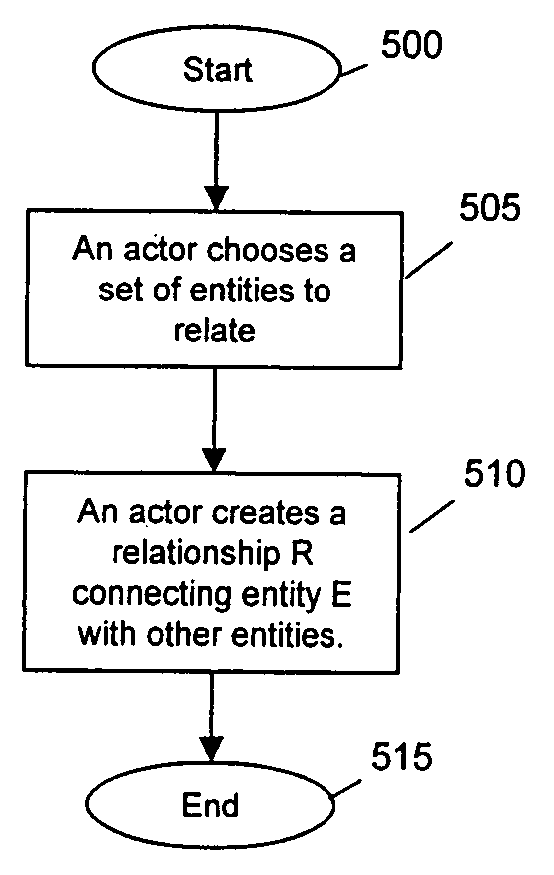
Patents
Literature
189 results about "Network operating system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A network operating system is a specialized operating system for a network device such as a router, switch or firewall. Historically operating systems with networking capabilities were described as network operating system, because they allowed personal computers (PCs) to participate in computer networks and shared file and printer access within a local area network (LAN). This description of operating systems is now largely historical, as common operating systems include a network stack to support a client–server model.
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
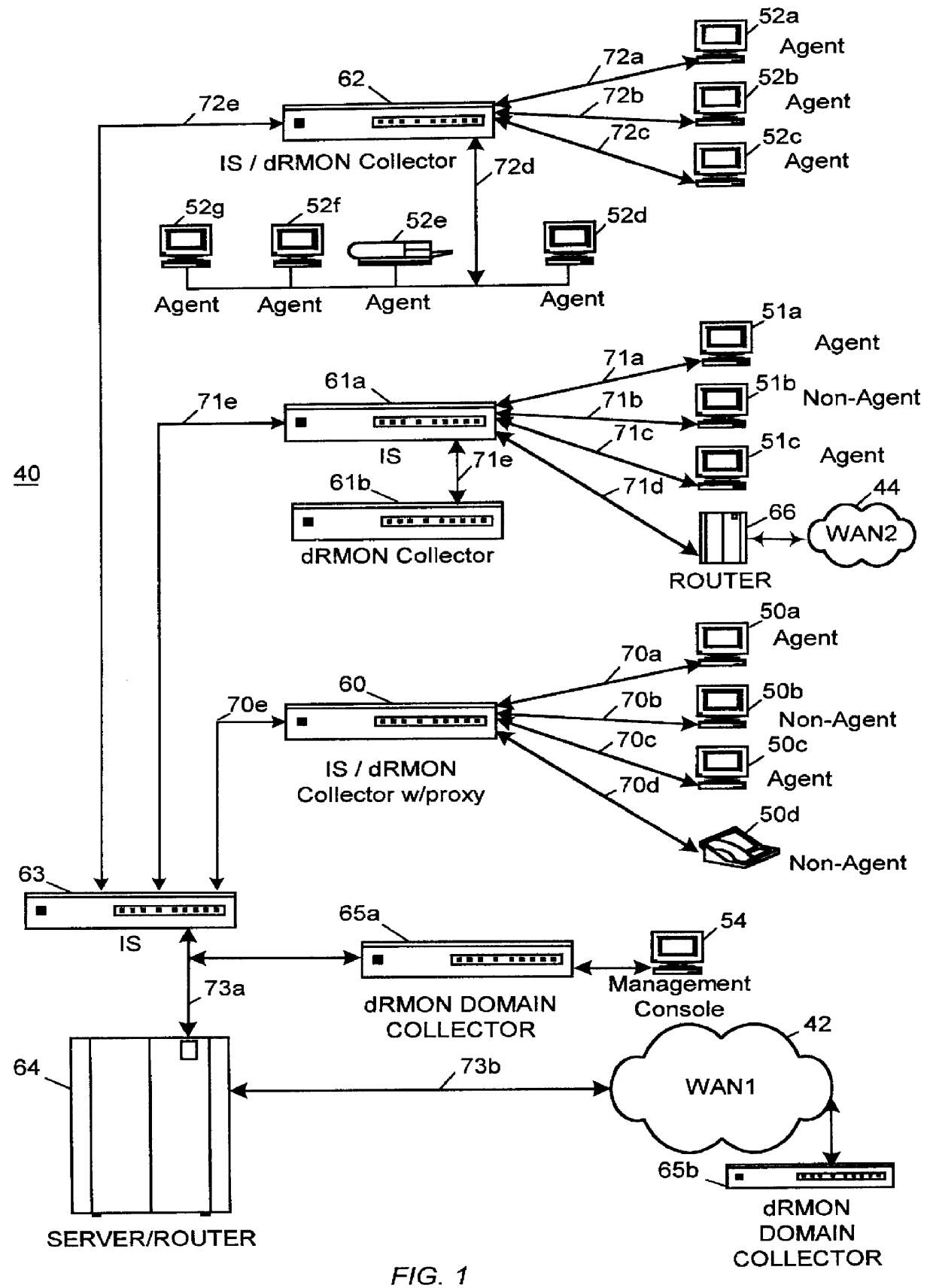
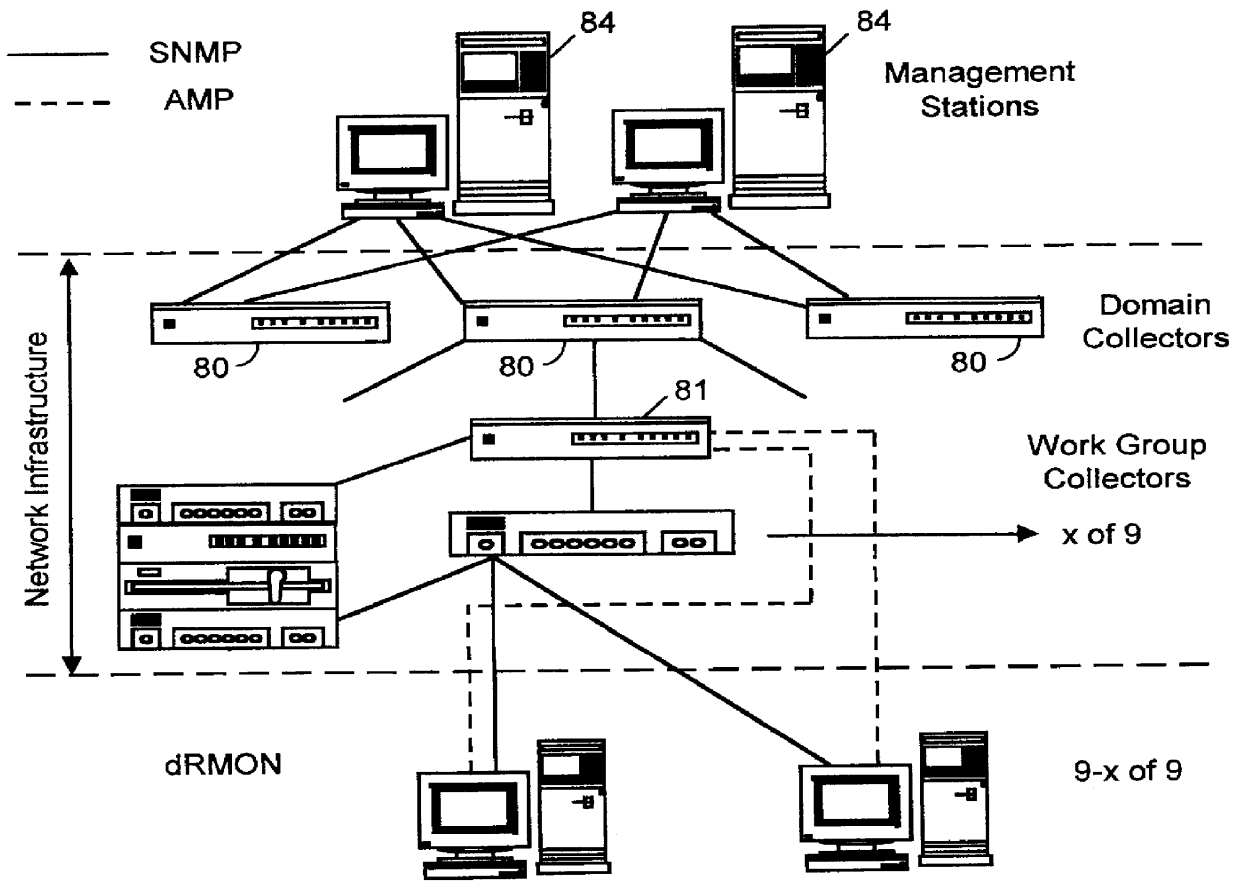
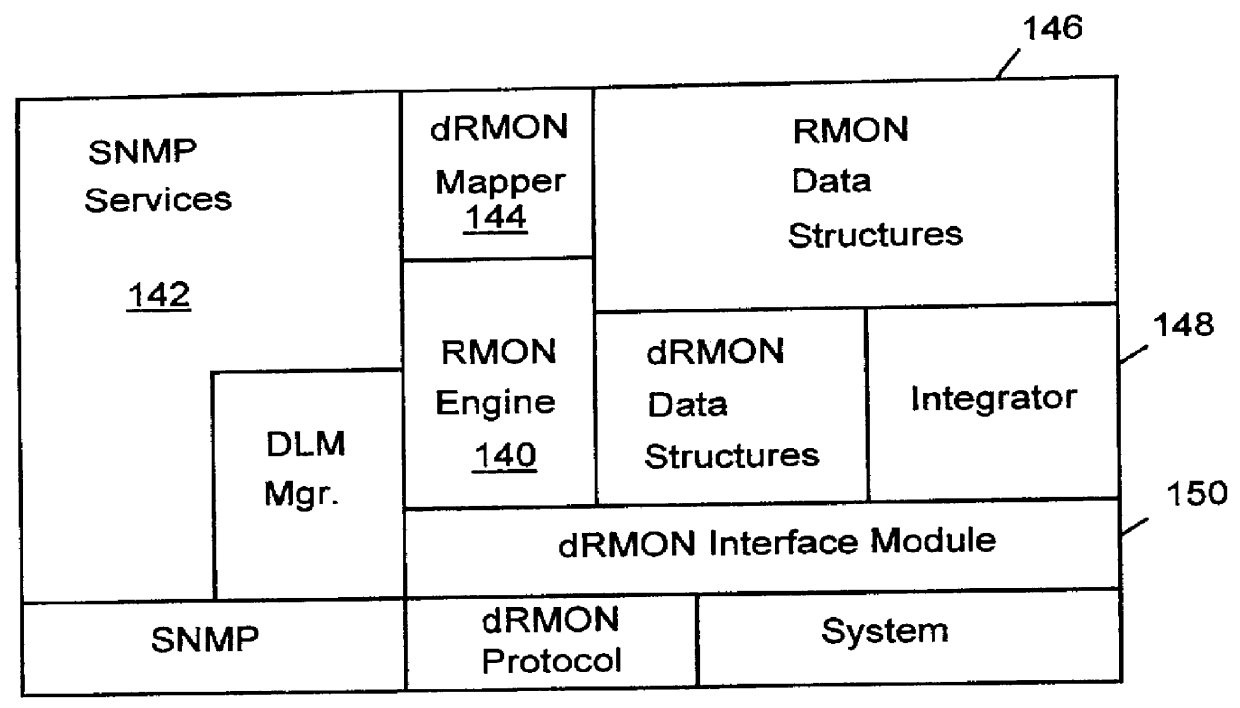
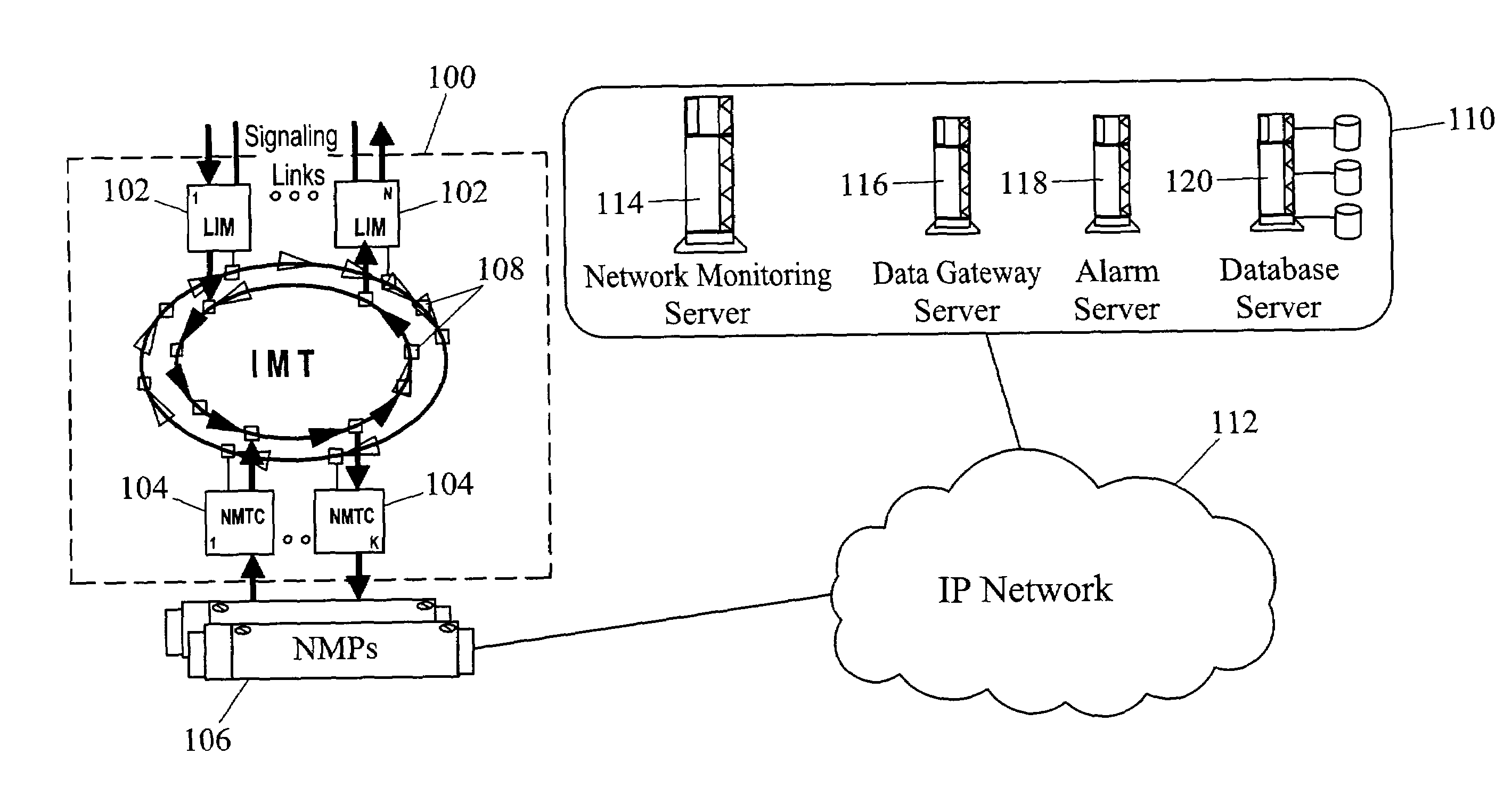
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Network operating system for managing and securing networks
ActiveUS20090138577A1Reduced power modeDigital computer detailsTransmissionTraffic capacityAuto-configuration
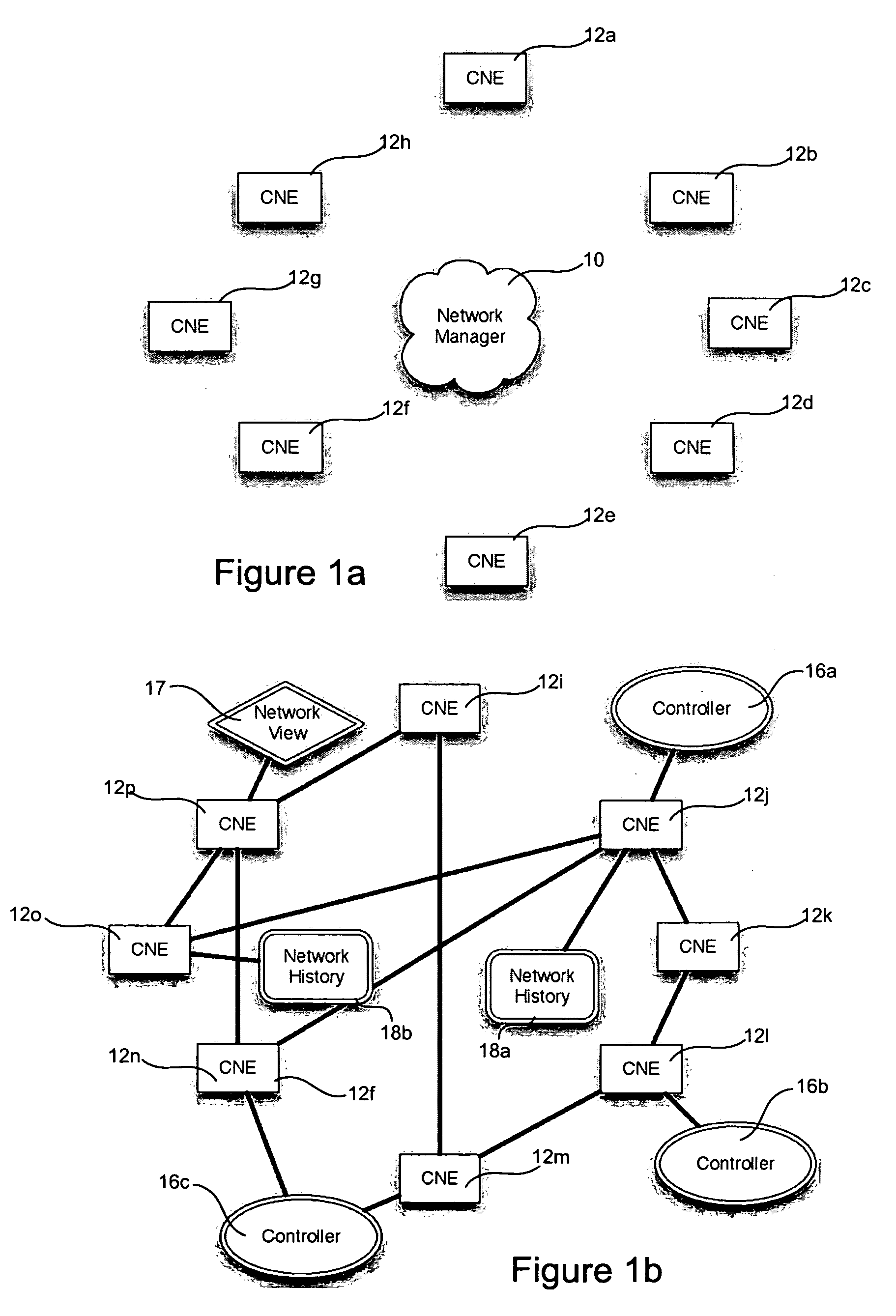
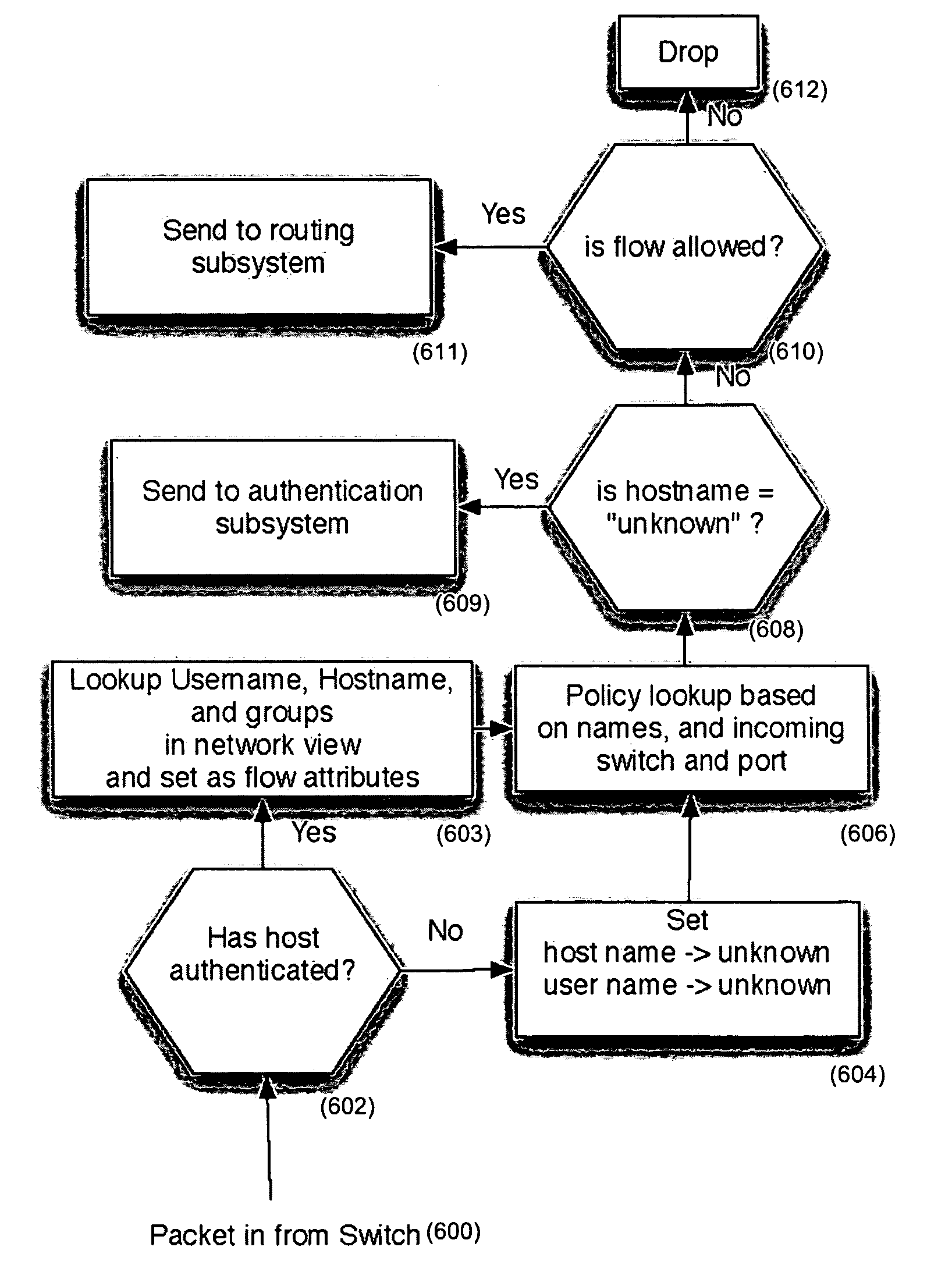
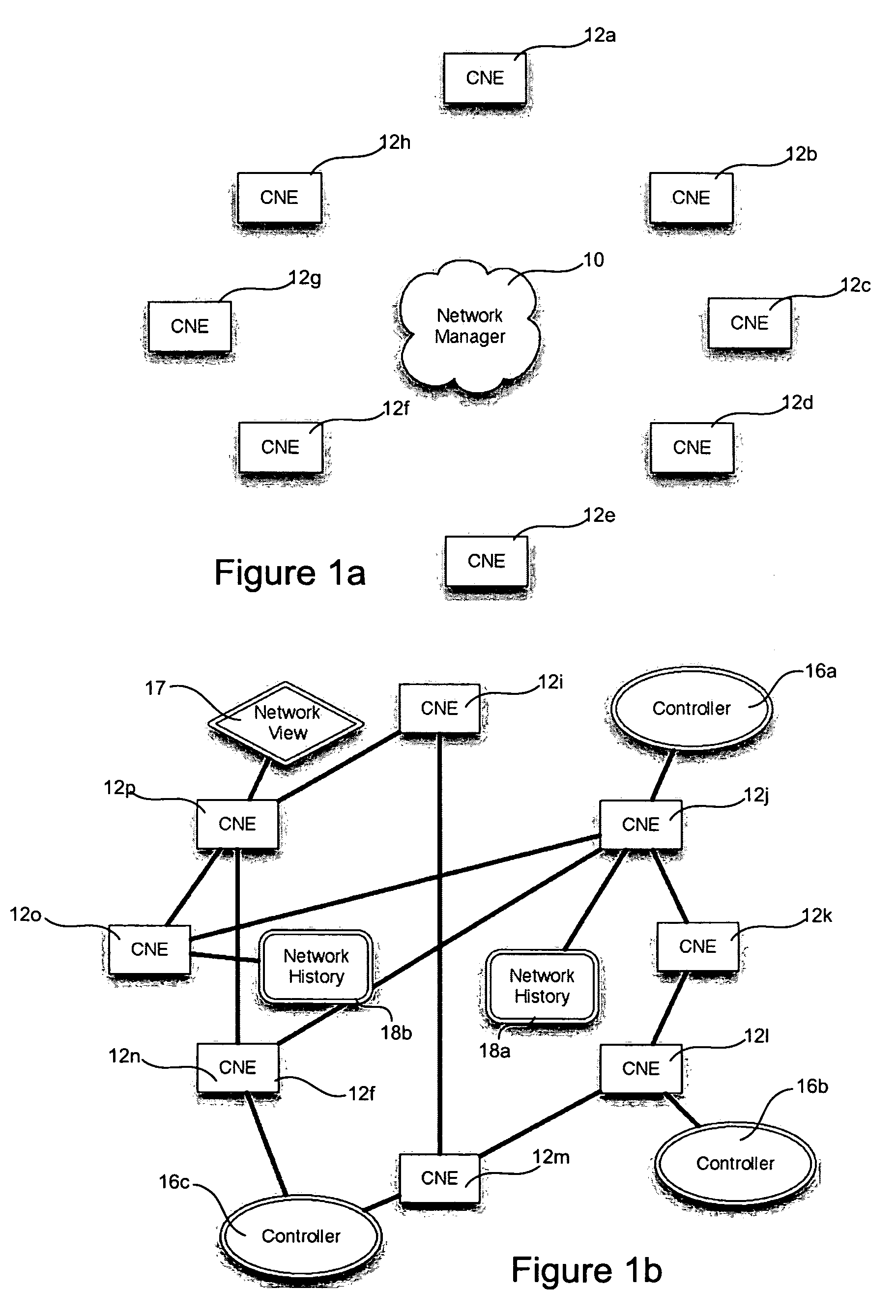
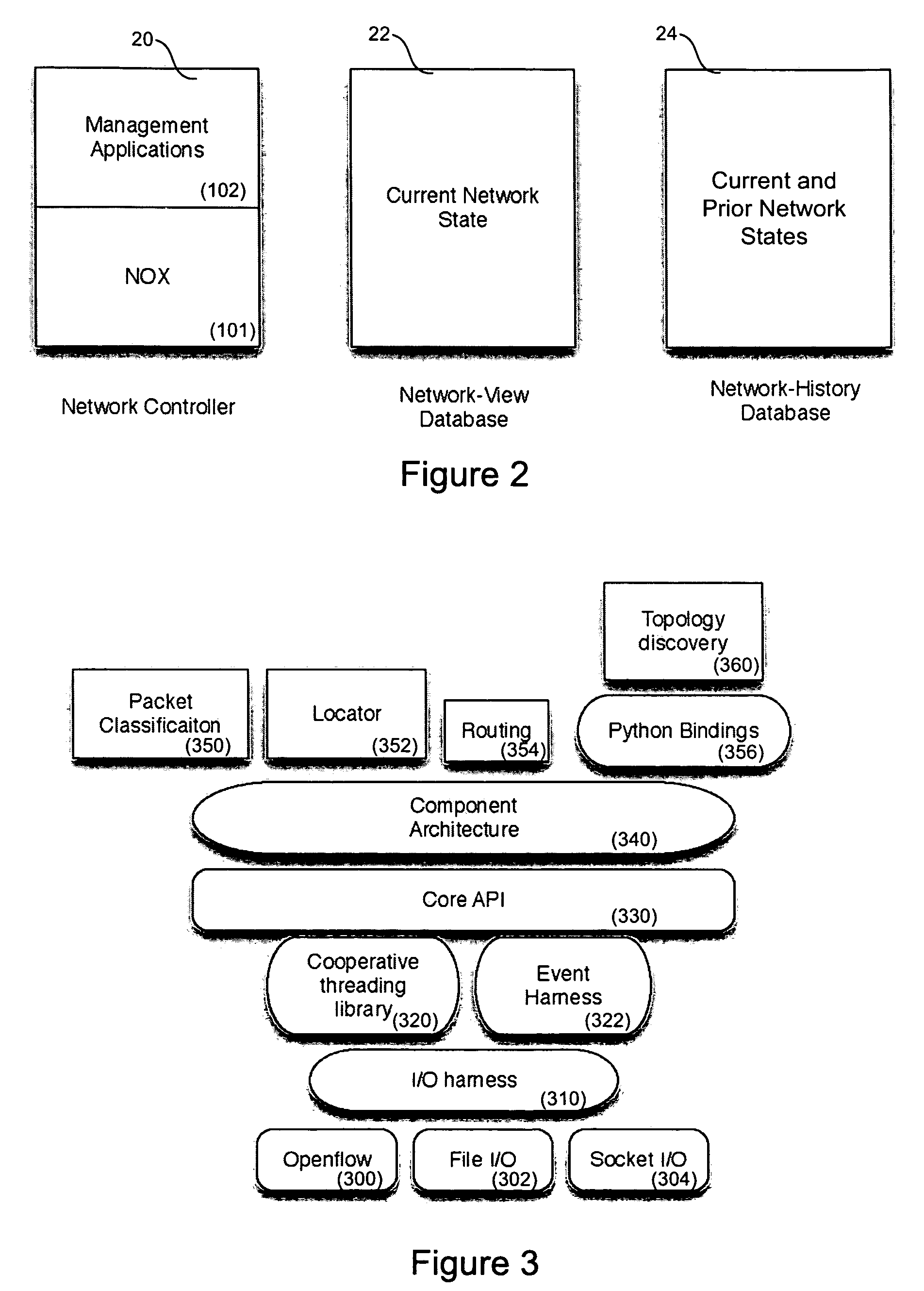
Systems and methods for managing a network are described. A view of current state of the network is maintained where the current state of the network characterizes network topology and network constituents, including network entities and network elements residing in or on the network. Events are announced that correspond to changes in the state of the network and one or more network elements can be configured accordingly. Methods for managing network traffic are described that ensure forwarding and other actions taken by network elements implement globally declared network policy and refer to high-level names, independently of network topology and the location of network constituents. Methods for discovering network constituents are described, whereby are automatically configured. Routing may be performed using ACL and packets can be intercepted to permit host to continue in sleep mode. The methods are applicable to virtual environments.
