Patents
Literature
537 results about "Managed object" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In telecommunication, the term managed object has the following meanings: 1. In a network, an abstract representation of network resources that are managed. With "representation", we mean not the actual device that is managed, but also the device driver, that communicates with the device. An example of a printer as a managed object is the window that shows information about the printer, such as the location, printer status, printing progress, paper choice, and printing margins. The database, where all managed objects are stored, is called Management Information Base. In contrast with a CI, a managed object is "dynamic" and communicates with other network recourses that are managed. Note: A managed object may represent a physical entity, a network service, or an abstraction of a resource that exists independently of its use in management. 2. In telecommunications management, a resource within the telecommunications environment that may be managed through the use of operation, administration, maintenance, and provisioning application protocols. This article incorporates public domain material from the General Services Administration document "Federal Standard 1037C".
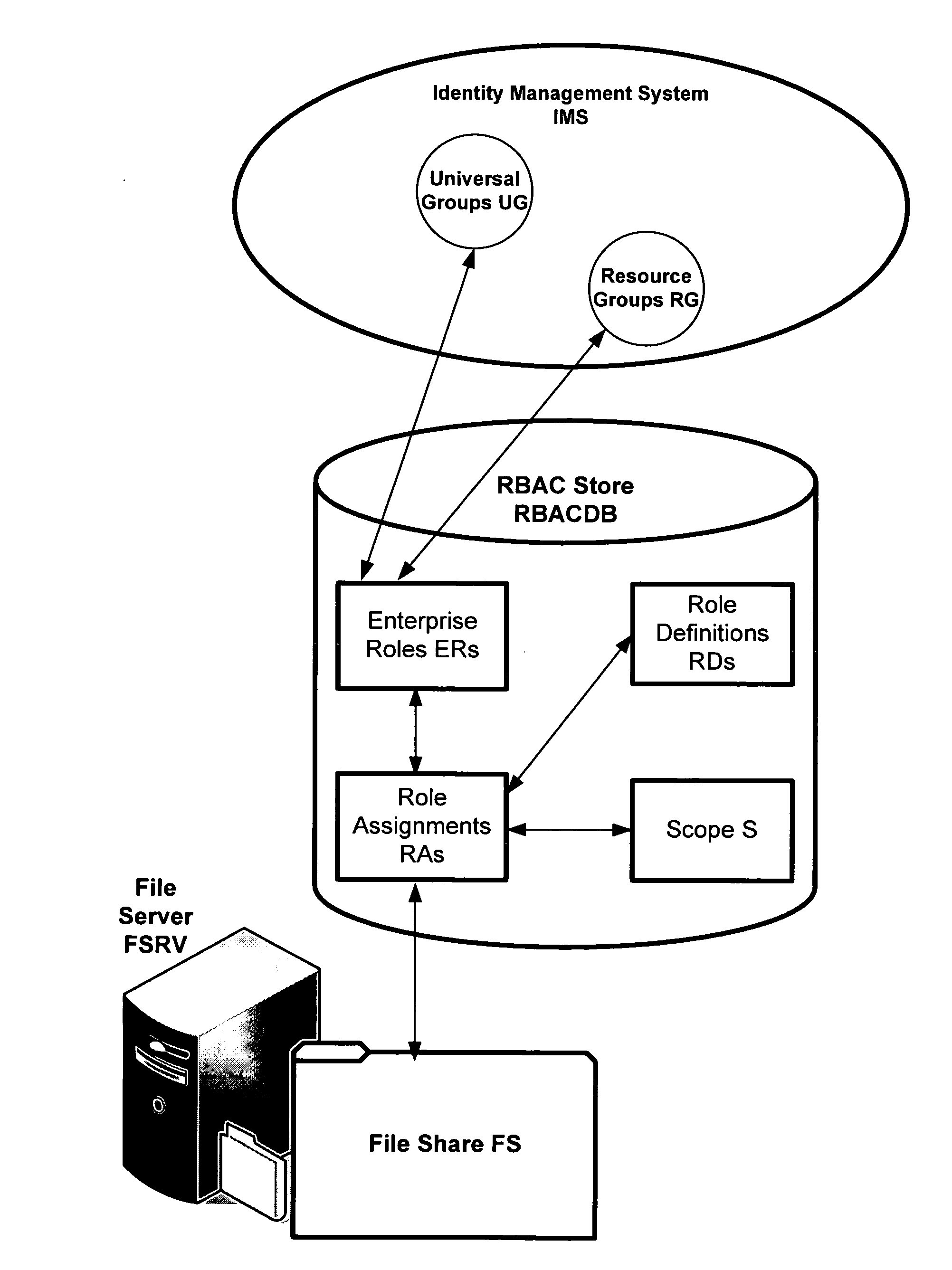
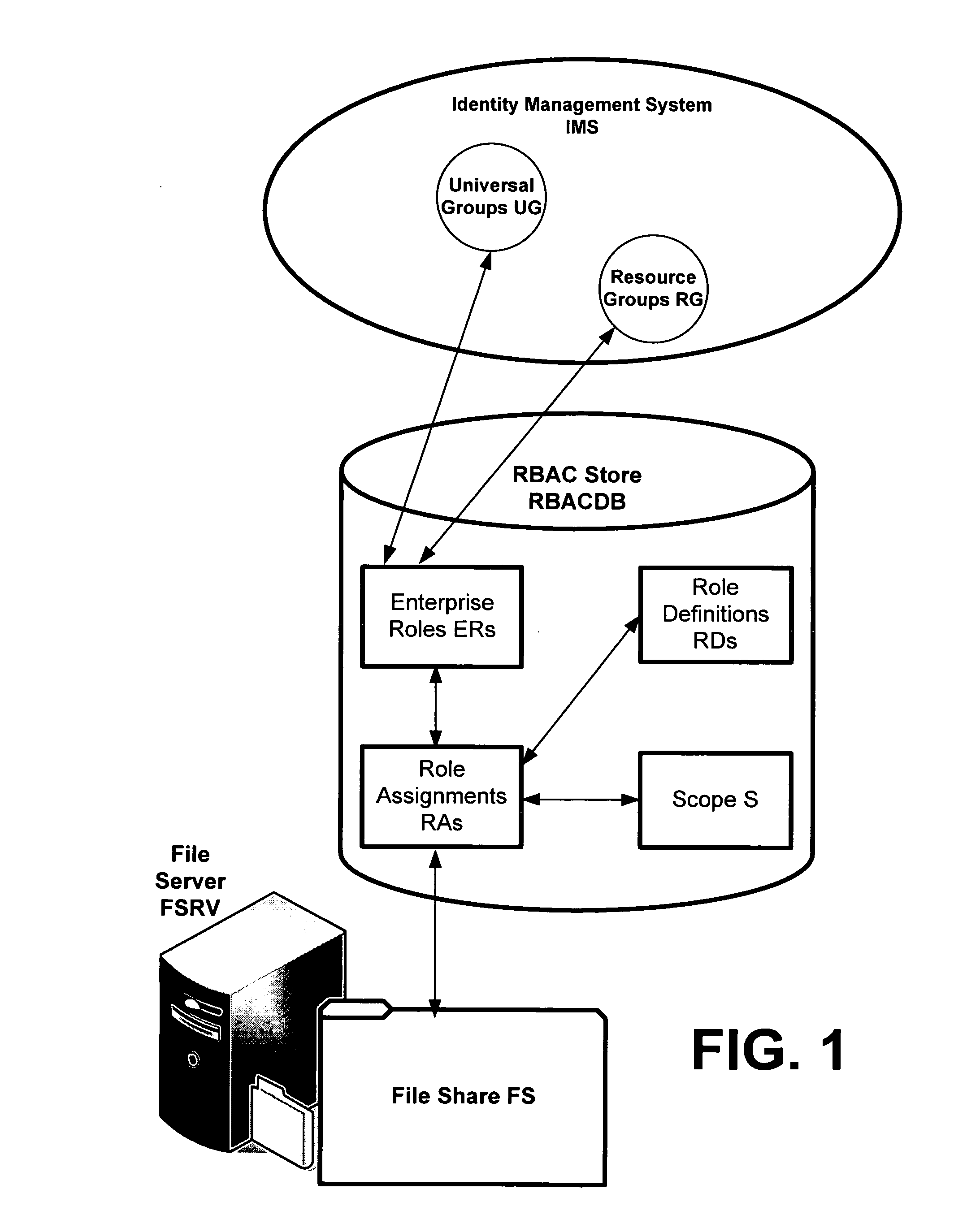
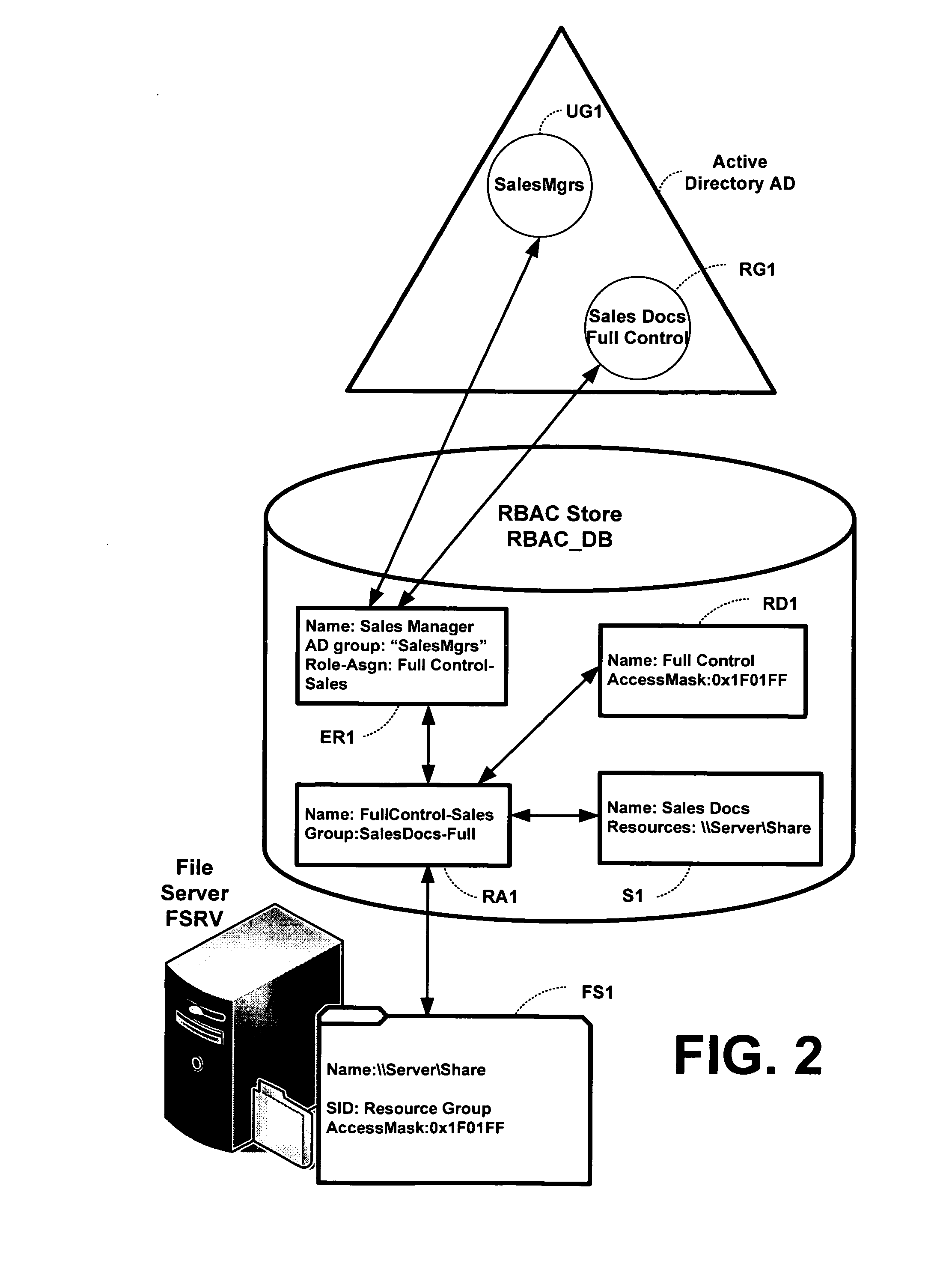
Translating role-based access control policy to resource authorization policy
ActiveUS20070283443A1Program control using stored programsDigital data processing detailsFile systemManaged object
Translation of role-based authoring models for managing RBAC “roles” to resource authorization policy (RAP), such as ACL-based applications, is provided. A generic RBAC system is defined from which mappings to other authorization enforcement mechanism make possible the translation of RBAC “roles” to resource authorization policies applied to resources managed by a resource manager, e.g., a file system resource manager. An implementation is described that uses Windows Authorization Manager as a storage mechanism and object model to manage object types and relationships translated from an RBAC system.
Owner:MICROSOFT TECH LICENSING LLC
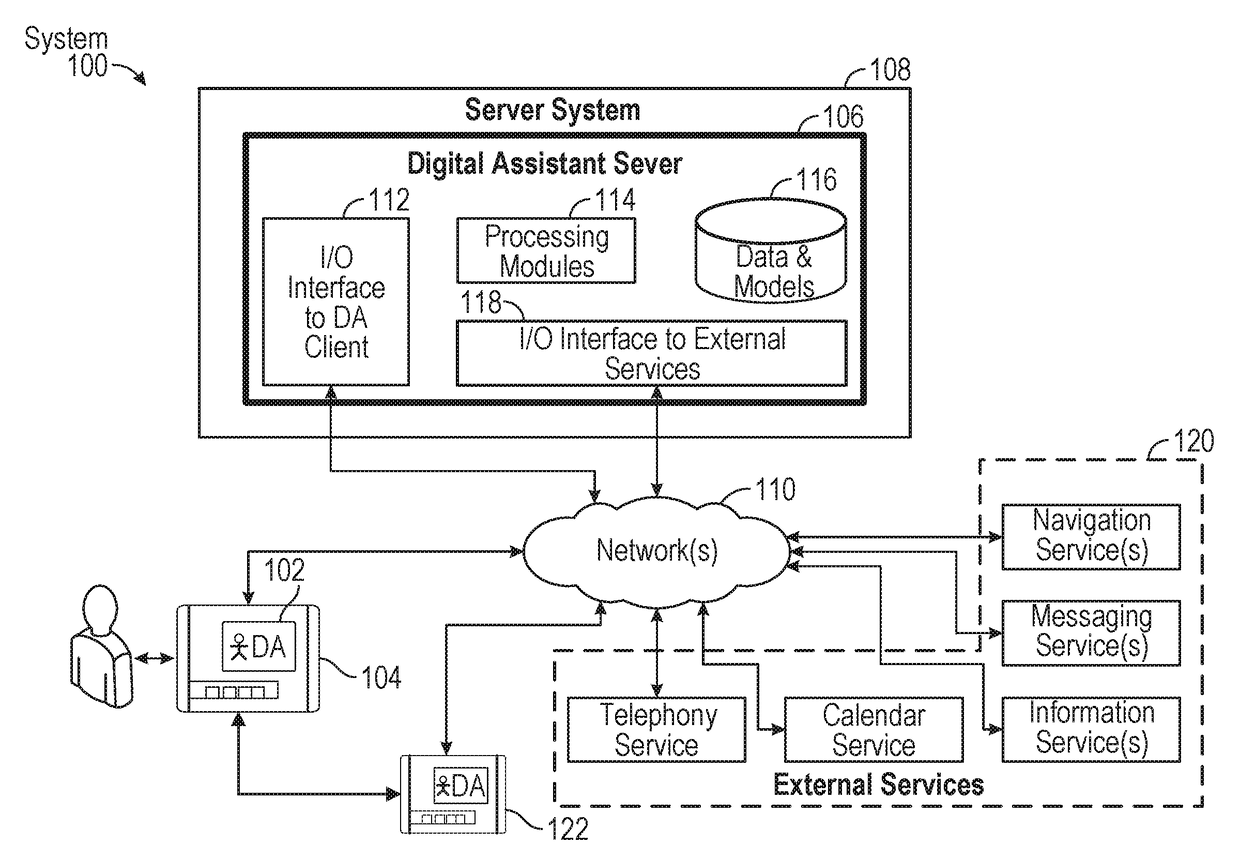
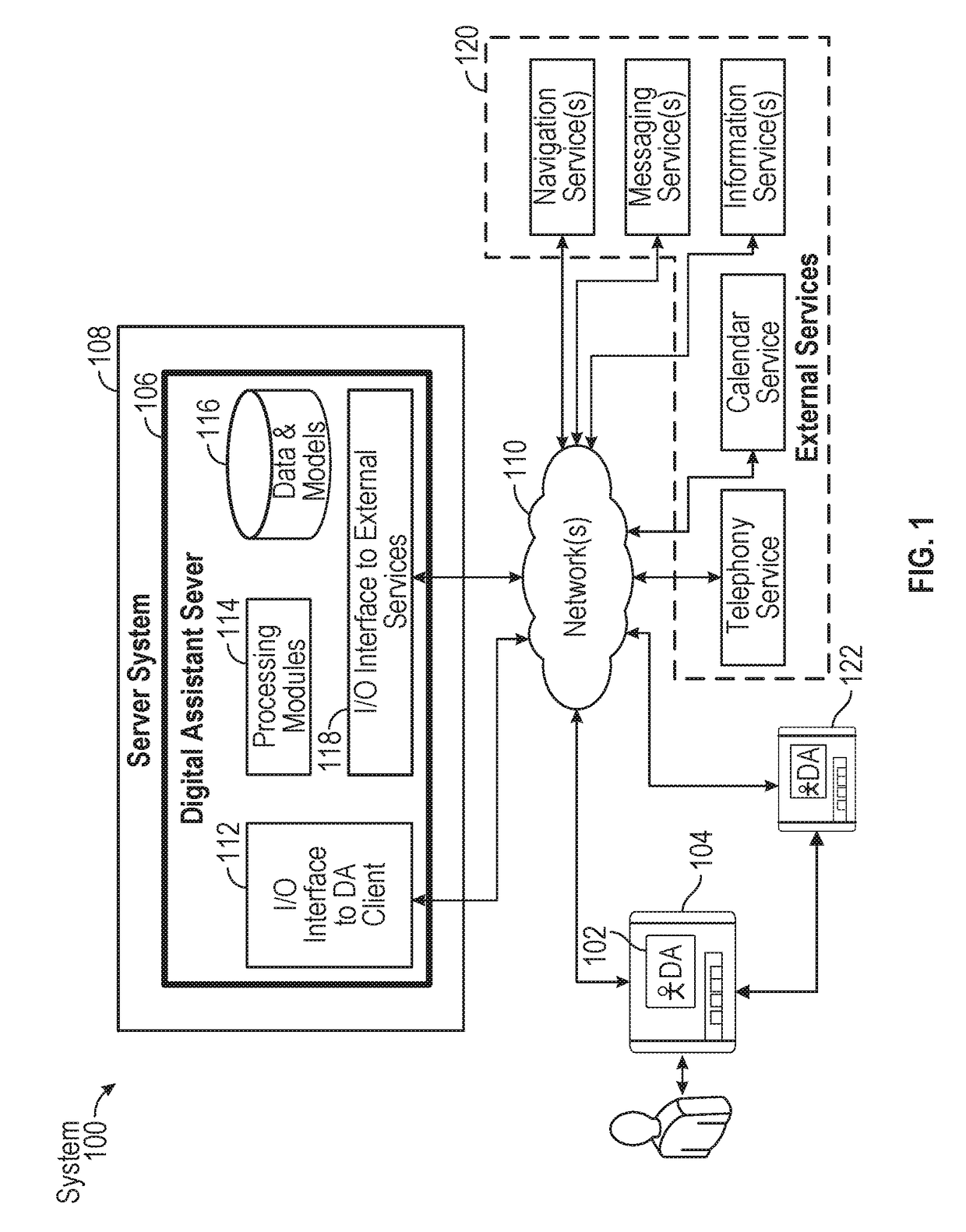
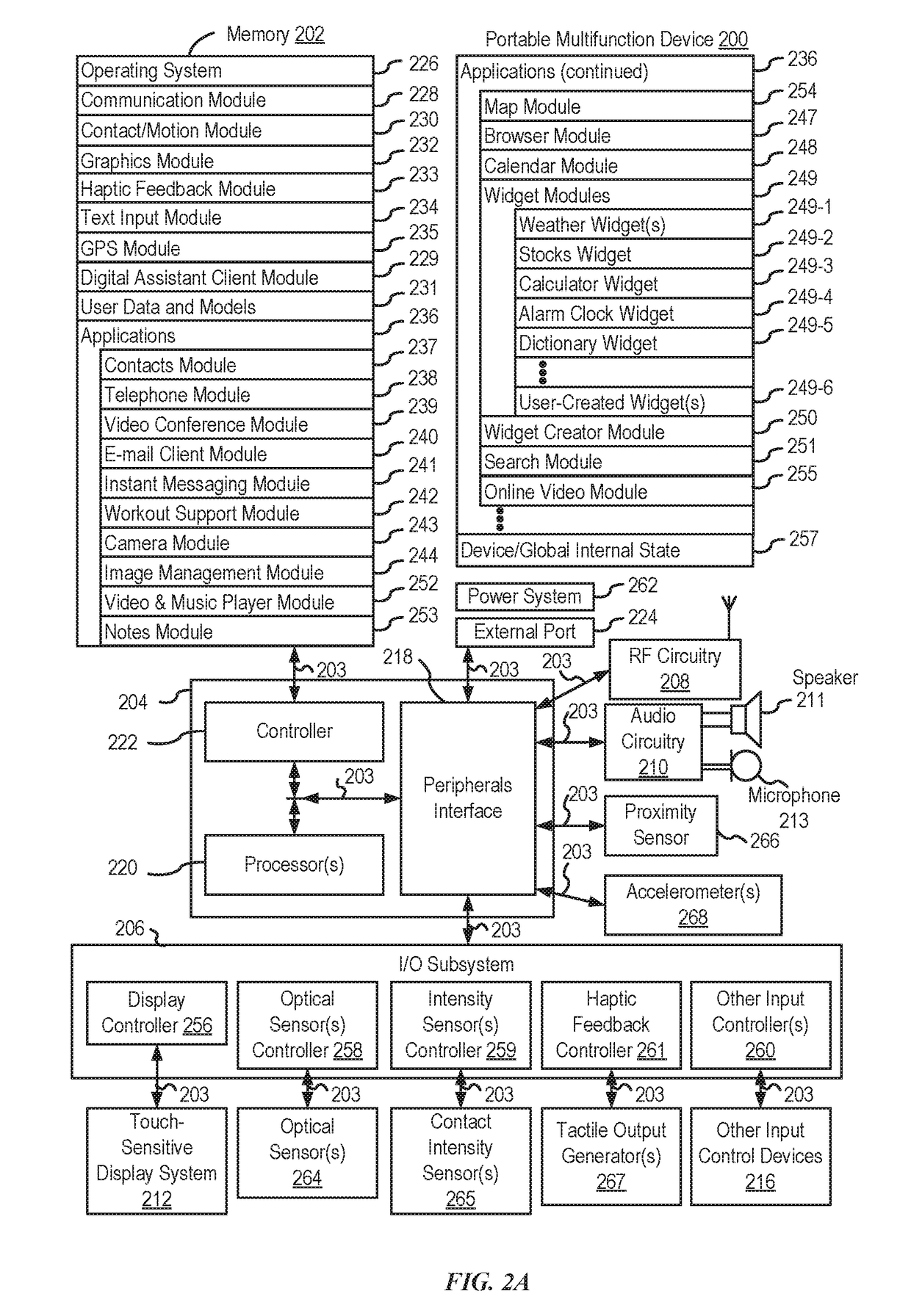
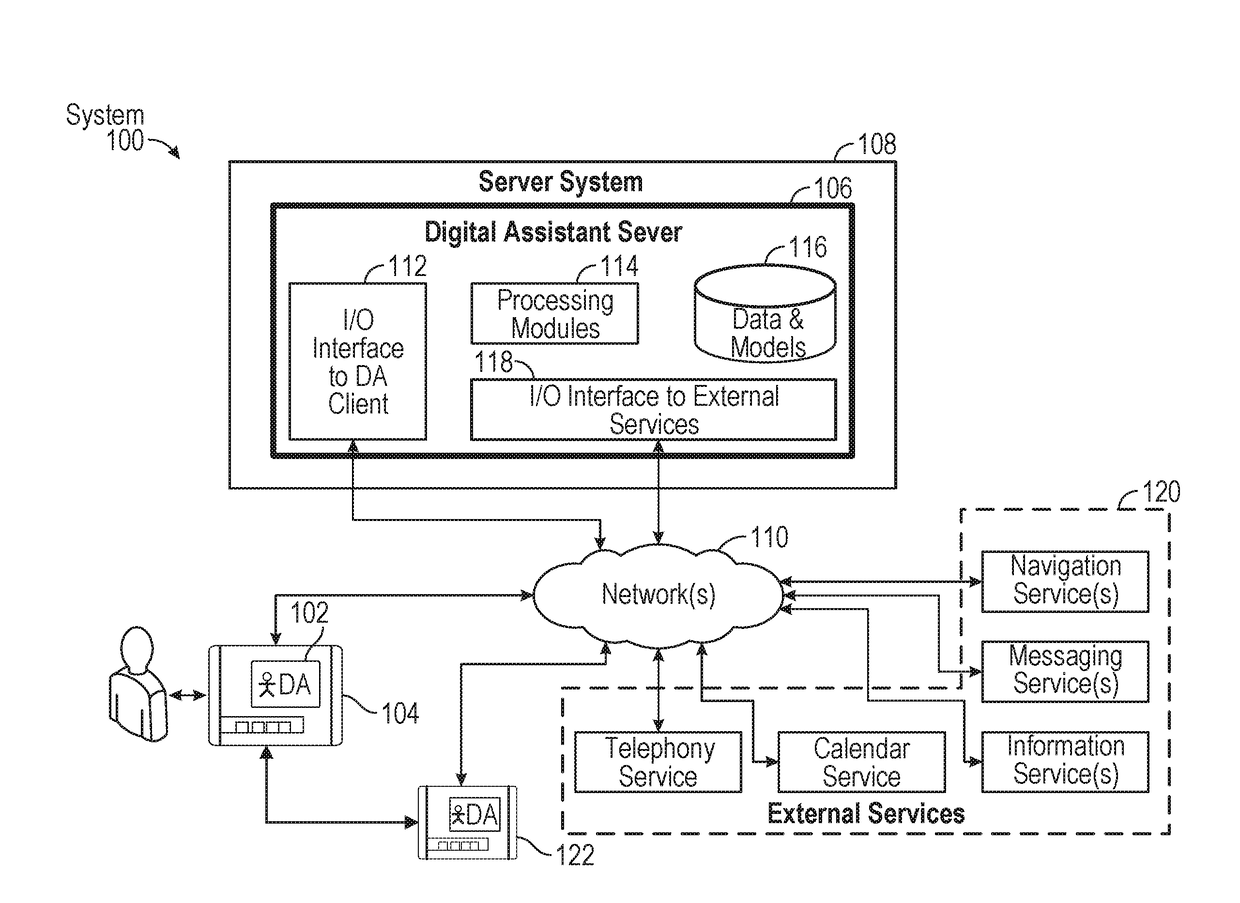
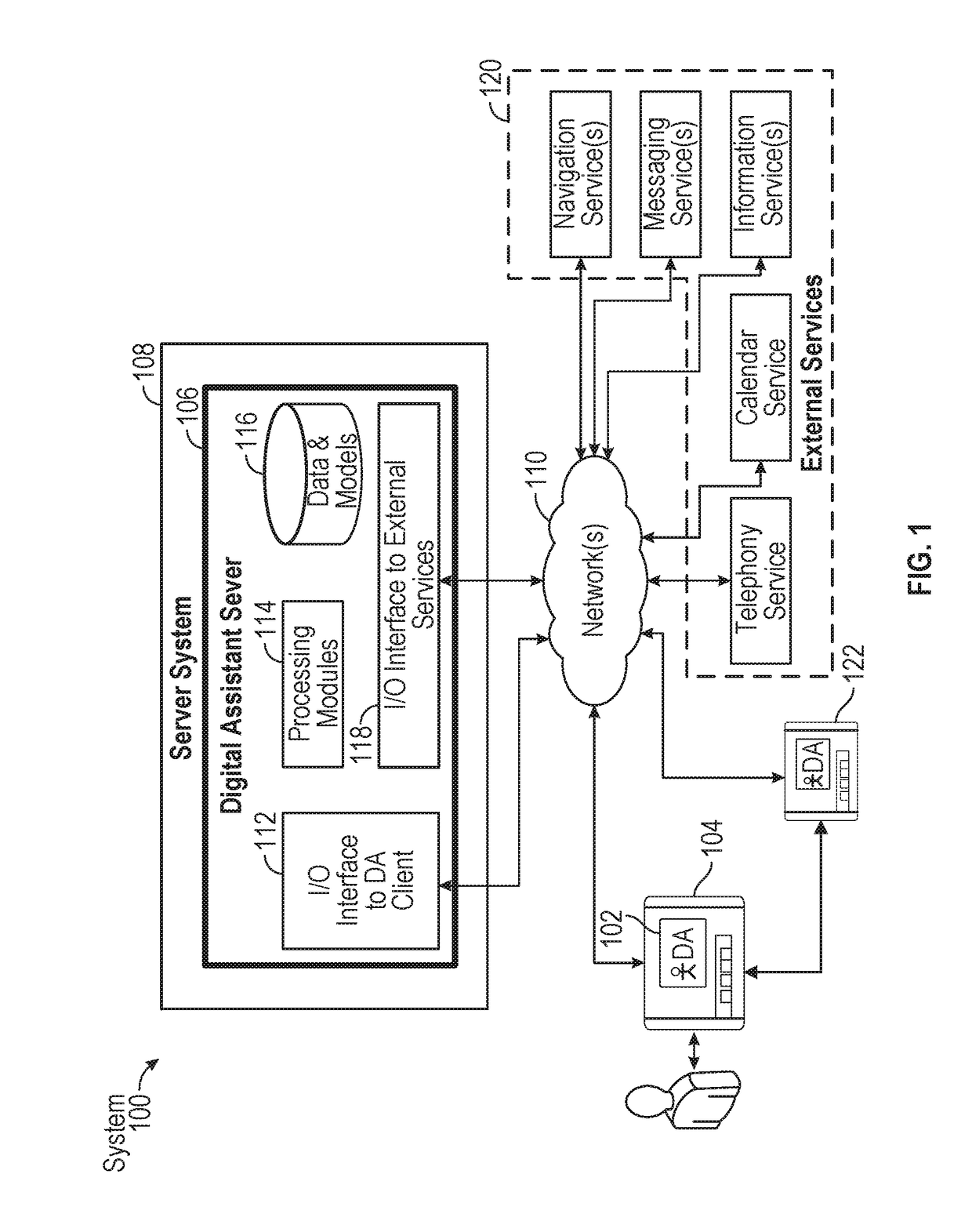
Intelligent digital assistant in a multi-tasking environment
ActiveUS20170358305A1Web data indexingNatural language data processingManagement objectManaged object
Systems and processes for operating a digital assistant are provided. In one example, a method includes receiving a first speech input from a user. The method further includes identifying context information and determining a user intent based on the first speech input and the context information. The method further includes determining whether the user intent is to perform a task using a searching process or an object managing process. The searching process is configured to search data, and the object managing process is configured to manage objects. The method further includes, in accordance with a determination the user intent is to perform the task using the searching process, performing the task using the searching process; and in accordance with the determination that the user intent is to perform the task using the object managing process, performing the task using the object managing process.
