Patents
Literature
537 results about "Management information base" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
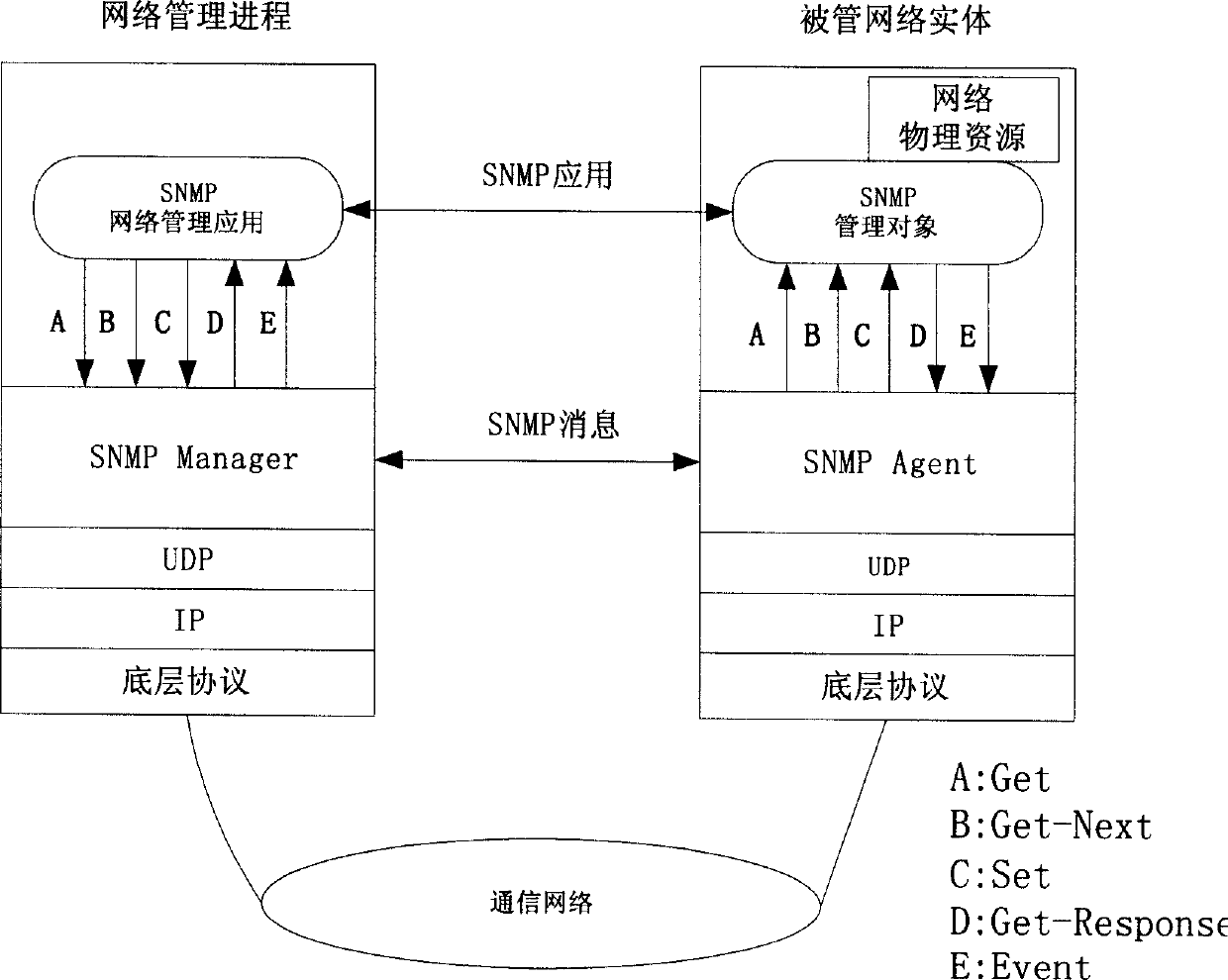
A management information base (MIB) is a database used for managing the entities in a communication network. Most often associated with the Simple Network Management Protocol (SNMP), the term is also used more generically in contexts such as in OSI/ISO Network management model. While intended to refer to the complete collection of management information available on an entity, it is often used to refer to a particular subset, more correctly referred to as MIB-module.
Software fault management system
InactiveUS6012152ASupervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsInformation repositoryManagement information systems
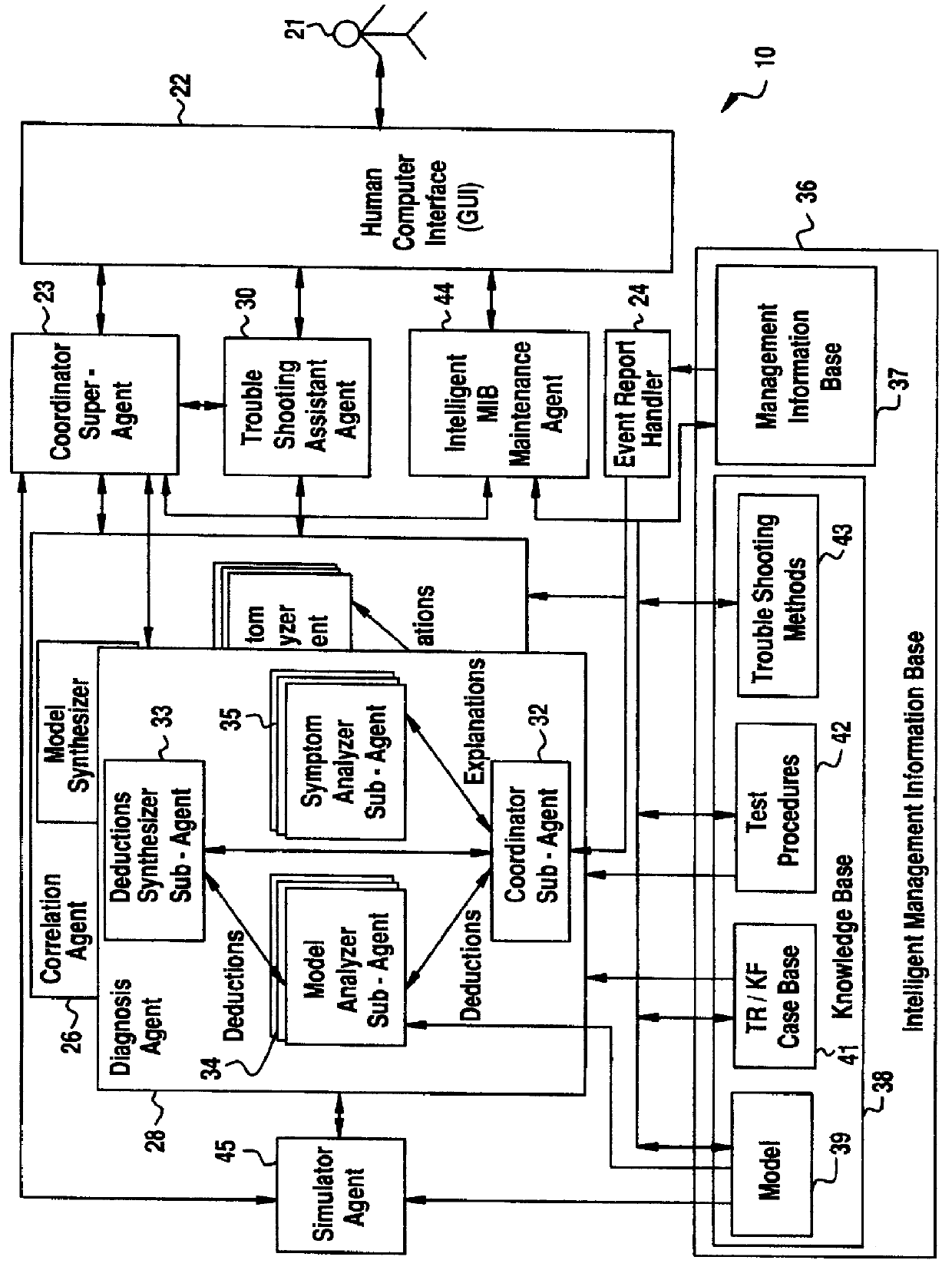
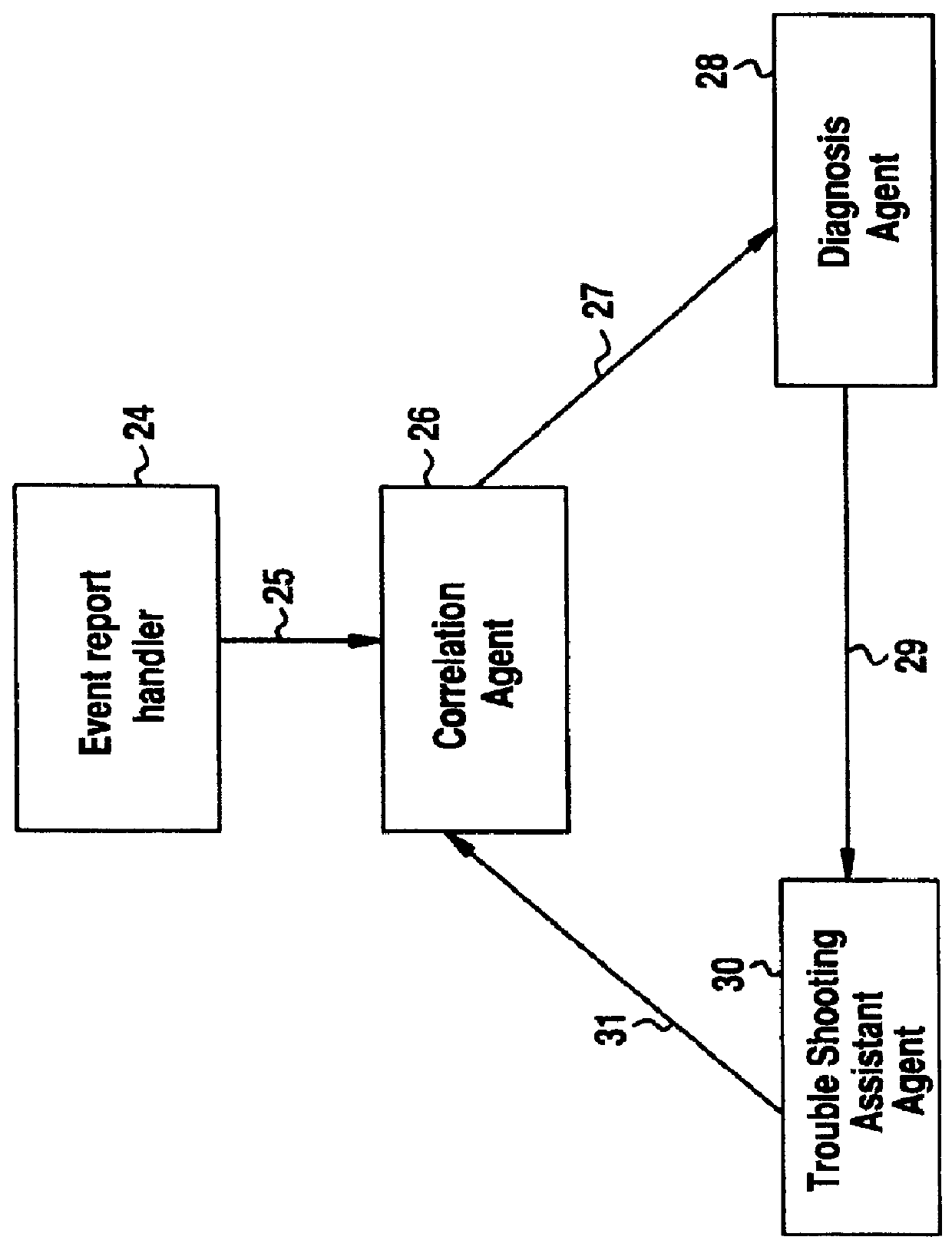
A Software Fault Management (SFM) system for managing software faults in a managed mobile telecommunications network. The SFM system includes an Intelligent Management Information Base (I-MIB) comprising a Management Information Base (MIB) and a Knowledge Base (KB) having a functional model of the managed network and a trouble report / known faults (TR / KF) case base. The SFM system also includes an intelligent multi-agent portion having a plurality of agents which process the software faults utilizing the functional model from the I-MIB, case-based information, and other management information. The I-MIB and the intelligent multi-agent portion are compliant with Telecomunications Management Network (TMN) principles and framework. Fault management is both proactive and reactive. The SFM system is made independent of technology-specific implementations by representing the underlying switch design knowledge in a modular and changeable form which is then interpreted by the intelligent multi-agent portion. A clear separation is maintained between the generic procedural inference mechanisms and agents, and the specific and explicit models of the different network elements of a mobile telecommunications network.
Owner:TELEFON AB LM ERICSSON (PUBL)
Virtual network management method, virtual network management program, virtual network management system, and virtual network means
InactiveUS7649851B2Lighten the taskDigital computer detailsData switching by path configurationManagement information baseNetwork management
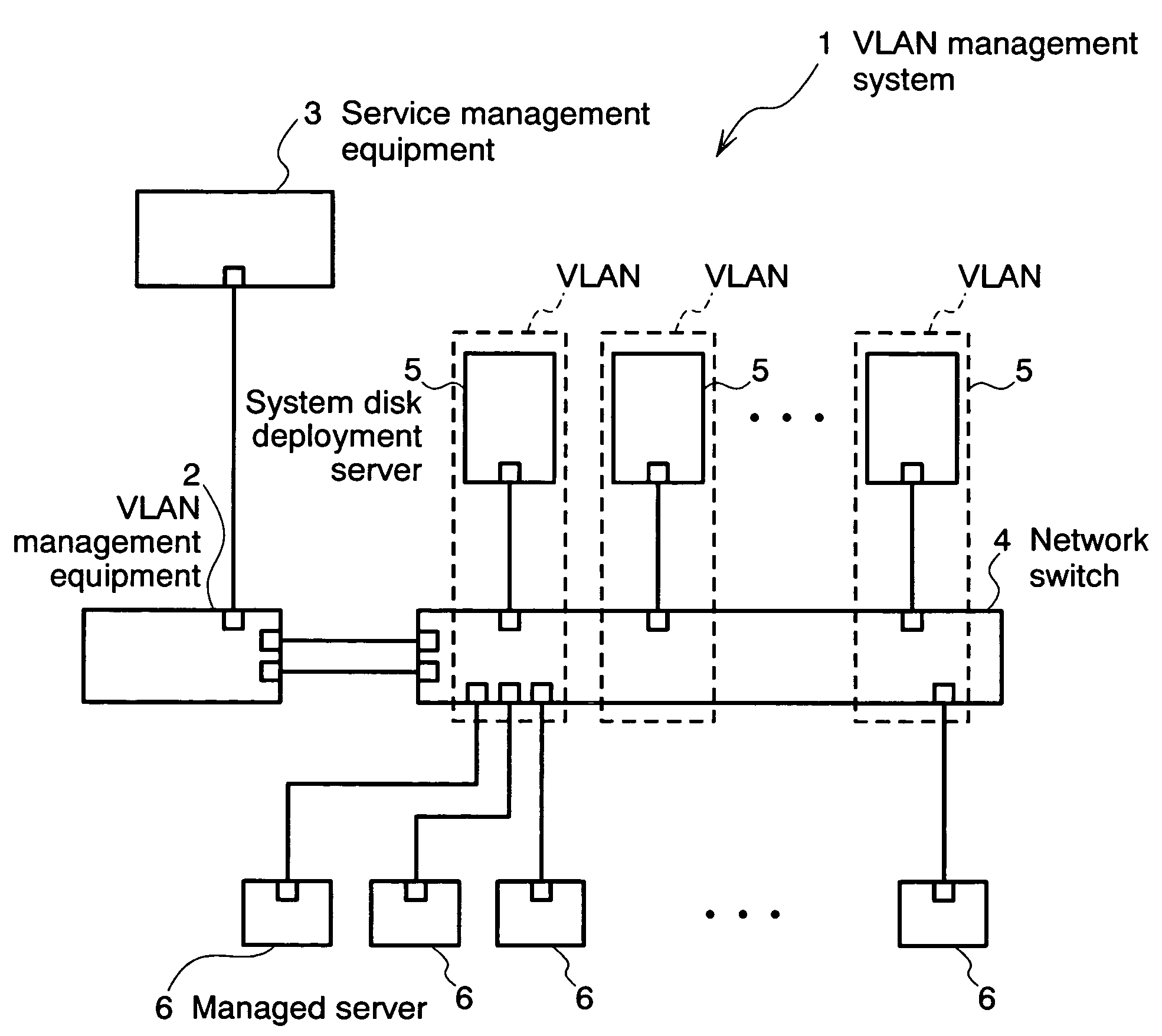
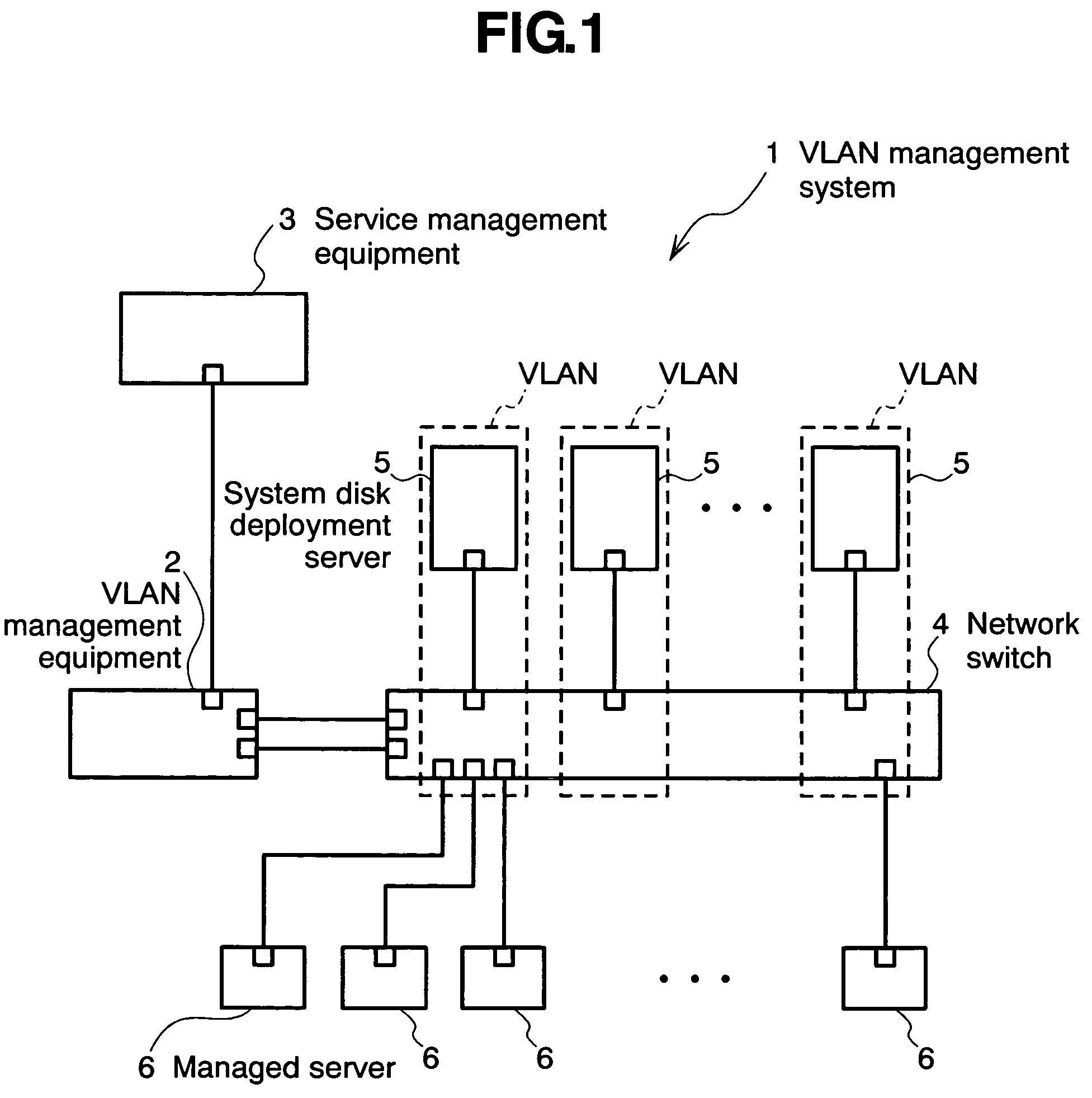
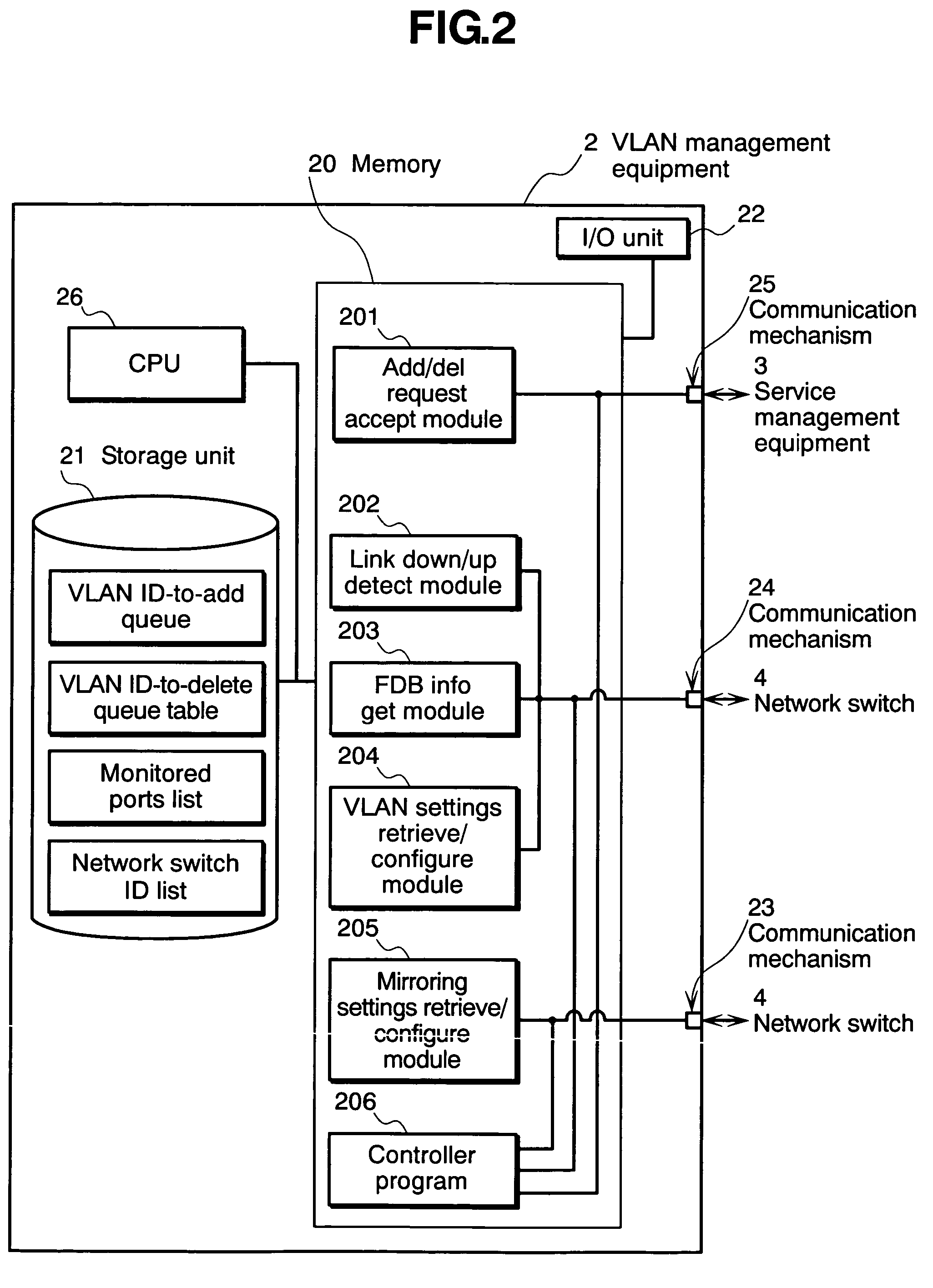
The invention relates to a network management method wherein: a service management equipment holds the mapping of services and virtual networks as management information; a managed server sends an advice to a VLAN management equipment when its status changes; and the VLAN management equipment receives the advice and refers to the information contained in the advice to thereby identify the managed server and the connection port of a network switch, and configures a virtual network belonging to the identified port of the network switch. The method alleviates the task of reconfiguration associated with the adding or deleting of servers.
Owner:HITACHI LTD
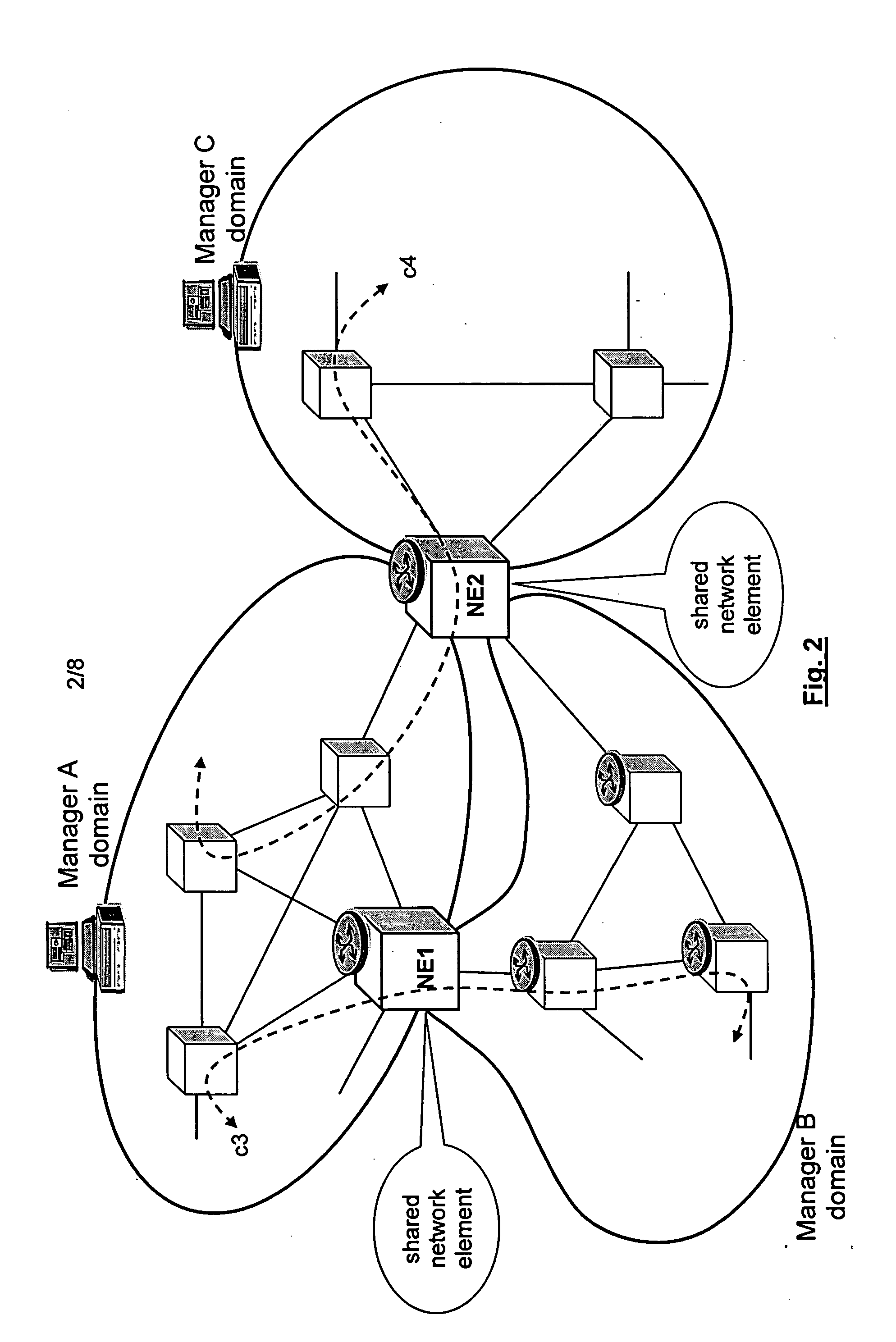
Shared resources in a multi manager environment
ActiveUS20060026225A1Reduce network element performanceMultiple digital computer combinationsTransmissionInformation repositoryManagement information base
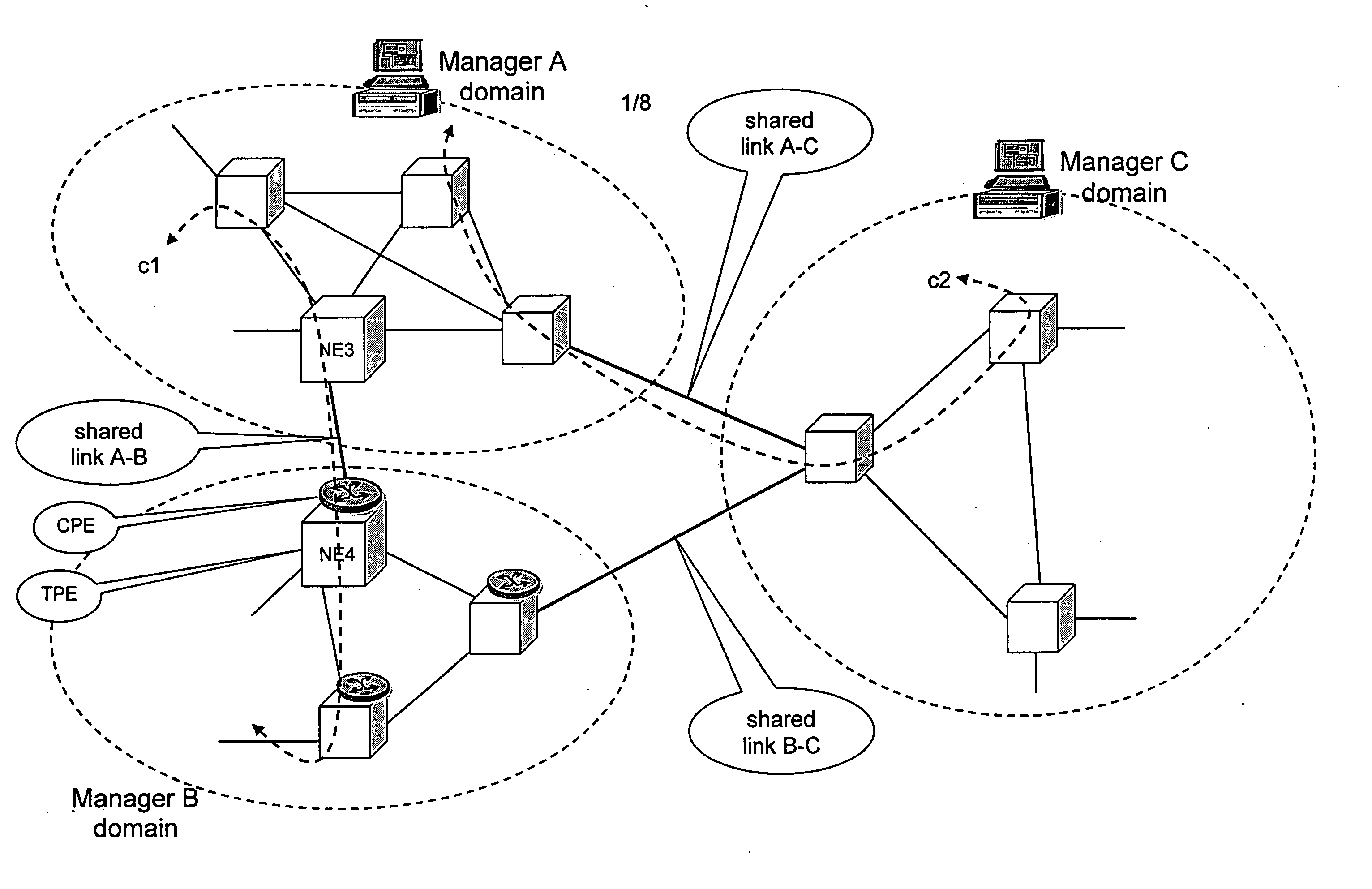
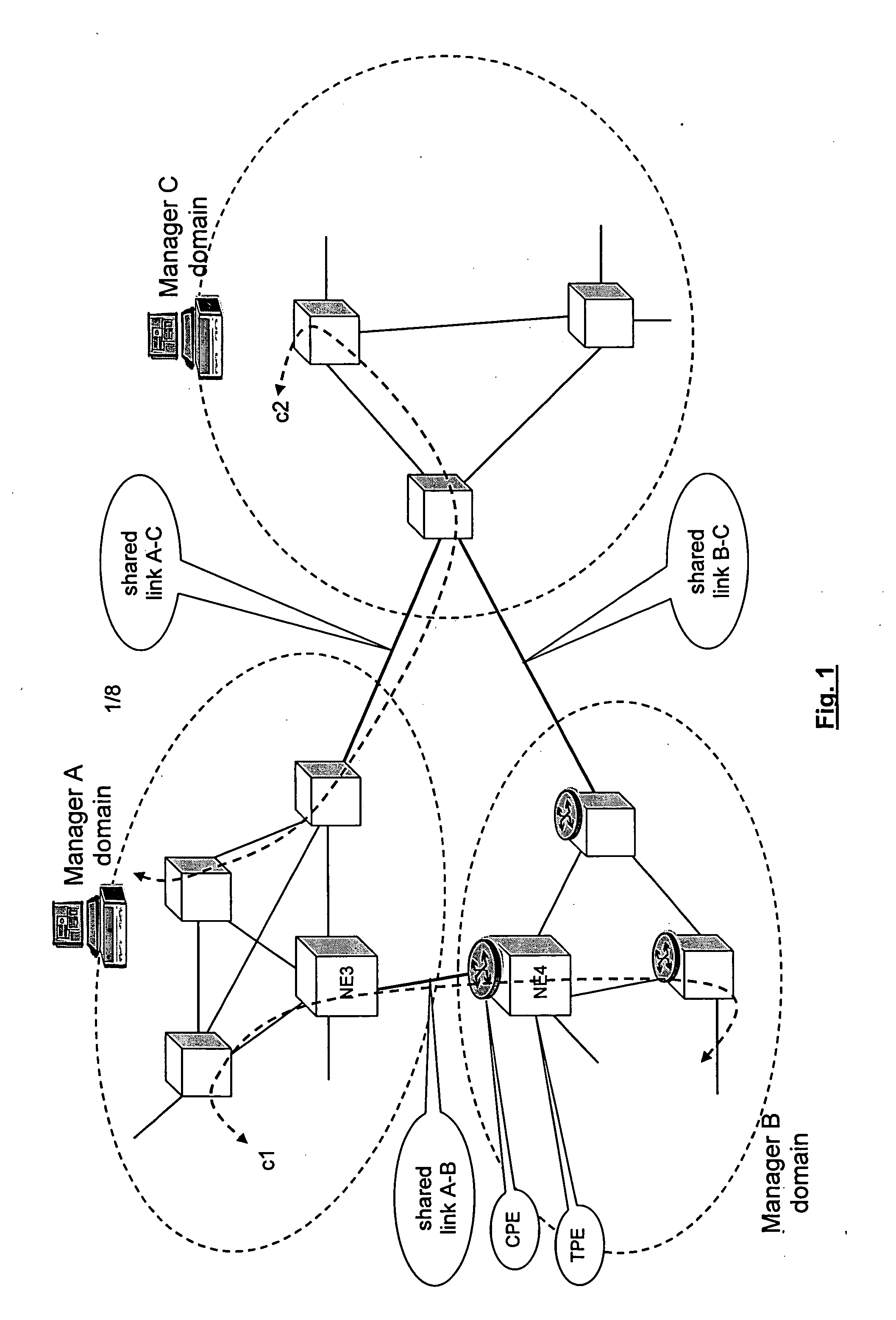
A method is described for controlling a shared resource for interconnecting two or more network domains being controlled by different Managers. Multiple Managers control the shared resource for the configuration of a segment of a connection between two different domains and the Managers cooperate in order to control dynamically the shared resource. Different network domains can be connected by a network element or by a link between different network elements belonging to the different network domains. In the first case the shared resource is a connection matrix of the network element, in the second case the shared resource includes the connection matrixes of the different network elements and the link between the network elements. A shared connection matrix includes some connection points for performing the cross-connections within the matrix: some connection points are controlled by one Manager, other connection points are controlled by another Manager and some shared connection points are controlled by both Managers. Multiple Managers control the shared resource by reading and writing information stored into a management information base, according to an explicit or implicit mode, or alternatevely by transmitting messages in the network directly between the Managers, according to a signalling protocol.