Owner:NICIRA
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS10129211B2Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsFiberNetwork operating system
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
Network operating system with distributed data architecture
ActiveUS7263290B2Dynamic reconfiguration of network connectivity, flexibility and scalabilityDynamic reconfiguration of network connectionsMultiplex system selection arrangementsOptical multiplexInformation repositoryNetwork operating system
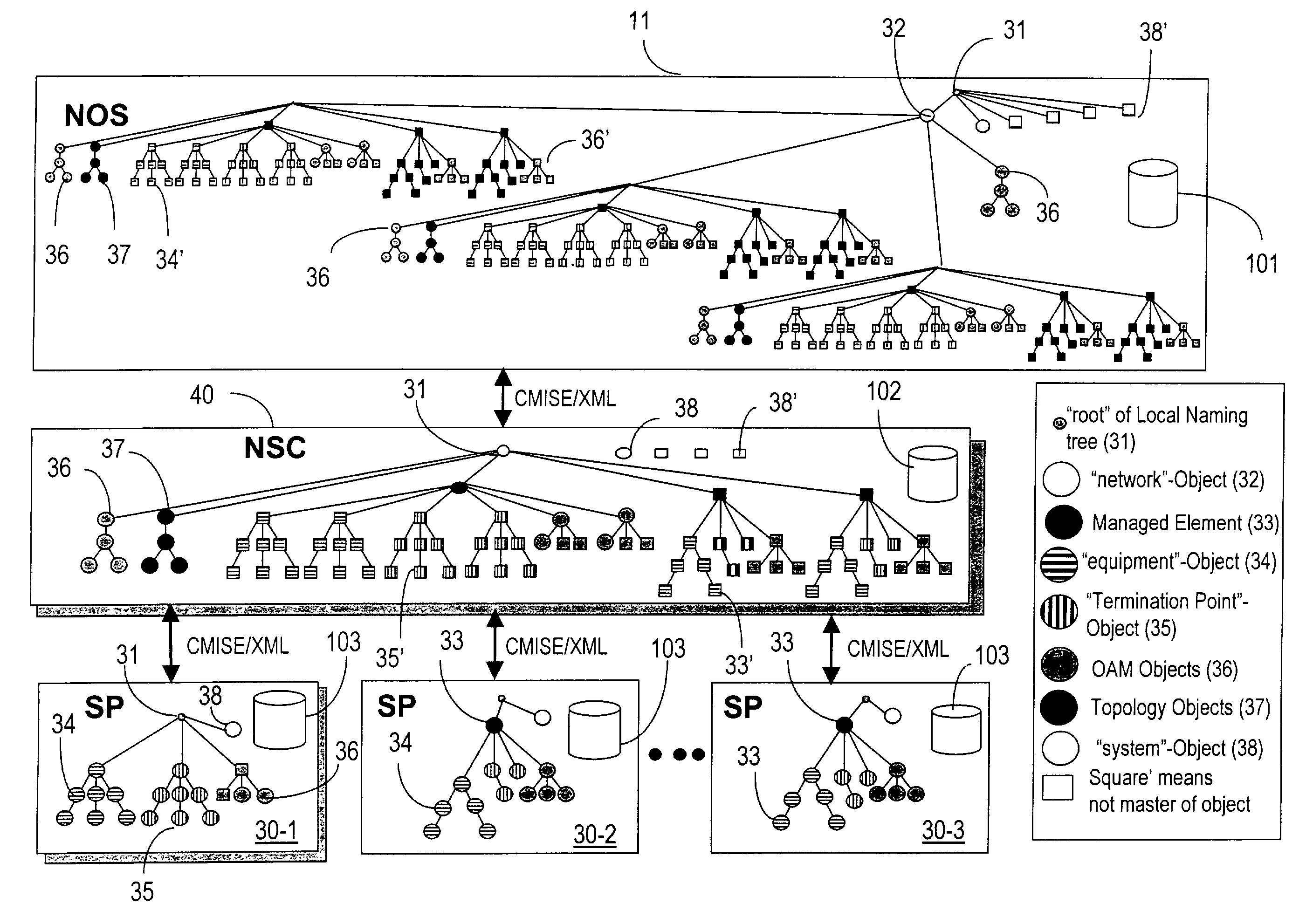
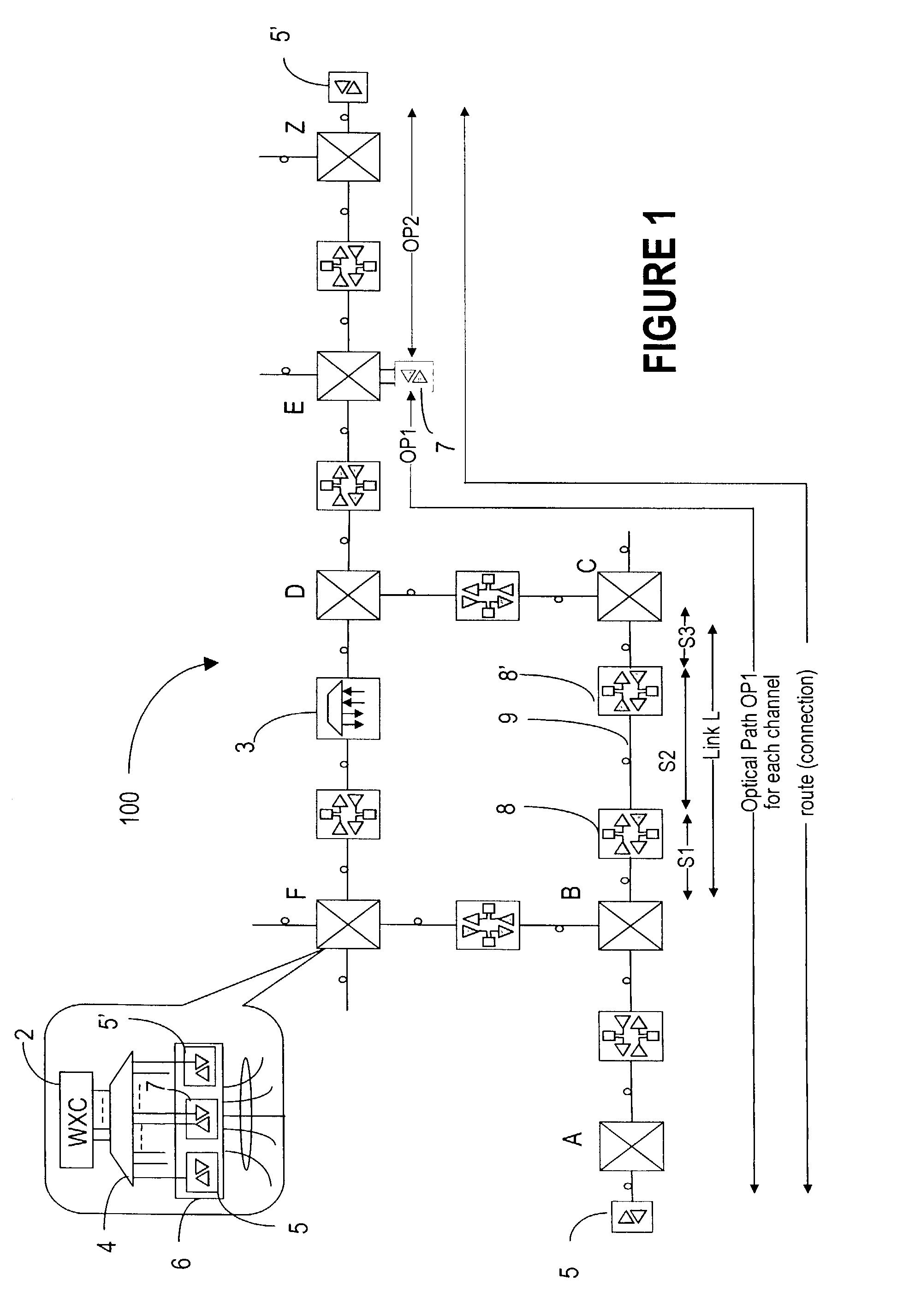
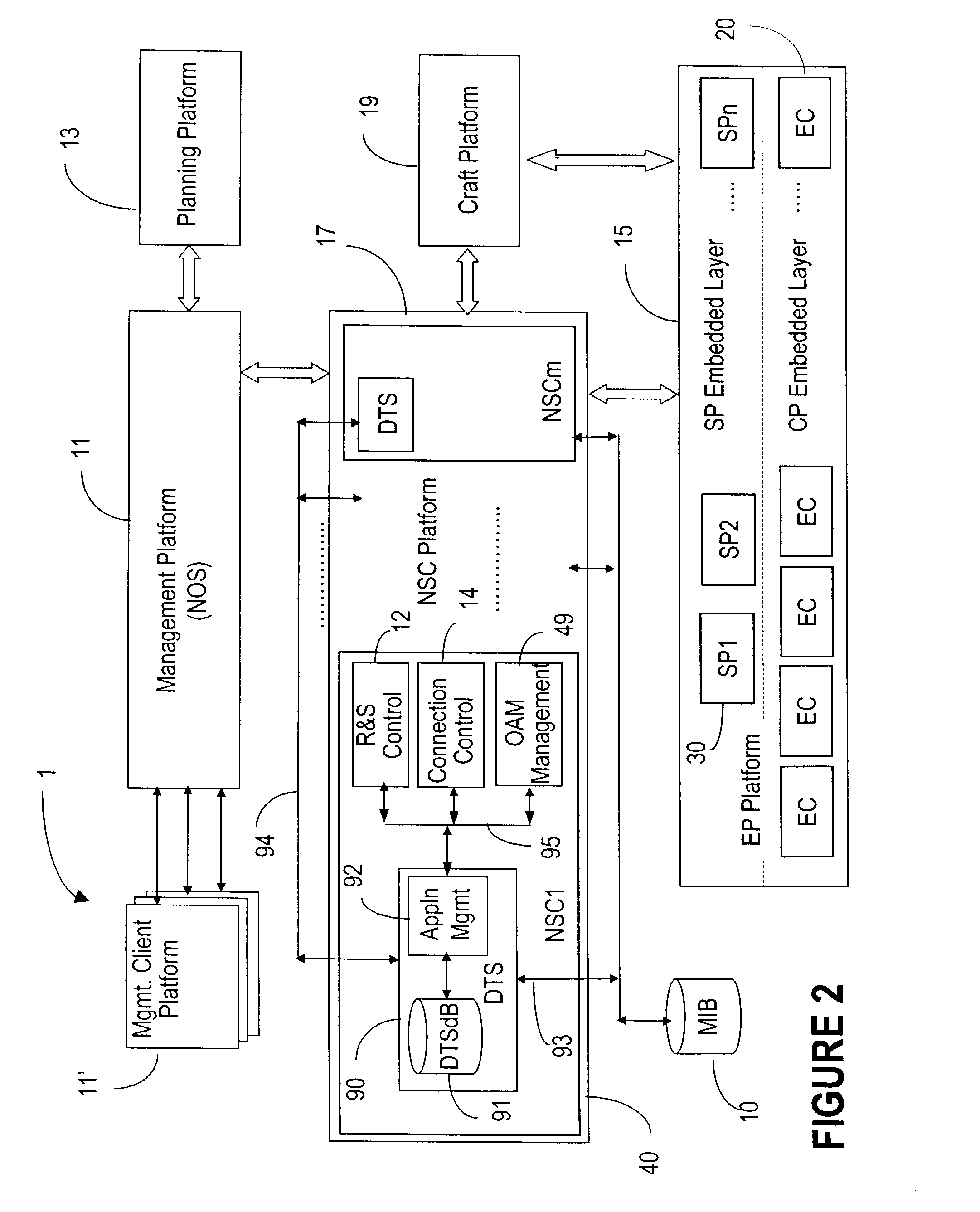
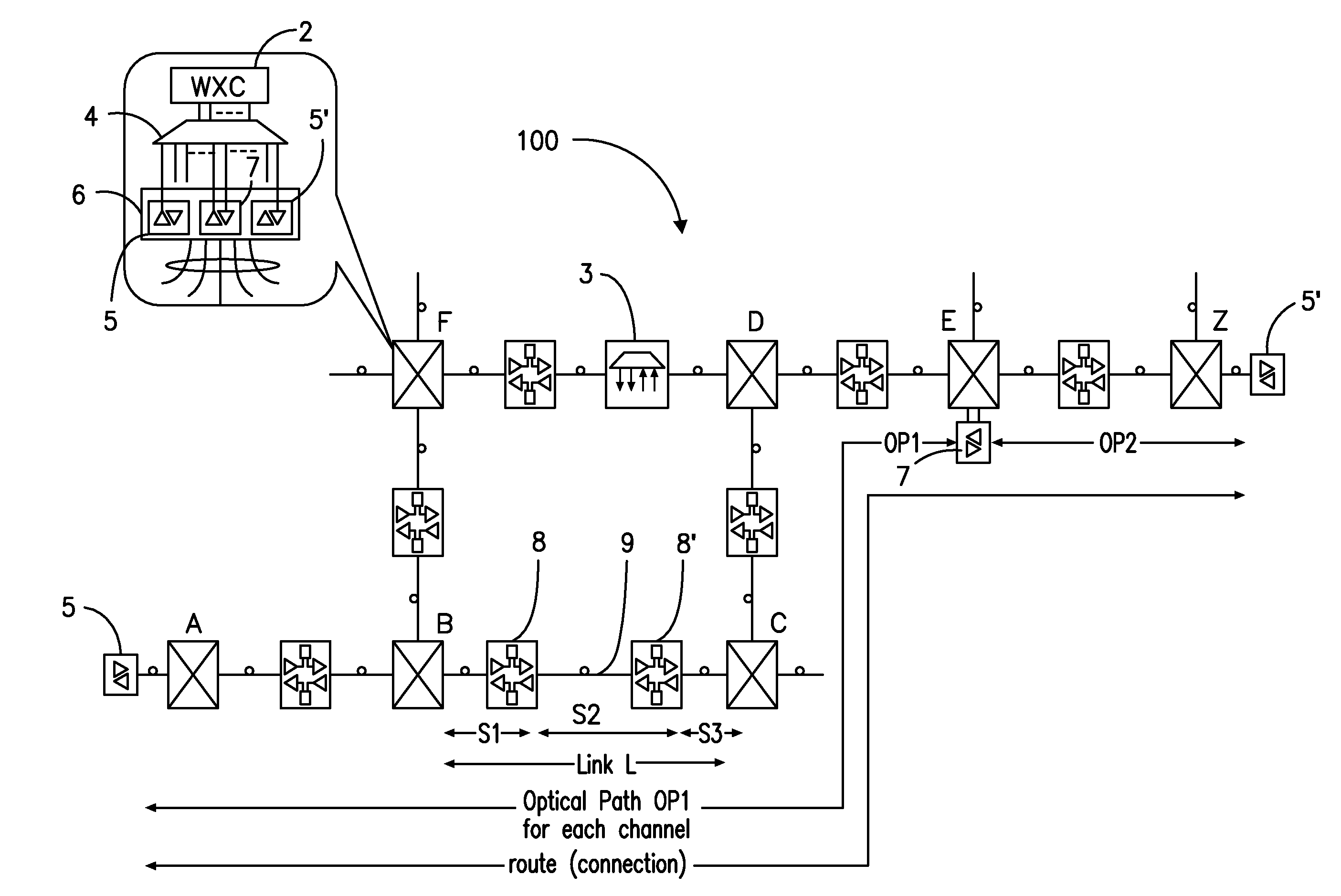
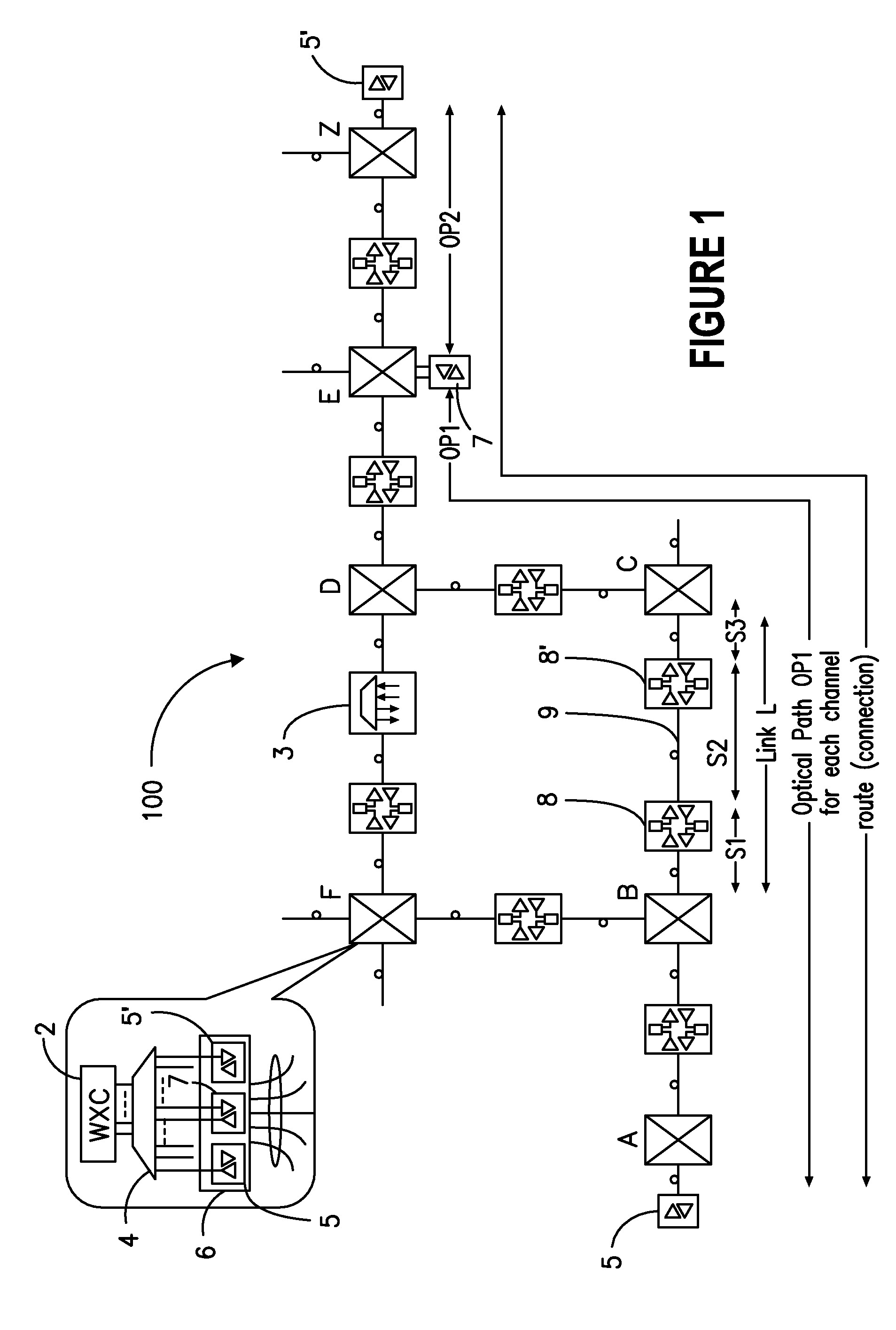
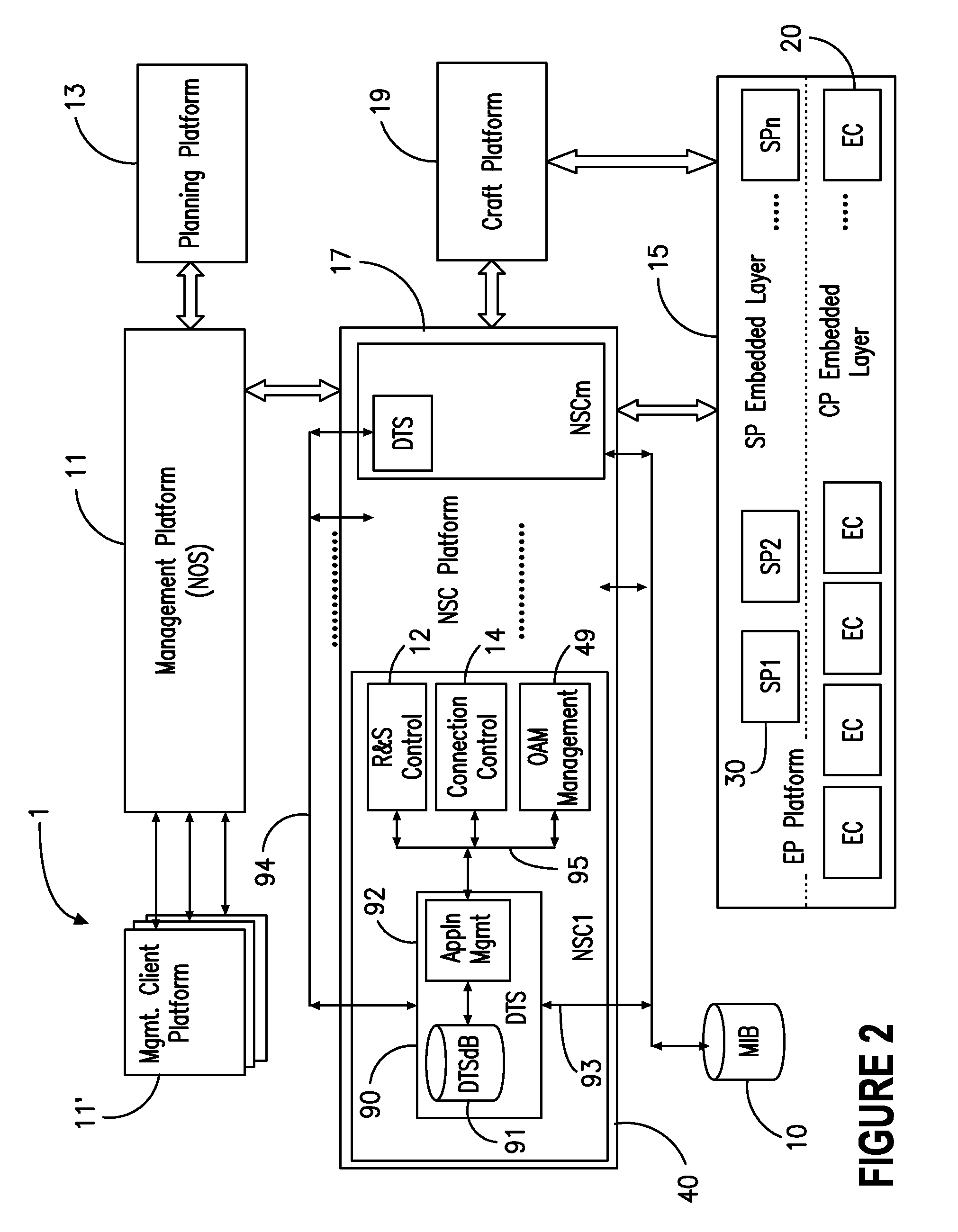
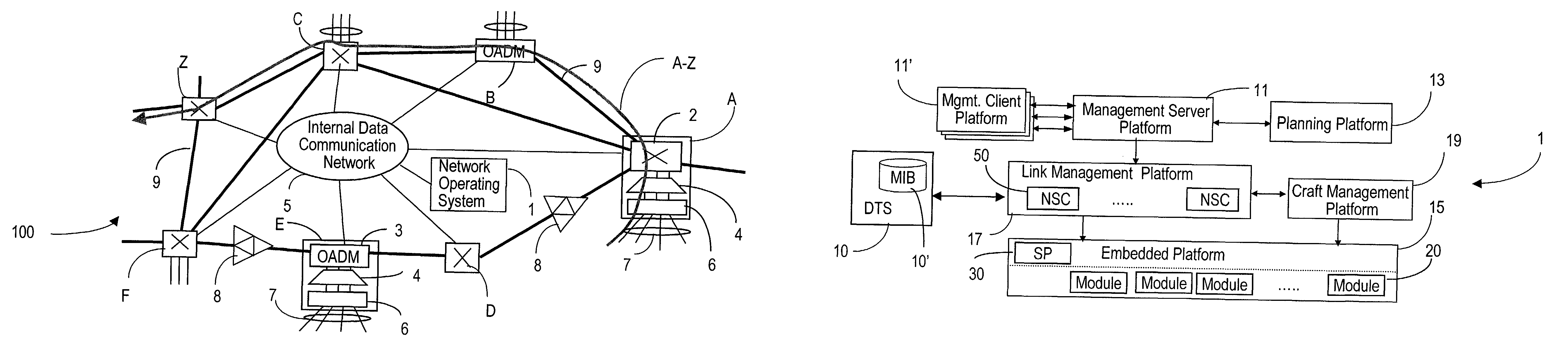
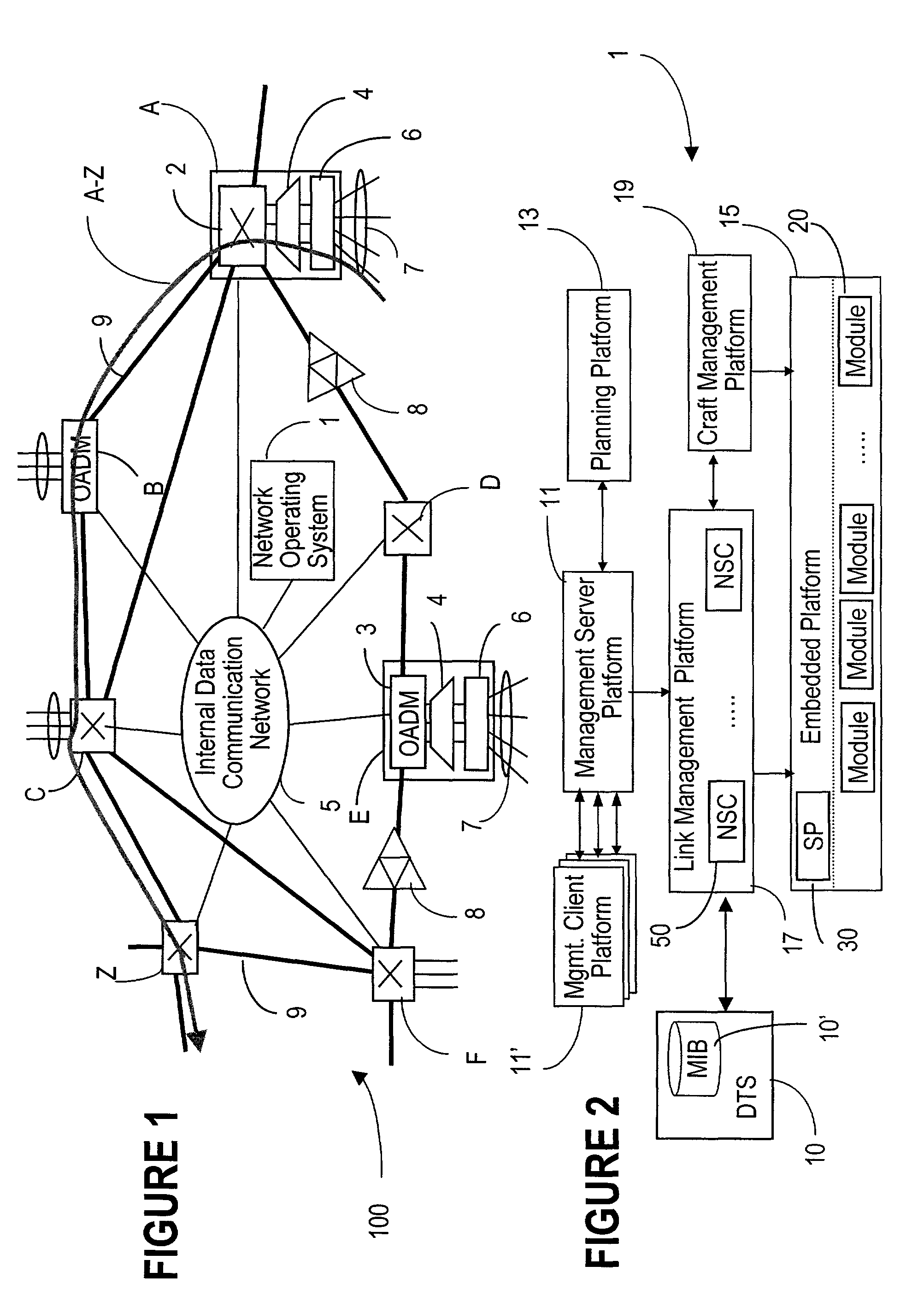
A network operating system NOS for an agile optical network with a plurality of mesh interconnected switching nodes, manages the network using an object-oriented network information model. The model is common to all applications requiring the data stored in the network managed information base. The core model can be expanded for serving specific application areas. The NOS is organized in layers, at the optical module level, connection level and network level. A distributed topology server DTS organizes the physical, logical and topological data defining all network entities as managed objects MO and topology objects TO for constructing a complete network view. The network information model associates a network element NE information model, specified by managed objects MO and a topological information model, specified by topology objects TO. The MOs are abstract specific NE data that define network implementation details and do not include any topological data, while the TOs abstract specific topological data for defining a trail established within the network, and do not include any NE data. The models are associated in a minimal number of points to construct the model of a trial in response to a connection request.
