Patents
Literature
1498 results about "Data link layer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
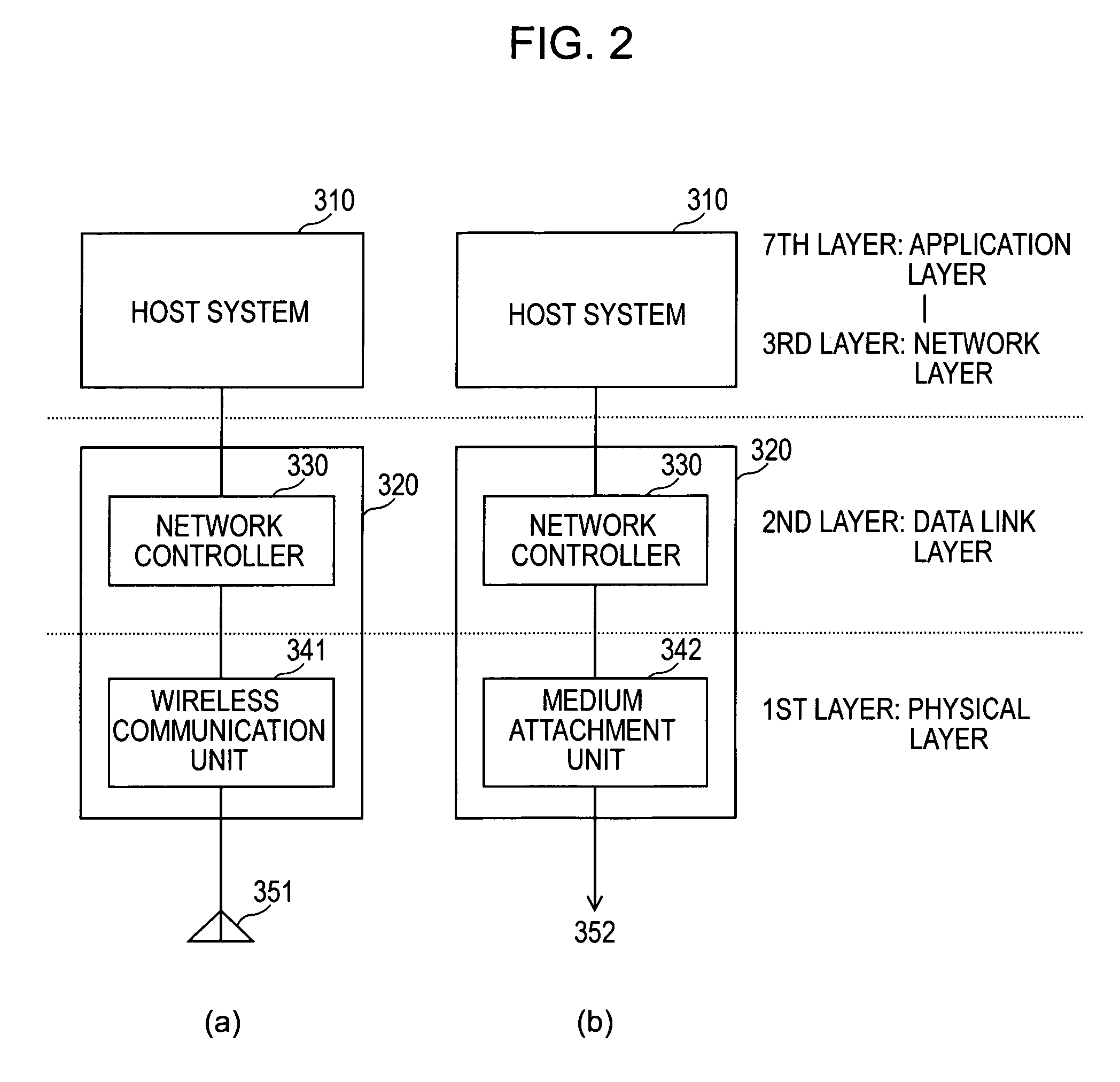
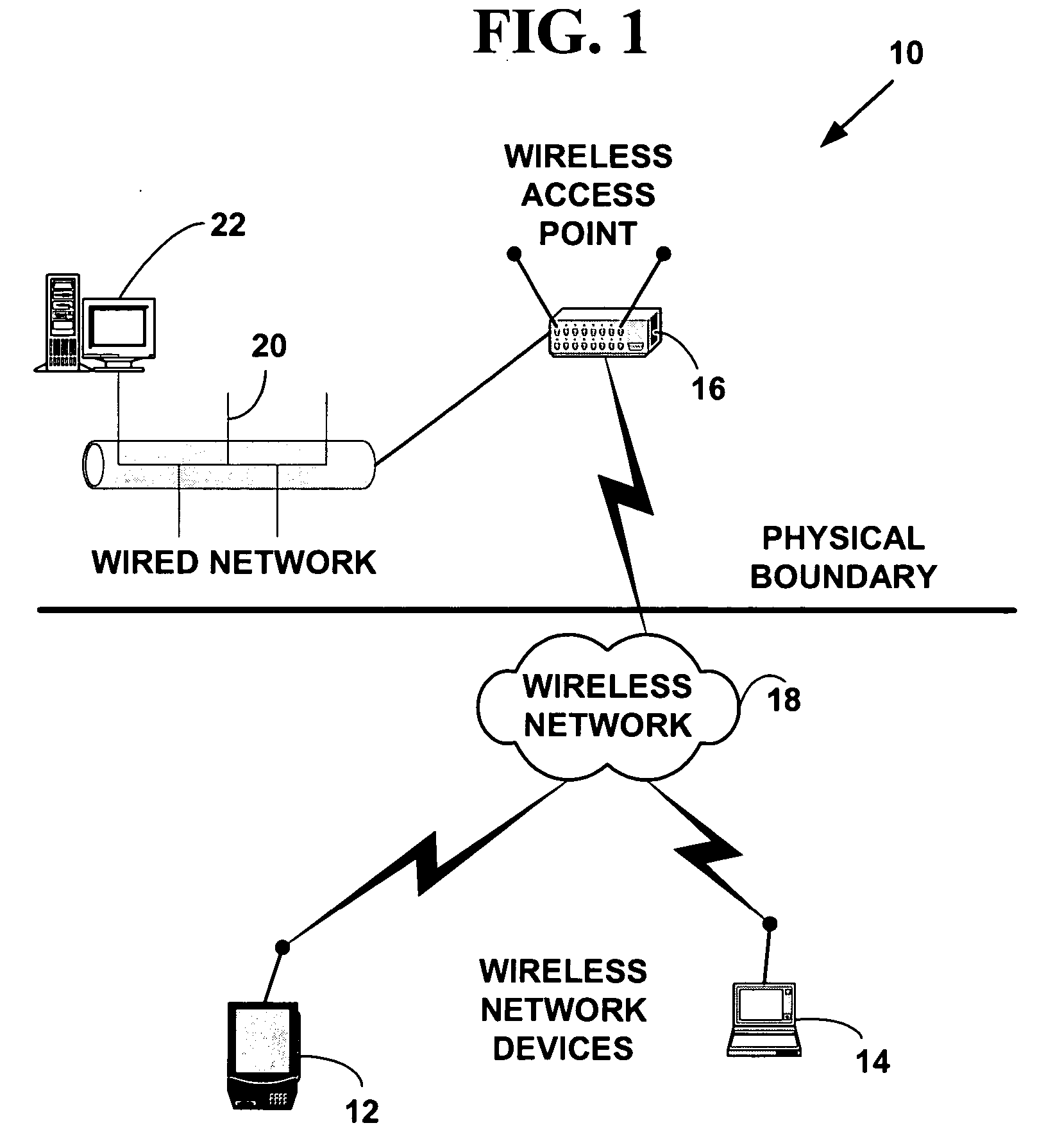
The data layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers data between adjacent network nodes in a wide area network (WAN) or between nodes on the same local area network (LAN) segment. The data link layer provides the functional and procedural means to transfer data between network entities and might provide the means to detect and possibly correct errors that may occur in the physical layer.
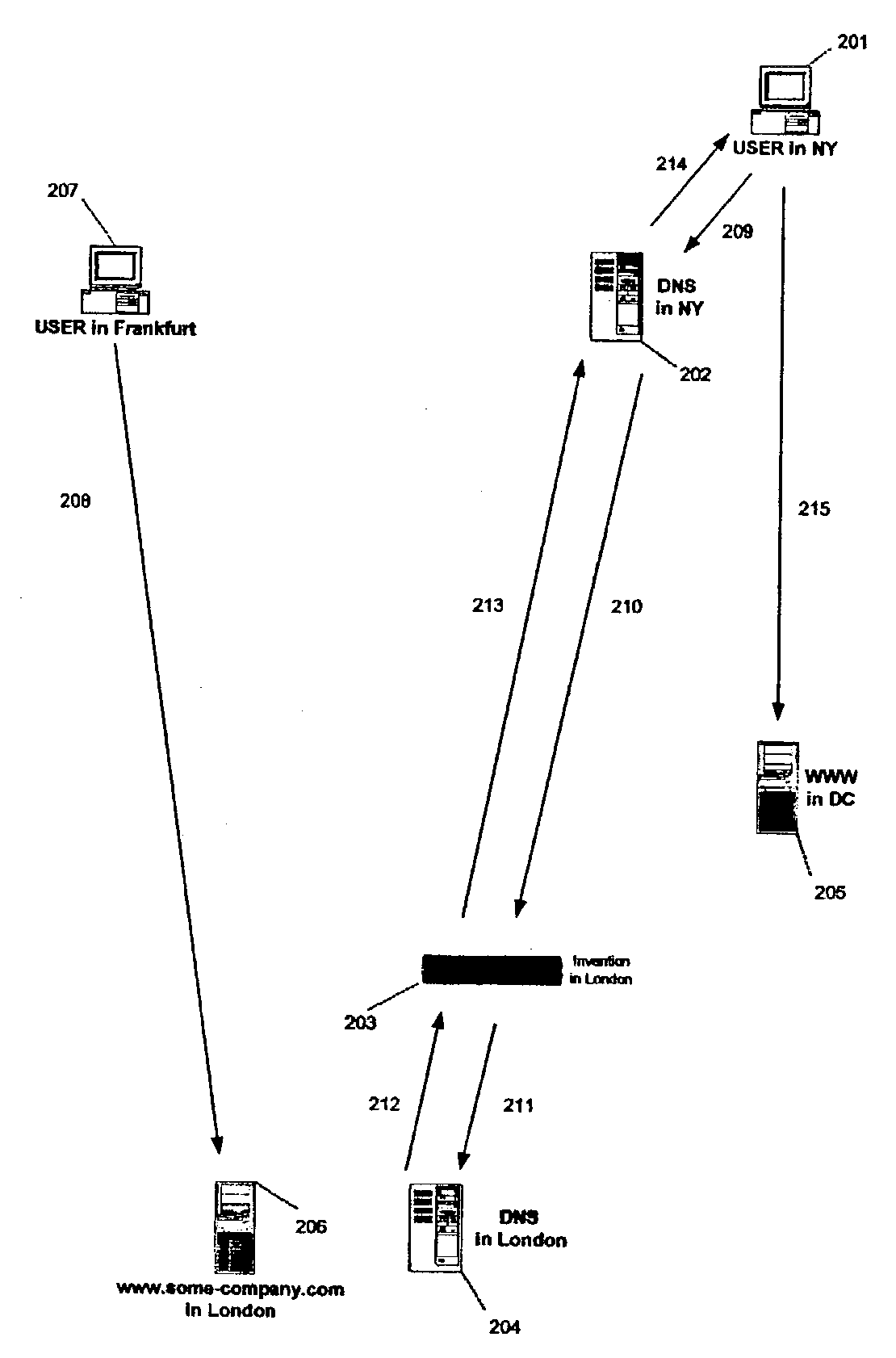
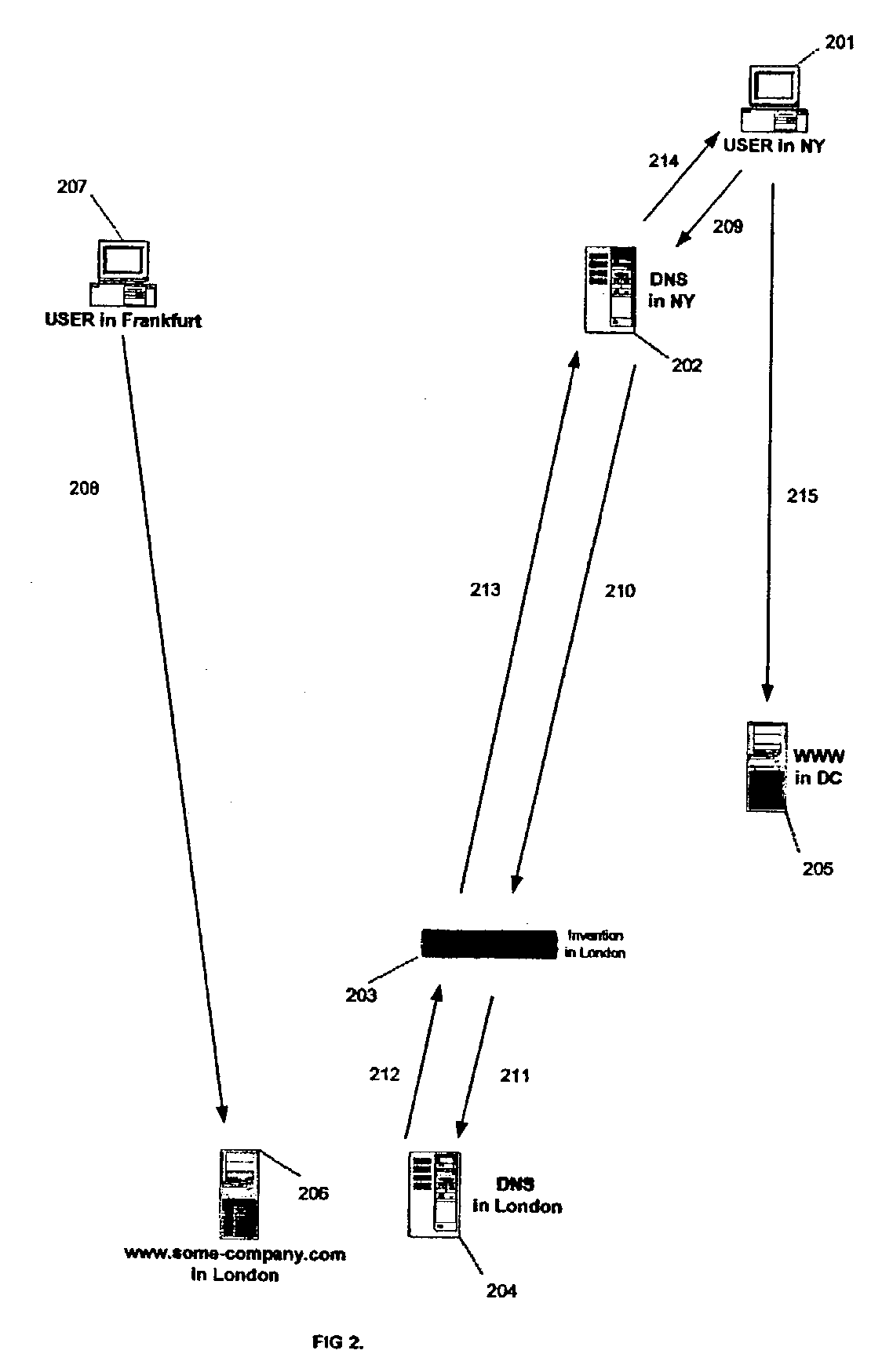
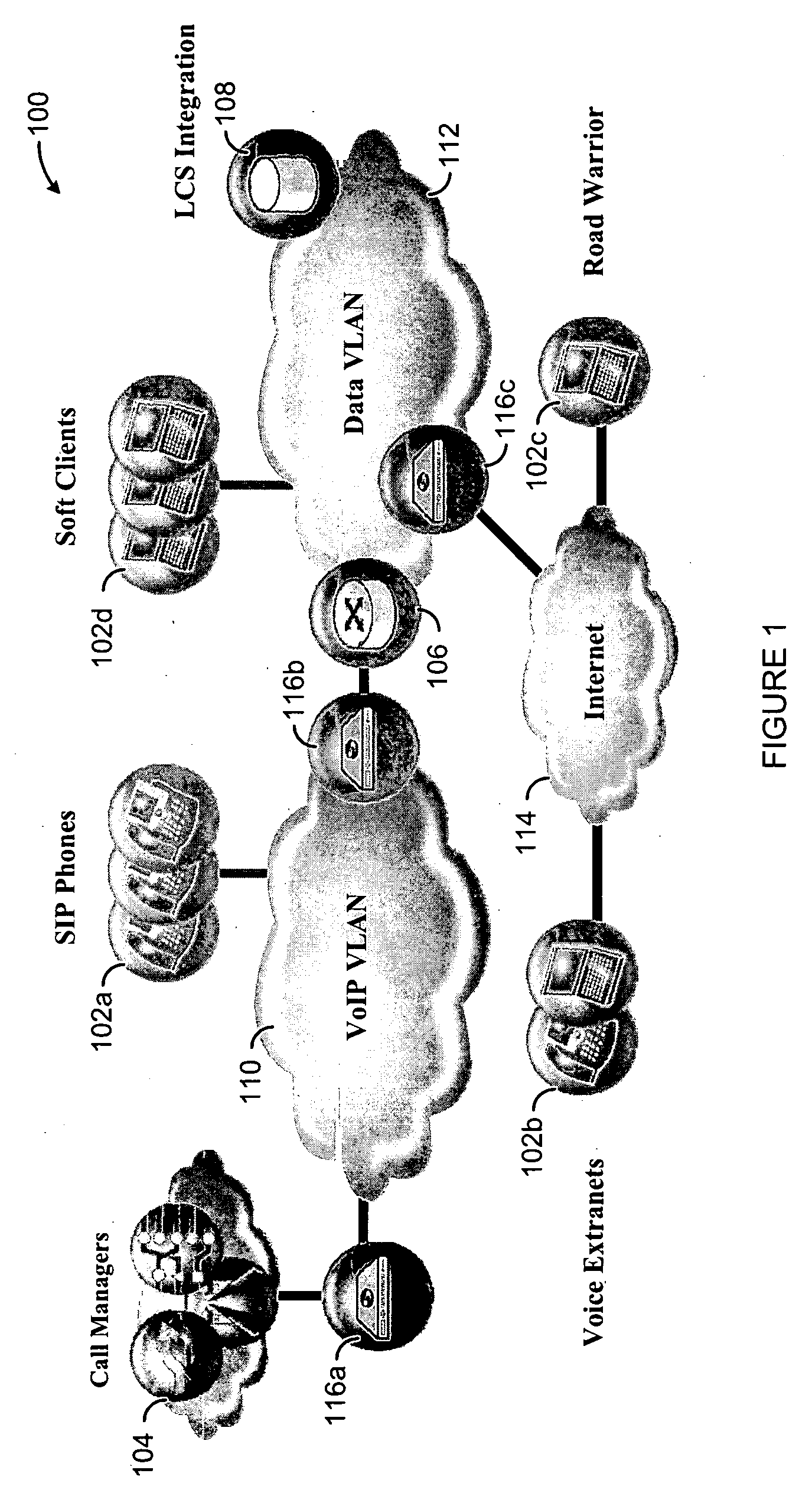
Apparatus and method for transparent selection of an Internet server based on geographic location of a user
ActiveUS7310686B2Data processing applicationsMultiple digital computer combinationsApplication serverGeolocation
This invention is an apparatus and a method that selects the optimum location of a service on the Internet according to the user's geo-location and the configuration of the invention by transparently altering the DNS messages. In the preferred embodiment, the invention operates at OSI model's data link layer and it is located in front of the DNS server so that it does not require any modification in the existing DNS or IP network setup or on the application servers. It provides a fast and transparent method of locating an Internet service without the overhead of server scripts, HTTP redirects, or extra steps by the user to find the desired location or content.
Owner:BUSHNELL HAWTHORNE
A method and systems for securing remote access to private networks
ActiveUS20060037071A1Reduce the burden onImprove experienceMultiple digital computer combinationsProgram controlPrivate networkNetwork address translation
A method for securing remote access to private networks includes a receiver intercepting from a data link layer a packet in a first plurality of packets destined for a first system on a private network. A filter intercepts from the data link layer a packet in a second plurality of packets transmitted from a second system on the private network, destined for an system on a second network. A transmitter in communication with the receiver and the filter performing a network address translation on at least one intercepted packet and transmitting the at least one intercepted packet to a destination.
Owner:CITRIX SYST INC
Method of controlling communication between devices in a network and apparatus for the same
InactiveUS20070064689A1Avoid collisionReduce communicationSpecial service provision for substationNetworks interconnectionAddress Resolution ProtocolVirtual firewall
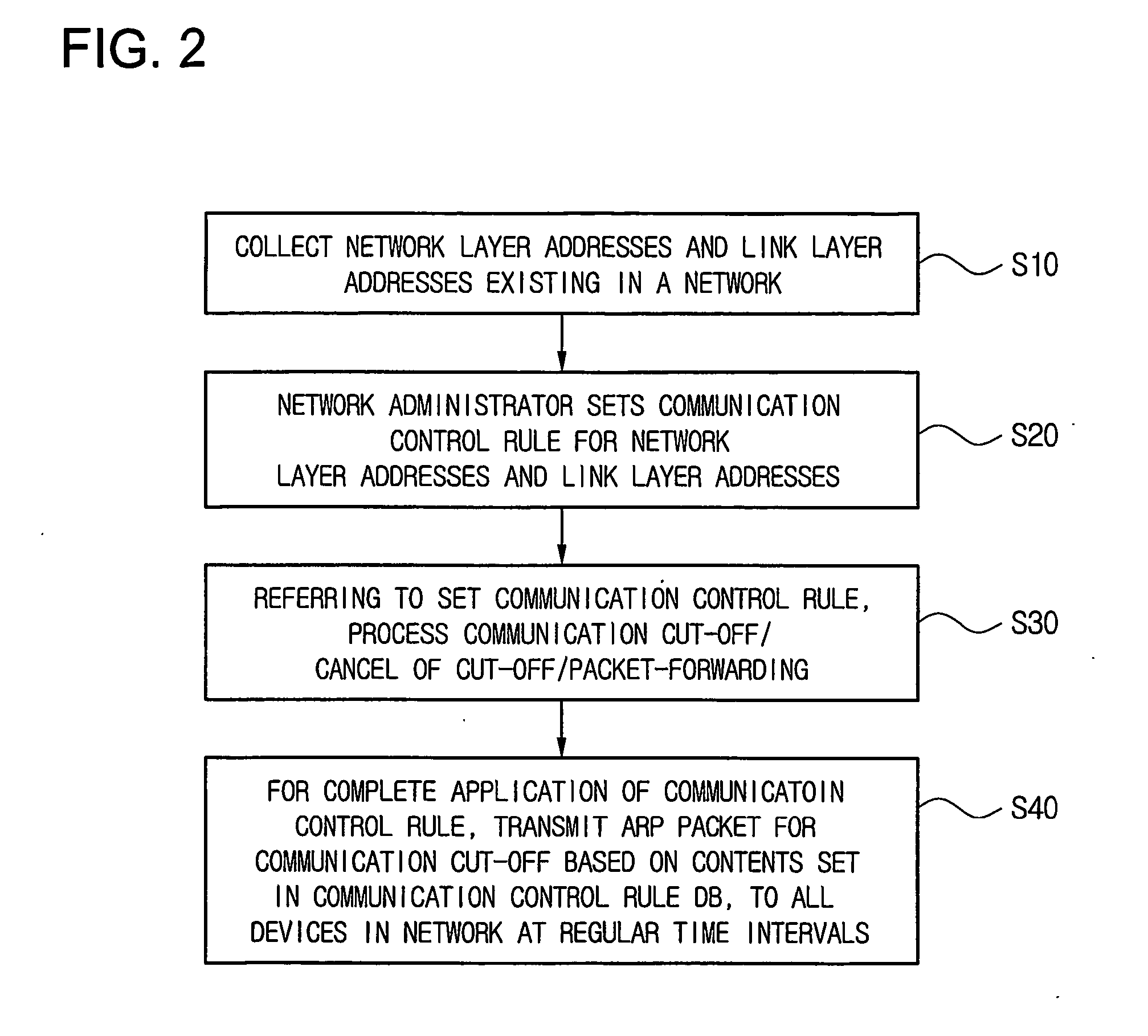
Disclosed is a technology by which rules on communication permission or control are enforced to network internal devices such that an environment which looks as if to have a virtual firewall existing between network internal devices can be established. A communication control apparatus for this is located on the same level in the network as other devices are located. By using this communication control apparatus, an address resolution protocol (ARP) packet in which a data link layer address is manipulated is provided to devices that are the objects of communication cut-off, such that data packets transmitted by the communication cut-off object devices are transmitted to manipulated abnormal addresses. By doing so, communication with the communication cut-off object devices is cut off. For a device which is in a communication cut-off state although the device is not an object of communication cut-off any more, the communication control apparatus transmits an ARP packet including normal address information to the device such that the communication cut-off state is canceled.
