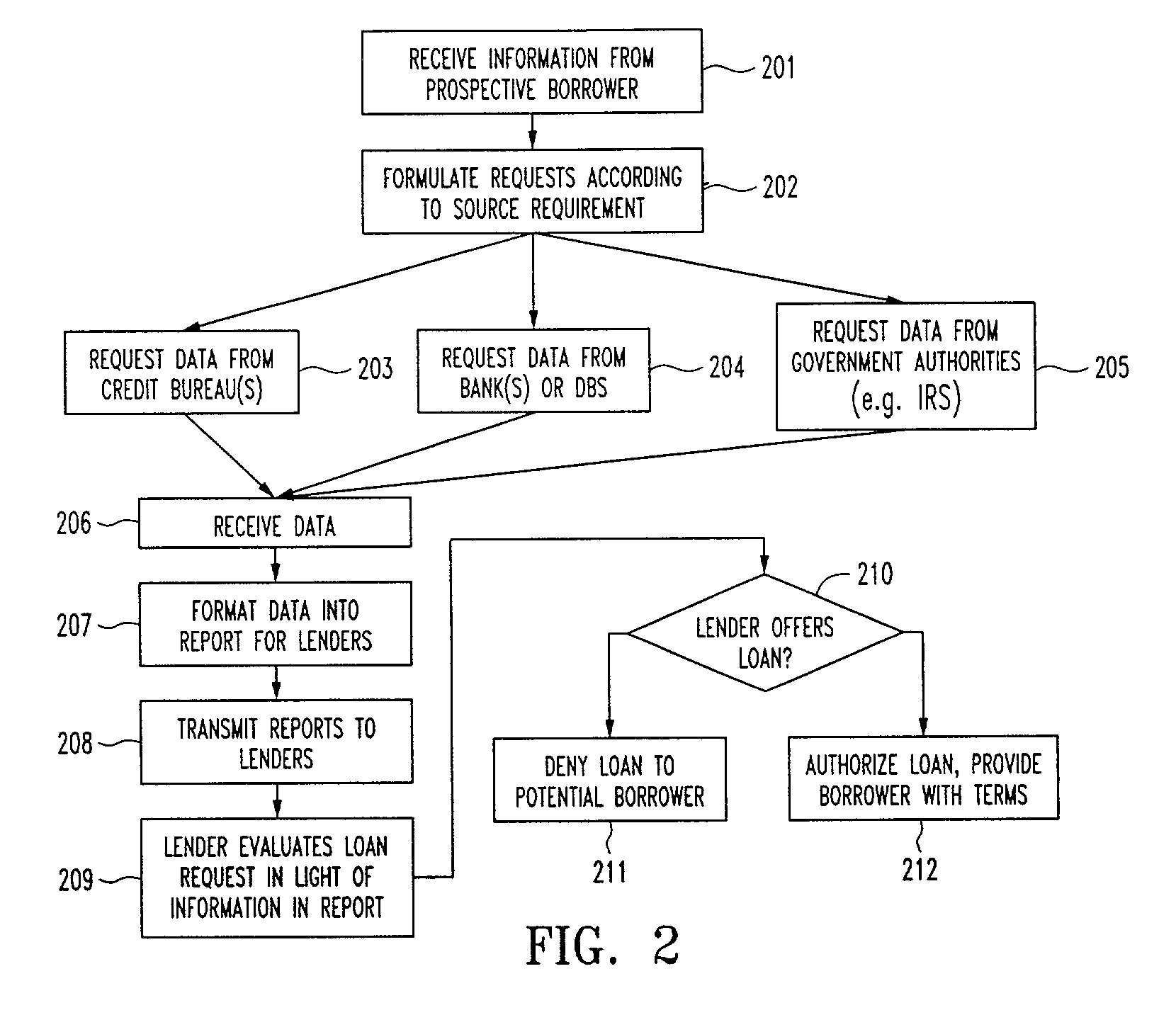
Systems and methods for electronically verifying and processing information
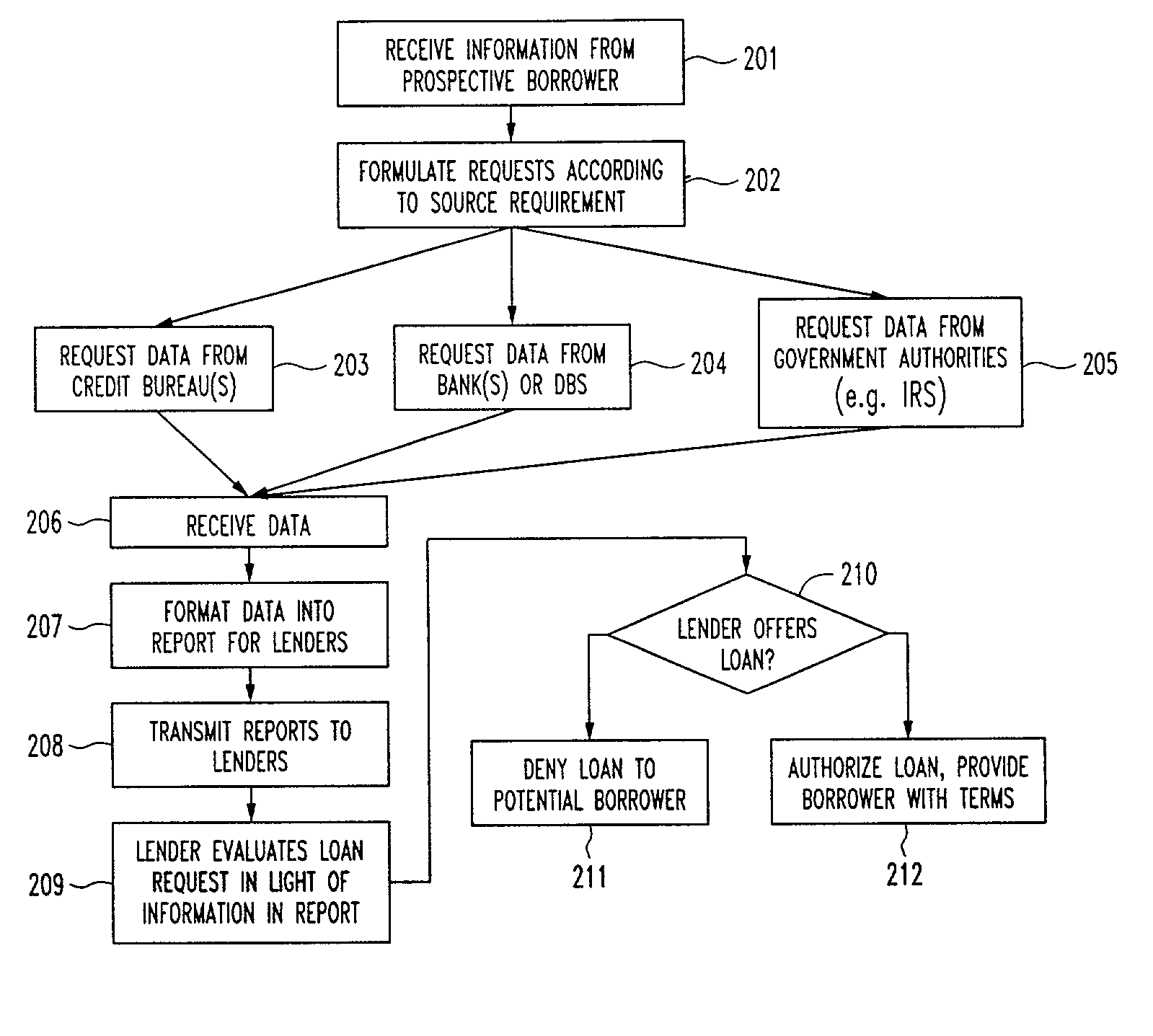
InactiveUS20030009418A1Reduce riskFacilitate a convenient, efficient and expeditious credit-risk evaluationFinanceLogisticsInternet privacyProcess information
A computer implemented method and system which provides current, reliable and accurate personal information regarding a prospective borrower and / or co-borrower. The system includes a central server which receives requests for personal information relating to proposed borrowers, which in turn parses out similar requests relating to that borrower to information sources such as, among others, the Internal Revenue Service, the Social Security Administration, the Daily Banking System and the pertinent credit bureaus. Information corresponding to the respective requests is retrieved from the information sources, and then compiled into a report format and forwarded to the requested party. The requested party may be the borrower / consumer individually, or may be a mortgage broker / agent, lending institution or other party authorized to request and obtain the information. An electronic signature or signatures accompany the request to the central server, which uses same to retrieve personal information data pertaining to the signatory(ies). Various encryption schemes may be employed for security purposes. The invention permits for the retrieval, compilation and reporting of relevant, personal data to a party or parties involved in the loan decision making process without any opportunity for the information to be tampered with by the proposed borrower(s) because the information is obtained electronically and directly from the information depositories.