Owner:APPLE INC
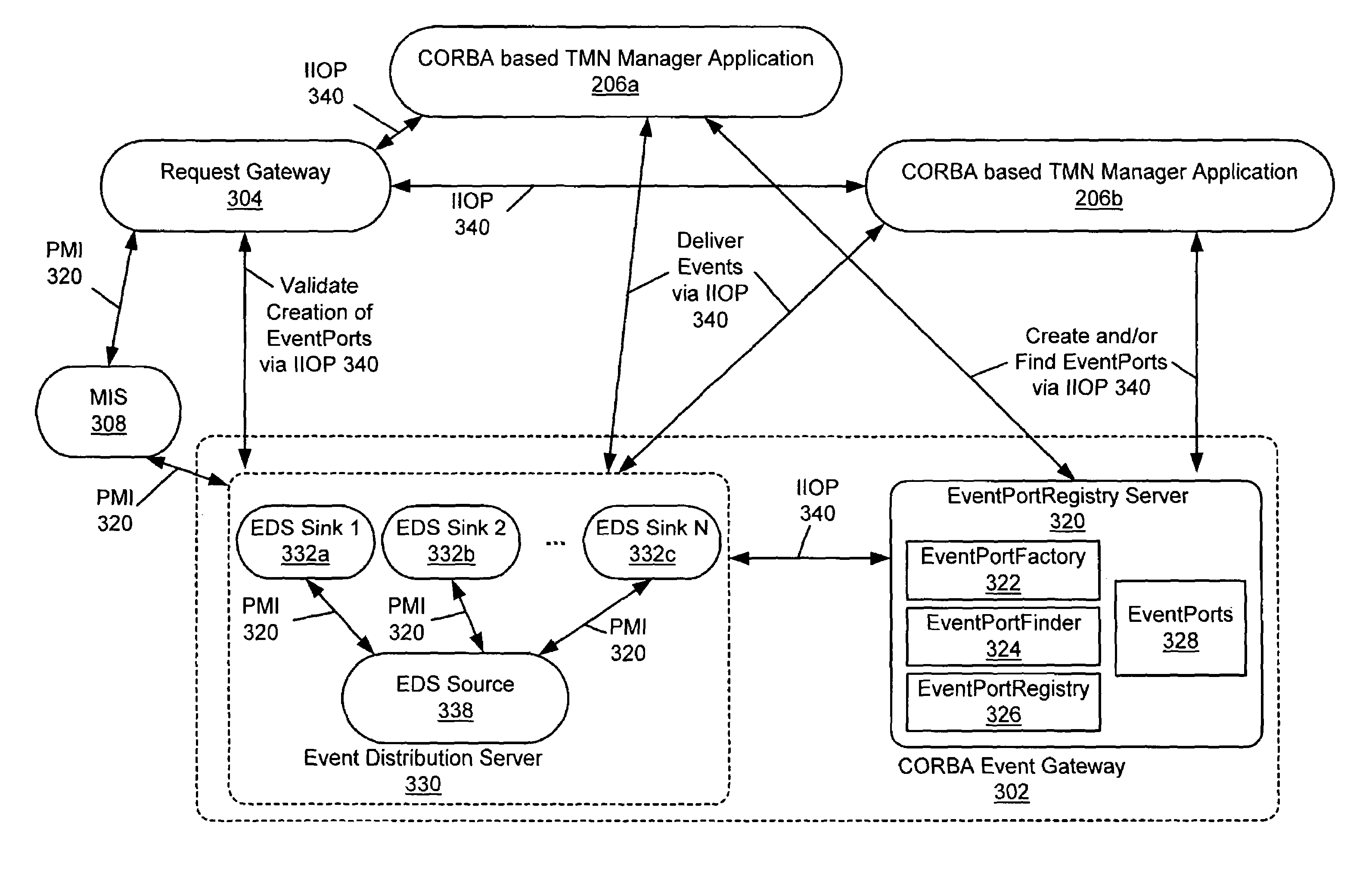
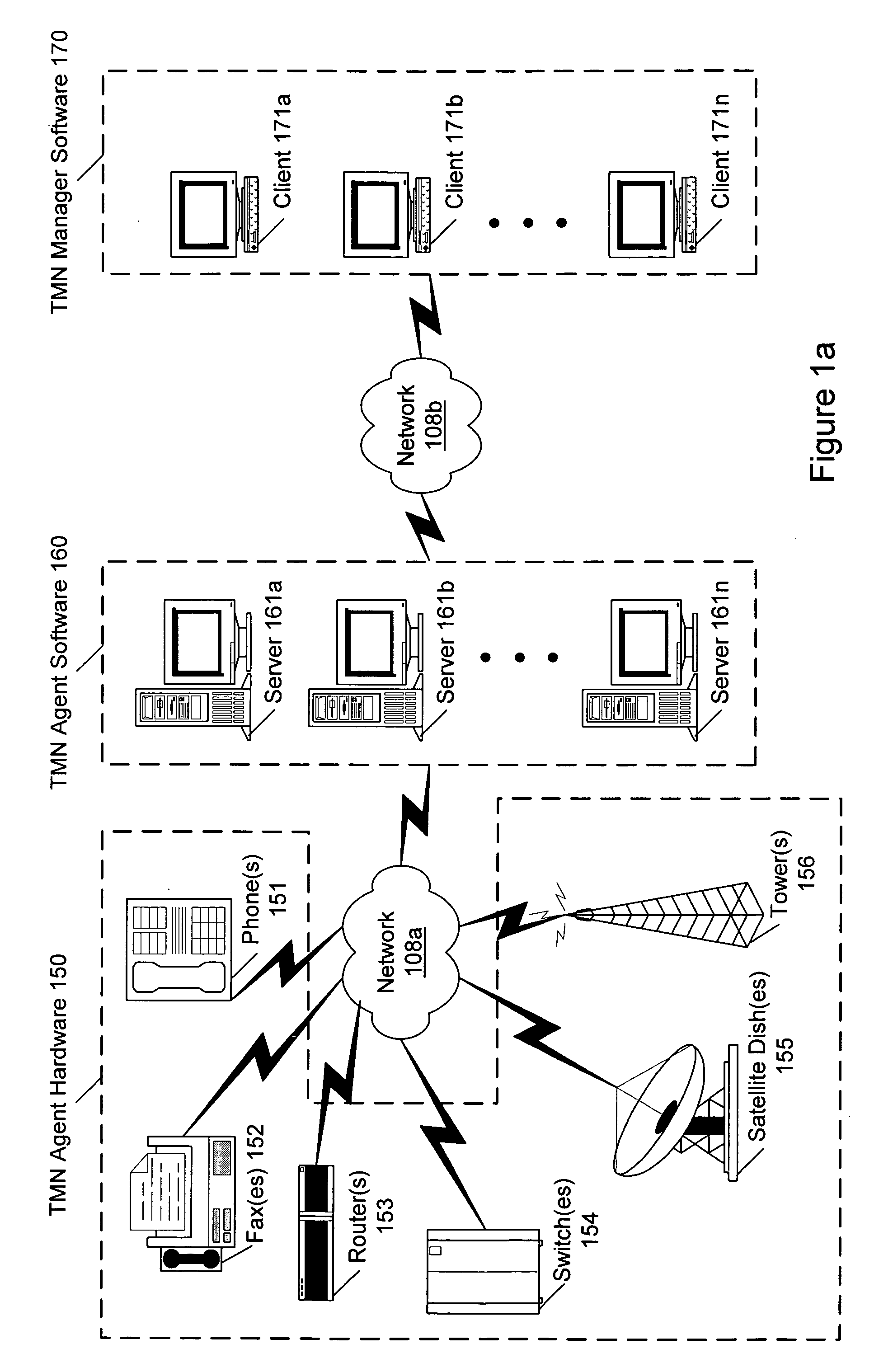
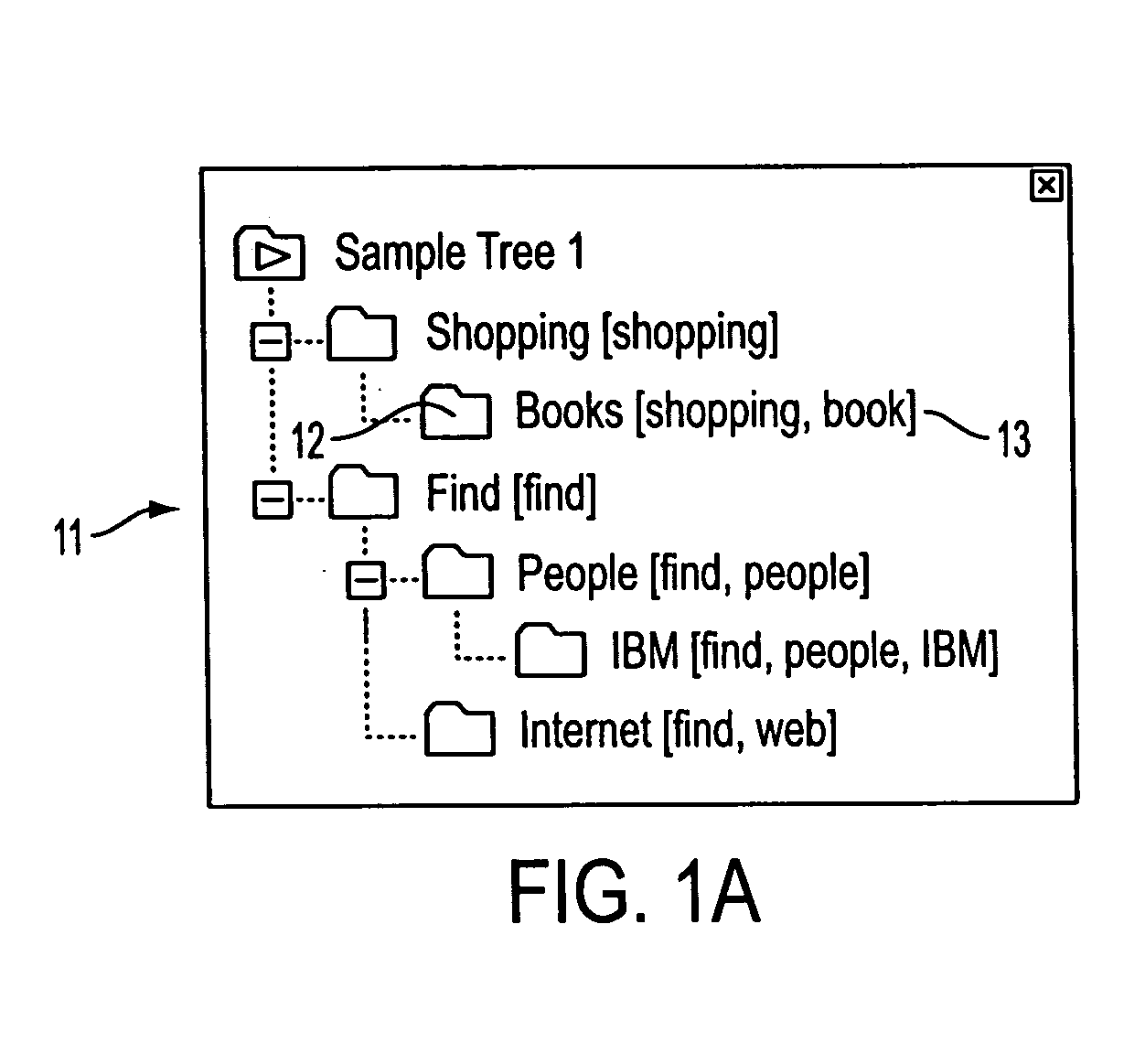
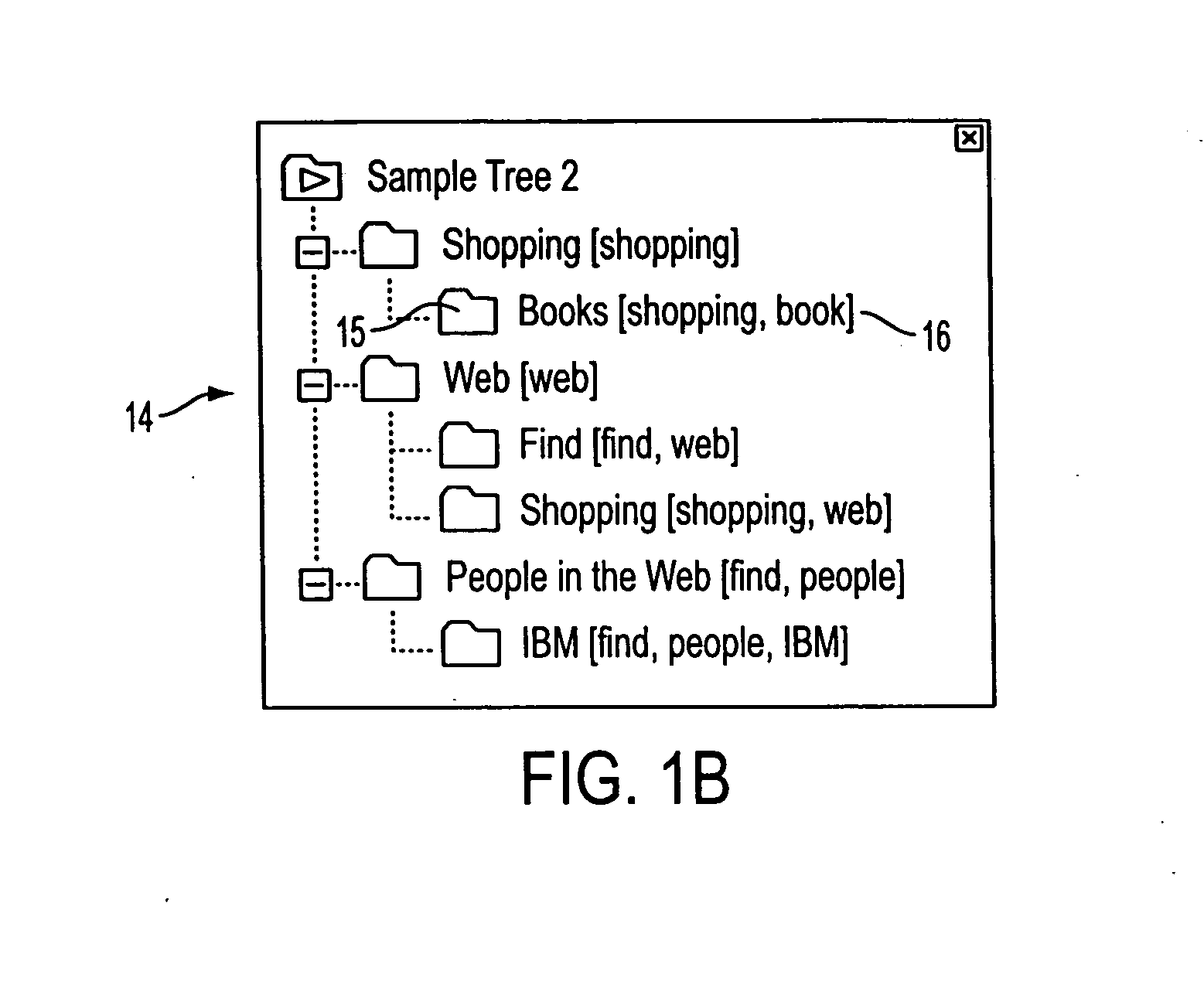
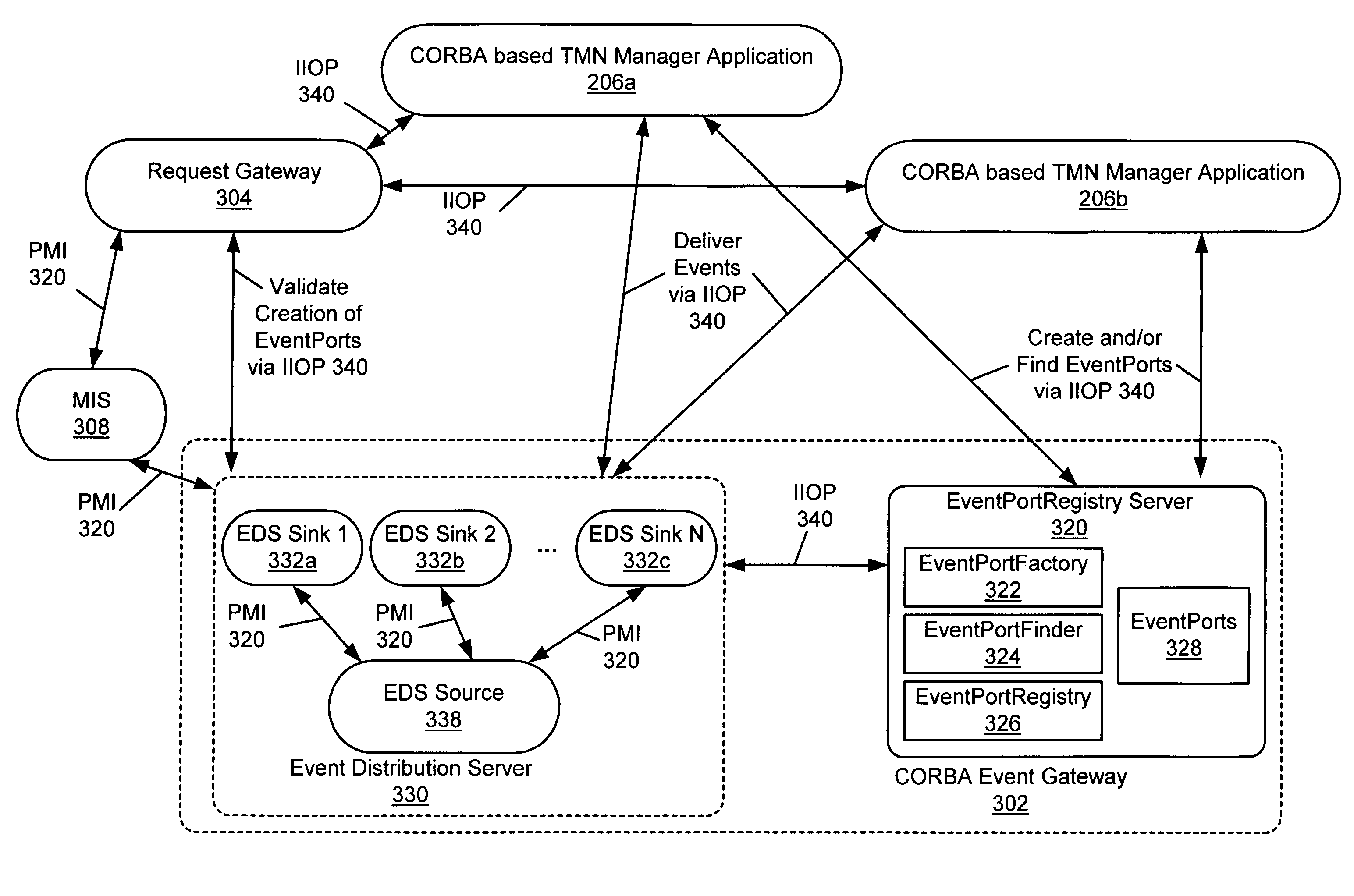
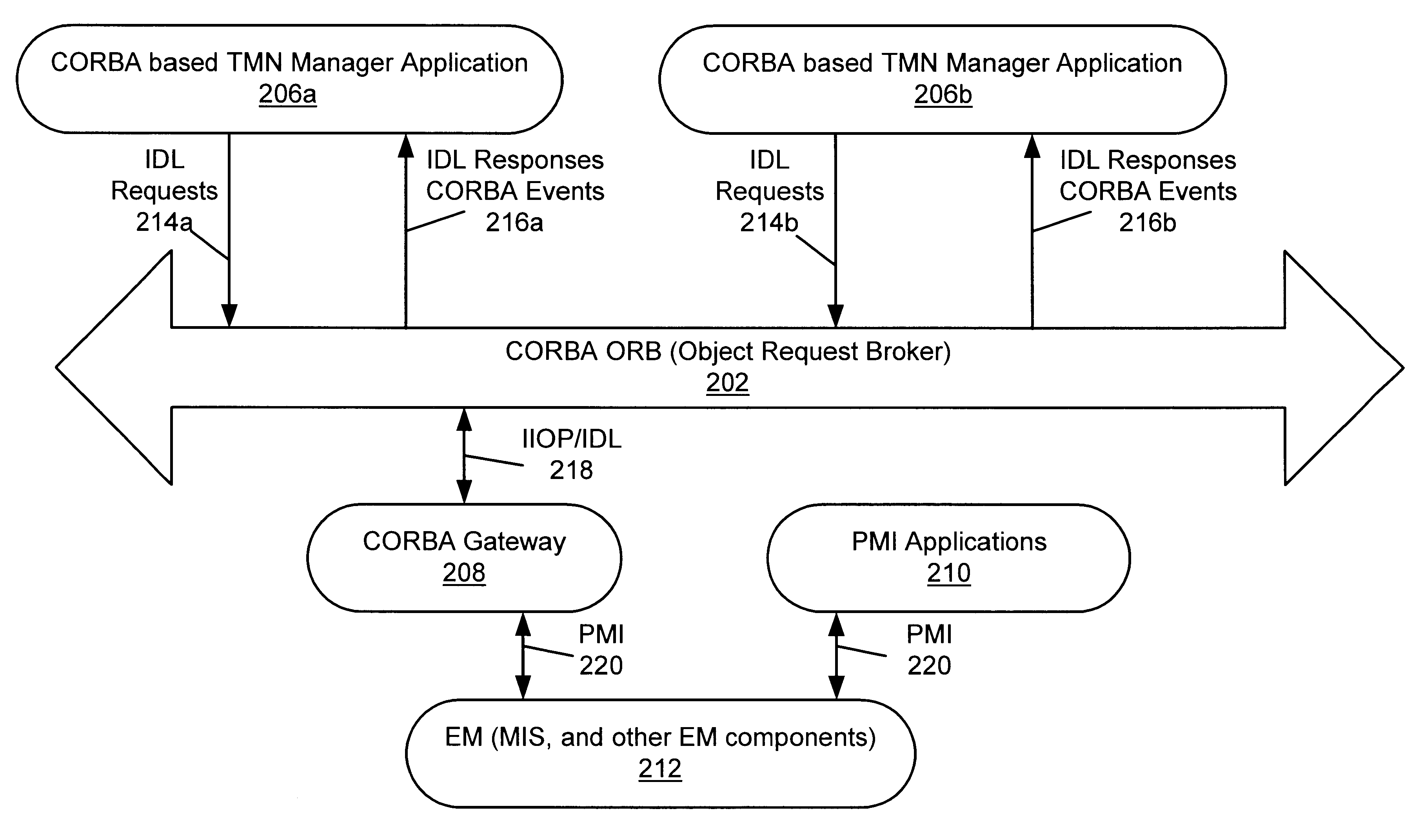
System and method for event subscriptions for CORBA gateway
InactiveUS7010586B1Improve performanceImprove scalabilityData switching by path configurationMultiple digital computer combinationsEvent typeInternet traffic
A CORBA Gateway between CORBA-based applications and an enterprise manager may be configurable to manage various networked objects, such as printers, scanners, copiers, telephone systems, cell phones, phone systems, faxes, routers, switches, etc., which may be interconnected via networks. Various embodiments of the CORBA Gateway may include an Event Gateway which manages object events. The CORBA Event Gateway is designed to leverage existing Event Distribution Server (EDS) sinks to provide EDS filtering functionality and EDS object level access control functionality. The approach leverages existing EDS solutions by providing a common sink for all events / notifications and using a unique Event Port Registry to manage the subscriptions of various TMN clients that subscribe for such events / notifications. Generally, the approach described provides the capability to filter events according to criteria presented by client event subscriptions. In one embodiment, the events may be filtered to enforce policy-based access control on TMN events / notifications, determining which CORBA client applications have access to which events. The filtering of events at the sink based upon client subscriptions decreases unnecessary network traffic in that events may be “pushed” to the client, rather than delivered upon client request. In addition, the approach may provide easy-to-use IDL APIs that allow CORBA clients to directly subscribe / unsubscribe to events based on criteria such as object class, object instance, and event type.
Owner:ORACLE INT CORP
Personalized multi-service computer environment
InactiveUS7062475B1Easy to useEasy to identifyGenetic modelsDigital computer detailsPersonalizationHyperlink
A system and method for tracking a user history, for presentation thereof within a browser display. An executable software construct operates at a client machine to trap object references, which are then transmitted to a server. The server analyzes the object references and organizes them into a display structure. The display structure is then displayed within the browser, including hyperlinks to allow the user to select a prior system state to which he seeks to return. Preferably, the software construct also manages objects associated with the object reference, for example cookies associated with URLs, in order to assure full definition of the desired state. The display structure may also be provided to browsers distinct from the originating browser.