Owner:ALCATEL LUCENT SAS
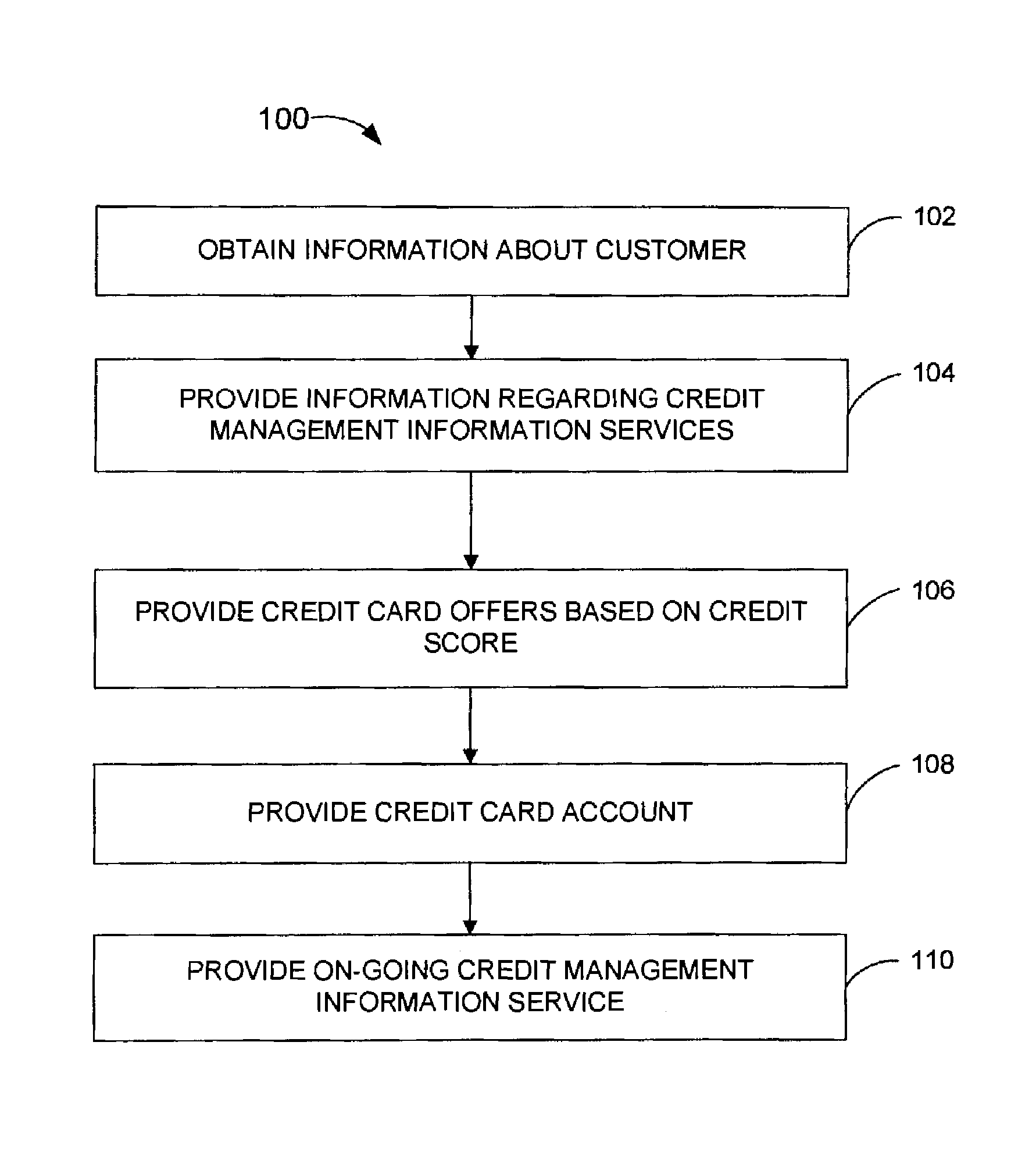
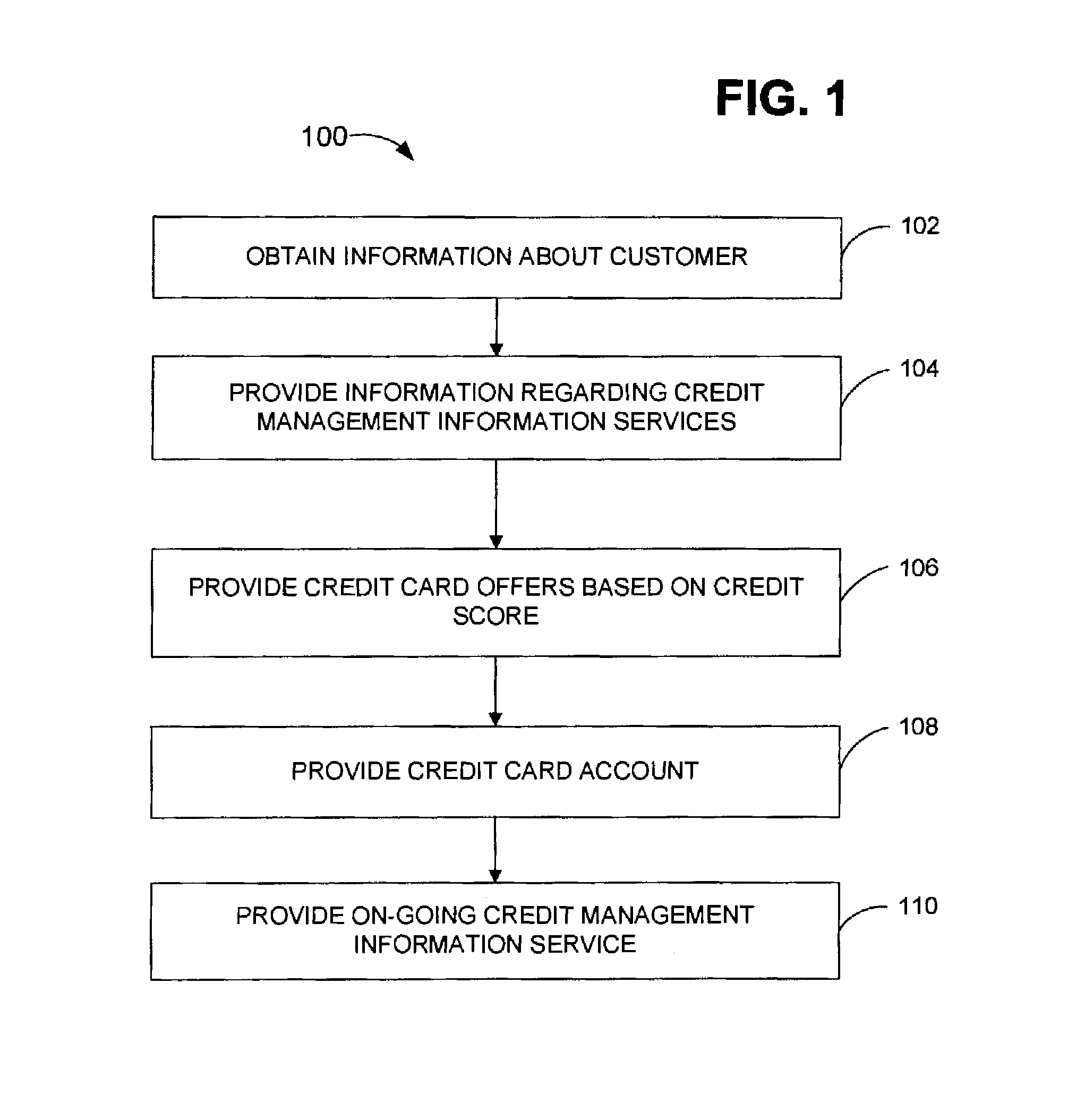
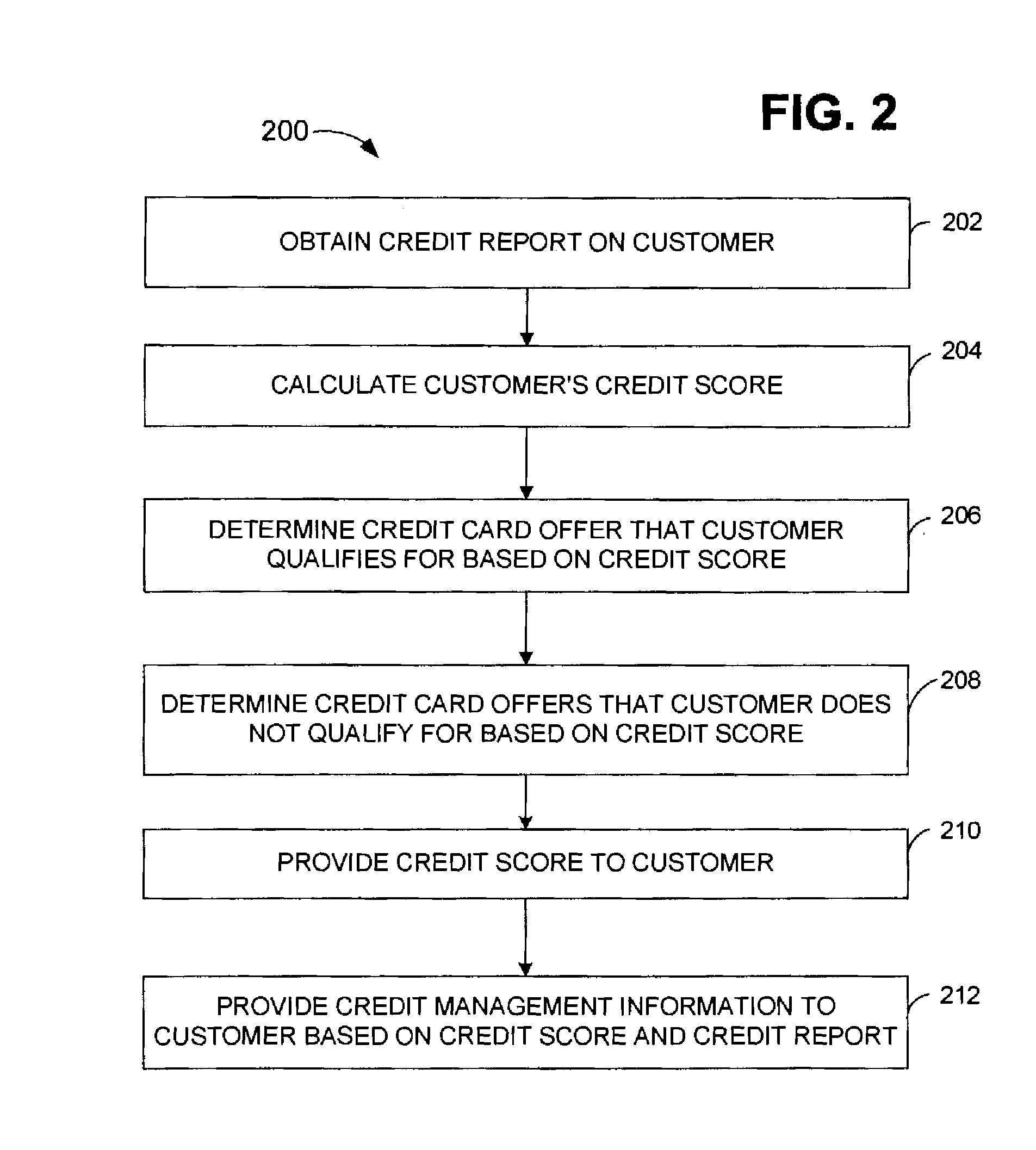
Method for providing credit offering and credit management information services
InactiveUS20080021802A1Improve customer satisfactionStrengthens customer loyaltyFinanceCredit cardManagement information base
The present invention is related to a method for issuing a credit card to a customer in combination with providing credit management information services for the customer. Customers are solicited by various means and a credit account is offered to the customer. The exact terms of the credit account offered depend on the creditworthiness of the customer. The customer also receives credit management information services including information as to what actions the customer could take to improve the customer's credit rating and improve the terms of the credit account. After a credit account is issued to the customer, the customer receives additional and on-going credit management information services, including credit management information based on the customer's use of the credit account.
Owner:CC SERVE
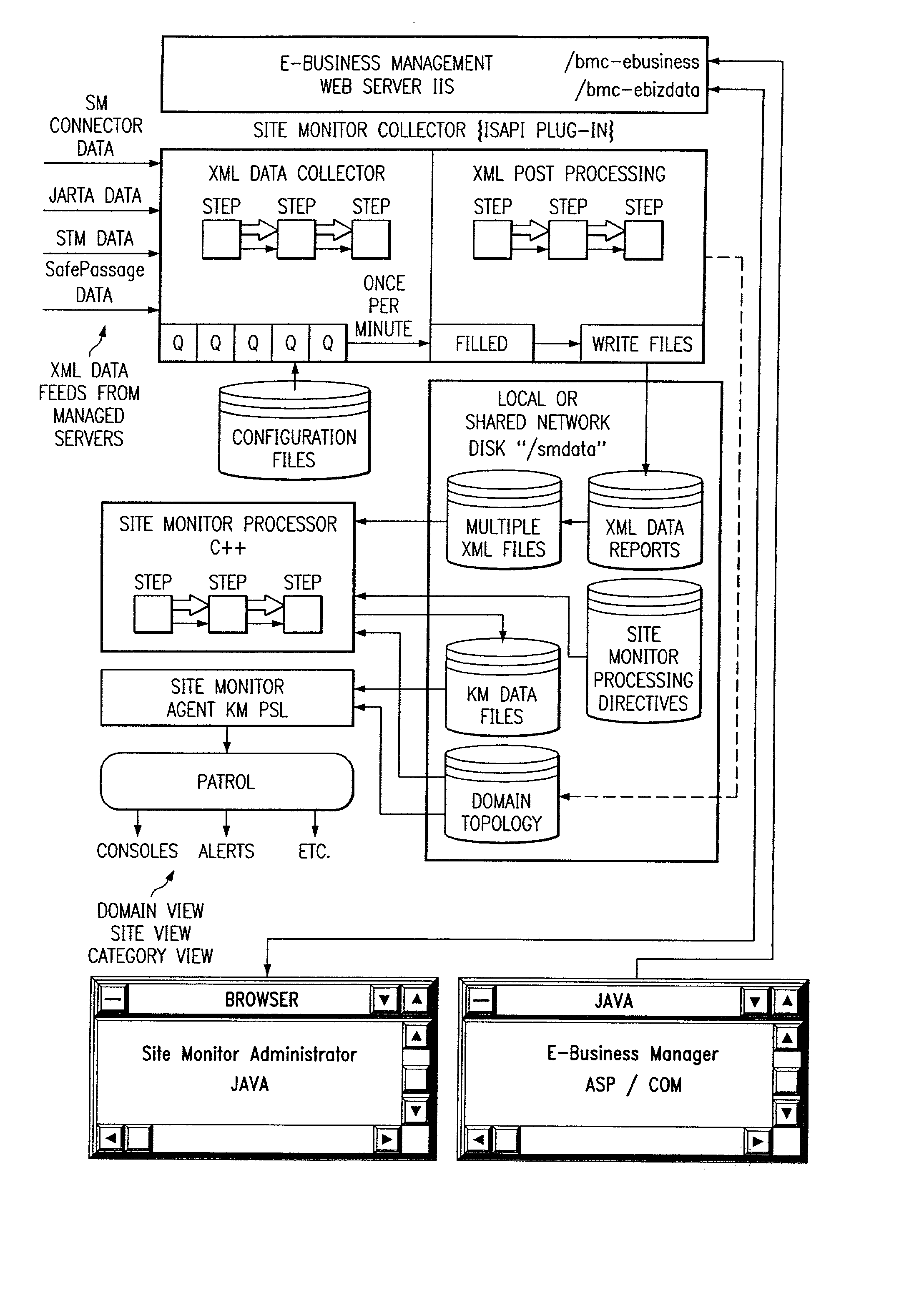
Site monitor
Systems and methods for network service management, wherein the internet service management system includes one or more components which collectively enable an administrator to obtain a site-wide view of network activities on servers such as web servers, FTP servers, e-mail servers, domain name servers, etc. In addition to collecting information relating to web server latency and processing time, the internet service management system may collect actual user transaction information and system information from end users on client computers. The internet service management system may provide domain summary information for a domain, or it may provide management information organized by "categories" according to how a site manager wants to view and manage his business; e.g., byline of business (books, auctions, music, etc.), by site function (searches, shopping cart, support, quotes, sales automation), or most any other categorization customers may choose.
Owner:BMC SOFTWARE
Method and apparatus for adjusting overflow buffers and flow control watermark levels
InactiveUS6084856AReduce congestionHigh trafficError prevention/detection by using return channelTransmission systemsShared memory architectureTraffic capacity
A network switch having a shared memory architecture for storing data frames includes configuration registers that are programmable by a host processor to adaptively adjust overflow buffer locations and flow control watermark levels based on monitored network traffic. The host processor allocates shared resources by setting memory configuration registers corresponding to an external memory, where the network switch uses the external memory for storing received data frames, Management Information Base (MIB) counter values, and output port overflow data. The host processor periodically reads the MIB counter values from the external memory, and adjusts flow control watermark levels or the memory configuration registers in the network switch based on rate-based network traffic derived from the MIB counter values. PCI burst transfers between the host processor and the external memory via the network switch ensure that stored data is not lost during reconfiguration of the external memory. The disclosed arrangement enables resources used by the network switch to be adjusted to minimize congestion by borrowing resources from network ports serving idle stations.
Owner:GLOBALFOUNDRIES INC
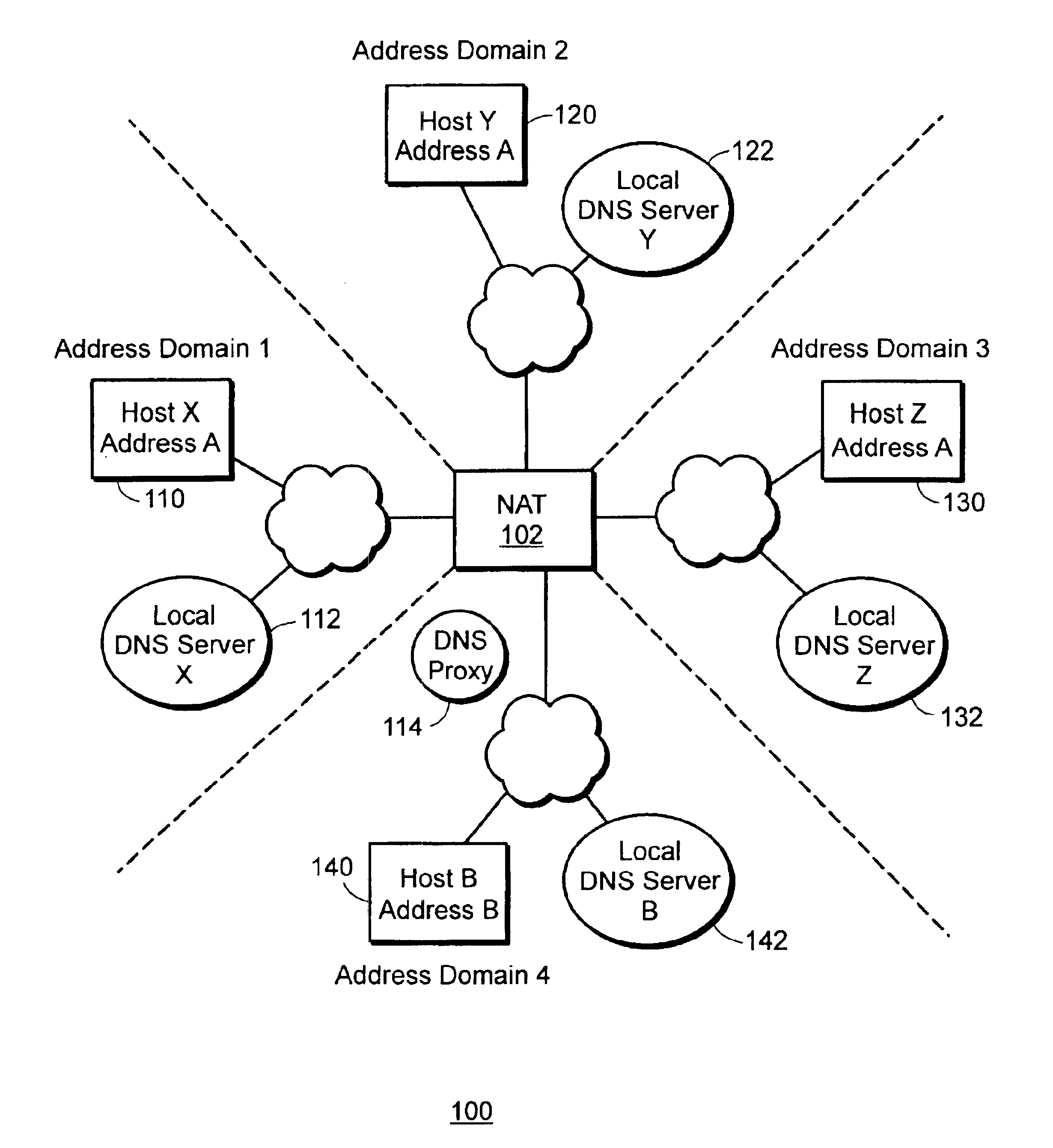
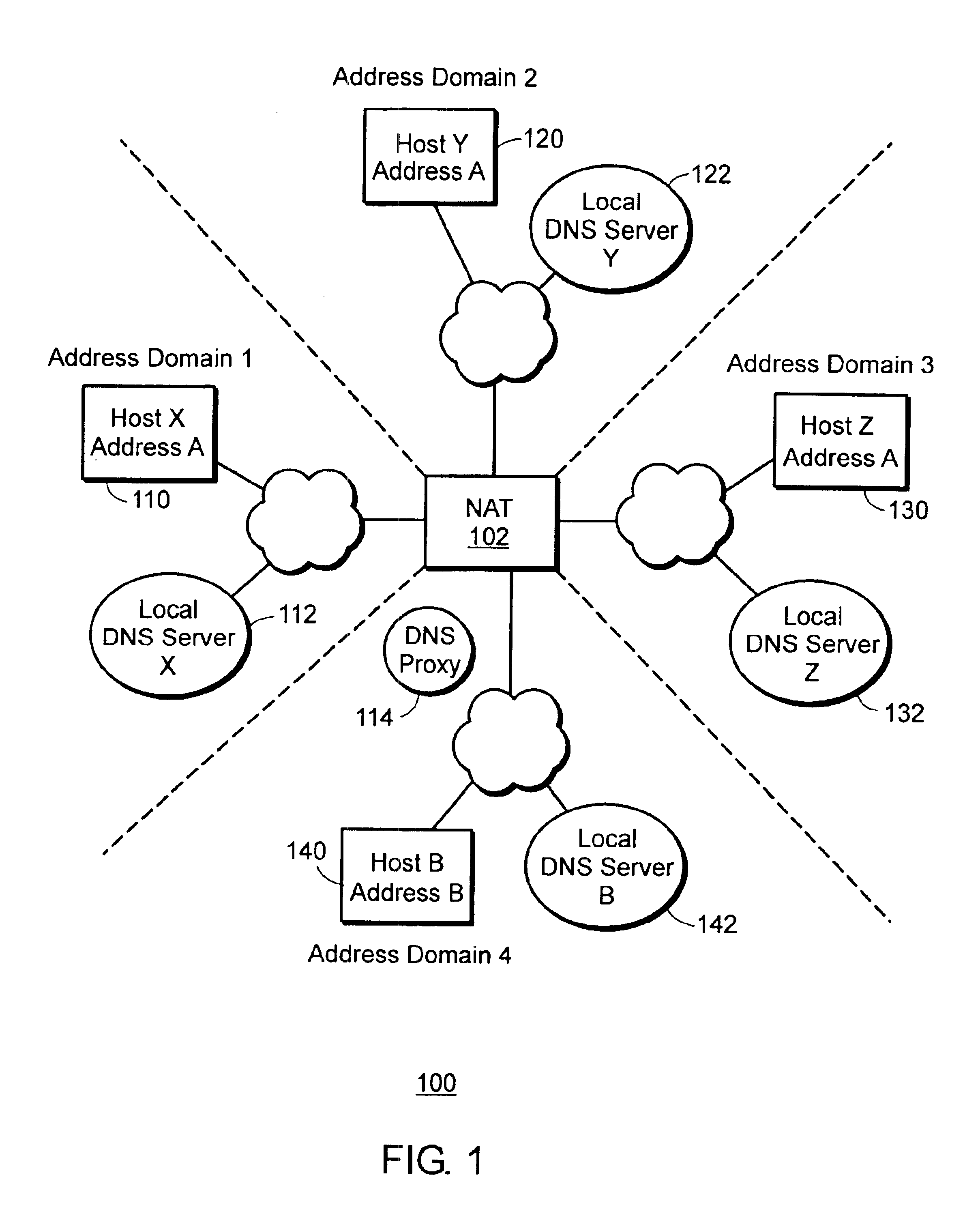
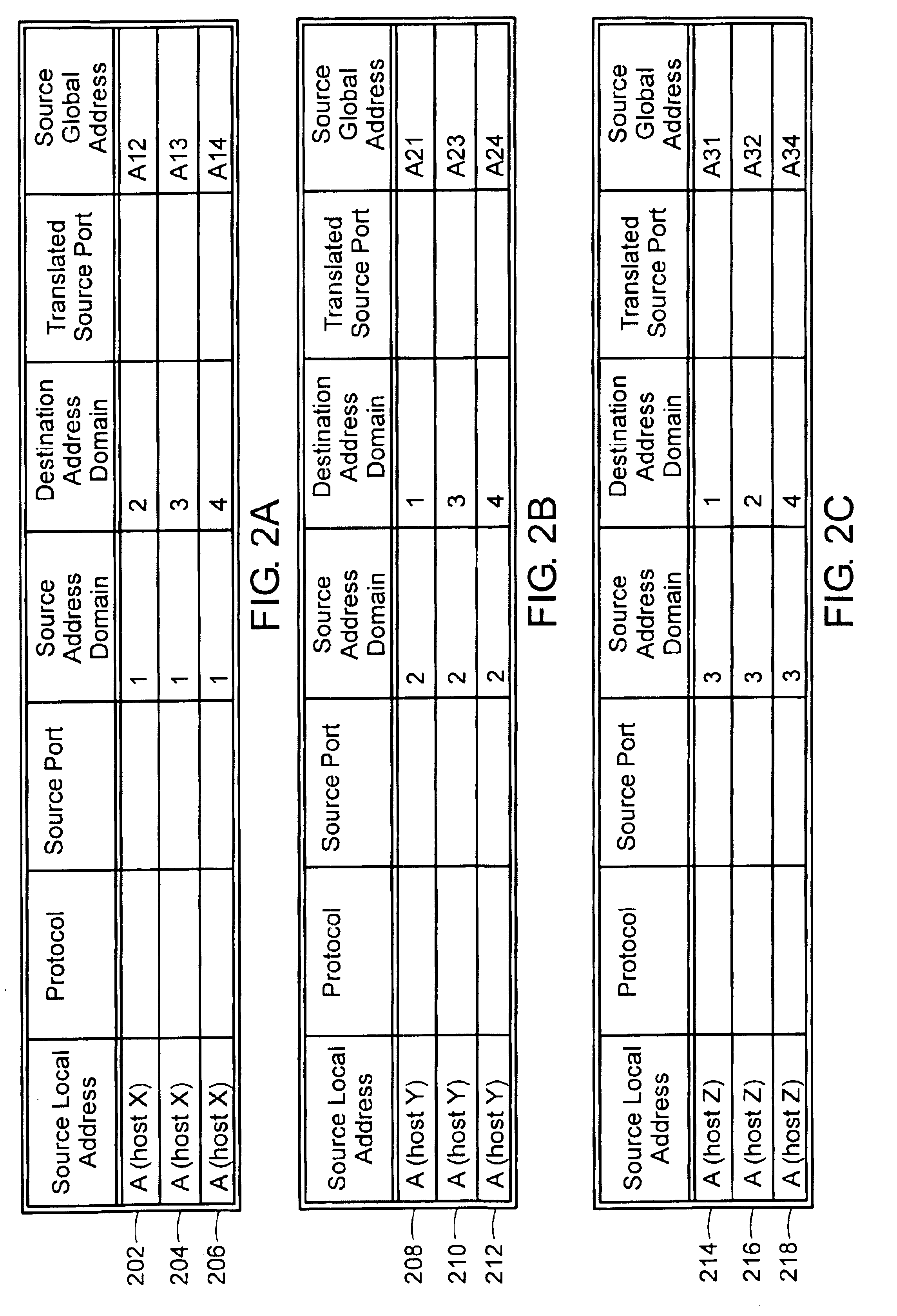
Management information base for a multi-domain network address translator
InactiveUS6892245B1Interconnection arrangementsMultiple digital computer combinationsManagement information baseInformation repository
A management information base (MIB) for a multi-domain network address translator provides management objects for configuring and controlling the multi-domain network address translator. The MIB includes management objects for defining a domain-specific source address filter range, which is a range of addresses used to detect domain-specific packets that require domain-specific network address translation forwarding. The domain-specific source address filter management objects include a beginning address, a prefix length, a domain indicator, and a domain-specific translation pool indicator. The MIB also includes management objects for defining a domain-specific translation pool, which is a range of addresses from which domain-specific translation addresses are selected for domain-specific network address translation forwarding. The domain-specific translation pool management objects include a beginning address, a prefix length, and a domain indicator.