Owner:WSOU INVESTMENTS LLC
Methods and systems for automatically configuring network monitoring system
ActiveUS7155512B2Requires some amountReduce laborDigital computer detailsData switching networksAuto-configurationNetwork operating system
Owner:TEKELEC GLOBAL INC
Network operating system with distributed data architecture
ActiveUS20080212963A1Dynamic reconfiguration of network connectivity, flexibility and scalabilityDynamic reconfiguration of network connectionsMultiplex system selection arrangementsOptical multiplexInformation repositoryNetwork operating system
A network operating system NOS for an agile optical network with a plurality of mesh interconnected switching nodes, manages the network using an object-oriented network information model. The model is common to all applications requiring the data stored in the network managed information base. The core model can be expanded for serving specific application areas. The NOS is organized in layers, at the optical module level, connection level and network level. A distributed topology server DTS organizes the physical, logical and topological data defining all network entities as managed objects MO and topology objects TO for constructing a complete network view. The network information model associates a network element NE information model, specified by managed objects MO and a topological information model, specified by topology objects TO. The MOs are abstract specific NE data that define network implementation details and do not include any topological data, while the TOs abstract specific topological data for defining a trail established within the network, and do not include any NE data. The models are associated in a minimal number of points to construct the model of a trial in response to a connection request.
Owner:WSOU INVESTMENTS LLC
Audio communications using devices with different capabilities
InactiveUS20060041616A1Facilitates distributed collaborationCompact integrationMultiple digital computer combinationsOffice automationComputer hardwareWide area
Owner:PRAGMATUS AV
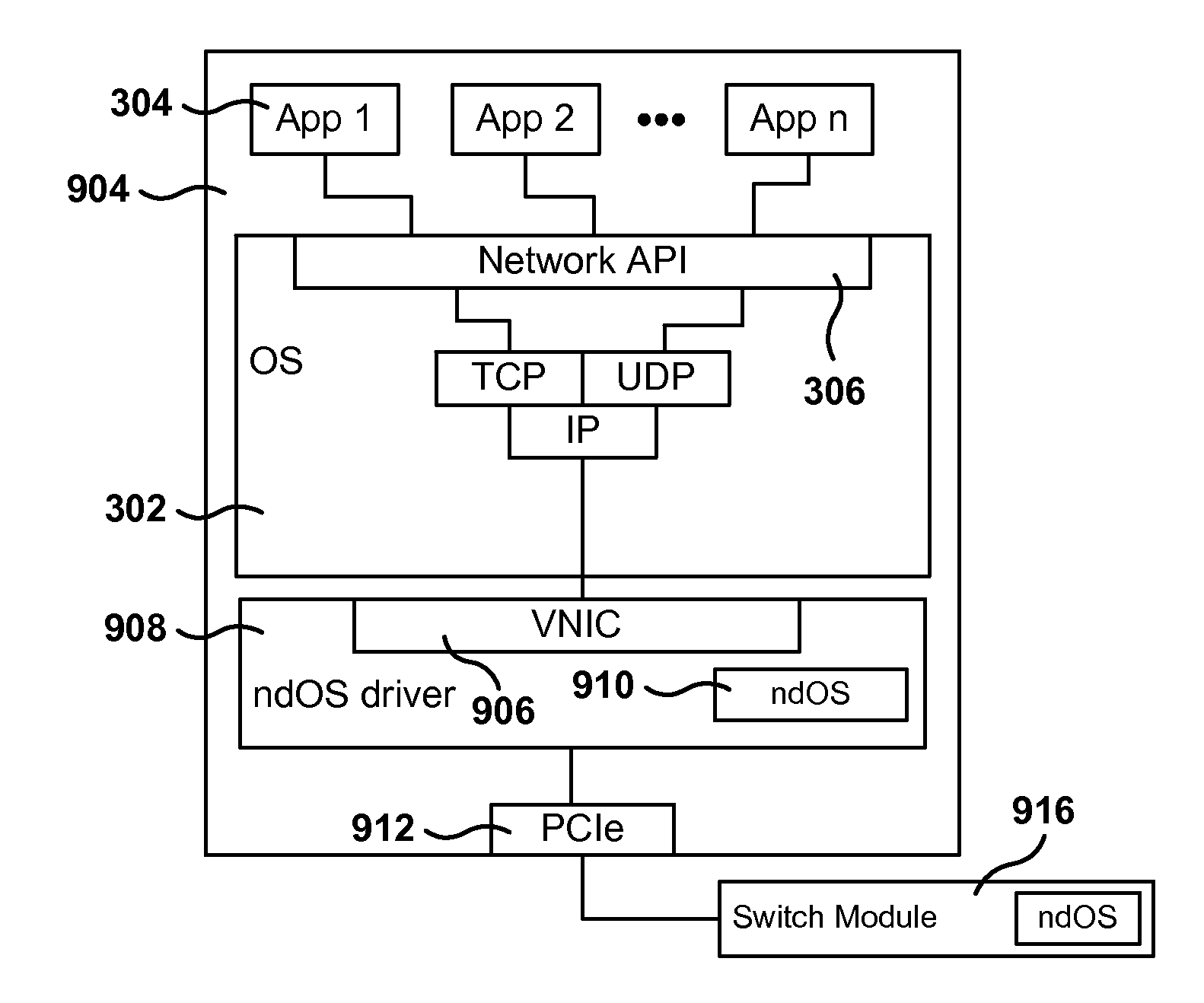
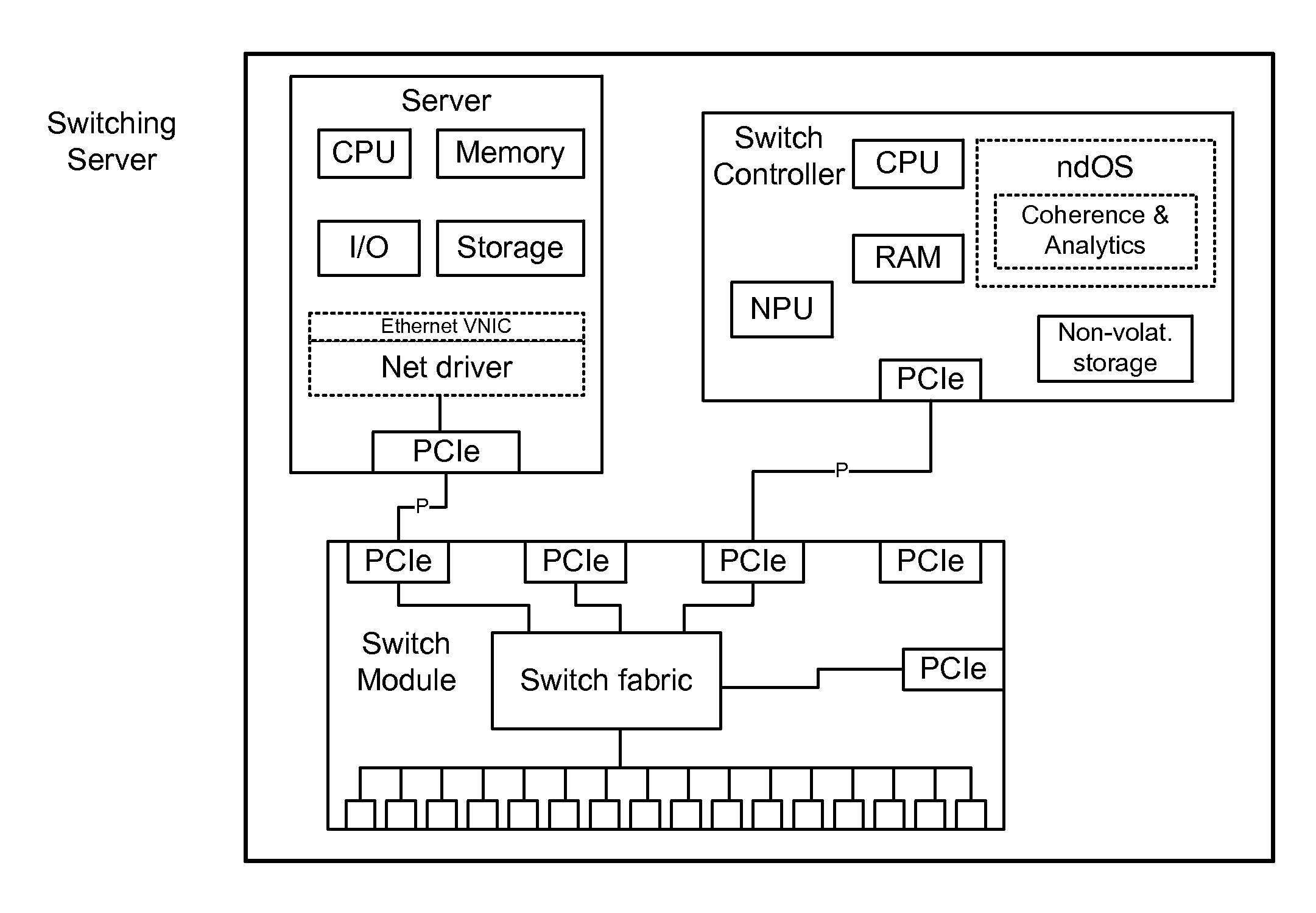
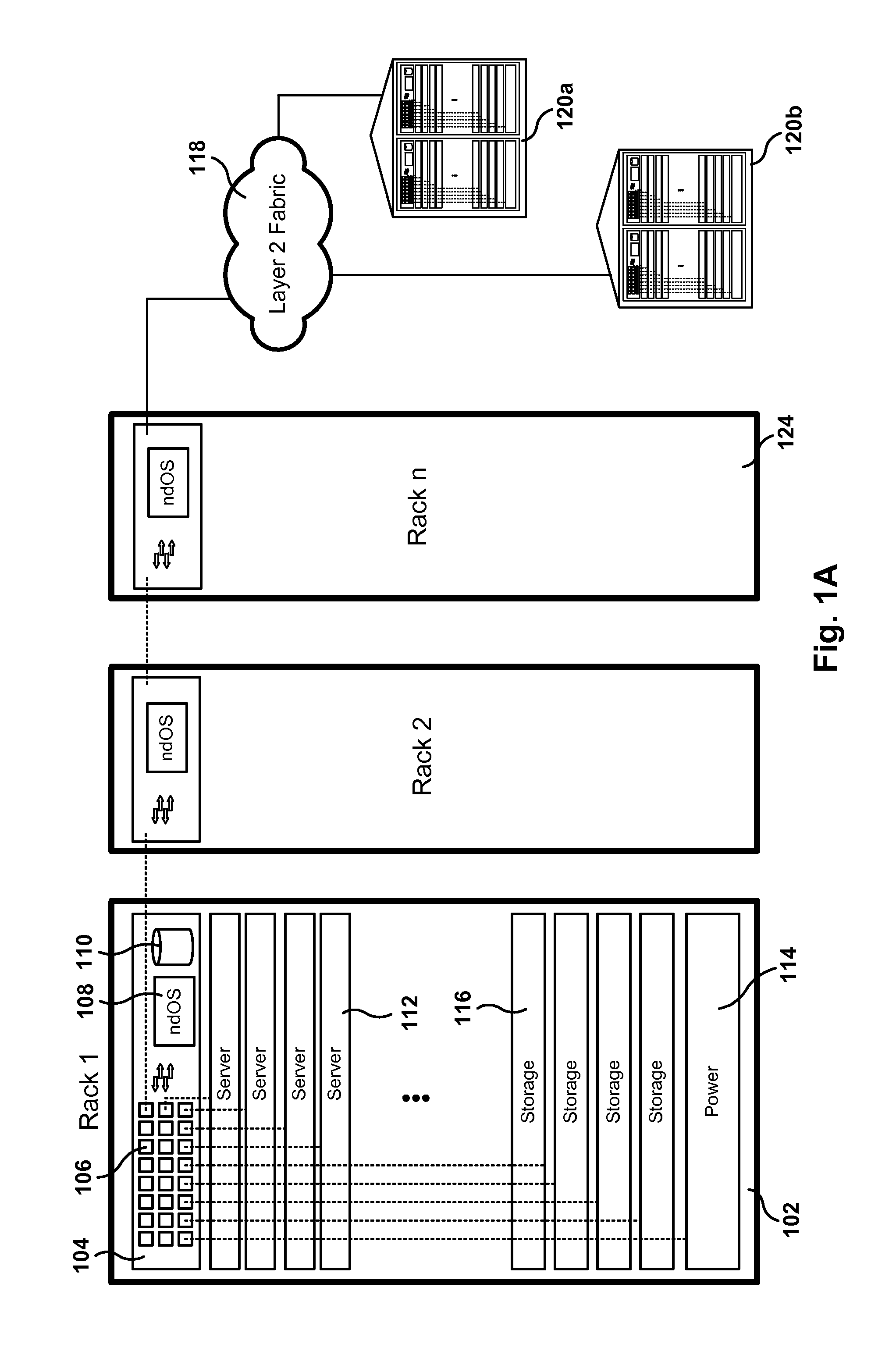
Servers, Switches, and Systems with Switching Module Implementing a Distributed Network Operating System
ActiveUS20130215754A1Error preventionFrequency-division multiplex detailsCommunication interfaceNetwork operating system
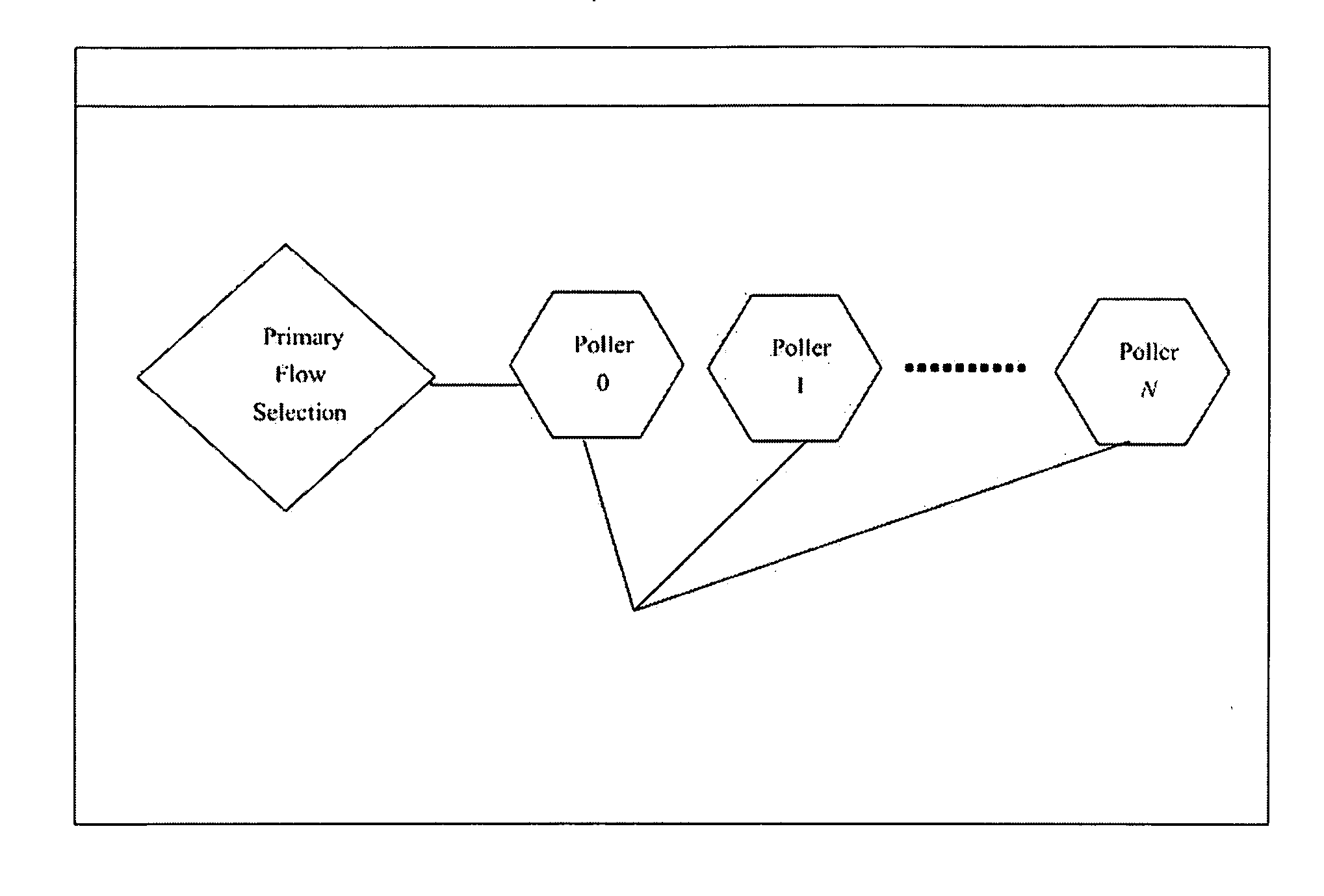
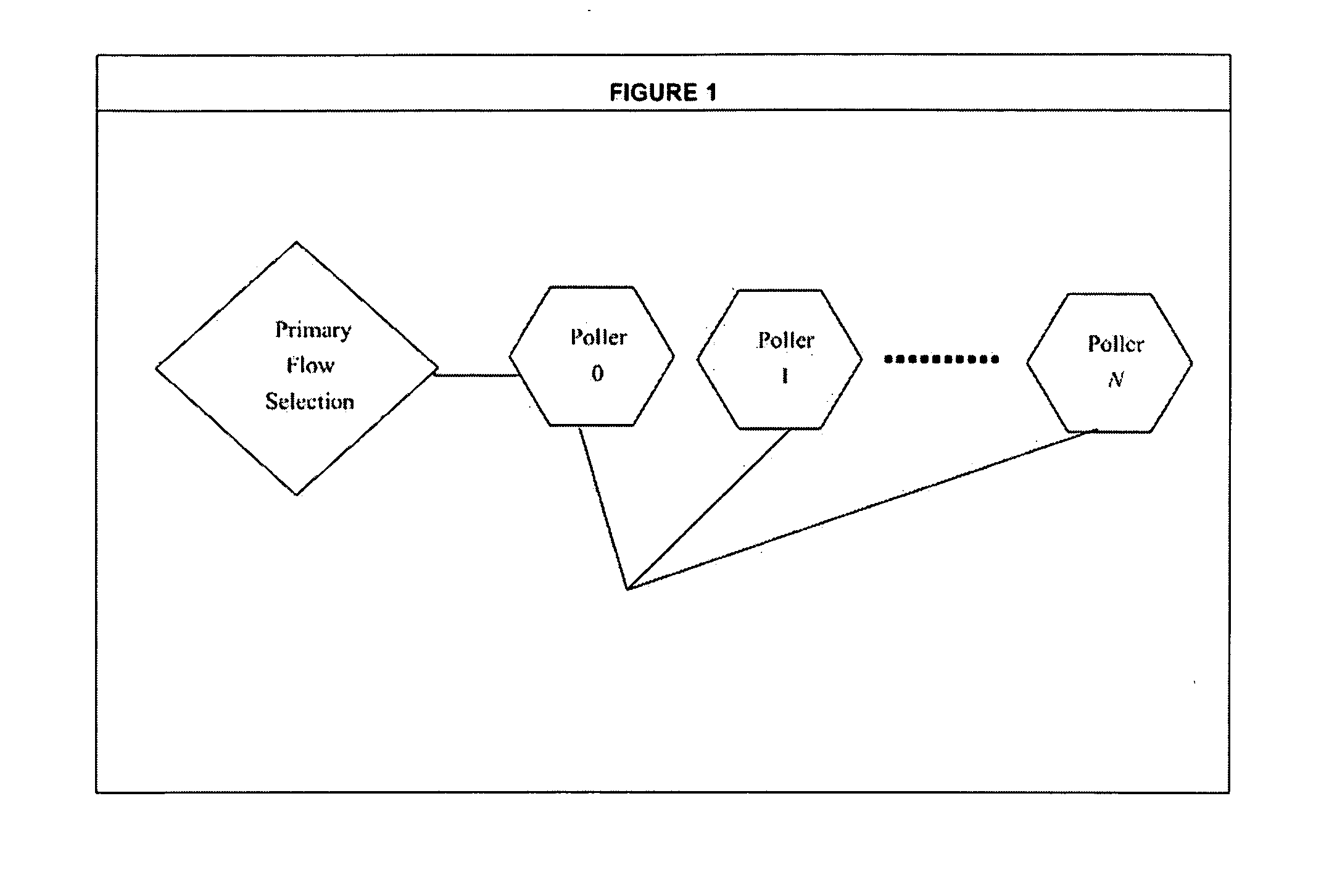
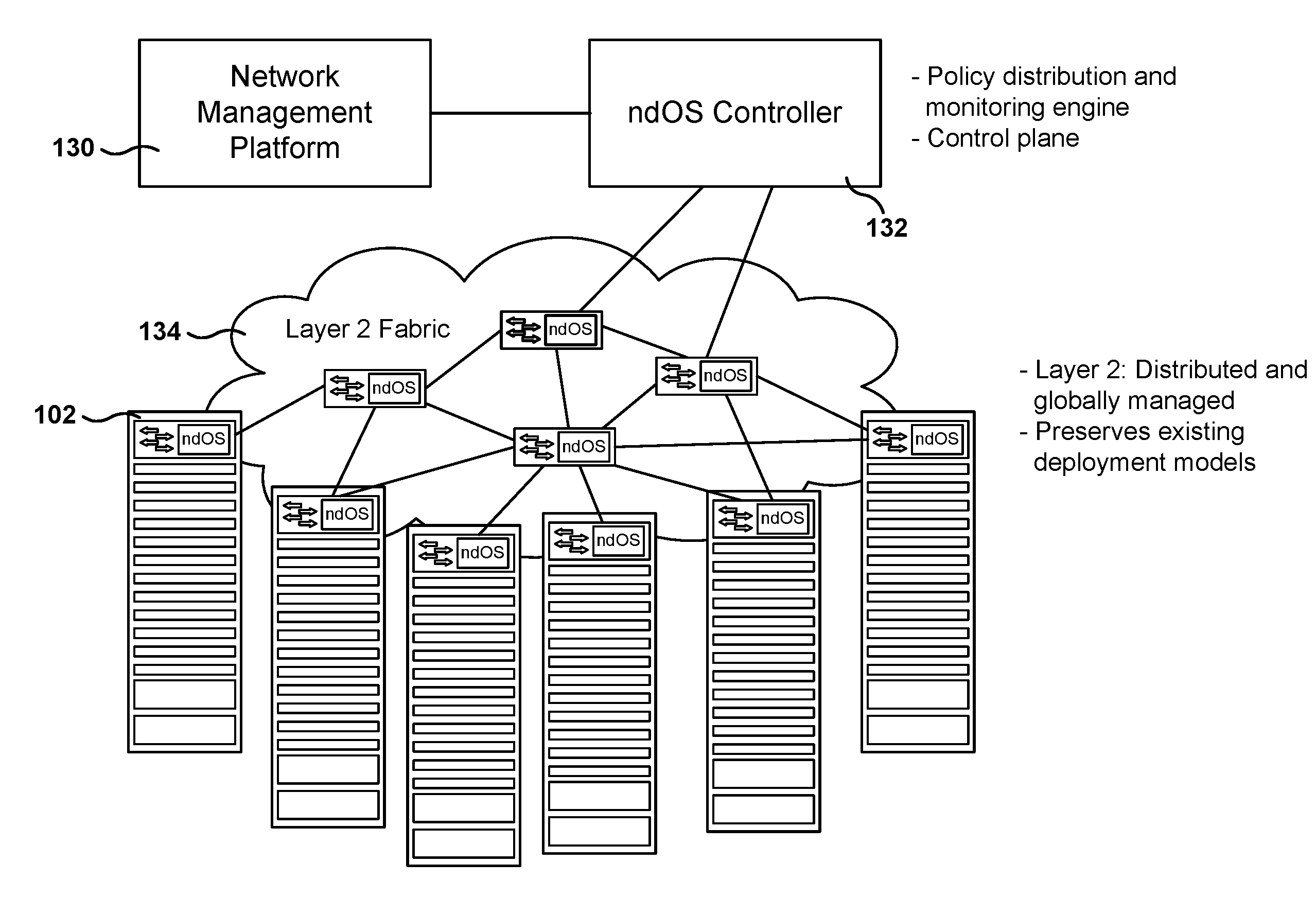
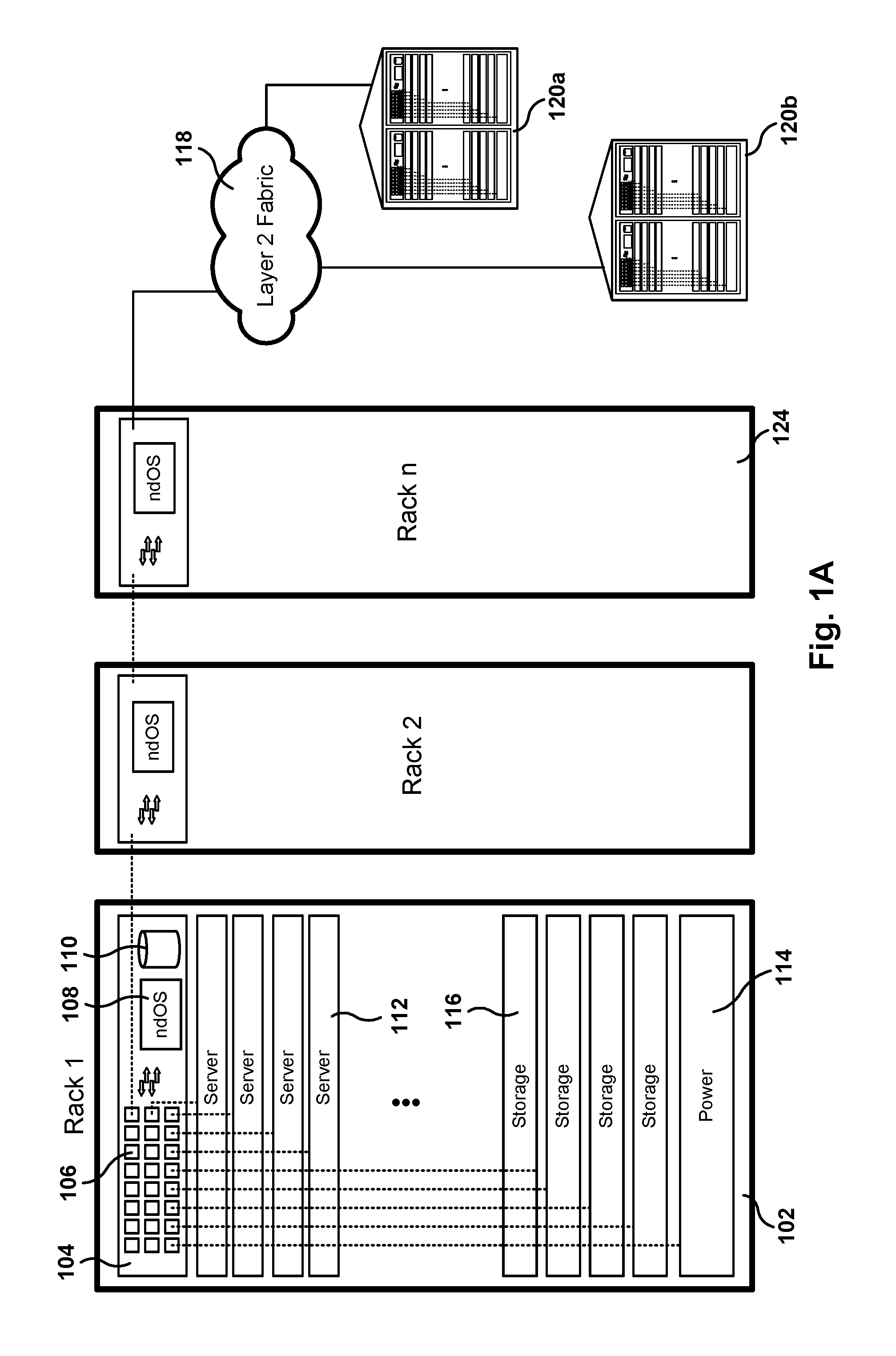
One networking device includes a switch module, a server, and a switch controller. The switch module has ports with a communications interface of a first type (CI1) and ports with a communications interface of a second type (CI2). The server, coupled to the switch module via a first CI2 coupling, includes a virtual CI1 driver, which provides a CI1 interface in the server, defined to exchange CI1 packets with the switch module via the first CI2 coupling. The virtual CI1 driver includes a first network device operating system (ndOS) program. The switch controller, in communication with the switch module via a second CI2 coupling, includes a second ndOS program controlling, in the switch module, a packet switching policy defining the switching of packets through the switch module or switch controller. The first and second ndOS programs exchange control messages to maintain a network policy for the switch fabric.