Owner:UNWIRED BROADBAND INC
Method and a System Relating to Network Management
InactiveUS20080294418A1OptimizationReduce the amount requiredData switching by path configurationMultiple digital computer combinationsNetwork managementManaged object
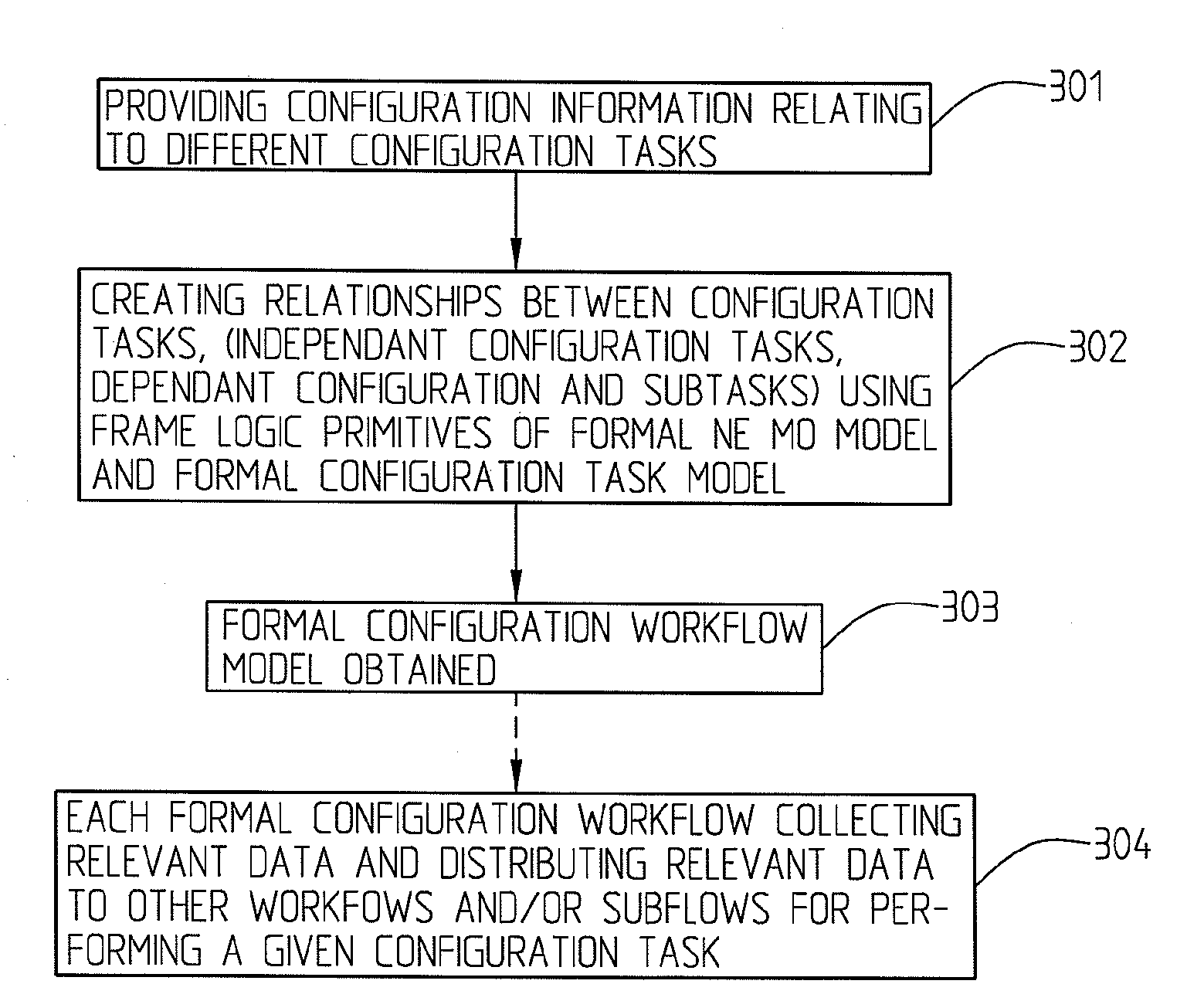
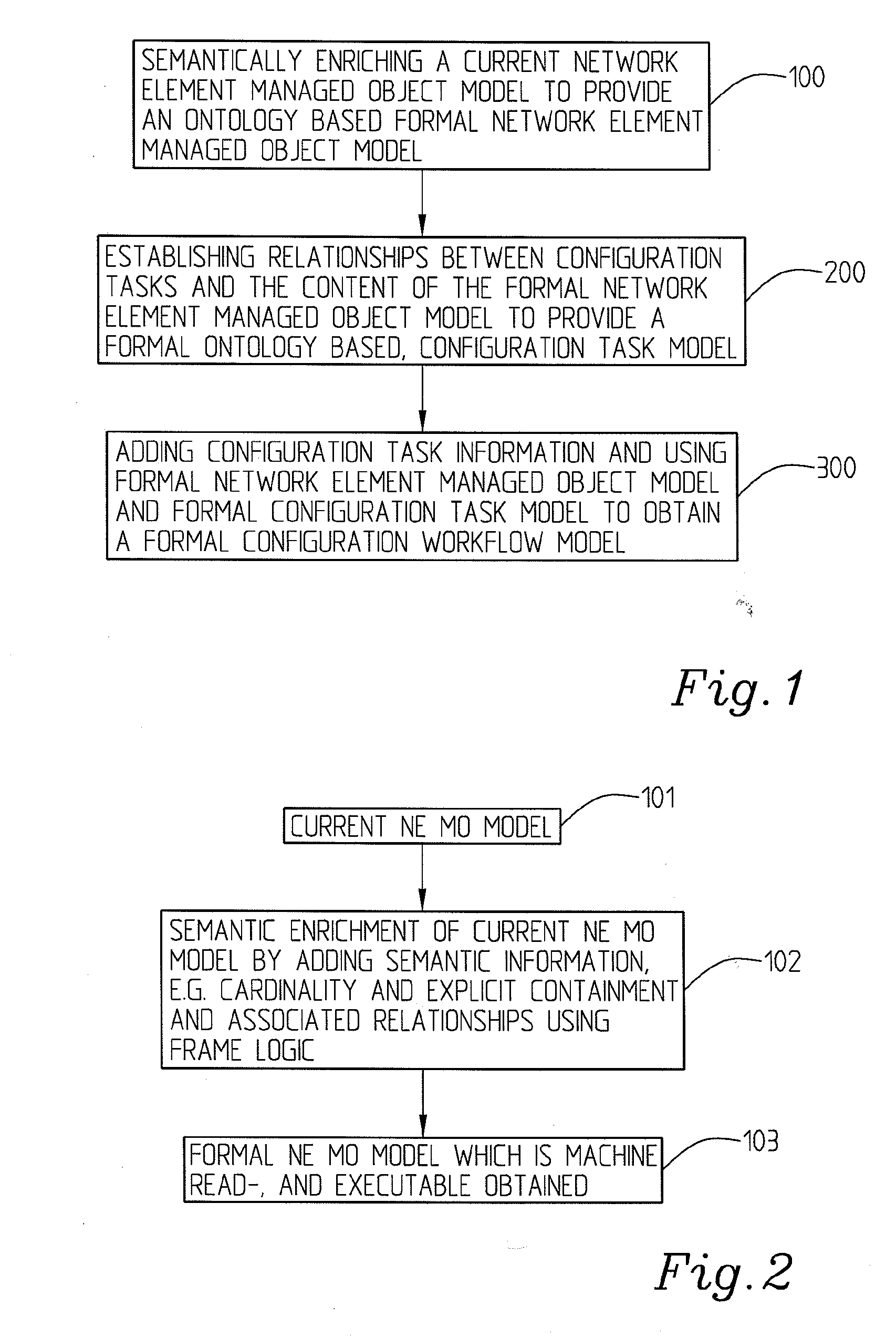
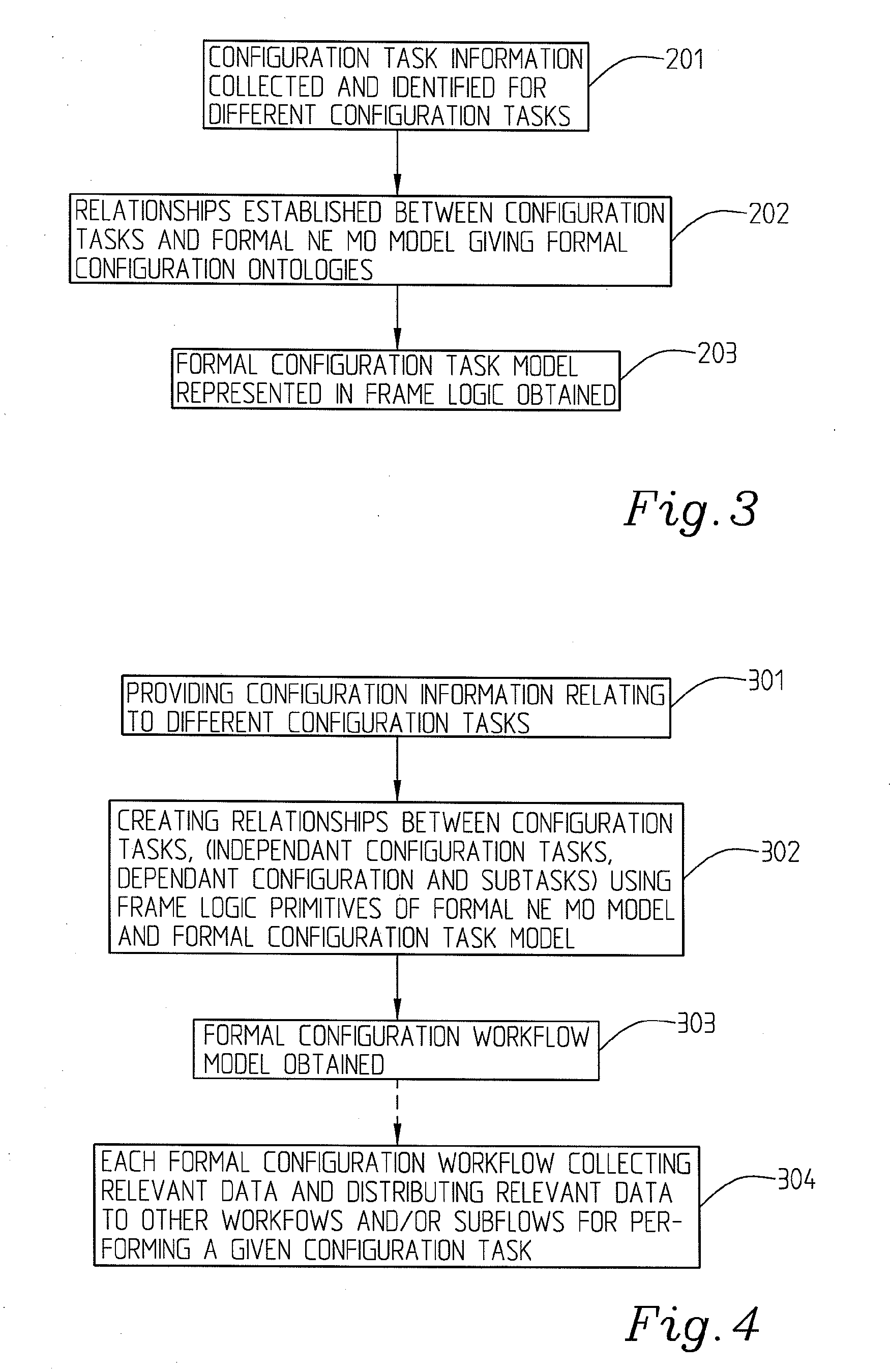
The present invention relates to a method for network management comprising configuration of control protocols between network elements in a network represented through a current, static, network element object model comprising a number of managed objects with attributes and instances and representing resources. It comprises the steps of: transforming the current network element object model to a machine readable and executable formal network element object model; identifying configuration tasks needed for the configuration of the relevant control protocols; modelling a formal configuration task model using information about the configuration tasks and the formal network element object model; building a formal configuration workflow model using the formal network element object model and the formal configuration task model, said formal configuration workflow model defining the relationships between different configuration tasks required for performing or completing a number of given actions or to achieve a number of given goals.
Owner:TELEFON AB LM ERICSSON (PUBL)
Non-overlapping graphical user interface workspace
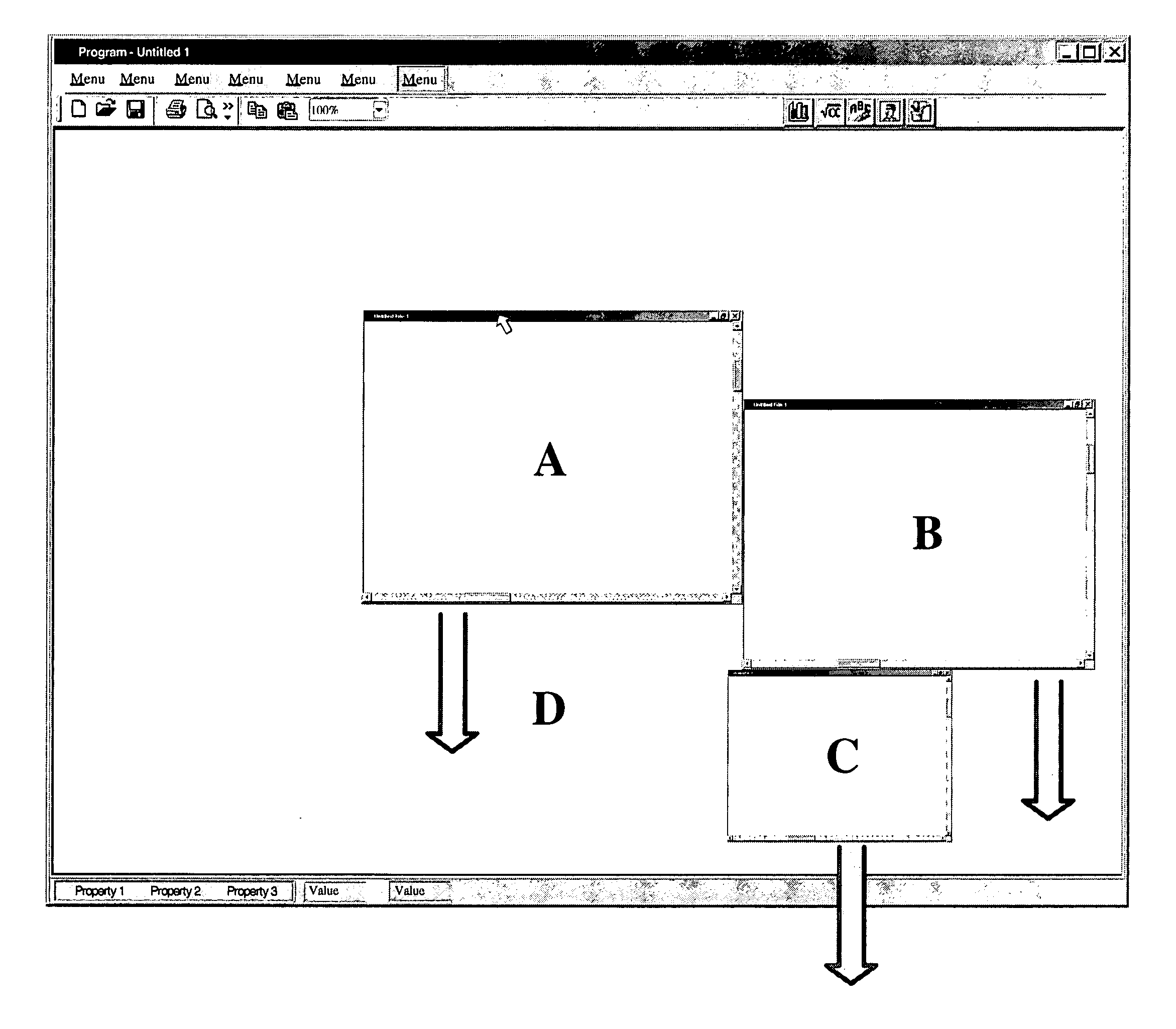
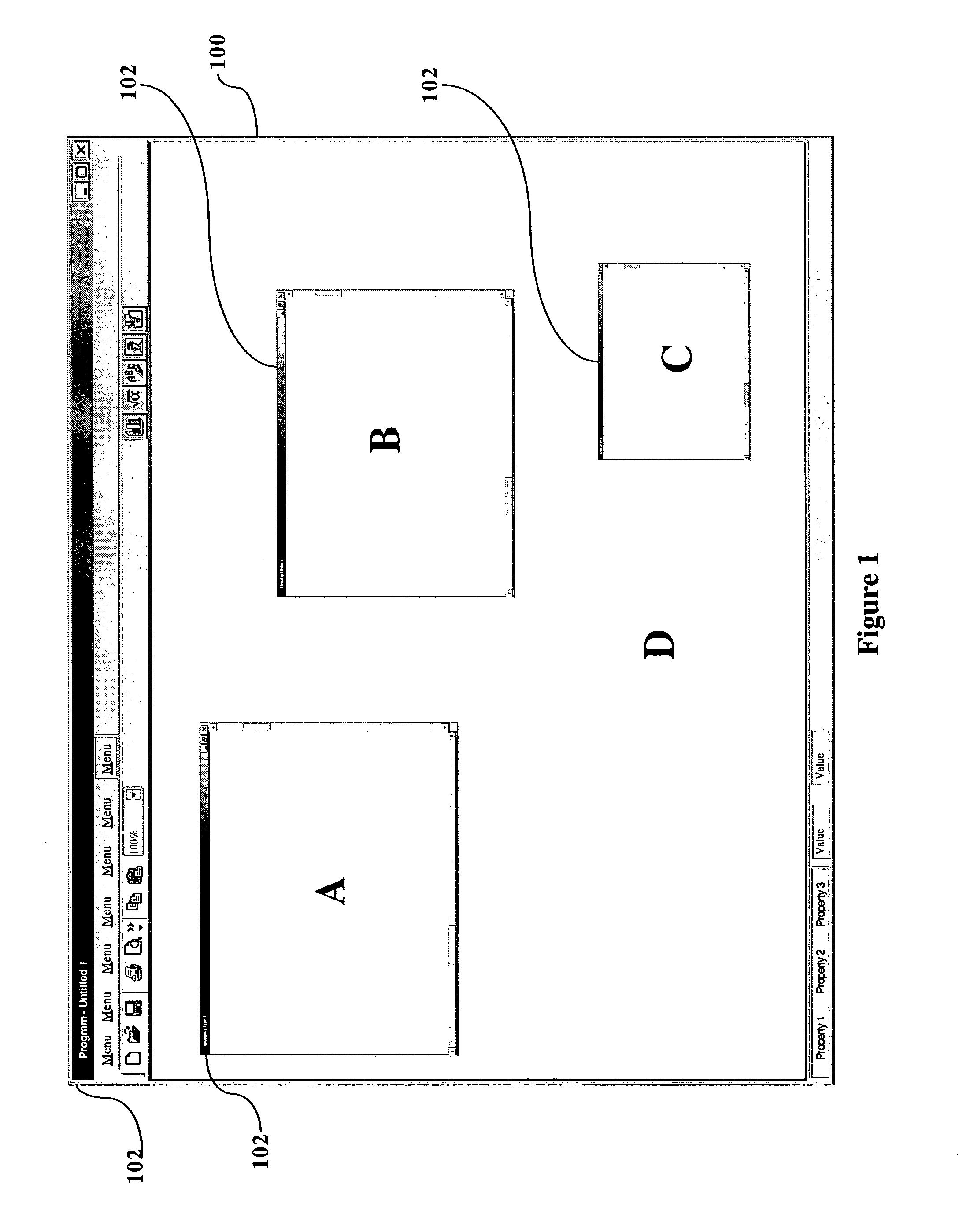
InactiveUS20050125742A1Increase in sizeInput/output processes for data processingGraphicsGraphical user interface
A user interface mechanism that introduces a novel concept referred to as a “non-overlapping workspace”. A system user can switch between the traditional overlapping workspace and the novel non-overlapping workspace, depending upon how they wish to move and manage objects in the workspace. In the non-overlapping mode, as the user moves a selected object to relocate it within the work area, as its border touches another object, the selected object pushes the other object (rather than cover it). In an alternative embodiment, when the system is in the non-overlapping mode, objects on the desktop have “sticky” borders, that is, as the border of a selected object comes into contact with the border of another object, the two objects are coupled to each other as though they were glued together, forming an “object unit”.
Owner:IBM CORP
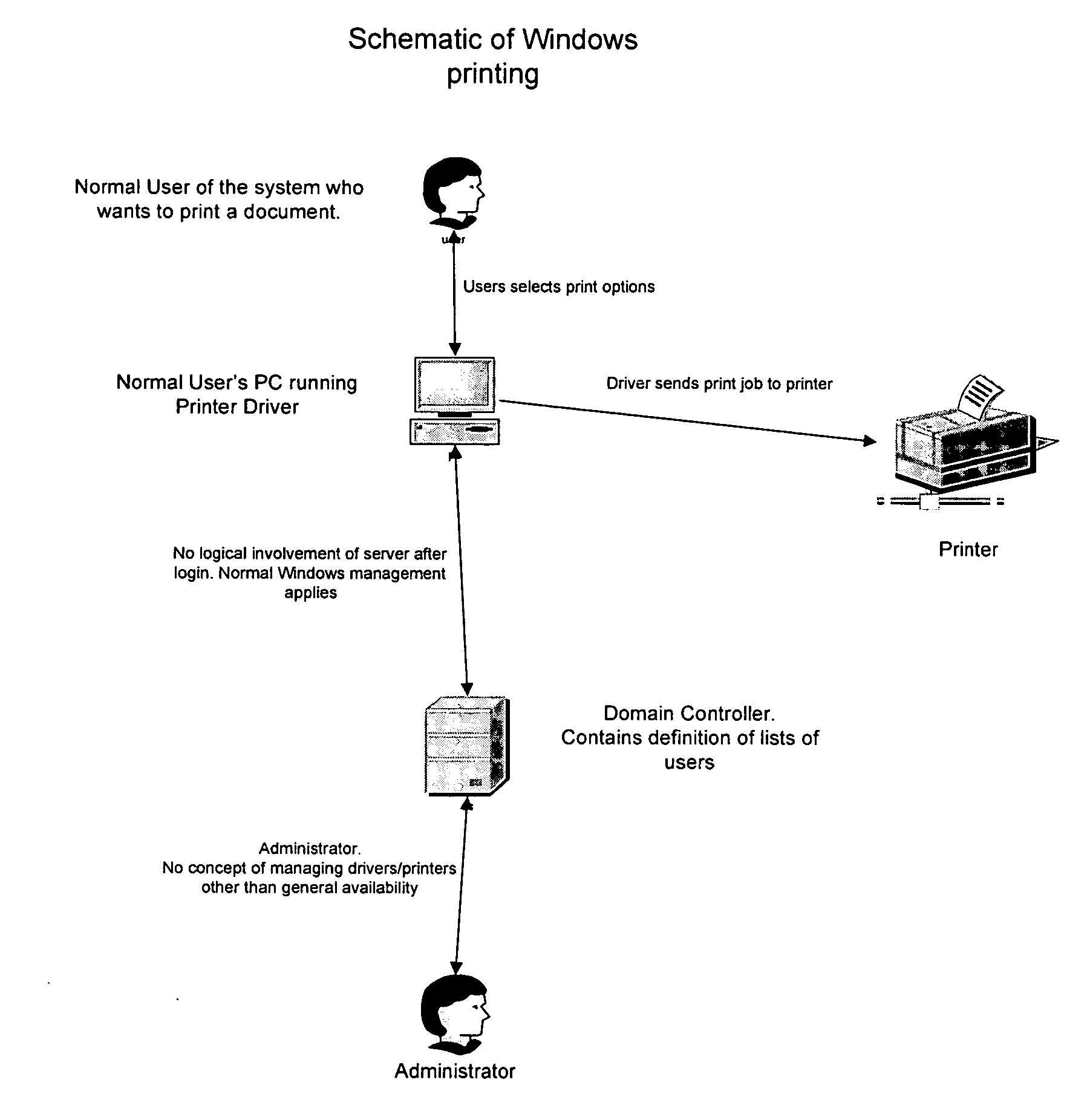
Managing user permissions in a computer system
InactiveUS20070079385A1Digital data processing detailsUser identity/authority verificationOperational systemUser Privilege
A method of operating a printer coupled to a computer, the method comprising associating one or more permissions of a printer driver resident on the computer with an operating system managed object and, when an attempt is made to print on said print device or a User Interface of the printer driver opened, setting the status of said permissions according to one or more security settings of the operating system managed object.
Owner:SOFTWARE IMAGING GROUP
Method and apparatus for harvesting file system metadata
InactiveUS20100088317A1Efficient storageEfficient accessDigital data processing detailsMultiple digital computer combinationsFile systemBusiness enterprise
A harvester is disclosed for harvesting metadata of managed objects (files and directories) across file systems which are generally not interoperable in an enterprise environment. Harvested metadata may include 1) file system attributes such as size, owner, recency; 2) content-specific attributes such as the presence or absence of various keywords (or combinations of keywords) within documents as well as concepts comprised of natural language entities; 3) synthetic attributes such as mathematical checksums or hashes of file contents; and 4) high-level semantic attributes that serve to classify and categorize files and documents. The classification itself can trigger an action in compliance with a policy rule. Harvested metadata are stored in a metadata repository to facilitate the automated or semi-automated application of policies.
Owner:IBM CORP
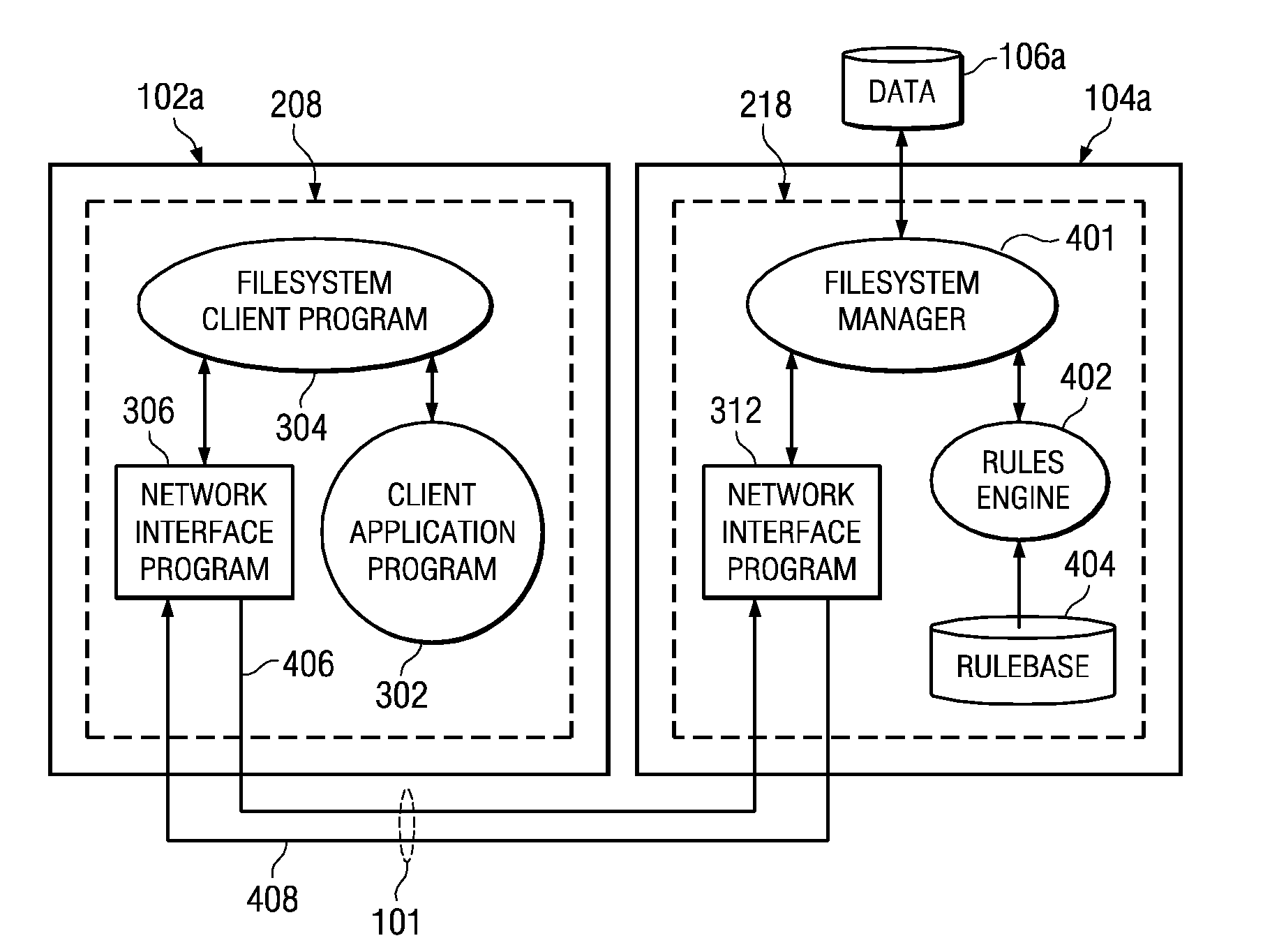
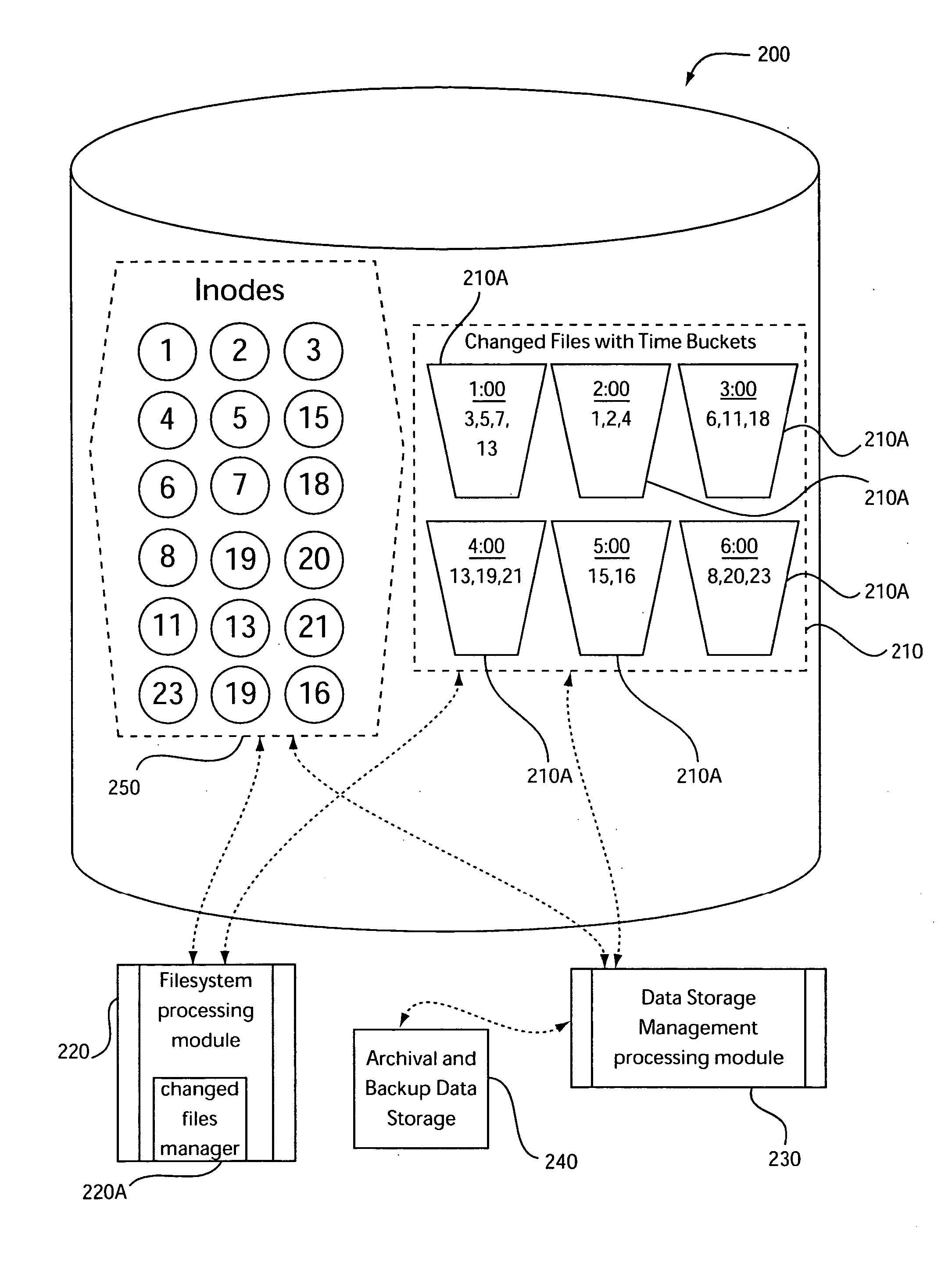
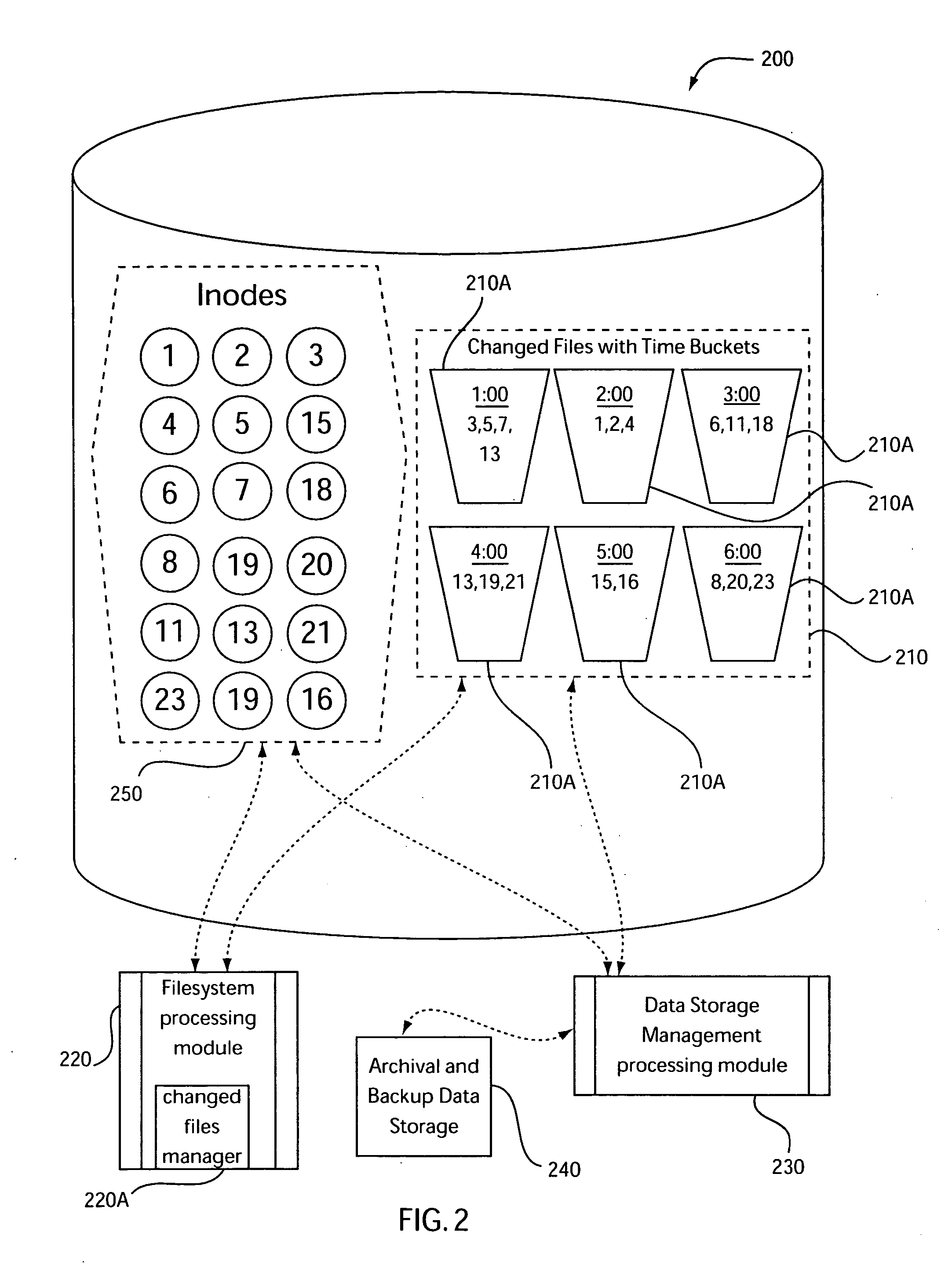
Changed files list with time buckets for efficient storage management
InactiveUS20060259527A1File access structuresSpecial data processing applicationsTimestampManagement object
There is provided, in a computer processing system, an apparatus for managing object data. The apparatus includes a changed objects manager for creating and managing a changed objects list that at least identifies the objects that have changed based on time of change. The changed objects list is associated with a plurality of time buckets. Each of the plurality of time buckets is associated with a respective date and time period and with object change records for objects having a timestamp falling within the respective date and time period. Each of the object change records is associated with a unique object identifier and the timestamp for a corresponding one of the objects. The timestamp specifies a date and a time corresponding to a latest one of a creation time or a most recent update time for the corresponding one of the objects.