Owner:RPX CLEARINGHOUSE
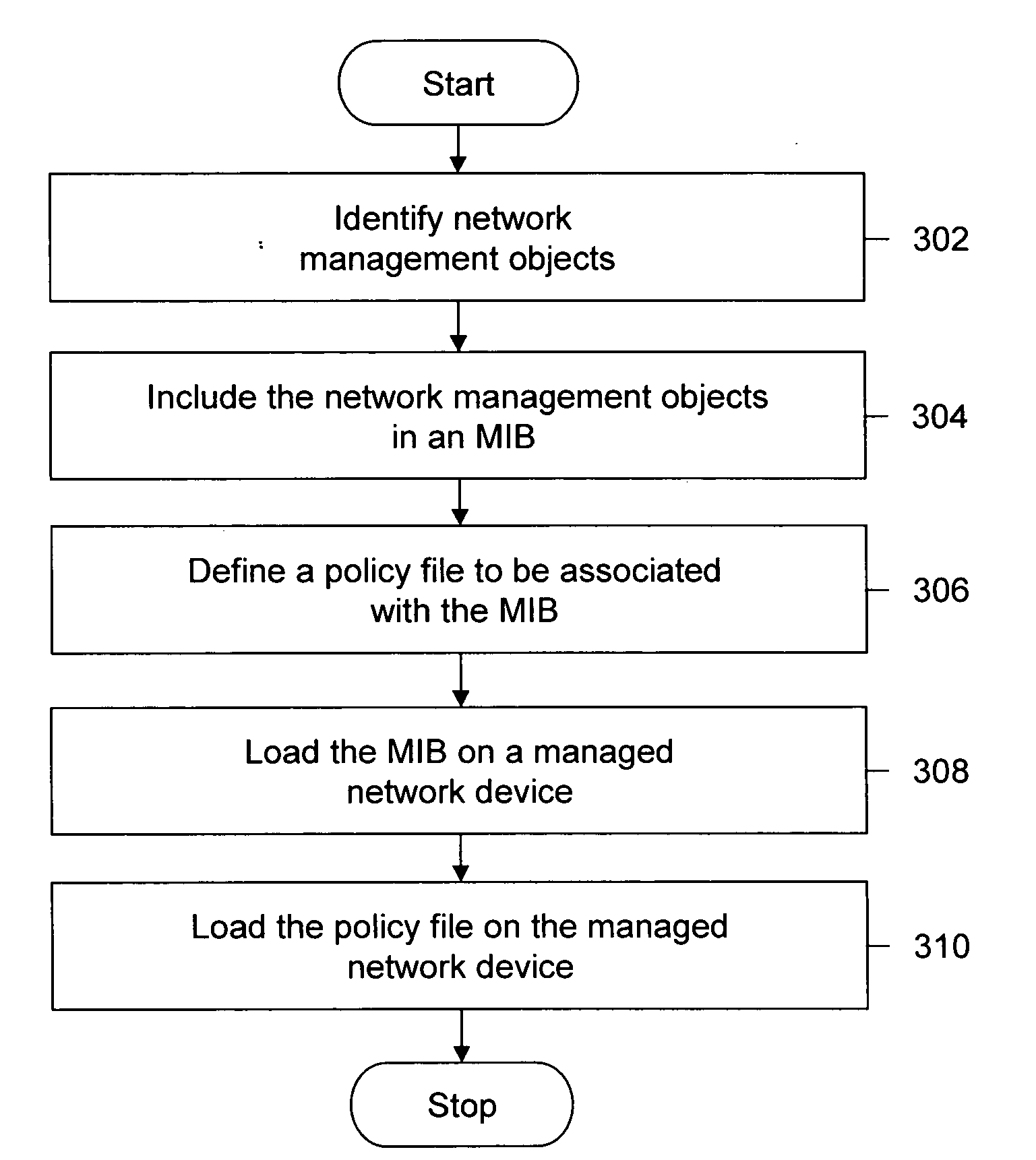
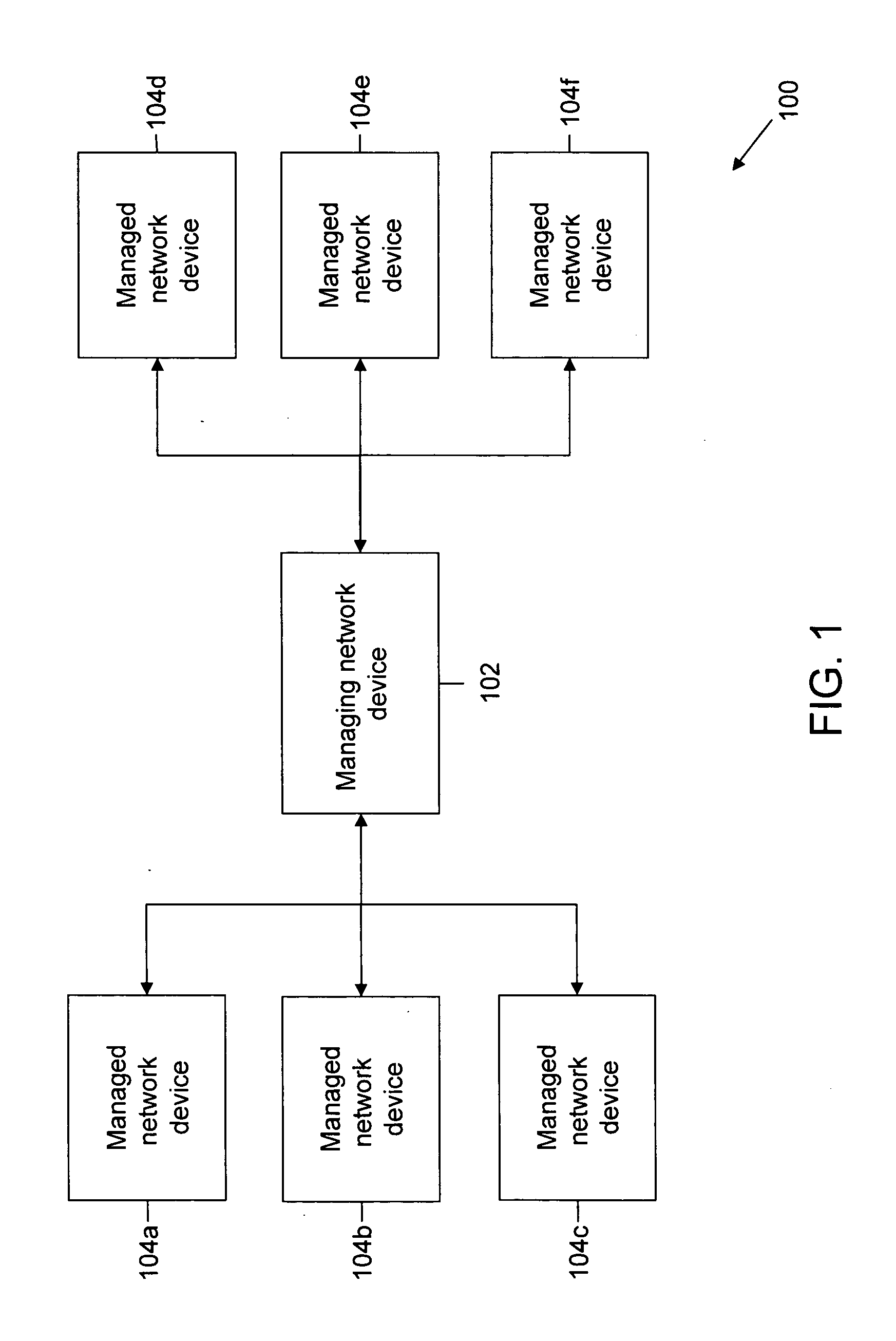
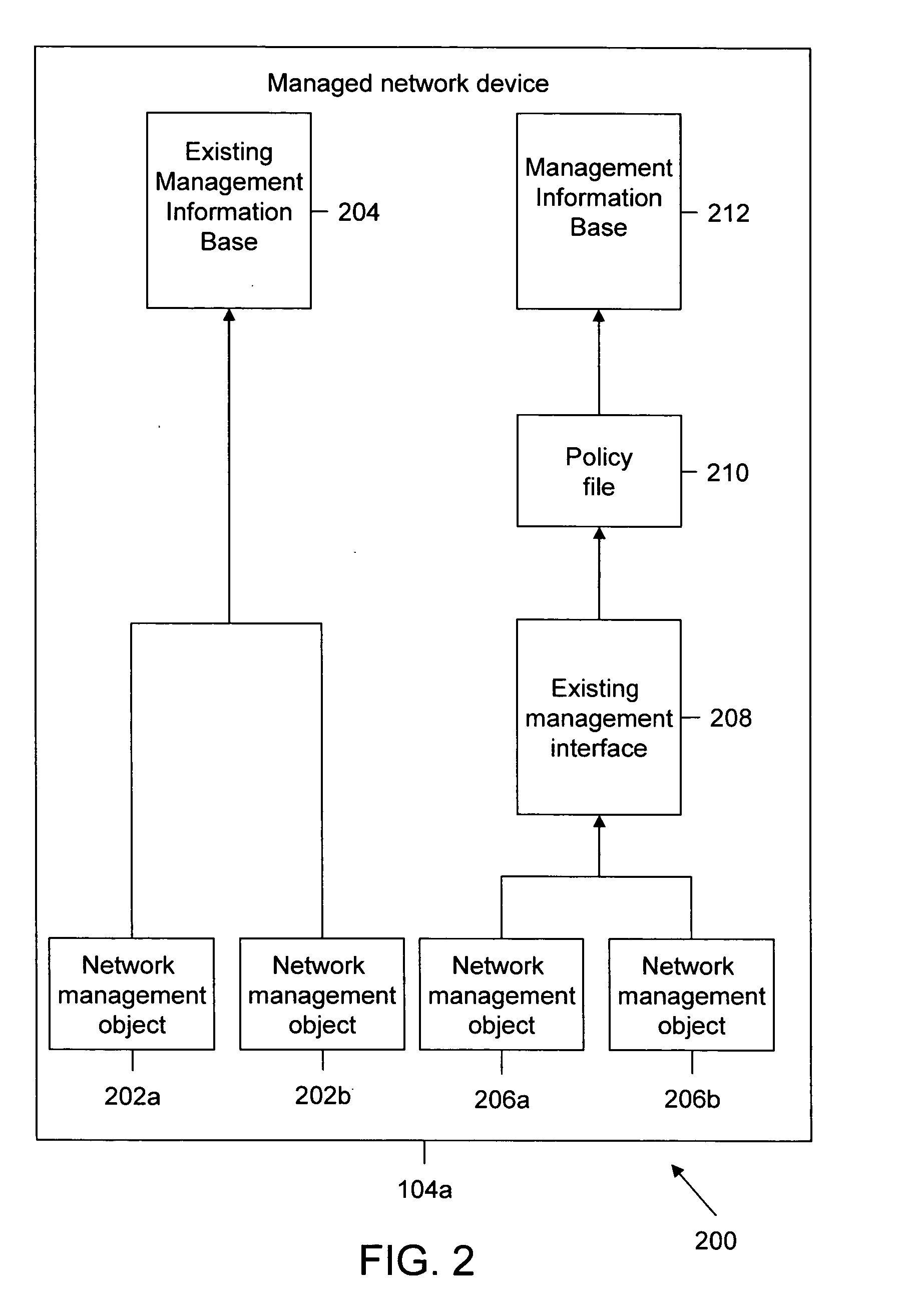
Method and system for dynamic loading of management information bases on network devices
ActiveUS20080040467A1Digital computer detailsTransmissionManagement information baseNetwork management
In one embodiment, a Management Information Base (MIB) is dynamically loaded on a managed network device that is managed by a managing network device using a management application. Initially, one or more network management objects are identified. The identified one or more network management objects are then included in the MIB. Thereafter, a policy file to be associated with the MIB is defined. Consequently, the MIB is loaded on the managed network device along with the associated policy file.
Owner:CISCO TECH INC
IP network topology discovering method based on SNMP
InactiveCN1756189ADiscover connectionsData switching by path configurationInformation repositoryManagement information base
Disclosed a method for automatically discovering the physical distribution of network and the connection relationship of IP network topology, based on the SNMP protocol, comprises following steps: constructing the condition of operating the SNMP network management; arranging a management information base on every network node of target network; the network management process via the application layer visits the SNMP management information base; the network management applies the information transmitted to the network management process to reach the managed network entity via the substratum protocol; discovering the topology of network layer; and discovering the topology of data chain circuit layer. In the network management, the inventive method can detect the topological structure of network layer and the data chain circuit layer, attain and maintain the existence information and connection relation information of network node, and protract the topological chart of total network. And the network manager can position the network breakage via the information of topological structure and discover the network bottleneck for optimizing the whole network.
Owner:BEIHANG UNIV
Discovery method and device based on Open Flow protocol for control plane device
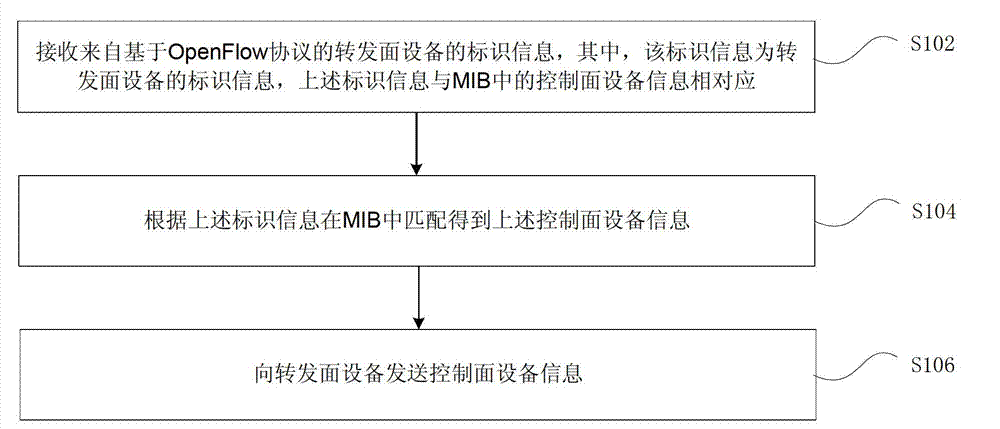
ActiveCN103209121AImplement auto-discoveryRealize adaptive adjustmentHybrid transportManagement information baseSelf adaptive
The invention provides a discovery method and device based on an Open Flow protocol for a control plane device. The method comprises the steps of receiving identification information from a forwarding plane device based on the Open Flow protocol, wherein the identification information is the identification information of the forwarding plane device, the identification information is corresponding to information of the control plane device in a management information base (MIB); matching the identification information in the MIB to obtain the information of the control plane device; and sending the information of the control plane device to the forwarding plane device. By means of the technical scheme, the technical problem that the forwarding plane device cannot discover the control plane device automatically and effectively in relevant technologies is solved, the forwarding plane device can discover the control plane device automatically and can further perform self-adaptive adjusting on the control plane device.
Owner:ZTE CORP
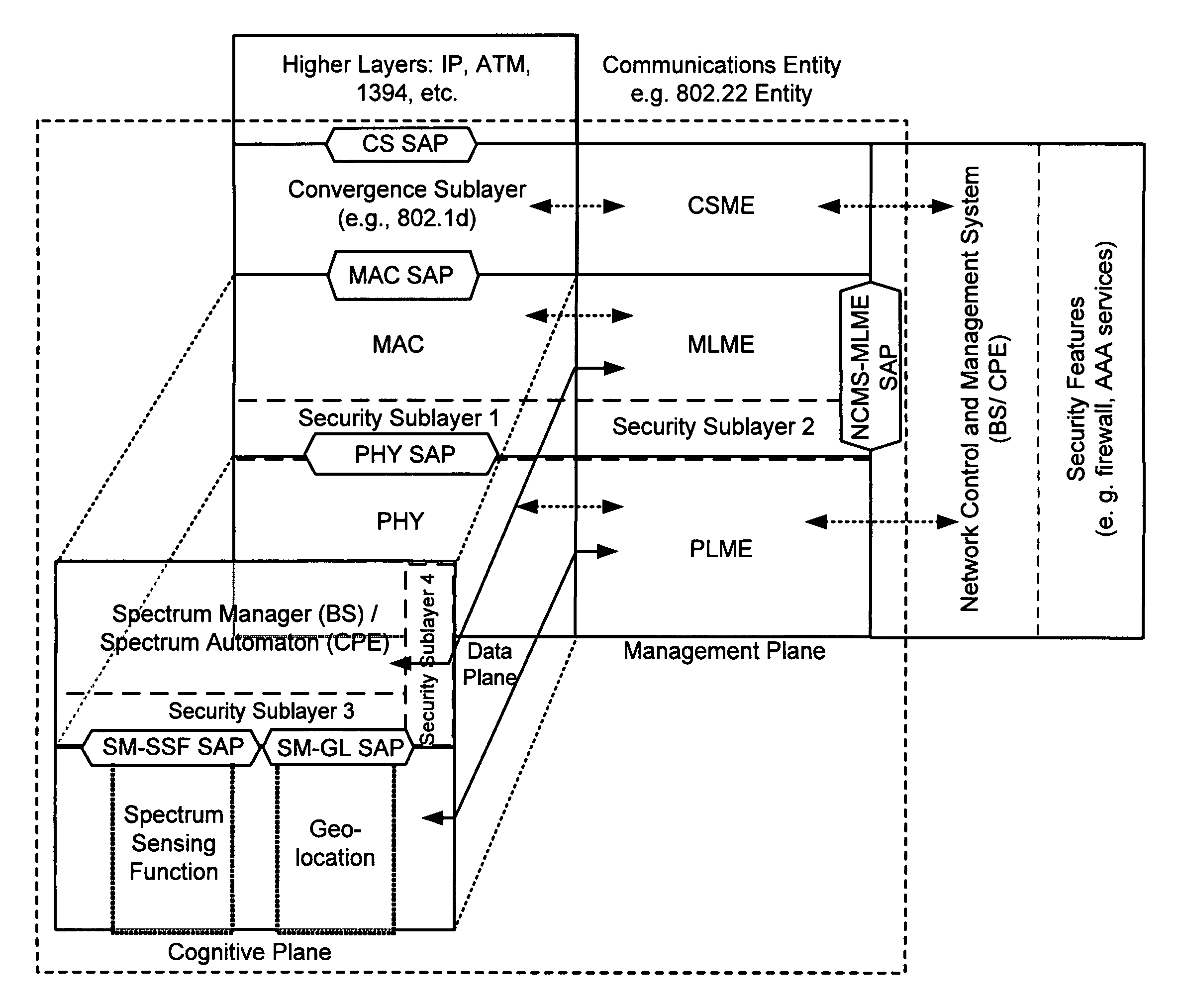
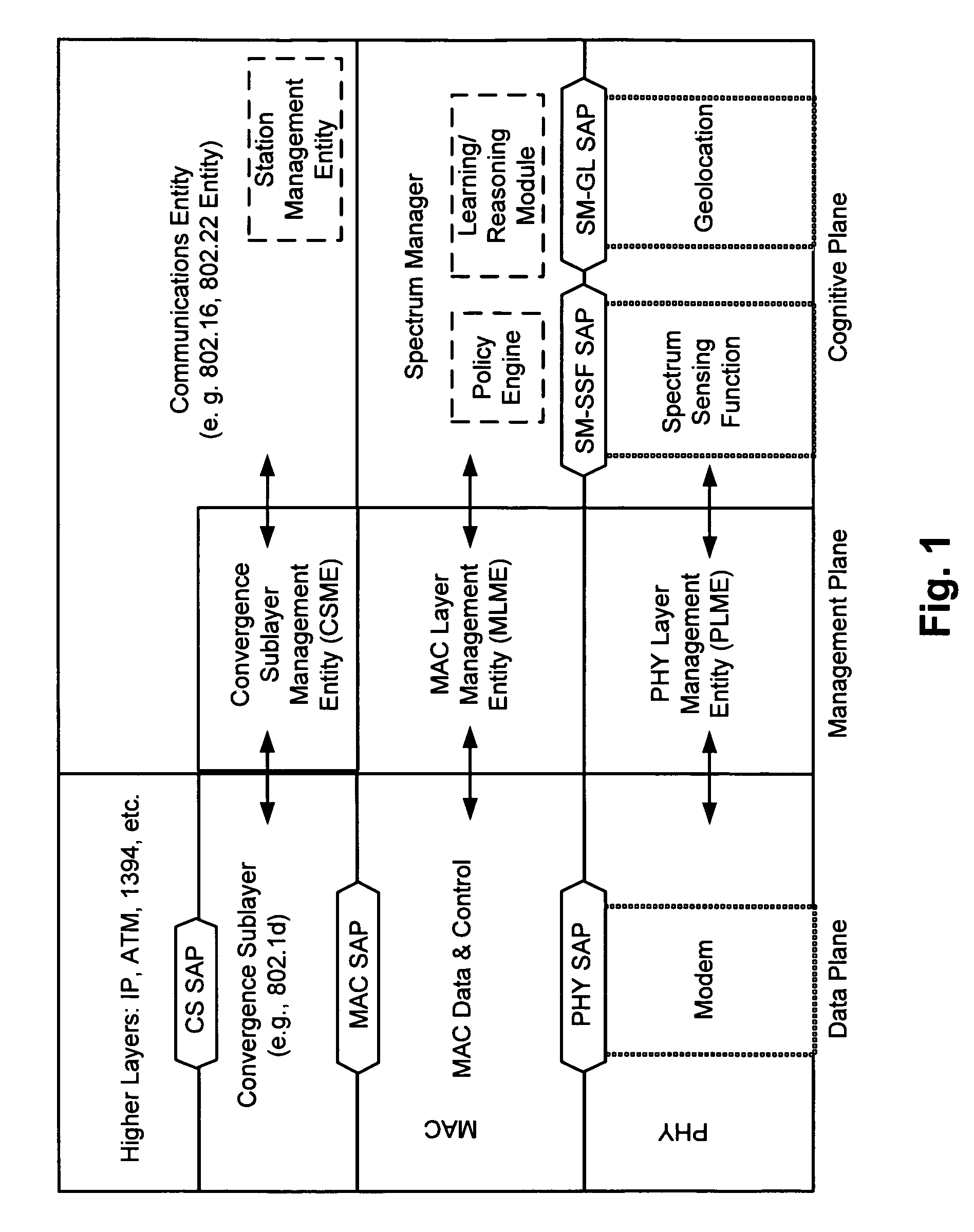
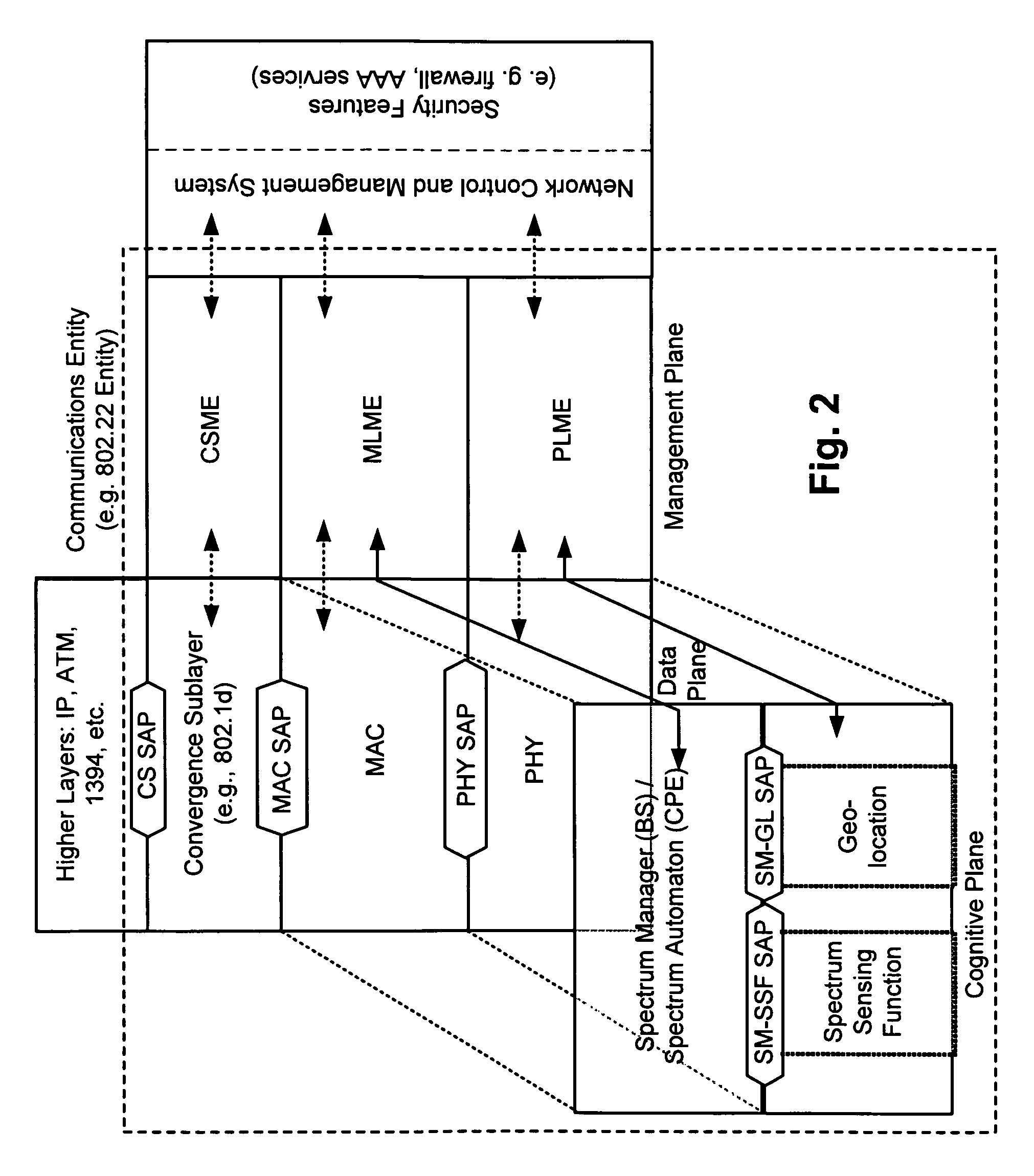
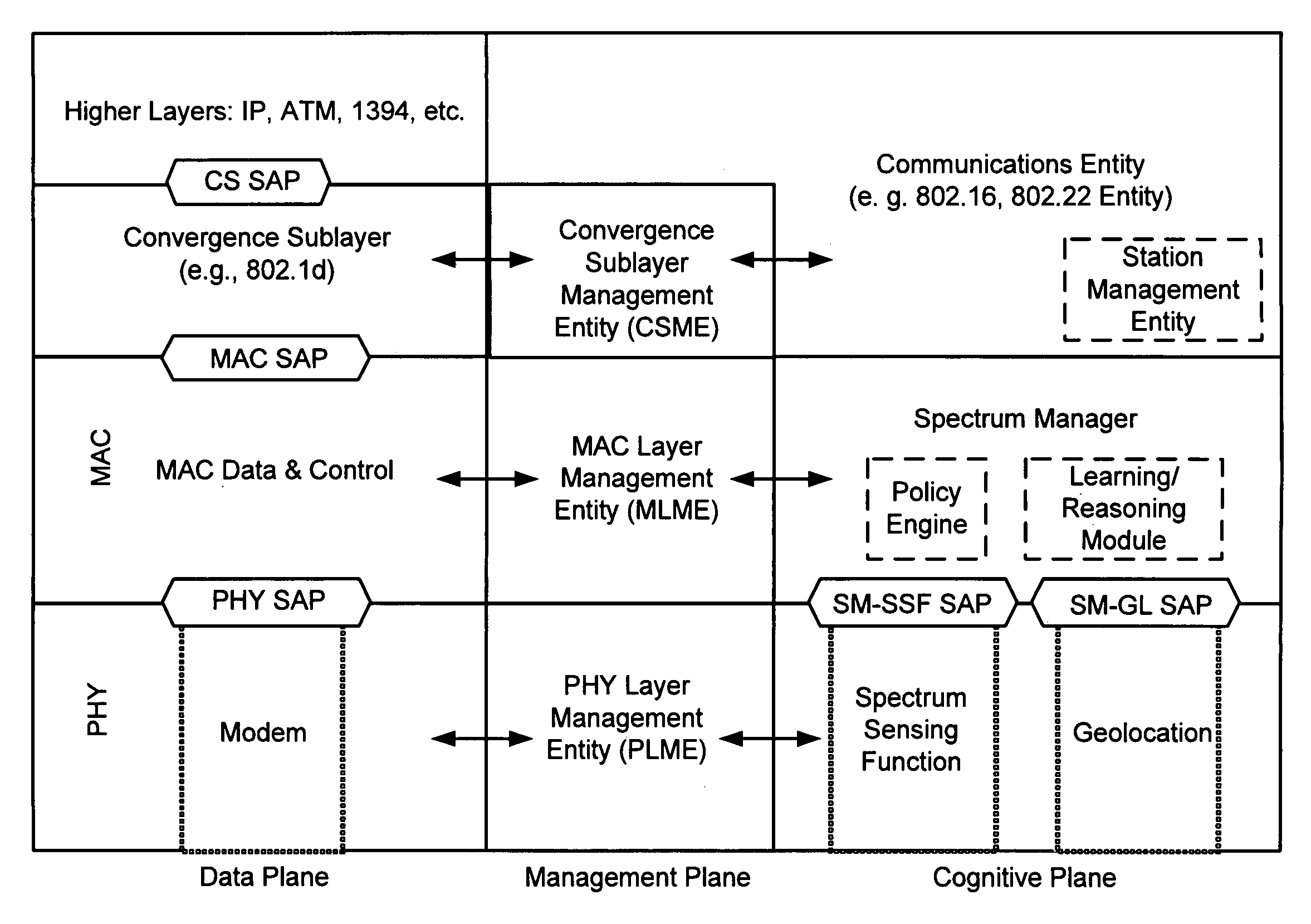
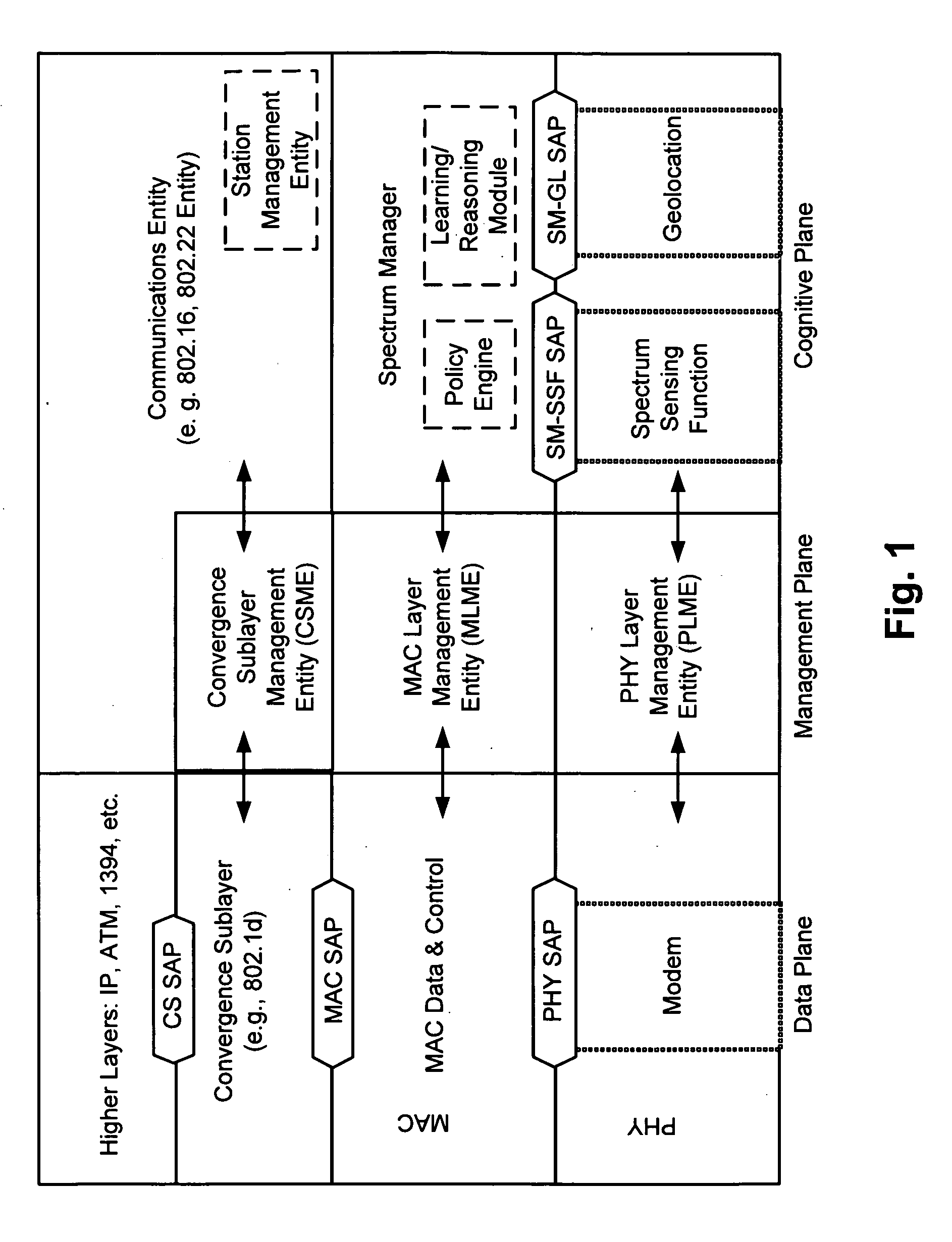
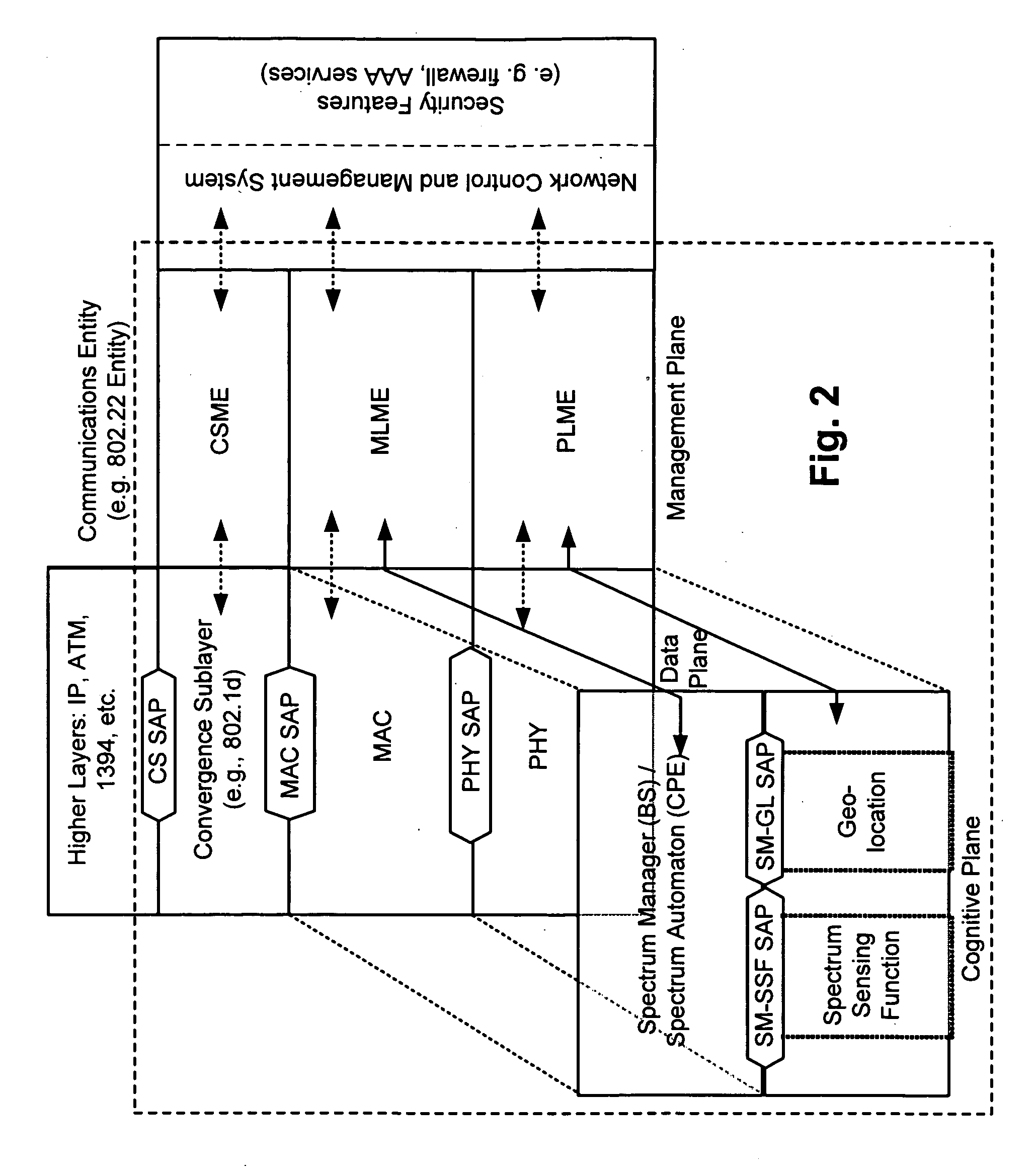
Protocol reference model, security and inter-operability in a cognitive communications system
Various cognitive communications system architectures and their corresponding Protocol Reference Models (PRMs) are disclosed. Such PRMs incorporate a Cognitive Plane in addition to conventional Data and Management Planes. The additional Cognitive Plane functionality may include, for example, spectrum sensing, spectrum management, geolocation, and security functions. The Cognitive Plane may further include a Policy Engine and a Learning and Reasoning Module. In some embodiments, Management Plane functions may be effectively combined to form a database of primitives (and their respective values) called a Management Information Base (MIB). In addition, techniques are provided by which various components of cognitive and non-cognitive, as well as mesh-enabled and non-mesh-enabled nodes in a network, inter-operate with each other. The architectures allow a Spectrum Manager (or Signal Space Manager) to combine information from various network layers (e.g., PHY / MAC Layers, Spectrum Sensing Function, Geolocation Function, and / or Security Sublayers), and to make informed decisions on spectrum utilization.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC +1
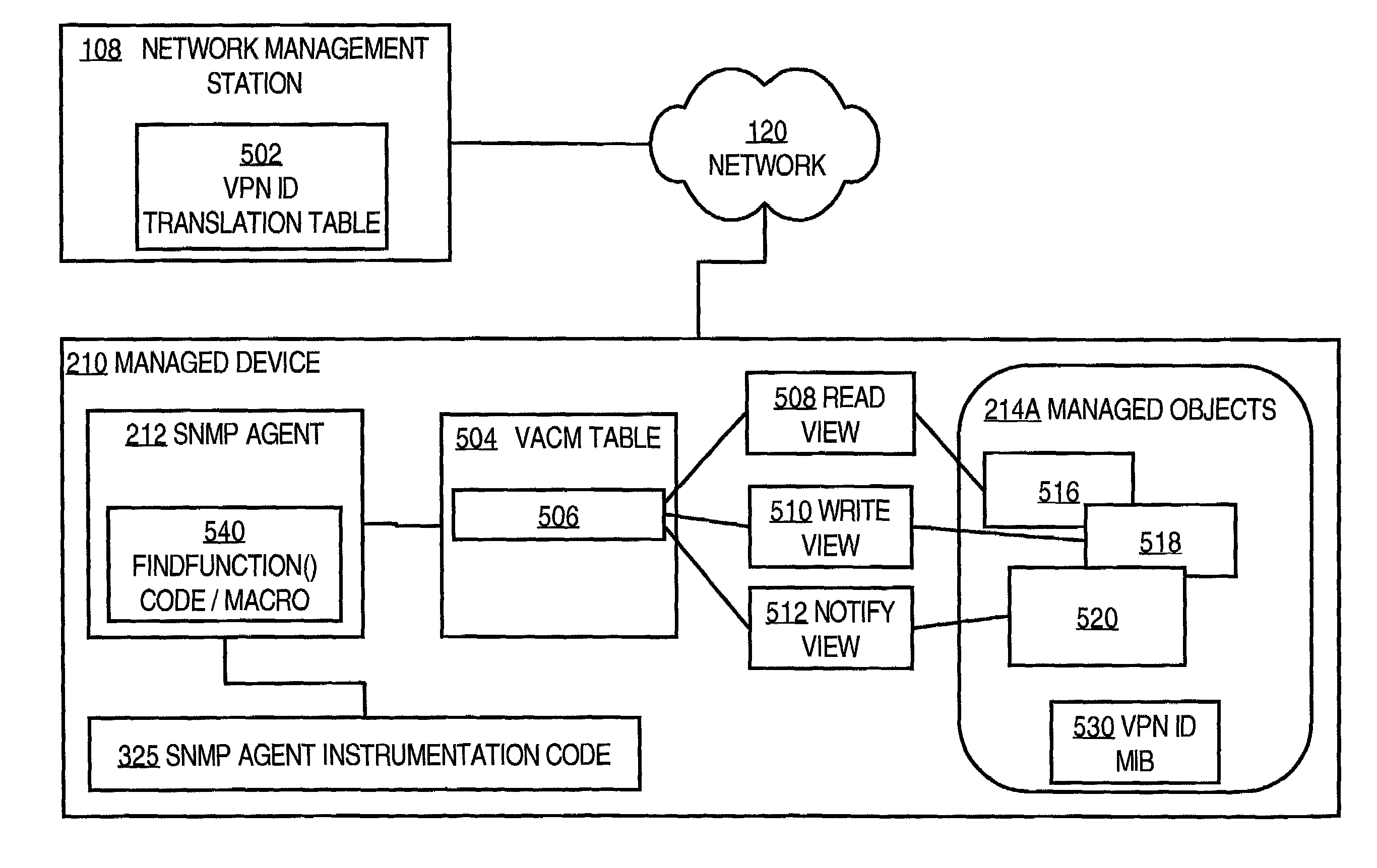
Method and apparatus providing controlled access of requests from virtual private network devices to managed information objects using simple network management protocol
InactiveUS7099947B1Prevent access to informationSimple and scalableUser identity/authority verificationMultiple digital computer combinationsManagement information baseView based
Access control approaches are disclosed wherein managed object in Simple Network Management Protocol (SNMP) Management Information Bases (MIBs) are accessed on a per-Virtual Private Network (VPN)-basis with no modifications to existing MIBs. A manager and an SNMP Agent operating in a VPN environment agree on a mapping between SNMP securityNames and VPN IDs. Under the agreed mapping, the target VPN of any SNMP management request can be unambiguously determined from the securityName alone. For each securityName, one or more MIB Views are configured using in a View-based Access Control Model MIB (VACM MIB) table; the MIB Views specify which portions of the managed object tree can be viewed or modified by a corresponding VPN. Thereafter, a VPN-enabled device provides SNMP requests in which a VPN ID value is passed in the securityName field of the context string in the community string. The receiving device extracts the securityName, locates corresponding MIB Views using the VACM MIB table, and allows the requesting device to access only objects that are identified in the MIB Views.