Owner:INIMAX
Method and apparatus for load balancing over virtual network links
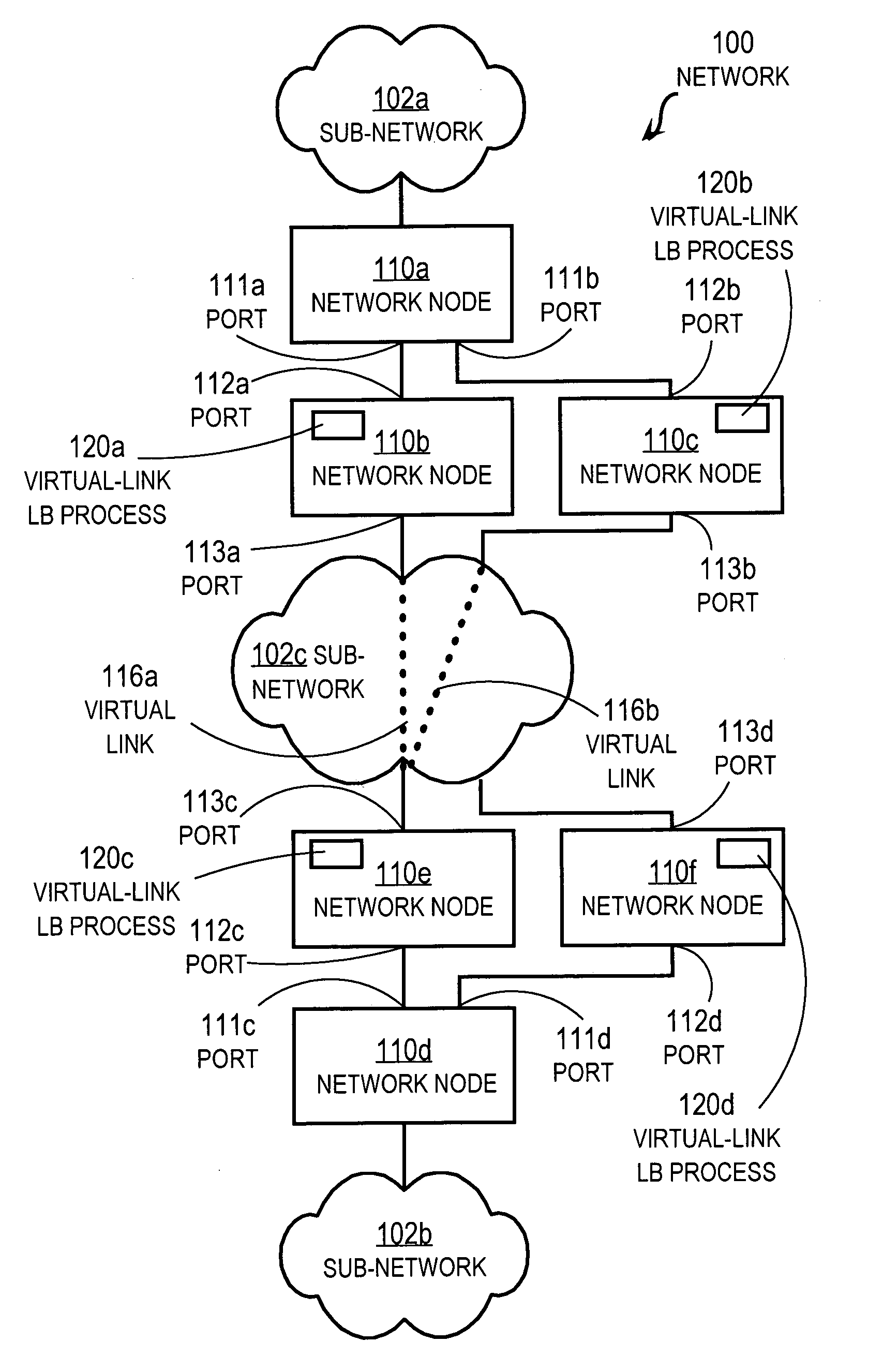
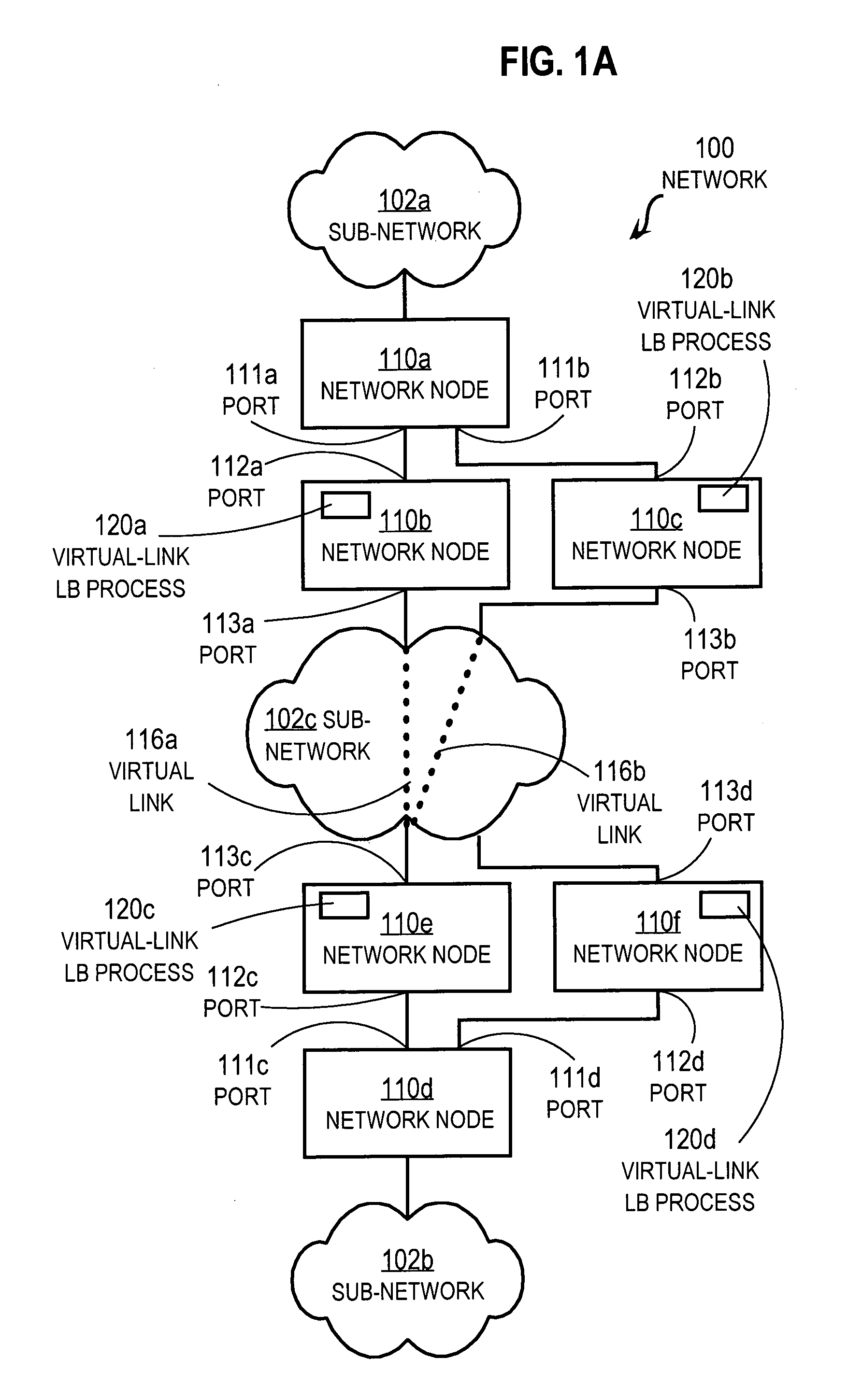
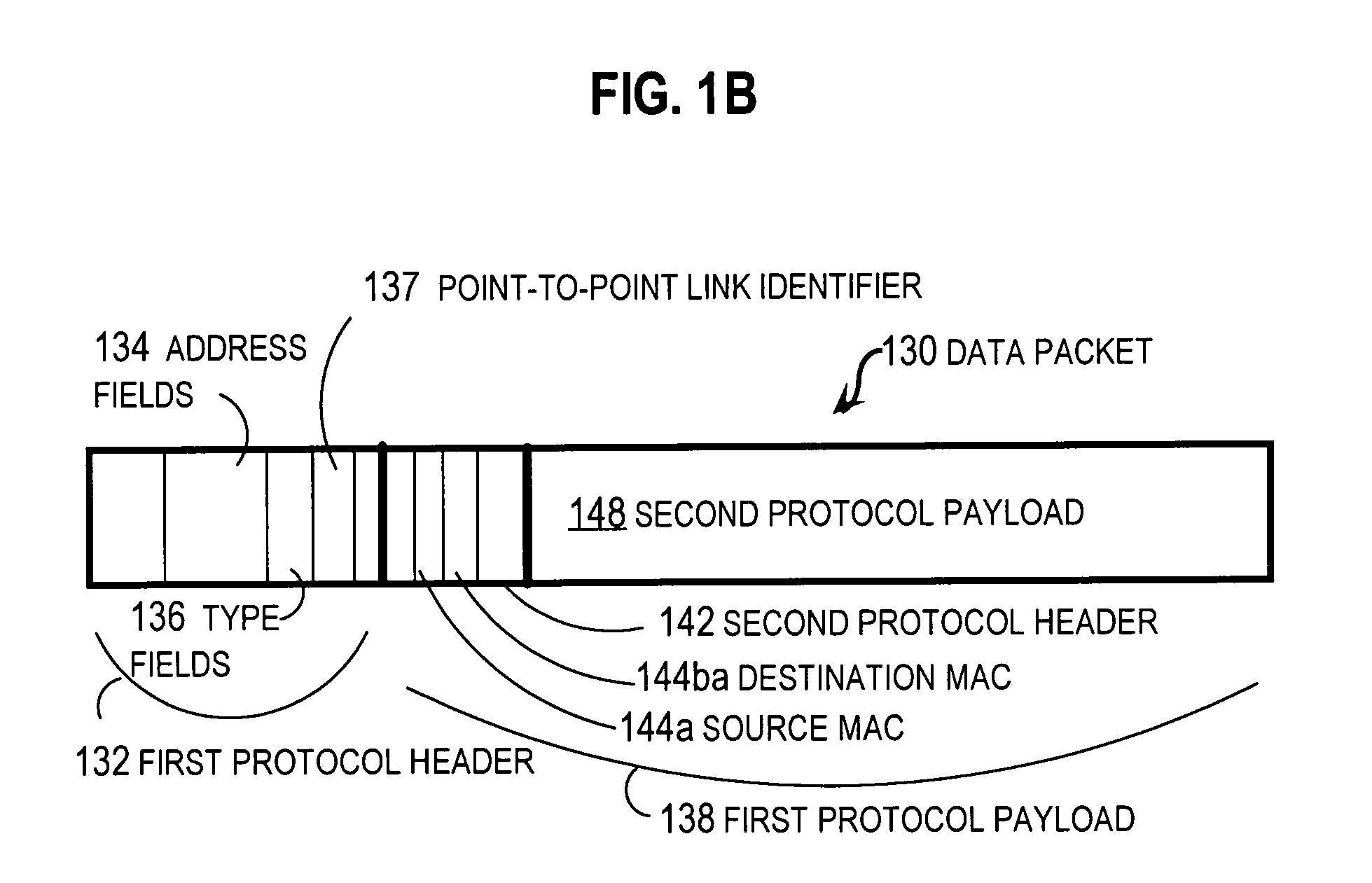
Techniques for load balancing network traffic over virtual point-to-point data links at a data-link layer include determining a particular group of virtual point-to-point data links that reach a particular local area network of one or more network nodes. A particular data-link address for a particular node of the particular local area network is associated with each virtual point-to-point data link of the particular group. When a data packet is received that includes data that indicates the particular data-link address as a destination; one virtual point-to-point data link of the group is determined to balance traffic among the group. The data packet is sent only over the one virtual point-to-point data link. These techniques enable virtual point-to-point data links through two or more intermediate network nodes, such as a pair of provider edge nodes, to be bundled for load balancing purposes.
Owner:CISCO TECH INC
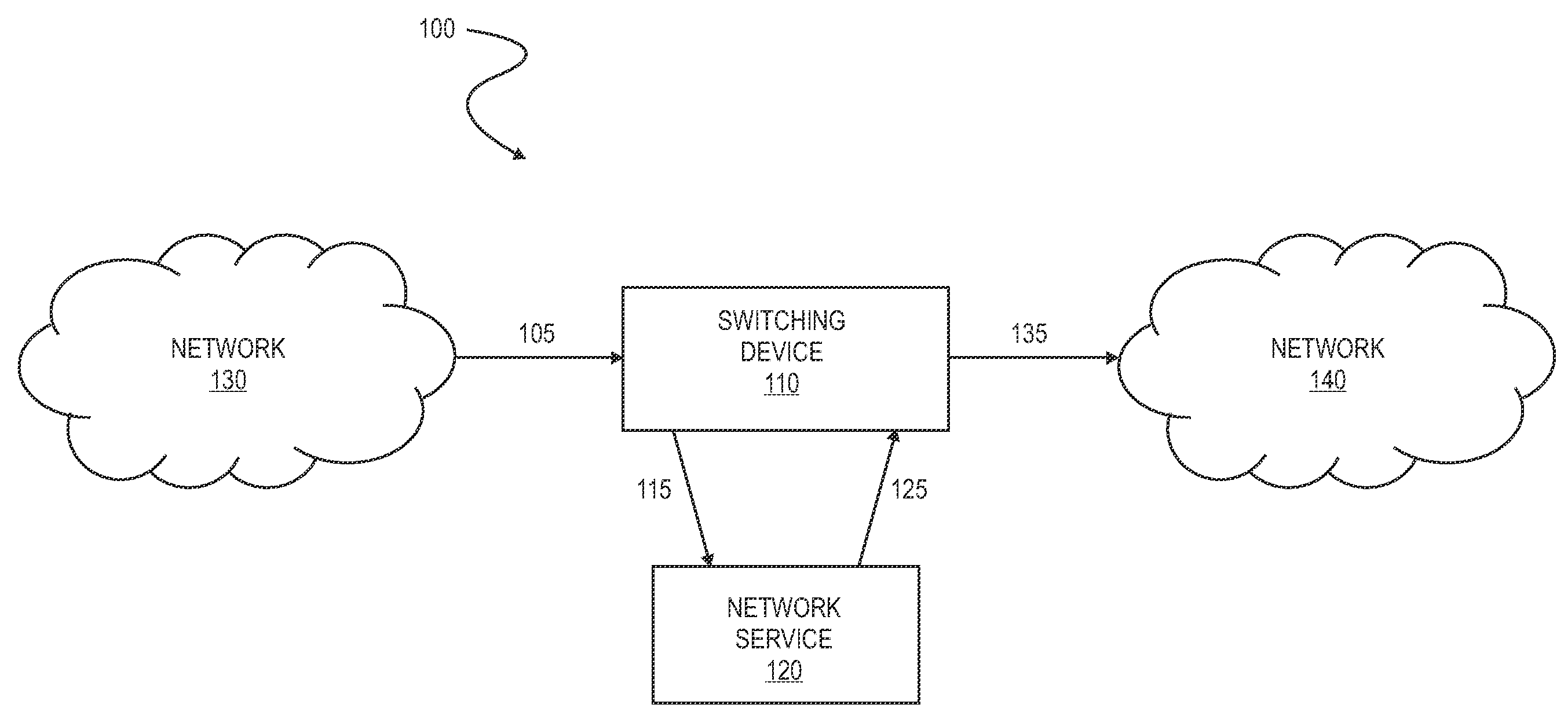
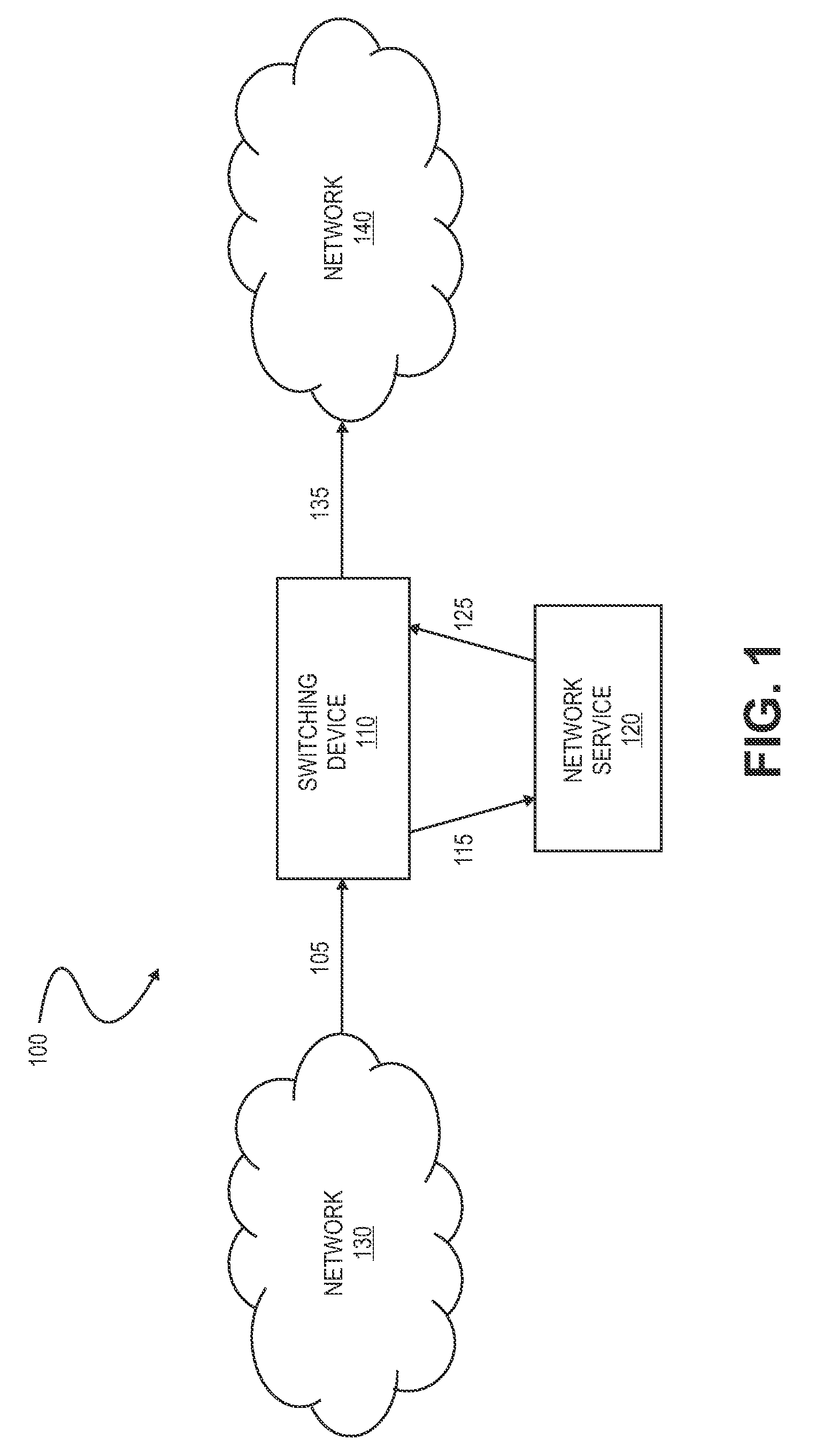
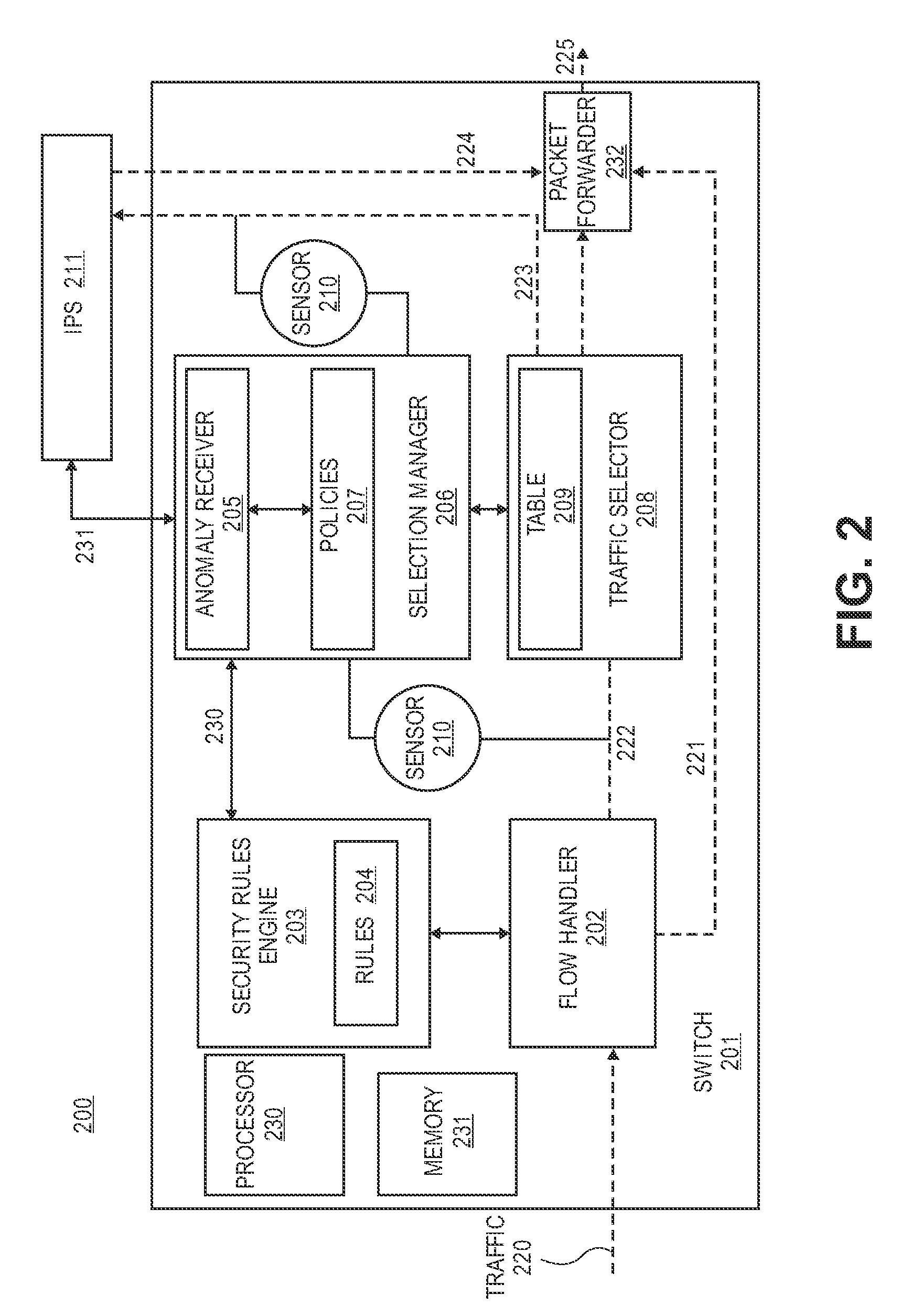
Method and mechanism for port redirects in a network switch
ActiveUS20090003317A1Memory loss protectionError detection/correctionNetwork switchSecurity analysis
A method for selectively redirecting a data packet to a port on a switching device which is associated with a corresponding network service. In one embodiment, the data packet is redirected to an intrusion prevention service (IPS) for security analysis of the data packet. In another embodiment, the switching device performs a data link layer redirecting of the data packet based at least in part on whether the data packet is to be flooded from the switching device.
Owner:EXTREME NETWORKS INC
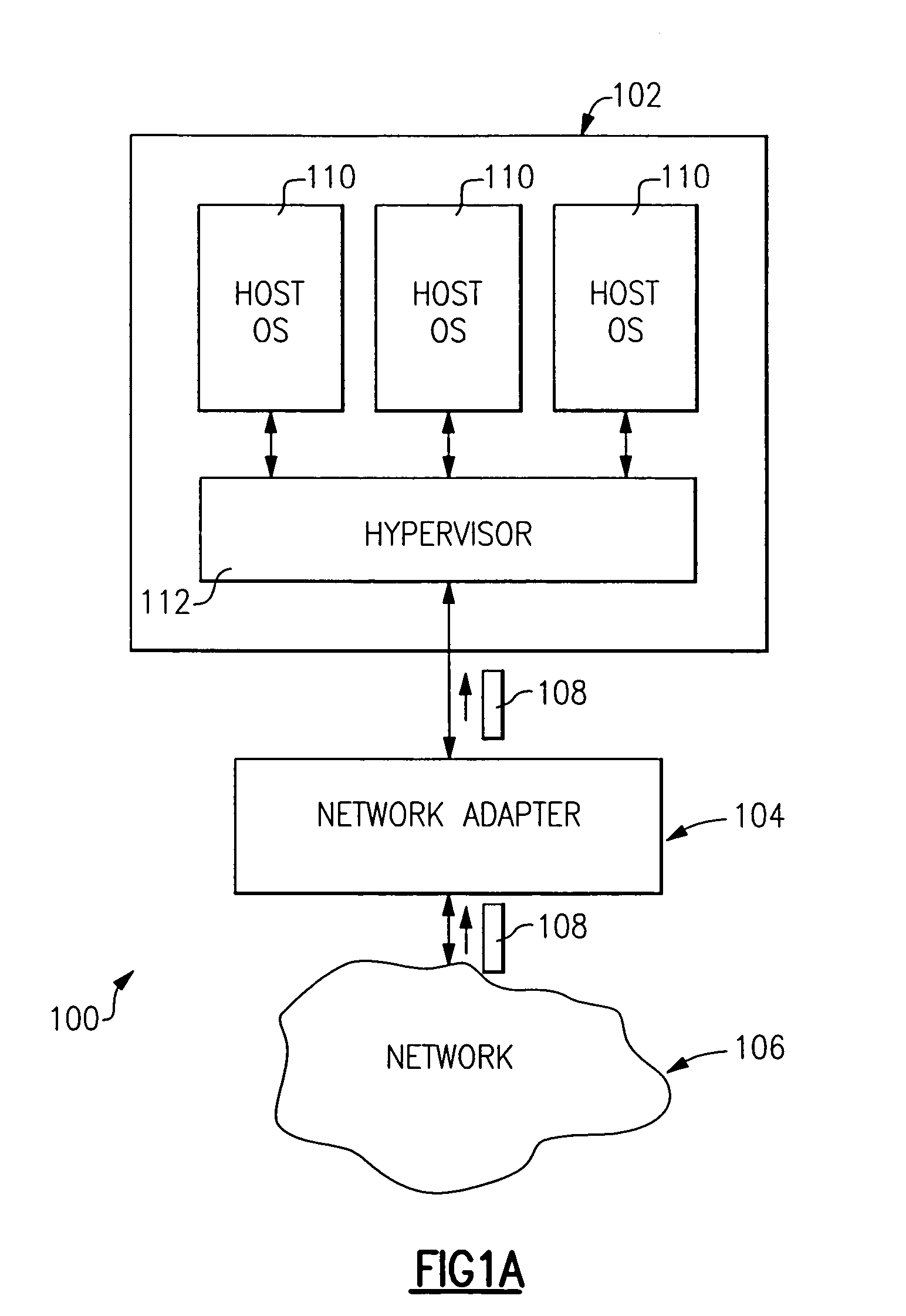
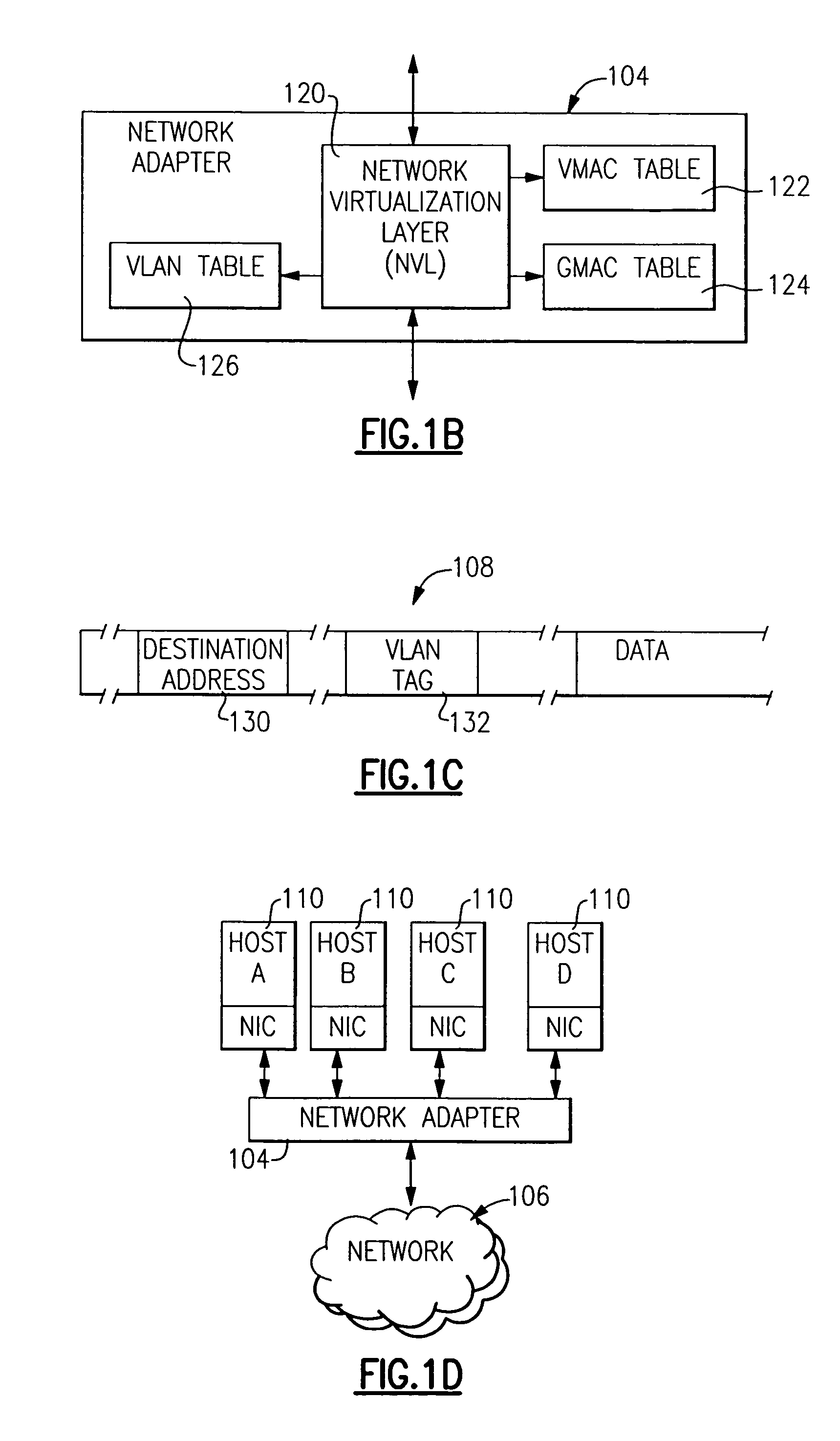
Method and apparatus for providing network virtualization
A network virtualization layer for an information handling system in which a physical machine coupled to a network is divided into a plurality of logical partitions, each of which has a host system residing thereon. In response to receiving a set command from one of the host systems specifying a data link layer (layer 2) address, the virtualization layer associates the data link layer address with the host system and forwards to the host system data packets specifying the data link layer address as a destination address. Unicast packets are forwarded to the single host system specifying the destination address as an individual MAC address, while multicast packets are forwarded to each host system specifying the destination address as a group MAC address. A host system may also specify a virtual LAN (VLAN) ID, which is used to scope the forwarding of packets to host systems sharing that VLAN ID.