Owner:IBM CORP
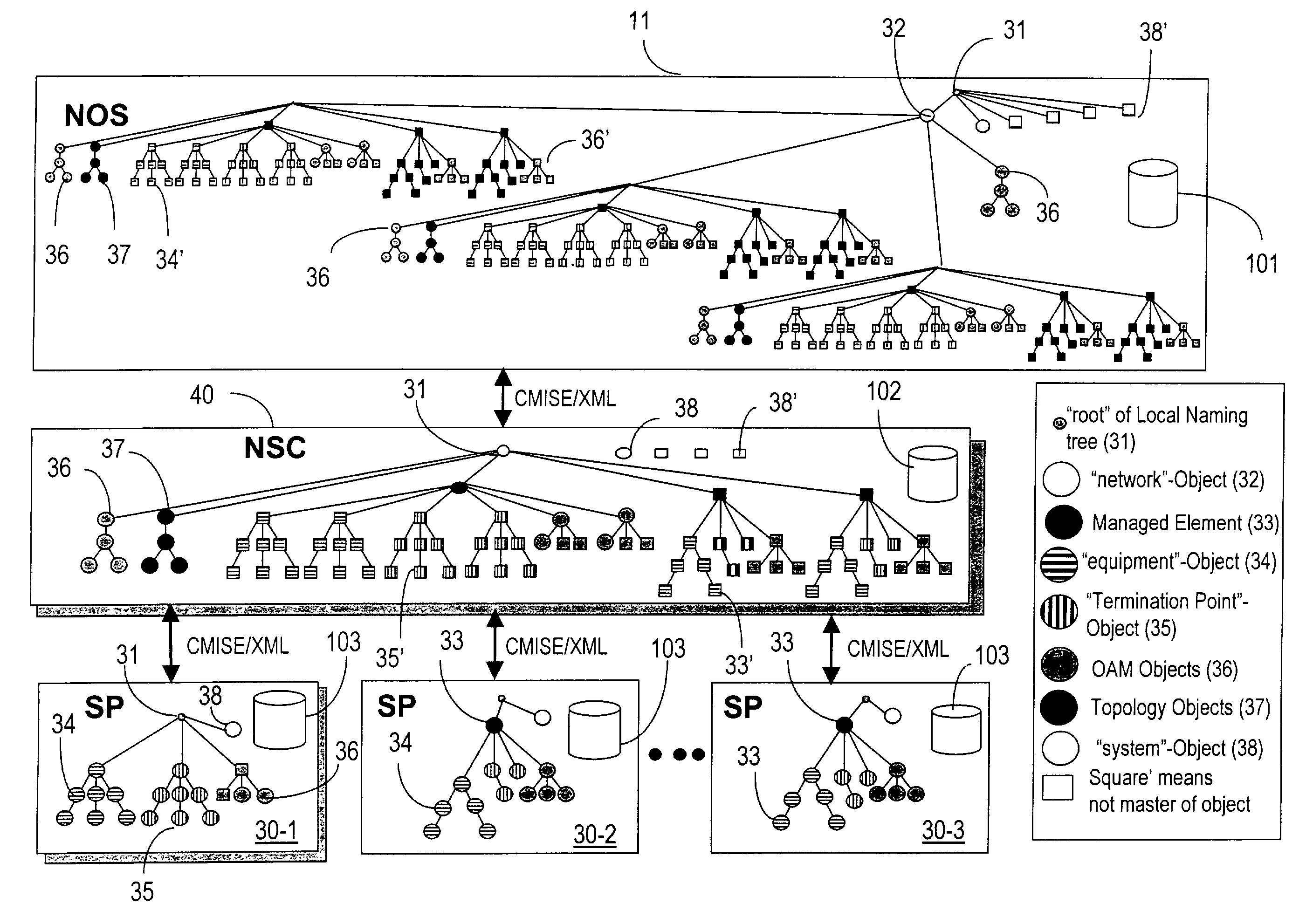
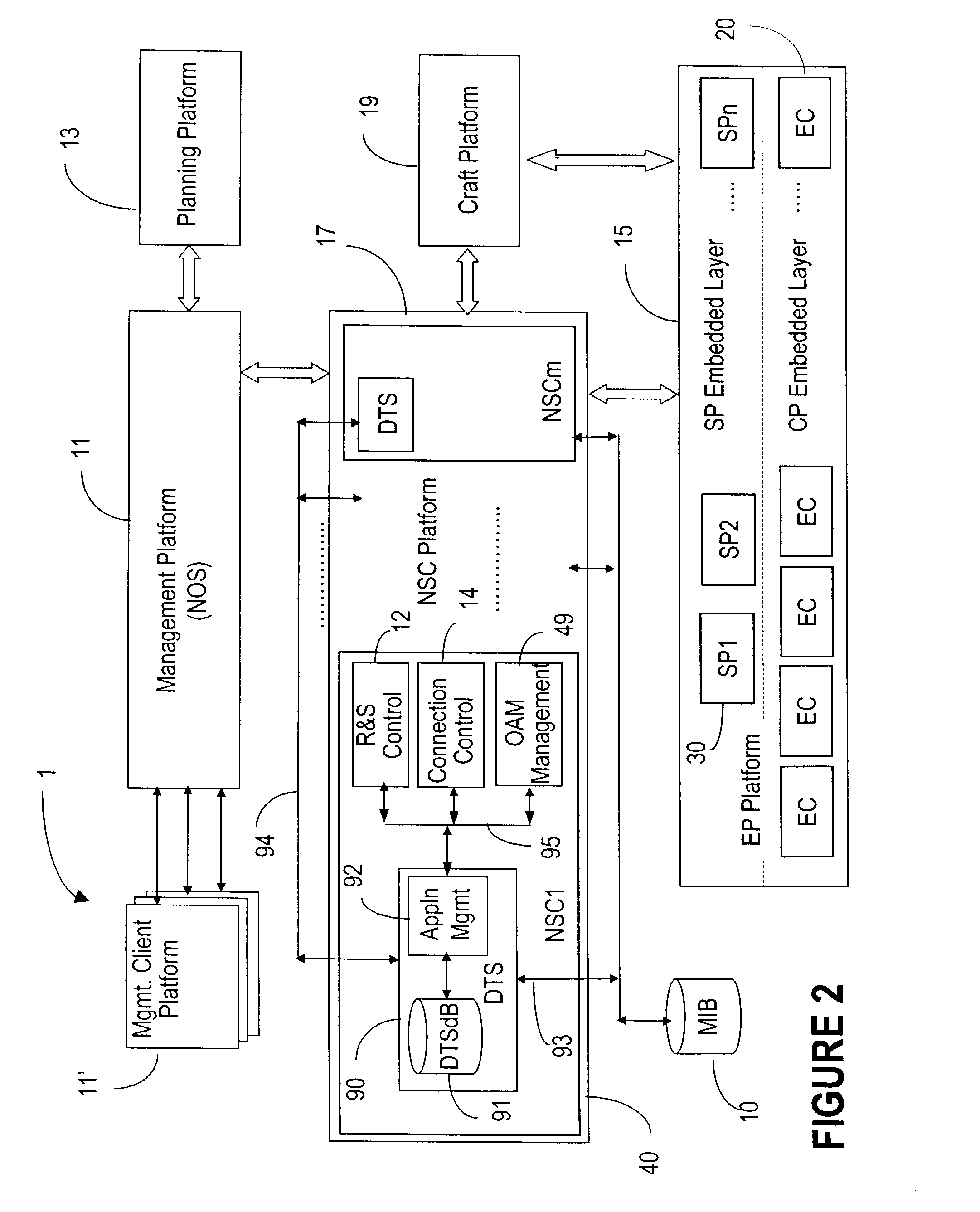
Network operating system with distributed data architecture
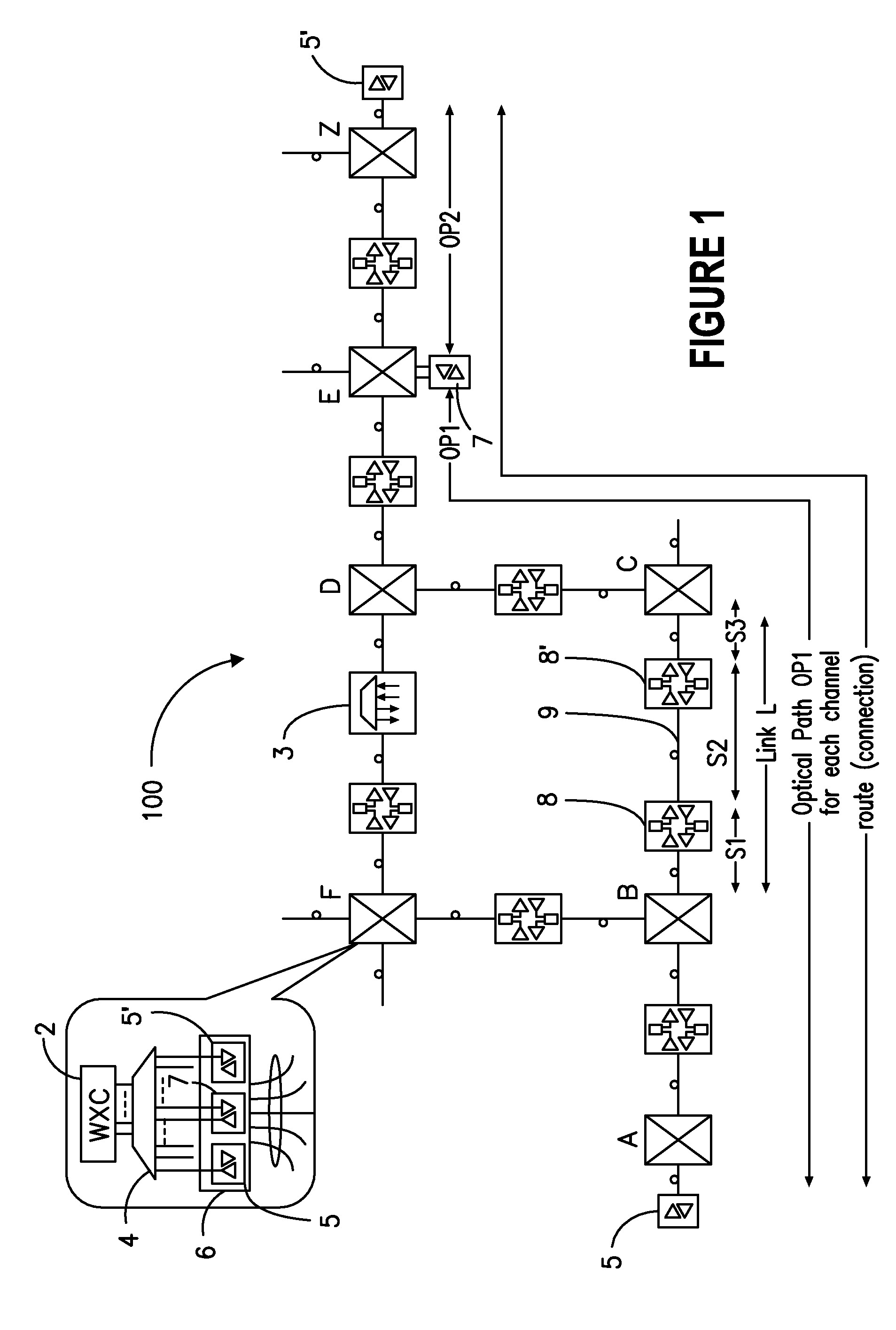
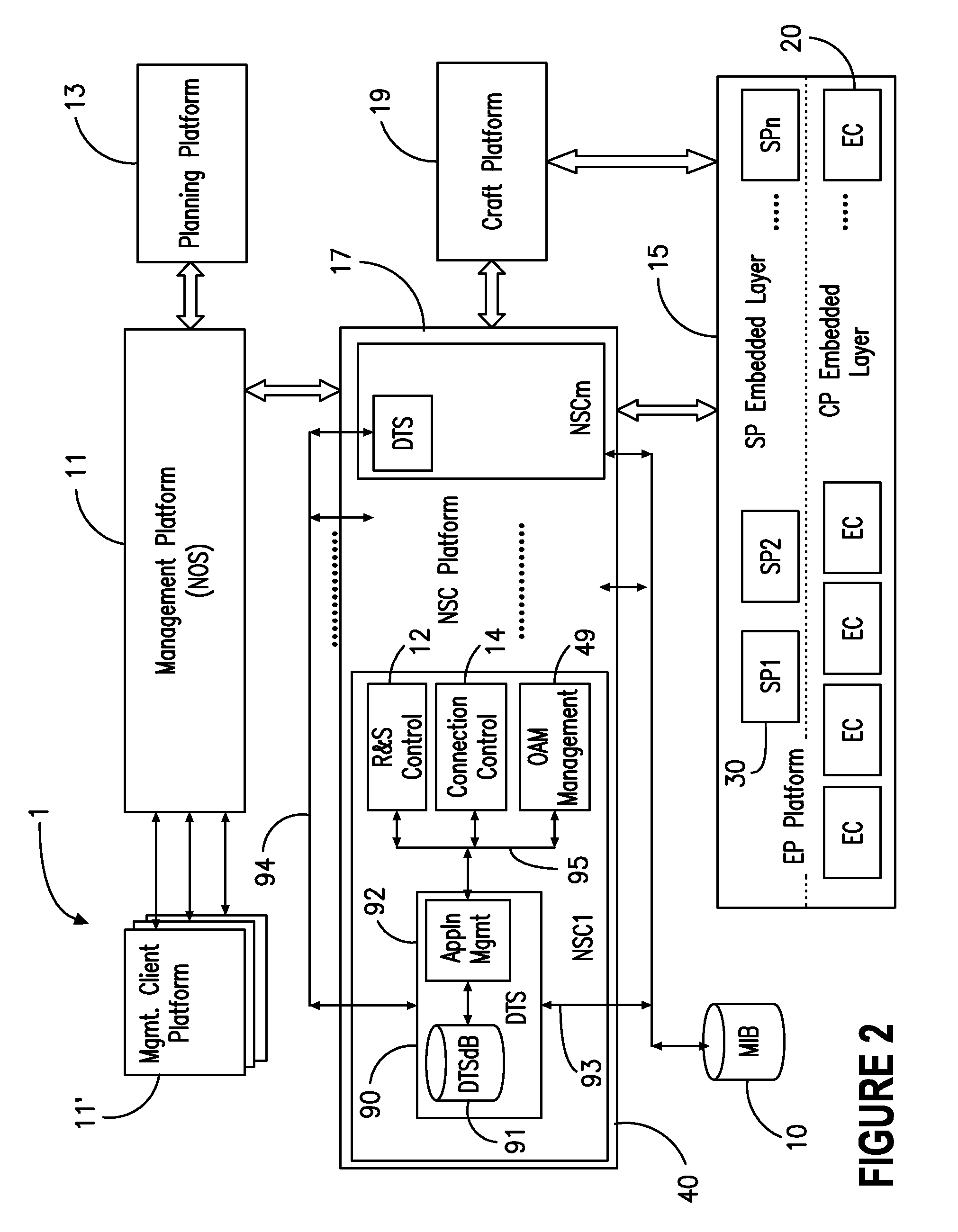
ActiveUS7263290B2Dynamic reconfiguration of network connectivity, flexibility and scalabilityDynamic reconfiguration of network connectionsMultiplex system selection arrangementsOptical multiplexInformation repositoryNetwork operating system
A network operating system NOS for an agile optical network with a plurality of mesh interconnected switching nodes, manages the network using an object-oriented network information model. The model is common to all applications requiring the data stored in the network managed information base. The core model can be expanded for serving specific application areas. The NOS is organized in layers, at the optical module level, connection level and network level. A distributed topology server DTS organizes the physical, logical and topological data defining all network entities as managed objects MO and topology objects TO for constructing a complete network view. The network information model associates a network element NE information model, specified by managed objects MO and a topological information model, specified by topology objects TO. The MOs are abstract specific NE data that define network implementation details and do not include any topological data, while the TOs abstract specific topological data for defining a trail established within the network, and do not include any NE data. The models are associated in a minimal number of points to construct the model of a trial in response to a connection request.
Owner:WSOU INVESTMENTS LLC
Intelligent digital assistant in a multi-tasking environment
ActiveUS20180308485A1Web data indexingNatural language data processingManagement objectManaged object
Systems and processes for operating a digital assistant are provided. In one example, a method includes receiving a first speech input from a user. The method further includes identifying context information and determining a user intent based on the first speech input and the context information. The method further includes determining whether the user intent is to perform a task using a searching process or an object managing process. The searching process is configured to search data, and the object managing process is configured to manage objects. The method further includes, in accordance with a determination the user intent is to perform the task using the searching process, performing the task using the searching process; and in accordance with the determination that the user intent is to perform the task using the object managing process, performing the task using the object managing process.
Owner:APPLE INC
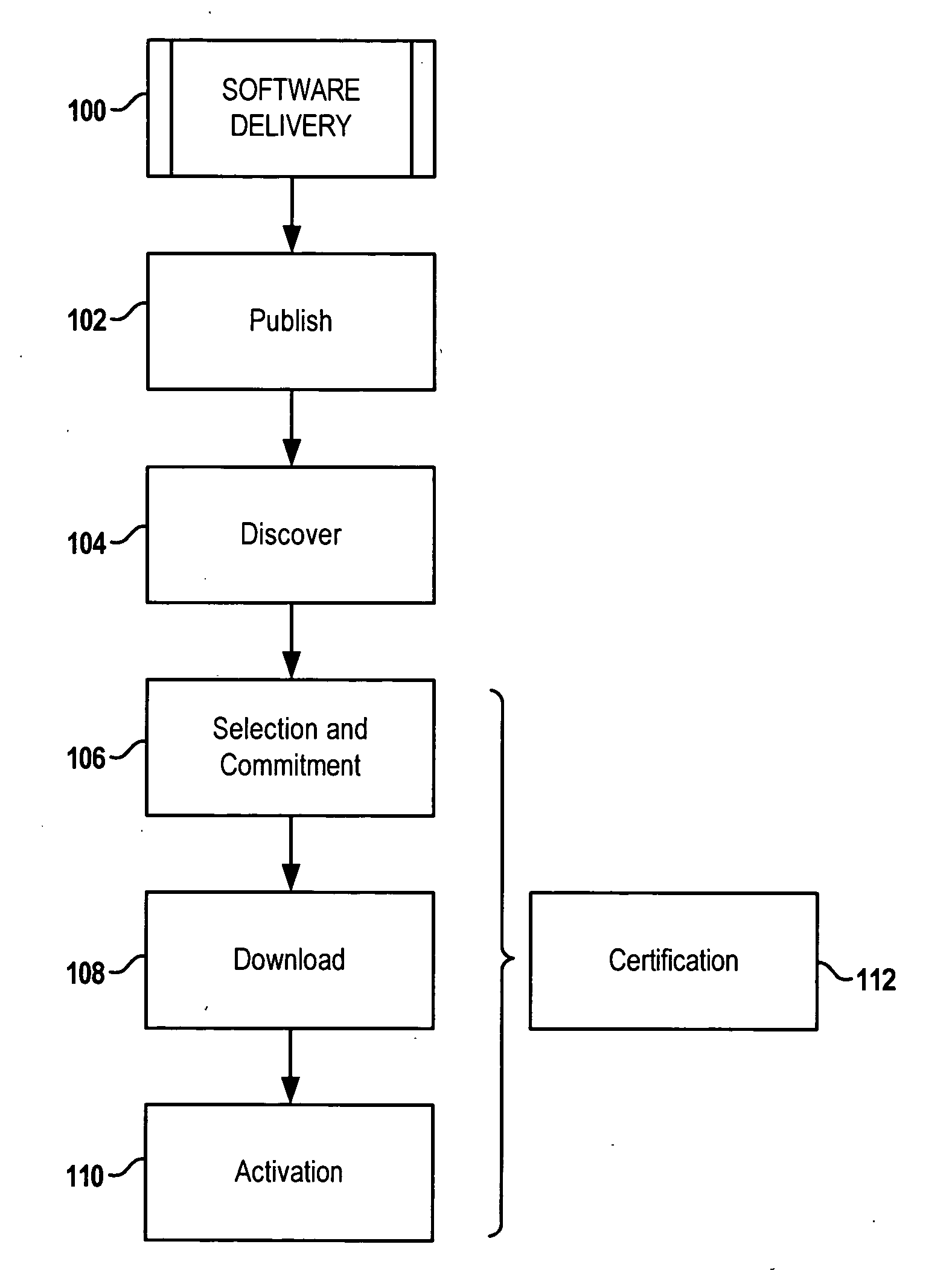
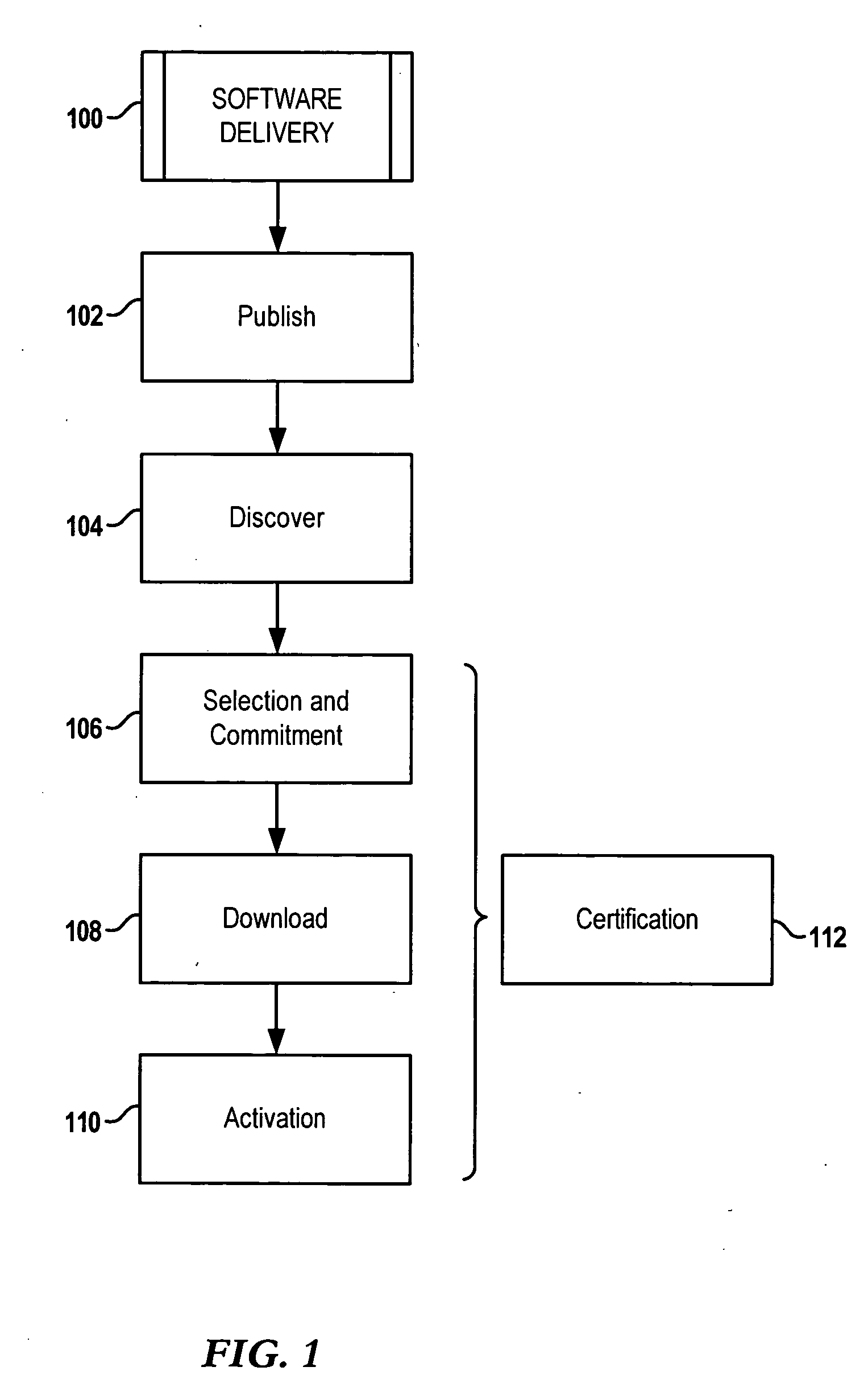
Software distribution with activation control
InactiveUS20060200814A1Specific program execution arrangementsMemory systemsSoftware distributionManagement object
Distributing software involves providing a software installation package configured to allow installing one or more programs on a computing arrangement. The software installation package is configured as a managed object compliant with the Open Mobile Alliance Device Management (OMA DM) specification. A certificate configured as a second managed object compliant with the OMA DM specification is also provided. One or more programs are installed to a computing arrangement using the software installation package. The one or more programs are bound to the computing arrangement using the certificate. Operation of the one or more programs is enabled based on the binding of the one or more programs to the computing arrangement.