Owner:GREEN GERALD M +1
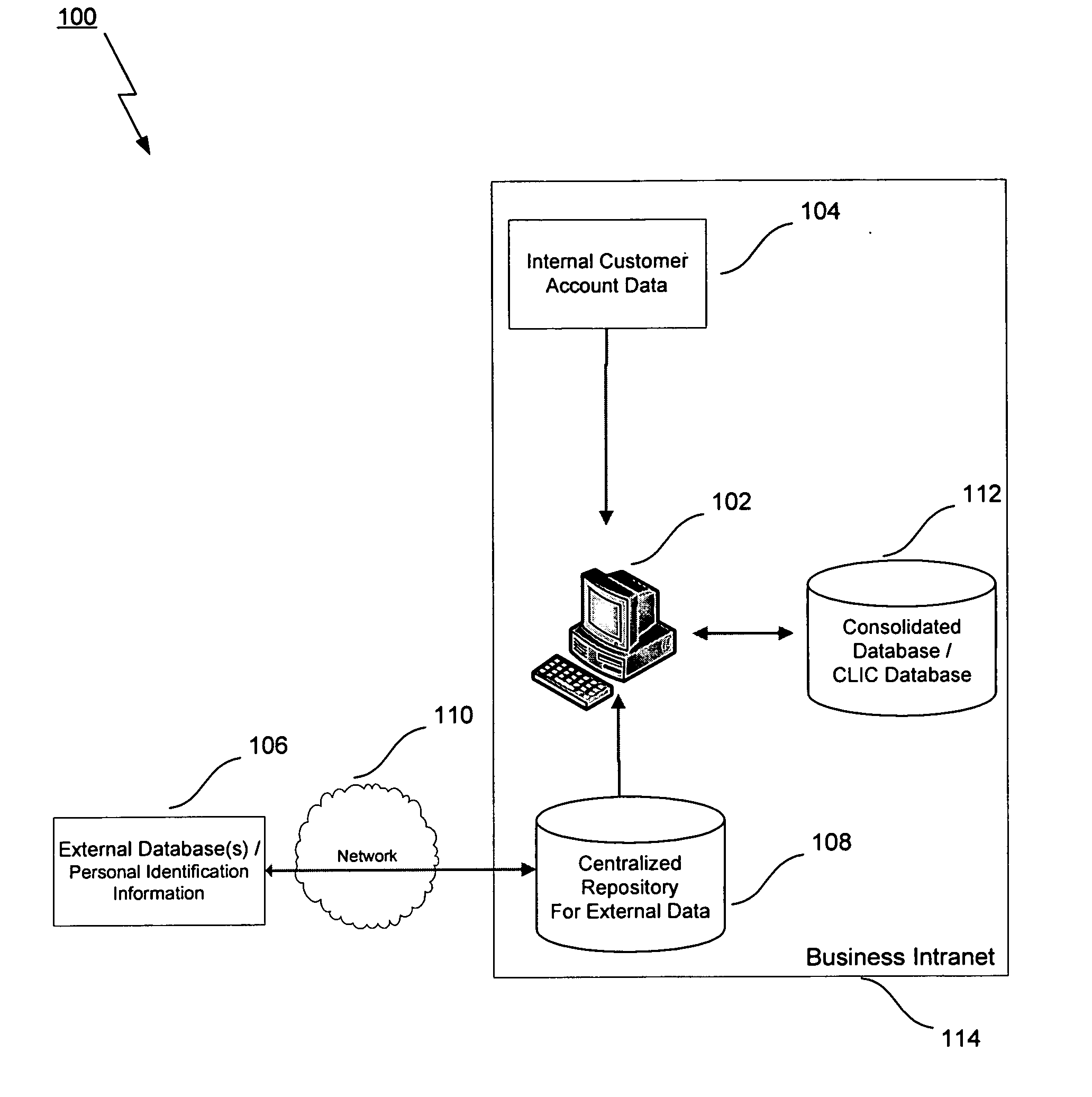
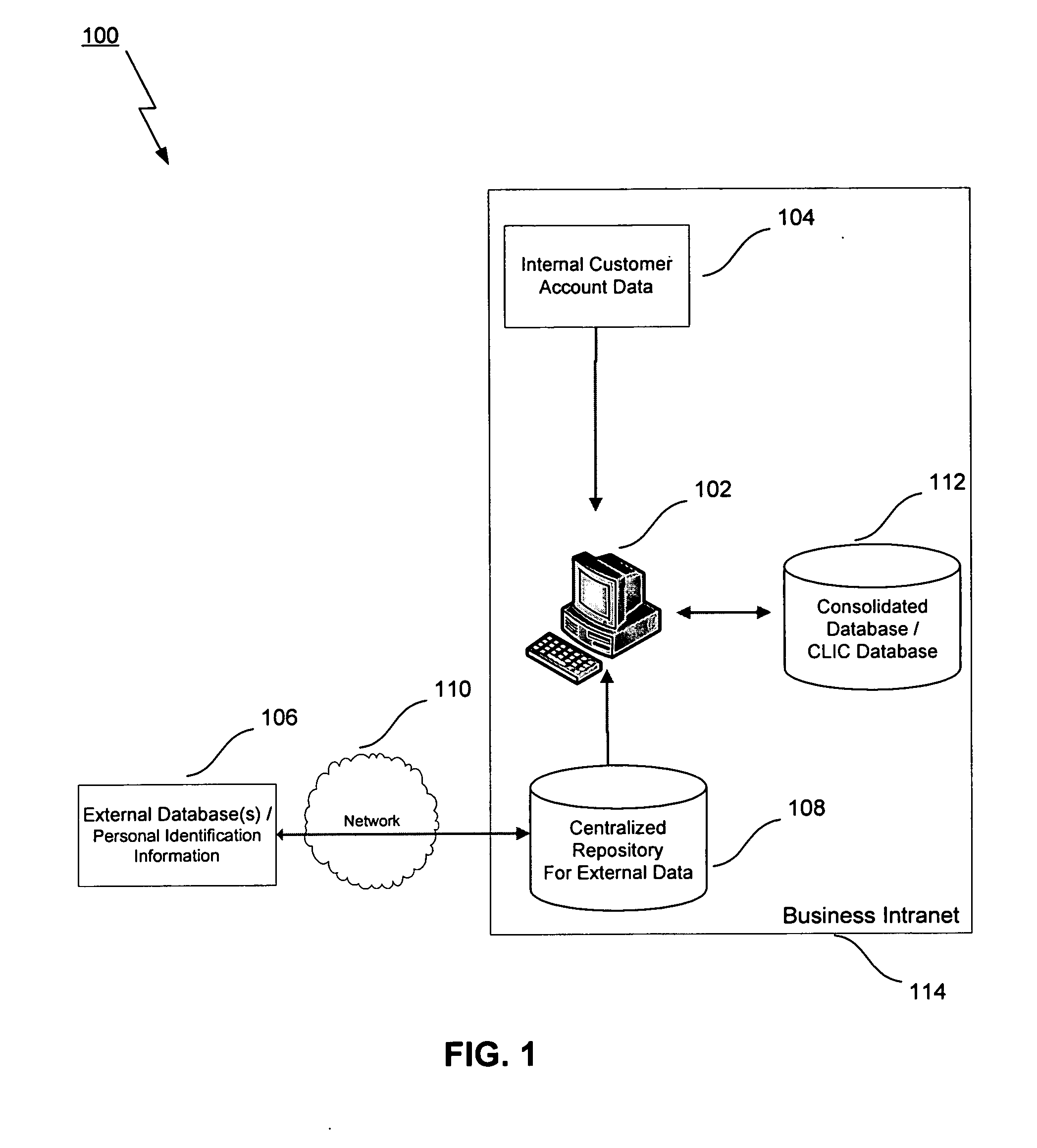
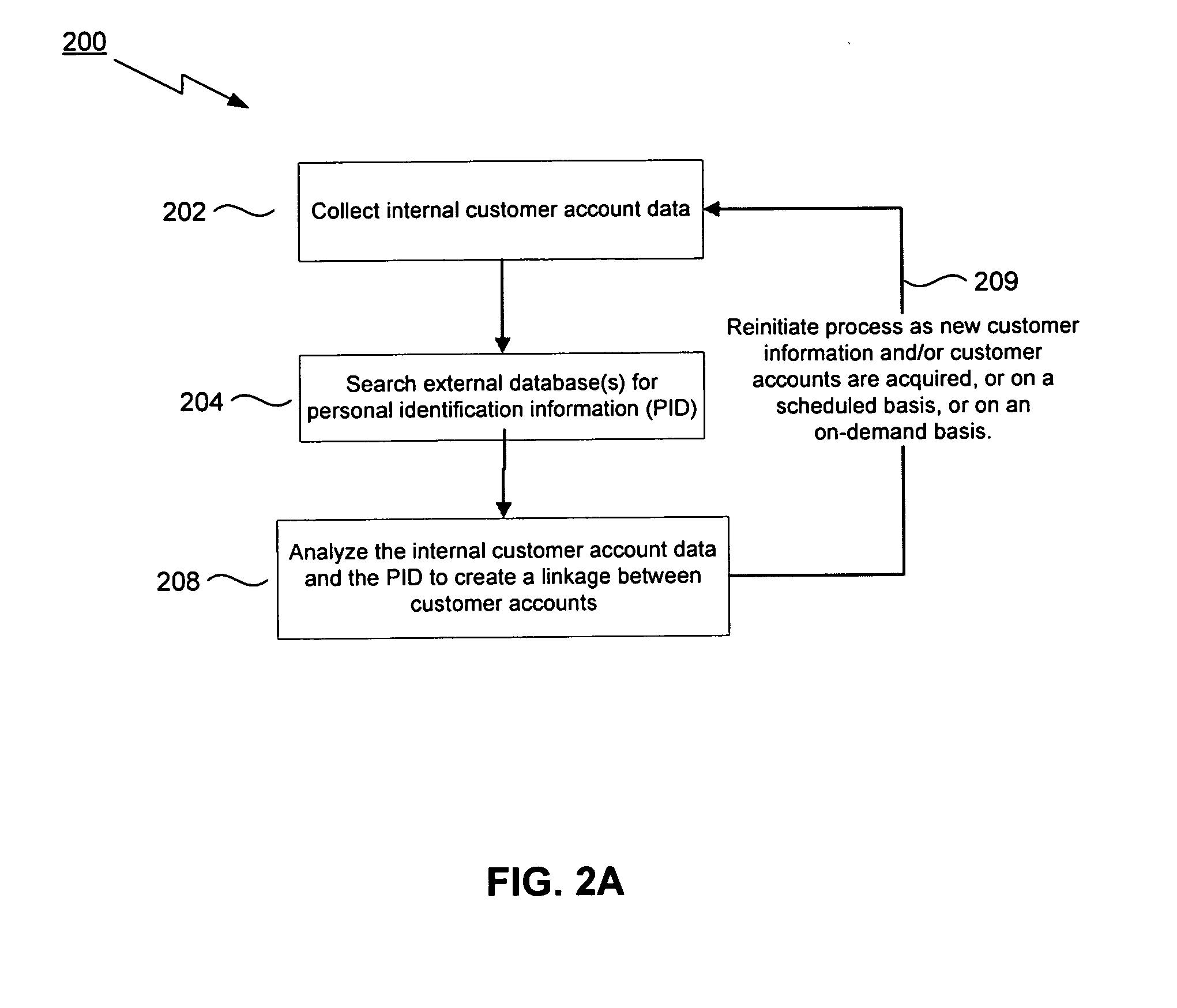
Method, system, and computer program product for linking customer information
InactiveUS20070192122A1Customer relationshipDigital data processing detailsCustomer informationInformation data
In a business where a database tracks customers and manages customer accounts, a method and system correctly link accounts with customers. The method entails reading customer information for a first customer and for a second customer, and then utilizing personal identification information obtained from other sources to determine if the first customer is the same as the second customer. If the first customer and the second customer are the same person, the first customer and the second customer are identified as being the same unique person. Accounts associated with the two customers are identified as belonging to the same unique person. Viewed another way, the method and system of the present invention takes an existing database of personal identification information, and cross-references that database against other sources of personal identification information to identify persons who appear to be separate persons, but who are actually one and the same individual.
Owner:LIBERTY PEAK VENTURES LLC
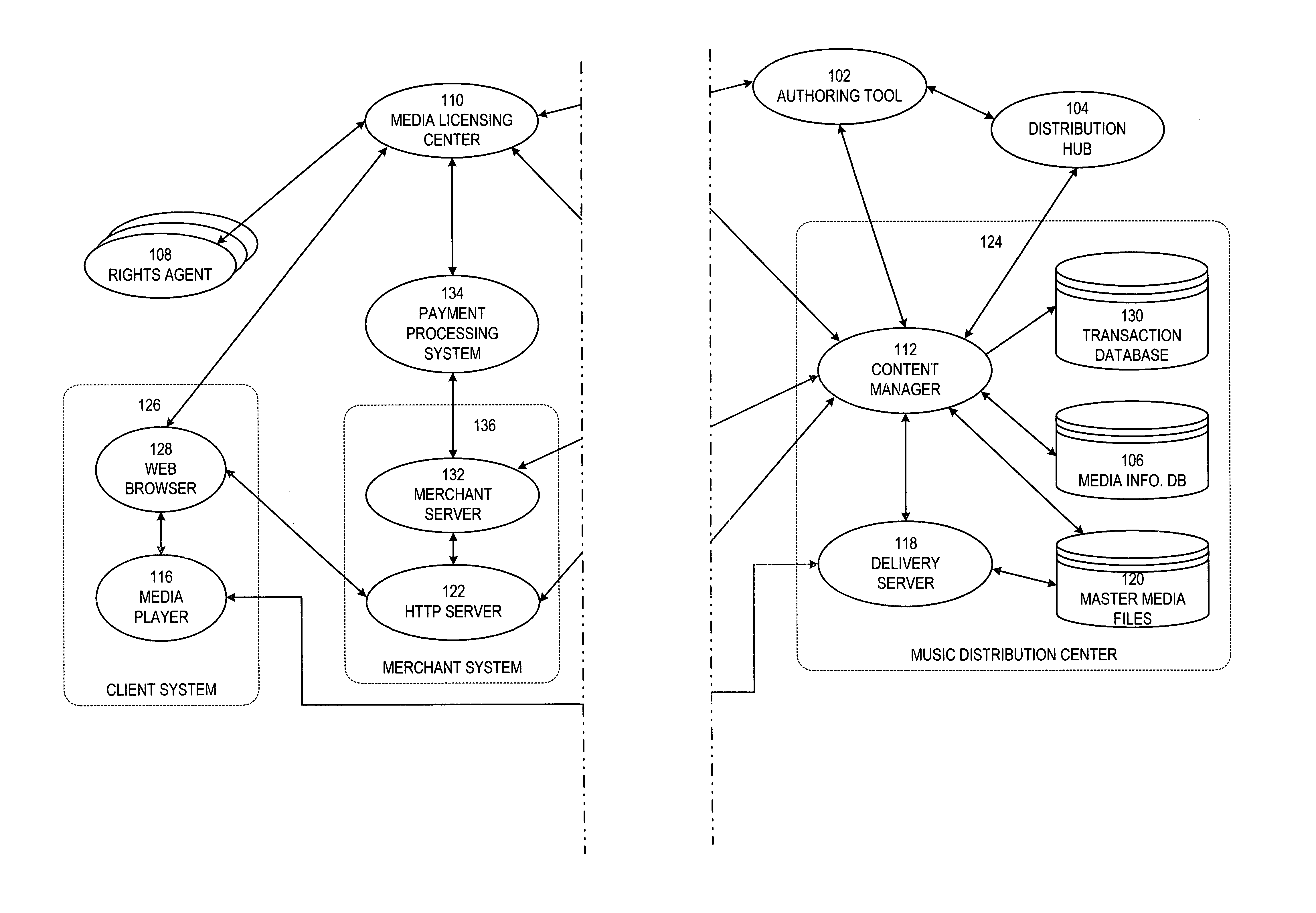
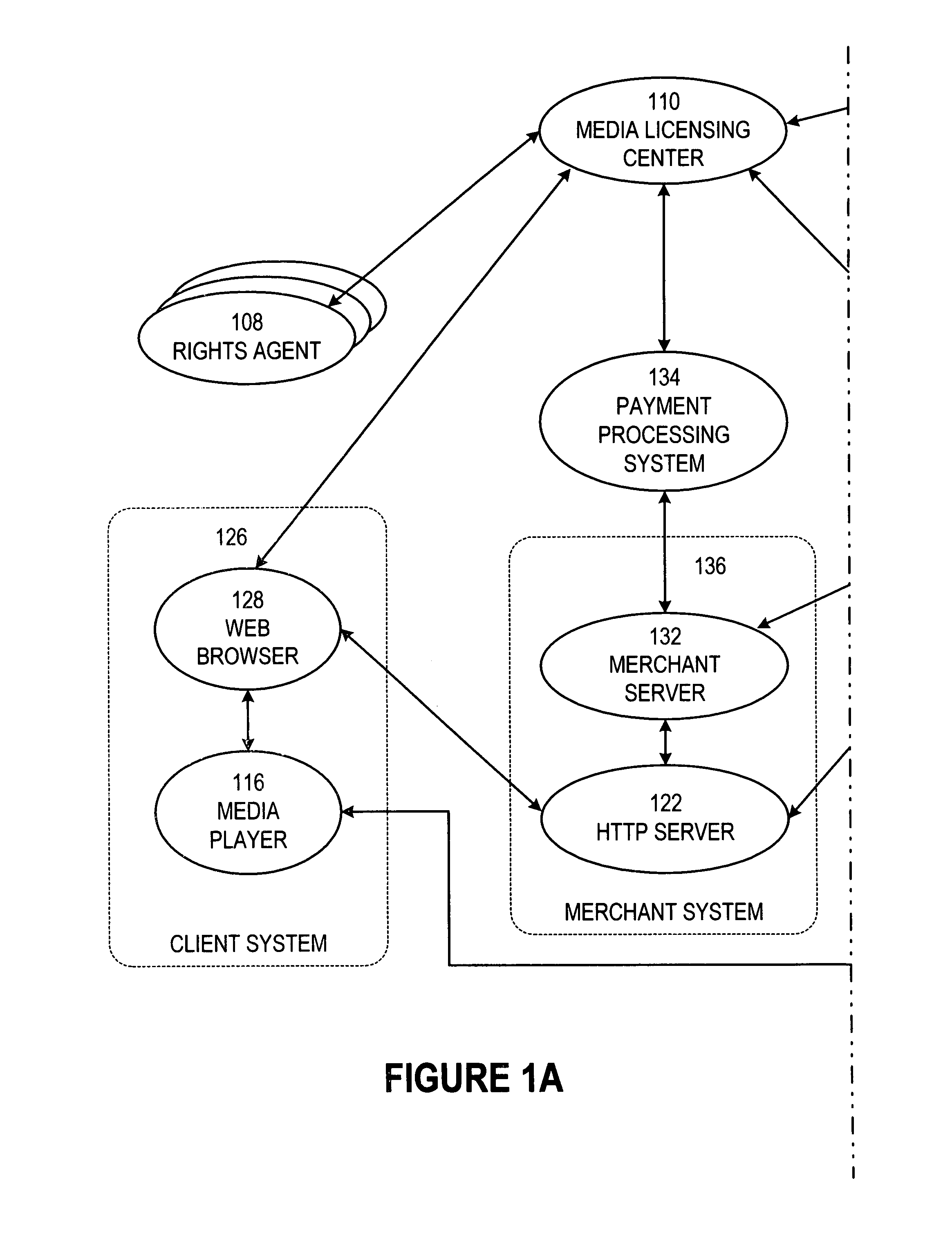
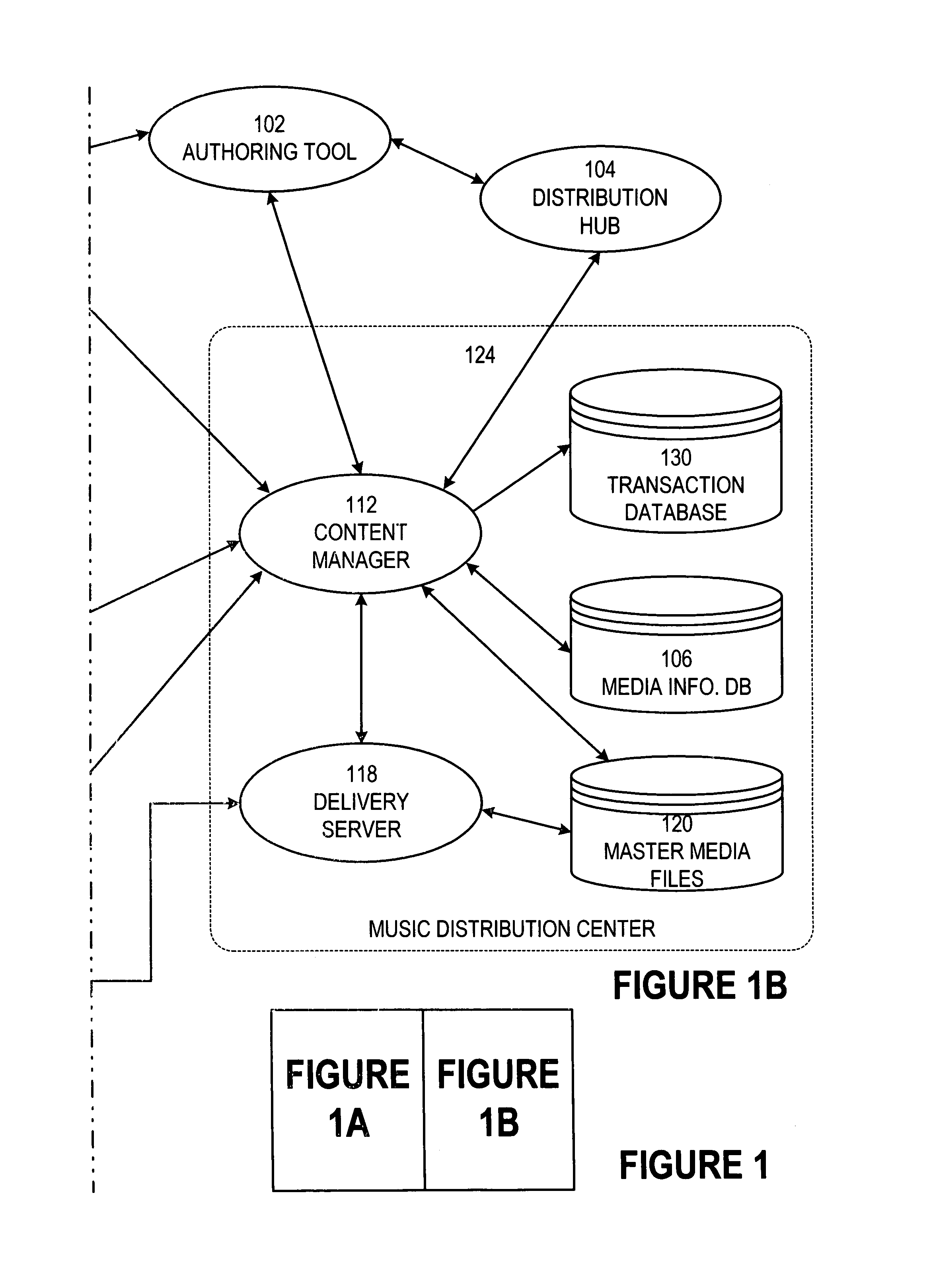
Secure online music distribution system
InactiveUS7263497B1Flexibility and ease of useGood flexibilityComputer security arrangementsPayment architectureContent managementInformation data
A secure music distribution system securely distributes digital products such as music, video, and / or computer software along with related media over a public telecommunications network, such as the Internet, employing a client-server architecture. The digital products are stored and controlled by a content manager computer system and are sold by separate merchant computer systems. The secure music distribution system includes a music distribution center which operates with any number of client systems and with any number of merchant systems. The music distribution center includes a content manager and at least one delivery server. The content manager maintains a media information database, a master media file system, and a transaction database. In addition, the music distribution center interfaces with a media licensing center, which in turn communicates with one or more distributed rights agent servers and the merchant servers. The merchant server executes in a merchant computer system, which also includes an HTTP (HyperText Transfer Protocol) server. The merchant servers interface with various payment processing systems. The client systems include a media player and a Web browser. Additional delivery servers and media licensing centers operate independently and externally to the music distribution center and interface with the music distribution center.
Owner:MICROSOFT TECH LICENSING LLC
Method for facilitating electronic communications