Owner:PLURIBUS NETWORKS
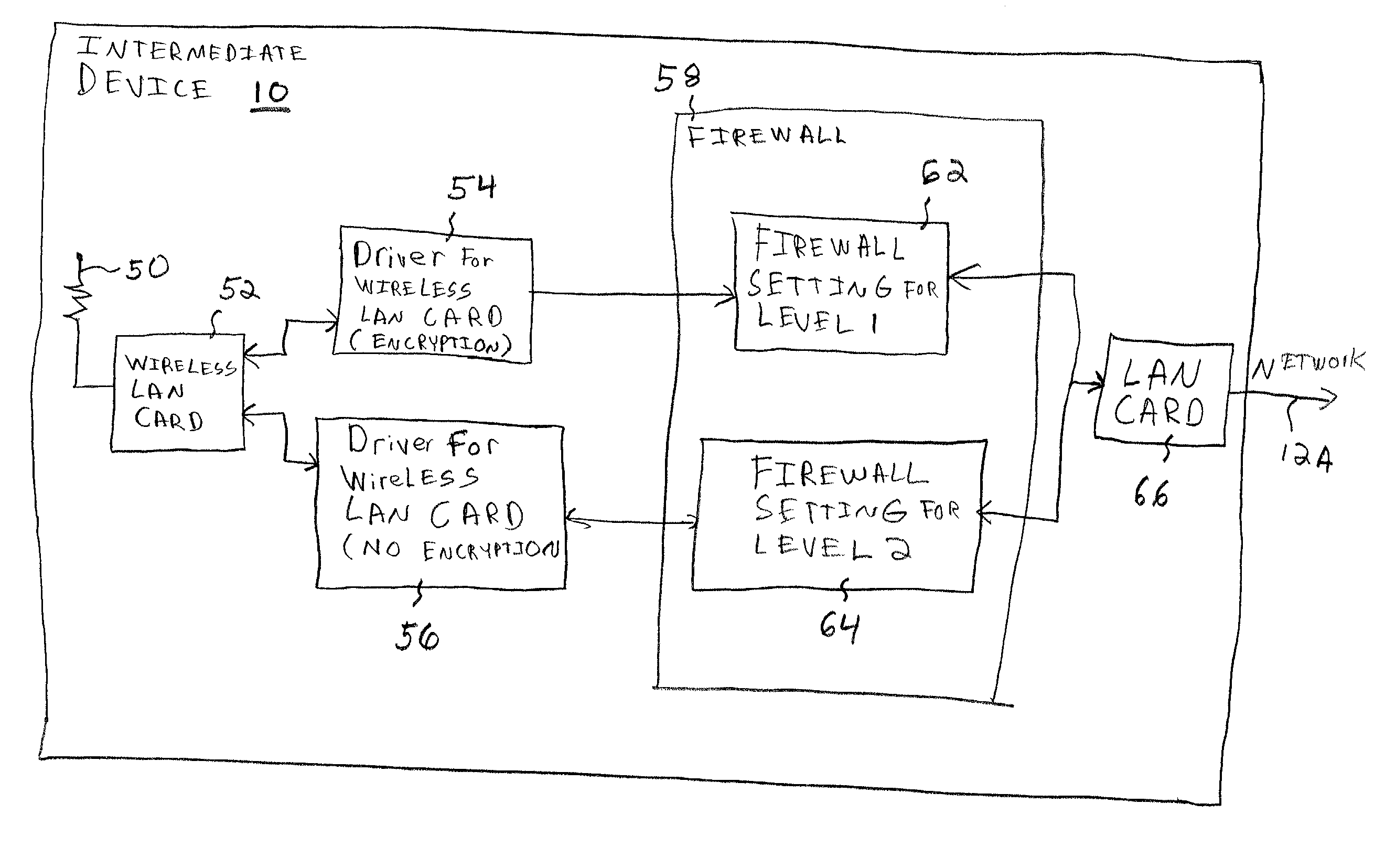
Method and system for controlling access to network resources based on connection security
InactiveUS20020178365A1Computer security arrangementsSecret communicationOperational systemNetwork operating system
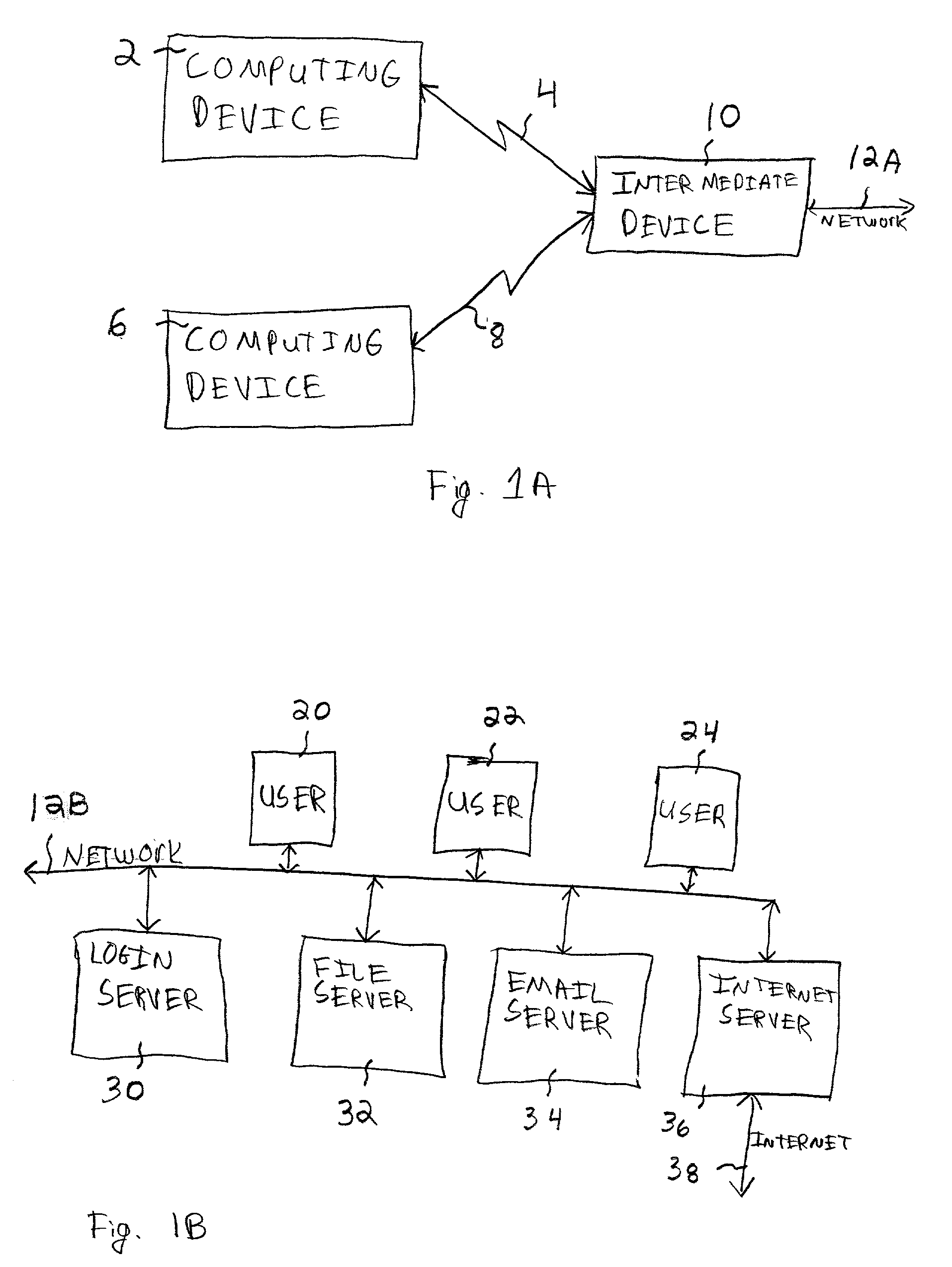
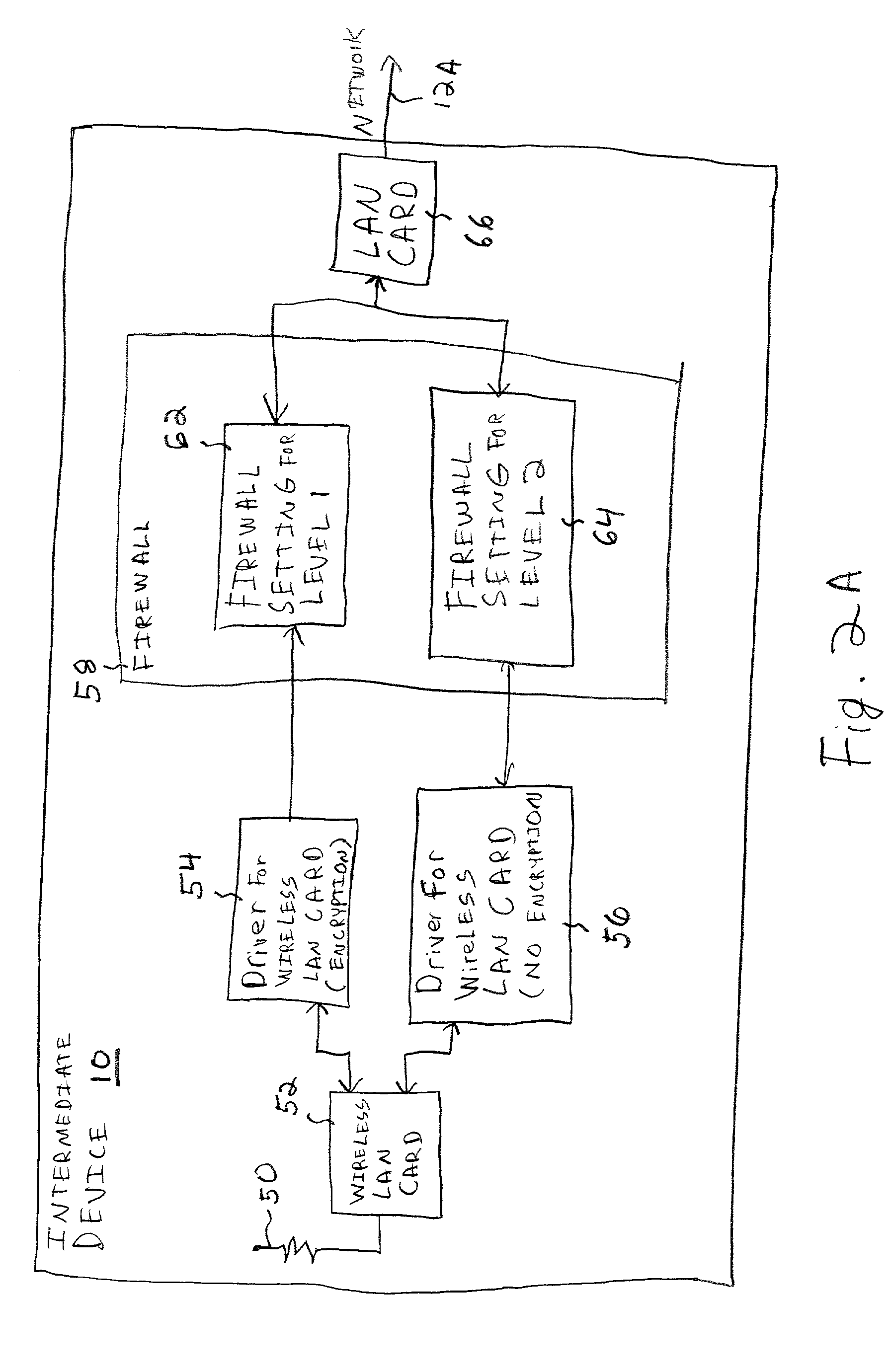
A method and system for controlling a network, such as a computer network. A computer network connection is established between one or more computers or computing devices and an intermediate device to which network resources are connected. There is a controlling of a level of access of the computer or computing device to the network resources based on the level of security of the computer network connection between the computer or computing device and the intermediate device. Such a controlling may be performed by the intermediate device, a separate firewall device, and / or components of a network operating system or network controlling software. The computing devices are connected to the intermediate device using a wireless connection, although as an alternative a wired connection may be utilized.
Owner:RICOH KK
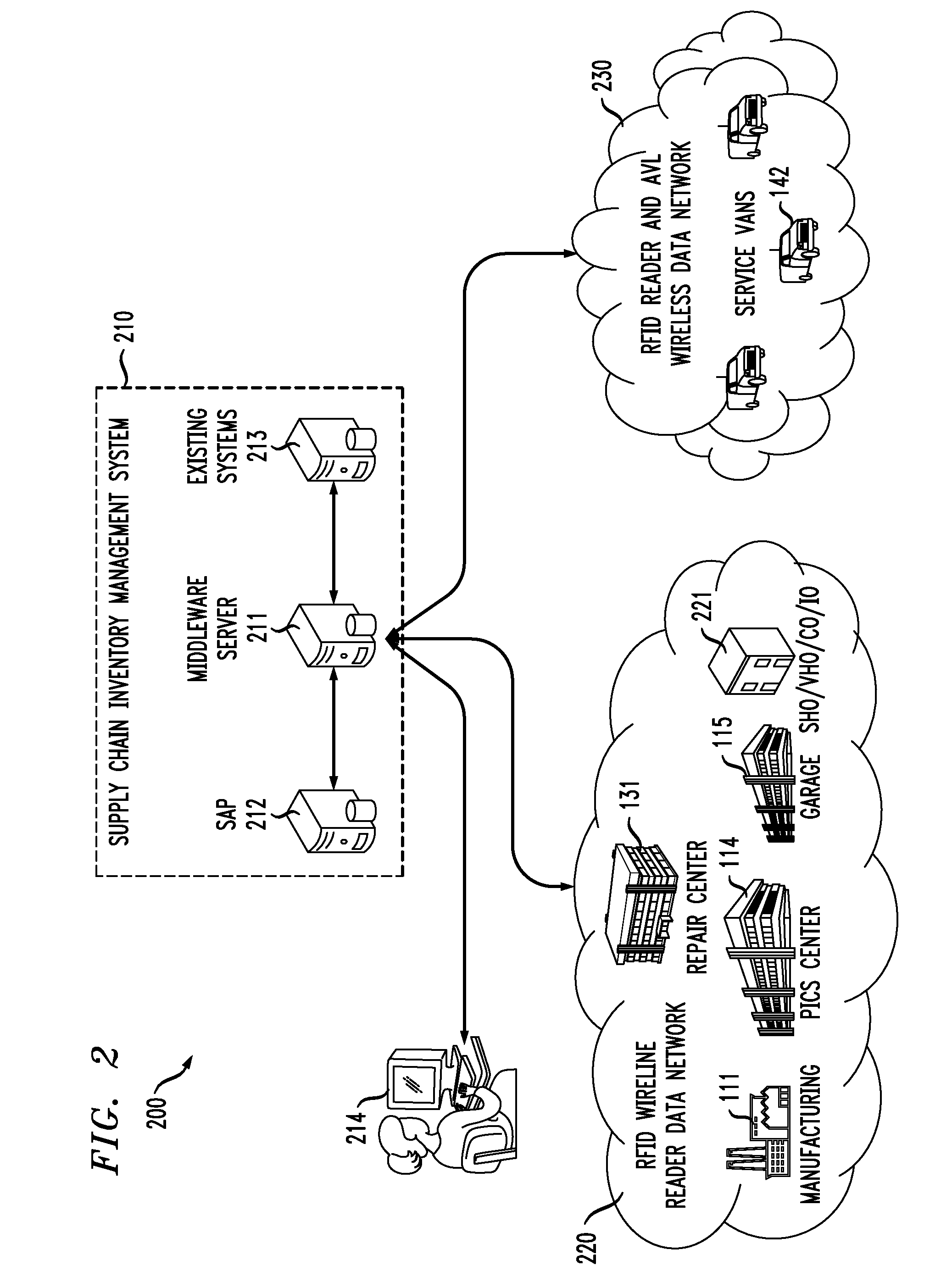
Radio-Frequency Identification Enabled Inventory Management and Network Operations System and Method
InactiveUS20090189743A1Programme controlElectric signal transmission systemsNetwork operating systemOperational system
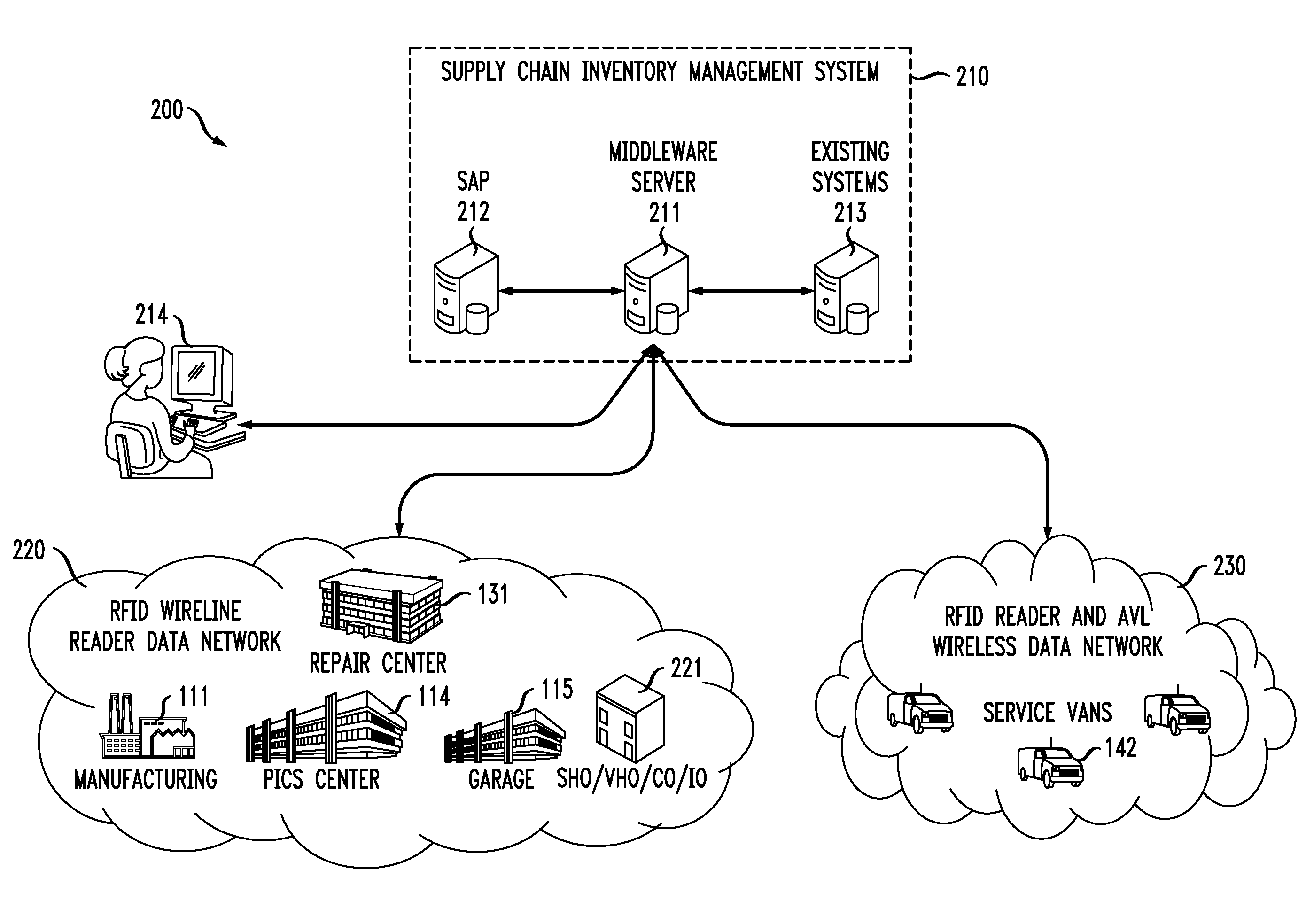
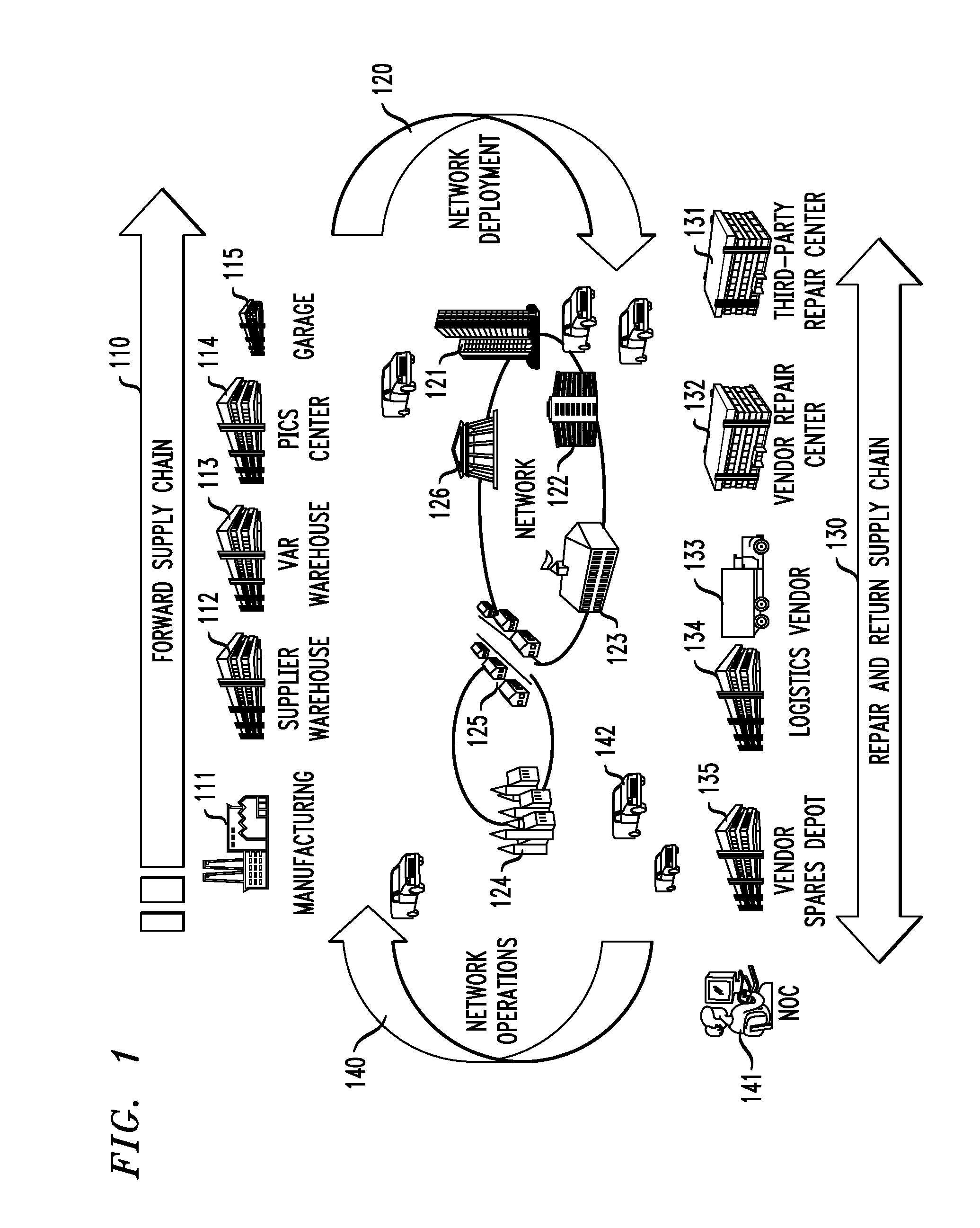
An inventory management and network operations system and method. In one embodiment, the system includes: (1) a radio-frequency identification (RFID) reader data network having RFID readers configured to read tag identifiers from RFID tags associated with equipment to be deployed to a target network and (2) a computer coupled to the RFID reader data network and the target network and configured to retrieve the tag identifiers from the RFID reader data network and network identifiers from equipment deployed in the target network, associate the tag identifiers and the network identifiers and display both the tag identifiers and the network identifiers of at least some of the equipment to a user.