Owner:IBM CORP
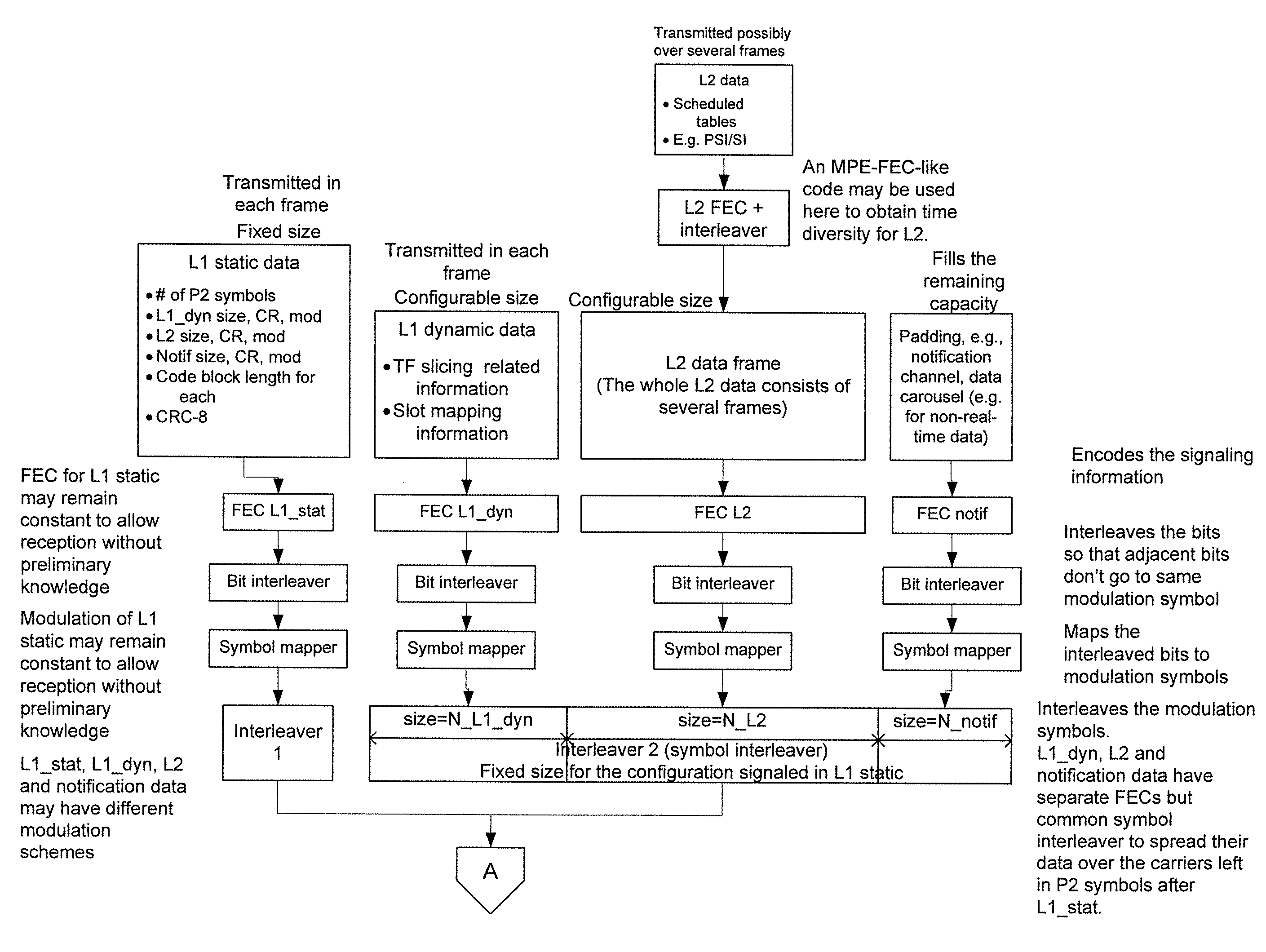
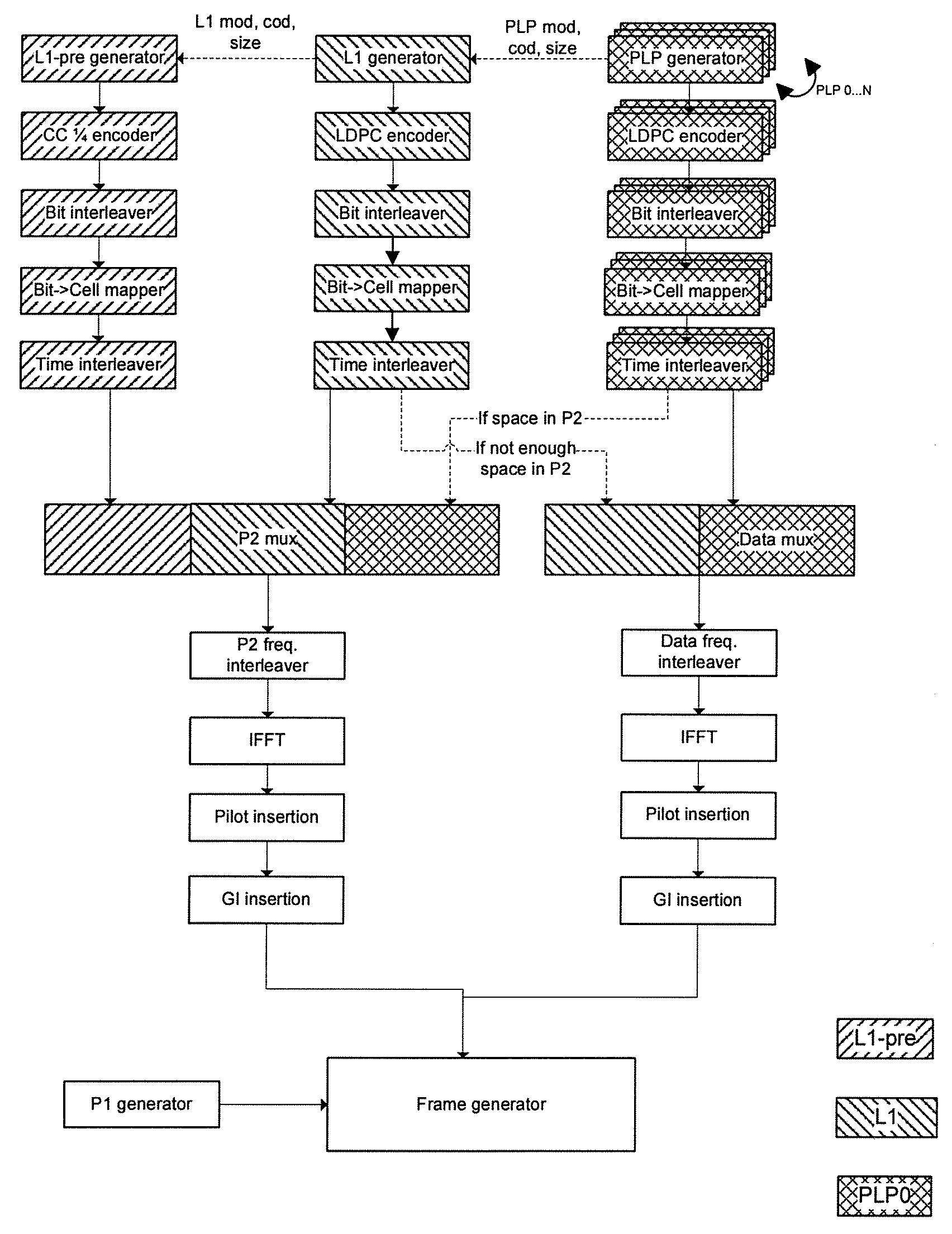
Digital Broadcast Signaling Metadata
ActiveUS20090103649A1Error correction/detection using convolutional codesError preventionDigital broadcastingData link layer
Embodiments are directed to transmitting L1 pre-signaling information with predetermined modulation and code rate such that L1 pre-signaling information can be received without preliminary knowledge on the network. L1 pre-signaling information makes it possible to receive the L1 signaling information, data link layer information, and notification data that may have configurable code rates and modulation. Therefore, L1 pre-signaling information can be thought of as signaling metadata (i.e., information about other signaling information). L1 signaling is divided into pre-signaling and signaling parts. The pre-signaling part includes parameters used for receiving the L1 signaling information. L1 pre-signaling signaling enables the receiver to receive the signaling itself (L1 signaling and data link layer information) by informing the receiver about the type of modulation, coding, and the like, used to transmit the L1 signaling, data link layer, and notification information.
Owner:SAMSUNG ELECTRONICS CO LTD
Network system and communication device
ActiveUS7848768B2Reduce power consumptionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsNetworked systemData link layer
A network system includes at least first and second communication devices connected in a network. The first communication device includes an inquiry device for inquiring the attributes of the second communication device to the second communication device via the network. The second communication device includes an attribute holding device for holding the attributes and a search device for searching for the attributes held in the attribute holding device in response to the inquiry and responds back with the search result to the inquiry device. The attribute holding device and the search device operate in a data link layer.
Owner:SONY CORP
Physical Layer and Data Link Layer Signalling in Digital Video Broadcast Preamble Symbols
Aspects of the invention are directed to physical layer and data link layer signaling in digital video broadcast preamble symbols. Embodiments are directed to distributing physical layer pre-signalling data among preamble symbols. If physical layer data is larger than a predetermined number of preamble symbols, then excess physical layer data is written to data symbols immediately following the preamble symbols in top-down order symbol by symbol or the predetermined number of preamble symbols is increased. If physical layer data is not larger than the predetermined number of preamble symbols such that there is excess preamble symbol space, physical layer pipe 0 data comprising link layer signaling and notification data is carried in the excess preamble symbols or the excess preamble symbols are left empty. Different permutation rules may be used to frequency interleave odd-numbered versus even-numbered orthogonal frequency division multiplexing symbols.
Owner:SAMSUNG ELECTRONICS CO LTD
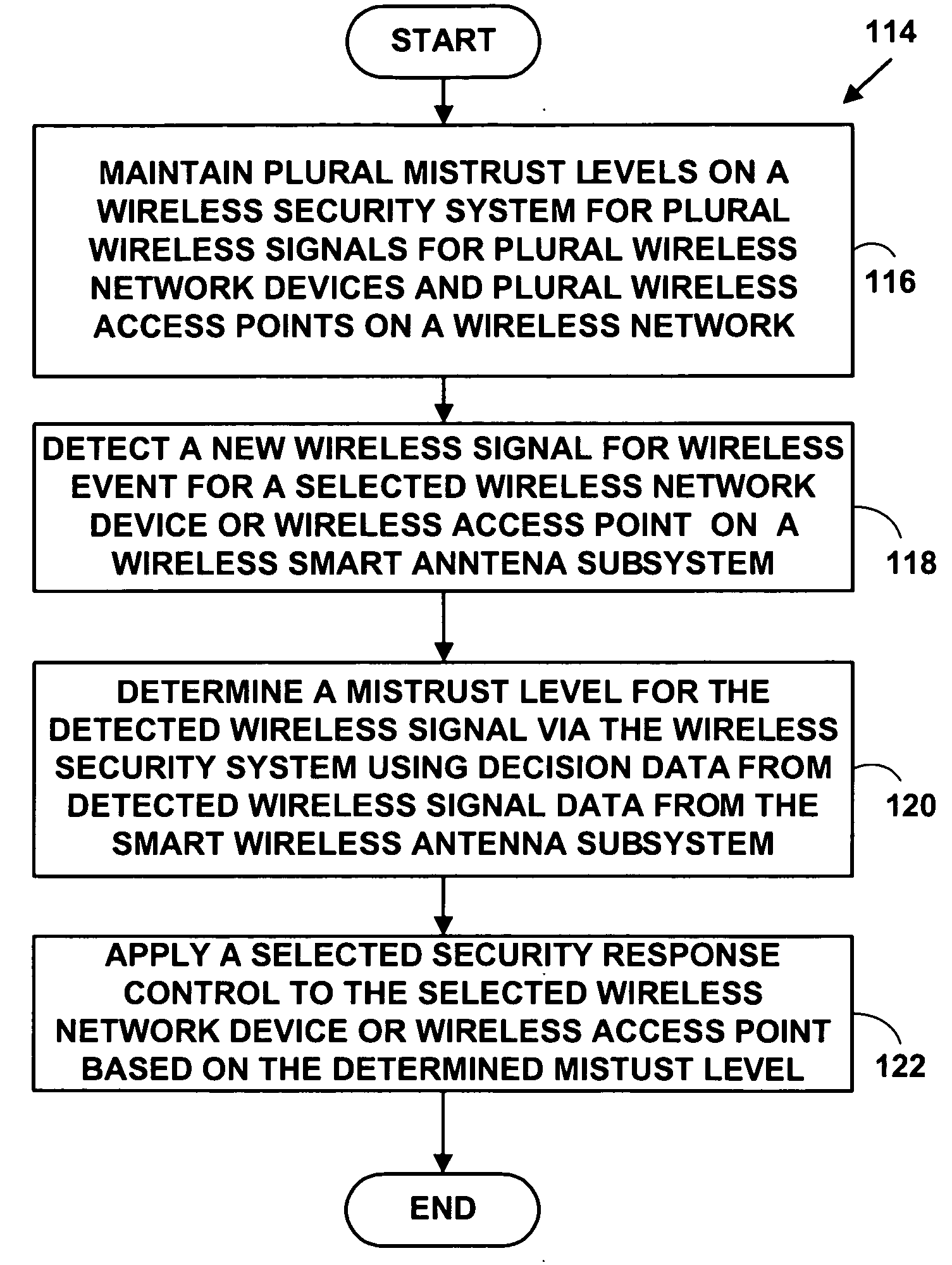
Method and system for wireless intrusion detection prevention and security management
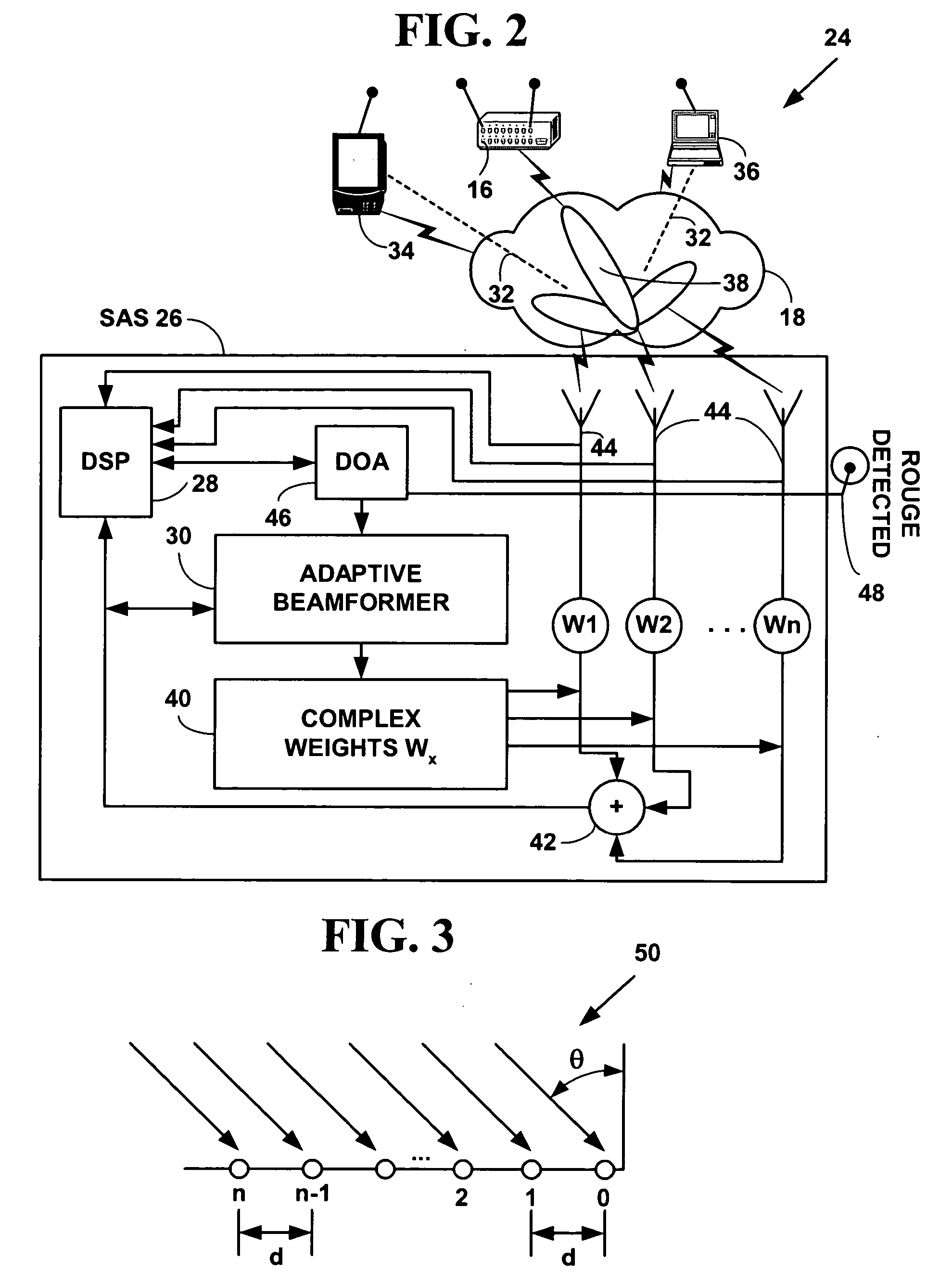
ActiveUS20050037733A1Spatial transmit diversityUnauthorised/fraudulent call preventionSystems managementIntrusion detection and prevention
A method and system for wireless intrusion detection, prevention and security management. The method and system provides autonomous wireless intrusion detection and prevention, with minimal or no operator intervention. The method and system integrates a physical layer (e.g., OSI layer 1) a smart wireless radio frequency (RF) antenna subsystem with a data-link layer (e.g., OSI layer 2) wireless security system management platform.
Owner:3E TECH INT
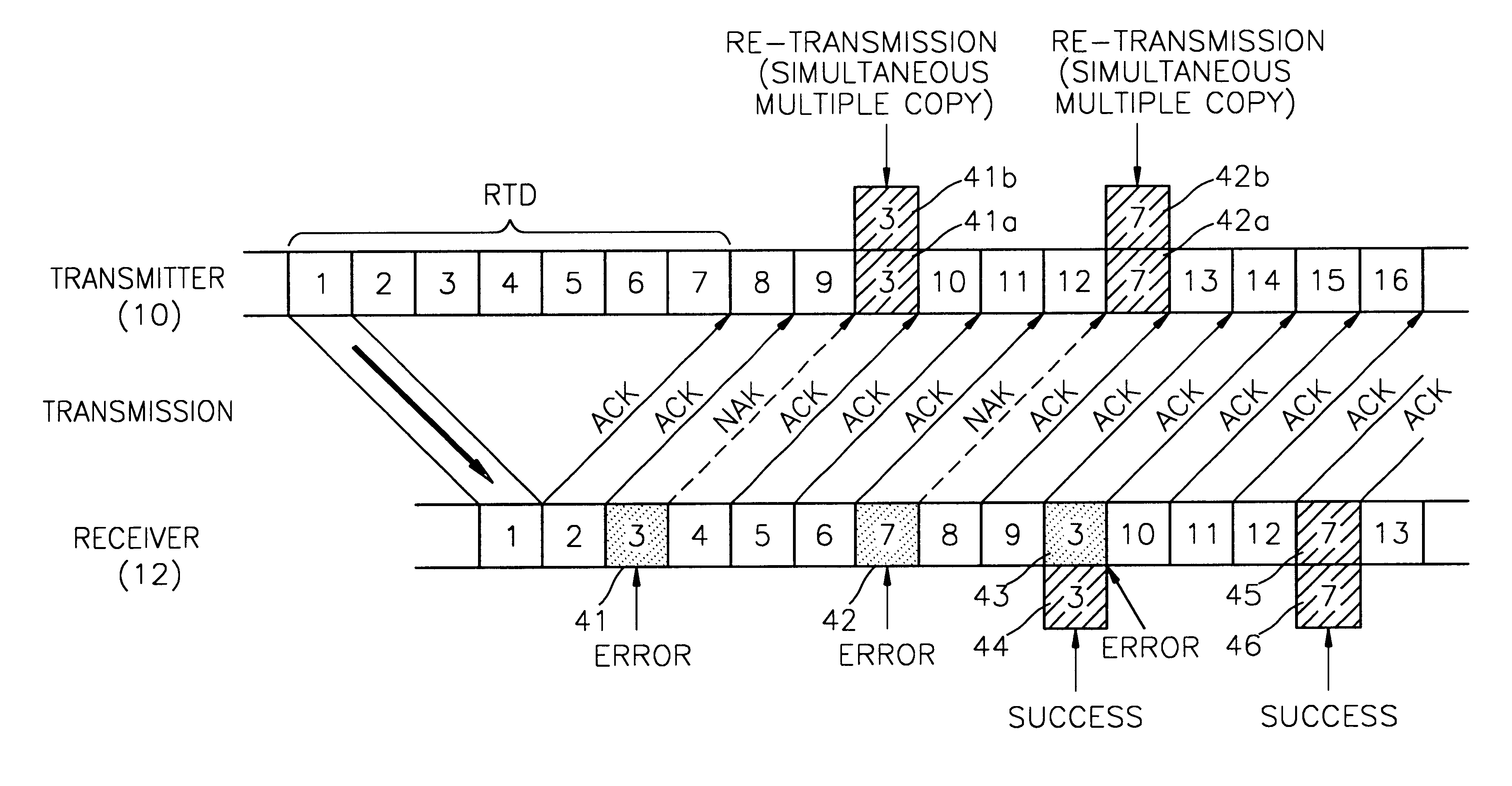
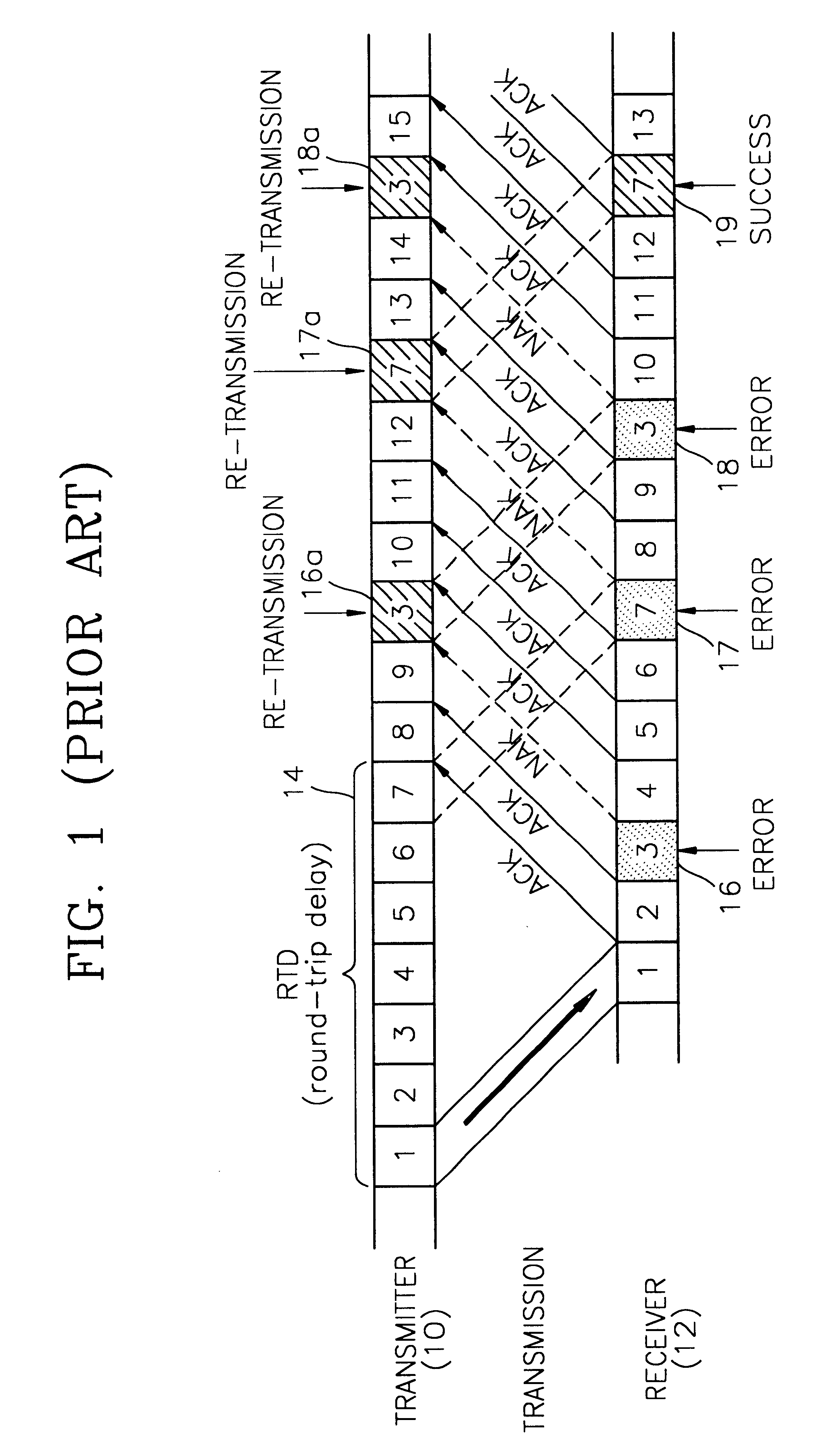
Method for controlling errors in link layer in wideband wireless communication and computer readable media therefor
InactiveUS6615382B1Error prevention/detection by using return channelTransmission systemsDelayed timeData link layer
A method for controlling errors in a wireless link layer using a simultaneous multiple copy scheme and an adaptive forward error correction (FEC) scheme in a wideband wireless communication is provided. The method for controlling errors in a link layer in wideband wireless communication using an automatic repeat request (ARQ) scheme, in which a wideband wireless channel is used for communication between a first node and a second node, includes the steps of (a) estimating the error ratio of a forward (a direction in which a cell is transmitted from the first node to the second node) channel using the state of a backward (a direction in which a cell is transmitted from the second node to the first node) channel, and transmitting a cell, in which a forward error correction (FEC) code having an encoding ratio that varies depending on the estimated error ratio is included in a protocol data unit (PDU) of a wireless link layer, through the forward channel and (b) re-transmitting the copy of a cell transmitted in the step (a), when feedback information that indicates that an error exists in the cell transmitted in the step (a) is received through the backward channel. It is possible to reduce the number of times of re-transmission by improving the probability of correcting forward errors using more error controlling bits as the state of the channel is worse and to minimize the waste of resources using less error controlling bits as the state of the channel is better, to thus obtain the optimal performance and guarantee the minimum delay time.
Owner:SAMSUNG ELECTRONICS CO LTD
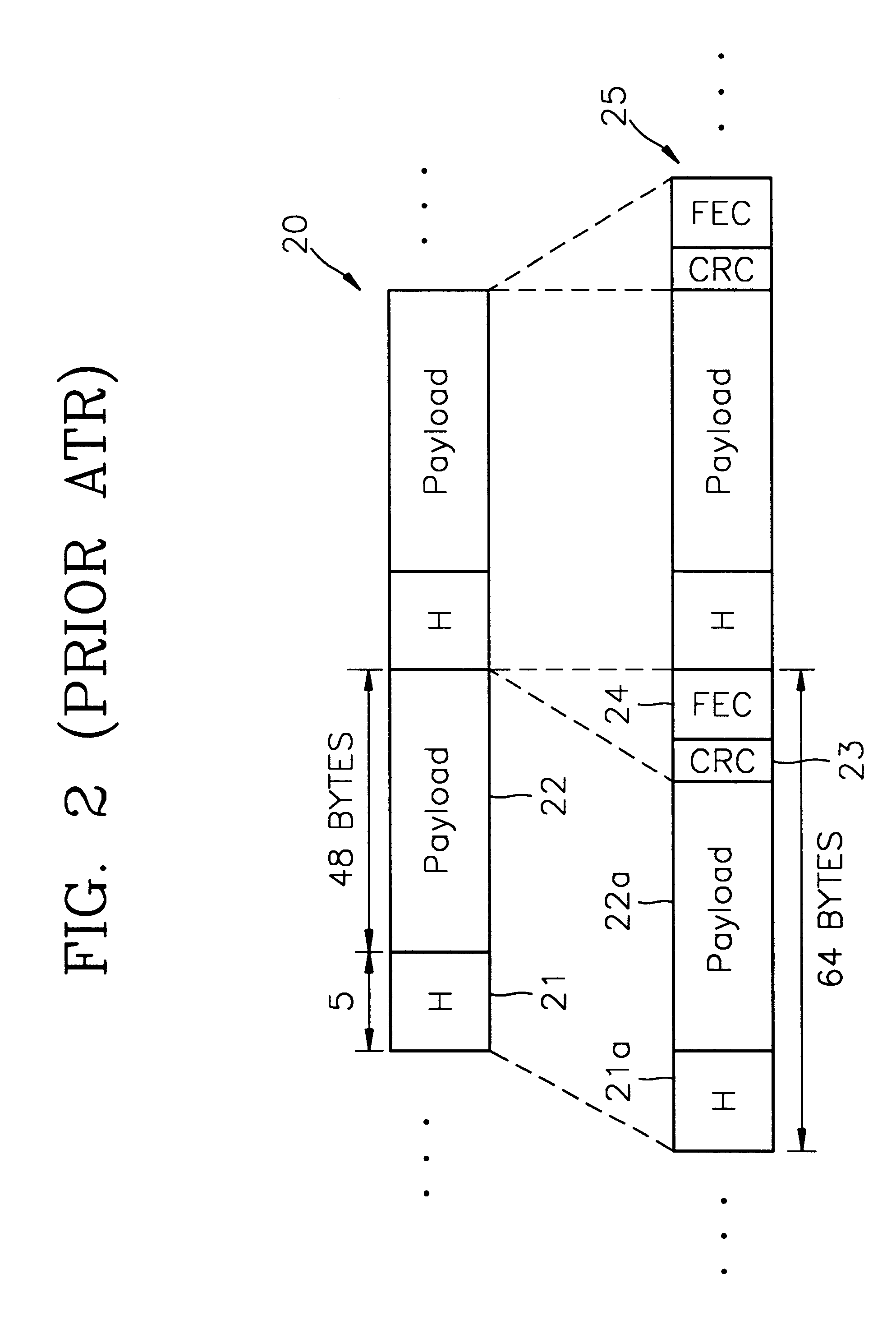
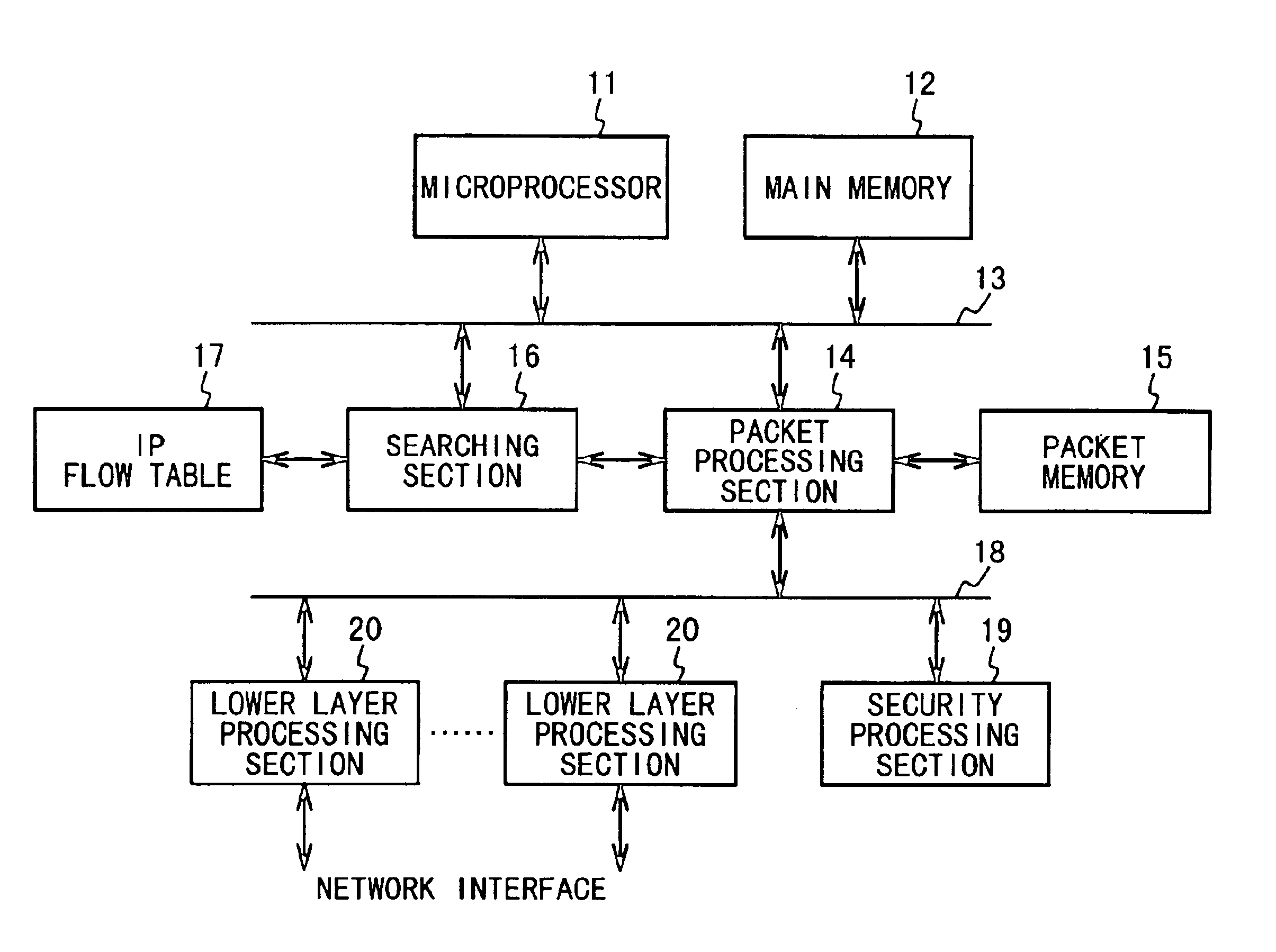
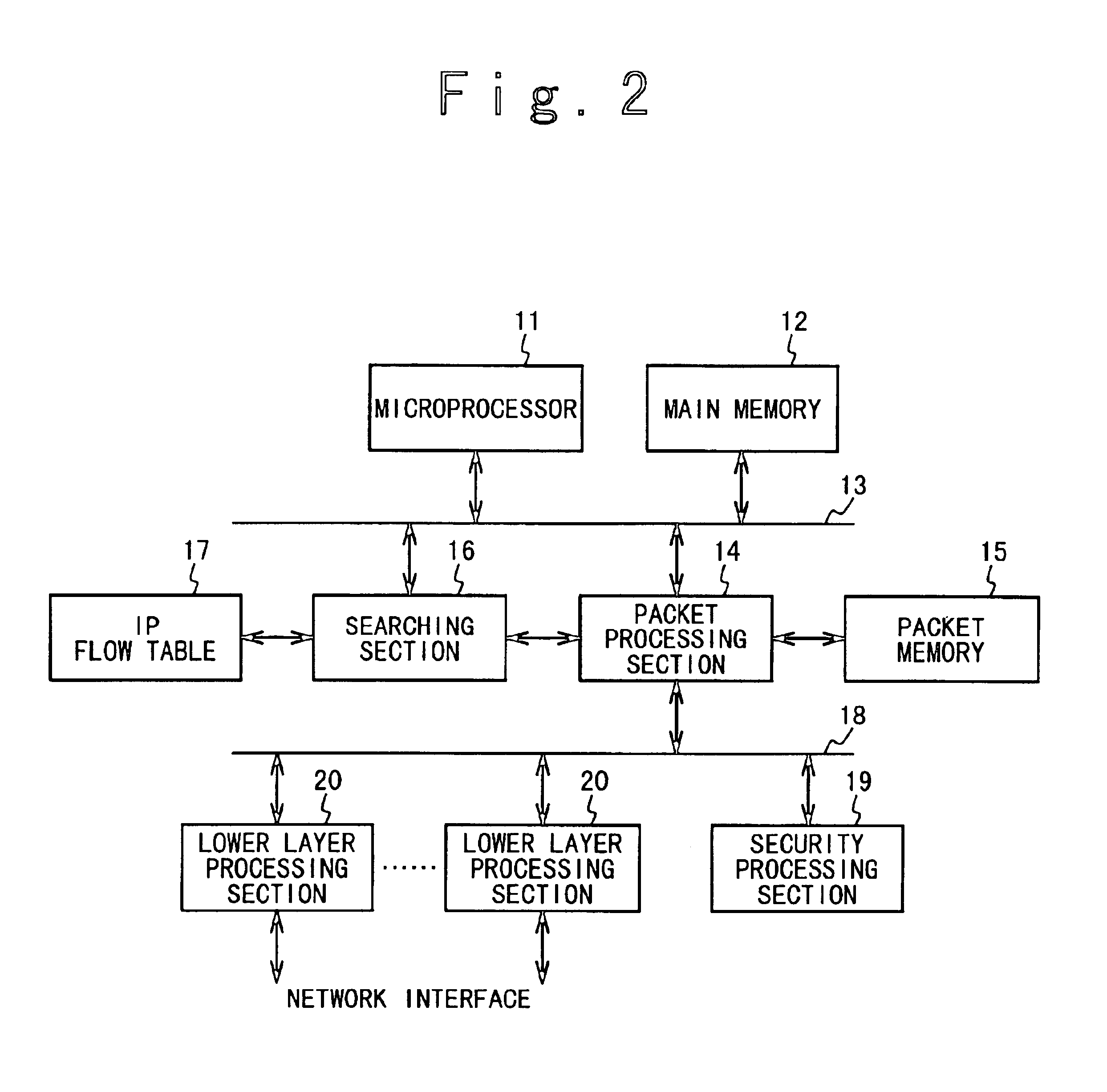
Packet switching apparatus with high speed routing function
InactiveUS6839346B1Reduce loadHigh speed packet switching processData switching by path configurationComputer hardwareData link layer
A packet switching apparatus includes a plurality of lower layer processing units, a table, and a processing unit. Each of the plurality of lower layer processing units carries out a process for a data link layer and a physical layer to a packet. The table stores flow data which includes a routing data and a search key. The processing unit searches the flow data from the table based on a search key of a routing packet received via one of the plurality of lower layer processing units, when the flow data for the search key of the routing packet is registered on the table. Also, the processing unit selectively transfers the routing packet to one of the plurality of lower layer processing units based on the routing data of the searched flow data.