InactiveUS6993325B1Special service provision for substationAutomatic call-answering/message-recording/conversation-recordingTelecommunicationsElectronic communication
A communication method allows members of an affinity group to obtain up-to-date information concerning the status of other members of the affinity group. Each member of the affinity group is provided with a communication device for communicating with other members. The communication device includes a memory for storing member status information. When the status of one member in the affinity group changes, a status update message is sent from the member whose status has changed to other members of the affinity group. When a status update message is receiving from other members, the status information data contained in the message is used to update the member status information stored in memory.
Owner:ERICSSON INC
Automatic authentication method and system in print process
ActiveUS7313699B2Improve securityEliminate needDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
This invention provides an automatic authentication method and system in a print process, which can obviate the need for user's input operations of the user ID and password and can improve security since authentication is automatically done based on print information embedded in a file or information from an application program without any user's input.In a print process that requires user authentication, a printer driver extracts information related to an application and / or a document for the print process as attribute information, and user authentication is made by comparing the attribute information with information stored in a user registration information database of a server. If user authentication has succeeded, the printer driver controls a printer to print, and the server manages and stores accounting information and the like for respective departments in a department management information database.
Owner:CANON KK
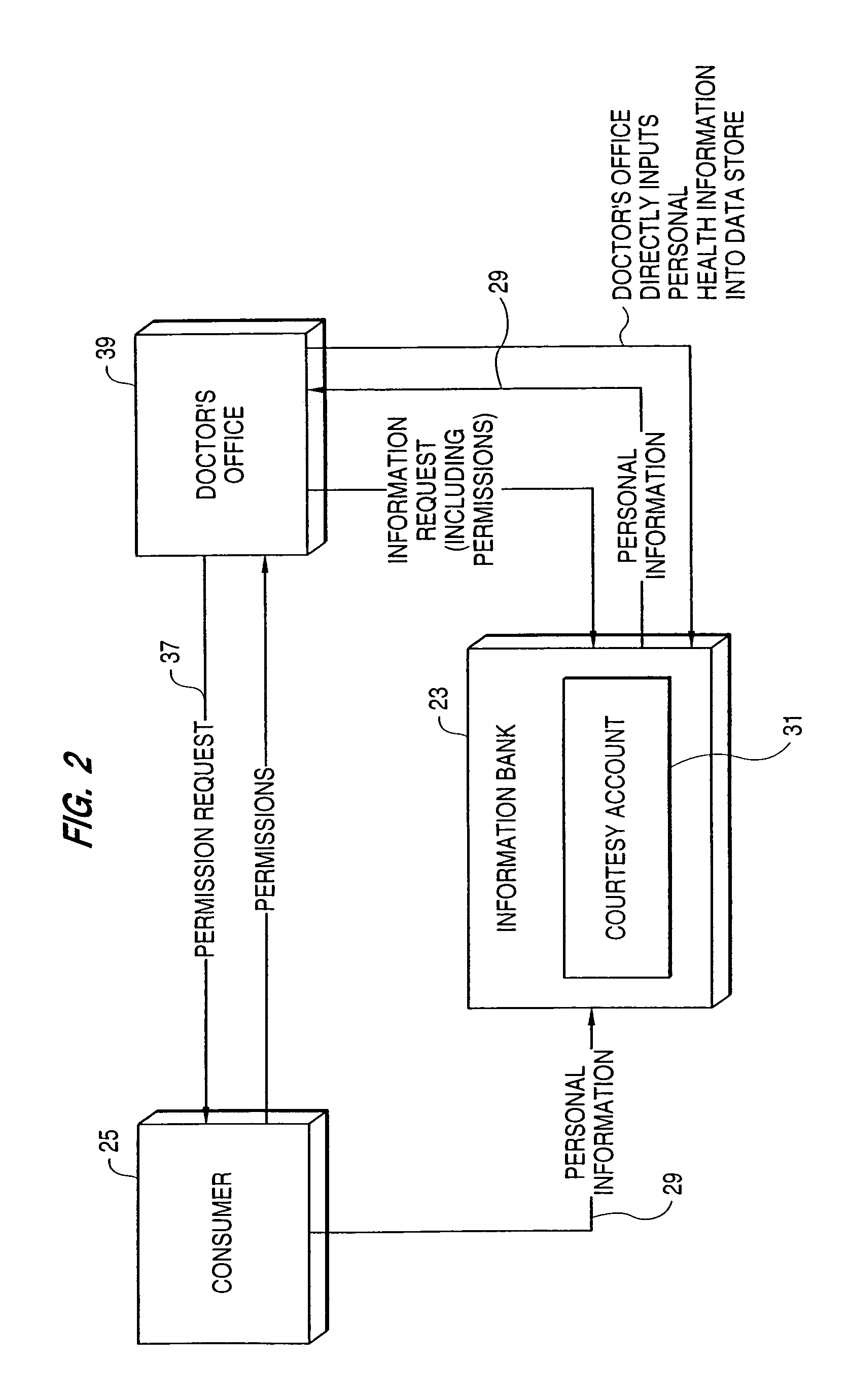
Method and system for anonymizing purchase data
InactiveUS7200578B2Easy accessEliminate needComplete banking machinesFinanceInternet privacyData storing
A system, in which information is the primary asset and in which investments may be made in information, includes multiple data stores for storing different types of a user's information. The safe, secure and properly authorized transfer of information while preserving individual privacy is provided. The system also provides for secure backup and storage, as well as for ubiquitous and nomadic access to information while maintaining the privacy of such information. A first data store includes static identification data about a user. A second data store includes moderately dynamic personal data about the user. A third data store includes dynamic demographic information data about the user. An electronic wallet can be used with the system to download selected portions of the data for use by the user. A method of use of the data includes using the data for billing out forms, providing services to the user and allowing merchants to selectively target users for sales while maintaining user anonymity.