Owner:ALCATEL LUCENT SAS
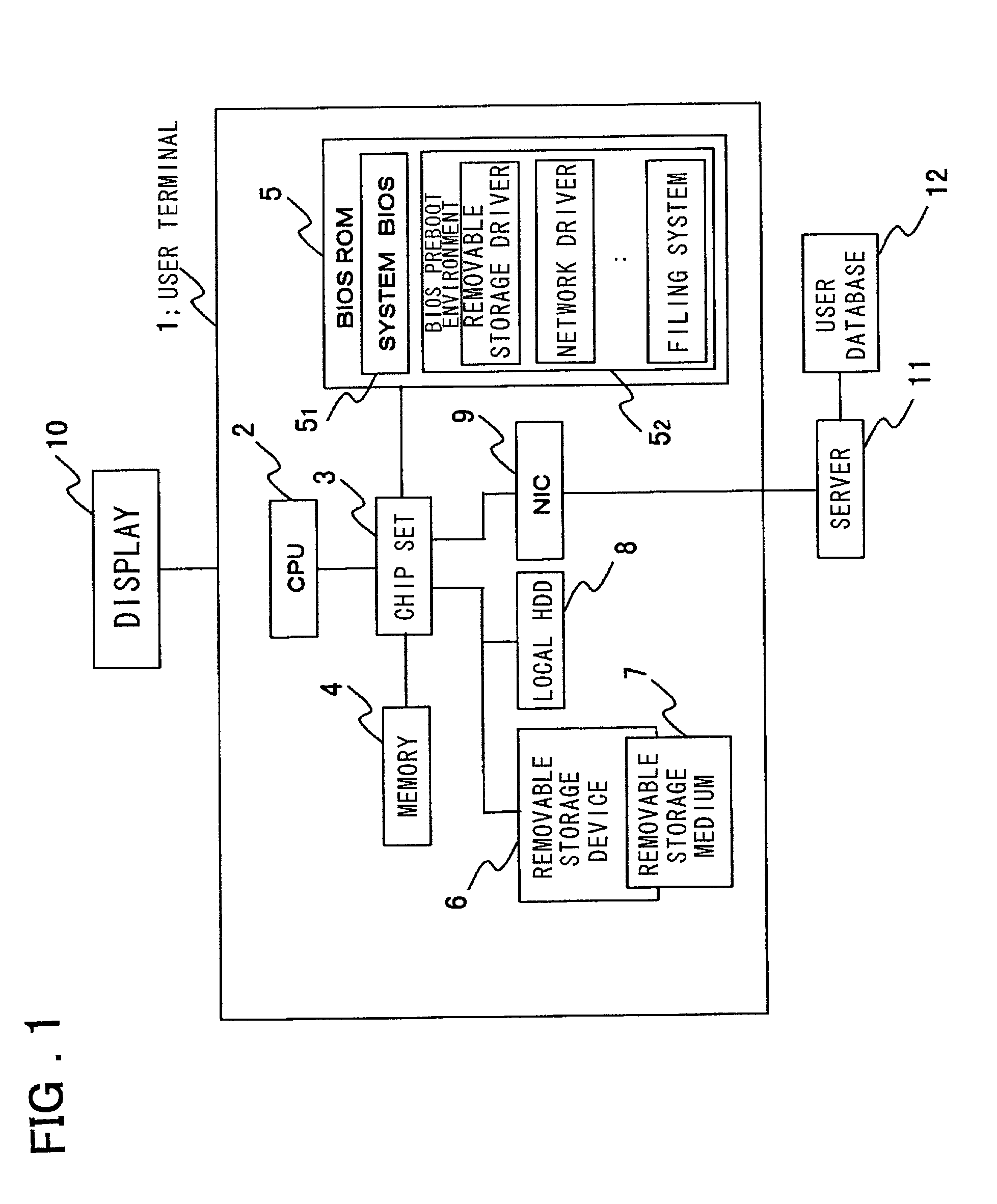
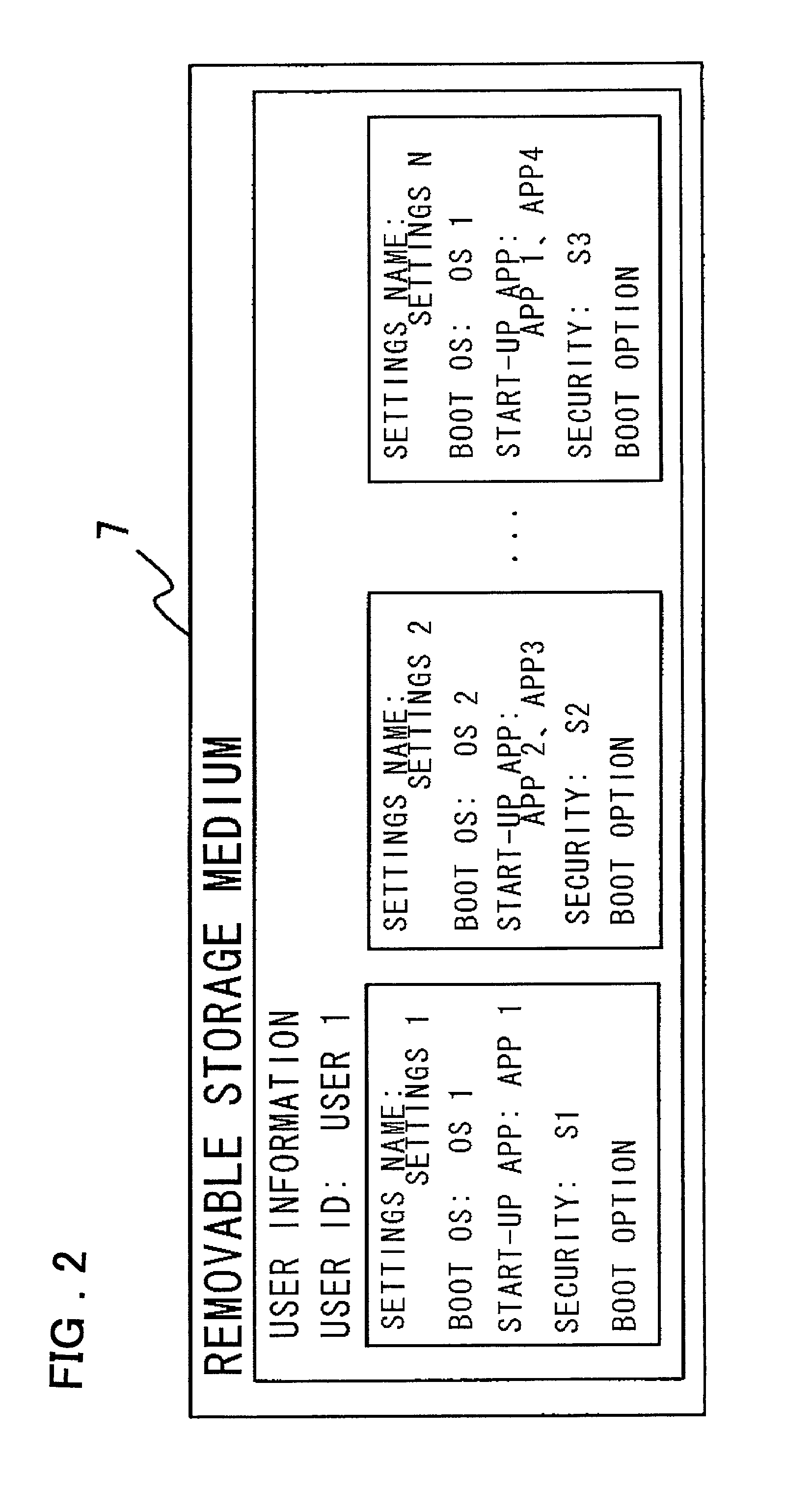
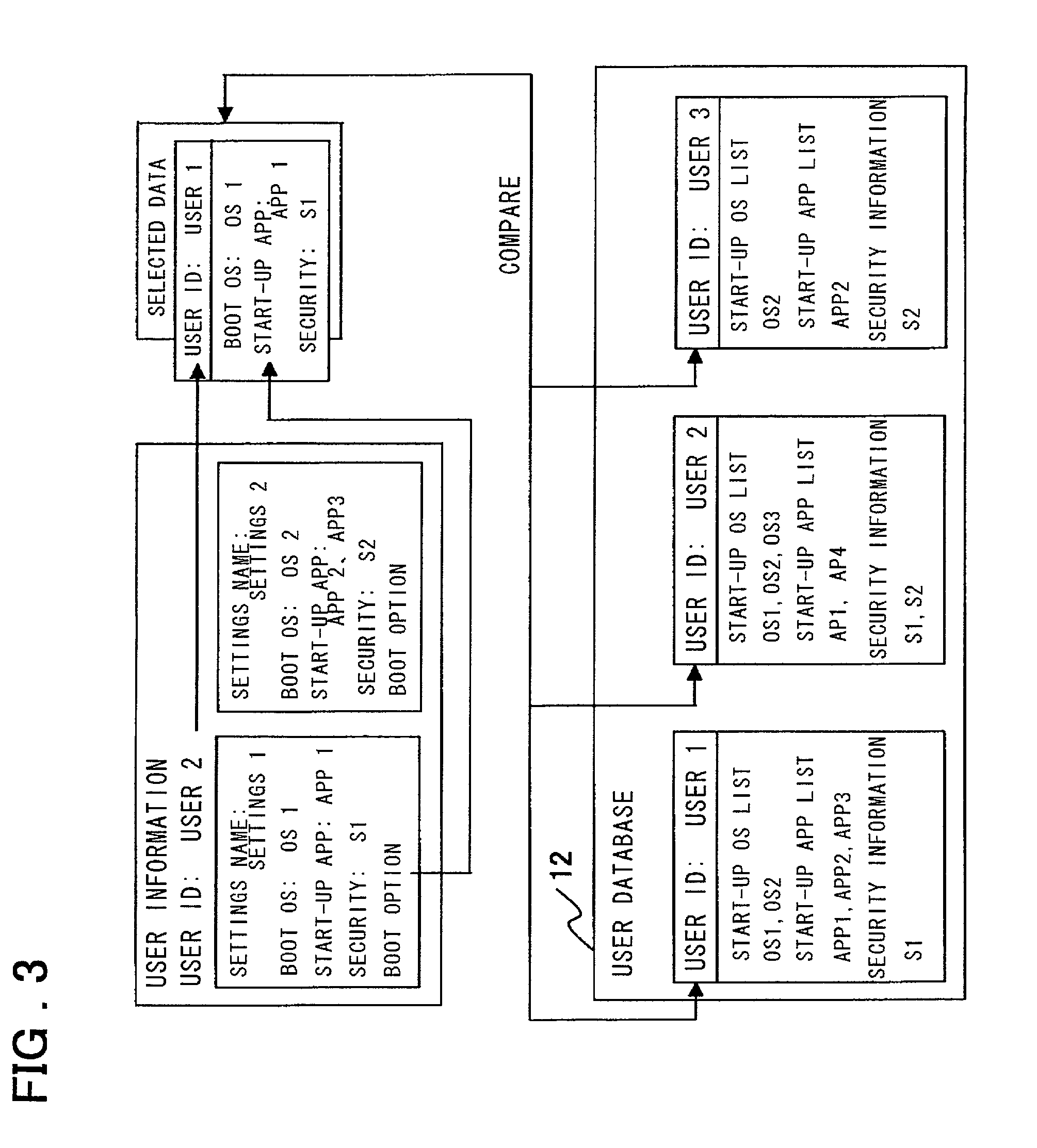
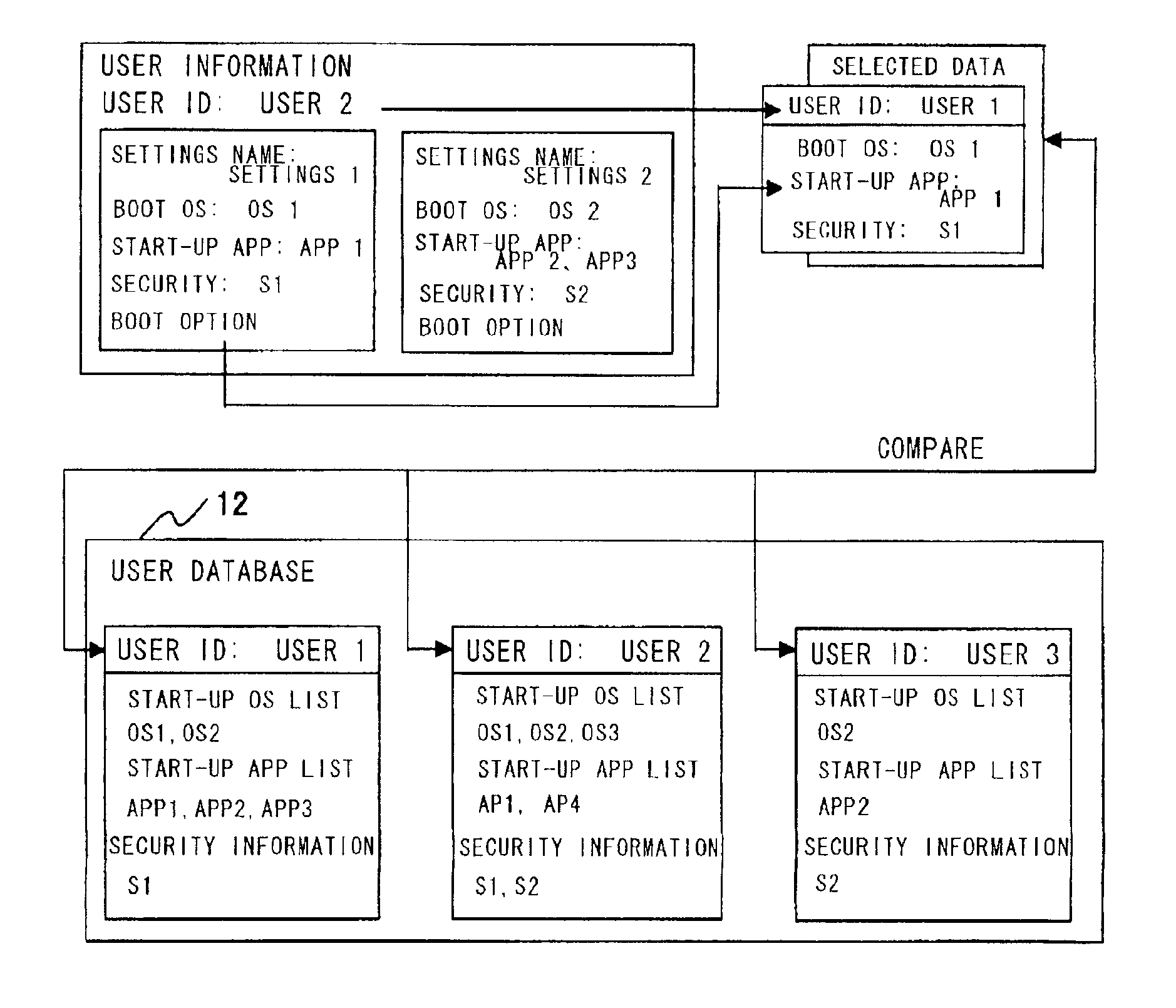
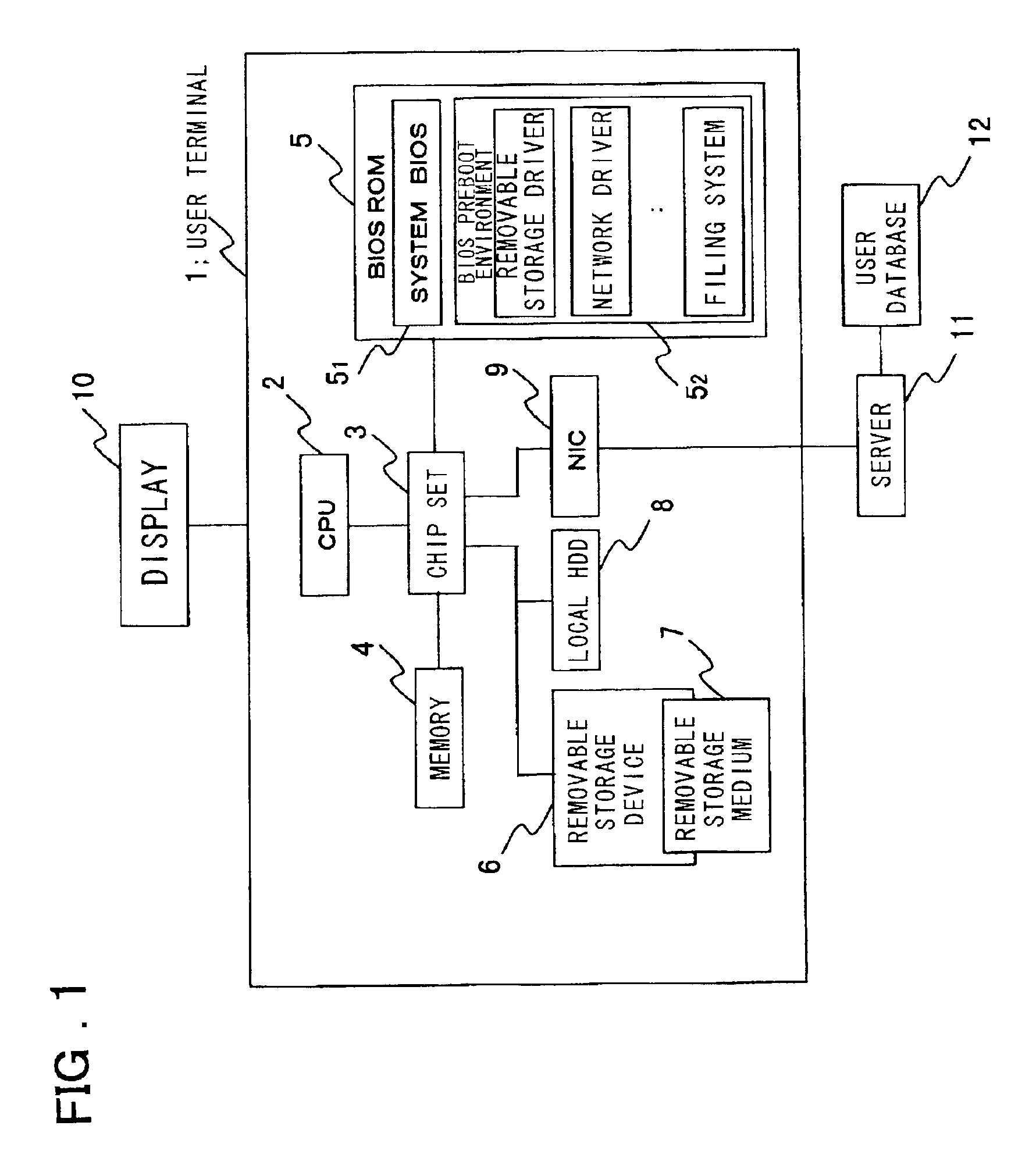
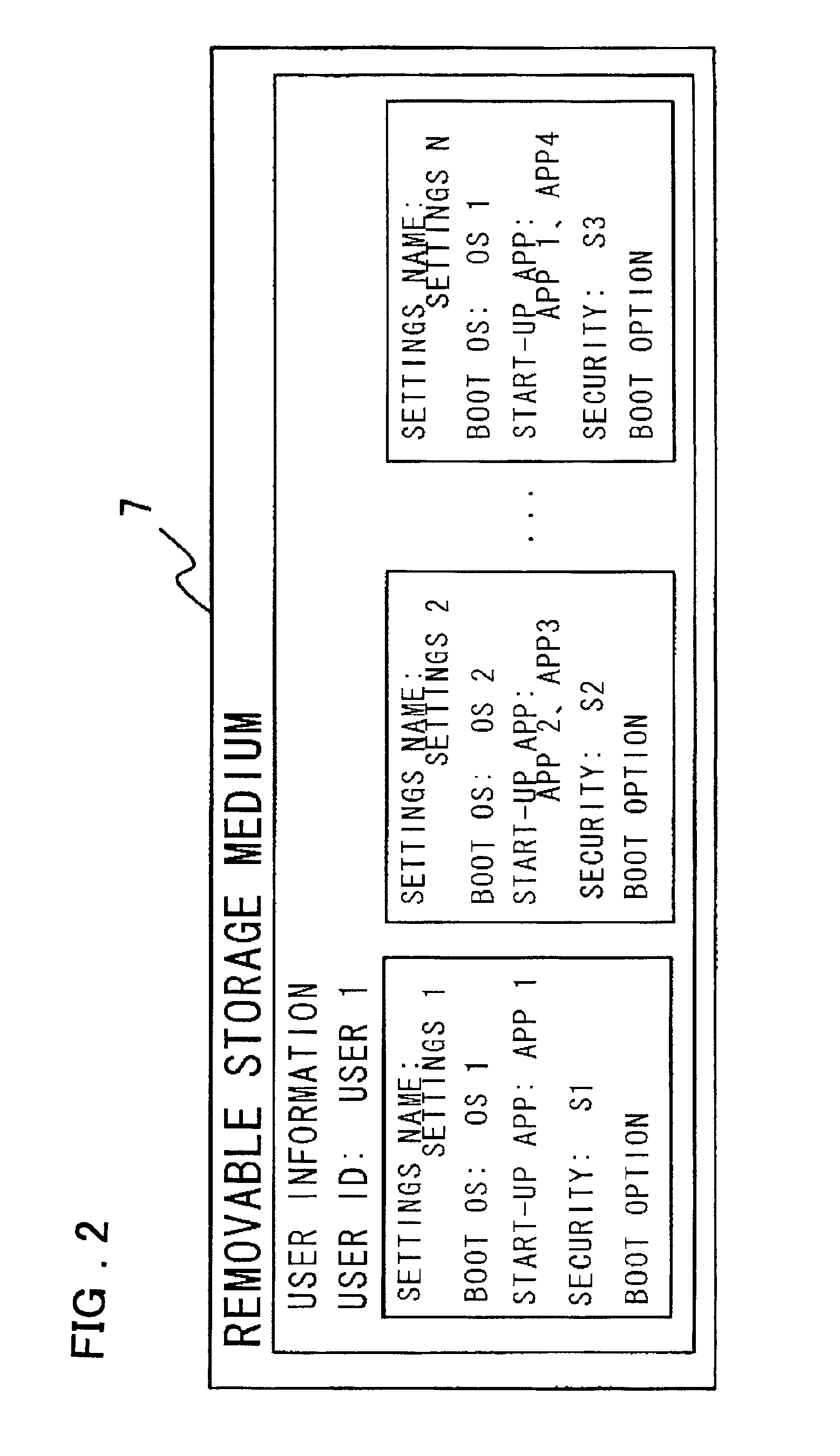
User-authentication-type network operating system booting method and system utilizing BIOS preboot environment
InactiveUS20010052069A1Easy to startImprove securityDigital computer detailsDigital data authenticationNetwork operating systemTerminal server
Disclosed is a system that make it possible for a user to readily boot an operating system from a user terminal with user-specific settings, thereby making it unnecessary for the server to register an image for each OS environment, as a result of which the required storage capacity of the server can be reduced. The user terminal, which is connected to the server by a network, is booted using an operating system stored in the server. In booting of the user terminal, user information that has been selected by the user from OS-booting user information stored on a removable storage medium of the user terminal is transmitted to the server under the control of a BIOS preboot environment stored in a storage device of the user terminal. On the basis of the user information, the server authenticates the user terminal, transmits the operating system to the user terminal and network-boots the operating system in a user-specific environment.
Owner:NEC CORP
Network operating system and method
InactiveUS20060101071A1Digital data processing detailsComputer security arrangementsProduction rateInformation processing
The invention provides a system and method for a network operating system. The system includes a complex data medium that enables the continuous reconciliation of the collaborative information process and product. The system generally increases productivity by enabling a network dynamic among knowledge workers. The system unifies e-mail and shared file management, synchronous and asynchronous collaboration, serial and parallel work flow, top-down and bottom-up collaboration, and information lifecycle management.
Owner:SKAI
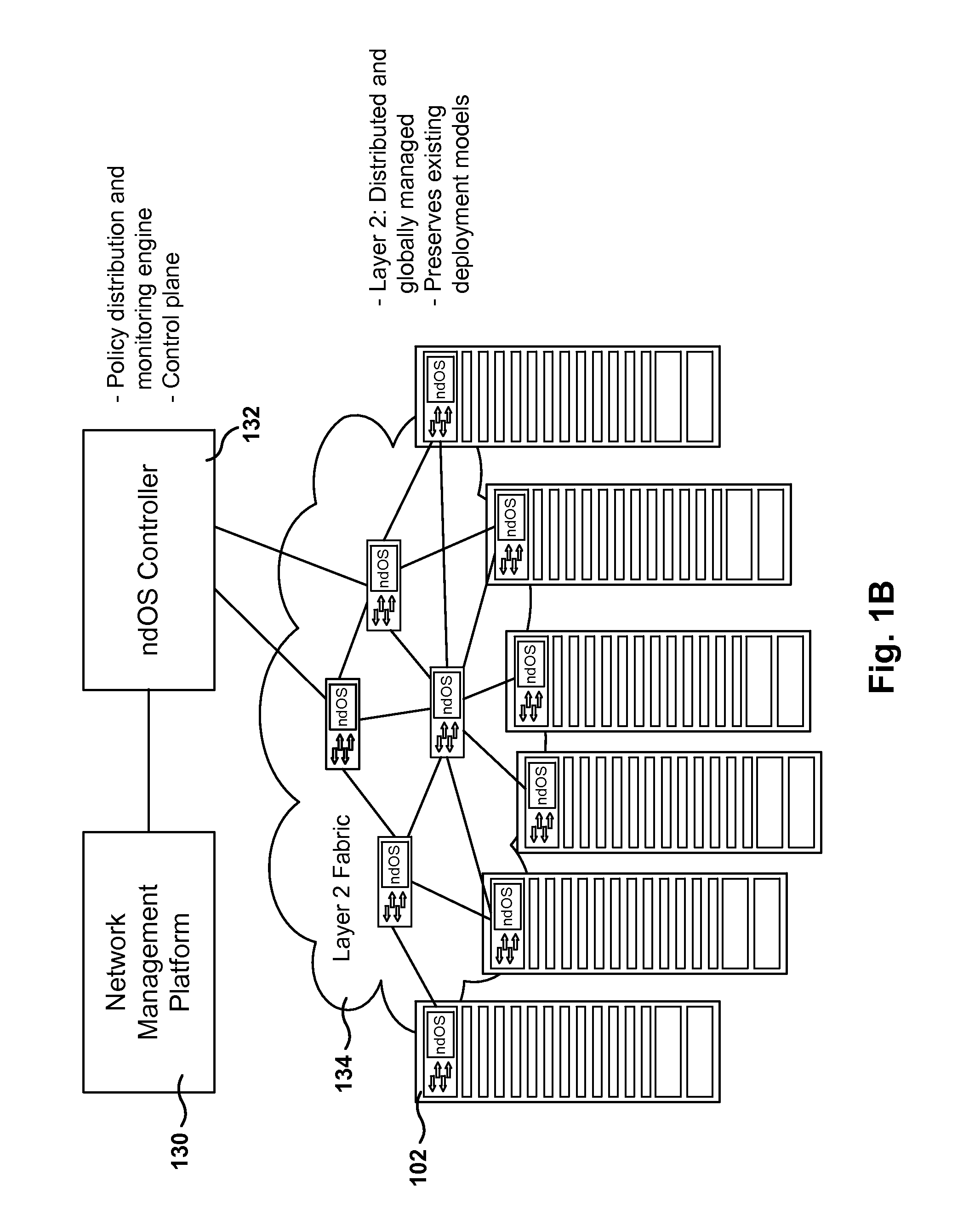
Methods, Systems, and Fabrics Implementing a Distributed Network Operating System
ActiveUS20130235870A1Data switching by path configurationService-level agreementNetwork operating system
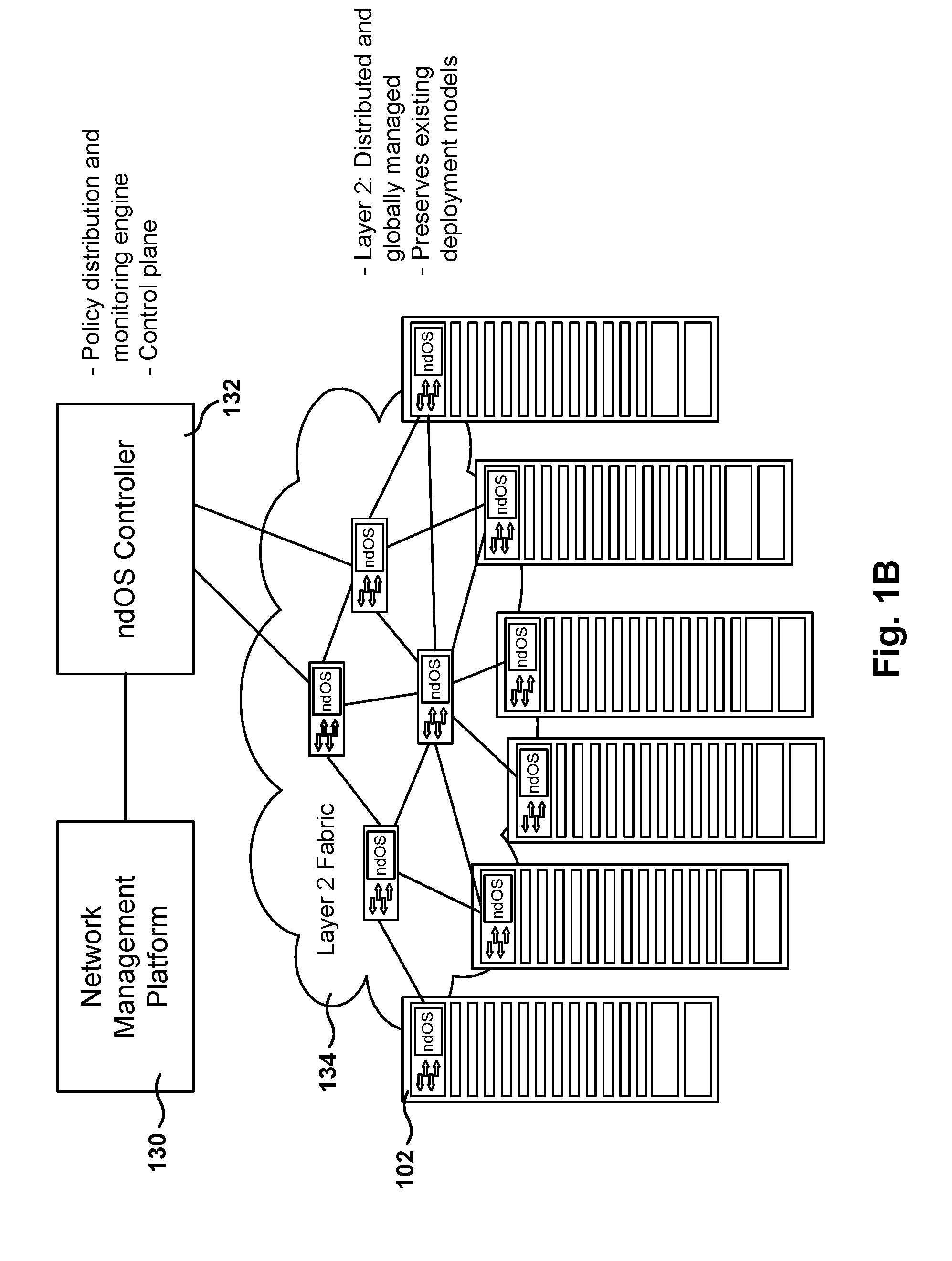
Methods, systems, and computer programs are presented for managing a switching layer fabric. A network device operating system (ndOS) program includes program instructions for exchanging switching policy regarding a switching of network packets in a plurality of ndOS switching devices having respective ndOS programs executing therein. The first ndOS program is executed in a first ndOS switching device, and the switching policy is exchanged with other ndOS programs via multicast messages. Further, the ndOS program includes program instructions for exchanging resource control messages with the other ndOS switching devices to implement service level agreements in the switching layer fabric, where the ndOS switching devices cooperate to enforce the service level agreements. Further yet, the ndOS program includes program instructions for receiving changes to the switching policy, and program instructions for propagating the received changes to the switching policy via message exchange between the ndOS programs. The ndOS switching devices are managed as a single logical switch that spans the plurality of ndOS switching devices.