Owner:NOKIA SOLUTIONS & NETWORKS OY
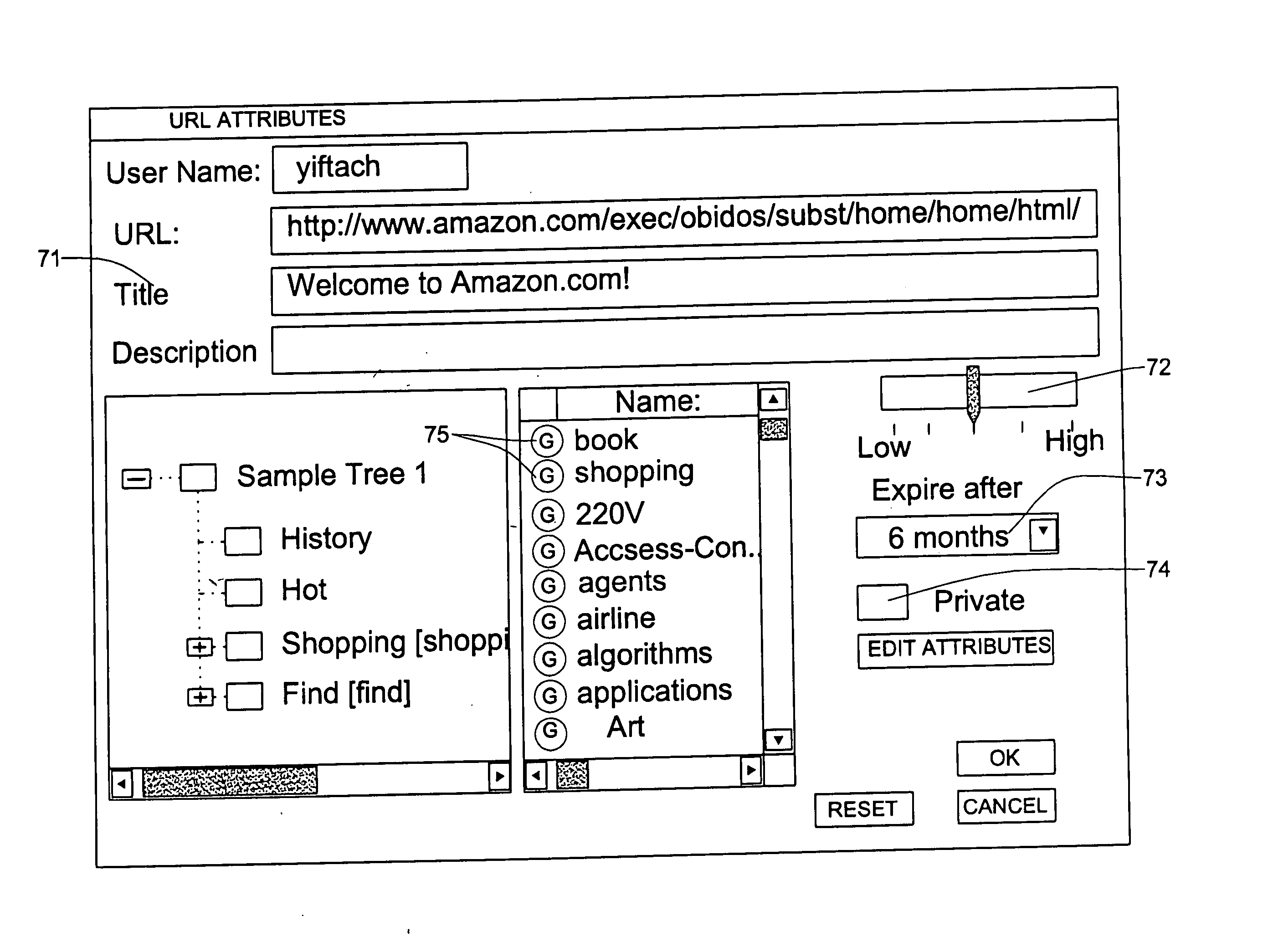
Managing objects and sharing information among communities
InactiveUS20050022132A1Much good performanceShorten the timeDigital computer detailsUnstructured textual data retrievalCommunity settingEngineering
A method for managing objects for users including providing a set of attributes and a set of containers each having attributes from the set. The method further provides a user interface for dynamically assigning attributes to the objects. The method further provides for selectively displaying, through a user interface, containers and objects in the containers. An object is displayed in a container if a condition is met. The condition is applied to the attributes of the container and the attributes of the object.
Owner:QUADRANT EPP +1
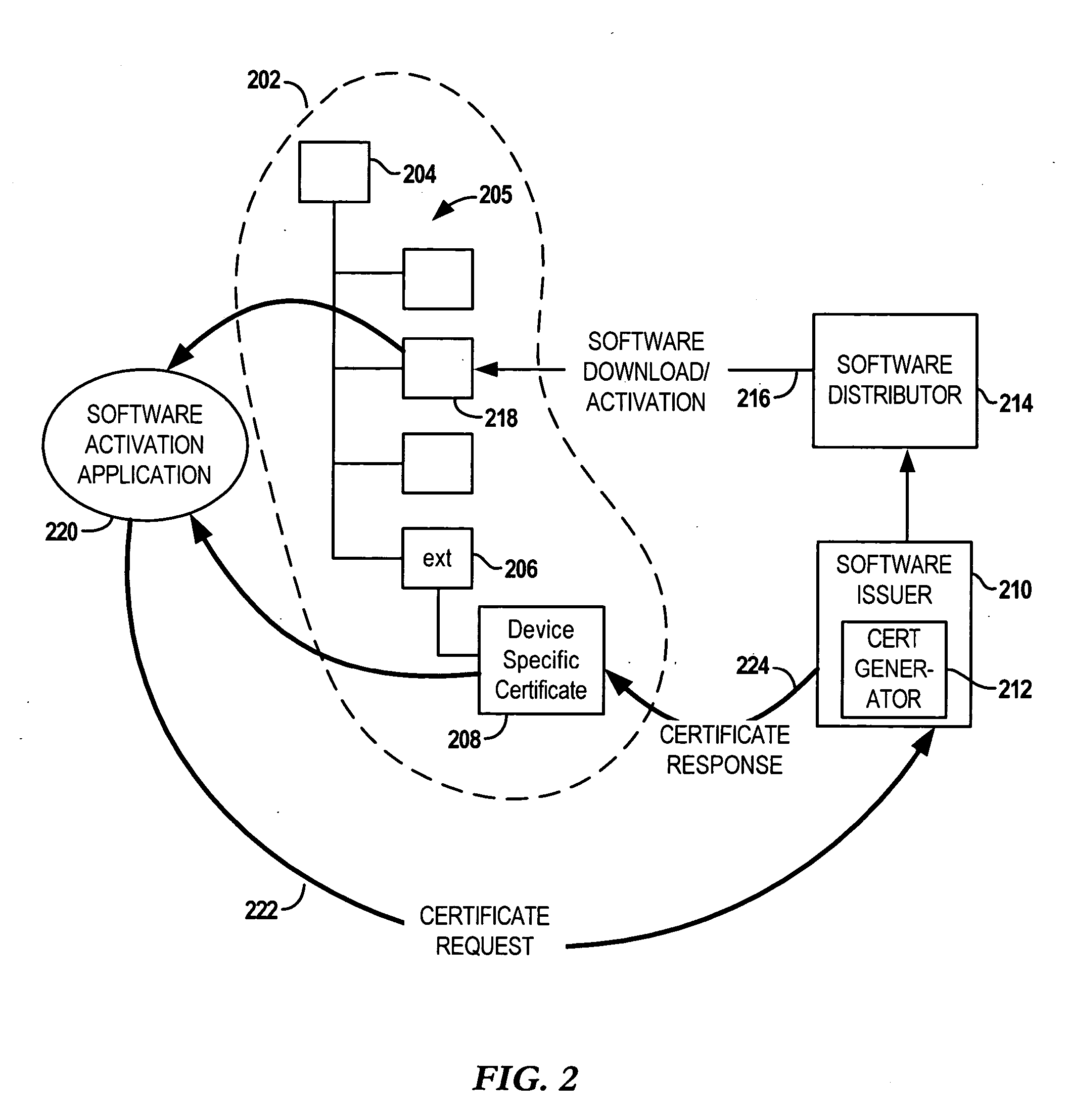
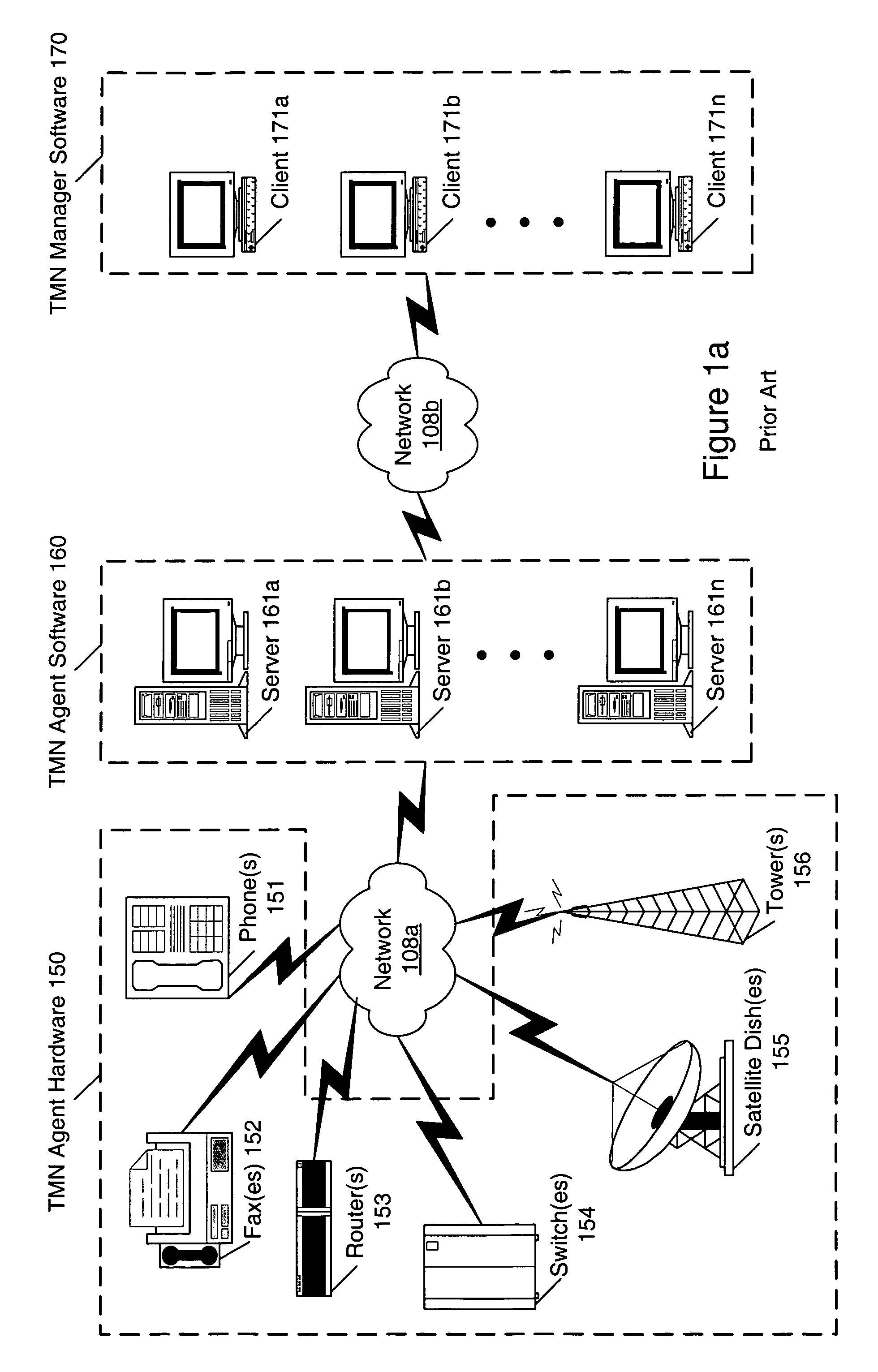
Secure access to managed network objects using a configurable platform-independent gateway providing individual object-level access control
InactiveUS7478403B1Data switching by path configurationMultiple digital computer combinationsManaged objectApplication software
A gateway between client manager applications and an enterprise manager may be provided to manage various networked objects. In one embodiment, CORBA-based TMN manager applications may be communicatively coupled to a CORBA Object Request Broker (ORB) and may be operable to send Interface Definition Language (IDL) requests to, and receive IDL responses and CORBA events from, managed objects through the CORBA ORB. The client manager may first be authenticated to the gateway by username and password, or other validation information associated with the client manager, which may be represented in a user profile. Once the initial client authentication is accomplished, the gateway may provide object-level access control between manager applications and managed objects at an individual object level so that one of the managers is granted access to one of the managed objects while being prevented from interfacing with a different one of the managed objects.
Owner:ORACLE INT CORP
Synchronous task scheduler for corba gateway
InactiveUS6839748B1Protect resourcesImprove performanceMultiple digital computer combinationsData switching networksManaged objectApplication software
A system and method for a synchronous task scheduler. The synchronous task scheduler may be used with a CORBA Gateway between CORBA-based client manager applications and an enterprise manager. The CORBA Gateway may include components such as an Event Gateway which manages events from managed objects, and a Request Gateway which manages requests and responses of managed objects. The Event Gateway and the Request Gateway may be designed as multi-threaded systems. A thread pool may be used to increase efficiency and performance of the CORBA Gateway. To ensure ordered delivery of events or replies to the CORBA gateway clients in a multi-threaded environment using a thread pool, a synchronous task scheduler may be used. There may be a synchronous task scheduler associated with each client manager to preserve the chronology of messages sent to each. The synchronous task scheduler may maintain an internal message list, and deliver one message at a time from that internal list. The synchronous task scheduler may hold a reference to a thread pool and use that thread pool to deliver messages. When a message is scheduled, the synchronous task scheduler may check if any message is already being delivered. If no prior message is currently being delivered, an available thread may be assigned from the thread pool for delivery of the message and the scheduler may initiate delivery of the message. If a prior message is being delivered, it may enqueue the message in the message list. Then, when the prior message delivery is completed, the scheduler may dequeue the message, assign another thread from the thread pool, and initiate delivery of the message. This may continue until the message list is empty.
Owner:ORACLE INT CORP
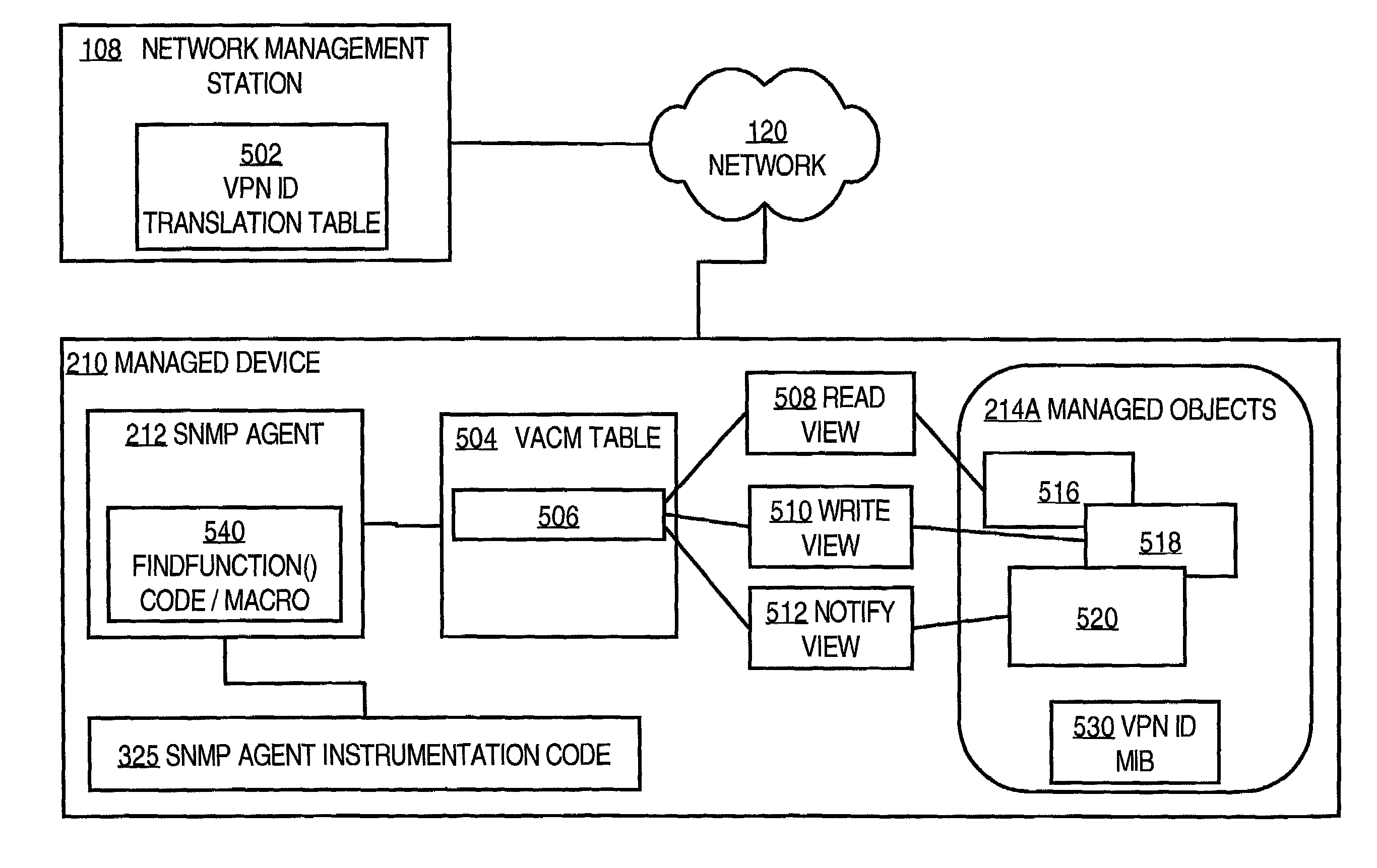
Method and apparatus providing controlled access of requests from virtual private network devices to managed information objects using simple network management protocol
InactiveUS7099947B1Prevent access to informationSimple and scalableUser identity/authority verificationMultiple digital computer combinationsManagement information baseView based
Access control approaches are disclosed wherein managed object in Simple Network Management Protocol (SNMP) Management Information Bases (MIBs) are accessed on a per-Virtual Private Network (VPN)-basis with no modifications to existing MIBs. A manager and an SNMP Agent operating in a VPN environment agree on a mapping between SNMP securityNames and VPN IDs. Under the agreed mapping, the target VPN of any SNMP management request can be unambiguously determined from the securityName alone. For each securityName, one or more MIB Views are configured using in a View-based Access Control Model MIB (VACM MIB) table; the MIB Views specify which portions of the managed object tree can be viewed or modified by a corresponding VPN. Thereafter, a VPN-enabled device provides SNMP requests in which a VPN ID value is passed in the securityName field of the context string in the community string. The receiving device extracts the securityName, locates corresponding MIB Views using the VACM MIB table, and allows the requesting device to access only objects that are identified in the MIB Views.