Owner:NEC CORP
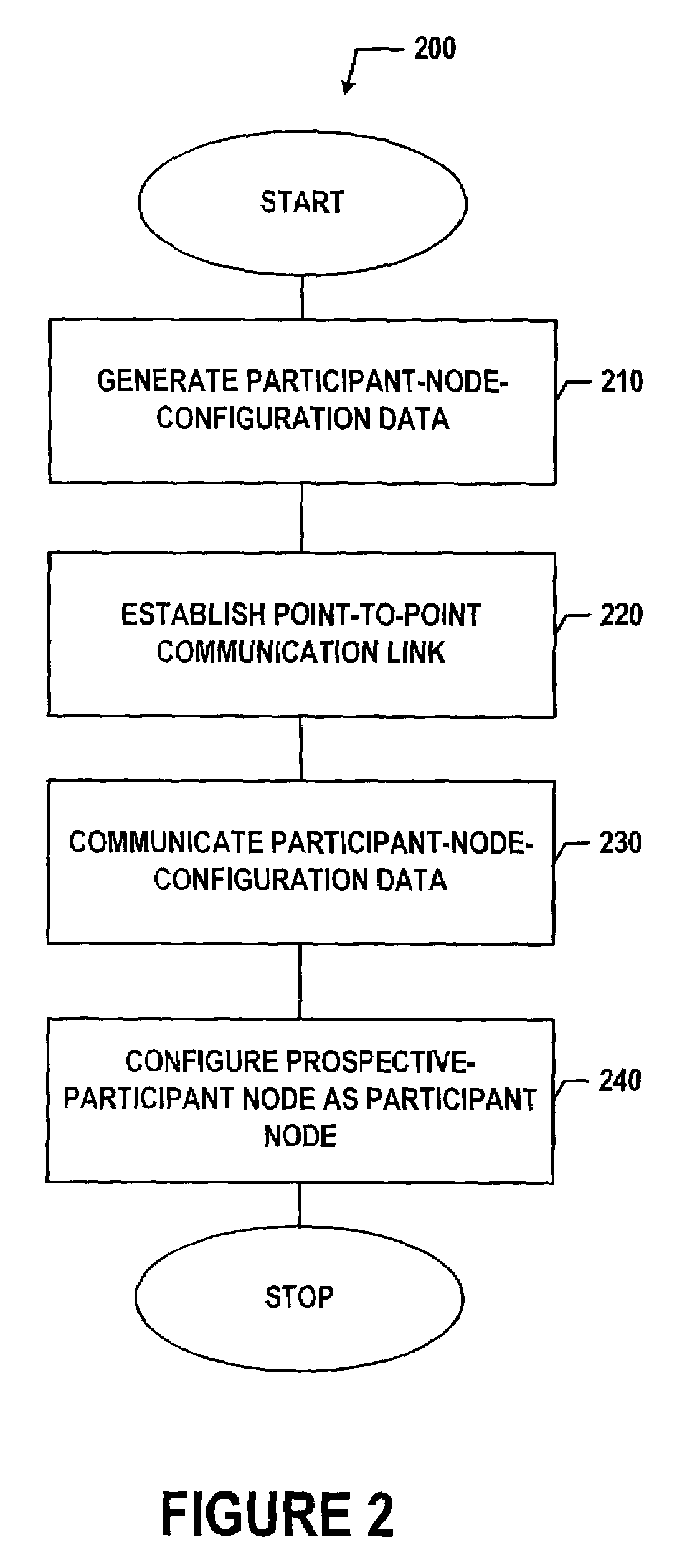
Method and system for automating node configuration to facilitate peer-to-peer communication
ActiveUS7263070B1Easy to set upConnection managementData switching by path configurationNetwork connectionCommunication link
A method and system for configuring one or more prospective-participant nodes as participant nodes so as to enable the prospective-participant nodes to engage in a peer-to-peer communication is provided. In one exemplary embodiment, the method and system may be embodied as a common application that includes logic, in hardware or software form, for carrying out one or more of the functions for configuring one or more prospective-participant nodes as a participant node in a peer-to-peer network. In carrying out these functions, one of the participant nodes discovers its network connection settings, and based on these settings, generates participant-node-configuration data that includes one or more network connection settings that define how to address the prospective-participant node as a participant node. When desiring to join the peer-to-peer network, the prospective-participant node and the participant node may establish a point-to-point communication link by engaging in a discovery process using so as to establish a data-link layer connection. After completing negotiation of the data-link-layer connection, the prospective-participant node and the participant node may communicate over the data-link-layer connection. The prospective-participant node may send to the participant node a request for network access. Responsively, the participant node sends to the prospective-participant node the participant-node-configuration data over the point-to-point connection. And the prospective-participant node configures itself using the participant-node-configuration data so as to become a participant node.
Owner:SPRINT SPECTRUM LLC
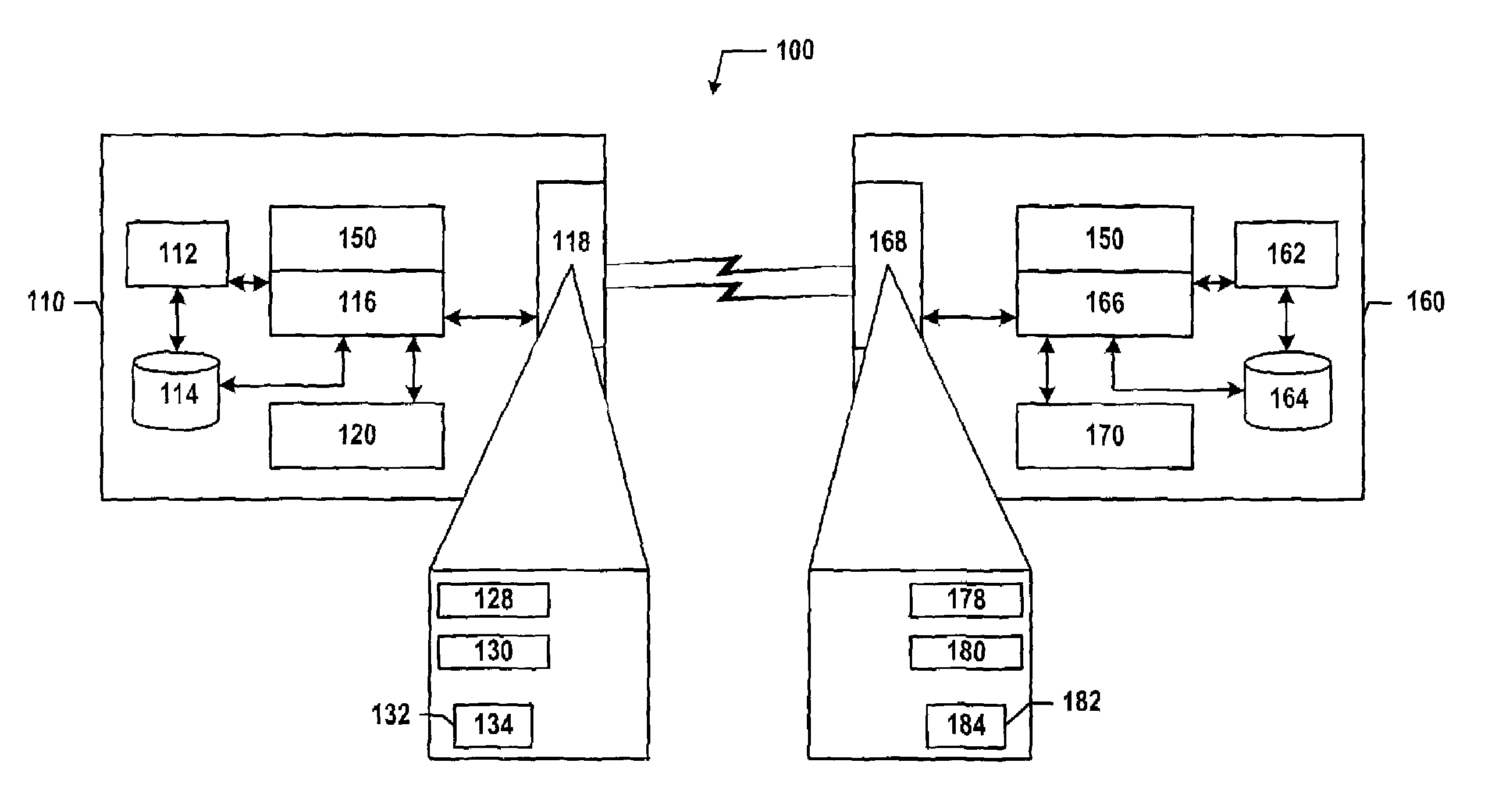
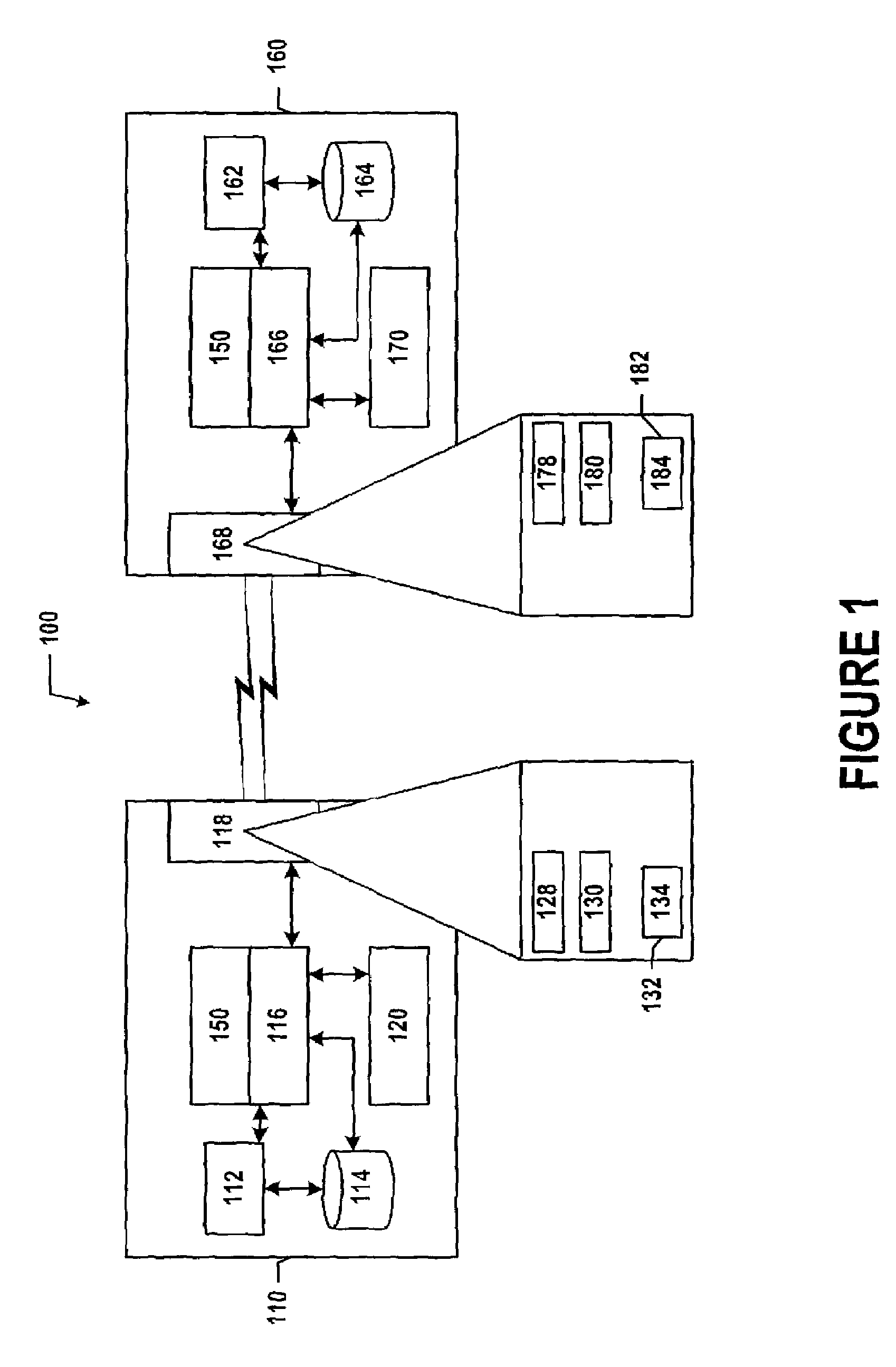
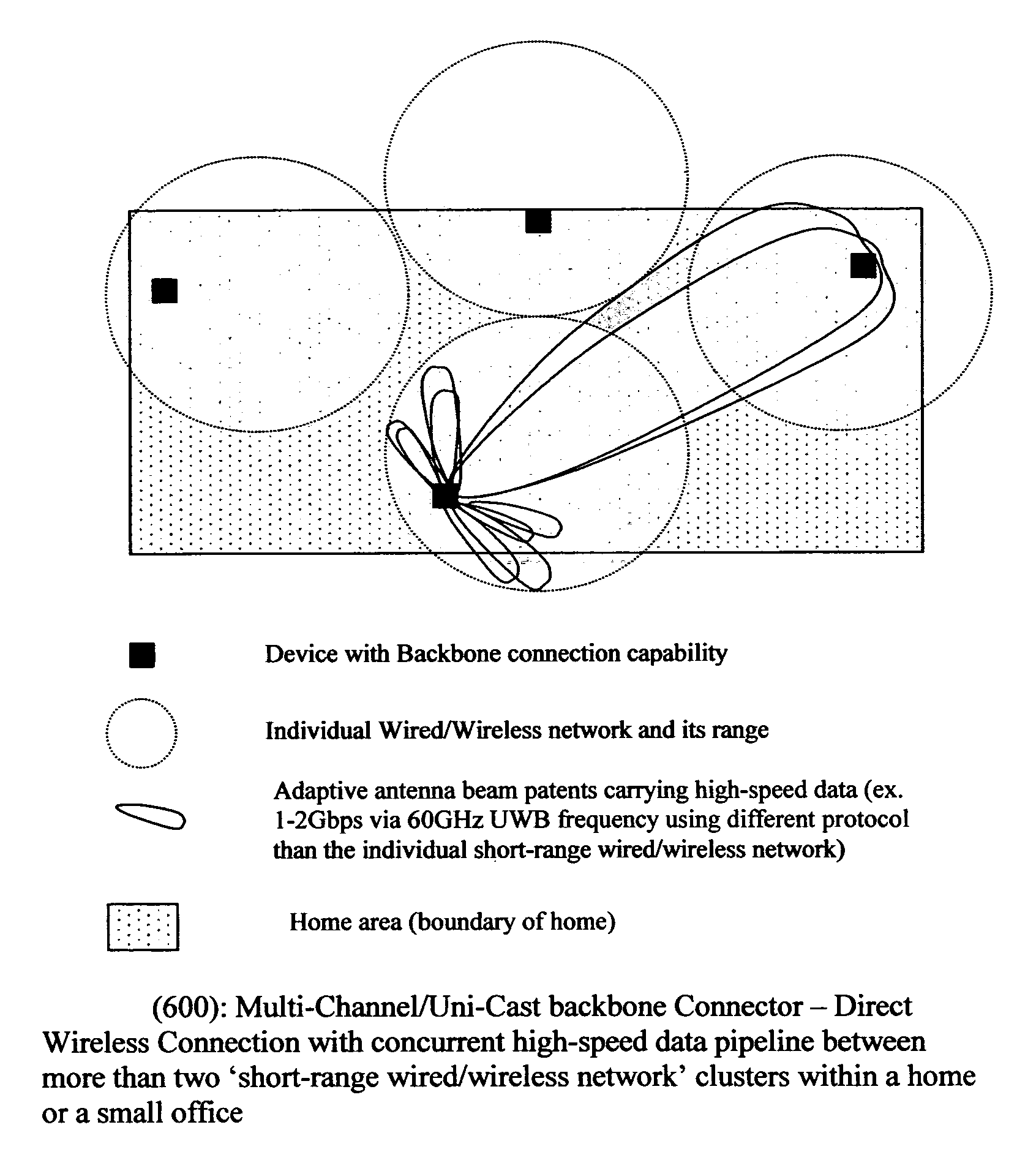
Method of constructing wireless high speed backbone connection that unifies various wired/wireless network clusters by means of employing the smart/adaptive antenna technique and dynamically creating concurrent data pipelines
InactiveUS7672271B2Reduce distractionsMinimize powerMultiplex system selection arrangementsEnergy efficient ICTTransmitted powerData link layer
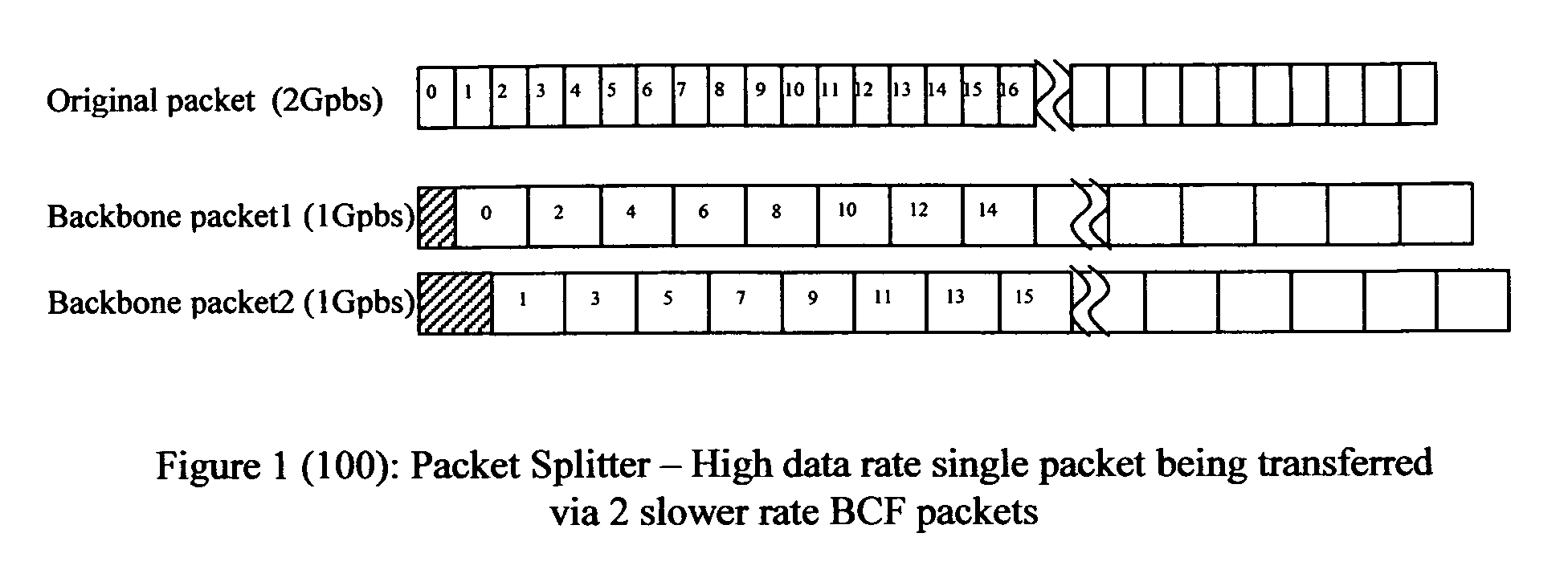
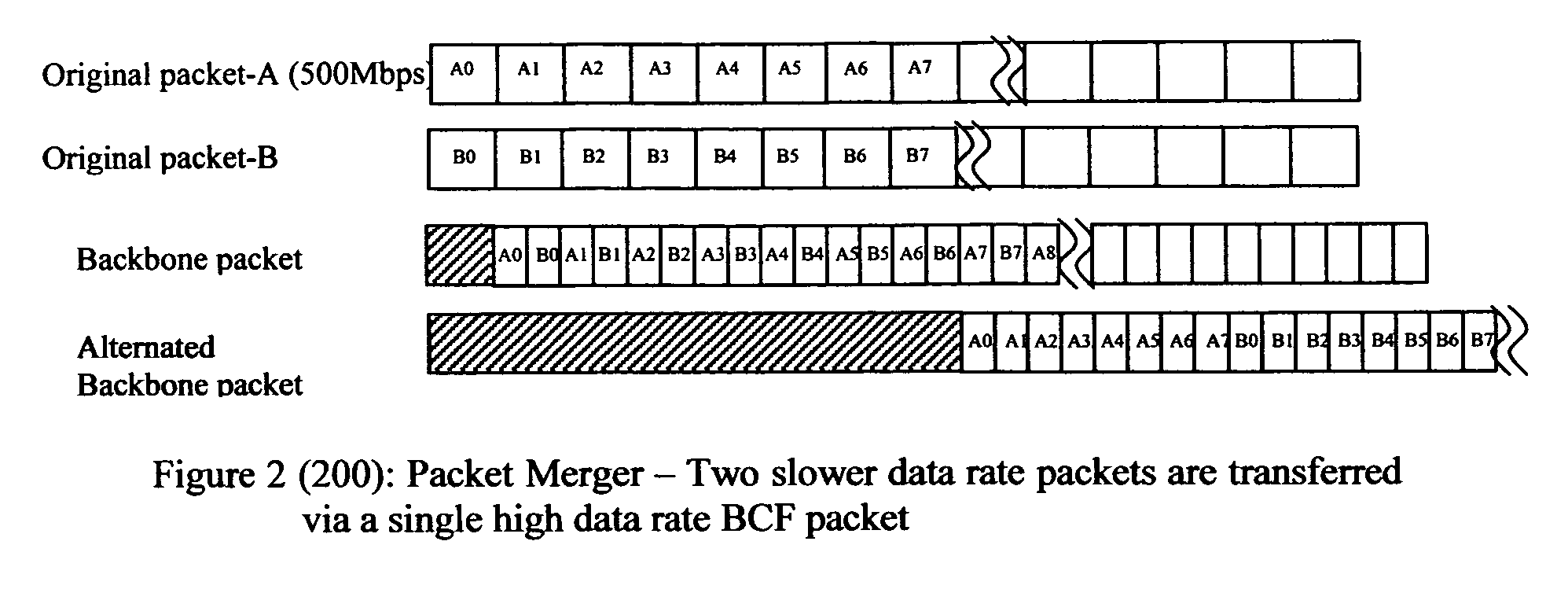
In accordance with the present invention, there is provided a high-speed wireless backbone connection, Backbone Connection Facilitator (BCF), to create a wireless home network, which may consist of many short-range wired / wireless networks. BCF dynamically creates concurrent data pipelines to meet the data bandwidth demand to transfer packets from one short-range wired / wireless network to another. BCF employs the newly developed antenna technologies (ex. MIMO, SDMA) to minimize the transmit power, to reduce the interferences, and to support the real time communication.BCF contains the BCF-PHY layer, the BCF-Data-Link-Layer, and the BCF-Network-Layer. The BCF-PHY layer consists of antenna array, a PHY Base Band controller, and a digital beam former. The BCF-Data-Link-Layer provides the MAC functionality. The BCF-Network-Layer assembles the packet, provides the source and destination address, and provides the BCF-PHY beam forming information. The BCF-Network-Layer is also responsible for parsing and assembling the packet payloads for the high-speed backbone connection.