Owner:CISCO TECH INC
Method and system for detecting a network anomaly in a network
InactiveUS20060047807A1Reduce expensesShorten the timeDigital computer detailsTransmissionInformation repositoryManagement information base
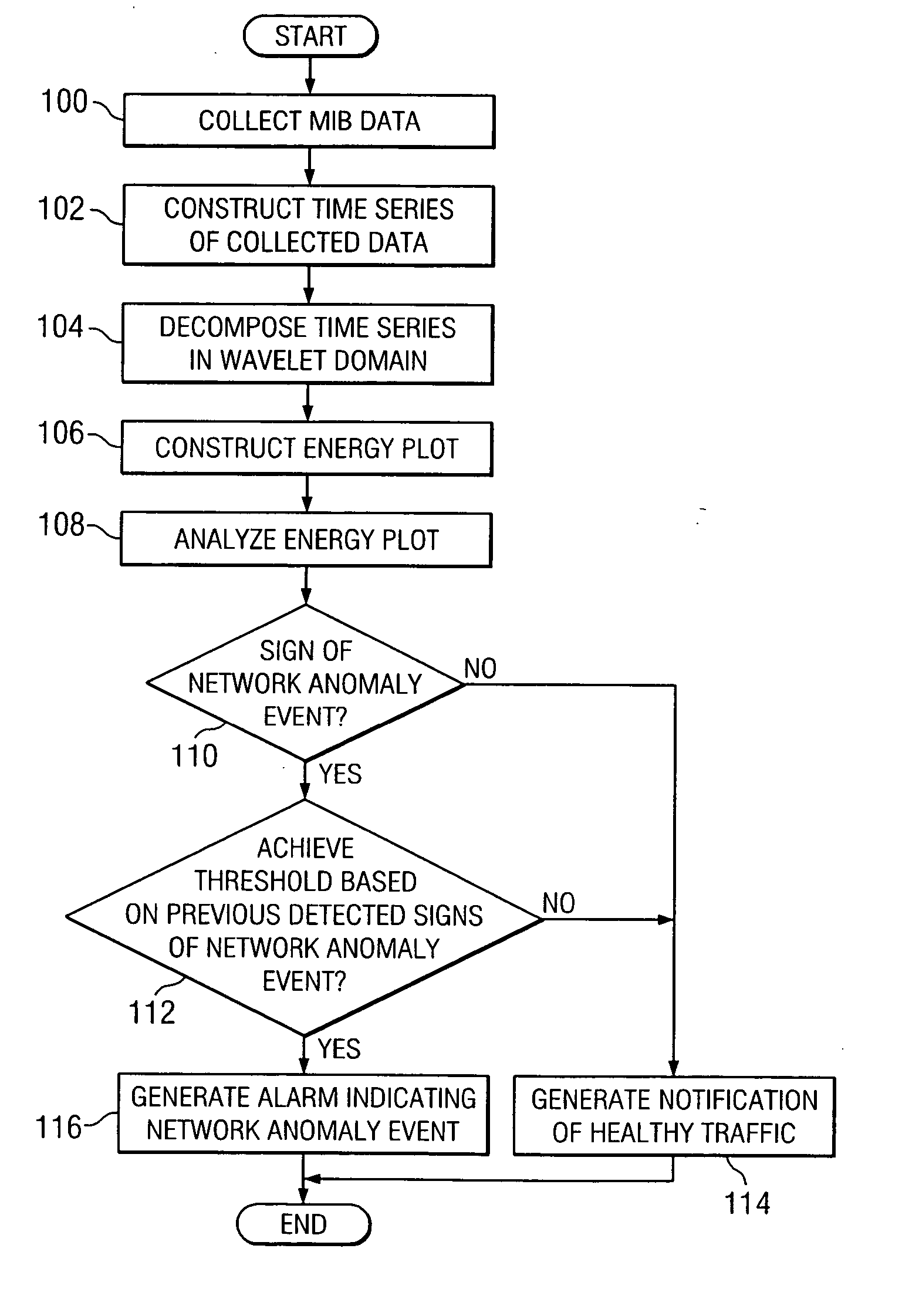
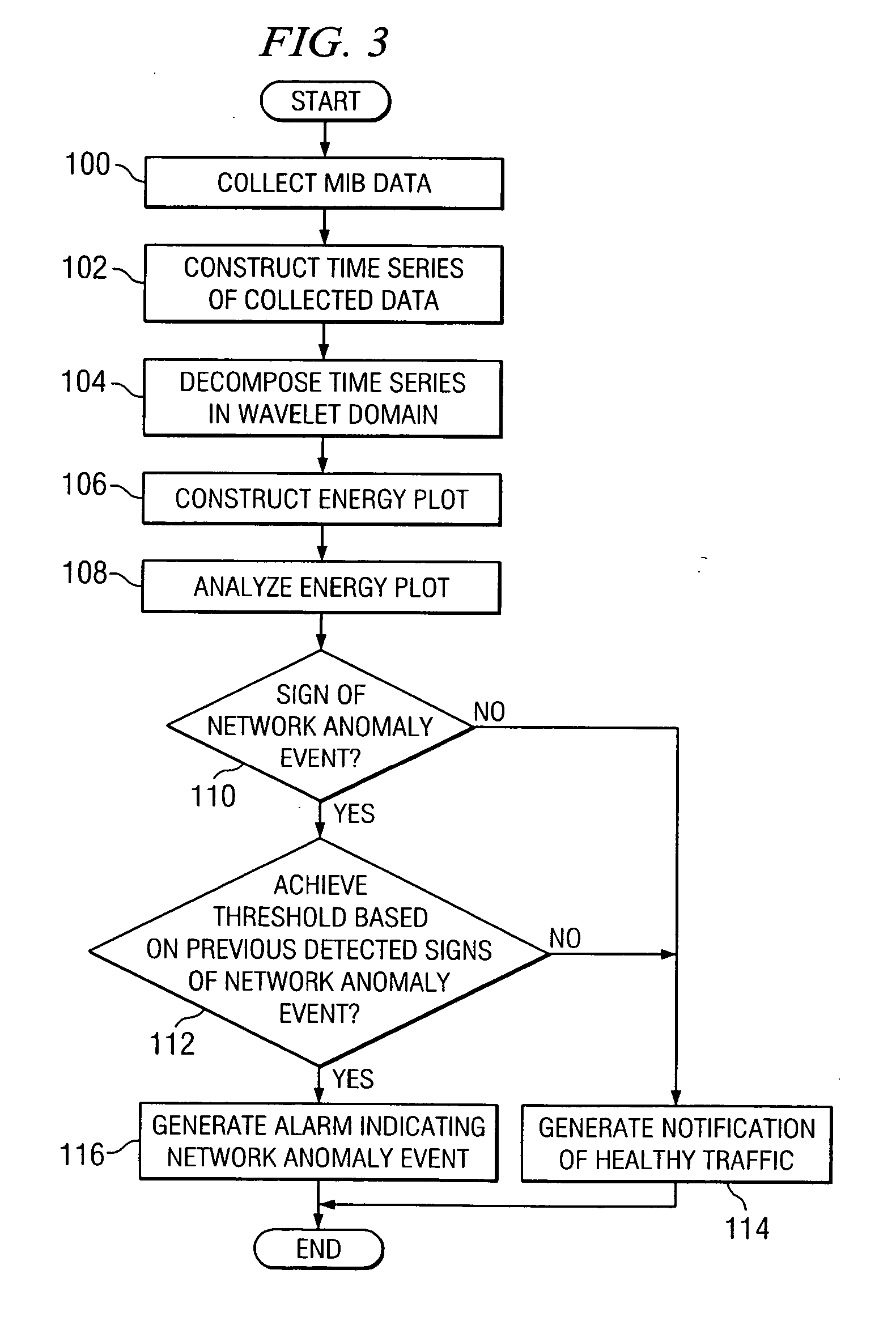
A method for detecting a network anomaly in a network includes collecting management information base (MIB) data from the network at an interval and constructing a time series of the collected data. The method also includes decomposing the time series of the collected data in the wavelet domain, constructing an energy plot based on the time series decomposed in the wavelet domain and analyzing the energy plot to determine a sign of a network anomaly event.
Owner:FUJITSU LTD
Method and apparatus for controlled access of requests from virtual private network devices to managed information objects using simple network management protocol and multi-topology routing
InactiveUS20050165834A1Simple and scalableSimple methodNetworks interconnectionSpecial data processing applicationsManagement information baseInformation repository
Access control approaches are disclosed wherein managed object in Simple Network Management Protocol (SNMP) Management Information Bases (MIBs) are accessed on a per- Virtual Private Network (VPN)-basis, taking into account multiple topologies that may exist under multi-topology routing (MTR) deployments, with no modifications to existing MIBs. One approach involves determining an identifier of a virtual private network in the request and a context name; determining, based on the context name, one or more sub-contexts that are either explicitly or implicitly specified in the context name; identifying, among a plurality of instances of managed objects that are associated with one or more routing topologies of a multi-topology routing system, a subset of object instances that requests associated with the virtual private network are permitted to access; and providing the request with access to only the subset of object instances.
Owner:CISCO TECH INC
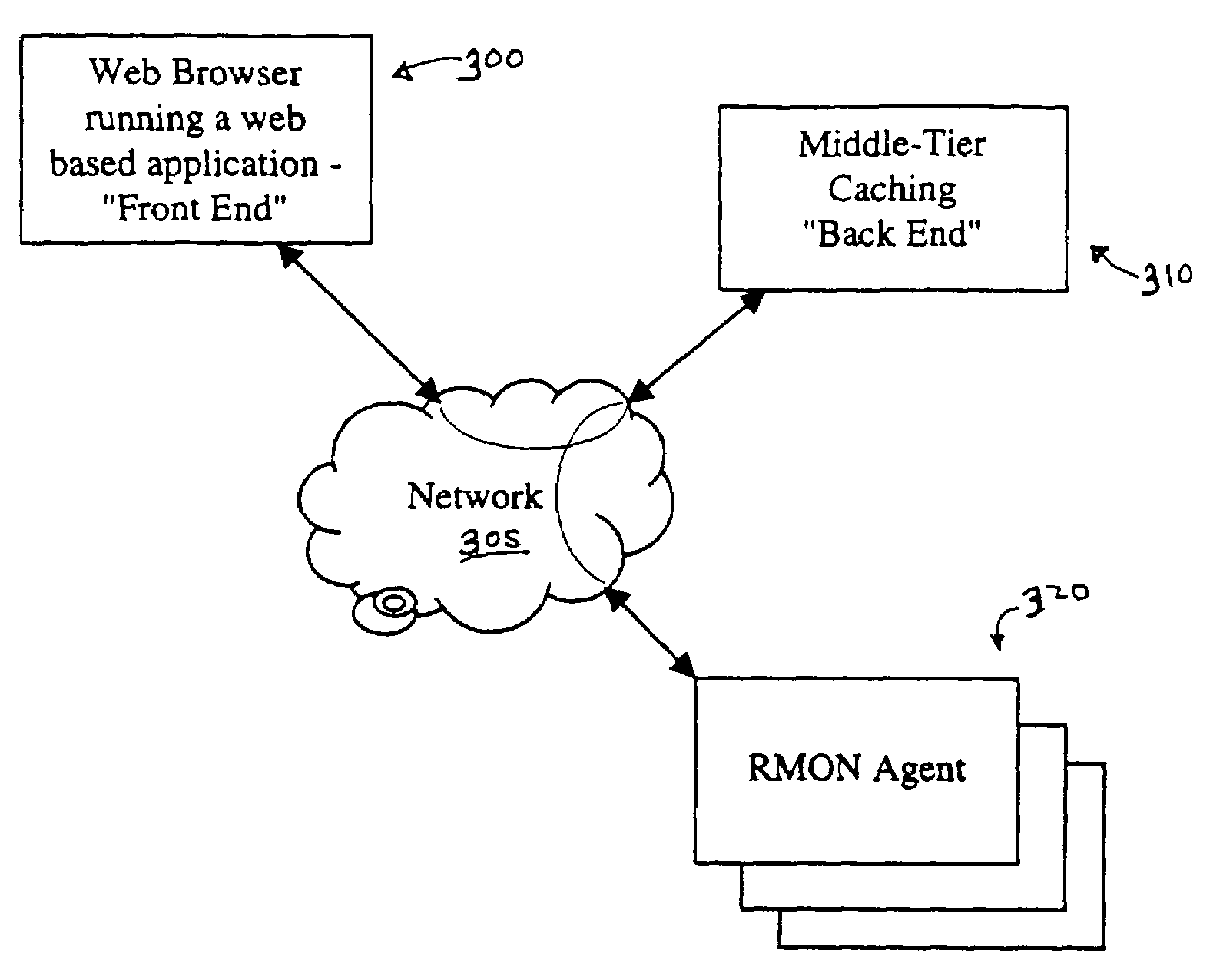
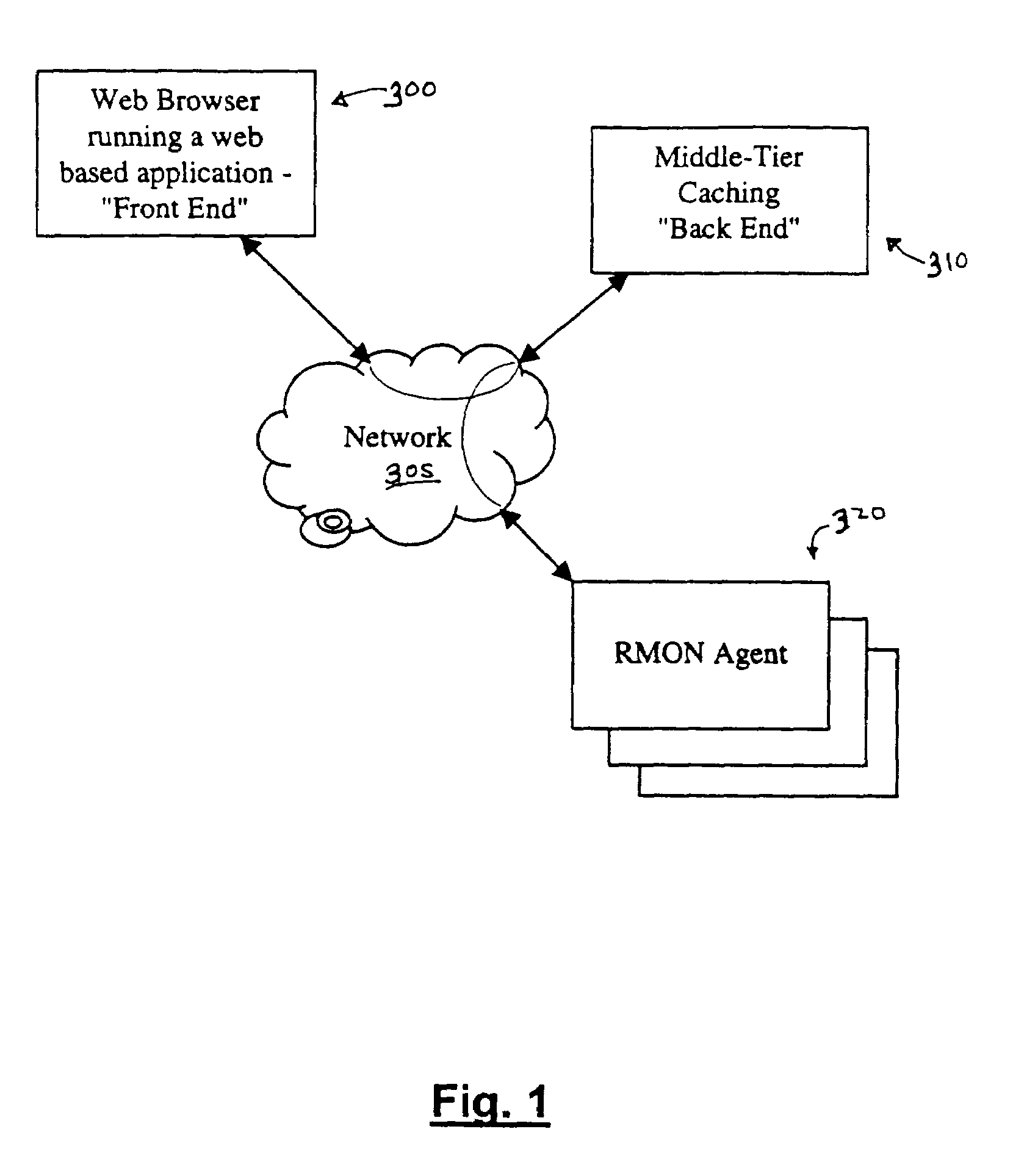
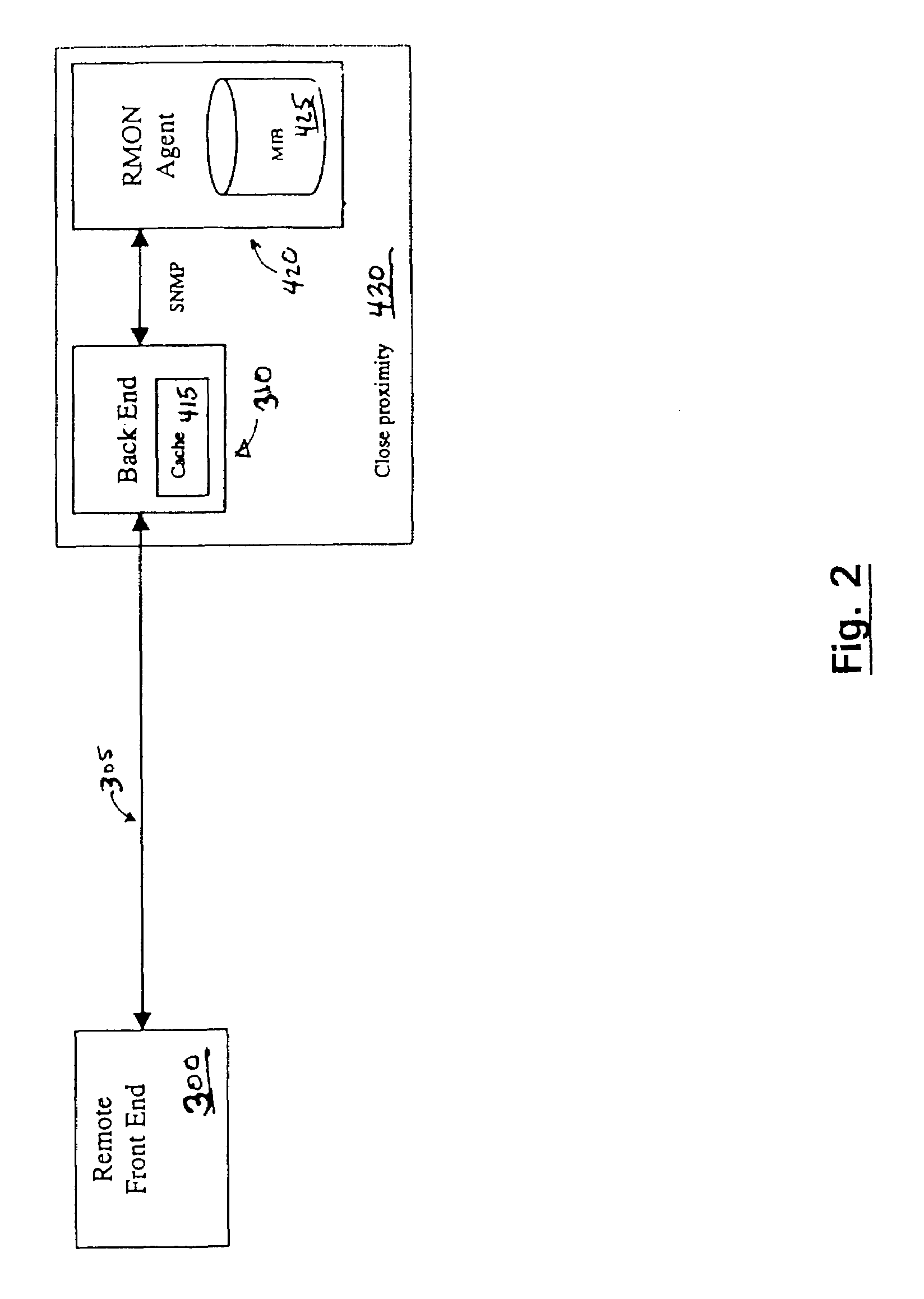
Method and architecture for a high performance cache for distributed, web-based management solutions
InactiveUS6954786B1Improve performanceReduce query timeMultiple digital computer combinationsData switching networksInformation repositoryManagement information base
An architecture for a management information system includes a backend that services information requests from a front end. The backend retrieves data from management information base(s) (MIBs) and prepares a response to the information requests. The backend maintains a cache of data recently retrieved from the MIBs and uses the cache to retrieve data, instead of making additional requests to the MIBs. The responses may be prepared from cache data only, MIB data only, or a combination of both. The back end is preferably maintained on a same segment of a network as the MIBs. Multiple MIBs may be queried from the back end, and the backend may coordinate with back ends on other segments of the network.
Owner:VALTRUS INNOVATIONS LTD
Methods and devices for discovering the topology of large multi-subnet LANs
InactiveUS20060256733A1Simple and efficient and practical mechanismHigh complexityData switching by path configurationInformation repositoryManagement information base
The physical topology of large, heterogeneous Ethernet LANs that may include multiple subnets may be discovered utilizing Management Information Base (MIB) information. Topology discovery tools and network management systems are introduced to carry out the topological discovery methods, features and functions of the present invention.