Owner:CISCO TECH INC
Network operating system with distributed data architecture
ActiveUS20080212963A1Dynamic reconfiguration of network connectivity, flexibility and scalabilityDynamic reconfiguration of network connectionsMultiplex system selection arrangementsOptical multiplexInformation repositoryNetwork operating system
A network operating system NOS for an agile optical network with a plurality of mesh interconnected switching nodes, manages the network using an object-oriented network information model. The model is common to all applications requiring the data stored in the network managed information base. The core model can be expanded for serving specific application areas. The NOS is organized in layers, at the optical module level, connection level and network level. A distributed topology server DTS organizes the physical, logical and topological data defining all network entities as managed objects MO and topology objects TO for constructing a complete network view. The network information model associates a network element NE information model, specified by managed objects MO and a topological information model, specified by topology objects TO. The MOs are abstract specific NE data that define network implementation details and do not include any topological data, while the TOs abstract specific topological data for defining a trail established within the network, and do not include any NE data. The models are associated in a minimal number of points to construct the model of a trial in response to a connection request.
Owner:WSOU INVESTMENTS LLC
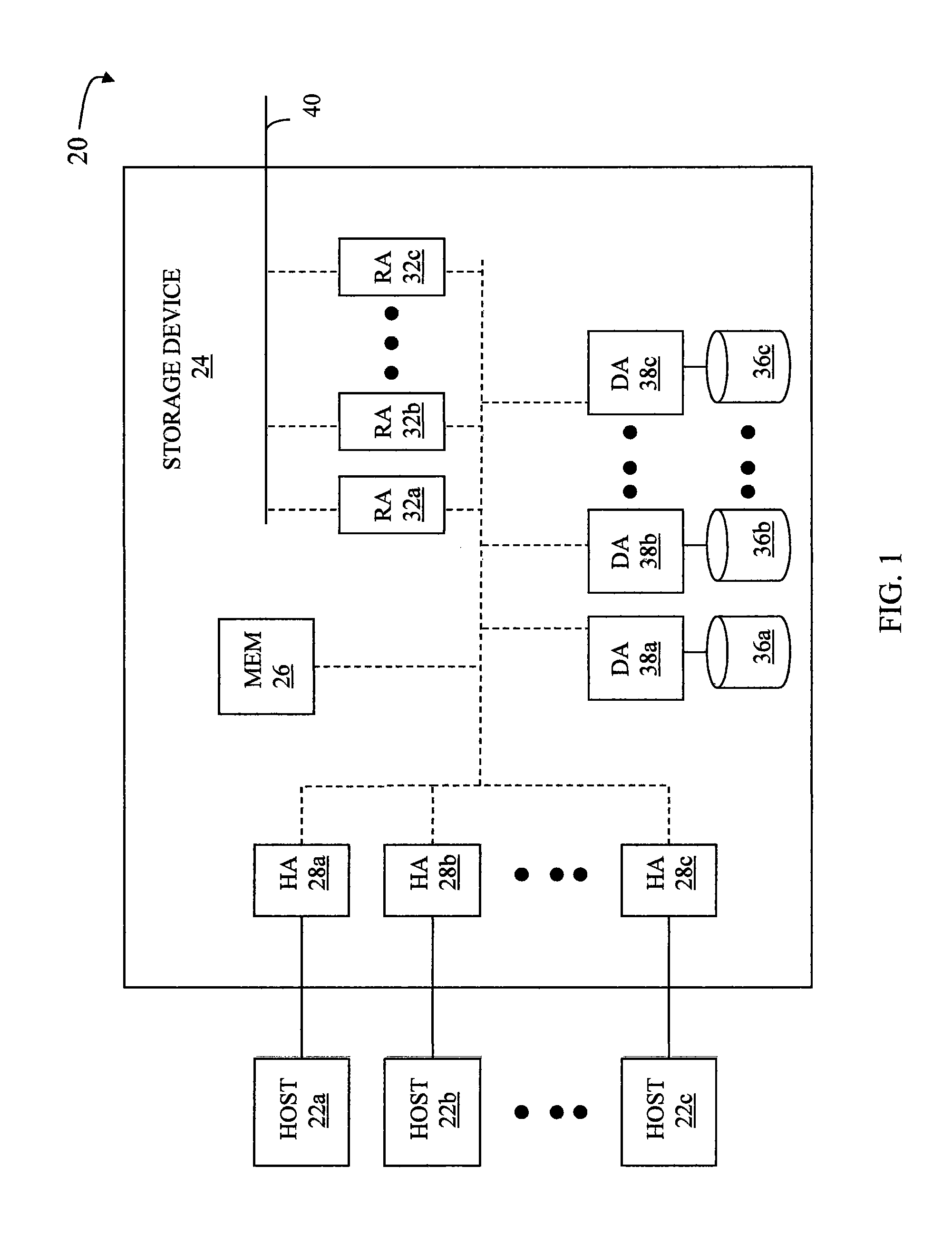
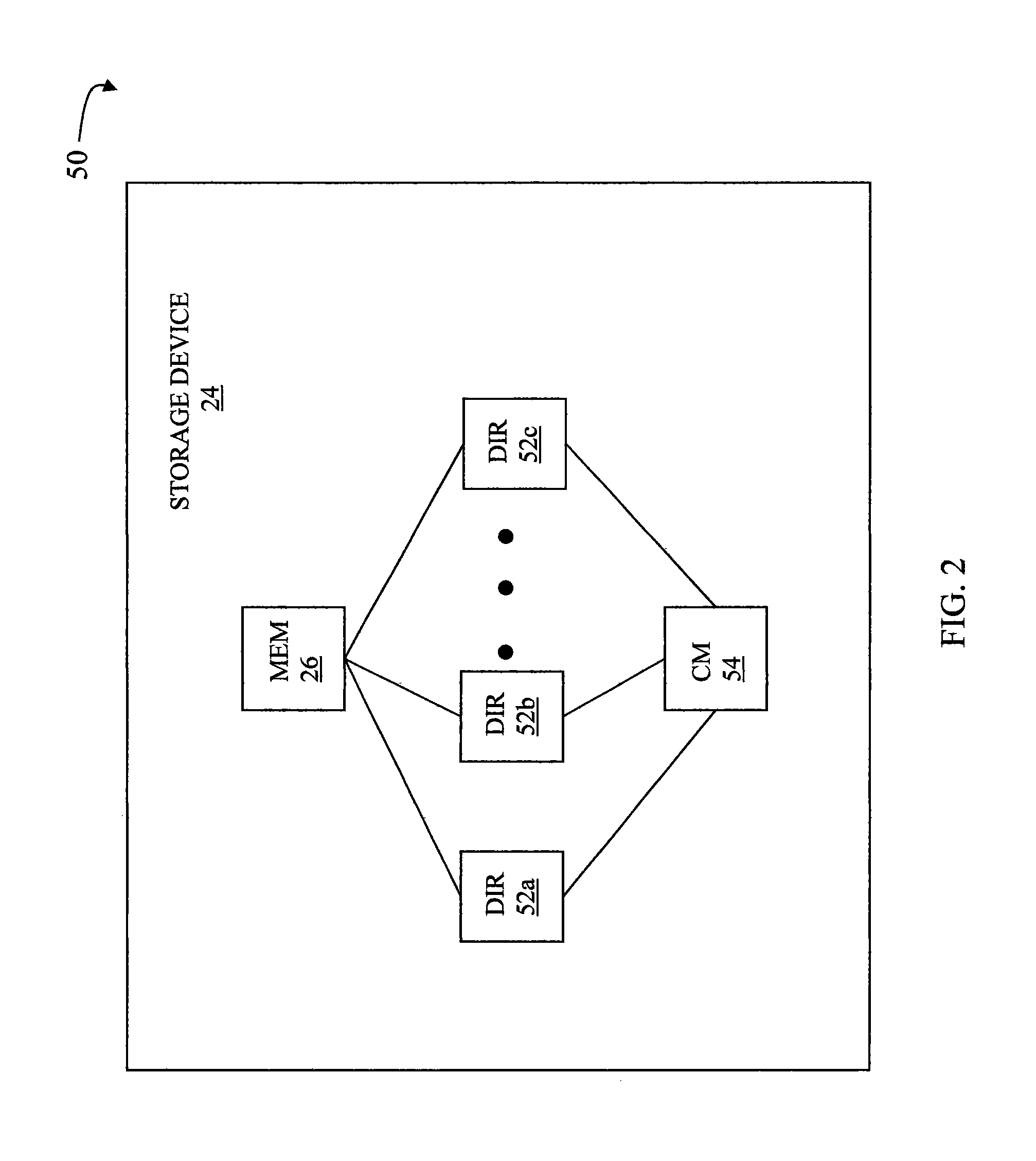
Techniques for maintaining high availability of networked systems
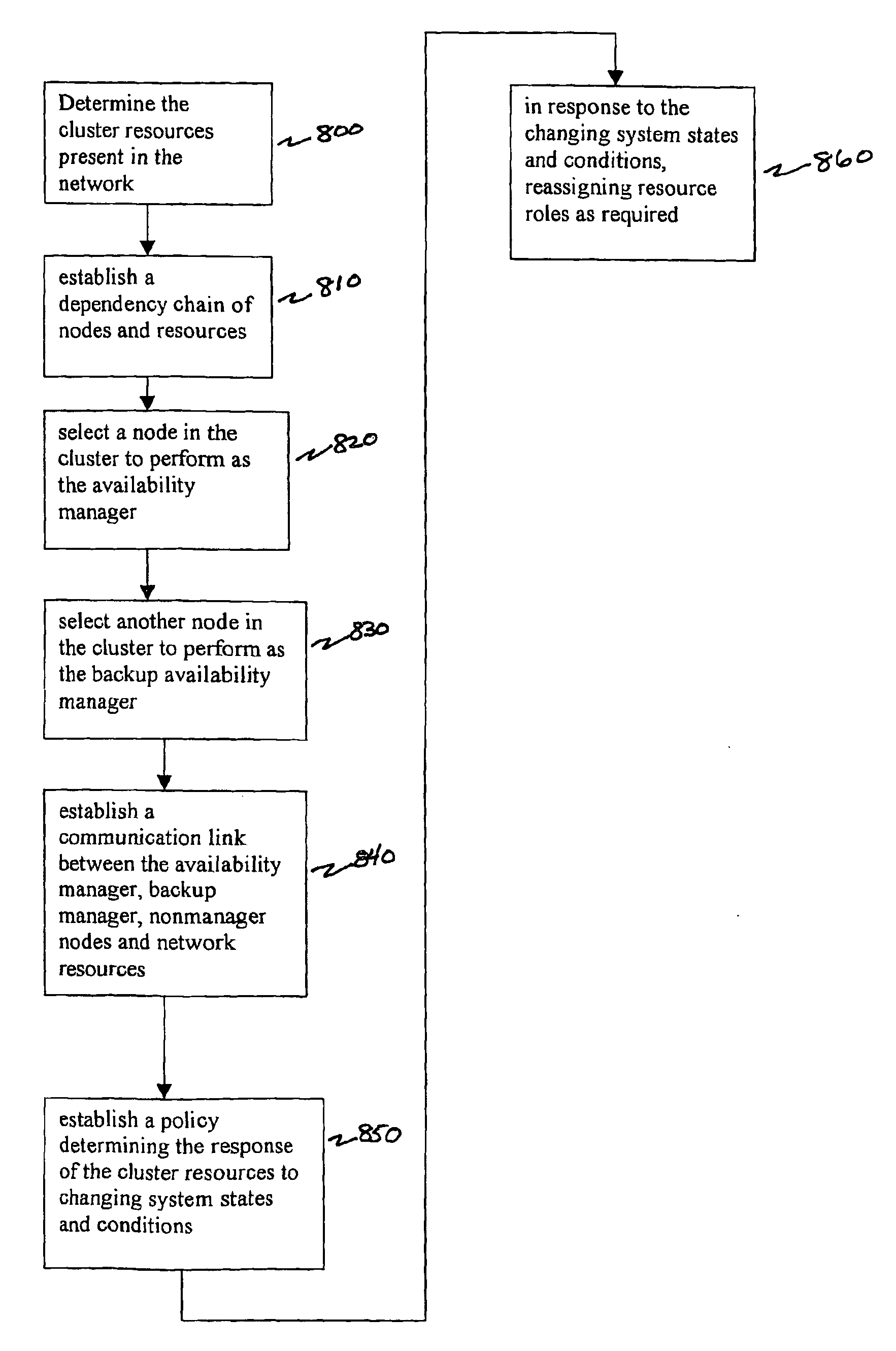
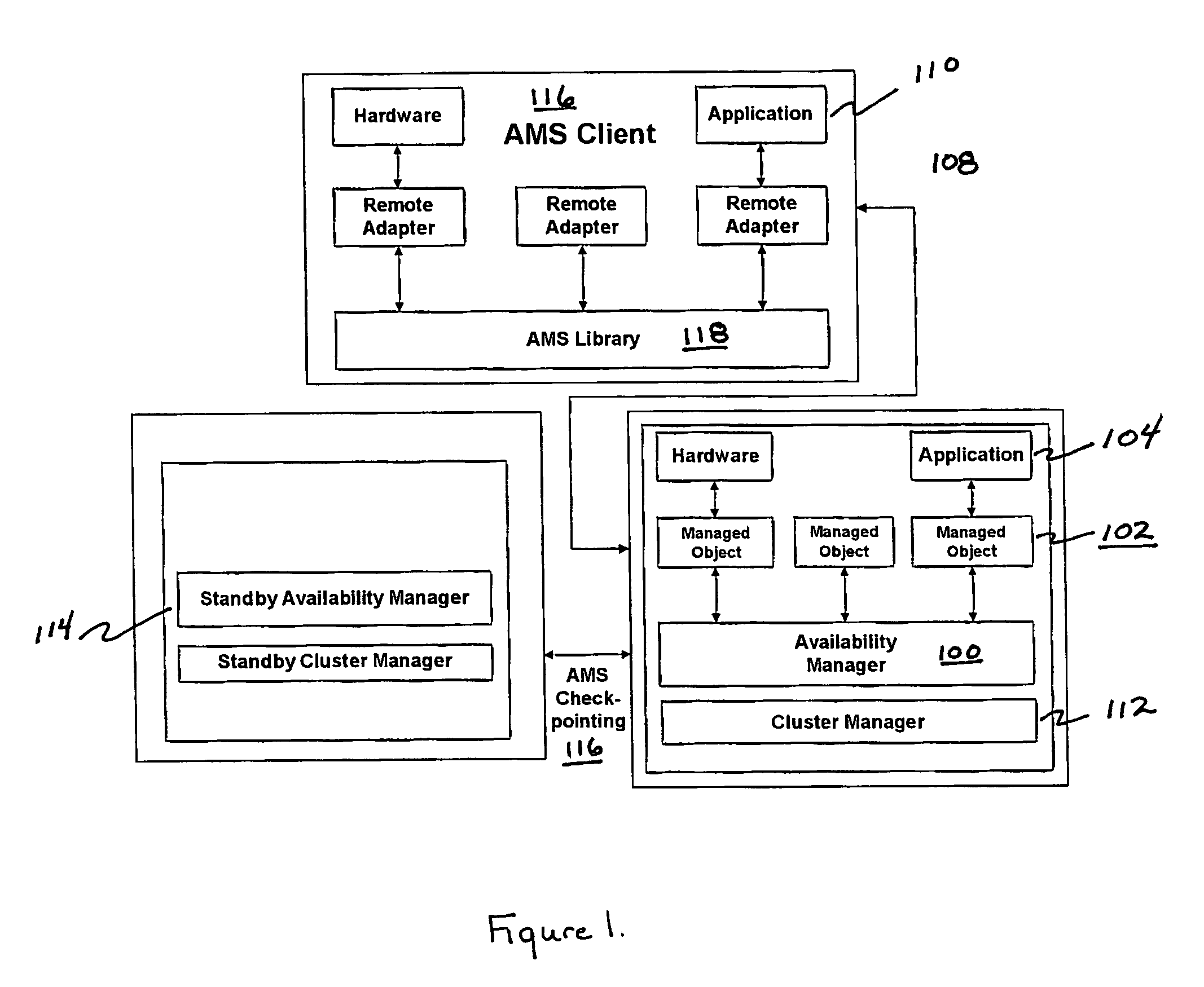
ActiveUS20050071470A1Improve usabilityMaintain availabilityDigital computer detailsData switching networksDowntimeHigh availability
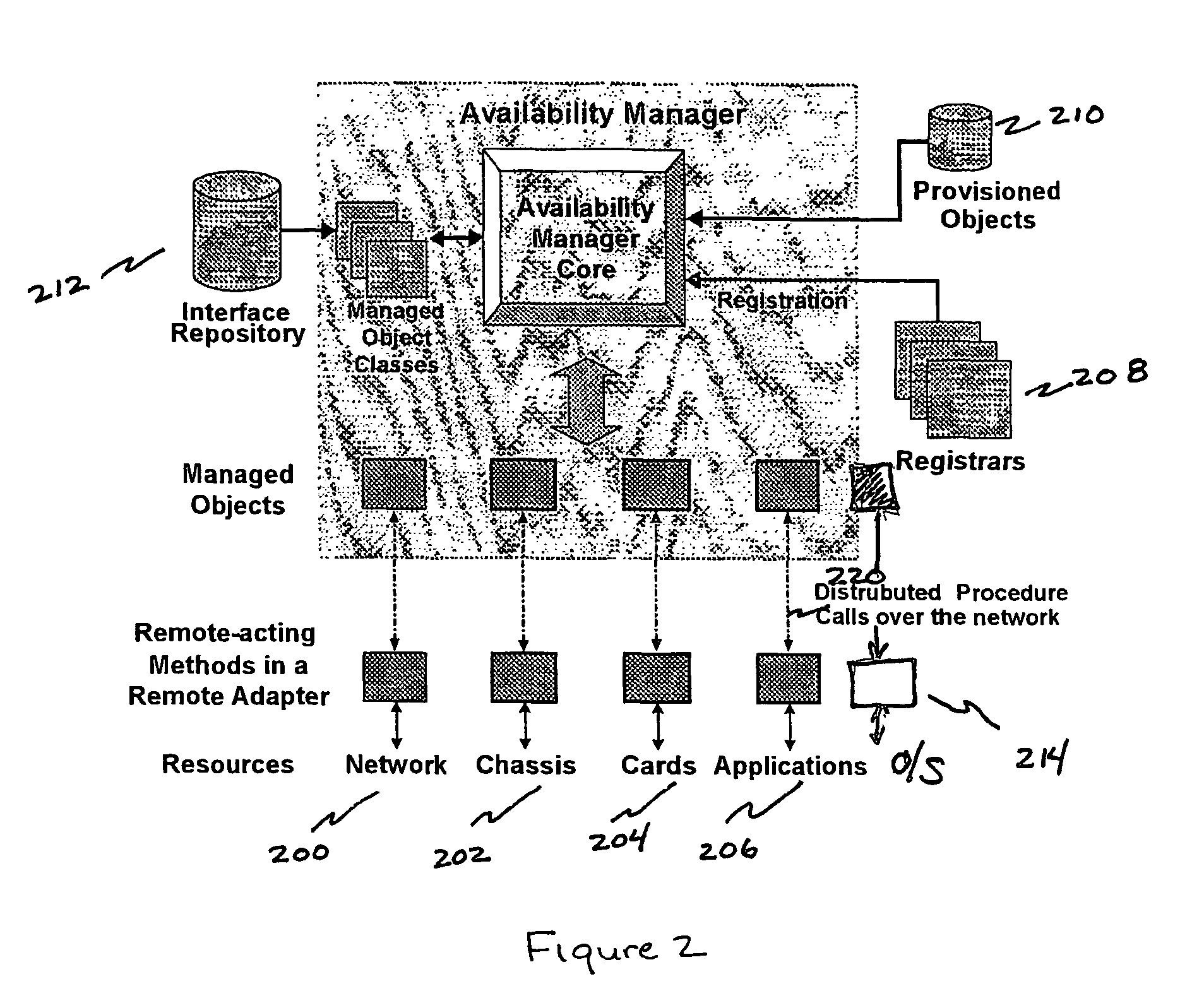
This computer implemented software invention supervises networked system resources with the goal of maximizing service availability, providing on-demand and uninterrupted access to service, and minimizing the down time due to failures. It is a cluster-wide solution that co-ordinates the states and activities of resources, assigns availability roles, implements recovery from failures, and implements overall system policy. To do this, it maintains a system model of the system's physical and logical configuration and models the resources using managed objects that provides an extensive representation of the states, roles, and relationships of the systems resources.
Owner:GOAHEAD SOFTWARE
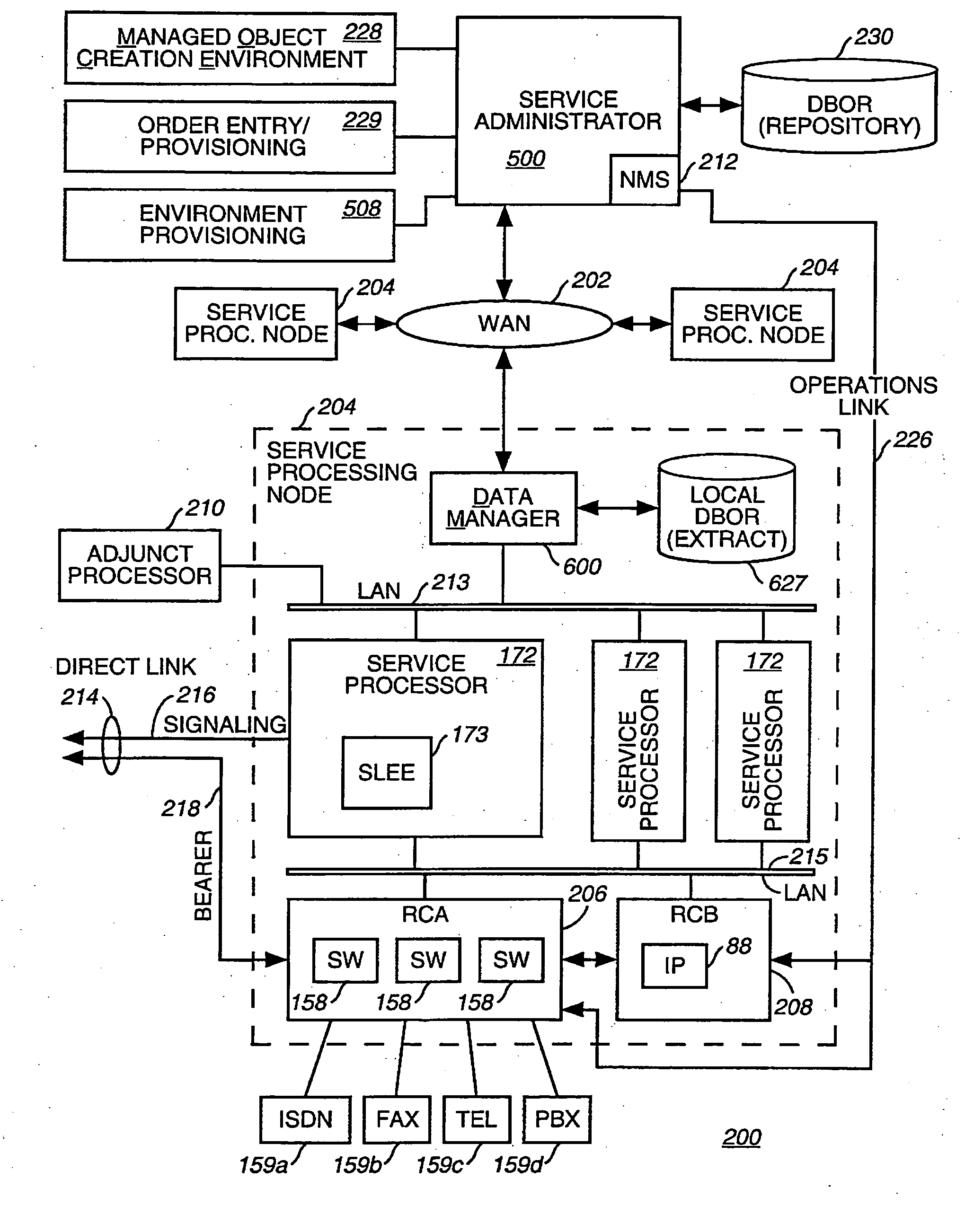
Method and apparatus for deploying service modules among service nodes distributed in an intelligent network
InactiveUS7024450B1Promote recoveryAvoid redundancySpecial service for subscribersMultiple digital computer combinationsIntelligent NetworkManagement object
Owner:VERIZON PATENT & LICENSING INC
Dynamic Scaling of Management Infrastructure in Virtual Environments
ActiveUS20110167421A1Increase the number ofTransmissionSoftware simulation/interpretation/emulationManagement objectManaged object
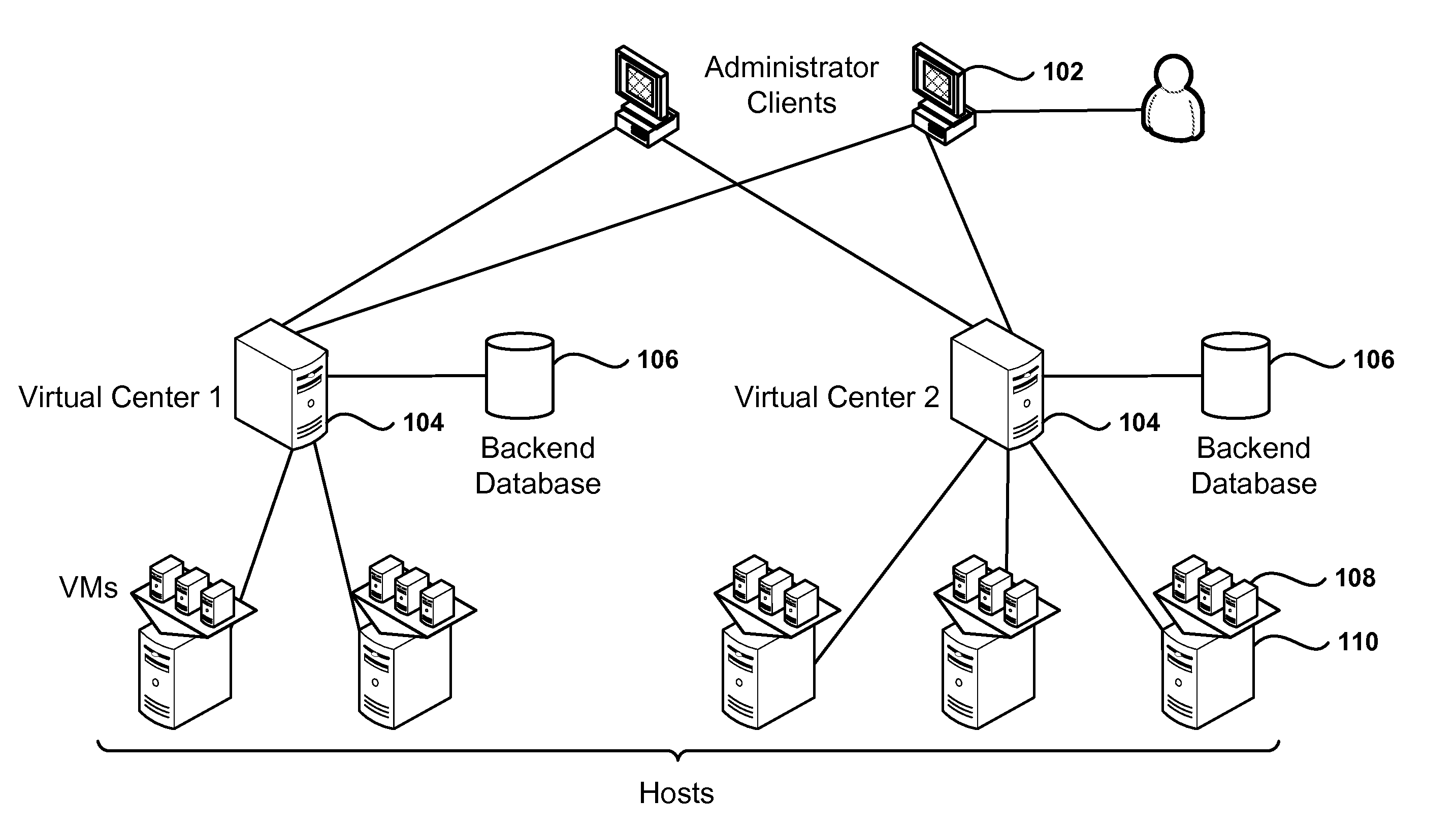
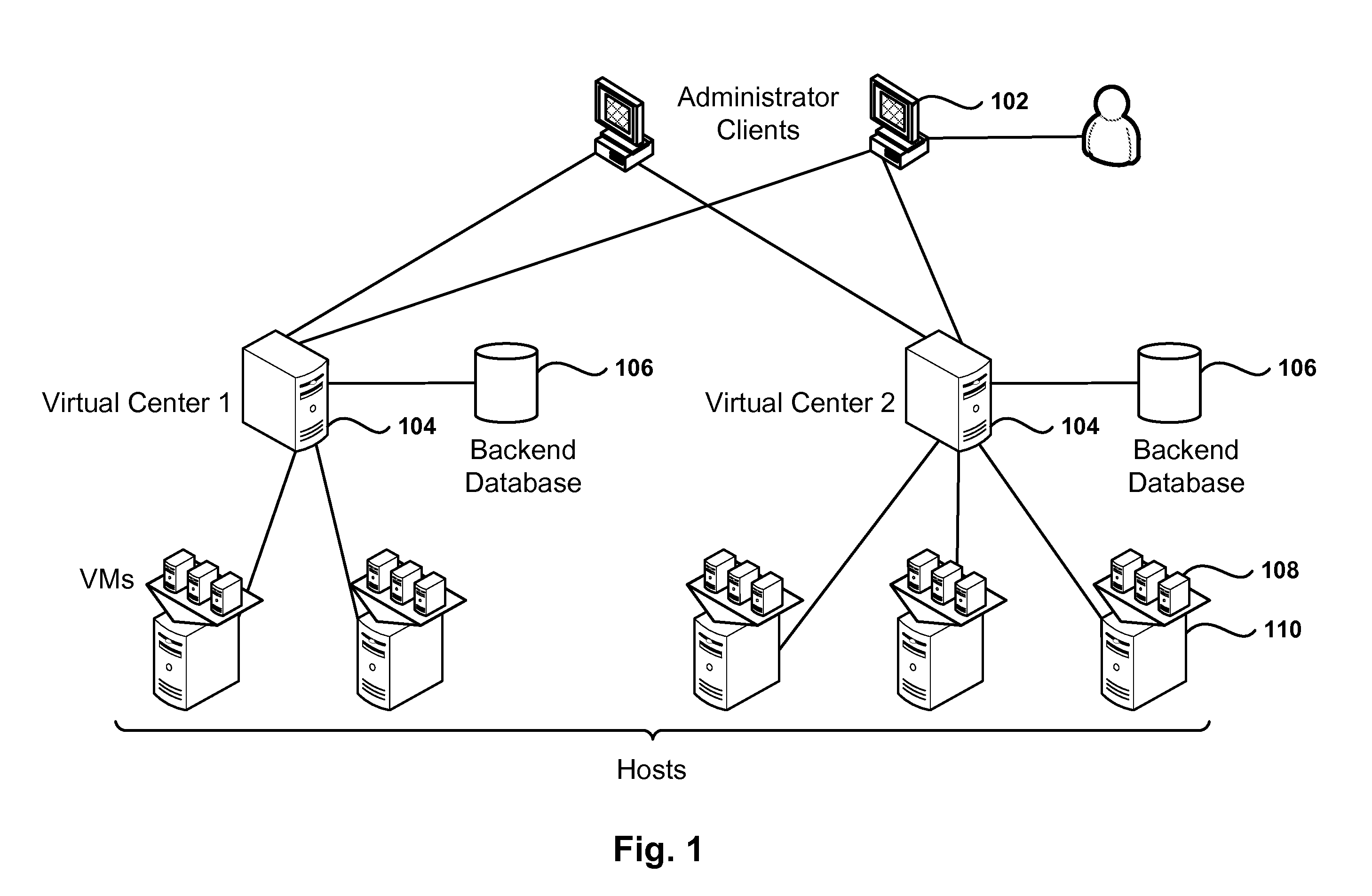
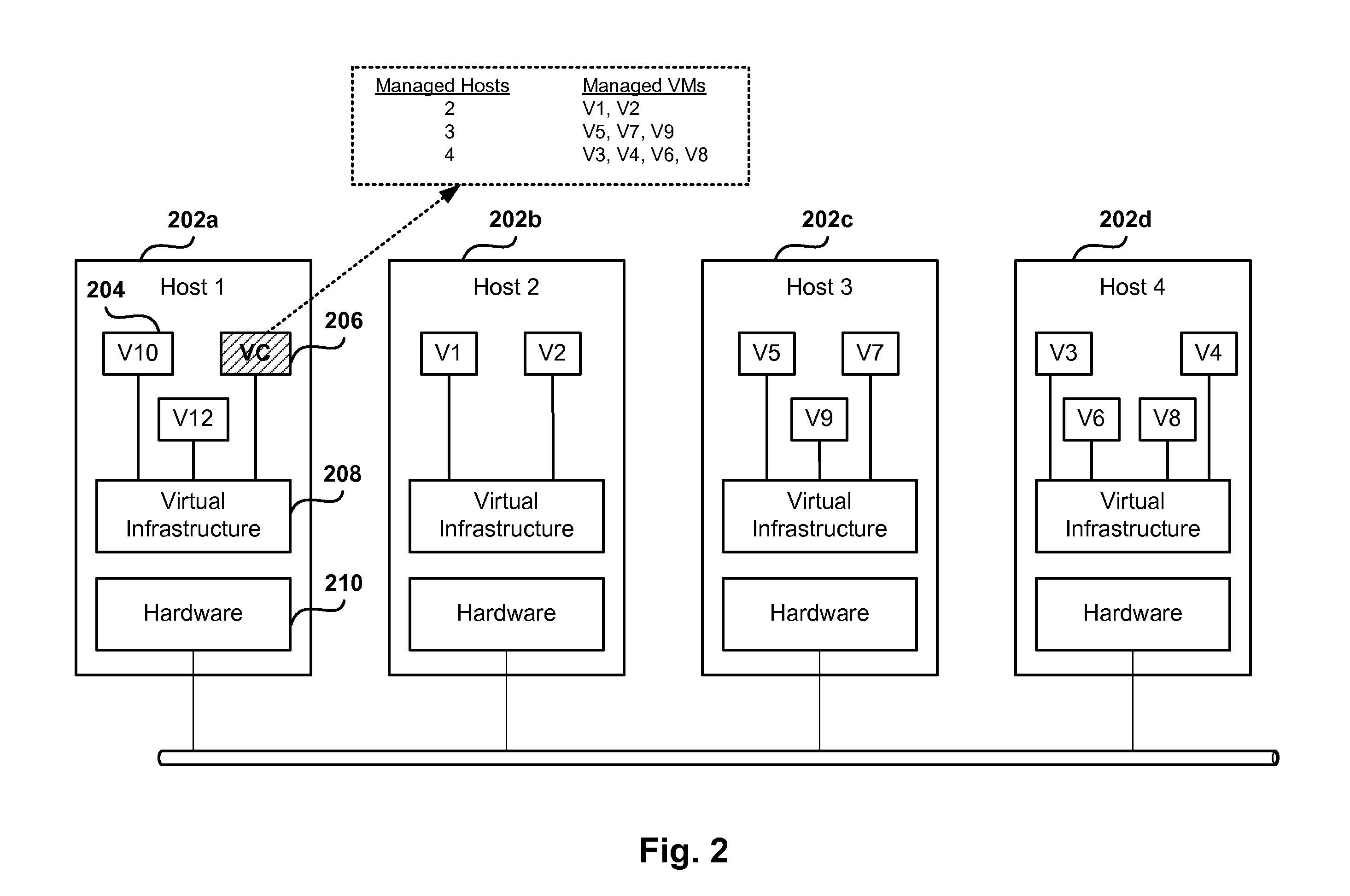
Methods, systems, and computer programs for performing management tasks in a virtual infrastructure are presented. The method includes detecting an increase, beyond a predetermined threshold, in the number of tasks waiting to be processed by a first virtual center (VC), which executes as a virtual machine (VM) in the virtual infrastructure. Further, the method includes operations for spawning one or more additional VCs executing as VMs in the virtual infrastructure and for distributing the managed objects handled by the first VC among the additional VCs. The tasks waiting to be processed are reallocated among the first VC and the additional VCs, and the reallocated tasks are then processed by the corresponding VC.
Owner:VMWARE INC
Automatically discovering management information about services in a communication network
An automatic service discovery approach allows a network management system to discover service managed objects from the network, eliminating the need for a user or other management application to provide such information. As a result, a network management system can automatically perform network-level or services level discovery of objects and services for which network components have no understanding. Embodiments are applicable, for example, in the context of management of packet voice (VoIP, VoATM) and metro Ethernet (TLS service) domains, as well as other domains.