Owner:LEE HYUN
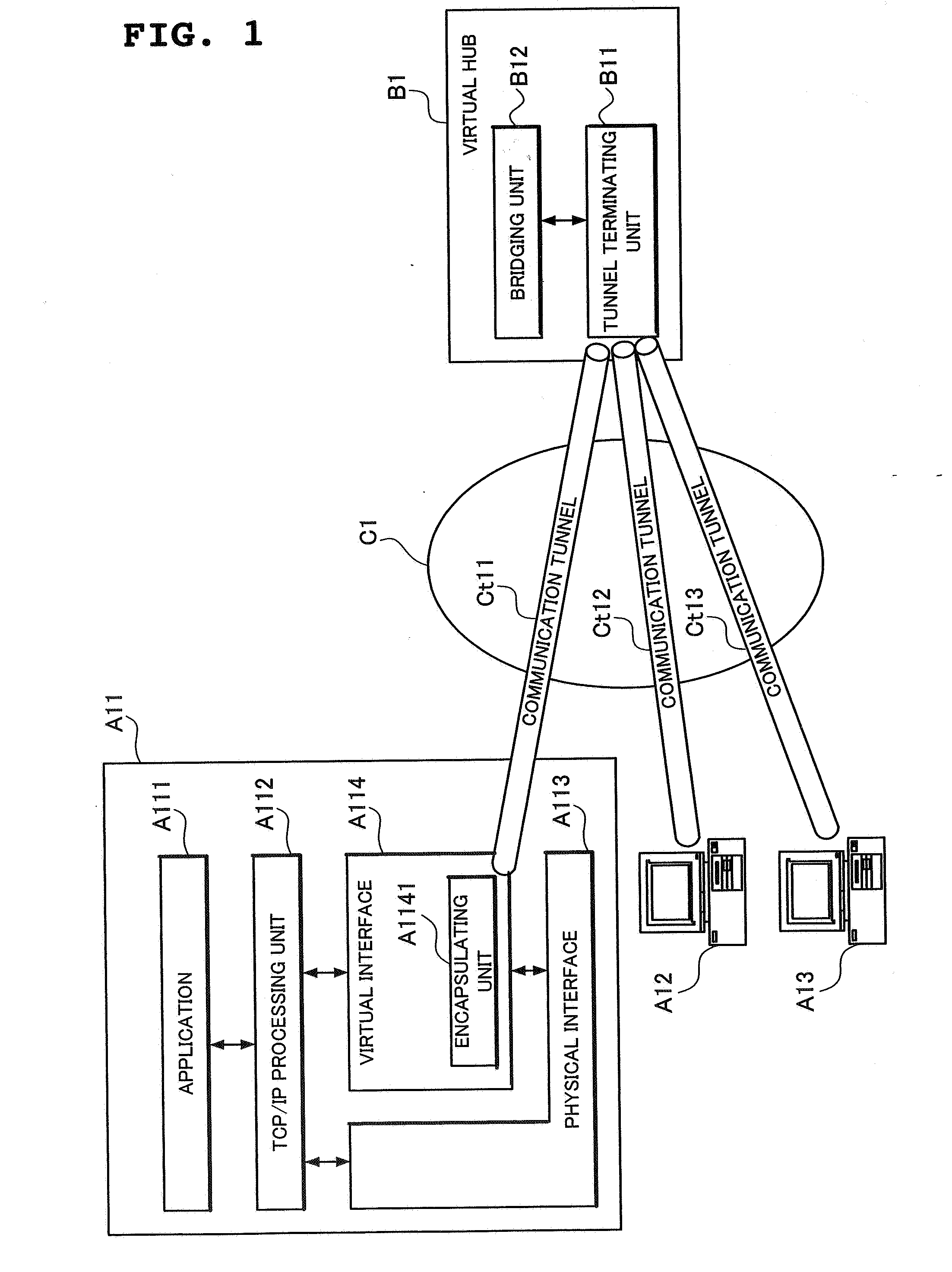
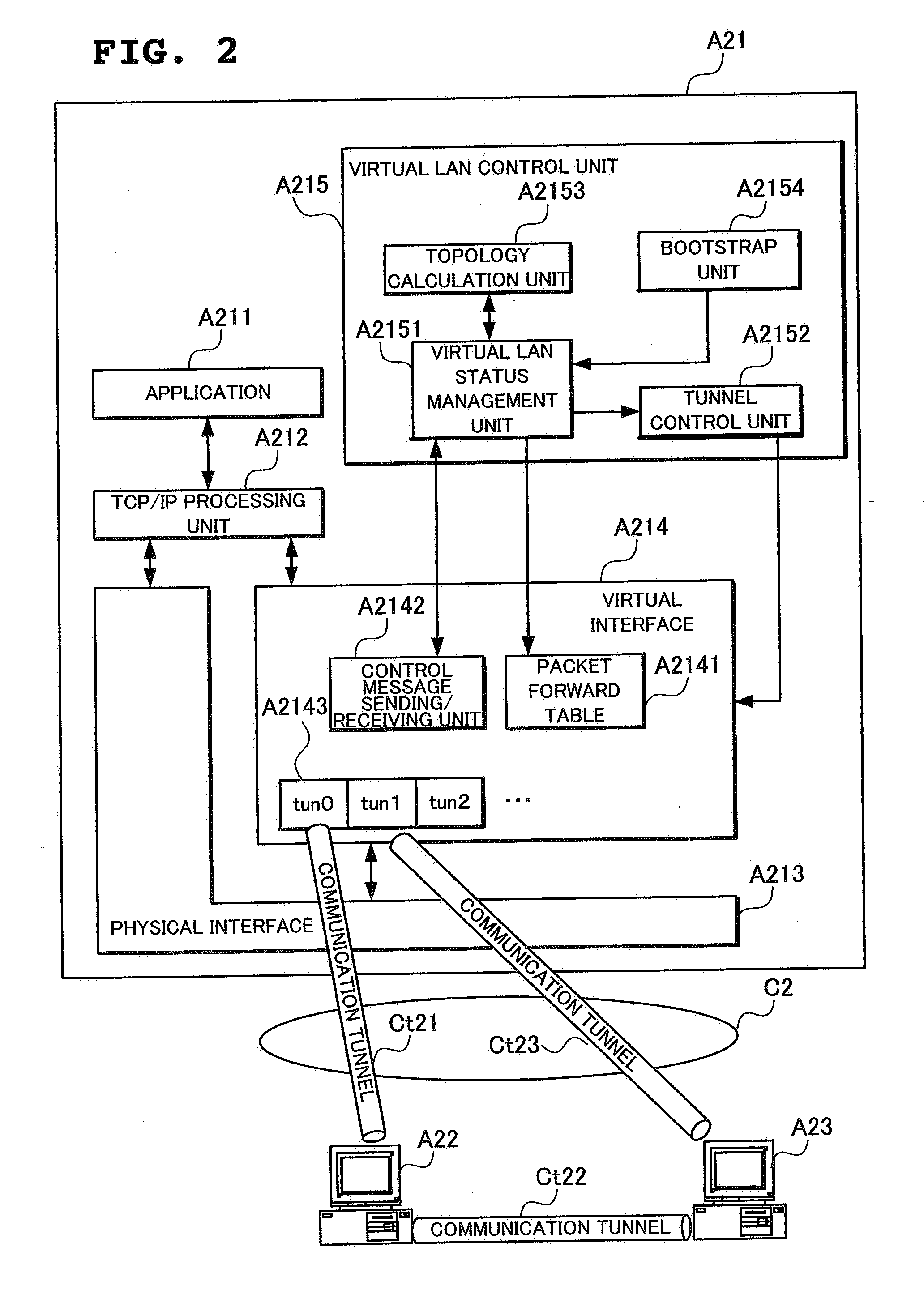
Virtual lan system and node device
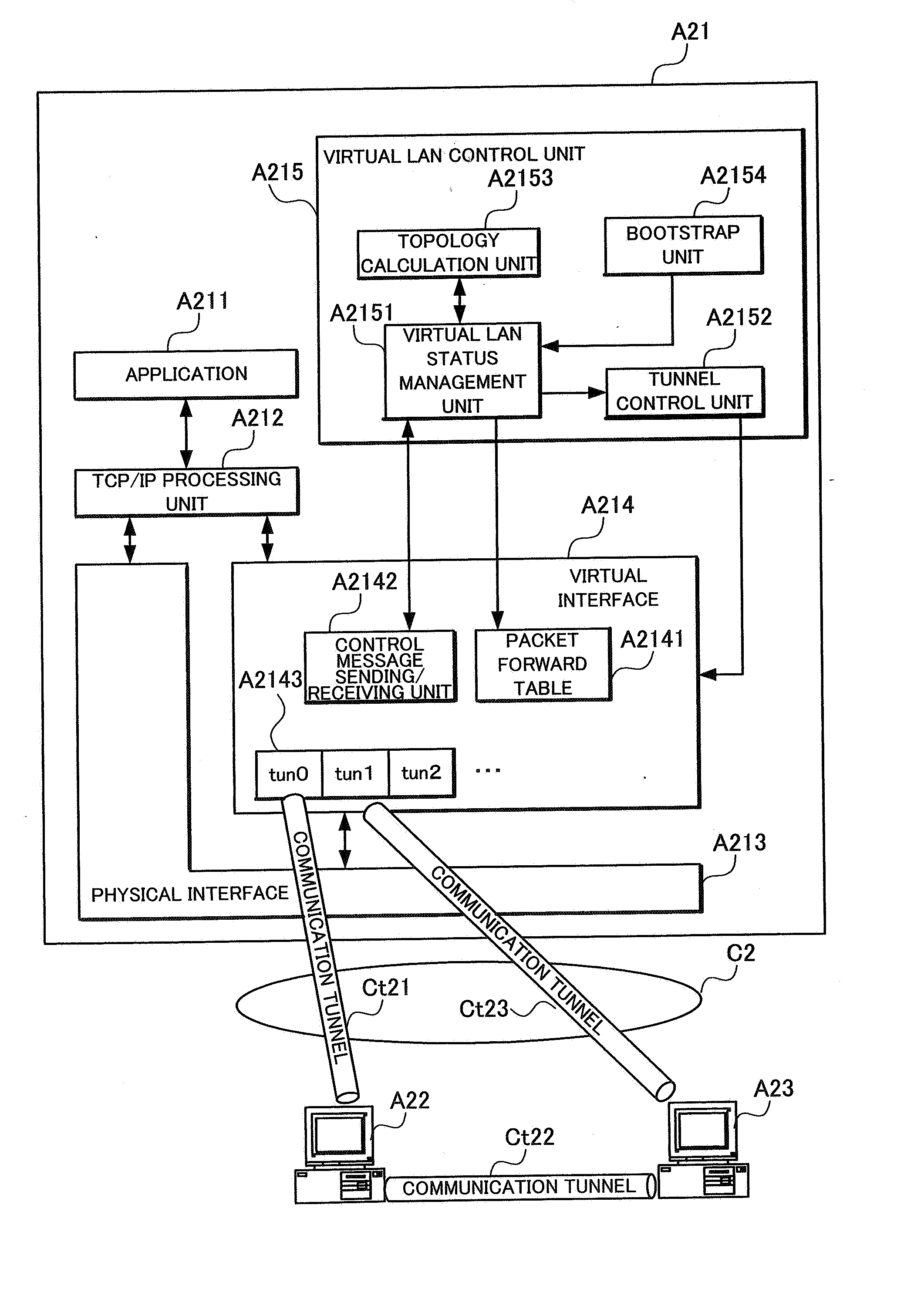
A node A21 sets a communication tunnel for encapsulating a data link packet with other nodes joining in a virtual LAN to a peer-to-peer type, and comprises a packet forward table A2141 for forwarding the data link layer packet received from a communication tunnel to another communication tunnel. In addition, the node A21 reconfigures the topology of the virtual LAN using a topology calculation unit A2153 when another node withdrew from the virtual LAN, and opens or removes communication tunnels according to the reconfigured topology using a tunnel control unit A2152.
Owner:NEC CORP
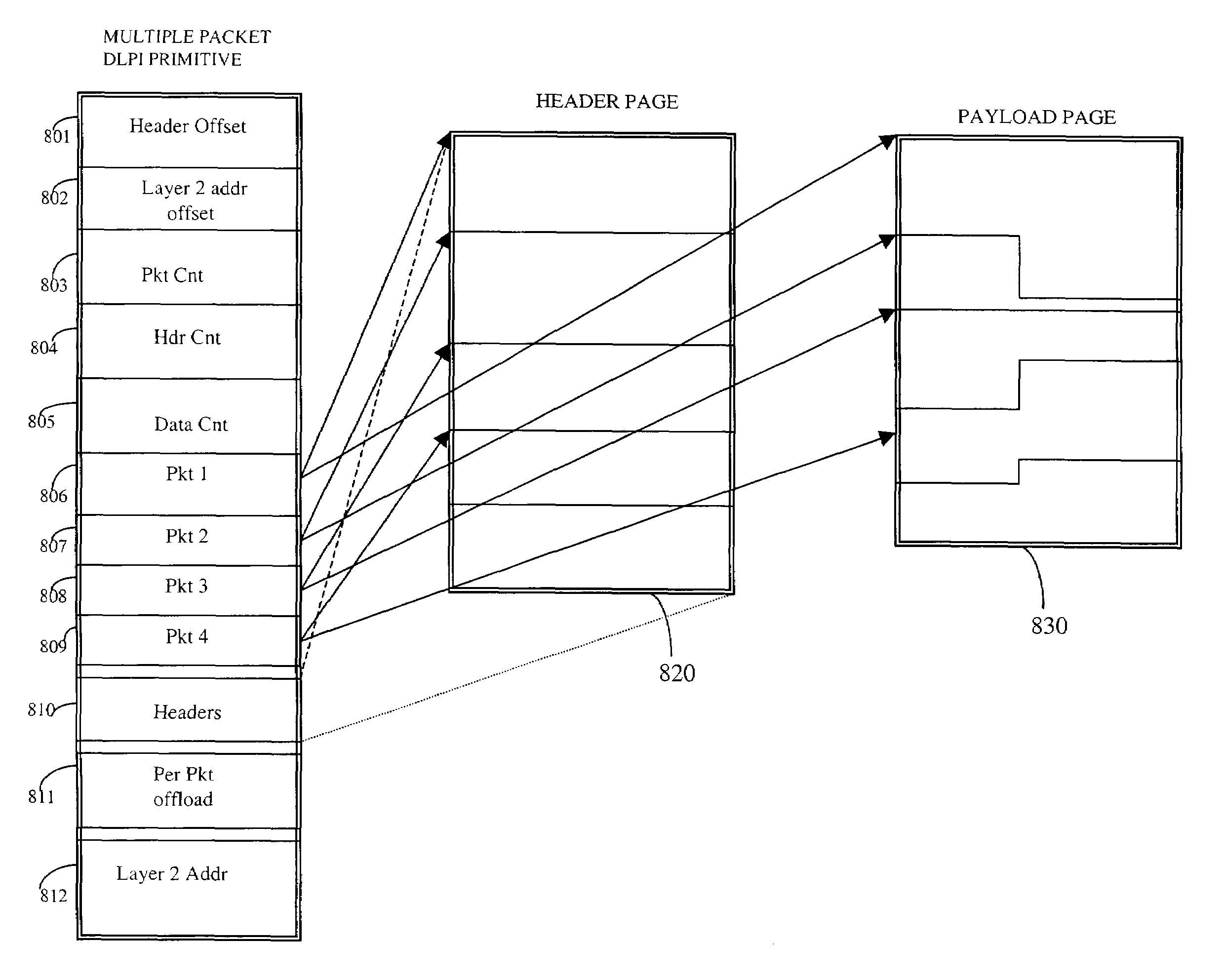
System and method for a multi-packet data link layer data transmission
ActiveUS7512128B2Fast network bandwidthWithout incurring the costly delayTime-division multiplexData switching by path configurationNetwork packetData link layer
A kernel data transfer method and system for transmitting multiple packets of data in a single block of data presented by application programs to the kernel's network subsystem for processing in accordance with data transfer parameters set by the application program. The multi-packet transmit system includes logic that allows header information of the multiple packets of data to be generated in a single buffer and appended to a second buffer containing the data packets to be transmitted through the network stack. The multi-data transmit system allows a device driver to amortize the input / output memory management related overhead across a number of packets. With some assistance from the network stack, the device driver needs to only perform the necessary IOMMU operations on two contiguous memory blocks representing the header information and the data payload of multiple packets during each transmit call.
Owner:ORACLE INT CORP
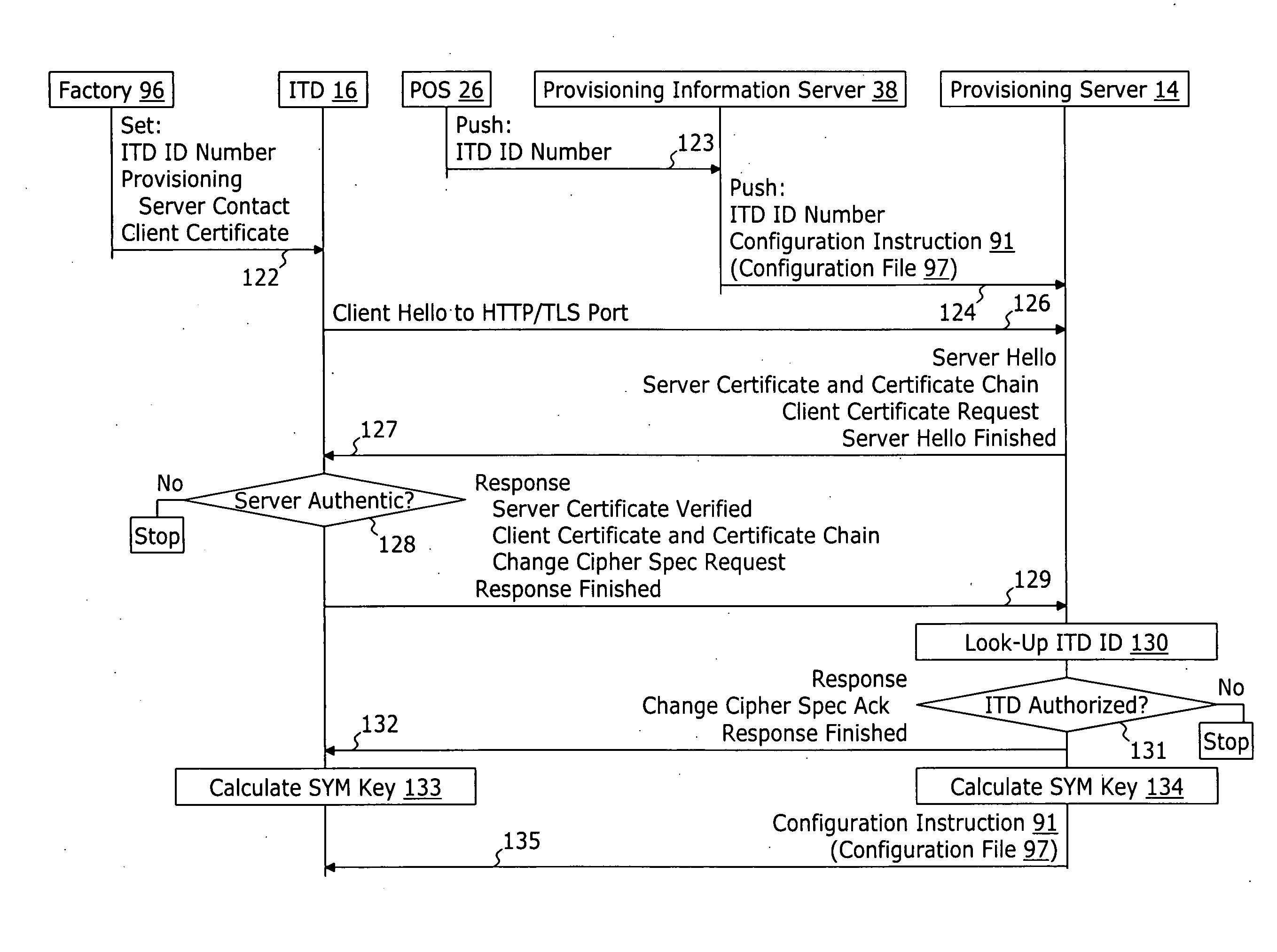
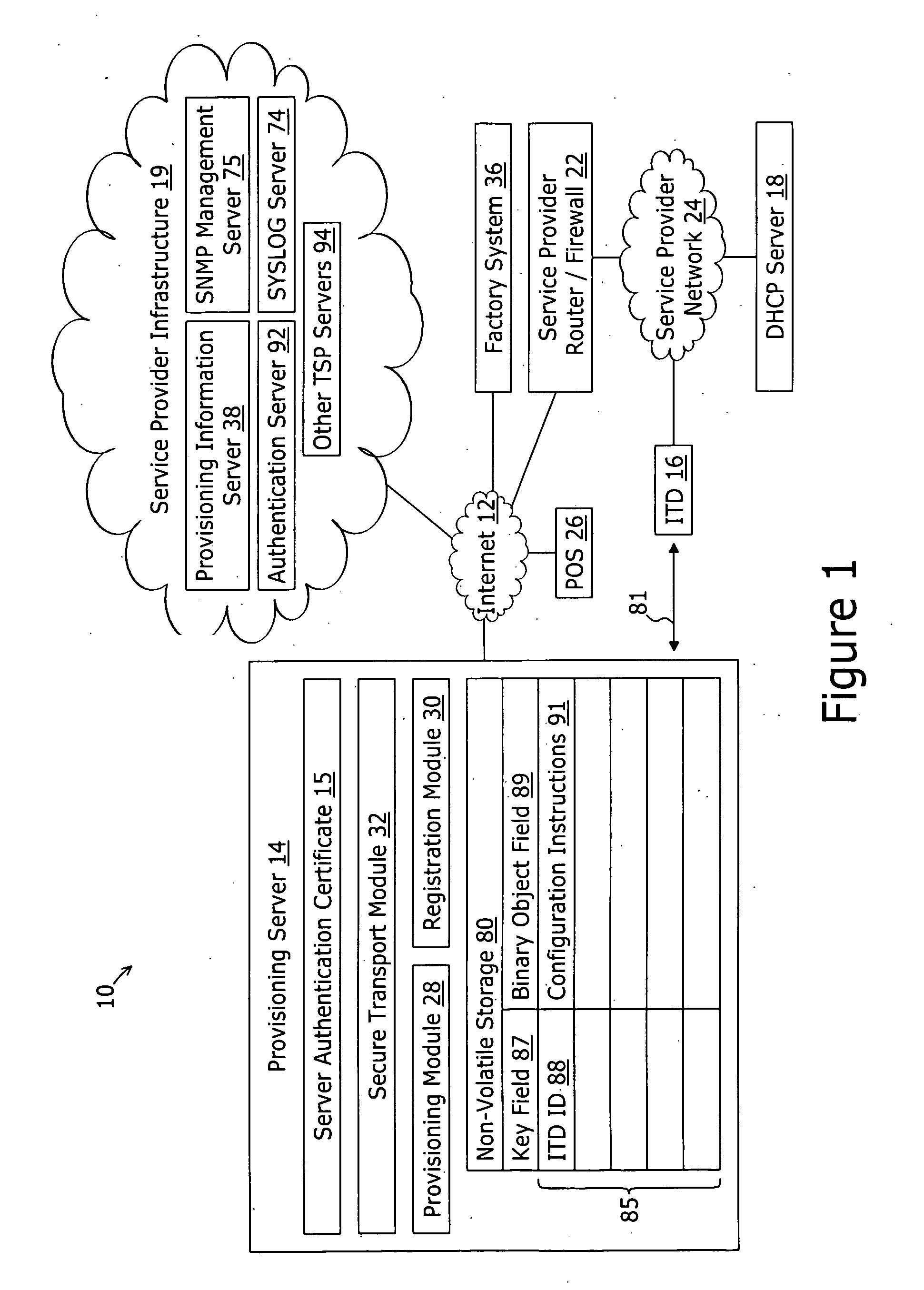
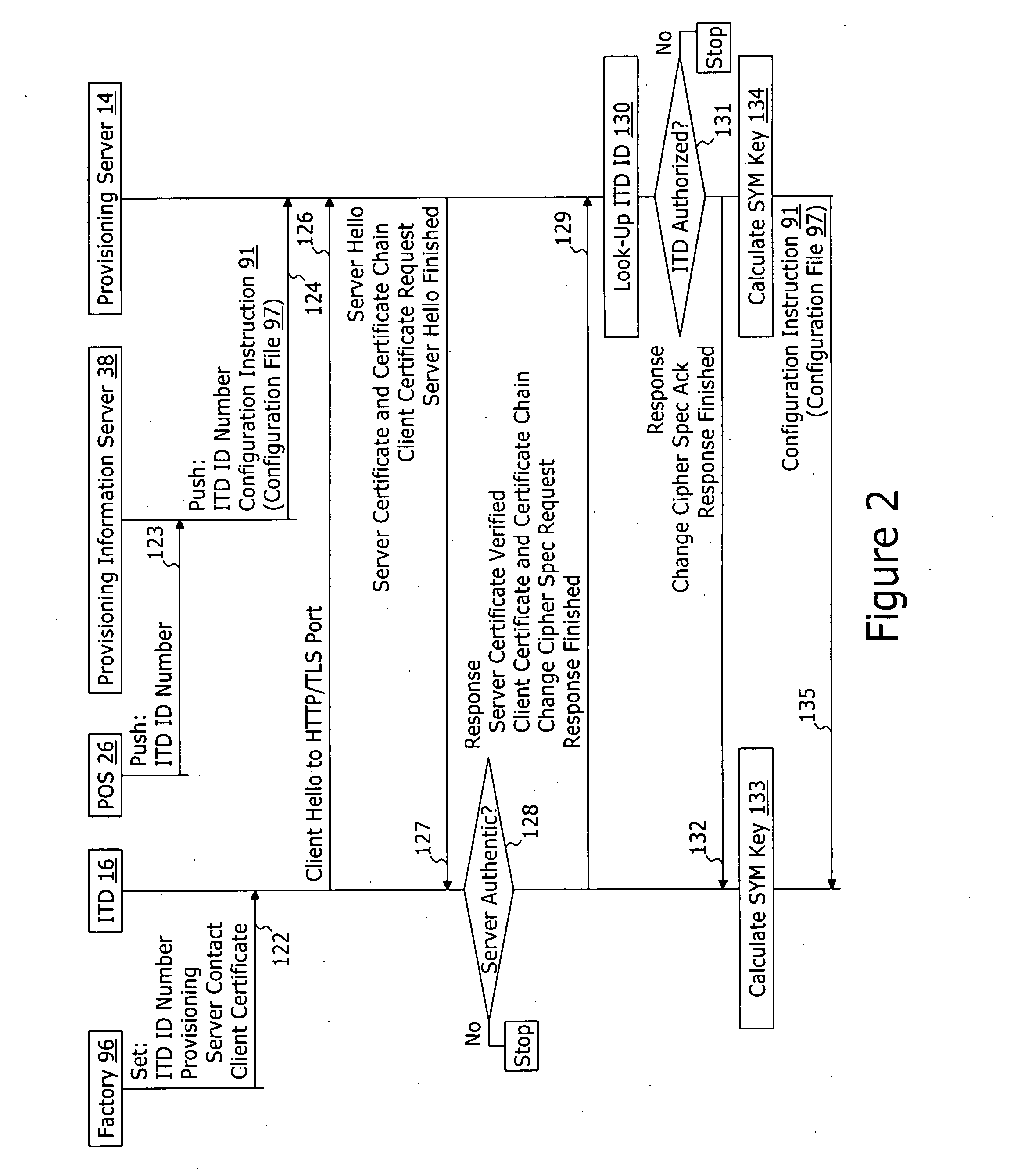
System and method for securely providing a configuration file over and open network
ActiveUS20060174018A1User identity/authority verificationUnauthorized memory use protectionDomain nameNetwork connection
A method for securely provisioning a device for operation within a service provider infrastructure over an open network comprises the device establishing physical and data link layer network connections for communication on at least a subnet of the open network and obtaining a network configuration data such as an IP address and a subnet mask from a provisioning server that responds to a network configuration broadcast request. A device establishes a secure hypertext transport protocol connection to a first provisioning server that corresponds to one of: i) and IP address and port number; and ii) a fully qualified domain name stored in a non-volatile memory of the device. After mutual authentication, the first provisioning server provides at least one of: i) a configuration file; and ii) identification of a second provisioning server and a cipher key through the secure connection. If the first provisioning server provided identification of a second provisioning server, the device establishes a transport connection to the identified second provisioning server. The second provisioning server provides an encrypted file which, when decrypted using the cipher key yields the configuration information needed by the device for operation with the service provider infrastructure.
Owner:INOMEDIA
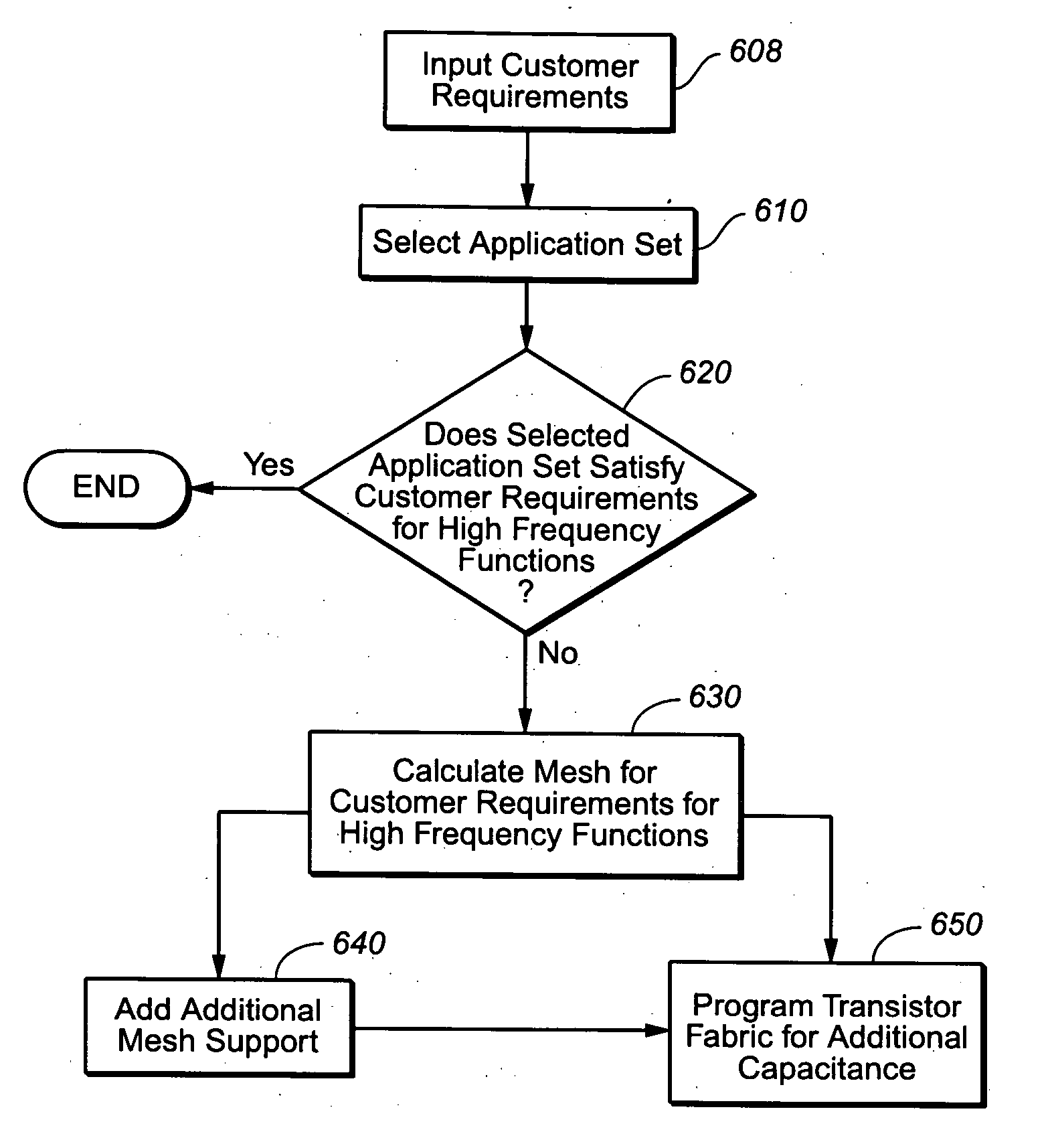
Power mesh for multiple frequency operation of semiconductor products
InactiveUS20060123376A1Decoupling capacitanceIncrease speedComputer programmed simultaneously with data introductionCAD circuit designCapacitanceTransceiver
The design of integrated circuits, i.e., semiconductor products, is made easier with a semiconductor platform having versatile power mesh that is capable of supporting simultaneous operations having different frequencies on the semiconductor product; e.g., higher frequency operations may be embedded as diffused blocks within the lower layers or may be programmed from a configurable transistor fabric above the diffused layers. Preferably the power mesh is located above the layers having the operations requiring the different frequencies, and may be fixed in an application set given to a chip designer or may be configurable by the designer her / himself. For example, to support high speed communications adjacent an embedded high speed data transceiver, the transistor fabric may be programmed as a data link layer having higher performance requirements than the rest of the integrated circuit. The data link layer may be connected to one of the localized grids of the versatile power mesh which may have an increased density and / or wider strap width of a power / ground grid. Additional decoupling capacitance can be embedded in the lower layers of the semiconductor product and / or can be programmed from the configurable transistors fabric.