Owner:LUCENT TECH INC
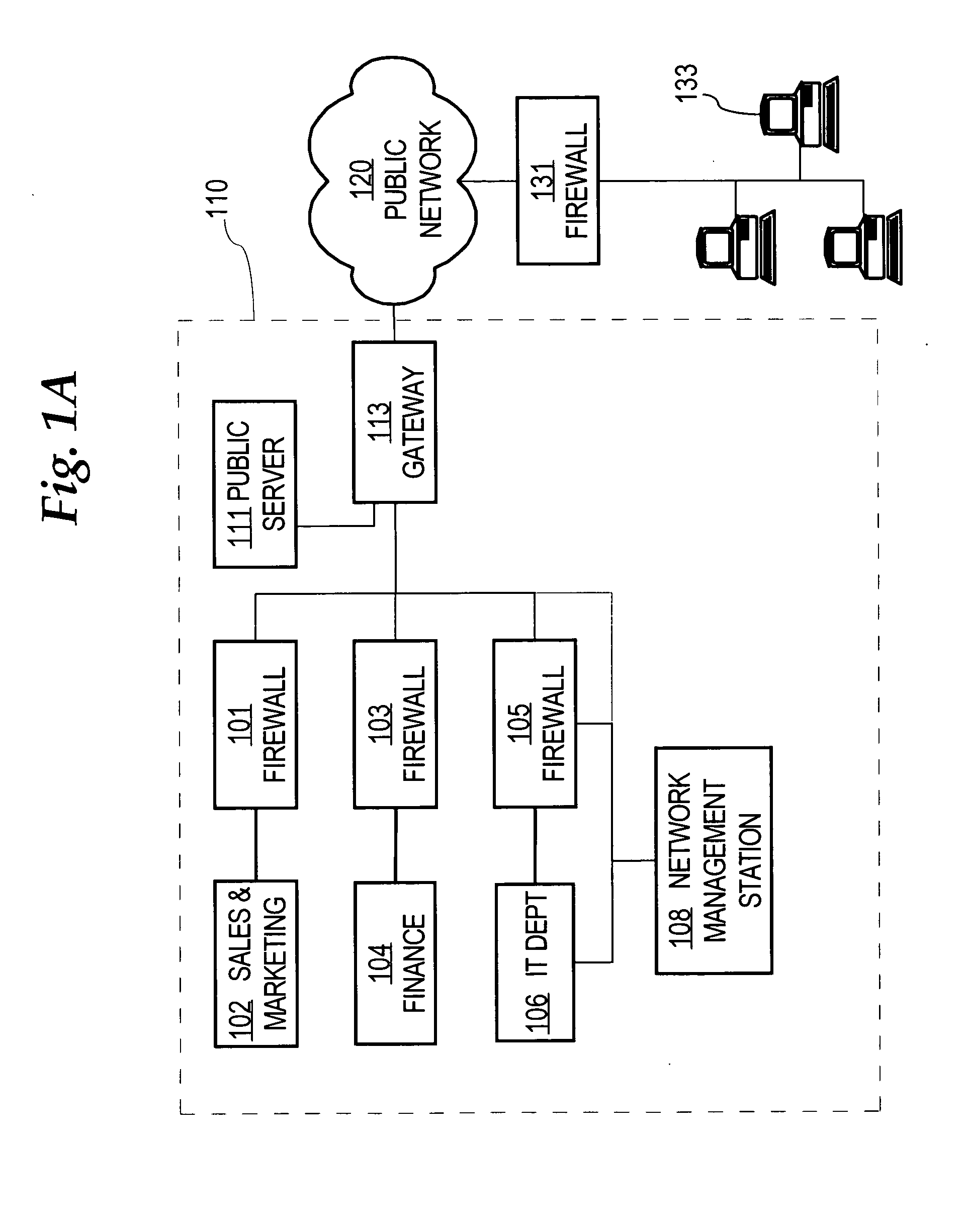
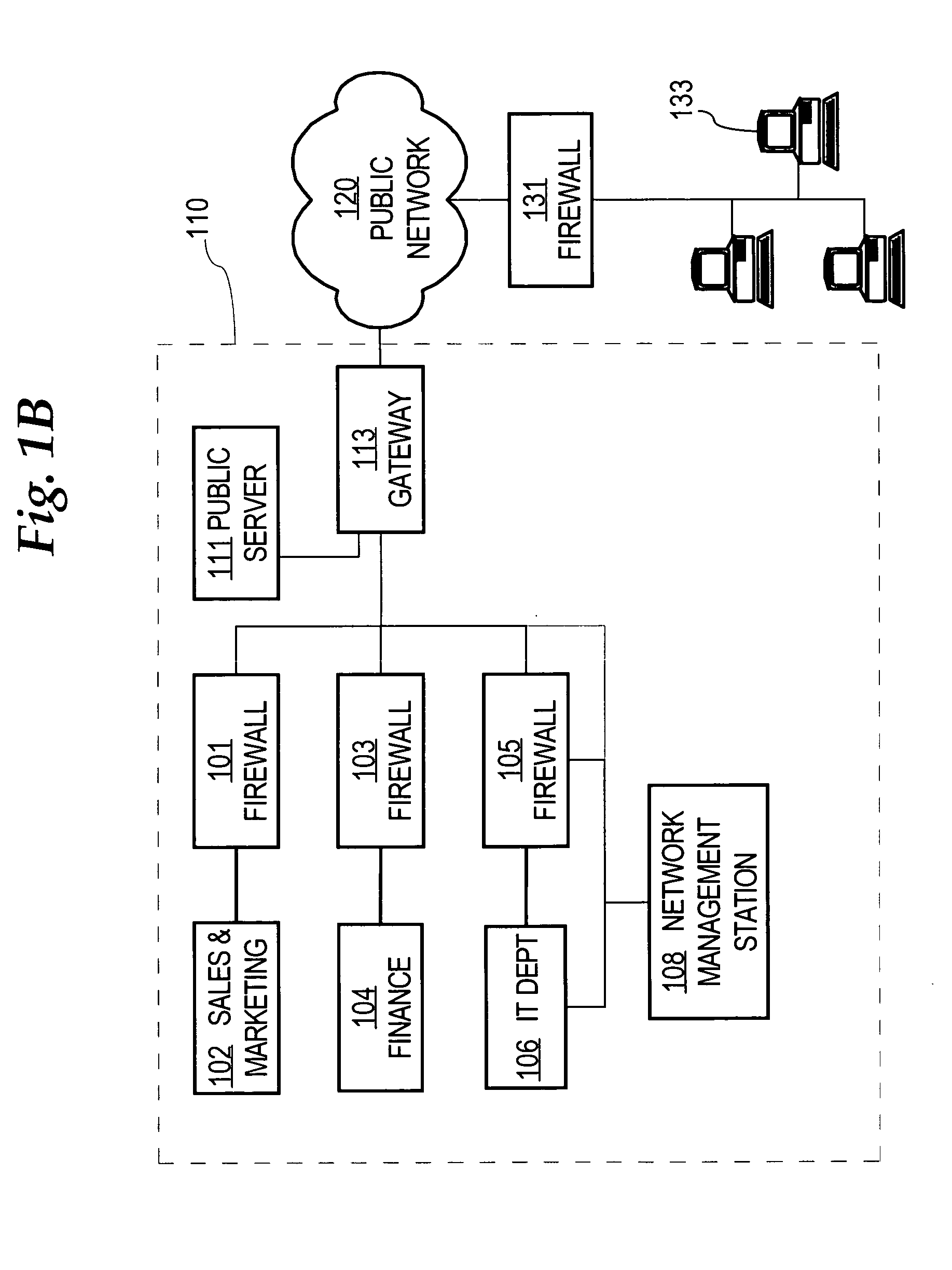
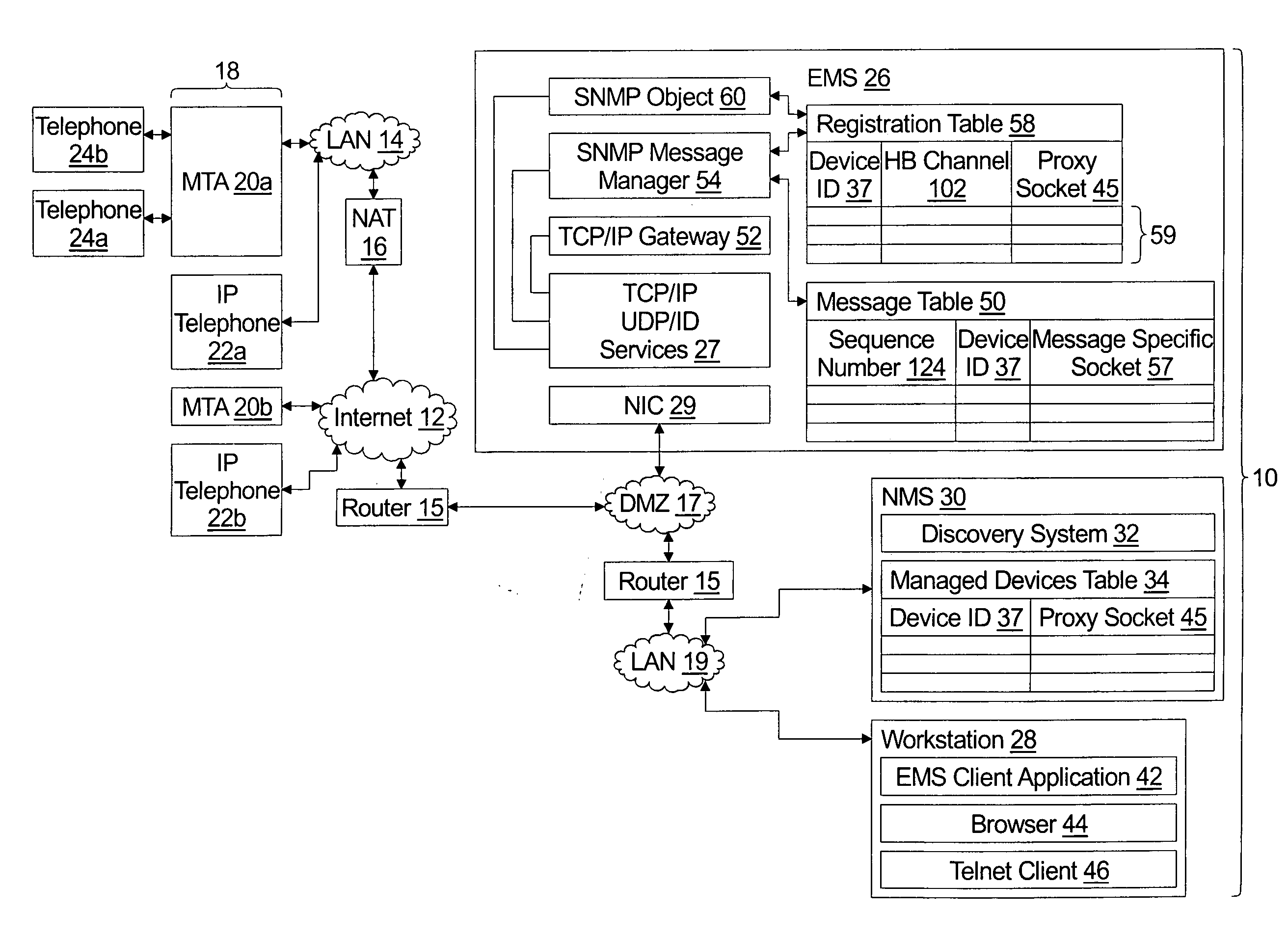
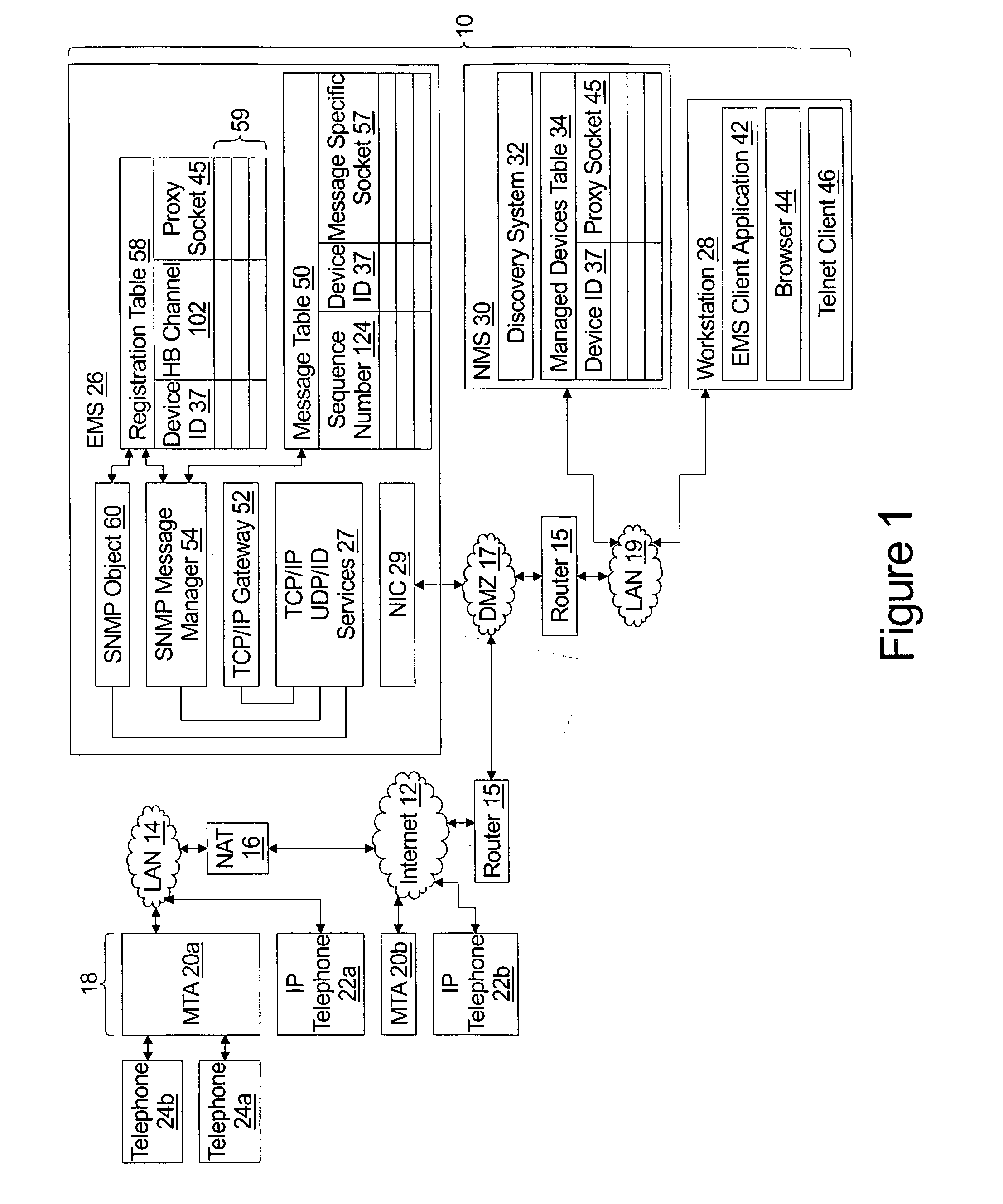
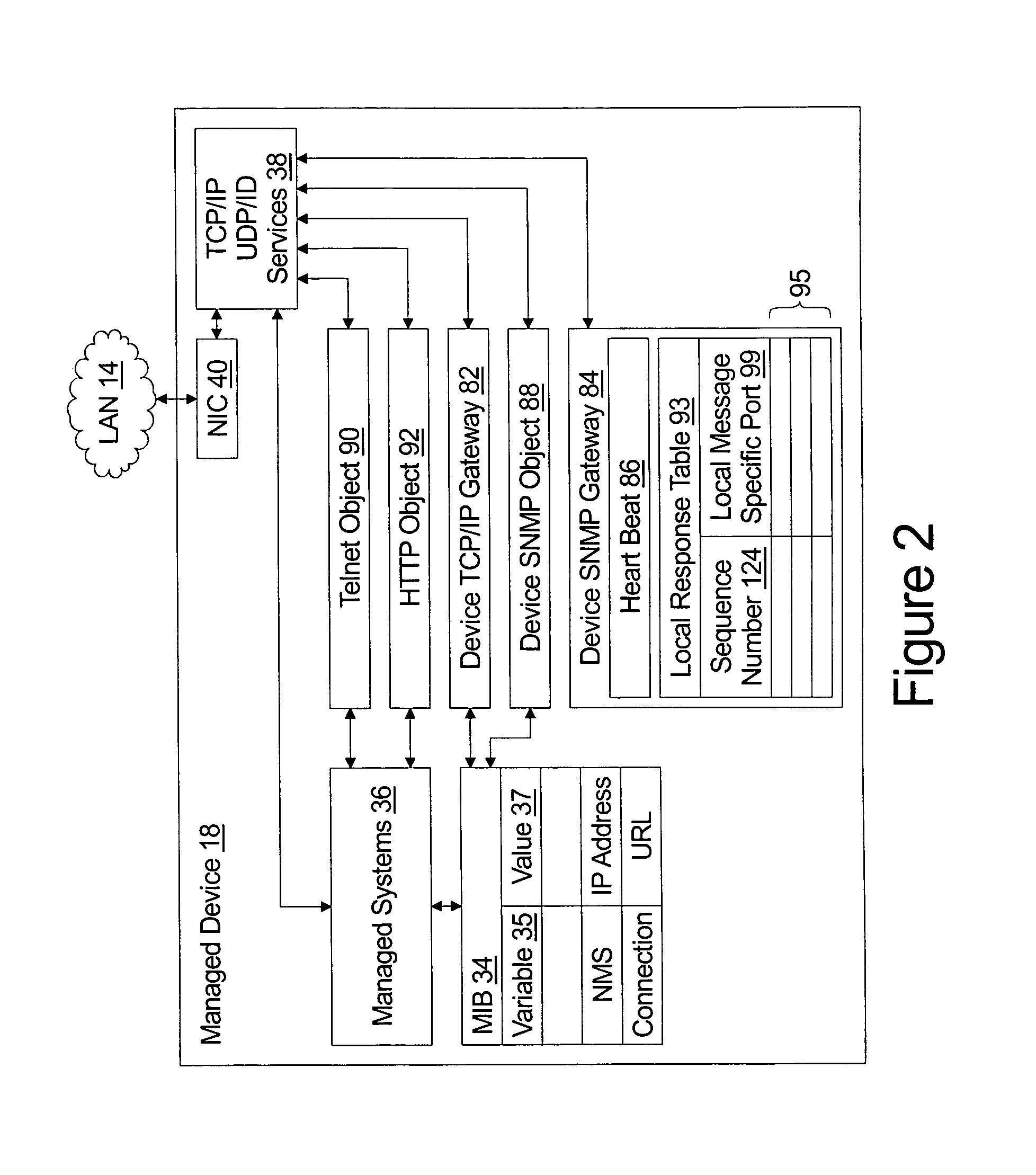
System for management of equipment deployed behind firewalls
ActiveUS20060077988A1Digital computer detailsData switching by path configurationInformation repositoryManagement information base
An element management system enables a network management server to provide a variable value to a management information base of a managed device independent of whether the managed device is served by a network address translation firewall. The element management system comprises an SNMP message manager which receives periodic heart beat frames from the managed device and stored identification of a heart beat channel in association with identification of the managed device in a registration table. The heart beat channel comprises the source socket and destination socket of the heart beat frame. The SNMP message manager further uniquely associates an assigned UDP port number with the managed device and provides the unique association of the assigned UDP port and the managed device to the network management server. The SNMP message manager further receives an SNMP Set from the network management server embodied as an IP frame addressed to the assigned UDP port number, looks up the managed device associated with the assigned UDP port number, and sends the SNMP Set to the managed device using the heartbeat channel.
Owner:INNOMEDIA PTE
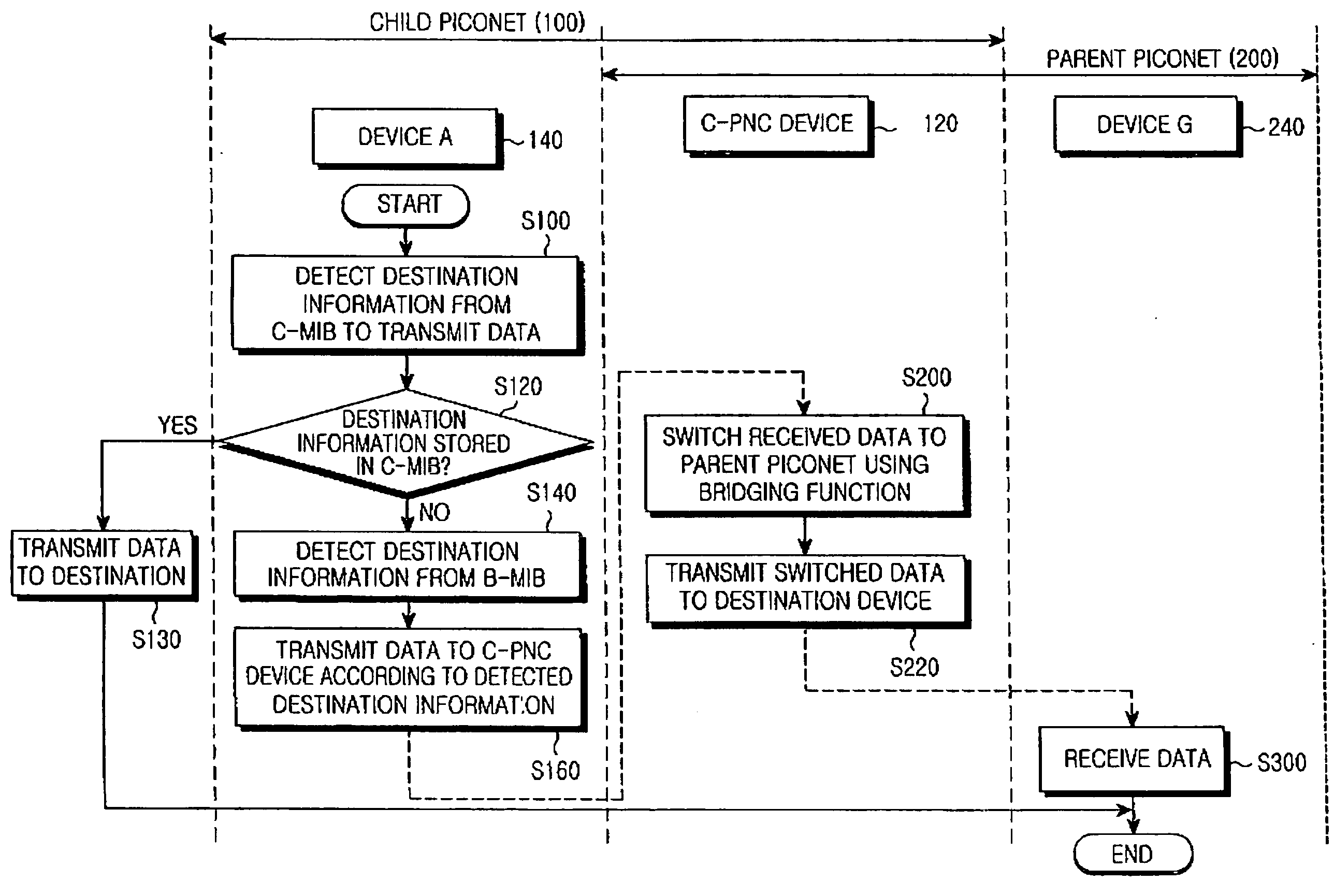
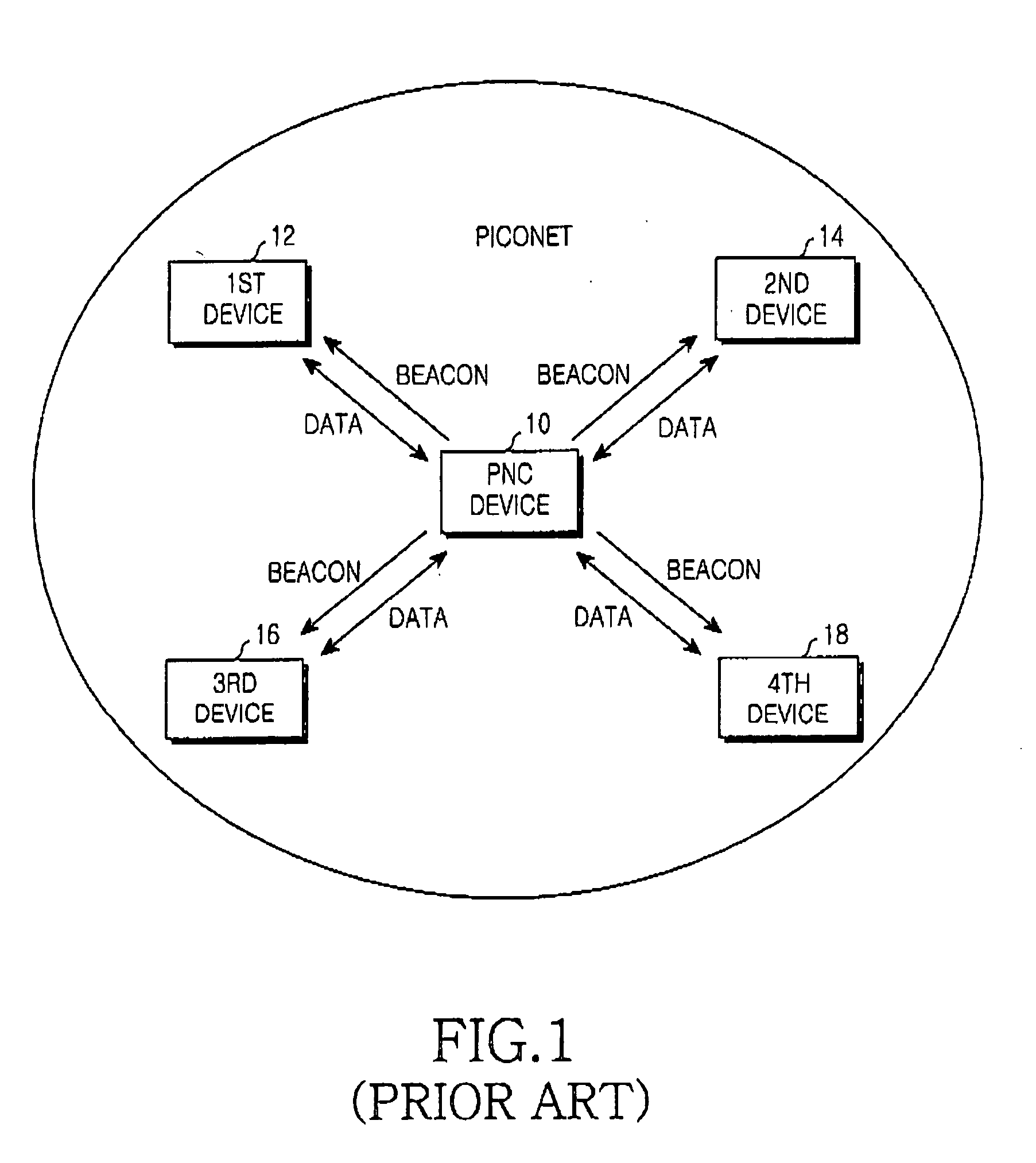
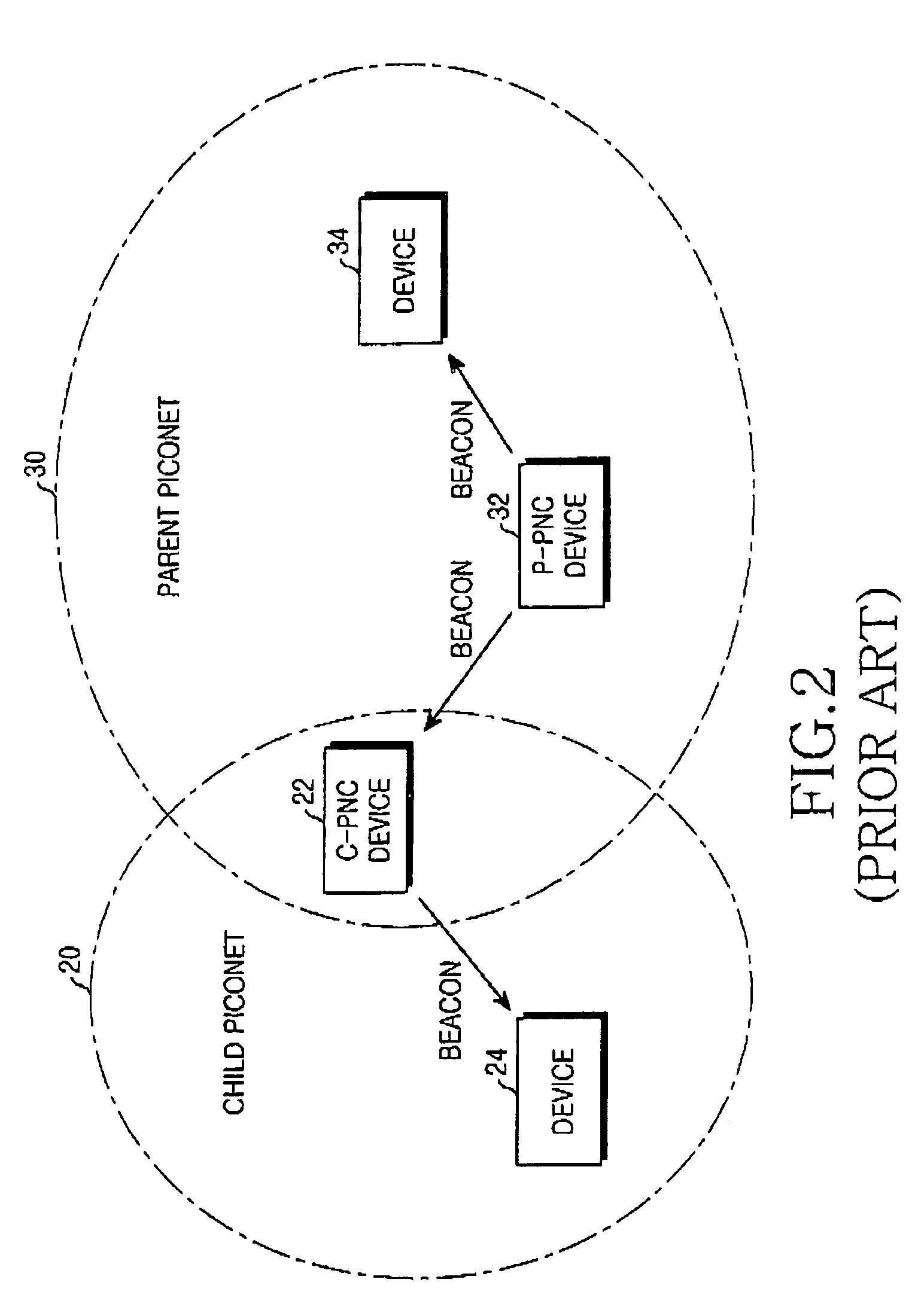
High-speed - WPAN and method for enabling communication between devices located in different piconets
ActiveUS20050026569A1Network topologiesCode division multiplexInformation repositoryManagement information base
A high-speed WPAN (Wireless Personal Area Network) system for enabling communication between piconets is configured by at least one first device located in the child piconet. A C-PNC (Child Piconet Coordinator) device includes a C-MIB (Child Piconet Management Information Base) stores mapping information associated with devices located in the child piconet and a P-MIB (Parent Piconet Management Information Base) stores mapping information associated with devices located in a parent piconet. At least one second device is located in the parent piconet. The first device includes a C-MIB and a first B-MIB (Bridging Management Information Base), detects destination information of data using the mapping information stored in the first B-MIB to transmit data to a device located in the parent piconet, and transmits the data containing the detected information to the C-PNC device. The C-PNC device broadcasts the mapping information stored in the C-MIB and P-MIB to different piconets, and switches and transmits the data from the first device to the parent piconet. The second device includes a P-MIB and a second B-MIB, and receives the data from the C-PNC device.
Owner:SAMSUNG ELECTRONICS CO LTD
Systems and methods for managing radio resources using extended management information bases in wireless networks
ActiveUS20100216467A1Facilitate data communicationError preventionFrequency-division multiplex detailsInformation repositoryMicrocell
A networked computing system, including multiple radio access nodes (RANs), multiple radio communications controllers (RCCs), and a data communications network facilitating communications amongst the RANs and the RCCs of the system. A regional RAN receives a default eMIB associated with a first type of RAN (e.g., a macrocell, microcell, picocells, or femtocell RAN types) from a RCC, in response to a registration event of a RAN initialization process. The regional RAN maintains a dynamic eMIB comprising network operating parameters determined by various self-optimization processes. The network operating parameters of the dynamic eMIB are selected to fall within a range designated by the default eMIB. During a network failure condition, the regional RAN is configured to use a temporary eMIB comprising failure level operating parameters in order to mitigate network deficiencies caused by the network failure condition.