Owner:PLURIBUS NETWORKS
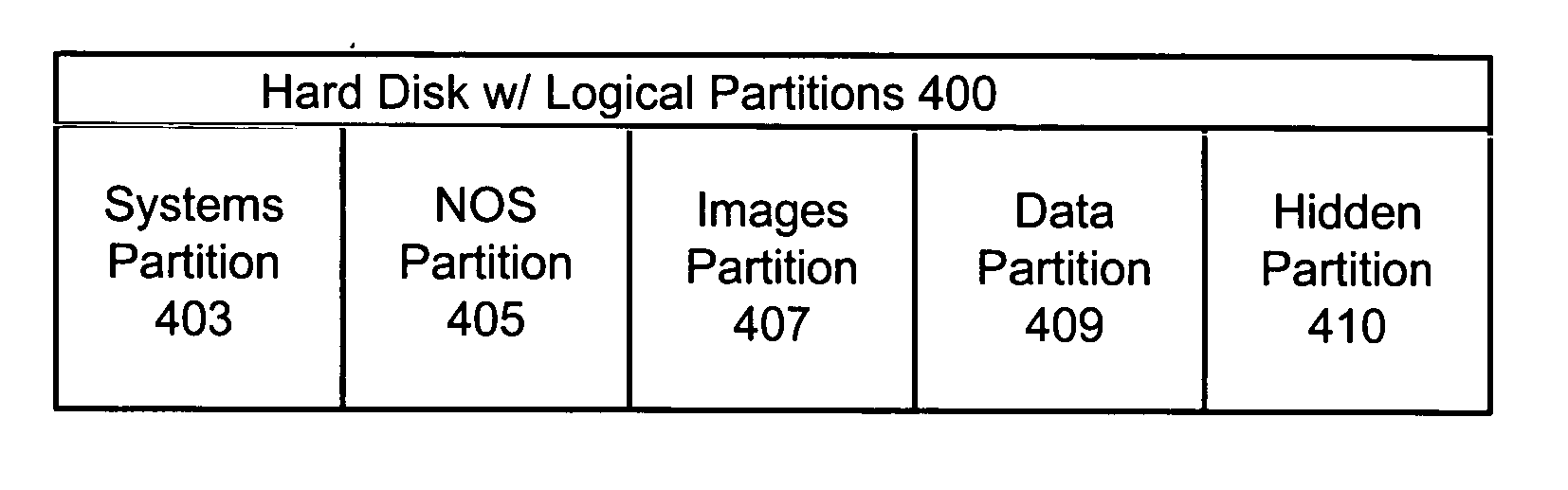
Method and system for protecting data associated with a replaced image file during a re-provisioning event
InactiveUS20050182796A1Input/output to record carriersSpecial data processing applicationsOperational systemNetwork operating system
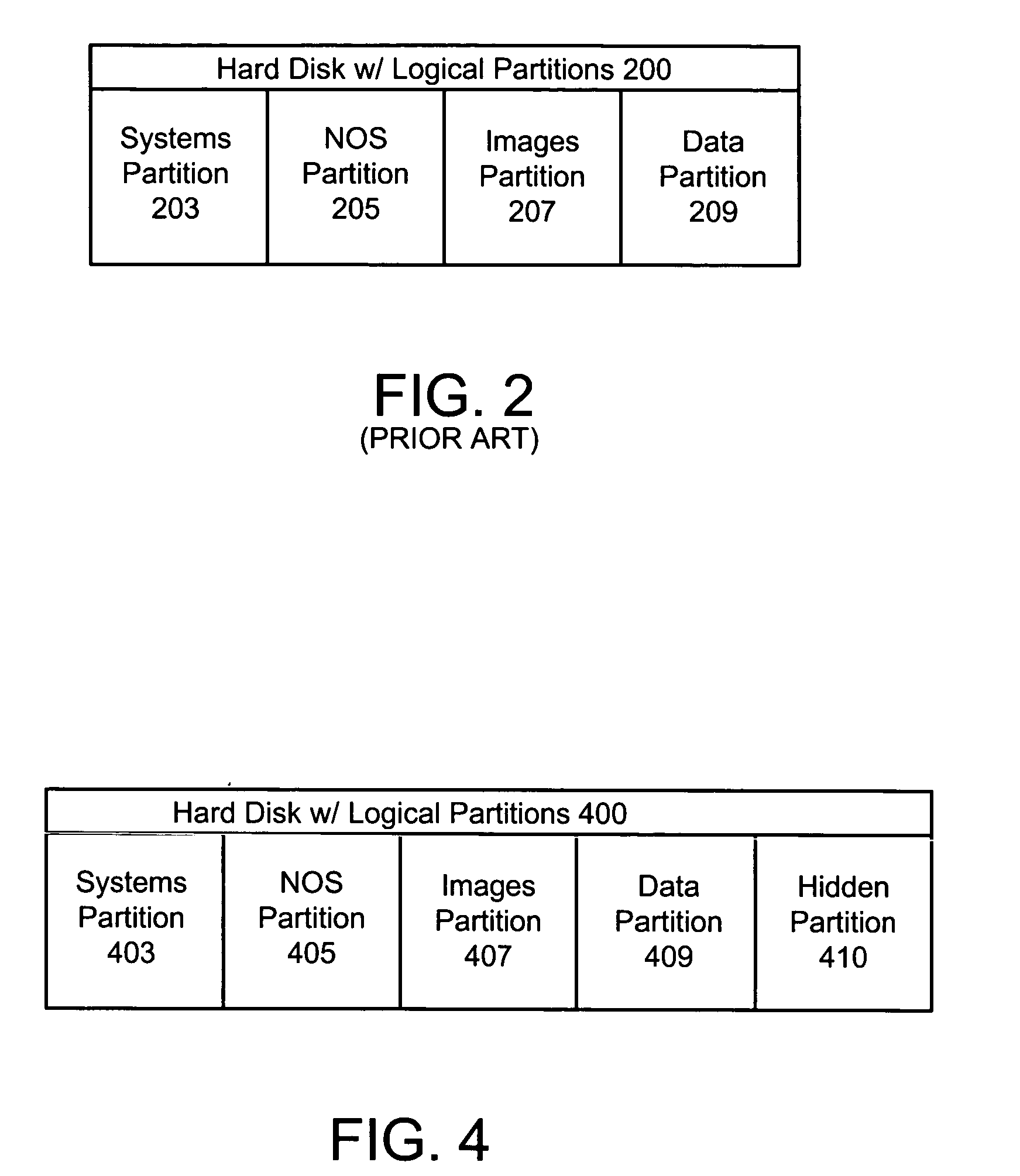
The present invention discloses a method and hard disk configuration for protecting data associated with a first image file in an appliance server after the first image file has been replaced with a second image file. In a first aspect, the method of the invention includes partitioning a hard disk of the appliance server into a plurality of partitions, wherein at least one of the plurality of partitions is a hidden partition and copying the data associated with the first image file to the hidden partition, wherein the data in the hidden partition is invisible to a network operating system during normal server operation. In another aspect, the hard disk of the invention includes a first partition for storing an image file, wherein the first partition stores one image file at one time, a second partition for storing data associated with the image file, wherein the second partition is visible to a network operating system in the first partition, a hidden partition, wherein the hidden partition is invisible to the network operating system in the first partition, means for replacing a first image file in the first partition with a second image file, and means for copying the data associated with the first image file from the second partition to the hidden partition when the first image file in the first partition is replaced with the second image file.
Owner:IBM CORP
Method and apparatus providing interoperation of execution images of different versions
ActiveUS7383541B1Error detection/correctionSpecific program execution arrangementsNetwork operating systemOperational system
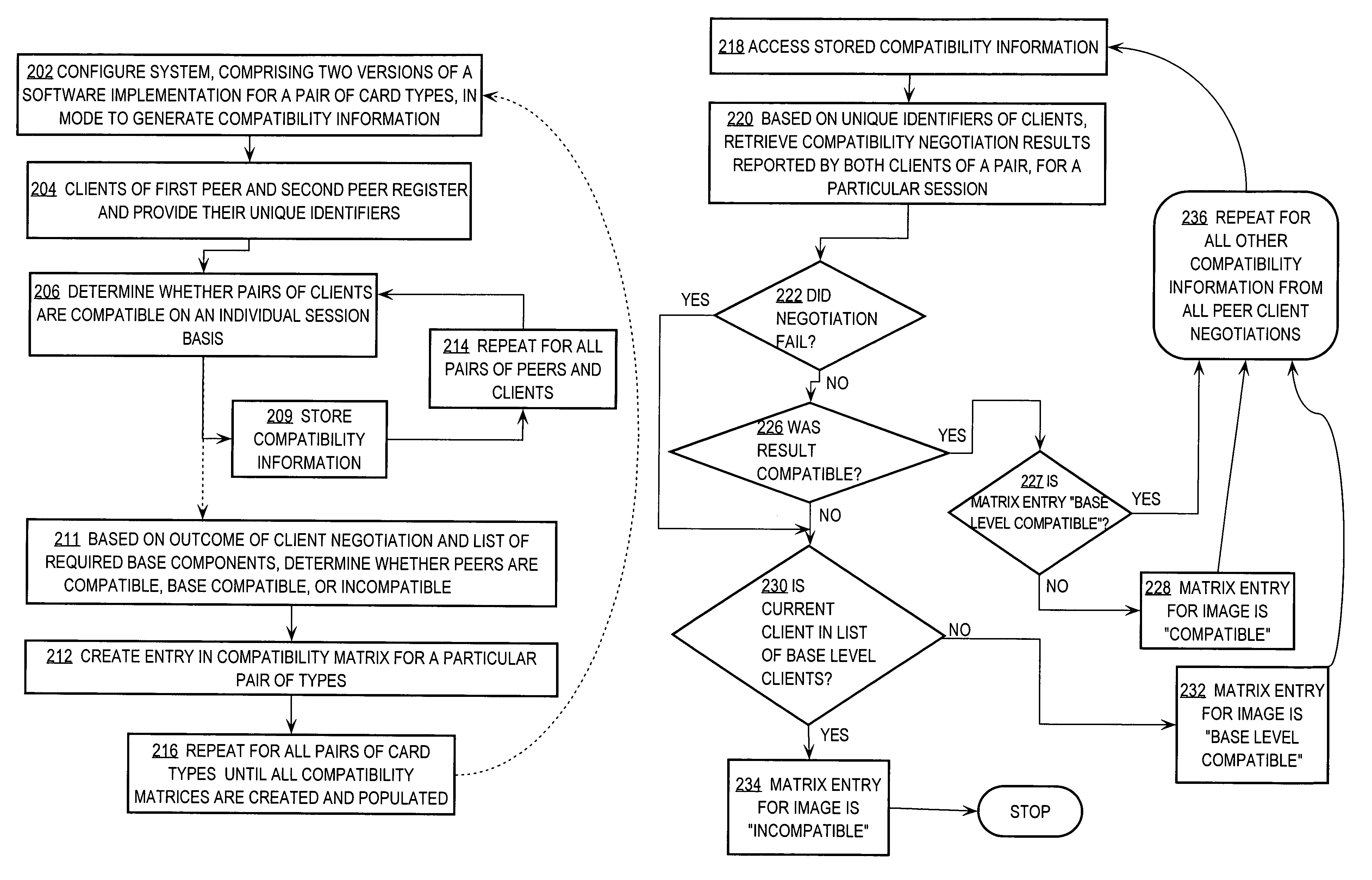
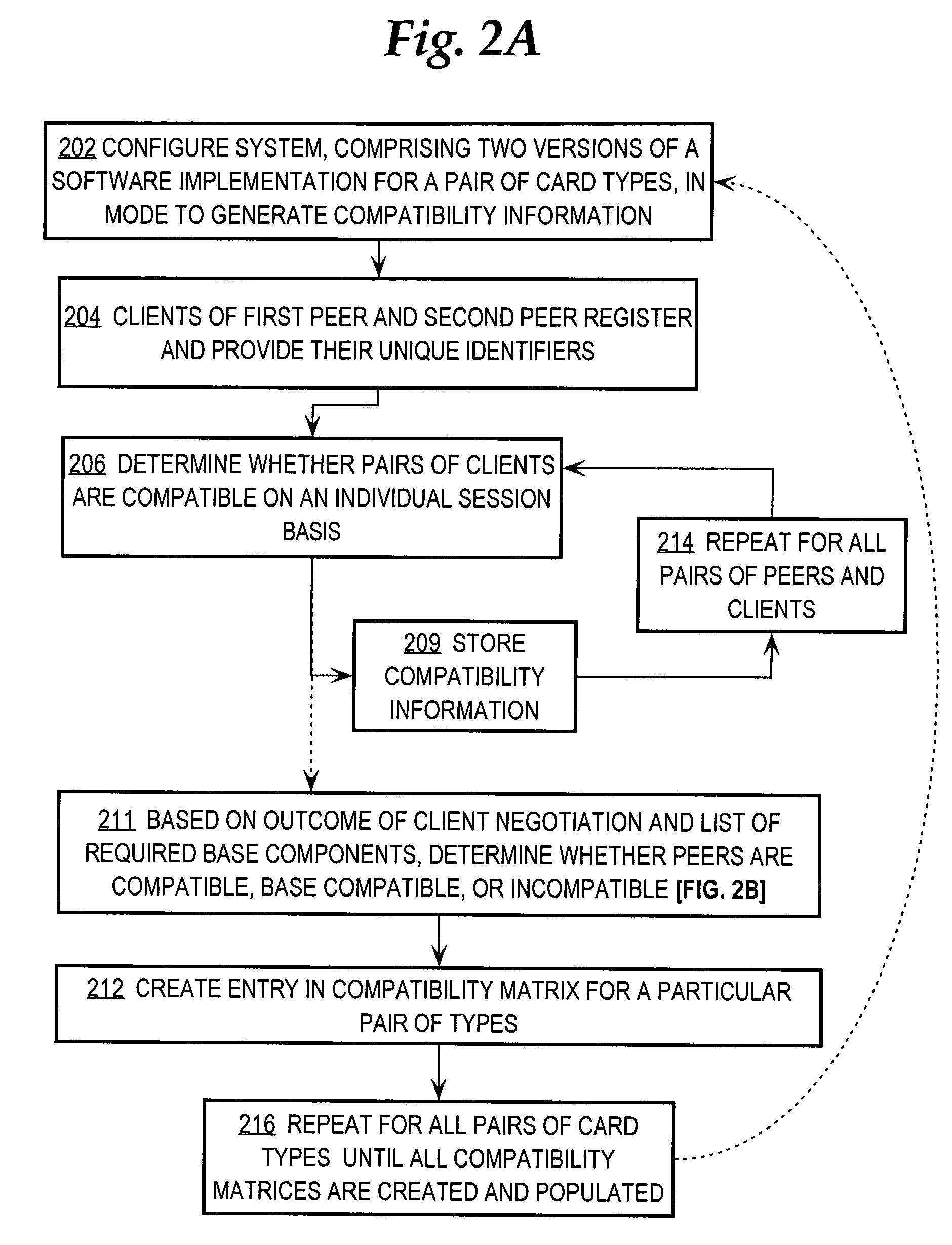
A method is disclosed for providing interoperation of a first execution image of a first version and a second execution image of a second version. A compatibility matrix specifies whether the versions are compatible, base-level compatible, or incompatible. In one embodiment, the compatibility matrix may comprise a sparse table that stores a compatibility indicator for all permutations of a plurality of versions of a network operating system. As part of initialization of a system that includes the first execution image and second execution image, version information for the execution images is determined. An entry in the compatibility matrix corresponding to the versions is identified. The execution images are operated in a fully synchronized state when the identified entry of the compatibility matrix specifies that the versions are either compatible or base-level compatible. Individual components of the execution images interoperate according to the results of individual session negotiations. If the versions are incompatible, an alternative redundancy operation mode may be used. Embodiments provide for negotiation of compatible message versions and capabilities among peer components or clients of the execution images as source information to generate the compatibility matrix.
Owner:CISCO TECH INC
Network operating system with topology autodiscovery
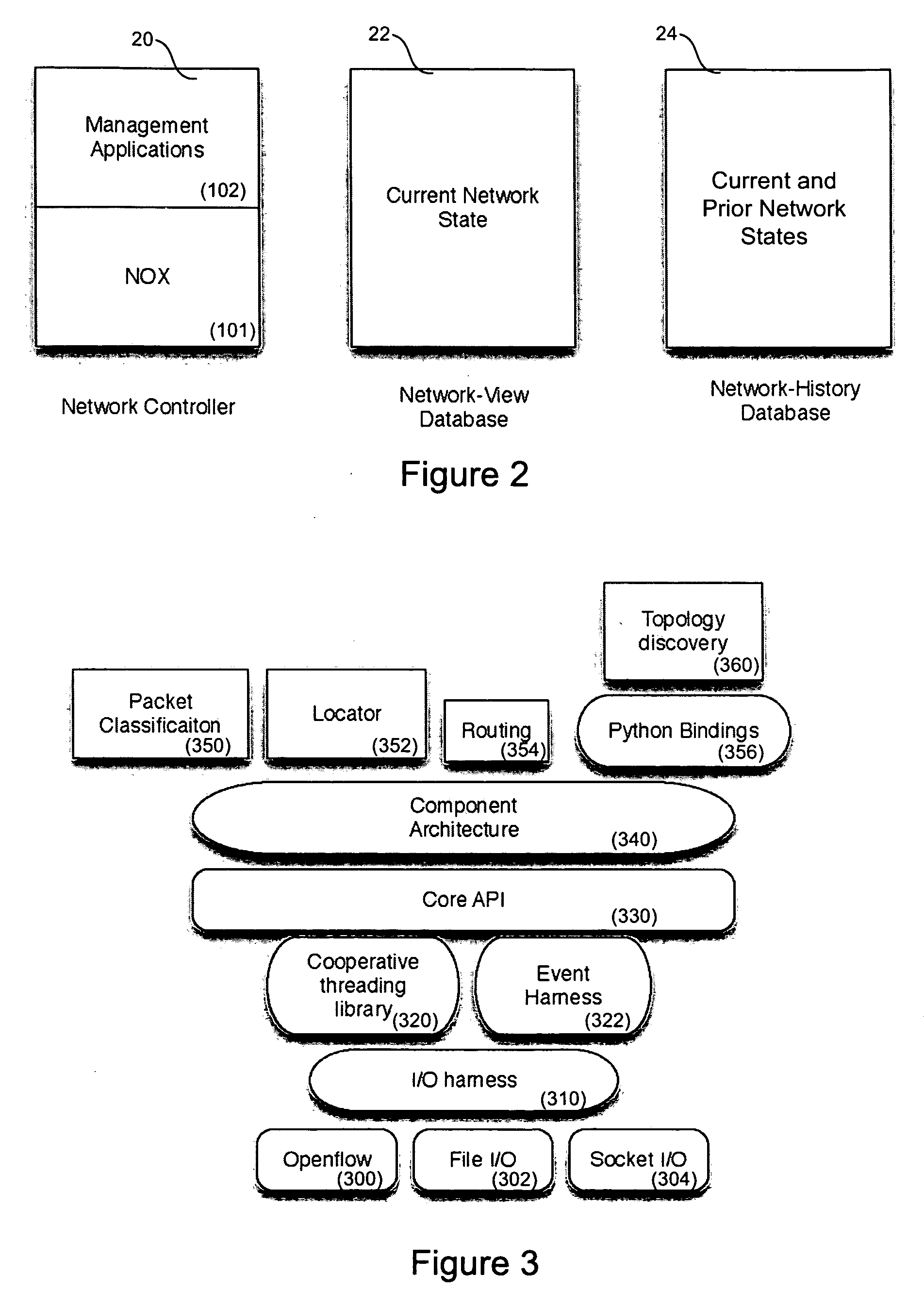
ActiveUS7747165B2Reduce the time required for installationReduce configuration timeMultiplex system selection arrangementsCoupling light guidesNetwork operating systemOperational system
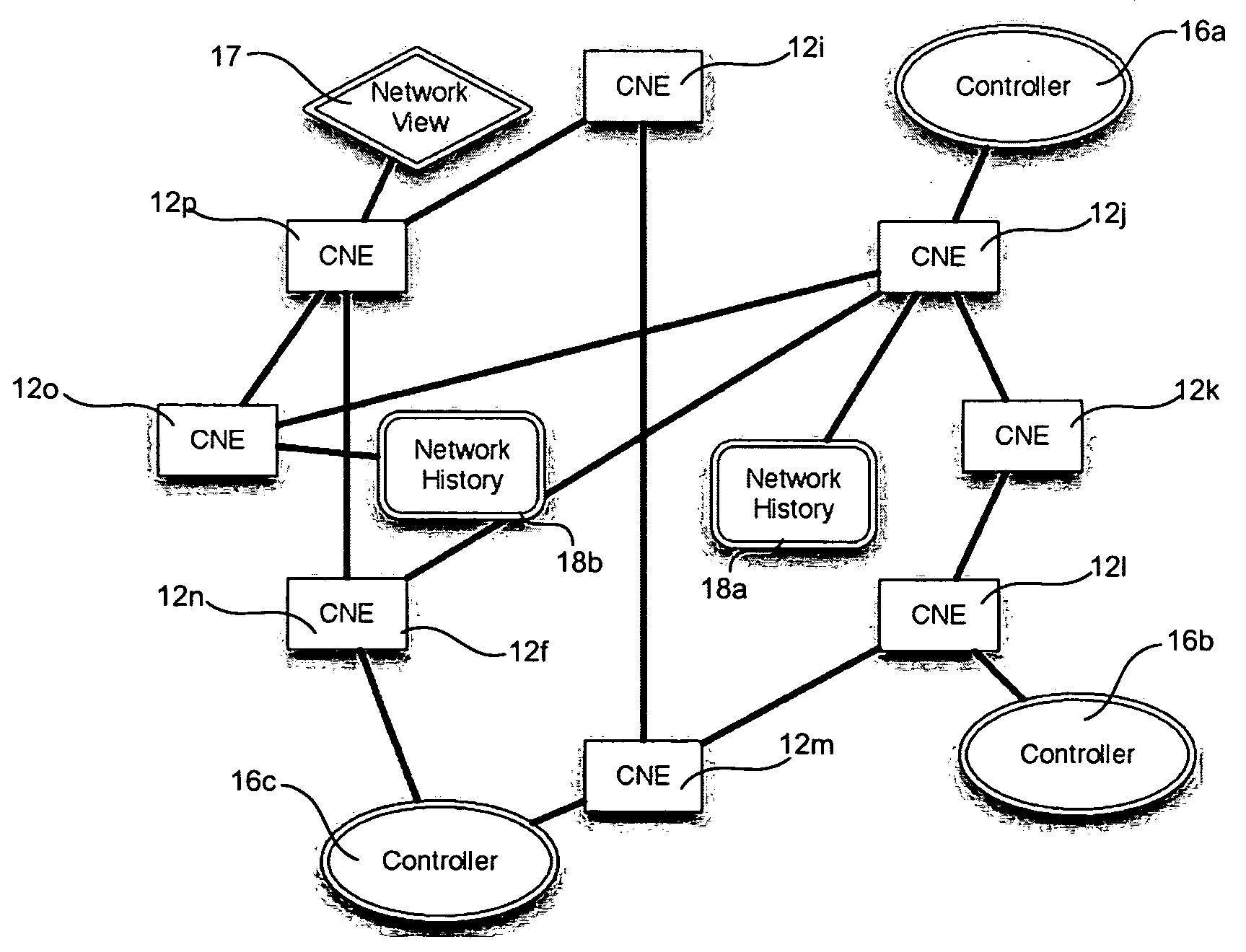
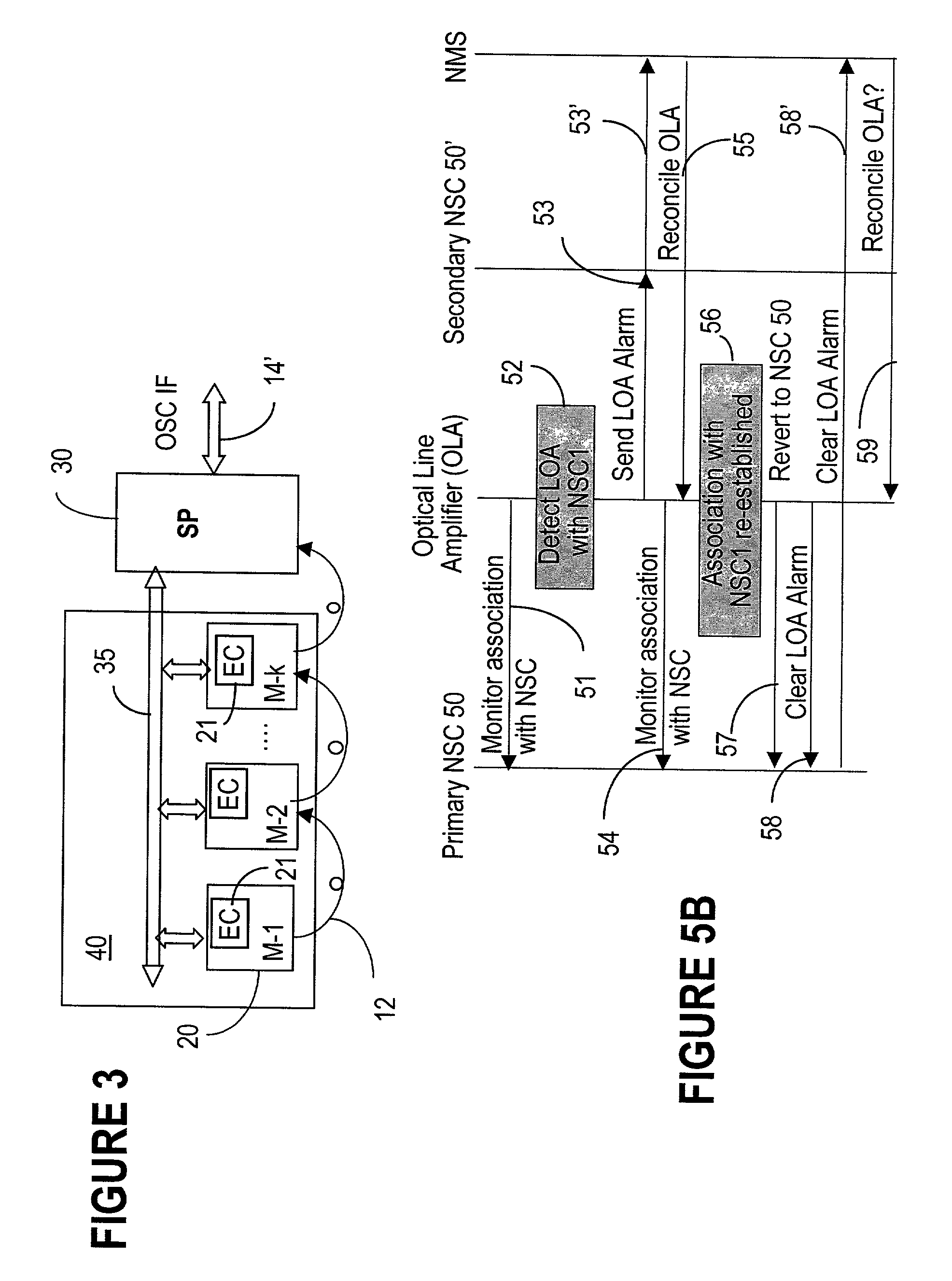
The network operating system includes an embedded platform for controlling operation of an agile optical network at the physical layer level. At the module embedded level, each module (card-pack) is provided with an embedded controller EC that monitors and control operation of the optical modules. At the next level, each shelf is provided with a shelf processor SP that monitors and control operation of the ECs over a backplane network. All optical modules are connected over an optical trace channel to send / receive trace messages that can then be used to determine network connectivity. At the next, link management level, a network services controller NSC controls the SPs in a negotiated span of control, over a link network. The control is address-based; each NSC receives ranges of addresses for the entities in its control, and distributes these addresses to the SPs, which in turn distribute addresses to the ECs in their control. One of the SPs operates as a router on the link network to relay signaling and control to all entities based on their address. Each NSC constructs, from queried information, a network topology fragment for the embedded elements under its control. A distributed topology system (DTS) shares this topology information with neighboring NSC's to build a complete network view, which can be used by all interested network applications.