Owner:AVAGO TECH INT SALES PTE LTD
Method for performing inter system handovers in mobile telecommunication system
ActiveUS6963745B2Radio/inductive link selection arrangementsWireless communicationDual modeData link layer
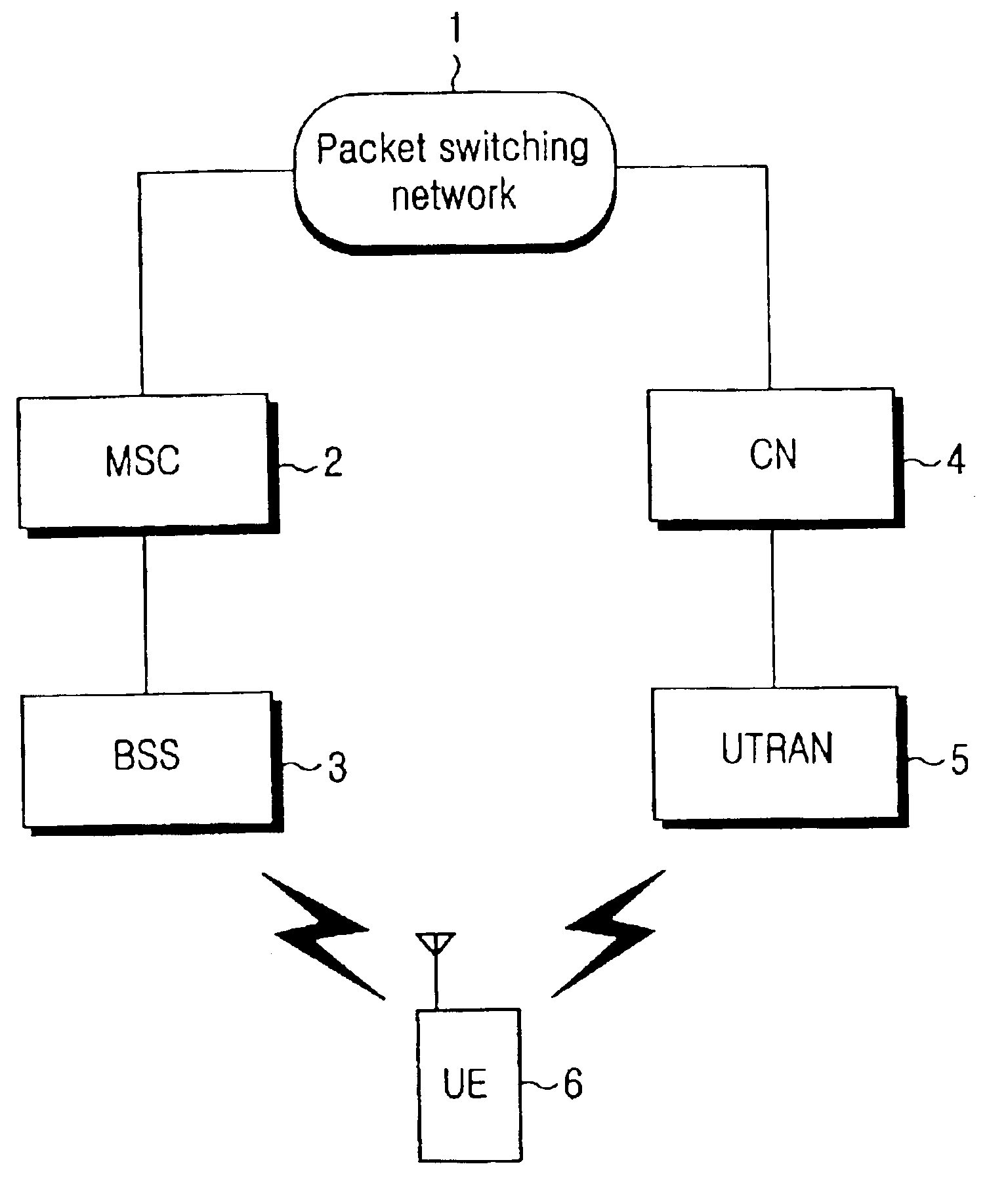
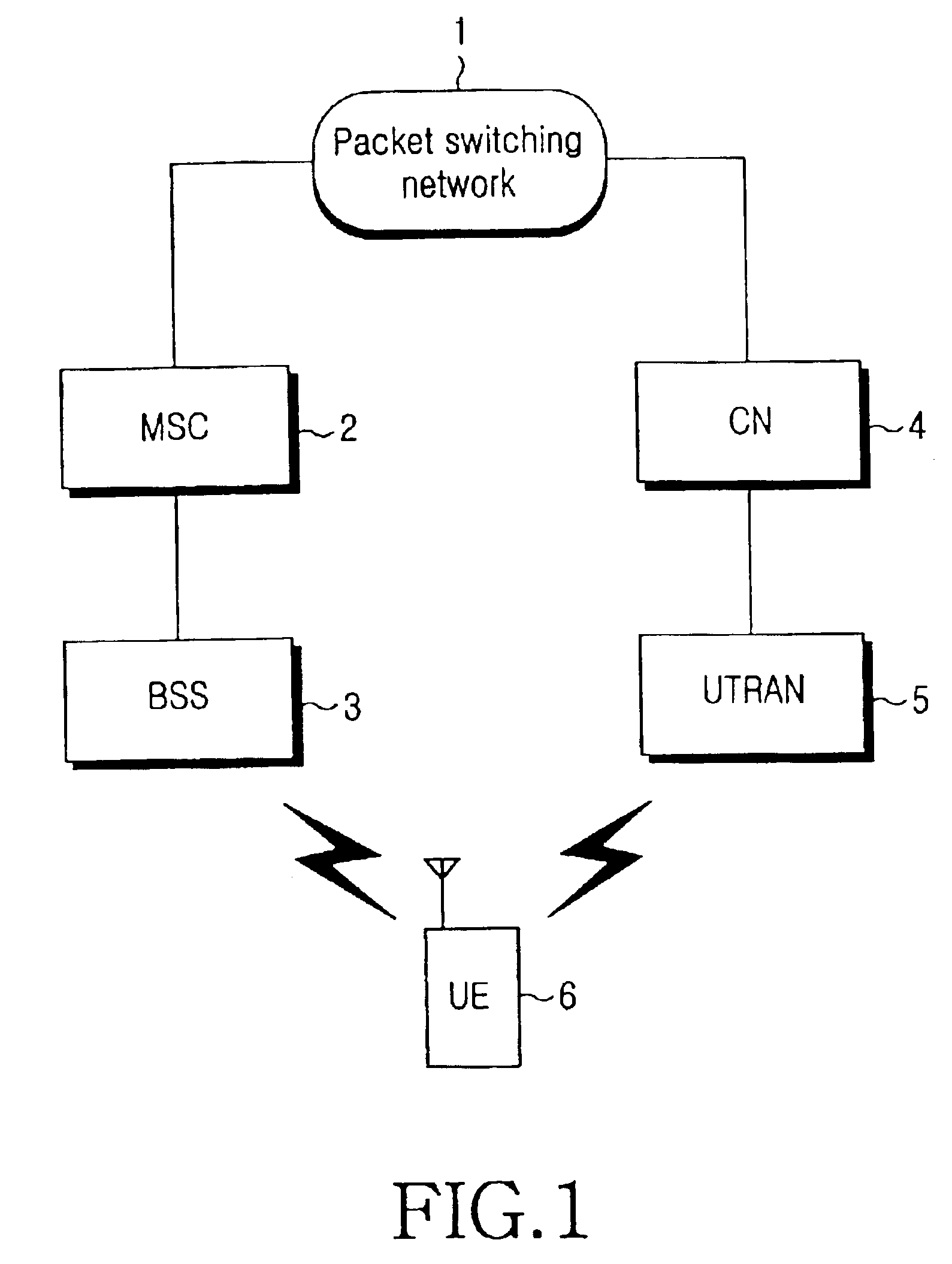
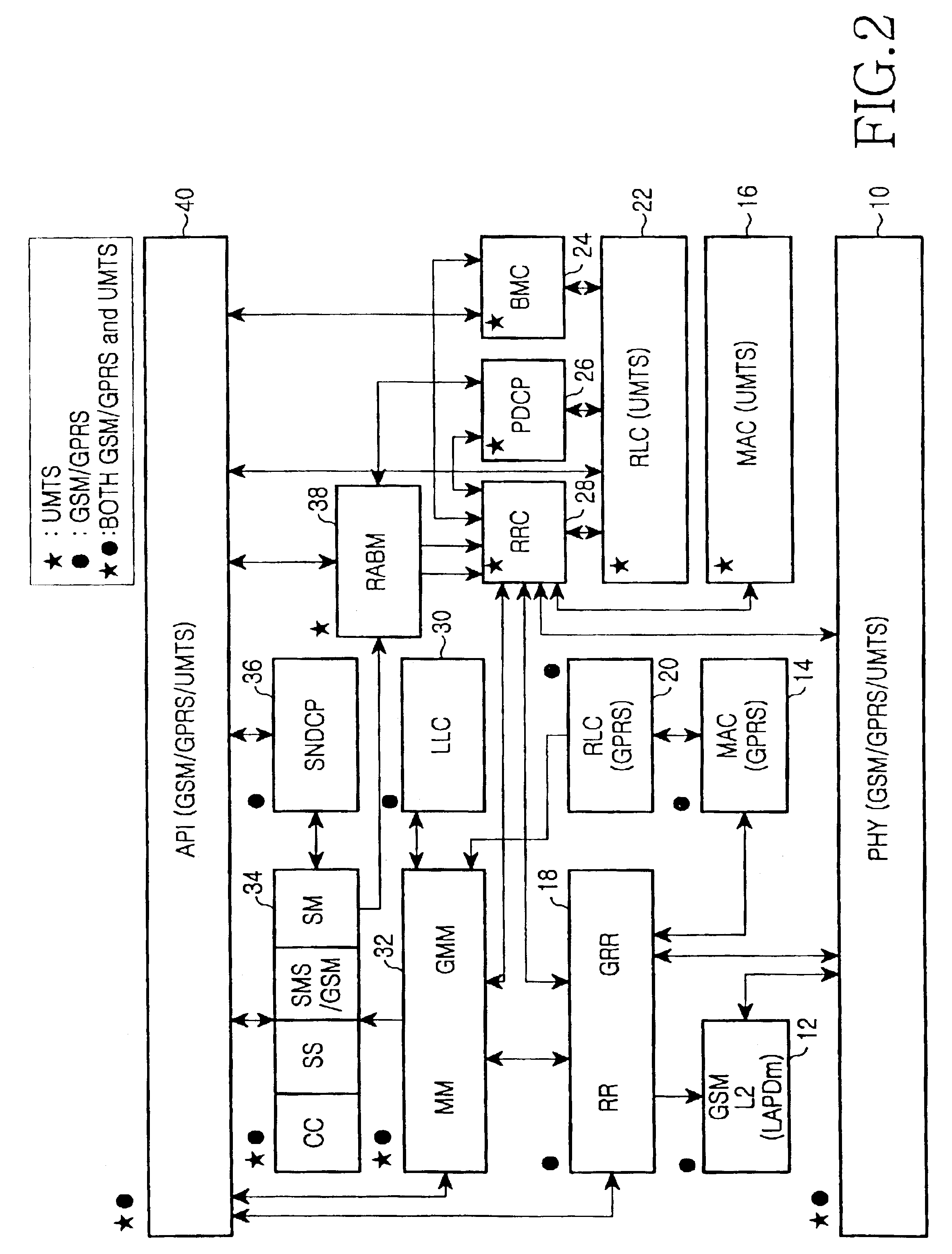
An inter system handovers in a mobile telecommunication system is performed when a dual mode user equipment (UE) covered by both GSM / GPRS network and UMTS network connects a dedicated channel and sets up a call in a BSS region where the GSM / GPRS provides coverage, and then moves to a UTRAN (UMTS Terrestrial Radio Access Network) where the UMTS provides coverage, wherein the method includes the steps of: if the dual mode UE receives an inter system handover command, i.e. from the BSS to the UTRAN, requesting GSM / GPRS data link layer to suspend a GSM / GPRS data link by a sublayer RR of GSM / GPRS network layer in the UE, requesting a GSM / GPRS physical layer to release a physical channel of the GSM / GPRS, and sending the inter system handover command to the UTRAN for authorizing a sublayer RRC of UMTS network layer in the UE to continue a call; requesting, at the RRC in the UE, a UMTS physical channel to be configured as a UMTS physical channel, and monitoring if the UMTS physical layer succeeds to have the configuration of the UMTS physical channel as requested; if the UMTS physical layer succeeds to have the configuration of the UMTS physical channel, requesting, at the RRC in the UE, a UMTS data link layer to configure a UMTS data link, and conveying information to the UTRAN through a UMTS channel that the handover between systems from the BSS to the UTRAN has been successfully performed; and sending, at the RRC, a GSM / GPRS resource release message to RR / GRR, thereby resetting the GSM / GPRS physical layer and the GSM / GPRS data link layer.
Owner:SAMSUNG ELECTRONICS CO LTD
System and Method for Optical Layer Management in Optical Modules and Remote Control of Optical Modules
ActiveUS20120275784A1Low costMultiplex system selection arrangementsTime-division optical multiplex systemsTransceiverNetwork connection
A system and method for managing the optical layer network data communications of an optical fiber data network by an optical transceiver module is disclosed. The management of the optical layer network data communications comprising data link layer functions or layer 2 functions in an OSI model. Benefits include reduction in reduced cost of network deployments from consolidation of network equipment, such as switches, and reduction in power consumed as well as enabling point-to-multipoint network connections from previously only point-to-point network connection.
Owner:SOTO ALEXANDER I +1
Vehicle failure detection method and device based on smart phone
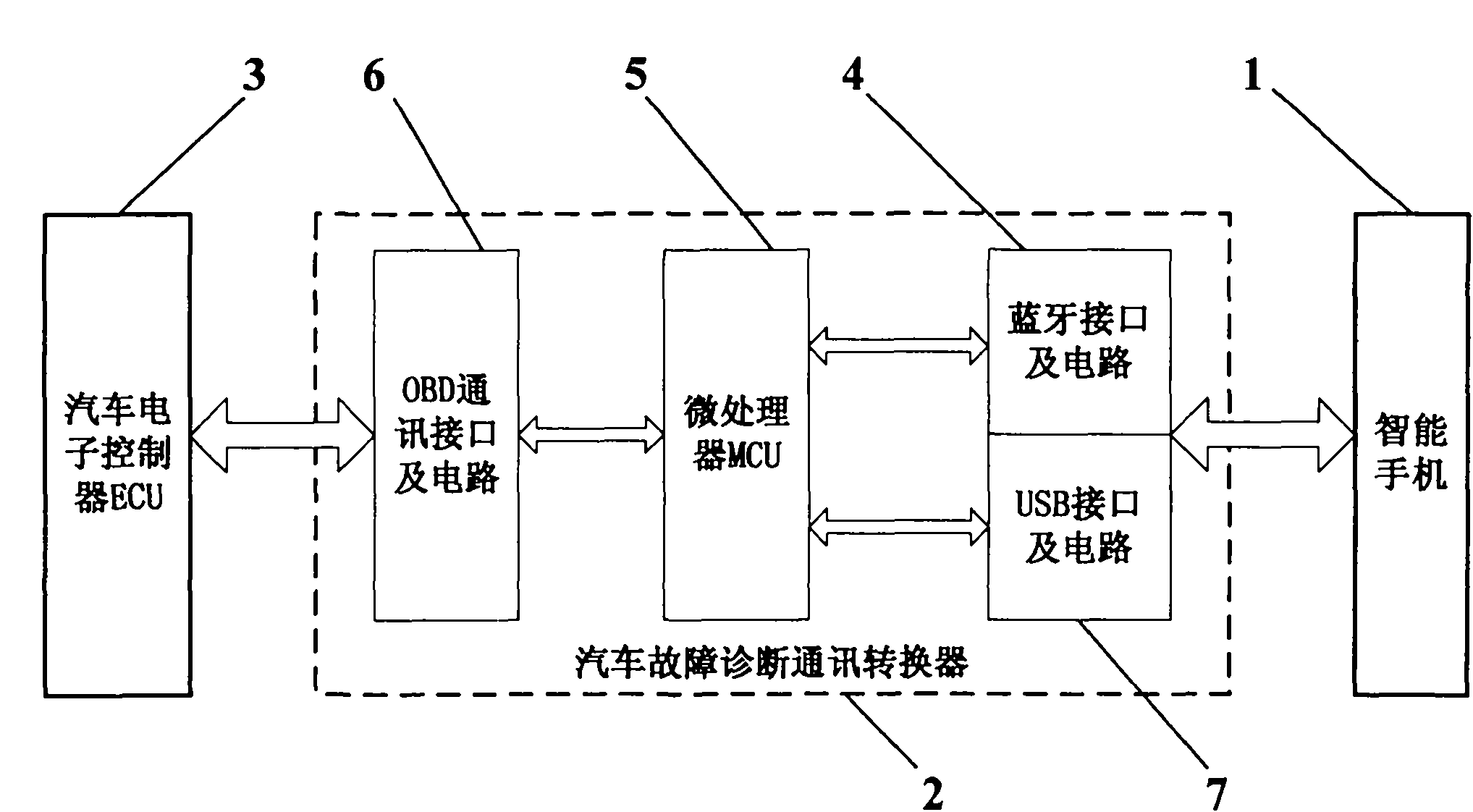
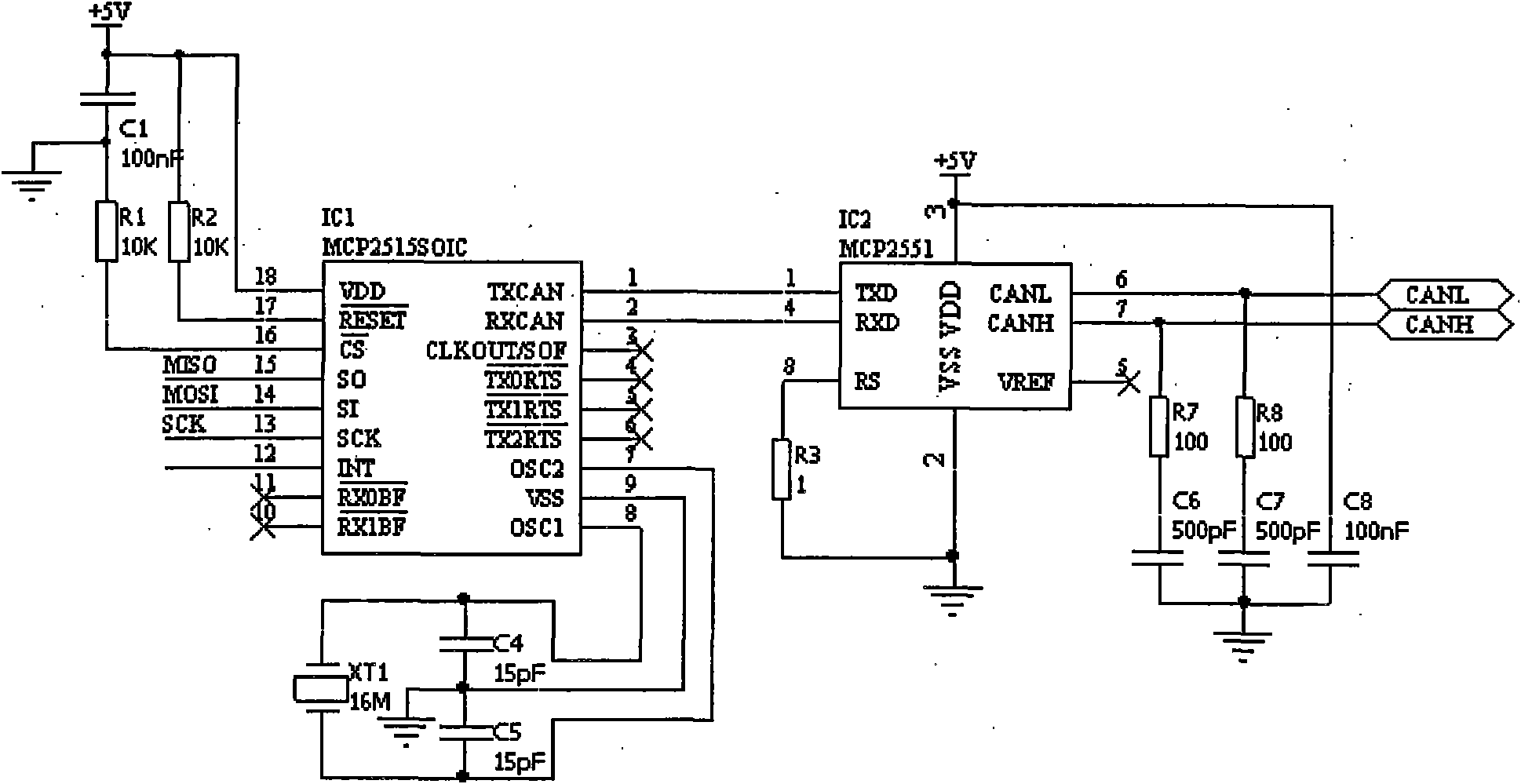
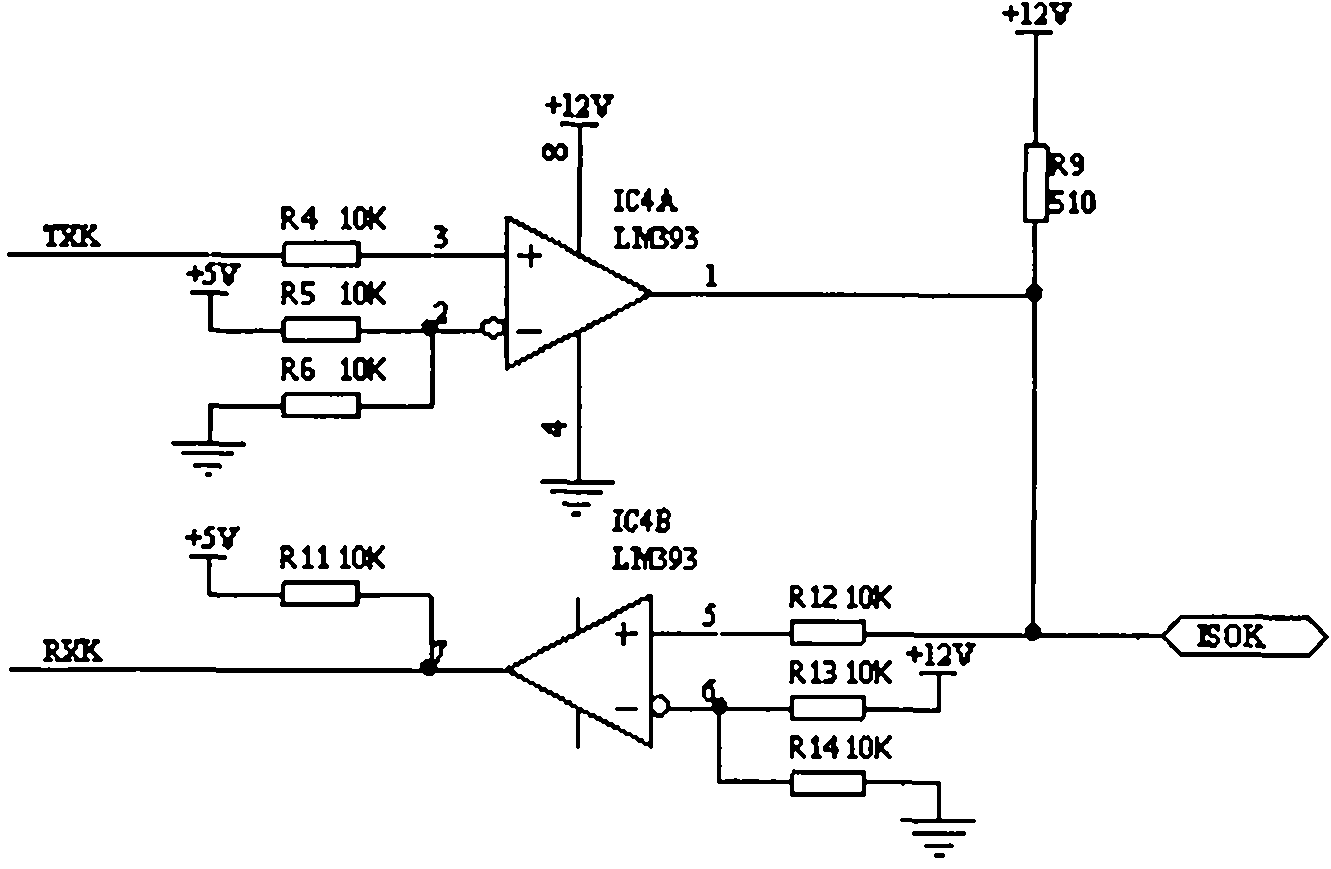
InactiveCN101929921AReduce volumeEasy to carryVehicle testingSubstation equipmentVehicle detectionEngineering
The invention discloses vehicle failure detection method and device, relating to a method and a device for realizing vehicle failure detection by using a smart phone. Failure detection software operating on the smart phone proposes a vehicle failure detection request, and the detection request is sent to a vehicle failure detection communication converter through a Bluetooth interface or a USB interface of the smart phone. The vehicle failure detection communication converter is directly connected with a vehicle detection port, and is used for converting the detection request from the smart phone into corresponding signals according to the requirements for application layers, data link layers, physical layers and the like specified by ISO 15031-5 and sending the corresponding signals to a vehicle electronic control unit (ECU) so as to realize vehicle failure detection. Meanwhile, the vehicle failure detection communication converter returns the feedback information of the vehicle electronic control unit (ECU) to the smart phone, and the feedback information is displayed by the smart phone.
Owner:钟桢
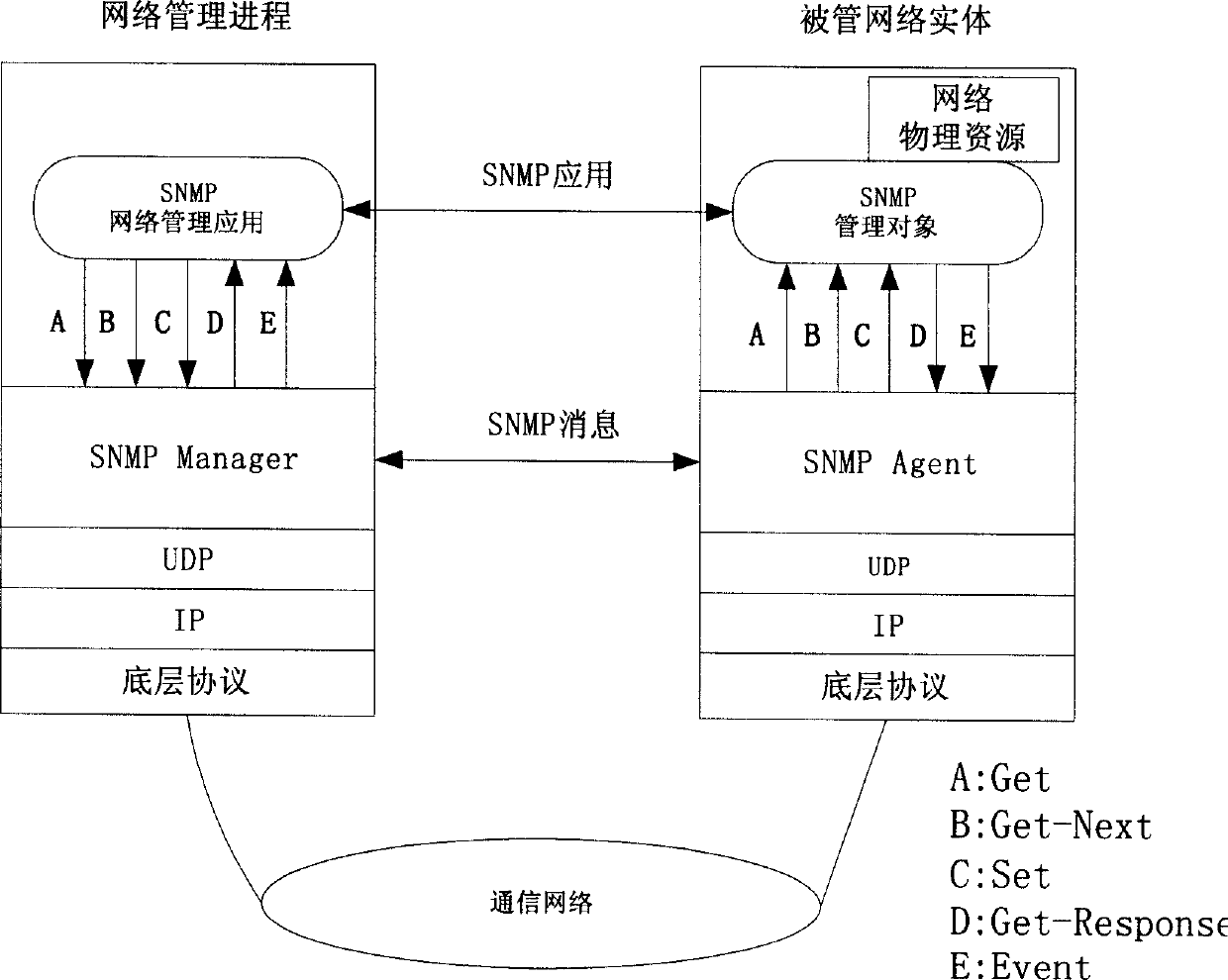
IP network topology discovering method based on SNMP
InactiveCN1756189ADiscover connectionsData switching by path configurationInformation repositoryManagement information base
Disclosed a method for automatically discovering the physical distribution of network and the connection relationship of IP network topology, based on the SNMP protocol, comprises following steps: constructing the condition of operating the SNMP network management; arranging a management information base on every network node of target network; the network management process via the application layer visits the SNMP management information base; the network management applies the information transmitted to the network management process to reach the managed network entity via the substratum protocol; discovering the topology of network layer; and discovering the topology of data chain circuit layer. In the network management, the inventive method can detect the topological structure of network layer and the data chain circuit layer, attain and maintain the existence information and connection relation information of network node, and protract the topological chart of total network. And the network manager can position the network breakage via the information of topological structure and discover the network bottleneck for optimizing the whole network.