Owner:CITICORP CREDIT SERVICES INC (USA)
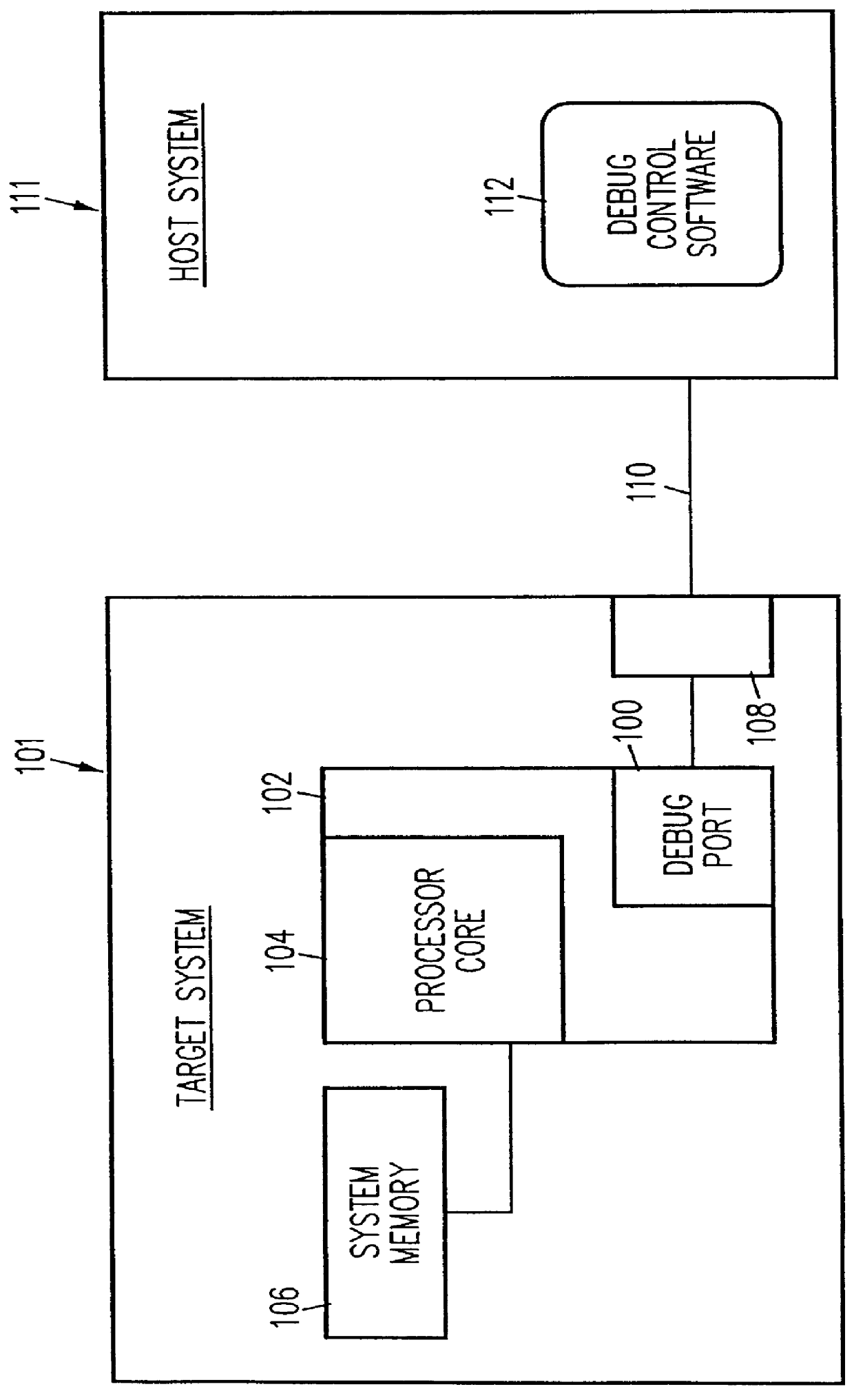
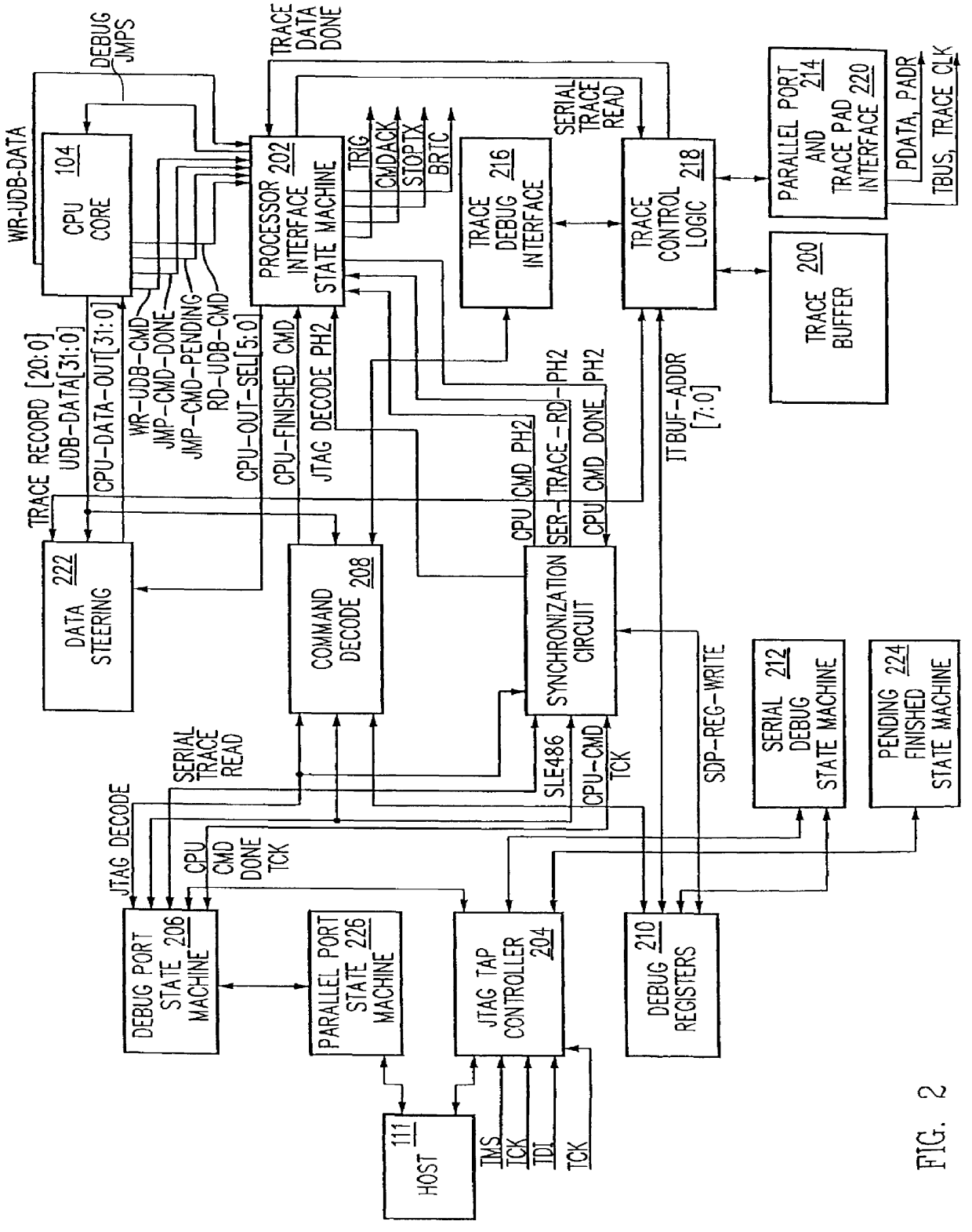
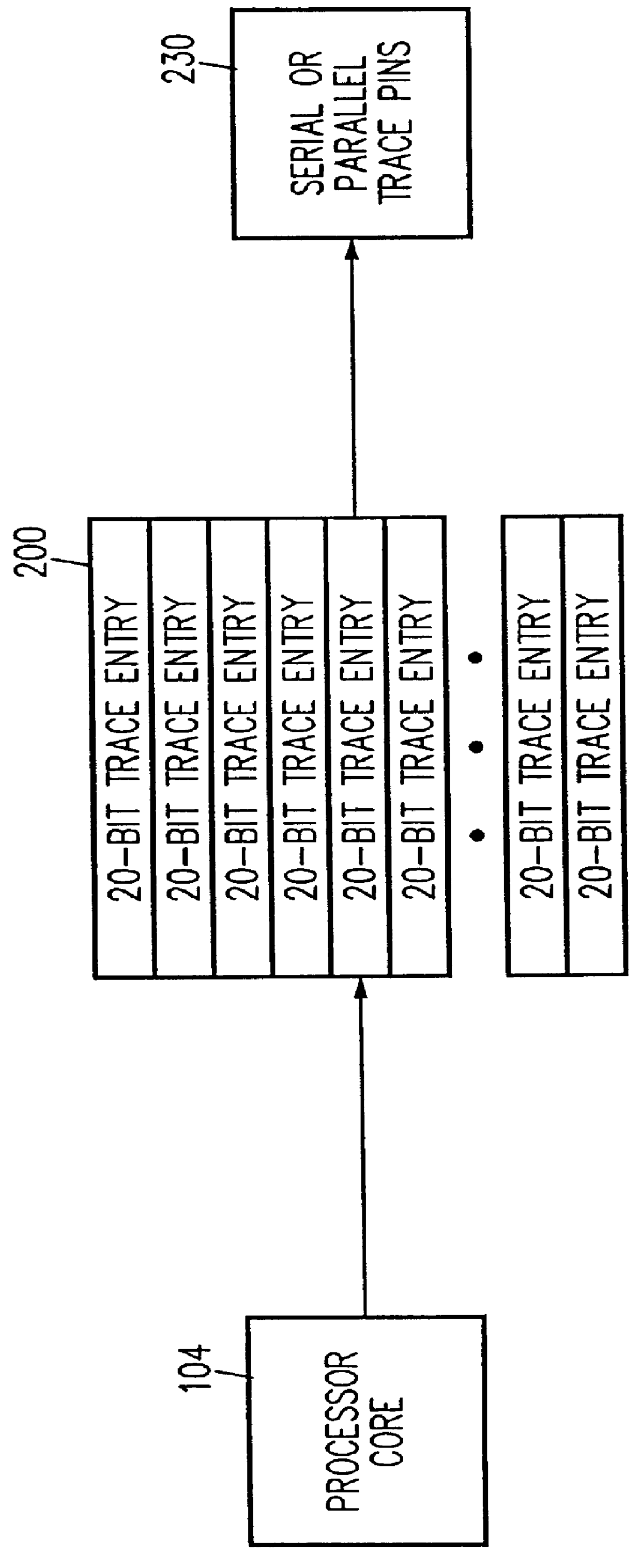
Debug interface including a compact trace record storage
InactiveUS6094729AReliability increasing modificationsHardware monitoringInformation typeParallel computing
In-circuit emulation (ICE) and software debug facilities are included in a processor via a debug interface that interfaces a target processor to a host system. The debug interface includes a trace controller that monitors signals produced by the target processor to detect specified conditions and produce a trace record of the specified conditions including a notification of the conditions are selected information relating to the conditions. The trace controller formats a trace information record and stores the trace information record in a trace buffer in a plurality of trace data storage elements. The trace data storage elements have a format that includes a trace code (TCODE) field indicative of a type of trace information and a trace data (TDATA) field indicative of a type of trace information data.