Owner:VIVO MOBILE COMM CO LTD
Automatic implementation of network configuration changes
InactiveUS6894983B1Lighten the computational burdenFunction increaseError preventionTransmission systemsInformation repositoryManagement information base
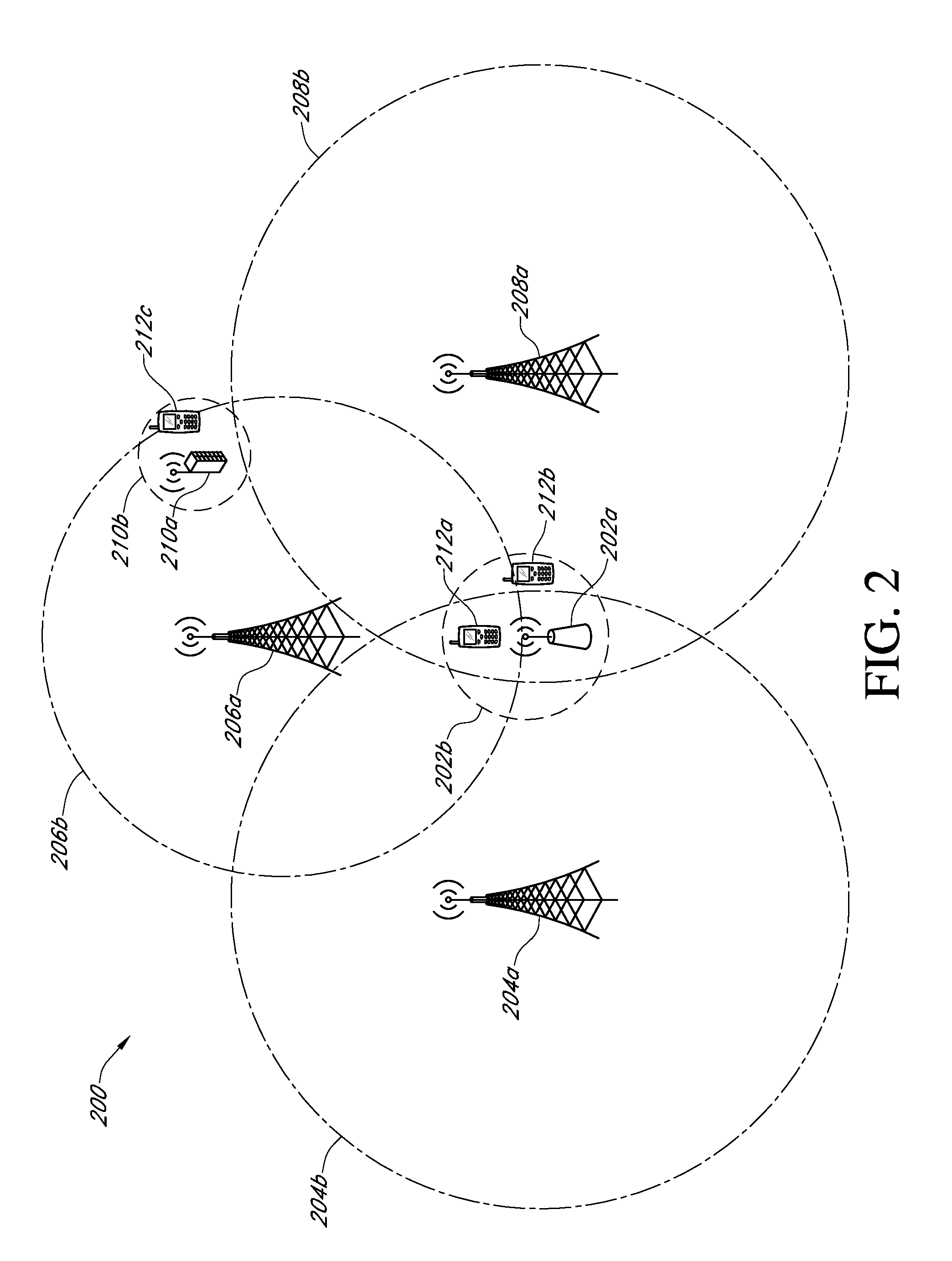
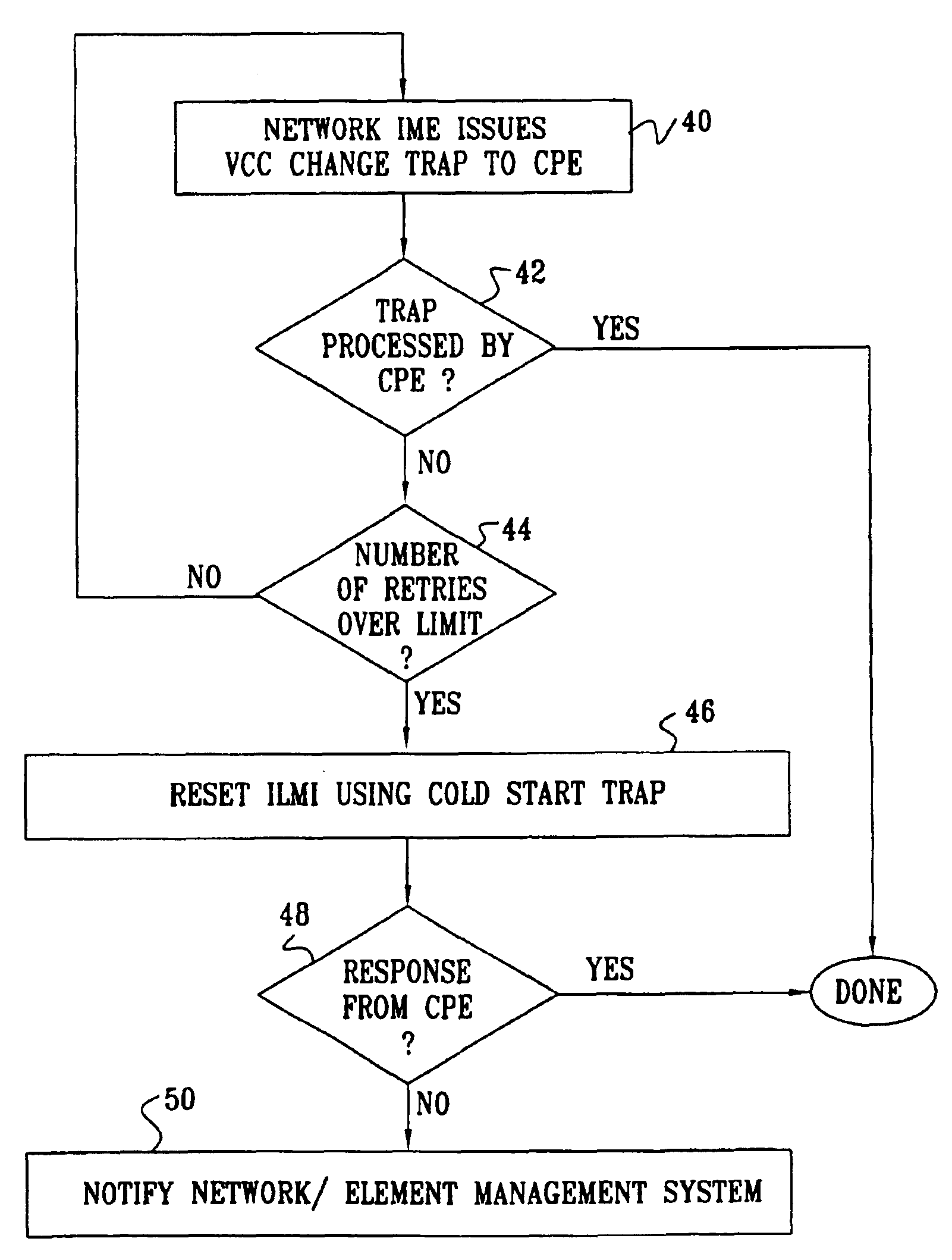
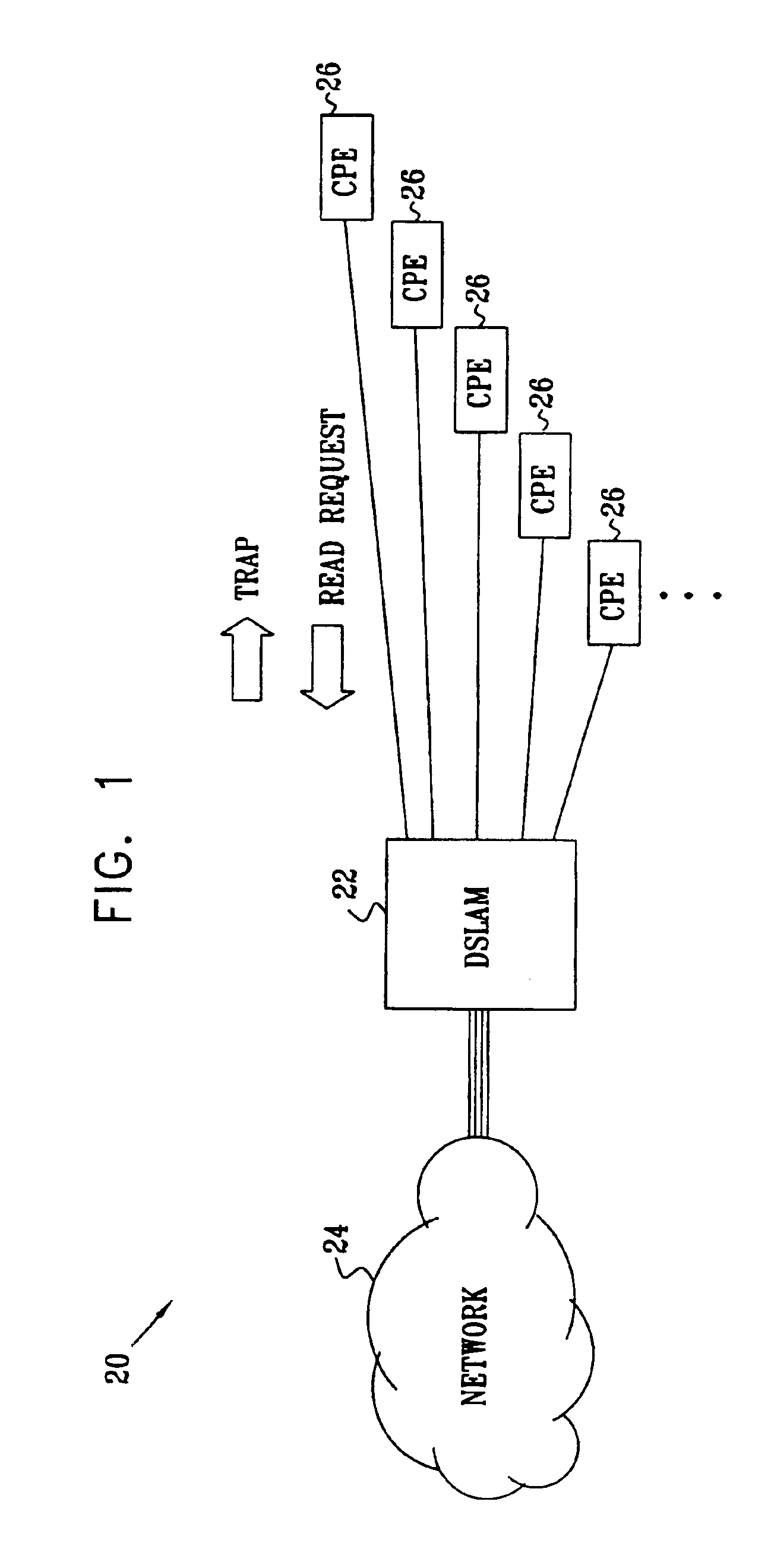
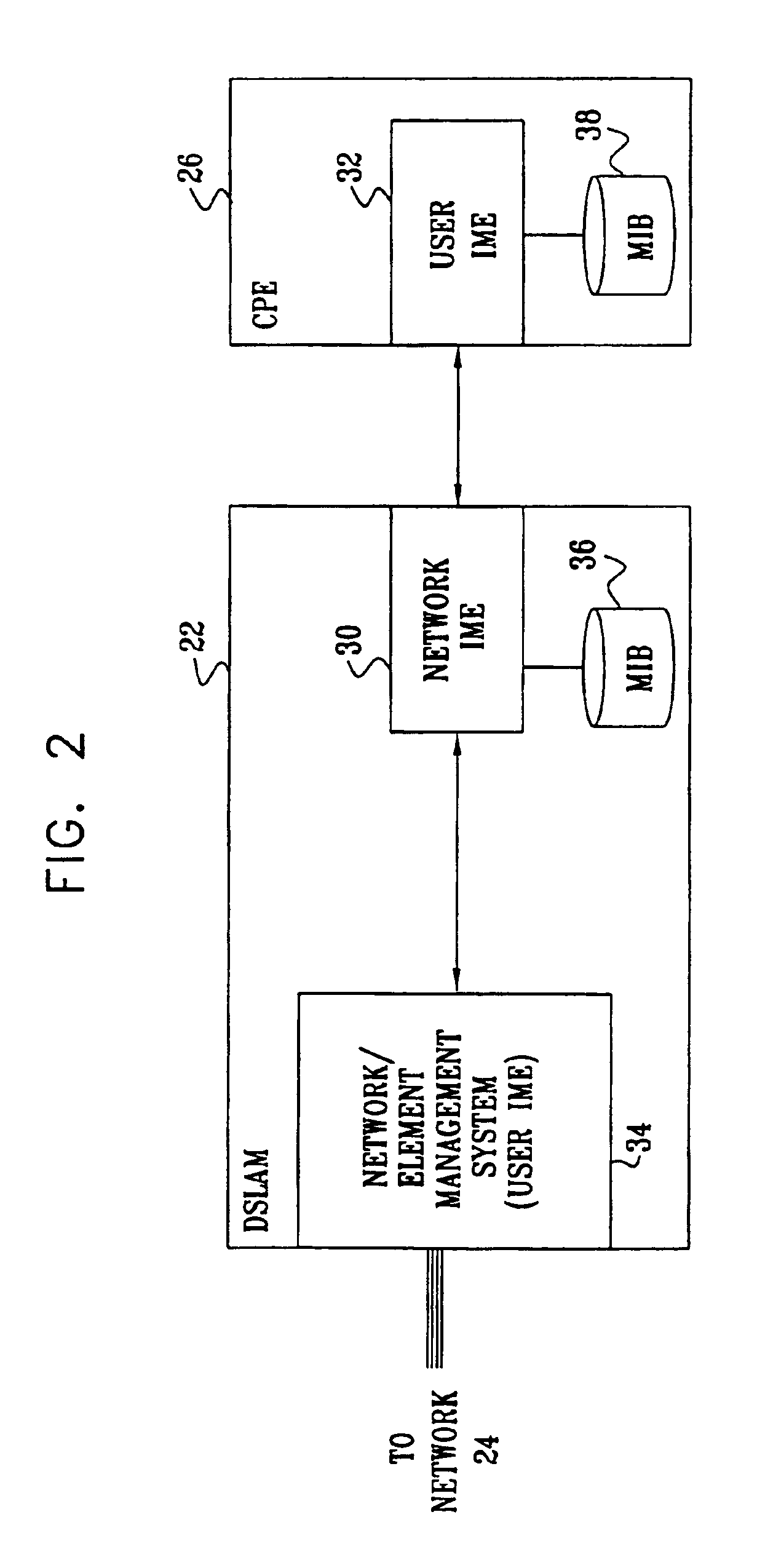
A method for network management includes sending a trap message from a network end switch to client premises equipment (CPE) over a network connection therebetween, informing the CPE of a change in a network management information base (MIB) of the end switch. A request from the CPE to the end switch, subsequent to the trap message, to read information from the MIB, and the information is provided from the end switch to the CPE responsive to the request. The change is determined to have been implemented by the CPE based on the request to read the information. There is thus no need for the CPE to poll the processor for further trap messages.
Owner:ORCKIT CORP
Automatic optimization for virtual systems
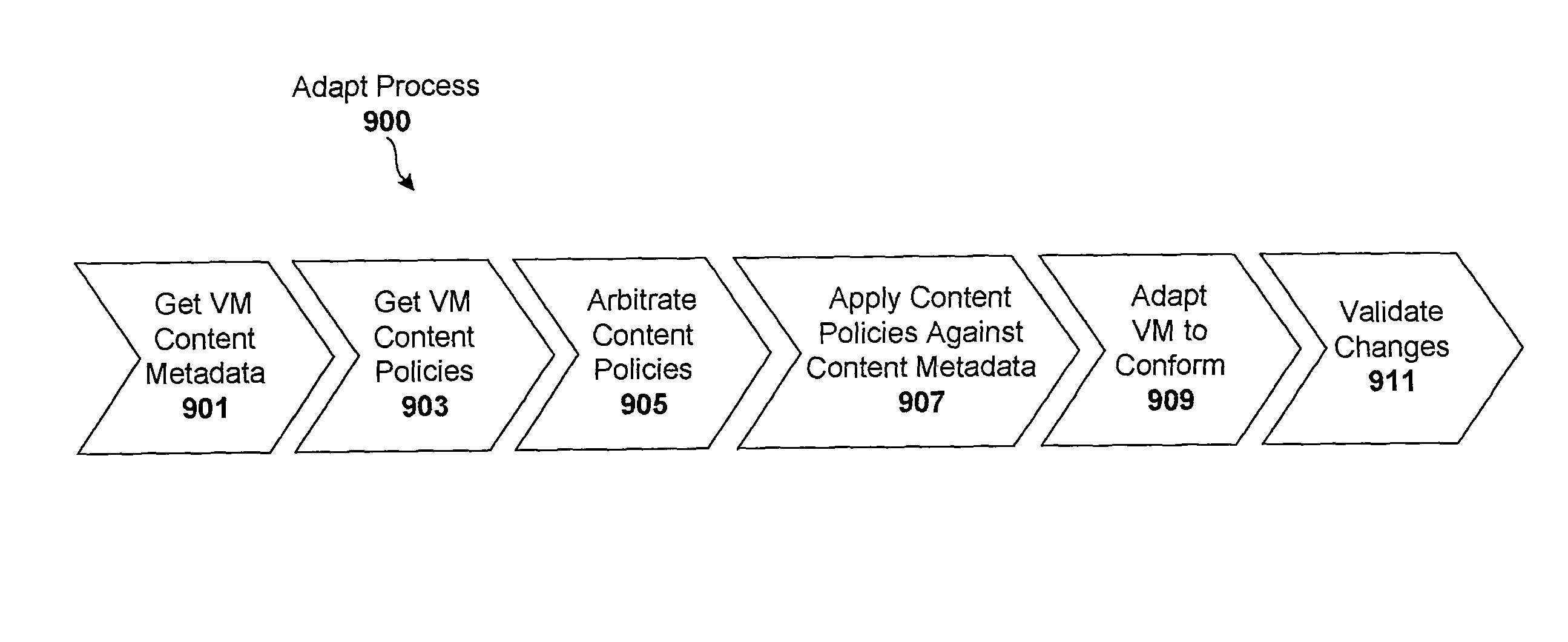
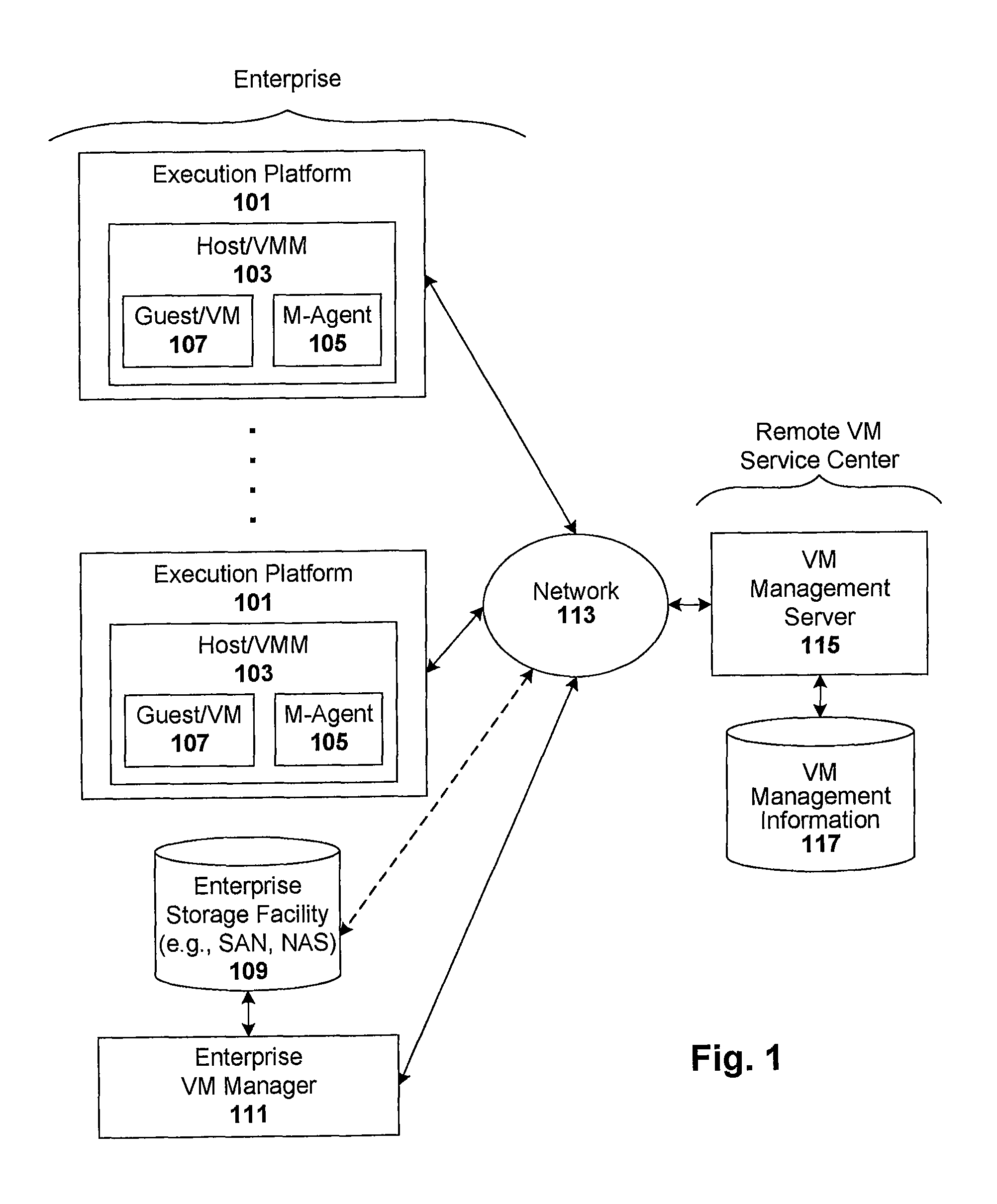
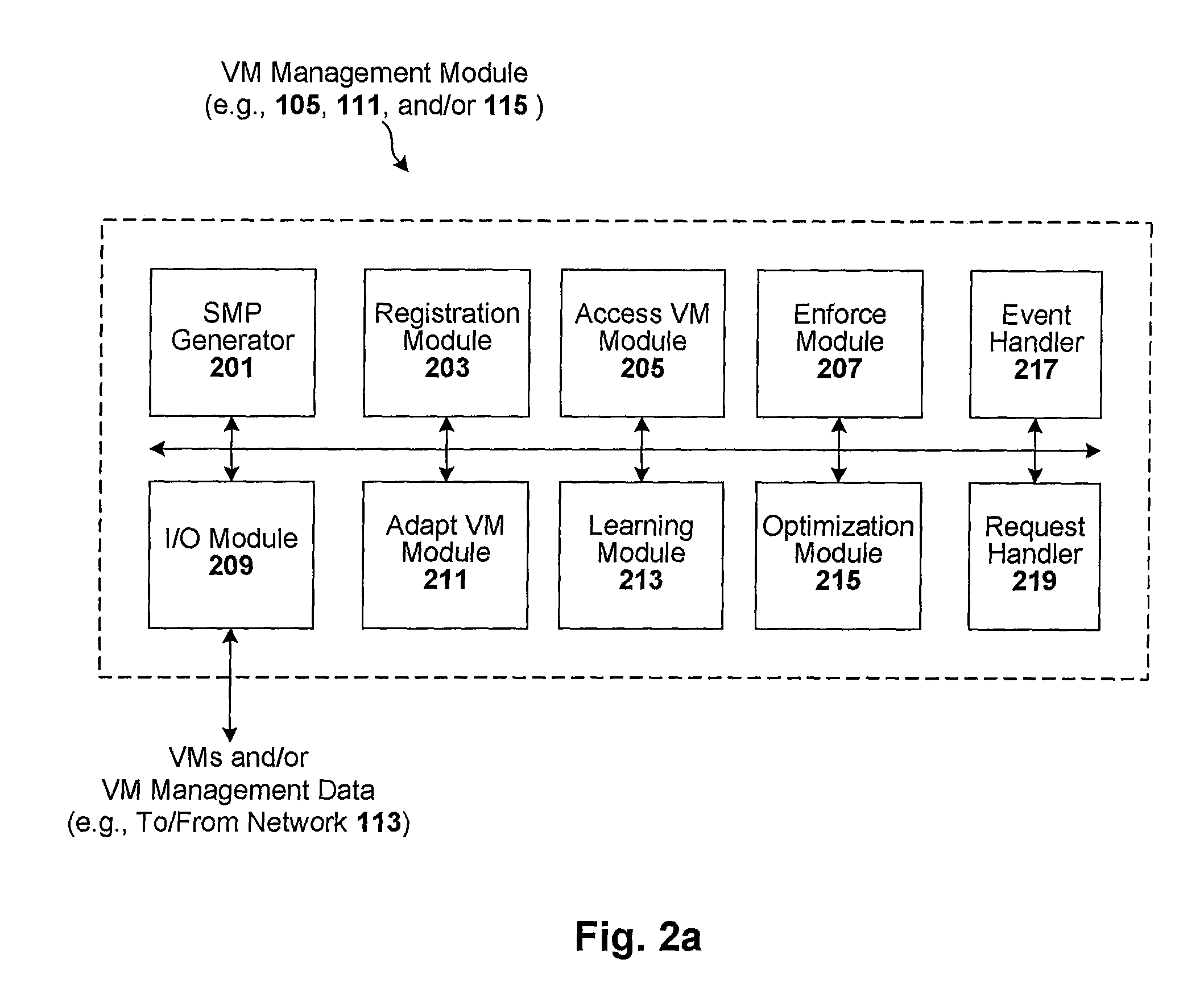
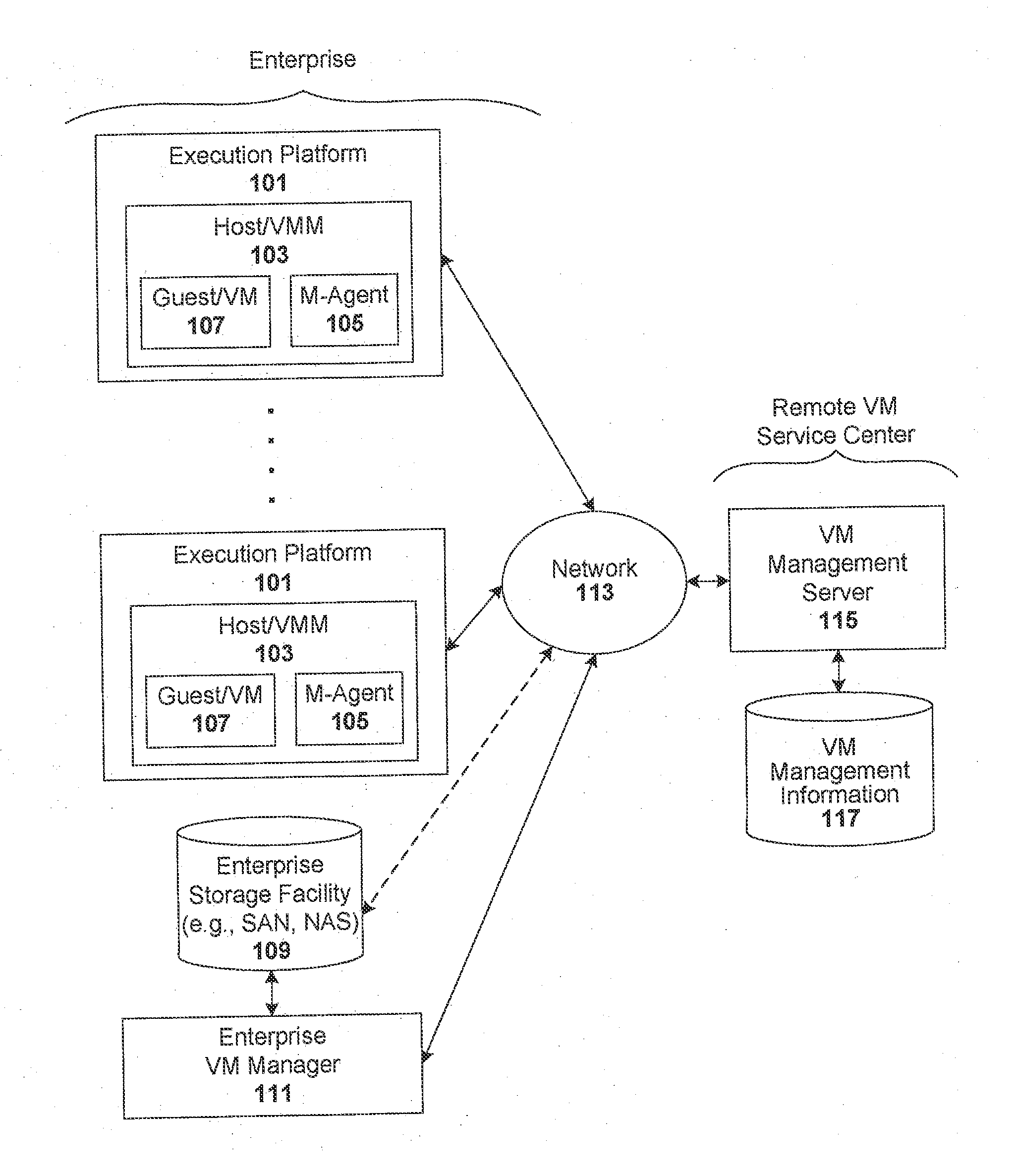
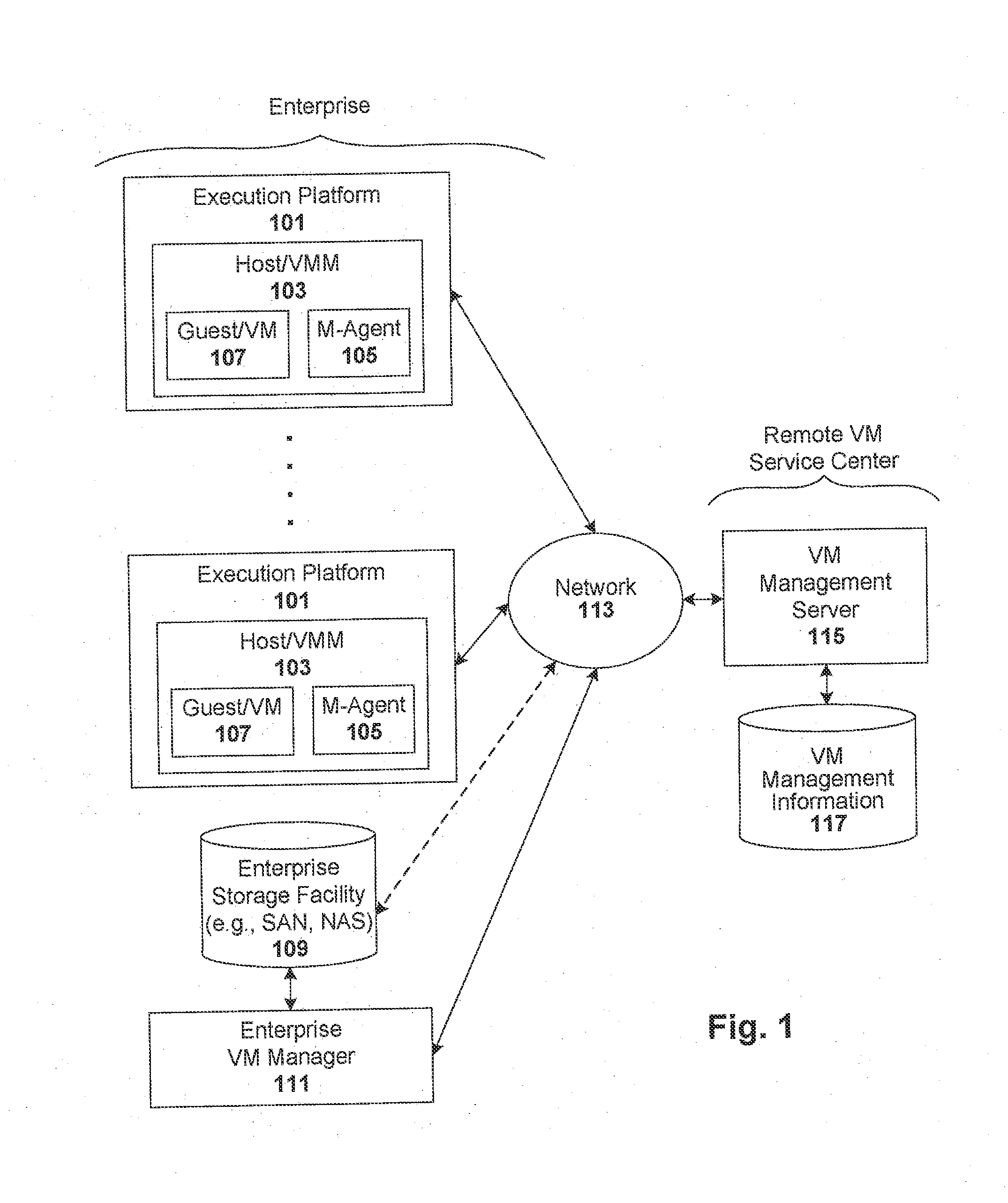
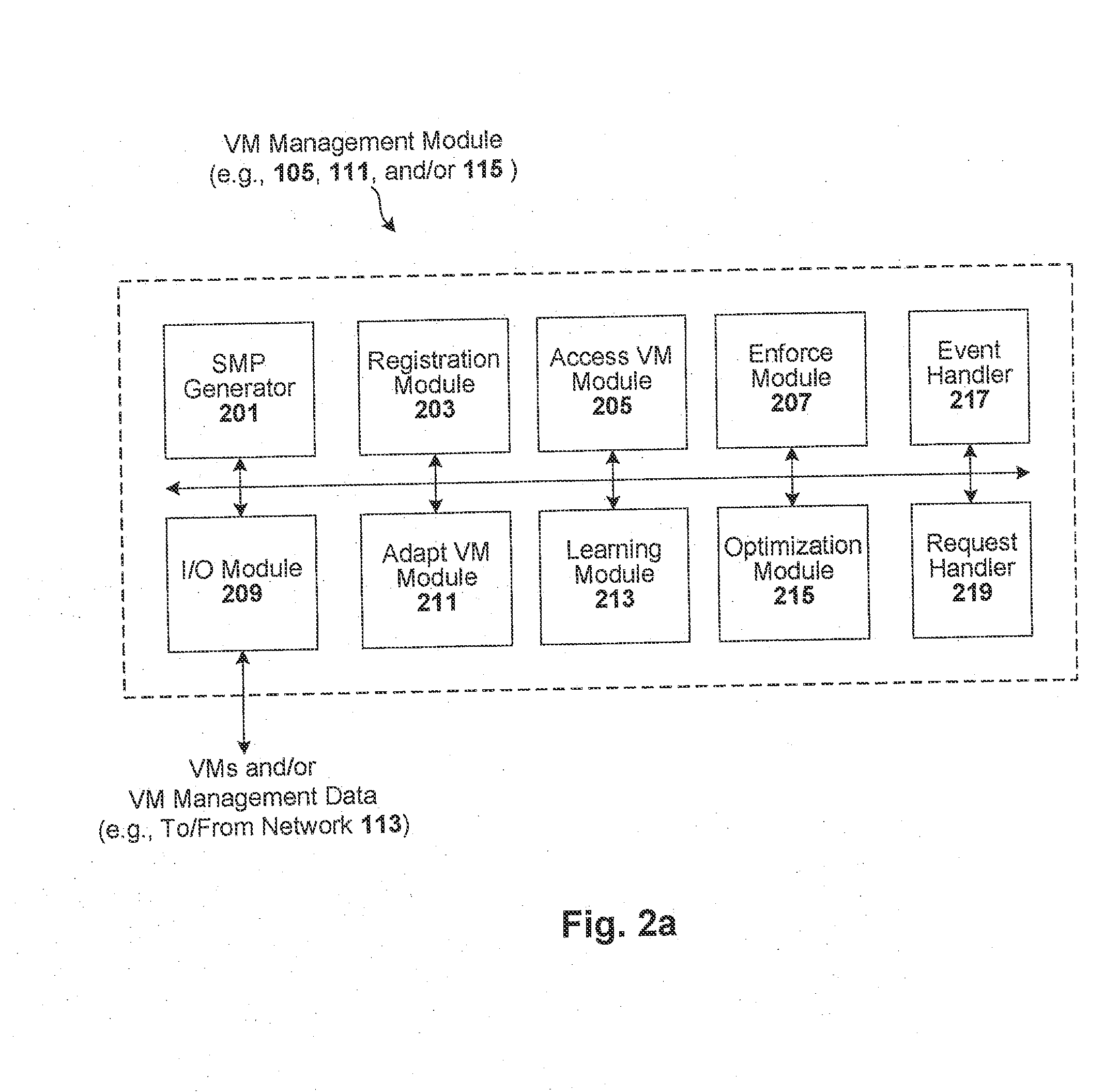
ActiveUS8458695B2Memory loss protectionError detection/correctionManagement information baseConsistency test
Techniques are disclosed for controlling and managing virtual machines and other such virtual systems. VM execution approval is based on compliance with policies controlling various aspects of VM. The techniques can be employed to benefit all virtual environments, such as virtual machines, virtual appliances, and virtual applications. For ease of discussion herein, assume that a virtual machine (VM) represents each of these environments. In one particular embodiment, a systems management partition (SMP) is created inside the VM to provide a persistent and resilient storage for management information (e.g., logical and physical VM metadata). The SMP can also be used as a staging area for installing additional content or agentry on the VM when the VM is executed. Remote storage of management information can also be used. The VM management information can then be made available for pre-execution processing, including policy-based compliance testing.