Owner:WSOU INVESTMENTS LLC
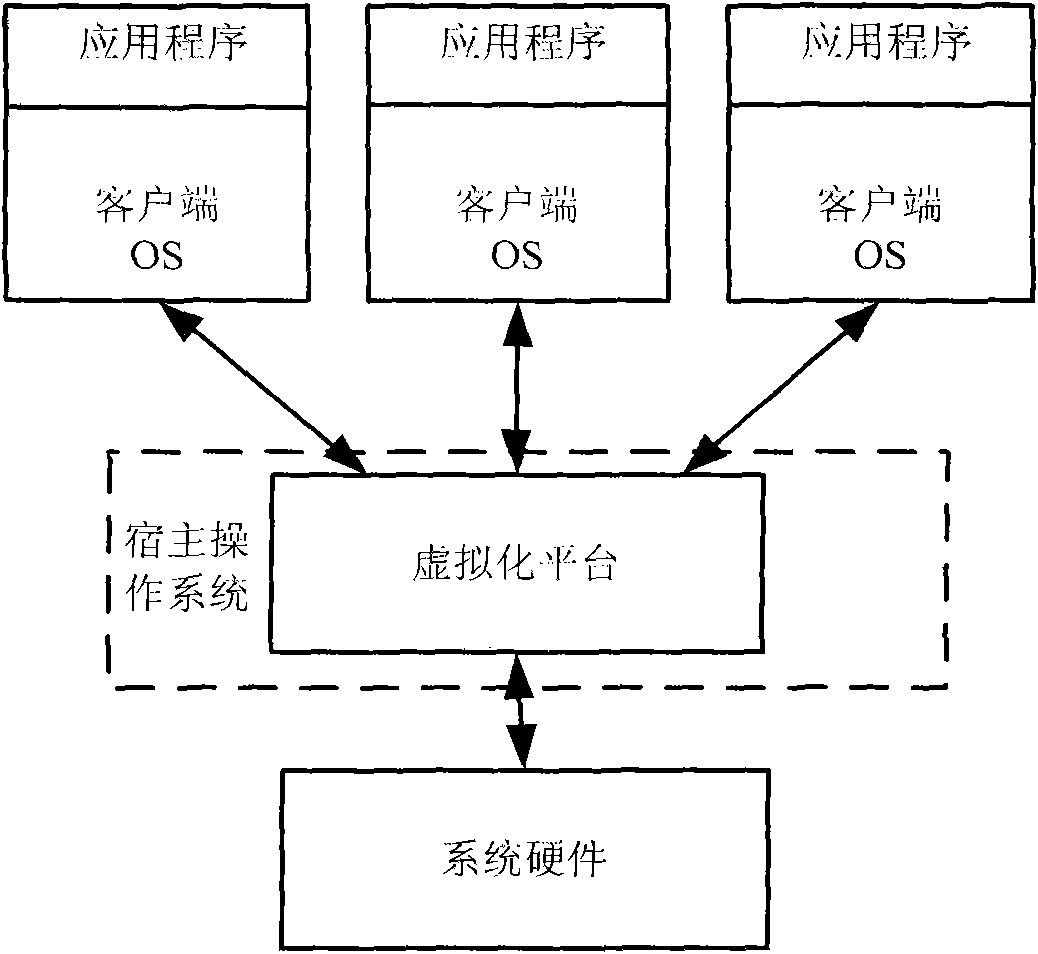
Virtualization Apparatus and Method
InactiveUS20110154328A1Input/output for user-computer interactionProgram initiation/switchingVirtualizationGraphics
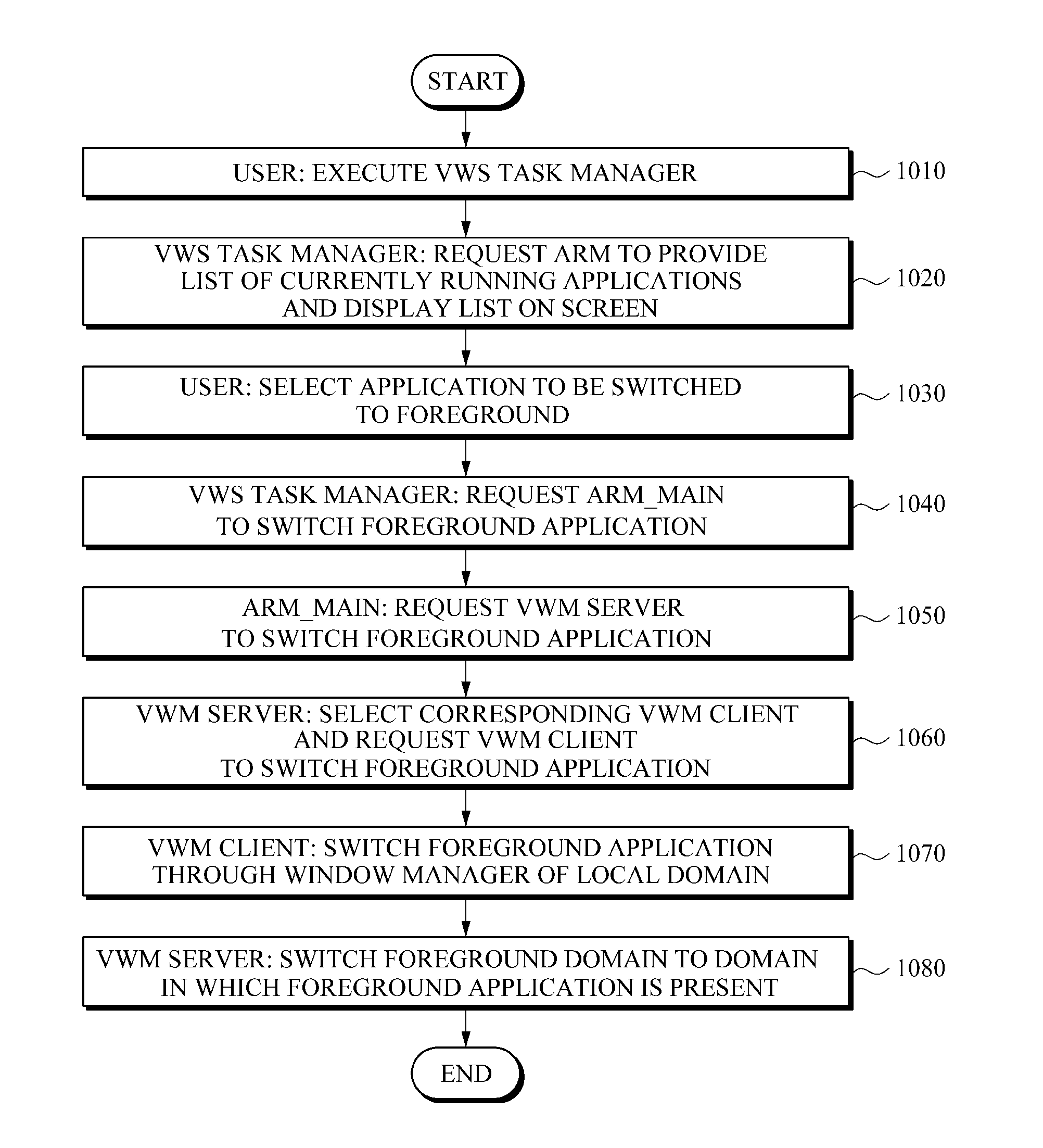
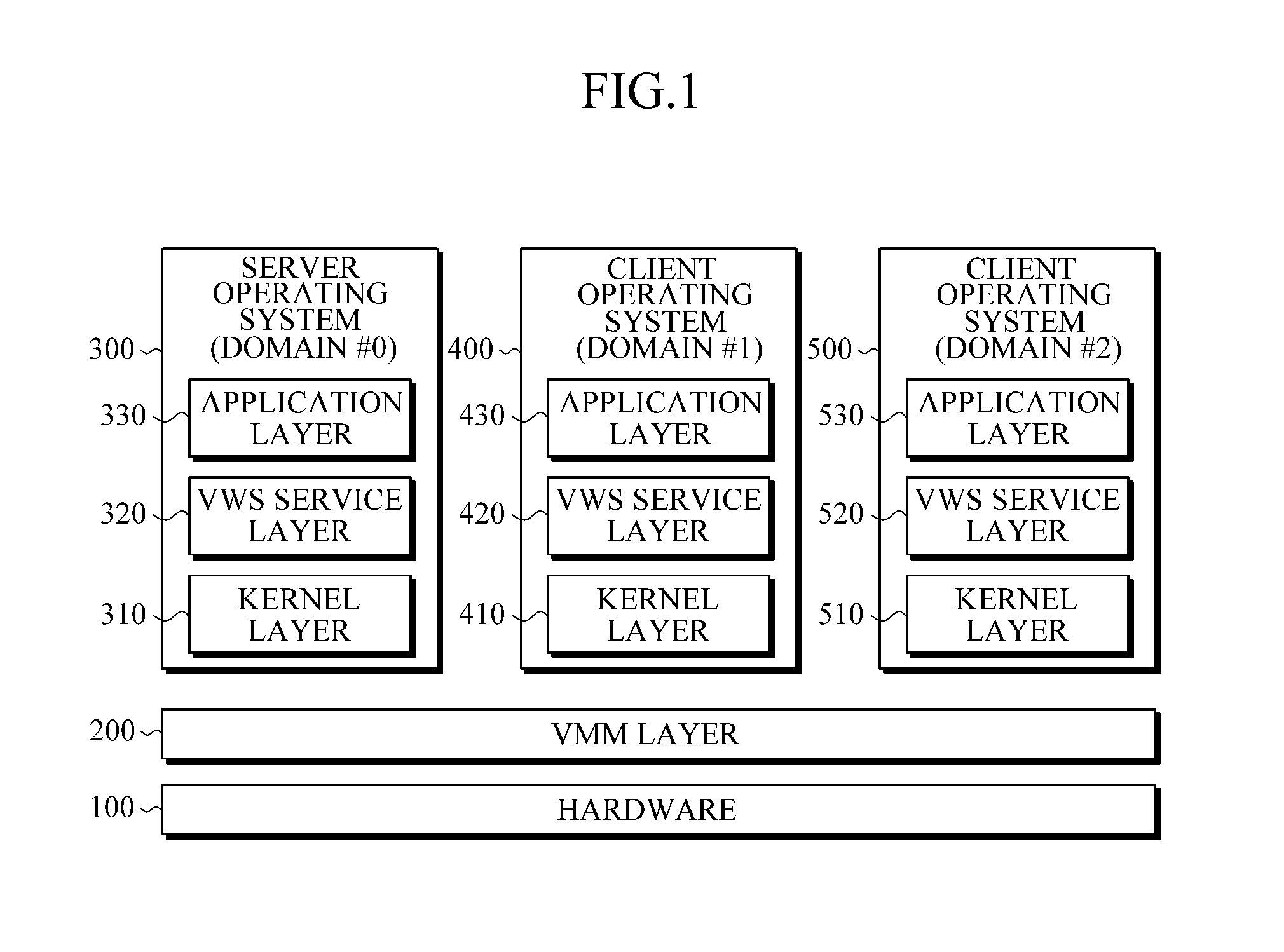
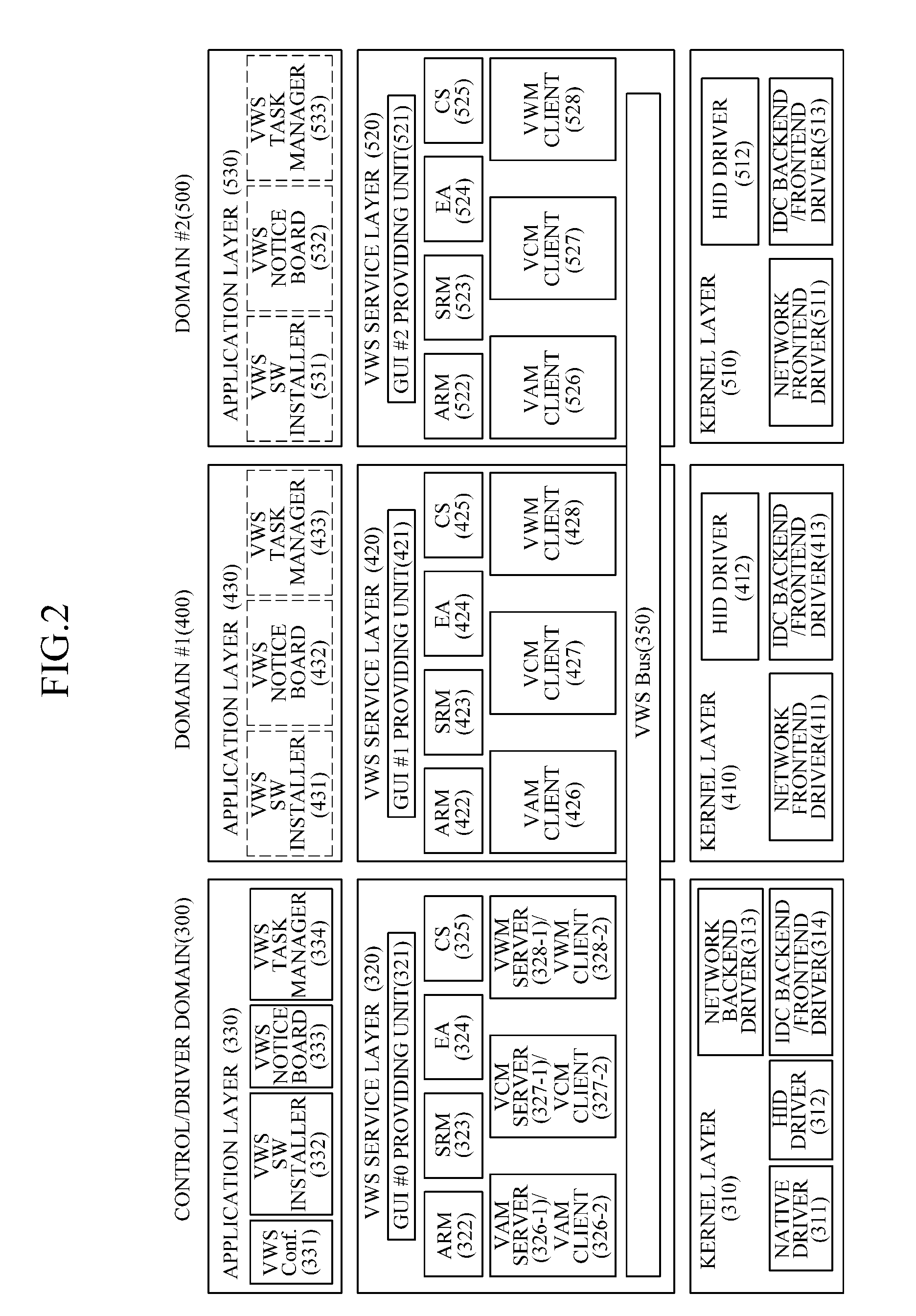
An apparatus and method for providing an integrated user interface for a variety of operating systems are provided. When a user request execution of an application included in a second operating system an application of a first operating system is in the foreground of a display, the apparatus switches the application included in the second operating system to the foreground of the display without the need for a separate window. One of a server operating system and client operating systems may be set as a main domain that provides an integrated graphic user interface with respect to applications executed on a plurality of operating systems. The operating systems not set to the main domain may be set as sub-domains each of which provides application information to the main domain in response to a request from the main domain. In response to an application execution request, the server operating system may switch an operating system in which the corresponding application is present to the foreground of the display.
Owner:SAMSUNG ELECTRONICS CO LTD
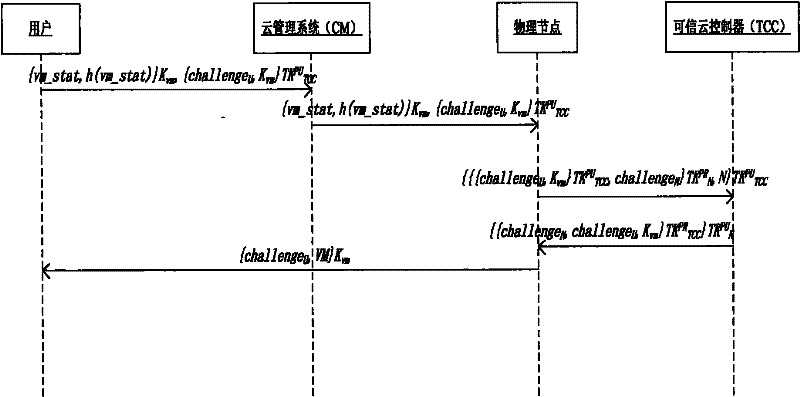
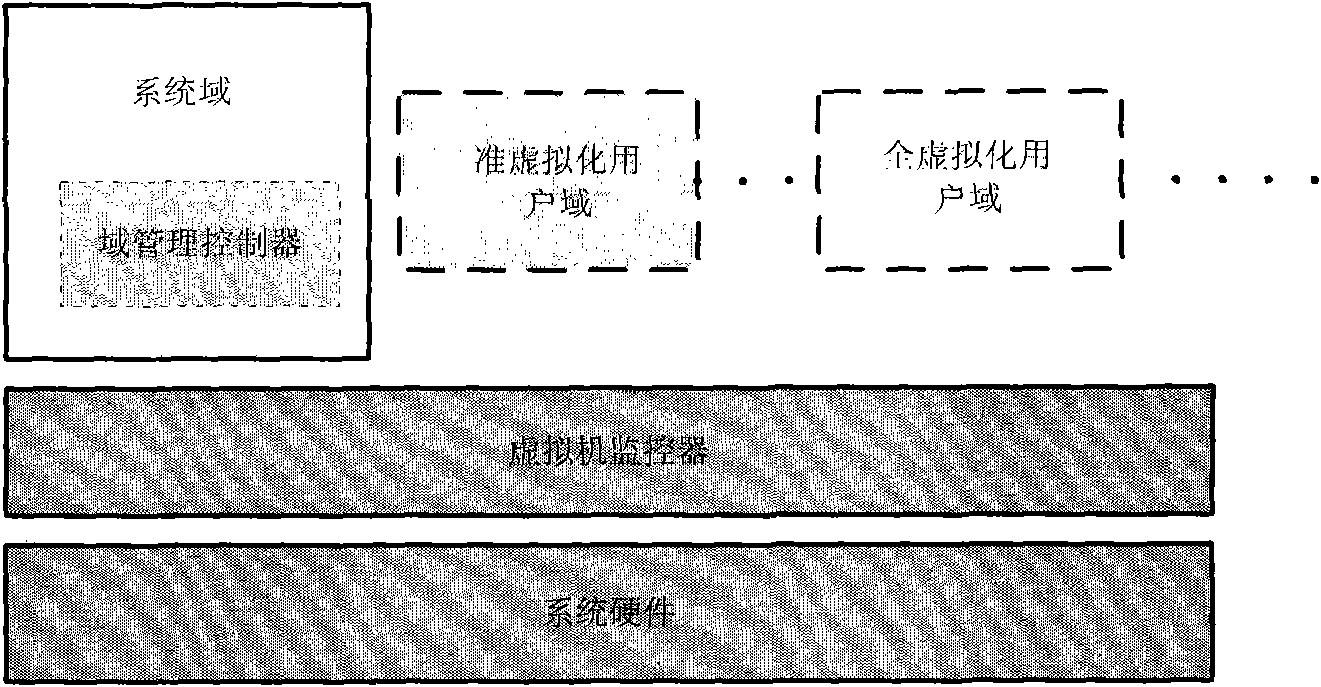
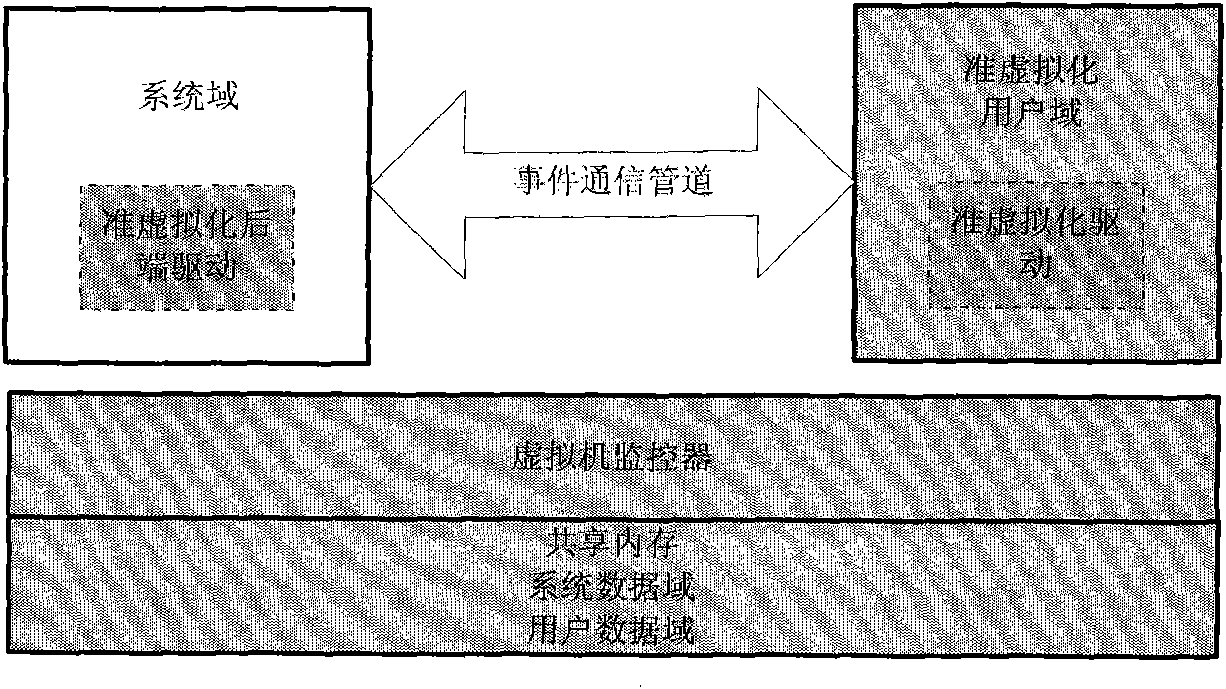
Network-operating-system-oriented trusted virtual operating platform
ActiveCN102202046APublic key for secure communicationUser identity/authority verificationThird partyNetwork operating system
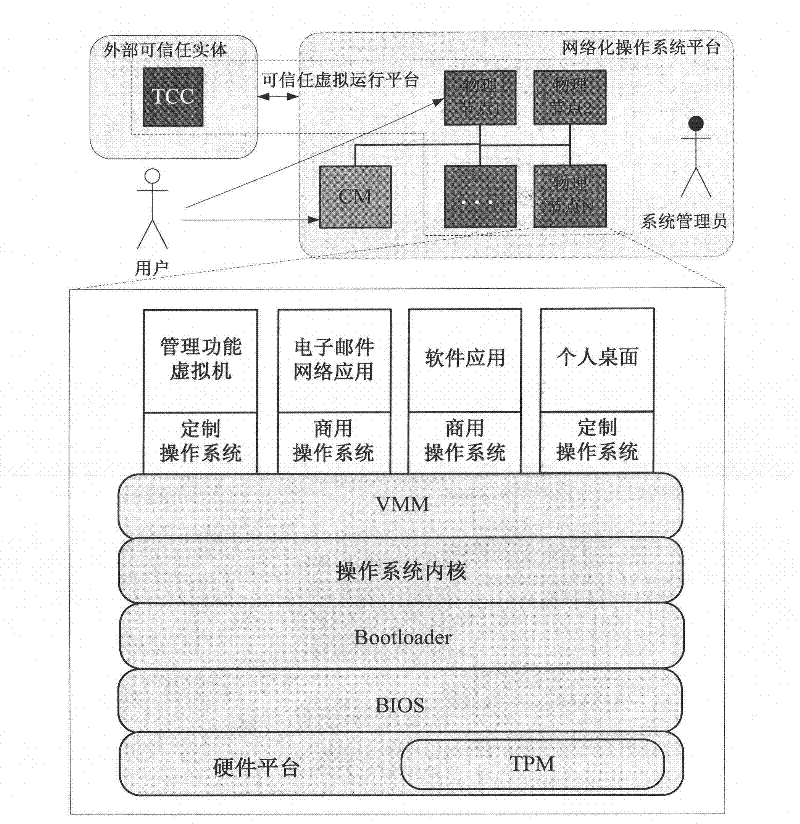
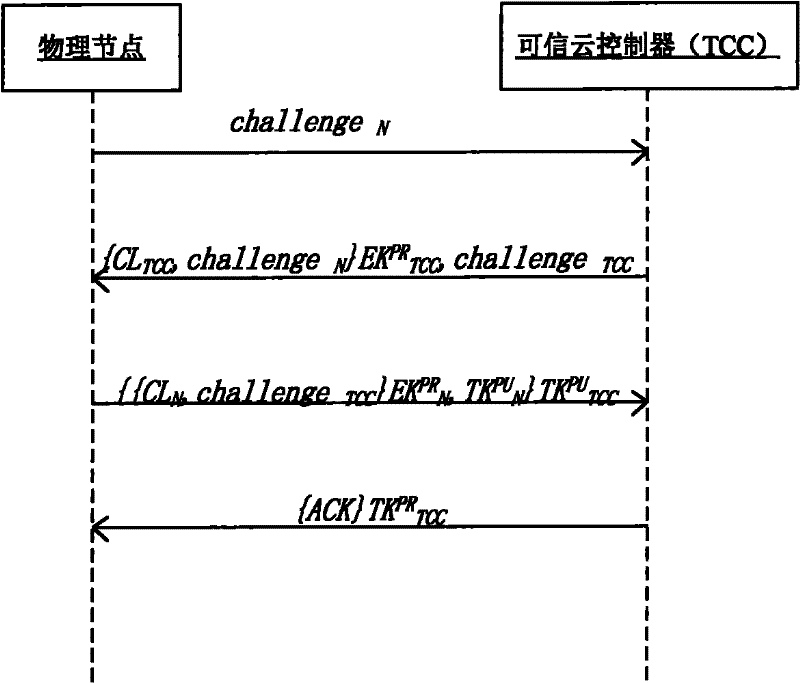
The invention discloses a network-operating-system-oriented trusted virtual operating platform technology, which belongs to the technical field of computer infrastructure software. In the technology, trusted registration and starting mechanisms are designed for each node in a network operating system by setting a third-party trusted authentication mechanism which is a trusted cloud controller for main threats to the main service range and main operations of the network operating system in a typical novel network application mode; and after passing through an authentication protocol of the trusted cloud controller, the nodes can become trusted nodes to provide a trusted host operating environment for virtual machines, ensure that damages to the integrity and accuracy of the virtual machines can be detected in a starting process and interrupt the starting and registration processes of damaged machines. Moreover, corresponding trusted ensuring mechanisms are designed for the main operations of the virtual machines, namely starting and migration processes.