Owner:GLOBALFOUNDRIES INC
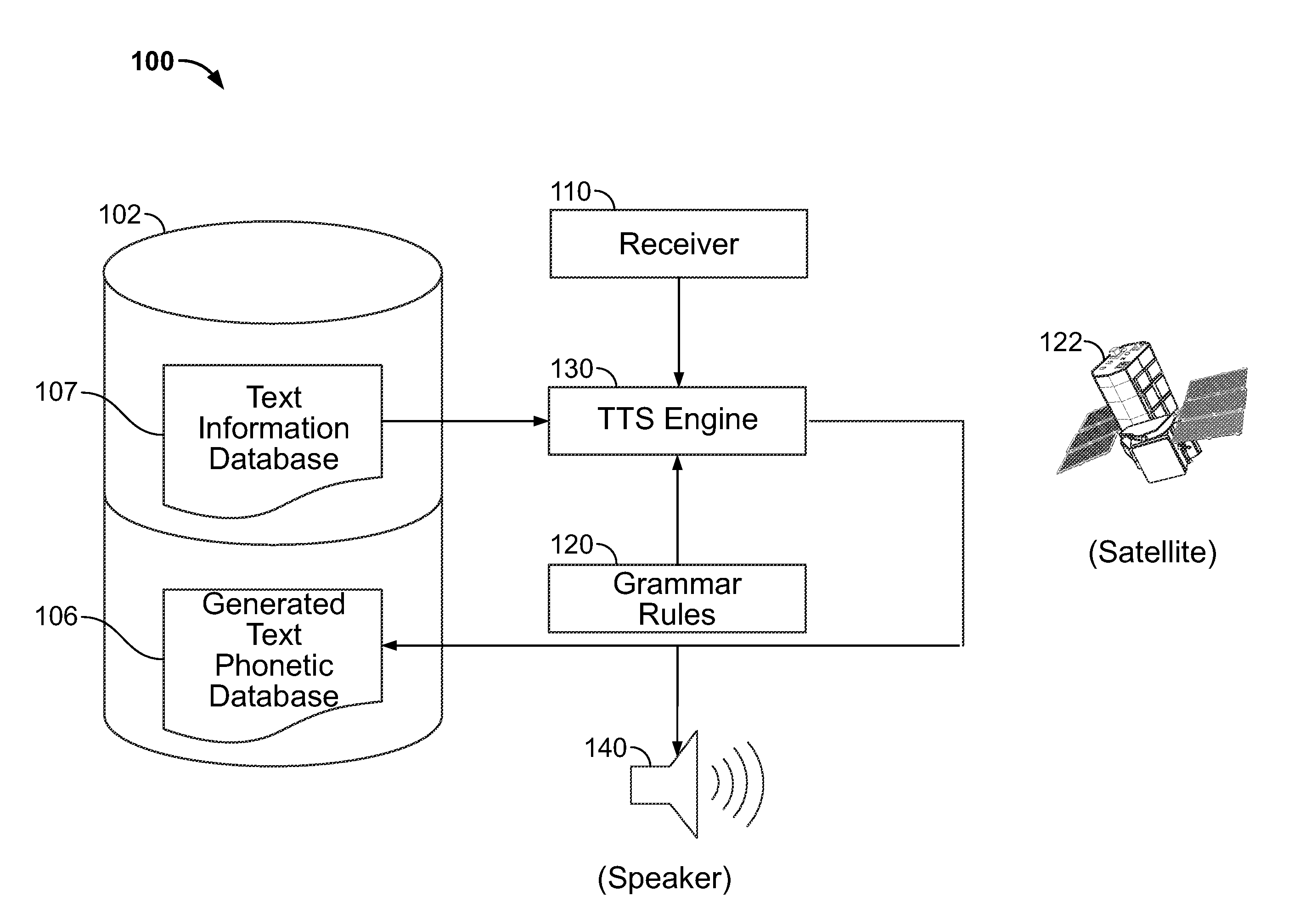
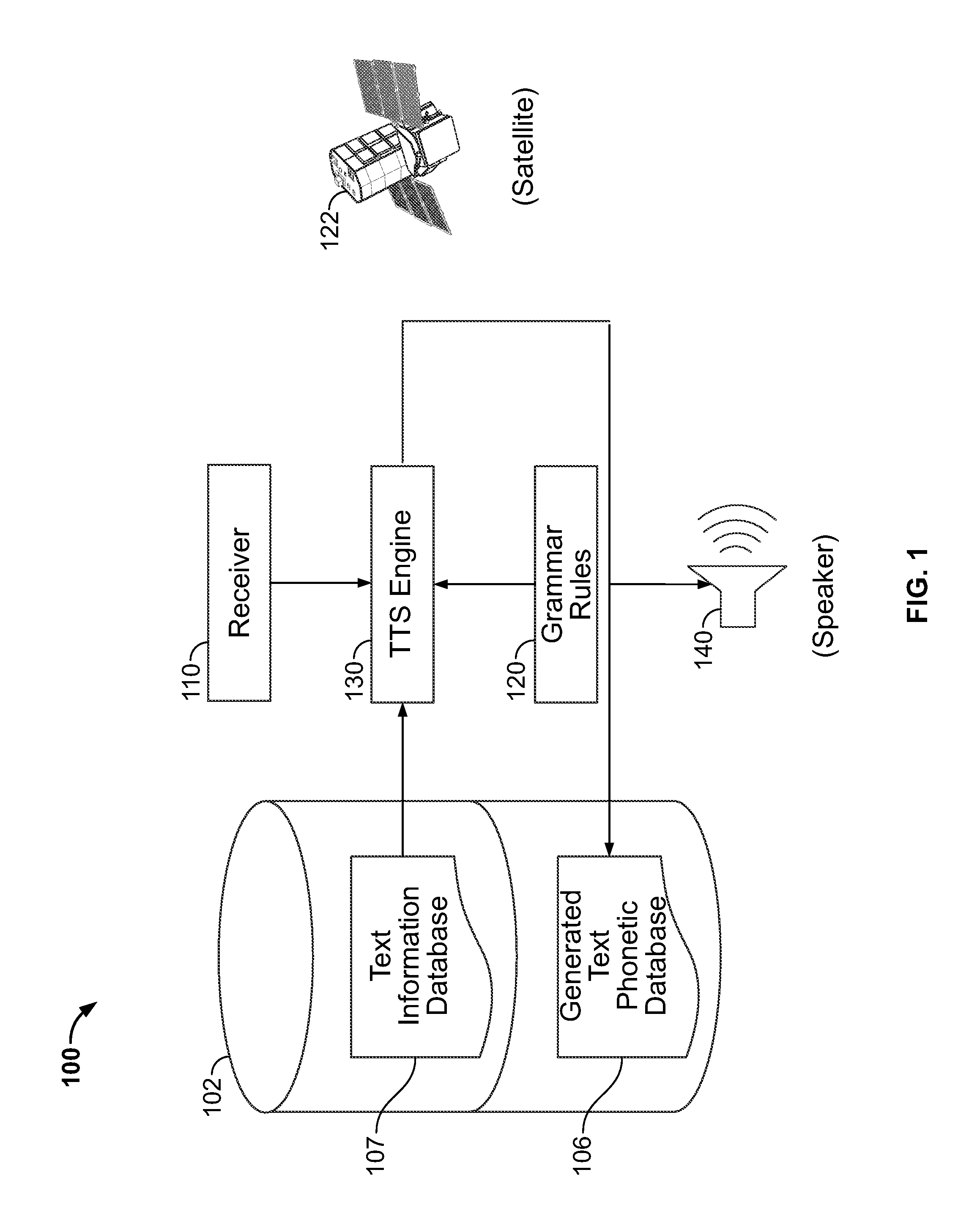
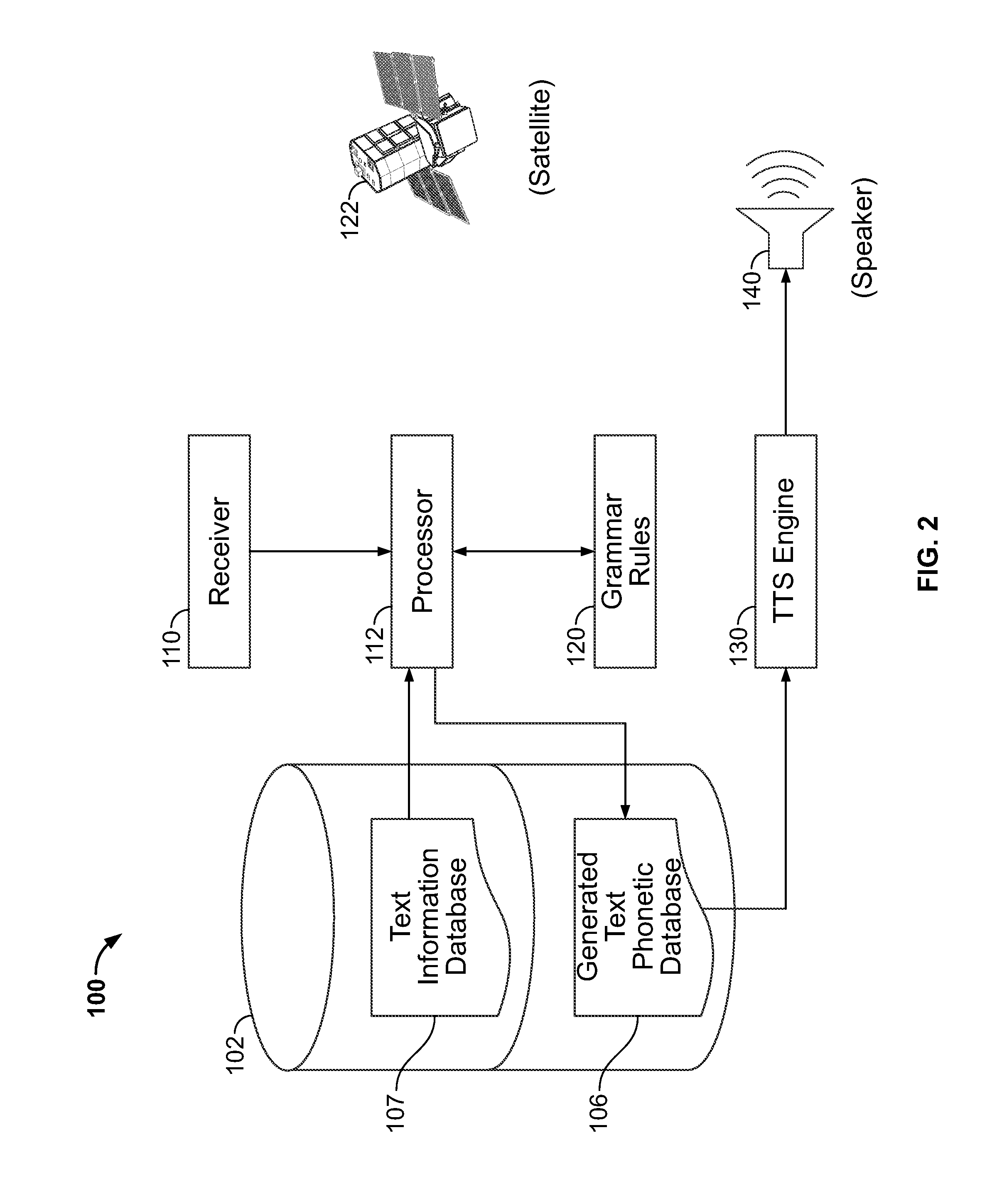
Text pre-processing for text-to-speech generation
A system and method are provided for improved speech synthesis, wherein text data is pre-processed according to updated grammar rules or a selected group of grammar rules. In one embodiment, the TTS system comprises a first memory adapted to store a text information database, a second memory adapted to store grammar rules, and a receiver adapted to receive update data regarding the grammar rules. The system also includes a TTS engine adapted to retrieve at least one text entry from the text information database, pre-process the at least one text entry by applying the updated grammar rules to the at least one text entry, and generate speech based at least in part on the least one pre-processed text entry.