Owner:RED HAT
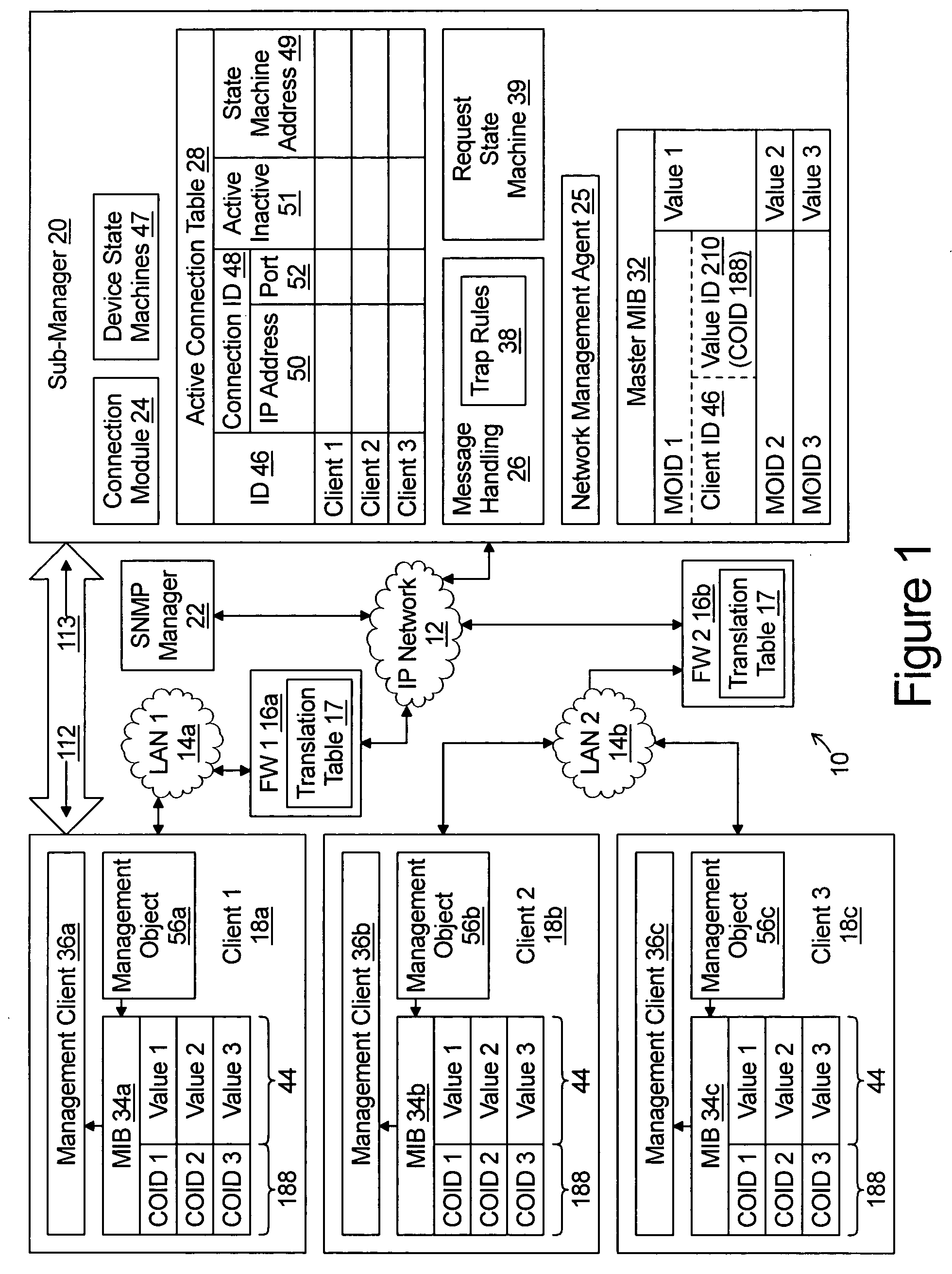
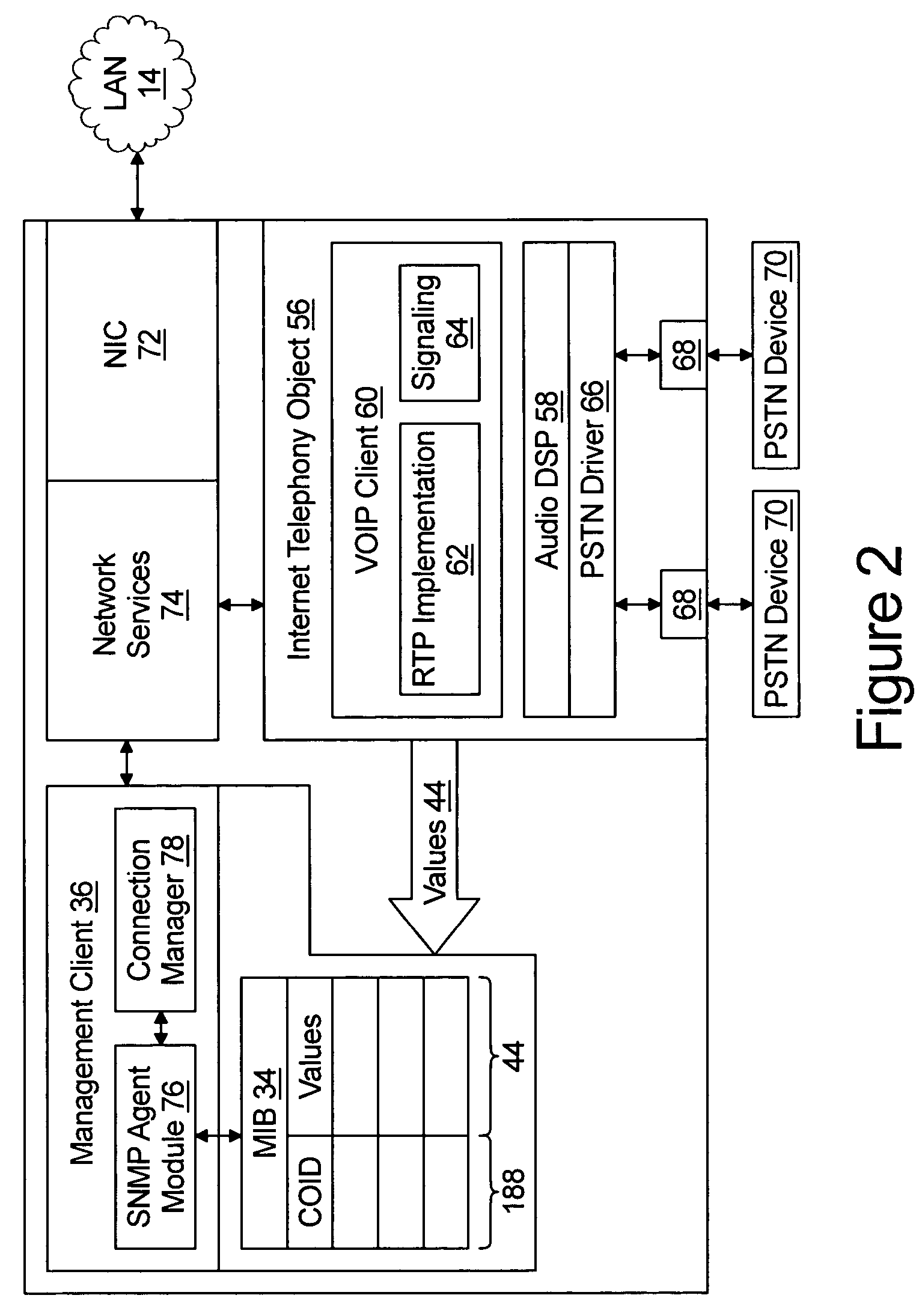
System for management of Internet telephony equipment deployed behind firewalls
A sub-manager interfaces between a traditional SNMP network management system (NMS) a plurality of clients, each of which may be served by a network address and port translation firewall. The sub-manager operates a master management information base and receives master network management request messages from the network management server. The master network management request message includes at least one master object identifier which comprises a client identifier which identifies a particular one of the clients and a variable portion that identifies a variable value within a client management information base. The sub-manager, in response, generates one or more client network management request messages to identified clients over TCP / IP connections through the firewall. The client network management request message includes a client object identifier that identifies the variable within the client management information base.
Owner:INNOMEDIA PTE
Automatic optimization for virtual systems
ActiveUS20140082621A1Software simulation/interpretation/emulationMemory systemsManagement information baseConsistency test
Techniques are disclosed for controlling and managing virtual machines and other such virtual systems. VM execution approval is based on compliance with policies controlling various aspects of VM. The techniques can be employed to benefit all virtual environments, such as virtual machines, virtual appliances, and virtual applications. For ease of discussion herein, assume that a virtual machine (VM) represents each of these environments. In one particular embodiment, a systems management partition (SMP) is created inside the VM to provide a persistent and resilient storage for management information (e.g., logical and physical VM metadata). The SMP can also be used as a staging area for installing additional content or agentry on the VM when the VM is executed. Remote storage of management information can also be used. The VM management information can then be made available for pre-execution processing, including policy-based compliance testing.
Owner:RED HAT
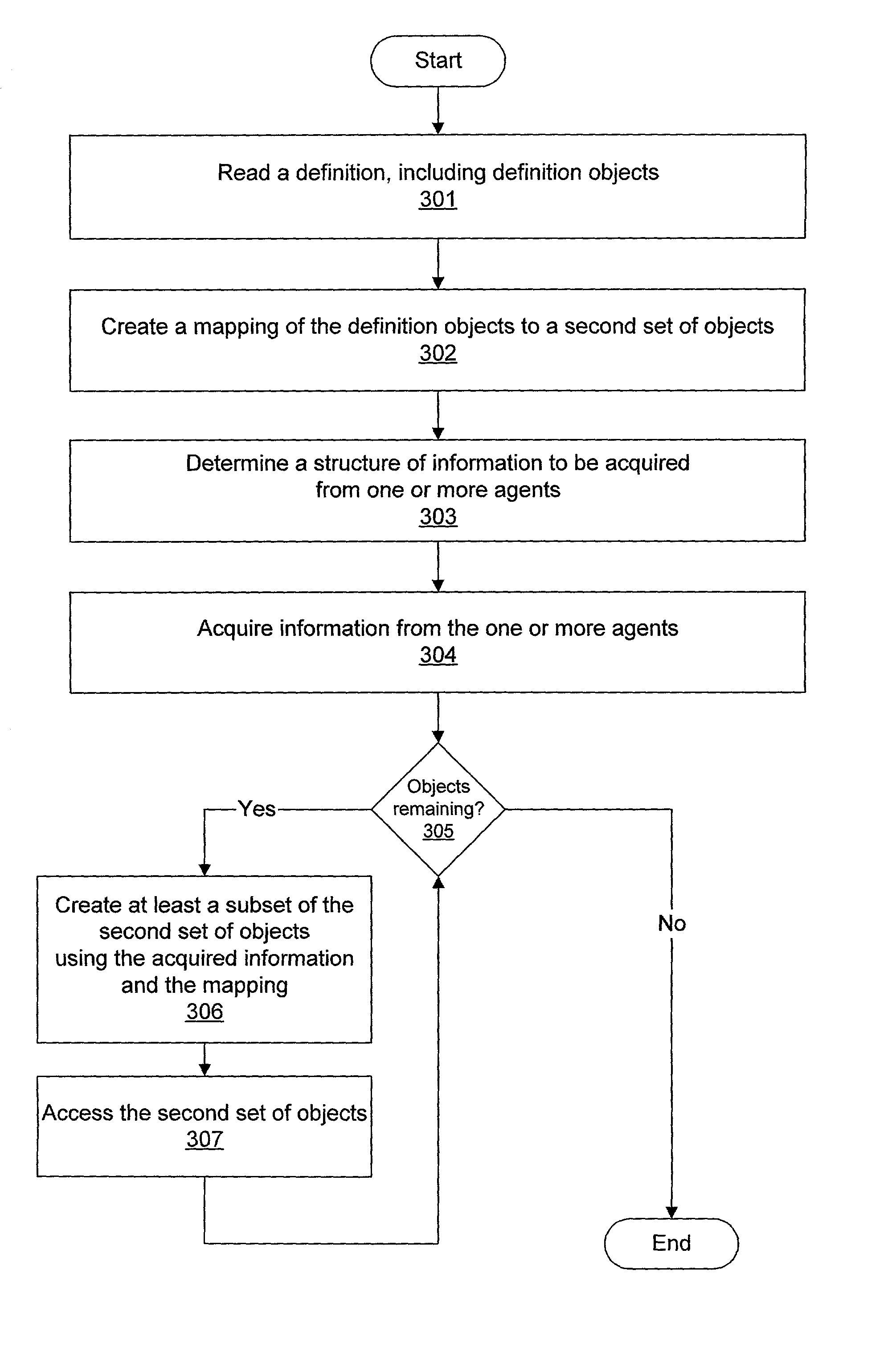
System and method for converting data structures
InactiveUS20030220963A1Multiple digital computer combinationsData switching networksManagement information baseImproved method
An improved method and system for converting data structures. A definition (e.g., a management information base definition) may be read. The definition may include definition objects. A mapping of the definition objects to a second set of objects may be created. The second set of objects may be common object system (COS) objects. A structure of information to be acquired from one or more agents may be determined, in response to reading the definition. The structure of the information may be metadata. The one or more agents may be simple network management protocol agents, or other types of agents, as desired. Information may be acquired from the one or more agents, in response to determining the structure of the information. At least a subset of the second set of objects may be created, using the acquired information and the mapping. The second set of objects may be accessed.
Owner:BMC SOFTWARE
Method for configuring and managing access point and access controller
InactiveUS20090141694A1Configuration managementReduce management costsNetwork topologiesData switching by path configurationComputer hardwareManagement information base
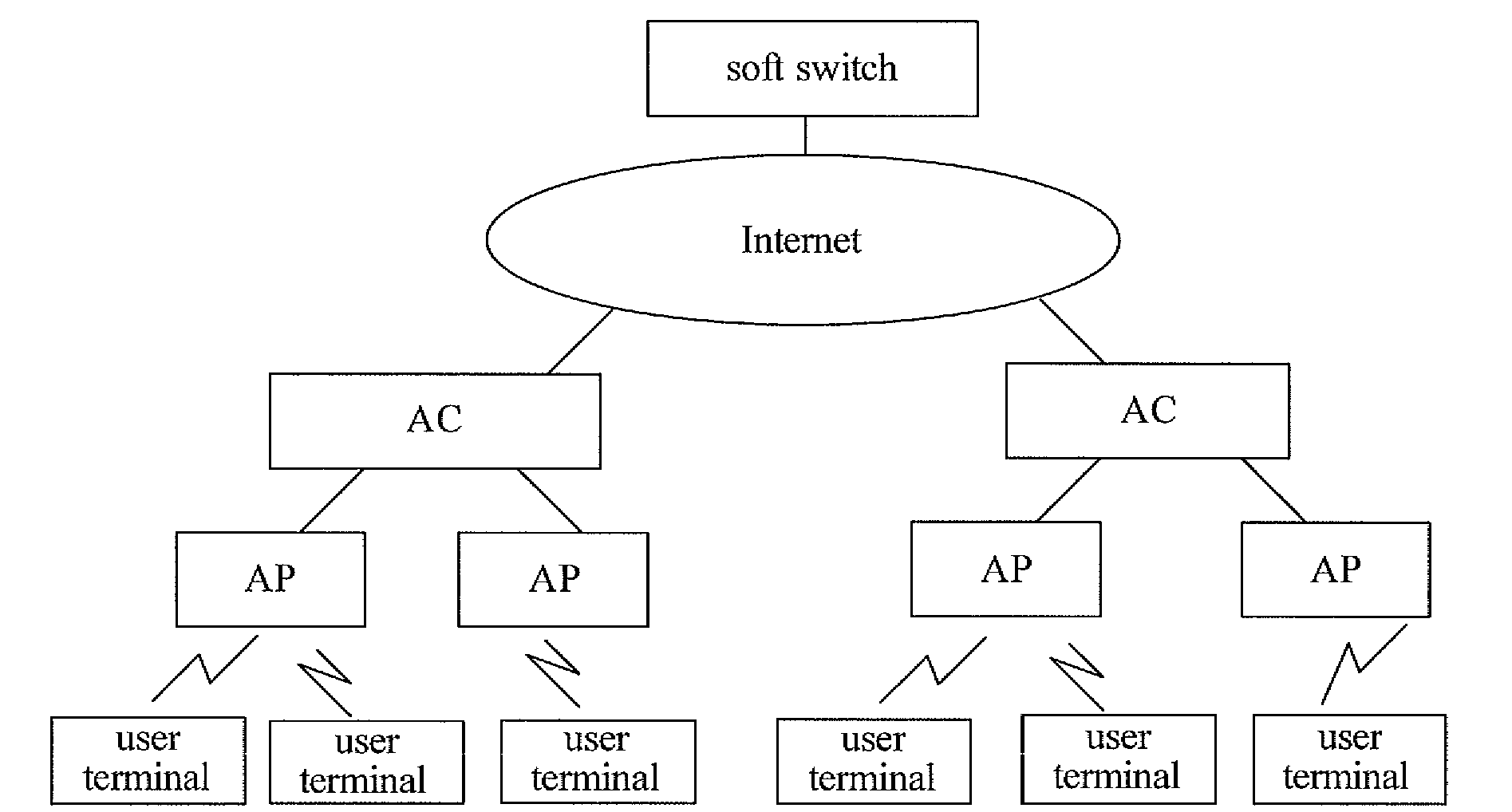
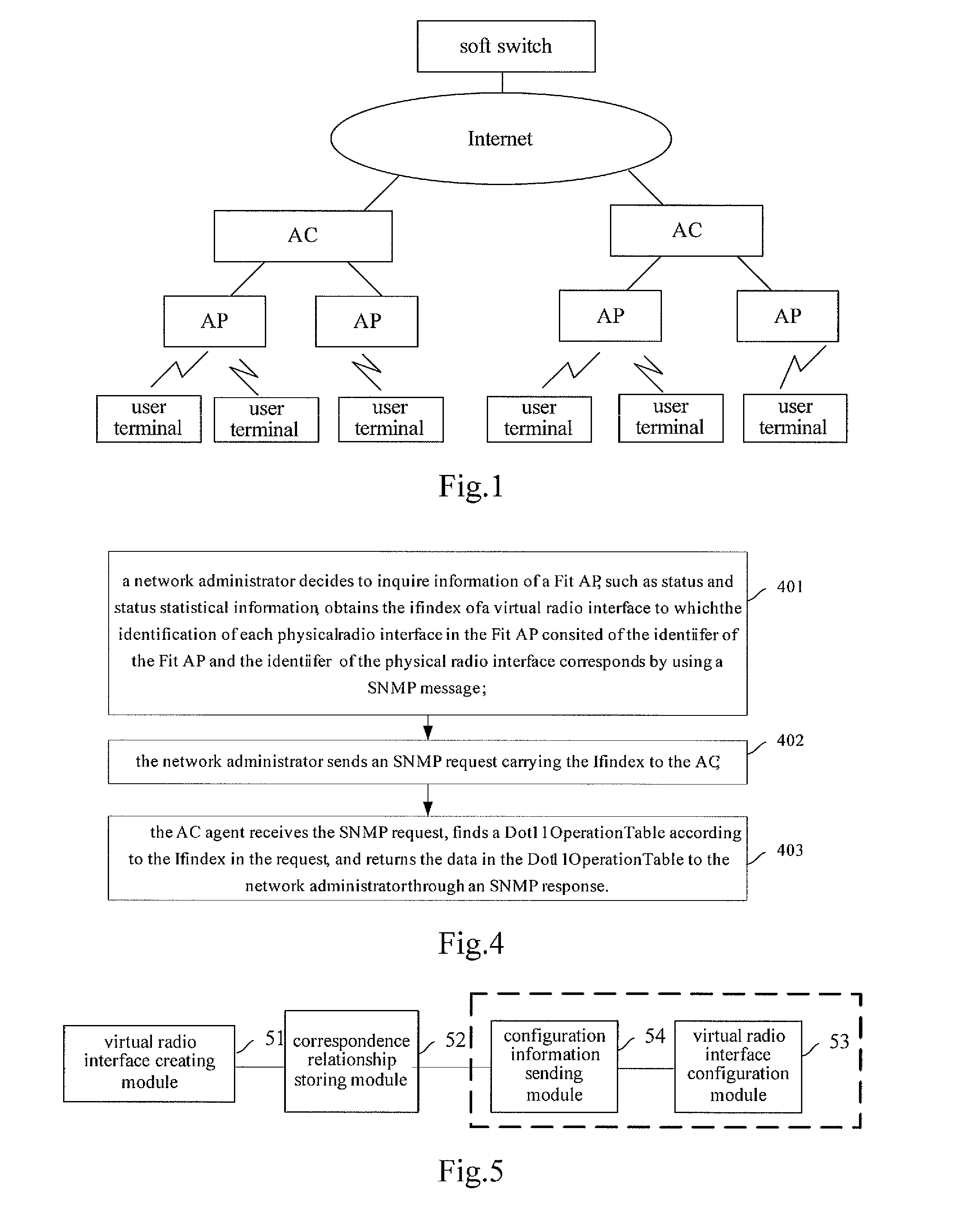
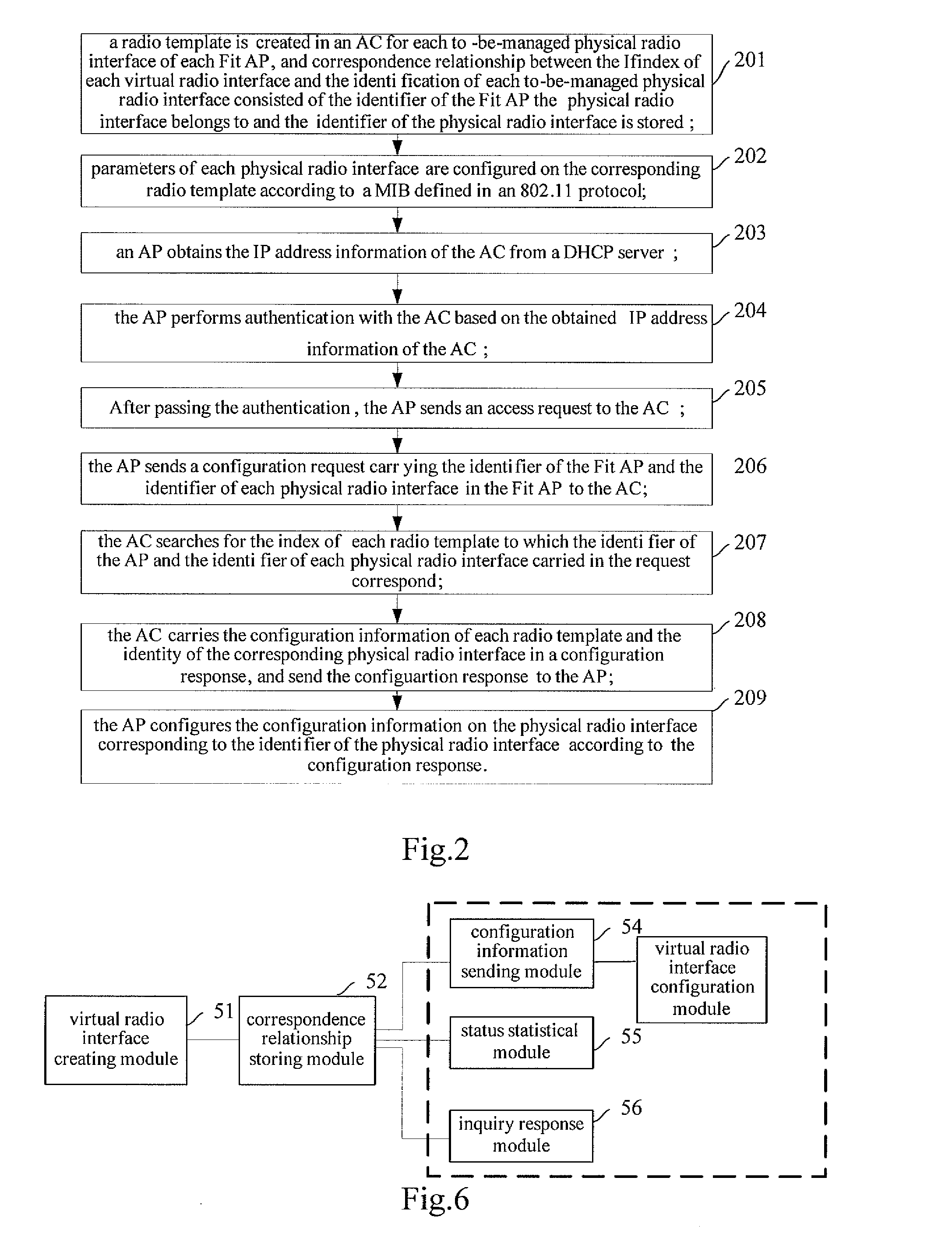
Embodiments of the present invention disclose a method for configuring and managing access points AP and an access controller AC. The method includes: creating at least one virtual radio interface, each of which is assigned a standard Management Information Base (MIB) interface index, wherein each of the at least one virtual radio interface corresponds to at least one physical radio interface of at least one AP; determining a physical radio interface to which a virtual radio interface corresponds and sending configuration information on the virtual radio interface to the determined physical radio interface when there is a need to send the configuration information to the physical radio interface. By using embodiments of the present invention, a standard MIB can be re-used for operating APs, thereby costs for managing the APs are reduced.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
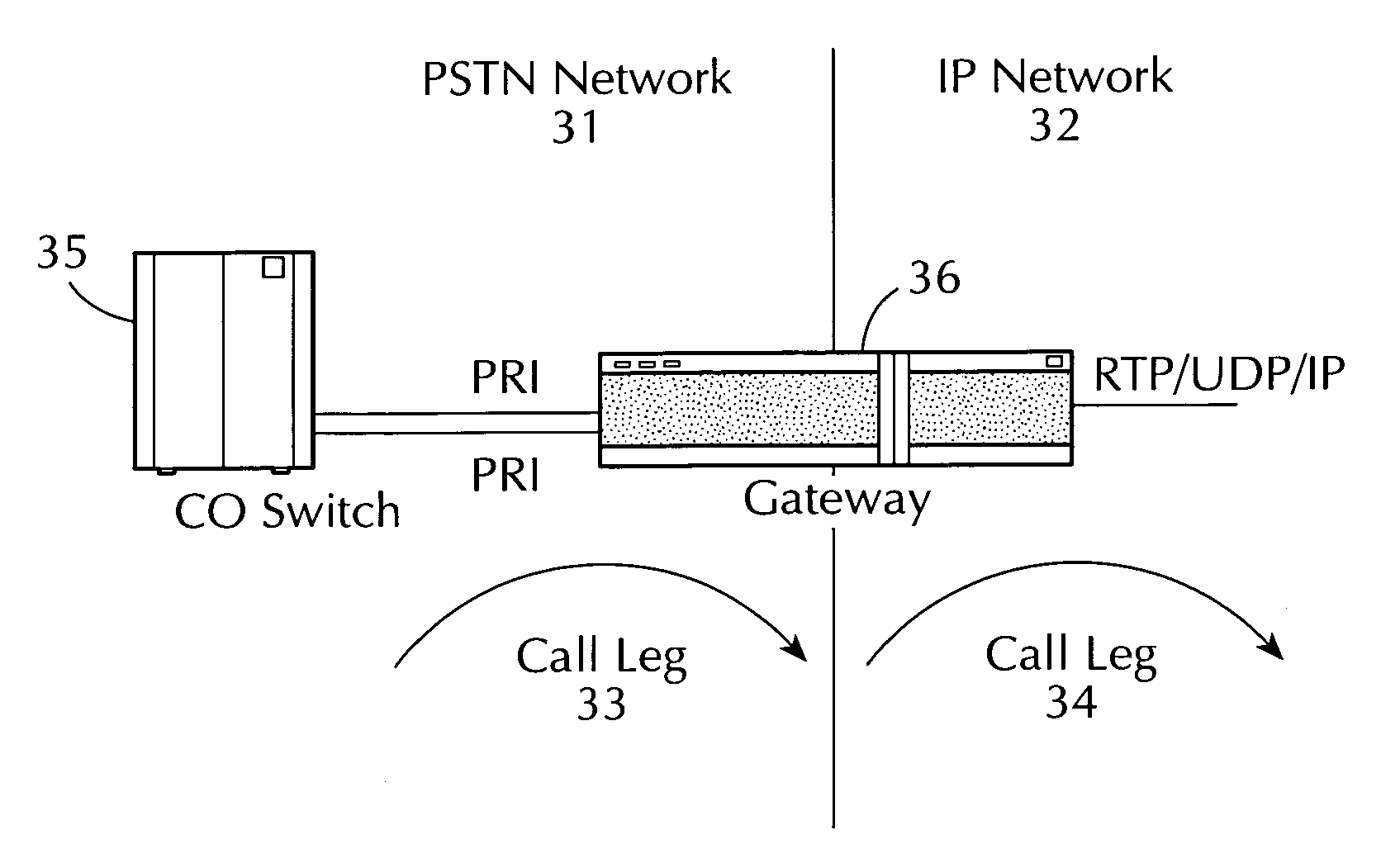
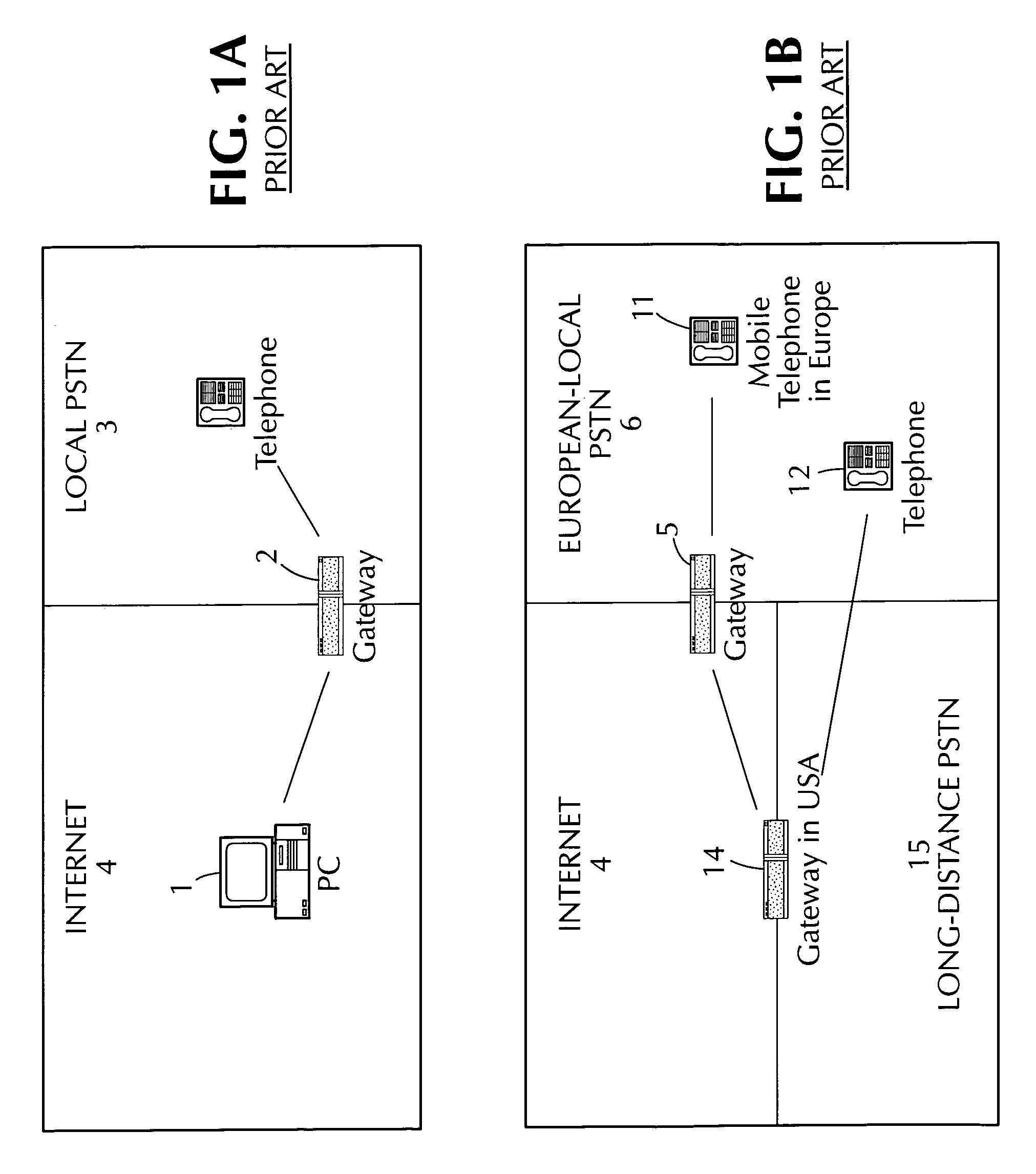
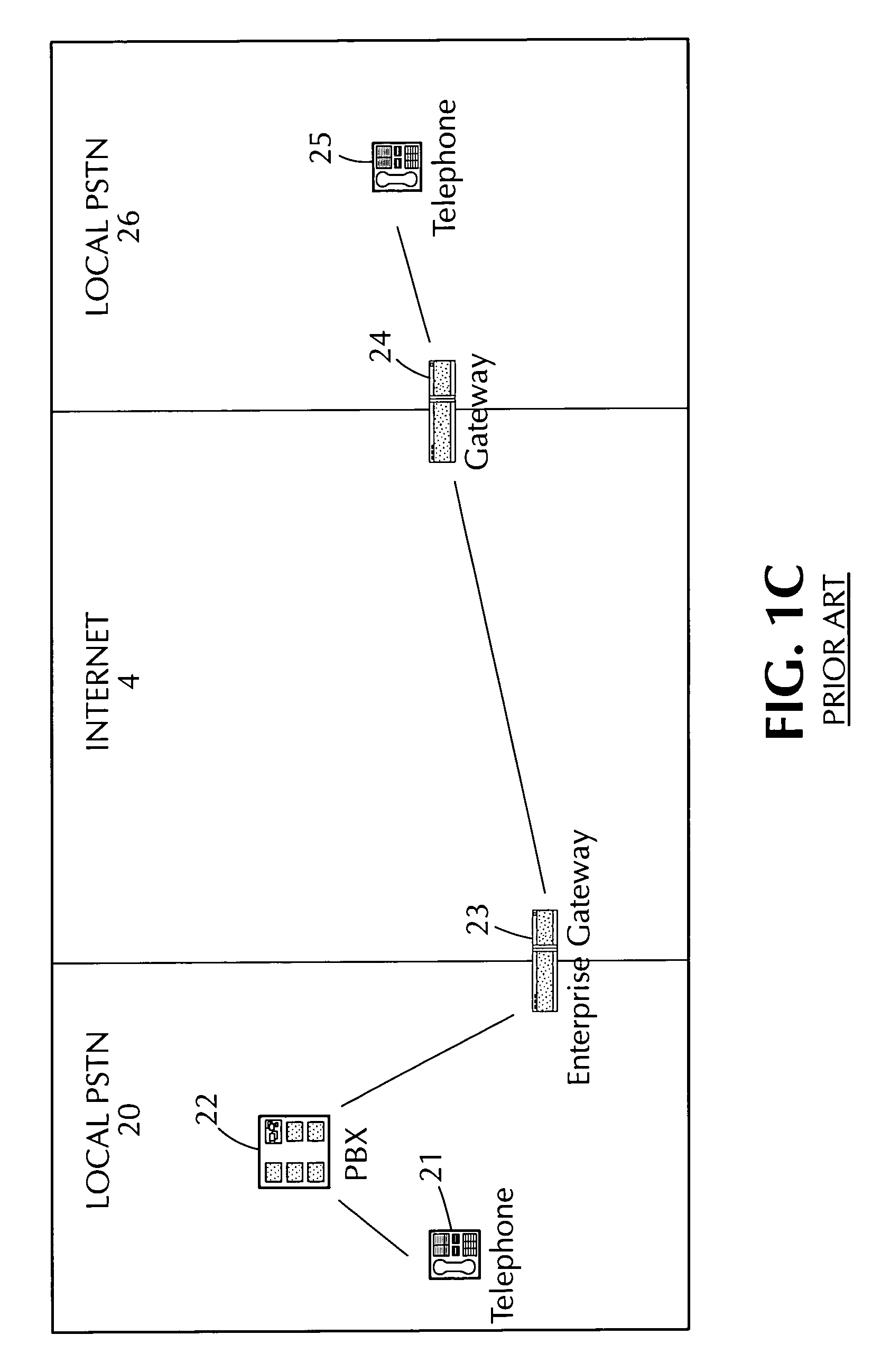
Method and apparatus for estimating the call grade of service and offered traffic for voice over internet protocol calls at a PSTN-IP network gateway
ActiveUS7054308B1Error preventionFrequency-division multiplex detailsManagement information baseGrade of service
An apparatus and method are provided for estimating the grade of service (52) and offered traffic (51) for voice over internet protocol calls at a gateway (2) bridging calls between a public switched telephone network (3) and an internet protocol network (4), the gateway (2) having a dial-control management information base. The method comprises the steps of periodically polling the dial-control management information base for dial peer traffic statistics (44), storing the polled data, estimating the carried traffic using the polled data (501), estimating the grade of service (52) by utilizing the Erlang-B formula in an inverse manner (502), operating on the estimated carried traffic obtained in the first estimating step (501), and estimating the offered traffic (51) using the estimated values for the carried traffic and the grade of service (52) obtained in the previous estimation steps (503). In a second embodiment of the invention, a system (FIG. 4) utilizing the method, continuously monitors the grade of service (52) and offered traffic (51) at gateways (2) in an internet protocol telecom network supporting voice over internet protocol. An enhancement of the system further comprises a world wide web interface (46) for generating monitoring reports.