Owner:SHENZHEN YUN AN BAO TECH CO LTD
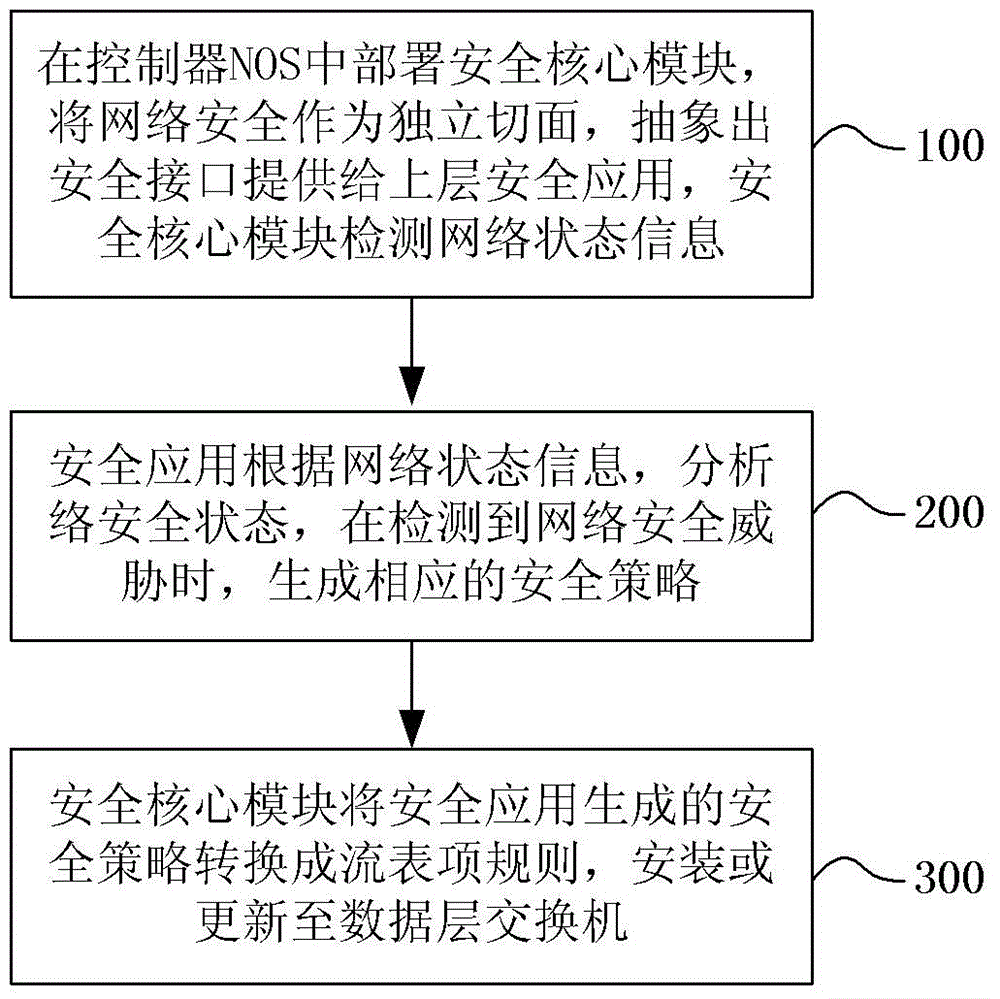
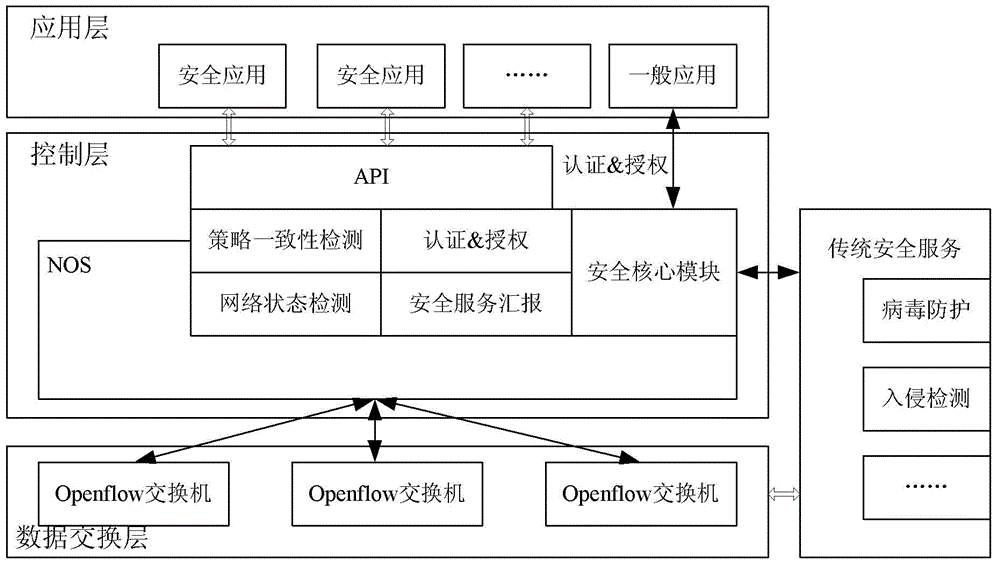
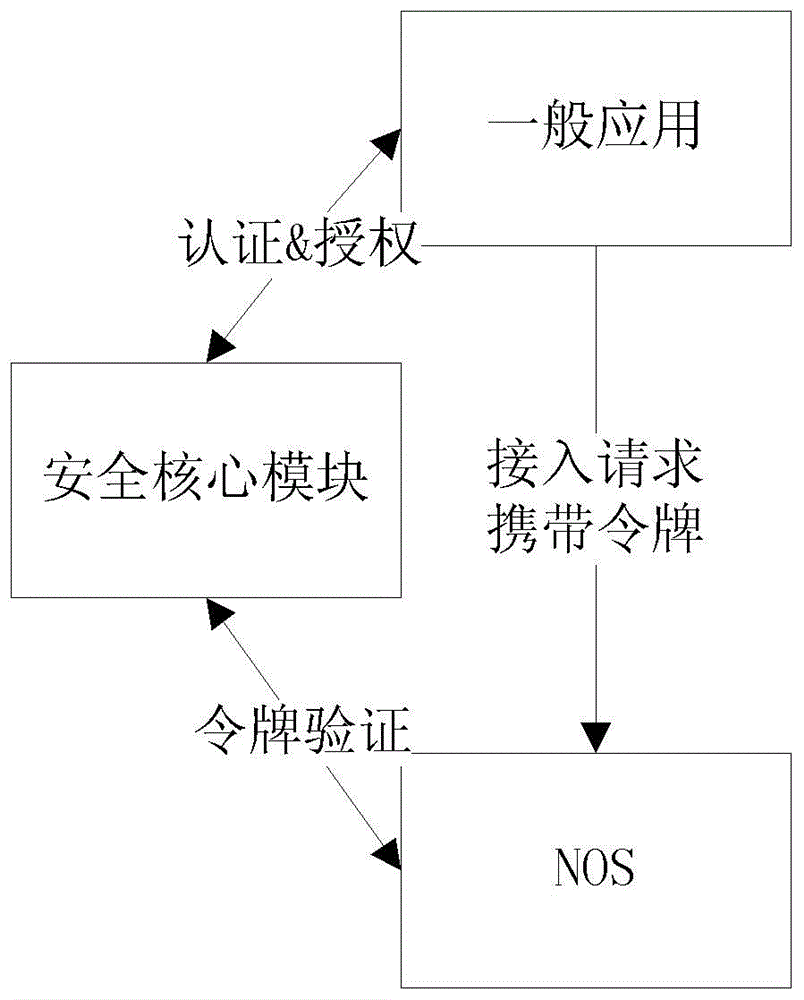
Software definition network safety enforcement method, system and controller thereof
The invention relates to a software definition network safety enforcement method, a system and a controller thereof and belongs to the network technology safety field. The software definition network safety enforcement method disclosed in the invention comprises the following steps that a safety core module deployed in a controller network operating system (NOS) detects network state information in real time; according to the network state information, a safety application analyzes a network safety state and generates a corresponding safety strategy when a network safety threat is detected,; the safety core module converts a safety strategy generated by the safety application into a flow table item rule which is installed or updated to a data layer switch. The invention also discloses another two software definition network safety enforcement methods, one software definition network safety enforcement system and the controller. By using the technical scheme in the invention, a safety problem of the software definition network is effectively solved.
Owner:ZTE CORP
User-authentication-type network operating system booting method and system utilizing BIOS preboot environment
InactiveUS6928541B2Easy to startImprove securityDigital computer detailsDigital data authenticationNetwork operating systemOperational system
Disclosed is a system that make it possible for a user to readily boot an operating system from a user terminal with user-specific settings, thereby making it unnecessary for the server to register an image for each OS environment, as a result of which the required storage capacity of the server can be reduced. The user terminal, which is connected to the server by a network, is booted using an operating system stored in the server. In booting of the user terminal, user information that has been selected by the user from OS-booting user information stored on a removable storage medium of the user terminal is transmitted to the server under the control of a BIOS preboot environment stored in a storage device of the user terminal. On the basis of the user information, the server authenticates the user terminal, transmits the operating system to the user terminal and network-boots the operating system in a user-specific environment.
Owner:NEC CORP
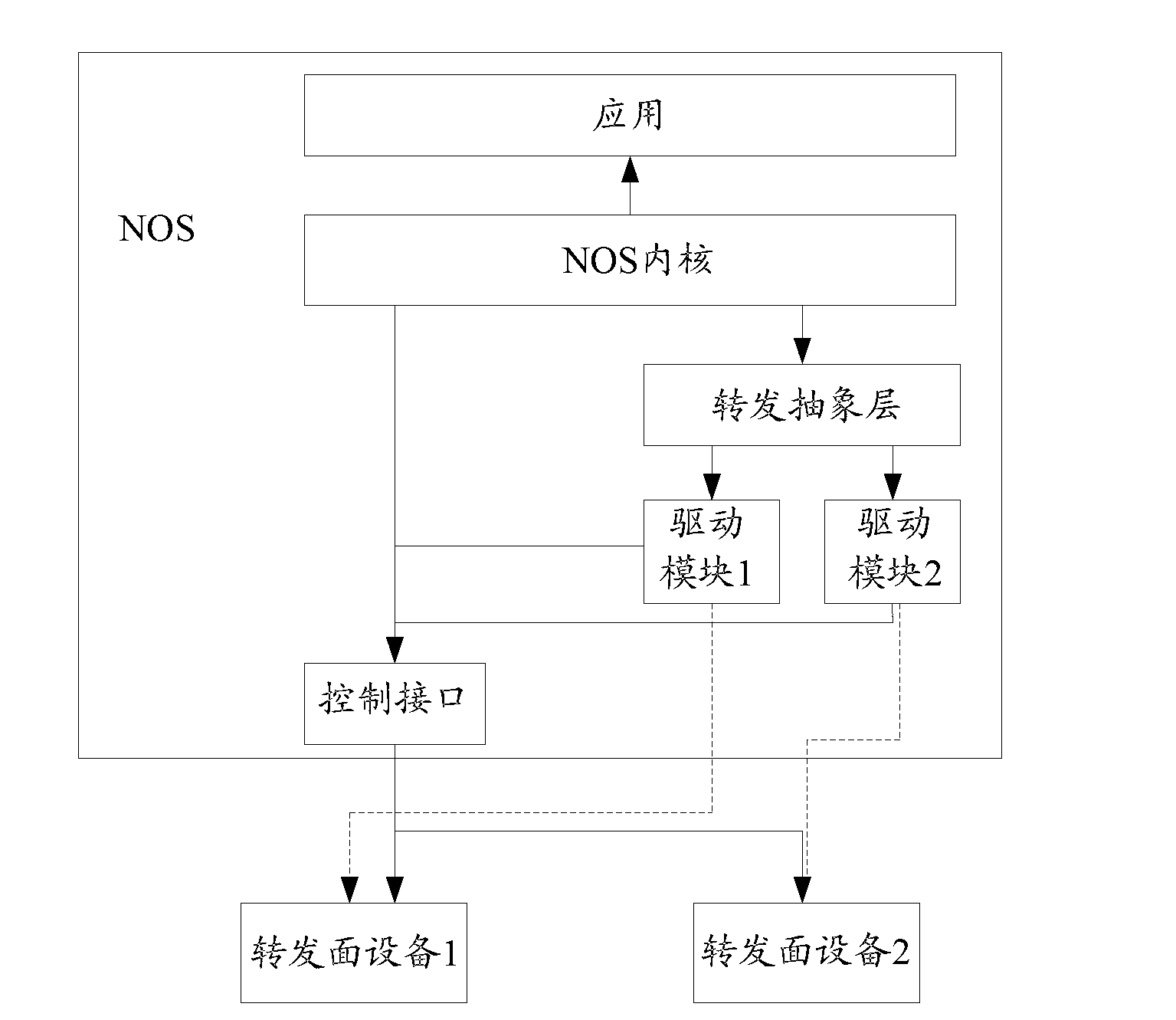
Software definition network operating system and implement method thereof
ActiveCN103095565AShorten the deployment cycleHigh feasibilityProgram loading/initiatingData switching networksProduction lineAbstraction layer
The invention discloses a self-defending network (SDN) operating system which comprises a network operating system (NOS) kernel, a control interface and application. The system further comprises a forwarding abstraction layer, and more than one drive modules of corresponding forwarding face equipment. The forwarding abstraction layer is arranged between the NOS kernel and the drive modules of the forwarding face equipment and used for managing the drive modules and converting forwarding list operating requests of the application or the NOS kernel into function interfaces which are of unified standards and not related to hardware. The drive modules of the corresponding forwarding face equipment are called. The drive modules are used for connecting the NOS kernel with the corresponding forwarding face equipment. According to call of the forwarding abstraction layer, standard operation is converted into specific forwarding list operation of a hardware production line. The invention further discloses an achieving method of the SDN operating system. According to the system and the method, under the circumstance that design details of the forwarding face hardware production line are unknown to the NOS, optimum control of the forwarding face equipment can be achieved.
Owner:ZTE CORP
Network operating system for managing and securing networks
Systems and methods for managing a network are described. A view of current state of the network is maintained where the current state of the network characterizes network topology and network constituents, including network entities and network elements residing in or on the network. Events are announced that correspond to changes in the state of the network and one or more network elements can be configured accordingly. Methods for managing network traffic are described that ensure forwarding and other actions taken by network elements implement globally declared network policy and refer to high-level names, independently of network topology and the location of network constituents. Methods for discovering network constituents are described, whereby are automatically configured. Routing may be performed using ACL and packets can be intercepted to permit host to continue in sleep mode. The methods are applicable to virtual environments.
Owner:NICIRA
High Performance, High Bandwidth Network Operating System
InactiveUS20120039336A1Reduce memory usageReduce context switchingData switching by path configurationProgram controlNetwork operating systemOperational system
The present subject matter relates to computer operating systems, network interface cards and drivers, CPUs, random access memory and high bandwidth speeds. More specifically, a Linux operating system has specially-designed stream buffers, polling systems interfacing with network interface cards and multiple threads to deliver high performance, high bandwidth packets through the kernel to applications. A system and method are provided for capturing, aggregating, pre- analyzing and delivering packets to user space within a kernel to be primarily used by intrusion detection systems at multi-gigabit line rate speeds.
Owner:RICHMOND ALFRED +2
Integrated server with switching capabilities and network operating system
Methods, systems, and computer programs are presented for a switching server. One switching server includes a server, a switch module coupled to the server, and a switch controller coupled to the server and to the switch module. The server includes a processor executing an operating system that includes a network driver, and the network driver includes a first network device operating system (ndOS) program. Further, the switch module includes a switch fabric and input / output ports. The switch controller includes a processor and non-volatile storage, where the processor is configured to execute a second ndOS program. The first and second ndOS programs implement a global networking policy for a plurality of devices executing ndOS programs, the global networking policy including a definition for switching incoming packets through the plurality of devices executing the ndOS programs.
Owner:PLURIBUS NETWORKS
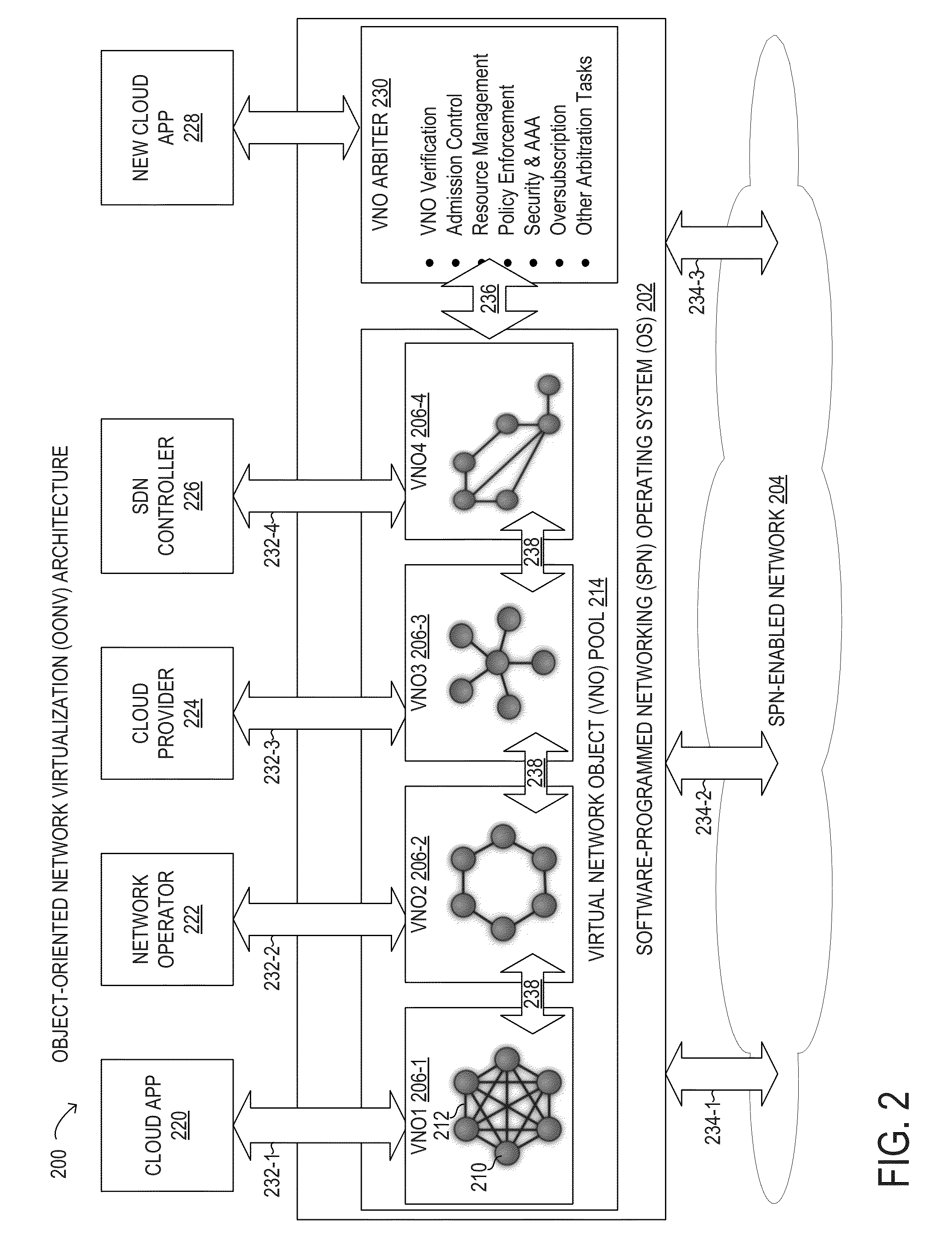
Object-oriented network virtualization
Object-oriented network virtualization may involve creating and operating virtual network objects (VNO) using a software-programmed networking operating system (SPN OS). A VNO may be a complete representation of a virtual network service provided under the SPN OS. A VNO may have a unique identity and properties, along with an internal set of methods for executing functionality encapsulated by the VNO. A VNO may exhibit persistence and autonomous control to enable improved virtual network services.
Owner:FUJITSU LTD
Log-in based communications plus two data types
InactiveUS20060041617A1Facilitates distributed collaborationCompact integrationMultiple digital computer combinationsOffice automationComputer hardwareWide area
A multimedia collaboration system that integrates separate real-time and asynchronous networks—the former for real-time audio and video, and the latter for control signals and textual, graphical and other data—in a manner that is interoperable across different computer and network operating system platforms and which closely approximates the experience of face-to-face collaboration, while liberating the participants from the limitations of time and distance. These capabilities are achieved by exploiting a variety of hardware, software and networking technologies in a manner that preserves the quality and integrity of audio / video / data and other multimedia information, even after wide area transmission, and at a significantly reduced networking cost as compared to what would be required by presently known approaches. The system architecture is readily scalable to the largest enterprise network environments. It accommodates differing levels of collaborative capabilities available to individual users and permits high-quality audio and video capabilities to be readily superimposed onto existing personal computers and workstations and their interconnecting LANs and WANs. In a particular preferred embodiment, a plurality of geographically dispersed multimedia LANs are interconnected by a WAN. The demands made on the WAN are significantly reduced by employing multi-hopping techniques, including dynamically avoiding the unnecessary decompression of data at intermediate hops, and exploiting video mosaicing, cut-and-paste and audio mixing technologies so that significantly fewer wide area transmission paths are required while maintaining the high quality of the transmitted audio / video.
Owner:PRAGMATUS AV
Virtualization method based on operating system layer
InactiveCN102339229AReduce overheadImprove performanceSoftware simulation/interpretation/emulationVirtualizationNetwork operating system
The invention provides a bottom virtualization process (namely, virtualization for an operating system layer). According to a method, virtualization is realized by adding a virtual server function in an operating system layer. The bottom virtualization process comprises the following steps of: forming a virtualized layer on a hardware layer, thereby finishing virtualized integration of physical equipment; installing a plurality of client operating systems on the virtualized layer; and running an application program in the client operating systems. The client operating systems are communicated with the hardware through a VMM (Virtual Machine Monitor) in the virtualized layer, wherein the VMM is used for determining the access of all virtual machines to physical resources. In a virtualization solution, the VMM plays a role of a traditional operating system in a software set and the traditional operating system as the client operating system runs on the virtualized layer at a position of the application program. Compared with other virtualization processes, the bottom virtualization process has the advantages that a manager need not install and maintain a single operating system embodiment for each application, thereby lowering the management cost.
Owner:戴元顺
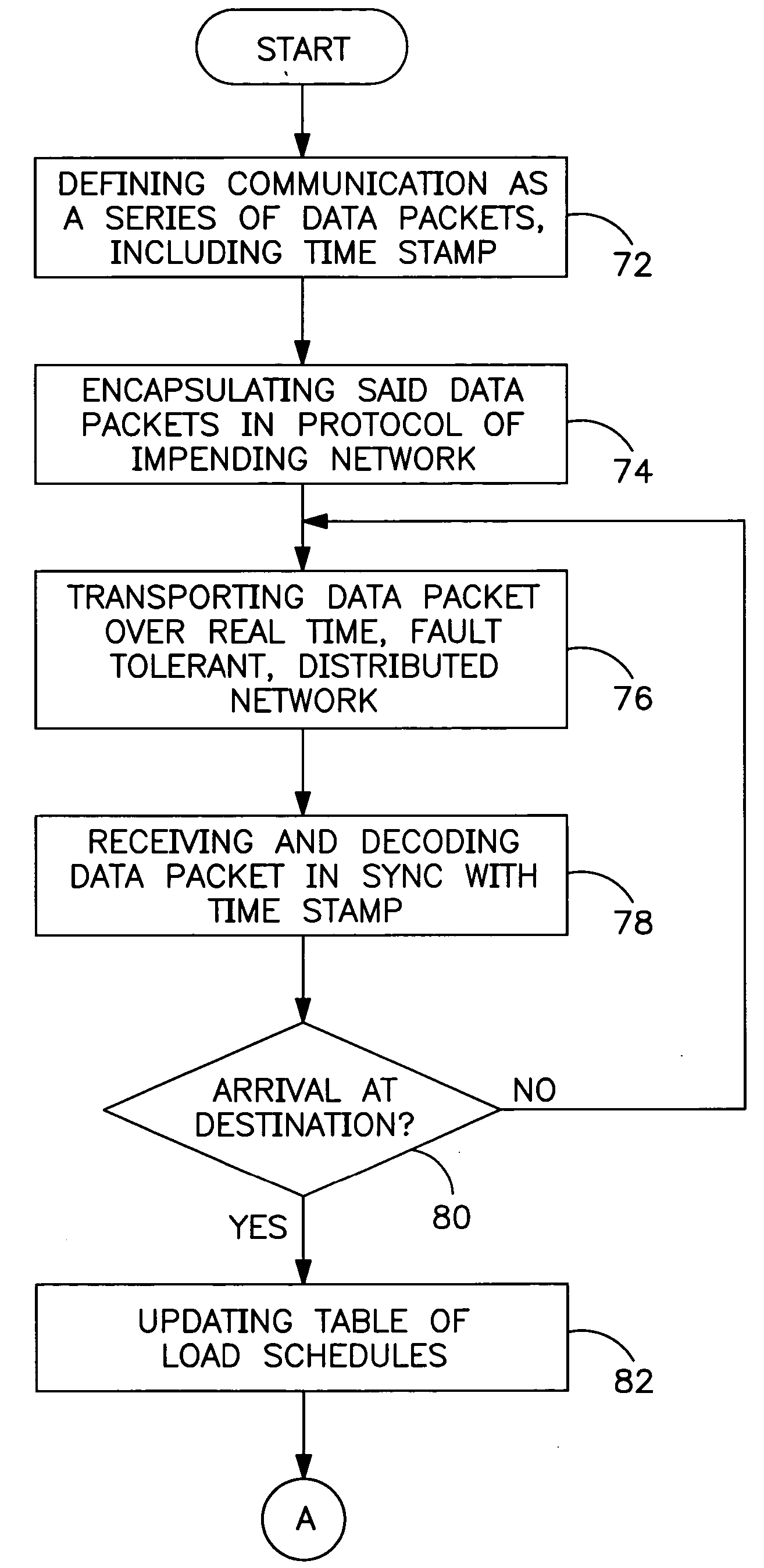
Operating system for telecommunications
InactiveUS20050111363A1Suitable for developmentMetering/charging/biilling arrangementsError preventionFault toleranceQuality of service
The present invention relates generally to telecommunications, and more specifically, to an improved operating system and apparatus for telecommunications networks. Currently, the majority of telecommunication services are provided over the Public Switched Telephone Network and Internet. Existing telephony systems suffer from a number of problems including system complexity, limited access and implementation of services on fixed hardware, which results in long time to bring new products to market. Internet applications cannot guarantee quality of service in the transmission. These systems are therefore inflexible and inefficient which limits their ability to carry new services. The invention provides a distributed and real-time operating system for use over varied telecommunications networks. As well, methods of implementing synchronized execution, fault tolerance and loading management over this network, are also described. The application of this operating system to existing networks allows new services to be provided.
Owner:WI LAN INC
Network operating system and method
InactiveUS7698346B2Digital data processing detailsComputer security arrangementsProduction rateNetwork operating system
A network operating system may be provided. Also, system and method may include a complex data medium that enables the continuous reconciliation of the collaborative information process and product. The system generally may increase productivity by enabling a network dynamic among knowledge workers. The system may unify e-mail and shared file management, synchronous and asynchronous collaboration, serial and parallel work flow, top-down and bottom-up collaboration, and information lifecycle management.
Owner:SKAI INC
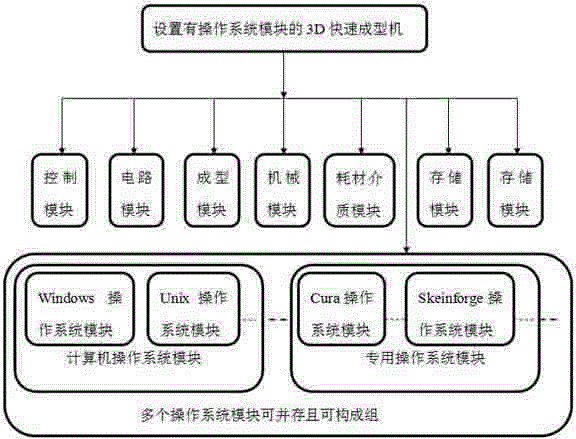
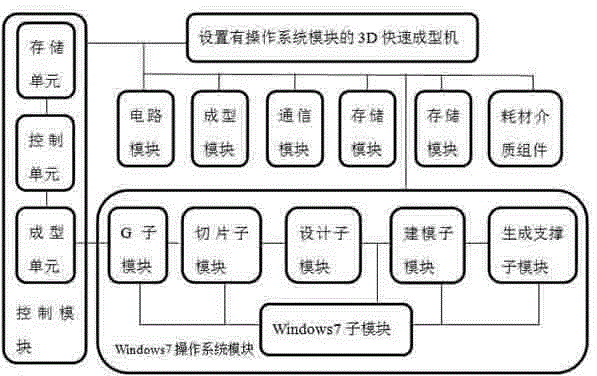
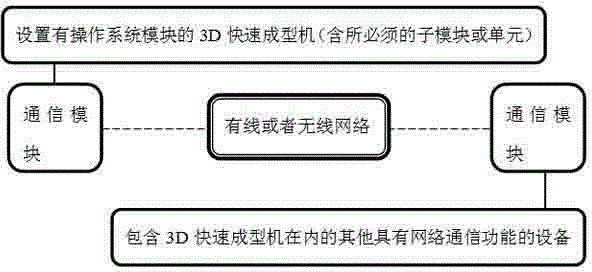
3-dimensional quick forming machine provided with operating system module
InactiveCN104699426AImprove management efficiencyRealize remote controlElectric signal transmission systemsDigital output to print unitsNumerical controlNetwork operating system
The invention discloses a 3-dimensional quick forming machine provided with an operating system module. The 3-dimensional quick forming machine comprises a control module, a storage module, a forming module, a mechanical module, a circuit module, a communication module, consumables and an auxiliary module, and is characterized in that the operating system module is further arranged inside the 3-dimensional quick forming machine, the operating system module is connected with the control module, the storage module and the communication module, and the operating system module can be a computer operating system module, an embedded operating system module, a network operating system module, a numerical control operating system module, an industrial control operating system module, a mobile phone operating system module or a 2D / 3D / 4D quick forming dedicated operating system module, and the like; the operating system module can comprises an open source or open type, research type or experiment type operating system module and the like. According to the machine provided by the invention, the 3-dimensional quick forming machine is enabled to have capabilities of independent calculation, independent communication, independent edition, independent operation, man-machine interaction, network operation, remote operation and mutual operation.
Owner:刘利钊
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com