Owner:CISCO TECH INC
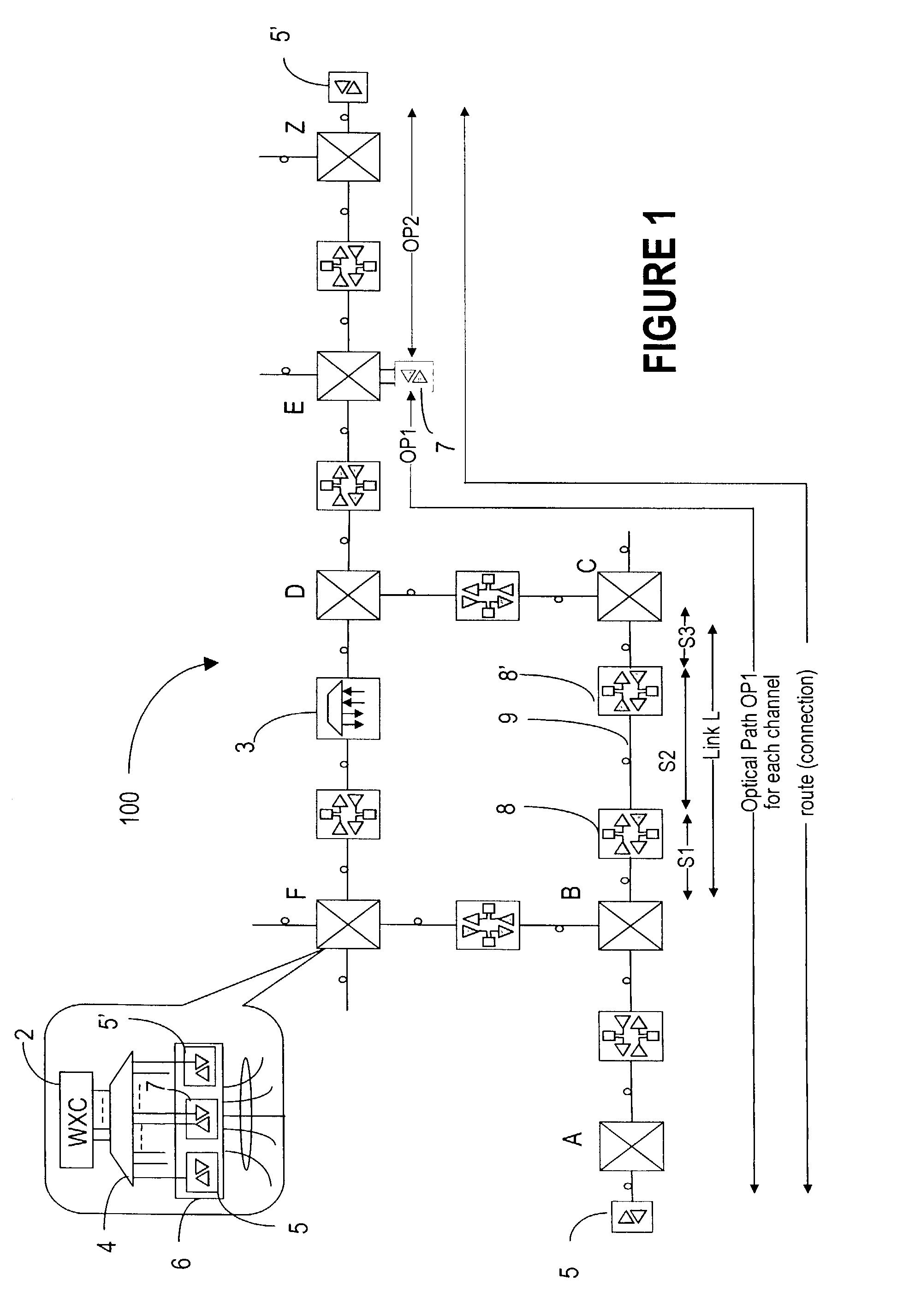
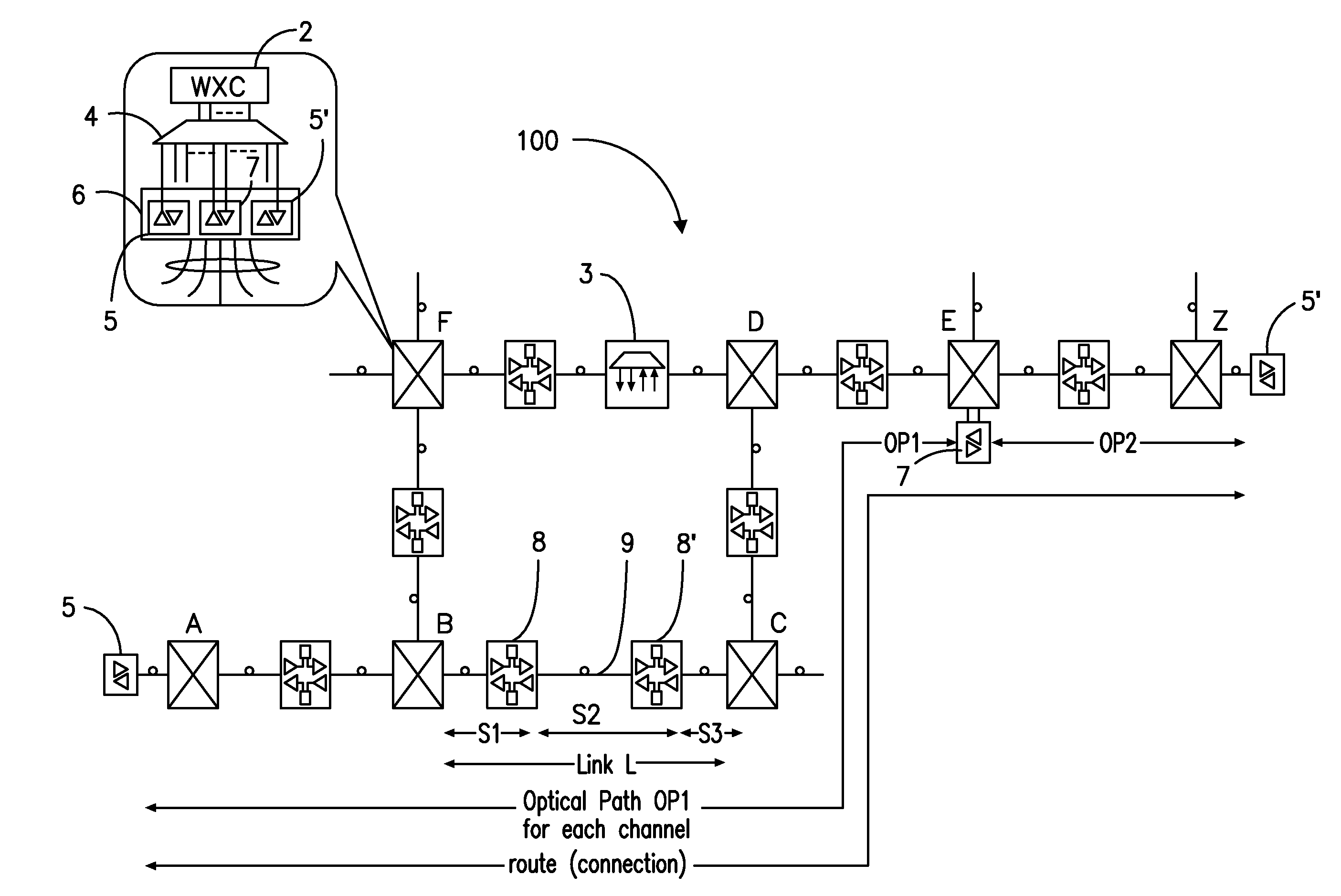
Detection of network topology changes affecting trail routing consistency
InactiveUS6564258B1Fast timeImprove scalabilityDigital computer detailsData switching by path configurationNetwork controlPhysical layer
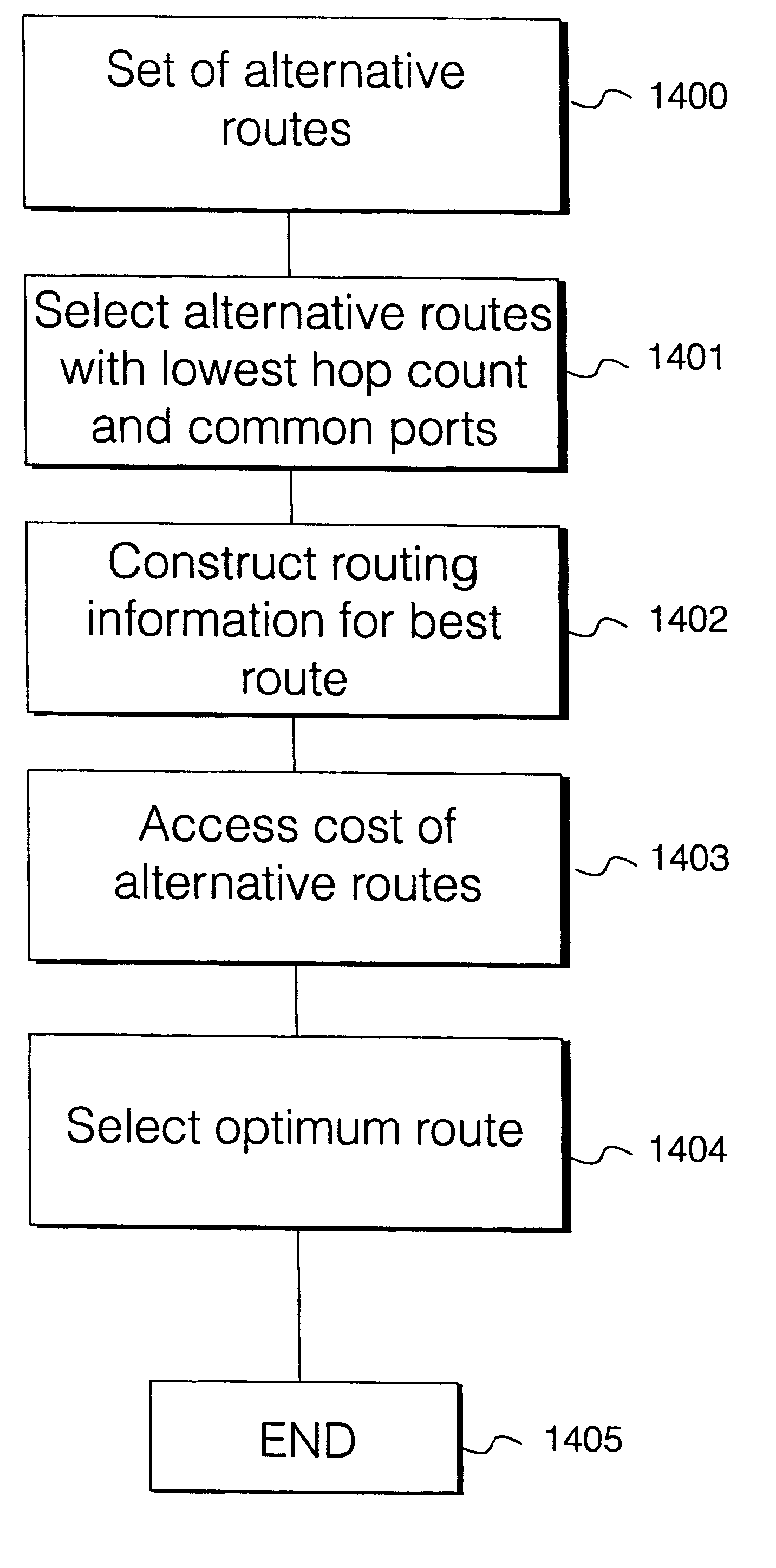
There is disclosed a method and apparatus for detection of client trails which may become unsupported due to reconfiguration of node elements within a network at a server layer, and a rerouting apparatus and method for proposing a set of alternative routes to support client trails during reconfiguration of a network at a physical layer. Data describing each trail, connection, node, link and other physical resource is maintained in a managed object database on a network controller. A trail detection algorithm investigates trail termination points corresponding to proposed deleted or created trails to see if those termination points support client trails at higher layers. If supported client trails are detected at higher layers, a routing algorithm is applied to find a set of alternative routes over which the client layer trails may be rerouted during network configuration at the physical or server layer.
Owner:CIENA
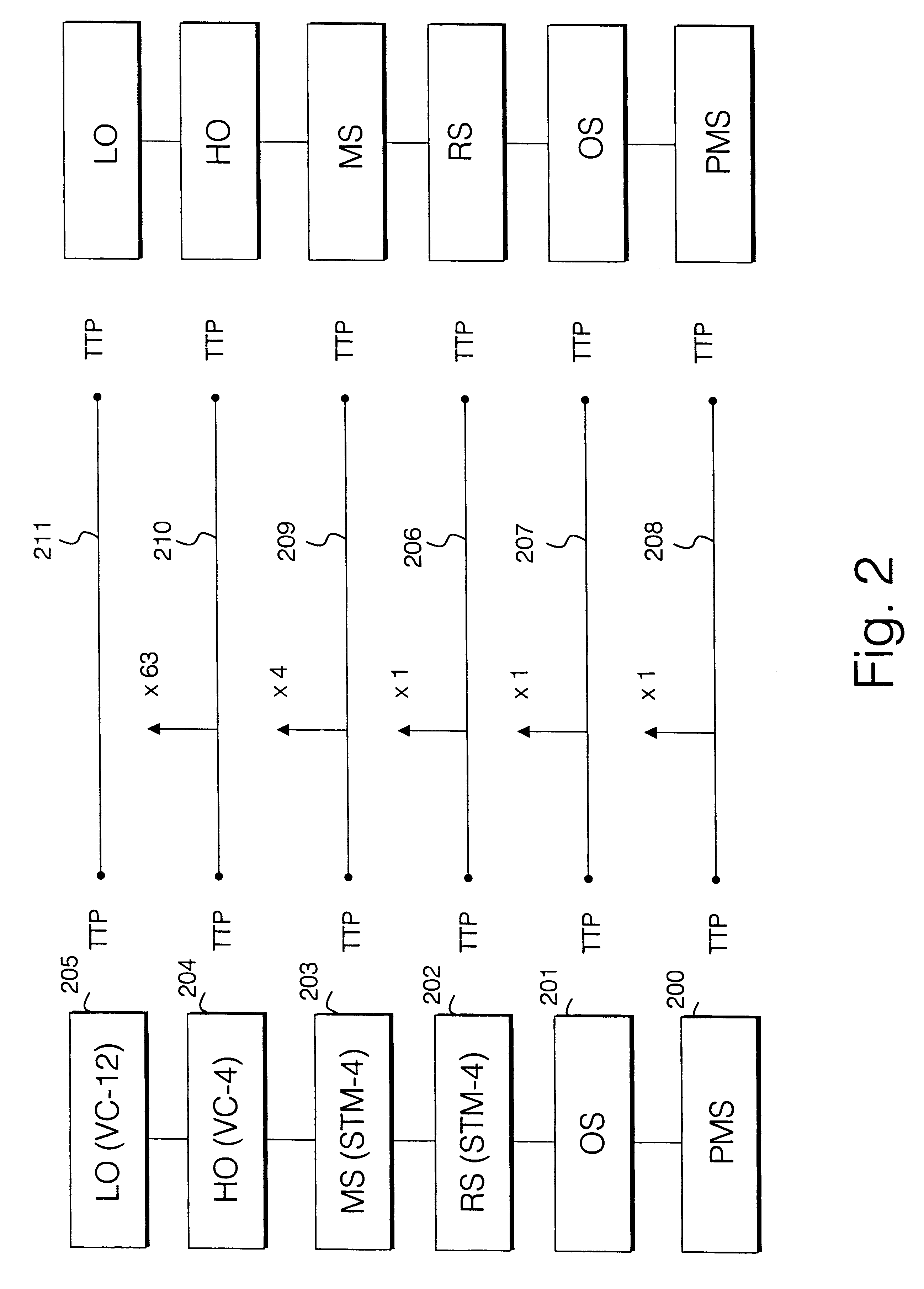
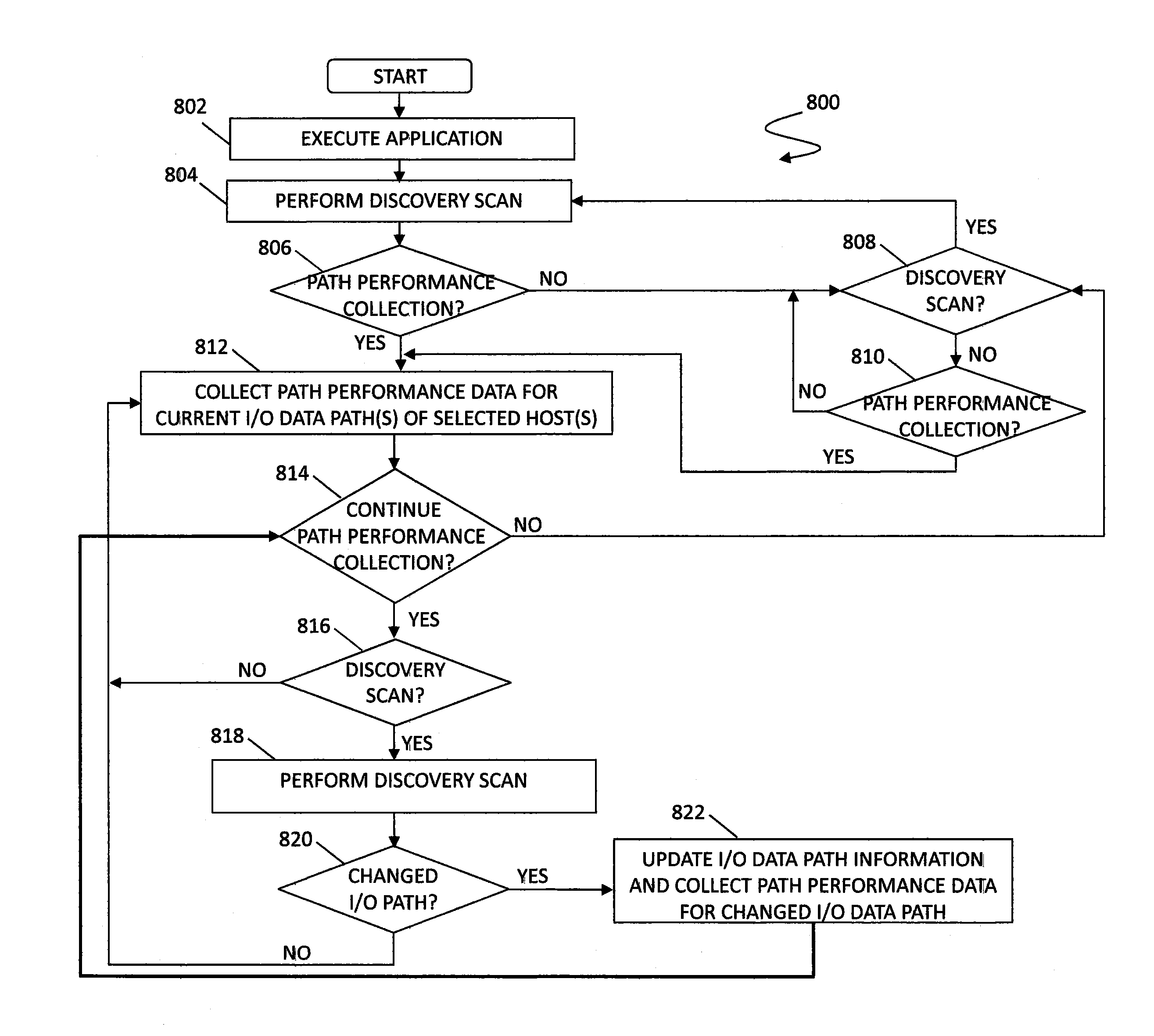
Path performance data collection
A system for controlled-tuning path performance data collection through a single application control. In an embodiment, performance data collection may be turned on or off from an application host running a path performance data application via a user interface. The tool may automatically update performance data collection characteristics as the application host I / O data path changes according to user controlled settings but without requiring further user intervention during the updating. In various embodiments, the tool may update continuously and / or at specified intervals. Turning on path performance data collection on the application host via the user interface may automatically set up synchronized performance data collection for all managed objects within I / O data path(s) of the managed objects.
Owner:EMC IP HLDG CO LLC
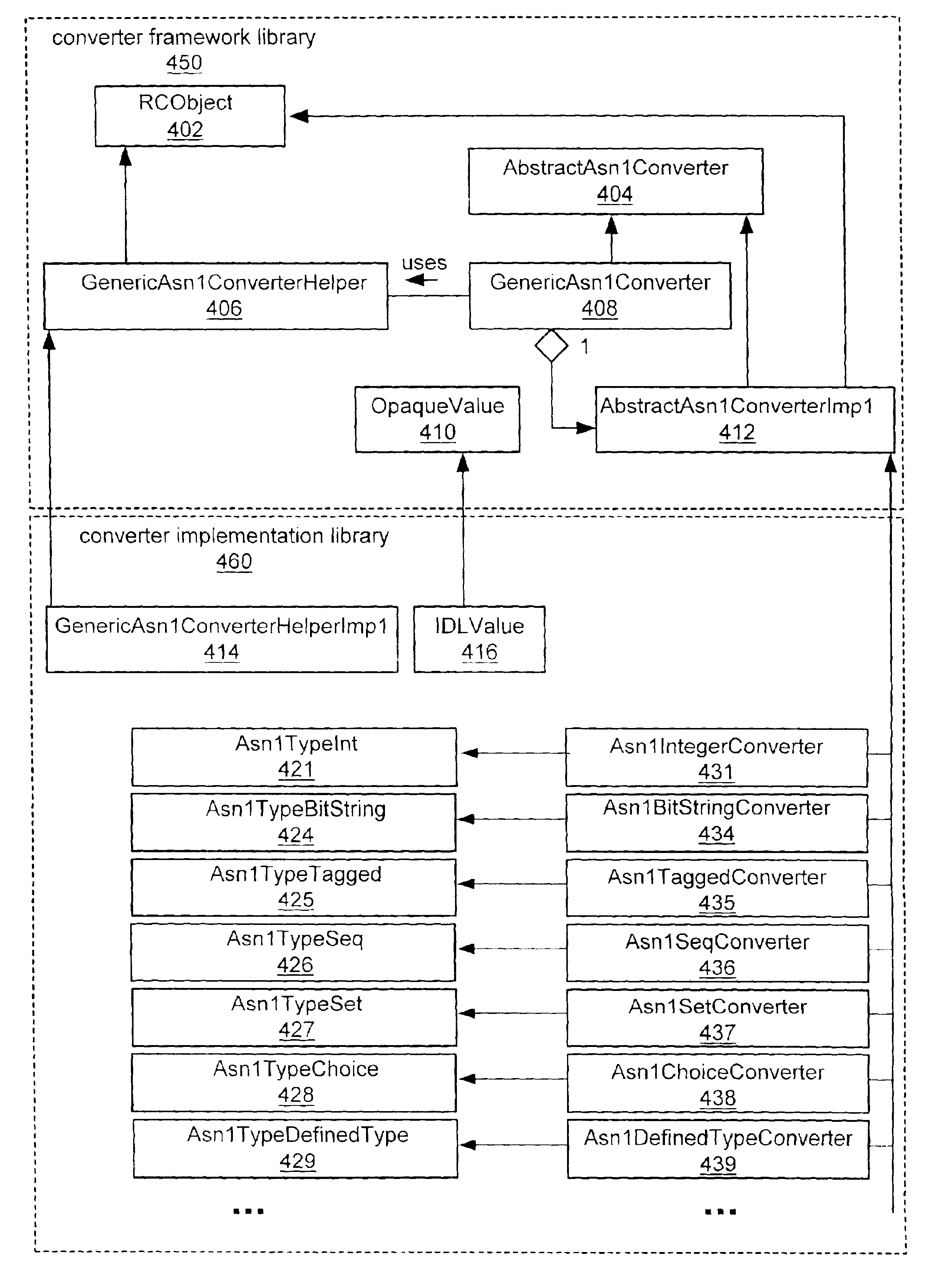
Abstract syntax notation to interface definition language converter framework for network management
InactiveUS6813770B1Multiprogramming arrangementsData switching networksType conversionData description
A system and method for managing network devices. The framework may provide a suitable system for managed object data type conversions between various data description languages, such as an interface definition language (e.g., OMG IDL) and an abstract syntax notation (e.g., ASN1). This conversion facility may be used in both request and event network traffic, so common libraries may be used. Two separate libraries may be used: a converter framework library and a converter implementation library. The framework library provides a collection classes that may be used by the clients of the converter libraries. Most classes in the converter framework library are handle classes (or wrappers) to the real implementation (or body) classes in the converter implementation library. Framework classes hide the details of the real implementation classes and provide a simple, consistent interface to any data type converter via IDL. The converter implementation library provides the implementation needed by the framework to function properly, and may allow various different mappings to be used easily by implementing them as plug-in modules. The combination of using IDL and generic typing provides an efficient, generic solution to mapping data types across multiple platforms, multiple programming languages, and multiple object classes.