Owner:BEIHANG UNIV
Frame transmission method in a multi-hop connection using a MAC address of data link layer identifier
InactiveUS20060256741A1Traffic loadReduce overheadTransmission control/equalisingNetwork topologiesCommunications systemData link layer
A frame transmission method is provided in which a multi-hop connection is established between access points and wireless terminals connected to the access points by using only a MAC address, the identifier of the data link layer (Layer 2). Various control frames are transmitted between access points to acquire the network topology. Over the unicast / broadcast communication system, data may be relayed and transferred in the form of frames from a wireless terminal connected to an access point to another wireless terminal via the optimum multi-hop path.
Owner:OKI ELECTRIC IND CO LTD
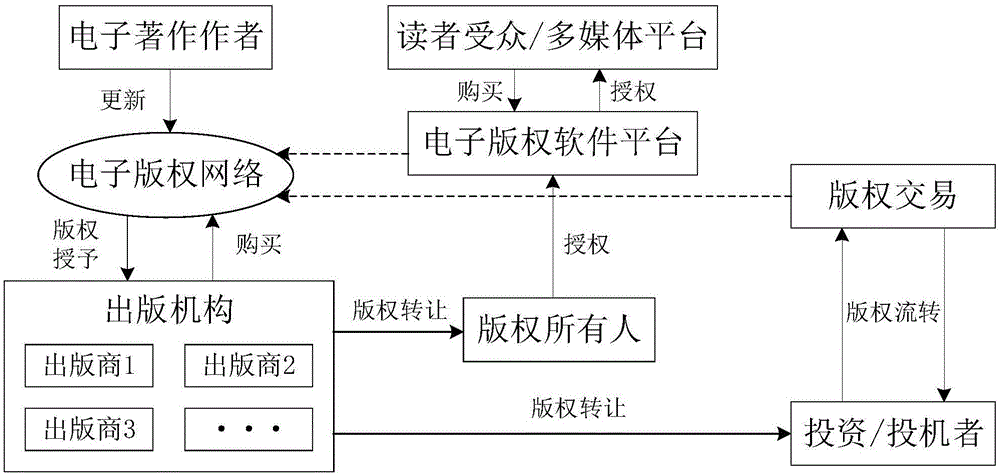
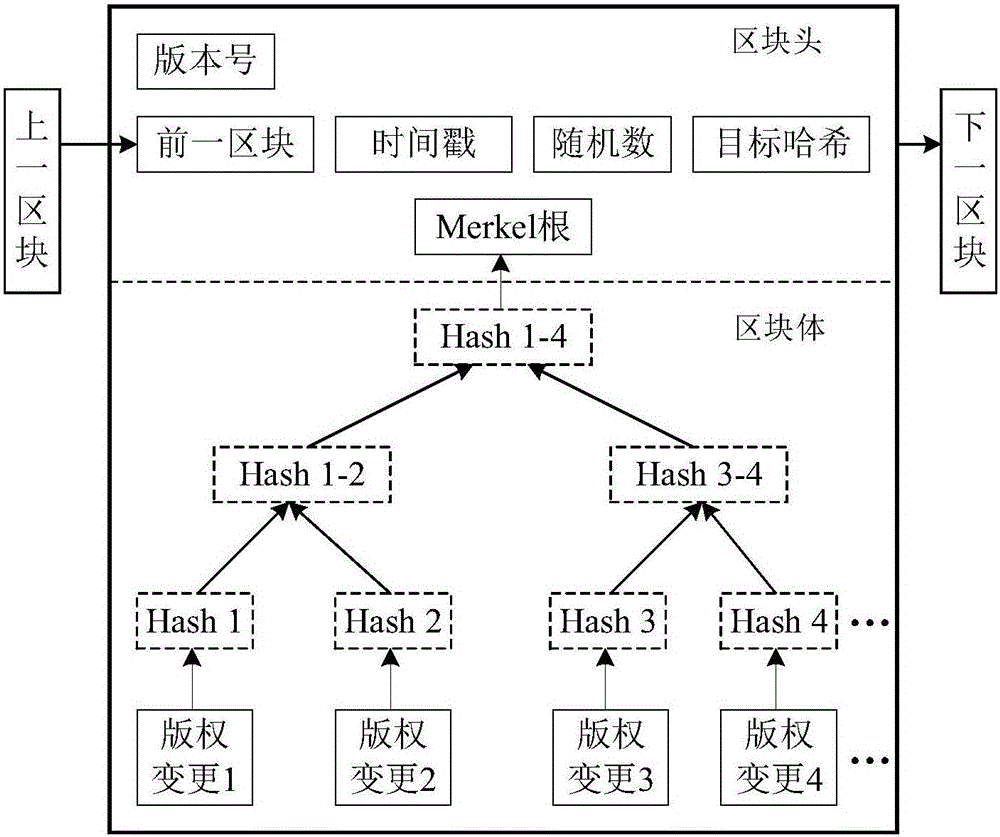
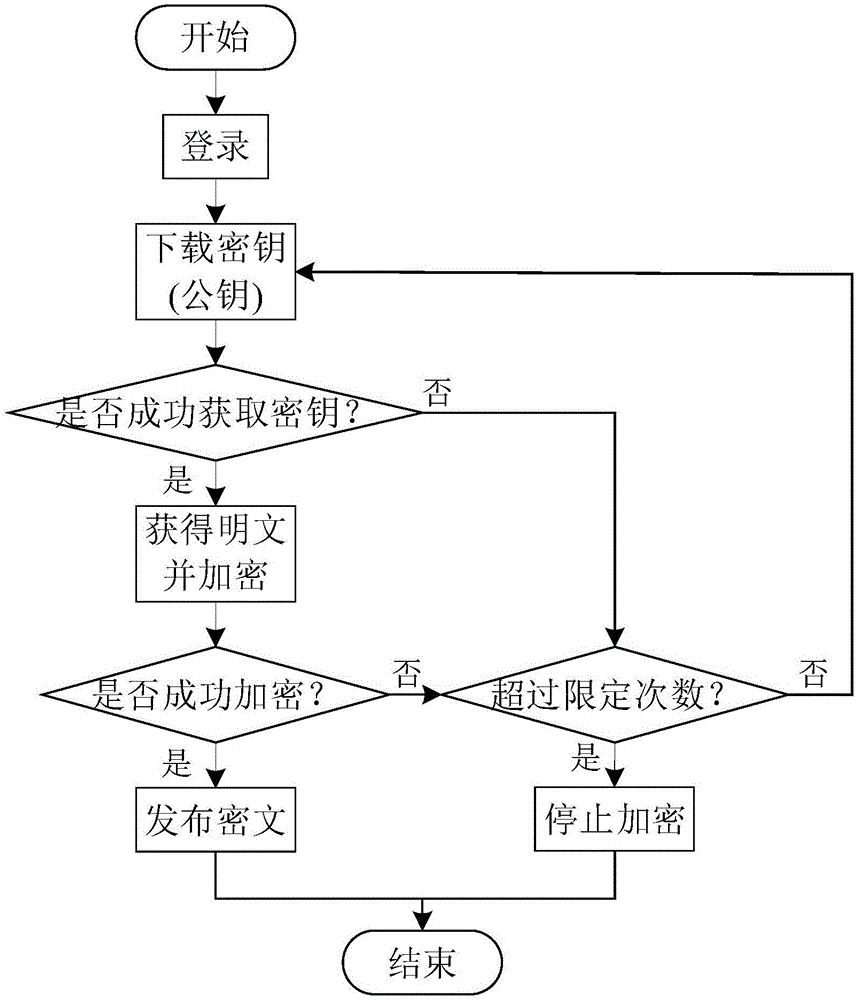
Block chain based electronic copyright protection method
InactiveCN106250721AEffective circulationStrengthen supervisionProgram/content distribution protectionPasswordData operations
The invention discloses a block chain-based electronic copyright protection method, which utilizes a brand-new, decentralized, distributed architecture called block chain and gradually emerging with digital encrypted currencies such as bitcoins. Electronic copyright protection for data calculation methods. The blockchain model usually includes a data layer, a network layer, a consensus layer, etc., which are respectively responsible for completing the tasks of time-stamped data encapsulation, distributed networking propagation mechanism, and consensus algorithm of distributed nodes. At the same time, the application of elliptic curve encryption (ECC), an asymmetric encryption algorithm in the blockchain, requires the use of two different public and private key ciphers for encryption and decryption, which can greatly enhance the security of the copyright database sex. The complete model architecture of the block chain of the present invention makes it have very broad application prospects in the field of electronic copyright protection.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Method and system for congestion marking
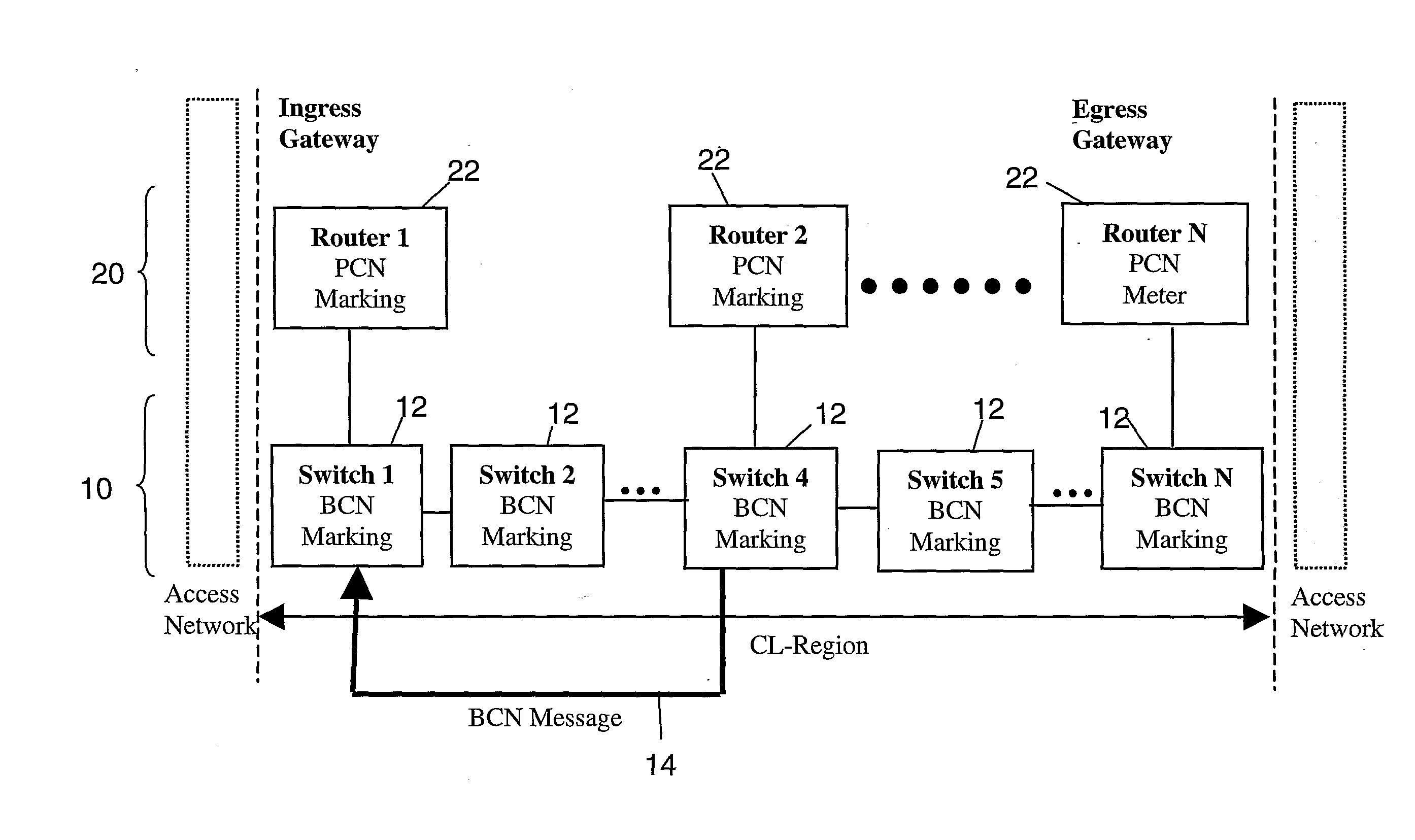
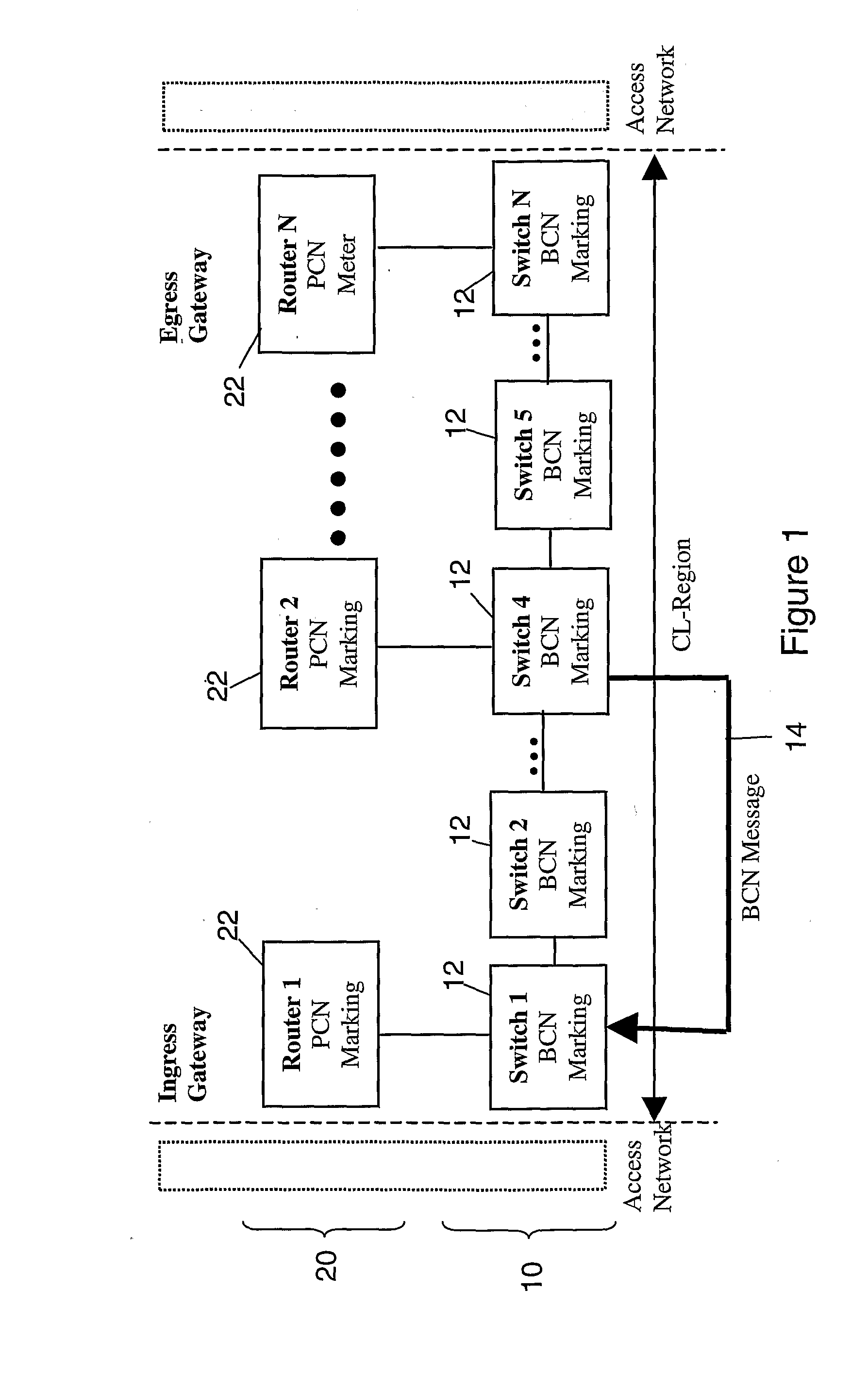
InactiveUS20090268614A1Error preventionFrequency-division multiplex detailsData link layerDistributed computing
The present invention provides a method and system wherein congestion information is taken from a lower level in the protocol stack and used for congestion marking in a higher layer. In particular, the method and system of the invention from a first aspect provide for congestion information in the lower layer to be generated downstream at a congested node, and to be fed back upstream to a source node. The source node then passes the congestion information, or information derived therefrom, up to the corresponding network element responsible for higher layer functions in the protocol stack, where higher level congestion marking can then be performed in dependence on the received lower level congestion information. Thus, congestion information from the lower layer which can typically be generated earlier before significant congestion occurs can be used in higher layer congestion control functions. Preferably the lower layer is the data link layer, and the higher layer is the network layer.
Owner:BRITISH TELECOMM PLC
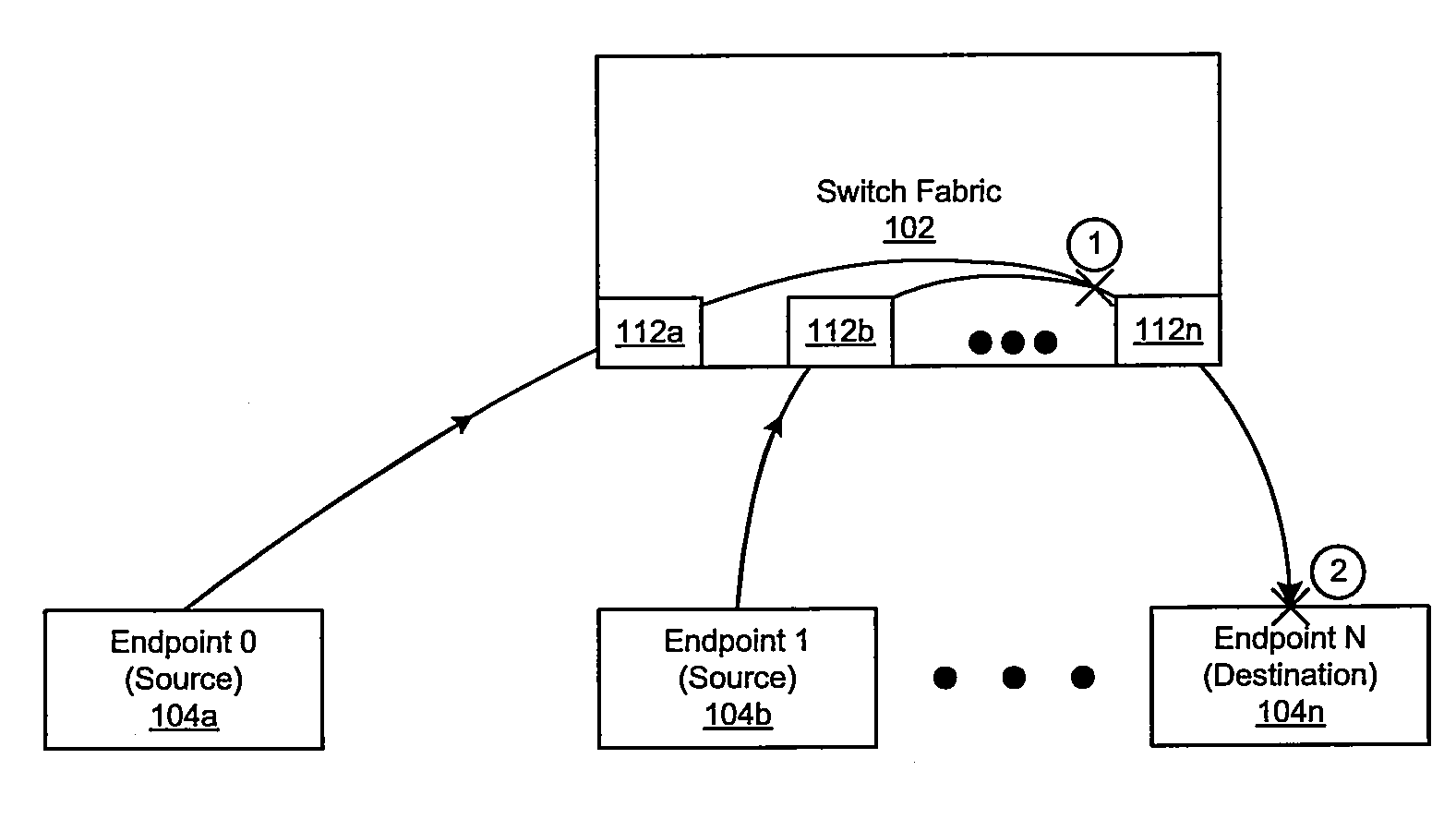
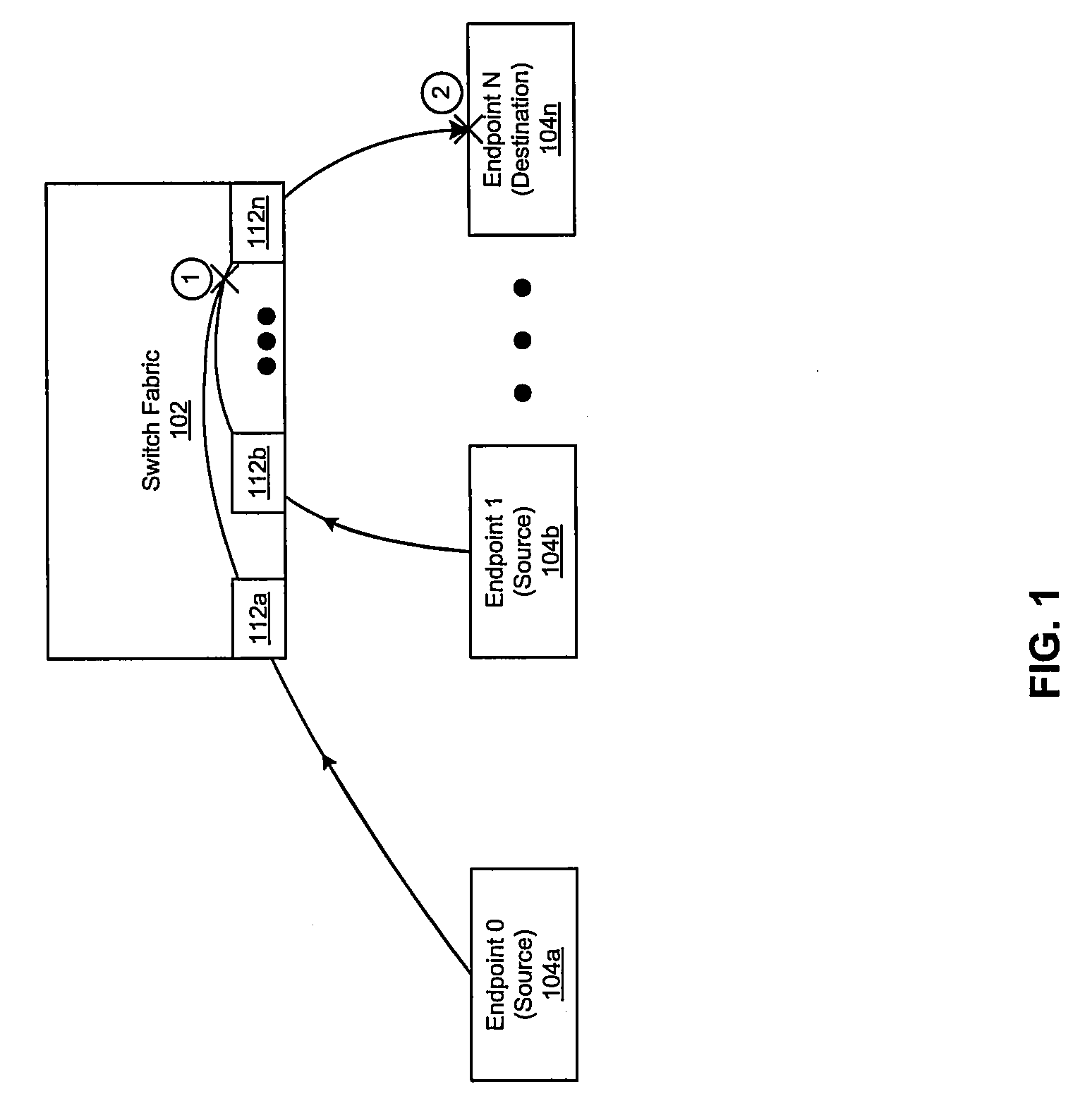
Switch fabric end-to-end congestion avoidance mechanism
Aspects of a switch fabric end-to-end congestion avoidance mechanism are presented. Aspects of a system for end-to-end congestion avoidance in a switch fabric may include at least one circuit that enables reception of a congestion notification message that specifies a traffic flow identifier. The circuitry may enable increase or decrease of a current rate for transmission of data link layer (DLL) protocol data units (PDU) associated with the specified traffic flow identifier as a response to the reception of the congestion notification message.