Owner:HONDA MOTOR CO LTD
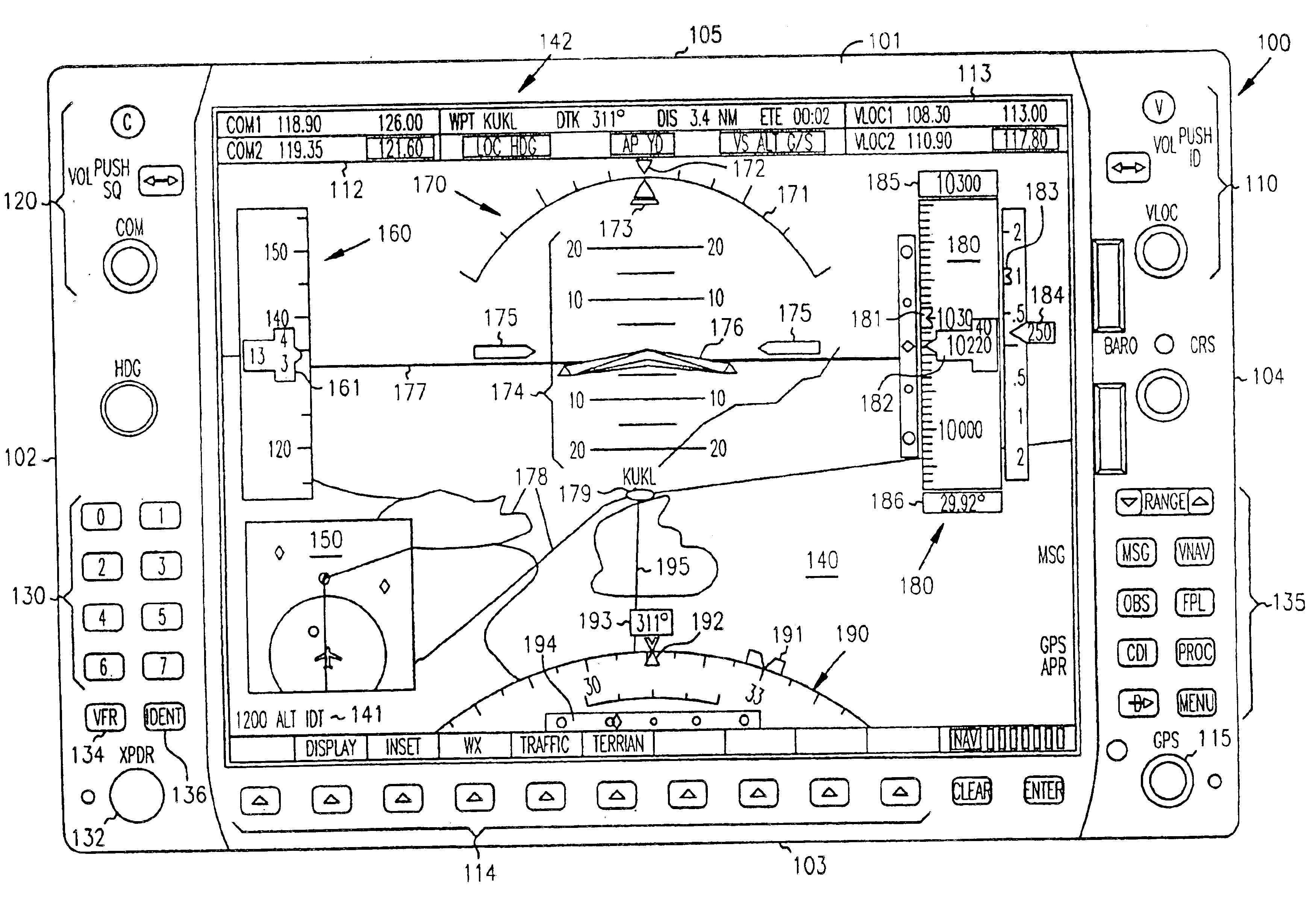
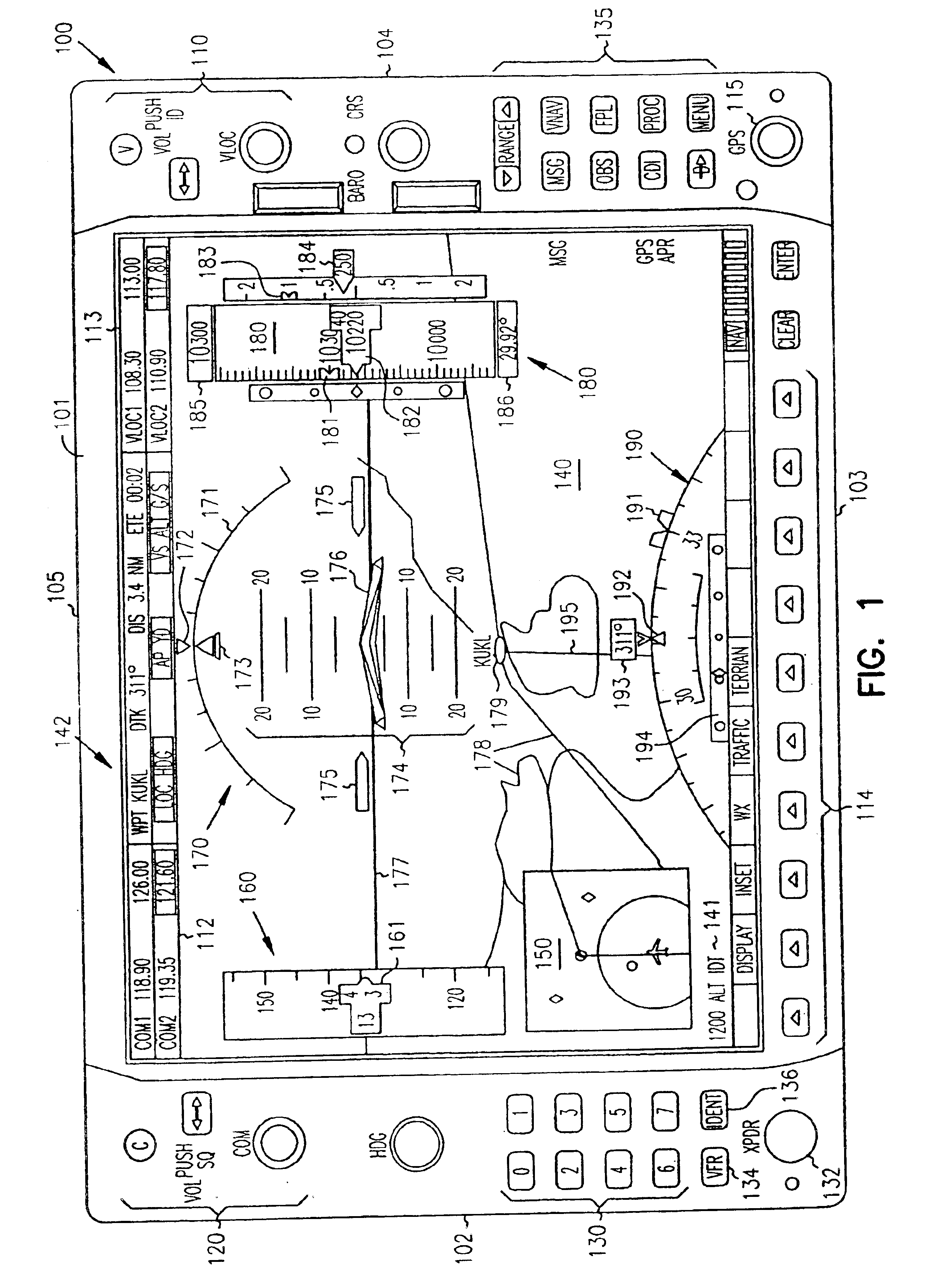
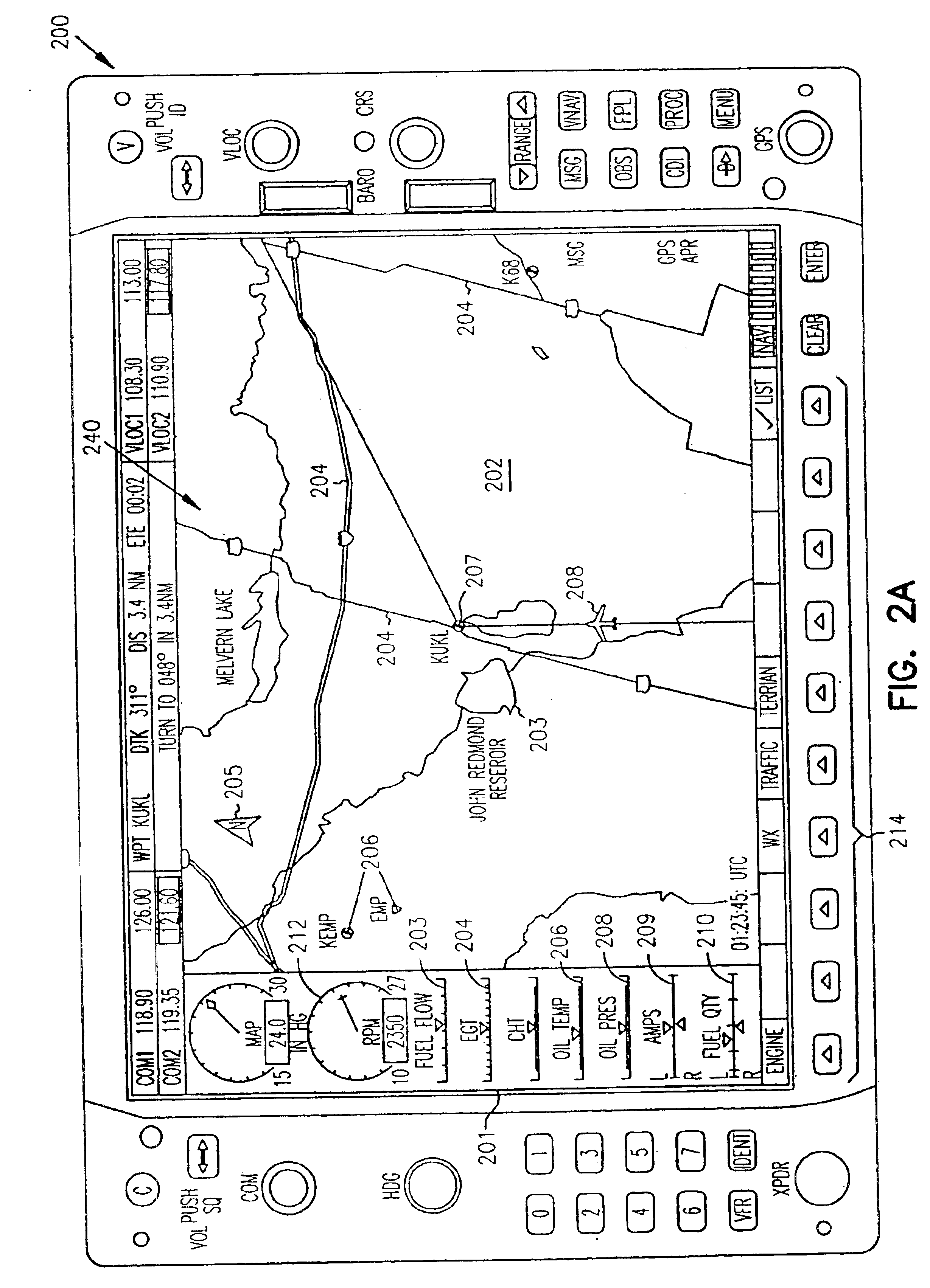
Cockpit instrument panel systems and methods with redundant flight data display
InactiveUS6842672B1Better backupEffective presentationAircraft controlAnalogue computers for trafficData displayDisplay device
Systems and methods are provided for integrated control, access, and presentation of flight information within the cockpit. Cockpit instrument systems and methods are provided which include a first cockpit instrument panel which has a first display proximately located to a first bezel. The first display is operable to present navigational data, communication data, and flight information data including airspeed, attitude, and altitude. The systems and methods further include a second cockpit instrument panel located adjacent to the first cockpit instrument panel. The second cockpit instrument panel has a second display proximately located to a second bezel. The second display is operable to present navigational data, communication data, and flight information data including detailed engine parameters. When either the first or the second cockpit instrument panel fails, the remaining functional, first or second display, is adapted to provide all of the important flight information data, including airspeed, attitude, altitude, and detailed engine parameters.