Owner:ORACLE INT CORP
Deploying service modules among service nodes distributed in an intelligent network
InactiveUS20050165906A1Avoid redundancyEasy to integrateMultiple digital computer combinationsTransmissionIntelligent NetworkManaged object
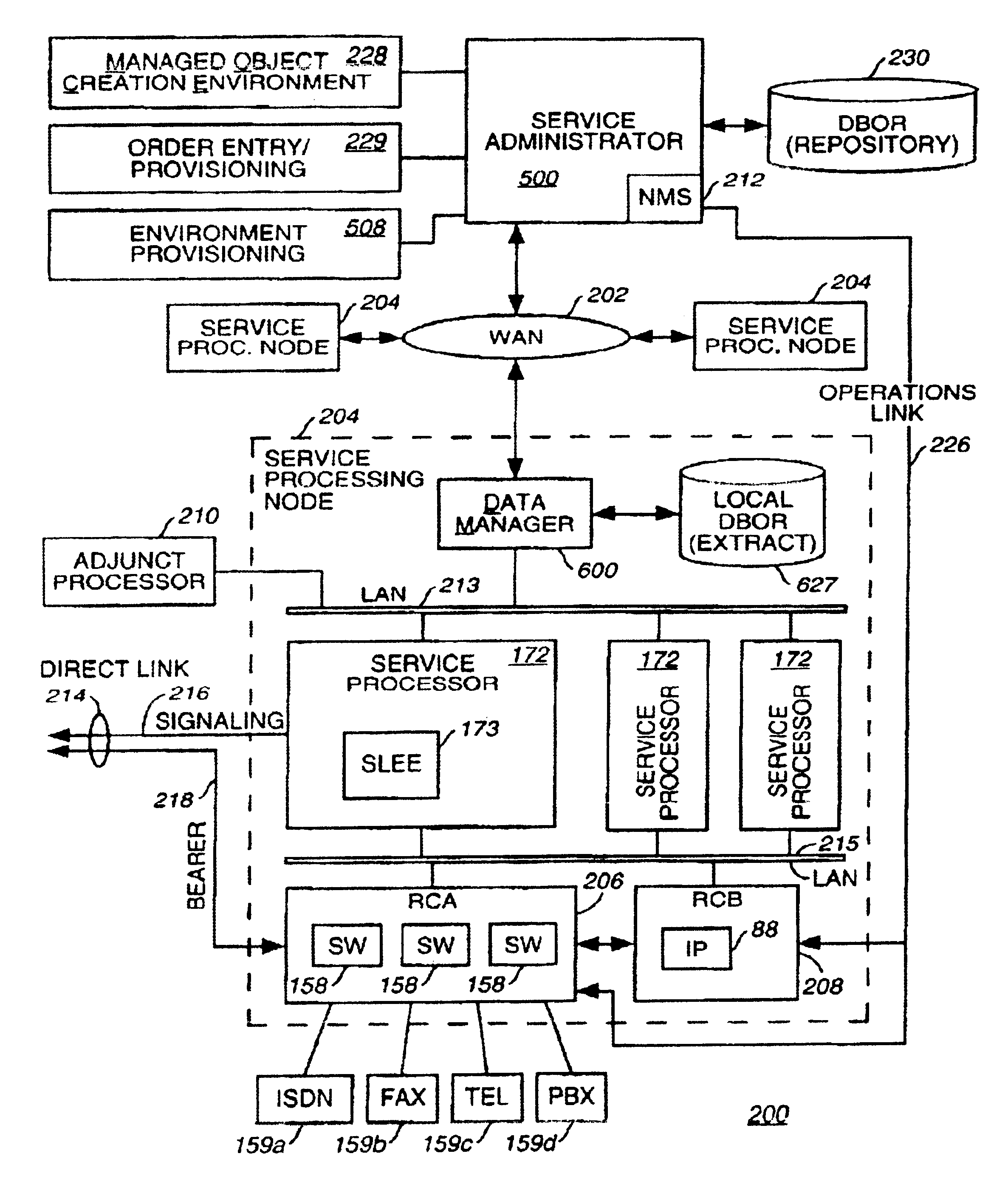
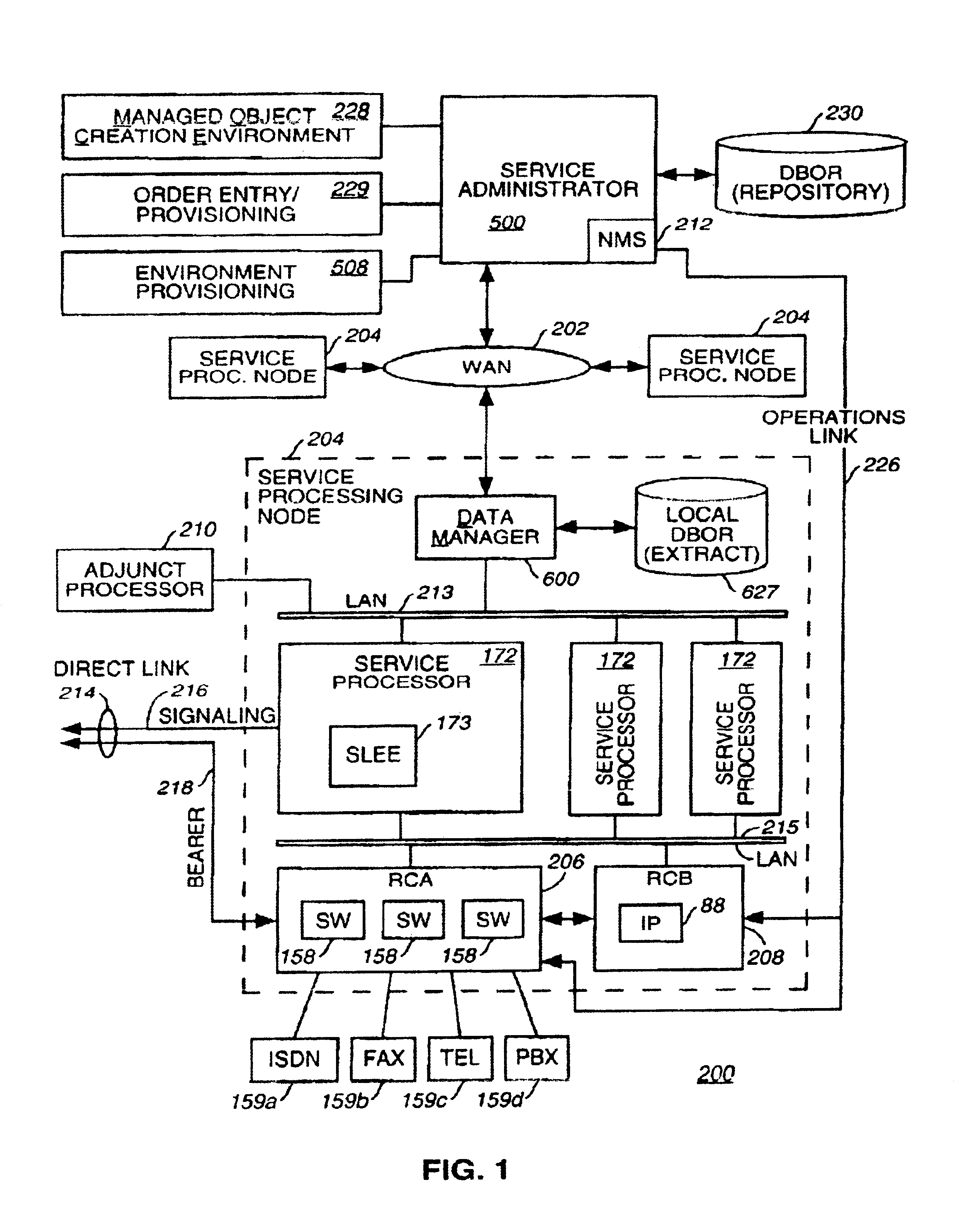
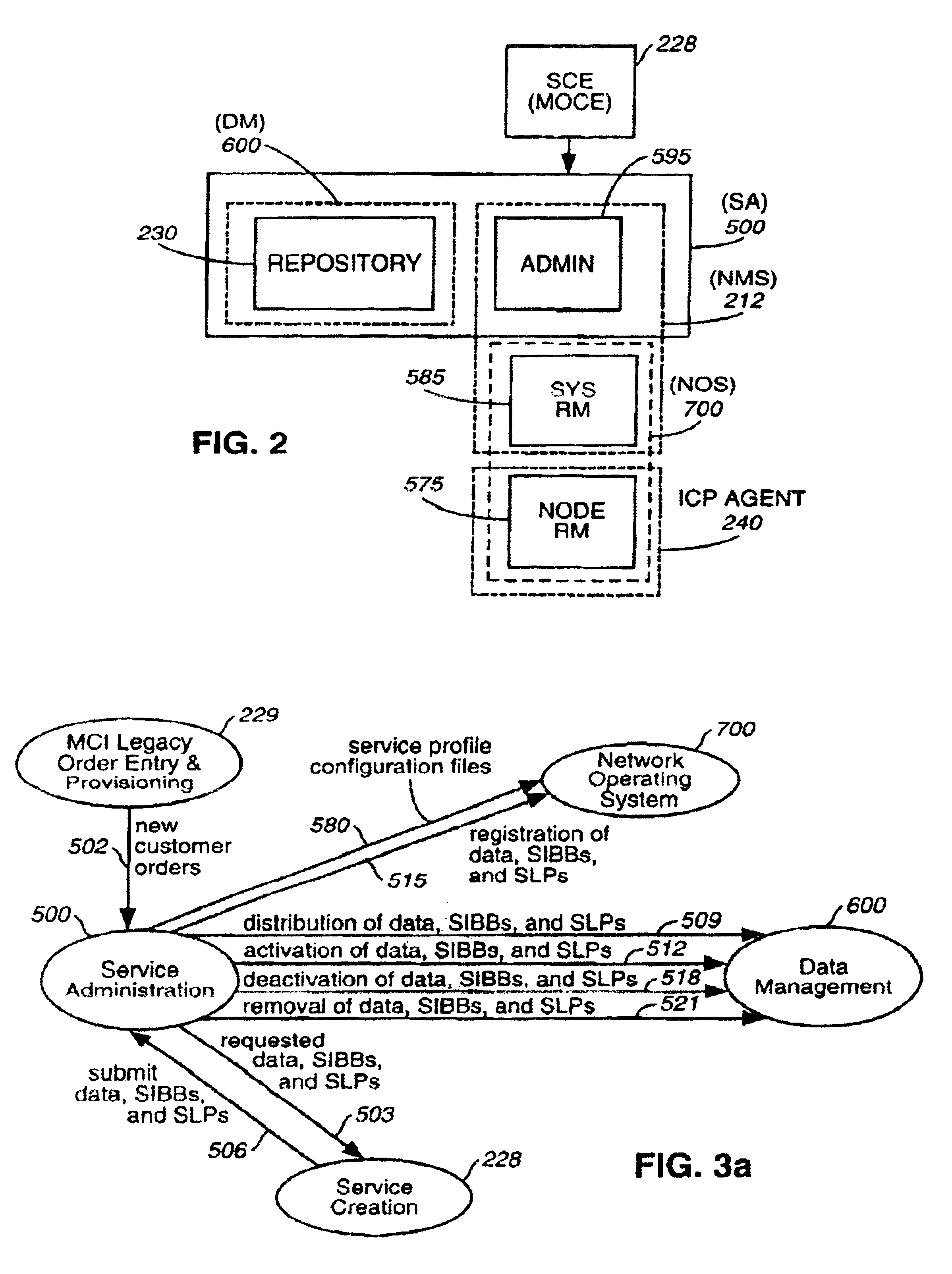
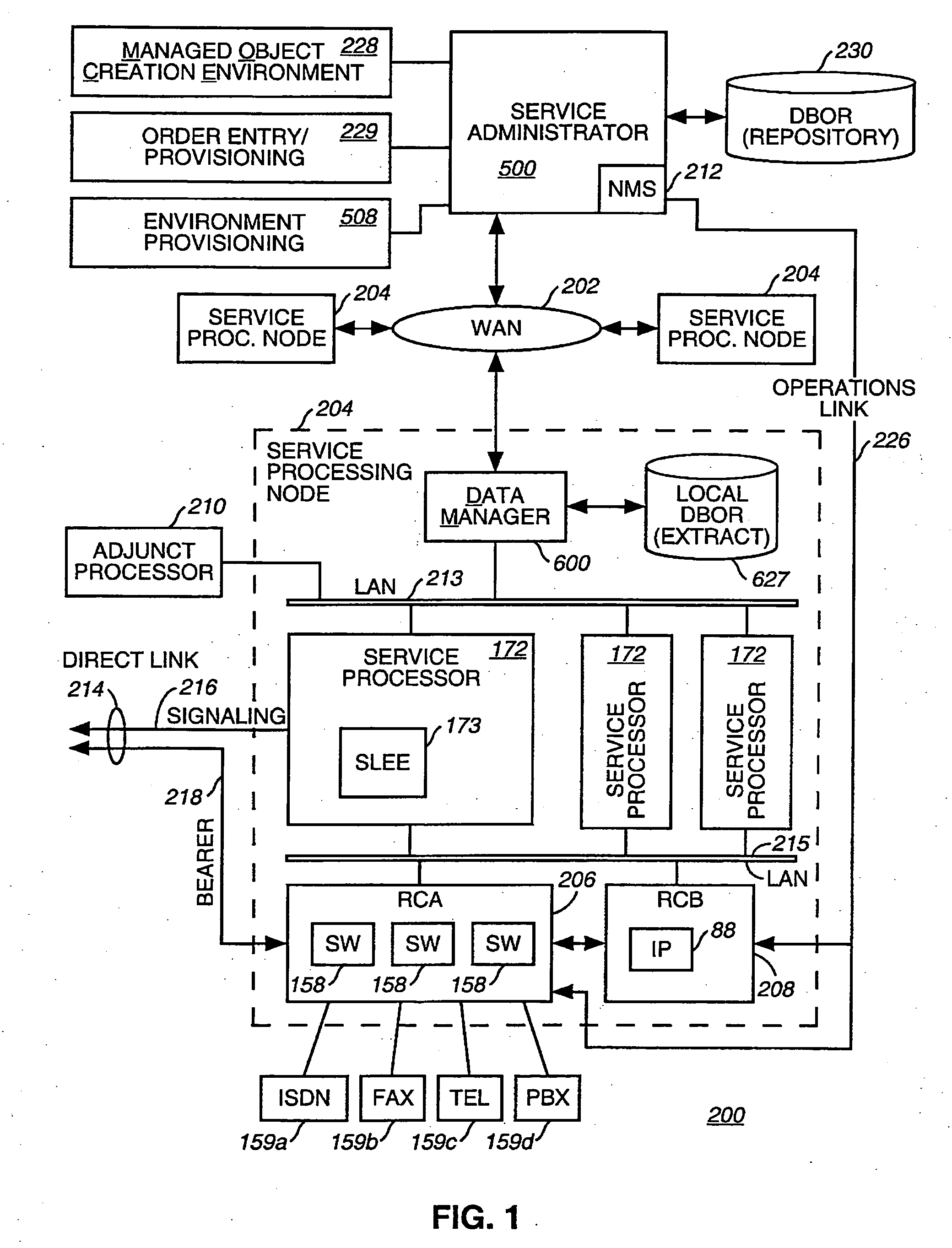
A method and apparatus for deploying and activating services in a communications network. In the context of a communications network that deploys service functionality by distributing managed software objects to service processing nodes, the present invention relates to selectively dispensing managed objects from a central repository and coordinating the instantaneous activation or deactivation of services throughout the network. Furthermore, where a managed object service creation environment is coupled to such a network, the method and apparatus of the present invention provides security, back-up, and version control of managed objects and other network data stored in the repository.
Owner:VERIZON PATENT & LICENSING INC
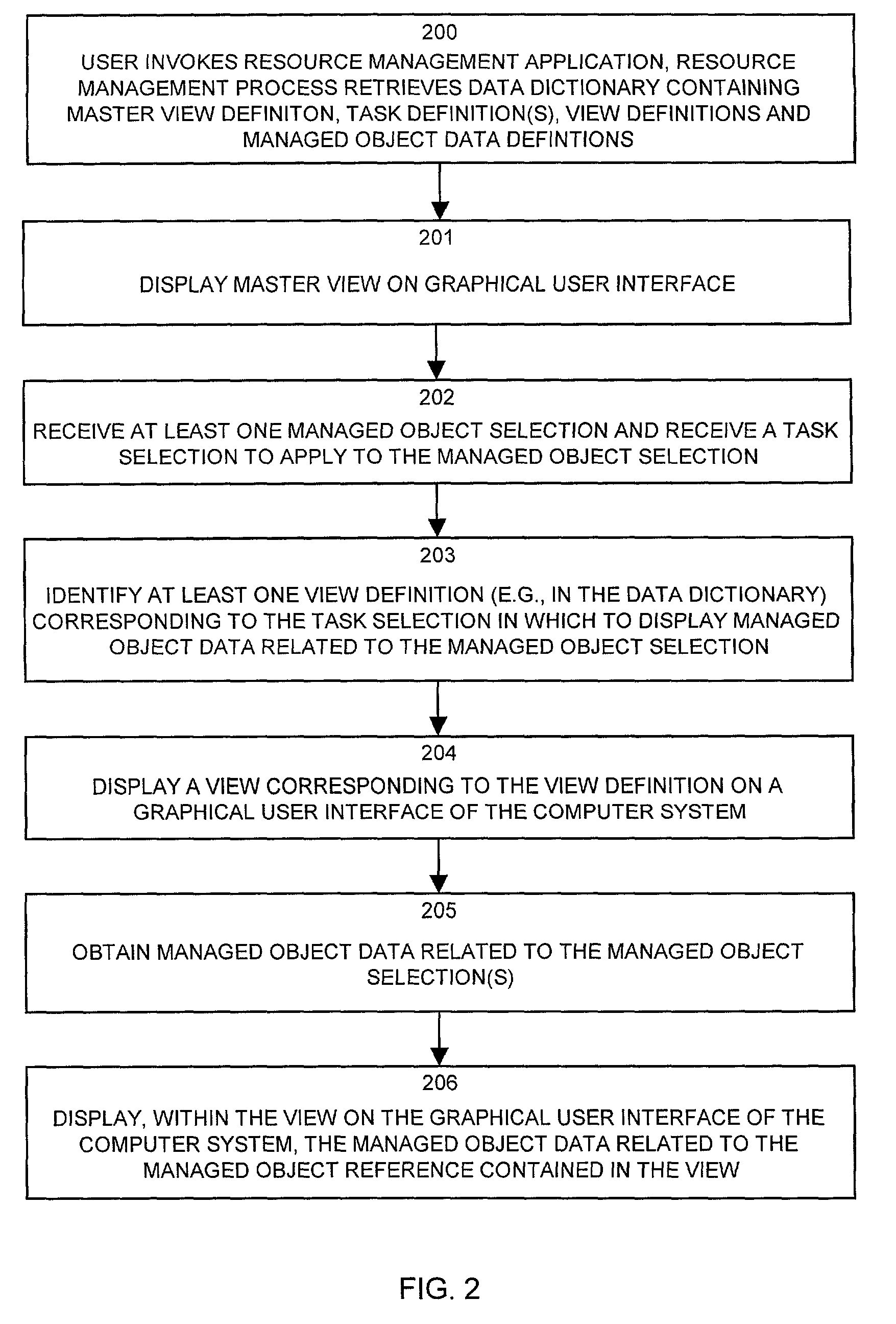
Methods and apparatus for displaying managed resource information
InactiveUS6978422B1Good flexibilityDigital computer detailsExecution for user interfacesGraphicsView based
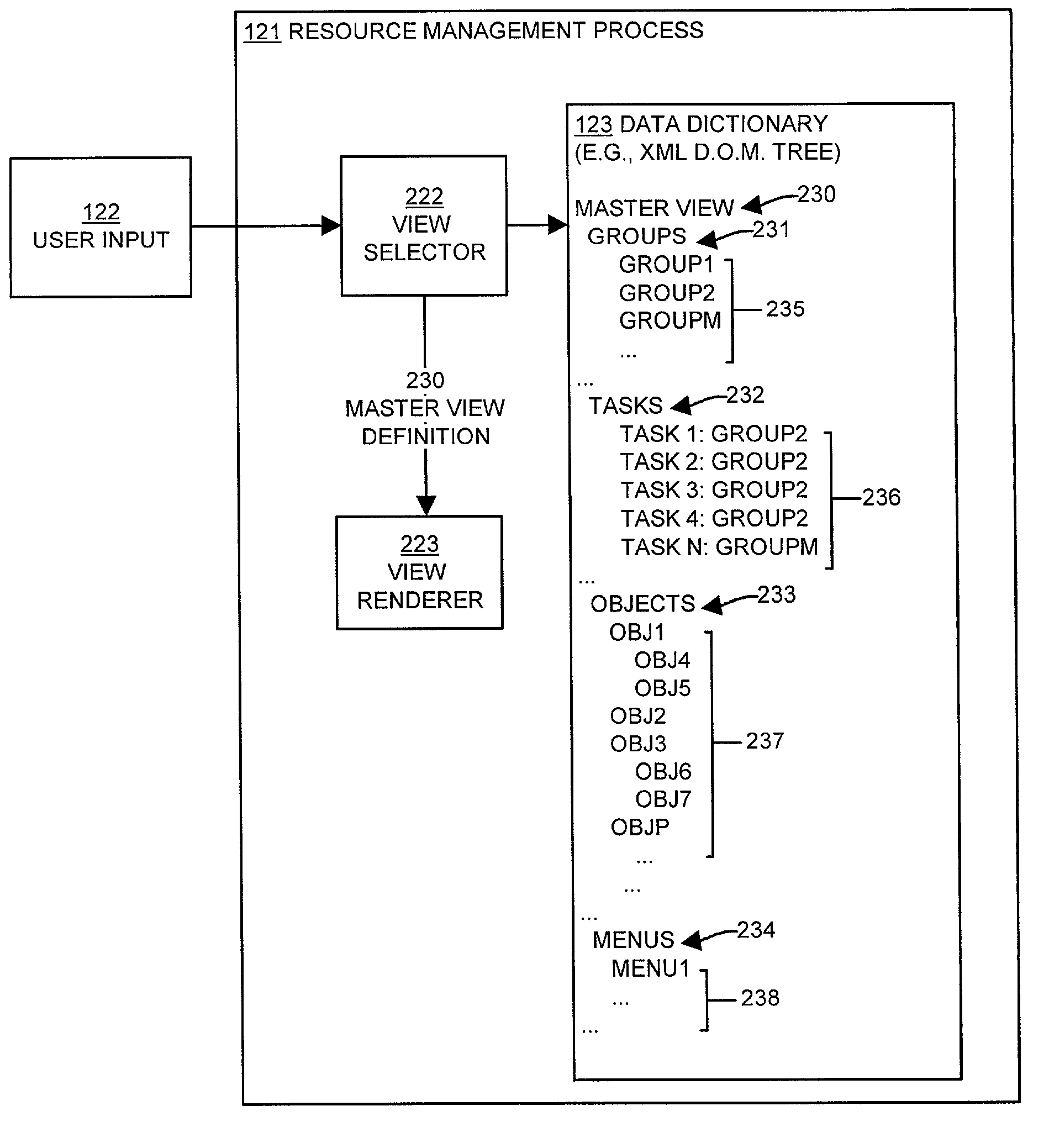
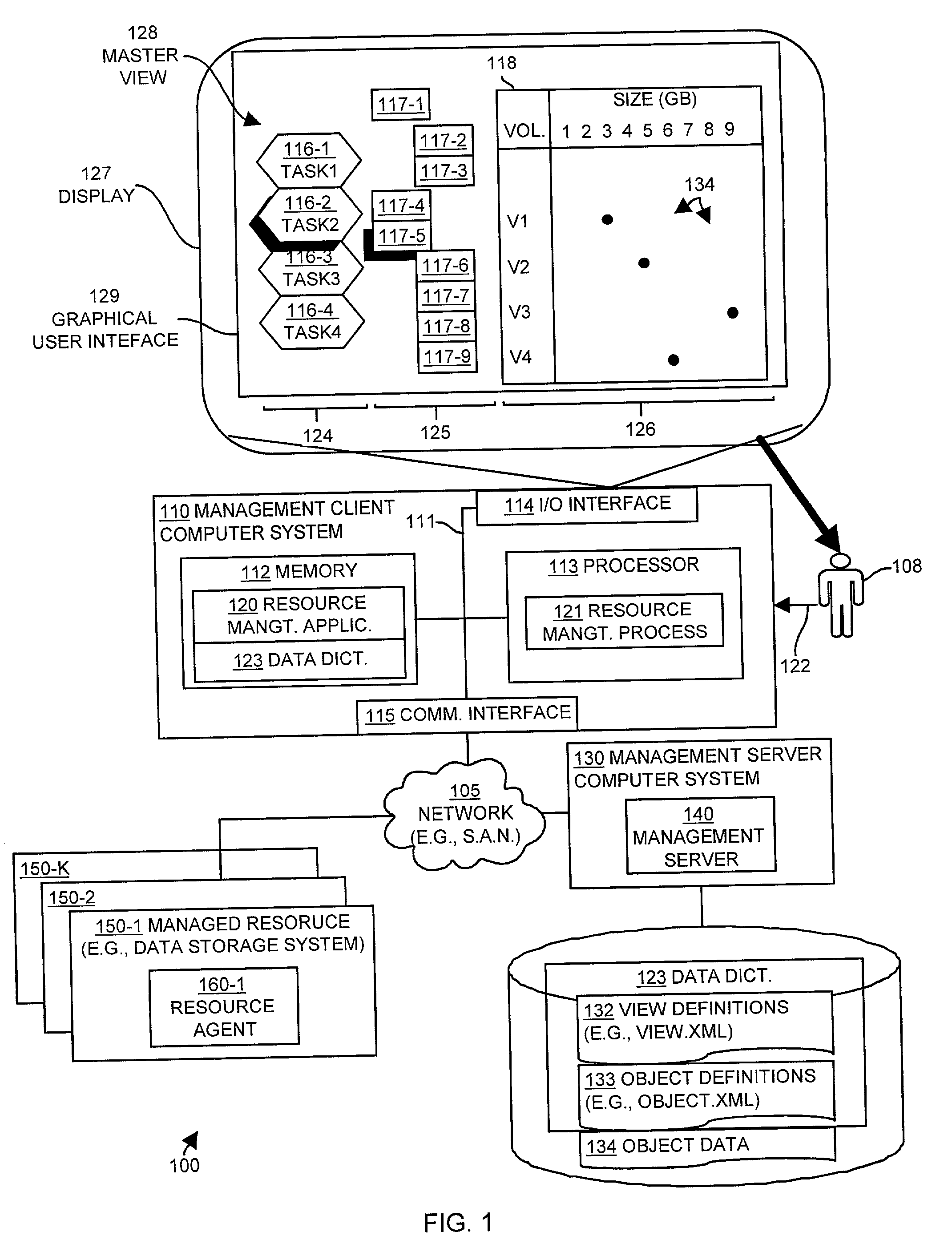
Methods and apparatus operate in a computer system for managing resources and provide a method for displaying managed object data associated with managed resources. Embodiments of the invention retrieve a data dictionary containing a master view definition, task definitions, view definitions and managed object data definitions. The embodiments then display the master view definition on the graphical user interface and receive a managed object selection and a task selection to apply to the managed object selection. The embodiments then identify a view definition corresponding to the task selection with which to display managed object data related to the managed object selection. The embodiments then display a view corresponding to the at least one view definition on a graphical user interface of the computer system and obtain managed object data related to the managed object selection based upon managed object data references contained in the view definition. The embodiments then display the managed object data related to the managed object selection within the view on the graphical user interface of the computer system.
Owner:EMC IP HLDG CO LLC
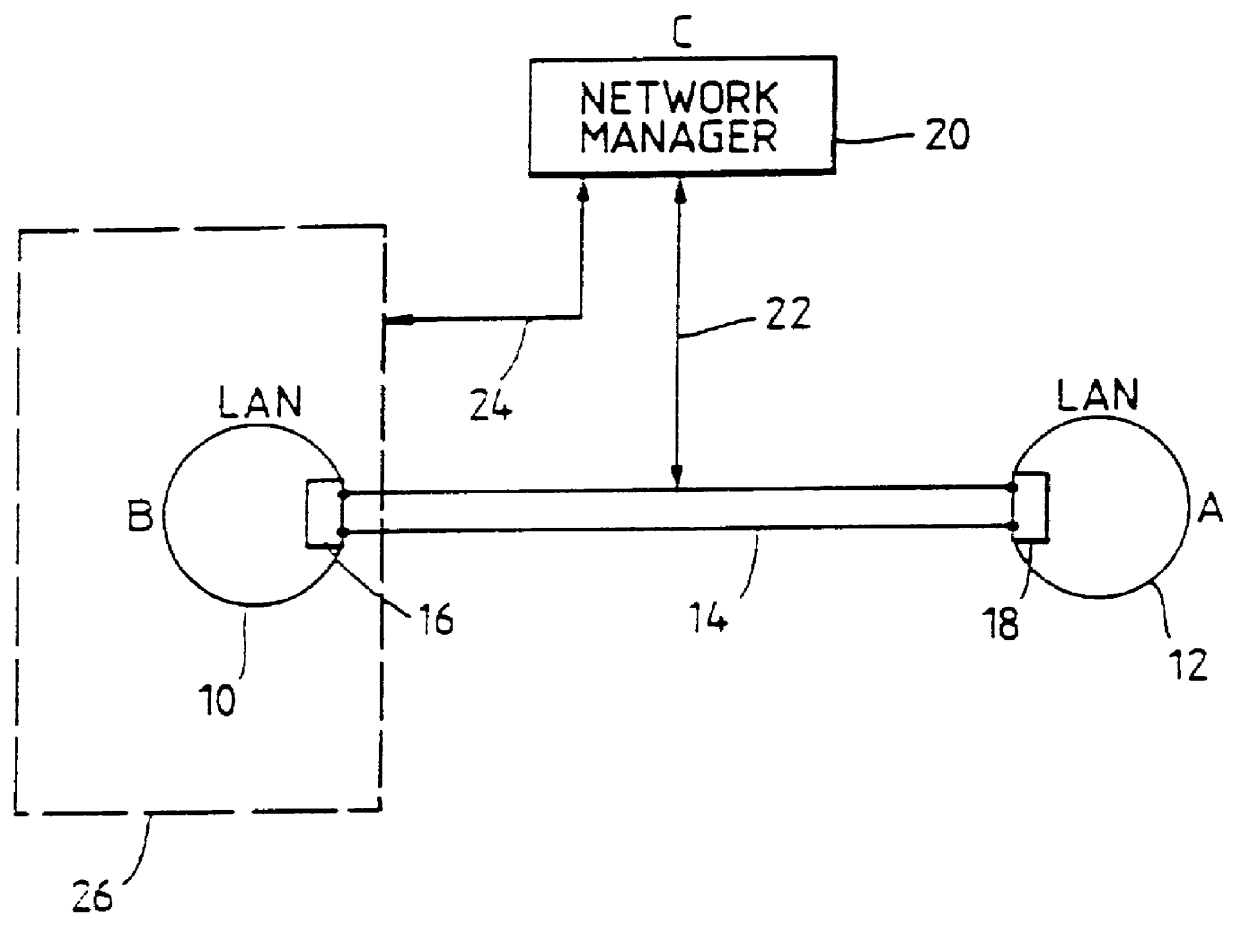
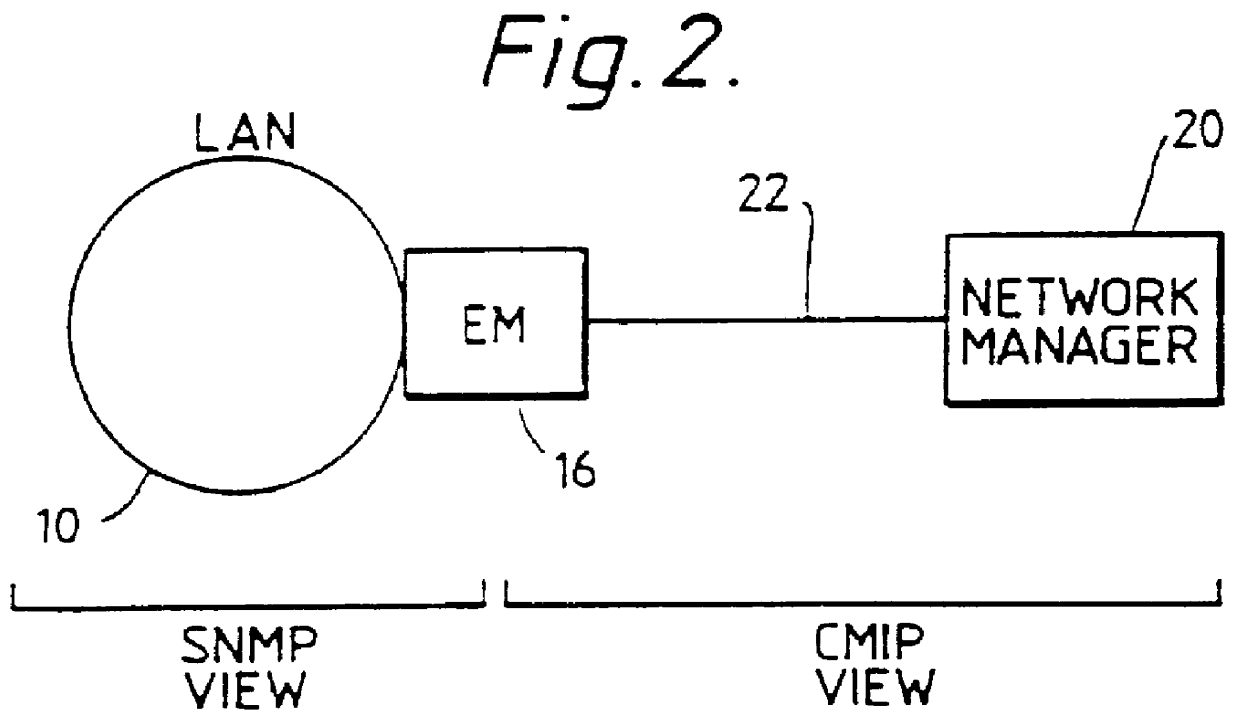
Generic managed object model for LAN domain
InactiveUS6101538AMultiple digital computer combinationsData switching networksThe InternetManaged object
PCT No. PCT / GB94 / 00429 Sec. 371 Date Oct. 18, 1995 Sec. 102(e) Date Oct. 18, 1995 PCT Filed Mar. 7, 1994 PCT Pub. No. WO94 / 23514 PCT Pub. Date Oct. 13, 1994An intemetwork system has several interlinked computer networks, each network having an associated element manager which is arranged to communicate with a router via a first network management protocol. Each element manager converts from the first network management protocol to a second protocol and also communicates via the network manager. The network manager allows a user of the system to control a router by issuing a command at the network manager and / or to view information on the status, configuration and / or performance of the router.
Owner:CISCO TECH INC
Network management system and method
InactiveUS6981266B1Dynamic loadingDigital computer detailsData switching by path configurationManagement objectNetwork management
A network management system and method is disclosed that can add or modify, for example, a managed object, without recompiling or stopping operations of an executing network management system. Thus, preferred embodiments of the present invention allow a dynamic management of managed objects in a network management system.
Owner:LG ERICSSON
System for managing object storage and retrieval in partitioned storage media
InactiveUS7136883B2Data processing applicationsInput/output to record carriersMedia typeManaged object
The invention is directed to a system for managing storage of an object in a storage system having a plurality of different storage media divided into different partitions, which includes a storage processor for determining whether a particular storage partition has reached a predetermined capacity threshold; a data migration processor for identifying within the particular storage partition an object to be moved and for identifying a target destination partition for the particular object in response to the capacity determination, the migration processor identifying the target destination partition based on one or more selected from the group consisting of (a) media type of the particular storage partition, and (b) information identifying related objects in the target destination partition; and a transfer processor for transferring data representing the particular object to the target destination partition.
Owner:CERNER INNOVATION
Method and apparatus for controlled access of requests from virtual private network devices to managed information objects using simple network management protocol and multi-topology routing
InactiveUS20050165834A1Simple and scalableSimple methodNetworks interconnectionSpecial data processing applicationsManagement information baseInformation repository
Access control approaches are disclosed wherein managed object in Simple Network Management Protocol (SNMP) Management Information Bases (MIBs) are accessed on a per- Virtual Private Network (VPN)-basis, taking into account multiple topologies that may exist under multi-topology routing (MTR) deployments, with no modifications to existing MIBs. One approach involves determining an identifier of a virtual private network in the request and a context name; determining, based on the context name, one or more sub-contexts that are either explicitly or implicitly specified in the context name; identifying, among a plurality of instances of managed objects that are associated with one or more routing topologies of a multi-topology routing system, a subset of object instances that requests associated with the virtual private network are permitted to access; and providing the request with access to only the subset of object instances.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com