Owner:LEVEL 3 COMM LLC
Protocol reference model, security and inter-operability in a cognitive communications system
ActiveUS20090124208A1Transmission monitoringWireless commuication servicesInformation repositoryInteroperability
Various cognitive communications system architectures and their corresponding Protocol Reference Models (PRMs) are disclosed. Such PRMs incorporate a Cognitive Plane in addition to conventional Data and Management Planes. The additional Cognitive Plane functionality may include, for example, spectrum sensing, spectrum management, geolocation, and security functions. The Cognitive Plane may further include a Policy Engine and a Learning and Reasoning Module. In some embodiments, Management Plane functions may be effectively combined to form a database of primitives (and their respective values) called a Management Information Base (MIB). In addition, techniques are provided by which various components of cognitive and non-cognitive, as well as mesh-enabled and non-mesh-enabled nodes in a network, inter-operate with each other. The architectures allow a Spectrum Manager (or Signal Space Manager) to combine information from various network layers (e.g., PHY / MAC Layers, Spectrum Sensing Function, Geolocation Function, and / or Security Sublayers), and to make informed decisions on spectrum utilization.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC +1
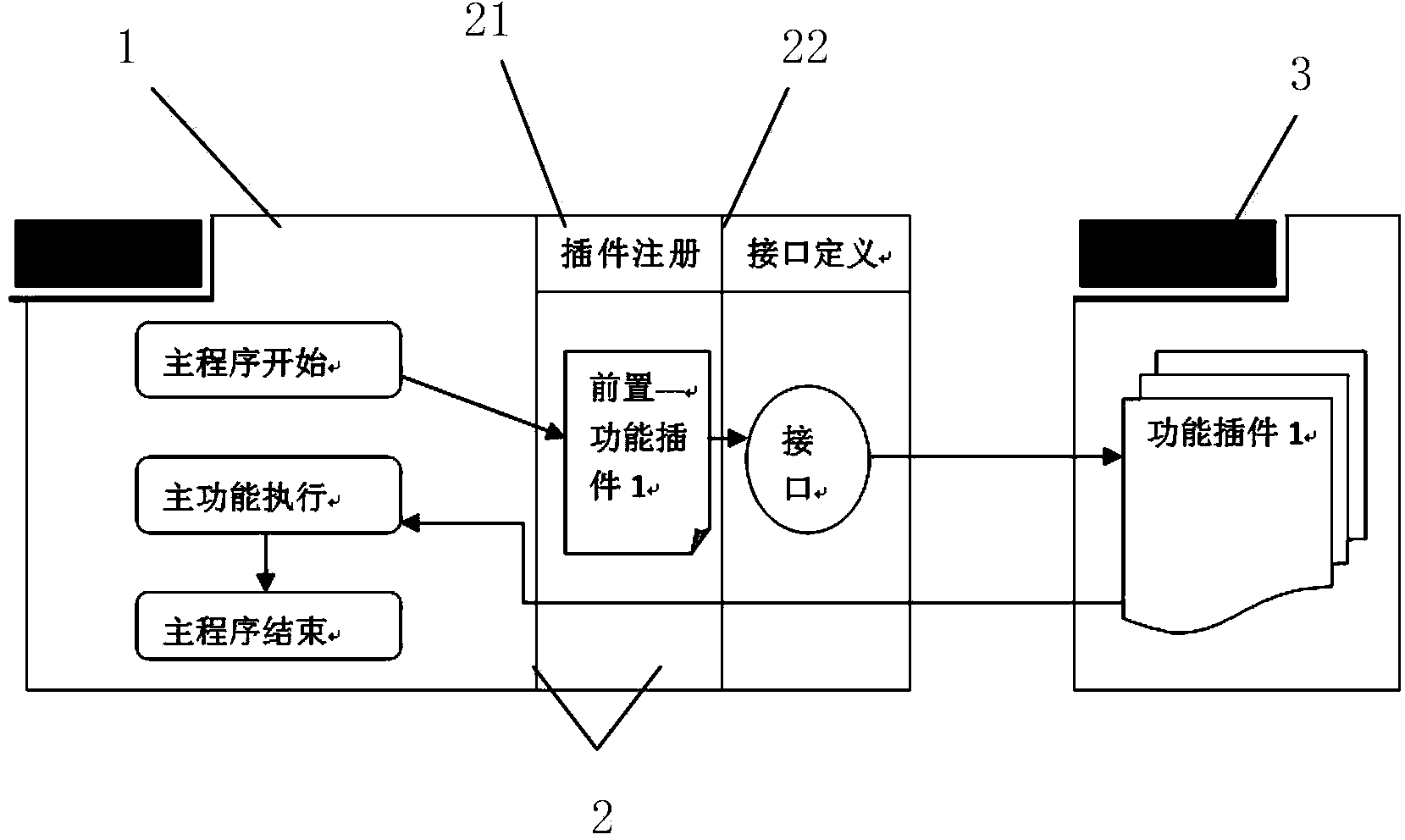
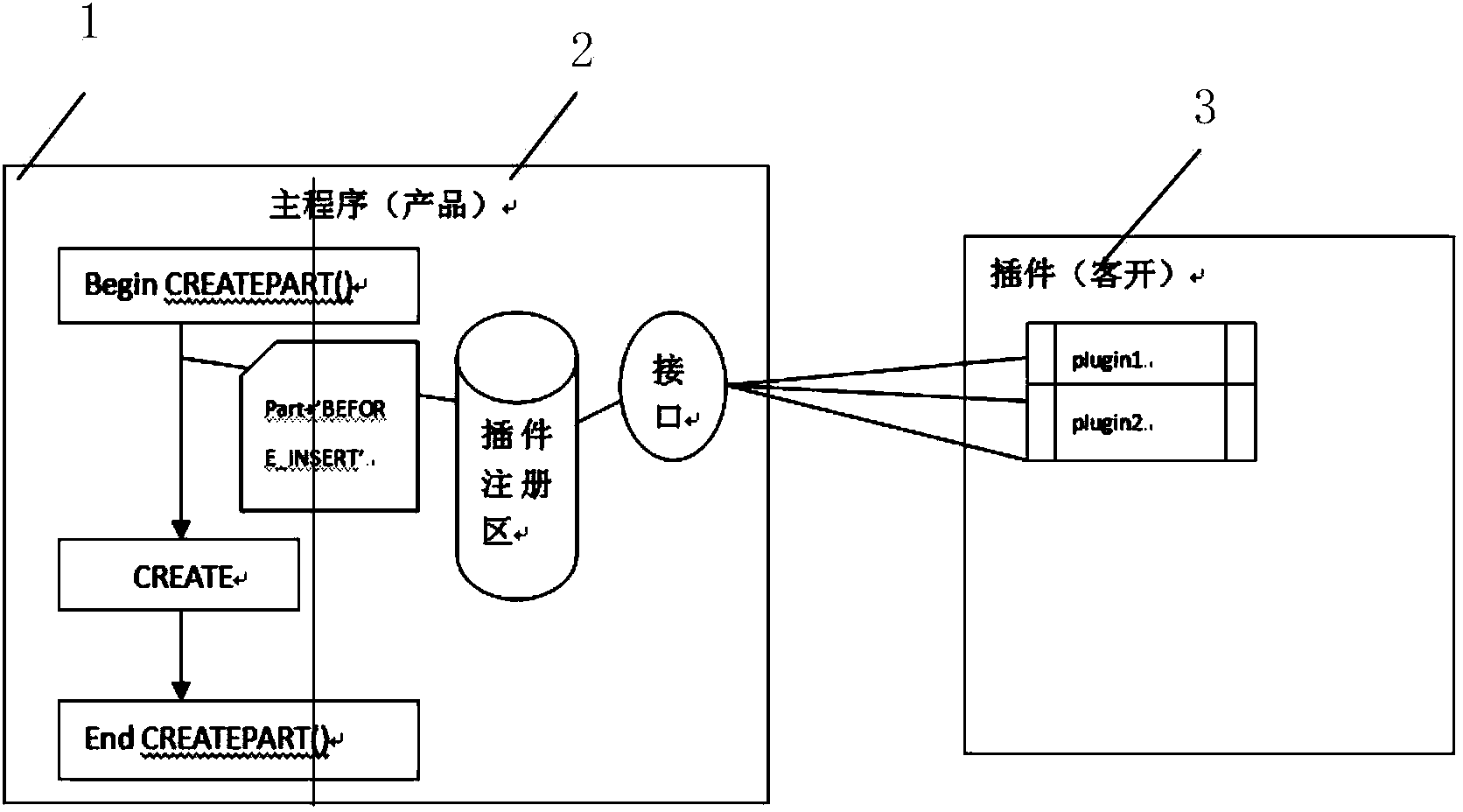
Method for extending functions of management information system through plugins
InactiveCN103645919AImprove scalabilityIncrease flexibilityProgram loading/initiatingManagement information basePersonalization
The invention discloses a device and a method for extending functions of a management information system through plugins. The plugin-extended management information system has a loosely-coupled function extension mechanism. The plugins are an independent part and can be developed, tested, increased and decreased independently, so that the extension and the continuous improvement on software functions can be realized; the plugins correspond to relationships between system standard functions and client personalized extension functions, and plugin interfaces are reserved in a standard function layer, so that the standard function layer turns into a plugin container; and during function extension, the plugin functions and registration are realized, so that the extended functions can be added to running logic of the system in a loose coupling manner. According to the method, on the basis of the standard management information system, the functions of the system are extended through a plugin mechanism, and loose coupling of the extended functions and the standard functions are realized, so that the flexibility and the independence of the customized development are improved.
Owner:YONYOU NETWORK TECH
Method and apparatus for discovering network resource and topology
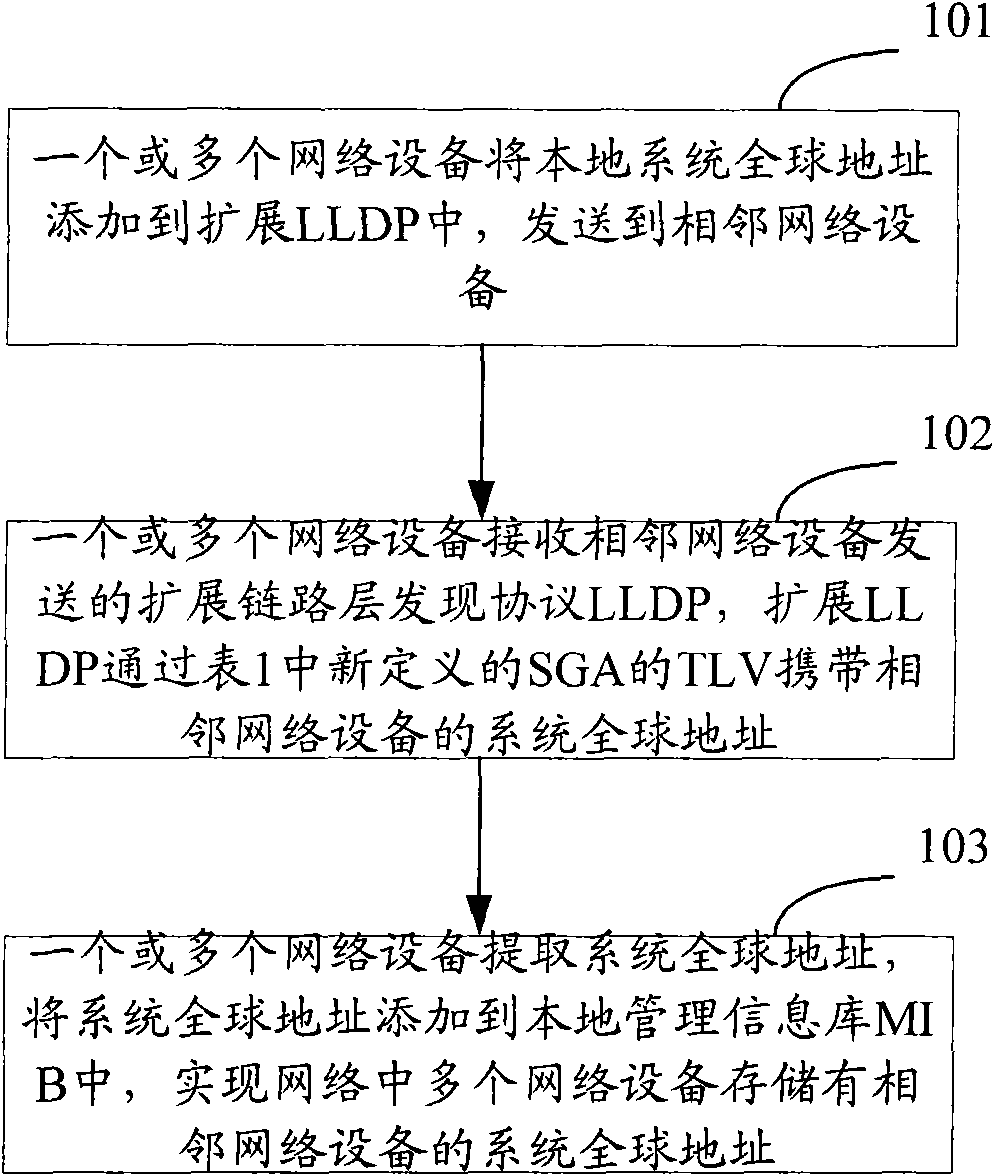
InactiveCN101621414ASolve the problem of incomplete discoveryImprove compatibilityEnergy efficient ICTData switching networksInformation repositoryManagement information base
The invention discloses a method for discovering network resource and topology, applied in a system including network IPv6 or double-stack network IPv6 / IPv4. The method comprises the following steps: one or more network devices receive an extendable link layer discover protocol LLDP transmitted by an adjacent network device, wherein the extendable LLDP carries a system global address of the adjacent network device and the system global address is address IPv6 and / or address IPv4; and one or more network devices extract the system global address and add the system global address into a local management information base MIB so that a plurality of network devices in the network store the system global address of the adjacent network device. In the invention, topology discovering is performed to the network IPv6 or double-stack network IPv6 / IPv4 by carrying IP address of mark network resources in the extendable LLDP.
Owner:NEW H3C TECH CO LTD
Method, apparatus and program for processing information
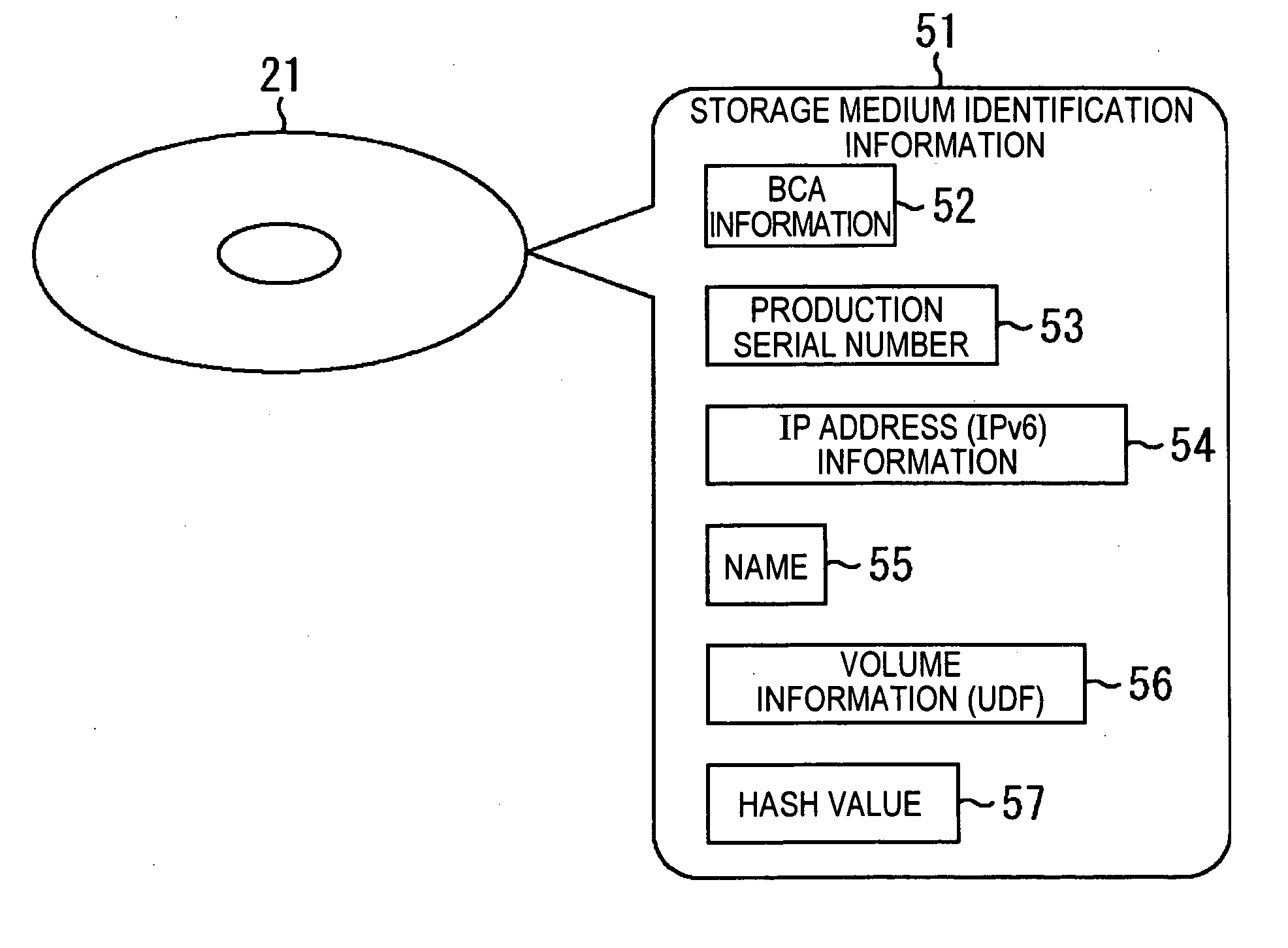
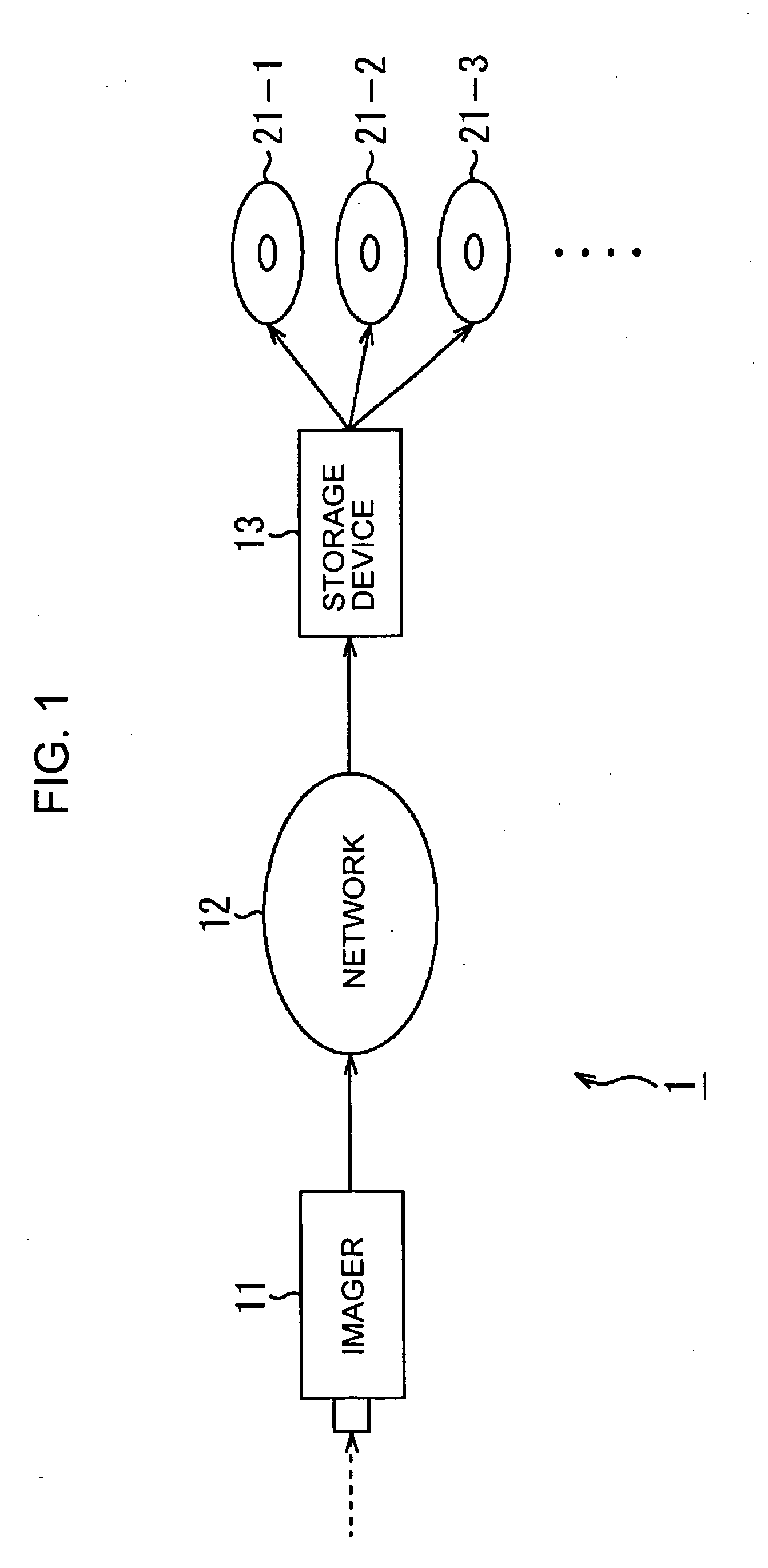
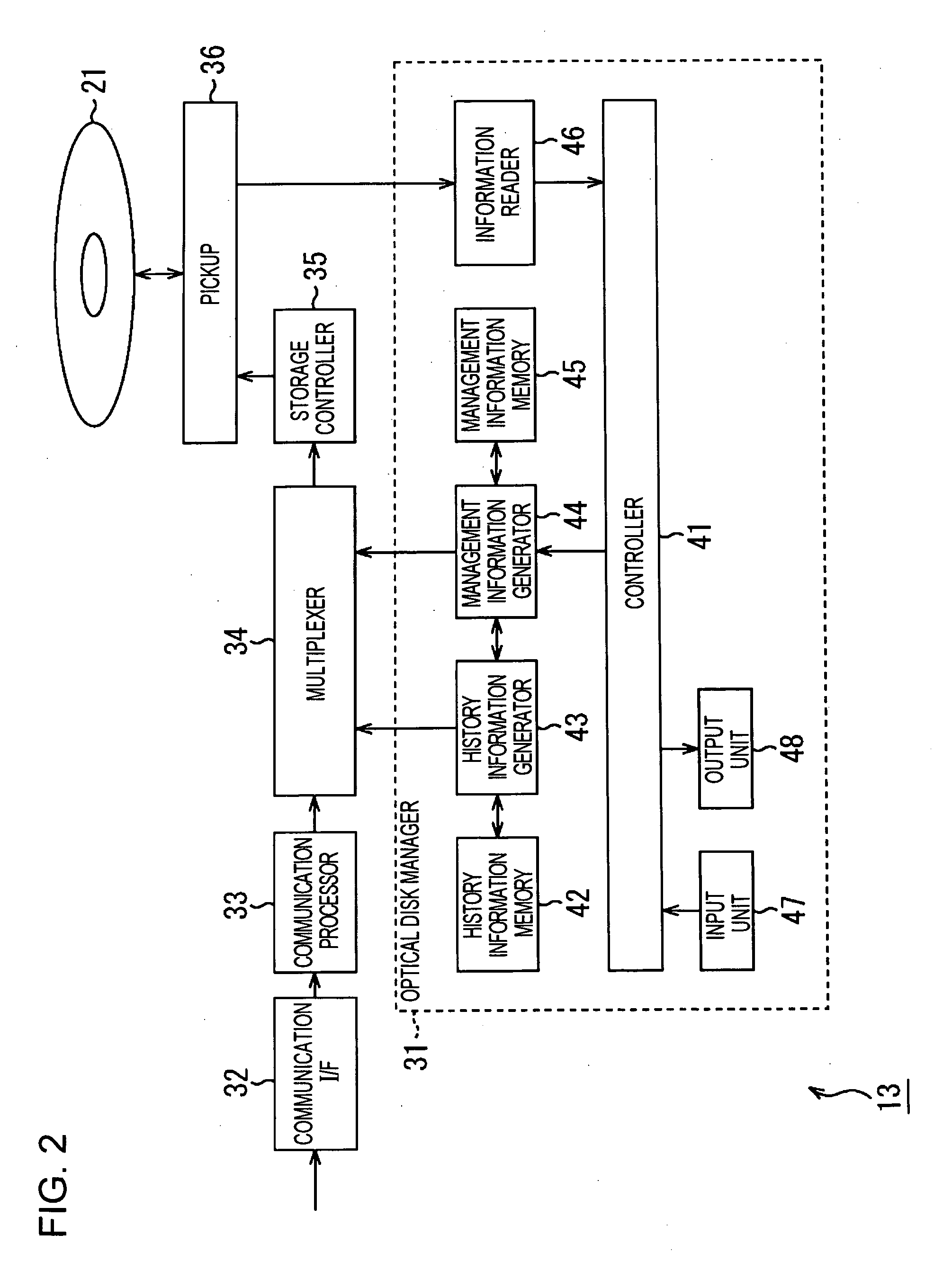
InactiveUS20050237865A1Easy to manageEasy to useTelevision system detailsDisc-shaped record carriersInformation processingManagement information base
In an information processing apparatus that stores data on a plurality of storage media, a management information generator generates management information based on which to manage an order in which data is stored on the storage media, using storage medium identification information identifying each storage medium, and a multiplexer multiplexes the management information generated by the management information generator on the data. A storage unit stores the data, including the management information multiplexed by the multiplexer, on the storage media such that the data can be easily managed and the storage media can be used in a very convenient manner.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com