Owner:GARMIN INT
Systems and methods for linking vehicles to telematics-enabled portable devices
Owner:HARTFORD FIRE INSURANCE
Real time data integration services for financial information data integration
InactiveUS20050222931A1Rapid and simplified developmentEasy accessFinanceDigital data processing detailsReal-time dataIntegration service
Financial information data integration is provided through real time data integration services deployed in a services oriented architecture.
Owner:IBM CORP
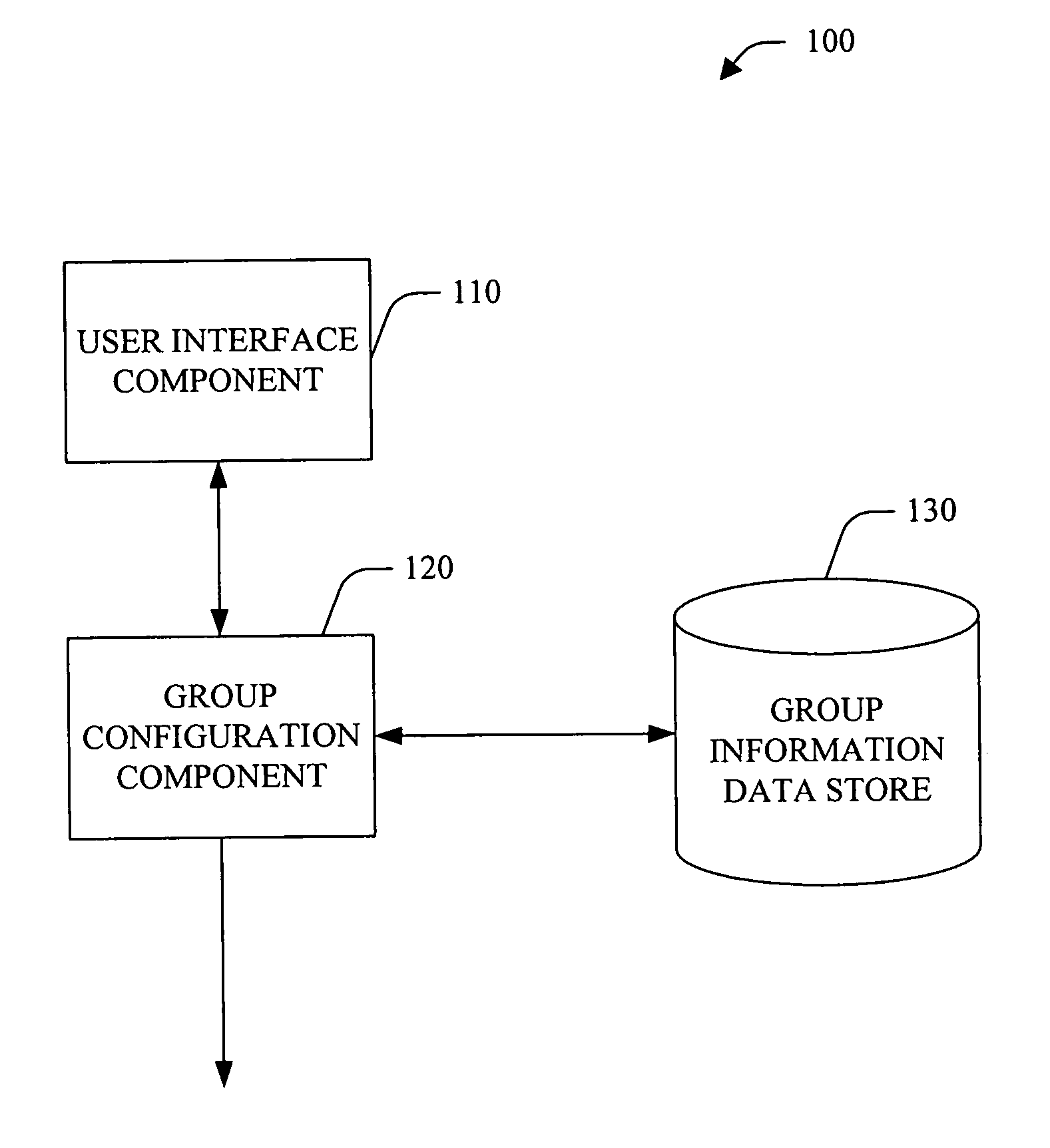
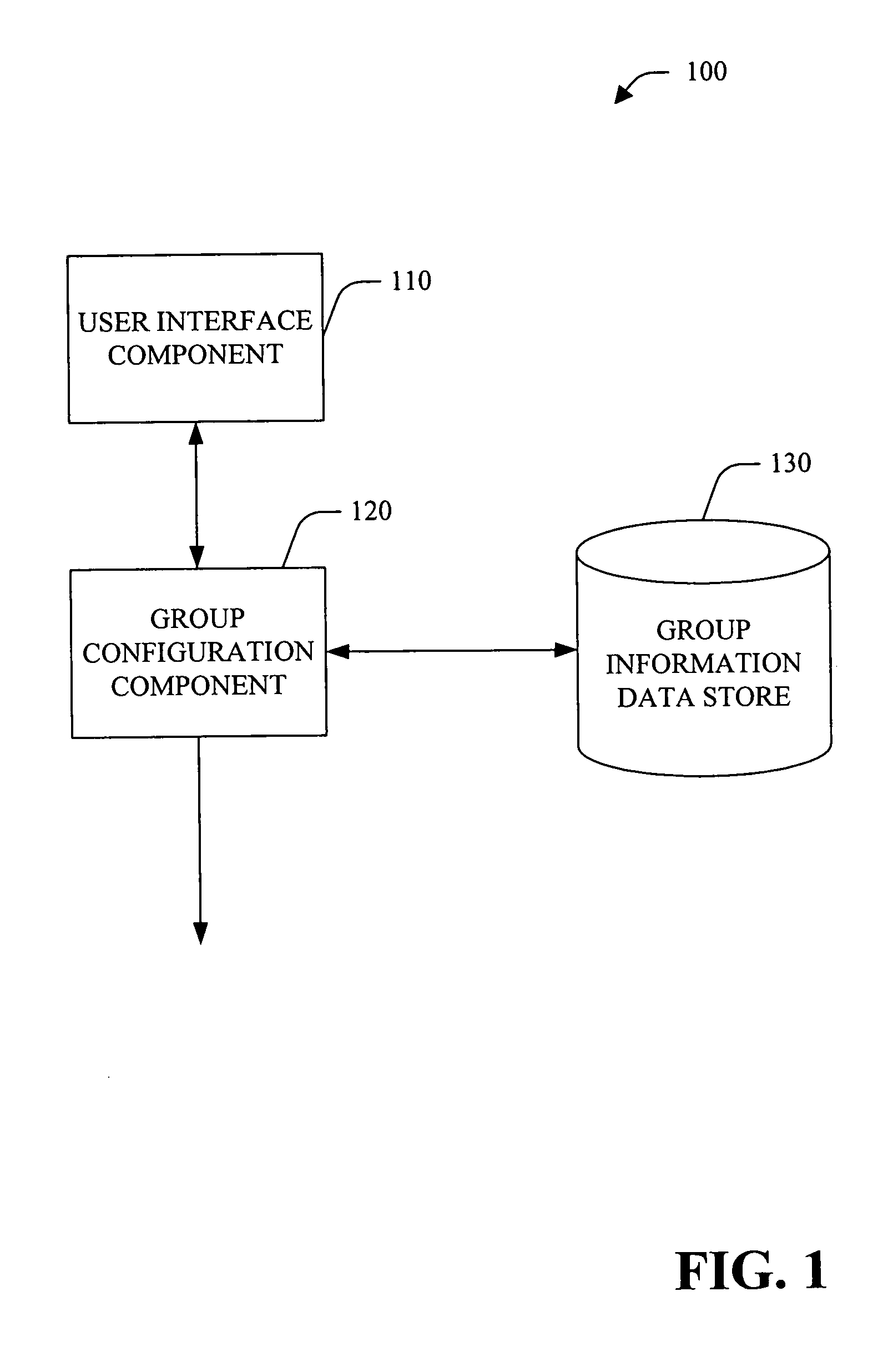
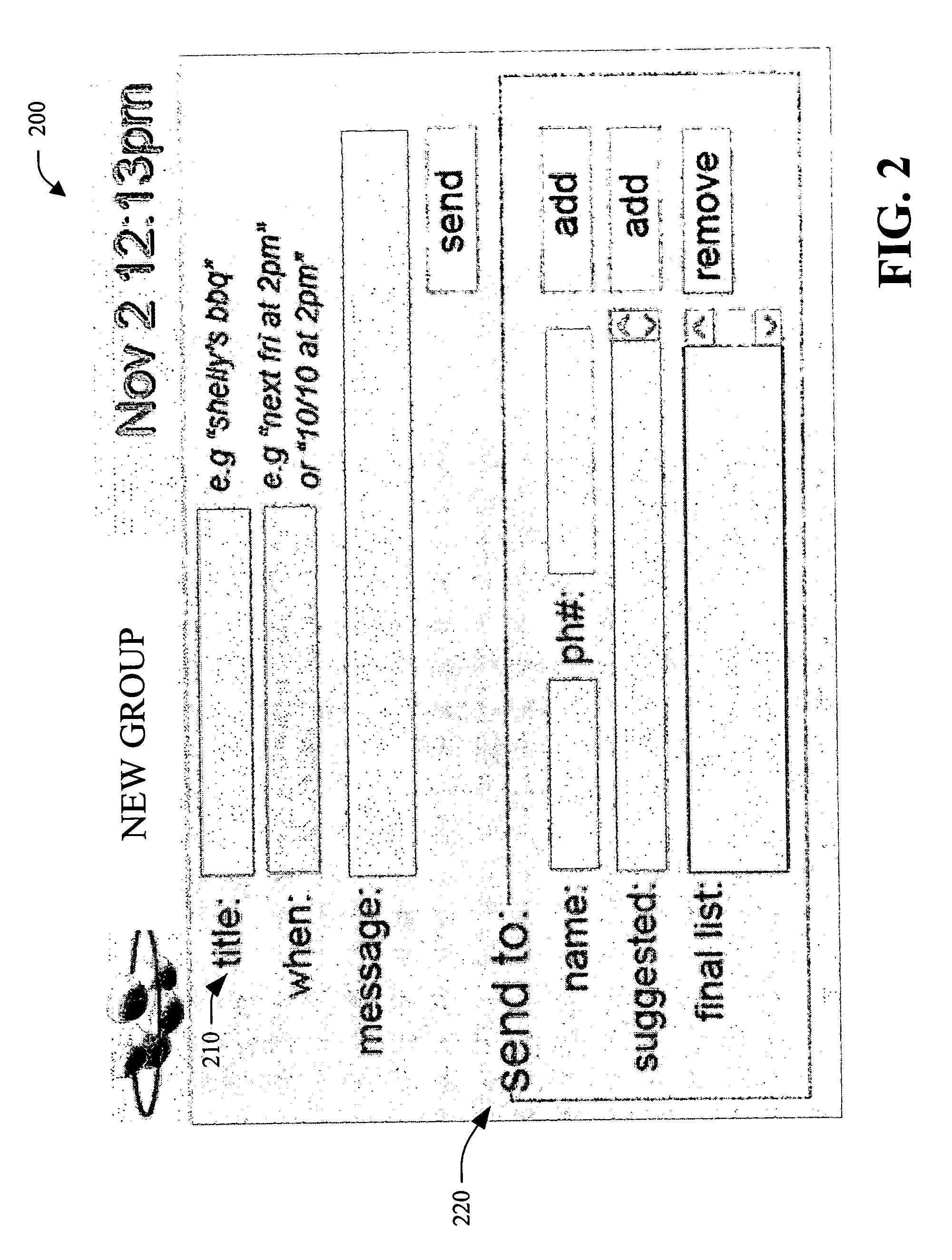
Dynamic group formation for social interaction
InactiveUS20060242234A1Good informationData processing applicationsNetwork traffic/resource managementWireless Application ProtocolTime-sharing
A system and method that facilitates dynamic group formation for social interaction and / or real-time sharing of content with the group is provided. A group formation system includes a user interface component that facilitates a user's entry of information and display of information regarding group formation. For example, the user interface component can be employed, for example, with a mobile communication device such as a mobile phone, personal digital assistant (PDA), a smart phone, a small, web based mobile or a wireless application protocol (WAP) client, and / or a regular web client. The system can further include a group formation component that forms a group based, at least in part, upon information received from a user via the interface component. The group configuration component can further store information regarding groups (e.g., a name / identifier, member(s), event(s) and / or shared context associated with the group) in a group information data store. For example, the group configuration component can form a group based, at least in part, upon information stored in the group information data store (implicit group formation). The group information data store can, optionally, provide archival access to communications and / or shared content (e.g., through a mobile communications device and / or a PC-based web browser).