Owner:AVAGO TECH INT SALES PTE LTD
Code generator tool for building software applications with reusable components
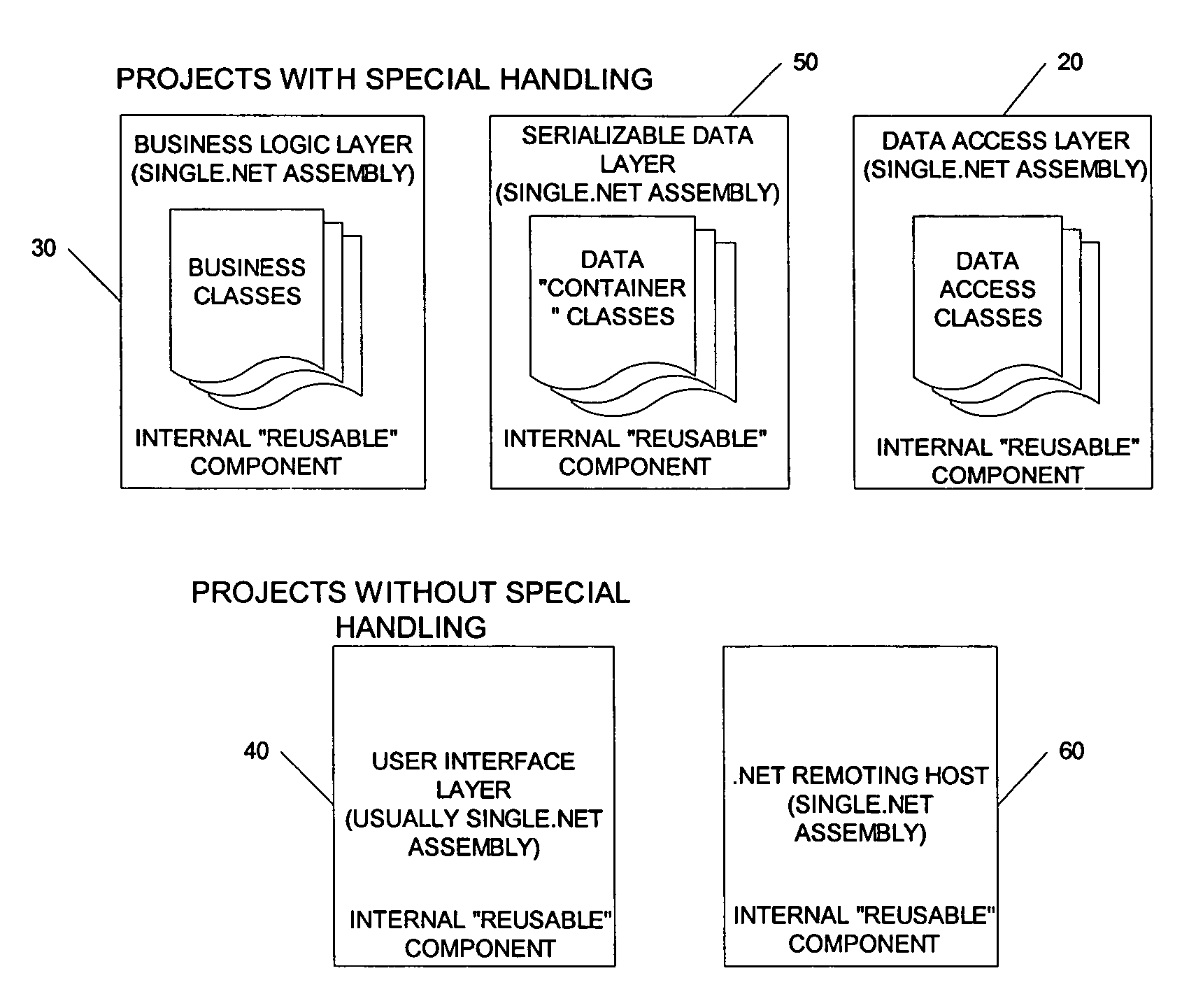
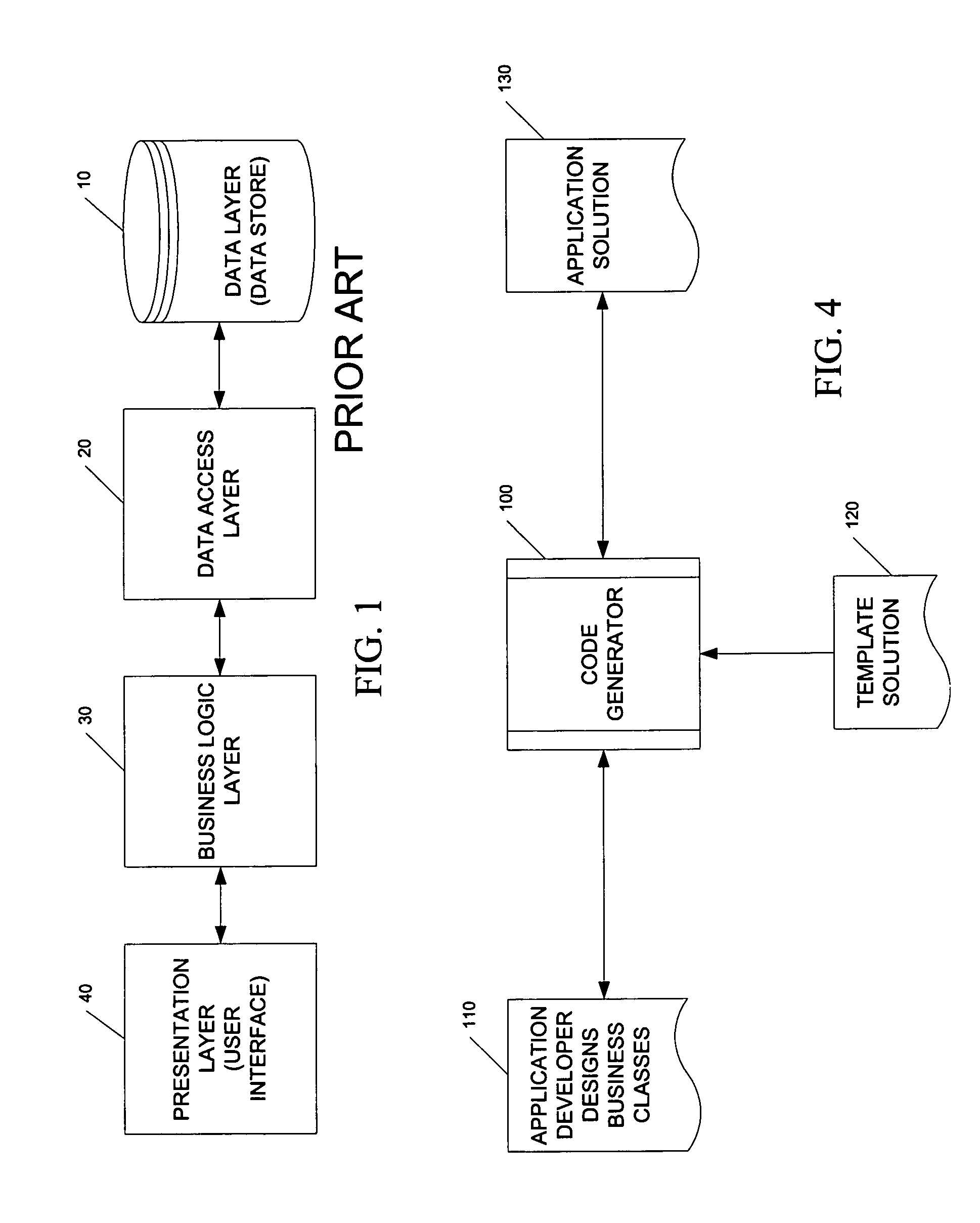
InactiveUS7761848B1Eliminate timeEliminate resourceDigital data processing detailsMultiple digital computer combinationsData setData access
A method and computer program product for building a multiple layer object-oriented software application with reusable components. The method includes the steps of creating business classes containing business logic for the software application; reading templates utilizing reusable components from a template solution file; and generating programming code for the software application based on the created business classes and selected template. The multiple layers include a data layer, a data access layer, a business logic layer and a user interface layer with executable logic for each layer placed into a corresponding assembly data structure. Security tokens are required to access the classes and methods in either the business logic assembly or data access assembly. A serializable data assembly includes container classes that are used to pass data between the business logic layer and data access layer when a dataset or data table is not appropriate. A code generator user interface enables an application developer to define a namespace, a deploy directory name, a database type, an application type, a target source code directory, and a plurality of class specifications and search criteria.
Owner:OPEN INVENTION NEWTORK LLC
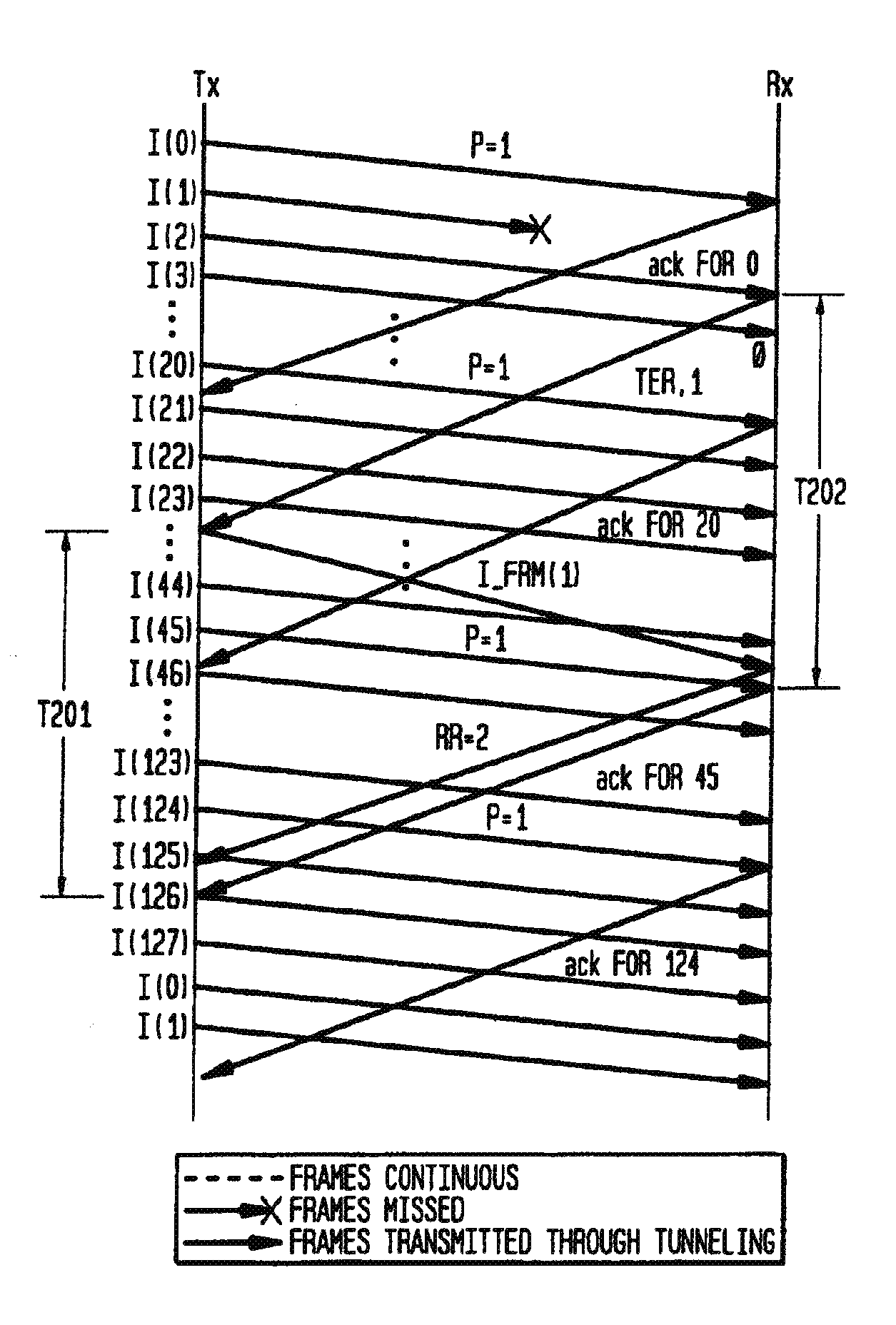
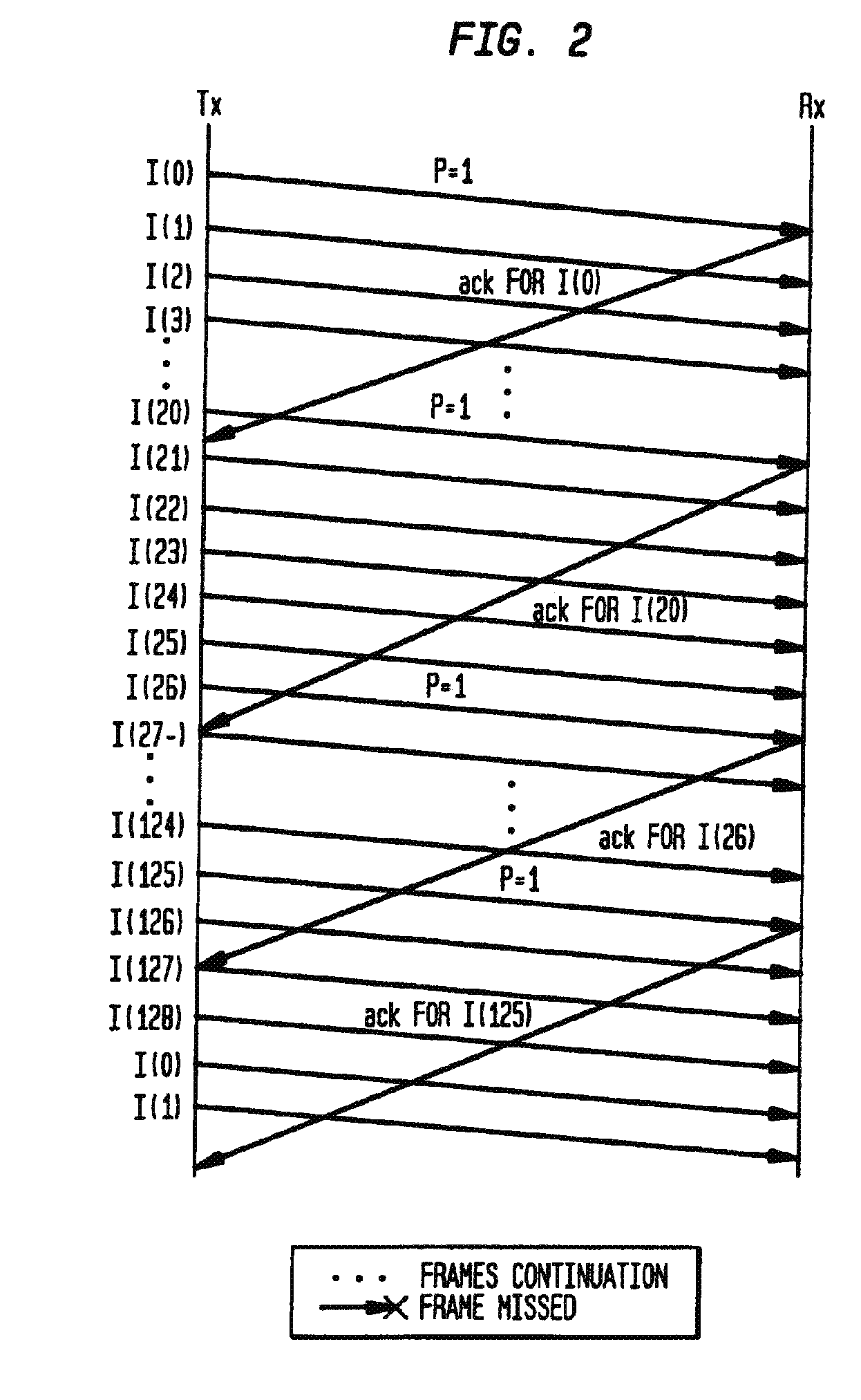
Data Link Layer Tunneling Technique for High-Speed Data in a Noisy Wireless Environment
InactiveUS20080235553A1Improve throughputAvoid large gapsError prevention/detection by using return channelFrequency-division multiplex detailsCommunications systemData link layer
In accordance with the invention, a data link layer tunneling technique is disclosed for improving the throughput of high speed data in noisy wireless environments. The method for recovering lost frames transmitted between a packet sending unit and a packet receiving unit in a data communications system, and generally comprises the steps of: (a) identifying a failure to successfully receive a missed frame at the packet receiving unit; (b) establishing a logical tunnel channel at the packet receiving unit to acknowledge the next successfully received frame; (c) starting a first timer at the packet receiving unit; (c) upon receiving a tunnel establishment request from the packet receiving unit, the packet sending unit resending the missed frame on the logical tunnel channel and starting a second timer; and (d) the packet sending unit resending the missed frame a specified number of times until receiving an acknowledgement from the packet receiving unit.
Owner:AT&T MOBILITY II LLC
Bit error resilience for an internet protocol stack
ActiveUS20020071432A1Accurate protectionWithout seriously degrading application qualityError preventionTransmission systemsInternet protocol suitePacket loss
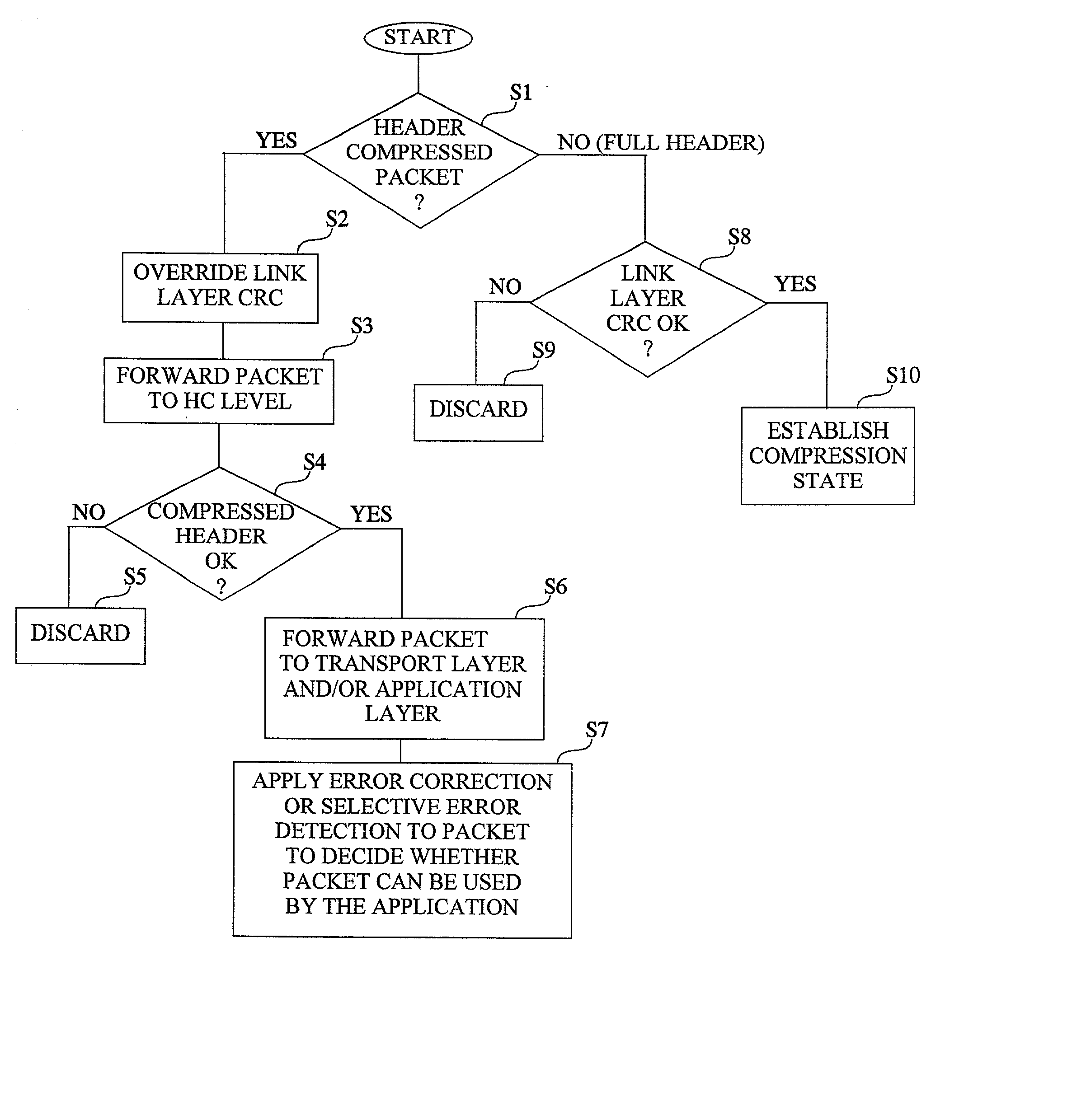
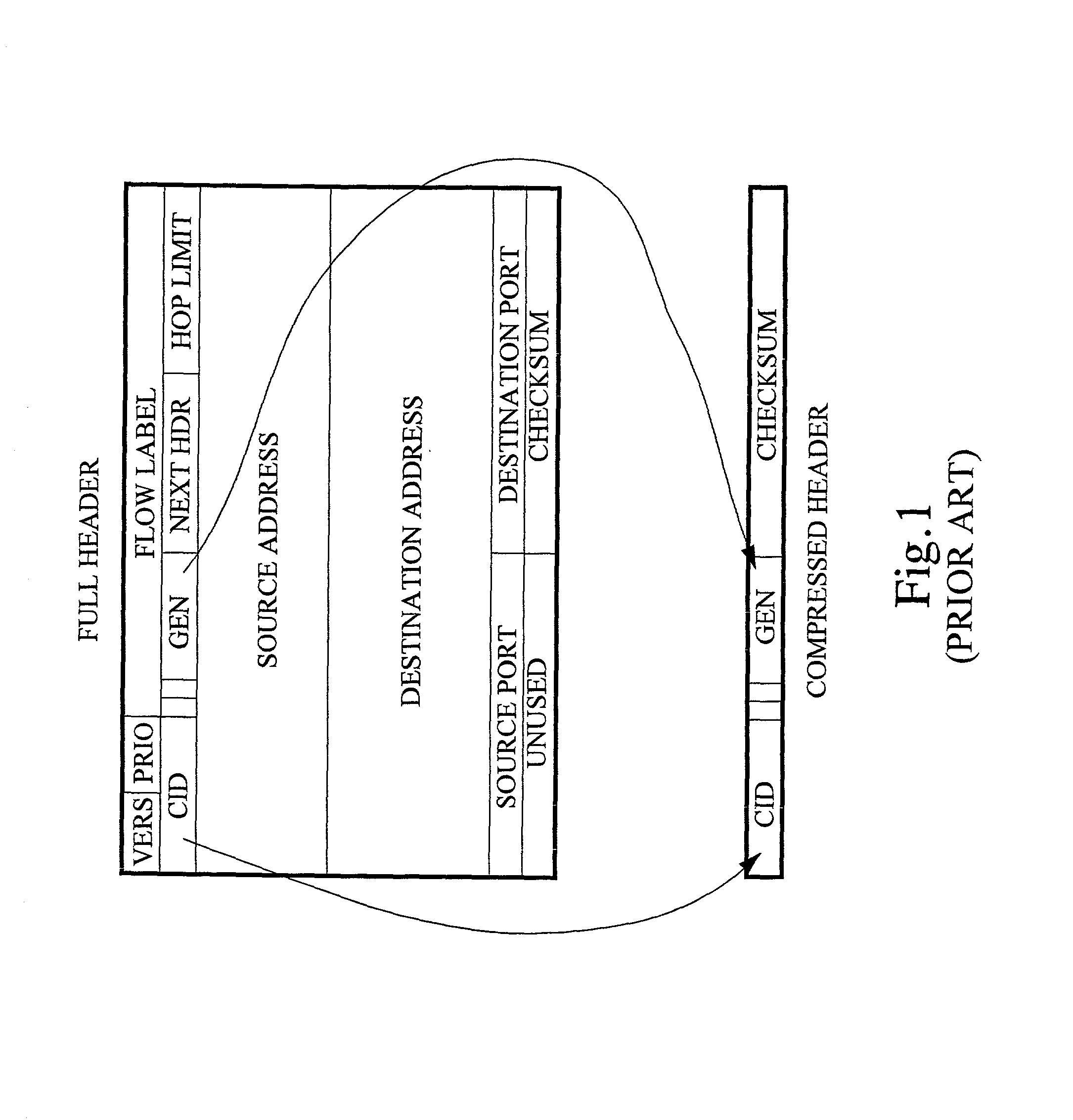
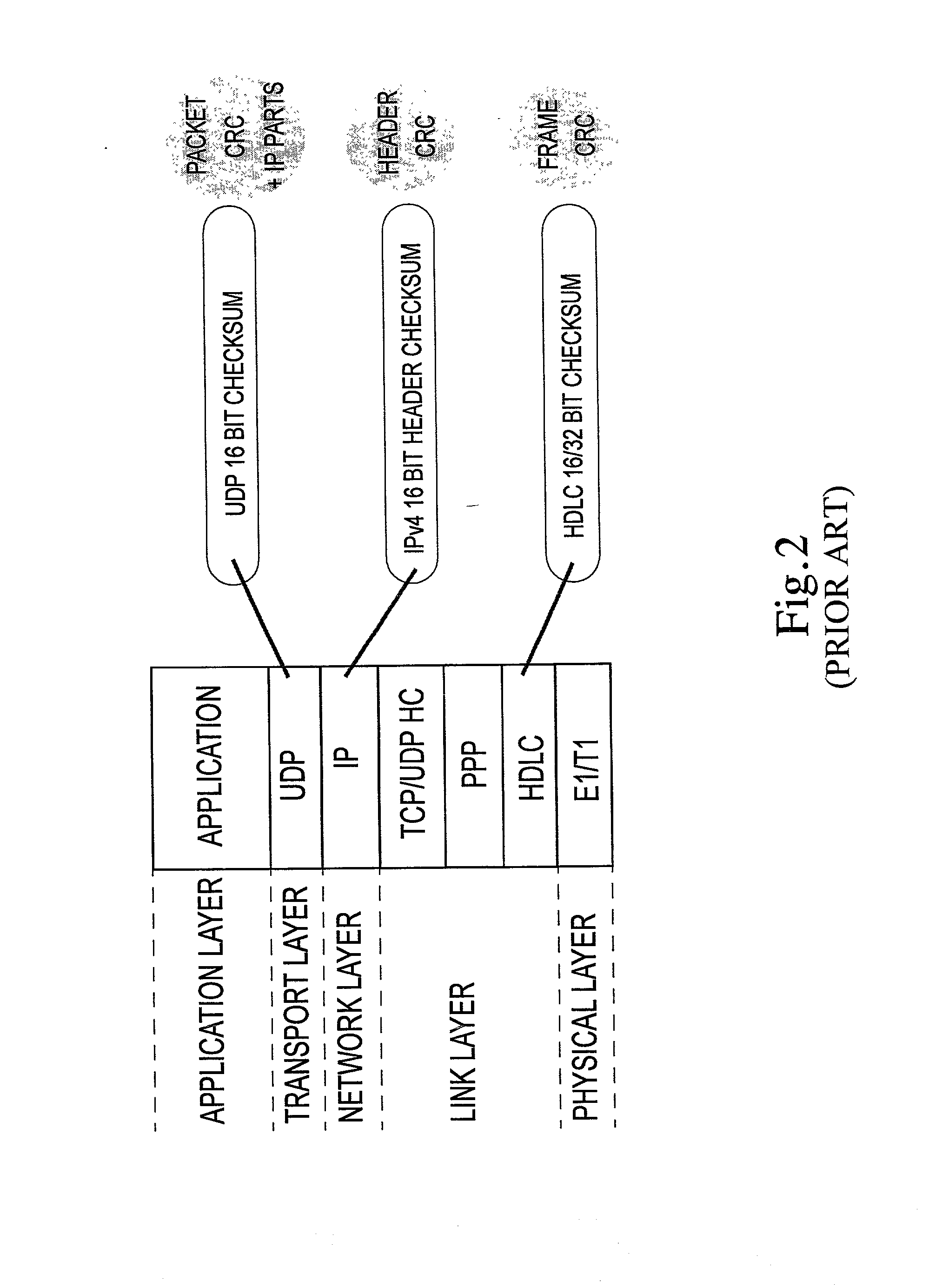
The invention concerns the bit error resilience of an IP protocol stack based on a secure link layer, in which packet flows are header compressed according to a suitable header compression standard. According to the invention, by analyzing each packet at the link layer it can be determined whether the packet is a full header packet, in which case the link layer checksum evaluation is used as normal for discarding faulty full header packets, or a header compressed packet in which case the link layer checksum evaluation is ignored and the packet is propagated upwards in the protocol stack. This solution not only opens up for more intelligent higher-level handling of faulty header compressed packets, but also solves the problem of properly protecting full header packets at the link layer. In order to compensate for ignoring the link layer checksum evaluation for header compressed packets, header protection is introduced at the header compression level of the link layer by using one or more local checksums. The invention is particularly applicable to delay-sensitive real-time data such as compressed voice or video.
Owner:TELEFON AB LM ERICSSON (PUBL)
System, Method and Apparatus for Providing Security in an IP-Based End User Device
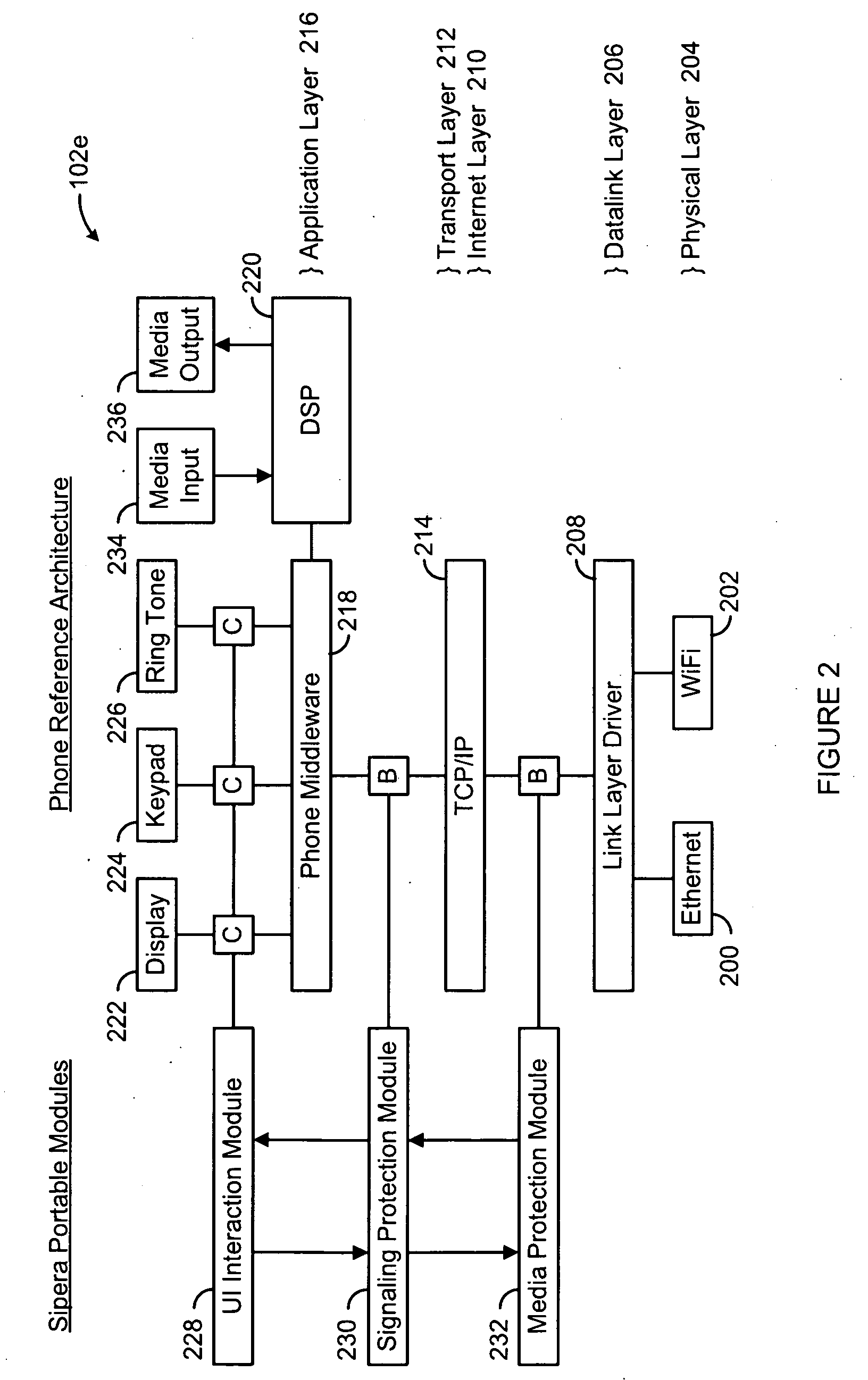
InactiveUS20090094671A1Special data processing applicationsSecuring communicationDual modeSecurity parameter
The present invention provides a system, method and apparatus for providing security in an IP-based end user device, such personal computer clients, hard phones, soft phones, cellular phones, dual-mode phones, handheld communication devices, wireless communications devices and any other device capable of supporting real time IP-based applications. An application layer, a TCP / IP layer and a datalink layer of the IP-based end user device are monitored. Whenever an incoming session is detected and analyzed, the incoming session is accepted whenever one or more session security parameter(s) are satisfied and the incoming session is denied whenever the session security parameter(s) are not satisfied. Whenever an incoming packet is detected and analyzed, the incoming packet is processed whenever one or more packet security parameter(s) are satisfied and the incoming packet is dropped whenever the packet security parameter(s) are not satisfied.
Owner:AVAYA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com