Owner:MICROSOFT TECH LICENSING LLC
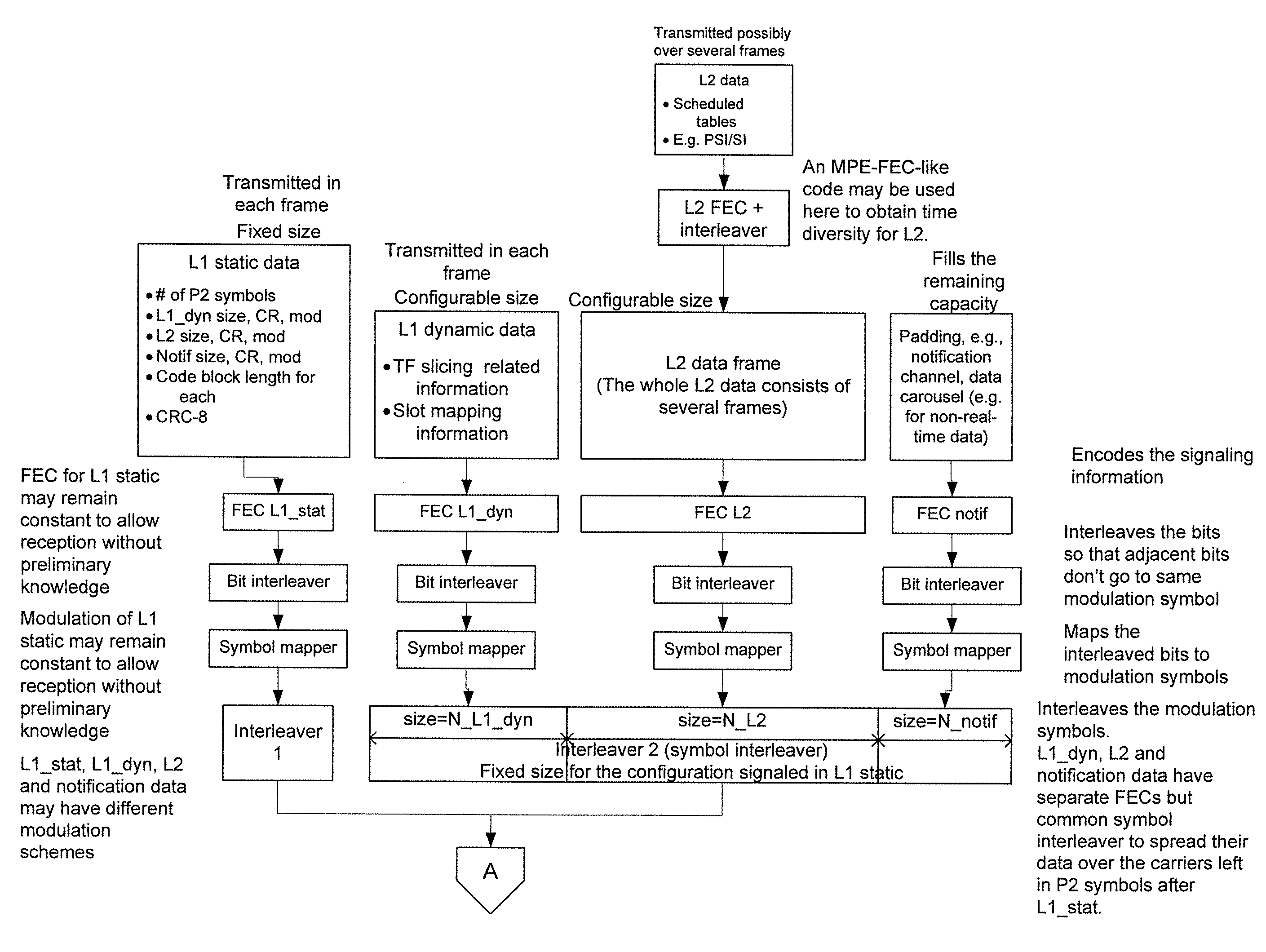
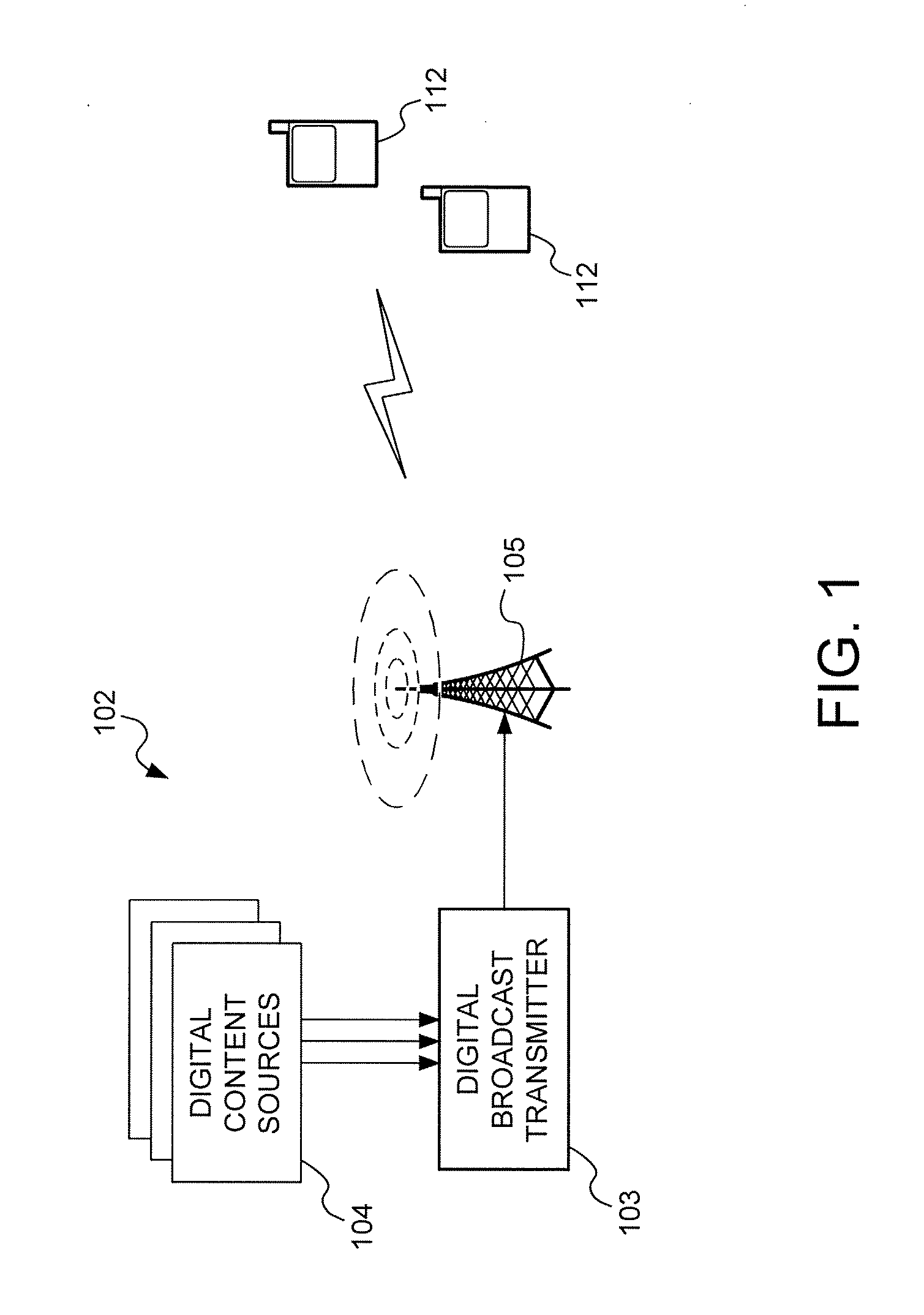
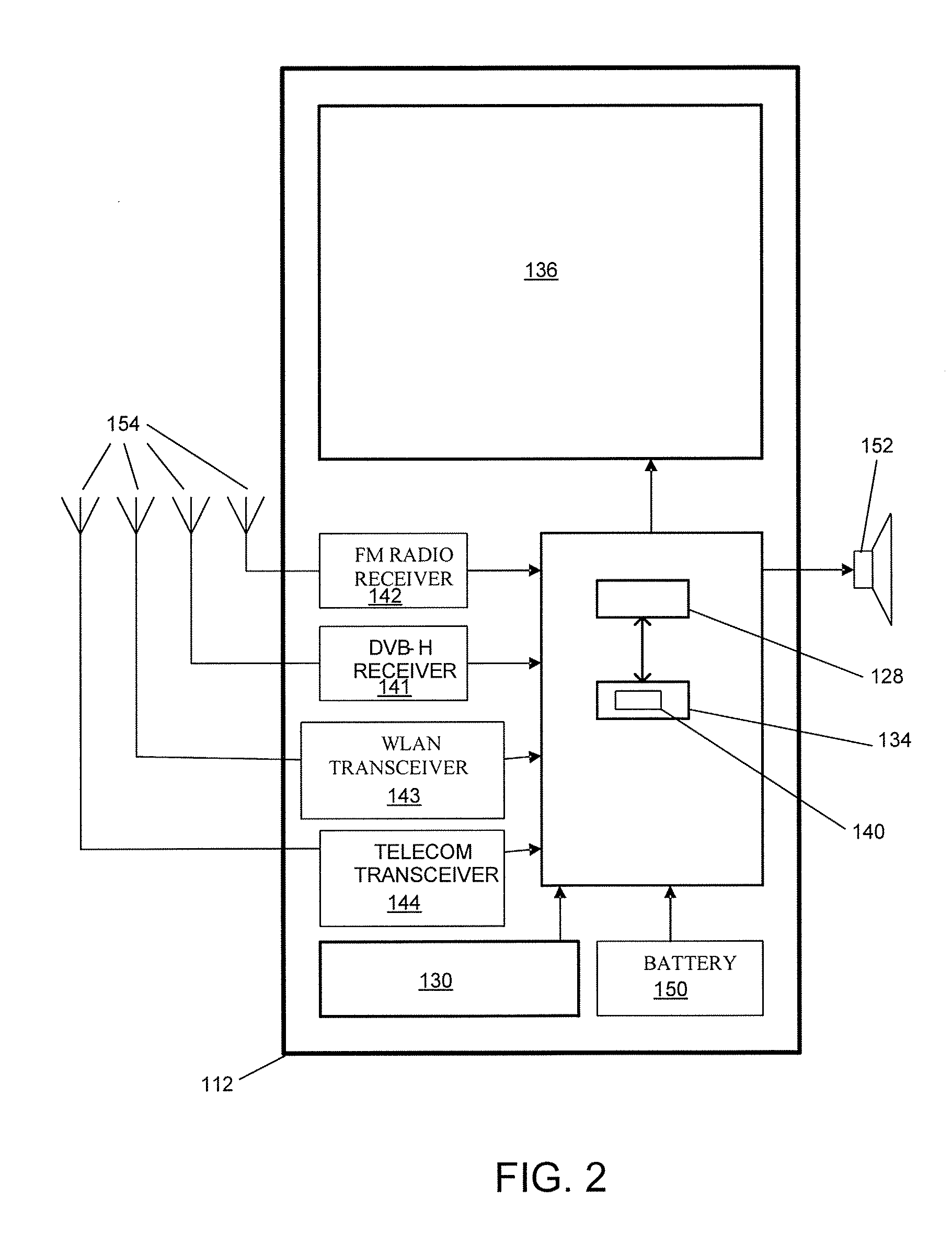
Digital Broadcast Signaling Metadata
ActiveUS20090103649A1Error correction/detection using convolutional codesError preventionDigital broadcastingData link layer
Embodiments are directed to transmitting L1 pre-signaling information with predetermined modulation and code rate such that L1 pre-signaling information can be received without preliminary knowledge on the network. L1 pre-signaling information makes it possible to receive the L1 signaling information, data link layer information, and notification data that may have configurable code rates and modulation. Therefore, L1 pre-signaling information can be thought of as signaling metadata (i.e., information about other signaling information). L1 signaling is divided into pre-signaling and signaling parts. The pre-signaling part includes parameters used for receiving the L1 signaling information. L1 pre-signaling signaling enables the receiver to receive the signaling itself (L1 signaling and data link layer information) by informing the receiver about the type of modulation, coding, and the like, used to transmit the L1 signaling, data link layer, and notification information.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com